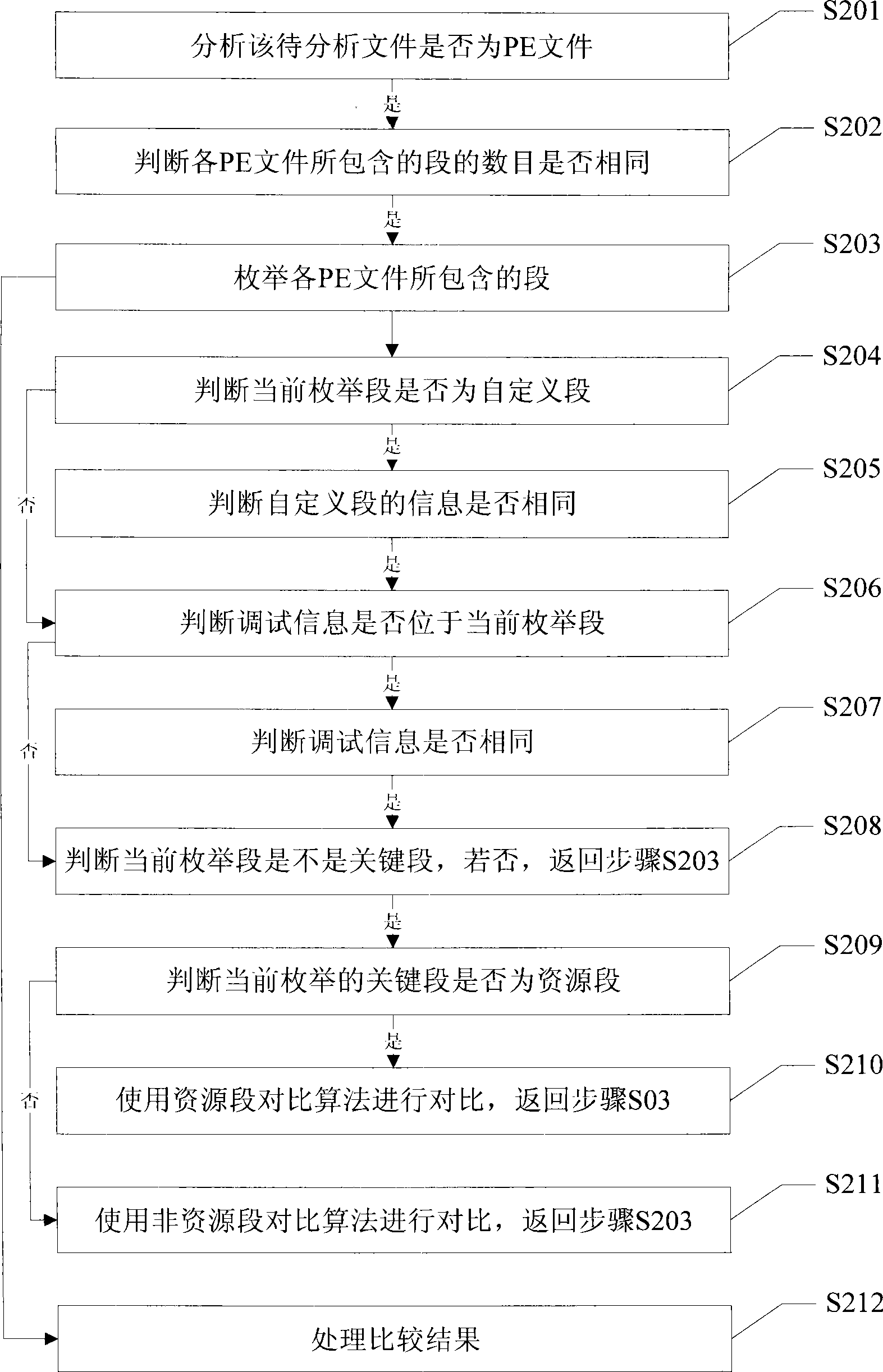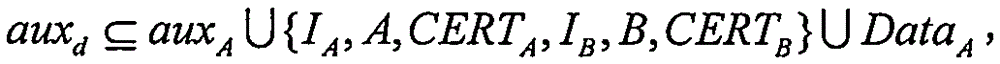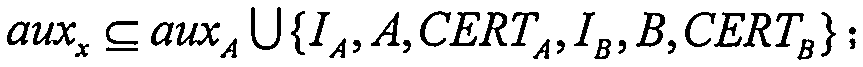Patents
Literature
288results about How to "Does not compromise security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
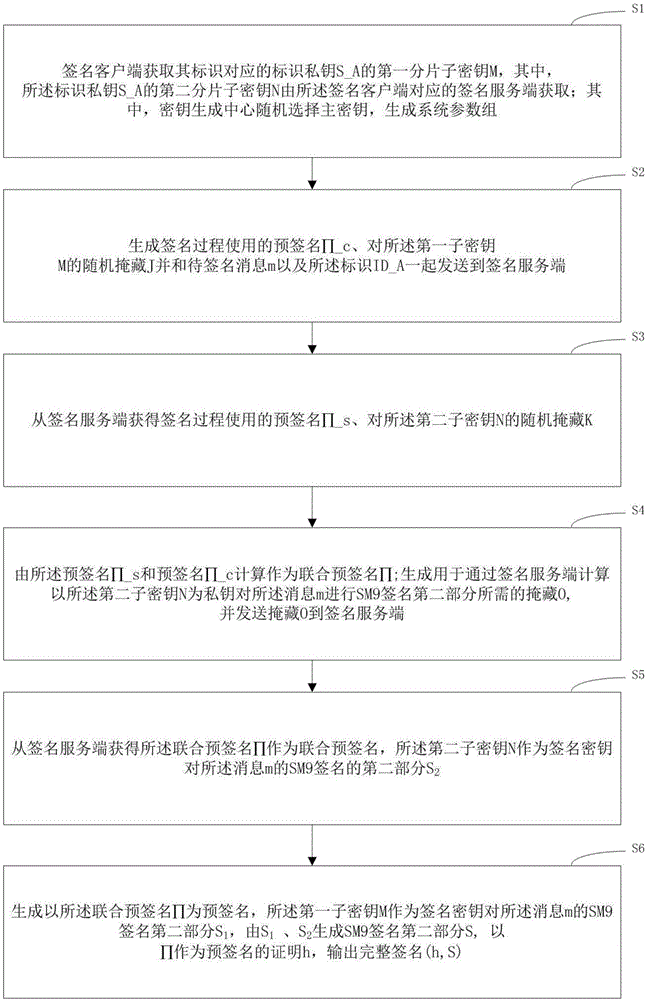
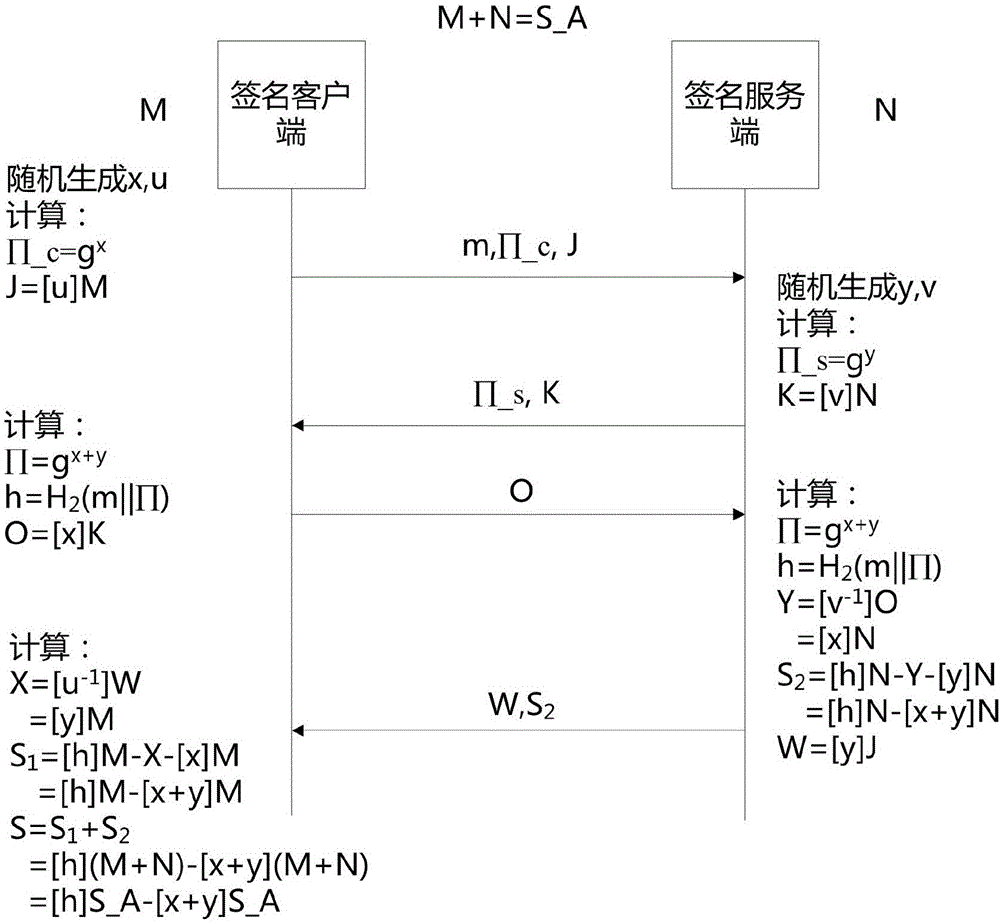
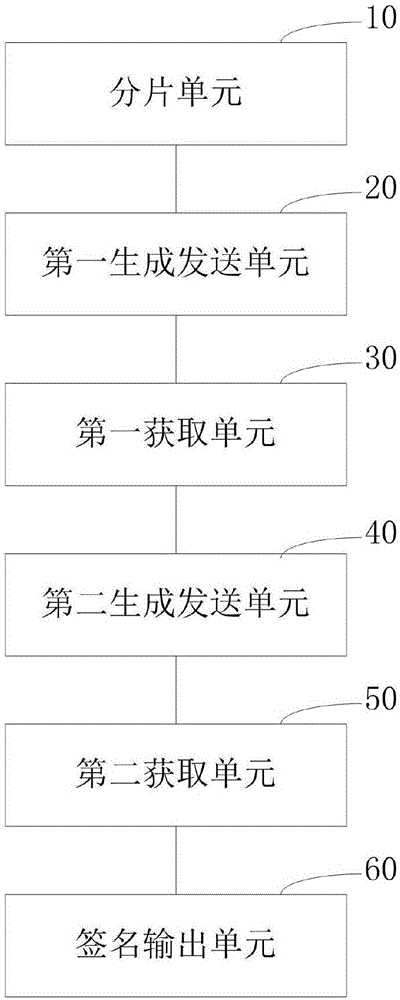
SM9 joint digital signature method and SM9 joint digital signature device
ActiveCN107438005ADoes not compromise securityImprove securityKey distribution for secure communicationPublic key for secure communicationClient-sideDigital signature forgery
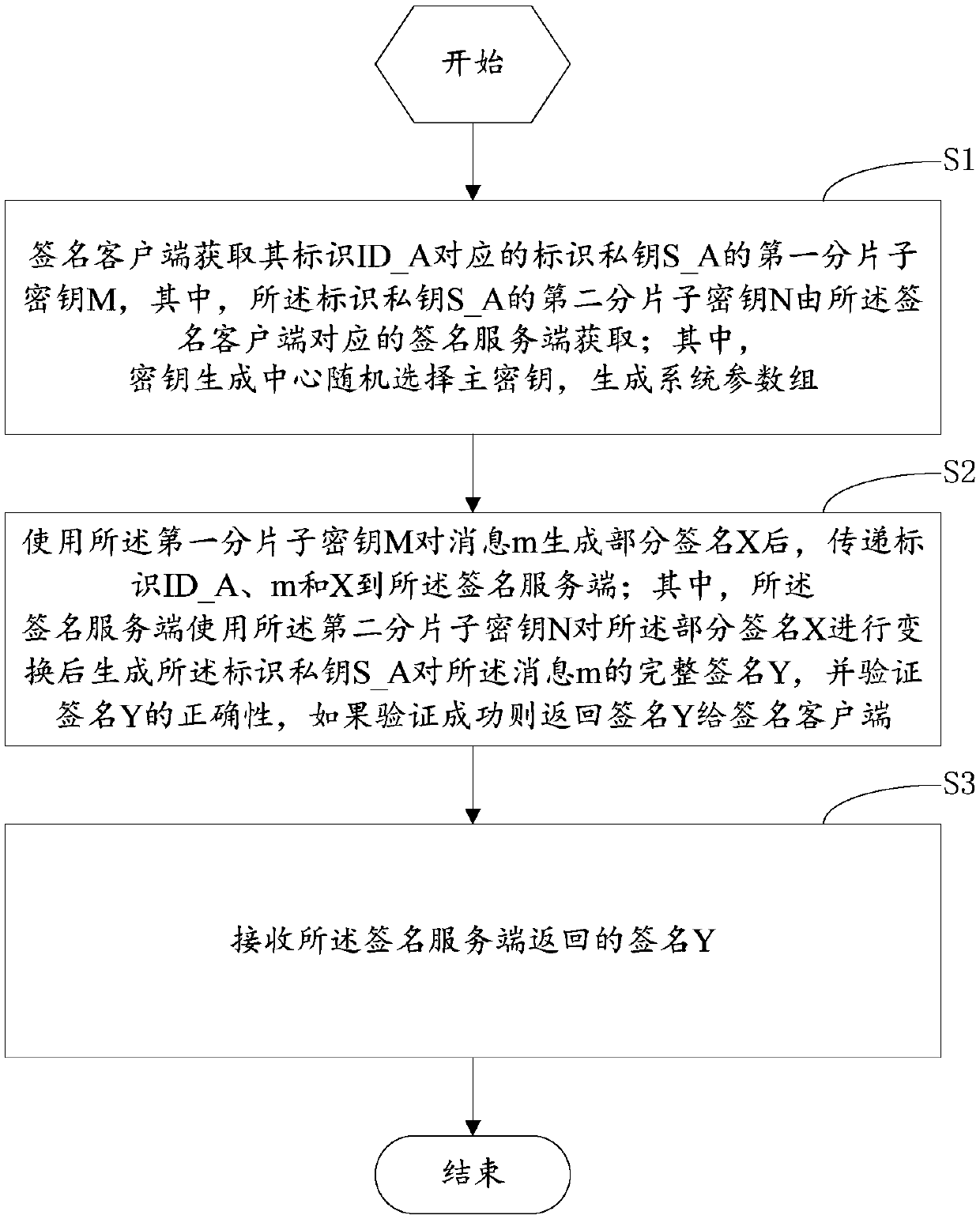
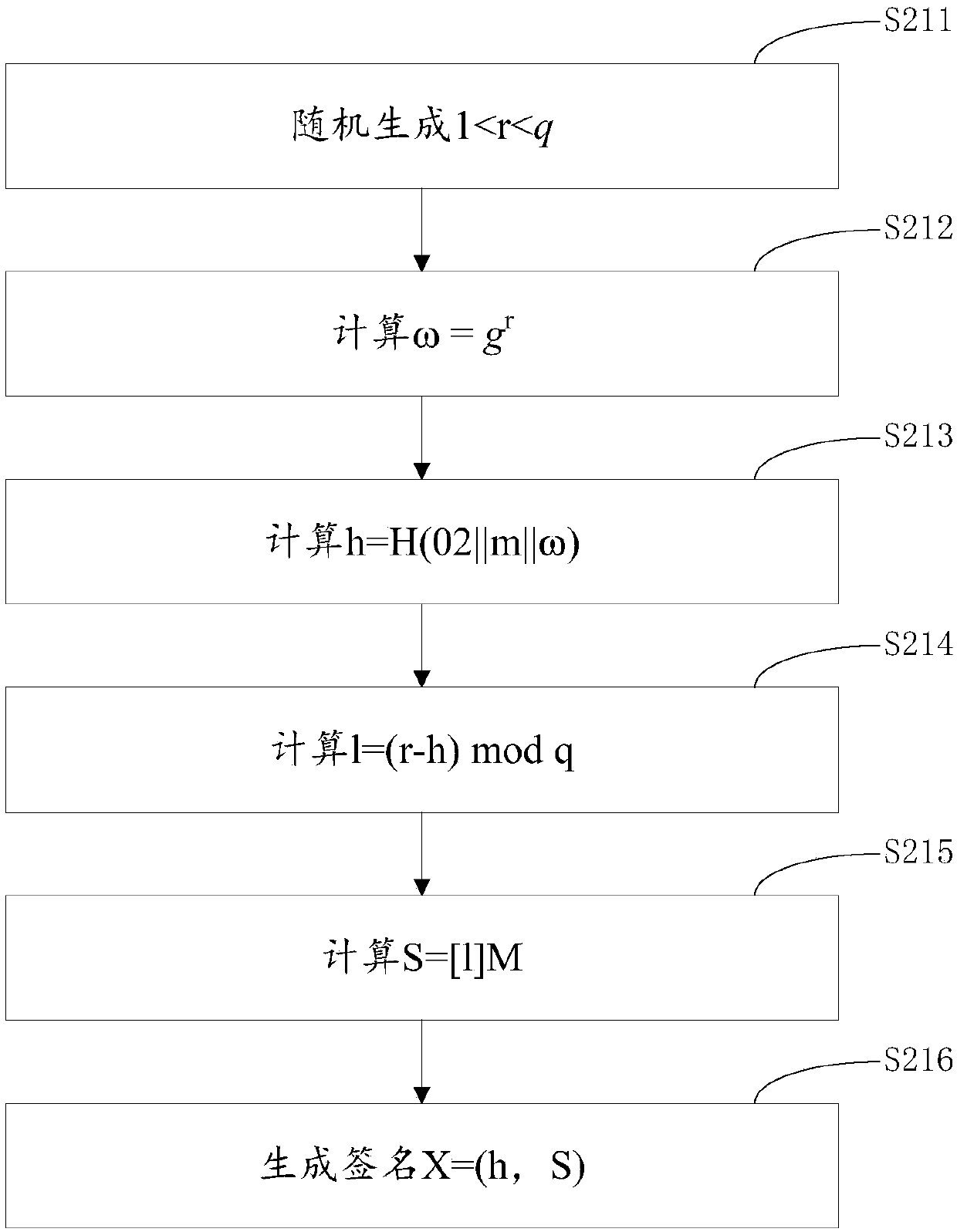
The invention discloses an SM9 joint digital signature method and an SM9 joint digital signature device. An identification private key S_A generated by a key generation center is divided to two parts: a first sub key M and a second sub key N at a signature client, a signature server, or a third party, the first sub key M and the second sub key N are stored in the two entities of the signature client and the signature server respectively, after the signature client and the signature server use the first sub key M and the second sub key N to sign a message m, a complete effective signature corresponding to the S_A is synthesized by the signature client, and when the sub key of any party of the signature client and the signature server gets lost, the integral security of the identification private key S_A is not influenced, and the digital signature security is further improved.
Owner:SHENZHEN OLYM INFORMATION SECURITY TECHOLOGY CO LTD
Non-fire-worker-driven two-stage compressing releasing mechanism
ActiveCN108298112AHeavy loadImprove vibration resistanceCosmonautic vehiclesCosmonautic component separationEngineeringDriven element
The invention provides a non-fire-worker-driven two-stage compressing releasing mechanism. Pretightening force applied to the mechanism can be accurately measured by means of strain gages; in the compressing state, a separating cap is limited by upper balls; a releasing pin is clamped by lower balls; the positions of the upper balls are determined by the separating cap, an upper retainer and the releasing pin; the positions of the lower balls are determined by the releasing pin, a sliding block and a lower retainer; and the sliding block is compressed by an anti-impact spring. During releasing, a non-fire-worker-driven element is powered on to start working to drive the sliding block to upwards move, after the sliding block upwards moves by a certain distance, the lower balls enter a groove of the sliding block, the releasing pin is unclamped and moves downwards under the effect of a driving spring, then the upper balls are unrestrained and fall into a groove of the releasing pin, theseparating cap is separated, and thus releasing is completed. In this mechanism, a plurality of spherical pairs are adopted, the influence of moment transferring on the part cooperation relationship and the releasing reliability is avoided, and meanwhile the mounting accuracy requirement is reduced; and control is convenient, vibration resistance is high, the borne load is large, and reliability is high.
Owner:北京深空动力科技有限公司
High strength coating cloth for tarpaulin of goods train and preparation thereof
InactiveCN101338522AHigh transparencyImprove thermal stabilityRailway componentsNon-woven fabricsEngineeringLow shrinkage
The invention discloses coated cloth with high strength for railway wagon tarp and making method thereof. The coating cloth includes high-strength and low-shrinkage terylene continuous filament yarn base cloth and PVC coating agent coated on the base cloth. The method comprises employing 800D-1300D high-strength and low-shrinkage terylene continuous filament yarns as warp yarn and weft yarn, or warp yarn, weft yarn and reinforced rib to make the base cloth; making base material and facing material of the PVC coating agent by PVC paste resin, plasticizer, temperature depressing plasticizer, stabilizer, flame retardant, stuffing, aging resistance agent, milew-proof agent and dye; evenly coating the base material on two sides of the base cloth with vertical coating method, and dyeing; coating one layer of facing material on vertically-coated two sides of the cloth by horizontal coating method, and tentering, plasticizing, drying, then performing surface treatment to make the coated cloth with high strength special for railway wagon tarp. The product of the invention has advantages of good stability, high strength, light weight, aging resistance, water-proof, dirt-proof, milew-proof, flame-proof, splite-proof performances, good weathering resistance and stripping performance. The method of the invention is simple, use and operation are convenient.
Owner:河北路篷塑胶有限公司 +1
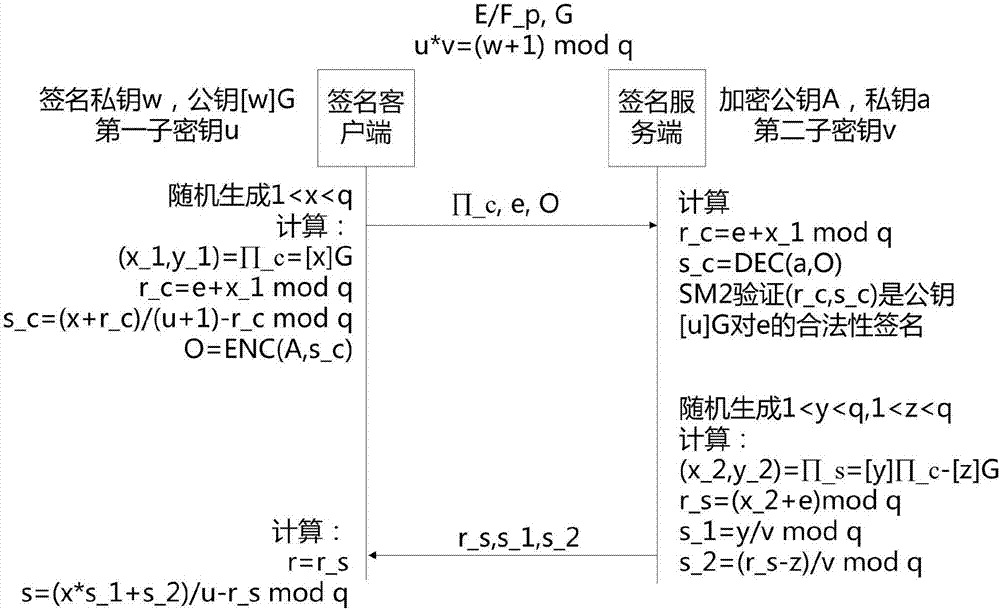
Digital signature method and device based on SM2
ActiveCN107124274ADoes not compromise securityImprove securityKey distribution for secure communicationPublic key for secure communicationDigital signatureComputer security
The invention discloses a digital signature method and device based on SM2. A signature private key is divided into two parts, which are respectively stored in a signature client and a signature server, the signature client and the signature server can only sign messages by joining up, and if a private key of any one party is lost, the overall security of the private key is not affected. According to the method and the system provided by the invention, the key of one party is protected by weak security mechanisms such as PIN codes and so on, so that a higher safety level is still remained.
Owner:SHENZHEN OLYM INFORMATION SECURITY TECHOLOGY CO LTD
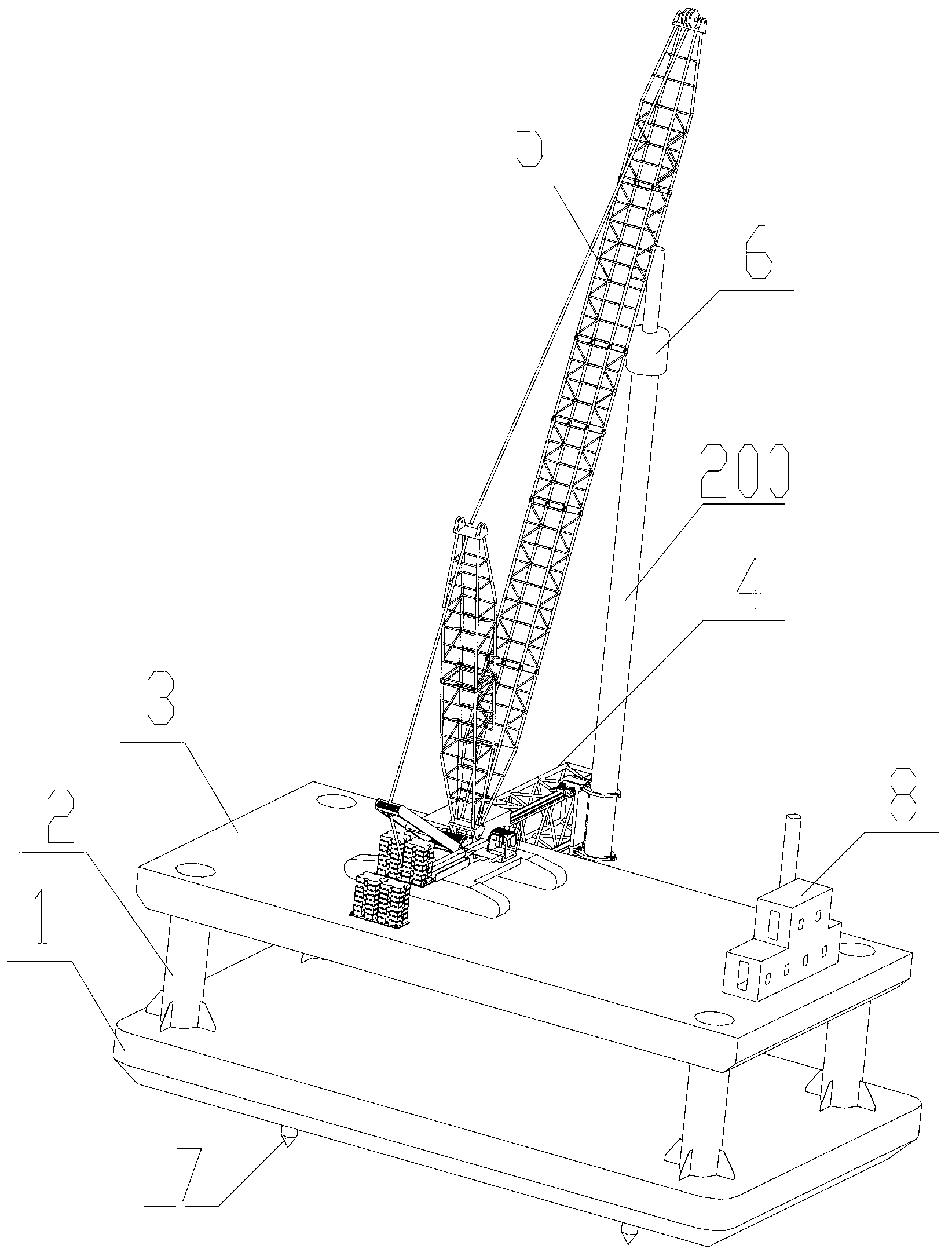
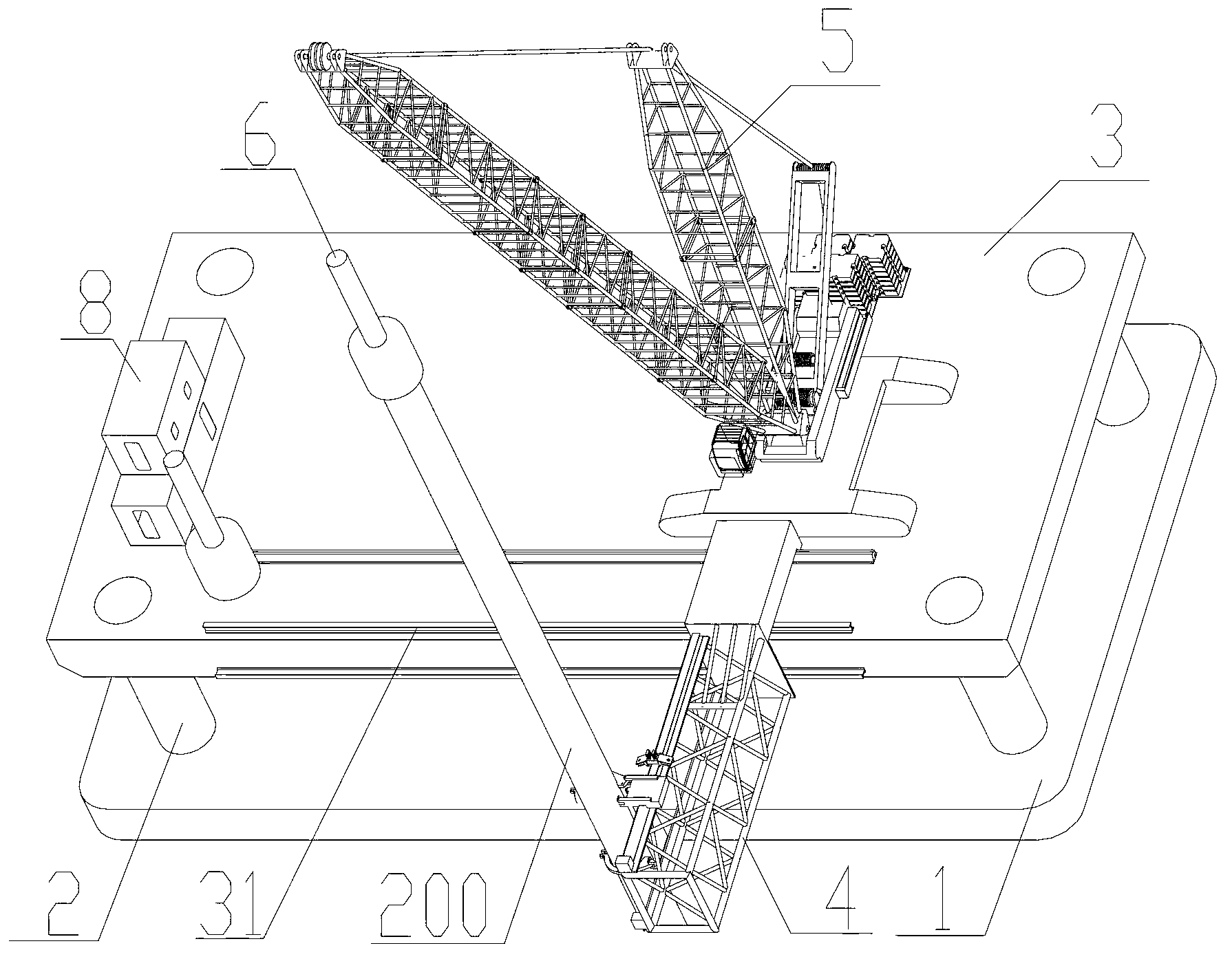
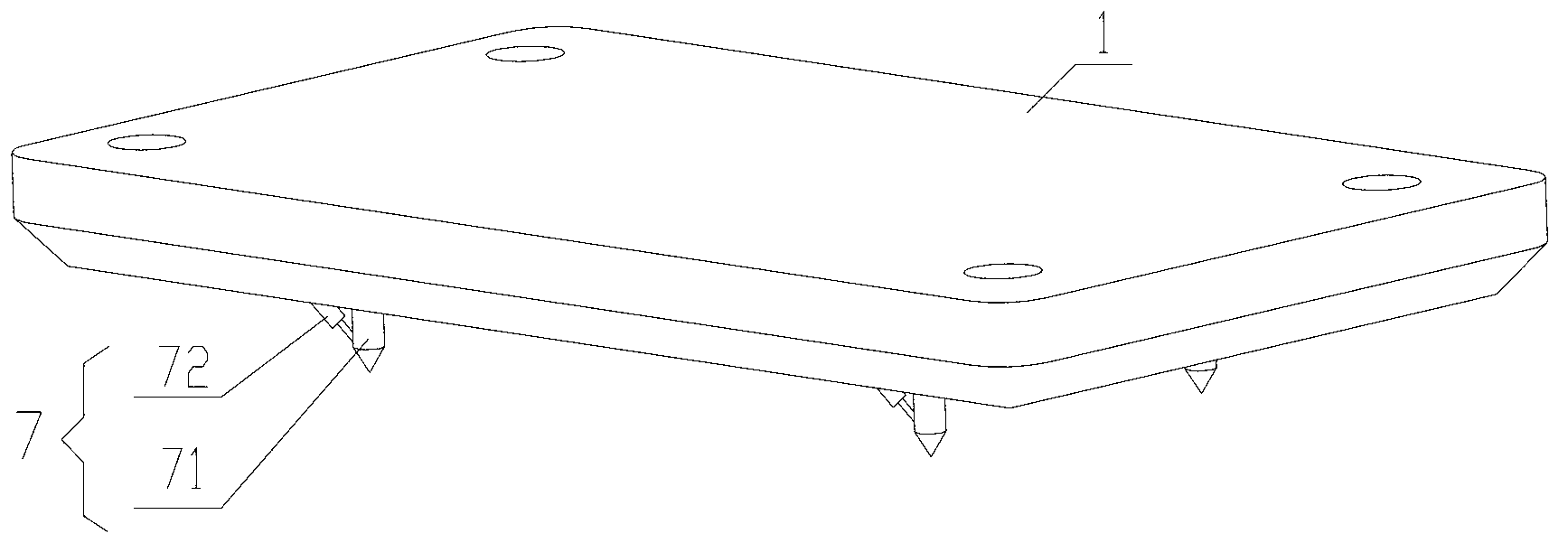
Bottom-supported floating pile-driving platform
ActiveCN102839666ADoes not compromise securityArtificial islandsUnderwater structuresShallow seaIntertidal zone
The invention discloses a bottom-supported floating pile-driving platform, which includes a caisson, a support device, an operating platform, a pile gripper and a crane. Inside the caisson are arranged a ballast tank and a water feeding / discharging system for controlling water feeding / discharging of the ballast tank; the support device is installed on the caisson, and supports the operating platform; the pile gripper is installed on the operating platform and used for positioning a pile body; the crane is used for hoisting the pile body and a pile hammer; the ballast water amount of the ballast tank in a sailing state is smaller than the ballast water amount of the ballast tank in a pile driving state; and the caisson floats on water in the sailing state, but comes into contact with the underwater ground in the pile driving state. With the caisson, the inventive bottom-supported floating pile-driving platform can adapt to pile foundation construction in shallow water areas such as intertidal zone and shallow sea area. As the caisson is always stably supported on the underwater ground in the process of pile driving, the pile foundation construction safety is not affected even in case of tide ebbing and stranding.
Owner:SANY MARINE HEAVY IND
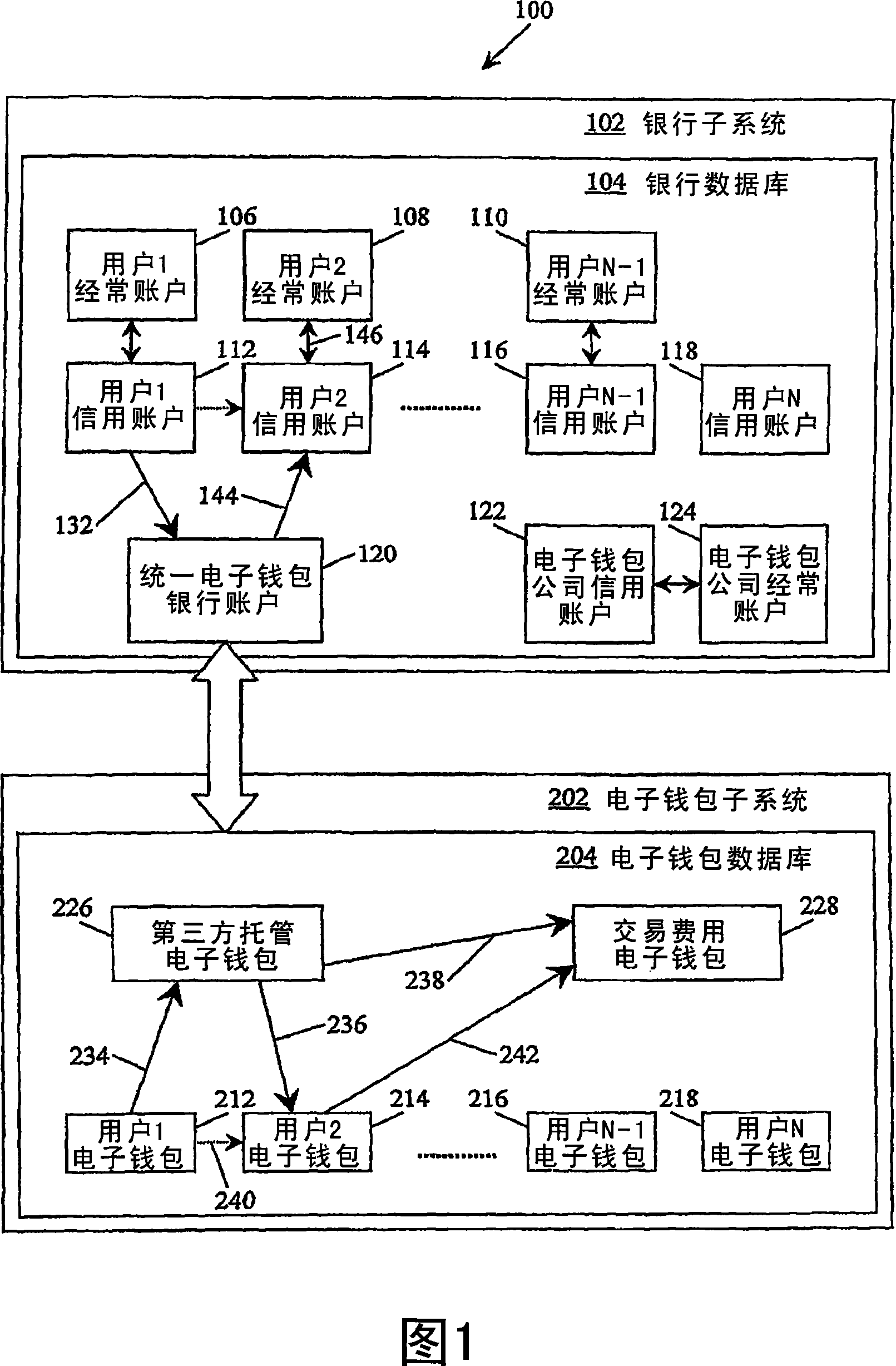
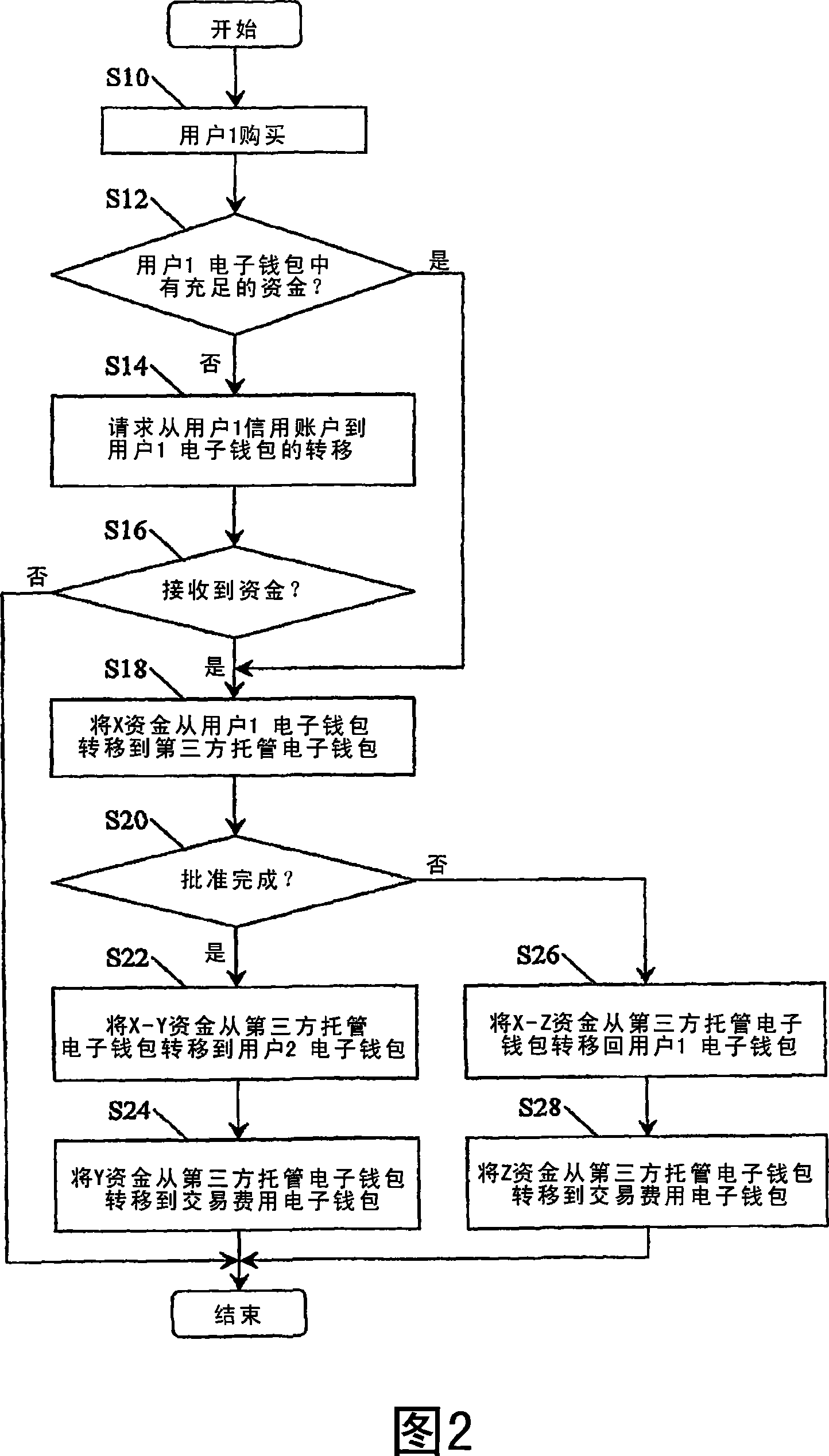
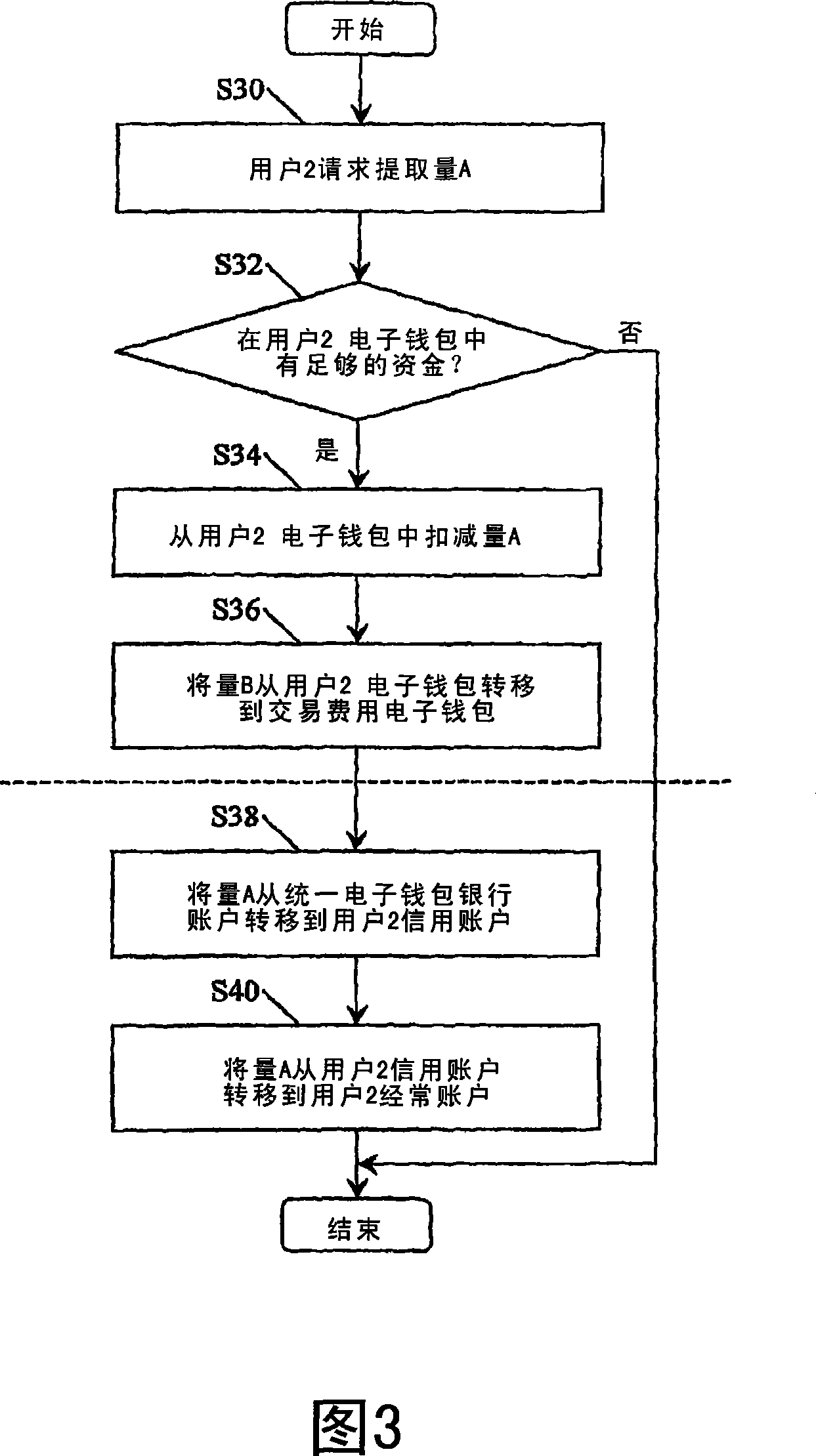
An electronic-purse transaction method and system
InactiveCN101099181AMinus transaction feesAccountableComplete banking machinesCoded identity card or credit card actuationBank accountPayment gateway
Users (302,403,406) of a bank (332,324) put funds into user credit account (112,114,116,118) from which the funds can be transferred to a consolidated e-pures ban account (120) within the bank (332,324). The consolidated e-pures bank account (120) i mirrored in a e-purse database (204), but wih fund allocated to different e-purese (212,214,216,218,226,228) the total of all funds in the different e-purse (212,214,216,218,226,228) beeing equal to the funds in the consolidated e-purse ban account. When a first user (302) wishes to make a purchase from a second user (304), h sends an SMS message (352) to a mobile telephone payment gateway (320) indicating th second user (304) and an amount. The indicated amount of funds is removed from the fir users's e-purese (212). When the purchase is confirmed, the funds are transferred into th second user's e-purse (214), less transaction charges. These funds are immediately availabl to the second user (304).
Owner:MOBILE MONEY INT SDN BHD
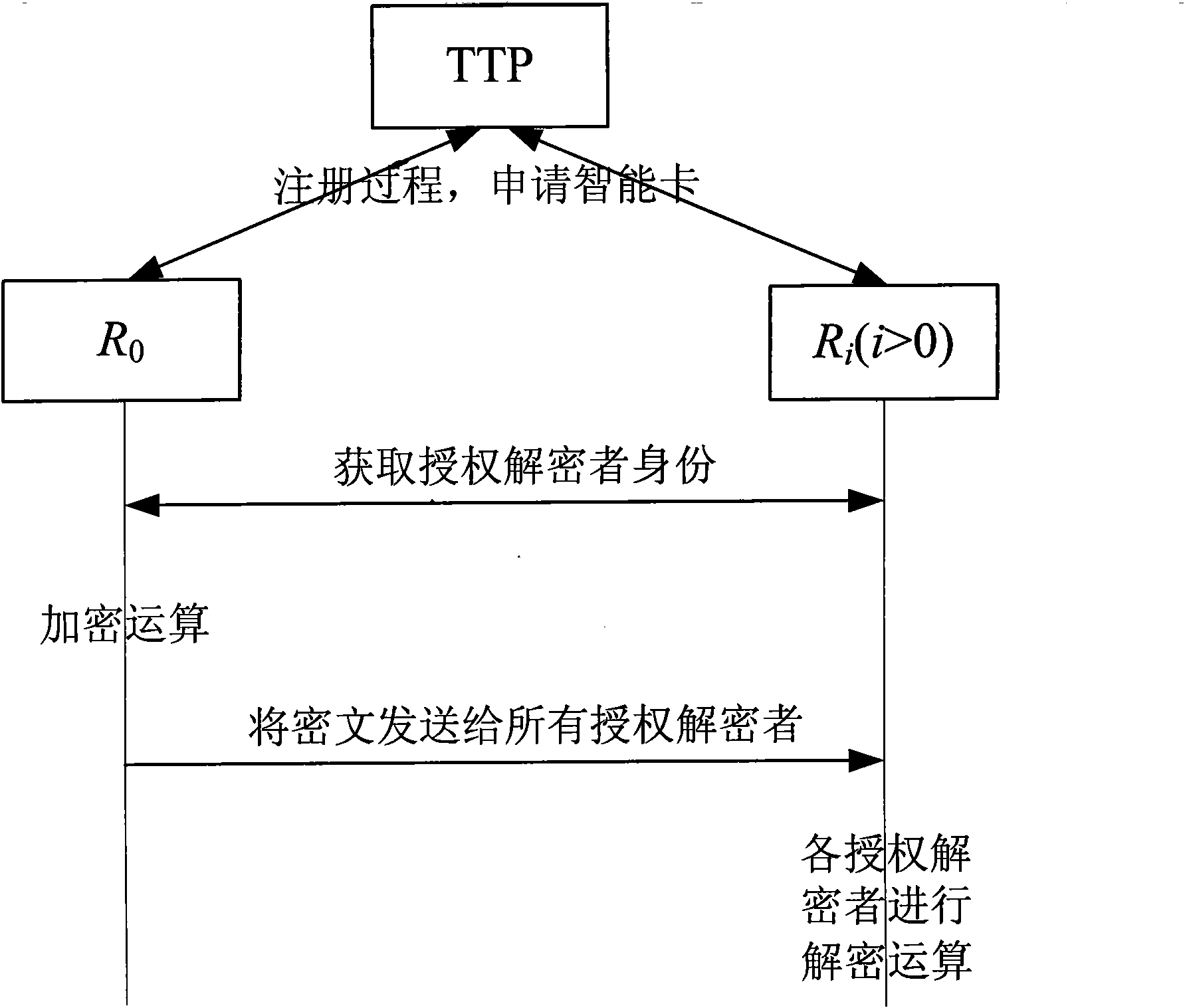
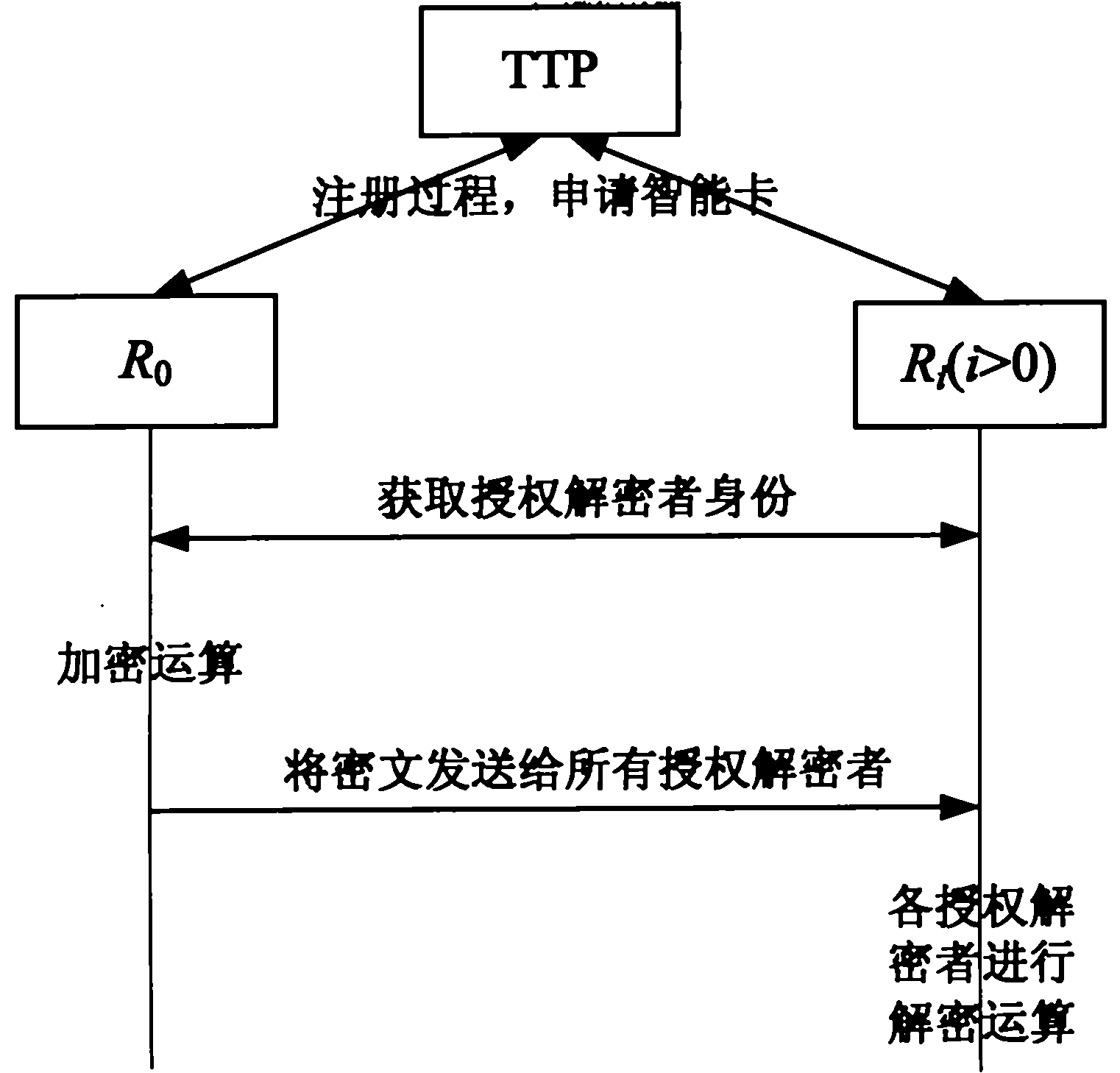
Multi-receiver encryption method based on biological characteristics
The invention provides a multi-receiver encryption method based on biological characteristics, overcoming various safety problems in secret key saving in the prior art by using the biological characteristics for replaying a secret key. When encrypting, encipherers only need to provide own biological characteristics, each authorized encipherer can use own biological characteristics as the secret key for deciphering without needing to save any secret key information, and meanwhile the identities of users are directly authenticated by using the information of the biological characteristics, thereby the avoidless problem of secret key abuse in cryptology is avoided, and the integral safety and reliability of the system are improved. The method comprises a registering process, an encrypting process and a deciphering process; and in the registering process, all users in the system register in a credible third party to obtain an intelligent card issued by the credible third party; in the encrypting process, the encipherers encrypt the information m through the own biological characteristics so that only authorized decipherers can decipher through the own biological characteristics; and in the deciphering process, each authorized decipherer deciphers the encrypted information through the own biological characteristics to obtain the information m.
Owner:XIDIAN UNIV
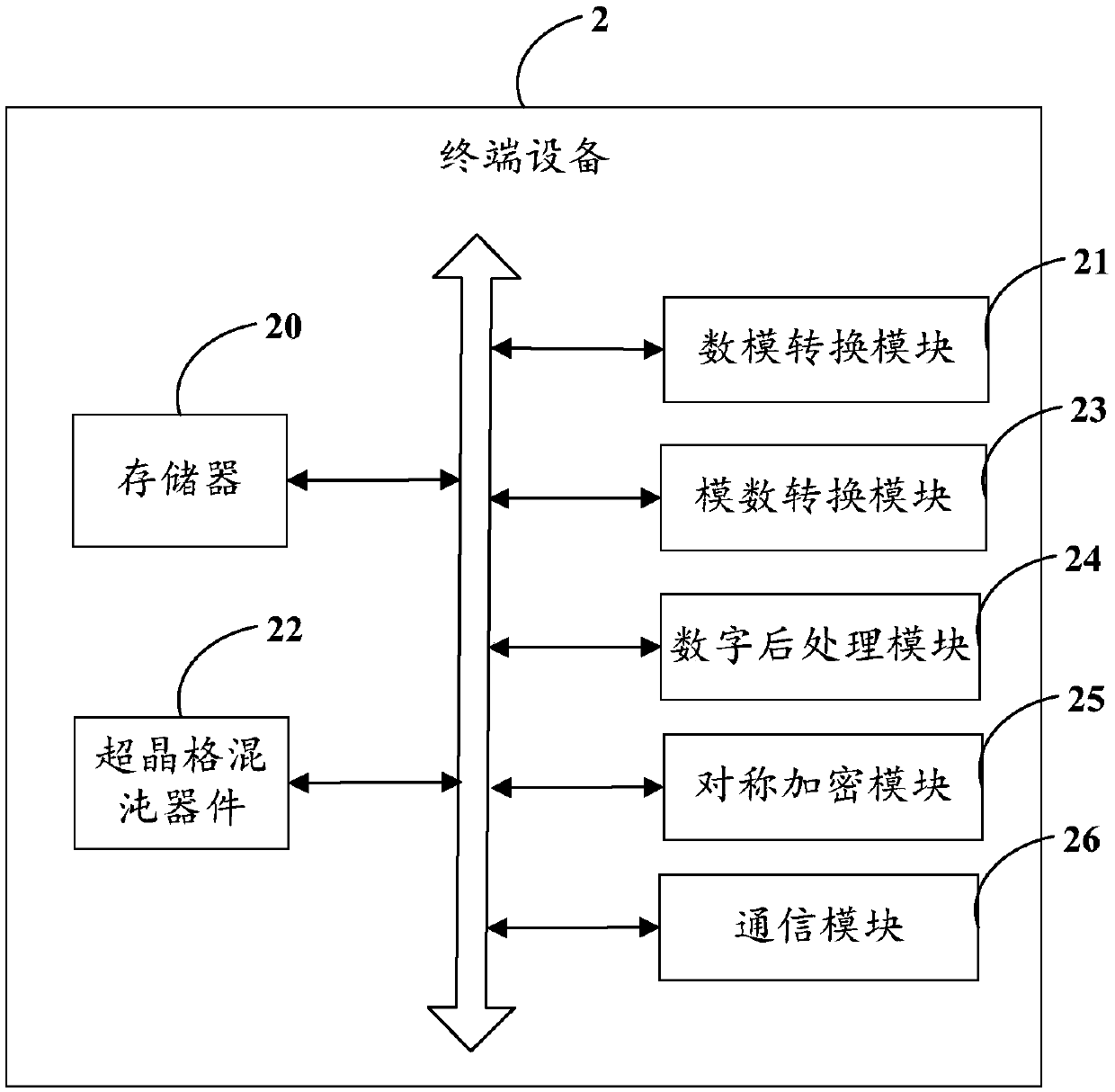
Data encryption transmission method, terminal equipment and use method of superlattice chaotic device
InactiveCN110519036AWith simplicityImprove convenienceKey distribution for secure communicationSecuring communication by chaotic signalsKey distributionSuperlattice
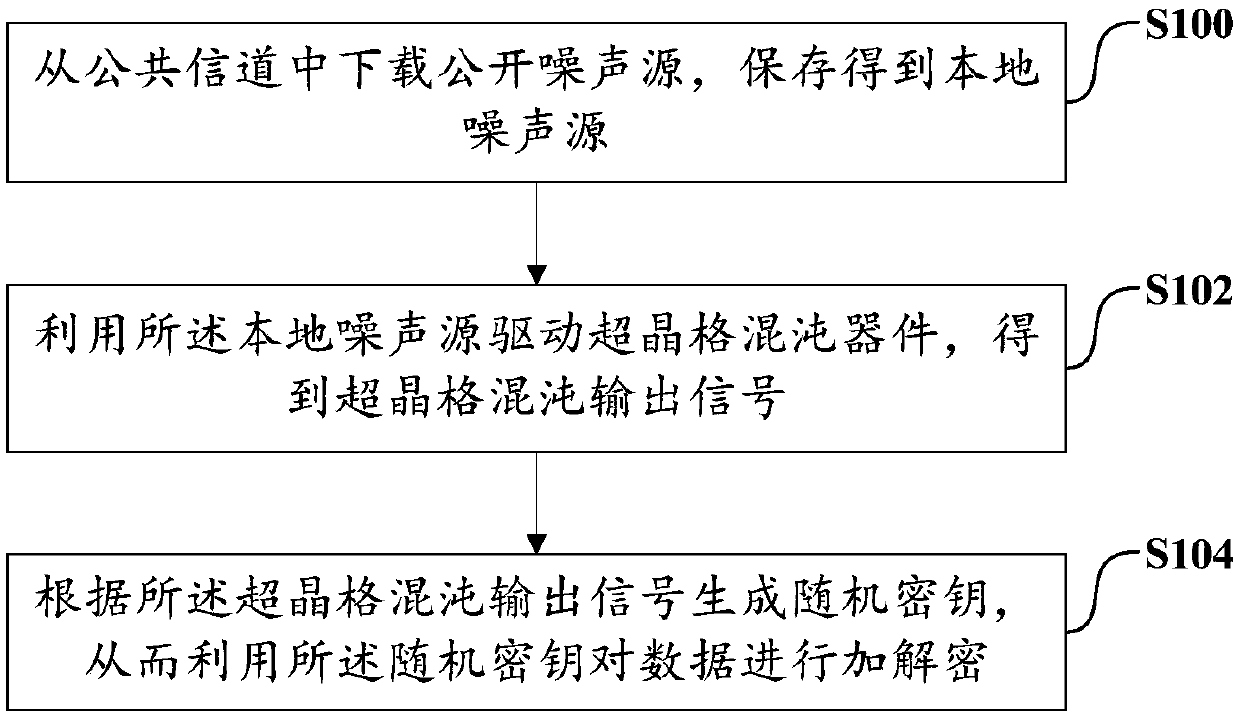
The invention discloses a data encryption transmission method, which comprises the following steps of: downloading a public noise source from a public channel, and storing the public noise sourceand obtaining a local noise source; driving a superlattice chaotic device by using the local noise source to obtain a superlattice chaotic output signal; generating a random key according to the superlattice chaotic output signal; and encrypting and decrypting the data by using the random key. The embodiment of the invention further discloses terminal equipment and a using method of the superlattice chaotic device. Therefore, the security of symmetric encryption and the convenience of key distribution can be improved.
Owner:SUZHOU INST OF NANO TECH & NANO BIONICS CHINESE ACEDEMY OF SCI
Method for providing trusted services using trusted execution environment system
ActiveCN111382445ADoes not compromise securityGuaranteed confidentialityDigital data protectionInternal/peripheral component protectionMonitor modeOperational system
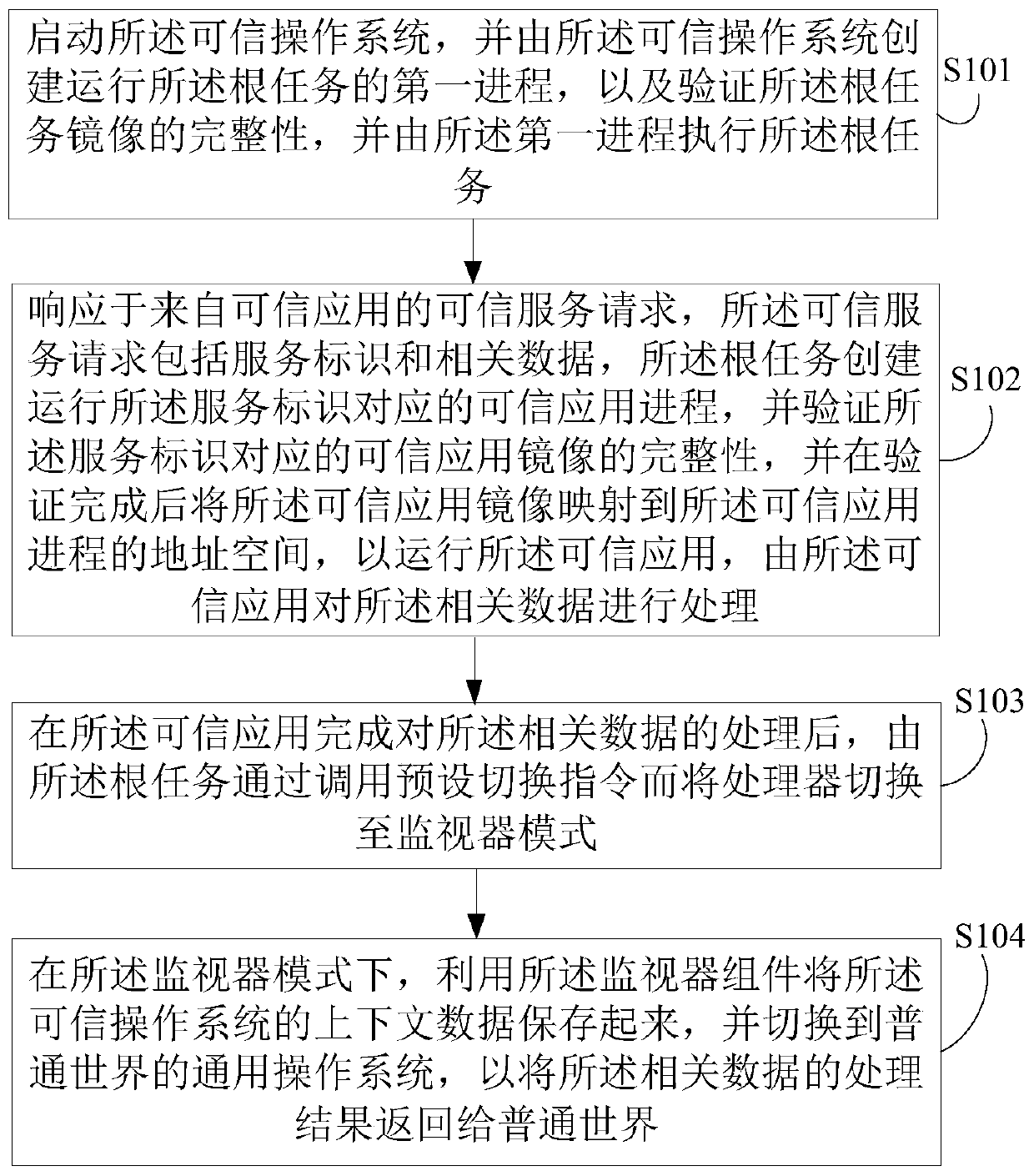
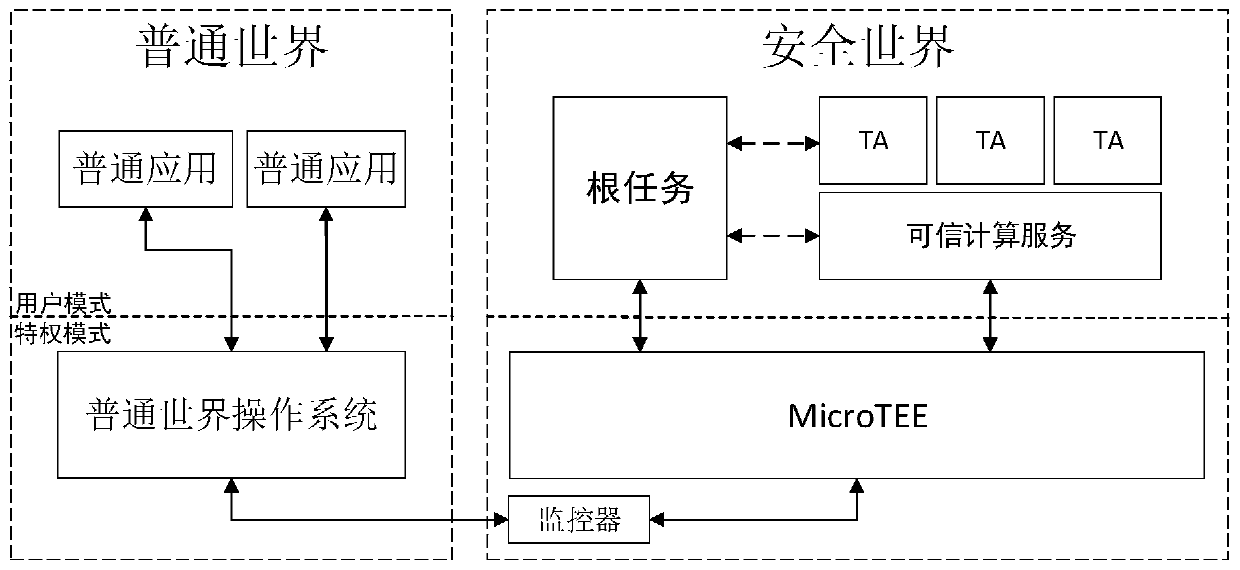
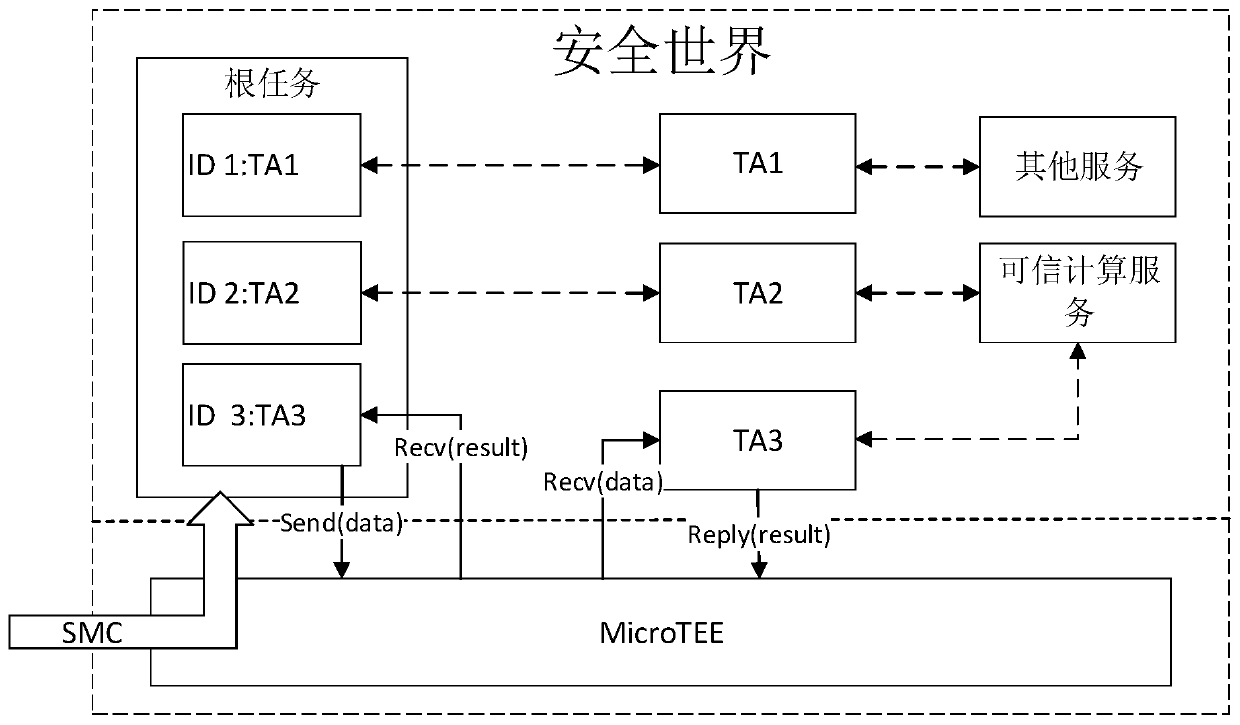
An embodiment of the invention discloses a method for providing trusted services by utilizing a trusted execution environment system based on a microkernel architecture. The method comprises the following steps of: starting a trusted operation system, creating a first process for running a root task by the trusted operation system, verifying the integrity of a mirror image of the root task, and executing the root task by the first process; in response to a service request from the common world, creating and running a trusted application process corresponding to a service identifier by the roottask, verifying the integrity of a trusted application mirror image corresponding to the service identifier, and creating a trusted application process based on the trusted application mirror image after the verification is completed; after the trusted application completes processing of the related data, switching a processor to a monitor mode by calling a preset switching instruction through the root task; and storing context data of the trusted operating system by using the monitor component in the monitor mode, and switching to a general operating system in the common world.
Owner:CAPITAL NORMAL UNIVERSITY
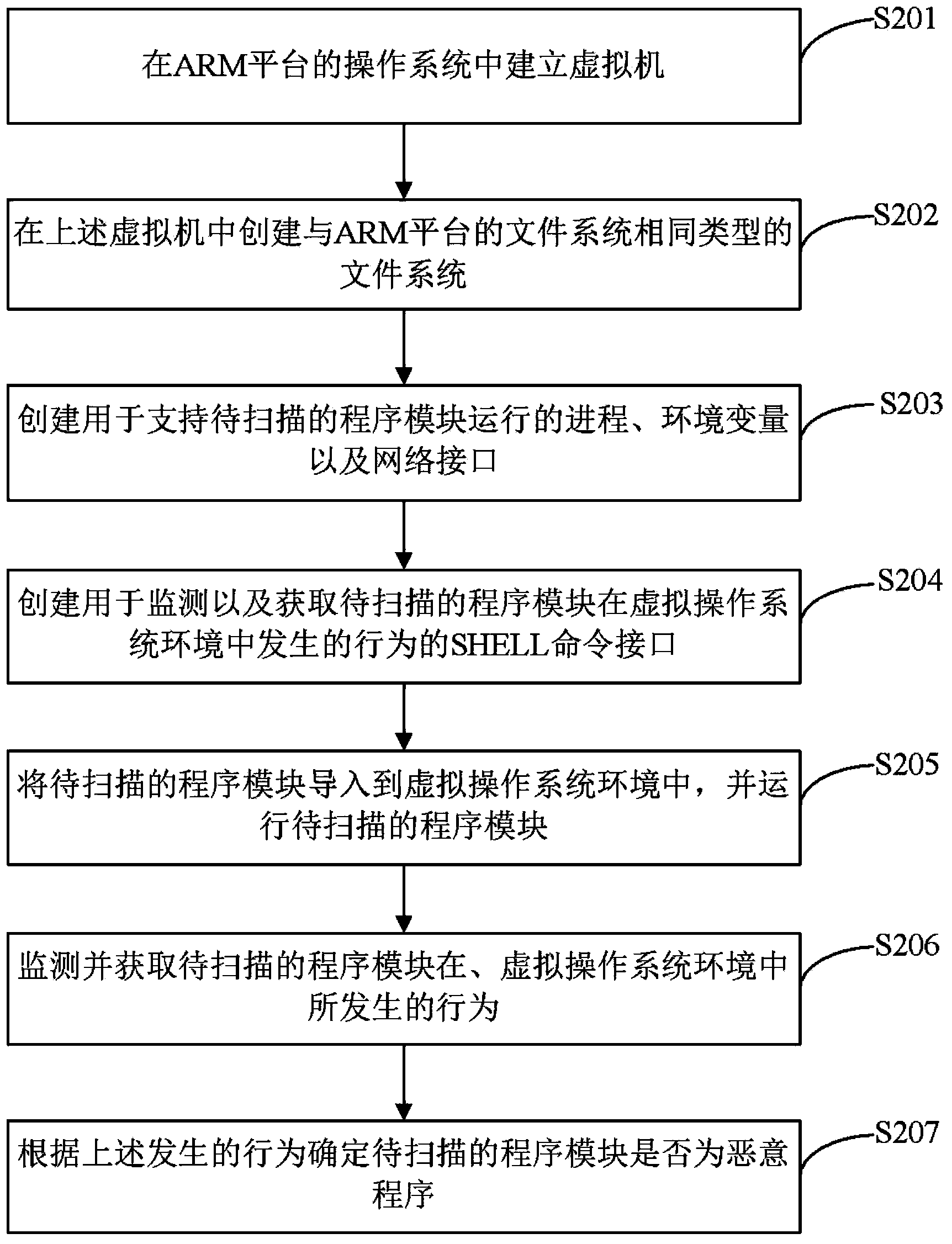
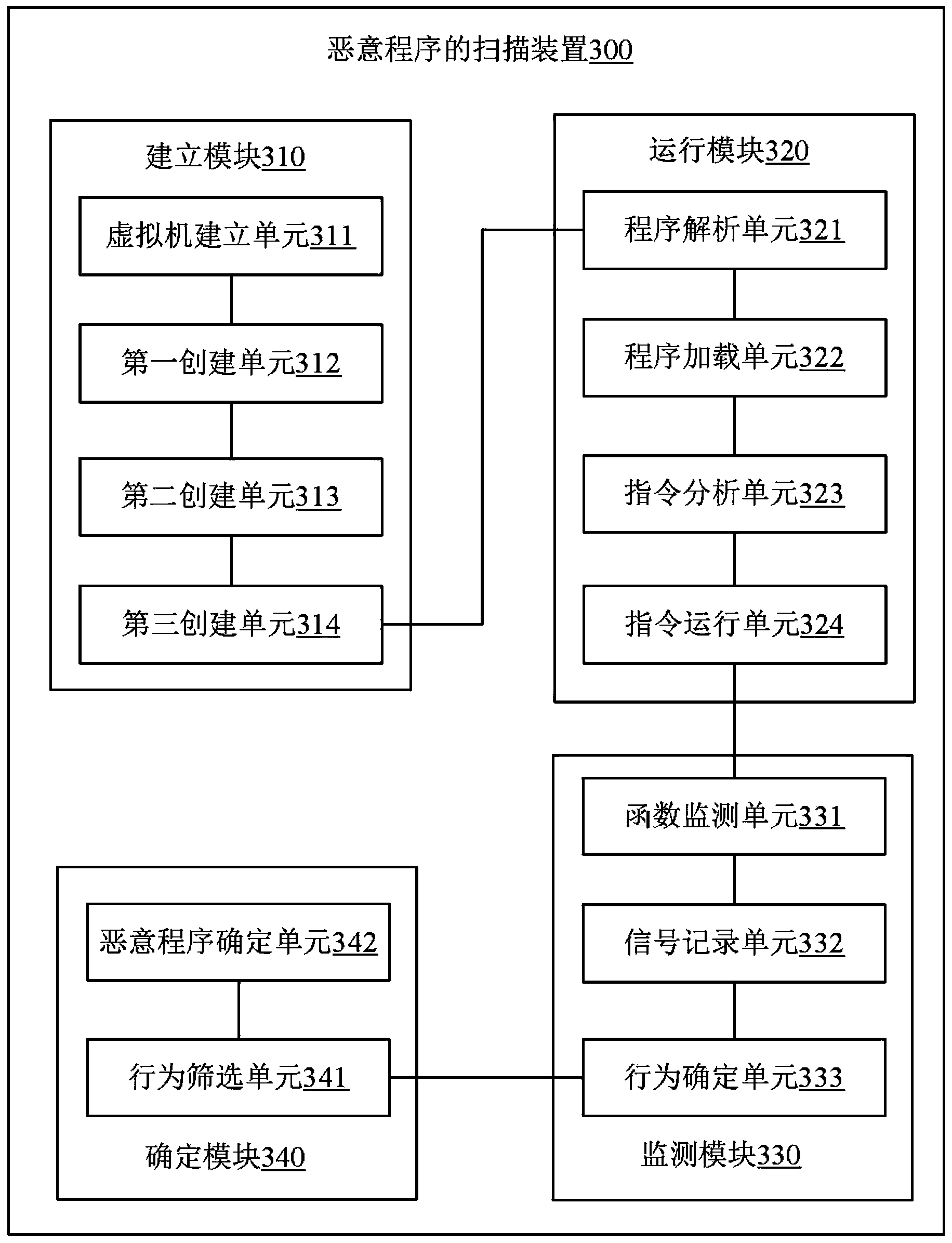
Scanning method and scanning device for malicious programs
ActiveCN103761479ADoes not compromise securitySolve the problem that malware scanning cannot be performedPlatform integrity maintainanceOperational systemInstruction set
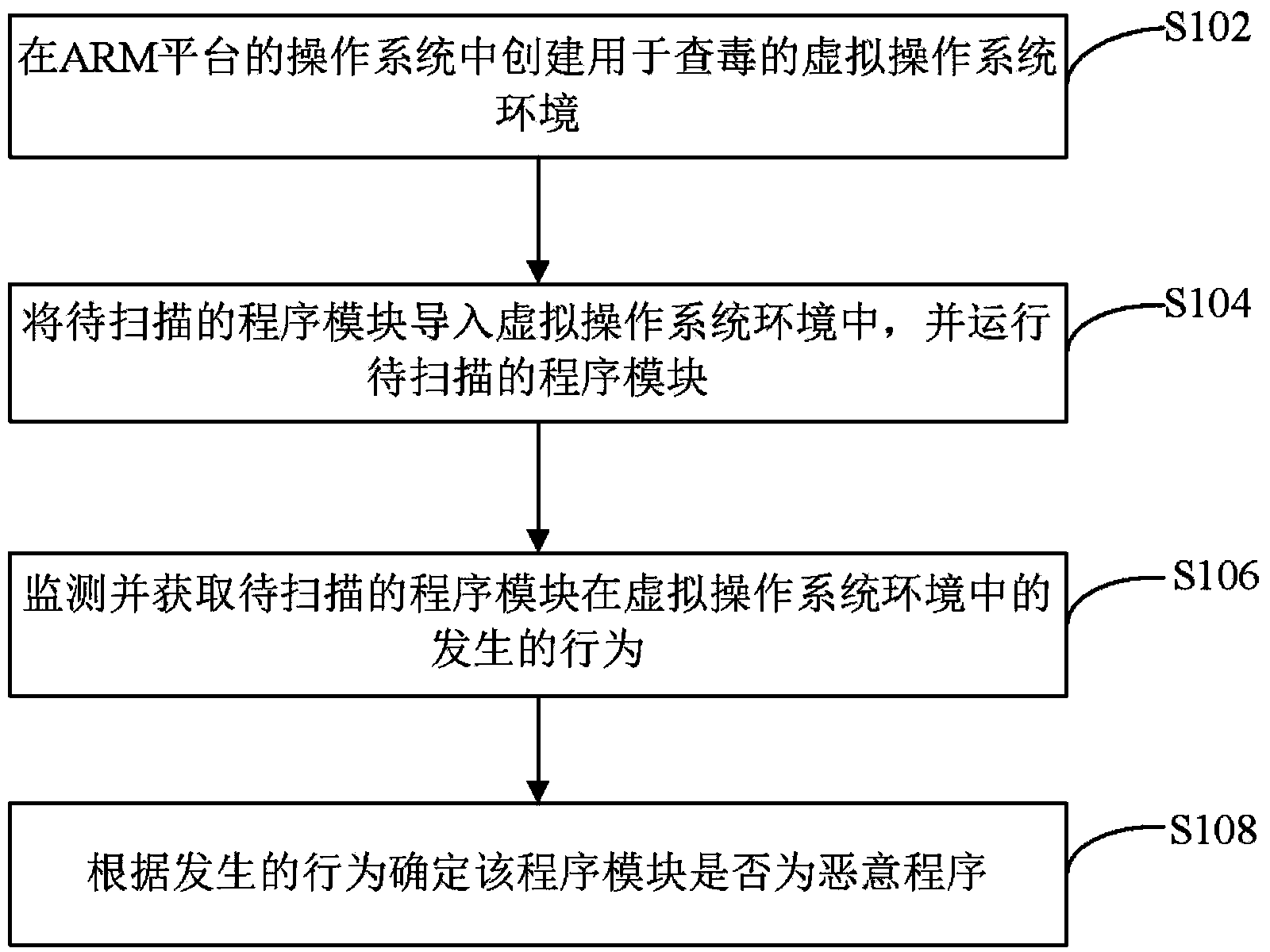
The invention provides a scanning method and a scanning device for malicious programs. The scanning method includes creating a virtual operating system environment used for virus scanning in an operating system of an ARM (acorn reduced-instruction-set-computer machine) platform, importing to-be-scanned program modules into the virtual operating system environment, running the to-be-scanned program modules, monitoring and acquiring behaviors of the to-be-scanned program modules in the virtual operating system environment, and determining whether the program modules are the malicious programs or not according to the behaviors. By the scanning method and the scanning device, the problem of incapability of scanning the malicious programs in the ARM platform due to mechanism characteristics is solved; the to-be-scanned program modules are embedded into the virtual operating system environment to run, so that whether the to-be-scanned program modules are the malicious programs or not can be judged according to the behaviors of the to-be-scanned program modules, and safety of a real operating system of a user is not affected.
Owner:北京鸿享技术服务有限公司
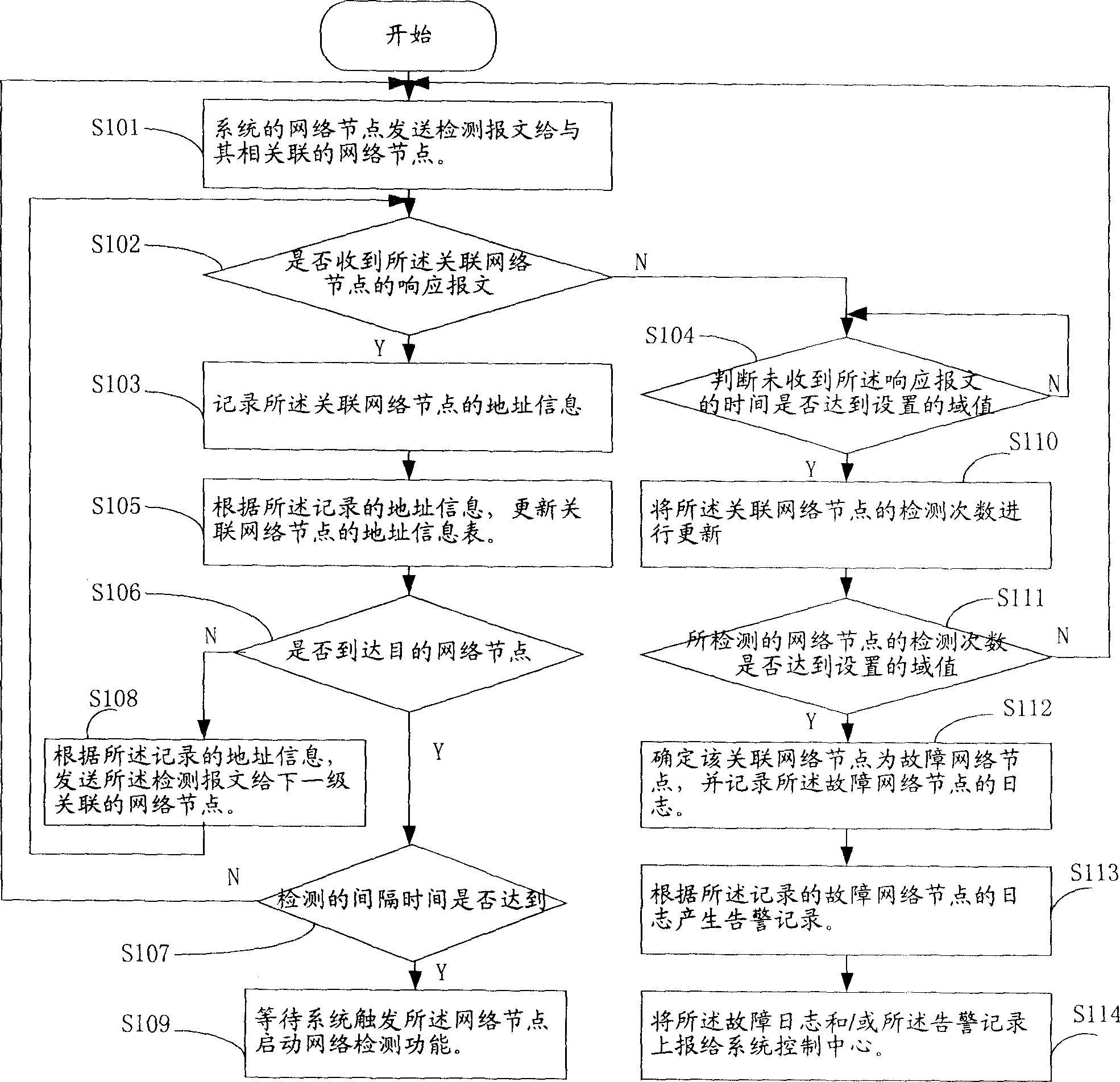
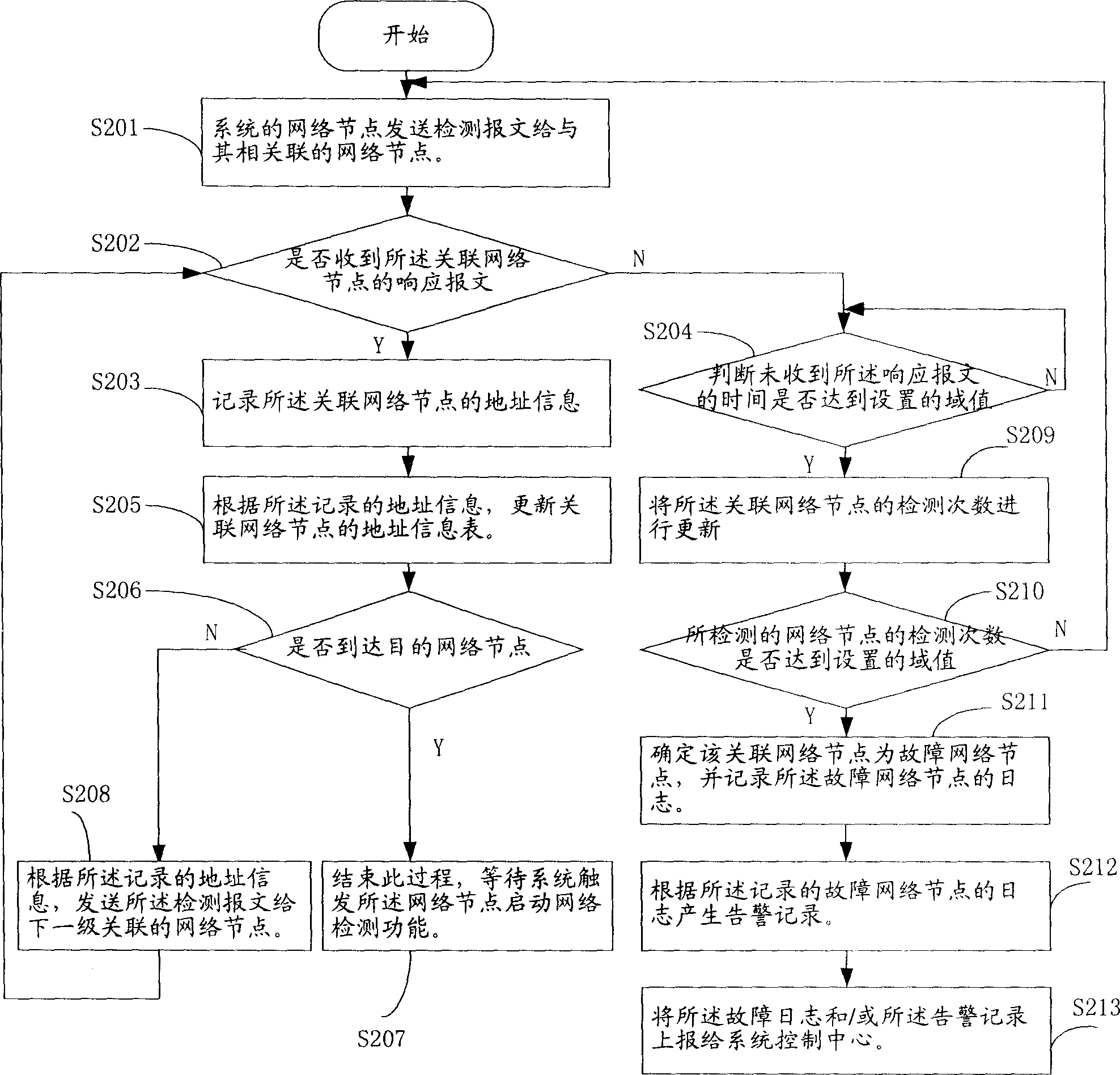
Method for recognizing failure node in network
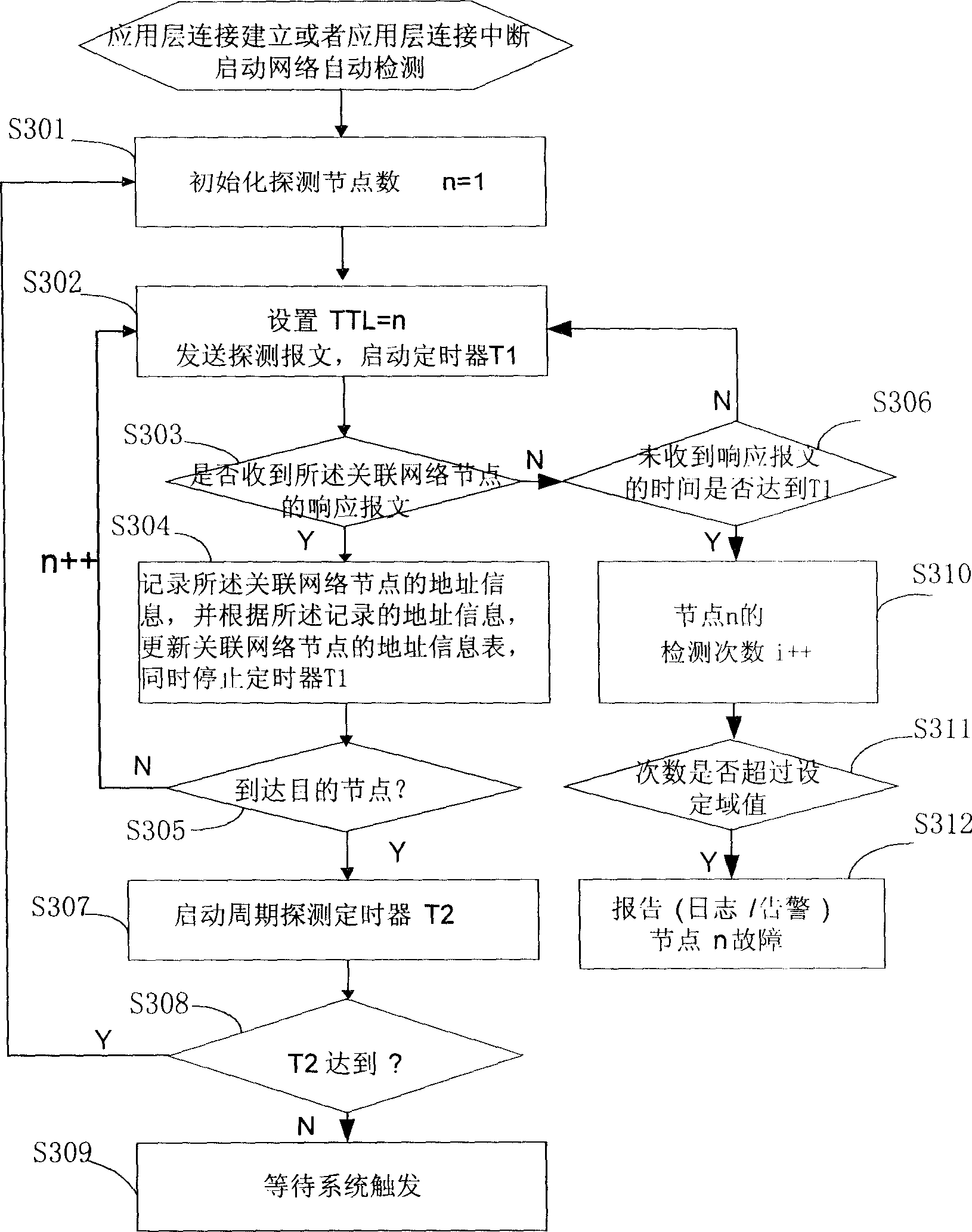
InactiveCN1874272ADoes not compromise securityImprove satisfactionData switching networksTechnicianReal-time computing
Core of the method is as following: first, network node of system sends detection message to other associated network nodes; then, monitoring response messages from the said associated network nodes; if verifying that response message from an associated network node is not received then the method determines the associated network node is a fault network node. Without need of preparing additional special network detection device, and without need of debugging fault nodes through manual work by technicians, the invention can position network fault accurately, and quicken speed for positioning fault. Advantages are: increasing efficiency of recognizing fault point of network, reducing maintenance cost of system, raising degree of satisfaction of users, and not influence on safety of network.
Owner:HUAWEI TECH CO LTD
SM9 joint digital signing method and device
InactiveCN107864037ADoes not compromise securityImprove securityKey distribution for secure communicationPublic key for secure communicationThird partyDigital signature
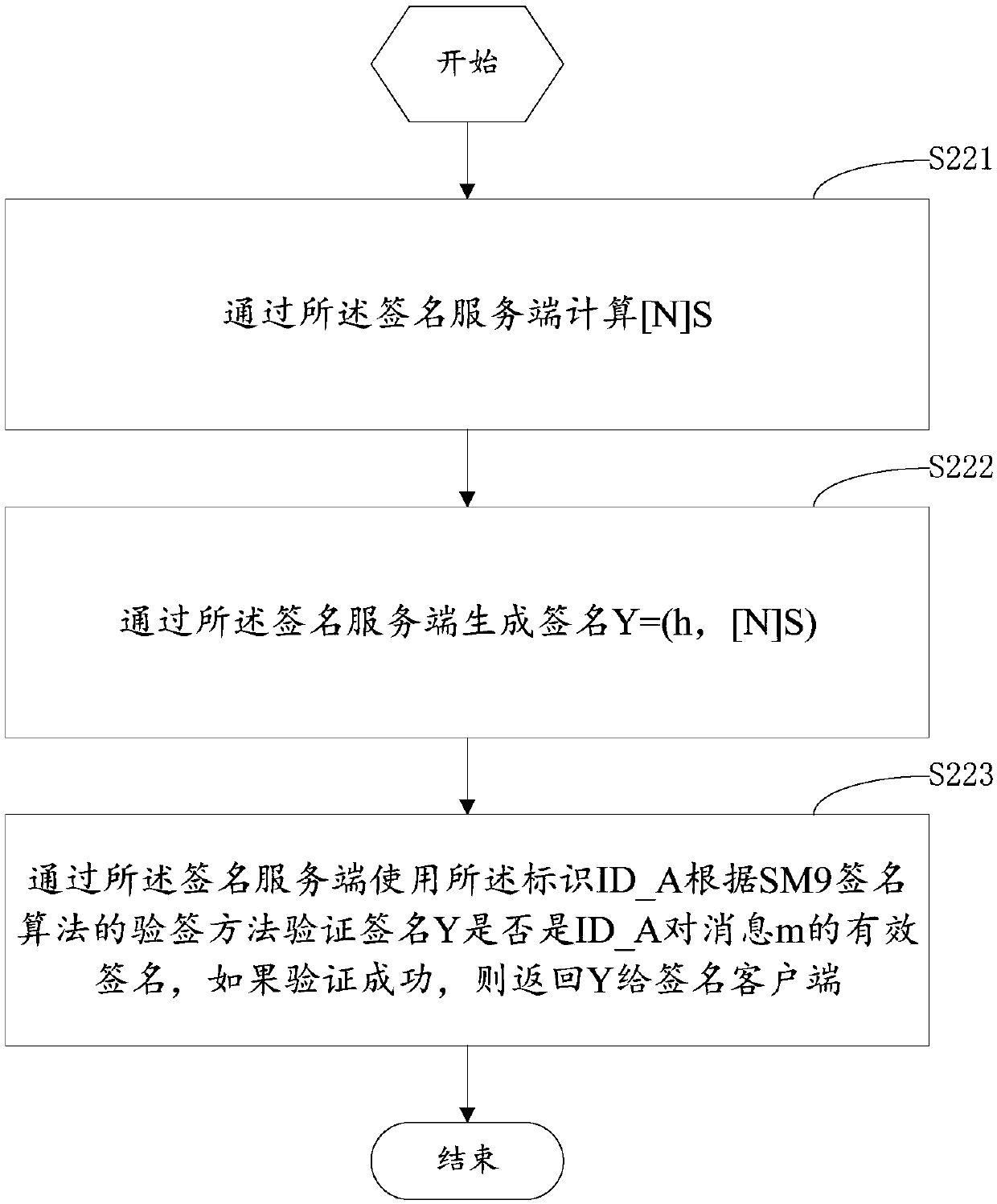
The invention discloses an SM9 joint digital signing method and device. According to the method and device, an identification private key S_A generated by a key generation center is divided into two parts, i.e., a first subkey M and a second subkey N, in a signing client, a signing server or a third party; the first subkey M and the second subkey N are respectively stored in two entities, i.e., the signing client and the signing server; the signing client carries out signing on a message m through the first subkey M and then transmits a signing result X to the signing server; the signing server converts the signing result X of the signing client through the subkey N to generate a signature Y of the identification private key S_A on the m, and sends the signing result Y to the signing client if verifying that the signing result Y is correct. Therefore, the overall security of the identification private key S_A is not affected by the loss of the subkey stored in either the signing clientor the signing server, and the digital signing security is further improved.
Owner:SHENZHEN OLYM INFORMATION SECURITY TECHOLOGY CO LTD
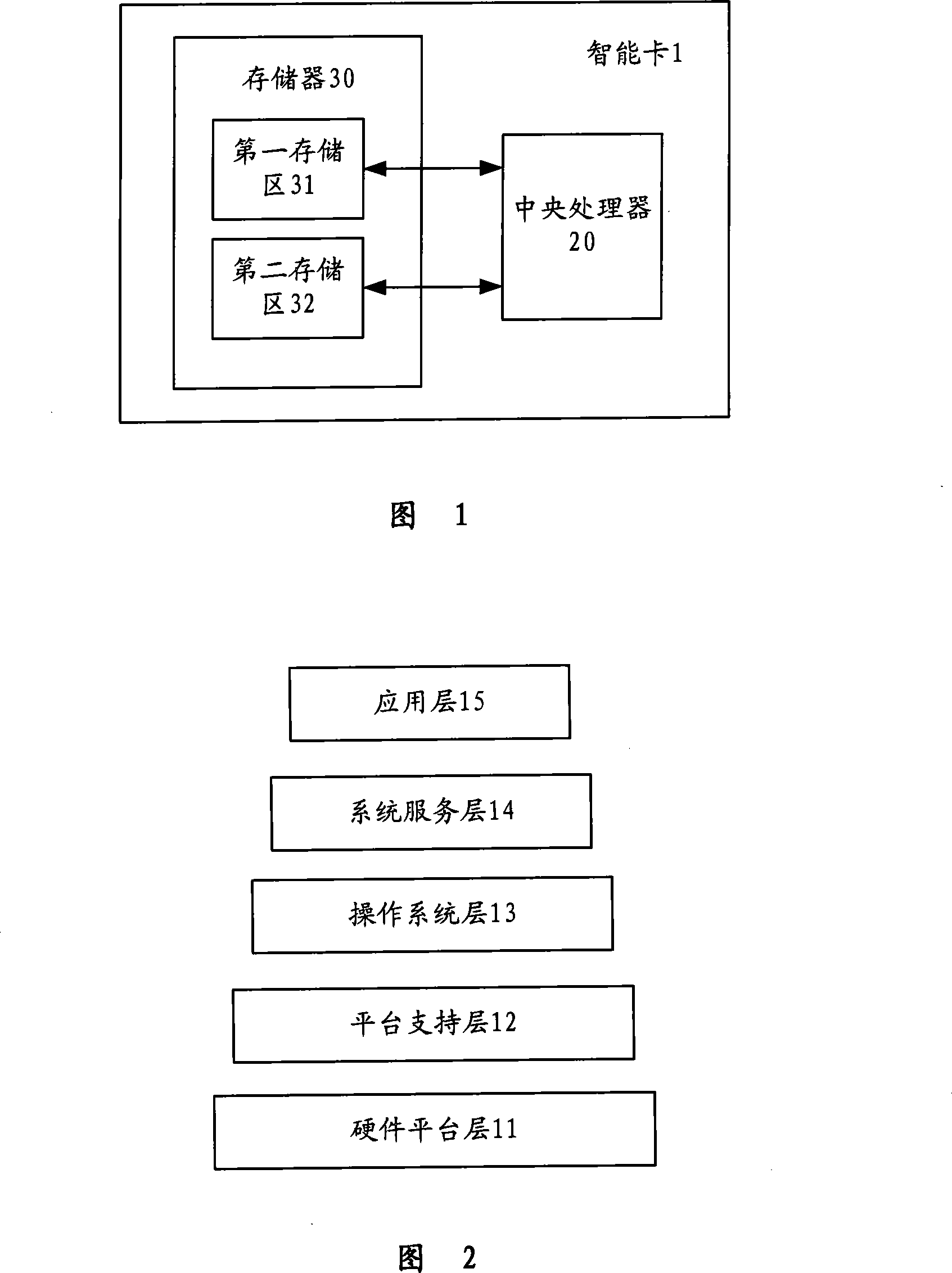
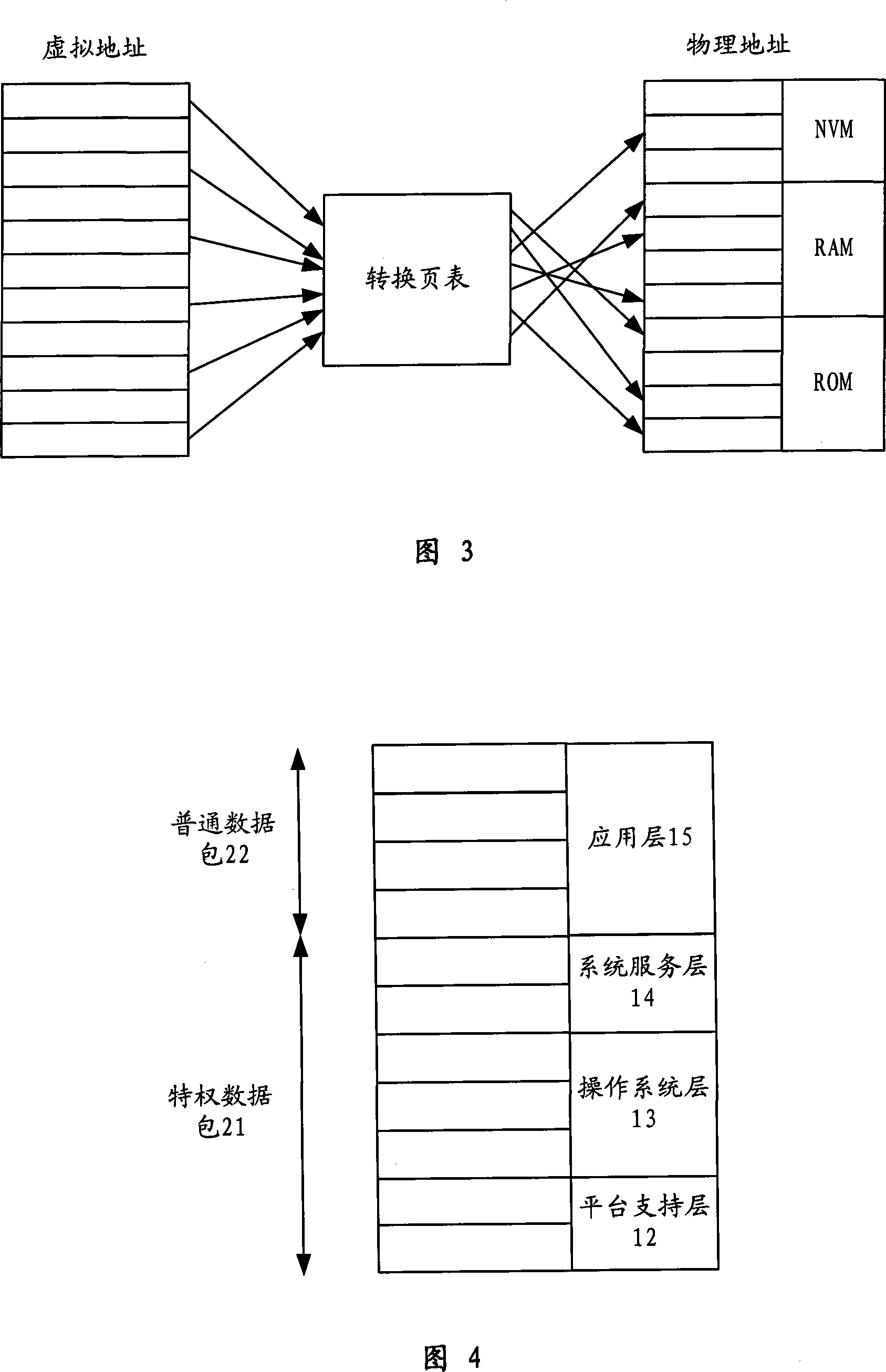
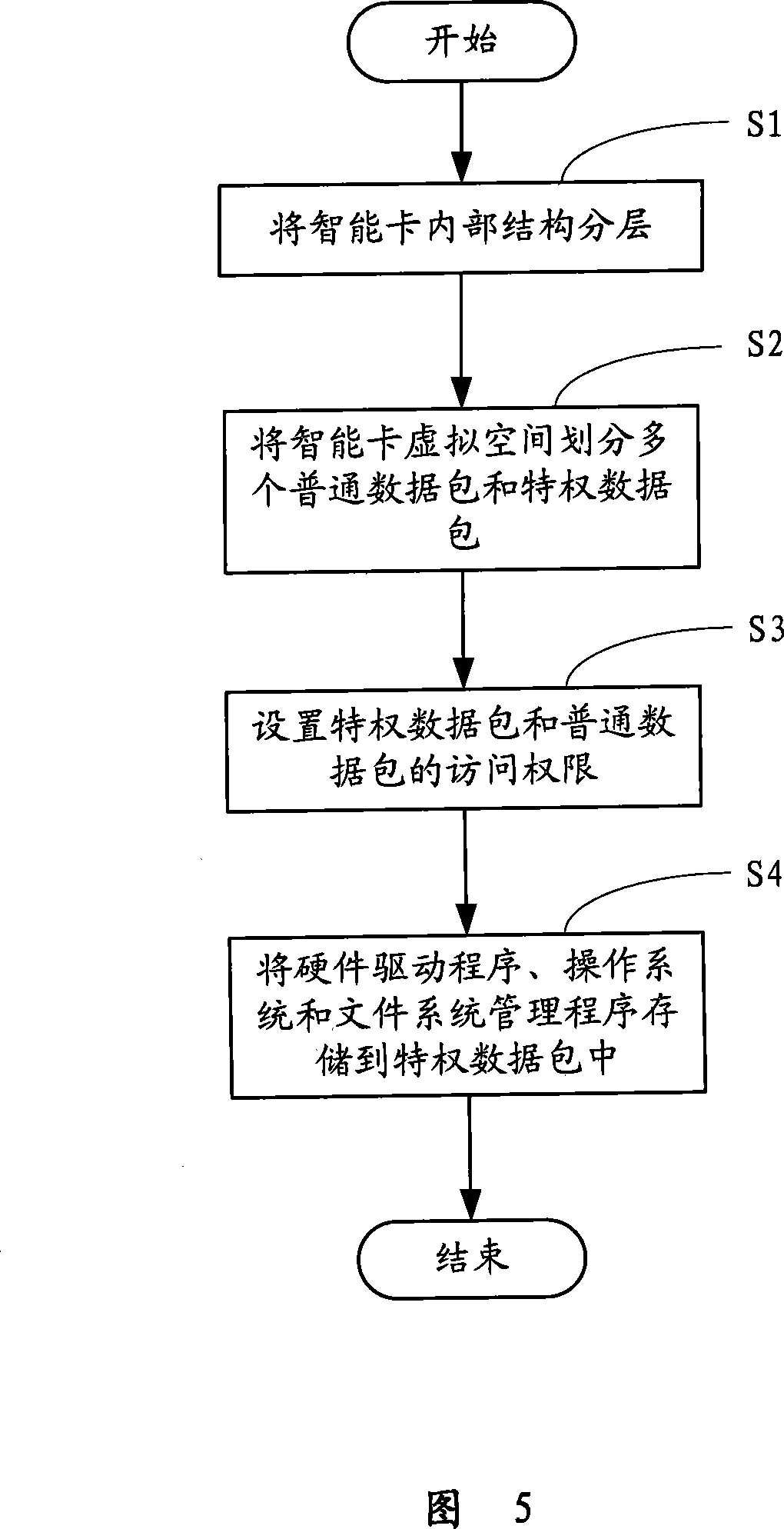
Smart card opening application development method
ActiveCN101216758ADoes not compromise securityEnsure safetySpecific program execution arrangementsThird partyOperational system
The invention provides a development method for open application of a smart card, comprising the following steps of: dividing the smart card into a hardware platform layer, a platform-supporting layer, an operating system layer and an application layer, dividing the virtual space of the smart card into a plurality of privilege data packages and common data packages, setting the access right for the privilege data packages and the common data packages, and storing the hardware driving program of the platform-supporting layer and the operating system of the operating system layer into the privilege data packages. The invention can make the smart card safely open to the open application system of a third party, and allow the third part (such as a bank), to apply the language which can be compiled into the machine instruction to develop the application program of the smart card and improve the running speed of the smart card.
Owner:EASTCOMPEACE TECH
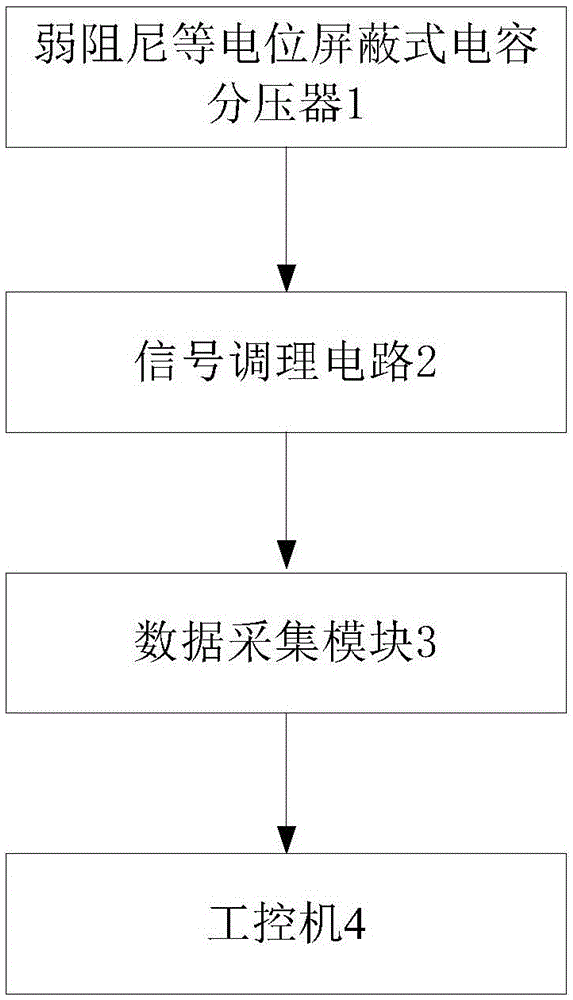
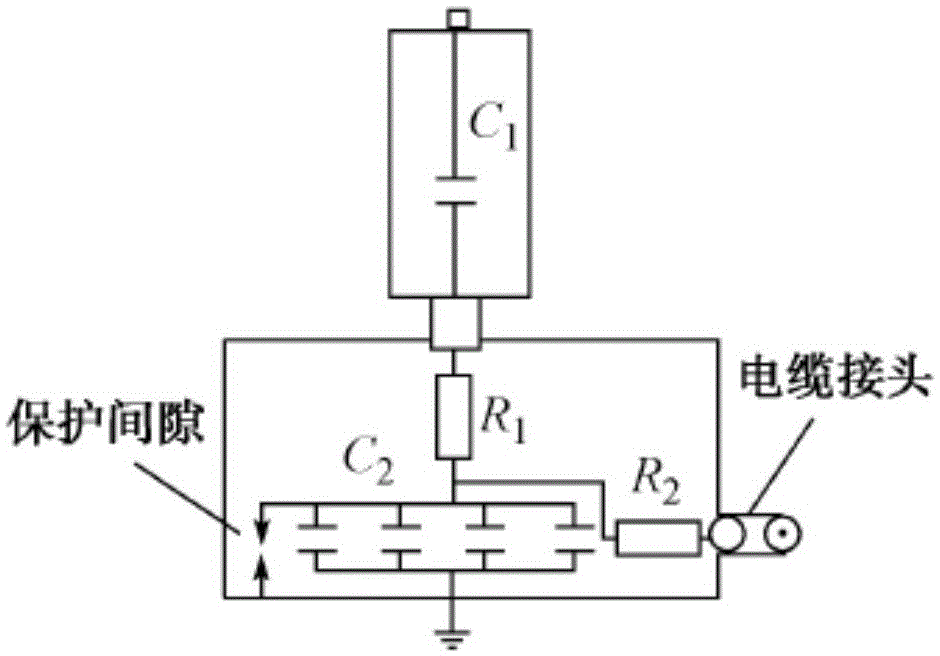
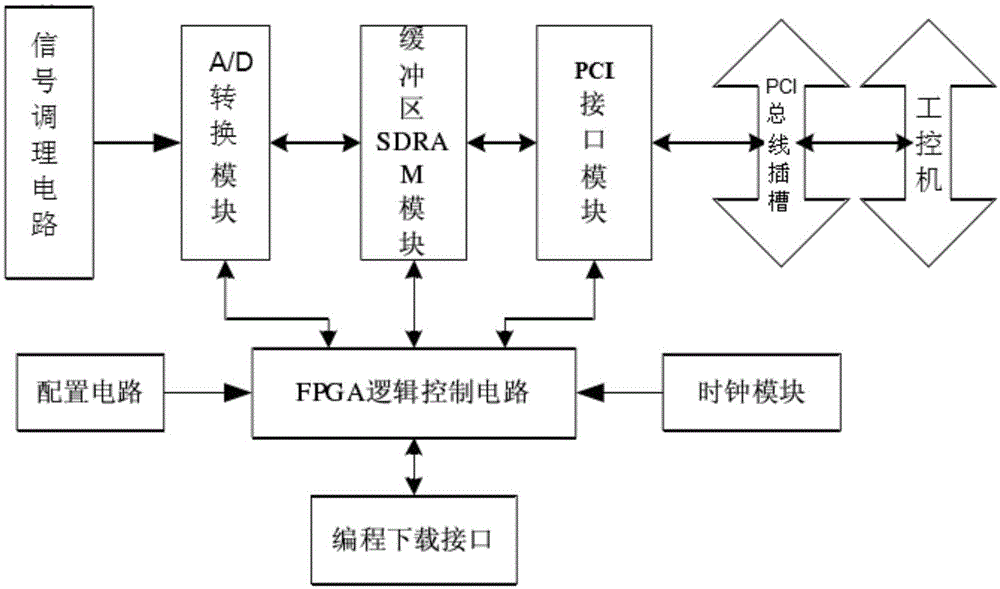
Power system temporary overvoltage monitoring system
InactiveCN105137158ADoes not compromise securityWill not affect normal operationCurrent/voltage measurementFault locationOvervoltageLightning strike
The invention provides a power system temporary overvoltage monitoring system, which comprises a weak damping equipotential shielding-type capacitive voltage divider, a signal conditioning circuit, a data acquisition module and an industrial control computer, wherein the weak damping equipotential shielding-type capacitive voltage divider acquires voltage signals of the power system and outputs the signals to the signal conditioning circuit; the signal conditioning circuit conditions the voltage signals to signals suitable for the data acquisition module; the data acquisition module carries out multichannel synchronous A / D conversion on the voltage signals after being conditioned by the signal conditioning circuit, and the converted digital signals enter the industrial control computer via a communication interface; and the industrial control computer processes signals acquired by the data acquisition module for realizing online monitoring, offline analysis and remote access and control on the power system temporary overvoltage. A temporary overvoltage response can be built; and after equipment is subjected to lightning strike and other temporary overvoltage damages, the system records related data, the data serve as a damage judgment basis, and correct insulated matching is realized.
Owner:SHANGHAI JUNSHI ELECTRICAL TECH +1
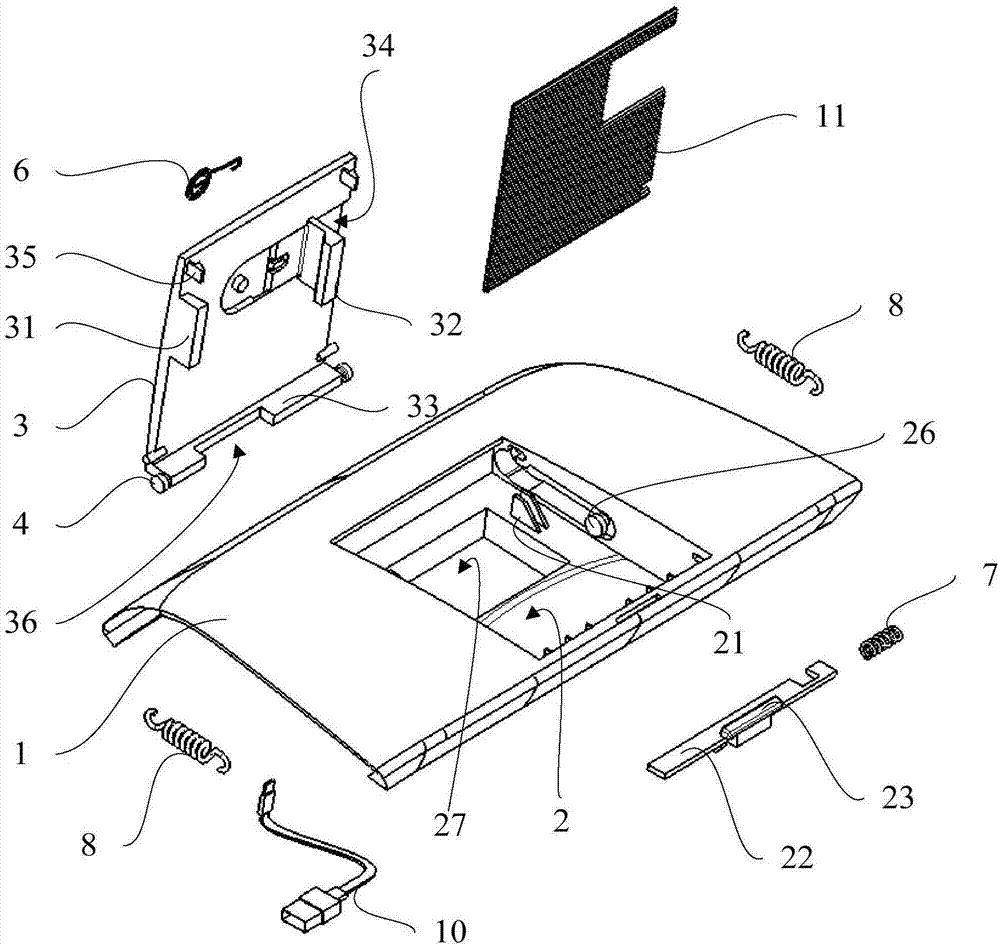
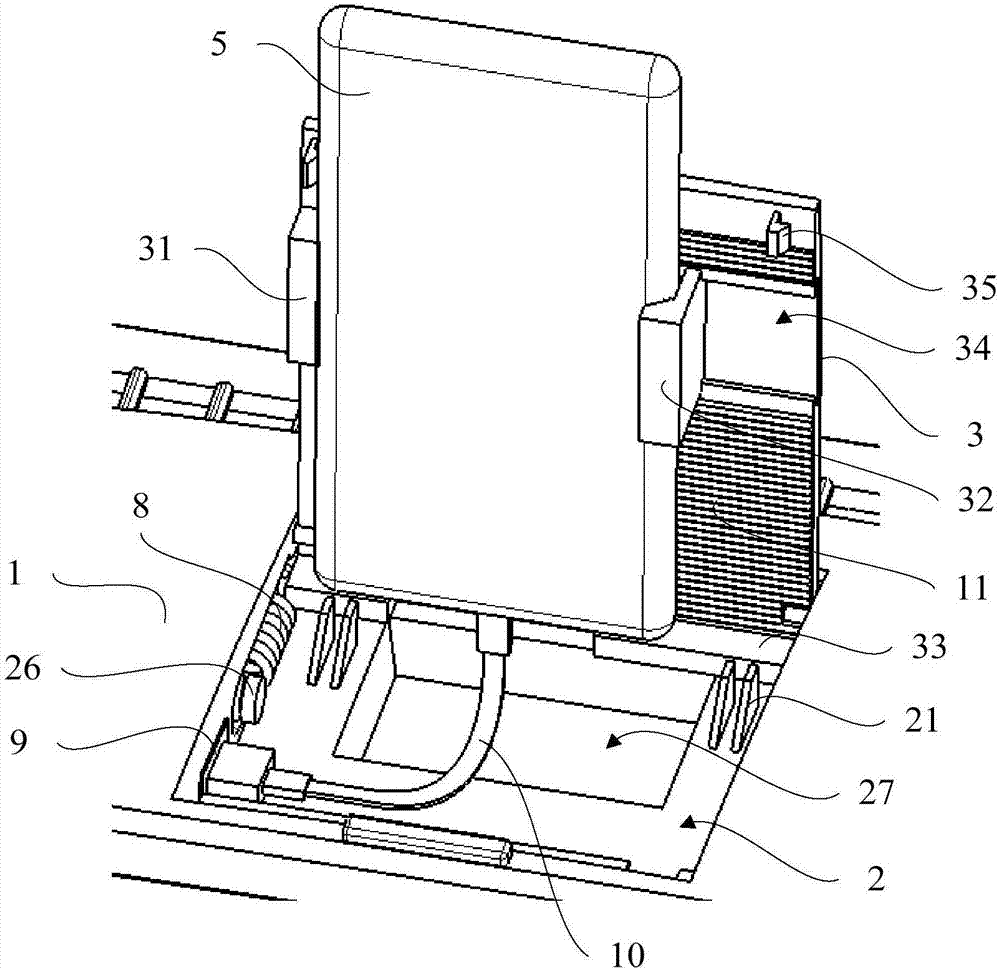
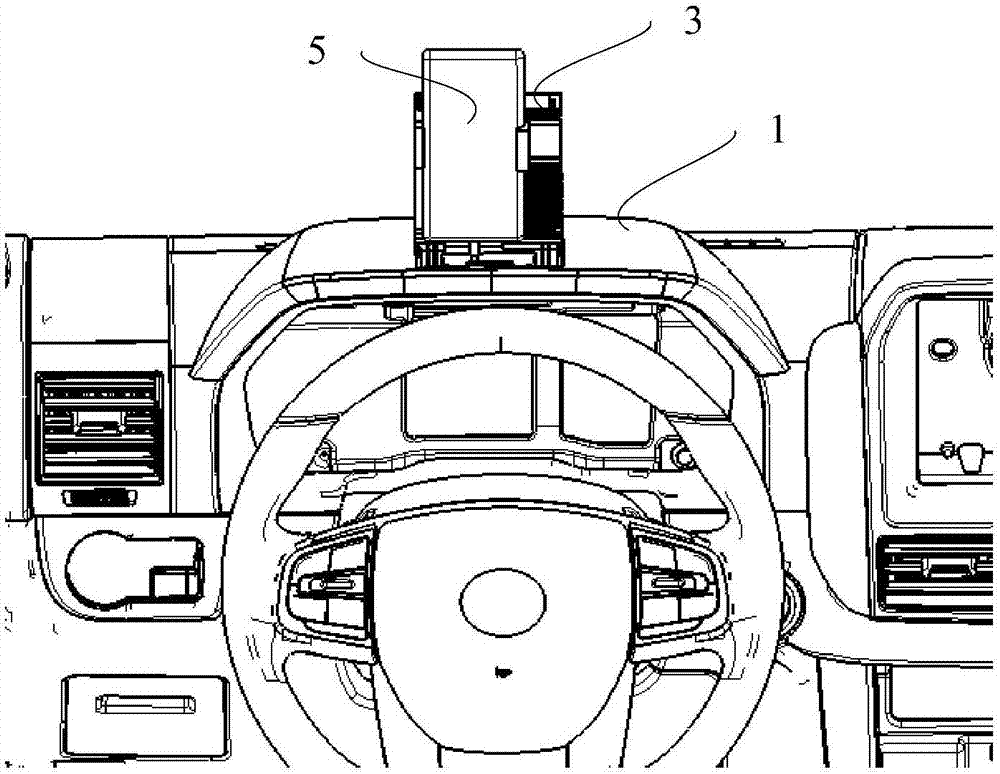
Vehicle instrument board and vehicle
PendingCN107499246AEasy to viewDoes not compromise securityDashboard fitting arrangementsSight lineMechanical engineering
The invention provides a vehicle instrument board and a vehicle. The instrument board is provided with a containing cavity and a cover plate, the cover plate is connected with the instrument board through a rotating shaft and rotates around the rotating shaft to open or close the containing cavity, a first clamping block and a second clamping block are arranged on a first surface of the cover plate, a laying plate is further arranged on the first surface of the cover plate, the first surface of the cover plate faces the containing cavity, a limit block is arranged at the bottom of the containing cavity, the laying plate approaches to the limit block along with opening of the cover plate, and the laying plate is abutted to the limit block when the opening angle of the cover plate reaches a preset angle. By the aid of the vehicle instrument board, a driver can conveniently check a navigation map in the vehicle driving process, the sight line of the driver is as same as the running direction of the vehicle, and vehicle driving safety cannot be affected.
Owner:BAIC GRP ORV CO LTD
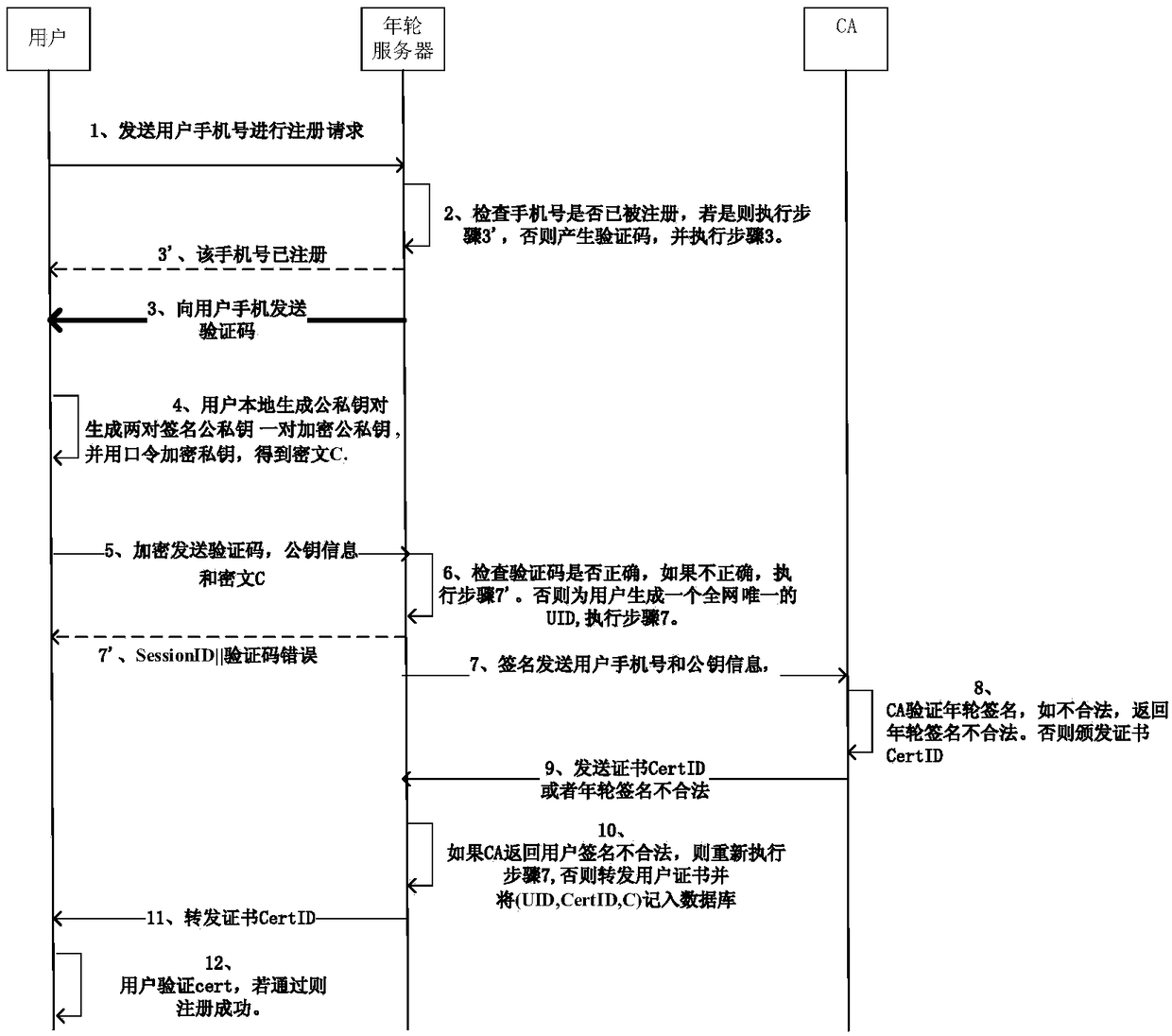
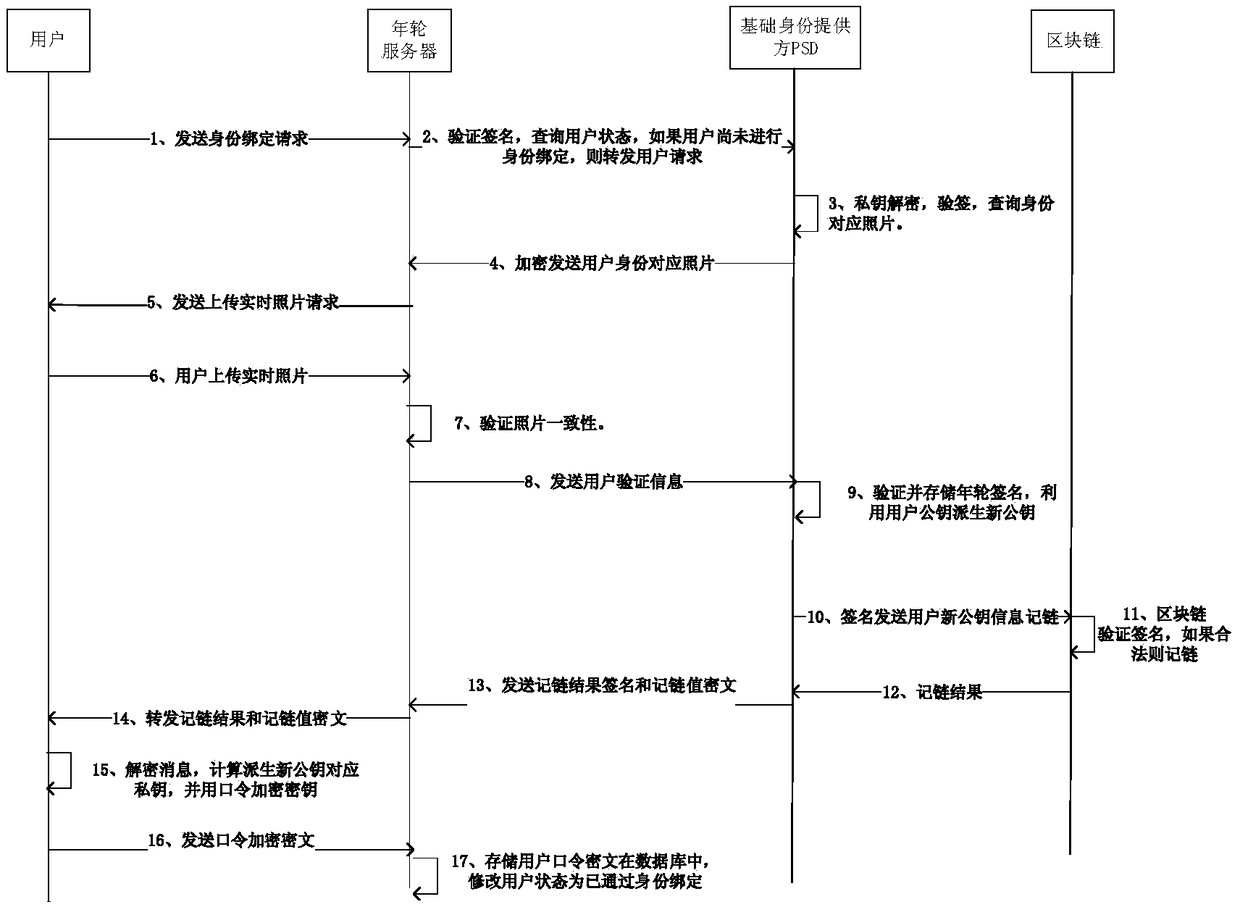
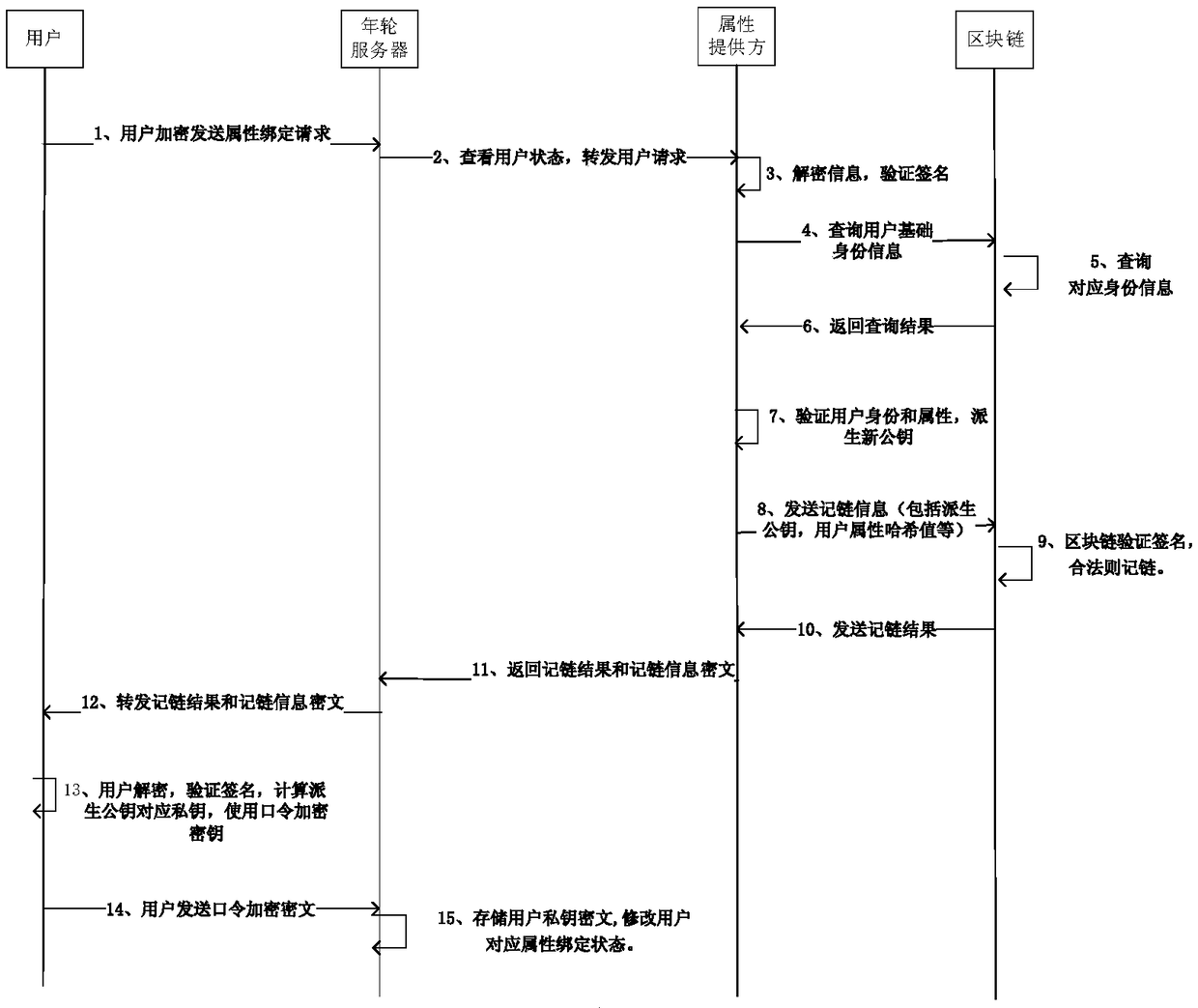
Unified identity authentication method based on blockchain
ActiveCN109495490AGuaranteed to be tamper-proofGuaranteed privacyTransmissionInternet privacyBound property
The invention discloses a unified identity authentication method based on a block chain, comprising the following four stages: 1. phase of user registration: a user registering with an annual ring server using his mobile phone number to obtain the certificate issued by the annual ring server CA; 2. phase of user binding identity: the annual ring server cooperating with a public security departmentto verify the identity of the user online with face, and recording the user identity verification result on the block chain; 3. phase of user attribute binding: the user initiating a binding requestfor the attribute to the annual ring server, and the annual ring server binding various attributes of the user to the block chain; 4. phase of user attribute presentation: the user presenting the successfully bound property to a relying party. Compared with the prior art, the positive effects of the present invention are that: the block chain technology ensures the incomprehensible modification ofvarious identity information of the user, and on the other hand, the cryptographic means is used to ensure the privacy of the user identity.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Semi-active dynamic vibration absorber for magneto-rheological elastomers and selection and installation method
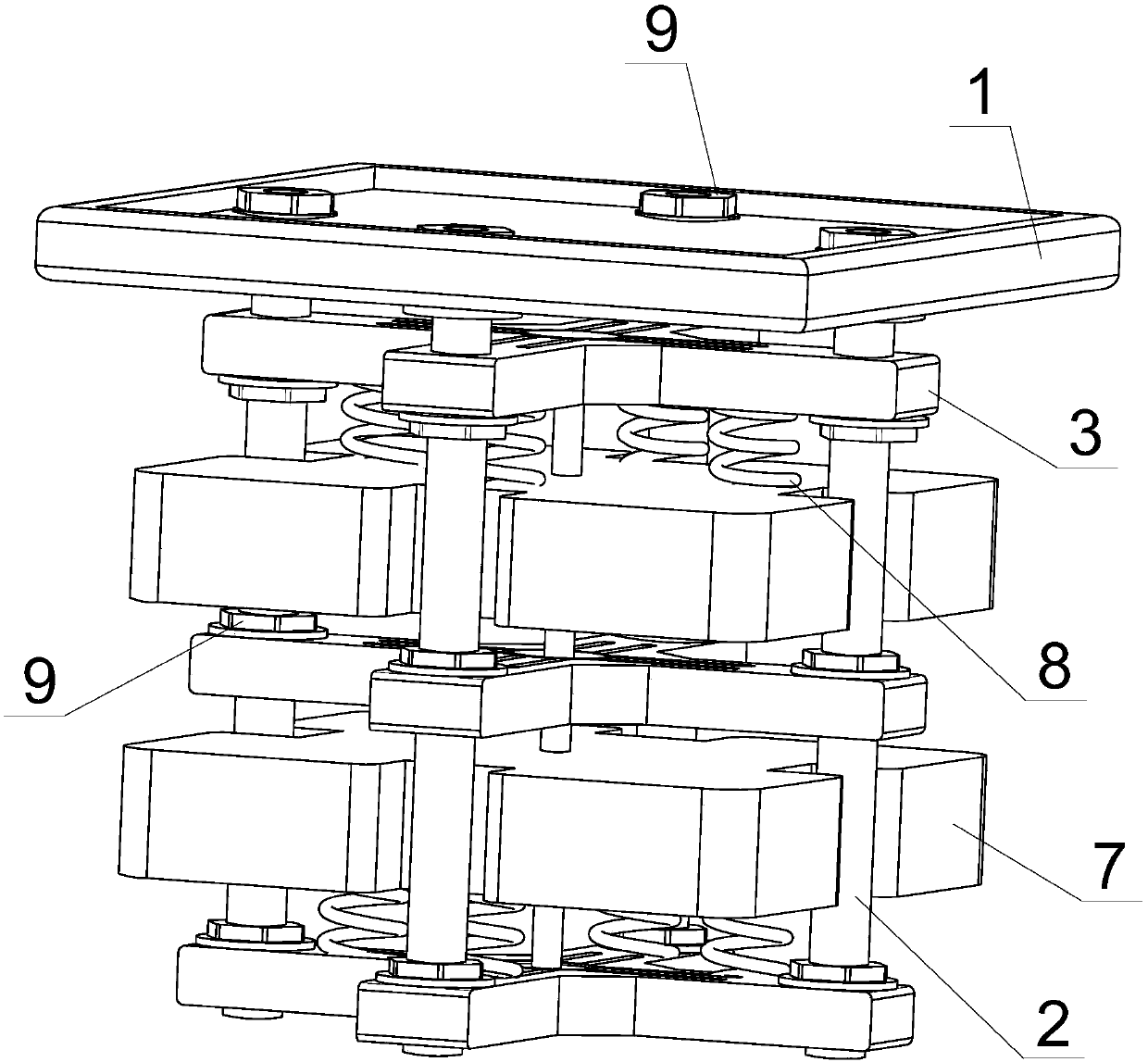
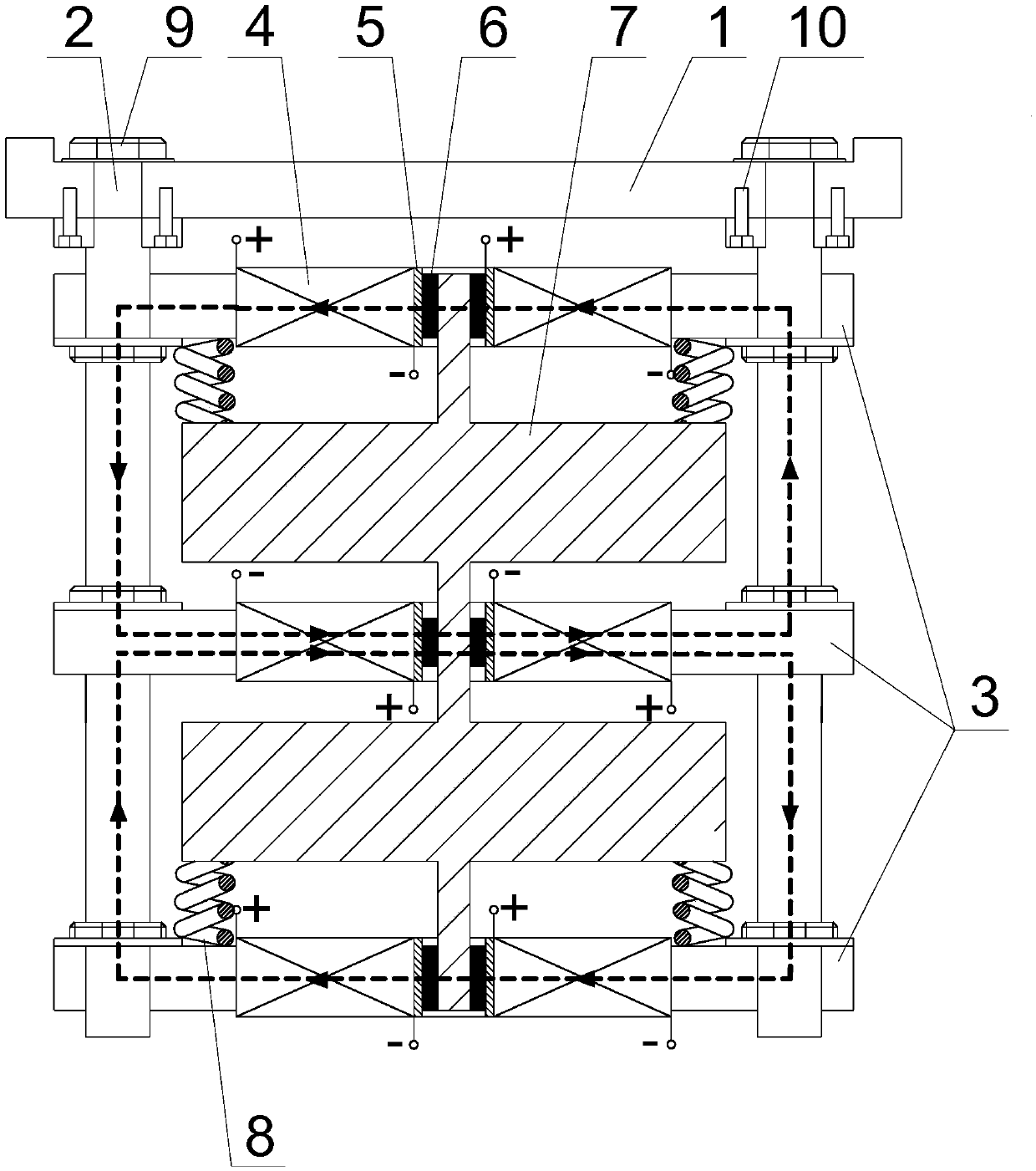
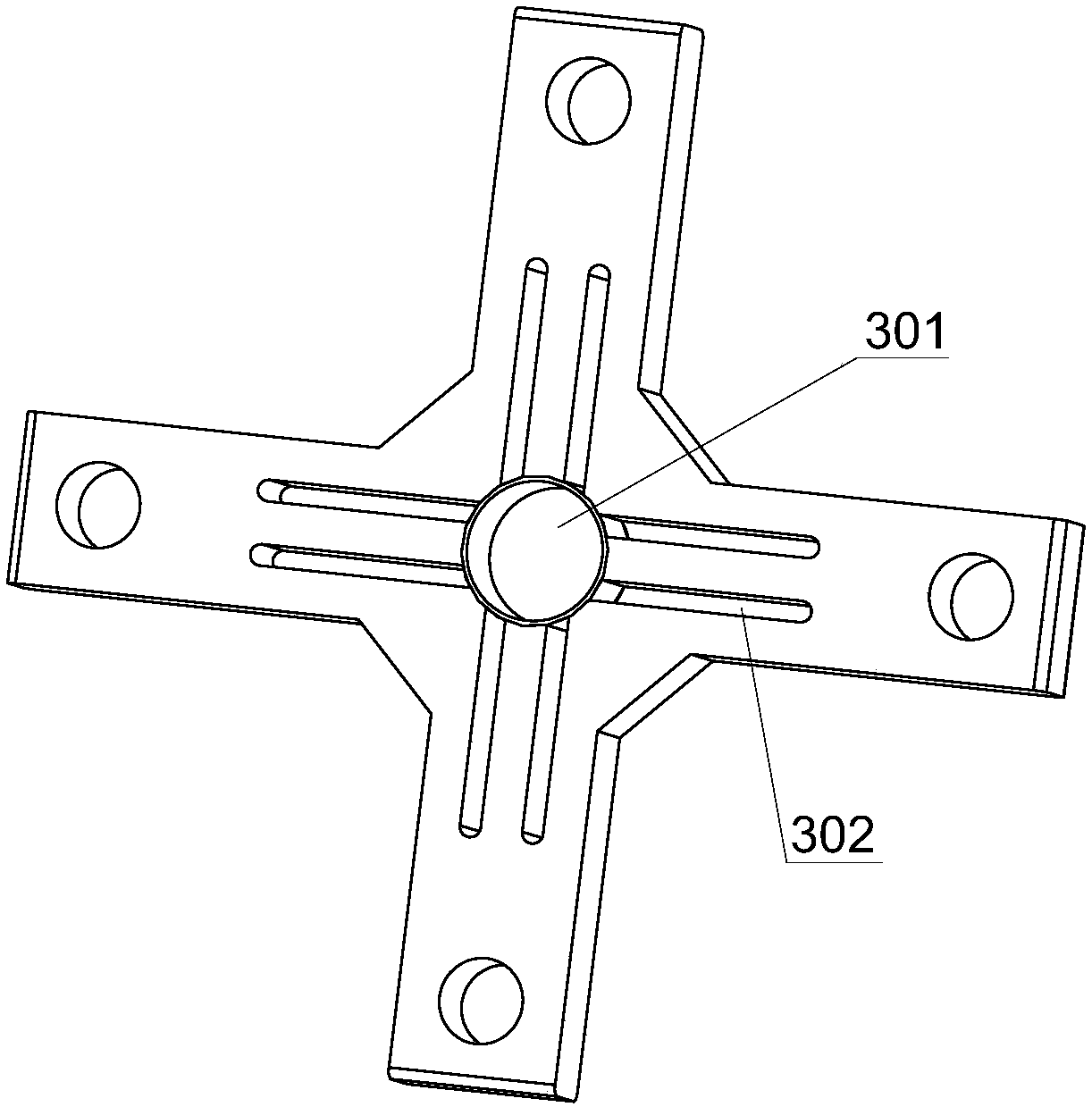
ActiveCN107939901ASuppress vertical vibrationAchieve broadband vibration reductionSpringsNon-rotating vibration suppressionElastomerSemi active
The invention discloses a semi-active dynamic vibration absorber for magneto-rheological elastomers and a selection and installation method. According to the semi-active dynamic vibration absorber andthe selection and installation method, multiple layers of cross-shaped cross beams arranged in parallel are fixed to the positions below a bottom frame base located at the bottom of a railway vehiclein a suspended mode through four vertical magnetic conductive rods arranged vertically and penetrating through the four end parts of cross-shaped beam arms; multiple layers of stacked structures which are spaced from each other are formed between multiple layers of grooving vibrators and the cross-shaped cross beams; vertical mounting through holes are formed in the centers of the cross-shaped cross beams; the annular magneto-rheological elastomers are arranged between the mounting through holes and a connecting shaft of the multiple layers of grooving vibrators; the multiple layers of grooving vibrators can vibrate up and down relative to the bottom frame base in the axial direction of the mounting through holes; winding grooves are formed in the beam arms of the cross-shaped cross beams; and excitation coils are wound in the winding grooves. The semi-active dynamic vibration absorber has the advantages that the vibration absorption effect is good, the energy consumption is small, the structure is simple and compact, the installation is easy, the safety and the reliability are high, the utilization of the residual space under the railway vehicle is reasonable, and vertical wide-frequency vibration reduction can be carried out on a railway vehicle body which suffers form an abnormal vibration problem due to the fact that a railway is unsmooth.
Owner:SHANGHAI UNIV OF ENG SCI
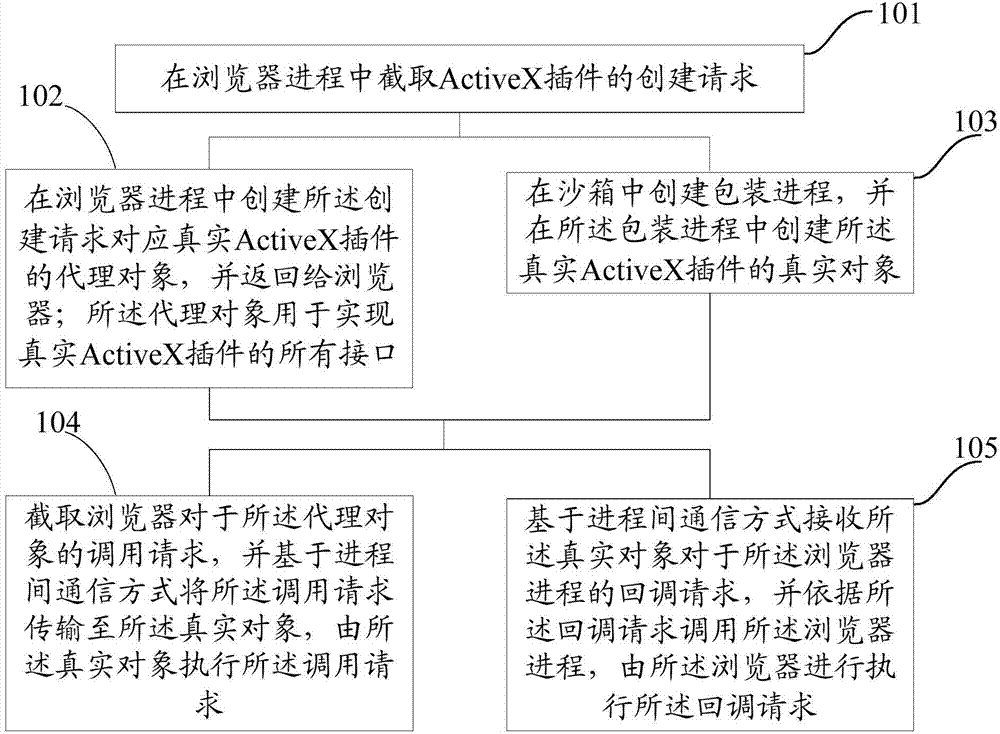
Browser based plug-in running method and device
InactiveCN103617092ADoes not compromise securityImprove stabilityInterprogram communicationPlatform integrity maintainanceProgramming language
The invention discloses a browser based plug-in running method and device. The method specifically includes: intercepting an ActiveX plug-in create request from a browser process; creating a proxy object of a real ActiveX plug-in corresponding to the create request in the browser process, and returning the proxy object, used for realizing all interfaces of the real ActiveX plug-in, to a browser; creating a packaging process in a sandbox, and creating a real object of the real ActiveX plug-in in the packaging process; intercepting a call request of the browser for the proxy object, transmitting the call request to the real object, and executing the call request via the real object. The proxy object can realize all the interfaces of the real ActiveX plug-in and applicable to all ActiveX plug-ins, and a special proxy object needs not to be created for a special ActiveX plug-in, so that the method has the advantage of good universality.
Owner:BEIJING QIHOO TECH CO LTD +1
Preparation method of mixed egg liquid and egg liquid obtained through preparation method
ActiveCN103564533AIncrease relative volatilityGuaranteed nutritionMulti-step food processesFood preparationIce waterSodium Caseinate
The invention provides a preparation method of mixed egg liquid. The preparation method comprises the following steps: (1) poultry eggs are disinfected, aired and broken to obtain egg liquid; (2) additives of sodium caseinate, sodium carboxymethylcellulose, hydroxypropyl starch and maltodextrin are added; (3) high-density carbon dioxide treatment is conducted on the egg liquid, and the treatment temperature is 38-42 DEG C; a high-density CO2 environment is formed in a treatment kettle; the treatment lasts for 20 minutes under 20 MPa; (4) the pressure is relieved after the treatment is finished; the egg liquid is taken out, and put in ice water for cooling, and then stored under the condition of 2-4 DEG C. The preparation method adopts the high-density CO2 cold disinfection mode to treat the mixed protein liquid, and regulates the disinfection treatment conditions according to the egg liquid properties; the used carbon dioxide has of properties of chemical inertness, no corrosion, high volatility and unique economy, so that energy is saved; as the disinfection and enzyme deactivating are conducted under the condition of low temperature, the qualities of nutrition, flavor and freshness and the like of the mixed protein liquid are kept to the maximum extent; compared with pasteurization, the disinfection method has the advantages that the shelf life of the mixed egg liquid is longer.
Owner:BEIJING HELEE BIO ENERGY TECH
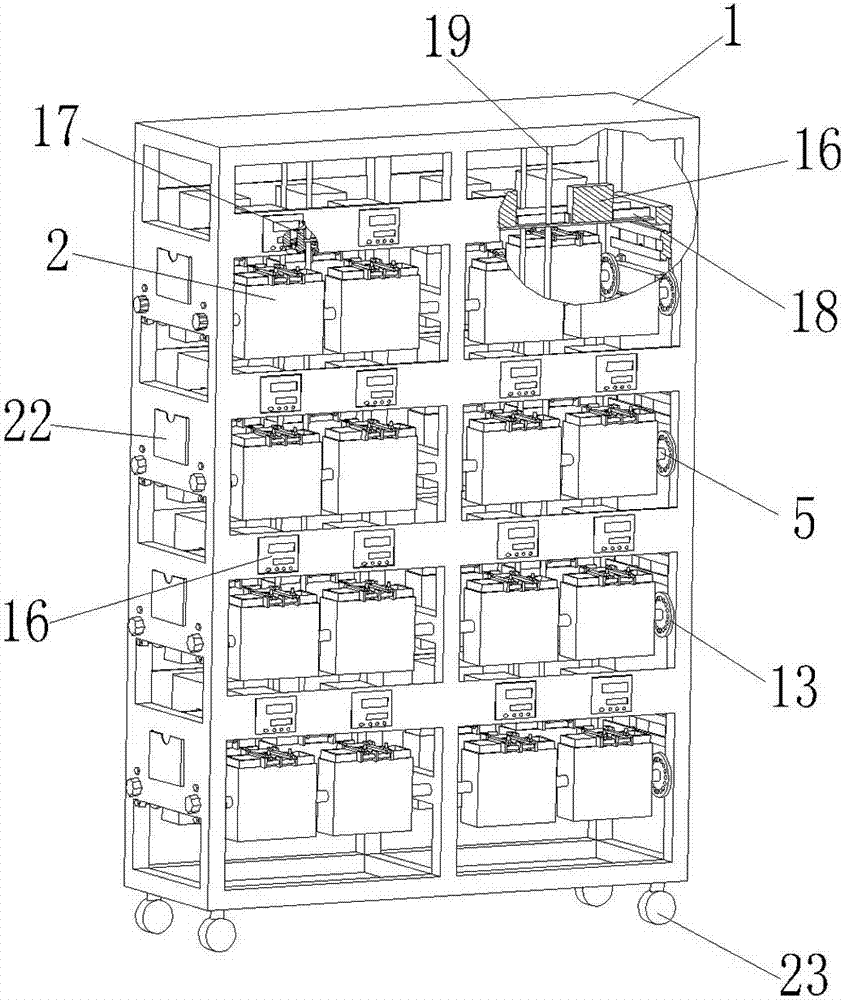
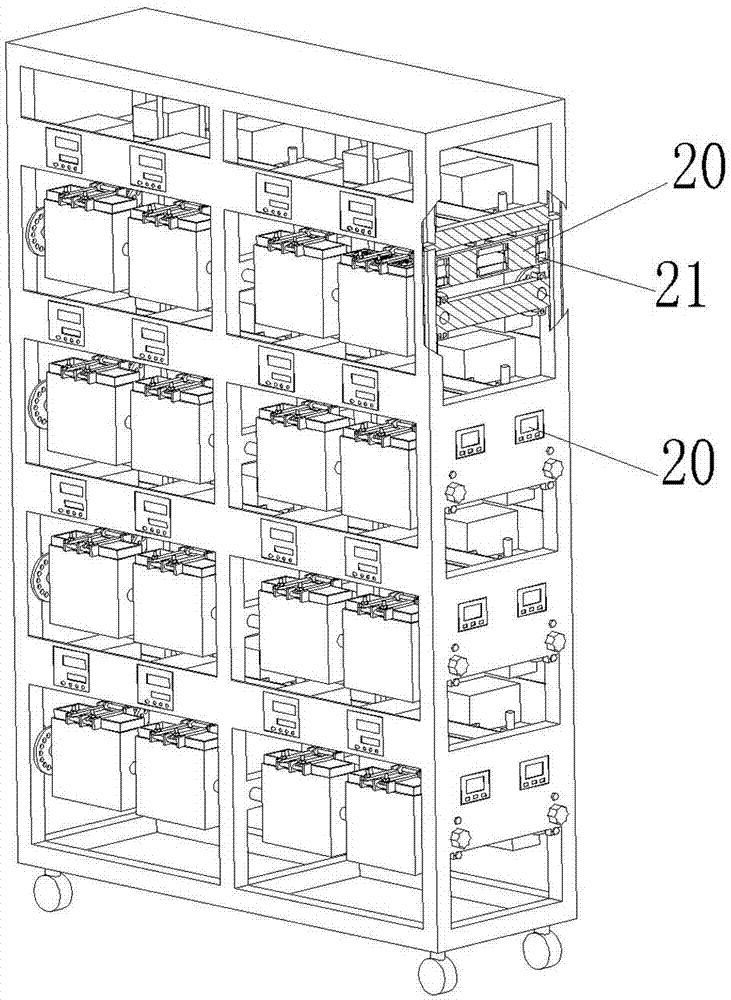
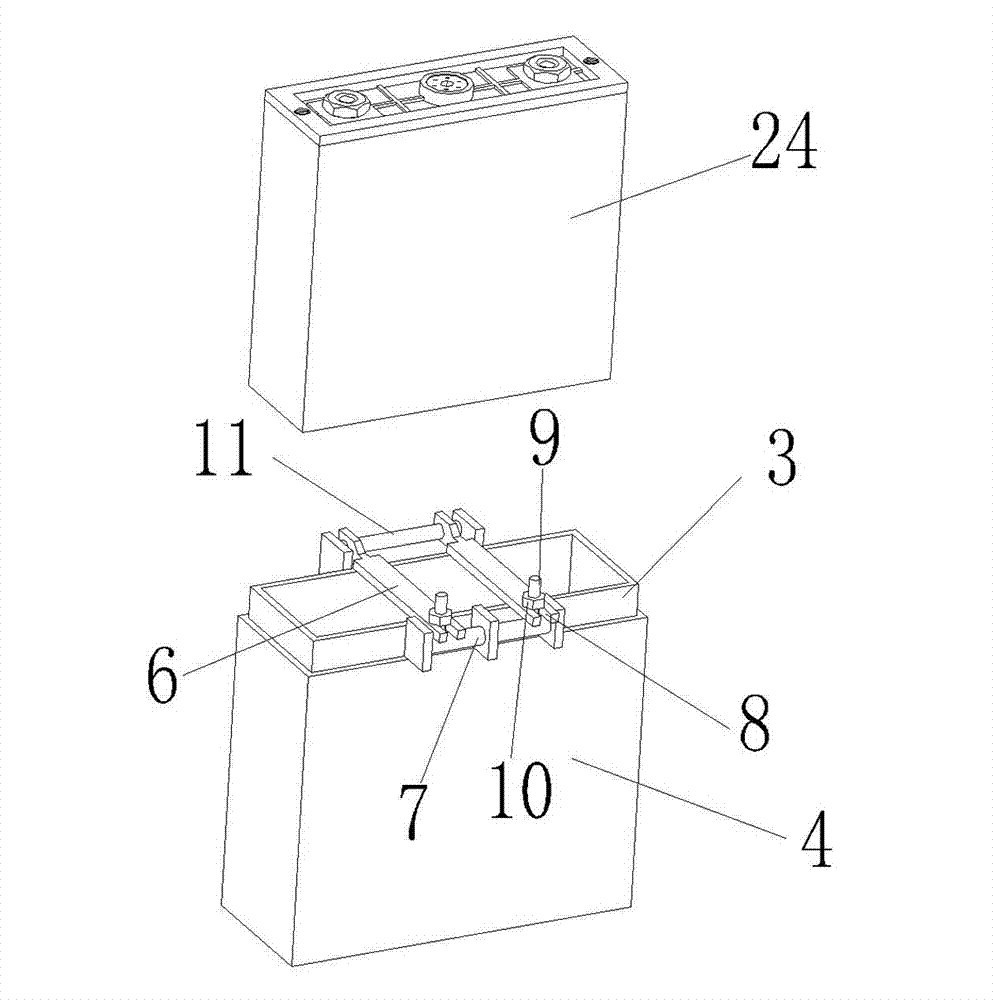
Safety device for formation and sub-capacity of lithium ion battery
ActiveCN102881942AAvoid short circuitAvoid manual flippingFinal product manufactureCell component detailsElectrical batteryEngineering
The invention discloses a safety device for formation and sub-capacity of a lithium ion battery. The safety device comprises a cabinet, wherein at least a row of battery compartments are arranged in the cabinet; an opening is formed at the upper end of each battery compartment; each battery compartment consists of an internal insulation fireproof layer and an external stainless steel layer; the battery compartments are connected in series by shafts so as to form a battery compartment row; rotating shafts are arranged at two ends of the battery compartment row; the two ends of each rotating shaft penetrate through the side wall of the cabinet; and a battery locating mechanism for locating the battery is arranged at the upper end of each battery compartment. Due to the adoption of the battery compartments of a two-layer structure, the battery has good insulation effect on the outside; and the short circuit of the battery caused by inappropriate operation of an operator or other accidents is avoided. The battery compartments of the two-layer structure further have high anti-explosion capability; and due to the adoption of the rotating shafts of the battery compartments, the battery can rotate in multiple angles in a standing stage (which can improve the infiltration effect of electrolyte); and the battery does not need to be manually rotated one by one. Therefore, the production efficiency of a workshop is greatly improved.
Owner:NINGBO SHIJIE NEW ENERGY TECH
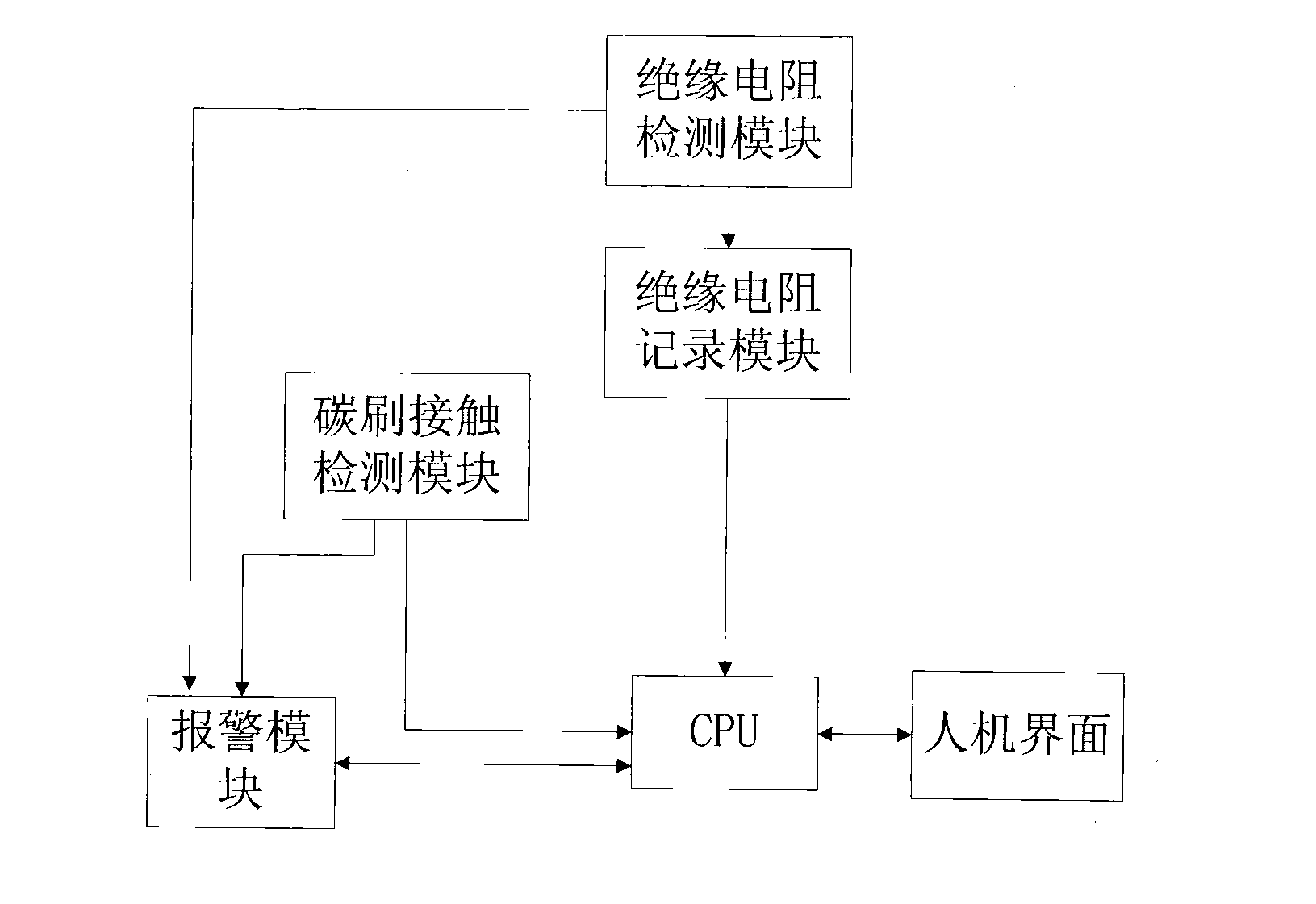
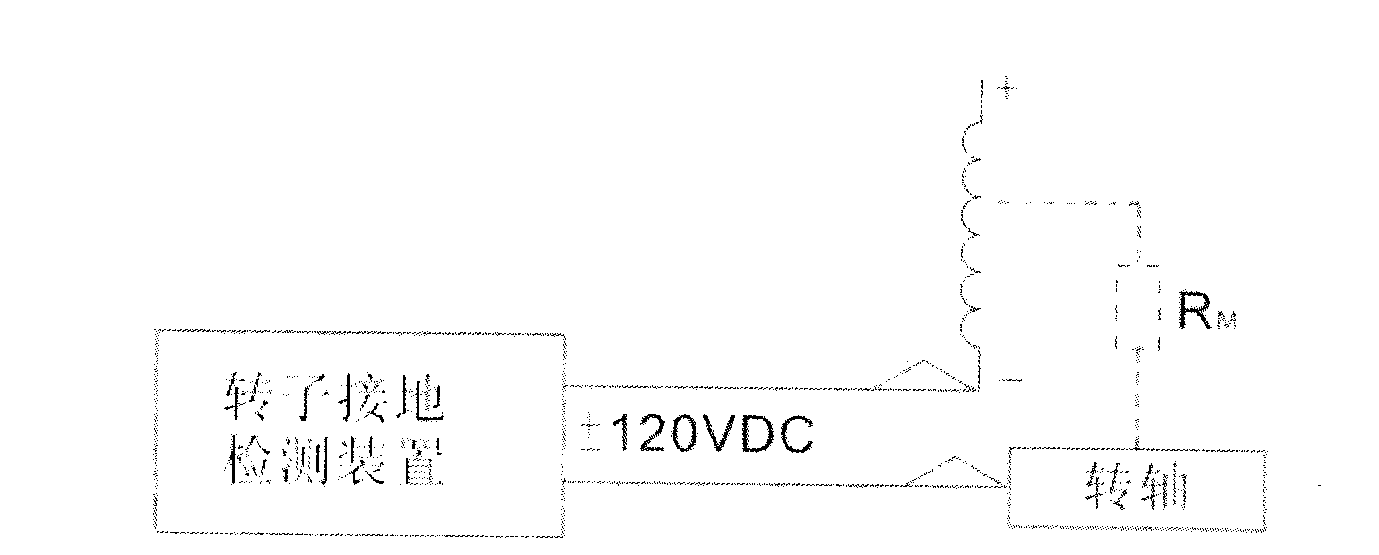
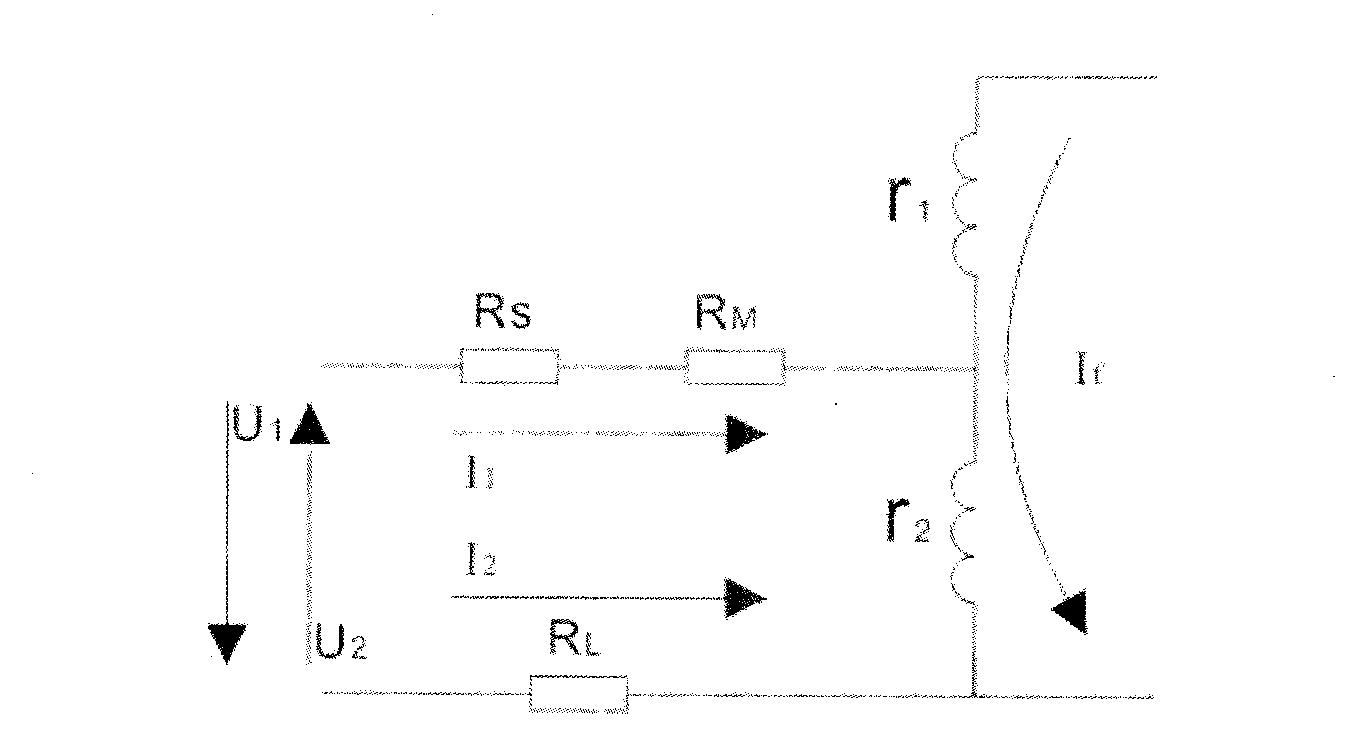
Rotor grounding detection device
InactiveCN103018567ADoes not compromise securityAchieve weak couplingResistance/reactance/impedenceElectrical resistance and conductanceHuman–machine interface
The invention provides rotor grounding detection device which is characterized by comprising a carbon brush contact detection module and an insulating resistance detection module, wherein an alarm module is connected with the carbon brush contact detection module and the insulating resistance detection module, the insulating resistance detection module is connected with a central processing unit (CPU) through an insulating resistance recording module, and the CPU is further connected with the carbon brush contact detection module, the alarm module and a man-machine interface. The rotor grounding detection device overcomes the shortcomings in the prior art, keeps weak coupling with a rotor without any mutual influence, is accurate in rotor insulating resistance detection and improves reliability of system operation.
Owner:SHANGHAI ELECTRIC POWER GENERATION EQUIPMENT CO LTD
Forming and verifying system and method for bill anti-fake code
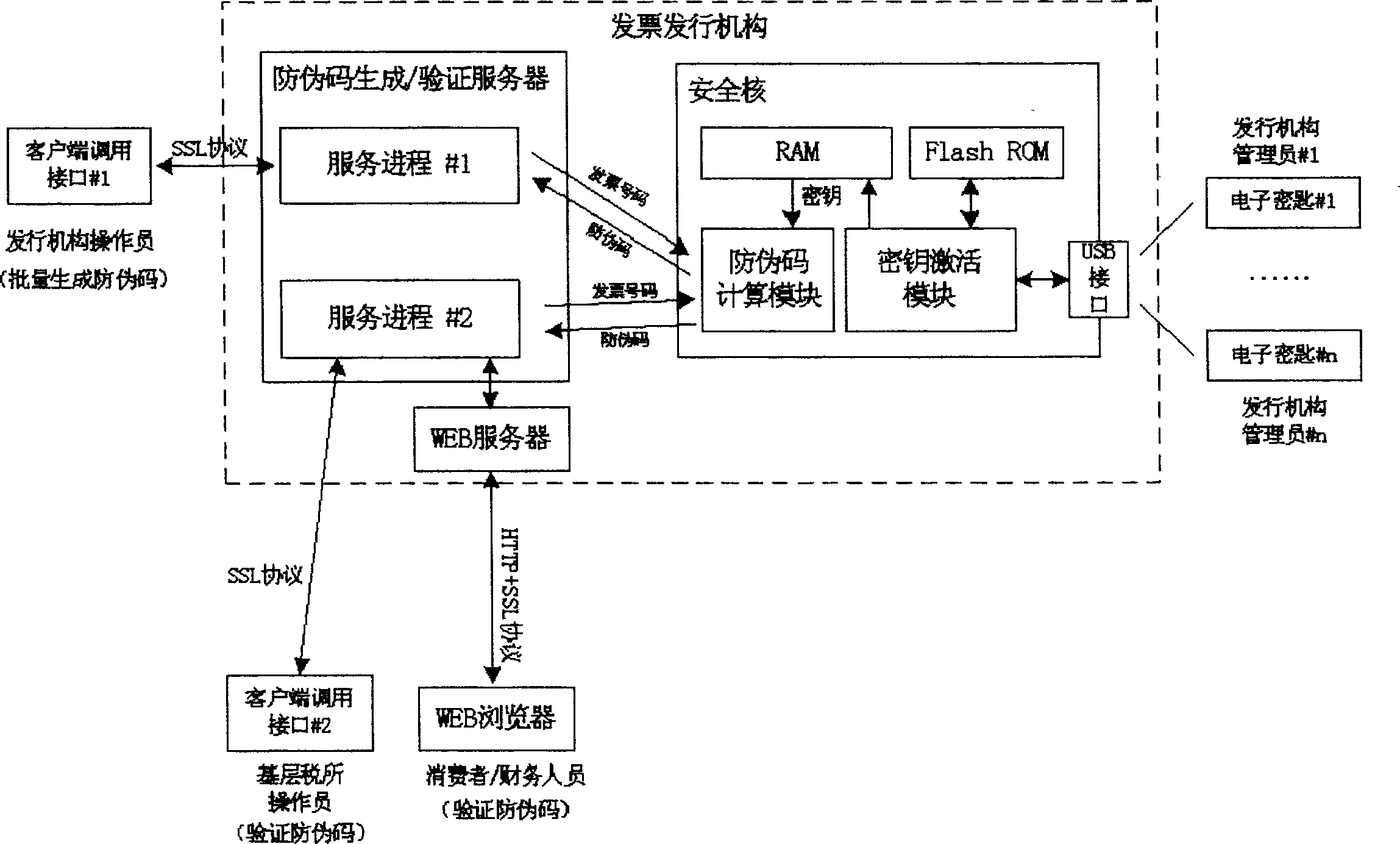
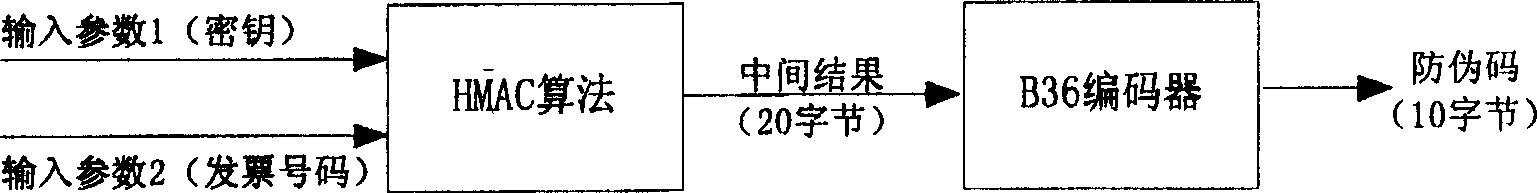
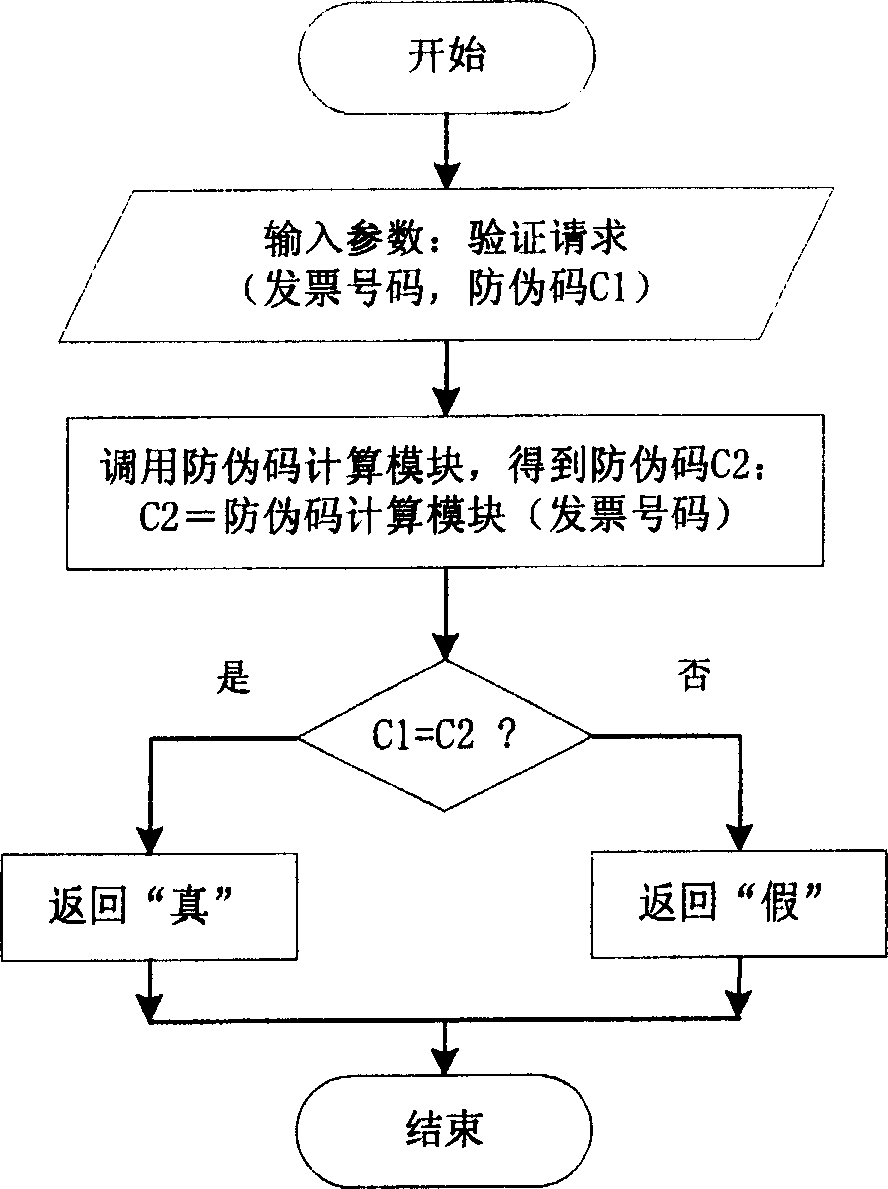
InactiveCN1588843AStrong ability to prevent hackers from tamperingImprove securityKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareWeb service
This invention relates to a method for generating a bill anti-false code and checking system composed of a customer end and a service end constituting a safety kernel, an anti-false code generation / check server and WEB server, the service end is interacted with the customer end via SSL protocol. This invention adopts a method of modern cryptography to apply an operation of cryptography based on ciphered code to get a bill anti-false code to be printed on the bill surface together with the number, when checking, the service end carries out ciphered code bill number operation to generate a bill anti-false code then to contrast it with the code on the bill surface to realize the check.
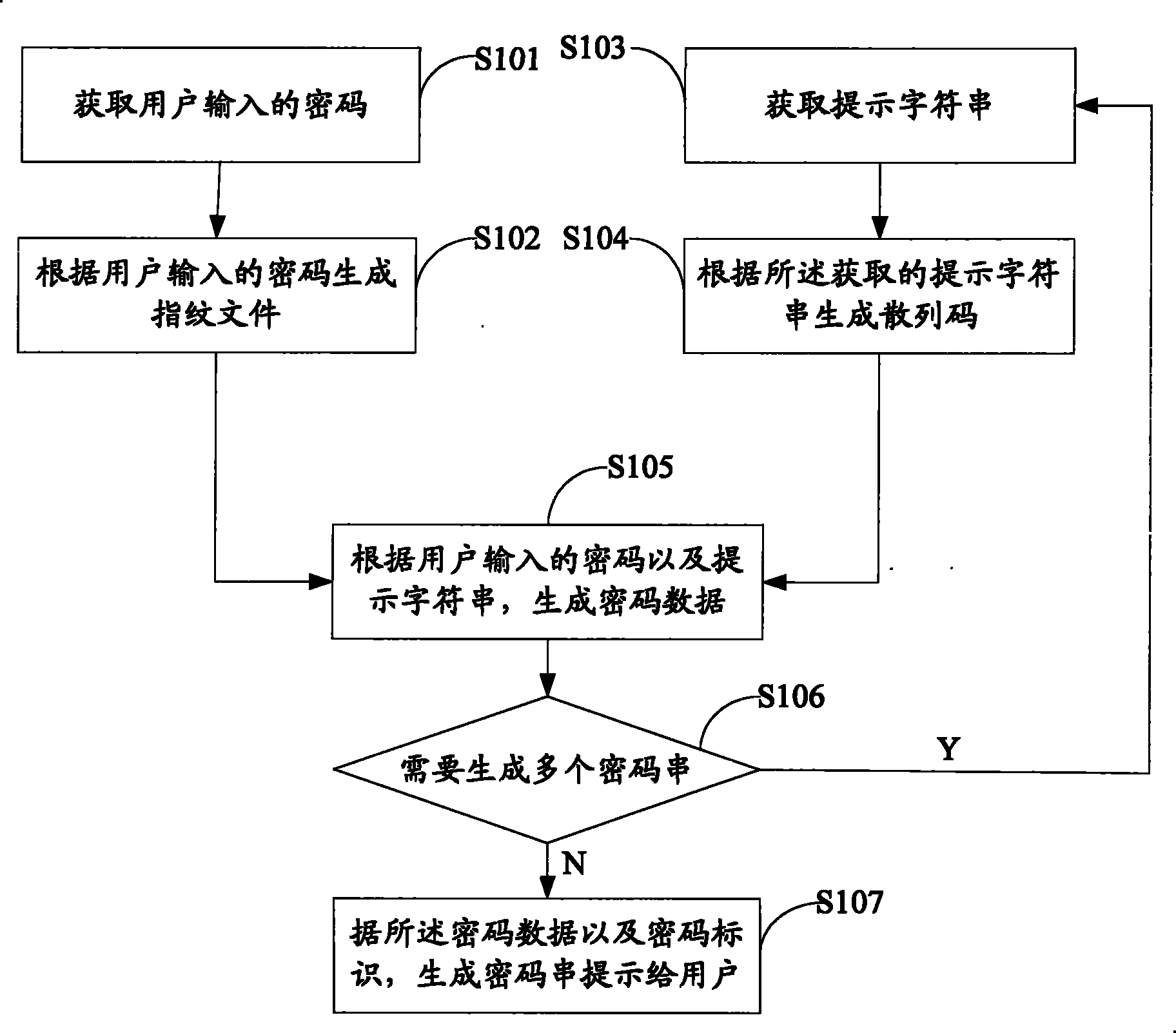
Owner:SOUTH CHINA UNIV OF TECH
Method and device for generating password string
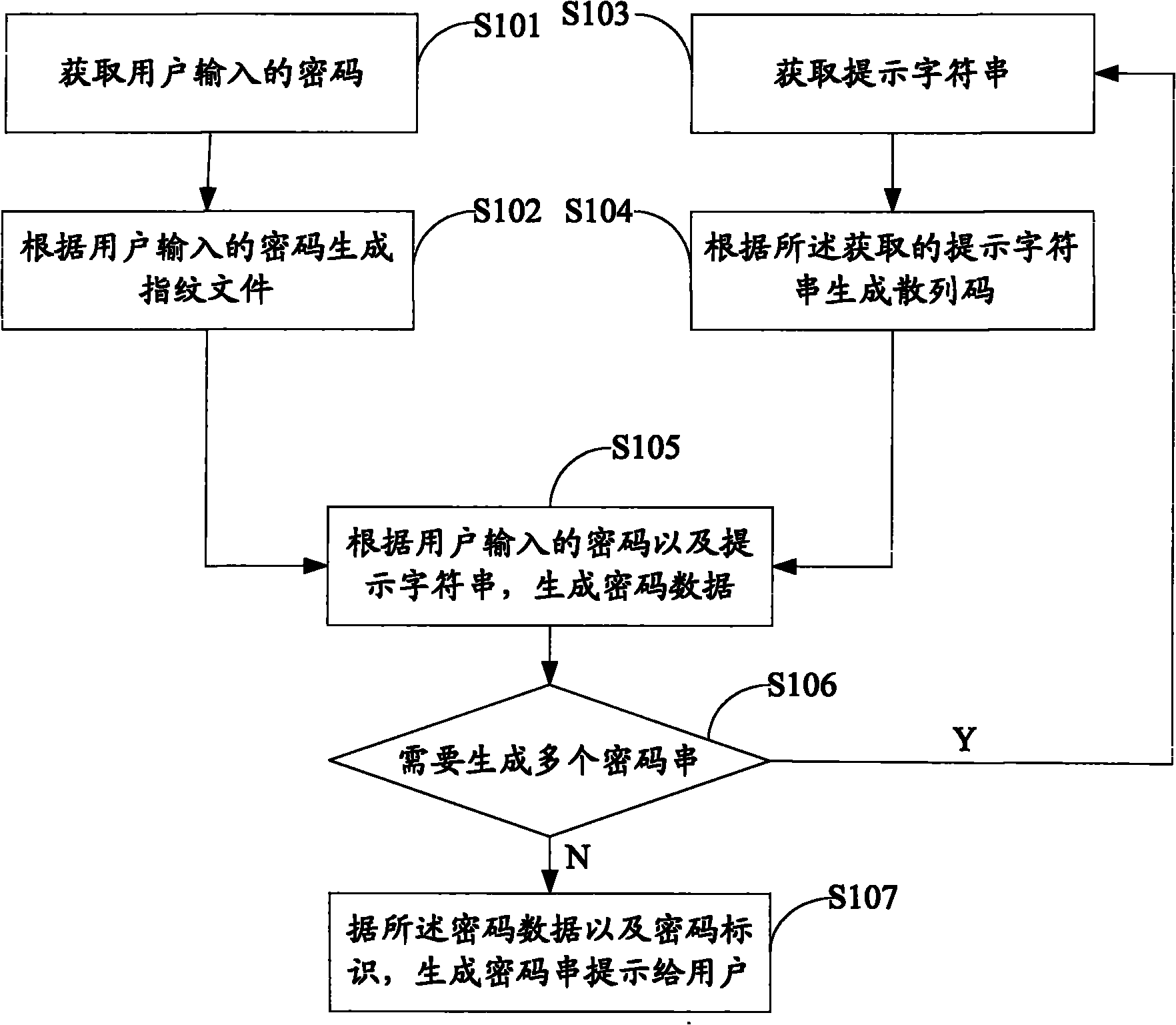
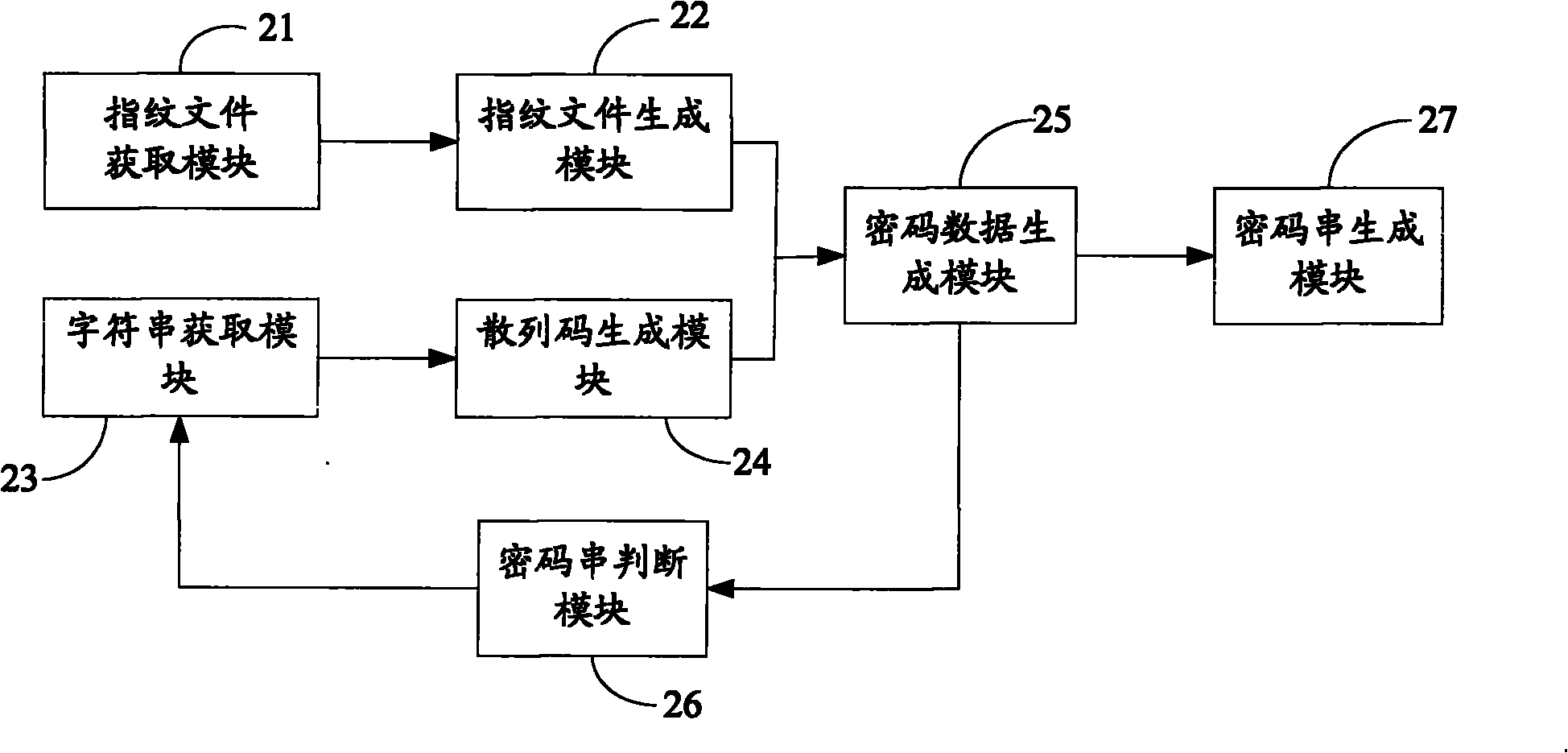
ActiveCN101873211AEasy to useDoes not compromise securitySecuring communicationFingerprintPassword strength
The invention belongs to the field of password safety and discloses a method and a device for generating a password string. The method comprises the following steps of: acquiring a fingerprint file of a user; acquiring a prompt string, wherein the prompt string is characteristic information of a password object input by the user; generating password data according to a password input by the user and the prompt string; and generating the password string according to the password data and a password identifier and prompting the password string to the user. In the invention, the user only needs to remember one password without remembering masses of other passwords so as to bring great convenience to the user.
Owner:WONDERSHARE TECH CO LTD
Battery cooling system and method
ActiveCN104868194AReduce the temperatureImprove cooling efficiencySecondary cellsBatteriesElectricityTemperature difference
The invention discloses a battery cooling system and method. The system comprises a battery box and a gas bottle filled with CO2 gas. A box air inlet and a box air outlet are arranged in the battery box, a gas bottle air outlet and the box air inlet are connected through a first pipeline, the box air outlet is connected with a second pipeline, a first control valve and a reducing valve are arranged on the first pipeline, a second control valve is arranged on a second pipeline, a first detection control device used for detecting the temperature of a battery is arranged in the battery box, and the first control valve, the reducing valve and the second control valve are all electrically connected with the first detection control device. The decompressed CO2 gas expands to absorb heat to cool the battery in the battery box, the temperature difference between the decompressed CO2 gas and the battery is 40 DEG C, heat exchange rate of the battery and the gas is greatly increased, and energy consumption is reduced because the CO2 gas does not require refrigeration before entering the battery box. In addition, the CO2 gas has a fire extinguishing function and can protect the battery.
Owner:HUBEI JINQUAN NEW MATERIALS CO LTD
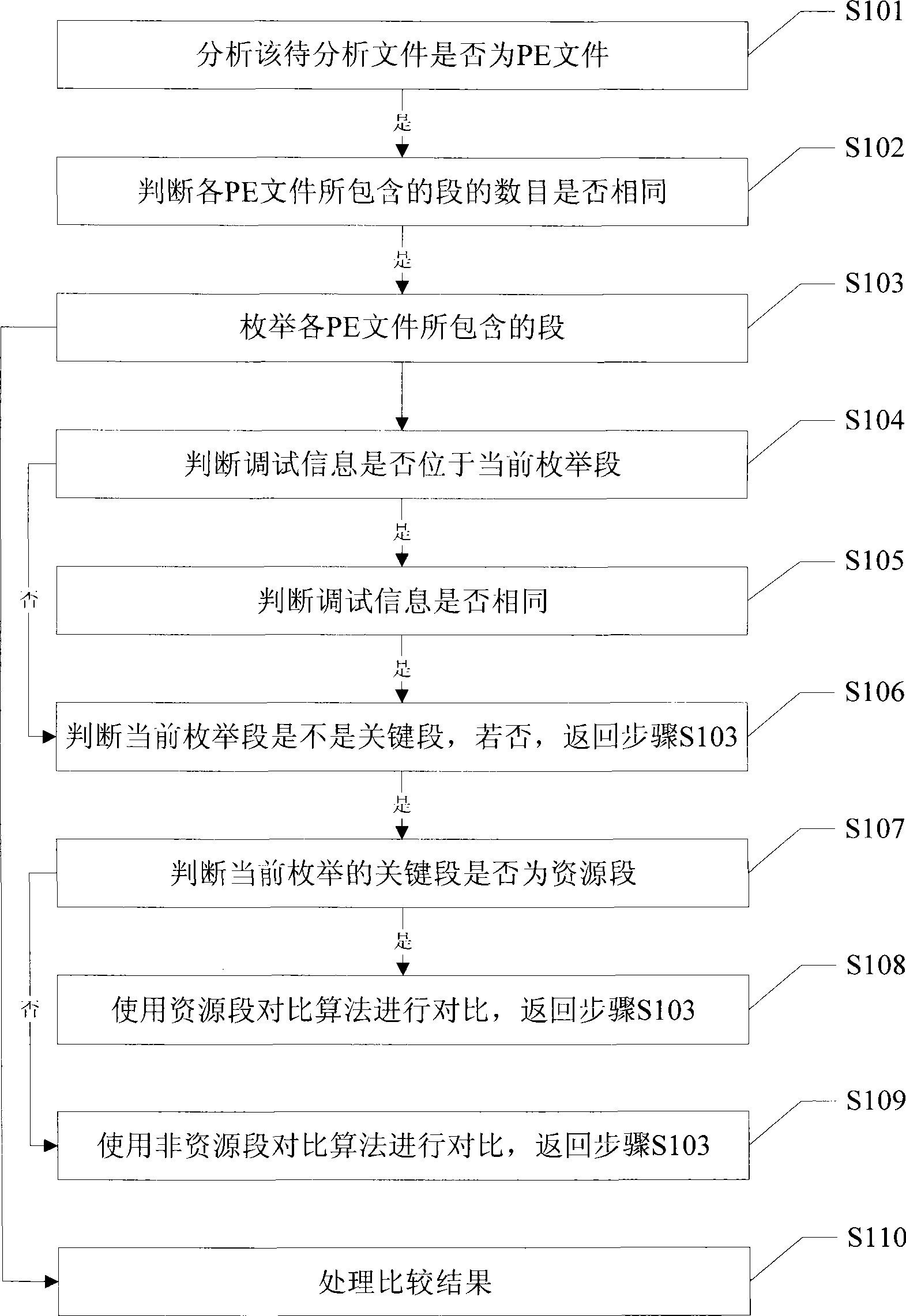
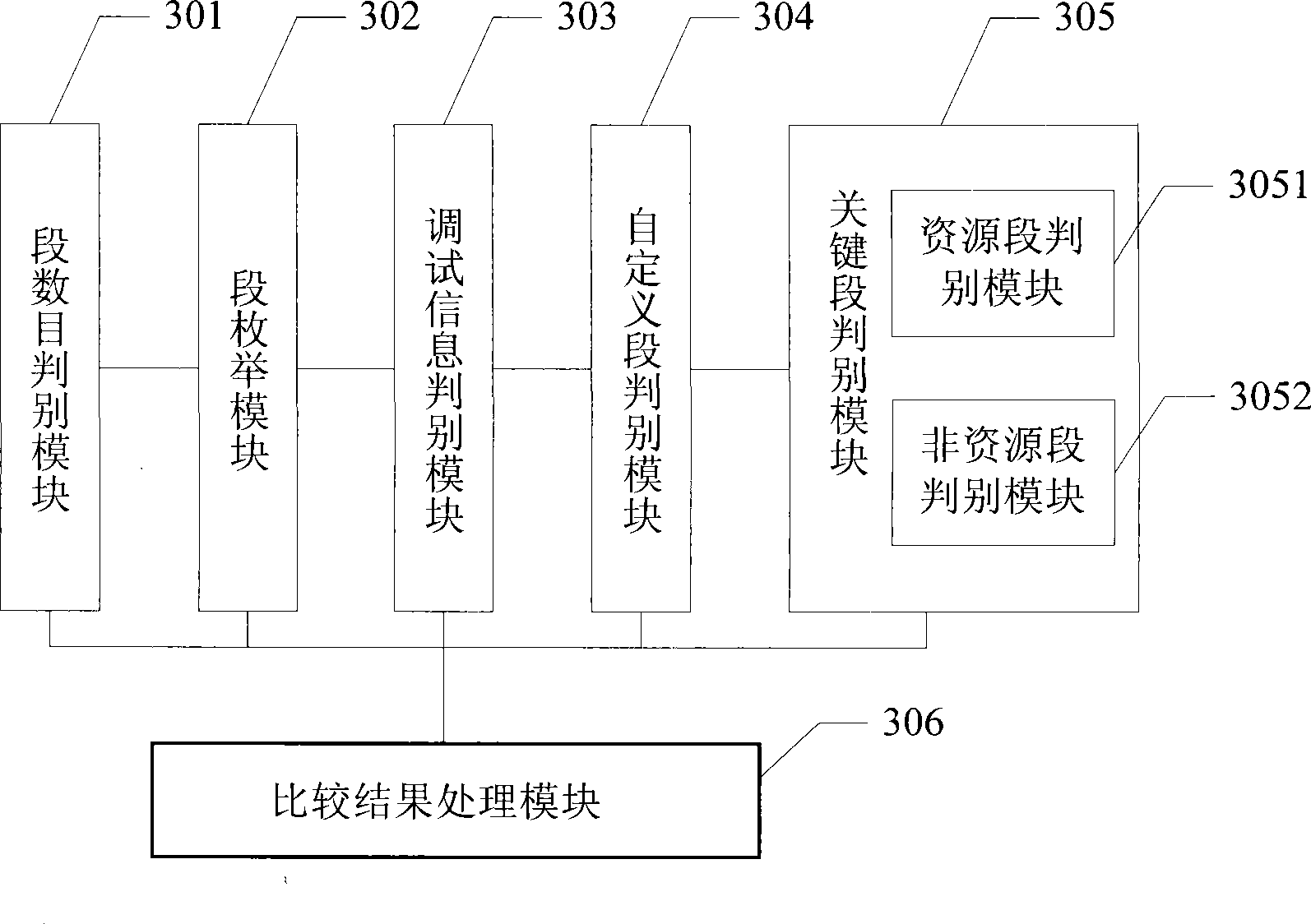
Method and apparatus for judging PE file source code consistency
ActiveCN101470620AEasy to operateDoes not compromise securityProgram controlMemory systemsDatabaseSource code
The invention discloses a method for judging the consistency of PE file source codes and a device, through analyzing a public structure of a PE file, whether various PE files awaiting to analyze are based on same source codes can be judged when the PE files awaiting to analyze comprise same number of segments and same content of critical segments. The method for judging the consistency of PE filesource codes does not depend on the content of original source codes, thereby being capable of not accessing a source code library, and guaranteeing the security safety of the source code library.
Owner:ZHUHAI KINGSOFT SOFTWARE CO LTD
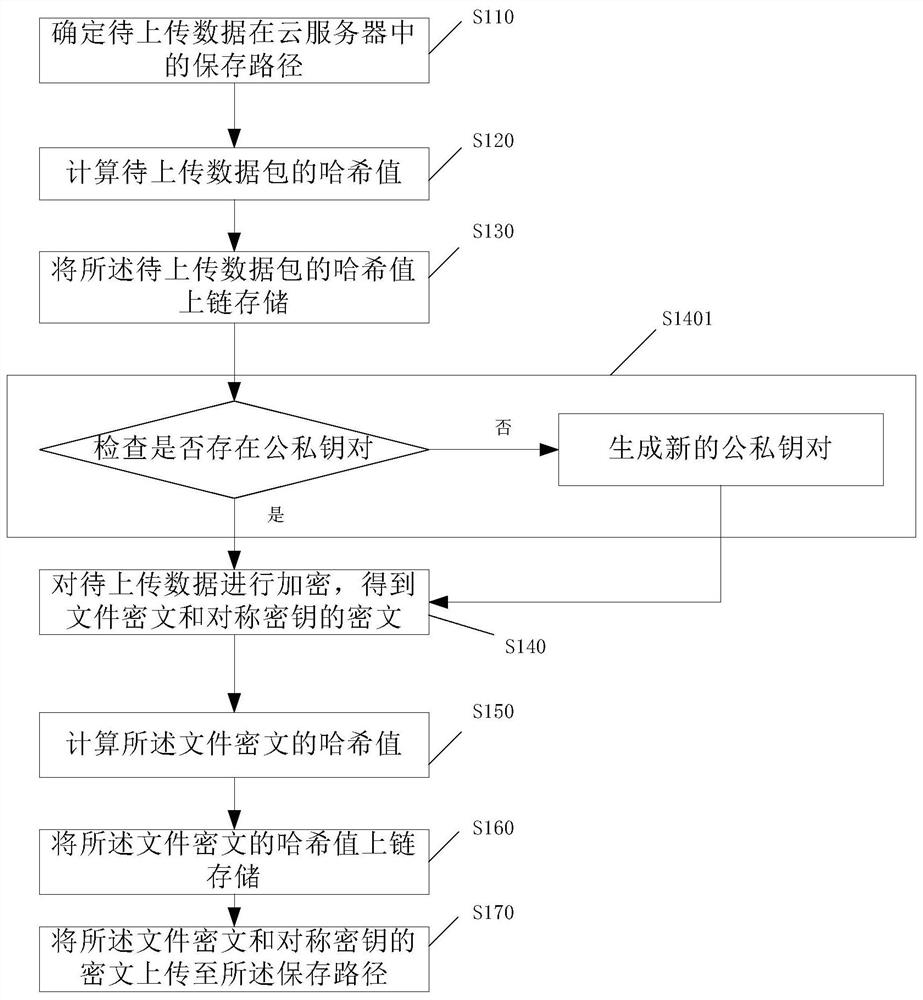
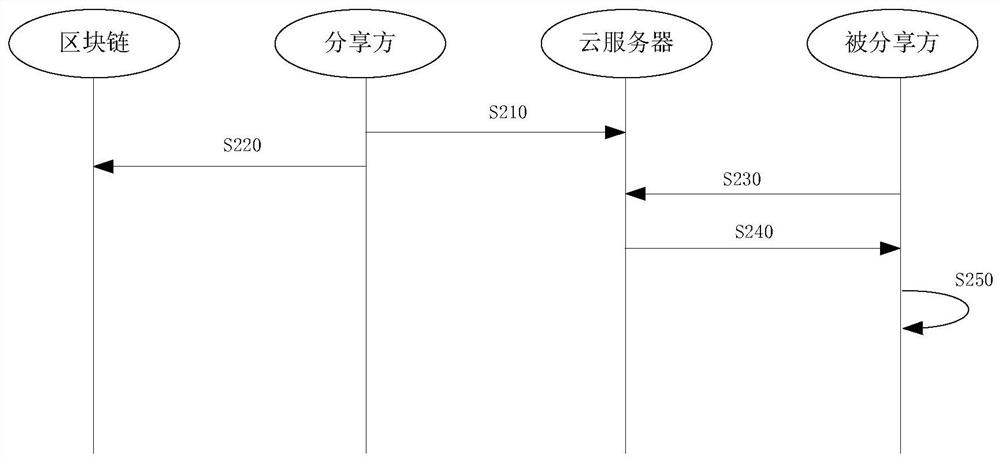
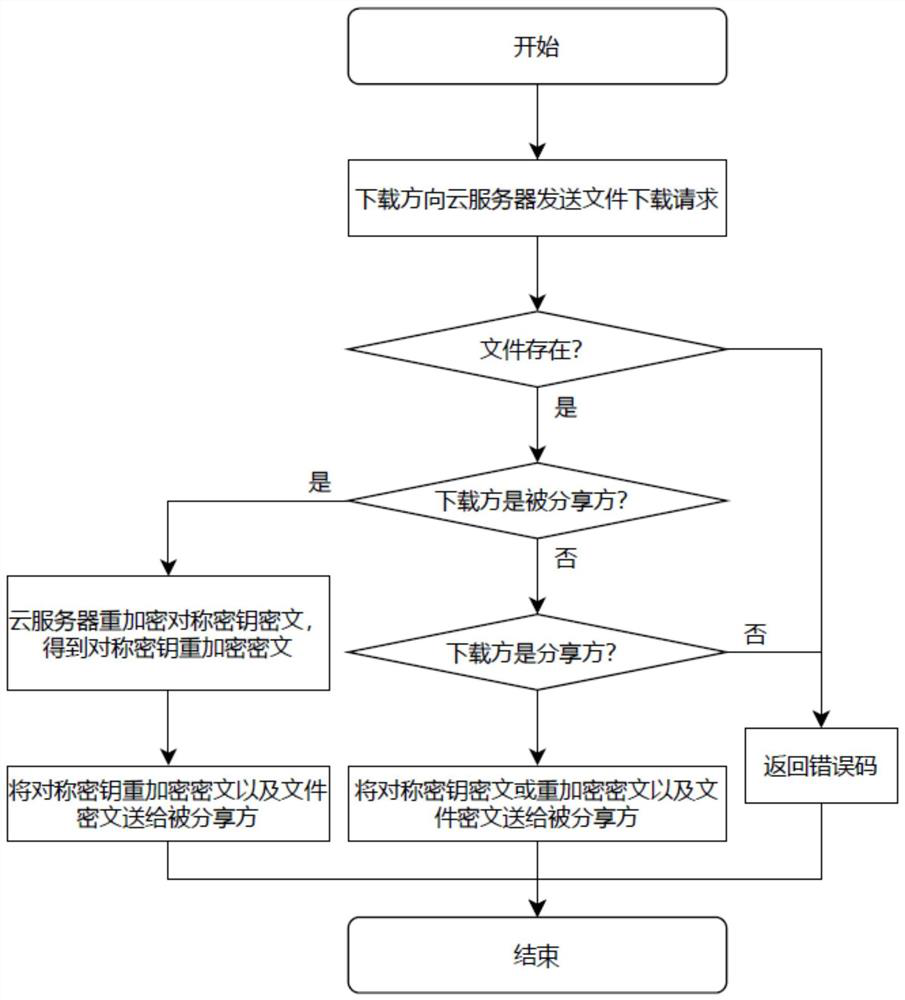
Cloud data encryption storage and sharing method, device and system
ActiveCN112702160ARealize encryption and decryptionEnsure safetyKey distribution for secure communicationPlaintextCiphertext
The invention discloses a cloud data encryption storage and sharing method. The method comprises an uploading step and a sharing step. The sharing step comprises the following steps: the sharing party generates an authorization re-encryption key for the shared party and uploads the authorization re-encryption key to the cloud server; the sharing party uplinks and stores the authorization record; the cloud server receives the sharing application of the shared party, obtains a verification result of the sharing application according to the authorization record, calls a file ciphertext of the to-be-shared file in the storage path and a ciphertext of the symmetric key if the verification succeeds, and sends the file ciphertext and the ciphertext to the shared party; and the shared party reads the local private key to decrypt the file ciphertext to obtain plaintext data of the to-be-shared file. File sharing is established on the premise of re-encrypting the uploaded file, and other parties including the cloud end cannot access the plaintext of the file except the two parties participating in file sharing, so that the file is prevented from being leaked, and the security of file privacy is improved.
Owner:江苏通付盾区块链科技有限公司 +1
Private key management method and apparatus for bastion host
ActiveCN107181589ADoes not compromise securityImprove securityKey distribution for secure communicationPasswordCiphertext
The invention provides a private key management method and apparatus for a bastion host. The private key management method for a bastion host includes the steps: when the bastion host is started, acquiring a first private key parameter in a bastion host process file, wherein the first private key parameter includes a first sharing key decryption password; acquiring a second private key parameter from a private key management platform, wherein the second private key parameter includes a second sharing key decryption password, a cryptograph private key and a private key encryption algorithm; according to the sharing key algorithm, calculating the first sharing key decryption password and the second sharing key decryption password, and obtaining the decryption key; and according to the private key encryption algorithm and the decryption key, decrypting the cryptograph private key, and obtaining a bastion host private key. The private key management method for a bastion host can improve storage safety of the bastion host private key.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
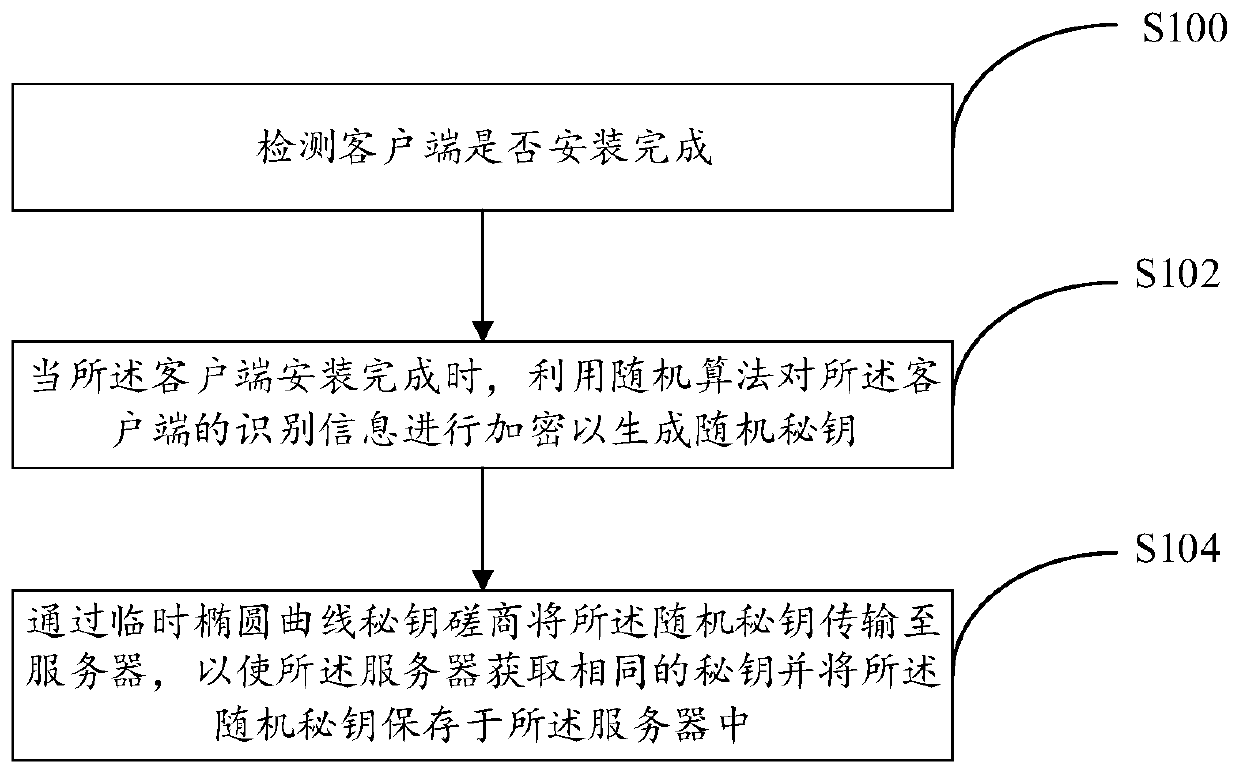
Encryption method and encryption system
InactiveCN110635898ADoes not compromise securityImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareIp address
The embodiment of the invention provides an encryption method. The encryption method comprises the following steps: detecting whether a client is installed; when the client is installed, encrypting the identification information of the client through a random algorithm to generate a random secret key, wherein the identification information at least comprises an MAC address, an IP address, a UUID,local time and a user mouse track; and transmitting the random secret key to a server through a temporary elliptic curve secret key negotiator, so that the server obtains the same secret key and stores the random secret key in the server. Through the embodiment of the invention, the security of the local data of the client can be greatly enhanced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Signcryption method with hidden identity and strong security
ActiveCN105306212AProtect identity privacyDoes not compromise securityPublic key for secure communicationUser identity/authority verificationSigncryptionModular exponentiation
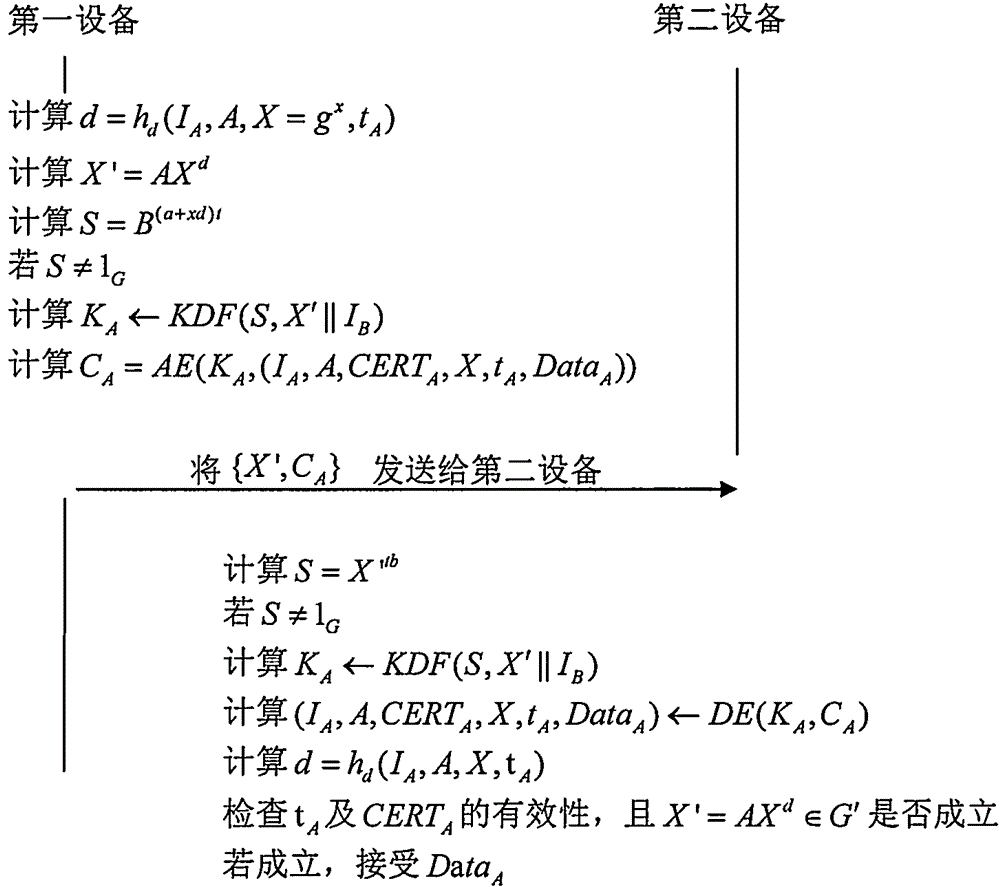
The invention provides a signcryption method with hidden identity and strong security. The signcryption method comprises the steps that: a first device calculates X' = AXd, wherein X = gx and d = hd (X, auxd), determines a preset shared key S according to a DH-index x, a private key a and a public key B = gb of a second device, determines KA based on S, determines CA = (IA, A, CERTA, X, DataA)) according to KA, and sends [X CA]' to the second device; the second device determines the preset shared key S according to the received X' and the private key b of the second device, determines KA based on S, and decrypts CA according to KA to obtain (IA, A, CERTA, X, DataA); and if a public key certificate CERTA is valid and X' = AX d is effective, DataA is accepted. In the signcryption method provided by the invention, the identity and the public key information of the first device are hidden, the first device only needs to operate 2.5 modular exponentiations, and the second device only needs to operate 1.5 modular exponentiations. In addition, the bandwidth consumed by the method provided by the invention is less than an existing signcryption scheme, and the leakage of a temporary DH-index x does not affect the security of the scheme of the invention.
Owner:赵运磊
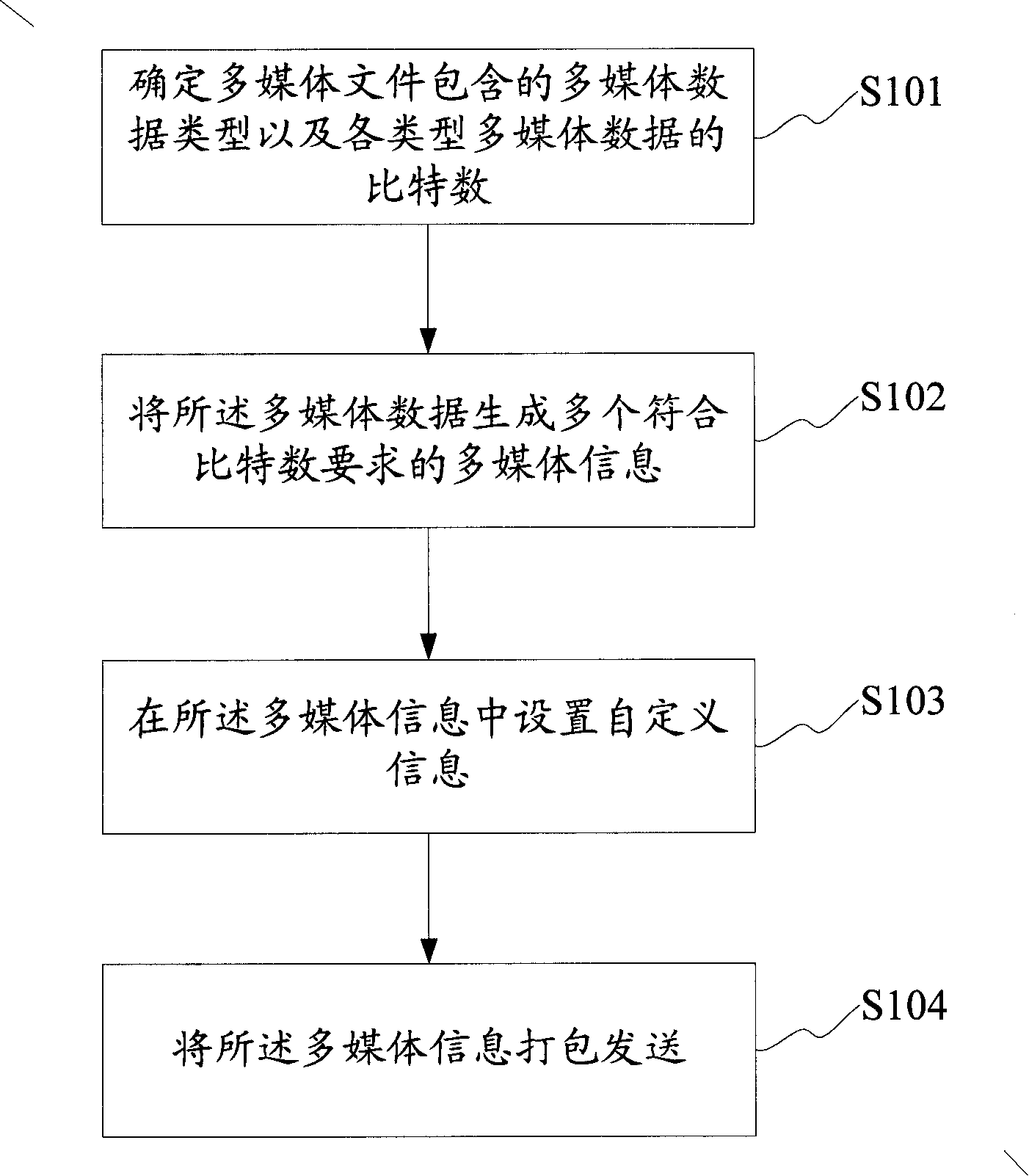
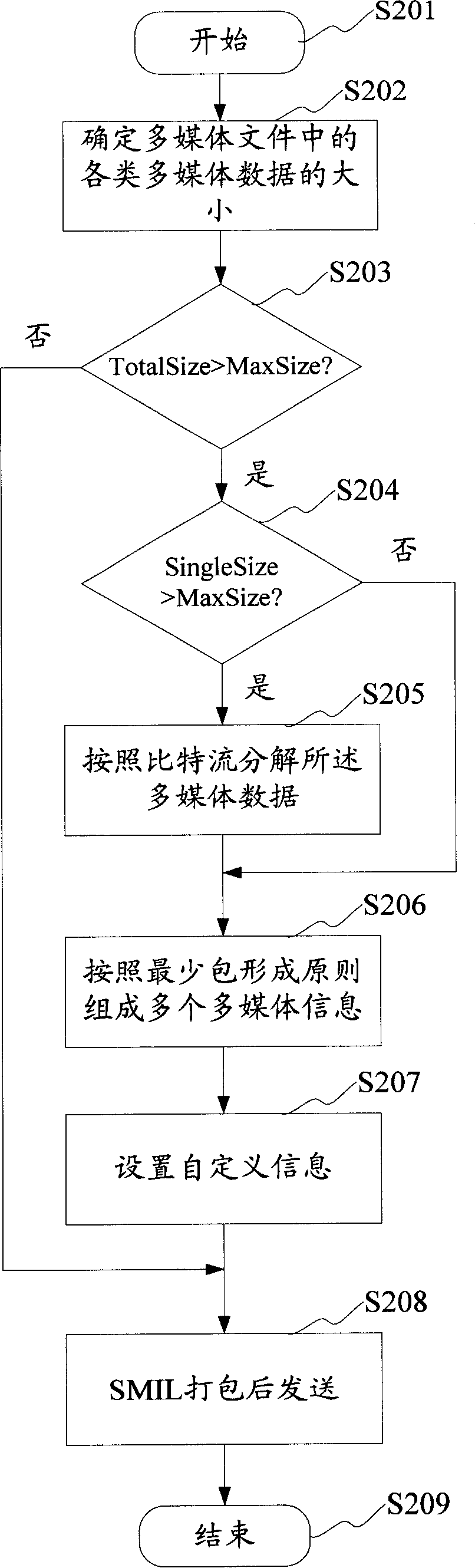
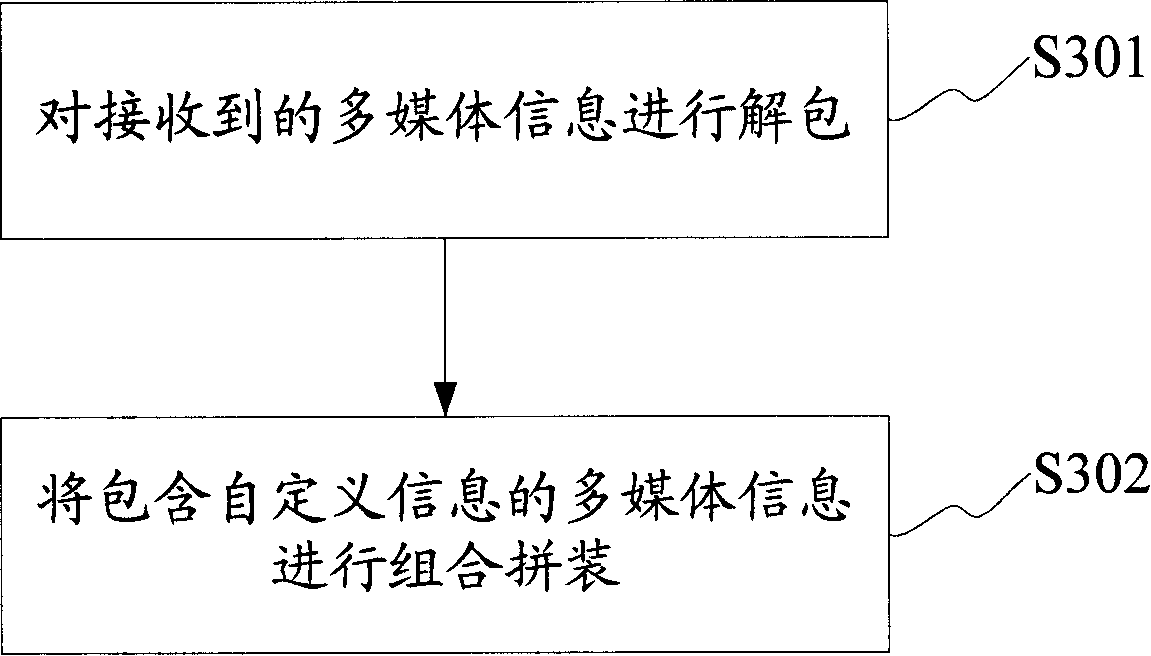
Method, device for sending multimedia document and method, device for receiving multimedia document
ActiveCN101202940ATo achieve the purpose of not being limited by the number of bitsDo not change the formatNetwork traffic/resource managementRadio/inductive link selection arrangementsData typeBit numbering
The invention discloses a sending method of multimedia files. The procedures includes: making certain of the multimedia data type comprised by multimedia files and the bit number of various multimedia data; generating a plurality of multimedia information meeting the requirement of the bit number from the multimedia data; setting user-defined information in the multimedia information; packing and sending of the multimedia information. The invention also discloses a multimedia file sending device the bit number of which is not limited. Simultaneously, the invention also provides a receiving method and device of multimedia files without any limitation to bit number. The invention decomposes the multimedia files into a plurality of multimedia information meeting the requirement of the bit number from the multimedia data; the multimedia information is recombined into the style of multimedia file in a receiving terminal, thereby realizing the purpose that the sent multimedia files are not limited by the bit number.
Owner:YINGHUADA (SHANGHAI) ELECTRONIC CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com