Patents
Literature
419 results about "Random pattern" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Definition of random pattern. The setting of diamonds in a bit crown without regard to a geometric pattern--without regular and even spacing.
Systems and methods for album playback in a random mode
ActiveUS20090222115A1Metadata audio data retrievalUsing non-detectable carrier informationRandom patternMultimedia
An embodiment relates generally to a method of playback in a media player. The method includes retrieving at least one song from a media library in a random mode on a media player and playing the at least one song through the media player. The method also includes initiating an album mode on the media player and retrieving remaining songs on an album associated with the at least one song.
Owner:RED HAT
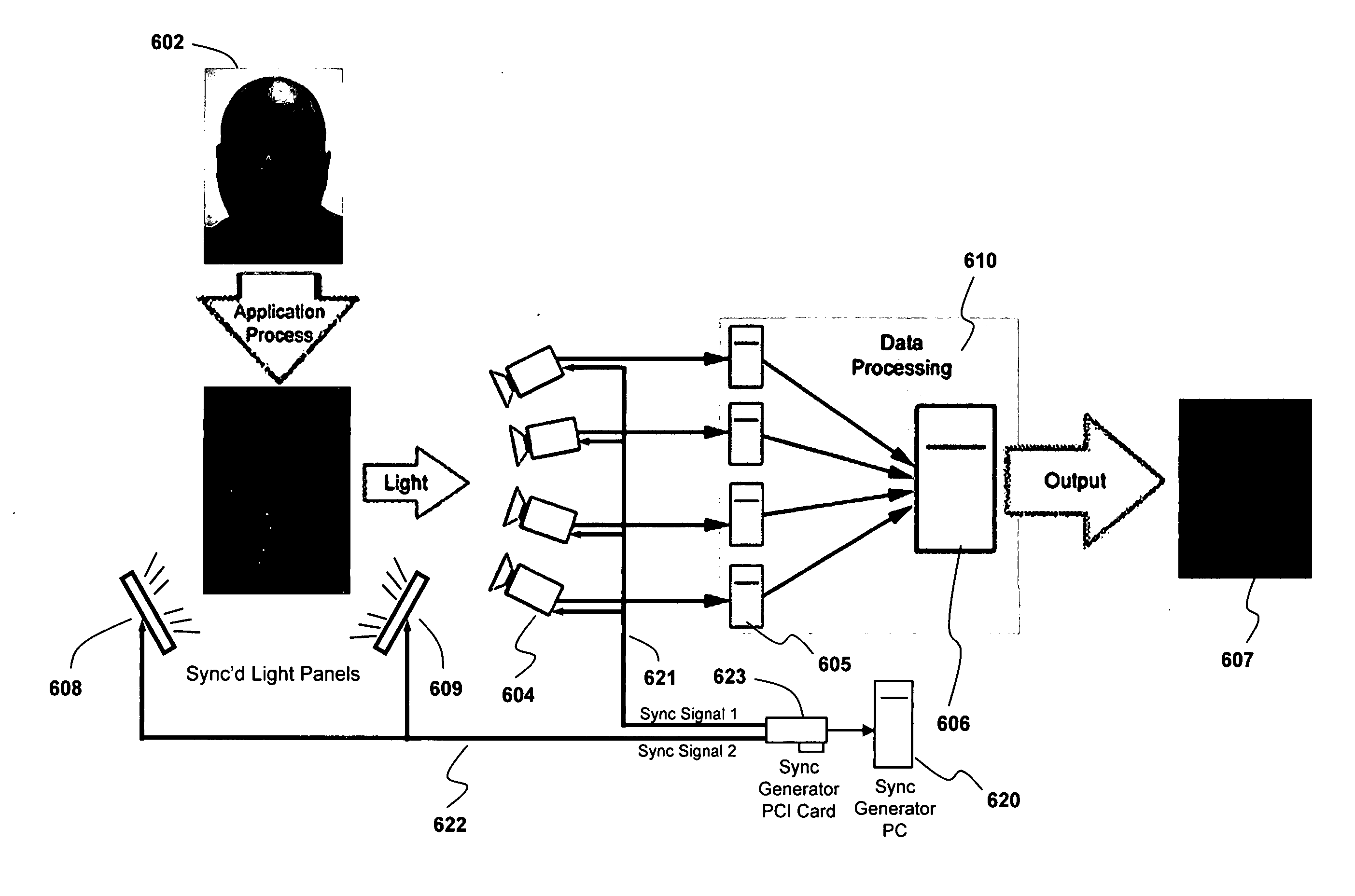
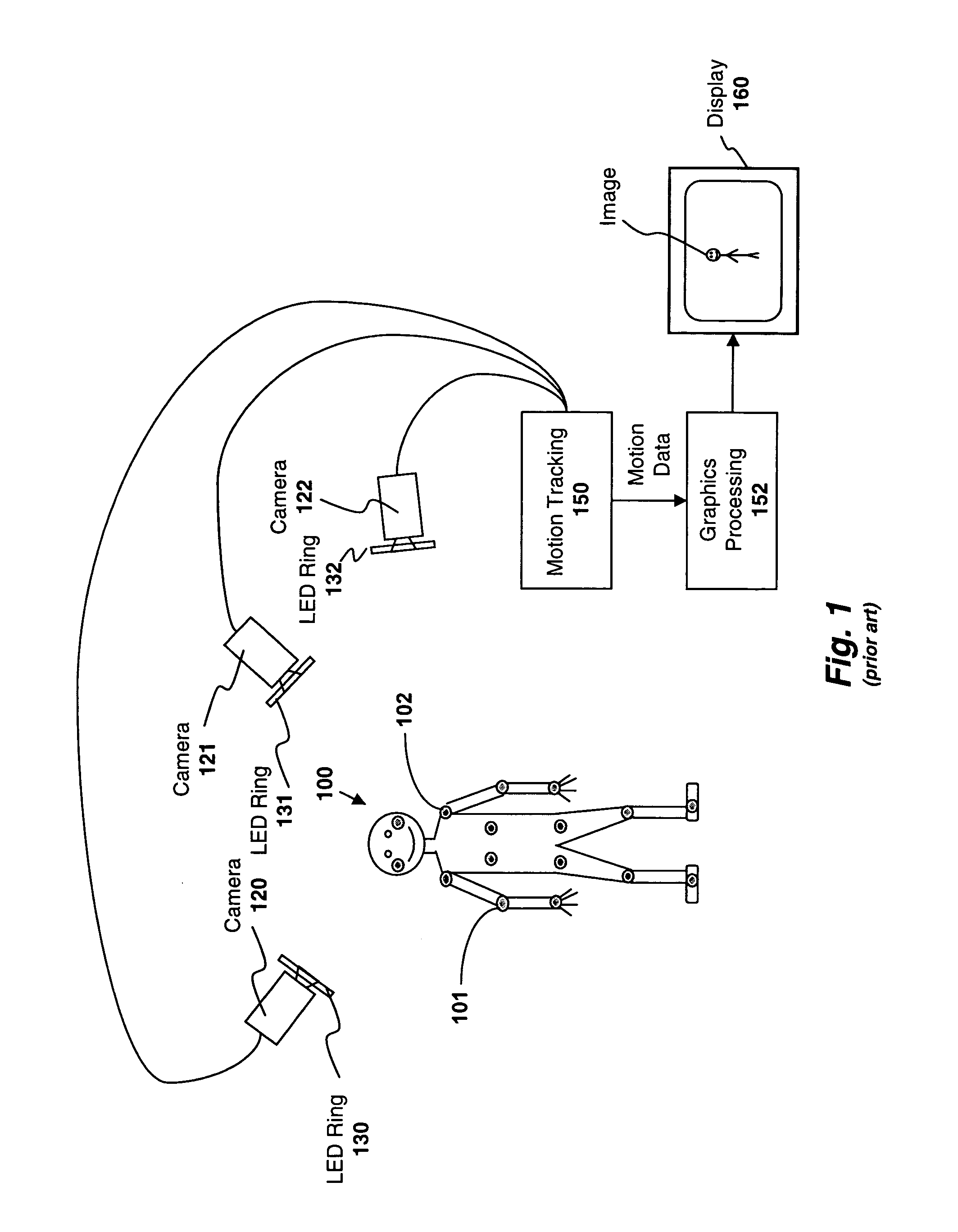
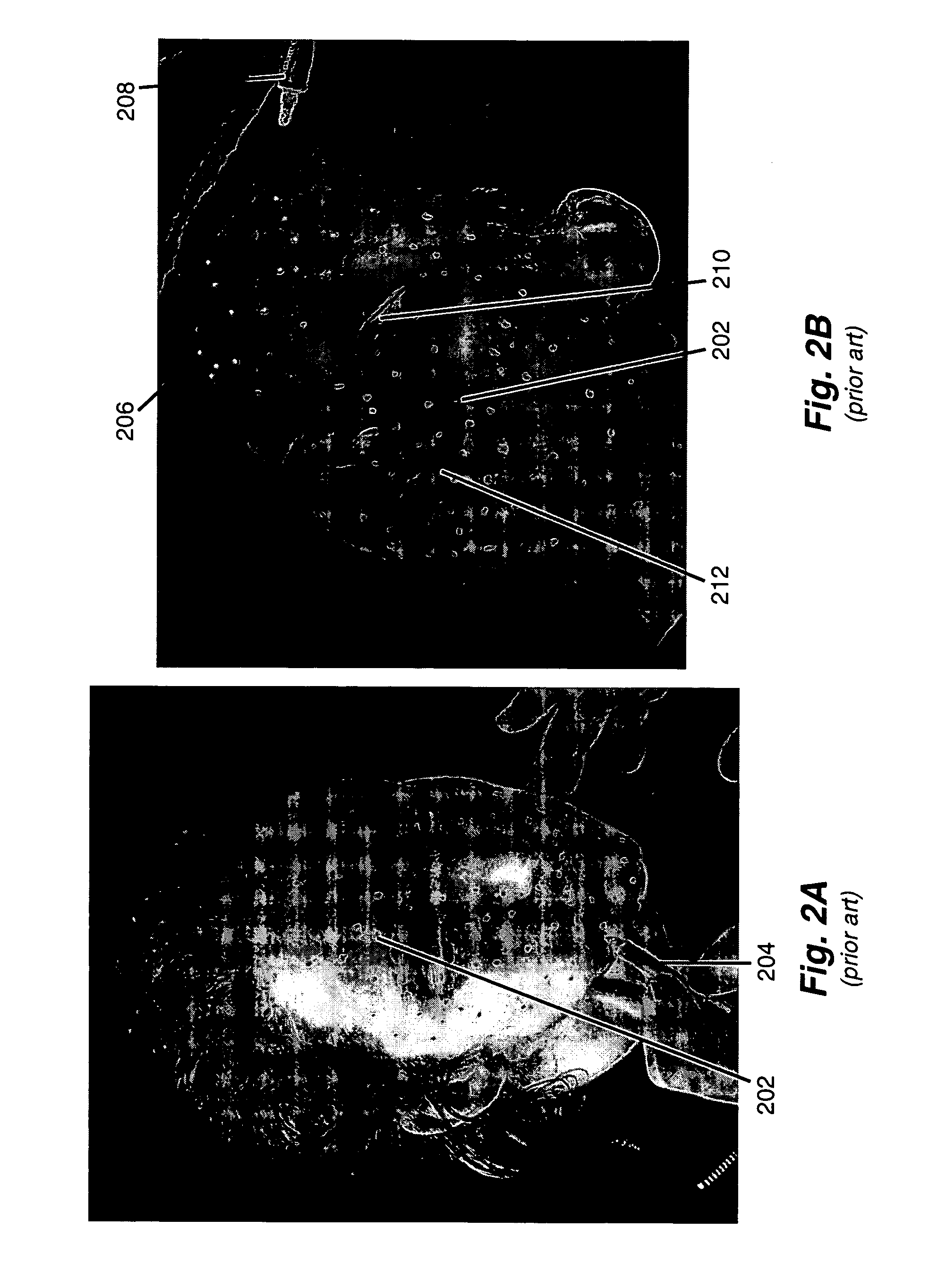
Apparatus and method for performing motion capture using a random pattern on capture surfaces
ActiveUS20070091178A1Image enhancementTelevision system detailsComputer graphics (images)Motion capture
A method is described comprising: applying a random pattern to specified regions of an object; tracking the movement of the random pattern during a motion capture session; and generating motion data representing the movement of the object using the tracked movement of the random pattern.
Owner:REARDEN
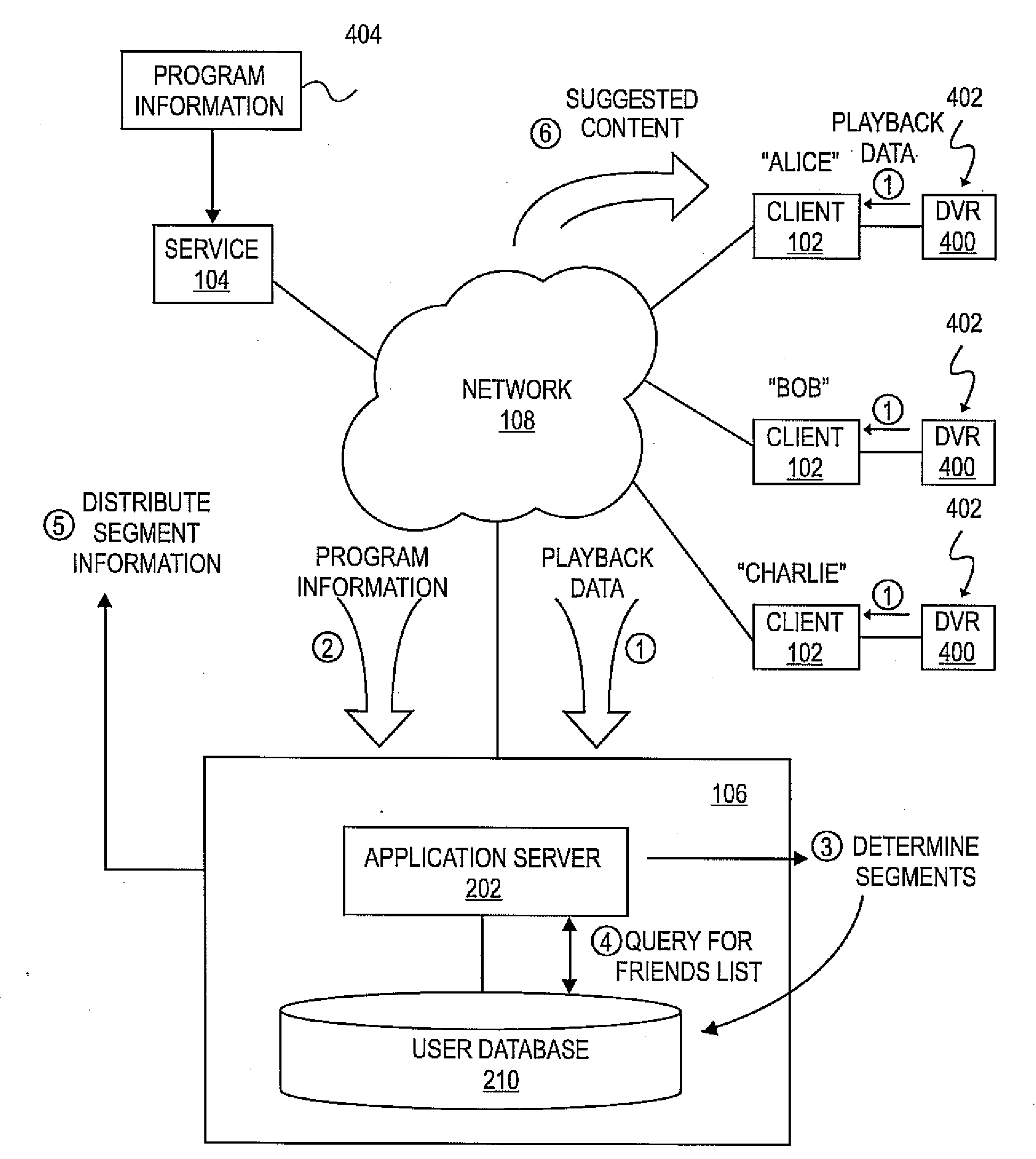
Method and system for preloading suggested content onto digital video recorder based on social recommendations
ActiveUS20080134039A1Metadata audio data retrievalTelevision system detailsDigital videoSocial network
Owner:RED HAT
Substrate for reducing electromagnetic interference and enclosure
InactiveUS6191475B1Magnetic/electric field screeningSemiconductor/solid-state device detailsElectromagnetic interferenceEngineering
A substrate for reducing electromagnetic emissions is provided. The substrate may include a plurality of ground layers, signal layers and power layers. All of the layers other than the ground layer are provided with a ground ring that may extend around the perimeter of the layer. The ground rings are electrically coupled together by ground stitching or vias that are randomly spaced. The random spacing of the ground stitching is based on the operating frequencies of the integrated circuit devices mounted on the substrate. Additional shielding may be provided by providing a cover assembly made of any conductive material that is coupled to the exposed ground rings on the uppermost and lowermost surfaces of the substrate. The cover assembly is coupled to the exposed ground rings in a randomized pattern. The device provides a virtual electrical ground cage in which the internal signal layers are totally enclosed, thereby reducing electromagnetic emissions.
Owner:INTEL CORP
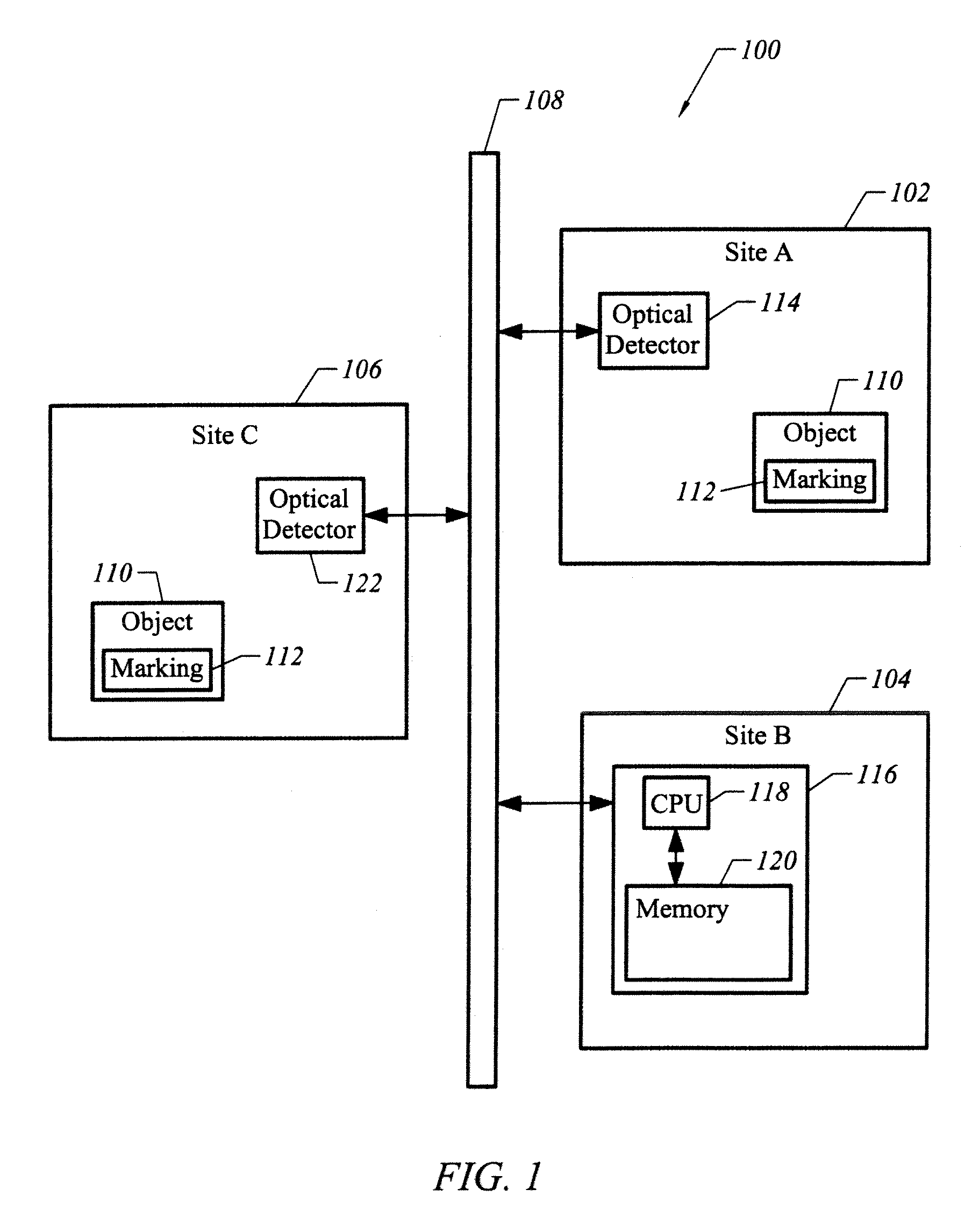
Authenticating and identifying objects using markings formed with correlated random patterns
InactiveUS20080138604A1Layered productsRecord carriers used with machinesQuantum efficiencyPhotoluminescence
Described herein are techniques for authenticating and identifying objects using markings formed with correlated random patterns. In one embodiment, an object to be authenticated includes a substrate and a marking adjacent to the substrate. The marking includes a luminescent material distributed in accordance with a correlated random pattern, and the luminescent material exhibits photoluminescence having a quantum efficiency of at least 10 percent.
Owner:OMNIPV
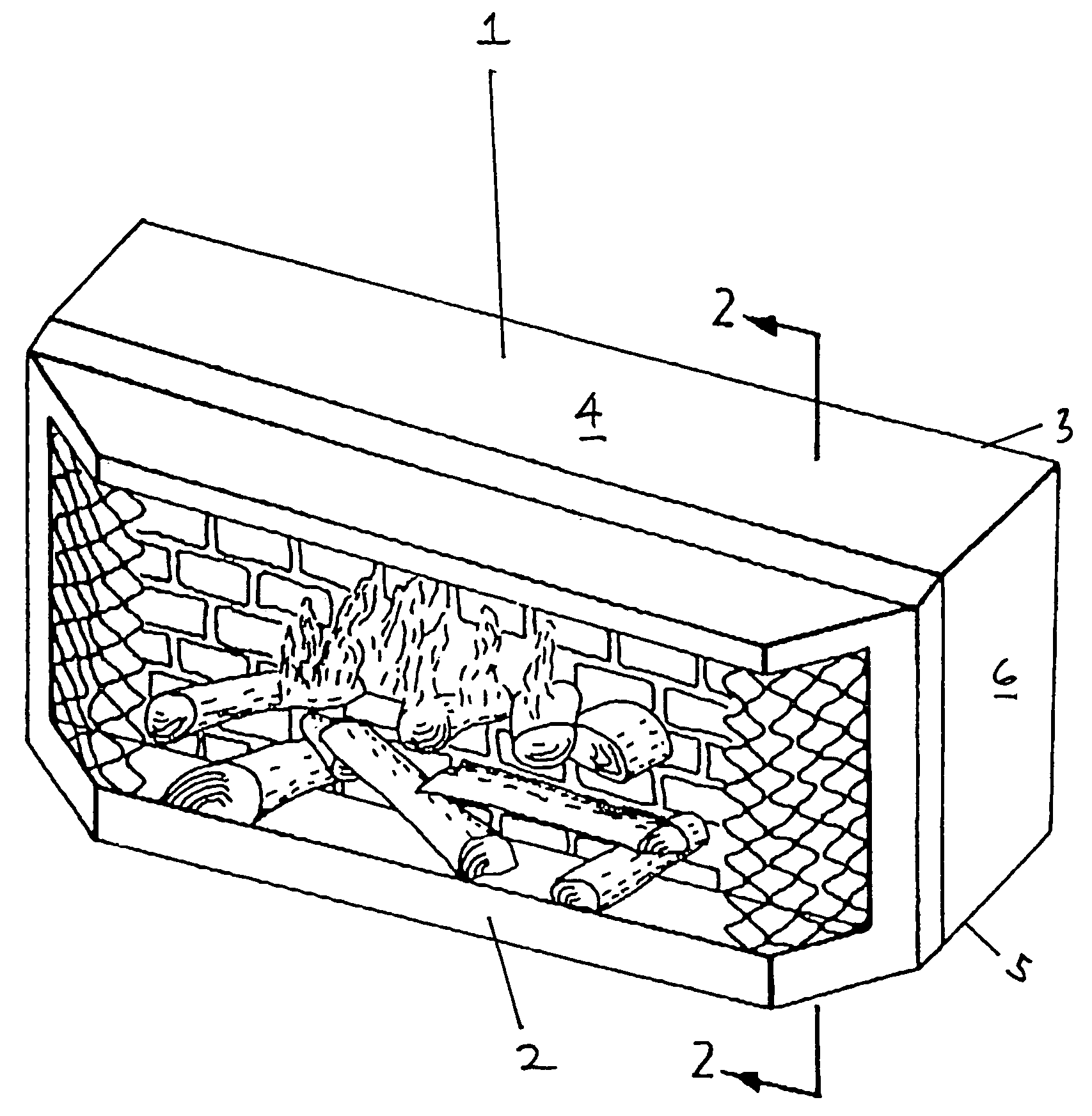
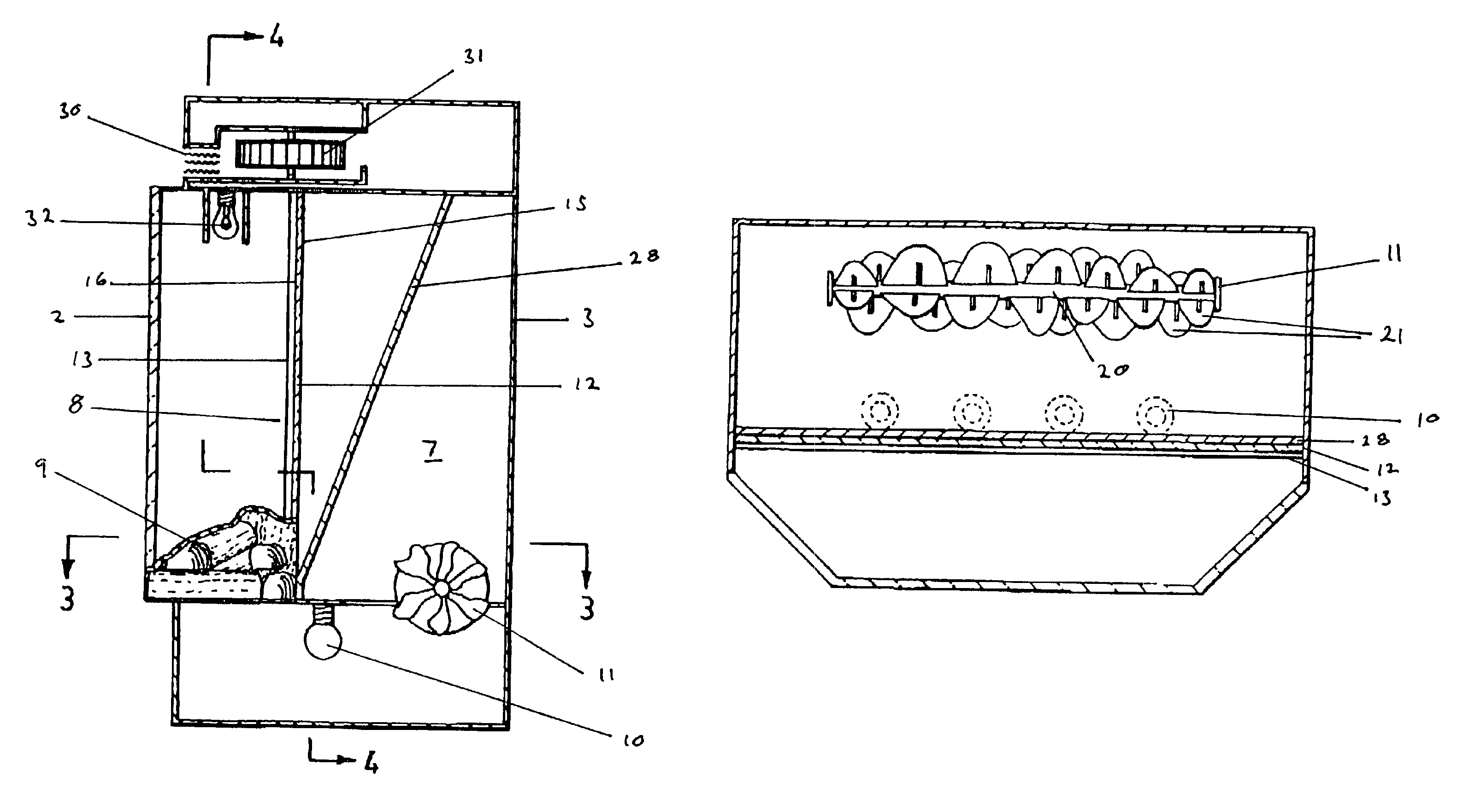
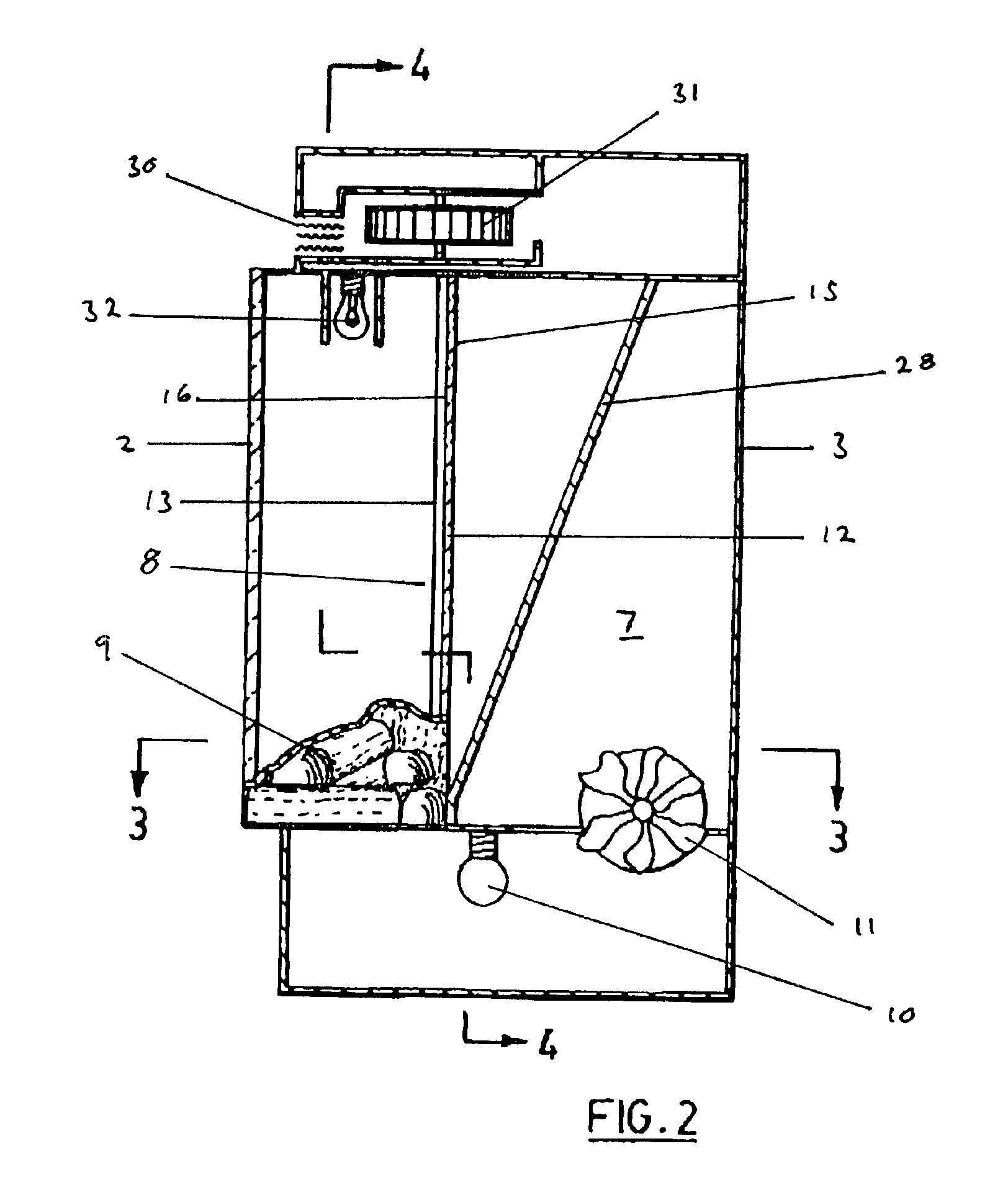
Flame simulating apparatus
A flame simulating apparatus to simulate flames emanating from a wood or fossil fuel burning fire. The flame simulating apparatus includes a light source, a light reflecting element, and a fire simulation screen. The light reflecting element produces a moving and generally random pattern of reflected light when light is cast upon it by the light source. The fire simulation screen has the image of a fire thereon and is positioned so that reflected light from the light reflecting element is cast upon its rear surface. The fire simulation screen includes at least one portion that is at least partially translucent such that light cast upon the partially translucent portion by the light reflecting element is diffused and at least partially passes through the translucent portion to present a moving flame image when viewed from a position in front of the fire simulation screen.
Owner:NAPOLEON SYST & DEV
Copy protection for digital motion picture image data
InactiveUS7043019B2Television system detailsUser identity/authority verificationComputer graphics (images)Copy protection
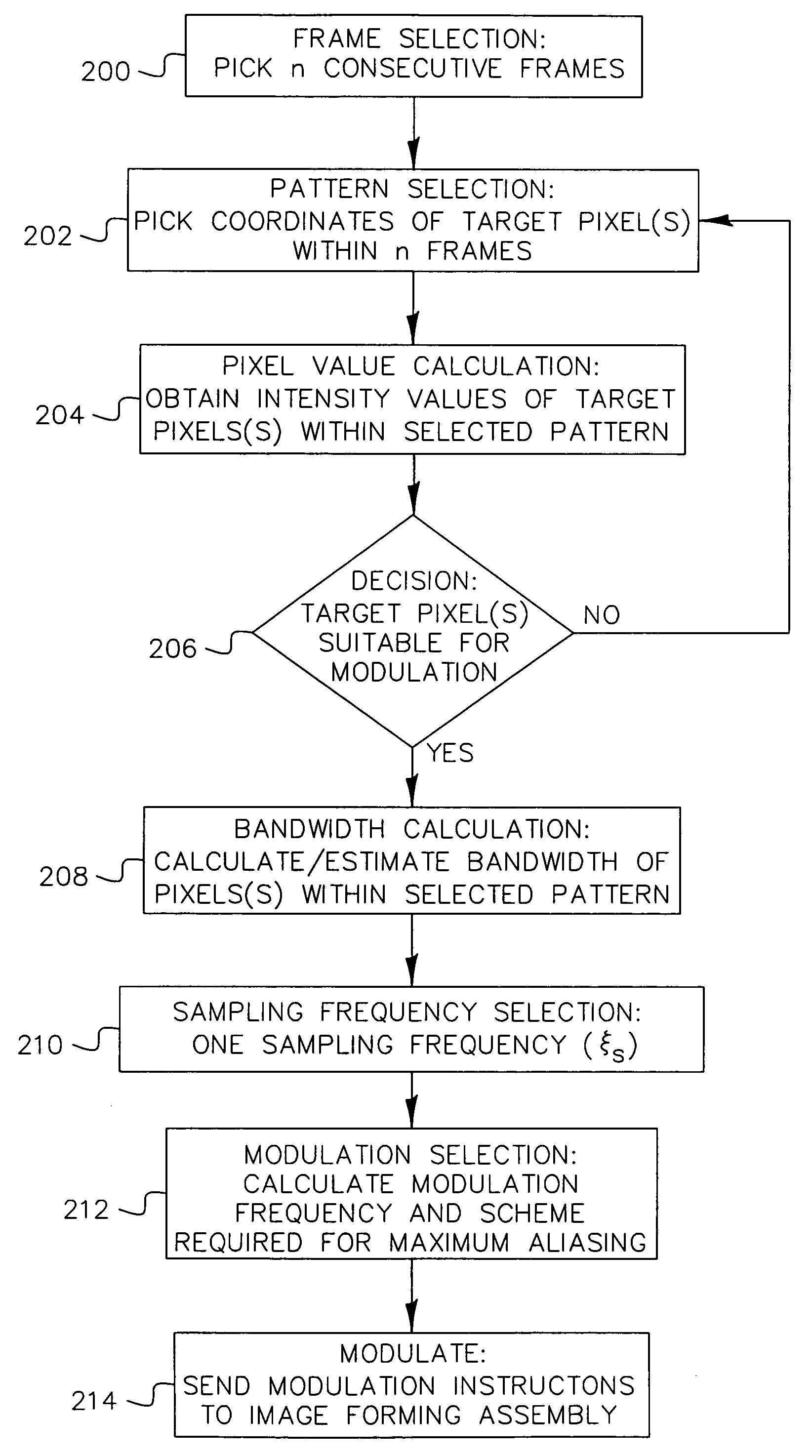
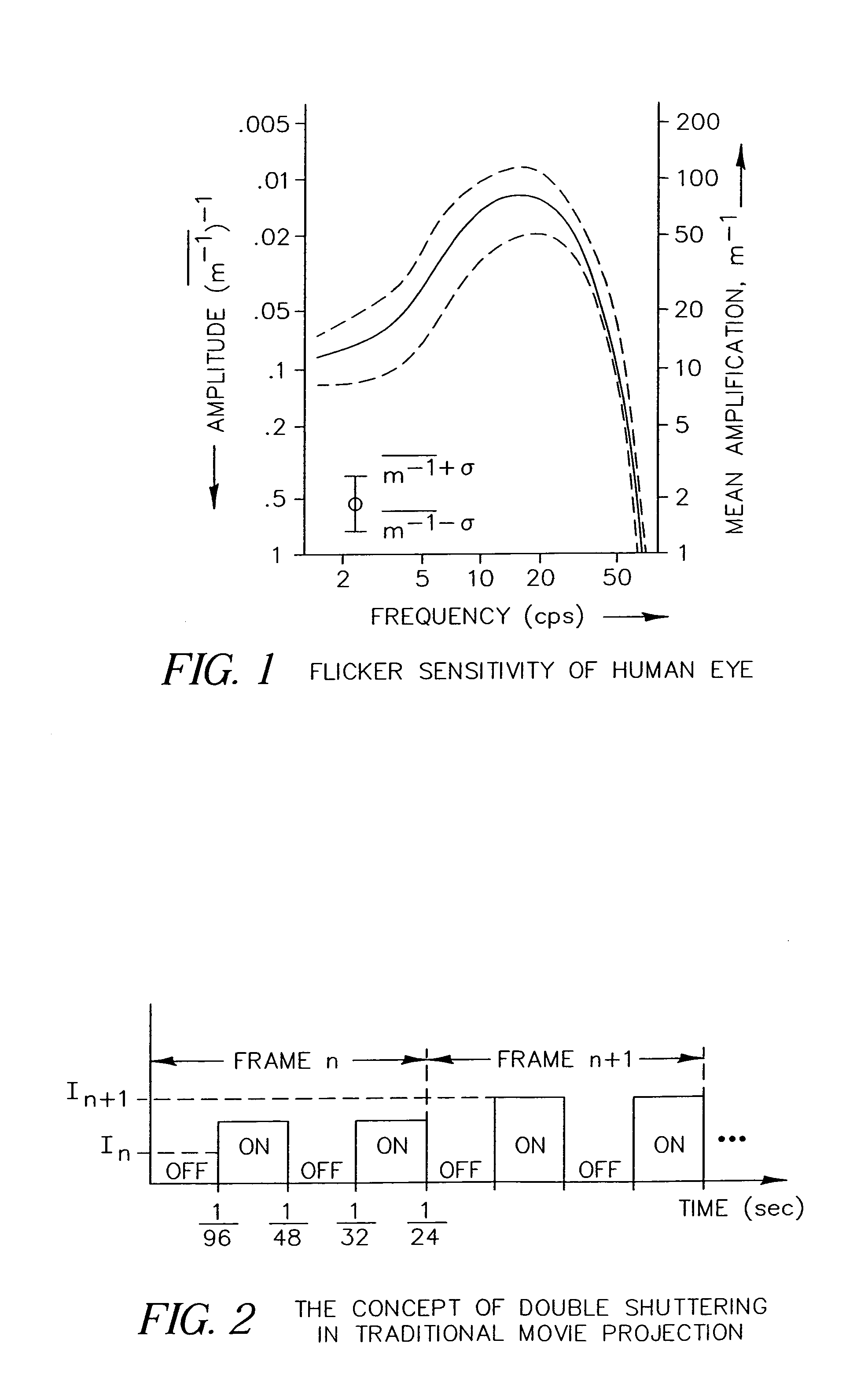
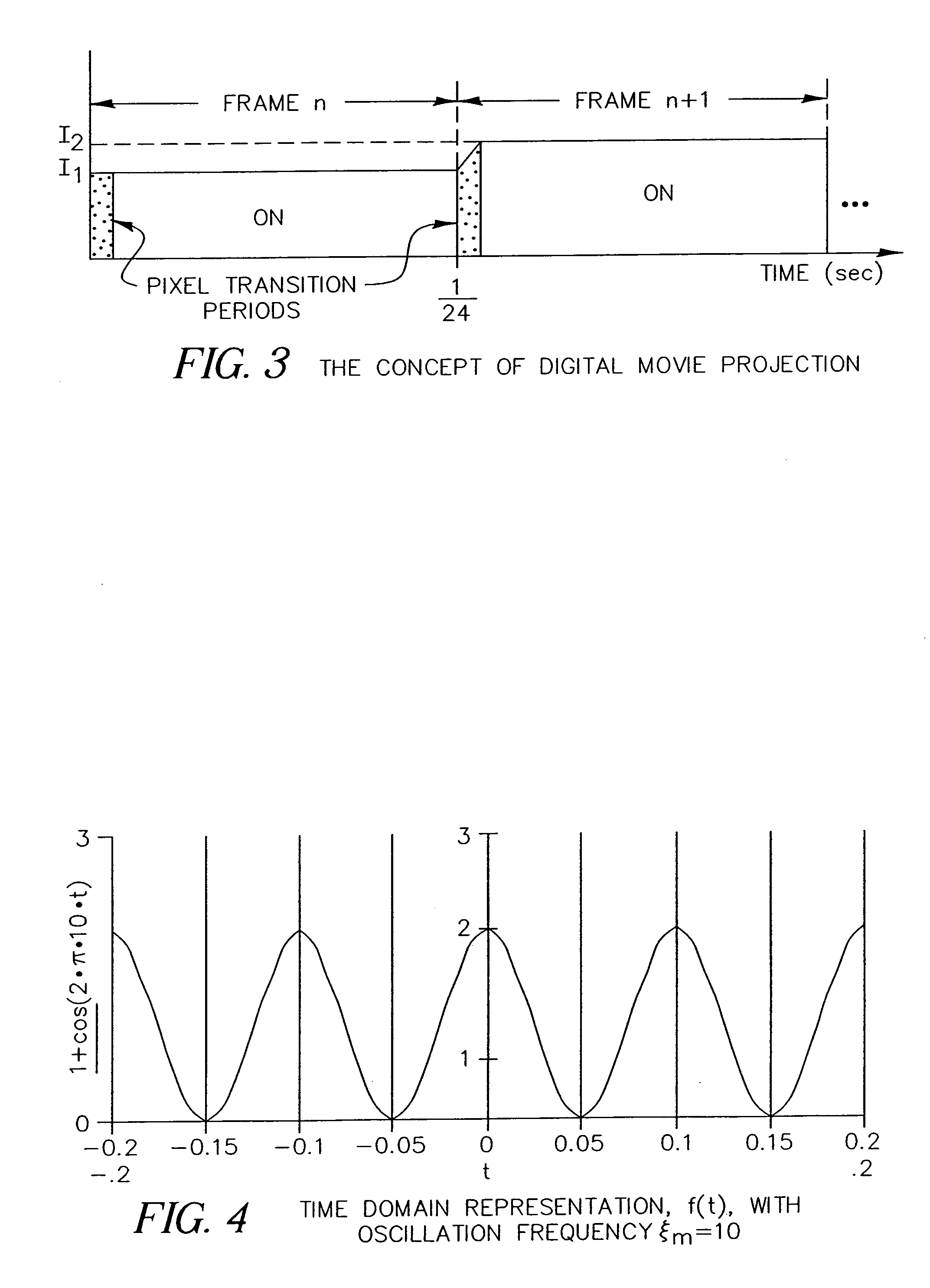
An apparatus and method for displaying a copy-deterrent pattern (104) within a digital motion picture in order to discourage recording of the motion picture using a video camera or other sampling recording device. A copy-deterrent pattern (104) could be, for example, one or more symbols, a random pattern, a digital watermark or a text message (106). The copy-deterrent pattern (104) comprises a plurality of pixels within each frame of the digital motion picture, and the displayed pixel intensities are modulated at a temporal frequency using modulation characteristics deliberately selected to be imperceptible to human observers while simultaneously producing objectionable aliasing in any copy made using a video camera.
Owner:EASTMAN KODAK CO
Method and apparatus for tissue expansion
InactiveUS20110251602A1Reduce presenceReduced likelihoodSkin implantsIncision instrumentsMedicineTissue expansion
Exemplary embodiments of the present disclosure provide method and apparatus for facilitating stretching of a bio-logical tissue by forming a plurality of micro-slits in the tissue. Each micro-slit can be less than about 2 mm or less than about 1.5 mm long, or even less than about 1 mm, such that small gaps that can heal quickly can be formed when the tissue is stretched. The micro-slits can be formed using a plurality of cutting arrangements or an ablative laser. The micro-slits can be formed in various patterns, including staggered rows, circular or spiral patterns, or random patterns.
Owner:THE GENERAL HOSPITAL CORP
Device for cell separation and analysis and method of using
ActiveUS20070161051A1Disrupt flowEasy to separateBioreactor/fermenter combinationsBiological substance pretreatmentsEngineeringMicroscopic exam
A microflow device for separating or isolating cells from a bodily fluid or other liquid sample uses a flow path where straight-line flow is interrupted by a pattern of transverse posts which are arranged across the width of a collection region in an irregular or set random pattern so as to disrupt streamlined flow. Sequestering agents, such as Abs, are attached to all surfaces in the collection region via a hydrophilic permeable hydrogel coating. The collection region is formed as a cavity in a body molded from PDMS, which flexible body is sandwiched between a glass slide or comparable flat plate and a rigid top cap plate, both of which are pressed into abutting relation with the PDMS body by a heat-shrunk polymeric sleeve. Following cell separation and washing, cells can be released from the sequestering agents and the device centrifuged to force said cells to collect adjacent the hydrogel-coated slide or plate. Slitting the polymeric sleeve allows the body to then be peeled from the slide or plate, using an integral tab, to expose the separated cells on the top surface thereof for ready microscopic examination.
Owner:BIOCEPT INC
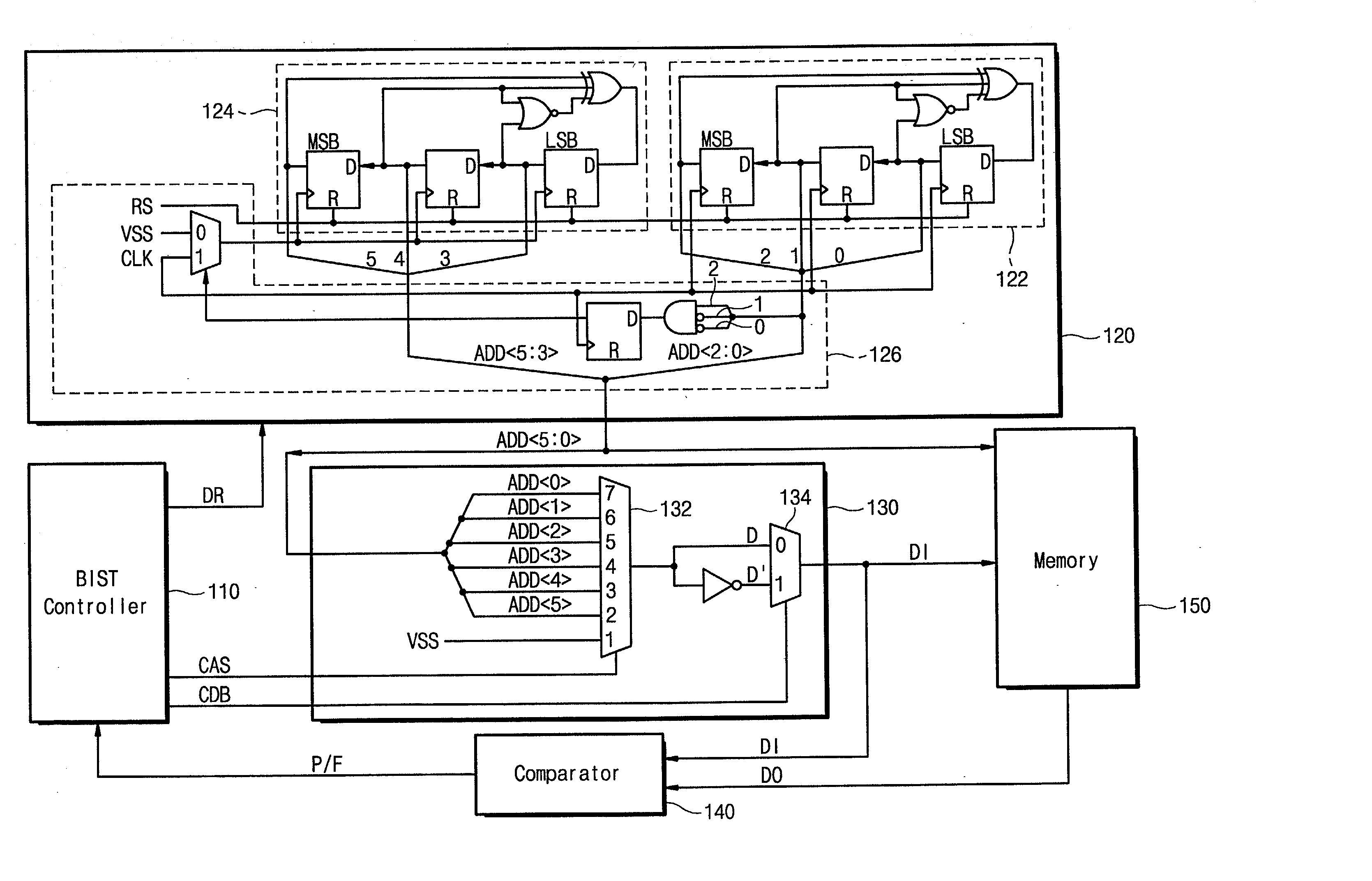
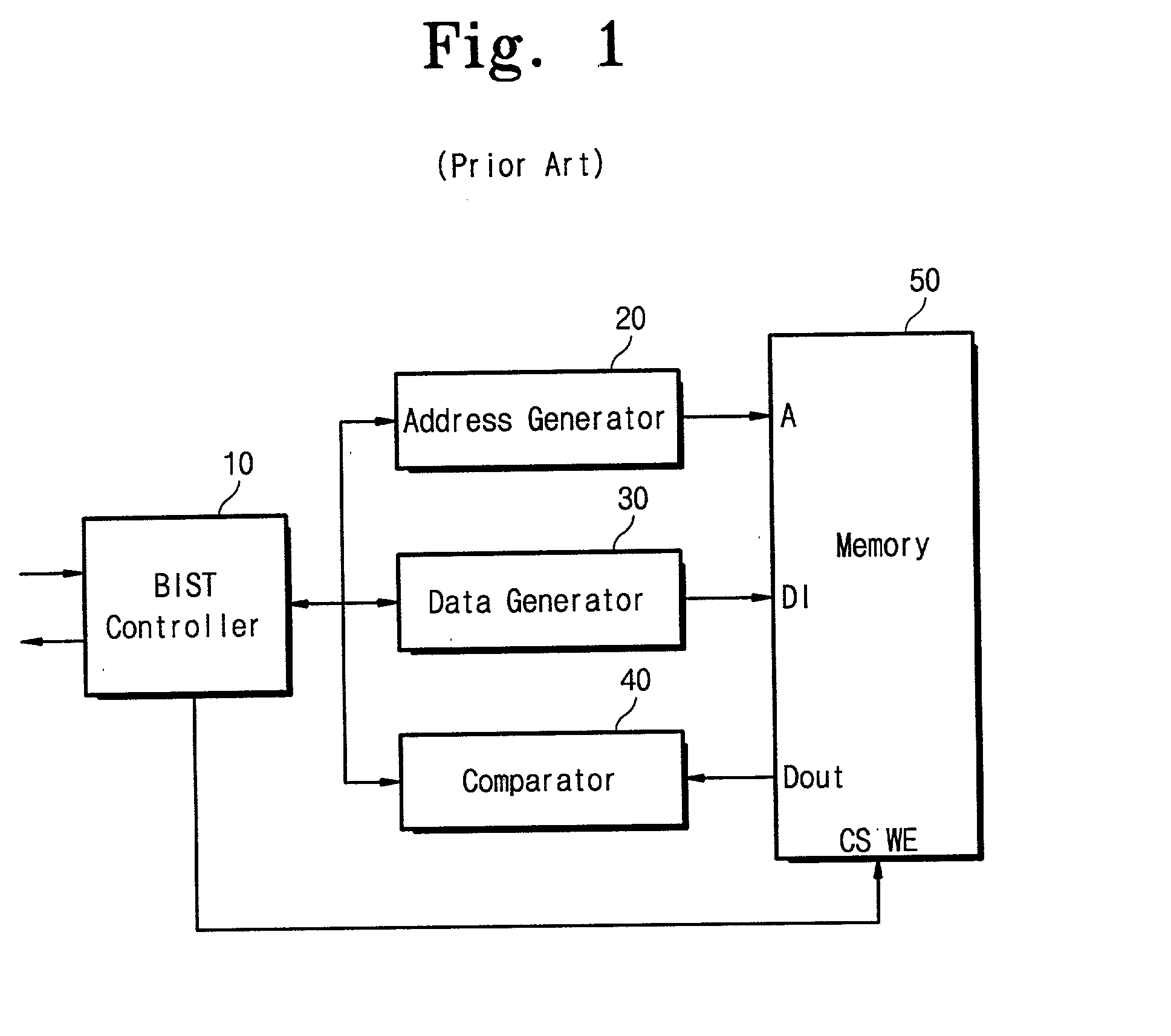
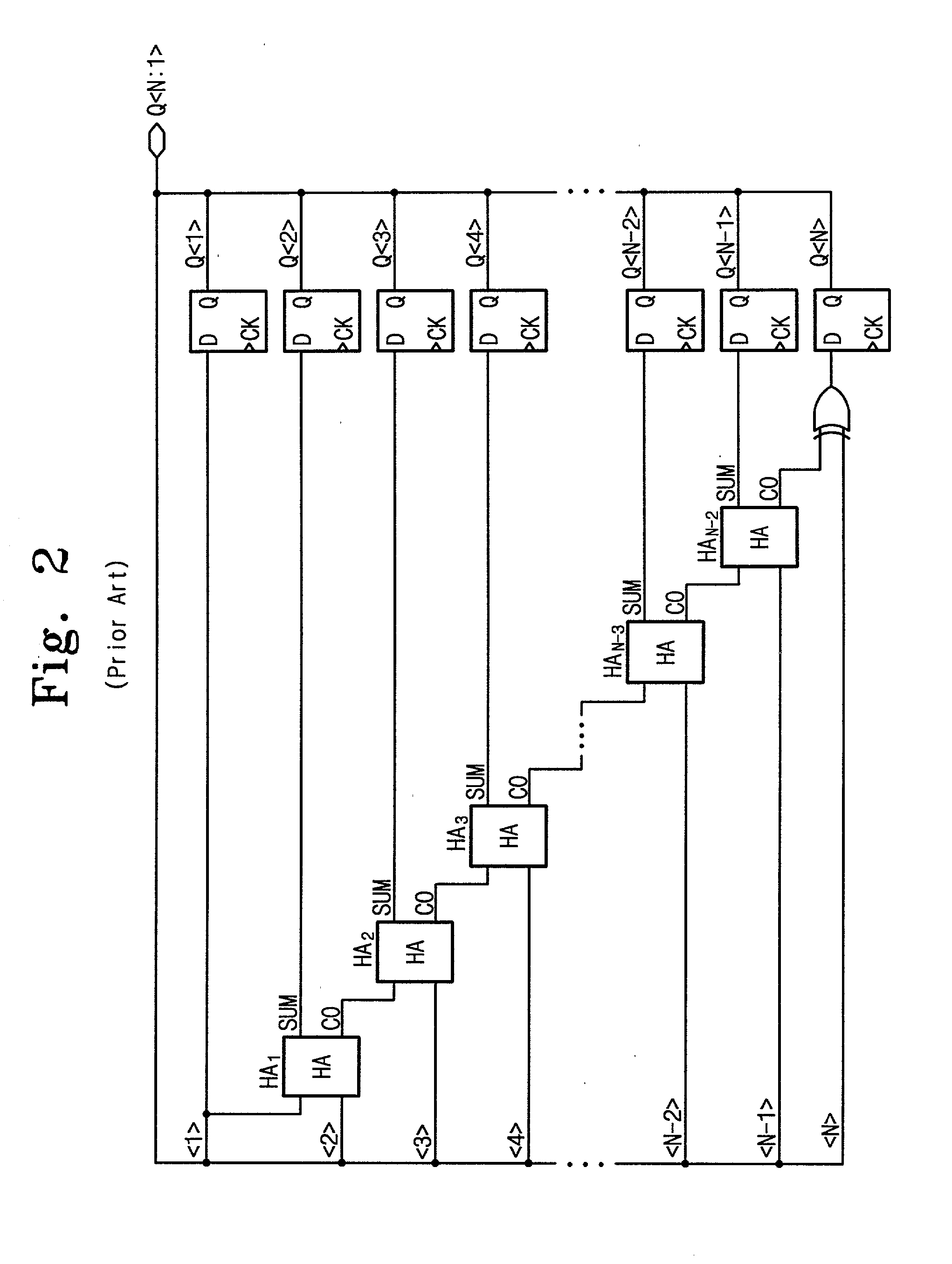
Built-in self test circuit using linear feedback shift register
A built-in self test (BIST) circuit comprising a linear feedback shift register is disclosed. The BIST circuit comprises a controller for controlling a self-testing operation of a memory chip embedded in an integrated circuit, an address generator for generating pseudo-random address patterns under control of the controller, a data generator for producing test data associated with data backgrounds of the address bits under the control of the controller, and a comparator for comparing the test data with memory data output from the memory chip to detect a defect, if any, of the memory chip. The pseudo-random random pattern comprises a single-random pseudo-random address pattern.
Owner:SAMSUNG ELECTRONICS CO LTD
Apparatus and method for the transfer of a fluid to a moving web material
An apparatus and method for enabling the transfer of a fluid to a web material, the apparatus comprising a fluid transfer component having a first surface, a second surface, and a non-random pattern of distinct pores. The pores connect the first surface and the second surface and are disposed at preselected locations to provide a desired pattern of permeability. The apparatus also comprises a fluid receiving component comprising a fluid receiving surface, a fluid supply adapted to provide a fluid in contact with the first surface of the fluid transfer component, and a fluid motivating component adapted to facilitate transport of the fluid from the first surface through the pores to the second surface. The method comprises steps of providing the apparatus, motivating a fluid through the pores and bringing the fluid receiving component into contact with the motivated fluid.
Owner:PROCTER & GAMBLE CO
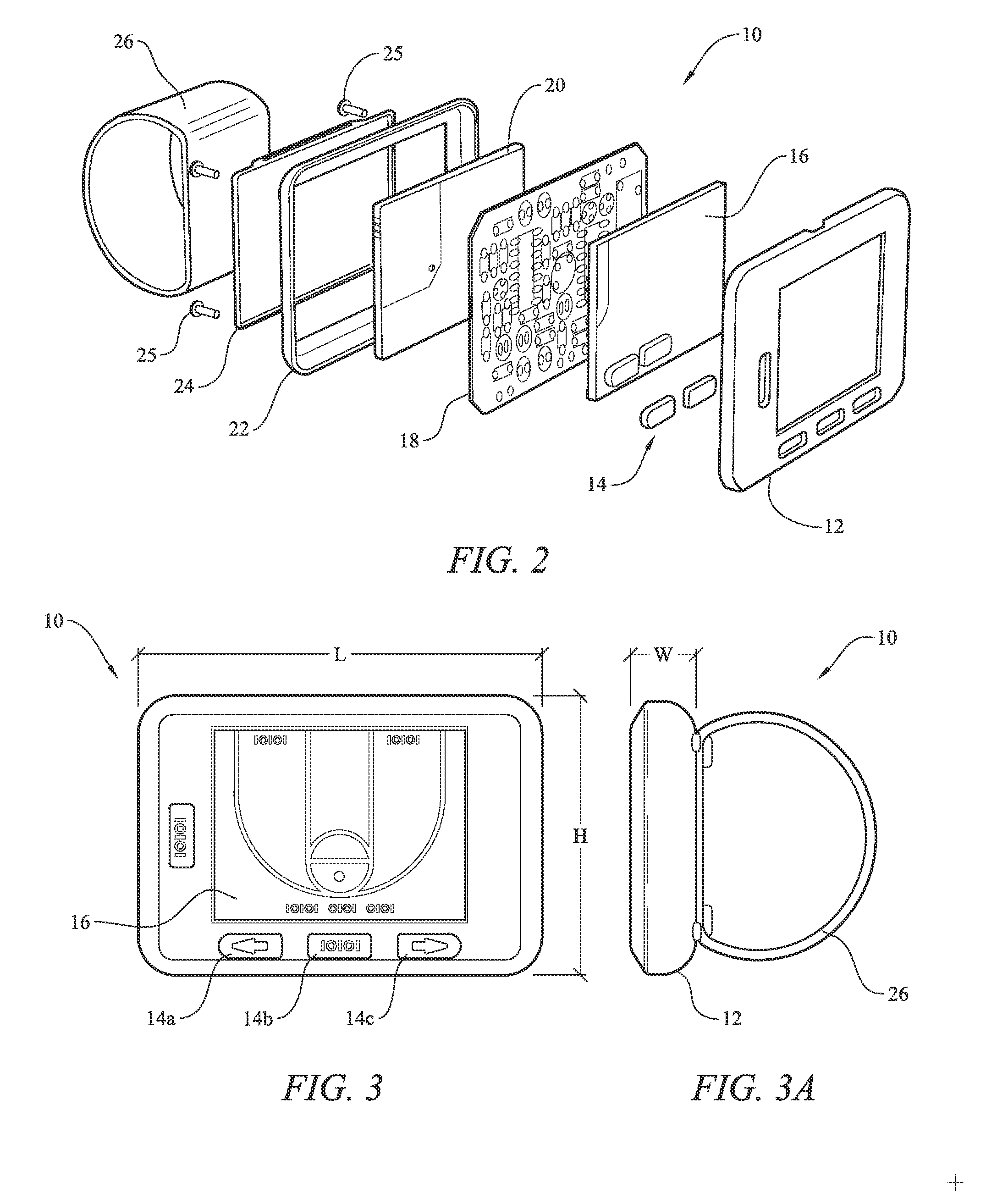
Hoop tracker
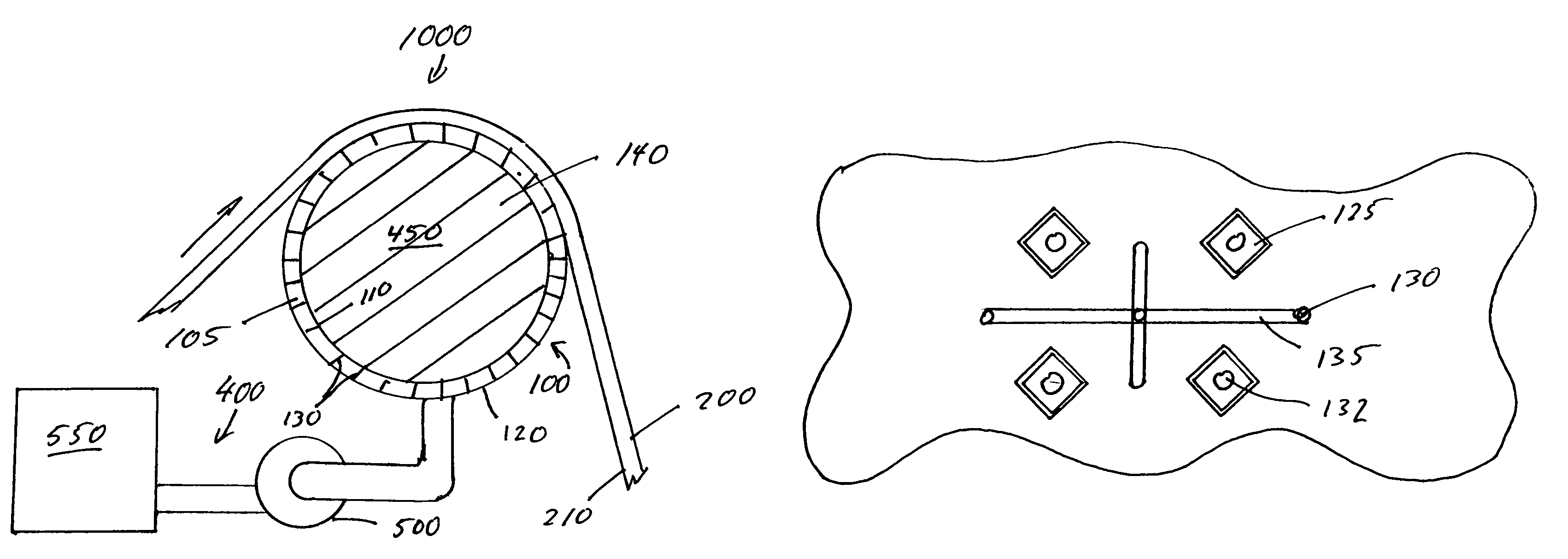
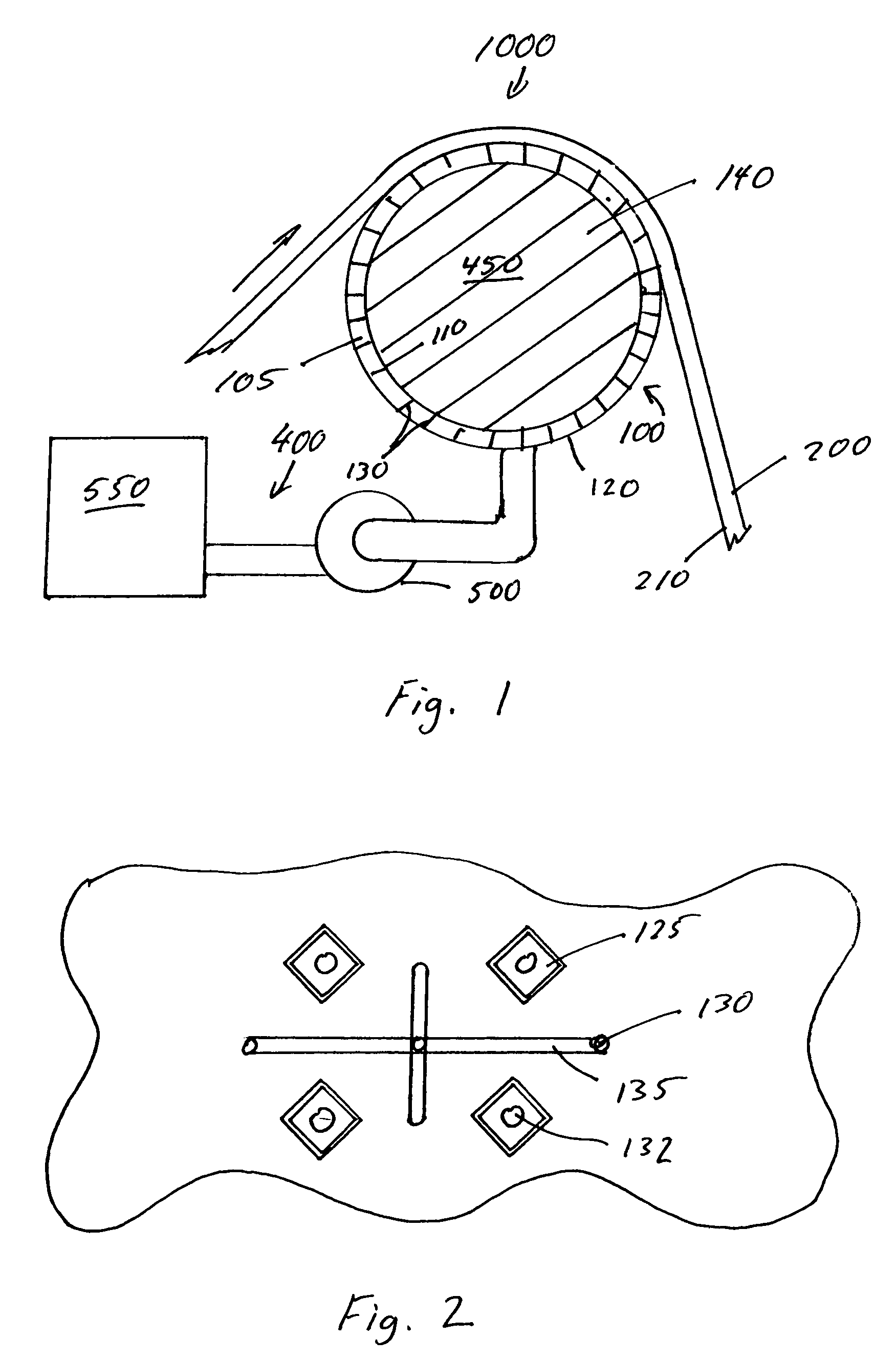
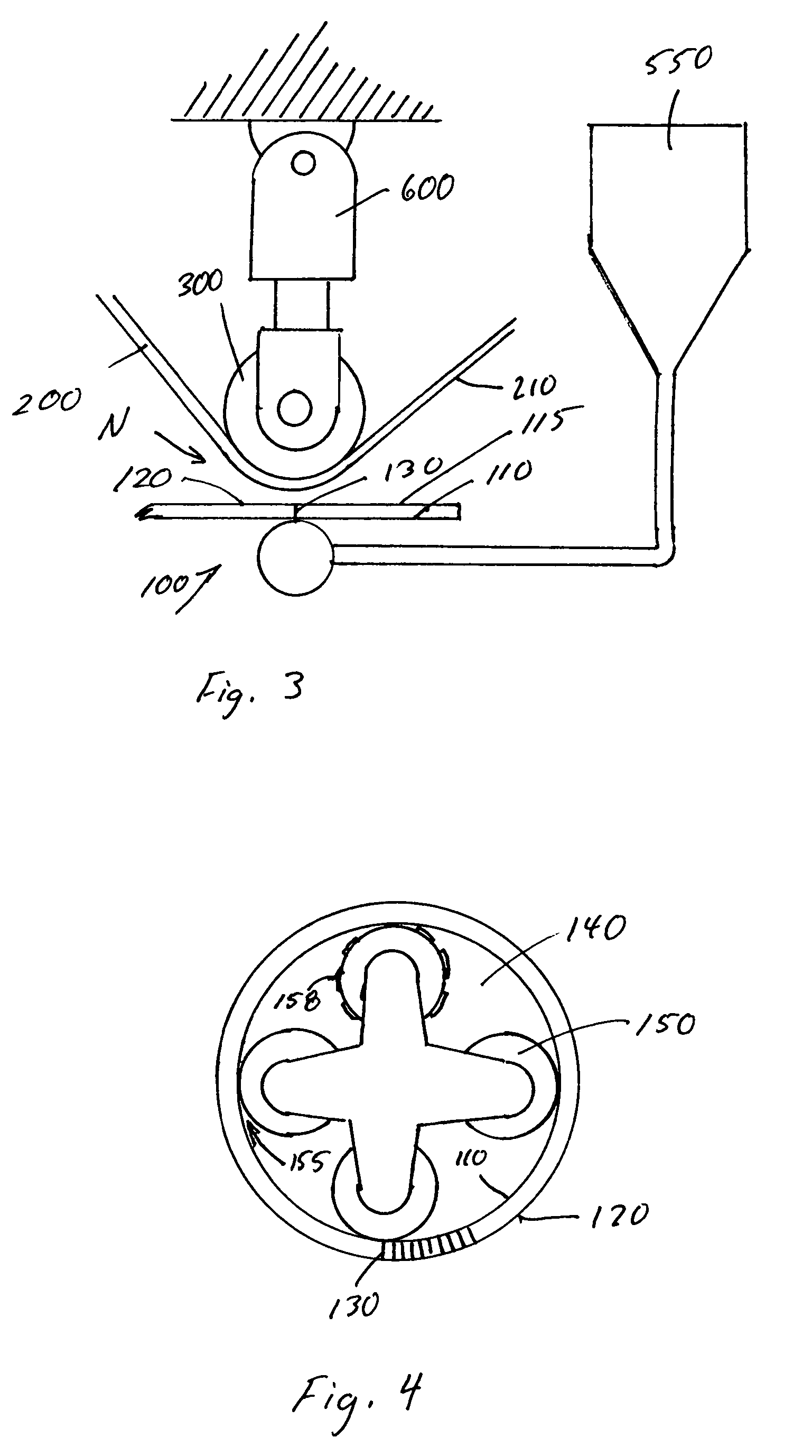
The present invention is directed to a wireless shot tracking system including a programmable electronic unit that is in electrical communication with a shot detector for automatically tracking and displaying real-time shooting percentages of basketball players during basketball shooting sessions, and a telescoping pole for mounting the shot detector to a basketball rim from the ground. The programmable electronic unit provides a program mode, a play mode, a review mode and a random mode to help improve the shooting skills of a basketball player from different shooting locations on a basketball court. The shot detector includes one or more vibration sensors to detect missed shots, and an activator that extends along a horizontal axis in a central region of the basketball hoop to detect made shots. The programmable electronic unit interfaces with a computer via a USB port for uploading or downloading program updates or shooting session data.
Owner:DUKE JASON
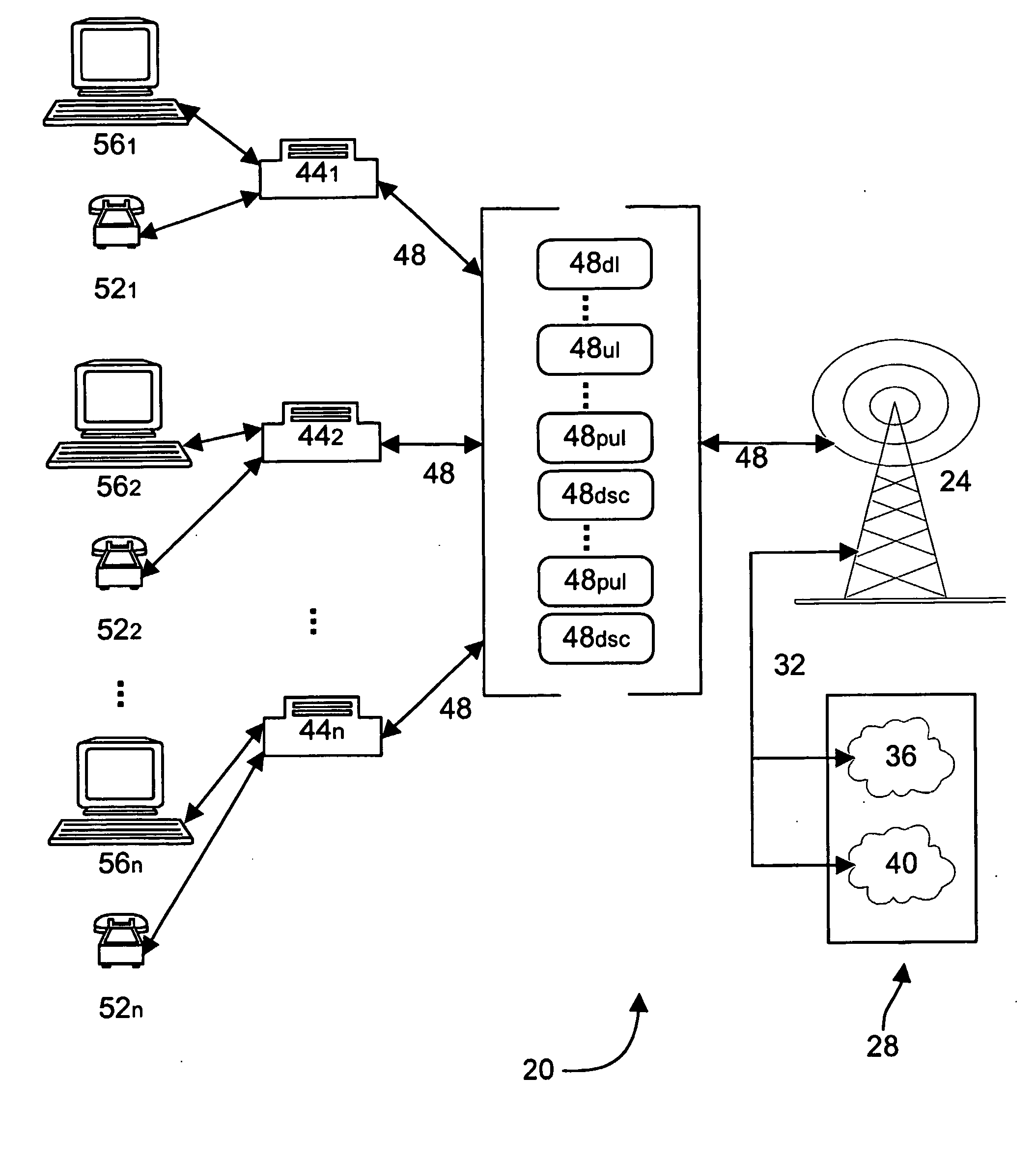
Communication channel structure and method
InactiveUS20050157678A1Improve transmission capacityImprove balanceNetwork traffic/resource managementTime-division multiplexOperational systemCommunications system
A novel communication channel structure and method in a wireless communication system is provided. In an embodiment of the invention, the communication system includes a base station and a plurality of subscriber stations and the subscriber stations are given access to a variety of channels, including at least one uplink data channel. The uplink data channel can operate in at least a random access mode and a polled access mode. The base station informs each subscriber station it serves of the current mode of the uplink channel via an associated downlink signaling channel and, in random access mode, each subscriber station is able to randomly access the shared uplink channel. In polled mode, each subscriber station waits for permission from the base station before sending data over the shared uplink channel. A method of operating the system monitors the collisions which occur on the uplink channel in random mode and / or the amount of data and / or the data's priority level and / or QoS requirements and switches the system between random and polled modes as appropriate. In polled mode, the method determines which subscriber stations should access the uplink and when.
Owner:WI LAN INC
Device for cell separation and analysis and method of using
ActiveUS7695956B2Easy to separateEasy to peelBioreactor/fermenter combinationsBiological substance pretreatmentsMicroscopic examEngineering
A microflow device for separating or isolating cells from a bodily fluid or other liquid sample uses a flow path where straight-line flow is interrupted by a pattern of transverse posts which are arranged across the width of a collection region in an irregular or set random pattern so as to disrupt streamlined flow. Sequestering agents, such as Abs, are attached to all surfaces in the collection region via a hydrophilic permeable hydrogel coating. The collection region is formed as a cavity in a body molded from PDMS, which flexible body is sandwiched between a glass slide or comparable flat plate and a rigid top cap plate, both of which are pressed into abutting relation with the PDMS body by a heat-shrunk polymeric sleeve. Following cell separation and washing, cells can be released from the sequestering agents and the device centrifuged to force said cells to collect adjacent the hydrogel-coated slide or plate. Slitting the polymeric sleeve allows the body to then be peeled from the slide or plate, using an integral tab, to expose the separated cells on the top surface thereof for ready microscopic examination.
Owner:BIOCEPT INC
Multi composition stick product and a process and system for manufacturing the same
A multi-composition stick product, such as a lip balm, sun screen, deodorant, or glue stick. The multi-composition stick product including a stick composition molded in the container so as to contact the walls thereof and be advanceable or ejected therefrom. The stick composition includes a first composition and a second composition. The first and second compositions differ in at least one component, such as a medicament, colorant, fragrance, flavorant, sunscreen, preservative, conditioner, moisturizer, emollient, or surfactant. Furthermore the first and second compositions are arranged in a predetermined non-random pattern that is reproducible. Also described is the method and apparatus for manufacturing the multi-composition stick product.
Owner:PF CONSUMER HEALTHCARE 1 LLC
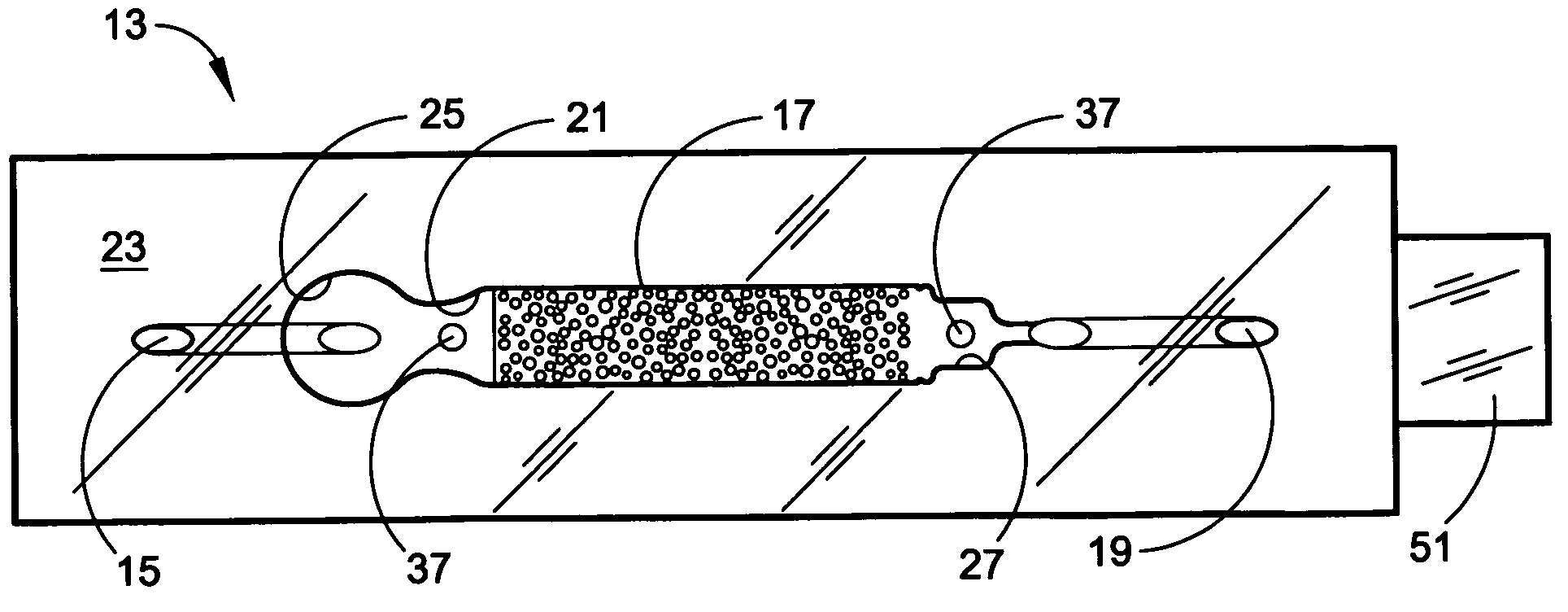
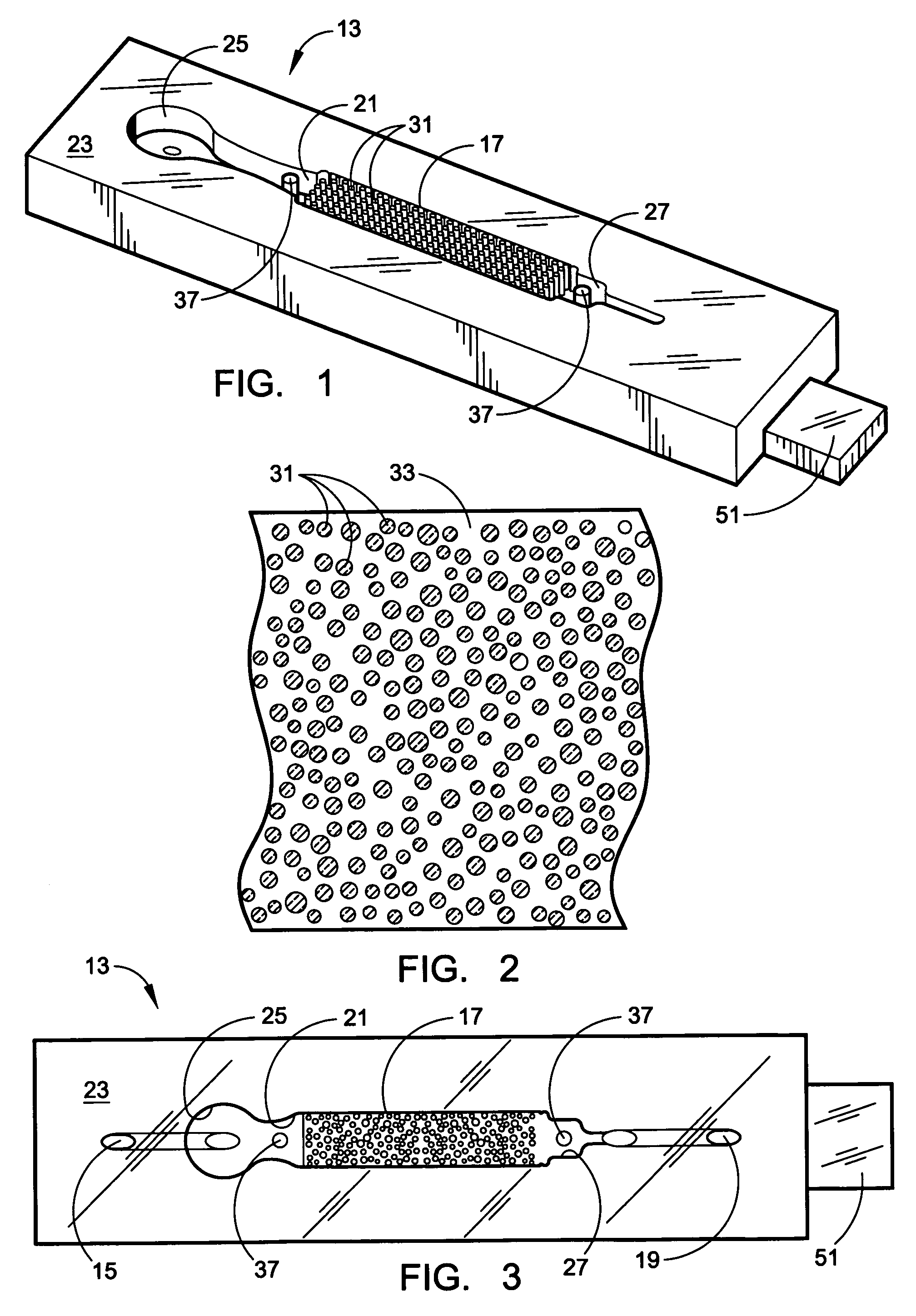
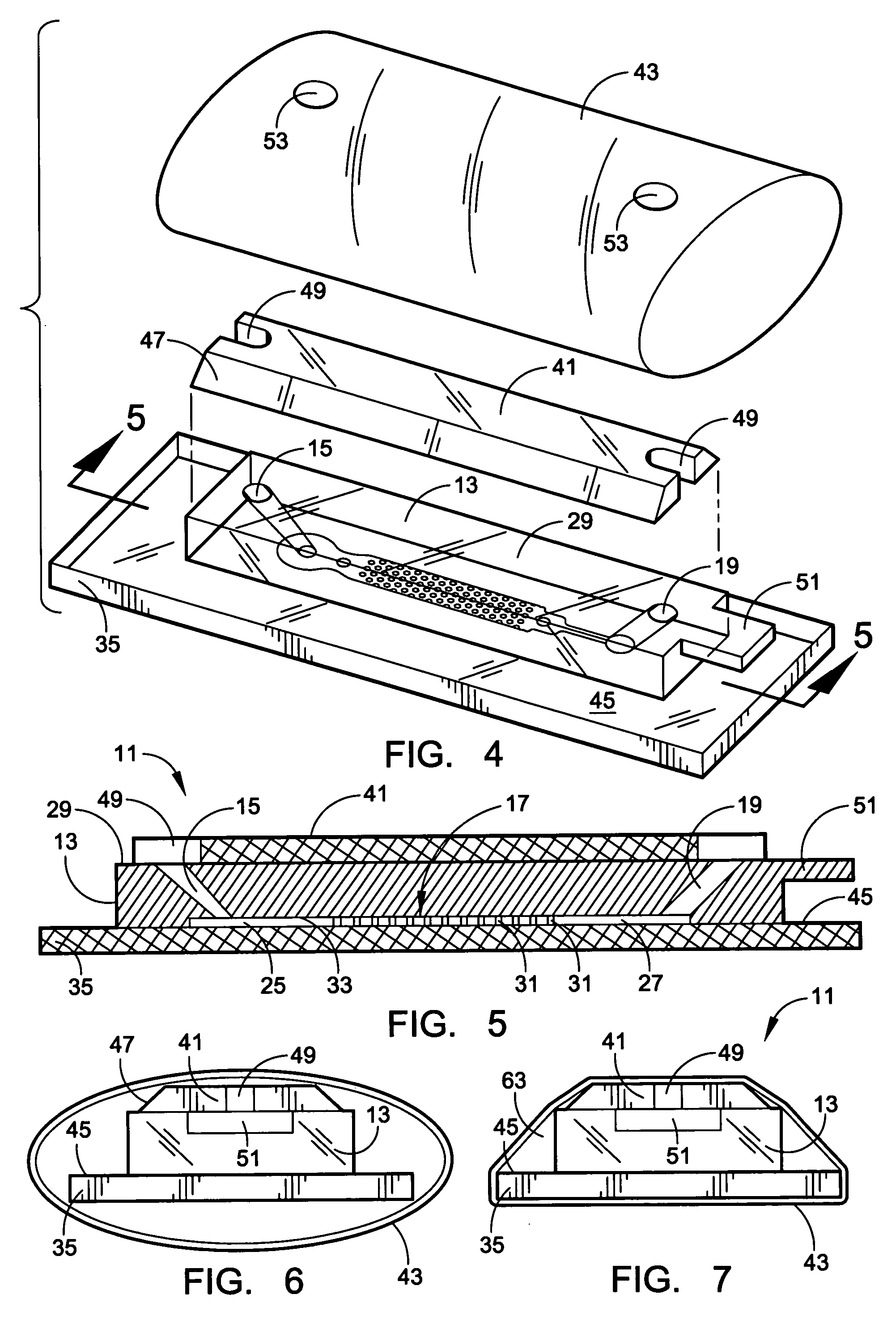
Holey optical fiber with random pattern of holes and method for making same
ActiveUS20050094954A1Glass making apparatusOptical fibre with multilayer core/claddingSilicon dioxideAir bubble
A random array of holes is created in an optical fiber by gas generated during fiber drawing. The gas forms bubbles which are drawn into long, microscopic holes. The gas is created by a gas generating material such as silicon nitride. Silicon nitride oxidizes to produce nitrogen oxides when heated. The gas generating material can alternatively be silicon carbide or other nitrides or carbides. The random holes can provide cladding for optical confinement when located around a fiber core. The random holes can also be present in the fiber core. The fibers can be made of silica. The present random hole fibers are particularly useful as pressure sensors since they experience a large wavelength dependant increase in optical loss when pressure or force is applied.
Owner:VIRGINIA TECH INTPROP INC
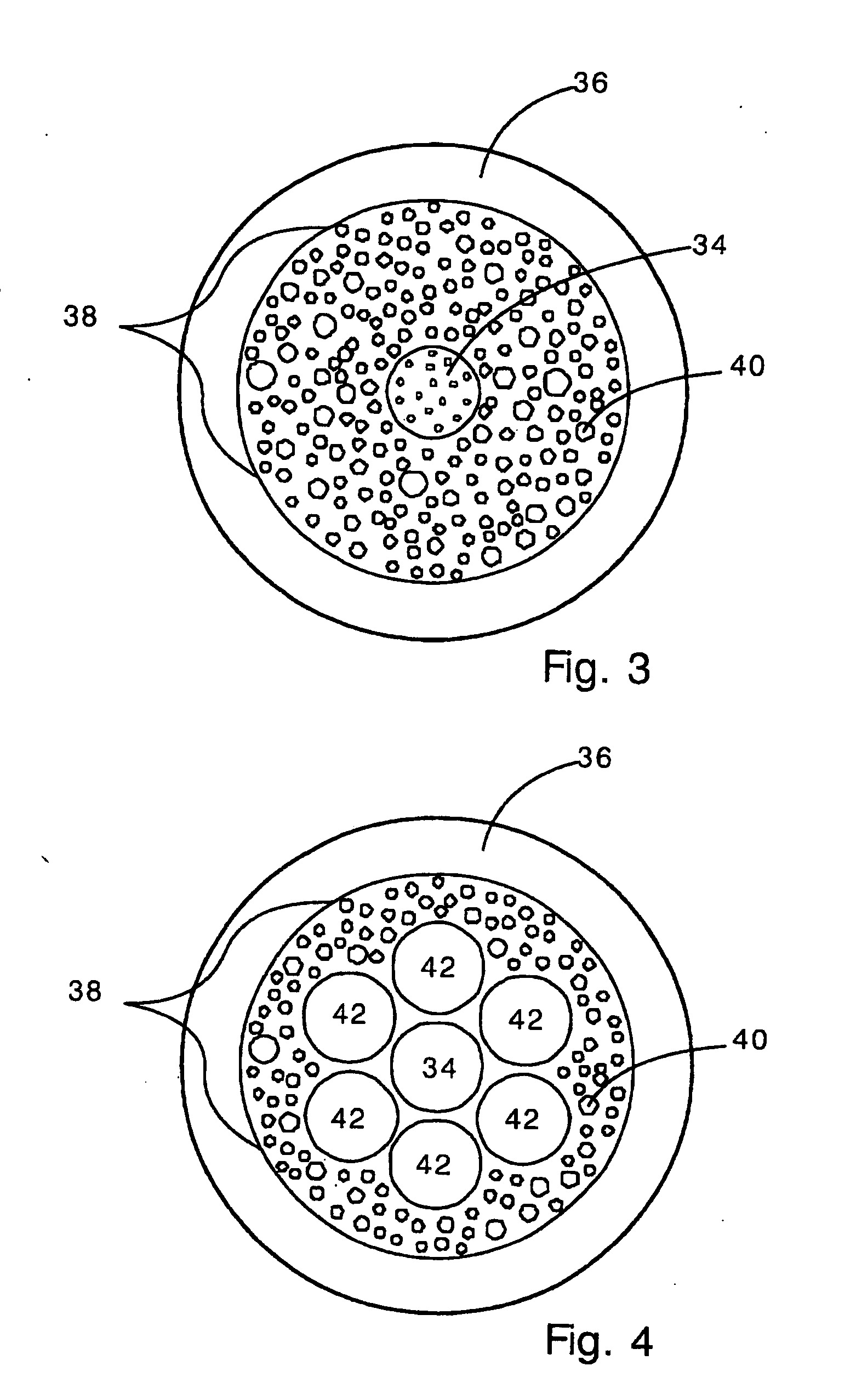
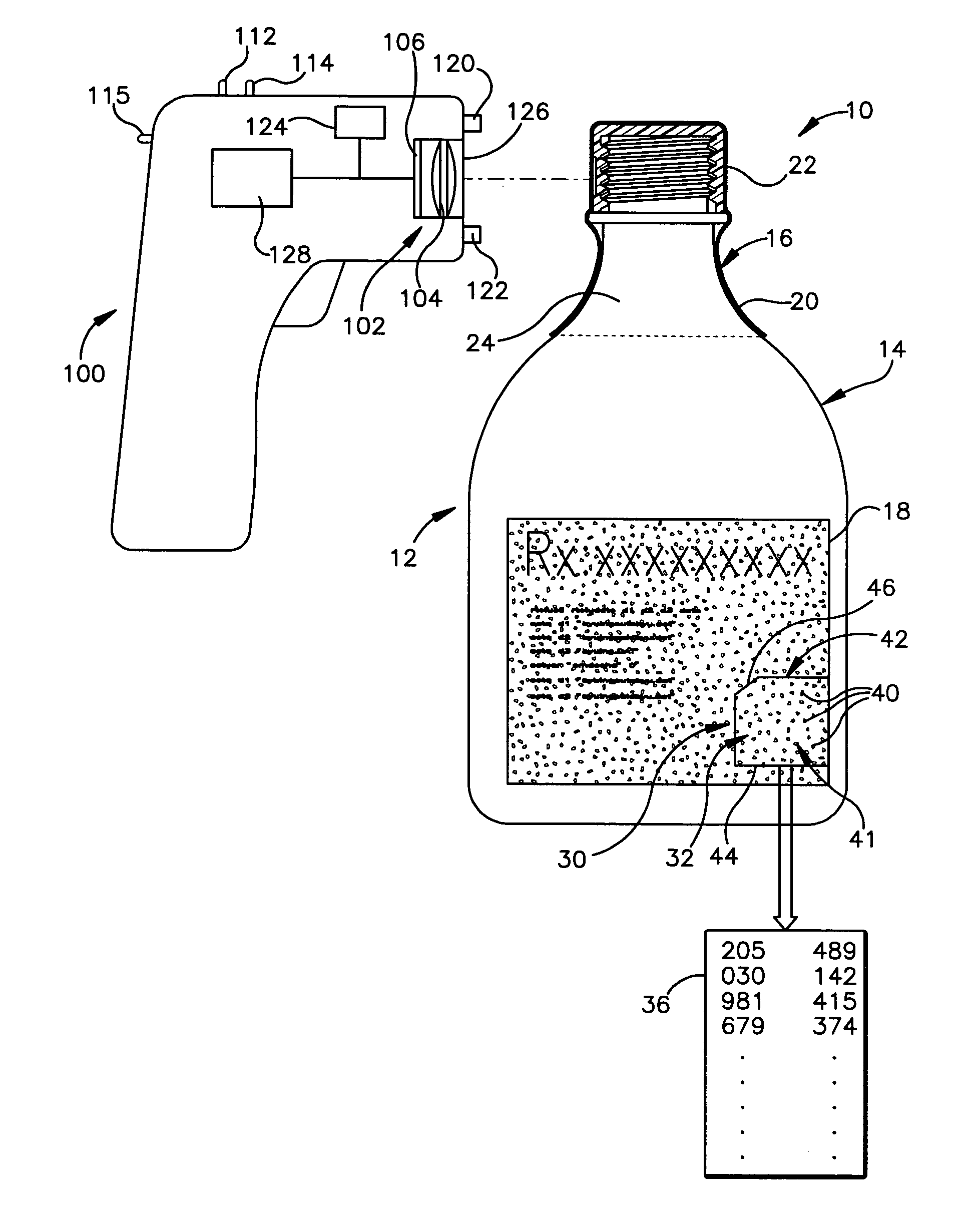
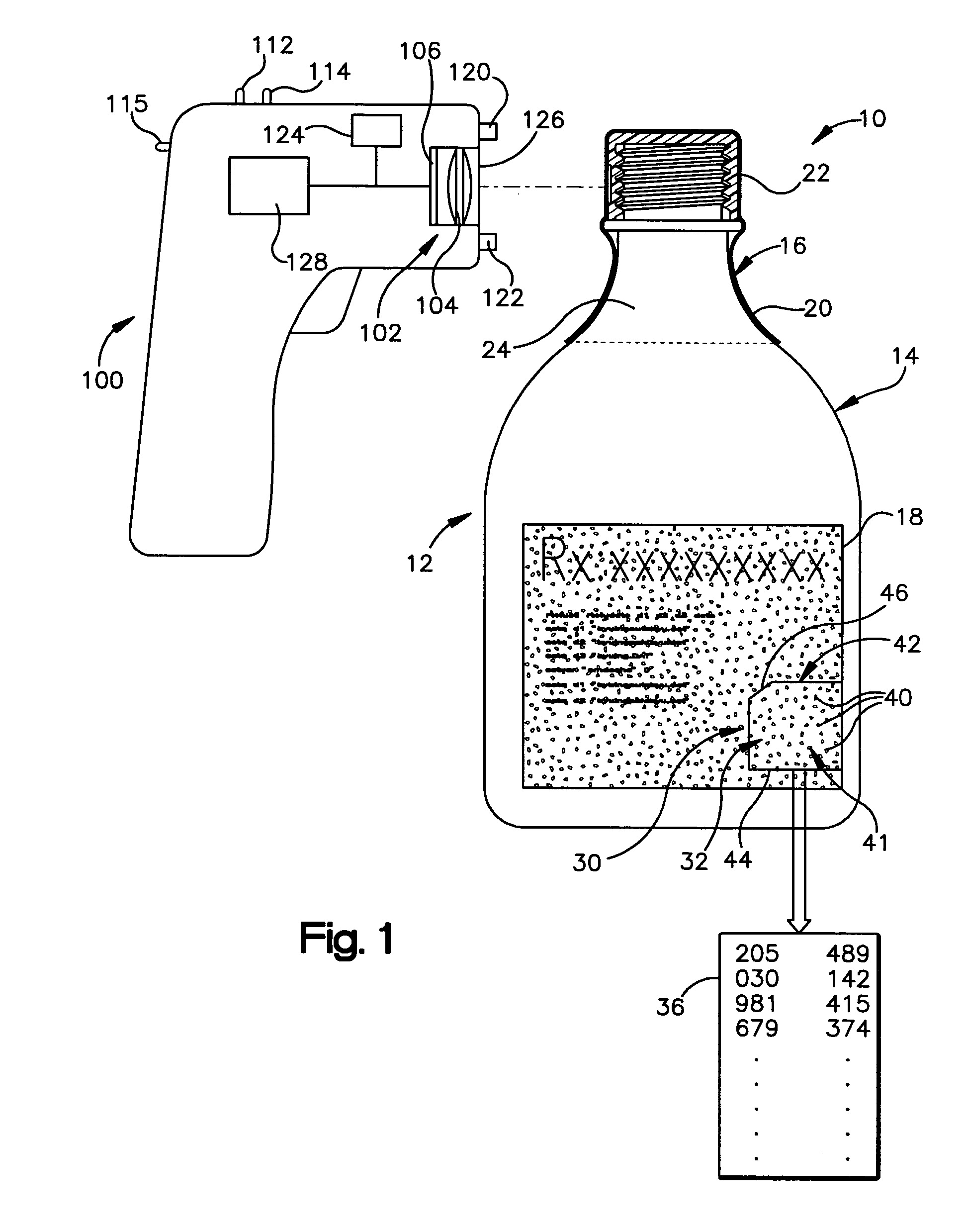
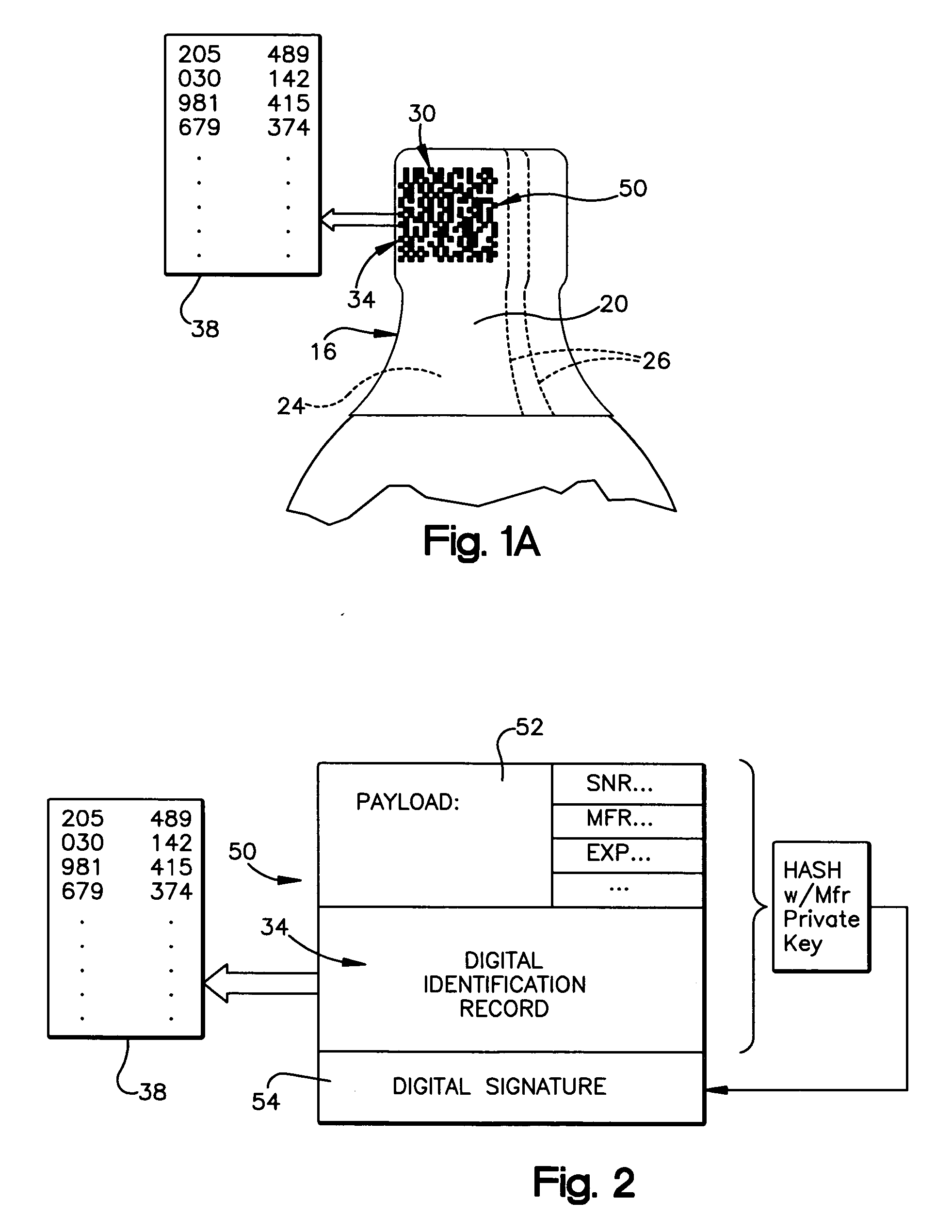
Method of authenticating products using analog and digital identifiers
A method of identifying or authenticating a product by providing an analog identification indicium including a randomized pattern of identification features on a first part of the product wherein one or more attributes of the randomized pattern of identification features correspond to an item identifier. A digital identification record is provided on a second part of the product including an encoded digital version of the item identifier, the first and second parts being separable when the product is used. The randomized pattern of identification features of the analog identification indicium is read and decoded to generate an item identifier and the digital identification record is read and decoded to generate an item identifier. The product is deemed authentic if the item identifier from the analog identification indicium substantially matches the item identifier from the digital identification record.
Owner:SYMBOL TECH LLC
Embossing process including discrete and linear embossing elements
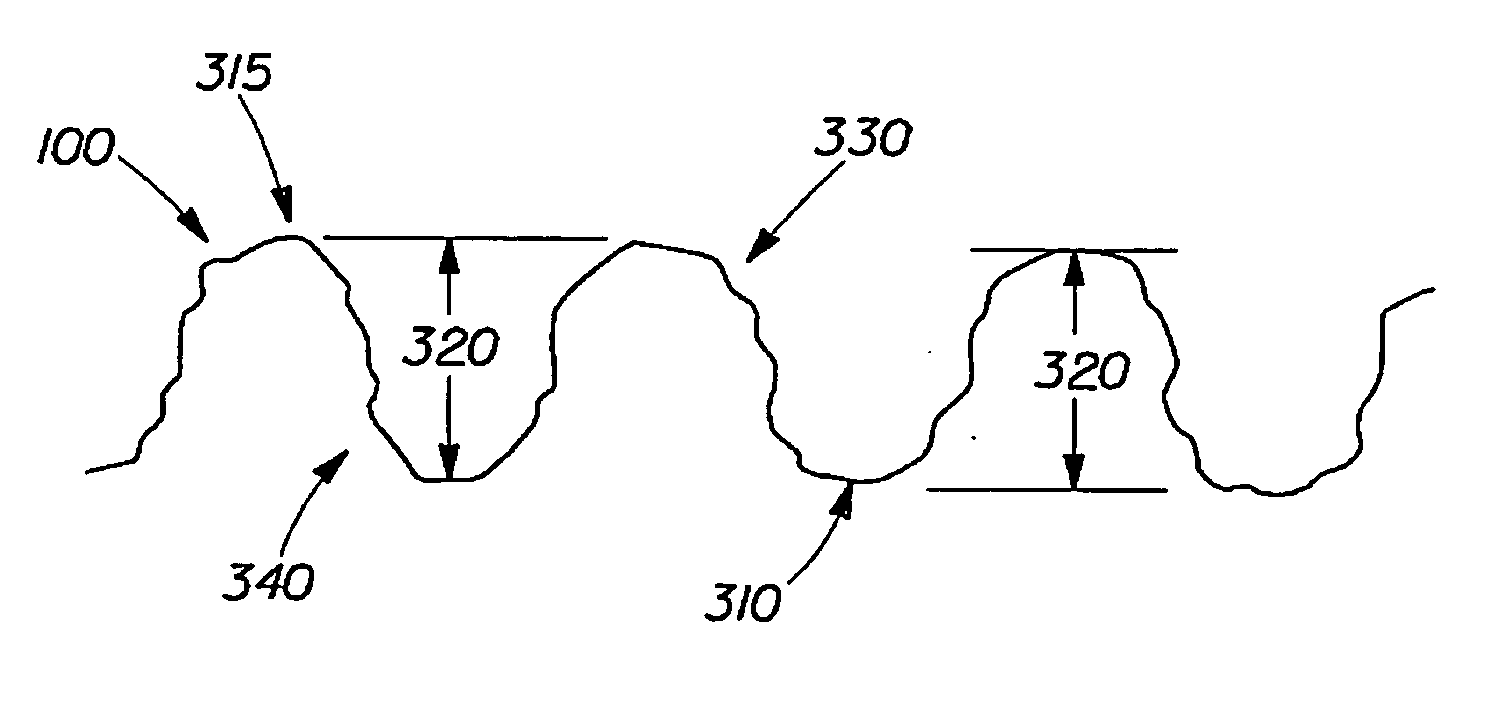
InactiveUS20060278355A1Non-fibrous pulp additionNatural cellulose pulp/paperEngineeringRandom pattern
An apparatus for producing an embossed product including a first embossing member having a plurality of discrete embossing elements disposed in a first non-random pattern having at least one first single pattern unit. The total area of the distal ends of the discrete embossing elements in the first single pattern unit is less than about 5.0 cm2. The apparatus also includes a second embossing member having a plurality of linear embossing elements disposed in a second non-random pattern having at least one second single pattern unit. The total area of the second distal ends in the second single pattern unit is less than about 10 cm2. The second non-random pattern is coordinated with the first non-random pattern such that when engaged with each other the first single pattern unit and the second single pattern unit make up an embossing pattern single pattern unit.
Owner:THE PROCTER & GAMBLE COMPANY
Secure Access by a User to a Resource
InactiveUS20140143844A1Shorten the lengthDigital data processing detailsMultiple digital computer combinationsArray data structureUser input
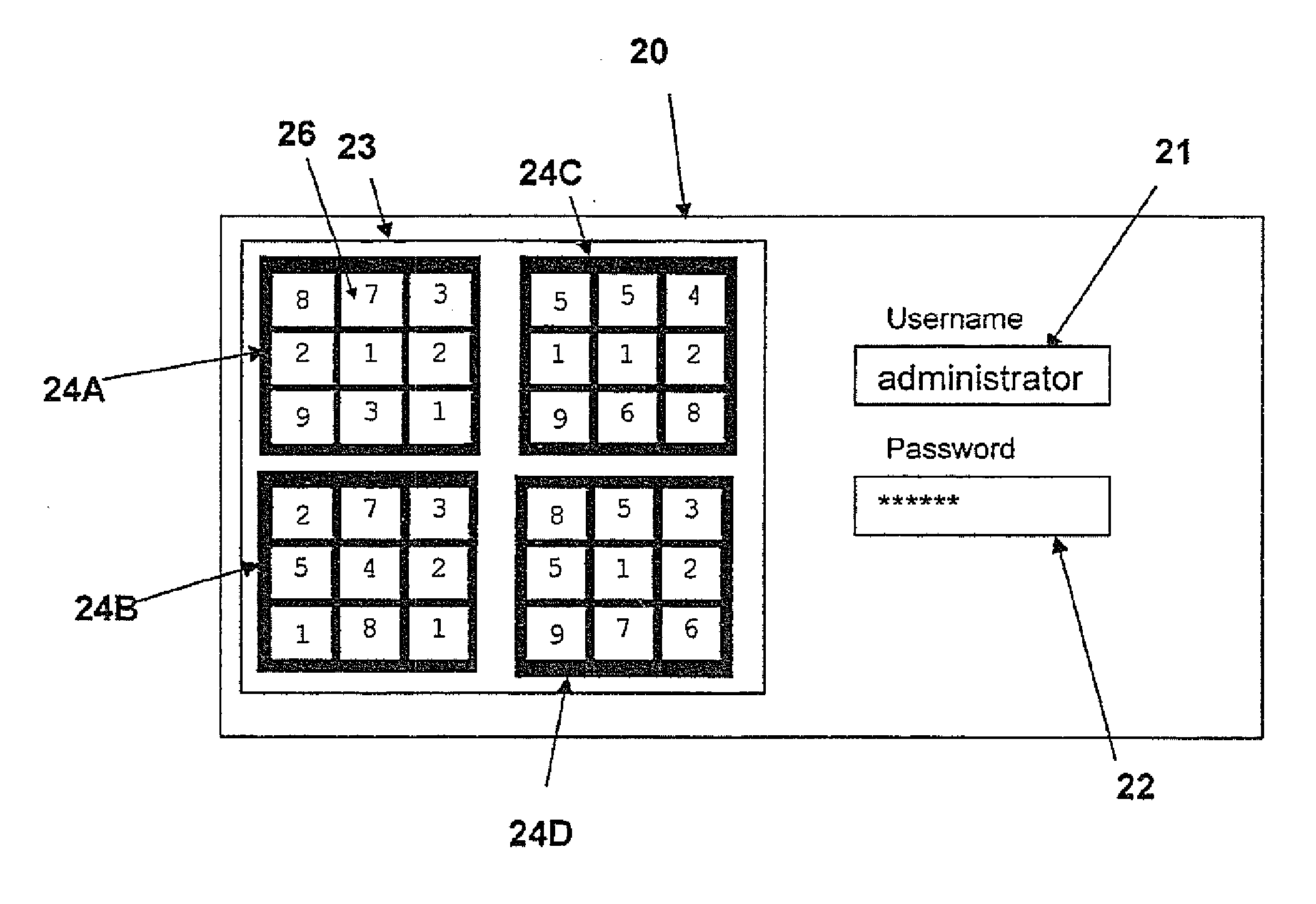
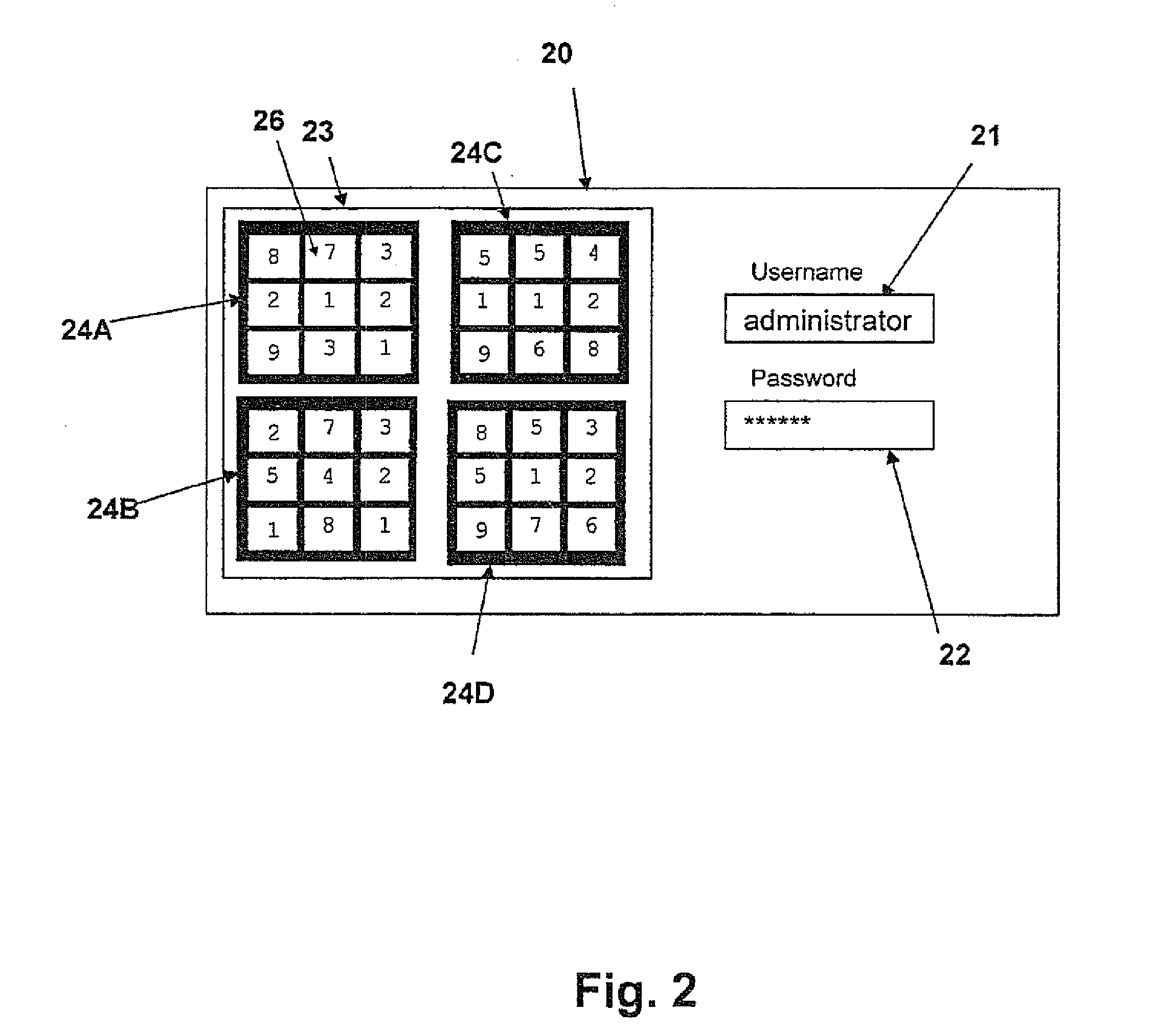
A method for allowing user access to a resource includes a large number of arrays of elements which are generated and stored for each user for use in a series of log-in sessions. A user input token is calculated by identifying a subset of the array by a pattern of the elements in the array, combined in an operation on the elements selected using one or more mathematical, relational and / or logical operations. The arrays are stored in a table with the tokens calculated from those arrays and withdrawn in a random pattern for use in the sessions for that user. Each array includes multiple possible solutions including the actual solution using the pattern and calculation of that user and these other possible solutions act as hacker traps to indicate the presence of a hacker who has calculated a solution but found the wrong solution
Owner:PASSRULES CANADIAN SECURITY
Visible authentication patterns for printed document
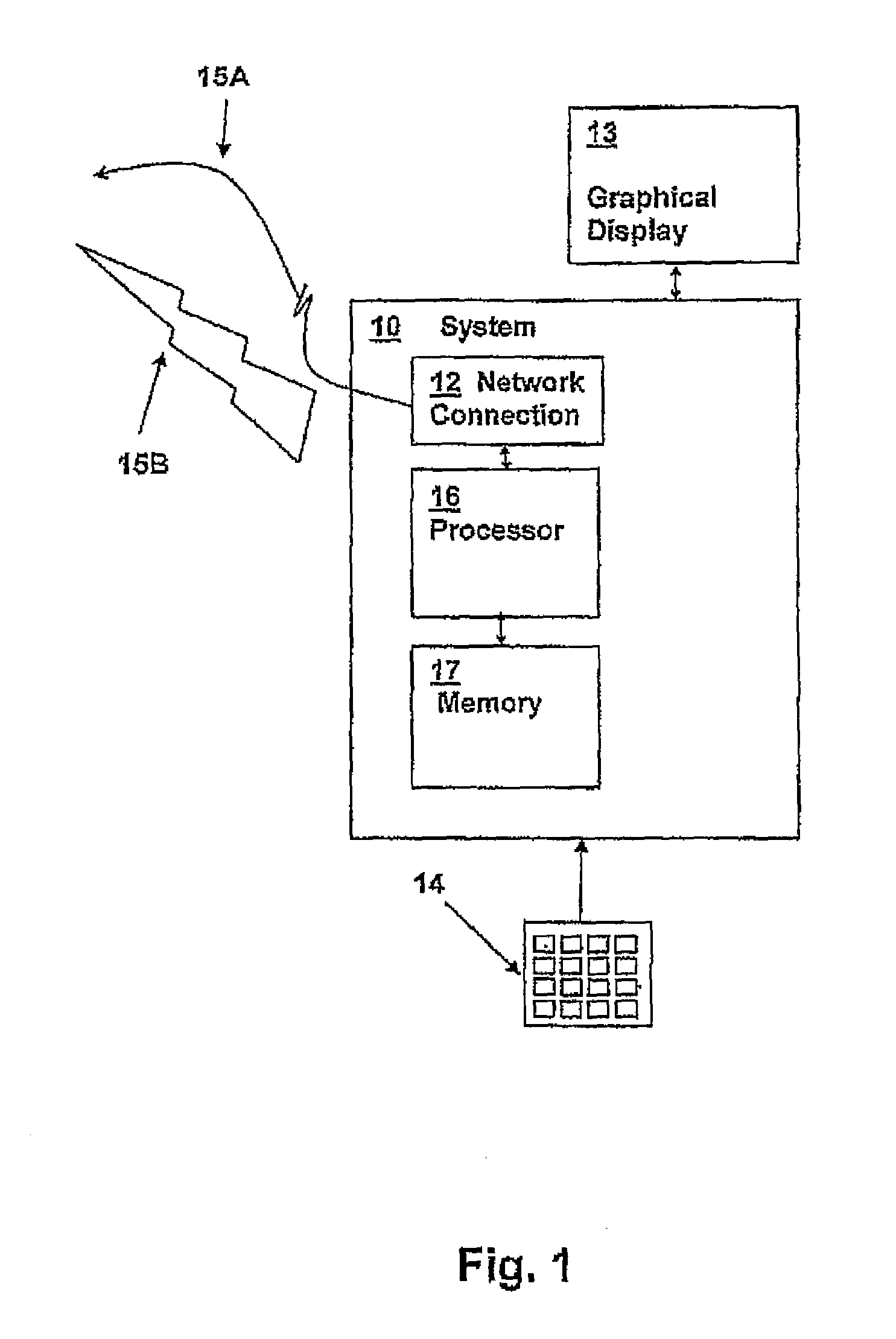
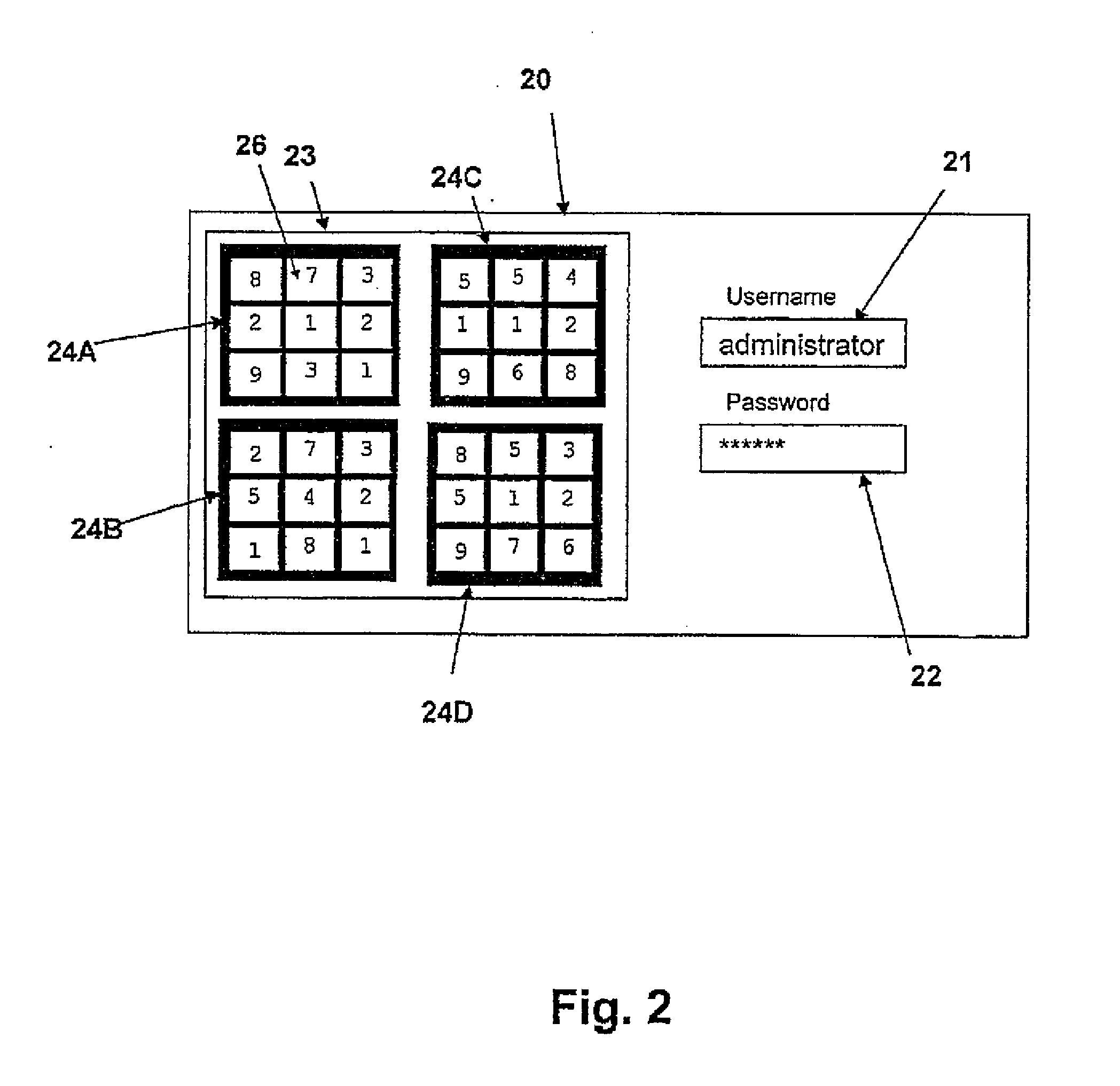
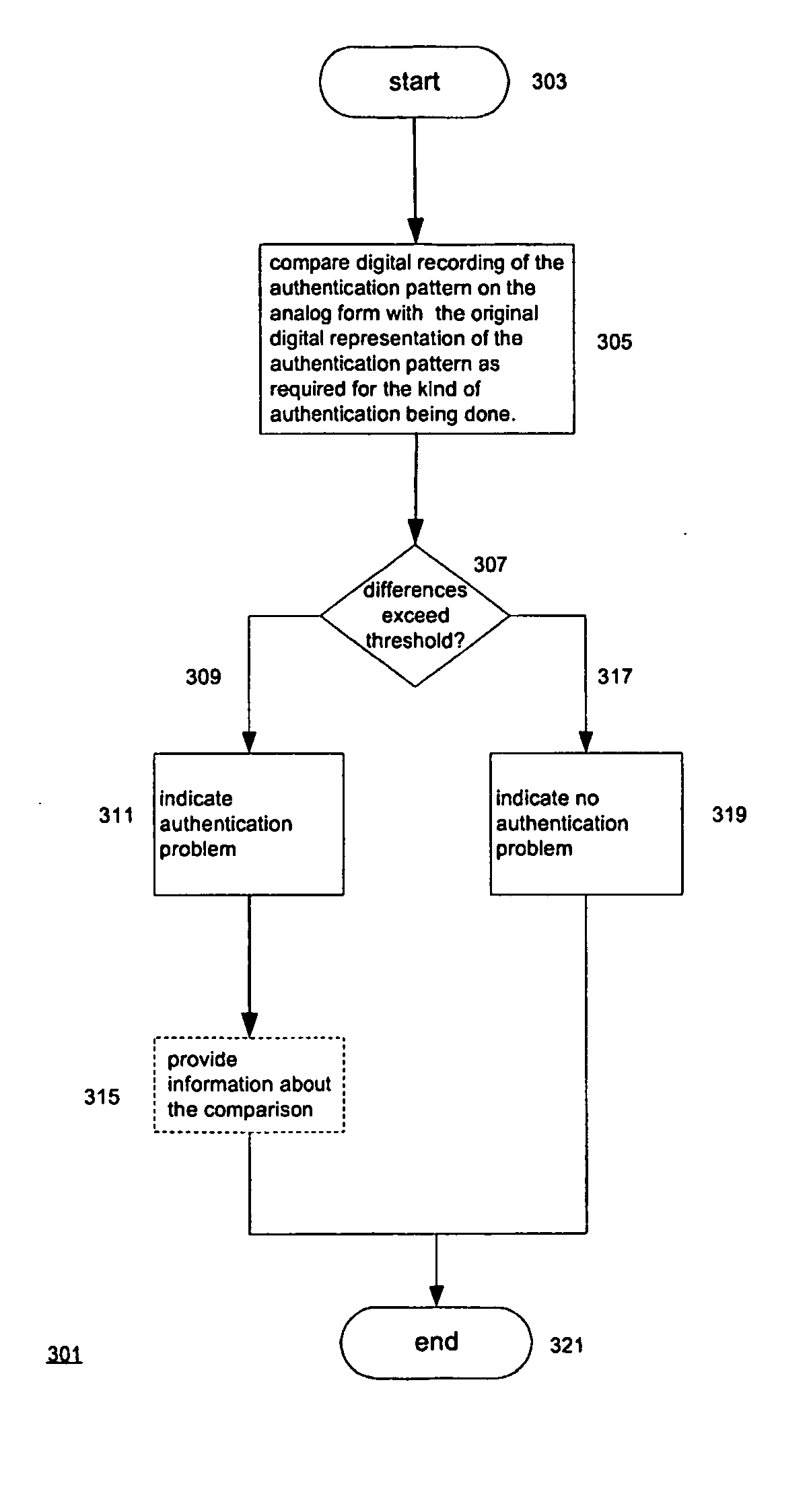
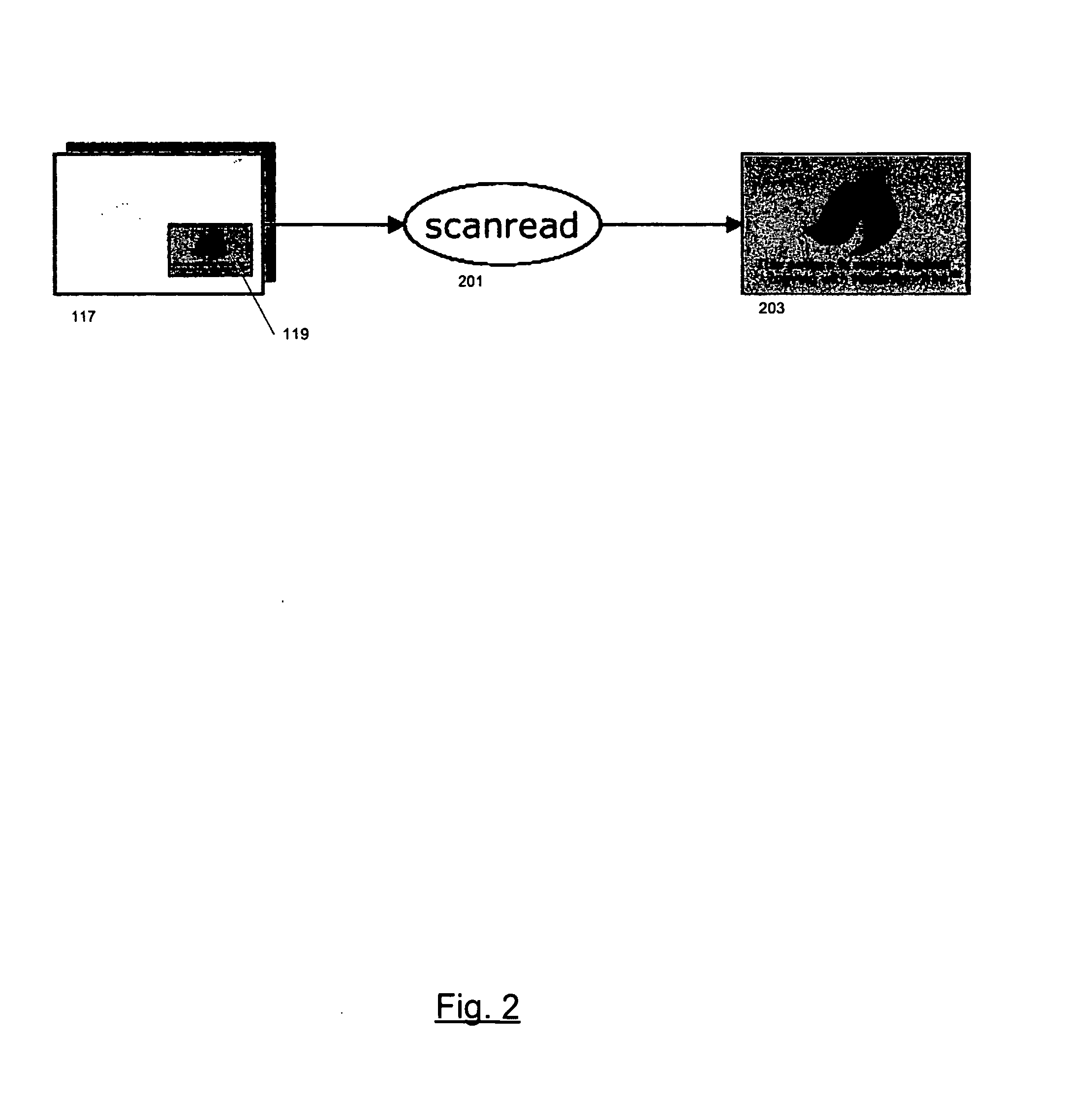
Techniques for determining authenticity of analog forms such as packaging or documents (117). One of the techniques determines whether the analog form has been made directly from a digital representation (903) or by photocopying or scanning an analog form. The technique makes the determination by comparing (911) an original digital representation of a portion of the analog form with a digital recording (203) of the portion from the analog form and measuring differences in features that are affected by the operations of photocopying or scanning. The original digital representation (105) and the analog form may have a “noisy”, i.e., random or pseudo random pattern. Such noisy patterns may further be used for other authentication purposes, such as determining whether the portion of the analog form that has the noisy pattern has been altered and to carry hidden messages. The noisy pattern may carry a logo or may be part or all of a barcode.
Owner:ADVANCED TRACK & TRACE SA
Secure Access by a User to a Resource
InactiveUS20110191592A1Shorten the lengthDigital data processing detailsMultiple digital computer combinationsArray data structureUser input
A method for allowing user access to a resource includes a large number of arrays of elements which are generated and stored for each user for use in a series of log-in sessions. A user input token is calculated by identifying a subset of the array by a pattern of the elements in the array, combined in an operation on the elements selected using one or more mathematical, relational and / or logical operations. The arrays are stored in a table with the tokens calculated from those arrays and withdrawn in a random pattern for use in the sessions for that user. Each array includes multiple possible solutions including the actual solution using the pattern and calculation of that user and these other possible solutions act as hacker traps to indicate the presence of a hacker who has calculated a solution but found the wrong solution
Owner:PASSRULES CANADIAN SECURITY
Precast concrete veneer panel system
InactiveUS20050210811A1Easily interconnect verticallyOptimize locationConstruction materialCovering/liningsEngineeringPrecast concrete
A pre-cast concrete veneer panel system for attaching to a wall surface. The pre-cast concrete veneer panels comprise a surface having simulated stone regions surrounded by simulated mortar regions. The concrete veneer panels are sized and shaped to allow the panels to interconnect both vertically and horizontally in a manner which results in a wall facade having a random pattern of unique stones.
Owner:NASVIK PAUL C
Composite material for a sensor for measuring shear forces
The present invention is related to a composite sheet material, a method of producing this material, and the application of this material as a sensor for monitoring and measuring shear forces (or lateral translation). In one embodiment, the present invention includes a composite sheet material having an upper and a lower surface comprising an elastomeric matrix, which is essentially non-conductive, and discrete electrically conductive elements within the matrix wherein the electrically conductive elements in a region of the composite sheet material are arranged into columns, and the orientation of these columns are in an essentially organized, non-random pattern with a majority of these columns oriented at angles less than about 90° and greater than about 15° to the lower surface of the composite sheet material. In another embodiment, the present invention provides for a method of forming the sensors.
Owner:GREAT LAKES NEUROTECH
Method for the continuous real time tracking of the position of at least one mobile object as well as an associated device
ActiveUS7139582B2Reduce cross-correlationMaximize accuracyDirection finders using radio wavesGymnastic exercisingBurst transmissionTemporal resolution
In a method for the continuous real time tracking of the position of at least one mobile object in a defined multidimensional space, at least one mobile transmitter module is attached to at least one mobile object and the signals from the at least one module are received by a stationary receiving and signal processing network and then centrally processed. The signals emitted by each transmitter module are electromagnetic waves sent within a frequency band range using time division multiplexing techniques. Due to the fact that the frequency band is used as a single channel for the purpose of maximizing the accuracy with which a position is detected, and due also to the fact that the communication process between the transmitters and the receivers is based on the principle of pseudo-random time division multiplexing using burst transmissions of low cross correlation with non synchronized pseudo-random patterns, there is created a method for the continuous tracking of the position of one or more mobile objects at any time and in any place which is of very high positional resolution and has a temporal resolution of just a few milliseconds.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Flame simulating apparatus
A flame simulating apparatus to simulate flames emanating from a wood or fossil fuel burning fire. The flame simulating apparatus includes a light source, a light reflecting element, and a fire simulation screen. The light reflecting element produces a moving and generally random pattern of reflected light when light is cast upon it by the light source. The fire simulation screen has the image of a fire thereon and is positioned so that reflected light from the light reflecting element is cast upon its rear surface. The fire simulation screen includes at least one portion that is at least partially translucent such that light cast upon the partially translucent portion by the light reflecting element is diffused and at least partially passes through the translucent portion to present a moving flame image when viewed from a position in front of the fire simulation screen.
Owner:NAPOLEON SYST & DEV
Randomization-based encryption apparatus and method
InactiveUS20050002531A1Reduce computational complexityIncrease variabilityDigital data protectionDigital storageObfuscationTheoretical computer science
A method for encryption data subdivided into segments of random lengths. A data source having a state corresponding to initialization parameters and the number of patterns output therefrom provides for a reversible encryption process. Decryption is accomplished by repeating encryption using a data source having an identical initial state. The data source consists random pattern generation machines (RPGMs). A portion of RPGMs may each contain patterns of a different length. Randomly selecting an RPGM and outputting a pattern therefrom effectively provides a pattern of random length. The data source may output patterns interpreted to govern the behavior of obfuscation operations. Patterns output from the data source may be interpreted as instructions as to what obfuscation to perform and what parameters shall define the obfuscation.
Owner:MICHAELSEN DAVID L
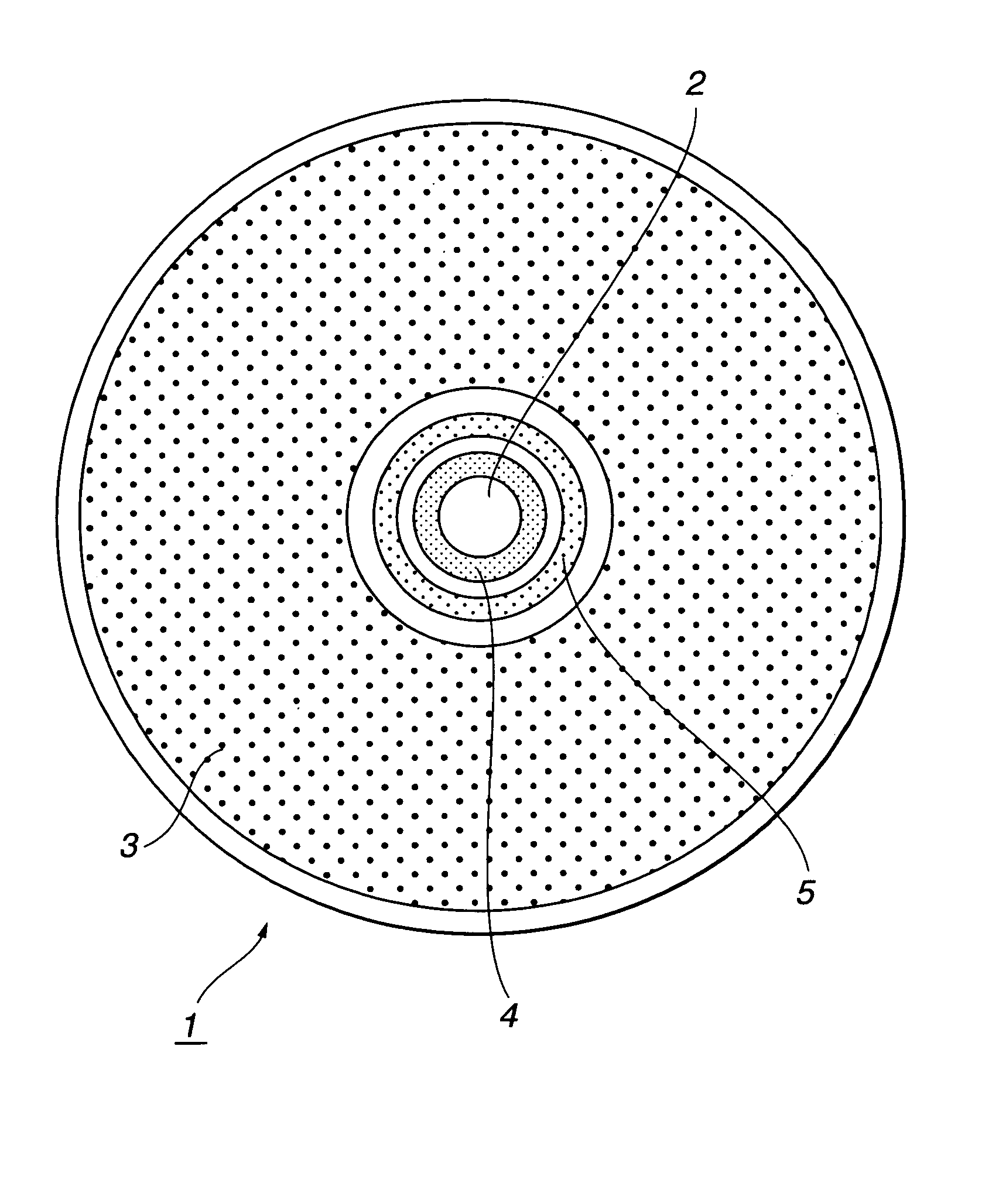
Information recording/reproducing system
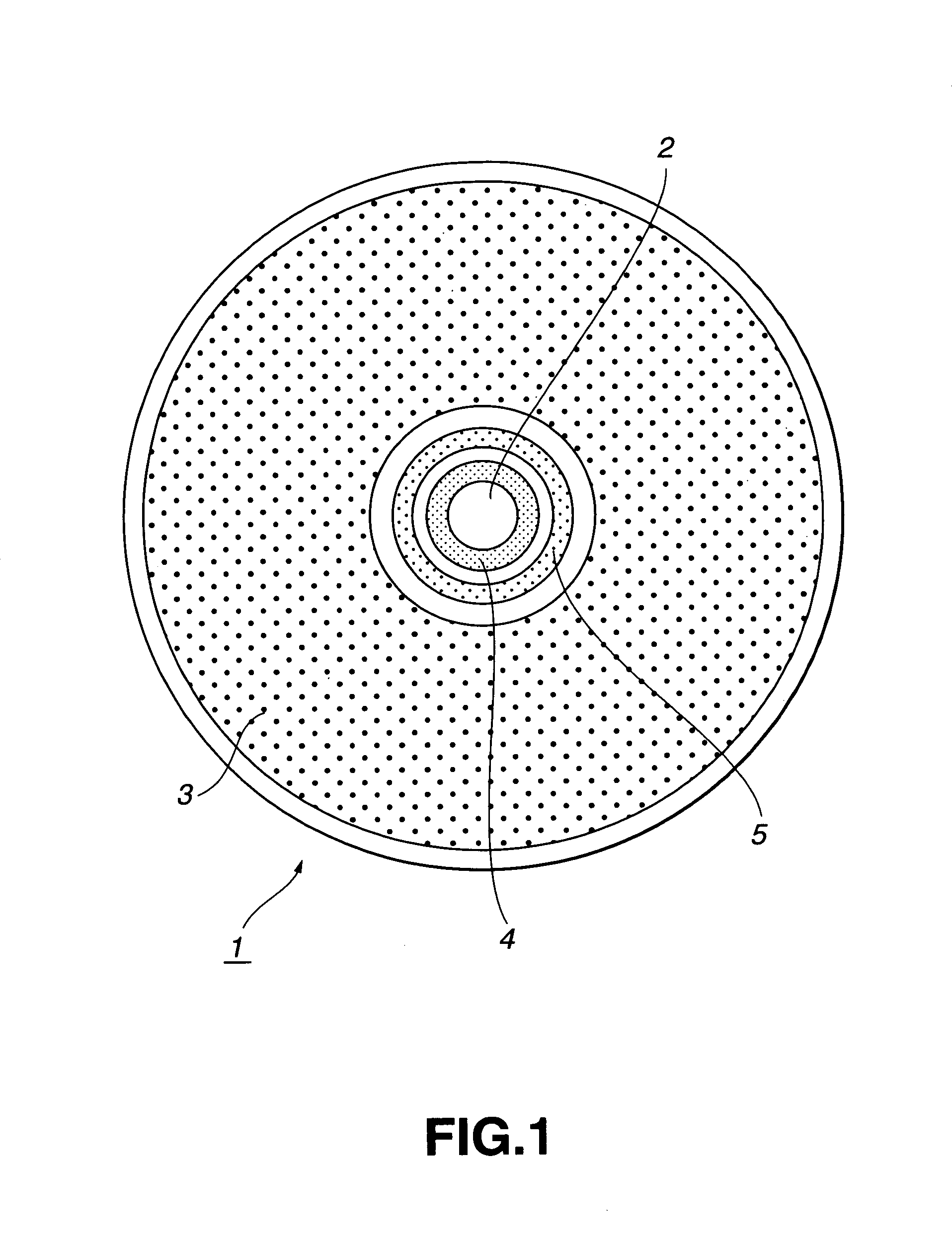
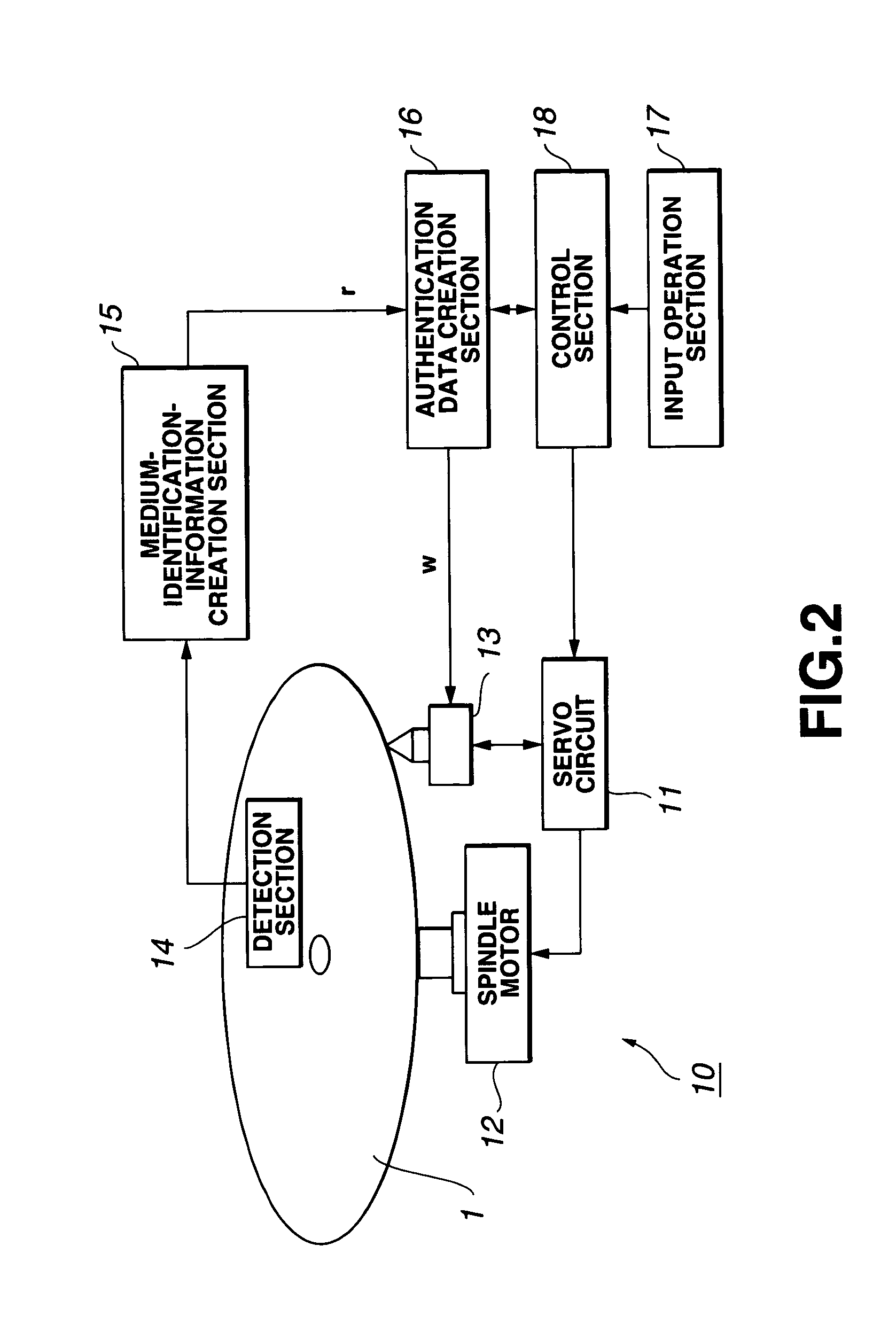
An information recording medium 1 is provided with: a user data recording part 3 which records user data; a random-patter-information recording part 4 which records random pattern information from a random physical phenomenon; and an authentication data recording part 5 which records, as authentication data, medium identification information created on the basis of the random pattern information detected from the random-pattern-information recording part 4 and a digital signature for each manufacturer with respect to the medium identification information.
Owner:SONY CORP
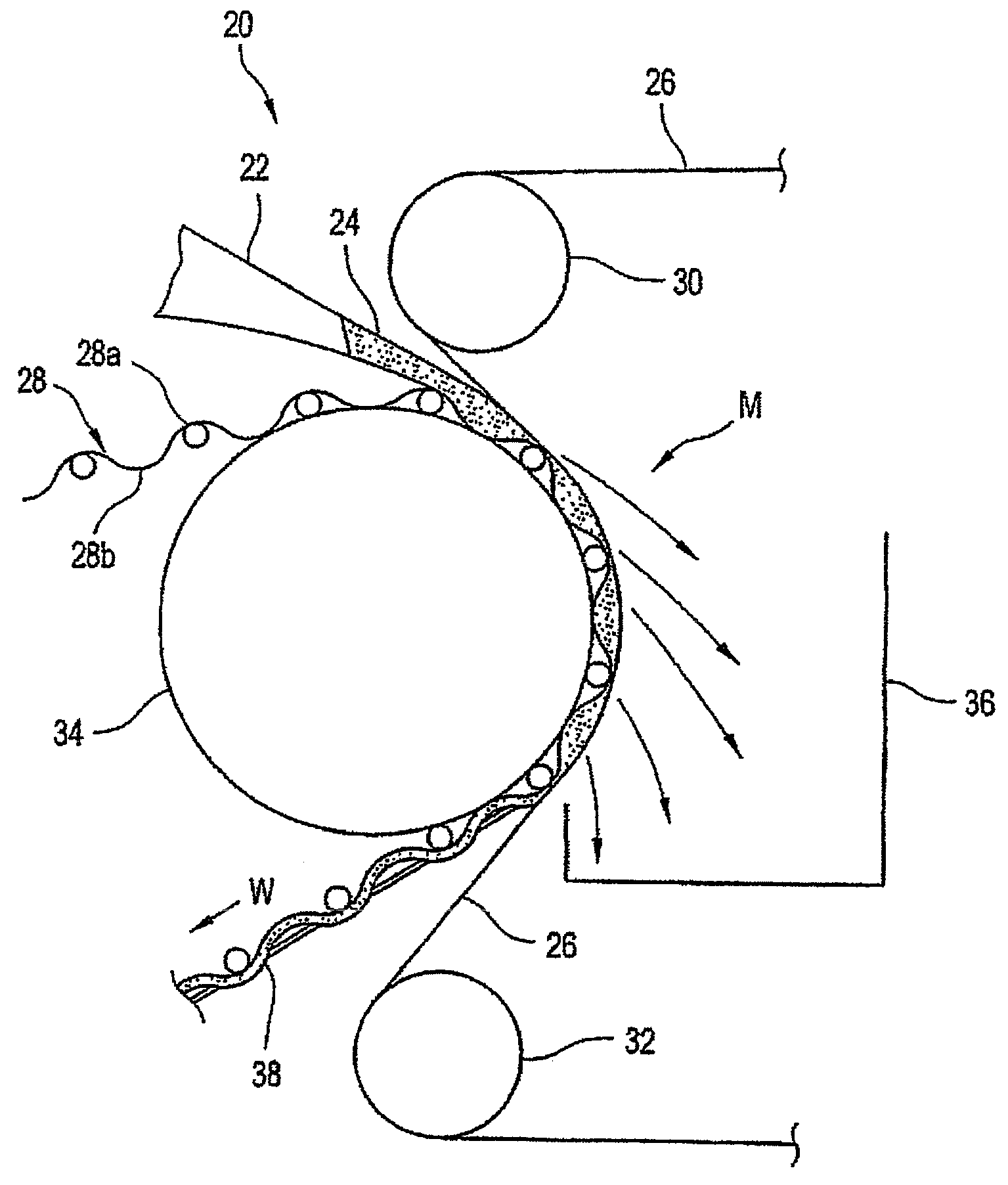
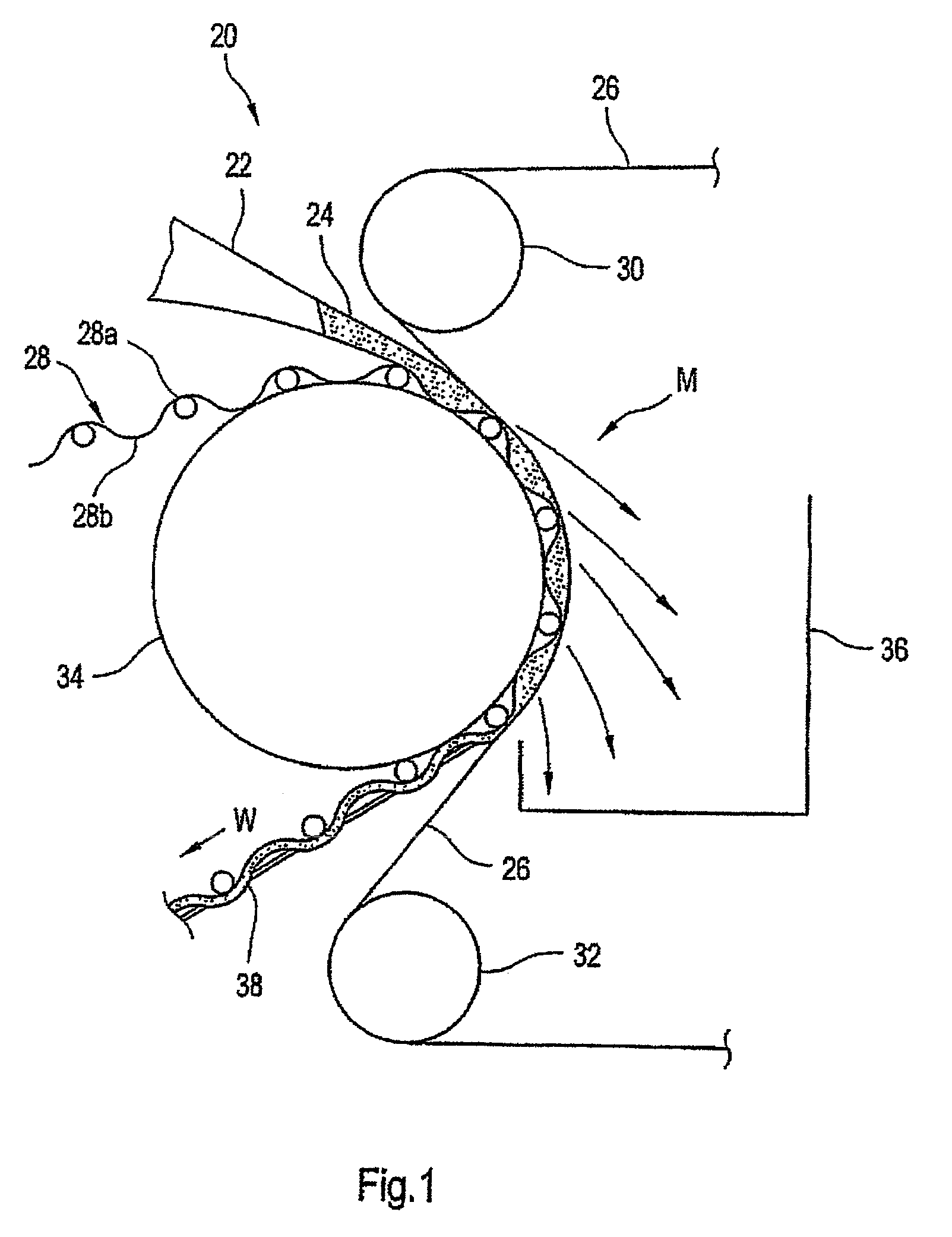
Forming fabric with extended surface
InactiveUS20090205797A1Large capacityQuality bulkSynthetic resin layered productsMachine wet endMechanical engineeringPolymer
A fabric for an advanced dewatering system having a woven fabric, the woven fabric having a paper side and a roll side, the paper side having a paper side surface and the roll side having a roll side surface and a polymer material. The polymer material is deposited onto the fabric and extends above the paper side surface. The polymer material has at least one of a random pattern, a random motif, a pseudo-random pattern, a pseudo-random motif, a predetermined pattern, and a predetermined motif.
Owner:VOITH PATENT GMBH
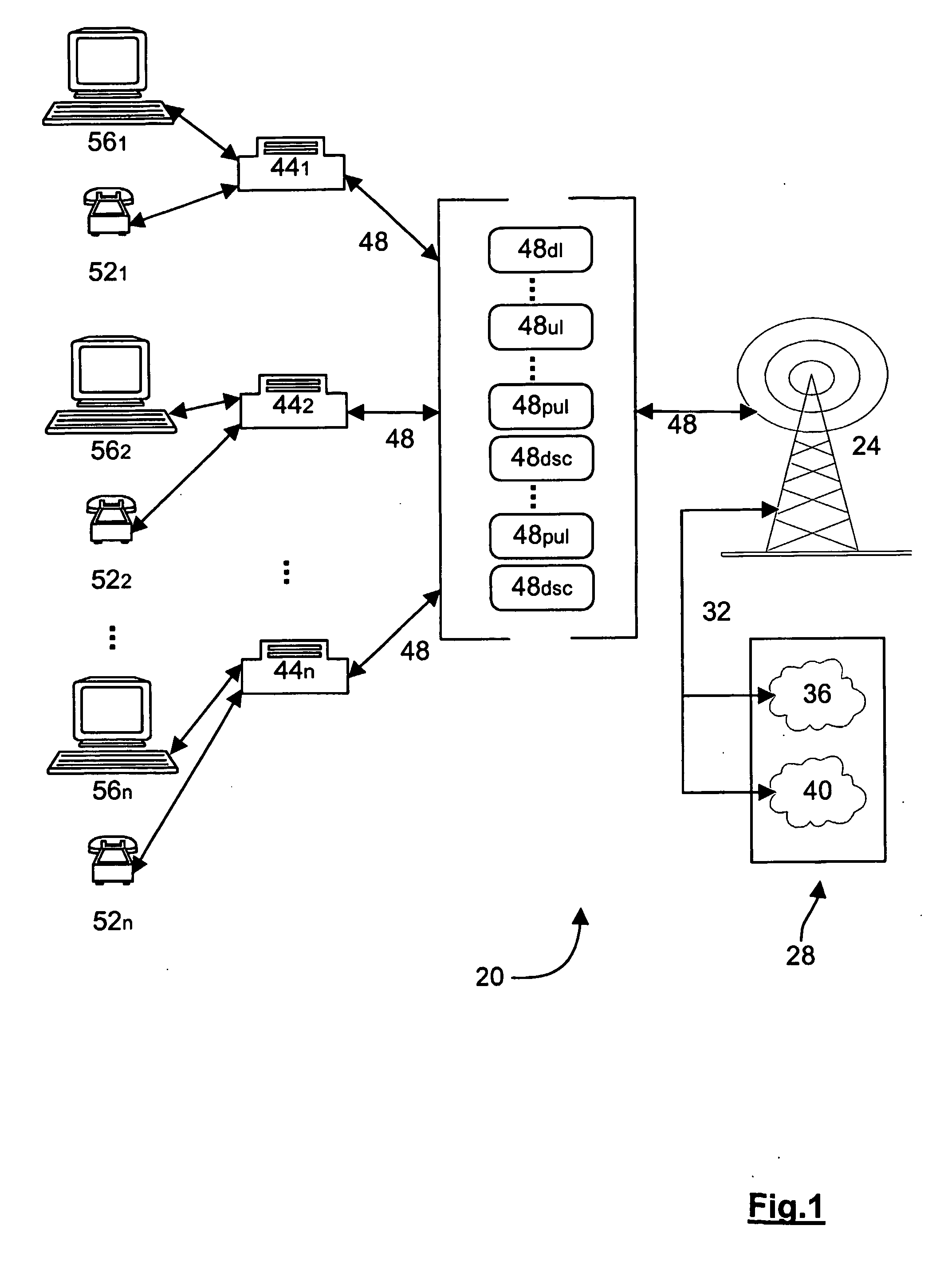
Communication channel structure and method
InactiveUS7385952B2Improve balanceIncrease capacityNetwork traffic/resource managementTime-division multiplexOperational systemCommunications system
A novel communication channel structure and method in a wireless communication system is provided. In an embodiment of the invention, the communication system includes a base station and a plurality of subscriber stations and the subscriber stations are given access to a variety of channels, including at least one uplink data channel. The uplink data channel can operate in at least a random access mode and a polled access mode. The base station informs each subscriber station it serves of the current mode of the uplink channel via an associated downlink signaling channel and, in random access mode, each subscriber station is able to randomly access the shared uplink channel. In polled mode, each subscriber station waits for permission from the base station before sending data over the shared uplink channel. A method of operating the system monitors the collisions which occur on the uplink channel in random mode and / or the amount of data and / or the data's priority level and / or QoS requirements and switches the system between random and polled modes as appropriate. In polled mode, the method determines which subscriber stations should access the uplink and when.
Owner:WI LAN INC
Method and system for protecting a user's password
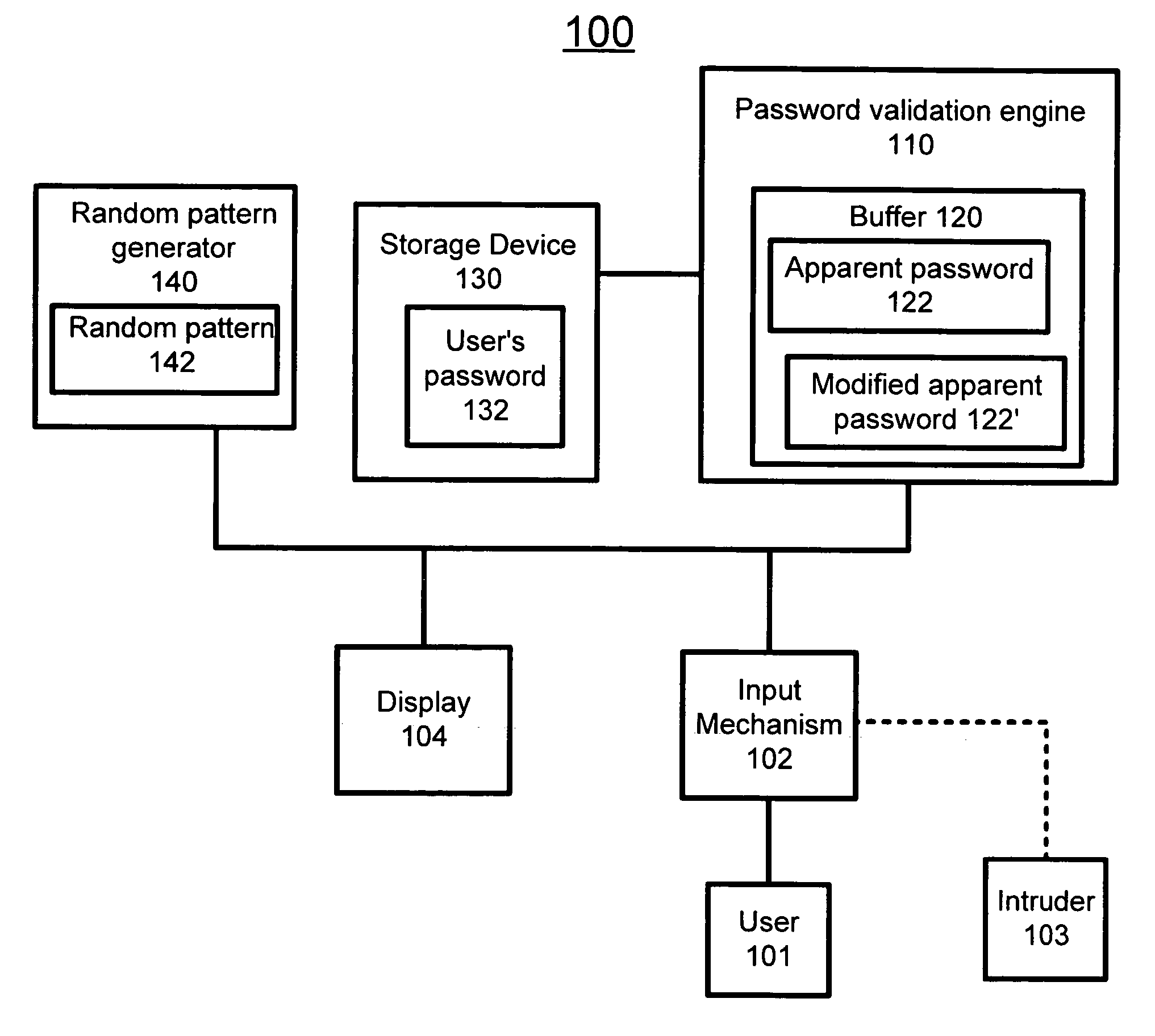
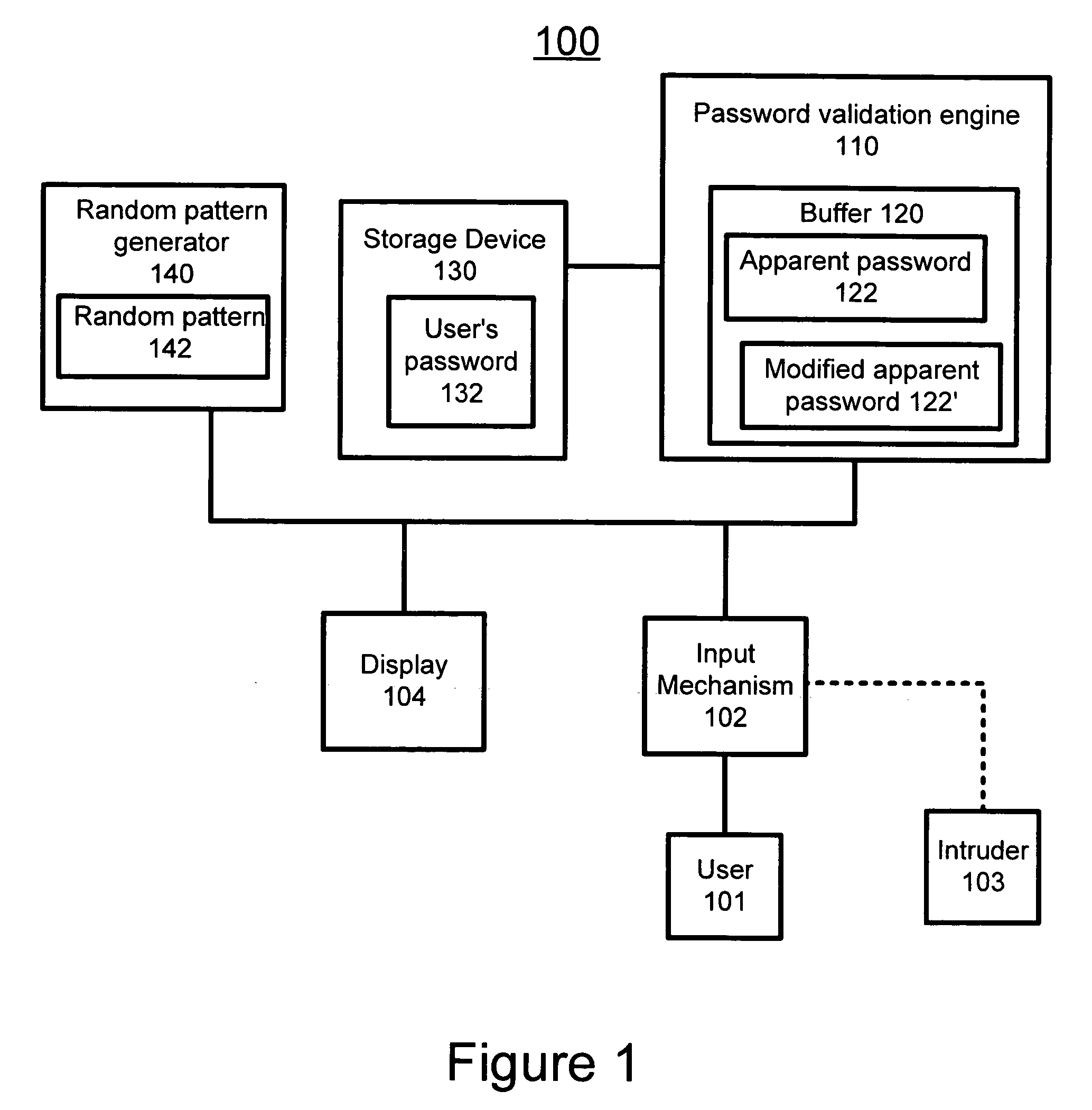
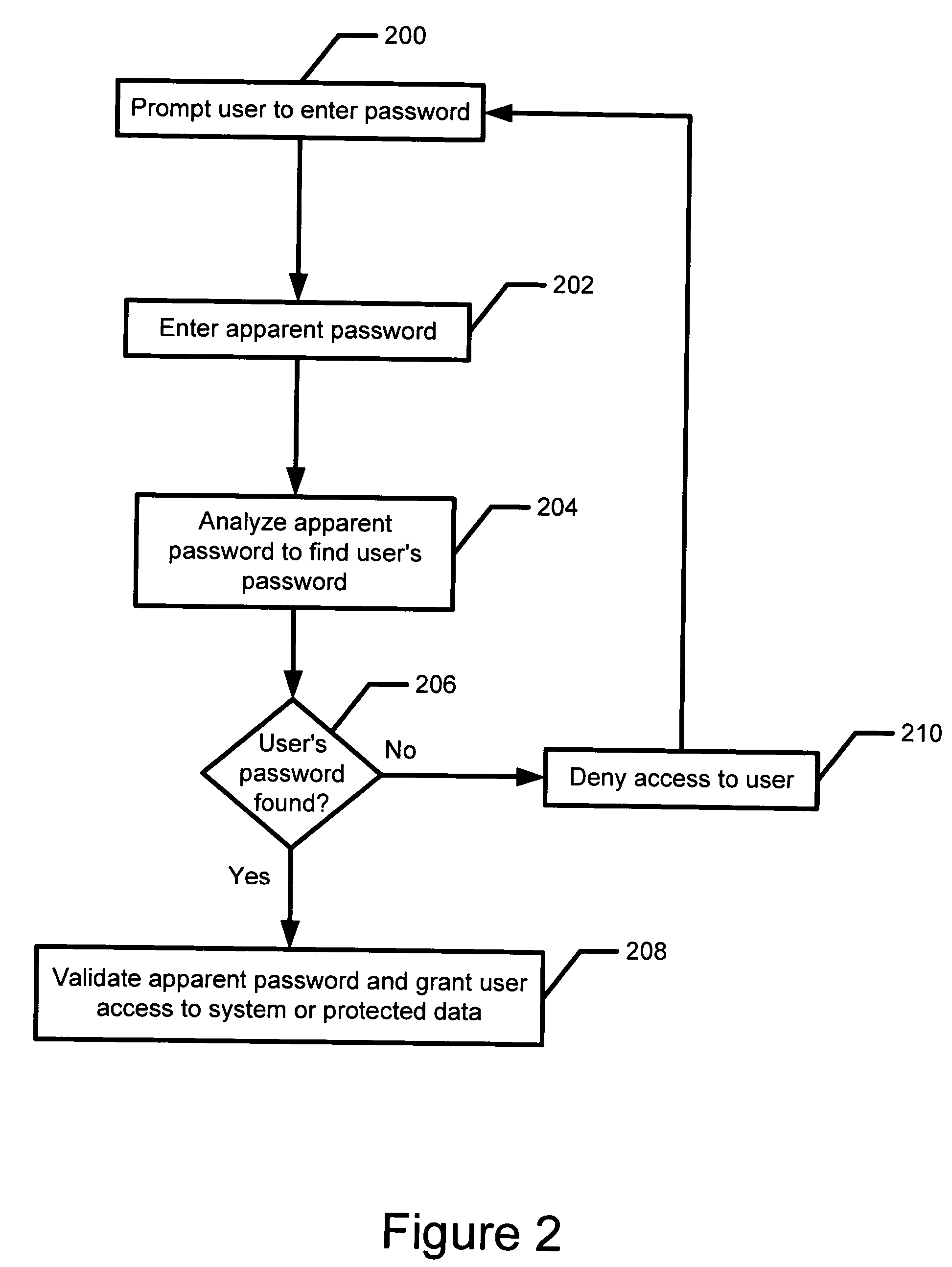
ActiveUS20050273625A1Reduce the possibilityMemory loss protectionError detection/correctionRandom patternPassword
The present invention relates to a method and system for protecting a password. In a first aspect, the method includes allowing a user to enter an apparent password into a computing system, wherein the apparent password is a string of characters and keystrokes including the password and an arbitrary number of non-password related characters and keystrokes. The method further includes analyzing the string of characters and keystrokes by the computing system to find the password, and validating the apparent password if the password is found in any position in the string of characters and keystrokes. In a second aspect, the method includes creating a random pattern in response to receiving a request from a user to access a protected resource in a computing system, wherein the random pattern is associated with the request, displaying the random pattern associated with the request to the user, and allowing the user to enter an apparent password into the computing system that controls access to the protected resource, wherein the apparent password is a string of characters and keystrokes including the password, the random pattern and an arbitrary number of non-password related characters and keystrokes. The method further includes analyzing the string of characters and keystrokes by the computing system to find the password and the random pattern associated with the request, and validating the apparent password if the password and the random pattern are found in any position in the string of characters and keystrokes.
Owner:LENOVO GLOBAL TECH INT LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com