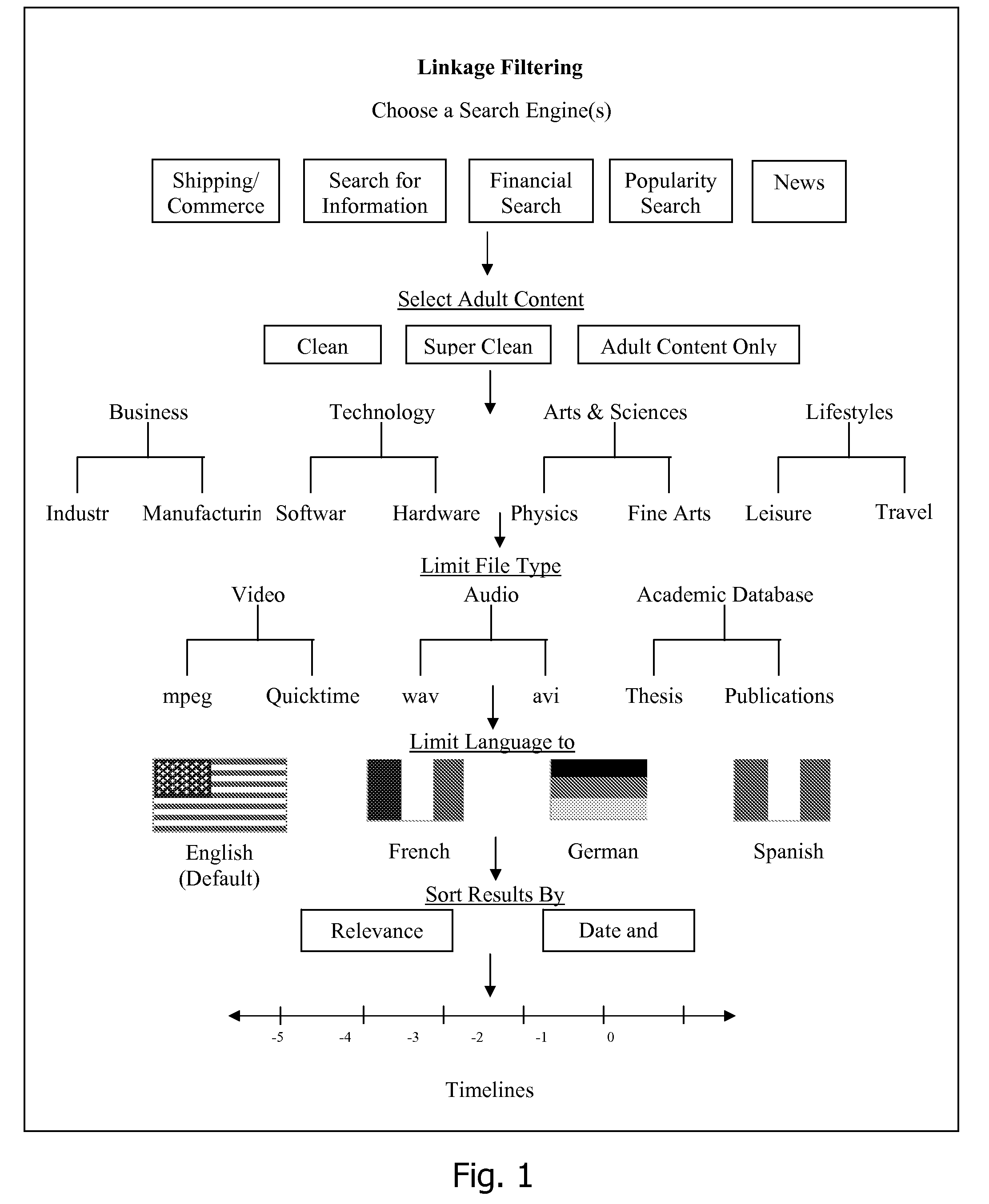
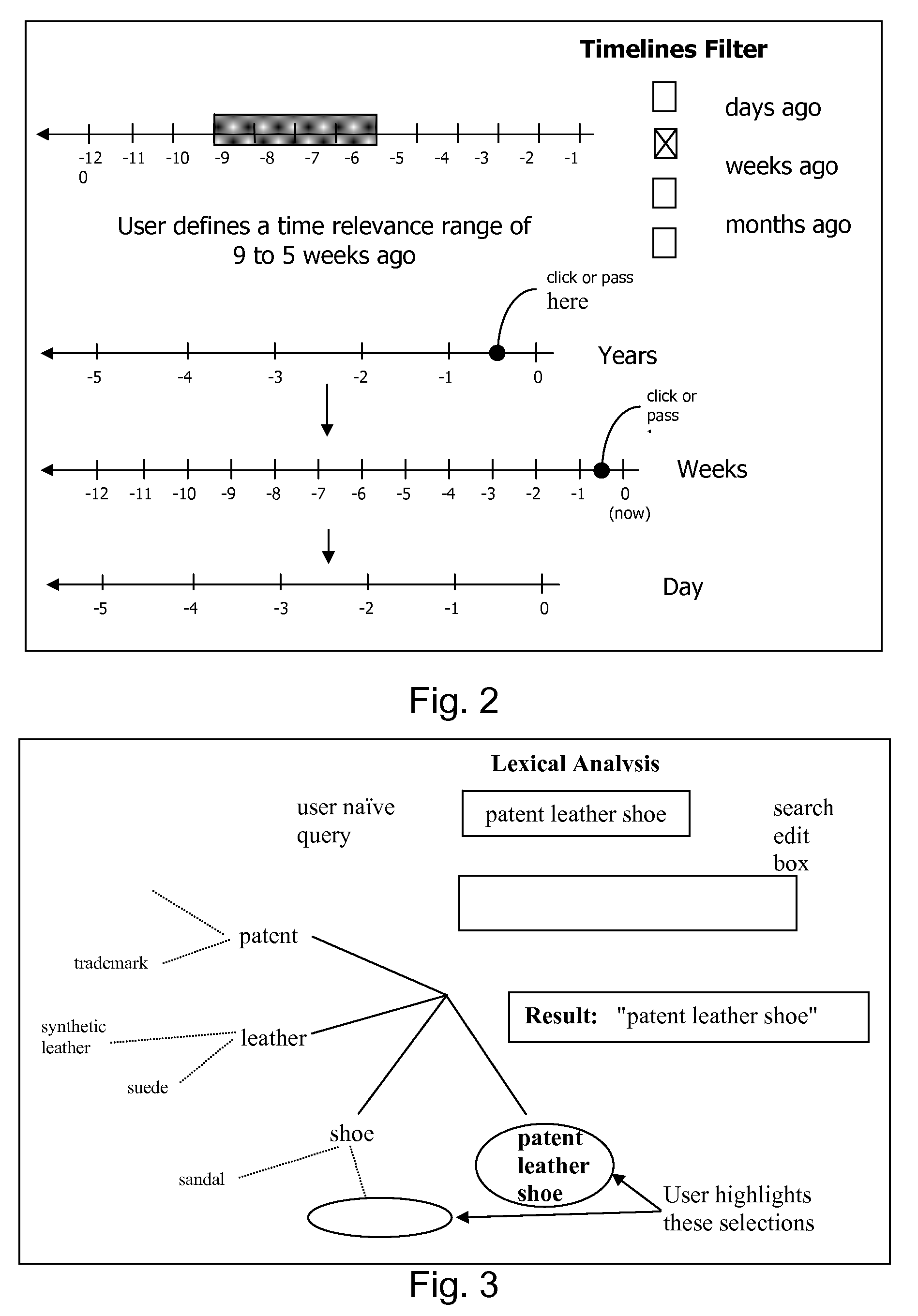
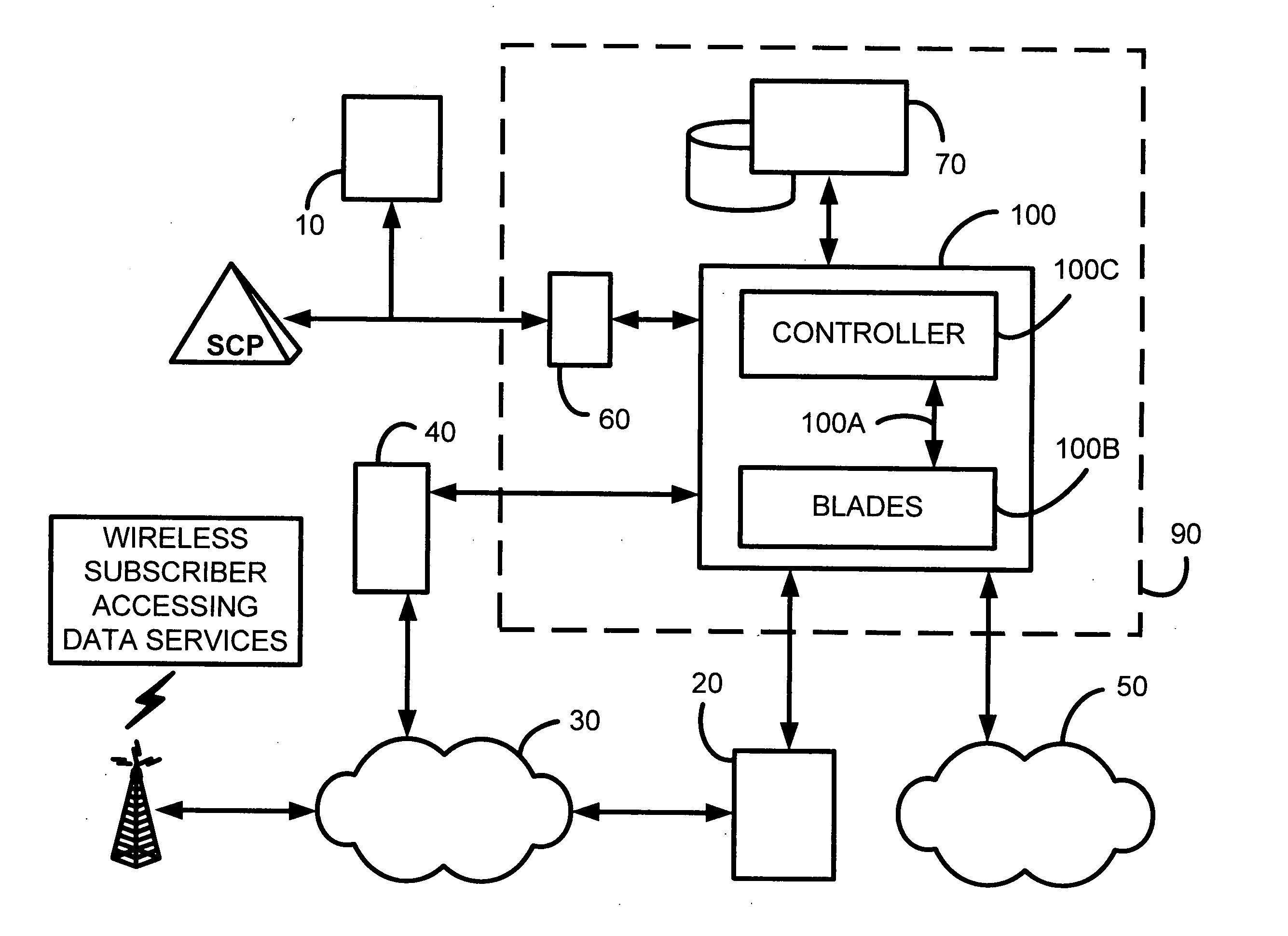
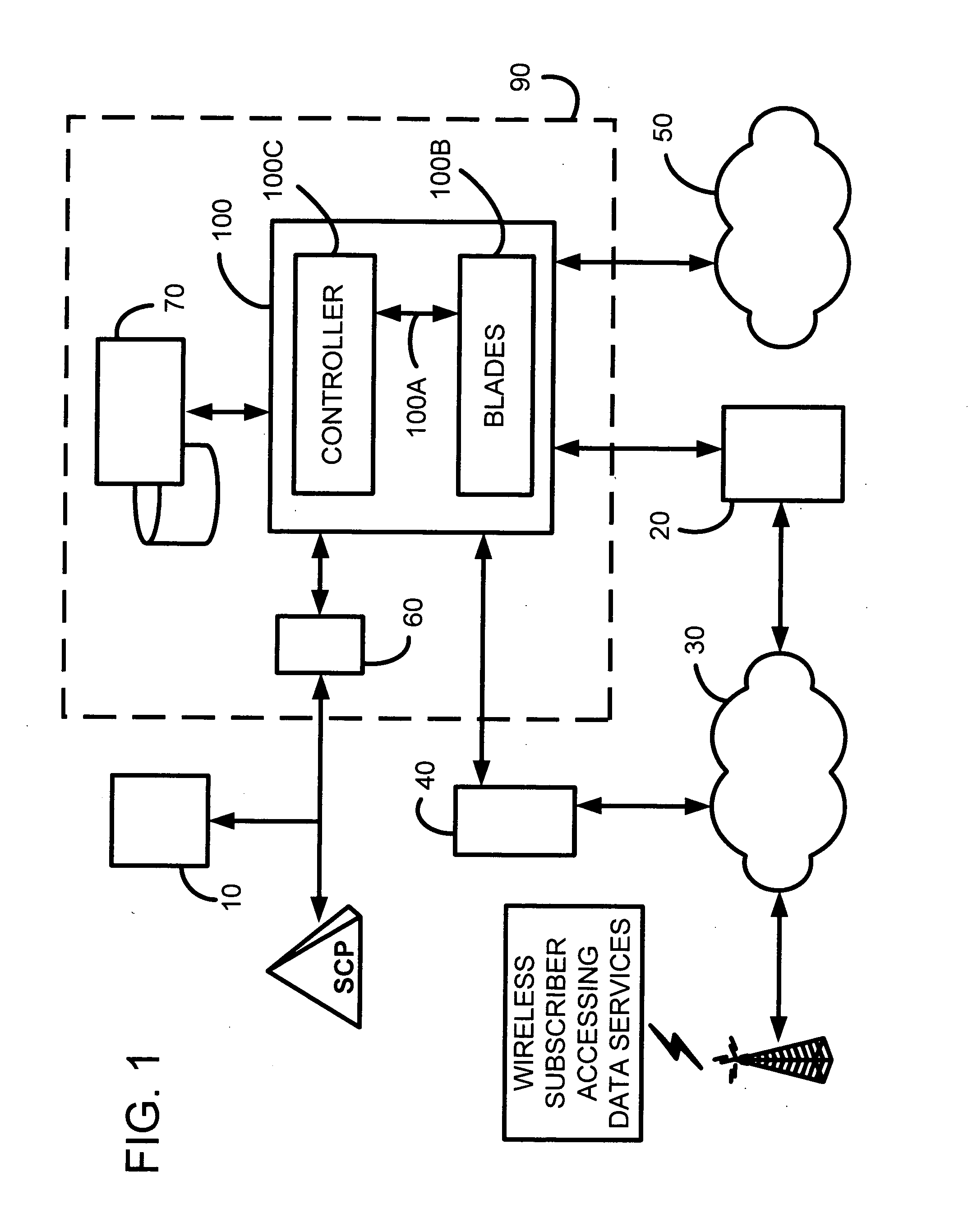
Patents
Literature
3020 results about "User privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
User Privacy Statement. This privacy statement addresses the personally identifiable information ( “data”) that we collect and process about users of our services ( “you” or “your” ). “Services” means any services that we offer, including visitors to our website.
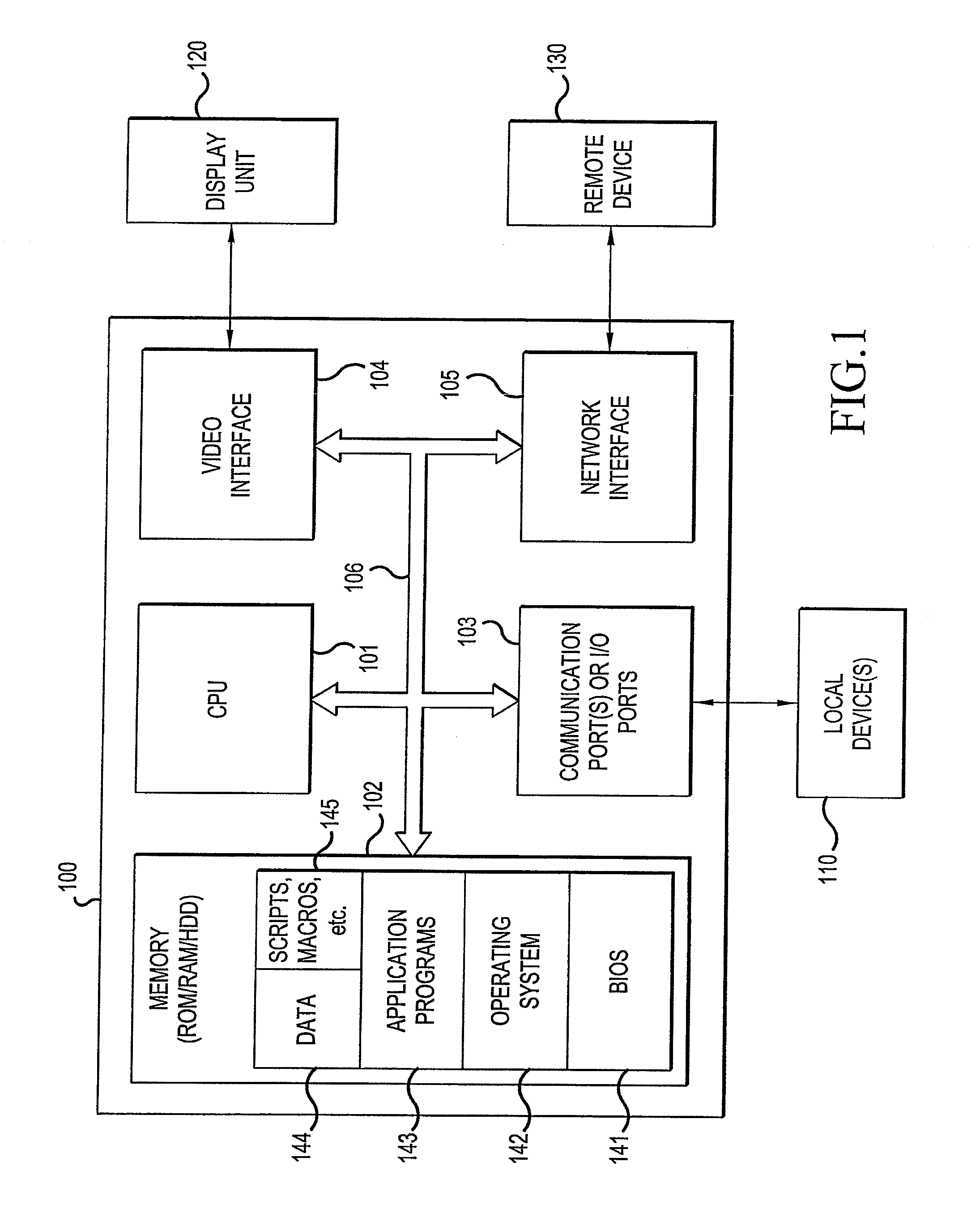
Database access system
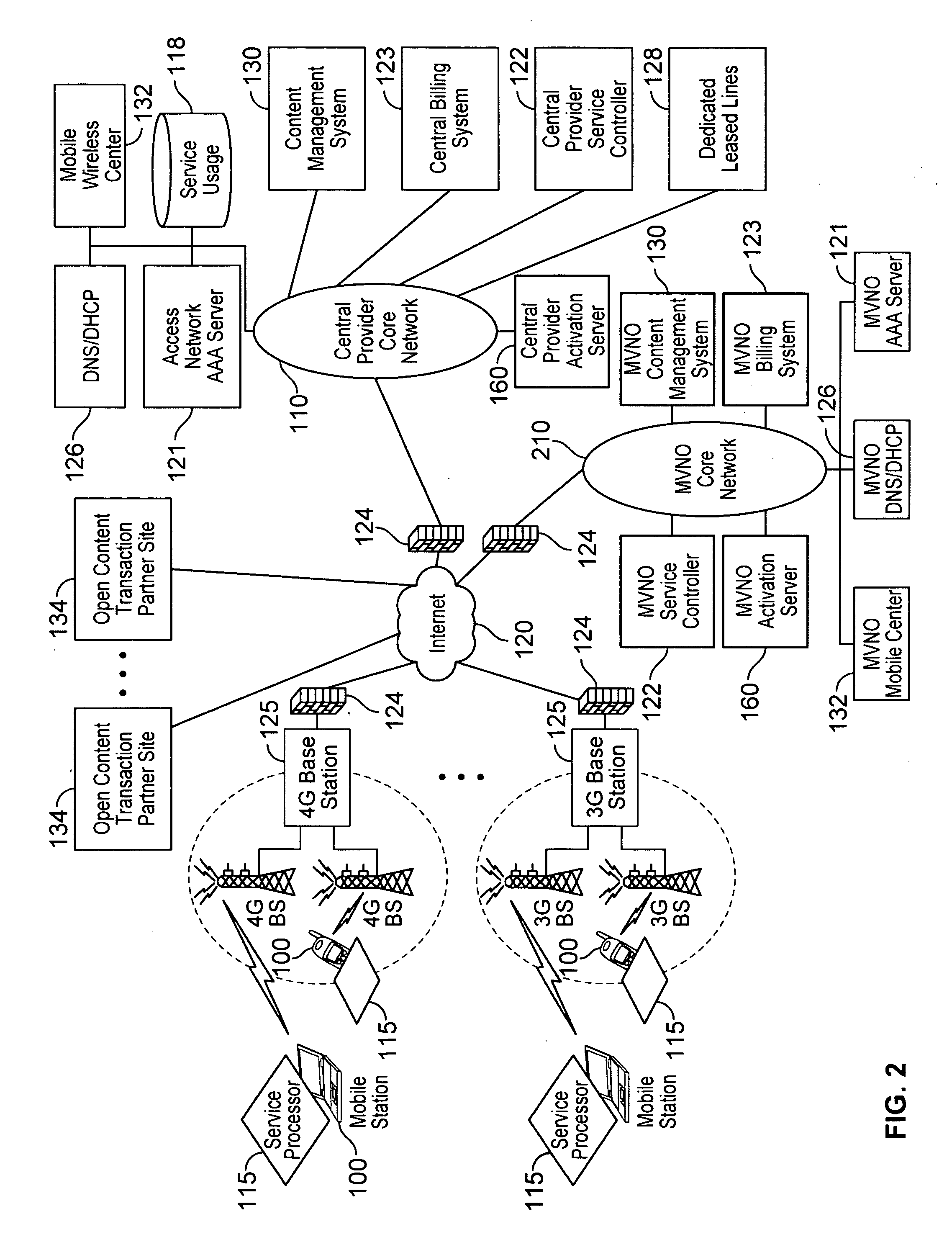
ActiveUS7181438B1Increased formationGood user interfaceDigital data information retrievalAdvertisementsAnonymityPopulation statistics
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
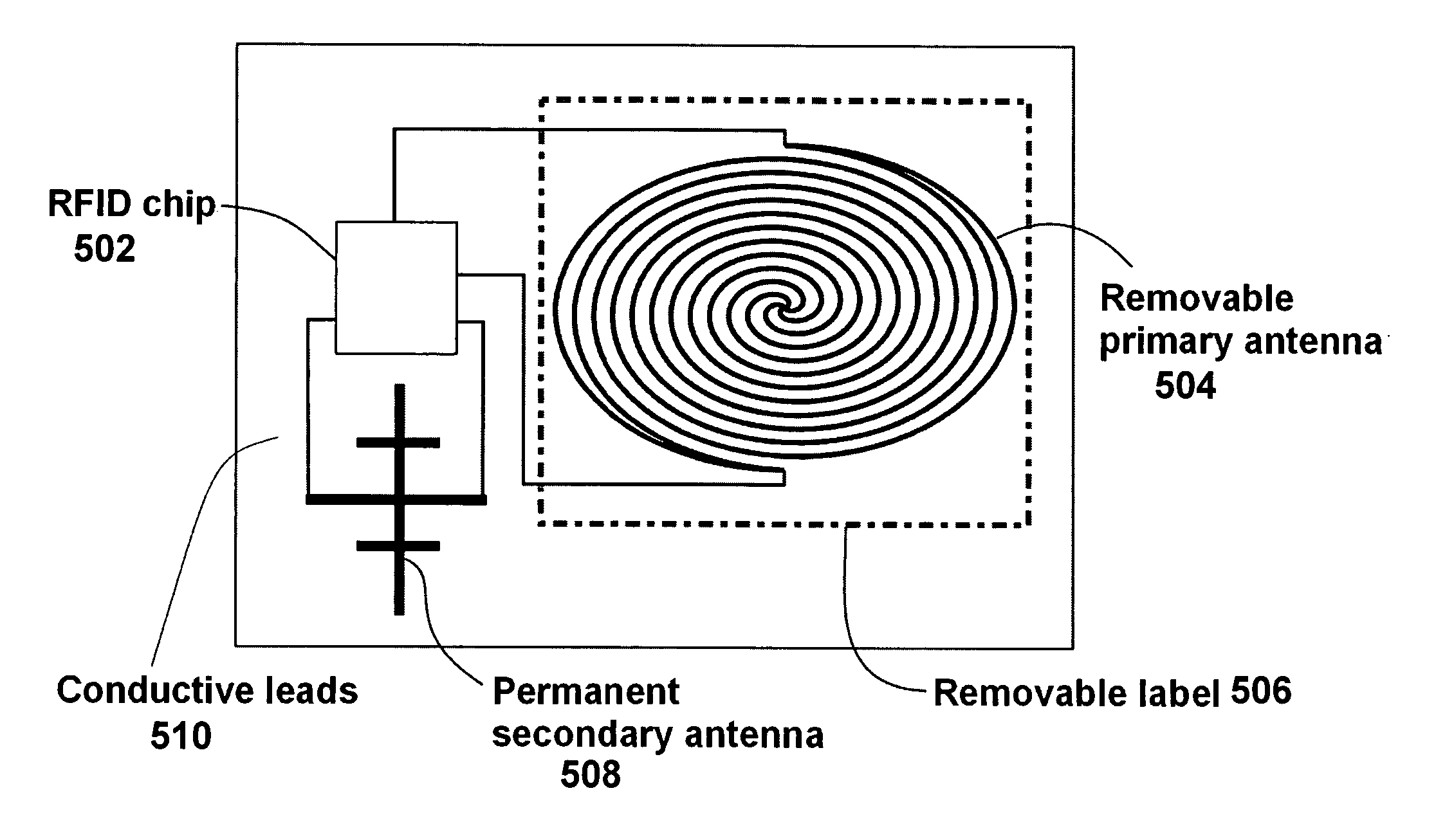
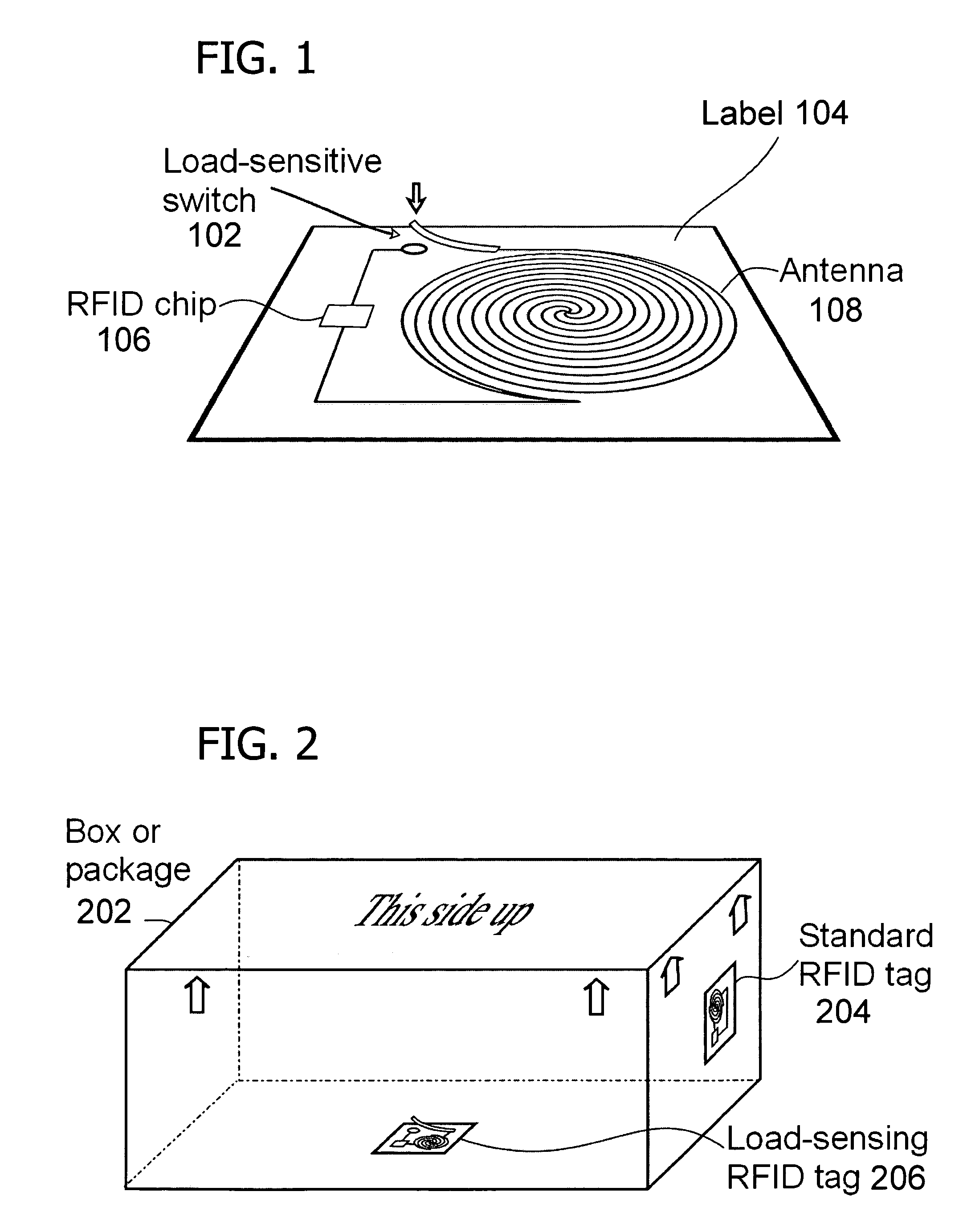
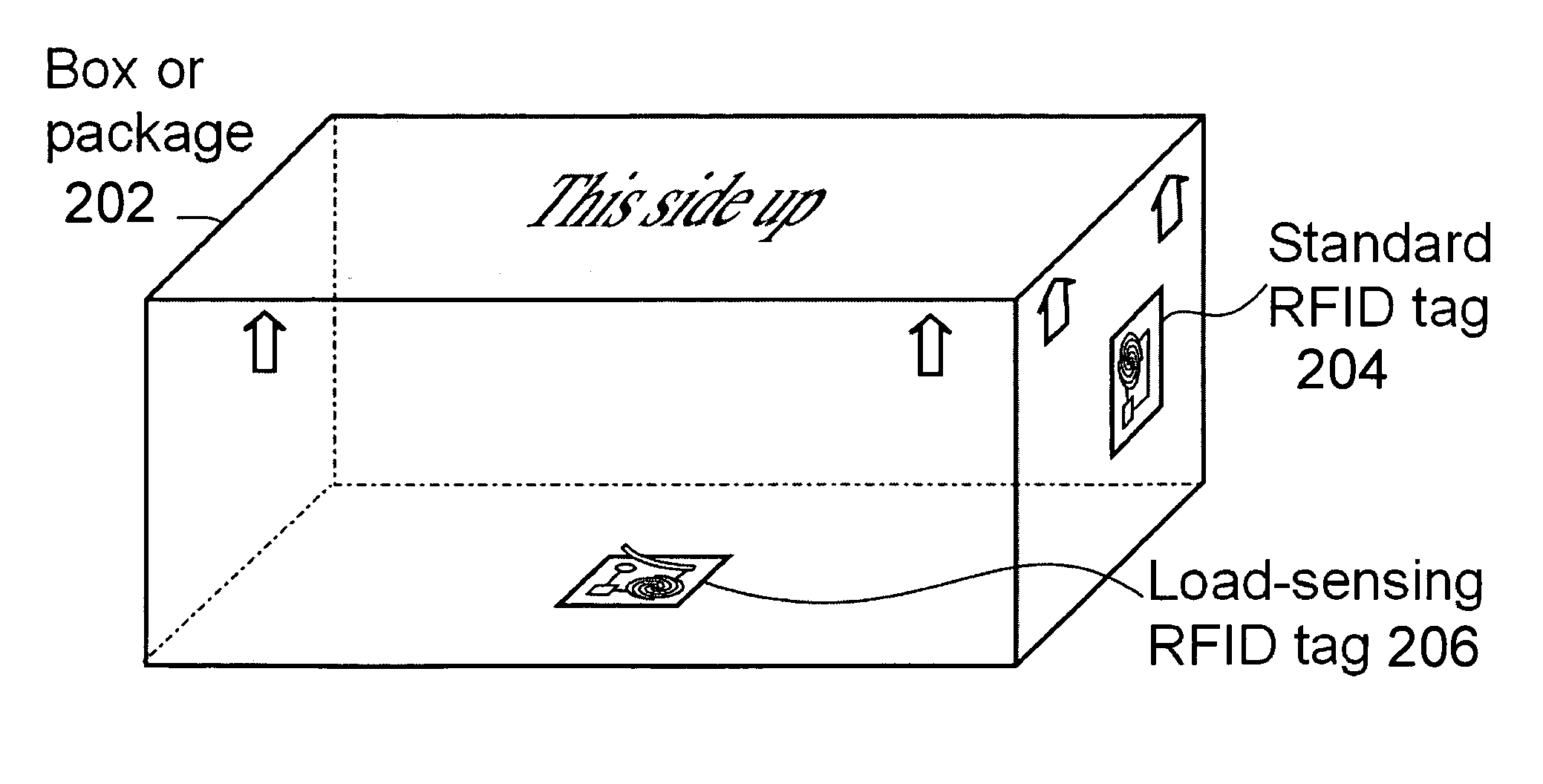
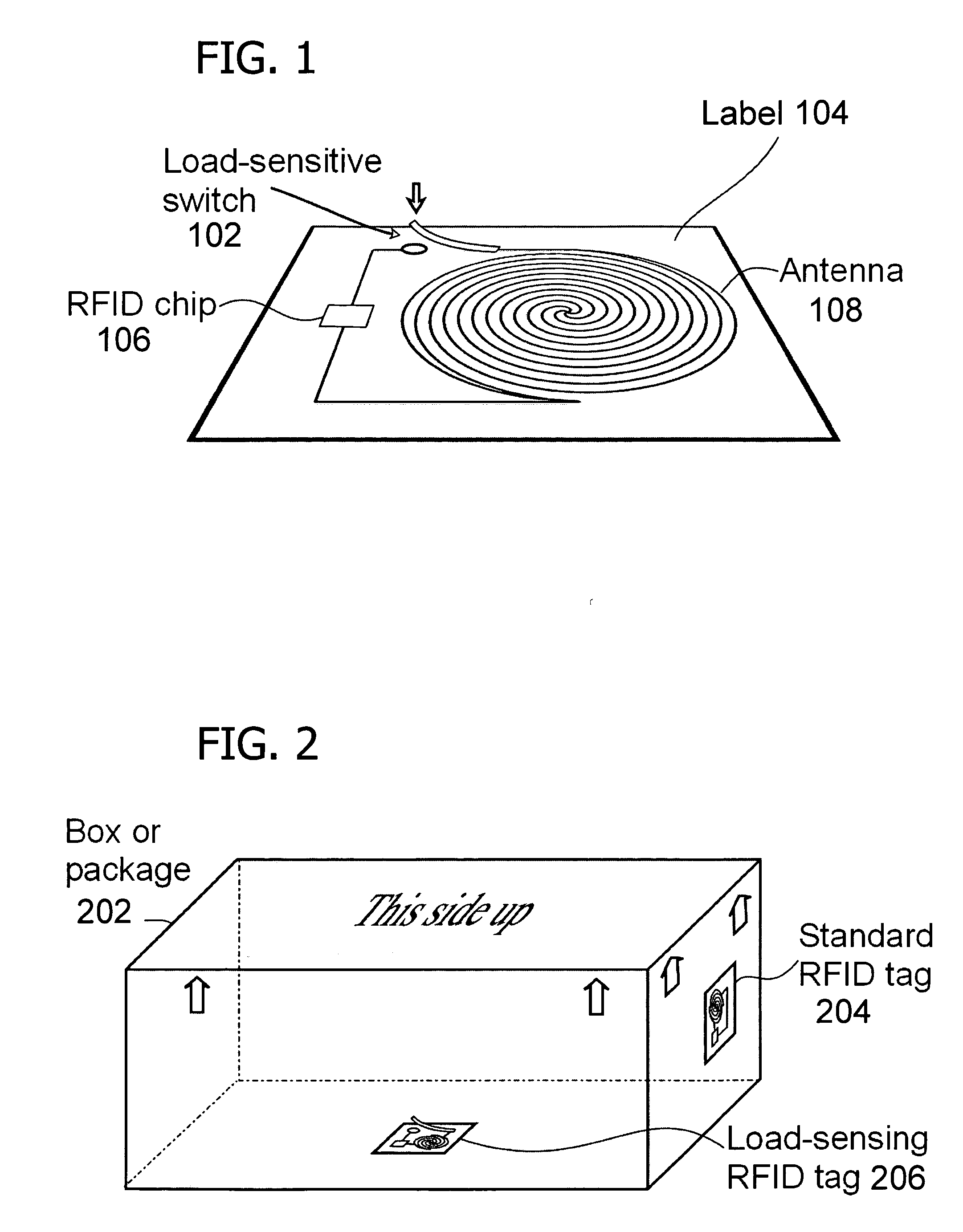
Deactivating a data tag for user privacy or tamper-evident packaging
ActiveUS7098794B2Facilitate communicationBurglar alarm by openingLocks for portable objectsUser privacyVIT signals
Deactivating a data tag attached to packaging for user privacy or tamper-evident reasons. A data circuit stores identification information. A plurality of antennas is coupled to the data circuit. At least one antenna of the plurality of antennas is a removable antenna capable of wireless signal transmission at a first range such that removal of the antenna substantially prevents communication of the identification information via the removed antenna and permits communication of the identification information via another antenna of the plurality of antennas at a second range relatively smaller than the first range.
Owner:BUFFALO PATENTS LLC
Database access system
InactiveUS20070156677A1Increased formationGood user interfaceDigital data information retrievalAdvertisementsPersonal detailsAnonymity
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
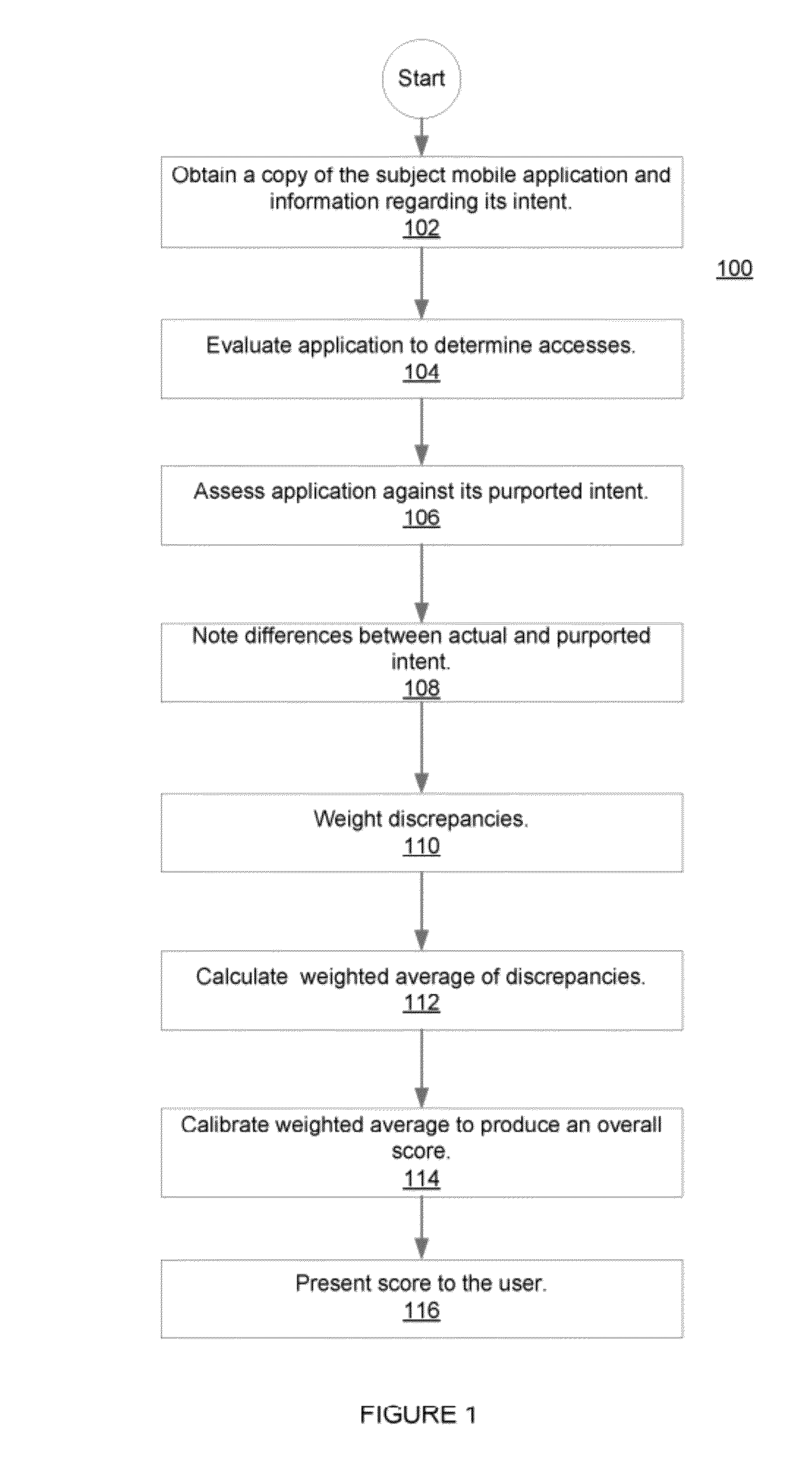
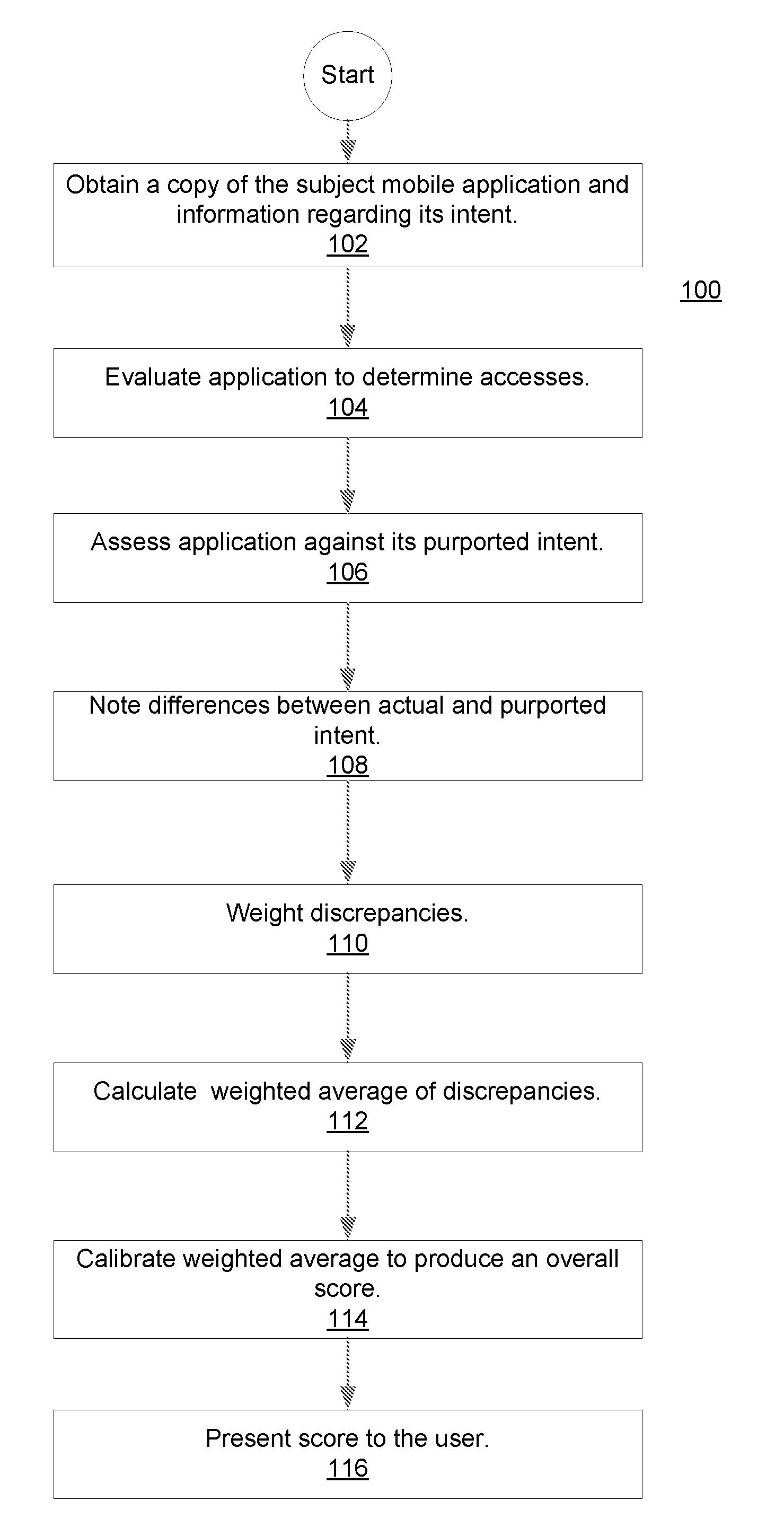
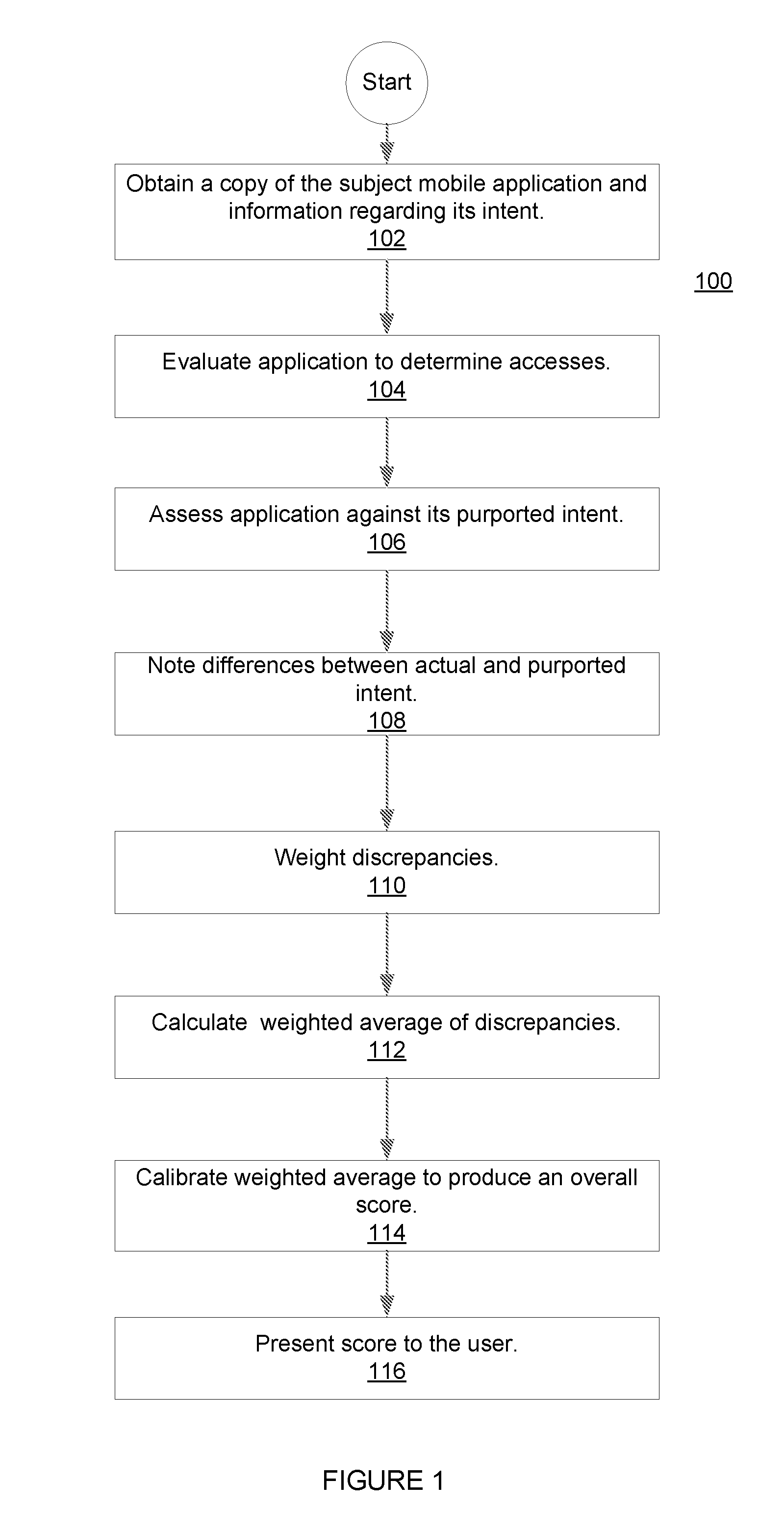
Methods and systems for rating privacy risk of applications for smart phones and other mobile platforms
InactiveUS20120110674A1Better-informed decisionService provisioningMemory loss protectionInternet privacyUser privacy
Methods and systems for evaluating and rating privacy risks posed by applications intended for deployment on mobile platforms. Validating the “intent” of a mobile platform application vis-à-vis its impact on user privacy, as viewed from an end-user's perspective allows those end-users to make better-informed decisions concerning the downloading, installation and / or operation of mobile platform applications. In making such assessments user preferences can be taken into account. Privacy scores are provided through sales channels for the applications, thereby affording potential users the opportunity to assess whether they wish to incur the associated privacy risk, before purchasing a subject application.
Owner:NCC GRP SECURITY SERVICES
Service profile management with user preference, adaptive policy, network neutrality and user privacy for intermediate networking devices
InactiveUS20100188992A1Error preventionFrequency-division multiplex detailsService profileCommunications system
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, an intermediate networking device provides a service intermediary or intermediate connection between a network and one or more communications devices; implements a service profile set for assisting control of the intermediate networking device use of a service set on the network, wherein the service profile set includes one or more service profiles, each profile being associated with either the intermediate networking device or a communications device, each profile further including a plurality of service policy settings; and monitors use of the service set based on the service profile set, in which the implementation of the first service profile set is verified.
Owner:ITSON
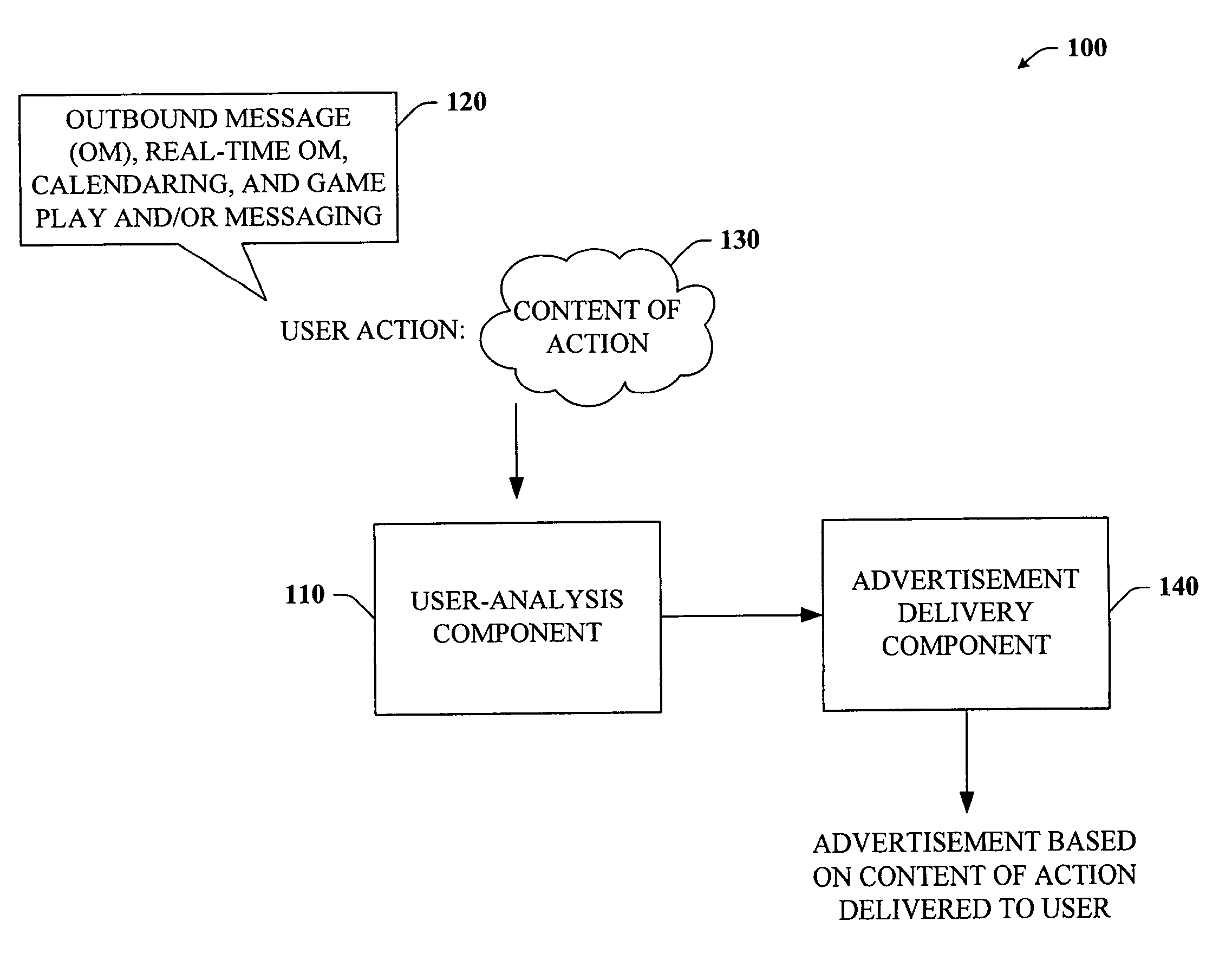
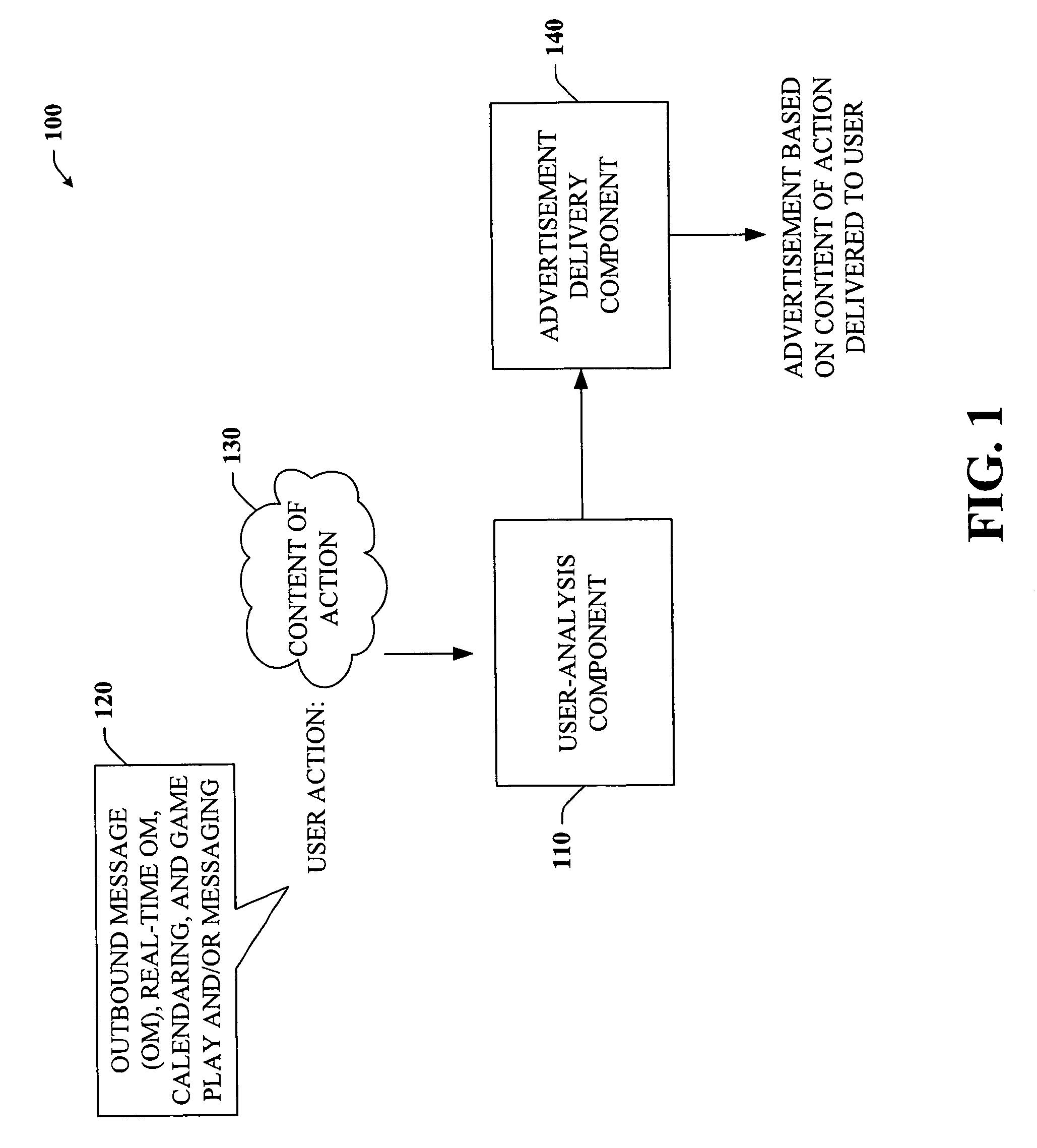
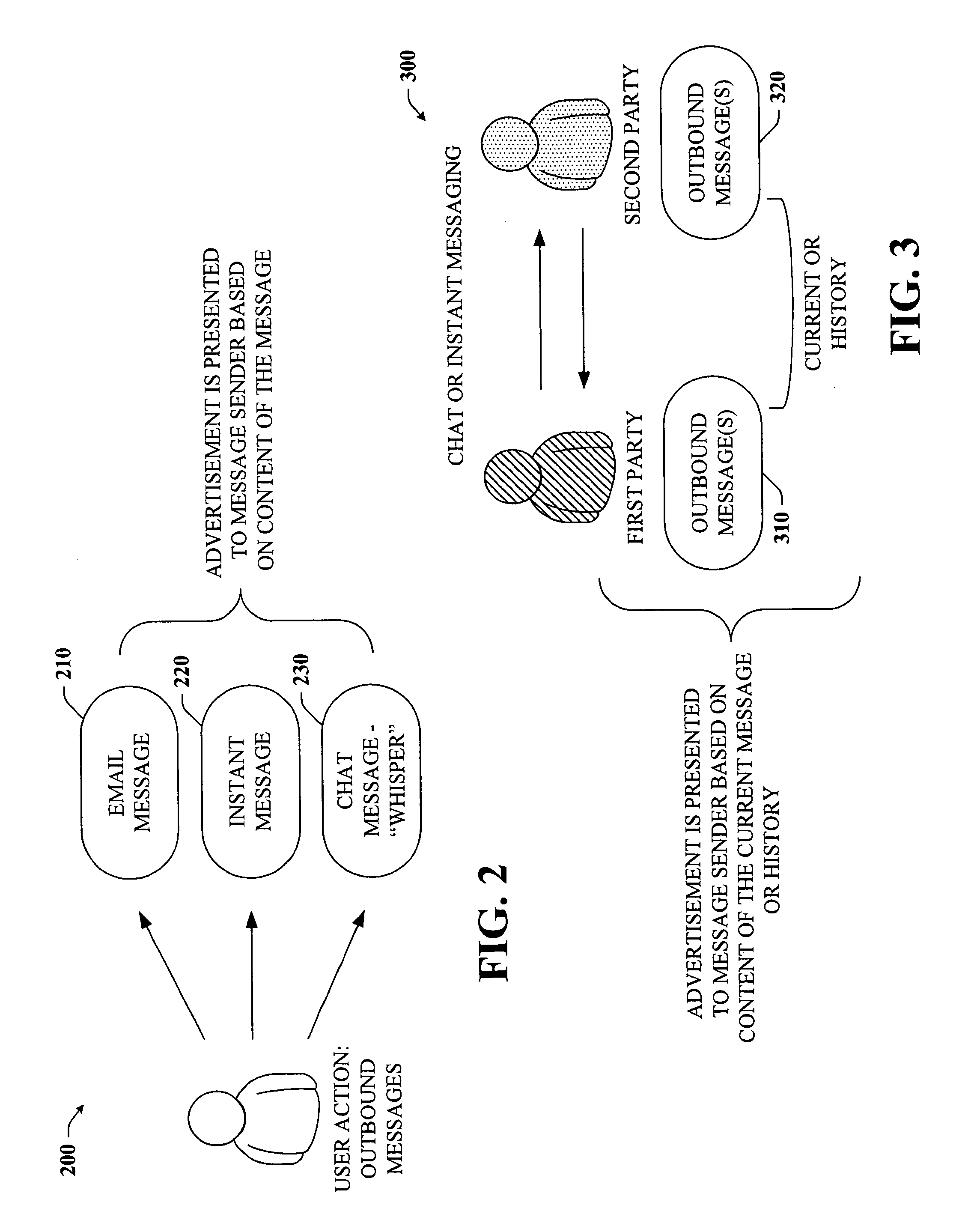
Content-targeted advertising for interactive computer-based applications
InactiveUS20060167747A1Reduce user experienceUser privacy is enhancedMarketingUser privacyContent analytics
The subject invention provides a unique system and method that facilitates providing content-targeted advertising to a user based at least in part on the content of a user action. The user action can be performed in connection with an outbound messaging system, a real-time messaging system such as a chat or instant messaging, a game environment, and / or calendaring system. The system and method analyze at the least the content of an outbound message and then present a content-targeted advertisement based on the content of the message. The same can be done with respect to calendar entries. However, outbound and inbound calendar entries, invitations, and responses to invitations can be analyzed for content and have content-targeted advertisements presented to the sender or receiver of such items. User privacy can be maintained and / or increased by allowing a user to opt out of content-targeting advertisements. Reasons for being targeted can also be provided to the user.
Owner:MICROSOFT TECH LICENSING LLC
Network based service profile management with user preference, adaptive policy, network neutrality, and user privacy
ActiveUS20100188990A1Error preventionFrequency-division multiplex detailsService profileControl communications
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a network device implements a service profile for assisting control of a communications device use of a service on a network, in which the service profile includes service policy settings for the communications device; monitors use of the service by the communications device based on the service profile; and modifies a service policy setting to achieve a service usage goal.
Owner:HEADWATER RES LLC
Device assisted service profile management with user preference, adaptive policy, network neutrality, and user privacy
InactiveUS20100192170A1Analogue secracy/subscription systemsTechnology managementService profileControl communications
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service profile for assisting control of the communications device use of a service on a network, in which the service profile includes service policy settings; monitors use of the service based on the service profile; and modifies a service policy setting to achieve a service usage goal.
Owner:HEADWATER RES LLC
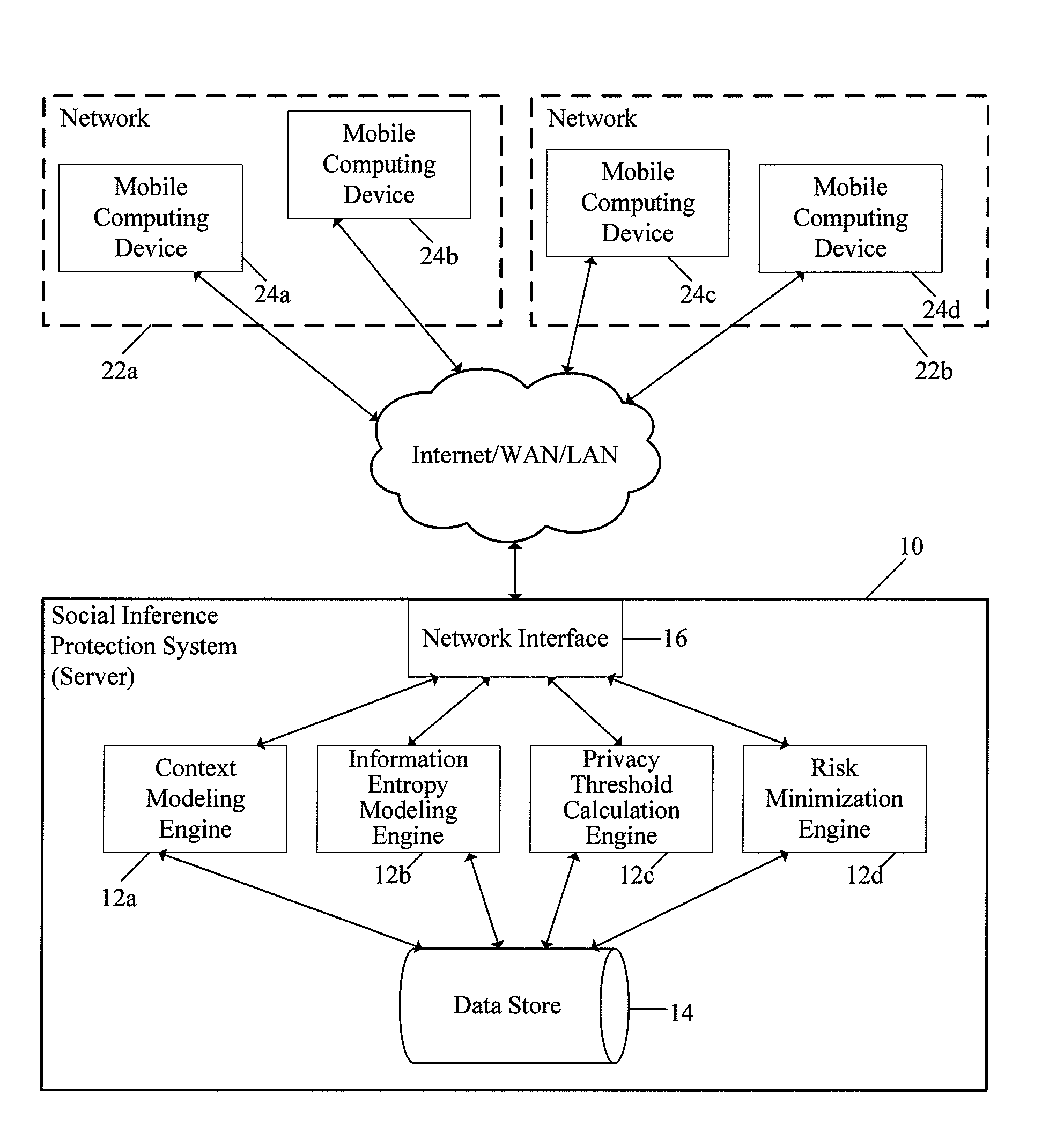
System and method for protecting user privacy using social inference protection techniques
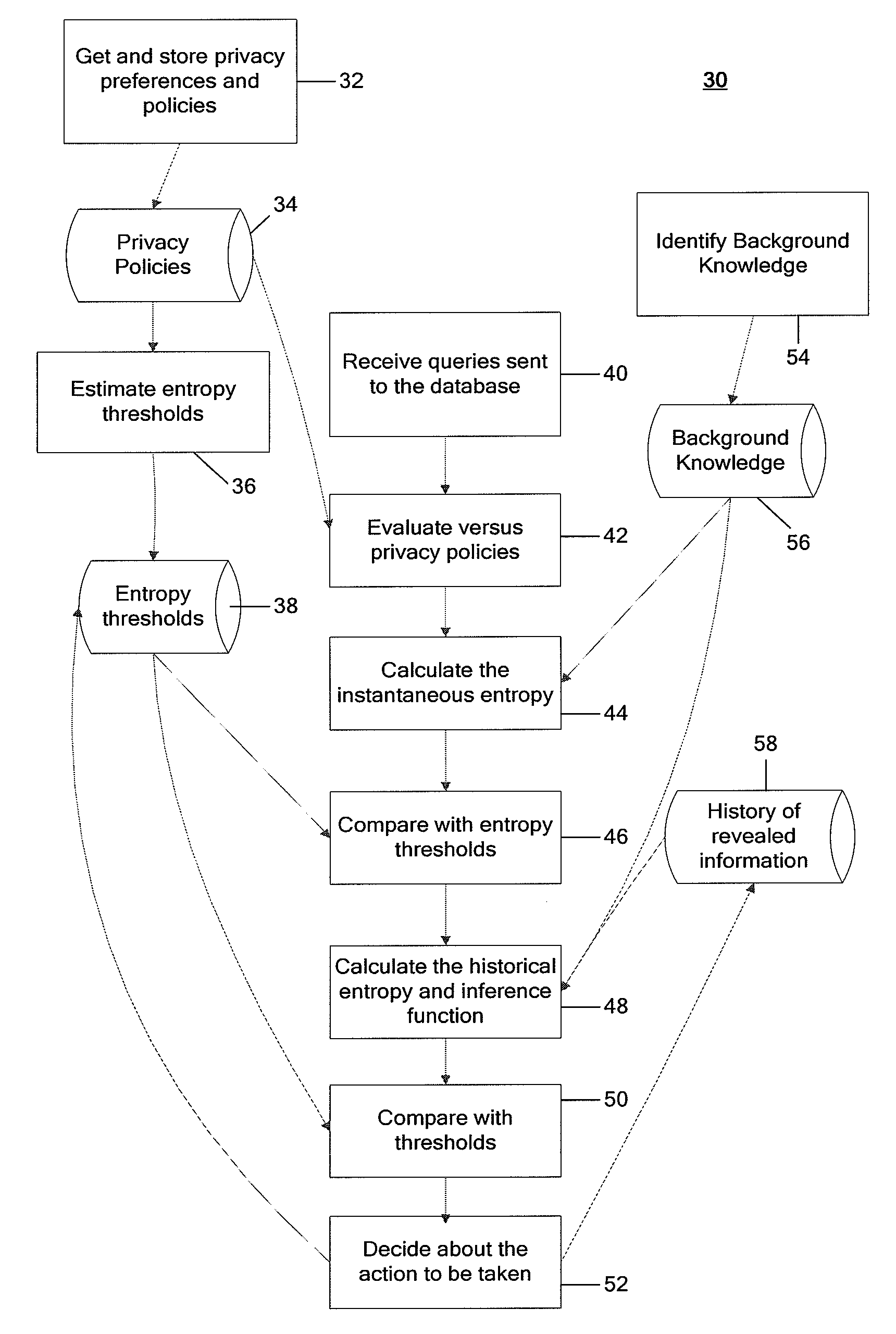
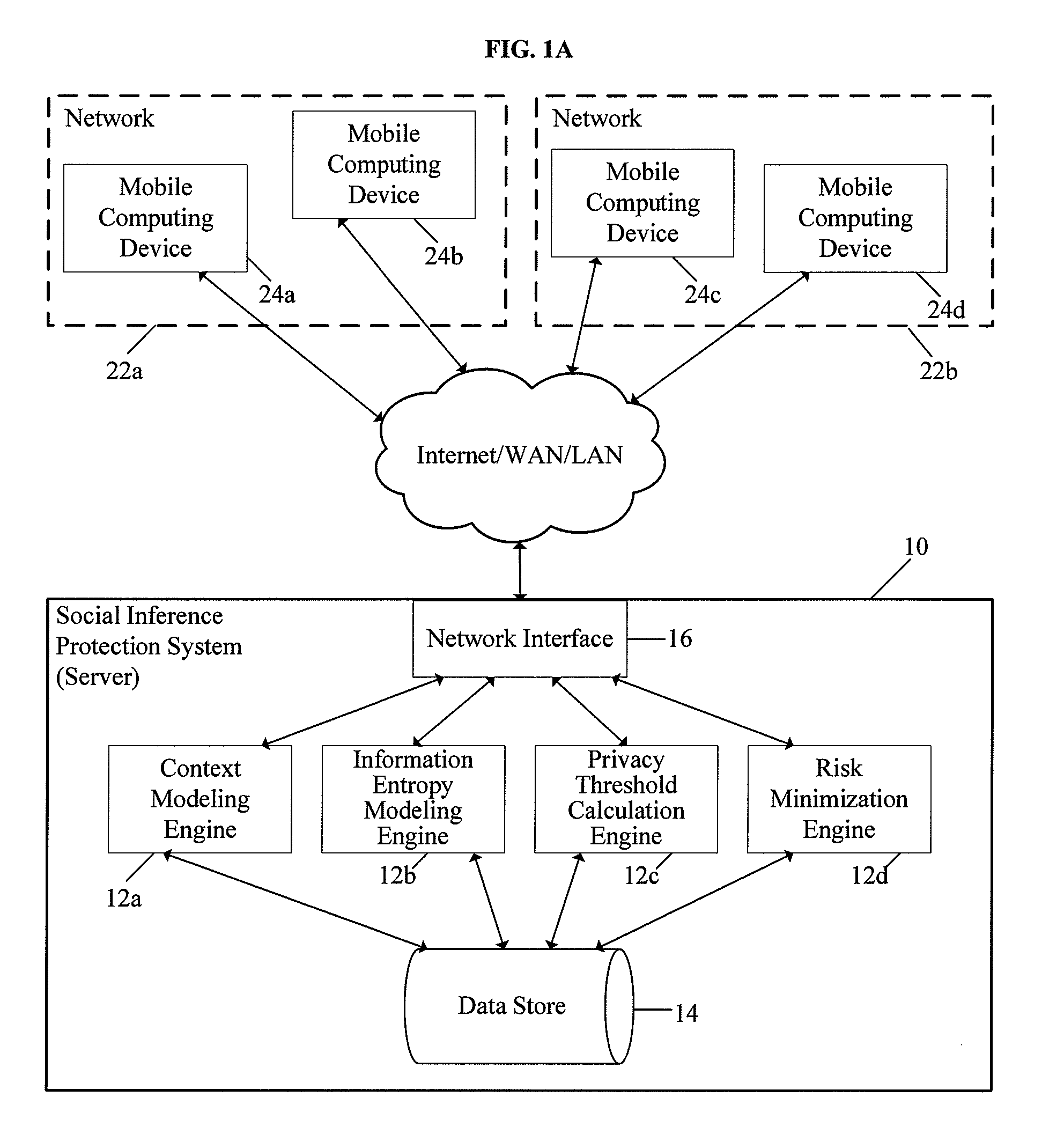
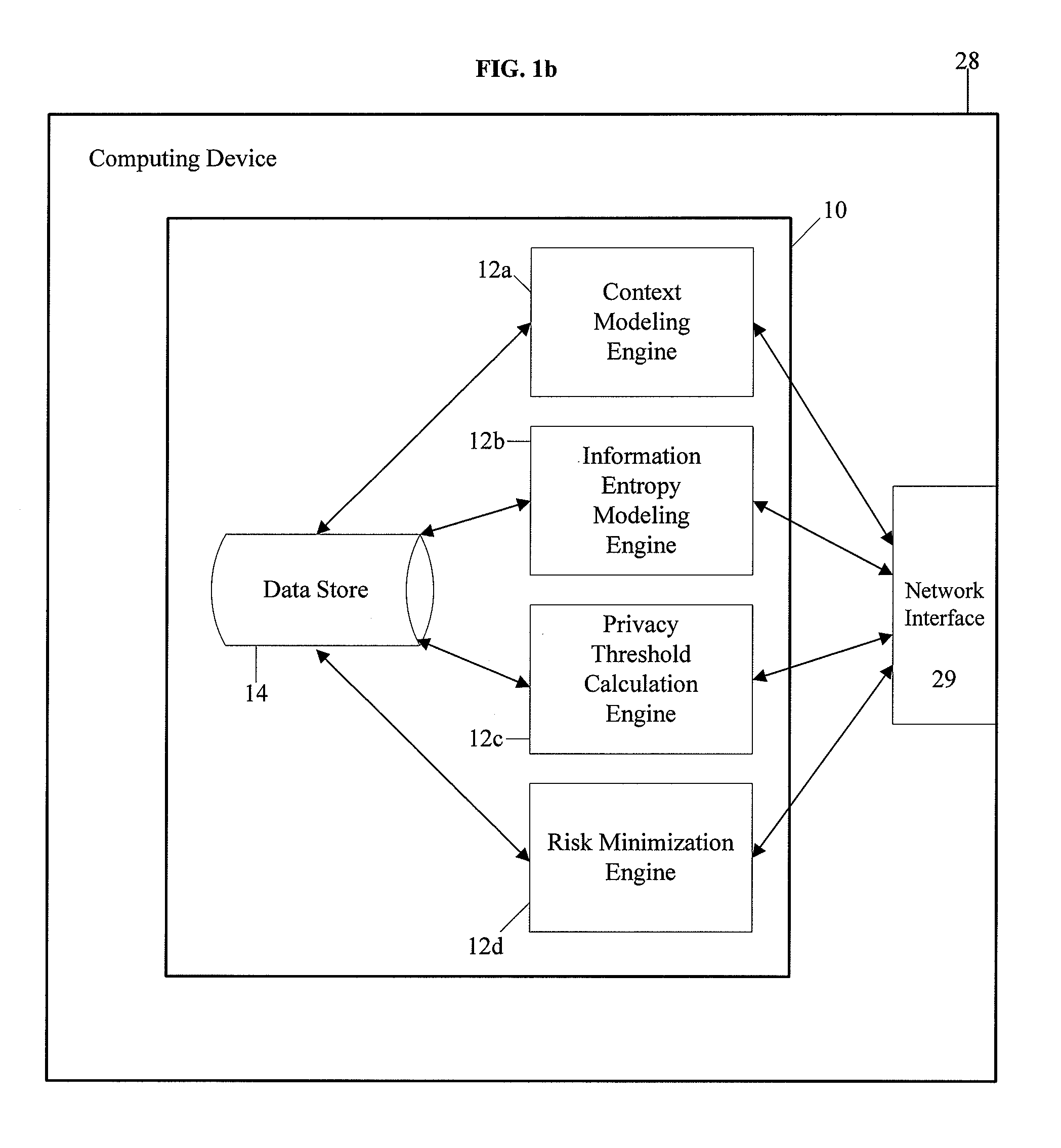
InactiveUS8504481B2Minimize privacy riskInhibit exchangeDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyUser privacy
A system and method for protecting user privacy using social inference protection techniques is provided. The system executes a plurality of software modules which model of background knowledge associated with one or more users of the mobile computing devices; estimate information entropy of a user attribute which could include identity, location, profile information, etc.; utilize the information entropy models to predict the social inference risk; and minimize privacy risks by taking a protective action after detecting a high risk.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
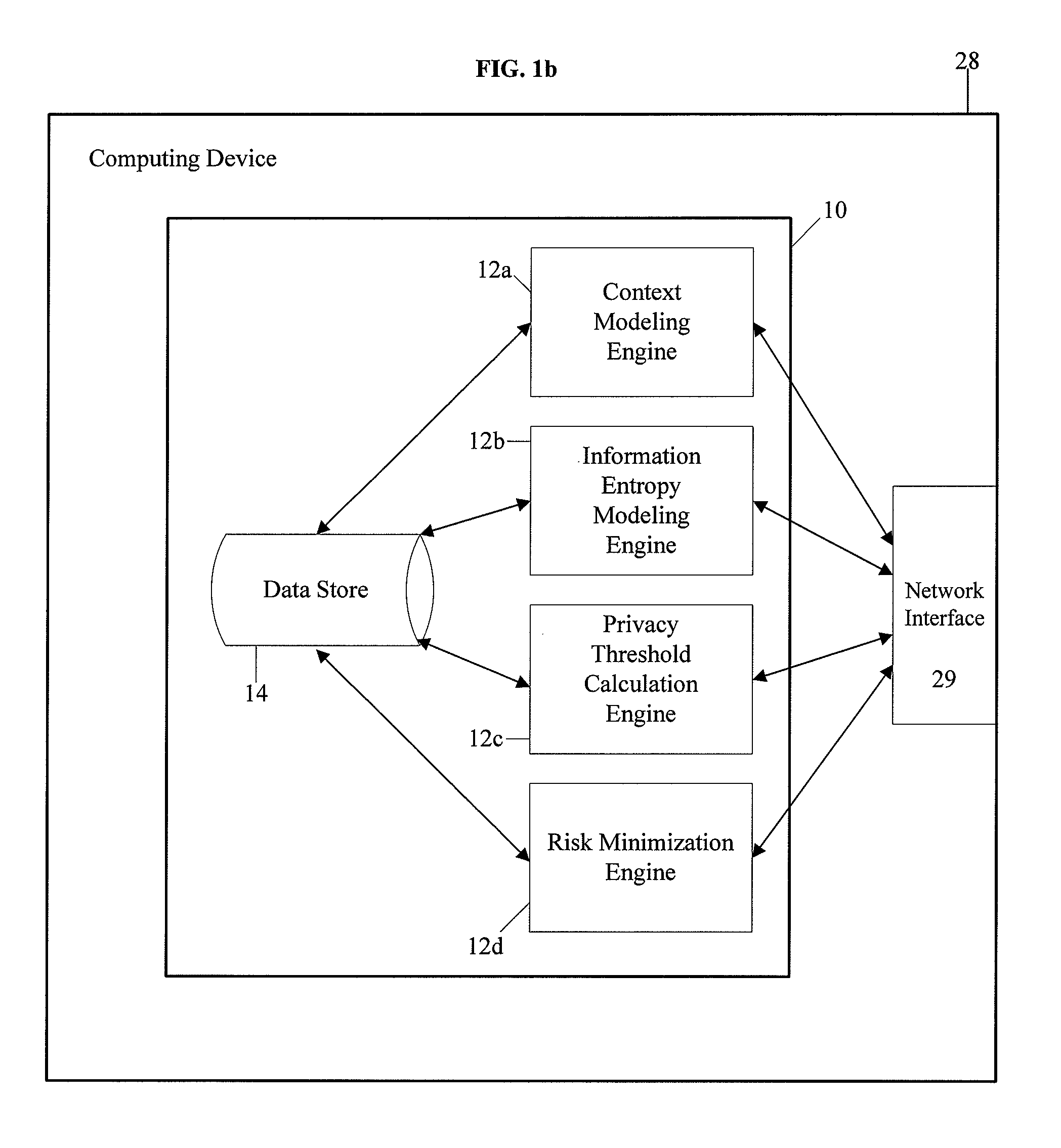
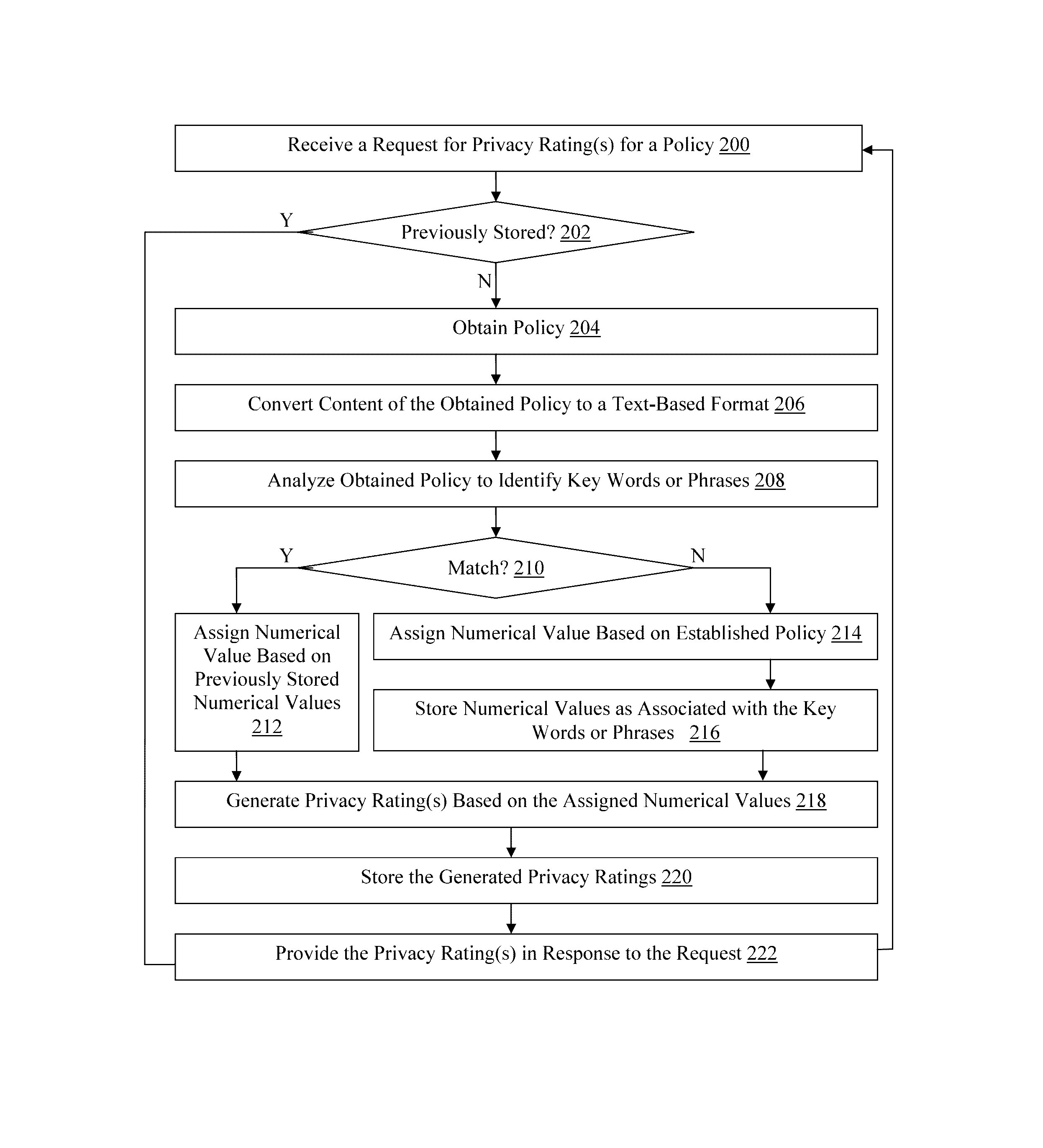
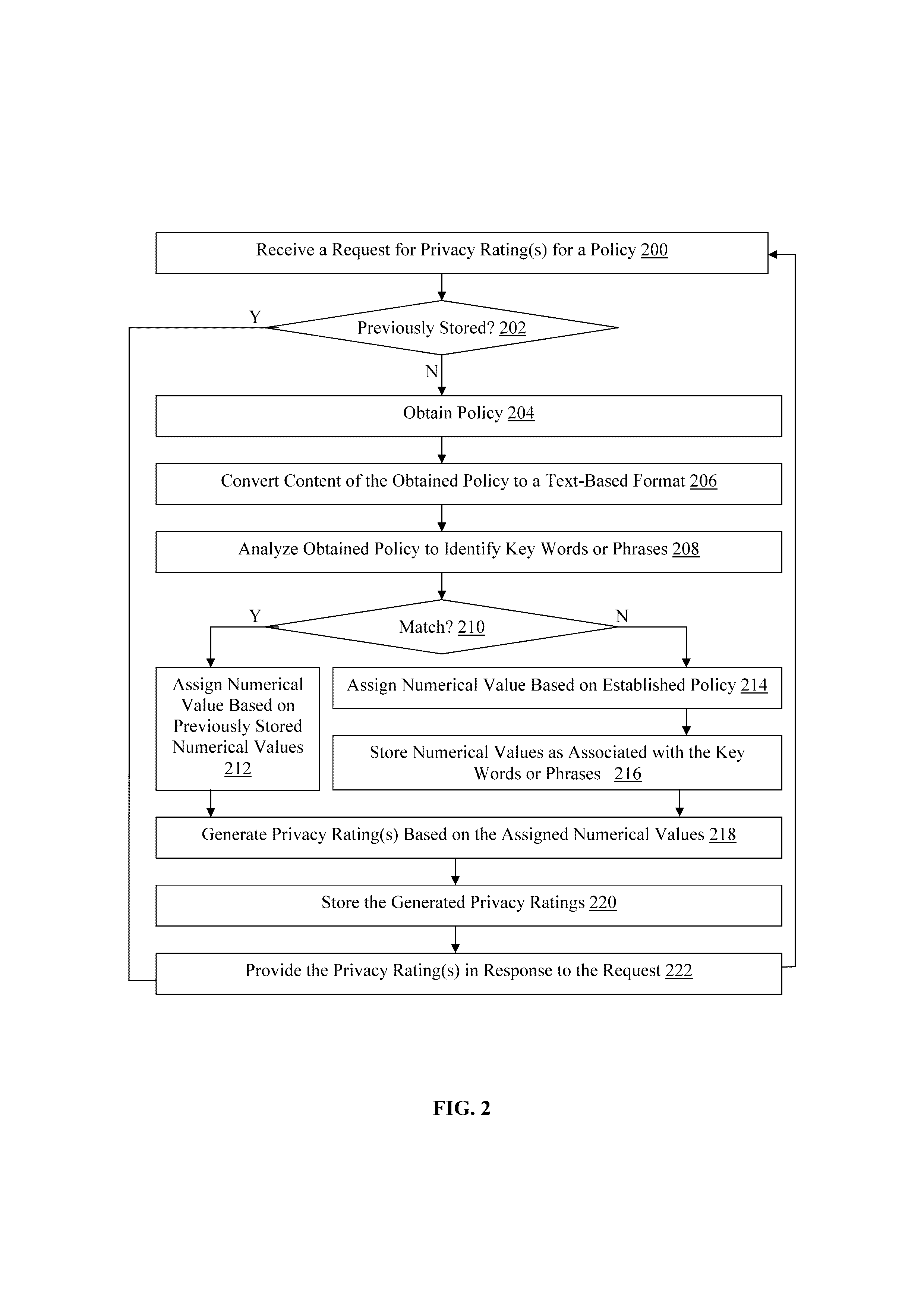
Methods and devices for analyzing user privacy based on a user's online presence
A method, non-transitory computer readable medium, and policy rating server device that receives a request from a client computing device for one or more privacy ratings. The request identifies at least one application, such as an application installed on the client computing device for example. A policy associated with the identified application is obtained. The obtained policy is analyzed to identify a plurality of key words or phrases associated with use by the at least one application of functionality of, or personal information stored on, the client computing device. One or more privacy ratings are generated based on numerical values assigned to each of the identified key words or phrases. The generated one or more privacy ratings are output to the client computing device in response to the request.
Owner:THE PRIVACY FACTOR
Deactivating a data tag for user privacy or tamper-evident packaging
ActiveUS20050242957A1Facilitate communicationBurglar alarm by openingAntenna arraysUser privacyComputer science
Deactivating a data tag attached to packaging for user privacy or tamper-evident reasons. A data circuit stores identification information. A plurality of antennae is coupled to the data circuit. At least one antenna of the plurality of antennae is a removable antenna capable of wireless signal transmission at a first range such that removal of the antenna substantially prevents communication of the identification information via the removed antenna and permits communication of the identification information via another antenna of the plurality of antennae at a second range relatively smaller than the first range.
Owner:BUFFALO PATENTS LLC
Database access system
InactiveUS7801896B2Increased formationGood user interfaceDigital data information retrievalAdvertisementsAnonymityPopulation statistics
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
Method for implementing an intelligent content rating middleware platform and gateway system
InactiveUS20050135264A1Highly scalable, manageable and reliableMetering/charging/biilling arrangementsError preventionCyber operationsMiddleware
The method for implementing an Intelligent Content Rating middleware platform and gateway system disclosed herewith provides telecommunications carriers and network operators with the ability to define routing and actions based on HTTP / SIP based content and subscriber context through a powerful, extensible Layer 4-7 switching fabric technology. The invention mediates communications between applications and networks for IP packet flows, personal messaging, location-based services and billing. Furthermore, it enables advanced context-sensitive dialogue scenarios with the wireless subscriber such as, but not limited to, Advice-of-Charge dialogues. The art permits telecommunications network operators and like entities to introduce real-time rating of data services for both prepaid and post-paid subscribers. Further advances in the art include the validation of digital signatures, combined with authentication and non-repudiation techniques to ensure subscriber privacy remains protected.
Owner:REDKNEE INC
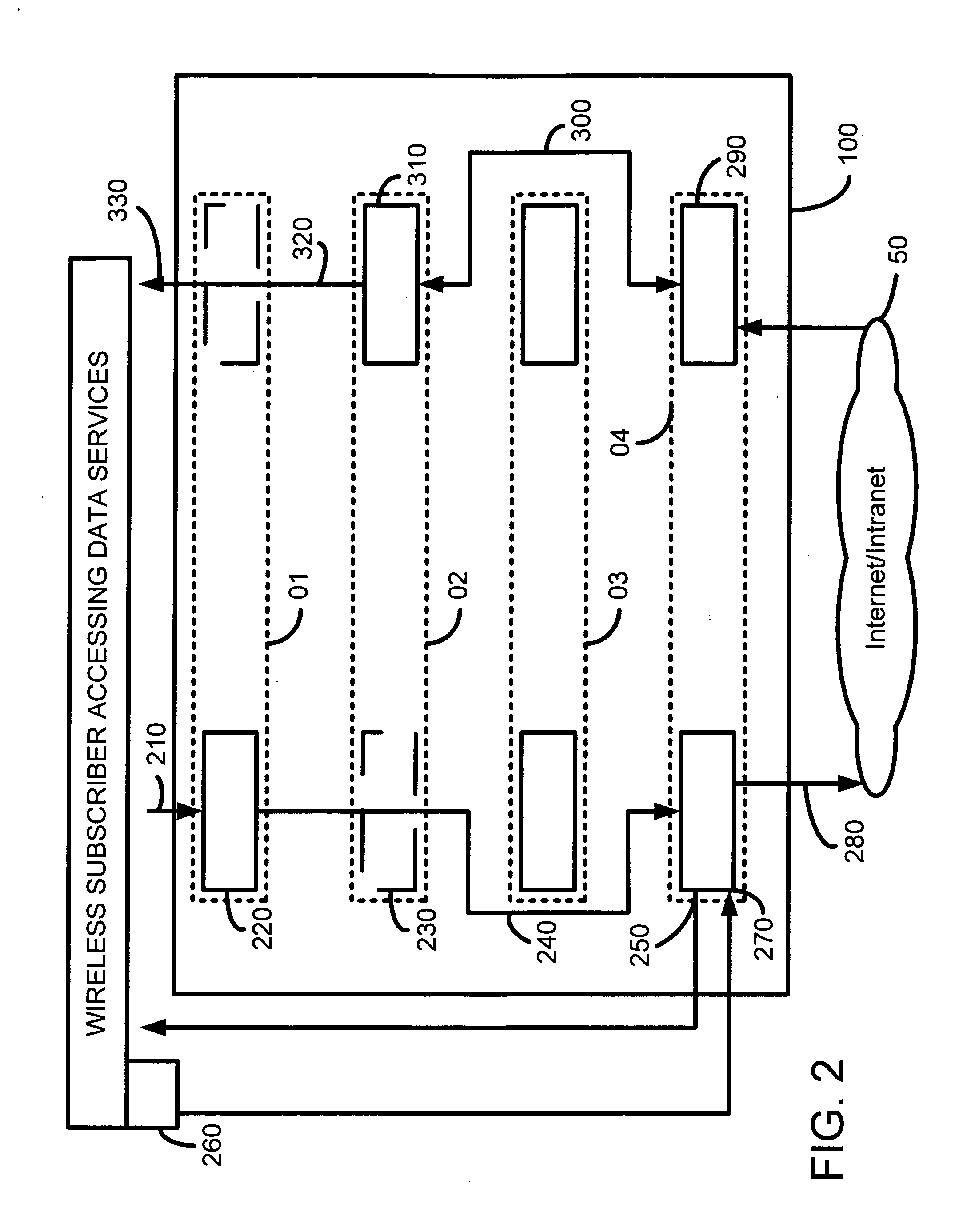
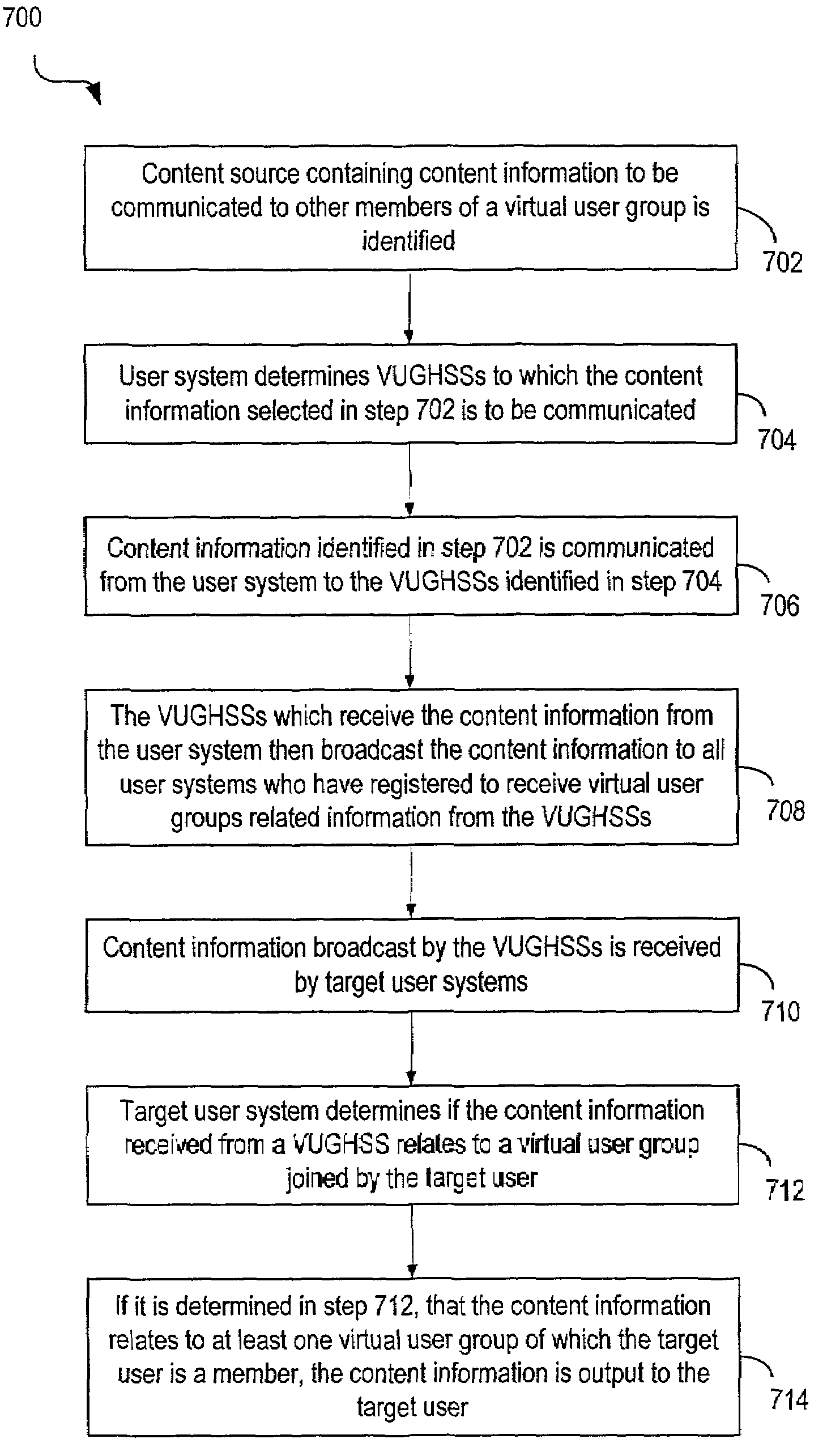
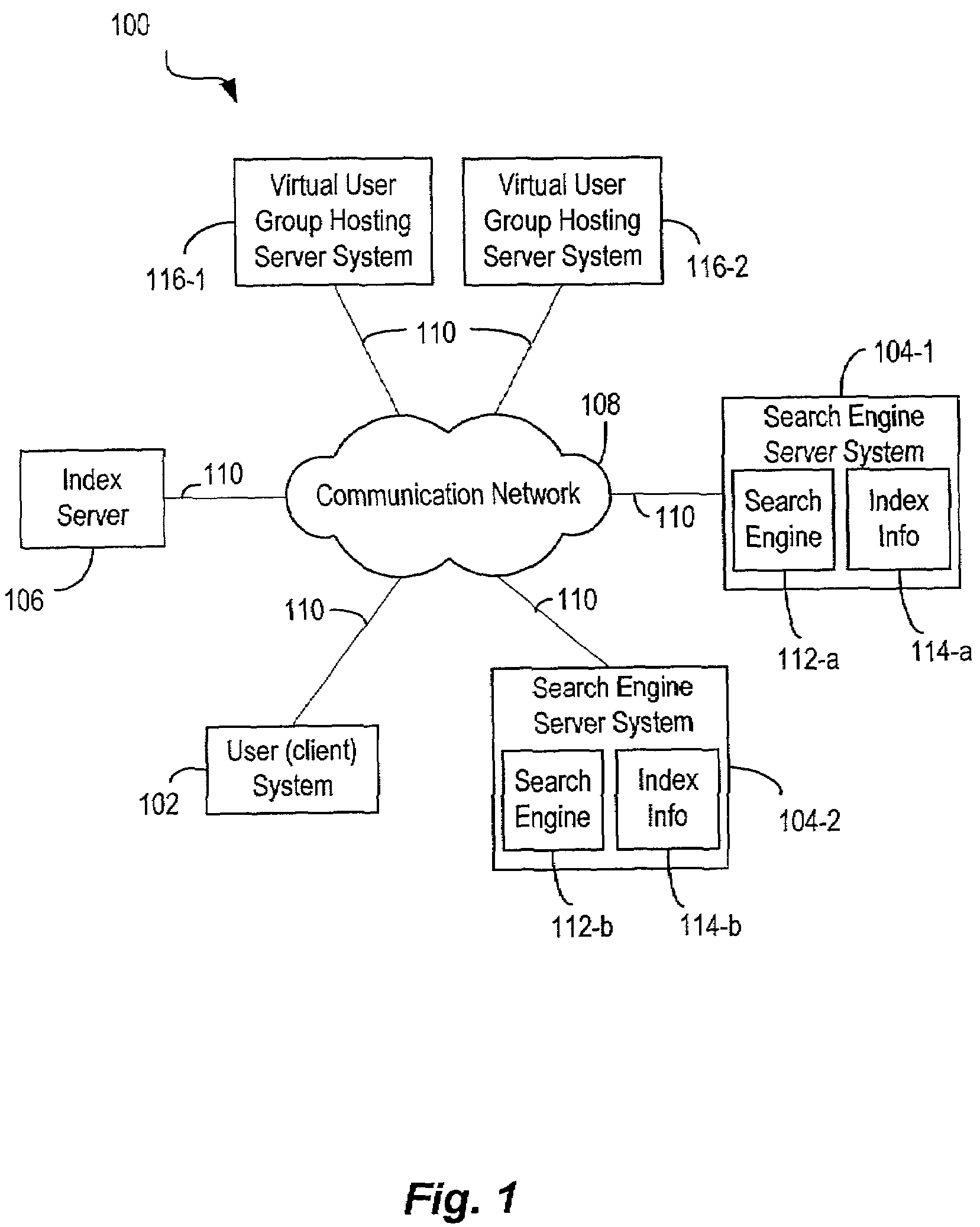
Techniques for sharing content information with members of a virtual user group in a network environment without compromising user privacy
InactiveUS7177904B1Protect user privacyWithout compromising the user's privacyComputer security arrangementsMultiple digital computer combinationsRelevant informationVirtual user
Techniques for sharing content information between members of a virtual user group without compromising the privacy of the members. A user can identify content information to be shared with other members of a virtual user group using a user computer system. The content information is then communicated to the other members of the virtual user group and can be accessed by members of the virtual user group in such a manner that the privacy of the user and of the other members of the virtual user group is not compromised. The present invention preserves user privacy by controlling and minimizing the amount of user-related information available / accessible to server systems hosting the virtual user groups.
Owner:MICRO FOCUS LLC
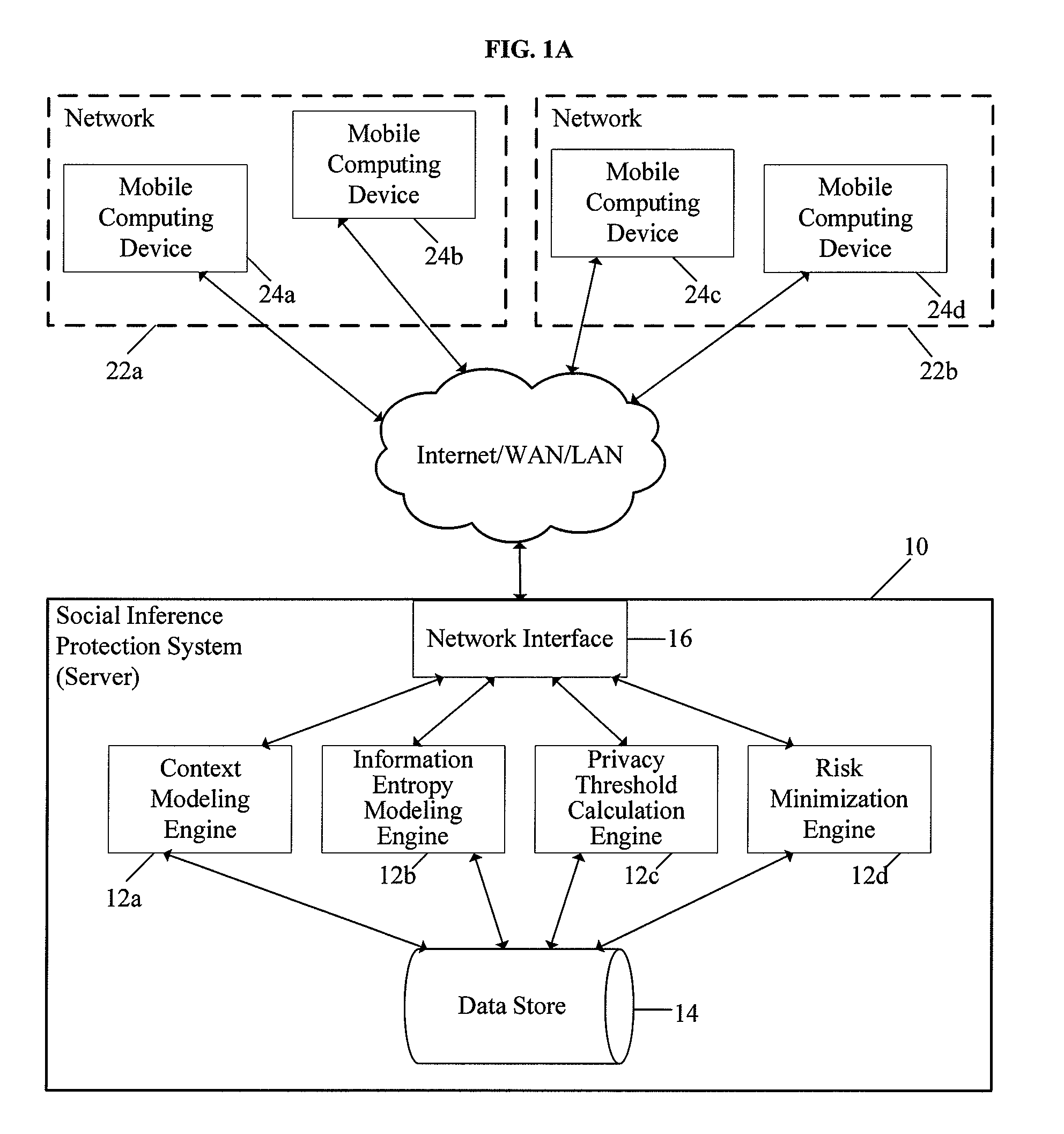
System and Method for Protecting User Privacy Using Social Inference Protection Techniques
InactiveUS20100024042A1Minimize privacy riskInhibit exchangeDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyUser privacy
A system and method for protecting user privacy using social inference protection techniques is provided. The system executes a plurality of software modules which model of background knowledge associated with one or more users of the mobile computing devices; estimate information entropy of a user attribute which could include identity, location, profile information, etc.; utilize the information entropy models to predict the social inference risk; and minimize privacy risks by taking a protective action after detecting a high risk.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
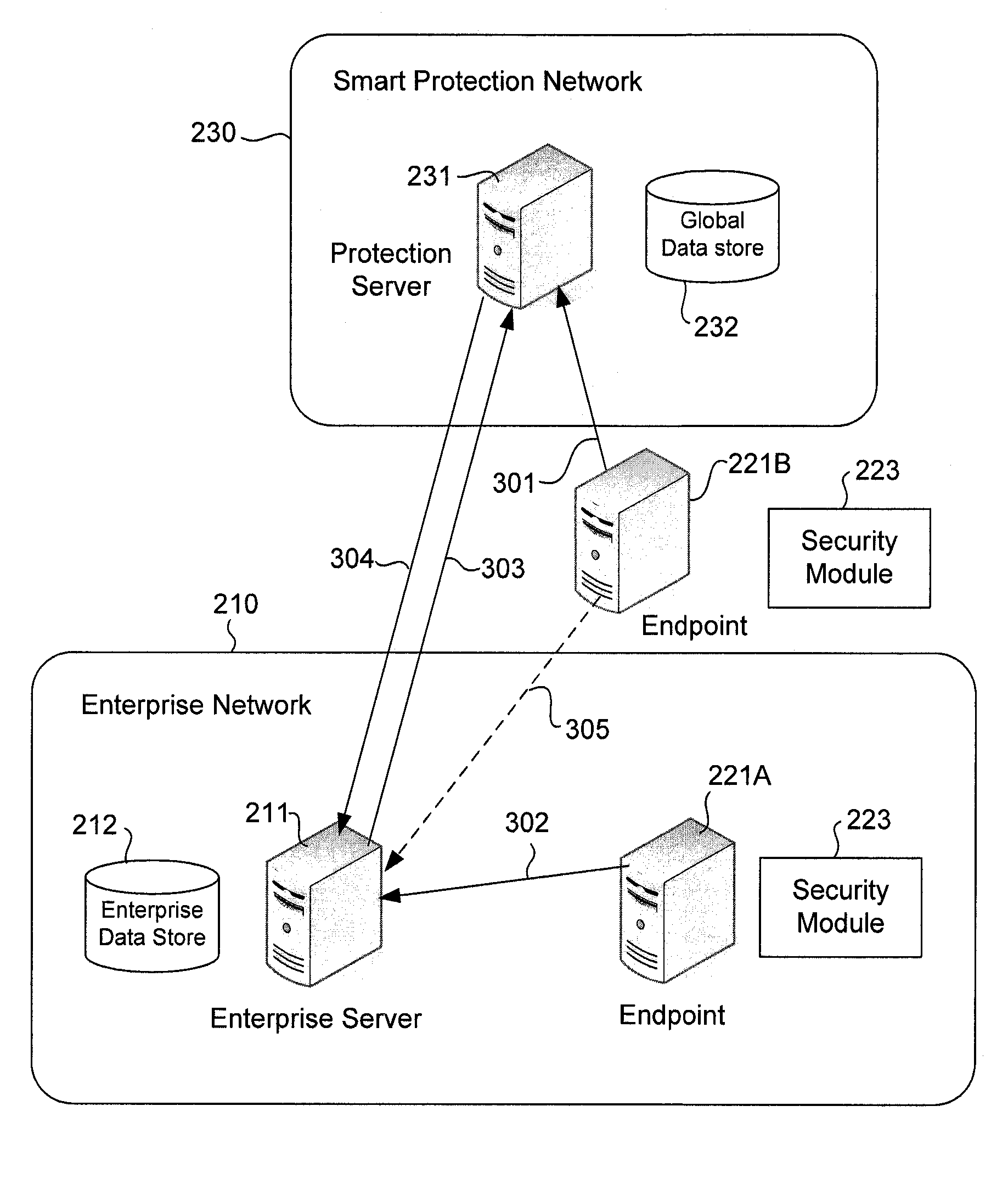
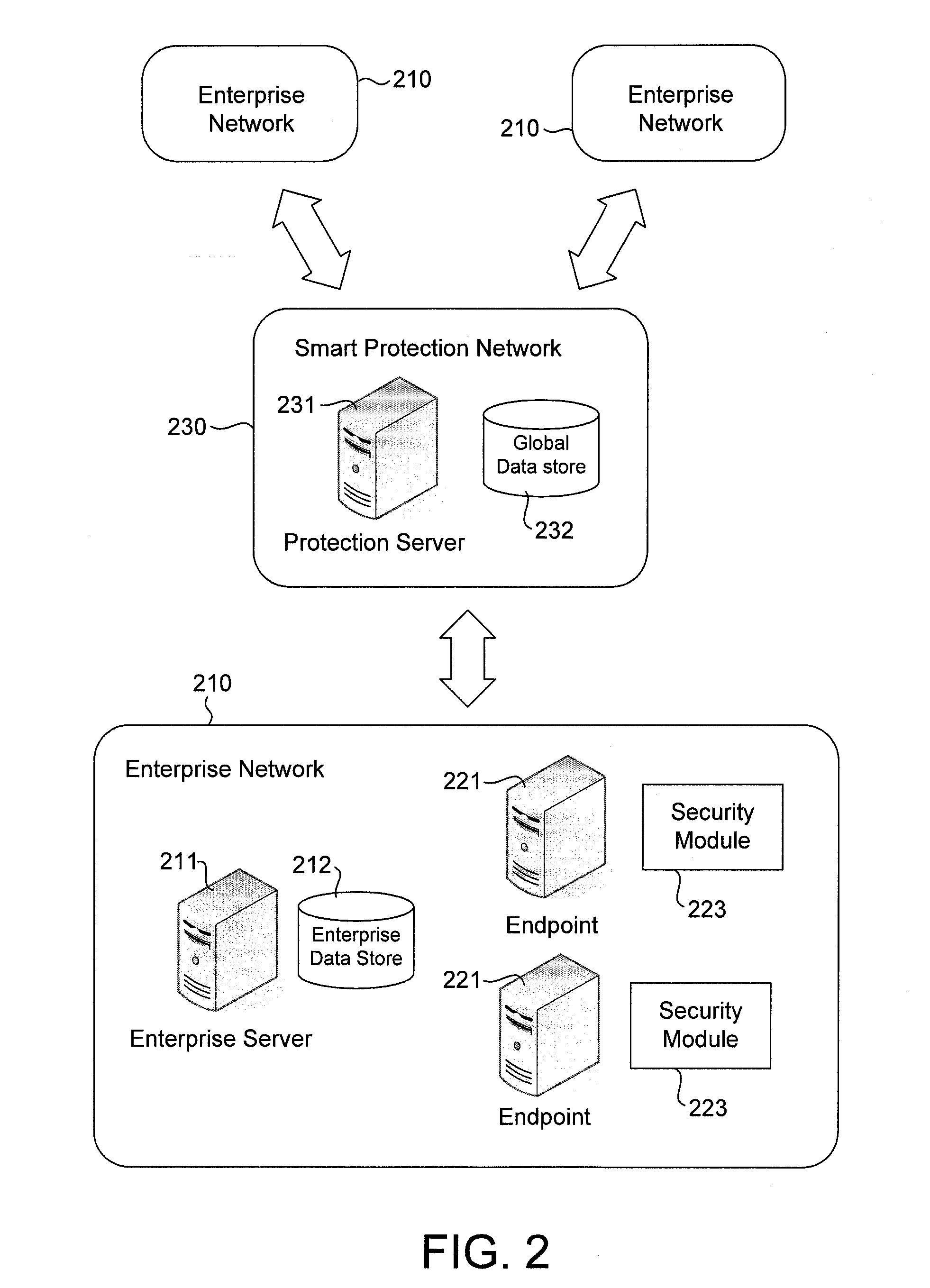
Computer security threat data collection and aggregation with user privacy protection
An endpoint computer in an enterprise network is configured to detect computer security threat events, such as presence of a computer virus. Upon detection of a threat event, the endpoint computer generates computer security threat data for the threat event. The threat data may include user identifiable data that can be used to identify a user in the enterprise network. The endpoint computer encrypts the user identifiable data prior to sending the threat data to a smart protection network or to an enterprise server where threat data from various enterprise networks are collected for analysis. The endpoint computer may also encrypt an identifier for the threat data and provide the encrypted identifier to the smart protection network and to an enterprise server in the enterprise network. The enterprise server may use the encrypted identifier to retrieve the threat data from the smart protection network to generate user-specific reports.
Owner:TREND MICRO INC
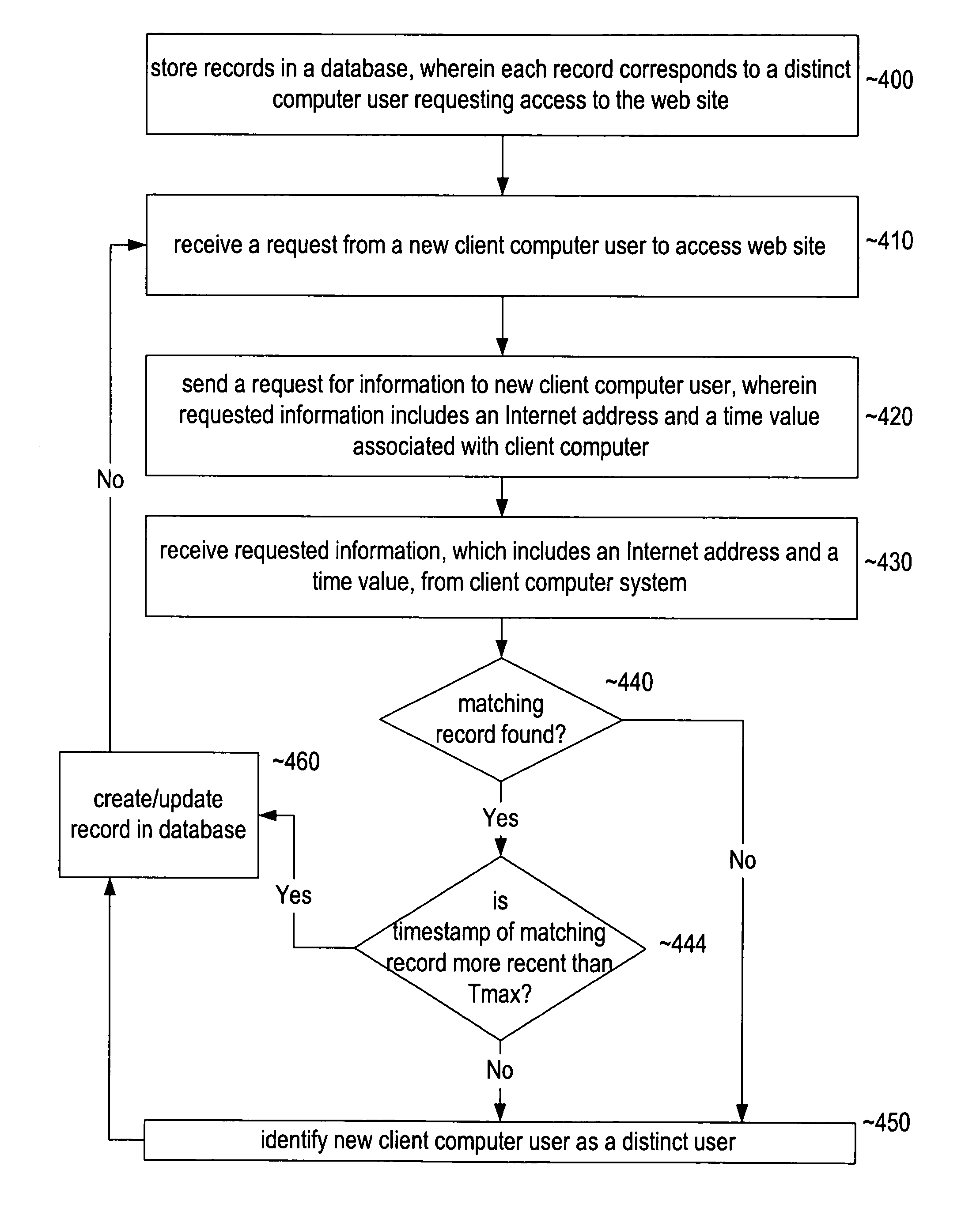
System and method for identifying individual users accessing a web site
ActiveUS7962603B1Digital computer detailsWebsite content managementUser identifierApplication software
An improved method and system for identifying individual users accessing a web site. A web site server is able to identify distinct users by using a unique identifier associated with each client computer system requesting access to the web site. The unique identifier comprises an Internet address, such as an Internet Protocol (IP) address, and a time value associated with each client computer system requesting access to the web site. On starting up a web browser, an application program or browser plug-in may synchronize the internal clock included with the client computer system with a global time standard. The synchronized time value may be based on an event associated with the client computer system, such as the start of a web browser. A web site server may determine the uniqueness of the client computer system by comparing unique identifier records of users accessing the web site. A user may be identified as distinct if no matching record exists in the database. Multiple client computer systems having a common Internet address may be identified by using this method. Users privacy is also protected as the unique identifiers are erased when the client computer system's user exits the web browser or powers down the computer.
Owner:NIHON DOT COM
Enhancing smart card usage for associating media content with households
InactiveUS7124938B1Improve privacyEasy to changeAcutation objectsPayment architectureUser privacySmart card security
Various enhancements are made to using smart cards that are associated with (or to be associated with) a household. In one embodiment, data that is expected to be of value to a user (e.g., electronic money) is attached to that user's smart card(s), thereby providing an incentive for the user to keep his or her smart card(s) secure. In another embodiment, the smart cards are used for parental control (e.g., by restricting the children's access to one or more of the smart cards). In yet another embodiment, smart cards are used to enhance user privacy by maintaining user-specific information on the smart cards (which can be de-coupled from the computing device whenever the user desires). In another embodiment, the boundaries of a network of computing devices are defined by multiple smart cards—any computing device to which a smart card is coupled is part of the network.
Owner:MICROSOFT TECH LICENSING LLC
Information content distribution based on privacy and/or personal information
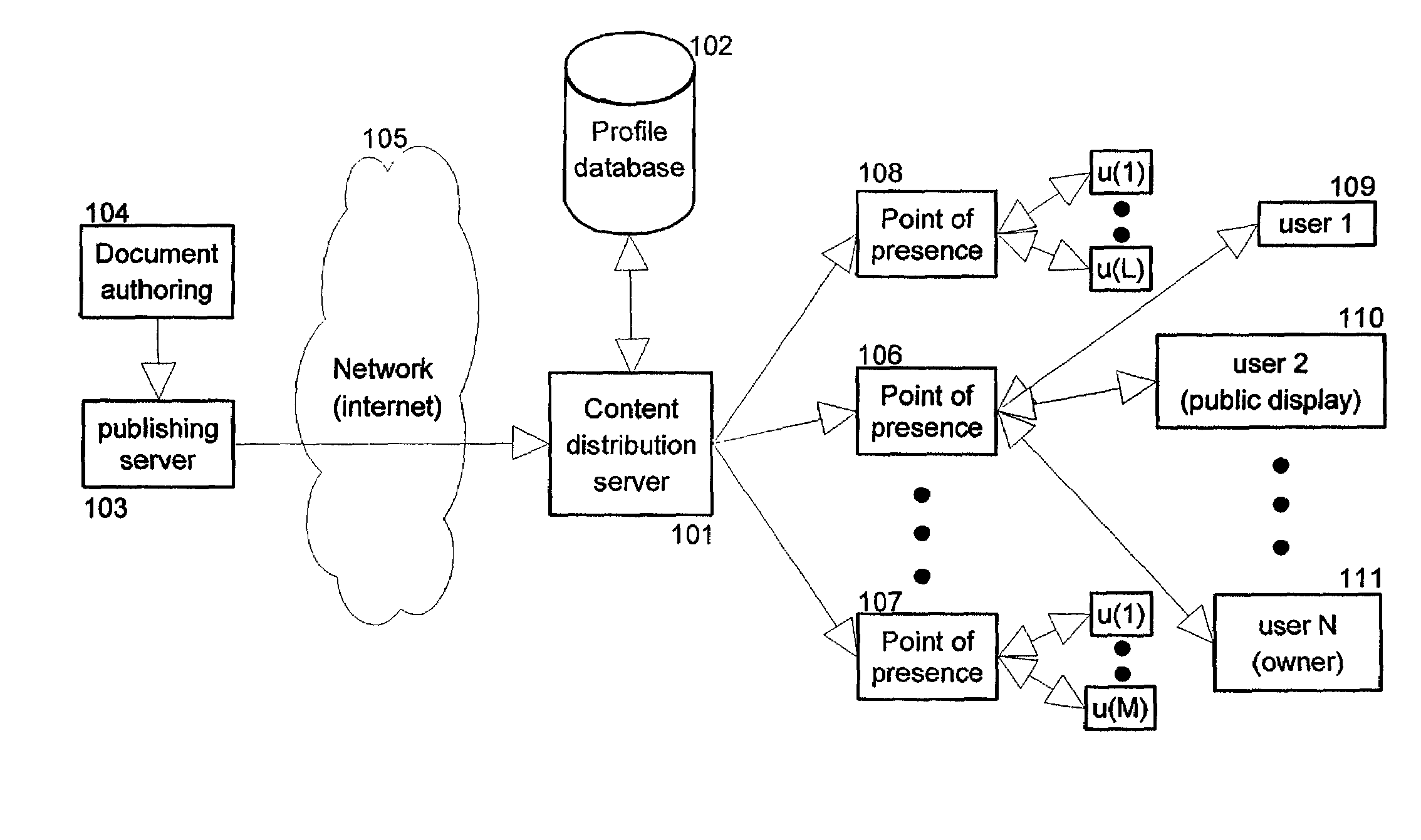
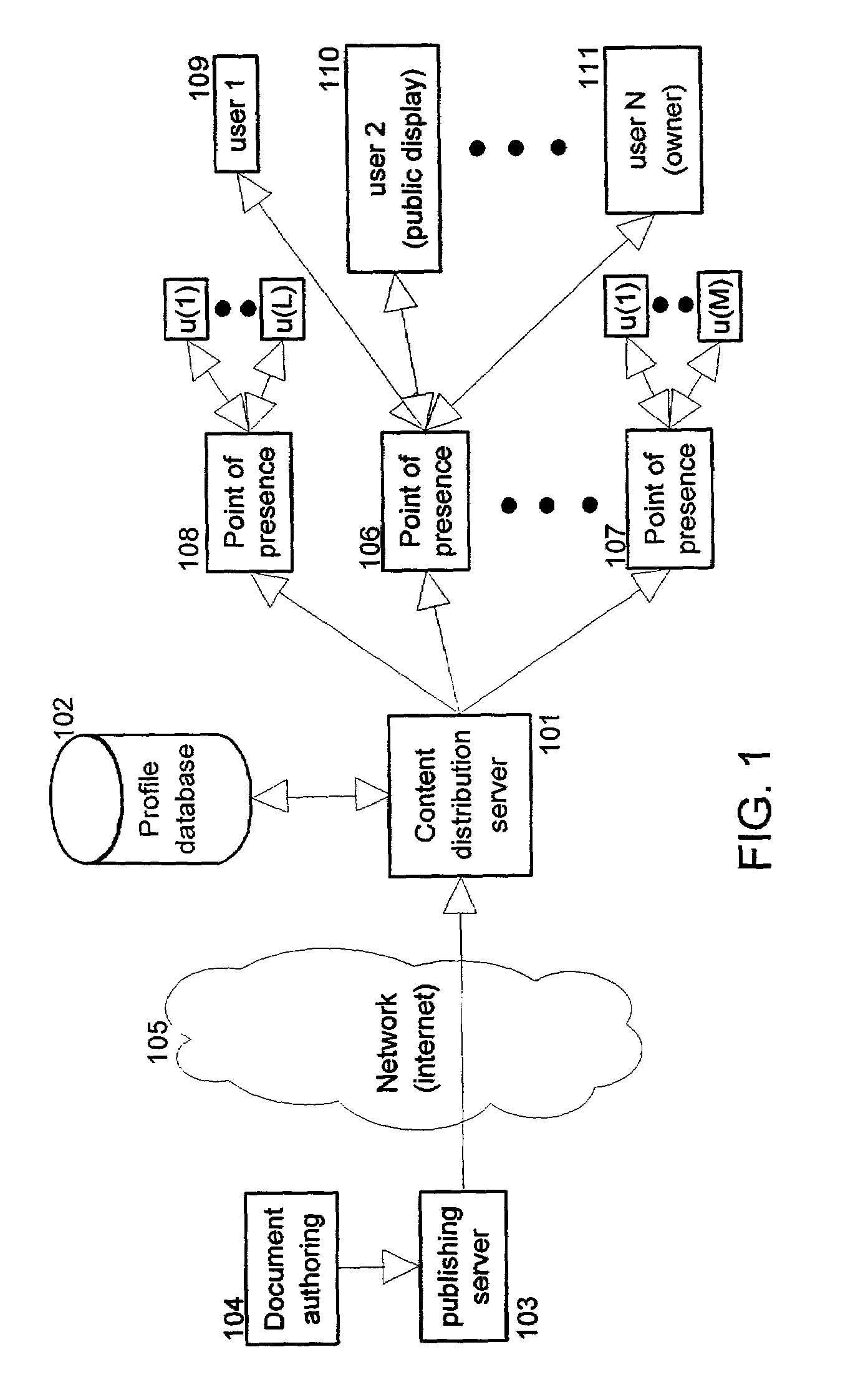
InactiveUS7162451B2Protect user privacyData representation error detection/correctionError preventionContent distributionPublic place
The present invention provides methods and apparatus to protect user privacy while accessing information in public places, using both public and personal devices. This is achieved by employing a mechanism that prevents private information from being displayed on public devices. Instead, this type of information is made available only to a user's personal device(s) that the user carries and / or trusts. An example embodiment of the invention shows relevant parts of the information content, referred to also as information documents or simply documents, to multiple devices based on privacy level and user preferences. Embodiments of the present invention also provide personalized services based on privacy levels defined by users. These users can for example be customers of a retail store. The service provided is sometimes also based on user history of accessing information documents. It permits personalized information to be sent to a customer's personal device.
Owner:IBM CORP
Mobile terminal security certification method and system and mobile terminal
InactiveCN104050402AImprove experienceEnsure safetyInput/output for user-computer interactionDigital data authenticationUser privacyComputer terminal
The invention provides a mobile terminal security certification method and system and a mobile terminal, wherein the method comprises the steps that the mobile terminal obtains first gesture information and receives security certification information sent by a wearable device; the mobile terminal carries out identity authentication on the wearable device according to the security certification information and authenticates the first gesture information; if the wearable device passes the identity authentication and the first gesture information passes the authentication, the wearable device passes the security certification of the mobile terminal. By applying the mobile terminal security certification method disclosed by the embodiment of the invention, security of user data stored in the mobile terminal is guaranteed, the user privacy is avoided being leaked, and the user experience is enhanced.
Owner:SHENZHEN GOODIX TECH CO LTD
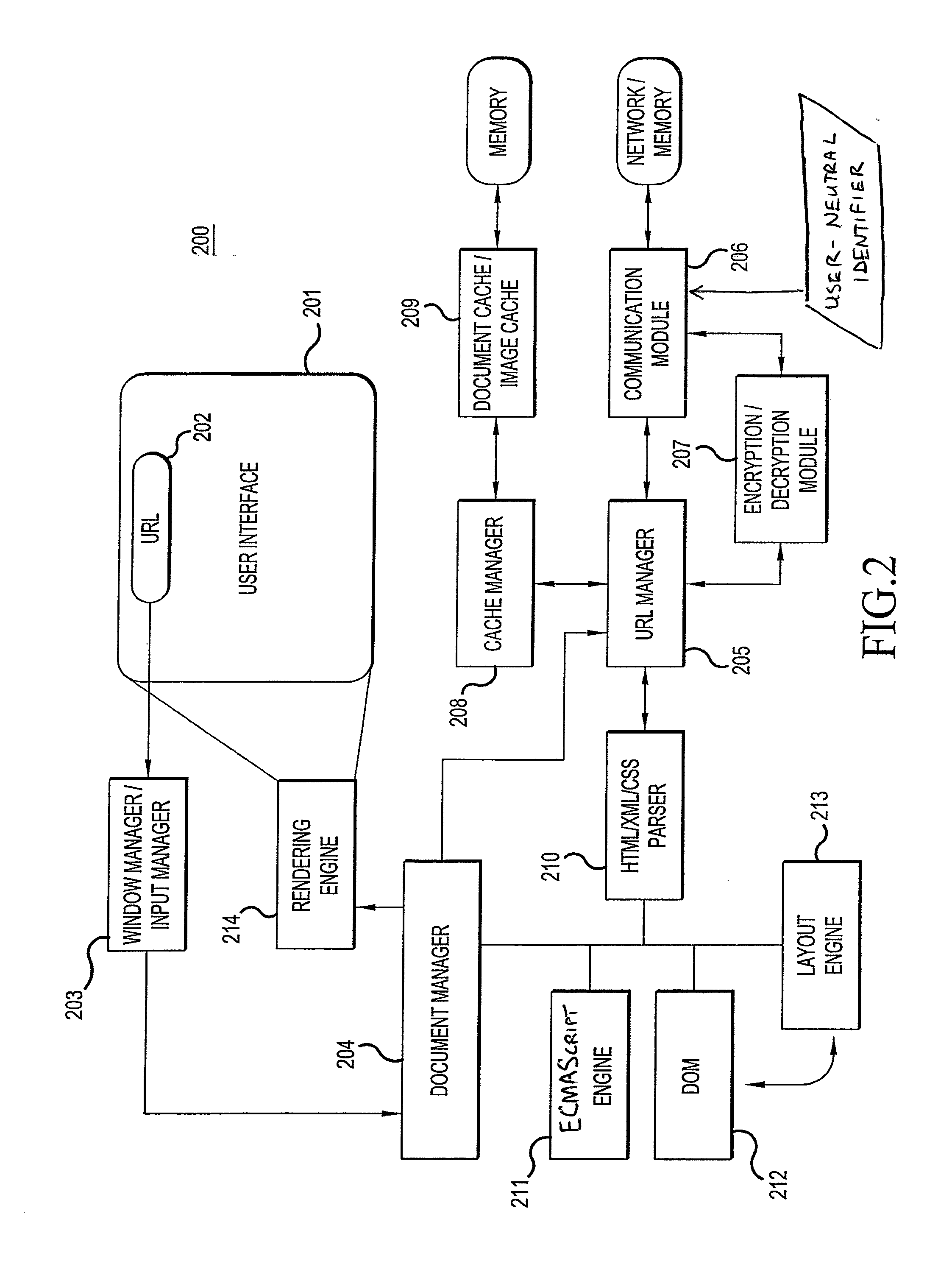
Server side mobile audience intelligence creation
ActiveUS20130080498A1Improve browsing experienceAvoid trackingAdvertisementsMultiple digital computer combinationsWeb siteWeb browser
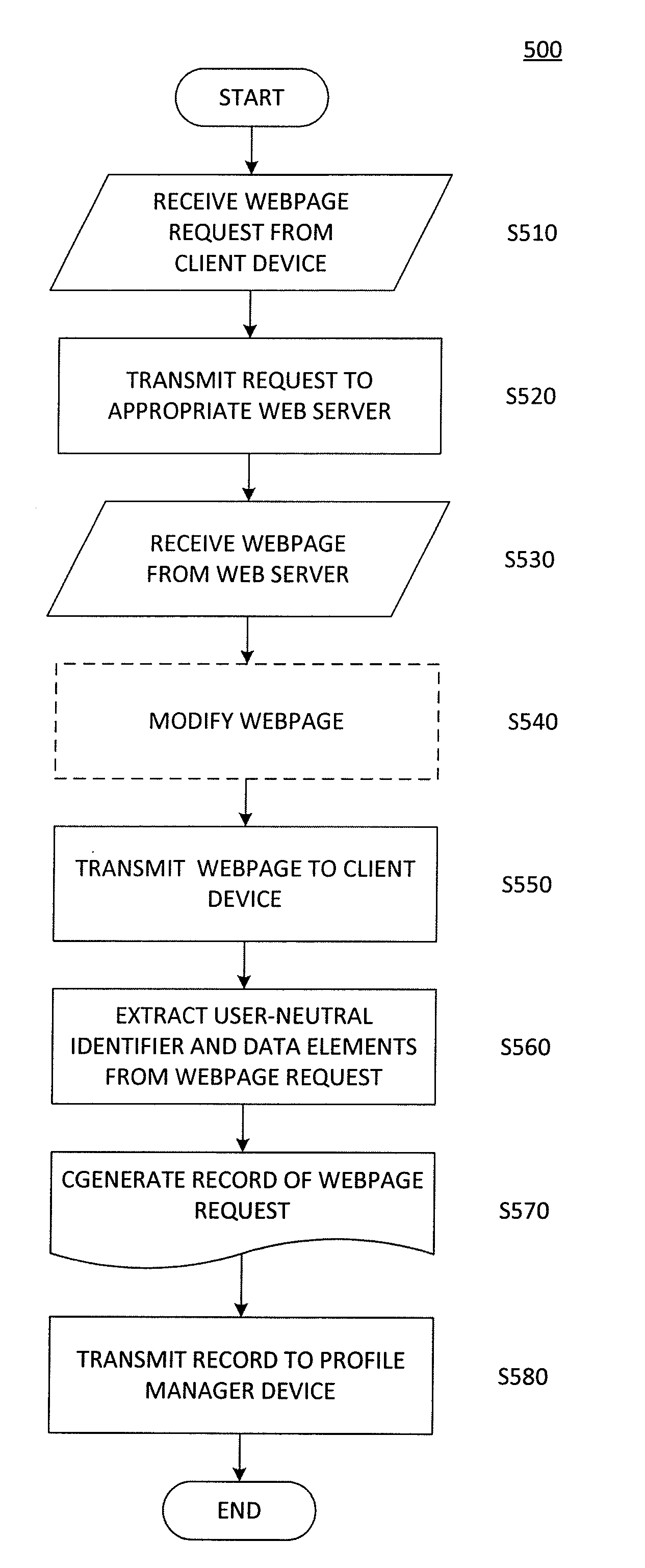
The present invention is directed toward a method and system for tracking webpage requests from web browsers without invading the privacy of the corresponding users. A server receives the webpage requests, and extracts from each of them a user-neutral identifier and URL. The server creates records of these webpage requests, and these records are used to create and update profiles for the corresponding user-neutral identifiers. Since the user-neutral identifiers are not tied to user-specific information, the profiles are made anonymous and user privacy can be protected. However, since each user-neutral identifier is tied to a particular web browser, useful information regarding individual browsing behavior can be obtained. Furthermore, the requested URL's can be categorized before being used to update the profiles, thus eliminating concerns that a user's browsing activity might be tracked from website to website.
Owner:OPERA SOFTVEAR AS
Method, system, and apparatus for maintaining user privacy in a knowledge interchange system
InactiveUS7730010B2Maintain privacyType is limitedDigital data processing detailsDigital computer detailsInternet privacyNoun phrase
A method, system, and apparatus are provided for maintaining user privacy in a knowledge interchange (“KI”) system. A user may provide privacy preferences relating to their participation in the KI system. The user may identify specific keywords, noun phrases, and contacts that should not be transmitted to a server computer. The user may also specify whether each keyword, noun phrase, or contact should be public or private. If a public keyword is identified during a search query as being associated with the user, the user's identity will be made available to a seeker If a private keyword is identified during a search query as being associated with the user, the user's identity will not be made available and a brokered communication process between the seeker and the user will be performed.
Owner:MICROSOFT TECH LICENSING LLC
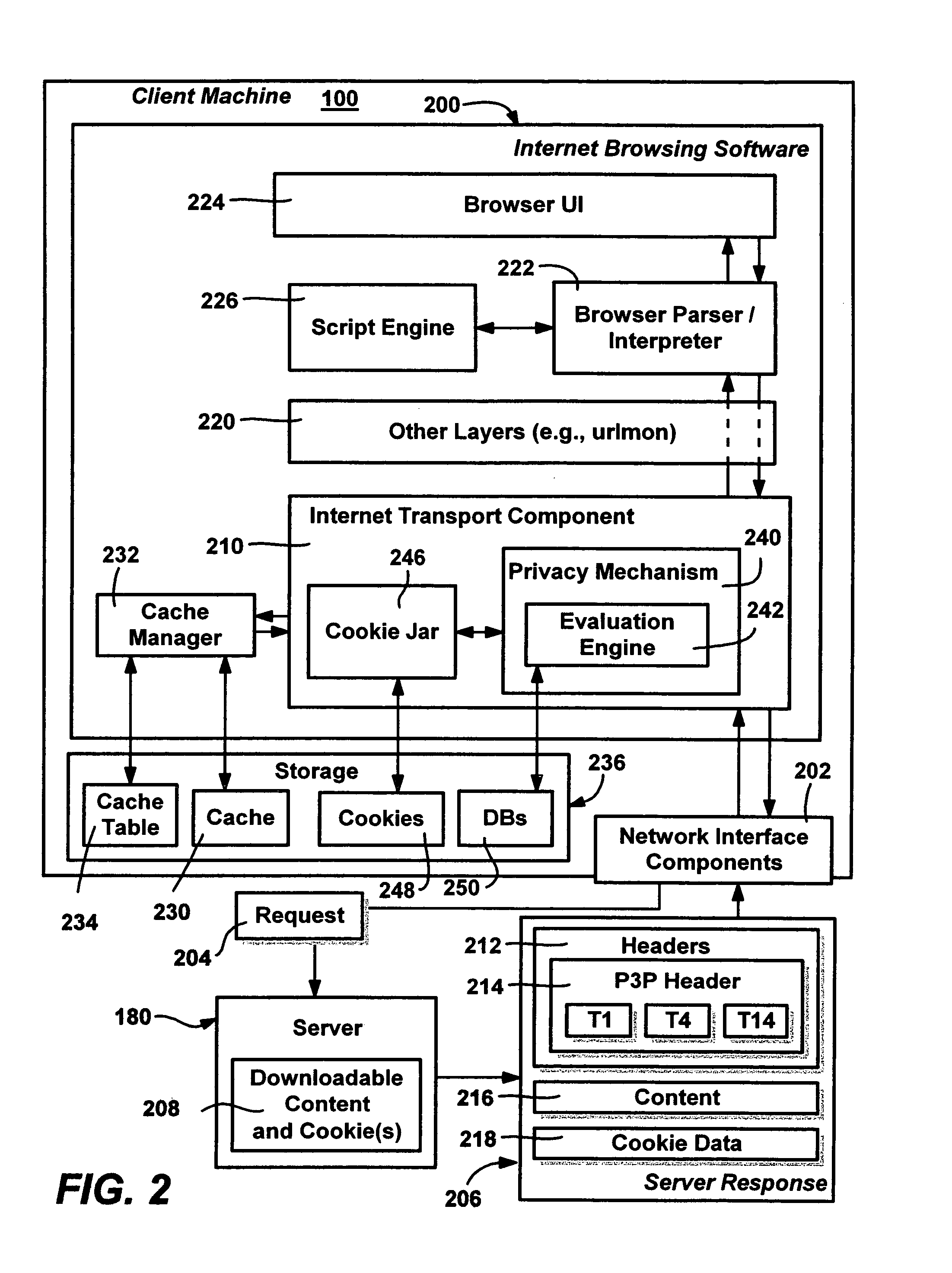
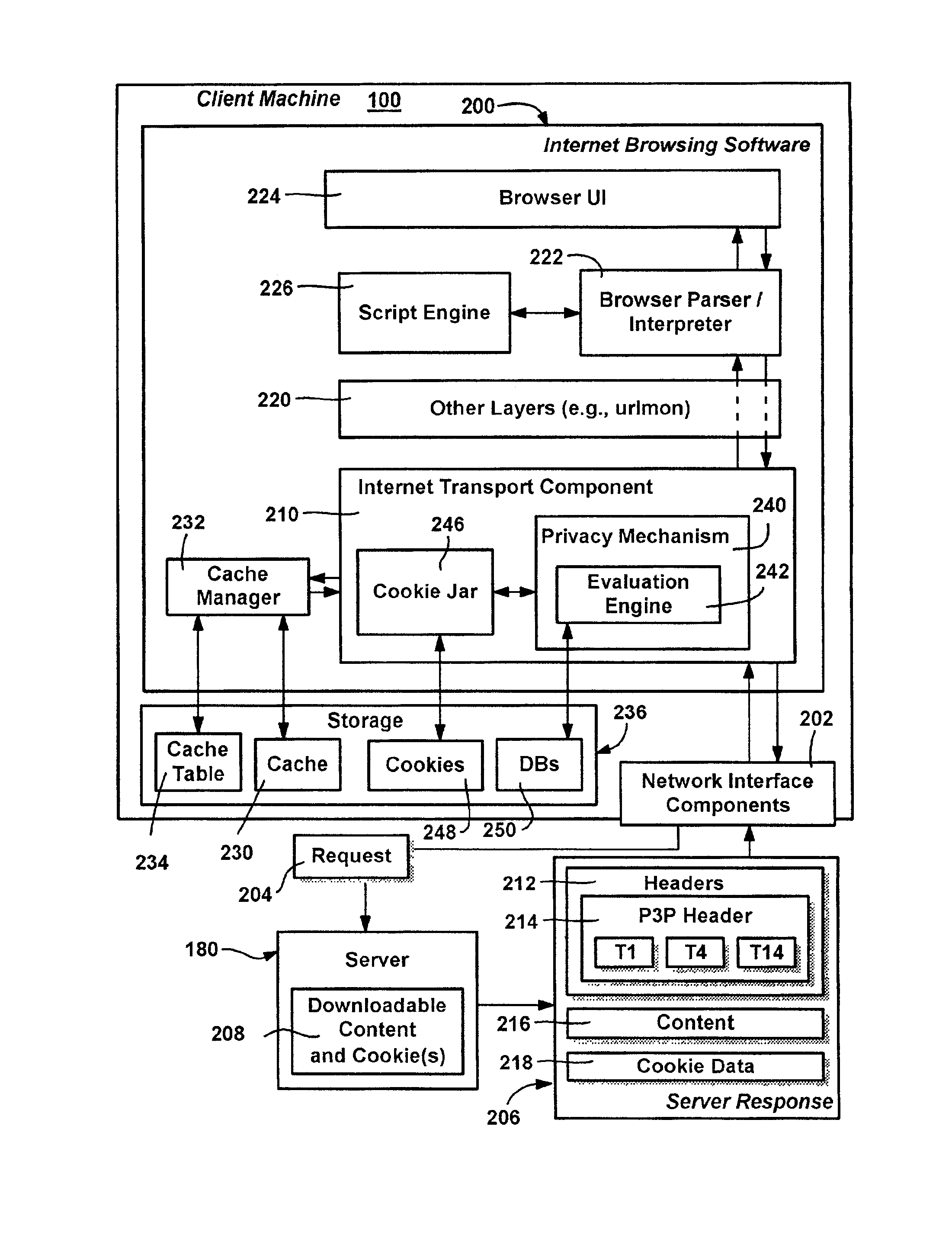
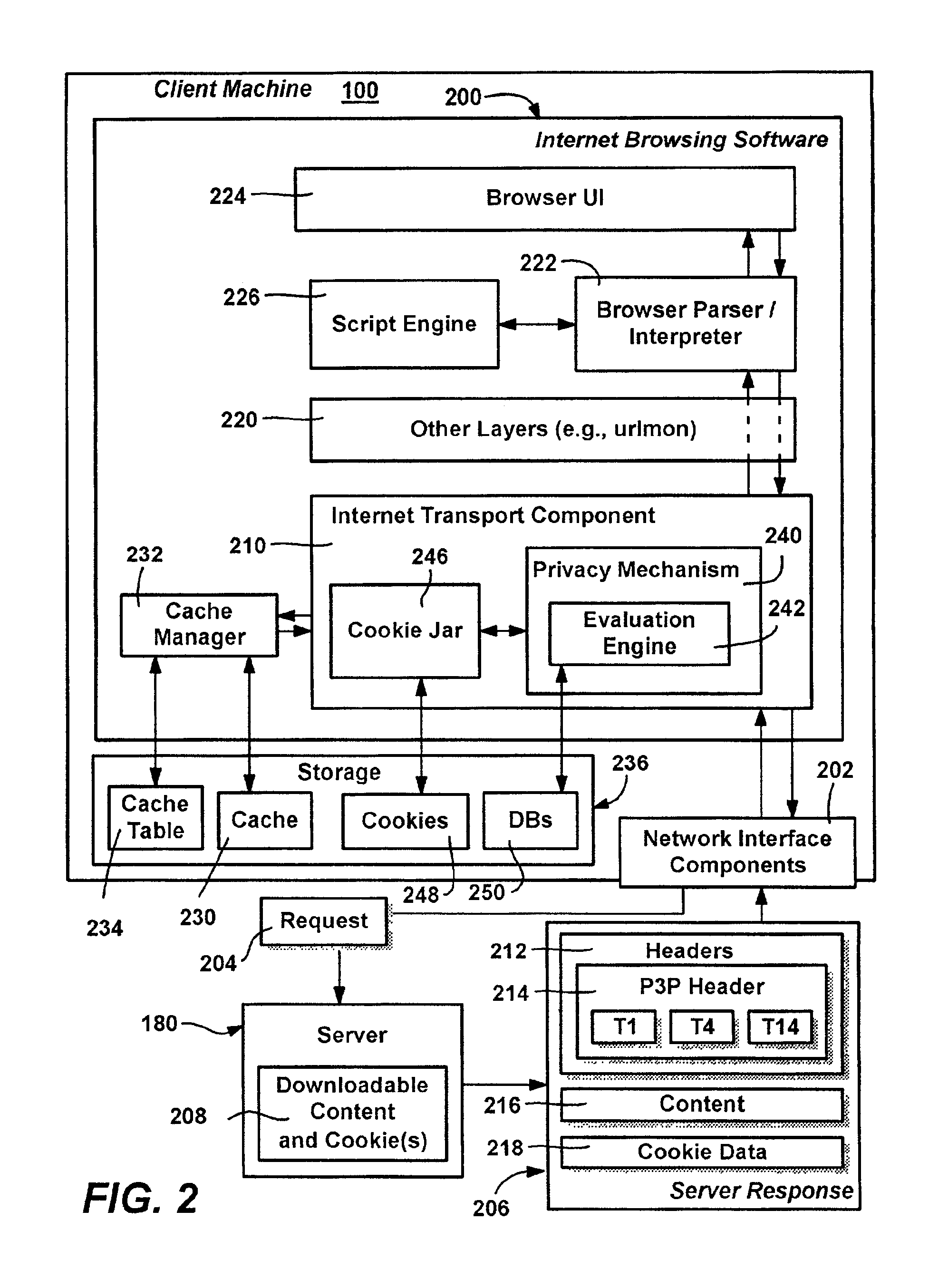
Method and system for protecting internet users' privacy by evaluating web site platform for privacy preferences policy
InactiveUS20050257250A1Digital data processing detailsUser identity/authority verificationThird partyWeb site
A system and method that evaluates privacy policies from web sites to determine whether each site is permitted to perform operations (e.g., store, retrieve or delete) directed to cookies on a user's computer. Various properties of each cookie and the context in which it is being used are evaluated against a user's privacy preference settings to make the determination. An evaluation engine accomplishes the evaluation and determination via a number of criteria and considerations, including the cookie properties, its current context, the site, the zone that contains the site, and any P3P data (compact policy) provided with the site's response. The user privacy preferences are evaluated against these criteria to determine whether a requested cookie operation is allowed, denied or modified. A formalized distinction between first-party cookies versus third-party cookies may be used in the determination, along with whether the cookie is a persistent cookie or a session cookie.
Owner:MICROSOFT TECH LICENSING LLC
Unified collection and distribution of data
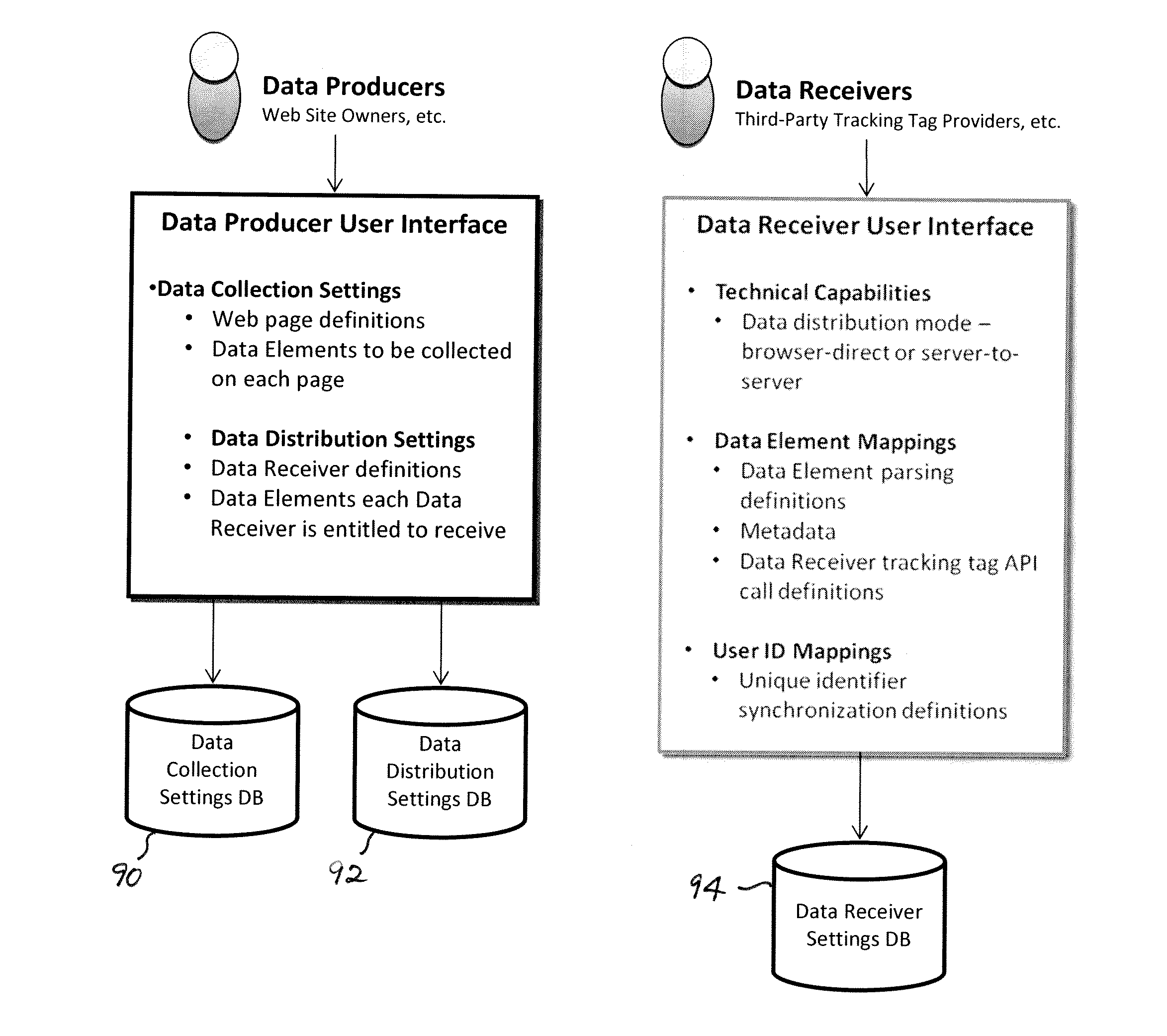
ActiveUS20110314092A1Multiple digital computer combinationsWebsite content managementUser deviceWeb browser
A stub tag in source code of a webpage allows for collection of numerous data elements according to tracking tags of various data receiver parties and for distribution of the collected data elements to those parties. The stub tag references a remotely cached script that enables a user device, e.g. a computer running a web browser, to retrieve a tag code for collecting the data elements. The tag code is constructed according to data collection settings, data distribution settings, data receiver settings, and / or user privacy settings. The tag code results in a single variable, common to all data receiver parties, for each data element. The common variable is transmitted to data receivers through the user device or through a server-to-server API.
Owner:SIGNAL DIGITAL
Methods and systems for rating privacy risk of applications for smart phones and other mobile platforms
ActiveUS20120072991A1Better-informed decisionService provisioningMemory loss protectionInternet privacyUser privacy
Methods and systems for evaluating and rating privacy risks posed by applications intended for deployment on mobile platforms. Validating the “intent” of a mobile platform application vis-à-vis its impact on user privacy, as viewed from an end-user's perspective allows those end-users to make better-informed decisions concerning the downloading, installation and / or operation of mobile platform applications. In making such assessments user preferences can be taken into account. Privacy scores are provided through sales channels for the applications, thereby affording potential users the opportunity to assess whether they wish to incur the associated privacy risk, before purchasing a subject application.
Owner:NCC GRP SECURITY SERVICES
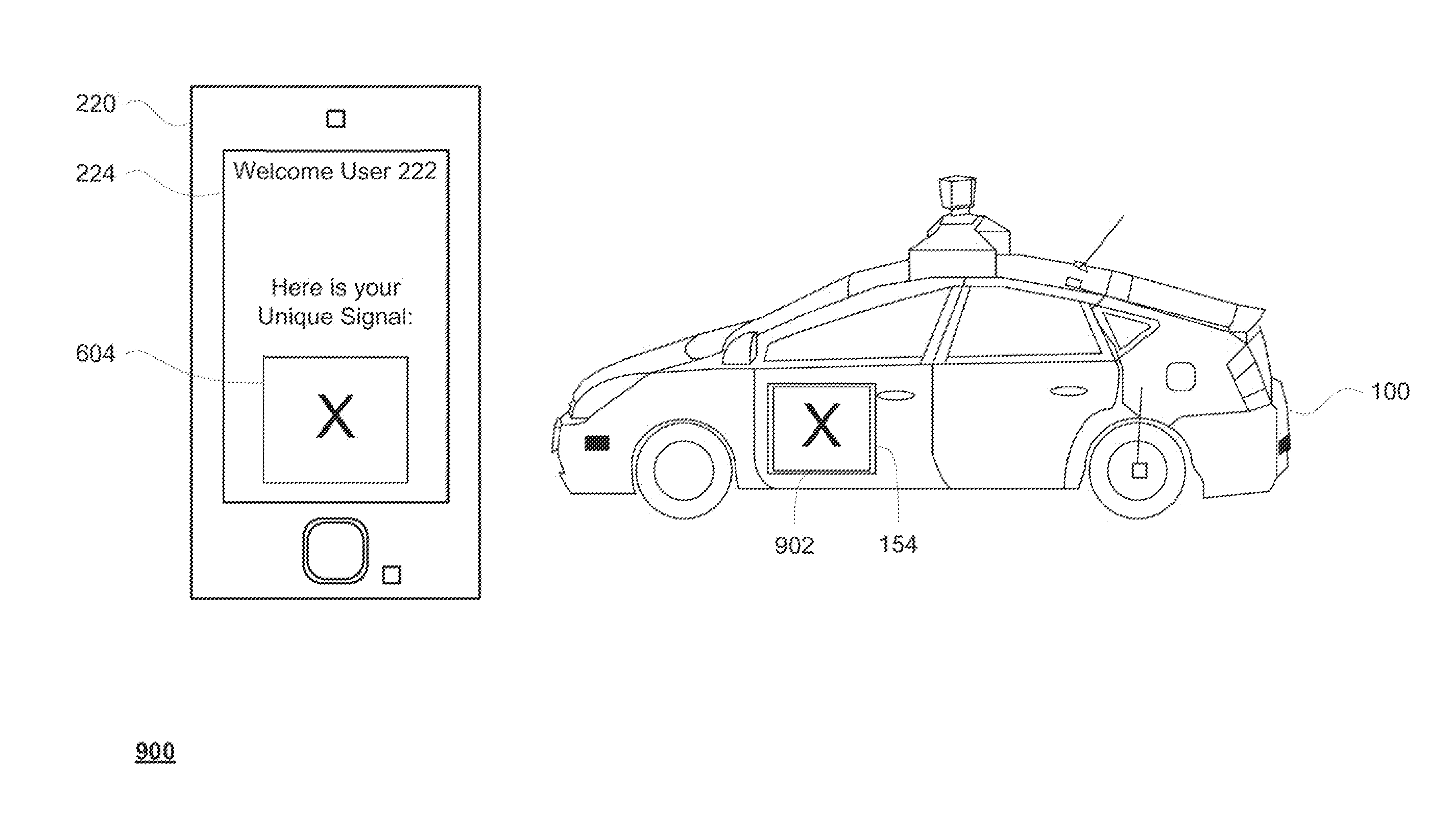
Unique signaling for autonomous vehicles to preserve user privacy
ActiveUS9494938B1Autonomous decision making processRoad vehicles traffic controlUser privacyReal-time computing
Aspects of the present disclosure relate to protecting the privacy of a user of a dispatching service for driverless vehicles. For example, a request for a vehicle identifying user information is received. A client computing device may be identified based on the user information. In response to the request, a driverless vehicle may be dispatched to the location of the client device. Signaling information may be generated based on a set of rules including a first rule that the signaling information does not identify, indirectly or directly, the user as well as a second rule that the signaling information does not identify, indirectly or directly, the user information. The location of the client computing device and the signaling information may be sent to the driverless vehicle for display. In addition, the signaling information may also be sent to the client computing device for display.
Owner:WAYMO LLC
Method and system for protecting internet users' privacy by evaluating web site platform for privacy preferences policy
A system and method that evaluates privacy policies from web sites to determine whether each site is permitted to perform operations (e.g., store, retrieve or delete) directed to cookies on a user's computer. Various properties of each cookie and the context in which it is being used are evaluated against a user's privacy preference settings to make the determination. An evaluation engine accomplishes the evaluation and determination via a number of criteria and considerations, including the cookie properties, its current context, the site, the zone that contains the site, and any P3P data (compact policy) provided with the site's response. The user privacy preferences are evaluated against these criteria to determine whether a requested cookie operation is allowed, denied or modified. A formalized distinction between first-party cookies versus third-party cookies may be used in the determination, along with whether the cookie is a persistent cookie or a session cookie.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for protecting private information in a mobile environment
InactiveUS20060123462A1Protect informationViolates privacyDigital data processing detailsUser identity/authority verificationInternet privacyUser privacy
Techniques for protecting non-public information in a mobile environment are provided. A request for non-public information about users in a mobile environment is received. Privacy policies, non-public and optional public information about the users affected by the request are determined. An optional privacy impact indicator is determined based on how satisfying the request increases the current public information about the users. Crowds of users having similar attribute name / values are optionally determined. User and optional requestor privacy policies which associate threshold release criteria such minimum crowd size, minimum consideration with the non-public information are determined. A privacy agreement is reached for the disclosure of the requested non-public information based on the compatibility of the requester and user privacy policies. Privacy protecting transformations are optionally determined and applied to create crowds or groups associated with the requested attribute.
Owner:PALO ALTO RES CENT INC
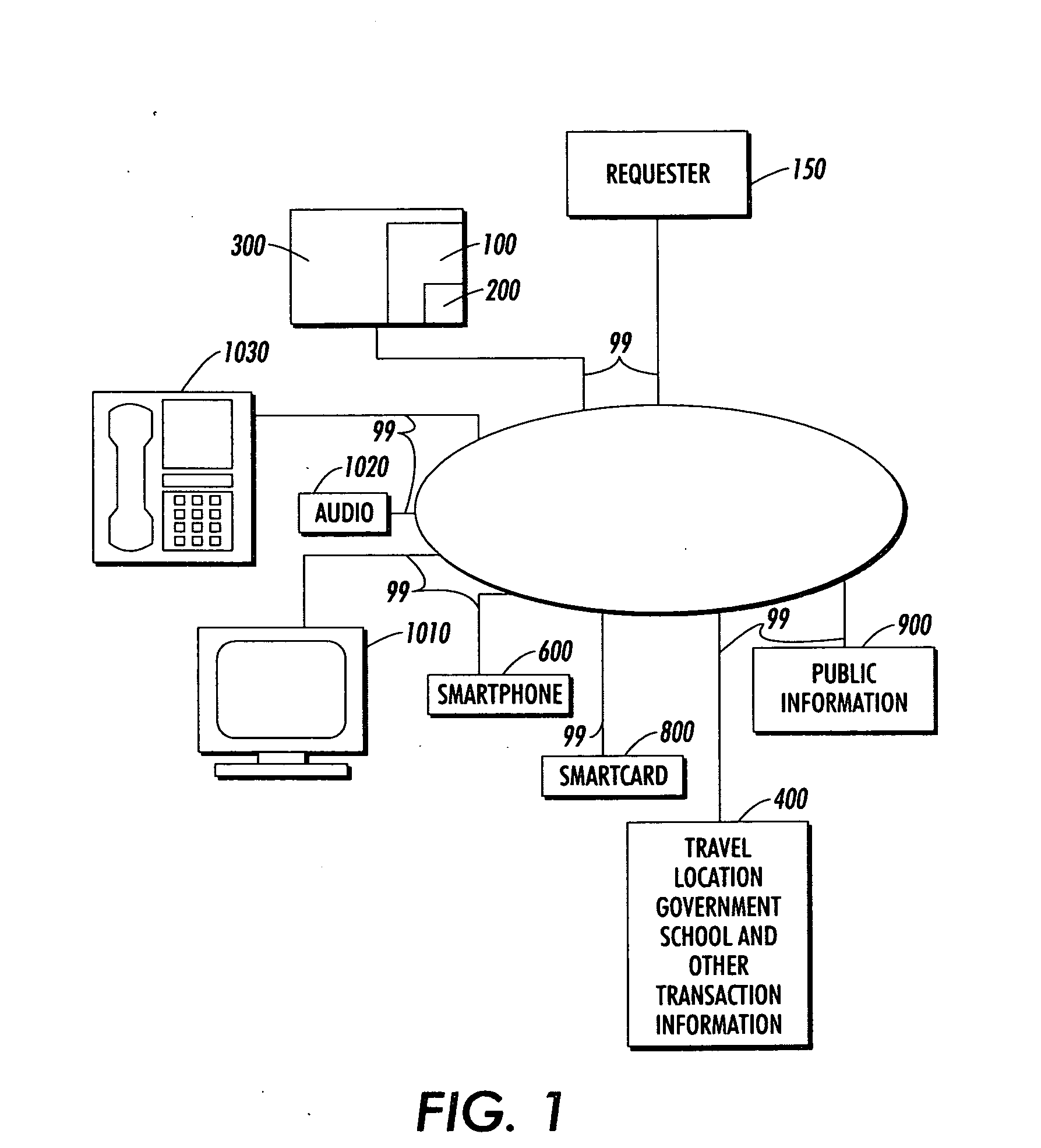
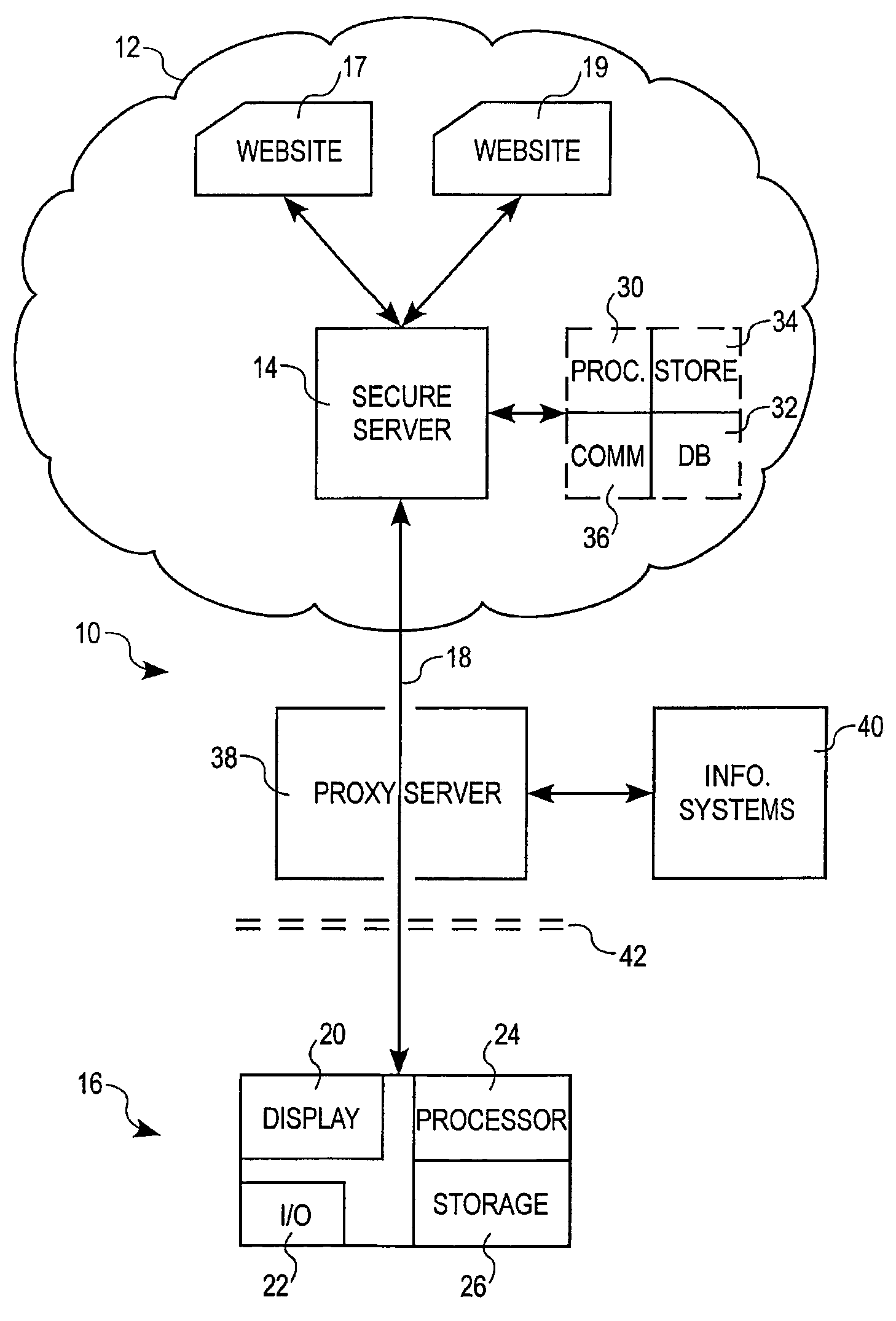
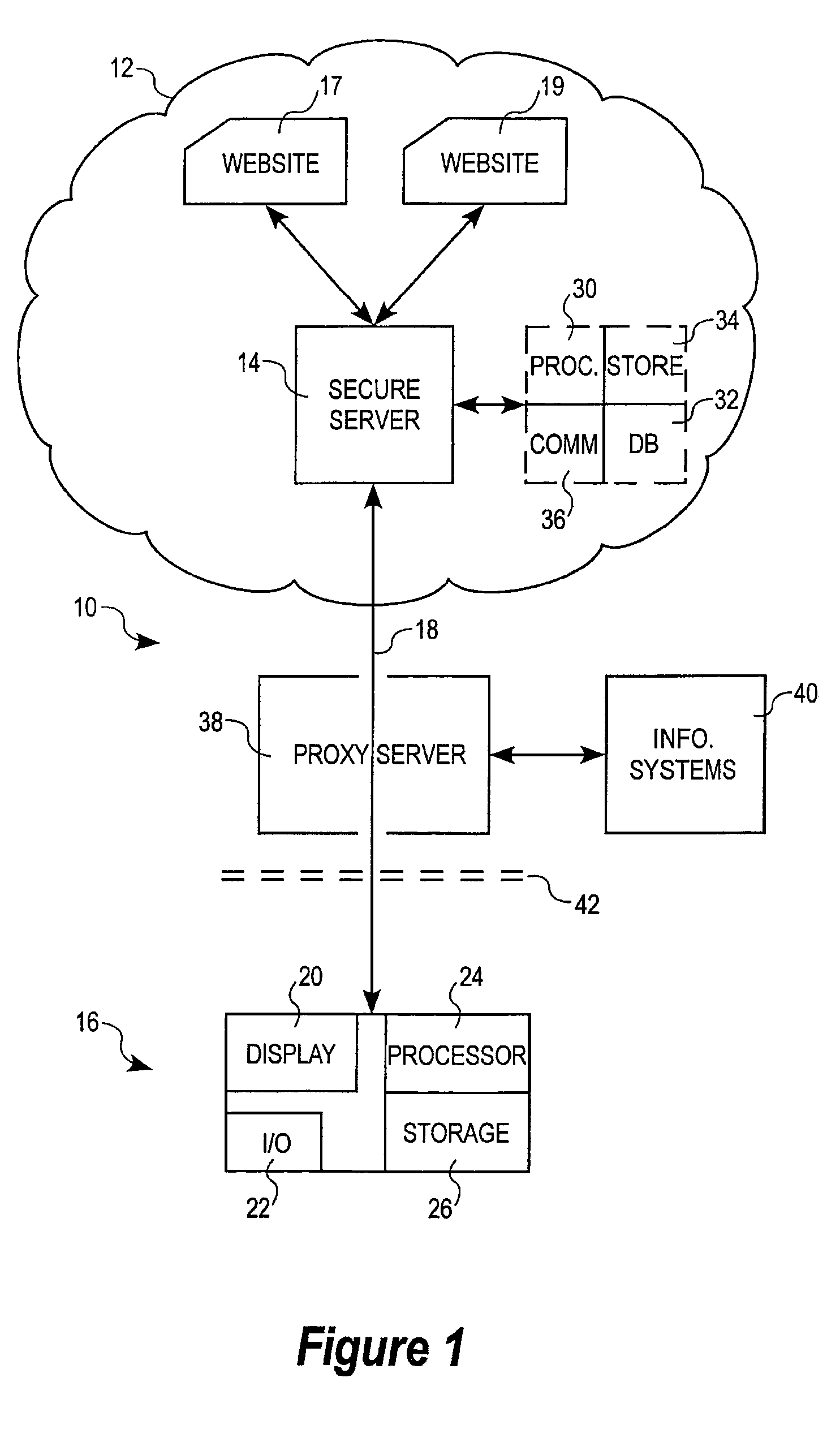
Method and apparatus for encrypted communications to a secure server
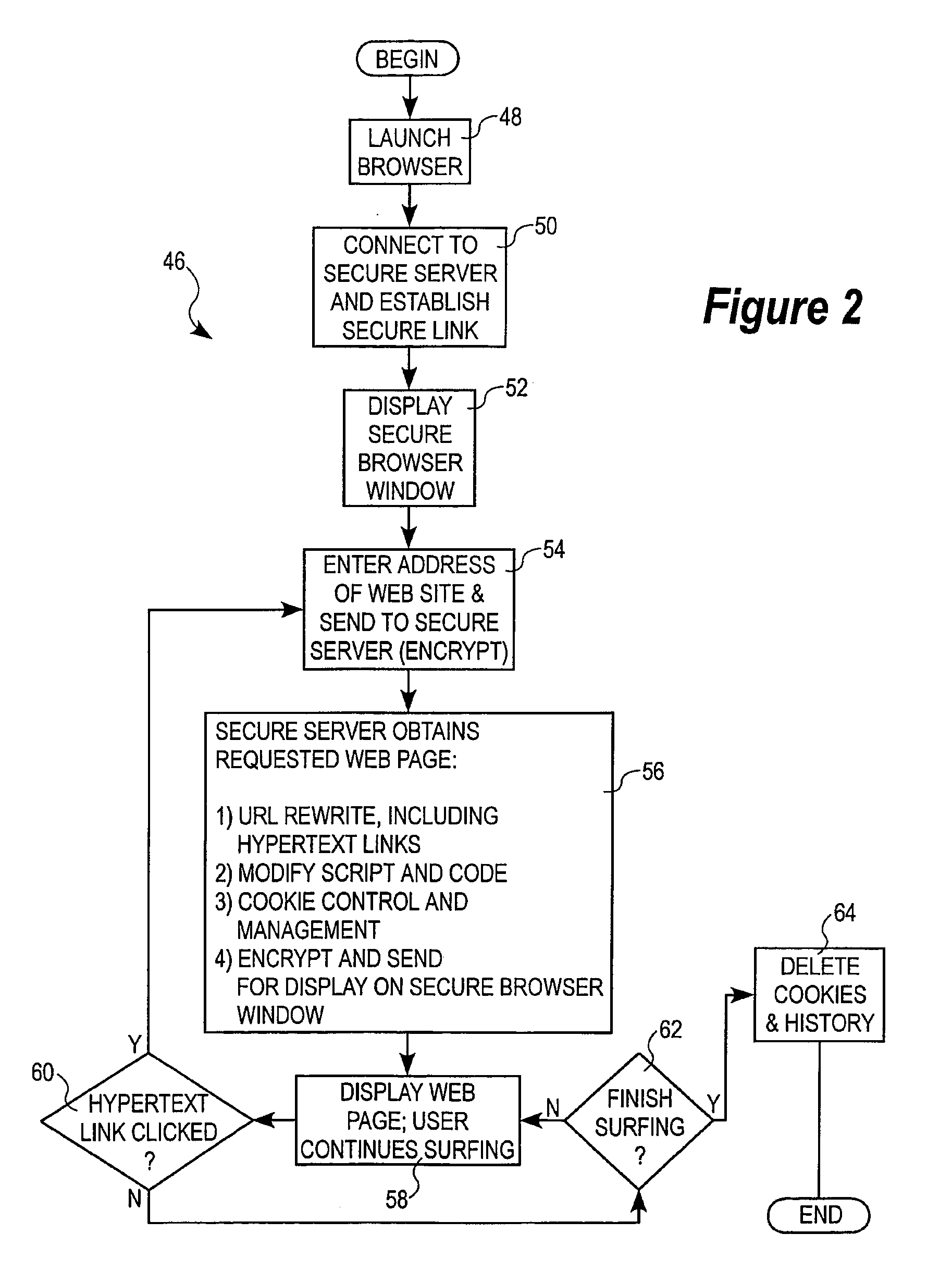
InactiveUS20090199000A1User identity/authority verificationAnonymous user systemsWeb siteUser privacy
An embodiment of the invention includes a secure server. A user at a terminal, communicatively coupled to the secure server by a secure link, can obtain web pages from web sites in a network, in encrypted form, via the secure link. Addresses associated with the web pages are altered to make it appear as if the web pages come from the secure server rather than from the web sites. Spoofing units may be used as alternative access points to the secure server, with the secure server sending the requested web pages directly to the terminal. In general, address rewriting and other manipulation can be performed on the requested web pages, such that the true sources of the web pages are disguised and such that subsequent communications from the terminal are directed to the secure server and / or spoofing unit, rather than to the true source of the web pages. Components of the user's privacy may be sold, or advertisements may be provided, in exchange for protection of the user's identity.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com