Unified identity authentication method based on blockchain
A technology of identity authentication and blockchain, applied in the transmission system, electrical components, etc., can solve the problems of unforgeability, unlinkability, convenience, anonymity, etc., and achieve the effect of ensuring privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
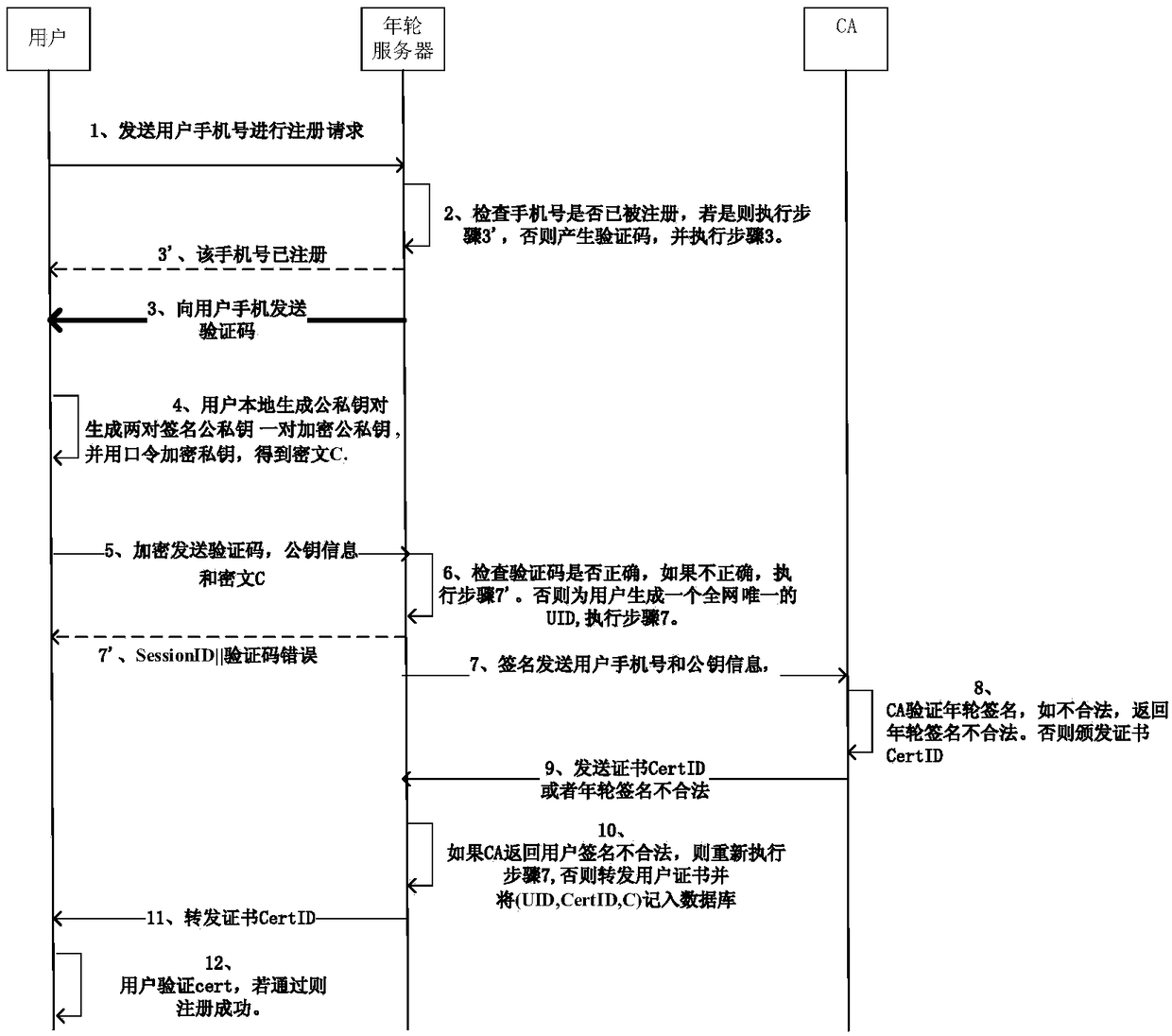
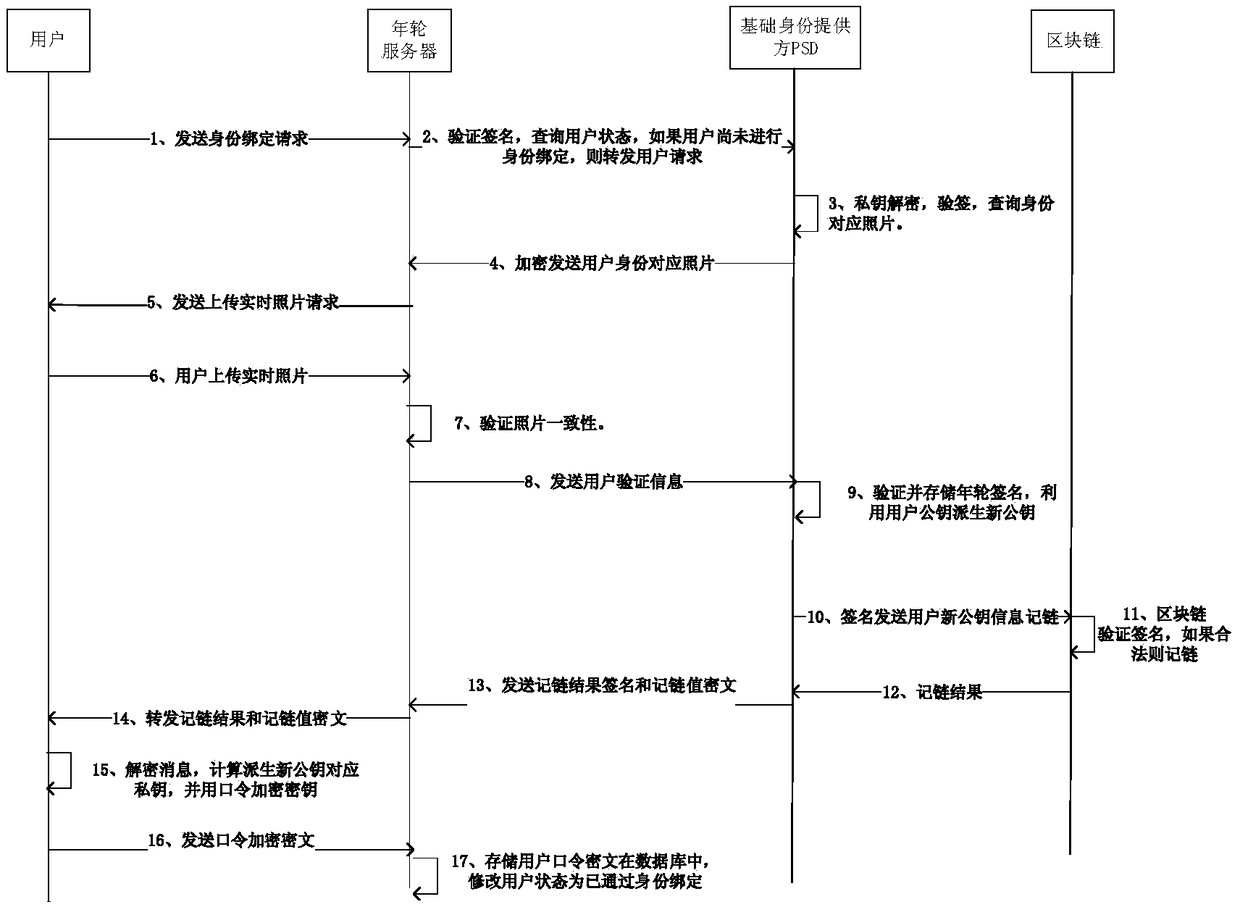
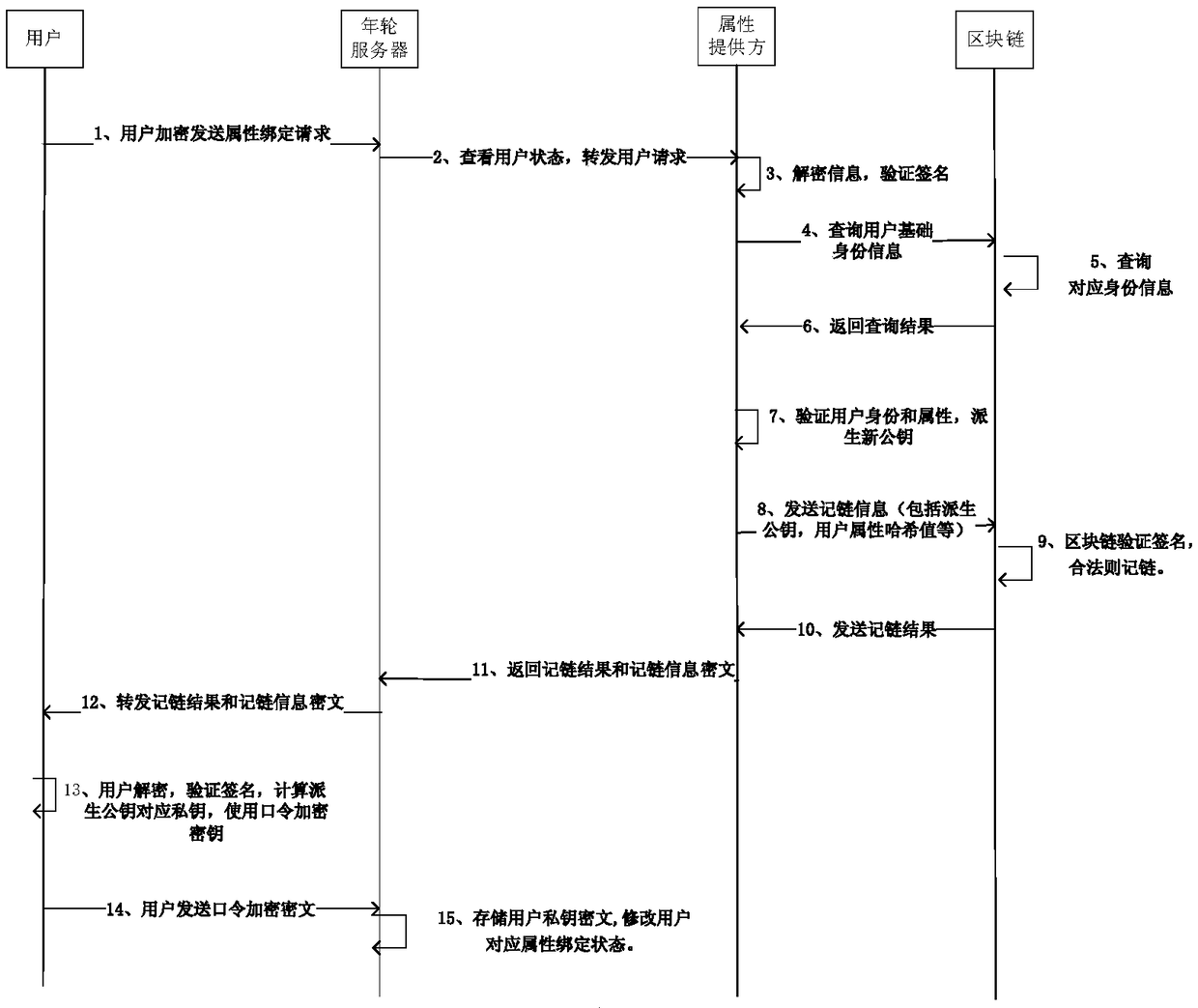
[0023] This patent designs a method for unified identity authentication of users based on the blockchain platform, which solves the problems of difficult verification and easy disclosure of privacy in current identity authentication.
[0024] In this method, there are six types of participants, users, annual ring server (referred to as server), basic identity provider (referred to as PSD), attribute provider (referred to as IDP), relying party (referred to as RP), and district blockchain. Among them, the annual ring server manages the application, serves as the medium of contact between the user and other participants, and is responsible for performing the comparison between the user's face and the user's identity information during the identity binding process. The underlying identity provider provides the underlying authentication of users. The attribute provider provides users with various attribute verifications. The relying party is the object to be presented as a user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com