Patents
Literature
32results about How to "Difficult to determine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
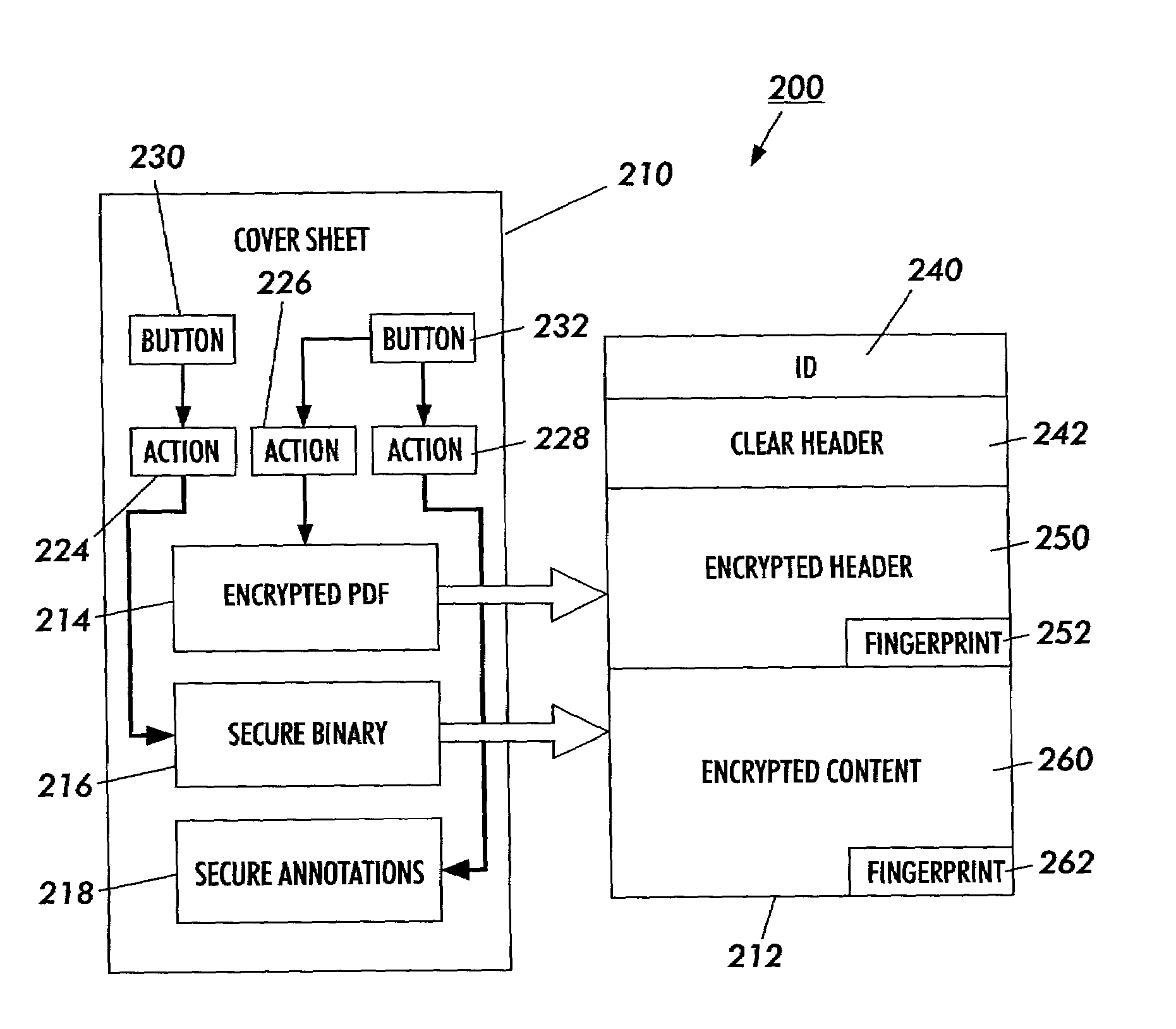
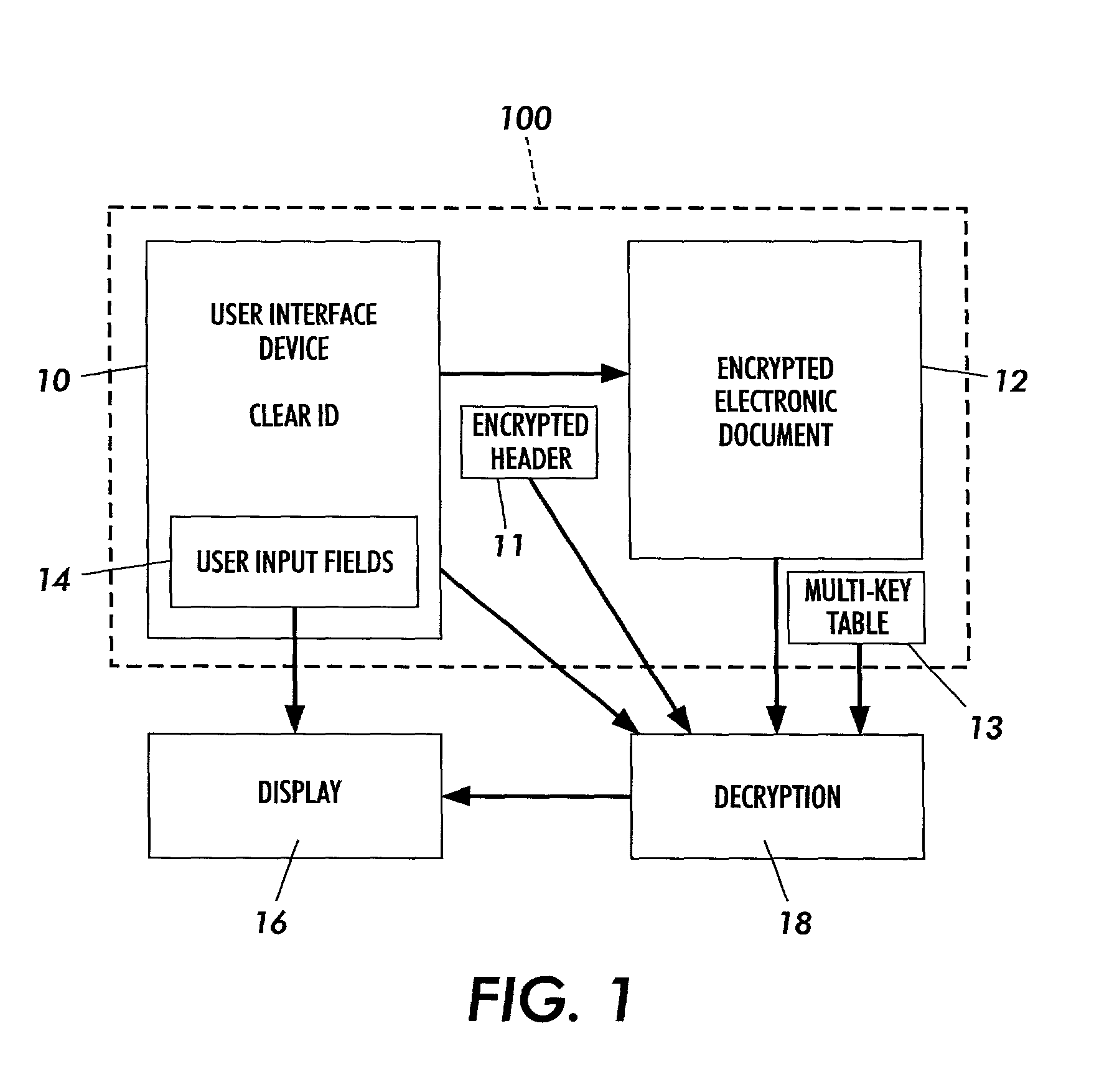
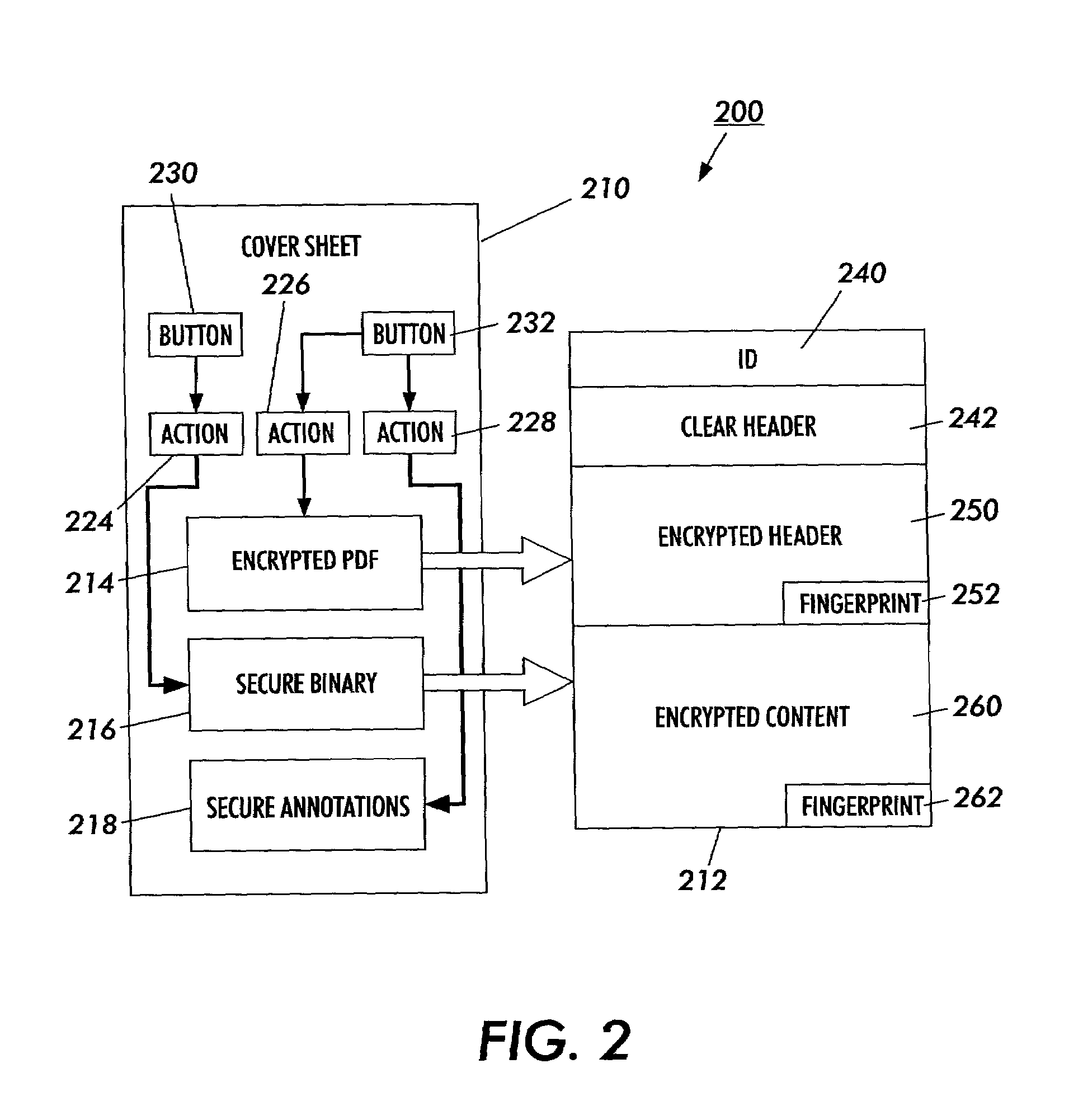
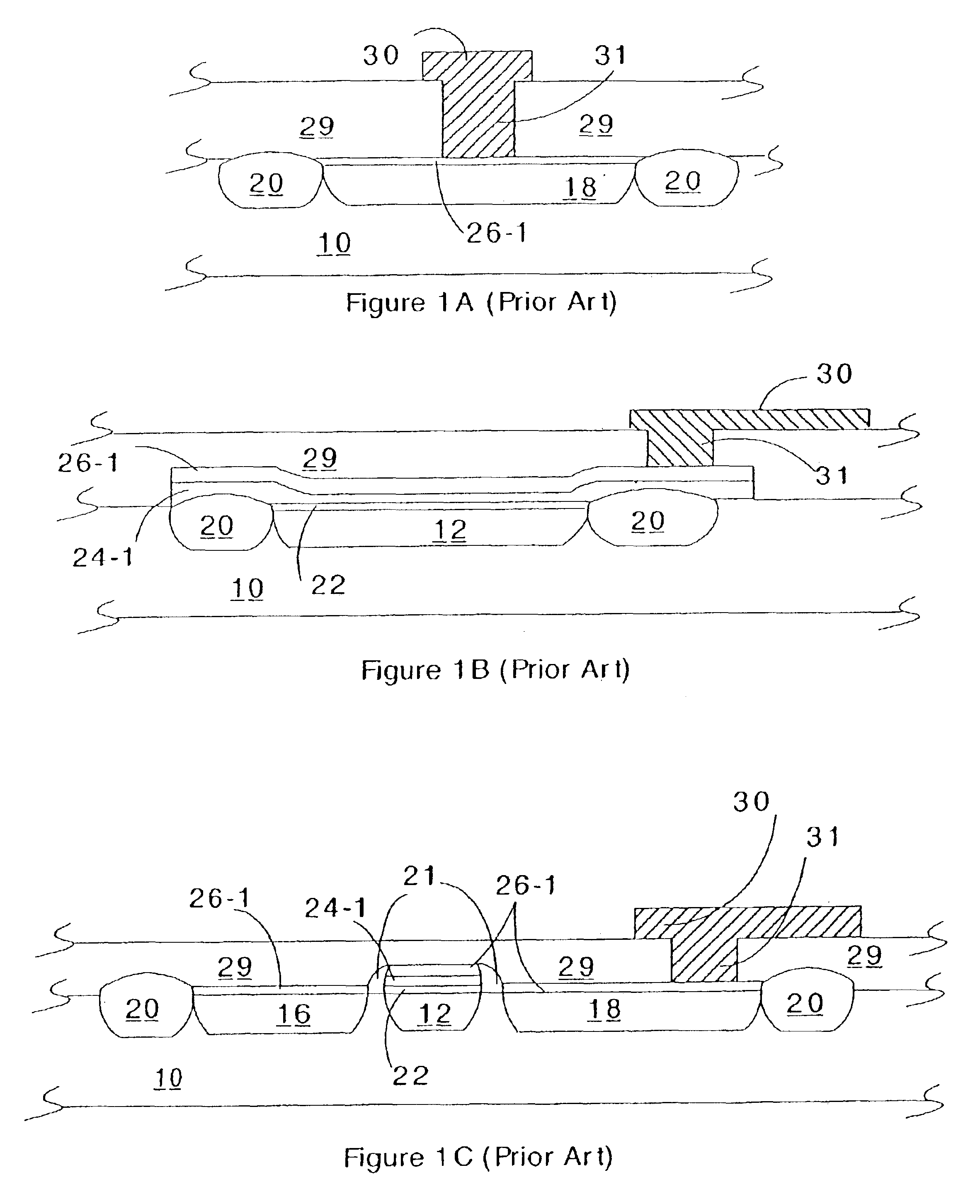
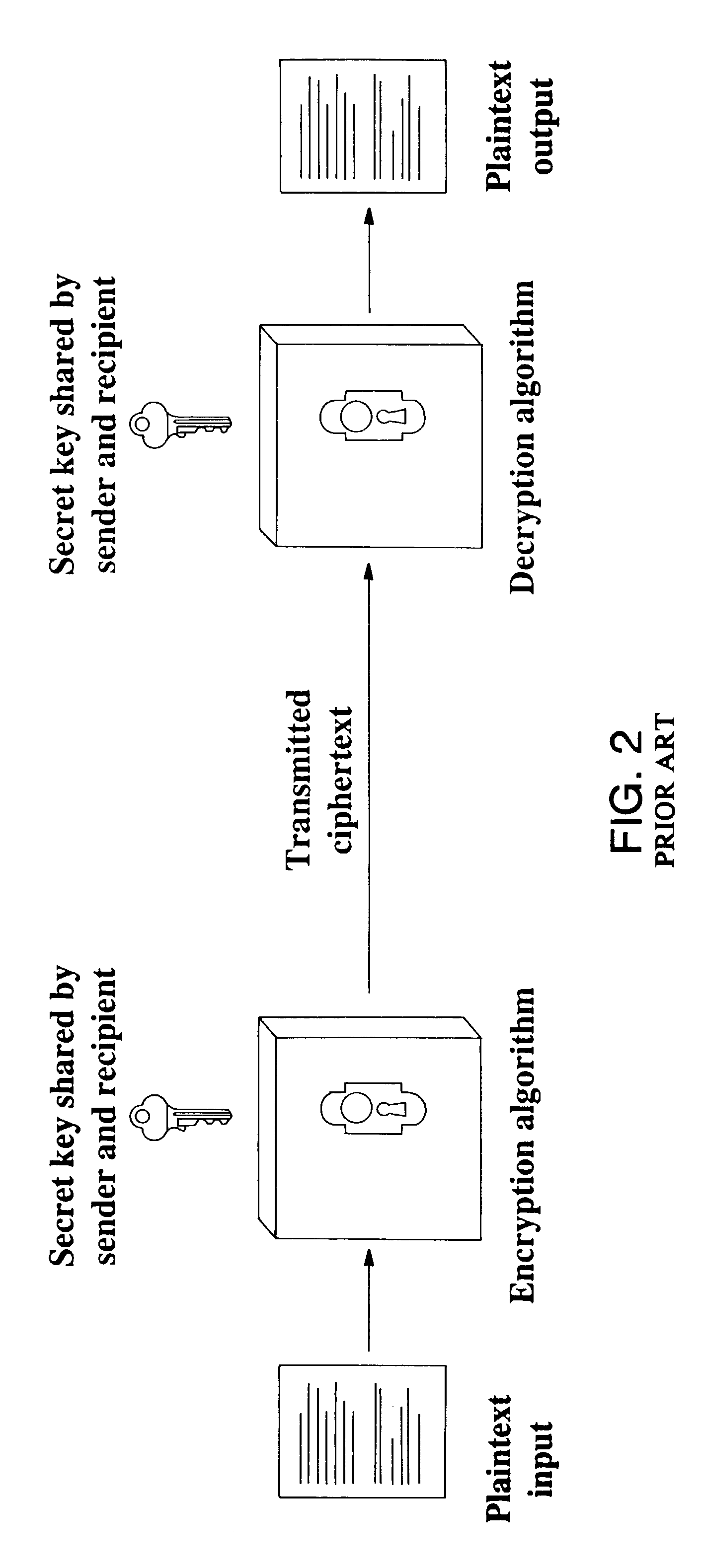
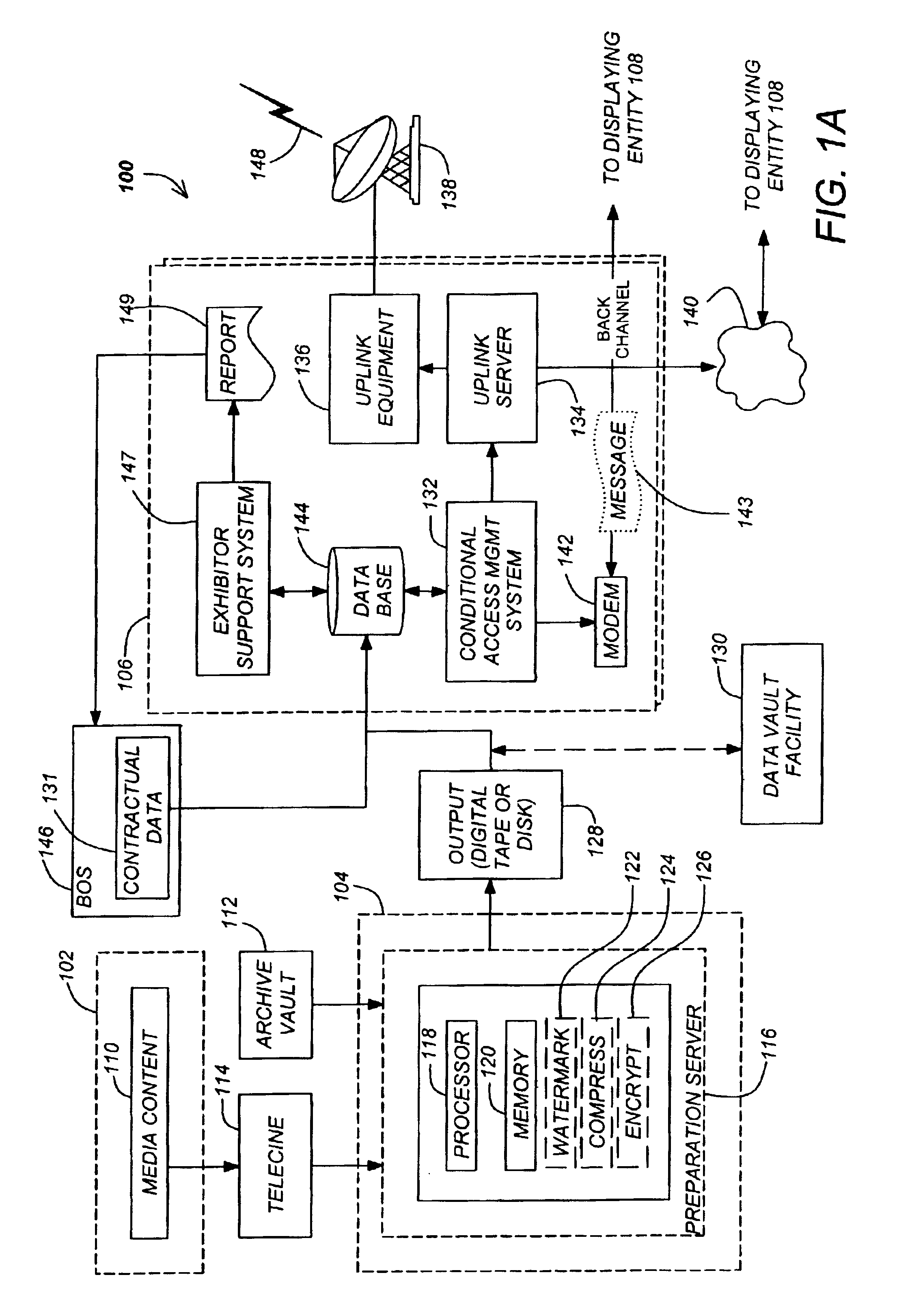
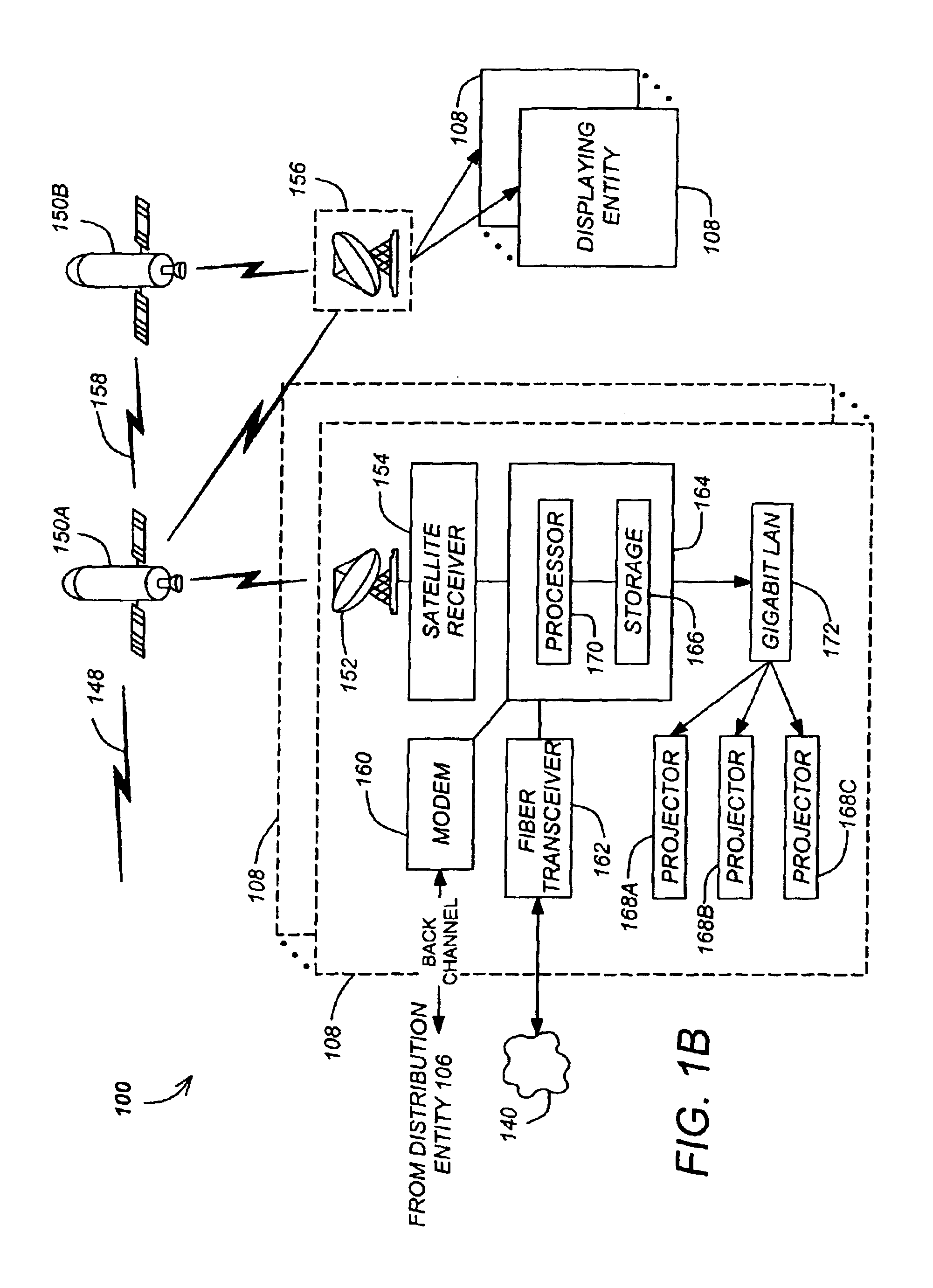
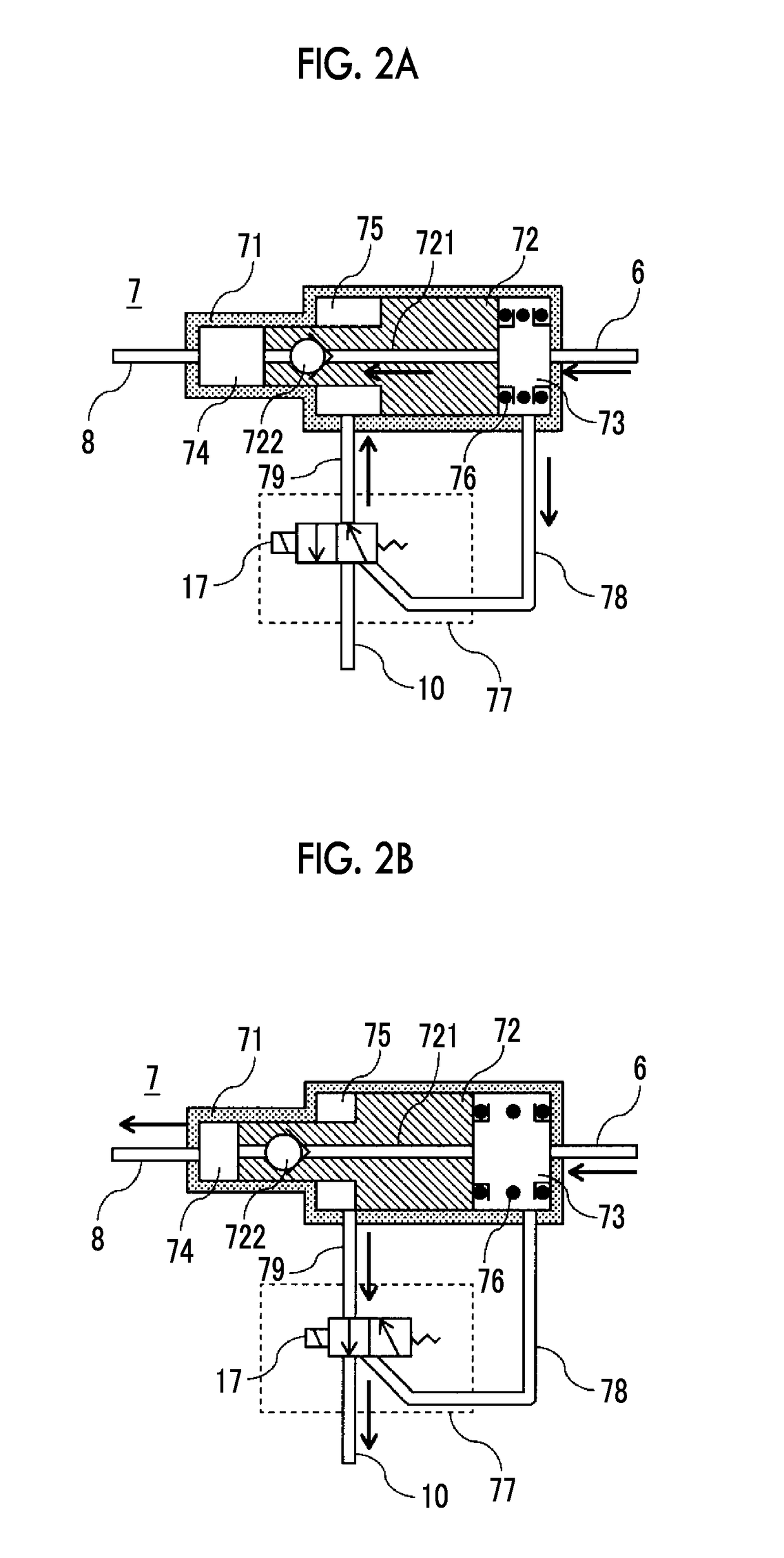
Secure content objects
InactiveUS7496767B2Easily brokenDifficult to determineMultiple keys/algorithms usageDigital data processing detailsElectronic documentDocument preparation
A secure content object protects electronic documents from unauthorized use. The secure content object includes an encrypted electronic document, a multi-key encryption table having at least one multi-key component, an encrypted header and a user interface device. The encrypted document is encrypted using a document encryption key associated with a multi-key encryption method. The encrypted header includes an encryption marker formed by a random number followed by a derivable variation of the same random number. The user interface device enables a user to input a user authorization. The user authorization is combined with each of the multi-key components in the multi-key encryption key table and used to try to decrypt the encrypted header. If the encryption marker is successfully decrypted, the electronic document may be decrypted. Multiple electronic documents or a document and annotations may be protected by the secure content object.
Owner:MAJANDRO LLC
Two factor authentication using a protected pin-like passcode
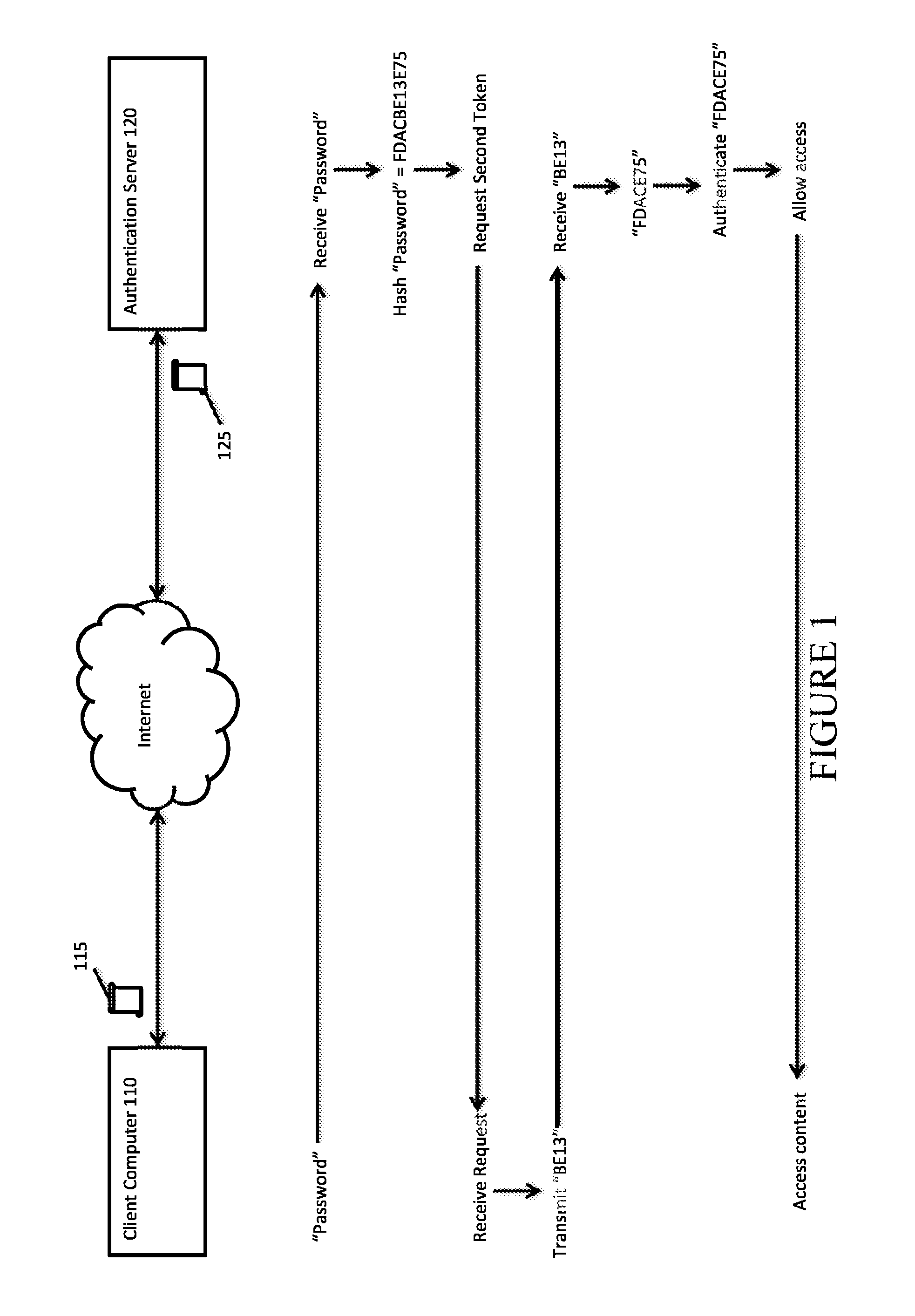
ActiveUS20150349960A1Difficult to determineUser identity/authority verificationCoding/ciphering apparatusMulti-factor authenticationPassword hashing
For example, an implementation of the present invention can comprise a method for authenticating a user. The method can comprise an authentication server receiving from a user a password. The server can then hash the password such that a password hash is created. The server can then receive a second token from the user. Using the second token, the server can identify a sequence of characters associated with the second token within the password hash. The server can create an authentication token by removing the sequence of characters from the password hash. If the authentication token matches a stored value, the server can authenticate the user.
Owner:TOKENYM
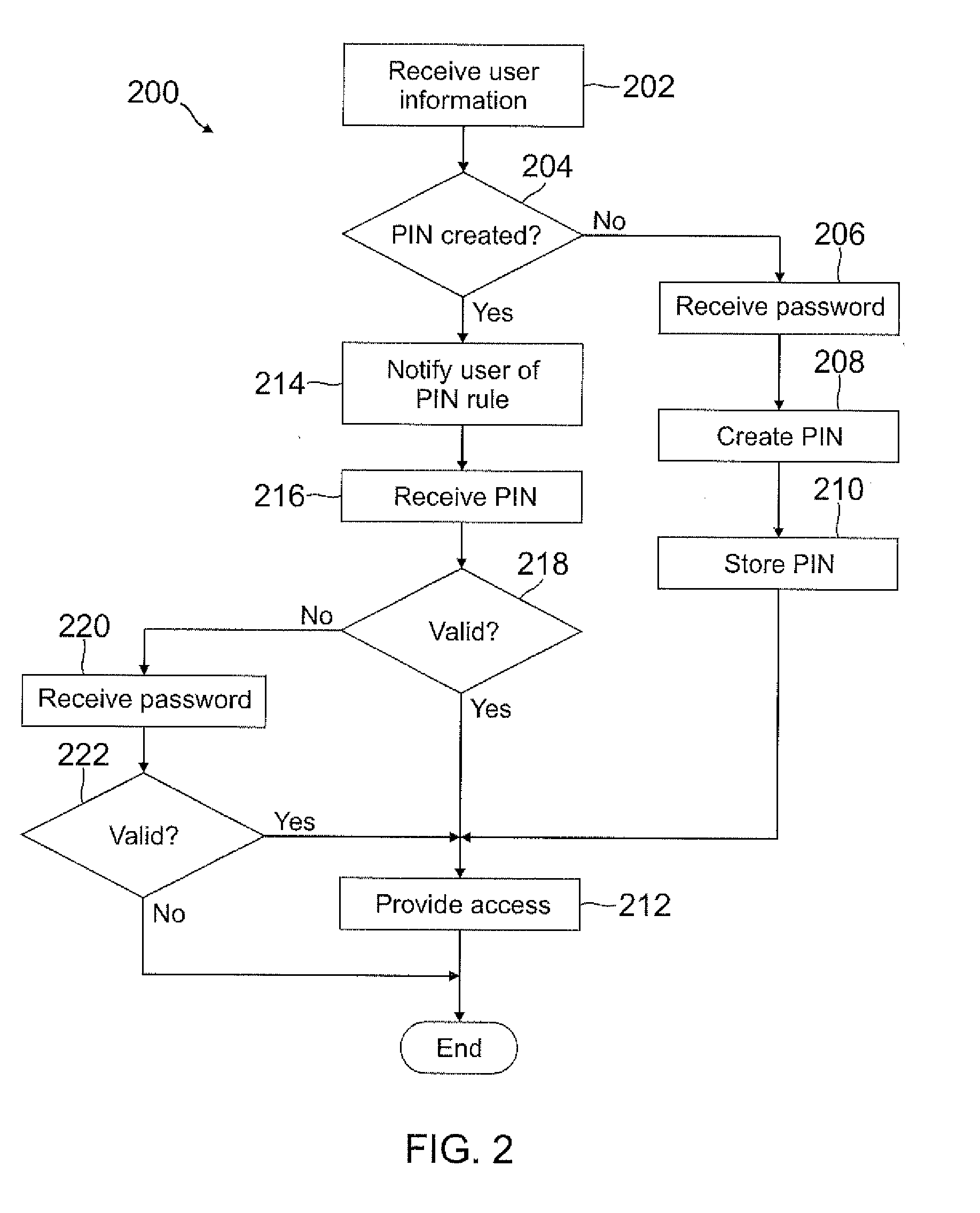
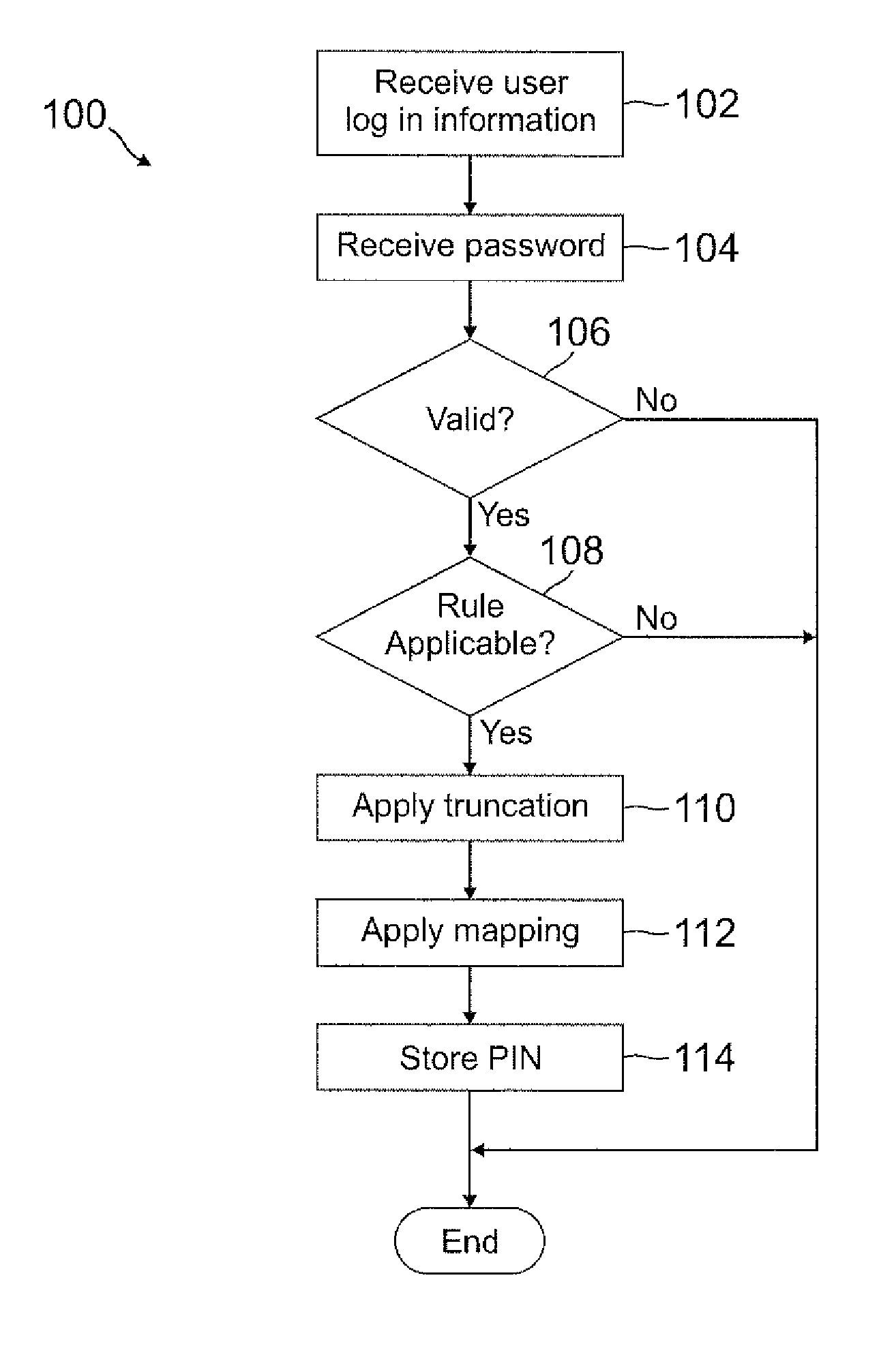
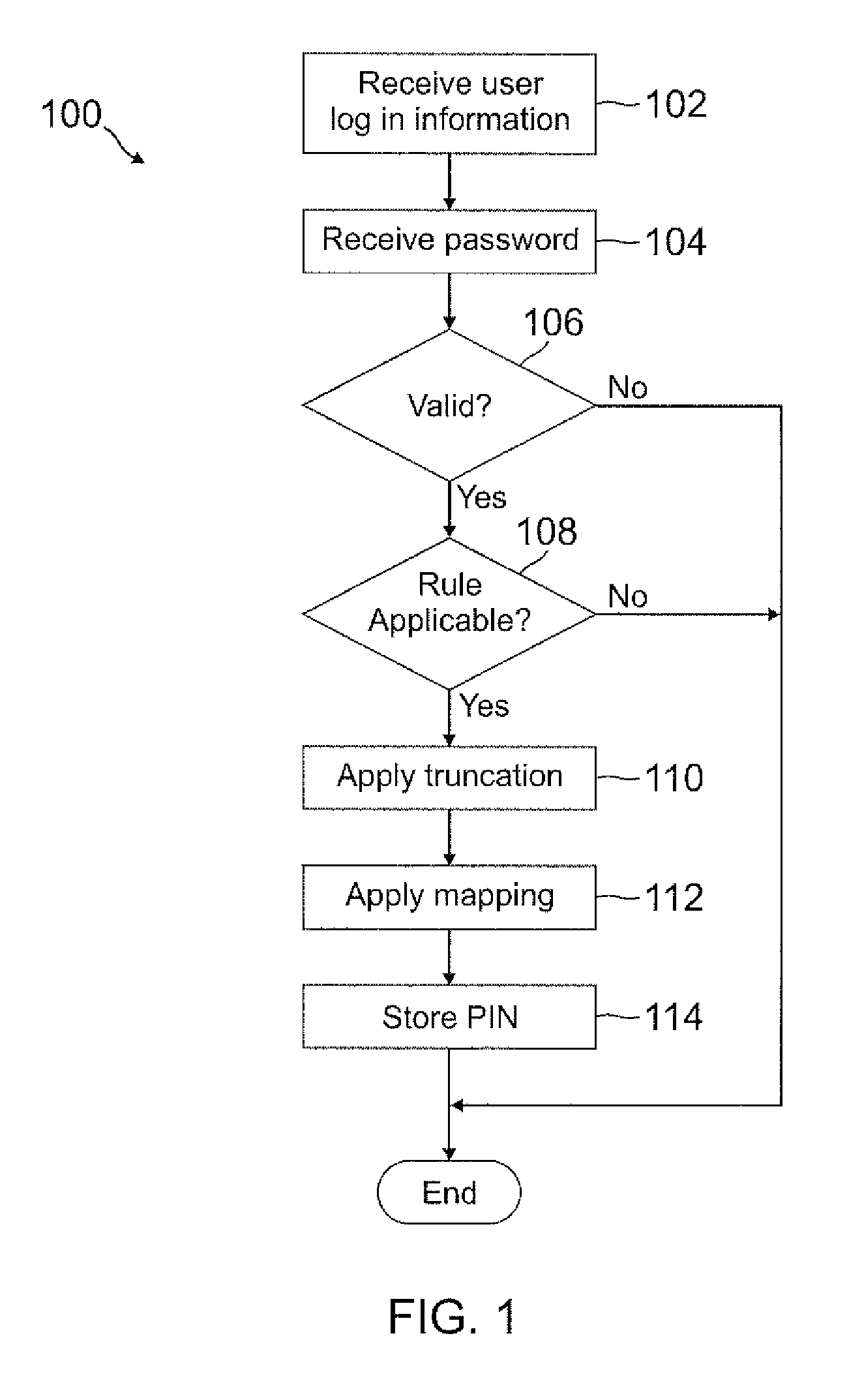
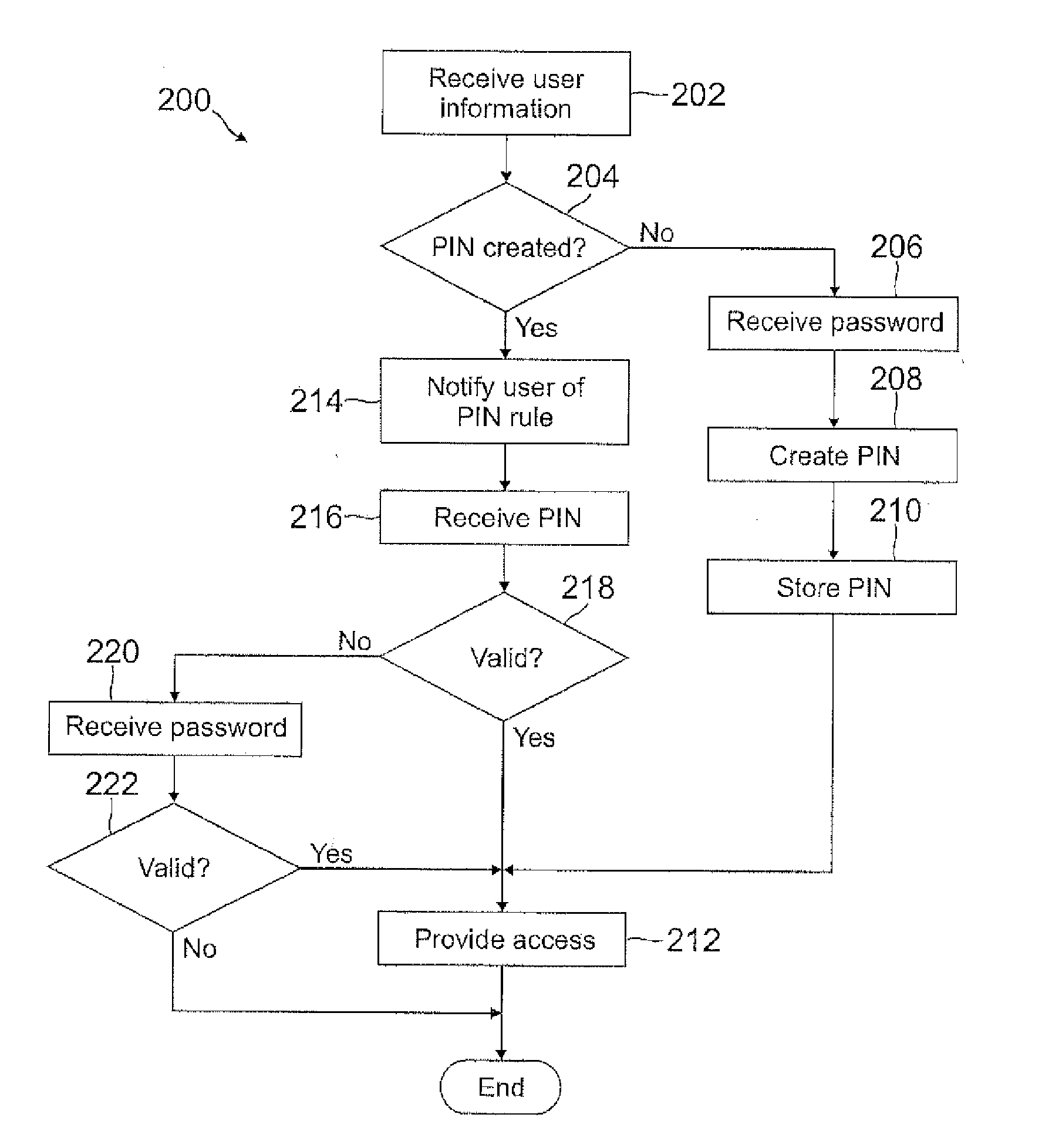
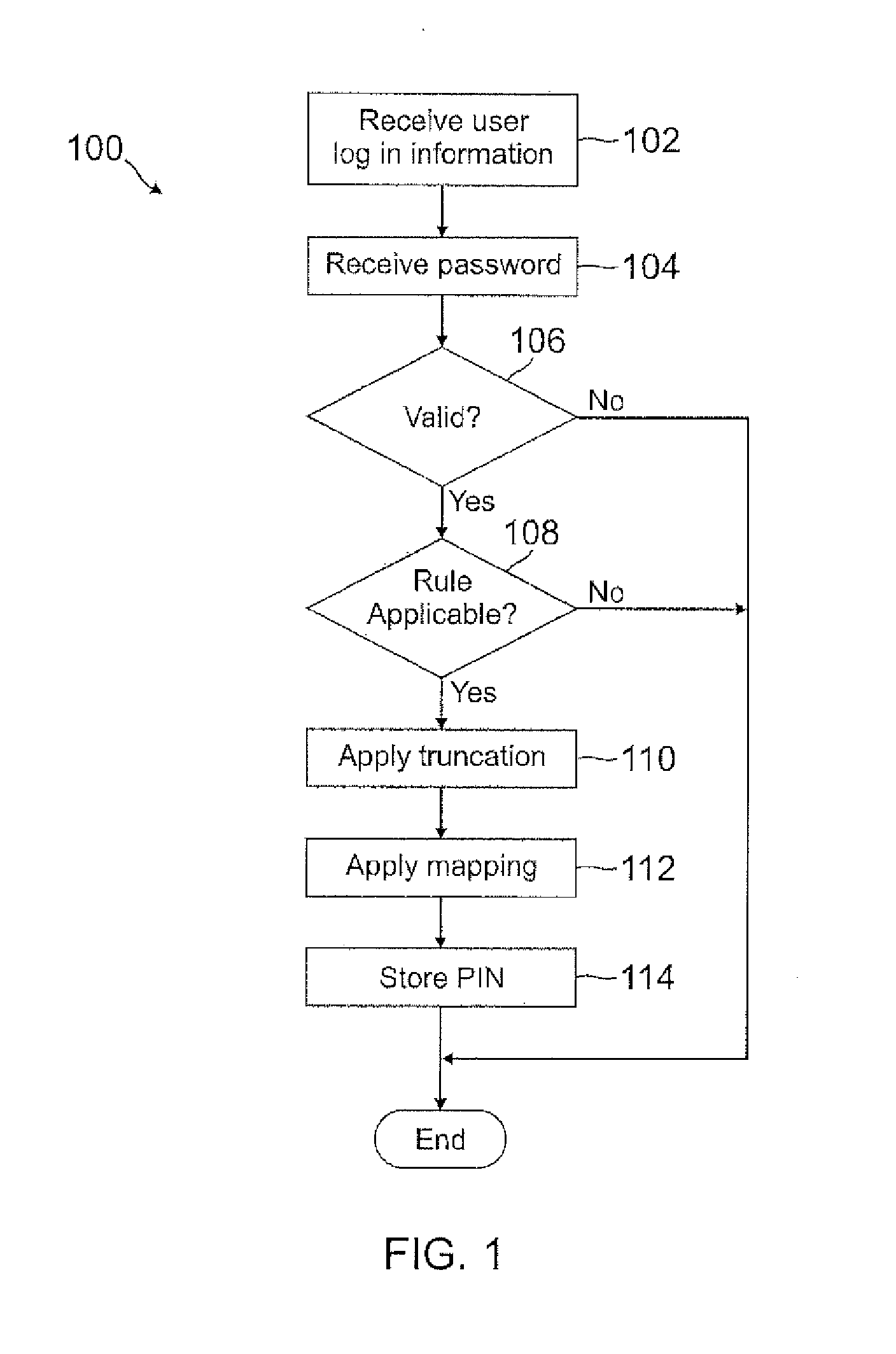
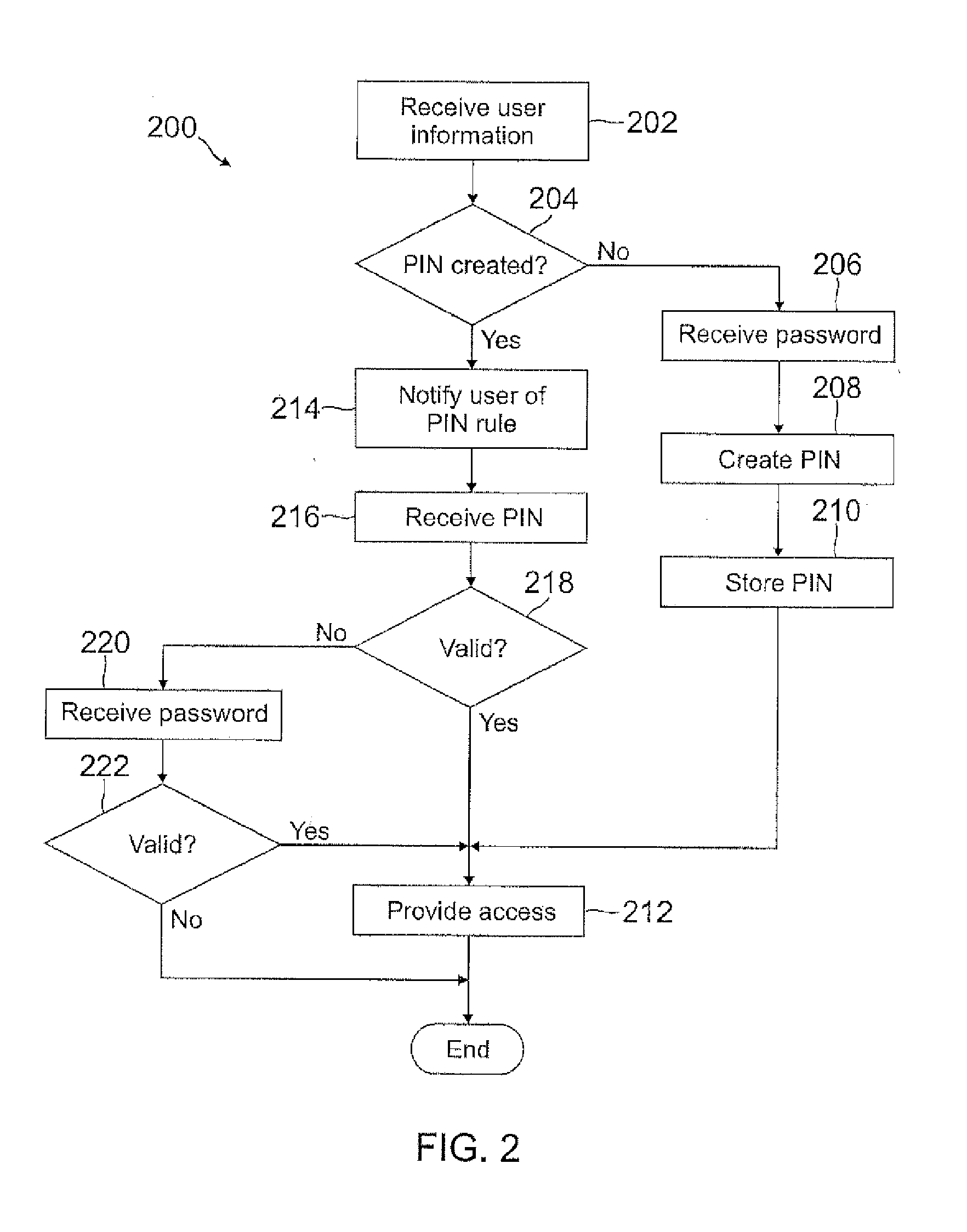
Automatic pin creation using password
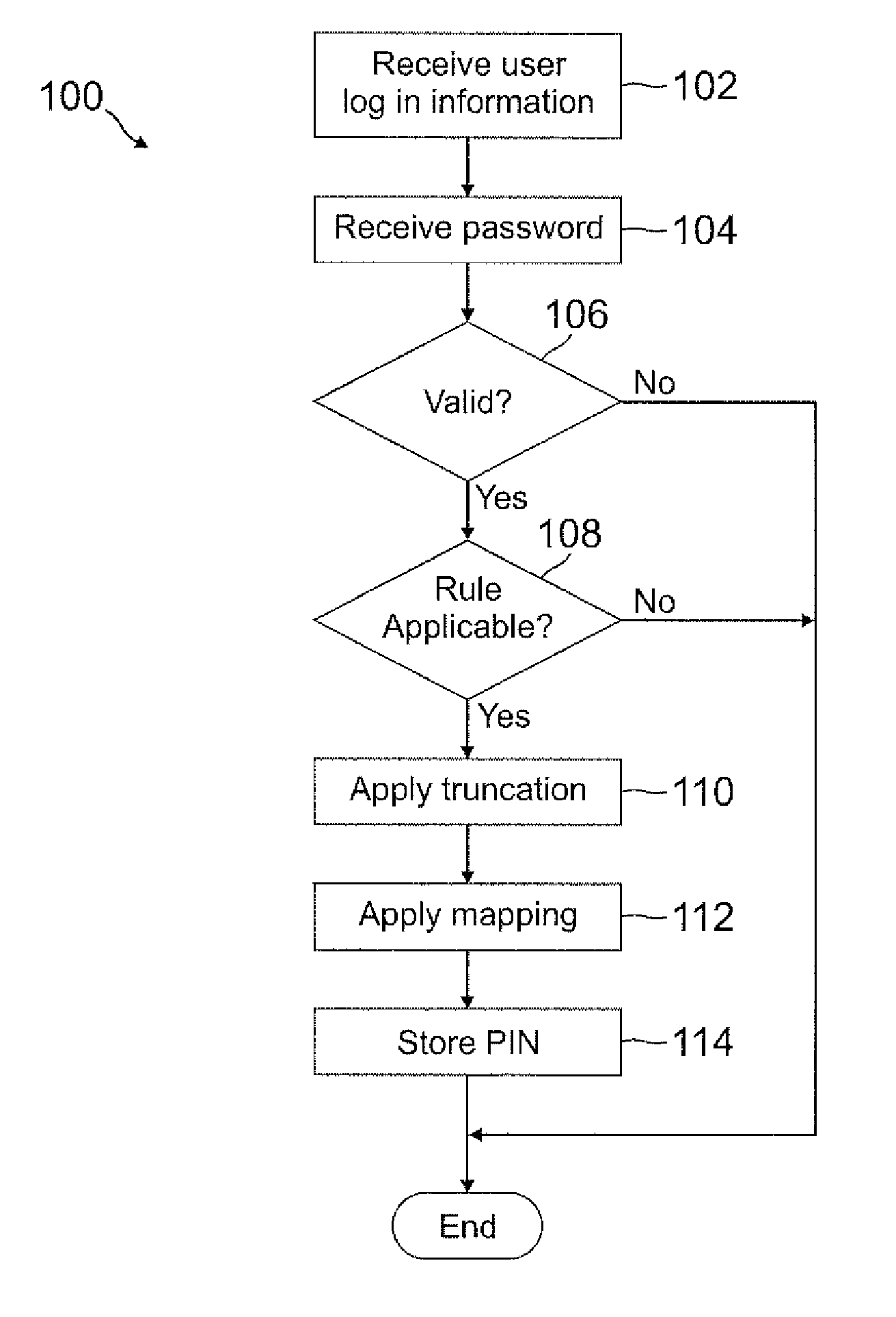
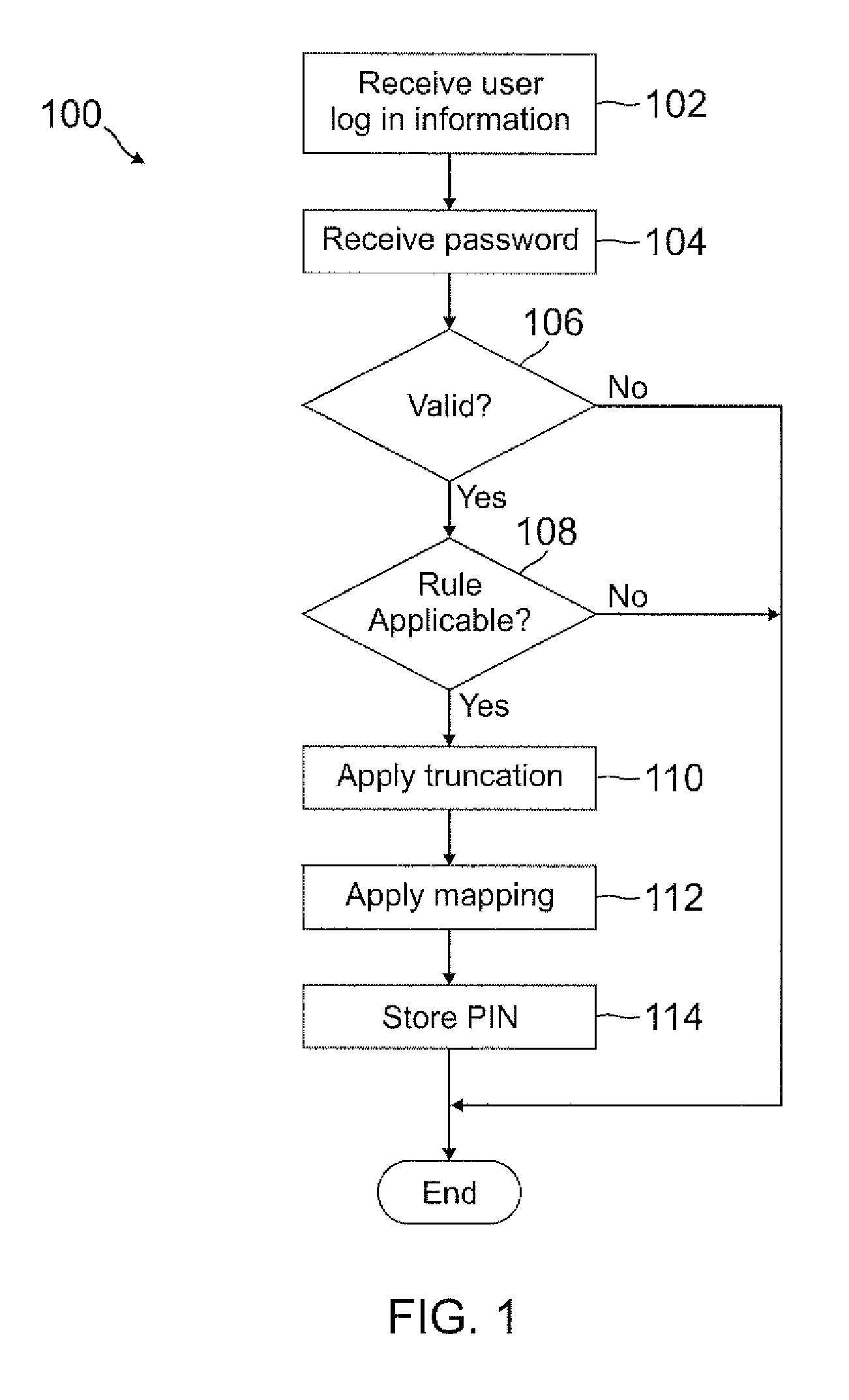
ActiveUS20120110634A1Easy to rememberMore experienceDigital data processing detailsMultiple digital computer combinationsUser devicePassword
A PIN is automatically generated based on at least one rule when the user enters a password through a user device. In one example, the PIN is a truncated version of the password where each character in the truncated version is mapped onto a number. The mapping can be a truncation at the beginning or end of the password, or the mapping can be with any pattern or sequence of characters in the password. This PIN generation may be transparent to the user, such that the user may not even know the PIN was generated when the password was entered. When the user attempts to access restricted content, the user may enter the PIN instead of the password, where the user may be notified of the rule used to generate the PIN so that the user will know the PIN by knowing the password.
Owner:PAYPAL INC
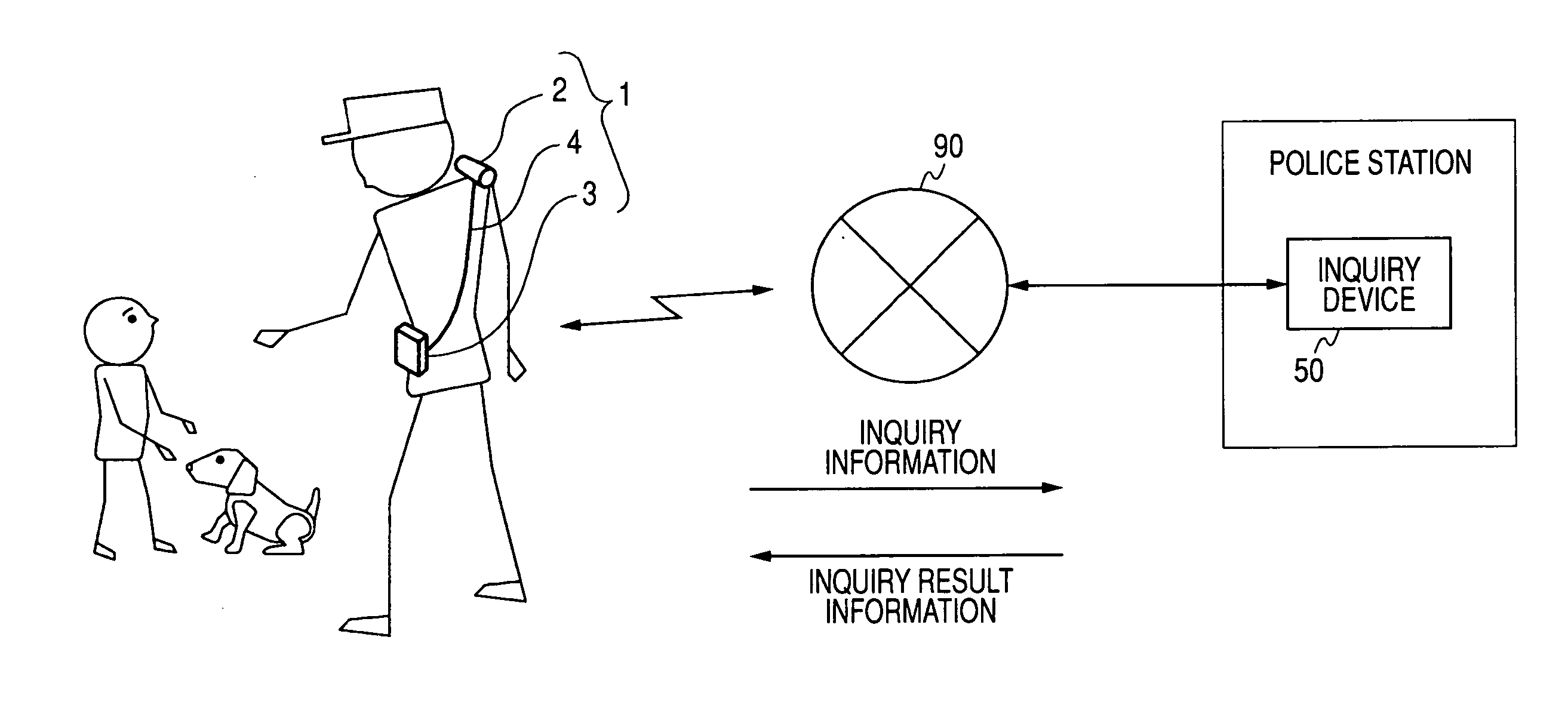
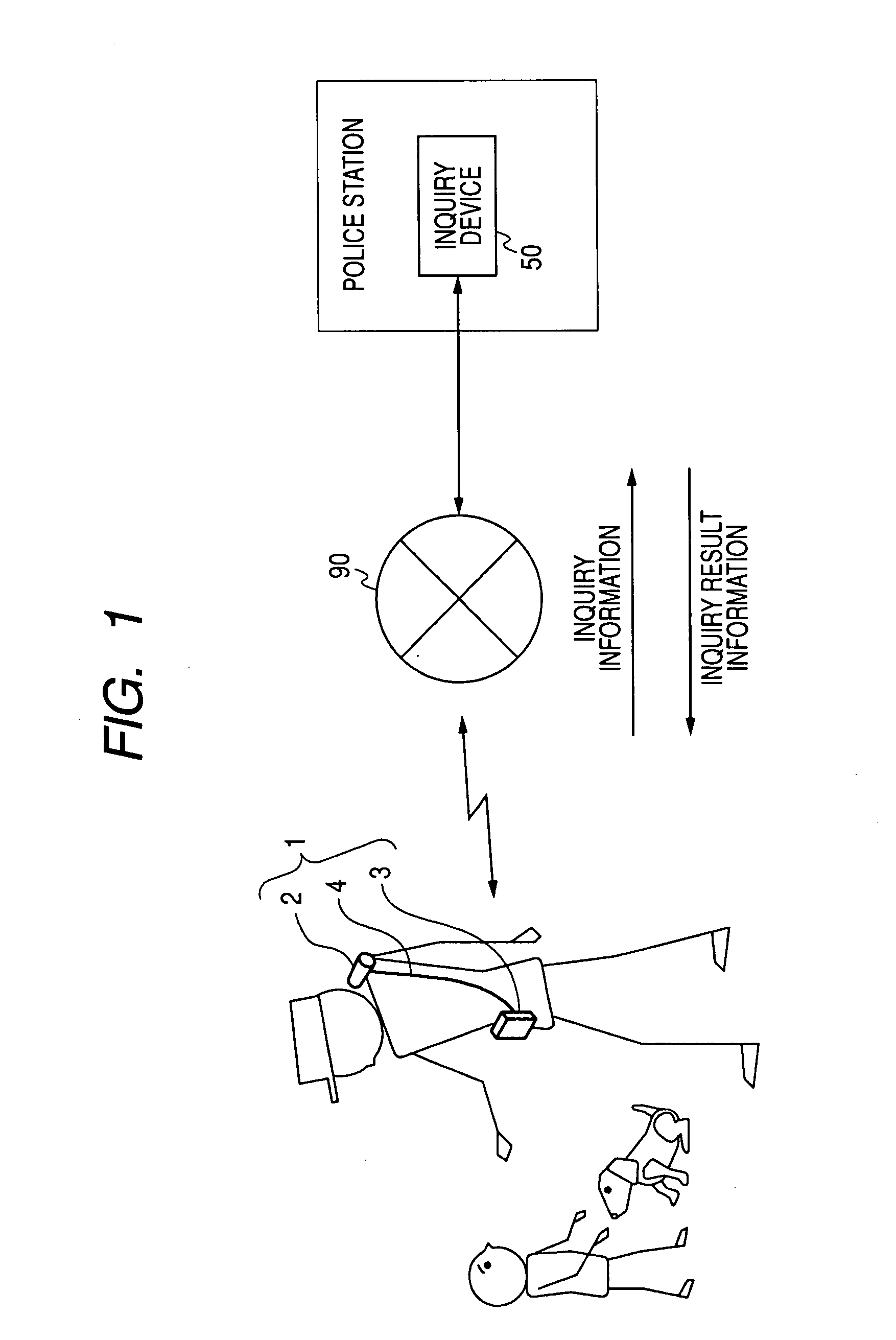
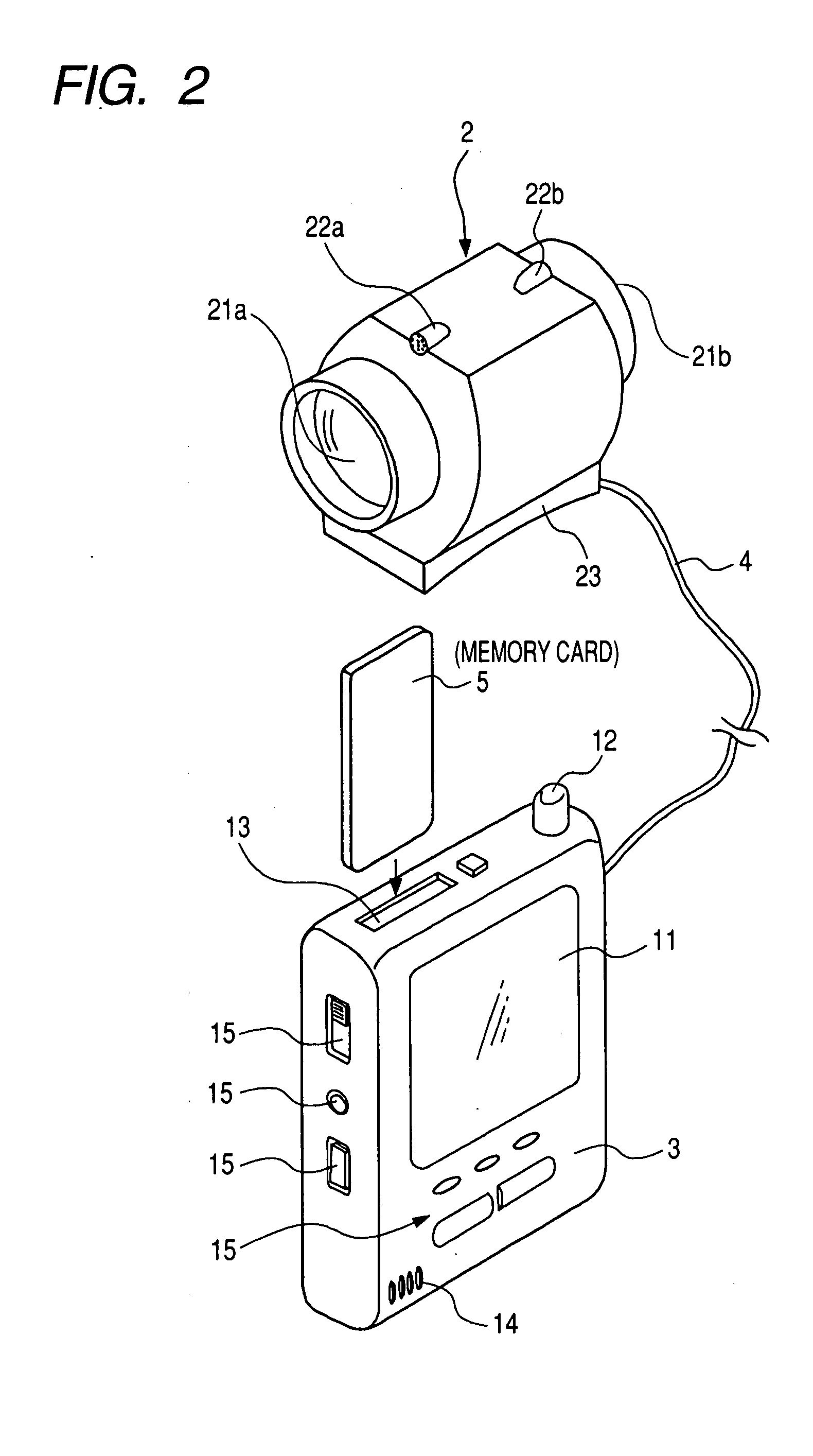
Inquiry system, imaging device, inquiry device, information processing method, and program thereof
InactiveUS20070228159A1Rapid responseAccurate measurementTelevision system detailsDigital data information retrievalInformation processingCommunication unit
An inquiry system which includes a portable imaging device and an inquiry device capable of communicating with the imaging device in two ways is provided. The imaging device includes an imaging unit, a communication unit, a face characteristic data generator extracting a face image from the image data picked up by the imaging unit and generating face characteristic data from the extracted face image, a transmission information generator generating inquiry information including the face characteristic data and transmitting the inquiry information to the inquiry device by using the communication unit, and a presentation processor performing a presentation process based on inquiry result information in response to reception of the inquiry result information transmitted from the inquiry device by using the communication unit. The inquiry device includes a communication unit, a face database, an inquiry processor, and a transmission information generator.
Owner:SONY CORP
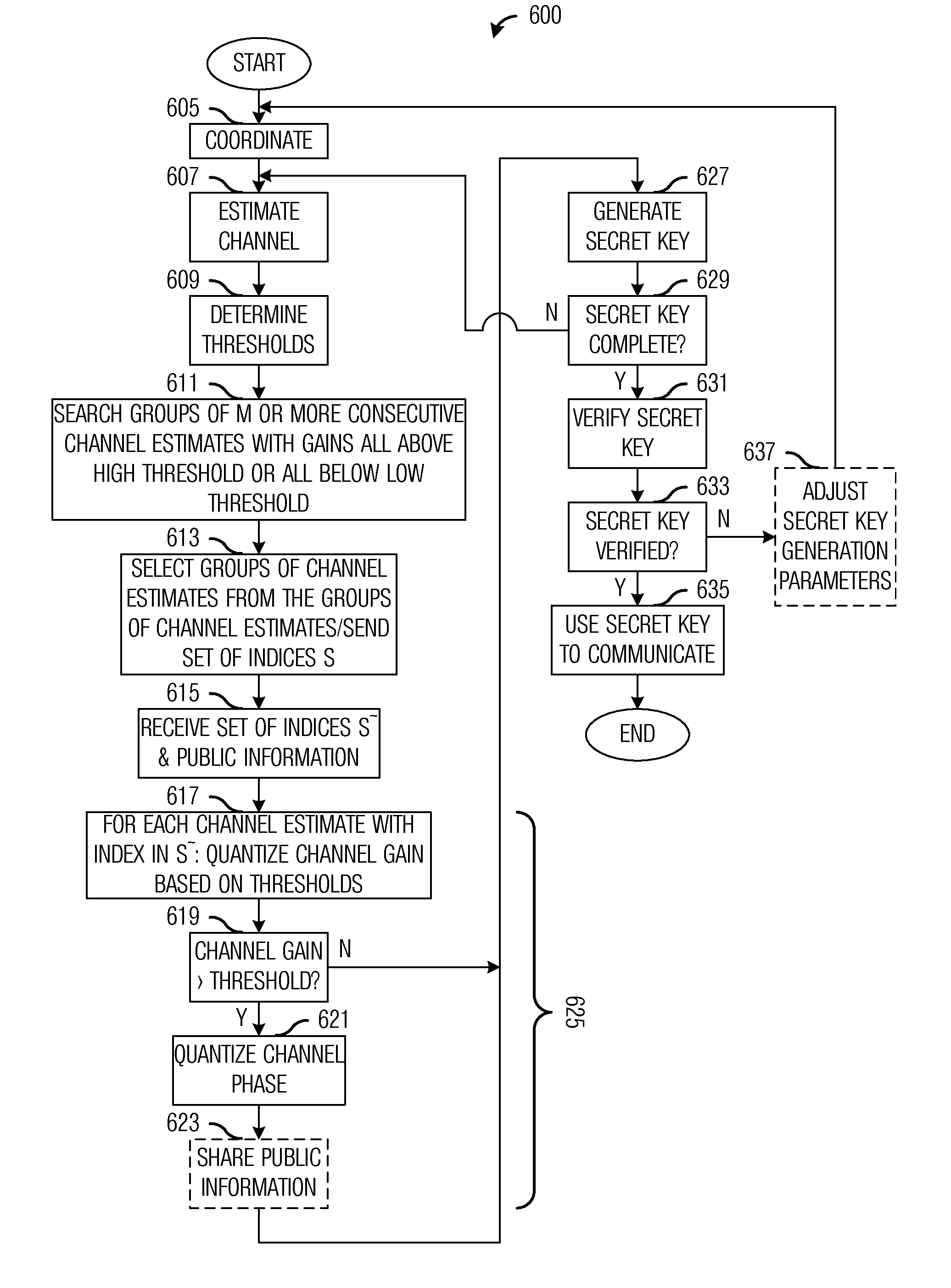
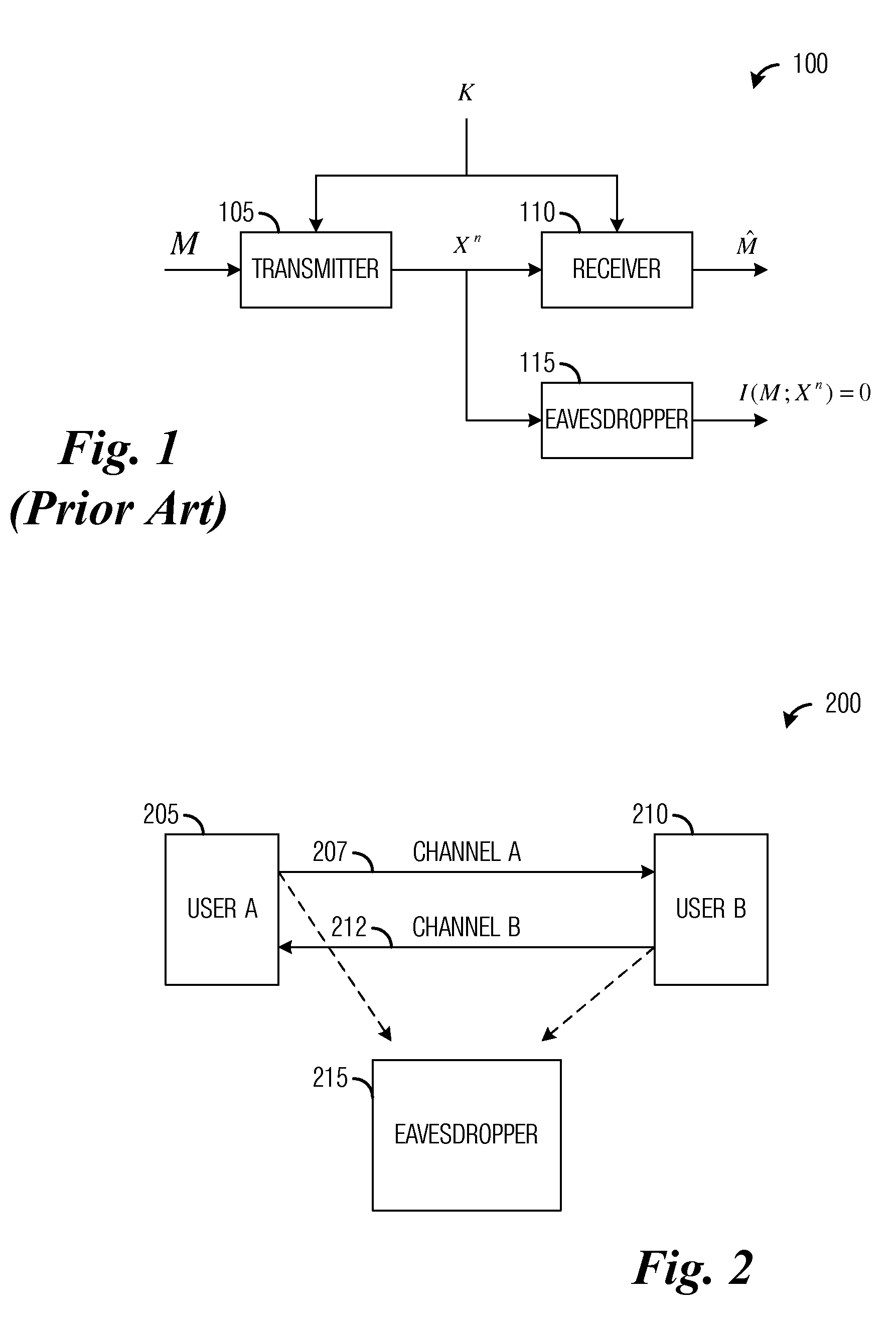
System and Method for Securing Wireless Communications
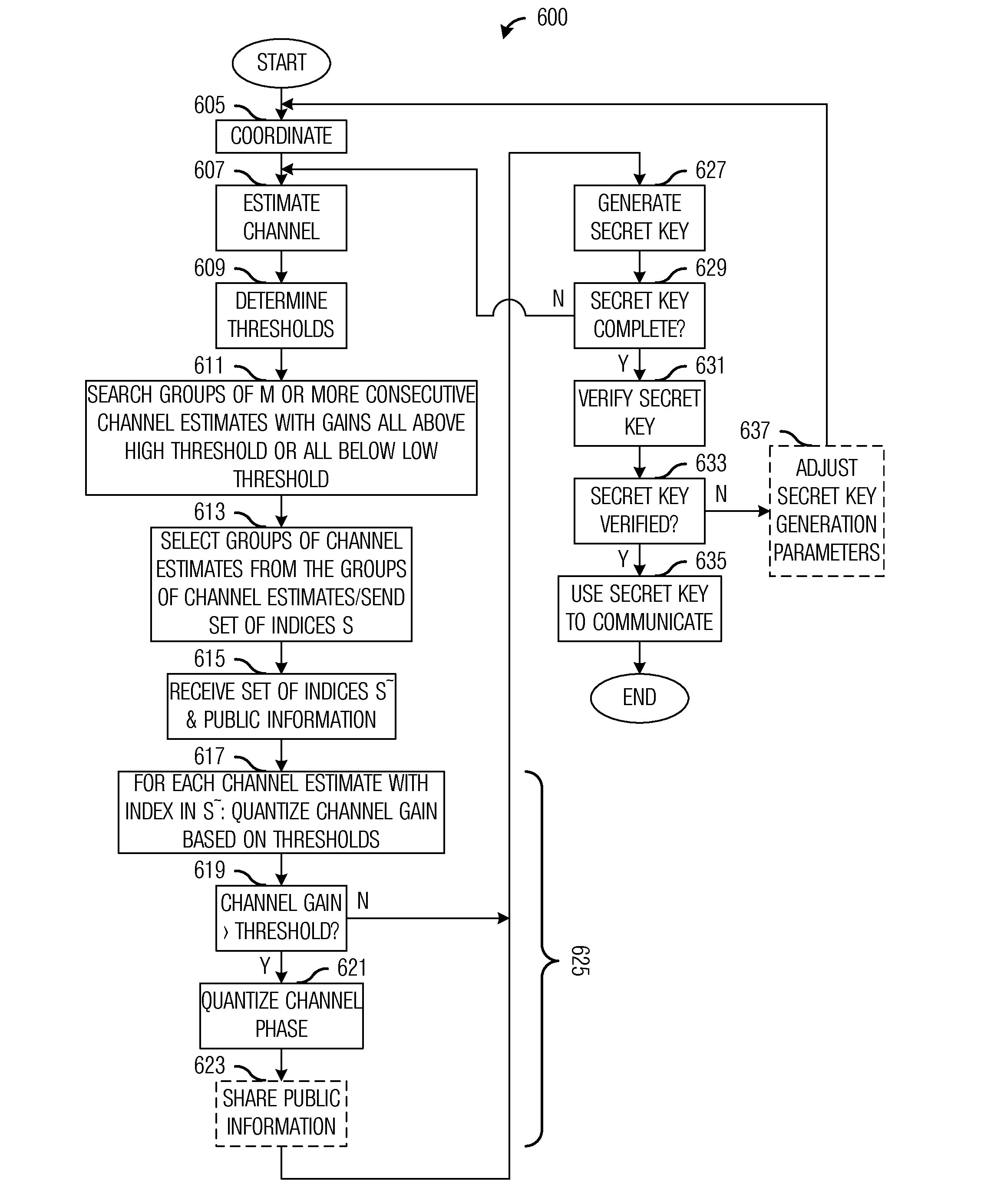
InactiveUS20120106739A1Increase probabilityIncreasing secret key generation ratePublic key for secure communicationSecret communicationSecure communicationComputer security
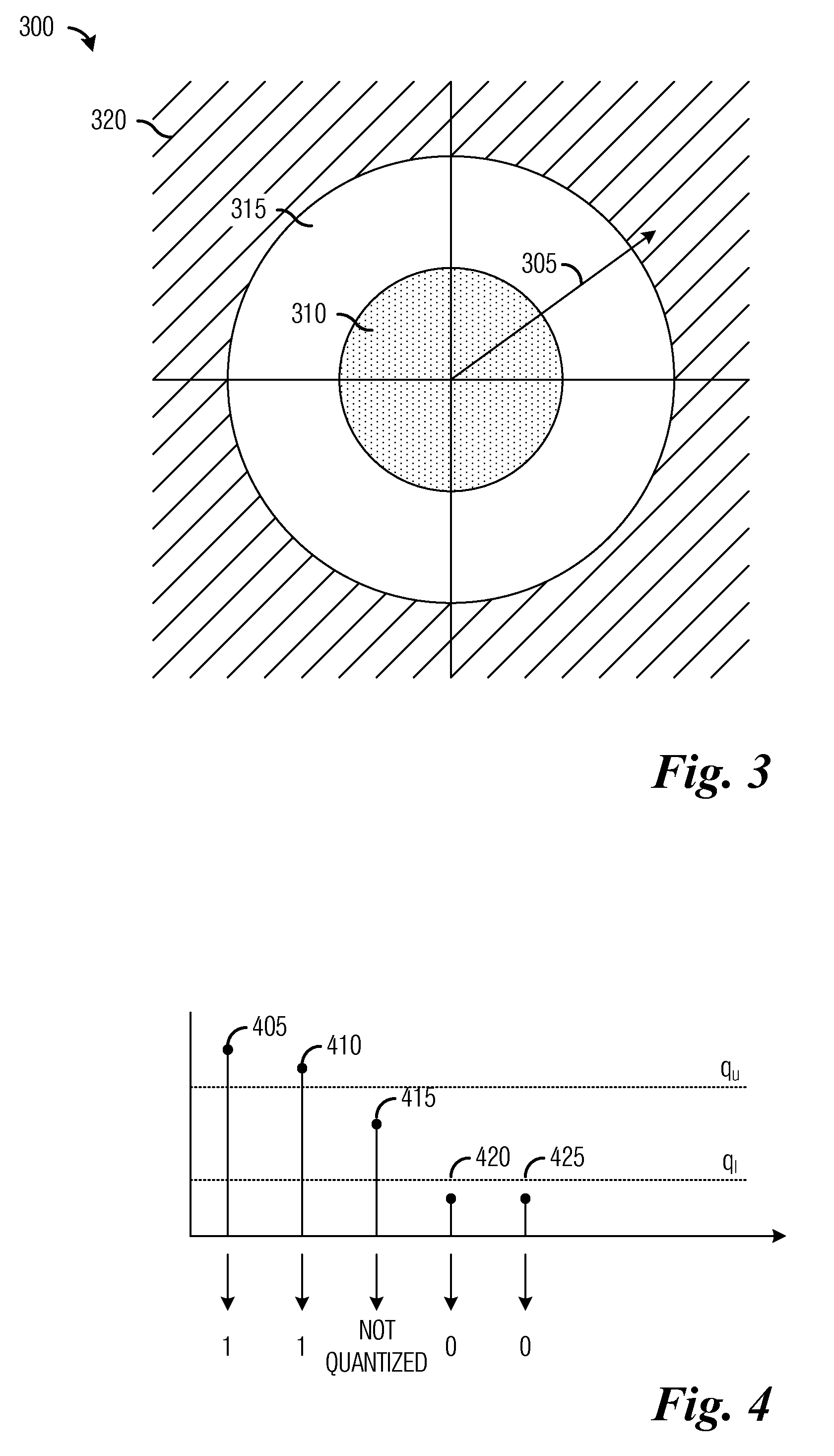
A system and method for securing wireless communications are provided. A method for secure communications by a first user includes estimating a channel between the first user and a second user based on a pilot signal transmitted by the second user, determining a first threshold and a second threshold based on the estimate of channel, selecting a first subset of channel estimates, signaling the first subset of channel estimates to the second user, receiving a second subset of channel estimates from the second user, for each channel estimate in the second subset of channel estimates, quantizing the channel estimate based on a relationship between a gain of the channel estimate and the first threshold and the second threshold, generating a first secret key based on quantized channel estimates, verifying that the first secret key matches a second secret key generated by the second user, and transmitting information to the second user.
Owner:FUTUREWEI TECH INC
Wireless Communication Device, Wireless Communication System, Wireless Communication Method, and Program
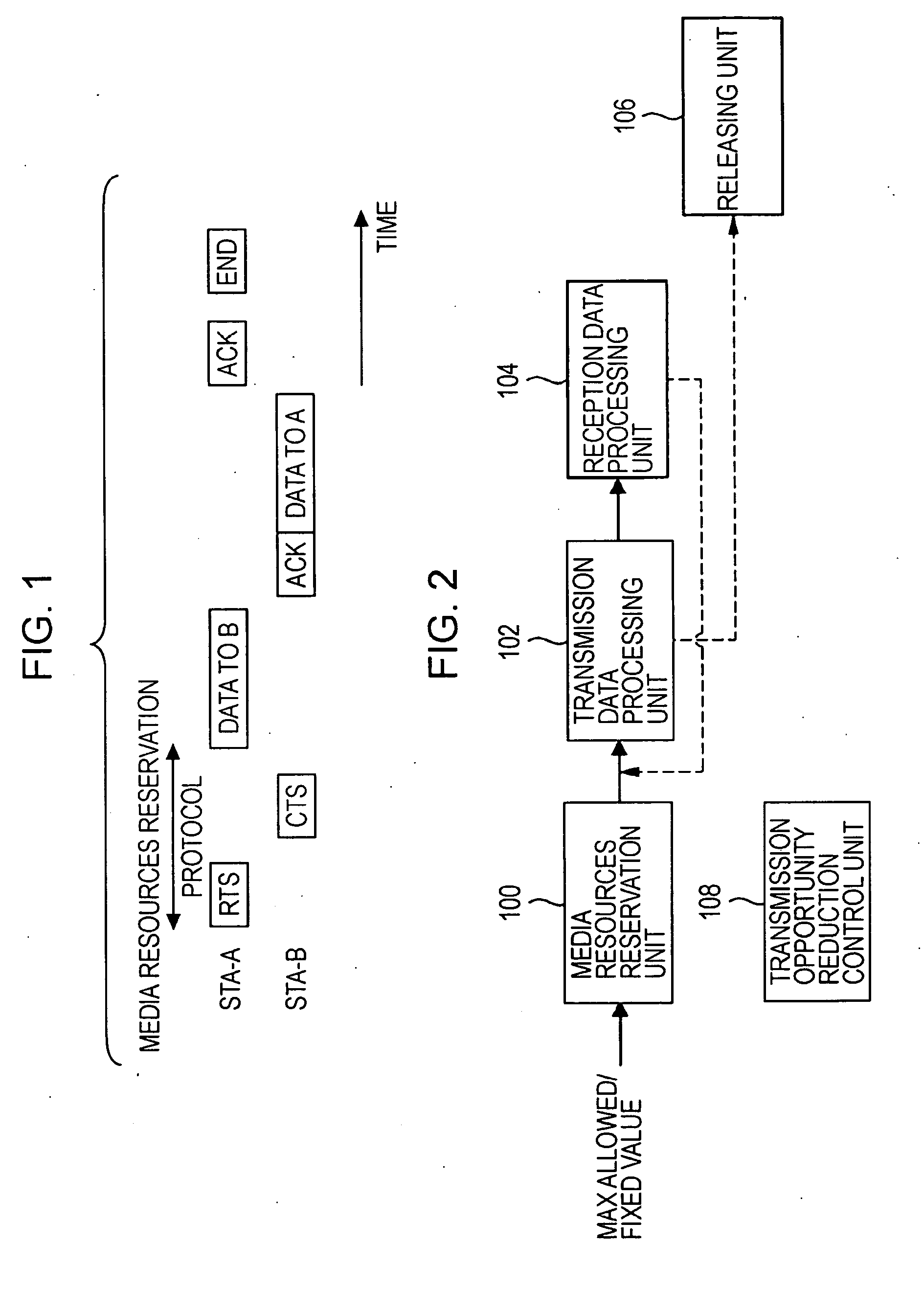
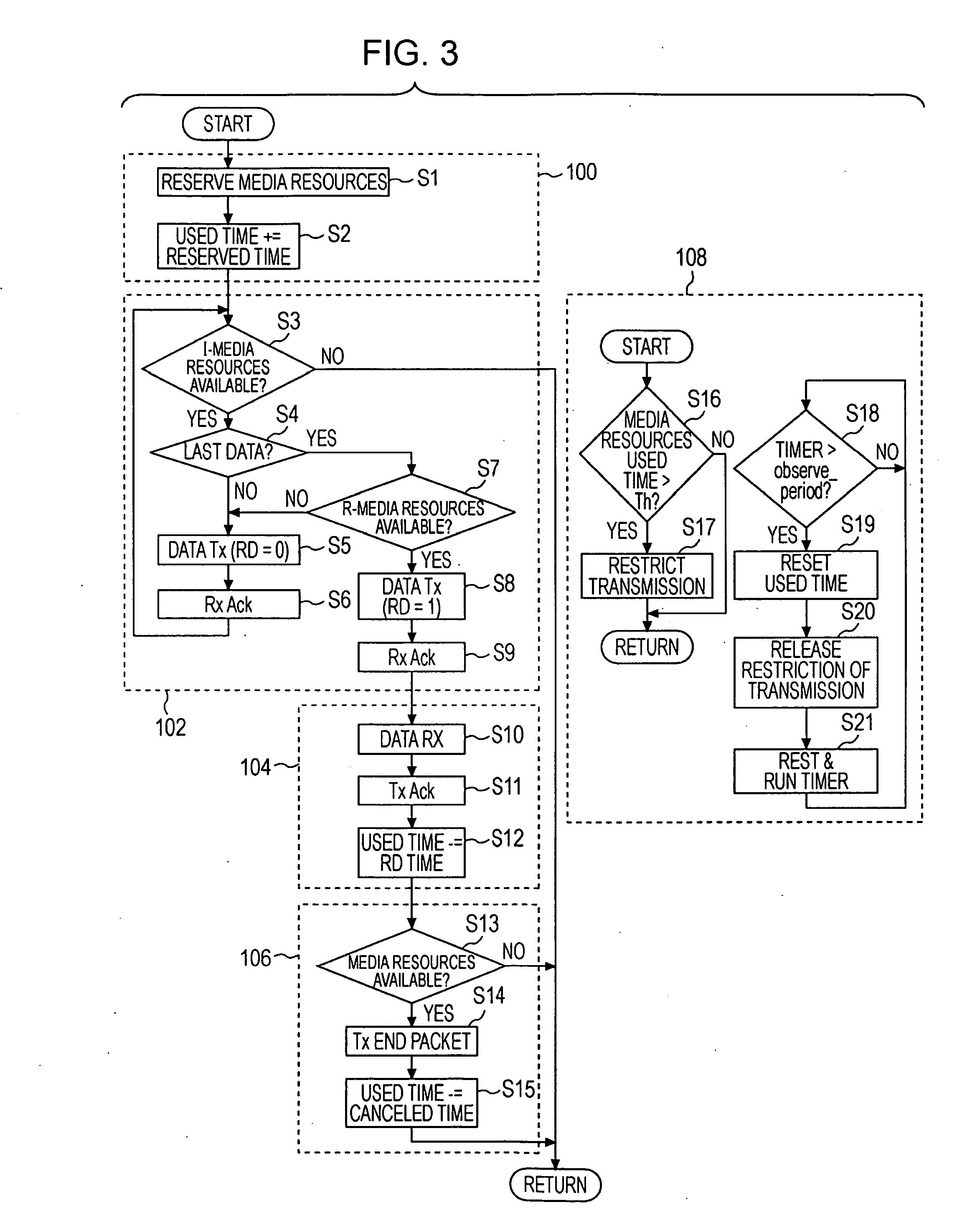
InactiveUS20090059792A1Avoid a lotMinimal amountError preventionFrequency-division multiplex detailsCommunications systemComputer science
A bandwidth-reservation wireless communication device that performs communication with a communication destination node connected thereto via a wireless communication network includes a traffic amount estimation unit configured to estimate an amount of traffic involved in receiving response data from the communication destination node, and a media resources reservation unit configured to reserve media resources on the basis of the estimated amount of traffic.
Owner:SONY CORP
Integrated circuit with reverse engineering protection
InactiveUS6897535B2Effectively frustrateDifficult to determineTransistorSemiconductor/solid-state device detailsIntegrated circuitReverse engineering
Technique and structures for camouflaging an integrated circuit structure. The integrated circuit structure is formed by a plurality of layers of material having controlled outlines and controlled thicknesses. A layer of dielectric material of a controlled thickness is disposed among said plurality of layers to thereby render the integrated circuit structure intentionally inoperable.
Owner:RAYTHEON CO
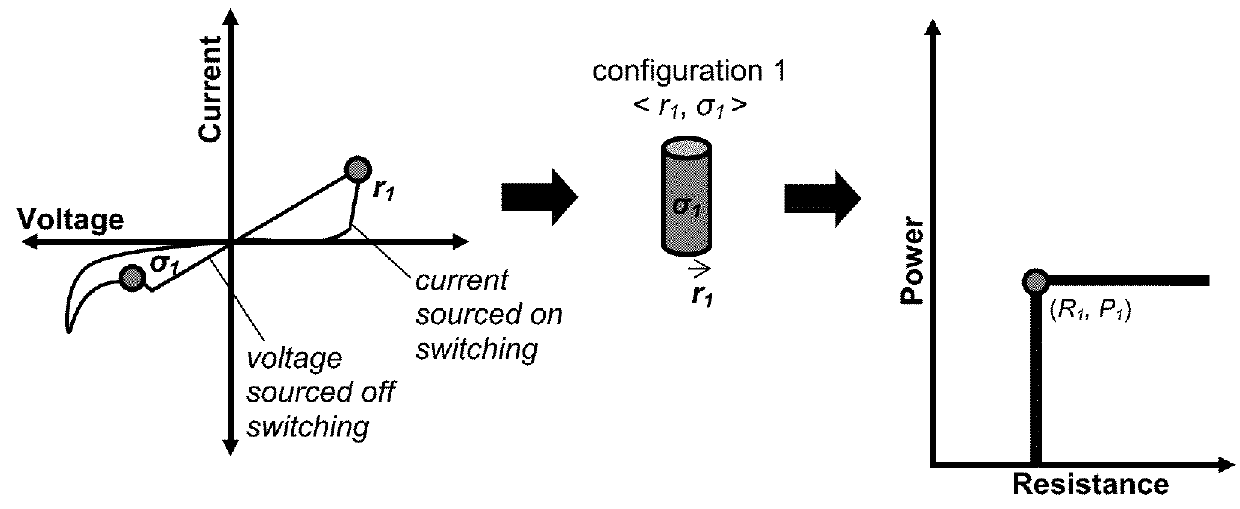
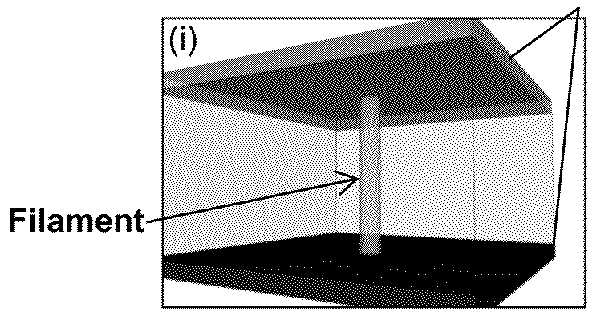
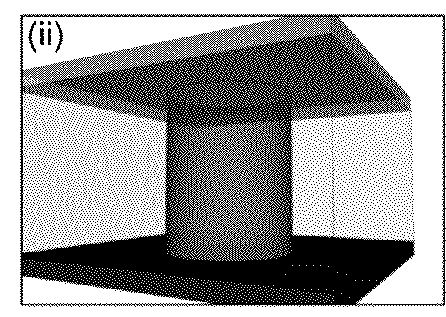
Methods for resistive switching of memristors
The present invention is directed generally to resistive random-access memory (RRAM or ReRAM) devices and systems, as well as methods of employing a thermal resistive model to understand and determine switching of such devices. In particular example, the method includes generating a power-resistance measurement for the memristor device and applying an isothermal model to the power-resistance measurement in order to determine one or more parameters of the device (e.g., filament state).
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
Test system and test method using virtual review
InactiveUS20070159179A1Difficult to determineEasy to detectSemiconductor/solid-state device testing/measurementResistance/reactance/impedenceComputer scienceTest facility
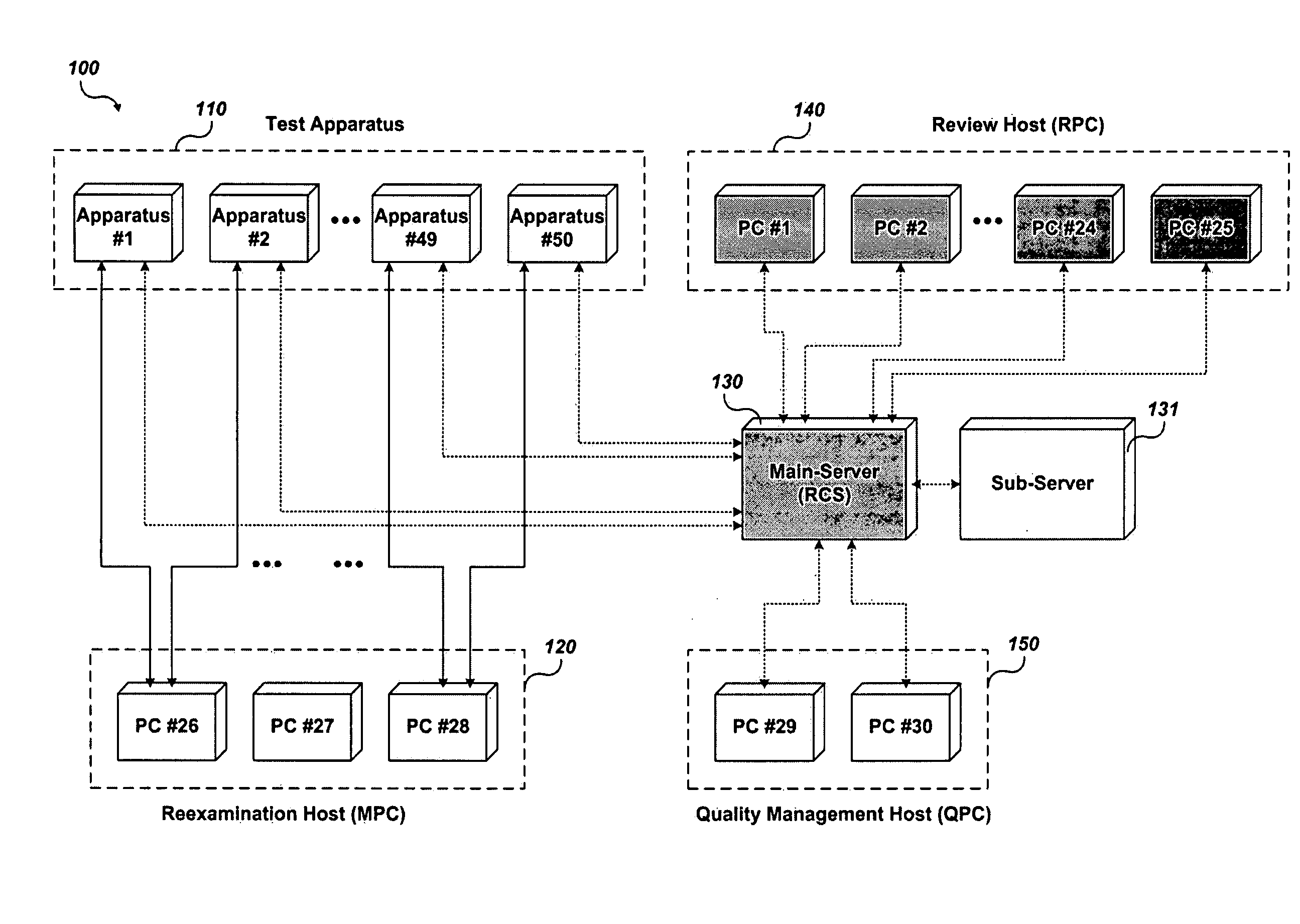
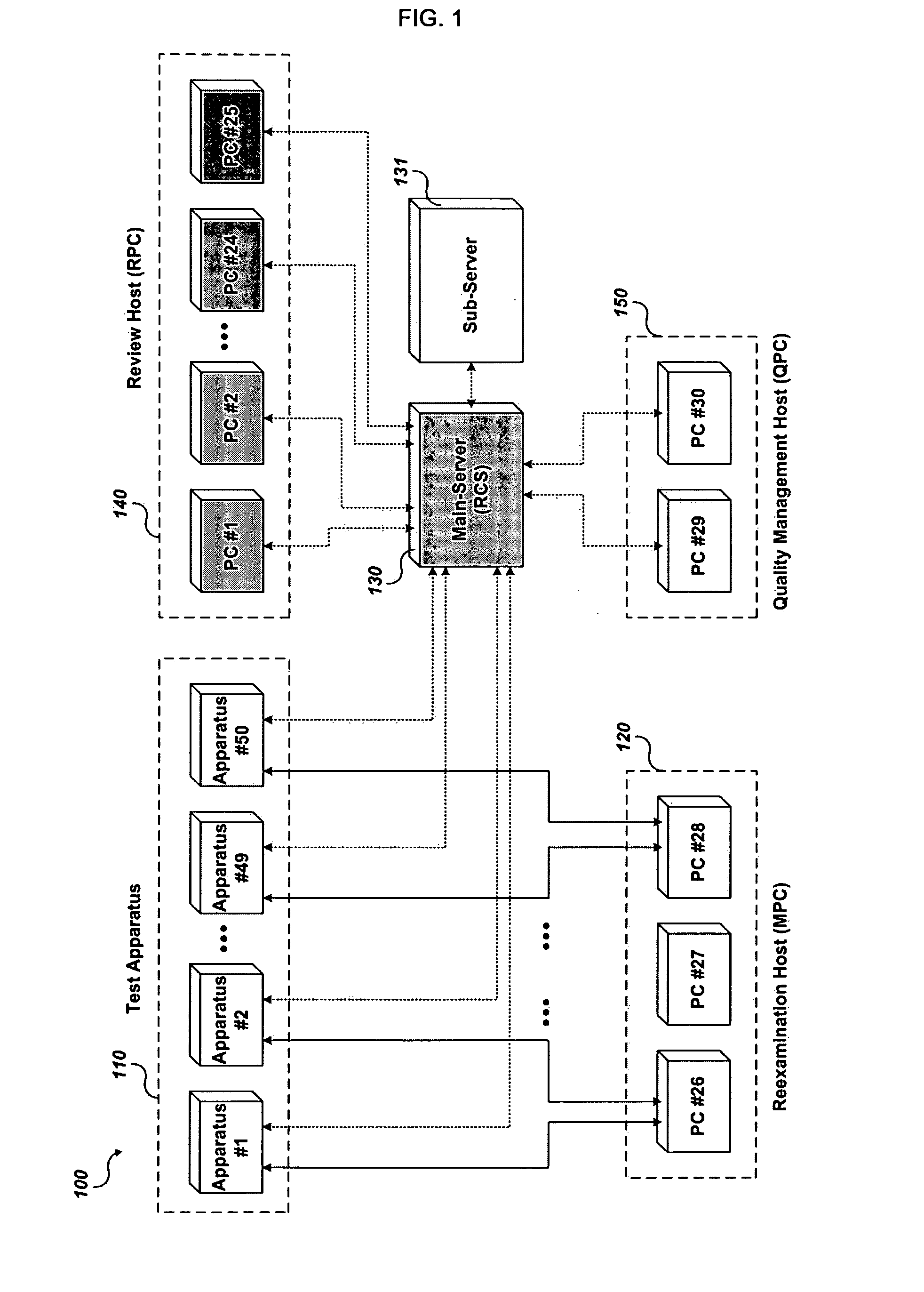
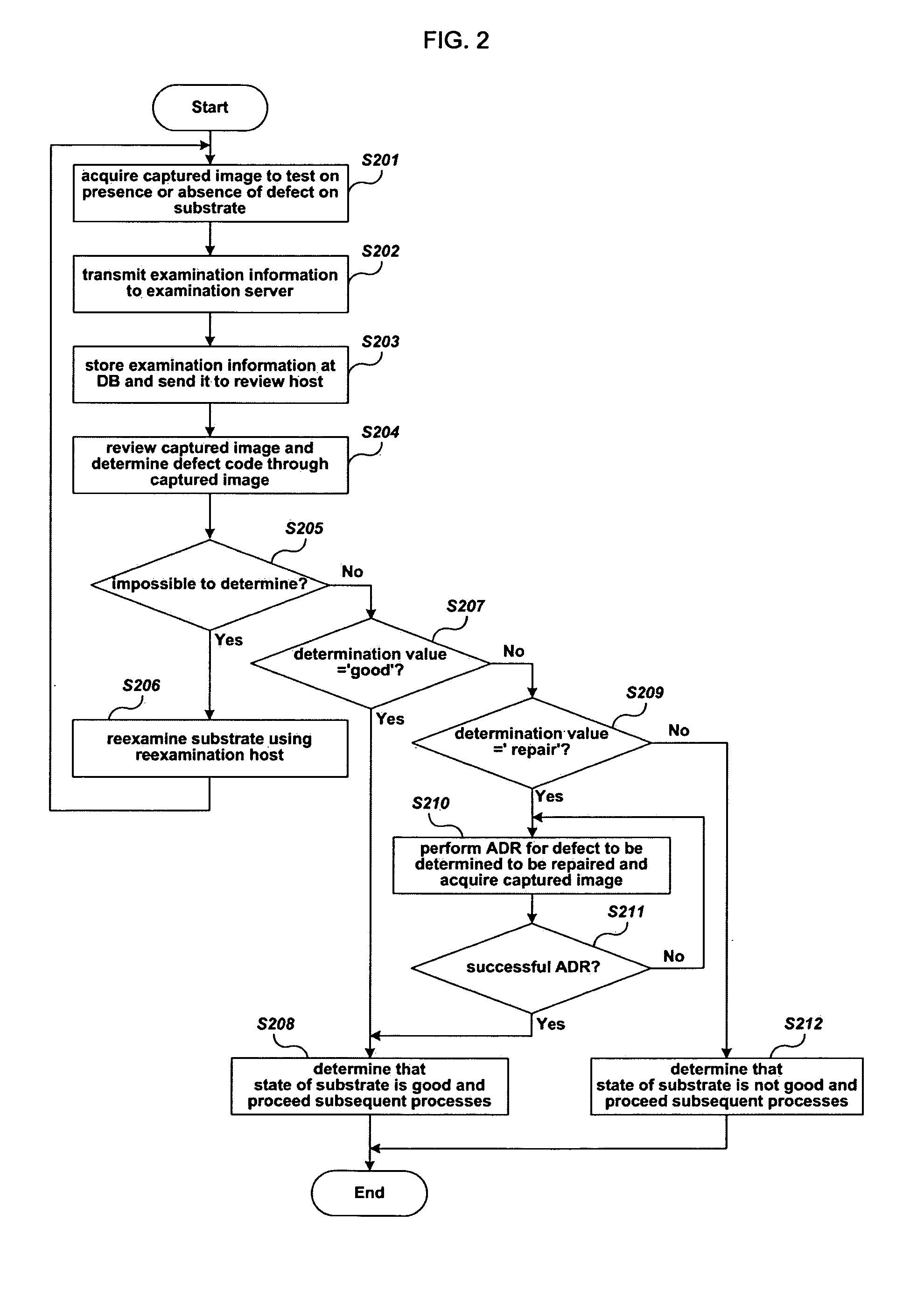
Disclosed are a test system and a test method using a virtual review, capable of driving a test device and reduce the number of operators by allowing an operator to perform review and determination based on a captured image of a defect on a substrate. The test system using a virtual review comprises: a test device that takes an image of a defect on an array substrate or color filter substrate to acquire a captured image and provides examination information related to the defect. A main server constructs the examination information from the test device as a database and transmits them to a review host. The review host determines whether a defect exosts on the array substrate or color filter substrate based on the examination information from the main server to yield a determination result and resends the determination result to the main server.
Owner:LG DISPLAY CO LTD
Parking assist system
ActiveUS20160078764A1Difficult to determineIndication of parksing free spacesAnti-collision systemsElectronic control unitParking space
A parking assist system includes an electronic control unit. The electronic control unit is configured to detect an obstacle, detect a boundary of a parking space, determine a target position to which a vehicle moves, and, when the vehicle is allowed to be located in a third area in which a first area and a second area overlap with each other, be allowed to determine the target position in the third area. The first area is an area across a limit line from the obstacle. The limit line is set substantially along an outer periphery of the obstacle at a position spaced a predetermined distance from the obstacle outward of the obstacle. The second area is an area out of the boundary.
Owner:AISIN SEIKI KK +1
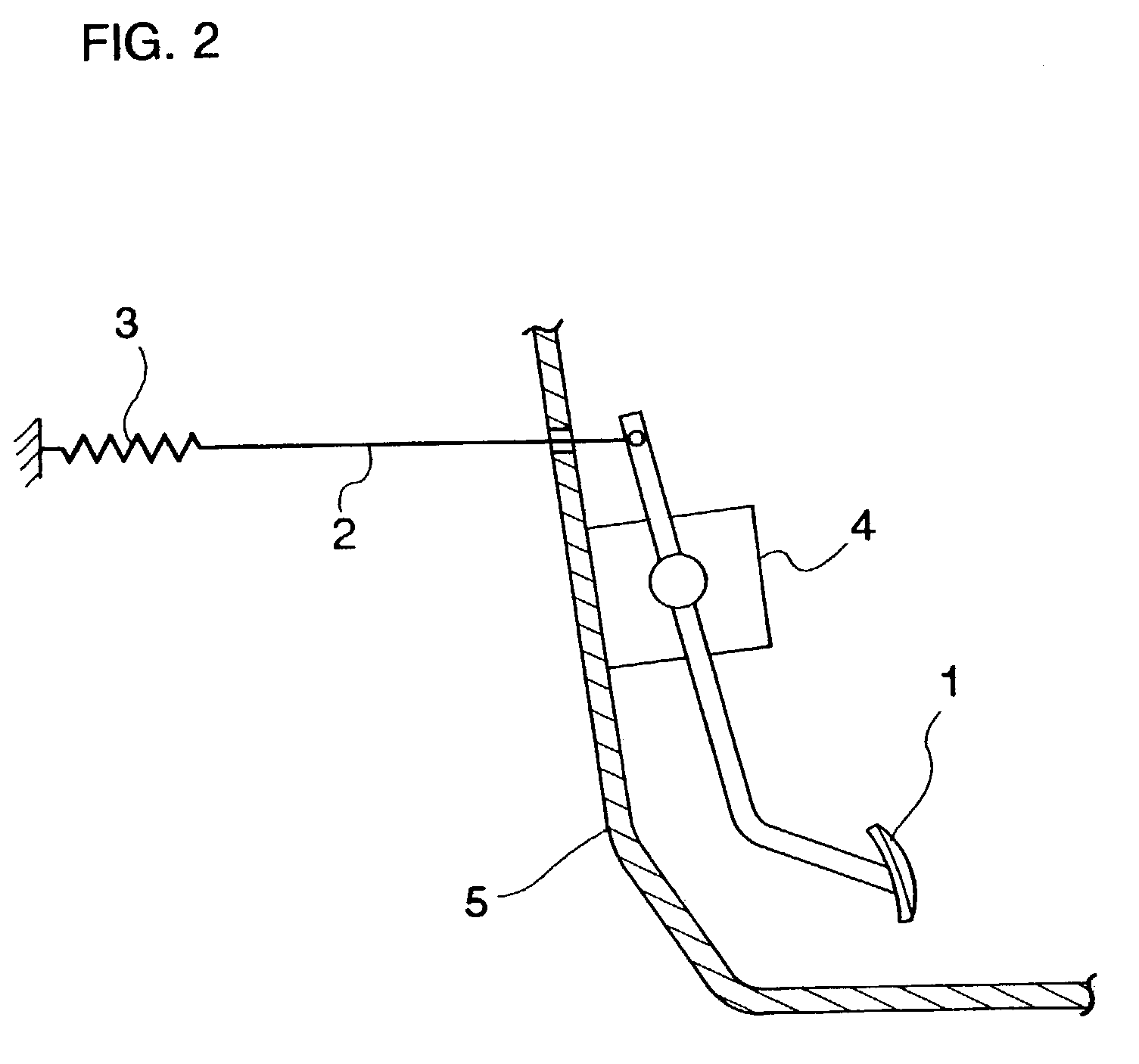
Driving assist system for vehicle
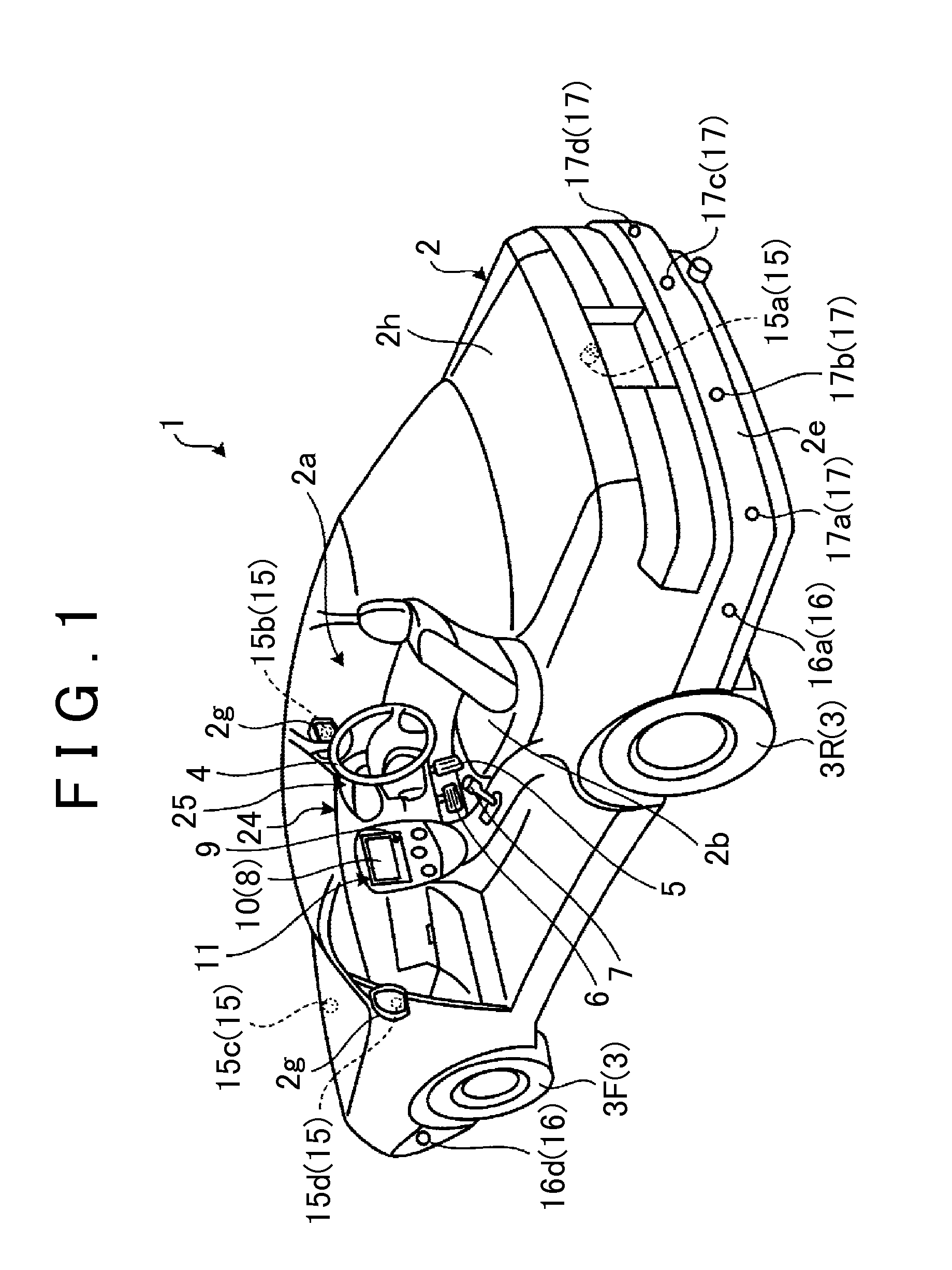
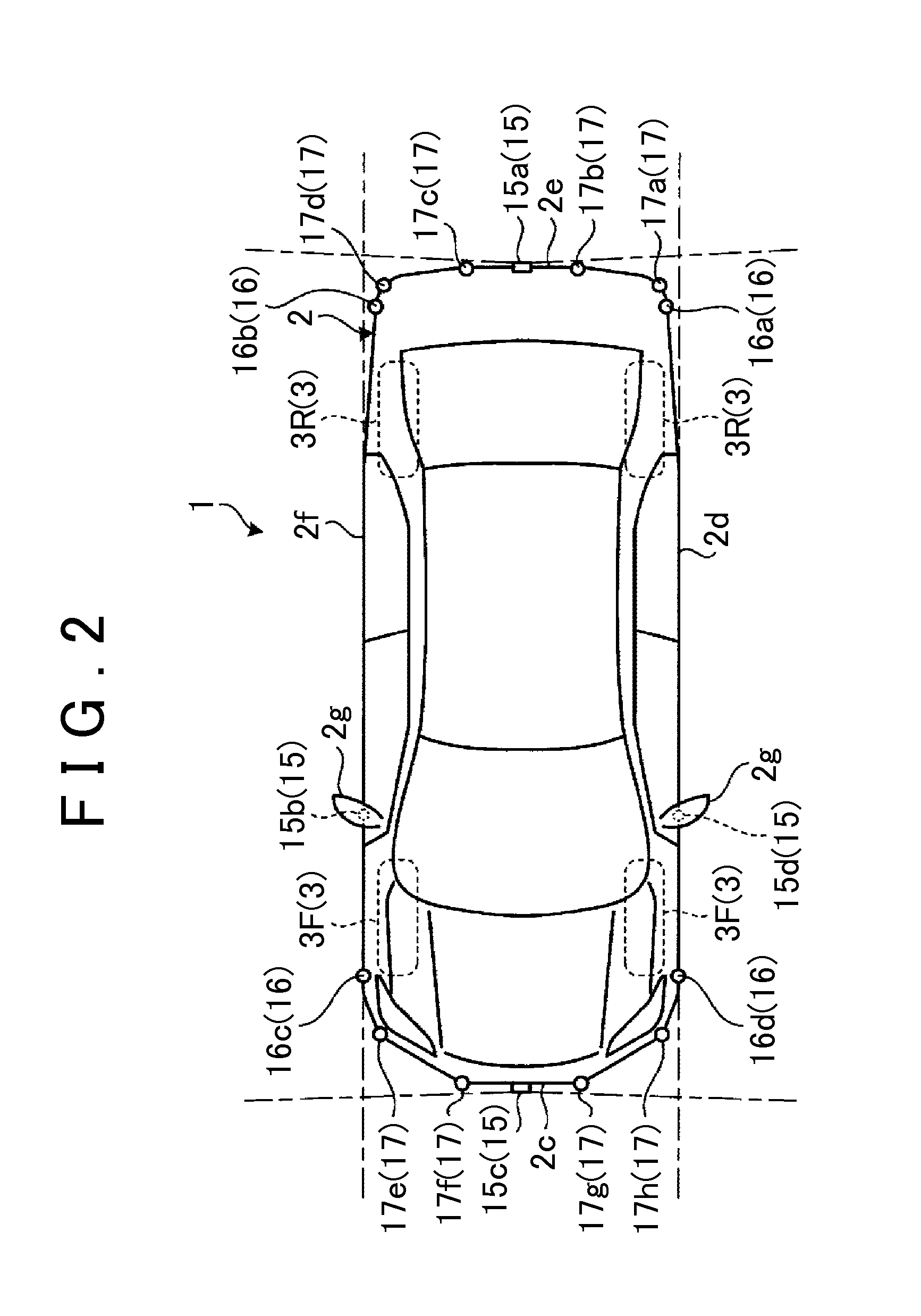
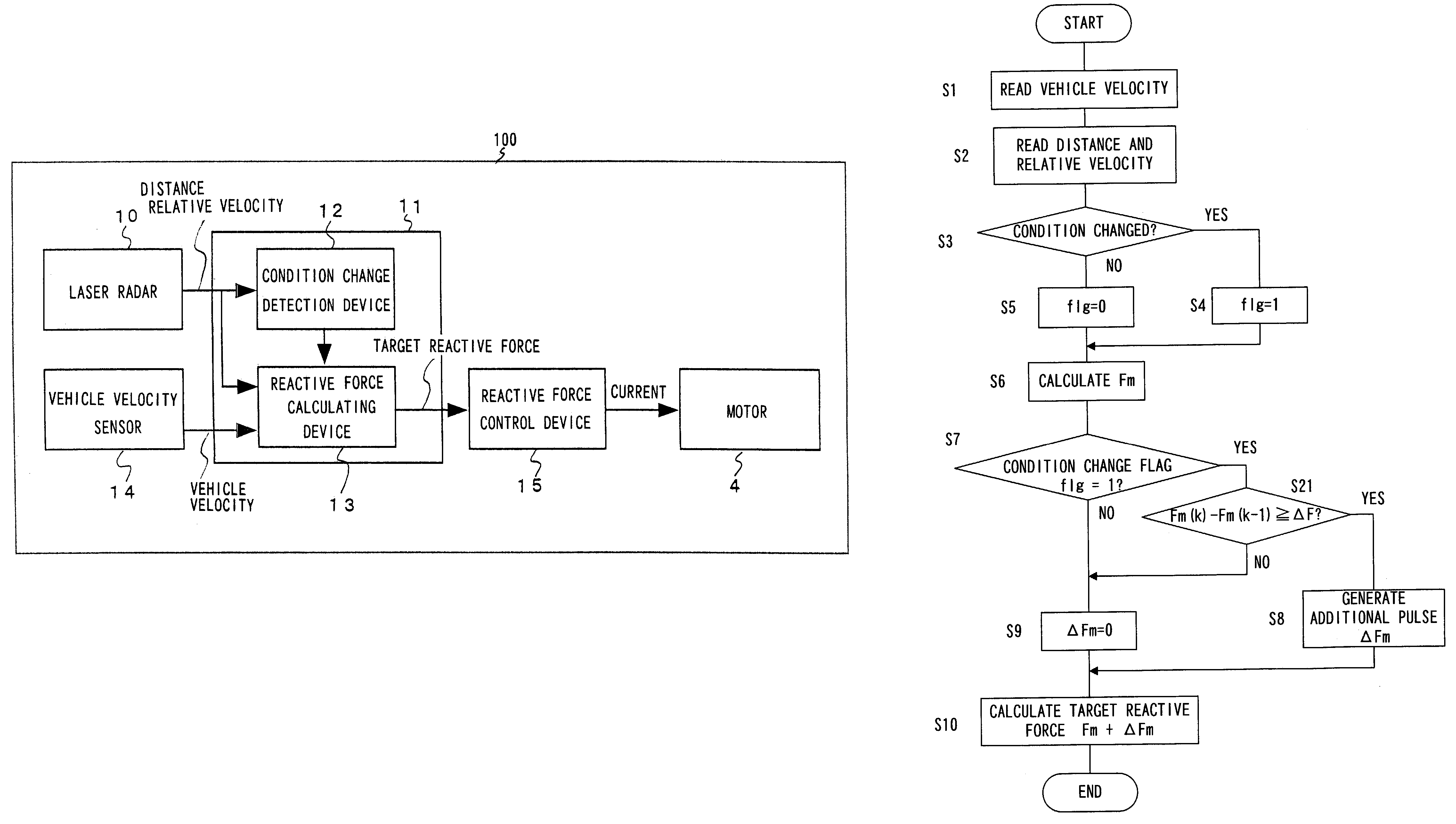
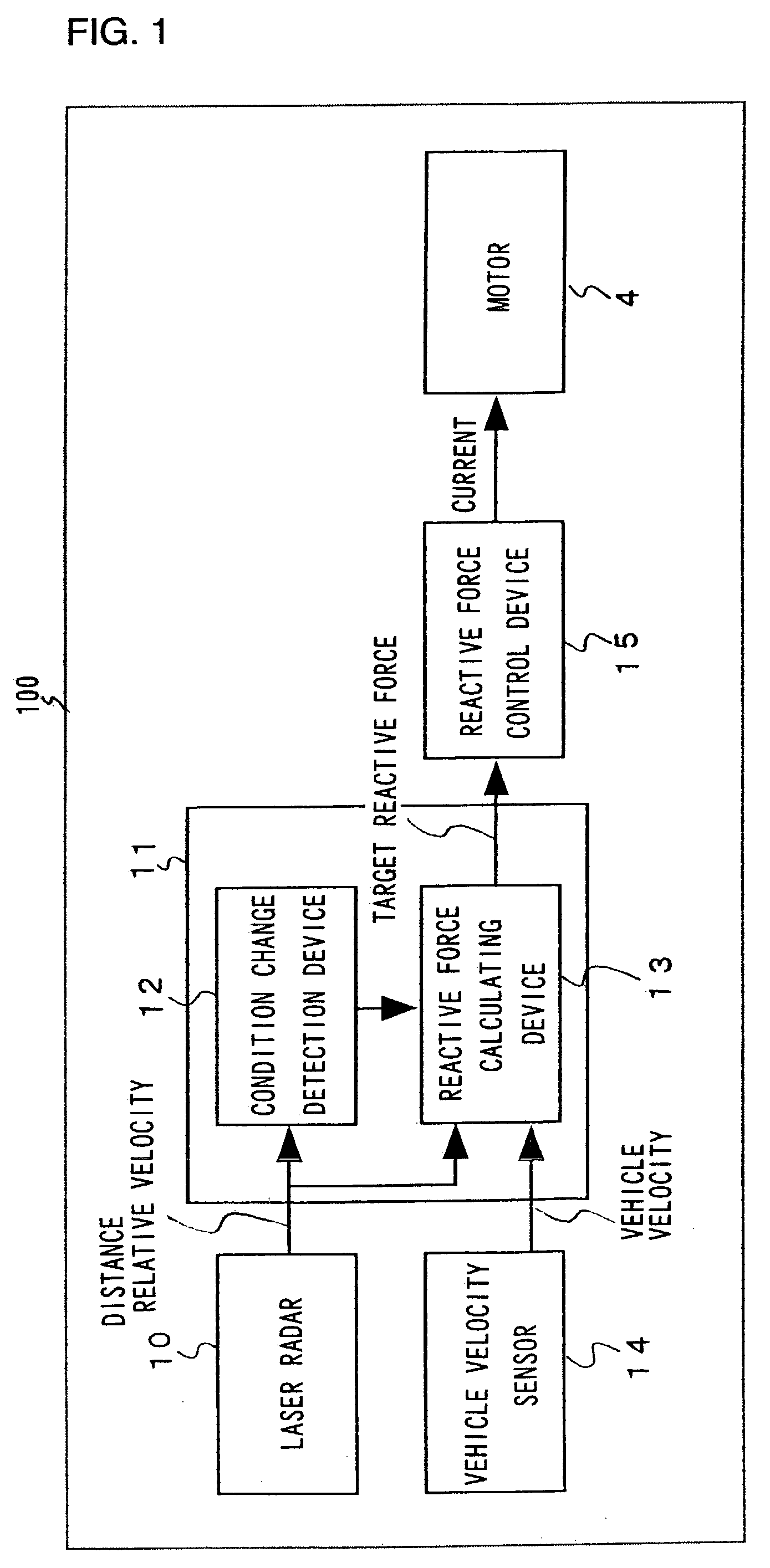
InactiveUS7124010B2Difficult to determineVehicle fittingsDigital data processing detailsEngineeringVehicle driving
A vehicle driving assist system comprises a condition recognition device that detects a vehicle condition and a traveling environment around a subject vehicle; a reactive force application device that applies a reactive force, in conformance to the vehicle condition and the travelling environment around the subject vehicle, to an operation device; a condition change detection device that detects a condition change occurring around the subject vehicle; and a reactive force variation device that adjusts the reactive force applied by the reactive force application device in a period of time, when the condition change detection device detects that a condition around the subject vehicle has changed discontinuously.
Owner:NISSAN MOTOR CO LTD
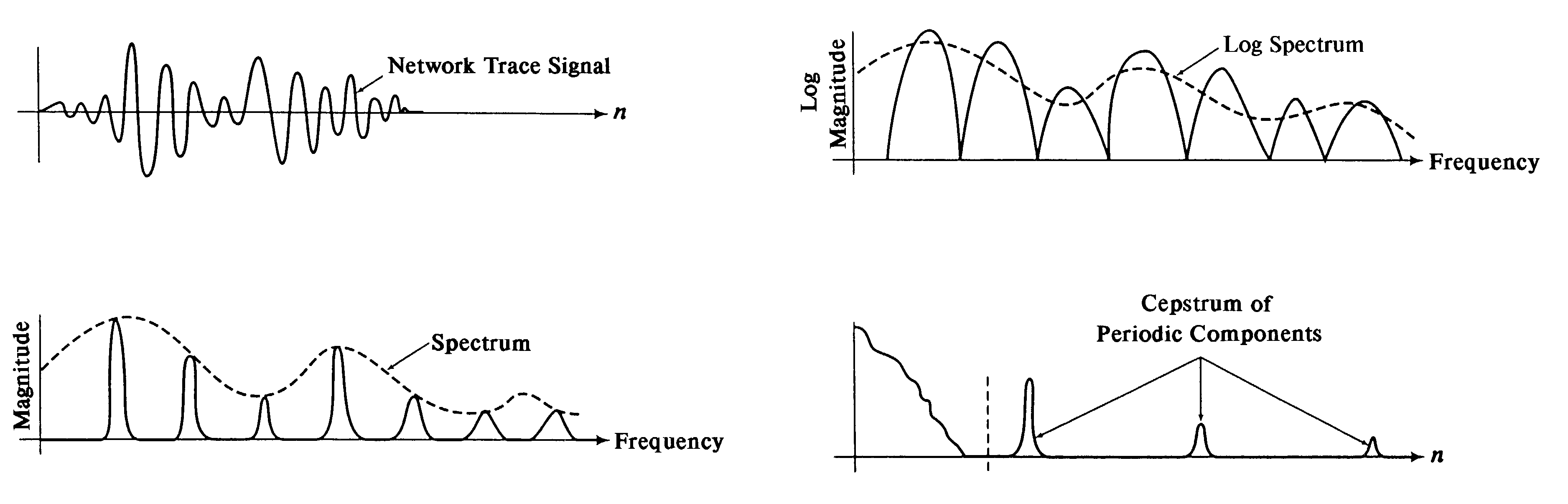
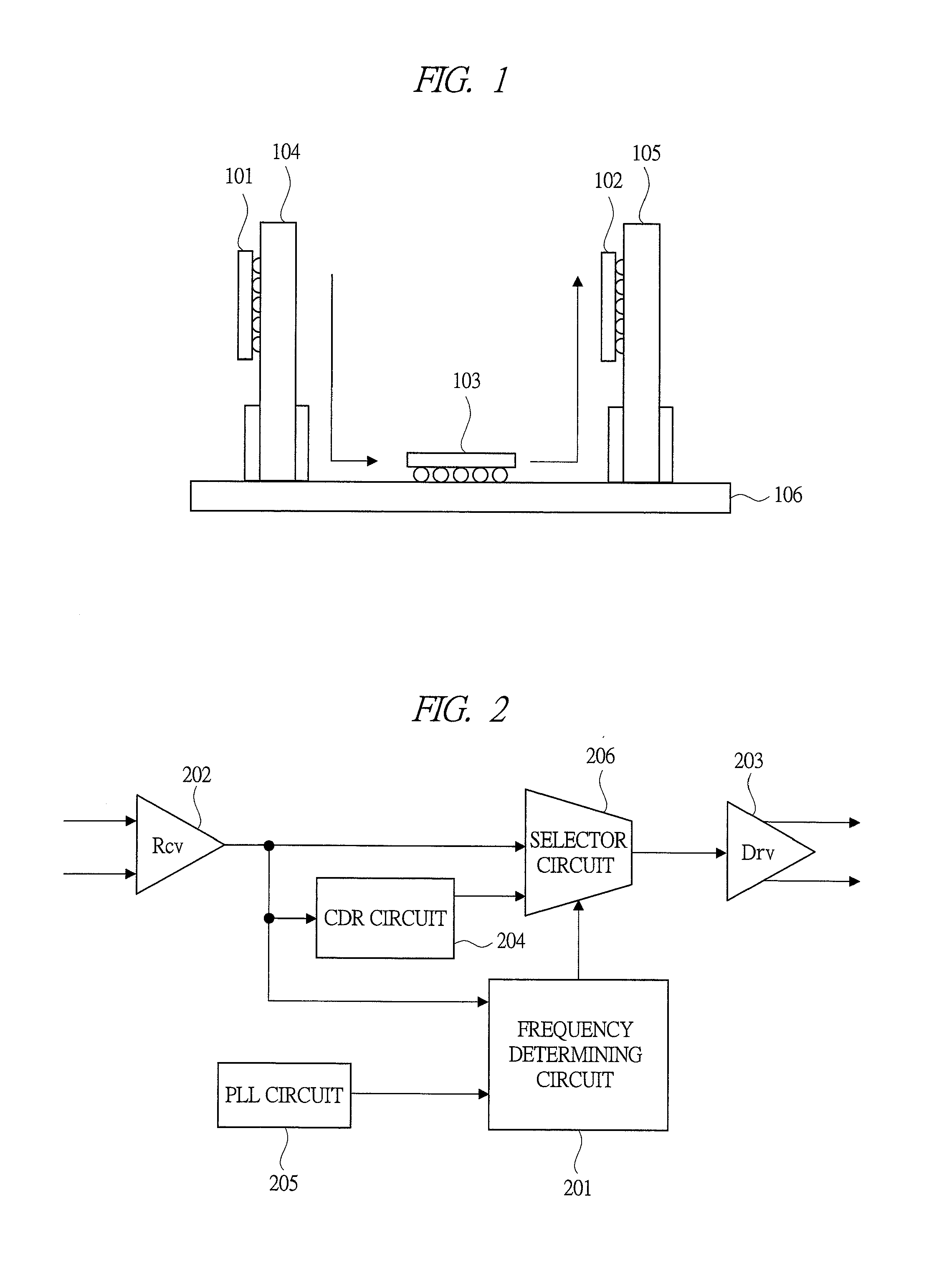
Method and system for passively analyzing communication data based on frequency analysis of encrypted data traffic, and method and system for deterring passive analysis of communication data
ActiveUS7170860B2Minimize presenceDeterring passive attacks on transmissionsError preventionTransmission systemsTraffic capacityNetwork link
A system for passively analyzing an aggregation of communication signals simultaneously passing through a network link performs spectral analysis on a trace of communication traffic through the network link. The spectral analysis identifies period components of the trace corresponding to different communication signals. A system for deterring the passive analysis of signals aggregates communication traffic through a network link, such that a plurality of signals simultaneously pass through the network link. The plurality of signals is regulated such that the data packets corresponding to the plurality of signals leave the network link at a common rate. A memory temporarily stores the data packets as they enter the network link, and a timer maintains a fixed time interval for releasing the data packets from the memory.
Owner:RAYTHEON BBN TECH CORP
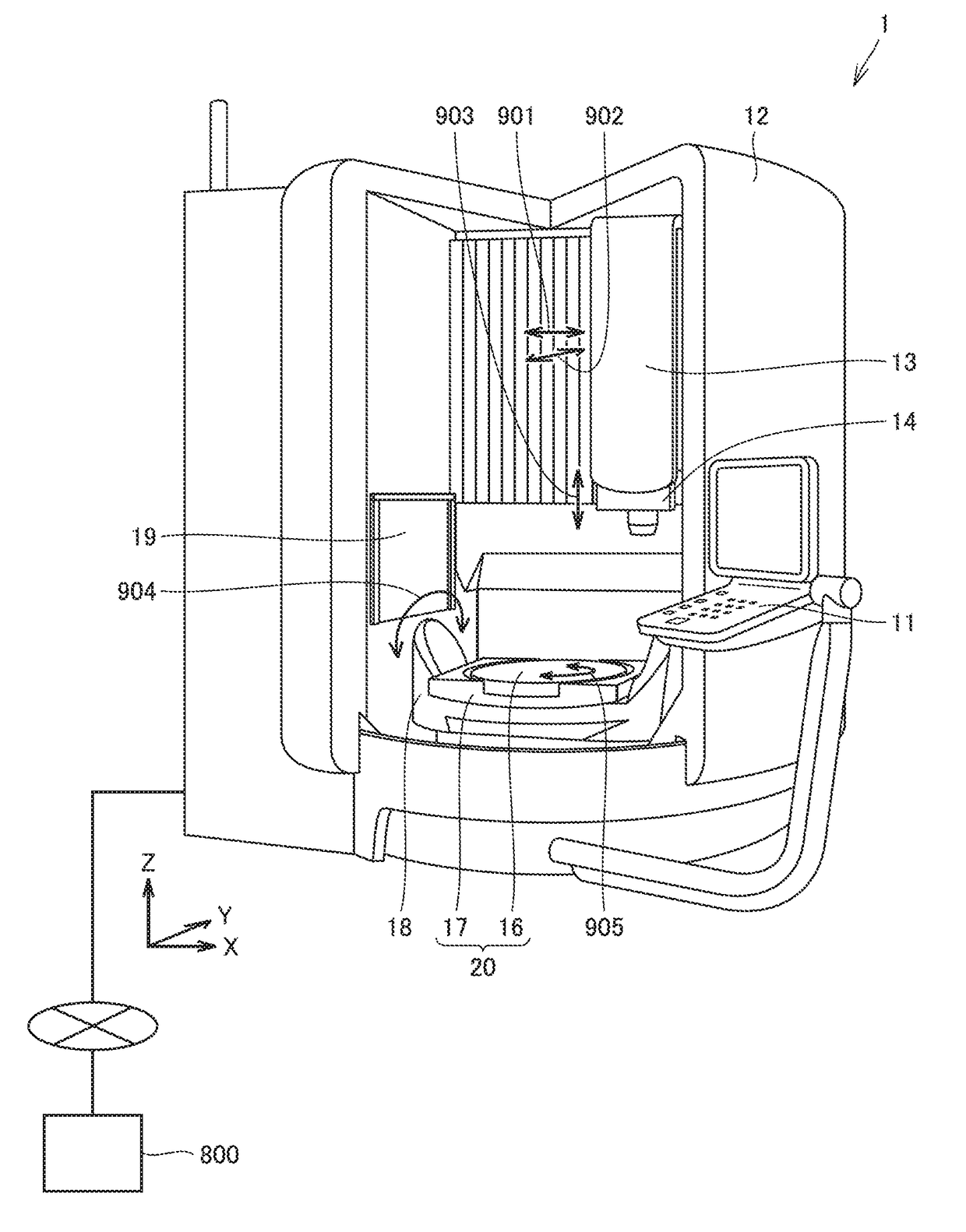
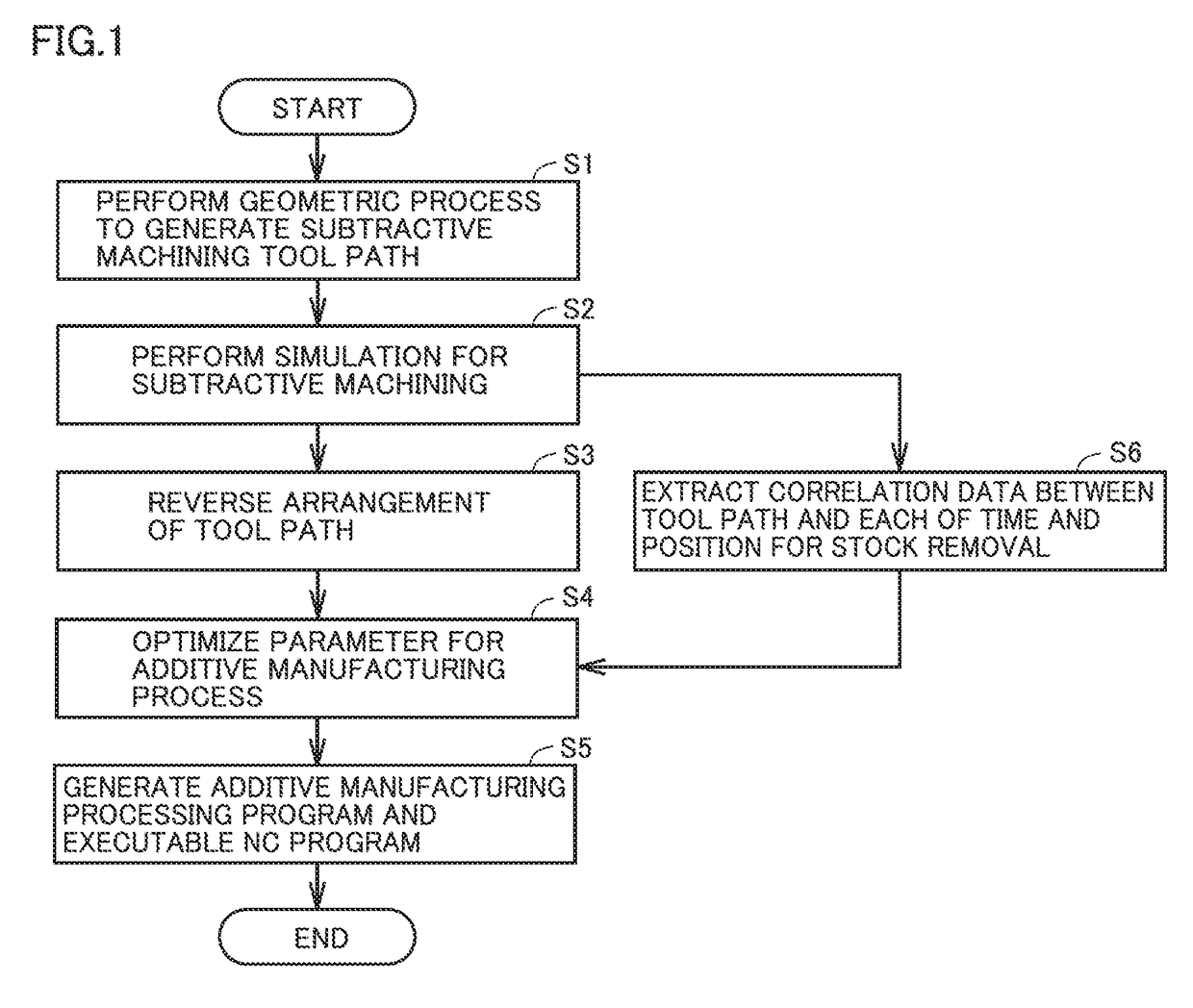
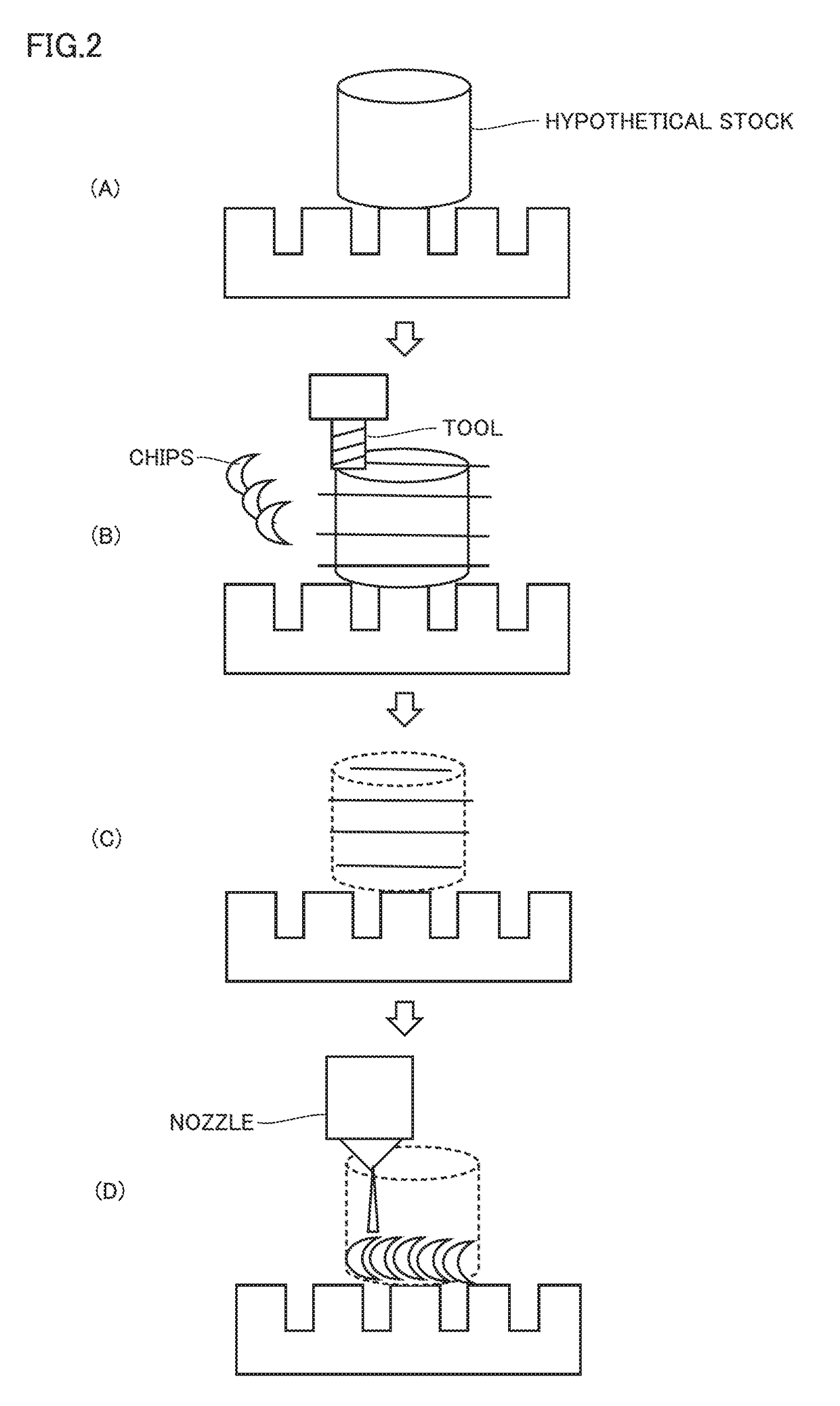
Method for generating control data, data processing device, machine tool, and program
ActiveUS20170297323A1Difficult to determineProgramme controlAdditive manufacturing apparatusManufacturing technologyControl data
A method for generating control data is a method for generating control data for manufacturing a product having a designated shape using an additive manufacturing technology. The control data includes a path of a nozzle for supplying a material. The method for generating the control data includes: determining a cutting path for cutting the designated shape by a tool; and determining the path of the nozzle by reproducing the cutting path temporally reversely.
Owner:MACHINE TOOL TECH RES FOUND +1
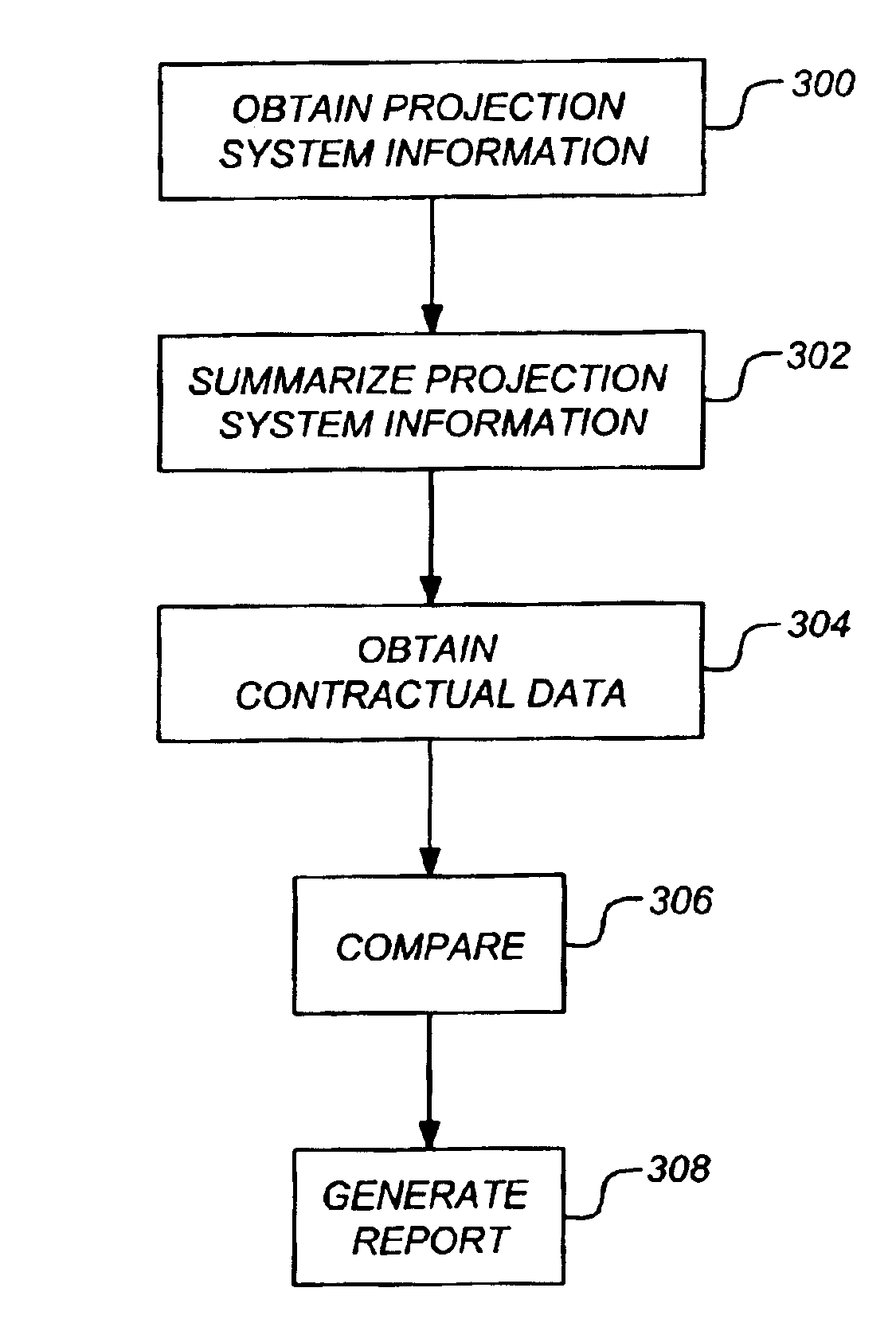
Method and apparatus for comparing actual use data with contract data
InactiveUS6954718B2Difficult to determineNuclear monitoringDigital computer detailsProjection systemActual use
Owner:THE BOEING CO
System and method for securing wireless communications
InactiveUS8744082B2Increase probabilityDifficult to determineKey distribution for secure communicationPublic key for secure communicationSecure communicationComputer science
Owner:FUTUREWEI TECH INC
Integrated circuits protected against reverse engineering and method for fabricating the same using vias without metal terminations
InactiveUS20020096777A1Difficult to determineTime-consume and expensiveSemiconductor/solid-state device detailsSolid-state devicesIntegrated circuitEngineering
A device adapted to protect integrated circuits from reverse engineering comprising a part looking like a via connecting two metal layers, but in fact attached only to one metal layer and spaced from the other. Having such "trick" via would force a reverse engineer to think there is a connection where there is none. A method for fabricating such device.
Owner:HRL LAB
Scanner and Scanning Method
A scanner is configured to scan an original sheet to generate image data, an image on the original sheet being subject to scanning, obtaining a first side of the original sheet area within one of a leading end side part and a trailing end side part of the image, the first end side part being a part where two edges having a common end do not exist, an outer side edge in the first end side part being obtained as the first side, obtaining a second side of the original sheet area within a second side part, the second end side part being a part where a pair of edges having a common end exists, one of the pair of edges closer to the first end side part being obtained as the second side, and determining the original sheet area based on the first and the second sides.
Owner:BROTHER KOGYO KK
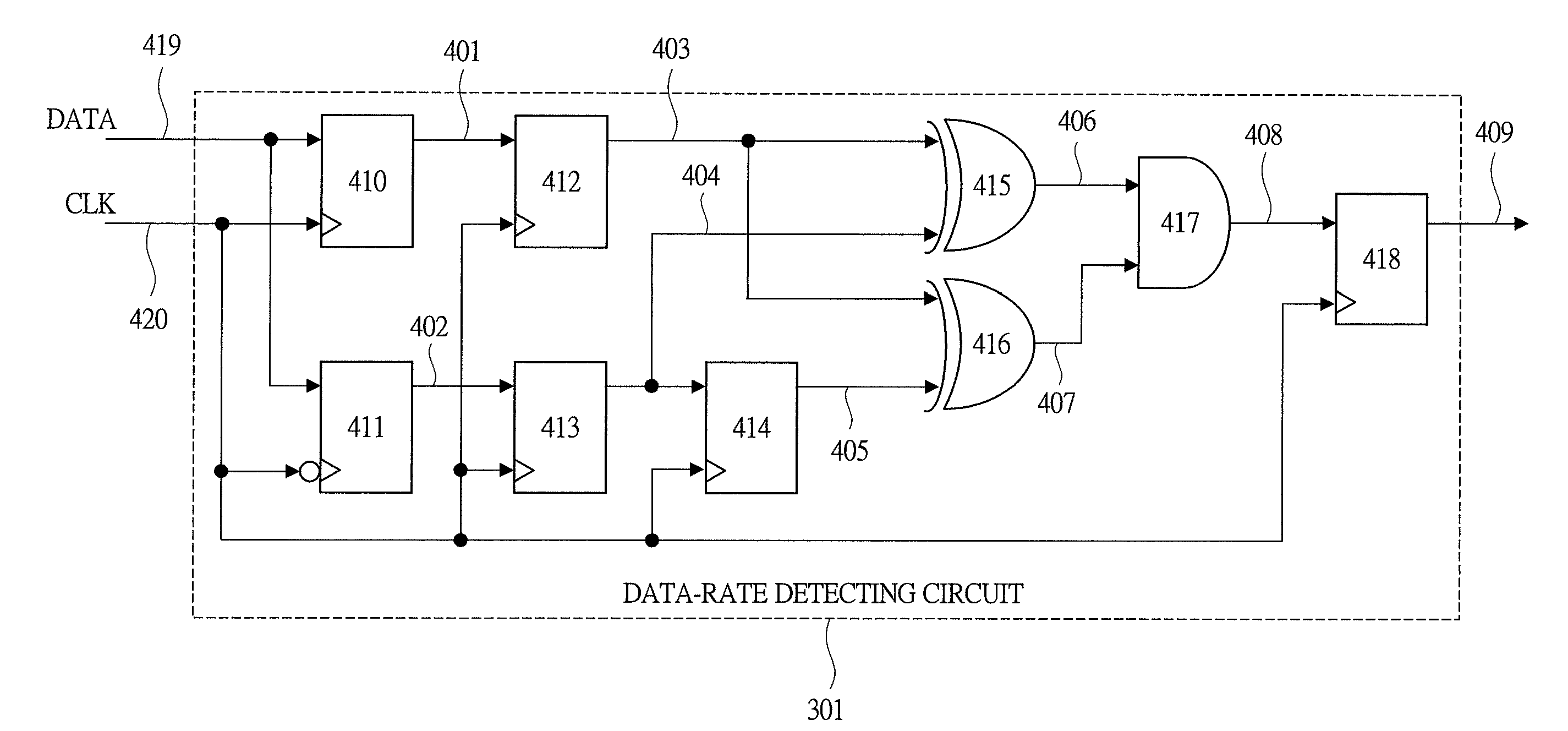
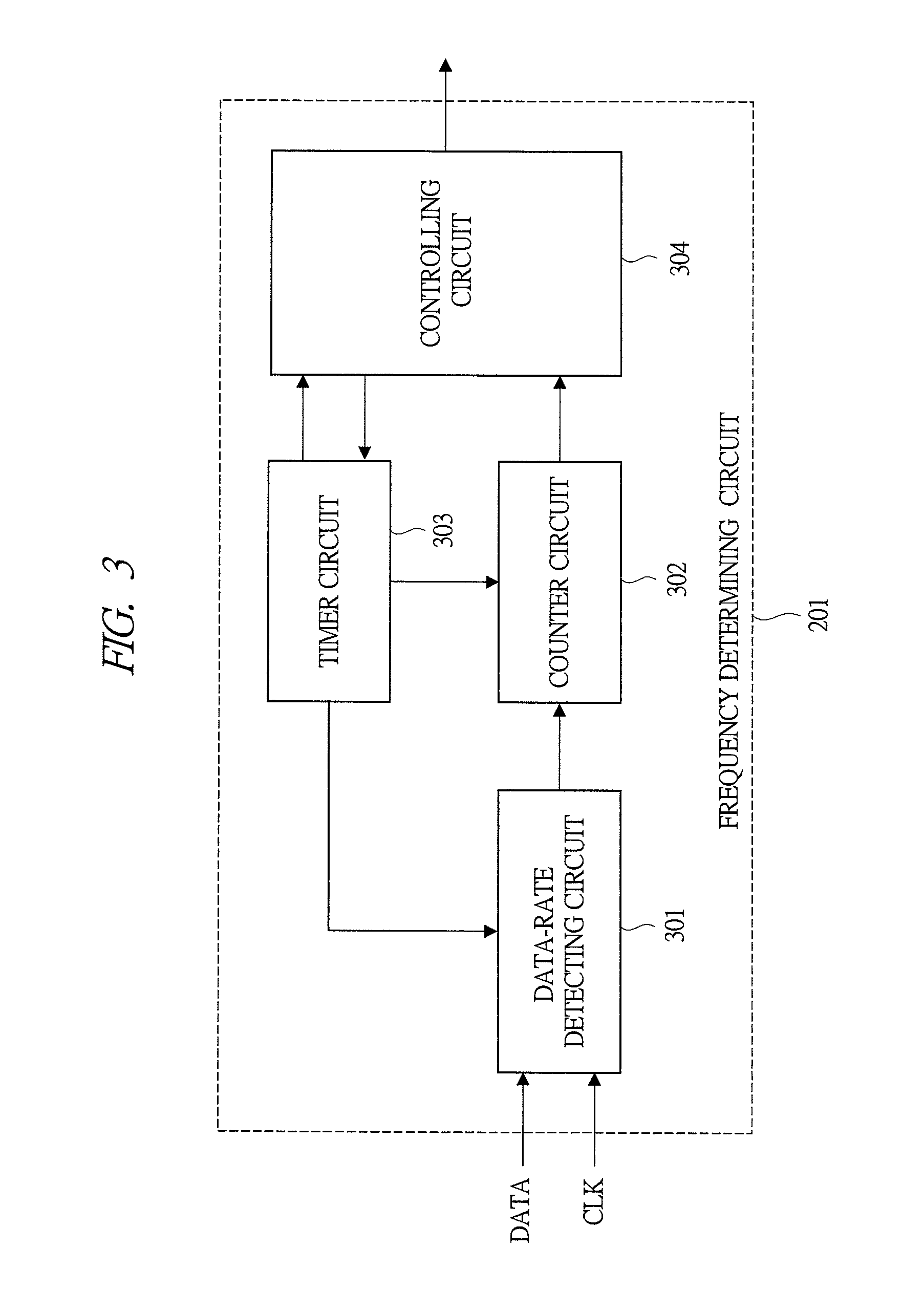
Frequency determining circuit and semiconductor device
InactiveUS20120191393A1Difficult to determineFrequency to pulse train conversionSpecial data processing applicationsPhysicsLong pulse
Owner:HITACHI LTD
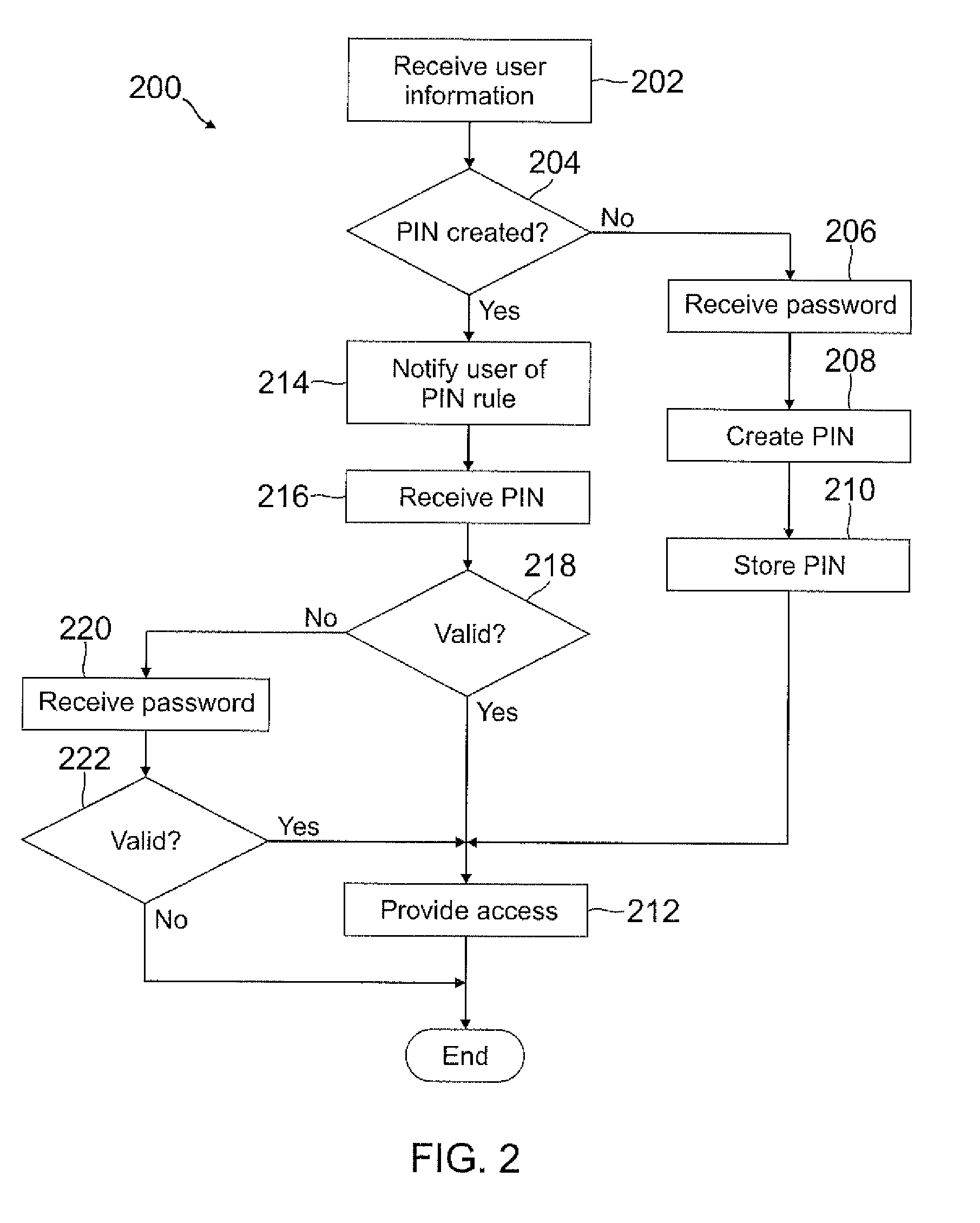
Automatic PIN creation using password
ActiveUS8756652B2Easy to rememberMore experienceDigital data processing detailsUnauthorized memory use protectionUser devicePassword
A PIN is automatically generated based on at least one rule when the user enters a password through a user device. In one example, the PIN is a truncated version of the password where each character in the truncated version is mapped onto a number. The mapping can be a truncation at the beginning or end of the password, or the mapping can be with any pattern or sequence of characters in the password. This PIN generation may be transparent to the user, such that the user may not even know the PIN was generated when the password was entered. When the user attempts to access restricted content, the user may enter the PIN instead of the password, where the user may be notified of the rule used to generate the PIN so that the user will know the PIN by knowing the password.
Owner:PAYPAL INC
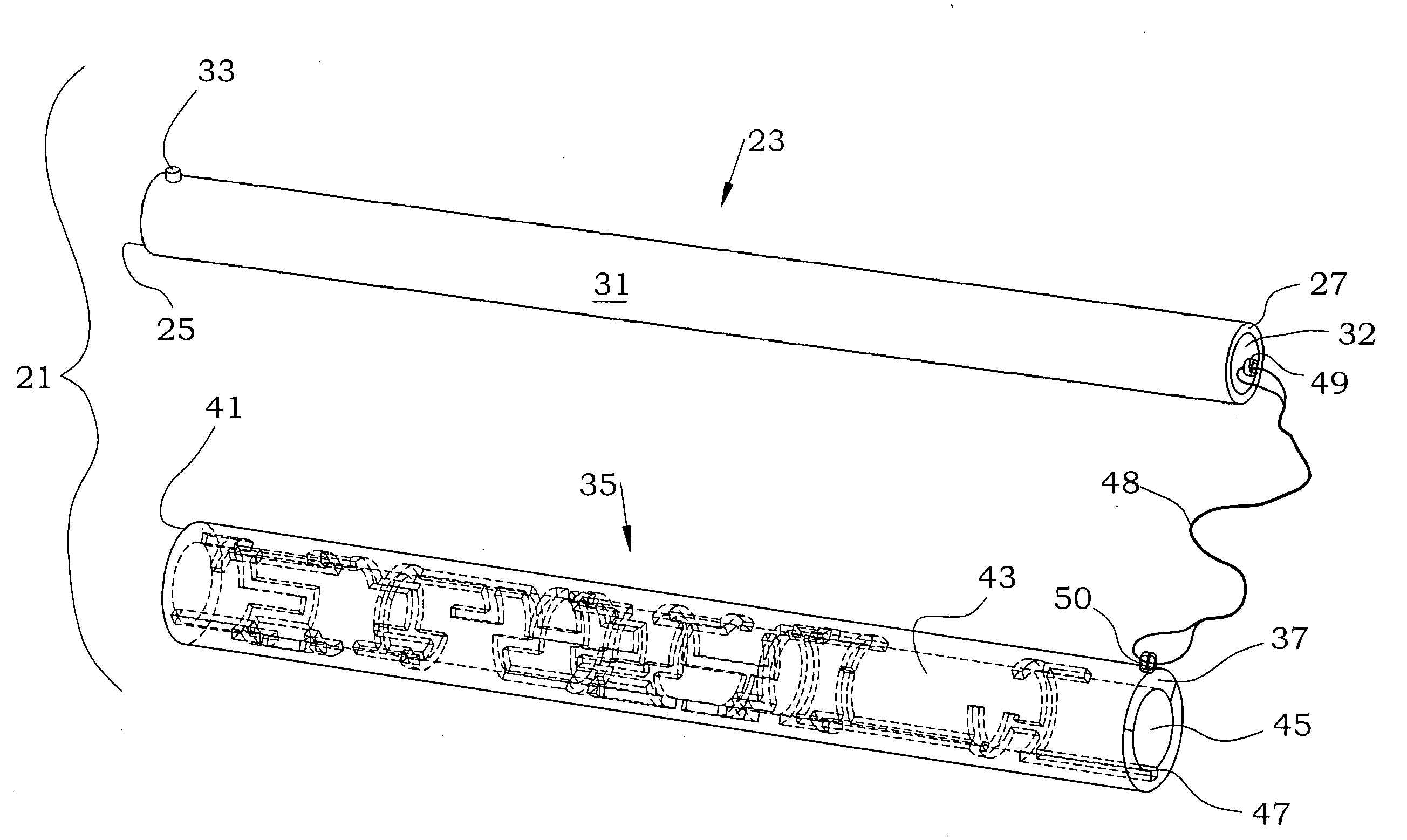
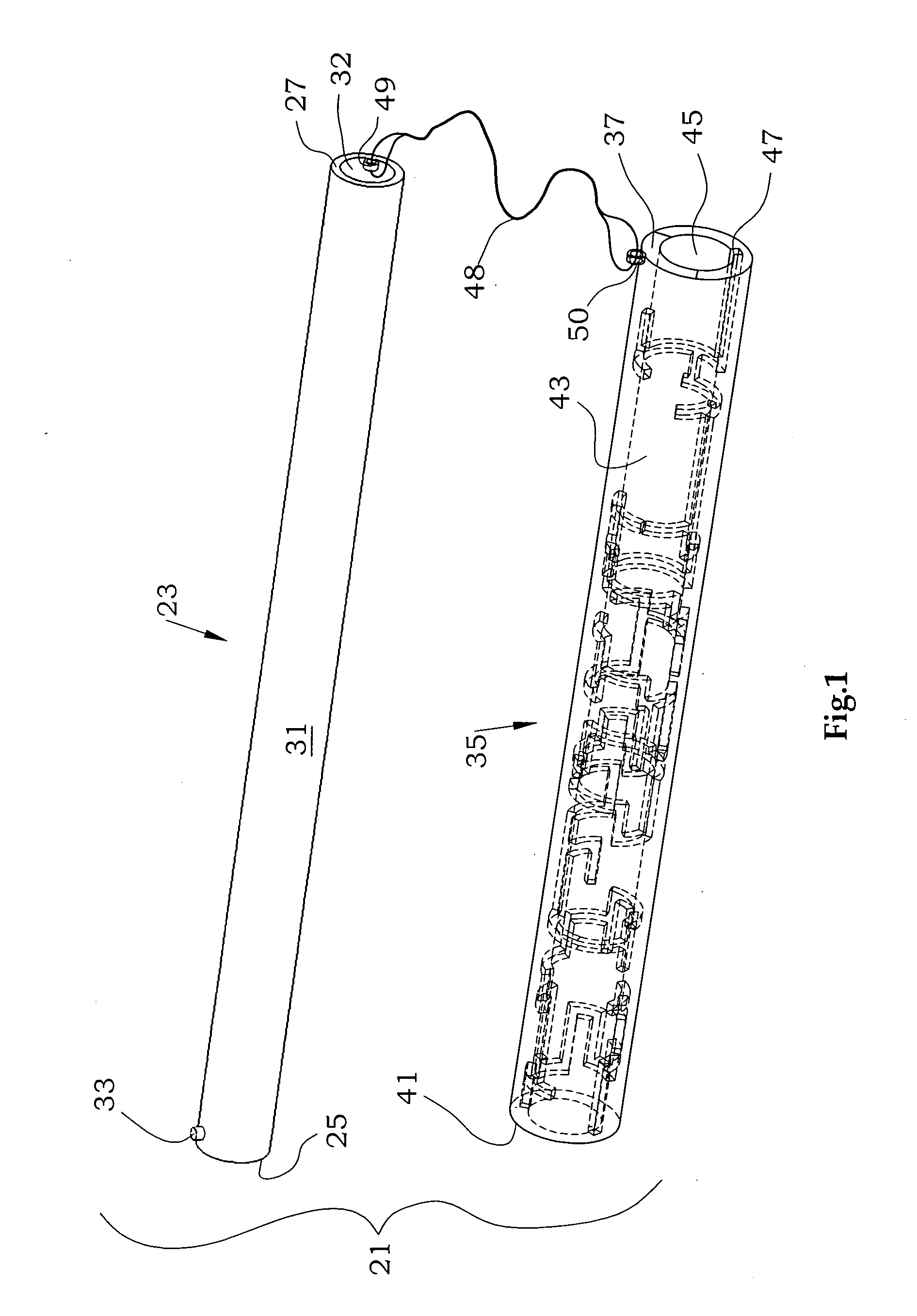
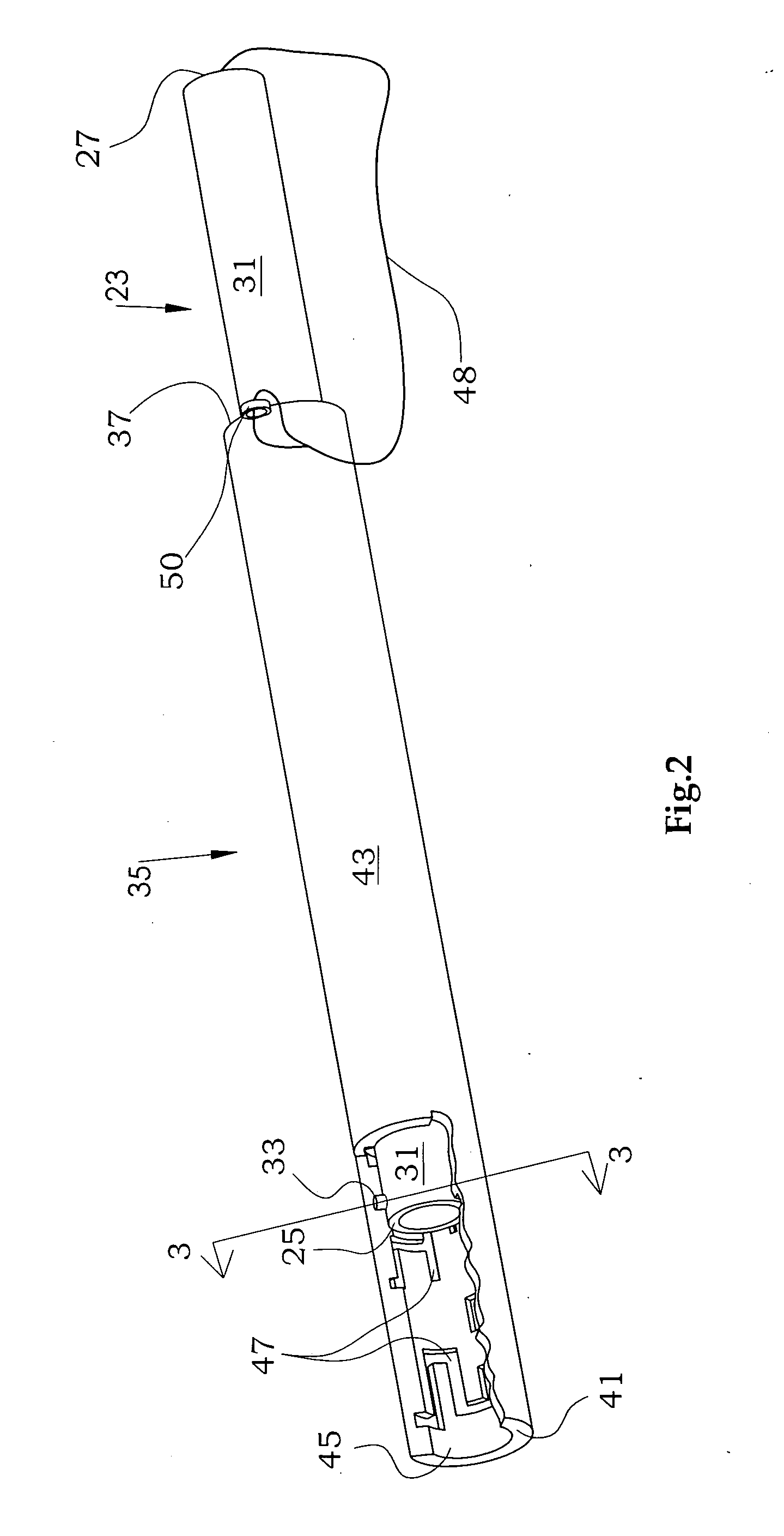
Mechanical maze puzzle
InactiveUS20100109240A1Sufficient varietyDifficult to determineIndoor gamesObsolescencePhysical ability
The mechanical puzzle of the present invention includes concentrically arrangeable cylinders in which a pin projects from a first cylinder to engage with a groove which forms a maze pattern on a concentrically adjacent second cylinder. The puzzle may be solved by rotating and advancing or retracting the cylinders with respect to one another to move the pin from a starting point through a continuous passage and to an ending point. The puzzle may have multiple cylinders with multiple pin / groove pairs, may have different pin / maze arrangements, may be constructed of plastic, wood, or other material, may include secret compartments, may vary in diameter and skill level to suit users of differing mental and physical abilities, and may have interchangeable components to minimize obsolescence from user fluency.
Owner:INGMAN SR ROBERT THOMAS MITCHELL
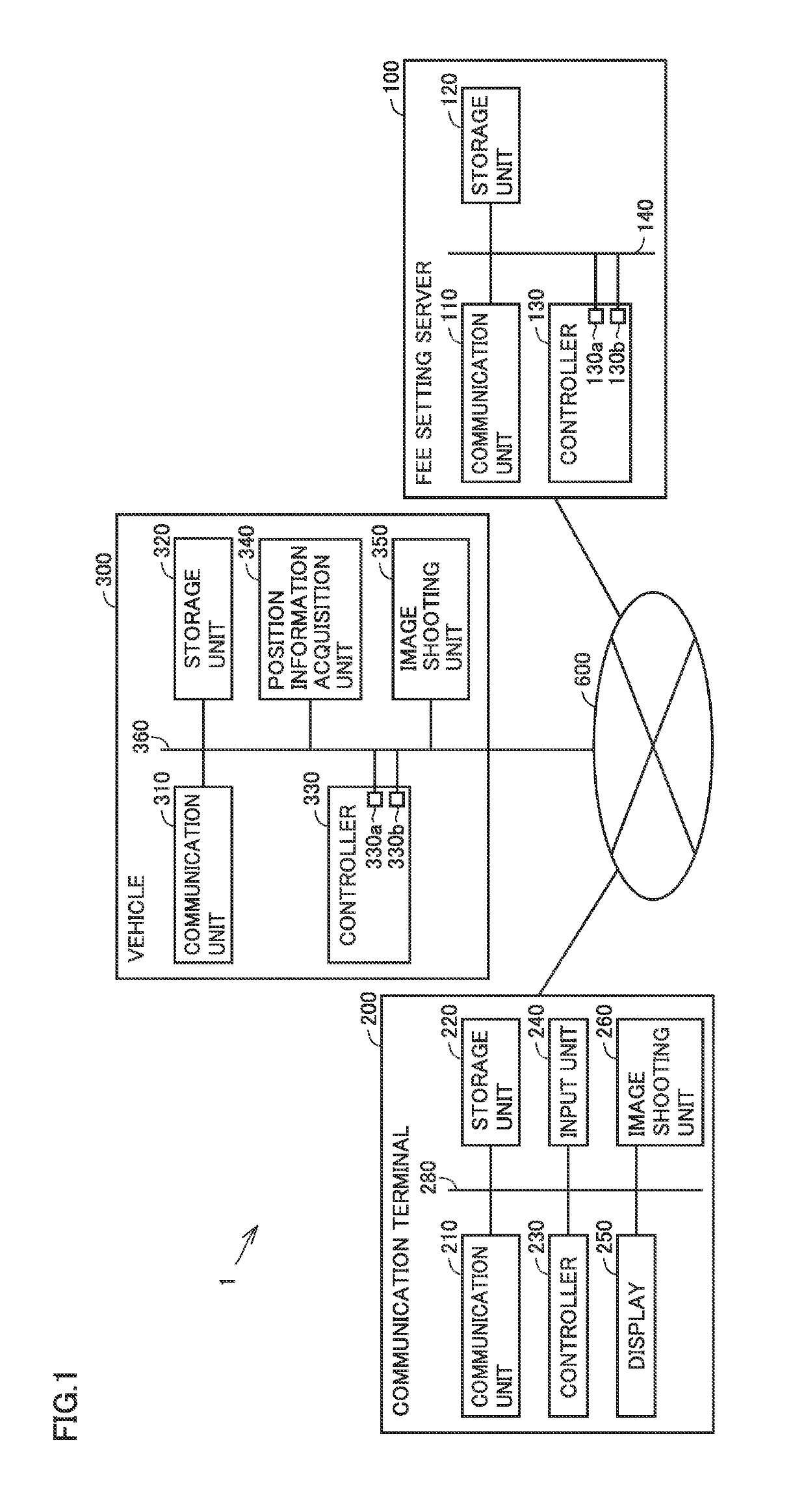
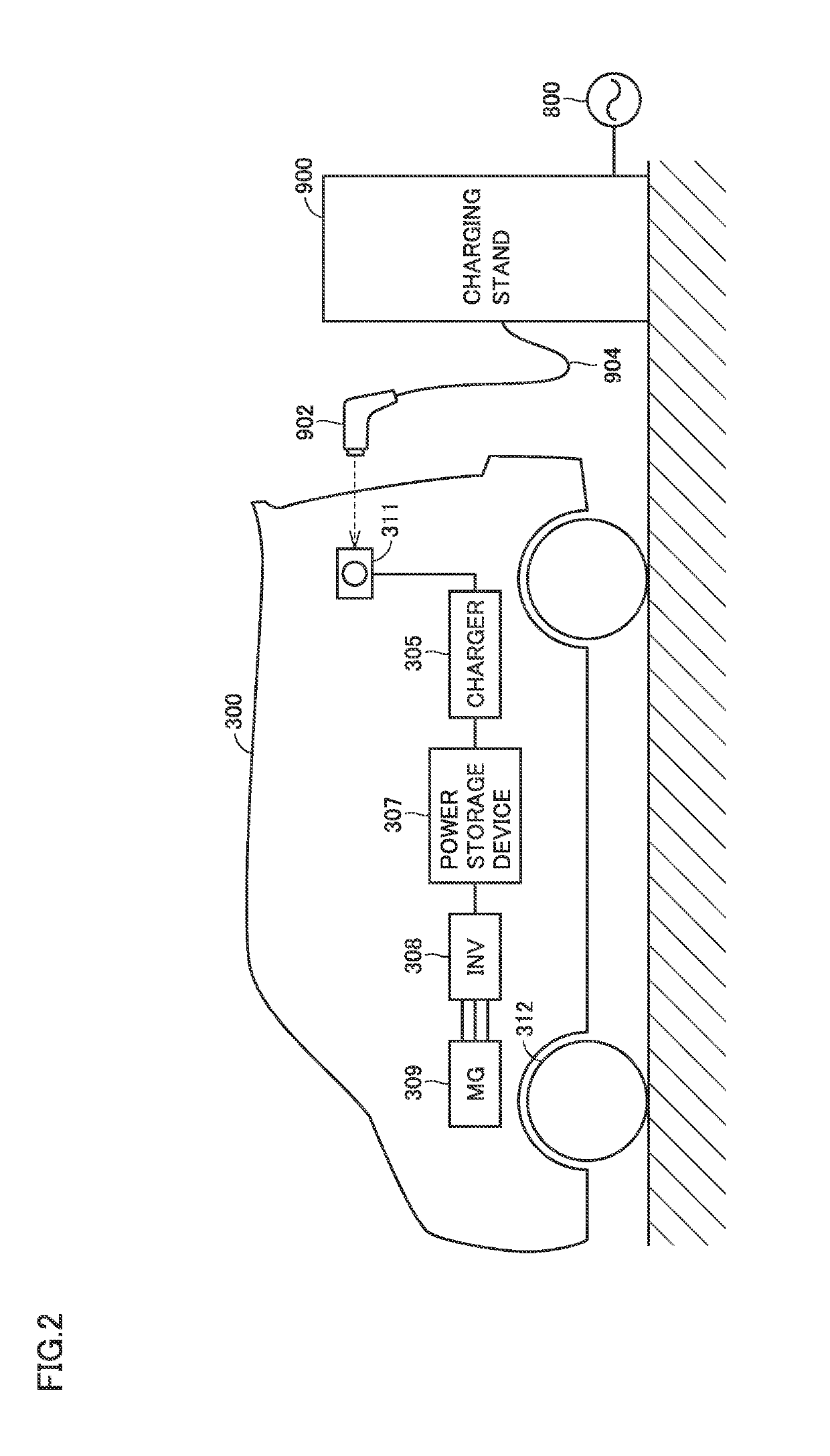
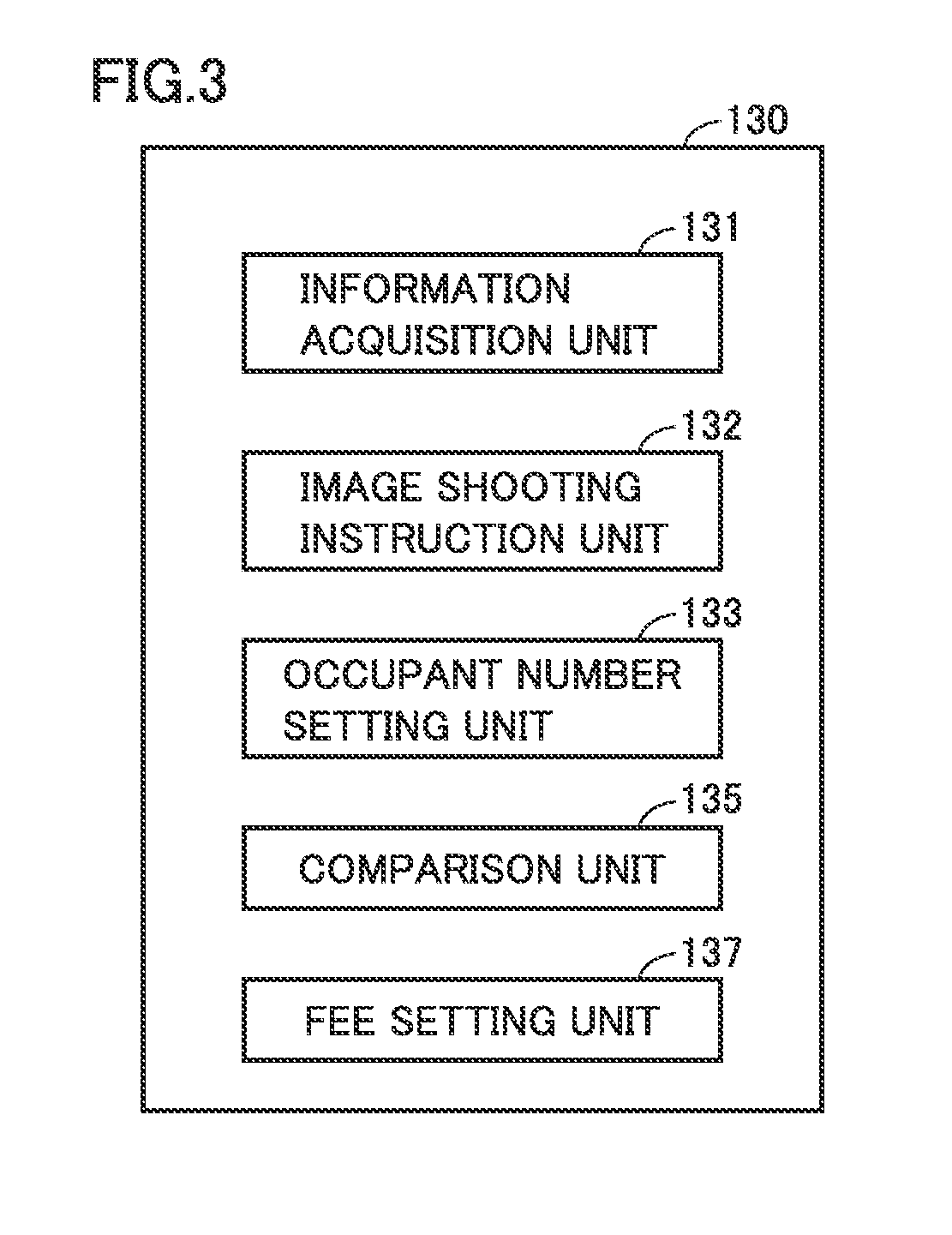
Fee setting server, fee setting method, and fee setting system for car sharing fee
InactiveUS20190164355A1Relieve congestionReduce congestionTicket-issuing apparatusMarketingIn vehicleCar sharing
When a fee setting server acquires end-of-utilization information from a vehicle, the fee setting server requests the vehicle to shoot an image serving as in-vehicle image data (information of the number of occupants). When the fee setting server acquires the in-vehicle image data from the vehicle, the fee setting server specifies the number of riding occupants from the acquired in-vehicle image data, and sets the number of occupants. In a case where the set number of occupants is large, the fee setting server sets a utilization fee for car sharing to be lower than that in a case where the number of occupants is small.
Owner:TOYOTA JIDOSHA KK
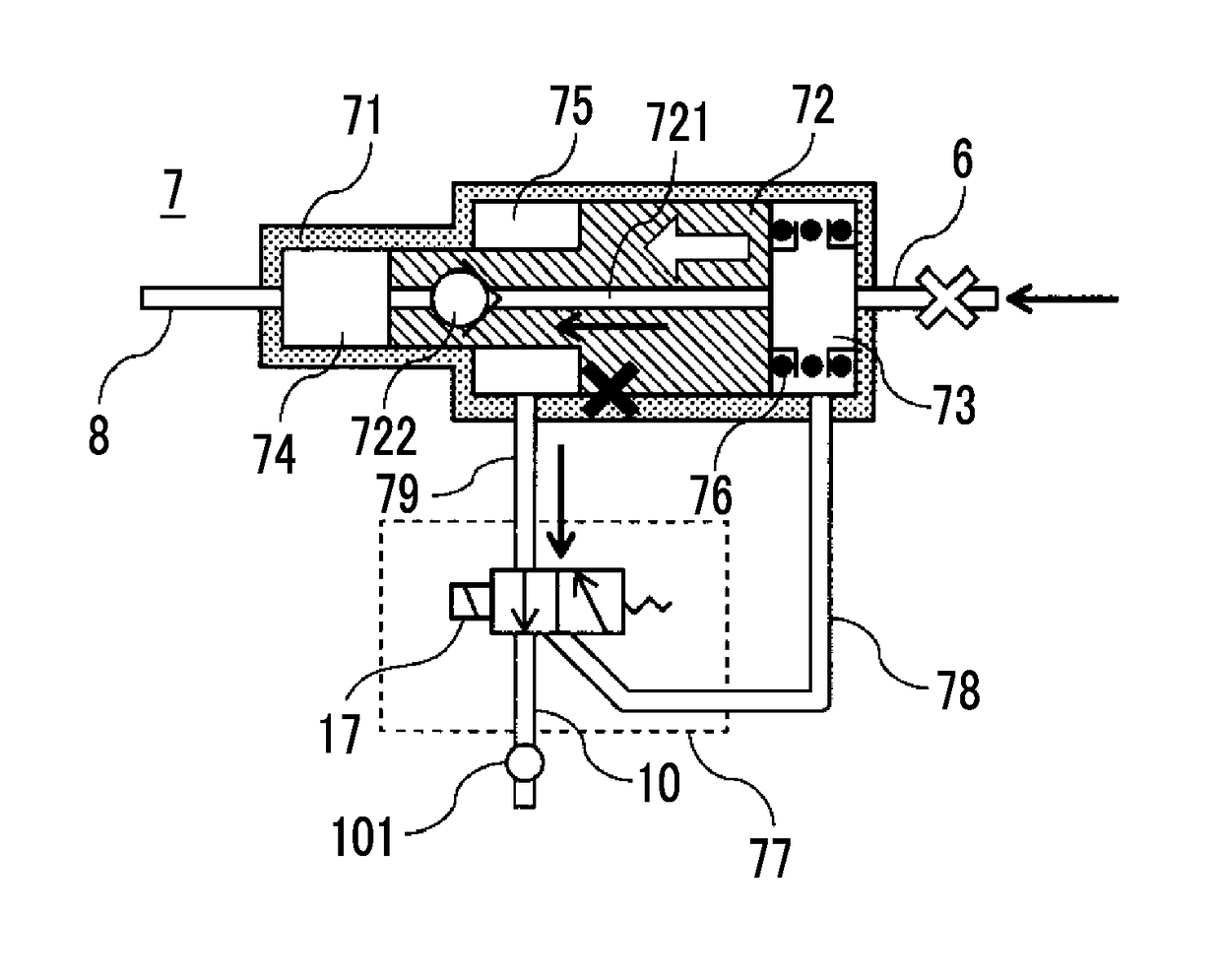
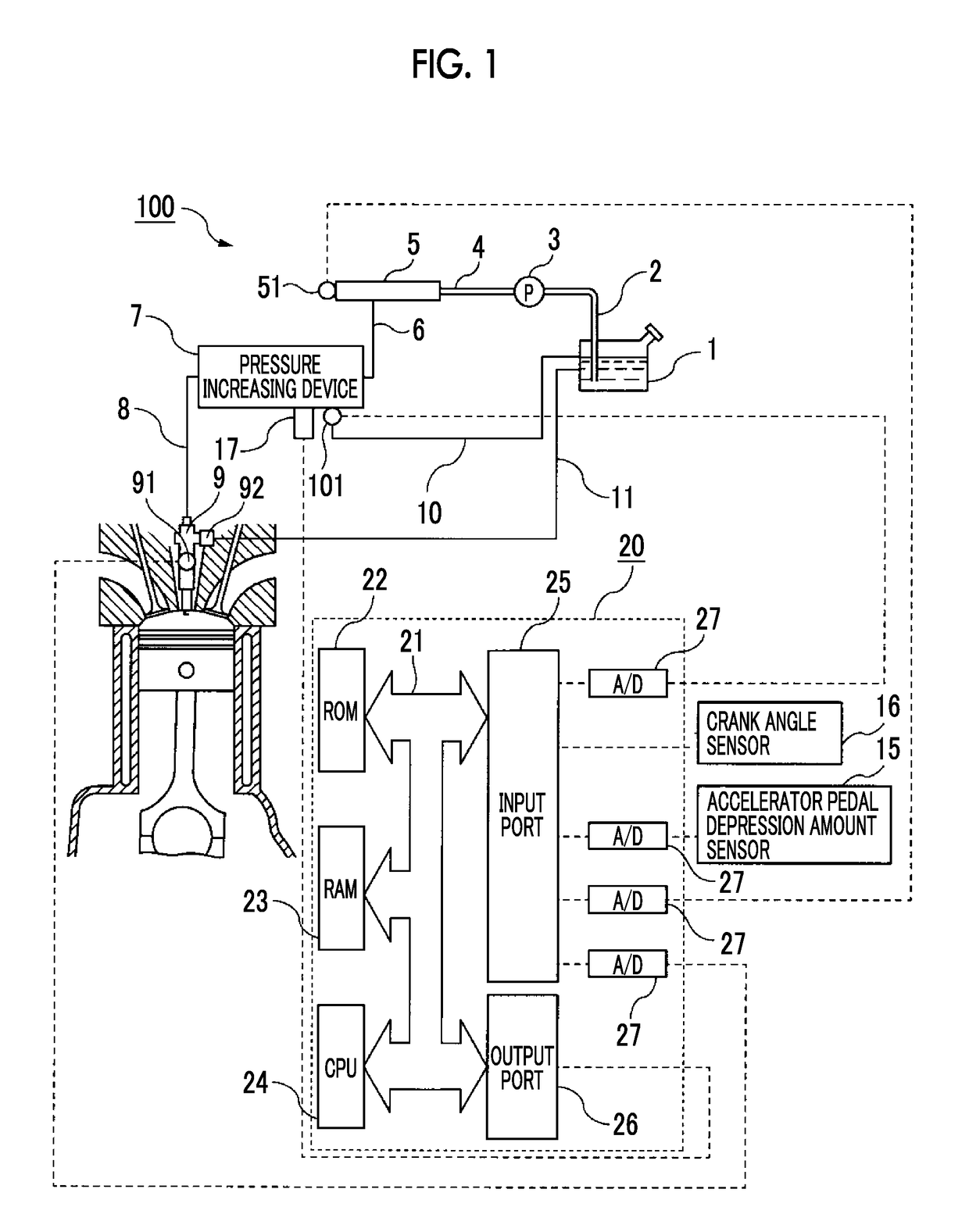
Control device for internal combustion engine
ActiveUS20180291831A1Difficult to determineElectrical controlMachines/enginesExternal combustion engineInternal combustion engine
A control device for an internal combustion engine includes a feel tank, a high pressure feel passage, a pressure increasing device, a switching device, a low pressure fuel passage, a temperature sensor, a fuel injector, and an electronic control unit. The electronic control unit is configured to determine that there is an abnormality in the switching device when a temperature measured by the temperature sensor when the pressure increase signal is output is not higher than a temperature measured by the temperature sensor when the pressure increase signal is not output. The electronic control unit is configured to stop fuel pressure increase by the pressure increasing device by stopping an output of the pressure increase signal regardless of the engine operation state when the electronic control unit determines that there is the abnormality in the switching device.
Owner:TOYOTA JIDOSHA KK
Automatic pin creation using password
ActiveUS20130125214A1Easy to rememberMore experienceDigital data processing detailsMultiple digital computer combinationsUser devicePassword
A PIN is automatically generated based on at least one rule when the user enters a password through a user device. In one example, the PIN is a truncated version of the password where each character in the truncated version is mapped onto a number. The mapping can be a truncation at the beginning or end of the password, or the mapping can be with any pattern or sequence of characters in the password. This PIN generation may be transparent to the user, such that the user may not even know the PIN was generated when the password was entered. When the user attempts to access restricted content, the user may enter the PIN instead of the password, where the user may be notified of the rule used to generate the PIN so that the user will know the PIN by knowing the password.
Owner:PAYPAL INC
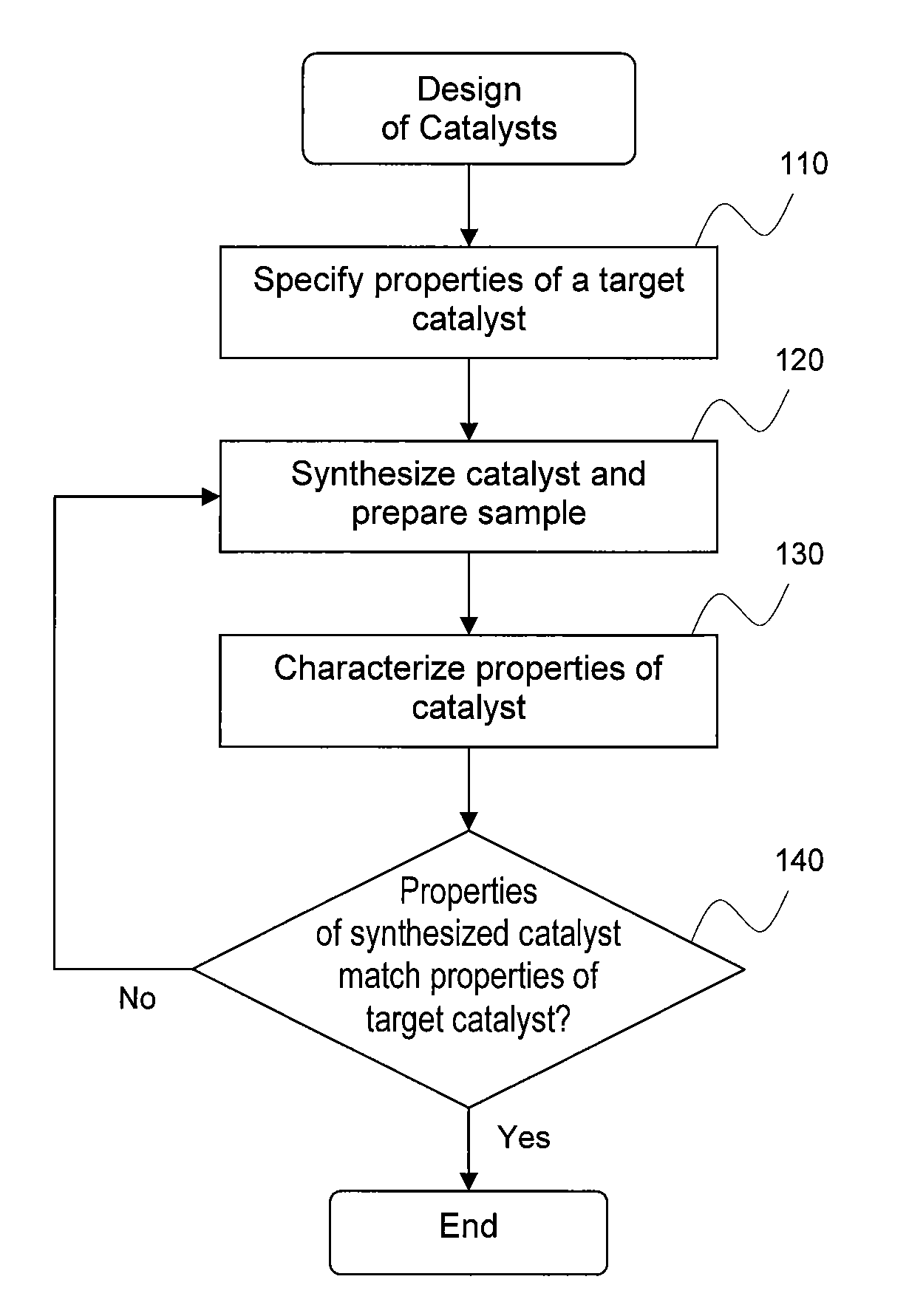
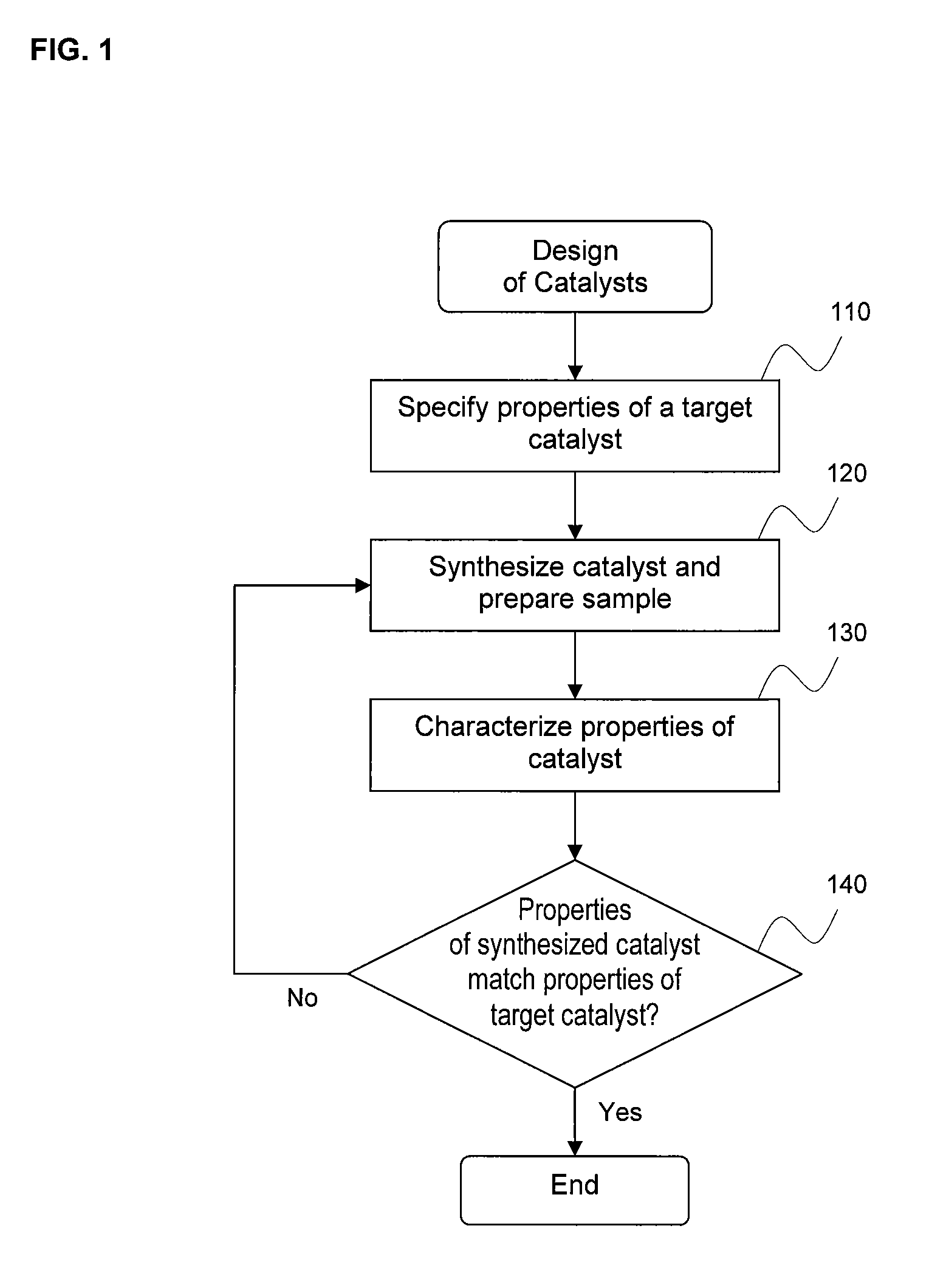
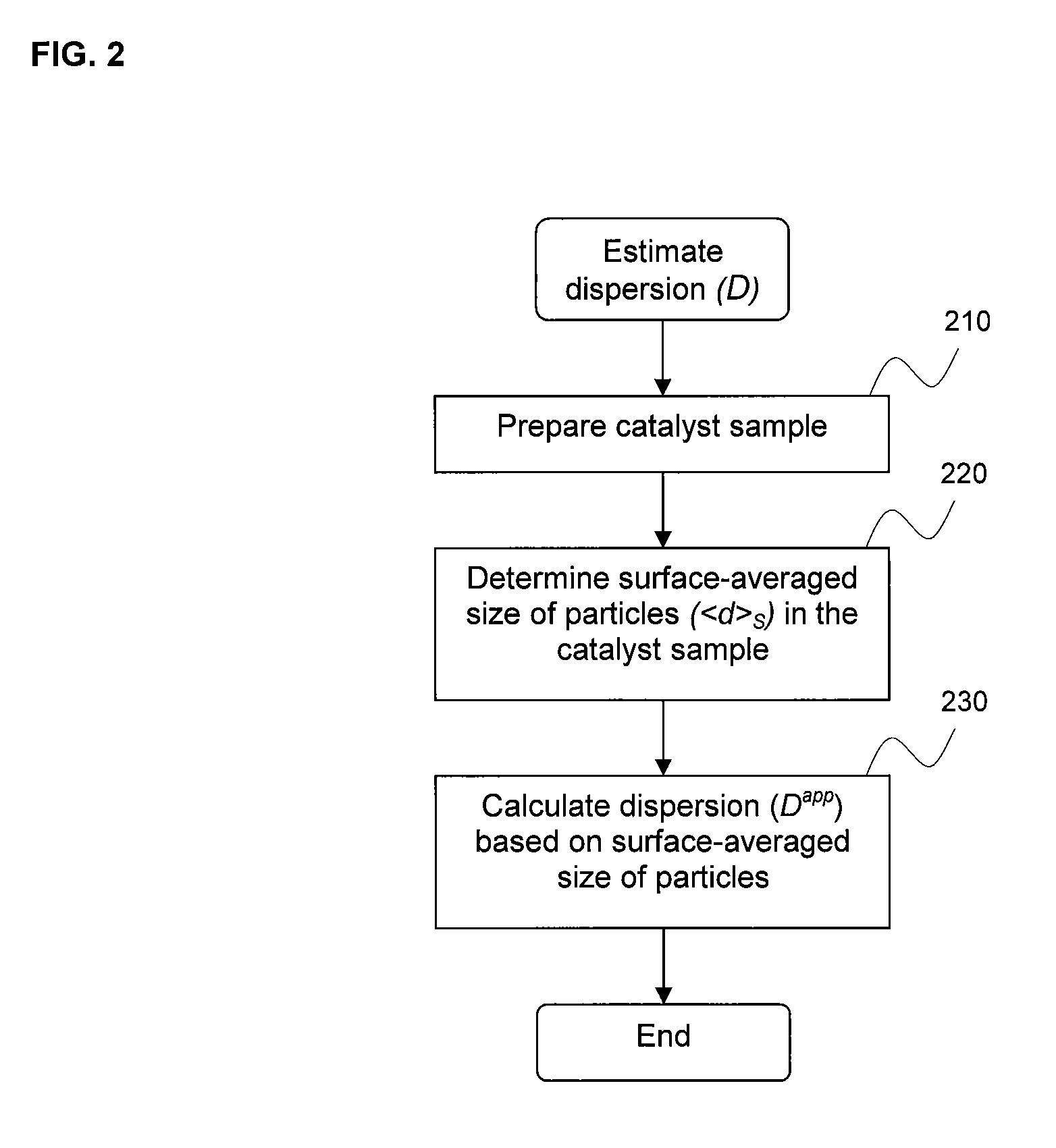
Dispersion and metal particle size characterization of nanocatalysts
InactiveUS7813523B1Difficult to determineSimple methodCharacter and pattern recognitionUsing wave/particle radiation meansNano catalystChemisorption
A relationship between dispersion and surface-averaged metal particle size is provided so that either dispersion can be determined from measured surface-averaged metal particle size or surface-averaged metal particle size can be determined from measured dispersion. The method can be applied to catalysts having a single metal species as well as catalysts having multiple metal species. The size of the supported metal particles in the catalyst sample may be determined using transmission electron microscopy images of supported metal particles in the catalyst sample. The dispersion of the supported metal particles in the catalyst sample may be determined using chemisorption tests on the catalyst sample.
Owner:SHUBIN
Method to secure a software code
ActiveUS11256786B2Improve securityDifficult to determineProgram/content distribution protectionSecurity softwareParallel computing
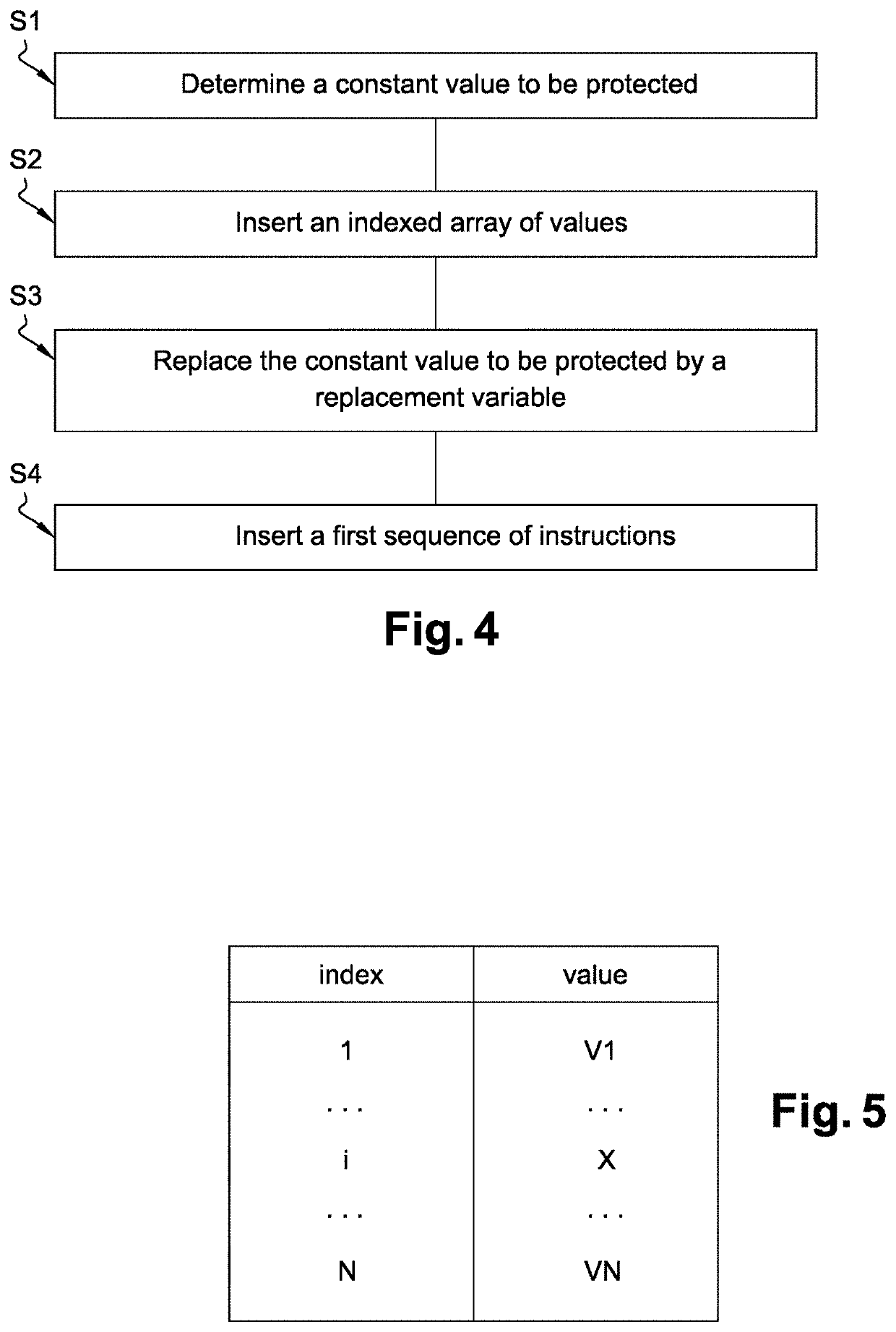
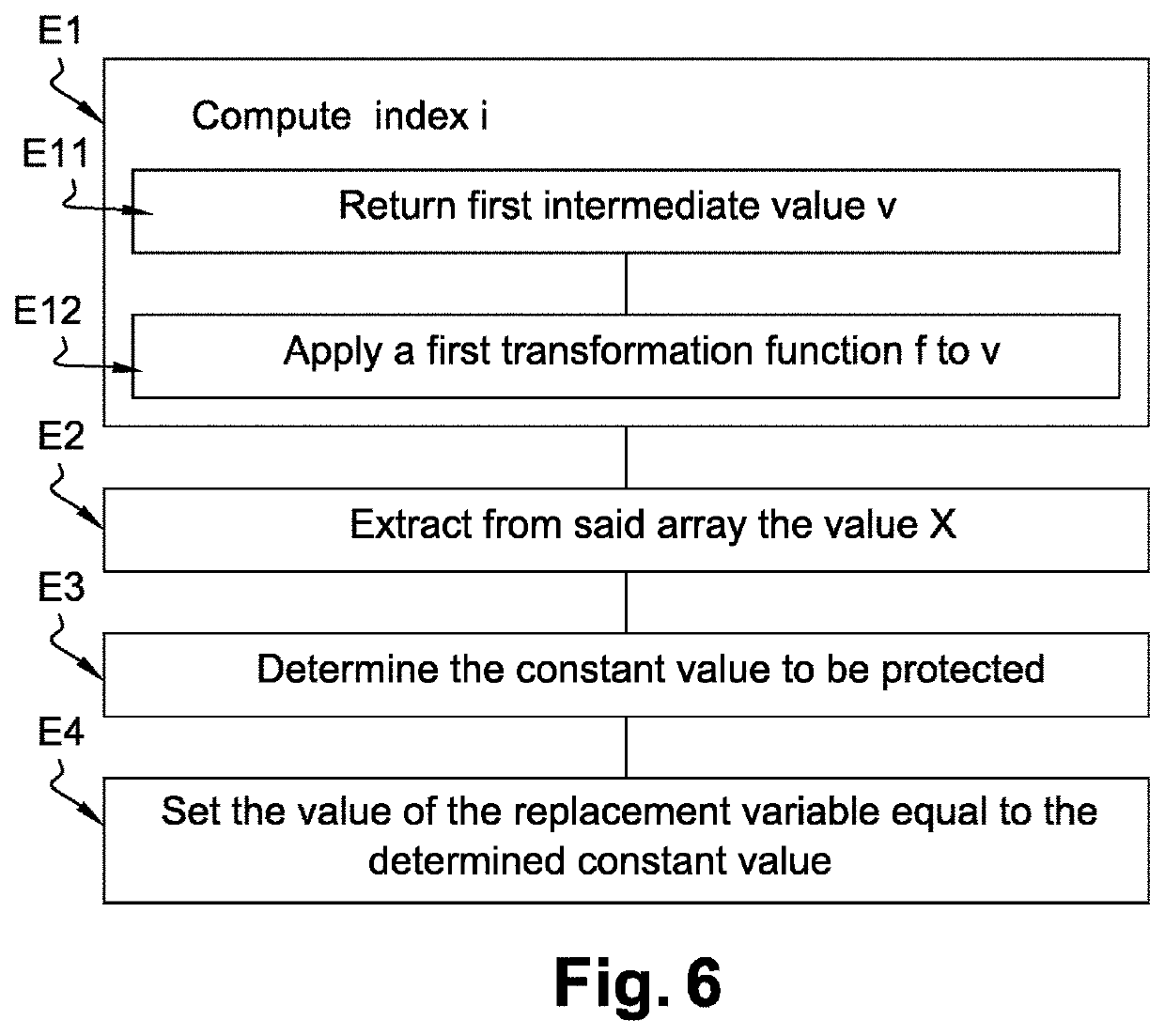
The present invention relates to method of securing a software code comprising at least one constant value, said method generating a secure software code and comprising the steps of: —determining (S1) by a processor in the software code a constant value to be protected, —inserting (S2) by the processor in the software code an indexed array of values such that the constant value to be protected can be determined from one value of the array, —replacing (S3) by the processor in the software code the constant value to be protected by a replacement variable, —inserting (S4) by the processor in the software code a first sequence of instructions which, when executed at runtime: •computes the index in the array of the value from which the constant value to be protected can be determined, •extracts from said array the value located at said computed index in said array, •from said extracted value, determines the constant value to be protected, •sets the value of said replacement variable equal to the determined constant value.
Owner:THALES DIS FRANCE SA
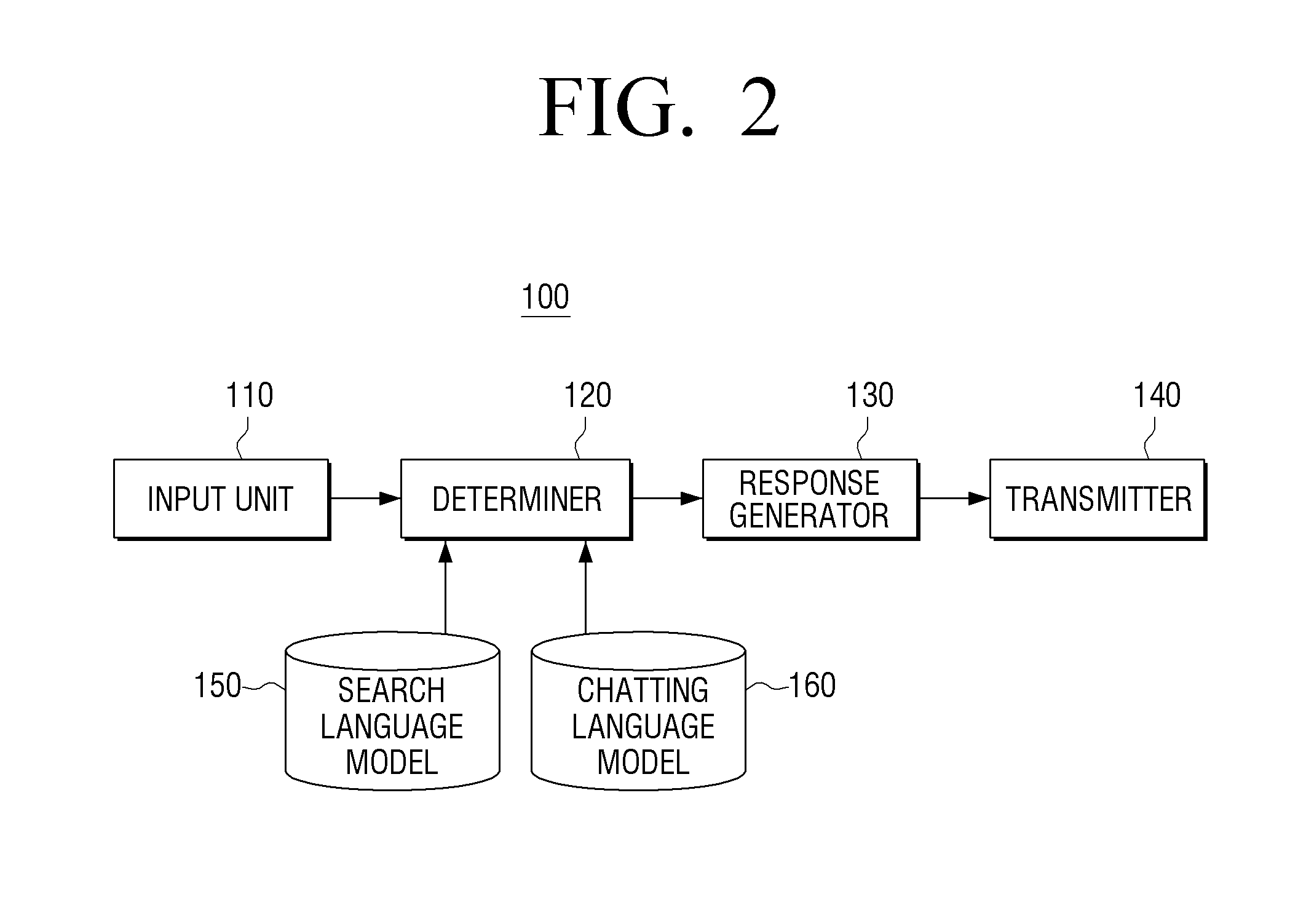
Interactive server and method for controlling the server
ActiveUS20150235643A1Difficult to determineNatural language analysisSpeech recognitionComputer networkSpeech sound
An interactive server and a controlling method thereof are provided. The method of controlling an interactive server includes receiving data corresponding to a user voice from a user terminal, determining an utterance type of the user voice, in response to determining that the utterance type of the user voice is an integrated utterance type, generating a search response and a chatting response in response to the user voice and generating an integrated response by combining the generated search response and the generated chatting response, and transmitting the generated integrated response to the user terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
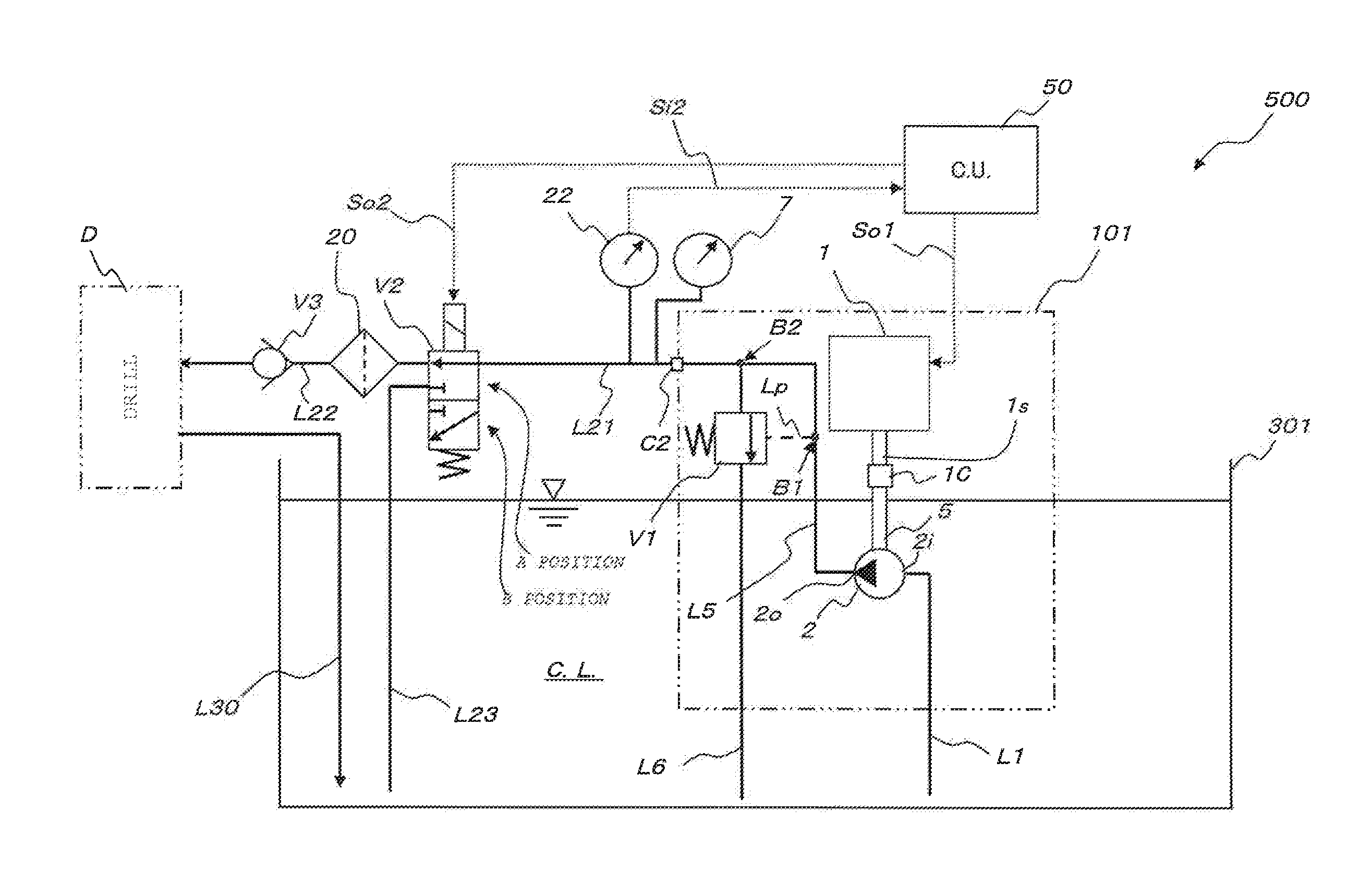
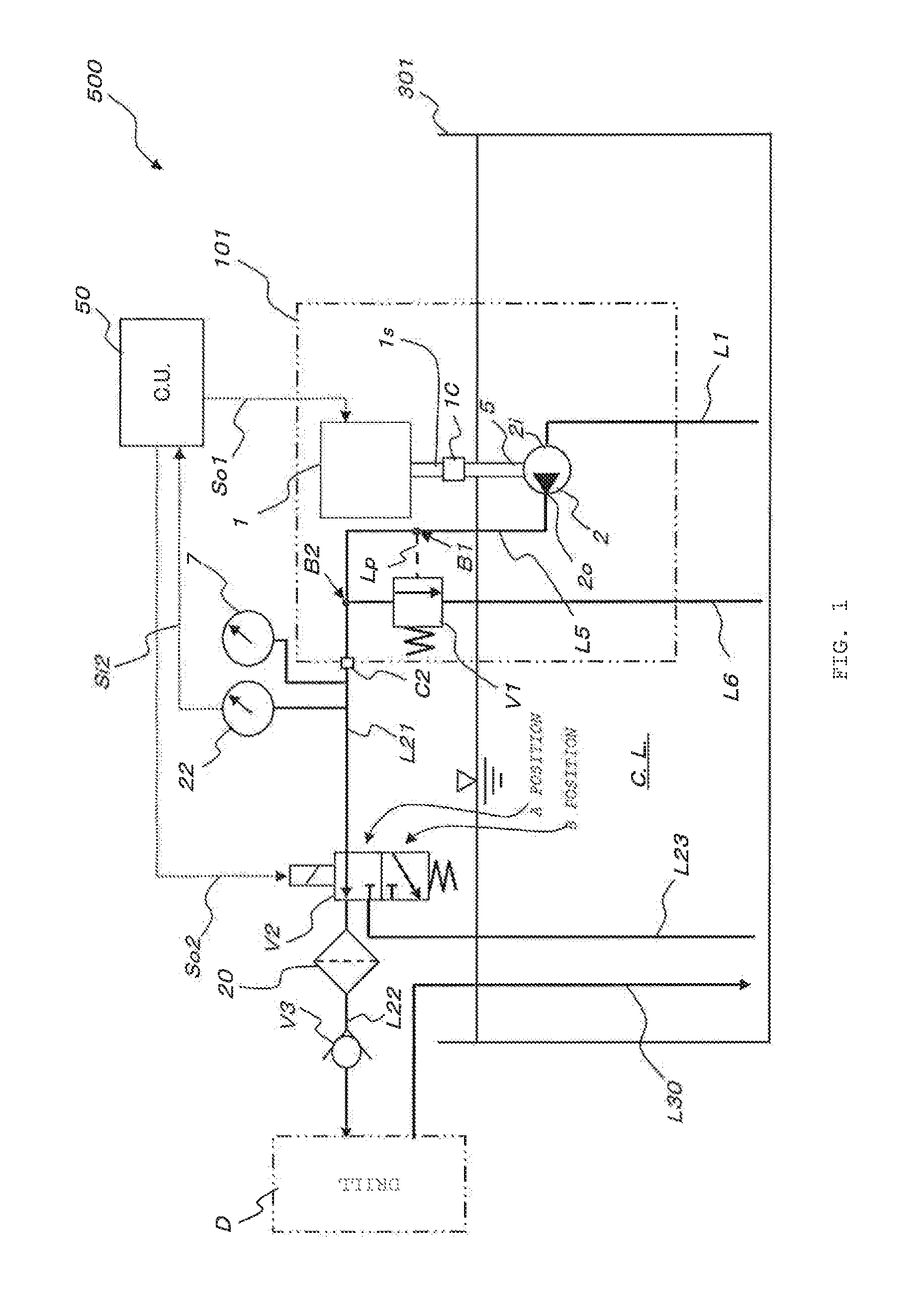
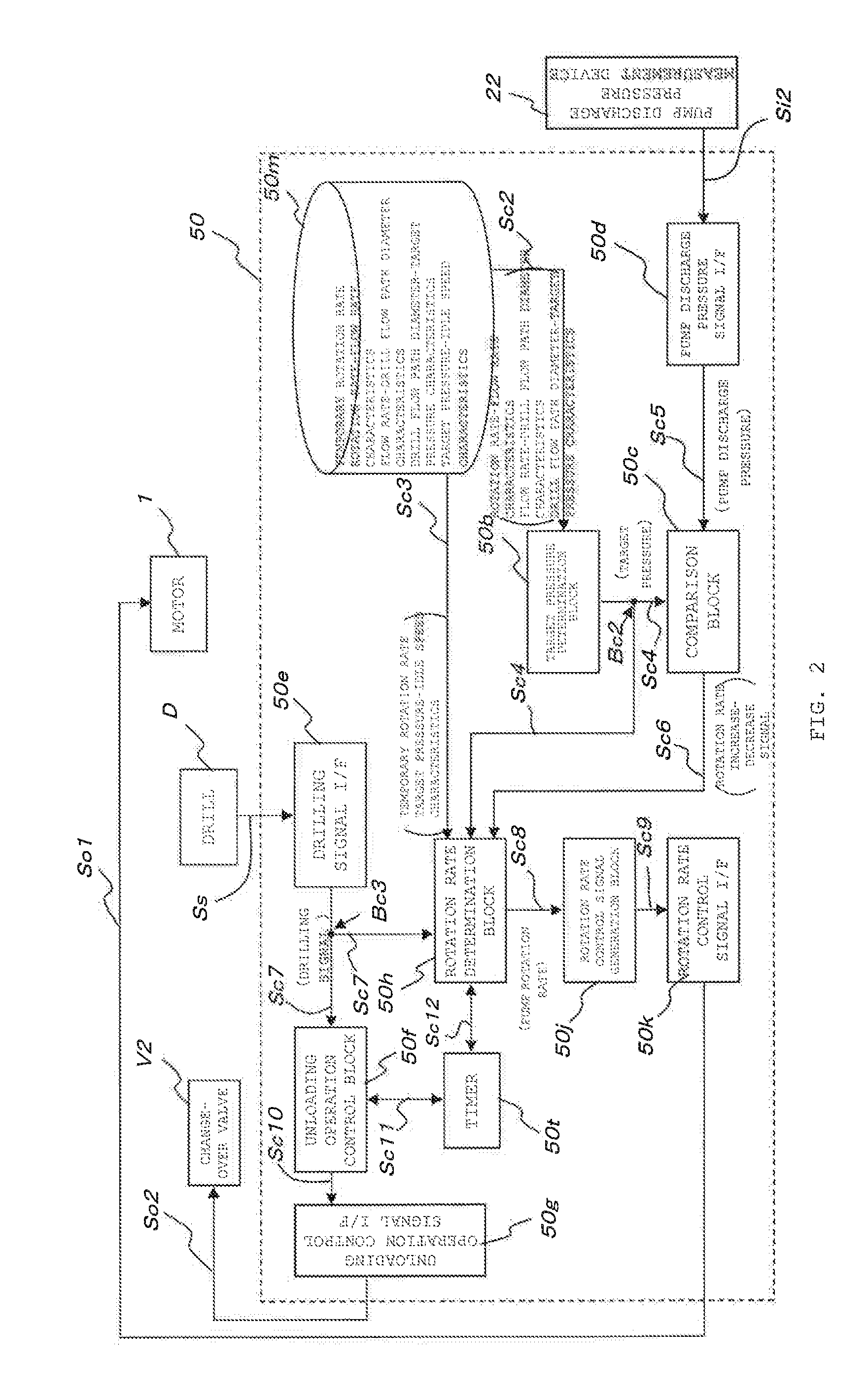
Coolant supply device and supply method
ActiveUS20140284041A1Difficult to determineAppropriate performanceTemperatue controlRotary piston pumpsCoolant flowEngineering
The purpose of the invention is to provide a coolant supply device and supply method that can appropriately control the spraying of coolant using a single parameter.To that end, the invention is provided with a pump (101) that supplies coolant to a tool (D), a measurement device (22) that measures the discharge pressure of the pump (101), and a control device (50). The control device (50) has a function for determining, from the rotation rate of the pump (101), the coolant flow path diameter for the tool (D) and the target value for the pump discharge pressure (target pressure) when the tool (D) is drilling.
Owner:NIPPON OIL PUMP
Information recording medium supply apparatus
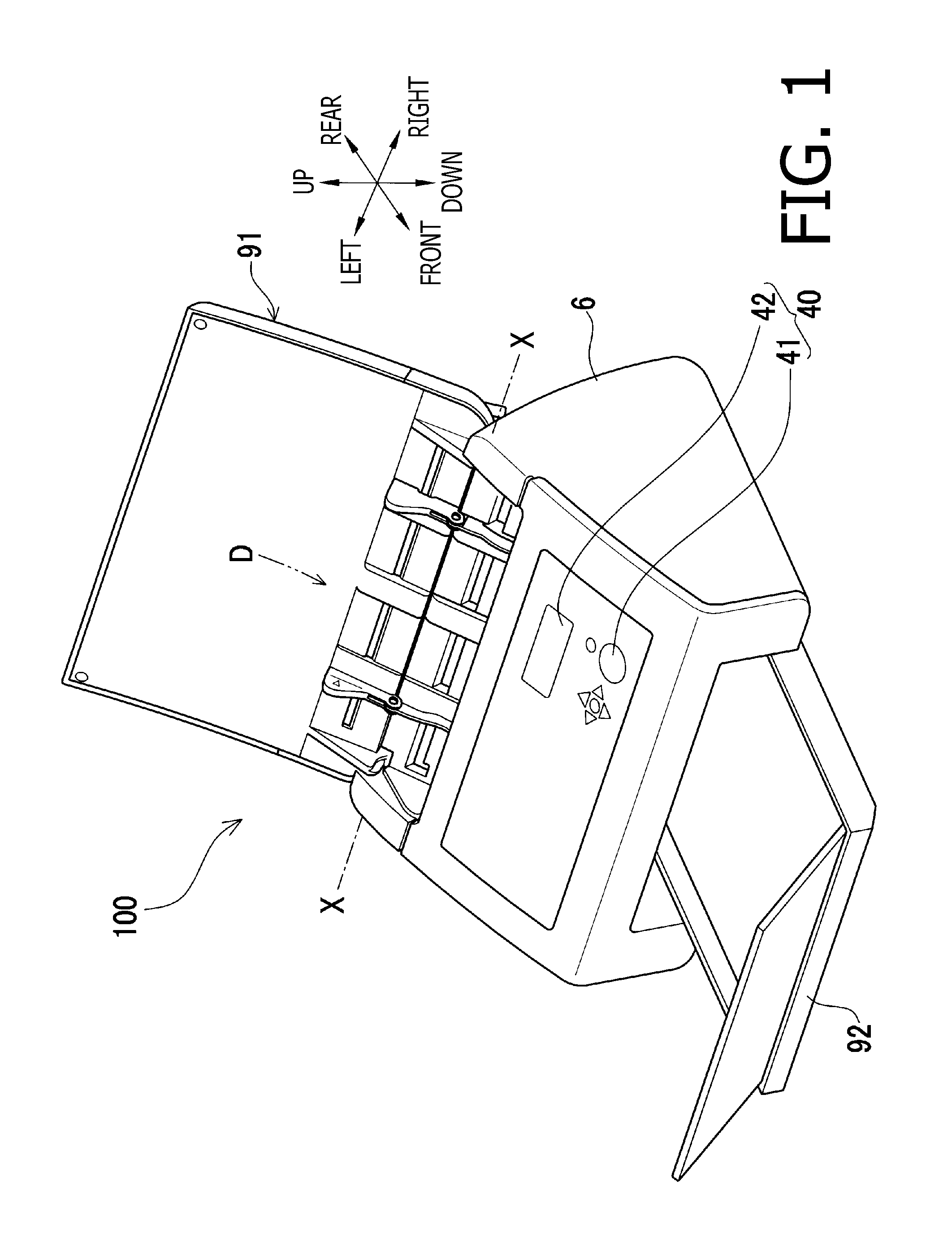
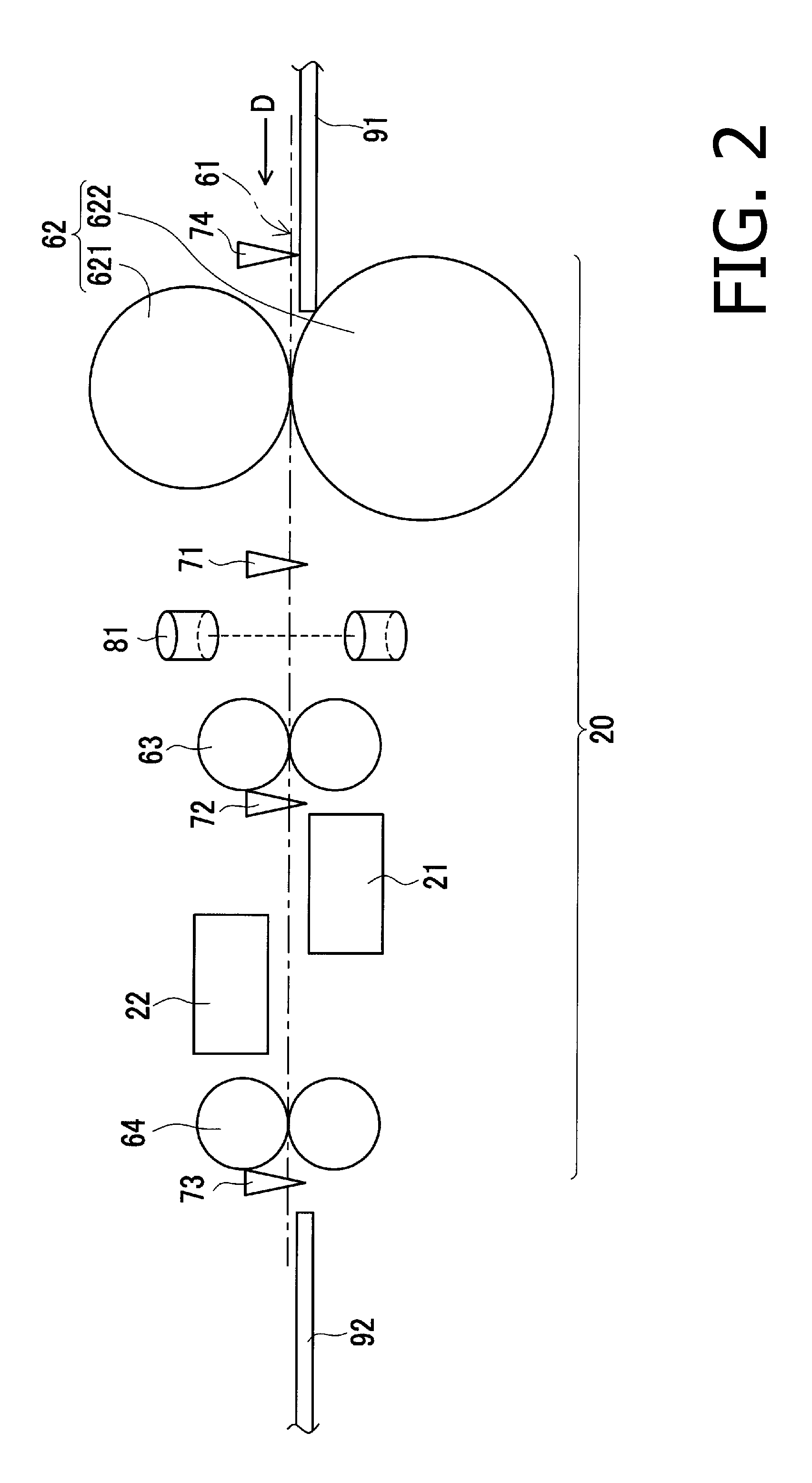
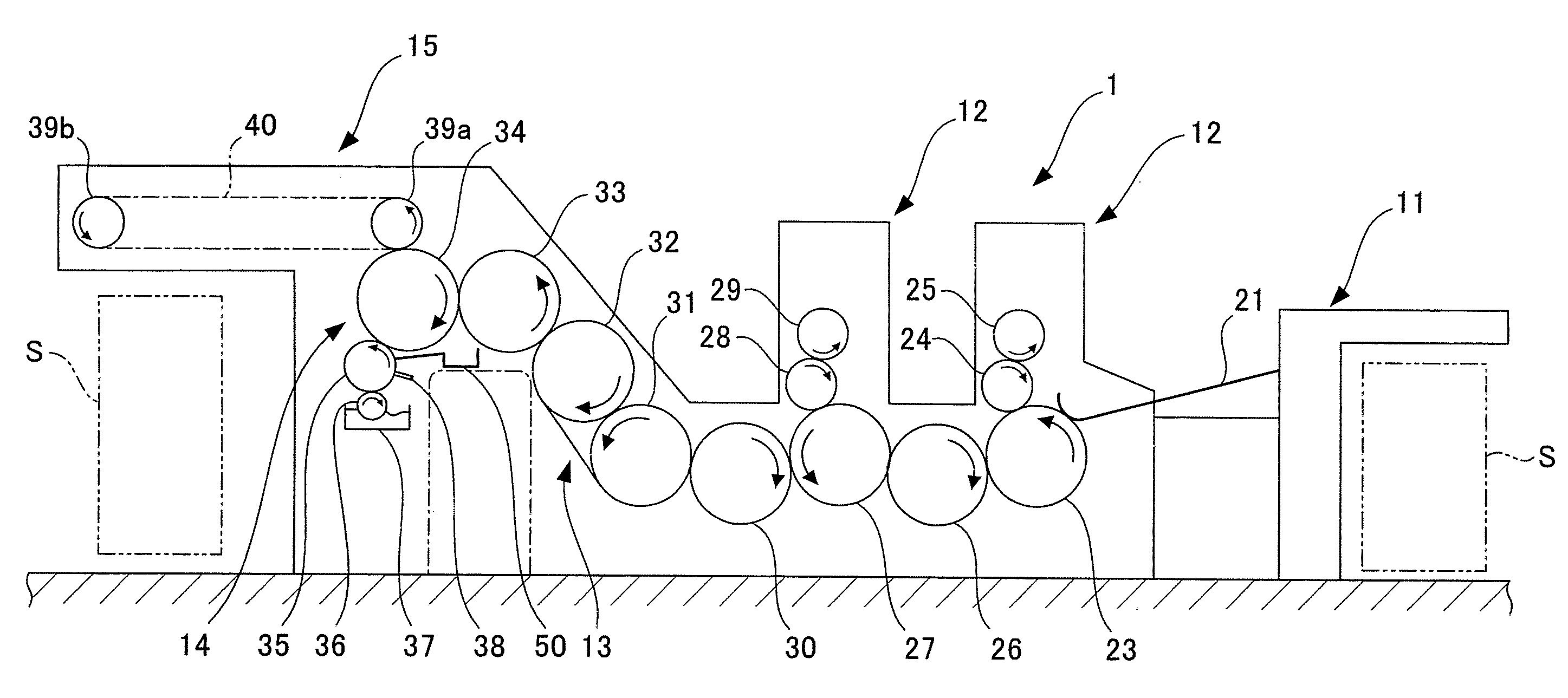
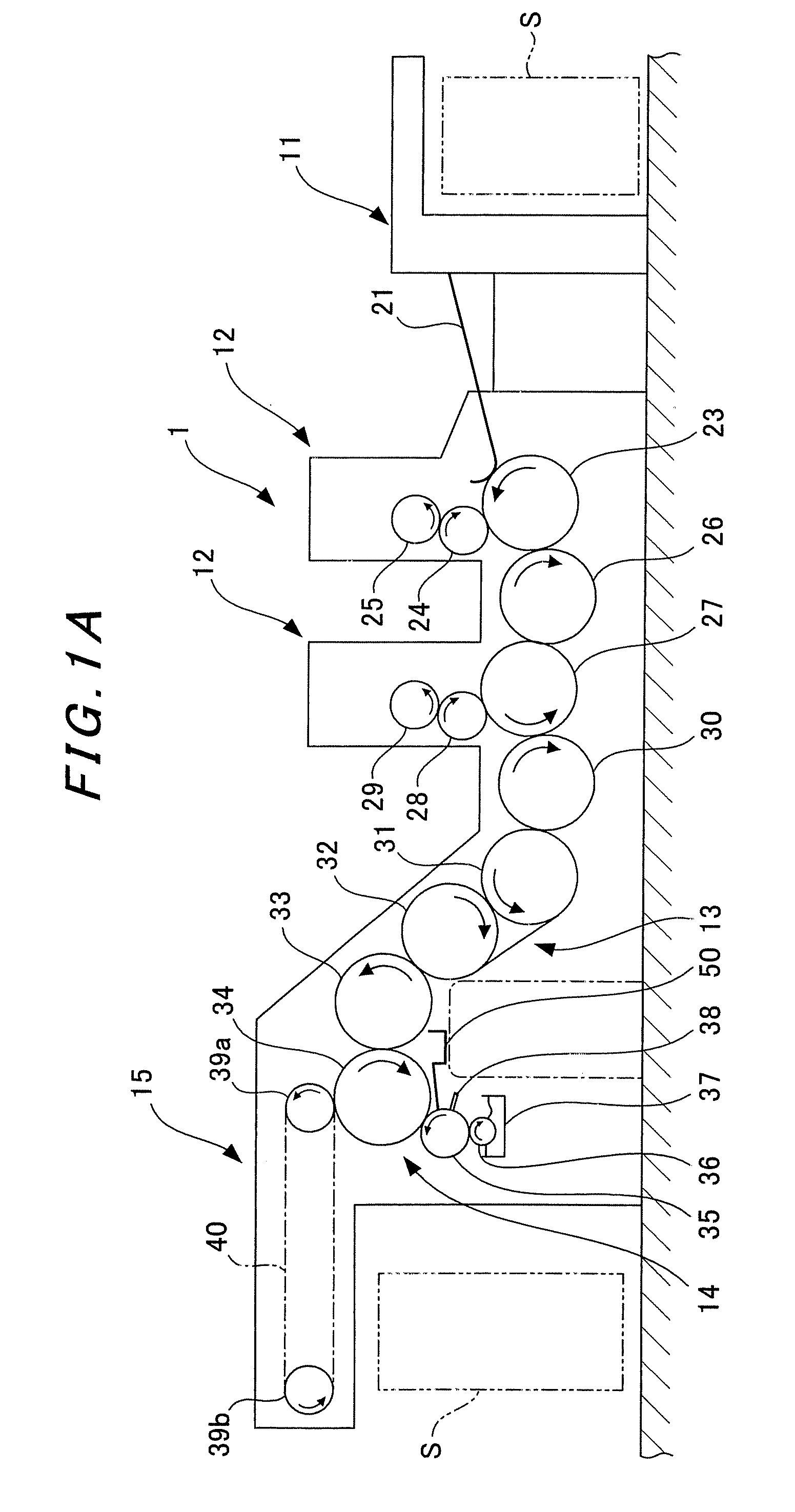
InactiveUS20080037401A1Improve anti-counterfeiting functionEmbedded in the sheet efficientlyTransfer printingRotary intaglio printing pressImage areaRecording media
An information recording medium supply apparatus comprises: a gravure plate cylinder supported having recessed image areas formed in the circumferential surface thereof; an ink roller for supplying ink from an ink reservoir to the circumferential surface of the gravure plate cylinder; a doctor for removing surplus ink adhering to non-image areas of the gravure plate cylinder; an impression cylinder supported rotatably and adapted to transfer the ink in the image areas to a sheet being transported in cooperation with the gravure plate cylinder; and an IC chip supply device for supplying an IC chip to the ink in the image area on a side downstream of the point of removal of the ink by the doctor in the rotating direction of the gravure plate cylinder, and on a side upstream of the point of contact with the impression cylinder in the rotating direction of the gravure plate cylinder.
Owner:KOMORI CORP
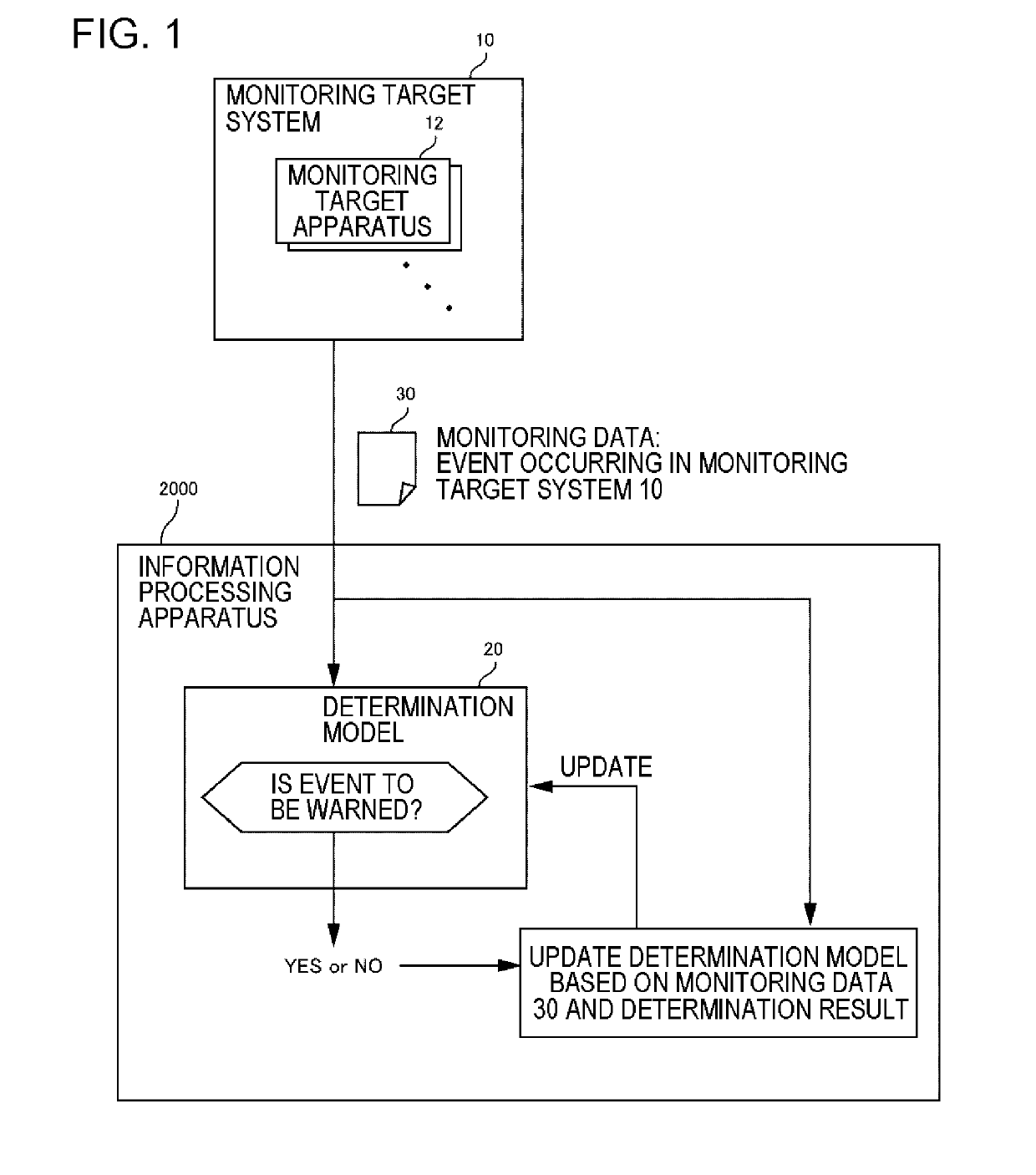
Information processing apparatus, control method, and program
ActiveUS20190306177A1Difficult to determineAccurately determineComputer security arrangementsTransmissionGoal systemMonitoring data
An information processing apparatus acquires monitoring data. The monitoring data is data representing an event occurring in the monitoring target system. The information processing apparatus determines whether or not the event represented by the monitoring data is an event to be warned. This determination is made using the determination model. The determination model is a model for determining whether or not the event is a warning target. The information processing apparatus updates the determination model, based on the monitoring data and the result of determination on the monitoring data by using the determination model.
Owner:NEC CORP
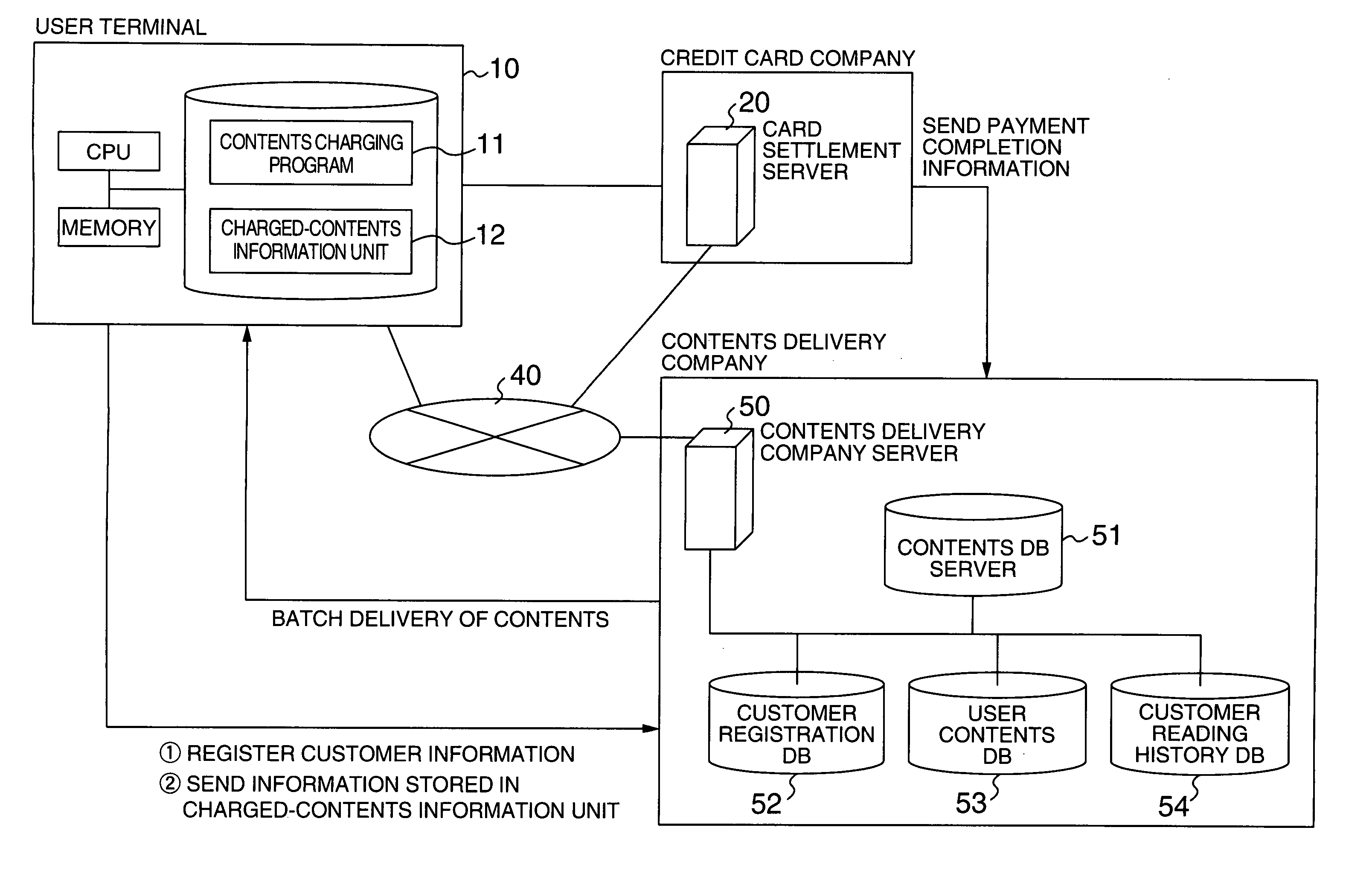
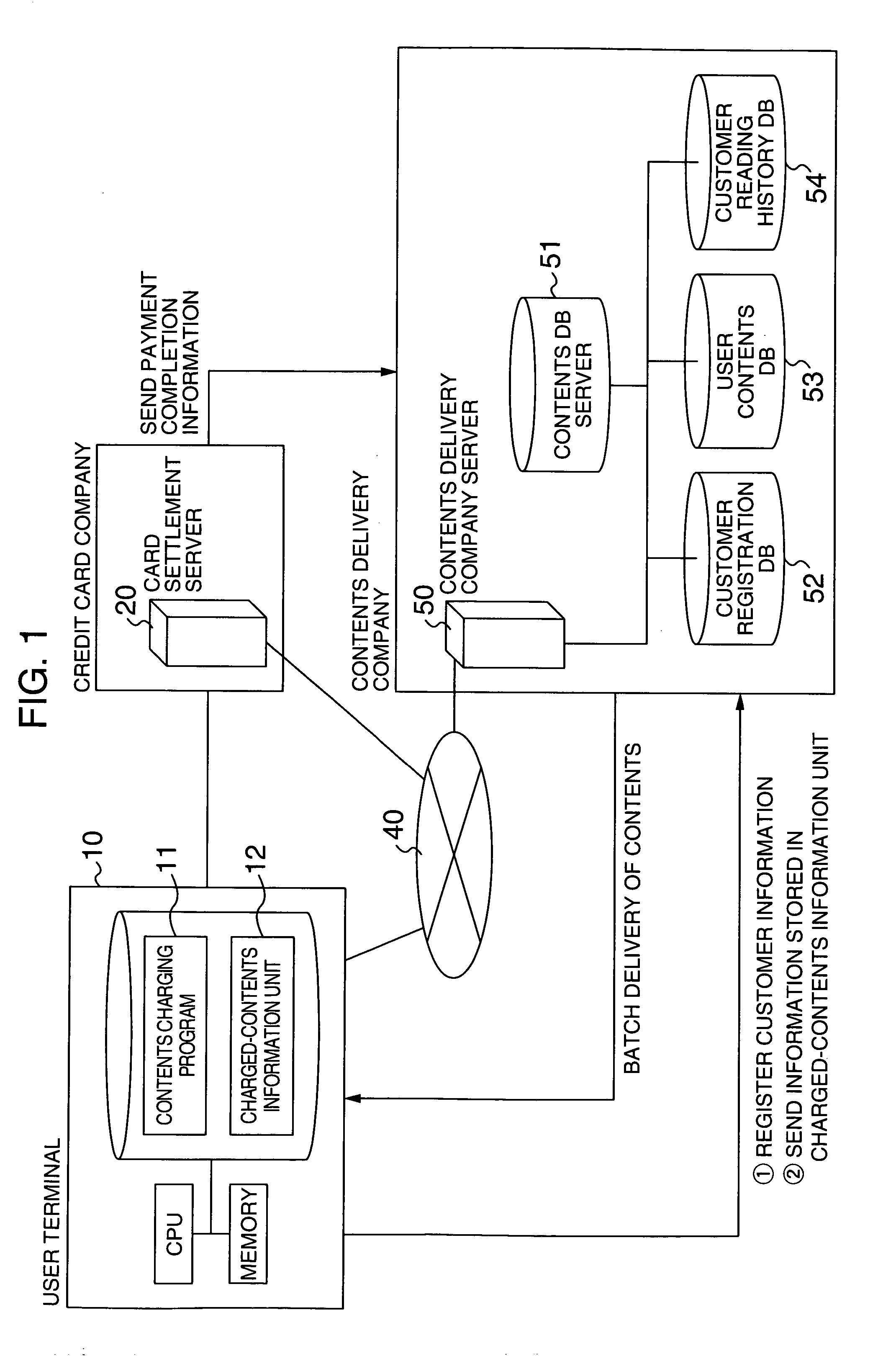
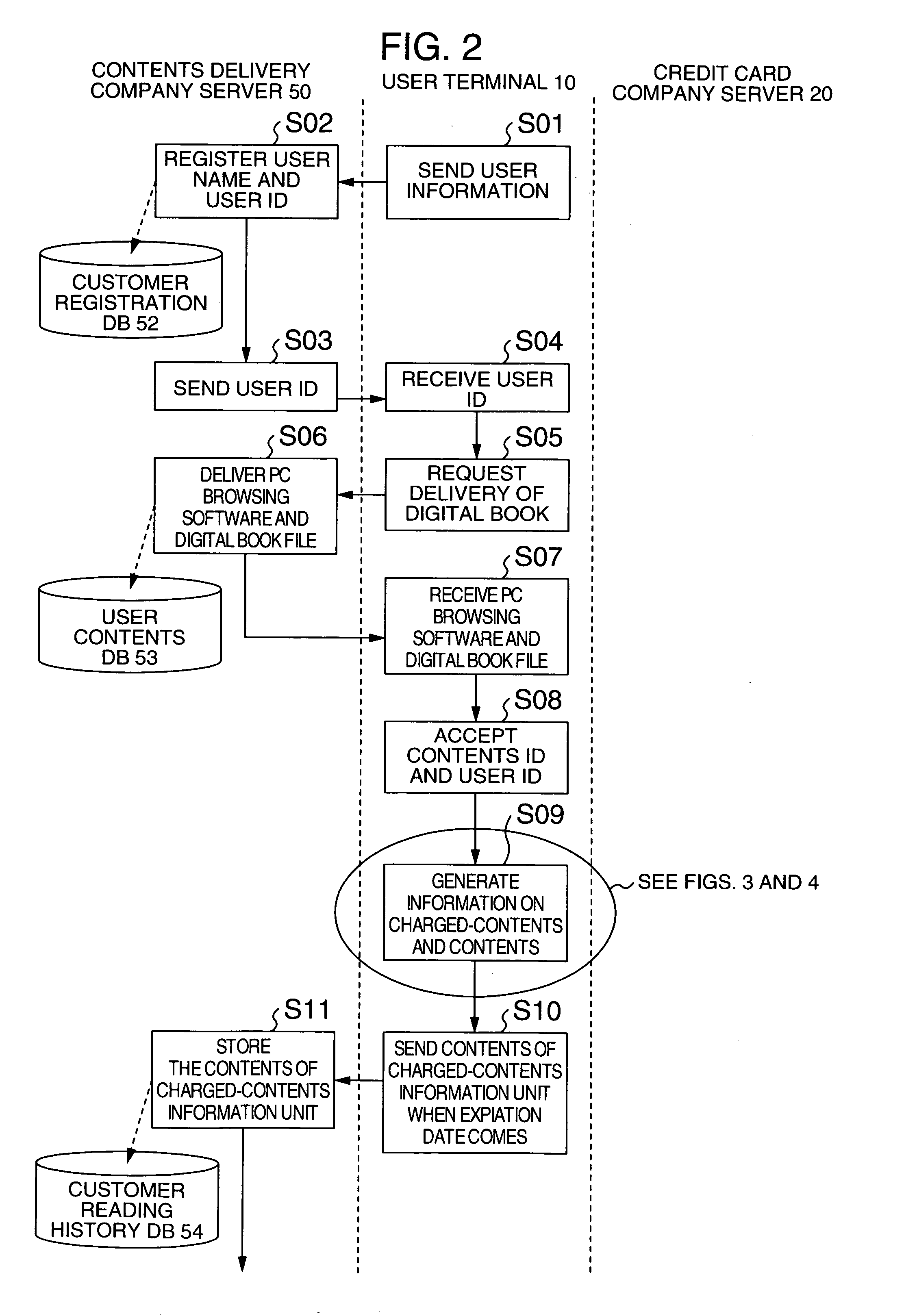
Contents delivering method
InactiveUS20060018206A1Difficult to determineTelevision system detailsFilamentary/web record carriersComputer graphics (images)Digital content
Owner:AKITOMO MIHO +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com