Patents
Literature
1290results about How to "Easy to remember" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Universal personal identifier for accessing patron information at a gaming venue
InactiveUS20050054438A1Easy to rememberApparatus for meter-controlled dispensingVideo gamesCard readerBluetooth
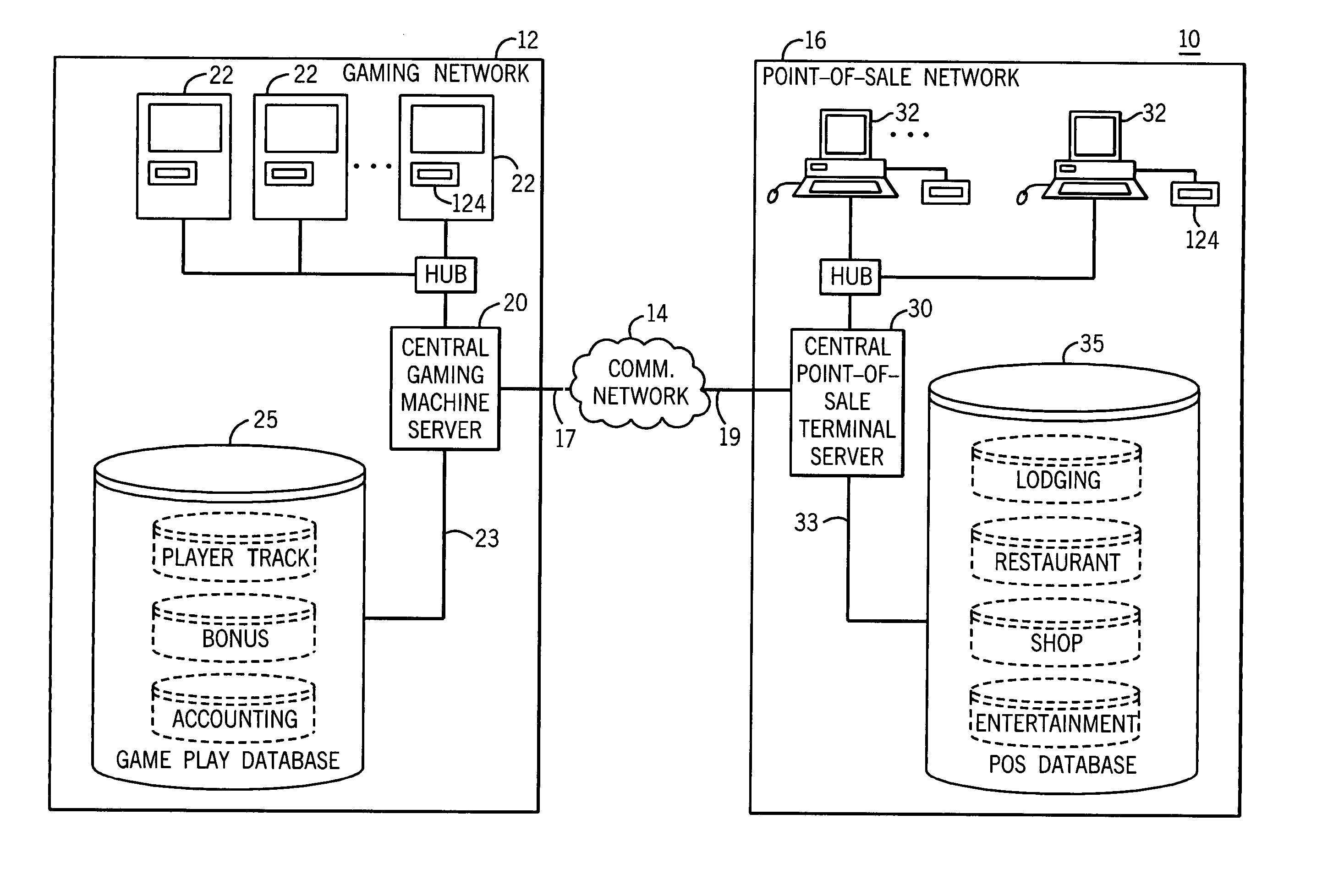
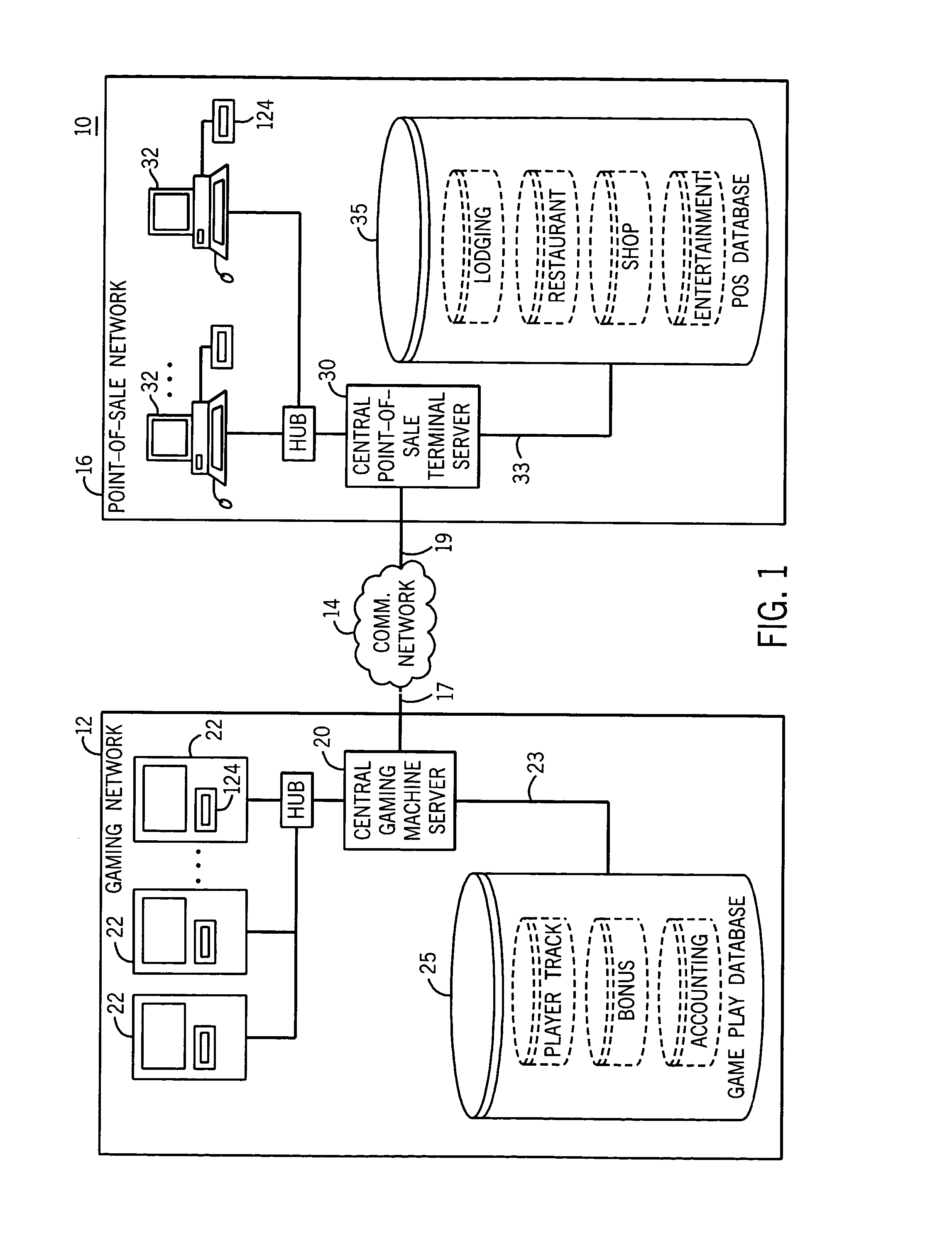
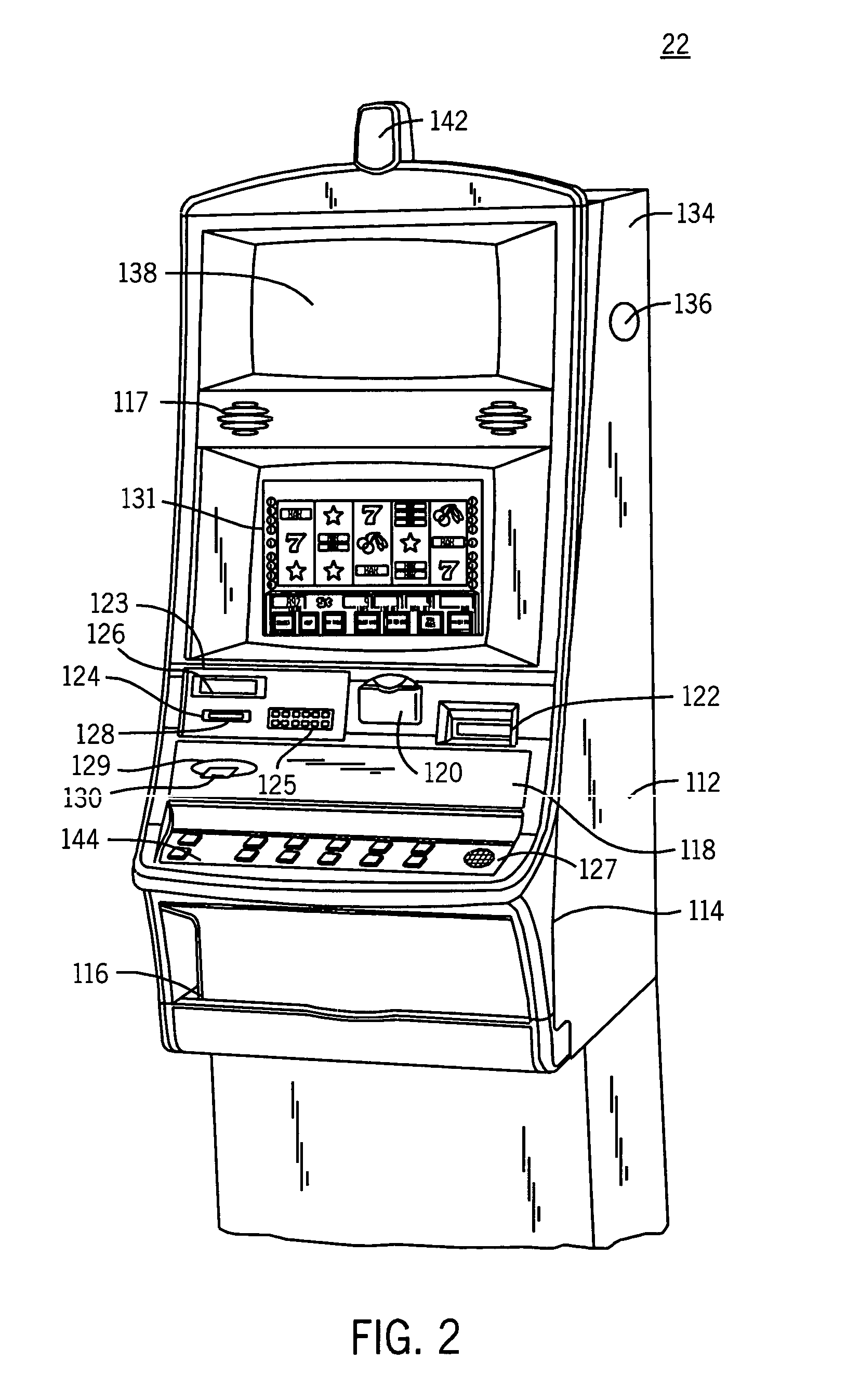
A method and apparatus for associating a patron with wagering game play at a gaming machine in a server-based gaming network is disclosed. The method includes associating a unique patron identification with the patron, establishing a patron account for the patron where the patron account is identified by the unique patron identification, associating the gaming machine with a universal personal identifier device for receiving a universal personal identifier having a patron identification where the universal personal identifier device is capable of detecting and transmitting the patron identification, receiving the patron identification, comparing the patron identification to the unique patron identification, and enabling collection of patron accounting data resulting from wagering game play if the patron identification matches the unique patron identification. The universal personal identifier device may be a card reader, a touch screen, a biometric device, a Bluetooth™ module device, a microchip scanner, or a combination thereof.
Owner:BALLY GAMING INC
Robust visual passwords
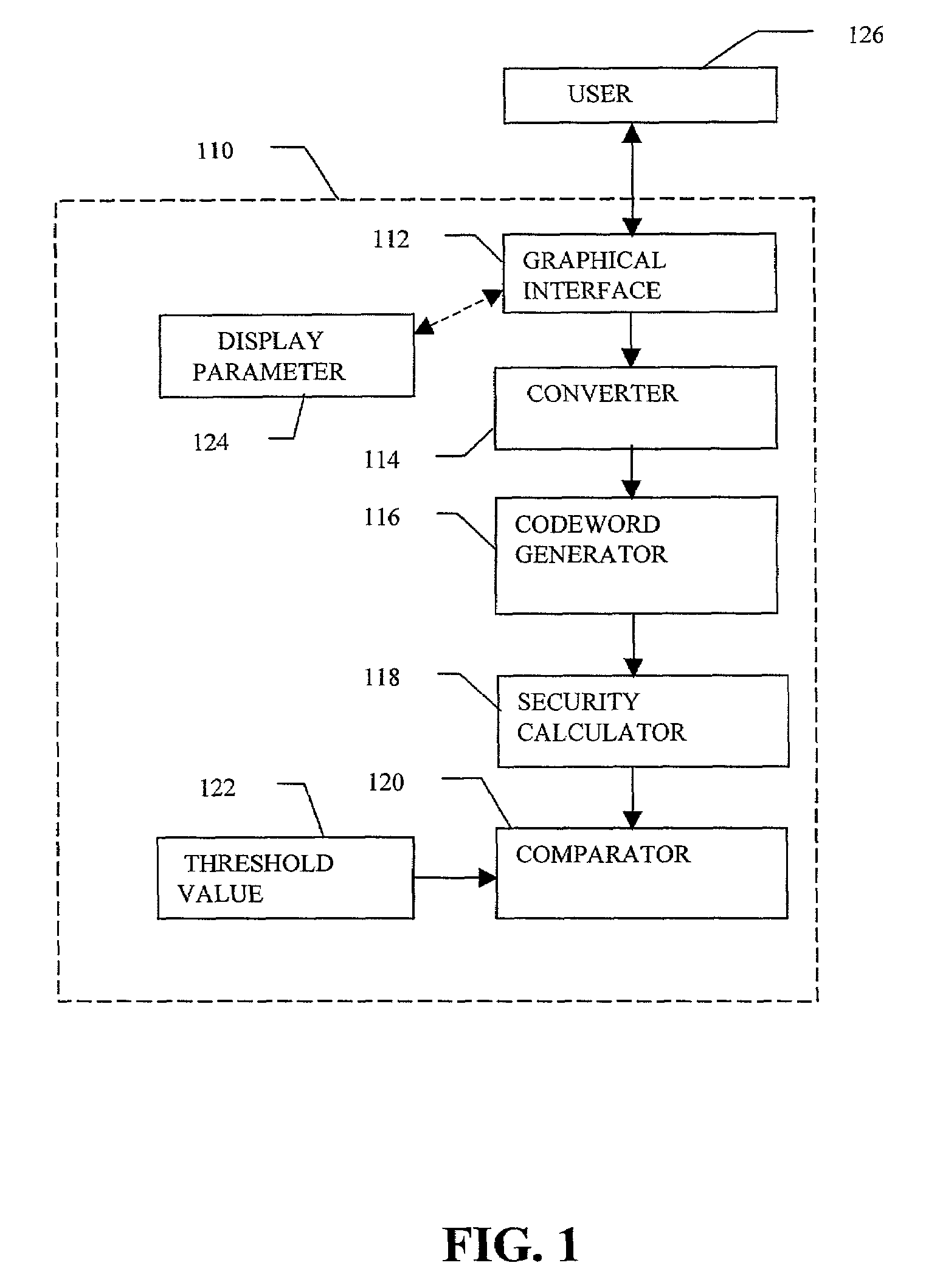
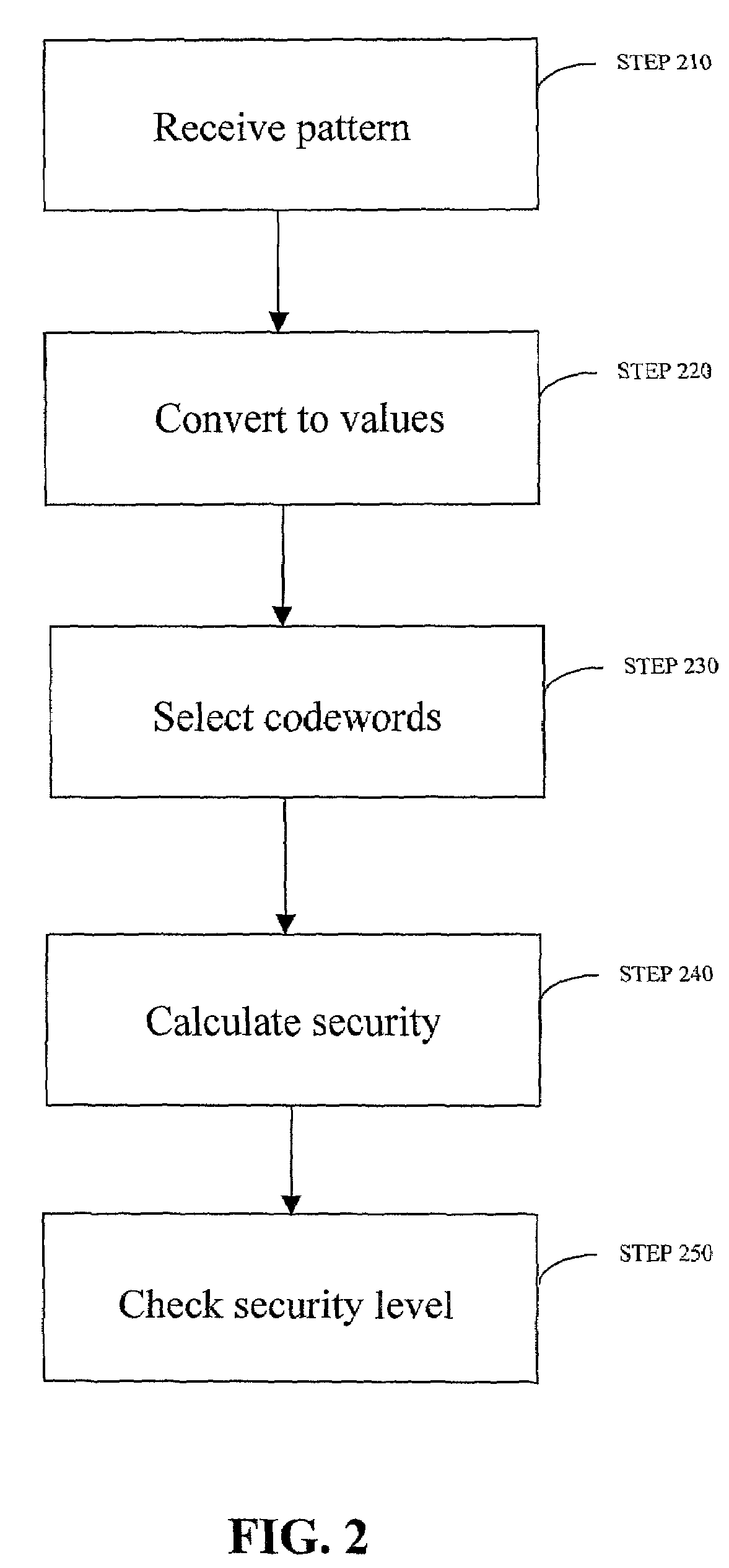
InactiveUS7219368B2Easy to rememberKey distribution for secure communicationPublic key for secure communicationGraphicsUser input
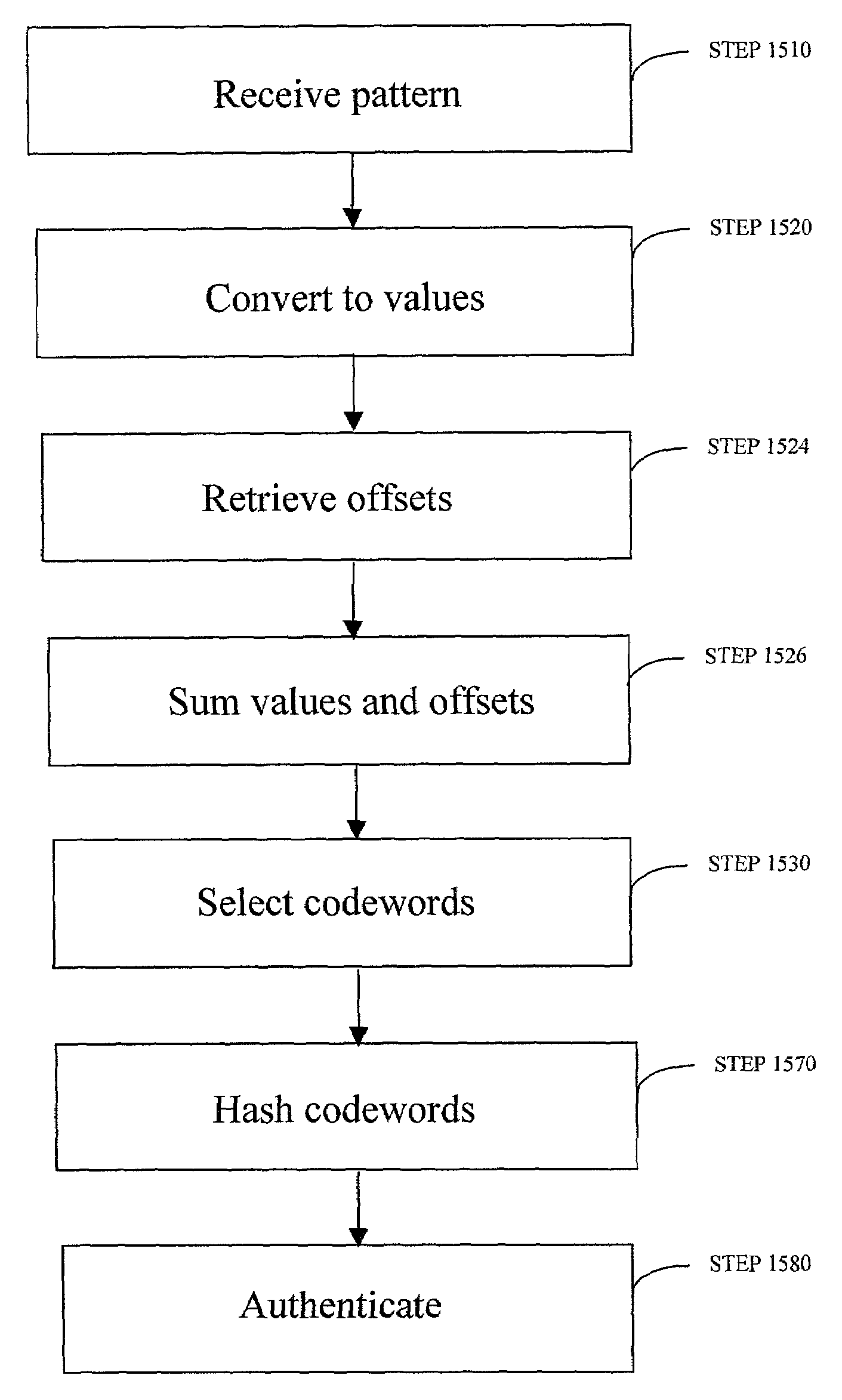
Enrollment and authentication of a user based on a sequence of discrete graphical choices is described. A graphical interface presents various images and memory cues that a user may associate with their original graphical choices. Enrollment may require the input to have a security parameter value that meets or exceeds a threshold. An acceptable sequence of graphical choices is converted to a sequence of values and mapped to a sequence of codewords. Both a hash of the sequence of codewords and a sequence of offsets are stored for use in authenticating the user. An offset is the difference between a value and its corresponding codeword. Authentication requires the user to enter another sequence of discrete graphical choices that is approximately the same as original. The offsets are summed with the corresponding values before mapping to codewords. Authentication requires the sequence of codewords, or a hash thereof, to match.
Owner:RSA
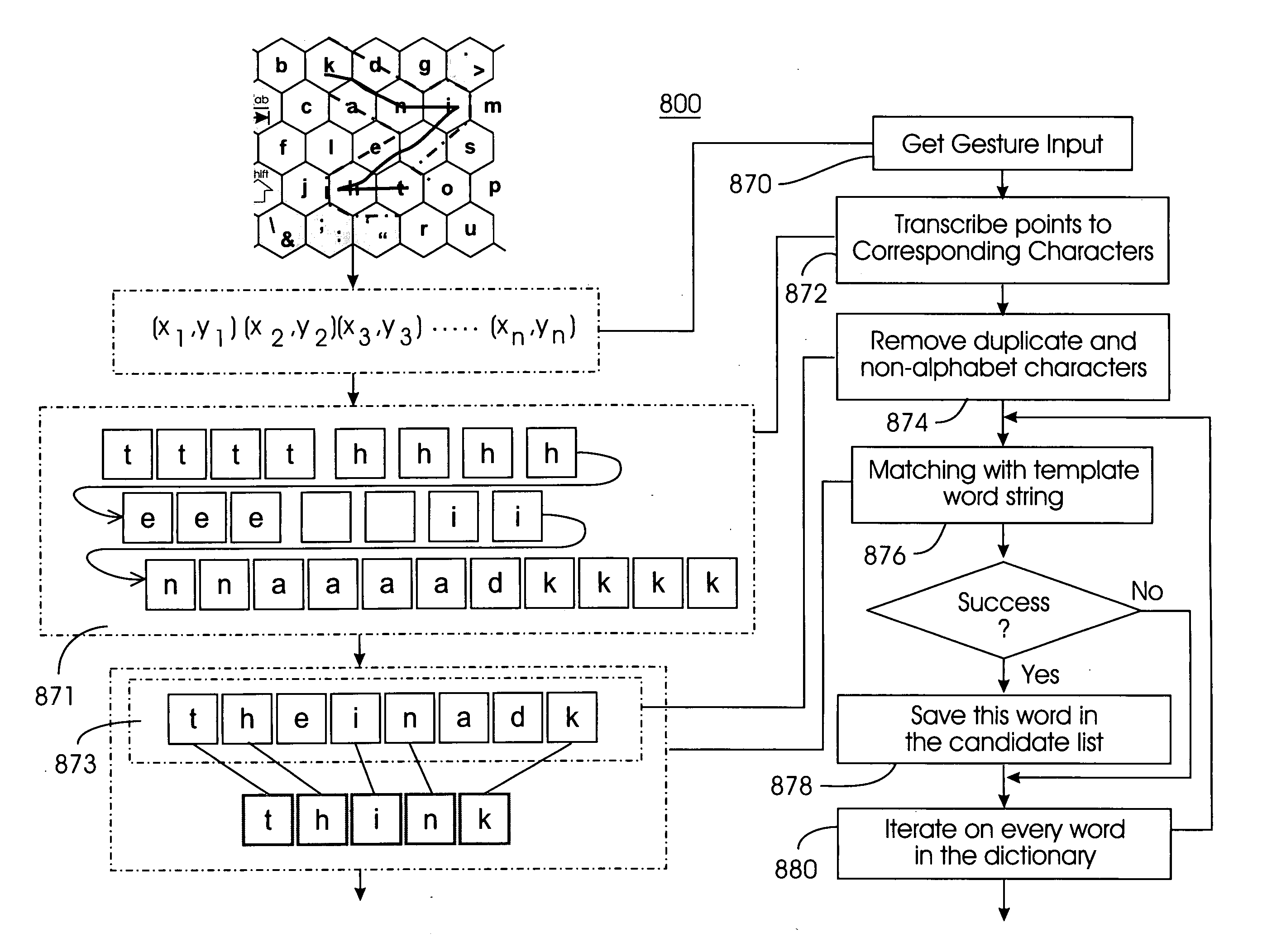
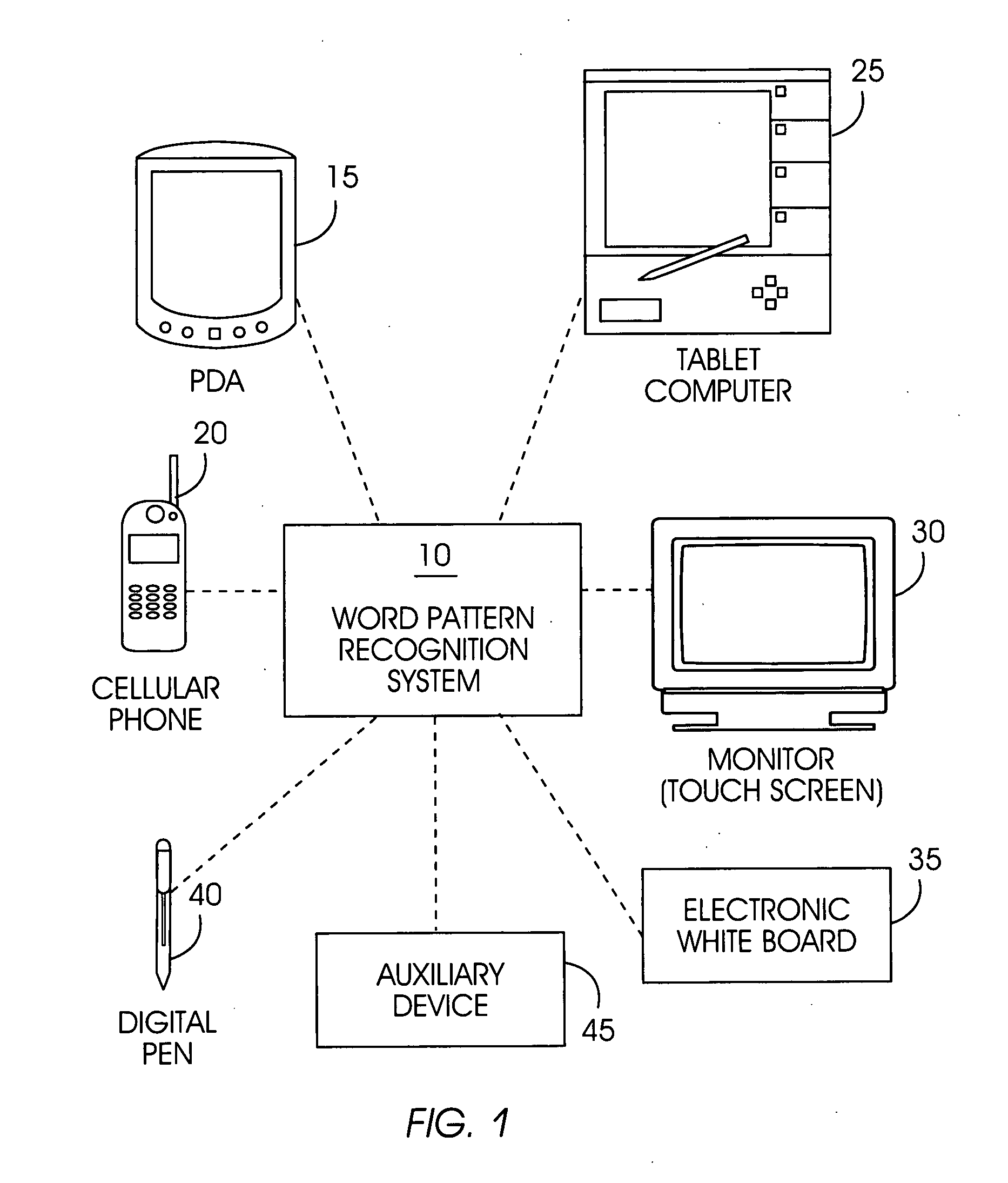
System and method for recognizing word patterns in a very large vocabulary based on a virtual keyboard layout
ActiveUS20050190973A1Reduce usageLess visual attentionCharacter and pattern recognitionSpecial data processing applicationsGraphicsText entry
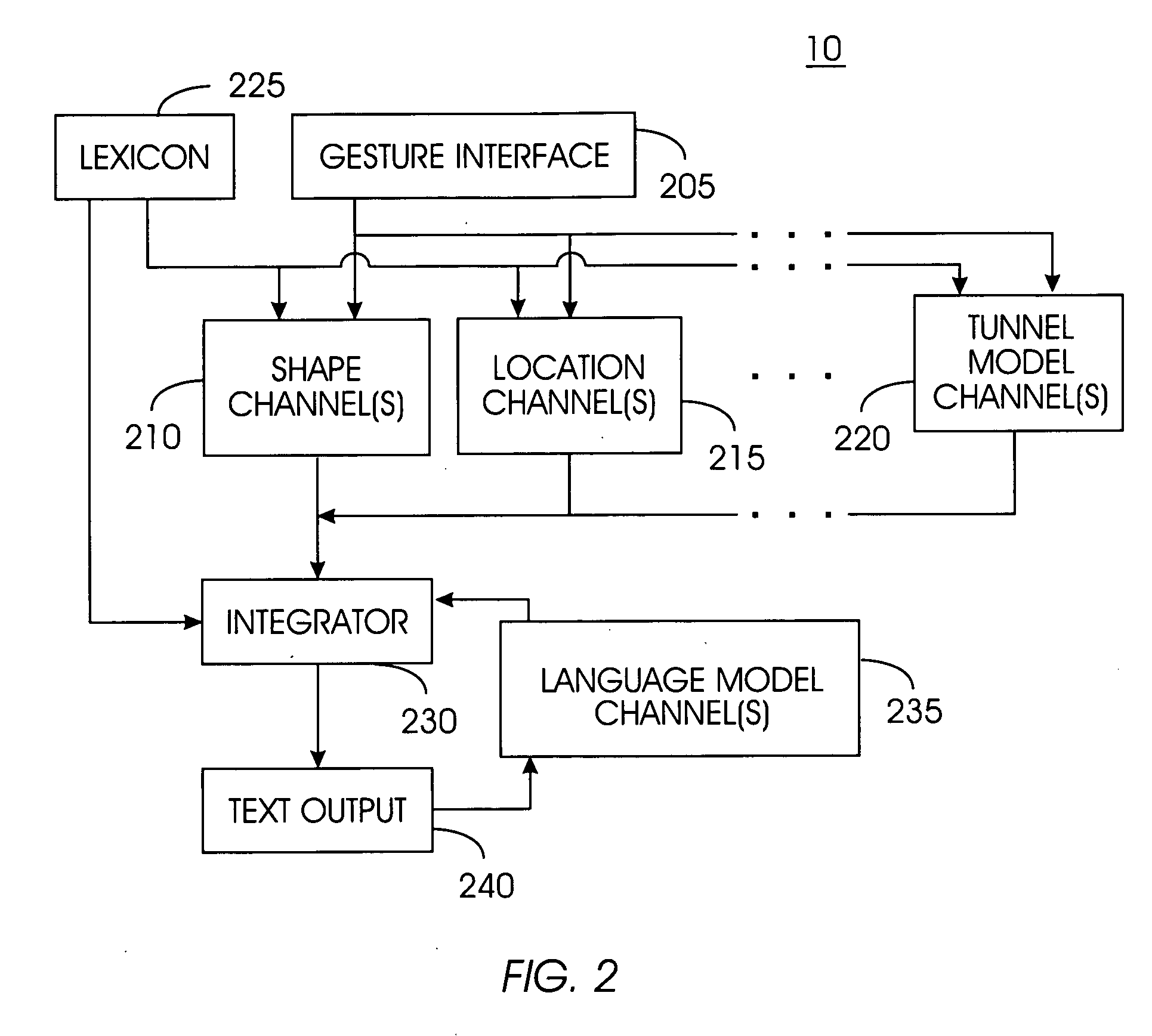
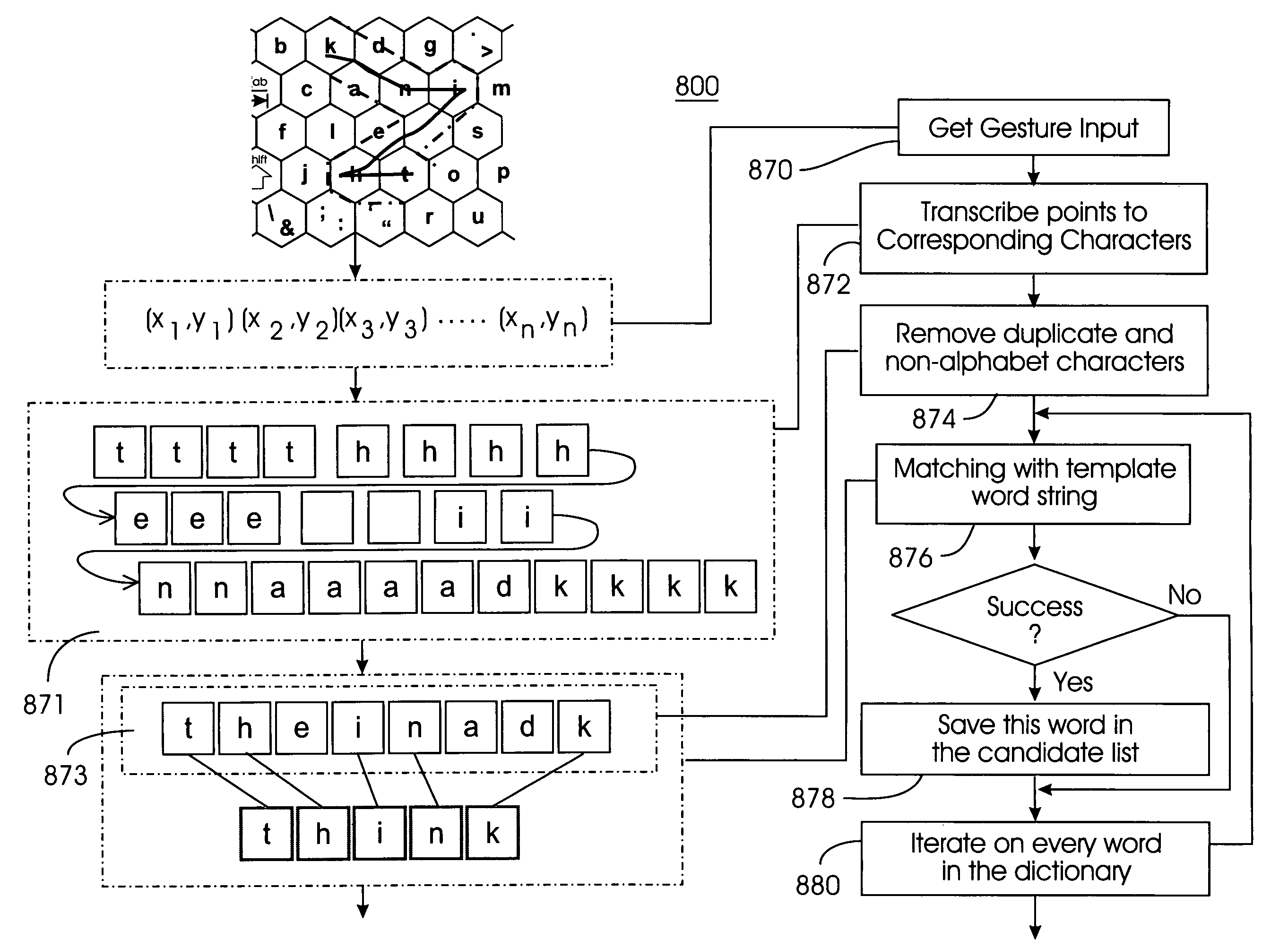
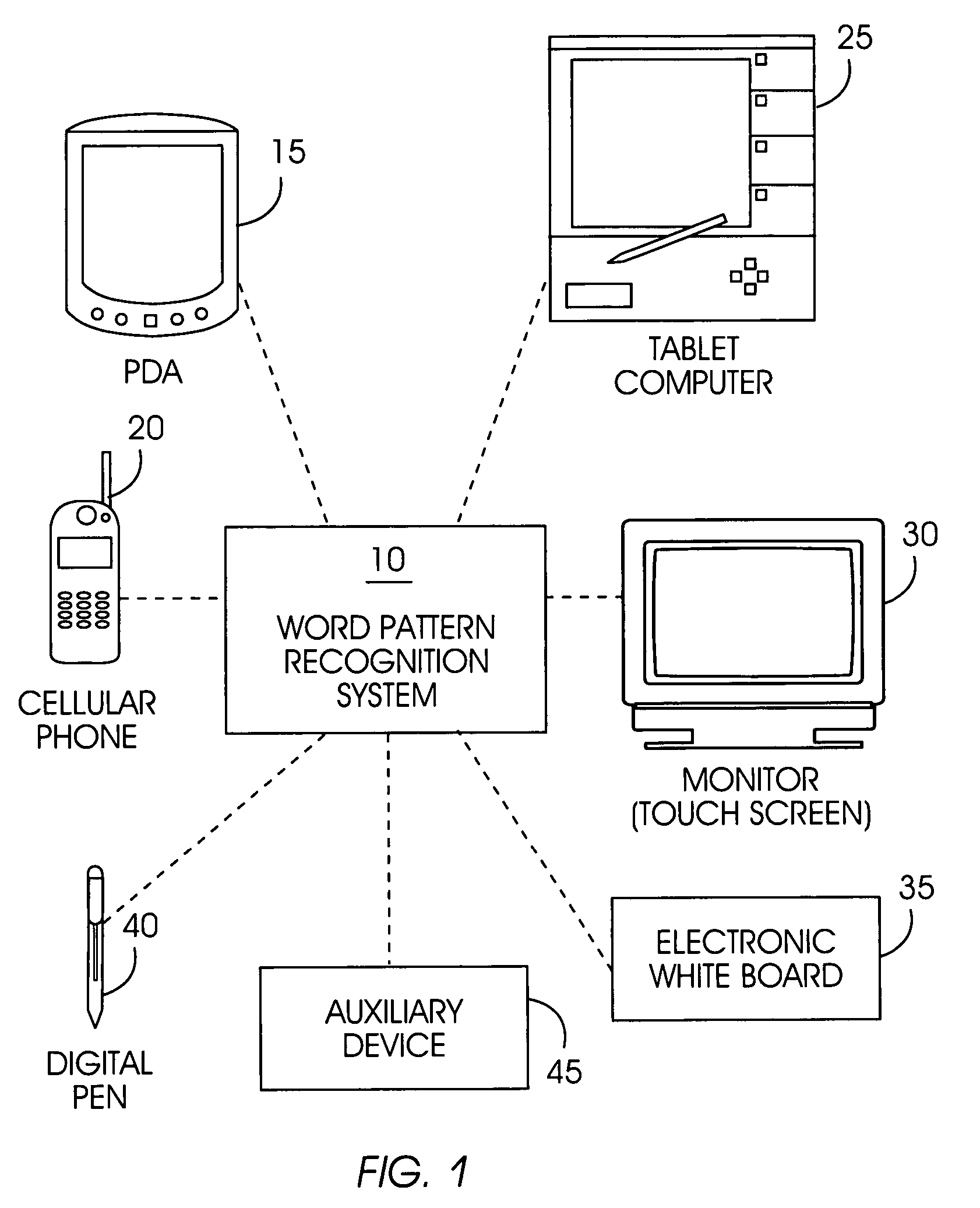
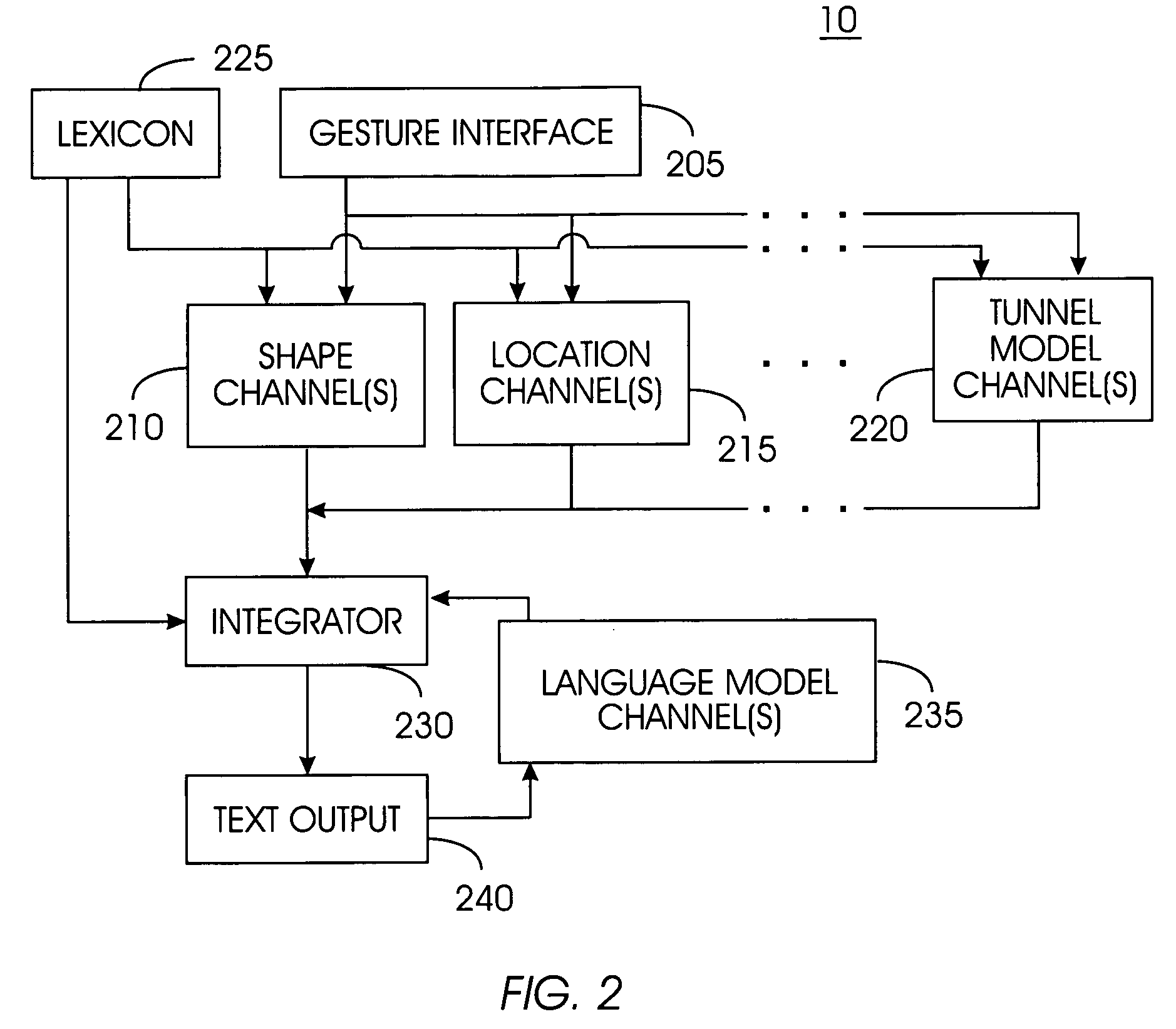
A word pattern recognition system based on a virtual keyboard layout combines handwriting recognition with a virtual, graphical, or on-screen keyboard to provide a text input method with relative ease of use. The system allows the user to input text quickly with little or no visual attention from the user. The system supports a very large vocabulary of gesture templates in a lexicon, including practically all words needed for a particular user. In addition, the system utilizes various techniques and methods to achieve reliable recognition of a very large gesture vocabulary. Further, the system provides feedback and display methods to help the user effectively use and learn shorthand gestures for words. Word patterns are recognized independent of gesture scale and location. The present system uses language rules to recognize and connect suffixes with a preceding word, allowing users to break complex words into easily remembered segments.
Owner:CERENCE OPERATING CO
Methods for providing cardless payment
ActiveUS7099850B1Convenient and easy to rememberConvenient and/orPublic key for secure communicationPayment protocolsComputer hardwareThe Internet
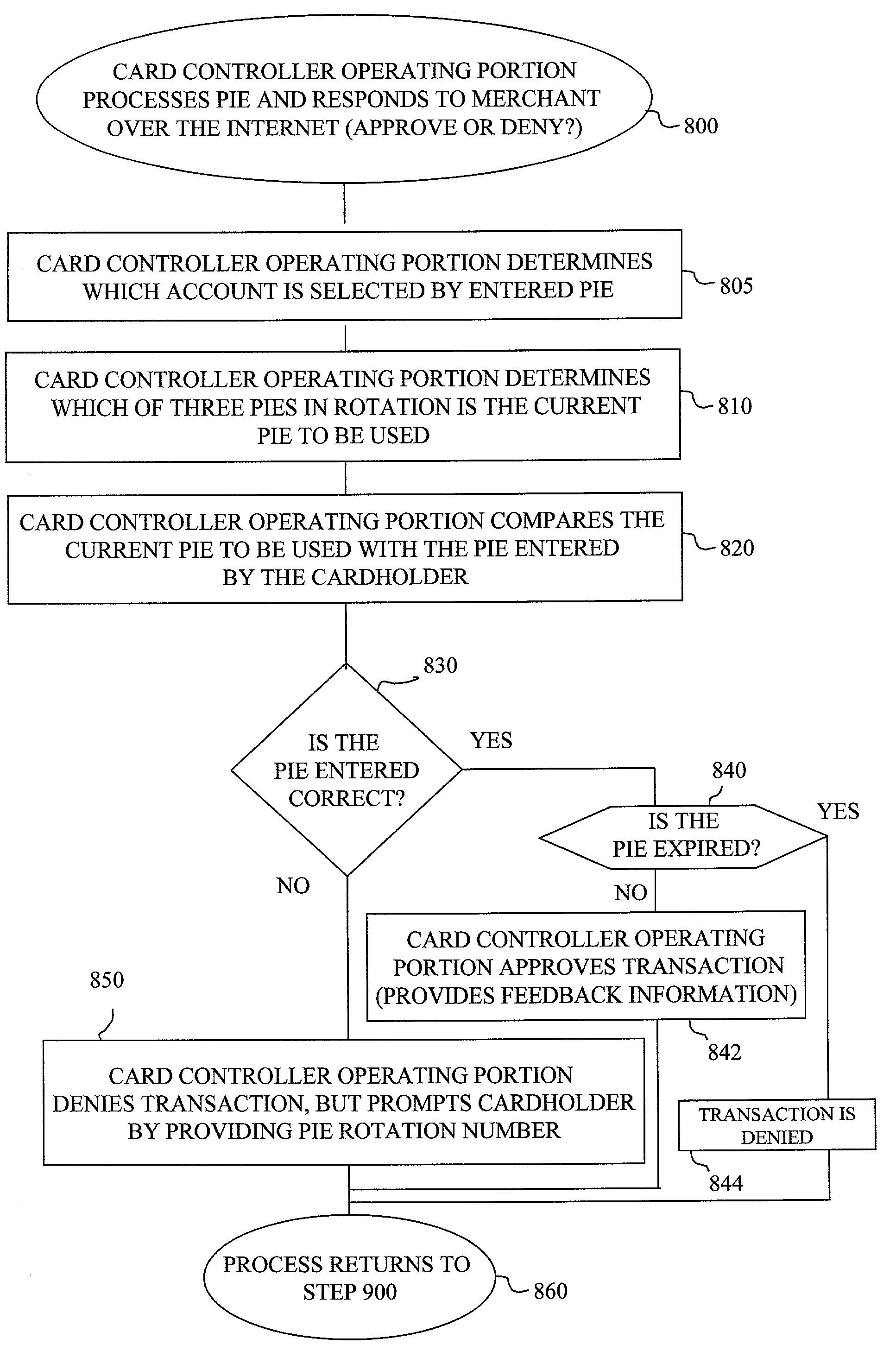
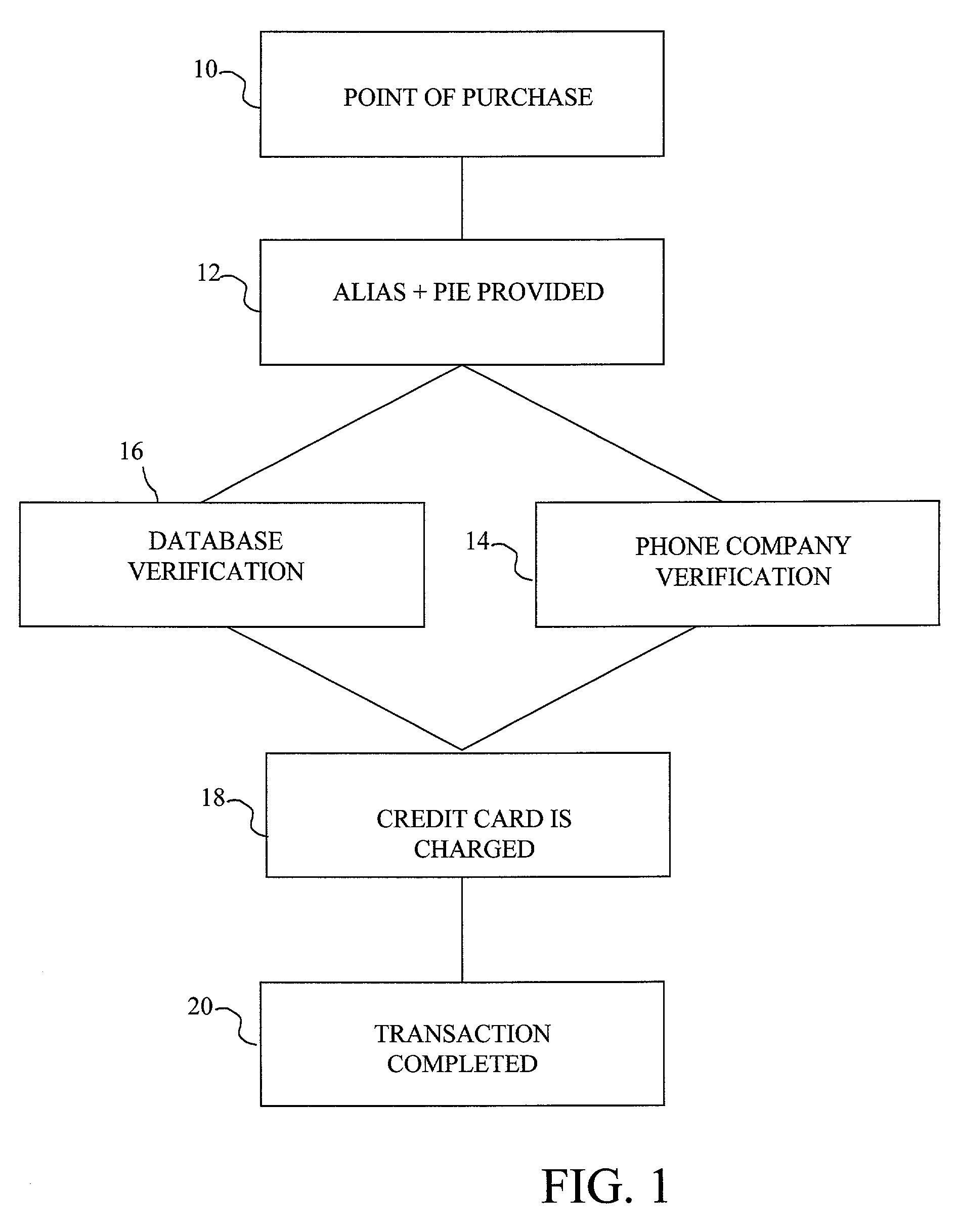
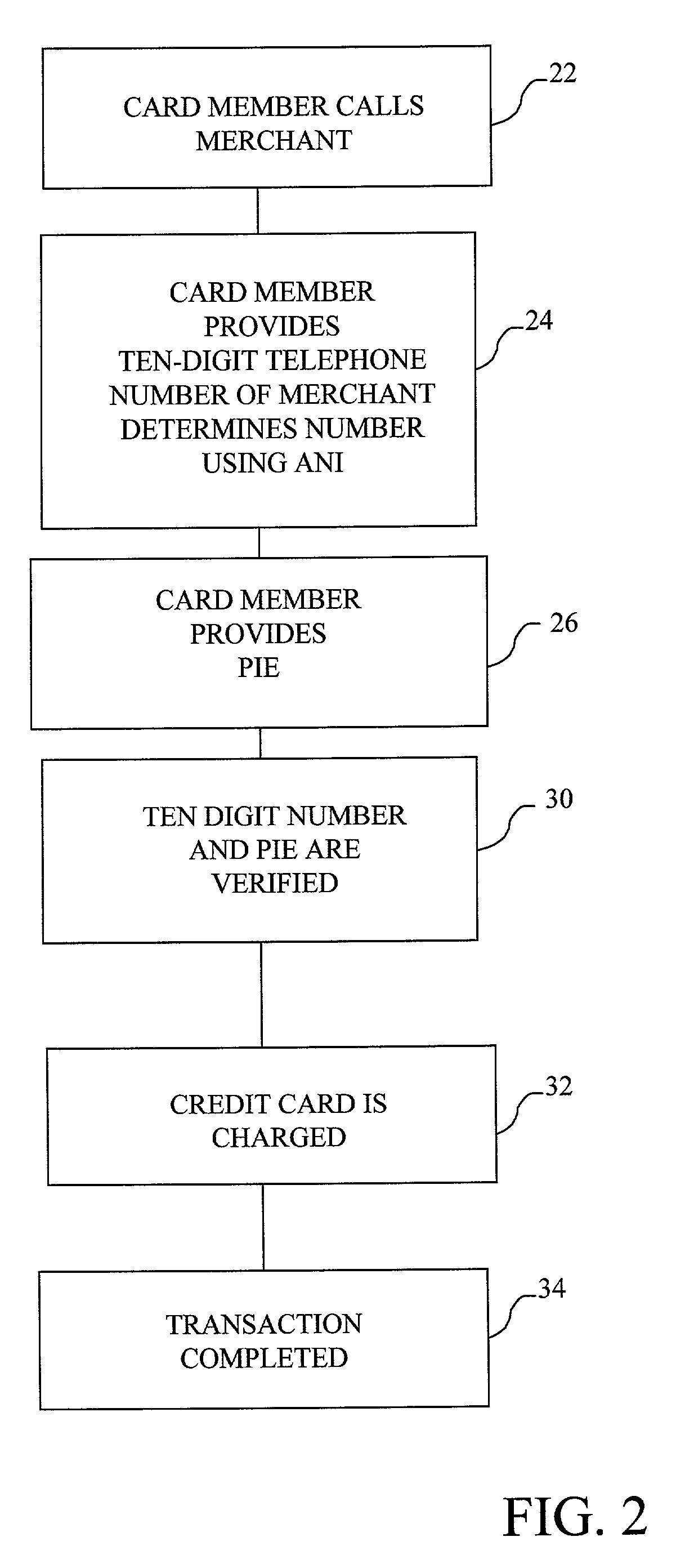
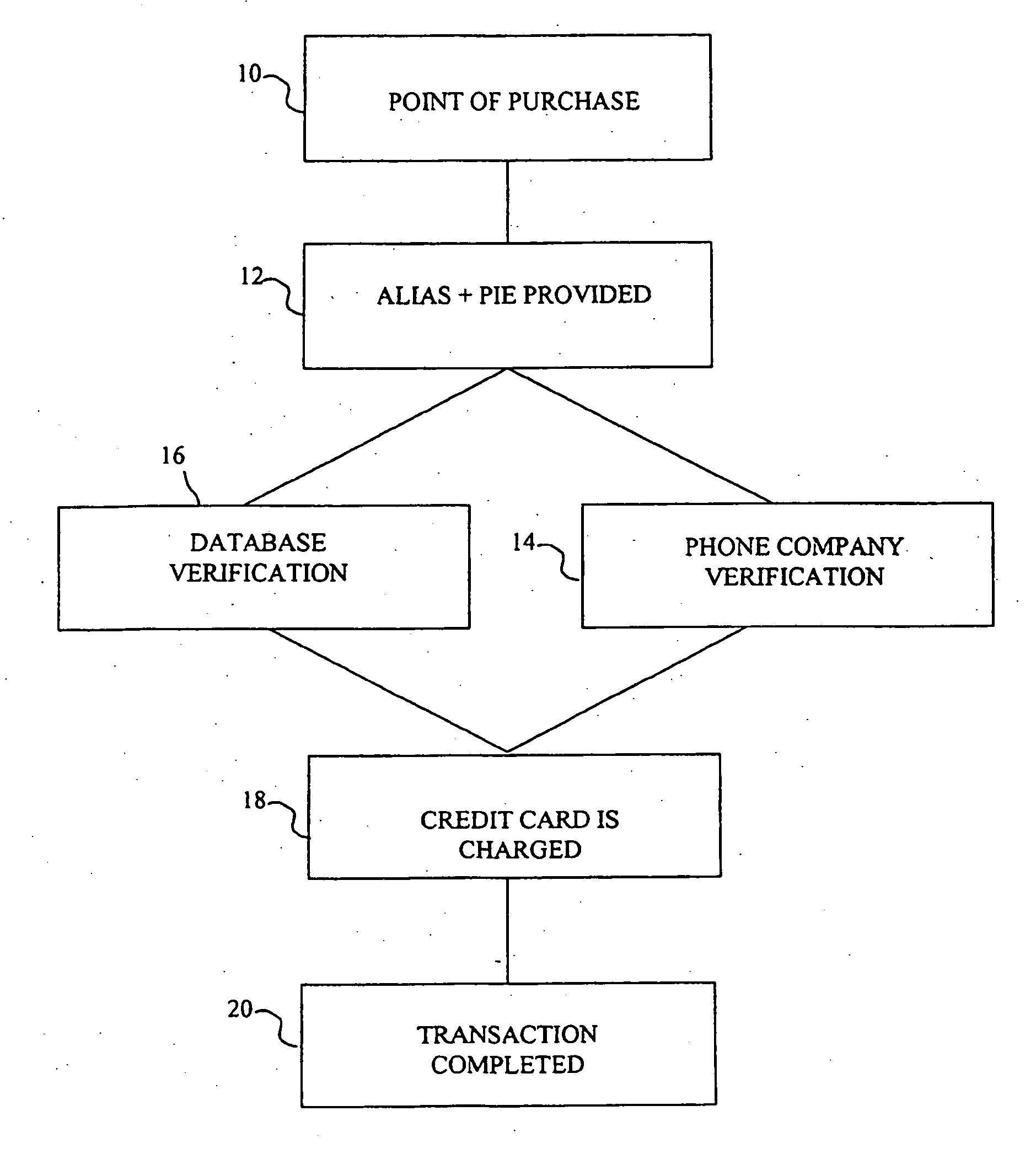
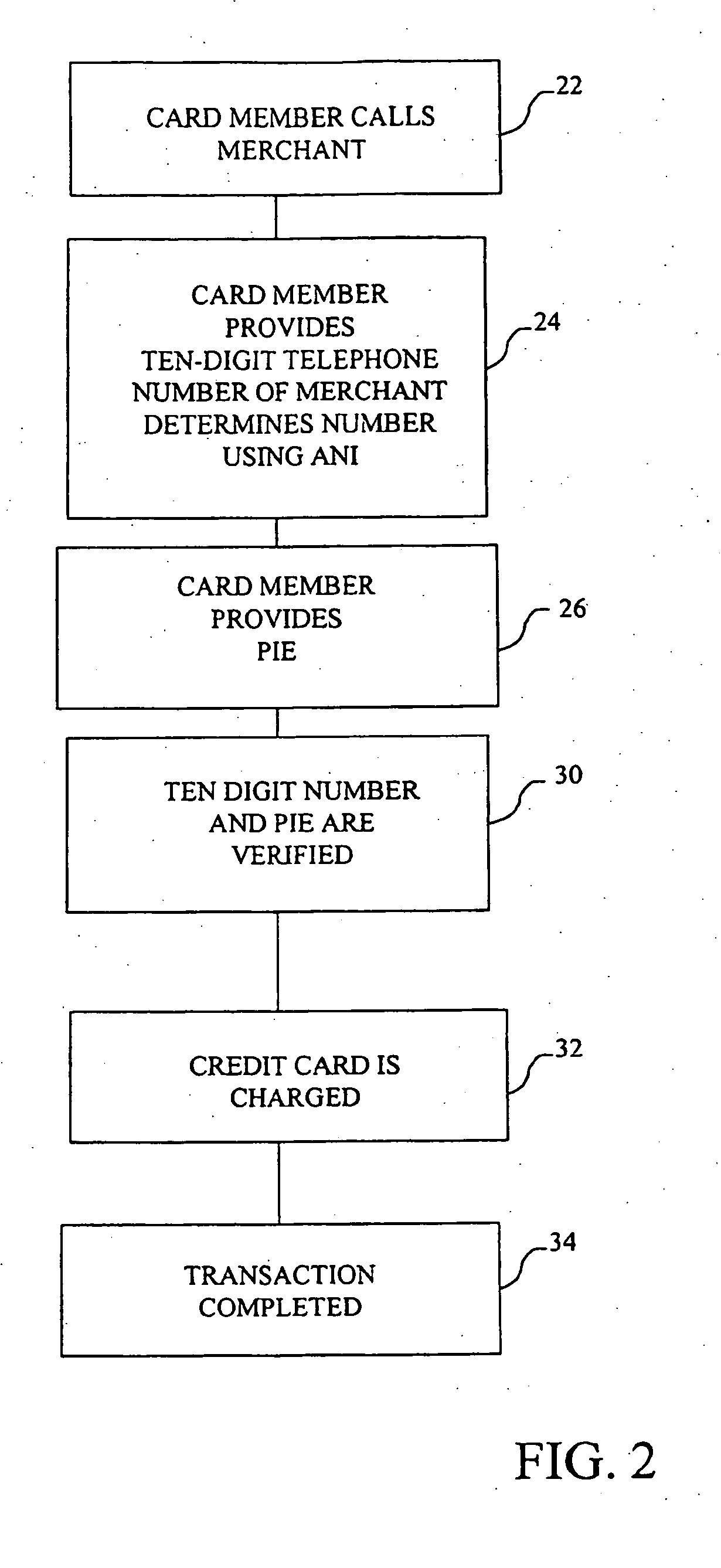
The method and system of the invention provide a variety of techniques for using a selected alias and a selected personal identification entry (PIE) in conjunction with use of a transaction card, such as a credit card, debit card or stored value card, for example. A suitable number or other identification parameter is selected by the account-holder as an alias. The account-holder is then required to choose a PIE for security purposes. The alias is linked to the account-holder's credit card number via a database. When the account-holder enters into a transaction with a merchant, the physical card need not be present. The account-holder simply provides his or her alias and then the PIE. This can be done at any point of sale such as a store, catalog telephone order, or over the Internet. The alias and PIE are entered and authorization is returned from the credit card company.
Owner:JPMORGAN CHASE BANK NA
Method and system of providing authentication of user access to a computer resource via a mobile device using multiple separate security factors
ActiveUS20160261411A1Easy to rememberPromote cloningKey distribution for secure communicationCryptography processingComputer resourcesPassword
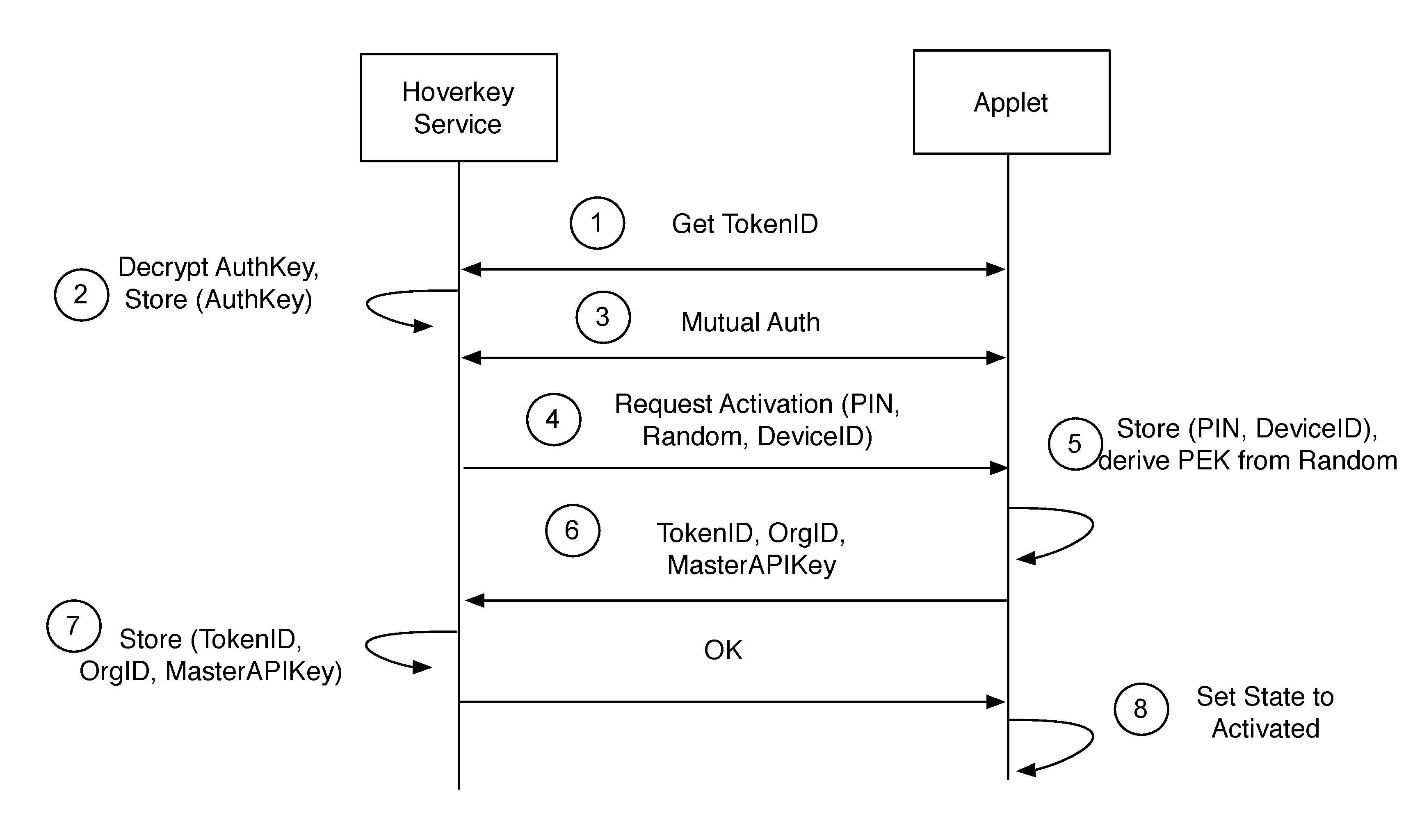
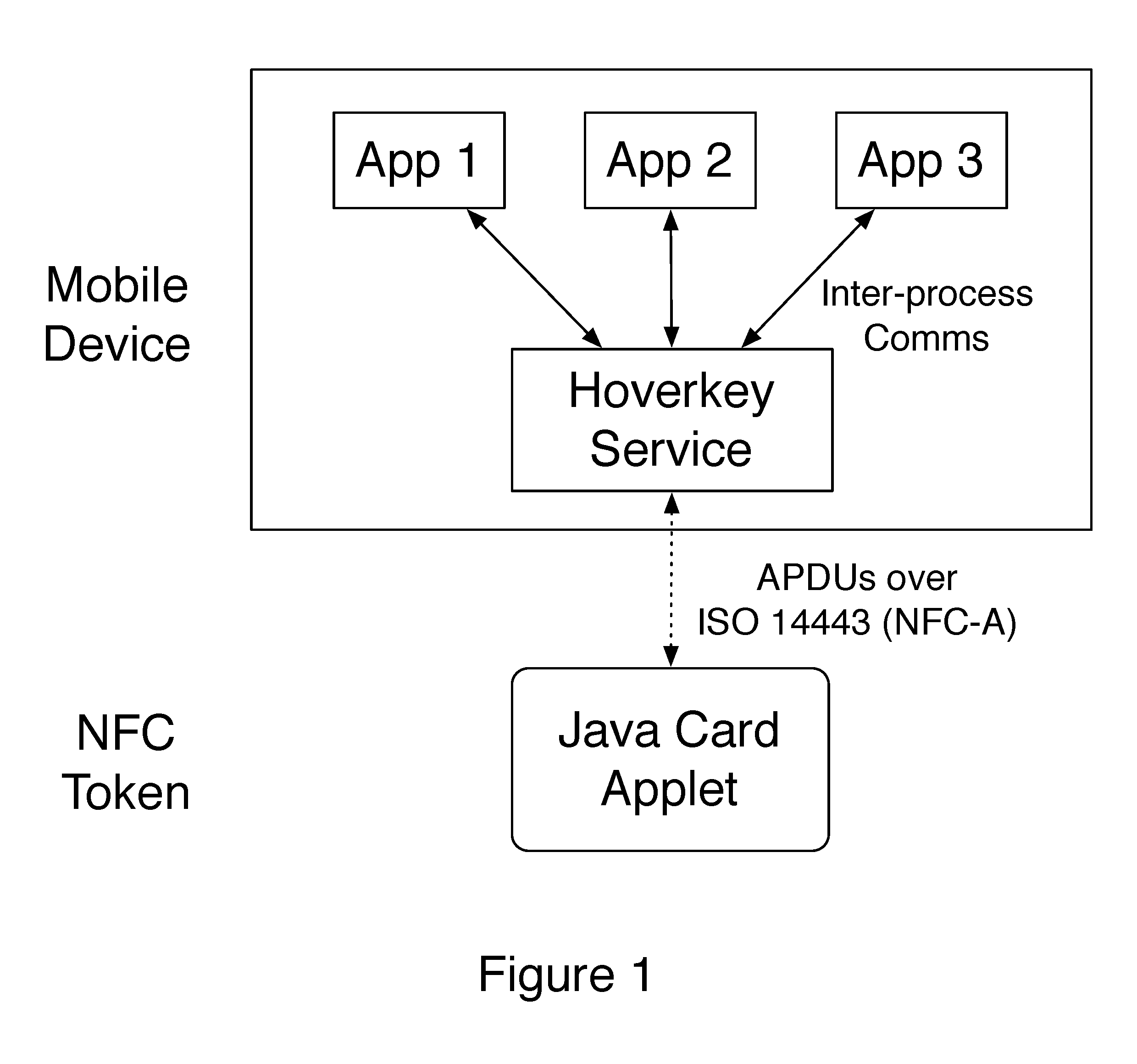
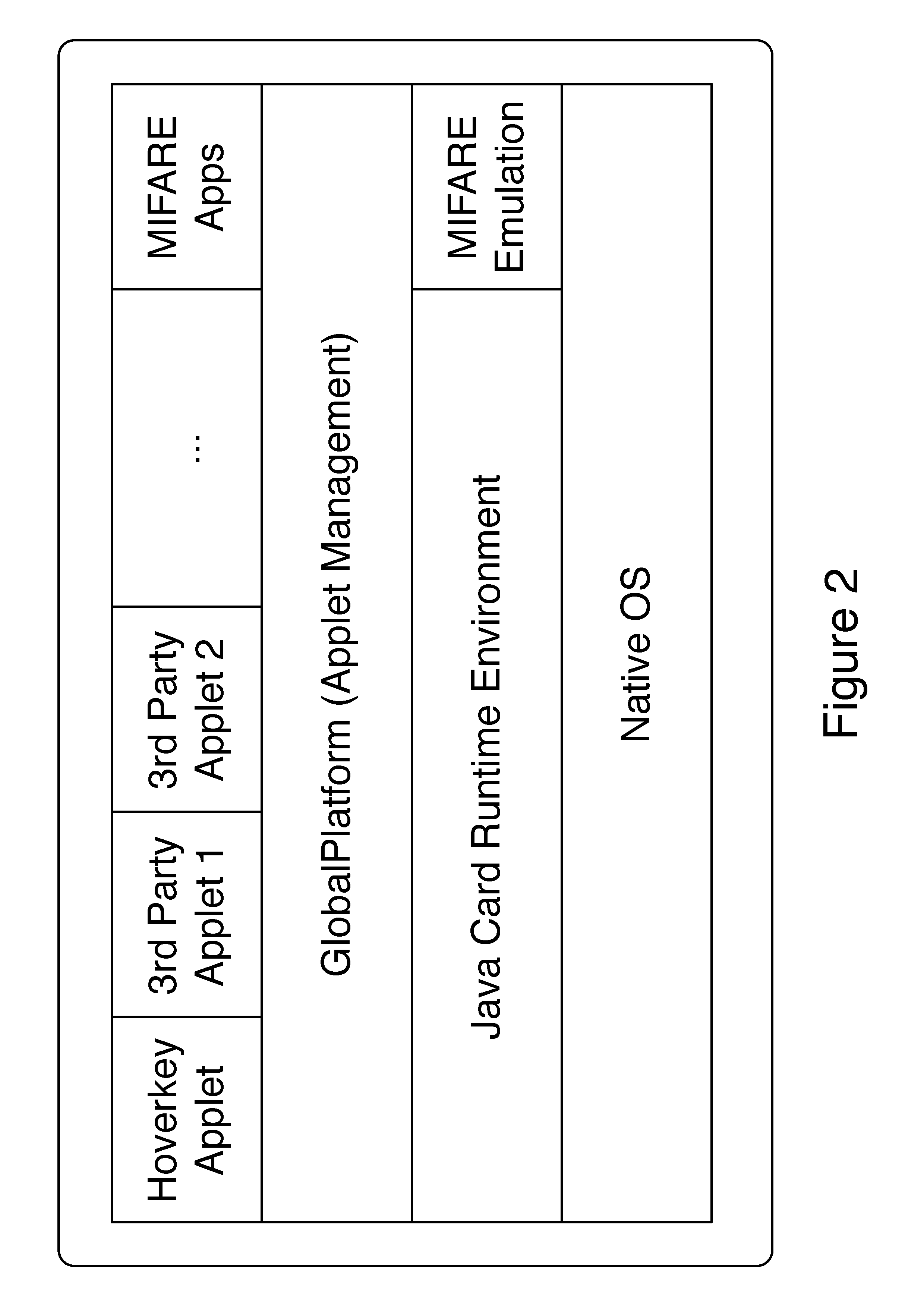
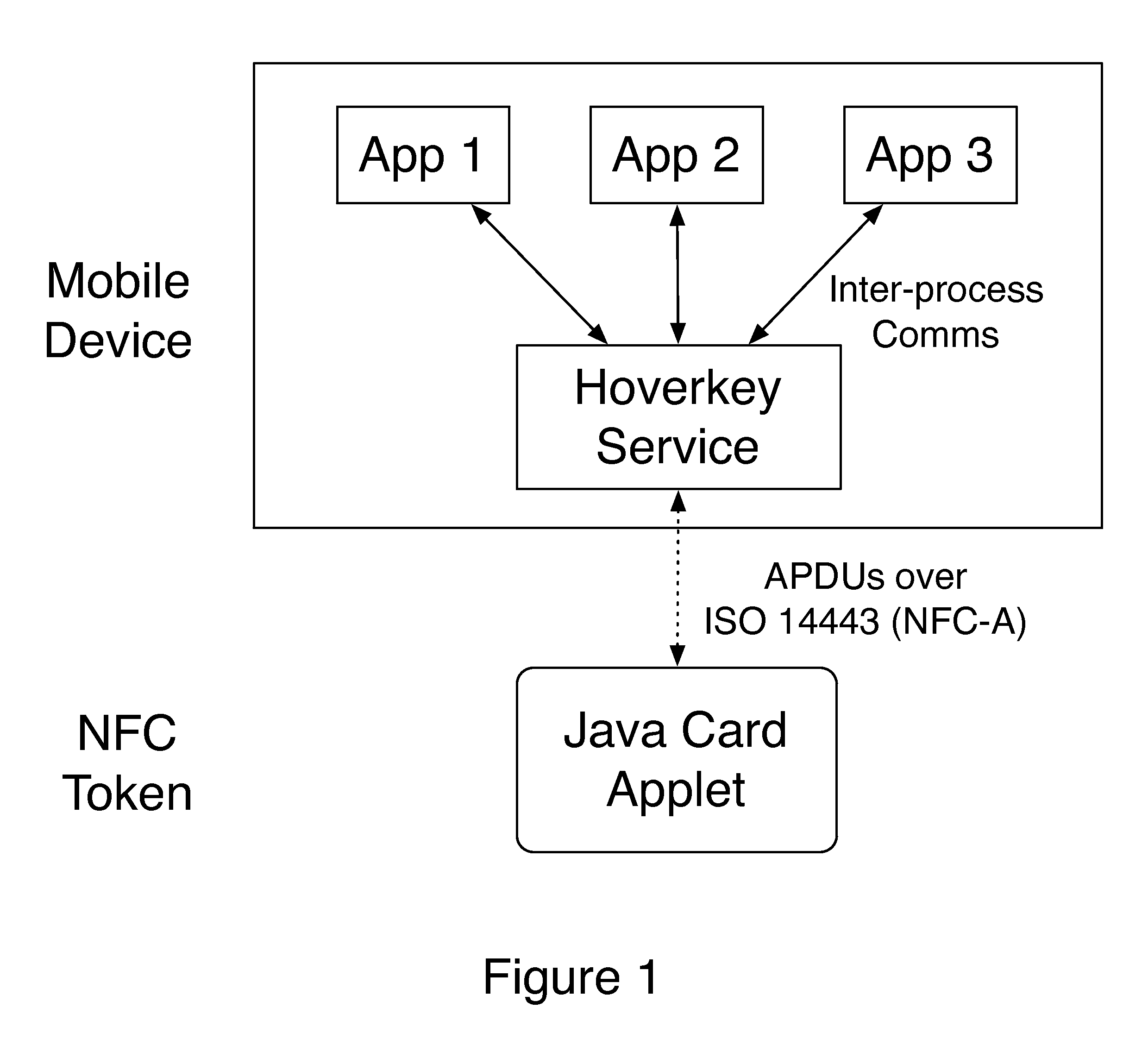
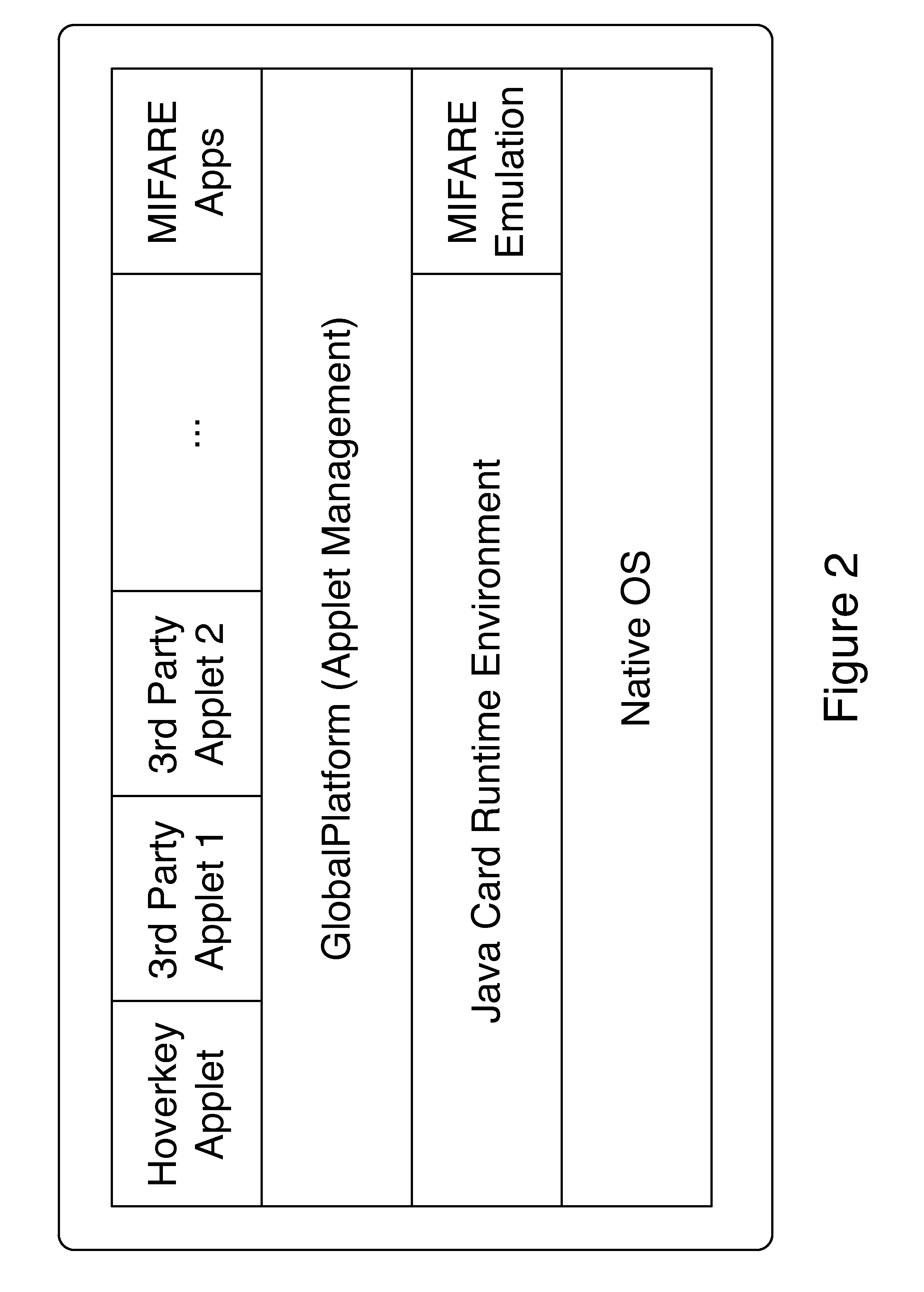
A method and system of authenticating a computer resource such as an application or data on a mobile device uses a contactless token to provide multi-factor user authentication. User credentials are stored on the token in the form of private keys, and encrypted data and passwords are stored on the device. When an application user requires access to the resource an encrypted password is transmitted to and decrypted on the token using a stored key. An unencrypted data encryption key or password is then transmitted back to the device under the protection of a cryptographic session key which is generated as a result of strong mutual authentication between the device and the token.
Owner:HOVERKEY
Flexible marking of recording data by a recording unit
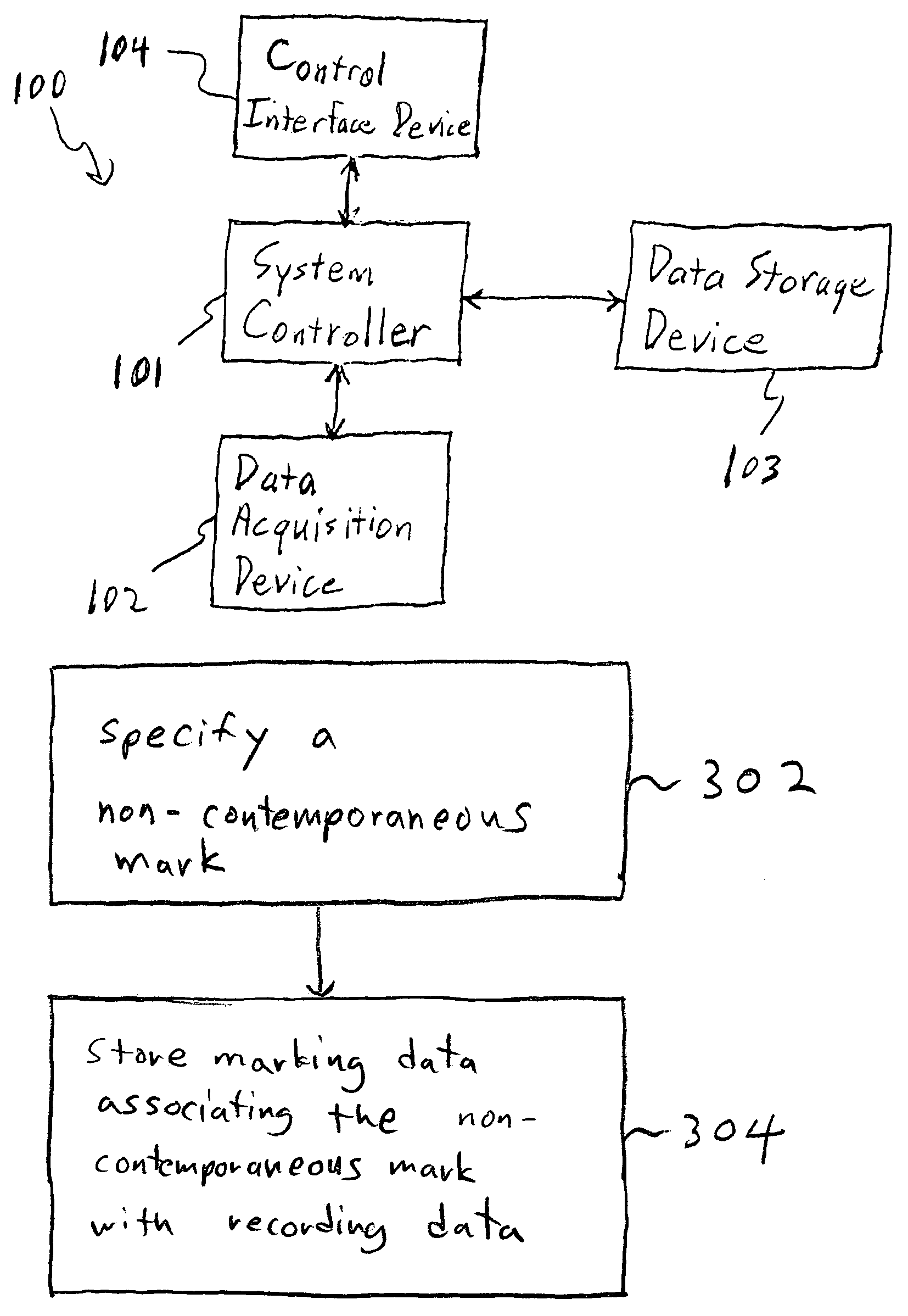
InactiveUS7194186B1Improve abilitiesLow attentionTelevision system detailsRecording carrier detailsComputer scienceLog data
Owner:VULCAN PATENTS
System and method for recognizing word patterns in a very large vocabulary based on a virtual keyboard layout
ActiveUS7706616B2Reduce usageLess visual attentionCharacter and pattern recognitionSpecial data processing applicationsGraphicsText entry
A word pattern recognition system based on a virtual keyboard layout combines handwriting recognition with a virtual, graphical, or on-screen keyboard to provide a text input method with relative ease of use. The system allows the user to input text quickly with little or no visual attention from the user. The system supports a very large vocabulary of gesture templates in a lexicon, including practically all words needed for a particular user. In addition, the system utilizes various techniques and methods to achieve reliable recognition of a very large gesture vocabulary. Further, the system provides feedback and display methods to help the user effectively use and learn shorthand gestures for words. Word patterns are recognized independent of gesture scale and location. The present system uses language rules to recognize and connect suffixes with a preceding word, allowing users to break complex words into easily remembered segments.
Owner:CERENCE OPERATING CO
System and method for generating language specific diacritics for different languages using a single keyboard layout
ActiveUS20060100848A1Conveniently generatedEliminate conflictElectronic switchingNatural language data processingUser inputSystem usage
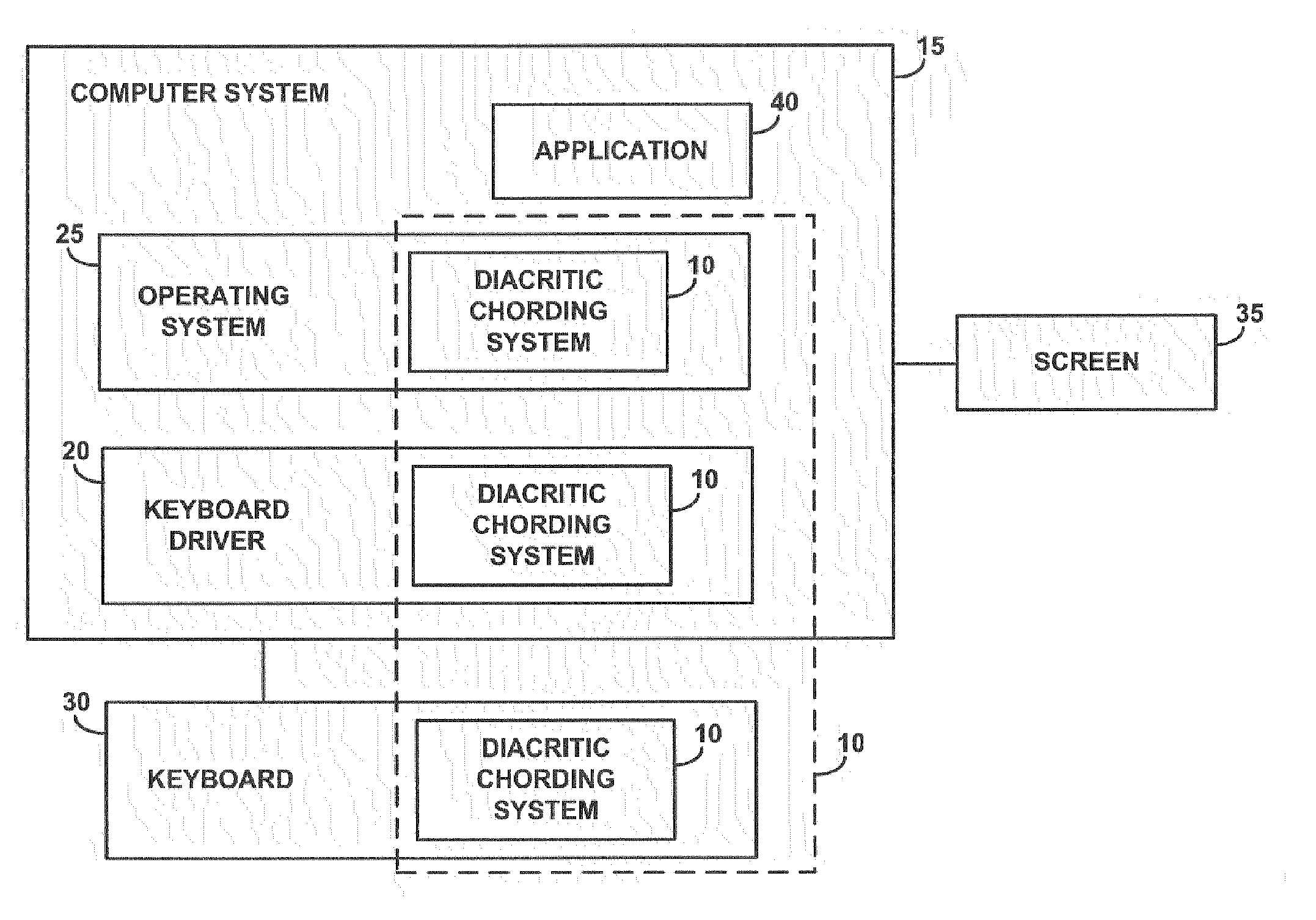
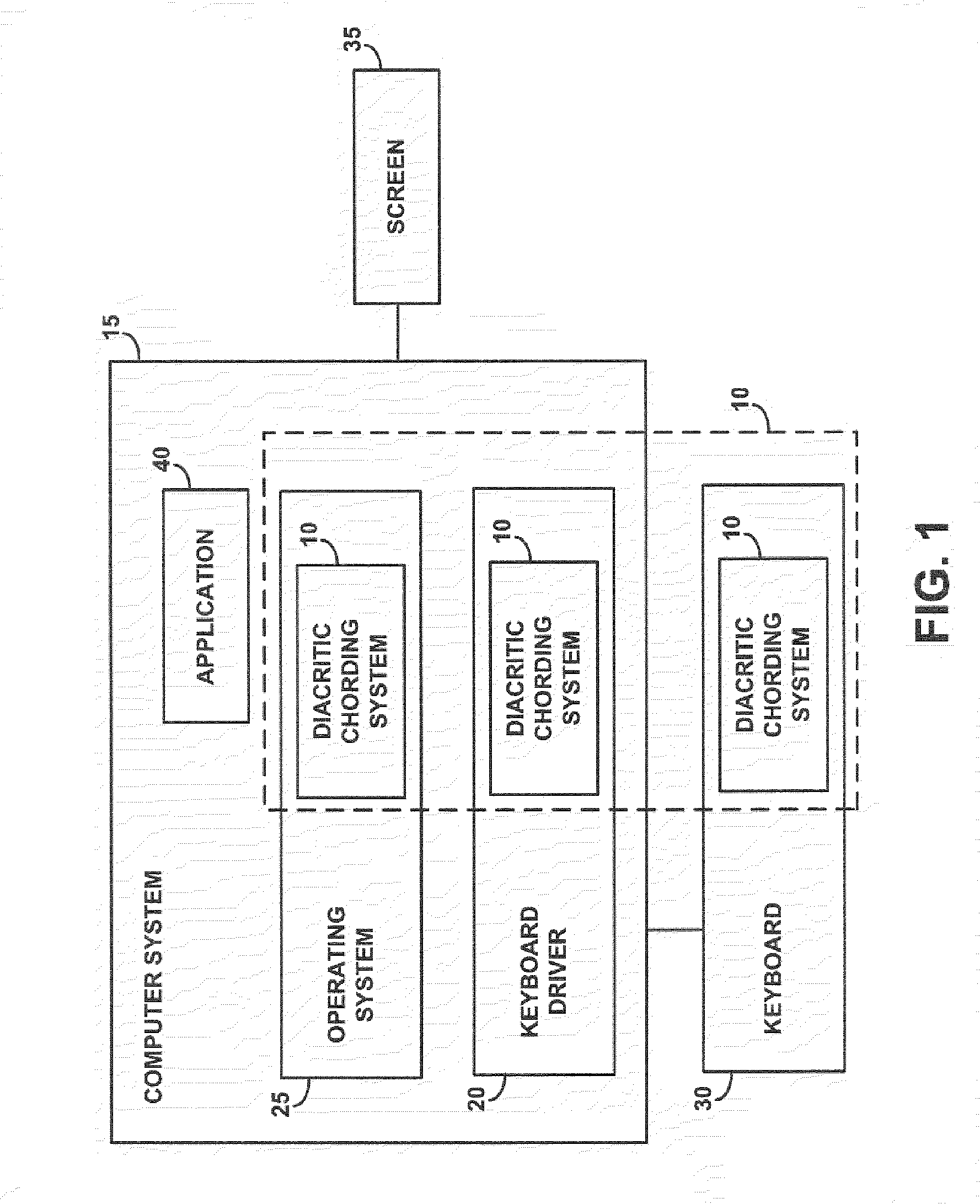
A diacritic chording system uses a single standard keyboard layout to generate diacritical characters used, for example, by Latin-based languages or languages based on a Roman character set, providing a universal keyboard The key combination required to select a diacritic is consistent, independent of the language the user is typing. The diacritic chording system uses chording to obtain characters modified by diacritics, i.e., diacritical characters. The key combinations in the diacritic chord are chosen in such a way to aid memorization by positional association of the keys or by logic association of the keys within the diacritic chord. The use of a combination of positional association and logical association eliminates conflicts in mapping diacritics for different languages. The diacritic chording system also provides a screen overlay as a mnemonic to illustrate which diacritic chords provide the desired diacritical character.
Owner:LENOVO PC INT
Unlocking method and device of operating system
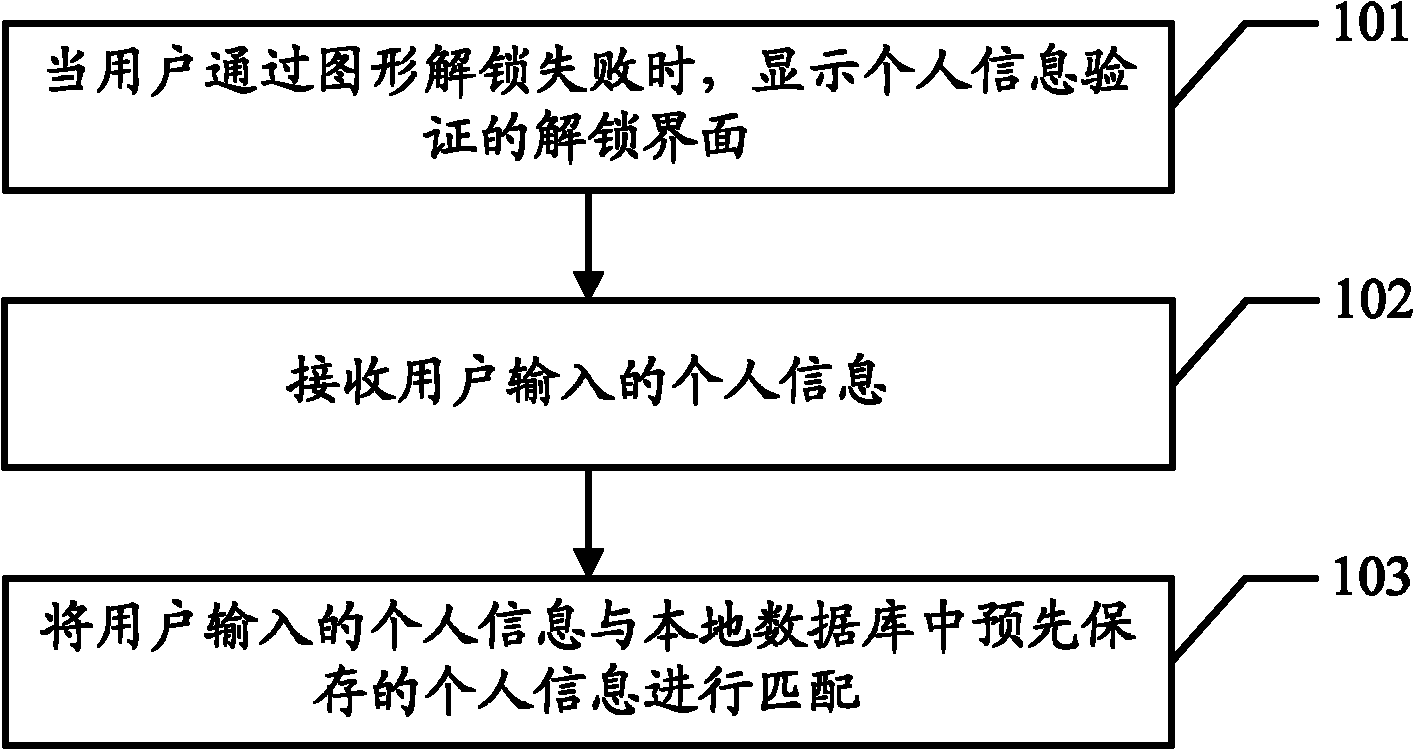
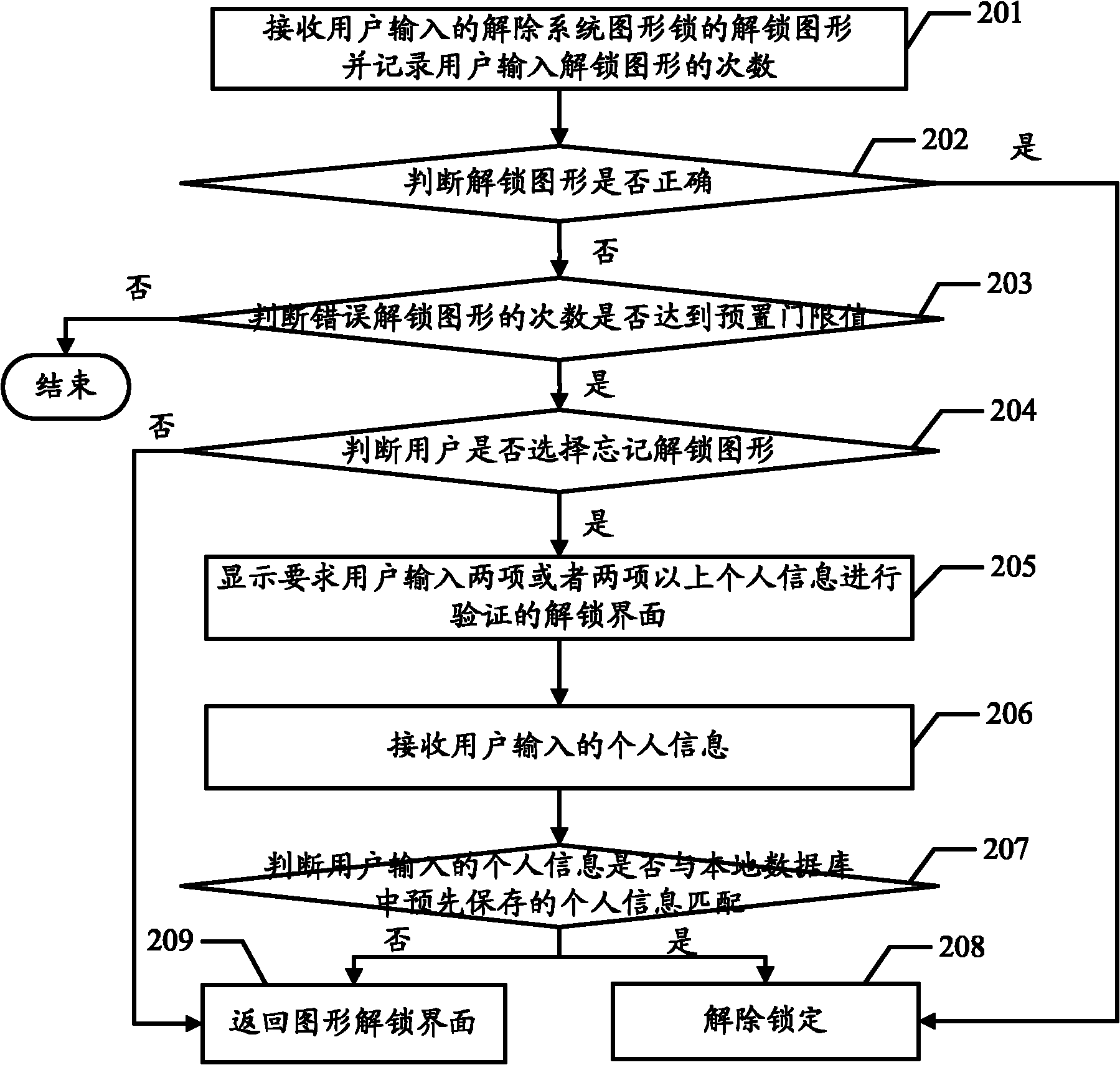
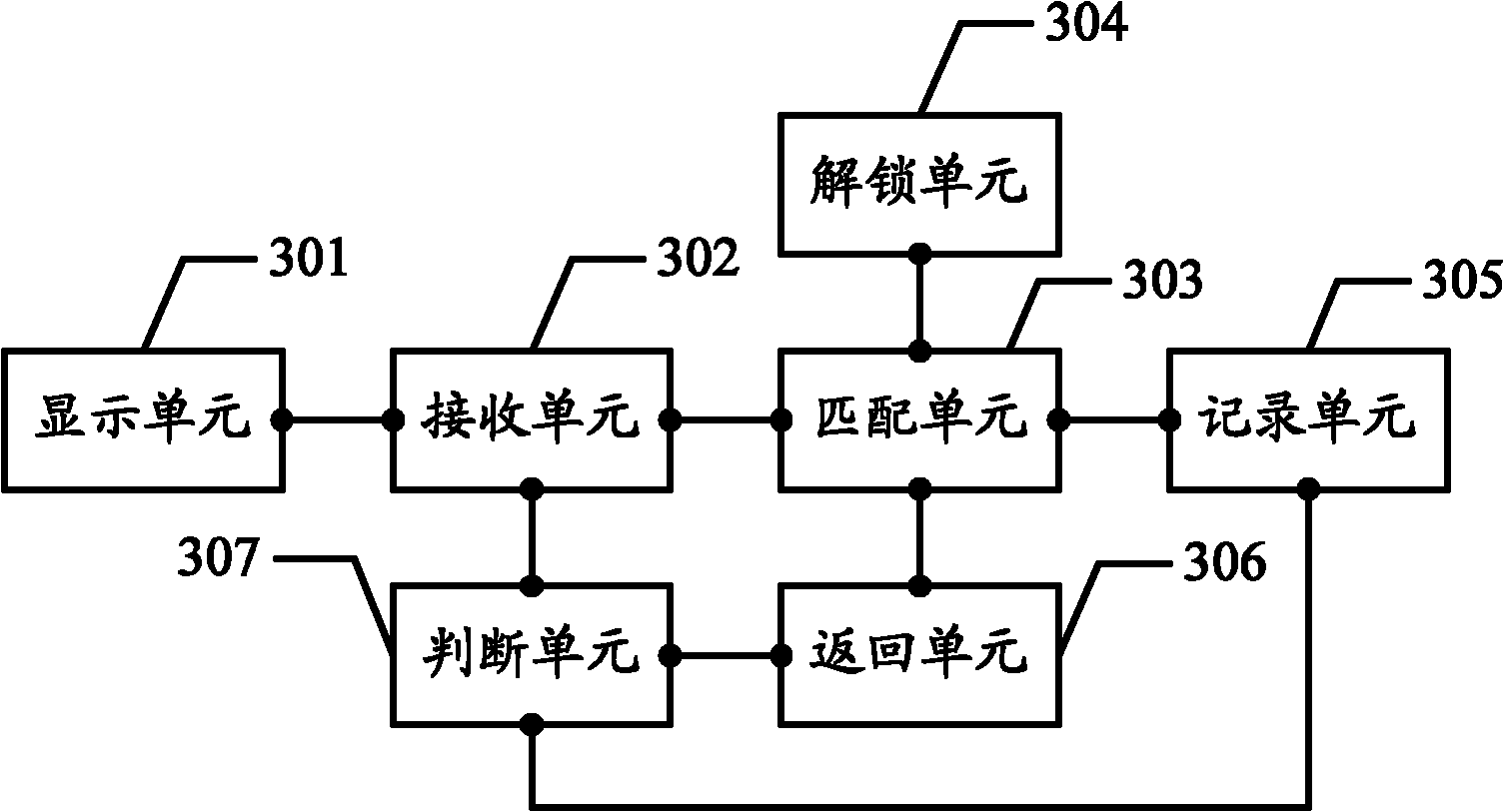
InactiveCN102096546AEasy to rememberIncrease the chance of unlocking successInternal/peripheral component protectionDigital data authenticationOperational systemPassword
The embodiment of the invention discloses an unlocking method and an unlocking device of an operating system, which are used for releasing system lock through personal information data when a user forgets a password to increase the success rate of unlocking by the user. The method in the embodiment of the invention comprises the following steps of: when the user fails during unlocking through a pattern, displaying an unlocking interface for verifying personal information; and matching personal information input by the user with personal information pre-stored in a local database.
Owner:HUAWEI DEVICE CO LTD
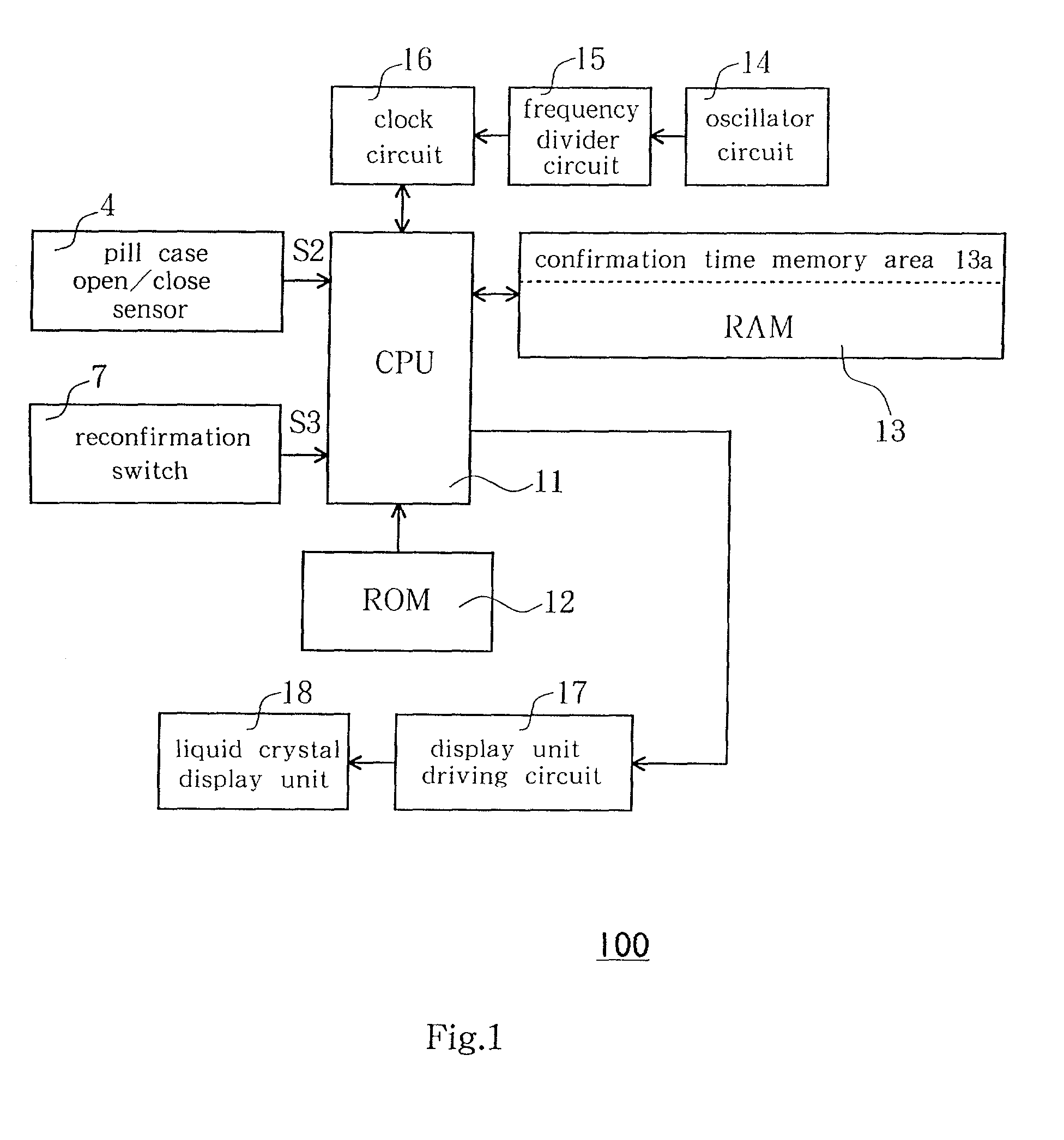
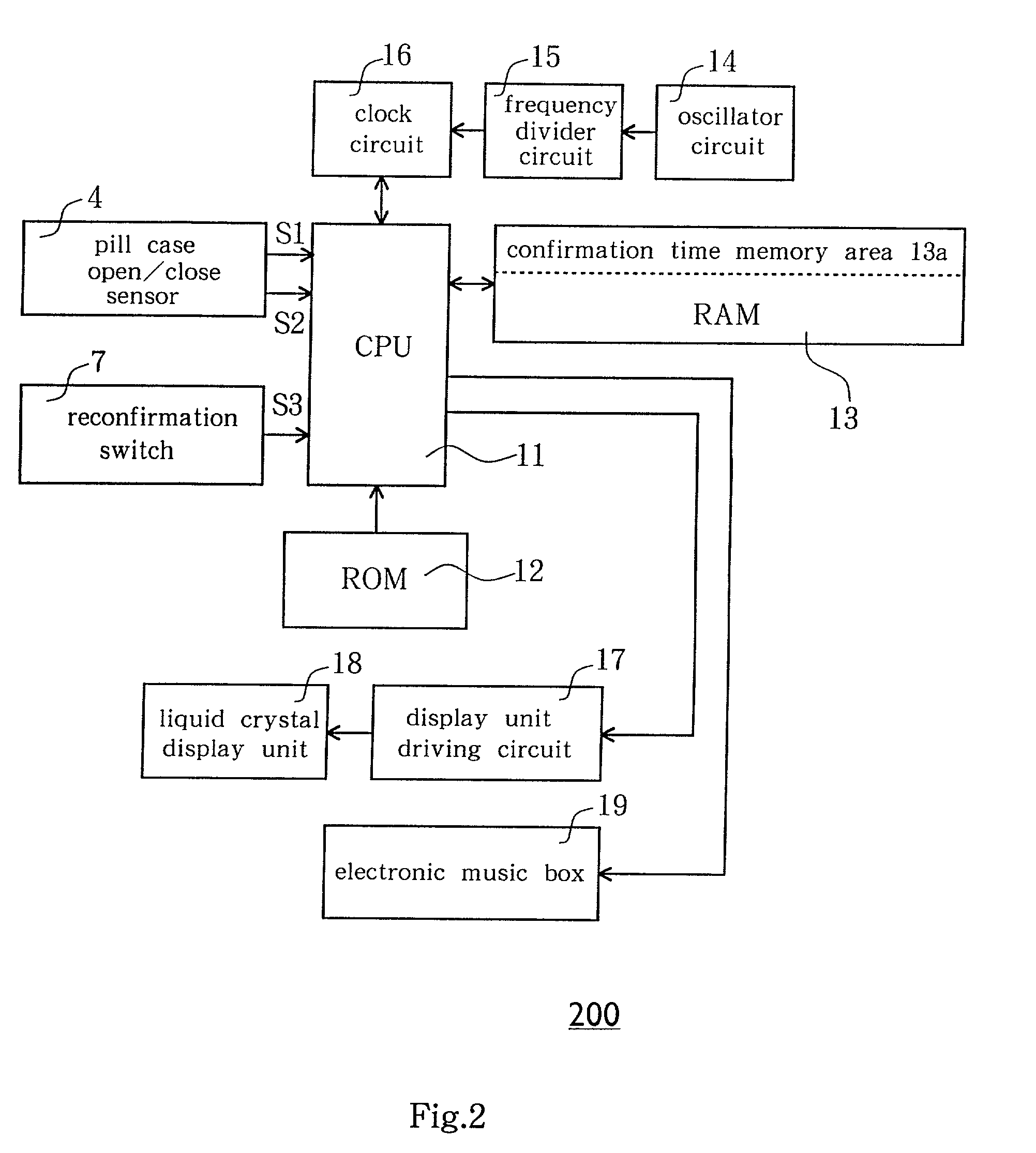
Medication-taking confirmation support device
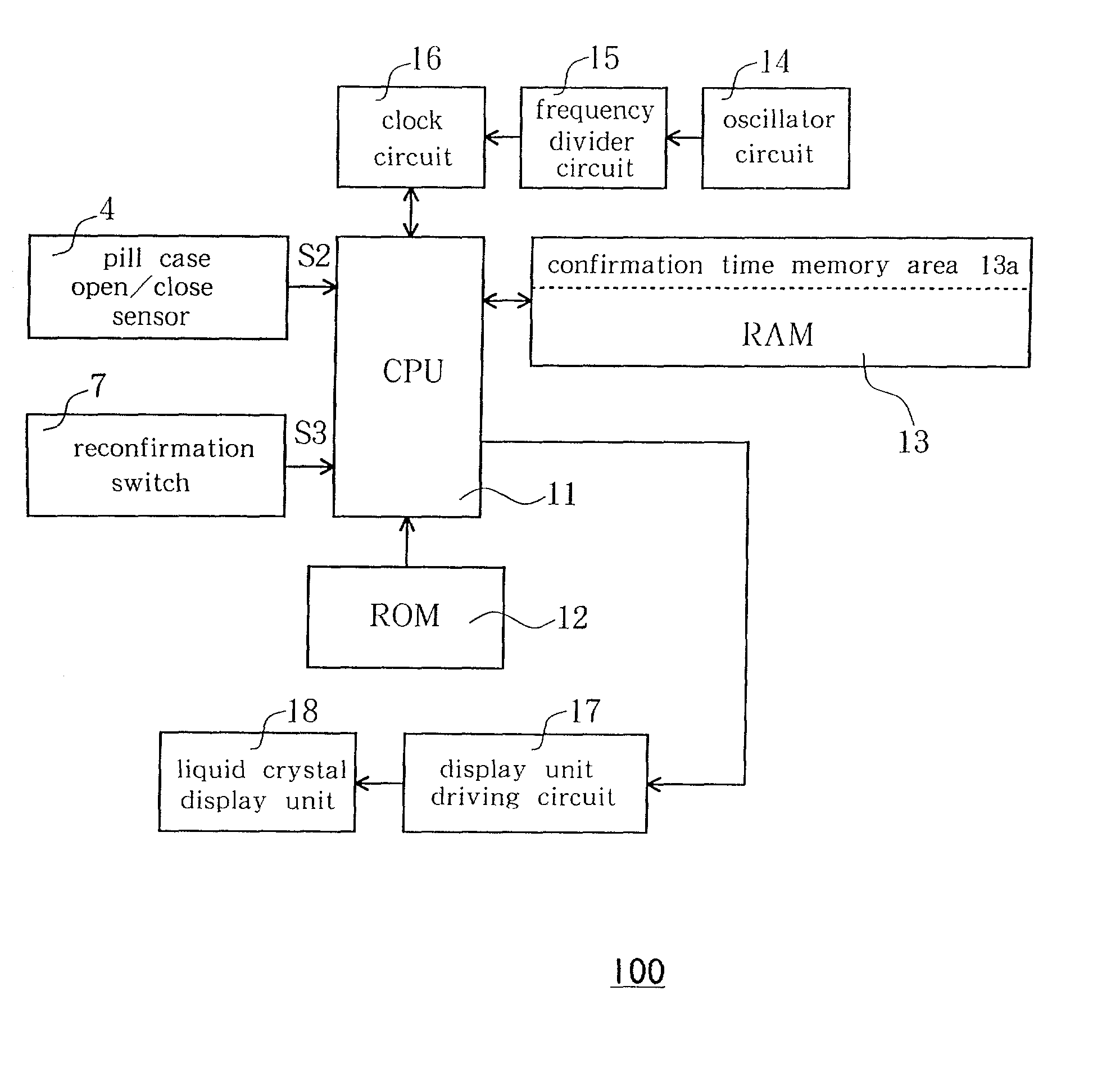
InactiveUS20020093429A1Easily and surely rememberEasy to rememberPharmaceutical containersMedical packagingEngineeringCLOCK
A medication-taking confirmation support device includes a pill case having a pill housing section, an electronic clock equipped with a memory, a notification unit and a controller, a pill case open / close sensor, and a reconfirmation signal input device. The controller makes the notification unit notify a medication-taking confirmation time on the basis of a detection signal from the pill case open / close sensor and also makes the memory store the medication-taking confirmation time at the time of taking medication. The controller further makes the notification unit re-notify the medication-taking confirmation time read out from the memory on the basis of a signal from the reconfirmation signal input device after having taken medication.
Owner:SELF SECURITY
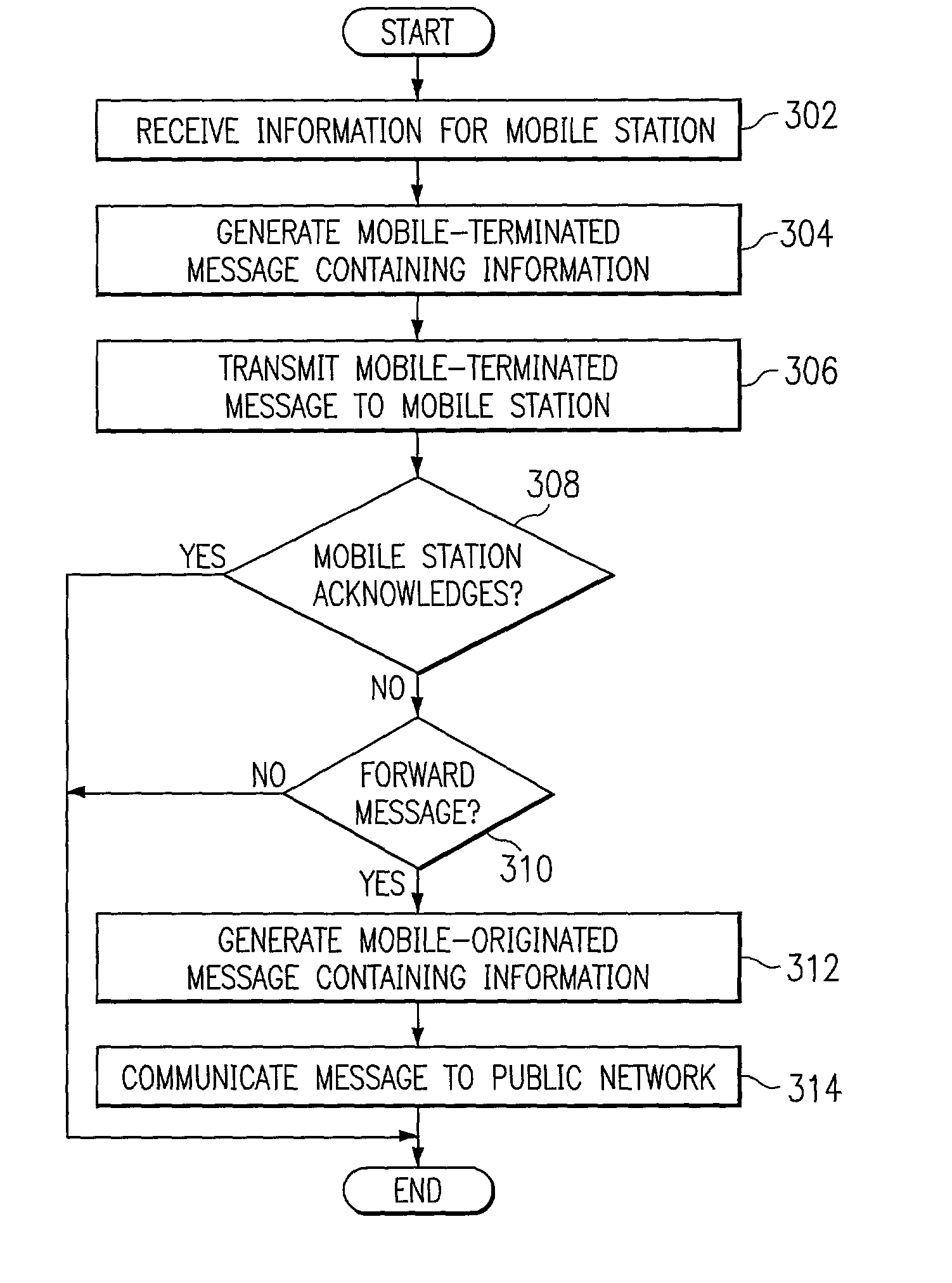
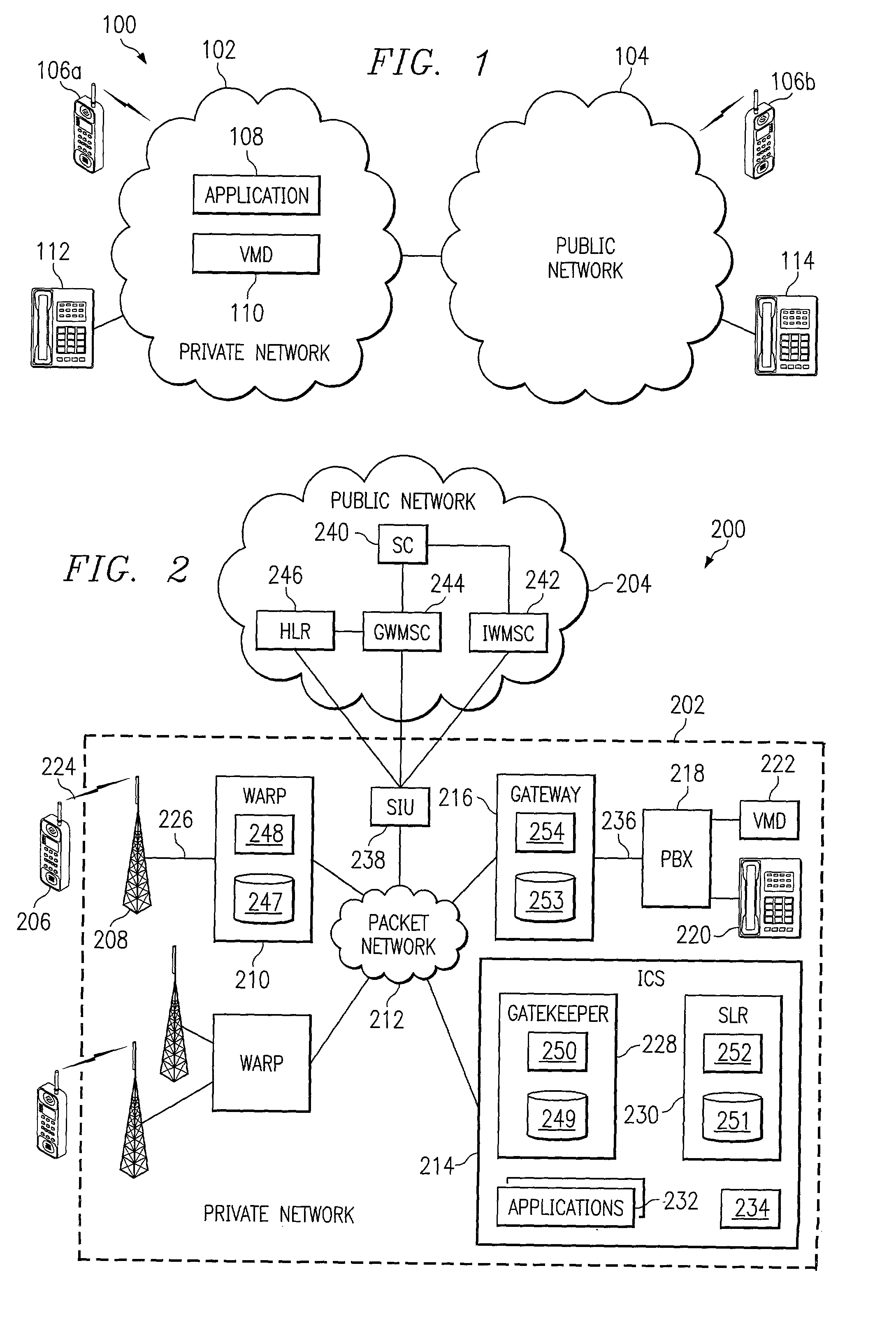
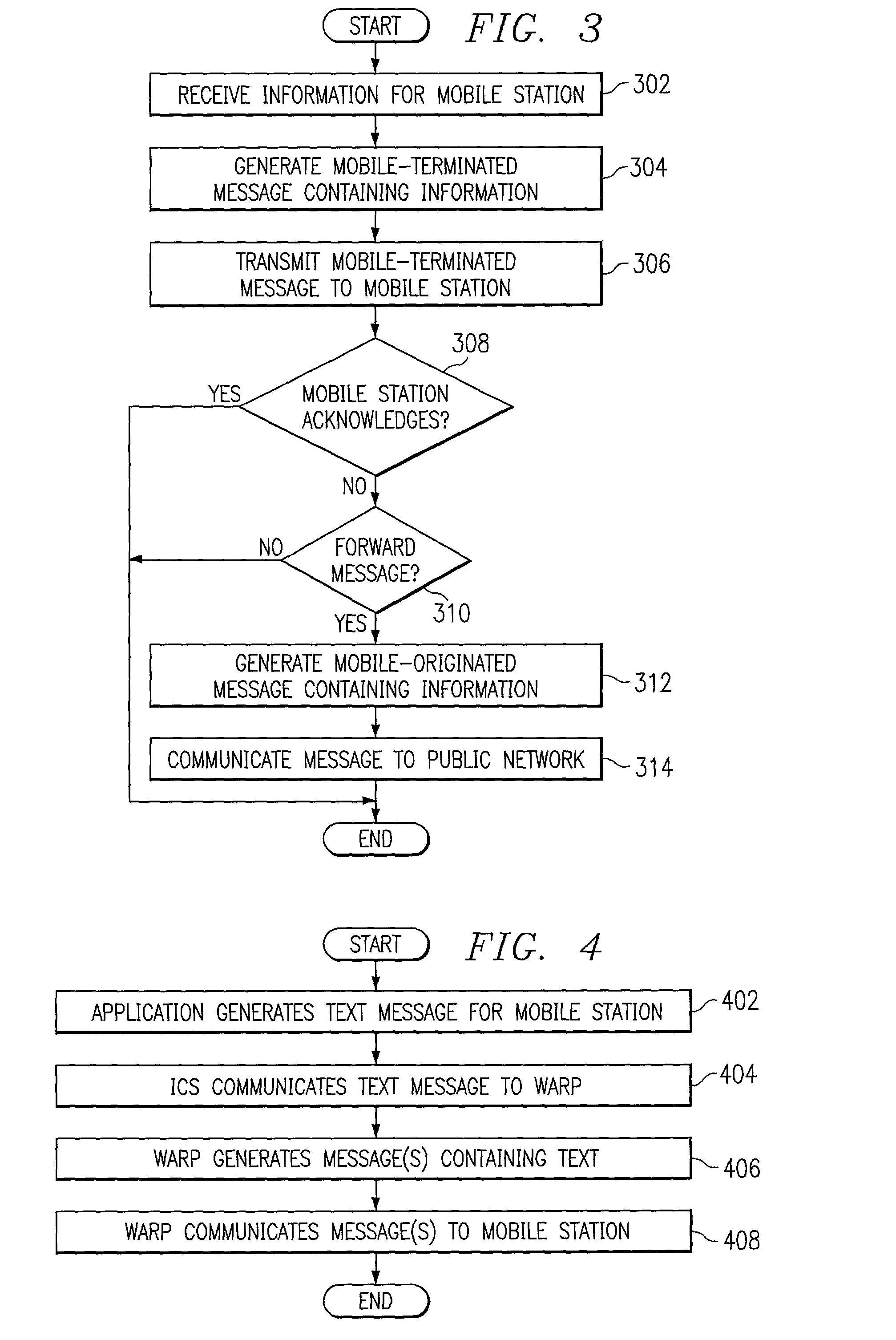
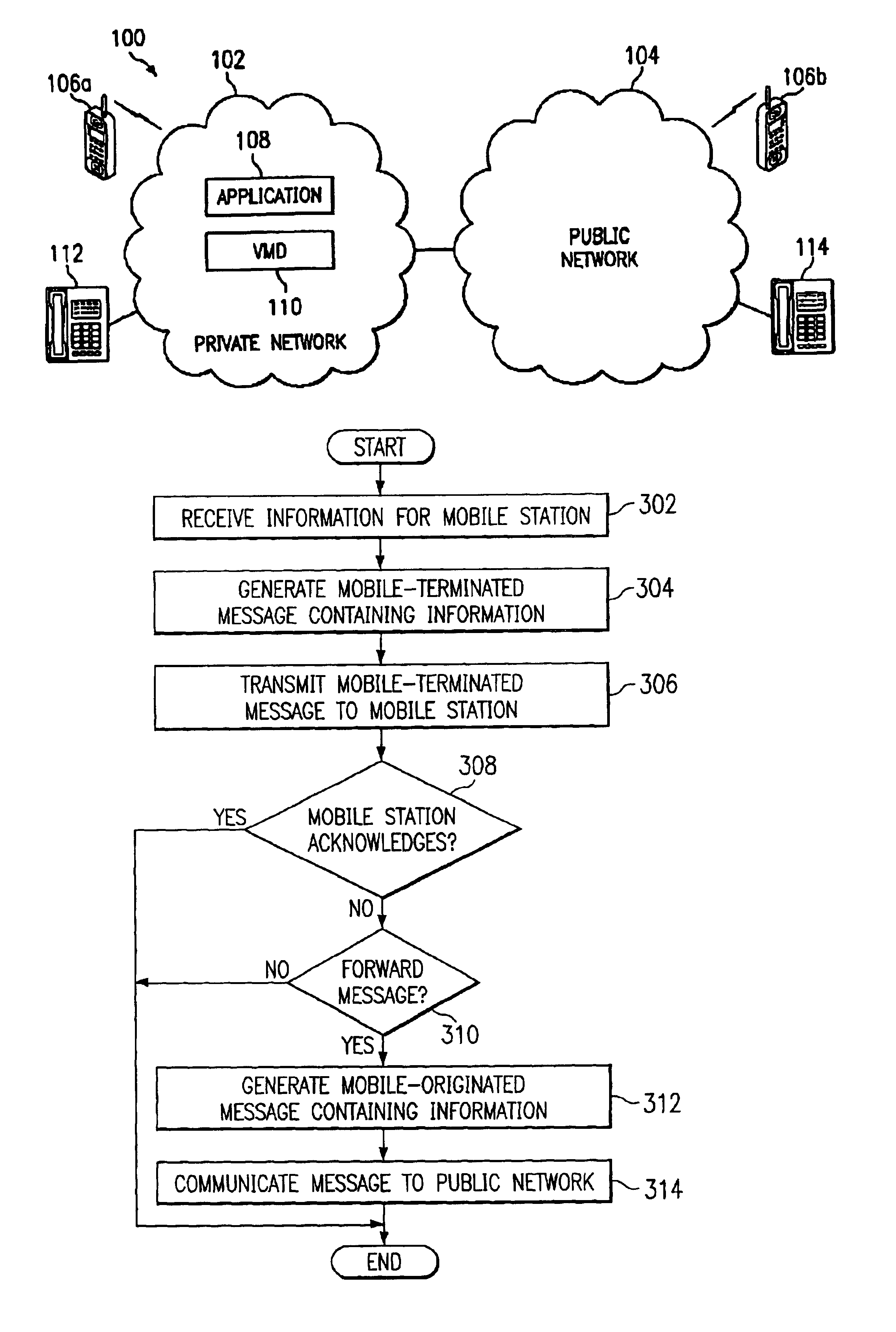
Method and system for providing message services in a communication system
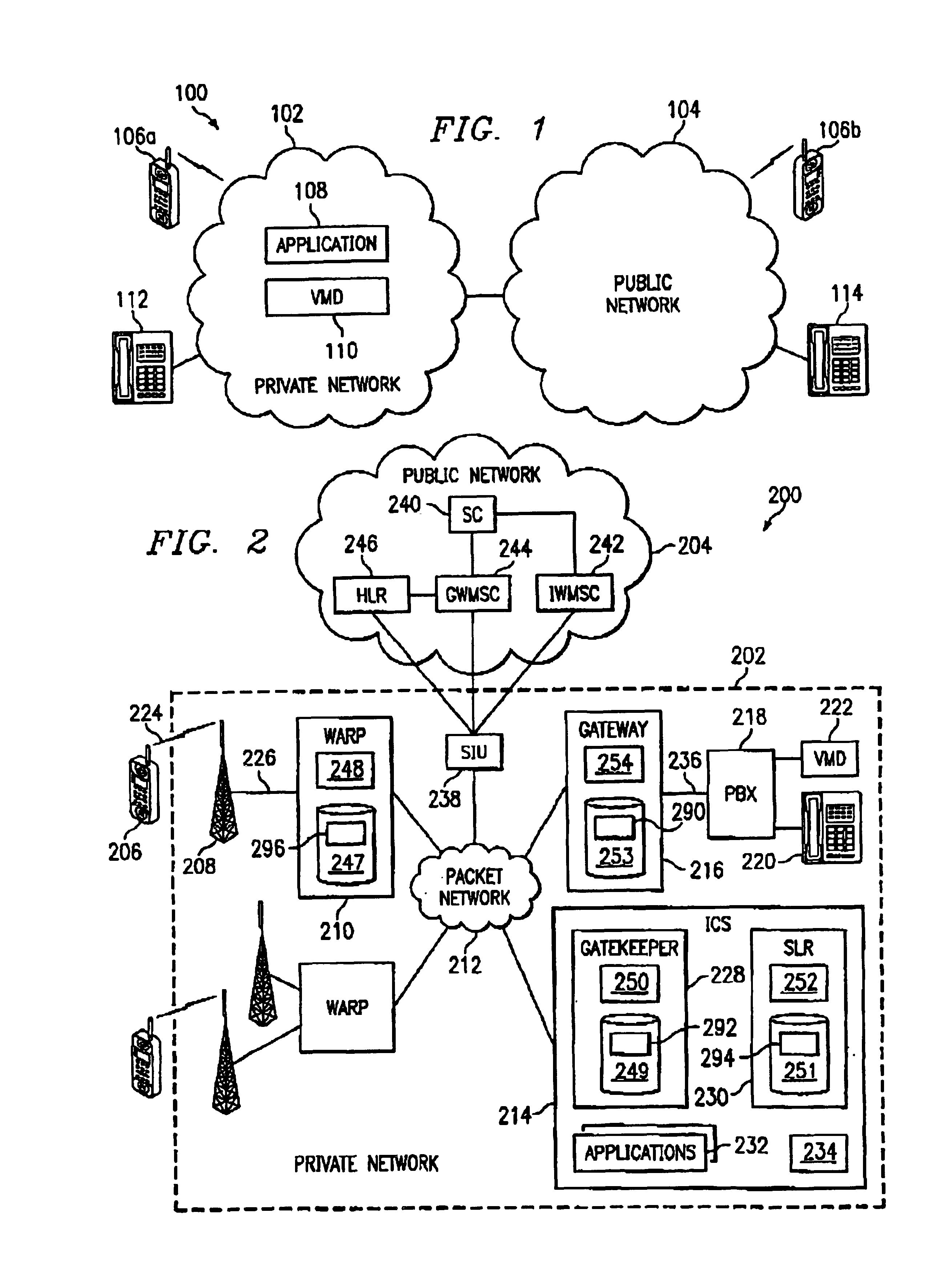
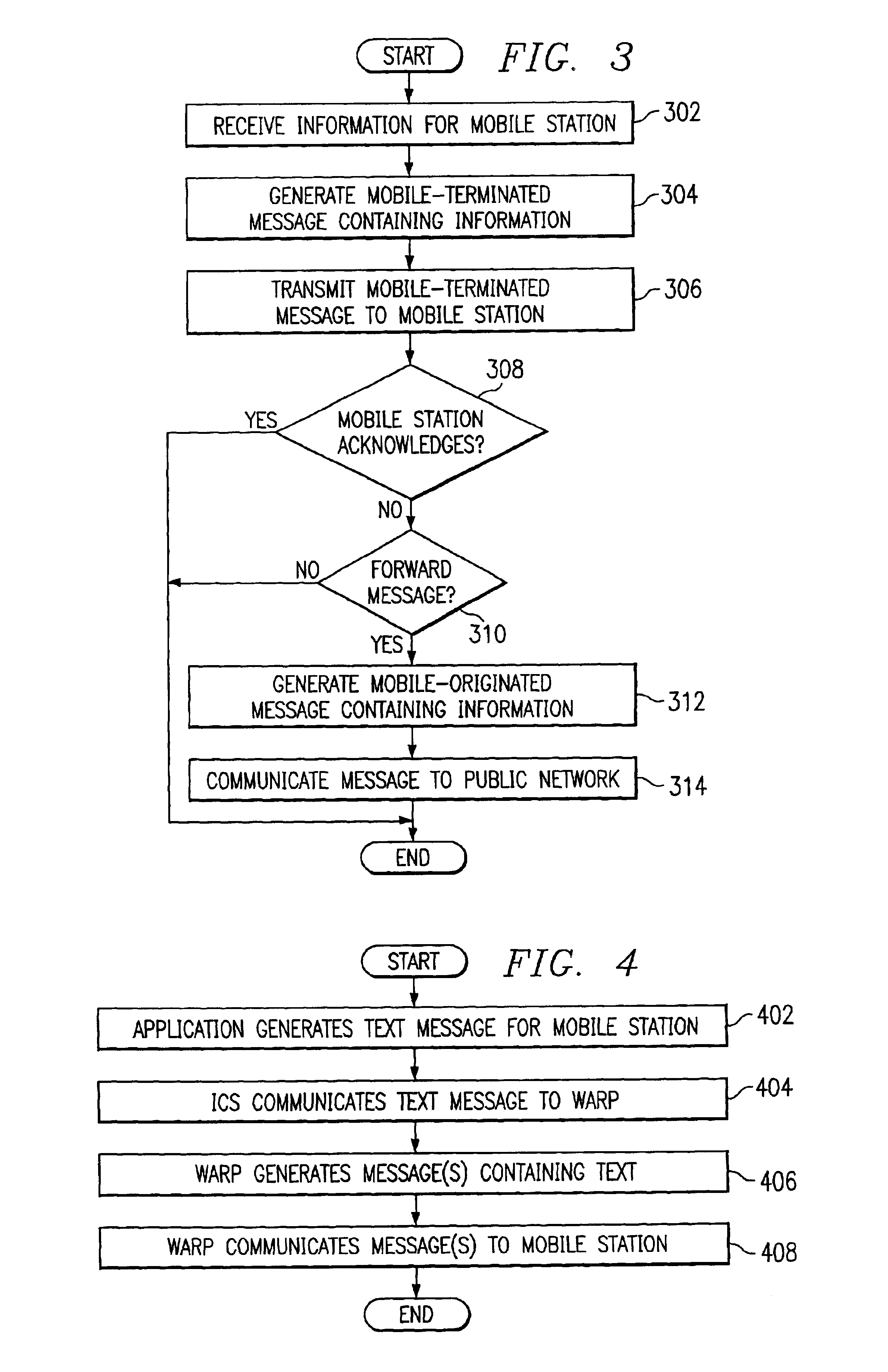
InactiveUS20020137500A1Eliminate and reduce disadvantageEliminate and reduce and problemSpecial service for subscribersSubstation equipmentCommunications systemPrivate network
A method for providing message services is provided that includes receiving a user notification message in an application. A user identifier for at least one recipient of the message is received in the application. The user identifier is operable to identify the recipient. The message and the user identifier are provided from the application to a private network. The private network is operable to transmit the message to a mobile station for the recipient. The mobile station has a corresponding mobile station identifier, and the user identifier is assigned to the mobile station identifier in the private network.
Owner:RINGCENTRAL INC
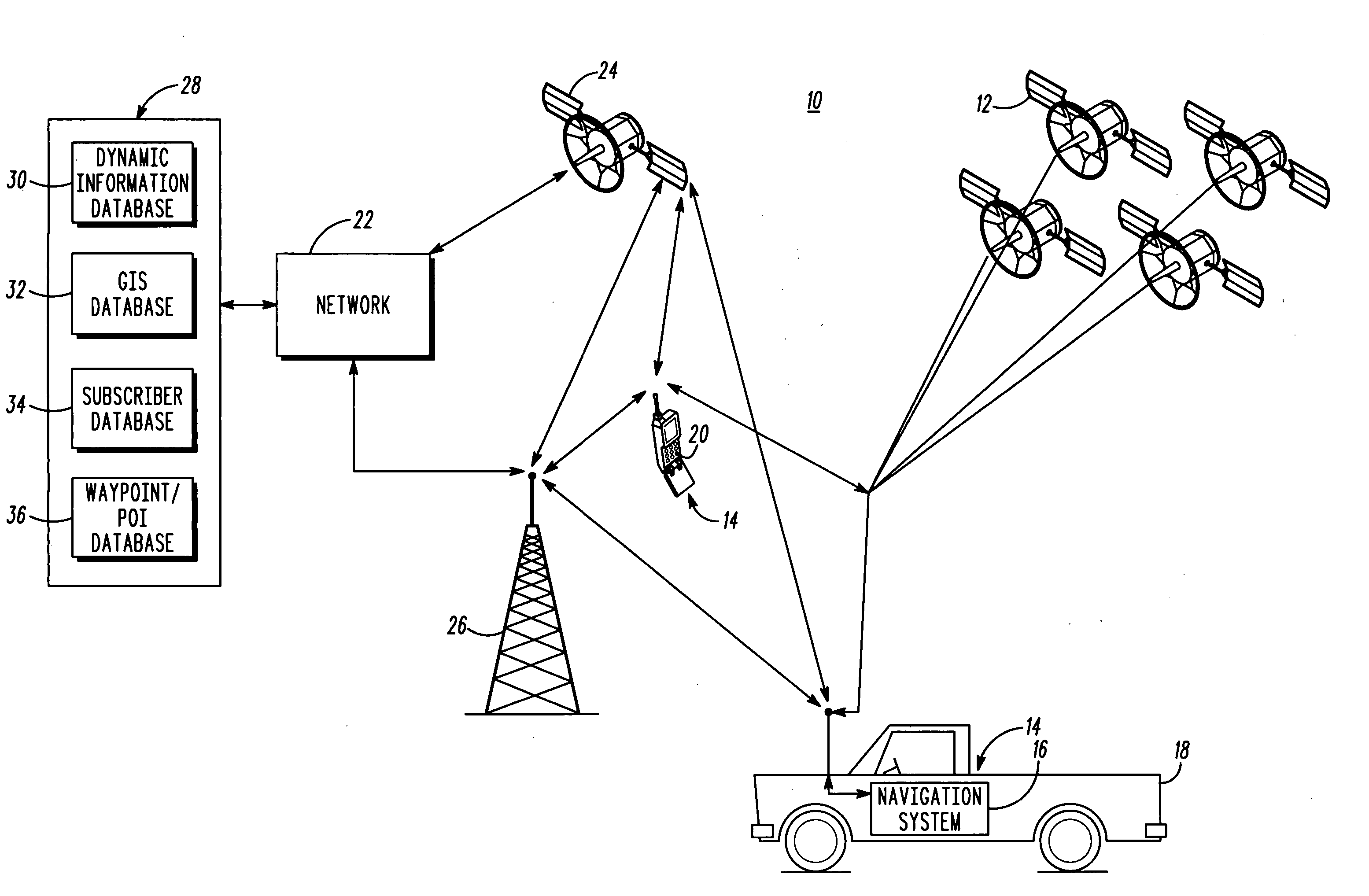
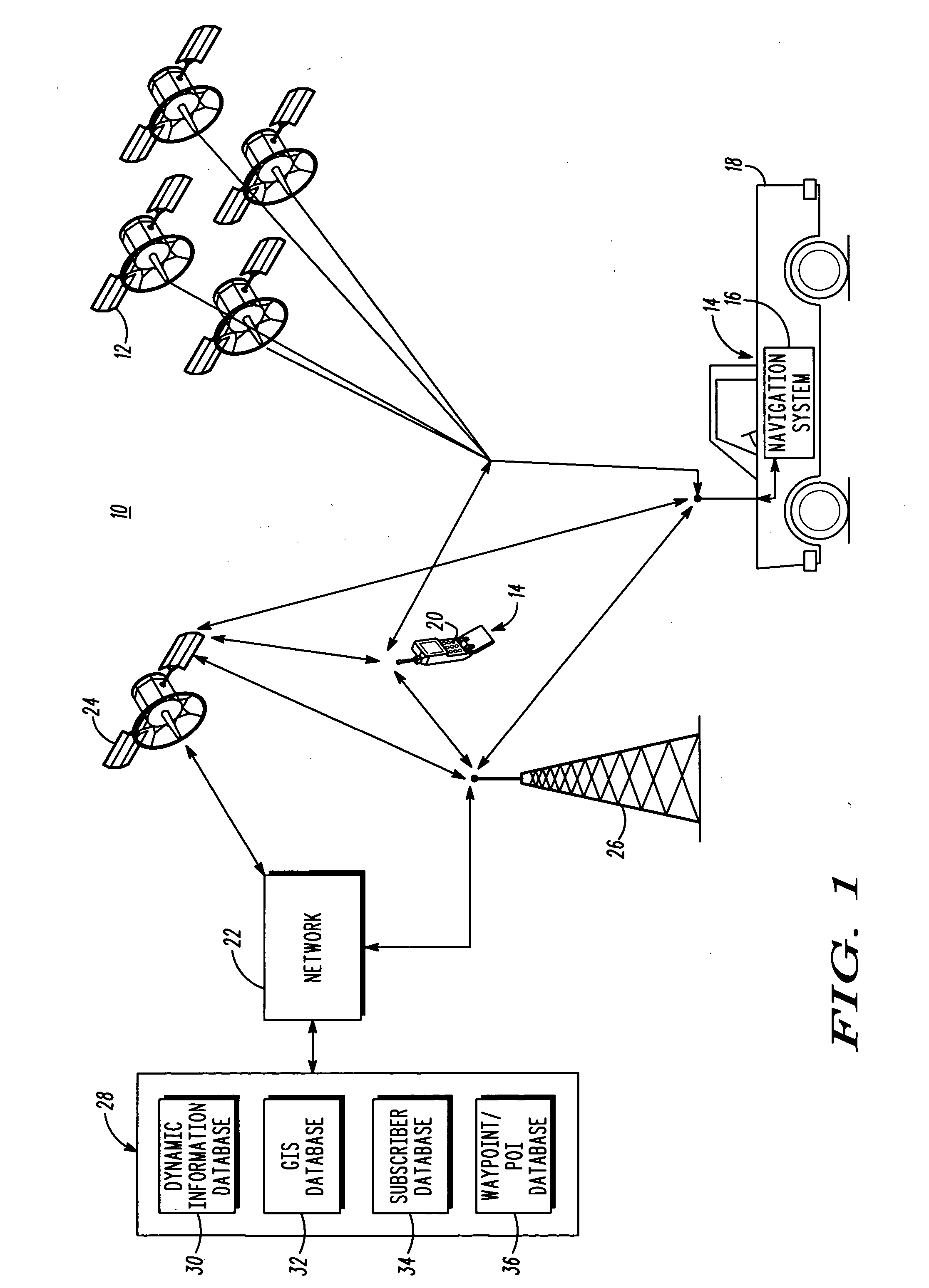
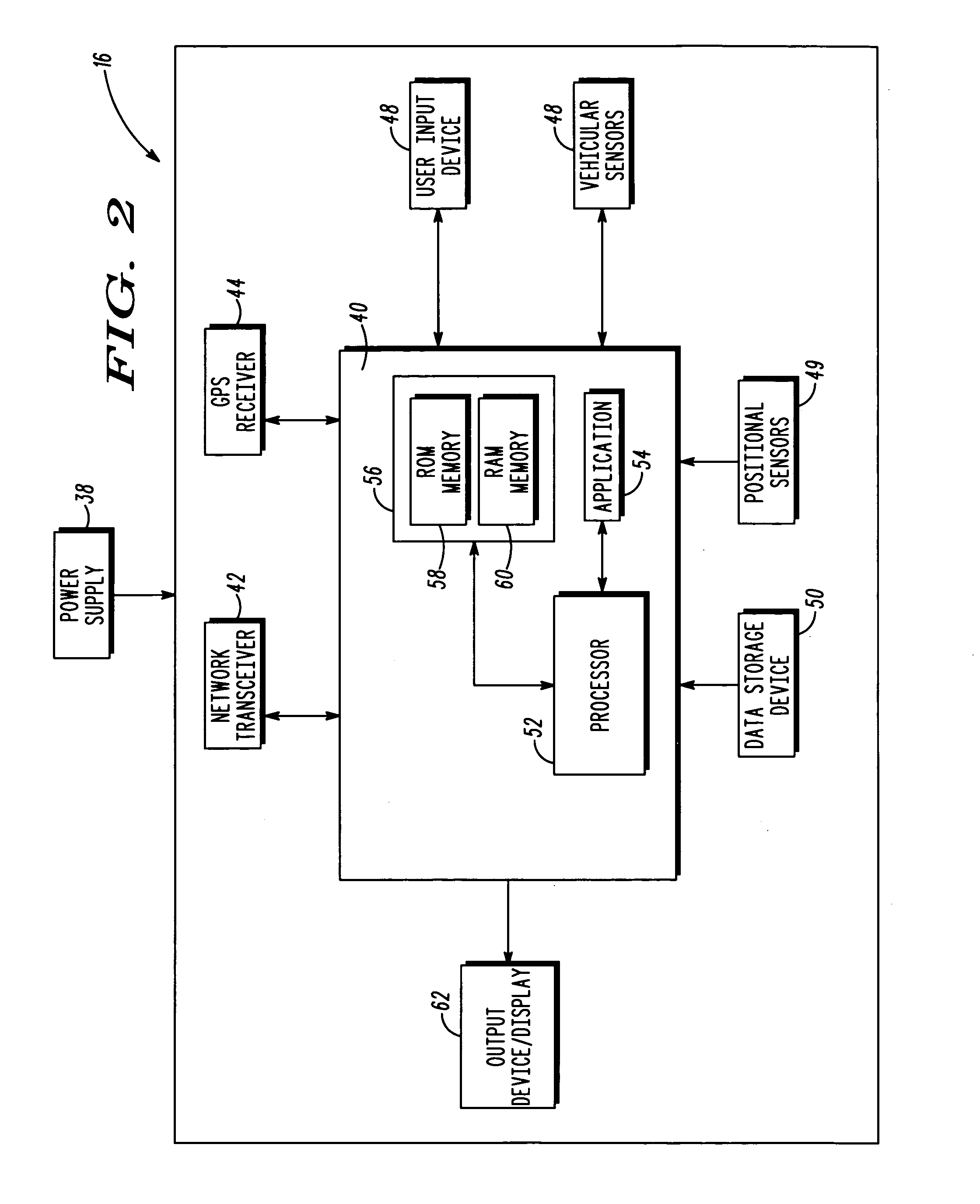
Method and apparatus for obtaining and providing information related to a point-of-interest
InactiveUS20050171686A1Easy to rememberEasy to enterInstruments for road network navigationRoad vehicles traffic controlInformation processingWorld Wide Web
In an exemplary embodiment of the present technique, a particular POI (66) may be assigned a code (68) representative thereof. Advantageously, by entering the code (68) into a telematics system (16), information about the POI (66) may be obtained. Moreover, in accordance with an exemplary aspect of the present technique, by entering the code (68) a route to the POI may be developed.
Owner:MOTOROLA INC
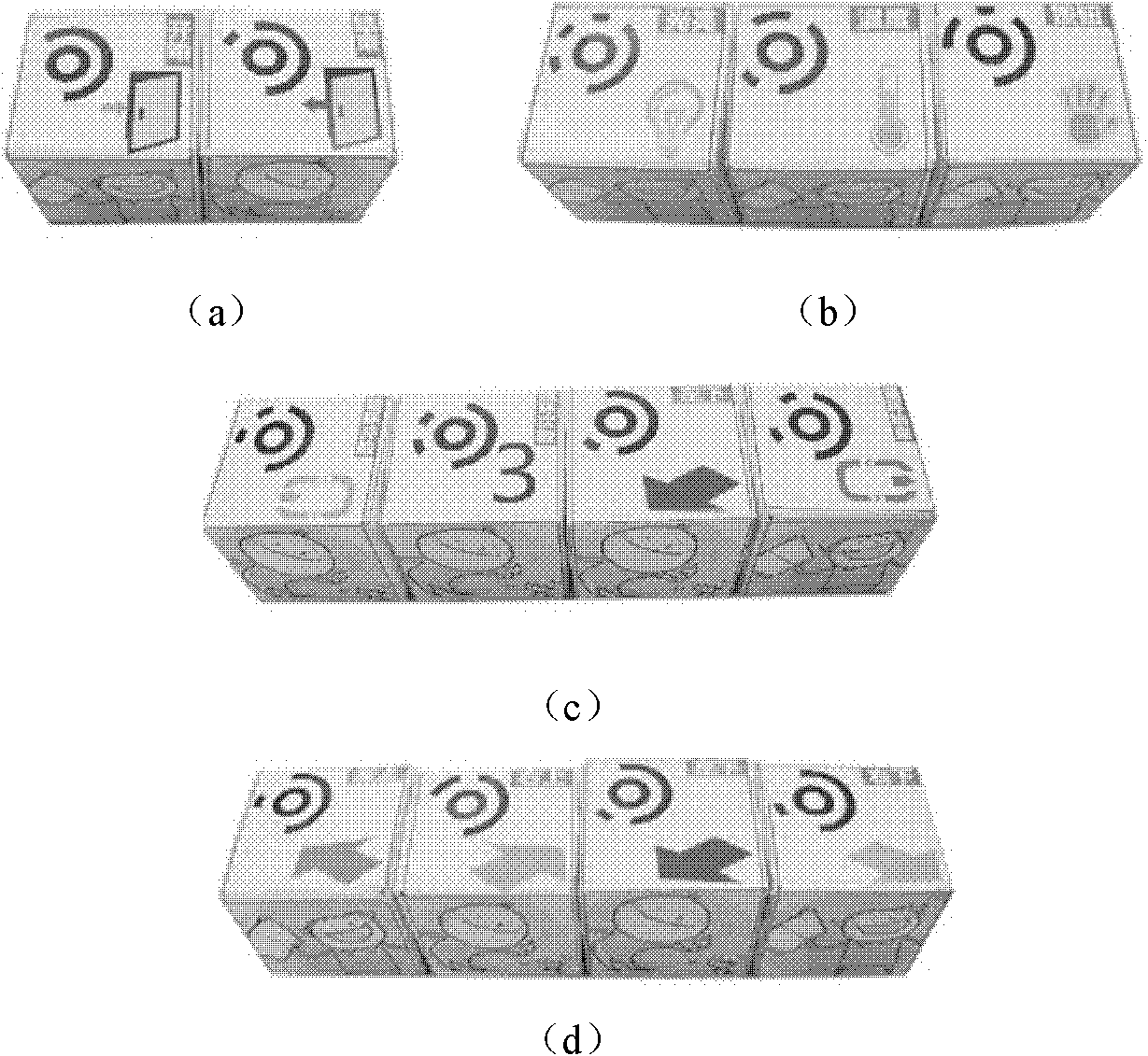
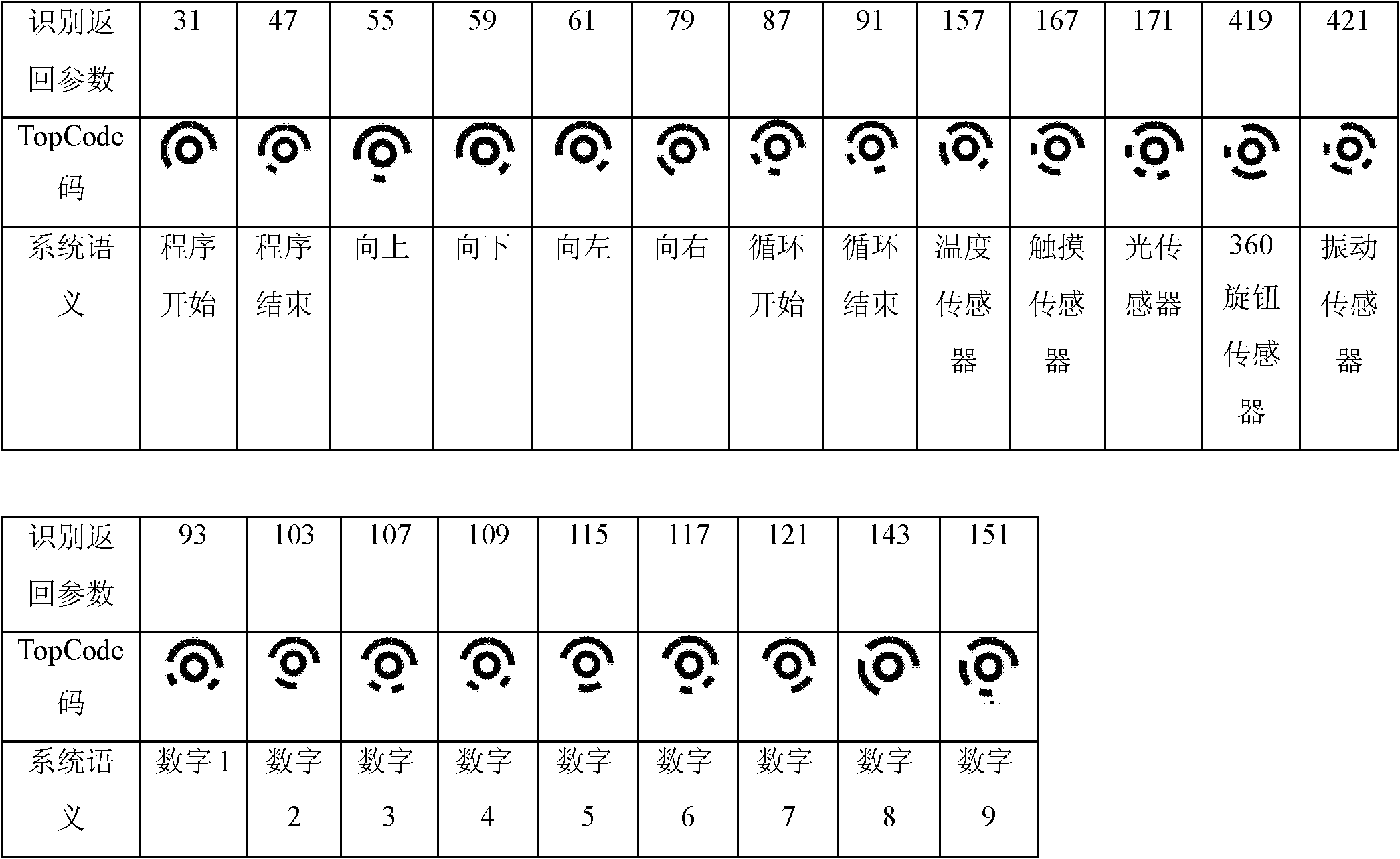
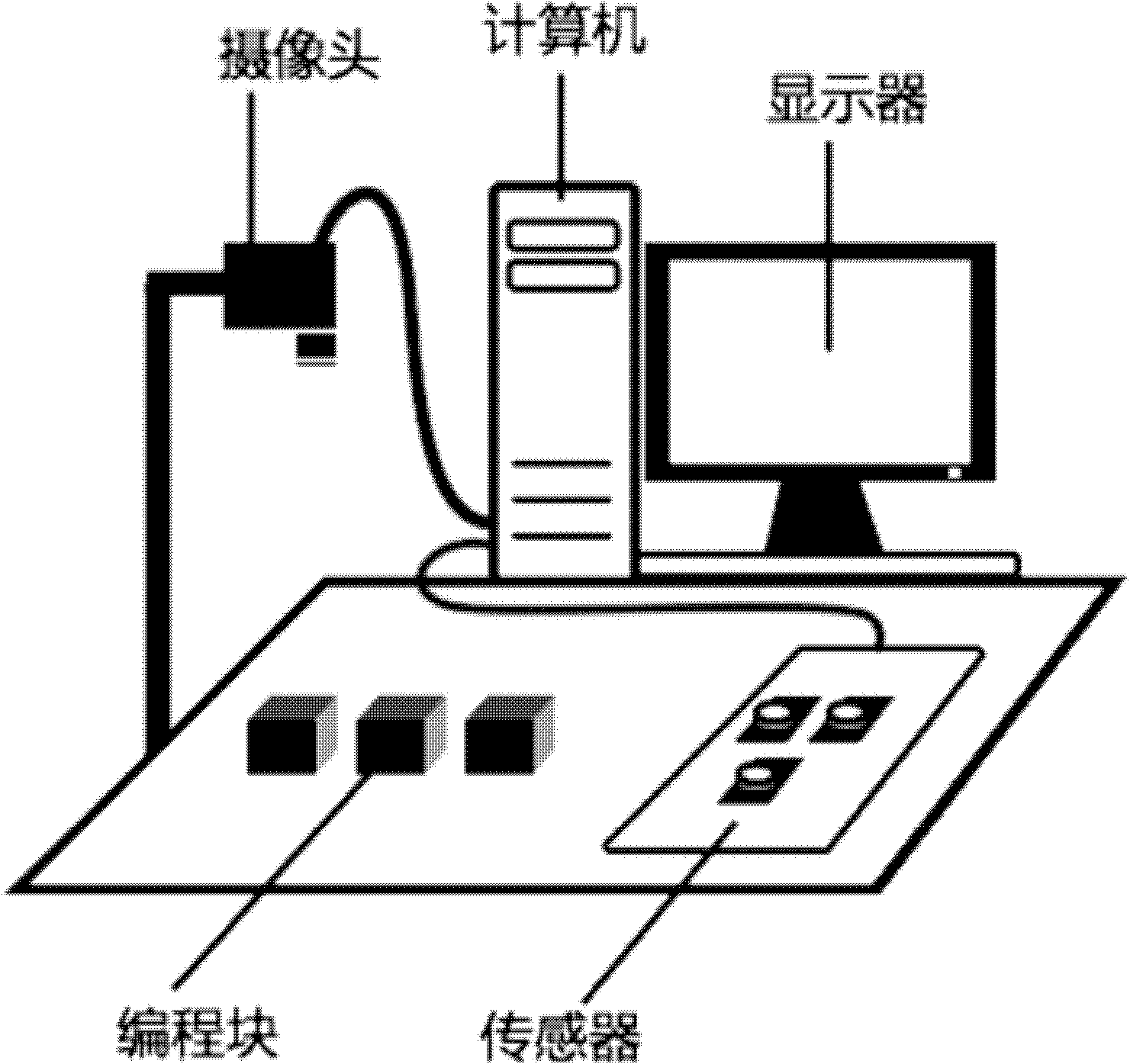
Material object programming method and system
The invention discloses a material object programming method and a material object programming system, which belong to the field of human-machine interaction. The method comprises the following steps of: 1) establishing a set of material object programming display environment; 2) shooting the sequence of material object programming blocks which are placed by a user and uploading the shot image toa material object programming processing module by using an image acquisition unit; 3) converting the sequence of the material object blocks into a corresponding functional semantic sequence by usingthe material object programming processing module according to the computer vision identification modes and the position information of the material object programming blocks; 4) determining whether the current functional semantic sequence meets the grammatical and semantic rules of the material object display environment or not, and if the current functional semantic sequence does not meet the grammatical and semantic rules of the material object display environment, feeding back a corresponding error prompt; 5) replacing the corresponding material object programming blocks by using the useraccording to the prompt information; and 6) repeating the steps 2) to 5) until the functional semantic sequence corresponding to the sequence of the placed material object programming blocks meets the grammatical and semantic rules of the material object display environment, and finishing a programming task. By using the method and the system, the problem that children and green hands are difficult to learn programming is solved, and the system has low cost and is easy to popularize.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
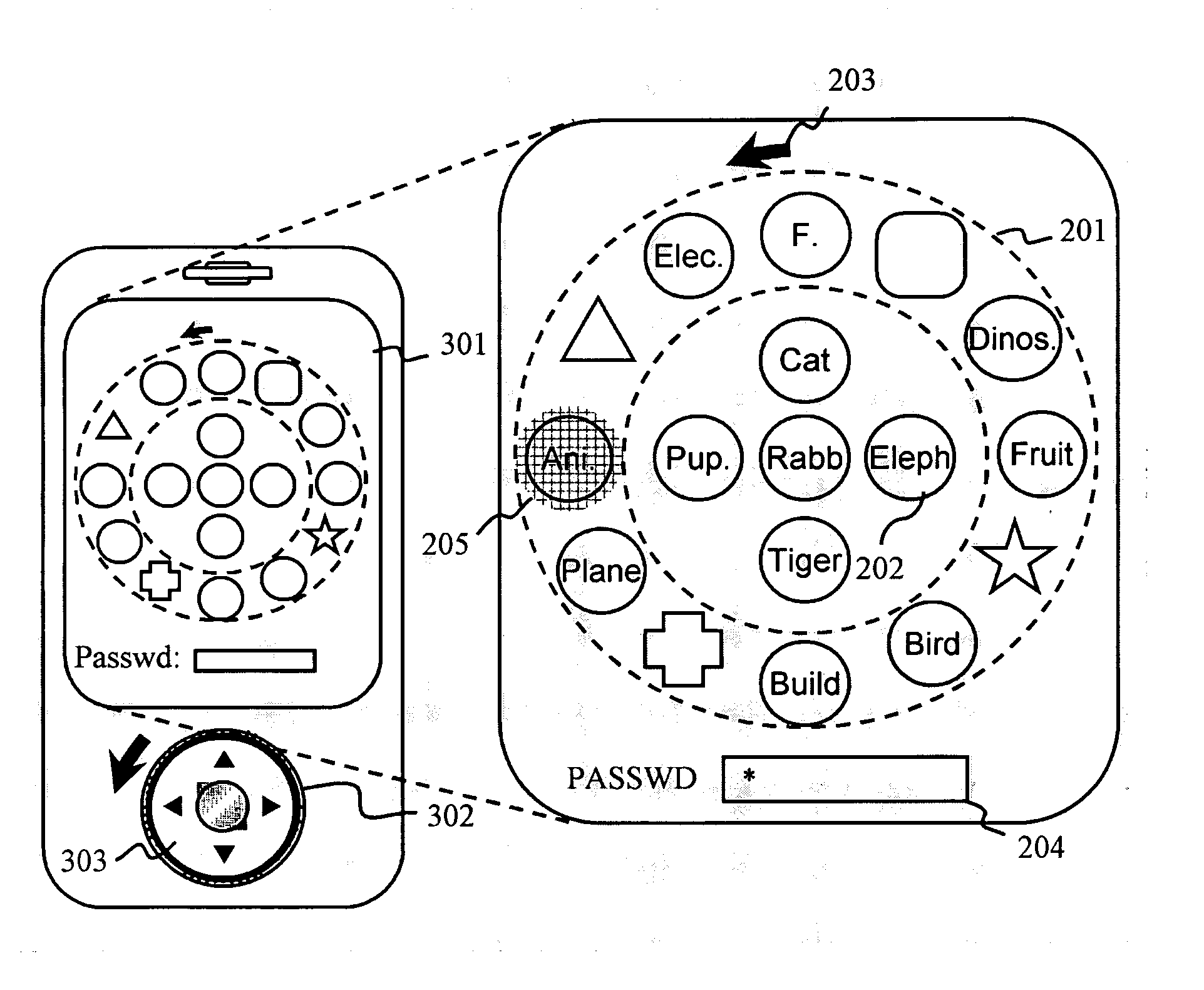
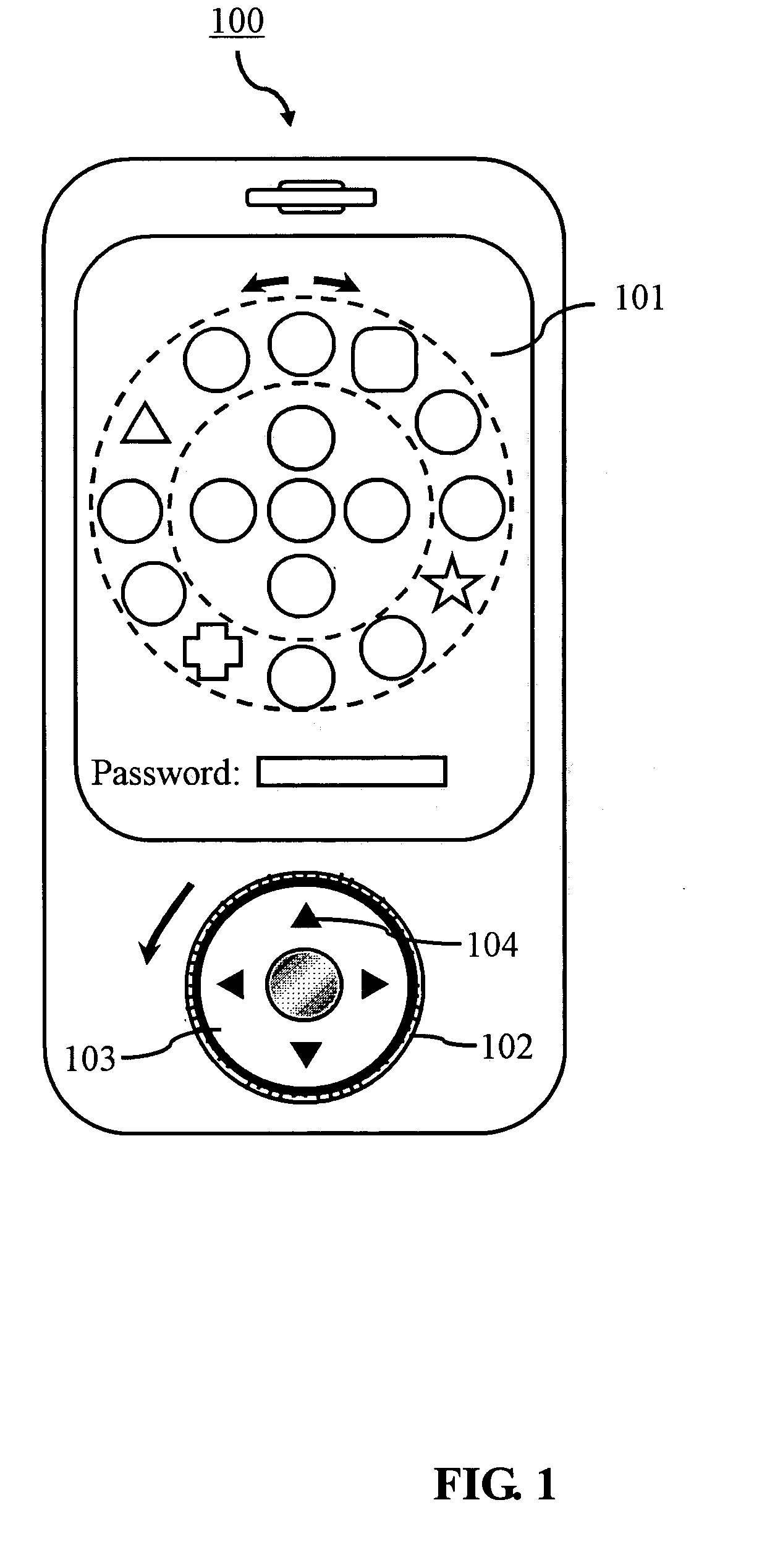
Apparatus and method for inputting graphical password using wheel interface in embedded system
InactiveUS20090172810A1Increase the number ofImprove convenienceDigital data processing detailsUser identity/authority verificationGraphicsPassword
Provided are an apparatus and method for inputting a graphical password that use representative pictures and elemental pictures of a graphic to form a graphical password and that receive the graphic via a wheel interface and a select button for user authentication. The apparatus includes: an input unit having a wheel interface and a select button; a display for displaying a graphic consisting of representative pictures and elemental pictures, and displaying a changed graphic in response to an input from the wheel interface; a memory for storing a graphical password of a user; and a controller for recognizing, when the select button is pressed, the graphic displayed on the display as a user-input graphical password, and determining whether the input graphical password matches the stored graphical password for user authentication. Thus, it is possible to increase the number of cases for a password using a wheel interface for a higher security level of an embedded system that has a low security level due to a limited type and length of letters input as a password.
Owner:RES & BUSINESS FOUND SUNGKYUNKWAN UNIV
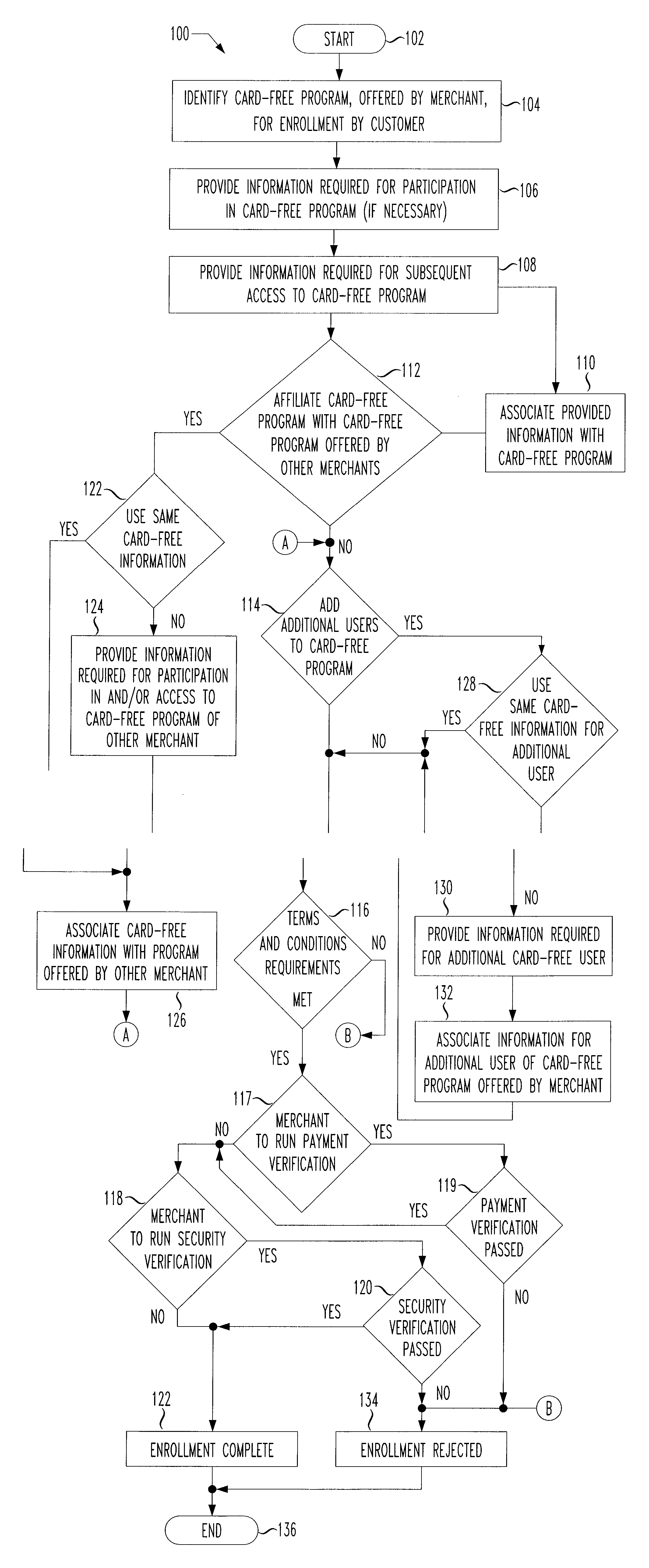
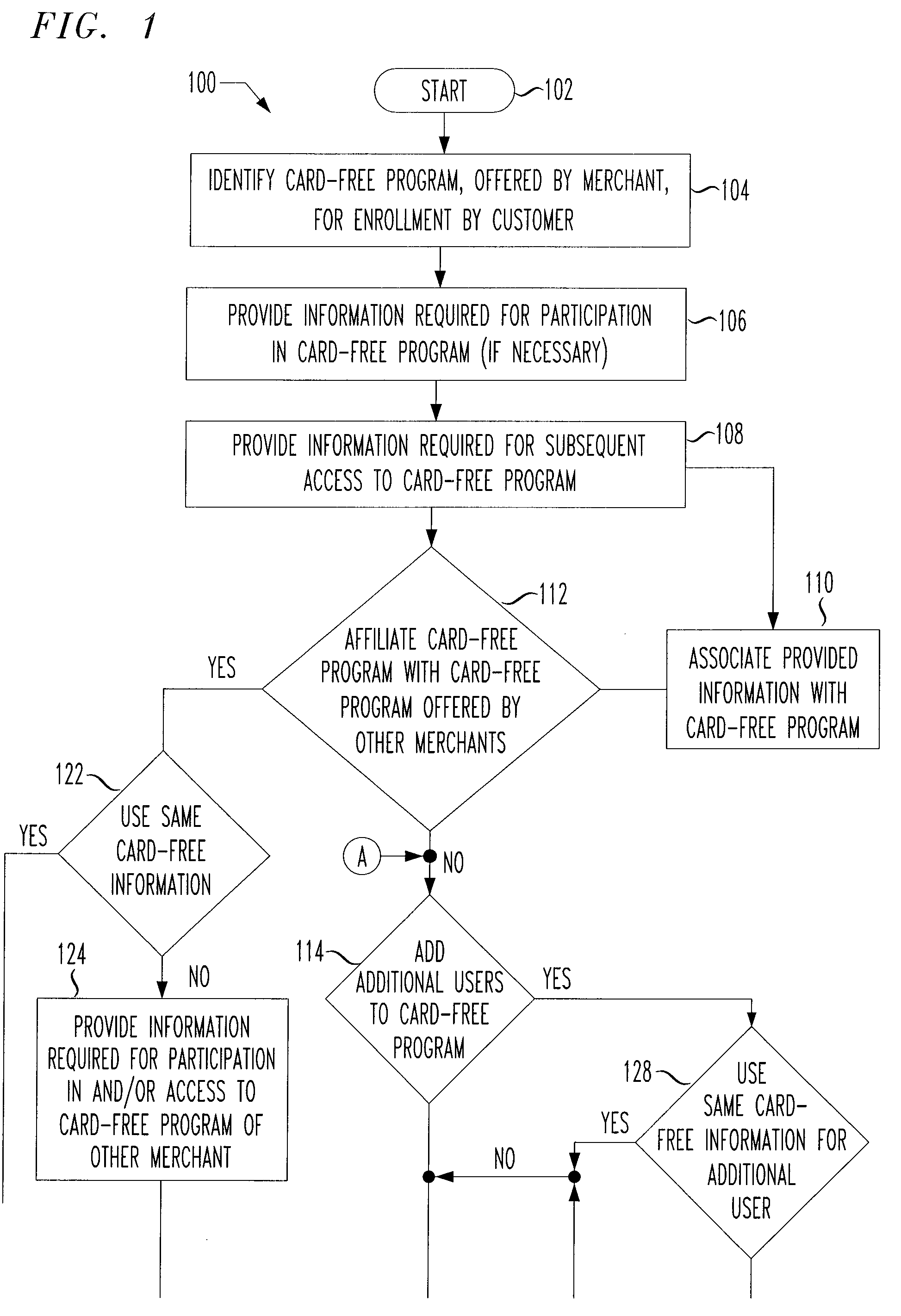
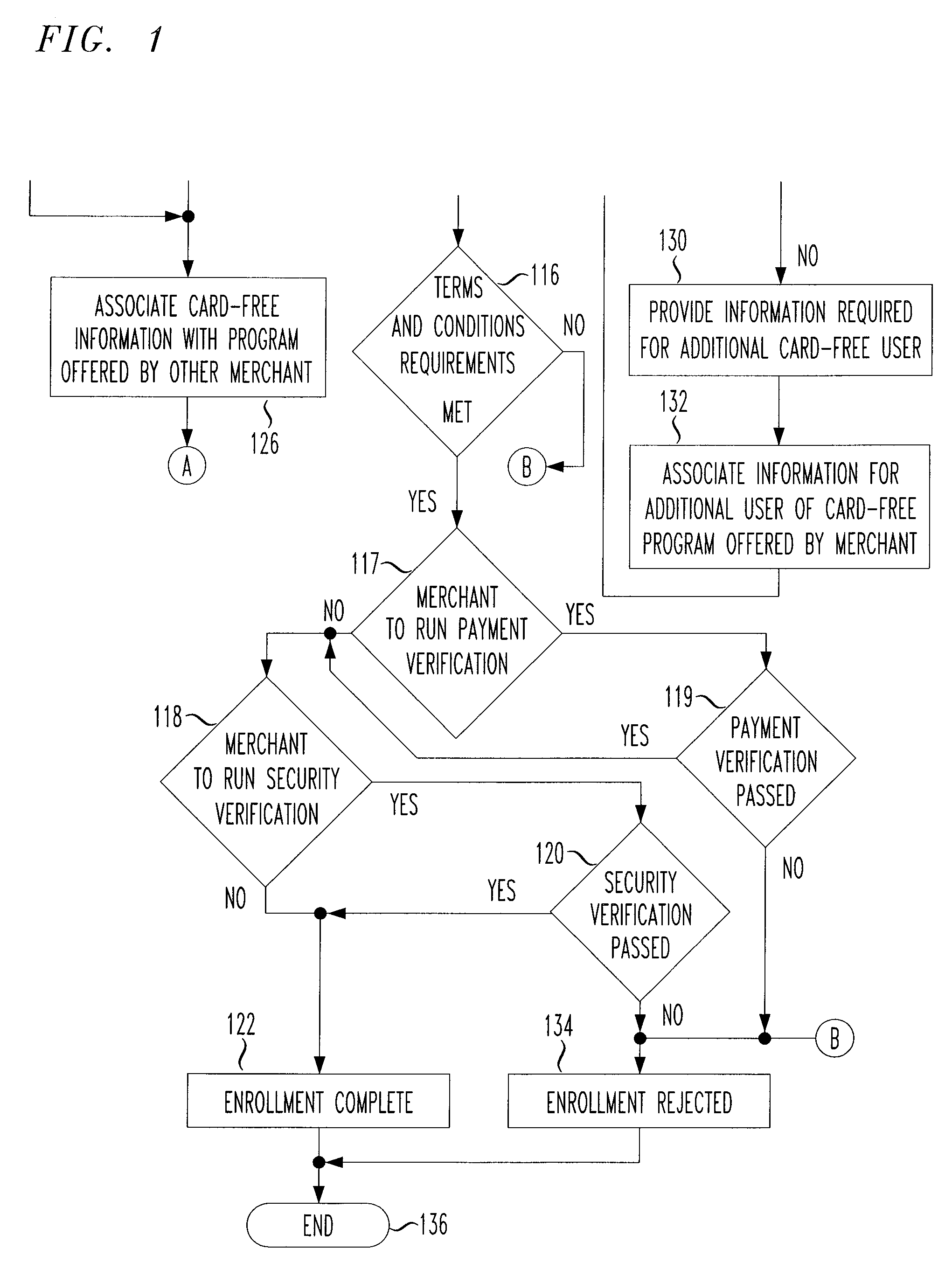
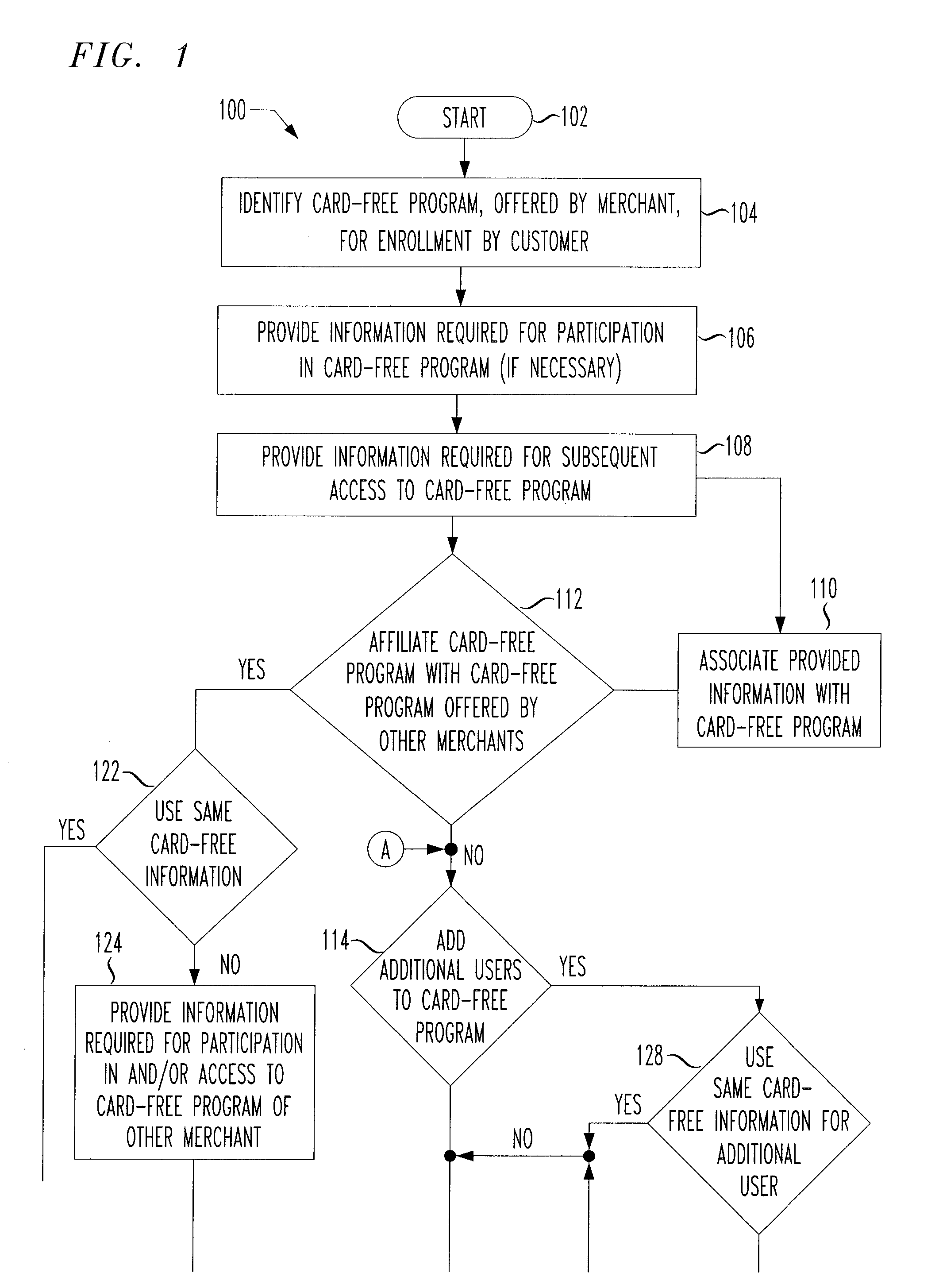
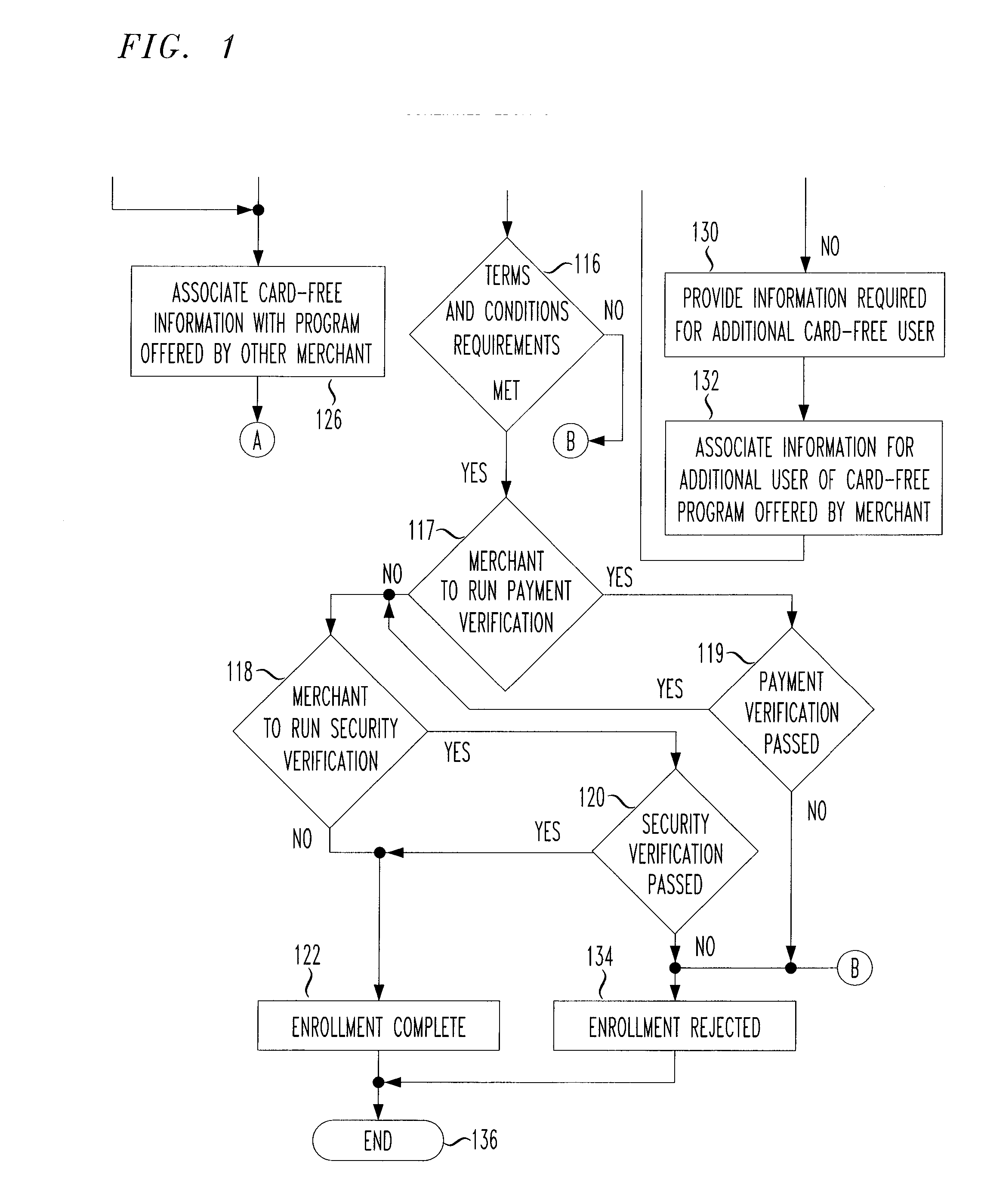
Payment program for use in point-of-sale transactions
ActiveUS20070022048A1Easy to rememberSuitable for useDiscounts/incentivesFinanceComputer hardwareBiometric data
In some embodiments, the present application relates to card-free programs provided by a merchant to a customer, whereby the customer has access to functions such as payment options and / or loyalty program benefits without needing to present a physical card at a point of sale. For example, a customer may make a card-free purchase of goods or services from a merchant, whereby the customer need not present a card such as a debit card, credit card, loyalty card, or other physical tender to make a purchase. Further, the customer need not provide biometric data or otherwise use an electronic device or identifier to make a purchase. Alternatively or additionally, the customer may access a loyalty program without needing to provide a physical card or data associated with a card.
Owner:SAFEWAY INC
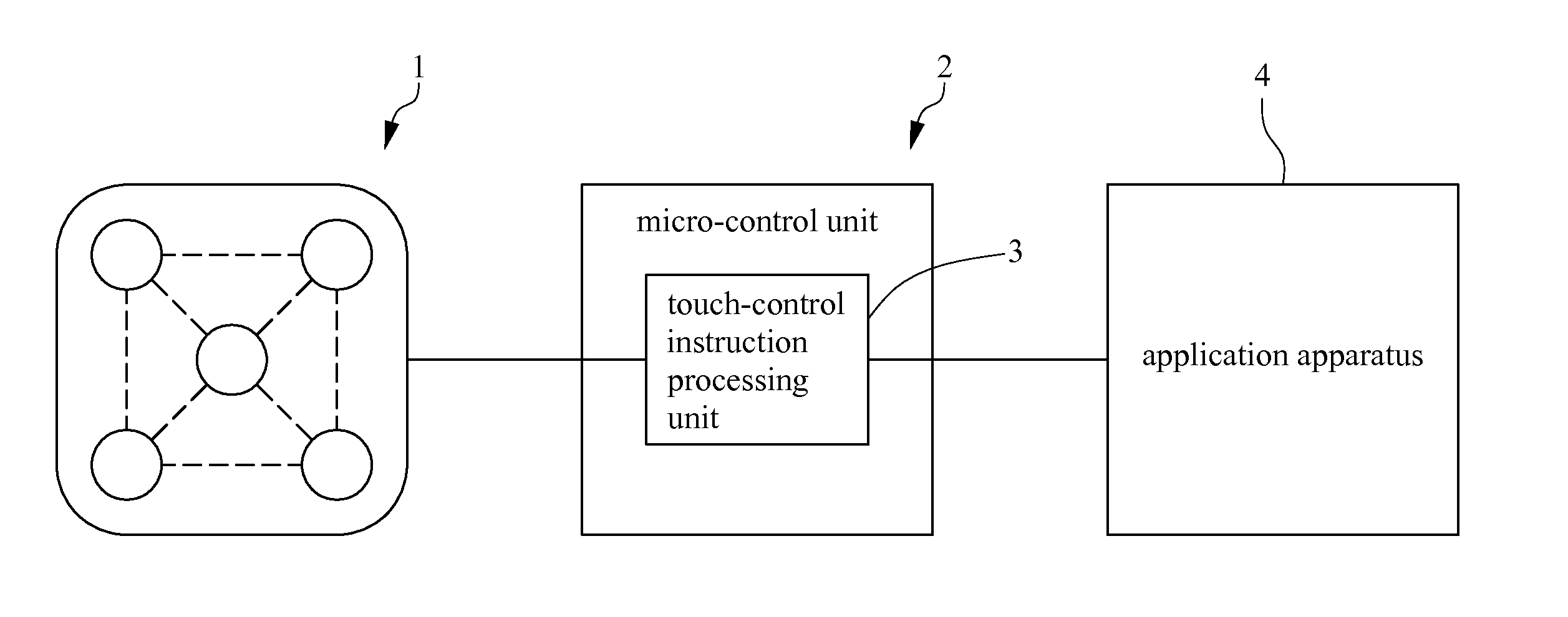
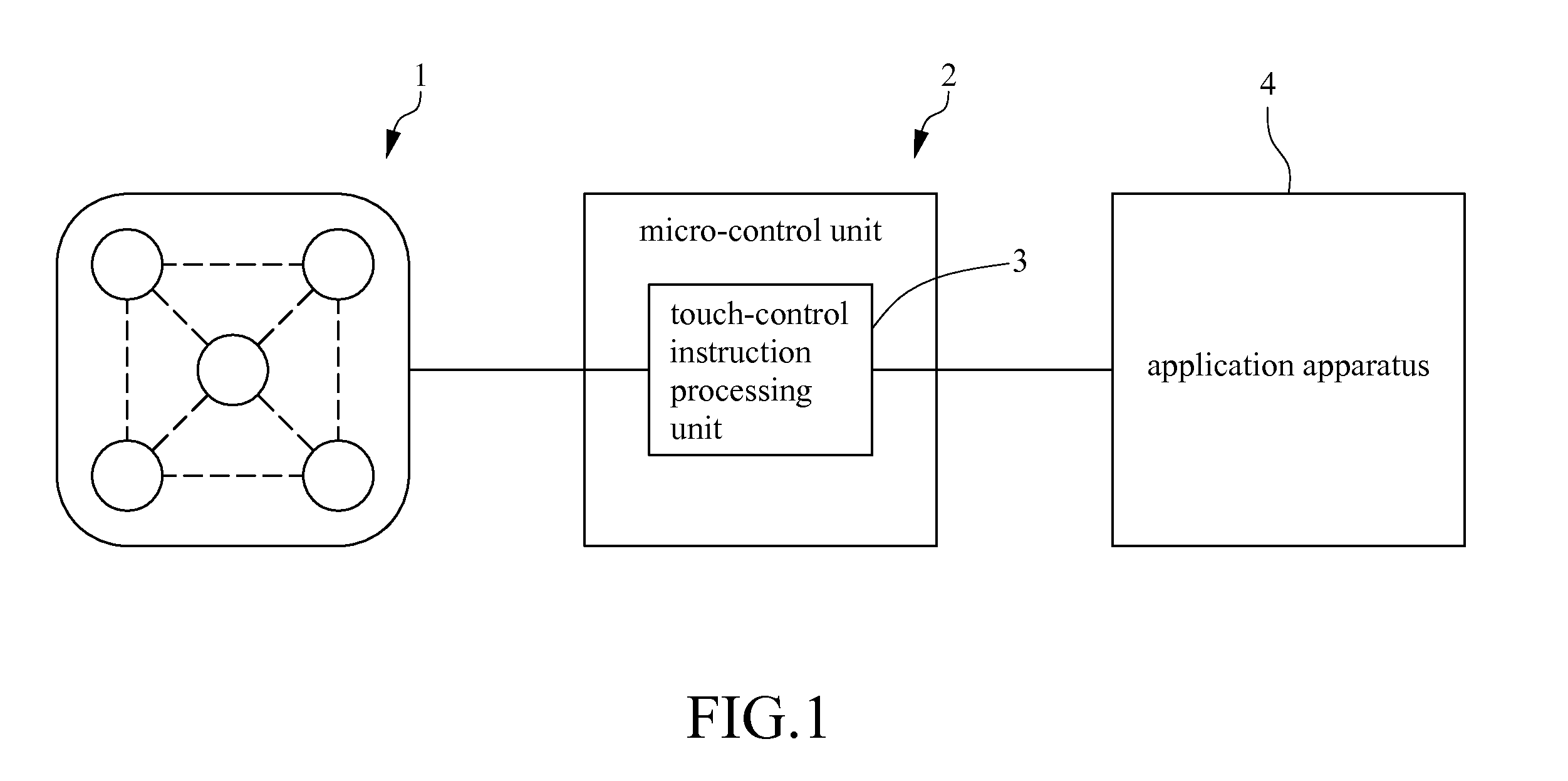
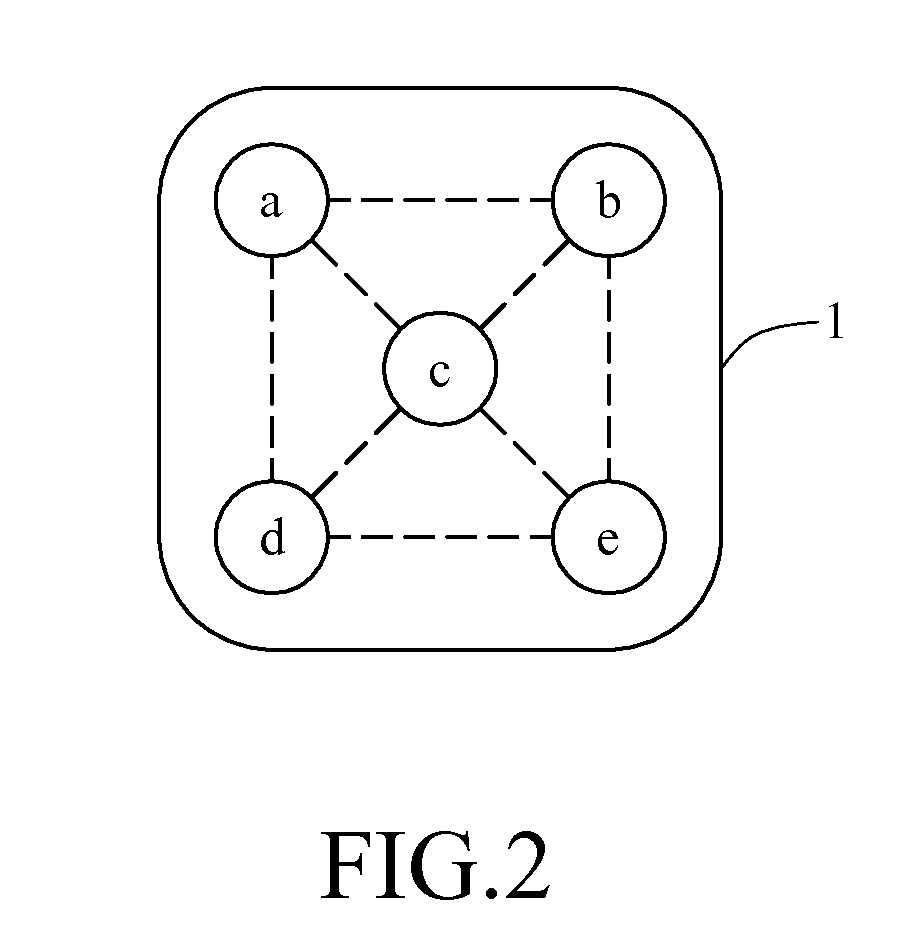
Touch-control lock
InactiveUS20110148572A1Avoid dataEasy to rememberProgramme controlElectric signal transmission systemsGraphicsInstruction processing unit
A method for operating a touch-control lock system according to a gesture or a figure, comprising steps of: (a) sensing a designated gesture or figure while a user uses his finger touches a touch-control panel of the touch-control lock system and outputting an electronic signal according to the designated gesture or figure; (b) processing the electronic signal by a micro-control unit and judging whether or not the electronic signal is a valid input by the micro-control unit; (c) determining whether or not the designated gesture or figure is valid by the micro-control unit; (d) loading correct data for the designated gesture or figure stored in a touch-control instruction processing unit and comparing the correct data with the designated gesture so as to determine if the designated gesture or figure is valid; and (e) outputting a control command to an application apparatus to react correspondingly.
Owner:BEST SOLUTIONS
System for providing cardless payment
InactiveUS20060173791A1Convenient and easy to rememberConvenient and/orFinancePayment circuitsComputer hardwareThe Internet
The method and system of the invention provide a variety of techniques for using a selected alias and a selected personal identification entry (PIE) in conjunction with use of a transaction card, such as a credit card, debit card or stored value card, for example. A suitable number or other identification parameter is selected by the account-holder as an alias. The account-holder is then required to choose a PIE for security purposes. The alias is linked to the account-holder's credit card number via a database. When the account-holder enters into a transaction with a merchant, the physical card need not be present. The account-holder simply provides his or her alias and then the PIE. This can be done at any point of sale such as a store, catalog telephone order, or over the Internet. The alias and PIE are entered and authorization is returned from the credit card company.
Owner:JPMORGAN CHASE BANK NA
Indirect disposable email addressing
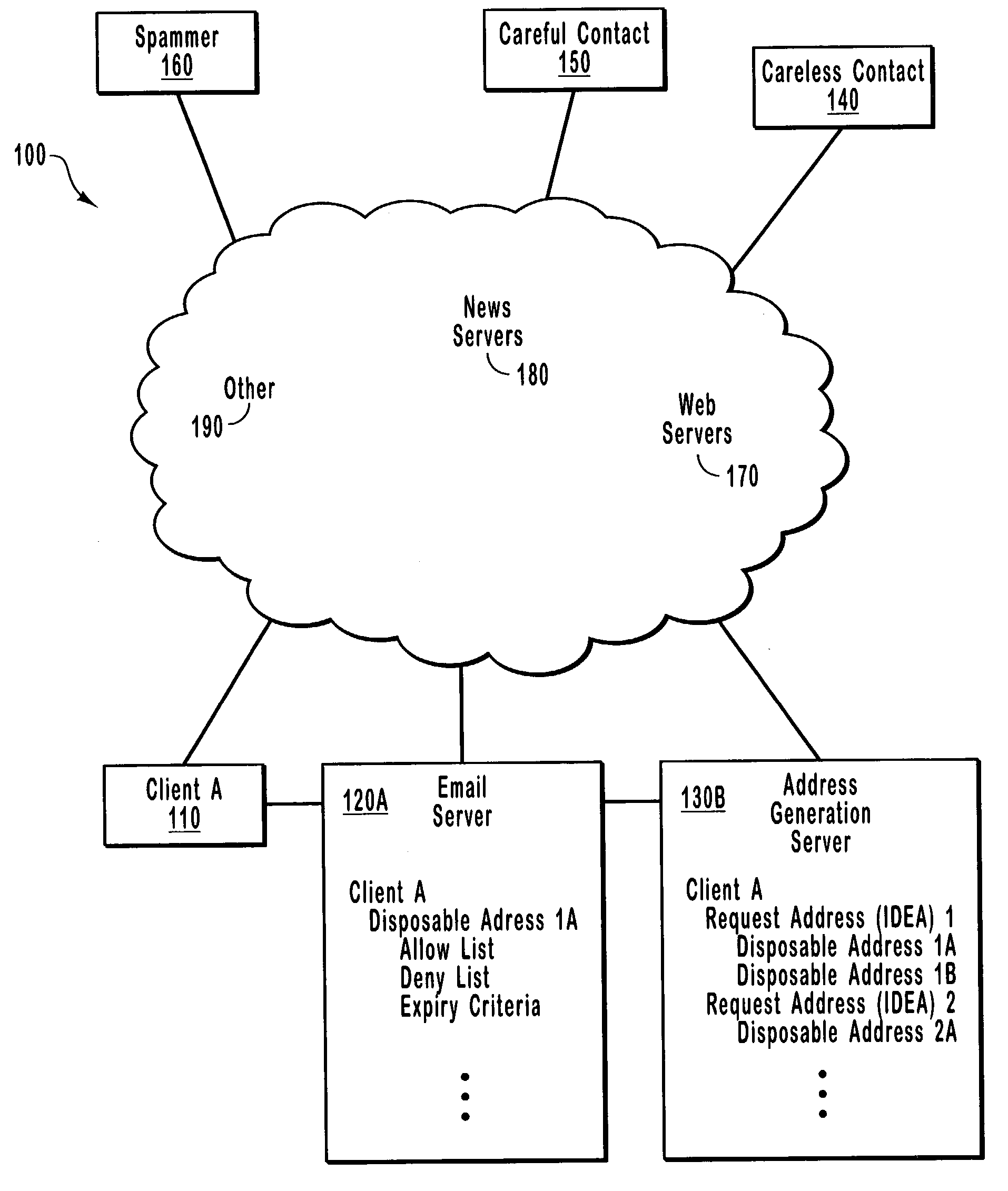
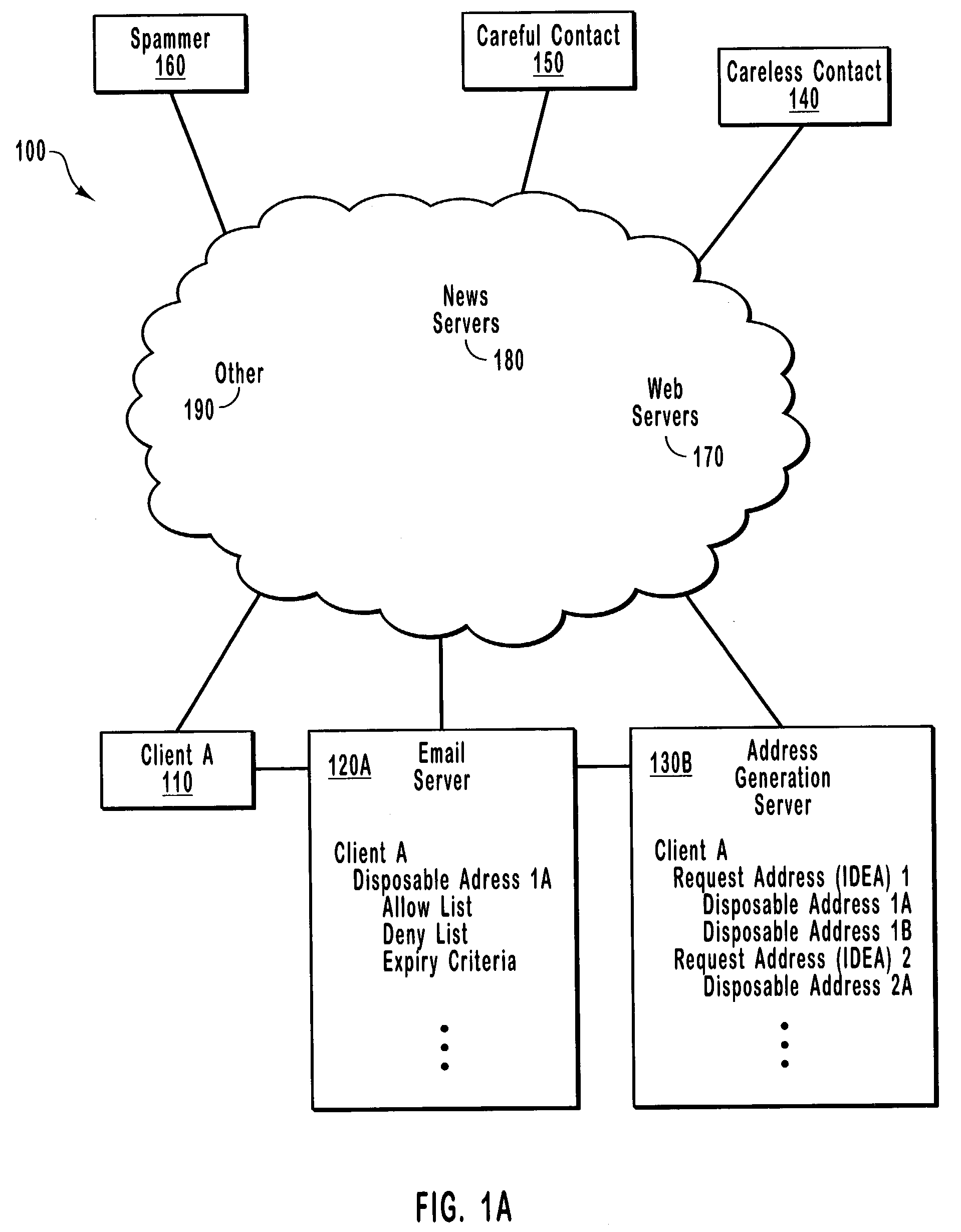
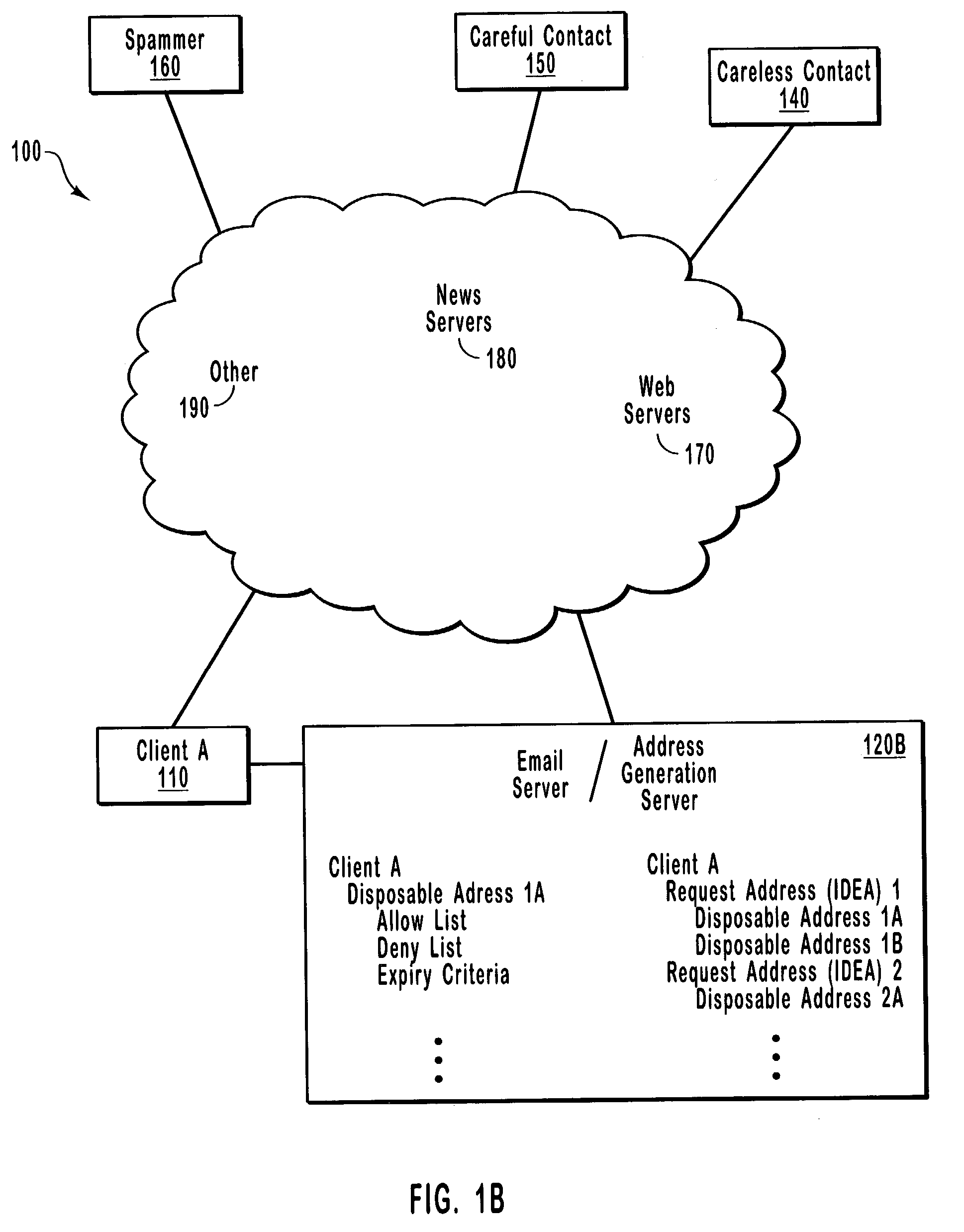
InactiveUS7305445B2ReducesEasy memorizationMultiple digital computer combinationsOffice automationProtocol for Carrying Authentication for Network AccessComputer program
Methods, systems, and computer program products for reducing unsolicited electronic messages by using immutable email identities in place of traditional email addresses. Over any of various protocols, an address generation server receives an electronic message requesting a disposable address for an intended recipient having an immutable email identity. The request also includes a return address for the sender, which discourages unsolicited messages because most senders of unsolicited messages prefer to remain anonymous. After receiving the request, the address generation server creates the disposable electronic message address, which may be limited in use. A challenge must be completed before the address may be discovered or used. This challenge further discourages unsolicited electronic messages because it imposes a burden that many senders of unsolicited messages are unwilling to bear.
Owner:MICROSOFT TECH LICENSING LLC
Anonymous disposable email addressing system and method of use thereo
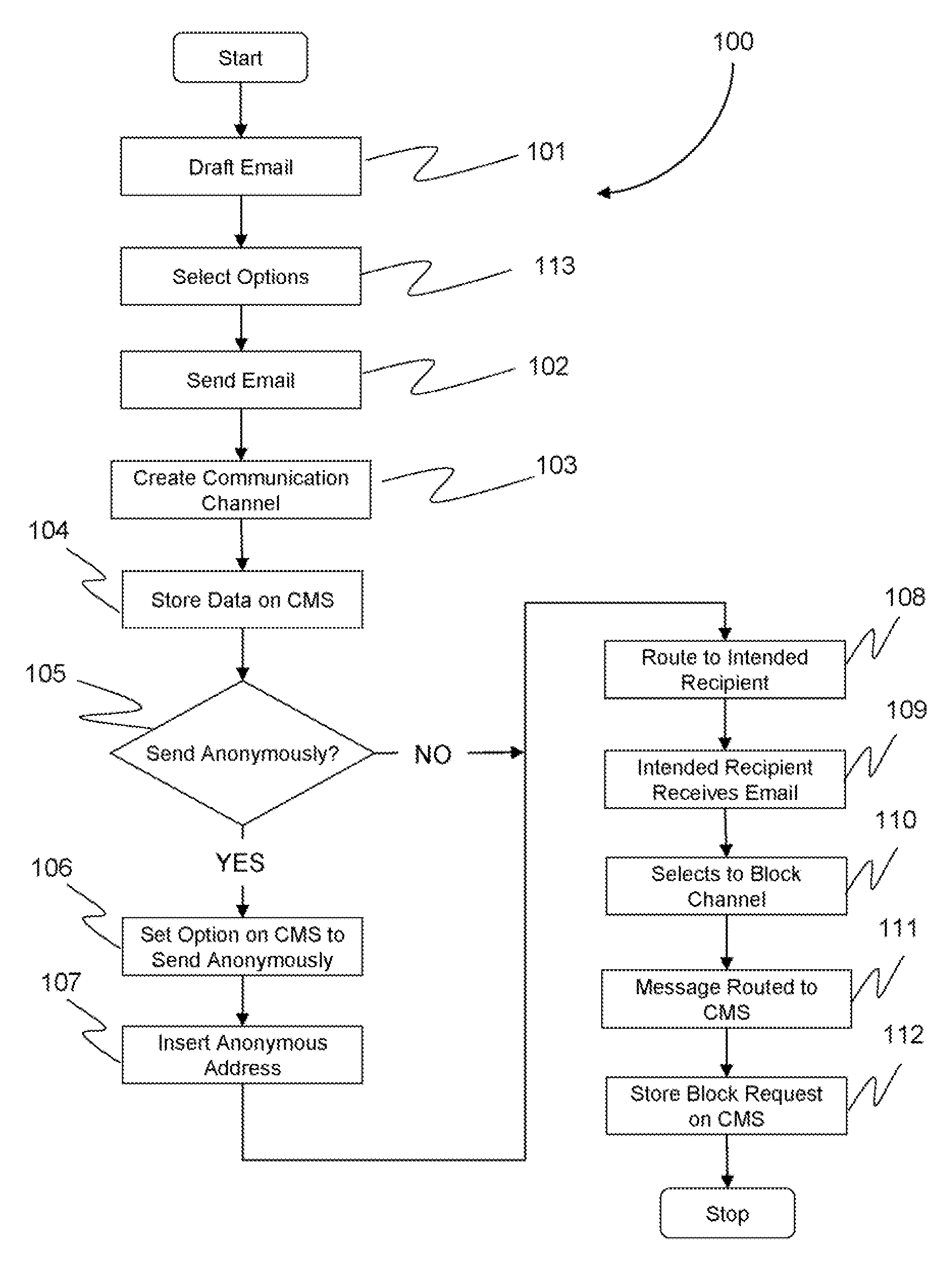
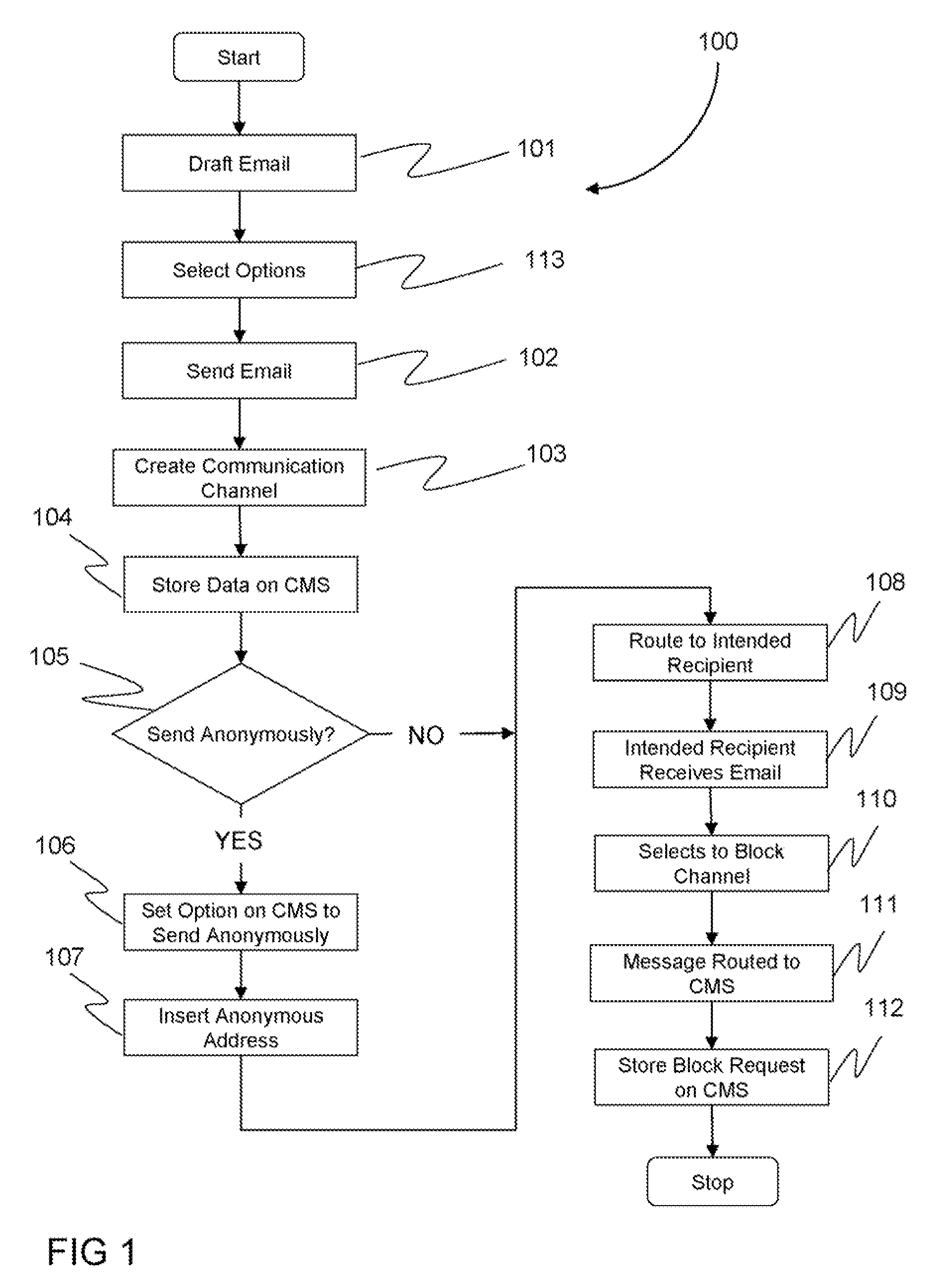
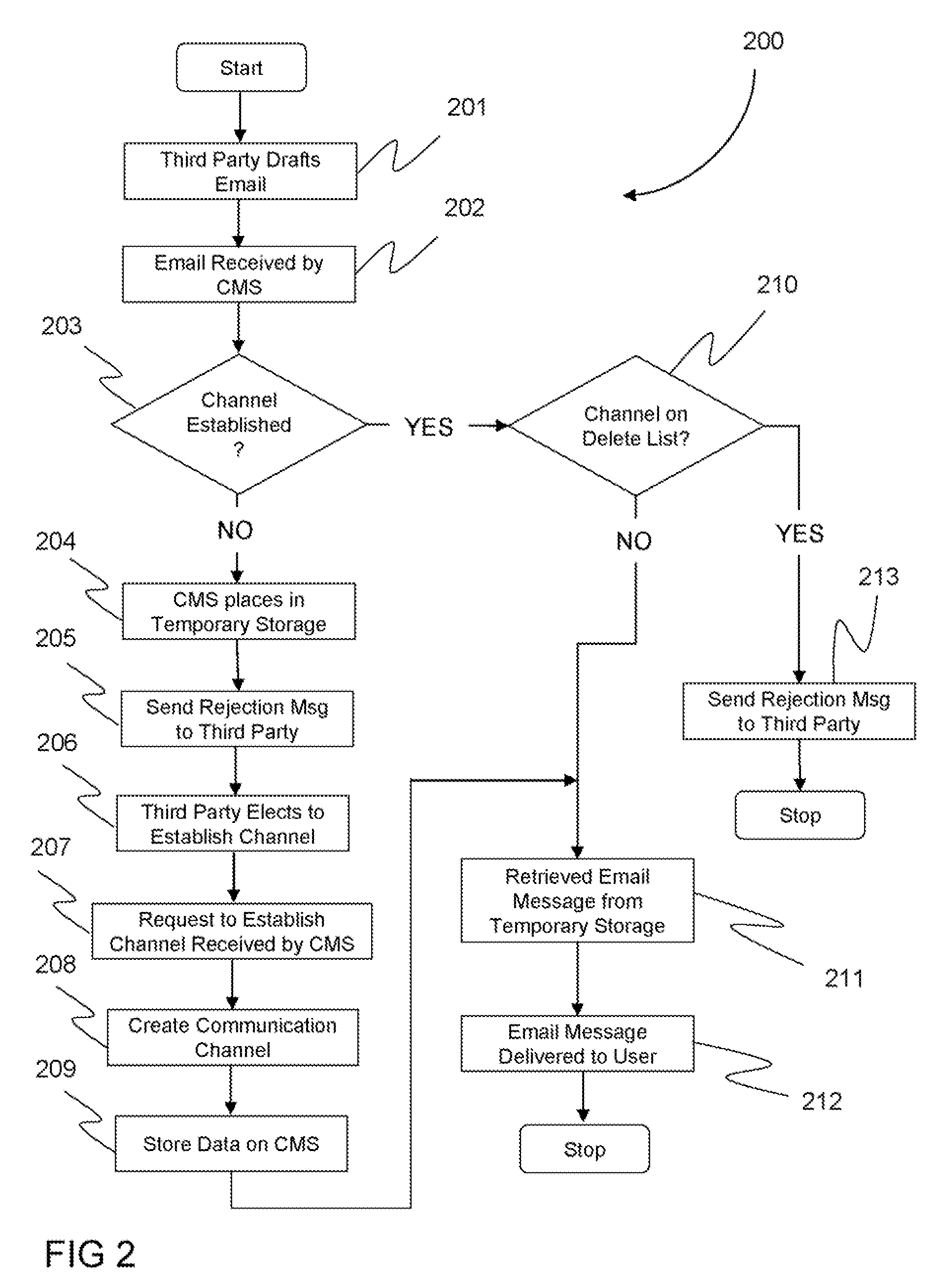
InactiveUS20070180039A1Reduces unsolicited electronic messagesEasy to rememberMultiple digital computer combinationsThird partyDisposable email address
A method and system directed toward establishing a communication channel for communication between an email user and third party email users, employing anonymous disposable email addresses of the email user associated with one or more third party email users to minimize email spam. The email user may further block email communication with a third party email user by electing to delete the communication channel associated with the third party email user. Moreover, the third party email user receiving an email through a communication channel may also elect to delete the communication channel to block receiving any further email communication from an email user.
Owner:SUTIDZE DAVID +3
Payment program for use in point-of-sale transactions
In some embodiments, the present application relates to card-free programs provided by a merchant to a customer, whereby the customer has access to functions such as payment options and / or loyalty program benefits without needing to present a physical card at a point of sale. For example, a customer may make a card-free purchase of goods or services from a merchant, whereby the customer need not present a card such as a debit card, credit card, loyalty card, or other physical tender to make a purchase. Further, the customer need not provide biometric data or otherwise use an electronic device or identifier to make a purchase. Alternatively or additionally, the customer may access a loyalty program without needing to provide a physical card or data associated with a card.
Owner:SAFEWAY INC
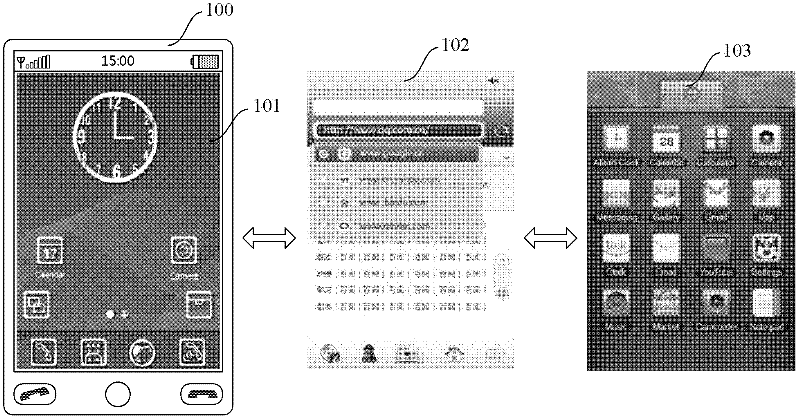
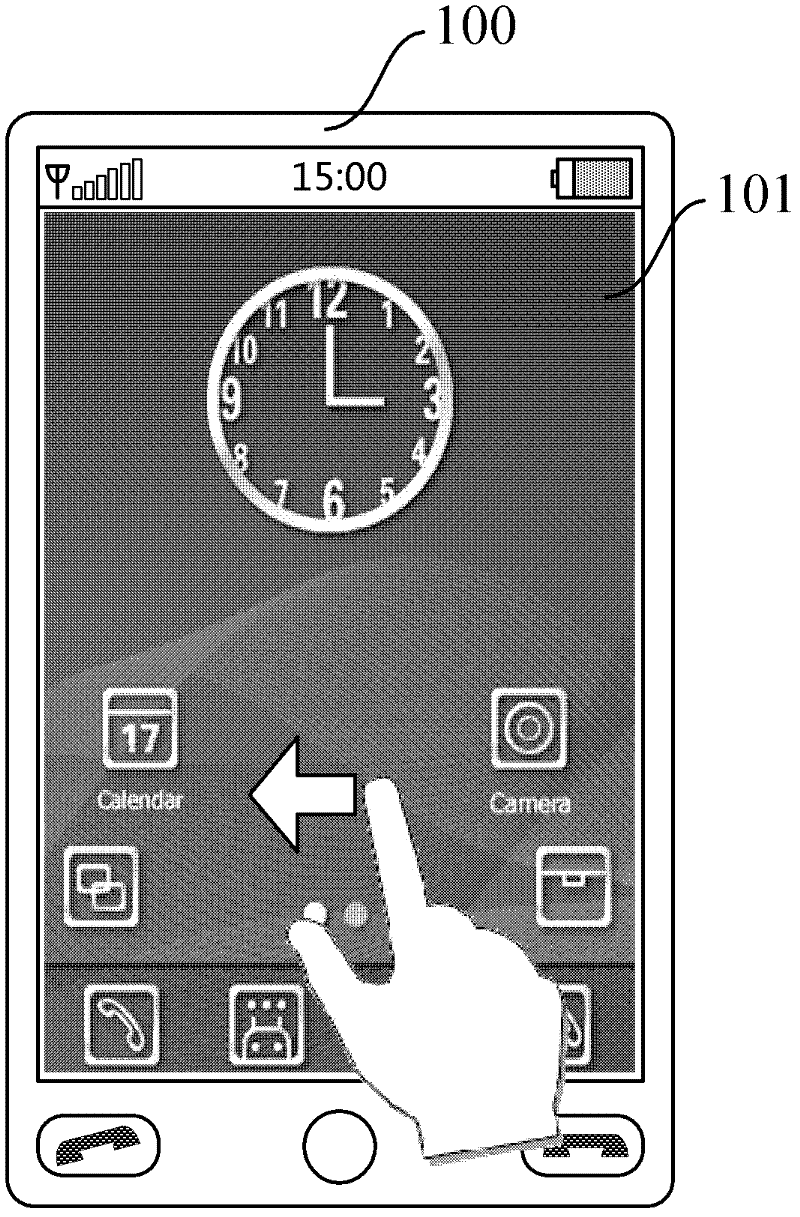
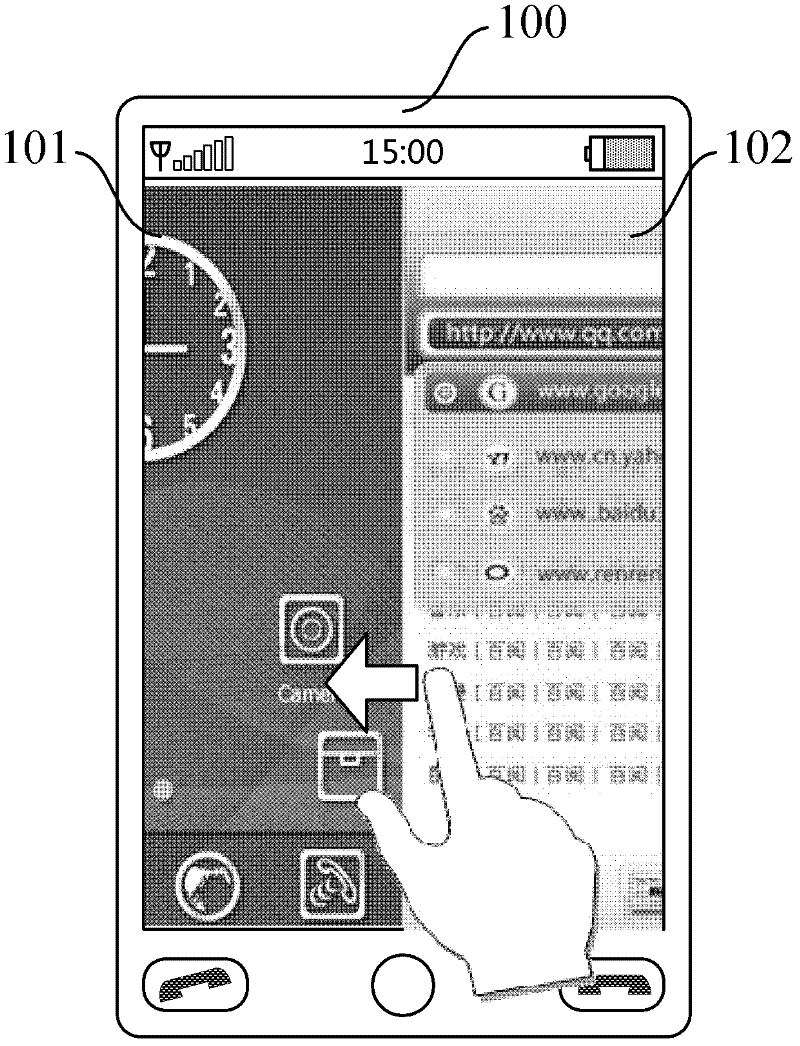
Method for displaying browser interface on mobile equipment
InactiveCN102243662AEasy to rememberImprove operational efficiencySubstation equipmentSpecial data processing applicationsComputer terminalMobile device
Owner:BEIJING FENGLING CHUANGJING TECH
Method and system for providing message services in a communication system
InactiveUS6920318B2Eliminate and reduce disadvantageEliminate and reduce and problemSpecial service for subscribersSubstation equipmentCommunications systemPrivate network
A method for providing message services is provided that includes receiving a user notification message in an application. A user identifier for at least one recipient of the message is received in the application. The user identifier is operable to identify the recipient. The message and the user identifier are provided from the application to a private network. The private network is operable to transmit the message to a mobile station for the recipient. The mobile station has a corresponding mobile station identifier, and the user identifier is assigned to the mobile station identifier in the private network.
Owner:RINGCENTRAL INC
Programmable liquid containers
InactiveUS20090206084A1Easy to rememberEasy to repeatPre-extraction tea treatmentHollow inflatable ballsMechanical engineering
The invention relates to liquid containers comprising a plurality of sealed additive chambers in communication with a vessel tillable with a liquid. The additive chambers comprise independently selected additives that may be added to a liquid in the container at the option of the user. The user can manually open the additive chambers of their choice and release the additive into a liquid in the vessel without destroying the integrity of the container. In this manner, the liquid containers are programmable by the users and various aspects of the liquid in the container, such as color and / or flavor, is controlled by the user.
Owner:IPIFINI INC
Method and system of providing authentication of user access to a computer resource via a mobile device using multiple separate security factors
InactiveUS20140149742A1Easy to rememberPromote cloningUser identity/authority verificationDigital data authenticationComputer resourcesPassword
A method and system of authenticating a computer resource such as an application or data on a mobile device uses a contactless token to provide multi-factor user authentication. User credentials are stored on the token in the form of private keys, and encrypted data and passwords are stored on the device. When application user requires access to the resource an encrypted password is transmitted to and decrypted on the token using a stored private key. An unencrypted data encryption key or password is then transmitted back to the device under the protection of a cryptographic session key which is generated as a result of strong mutual authentication between the device and the token.
Owner:HOVERKEY
Method and systems for accessing information on a network using message aliasing functions having shadow callback functions
InactiveUS7058726B1Easy to rememberEasy inputMultiple digital computer combinationsTransmissionOperational systemHome page
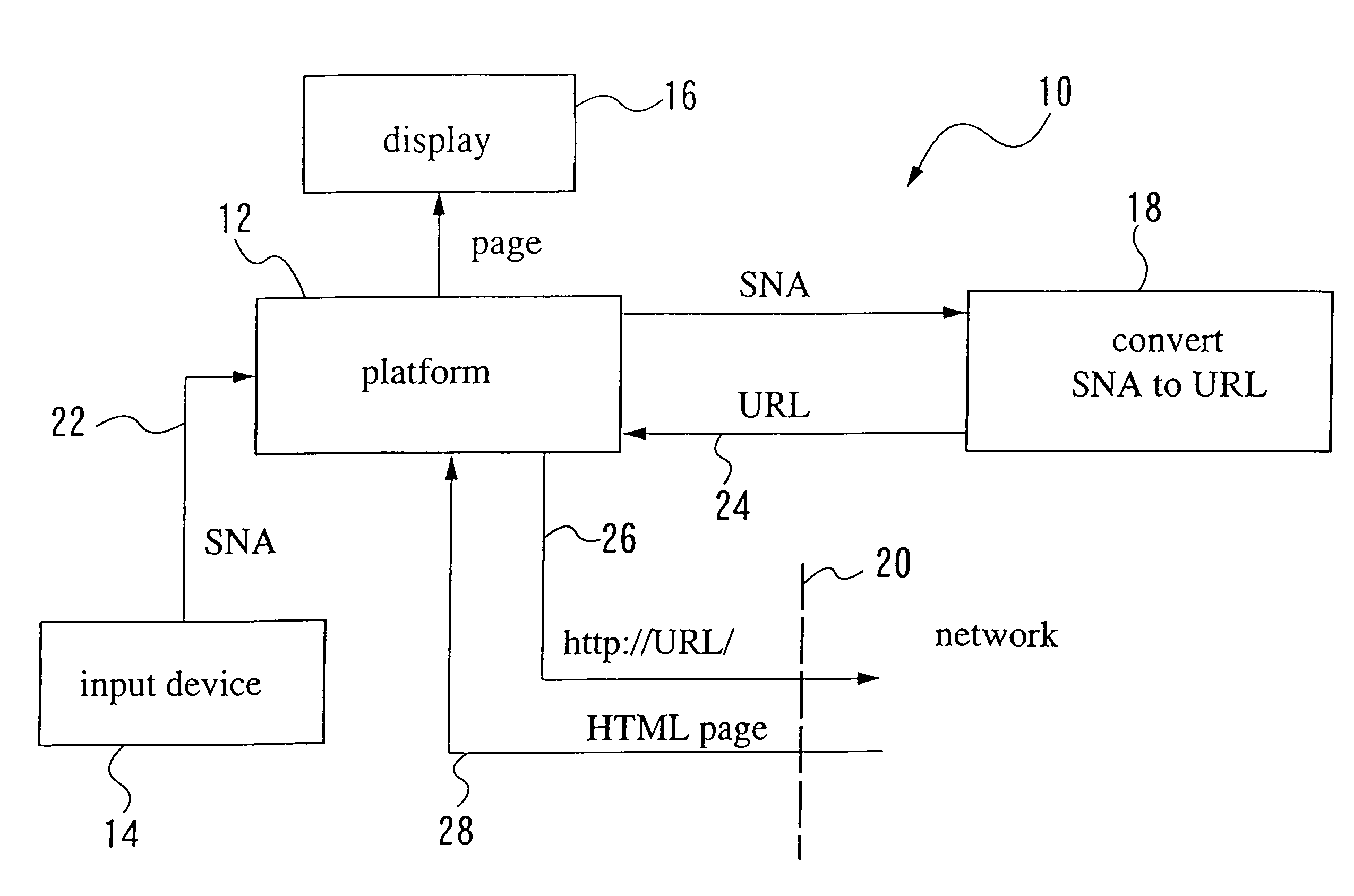
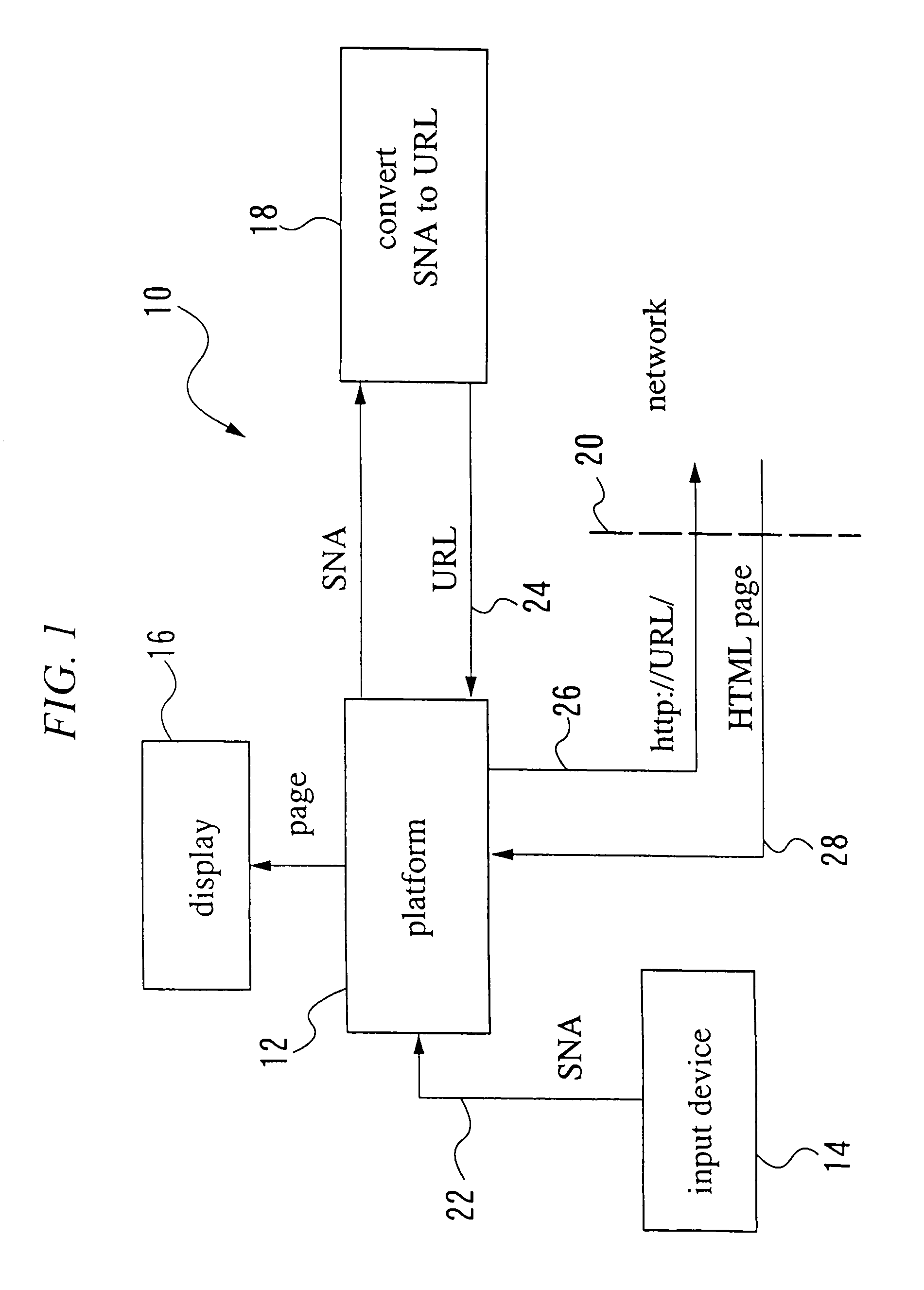
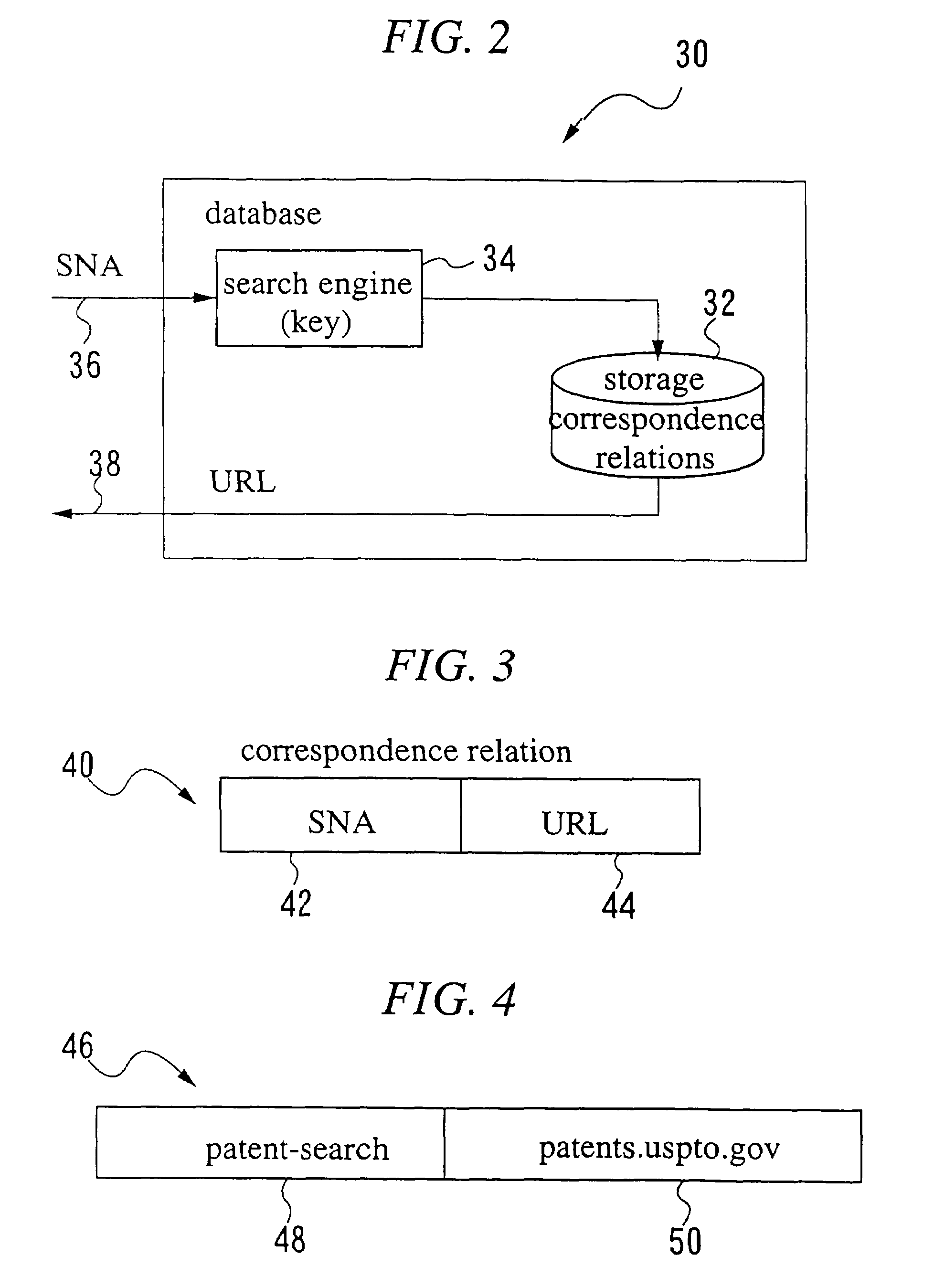
The present invention provides methods and systems for accessing a network URL through a pre-assigned simplified network address, correlating to the URL, and for displaying the home page having the URL as its address. These methods and systems provide easier URL and home page access because persons wanting to access the home page need only input the simplified network address, thereby avoiding the need to know and input the URL character string. The simplified network addresses of the present invention include numbers. Methods are provided for selecting numbers for assignment to URLs. The URL and home page access and display methods of the present invention include: assigning a simplified network address such as a number to a URL, storing the URL and number conversion in a network accessible storage system, inputting the assigned number in a network accessible computer, communicating the inputted number to the storage system, converting the number to the URL, retrieving the home page corresponding to the URL and displaying the home page on the computer. Additionally, the invention provides methods for use in message passing operating systems wherein system level messages to specific objects are intercepted, creating an alias message. The invention further defines networked systems and methods for operating the networked systems that rely on the interception and rule-based modification of messages passing between system applications.
Owner:INTERNET NUMBER
Tracking web server
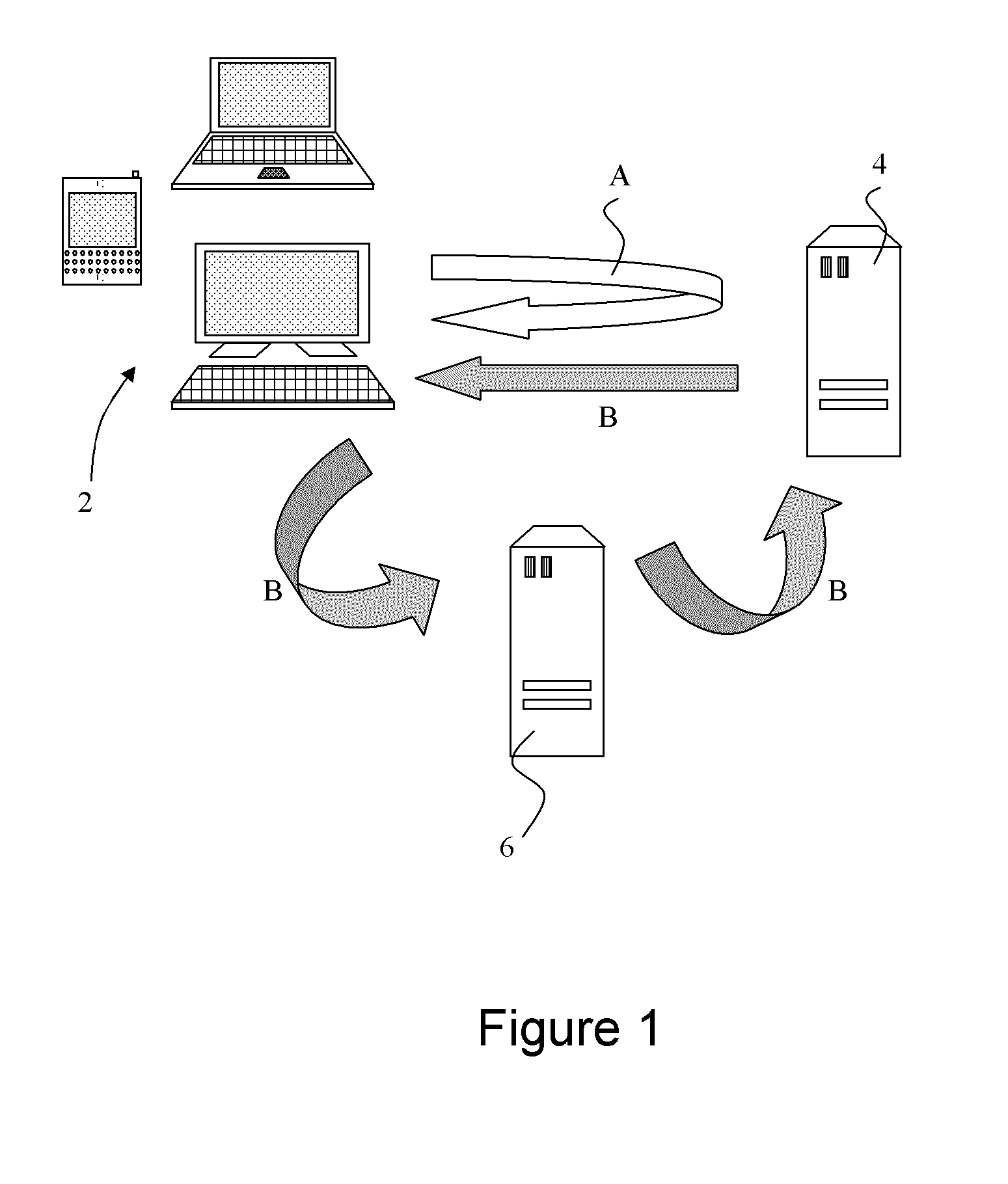
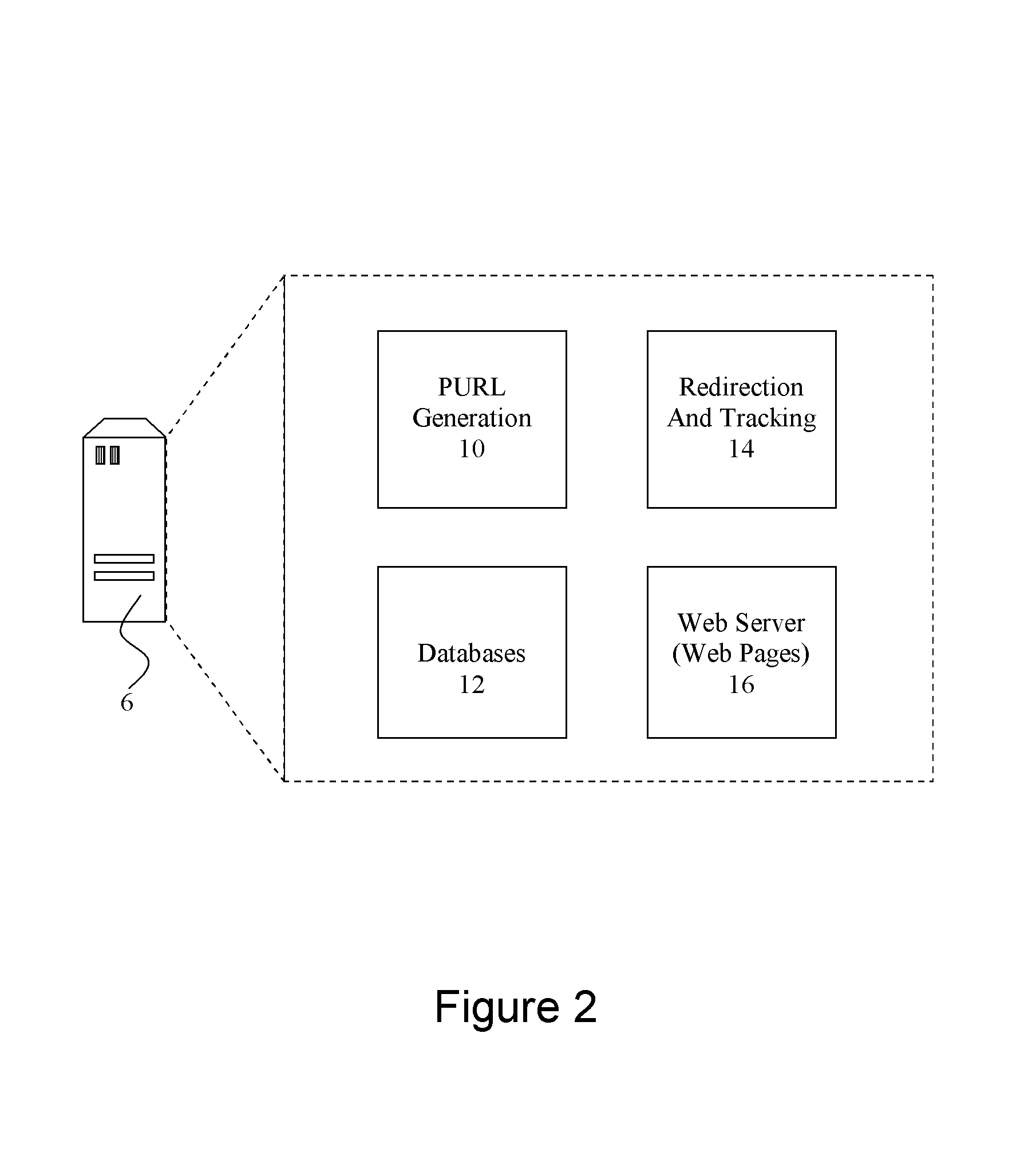
InactiveUS20080195665A1Easy to rememberURL user friendlyDigital data information retrievalTransmissionPersonalizationThird party
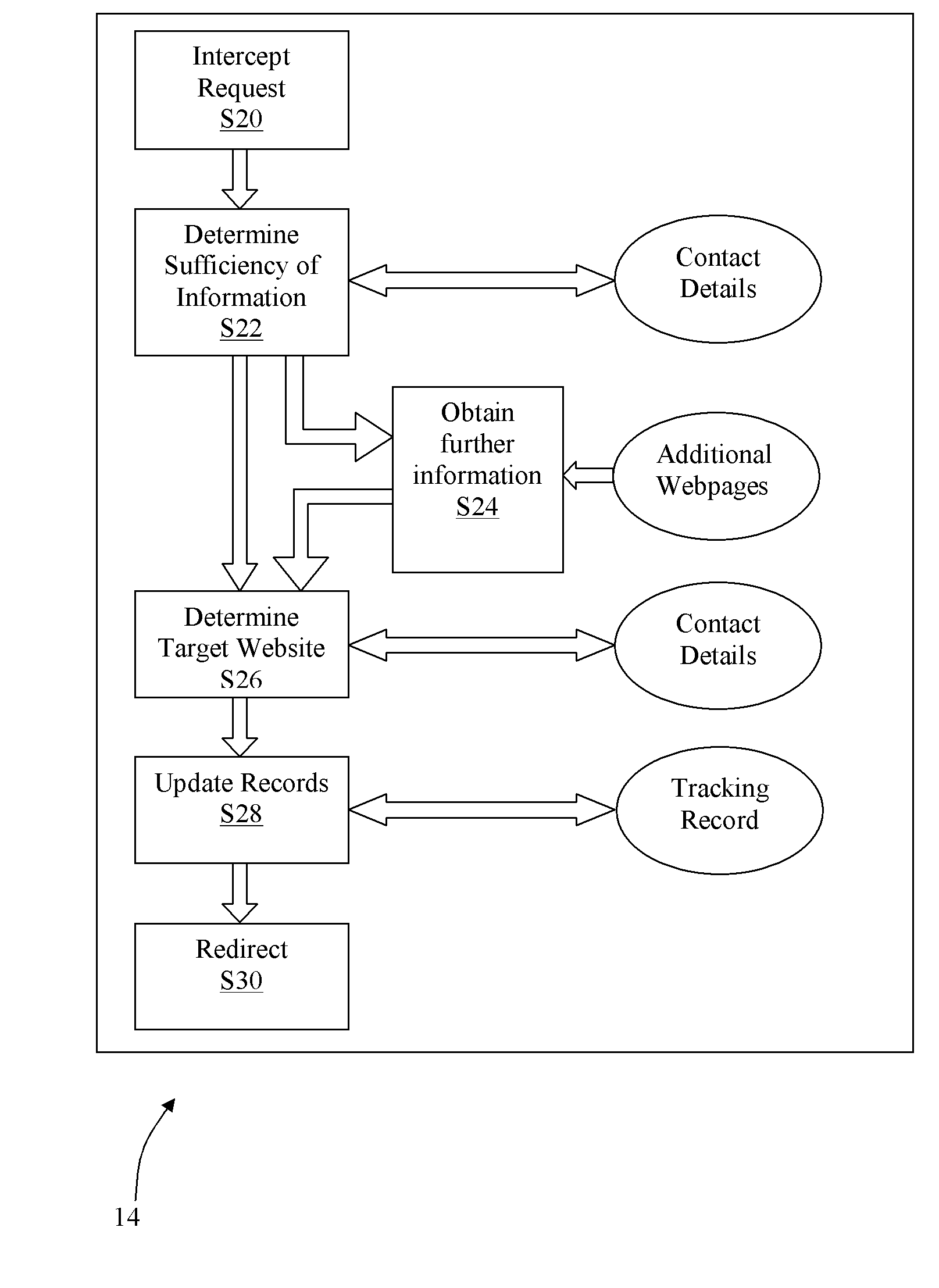
A web server is disclosed that is configured to track requests for web pages on a third party web server. The tracking web server traps a web page request, such as a PURL (Personalised URL) for a personalised web page, before it attempts to serve the web page requested. The URL of the web page request is analysed to determine the location of the requested page on a third party server, and details of the contact with which the personalised web page is associated. Receipt of the web page request is then recorded in a memory associated with the server, and the web page request is forwarded to the third party server for processing. The redirection to the third party web server may be seamless, such that the contact requesting the page does not know of the redirection. In this way, a tracking web server is provided which can supply a personalised tracking and forwarding function.
Owner:INTIMIS LTD
Reprogrammable fluid delivery system and method of use
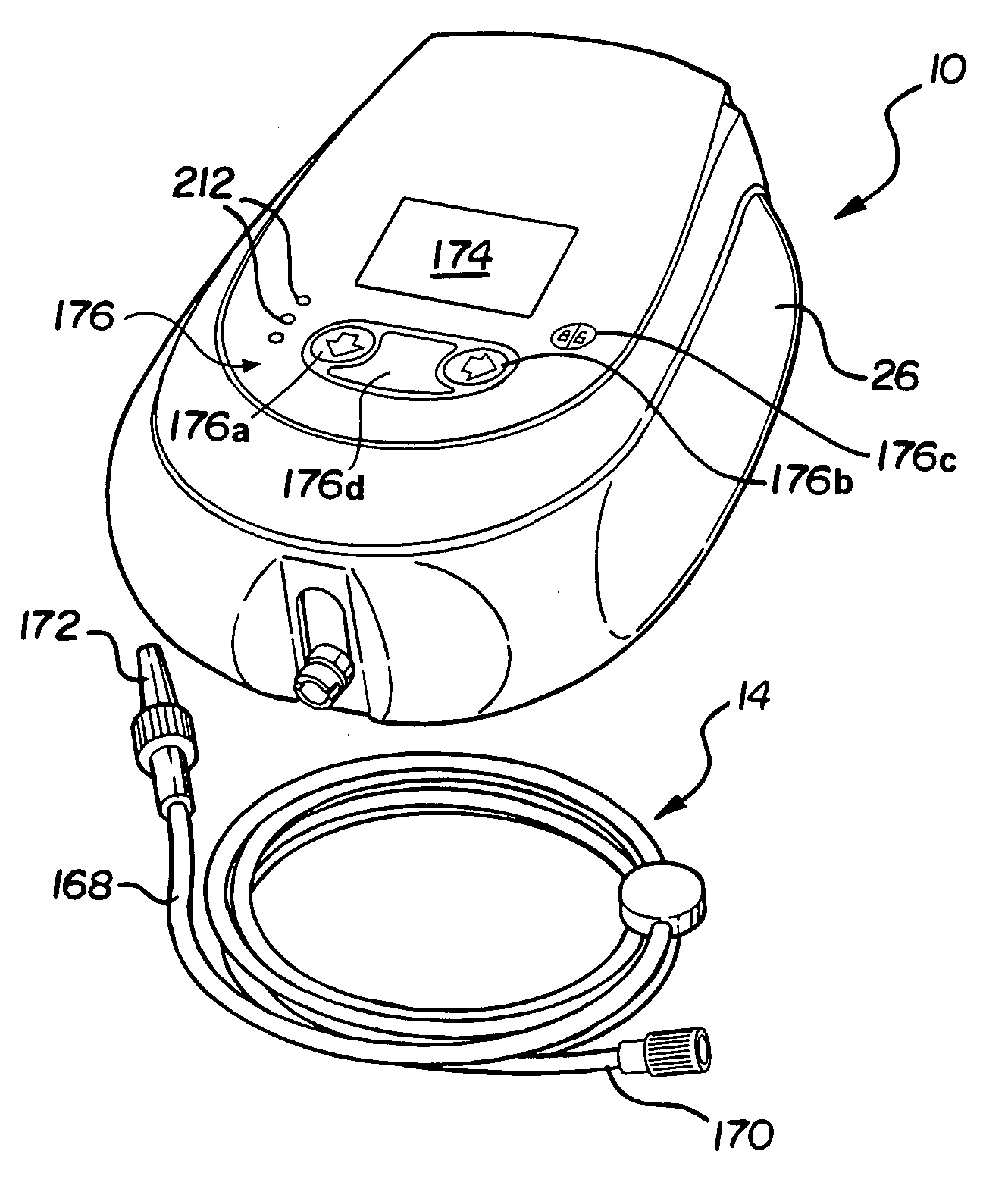
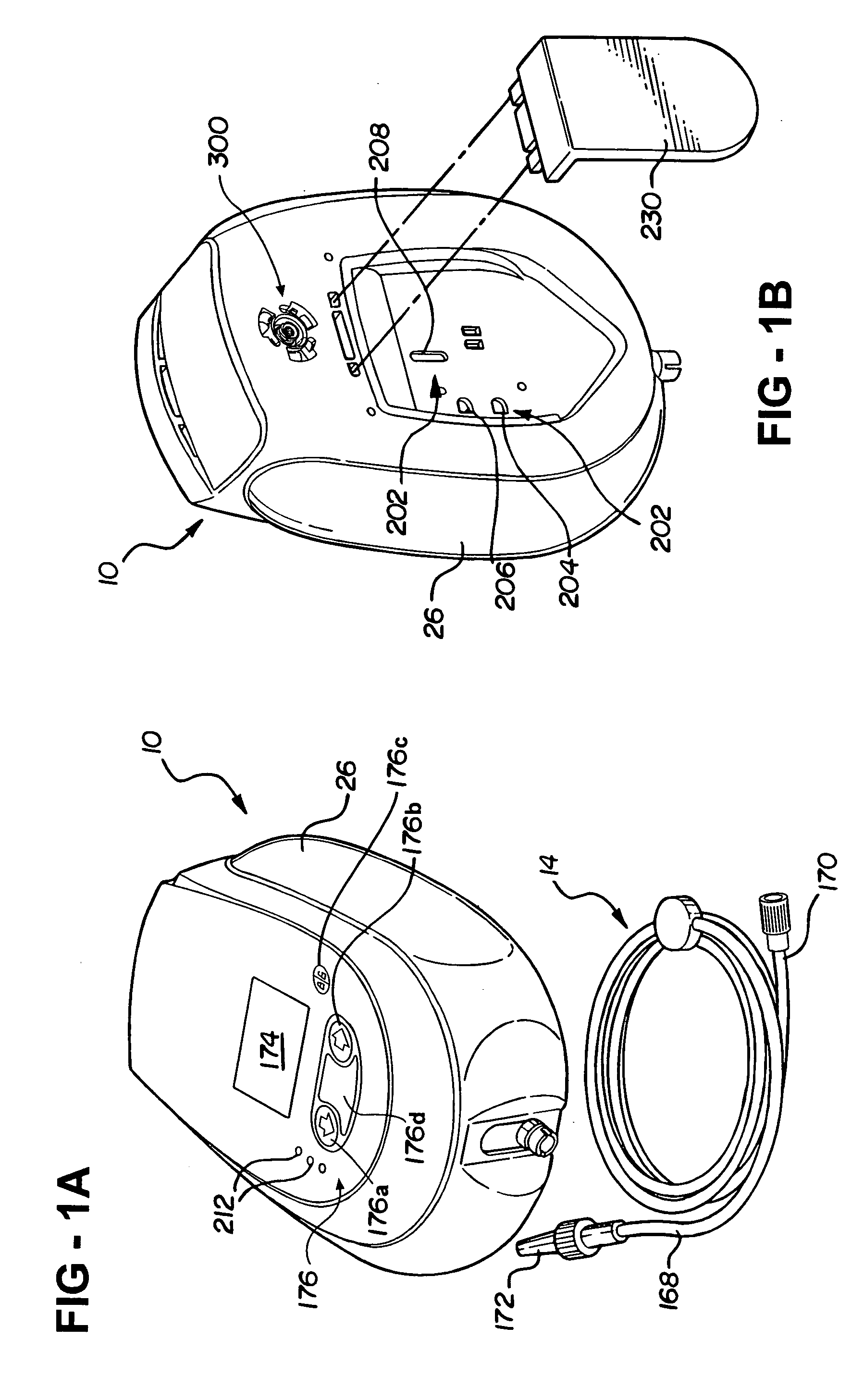
ActiveUS20060184121A1Easy to rememberEasily recognizeMedical devicesFlow monitorsElectronic communicationParameter control
A fluid delivery system is provided for delivering fluid to a patient. The system comprises a reservoir for storing the fluid to be delivered to the patient and a fluid discharge device operatively coupled to the reservoir for delivering the fluid from the reservoir to the patient. A controller is configured to operate the fluid discharge device. An input device is in electronic communication with the controller and configured for setting at least one operating parameter of the system. The controller operates the fluid discharge device based on the at least one operating parameter and locks the system after the at least one operating parameter is set such that the at least one operating parameter is unable to be modified. A display is in electronic communication with the controller to at least periodically display a code for resetting the at least one operating parameter. The code is altered at least once during use. The controller is further configured to unlock the system upon receiving the code thereby allowing a user to reset the at least one operating parameter.
Owner:STRYKER CORP
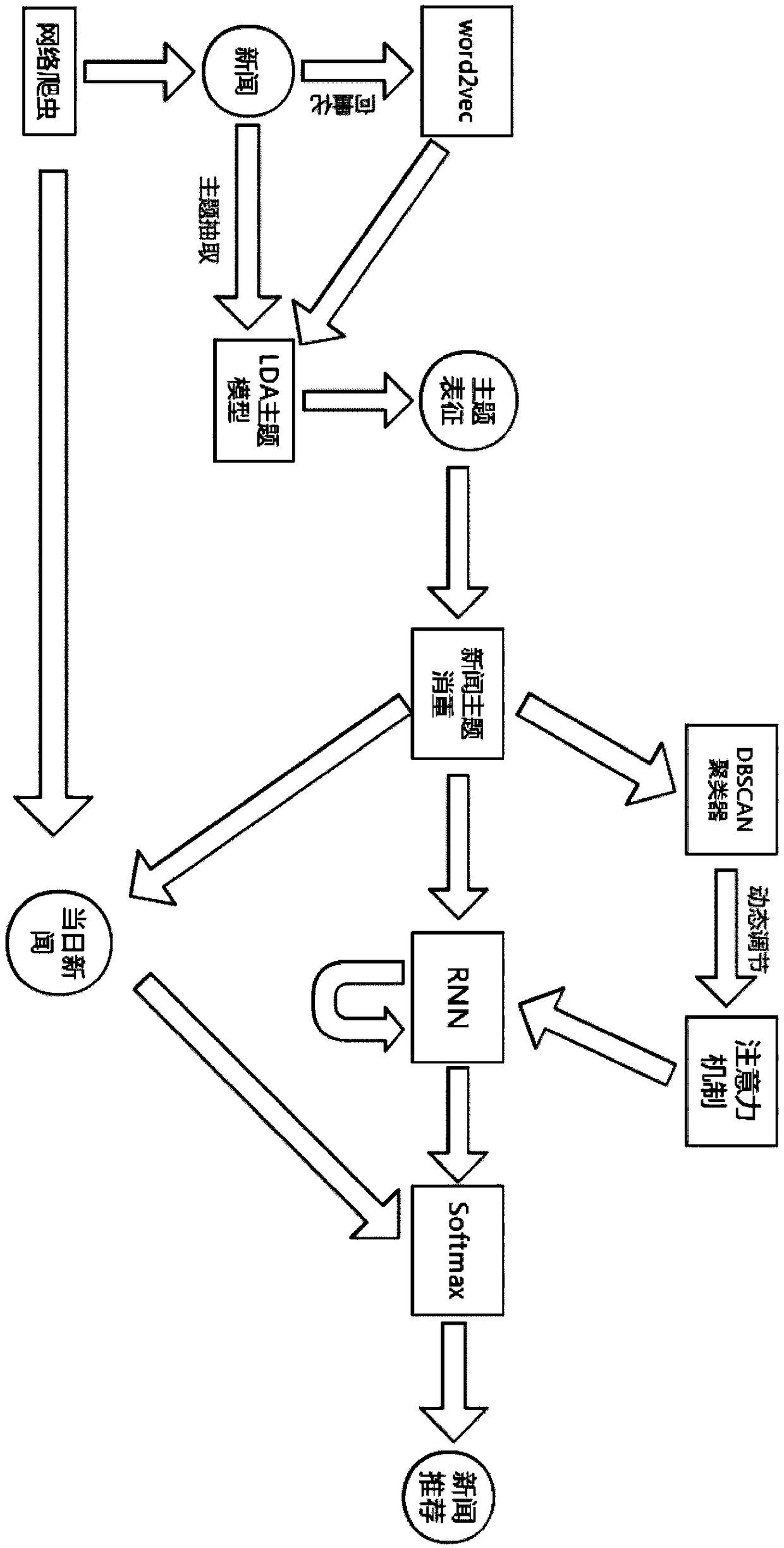
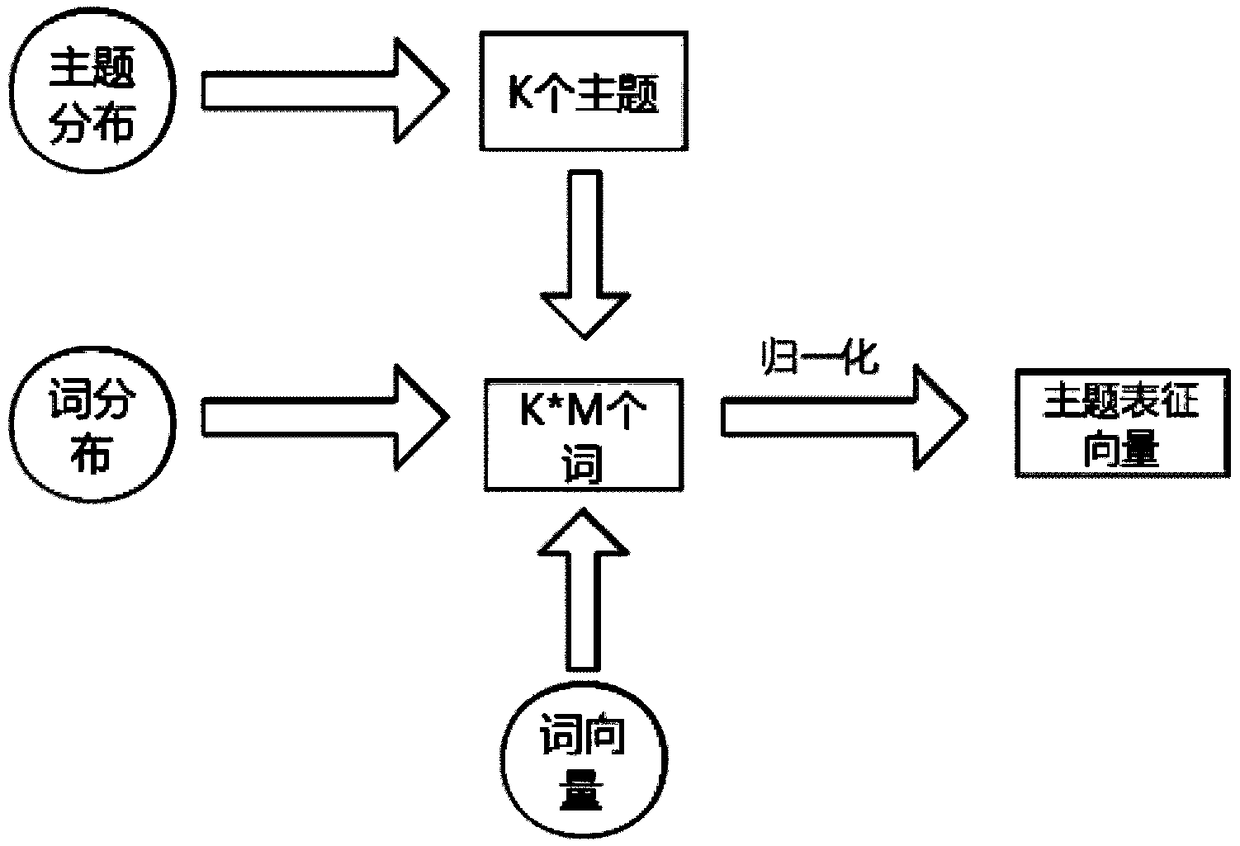
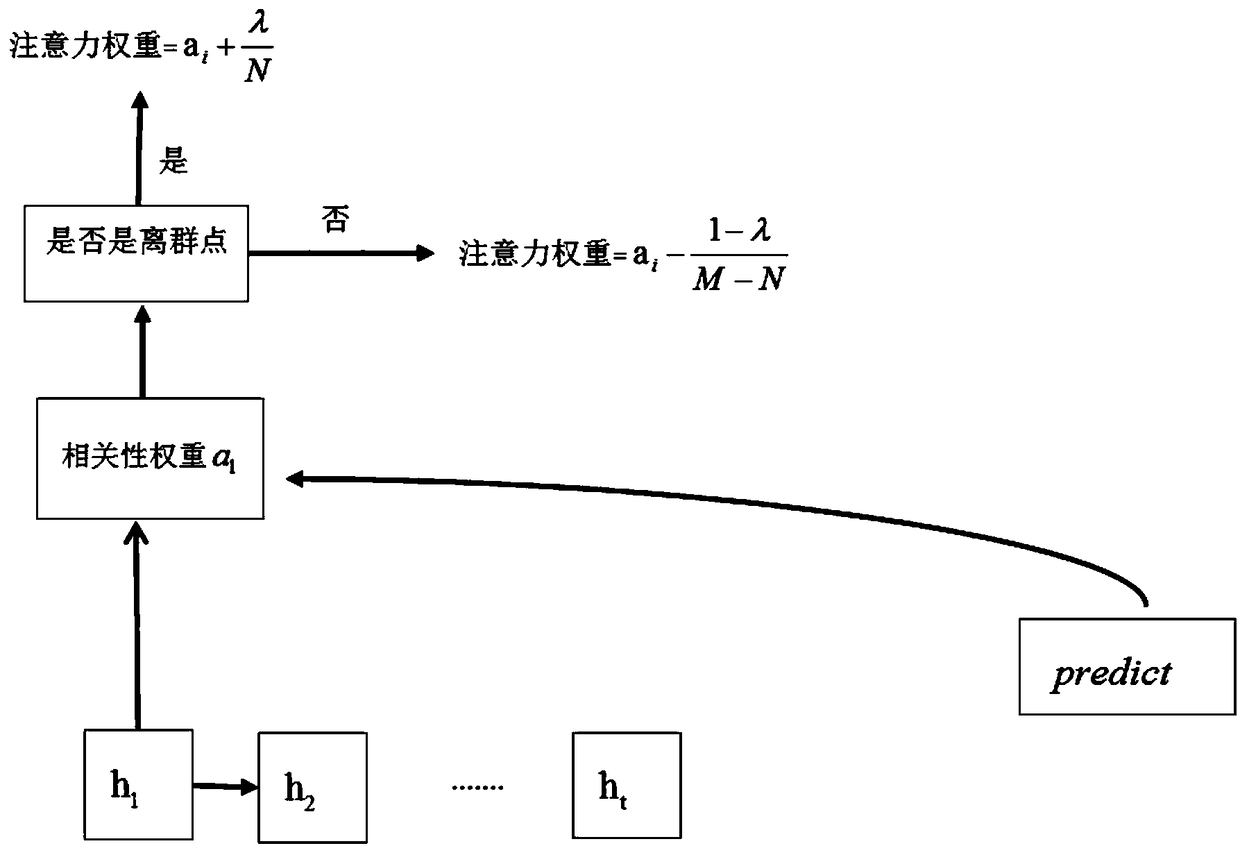
News recommendation method and topic characterization method based on RNN and attention mechanism
ActiveCN109492157AAccurate representationMake up for the lack of semantic expressionDigital data information retrievalCharacter and pattern recognitionCluster algorithmPersonalization
The invention relates to an RNN and attention mechanism-based news recommendation method and a topic representation method, which combine a traditional topic model with a neural network word vector and can effectively improve the accuracy of semantic extraction and representation of news content texts. The RNN is used for describing the seriality characteristics of news browsing of the user, so that the timeliness of the personalized news recommendation content can be greatly improved; influence weights of different news on recommendation prediction are distinguished by utilizing an attentionmechanism, user interest migration can be captured, and the accuracy and novelty of personalized news recommendation contents are improved; and finally, in combination with an attention mechanism of aDBSCAN density clustering algorithm; performing heuristic discovery on the new topics and the old topics through density clustering, and dynamically calculating influence weights of news by utilizinga topic clustering result, so that the novelty of the recommended topics is improved.
Owner:HUAQIAO UNIVERSITY
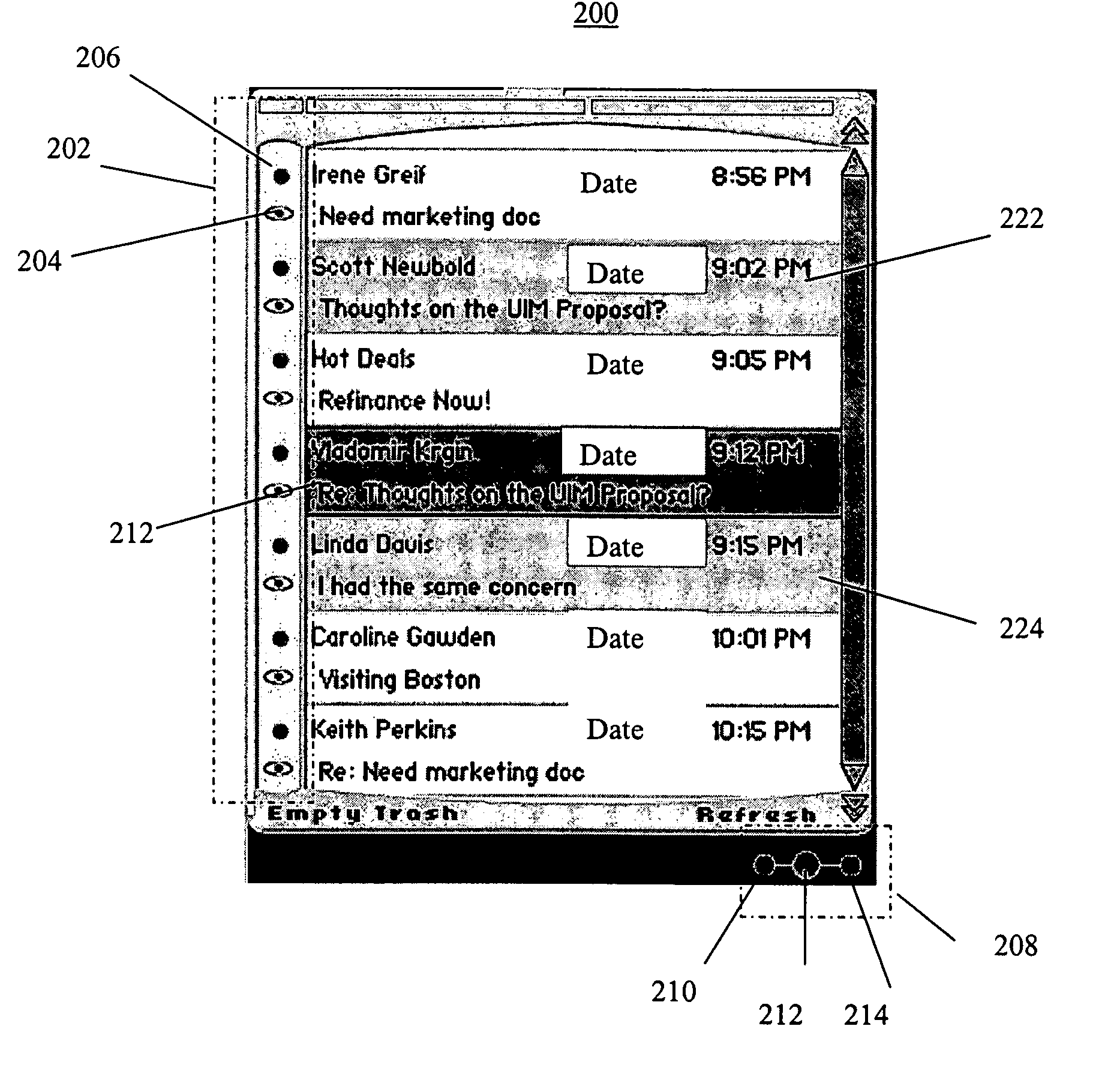
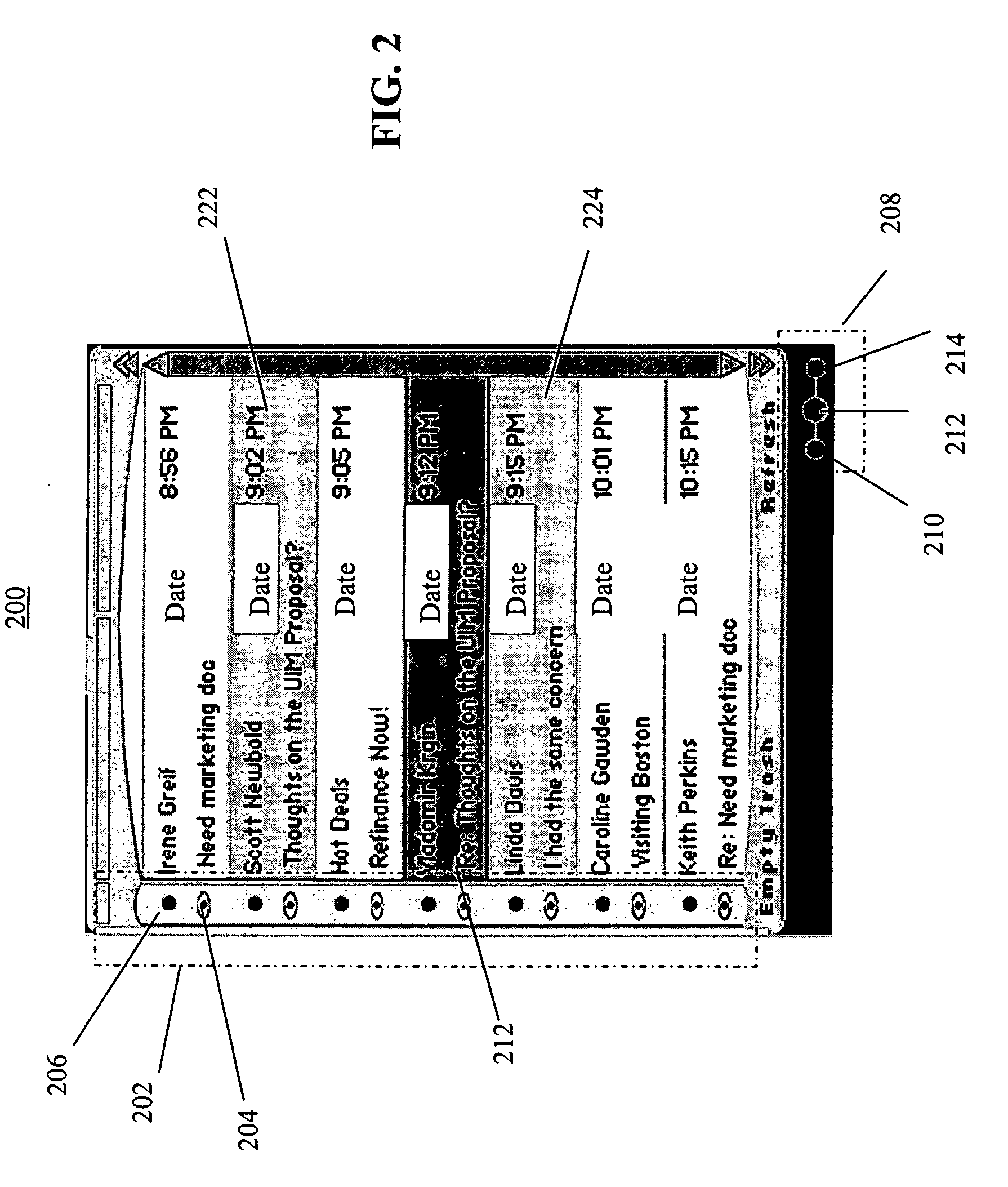
Method and apparatus for setting attributes and initiating actions through gestures
ActiveUS20050160372A1Easily rememberEasy to rememberInput/output processes for data processingHuman–computer interaction
An apparatus and method is provided for setting attributes and initiating actions associated with list items. An action icon menu is displayed with options for a user to select related to each item in the list. The user may set an item from the list for a selected action by choosing from the action icon menu or by performing a gesture associated with the desired action.
Owner:IBM CORP
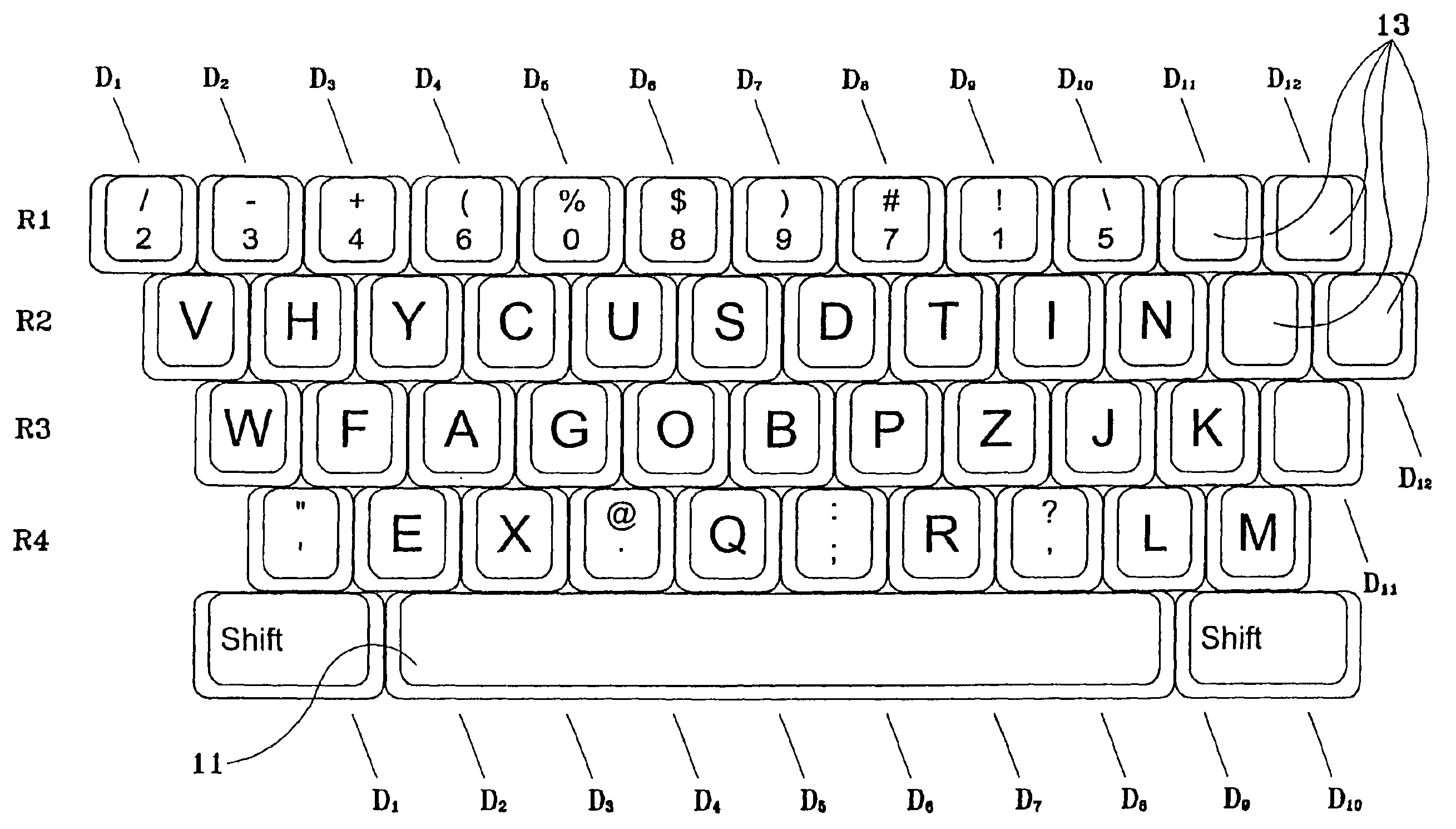
Keyboard arrangement for easy acquisition of typing skills
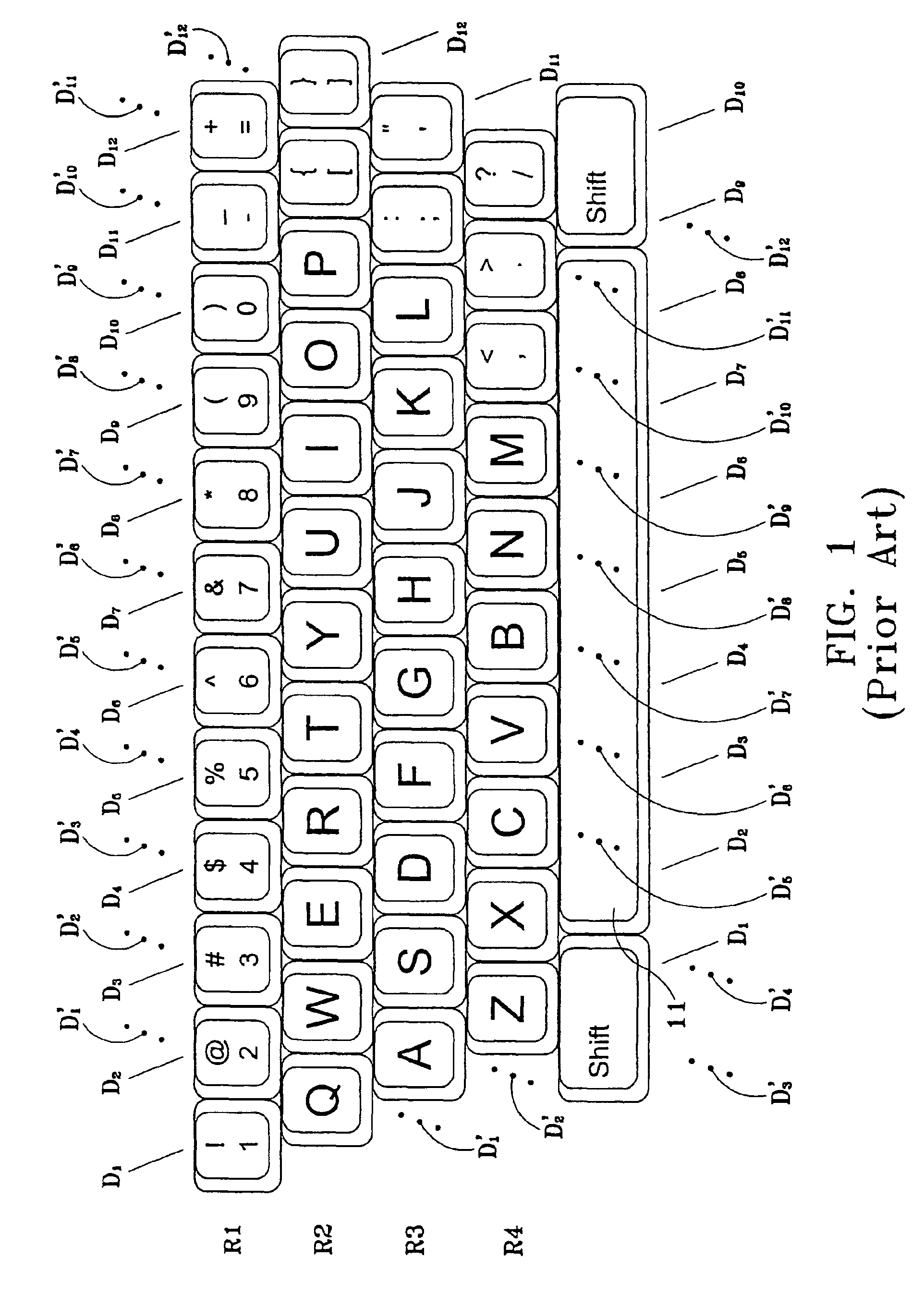
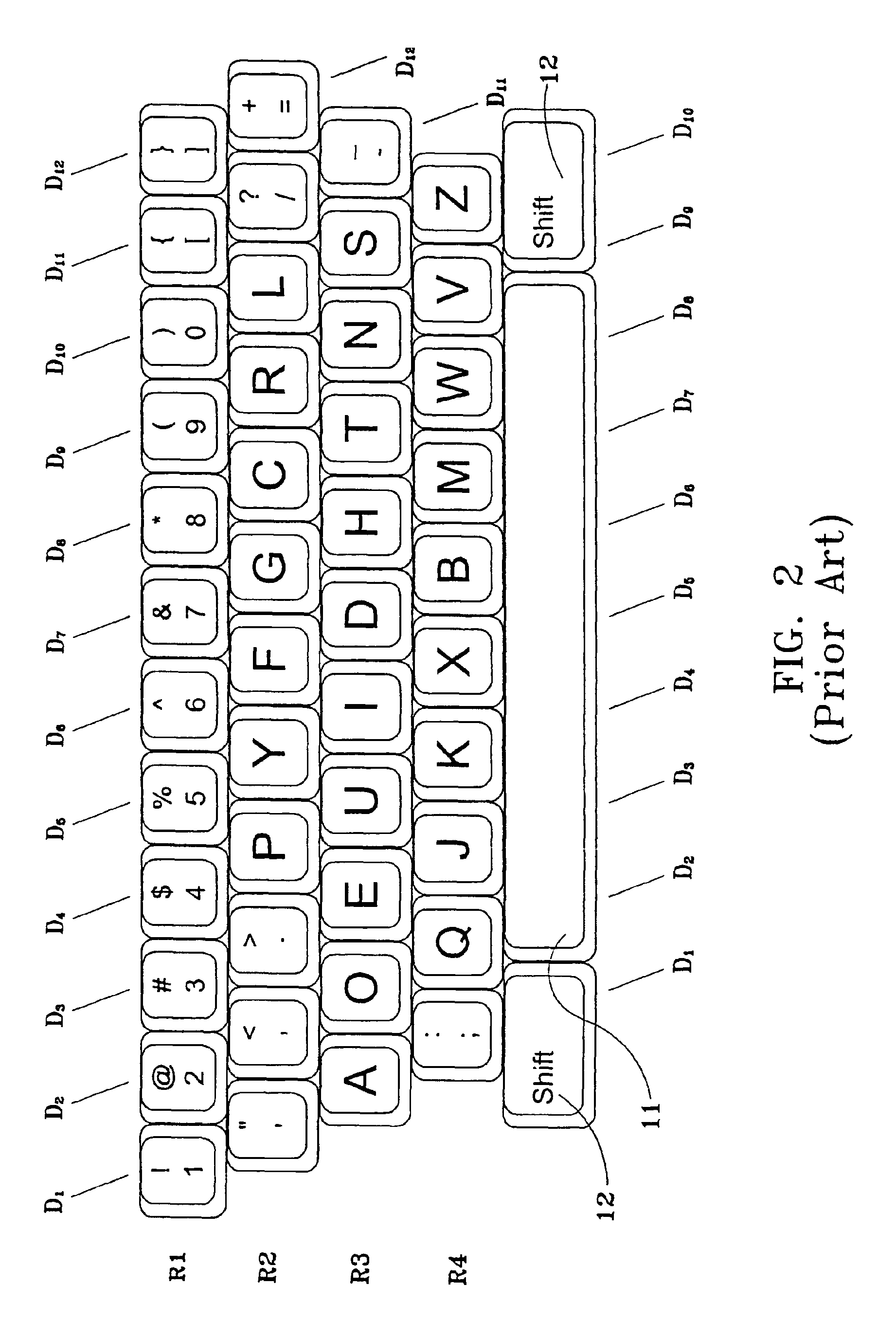
InactiveUS6932525B2Facilitate easy and rapid masteryEasy to understandOther printing apparatusInput/output processes for data processingTypingLettering
A keyboard arrangement that assigns alphanumeric and special character symbols to keys based upon the shapes of the symbols in order to facilitate learning to type. Attribute classes are defined according to the number, position, direction, or contours of the line segments that comprise the symbols. As an aid to memorization of a keyboard arrangement, symbols are assigned to keys such that a substantial number of keys in a column of keys belong to the same attribute class. To convert any prior art or other kind of electronic keyboard to a keyboard arrangement within the scope of the invention, hardware and / or software components are provided that reassign the keys so that substantially all keys within the same column will correspond to symbols within the same attribute class.
Owner:TROTMAN DOUGLAS L
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com