Patents
Literature
12560results about How to "Suitable for use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
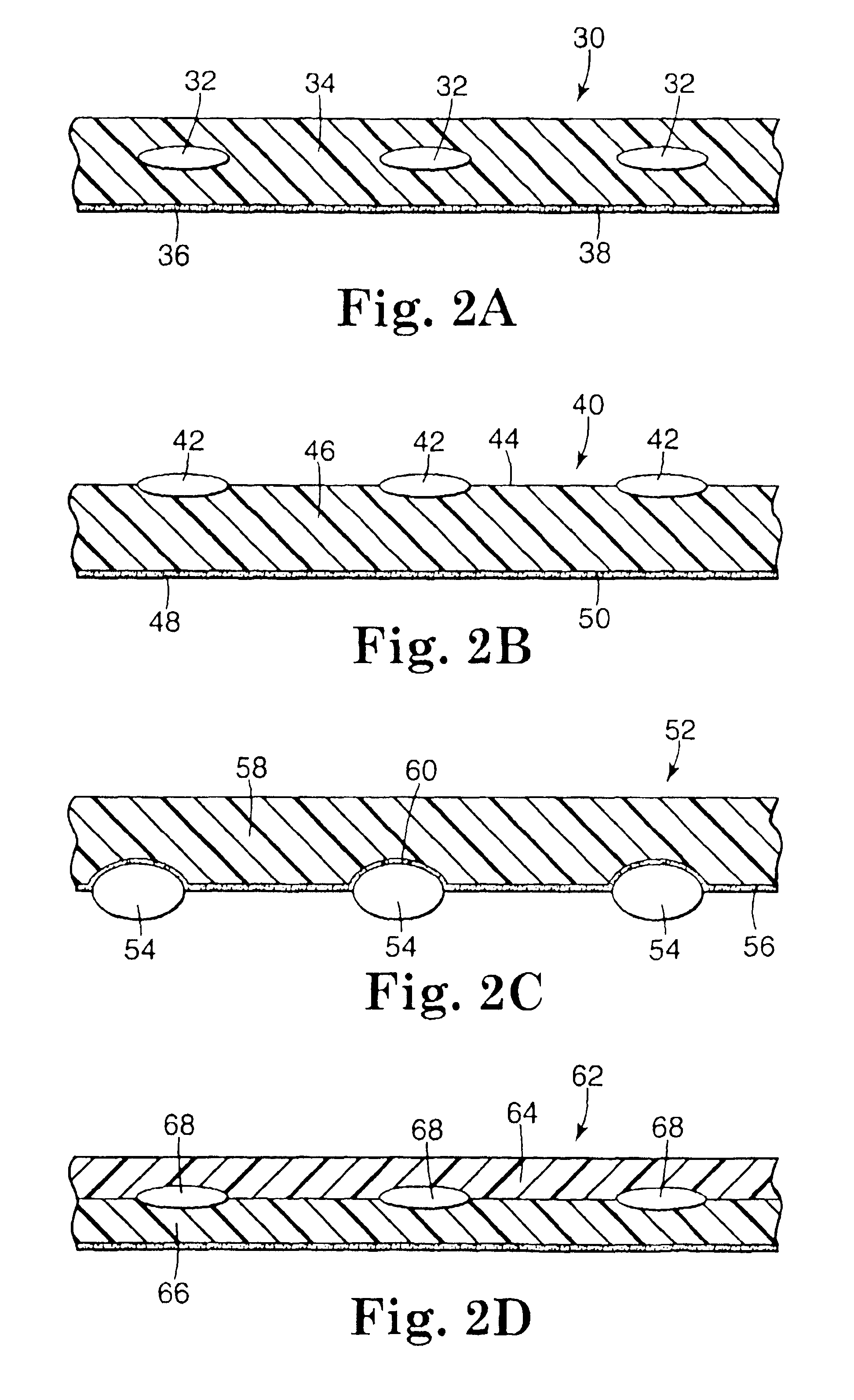
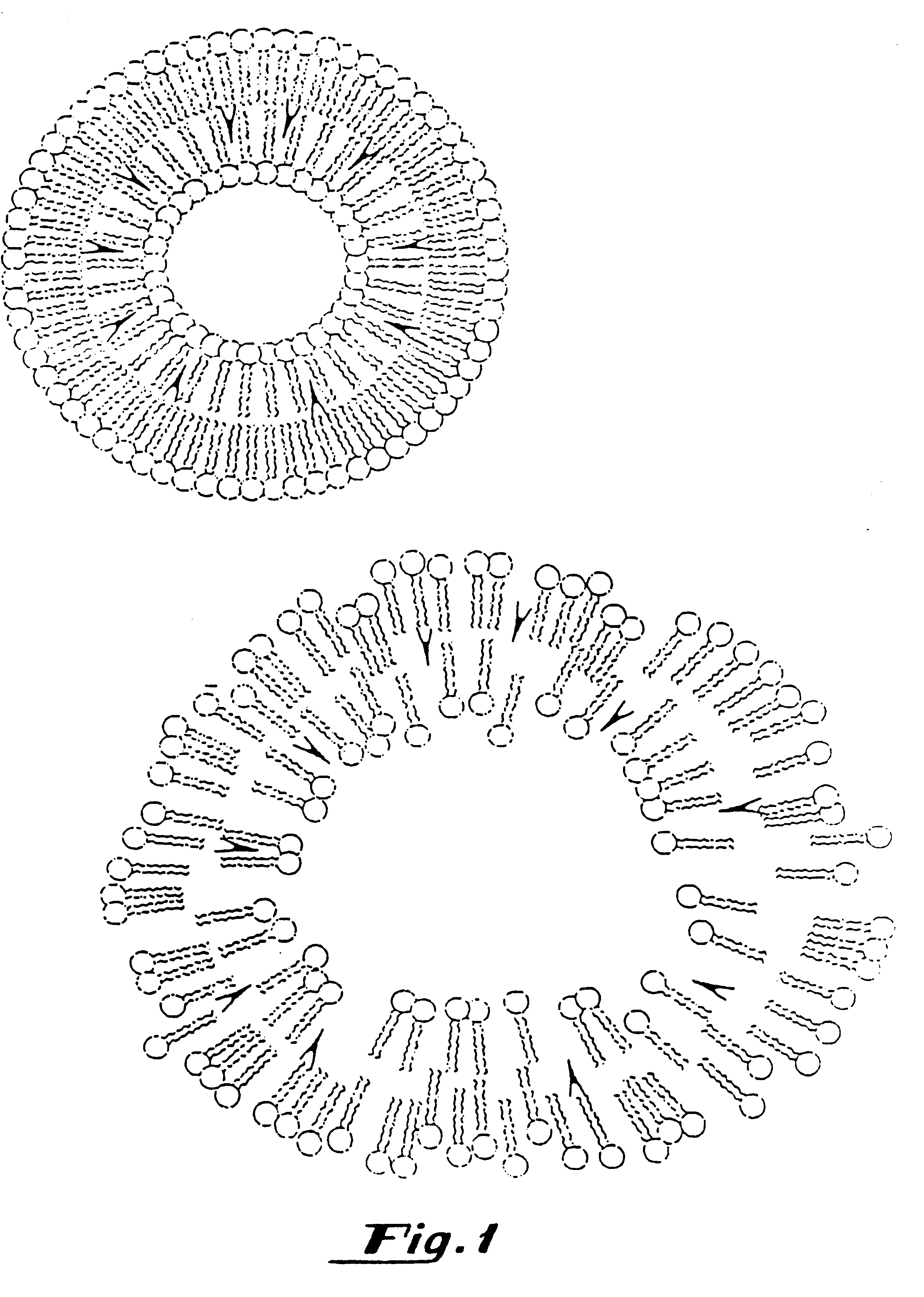
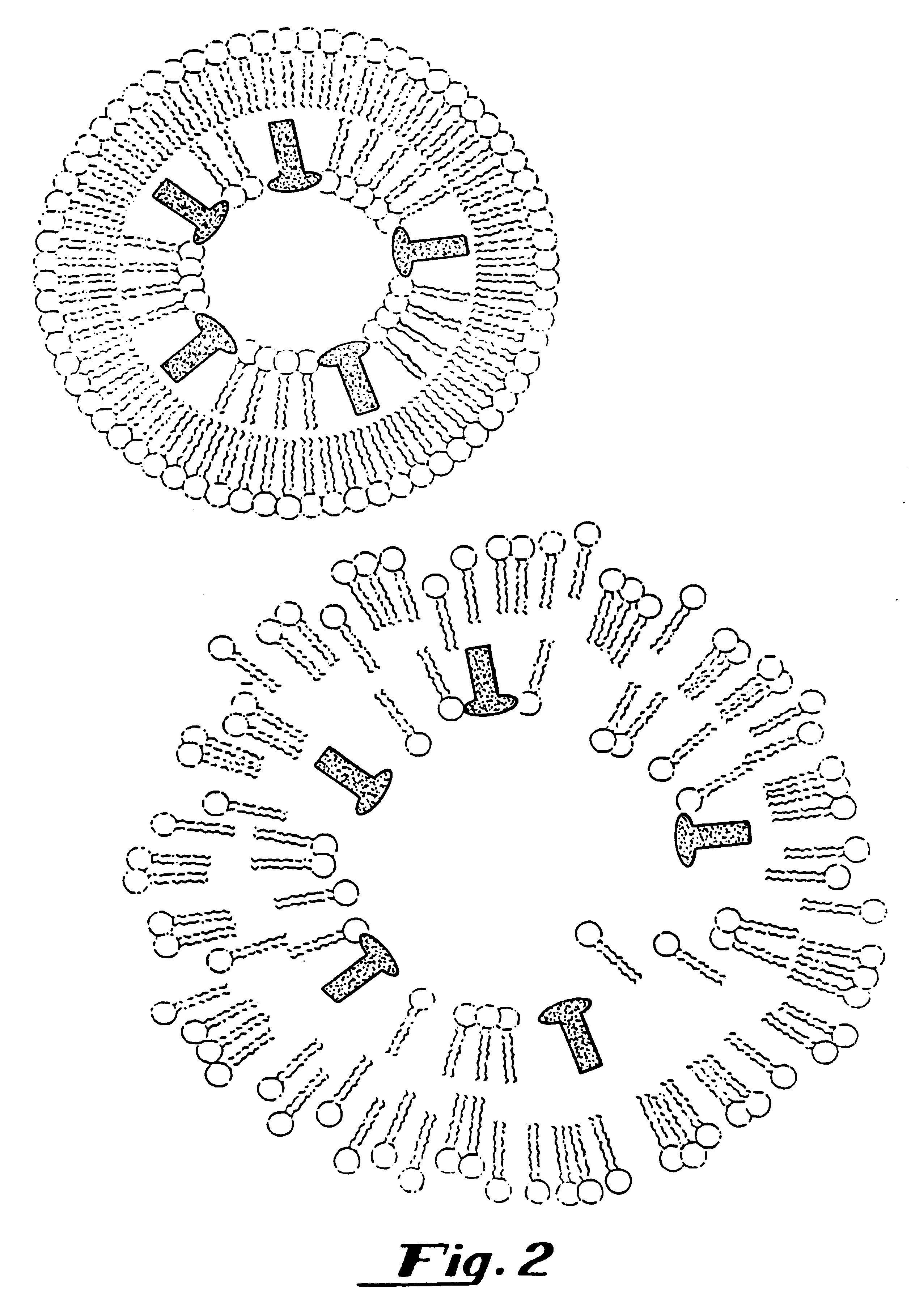
Composite self-cohered web materials
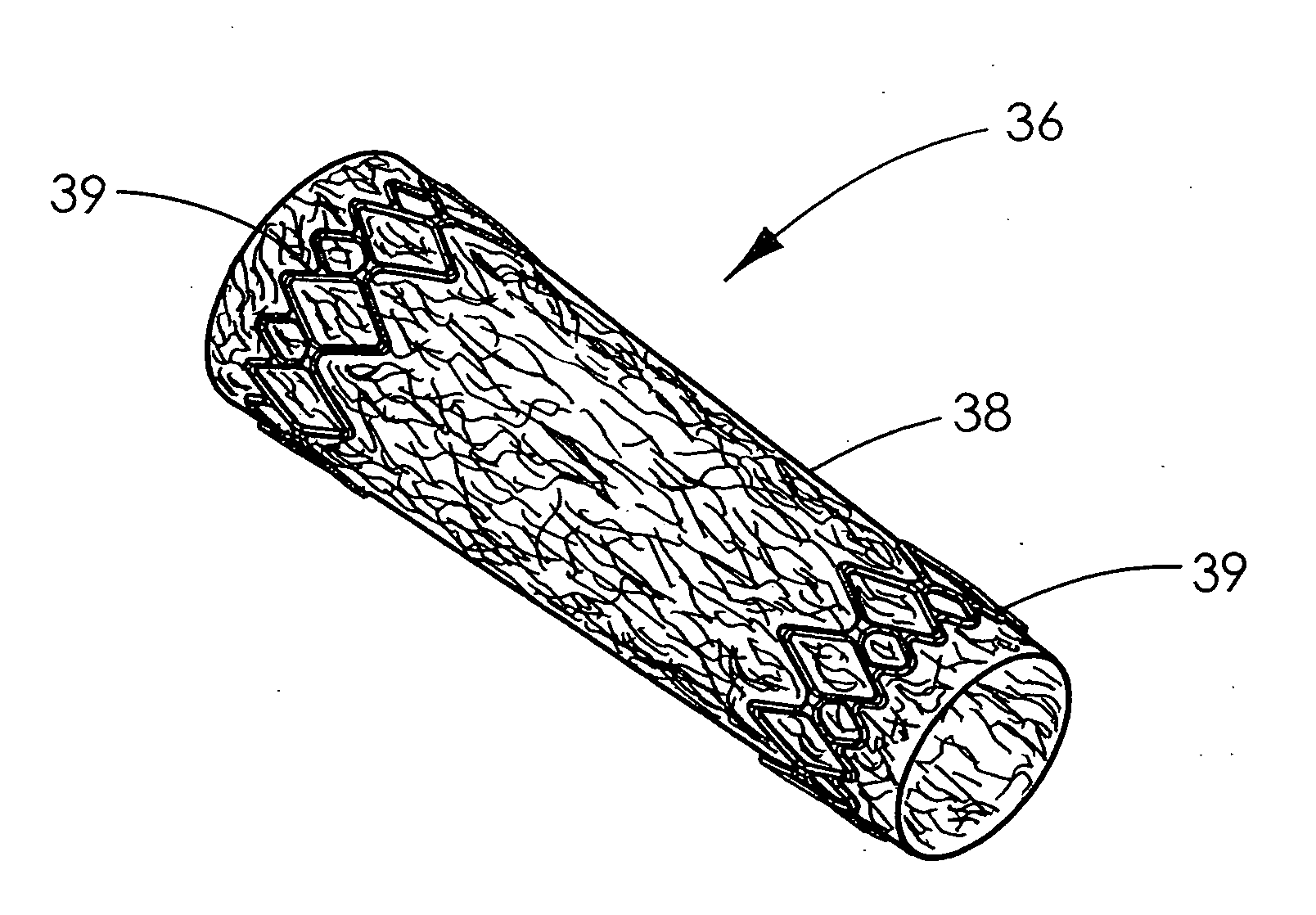
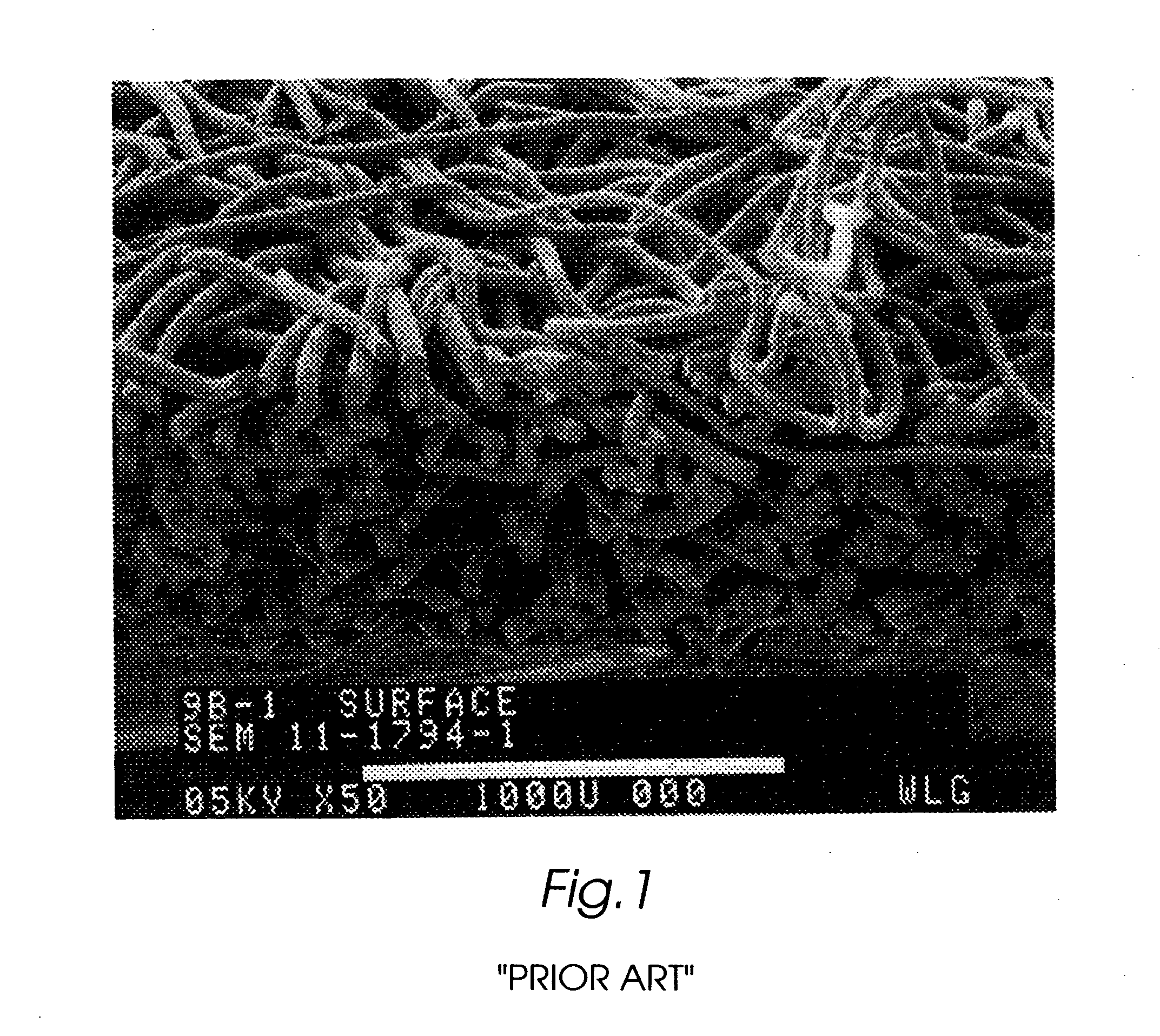
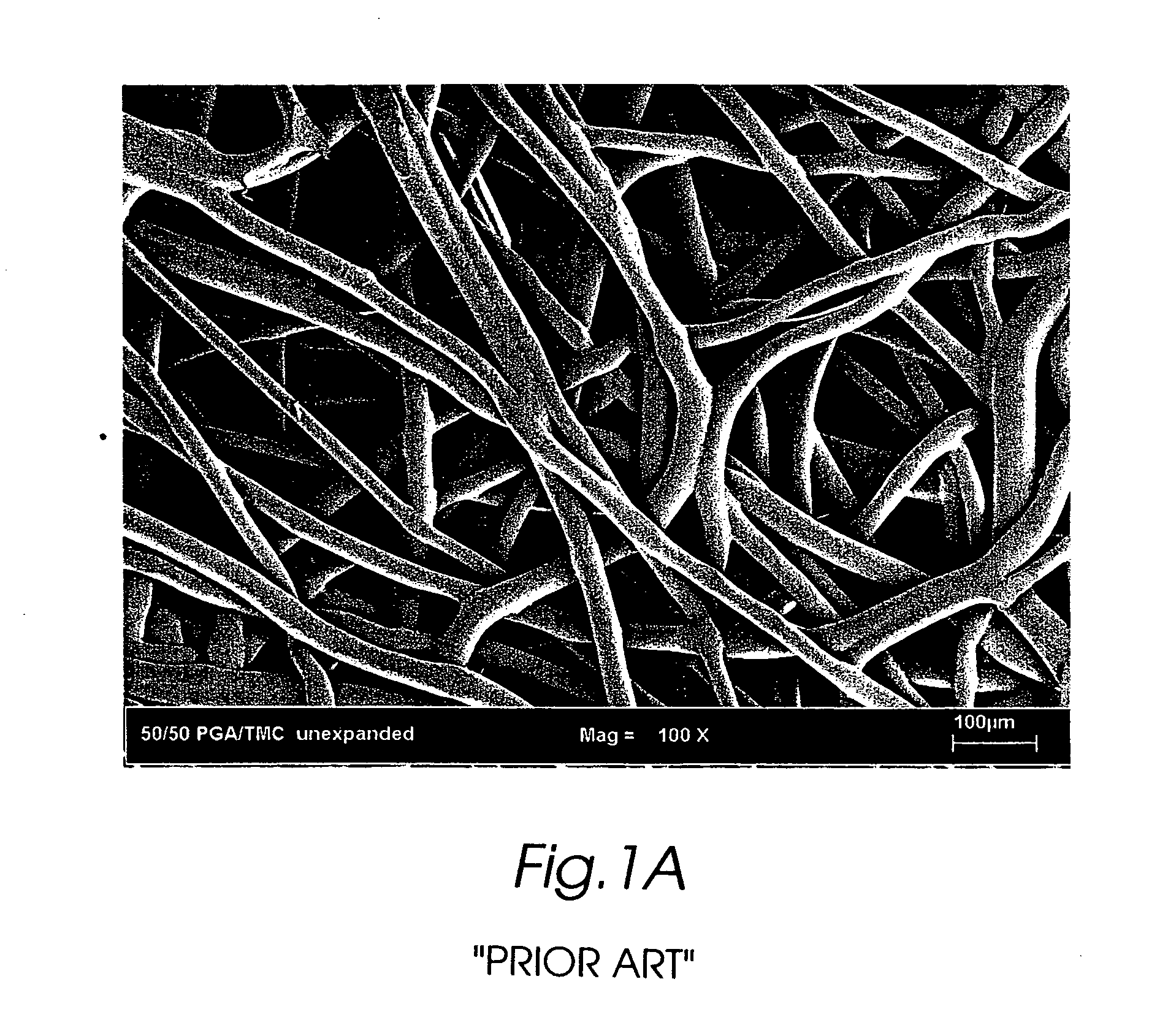
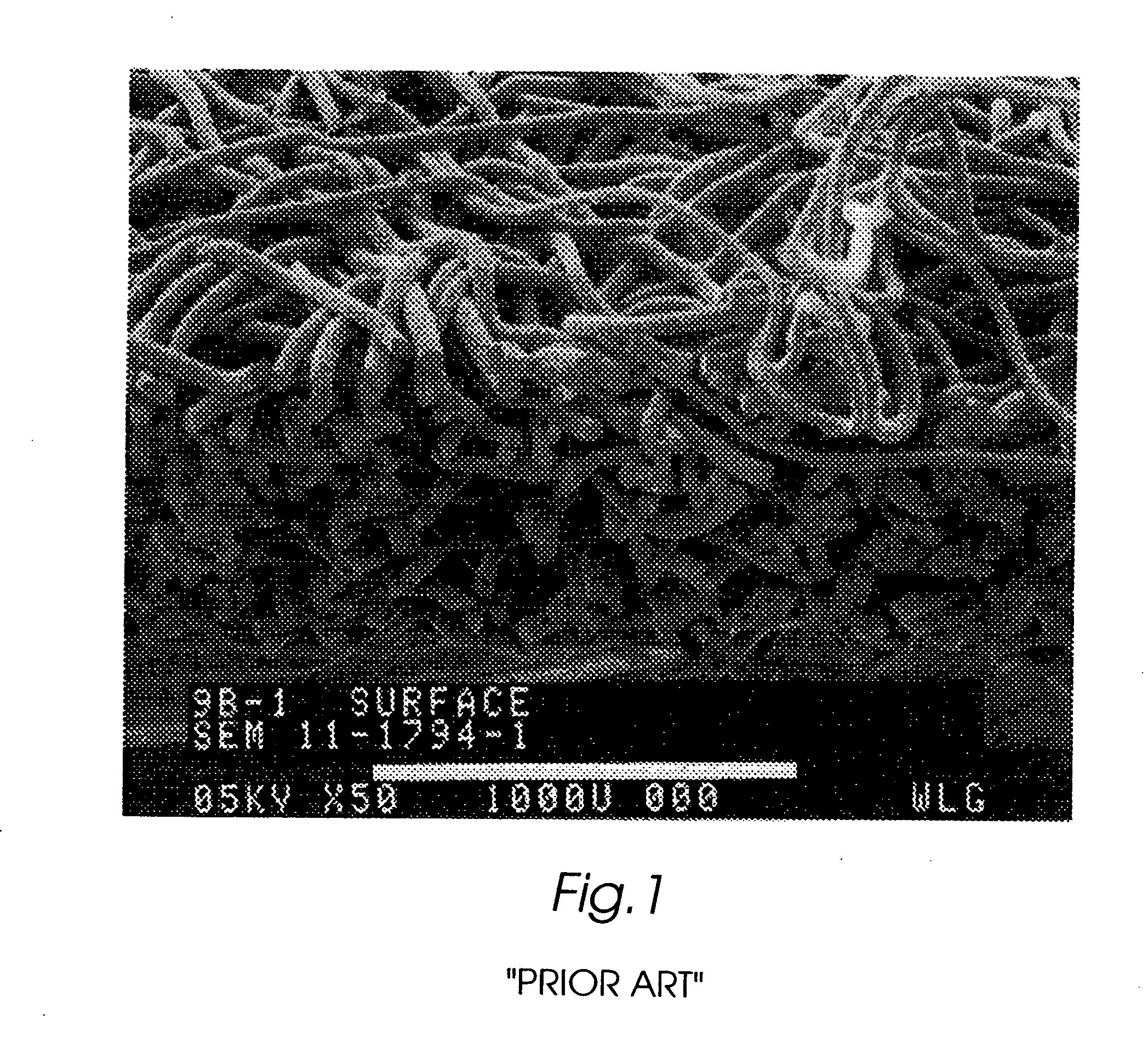
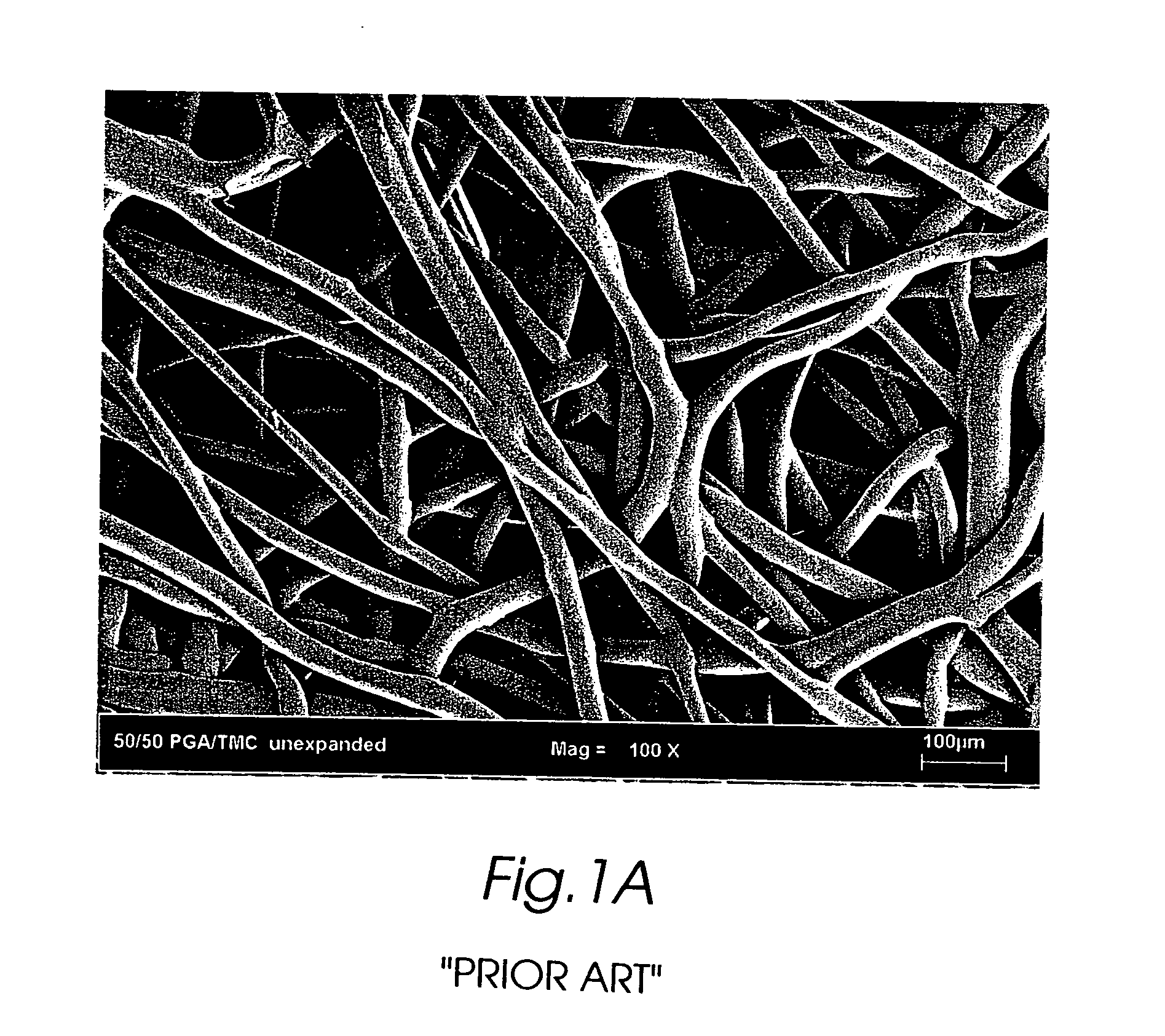
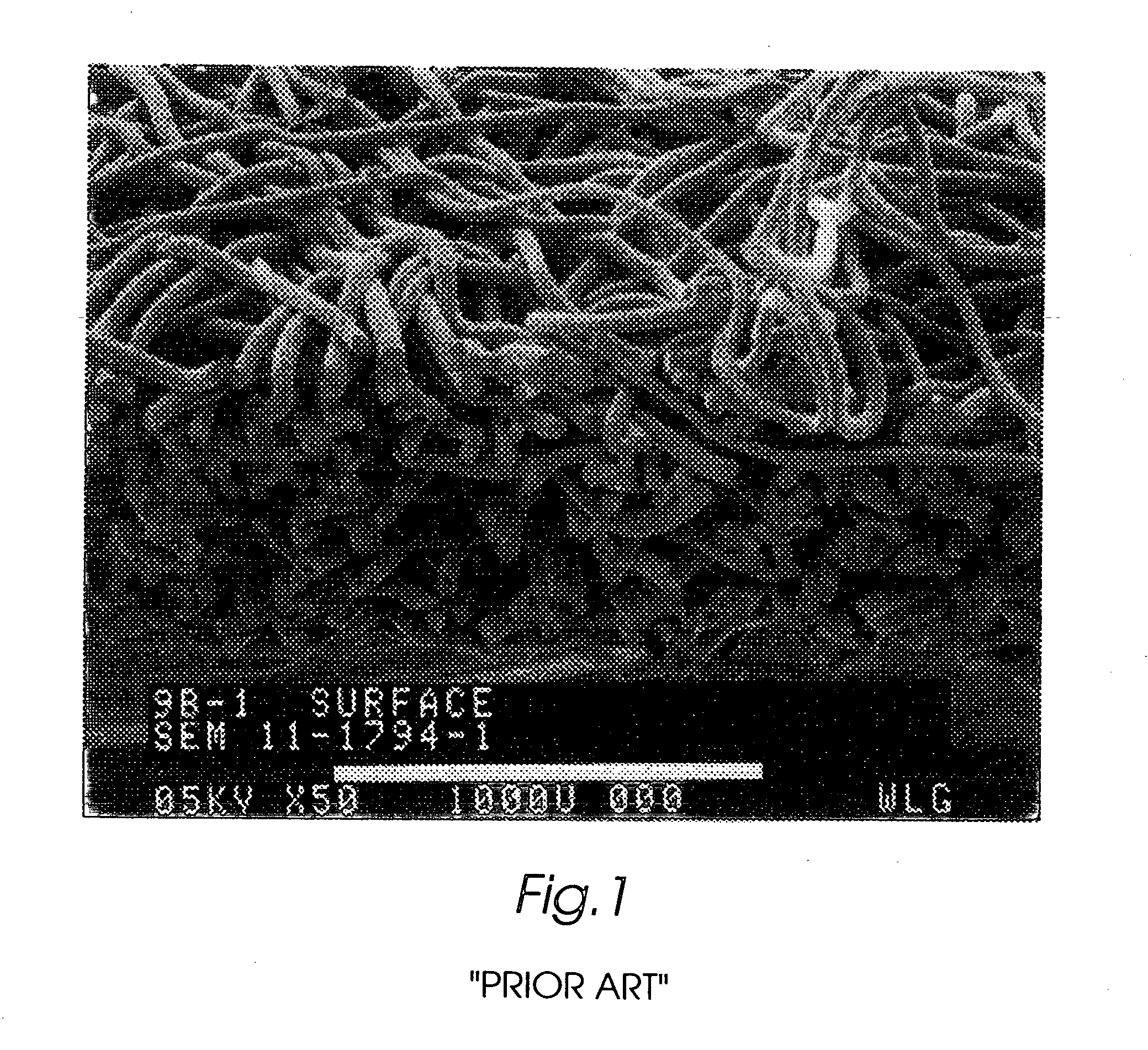
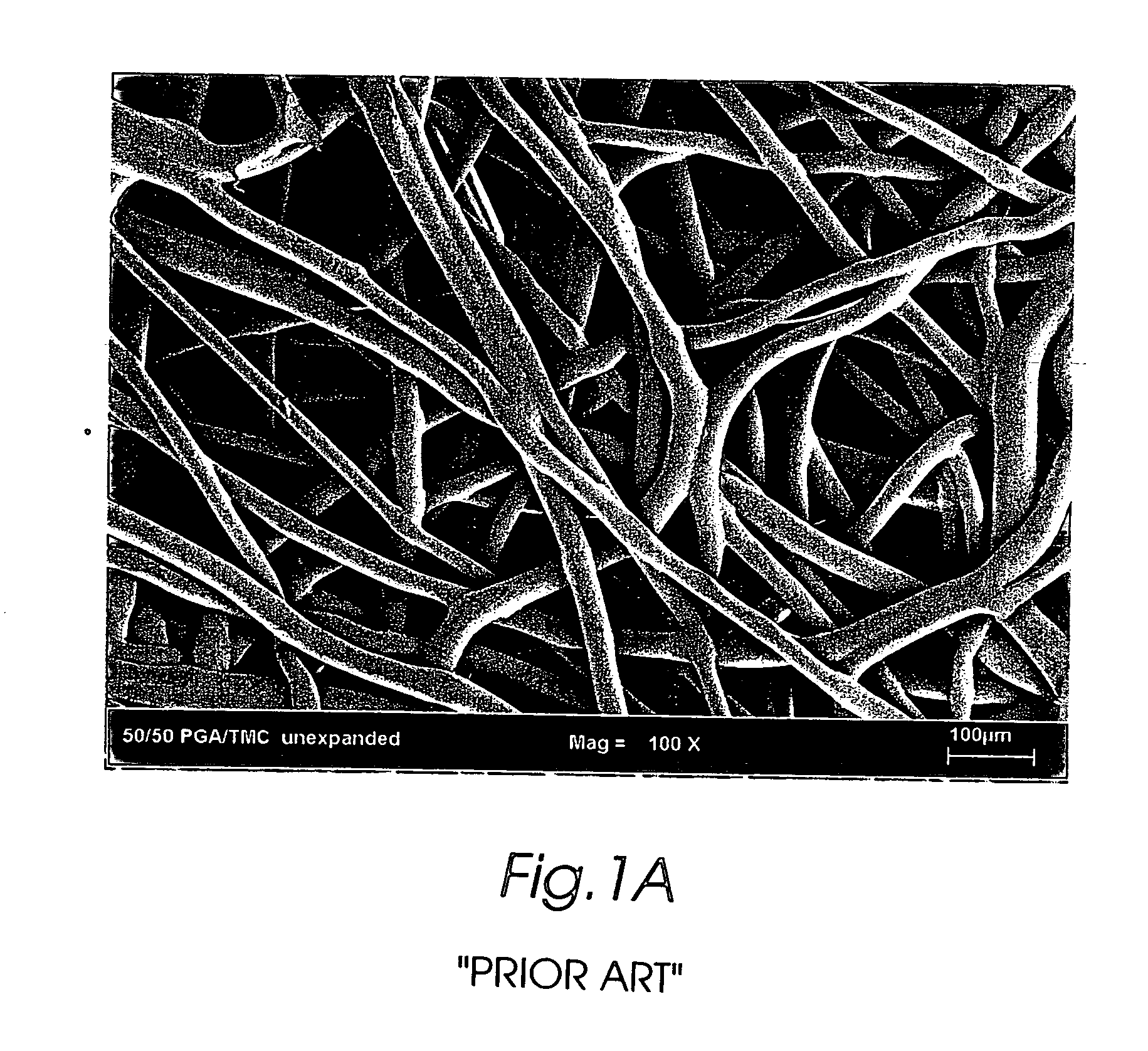
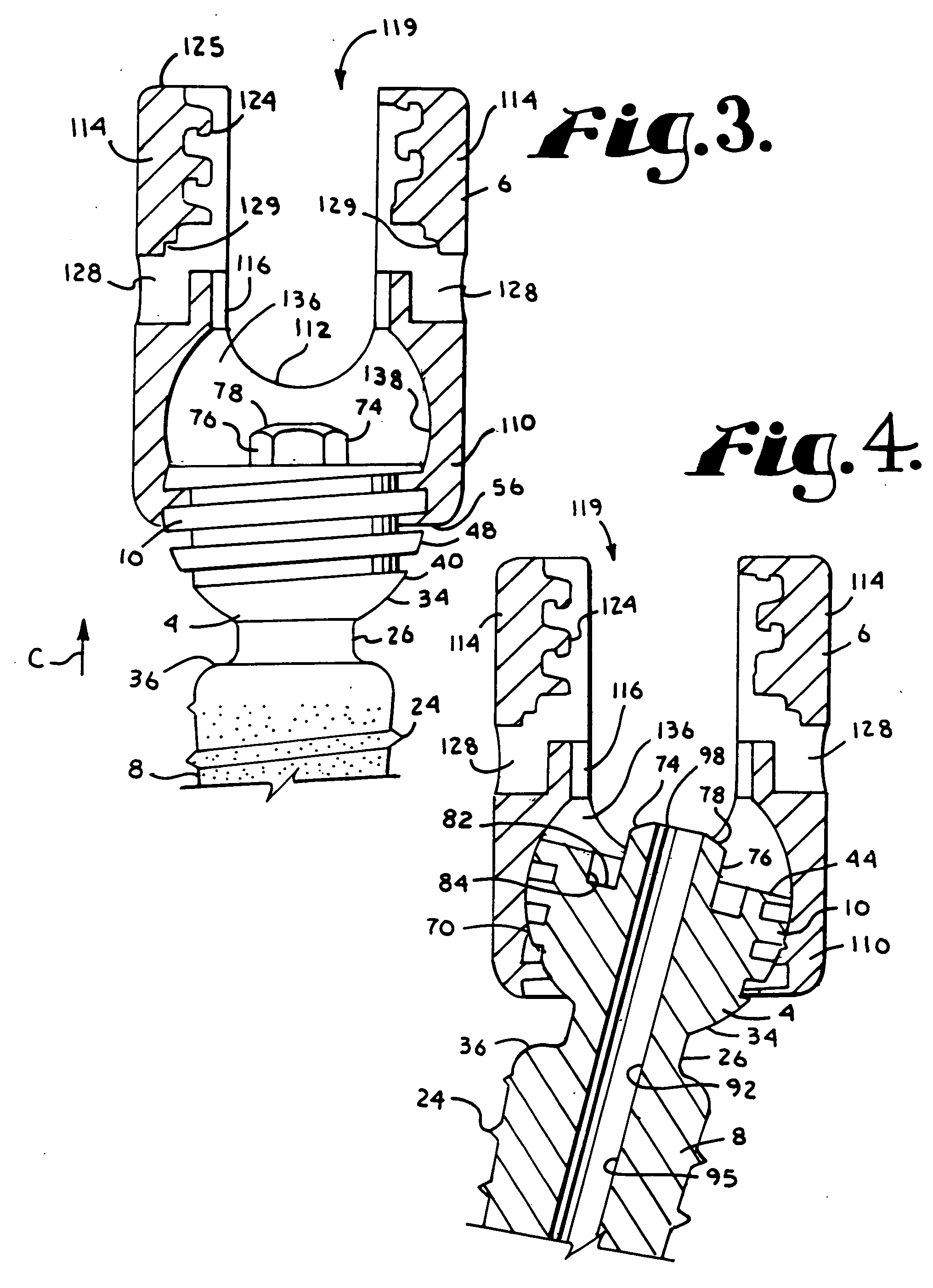
The present invention is directed to implantable bioabsorbable non-woven self-cohered web materials having a high degree of porosity. The web materials are very supple and soft, while exhibiting proportionally increased mechanical strength in one or more directions. The web materials often possess a high degree of loft. The web materials can be formed into a variety of shapes and forms suitable for use as implantable medical devices or components thereof.
Owner:WL GORE & ASSOC INC
Composite self-cohered web materials
InactiveUS20070026040A1High porositySuitable for useSurgical staplesProsthesisPorosityUltimate tensile strength
The present invention is directed to implantable bioabsorbable non-woven self-cohered web materials having a high degree of porosity. The web materials are very supple and soft, while exhibiting proportionally increased mechanical strength in one or more directions. The web materials often possess a high degree of loft. The web materials can be formed into a variety of shapes and forms suitable for use as implantable medical devices or components thereof.
Owner:WL GORE & ASSOC INC
Composite self-cohered web materials
InactiveUS20070026039A1High porositySuitable for useAntipyreticAnalgesicsBiomedical engineeringPorosity
The present invention is directed to implantable bioabsorbable non-woven self-cohered web materials having a high degree of porosity. The web materials are very supple and soft, while exhibiting proportionally increased mechanical strength in one or more directions. The web materials often possess a high degree of loft. The web materials can be formed into a variety of shapes and forms suitable for use as implantable medical devices or components thereof.
Owner:WL GORE & ASSOC INC
System and Method for Managing Malware Protection on Mobile Devices
InactiveUS20070240222A1Reliable detectionAmount of memory can be minimisedMemory loss protectionError detection/correctionClient-sideMalware
A system and method for providing malware protection on client mobile platforms in a mobile network. The system and method manages the malware scanning agents of the client mobile platforms from a management server using a device independent secure management protocol. The management server downloads new malware definitions to client mobile platforms and remotely initiates malware scanning on the client mobile platforms.
Owner:PULSE SECURE
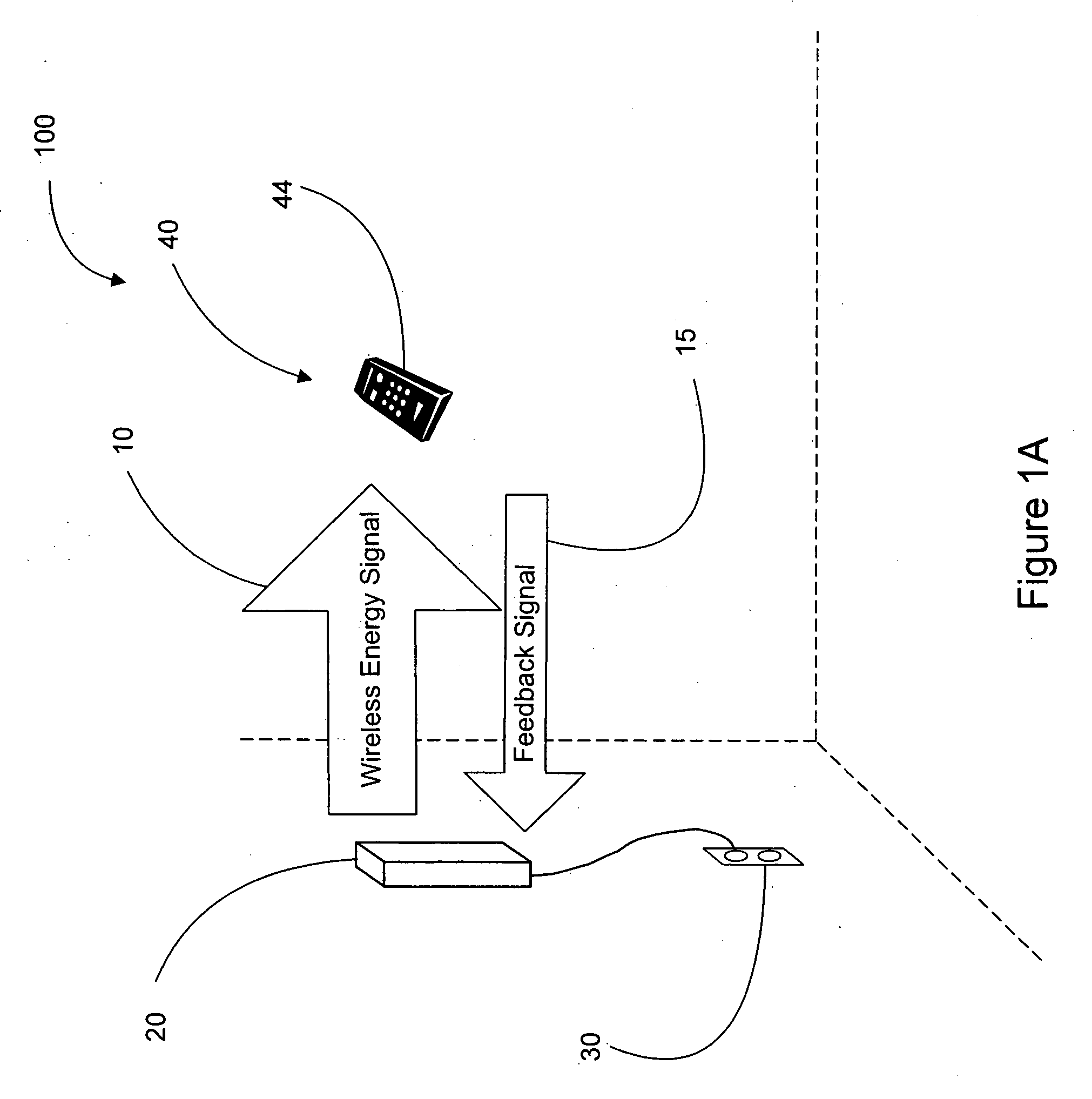
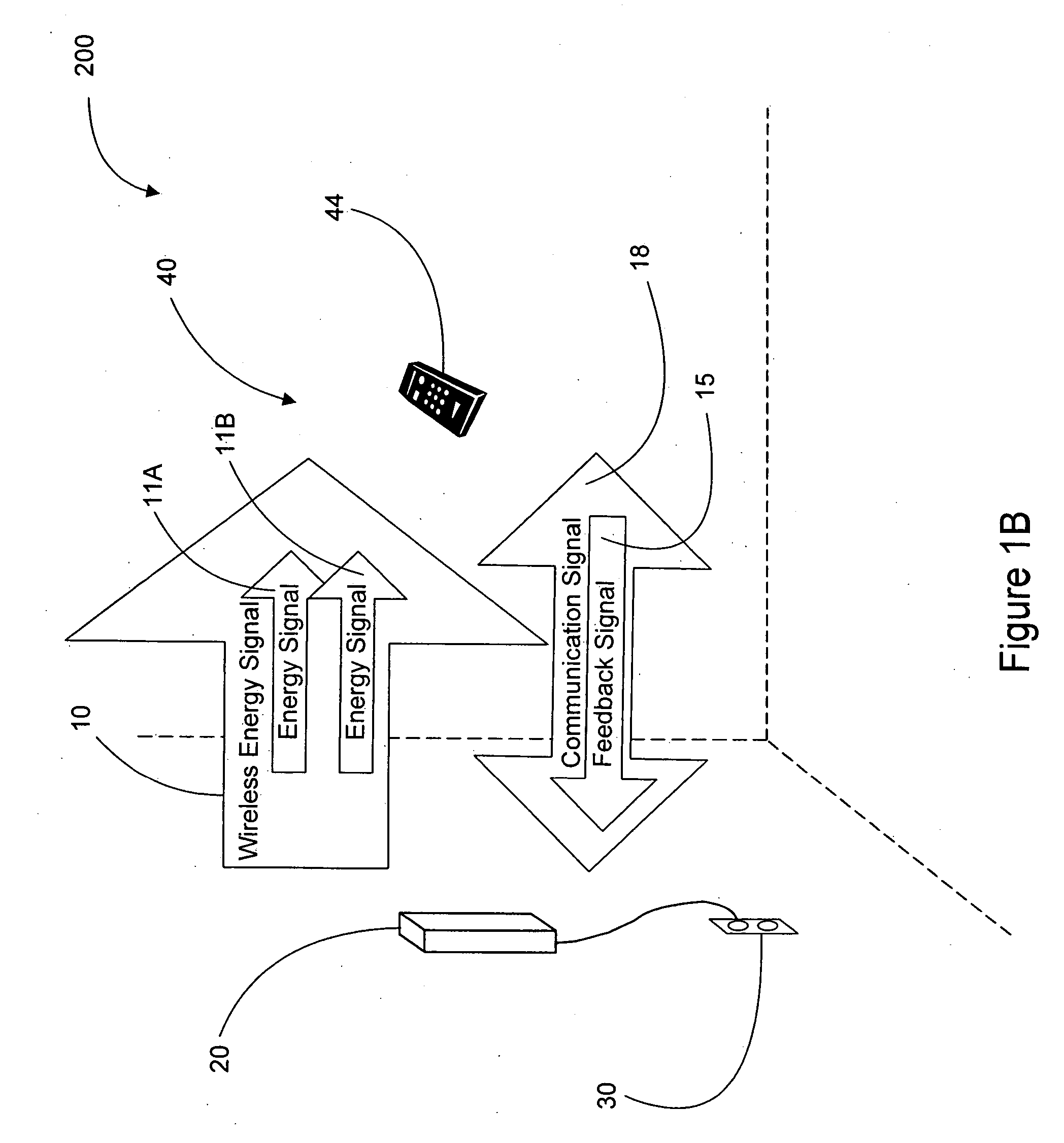
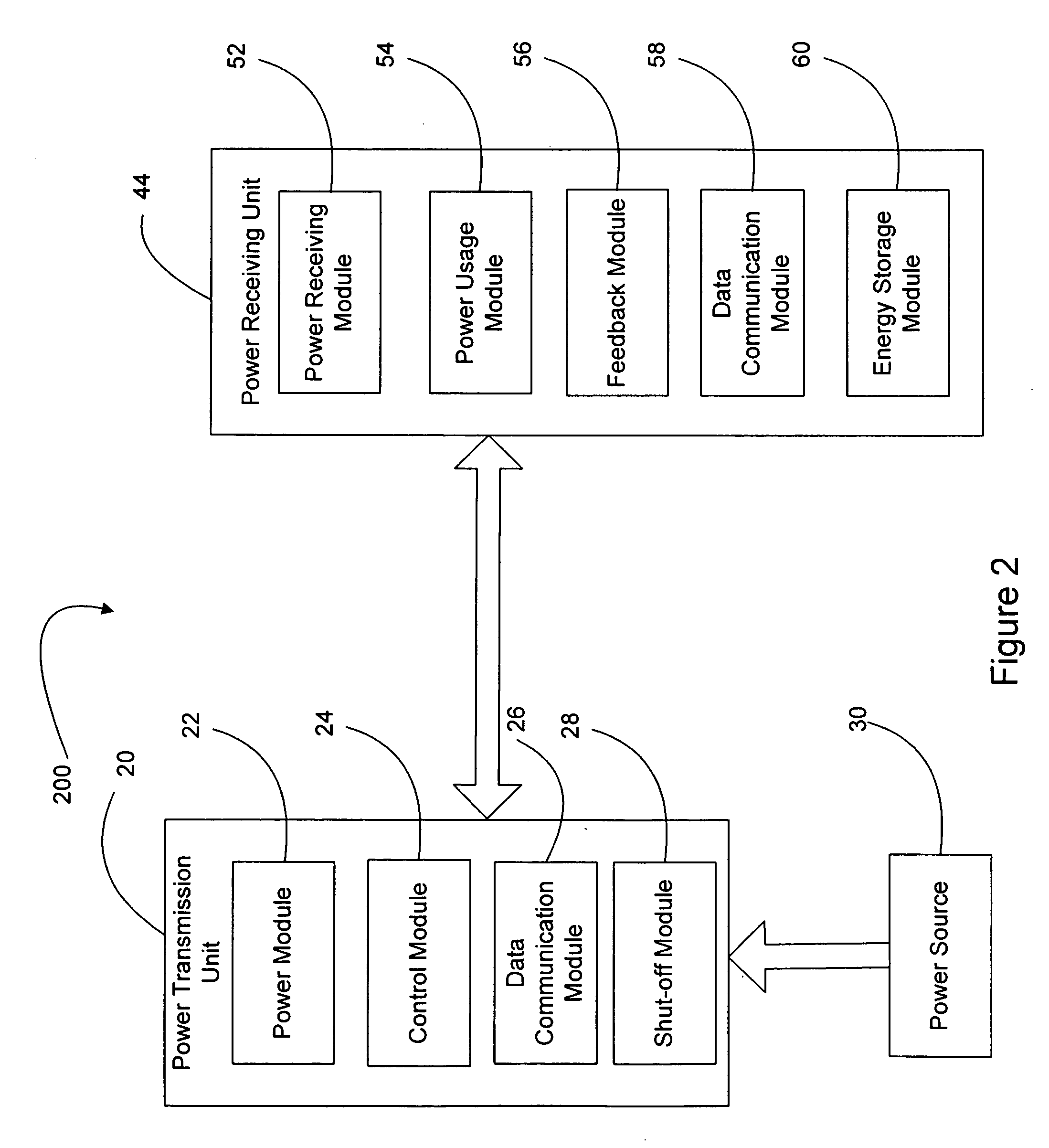
Remote power charging of electronic devices
InactiveUS20060113955A1Suitable for useElectromagnetic wave systemElectric powerElectric power transmissionInductive charging
A wireless charging and power system for electronic devices and method for communicating power to a power receiver employing wireless energy transmission are disclosed. The remote charging system includes a power transmission unit, which transmits energy as a plurality of constructive transmitted frequencies, and a power receiver system that receives the transmitted frequencies. The power receiver system is preferably incorporated in a device and includes an energy receptor capable of receiving the wireless transmitted energy and transferring the energy from the transmitted frequencies to an energy storage device included in the device. The power transmission unit receives and tracks a power request signal from the power receiver system to track the power receiver system location during energy transmission. Data streams may be incorporated into the wireless signals of the remote charging system, allowing the remote charging system to function as a communications pathway as well as a power delivery system.
Owner:PATRICK NUNALLY
Implantable product with improved aqueous interface characteristics and method for making and using same
InactiveUS20050129735A1Rapidly and accurately visualizedEliminates air-interference issueUltrasonic/sonic/infrasonic diagnosticsStentsLaparoscopyCardiac echo
An implantable medical device including a porous membrane that is treated with a hydrophilic substance to obtain rapid optimum visualization using technology for viewing inside of a mammalian body. These technologies include ultrasound echocardiography and video imaging such as that used during laparoscopic procedures.
Owner:WL GORE & ASSOC INC
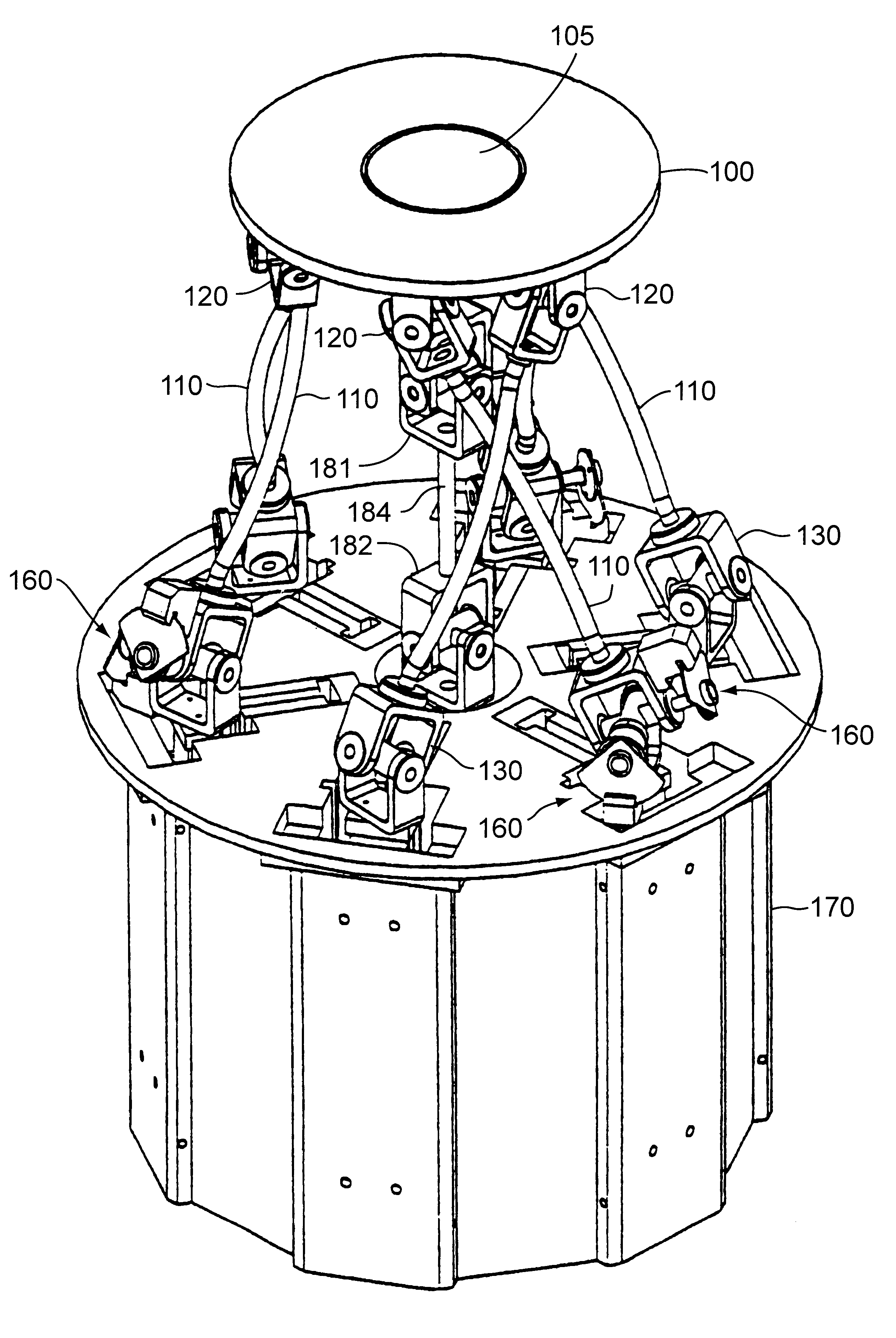
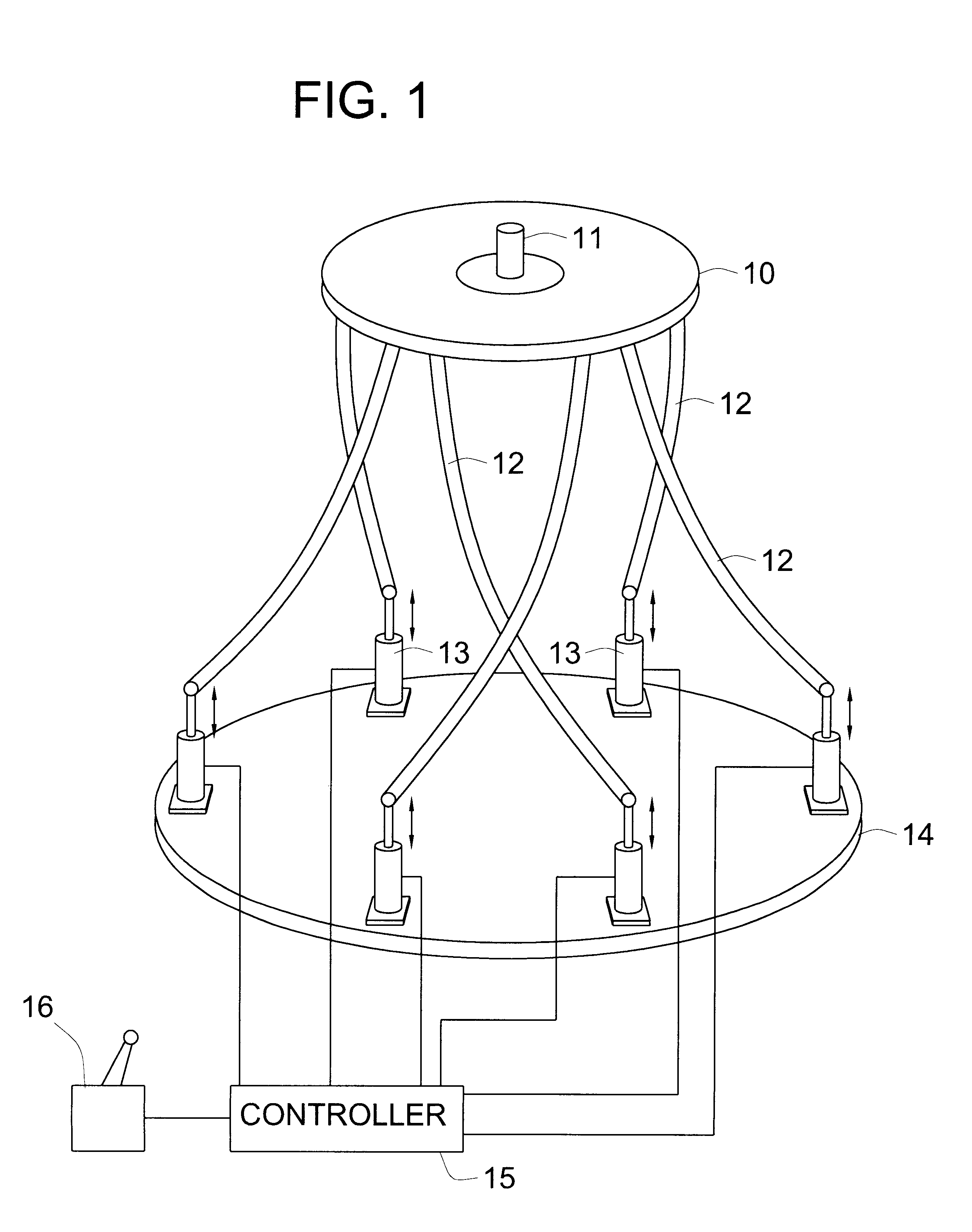
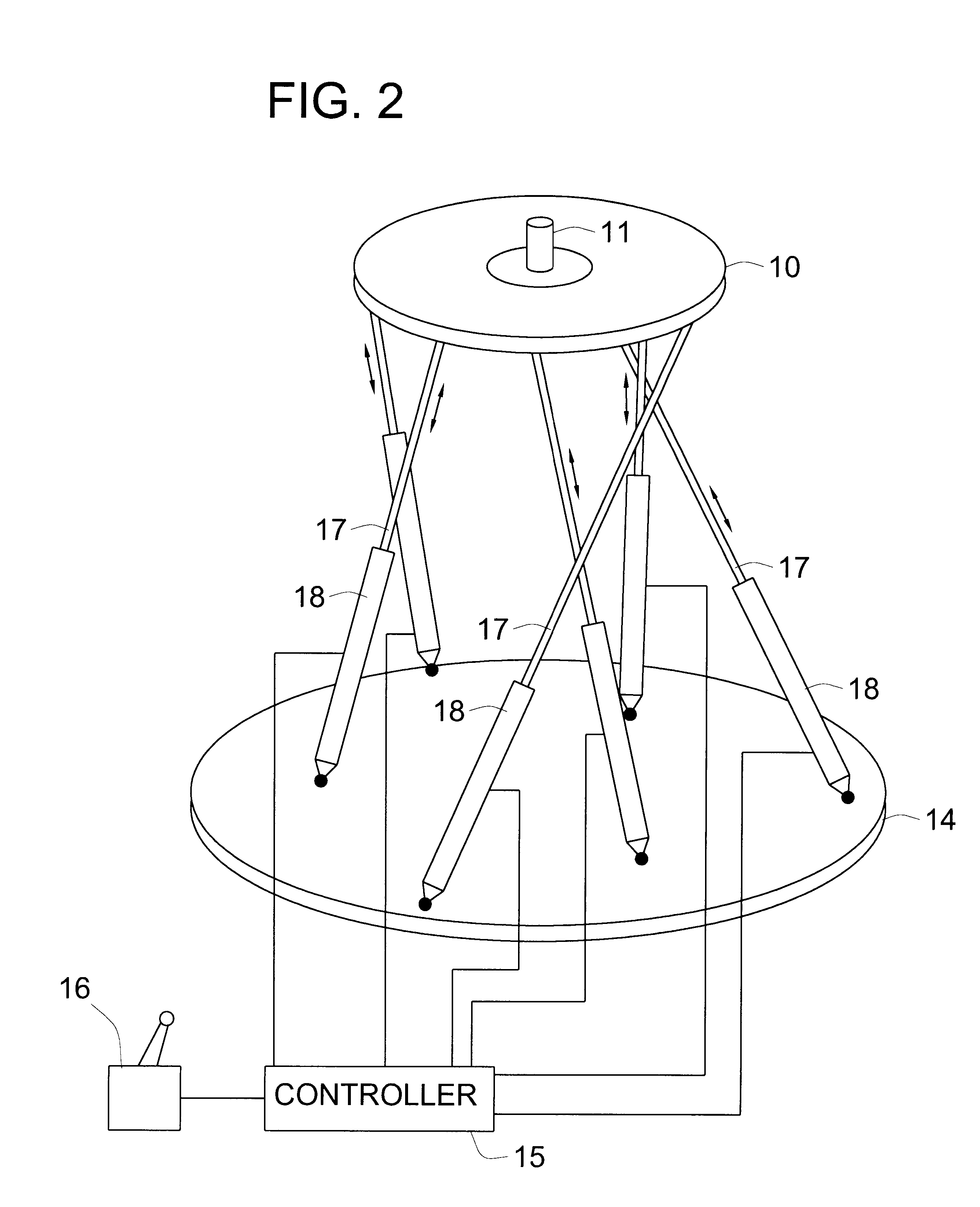
Parallel mechanism
InactiveUS6330837B1Reduce inertiaHigh speedMechanical apparatusJointsRange of motionDegrees of freedom
A parallel mechanism is capable of positioning and orienting an end platform with up to six or more degrees of freedom. In preferred embodiments, the mechanism includes six links having a first and second ends. The first end is connected to an end platform for supporting a tool, while the second end is connected to an actuator capable of translating the second end. A rotational drive mechanism may be provided for rotating an object mounted on the end platform at varying orientations of the end platform independently of movement of the end platform as a whole. The links may be curved in order to avoid interference between adjoining links, thereby permitting an increased range of motion and improved dexterity of the mechanism.
Owner:MOORE RUSSELL
Arrayed biomolecules and their use in sequencing
InactiveUS7232656B2Reduce interferencePermit resolutionBioreactor/fermenter combinationsSequential/parallel process reactionsGenome variationComputational biology
The invention is directed to a method for analysing genome wide variation in an individual. The method comprises randomly fragmenting the individual's genome and generating sequence reads of multiple bases on all fragments of the individual's genome, aligning the sequence reads generated with a known genomic reference sequence, and analysing variations between the sequence reads derived from the individual's genome and the known genomic reference sequence.
Owner:ILLUMINA CAMBRIDGE LTD
Adhesive composite having distinct phases
InactiveUS6927315B1Increase stiffnessHigh tensile strengthPlastersAdhesive dressingsMoisture vapor transmission rateEngineering
A conformable adhesive article for use as a sterile medical dressing is described. The article includes a breathable polymeric matrix, a plurality of phases, and an adhesive composition positioned on the polymeric matrix. The plurality of phases preferably provide reinforcement and stiffness to the article. The article permits transport of moisture across the breathable polymeric matrix, preferably at an Inverted water moisture vapor transmission rate of at least 300 g / m2 / 24 hours.
Owner:3M INNOVATIVE PROPERTIES CO
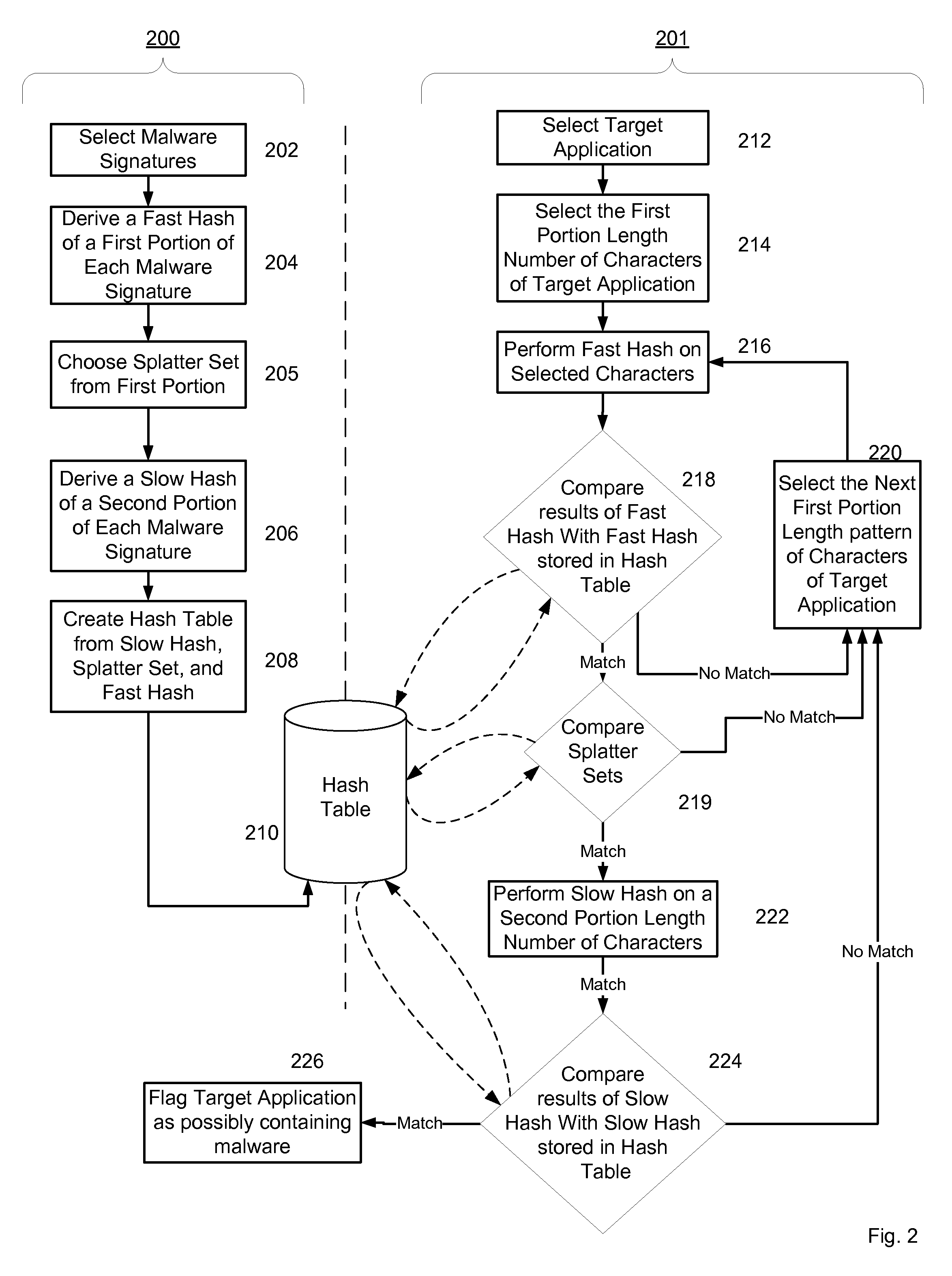
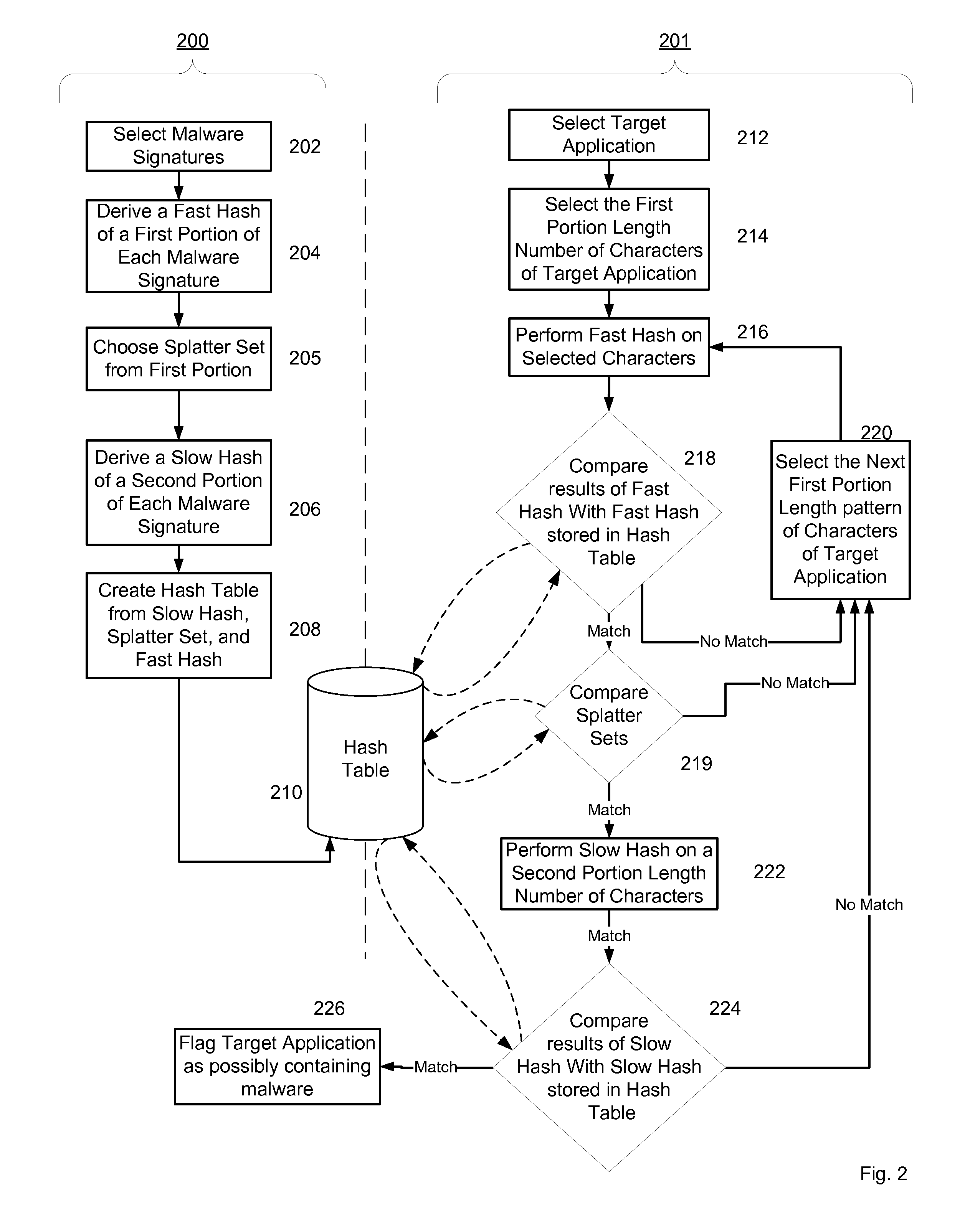
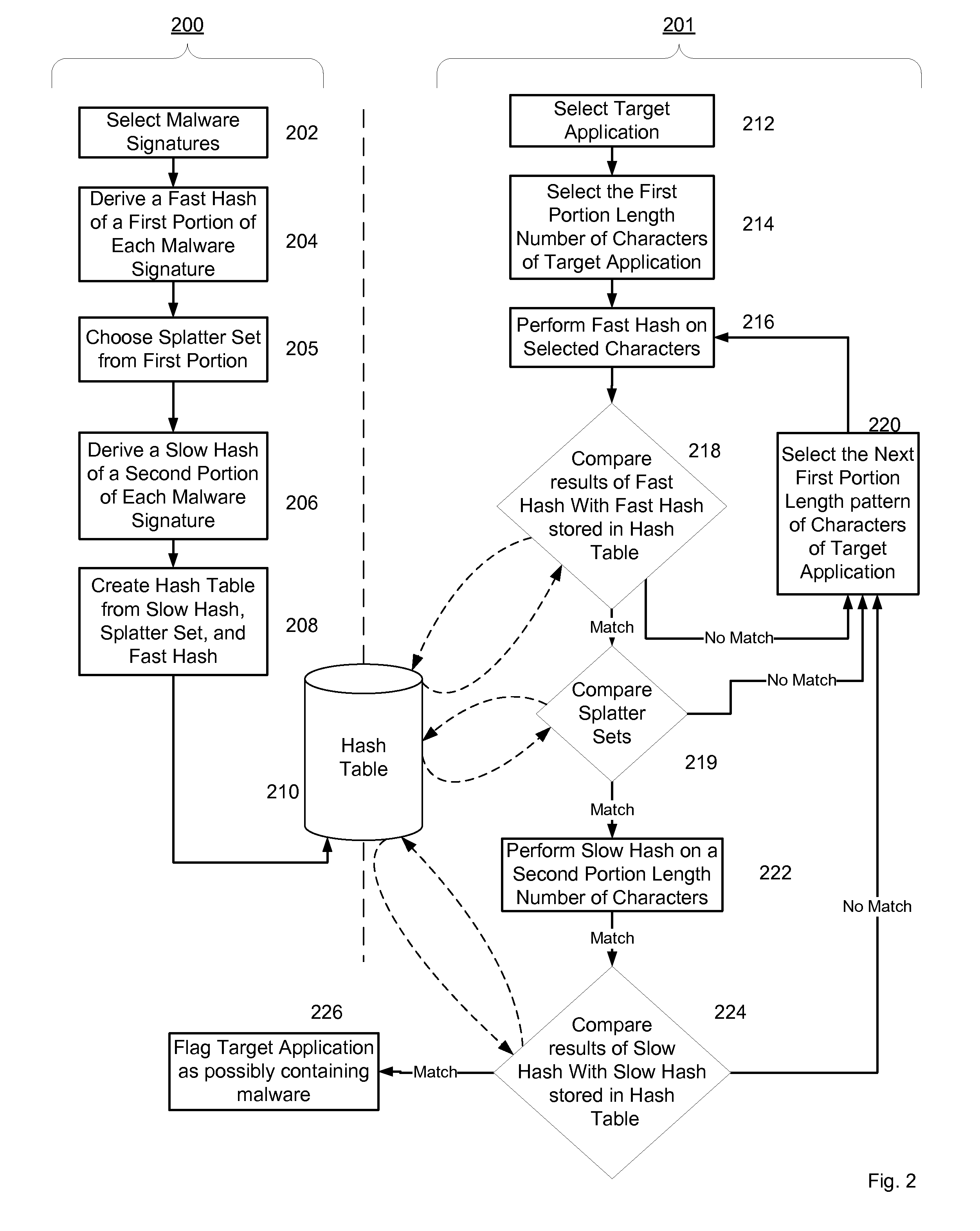
System and method for managing malware protection on mobile devices
ActiveUS20070240220A1Suitable for useReliable detectionMemory loss protectionError detection/correctionLimited accessFeature set
A system and method for detecting malware on a limited access mobile platform in a mobile network. The system and method uses one or more feature sets that describe various non-executable portions of malware-infected and malware-free applications, and compares a application on the limited access mobile platform to the features sets. A match of the features in a suspect application to one of the feature sets provides an indication as to whether the suspect application is malware-infected or malware-free.
Owner:PULSE SECURE
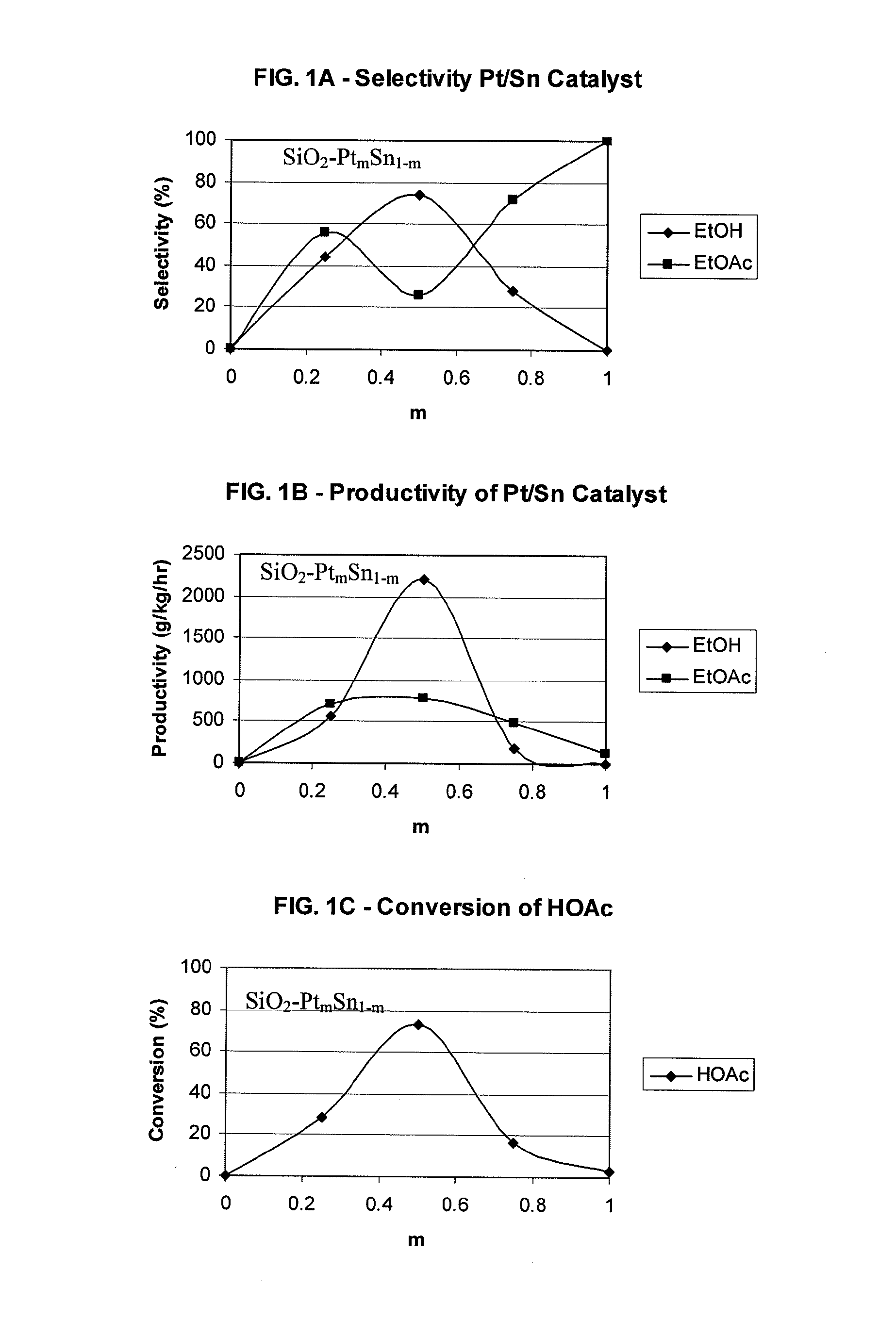
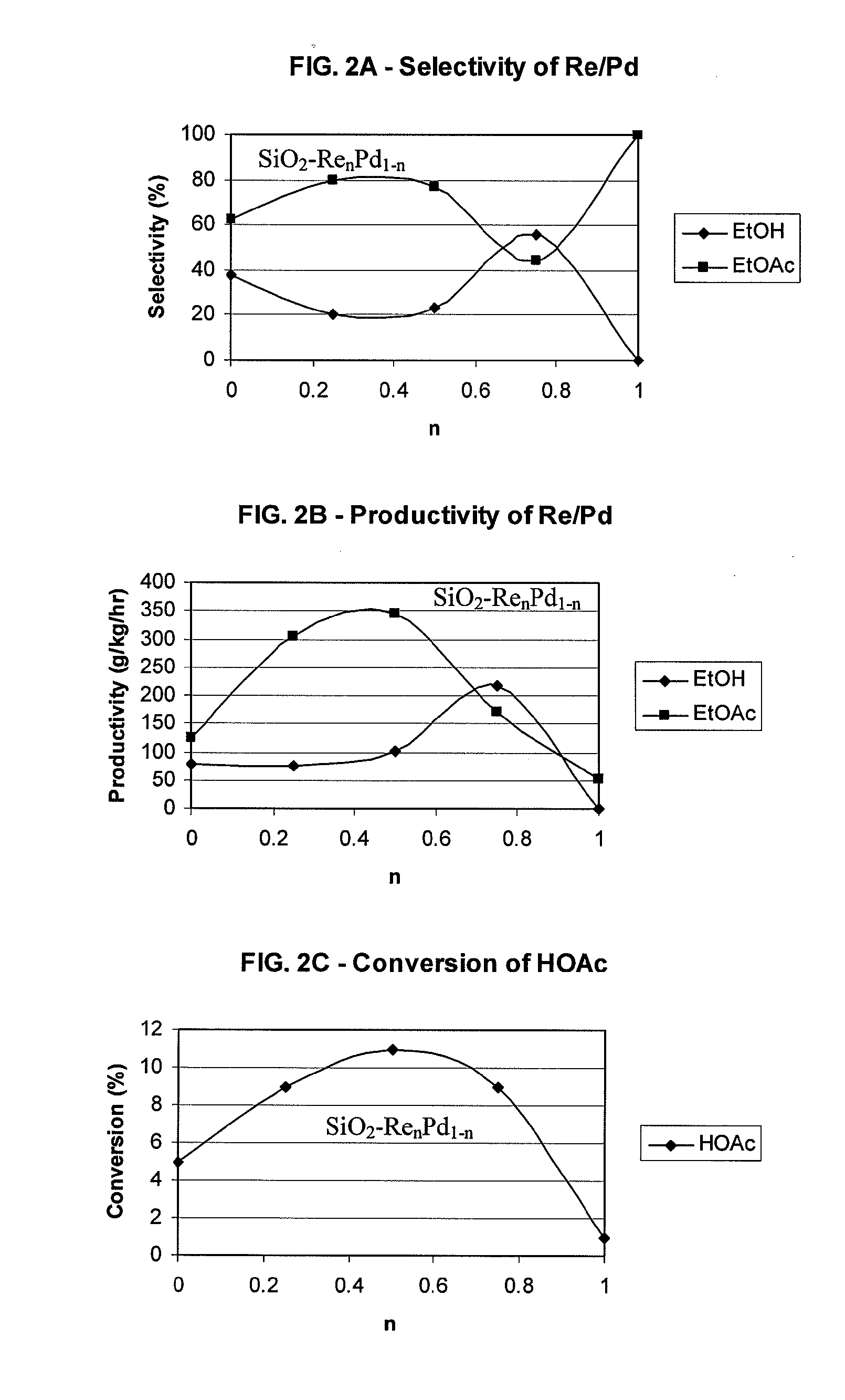
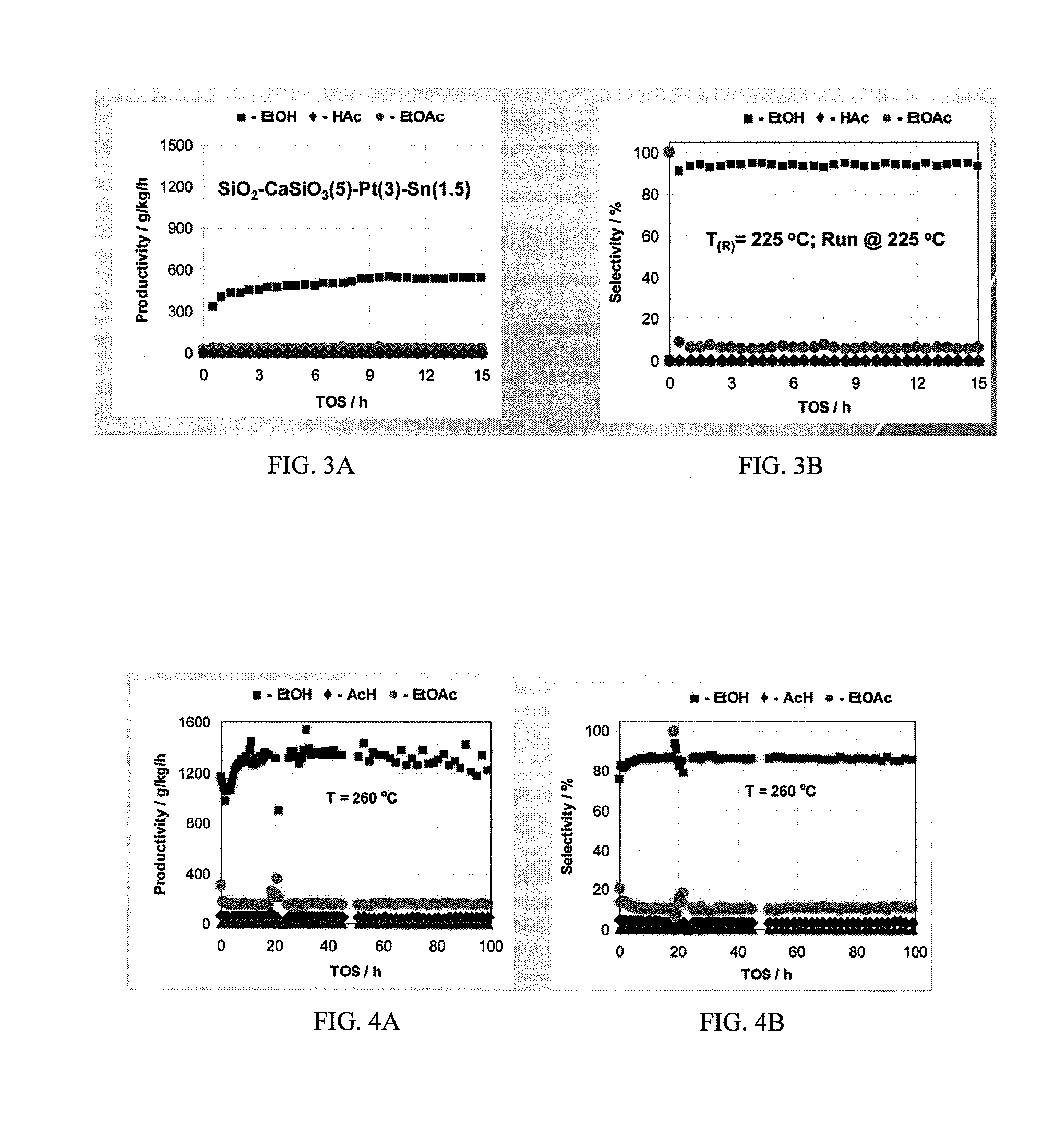
Catalysts for making ethanol from acetic acid
InactiveUS20100197485A1High selectivitySuitable for useMolecular sieve catalystsOrganic compound preparationTungstenIridium
Catalysts and processes for forming catalysts for use in hydrogenating acetic acid to form ethanol. In one embodiment, the catalyst comprises a first metal, a silicaceous support, and at least one metasilicate support modifier. Preferably, the first metal is selected from the group consisting of copper, iron, cobalt, nickel, ruthenium, rhodium, palladium, osmium, iridium, platinum, titanium, zinc, chromium, rhenium, molybdenum, and tungsten. In addition the catalyst may comprise a second metal preferably selected from the group consisting of copper, molybdenum, tin, chromium, iron, cobalt, vanadium, tungsten, palladium, platinum, lanthanum, cerium, manganese, ruthenium, rhenium, gold, and nickel.
Owner:CELANESE INT CORP
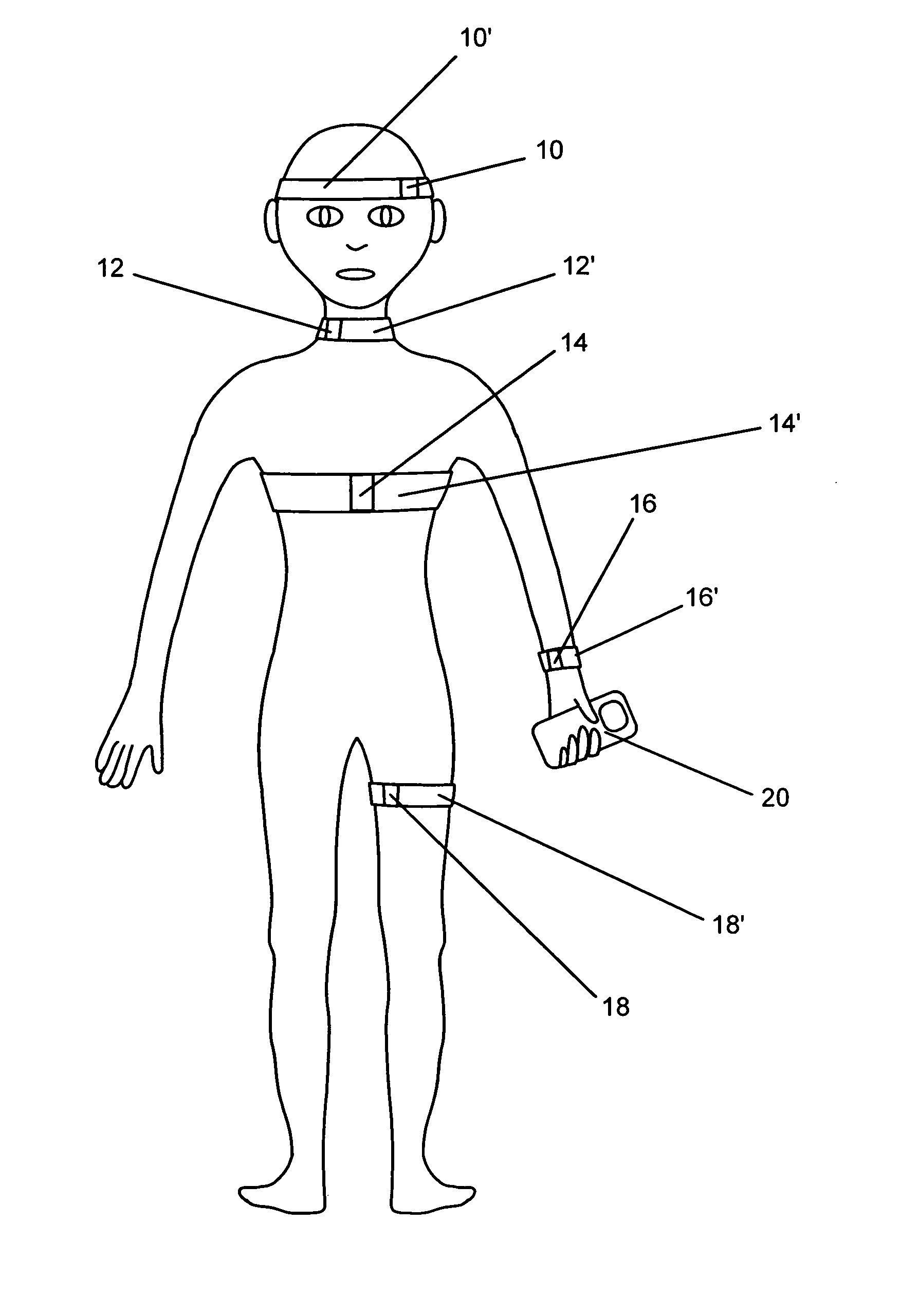
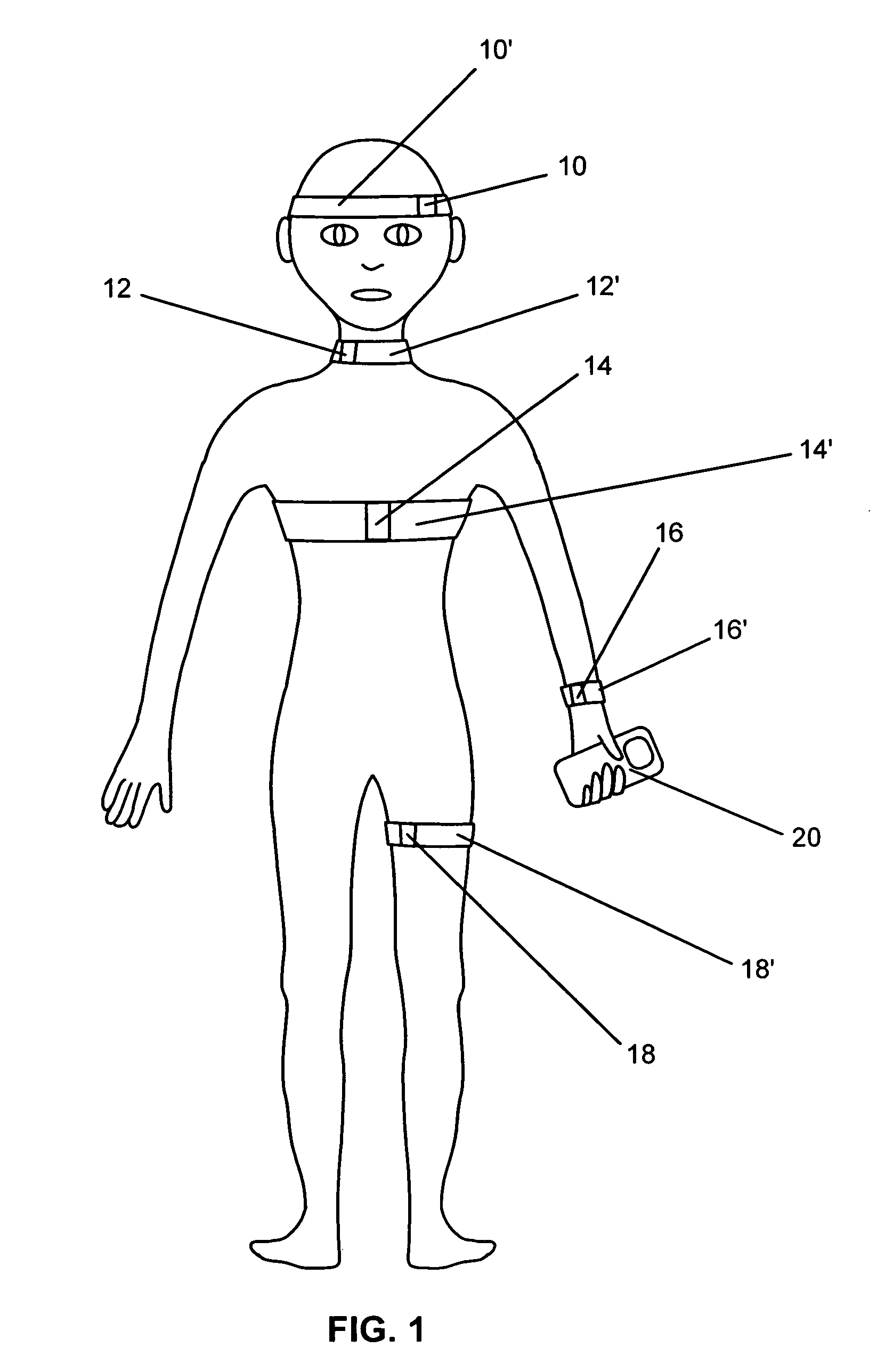
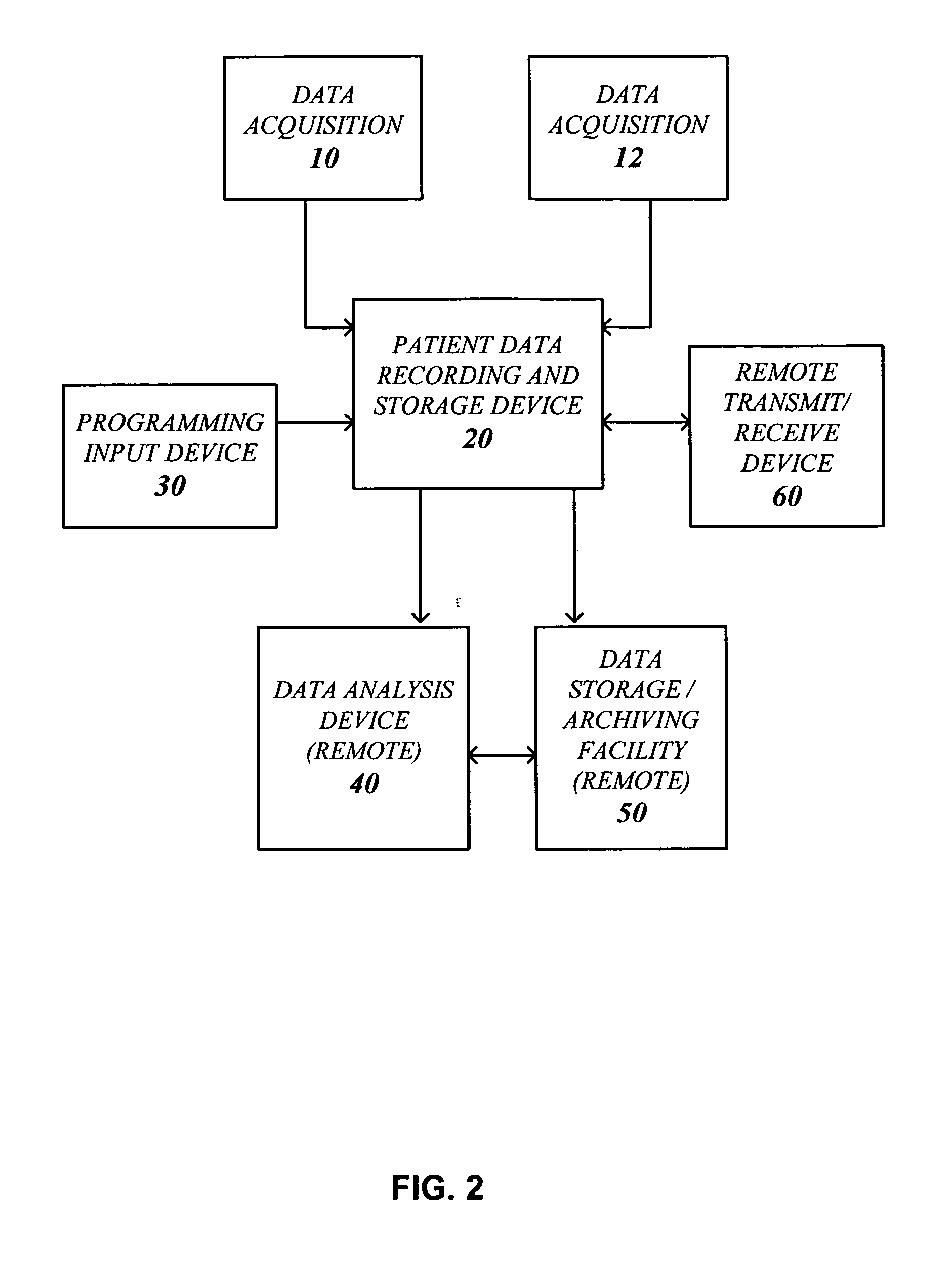
Systems and methods for non-invasive detection and monitoring of cardiac and blood parameters
InactiveUS20060100530A1Easy to detectEffective assessmentBlood flow measurement devicesCatheterData acquisitionNon invasive
Methods and systems for long term monitoring of one or more physiological parameters such as respiration, heart rate, body temperature, electrical heart activity, blood oxygenation, blood flow velocity, blood pressure, intracranial pressure, the presence of emboli in the blood stream and electrical brain activity are provided. Data is acquired non-invasively using ambulatory data acquisition techniques.
Owner:UNIV OF WASHINGTON +1
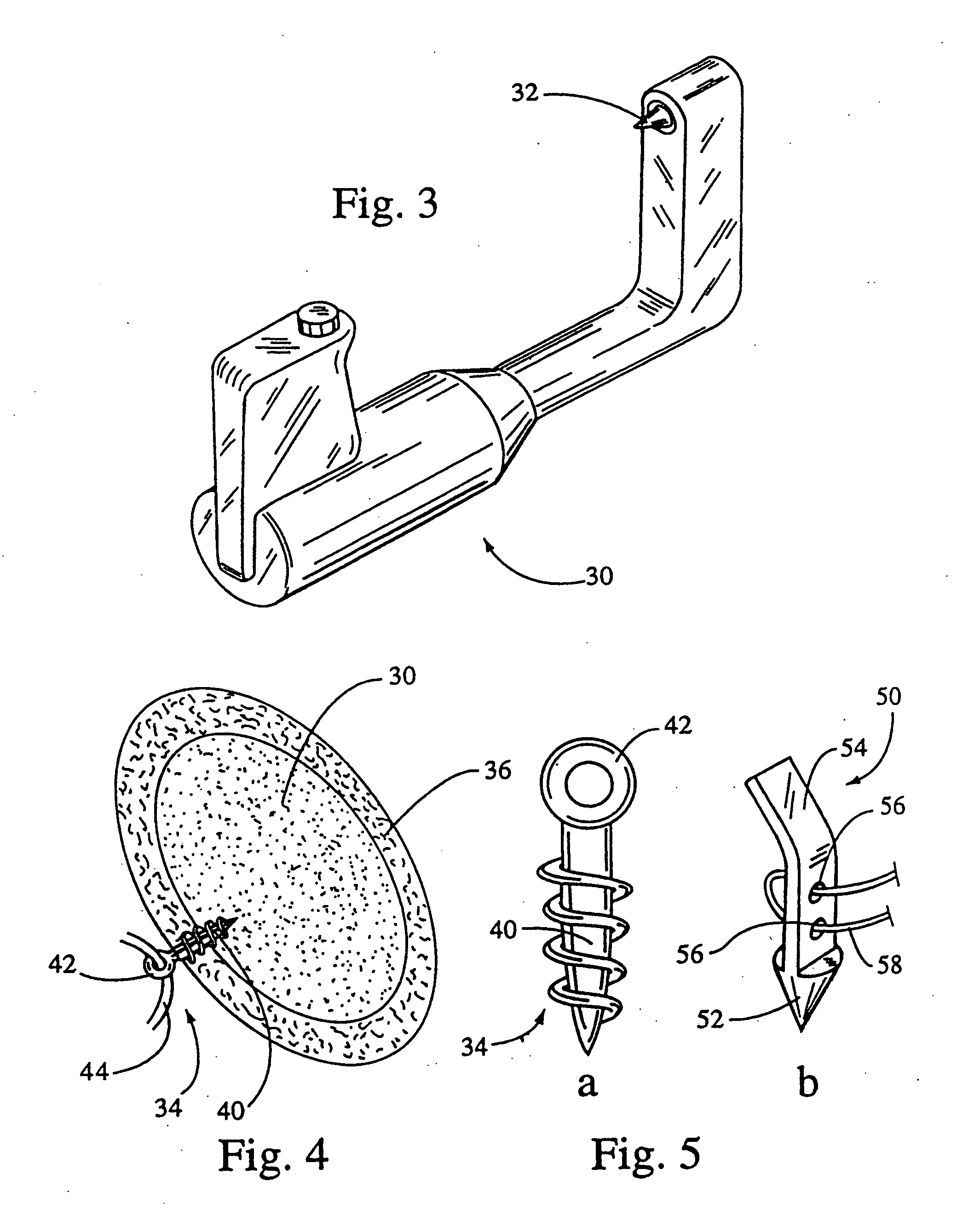
Fixed and variable locking fixation assembly
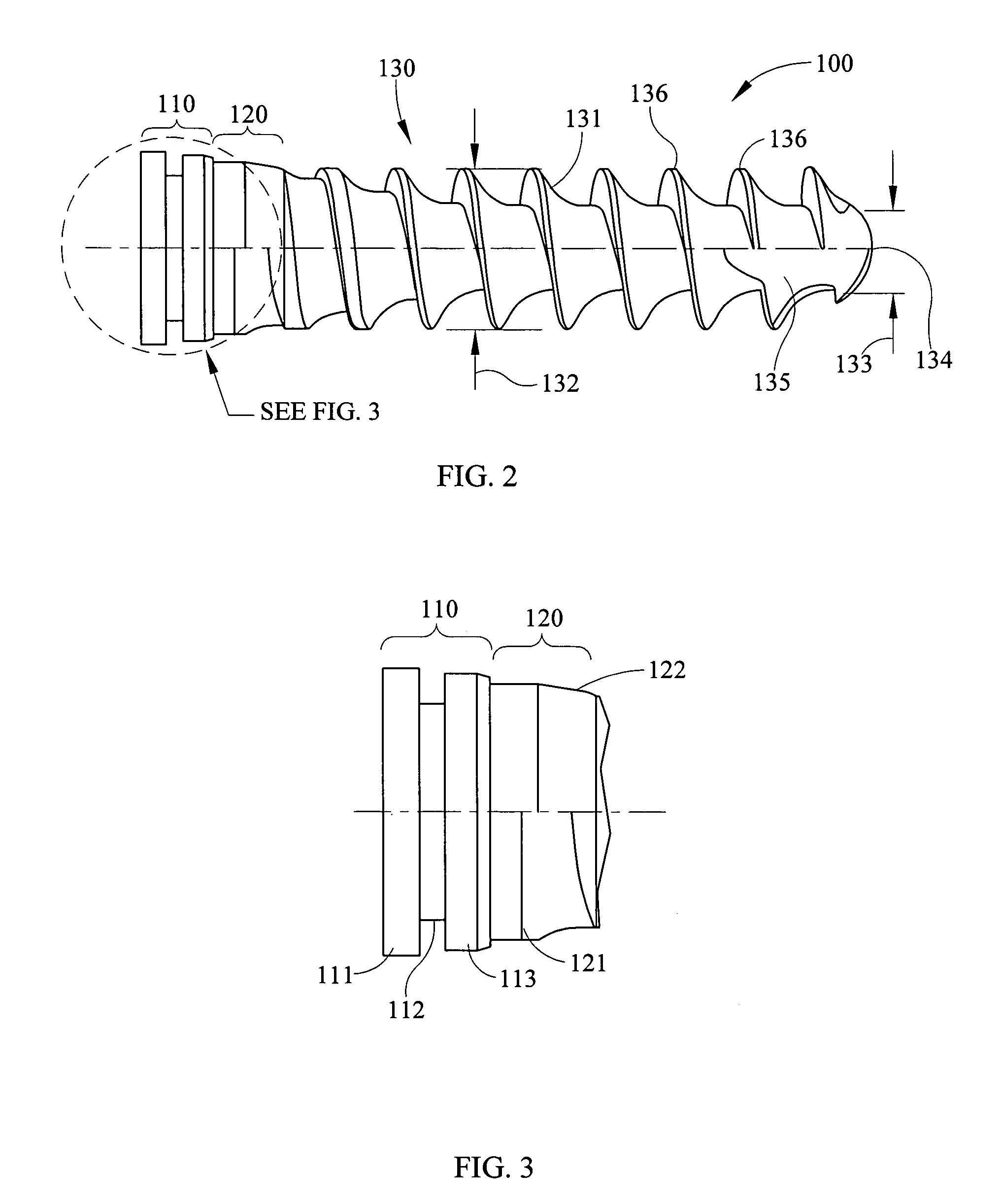
InactiveUS7001389B1Smoother transitionFacilitate smoothingSuture equipmentsInternal osteosythesisFastenerEngineering
A locking screw assembly is provided which allows installation into a plate-like member using relatively little force, but which requires relatively great force for removal. The fastener has an annular locking ring provided within a groove in the head of the screw to allow the screw to sit within or flush with the anterior surface of the plate. The through-hole in the plate which receives the locking screw comprises an entrance, a collar section, an undercut, and an exit. The locking ring resides within the undercut. The locking ring has a leading surface that is chamfered or radiused and a trailing surface that is flat. The chamfer allows the locking ring to easily be inserted into the through-hole by interacting with a lead chamfer in the entrance. After installation, the flat trailing surface abuts a lip adjoining the collar section and the undercut and prevents the screw from being easily removed from the through-hole.
Owner:THEKEN SPINE
Method and apparatus for training a multilingual speech model set
InactiveUS6912499B1Reduce development costsShorten development timeSpeech recognitionSpecial data processing applicationsMore languageSpeech identification
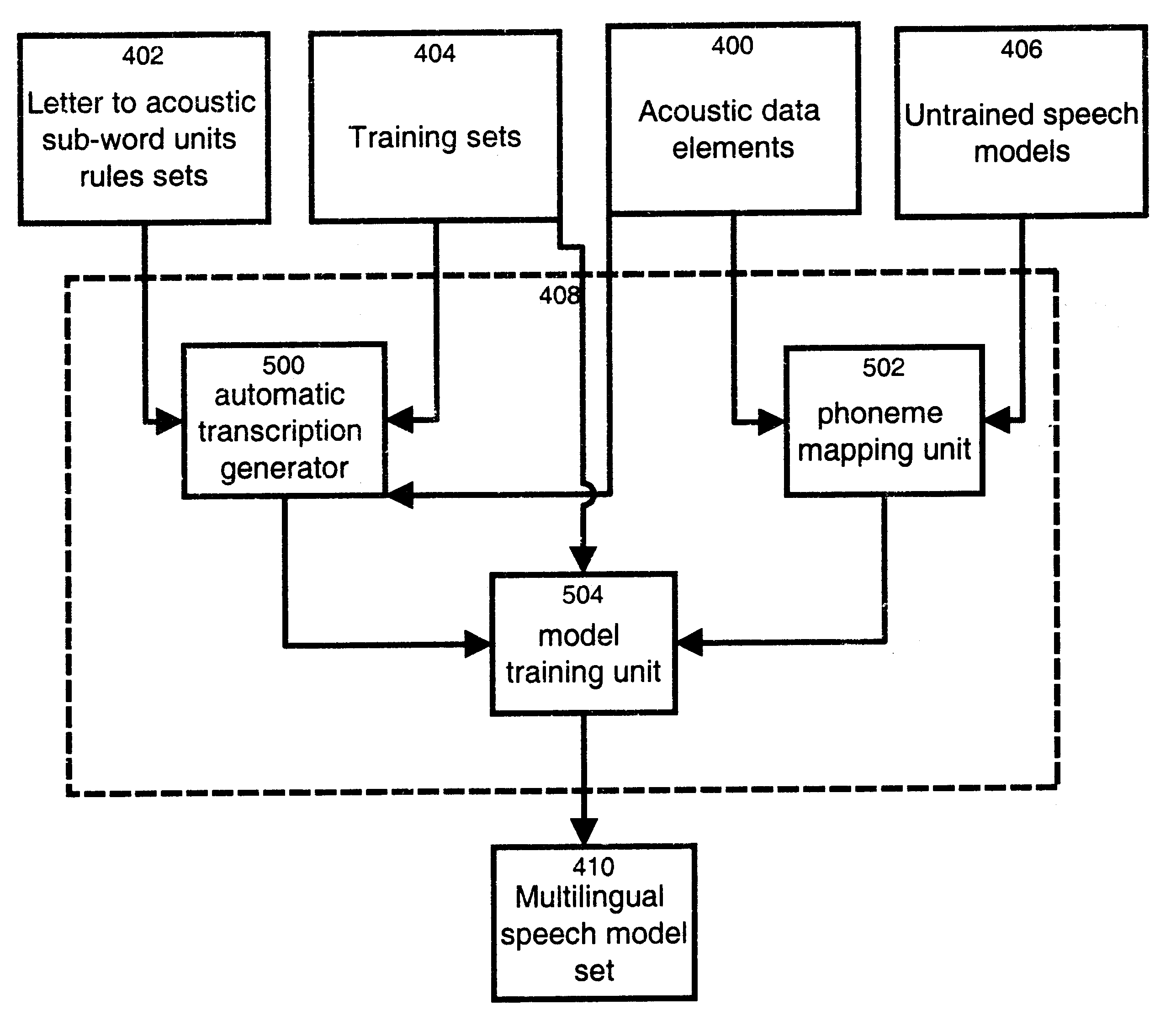
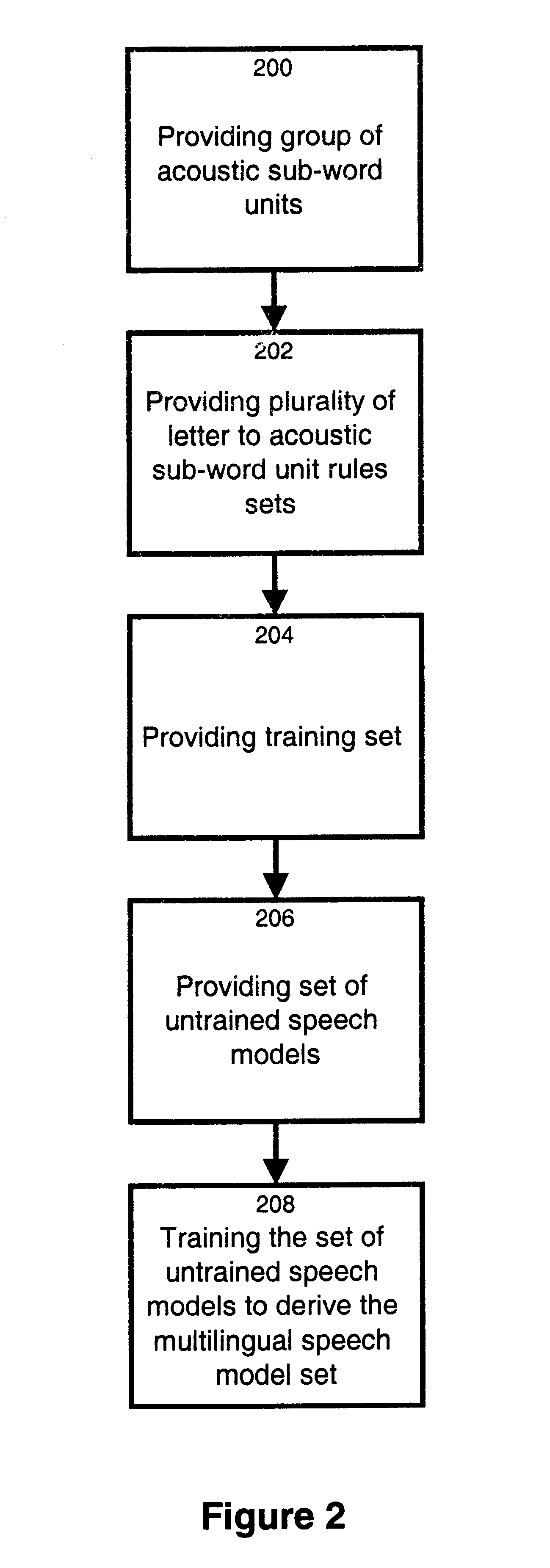
The invention relates to a method and apparatus for training a multilingual speech model set. The multilingual speech model set generated is suitable for use by a speech recognition system for recognizing spoken utterances for at least two different languages. The invention allows using a single speech recognition unit with a single speech model set to perform speech recognition on utterances from two or more languages. The method and apparatus make use of a group of a group of acoustic sub-word units comprised of a first subgroup of acoustic sub-word units associated to a first language and a second subgroup of acoustic sub-word units associated to a second language where the first subgroup and the second subgroup share at least one common acoustic sub-word unit. The method and apparatus also make use of a plurality of letter to acoustic sub-word unit rules sets, each letter to acoustic sub-word unit rules set being associated to a different language. A set of untrained speech models is trained on the basis of a training set comprising speech tokens and their associated labels in combination with the group of acoustic sub-word units and the plurality of letter to acoustic sub-word unit rules sets. The invention also provides a computer readable storage medium comprising a program element for implementing the method for training a multilingual speech model set.
Owner:RPX CLEARINGHOUSE
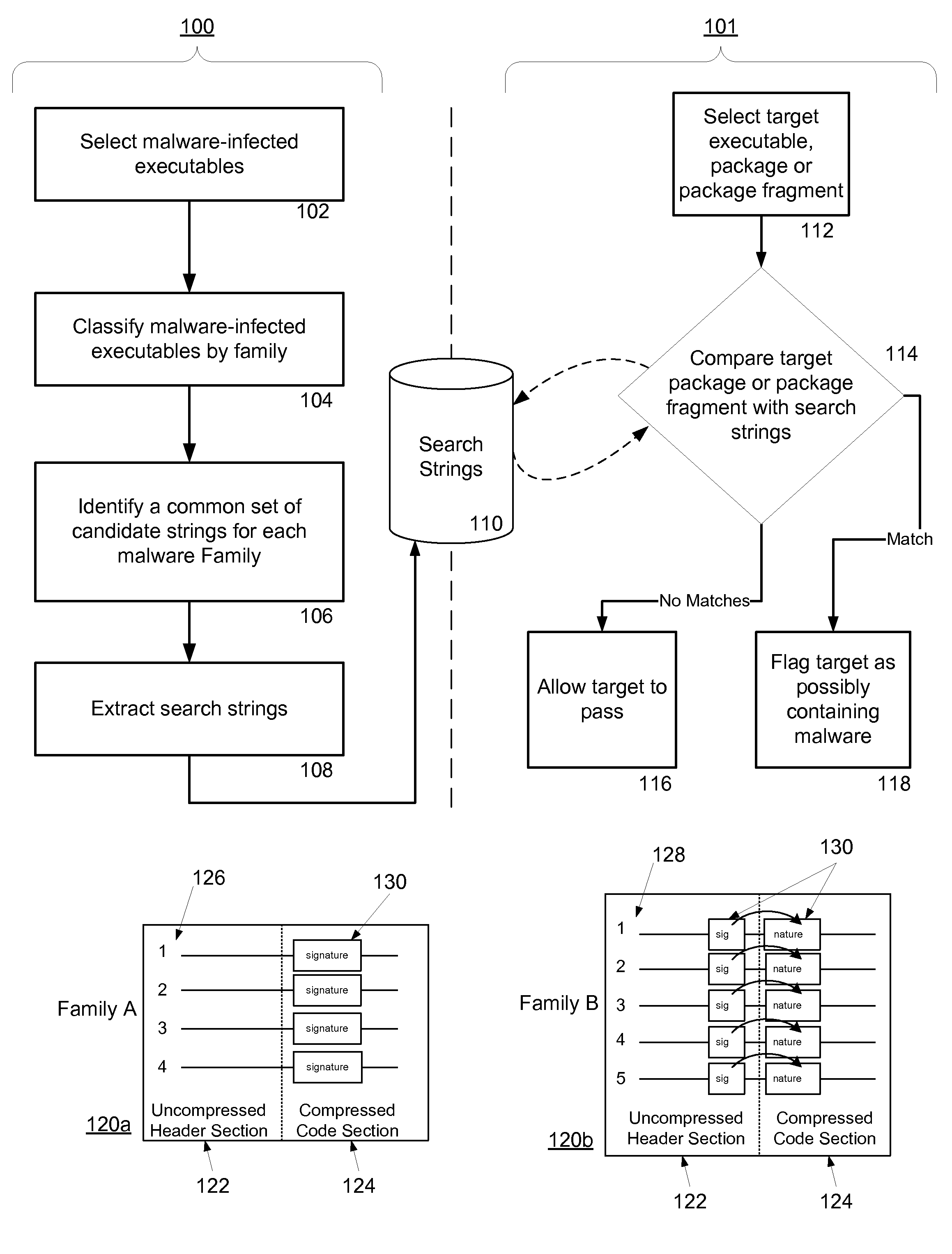
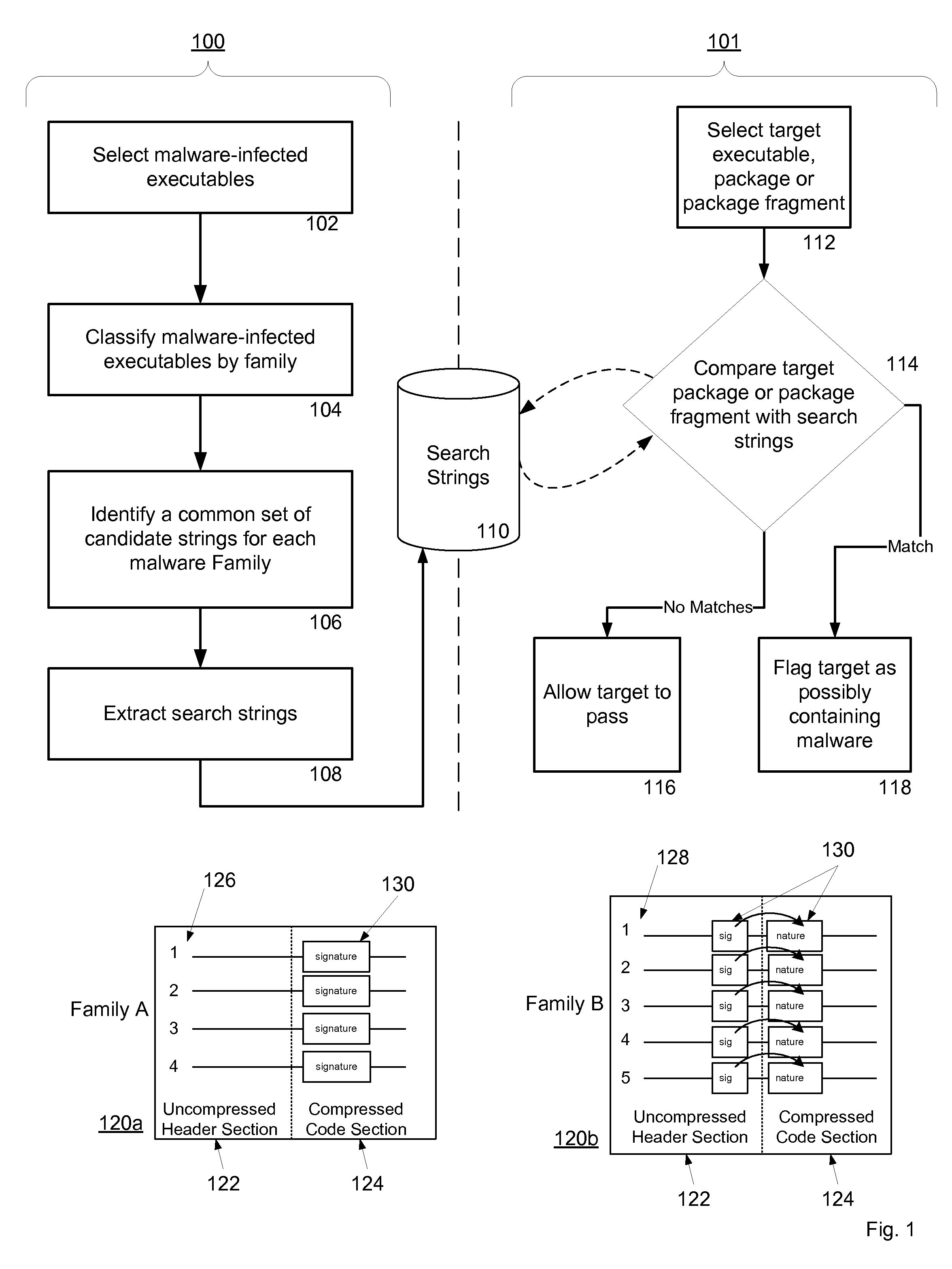
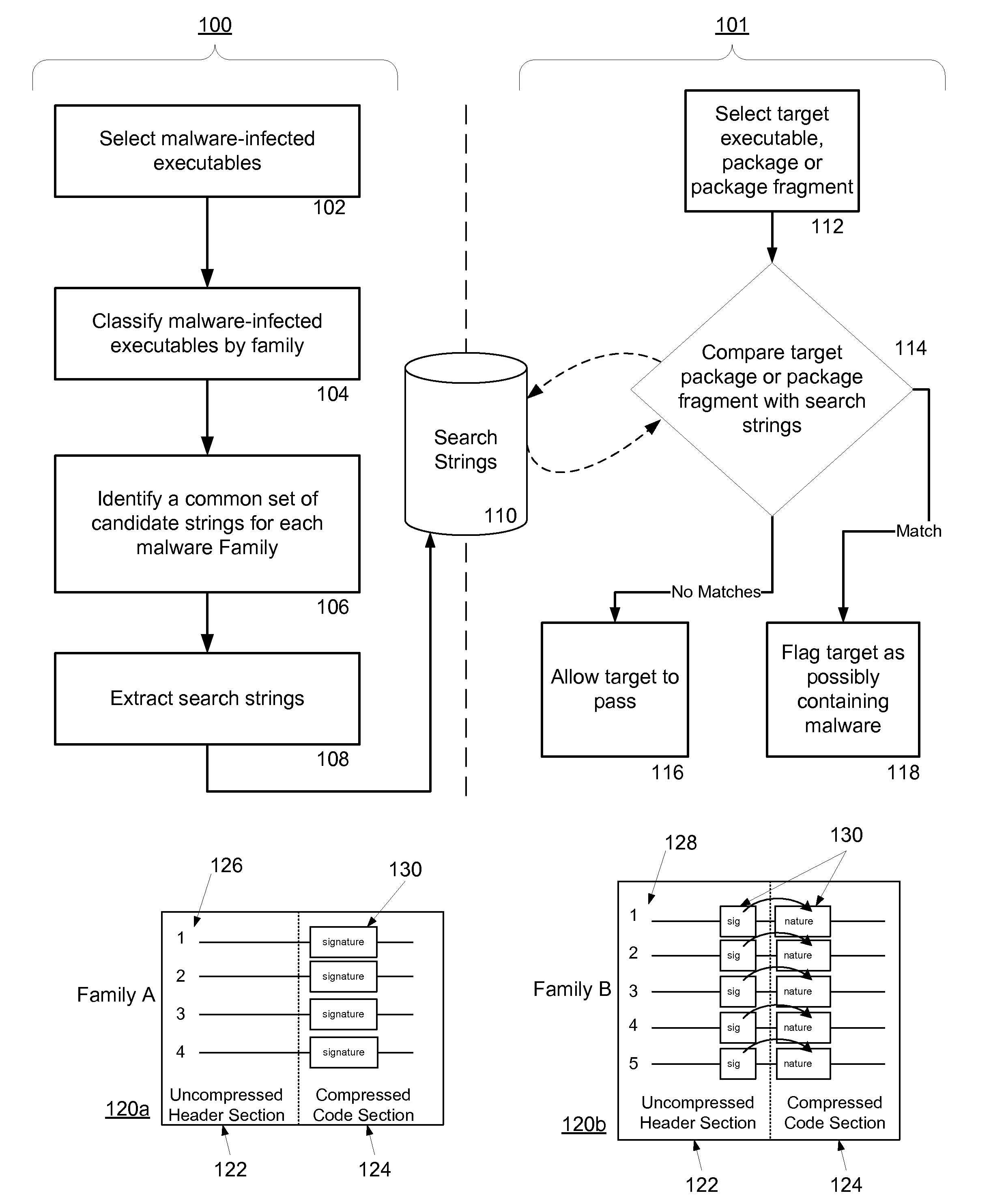
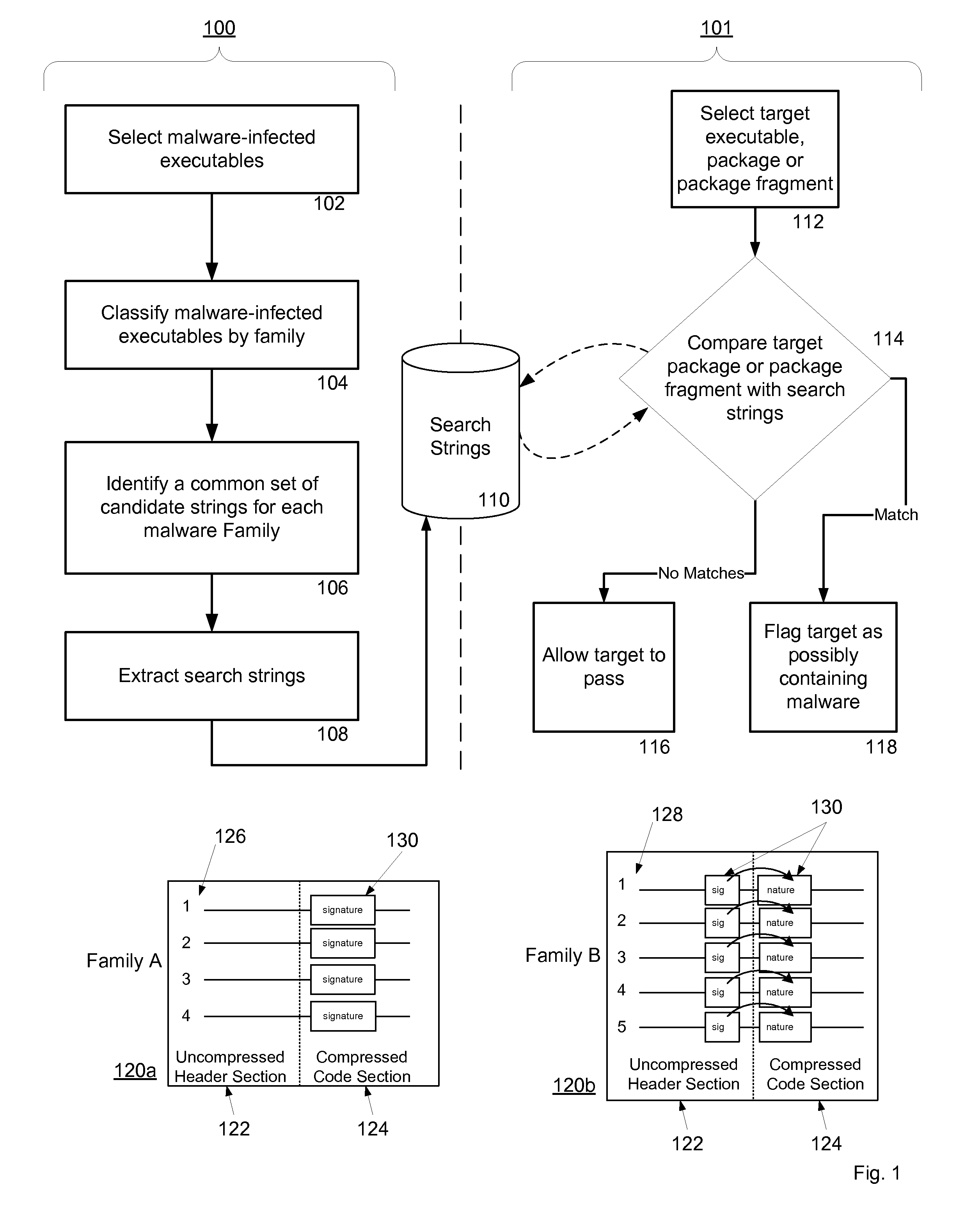
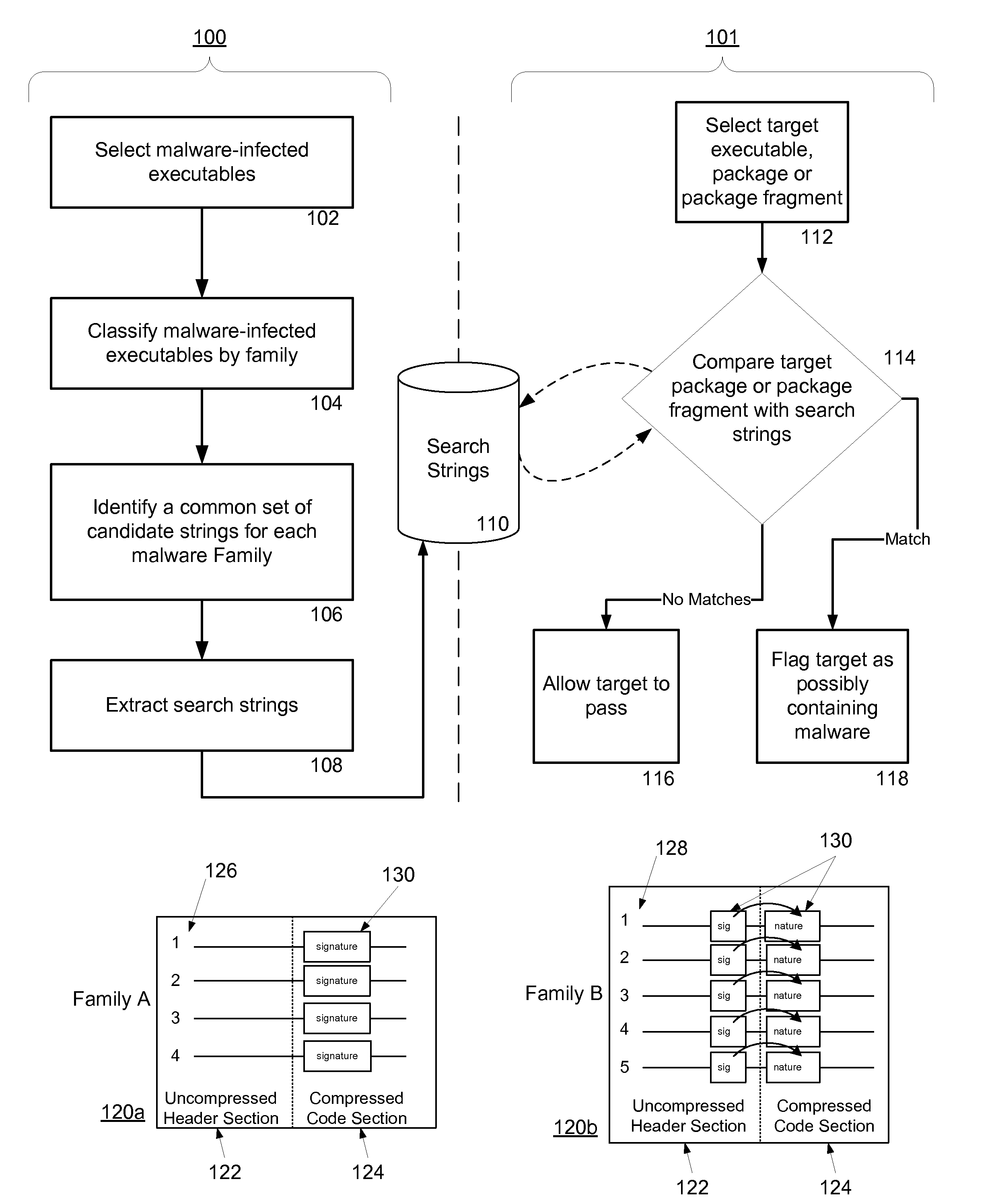
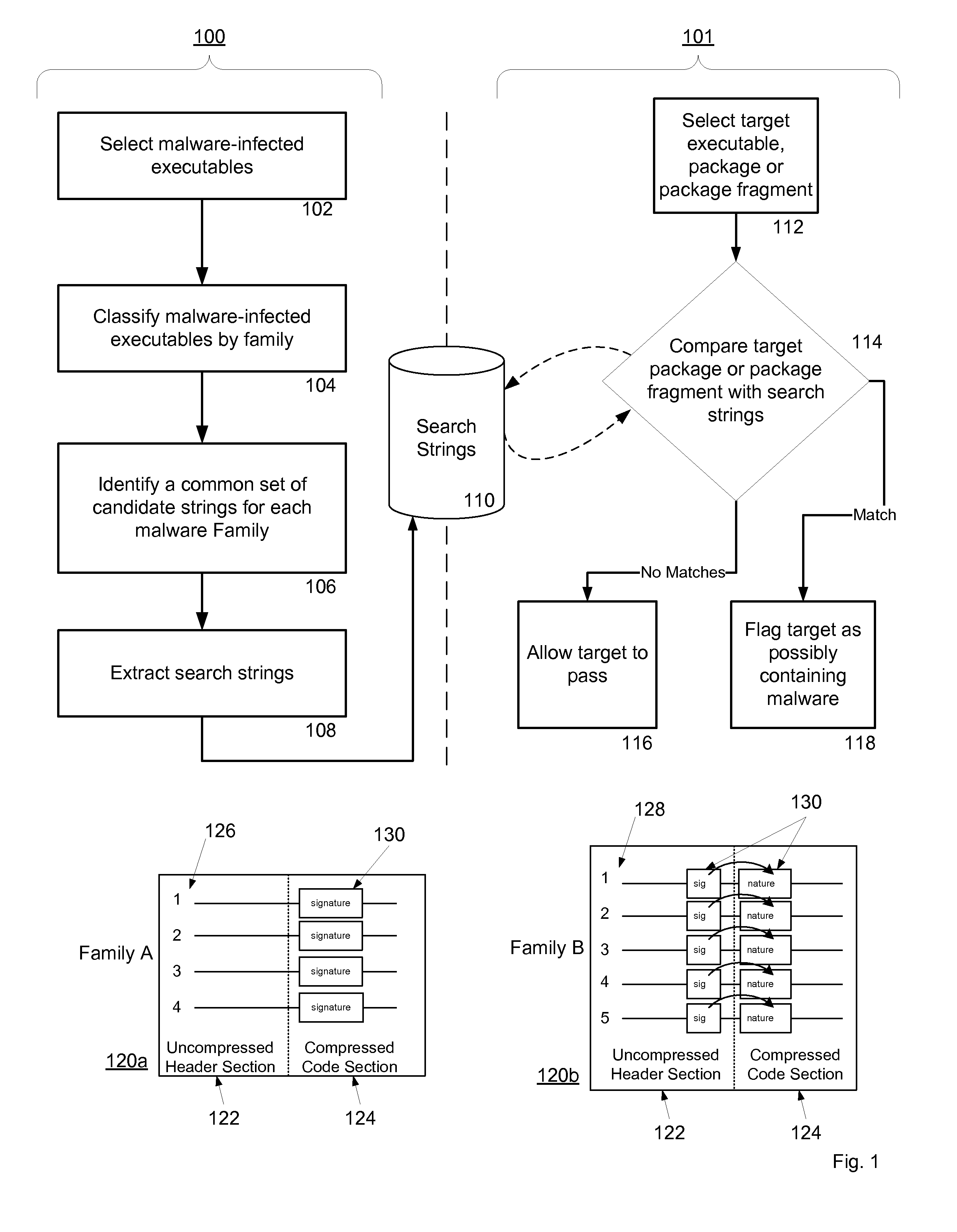
Malware Detection System And Method for Compressed Data on Mobile Platforms
ActiveUS20070240219A1Reliable detectionAmount of memory can be minimisedMemory loss protectionError detection/correctionMalwareExecutable
A system and method for detecting malware in compressed data. The system and method identifies a set of search strings extracted from compressed executables, each of which is infected with malware from a family of malware. The search strings detect the presence of the family of malware in other compressed executables, fragments of compressed executables, or data streams.
Owner:PULSE SECURE
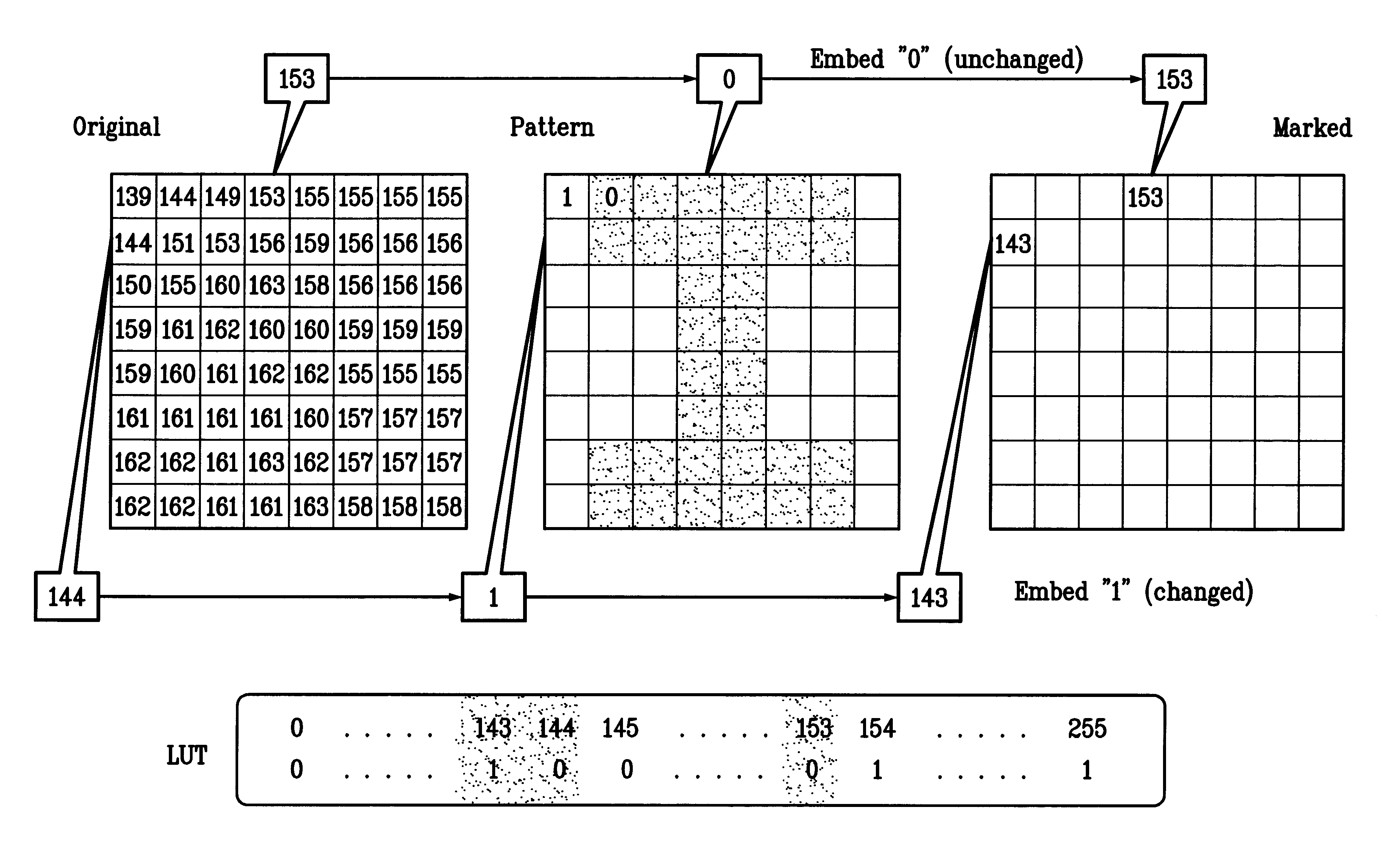
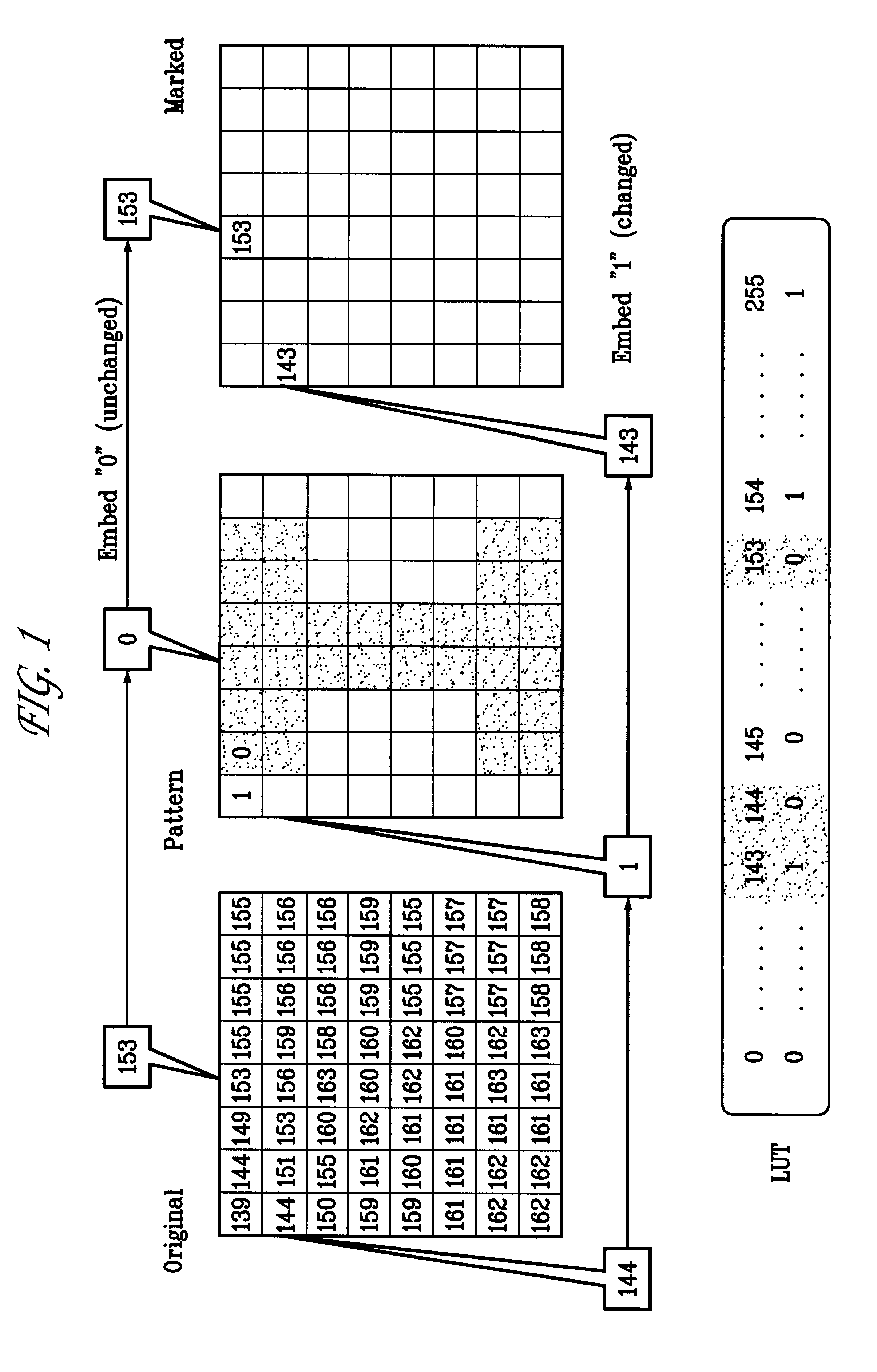
Watermarking scheme for image authentication
InactiveUS6285775B1Effective distributionQuick checkCharacter and pattern recognitionImage data processing detailsWatermark methodJPEG
A digital watermarking process whereby an invisible watermark inserted into a host image is utilized to determine whether or not the image has been altered and, if so, where in the image such alteration occurred. The watermarking method includes the steps of providing a look-up table containing a plurality of coefficients and corresponding values; transforming the image into a plurality of blocks, wherein each block contains coefficients matching coefficients in the look-up table; and embedding the watermark in the image by performing the following substeps for at least some of the blocks: First, a coefficient is selected for insertion of a marking value representative of a corresponding portion of the watermark. Next, the value of the selected coefficient to used to identify a corresponding value in the look-up table. Finally, the identified coefficient is left unchanged if the corresponding value is the same as the marking value, and is changed if the corresponding value is different from the marking value. After the insertion of the watermark, the image may be stored in a lossy-compression form, thus permitting efficient storage and distribution. Moreover, the method may be used to produce two output signals for authentication: (1) a meaningful pattern to facilitate a quick visual check, and (2) an additional signal to detect unauthorized alteration. The method can be applied to an image compressed using JPEG or other techniques, such as Wavelet compression, and the marked image can be kept in the compressed format. Any alteration made on the marked image can be localized, making the method suitable for use in a "trustworthy" digital camera or camcorder.
Owner:TRUSTEES OF THE UNIV OF PRINCETON THE
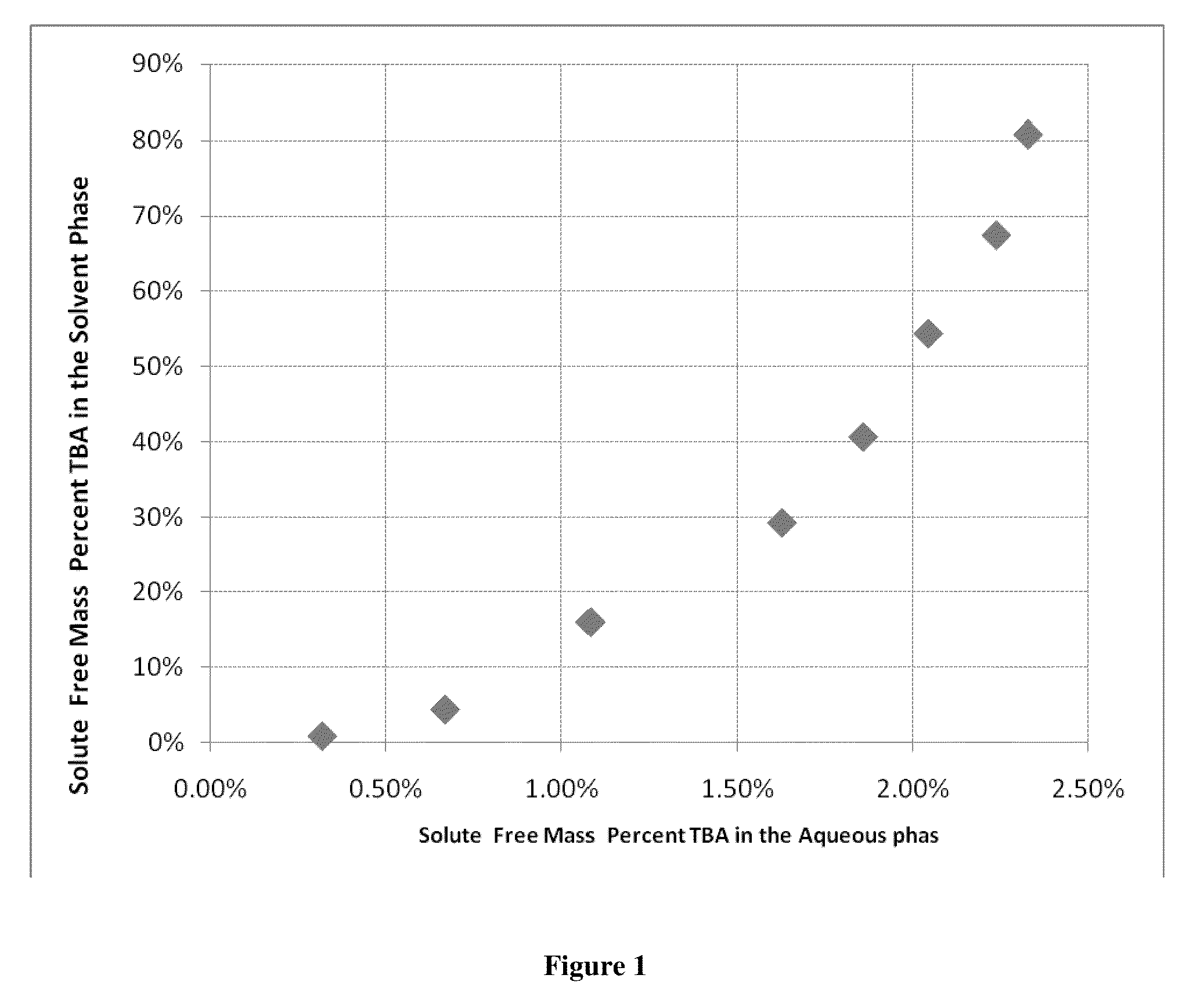
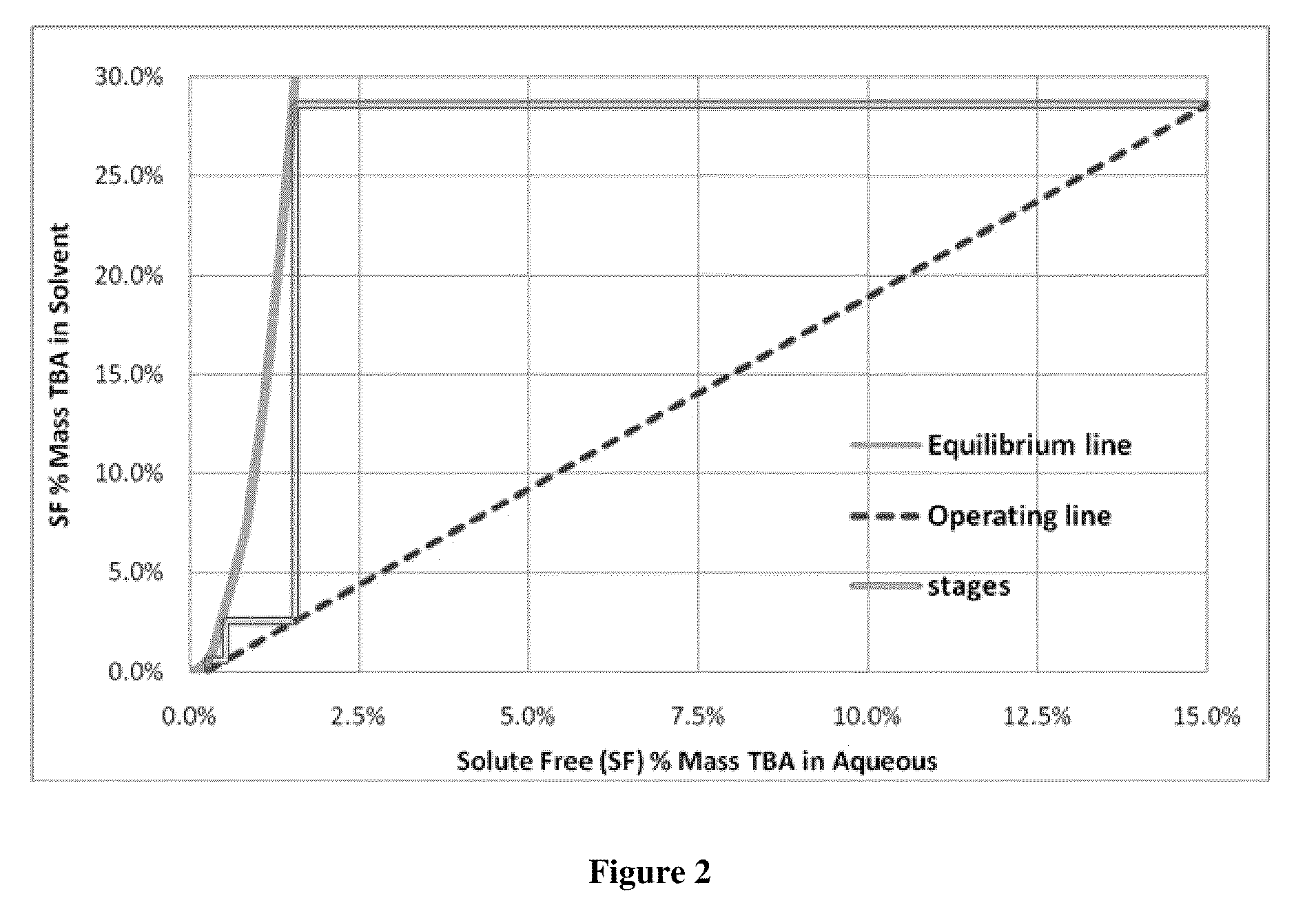
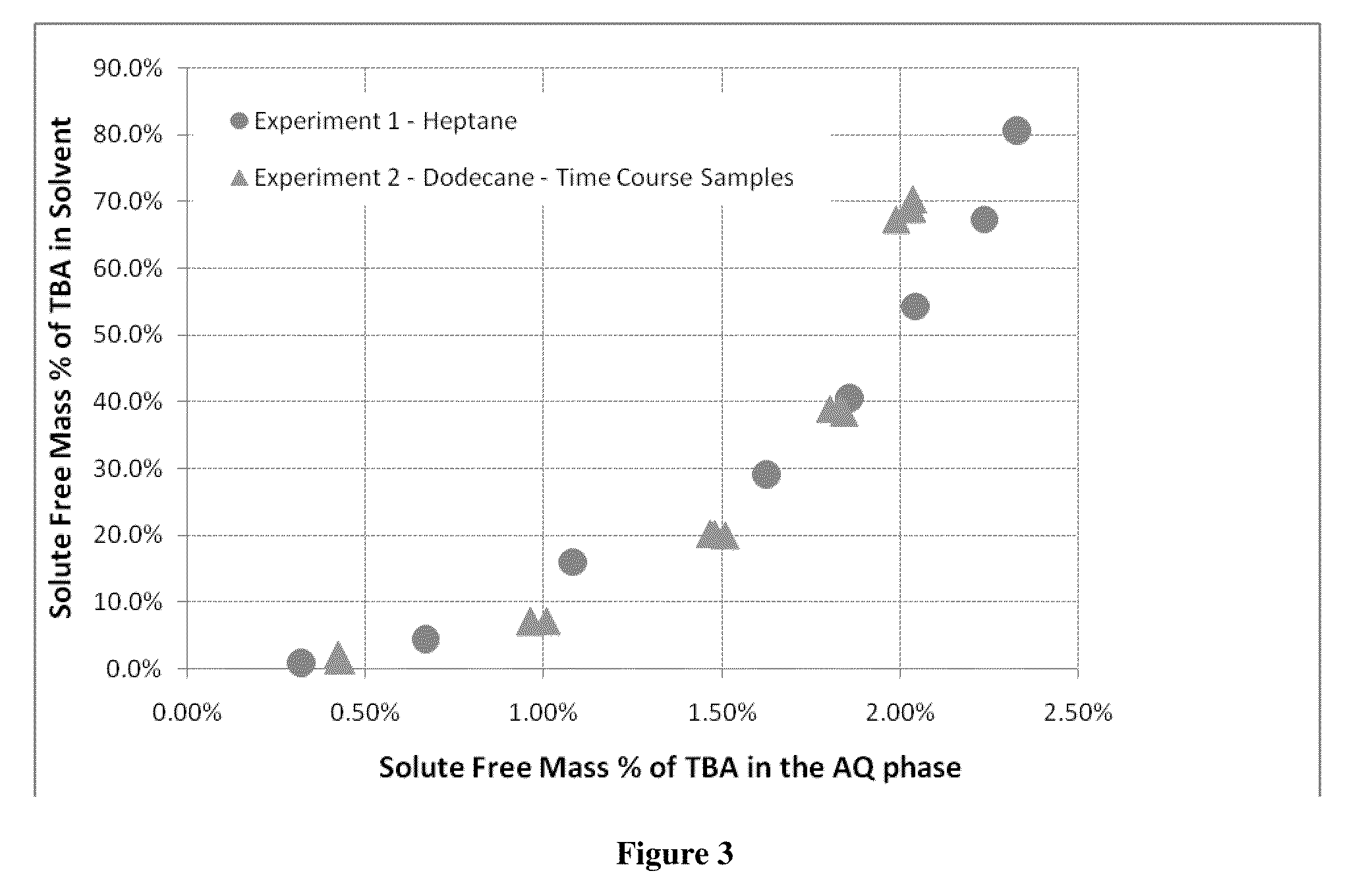
Recovery of organic acids
InactiveUS20090281354A1Promote recoveryOvercome consumptionPreparation from carboxylic acid saltsOrganic compound preparationOrganic acidReactive distillation
A method is disclosed for the recovery of an organic acid from a dilute salt solution in which the cation of the salt forms an insoluble carbonate salt. An amine and CO2 are introduced to the solution to form the insoluble carbonate salt and a complex between the acid and the amine. The acid / amine complex is thermally dissociated, or “cracked”, in the presence of a water immiscible solvent in which the amine is selectively soluble and in which the acid is not appreciably soluble. The organic acid may then be recovered from the water by any suitable means such as distillation, reactive distillation, extraction, or reactive extraction.
Owner:ZEACHEM
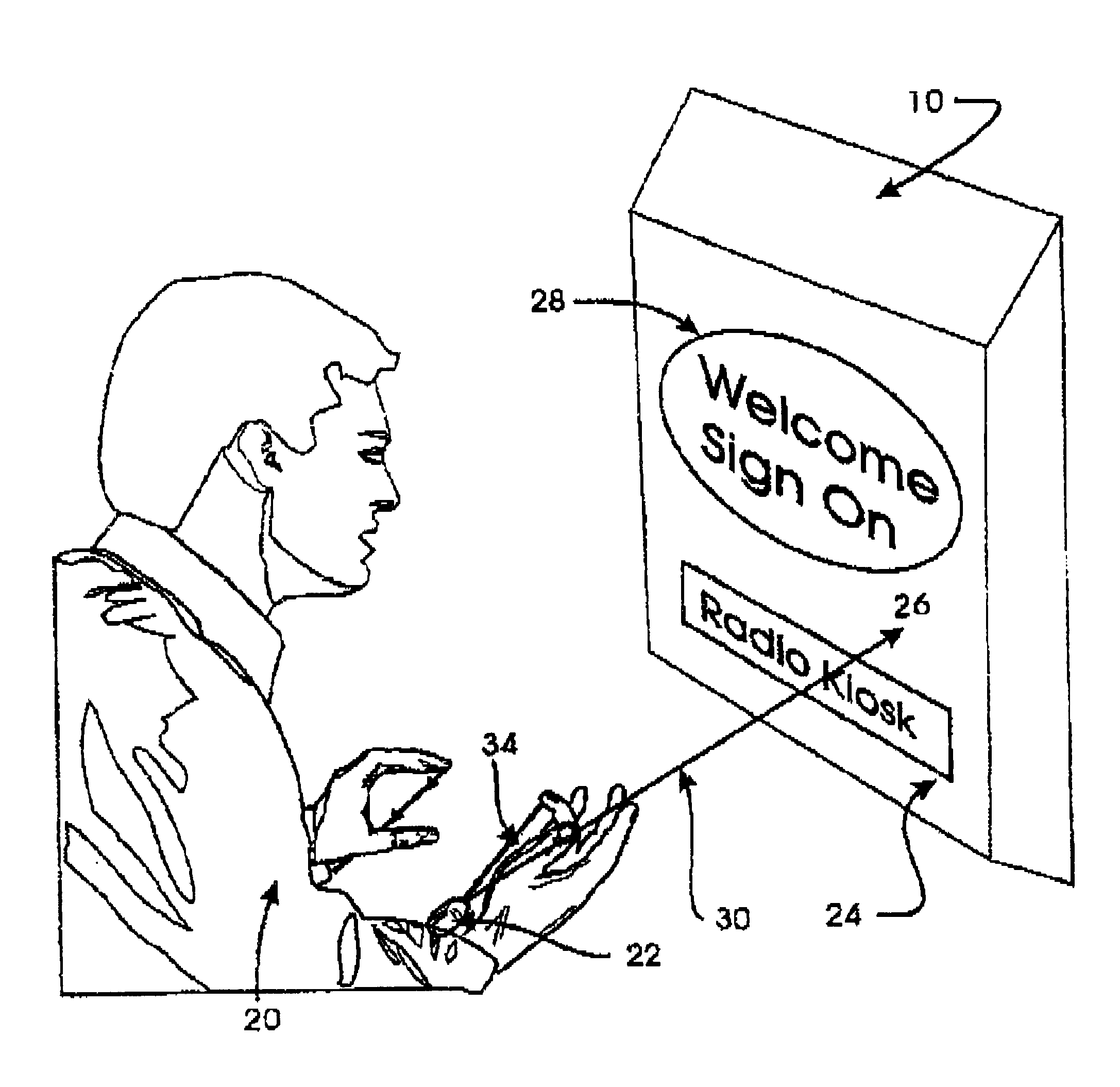
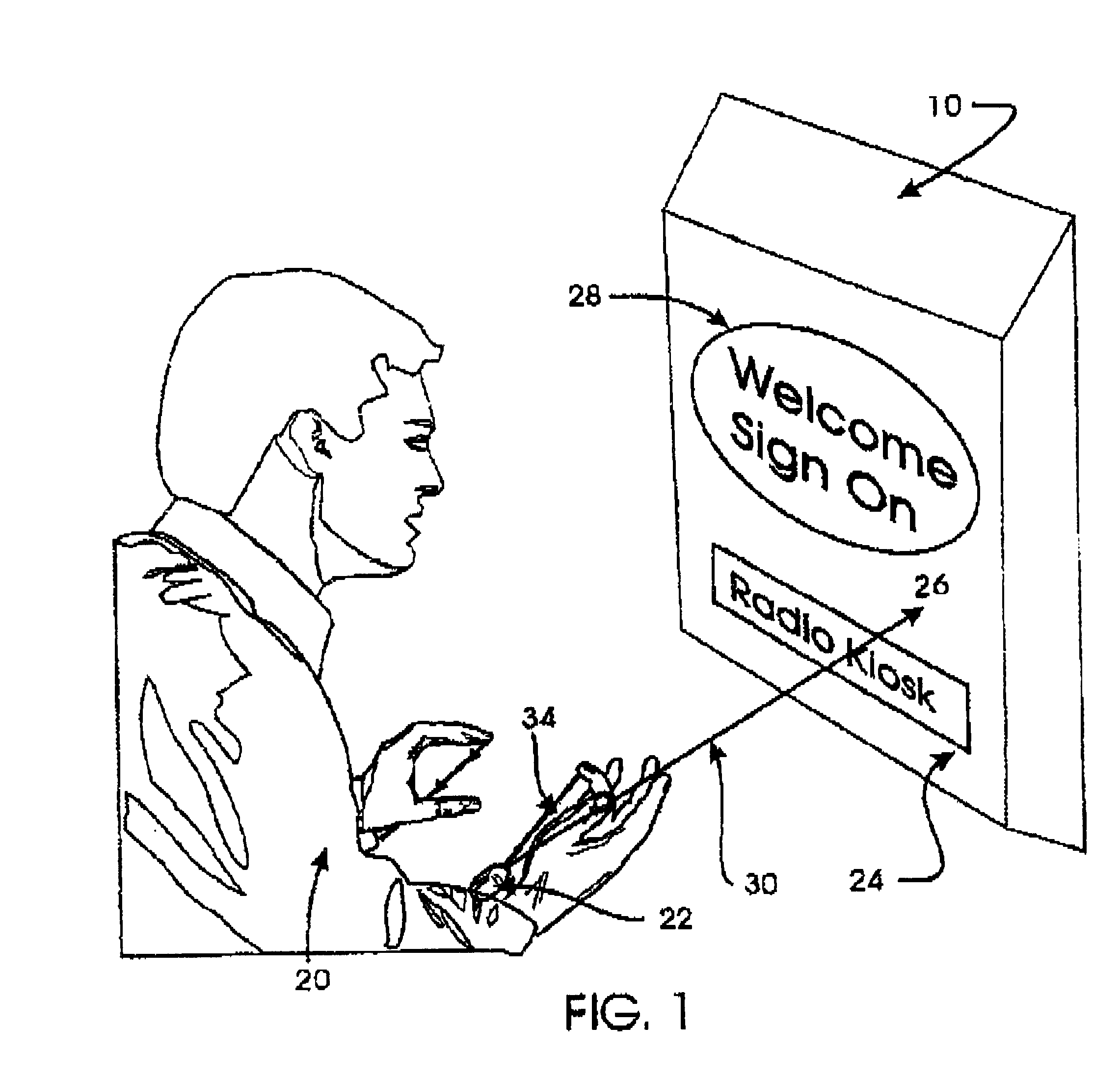
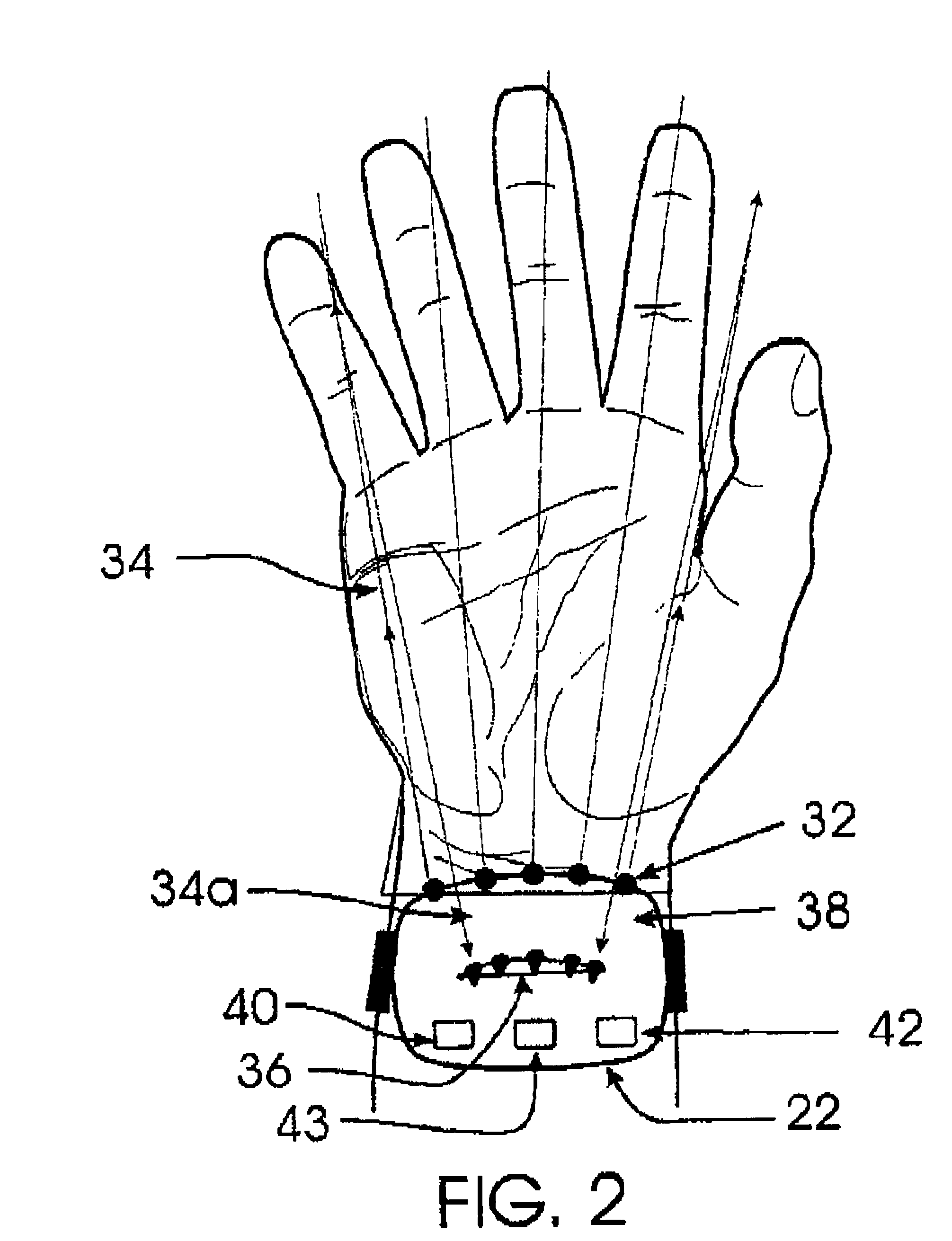
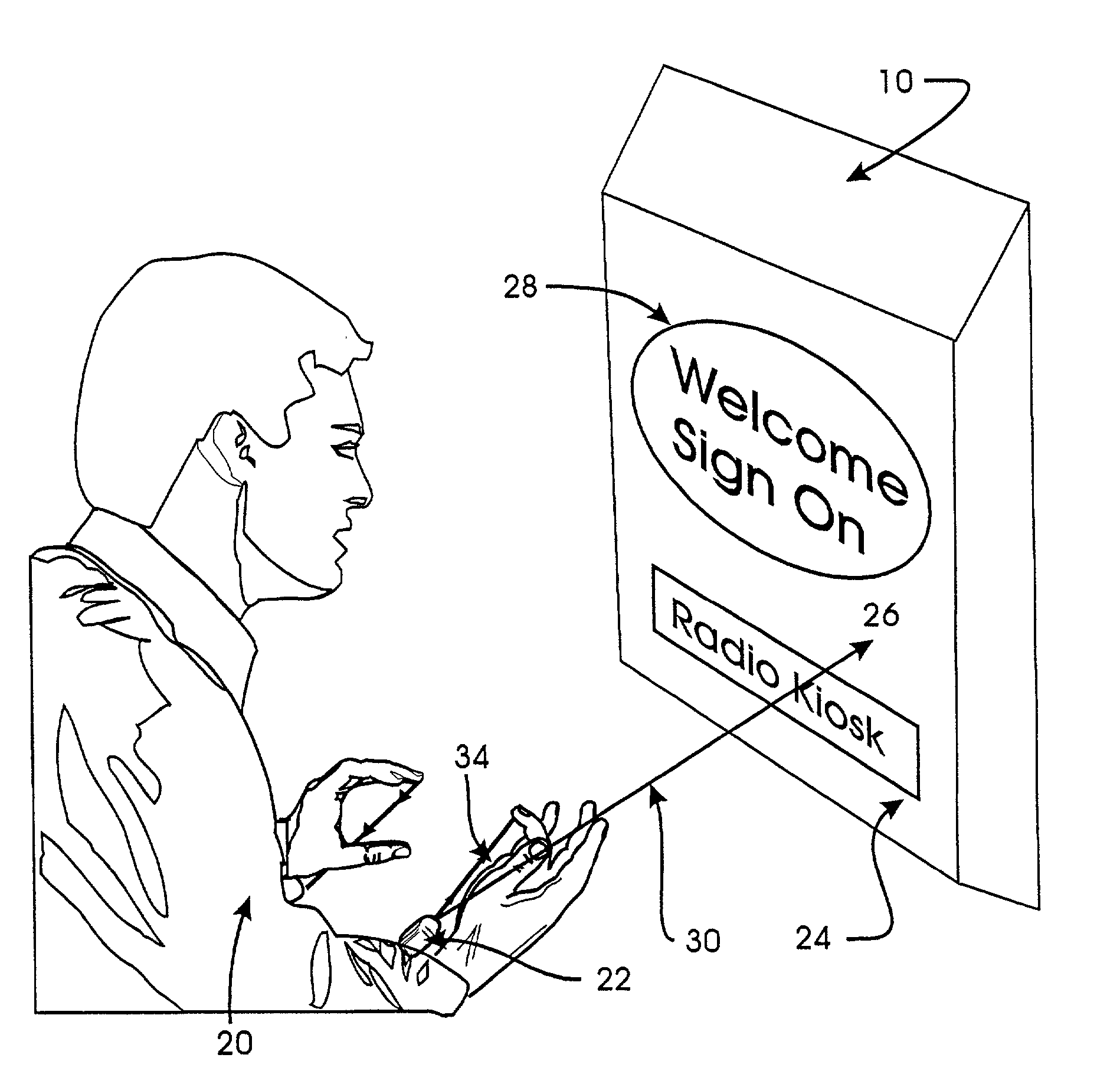
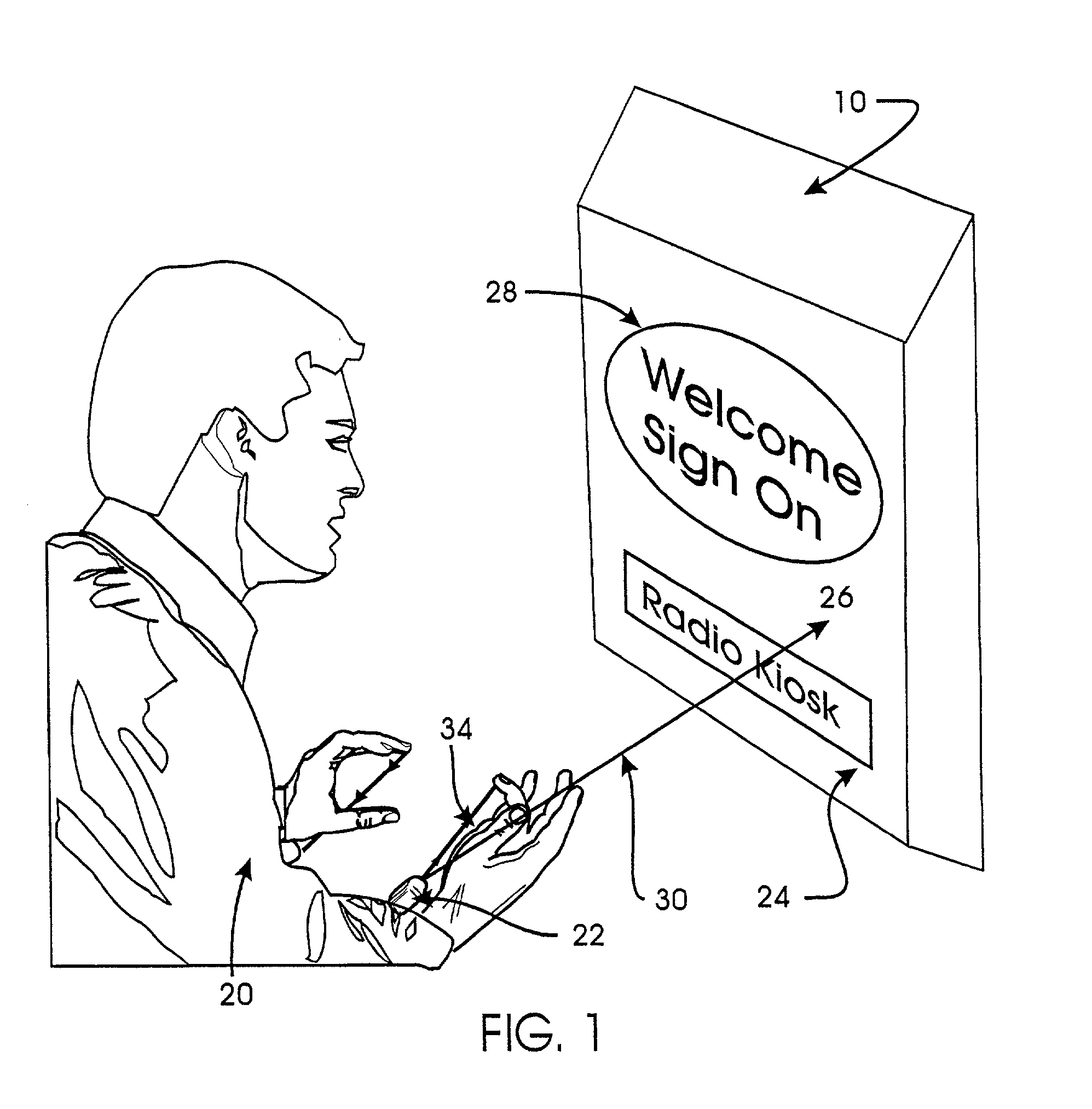
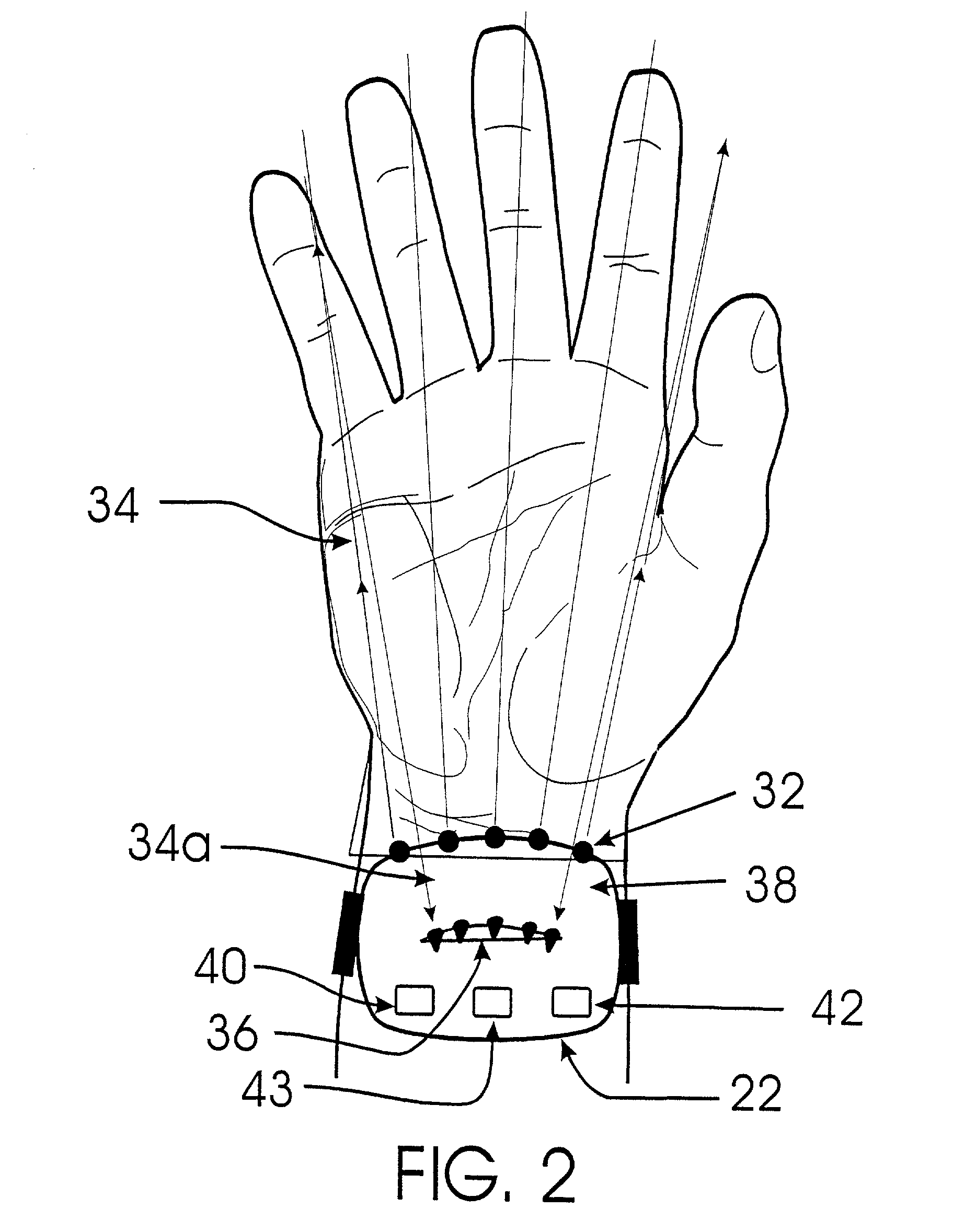
Wireless control device
InactiveUS6747632B2Rule out the possibilitySuitable for useInput/output for user-computer interactionElectrophonic musical instrumentsWireless controlDisplay device
A wireless control device includes a small, lightweight housing worn by an operator, for example on the operator's wrist, and a controlled device, for example a personal computer. Several optical emitters, preferably light emitting diodes operating in the infrared range, and several optical detectors are provided on the housing. At least one x-axis emitter-detector pair operates to detect an x-direction of a pointing motion or gesture, and at least one y-axis emitter-detector pair operates to detect a y-direction of a pointing motion or gesture. This motion can then be used to cause a response in the controlled device. For example, angles of the operator's hand at the wrist can be interpreted to induce motion of a cursor on a computer display. The device may also include a motion sensor, an environmental condition sensor, or a voice recognition sensor, and can also be adapted for gesture recognition and image scanning applications.
Owner:HARMONIC RES
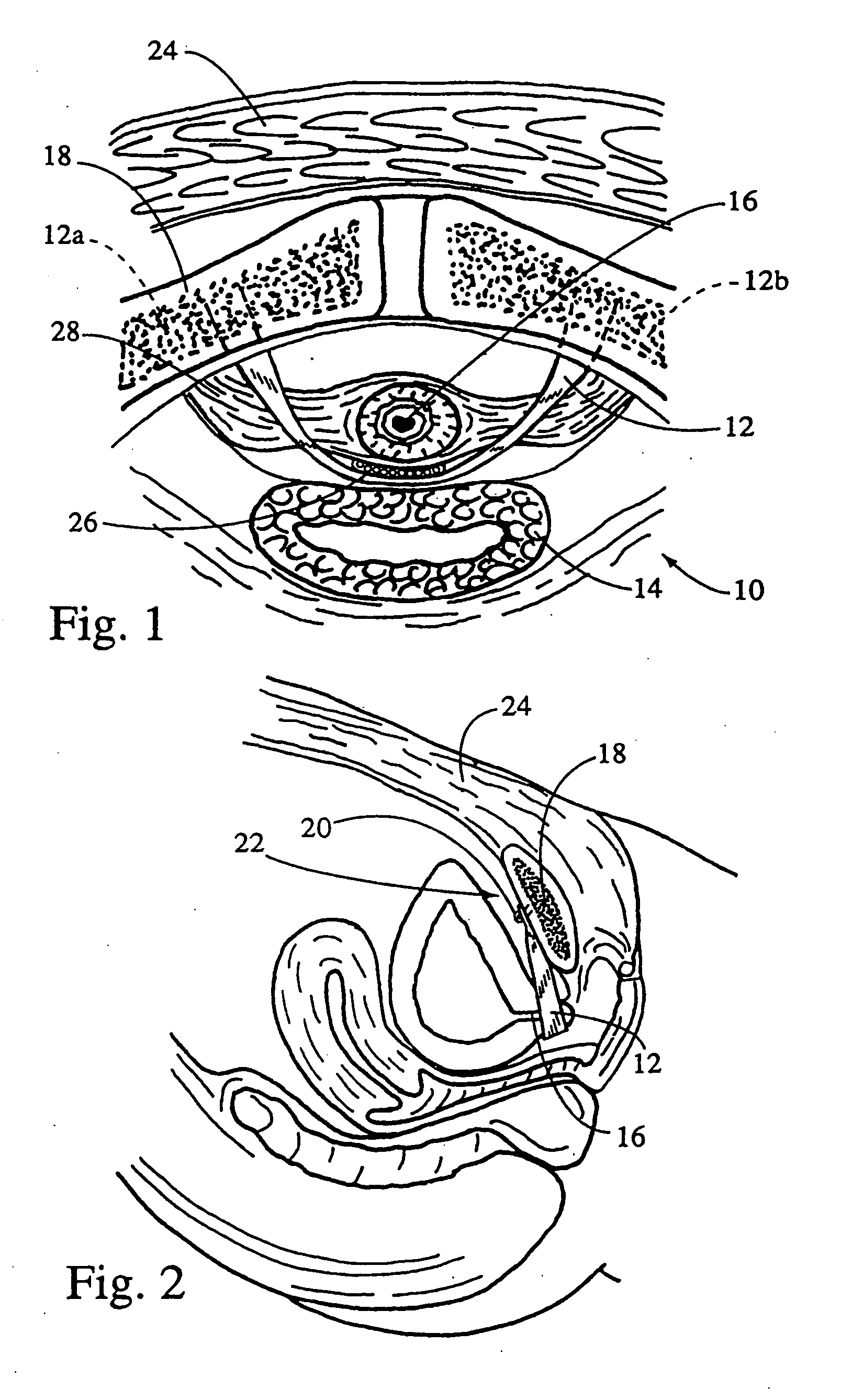
System for securing sutures, grafts and soft tissue to bone and periosteum
InactiveUS20050004576A1Easy constructionEasy to useSuture equipmentsAnti-incontinence devicesEngineeringPeriosteum
Self-anchoring slings and deployment mechanisms for use therewith in selectively positioning a sling into position within the body. According to a preferred embodiment, the sling comprises an elongate sling portion having opposed ends. Formed upon each respective opposed end is an anchor member operative to be percutaneously advanced through soft tissue at a selected target site in a first direction but resist movement in an opposed direction. Such anchor members are operative to extend in opposed directions to thus enable a sling to be securely affixed into position and resist sag or otherwise lose its ability to support a given structure.
Owner:SPRINGBOARD MEDICAL VENTURES
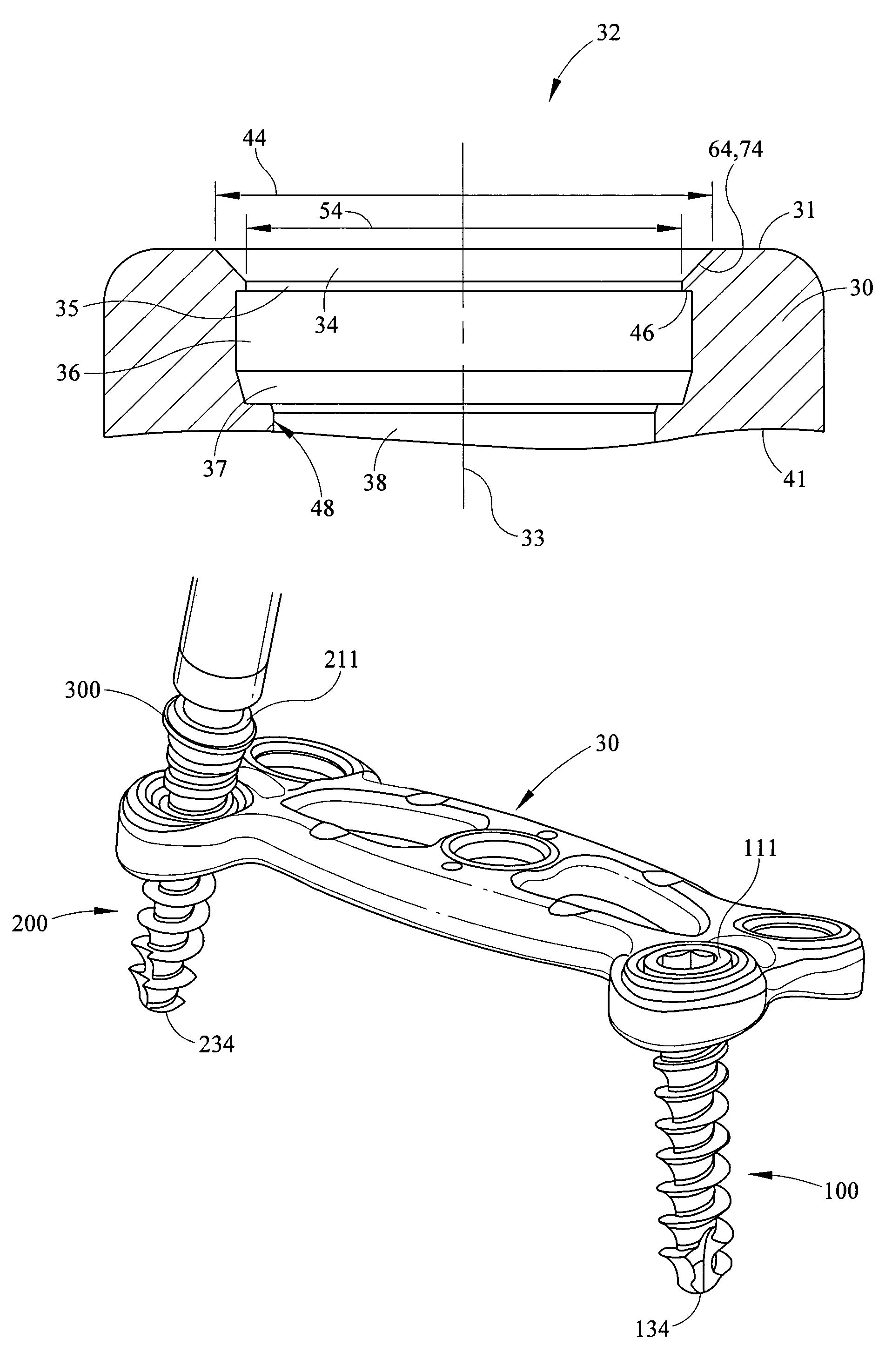
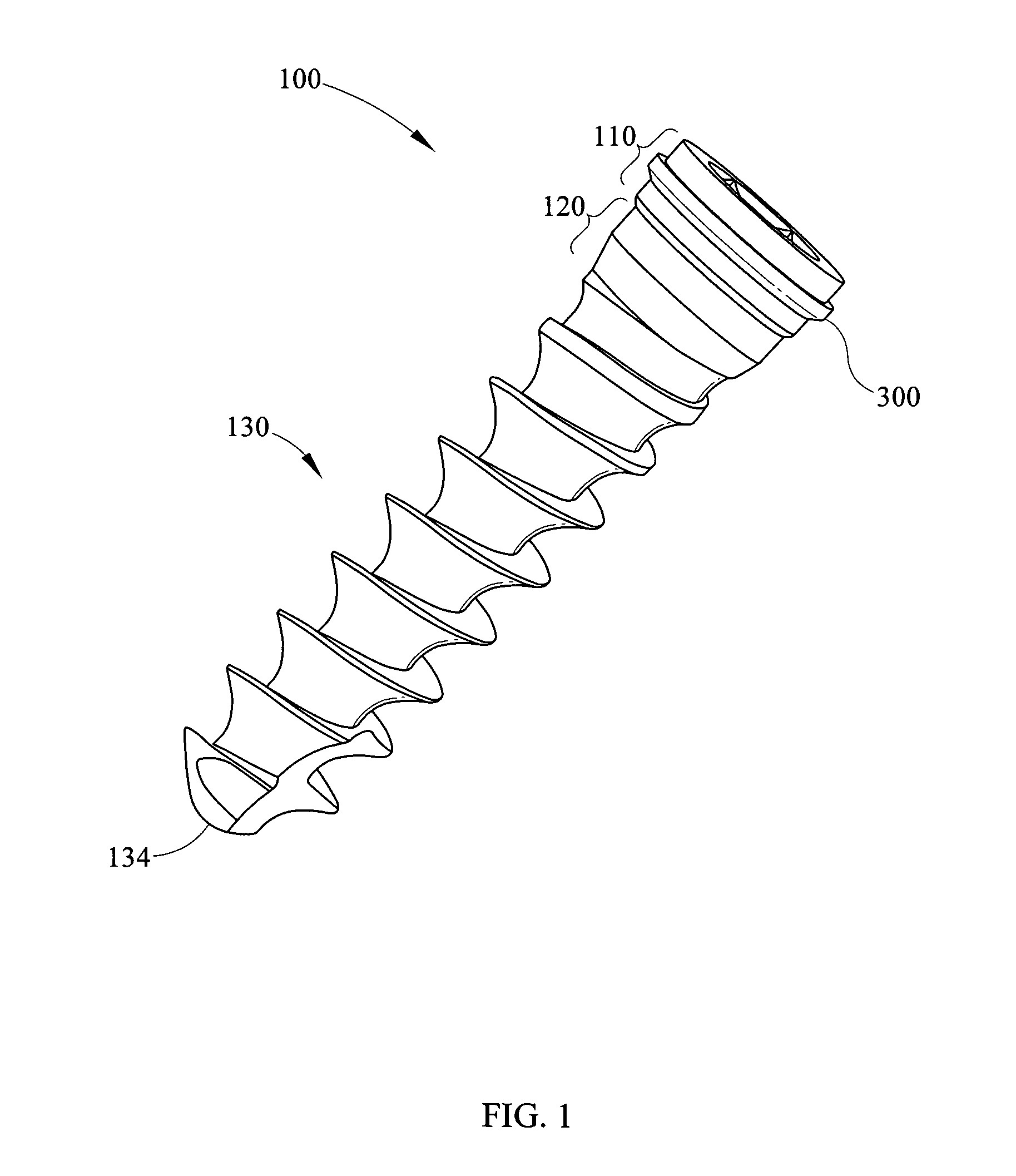
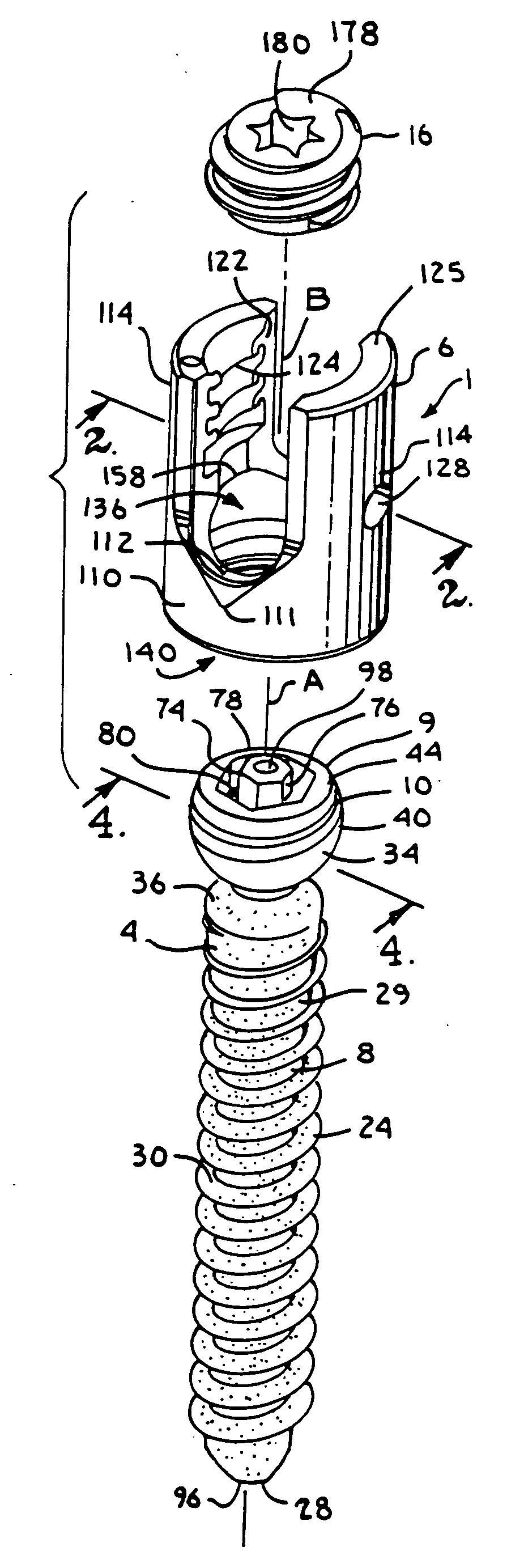
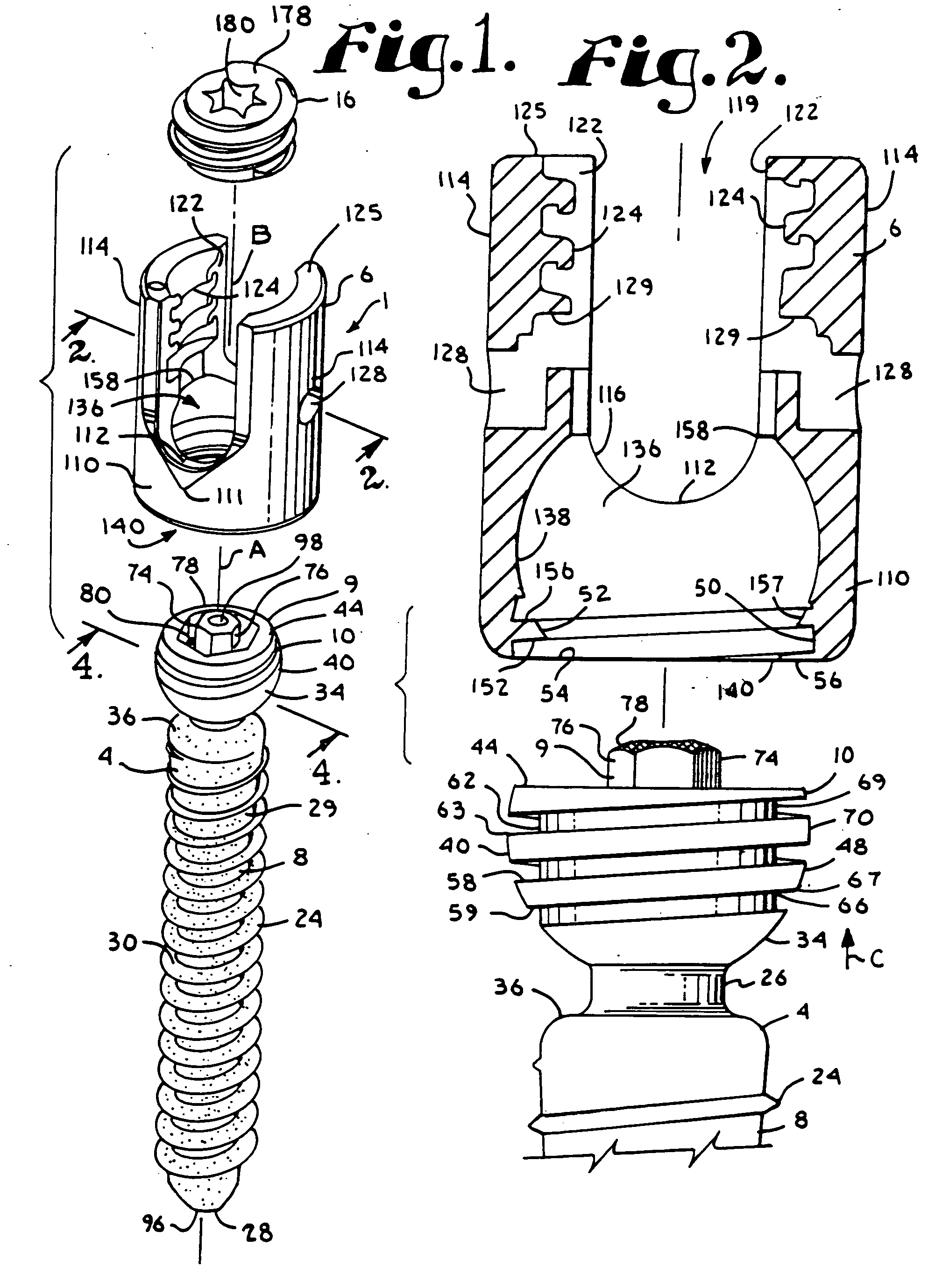
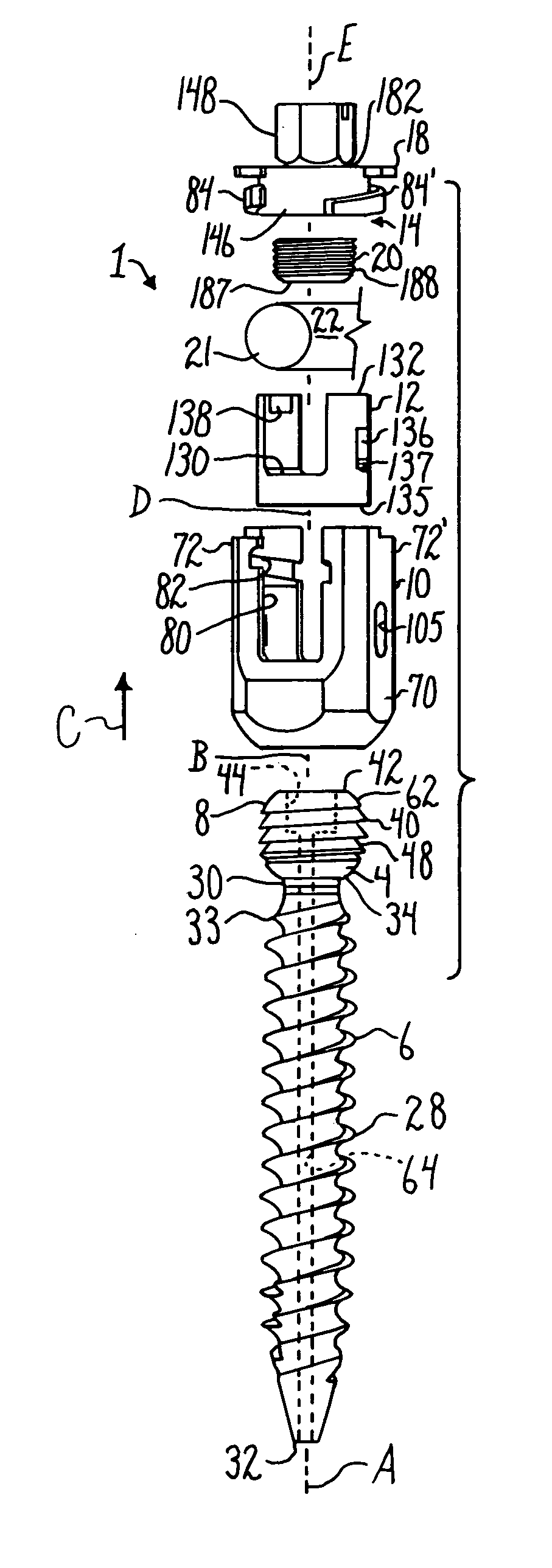
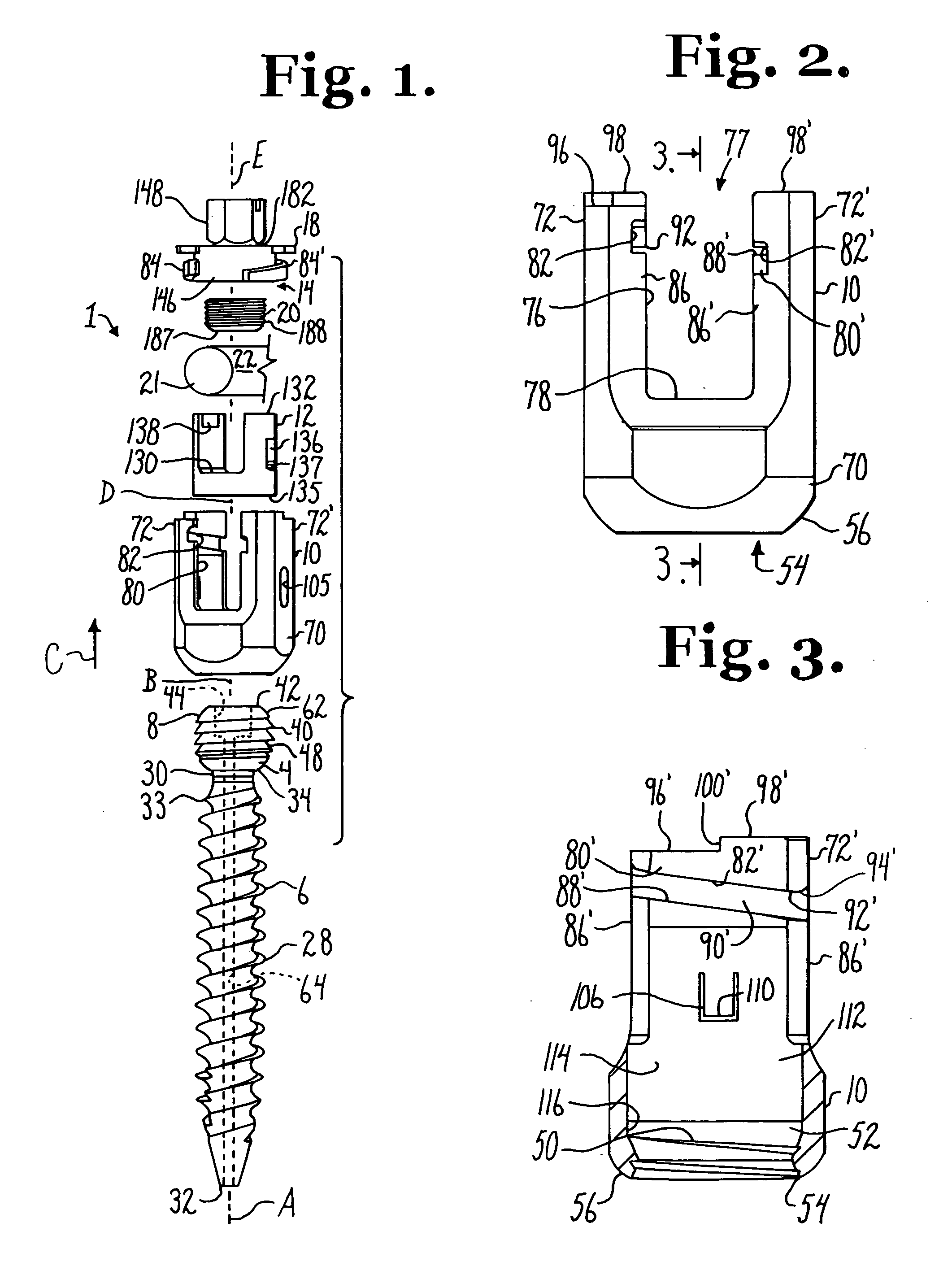
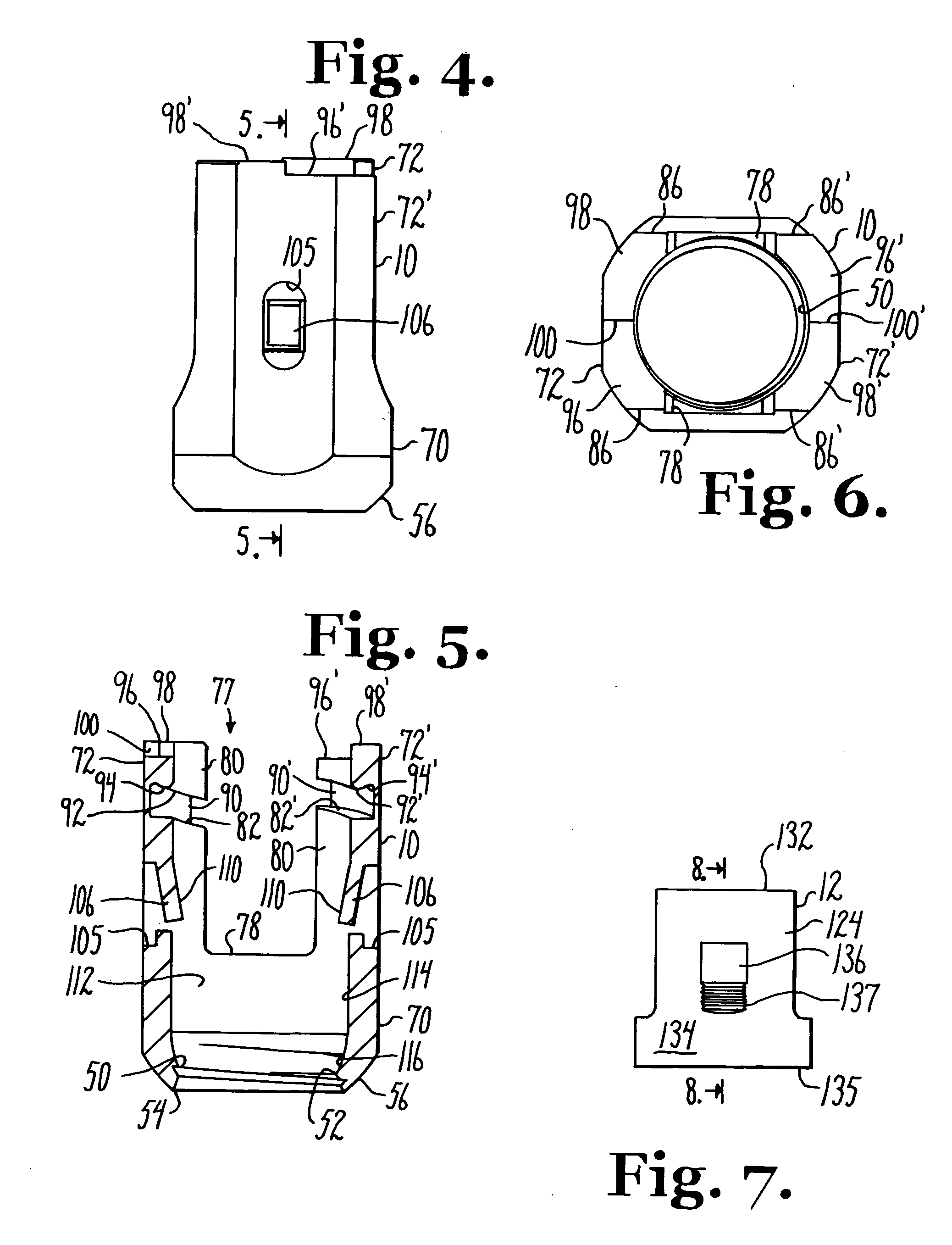
Dynamic stabilization medical implant assemblies and methods
InactiveUS20070016200A1Easy to useCheap to makeInternal osteosythesisDiagnosticsBiomedical engineeringBone screws
Bone screw assemblies include longitudinal connecting members that provide for dynamic stabilization, some including non-uniform portions that are configured to flex, contract or expand. Composite longitudinal connecting members include longitudinal segments made from different materials having different flexibilities. Polyaxial bone screw assemblies include change-out receivers for cooperating with replacement longitudinal connecting members having a different flexibility. Bone screw shanks for cooperating with one or more open receivers include treatment or coating to provide biologically active interface with bone.
Owner:JACKSON
Aseptic connector and fluid delivery system using such an aseptic connector
InactiveUS6096011ASimple in design and operationInexpensive to fabricateValve arrangementsInfusion devicesBiomedical engineeringHigh pressure
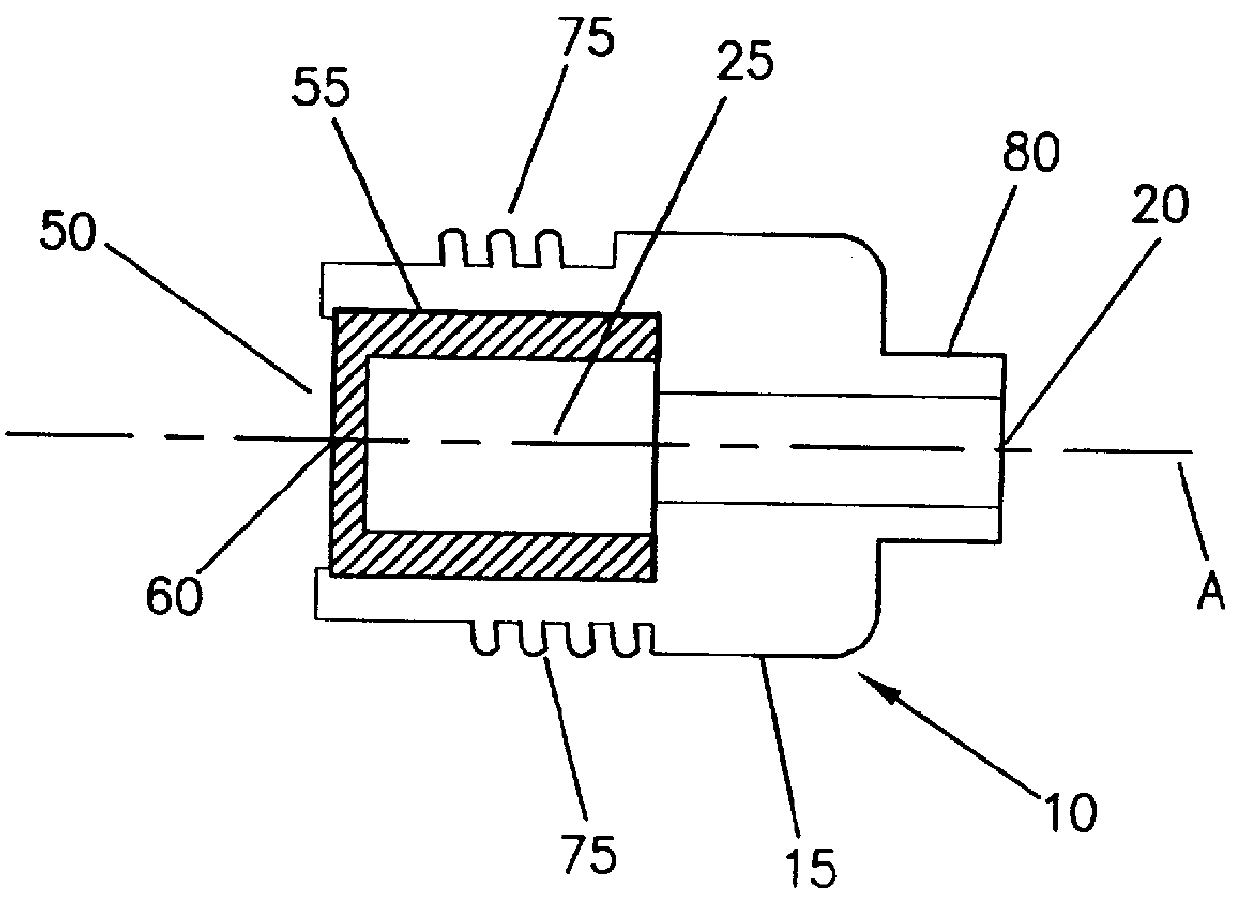
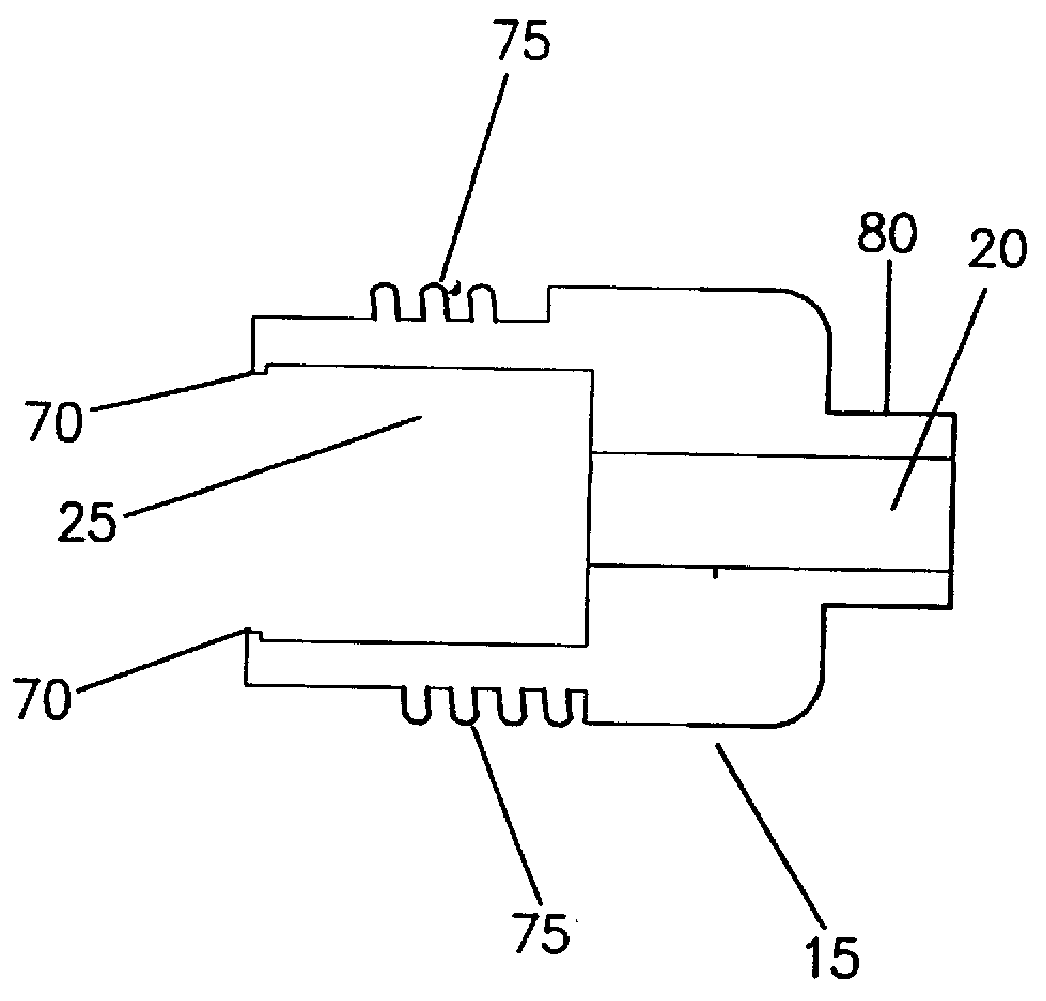
An aseptic connector comprises a first member and a second member. The first member preferably includes a resilient septum, and the second member preferably includes a penetrating member. Preferably, the septum is formed from an elastomeric material such as a silicone elastomer. The penetrating member preferably includes an extending penetrating element to penetrate the resilient septum. The aseptic connector further comprises a resilient sealing element that contacts the penetrating member and one of an inner wall of the first member and an inner wall of the second member to create a seal between the penetrating member and one of the inner wall of the first member and the inner wall of the second member. The seal created is suitable to withstand relatively high pressures (for example, those experienced during the injection of contrast media in CT procedures). A fluid delivery system comprising at least a first aseptic connector as described above is also provided.
Owner:BAYER HEALTHCARE LLC
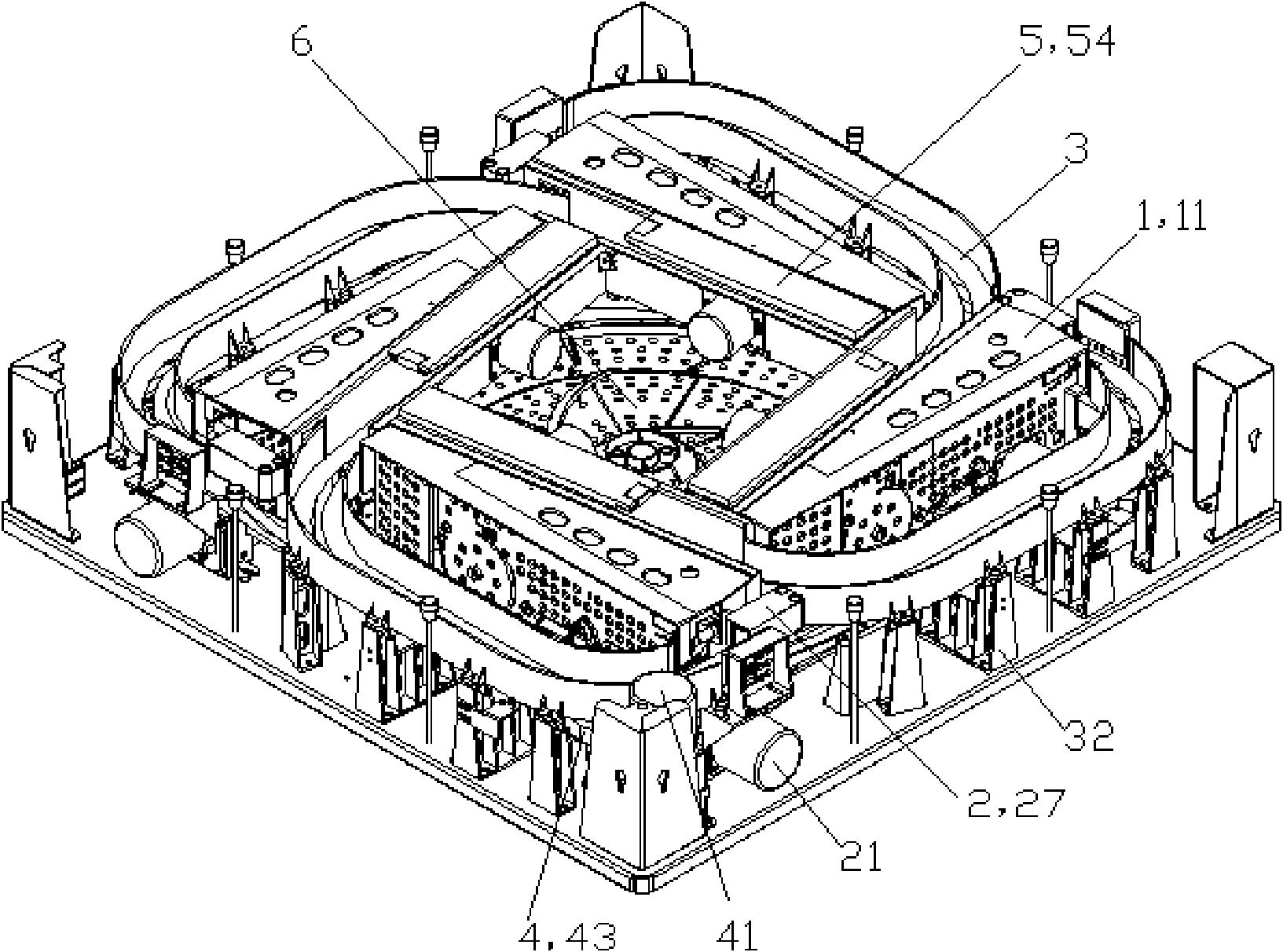
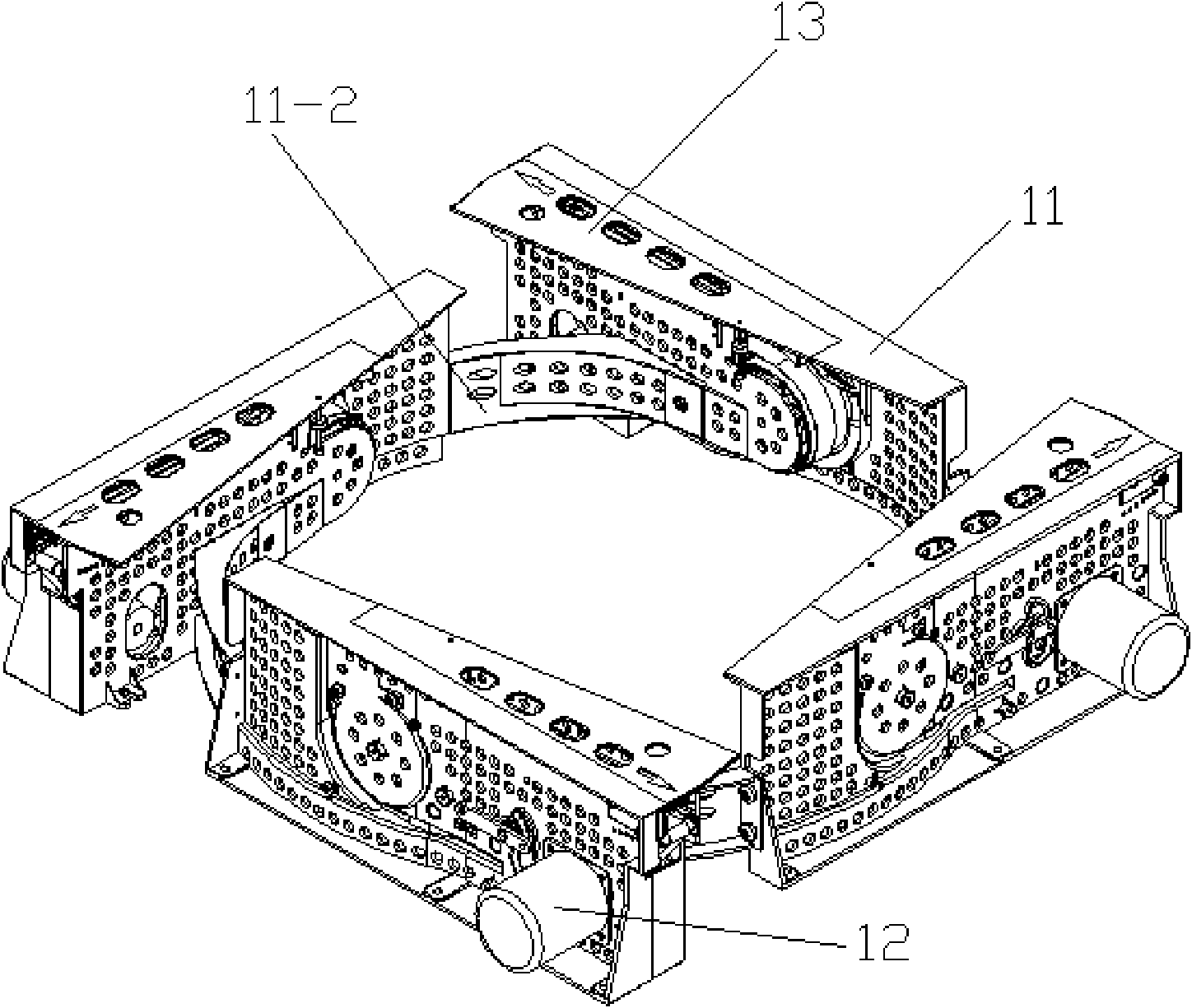
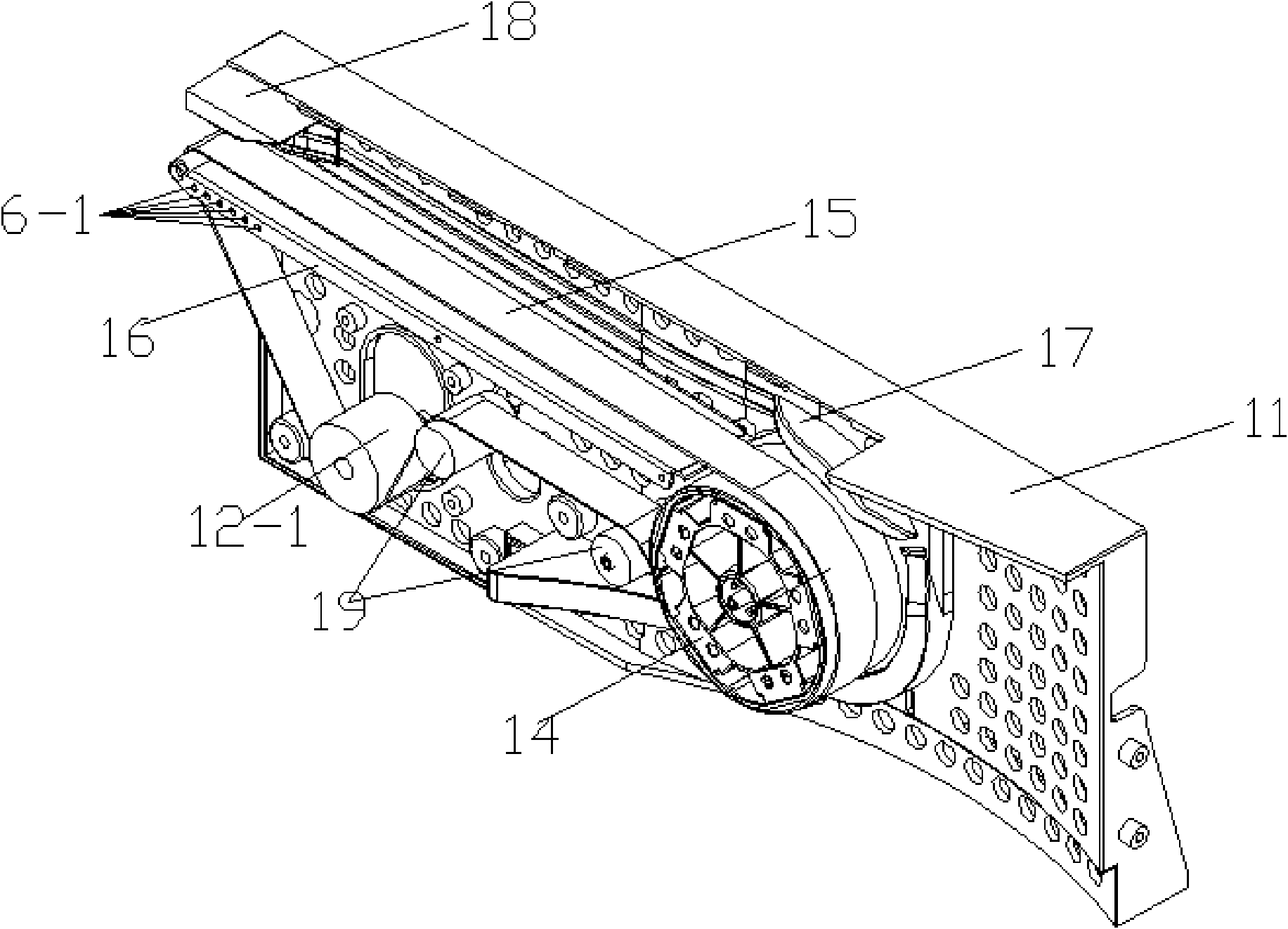
Fully-automatic mahjong machine
InactiveCN102133480AReduce manufacturing costGuaranteed uptimeIndoor gamesInlet channelTransmission belt
The invention relates to a fully-automatic mahjong machine comprising a board sending system, a board loading system, a board lifting system and a large shuffling disc. The board sending system comprises four board sending mechanisms, each board sending mechanism comprises a transmission rack, and a board sending motor, a board absorbing wheel, a transmission belt, a transmission platform, a board inlet guiding piece and a board outlet guiding piece fixed on the transmission rack; a board sending channel is arranged at the upper end of the transmission platform, the board absorbing wheel is tightly attached at the lower end of a board inlet opening of the board sending channel, the board inlet guiding piece is positioned above the board absorbing wheel, the board outlet guiding piece is positioned at a board outlet opening of the board inlet channel, the board sending motor is used for driving a motor guiding wheel, the motor guiding wheel is positioned below the transmission platform, and the transmission belt loops the motor guiding wheel, the board absorbing wheel and the transmission platform. In the invention, for the mahjong boards with different widths, the board sending mechanism of the mahjong machine can run normally by only replacing the corresponding board inlet guiding piece and the board outlet guiding piece, and a transmission rack cover does not need to be changed, so that the operation is simple and convenient, and the board inlet guiding piece and the board outlet guiding piece has extremely low production cost relative to the transmission rack cover.
Owner:程亮星
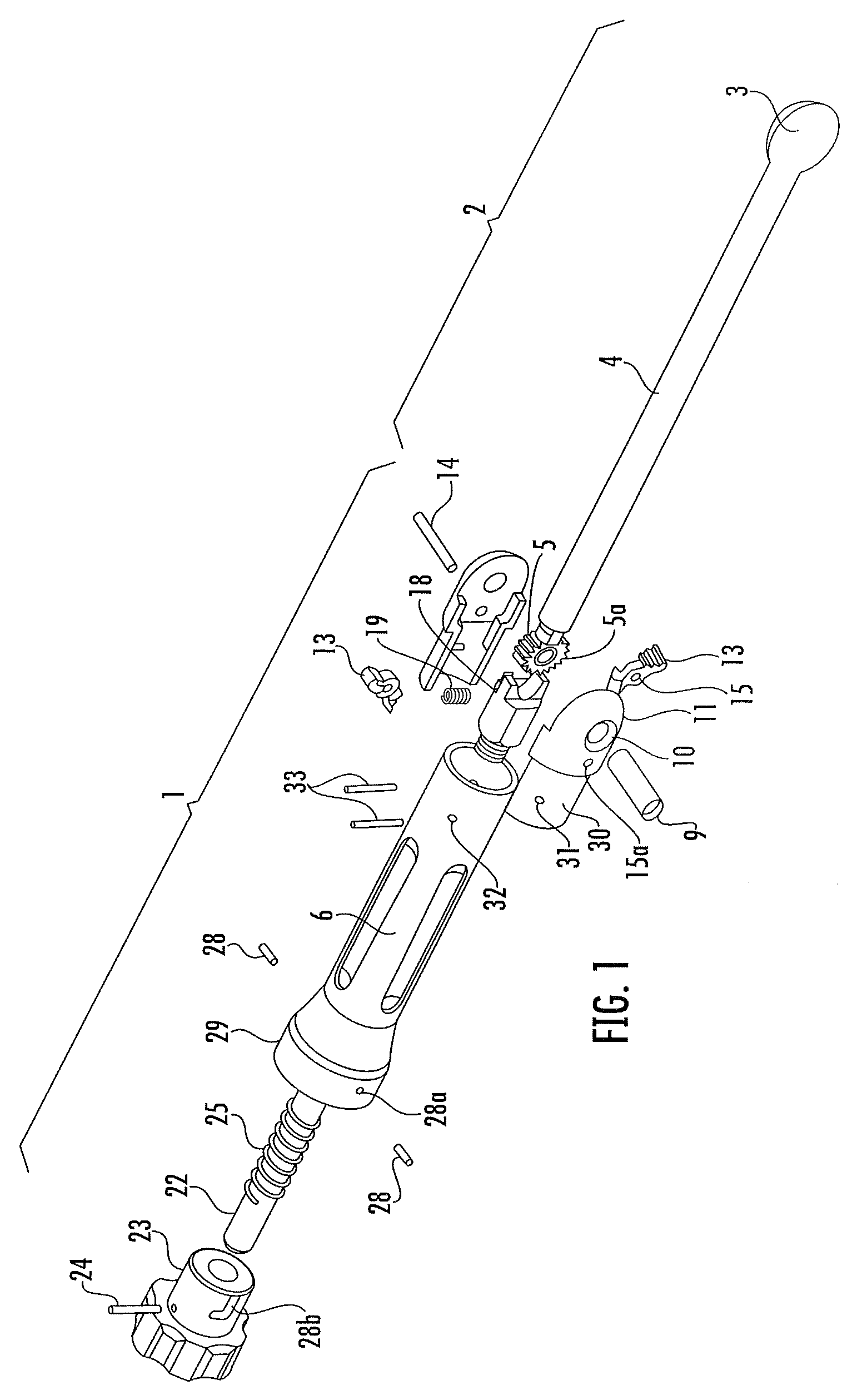
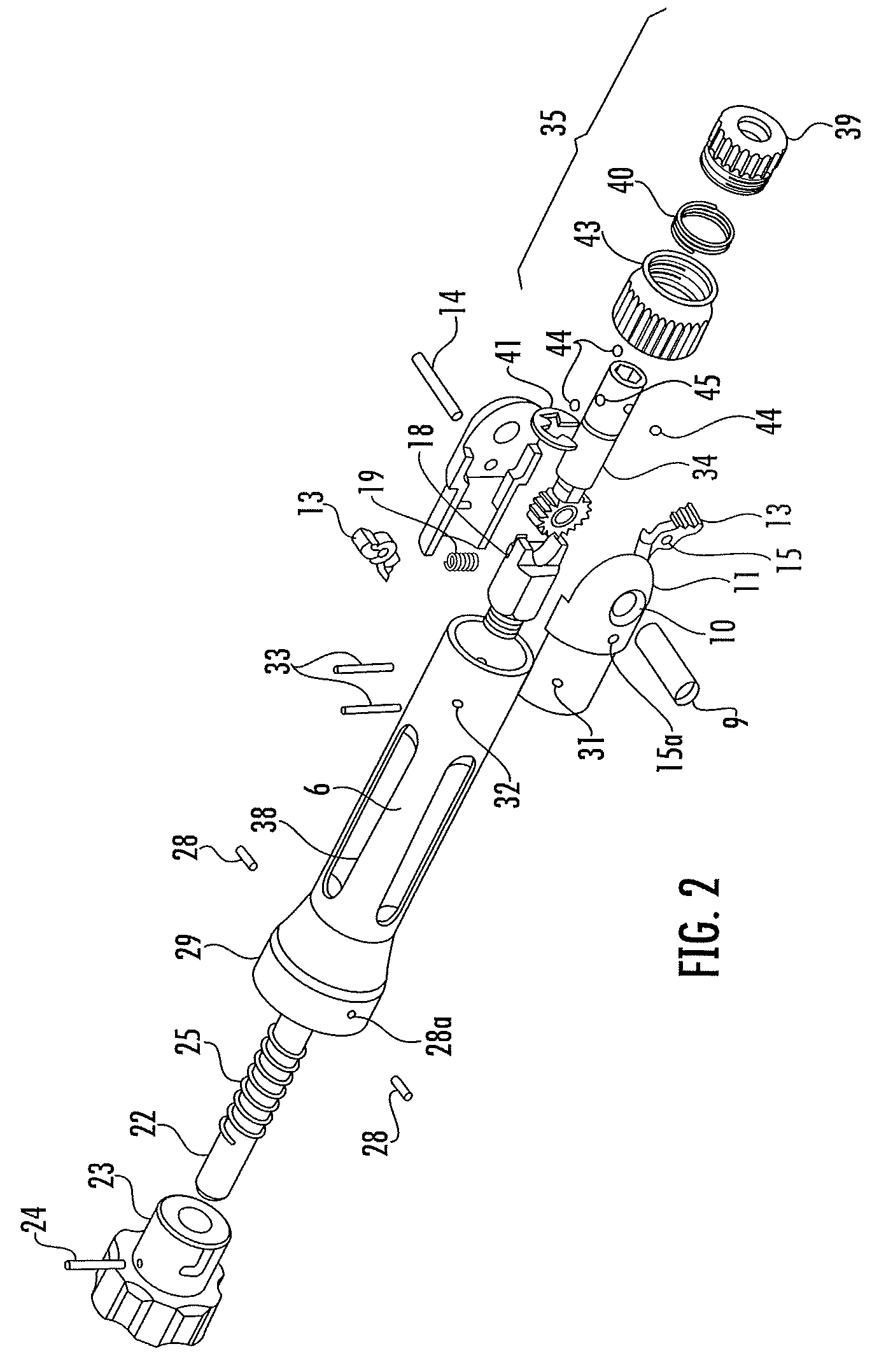
Adjustable angle pawl handle for surgical instruments
InactiveUS7922719B2Better grip for the surgeonEasy to adjustCannulasSpannersEngineeringOperative instrument
A two piece, adjustable angle handle for a surgical instrument, capable of easy adjustment to a number of angles, permitting the handle of the instrument to be grasped with one hand, and the other hand to guide the operating end of the instrument, said handle permanently affixed to an instrument, or capable if attachment to a number of different instruments by means of a firm but releasable fastening to the shaft of the instrument, as with a Hudson fitting; the adjustable angle fastening comprising a radial array of teeth as in a ratchet wheel and a reverse scissor pawl.
Owner:FIRST COMMERCE BANK
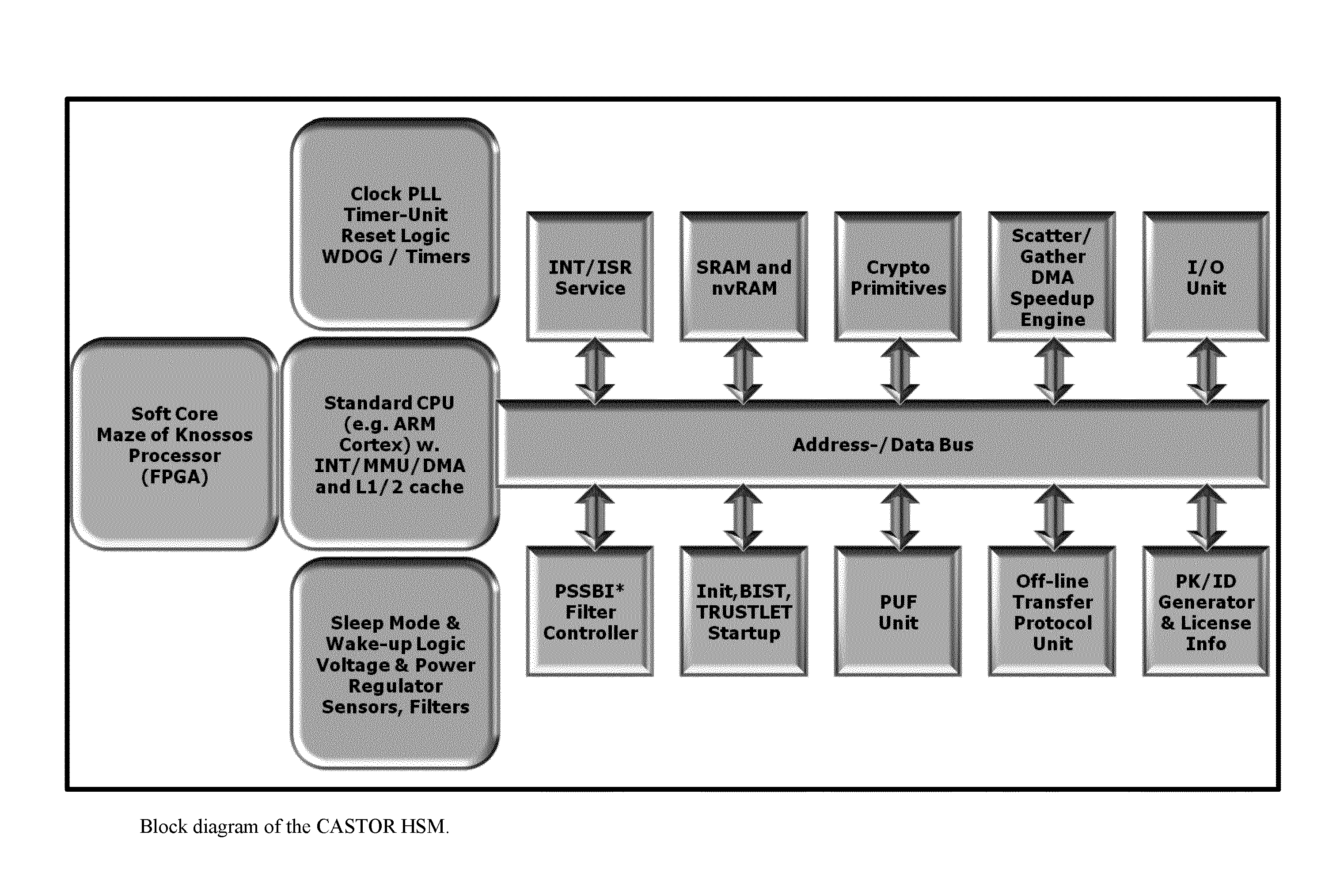
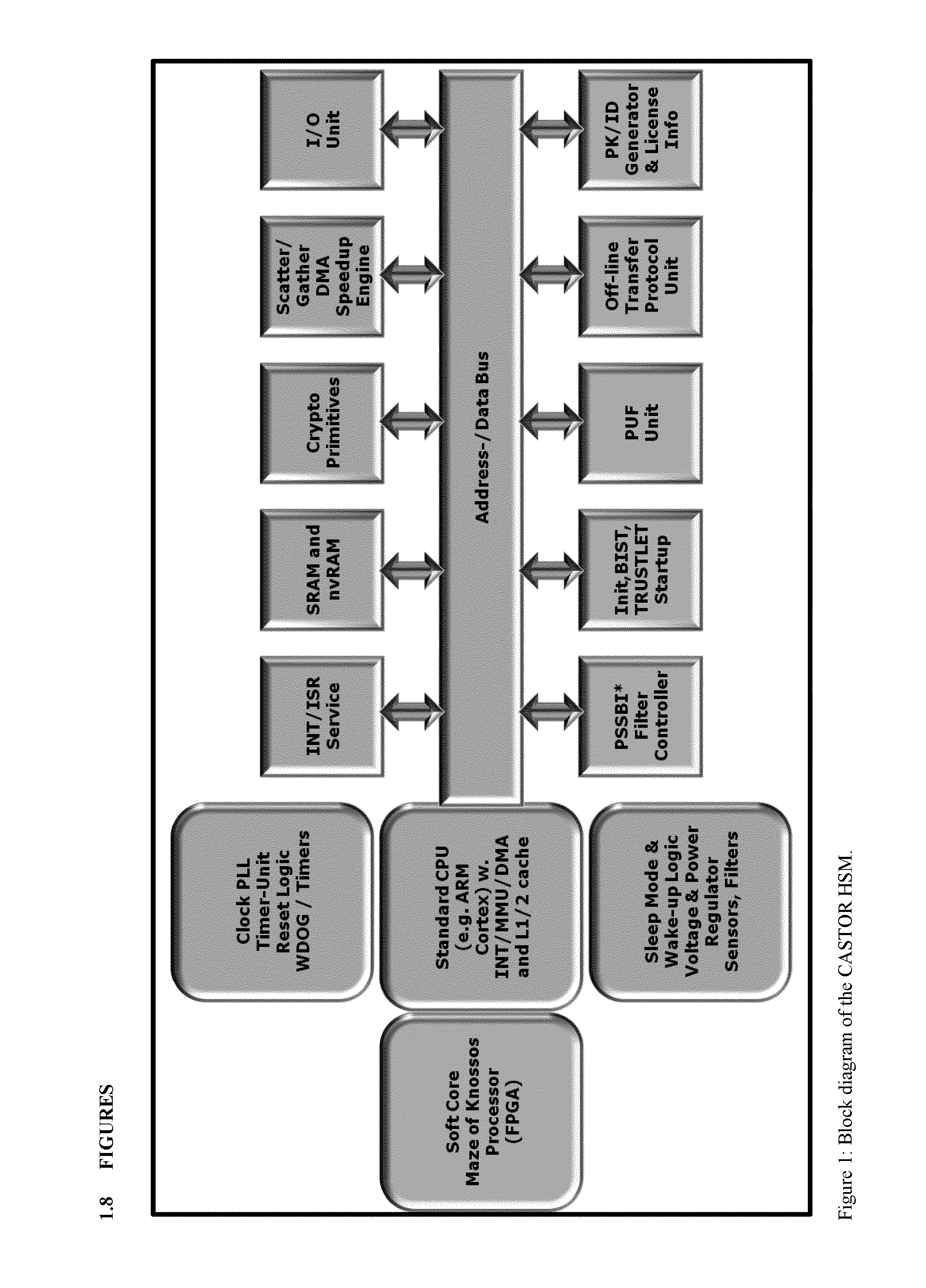
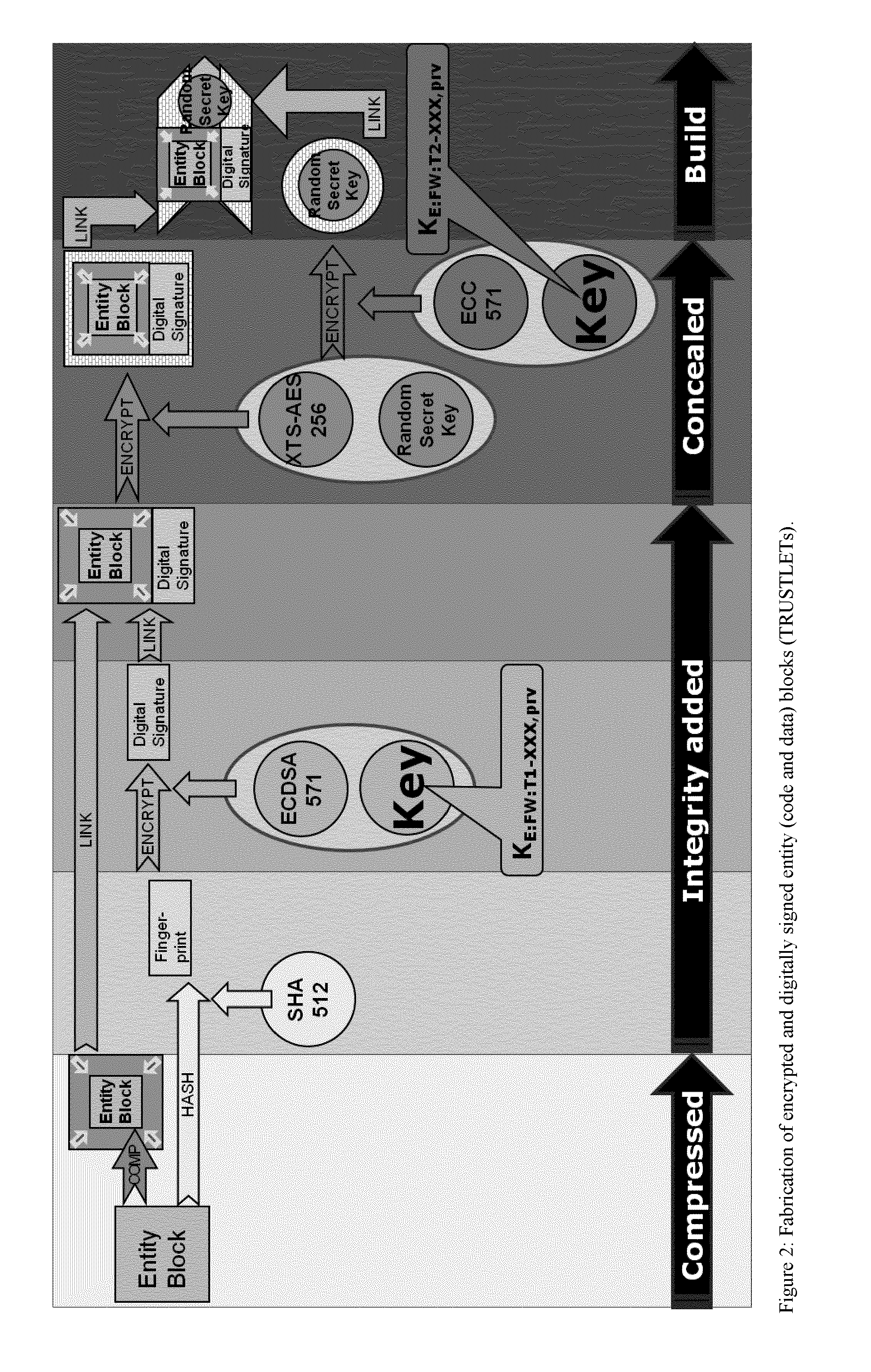
Tamper-protected hardware and method for using same
ActiveUS20140108786A1Execution of malicious code is preventedPreventing executionKey distribution for secure communicationMultiple keys/algorithms usageTamper proof hardwareComputer module
One of the various aspects of the invention is related to suggesting various techniques for improving the tamper-resistibility of hardware. The tamper-resistant hardware may be advantageously used in a transaction system that provides the off-line transaction protocol. Amongst these techniques for improving the tamper-resistibility are trusted bootstrapping by means of secure software entity modules, a new use of hardware providing a Physical Unclonable Function, and the use of a configuration fingerprint of a FPGA used within the tamper-resistant hardware.
Owner:EMSYCON
Wireless control device
InactiveUS20020024500A1Rule out the possibilitySuitable for useInput/output for user-computer interactionElectrophonic musical instrumentsOptical detectorsOptical detector
A wireless control device includes a small, lightweight housing worn by an operator, for example on the operator's wrist, and a controlled device, for example a personal computer. Several optical emitters, preferably light emitting diodes operating in the infrared range, and several optical detectors are provided on the housing. At least one x-axis emitter-detector pair operates to detect an x-direction of a pointing motion or gesture, and at least one y-axis emitter-detector pair operates to detect a y-direction of a pointing motion or gesture. This motion can then be used to cause a response in the controlled device. For example, angles of the operator's hand at the wrist can be interpreted to induce motion of a cursor on a computer display. The device may also include a motion sensor, an environmental condition sensor, or a voice recognition sensor, and can also be adapted for gesture recognition and image scanning applications.
Owner:HARMONIC RES
RFID antenna
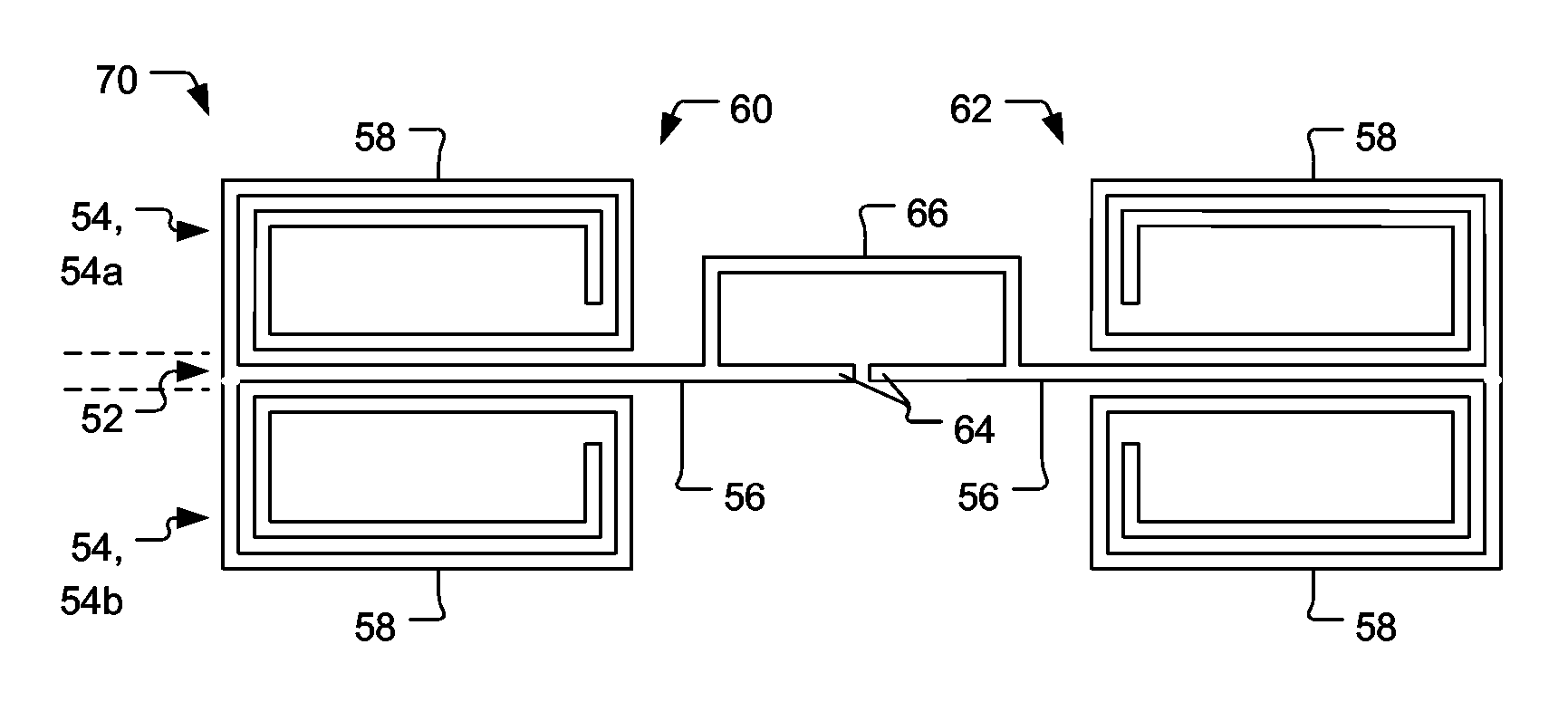
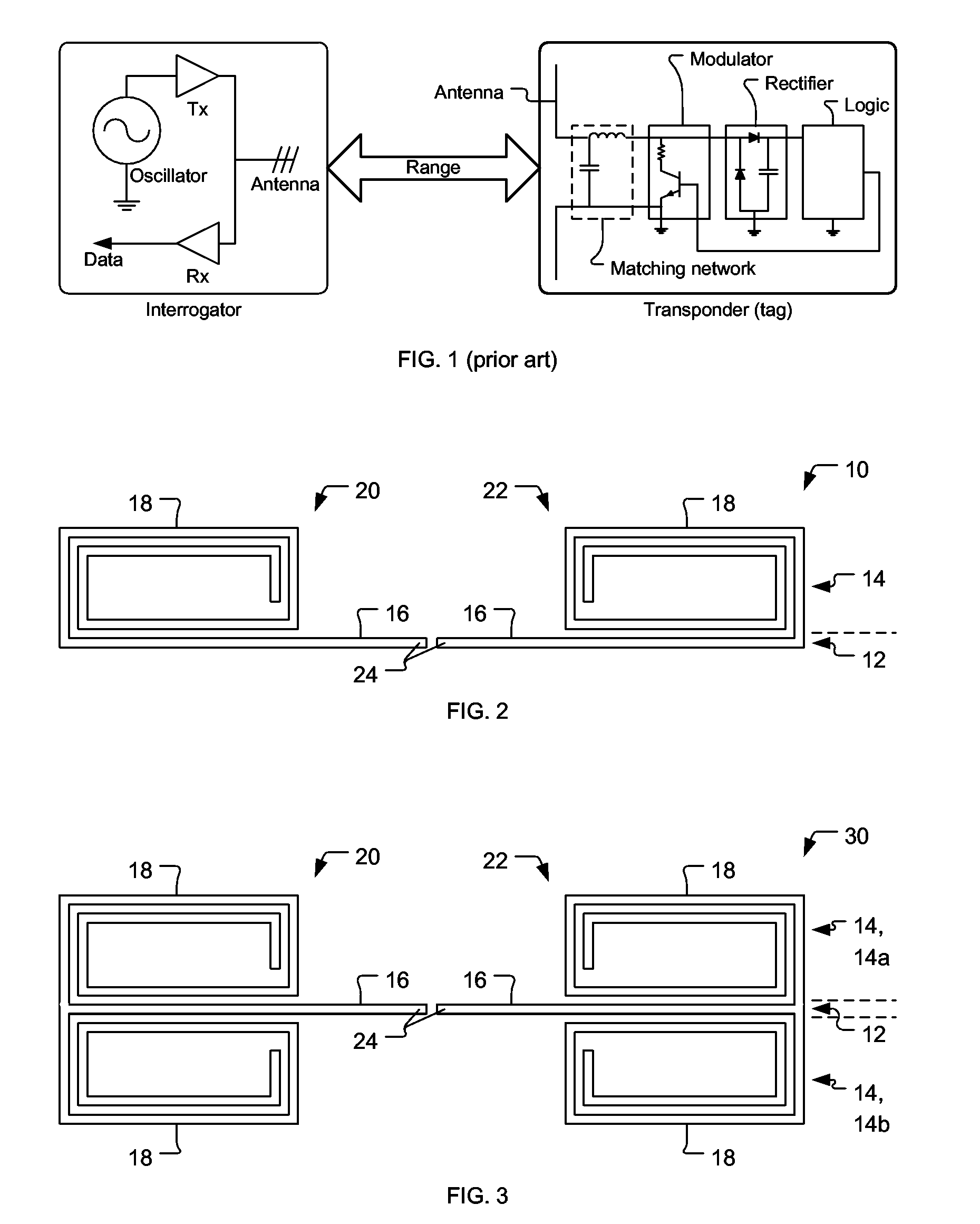
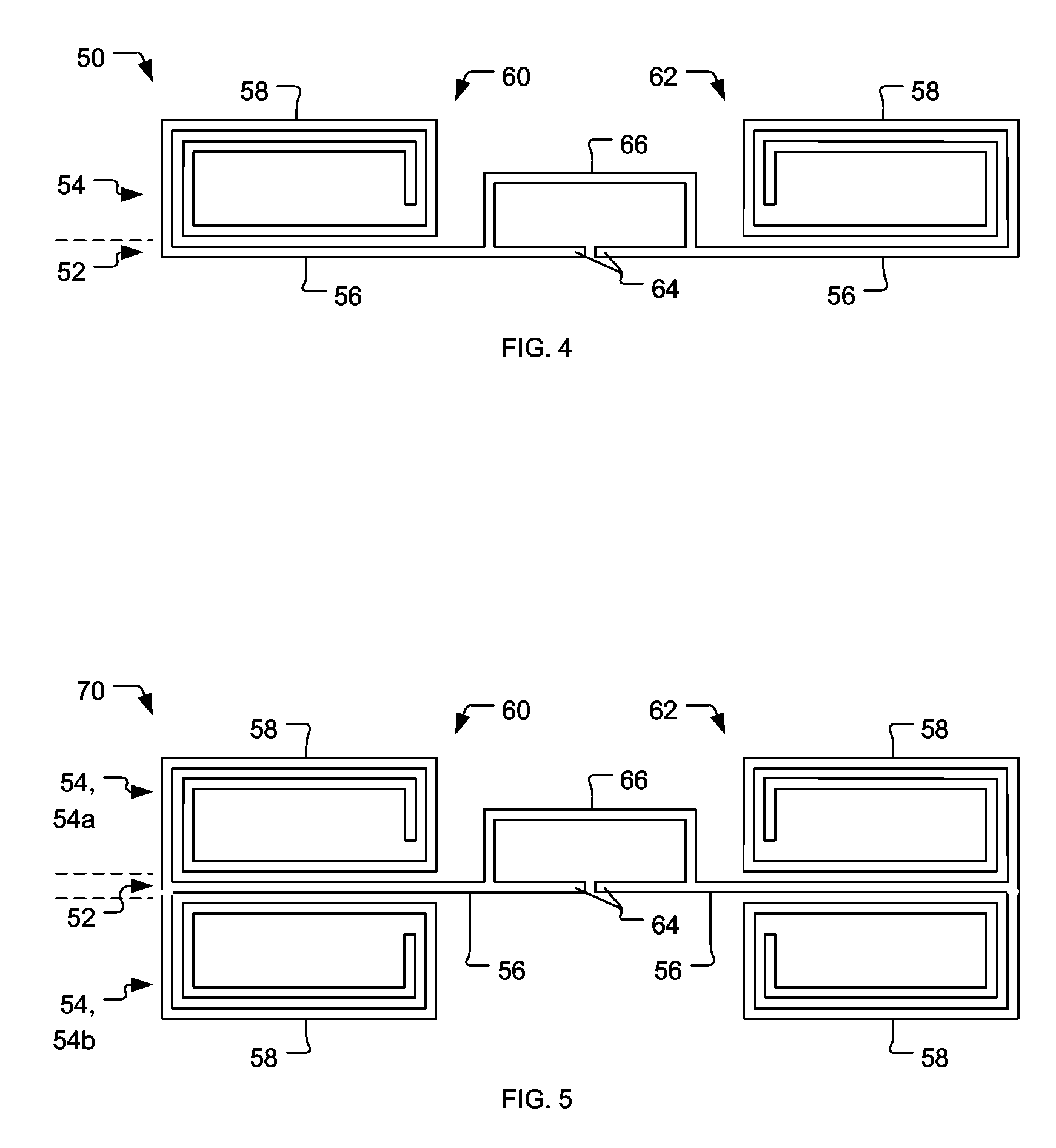
InactiveUS20060208900A1High efficiencySmall sizeAntenna supports/mountingsRadiating elements structural formsEngineeringFeed point
An antenna particularly suitable for use in radio frequency identification (RFID) transponders. First and second half portions each include nominally straight conductive sections primarily defining a radiating characteristic and nominally spiral conductive sections creating a positive reactive characteristic of the antenna. The straight conductive sections have feed points for connecting the antenna into the RFID transponder, and further connect with the respective spiral conductive sections. The first and said second half portions characterize the antenna as being a dipole type, and adding an optional loop section connecting the straight conductive sections can further characterize it as being of a folded dipole type.
Owner:TRANSPACIFIC TECH
Therapeutic delivery systems
InactiveUS6443898B1Low costSuitable for useUltrasonic/sonic/infrasonic diagnosticsPowder deliveryMicrosphereLiposome
Therapeutic delivery systems comprising gaseous precursor-filled microspheres comprising a therapeutic are described. Methods for employing such microspheres in therapeutic delivery applications are also provided. Therapeutic delivery systems comprising gaseous precursor-filled liposomes having encapsulated therein a contrast agent or drug are preferred. Methods of and apparatus for preparing such liposomes and methods for employing such liposomes in therapeutic delivery applications are also disclosed.
Owner:CEREVAST MEDICAL
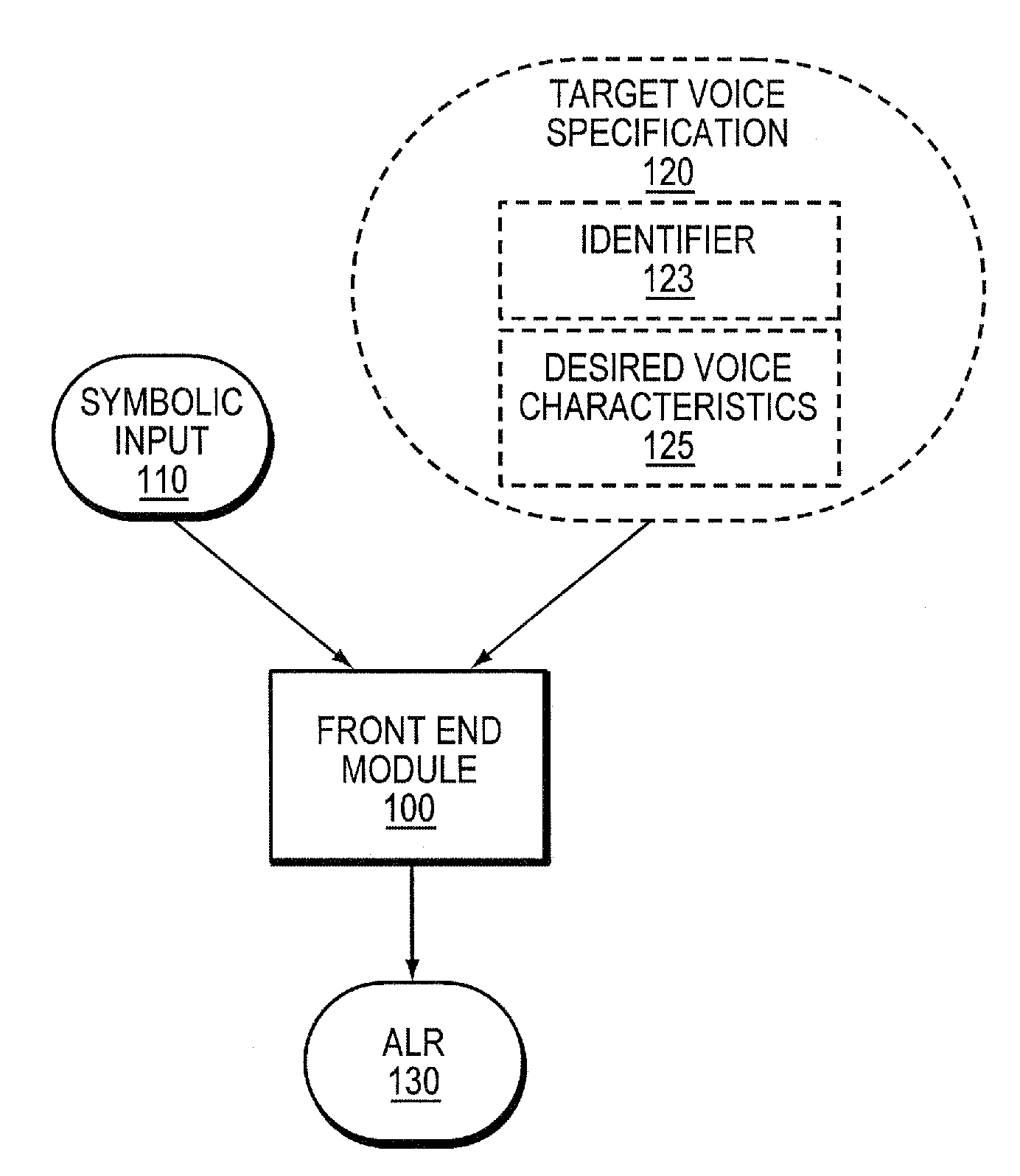
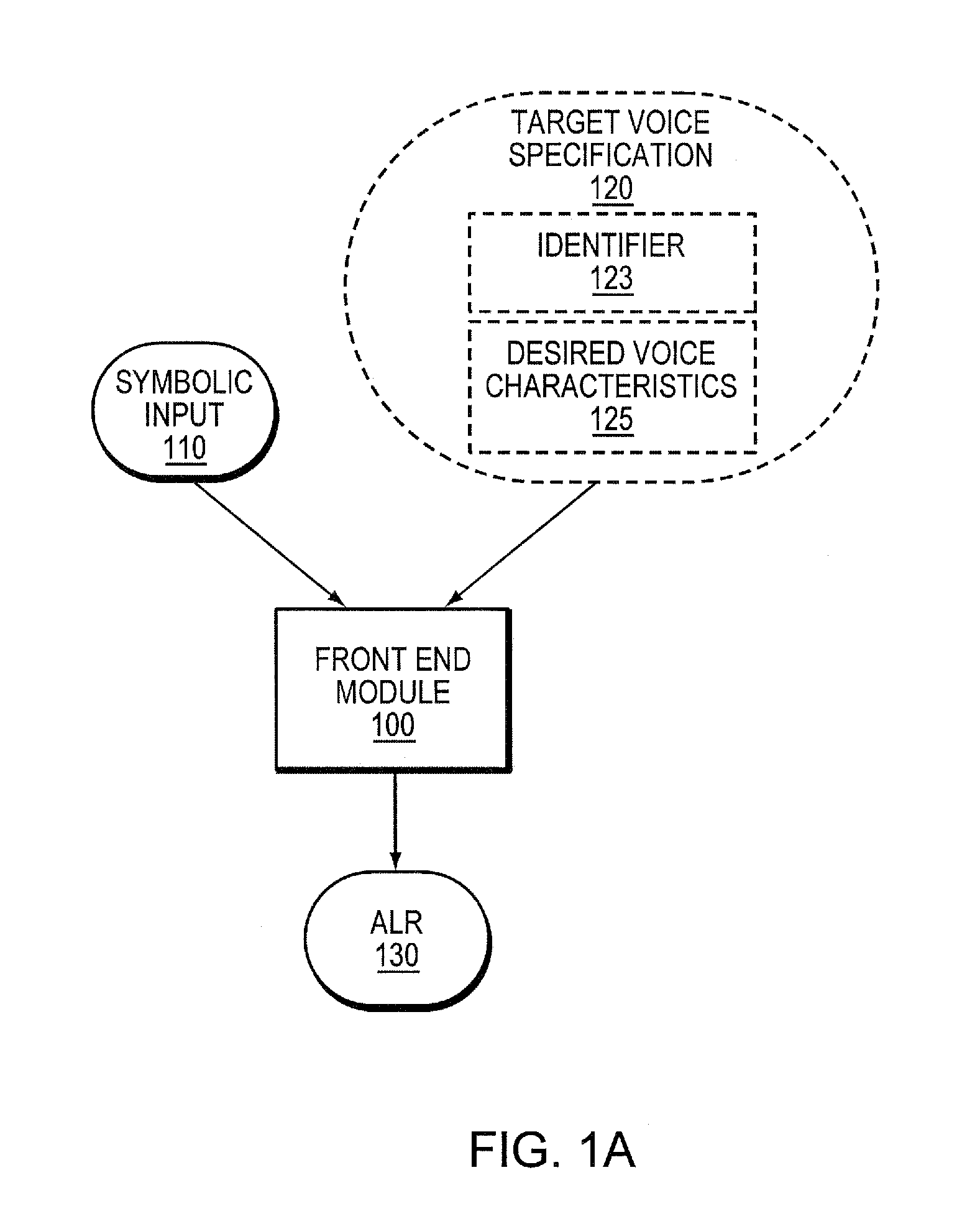
System and method for hybrid speech synthesis
ActiveUS20080270140A1Cost-efficientlySolve the real problemSpeech synthesisSpeech corpusSpeech sound
A speech synthesis system receives symbolic input describing an utterance to be synthesized. In one embodiment, different portions of the utterance are constructed from different sources, one of which is a speech corpus recorded from a human speaker whose voice is to be modeled. The other sources may include other human speech corpora or speech produced using Rule-Based Speech Synthesis (RBSS). At least some portions of the utterance may be constructed by modifying prototype speech units to produce adapted speech units that are contextually appropriate for the utterance. The system concatenates the adapted speech units with the other speech units to produce a speech waveform. In another embodiment, a speech unit of a speech corpus recorded from a human speaker lacks transitions at one or both of its edges. A transition is synthesized using RBSS and concatenated with the speech unit in producing a speech waveform for the utterance.
Owner:NOVASPEECH
Counter top reverse osmosis water purification system
InactiveUS6099735AEasy to operate and maintainSafely maintainSolid sorbent liquid separationReverse osmosisIon exchangeCarbon adsorption
A counter top reverse osmosis water purification system, suitable for home use, is connected to a water supply and contains a closed fluid treatment circuit extending to a water outlet. The closed fluid circuit flows through a plurality of replaceable water treatment modules mounted on a flowboard and each having a specific water treatment function, such as the removal of a particular material from the water by the use of reverse osmosis, filtration, carbon adsorption, ion exchange or the addition of a chemical to balance the desired water conditions. Preferably the circuit also includes traversing a radiation device, for example an ultraviolet light, for the purpose of sanitizing the water.
Owner:KELADA MAHER I
Polyaxial bone anchor with helical capture connection, insert and dual locking assembly
InactiveUS20090062866A1Easy to useInexpensiveSuture equipmentsInternal osteosythesisScrew threadBiomedical engineering
A medical implant assembly includes a polyaxial bone anchor having a shank, a receiver, a lower compression insert with surfaces for closely receiving an elongate connecting member and a dual closure structure that may include a single flange or helical flange. The dual closure structure independently engages the connecting member and the lower compression insert. A threaded capture connection of the bone anchor includes a shank upper surface exclusively engaging the lower compression insert and a retainer threadably attached to the shank and spaced from the upper surface, the retainer configured for polyaxial motion with respect to the receiver prior to locking.
Owner:JACKSON
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com