Patents
Literature
17818results about "Image data processing details" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
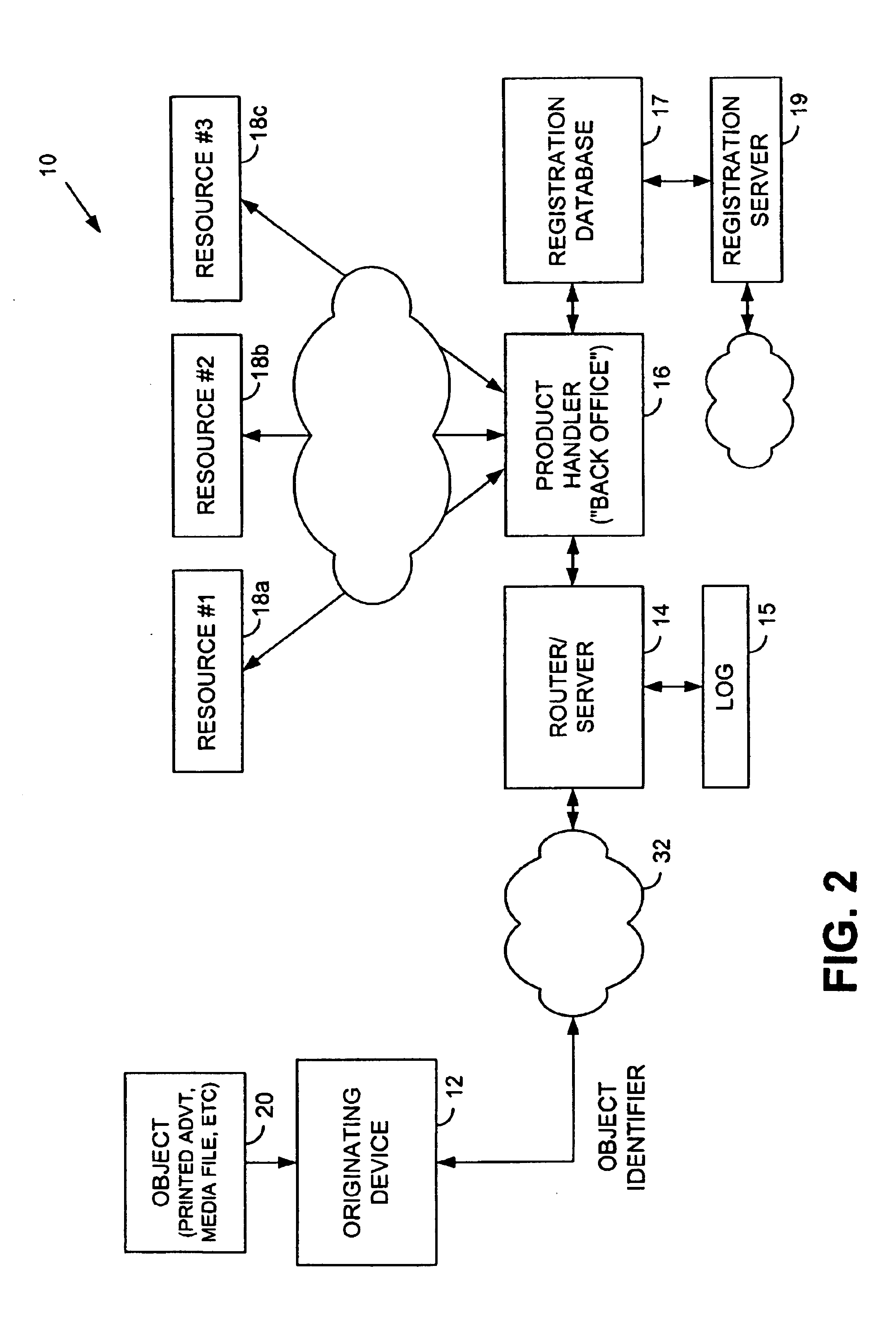
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
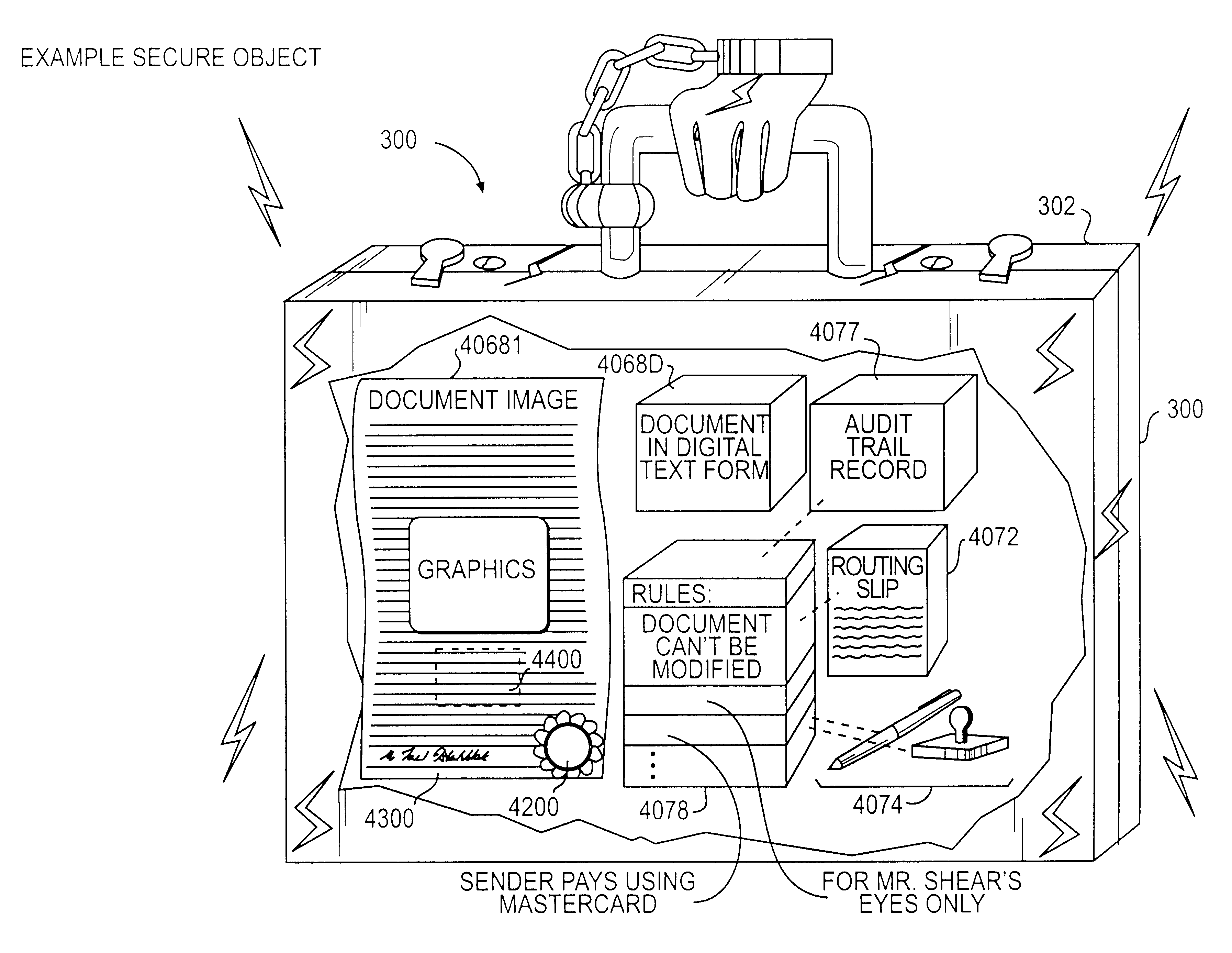
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
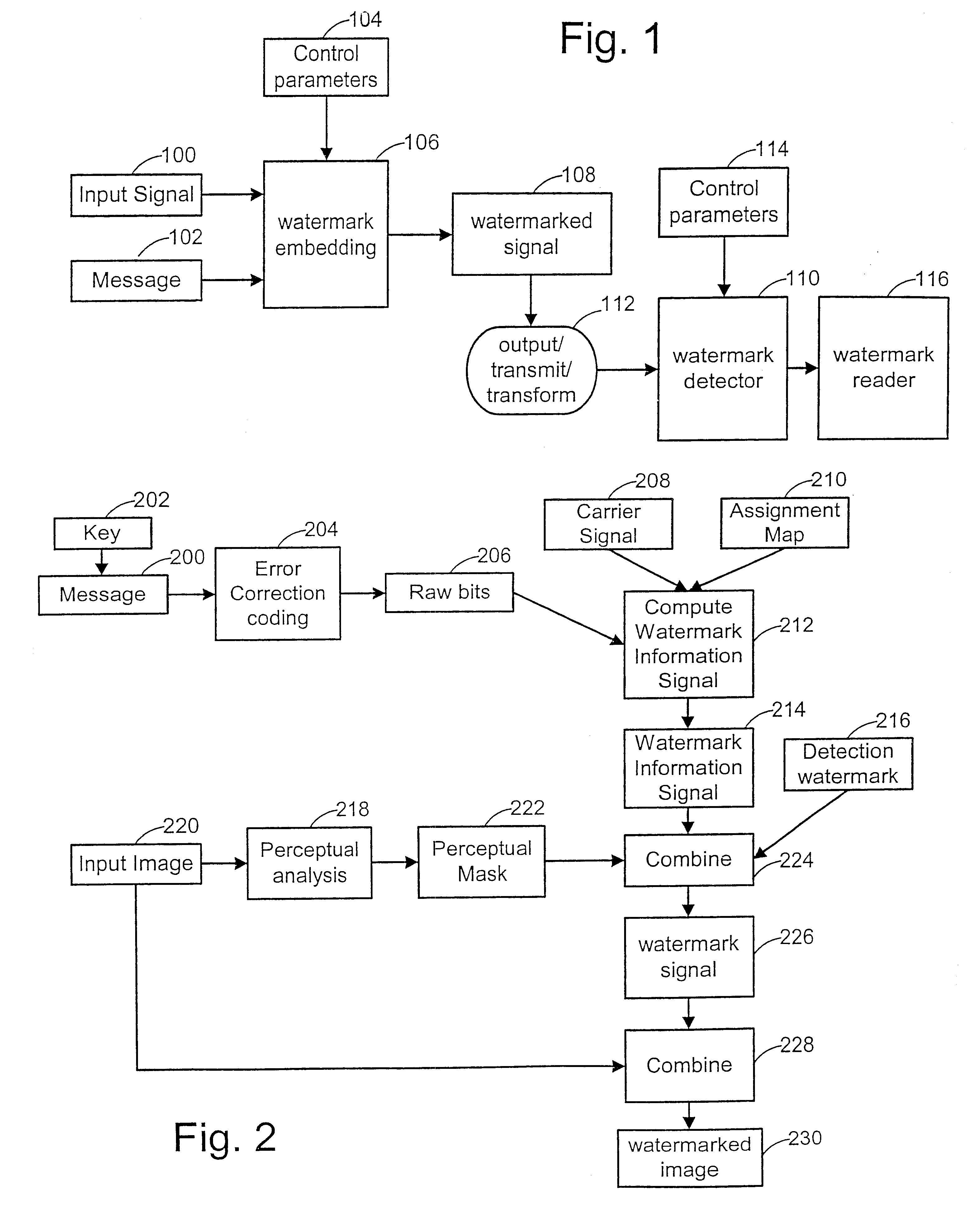
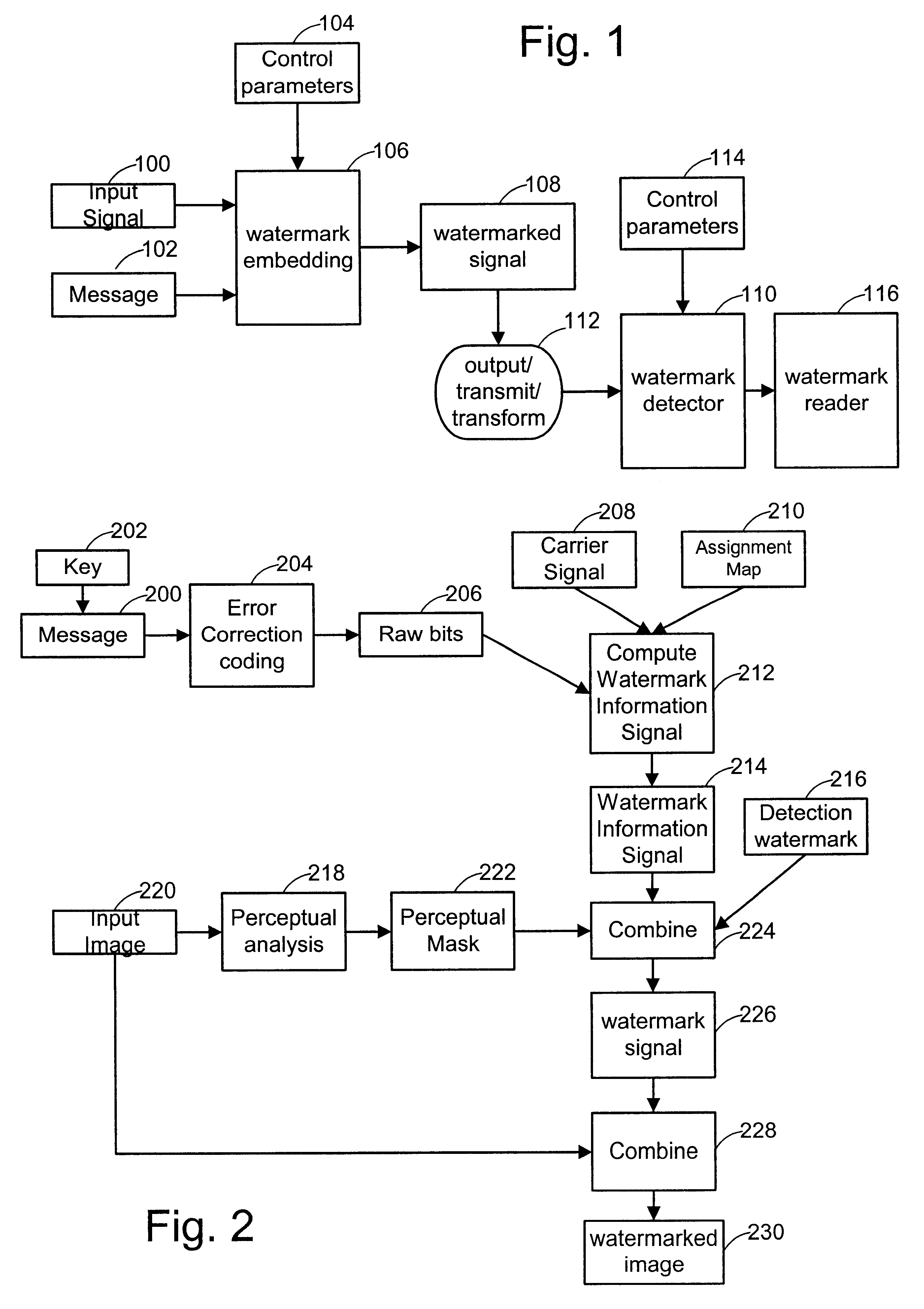
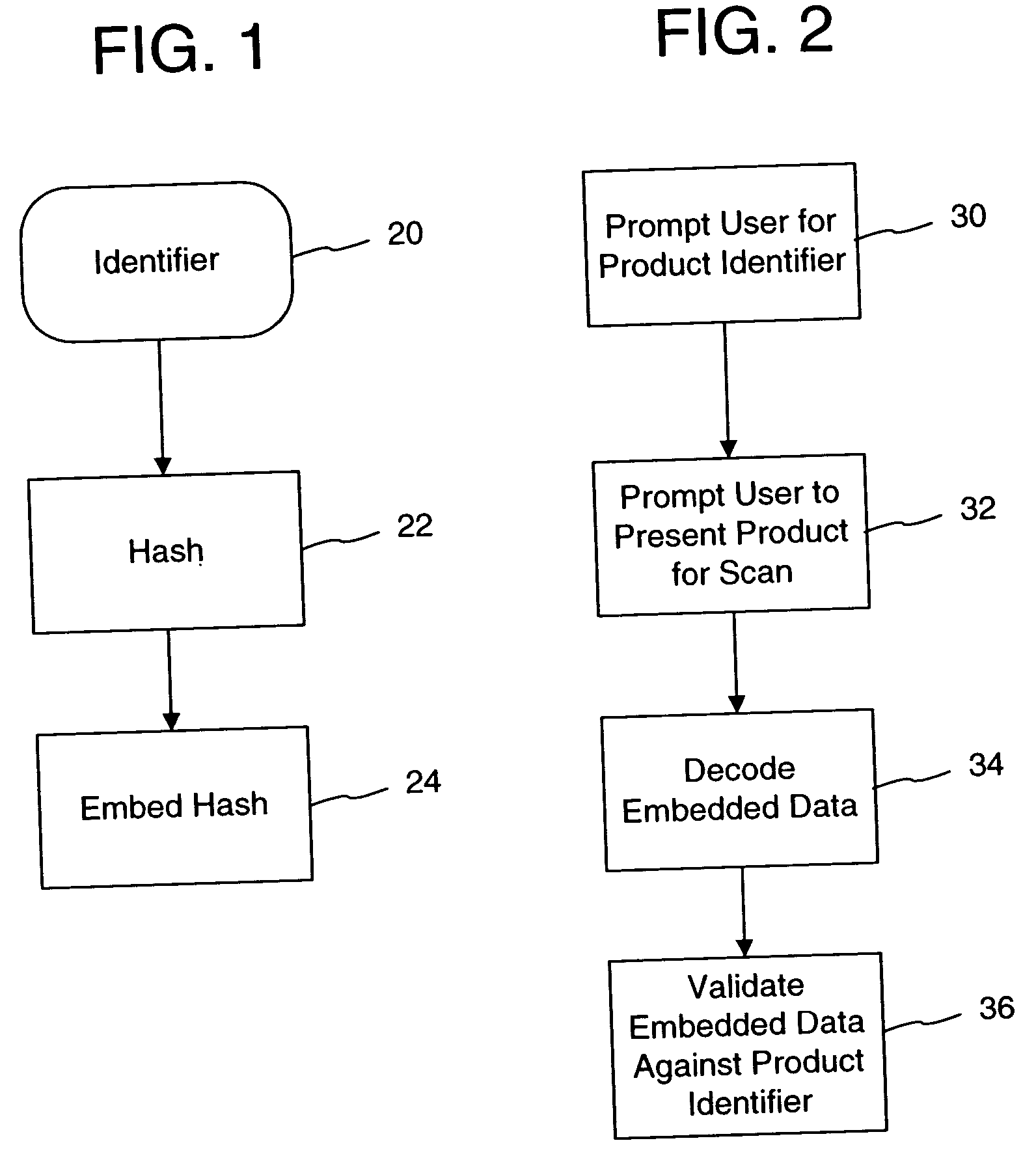
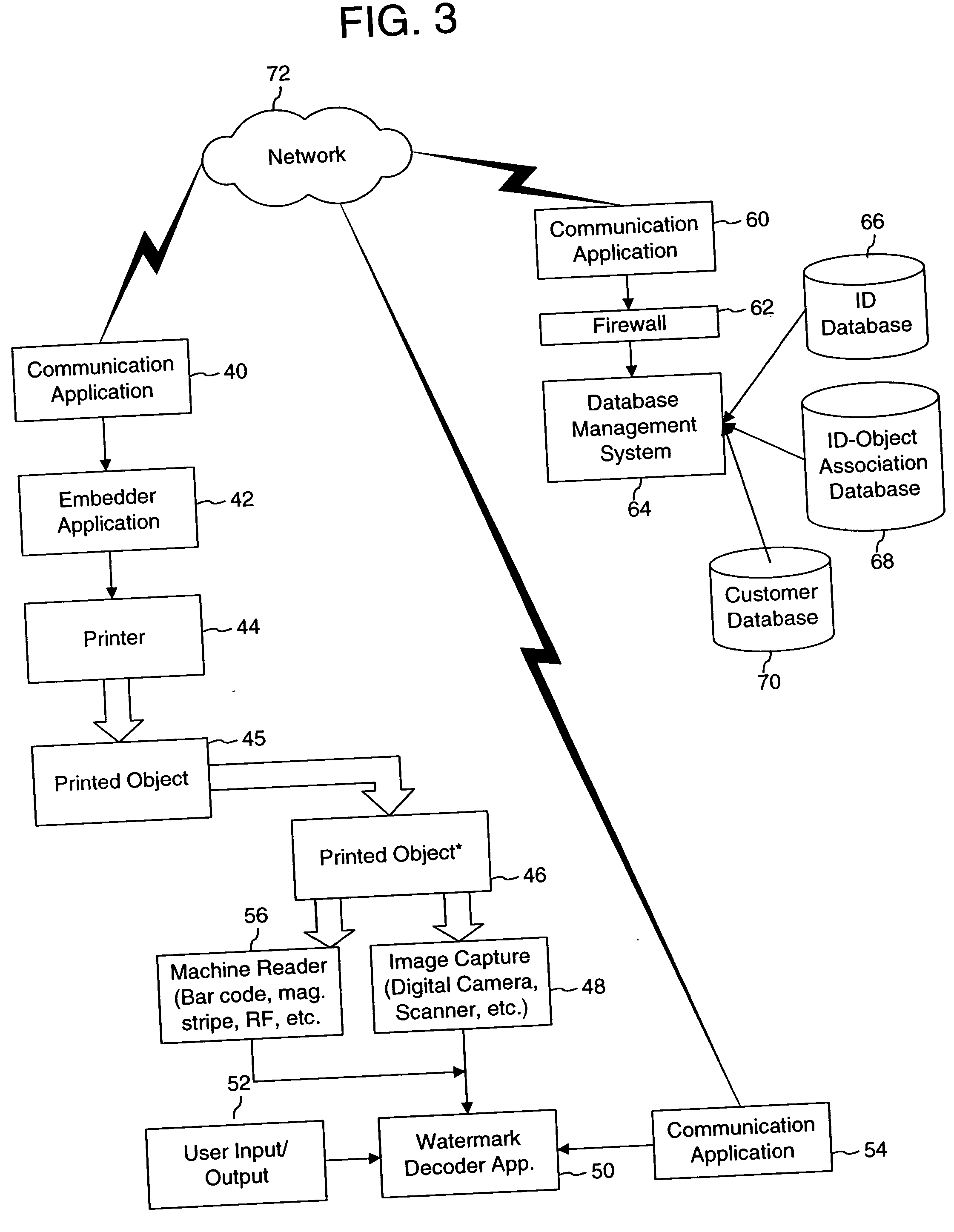
Watermark embedder and reader
InactiveUS6614914B1Mitigates effect of printingEasy to detectCoin-freed apparatusRecord information storageGraphicsComputer hardware
A watermark system includes an embedder, detector, and reader. The watermark embedder encodes a watermark signal in a host signal to create a combined signal. The detector looks for the watermark signal in a potentially corrupted version of the combined signal, and computes its orientation. Finally, a reader extracts a message in the watermark signal from the combined signal using the orientation to approximate the original state of the combined signal. While adapted for images, video and audio, the watermark system applies to other electronic and physical media. For example, it can be applied to mark graphical models, blank paper, film and other substrates, texturing objects for ID purposes, etc.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
Linking of computers based on optical sensing of digital data
InactiveUS6311214B1Reduce businessLow costCoin-freed apparatusRecord information storageDigital dataBusiness card
A printed object, such as an item of postal mail, a book, printed advertising, a business card, product packaging, etc., is steganographically encoded with plural-bit data. When such an object is presented to an optical sensor, the plural-bit data is decoded and used to establish a link to an internet address corresponding to that object.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
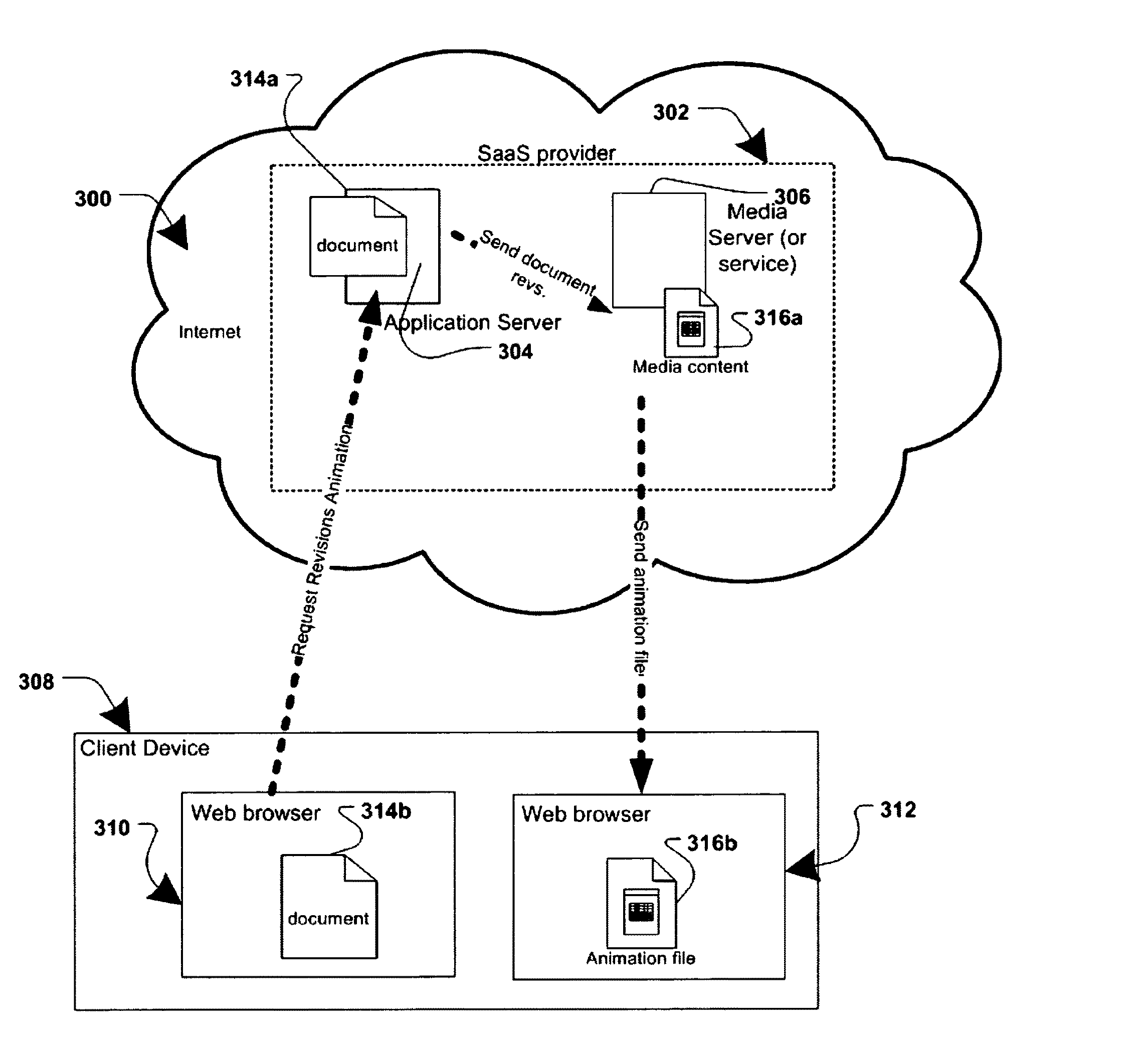
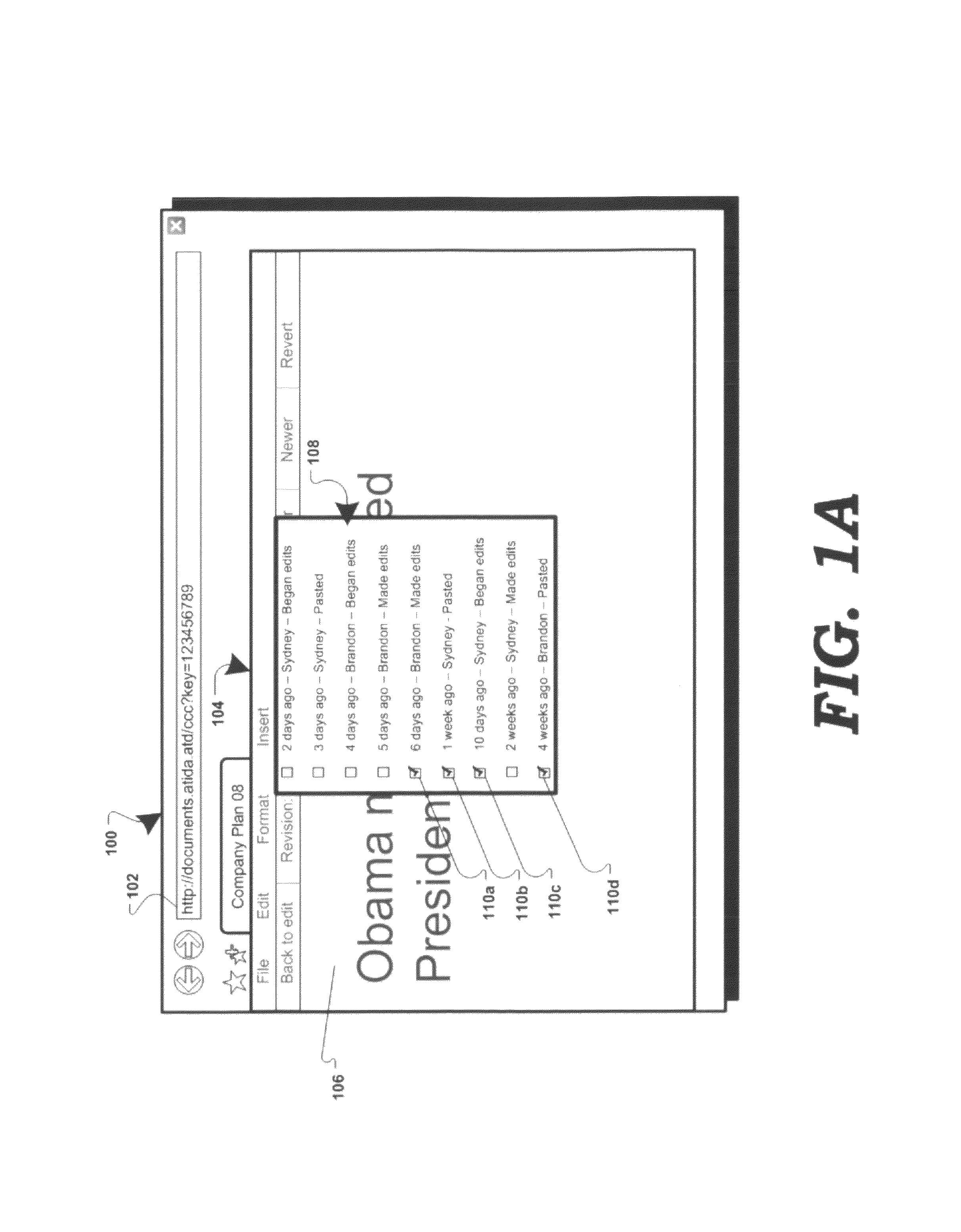
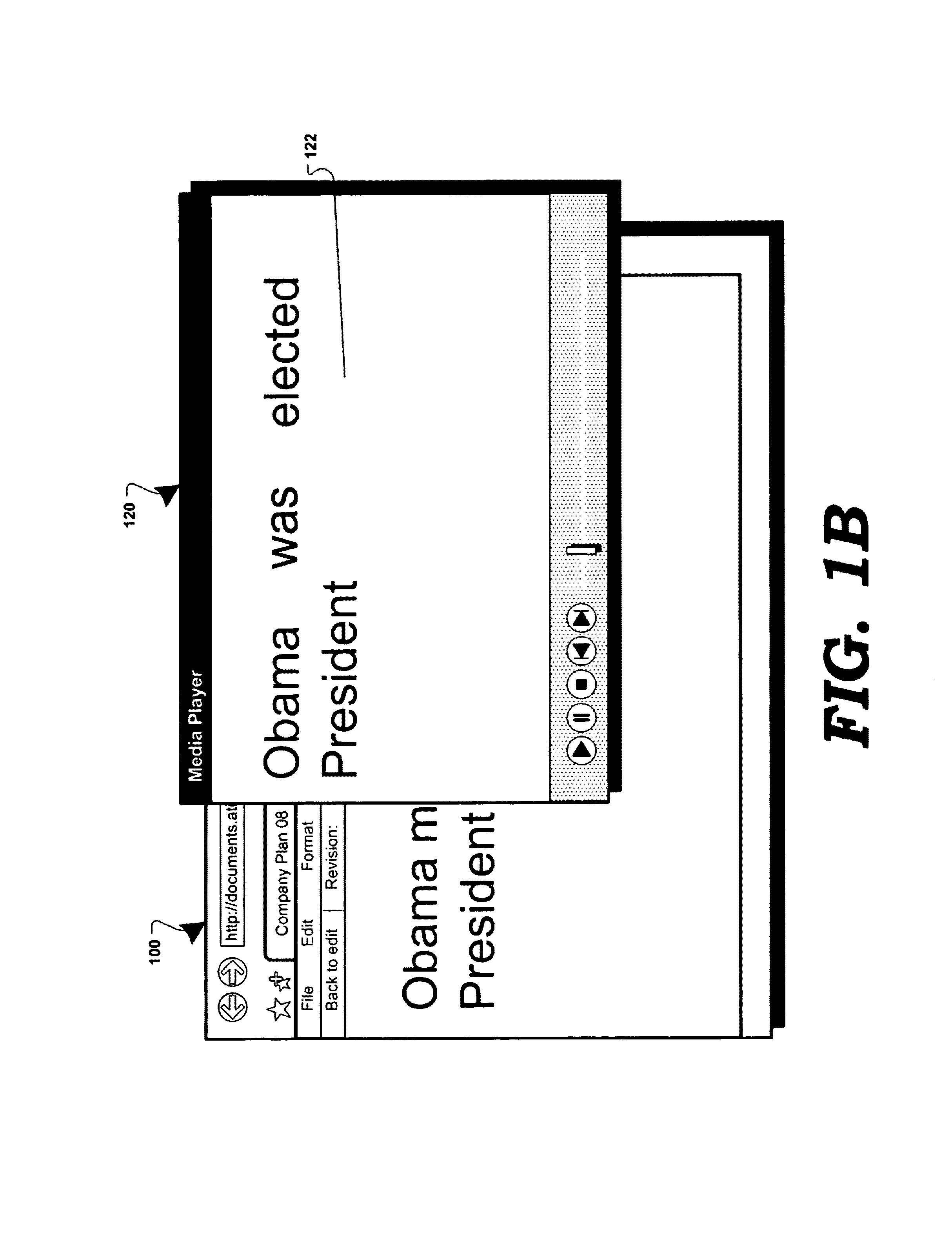
Document revisions in a collaborative computing environment
ActiveUS8566301B2Digital data processing detailsNatural language data processingElectronic documentDocumentation procedure
In a collaborative computing environment, a method and system for displaying revisions associated with a hosted electronic document are disclosed. In accordance with the disclosed method and system, select revisions of an electronic document may be displayed to a user as media (e.g. Flash™ animation, QuickTime™, MPEG, Windows™ Media Video, RealMedia™, DivX™, DHTML, etc.) in which the revisions are animated, recreating a visual history play-back of the evolution of the document. The animation may include an image of each selected revision, morphing into another image of another revision. The animation may be displayed in various orders (e.g. chronologically, by user, etc.) The user may use an application on a client device (e.g. a web-browser, a web-browser with a media plug-in, a media players, etc.) to view the media file and control various properties of the animation playback (e.g. speed, direction, pausing, skipping forward or back, etc.).
Owner:DOMO
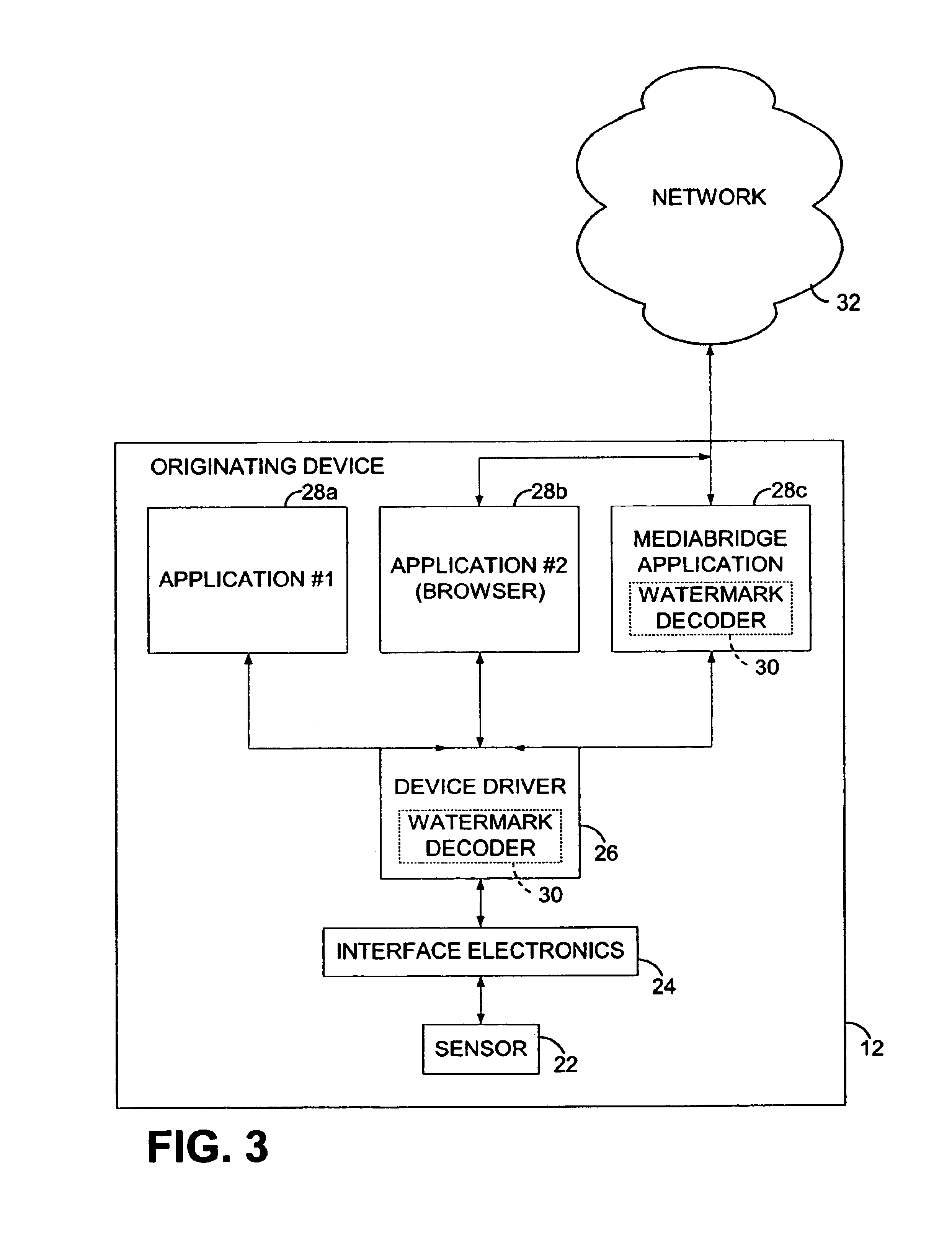
Cell phones with optical capabilities, and related applications
A cell phone is equipped with a 2D optical sensor, enabling a variety of applications. For example, such a phone may also be provided with a digital watermark decoder, permitting decoding of steganographic data on imaged objects. Movement of a phone may be inferred by sensing movement of an imaged pattern across the optical sensor's field of view, allowing use of the phone as a gestural input device through which a user can signal instructions to a computer-based process. A variety of other arrangements by which electronic devices can interact with the physical world are also detailed, e.g., involving sensing and responding to digital watermarks, bar codes, RFIDs, etc.
Owner:DIGIMARC CORP
Flexible transparent touch sensing system for electronic devices
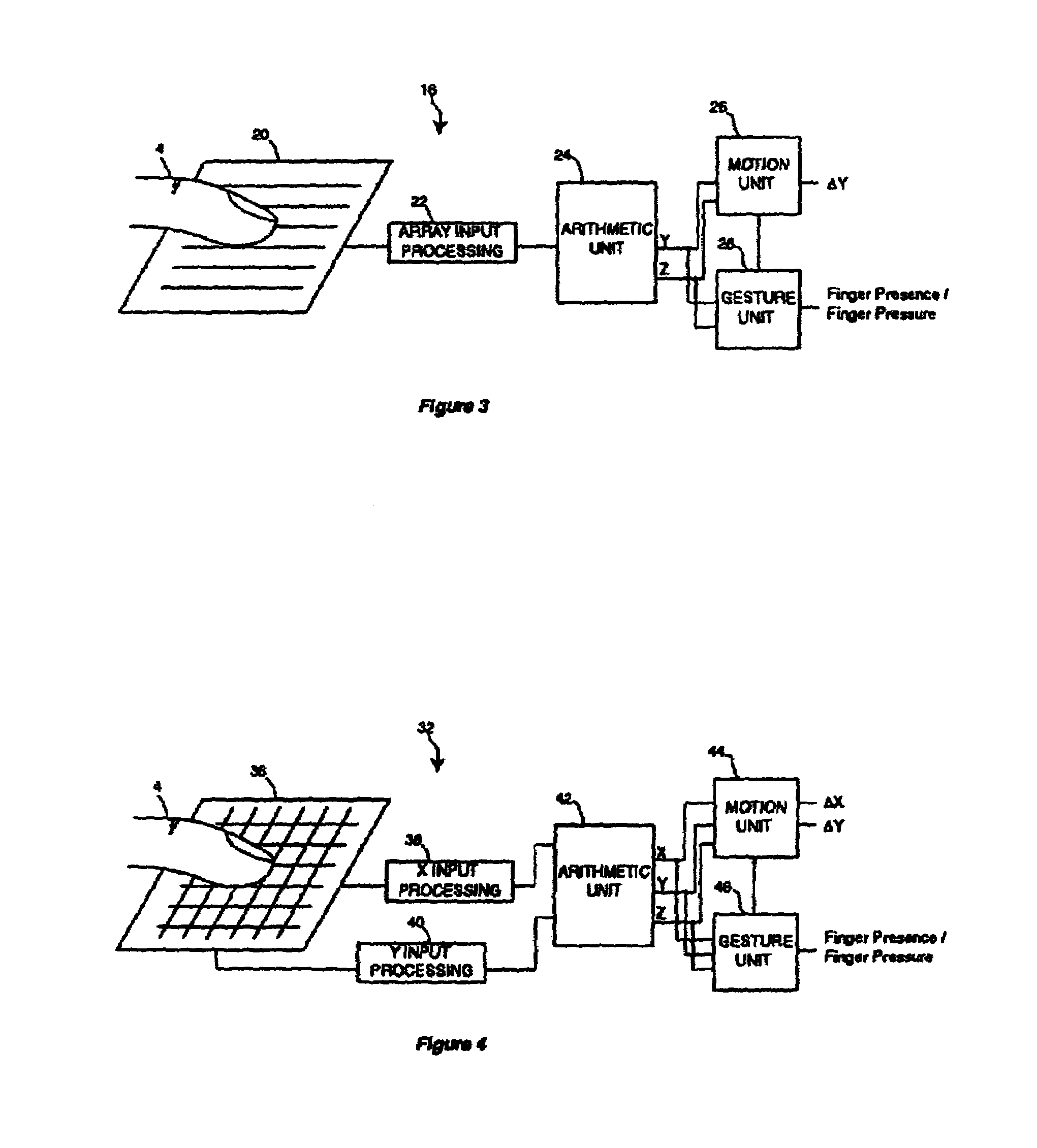
InactiveUS7030860B1Maximize transparencyAmount of overlapInput/output for user-computer interactionTransmission systemsDisplay deviceSensor observation
A transparent, capacitive sensing system particularly well suited for input to electronic devices is described. The sensing system can be used to emulate physical buttons or slider switches that are either displayed on an active display device or printed on an underlying surface. The capacitive sensor can further be used as an input device for a graphical user interface, especially if overlaid on top of an active display device like an LCD screen to sense finger position (X / Y position) and contact area (Z) over the display. In addition, the sensor can be made with flexible material for touch sensing on a three-dimensional surface. Because the sensor is substantially transparent, the underlying surface can be viewed through the sensor. This allows the underlying area to be used for alternative applications that may not necessarily be related to the sensing system. Examples include advertising, an additional user interface display, or apparatus such as a camera or a biometric security device.
Owner:SYNAPTICS INC
System for managing data objects
InactiveUS20020033848A1Television system detailsCo-operative working arrangementsUser inputThumbnail
A device for managing image and audio files displays thumbnails, which are representative of the files, on a screen in different arrangements, depending on the selected layout and order. When the user enters input to indicates that he or she wishes to browse through the thumbnails, the thumbnails move across the screen in sequence, following a path through a focus outline in the center of the screen. The path followed by the thumbnails depends on the selected layout.
Owner:TESSERA ADVANCED TECH
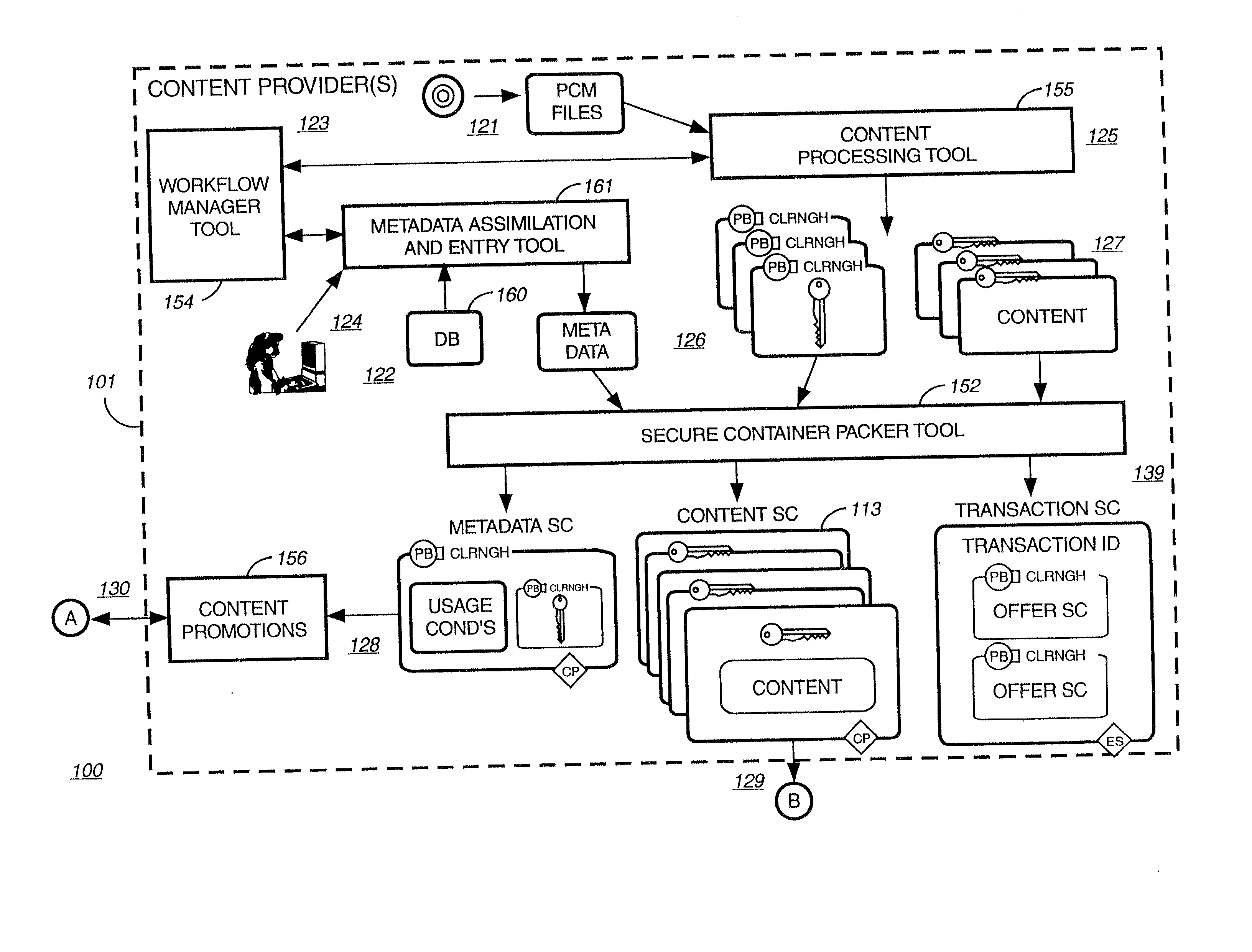
Secure electronic content distribution on CDS and DVDs
InactiveUS6611812B2Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
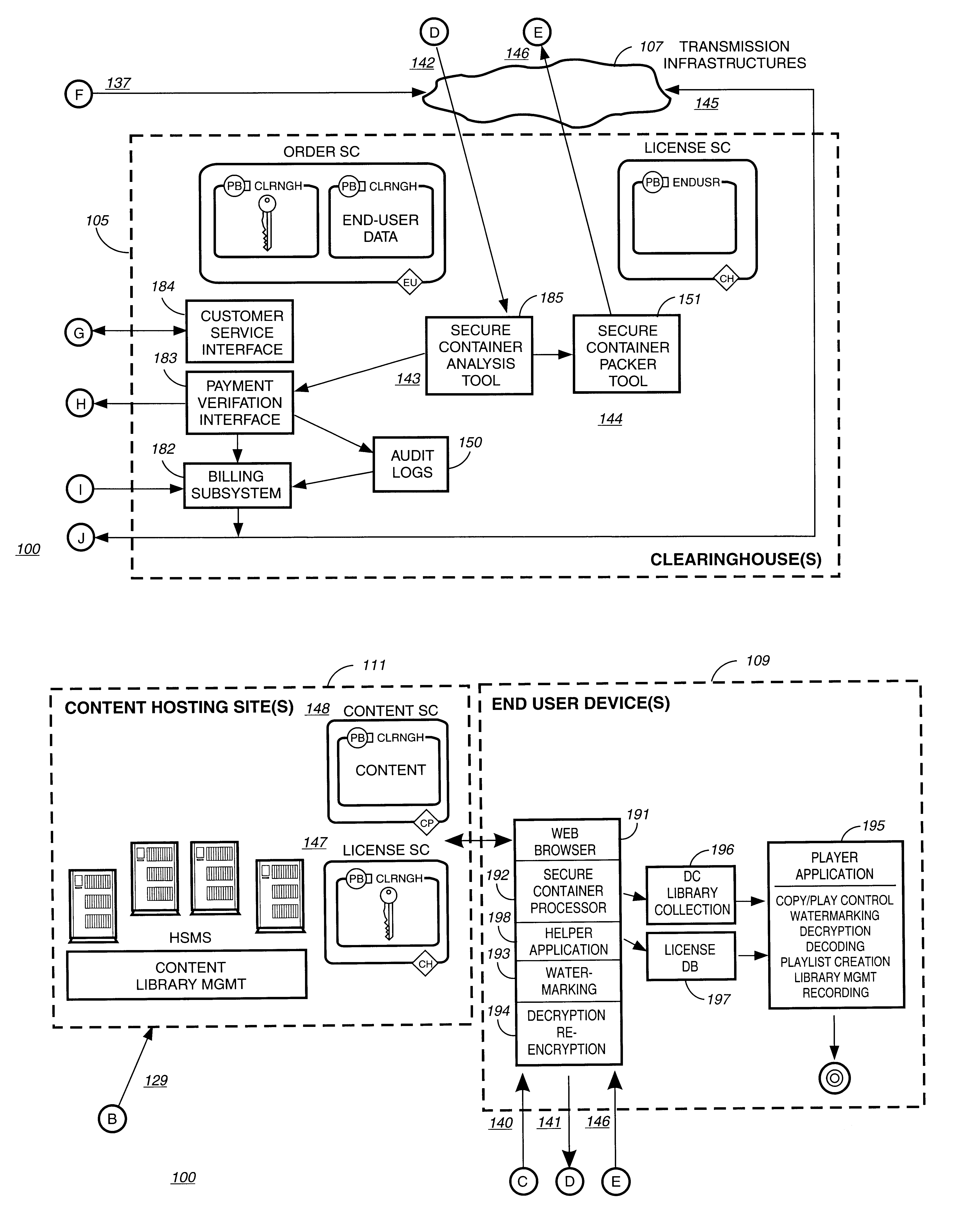
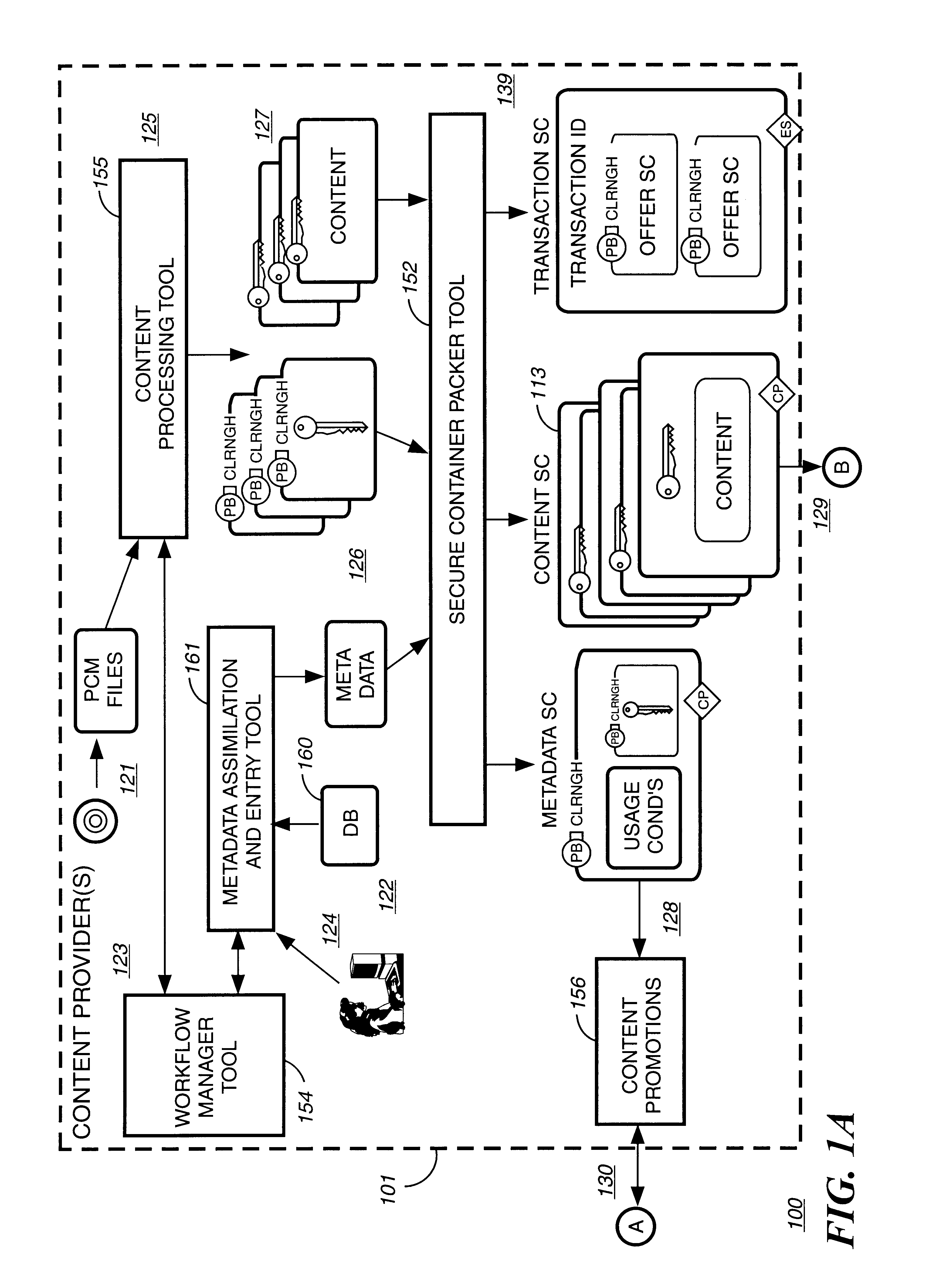
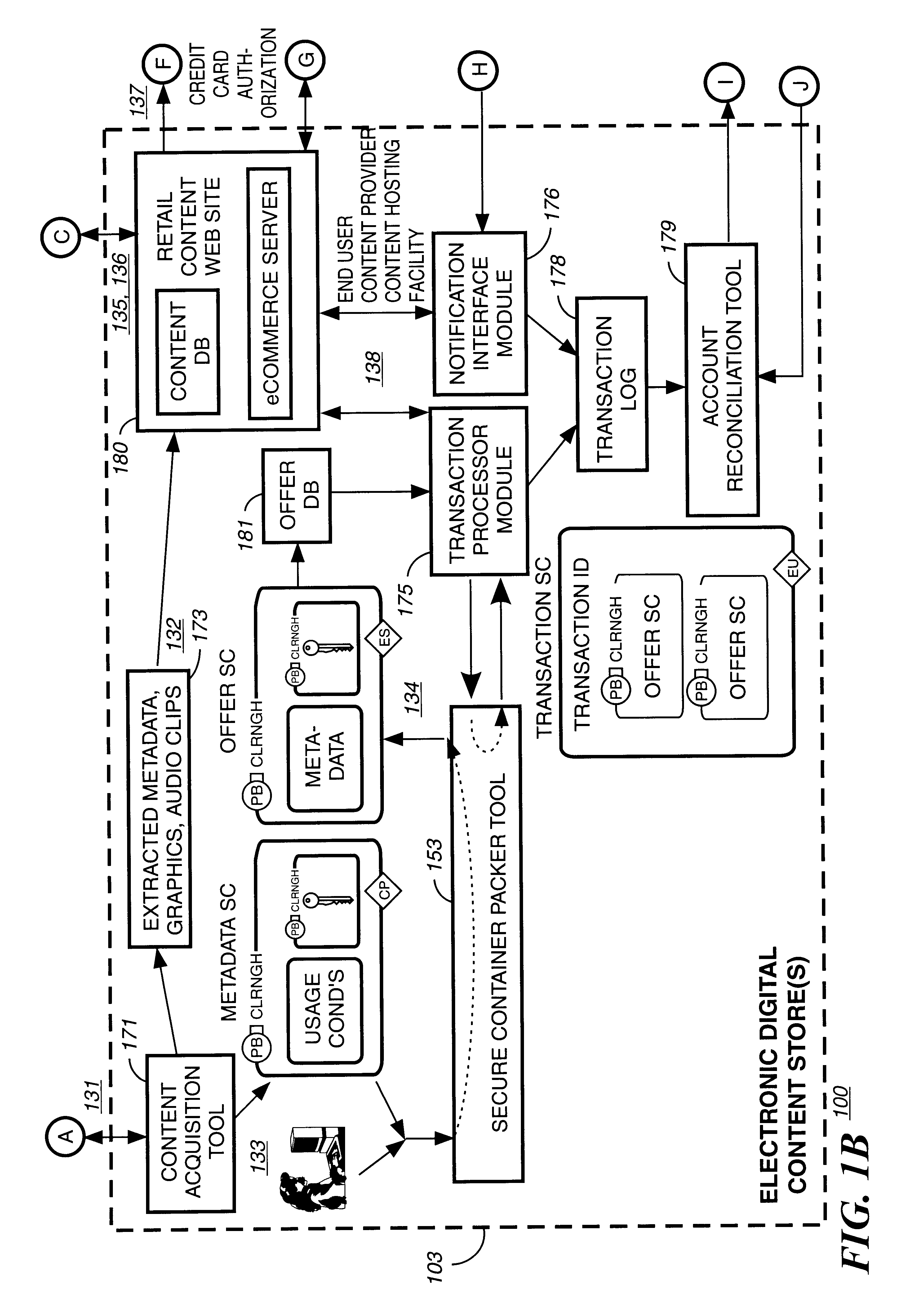
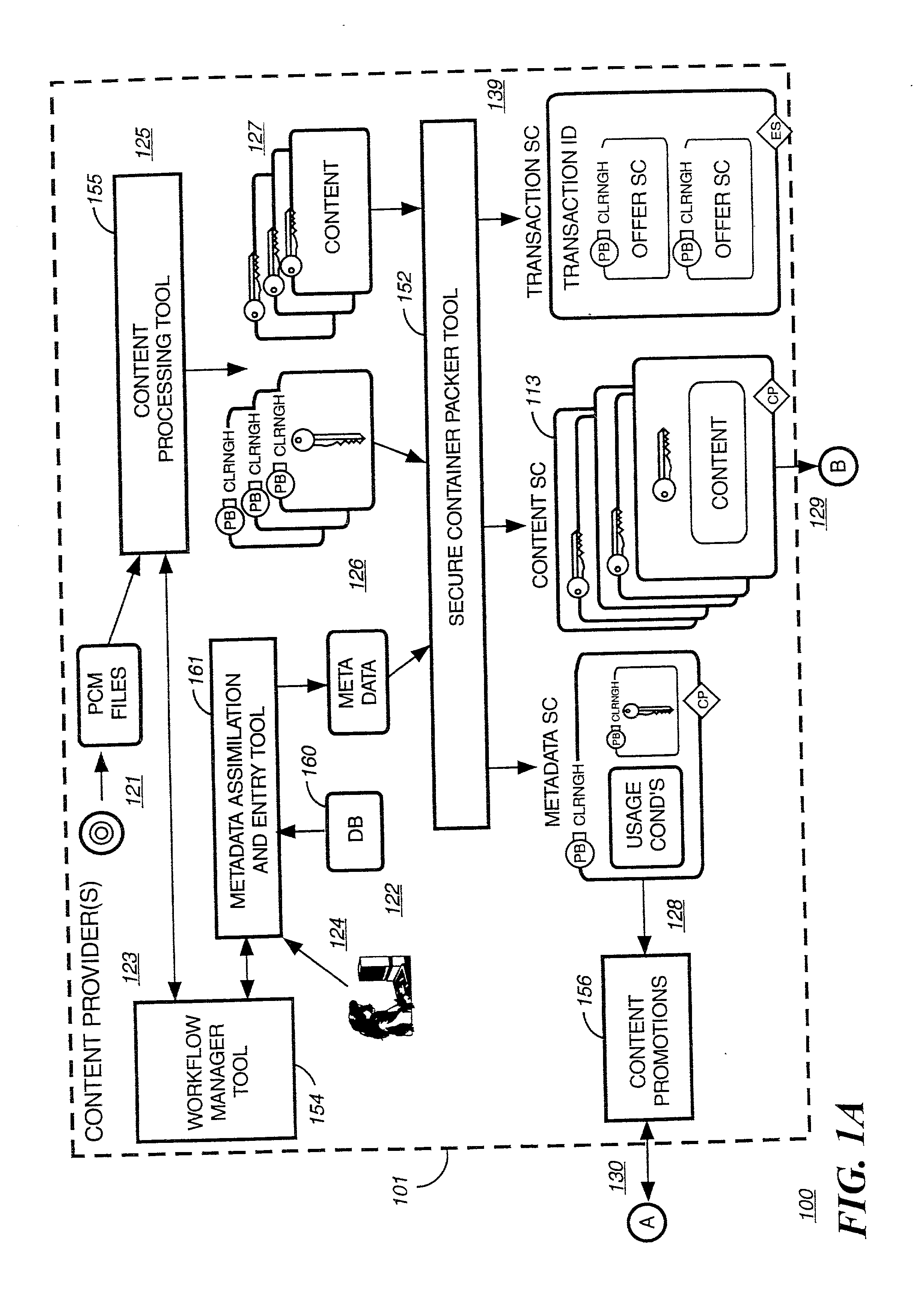
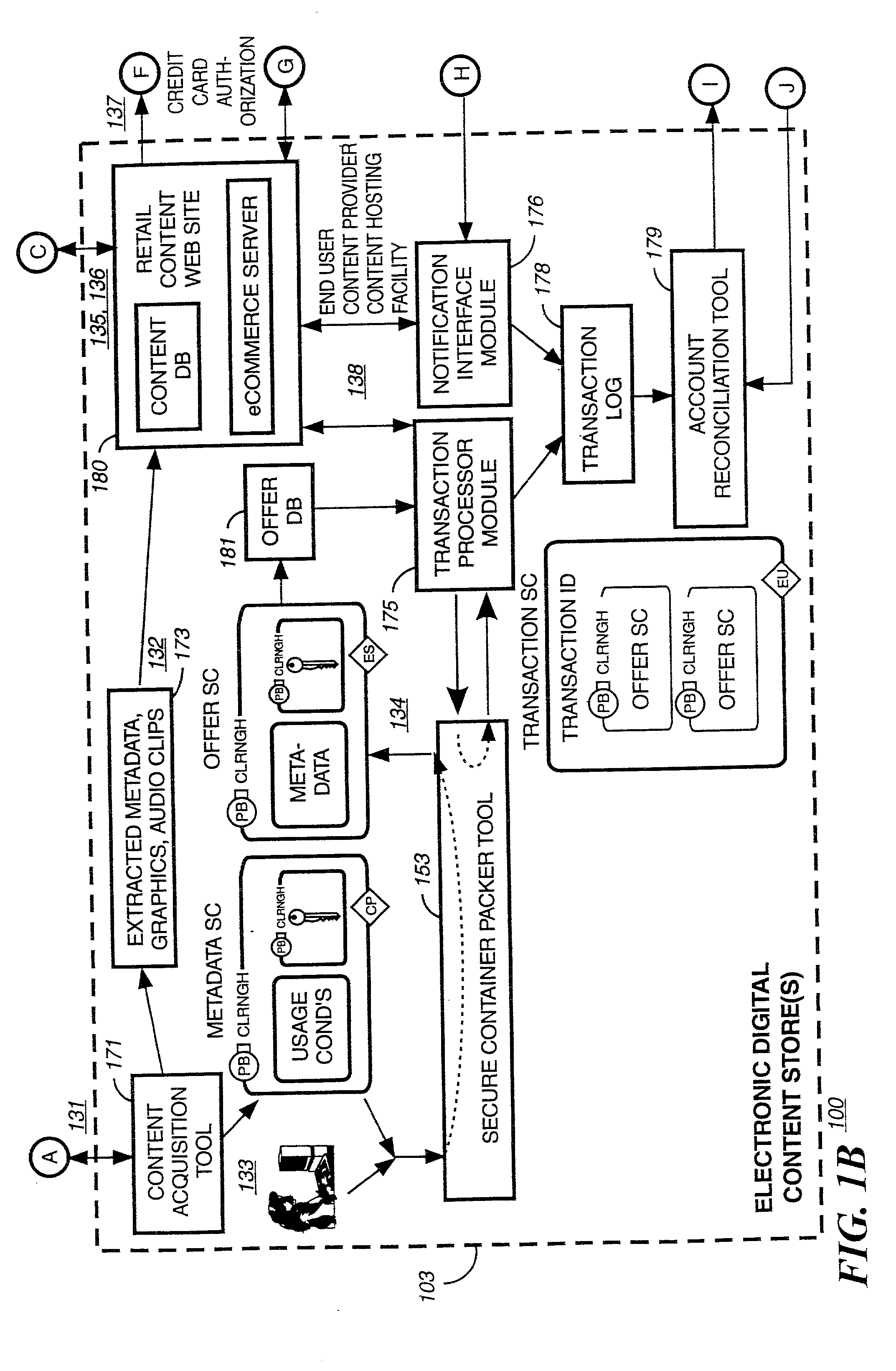
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
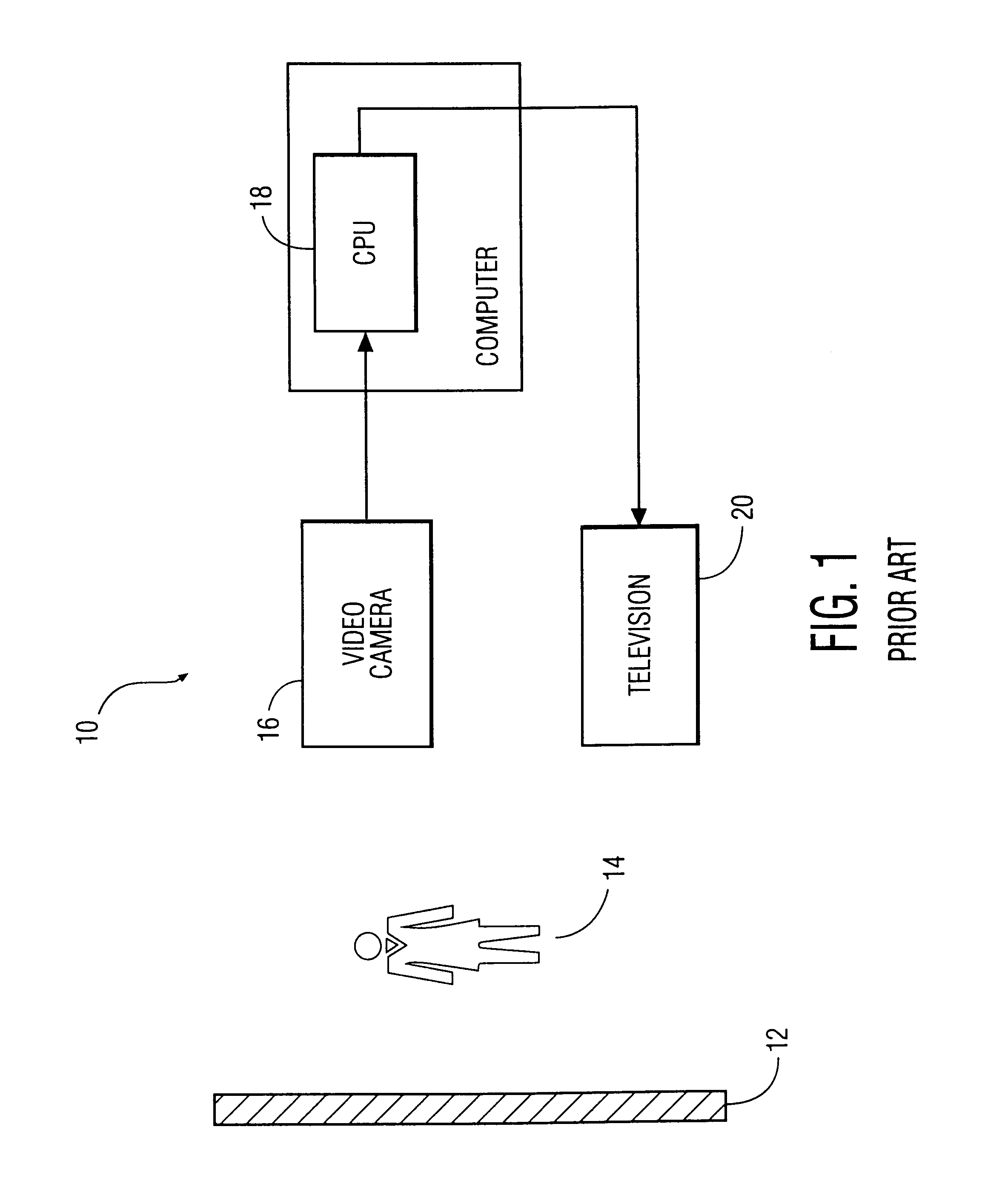
System and method for permitting three-dimensional navigation through a virtual reality environment using camera-based gesture inputs
InactiveUS6181343B1Input/output for user-computer interactionCosmonautic condition simulationsDisplay deviceThree dimensional graphics
A system and method for permitting three-dimensional navigation through a virtual reality environment using camera-based gesture inputs of a system user. The system comprises a computer-readable memory, a video camera for generating video signals indicative of the gestures of the system user and an interaction area surrounding the system user, and a video image display. The video image display is positioned in front of the system user. The system further comprises a microprocessor for processing the video signals, in accordance with a program stored in the computer-readable memory, to determine the three-dimensional positions of the body and principle body parts of the system user. The microprocessor constructs three-dimensional images of the system user and interaction area on the video image display based upon the three-dimensional positions of the body and principle body parts of the system user. The video image display shows three-dimensional graphical objects within the virtual reality environment, and movement by the system user permits apparent movement of the three-dimensional objects displayed on the video image display so that the system user appears to move throughout the virtual reality environment.
Owner:PHILIPS ELECTRONICS NORTH AMERICA
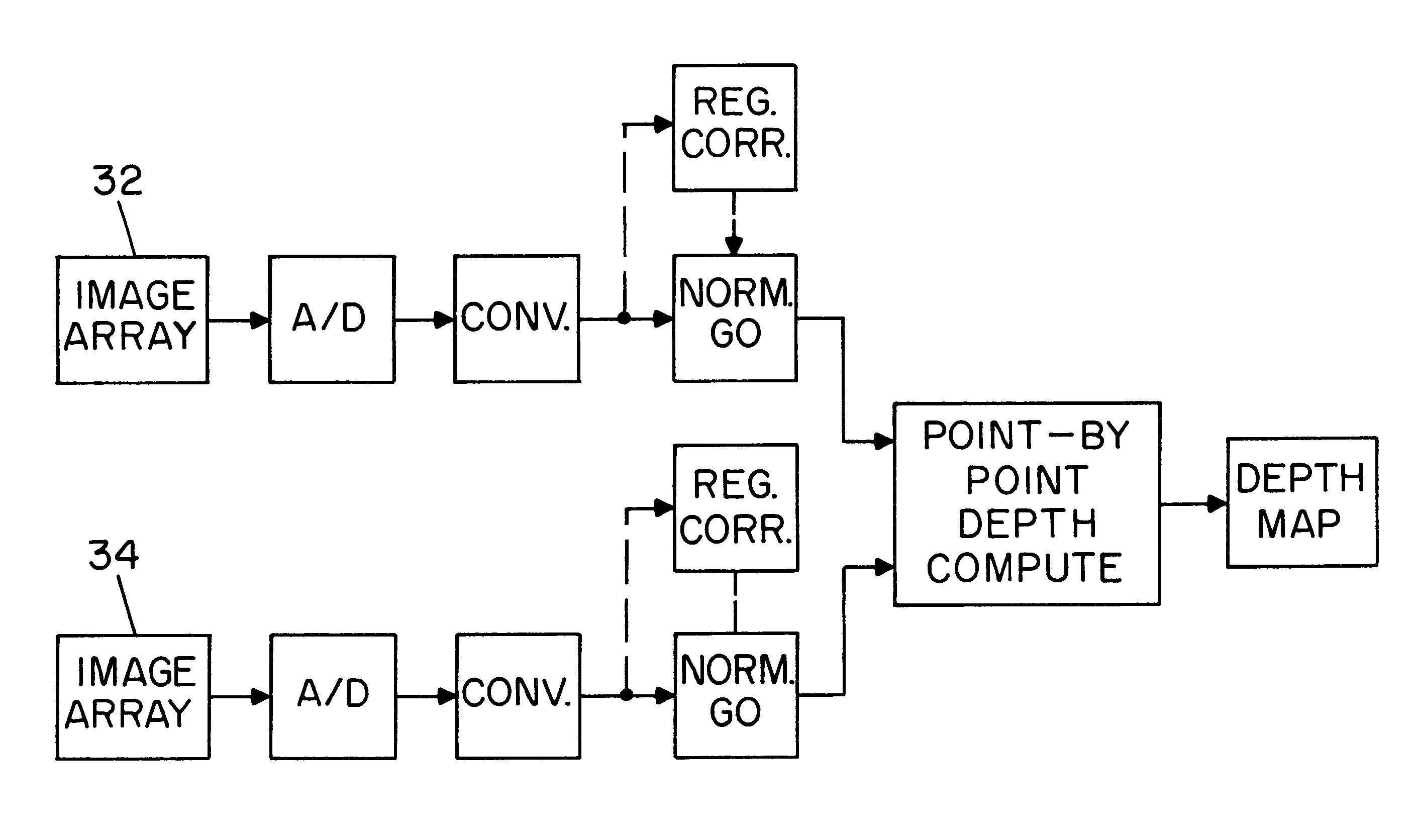
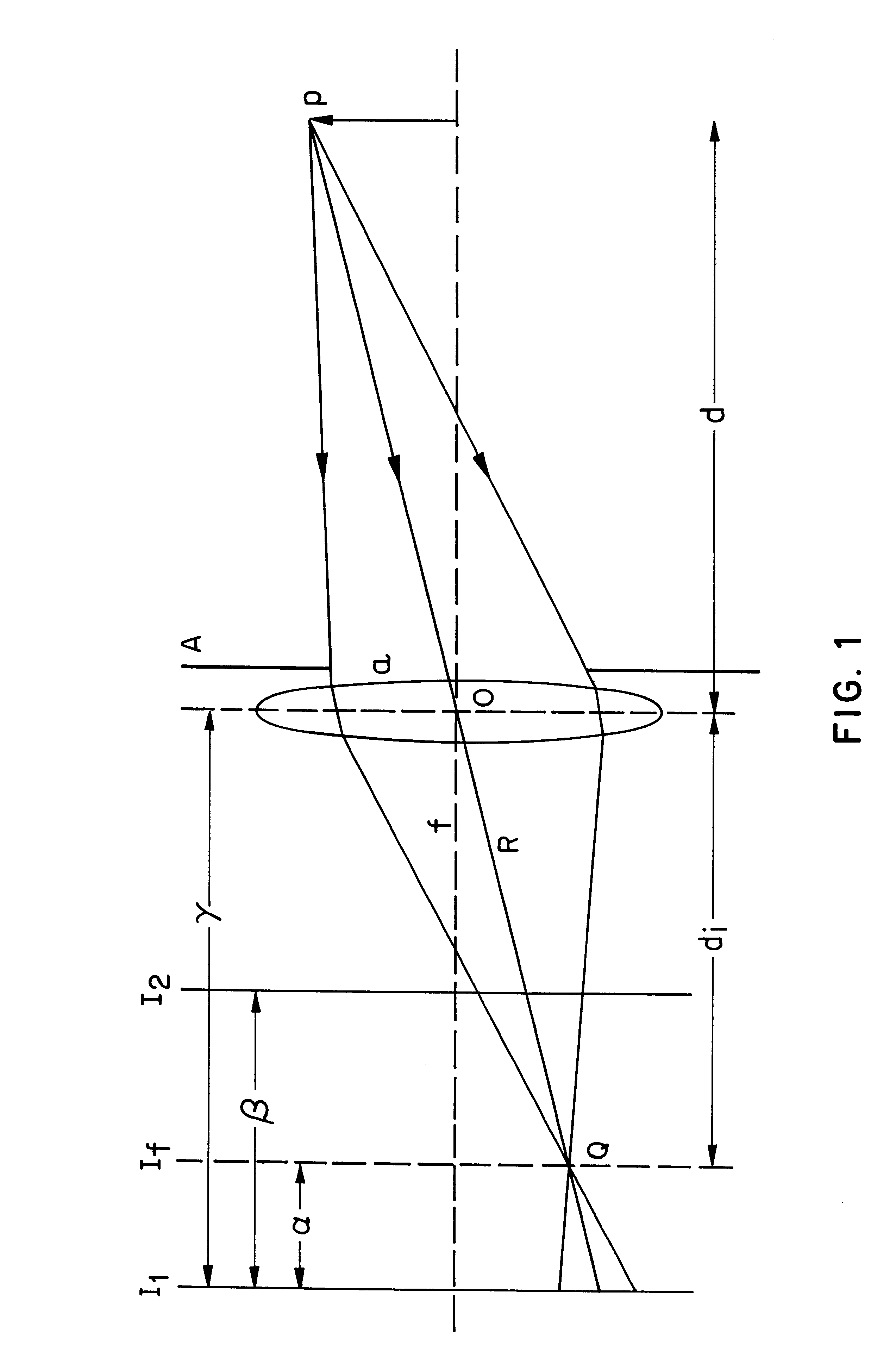
Apparatus and methods for determining the three-dimensional shape of an object using active illumination and relative blurring in two images due to defocus
A method and apparatus for mapping depth of an object (22) in a preferred arrangement uses a projected light pattern to provide a selected texture to the object (22) along the optical axis (24) of observation. An imaging system senses (32, 34) first and second images of the object (22) with the projected light pattern and compares the defocused of the projected pattern in the images to determine relative depth of elemental portions of the object (22).
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
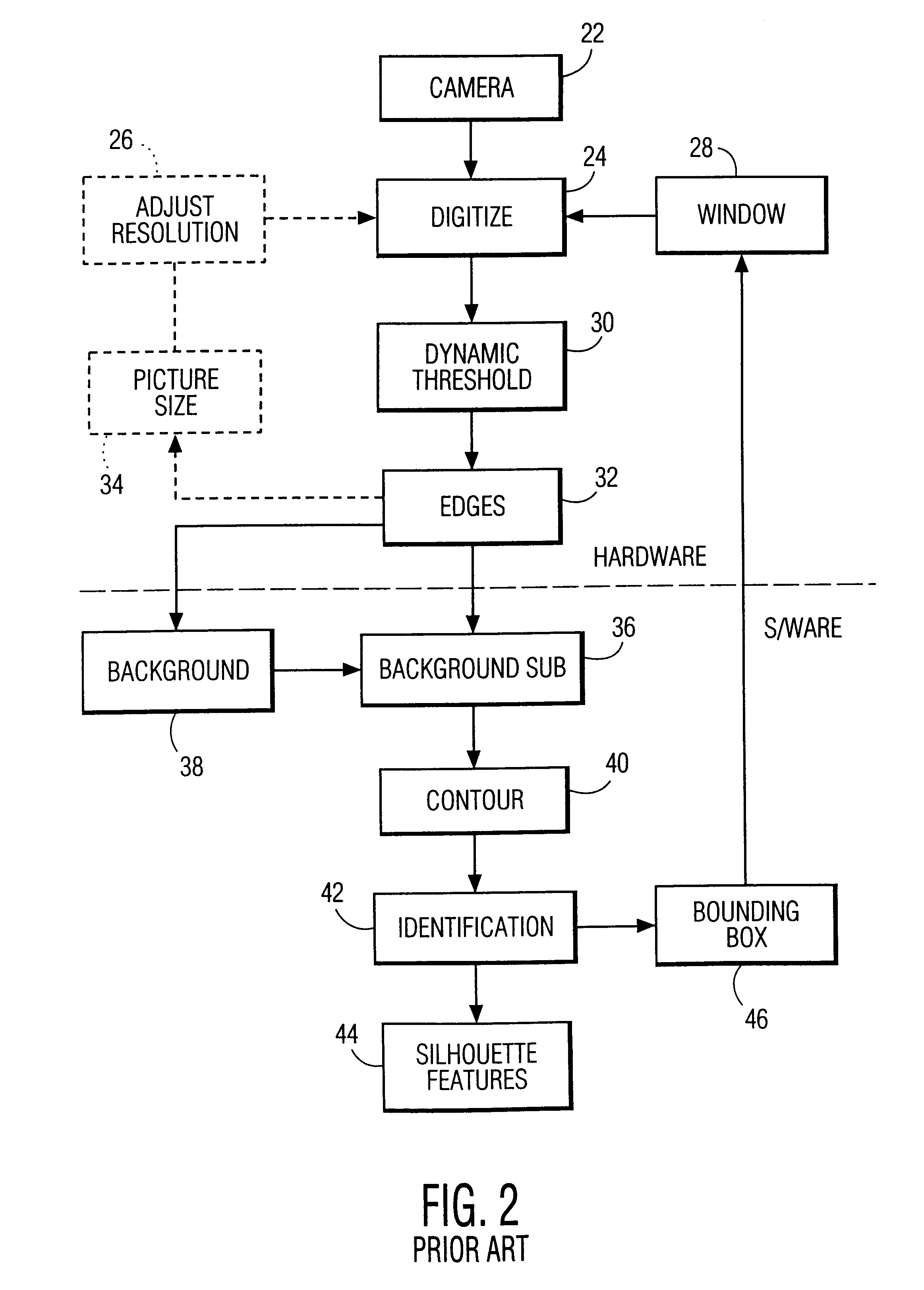
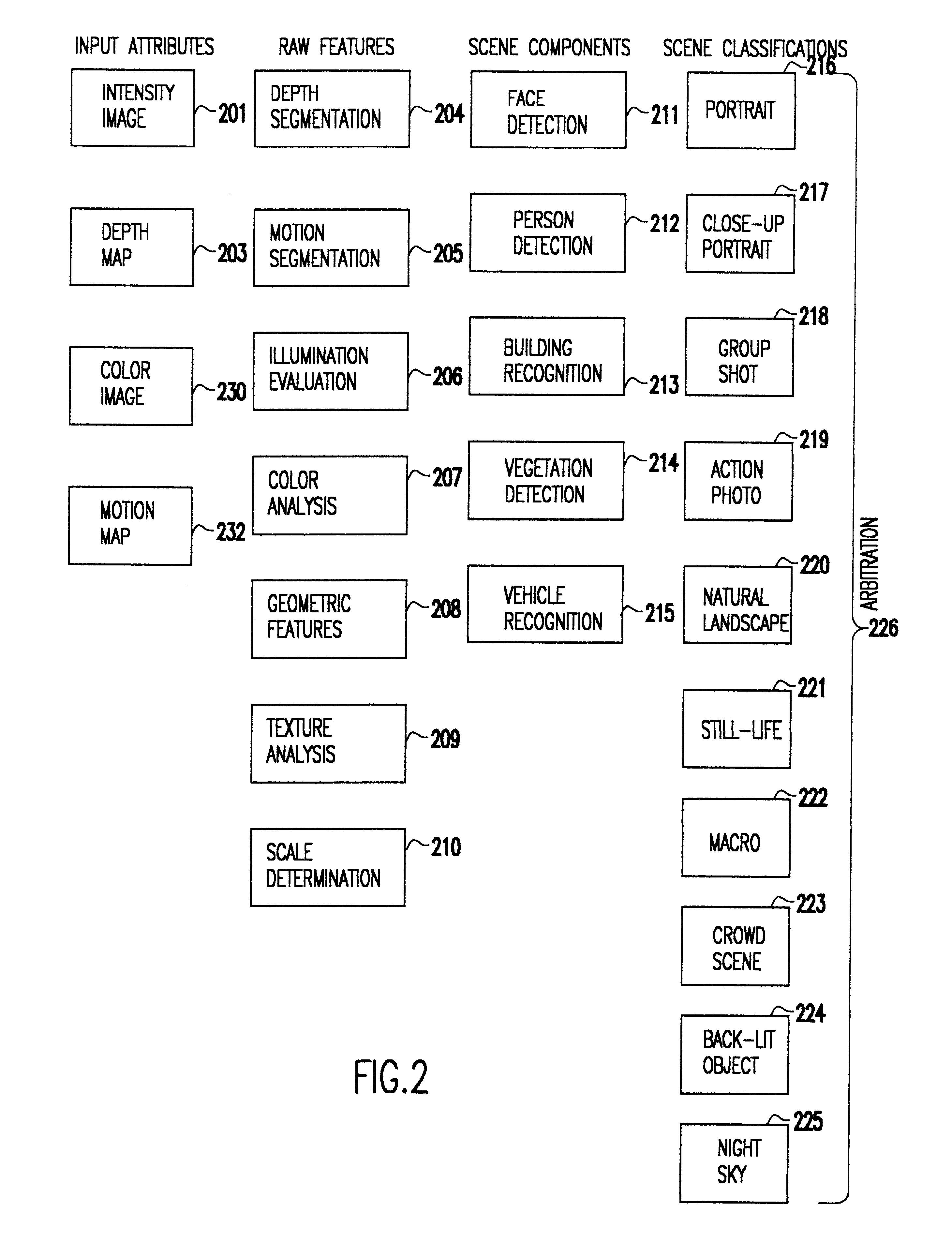
Face detecting camera and method
InactiveUS6940545B1Improve photo experienceGood and more pleasing photographTelevision system detailsImage analysisFace detectionPattern recognition
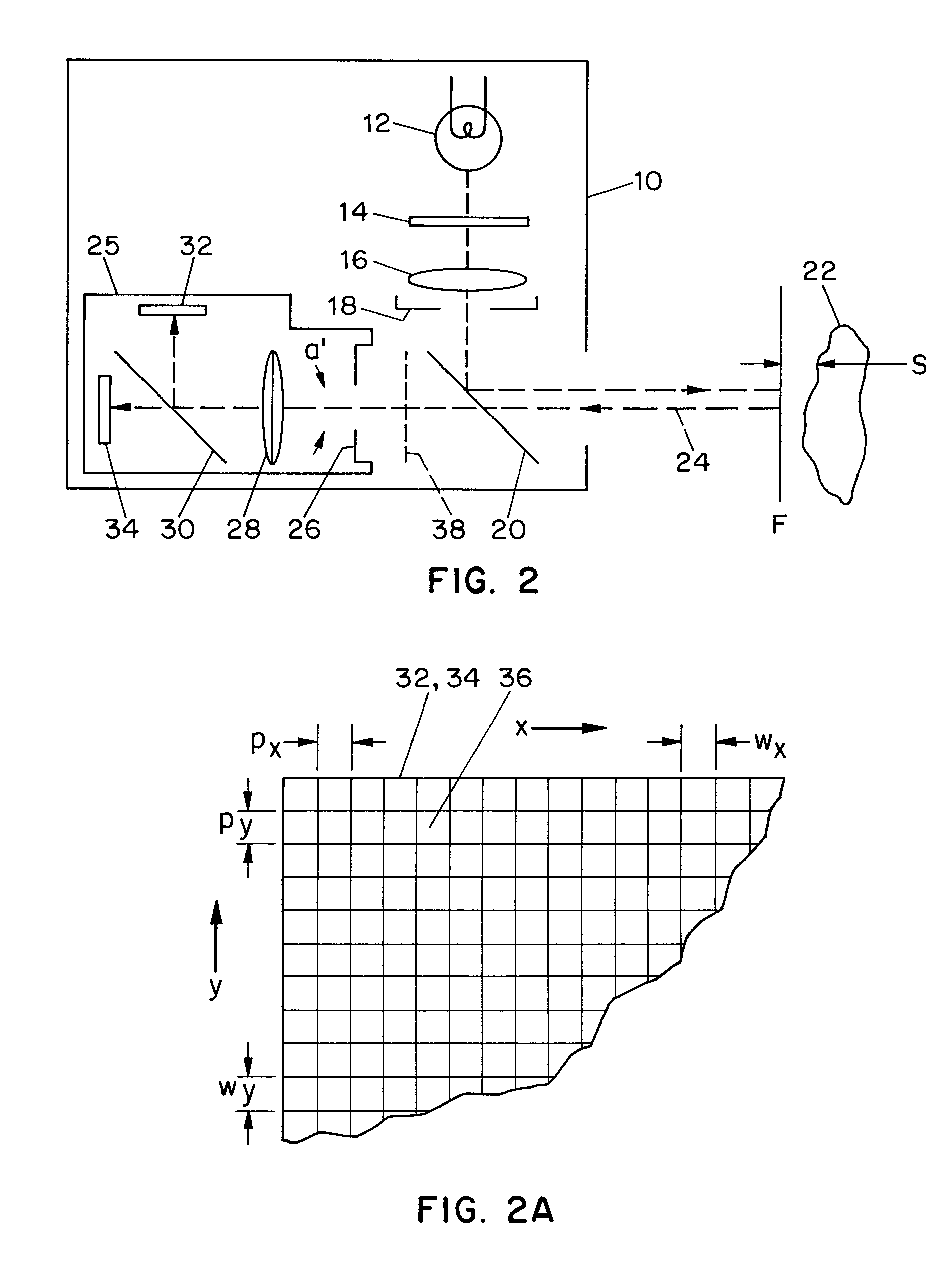
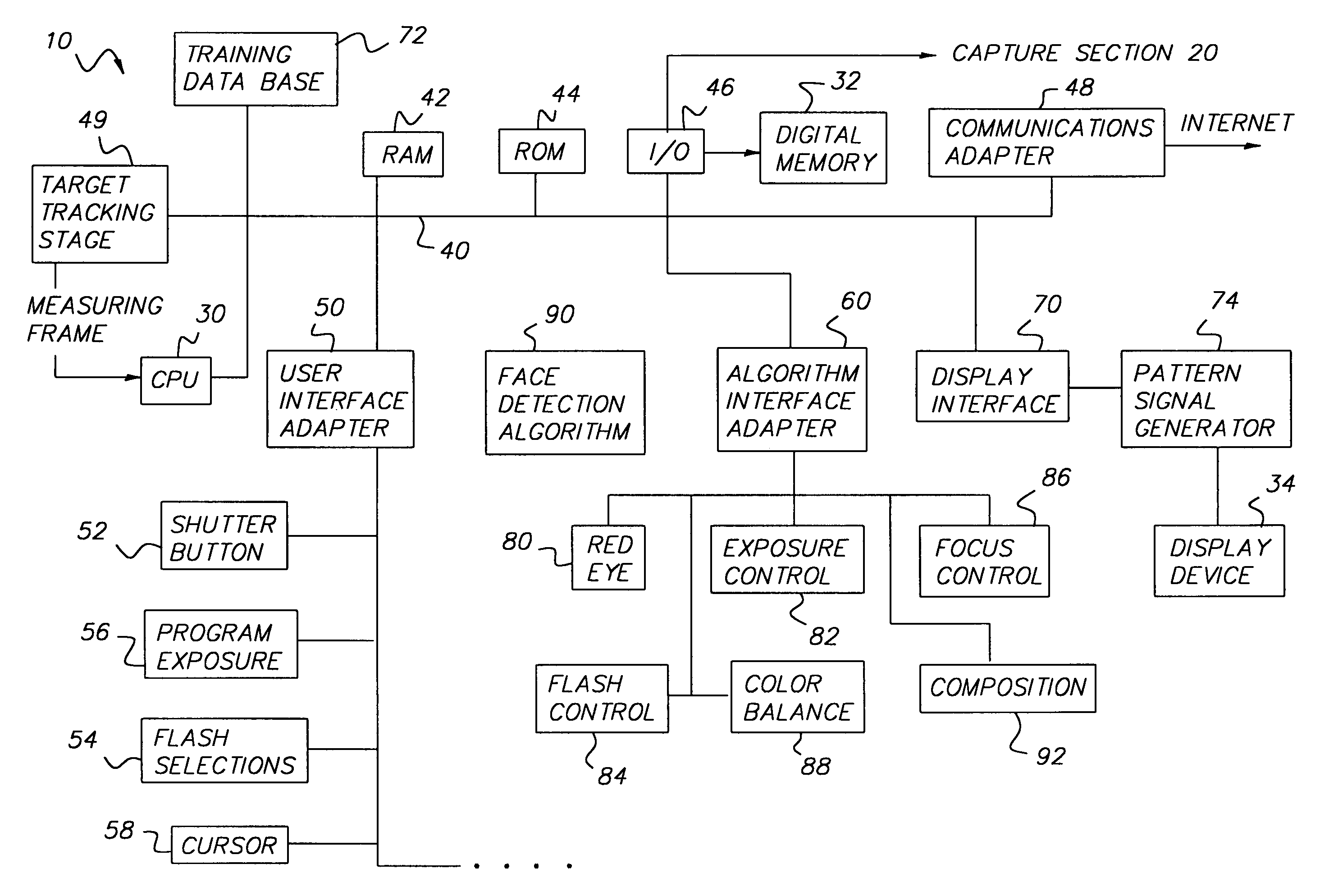
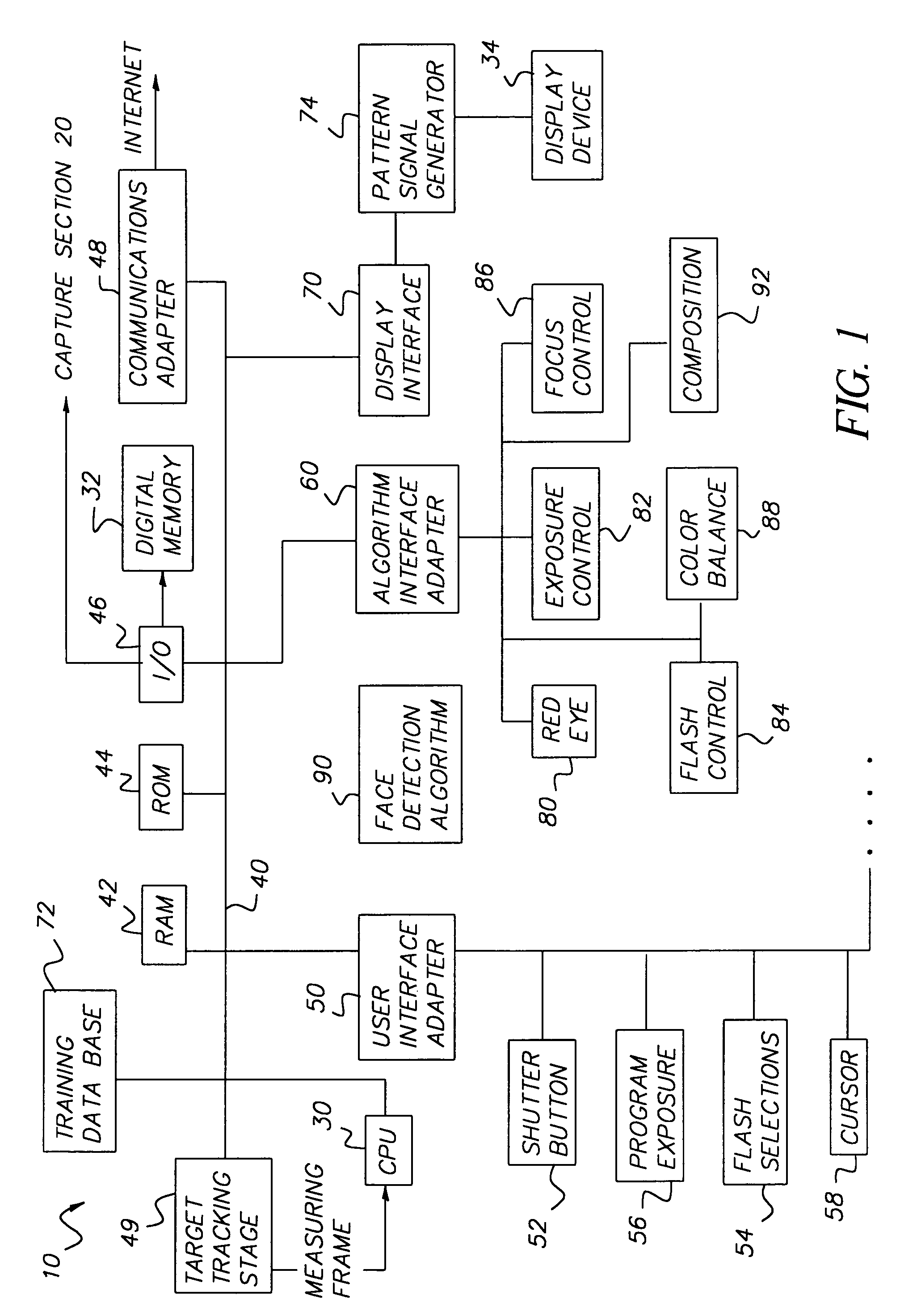
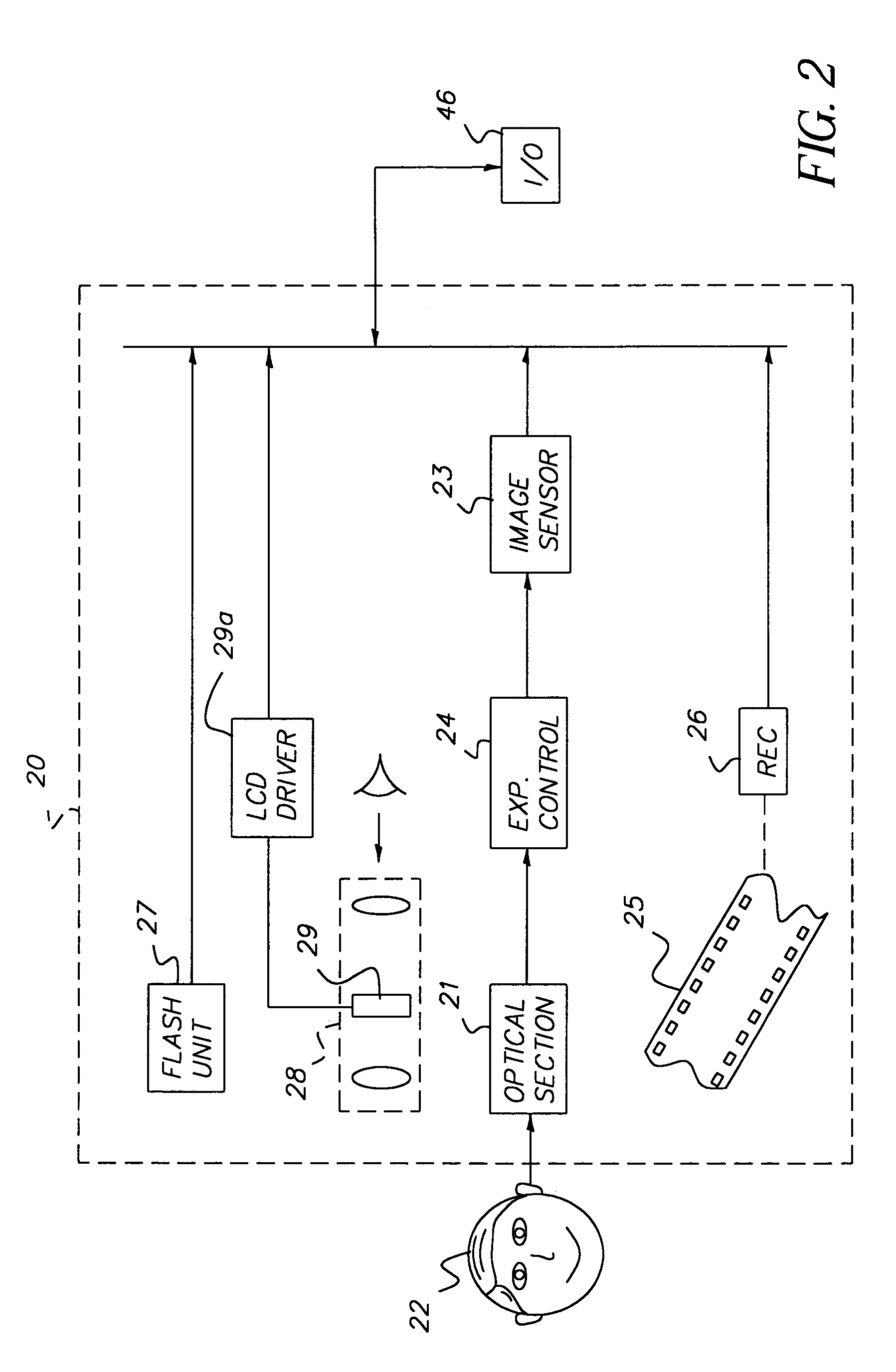
A method for determining the presence of a face from image data includes a face detection algorithm having two separate algorithmic steps: a first step of prescreening image data with a first component of the algorithm to find one or more face candidate regions of the image based on a comparison between facial shape models and facial probabilities assigned to image pixels within the region; and a second step of operating on the face candidate regions with a second component of the algorithm using a pattern matching technique to examine each face candidate region of the image and thereby confirm a facial presence in the region, whereby the combination of these components provides higher performance in terms of detection levels than either component individually. In a camera implementation, a digital camera includes an algorithm memory for storing an algorithm comprised of the aforementioned first and second components and an electronic processing section for processing the image data together with the algorithm for determining the presence of one or more faces in the scene. Facial data indicating the presence of faces may be used to control, e.g., exposure parameters of the capture of an image, or to produce processed image data that relates, e.g., color balance, to the presence of faces in the image, or the facial data may be stored together with the image data on a storage medium.
Owner:MONUMENT PEAK VENTURES LLC
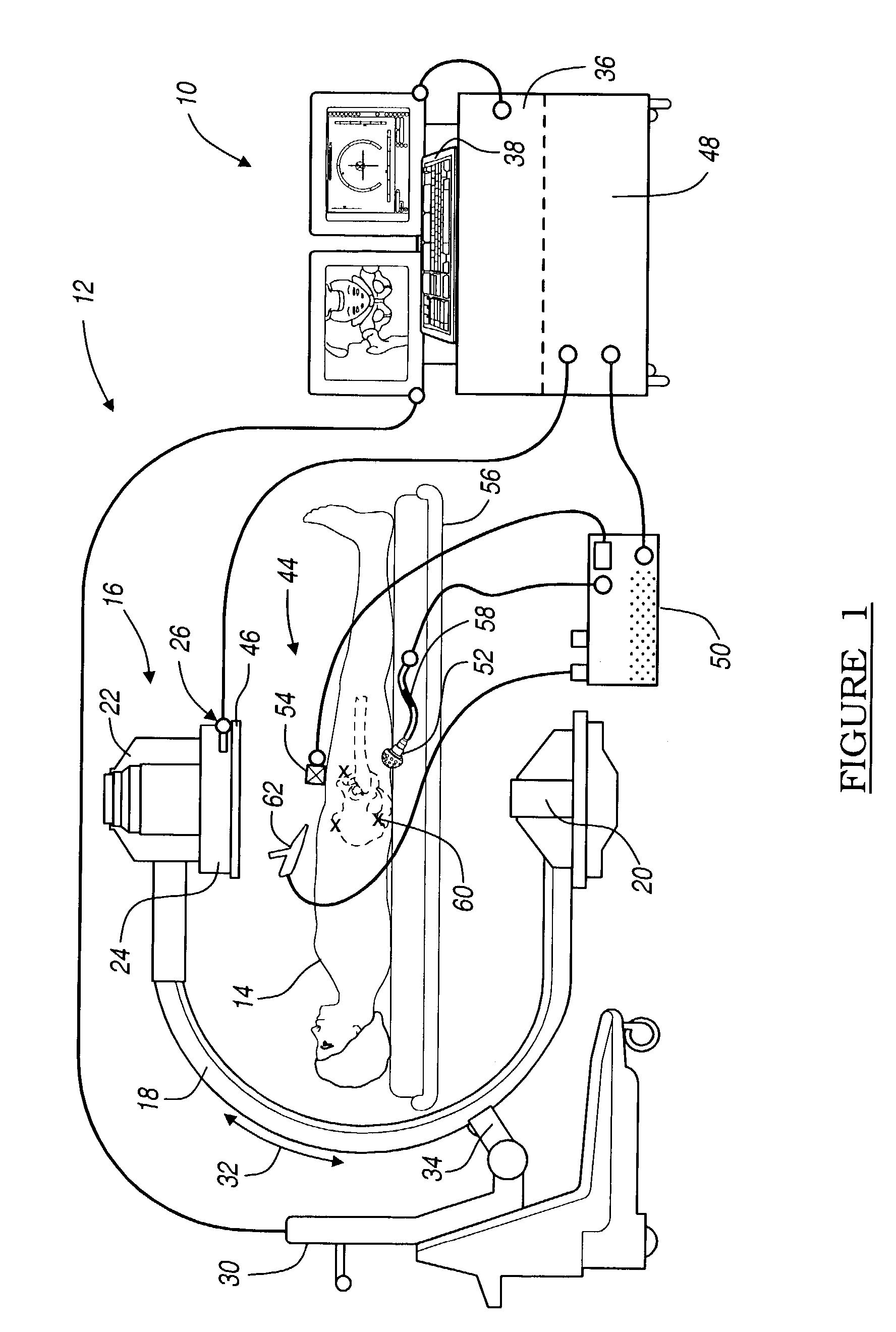
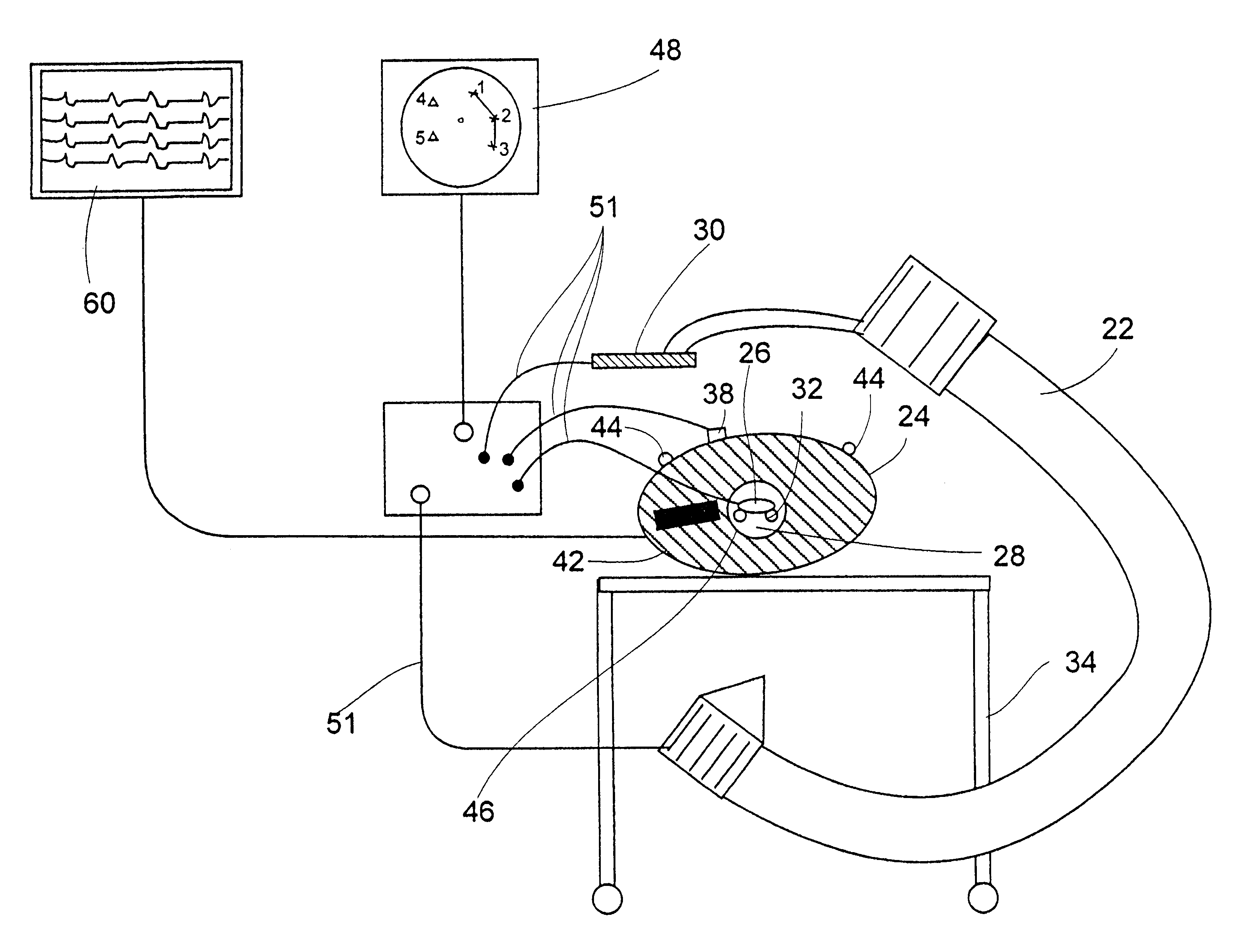
System and method for determining the location of a catheter during an intra-body medical procedure
A system and method of displaying at least one point-of-interest of a body during an intra-body medical procedure. The method is effected by (a) establishing a location of the body; (b) establishing a location of an imaging instrument being for imaging at least a portion of the body; (c) defining at least one projection plane being in relation to a projection plane of the imaging instrument; (d) acquiring at least one point-of-interest of the body; and (c) projection said at least one point-of-interest on said at least one projection plane; such that, in course of the procedure, the locations of the body and the imaging instrument are known, thereby the at least one point-of-interest is projectable on the at least one projection plane even in cases whereby a relative location of the body and the imaging instrument are changed.
Owner:TYCO HEALTHCARE GRP LP
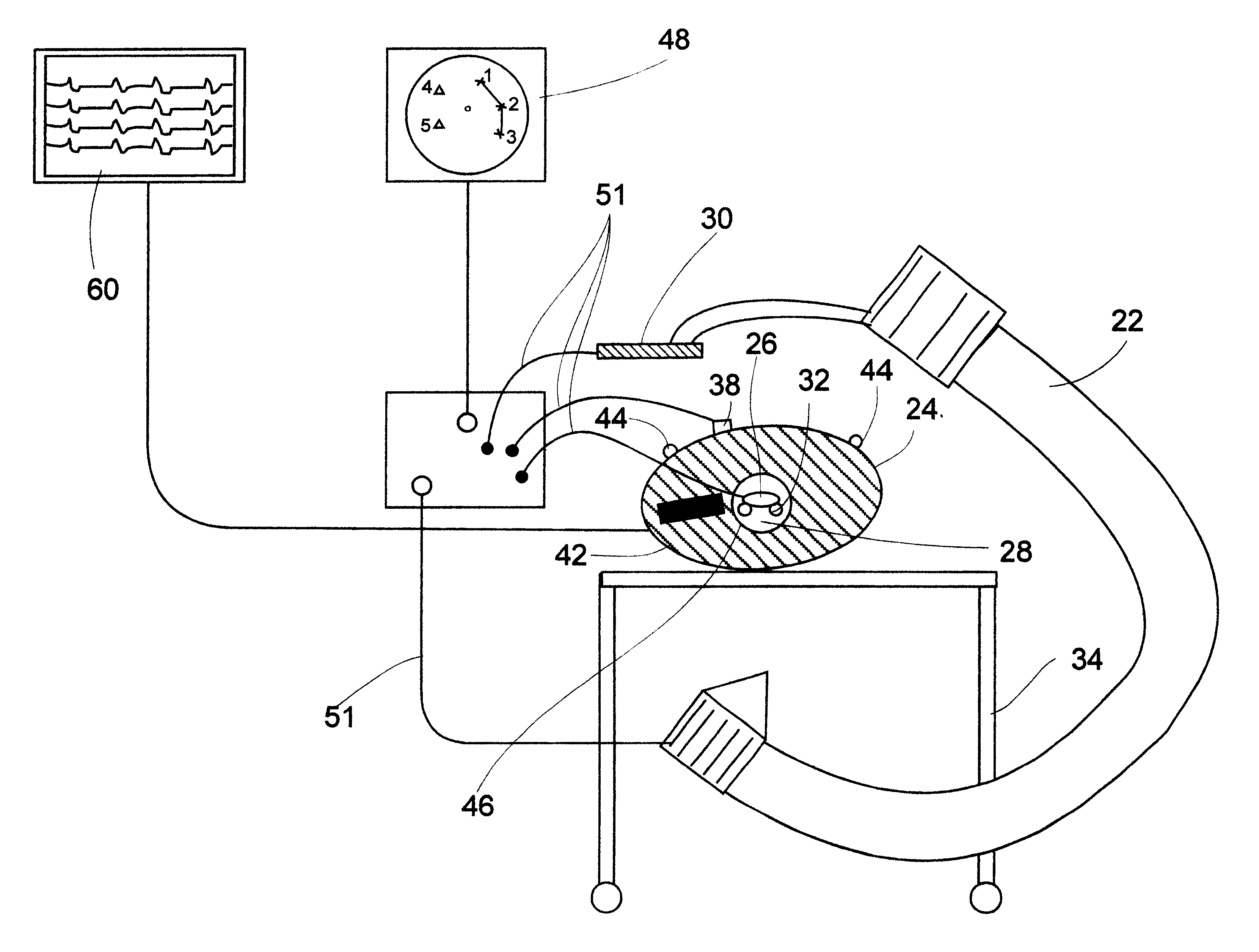
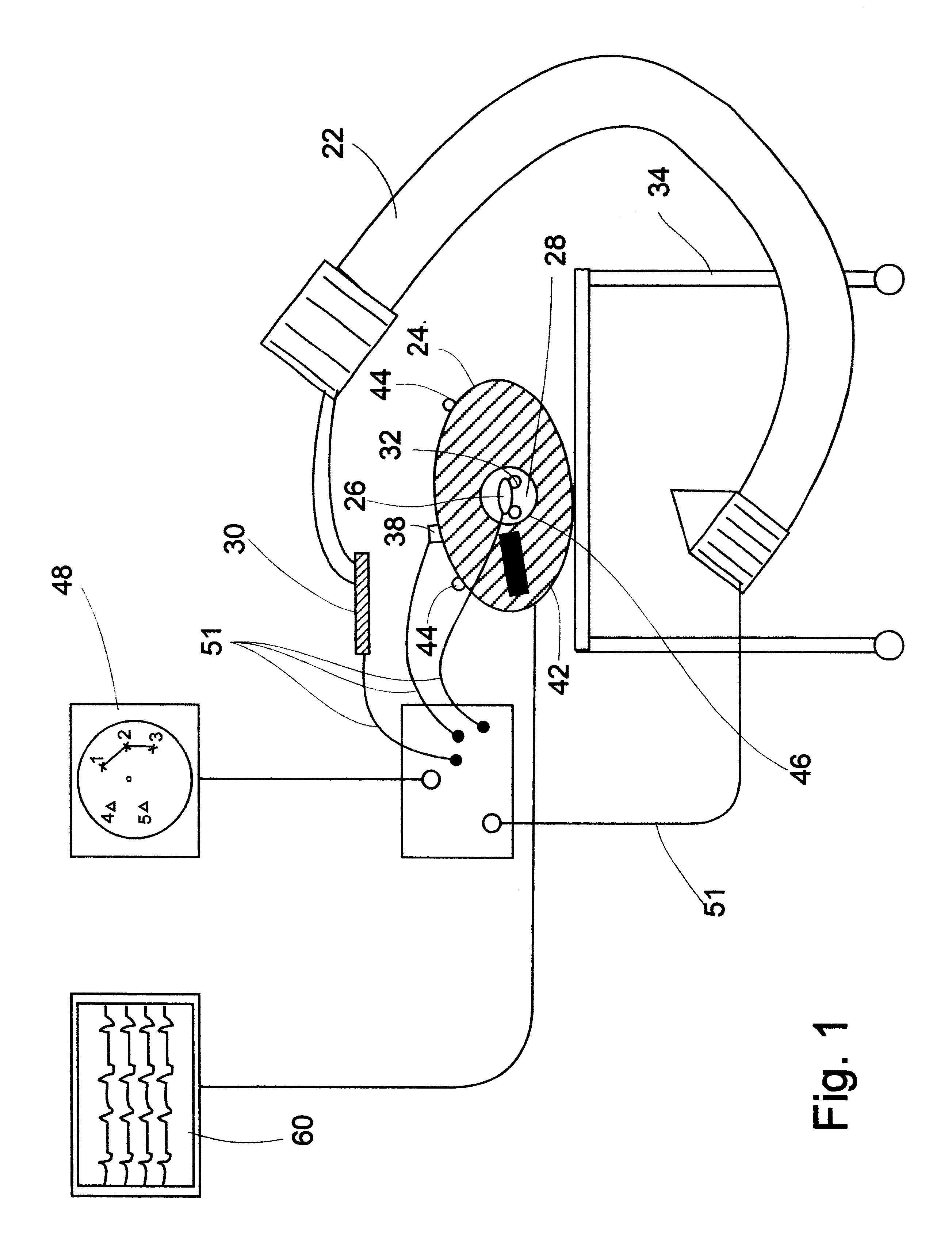
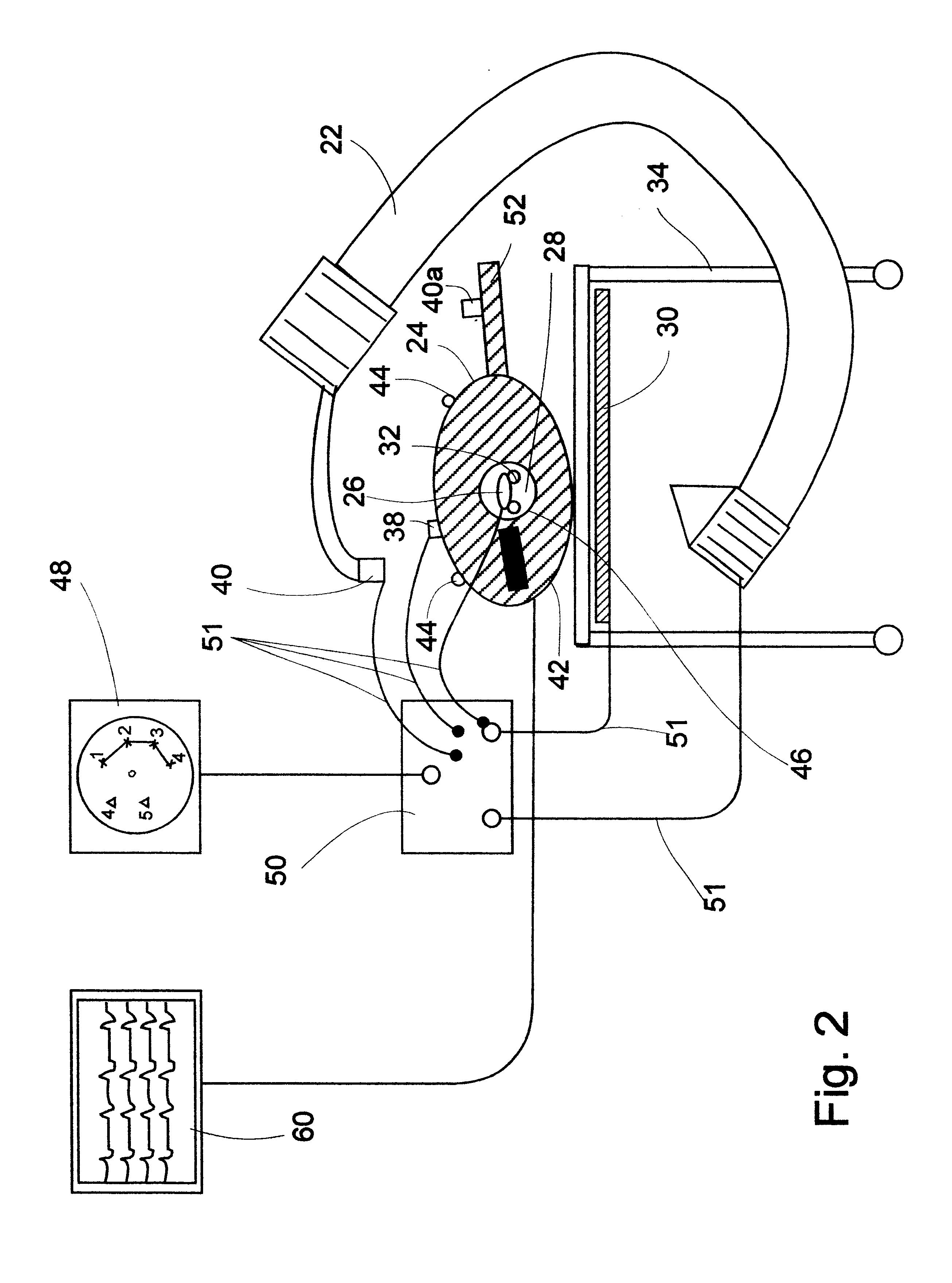
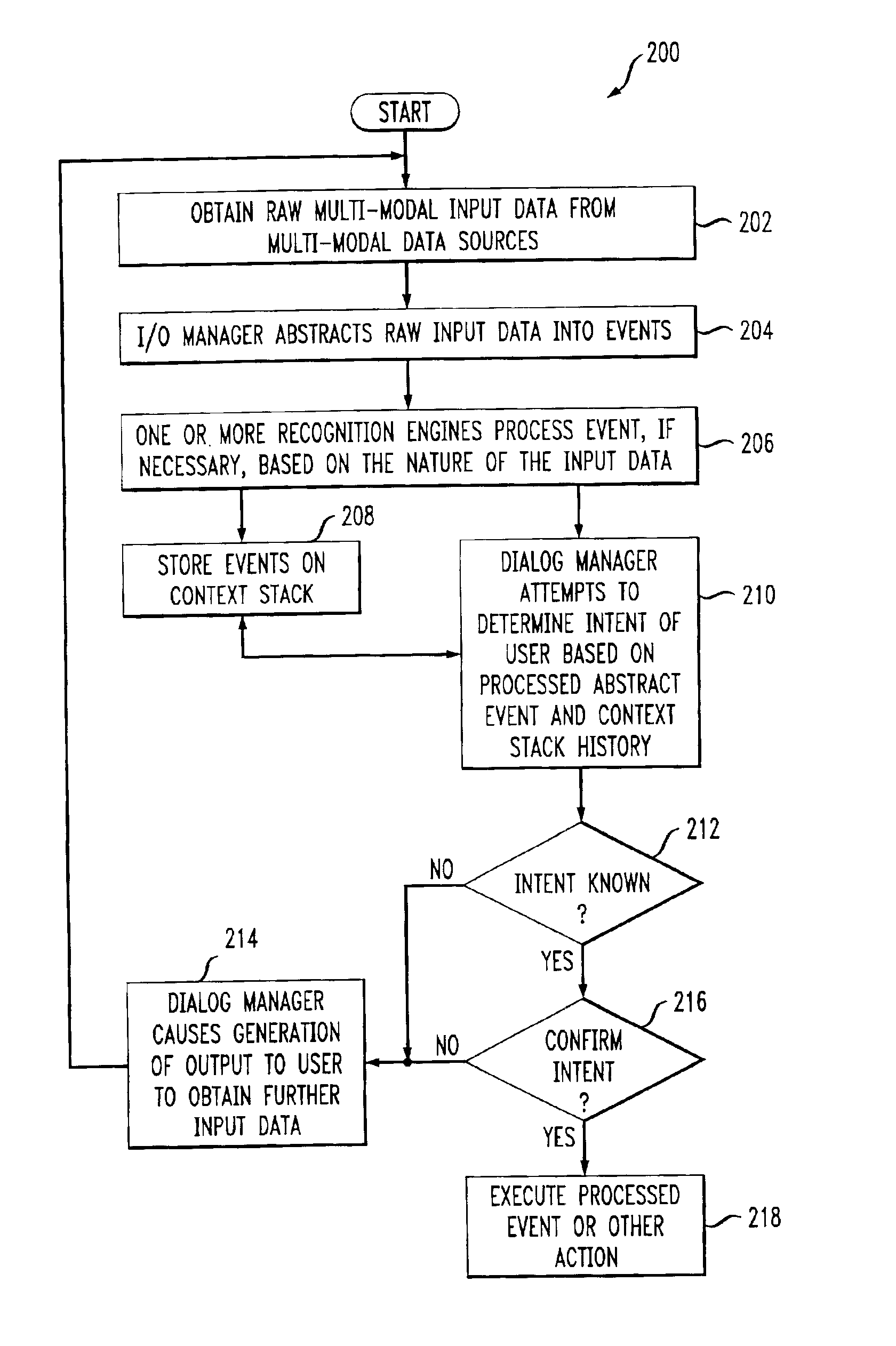
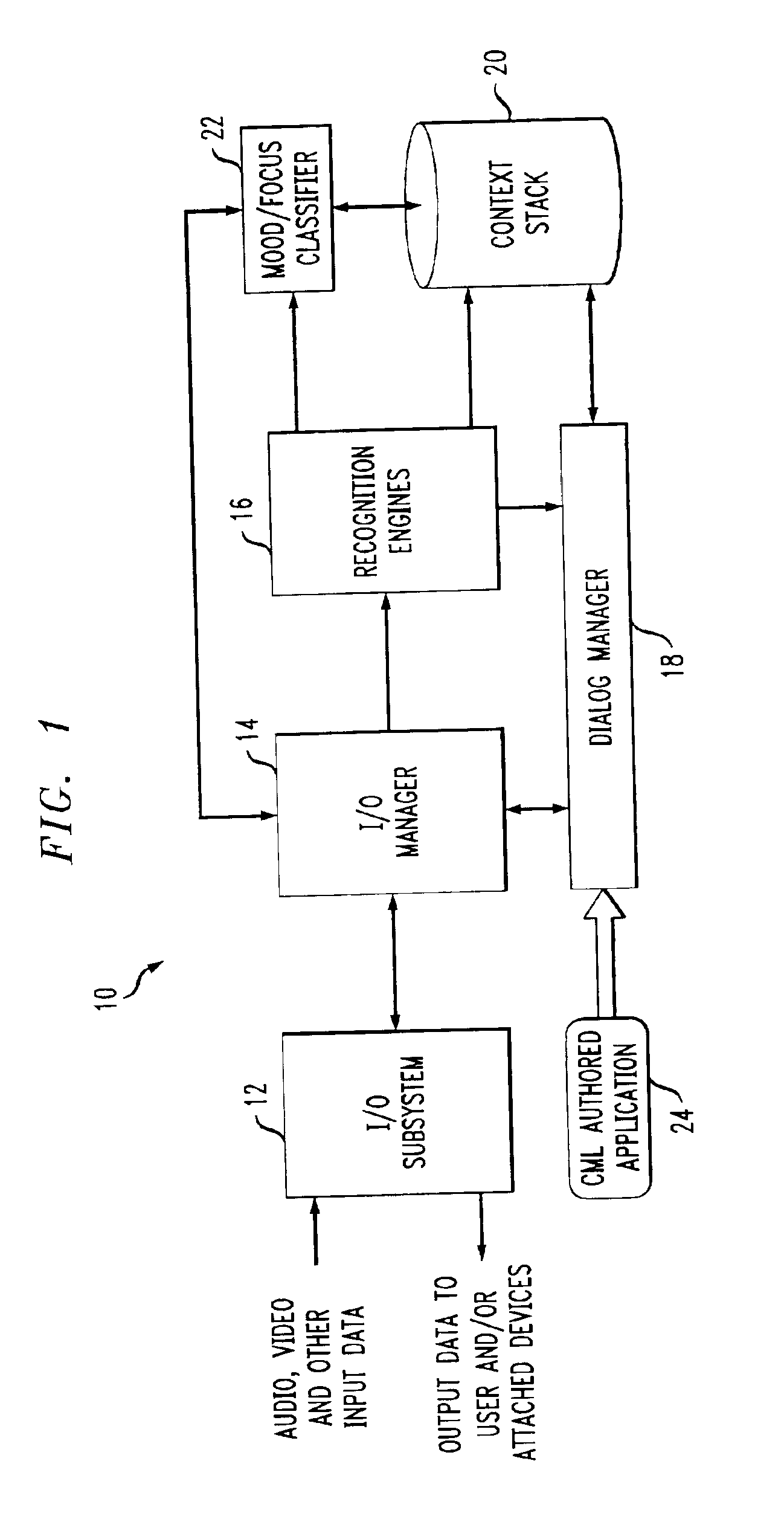
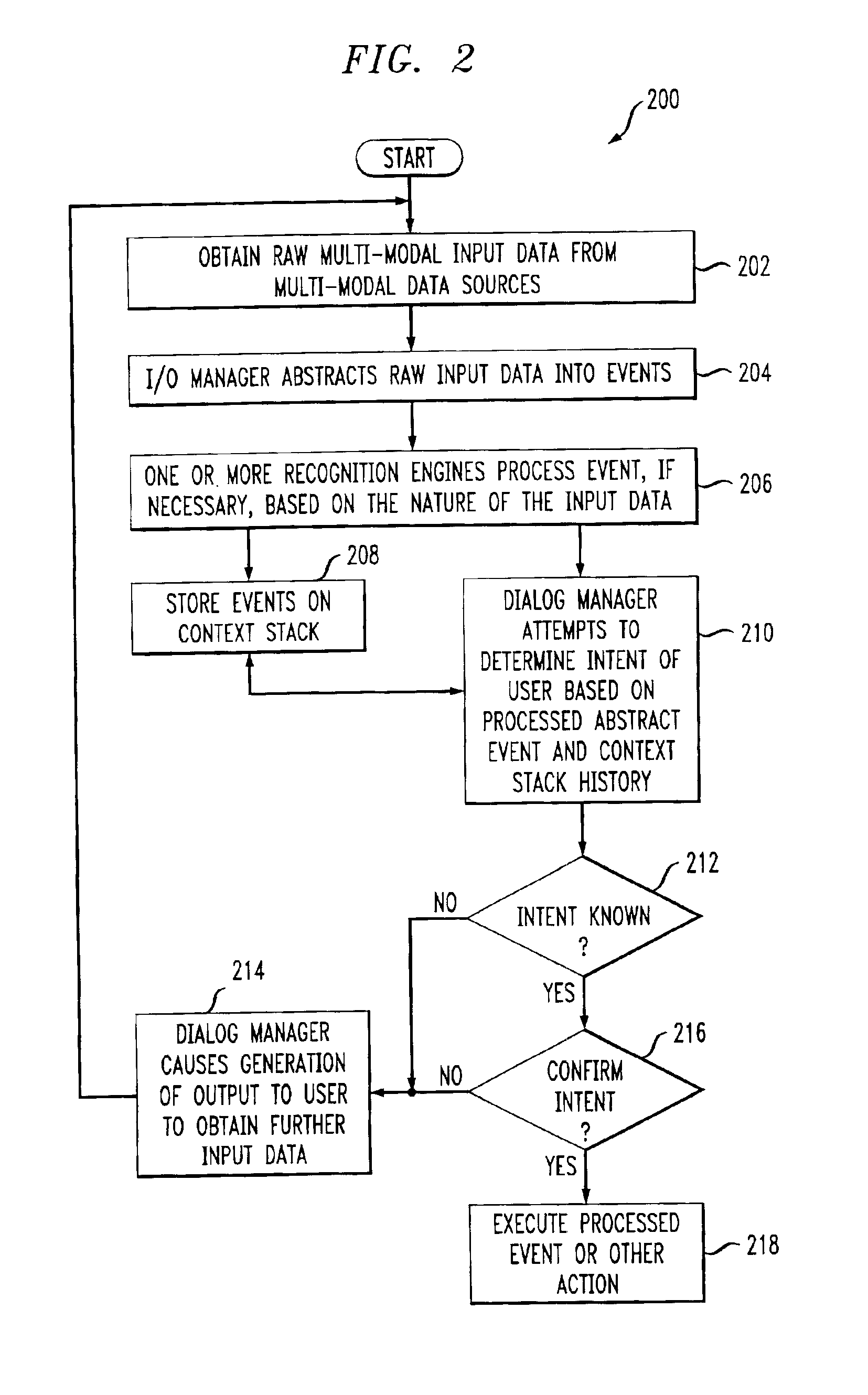
System and method for multi-modal focus detection, referential ambiguity resolution and mood classification using multi-modal input
InactiveUS6964023B2Effective conversational computing environmentInput/output for user-computer interactionData processing applicationsOperant conditioningComputer science
Owner:IBM CORP
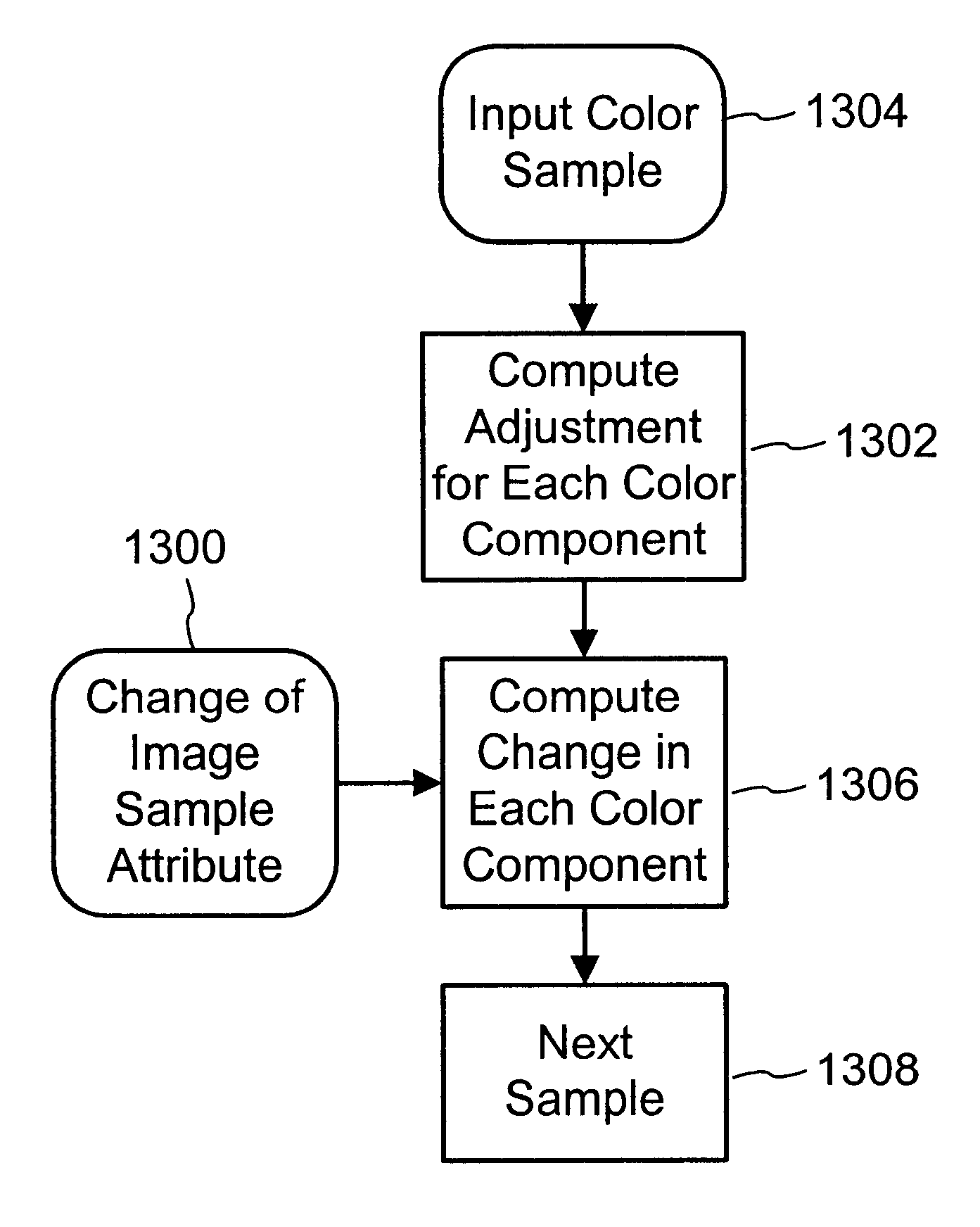
Color adaptive watermarking
InactiveUS6590996B1Effectively create and manipulateReduce the amount requiredPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningColor mappingComputer graphics (images)
A color mapping process enhances a watermark by computing a change in colors that is less visible for a given watermark strength. The mapping process provides smooth transitions from one color region to another, and may be implemented efficiently with a 3D look up table. A user interface scheme enables the user to control encoding of the watermark in desired color regions.
Owner:DIGIMARC CORP
Fingerprint-reading system
InactiveUS6289114B1Image analysisElectric/magnetic contours/curvatures measurementsEffective surfaceRelative motion
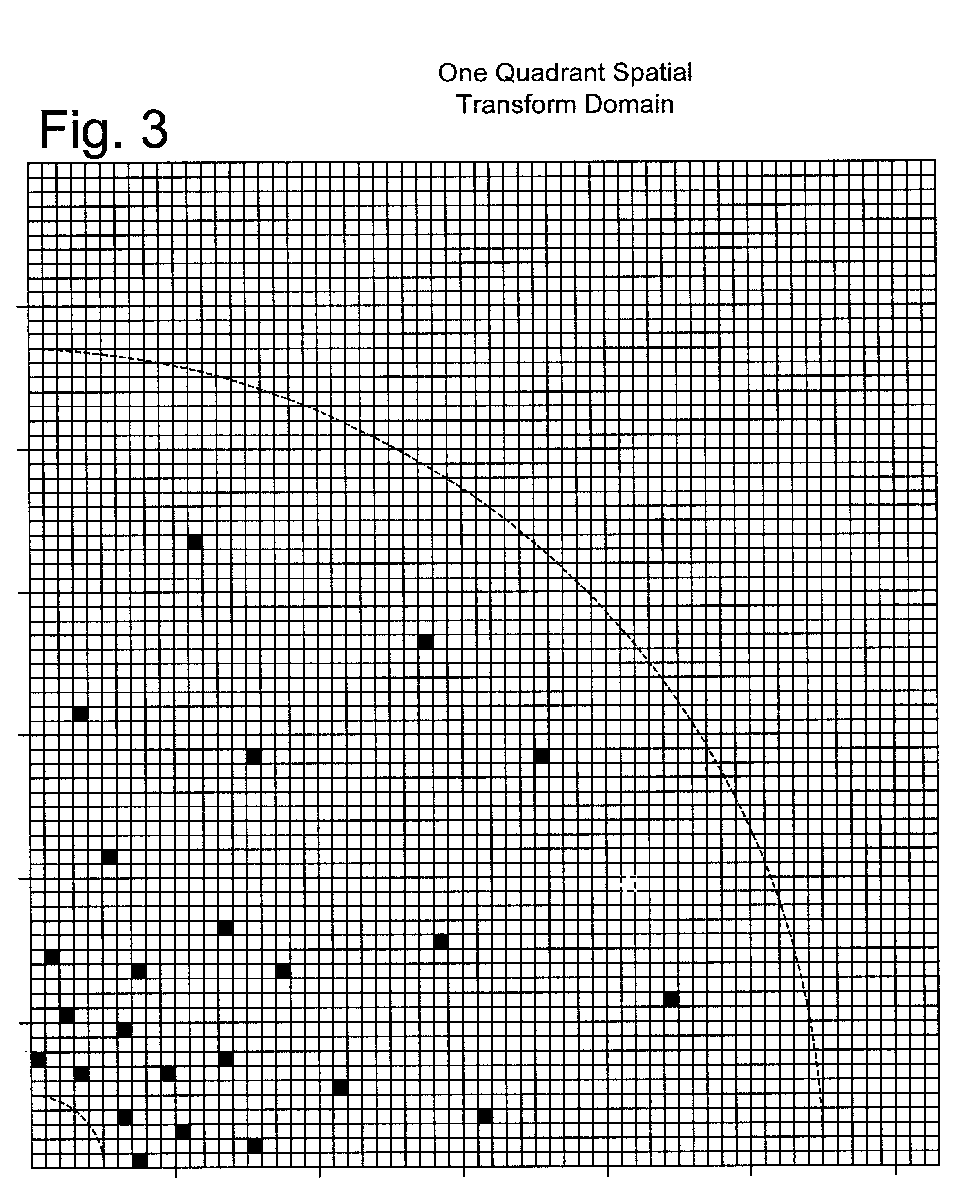
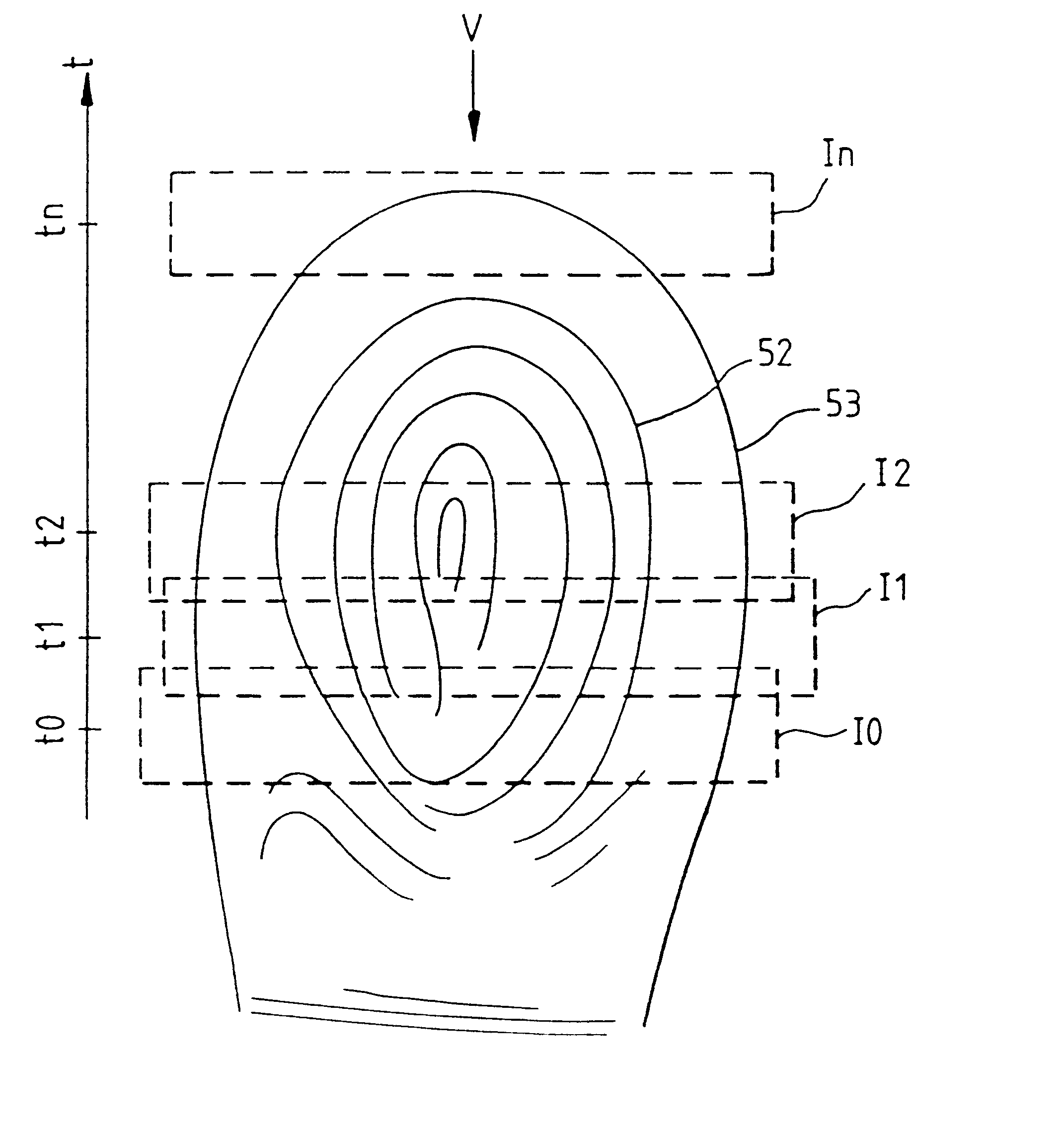
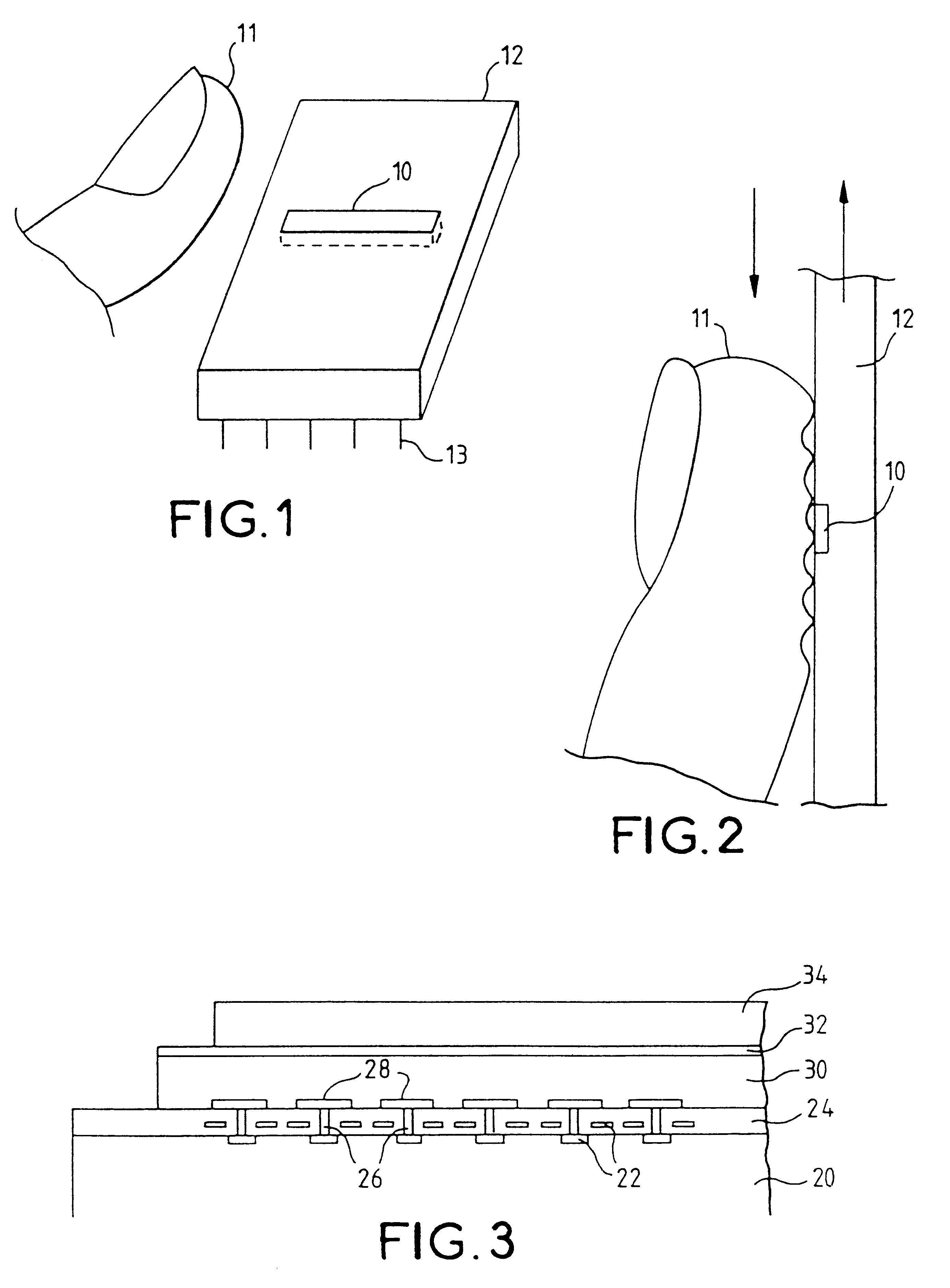
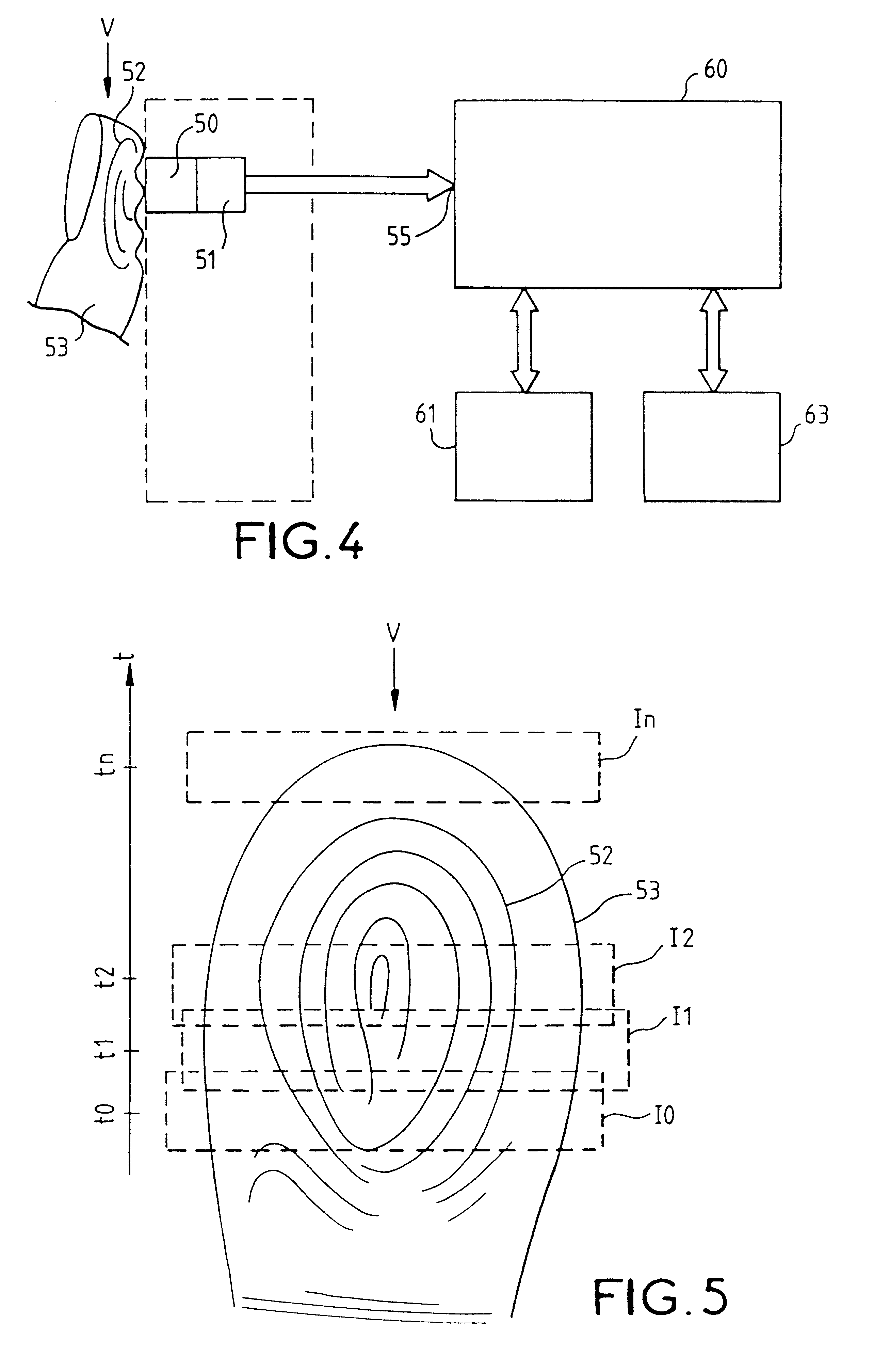
A fingerprint-reading system includes a fingerprint sensor having an active surface sensitive to the pressure and temperature of a finger. The surface area of this sensor is far smaller than the surface area of the fingerprint to be read. The reading is done when the sensor and the finger are in contact and in a relative motion of sliding of the sensor and the finger with respect to each other. The system reconstitutes a complete image of the fingerprint from the partial images given by the sensor during this motion.
Owner:APPLE INC
Cryptographic methods, apparatus and systems for storage media electronic rights management in closed and connected appliances
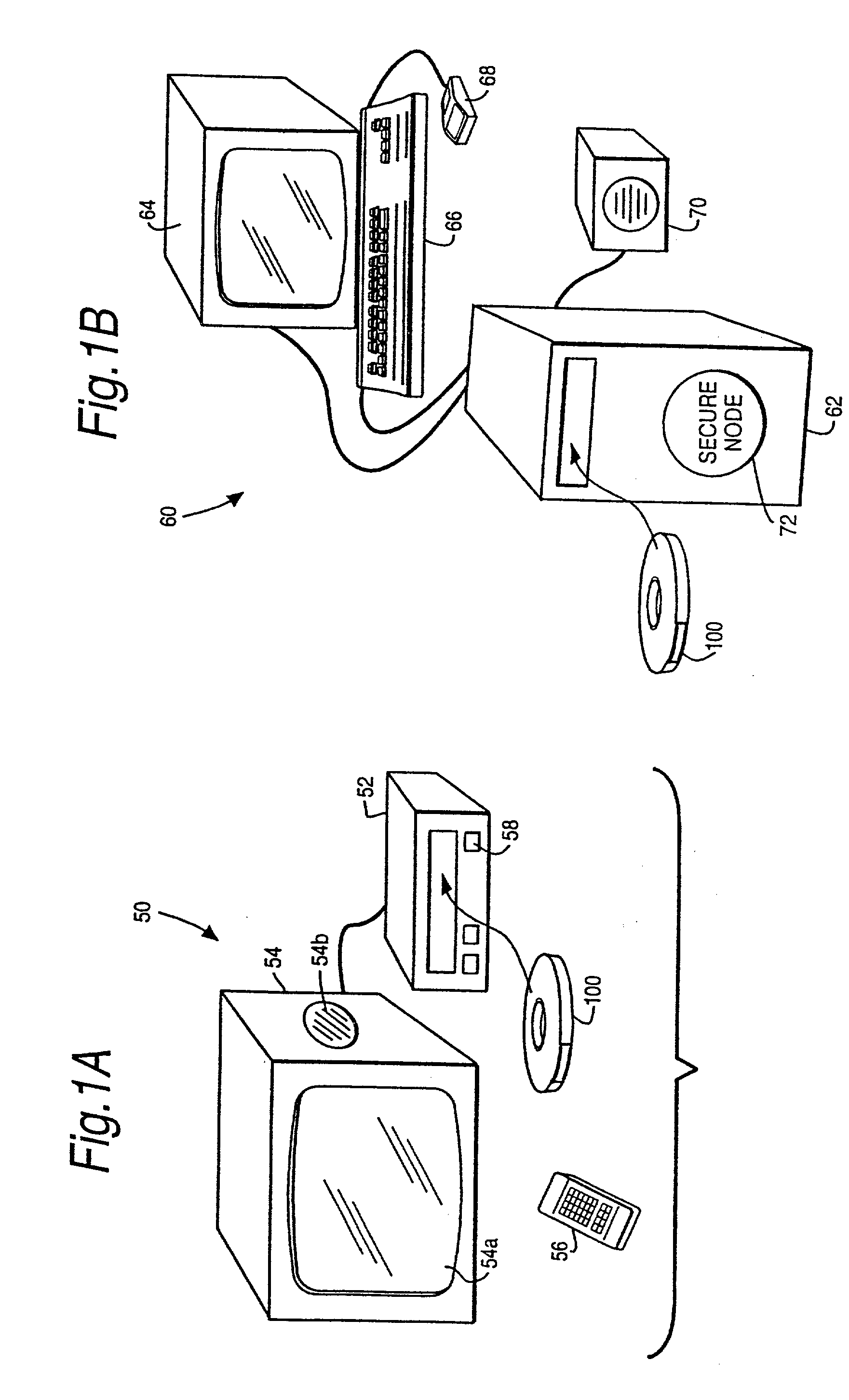
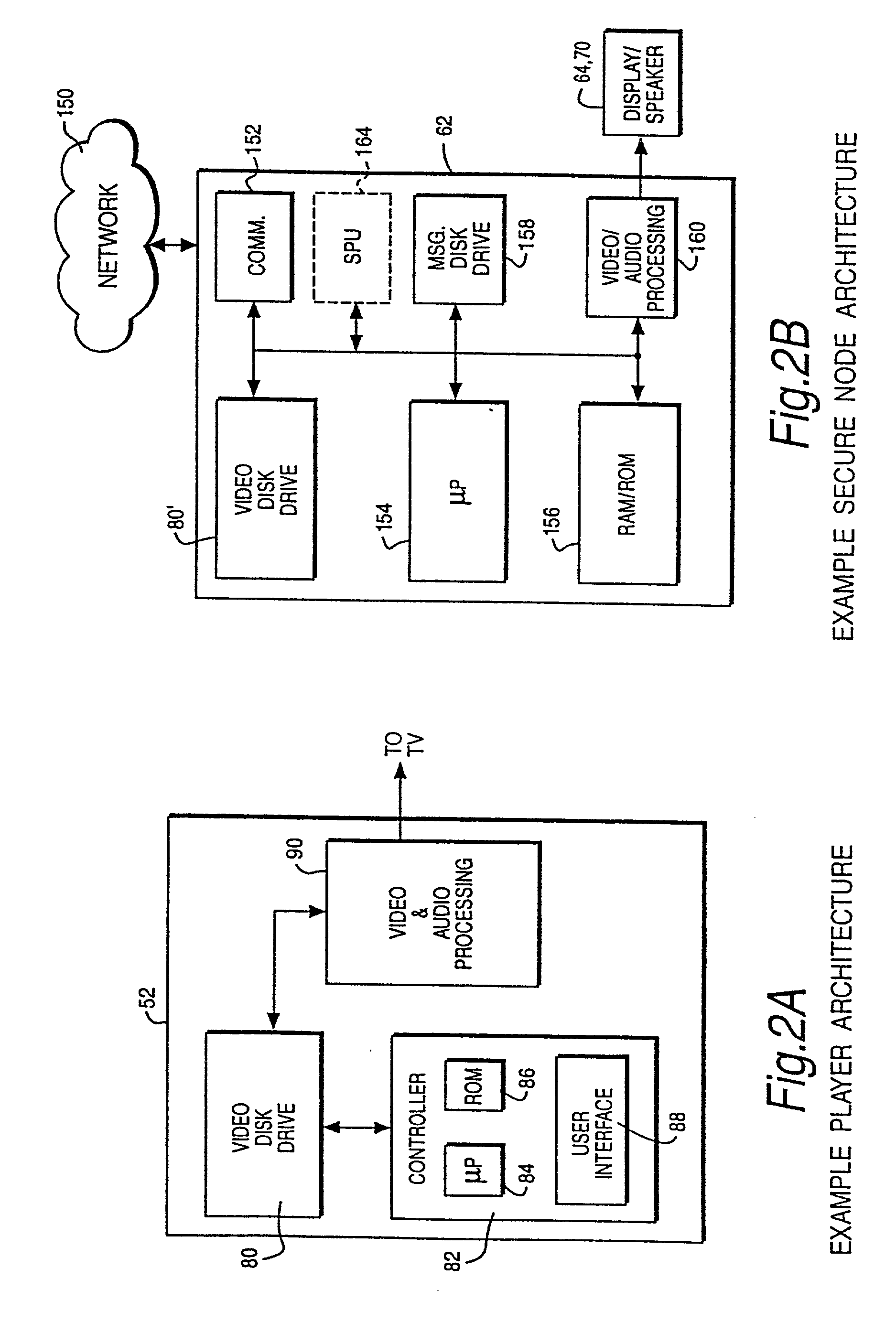
InactiveUS20010042043A1Low costGuaranteed to continue to useTelevision system detailsDigital data processing detailsControl setGeneral purpose
A rights management arrangement for storage media such as optical digital video disks (DVDs, also called digital versatile disks) provides adequate copy protection in a limited, inexpensive mass-produceable, low-capability platform such as a dedicated home consumer disk player and also provides enhanced, more flexible security techniques and methods when the same media are used with platforms having higher security capabilities. A control object (or set) defines plural rights management rules for instance, price for performance or rules governing redistribution. Low capability platforms may enable only a subset of the control rules such as controls on copying or marking of played material. Higher capability platforms may enable all (or different subsets) of the rules. Cryptographically strong security is provided by encrypting at least some of the information carried by the media and enabling decryption based on the control set and / or other limitations. A secure "software container" can be used to protectively encapsulate (e.g., by cryptographic techniques) various digital property content (e.g., audio, video, game, etc.) and control object (i.e., set of rules) information. A standardized container format is provided for general use on / with various mediums and platforms. In addition, a special purpose container may be provided for DVD medium and appliances (e.g., recorders, players, etc.) that contains DVD program content (digital property) and DVD medium specific rules. The techniques, systems and methods disclosed herein are capable of achieving compatibility with other protection standards, such as for example, CGMA and Matsushita data protection standards adopted for DVDs. Cooperative rights management may also be provided, where plural networked rights management arrangements collectively control a rights management event on one or more of such arrangements.
Owner:INTERTRUST TECH CORP
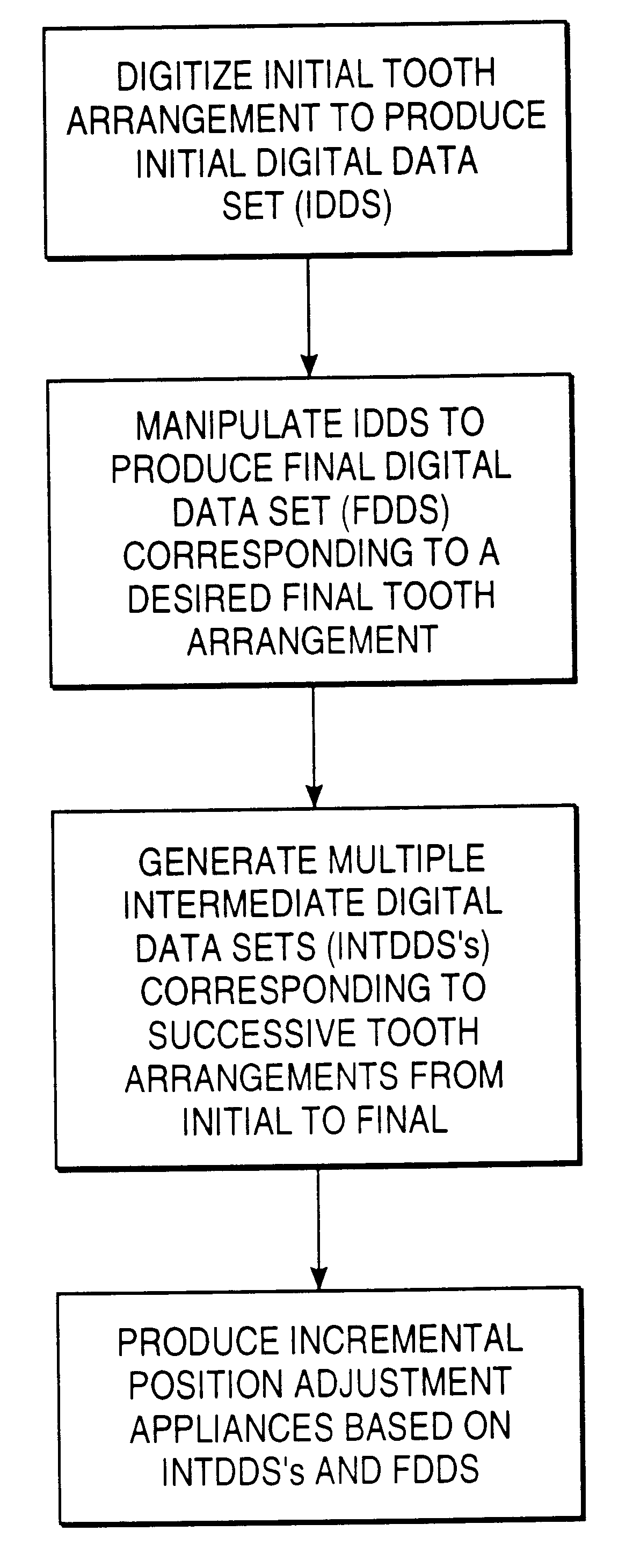
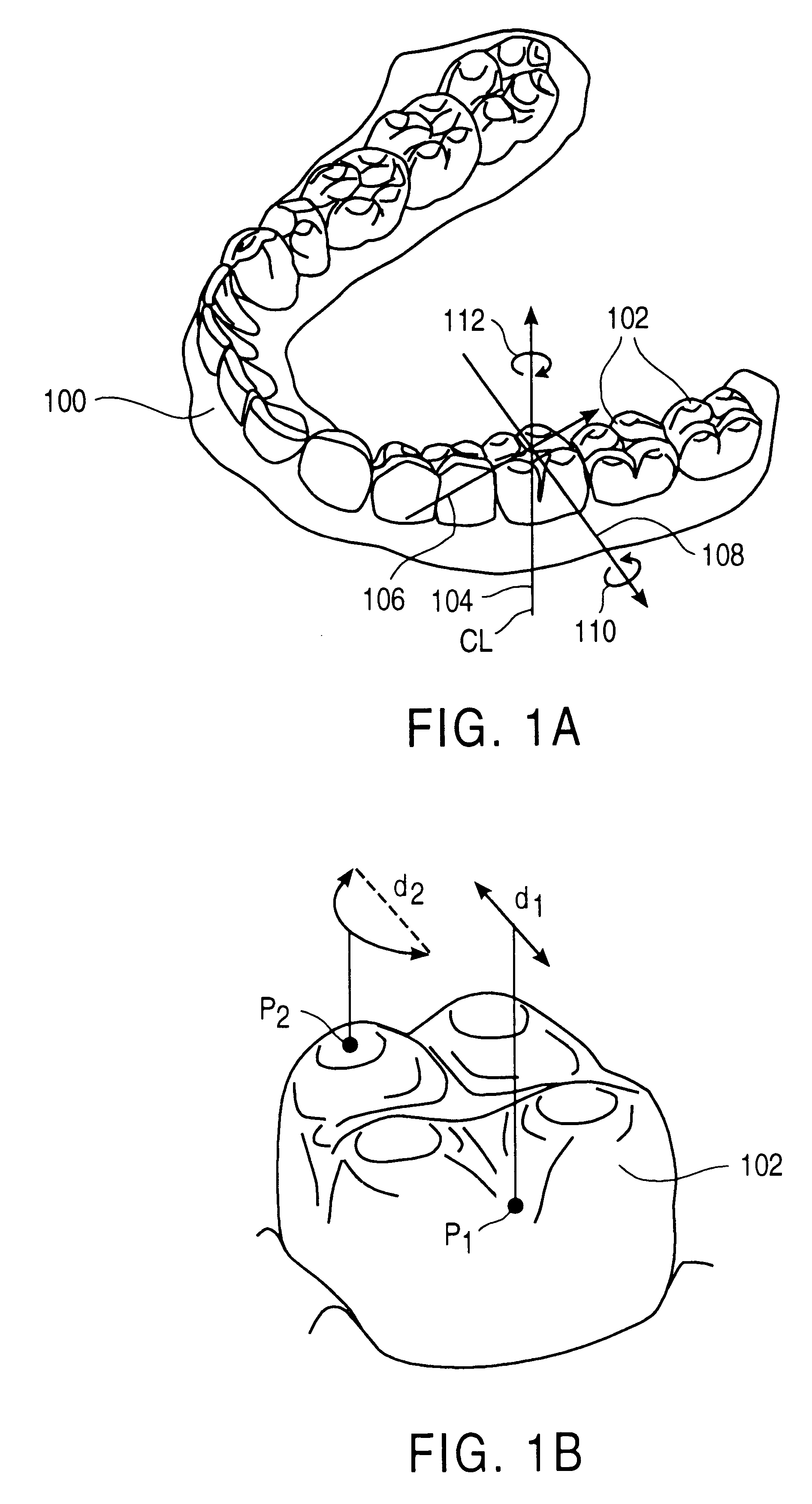
Method and system for incrementally moving teeth
A system for repositioning teeth comprises a plurality of individual appliances. The appliances are configured to be placed successively on the patient's teeth and to incrementally reposition the teeth from an initial tooth arrangement, through a plurality of intermediate tooth arrangements, and to a final tooth arrangement. The system of appliances is usually configured at the outset of treatment so that the patient may progress through treatment without the need to have the treating professional perform each successive step in the procedure.
Owner:ALIGN TECH
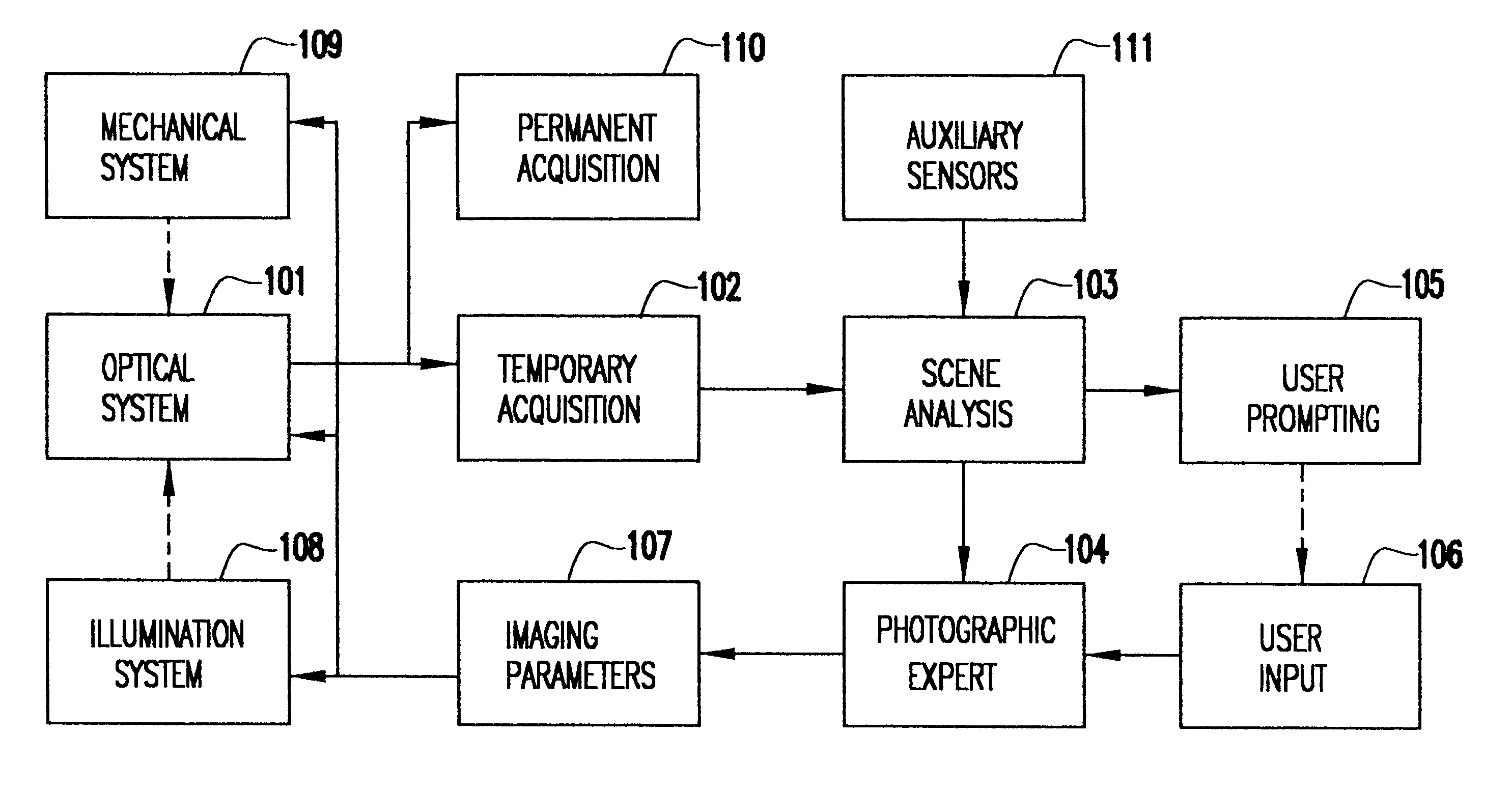
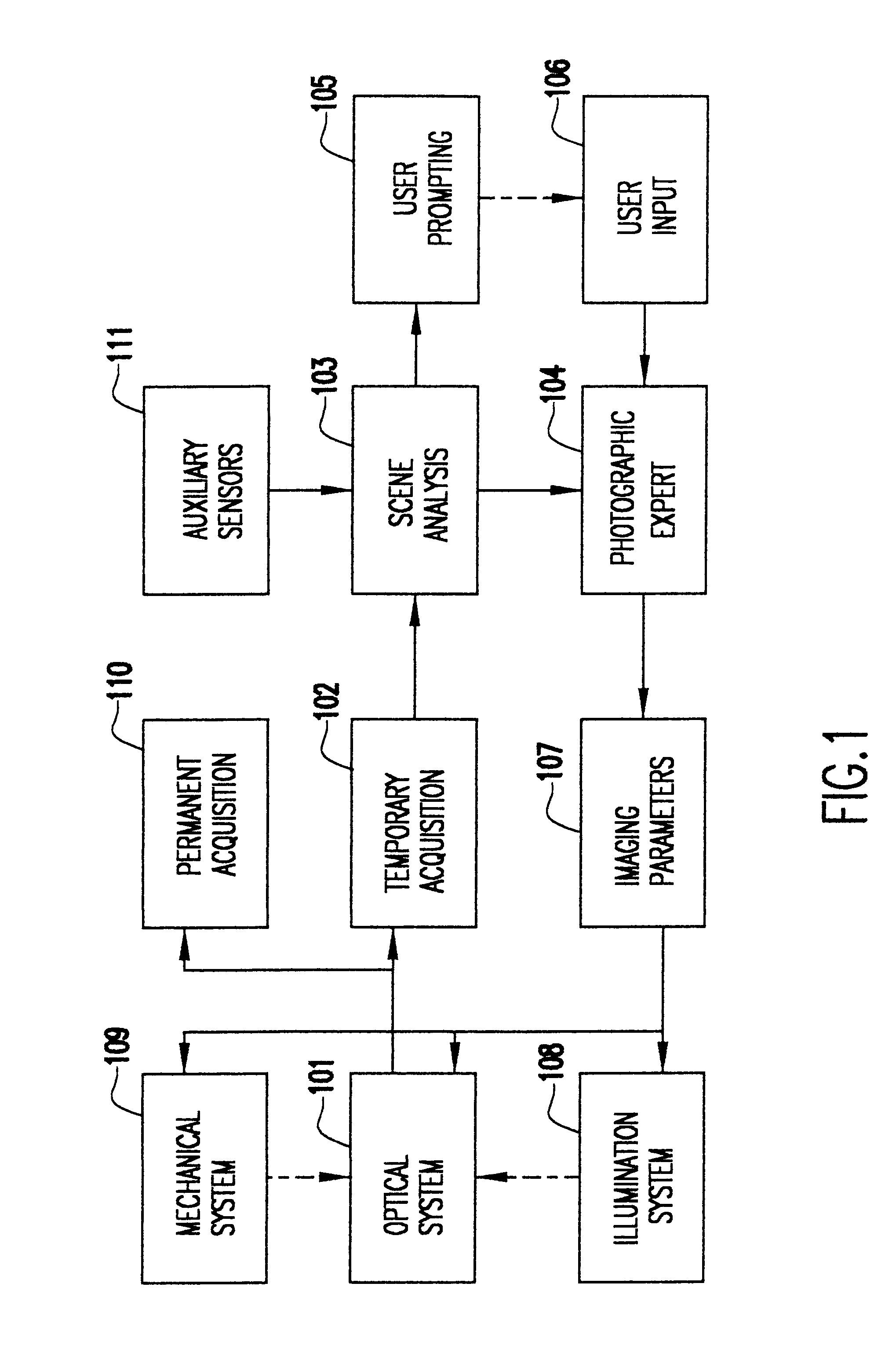
System and method for automatically setting image acquisition controls
InactiveUS6301440B1Television system detailsProjector focusing arrangementSubject matterComputer image
A system and method use computer image processing for setting the parameters for an image acquisition device of a camera. The image parameters are set automatically by analyzing the image to be taken, and setting the controls according to the subject matter, in the same manner as an expert photographer would be able to. The system can run in a fully automatic mode choosing the best image parameters, or a "guided mode" where the user is prompted with choices where a number of alternate settings would be reasonable.
Owner:ASML NETHERLANDS BV +1
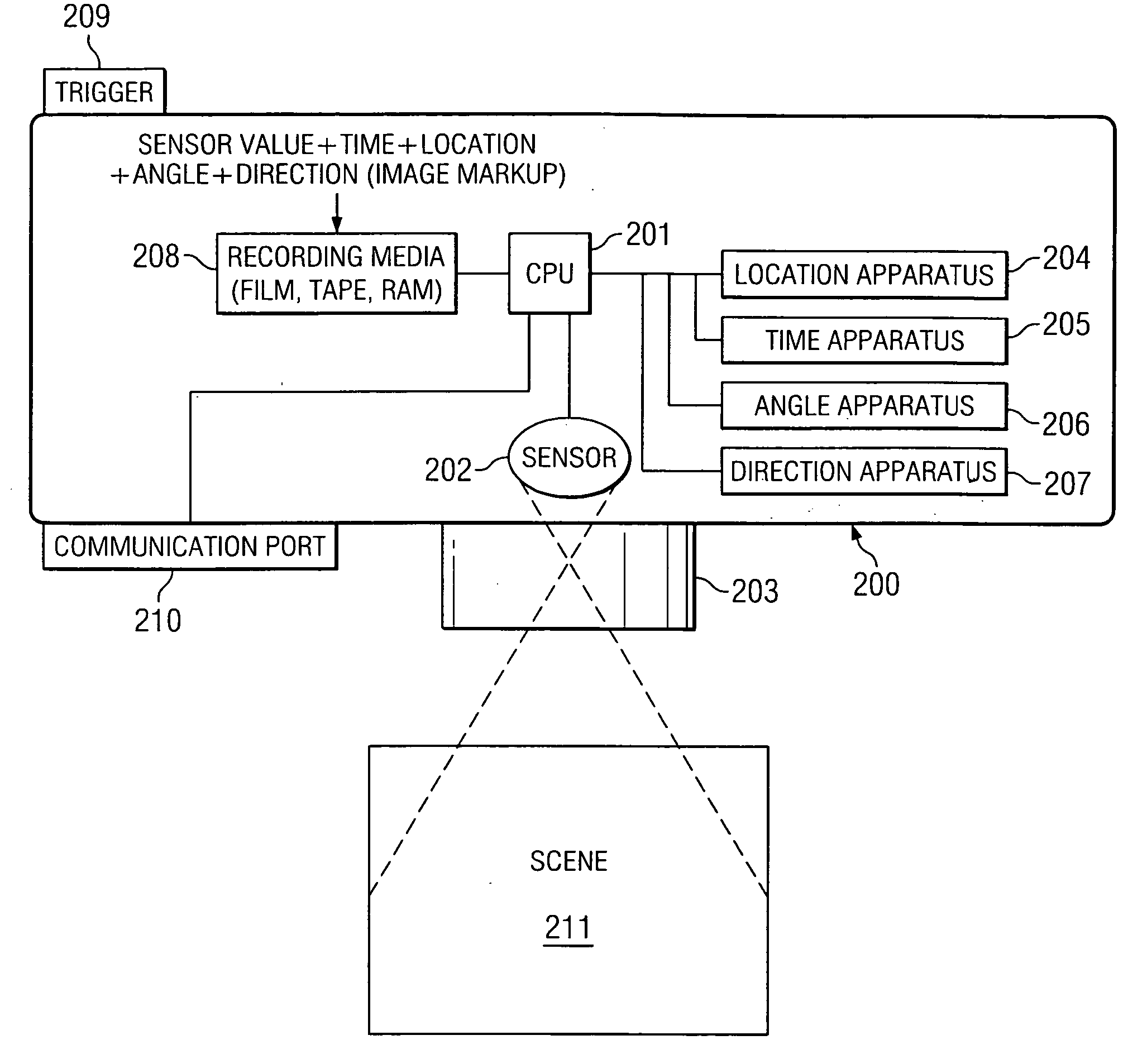
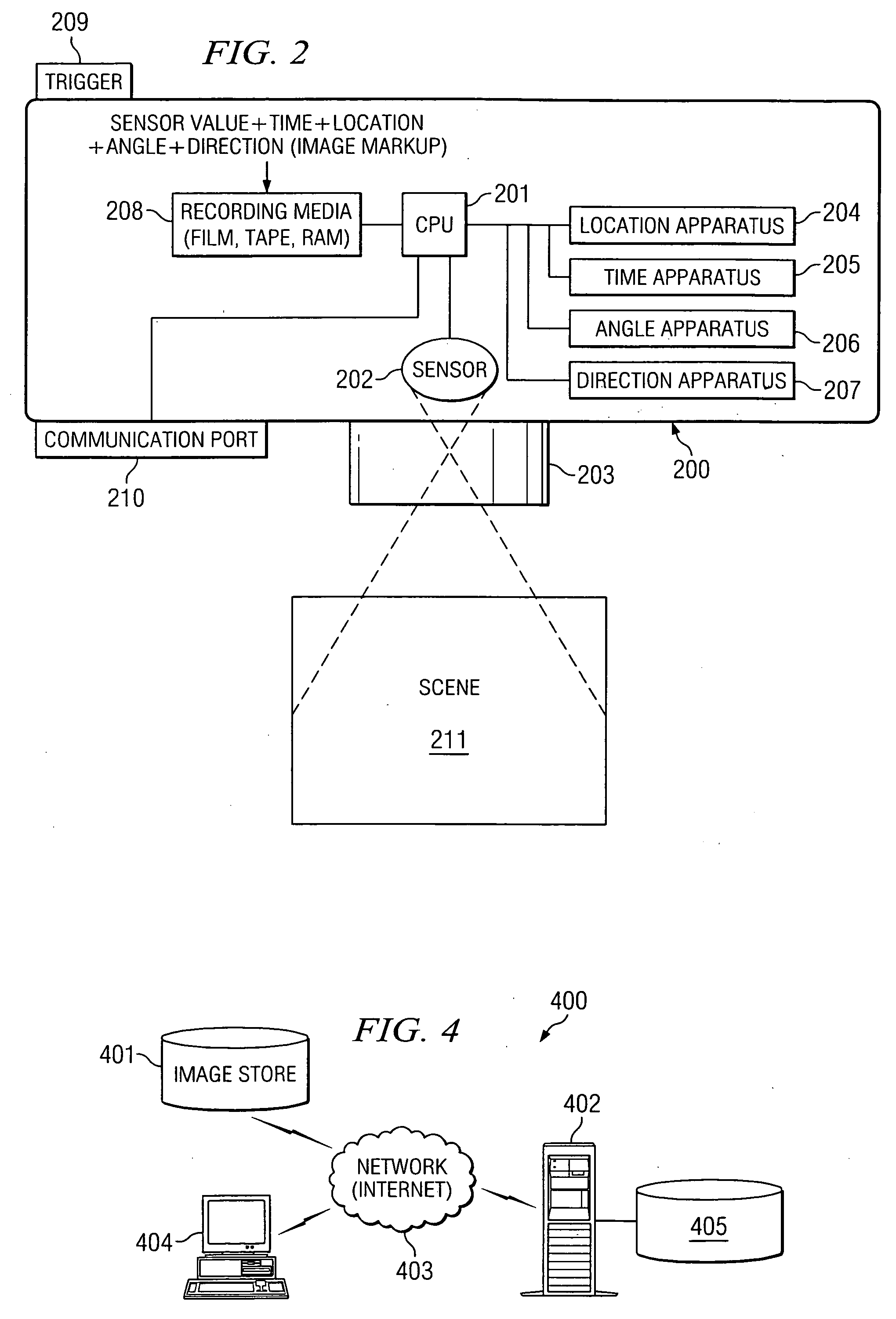
System and method for applying inference information to digital camera metadata to identify digital picture content
InactiveUS20050104976A1Television system detailsColor television signals processingDigital picturesInformation searching
The present invention is directed to a system and method for correlating an image with information associated with the image comprising identifying image metadata for the image, wherein the image metadata includes information associated with conditions at the time of image capture, searching one or more information sources using parameters in the image metadata to collect inference information from the information sources, and displaying the inference information to a user.
Owner:HEWLETT PACKARD DEV CO LP
Apparatus and method for digital filing
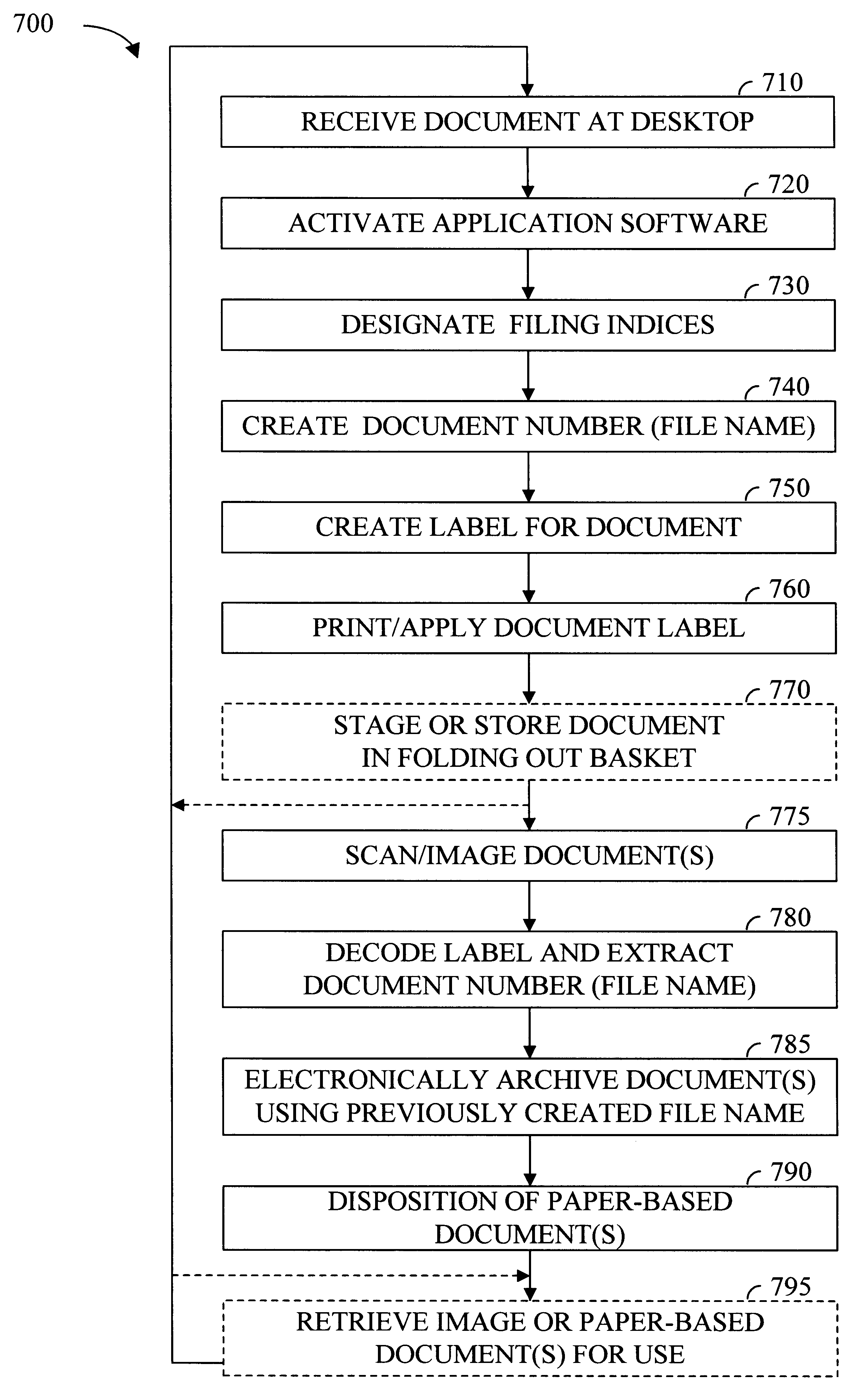
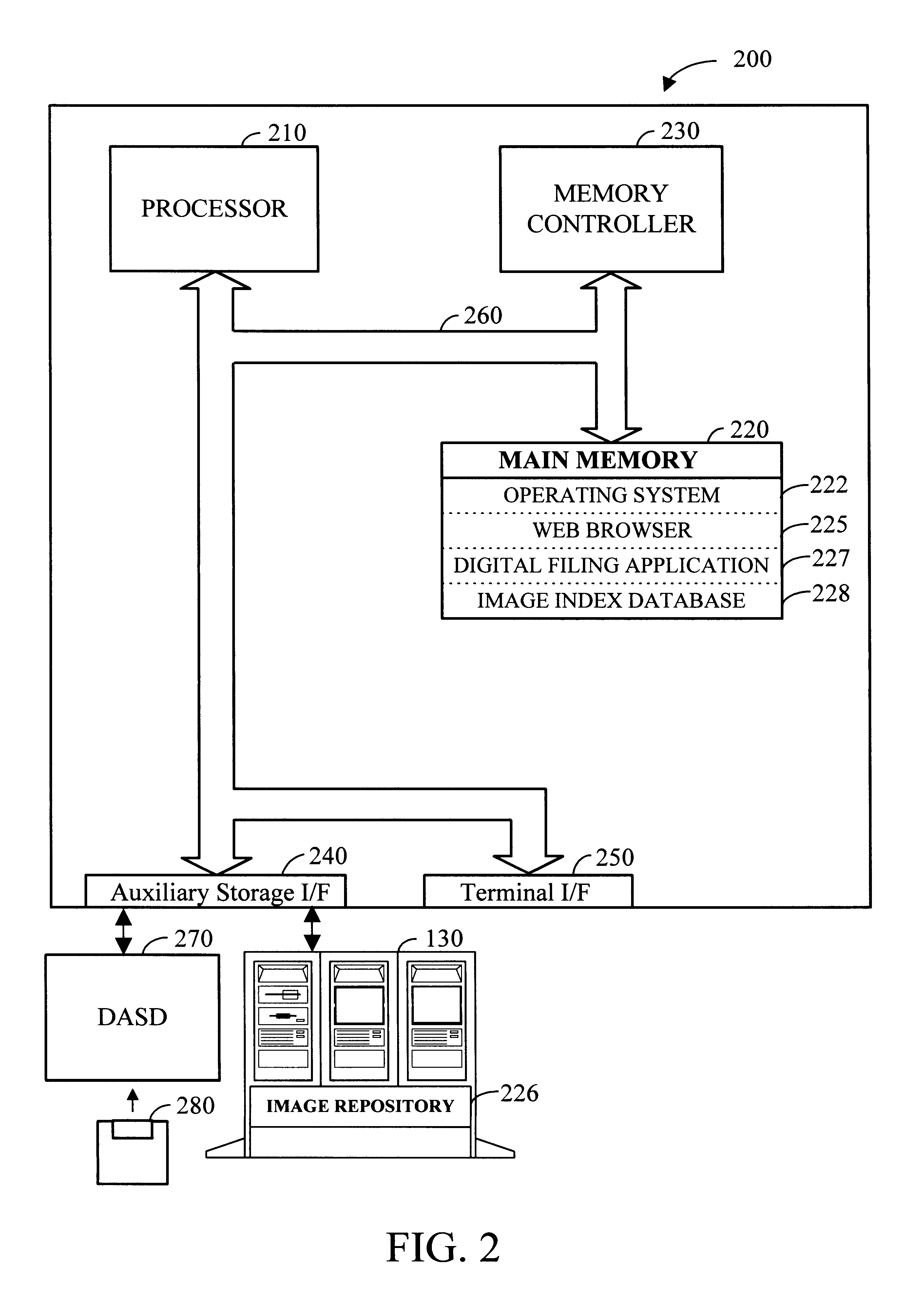
InactiveUS6192165B1Easy and effective and imagingEasy and effective indexingData processing applicationsDigital computer detailsElectronic documentWeb browser
According to the preferred embodiments of the present invention, an apparatus and method for a digital filing system is disclosed. In this context, digital filing refers to the efficient management of paper-based information from its receipt at the desktop through an indexing, scanning, image storage and image retrieval process. The preferred embodiments of the present invention provide for easy and effective indexing, imaging, storing, retrieving and managing of paper-based documents, transforming them into electronic documents using a system which incorporates many existing office resources. The proposed system and method implements a desktop solution for digital filing, which can be made available to each worker. In one embodiment of the present invention, an individual has complete control over the electronic storage and retrieval of their documents from a standard desktop computer, using a standard web browser application. Uniquely, the digital filing system of the present invention also allows users to index and label documents prior to scanning / imaging by using a dedicated desktop labeling mechanism.
Owner:IMAGETAG
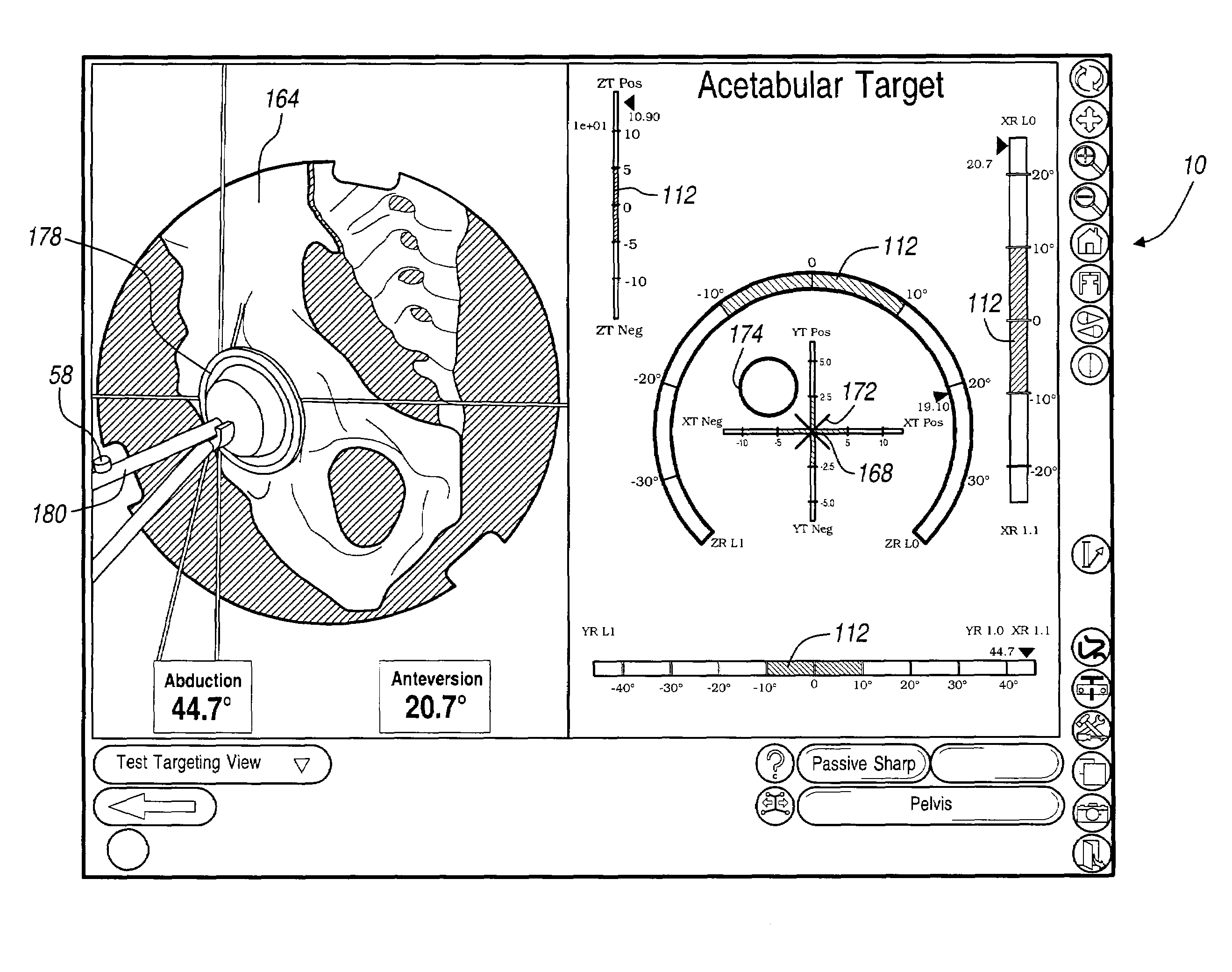
Six degree of freedom alignment display for medical procedures
A display and navigation system for use in guiding a medical device to a target in a patient includes a tracking sensor, a tracking device and display. The tracking sensor is associated with the medical device and is used to track the medical device. The tracking device tracks the medical device with the tracking sensor. The display includes indicia illustrating at least five degree of freedom information and indicia of the medical device in relation to the five degree of freedom information.
Owner:SURGICAL NAVIGATION TECH
Methods and arrangements for identifying objects
ActiveUS20130223673A1Increase check-out speedImprove accuracyStatic indicating devicesCash registersPattern recognitionGeometric primitive
In some arrangements, product packaging is digitally watermarked over most of its extent to facilitate high-throughput item identification at retail checkouts. Imagery captured by conventional or plenoptic cameras can be processed (e.g., by GPUs) to derive several different perspective-transformed views—further minimizing the need to manually reposition items for identification. Crinkles and other deformations in product packaging can be optically sensed, allowing such surfaces to be virtually flattened to aid identification. Piles of items can be 3D-modelled and virtually segmented into geometric primitives to aid identification, and to discover locations of obscured items. Other data (e.g., including data from sensors in aisles, shelves and carts, and gaze tracking for clues about visual saliency) can be used in assessing identification hypotheses about an item. A great variety of other features and arrangements are also detailed.
Owner:DIGIMARC CORP
System and method for constructing three-dimensional images using camera-based gesture inputs
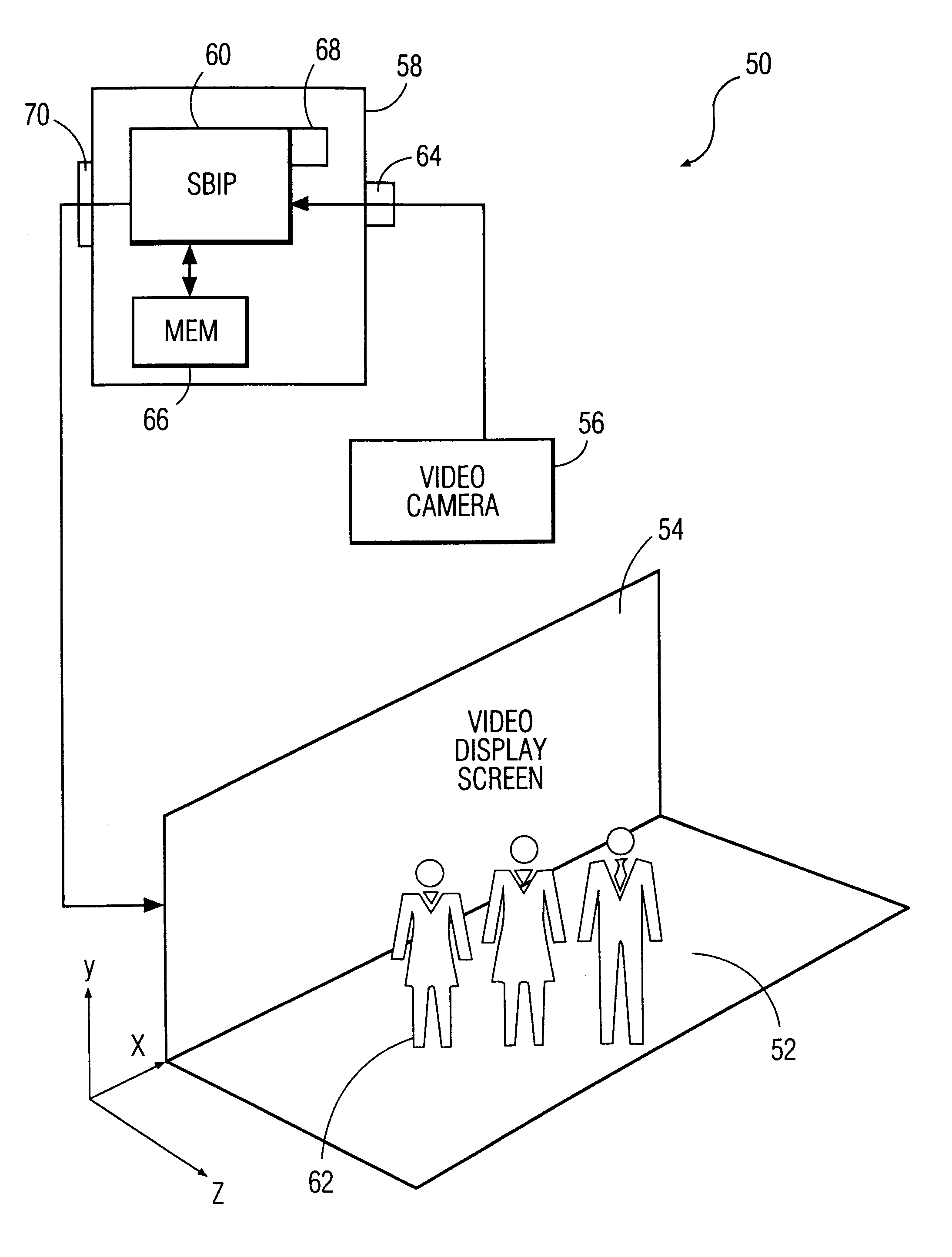
InactiveUS6195104B1Input/output for user-computer interactionTelevision system detailsBody areaDisplay device
A system and method for constructing three-dimensional images using camera-based gesture inputs of a system user. The system comprises a computer-readable memory, a video camera for generating video signals indicative of the gestures of the system user and an interaction area surrounding the system user, and a video image display. The video image display is positioned in front of the system users. The system further comprises a microprocessor for processing the video signals, in accordance with a program stored in the computer-readable memory, to determine the three-dimensional positions of the body and principle body parts of the system user. The microprocessor constructs three-dimensional images of the system user and interaction area on the video image display based upon the three-dimensional positions of the body and principle body parts of the system user. The video image display shows three-dimensional graphical objects superimposed to appear as if they occupy the interaction area, and movement by the system user causes apparent movement of the superimposed, three-dimensional objects displayed on the video image display.
Owner:PHILIPS ELECTRONICS NORTH AMERICA
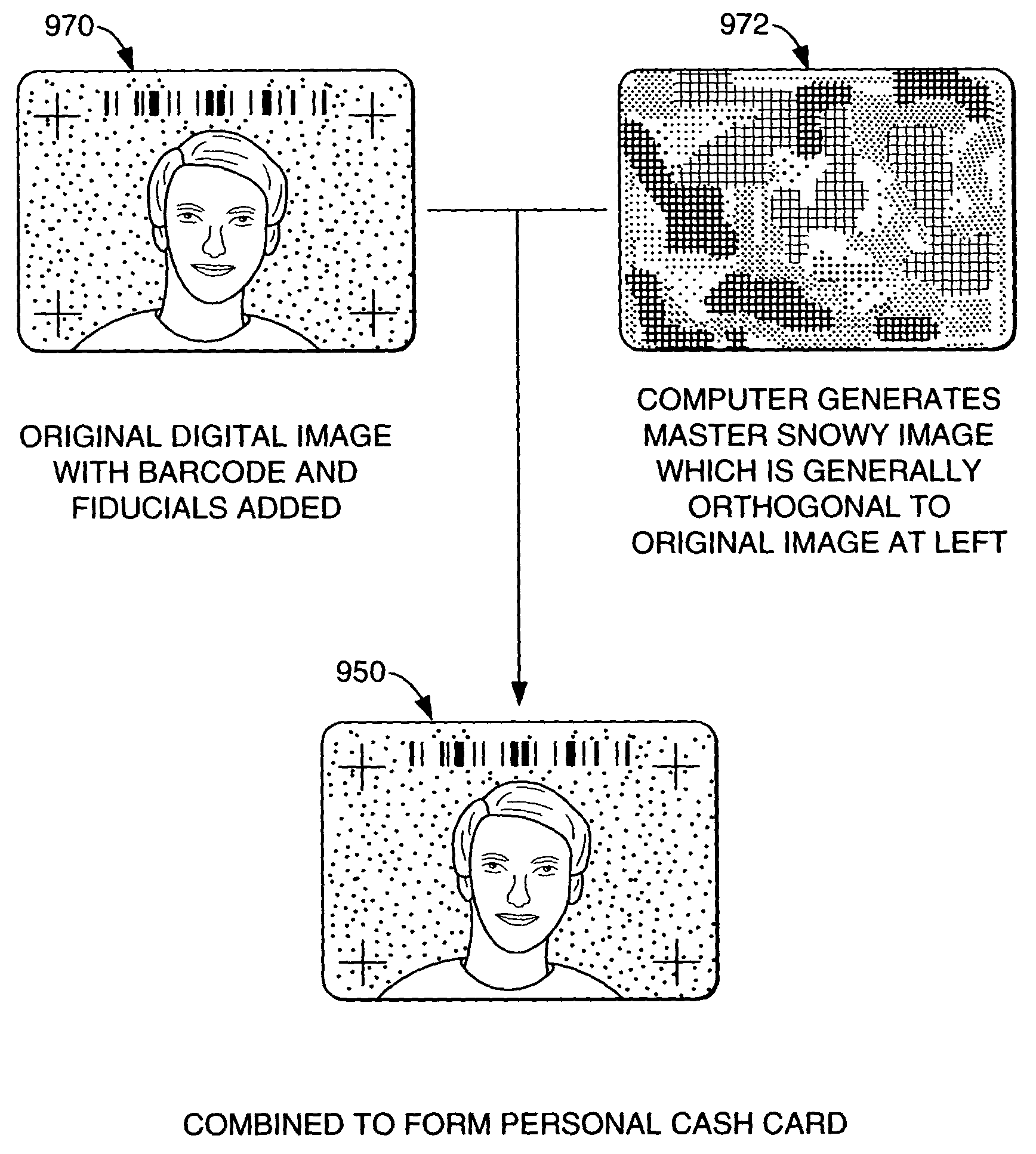
Digital authentication with digital and analog documents
InactiveUS20040153649A1More dataCompact formDigitally marking record carriersDigital data processing detailsAuthentication information
The disclosure describes systems for creating and authenticating printed objects using authentication information. Techniques for incorporating authentication information into digital representations of objects and using the authentication information to authenticate the objects are also provided.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
Method and system for securing local database file of local content stored on end-user system
InactiveUS20020002468A1Digital data processing detailsUnauthorized memory use protectionDatasheetDigital content
A method and system for forming a data table in memory on an end user system. The data table forming a library index of storage locations to electronic digital content in memory. The method consists of retrieving an encrypted file from storage. The file has a beginning, an end and a trailer section located just prior to the end. The file is read from the end a predetermined distance to verify if an identifier is present. Reading and decrypting the trailer section from the file read. Determining if there are any updates in the trailer section. In the case there are no updates in the trailer section then decrypting the reference table containing one or more data table location indicators for data items with the first decrypting key. Next, decrypting one or data items with the first decrypting key. Populating the data table with data items at locations specified in the reference table.
Owner:IBM CORP
Method and apparatus for the generation of computer graphic representations of individuals
InactiveUS7184047B1Color signal processing circuitsCharacter and pattern recognitionGraphicsThe Internet
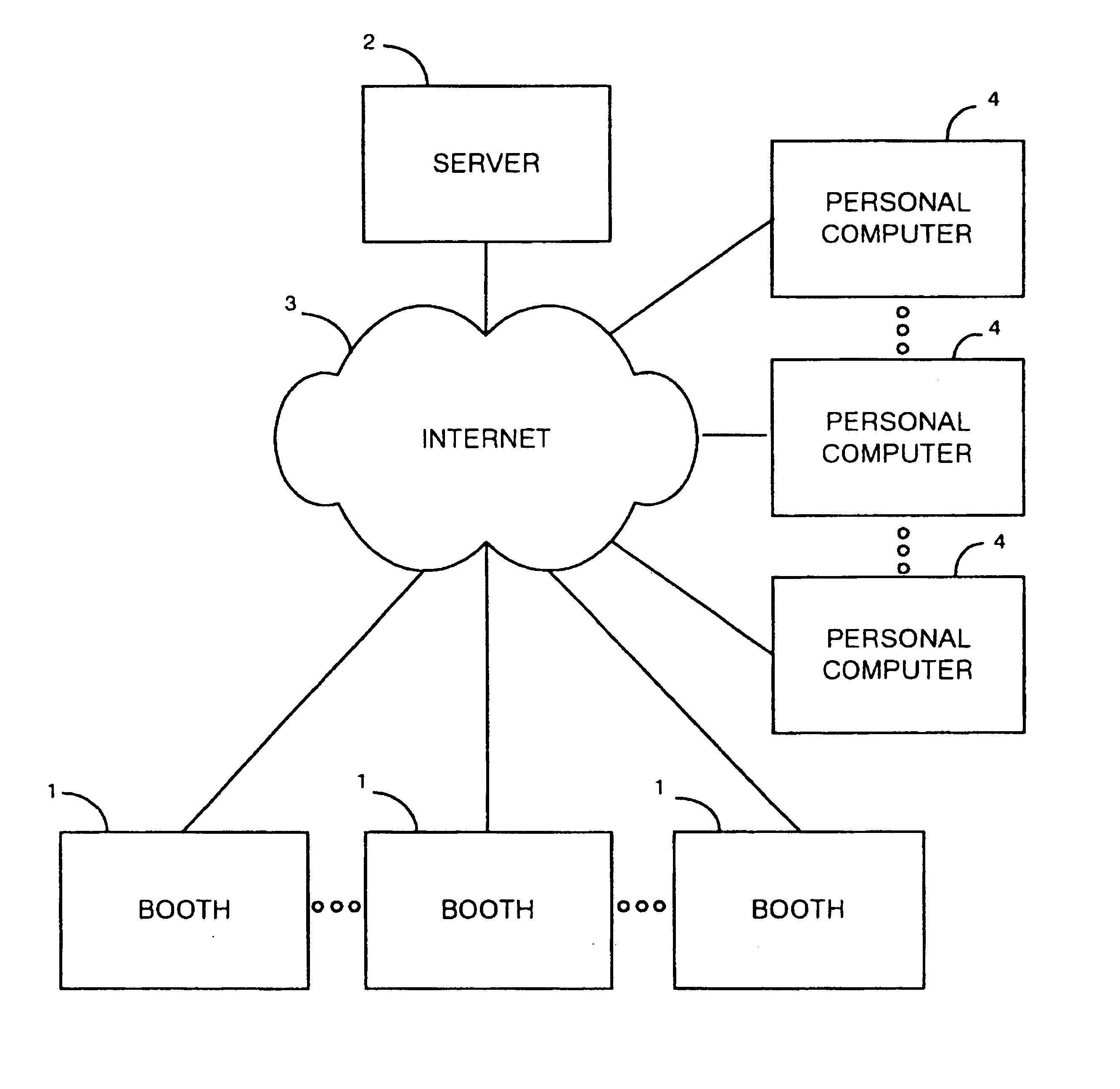
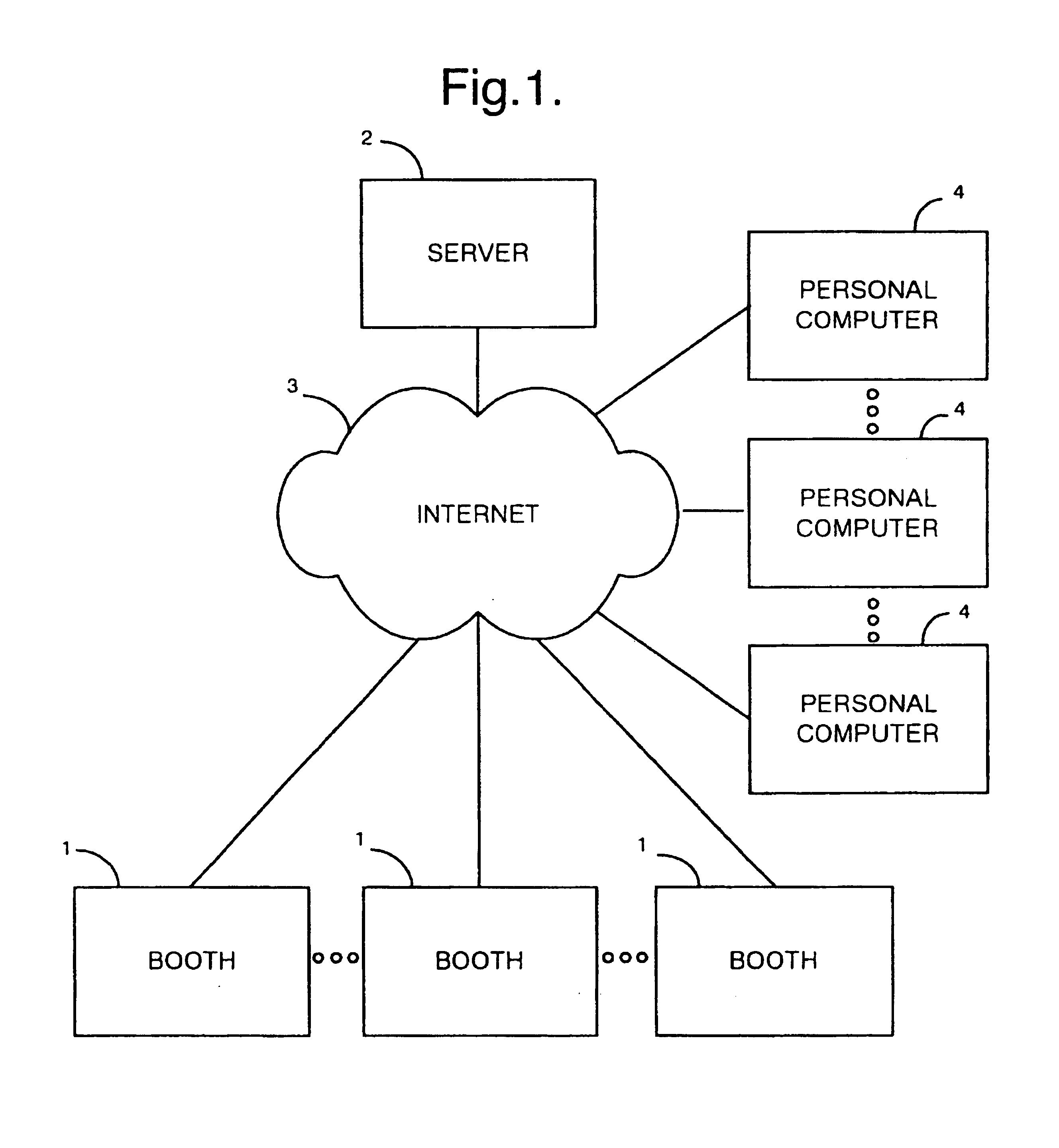
Apparatus for generating computer models of individuals is provided comprising a booth (1) that is connected to a server (2) via the Internet (3). Image data of an individual is captured using the booth (1) and a computer model corresponding to the individual is then generated by comparing the captured image data relative to a stored generic model. Data representative of a generated model is then transmitted to the server (2) where it is stored. Stored data can then be retrieved via the Internet using a personal computer (4) having application software stored therein. The application software on the personal computer (4) can then utilise the data to create graphic representations of an individual in any one of a number of poses.
Owner:CRAMPTON STEPHEN JAMES
Associating data with images in imaging systems
InactiveUS7010144B1Data processing applicationsUser identity/authority verificationExternal storageImage capture
A steganographic embedder associates data with an image by encoding the data, a link to the data, or a combination of both into the image. The embedder may be located in an image capture device or an external process or device. In one application, for example, an embedder process steganographically encodes data into an image as part of the process of uploading the image from the image capture device to external storage.
Owner:DIGIMARC CORP
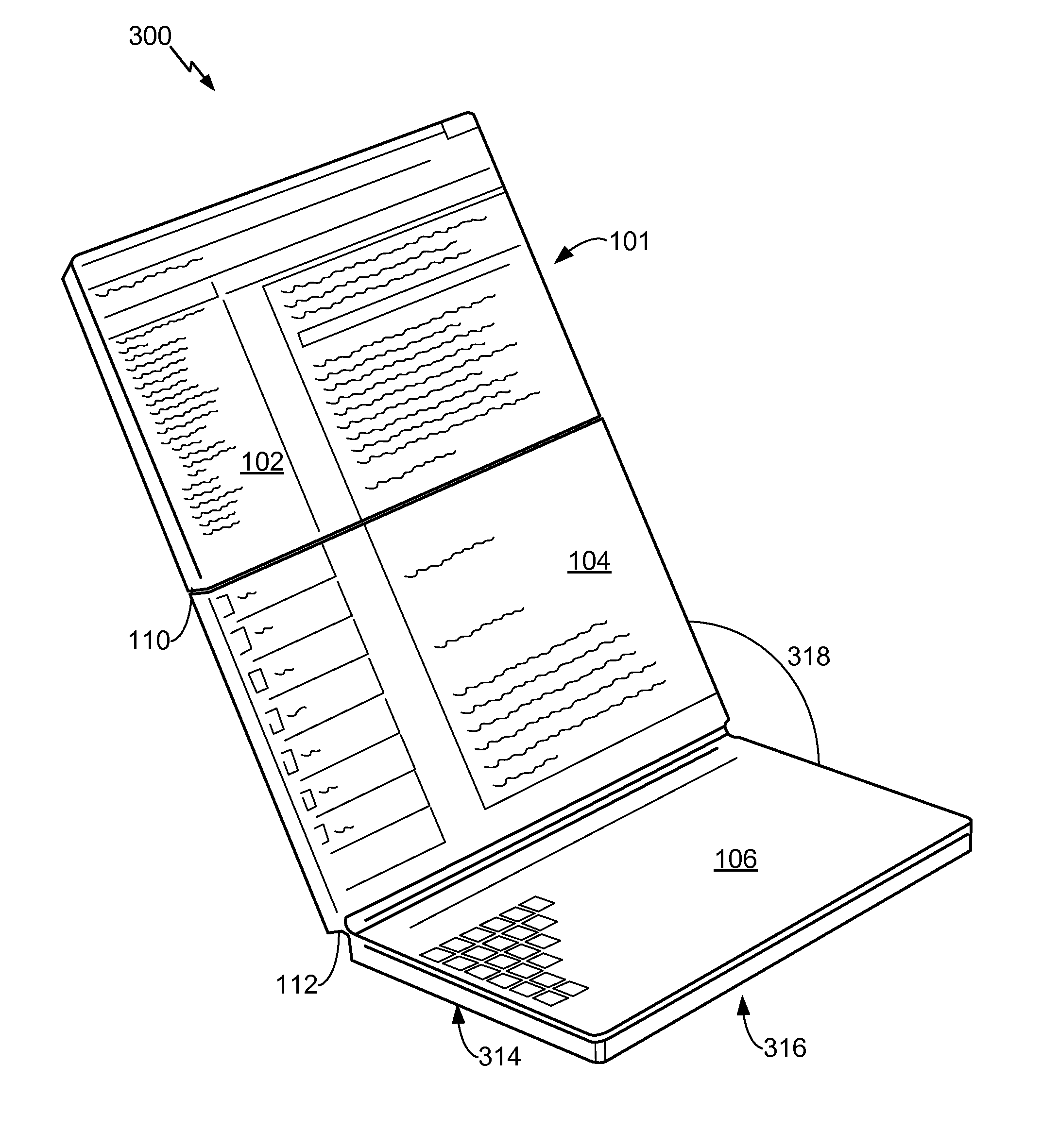
Sending a parameter based on screen size or screen resolution of a multi-panel electronic device to a server
ActiveUS20110216064A1Easy to operateDevices with multiple display unitsStatic indicating devicesComputer hardwareImage resolution
In a particular embodiment, a method includes detecting a hardware configuration change at an electronic device. The electronic device includes at least a first panel having a first display surface and a second panel having a second display surface. An effective screen size or a screen resolution corresponding to a viewing area that includes the first display surface and the second display surface is modified in response to the hardware configuration change. The method also includes sending at least one parameter associated with or based on the modified effective screen size or the modified screen resolution to a server.
Owner:QUALCOMM INC
System and method of recording and displaying in context of an image a location of at least one point-of-interest in a body during an intra-body medical procedure
The present invention provides a method of recording and displaying in context of an image a location of at least one point-of-interest in a body during an intra-body medical procedure. The method is effected by (a) establishing a location of the body; (b) inserting at least one catheter into a portion of the body, the at least one catheter including a first location implement; (c) using an imaging instrument for imaging the portion of the body; (d) establishing a location of the imaging instrument; (e) advancing the at least one catheter to at least one point-of-interest in the portion of the body and via a locating implement recording a location of the at least one point-of-interest; and (f) displaying and highlighting the at least one point-of-interest in context of an image of the portion of the body, the image being generated by the imaging instrument; such that, in course of the procedure, the locations of the body, the at least one catheter and the imaging instrument are known, thereby the at least one point-of-interest is projectable and displayable in context of the image even in cases whereby a relative location of the body and the imaging instrument are changed.
Owner:TYCO HEALTHCARE GRP LP
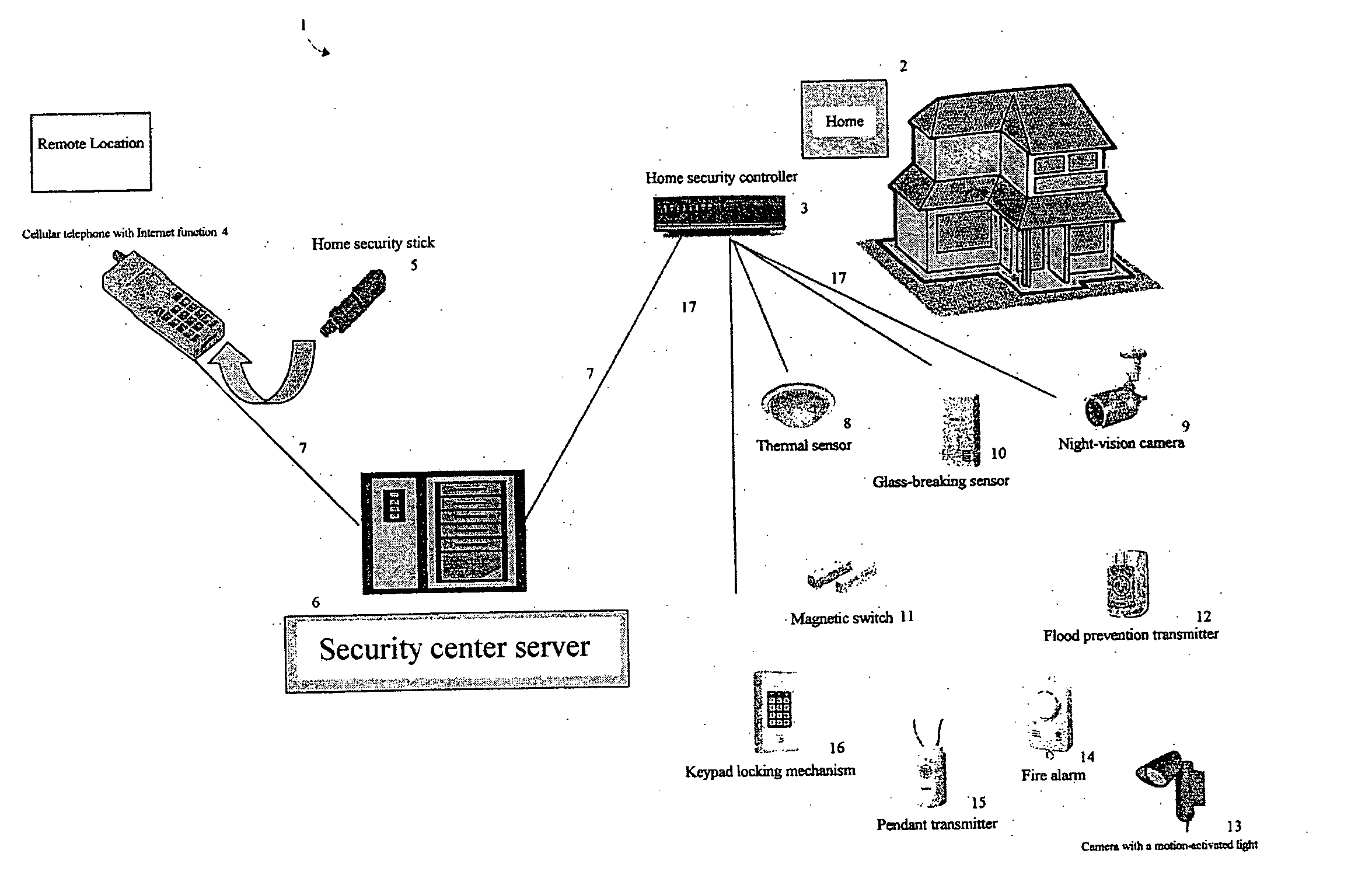
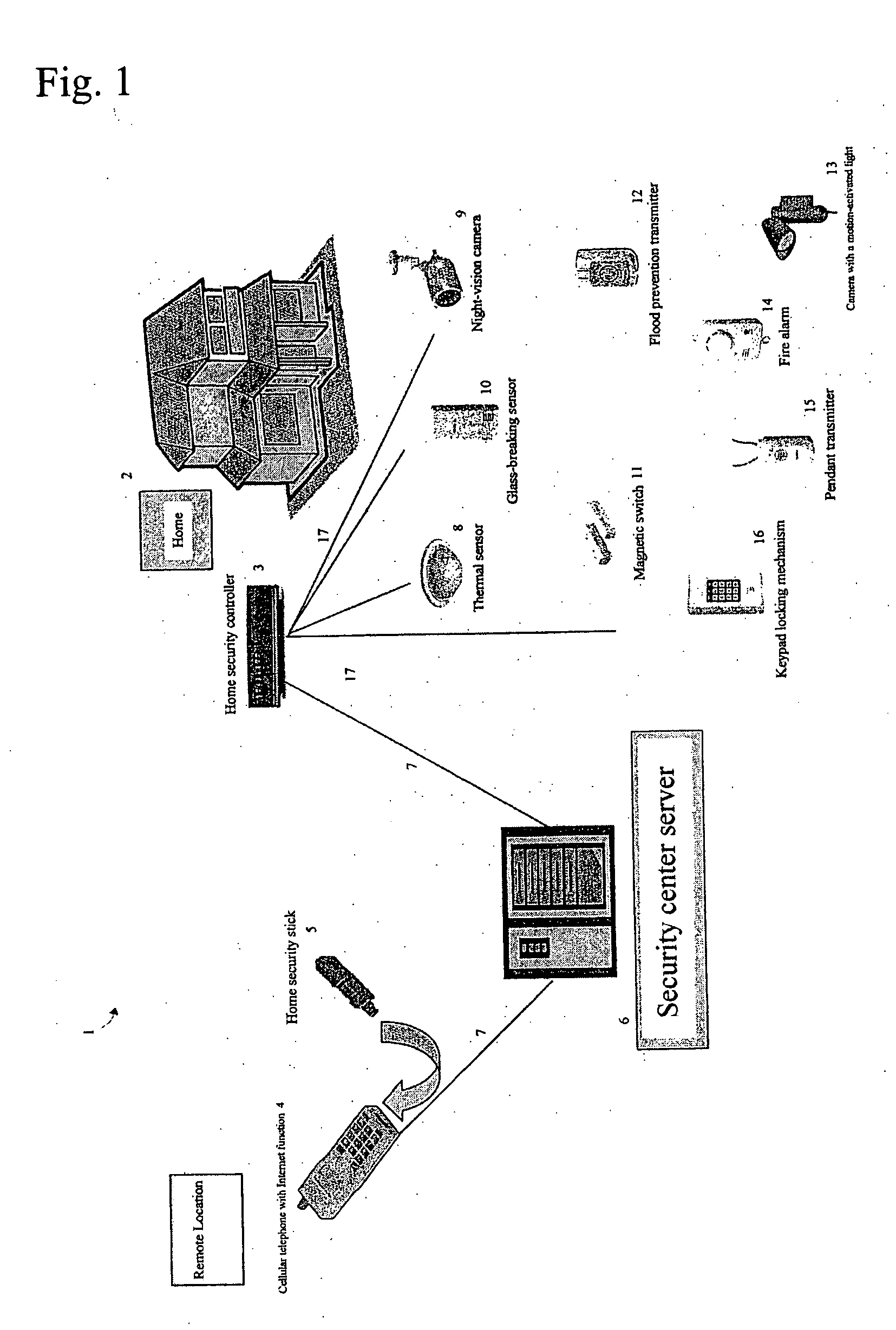
Home security system
InactiveUS20060022816A1Prevent intrusionEasy to operateElectric signal transmission systemsImage analysisRemote controlEngineering
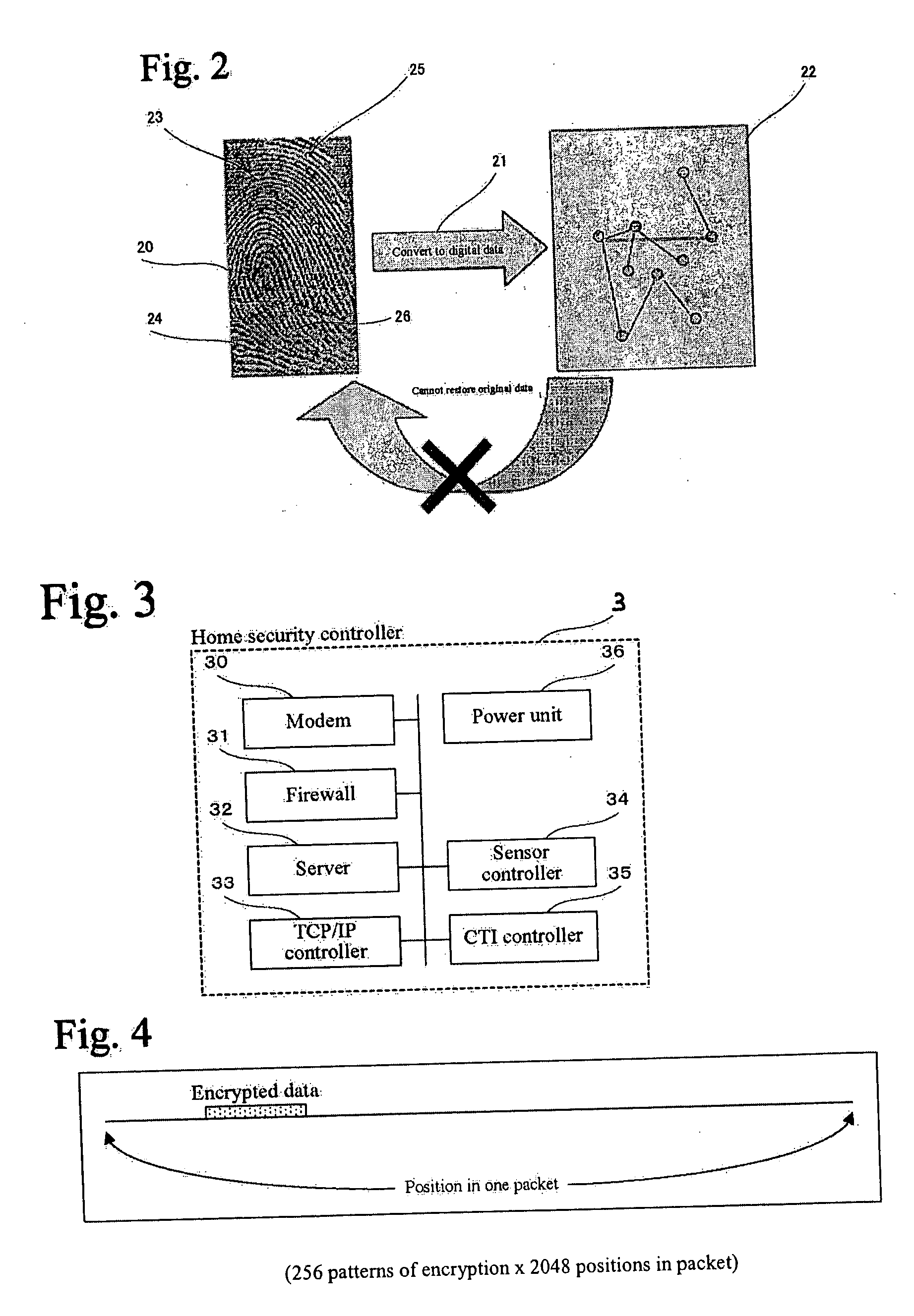
The present invention provides a home security system that includes a home security controller for collecting monitor data from various crime prevention and disaster prevention sensors installed in a home via a home network and notifying the portable terminal when a state of emergency occurs. The home security controller also enables devices in the home to be operated through remote control signals via an external network. The home security system further includes a portable terminal capable of connecting to the external network and having fingerprint data inputting means mounted on the body of the portable terminal for inputting fingerprints used for authentication. The fingerprint data inputting means has an assigned ID number. The home security system further includes a security center server having fingerprint authenticating means for receiving fingerprint data from the portable terminal via the external network and authenticating the fingerprint data through comparisons with registered fingerprint data. The fingerprint authenticating means completes authentication by checking the assigned ID number of the fingerprint data inputting means and matching the received fingerprint data with fingerprint data registered in association with the ID number. The security center server allows a connection between the portable terminal and the home security controller and controls bi-directional communications between the two after the security center server has completed authentication, enabling the portable terminal to receive monitor data from and transmit remote control signals to the home security controller via the external network.
Owner:AMERICAN TECH GRP JAPAN
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com