Patents
Literature
548 results about "Copy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Copy protection, also known as content protection, copy prevention and copy restriction, is any effort designed to prevent the reproduction of software, films, music, and other media, usually for copyright reasons. Various methods have been devised to prevent reproduction so that companies will gain benefit from each person who obtains an authorized copy of their product. Unauthorized copying and distribution accounted for $2.4 billion in lost revenue in the United States alone in the 1990s, and is assumed to be causing impact on revenues in the music and the game industry, leading to proposal of stricter copyright laws such as PIPA. Some methods of copy protection have also led to criticisms because it caused inconvenience for honest consumers, or it secretly installed additional or unwanted software to detect copying activities on the consumer's computer. Making copy protection effective while protecting consumer rights is still an ongoing problem with media publication.
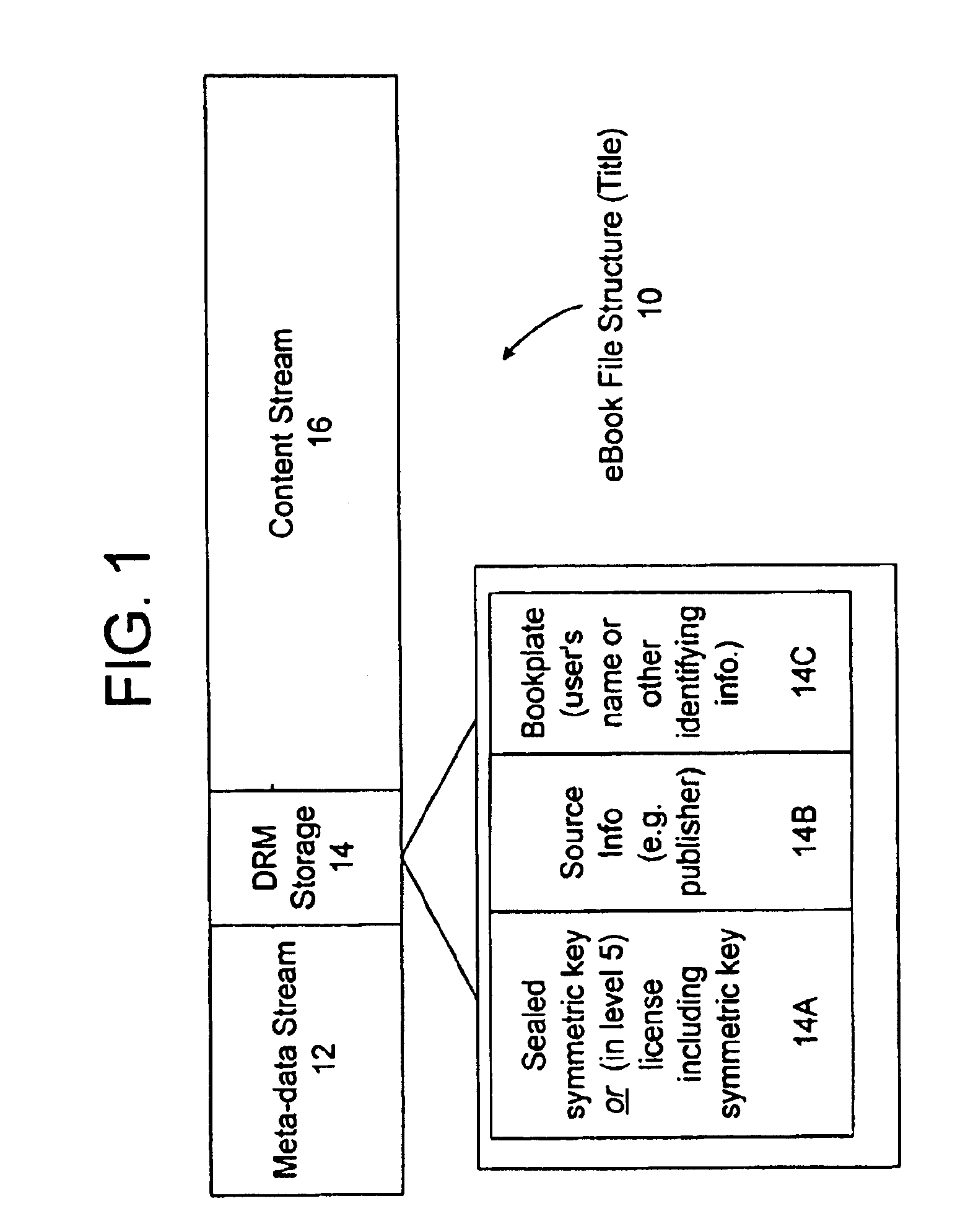
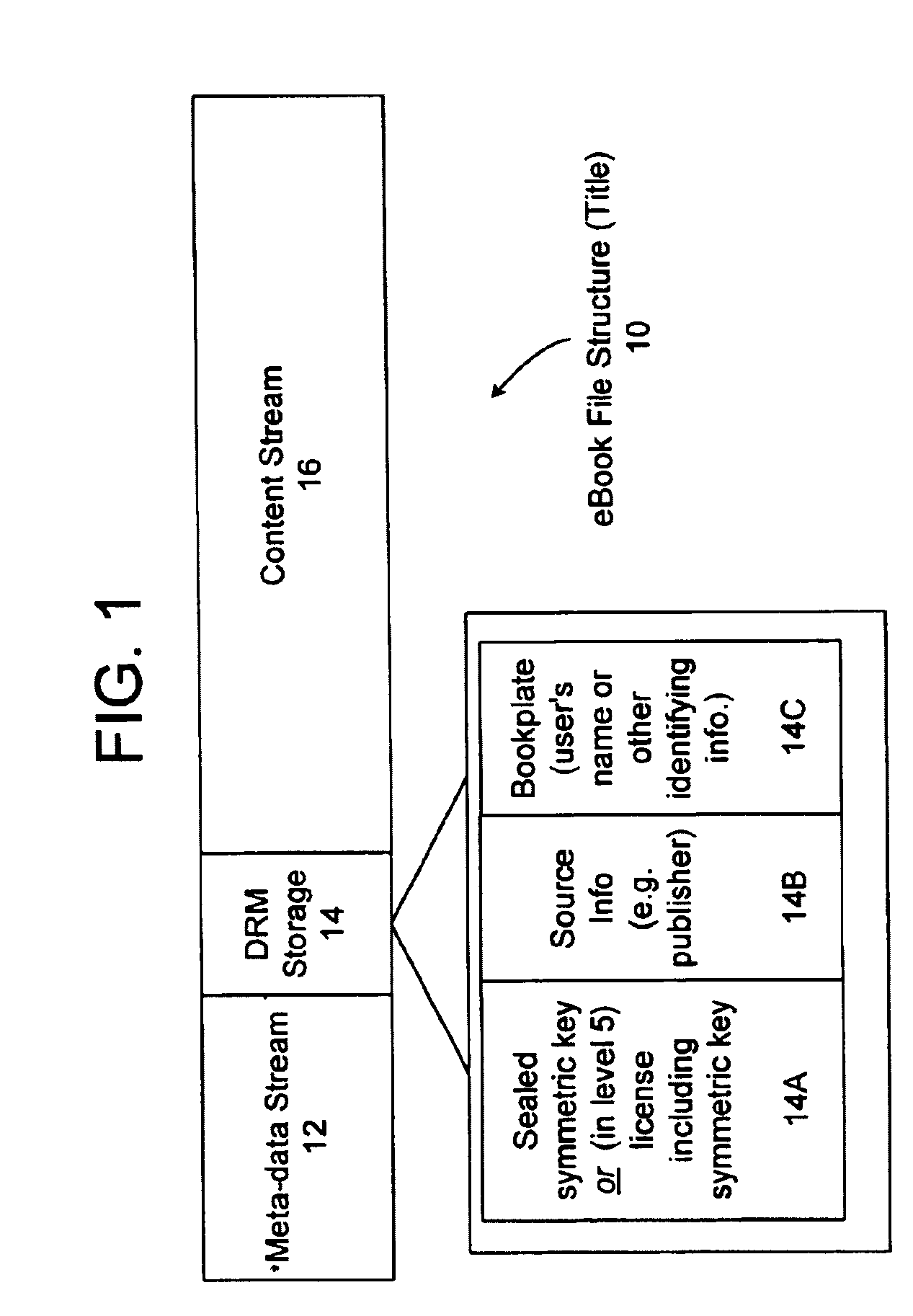
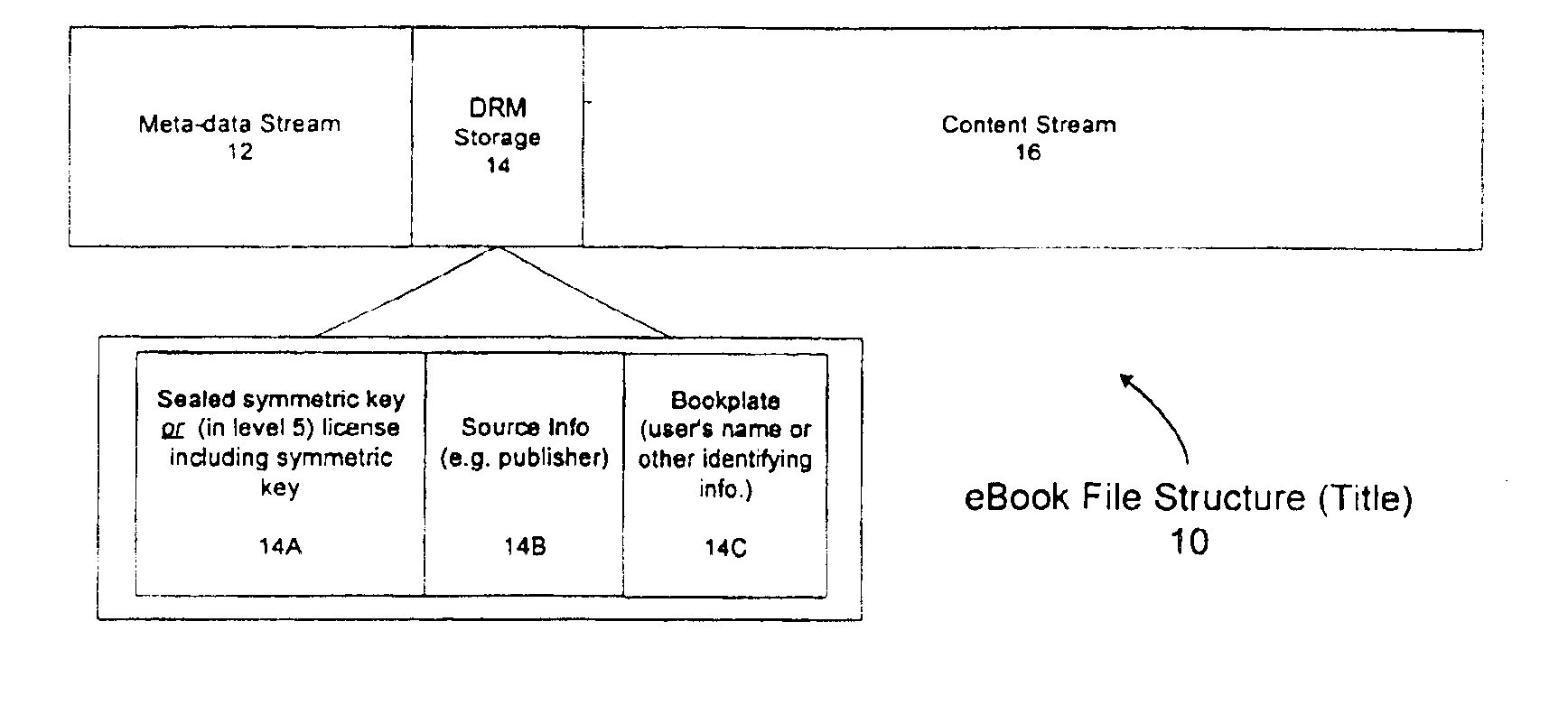
Cryptographic methods, apparatus and systems for storage media electronic rights management in closed and connected appliances
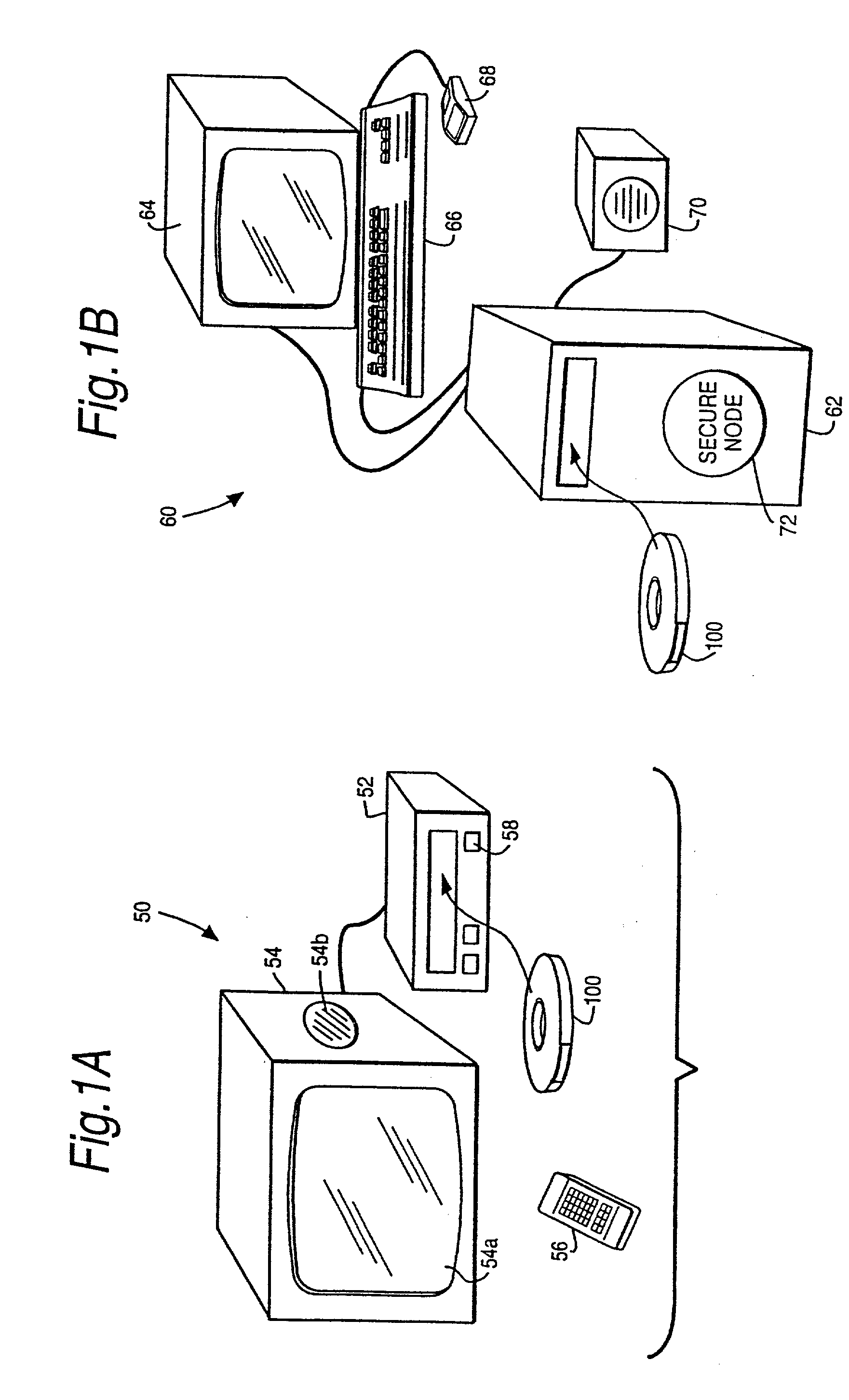
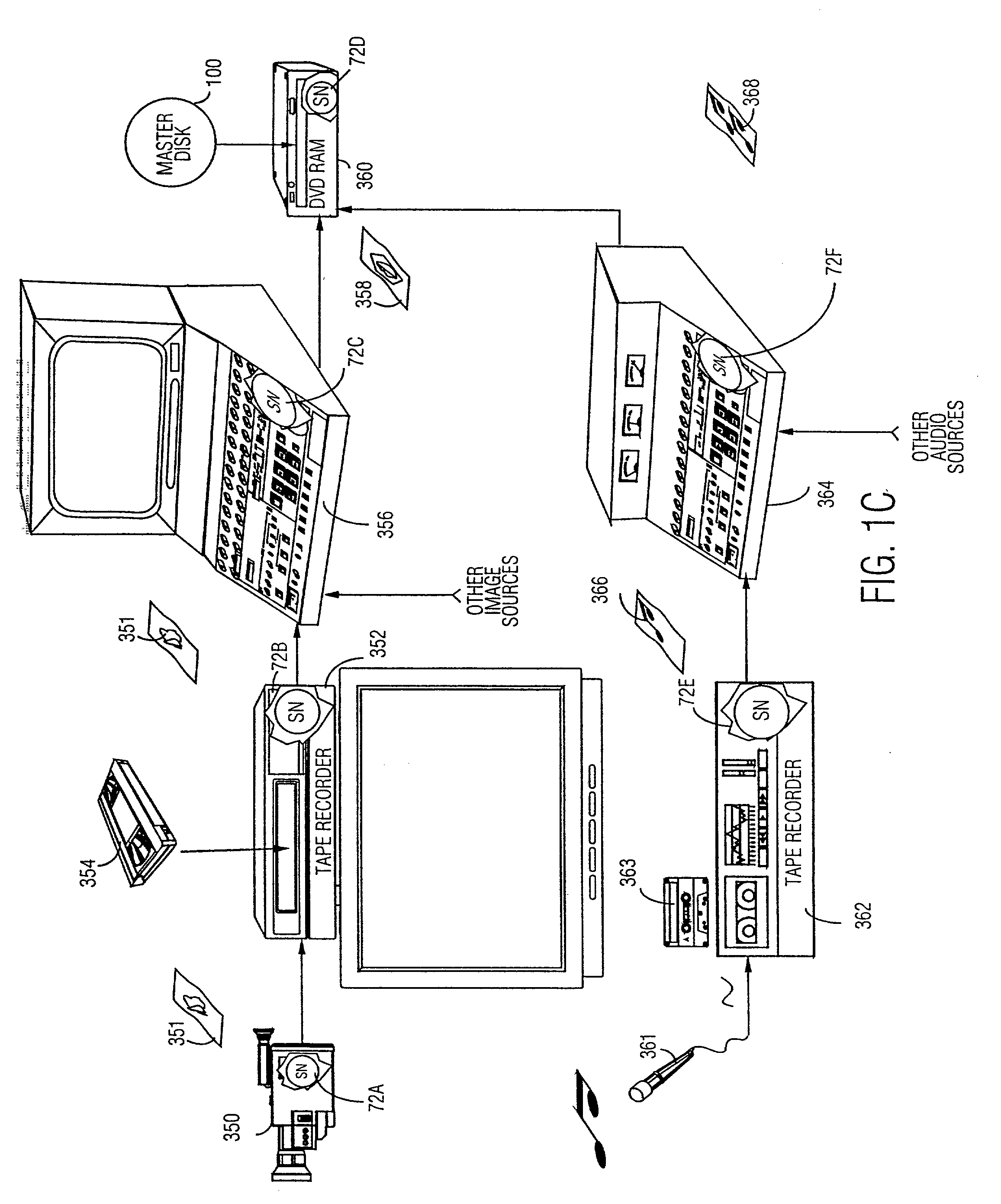
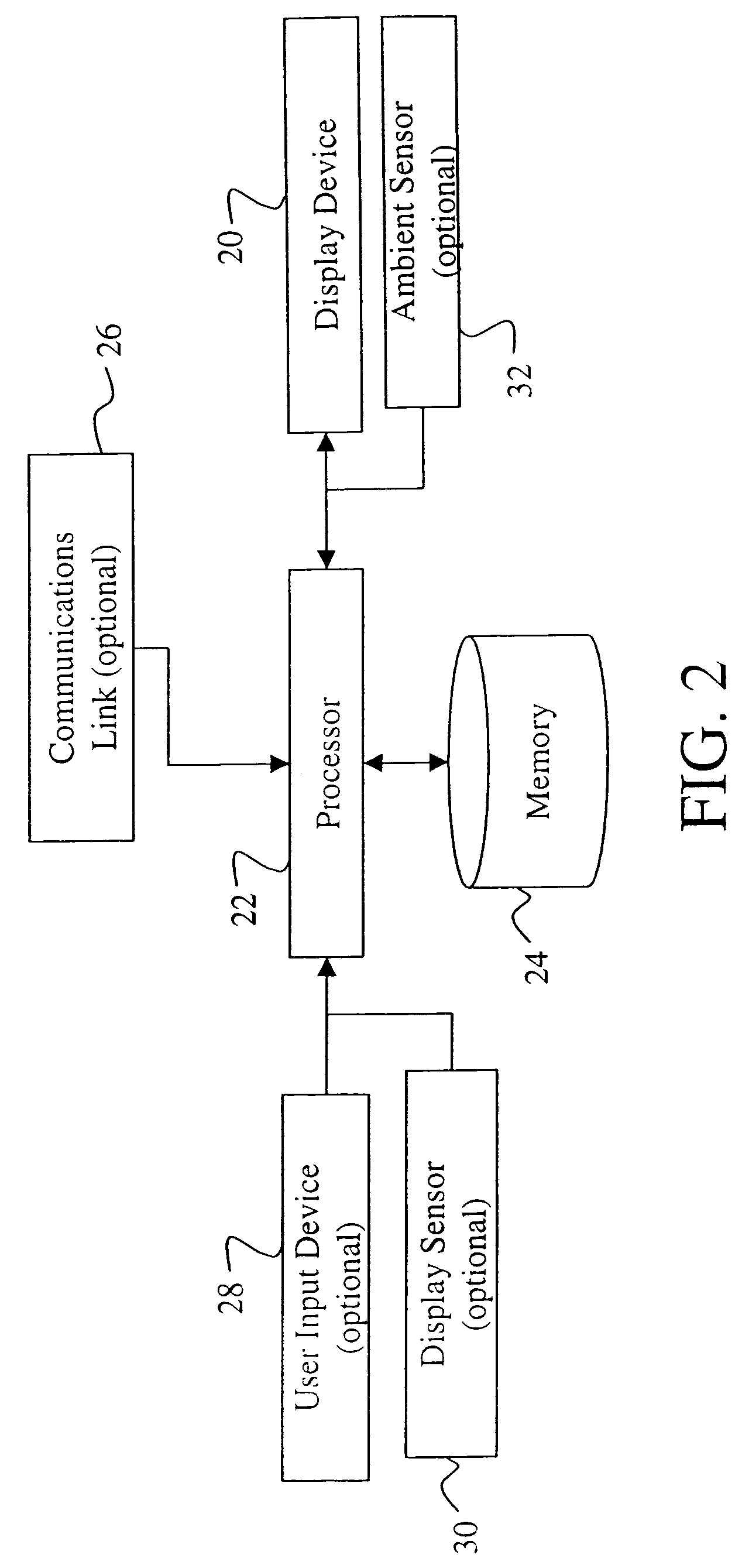
InactiveUS20010042043A1Low costGuaranteed to continue to useTelevision system detailsDigital data processing detailsControl setGeneral purpose
A rights management arrangement for storage media such as optical digital video disks (DVDs, also called digital versatile disks) provides adequate copy protection in a limited, inexpensive mass-produceable, low-capability platform such as a dedicated home consumer disk player and also provides enhanced, more flexible security techniques and methods when the same media are used with platforms having higher security capabilities. A control object (or set) defines plural rights management rules for instance, price for performance or rules governing redistribution. Low capability platforms may enable only a subset of the control rules such as controls on copying or marking of played material. Higher capability platforms may enable all (or different subsets) of the rules. Cryptographically strong security is provided by encrypting at least some of the information carried by the media and enabling decryption based on the control set and / or other limitations. A secure "software container" can be used to protectively encapsulate (e.g., by cryptographic techniques) various digital property content (e.g., audio, video, game, etc.) and control object (i.e., set of rules) information. A standardized container format is provided for general use on / with various mediums and platforms. In addition, a special purpose container may be provided for DVD medium and appliances (e.g., recorders, players, etc.) that contains DVD program content (digital property) and DVD medium specific rules. The techniques, systems and methods disclosed herein are capable of achieving compatibility with other protection standards, such as for example, CGMA and Matsushita data protection standards adopted for DVDs. Cooperative rights management may also be provided, where plural networked rights management arrangements collectively control a rights management event on one or more of such arrangements.
Owner:INTERTRUST TECH CORP
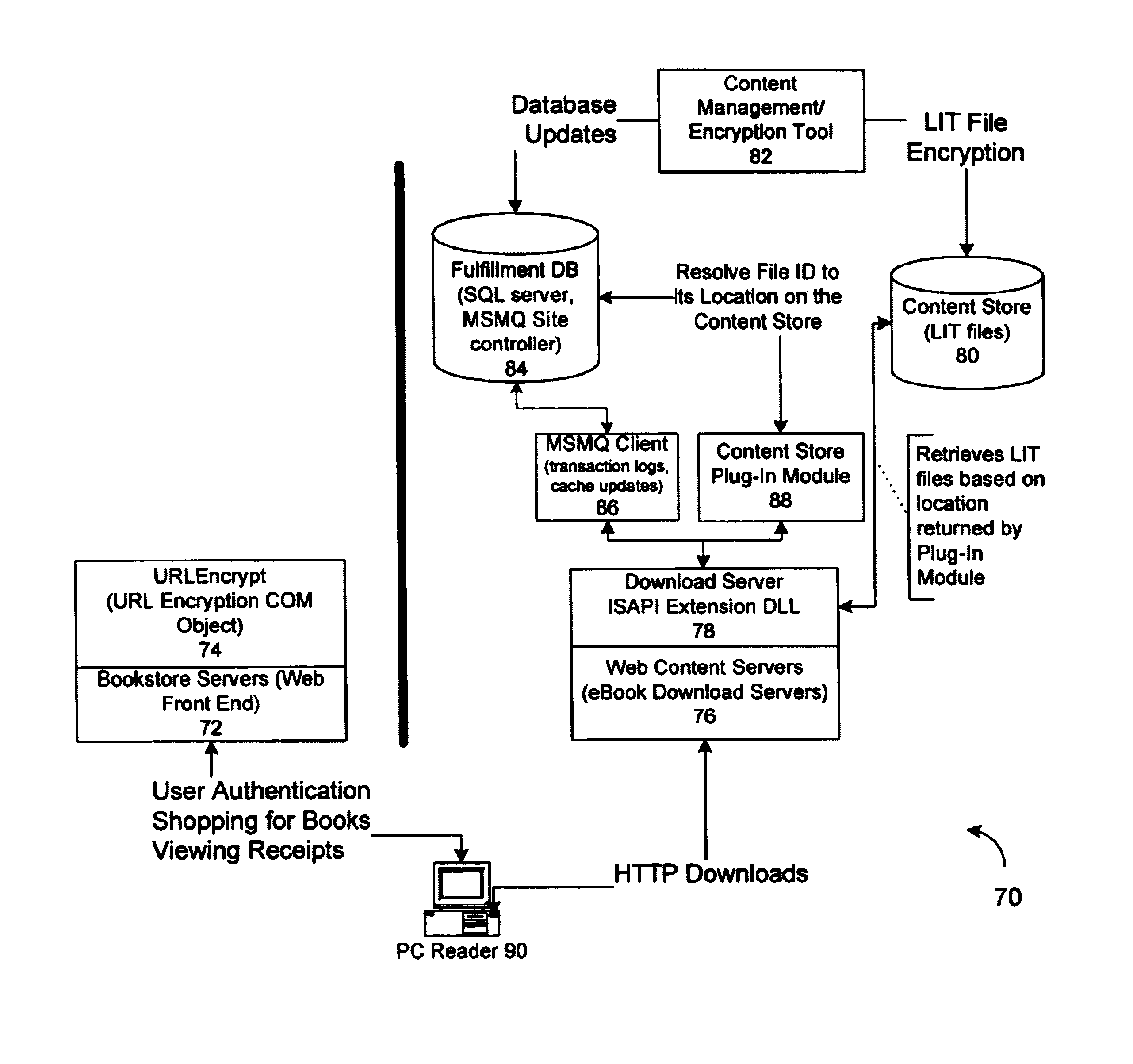
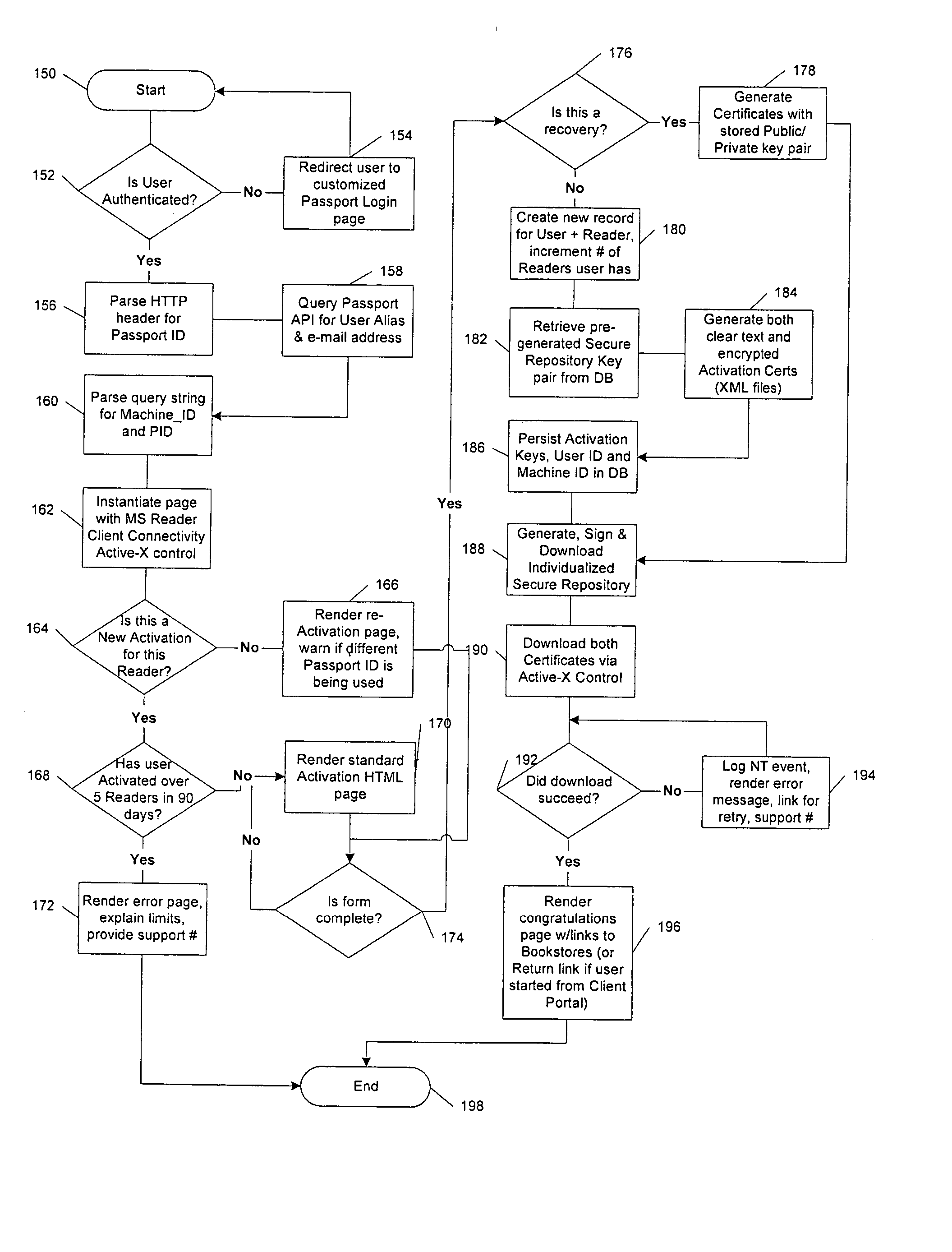
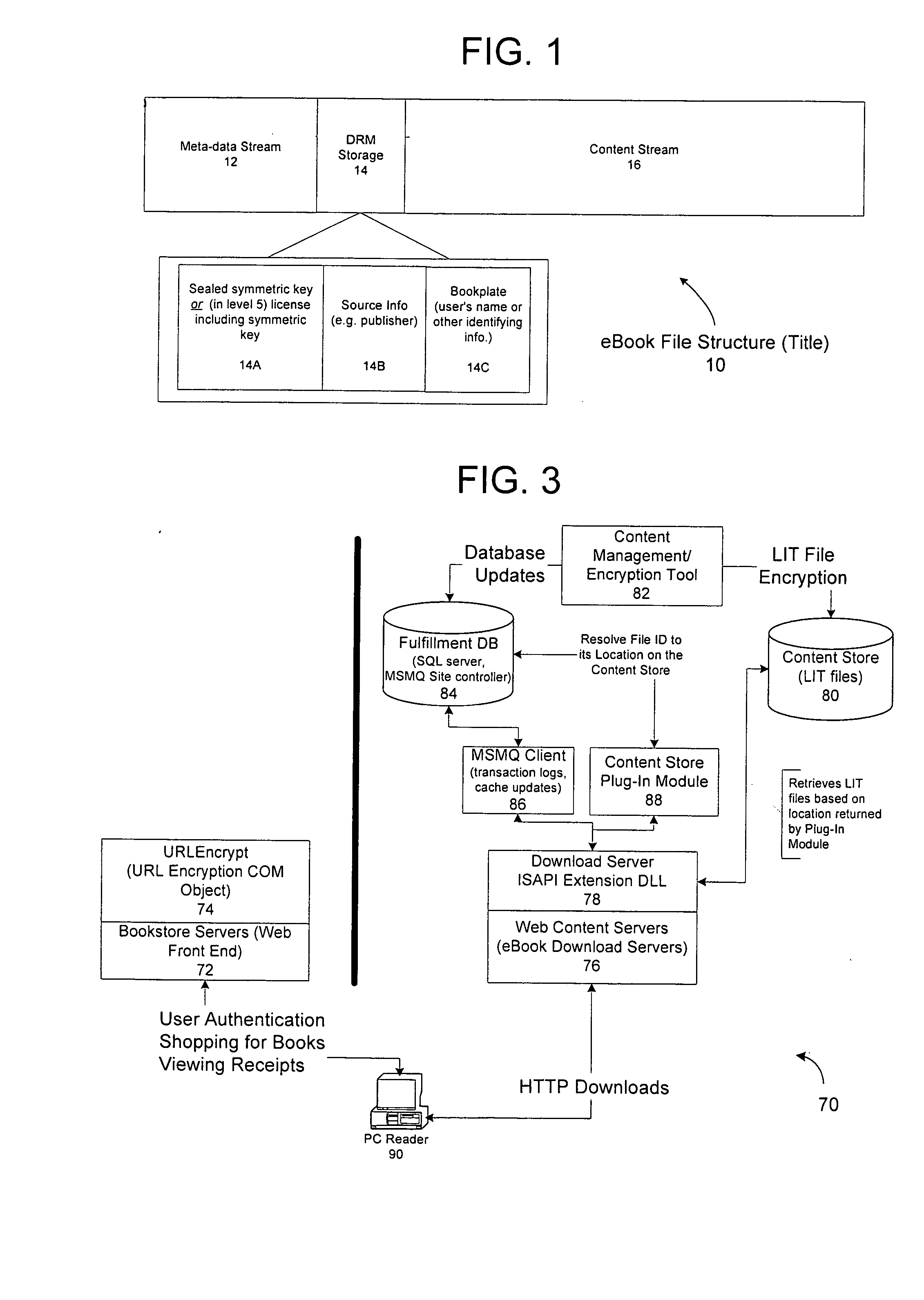
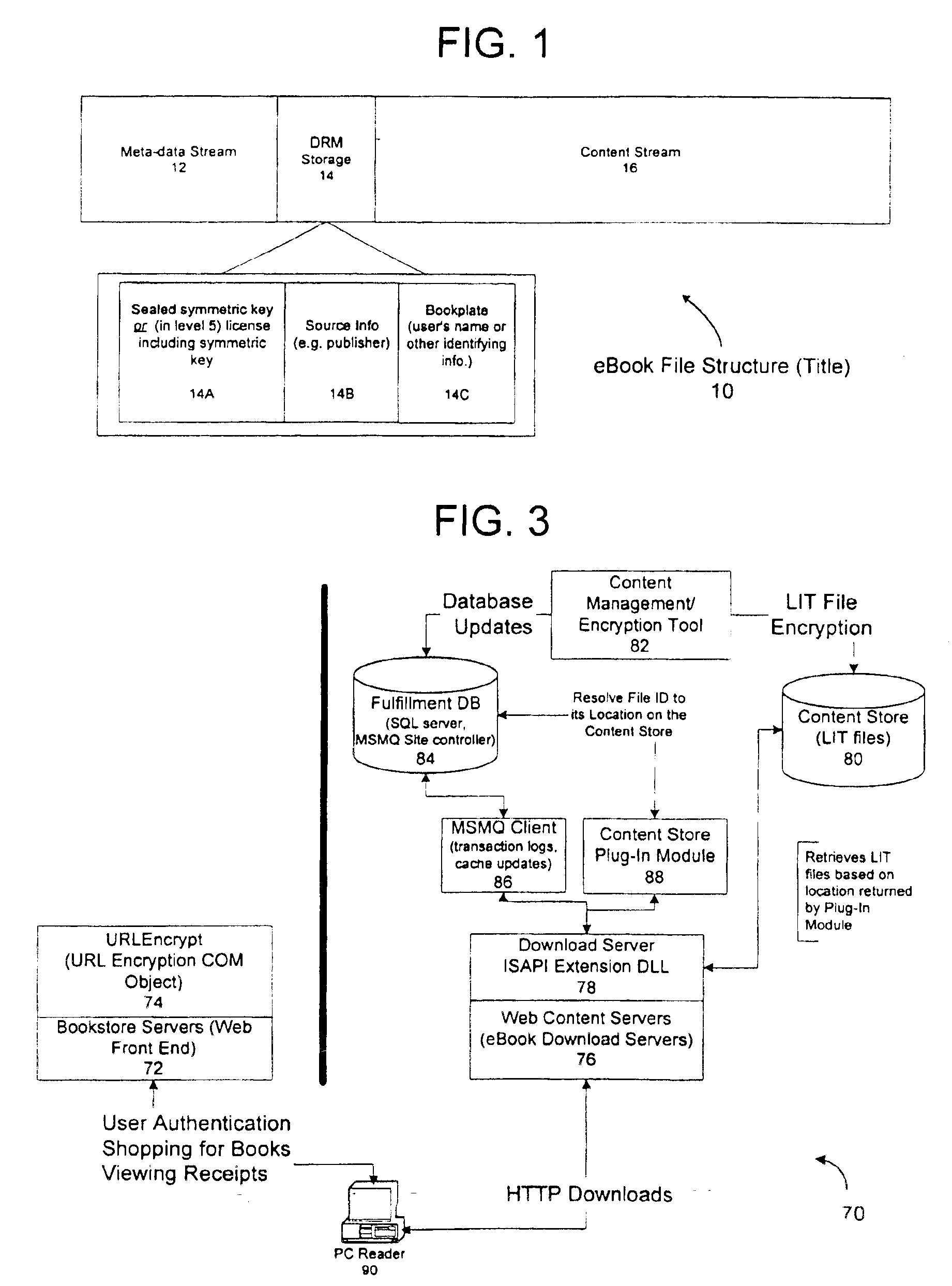
Method and system for binding enhanced software features to a persona
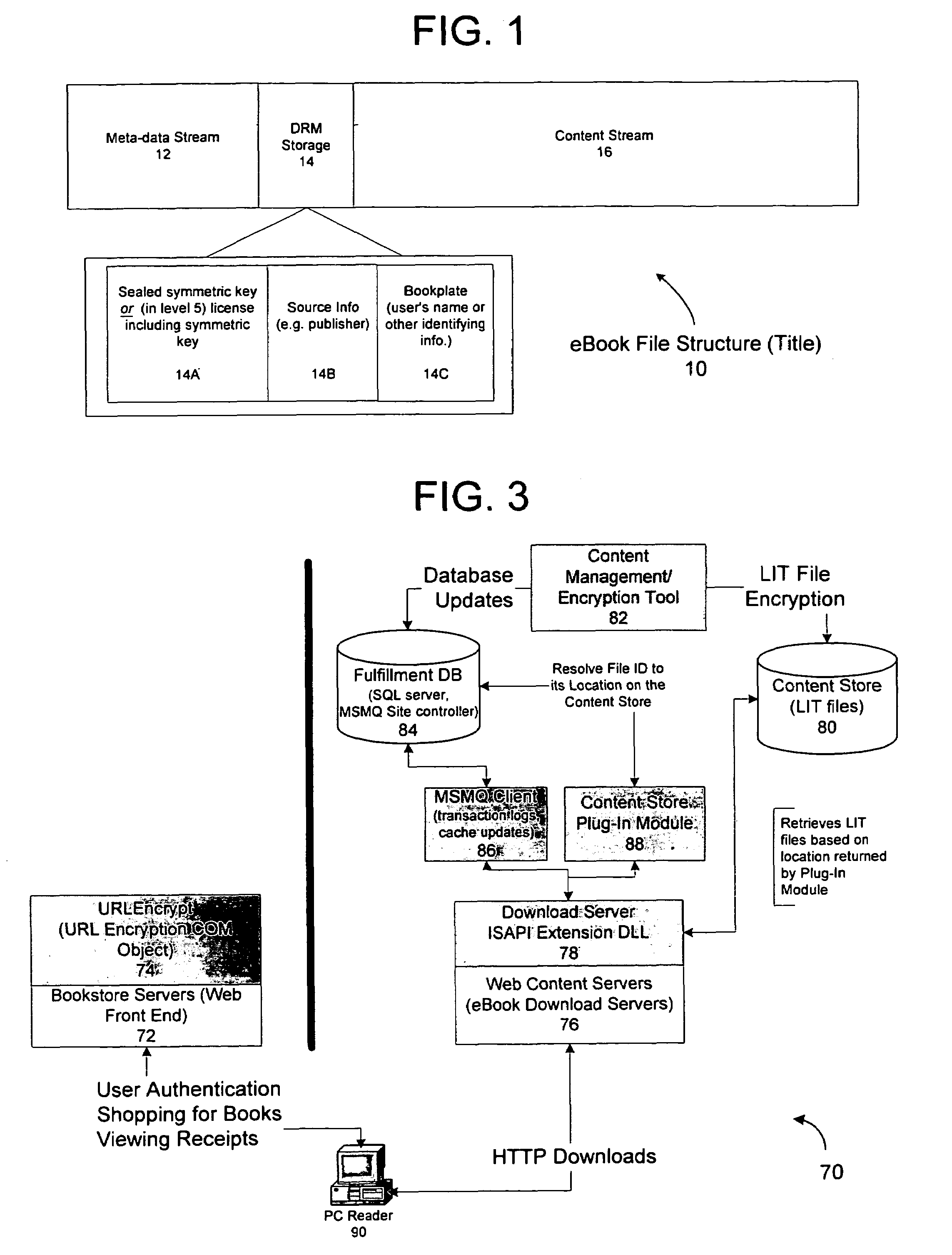
InactiveUS6891953B1Preventing unchecked proliferationKey distribution for secure communicationDigital data processing detailsBiological activationUniform resource locator
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
Server for an electronic distribution system and method of operating same
ActiveUS7047411B1Preventing unchecked proliferationKey distribution for secure communicationUser identity/authority verificationStore and forwardDigital rights management system
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content items, the retail site transmits to the purchase a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon the following the link, the fulfillment site downloads the ordered content to the consumer preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enable those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
Tamper resistant software encoding
InactiveUS6842862B2Improvement in tamper-resistanceIncreased complexityMemory loss protectionUnauthorized memory use protectionTamper resistancePassword
The present invention relates generally to computer software, and more specifically, to a method and system of making computer software resistant to tampering and reverse-engineering. “Tampering” occurs when an attacker makes unauthorized changes to a computer software program such as overcoming password access, copy protection or timeout algorithms. Broadly speaking, the method of the invention is to increase the tamper-resistance and obscurity of computer software code by transforming the data flow of the computer software so that the observable operation is dissociated from the intent of the original software code. This way, the attacker can not understand and decode the data flow by observing the execution of the code. A number of techniques for performing the invention are given, including encoding software arguments using polynomials, prime number residues, converting variables to new sets of boolean variables, and defining variables on a new n-dimensional vector space.
Owner:IRDETO ACCESS
Method and system for limiting the use of user-specific software features
InactiveUS20050060266A1Preventing unchecked proliferationDigital data processing detailsUser identity/authority verificationSchema for Object-Oriented XMLUniform resource locator
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
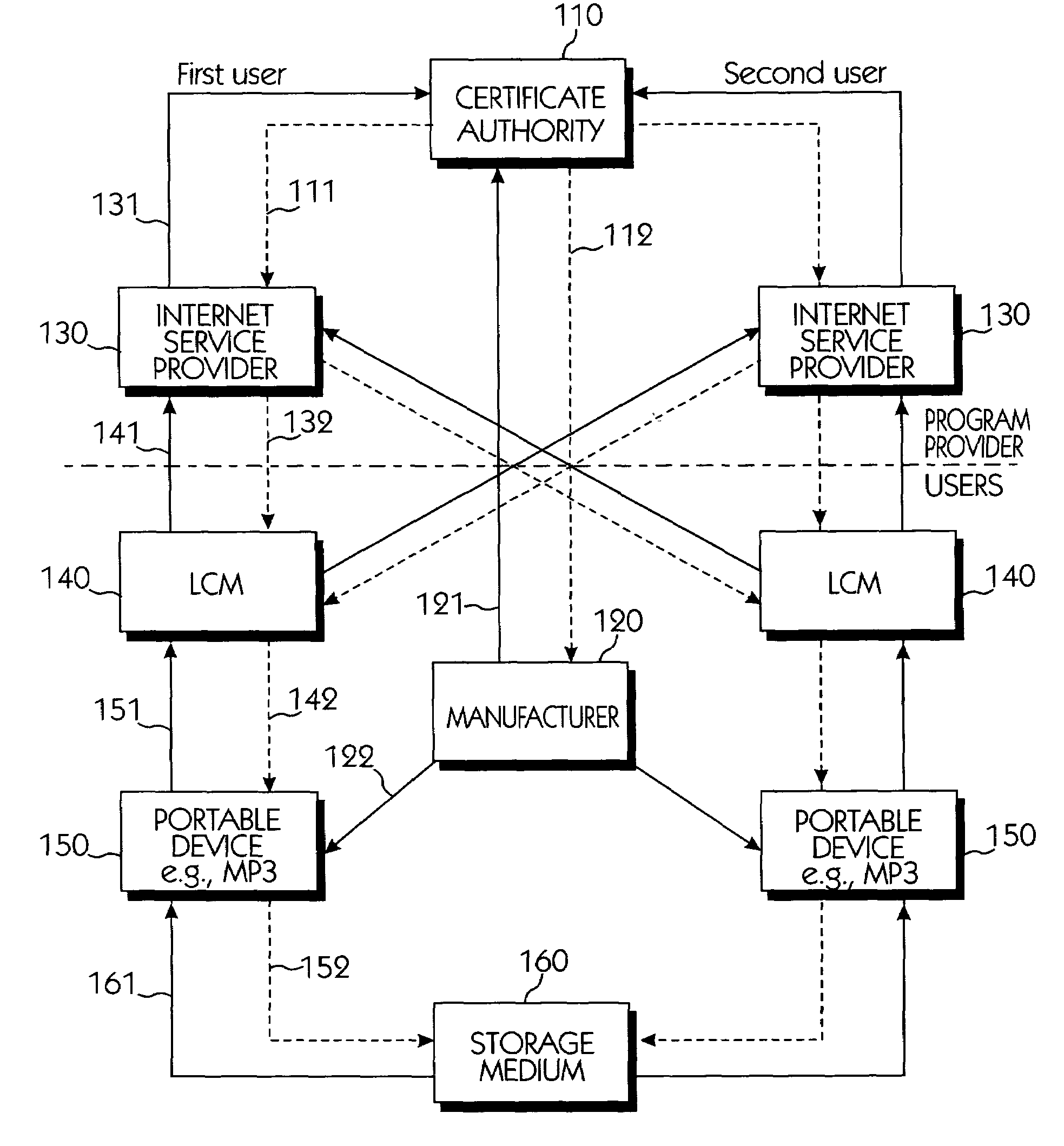
Copy protection system for portable storage media
InactiveUS6950941B1Limited abilityKey distribution for secure communicationData processing applicationsDevice formDigital content
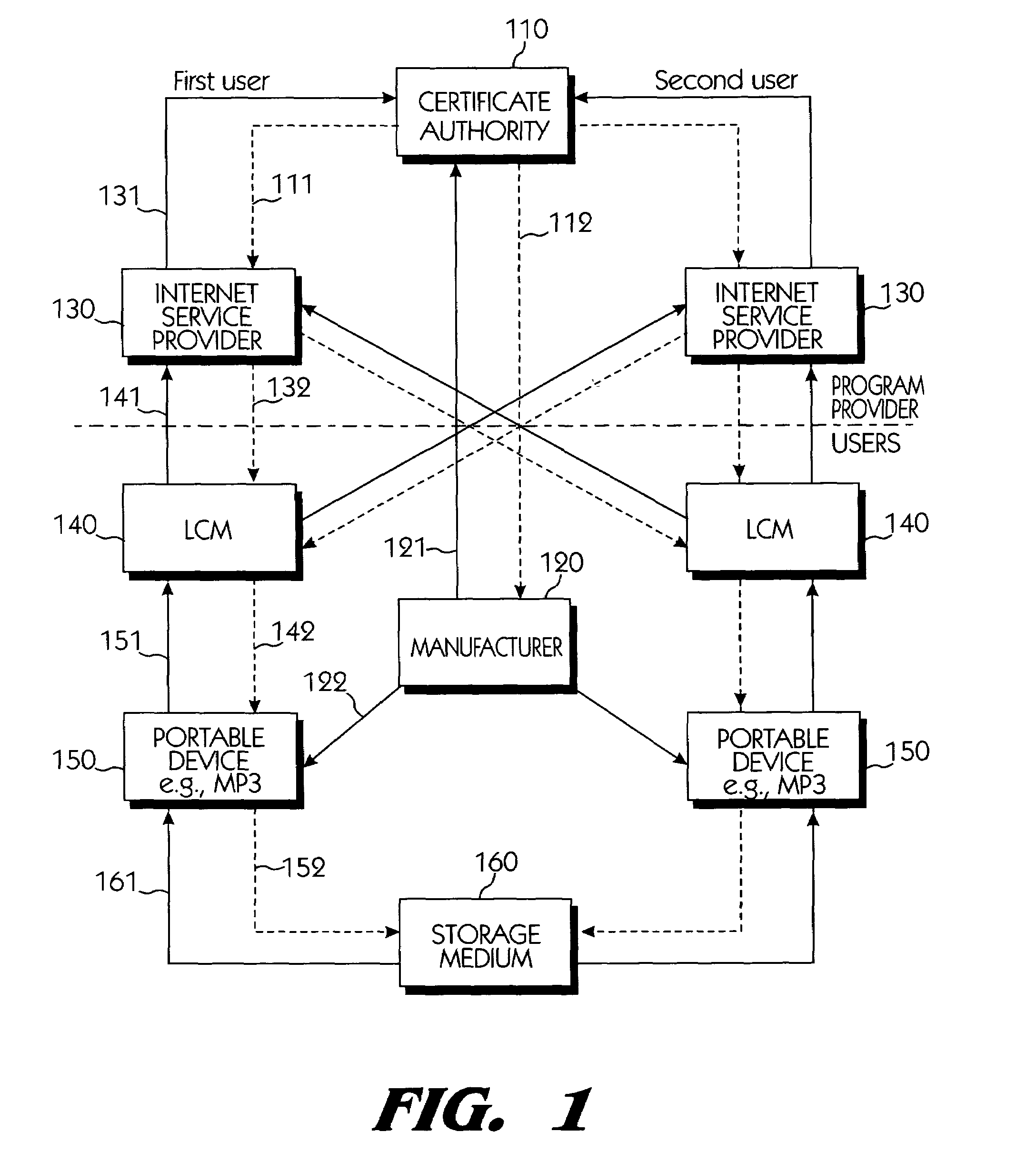
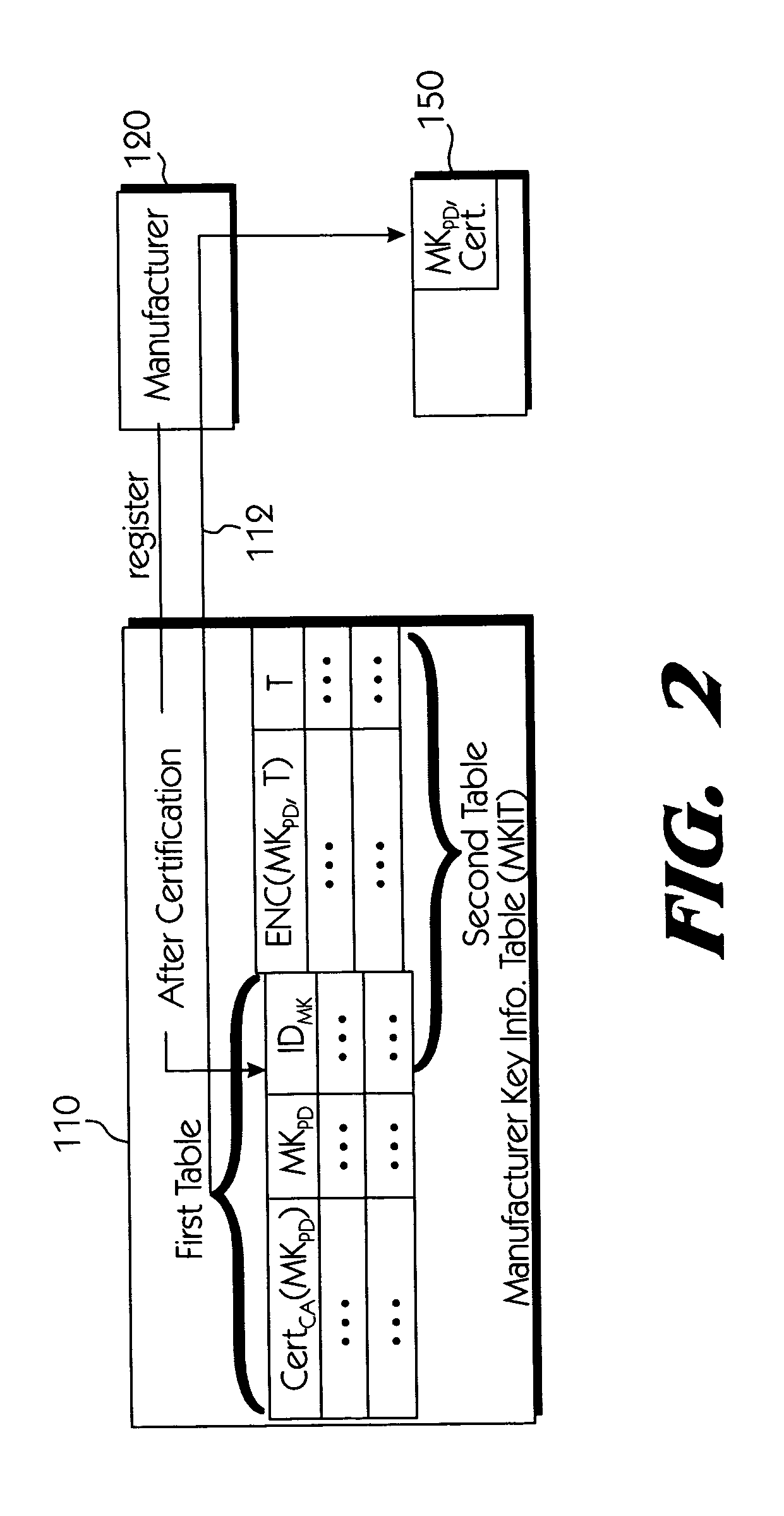
Systems connected to users generate a plurality of keys which are mutually shared, and download and upload digital contents by using secret channels formed between the systems. An information provider receives an authorization from a certificate authority. A licensed SDMI compliant module (LCM) is authenticated through the information provider, and the information provider and the LCM form a channel. A portable device is authenticated from the information provider through the LCM, and the LCM and the portable device form a channel. The digital content between the LCM and the portable device is downloaded and uploaded according to respective control state data of the LCM and the portable device. The system can use a physical address of a bad sector formed in the portable medium during the manufacturing process for preventing an illegal copy of the downloaded digital contents through the portable device after the digital contents have been downloaded.
Owner:SAMSUNG ELECTRONICS CO LTD
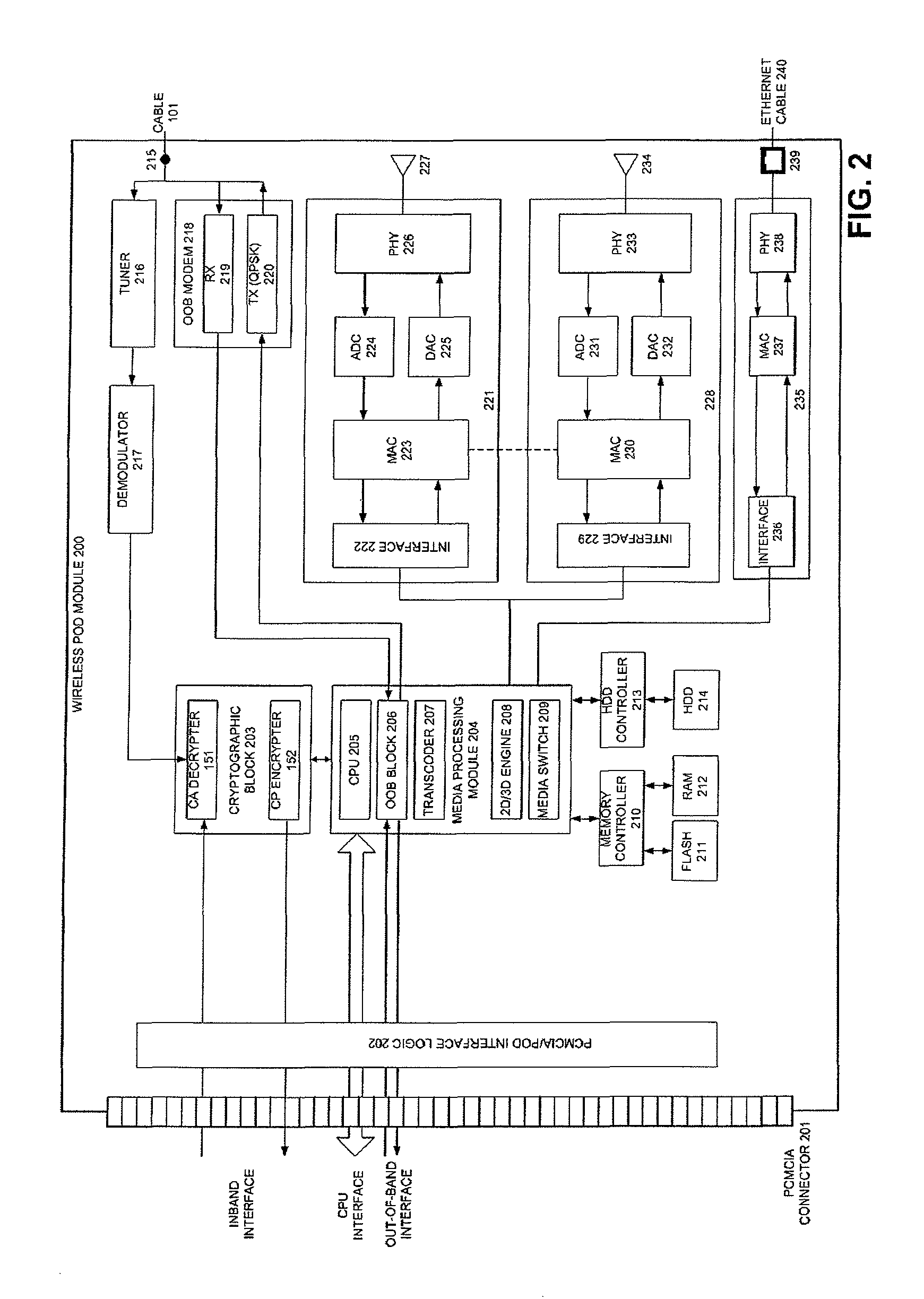
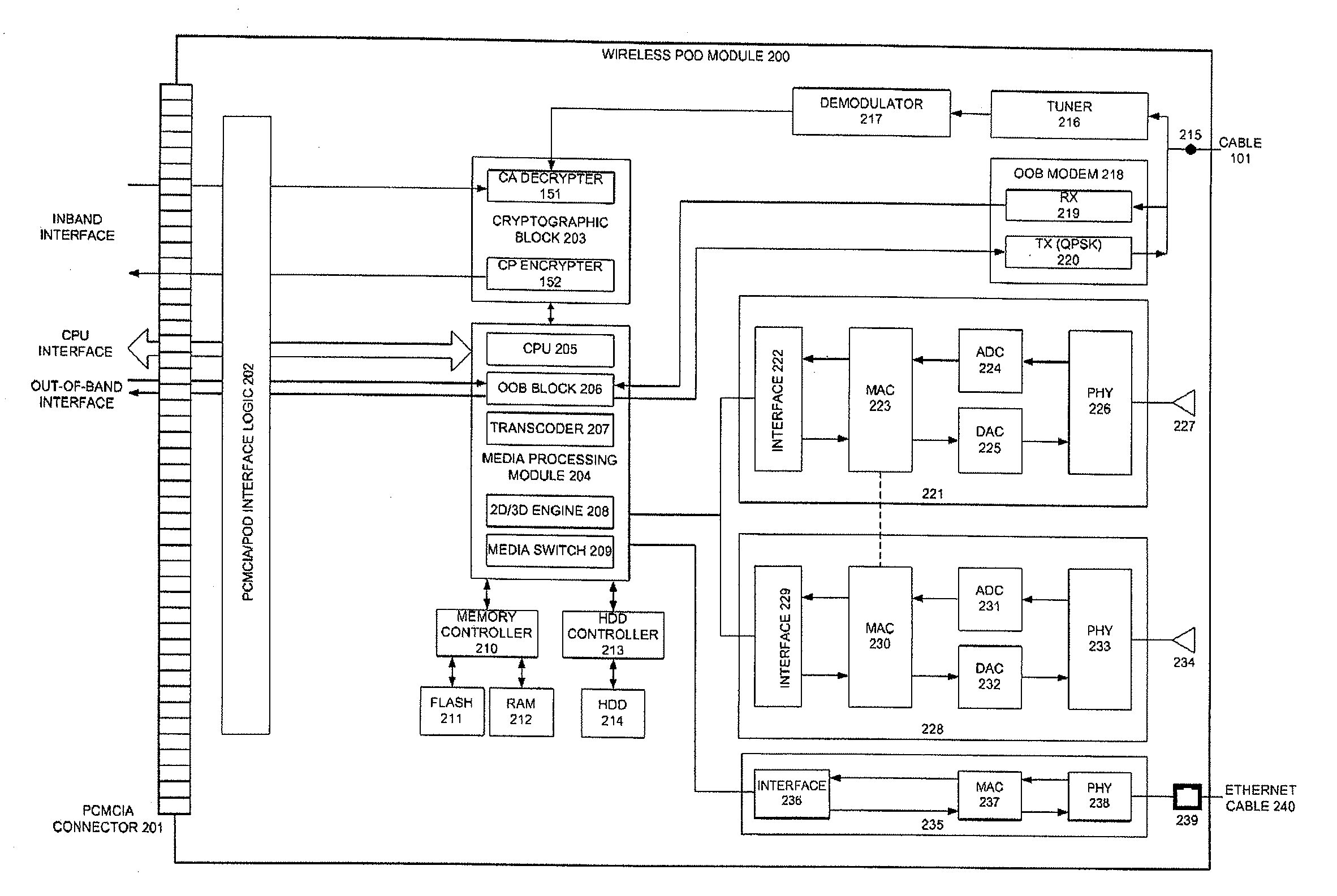
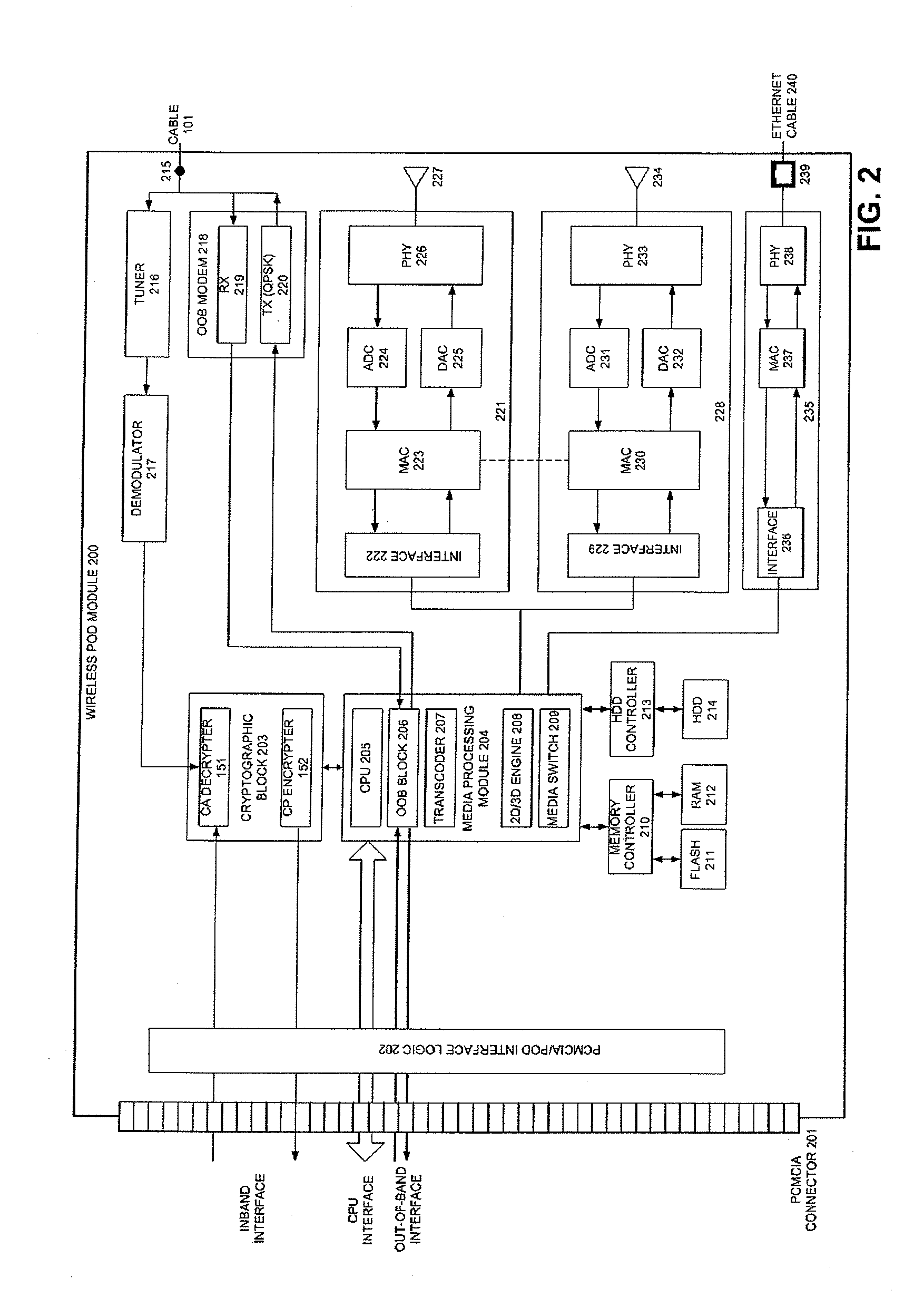
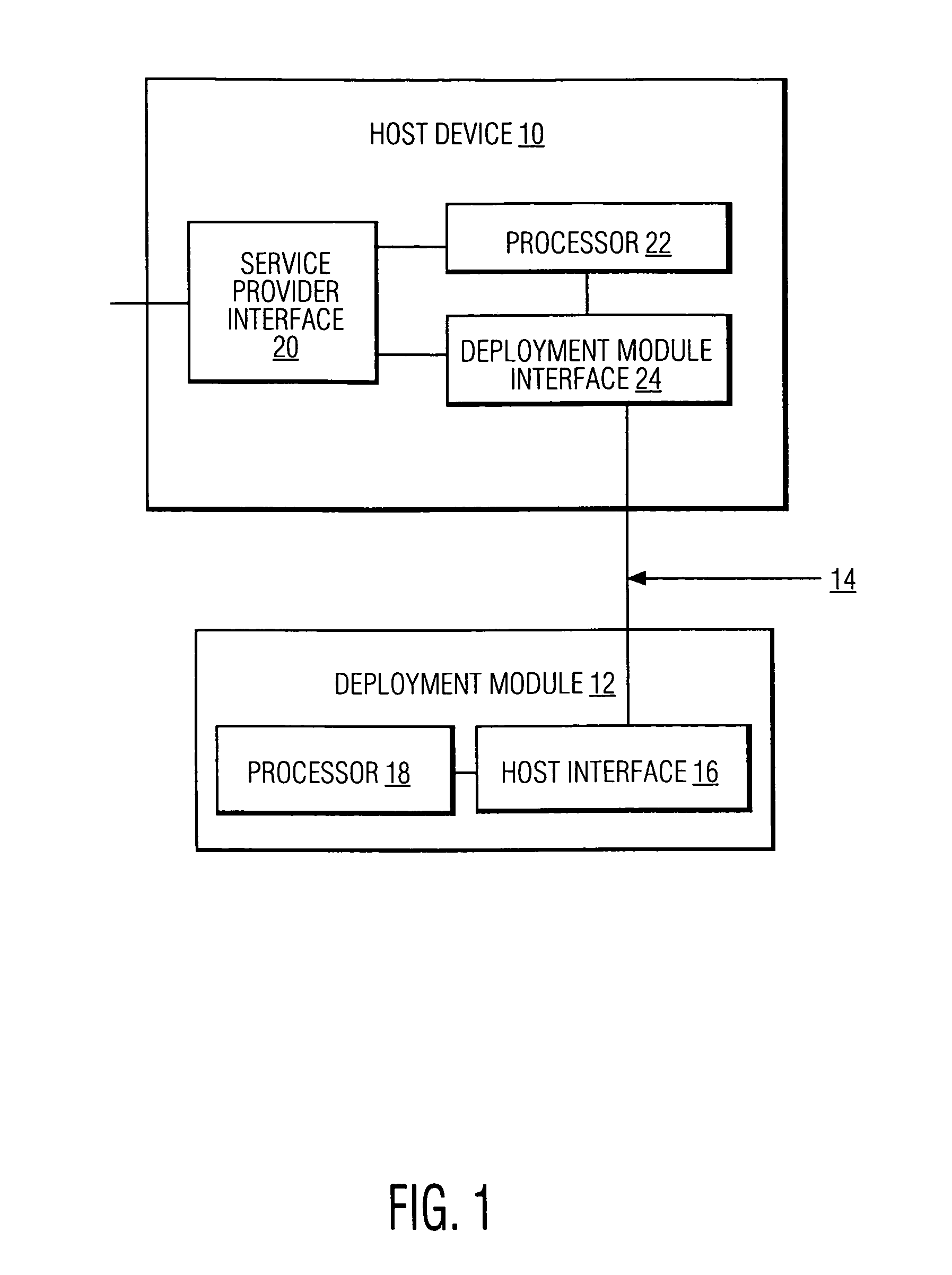
Extended connectivity point-of-deployment apparatus and concomitant method thereof
ActiveUS8887212B2Secure transmissionEasy to useNear-field transmissionDigital data processing detailsCoaxial cableComputer module
A POD module system includes a housing, a coaxial cable connector formed on the housing and connectable to a first device to receive a cable signal, a port formed on the housing to receive a wire or wireless signal from a second device, a module unit to process at least one of the cable signal and the at least one of the wireless signal to generate at least one of a copy protection signal and one of video and audio signals, respectively, and a connector formed on the housing and connectable to a third device to transmit the at least one of the copy protection signal and the one of video and audio signals to the third device such that the third device generates at least one of an image and a sound to correspond to the at least one of the copy protection signal and the one of video and audio signals.
Owner:SYNDEFENSE
Pod module and method thereof
ActiveUS20070250872A1Secure transmissionEasy to useAssess restrictionGHz frequency transmissionCoaxial cableEngineering
A POD module system includes a housing, a coaxial cable connector formed on the housing and connectable to a first device to receive a cable signal, a port formed on the housing to receive a wire or wireless signal from a second device, a module unit to process at least one of the cable signal and the at least one of the wireless signal to generate at least one of a copy protection signal and one of video and audio signals, respectively, and a connector formed on the housing and connectable to a third device to transmit the at least one of the copy protection signal and the one of video and audio signals to the third device such that the third device generates at least one of an image and a sound to correspond to the at least one of the copy protection signal and the one of video and audio signals.
Owner:SYNDEFENSE
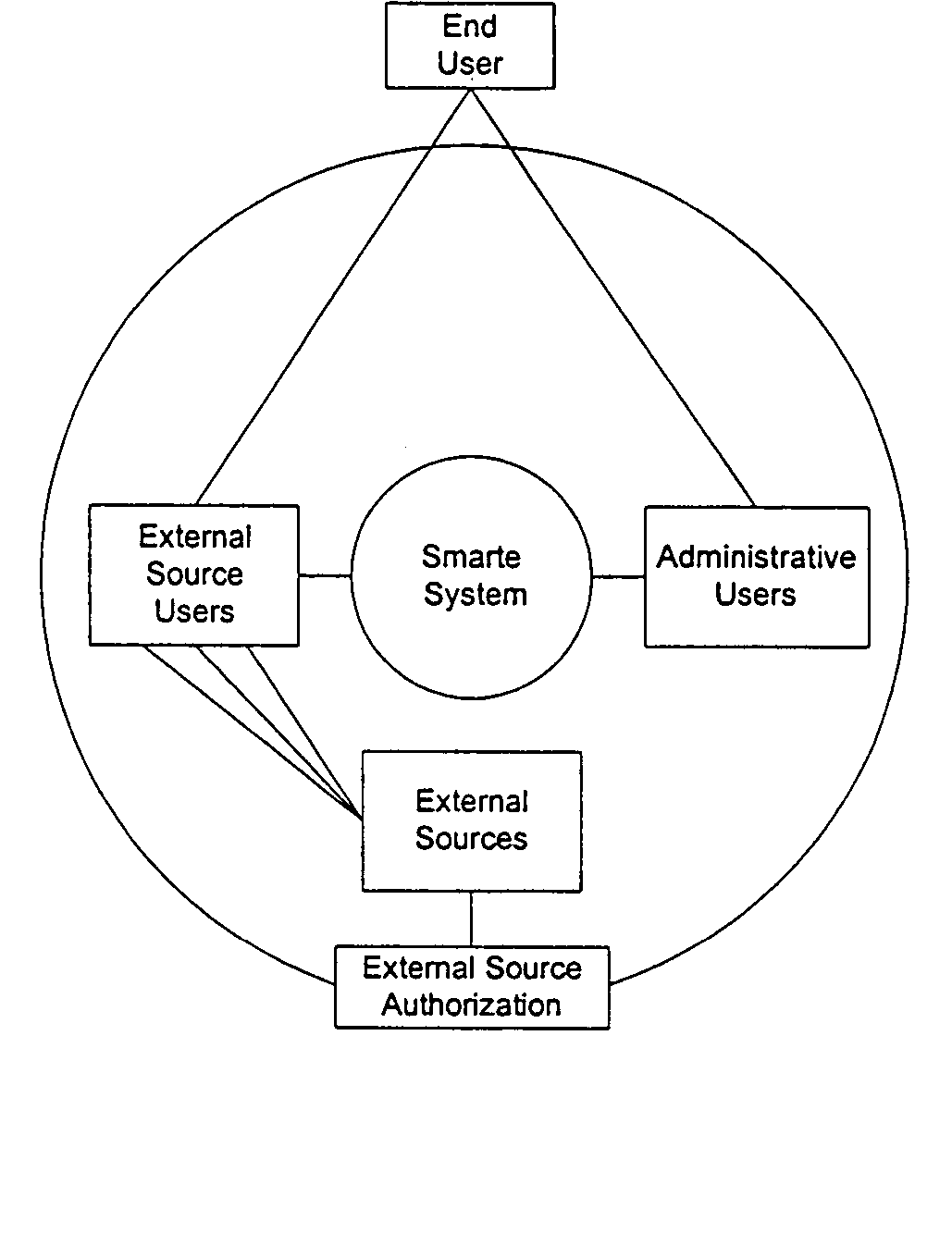
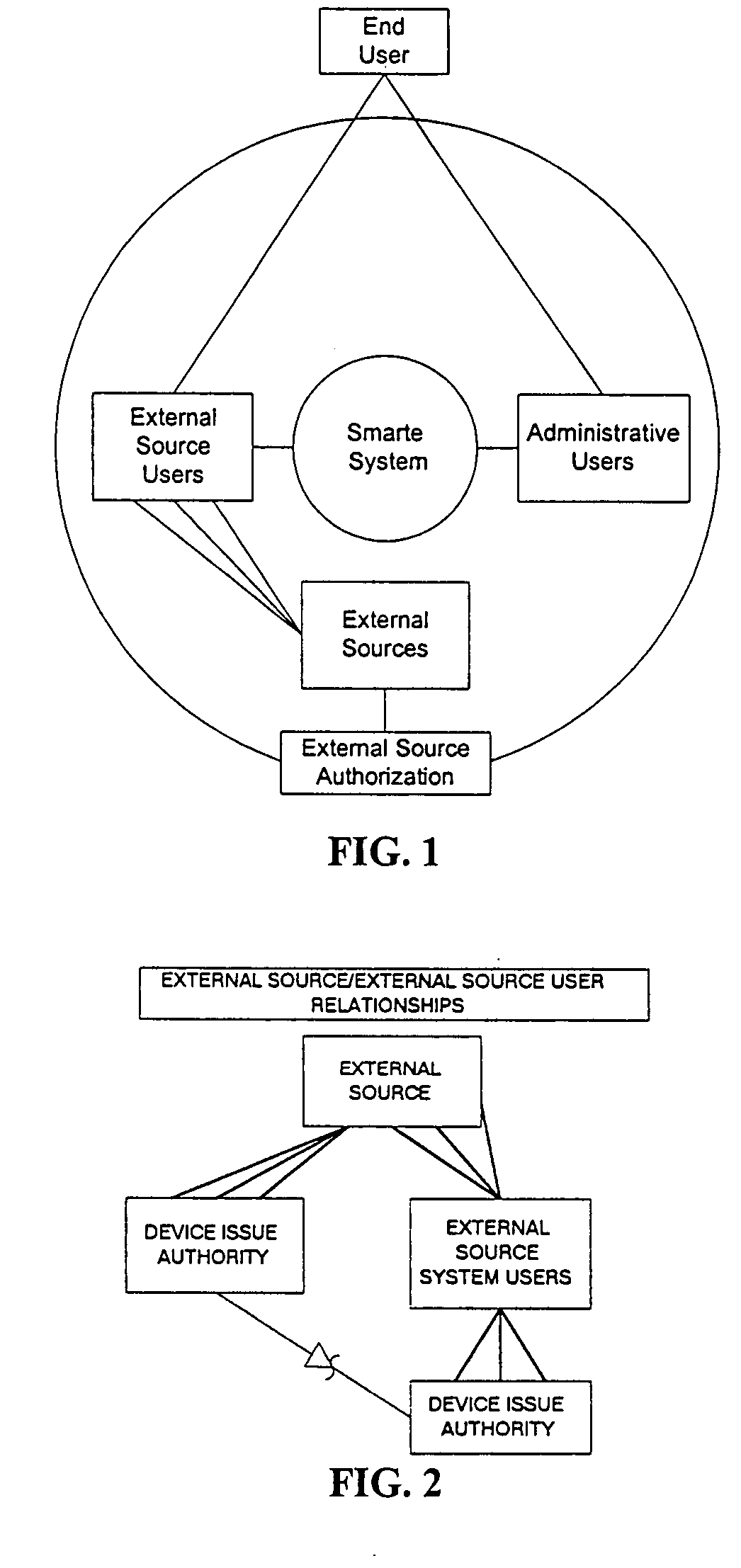
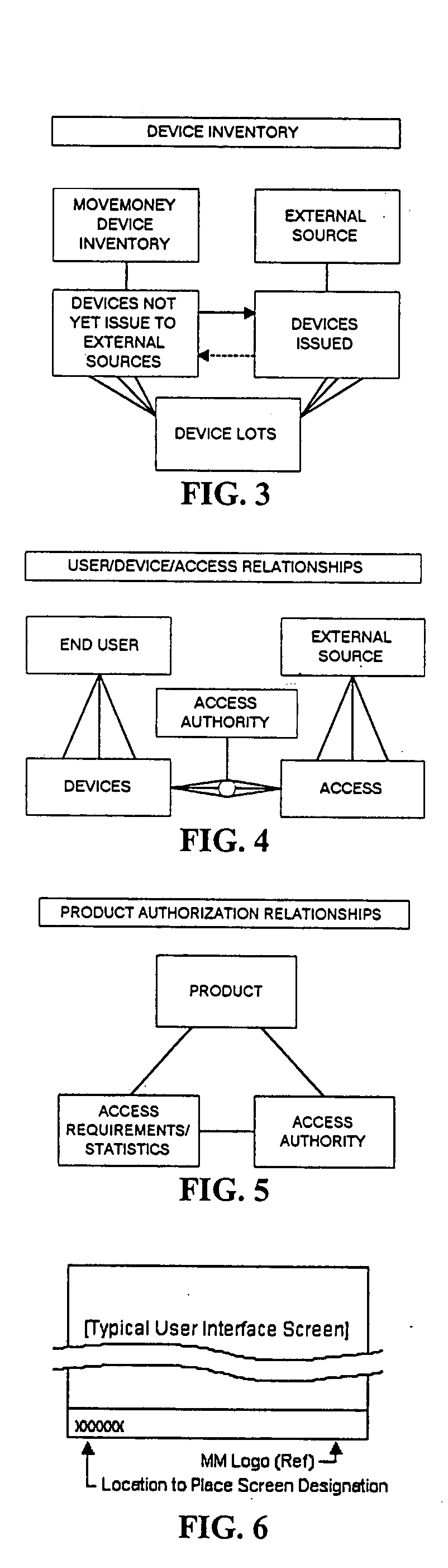
User/product authentication and piracy management system
InactiveUS20050149759A1Reduce potentialPrevent illegal useDigital data processing detailsMultiple digital computer combinationsDigital identitySerialization
A system in the form of a software solution that provides new and unique solutions to the need to secure digital environments. The present invention uses innovative and new forms of multi-factor user authentication and digital identity management, providing levels of security unmatched in the industry. In addition, the system provides new and unique methods of software piracy management including CD media-based copy protection, remote CD media validation, embedded product serialization, protection of electronically distributed software, and remote product installation tracking.
Owner:MOVEMONEY
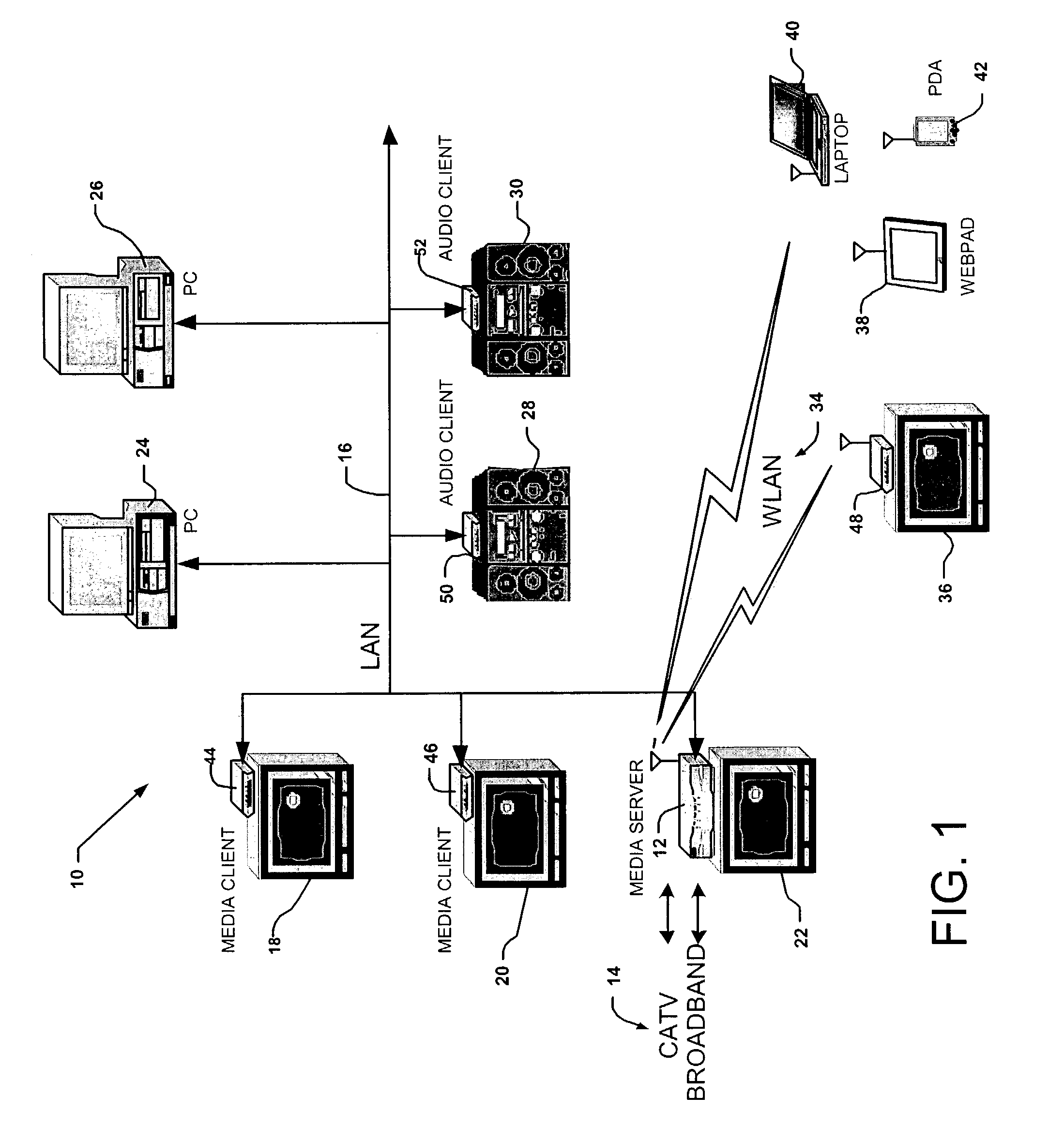
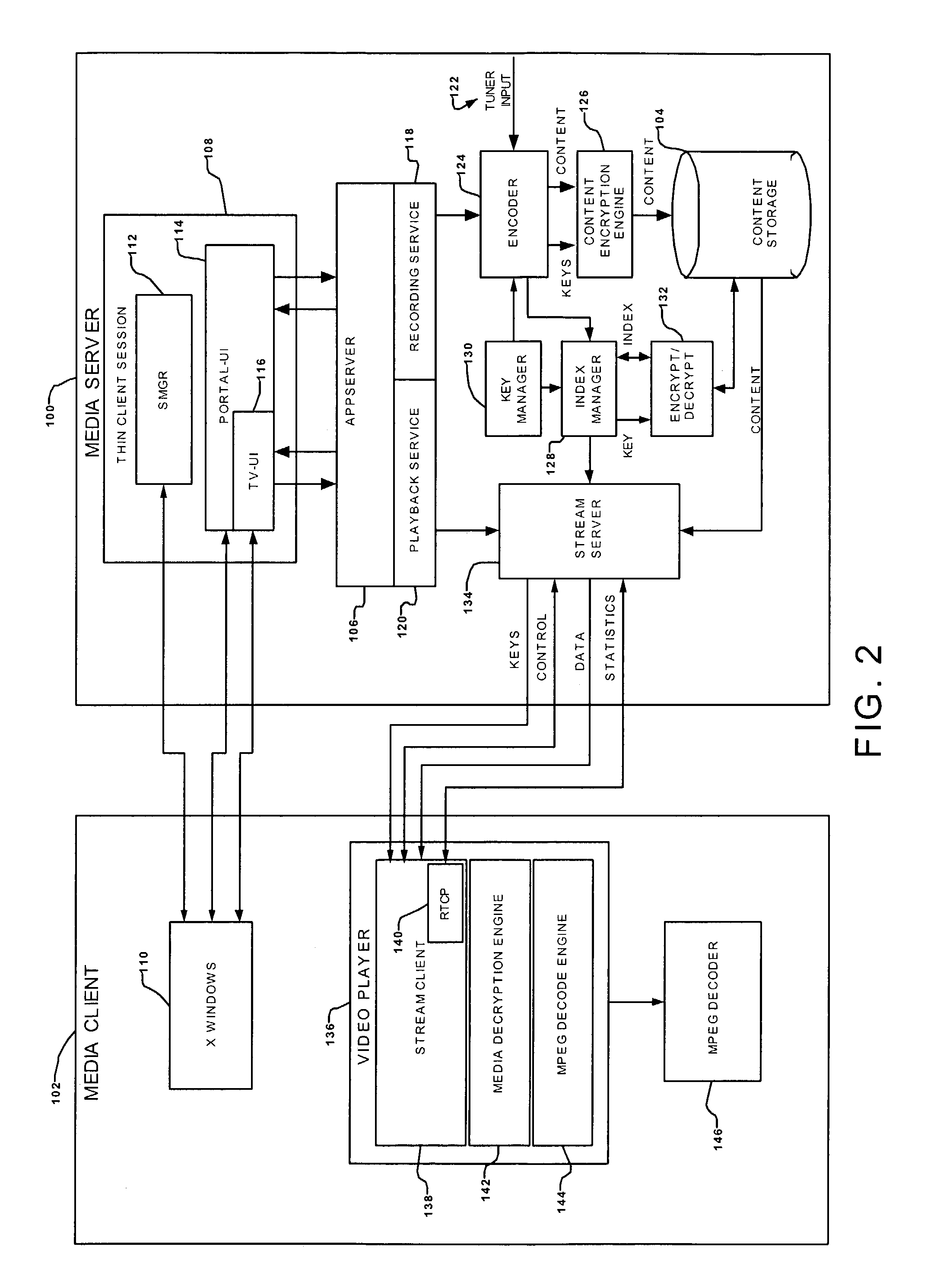
Networked digital video recording system with copy protection and random access playback
ActiveUS7231516B1Effective positioningHigh rateTelevision system detailsData resettingDigital videoDigital recording
In a multimedia recording and playback network for receiving from a content server a service package of multimedia content, the network including a media server in communication with the content server, a method of securely transmitting a master encryption key from the content server to the media server, including the steps downloading a service package certificate from the content server to the media server, authenticating, in the media server, the received service package certificate, the content server providing to the media server a key server certificate, a public key of the content server, and a client certificate request, the media server authenticating the key server certificate, providing to the content server, upon authentication of the key server certificate by the media server, a client certificate including a challenge signature, and a public key of the media server, the content server authenticating the client certificate including the challenge signature received from the media server, the media server requesting the master encryption key from the content server, and the content server responding by transmitting the master encryption key to media server.
Owner:GOOGLE TECH HLDG LLC
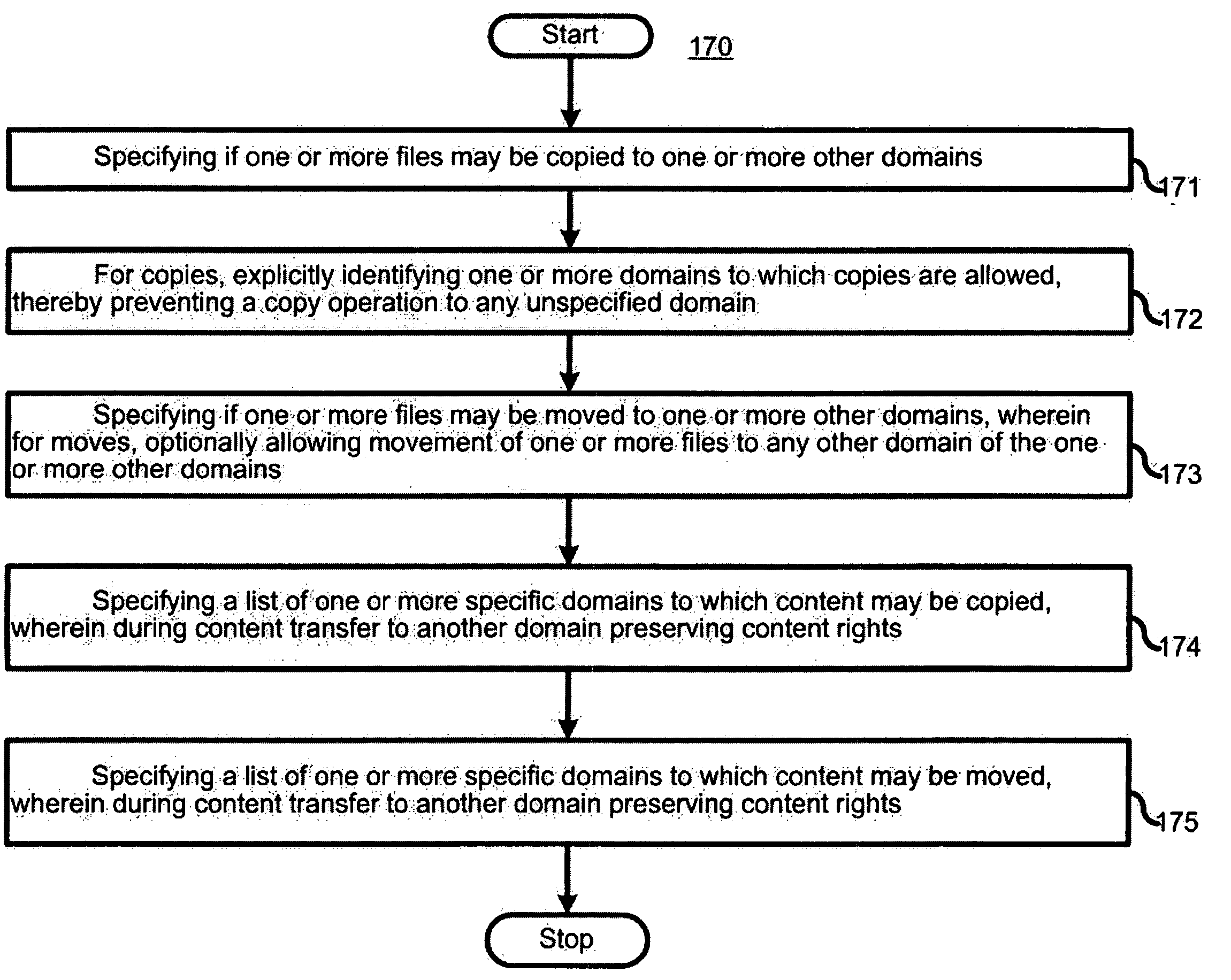
Separation of copy protection rules
InactiveUS20050071669A1Digital data processing detailsAnalogue secracy/subscription systemsDigital rights management systemCopy protection
A copyright protection method (150) and apparatus (190) employs (151) a first protection scheme (160) within a single authorized domain (195), in which all interfaces (194a-c) are protected with digital rights management system and employs (152) a second protection scheme (170) for use in inter-domain file transfers. The method (150) and apparatus (190) may employ (153) a third protection scheme (180) for external outputs (197a-c) not protected by a digital rights management system. The first protection scheme (160) includes specifying (161) whether a copy of files is allowed to be stored anywhere within the single authorized domain; specifying (162) whether files may be stored only on specific devices within the single authorized domain; or specifying (163) how many simultaneous rendering devices are permitted when rendering files. The second protection scheme (170) may include: specifying (171) if the files may be copied to other domains; and explicitly identifying (172) domains to which copies are allowed; specifying (173) if files may be moved to other domains, and optionally allowing movement of files to any other domain; specifying (174) a list of specific domains to which content may be copied, and preserving content rights during content transfer to another domain; or specifying (175) specific domains to which content may be moved, and preserving content rights during content transfer. The third protection scheme (180) may include: specifying (181) copy protection information separately for analog, digital uncompressed and digital compressed outputs; specifying (182) a CGMS Copy protection state; specifying (183) MACROVISION parameters for analog outputs; specifying (184) if a particular type of output is allowed at all; or disabling (185) the particular type of output if the particular output type is not allowed.
Owner:GOOGLE TECH HLDG LLC
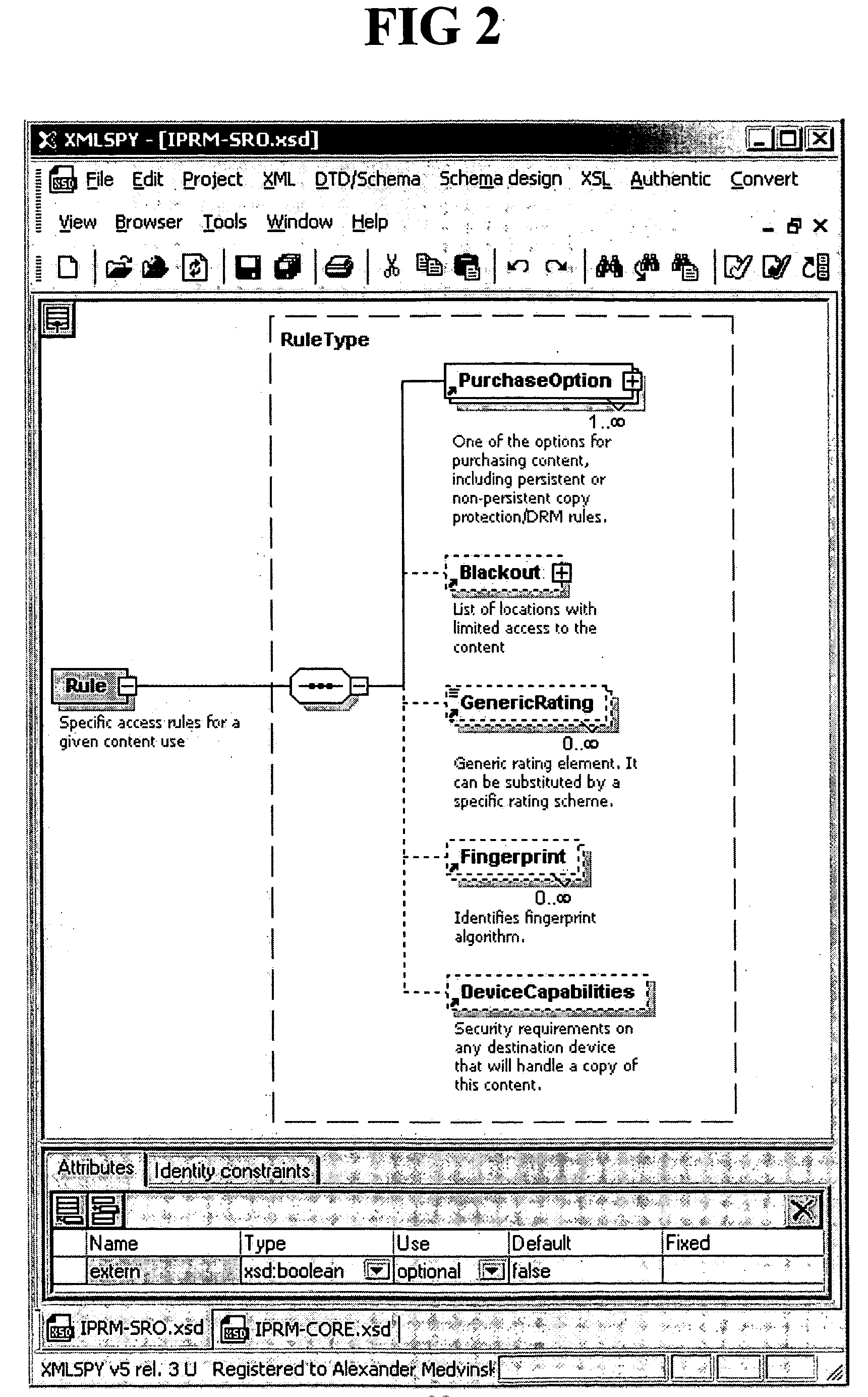
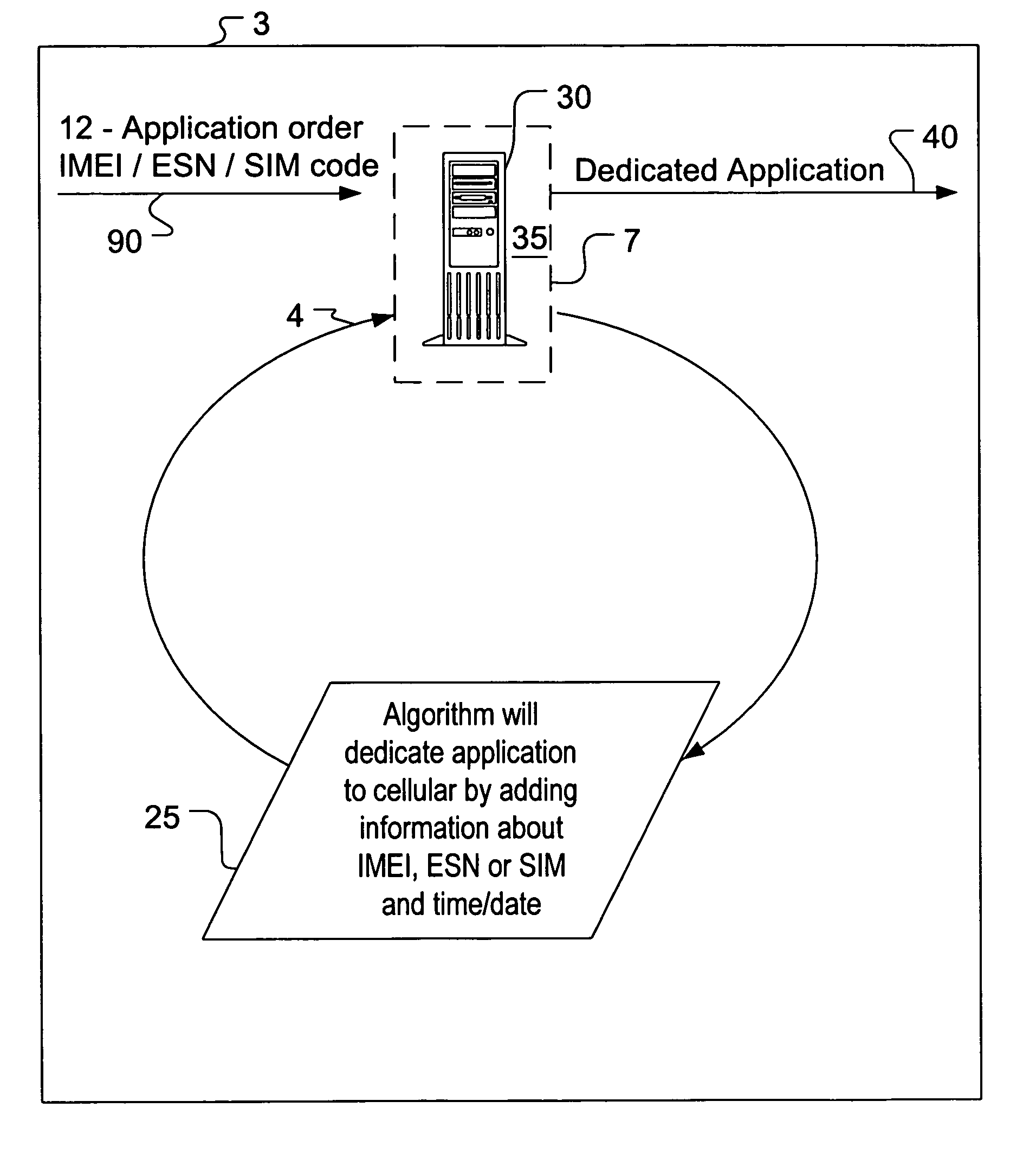
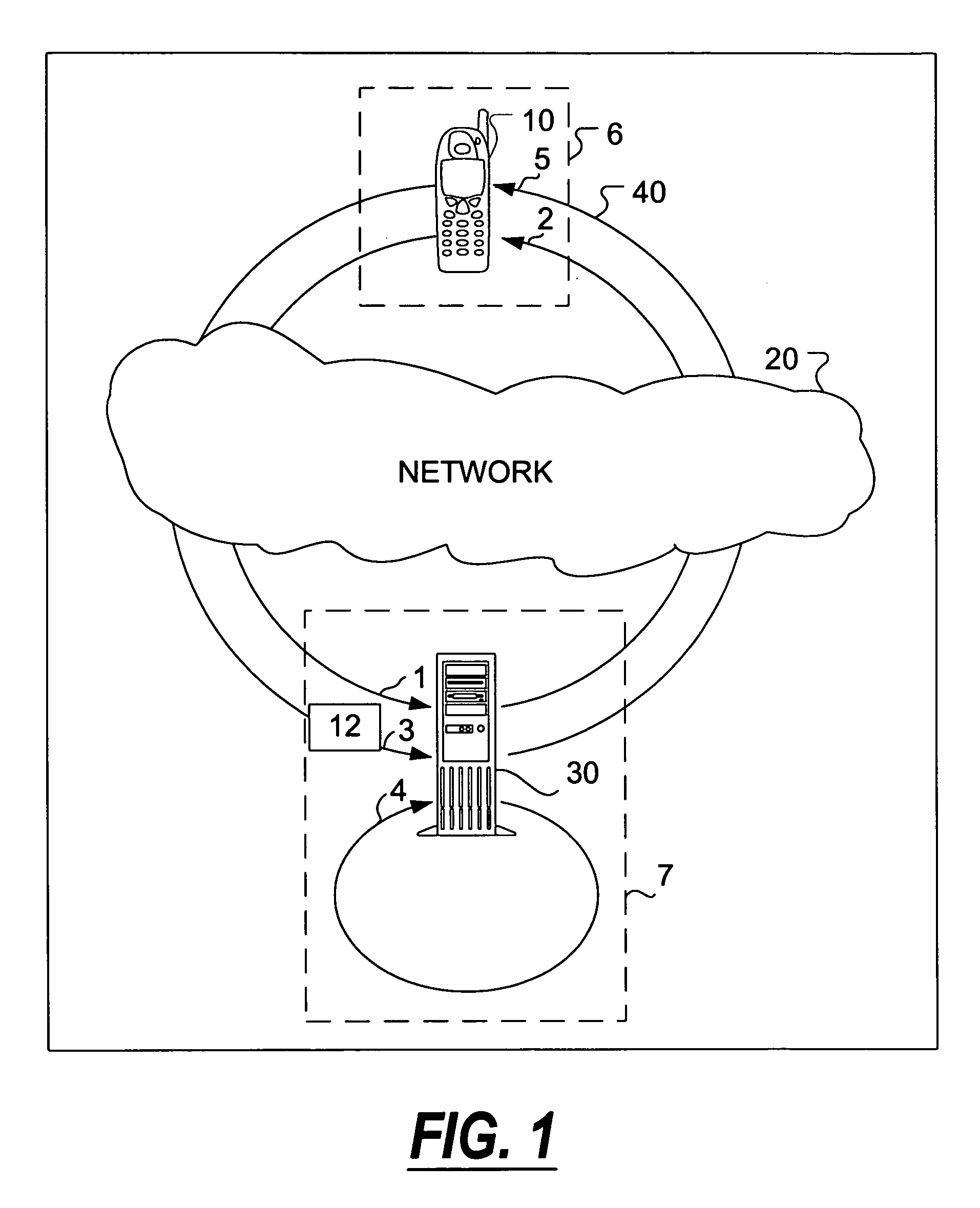
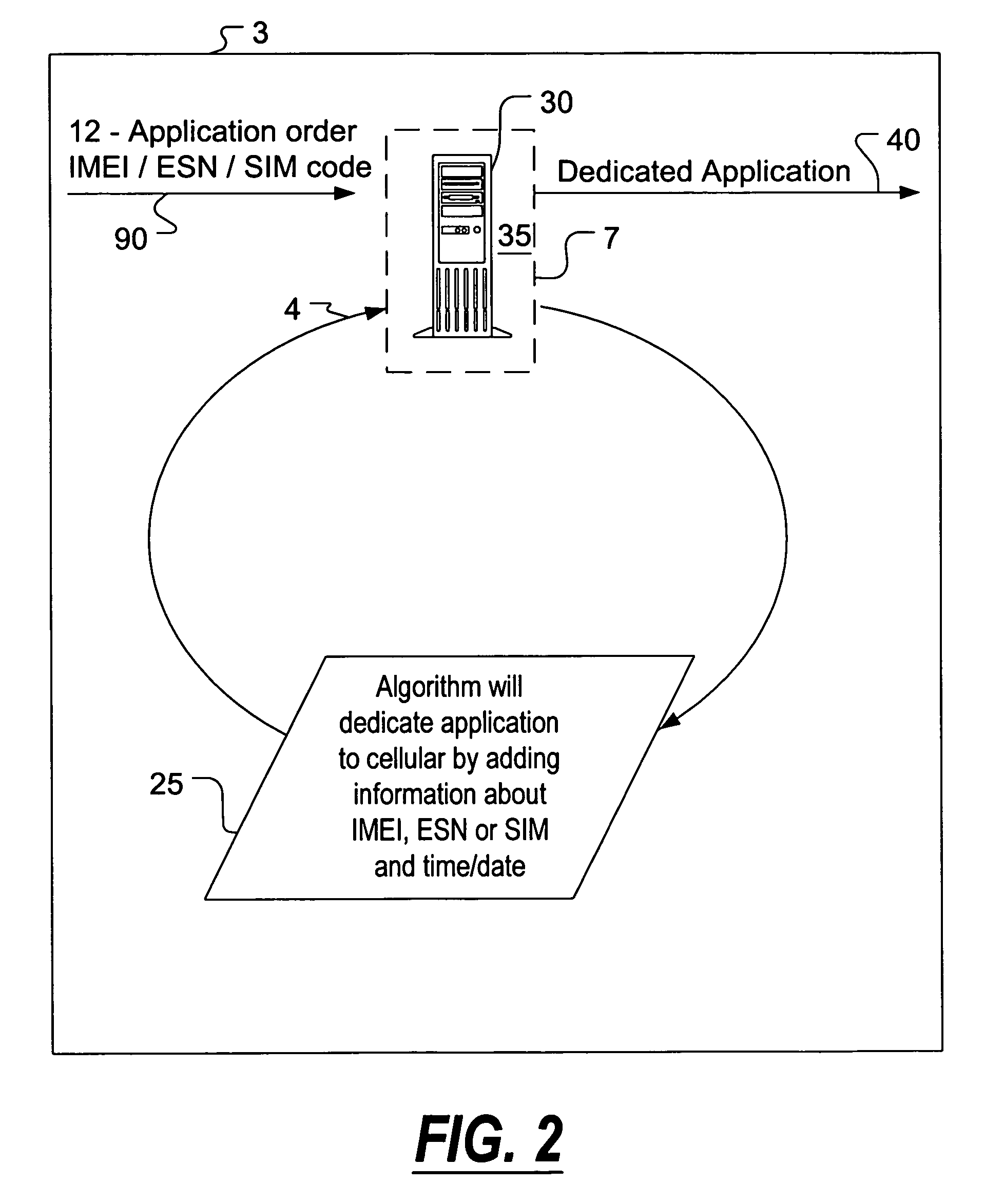
Dedicated applications for user stations and methods for downloading dedicated applications to user stations
The present invention is directed to a copy-protected dedicated software application and methods for downloading copy-protected dedicated applications to user stations so that the unique dedicated applications are executable upon downloading to the user station and so that the unique dedicated applications will only run on that particular authorized user station. A method of downloading the unique dedicated applications directly from a distributor to the user station is also included which eliminates the need for contact between the original manufacturer of an application and the user station.
Owner:NOKIA TECHNOLOGLES OY
Separation of copy protection rules for digital rights management
InactiveUS20050071663A1Digital data processing detailsAnalogue secracy/subscription systemsRights managementDigital rights management
Management of rights to content is provided within an authorized domain. In a single authorized domain, where a plurality of domain interfaces are protected using a common rights management system, a copy of particular content may be allowed to be provided on all devices or only on specific devices coupled to the domain via the interfaces. Copy protection information, for outputs to external devices not protected by the common rights management system, is also specified. Rules can be provided for specifying whether particular content may be copied or moved to another protected domain. A number of rendering devices permitted to render the content simultaneously may be specified. Content rules are provided for use in managing rights to content within an authorized domain. Such rules can be associated with content that is persistently stored by a consumer device, as well as with content that is only rendered by a consumer device.
Owner:GENERAL INSTR CORP +1
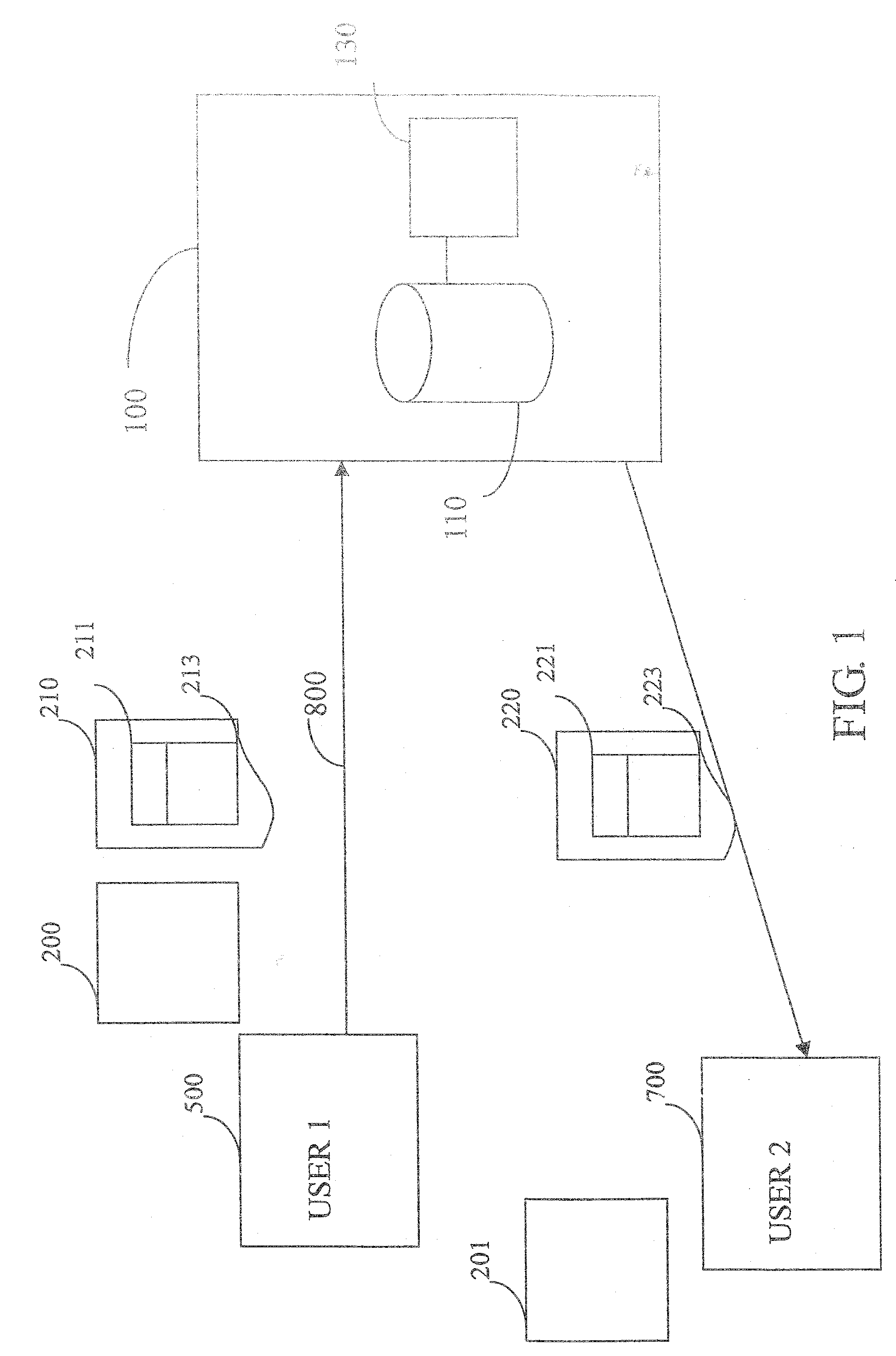
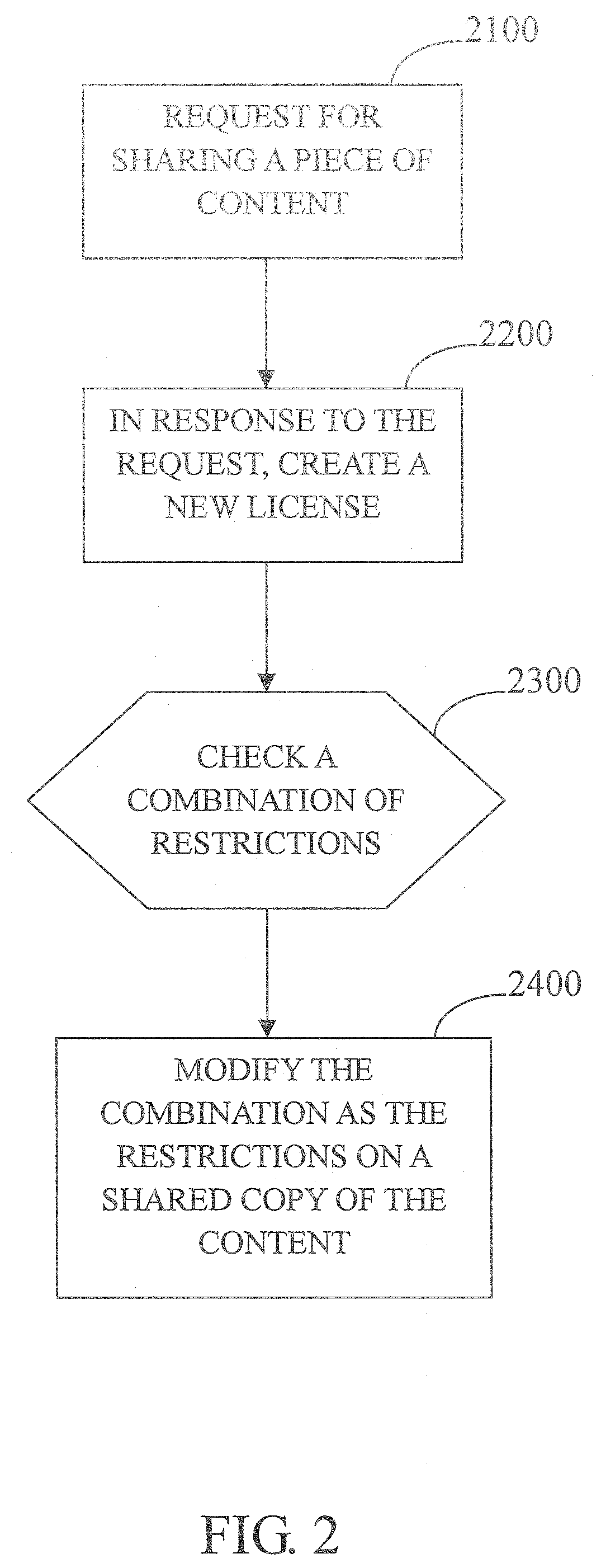
Content protection system and method for enabling secure sharing of copy-protected content
InactiveUS20080040283A1Data processing applicationsProgram/content distribution protectionManagement unitCopy protection
A content protection system for enabling secure sharing of a piece of content encrypted for copy-protection and a method therefor. The system includes a first processing unit and a license management unit. The first processing unit is for enabling the first user to send a request for sharing the piece of content with at least a second user. The license management unit, in response to the request, is used for generating a second license file for the second user which is associated with the first license file, the piece of content, and the second user, wherein the second license file securely includes a second decryption key needed to decrypt the piece of content and restrictions on the piece of content with respect to the second user. The second user is authorized to use a shared copy of the piece of content according to the restrictions in the second license file.
Owner:ARCADYAN
Inter-server communication using request with encrypted parameter
InactiveUS6970849B1Preventing unchecked proliferationDigital data processing detailsUser identity/authority verificationUniform resource locatorBiological activation
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
Character and vector graphics watermark for structured electronic documents security
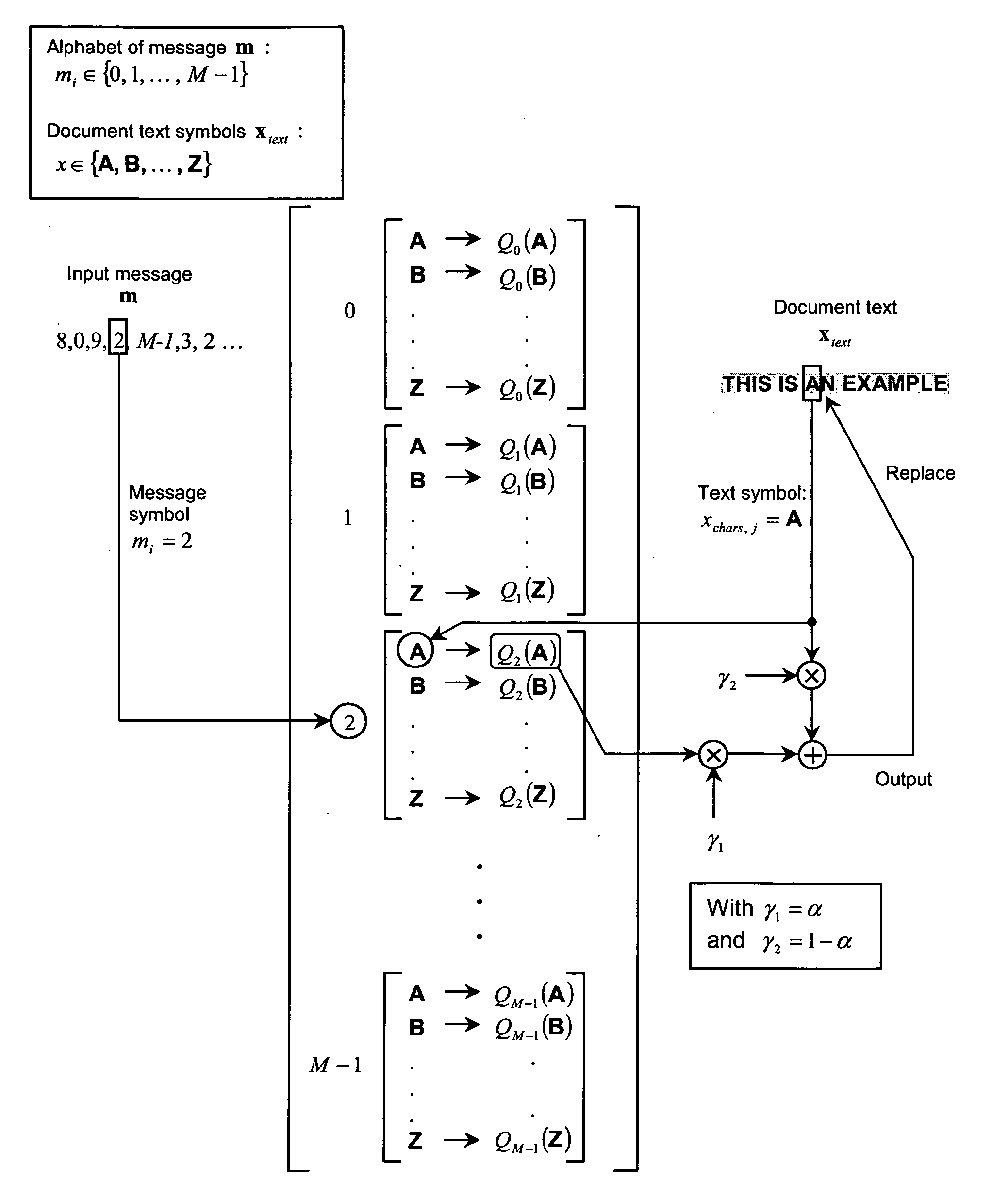
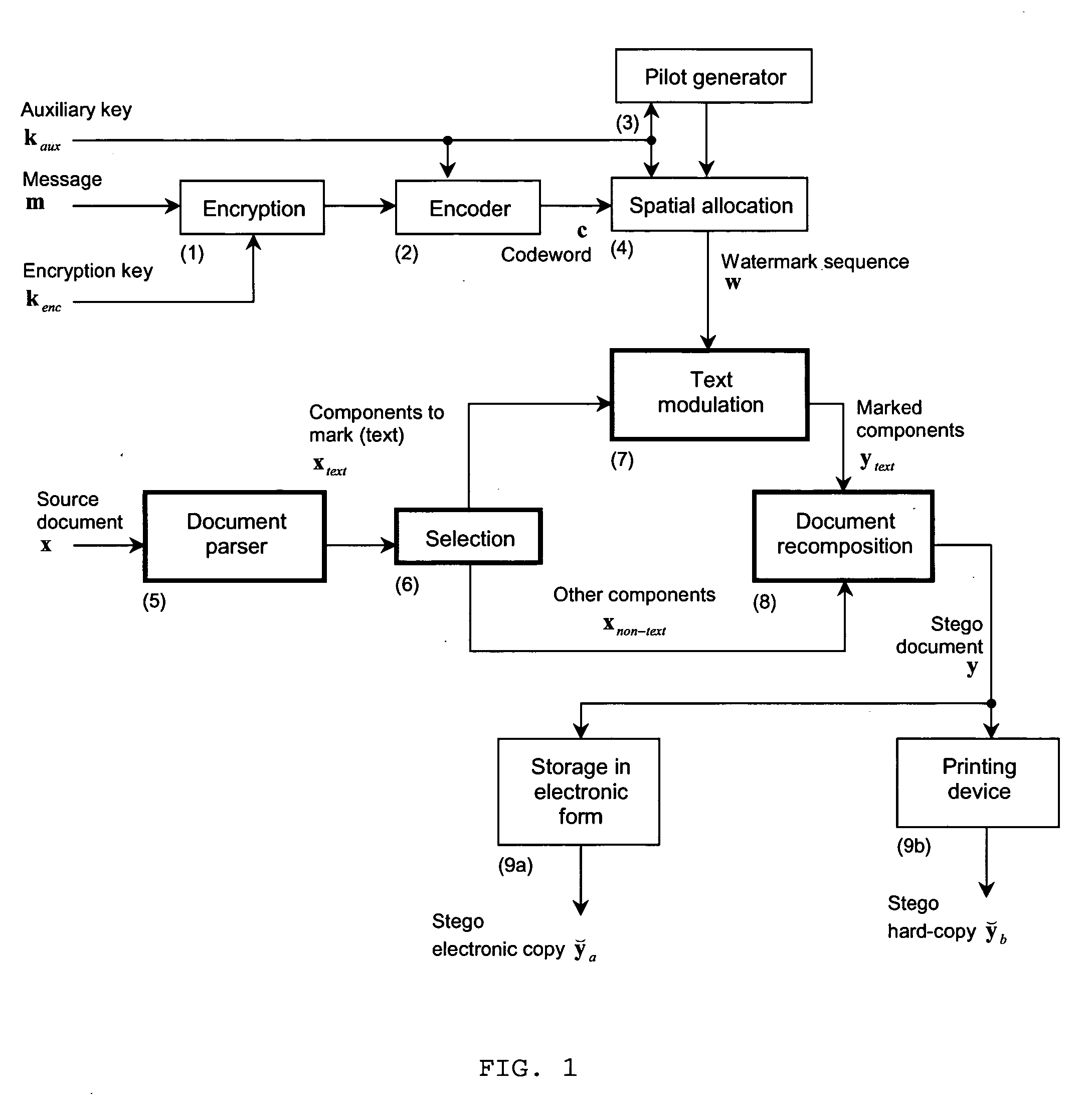
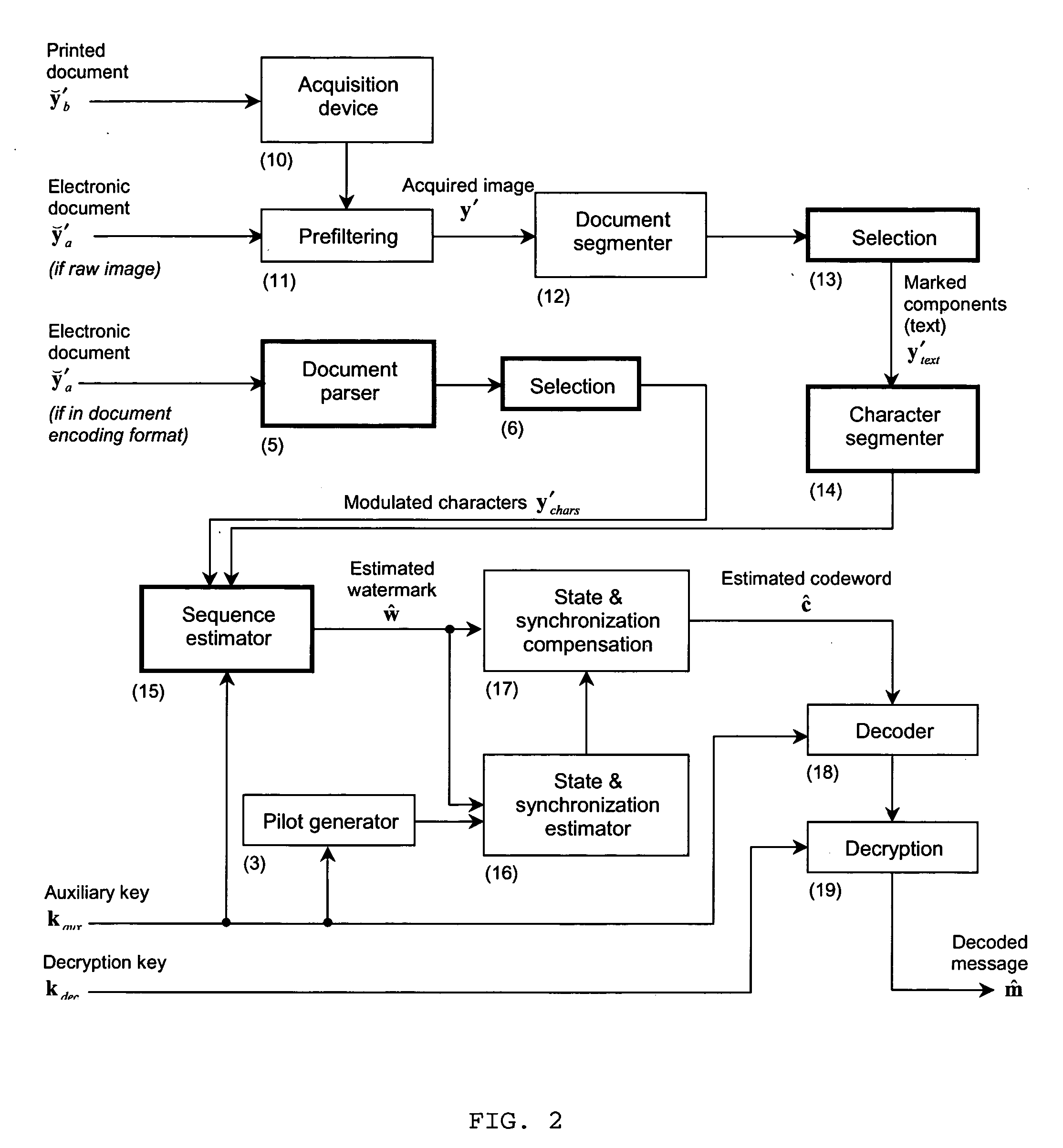
ActiveUS20060075241A1Reasonable data-hiding rateIncrease chanceUser identity/authority verificationDigital data protectionDocumentation procedurePaper document
The present invention is a method and apparatus for watermarking text or vector graphics documents. It is based on character-wise or vector graphics element-wise grayscale or color modulation. At high resolution, halftone or dither modulation can also be used in addition or in place of grayscale / color modulation, for printed representation of electronic document. For the detection, the document is acquired through an acquisition device, document segmentation is performed, characters / elements are segmented, the watermark signal is estimated and the information is decoded. Although the proposed scheme mostly addresses the watermarking of hard-copy documents, it can easily be integrated into electronic document editing and acquisition tools, and the watermark is attached to the document electronic version. The invention is applicable either using expensive high- resolution printing and acquisition devices, either using common cheap low-resolution devices, depending on the application needs. The proposed scheme is suitable for example to the protection of security documents, contracts, technical and commercial documentation; it can use any physical support like paper, cellulose, or plastic; it can be used for copy protection, authentication, or tamper proofing; finally it can also be applied to other non security-related applications, such as document tracking, as well as document embedded annotation and watermarked-assisted automatic processing.
Owner:UNIVERSITY OF GENEVA +1
Method and arrangement for detecting a watermark using statistical characteristics of the information signal in which the watermark is embedded
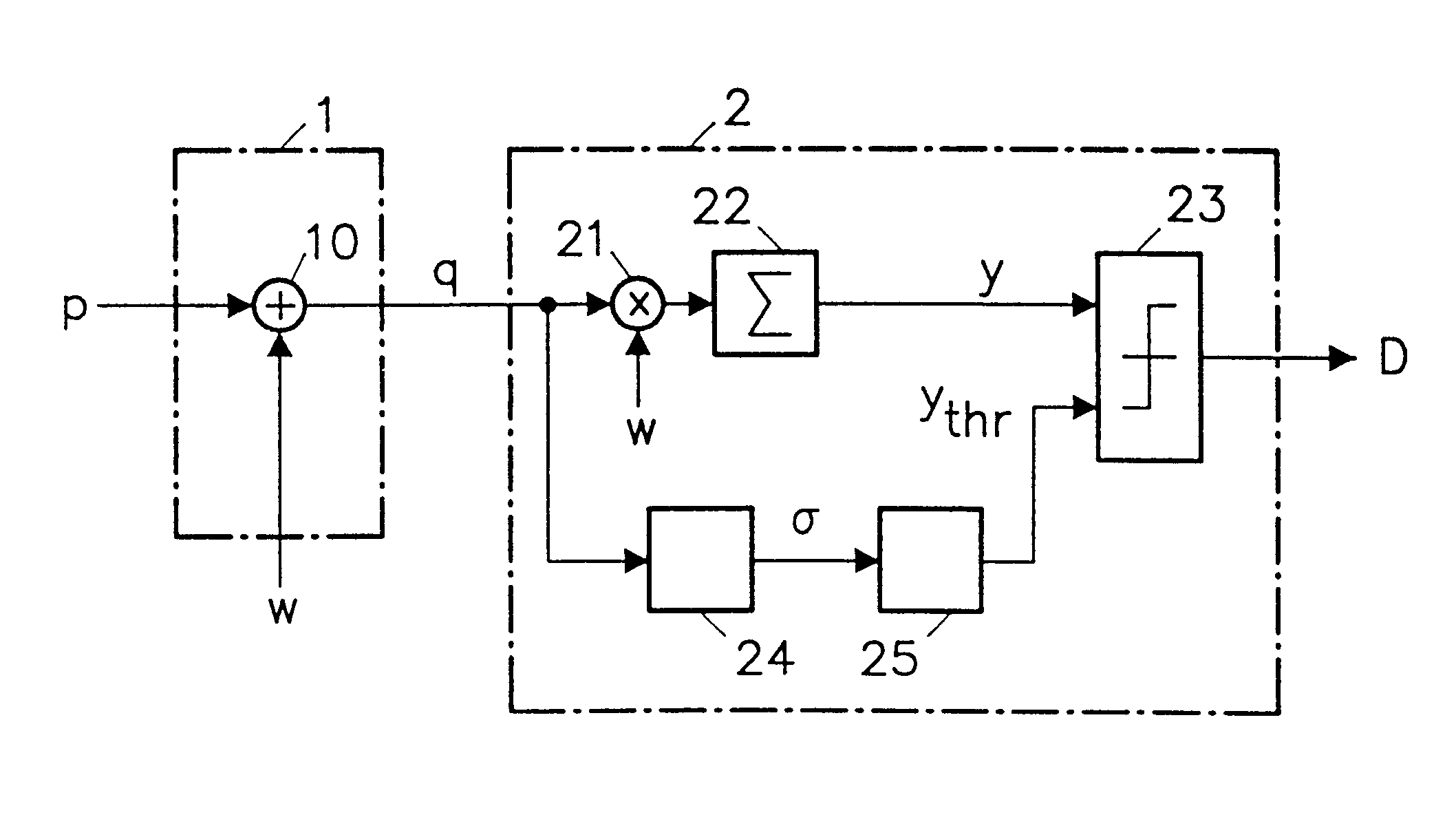
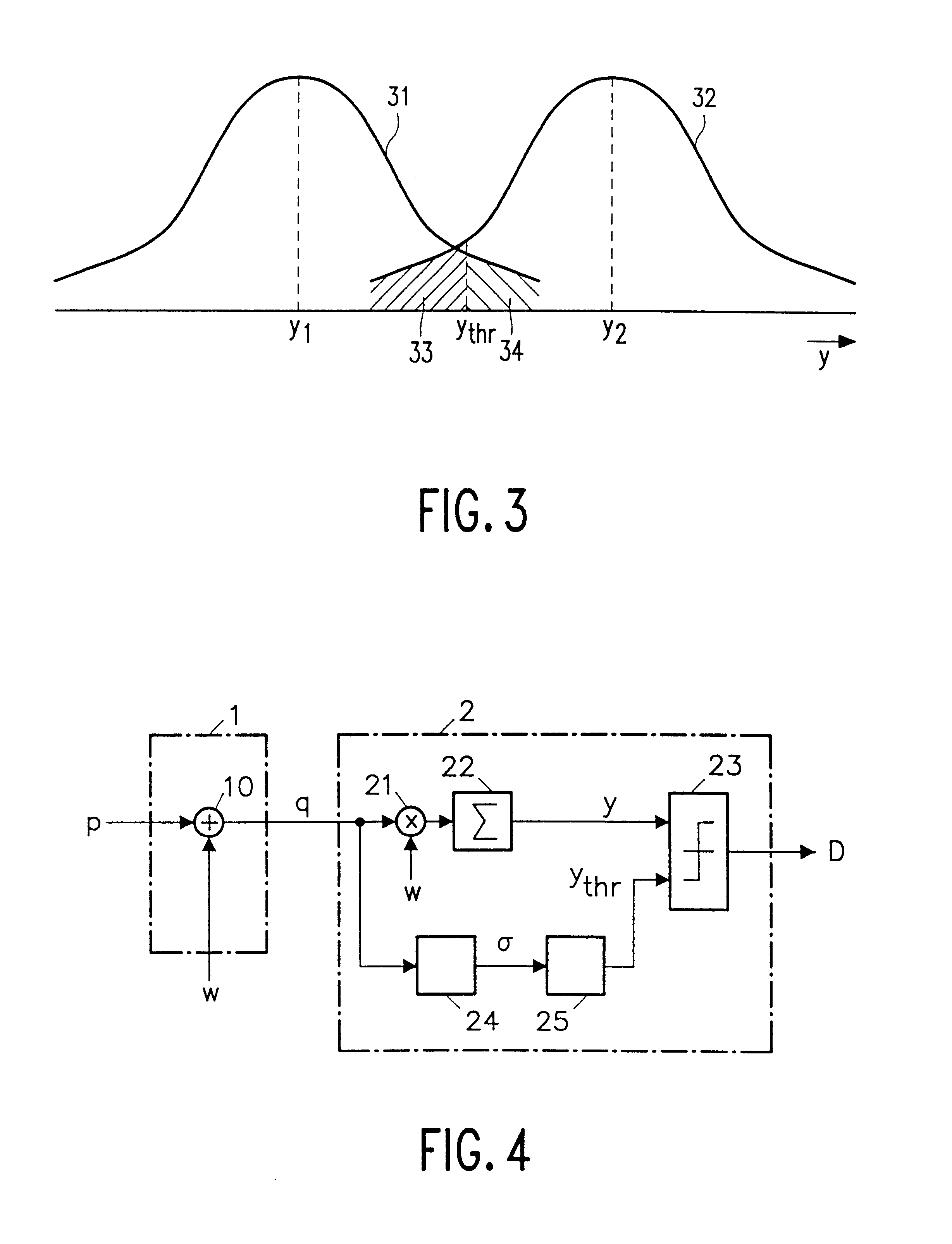
Recently developed methods for copy protection rely on a watermark detector to judge whether multimedia content can be copied or not. In such copy protection schemes, a watermark detector examines the multimedia content and outputs a signal (D) indicating whether a watermark is present or not. Known watermark detectors determine a decision variable (y) indicating to which extent the watermark is present, for example, the amount of correlation between input signal and a reference copy of the watermark to be detected. The watermark is detected if the decision variable exceeds a predetermined threshold (ythr)In accordance with the invention, the threshold value (ythr) is adaptively controlled in dependence upon statistical characteristics of the information signal and a desired probability of false alarms (watermark detected whereas the signal is not watermarked). In an embodiment, the watermark detector determines the standard deviation (sigma) of the pixel values threshold level and calculates the threshold value in accordance with the relationin which erfc is the error function and sigma is said standard deviation of the information signal values.
Owner:U S PHILIPS CORP +1
Copy protection for digital motion picture image data
InactiveUS7043019B2Television system detailsUser identity/authority verificationComputer graphics (images)Copy protection
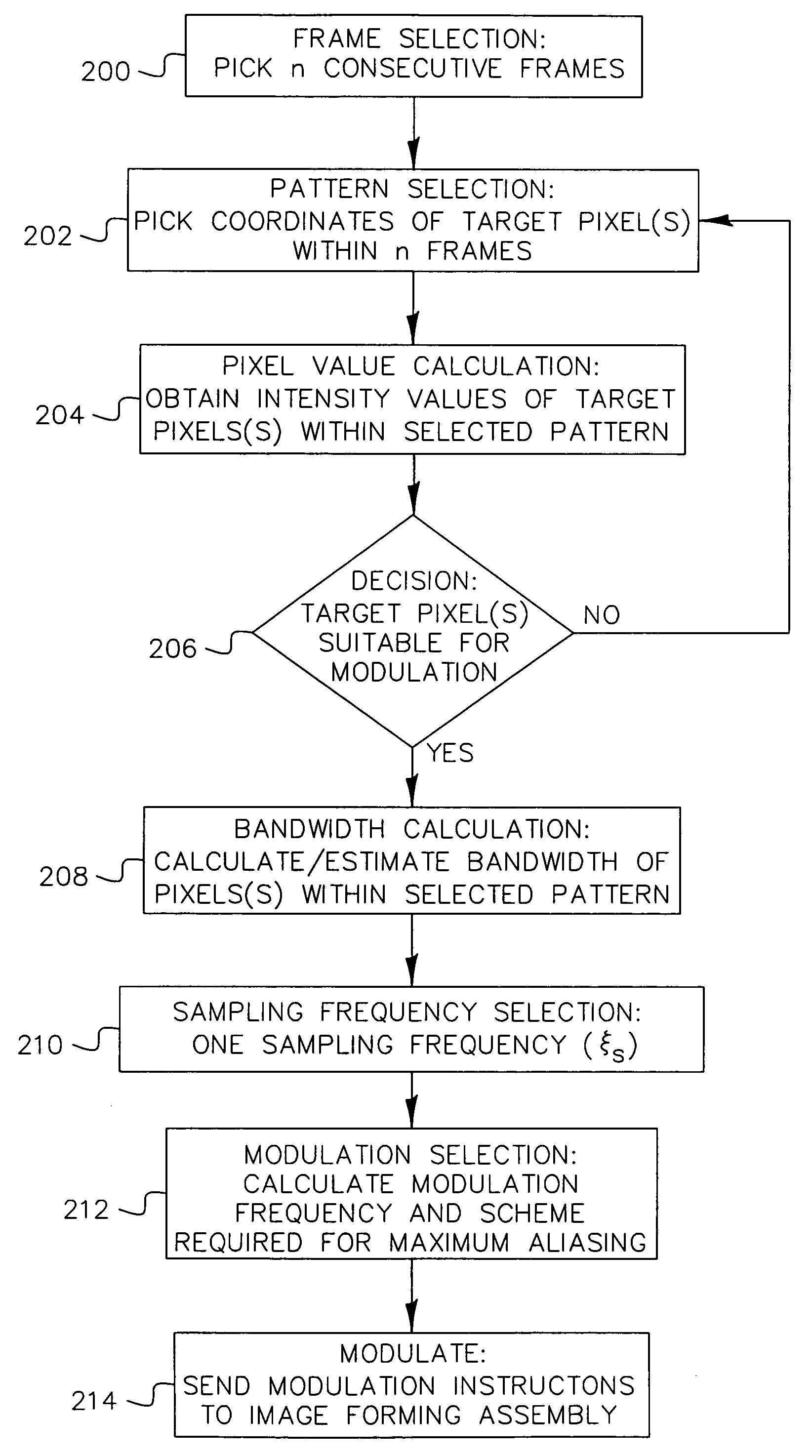
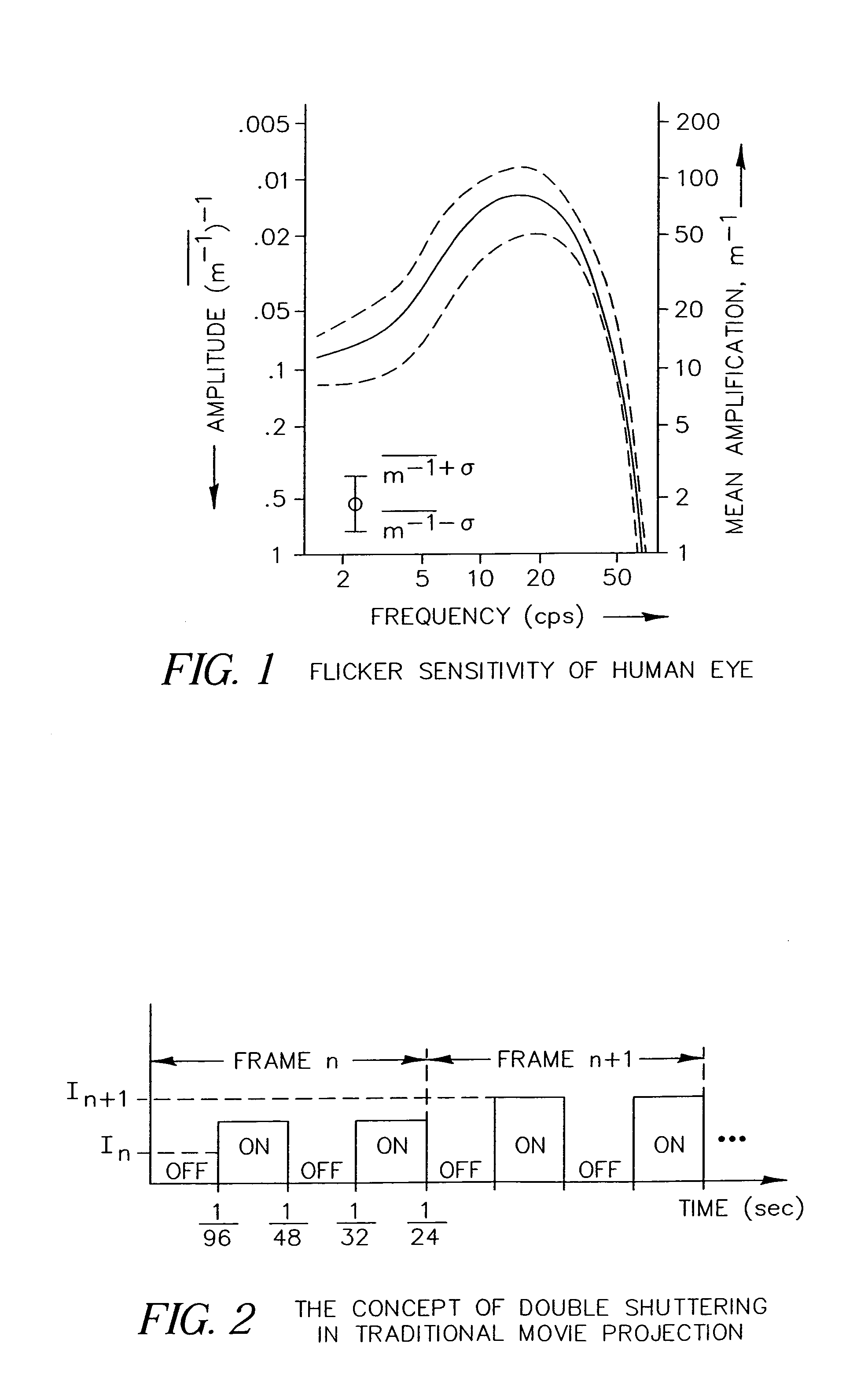
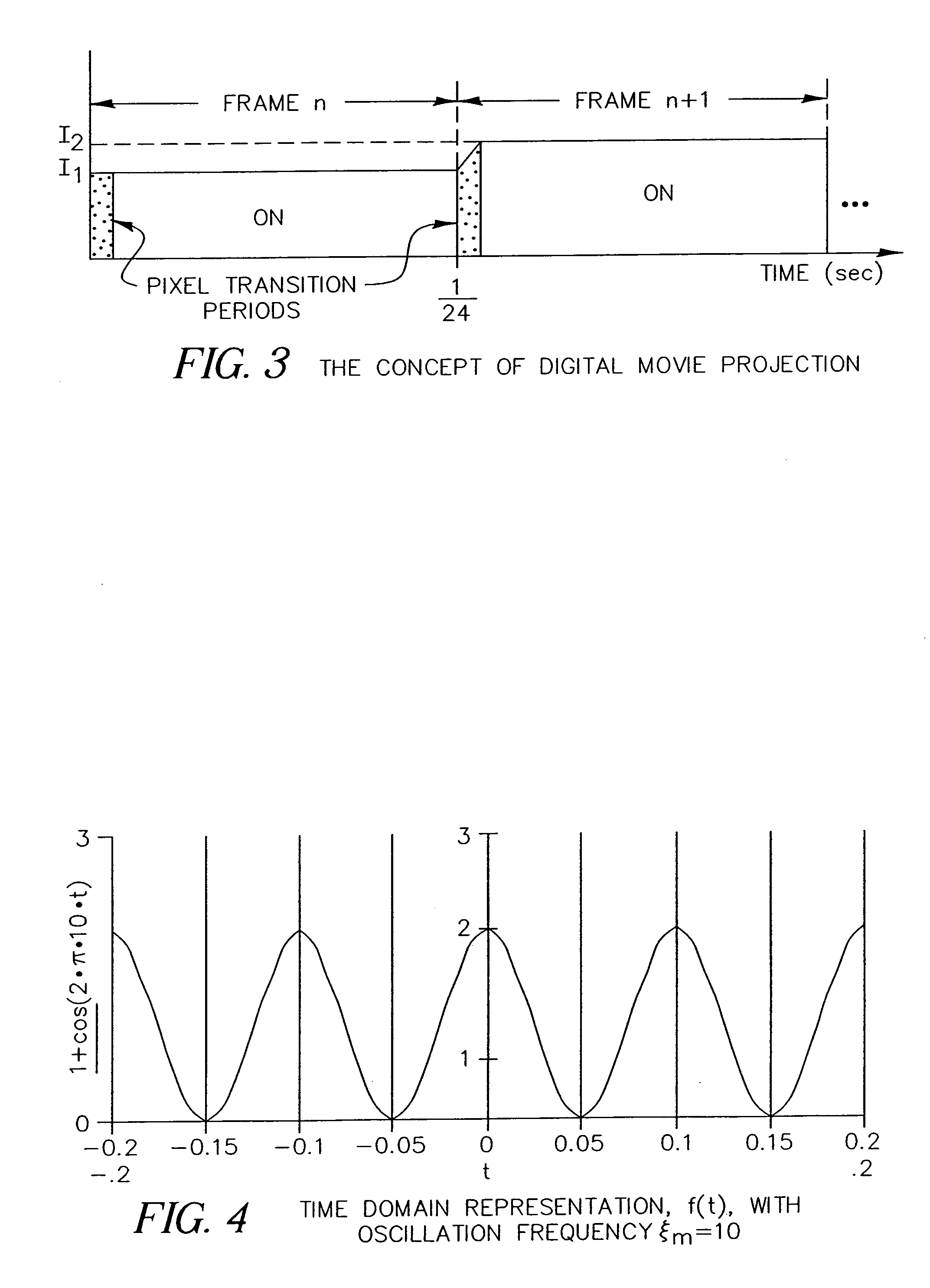
An apparatus and method for displaying a copy-deterrent pattern (104) within a digital motion picture in order to discourage recording of the motion picture using a video camera or other sampling recording device. A copy-deterrent pattern (104) could be, for example, one or more symbols, a random pattern, a digital watermark or a text message (106). The copy-deterrent pattern (104) comprises a plurality of pixels within each frame of the digital motion picture, and the displayed pixel intensities are modulated at a temporal frequency using modulation characteristics deliberately selected to be imperceptible to human observers while simultaneously producing objectionable aliasing in any copy made using a video camera.
Owner:EASTMAN KODAK CO
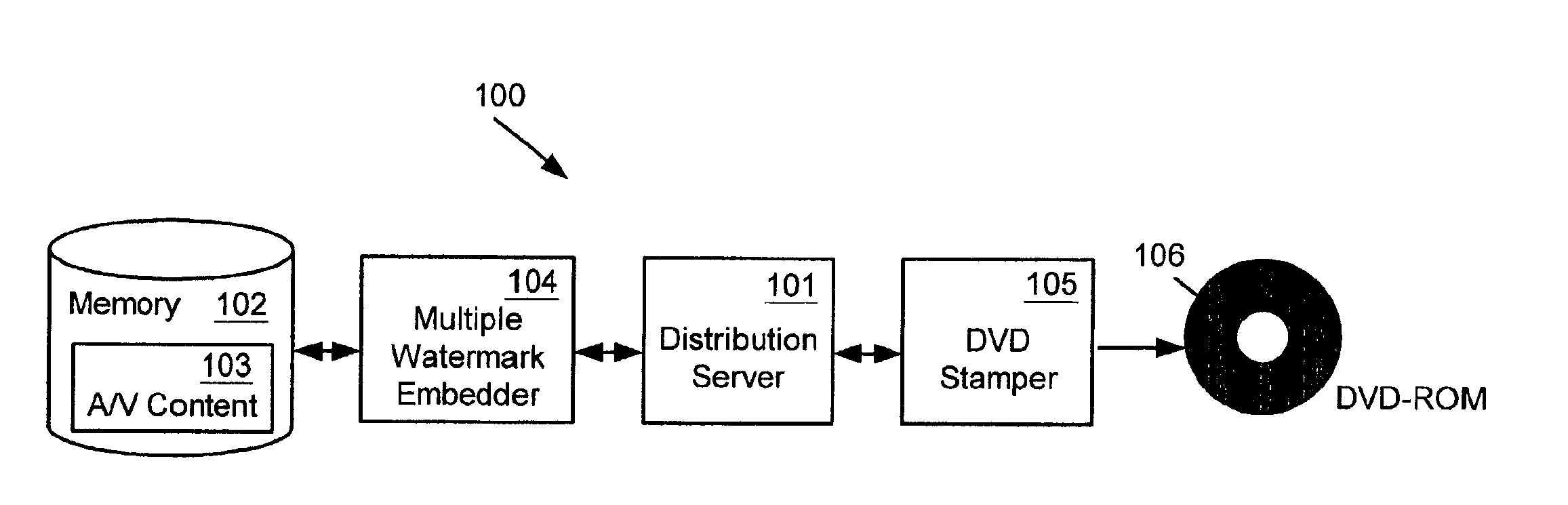
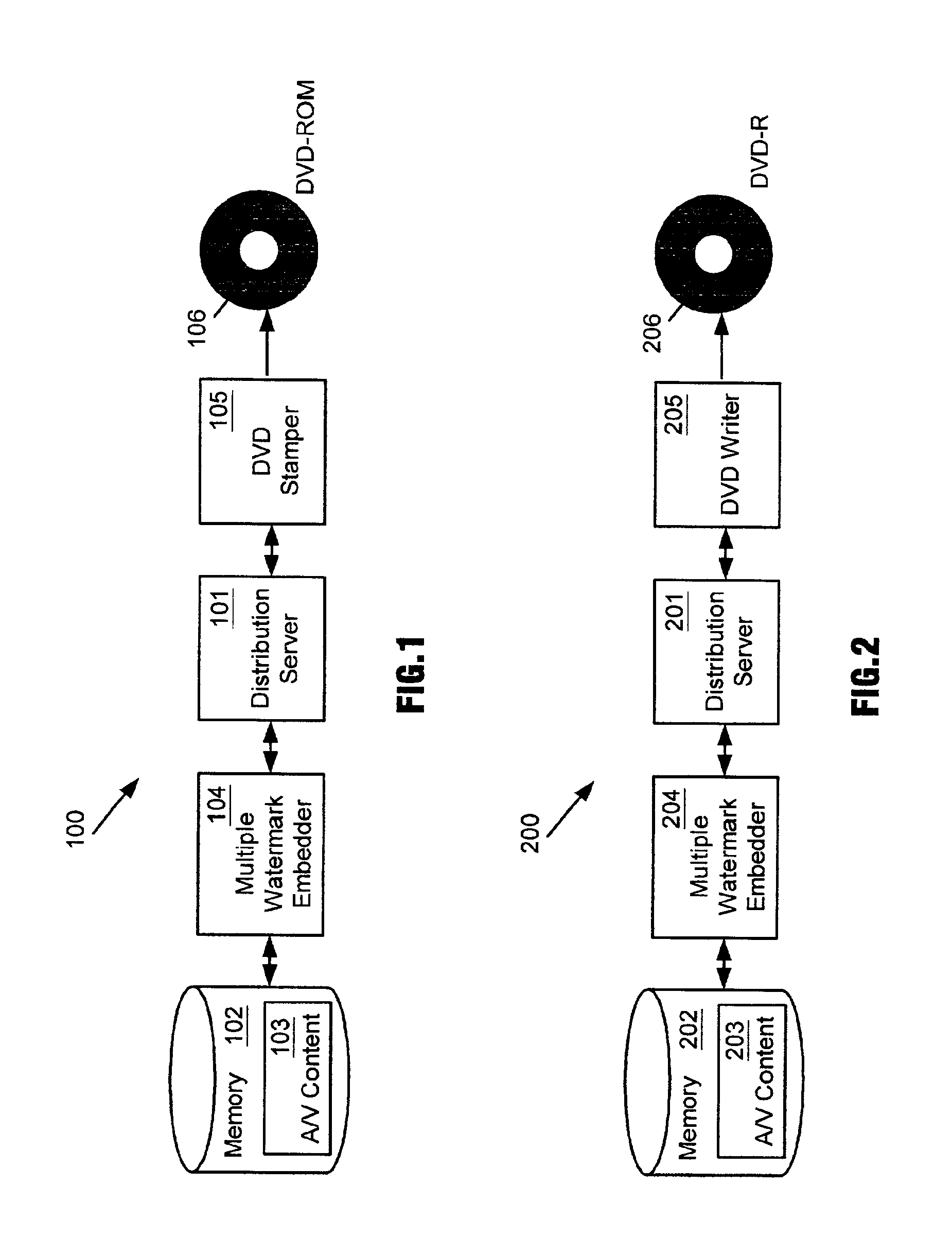
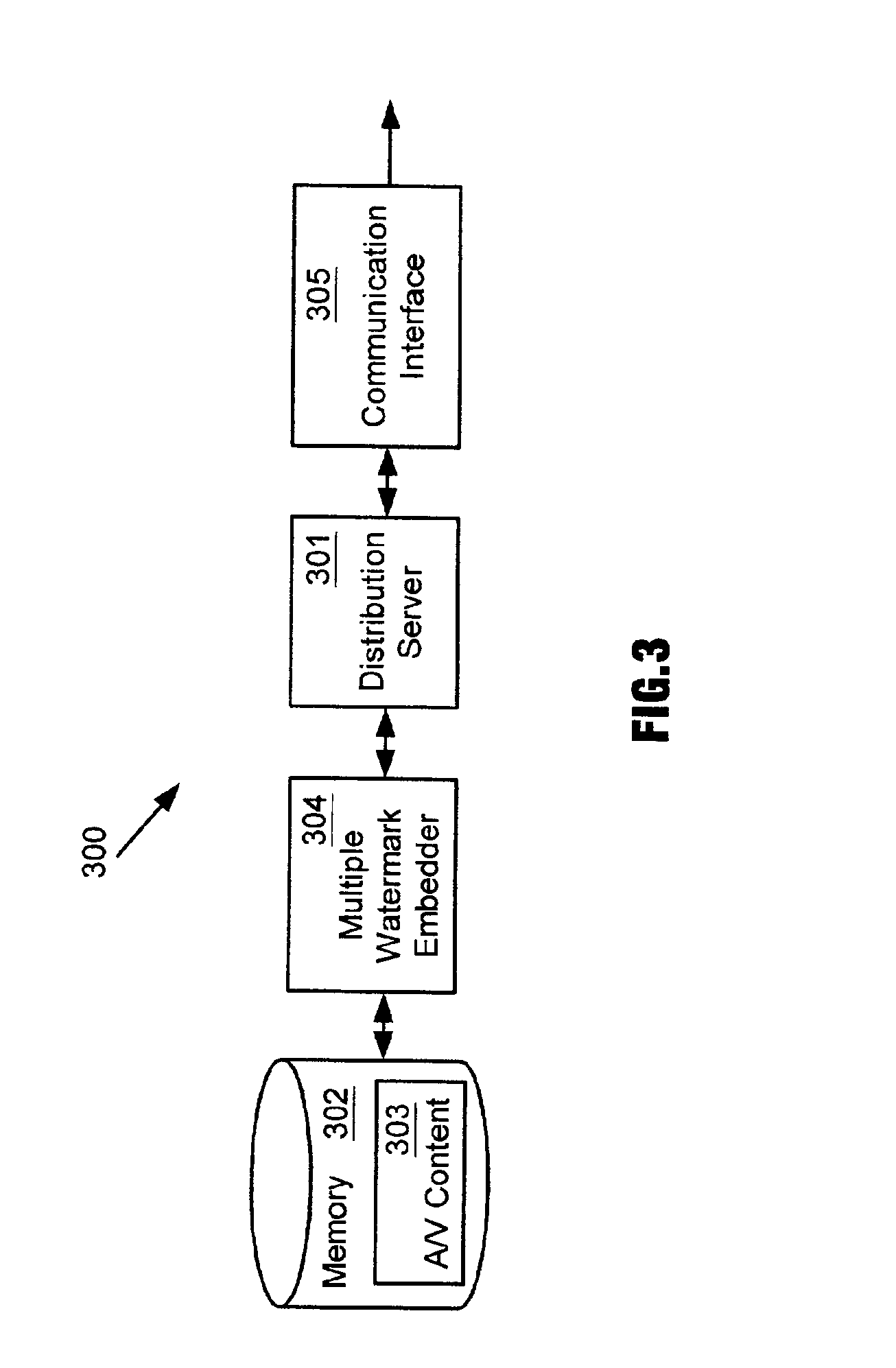
Enhanced copy protection of proprietary material employing multiple watermarks
InactiveUS6931536B2Enhanced copyEnhanced play protectionDigital data processing detailsUser identity/authority verificationComputer hardwareCopy protection
A method and apparatus for distributing proprietary material employs multiple watermarks embedded in the proprietary material for enhanced copy protection. A first watermark is to be processed by programmable and non-programmable devices configured to process the first watermark for copy protection of the proprietary material. If a programmable device eliminates the first watermark so that unauthorized copies of the proprietary material can be made, then non-programmable devices configured to process a second watermark as well as the first watermark look for and process the second watermark for copy protection of the proprietary material upon their failure to detect the first watermark.
Owner:MARKING OBJECT VIRTUALIZATION INTELLIGENCE LLC
Method and system for a generic key packet for mpeg-2 transport scrambling
Methods and systems for a generic key packet for MPEG-2 transport scrambling and descrambling are disclosed and may comprise descrambling multiple package identifier channels in a transport stream utilizing a single generic key packet. The single generic key packet may comprise scrambling keys for each of the multiple package identifier channels, and may comprise scrambling keys for time intervals corresponding to two or more successive key change points. A key change point may be enabled to occur at the same time instant for each of the multiple package identifier channels, or may be enabled to occur at different time instants for one or more of the multiple package identifier channels. The scrambling / descrambling may comprise copy protection or conditional access descrambling. The generic key change packet may comprise information identifying a scrambling / descrambling algorithm, such as AES, DES and 3-DES, for example.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
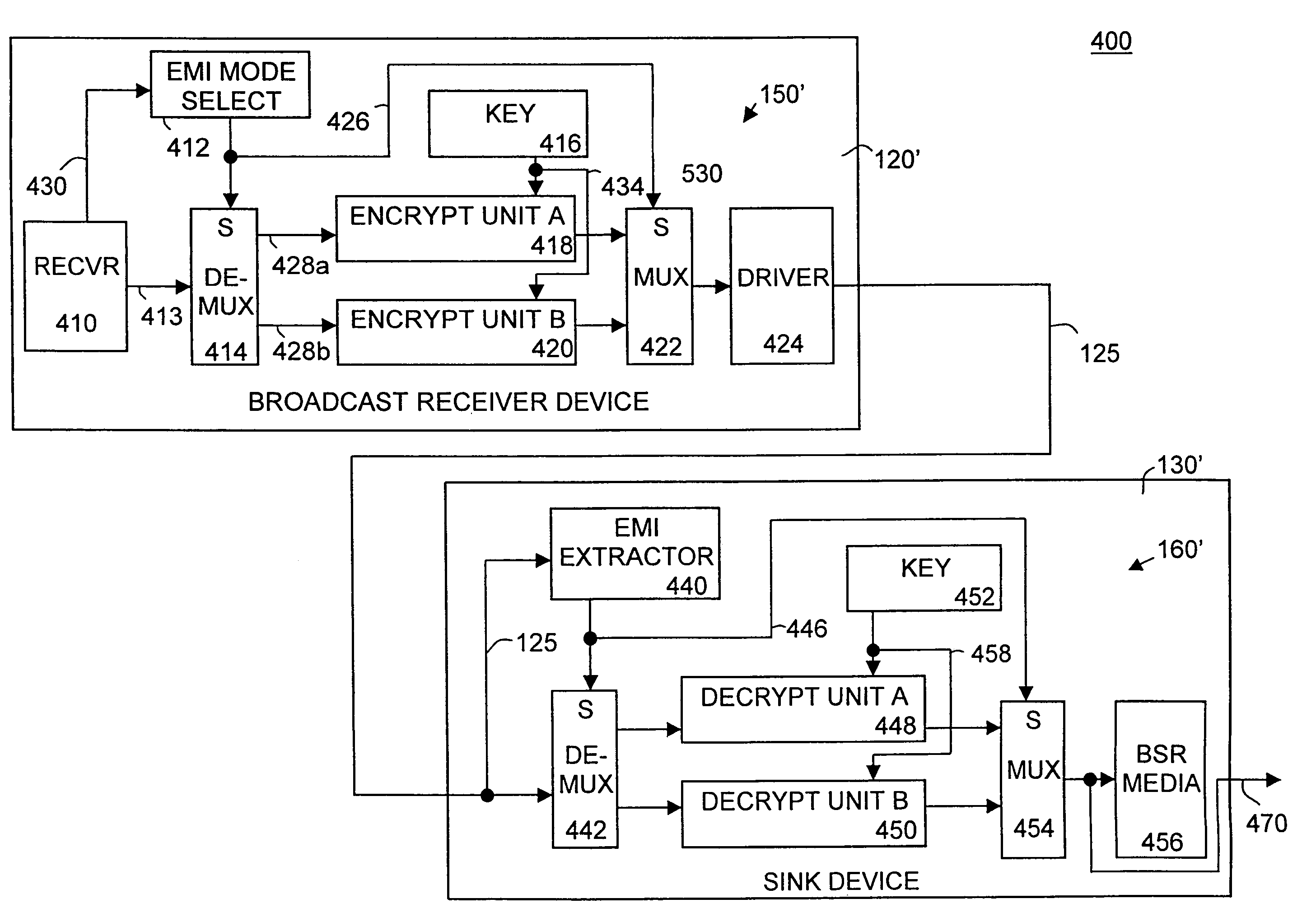
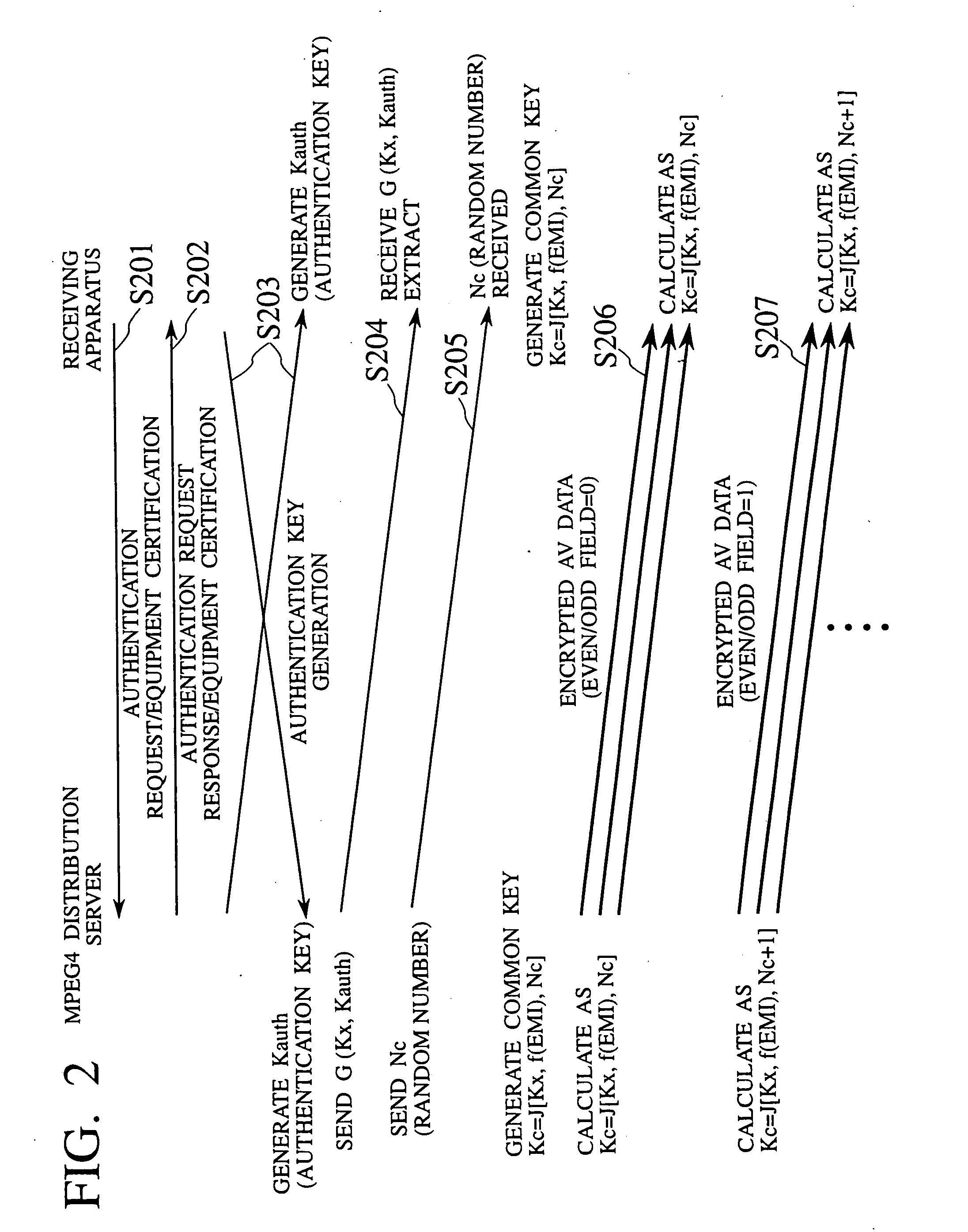
Method and system for transferring information using an encryption mode indicator
A method and system for transferring information using an encryption mode indicator (EMI). The present invention provides several secure information communication modes in which data (e.g., representing an audio / visual work) can be transmitted from a source device to a sink device (receiving station) in a number of secure modes. In one secure mode, EMI mode A, the information of the transmission is not allowed to be copied as a whole work; this is the highest level of copy protection. In second secure mode, EMI mode B, the information of the transmission is allowed to be copied once and once only by the sink device. In a third transmission mode, no encryption is used and free copying is available.
Owner:SONY CORP +1
Recording medium, apparatus for forming the recording medium, and apparatus and method for reproducing the recording medium
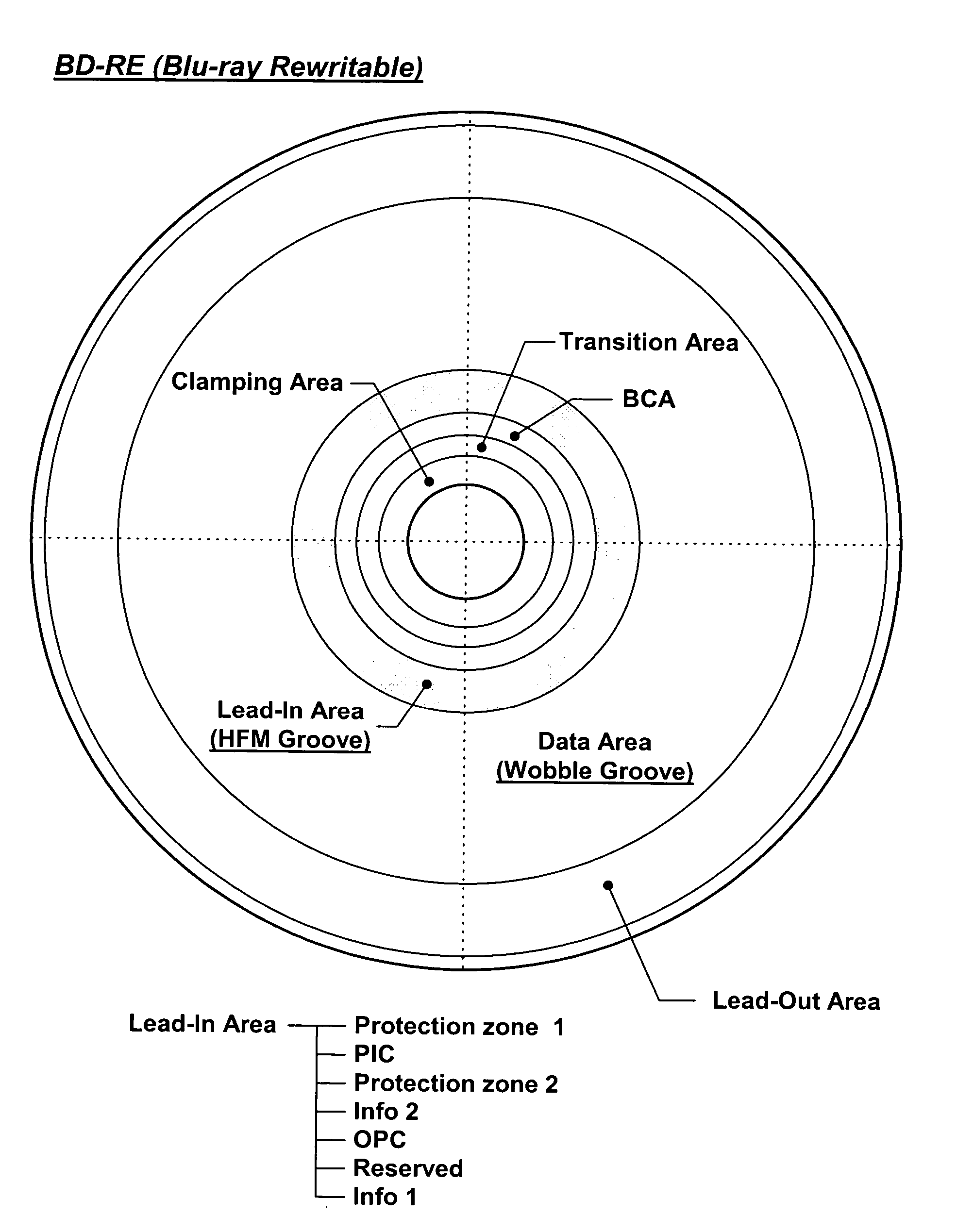
InactiveUS20040223427A1Accurate and easy distinctionEffective protectionElectronic editing digitised analogue information signalsFilamentary/web record carriersHigh densityControl data
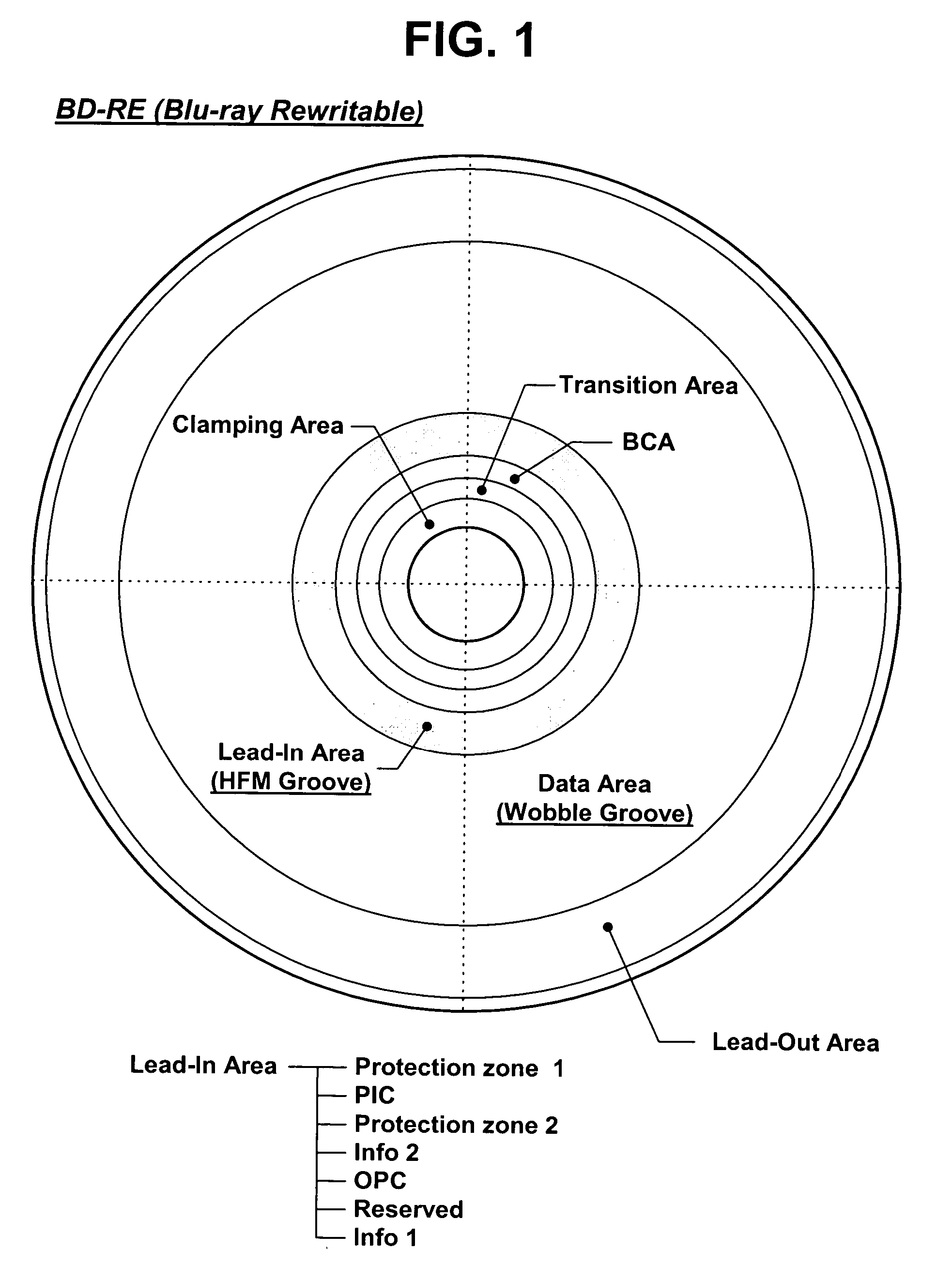
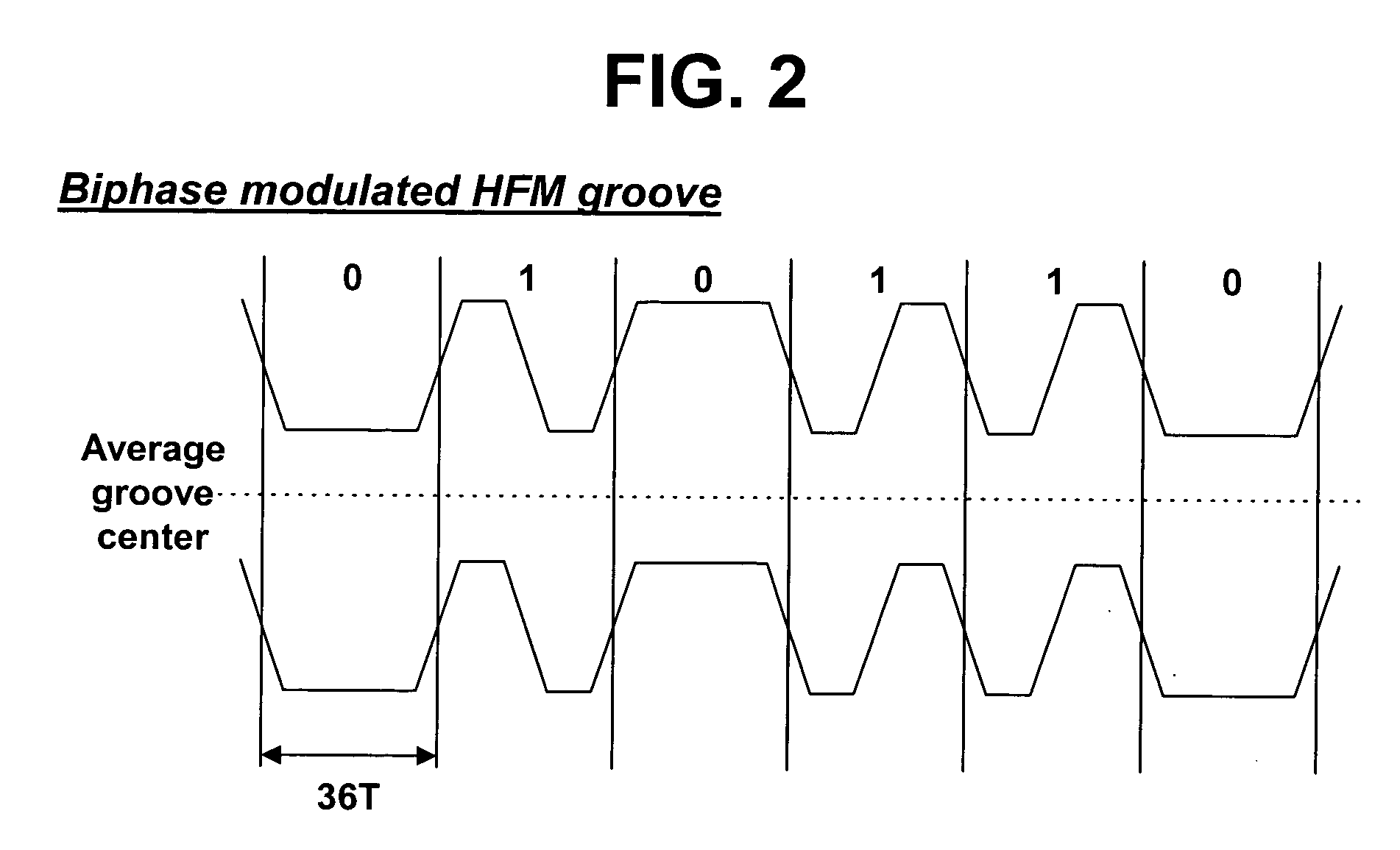
Disclosed herein are a recording medium, an apparatus for forming the recording medium, and an apparatus and method for reproducing the recording medium. CPI (Copy Protection-related Information), identification information (CPI_Flag) indicative of recording or non-recording of the CPI, and / or a plurality of contents specific information (CSI) with different formats are recorded in a PIC (Permanent Information & Control data) zone of a high-density optical disc such as a BD-ROM (Blu-ray Disc-ROM). A formatting operation and mastering operation are performed under the condition that control data including the CPI, CPI_Flag and / or CSI is separated from main data. An optical disc device judges whether the optical disc has been illegally copied, with reference to the CPI, CPI_Flag and / or CSI read from the optical disc, and compulsorily stops a data playback operation upon judging that the disc has been illegally copied. Therefore, it is possible to effectively protect an optical disc from illegal copying, make an accurate and easy distinction between a legally made optical disc and an illegally made optical disc, and restrict reproduction of an illegally made optical disc.
Owner:LG ELECTRONICS INC
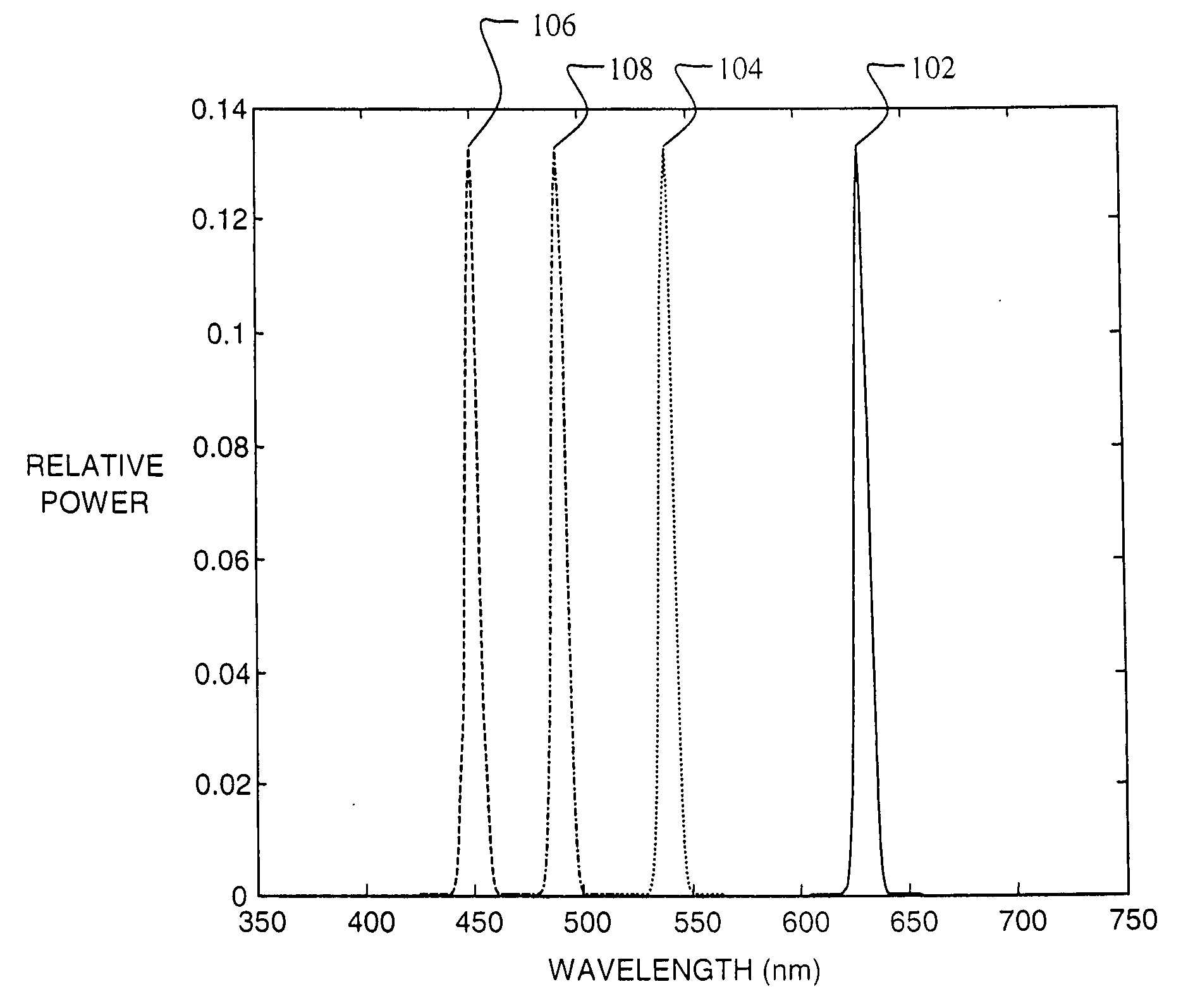
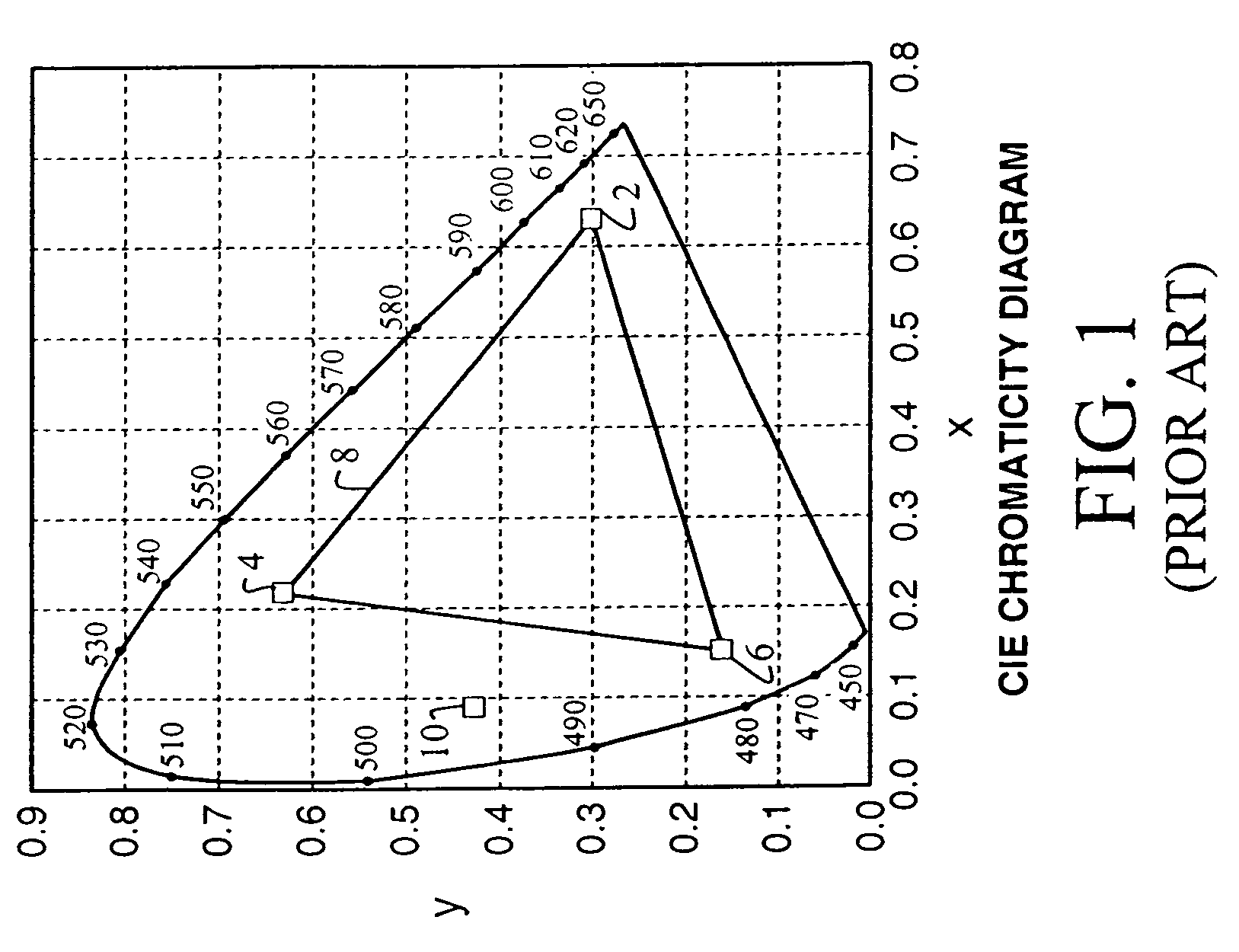
Four color digital cinema system with extended color gamut and copy protection
A color display system including a display device for four or more visible color primaries and a processor for controlling the four or more color primaries to selectively render portions of an image or image sequence such that visually equivalent colors displayed in two or more image portions differ in their spectral composition.
Owner:IMAX THEATERS INT
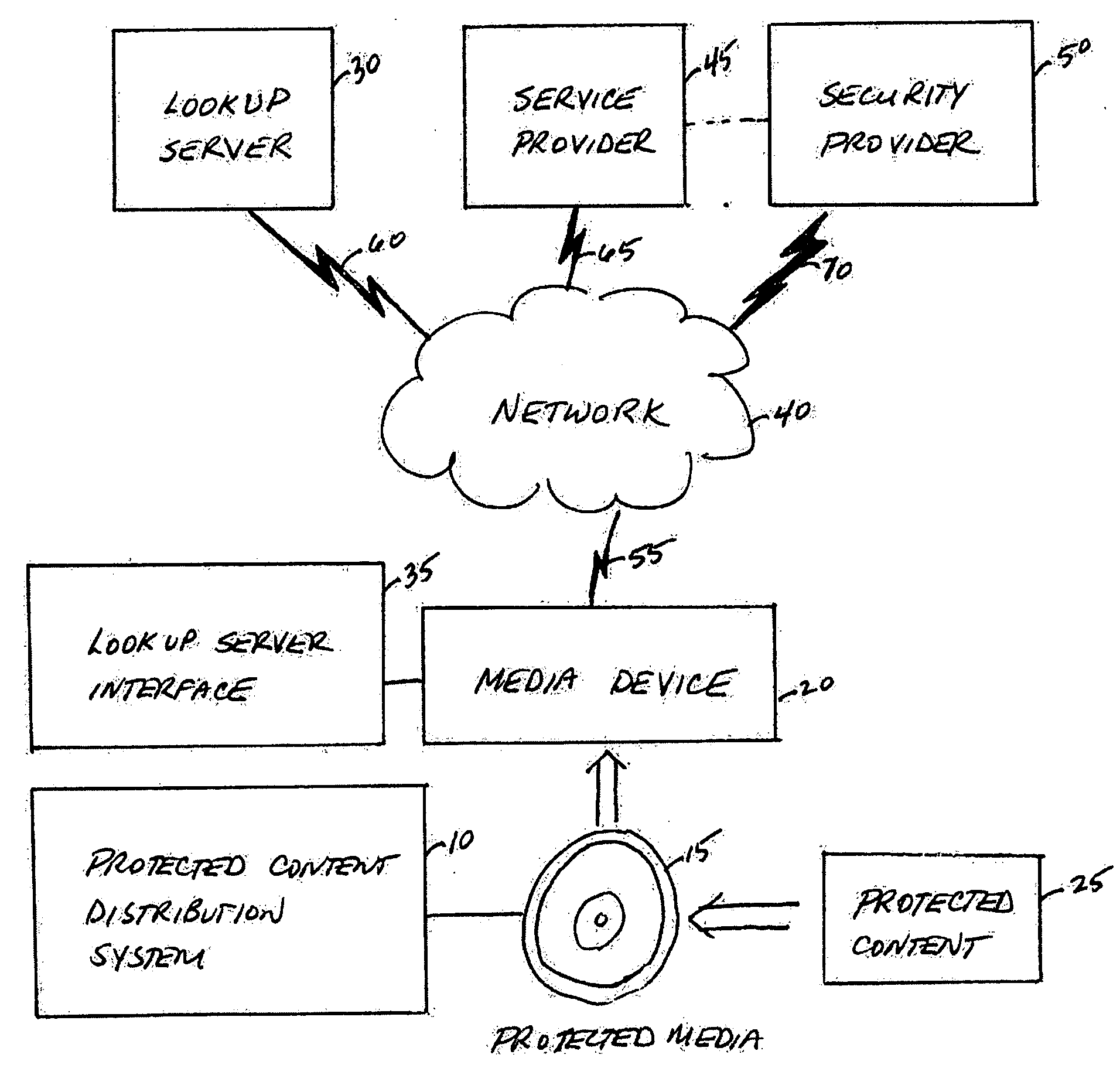
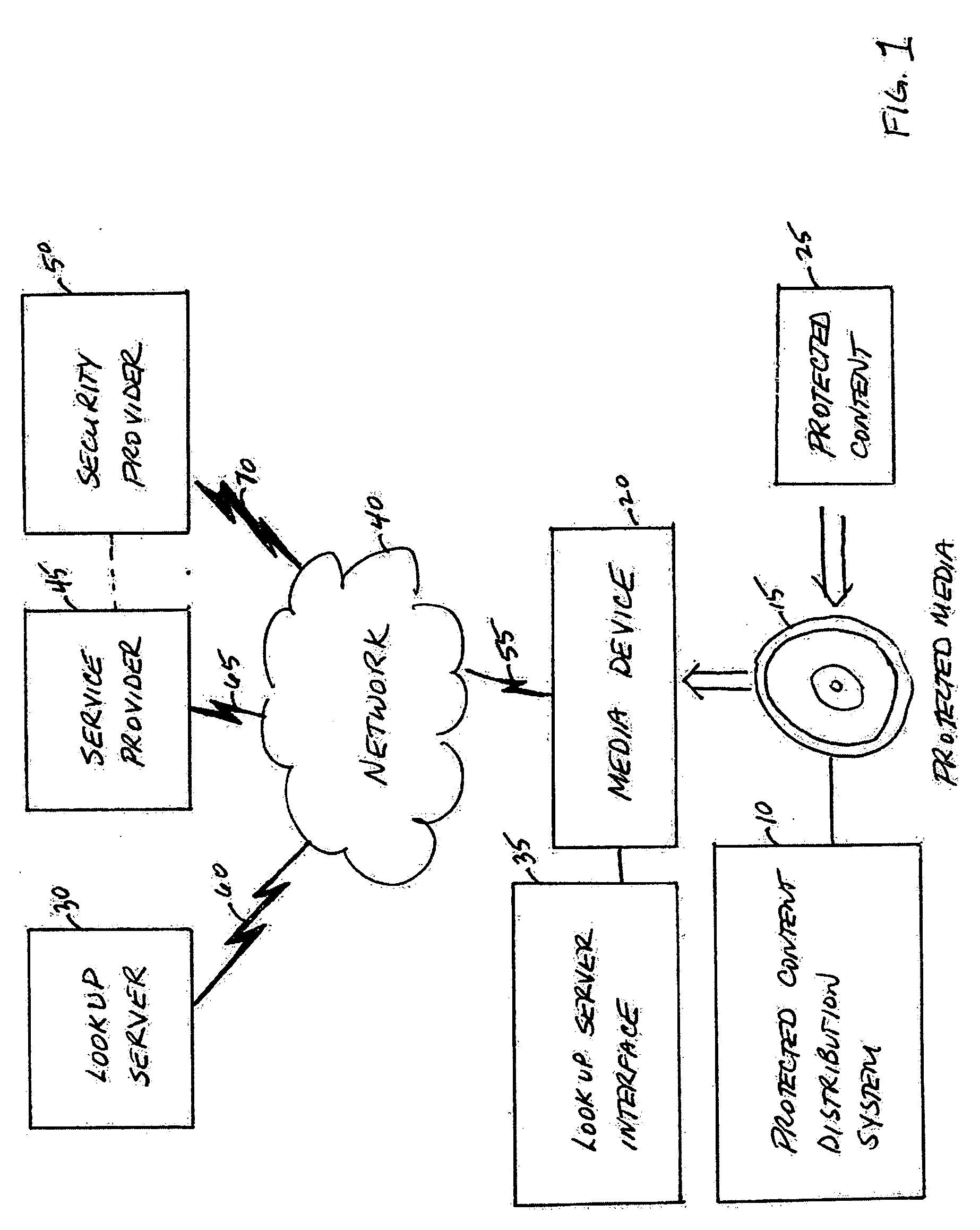
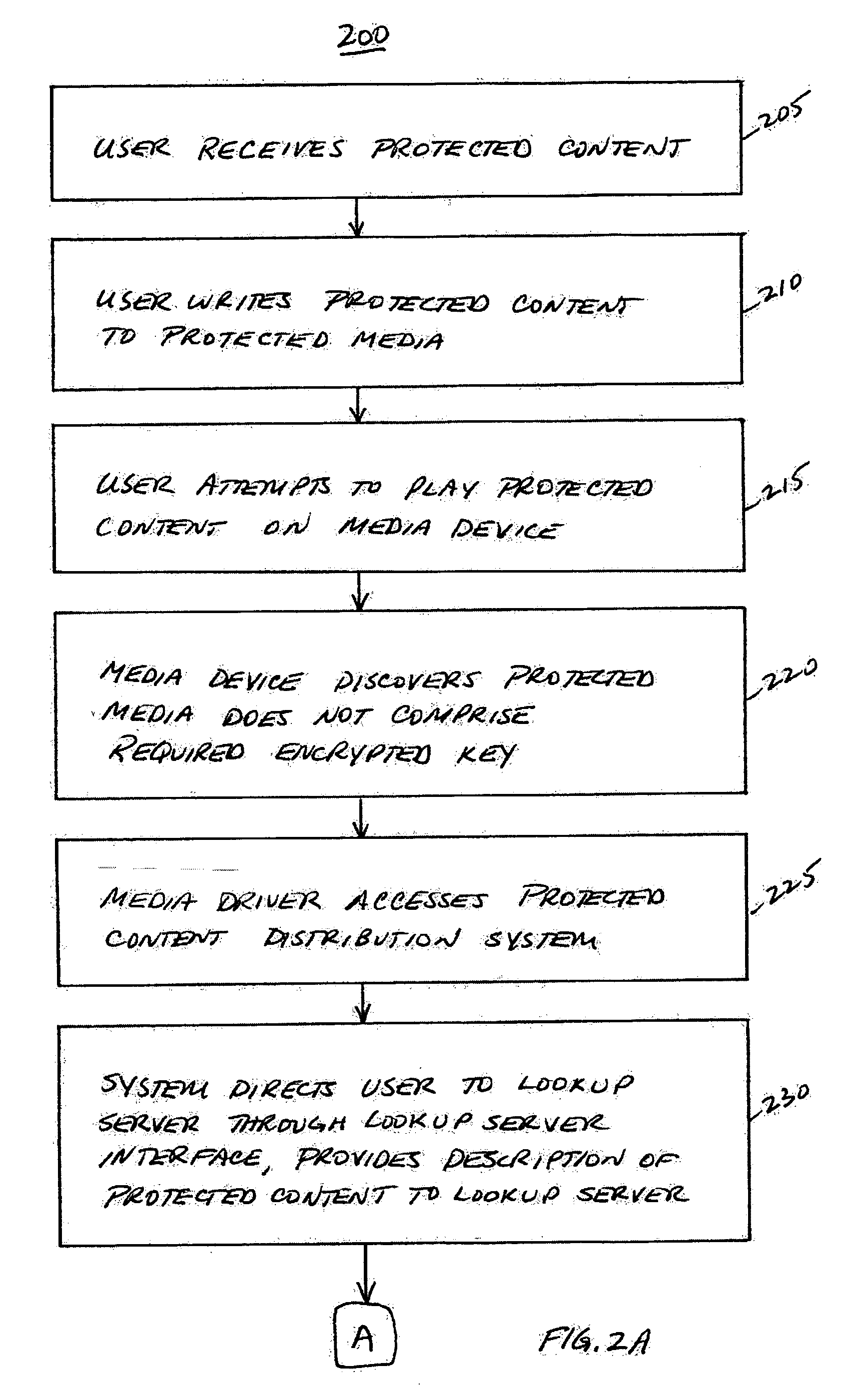
System, service, and method for enabling authorized use of distributed content on a protected media
InactiveUS20060200865A1Avoid playingEliminate needDigital data processing detailsUser identity/authority verificationContent distributionCopy protection
A protected content distribution system utilizes media-based copy protection to support online distribution of protected content in a secure and legitimate fashion. Using a media-based copy protection scheme based on broadcast encryption, the protected content distribution system realizes online distribution of protected content such as, for example audio files, movies, etc, authorizing consumption of unlicensed content by transfer of a unique encrypted key to the protected media. This transaction is fast, involving the transfer of an encrypted binding key rather than the protected content. Content is enabled through a unique encrypted key on protected media accessed through a device separate from the media driver.
Owner:IBM CORP
Method and system for limiting the use of user-specific software features
InactiveUS7158953B1Preventing unchecked proliferationDigital data processing detailsUnauthorized memory use protectionDigital rights management systemClient-side
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
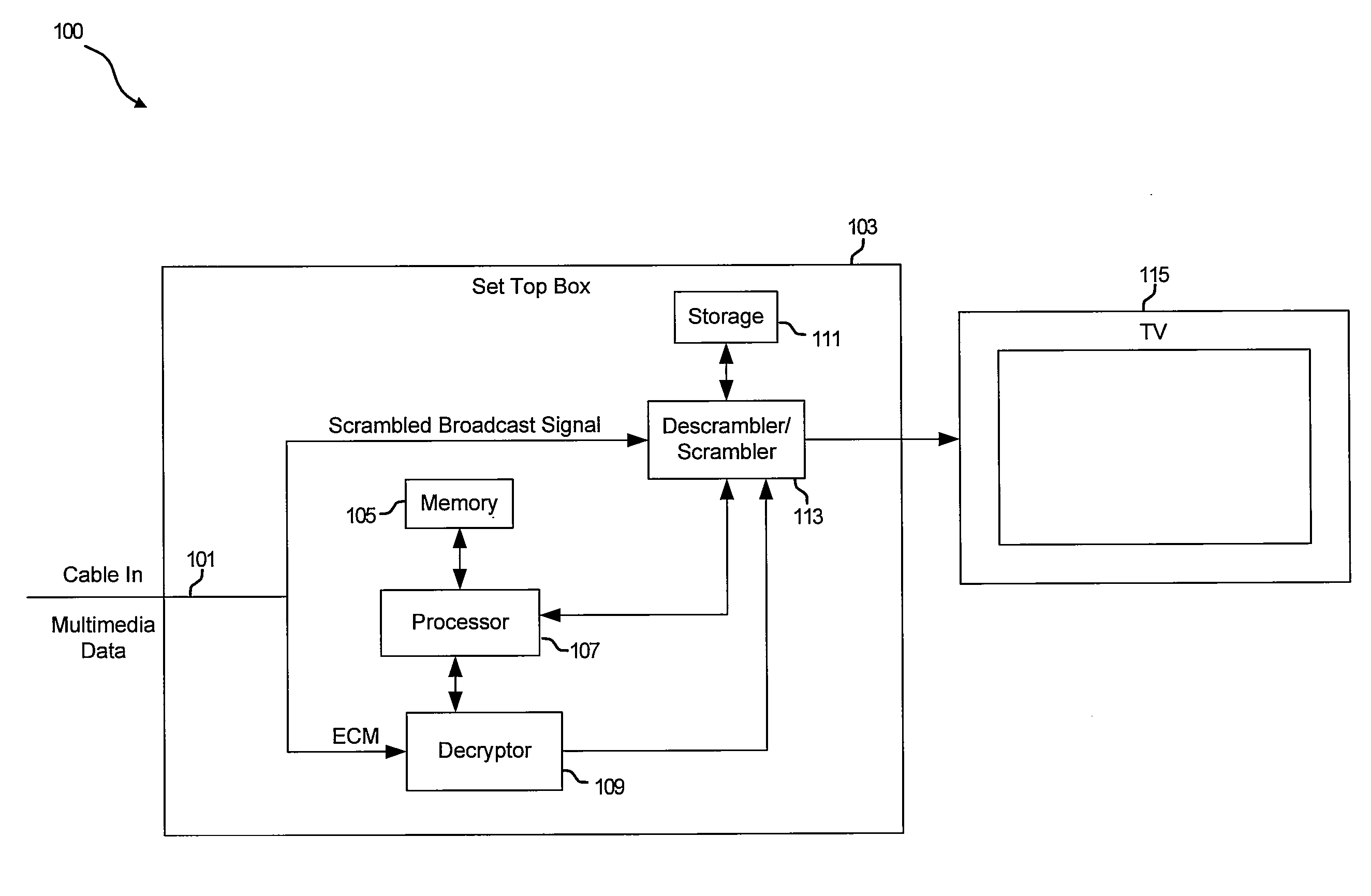
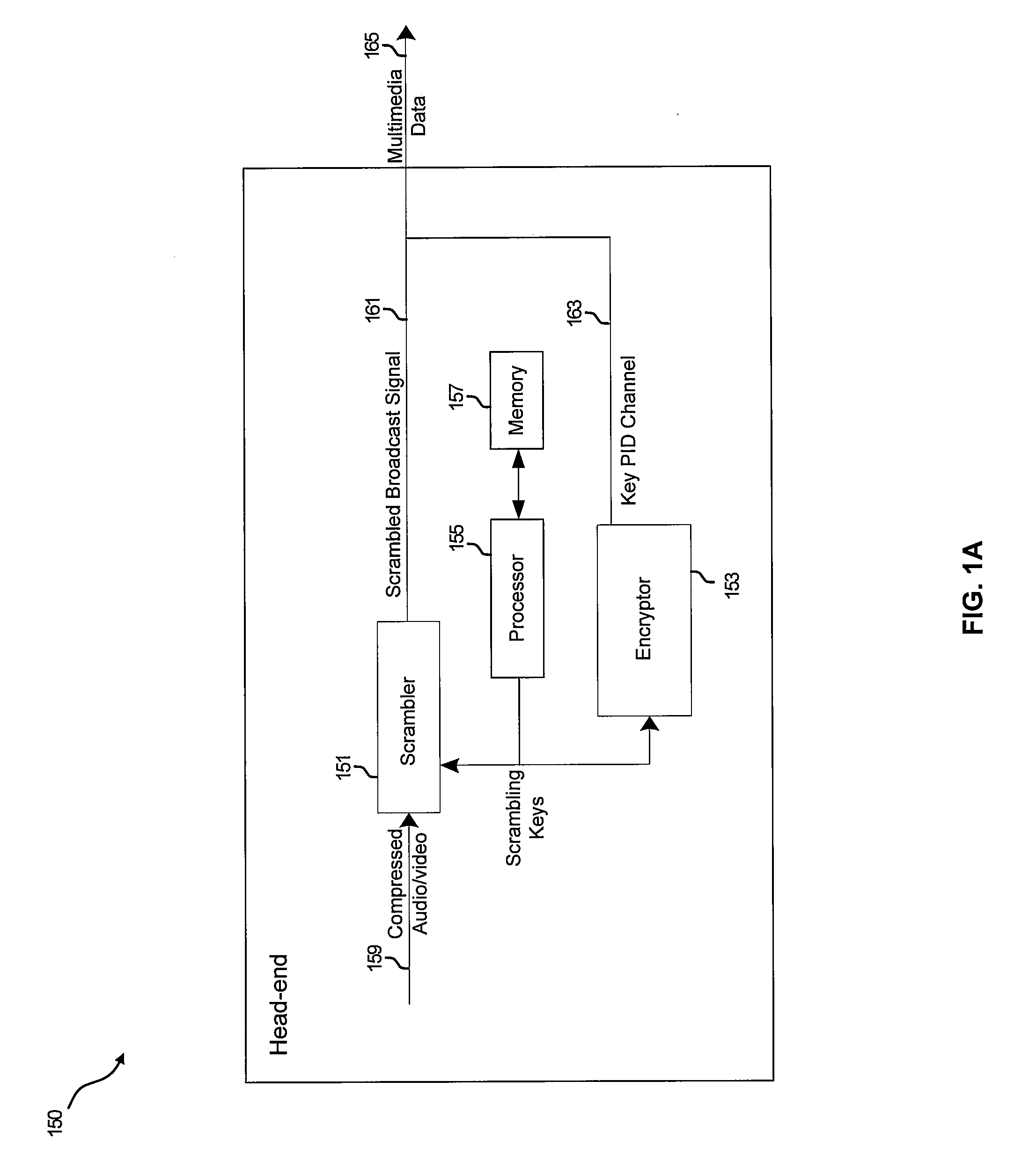
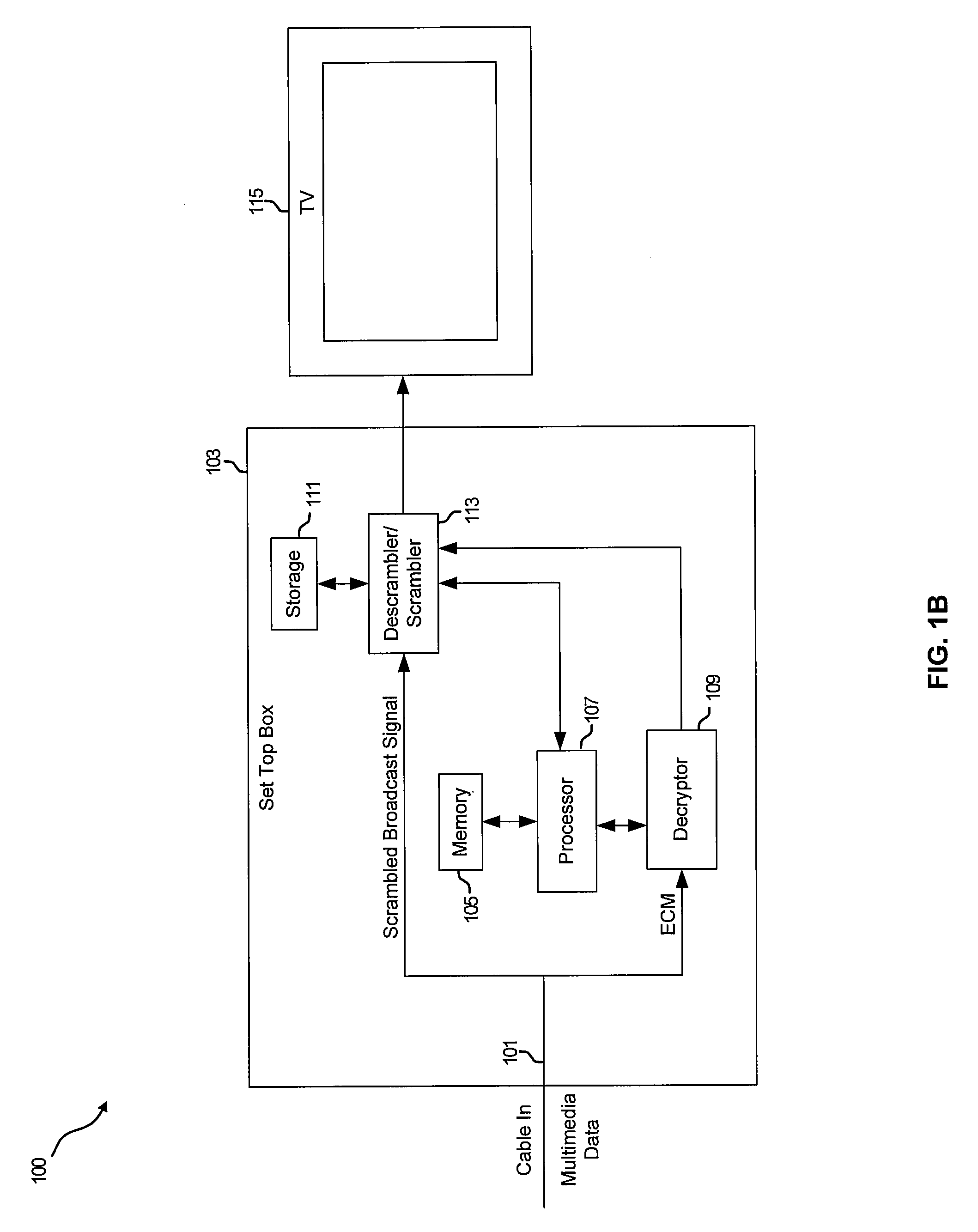
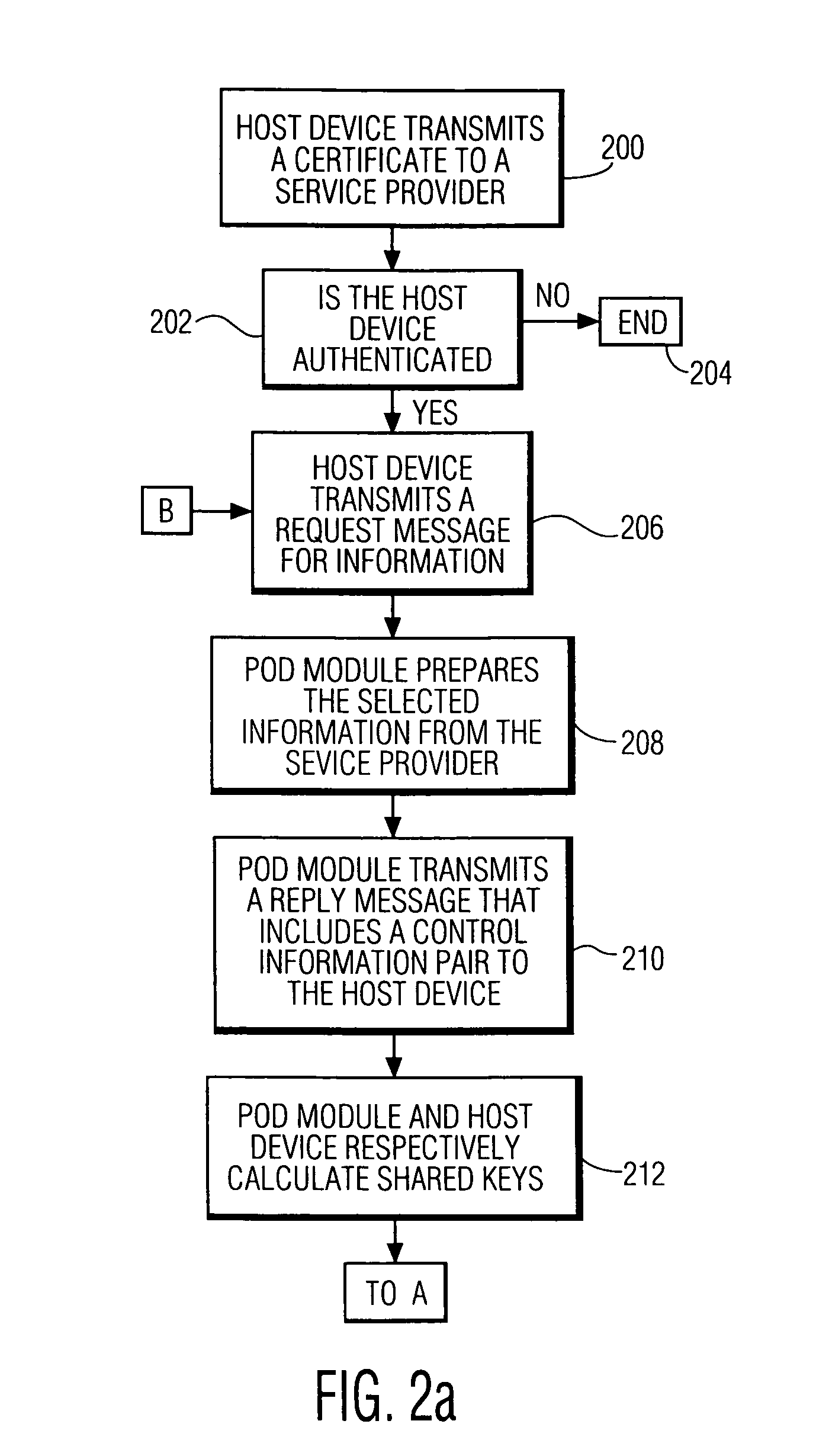
System and method for copy protecting transmitted information
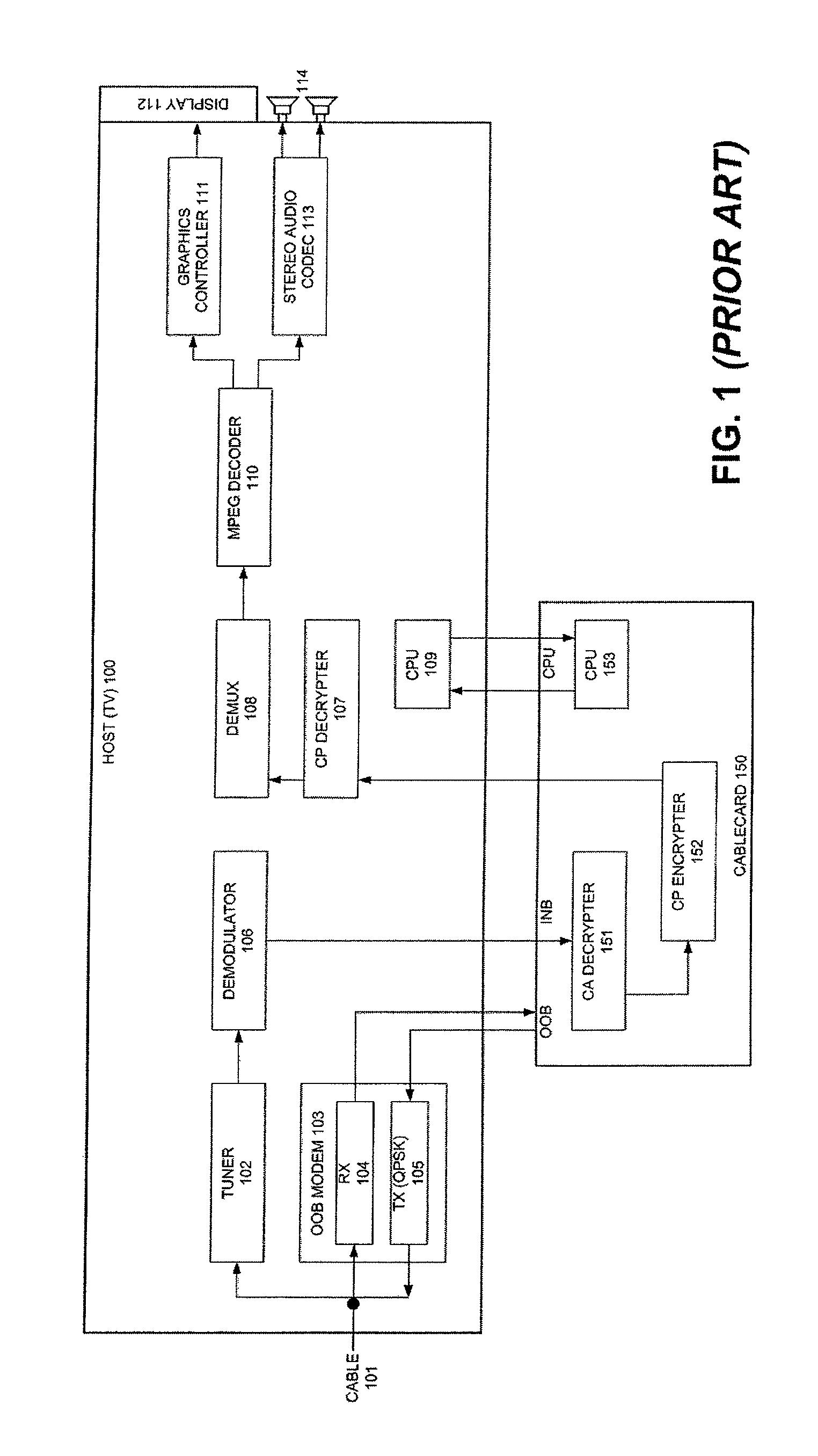
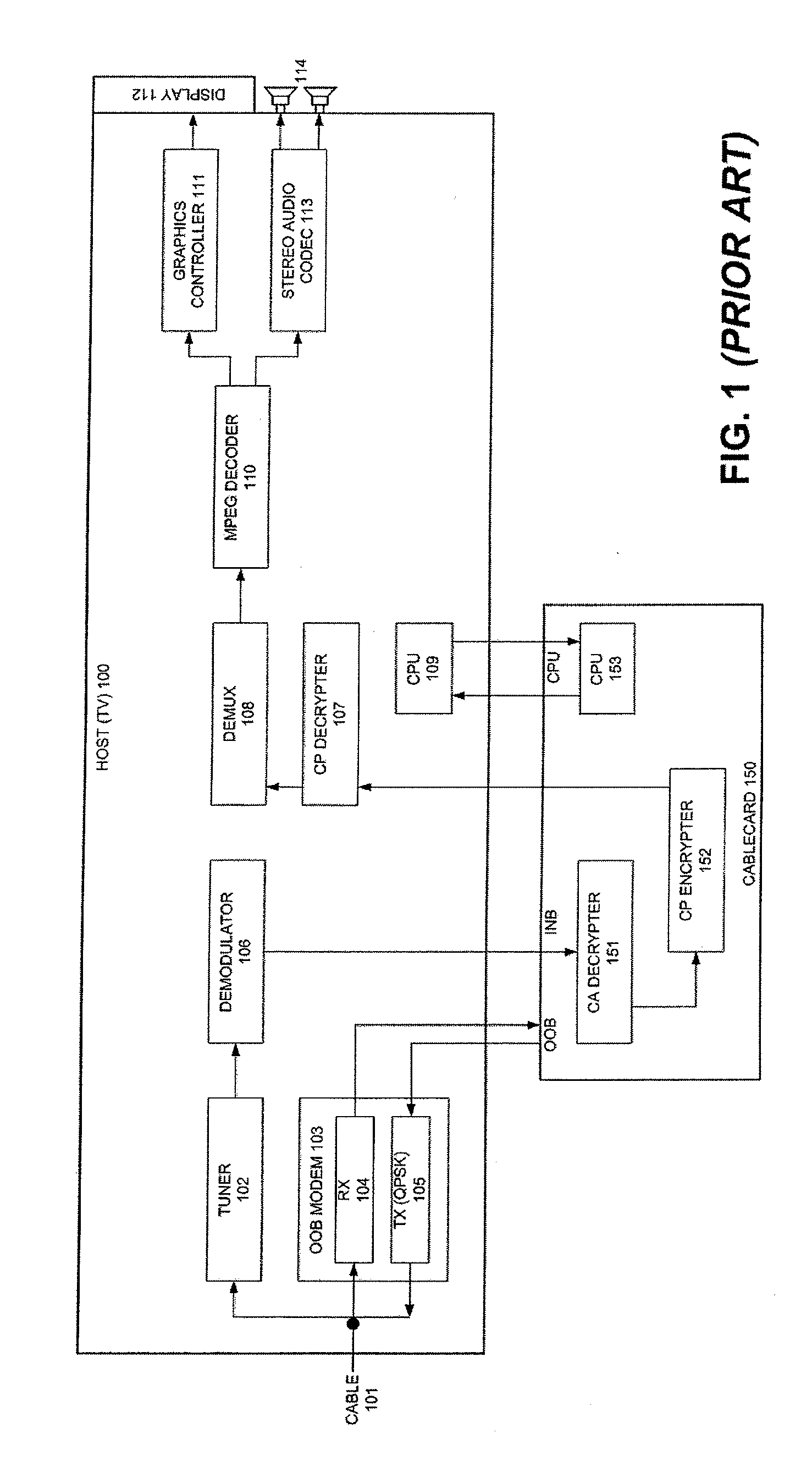
InactiveUS7336785B1Protect informationEliminate useTelevision system detailsKey distribution for secure communicationTransfer procedureService provision
To afford copy protection for information, e.g. elementary streams, from a service provider while in transit between a point of deployment (POD) module and a set-top box, the information is accompanied by control information pairs. The pairs are respectively associated with the portions of the copy protected information and are incorporated into a shared key calculation in the POD module and set-top box. The shared keys are used by the POD module and set-top box to encrypt and decrypt the information. Tampering with a control information pair, as by an intruder or hacker, prevents keys shared by the set-top box and POD module from matching. A mismatch prevents the set-top box from correctly decrypting information received from the deployment module.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
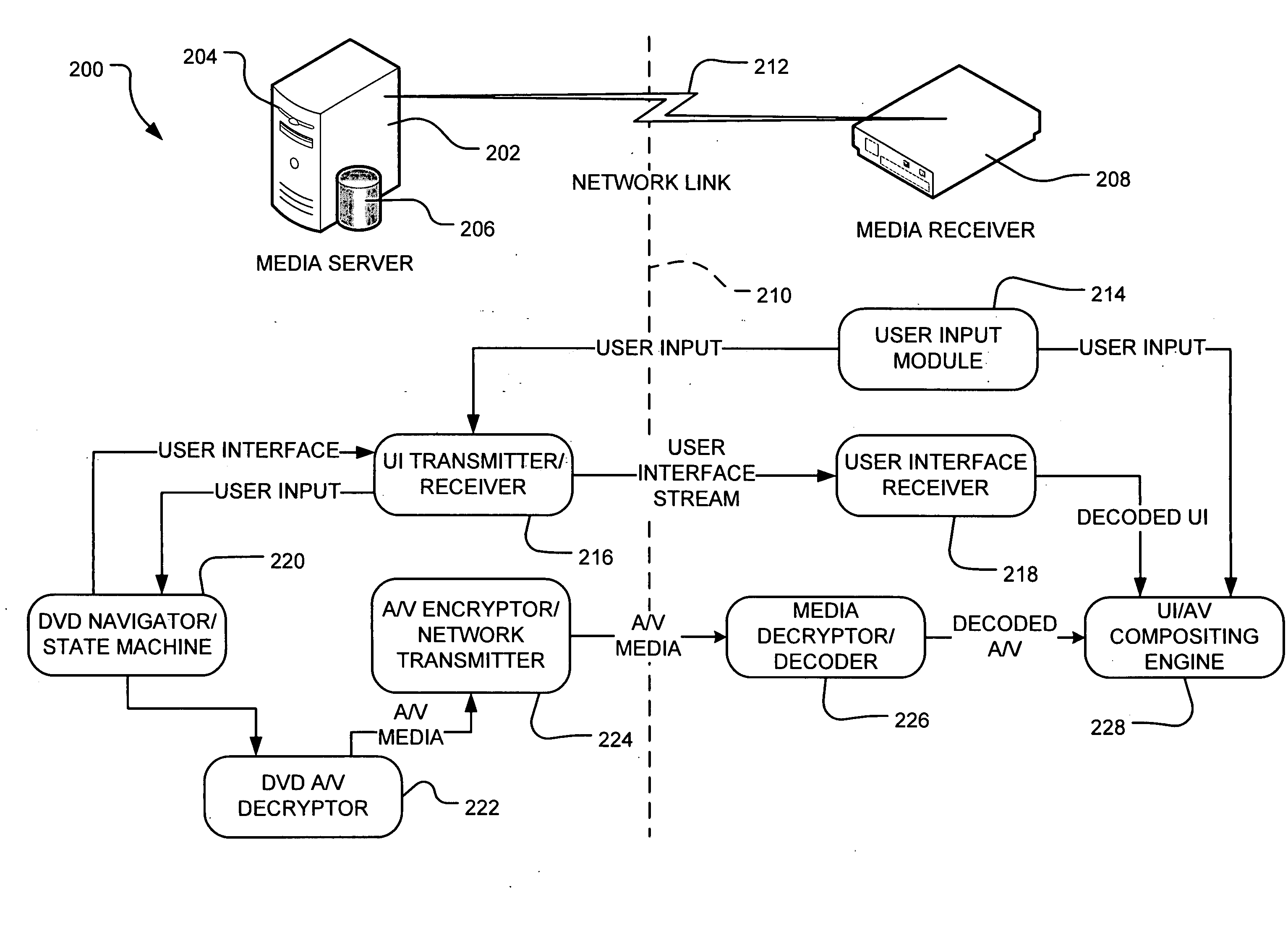
Control and playback of media over network link
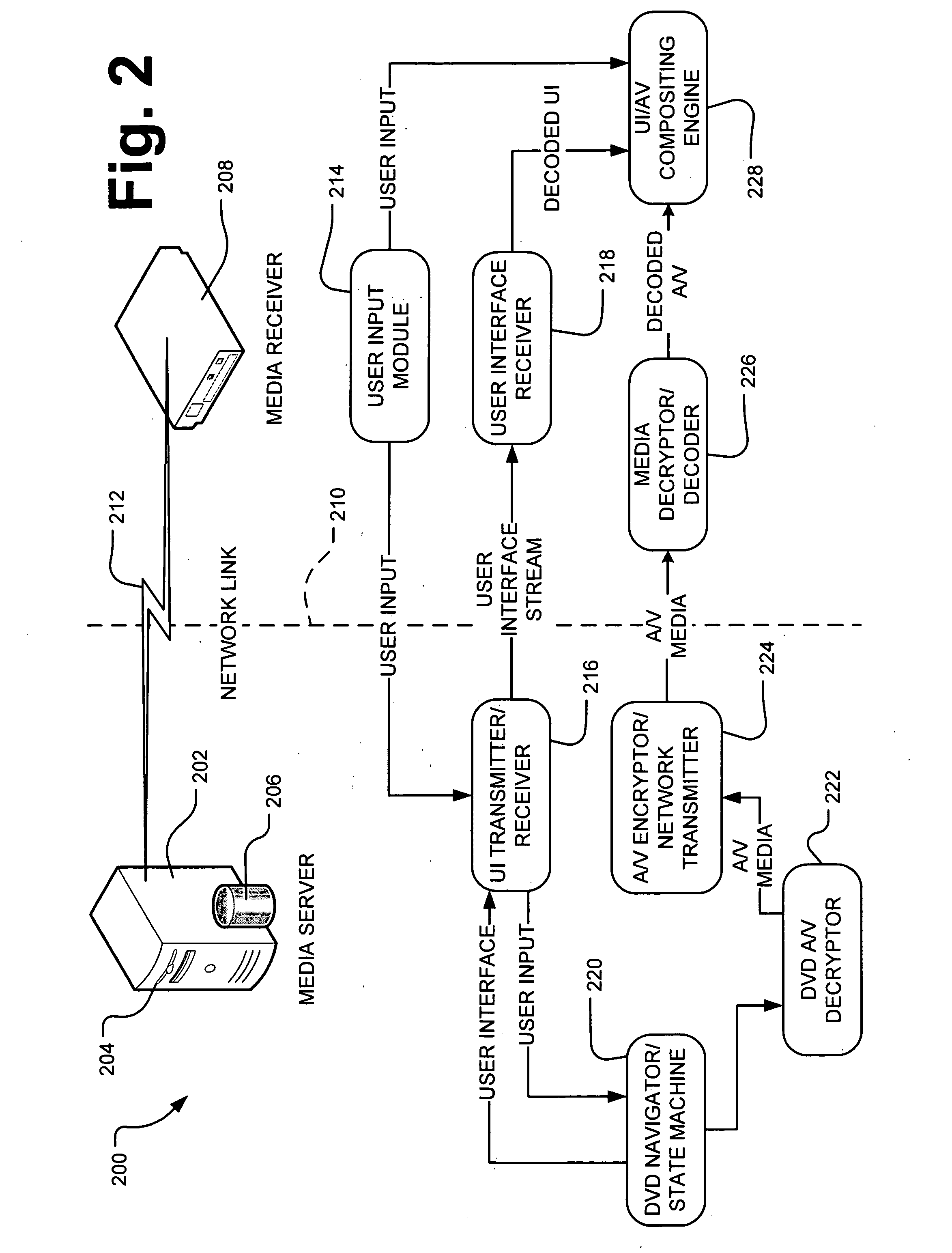
InactiveUS20080005676A1Well formedUnauthorized memory use protectionHardware monitoringNetwork linkUser input
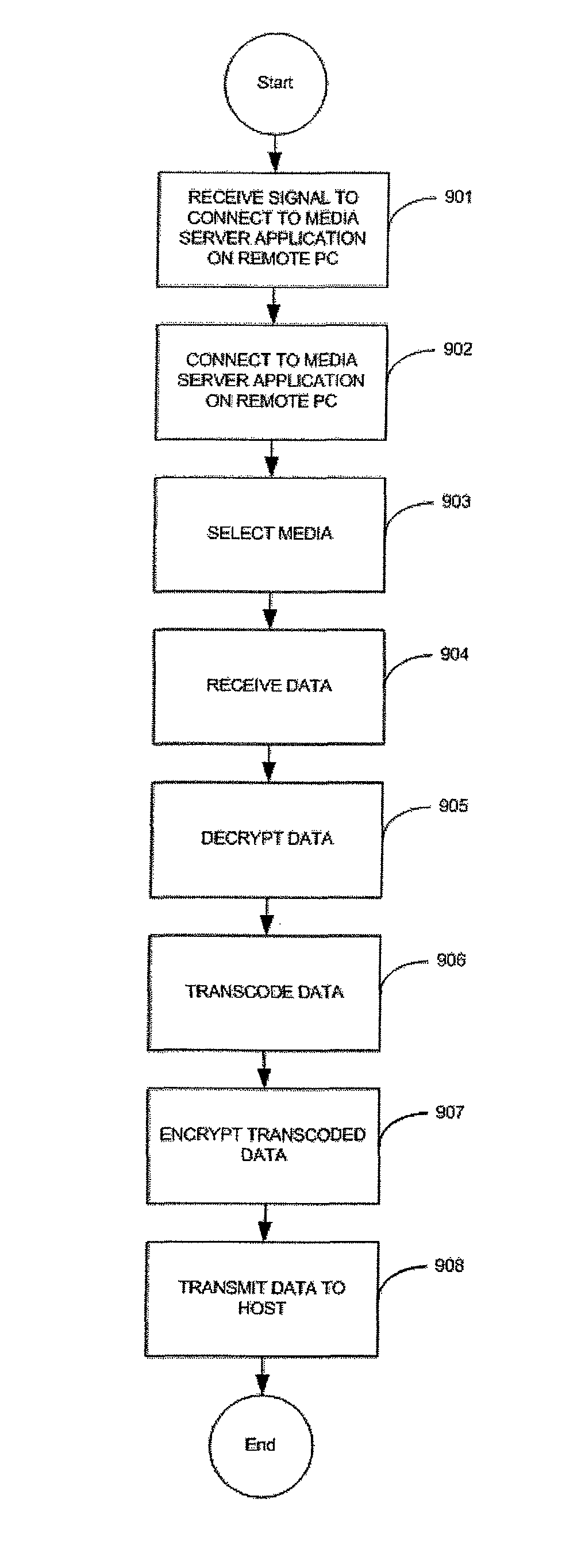
A home entertainment network transmits audio / video decrypted from a DVD over a network to a media receiver using a secure channel. The A / V data is re-encrypted in a second encryption format amenable to transmission over the network. The media stream is thereby compliant with copy protection and digital rights management requirements. The media server constructs an emulated user interface corresponding to an actual instantiation of a navigation menu on the media server to solicit user input at the media receiver. The media server alternatively constructs a unique identifier of the DVD based upon the file structure on the DVD to search for menu navigation commands over an external network for heuristic navigation control.
Owner:MICROSOFT TECH LICENSING LLC
Copy protection of data
InactiveUS7079649B1Provide securityReduce riskProgram control using stored programsData taking preventionCopy protectionClient-side
A copyright protection scheme downloads data from a server, typically over the World Wide Web to a client for presentation to a user. The downloaded data is cryptographically protected, by encryption and hashing. When displayed by the client, storing and copying functions are selectively disabled in respect of the data, in order to prevent unauthorized copying.
Owner:COPY PROTECTION LLC
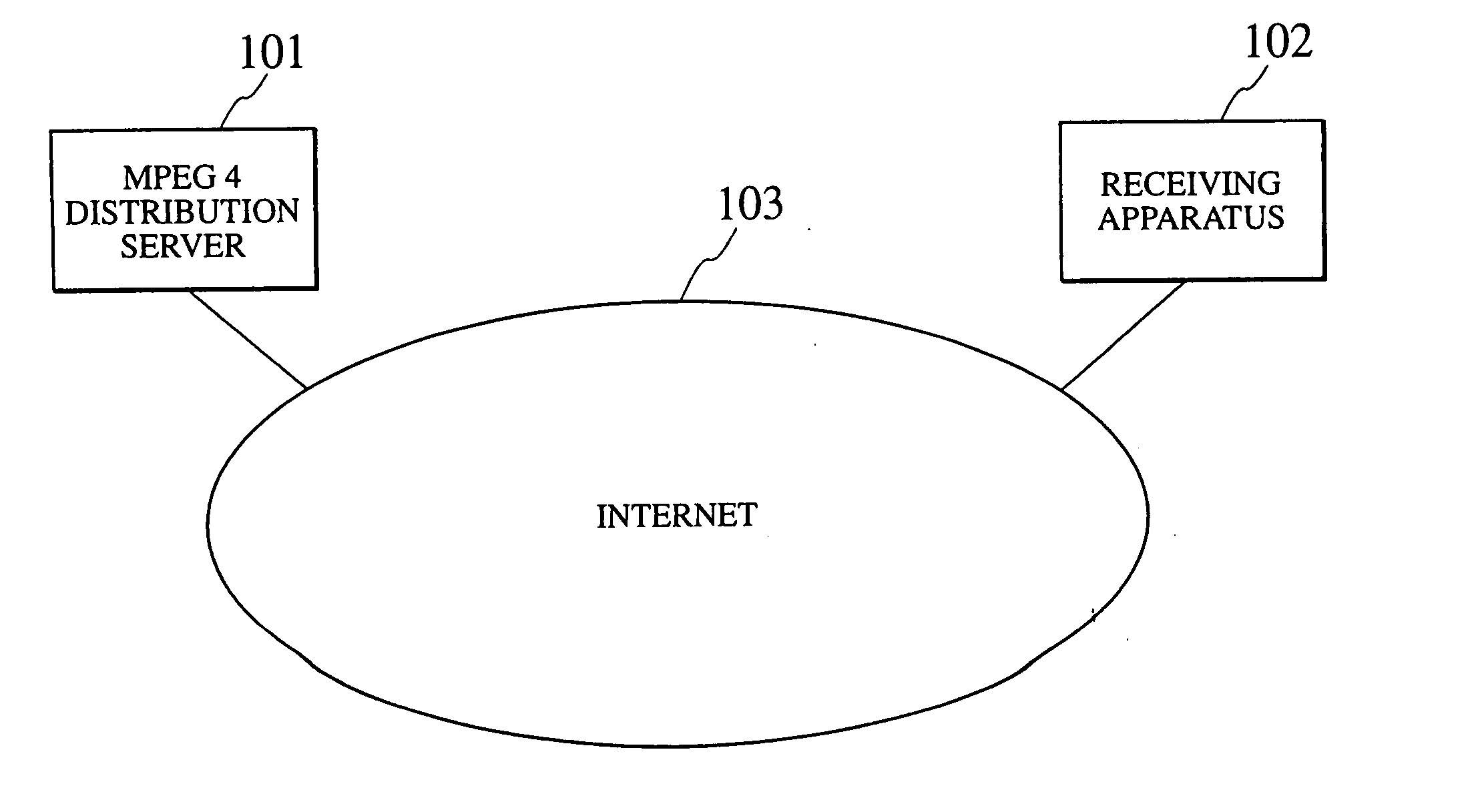
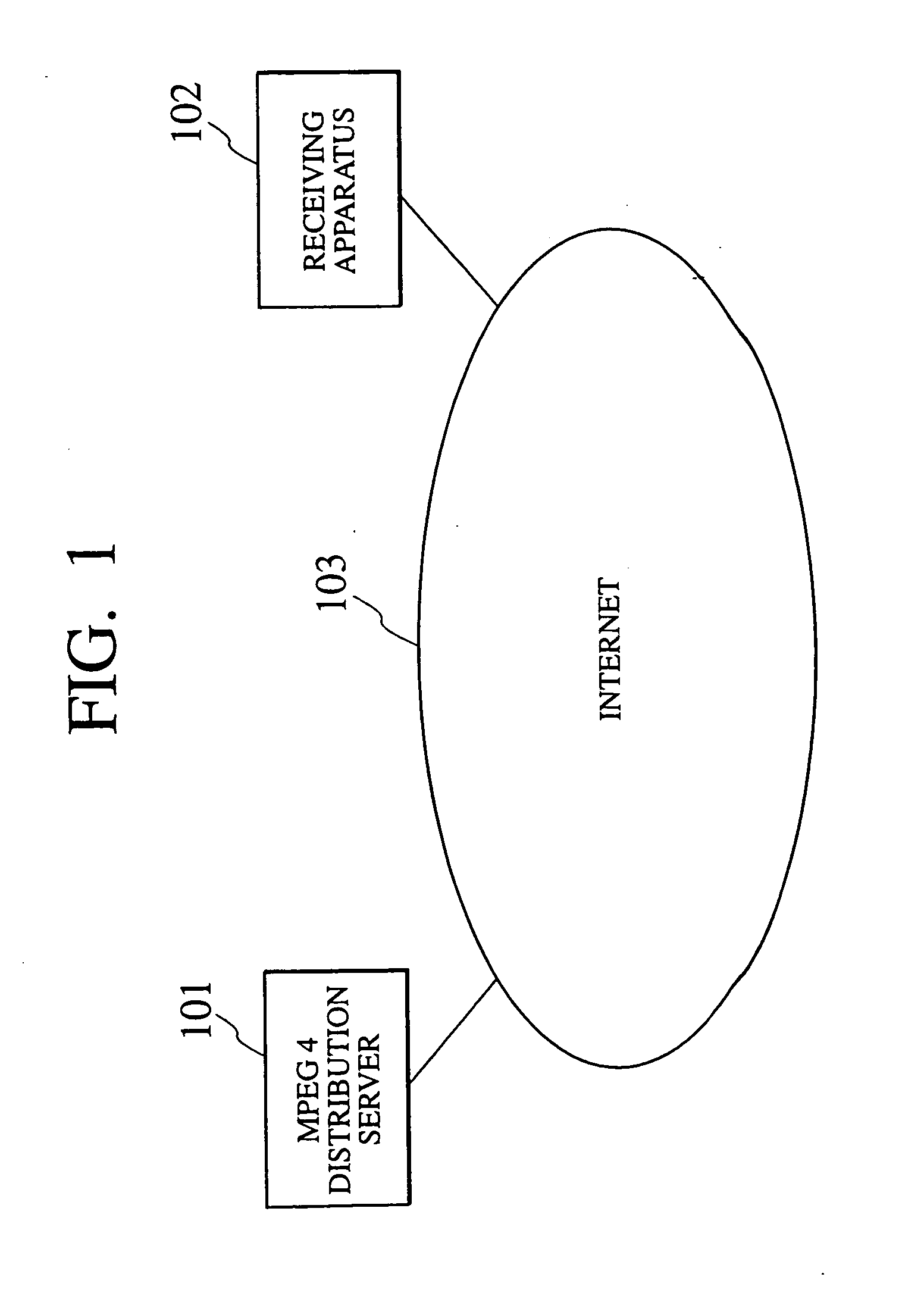
Content distribution apparatus, content receiving apparatus, and content distribution method
InactiveUS20050216731A1Television system detailsKey distribution for secure communicationKey exchangeContent distribution
A content distribution apparatus for implementing copy protection when distributing digital content as a real-time stream on the Internet is provided. This apparatus encrypts content and distributes them to a receiving apparatus via the Internet, and performs an authentication procedure and a key exchange procedure between with the receiving apparatus. The encoded content encoded by a prescribed encoding system is encrypted, an encryption expansion header is generated that includes at least one attribute information of attribute information indicating whether or not the content is encrypted and attribute information indicating the encryption system used, transport protocol processing required to transfer the content is performed and a basic transport header is generated, a packet being sent which includes the basic transport header, the encryption expansion header, and the encrypted content.
Owner:KK TOSHIBA
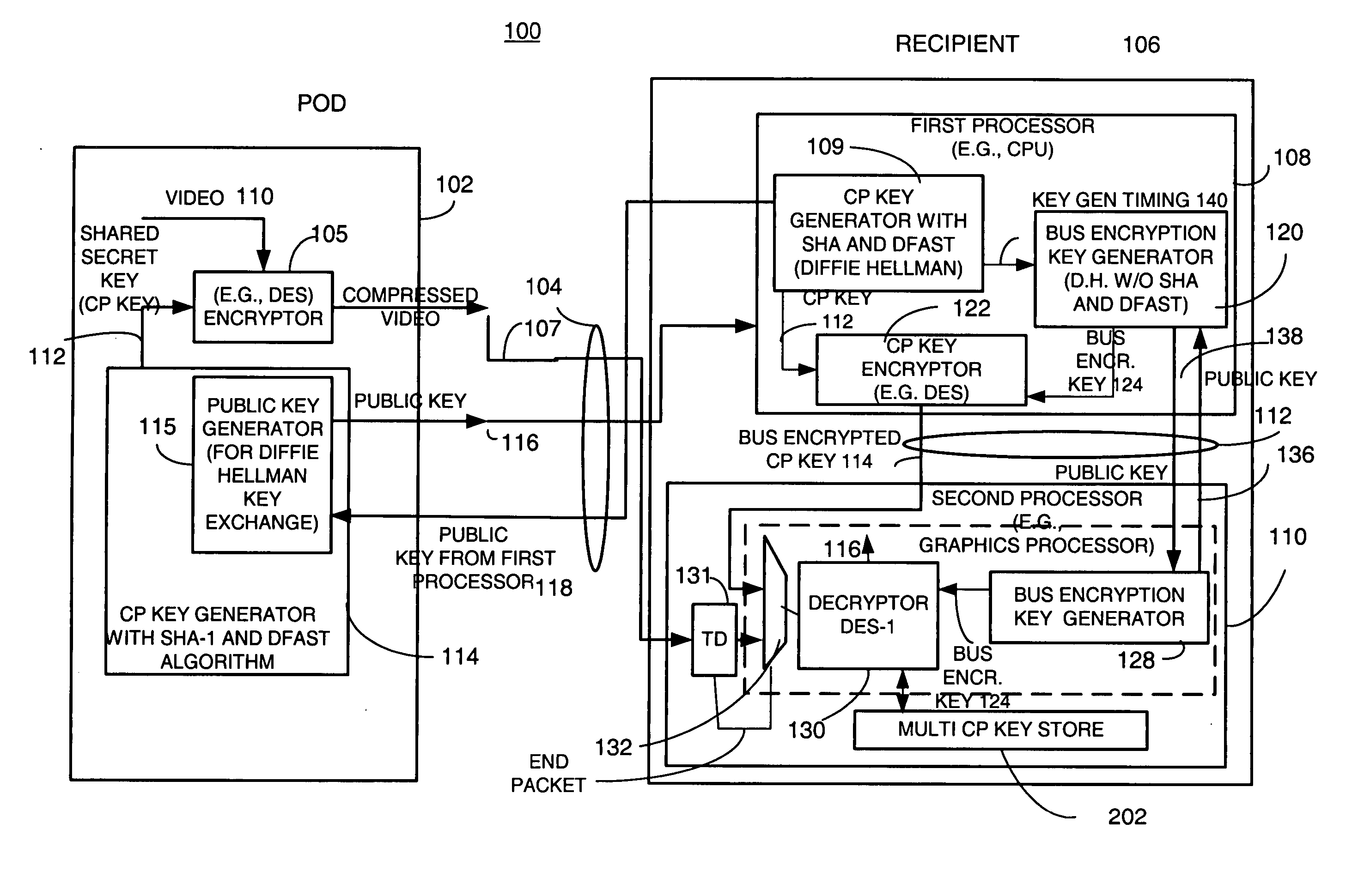
Method and apparatus for providing a bus-encrypted copy protection key to an unsecured bus
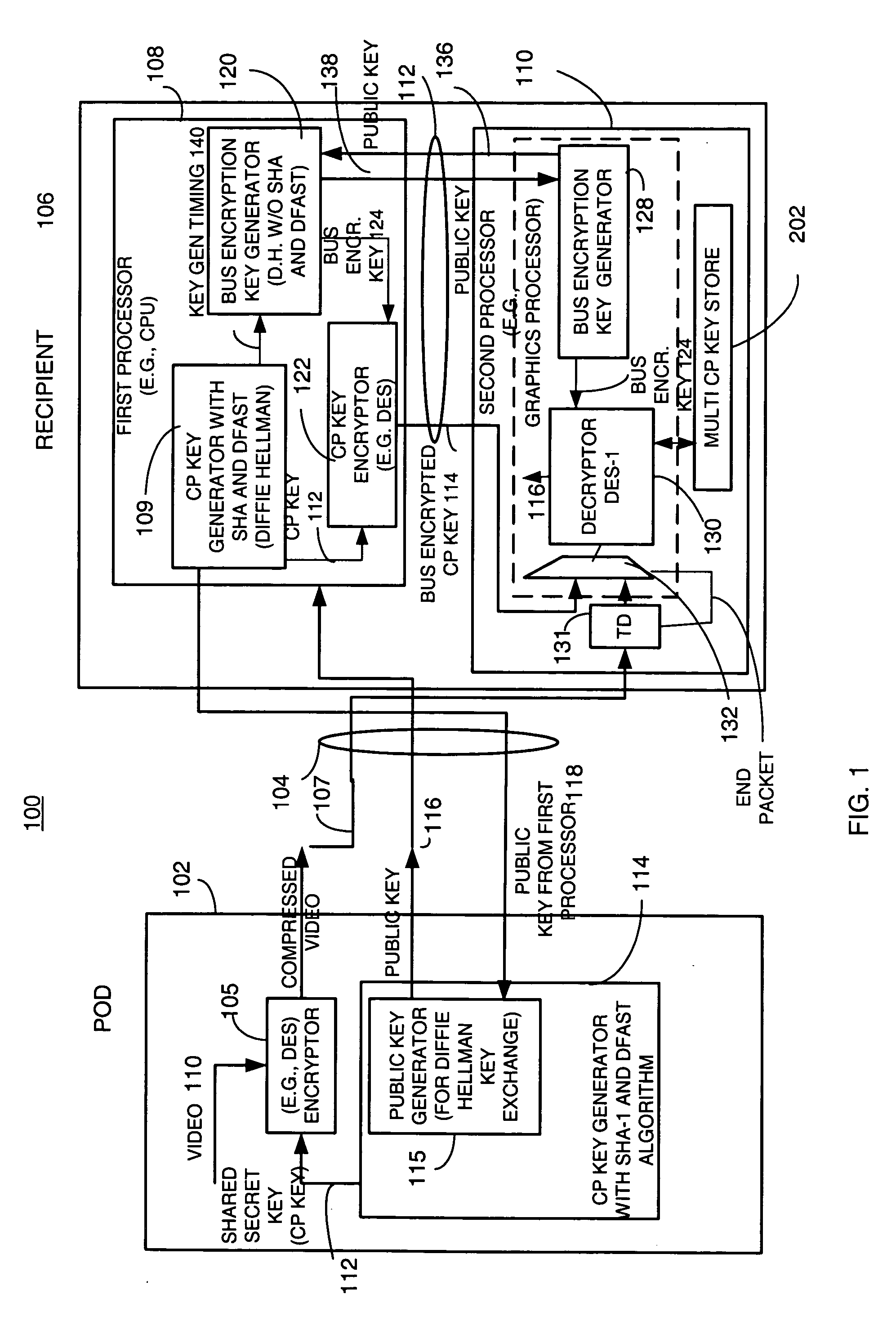
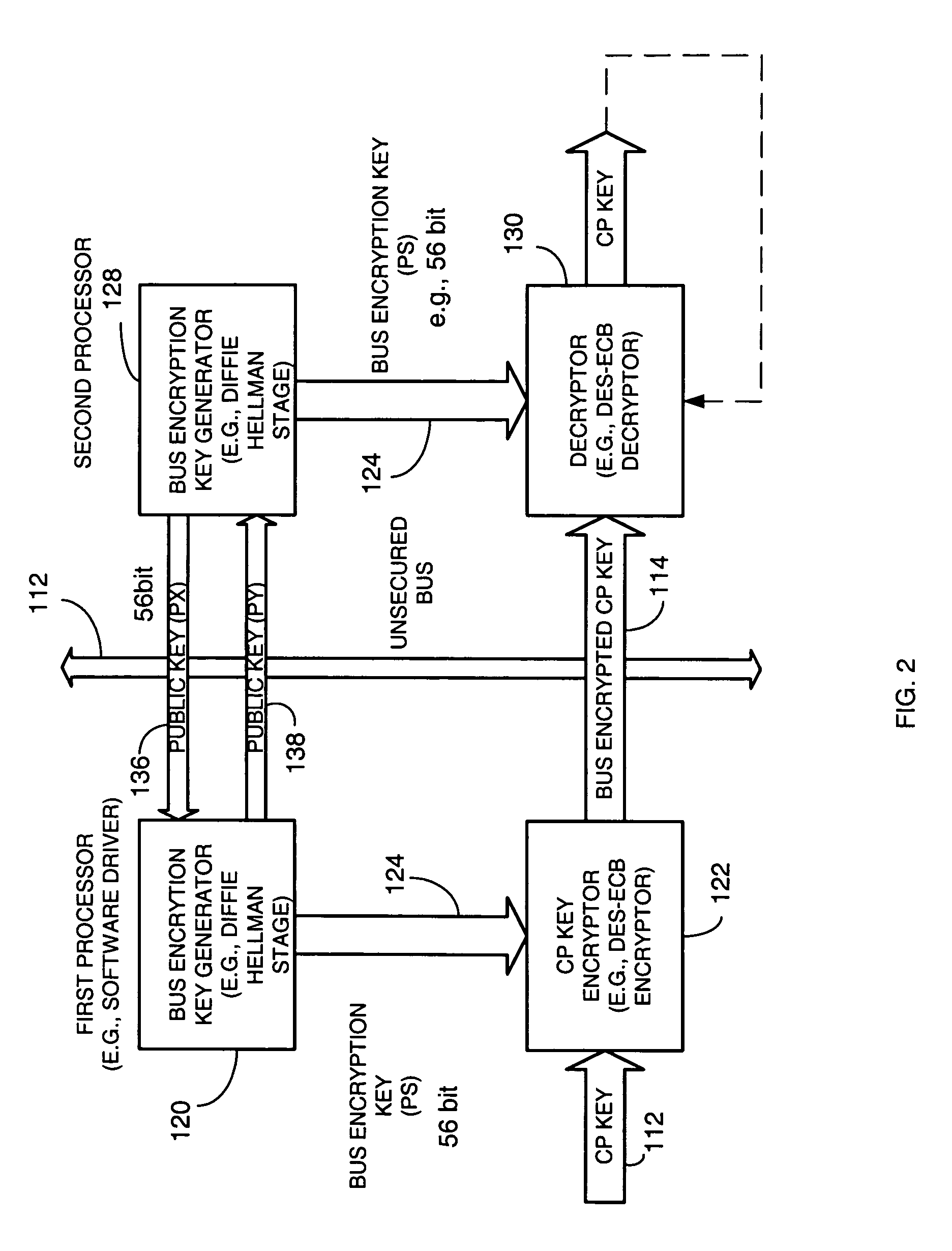
InactiveUS20050265547A1Key distribution for secure communicationPublic key for secure communicationComputer hardwareGraphics
A copy protection (CP) key used by a sending source, such as a POD, to encrypt content such as audio and / or video information is derived by a first key generator associated with a first processor and is locally encrypted by the first processor using a locally generated bus encryption key to produce a bus encrypted CP key that is sent over a local unsecure bus to a second processor, such as a graphics processor. The second processor decrypts the bus encrypted copy key using a decryption engine to obtain the CP key. The second processor receives the encrypted content and in one embodiment, also uses the same decryption engine to decrypt the encrypted content. The first and second processors locally exchange public keys to each locally derive a bus encryption key used to encrypt the CP key before it is sent over the unsecure bus and decrypt the encrypted CP key after it is sent over the bus. The locally exchanged public keys are shorter in length than those used between the CPU and POD to produce the original CP key.
Owner:ATI TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com