Patents
Literature
31results about How to "Data can be secured" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
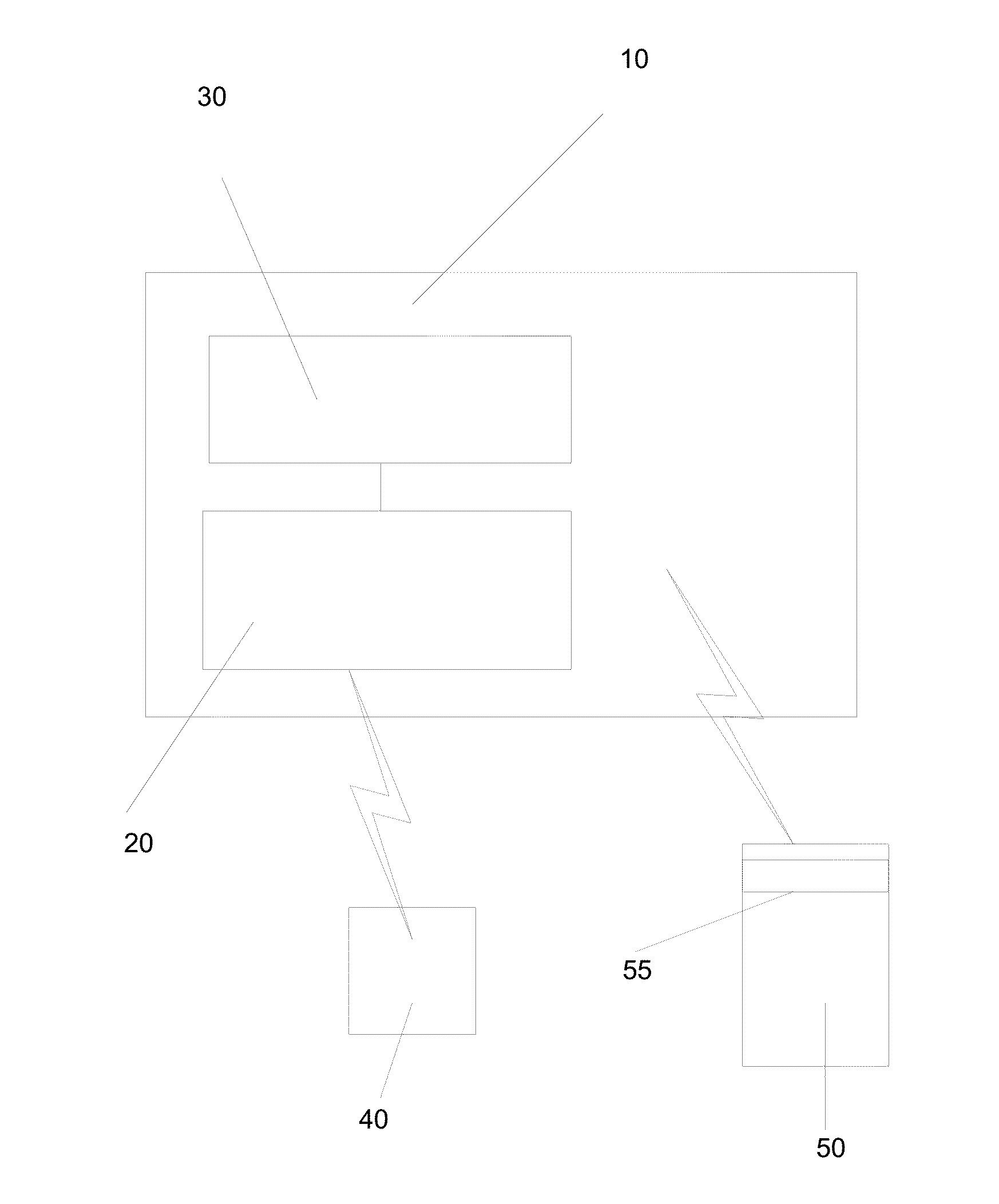
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
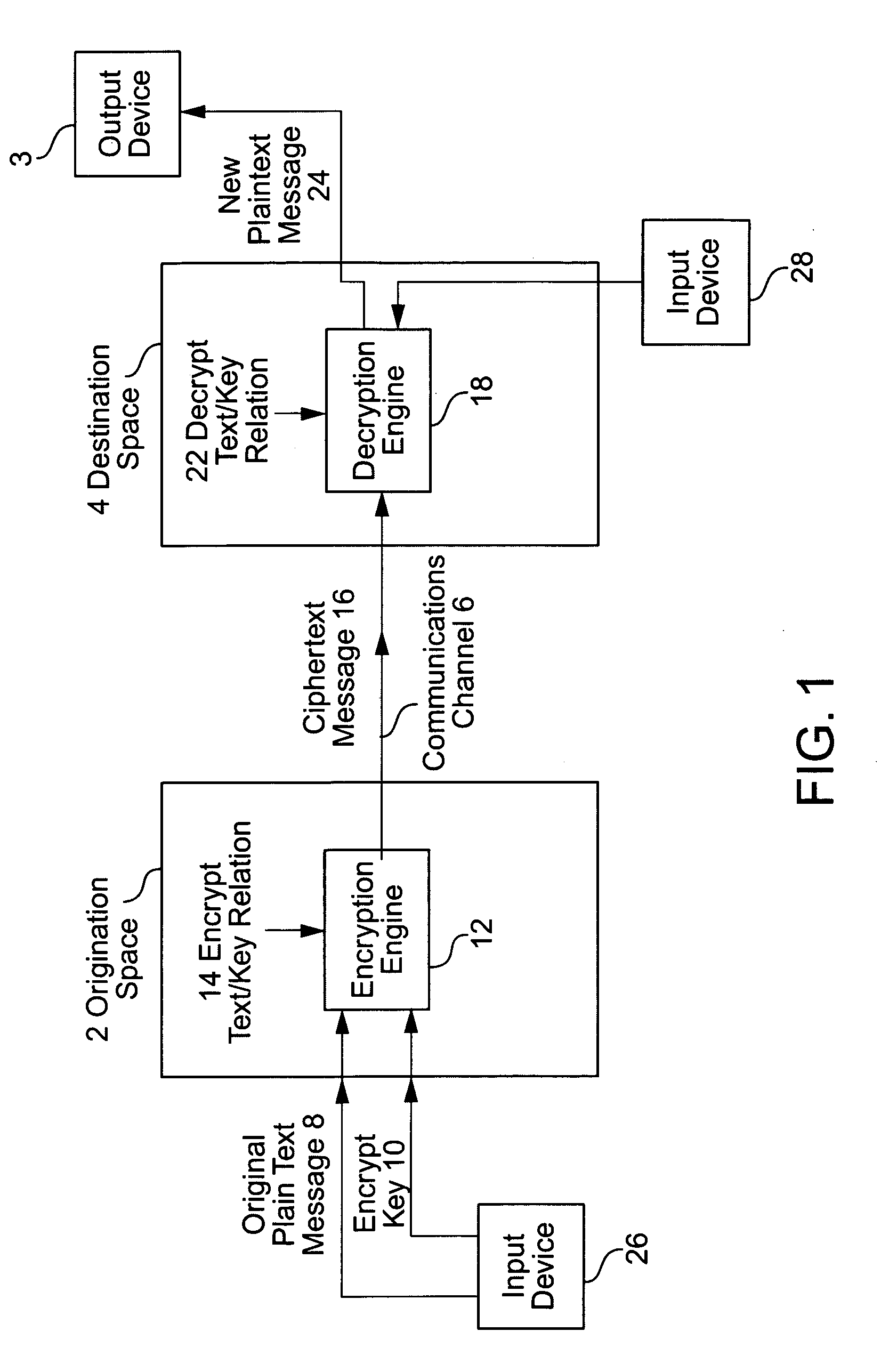
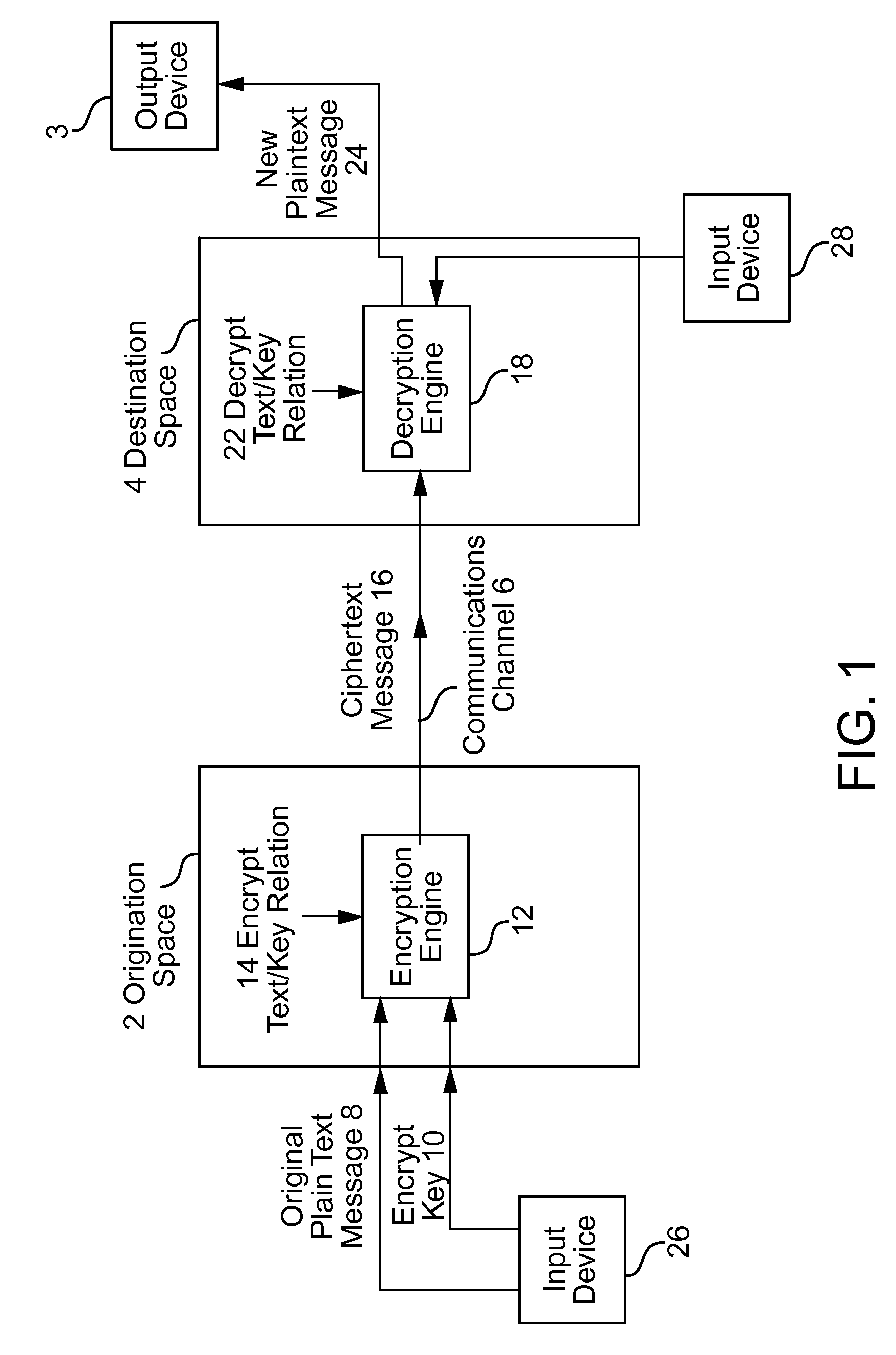
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS10129211B2Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsFiberNetwork operating system
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
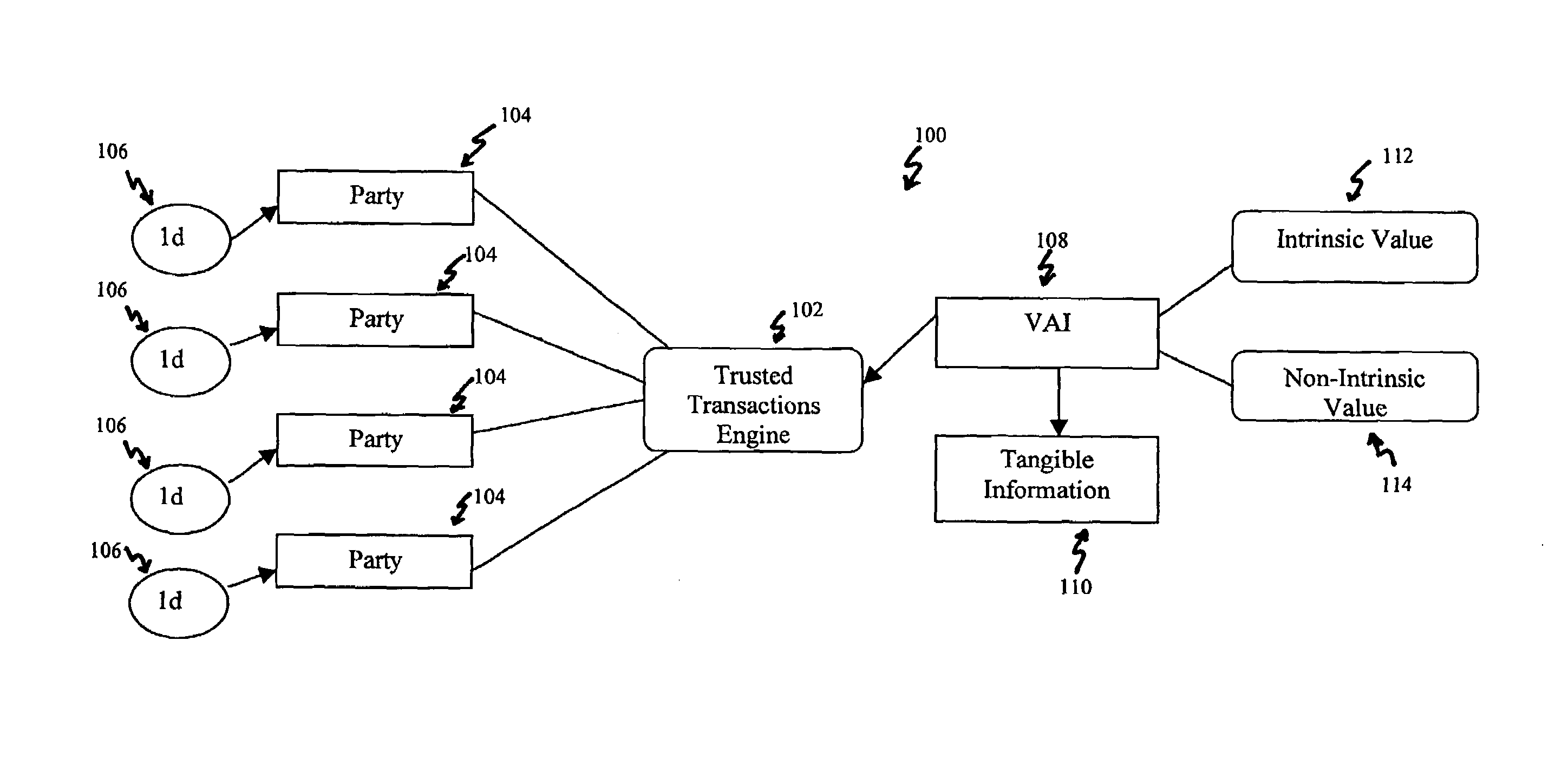
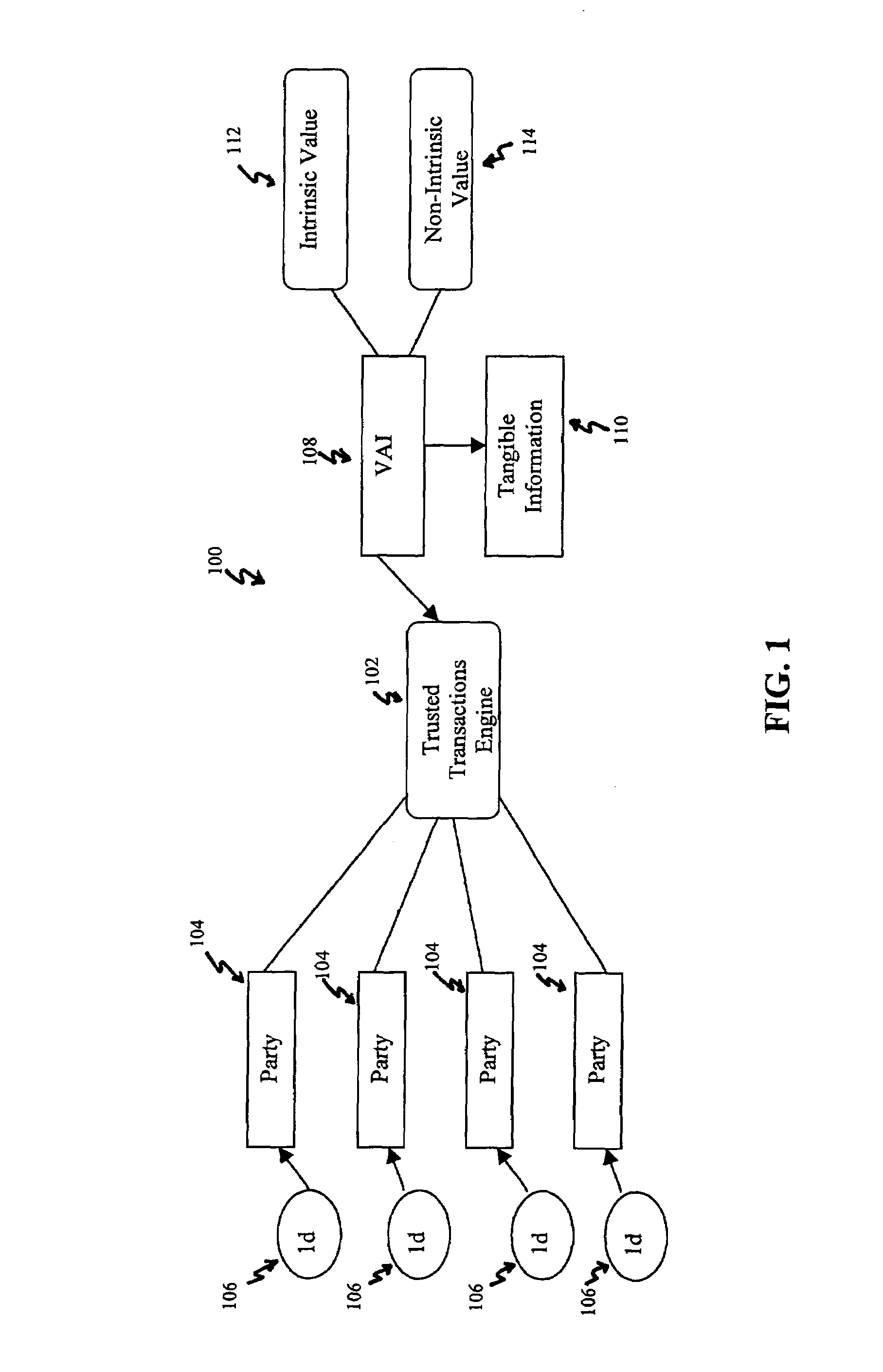
Systems, methods and devices for trusted transactions
InactiveUS7159116B2Convenient transactionLittle processing resourceMultiple keys/algorithms usagePublic key for secure communicationThe InternetSubject matter
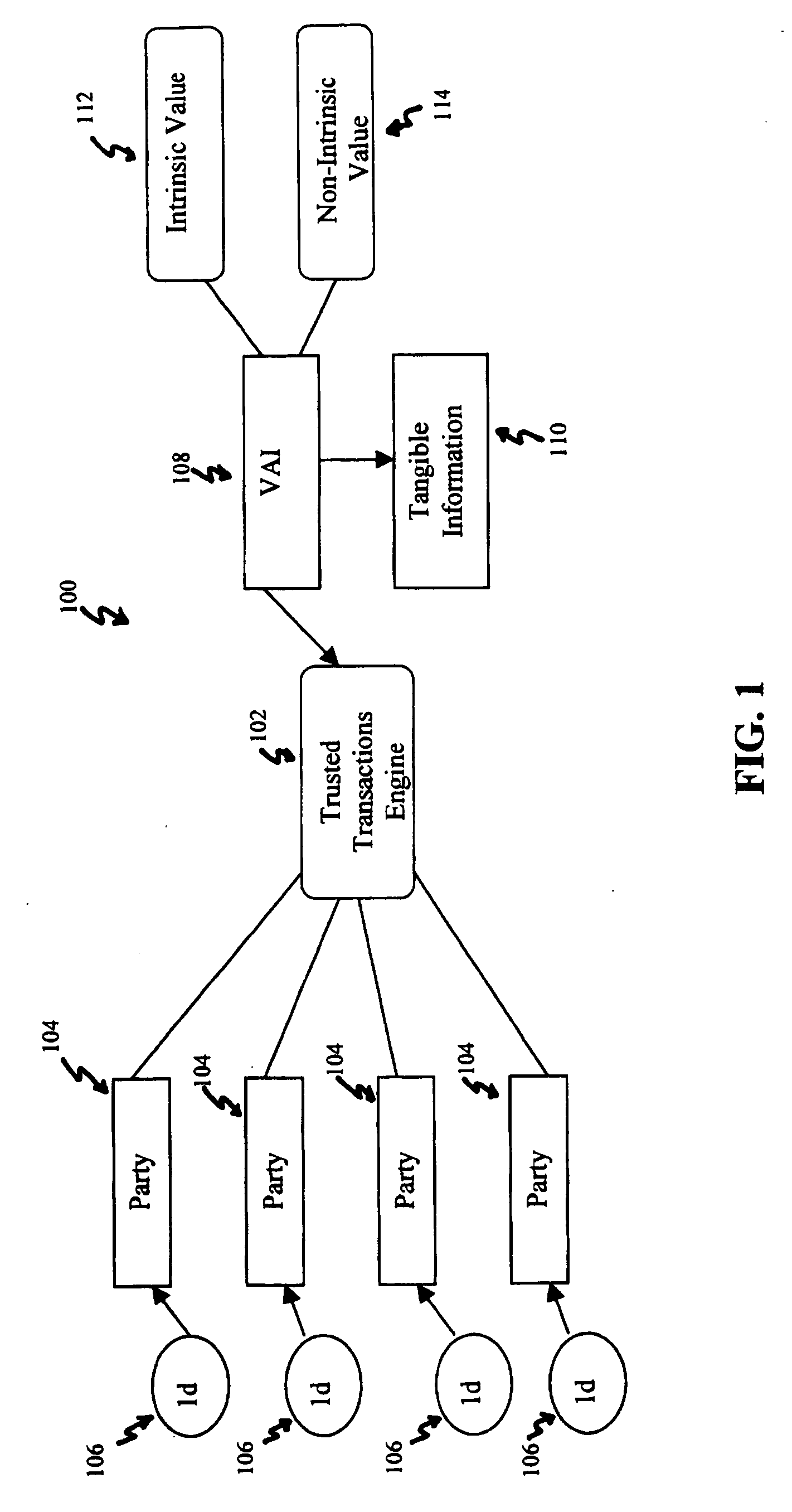
The invention discloses a system for enhancing trust in transactions, most particularly in remote transactions between a plurality of transactional parties, for instance a seller and buyer(s) of goods and / or services over a public computer network such as the internet. Trust is disclosed to be a multivalent commodity, in that the trust that is to be enhanced relates to information about the subject matter of the transactions (e.g., the suitability of the goods and services sold), the bona fides of the supplier of the goods and services, the appropriateness of a pricing structure for a particular transaction or series of transactions, a quantum of additional transactional value that may be imparted to the transactional relationship, security of information exchange, etc. An important contributor to trust for such aspects of the transaction is disclosed to be the use of highly-secure steganographic computer processing means for data identification, authentication, and transmission, such that confidence in the transaction components is enhanced. By providing an integrated multivalent system for enhancing trust across a variety of categories (for a variety of transaction species, including those in which the need for trust is greater on the part of one party than of another, as well as those in which both require substantial trust enhancement), the invention reduces barriers to forming and optimizing transactional relationships.
Owner:WISTARIA TRADING INC
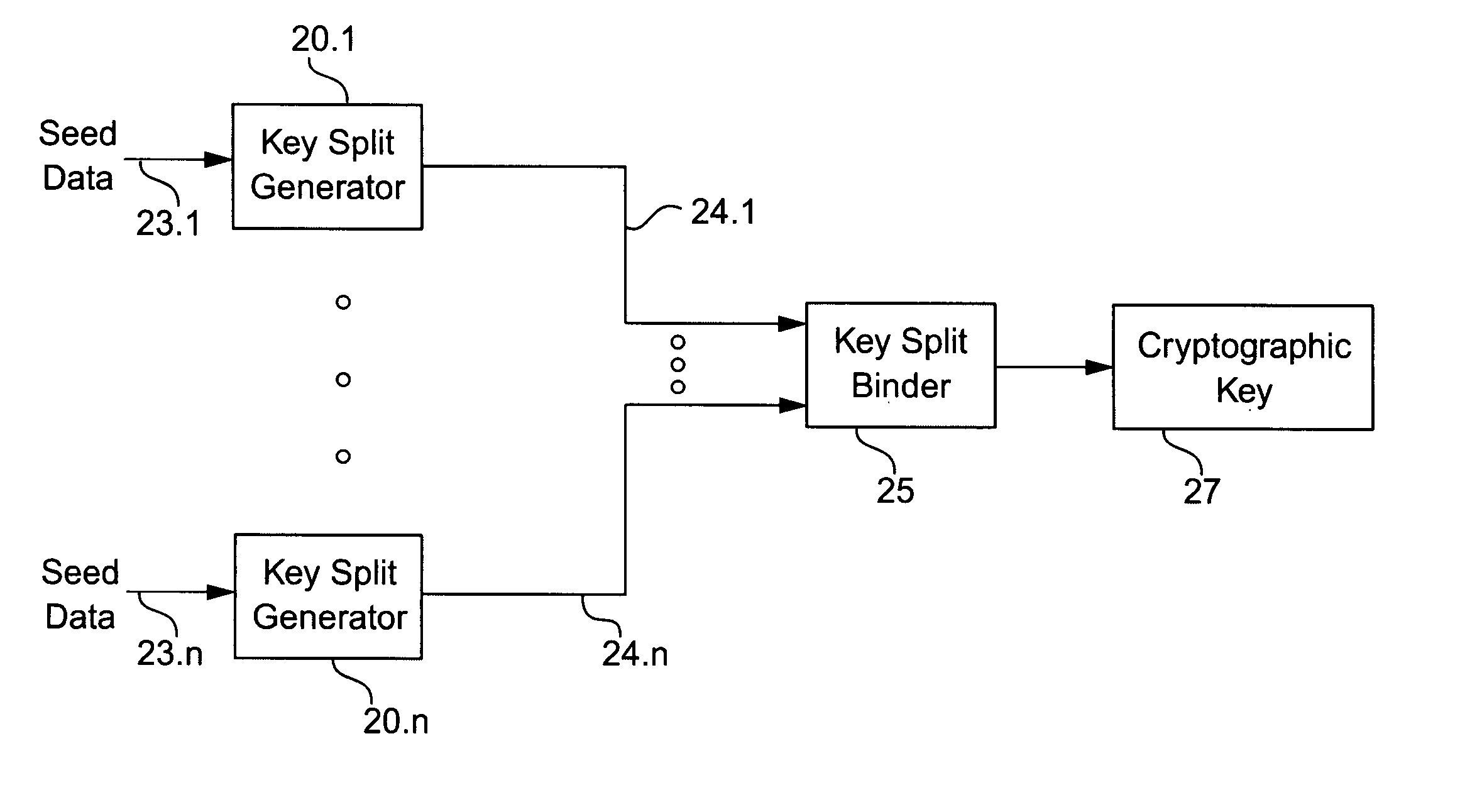
Cryptographic key split binder for use with tagged data elements
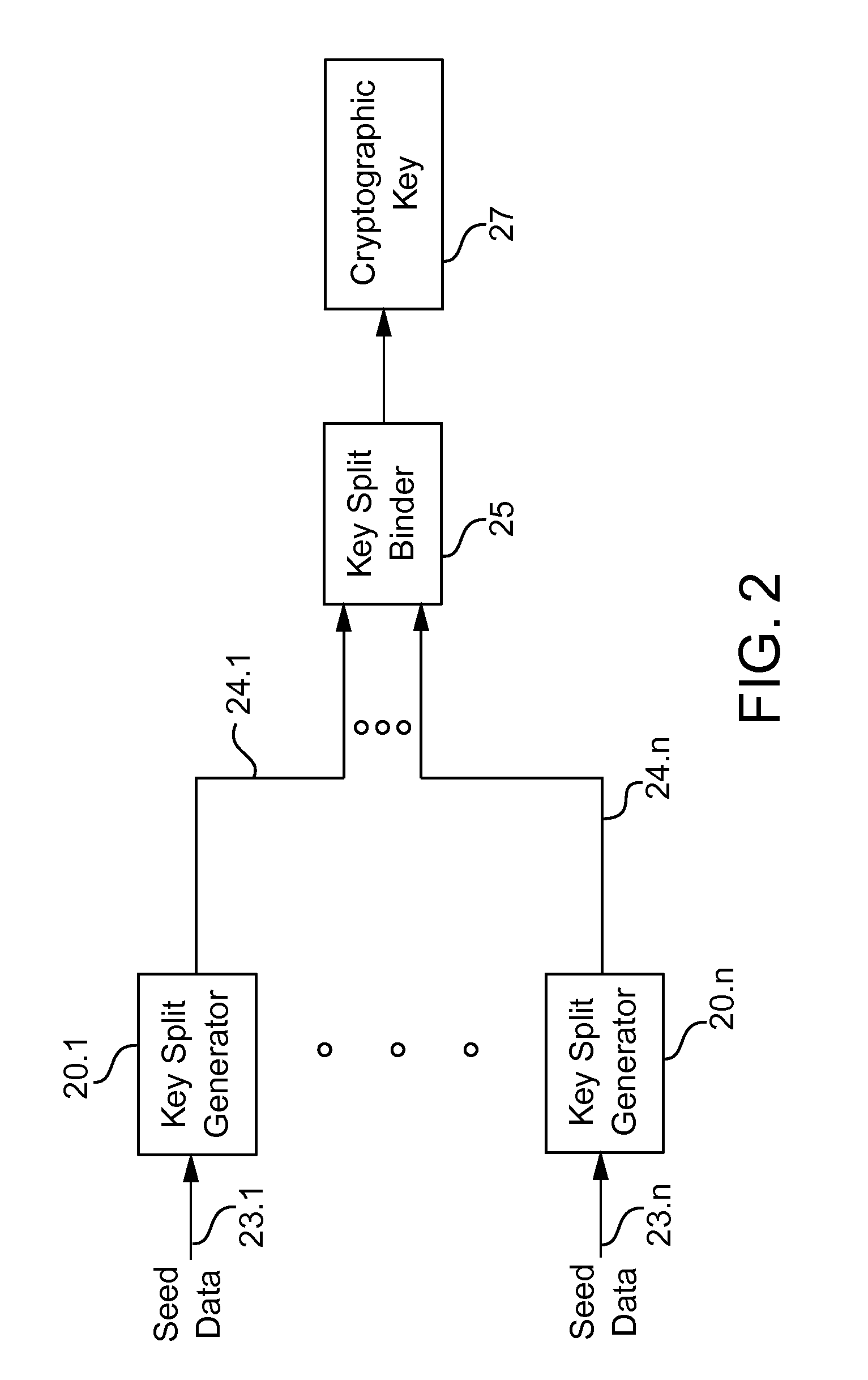
InactiveUS7095852B2Weight increaseData can be securedKey distribution for secure communicationComputer hardwareBiometric data
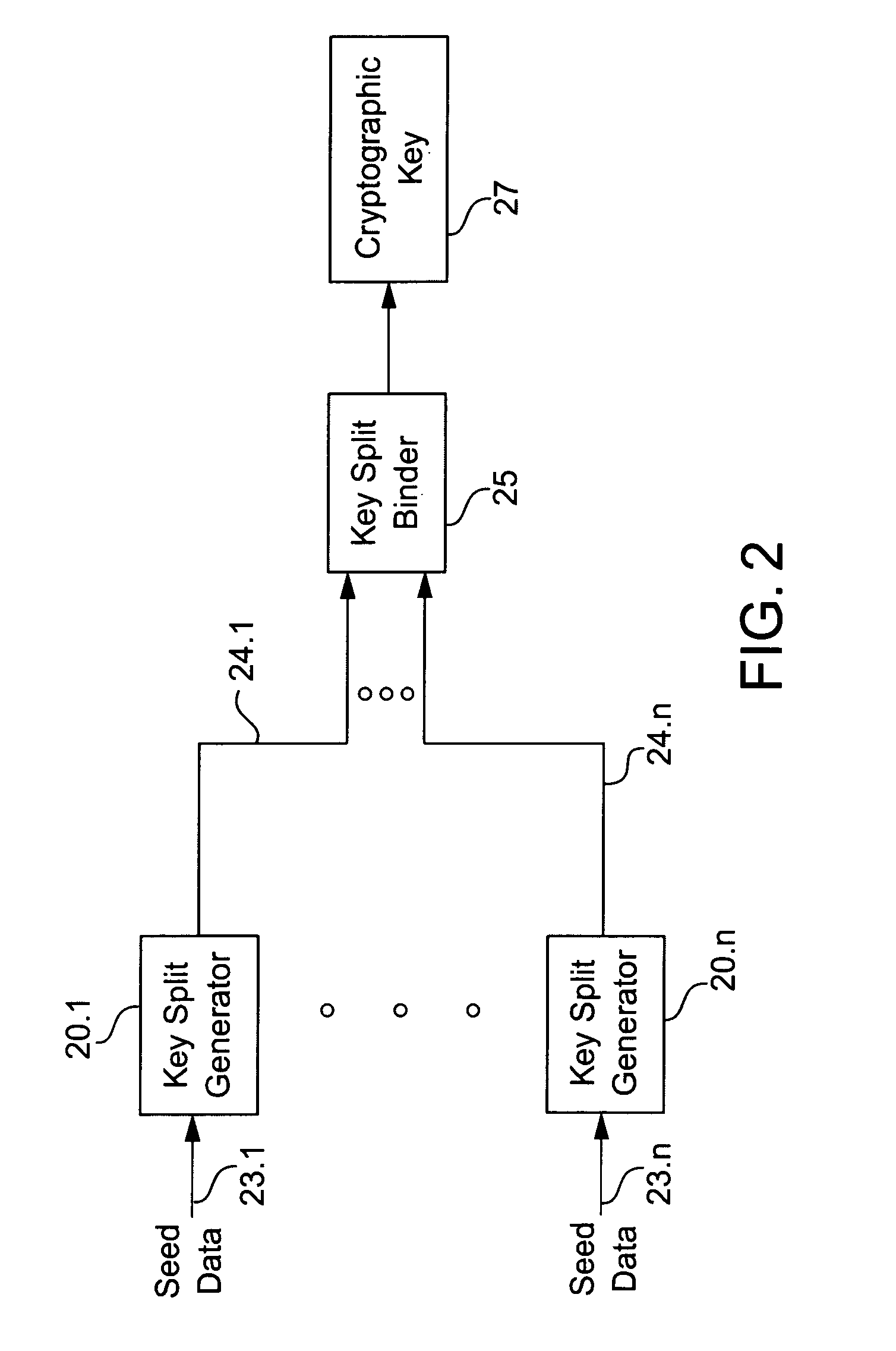
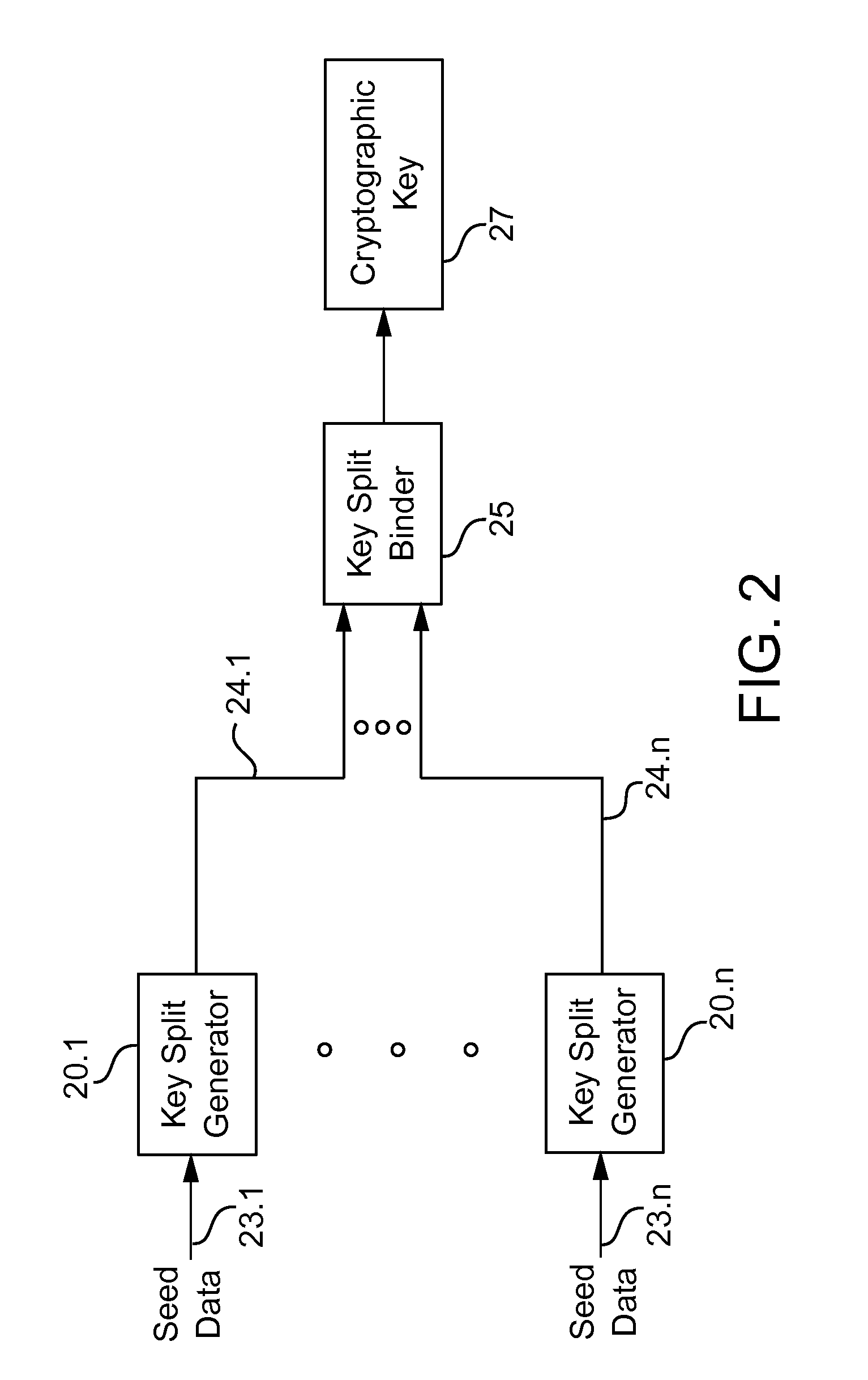
A cryptographic key split binder includes key split generators that generate cryptographic key splits from seed data and a key split randomizer for randomizing cryptographic key splits to produce a cryptographic key, and a process for forming cryptographic keys. Key split generators can include a random split generator for generating a random key split based on reference data, a token split generator for generating a token key split based on label data, a console split generator for generating a console key split based on maintenance data or a biometric split generator for generating a biometric key split based on biometric data. Any key split can further be based on static data, which can be updated. Label data can be read from a storage medium, and can include user authorization data. A cryptographic key can be, for example, a stream of symbols, at least one symbol block, or a key matrix.
Owner:TECSEC
Systems, methods and devices for trusted transactions
ActiveUS20070028113A1Little processing resourceMaximize its usefulnessMultiple keys/algorithms usageCryptography processingThe InternetSubject matter
The invention discloses a system for enhancing trust in transactions, most particularly in remote transactions between a plurality of transactional parties, for instance a seller and buyer(s) of goods and / or services over a public computer network such as the internet. Trust is disclosed to be a multivalent commodity, in that the trust that is to be enhanced relates to information about the subject matter of the transactions (e.g., the suitability of the goods and services sold), the bona fides of the supplier of the goods and services, the appropriateness of a pricing structure for a particular transaction or series of transactions, a quantum of additional transactional value that may be imparted to the transactional relationship, security of information exchange, etc. An important contributor to trust for such aspects of the transaction is disclosed to be the use of highly-secure steganographic computer processing means for data identification, authentication, and transmission, such that confidence in the transaction components is enhanced. By providing an integrated multivalent system for enhancing trust across a variety of categories (for a variety of transaction species, including those in which the need for trust is greater on the part of one party than of another, as well as those in which both require substantial trust enhancement), the invention reduces barriers to forming and optimizing transactional relationships.
Owner:WISTARIA TRADING INC
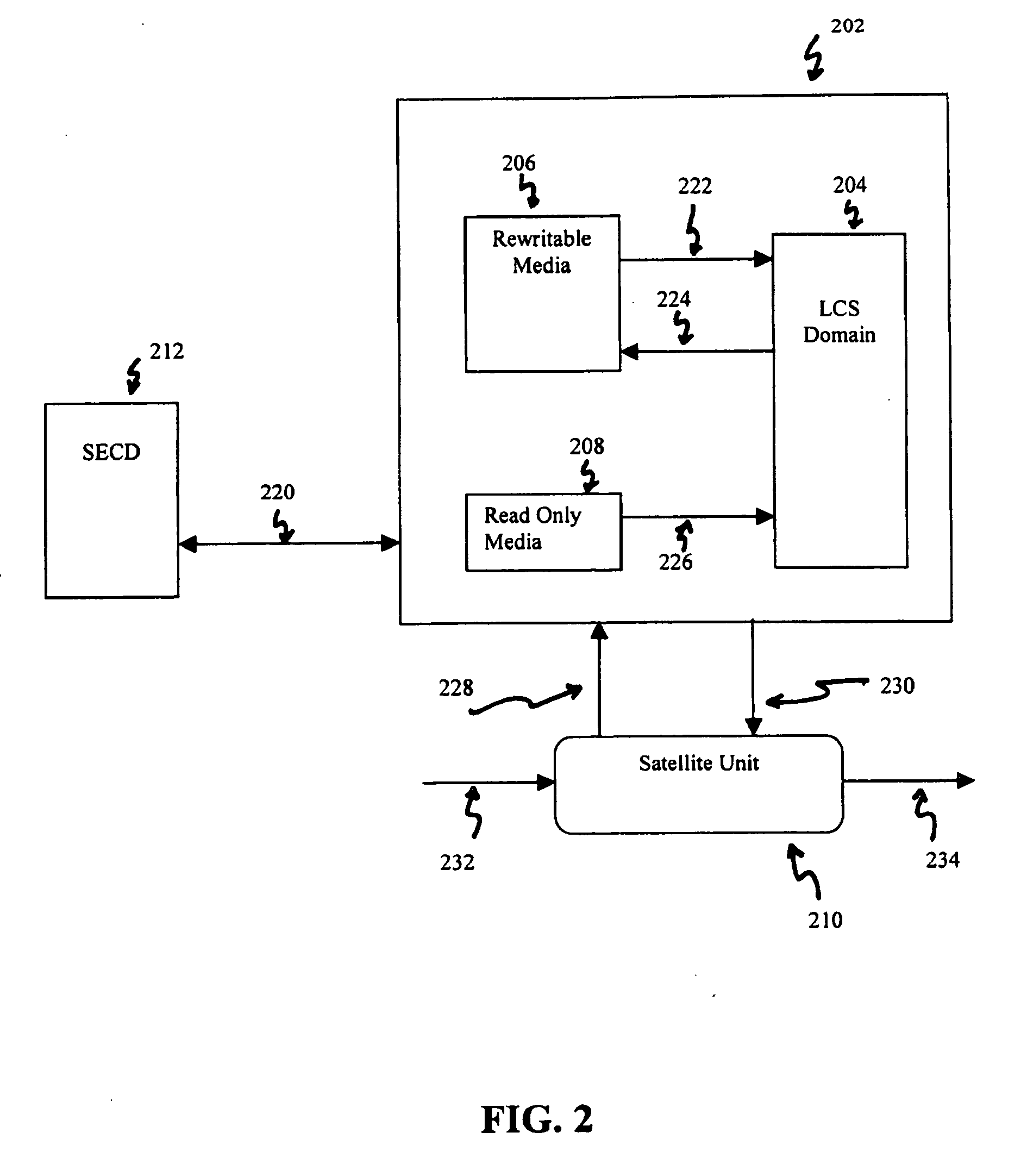
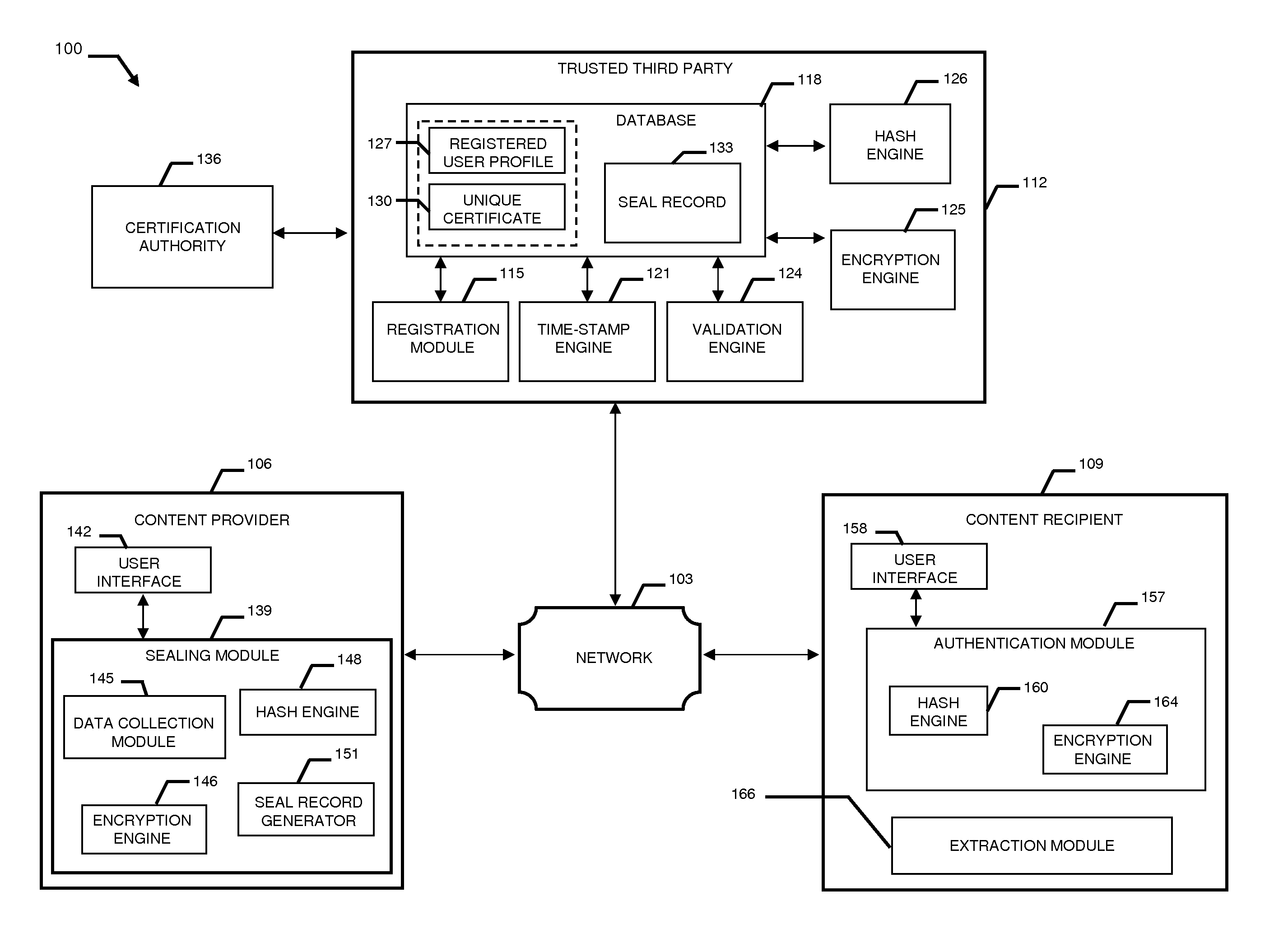
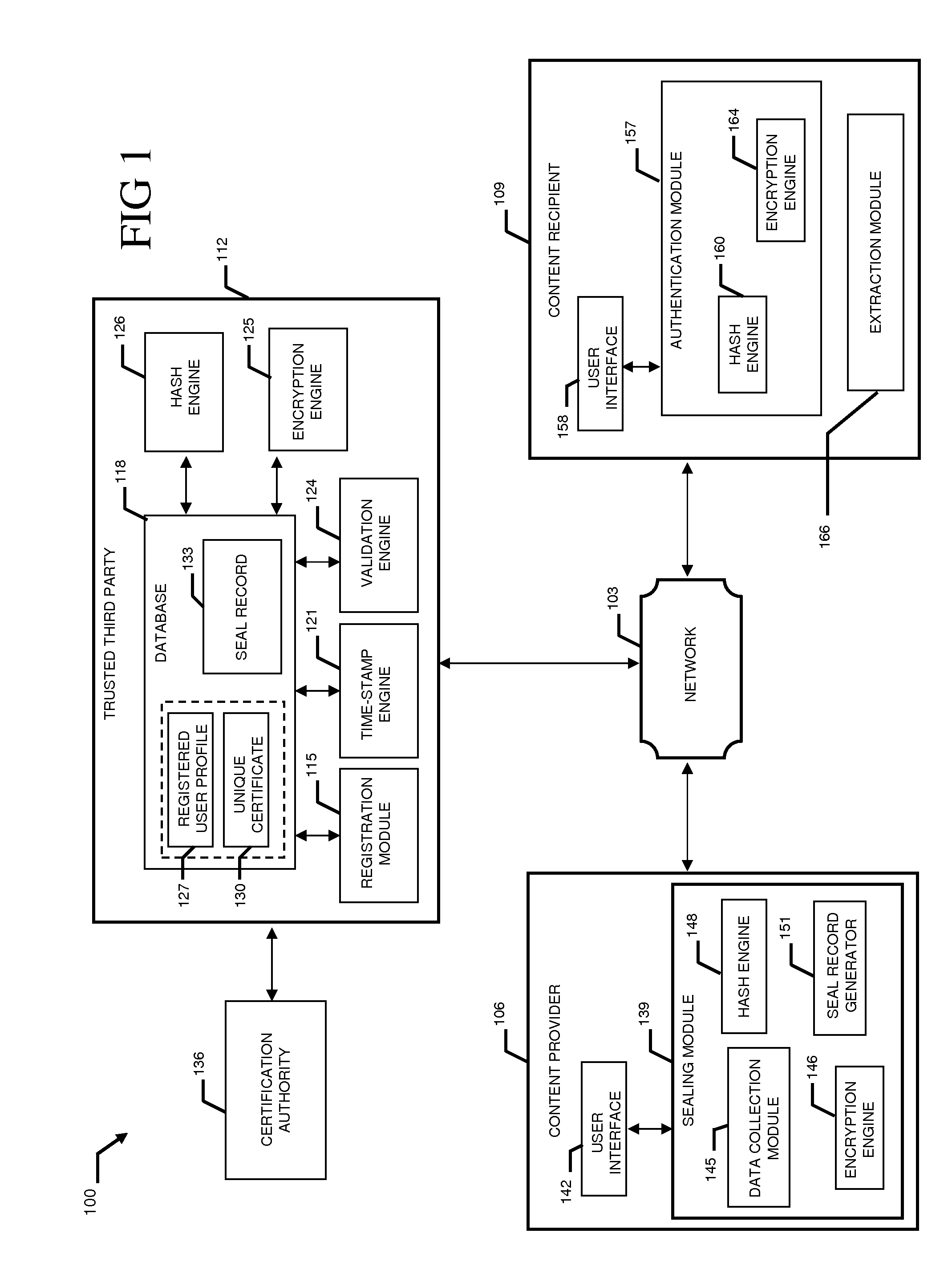
System and method to validate and authenticate digital data
InactiveUS20110231645A1Data can be securedDigital data processing detailsUser identity/authority verificationDigital dataDocument Identifier
A system and method combining registration with a trusted third party, certificate generation, hashing, encryption, customizable file identification fields, and time-stamping technology with recognized “best practice” procedures to achieve the legal admissibility and evidential weight of any form of digital file or collection of digital files. Generally, the originator of the file (the first party) and the originator's employing organization are registered with a Trusted Third Party. The originator reduces the file, by means of a hashing algorithm, to a fixed bit length binary pattern. This provides a unique digital fingerprint of the file. The resultant hash value, the originator's identity details, the employing organization details associated and securely linked to the digital certificate, the title of the file, customizable file identification fields, and other relevant data are forwarded to a Trusted Third Party where the date and time from a known and trusted time source are added. The customizable file identification fields can provide the originator with a mechanism for configuring the seal to incorporate as much additional information as deemed necessary to prove the authenticity of the digital content and / or provide data for the purposes of adding value in functions such as source identification, sorting, analysis, investigation, and compliance. Such information could include, but would not be limited to, location / GPS coordinates, machine id, biometric information, smart-card data, reason for sealing. The original file does not leave the control of the originating party. When combined, the forwarded details and date and time create a Seal Record. The Seal Record is encrypted and hashed. The Seal Record along with all other relevant information are retained on a central secure server. The recipient of the file (the second party) can confirm the file has been received in an unaltered state with integrity retained and it is the authentic version by validating the file.
Owner:CYBERCUBE
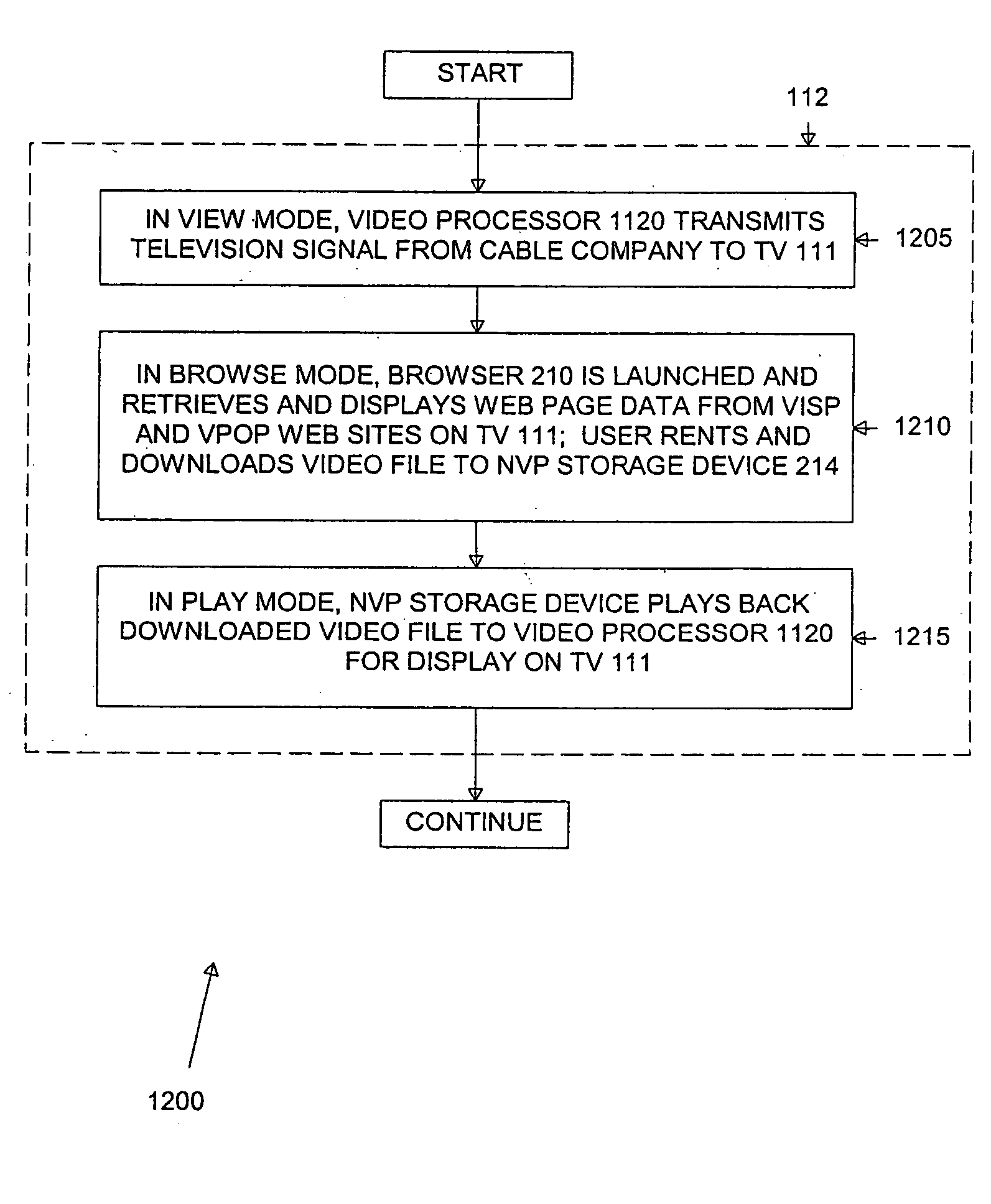
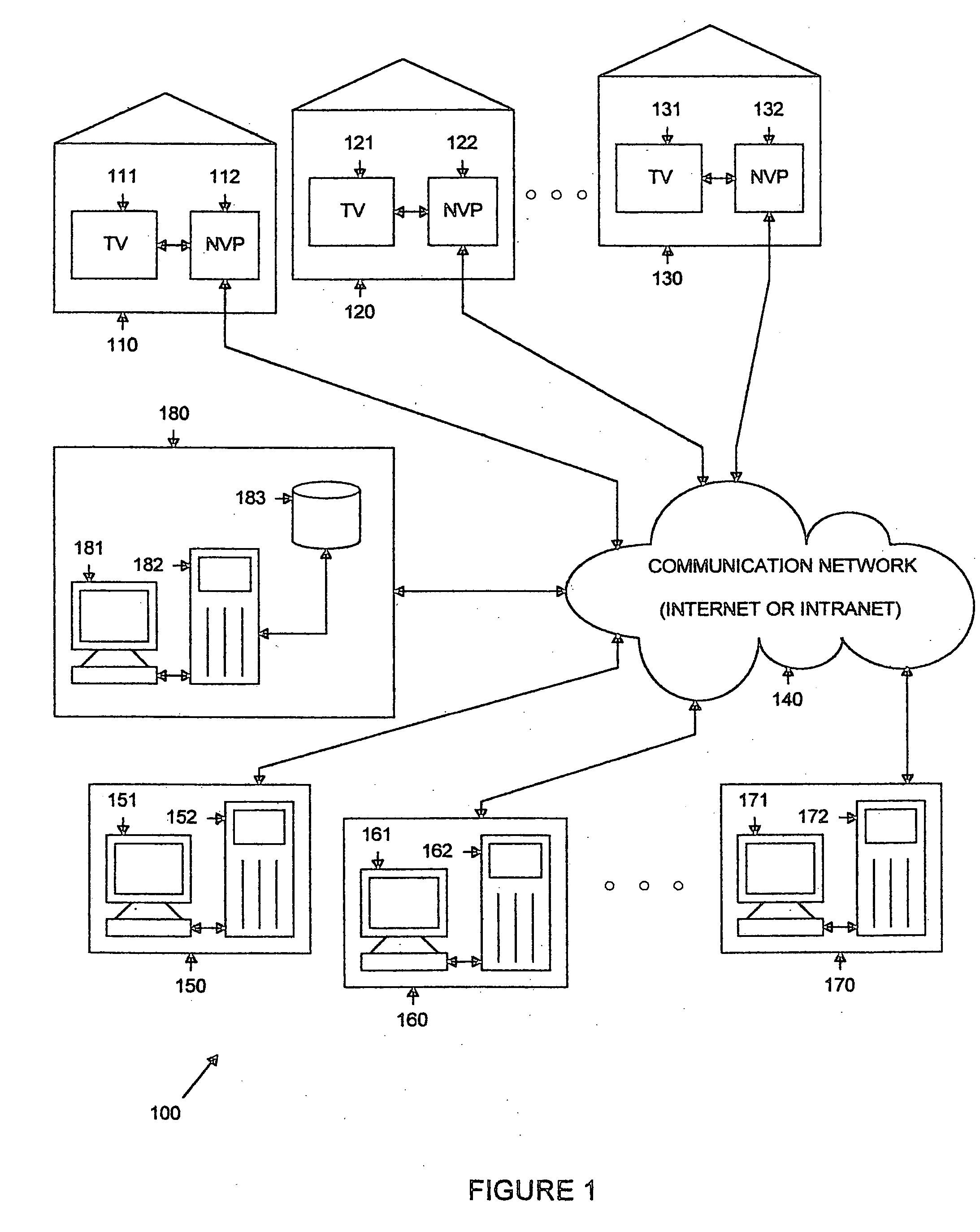
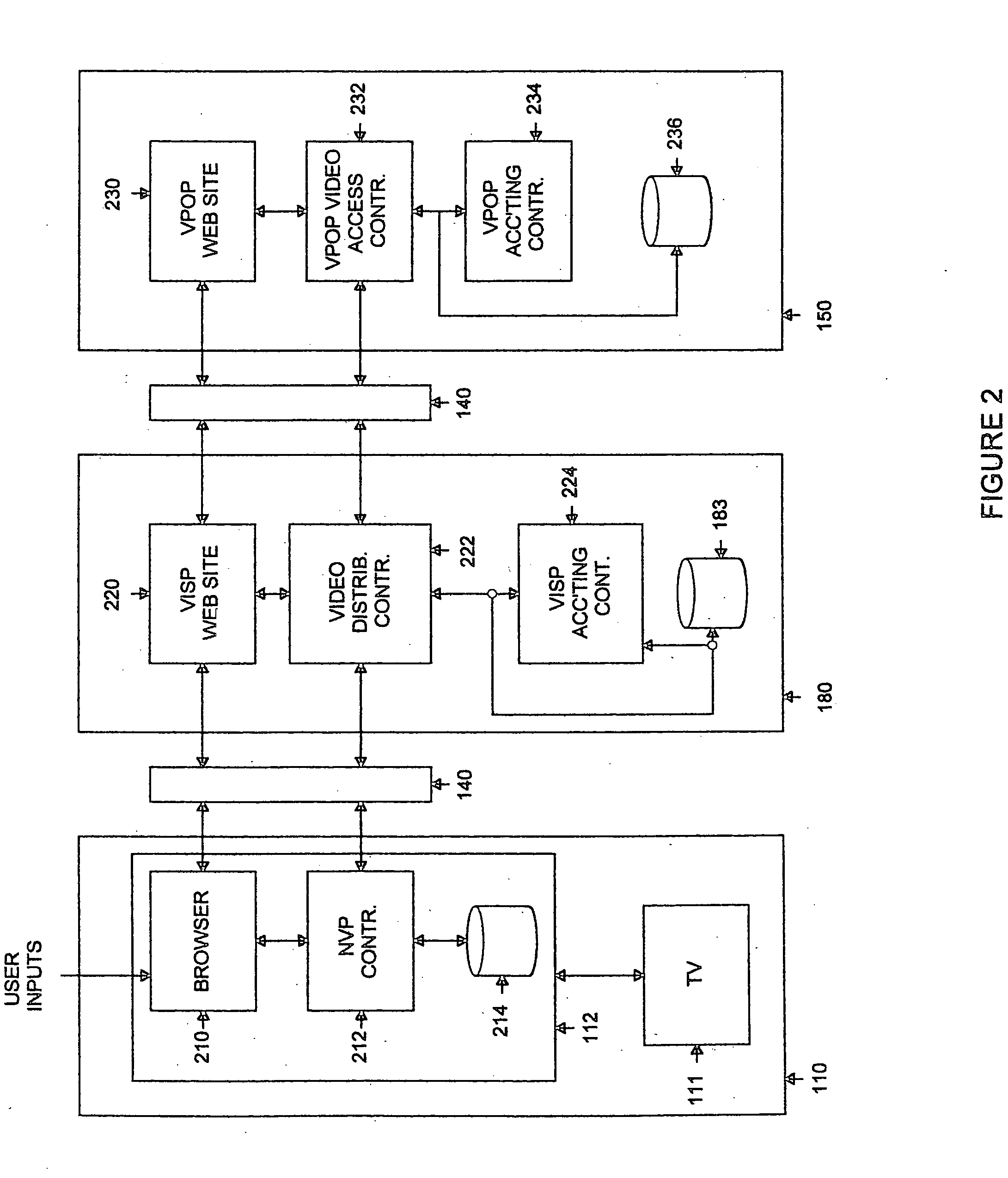
Set-top box for internet-based distribution of video and other data
InactiveUS20050273827A1Data can be securedAnalogue secracy/subscription systemsTwo-way working systemsVideo playerWeb page
A subscriber video player for use in a communication network that communicates with a plurality of video content servers that provide a plurality of video files for download to a subscriber. The subscriber video player comprises: 1) a storage medium for storing selected ones of the plurality of video files downloaded from the plurality of video content servers; 2) a first controller for receiving inputs from a first subscriber using the subscriber video player; and 3) a browser application coupled to the first controller and responsive to the inputs from the first subscriber, the browser application for accessing the video content servers and retrieving therefrom web page data associated with the plurality of video files and displaying the web page data on a display screen coupled to the subscriber video player.
Owner:JAVED SHOEB M +2
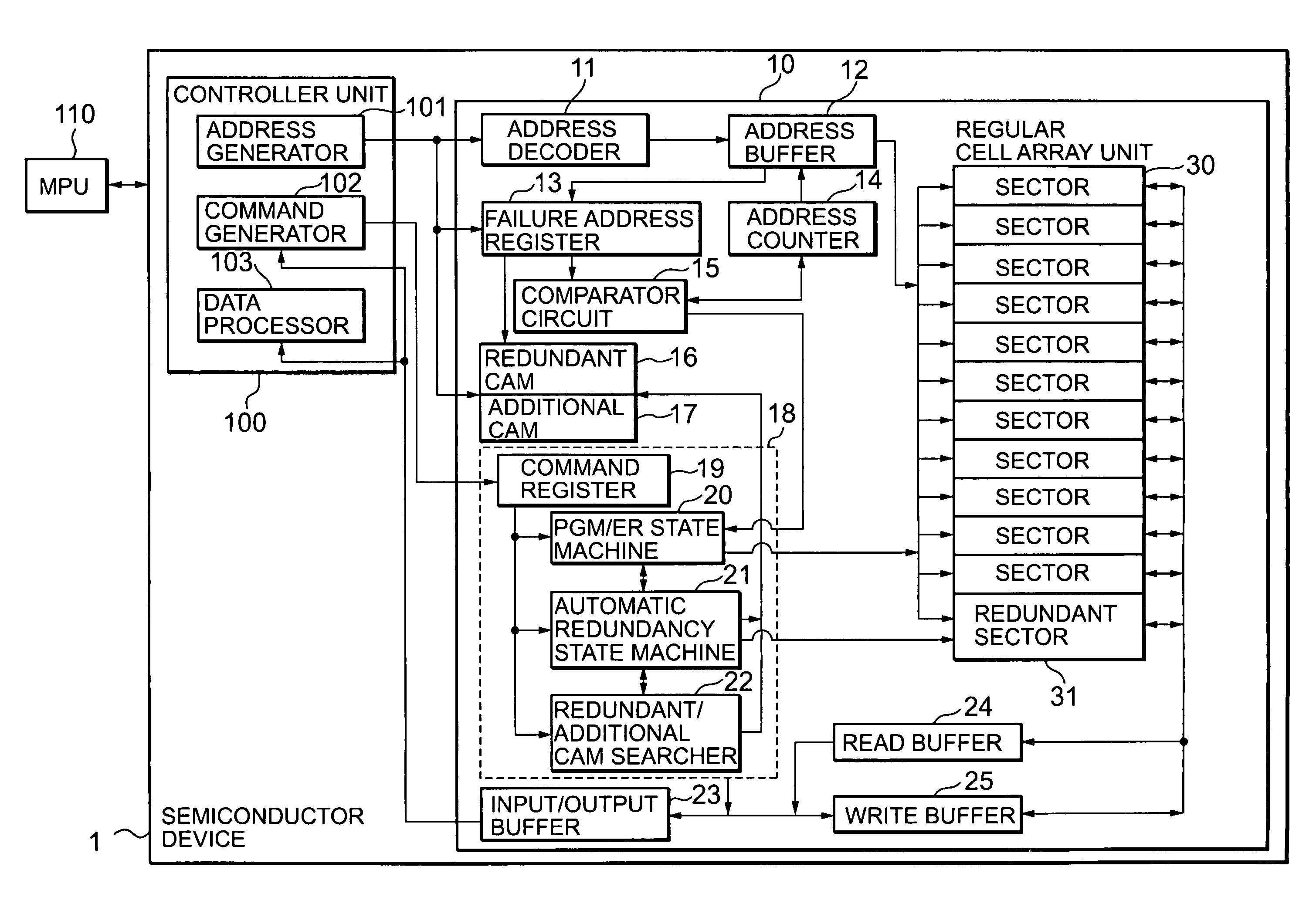
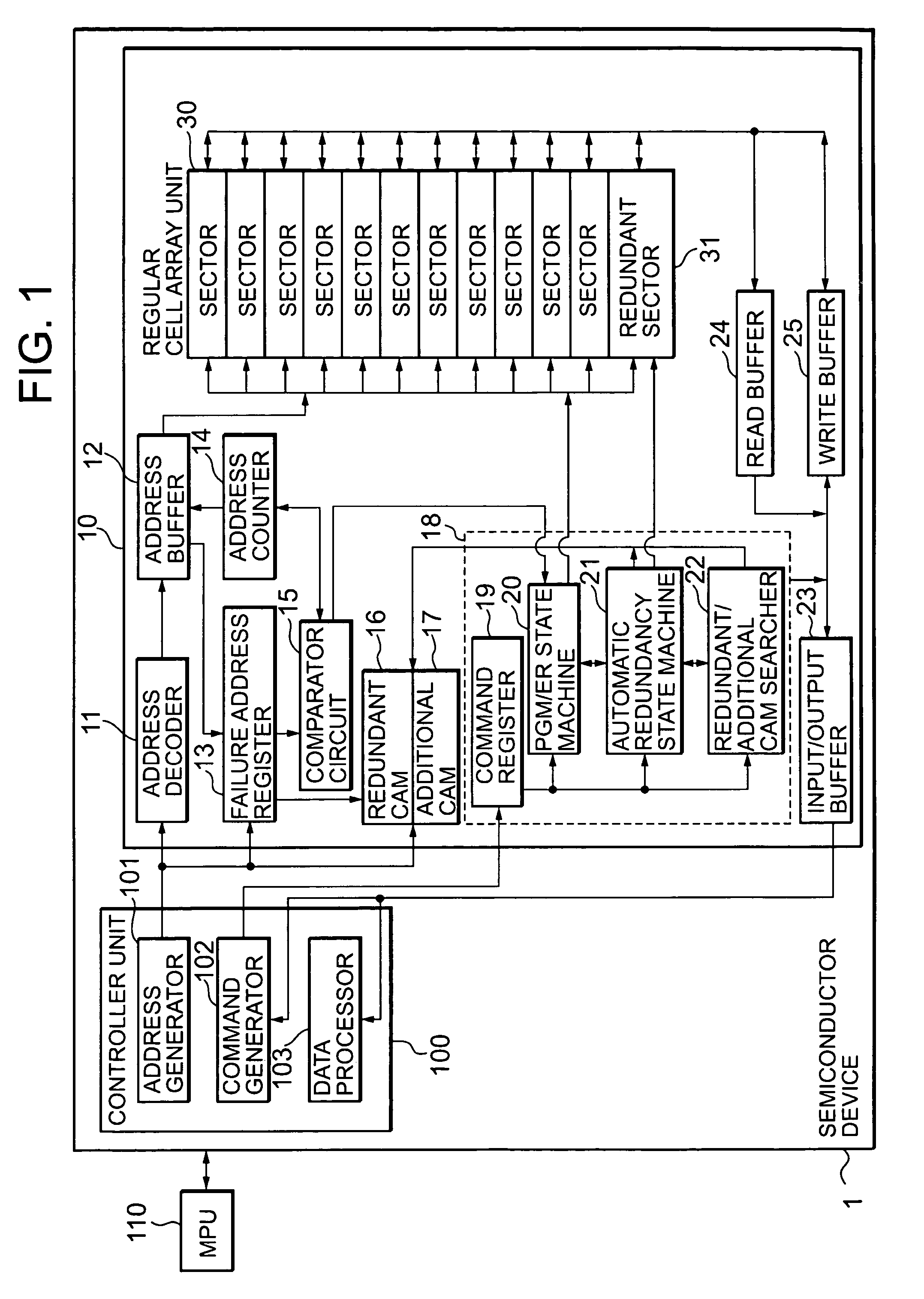
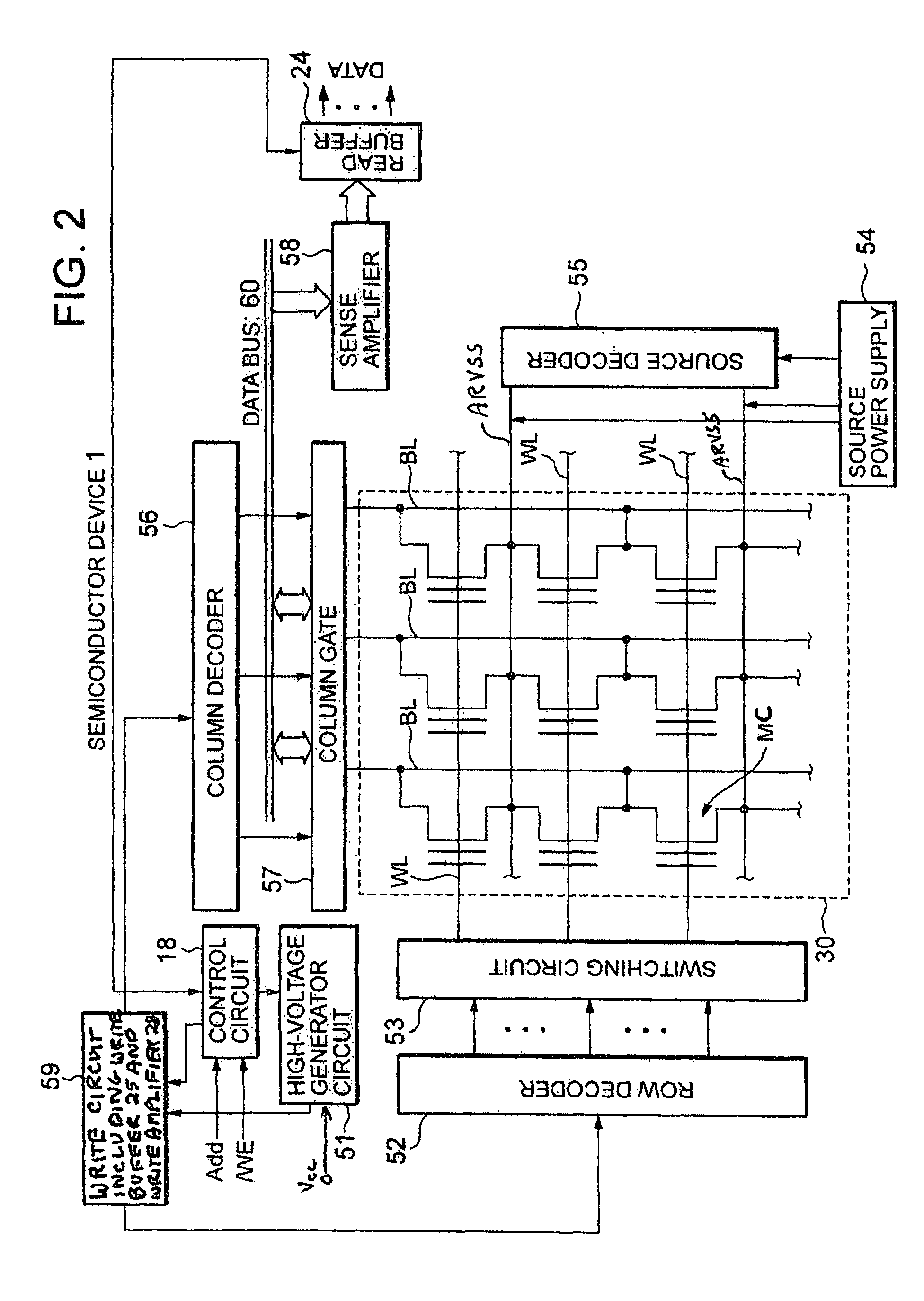
Semiconductor device and program data redundancy method therefor
A semiconductor device (1) is provided which includes a regular cell array unit (30), a redundant cell array unit (31) that is provided in relation to the regular cell array unit (30), and a PGM / ER state machine (20) that controls reprogramming in which, when programming of a sector in the regular cell array unit fails (step S3), data involved in the programming that fails and data already stored in the sector in the regular cell array unit are written (step S8) into the redundant cell array unit (31). Since reprogramming is performed to write the data already written in the sector as well as the data involved in the programming that fails into the redundant cell array unit (31), data loss can be prevented and data can be secured, thereby increasing the reliability of the system.
Owner:VALLEY DEVICE MANAGEMENT
Cryptographic key split binder for use with tagged data elements
InactiveUS20110116628A1Weight increaseData can be securedKey distribution for secure communicationTelevision systemsData elementData labeling
A process of cryptographically securing a data object including one or more respectively tagged data elements includes selecting a tagged data element from among a plurality of tagged data elements, based on an associated data tag. A plurality of cryptographic key splits is generated from seed data. The cryptographic key splits are bound together to produce a first cryptographic key. A second cryptographic key is generated based on security requirements of the data object. The tagged data element is encrypted using the first cryptographic key. The data object encrypting using the second cryptographic key. At least one of the cryptographic key splits is based on the associated data tag.
Owner:TECSEC
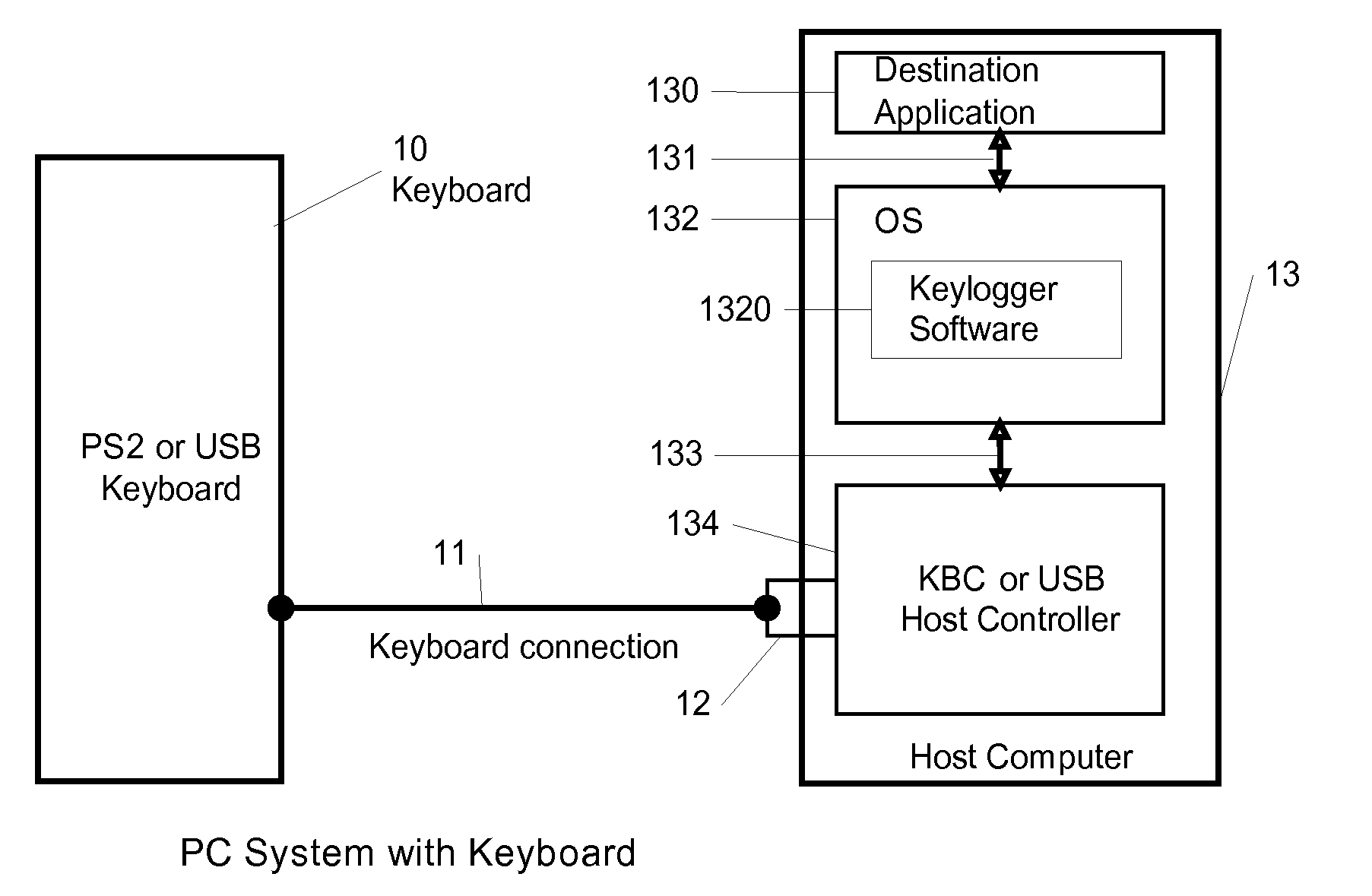
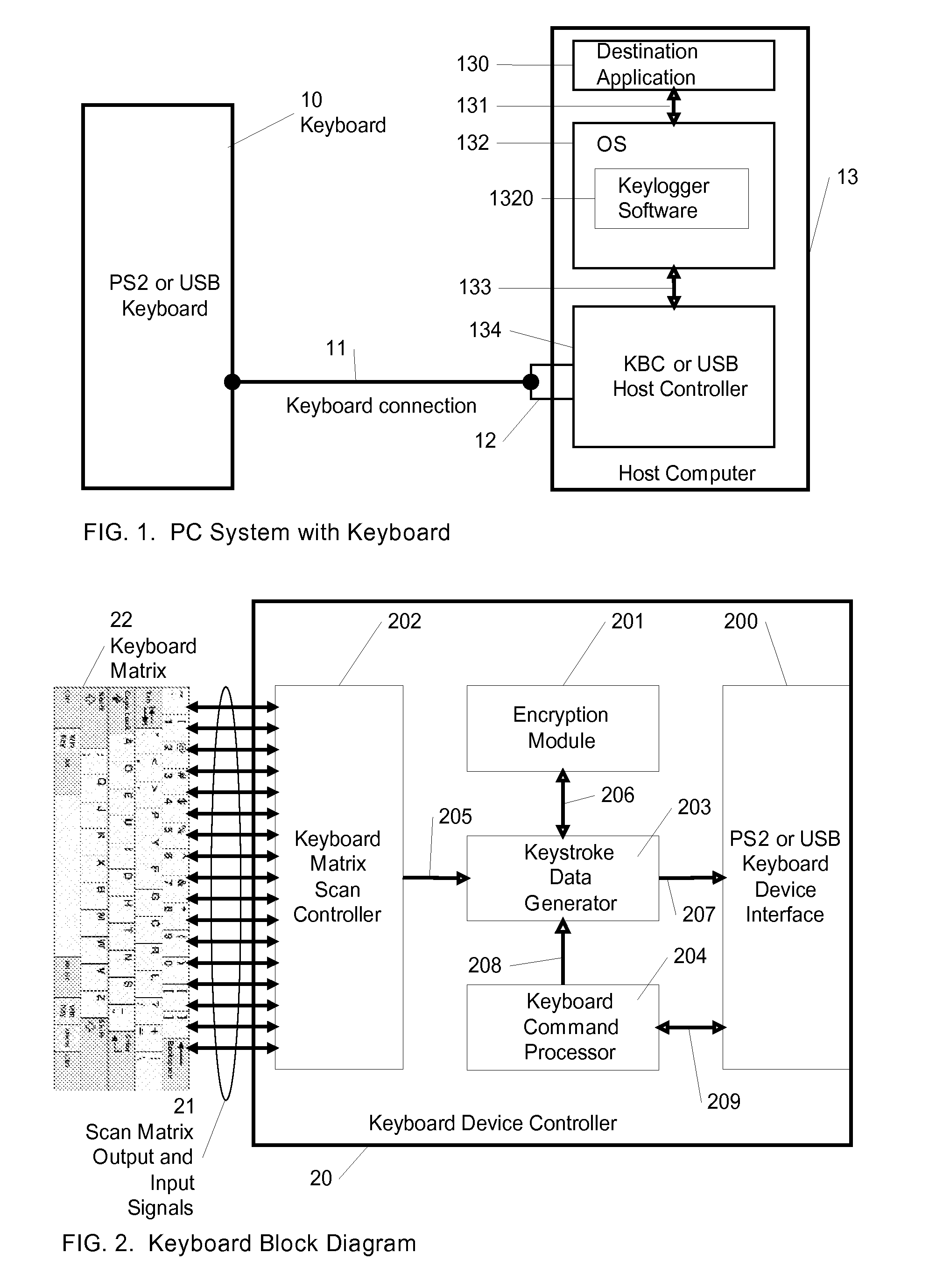
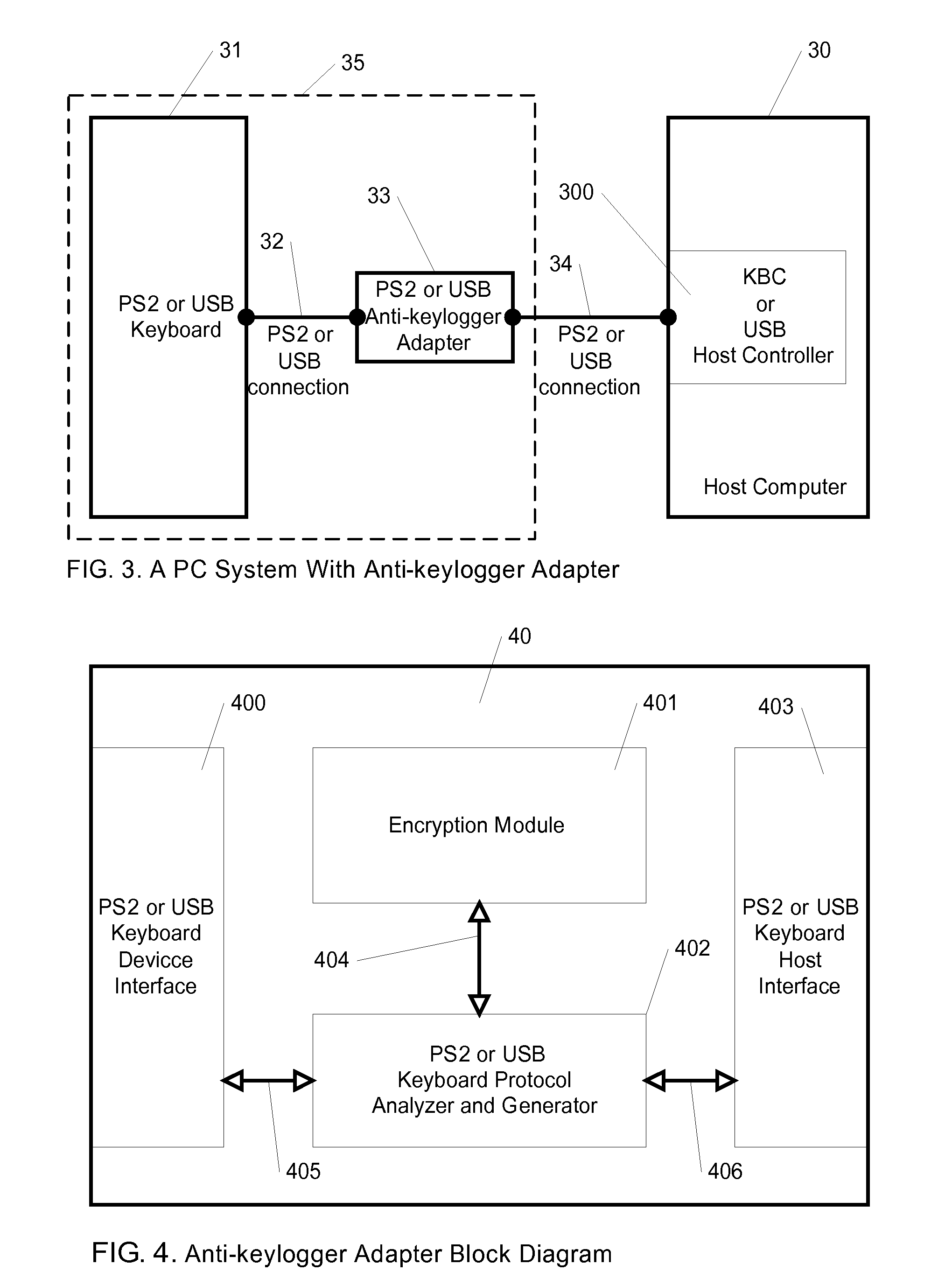
Method For Anit-Keylogger
InactiveUS20090144558A1Easy to fixImprove securityUnauthorized memory use protectionHardware monitoringComputer usersComputer science
A method for preventing keyloggers from logging text data, that is outputted by a computer user data input device. By encrypting the text data of the user data input device, the keyloggers cannot understand the text data of the user data input device in a computer.
Owner:WANG CHI PEI
Cryptographic key split binder for use with tagged data elements
InactiveUS8077870B2Data can be securedKey distribution for secure communicationTelevision systemsData elementData labeling
A process of cryptographically securing a data object including one or more respectively tagged data elements includes selecting a tagged data element from among a plurality of tagged data elements, based on an associated data tag. A plurality of cryptographic key splits is generated from seed data. The cryptographic key splits are bound together to produce a first cryptographic key. A second cryptographic key is generated based on security requirements of the data object. The tagged data element is encrypted using the first cryptographic key. The data object encrypting using the second cryptographic key. At least one of the cryptographic key splits is based on the associated data tag.
Owner:TECSEC
Telecommunication method for securely exchanging data
ActiveUS20160127326A1Improve security levelData can be securedUser identity/authority verificationSecurity arrangementTelecommunications DeviceMobile end
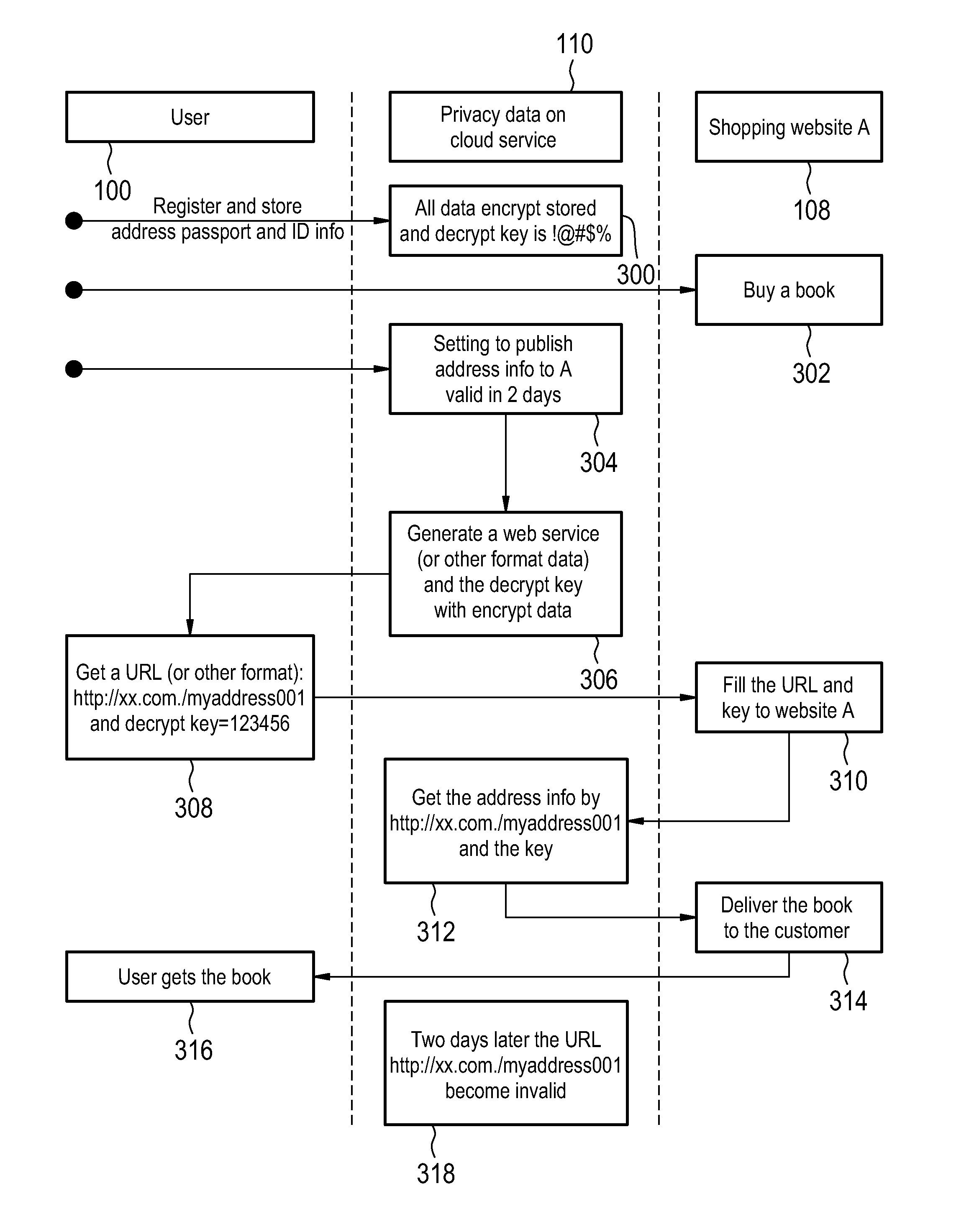
The invention provides for a telecommunication method of securely exchanging unencrypted data between a telecommunications device and a first server computer system via a digital cellular wireless telecommunications network, wherein the telecommunications device is a battery powered mobile end user telecommunications device, wherein the method comprises the steps of: encrypting the unencrypted data using a first encryption algorithm into first encrypted data, sending the first encrypted data to a second server computer system via a first network connection of the digital cellular wireless telecommunications network, storing the first encrypted data by the second server computer system, sending an order request to the first server computer system via a second network connection of the digital cellular wireless telecommunications network by the telecommunications device, sending a data publishing request to the second server computer system, generating a cryptographic key pair, sending the first encrypted data, the public key, and the private key to the telecommunications device, decrypting the first encrypted data into the unencrypted data, encrypting the unencrypted data into second encrypted data using the public key, sending the second encrypted data to the second, generating a web service for providing the second encrypted data via an URL, sending the URL to the telecommunications device, sending the URL and the private key, requesting the second encrypted data from the second server computer system, sending the second encrypted data to the first server computer system by the second server computer system using the wired network connection, decrypting the second encrypted data by the first server computer system into the unencrypted data, and combining the order request with the unencrypted data.
Owner:SAP AG
Keypad for the entry of authentication data
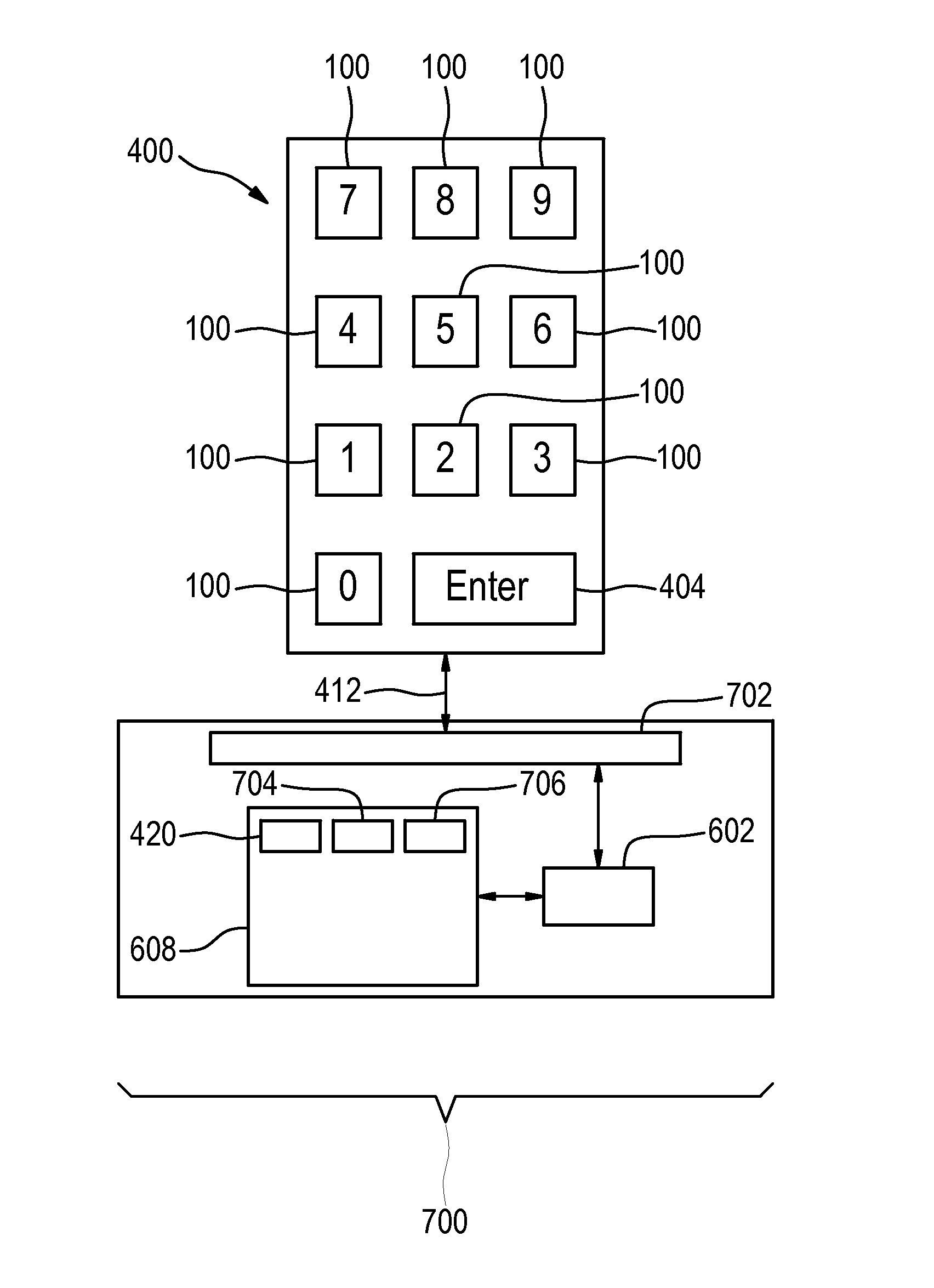
ActiveUS20160093131A1Difficult to determineData can be securedElectric signal transmission systemsDigital data processing detailsData connectionKey pressing
The invention provides for an electronic system with a keypad for manual entry of authentication data by a user. The keypad comprises: multiple keys for entering the authentication data. At least one of the multiple keys comprises a three position switch with an elastic element for restoring the three position switch to a first position. The three position switch is operable to be depressed in a motion direction to a second position and a third position. The motion direction is perpendicular to a surface where the keys are mounted. A first force is required to depress the three position switch to the second position and a second force is required to depress the three position switch from the second position to the third position. The second force is greater than the first force.The keypad further comprises a controller configured for monitoring key presses of the multiple keys and for monitoring key position data of the three position switch of each of the at least one of the multiple keys during the key presses. The controller is further configured for decoding the key presses and the key position data into the authentication data. The keypad is further configured for outputting the authentication data via a data connection.
Owner:SAP AG
Payment unit, system and method
InactiveUS20150161594A1Improve the level ofReduce ticket fraudAcutation objectsFinancePaymentCard reader
A payment unit, method and system are disclosed. In one arrangement, the payment unit includes a payment card reader to participate in a payment communication to obtain payment data, a secondary reader to obtain supplementary data from a machine readable entity that is physically proximate to the unit, the supplementary data being obtained via a communication that is separate from the payment communication, and a controller to operate the payment card reader and secondary reader and to generate a payment record from said payment data and said supplementary data.
Owner:VANCLARE SE
Embedded control device
InactiveUS20120303216A1Enhance real time performanceData be secureProgram synchronisationDigital data processing detailsEmbedded system
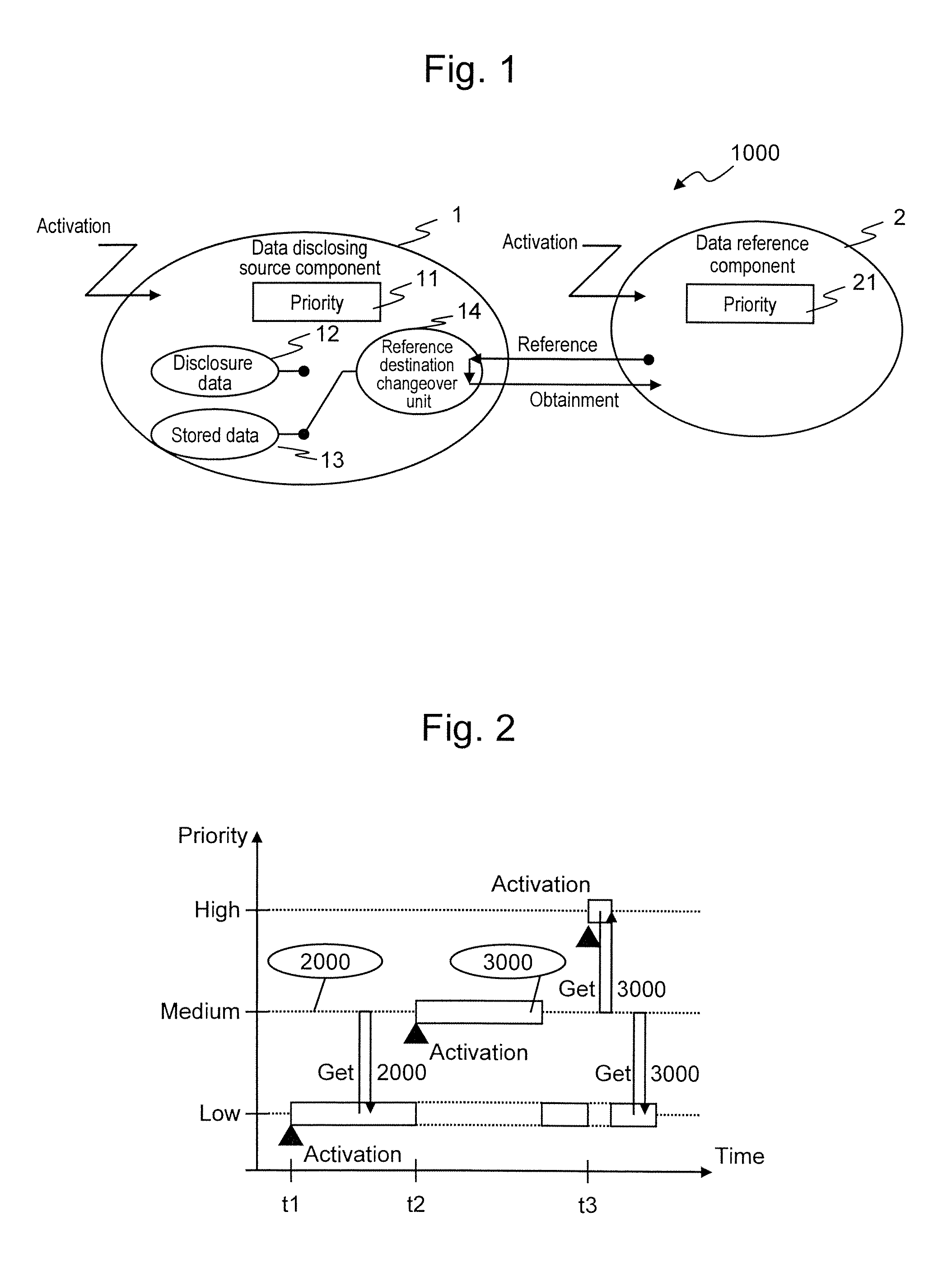
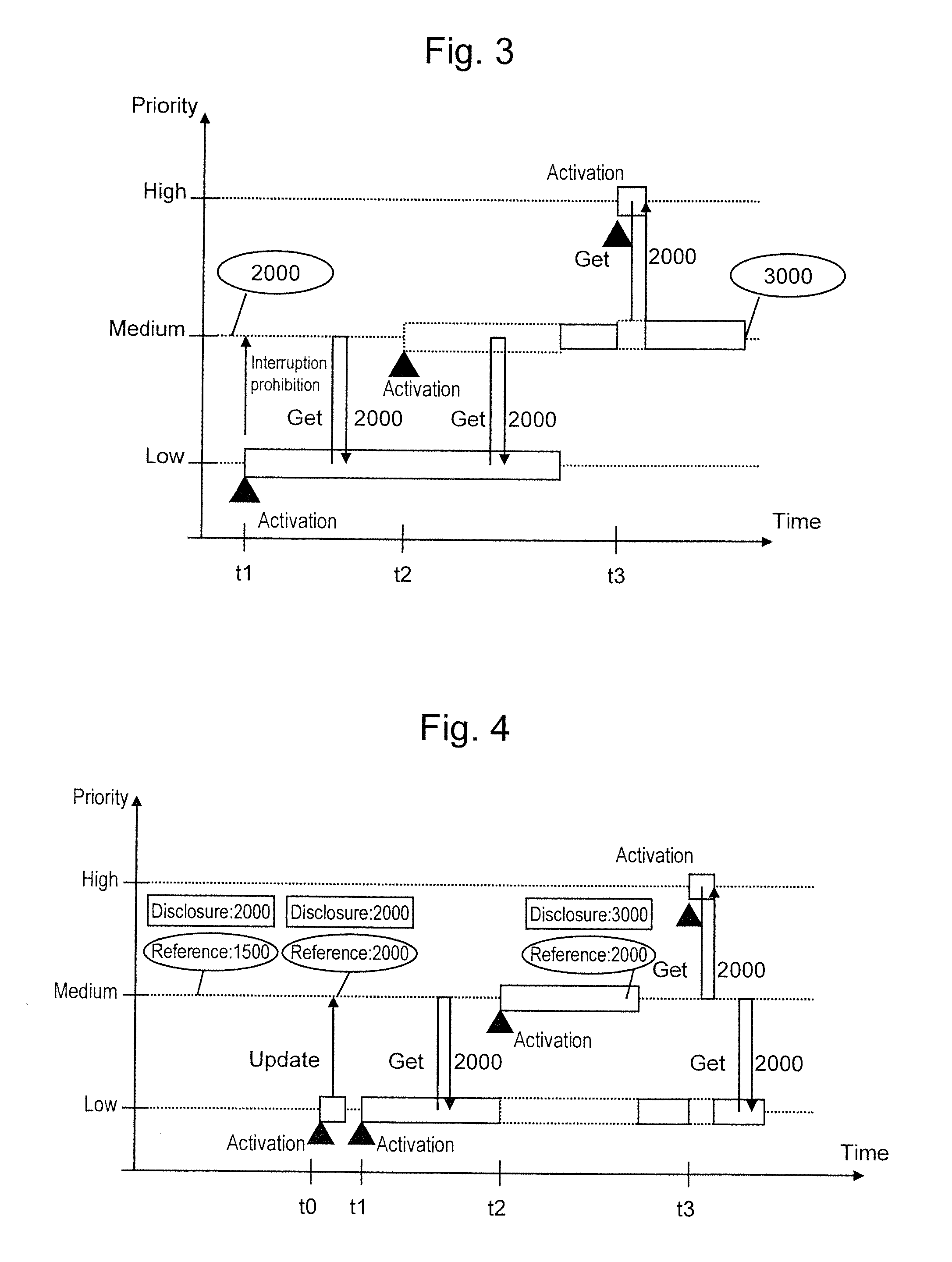
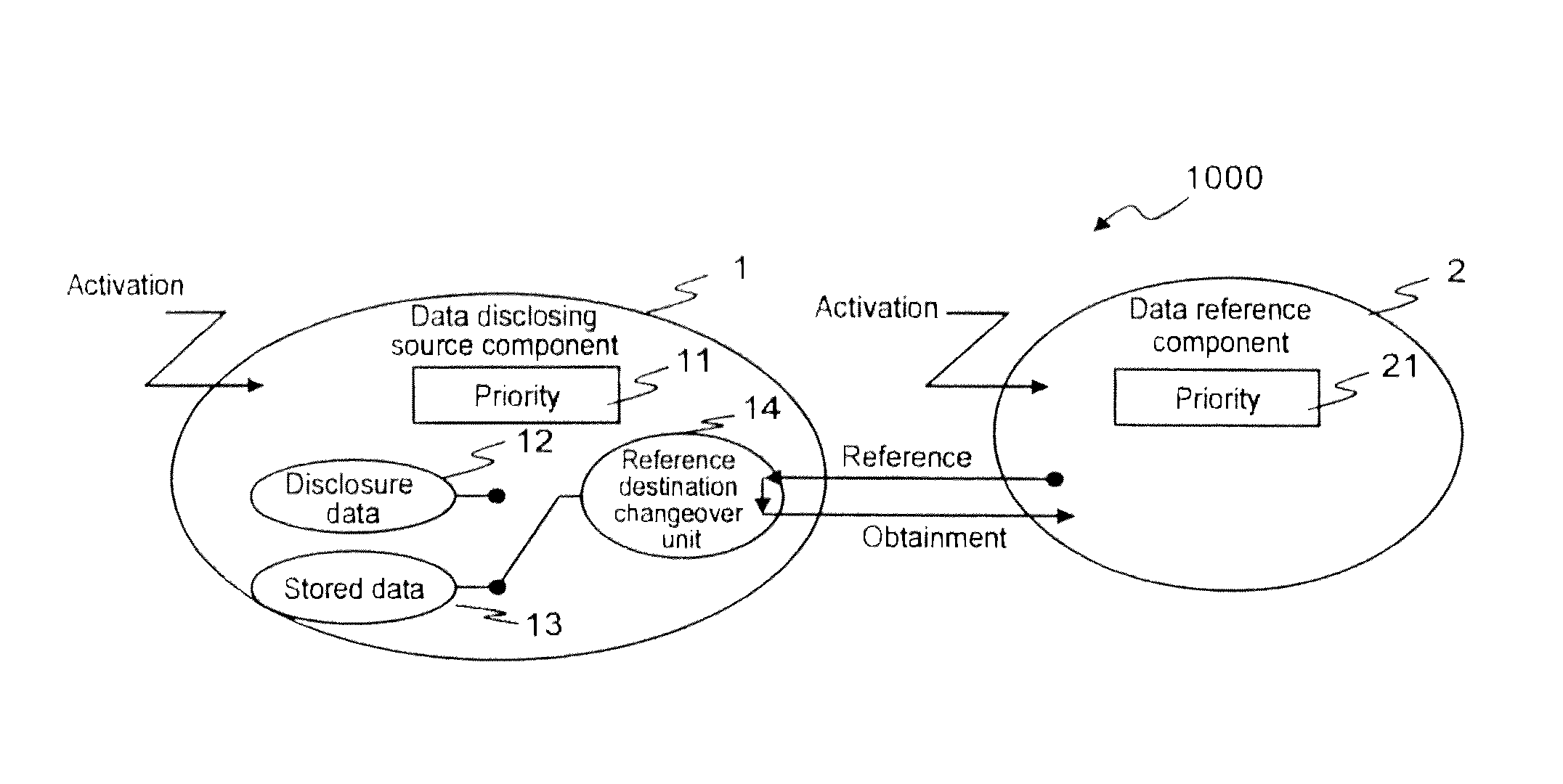
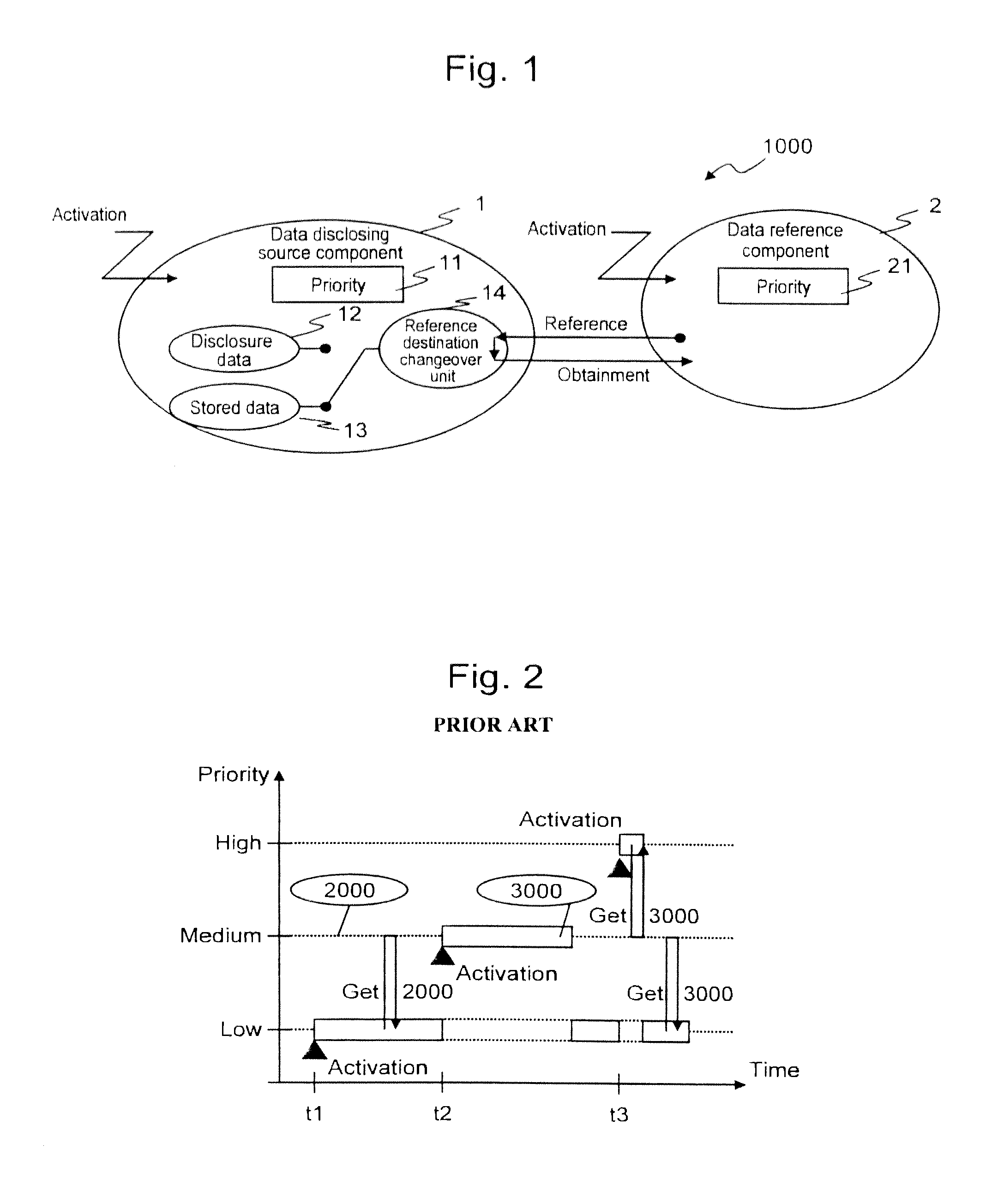
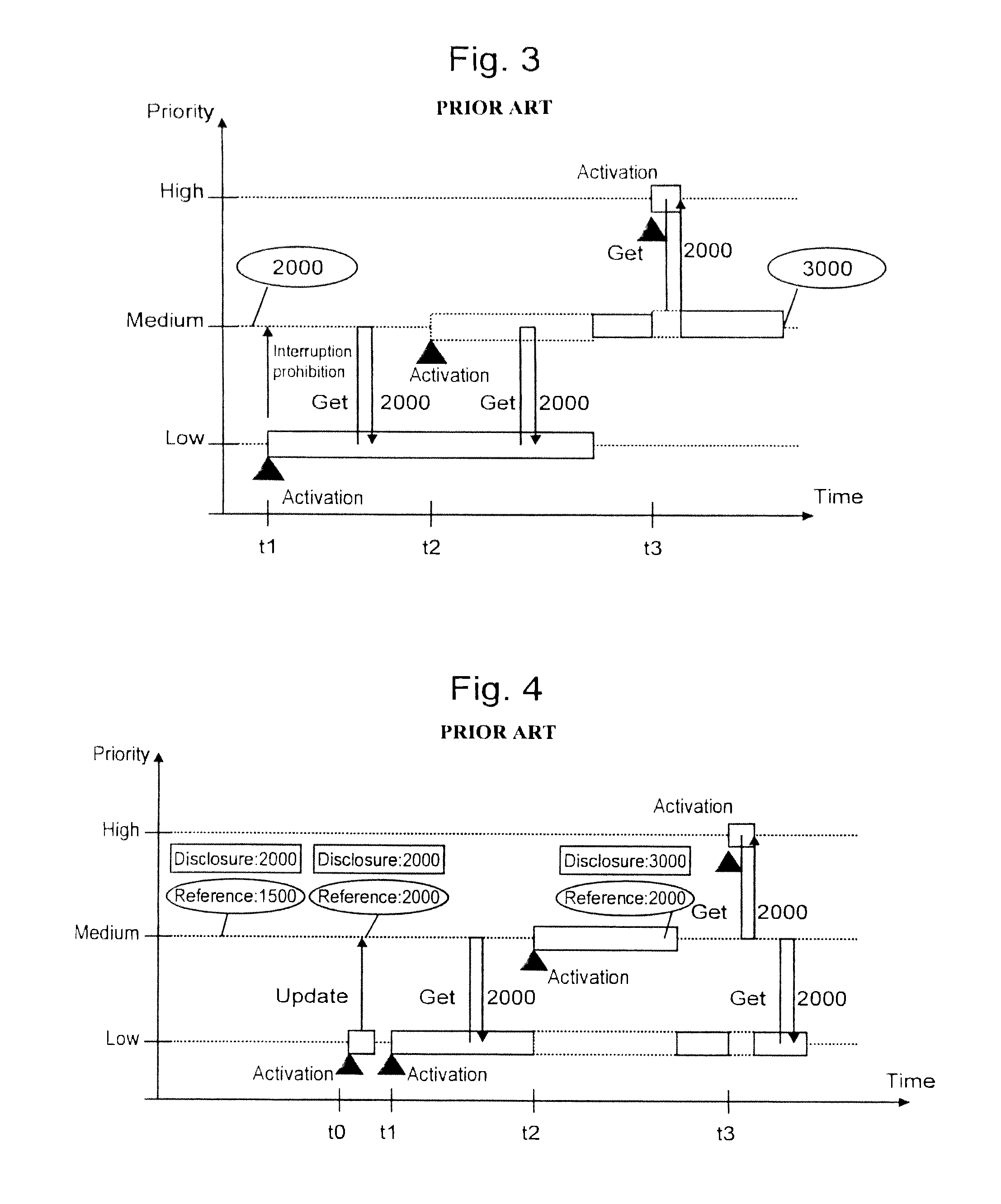
There is provided an embedded control device having high real time performance and capable of securing data concurrency. The embedded control device according to the present invention includes disclosure data and stored data as control data to be disclosed to a data reference component. The embedded control device changes over a reference destination for the data reference component either to the disclosure data or to the stored data, depending on which of the execution priority of the data disclosing source component and the execution priority of the data reference component is higher.
Owner:HITACHI LTD
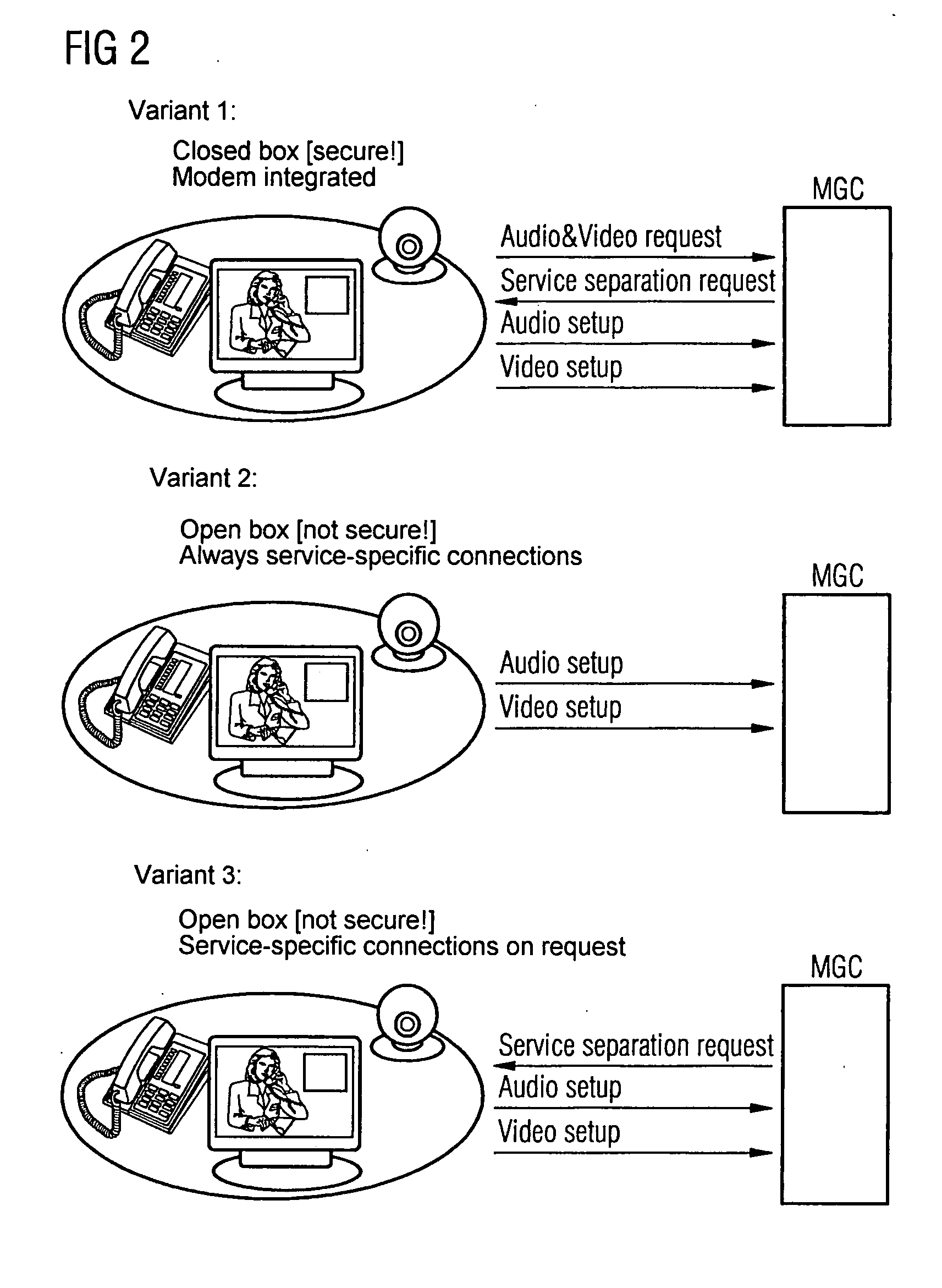
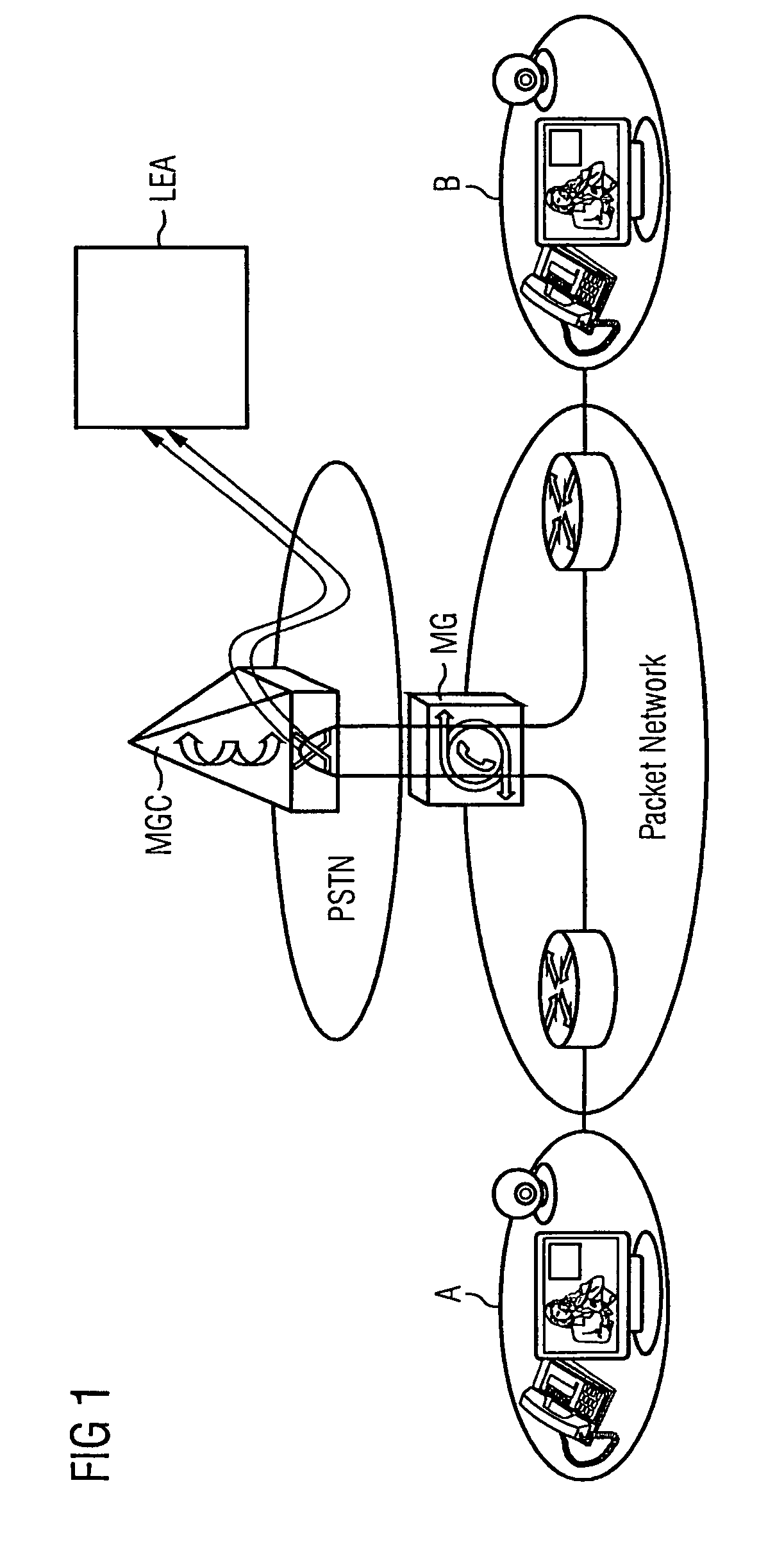
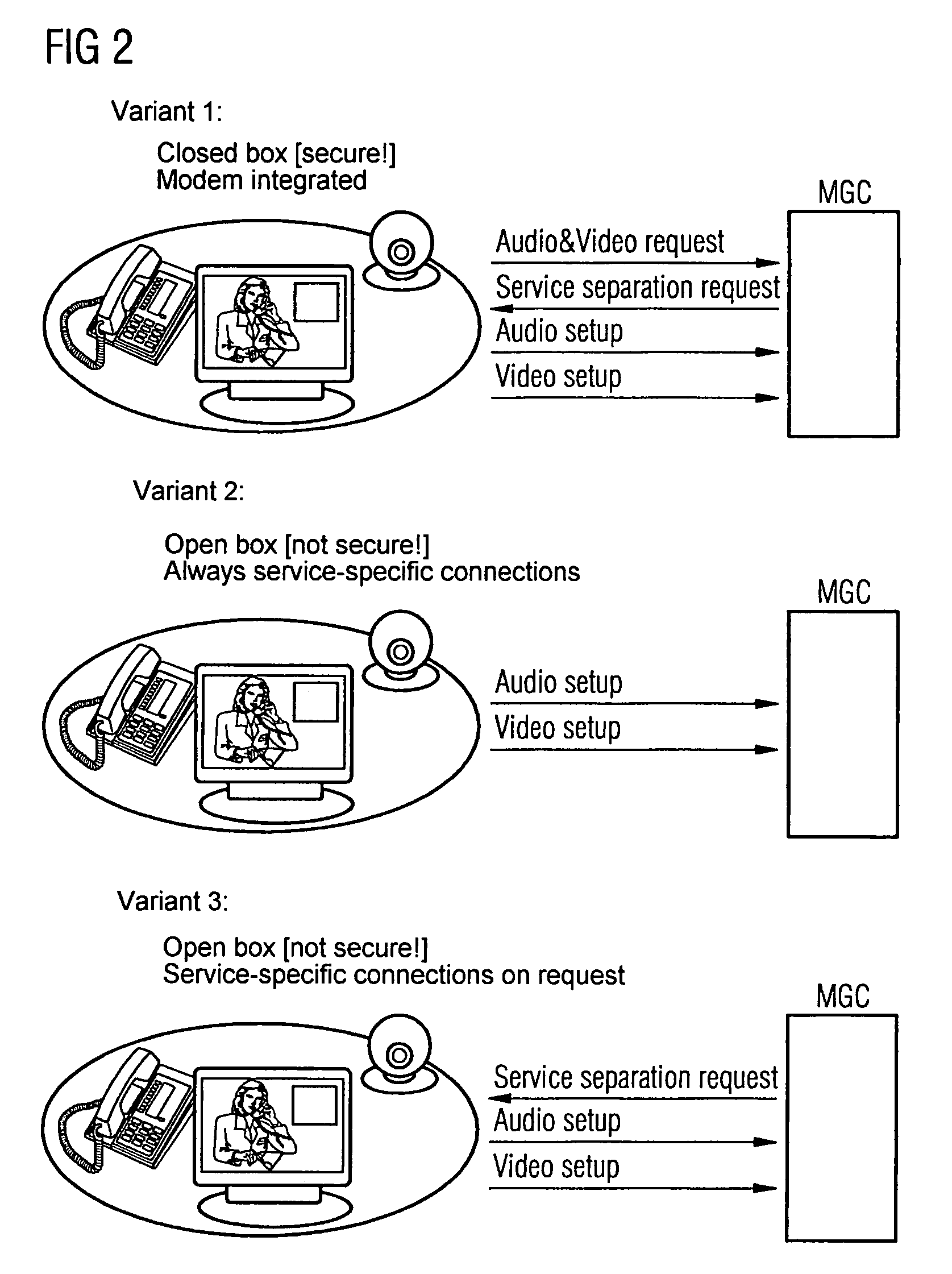
Method and Device for Apping the Payload Data of Multimedia Connections in a Packet Network
ActiveUS20070217423A1Reduce riskData can be securedInterconnection arrangementsTime-division multiplexComputer networkAudio frequency
Owner:HMD GLOBAL
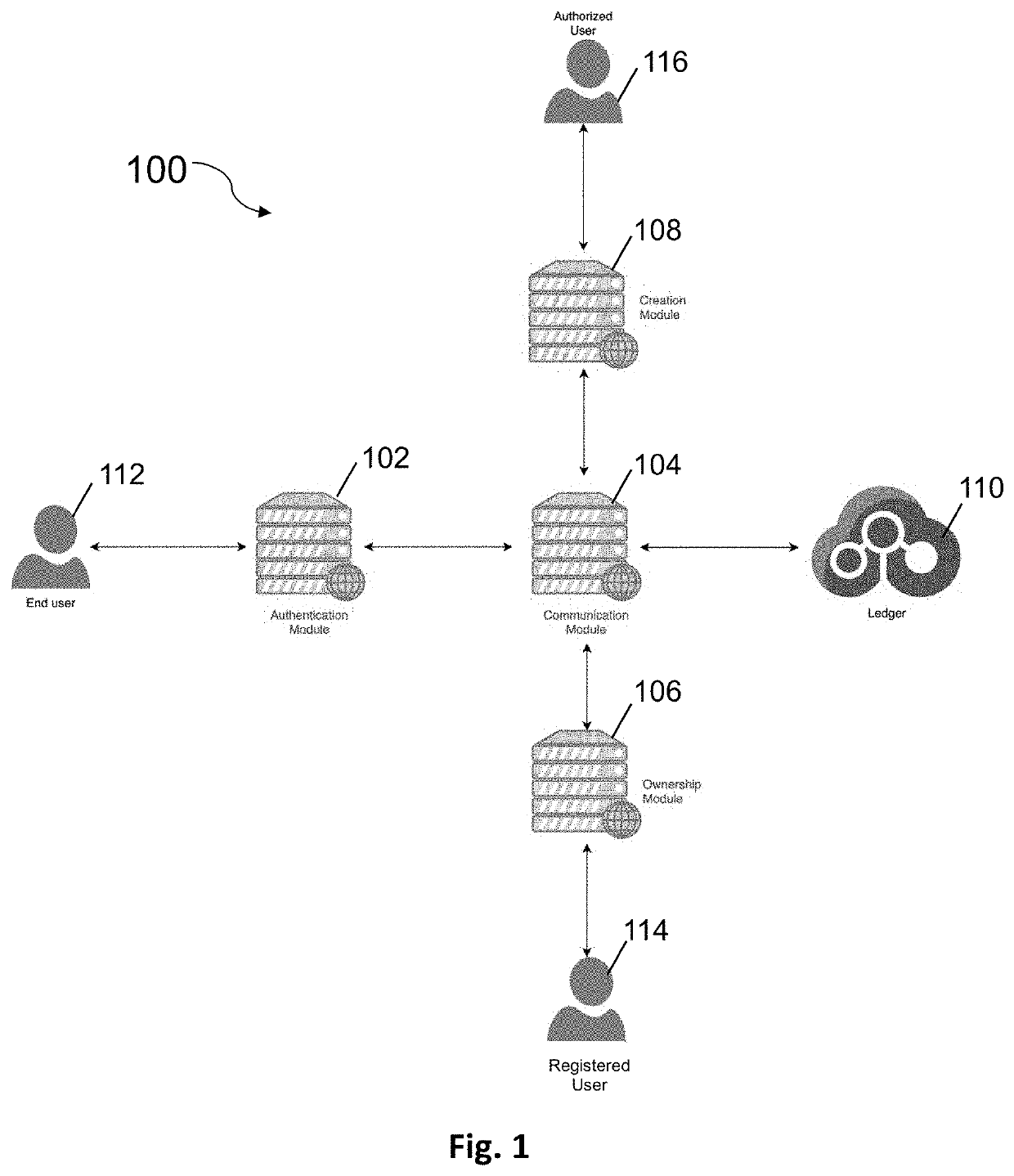
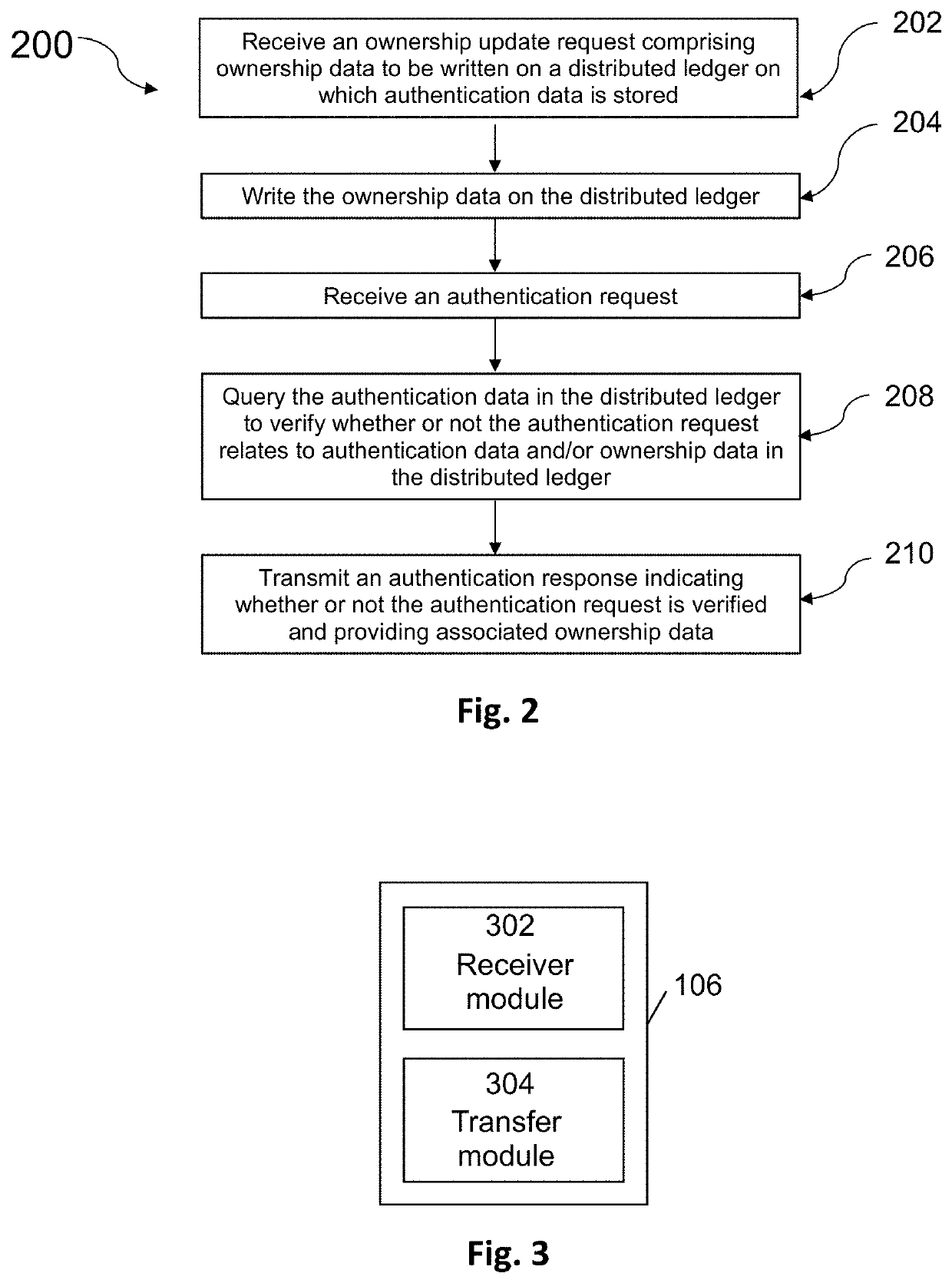
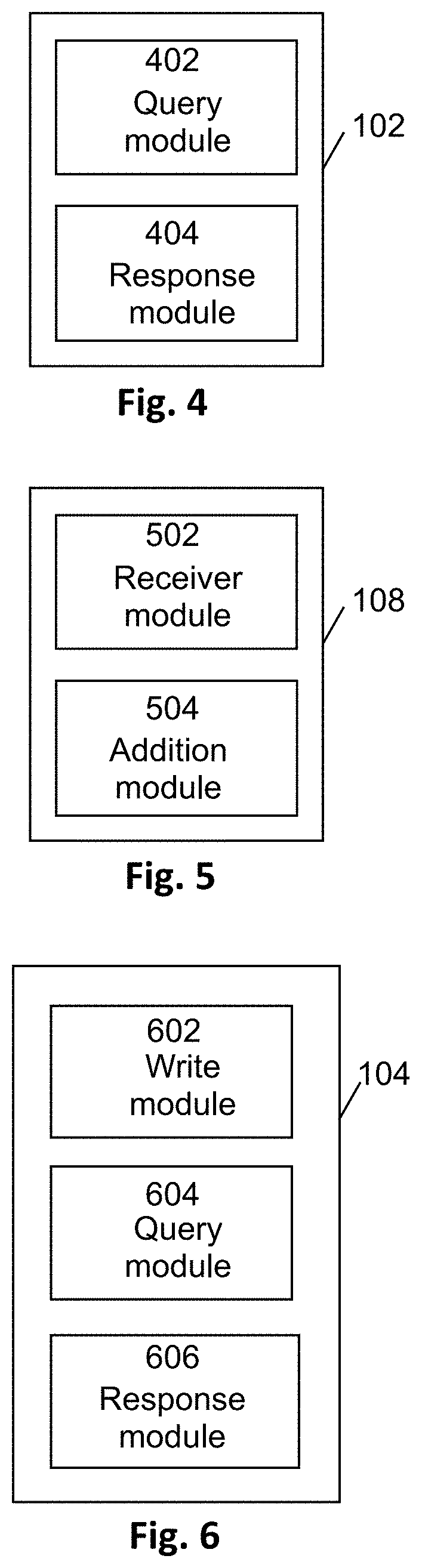
System and Method for Product Authentication
InactiveUS20200357004A1Increase authenticityData can be securedCustomer relationshipUser identity/authority verificationAuthentication systemDatabase
A product authentication system is described comprising a distributed ledger on which authentication data and ownership data for a product is stored. An ownership module is configured to add ownership data to the distributed ledger upon receipt of an ownership update request from a registered user. An authentication module is configured to i) query the authentication data and ownership data on the distributed ledger upon receipt of an authentication request from a user and to ii) relay an authentication response to the user wherein the authentication response indicates whether the product is authenticated and, if authenticated, identifies an owner of the product. A method of product authentication is also described.
Owner:ESCUDO WEB SOFTWARE SL
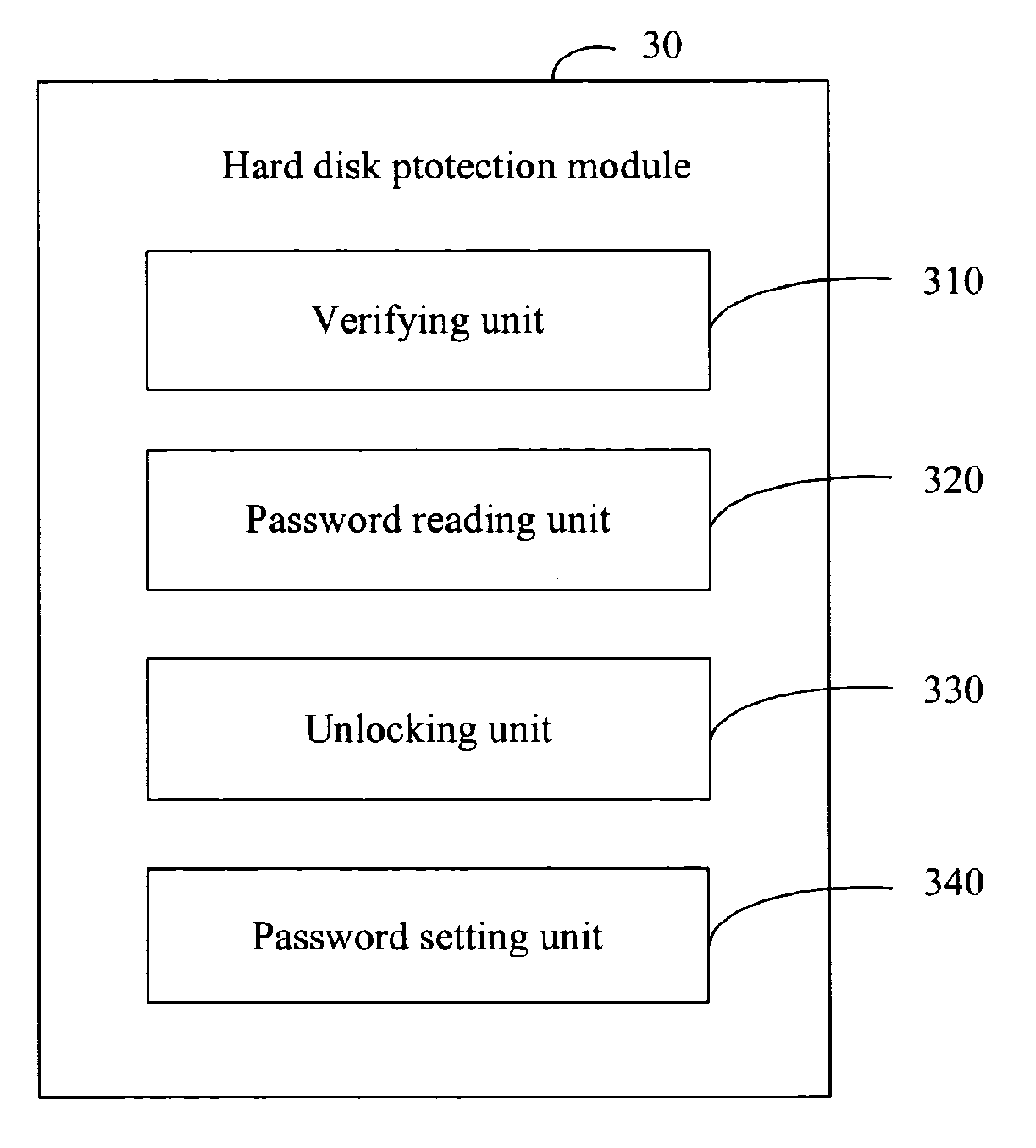
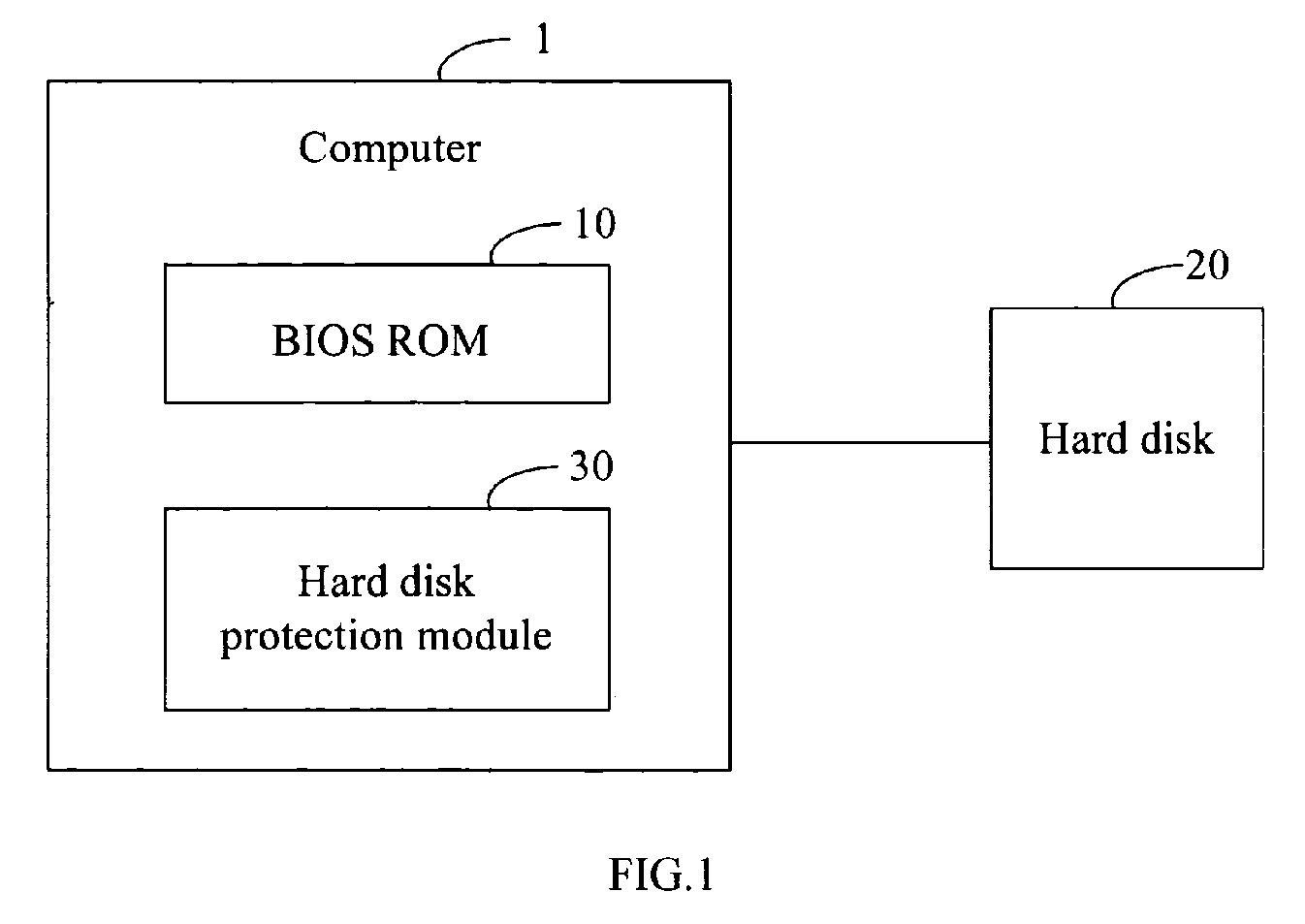
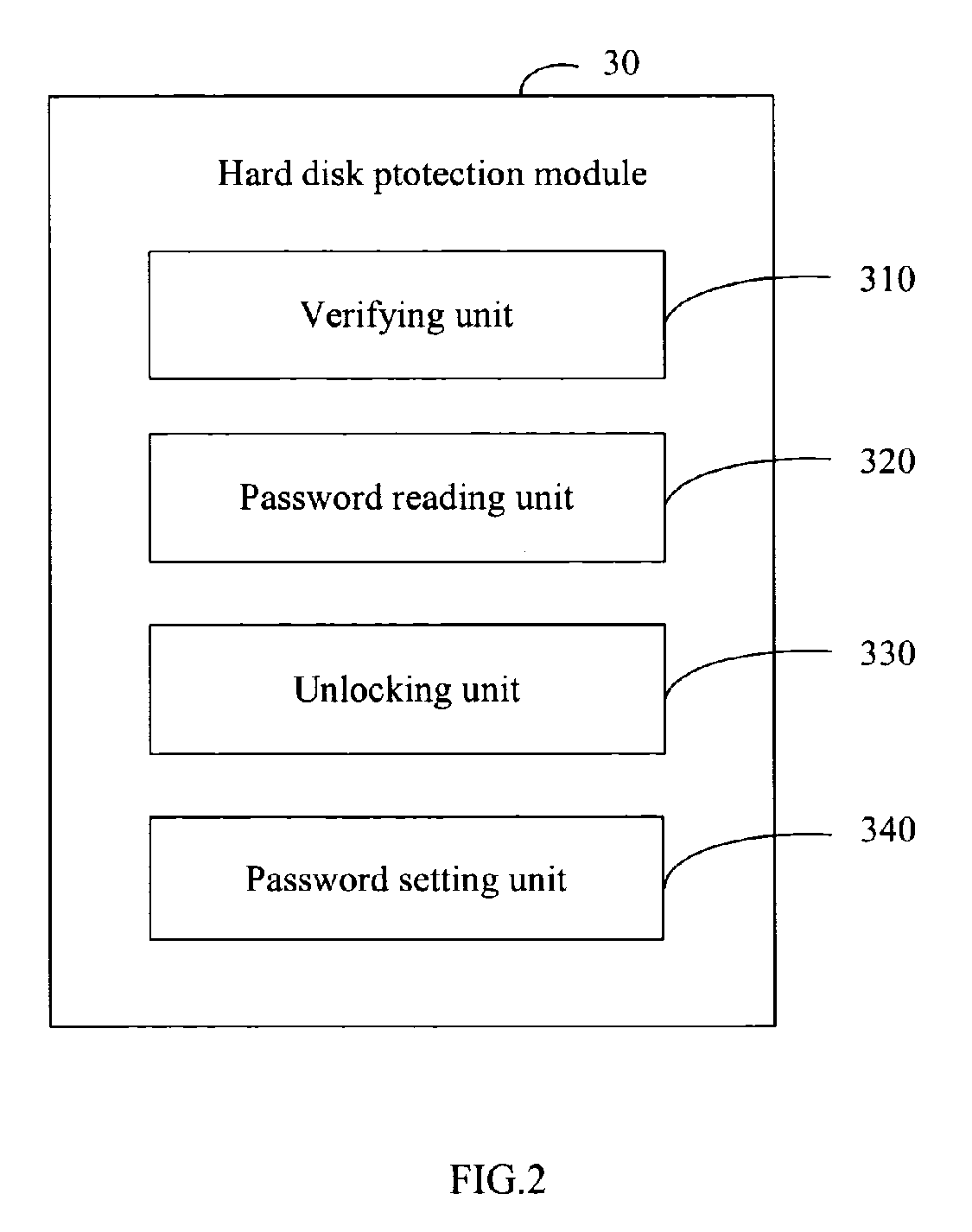
System and method for hard disk protection
InactiveUS20070089169A1Not easy to be stolenData can be securedDigital data processing detailsUnauthorized memory use protectionBIOSProtection system
A system for hard disk protection includes a computer. The computer includes a hard disk protection module, which includes: a verifying unit for determining whether a hard disk linked to the computer is locked, determining whether there is a generated password in a BIOS ROM of the computer, and determining whether an hard disk password setting in the hard disk is identical with the generated password or a factory default password stored in the BIOS ROM; a password reading unit for reading a factory default password or the generated password stored in the BIOS ROM, and reading an hard disk password setting in the hard disk; an unlocking unit for sending a request of unlocking the hard disk by the generated password or by the factory default password; and a password setting unit for writing the generated password to the hard disk to replace the hard disk password setting.
Owner:HON HAI PRECISION IND CO LTD
Method and device for tapping the payload data of multimedia connections in a packet network
ActiveUS7742465B2Data can be securedReduce riskInterconnection arrangementsTime-division multiplexComputer networkComputer science
Owner:HMD GLOBAL
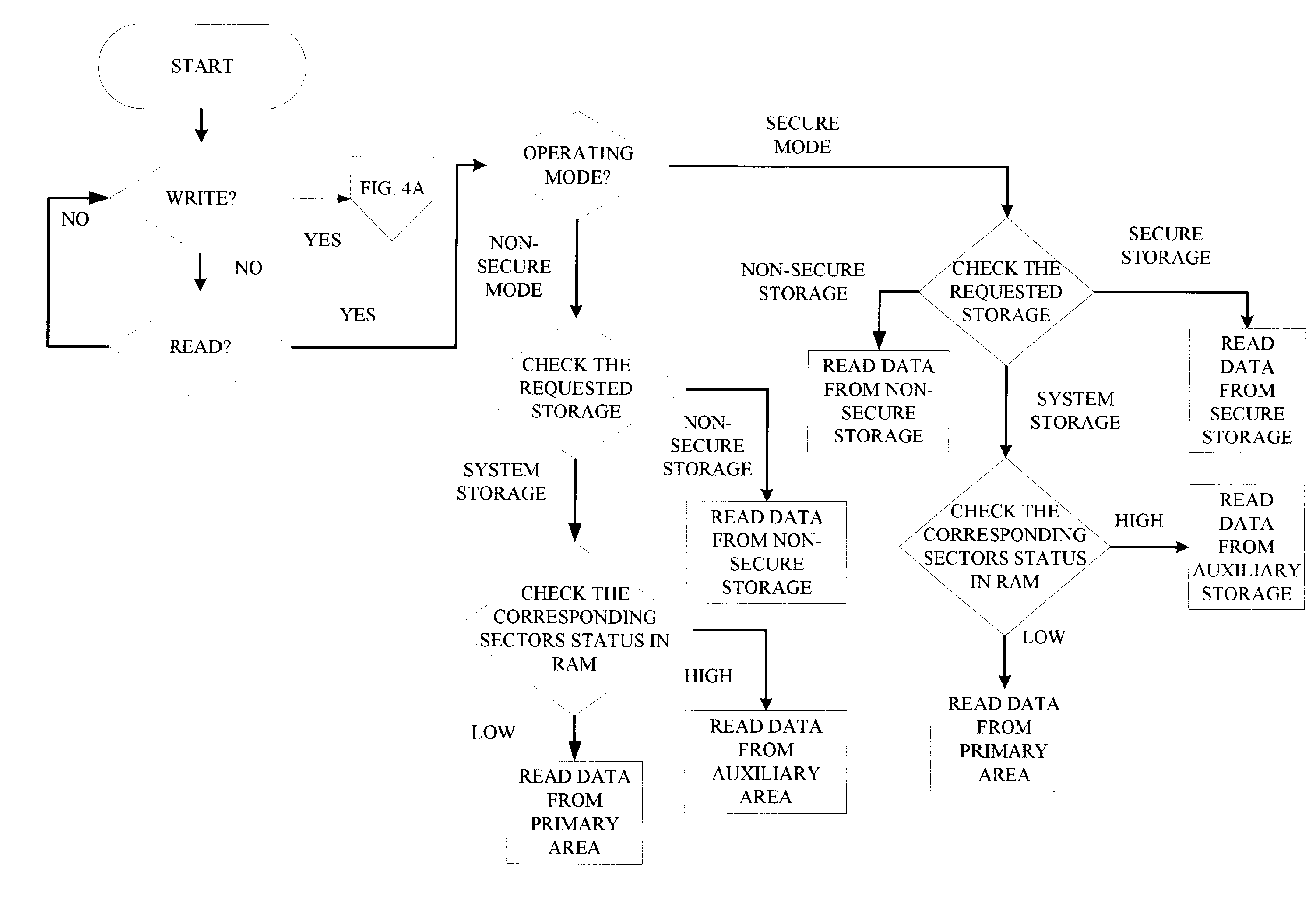
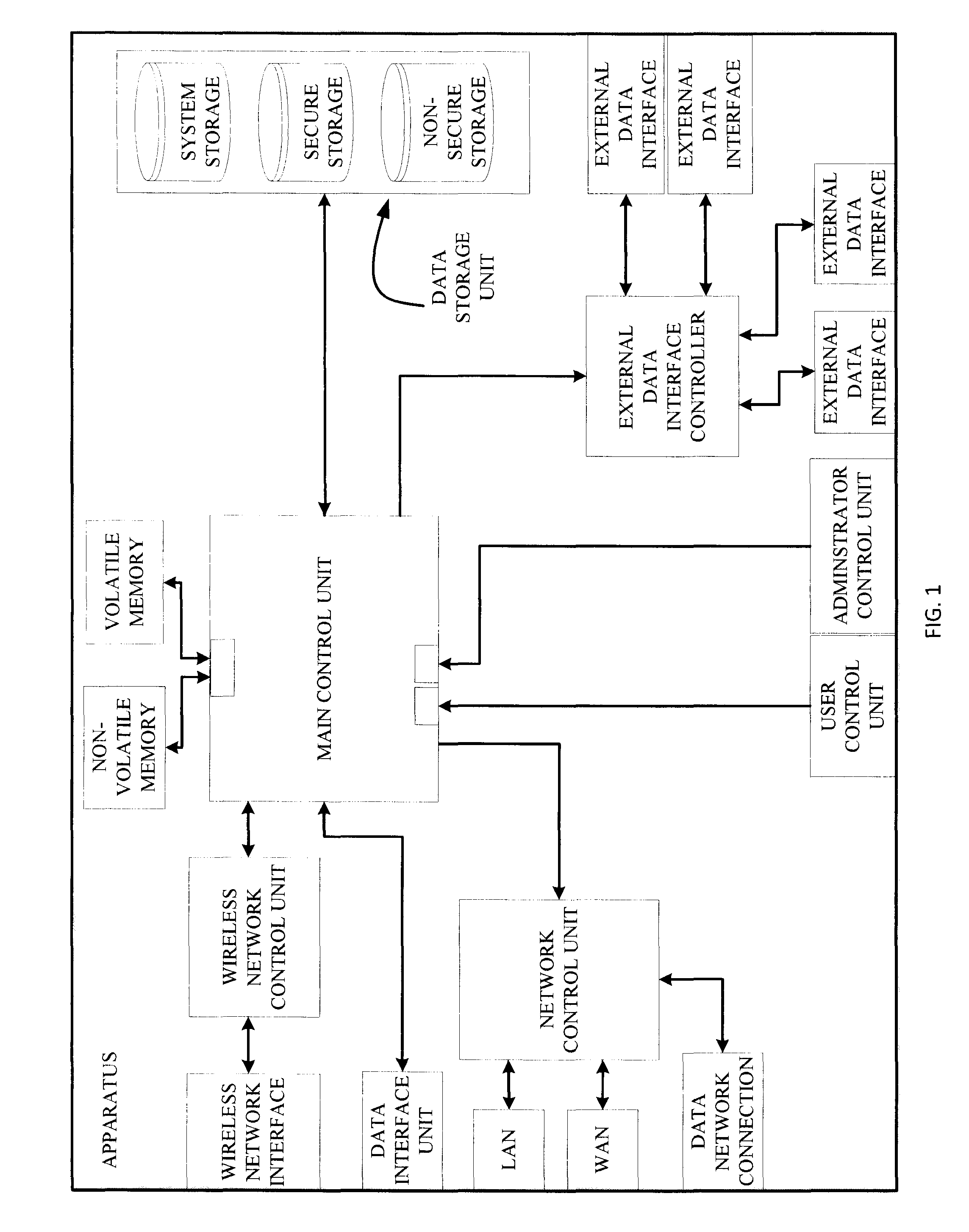
Apparatus and method for protection of stored data
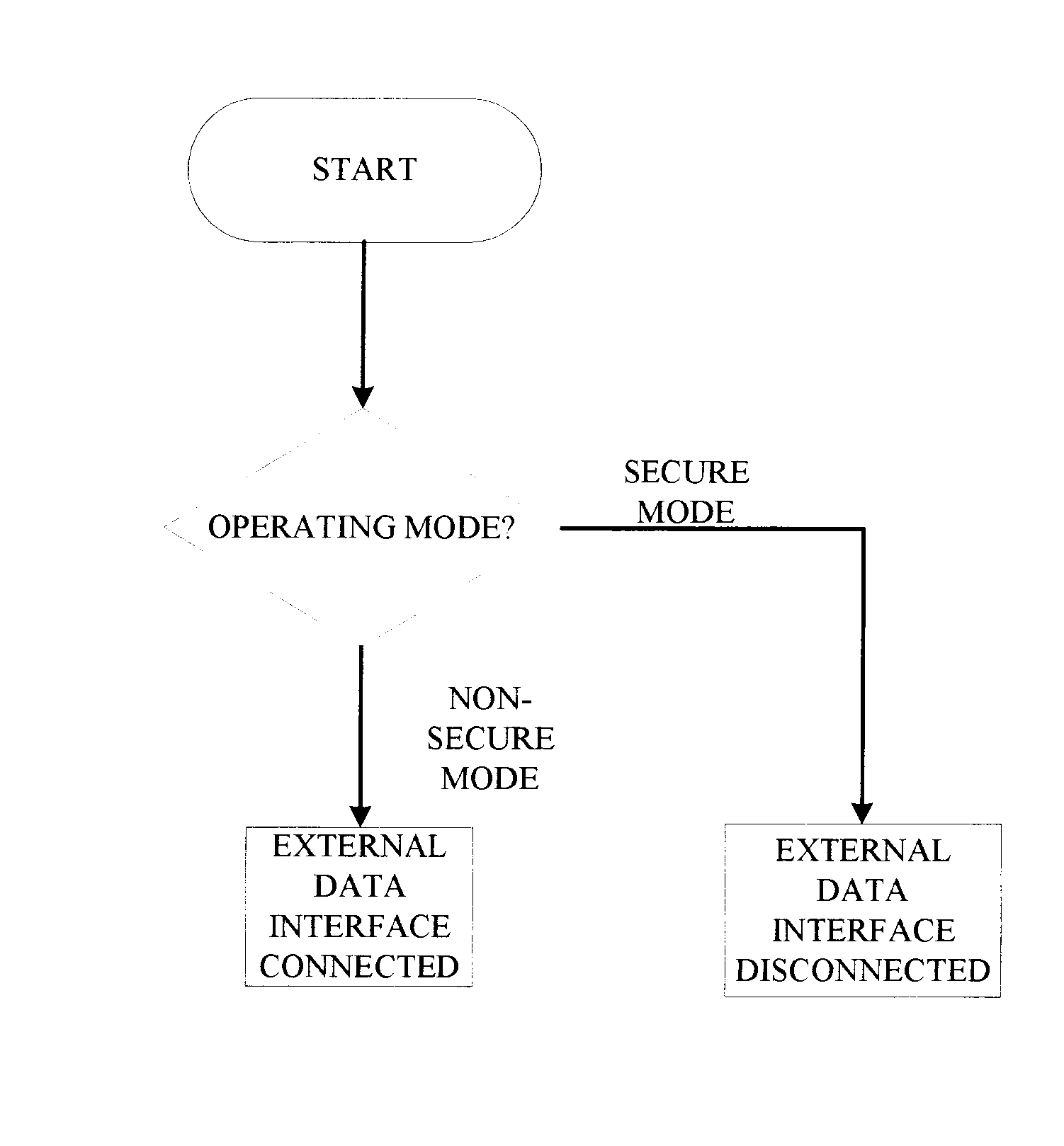
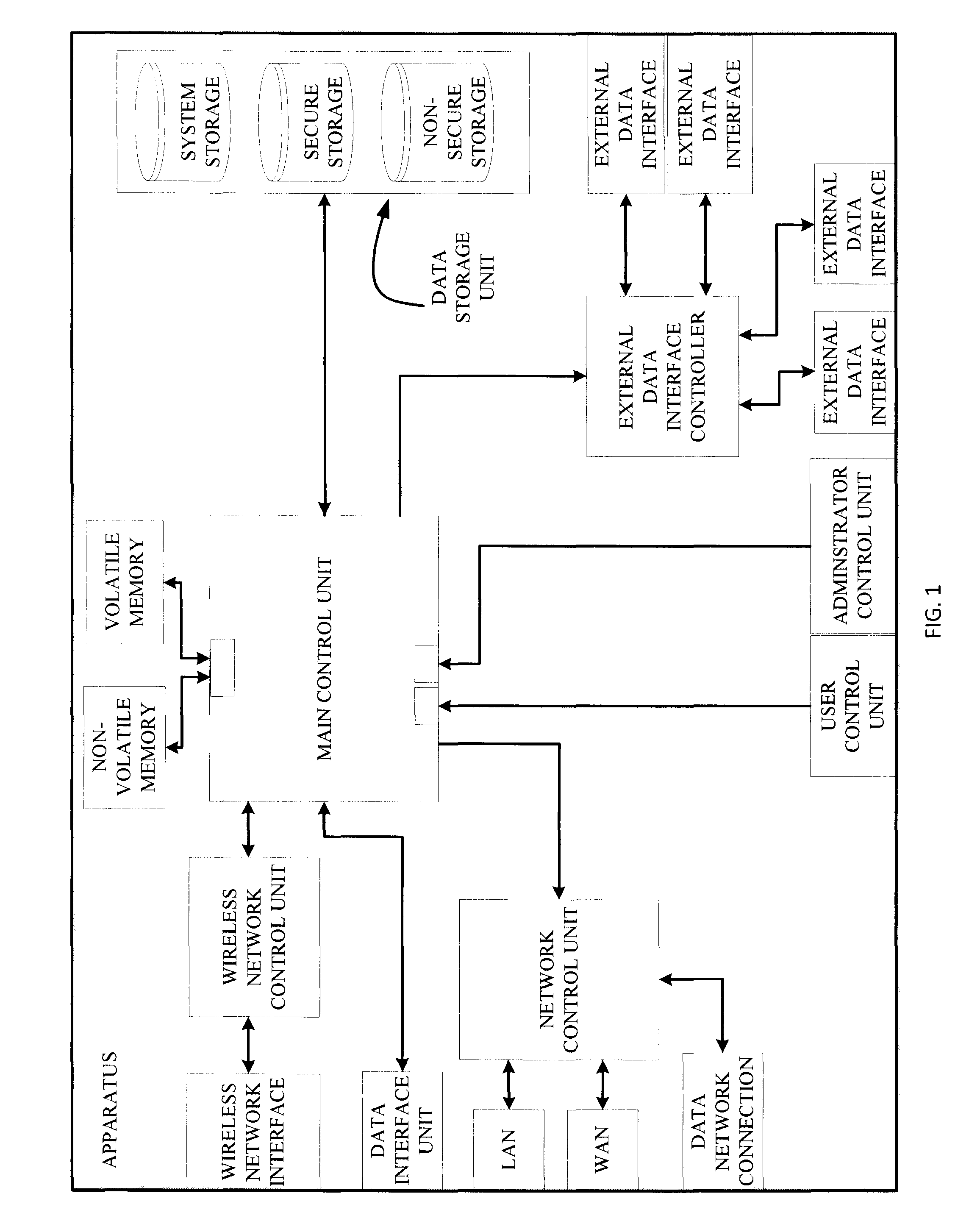
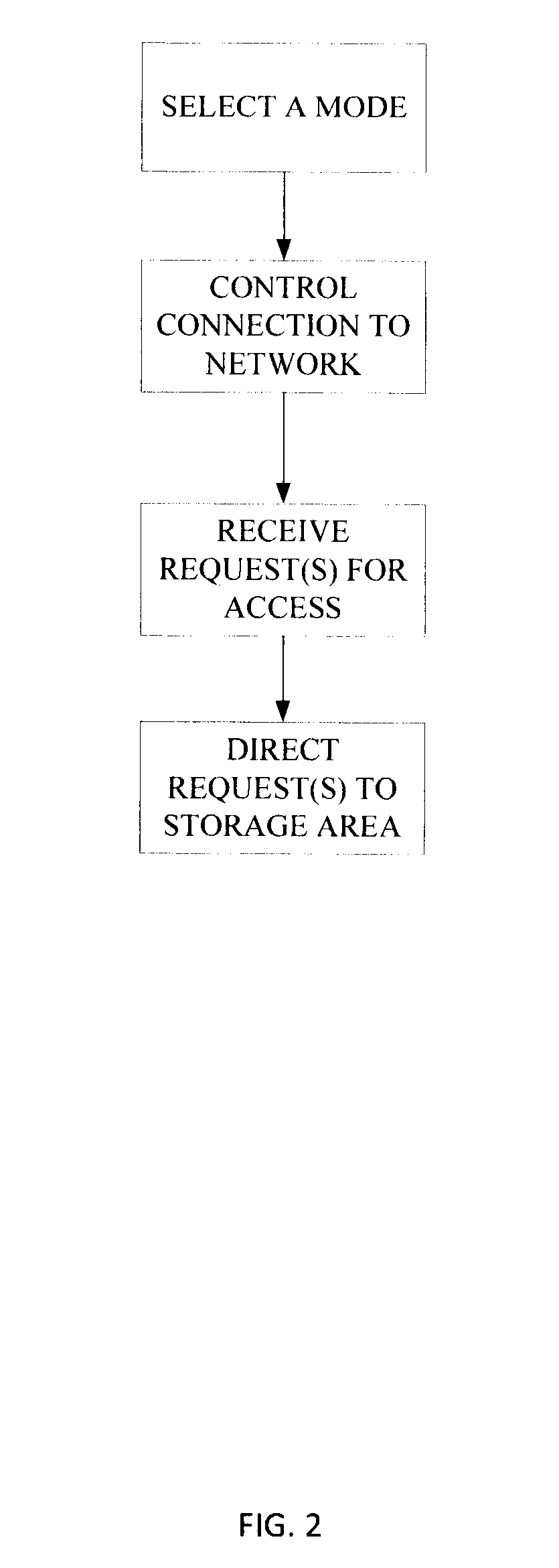
ActiveUS20150199144A1Reduce the impactPrevent intrusionInput/output to record carriersDigital data processing detailsMode controlControl cell
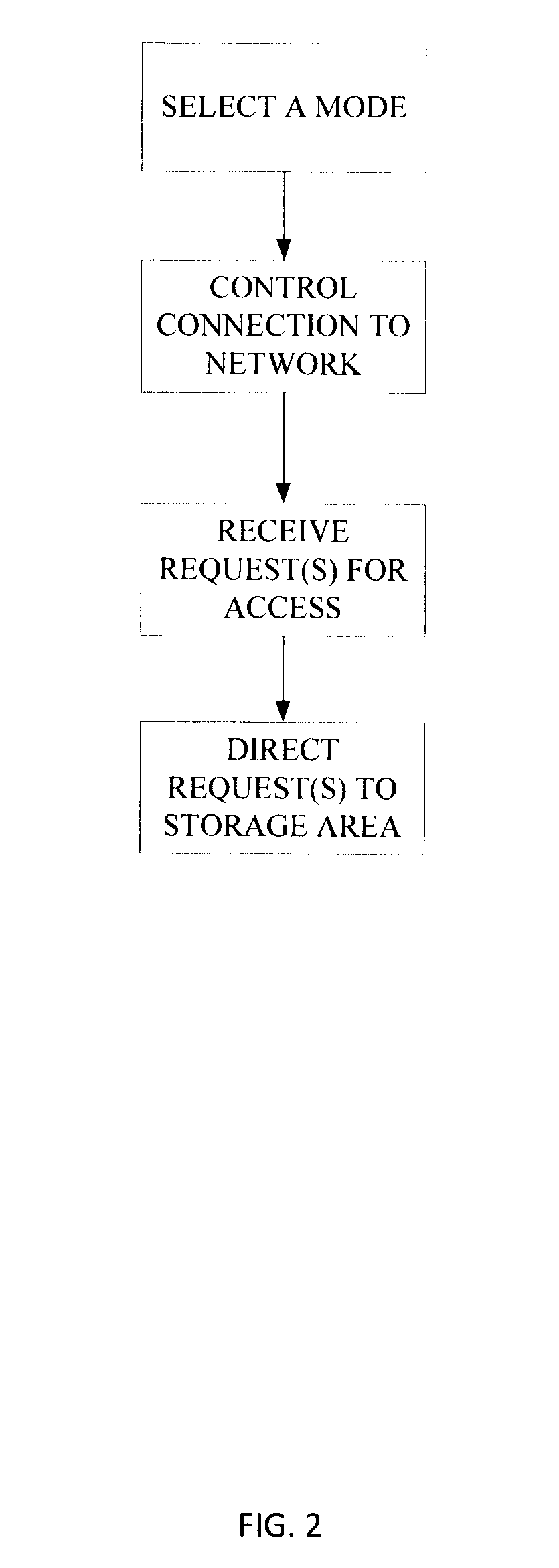
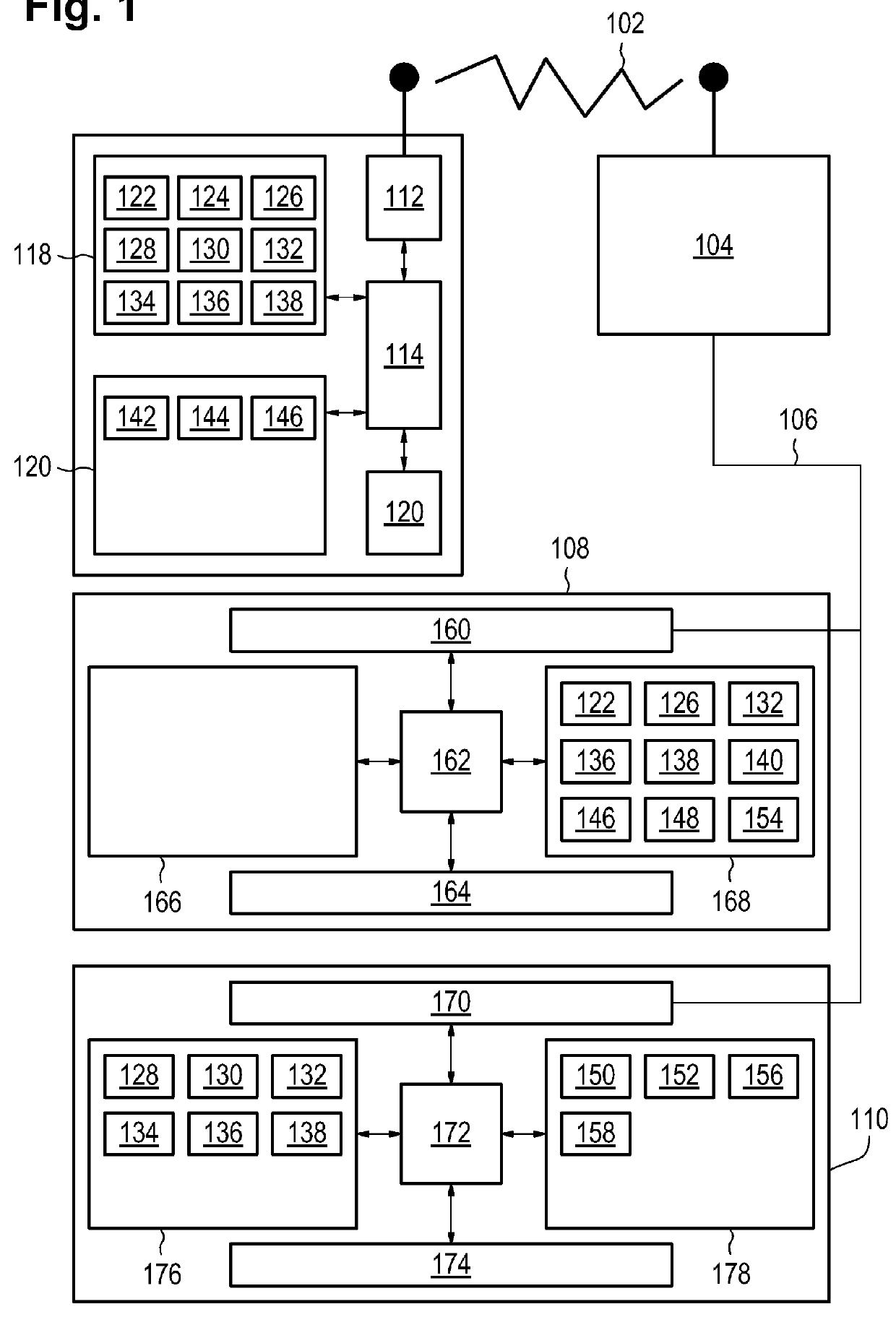
An apparatus and a method for protection of data stored in a data storage unit that comprises a plurality of storage areas. A data interface connects to a computer system and transfer of a data signal from the computer system to the apparatus requests access to the data storage unit. A main control unit is configured to receive the data signal and is connected to the data storage unit. A user control unit is connected to the main control unit and is arranged to be set in different modes and generates a mode selection signal indicating the selected mode. The main control unit is configured to receive the mode selection signal, and depending on the selected mode, control connection of the apparatus to a plurality of networks, and direct the request to a storage area of the plurality of storage areas of the data storage unit.
Owner:DROSCH KLAUS
Telecommunication method for securely exchanging data
ActiveUS9344410B1Data can be securedMore confidenceTransmissionSecurity arrangementWeb serviceNetwork connection
The invention provides for a telecommunication method of securely exchanging unencrypted data between a telecommunications device and a first server computer system via a digital cellular wireless telecommunications network, wherein the telecommunications device is a battery powered mobile end user telecommunications device, wherein the method comprises the steps of: encrypting the unencrypted data using a first encryption algorithm into first encrypted data, sending the first encrypted data to a second server computer system via a first network connection of the digital cellular wireless telecommunications network, storing the first encrypted data by the second server computer system, sending an order request to the first server computer system via a second network connection of the digital cellular wireless telecommunications network by the telecommunications device, sending a data publishing request to the second server computer system, generating a cryptographic key pair, sending the first encrypted data, the public key, and the private key to the telecommunications device, decrypting the first encrypted data into the unencrypted data, encrypting the unencrypted data into second encrypted data using the public key, sending the second encrypted data to the second, generating a web service for providing the second encrypted data via an URL, sending the URL to the telecommunications device, sending the URL and the private key, requesting the second encrypted data from the second server computer system, sending the second encrypted data to the first server computer system by the second server computer system using the wired network connection, decrypting the second encrypted data by the first server computer system into the unencrypted data, and combining the order request with the unencrypted data.
Owner:SAP AG
Embedded control device
InactiveUS8649939B2Data can be securedImprove real-time performanceResource allocationProgram synchronisationControl dataEmbedded system
There is provided an embedded control device having high real time performance and capable of securing data concurrency. The embedded control device according to the present invention includes disclosure data and stored data as control data to be disclosed to a data reference component. The embedded control device changes over a reference destination for the data reference component either to the disclosure data or to the stored data, depending on which of the execution priority of the data disclosing source component and the execution priority of the data reference component is higher.
Owner:HITACHI LTD
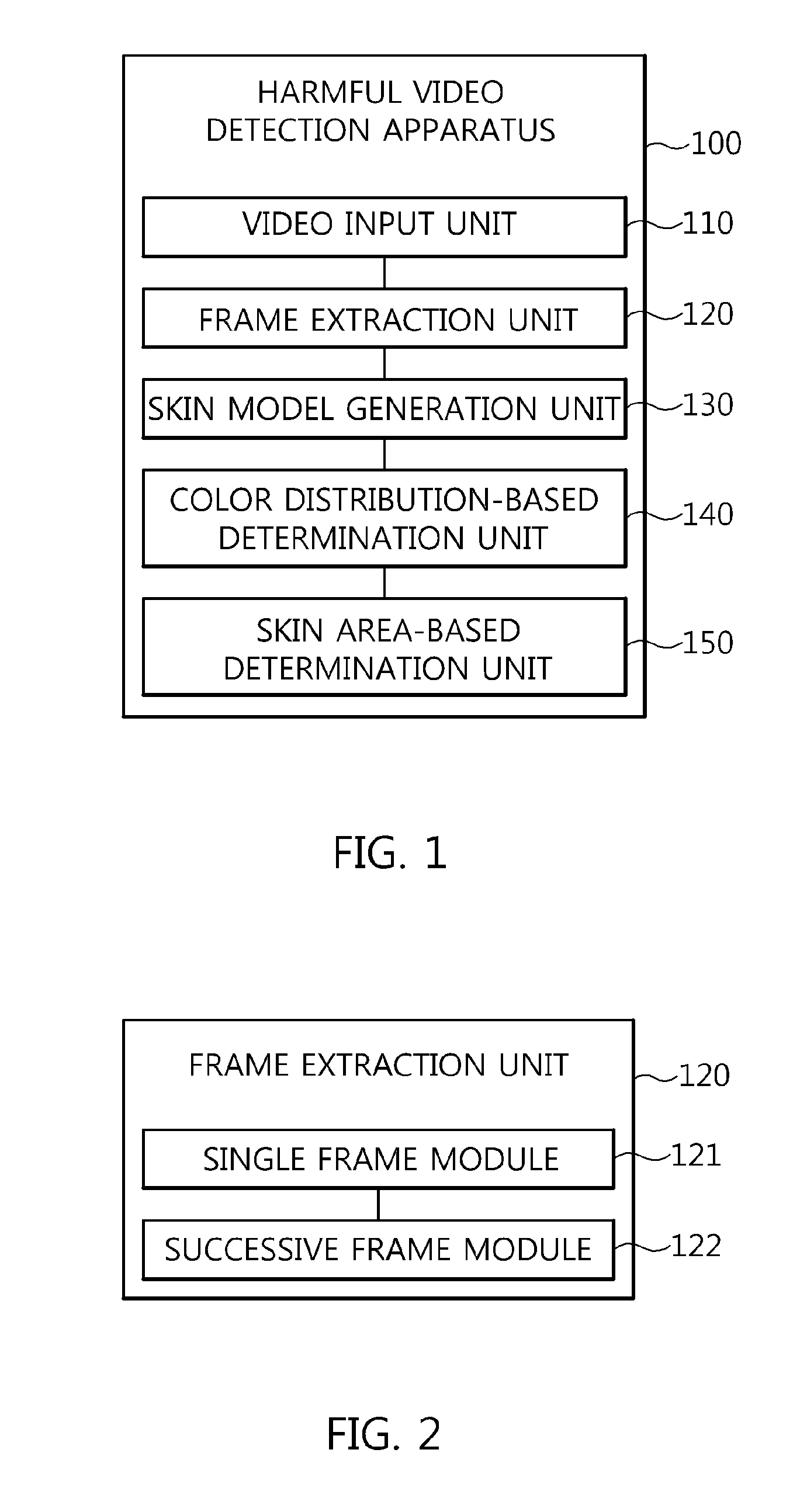
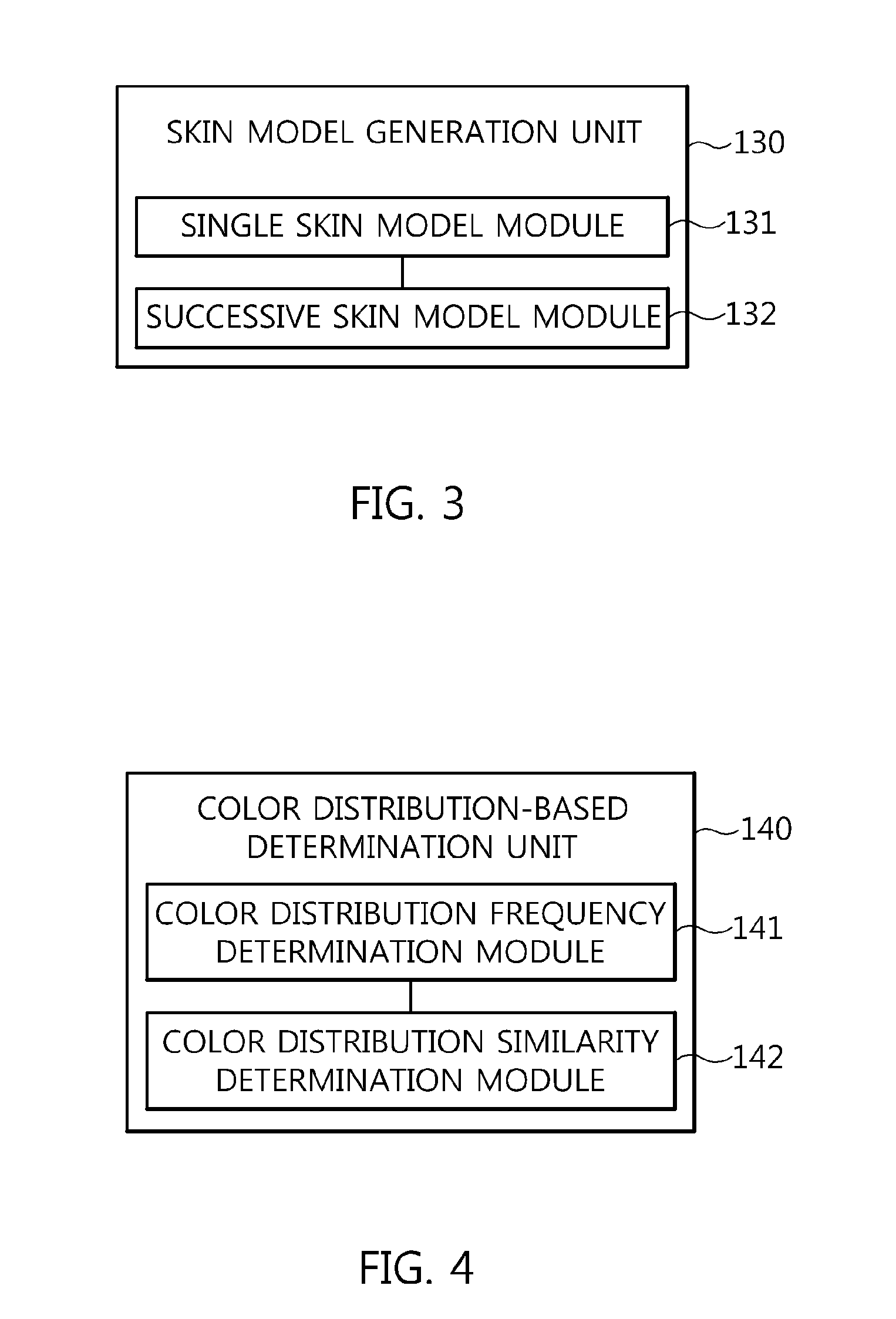
Apparatus and method for detecting harmful videos
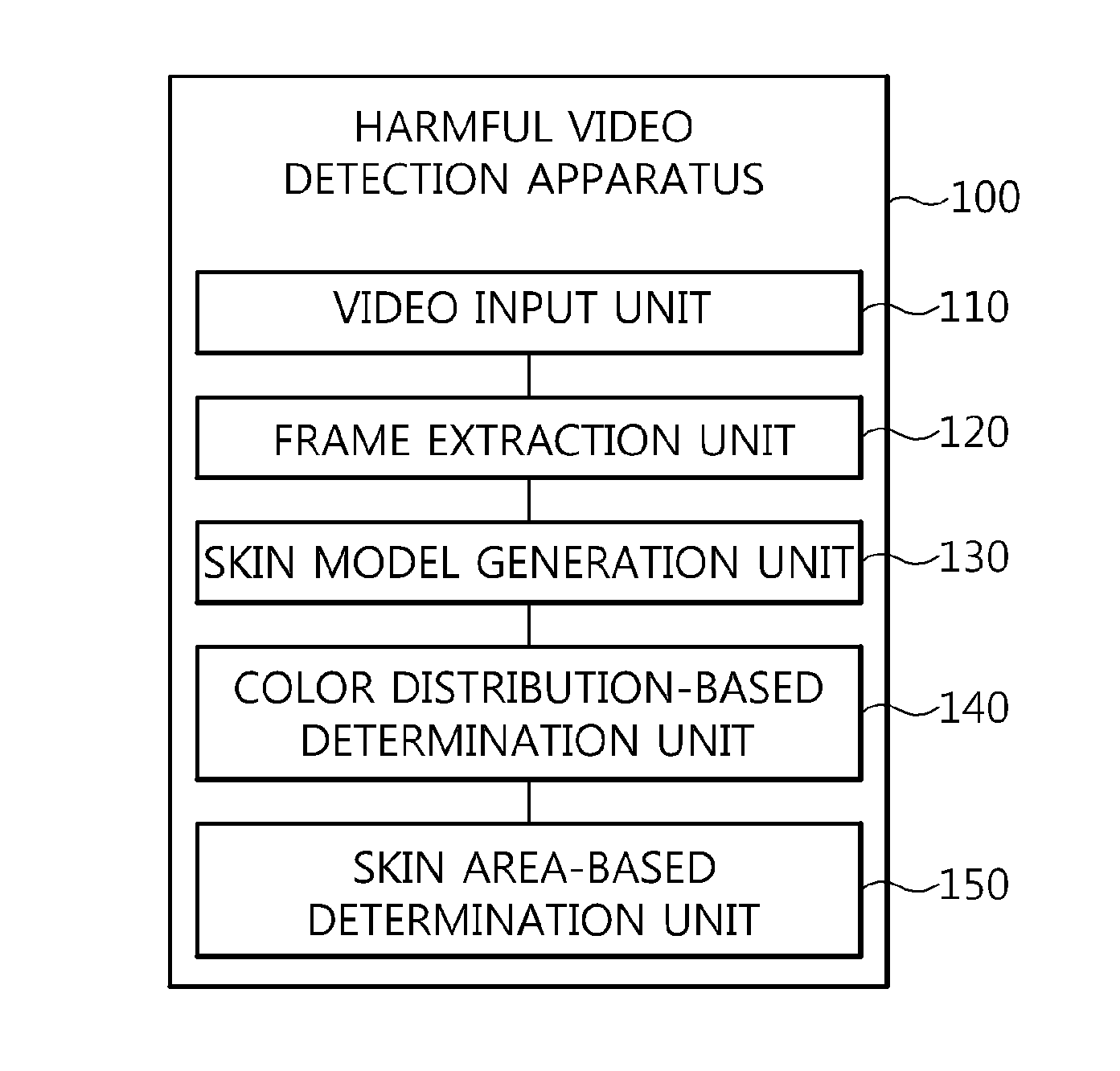
InactiveUS20150139541A1Accurate detectionData can be securedImage enhancementImage analysisPattern recognition
Disclosed herein is an apparatus and method for detecting harmful videos. The apparatus includes a video input unit for receiving an input video. A frame extraction unit extracts frames from the input video. A skin model generation unit generates a skin model for the frames extracted by the frame extraction unit. A color distribution-based determination unit determines whether the input video corresponds to a harmful video by comparing harmful color distribution information that is information related to a color distribution of preset harmful videos with target color distribution information. A skin area-based determination unit determines whether the input video corresponds to a harmful video by comparing a target skin area with harmful skin area information that is skin area information of preset harmful videos, the target skin area being extracted from the input video by separating an area corresponding to the skin model from the input video.
Owner:ELECTRONICS & TELECOMM RES INST
Keypad for the entry of authentication data
ActiveUS9489663B2Data can be securedComplete banking machinesPayment architectureKey pressingData connection
The invention provides for an electronic system with a keypad for manual entry of authentication data by a user. The keypad comprises: multiple keys for entering the authentication data. At least one of the multiple keys comprises a three position switch with an elastic element for restoring the three position switch to a first position. The three position switch is operable to be depressed in a motion direction to a second position and a third position. The motion direction is perpendicular to a surface where the keys are mounted. A first force is required to depress the three position switch to the second position and a second force is required to depress the three position switch from the second position to the third position. The second force is greater than the first force.The keypad further comprises a controller configured for monitoring key presses of the multiple keys and for monitoring key position data of the three position switch of each of the at least one of the multiple keys during the key presses. The controller is further configured for decoding the key presses and the key position data into the authentication data. The keypad is further configured for outputting the authentication data via a data connection.
Owner:SAP AG
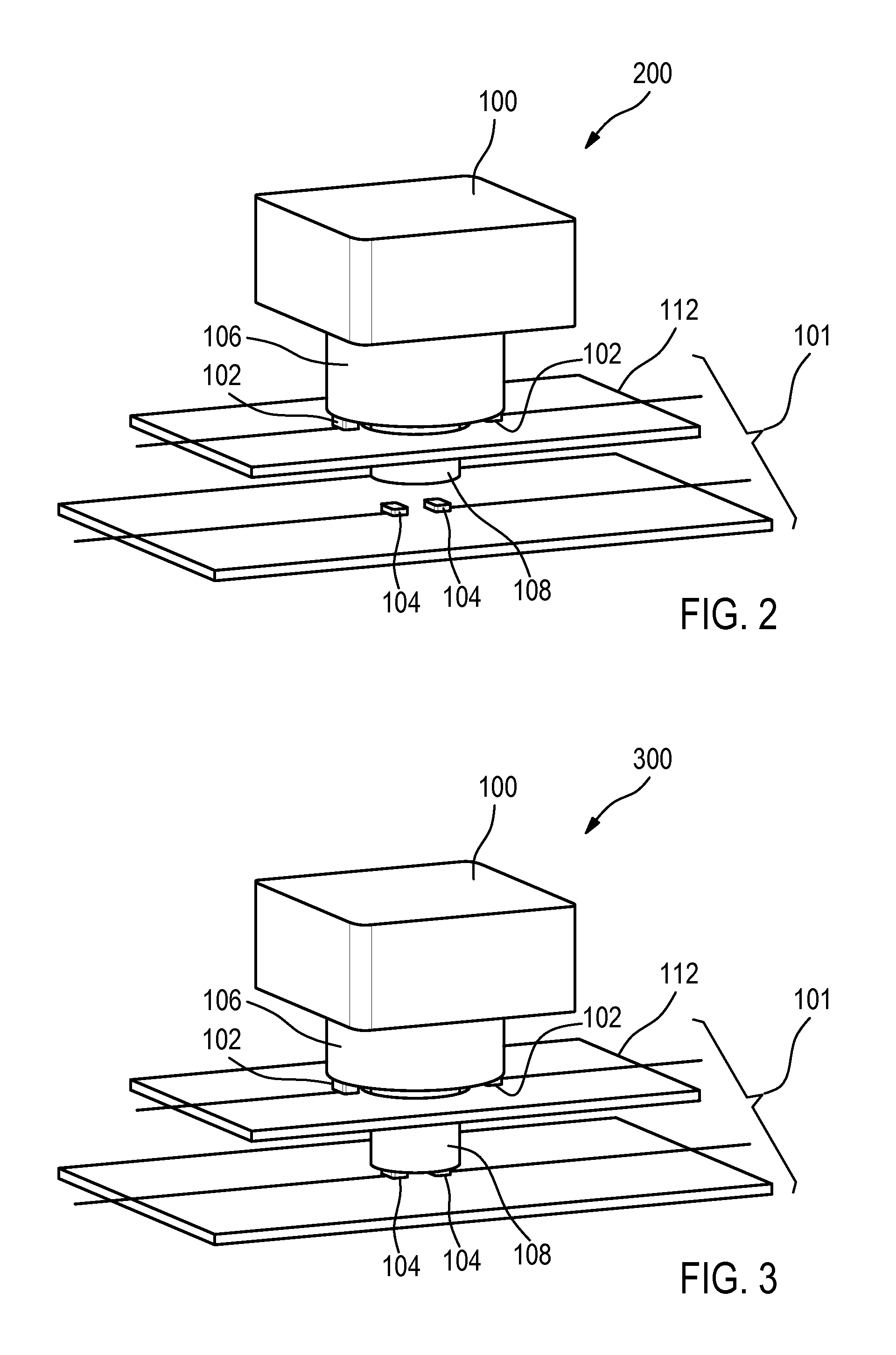
Method and system for calculating personalised values of parameters of a sole with a view to designing made-to-measure soles
PendingUS20220312902A1Improve the level ofImprove performanceFoot measurement devicesAdditive manufacturing apparatusPersonalizationEngineering
Owner:BAL INC
Apparatus and method for protection of stored data
ActiveUS9442667B2Data can be securedPrevent theftInput/output to record carriersDigital data protectionComputerized systemData signal
Owner:DROSCH KLAUS
Storing and using multipurpose secret data
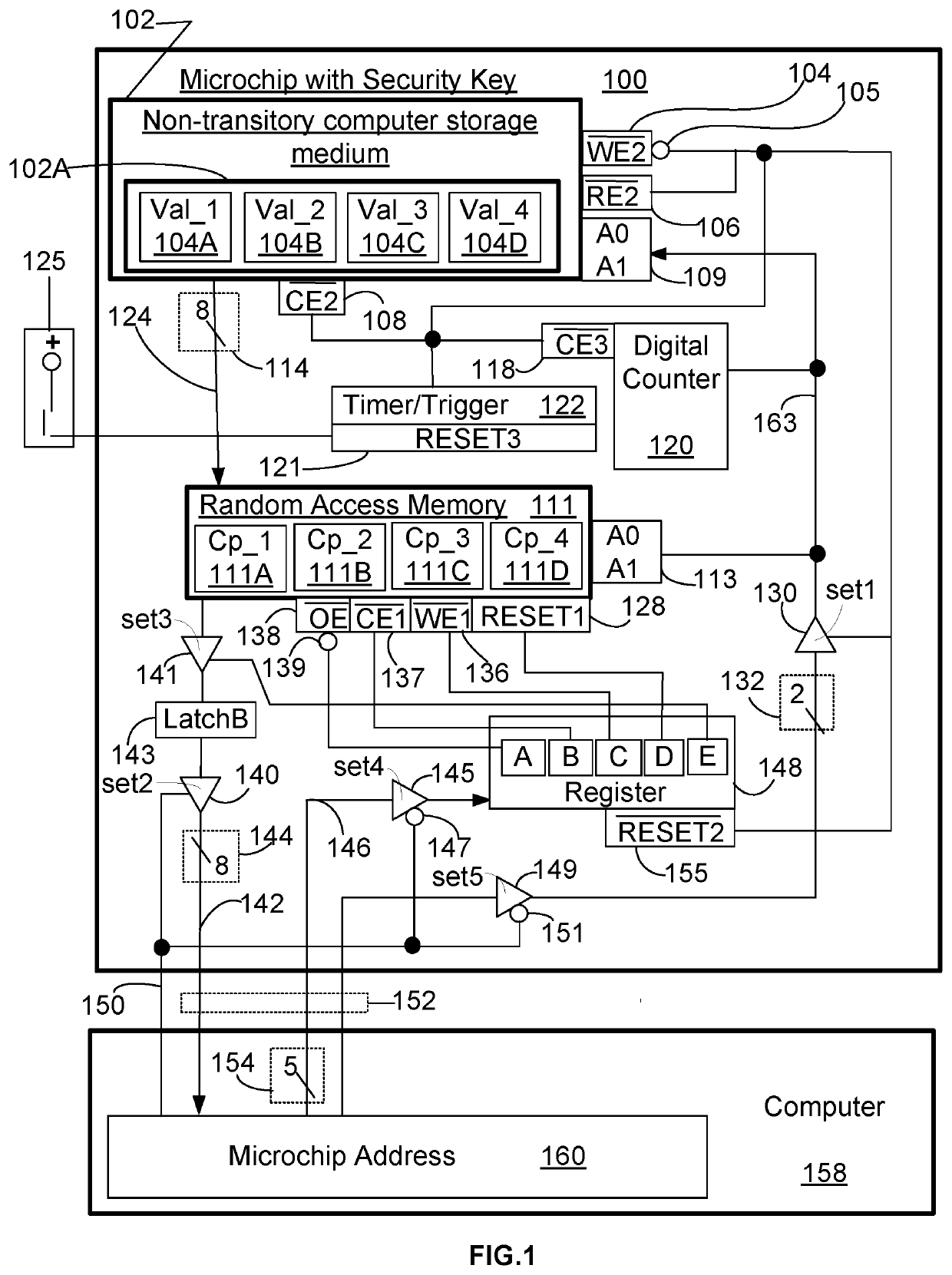
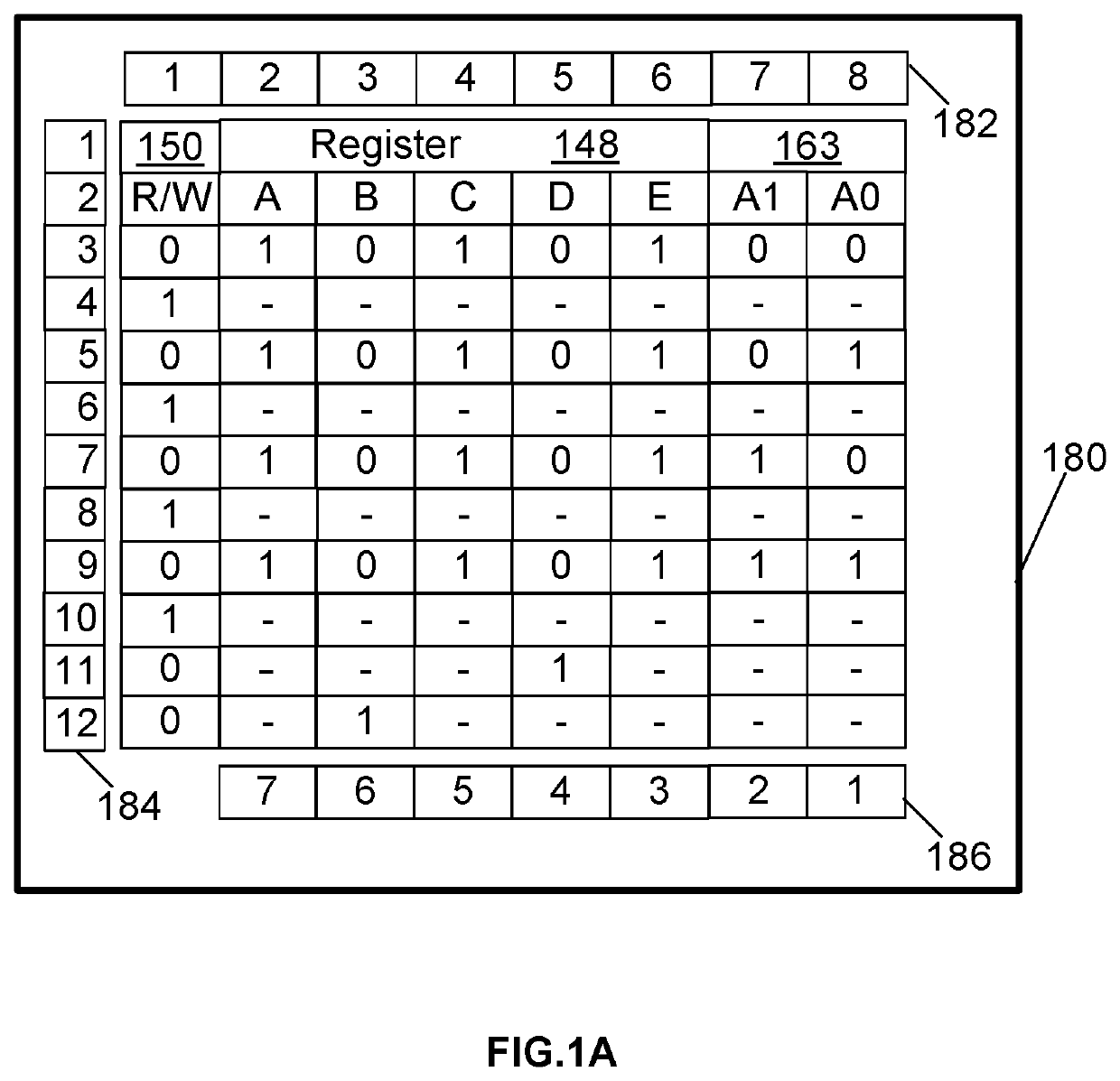
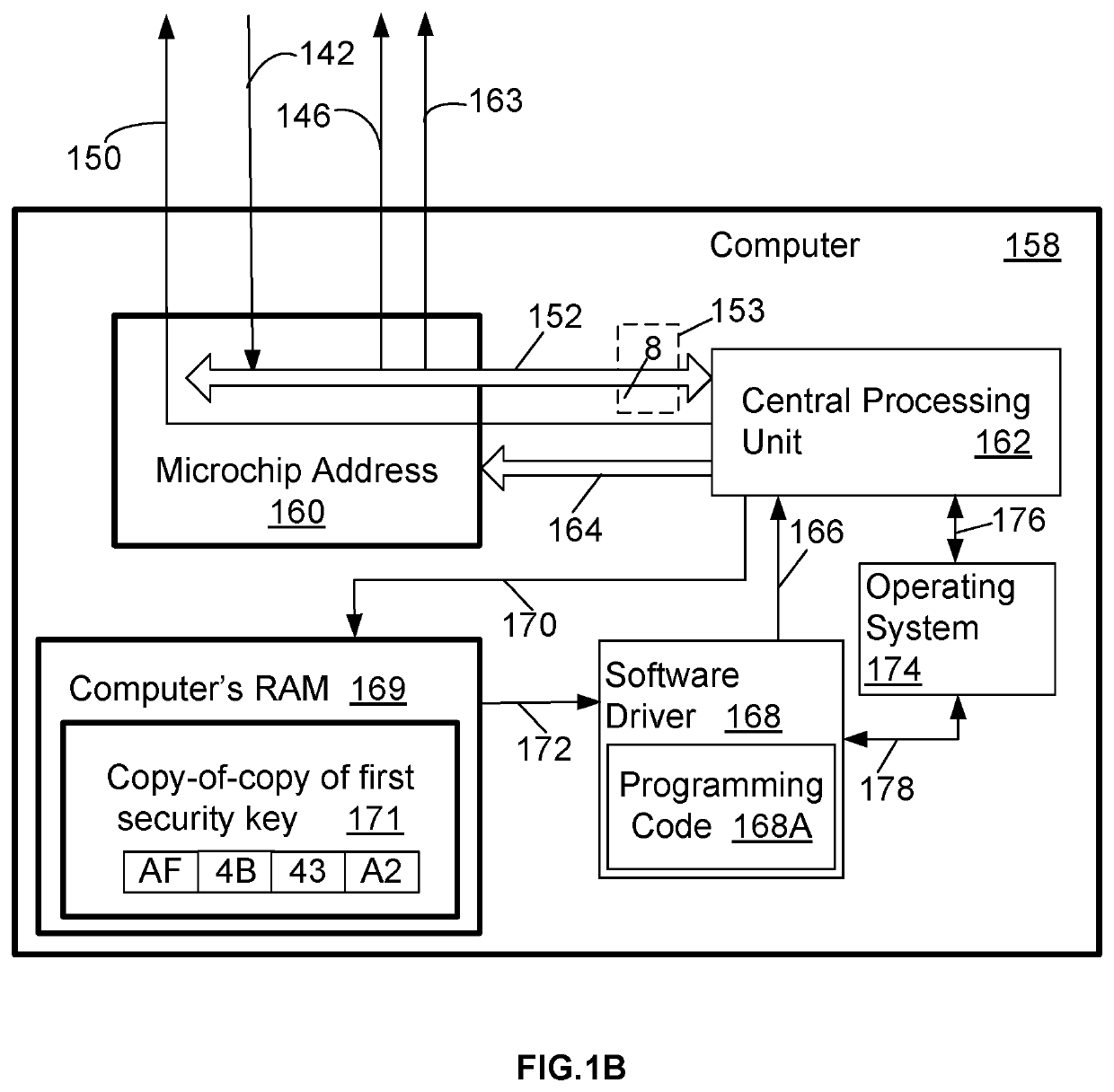
InactiveUS20210004472A1Hinder availabilityData can be securedDigital data protectionInternal/peripheral component protectionRandom access memoryData storing
A system and method improves operational performance of a computer by enhancing digital security with an added electronic circuit. The electronic circuit stores sensitive data in an un-erasable state such that the sensitive data may not be altered. The electronic circuit limits transfer of the sensitive data only once after each power-up or after each reset of the computer. The electronic circuit prevents access to the sensitive data by an authorized program. The electronic circuit utilizes its own storage medium and a random access memory, the latter of which can receive and store the sensitive data from the non-transitory computer storage medium. The method uses a software driver and a copy-of-copy of first security key obtained from the sensitive data stored on the electronic circuit. The software driver installs a software module on the computer using the copy-of-copy of first security key to encrypt each installed file.
Owner:ATENSE INC
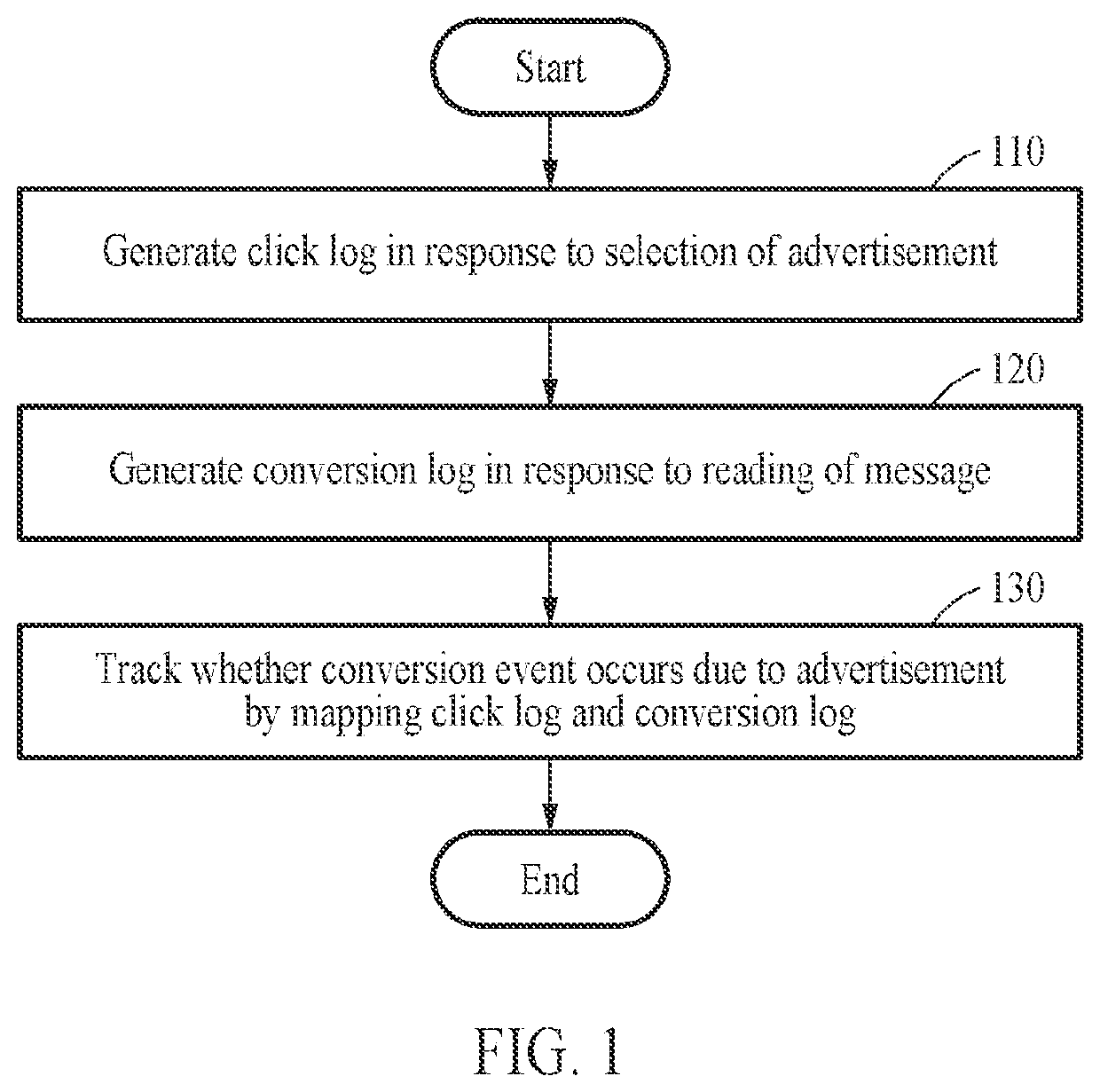
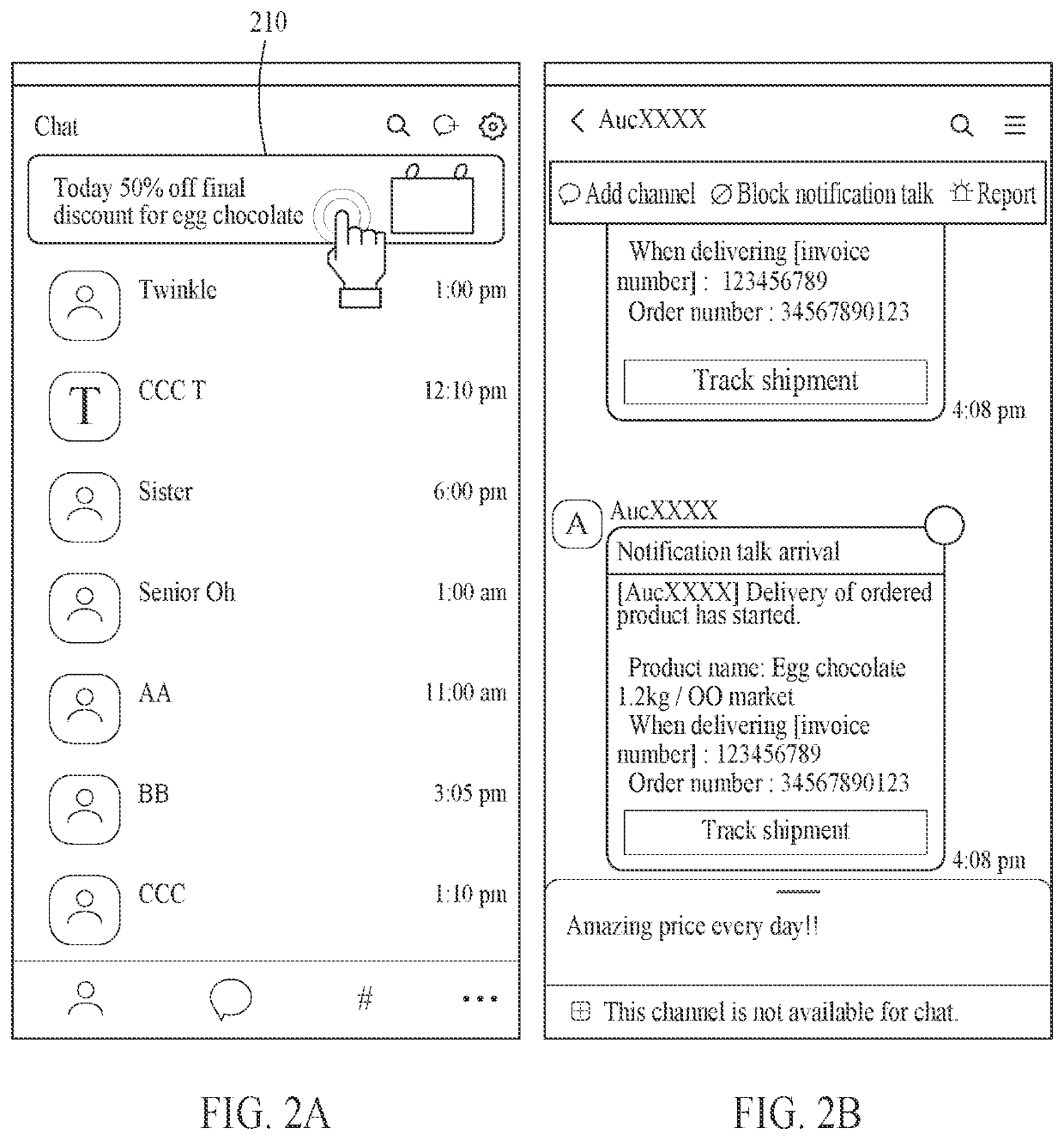
Method and apparatus for tracking conversion of advertisements provided through application
PendingUS20220108350A1Secure conversion tracking dataData can be securedAdvertisementsData switching networksEngineeringUser identifier
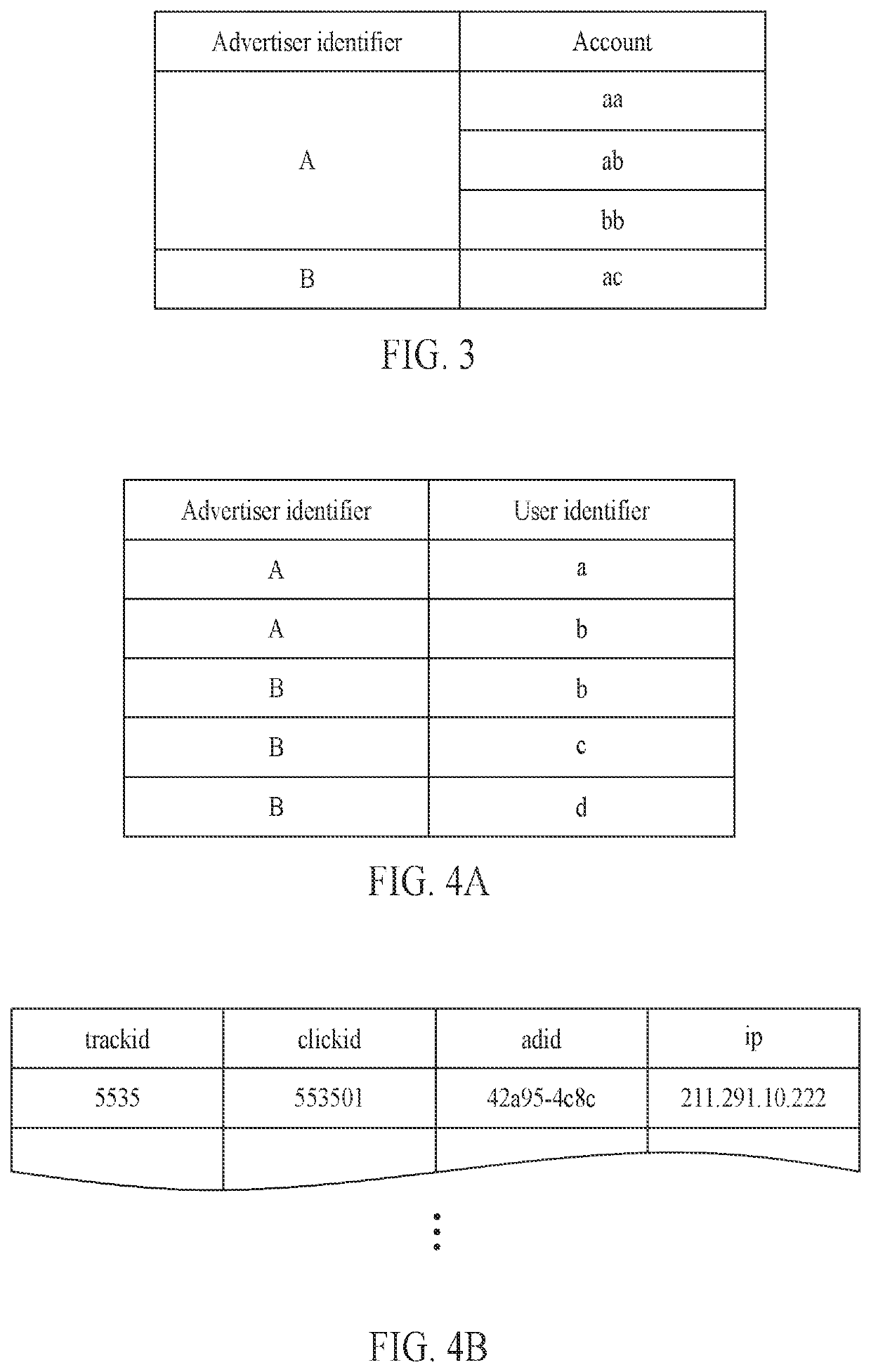
A method and apparatus for tracking a conversion of an advertisement provided through an application are disclosed. The method includes generating, in response to selection of an advertisement through a first application installed on a first user terminal, a click log including a first advertiser identifier corresponding to an advertiser of the advertisement and a first user identifier corresponding to the first user terminal, generating, in response to reading of an informational message through a second application installed on a second user terminal, a conversion log including a second advertiser identifier corresponding to a sender of the informational message and a second user identifier corresponding to the second user terminal, and tracking whether a conversion event occurs due to the advertisement by mapping the click log and the conversion log.
Owner:KAKAO CORP
Human capital management data transfer systems
ActiveUS20190349339A1Data can be securedComputer security arrangementsSecret communicationInternet privacyData pack
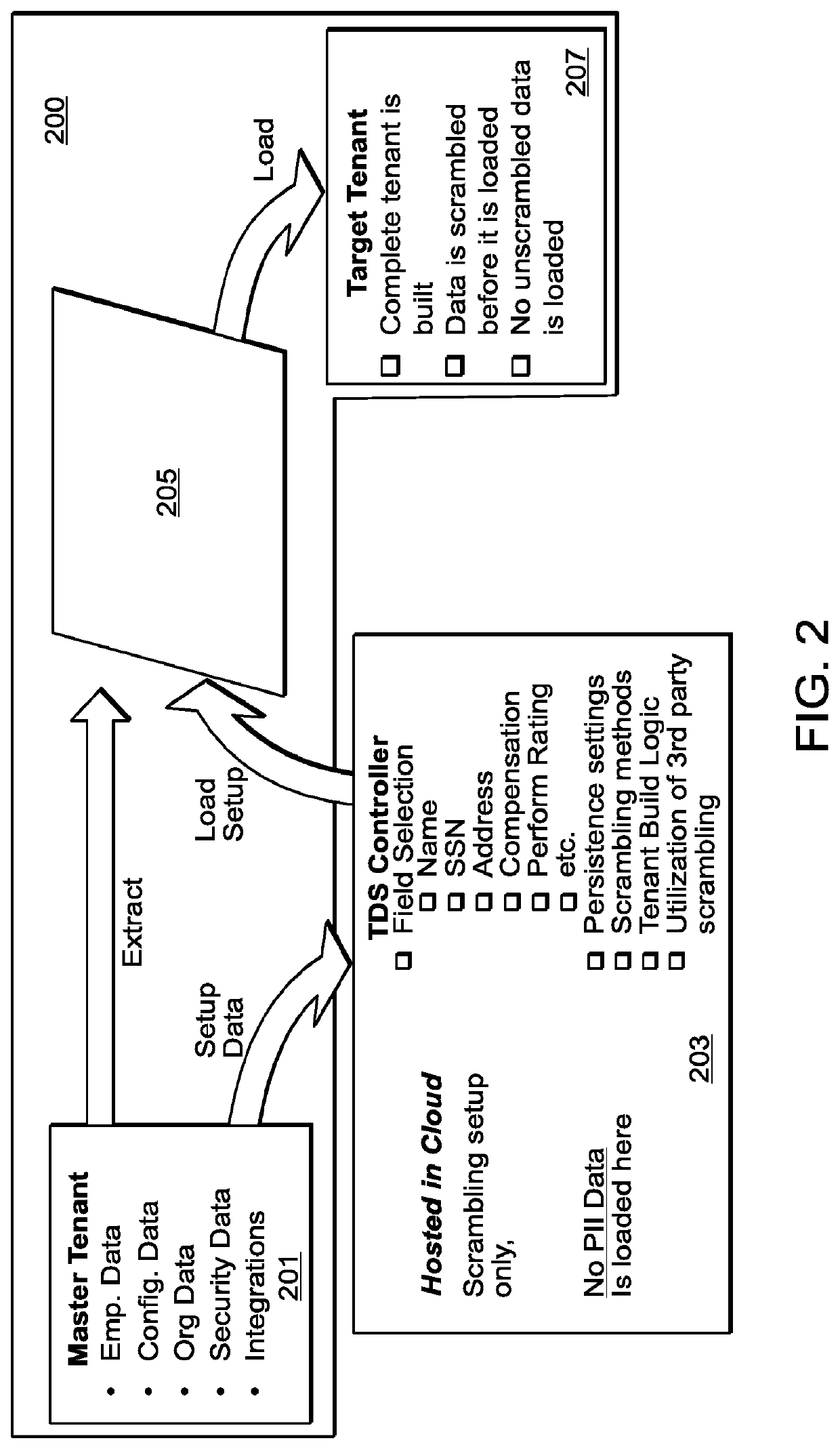
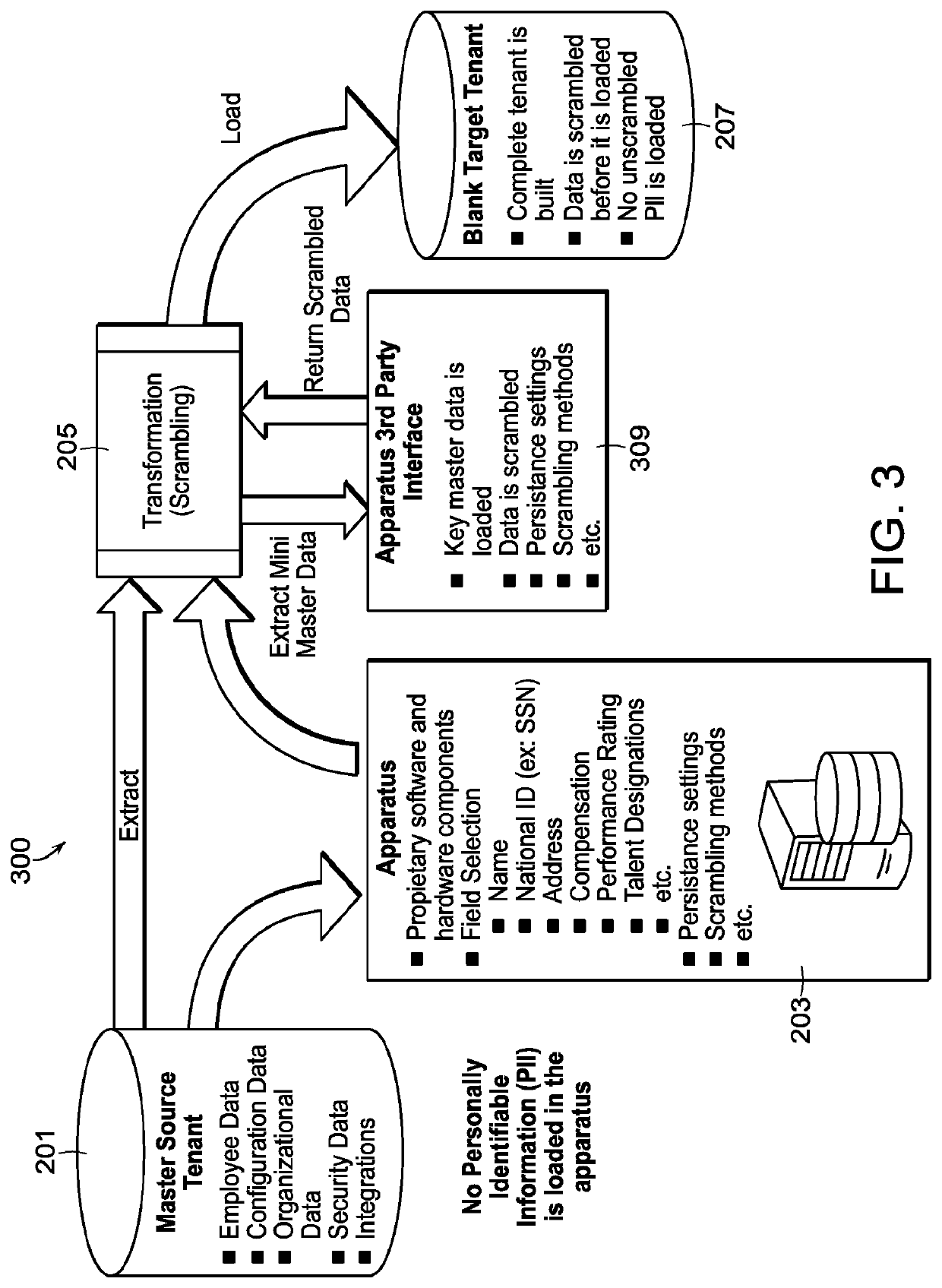
A computer implemented method for securely extracting secure data from a human capital management (HCM) system, includes receiving setup data from a production tenant of the HCM system, wherein the setup data includes one or more field types describing what type of secure data is stored on the production tenant, creating a scrambling module based on the setup data that is configured to scramble the secure data based on scrambling settings, wherein the scrambling module is configured to upload and install onto the HCM system and to communicate with the production tenant to receive the secure data to scramble the secure data, and uploading the scrambling module to the HCM system.
Owner:INTECROWD LLC
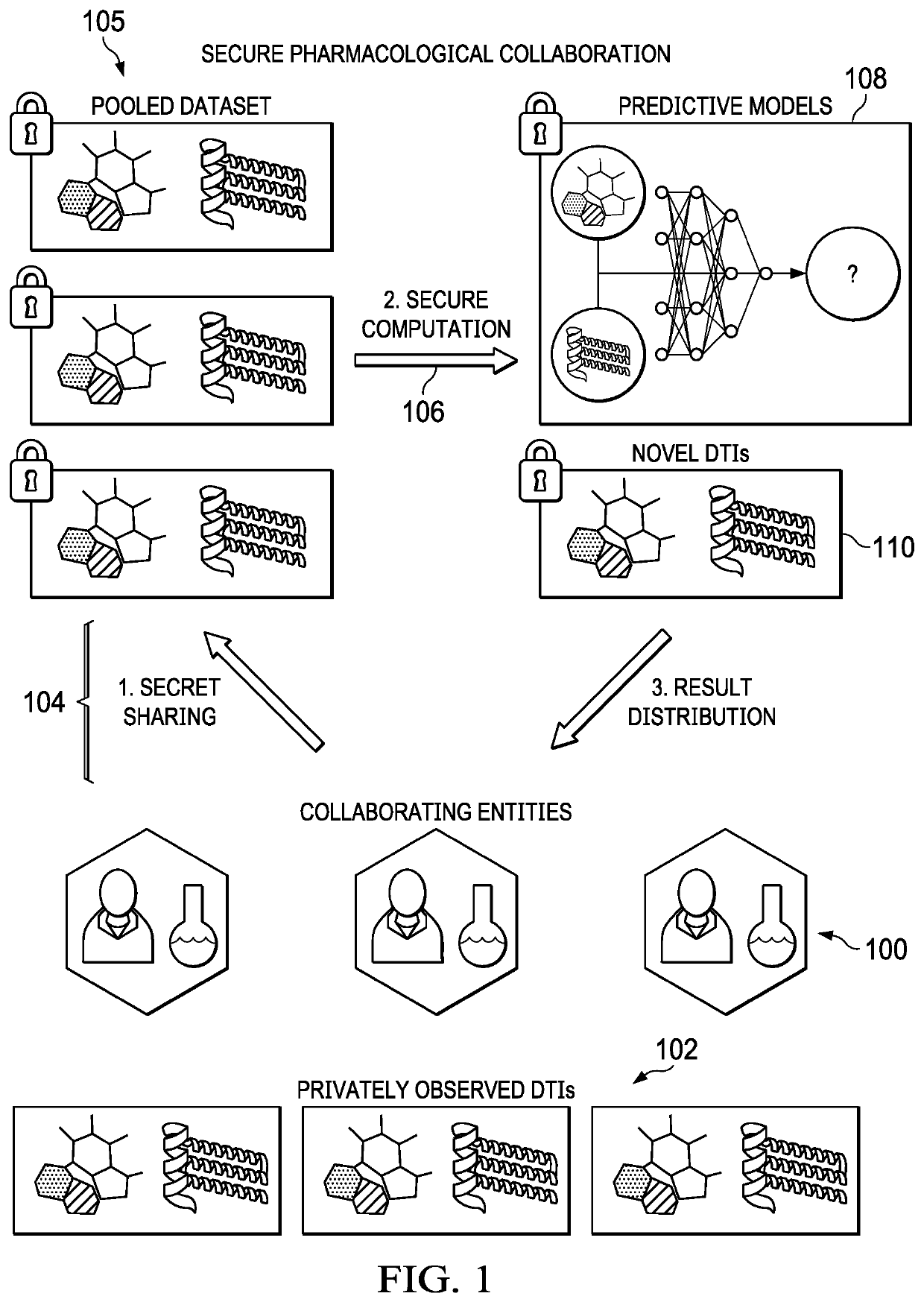
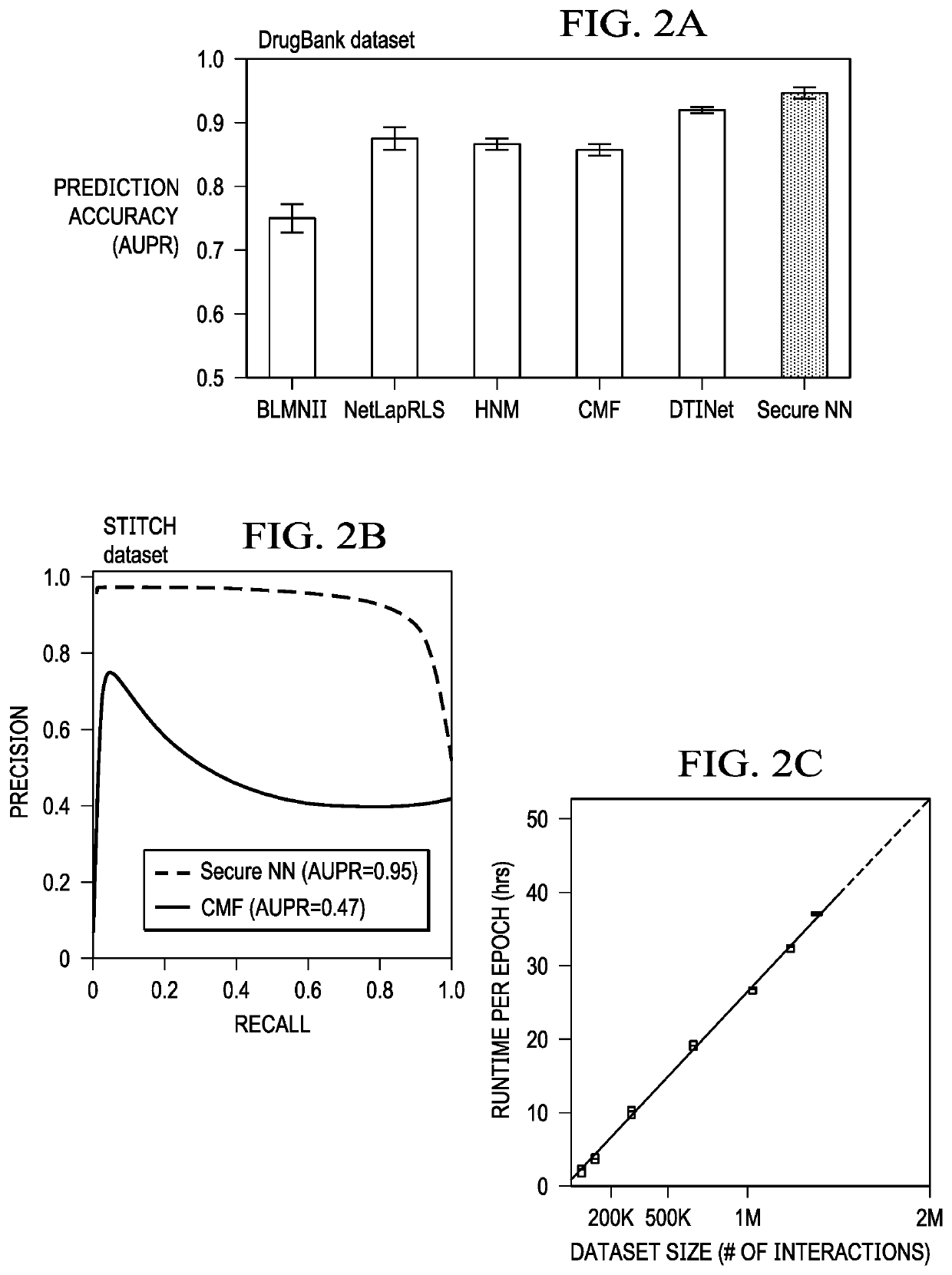
Realizing private and practical pharmacological collaboration using a neural network architecture configured for reduced computation overhead
ActiveUS11450439B2State-of-the-art prediction accuracyMore effective and collaborative biomedical researchMolecular designKernel methodsData setTheoretical computer science
Computationally-efficient techniques facilitate secure pharmacological collaboration with respect to private drug target interaction (DTI) data. In one embodiment, a method begins by receiving, via a secret sharing protocol, observed DTI data from individual participating entities. A secure computation then is executed against the secretly-shared data to generate a pooled DTI dataset. For increased computational efficiency, at least a part of the computation is executed over dimensionality-reduced data. The resulting pooled DTI dataset is then used to train a neural network model. The model is then used to provide one or more DTI predictions that are then returned to the participating entities (or other interested parties).
Owner:HIE BRIAN +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com