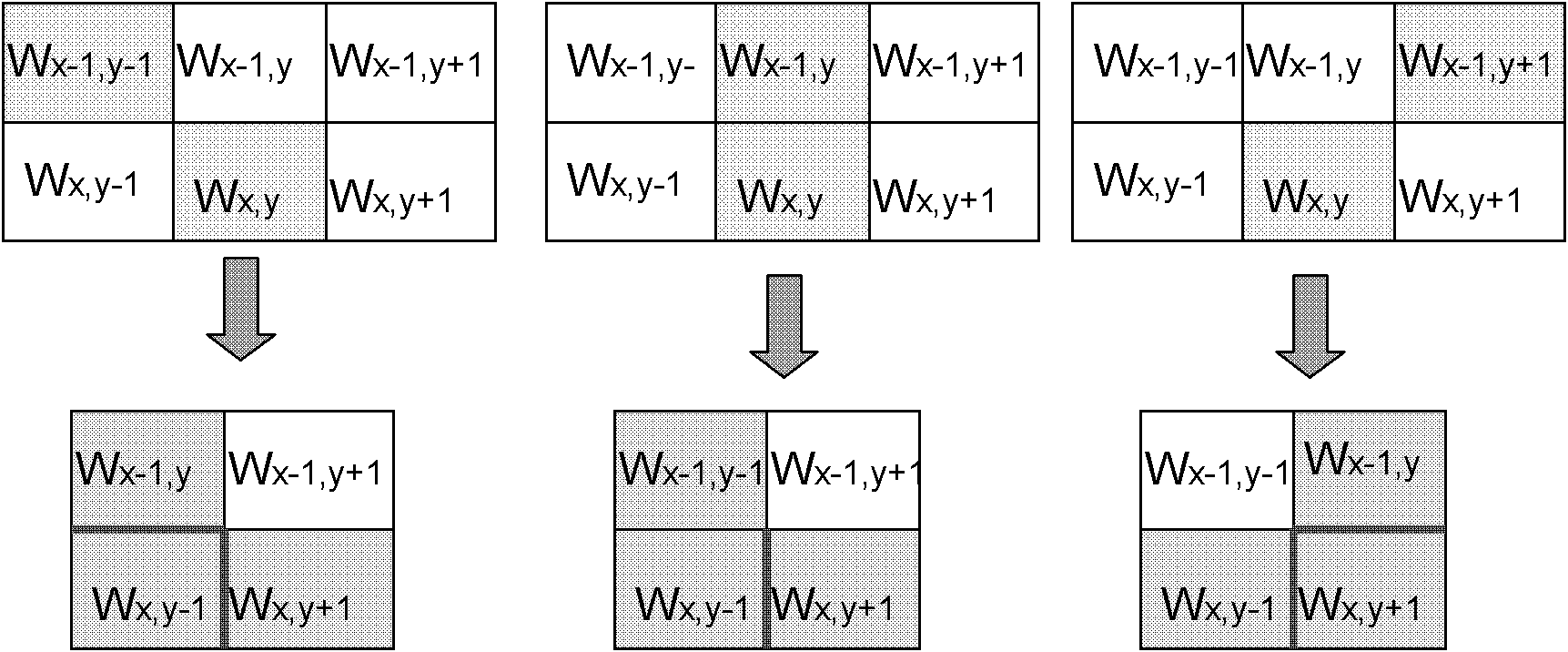Patents
Literature
117results about How to "Protect information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
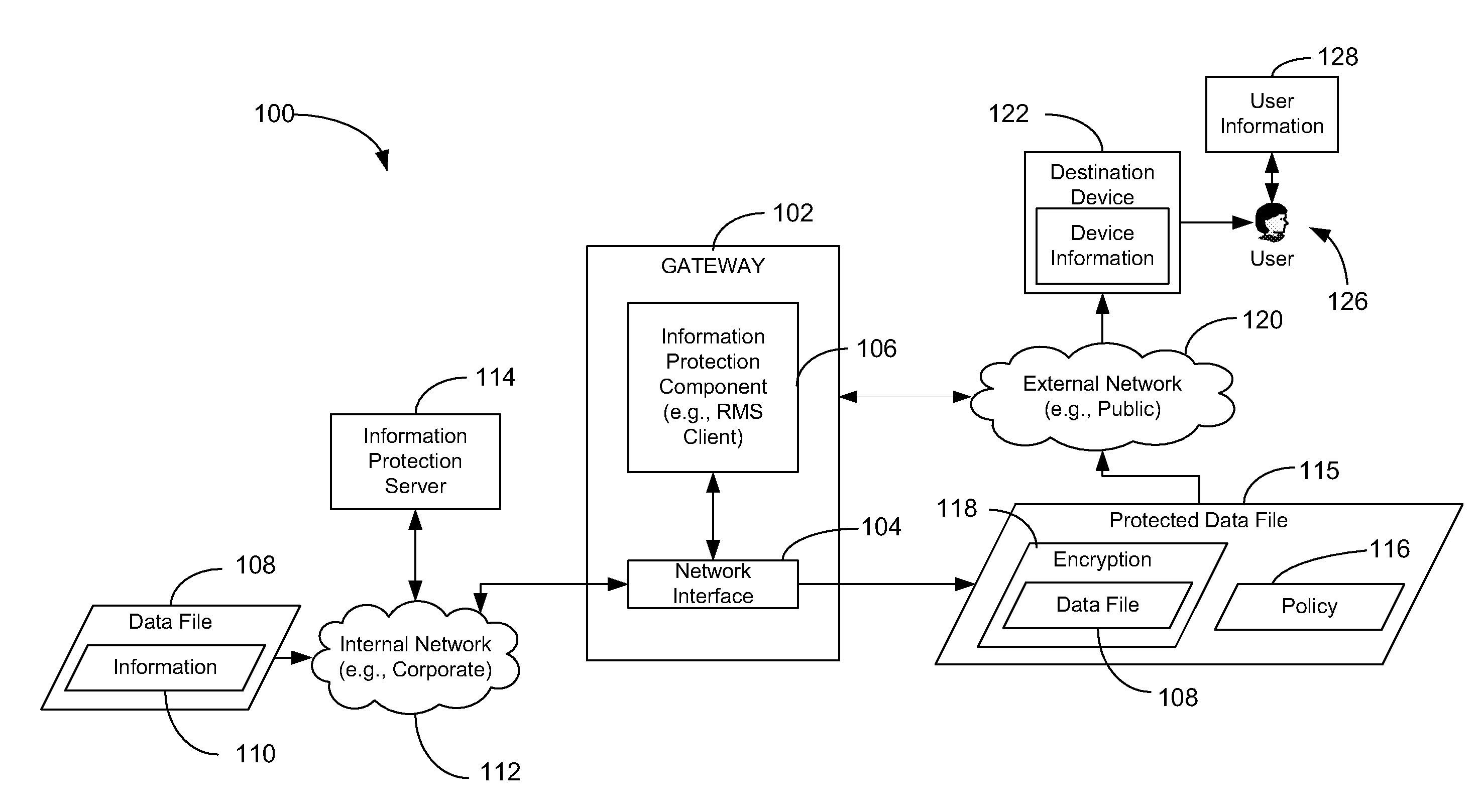
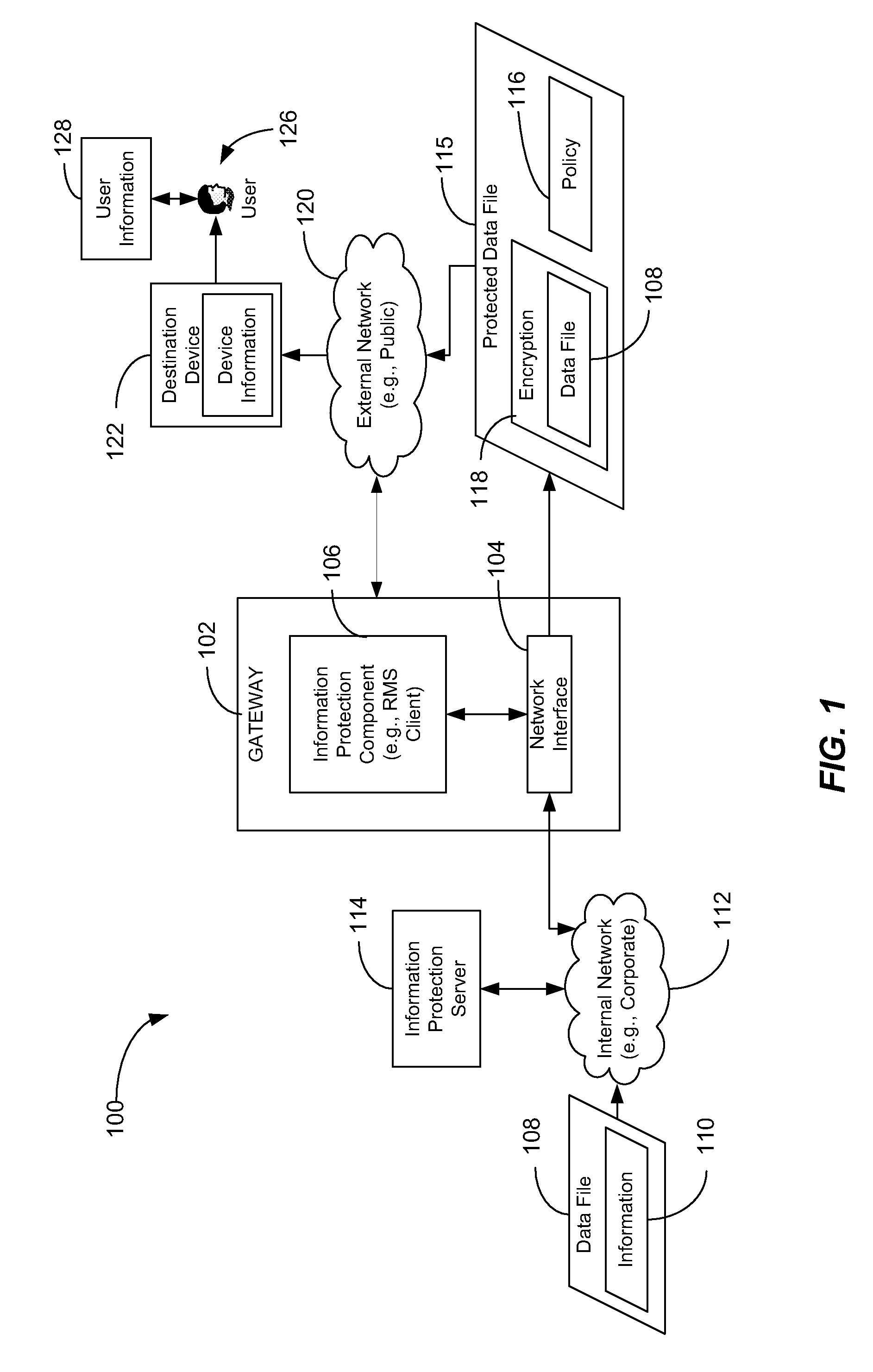
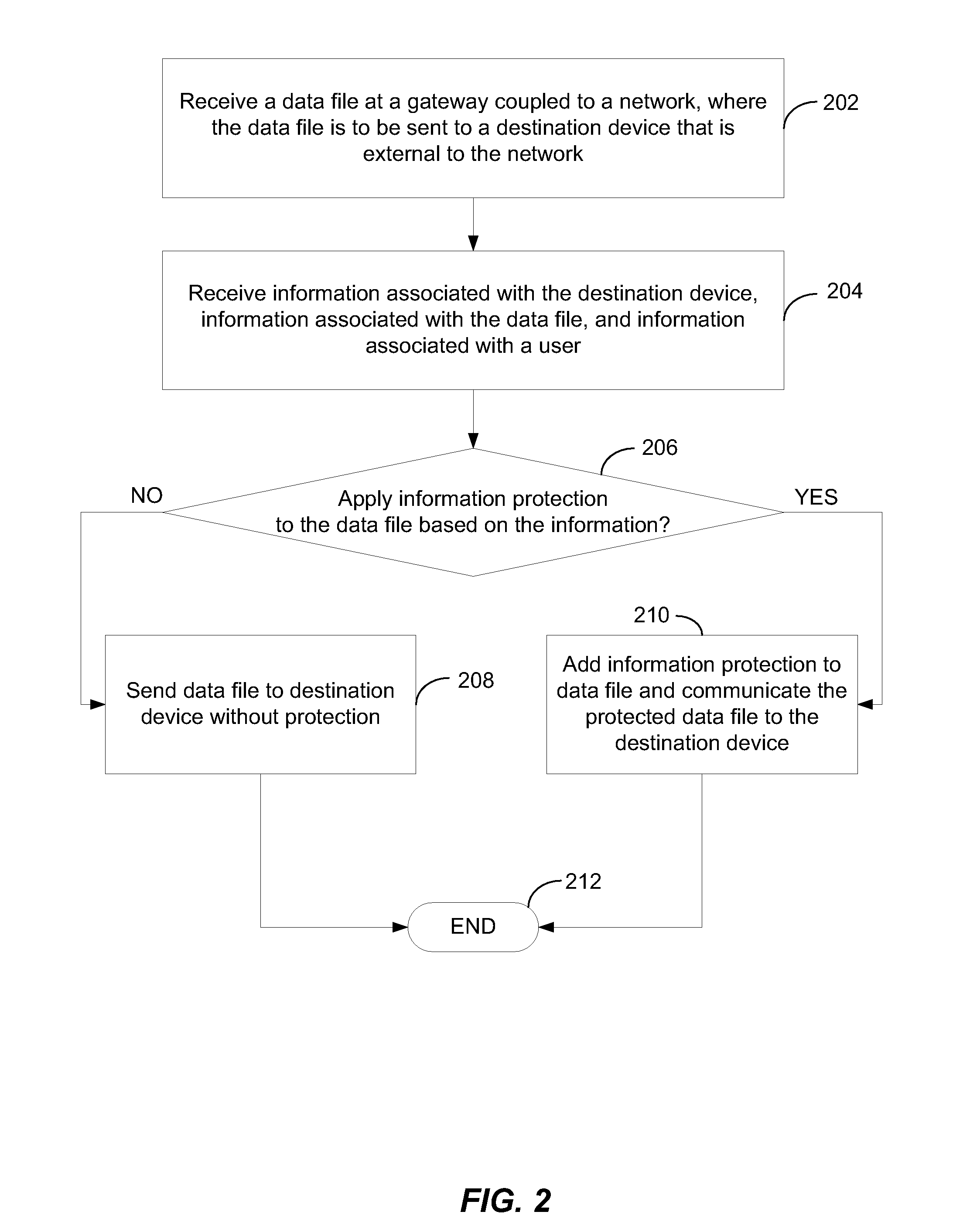
Information protection applied by an intermediary device
ActiveUS20100180332A1Protect informationWell formedComputer security arrangementsMultiple digital computer combinationsData fileComputer security
Methods, systems, and computer-readable media are disclosed for applying information protection. A particular method includes receiving a data file at a gateway coupled to a network. The data file is to be sent to a destination device that is external to the network. The method also includes selectively applying information protection to the data file at the gateway prior to sending the data file to the destination device. The information protection is selectively applied based on information associated with the destination device, information associated with the data file, and information associated with a user of the destination device.
Owner:MICROSOFT TECH LICENSING LLC
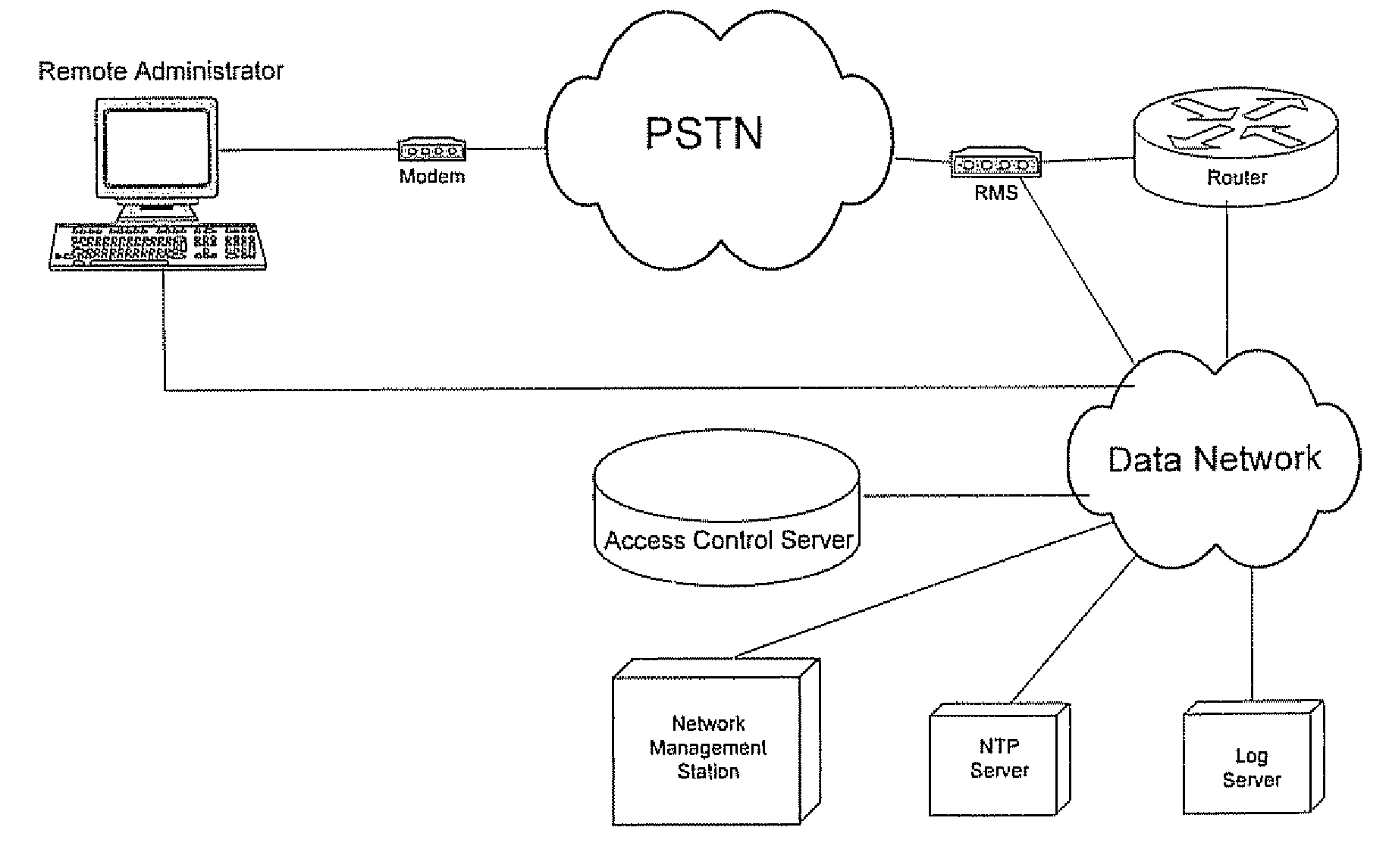
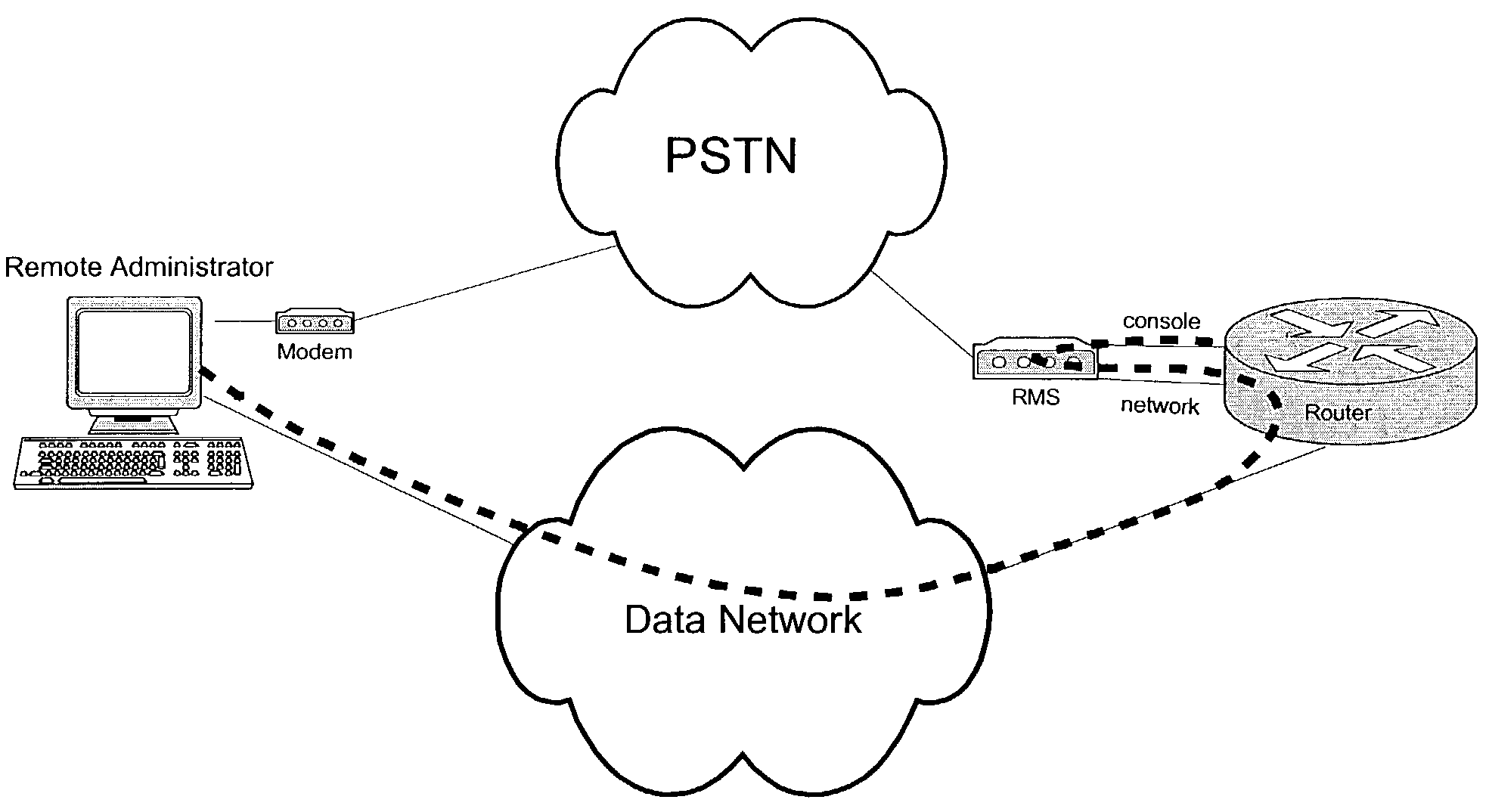
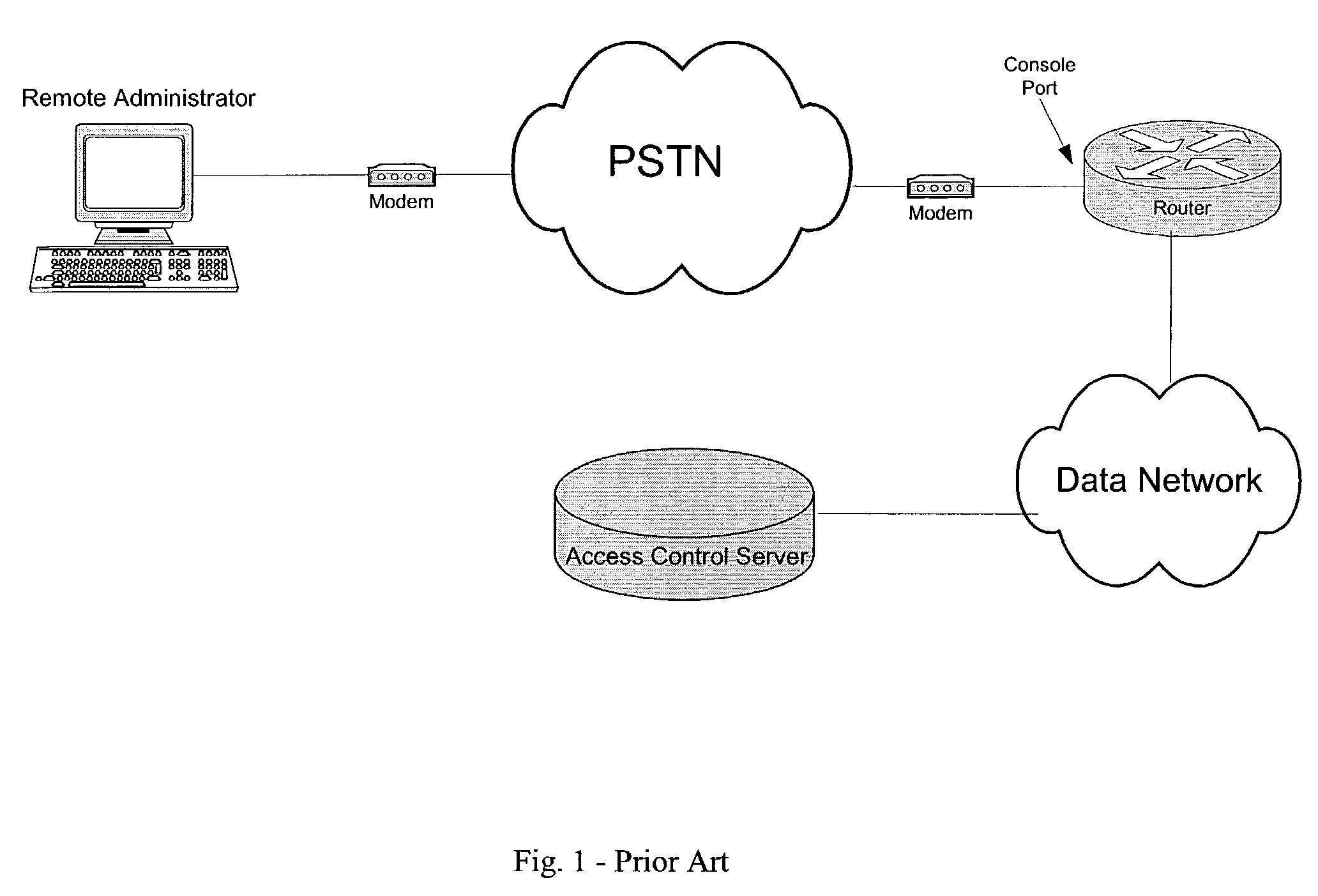
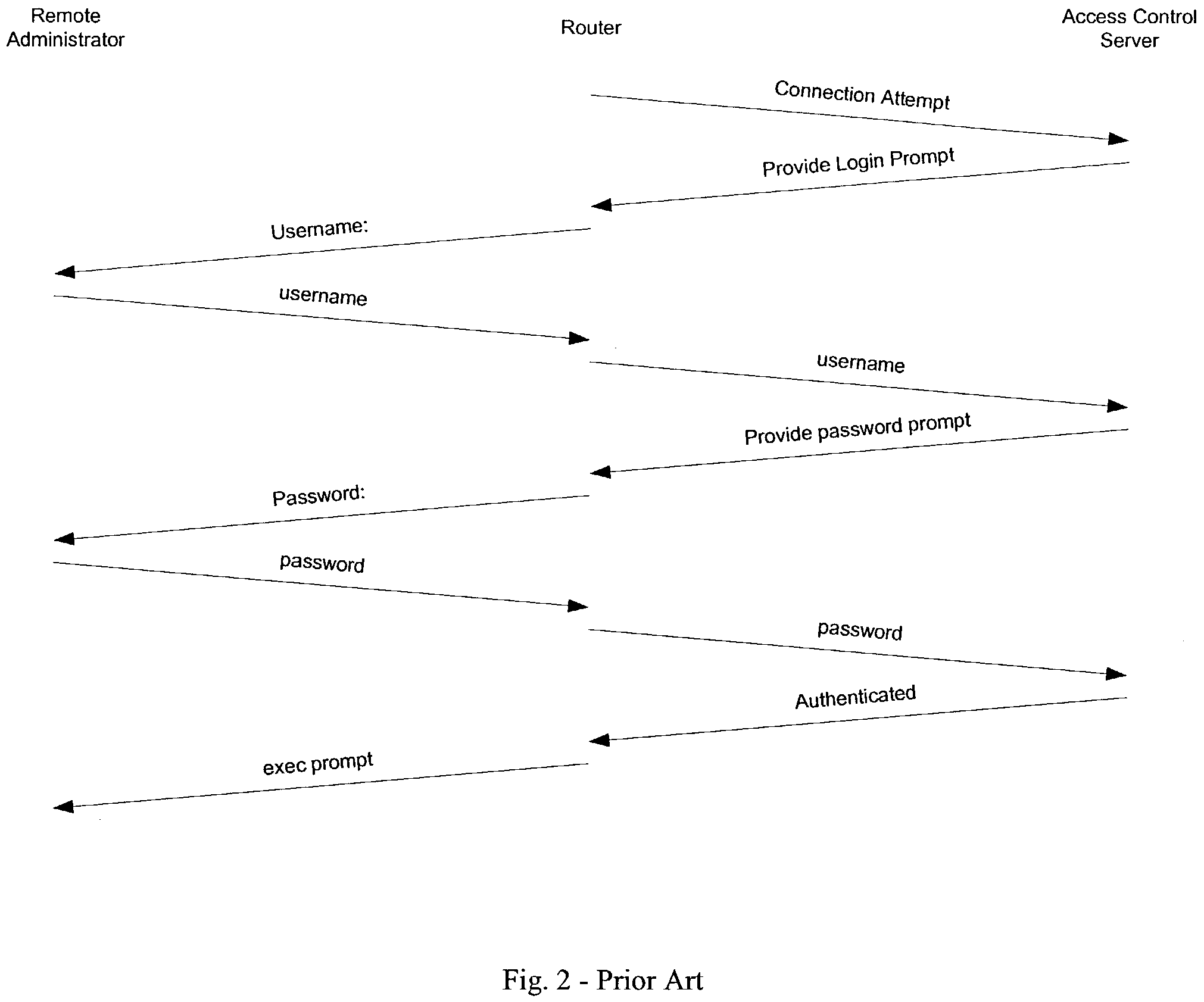
Out-of-band remote management station
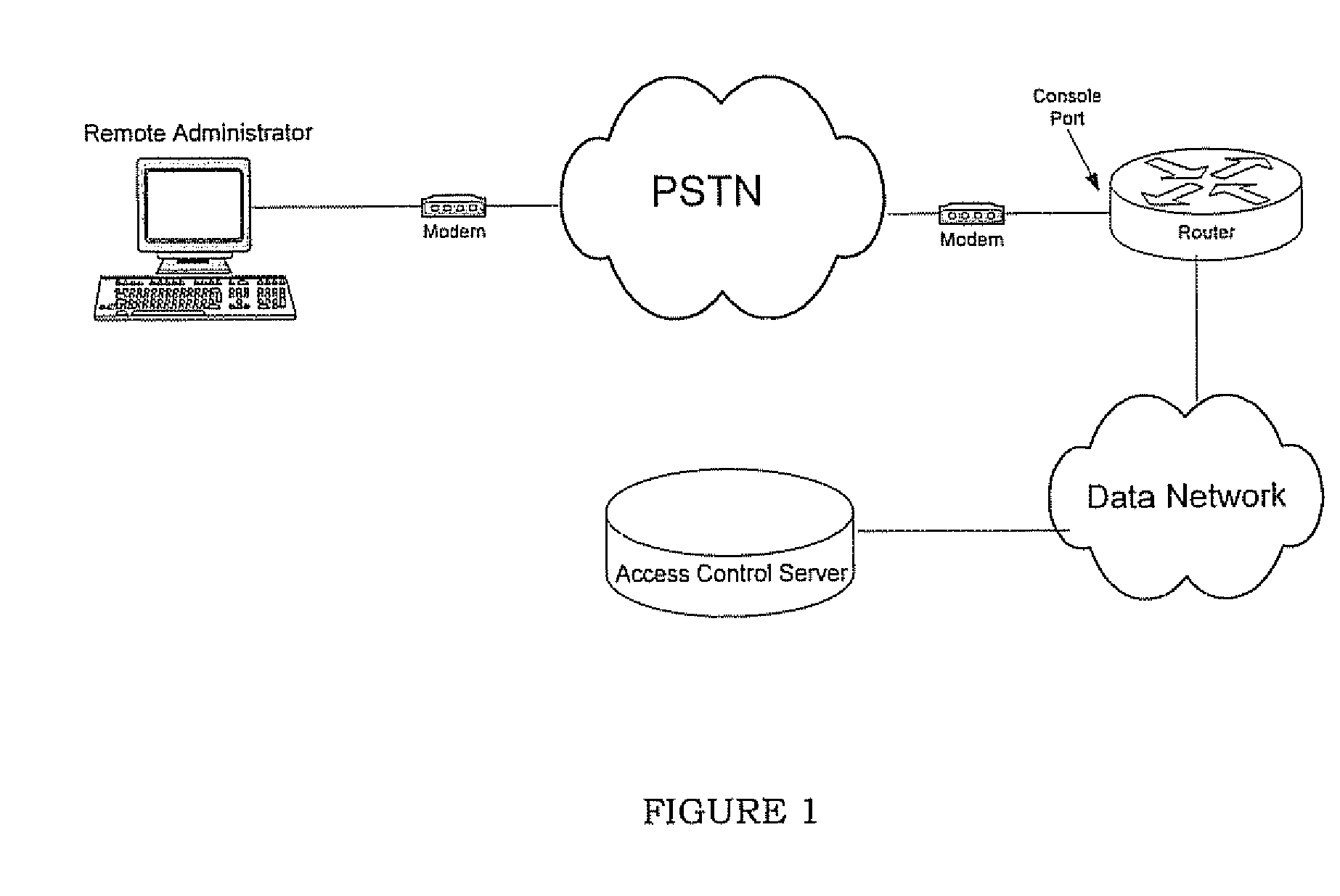
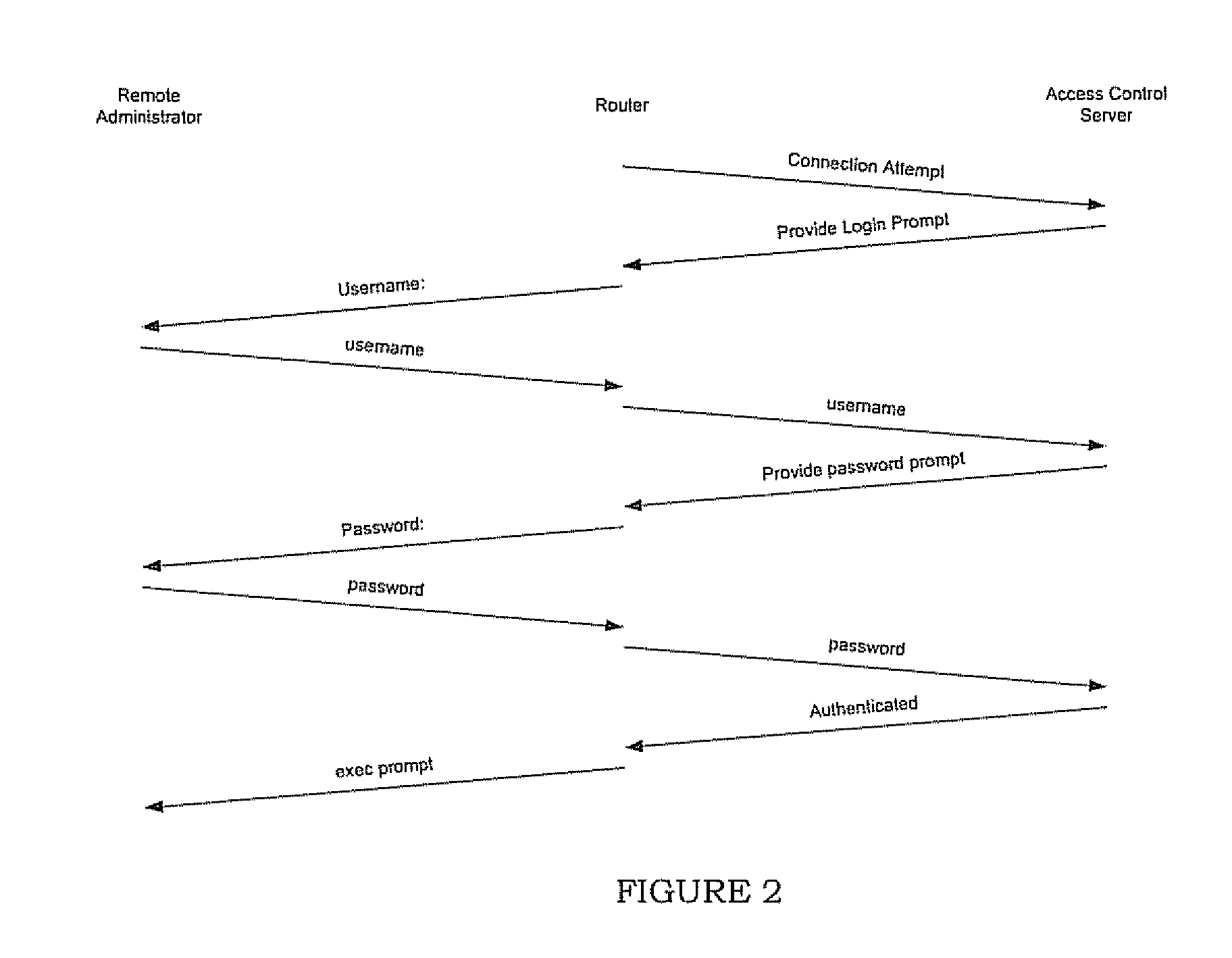
InactiveUS20070130334A1Eliminate security concernsProtect informationDigital computer detailsSupervisory/monitoring/testing arrangementsCommunications systemEngineering
A management system for a computer data network comprises a remote management station connected to an analog communication system and connected to a device console port of a co-located computer device. The remote management station comprises (a) an embedded processor, (b) a connecting means to the analog communication system, and (c) a connecting means to the device console port. The remote management station is configured to detect a user connecting to or disconnecting from the device console port via the remote management station. The remote management station is configured for one or more of the following: (a) logging the user off the device console port when the user disconnects or is disconnected from the console port; (b) logging a previous user off the device console port before allowing a new user to access the device console port; or (c) monitoring messages sent to the device console port.
Owner:INFINITE BAY TELECOM LIABILITY +1
System and method for supporting virtualized links at an exterior network-to-network interface
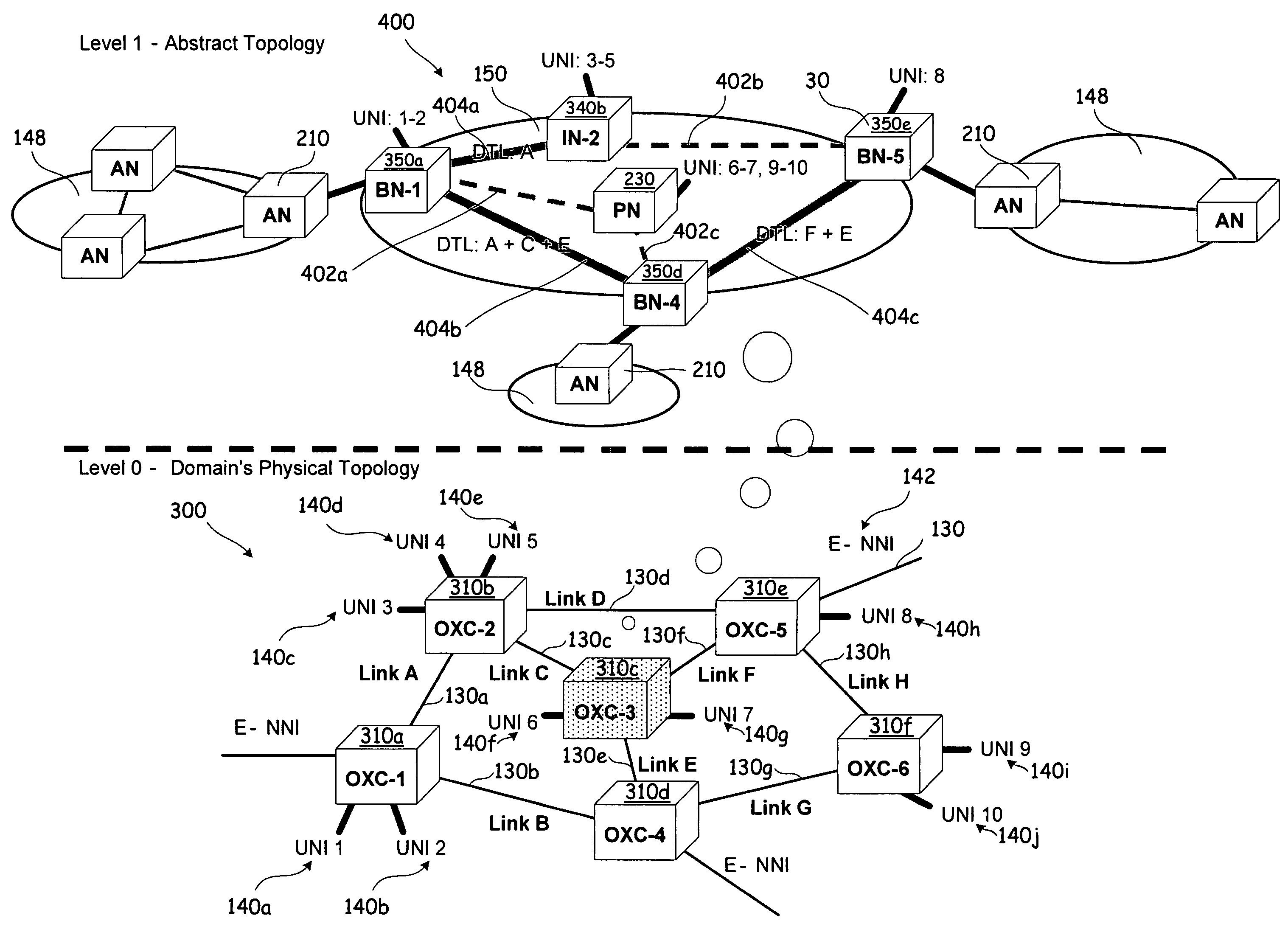
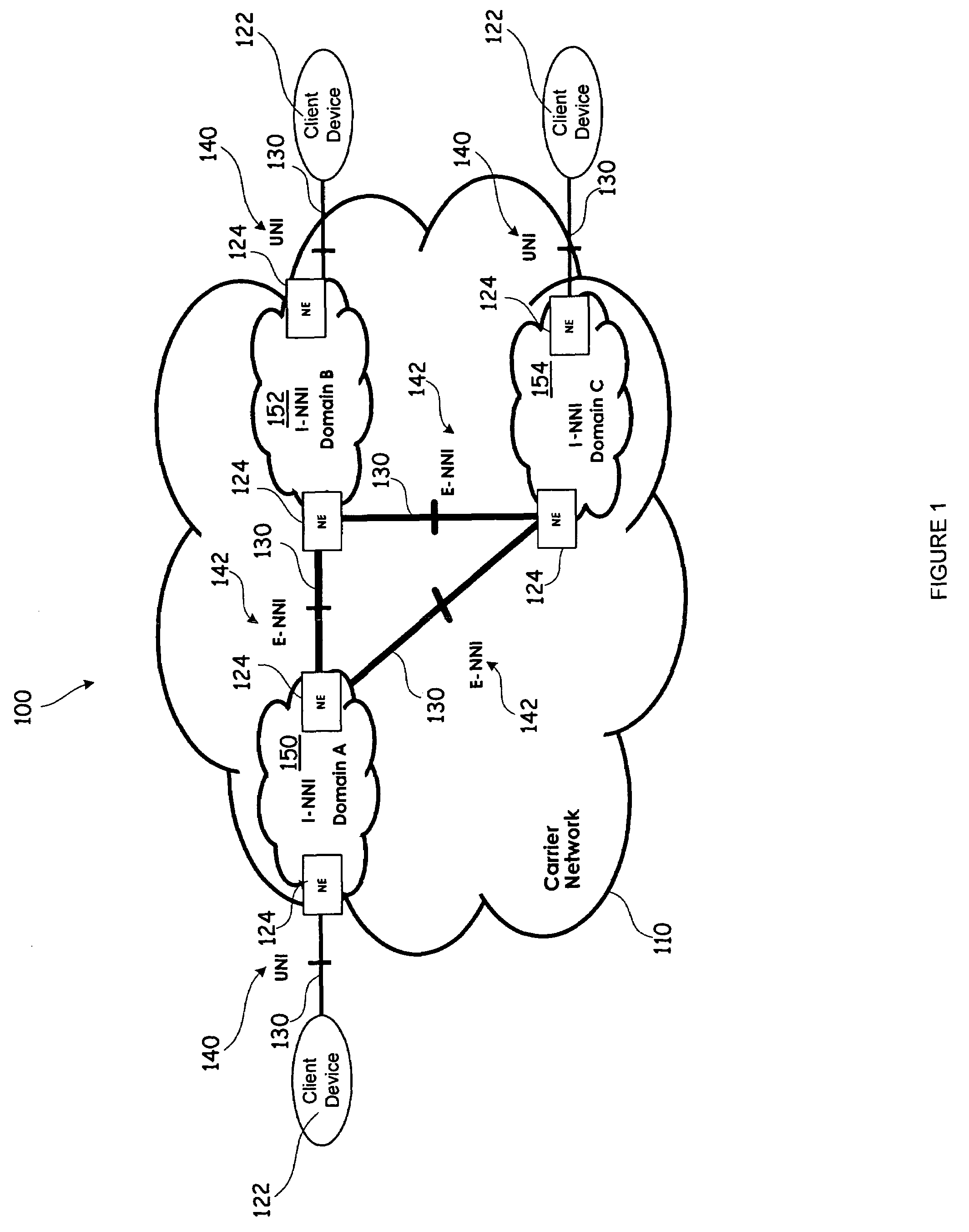
ActiveUS20080095176A1Reduce complexityProvide controlData switching by path configurationNetwork-to-network interfaceVirtualization
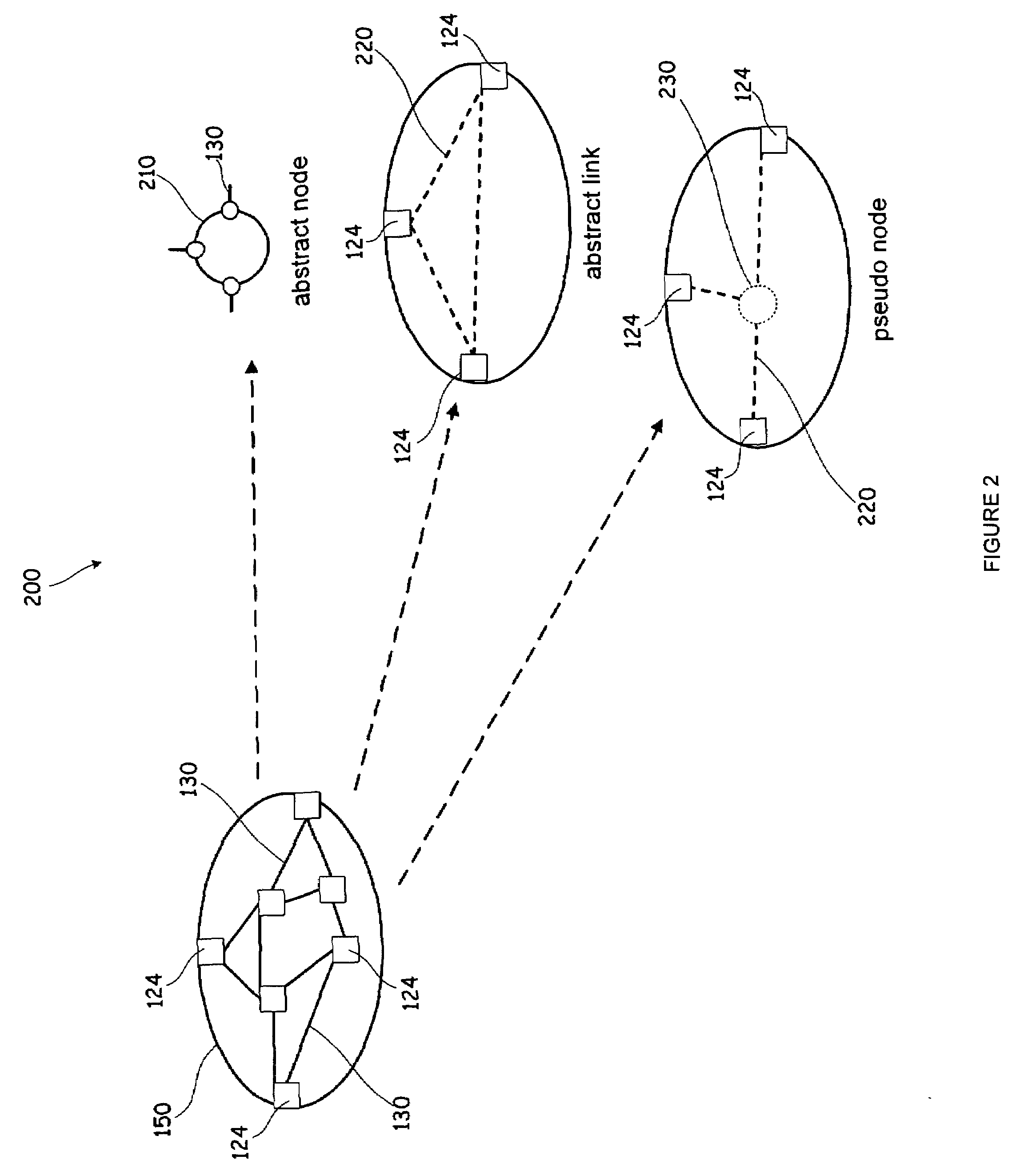
The present invention provides systems and methods for abstracting a network topology into virtual links and supporting both generic and instantiated virtualized links for linking a virtualized topology with actual resources within a domain, providing security over network topology information, providing control over the allocation of resources, and reducing the complexity of advertising.
Owner:CIENA
Method for generating and authenticating address automatically in IPv6-based internet and data structure thereof
InactiveUS20060077908A1Protect informationPublic key for secure communicationData switching by path configurationIPv6 packetTimestamp
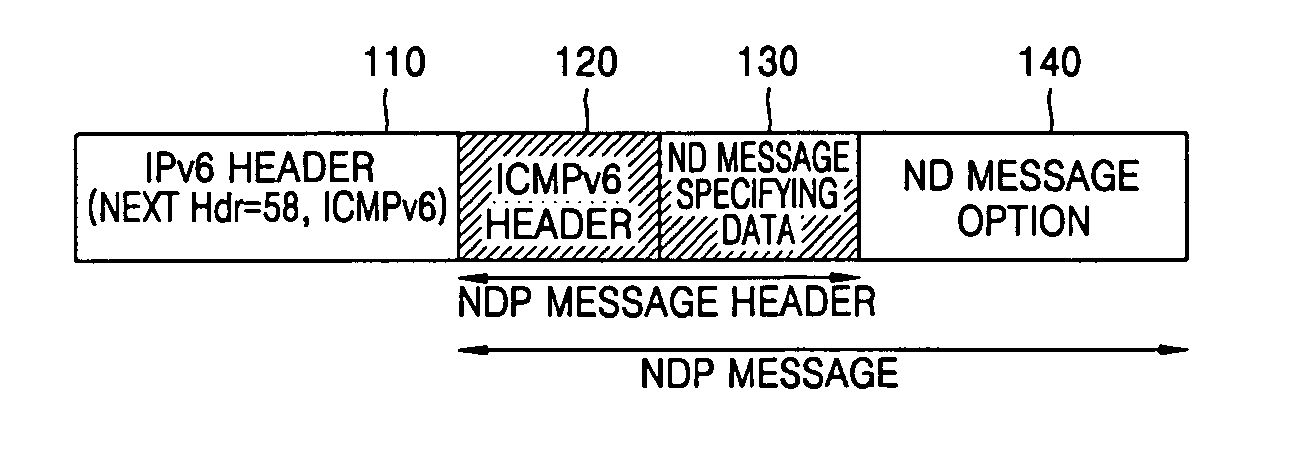
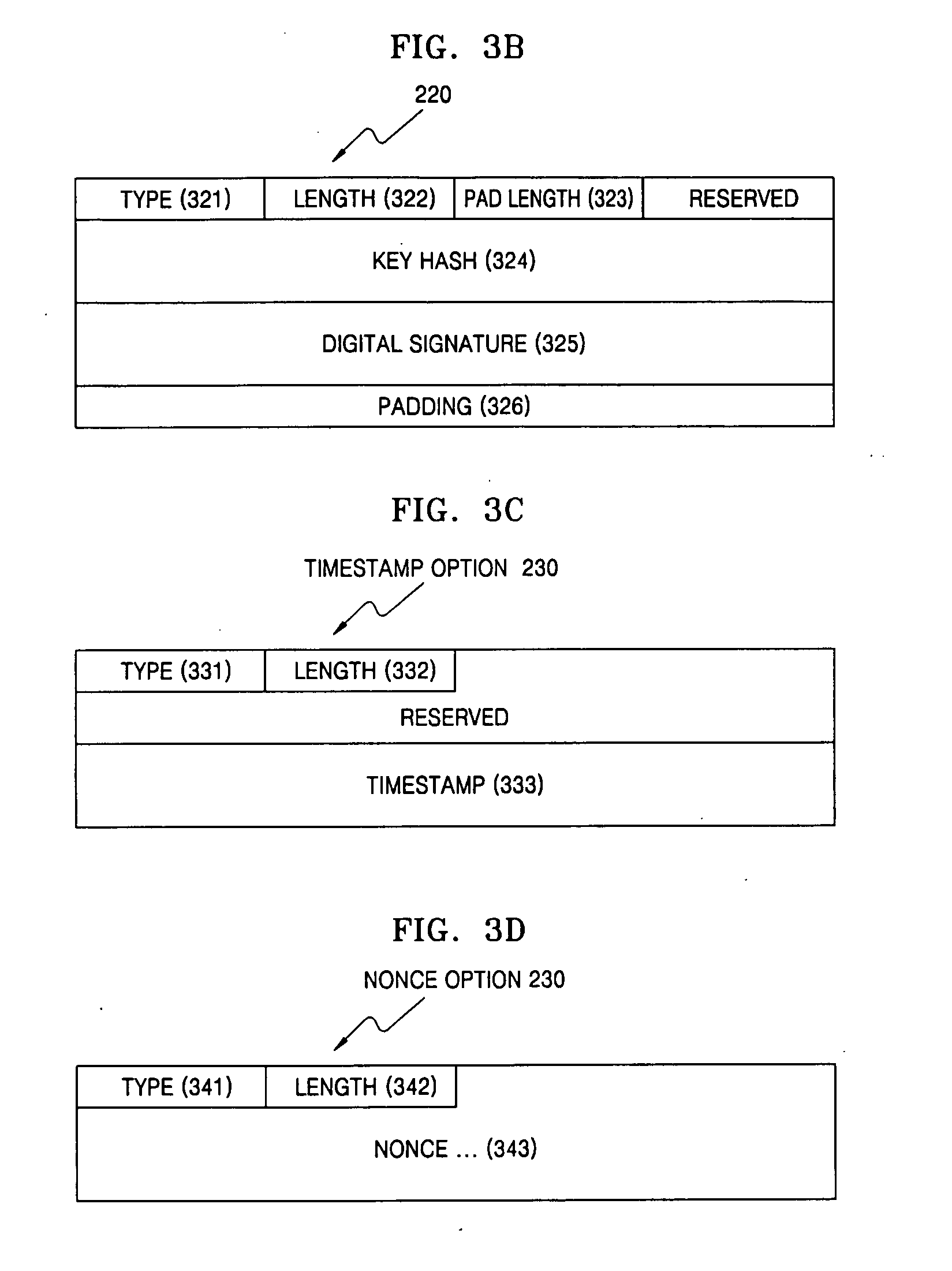
Provided are a method for automatically generating an address in the IPv6-based Internet when a sender having a pair of a public key and a private key establishes a network connection, and a data format thereof. The method includes generating a CGA address and a CGA option based on the public key and a predetermined parameter, generating a signature option for verifying the CGA option, additionally generating a timestamp option in a case where a unidirectional message is transmitted to the network, and additionally generating a nonce option containing random numbers in a case where a bidirectional message is transmitted to the network, and adding the signature option, the timestamp option and the nonce option to a Neighbor Discovery (ND) option field to form an ND message, and transmitting the ND message to the network. When a host enters the network in a Zero Configuration over the IPv6-based Internet, the host can securely generate its own address without using a manual key. The method can also be applied to general IPv6 packet authentication or position authentication of a mobile node.
Owner:ELECTRONICS & TELECOMM RES INST
Method of tracking a large number of tools
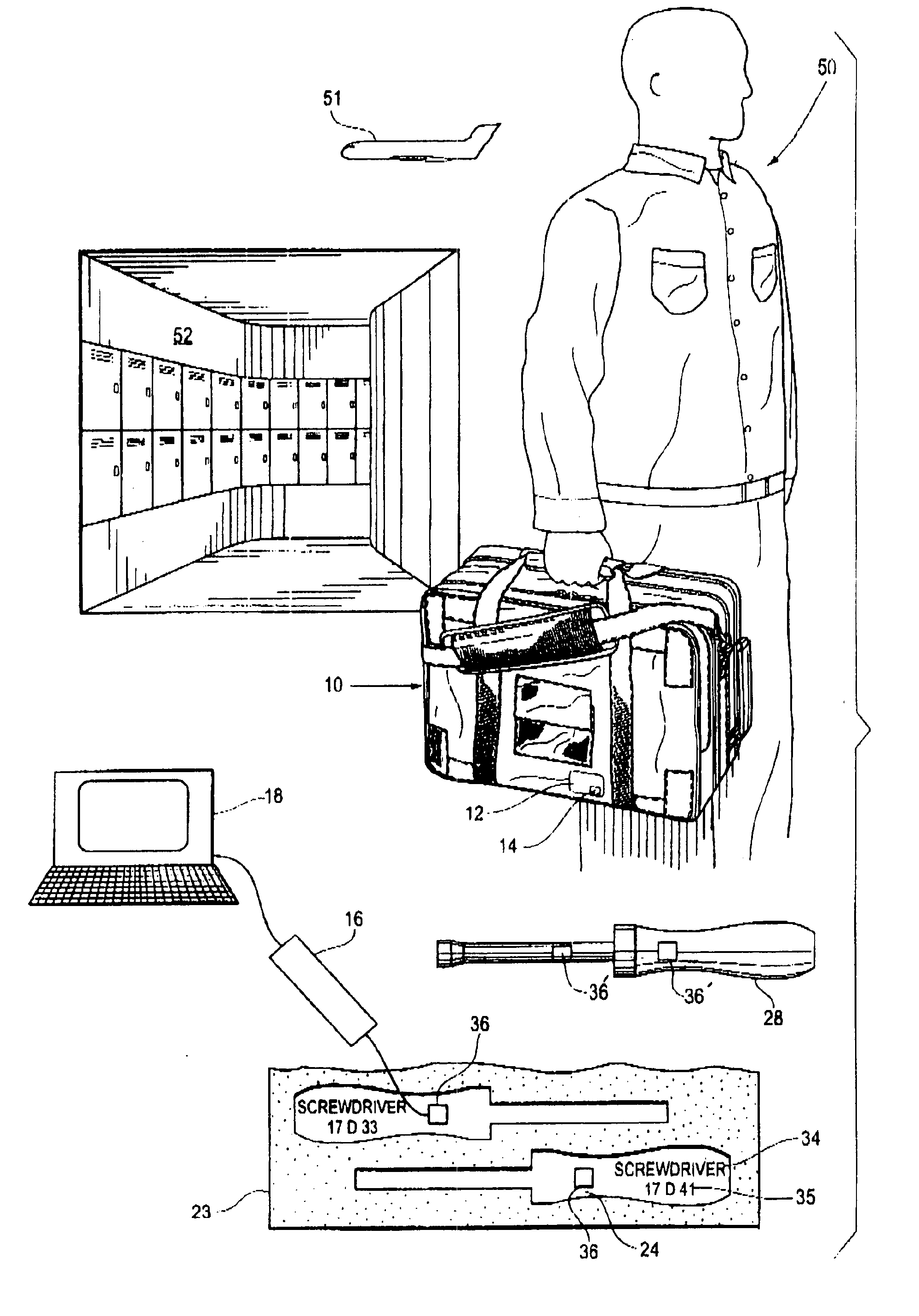
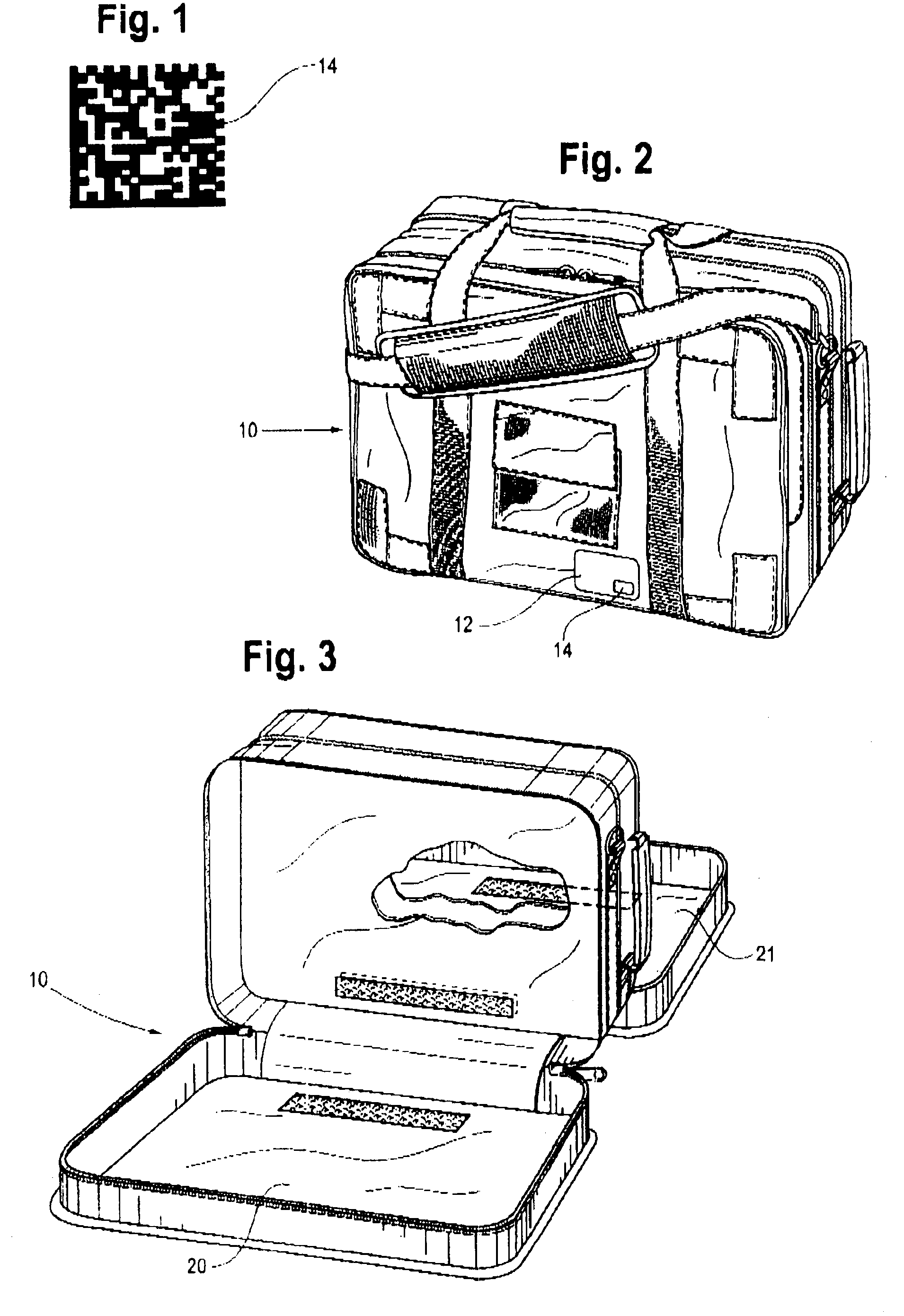
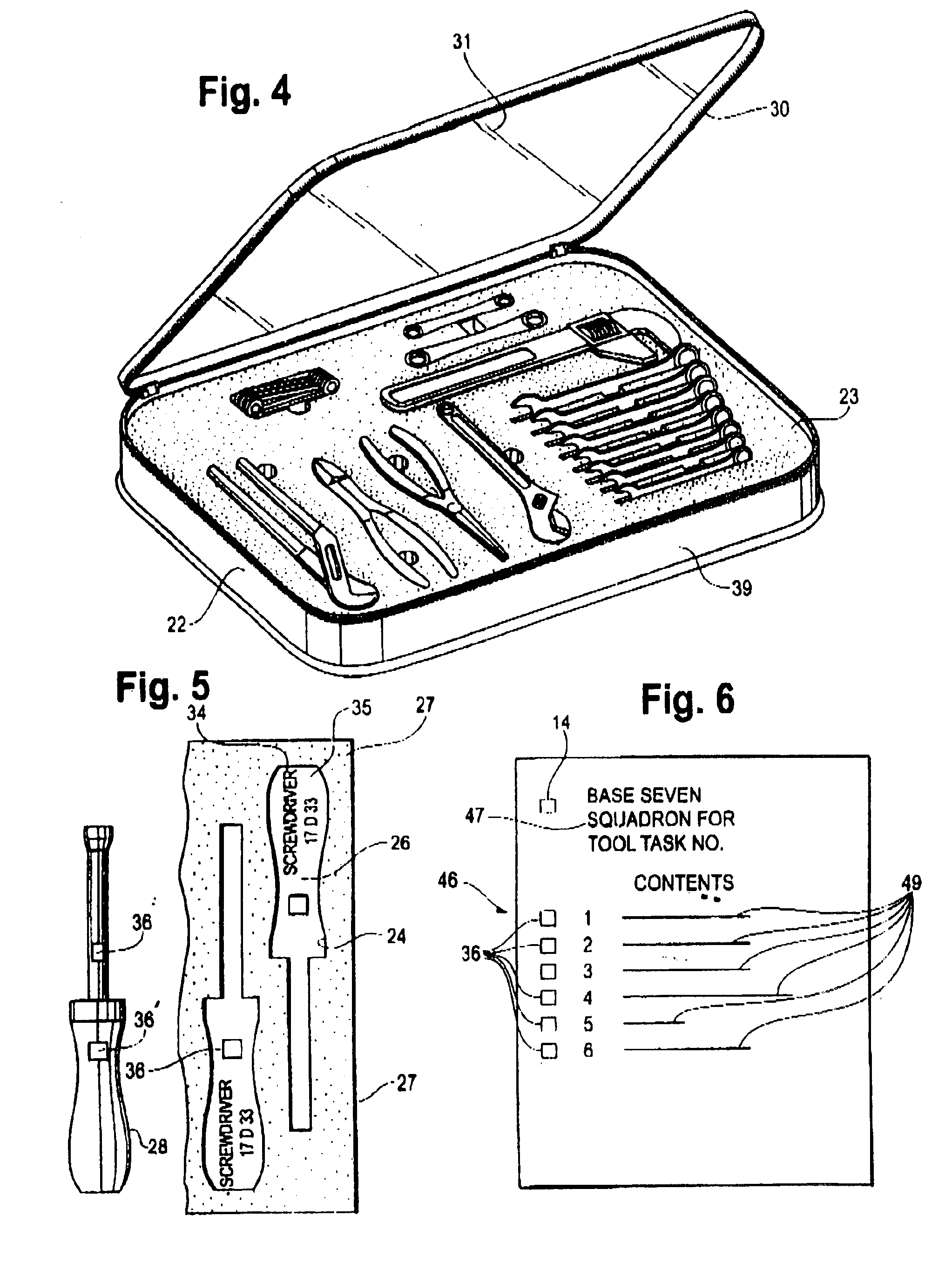
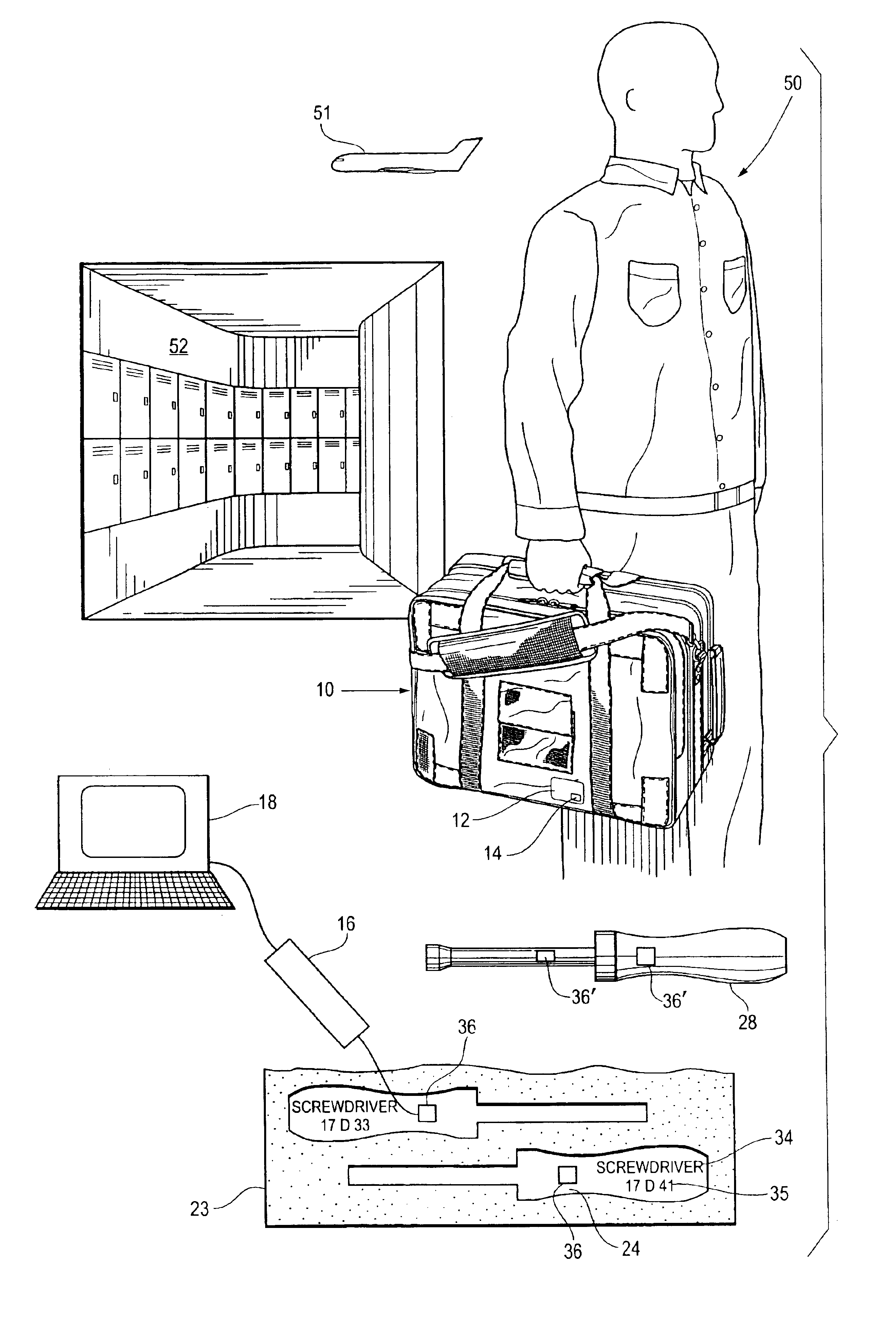
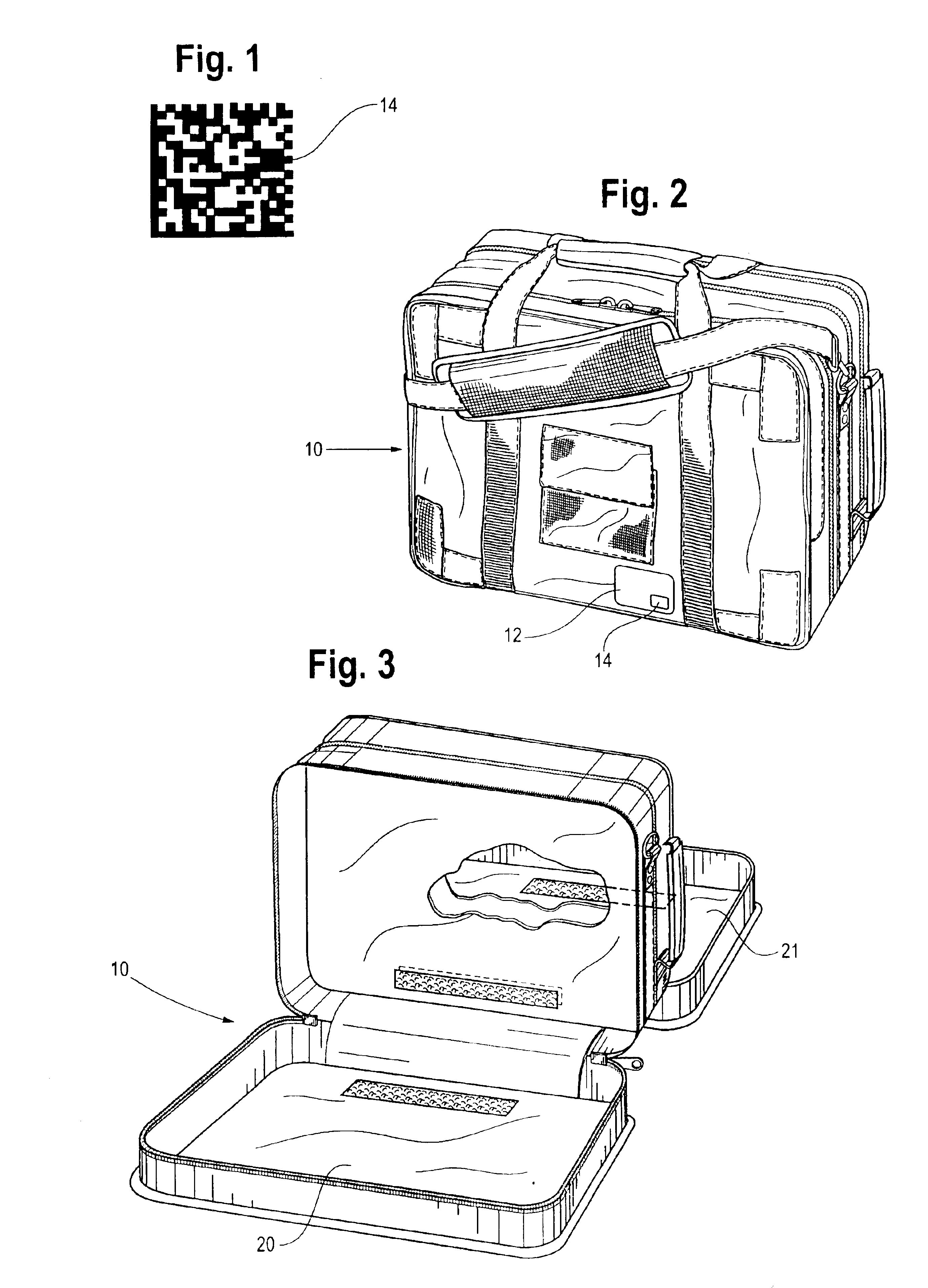
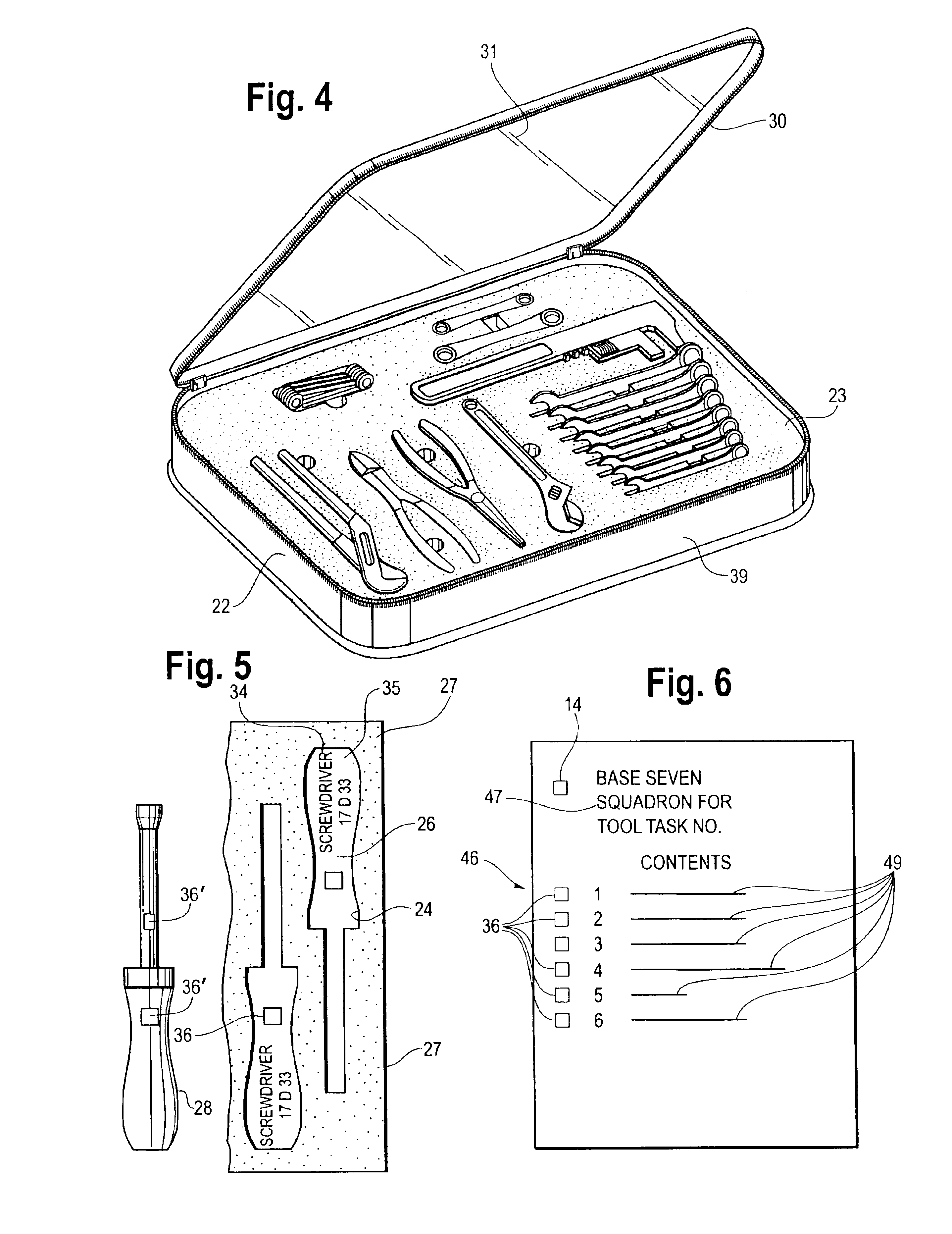
InactiveUS6840451B2Protection loss of informationReliably readableCharacter and pattern recognitionWork tools storageProgramming languageData Matrix
To track a large number of tools, the tools are kept in sets with each set having a container. A silhouette of each tool stored in the container is printed at the point of storage along with a data matrix code that has stored in binary code a description of the too, the part number, and an identification of the kit of which it is a part. The associated tool has etched into the surface thereof a data matrix code containing the same information as the code printed at the point of storage. The data matrix codes are readable by a scanner and a record of all the tools is maintained on a computer.
Owner:UFP TECHNOLOGIES
Apparatus and method of mirroring firmware and data of embedded system
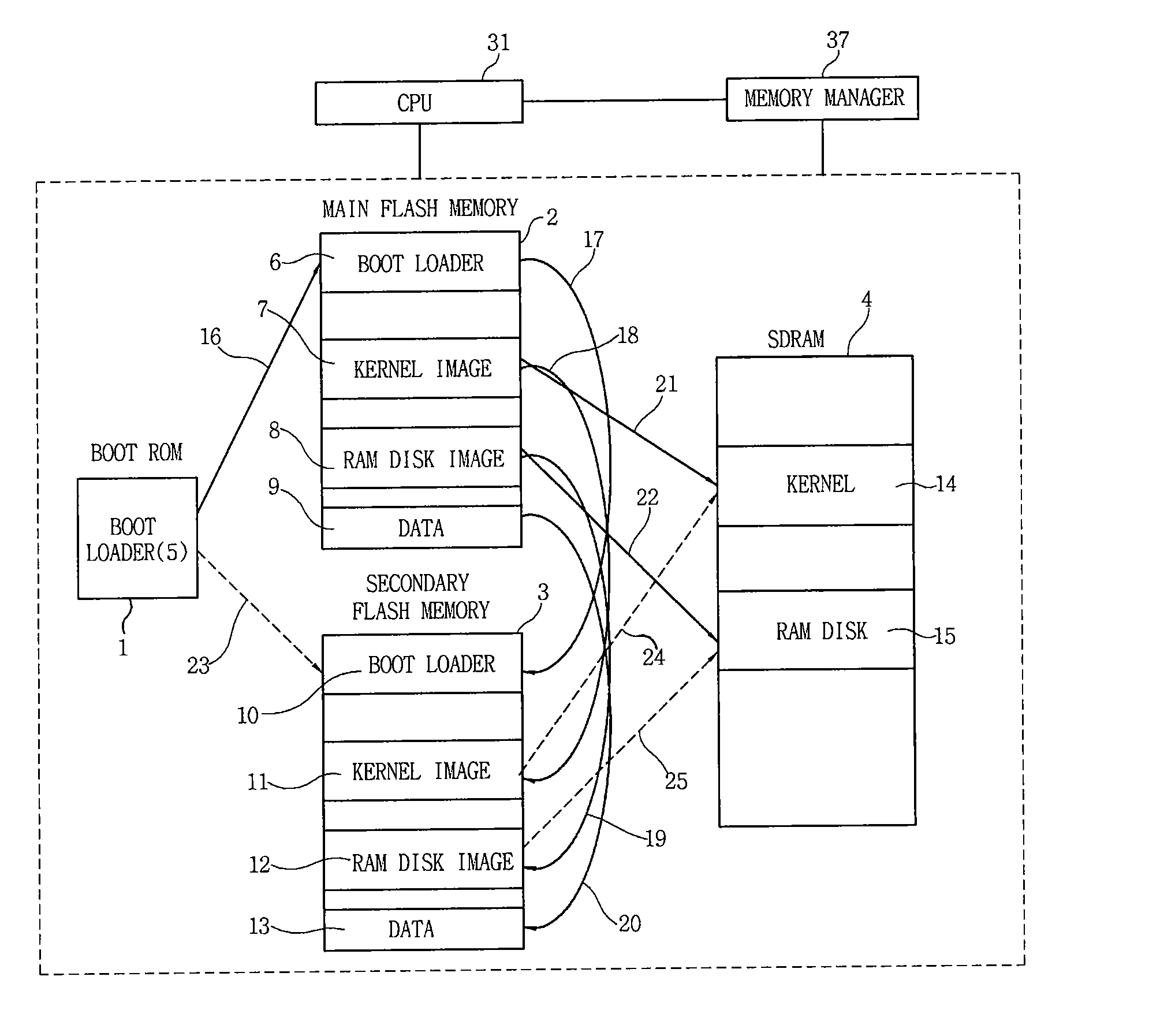
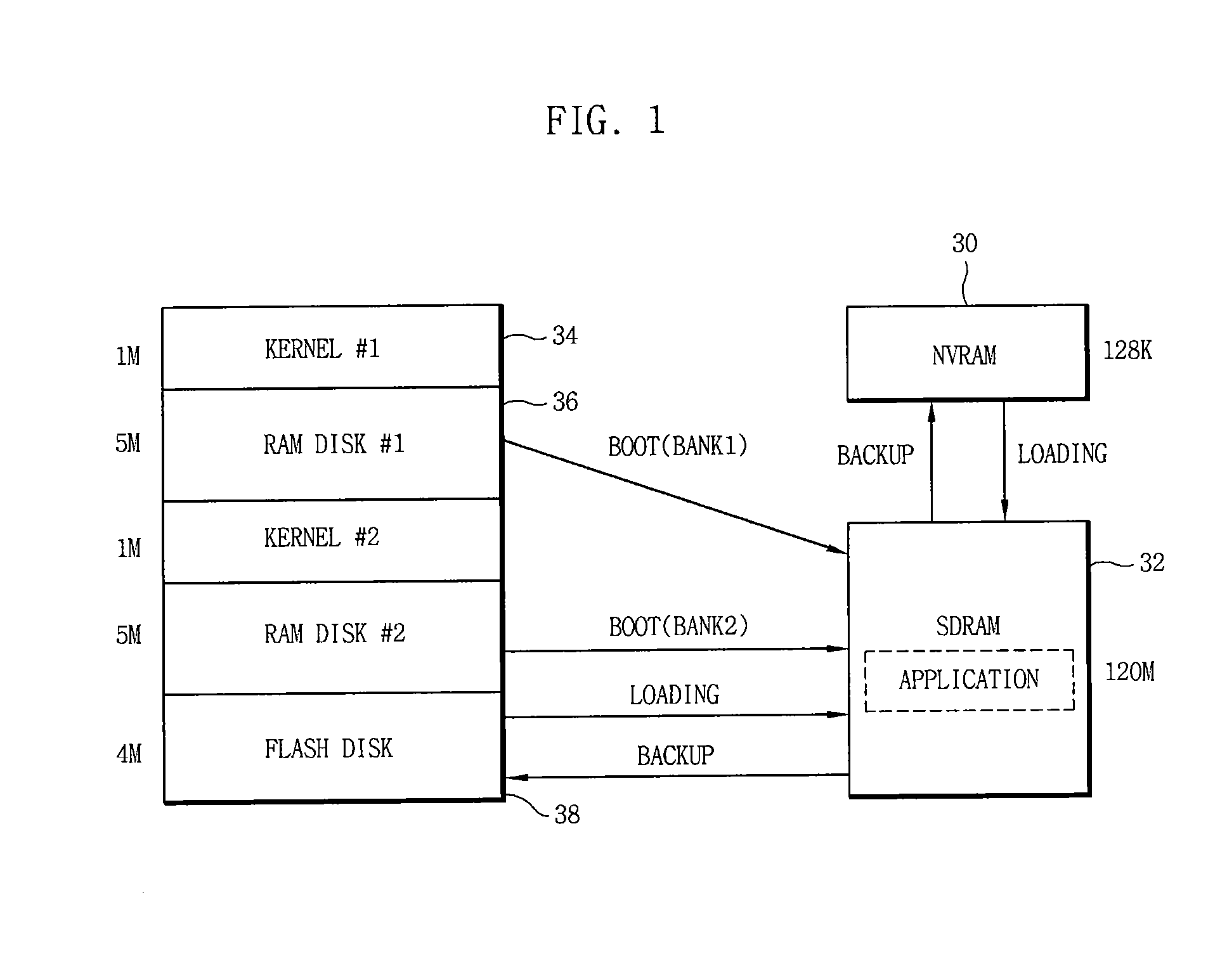
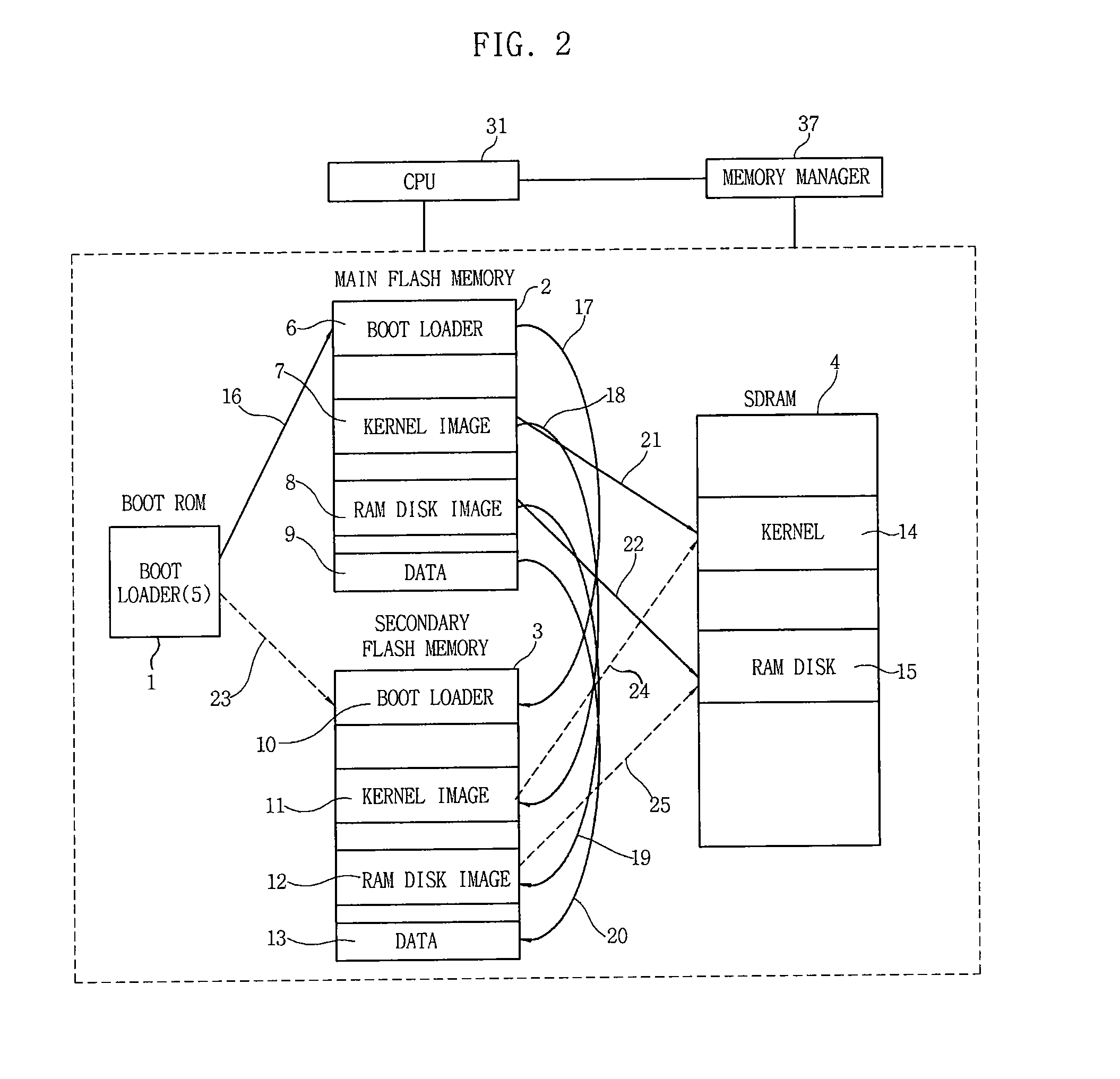
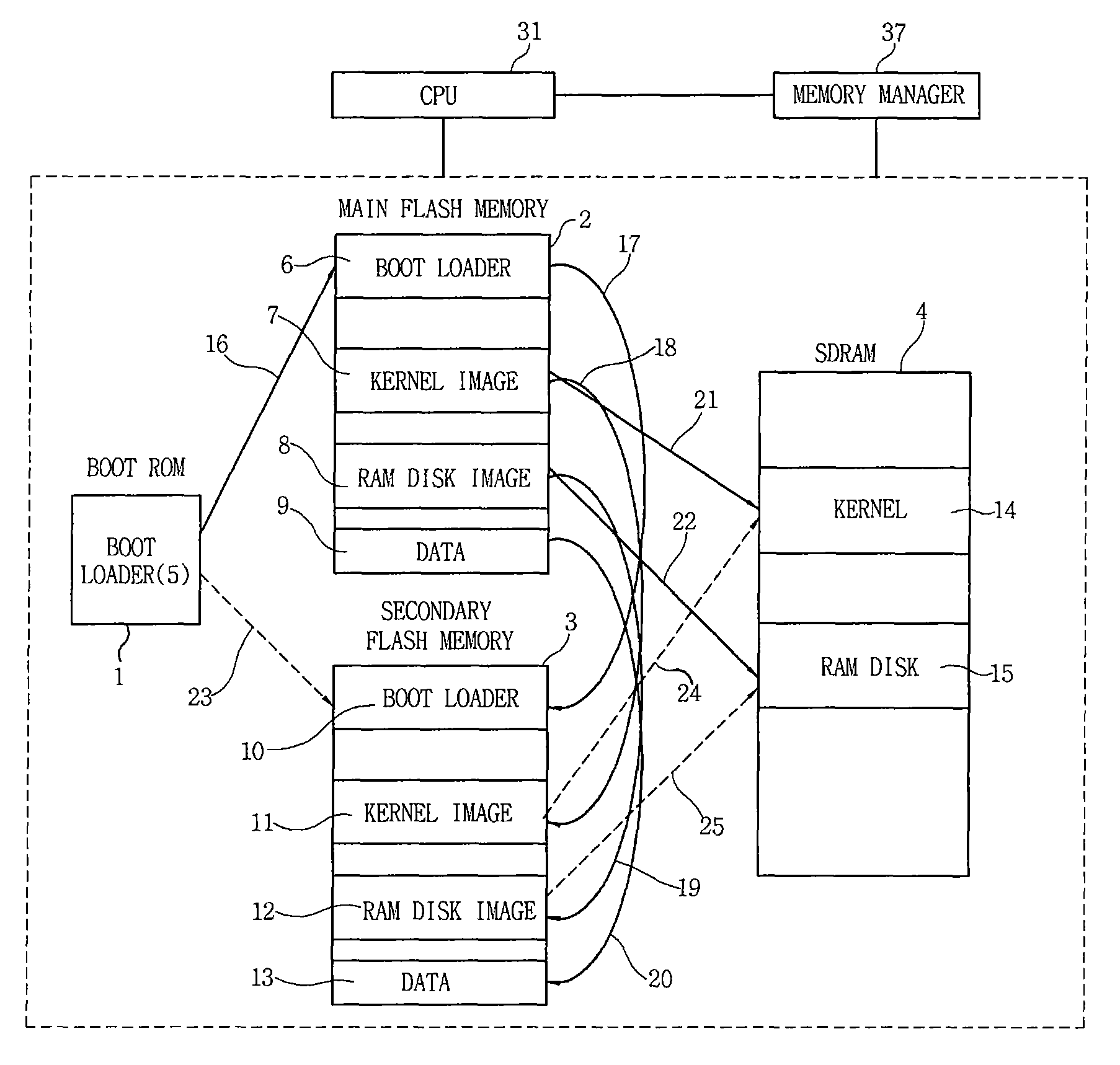
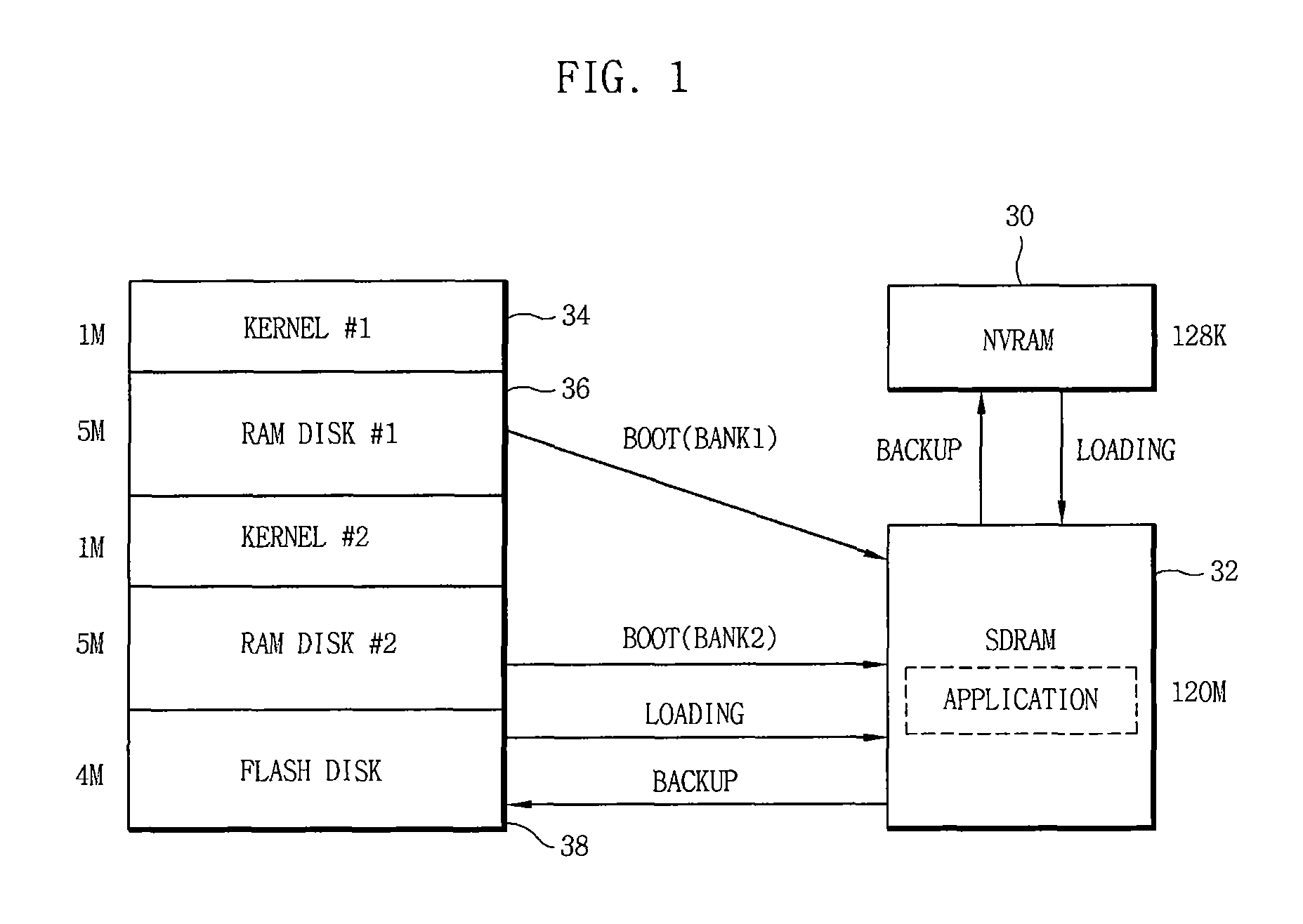
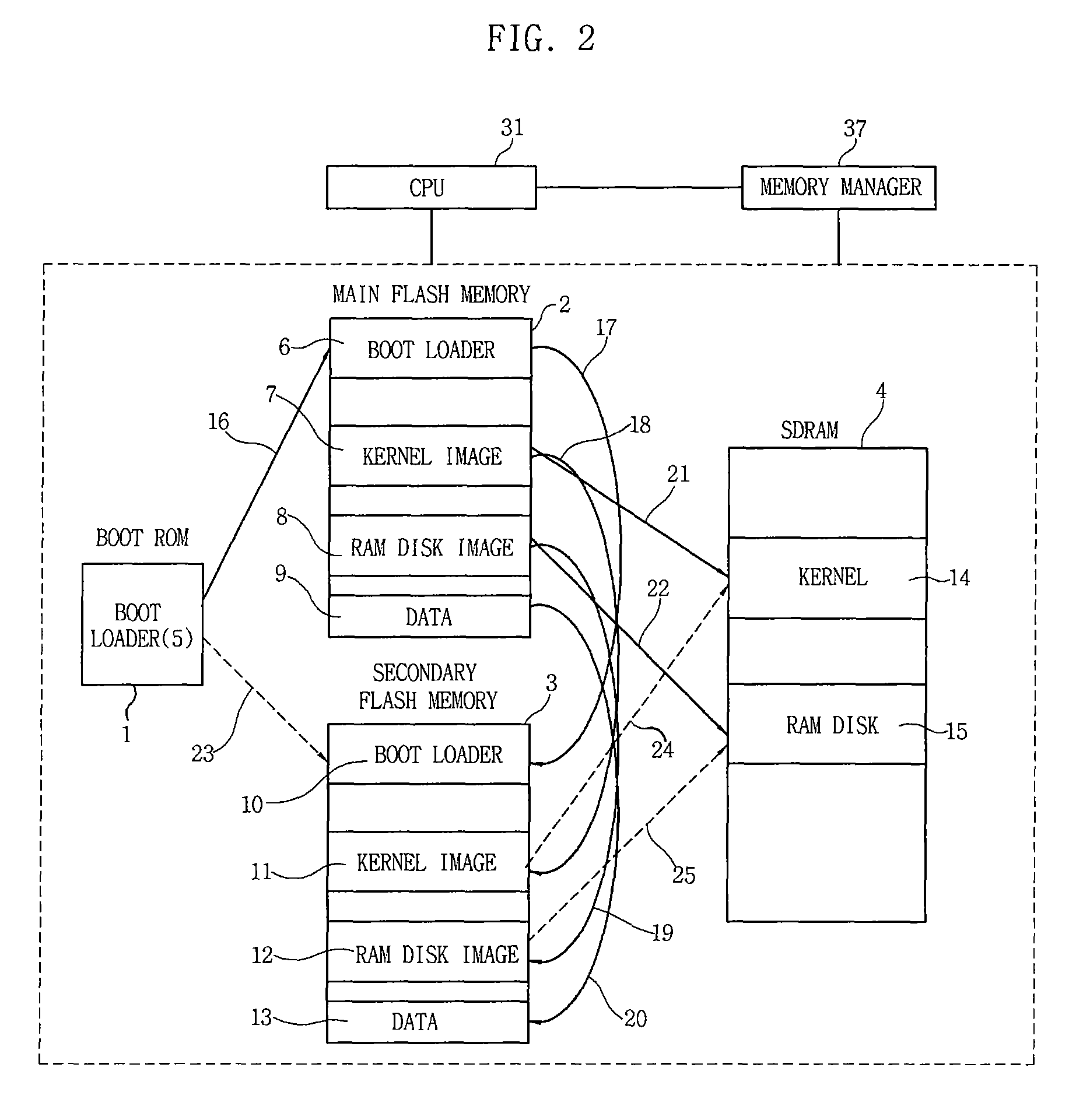
InactiveUS20090150598A1Improve reliabilityEasy to operateMemory loss protectionMemory adressing/allocation/relocationOperabilityData loss
Disclosed is an apparatus and method of mirroring firmware and data of an embedded system. The embedded system mirrors a boot loader image, a kernel image, a RAM disk image and data that are stored on a main flash memory to be operated onto a secondary flash memory. Therefore, when a main flash memory does not normally work, the firmware and data that are stored on the main flash memory to be operated is mirrored onto the secondary flash memory, which prevents the loss of data and maintains the operation of the embedded system. As a result, it is possible to secure the reliability and operability of the system.
Owner:ELECTRONICS & TELECOMM RES INST
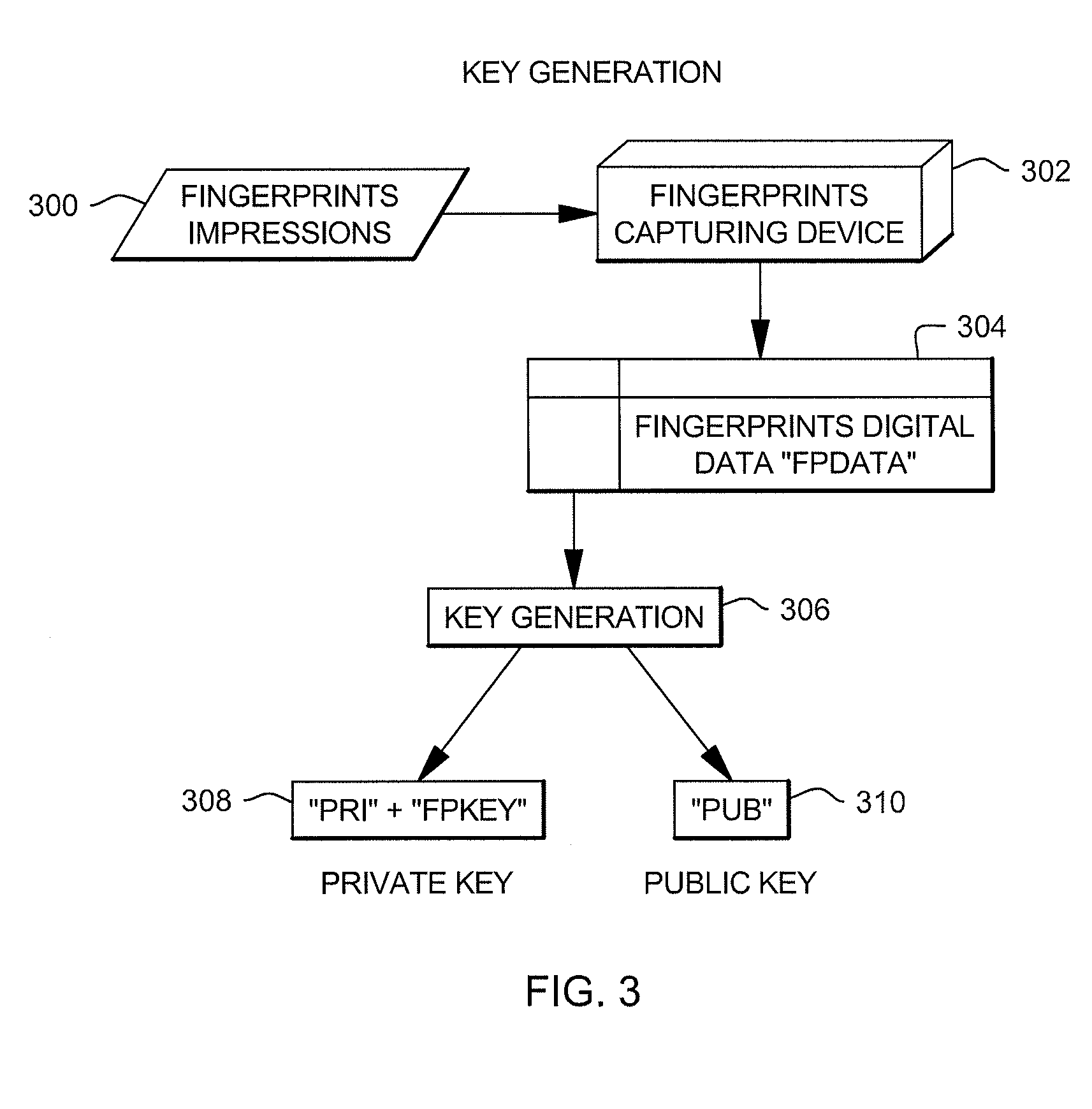
Generating secure private keys for use in a public key communications environment
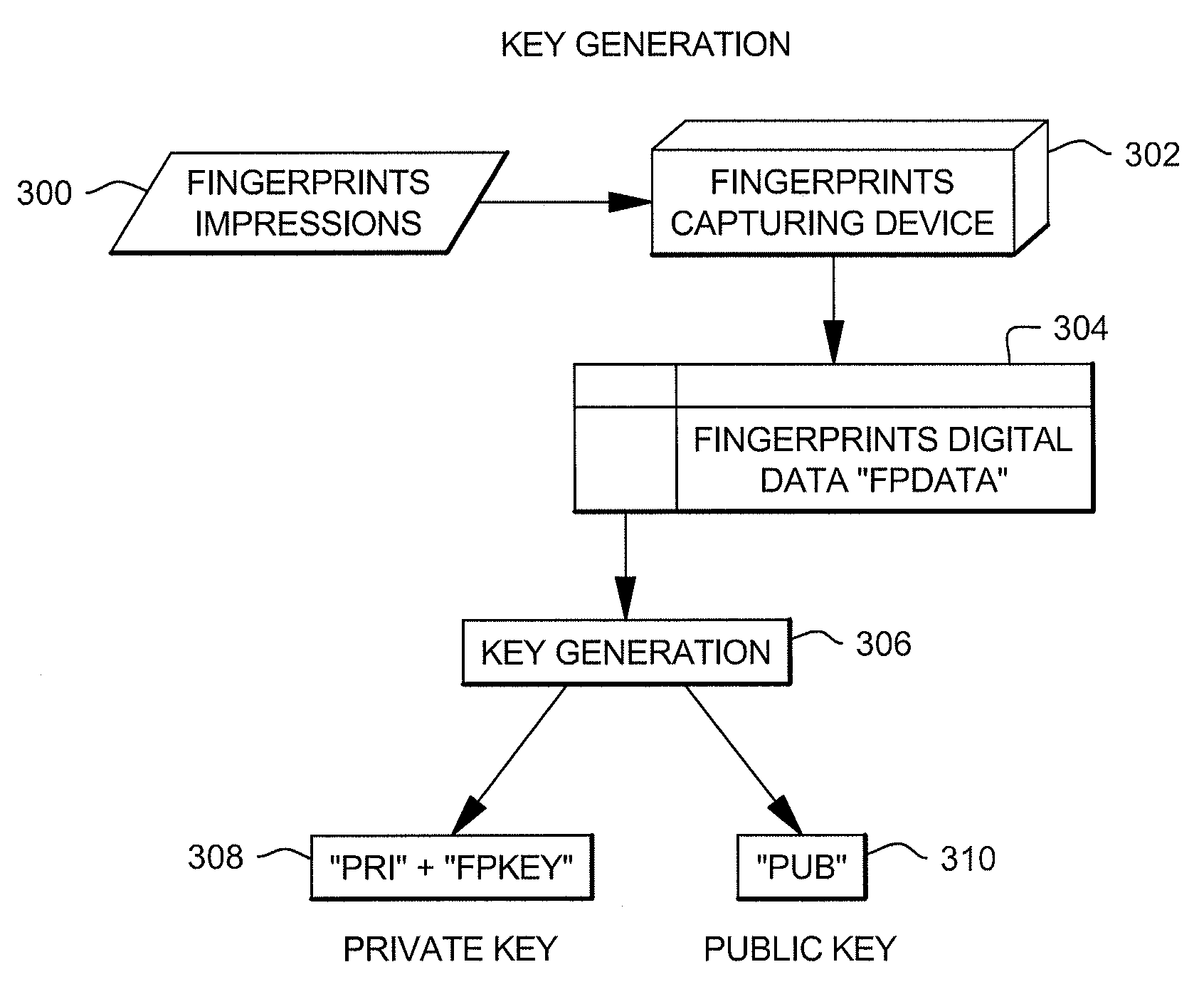
ActiveUS20100119061A1Protect informationOvercomes shortcomingEncryption apparatus with shift registers/memoriesBiometric dataEncryption decryption
A private key is generated for use in a public key communications environment, and the private key includes a partial private key and processed biometric data. The partial private key is known to the user, but the processed biometric data is not. The processed biometric data is generated on the fly and is not provided to the user. This enables a more secure and robust private key to be created and used in encryption / decryption.
Owner:IBM CORP
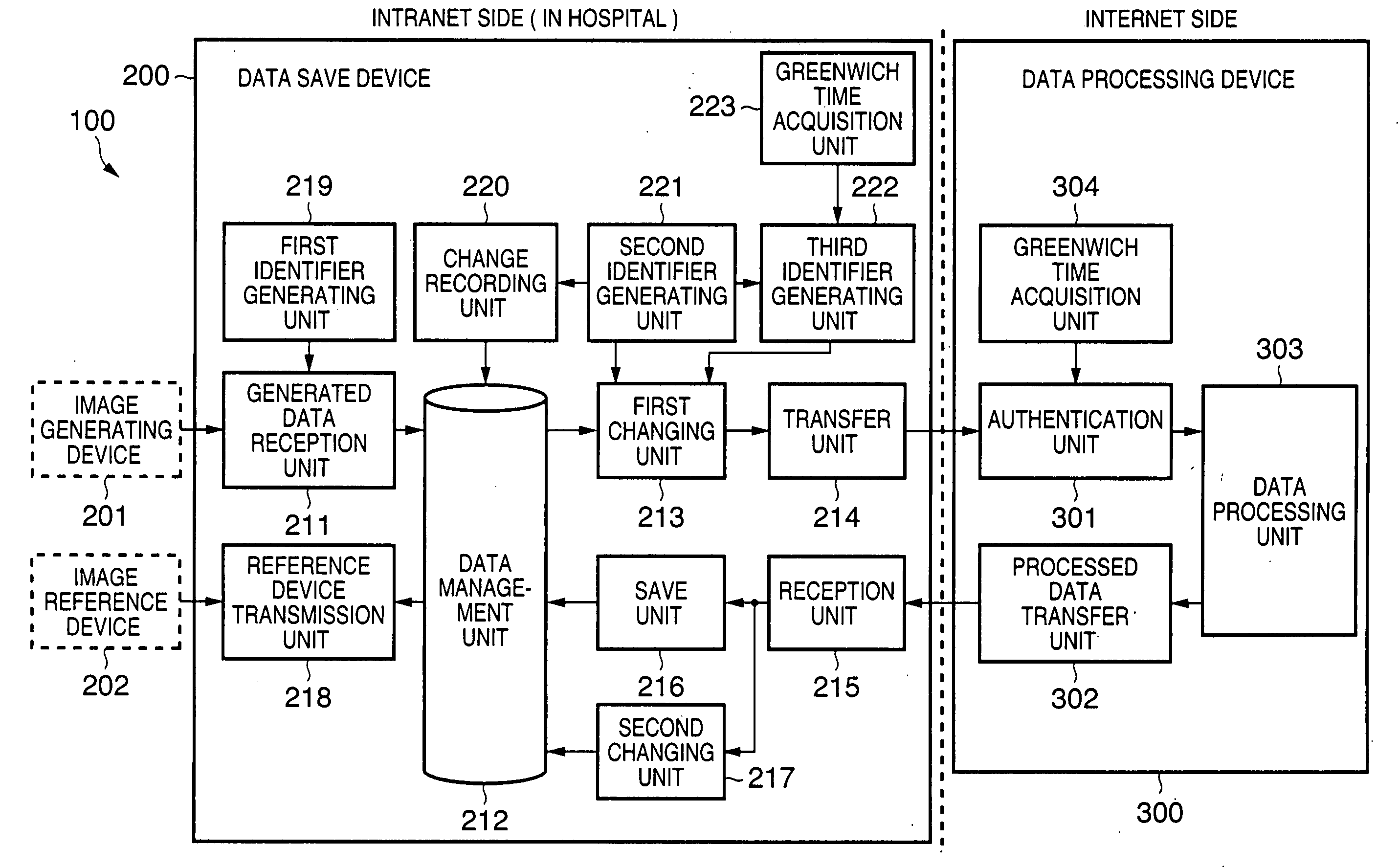
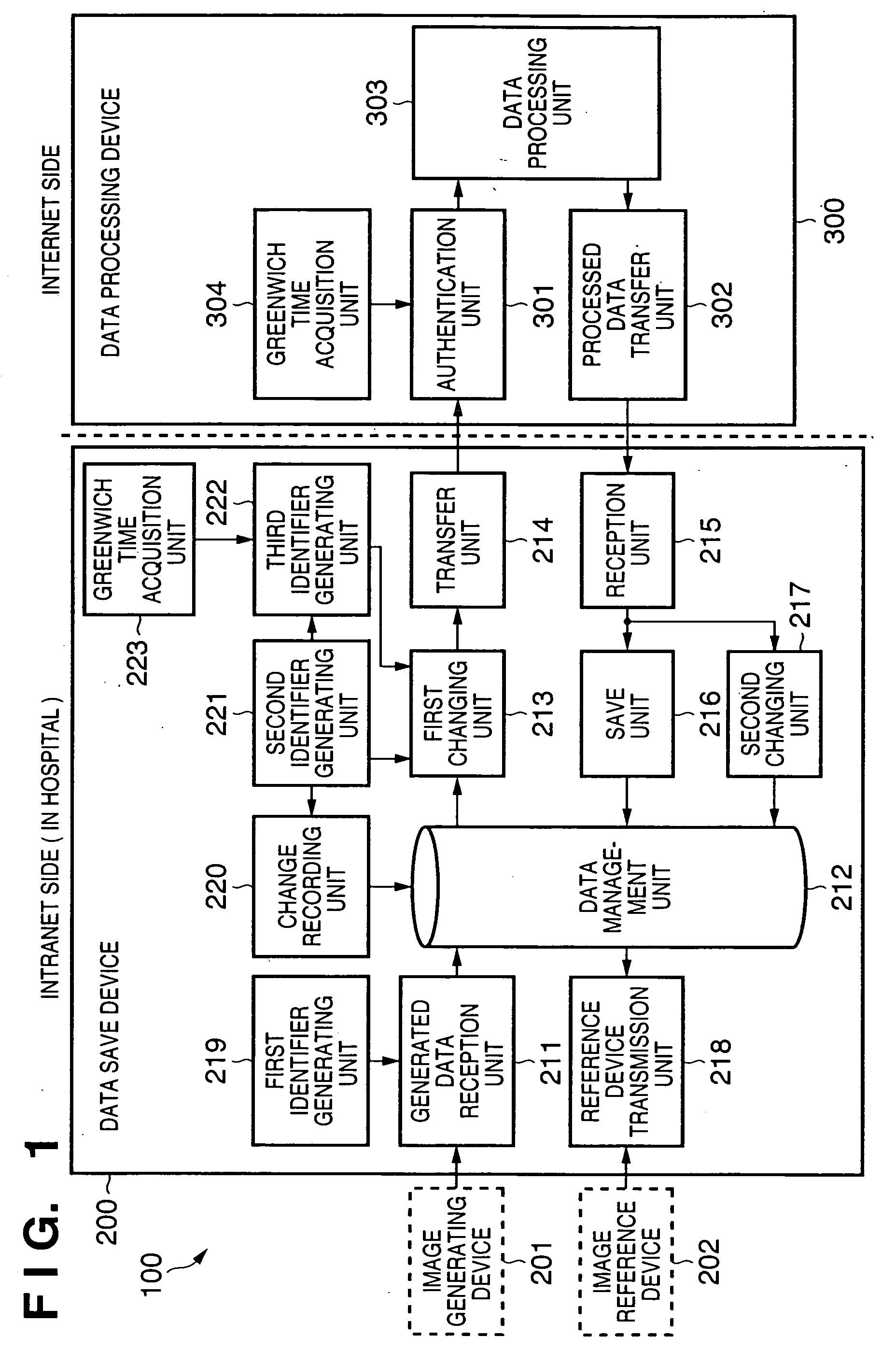
Information processing apparatus, information processing system, information processing method, storage medium, and program
InactiveUS20050086720A1Inhibition of informationProtect informationUltrasonic/sonic/infrasonic diagnosticsDigital data processing detailsInformation processingManagement unit
In an information processing apparatus which transfers target information to an external data processing device to process the information, and saves the processed information, a data management unit stores second identification information corresponding to the target information in association with the target information to which first identification information is attached. The first changing unit deletes the first identification information from the target information and adds the corresponding second identification information to the target information in the data management unit. The transfer unit transfers the target information processed by the first changing unit to the external data processing device.
Owner:CANON KK
Method for voice recognition and electronic equipment
InactiveCN103903621ASolve the technical problem of speech recognition inefficiencyImprove Speech Recognition EfficiencySpeech recognitionData needsSpeech identification
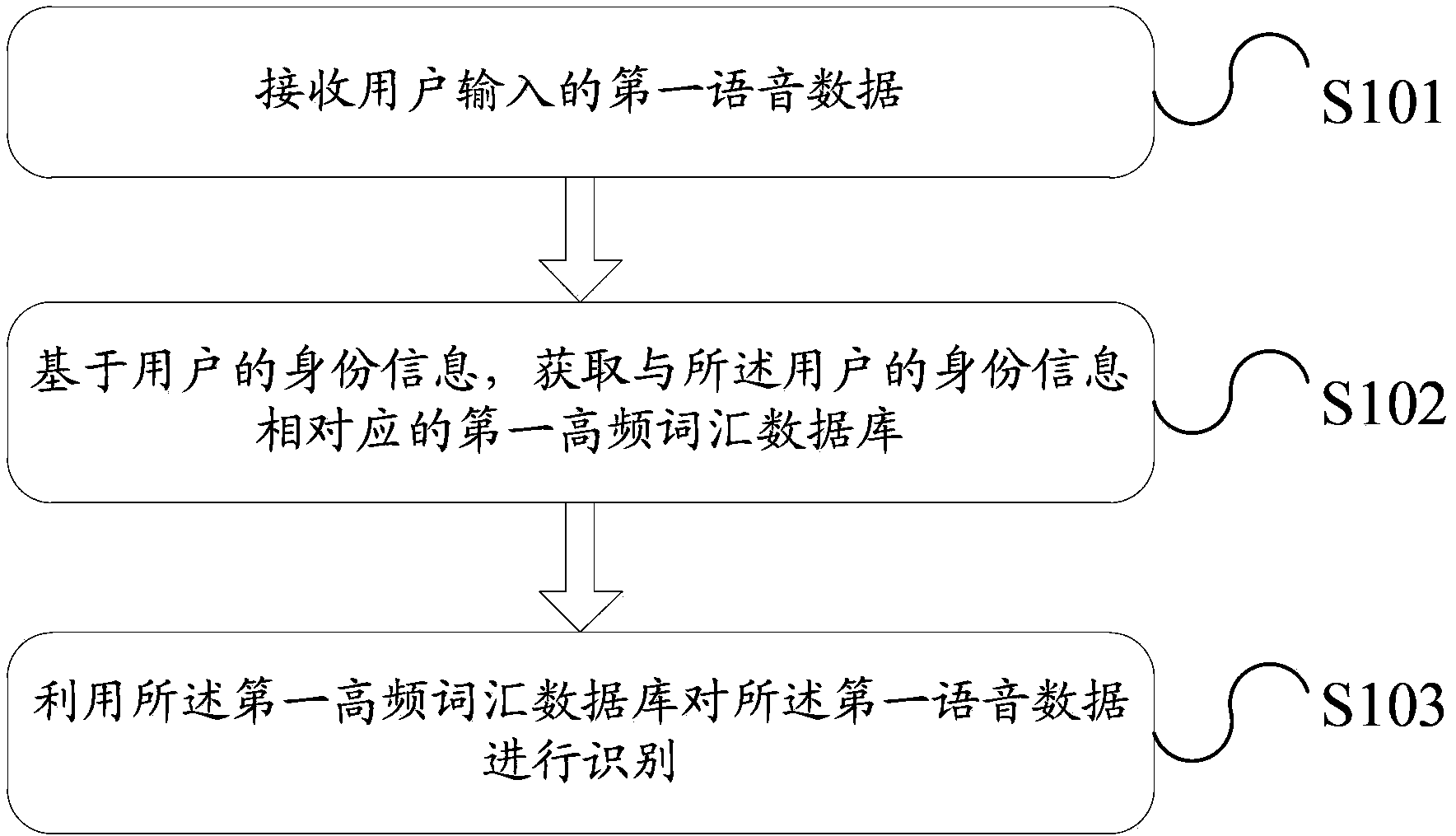
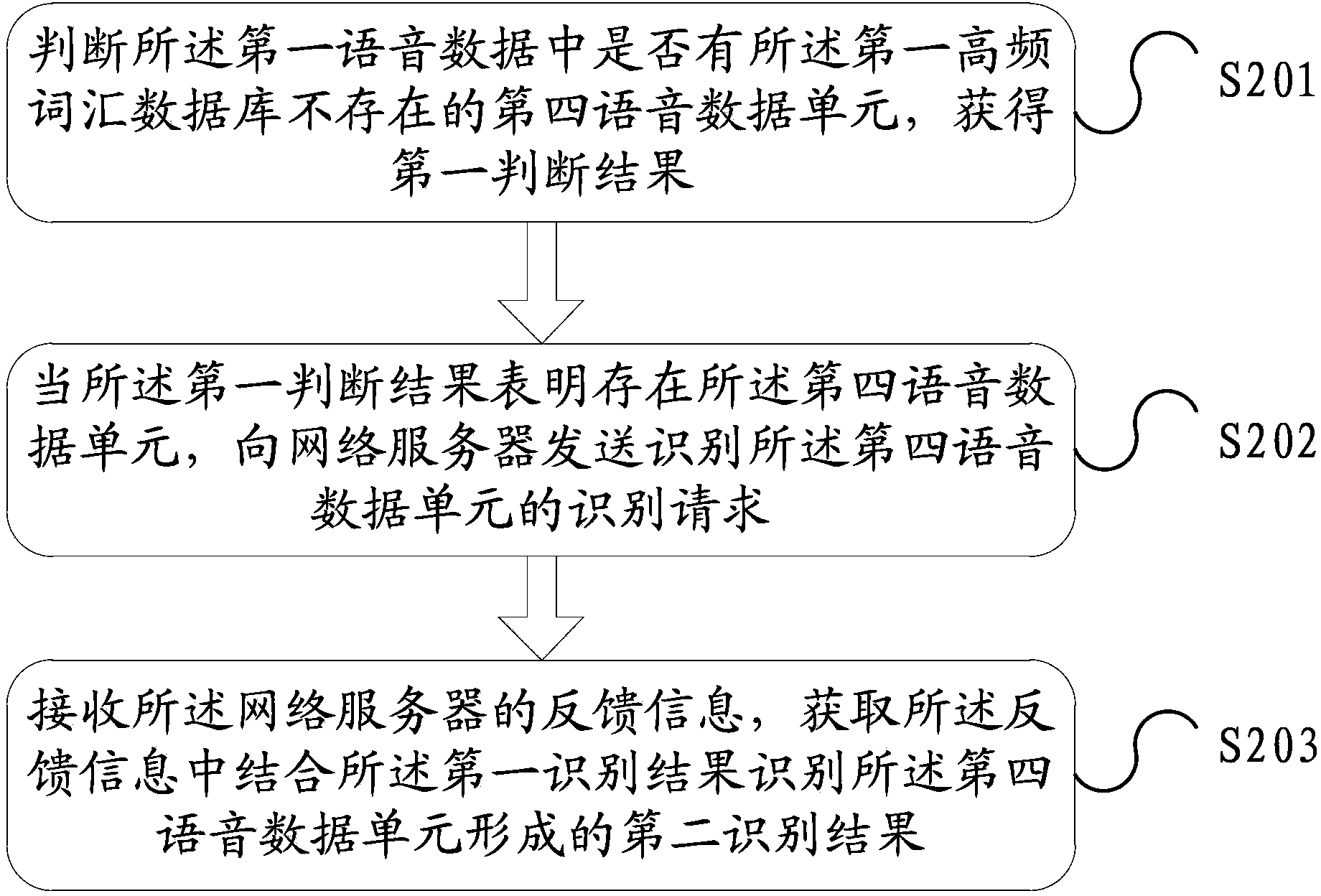
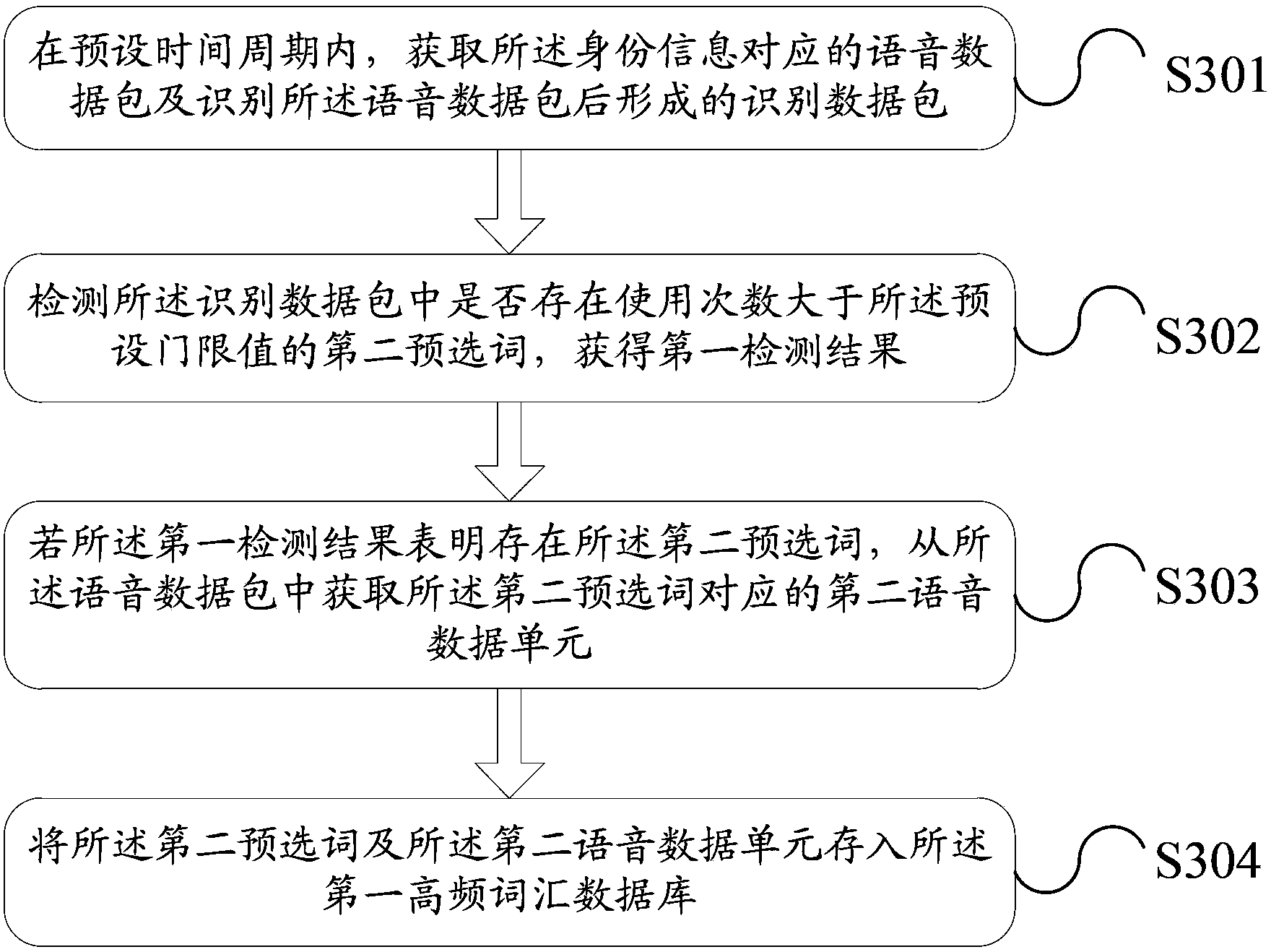
The invention discloses a method for voice recognition and electronic equipment. The method for voice recognition is applied to the electronic equipment, and the method includes: receiving first voice data input by a user; based on identity information of the user, obtaining first high-frequency vocabulary database corresponding to the identity information of the user; and utilizing the first high-frequency vocabulary database to recognize the first voice data. Corresponding voice recognition is performed on the voice data input by the user through the high-frequency vocabulary database corresponding the user, thereby solving the technical problem in the prior art that since all voice data need to be compared and recognized in a standard vocabulary database, the efficiency of voice recognition is low, and achieving the technical effect of improving the efficiency of voice recognition.
Owner:LENOVO (BEIJING) CO LTD
Method and system for calculating performance parameters for a processor
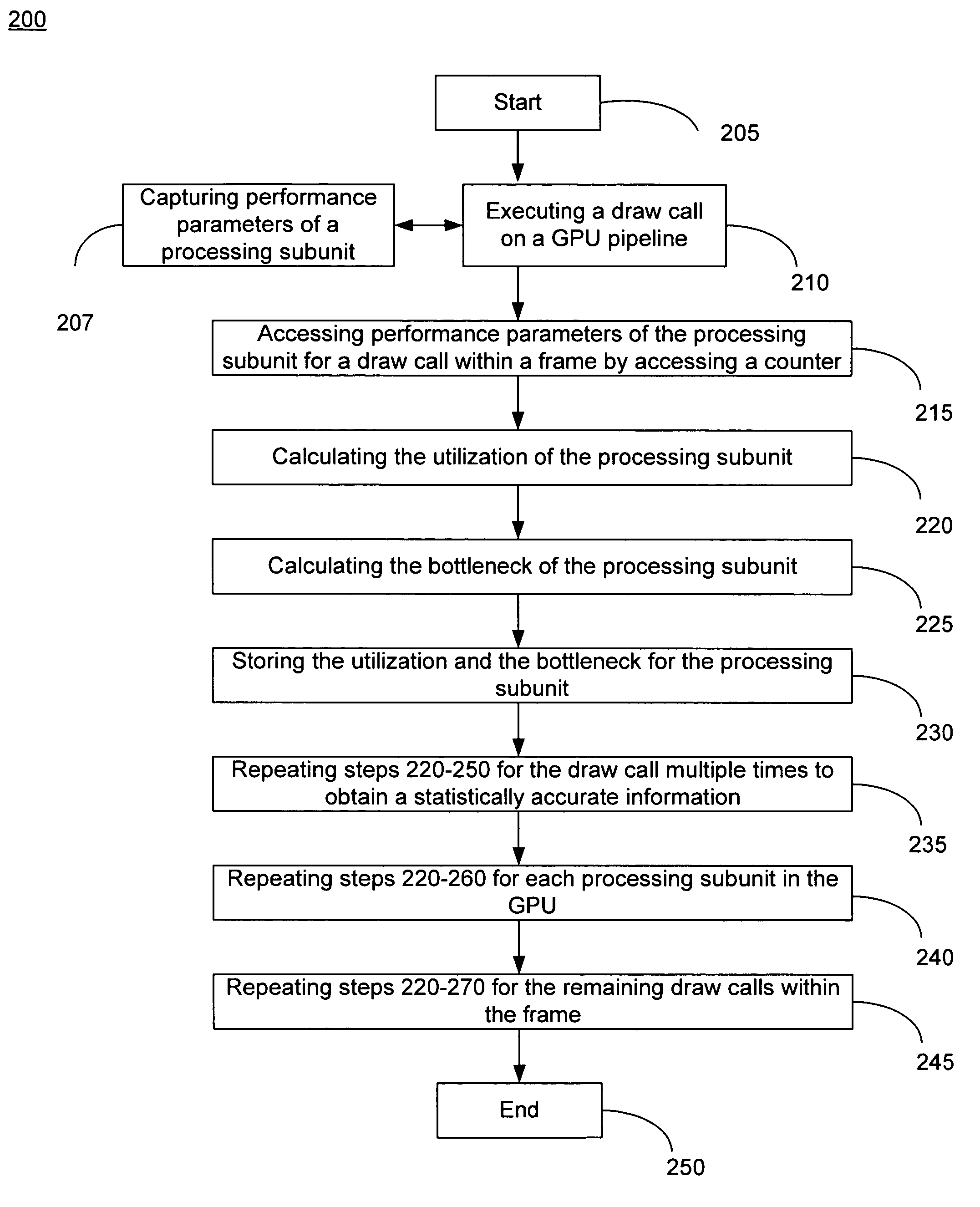
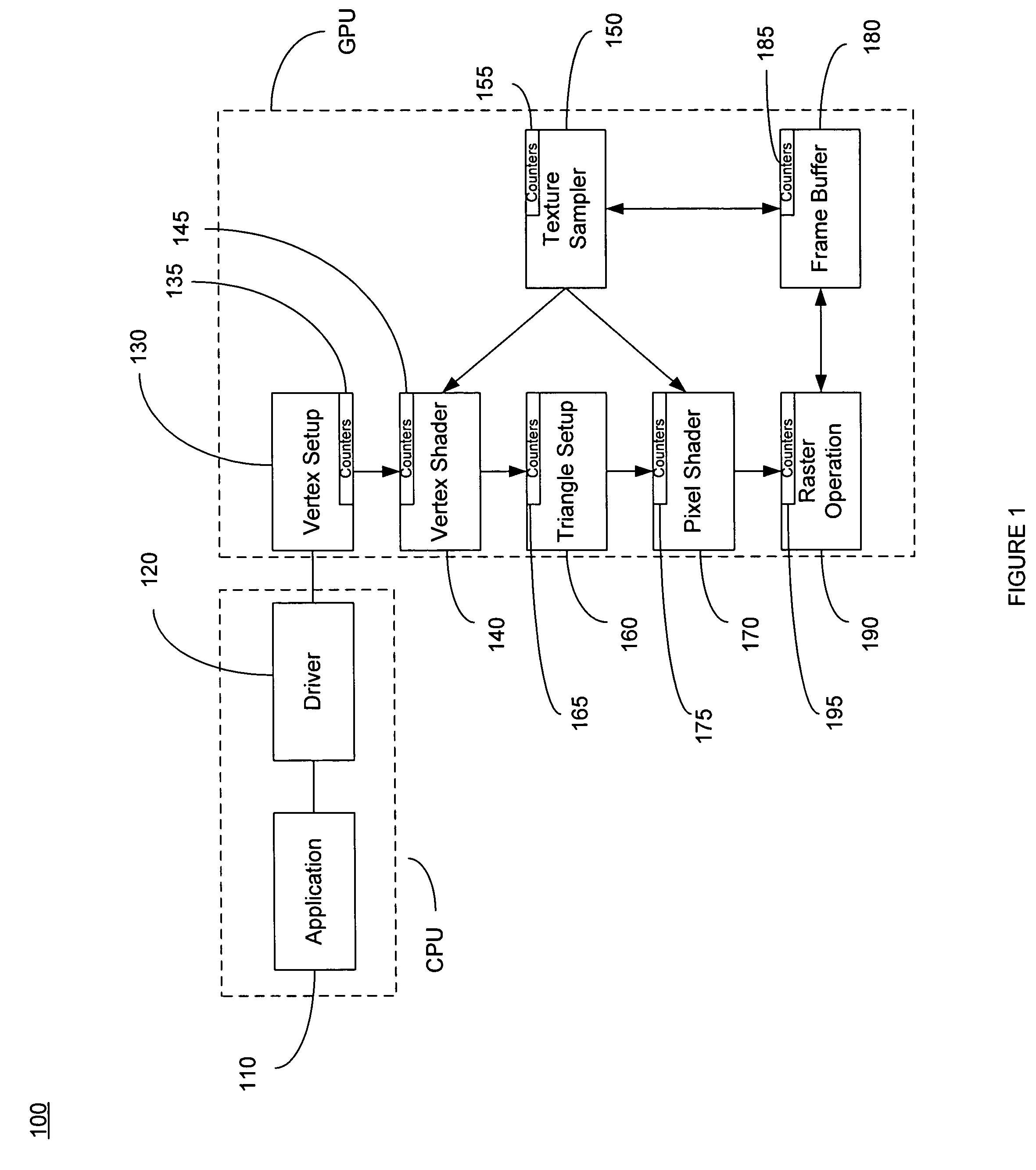
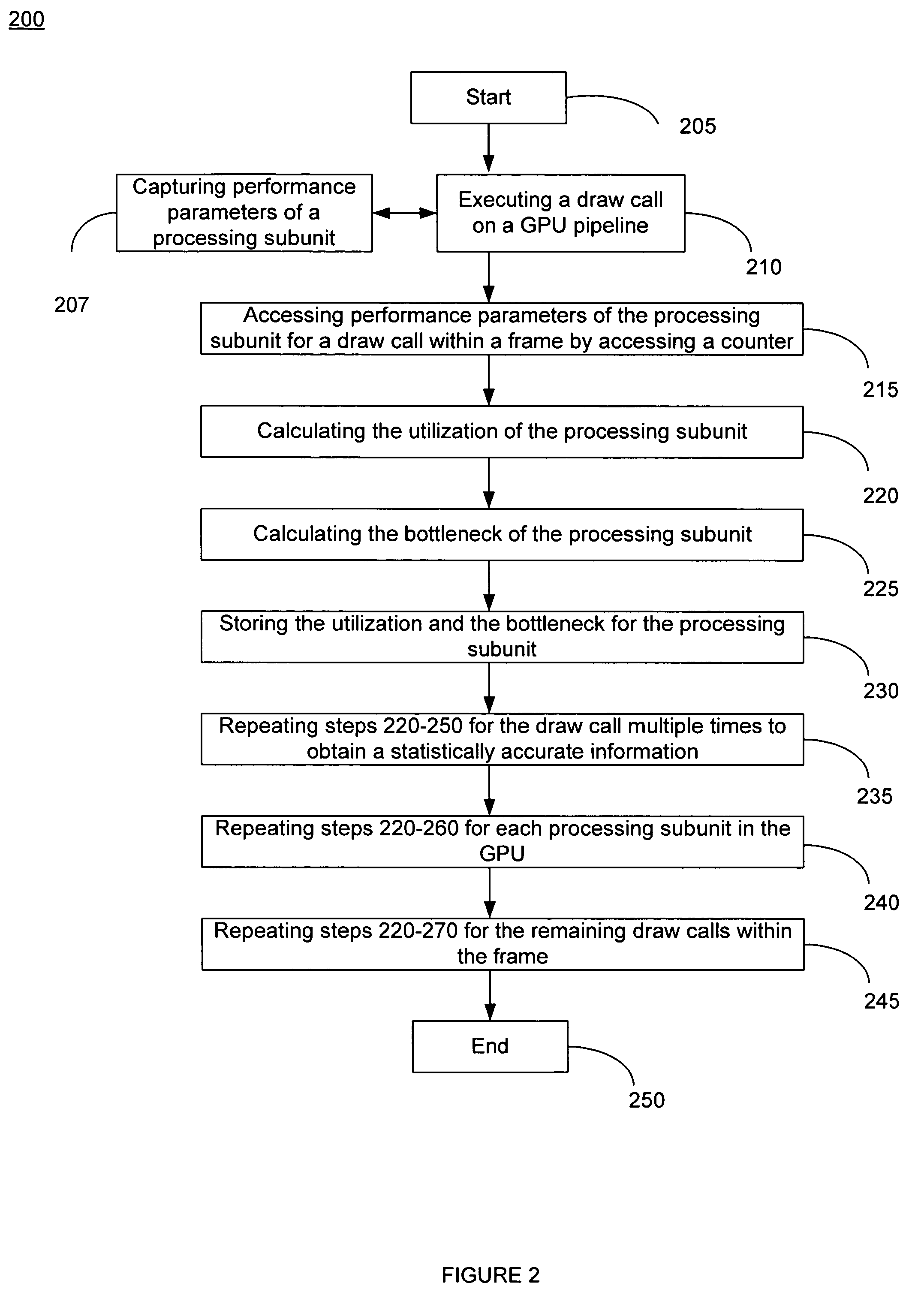
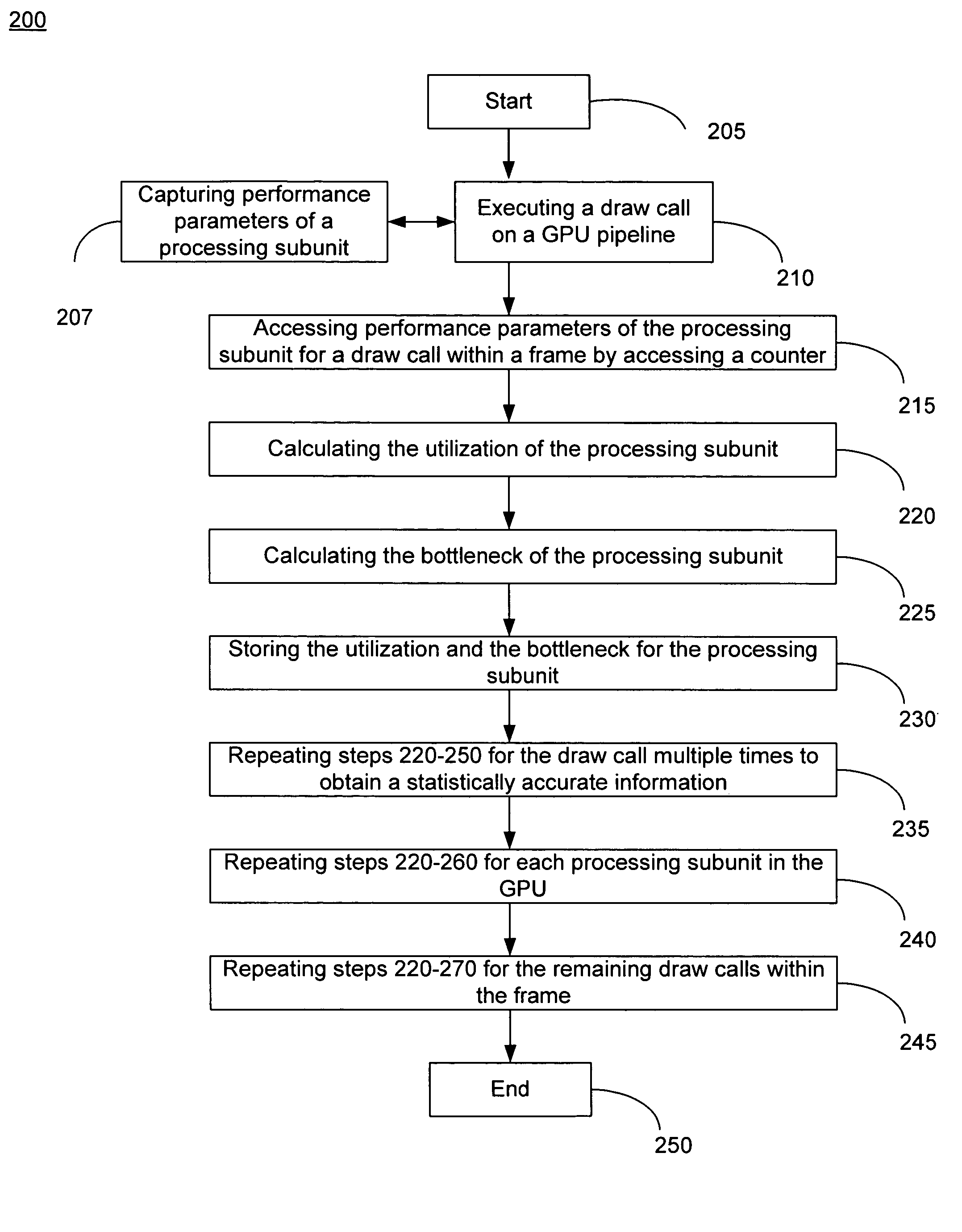
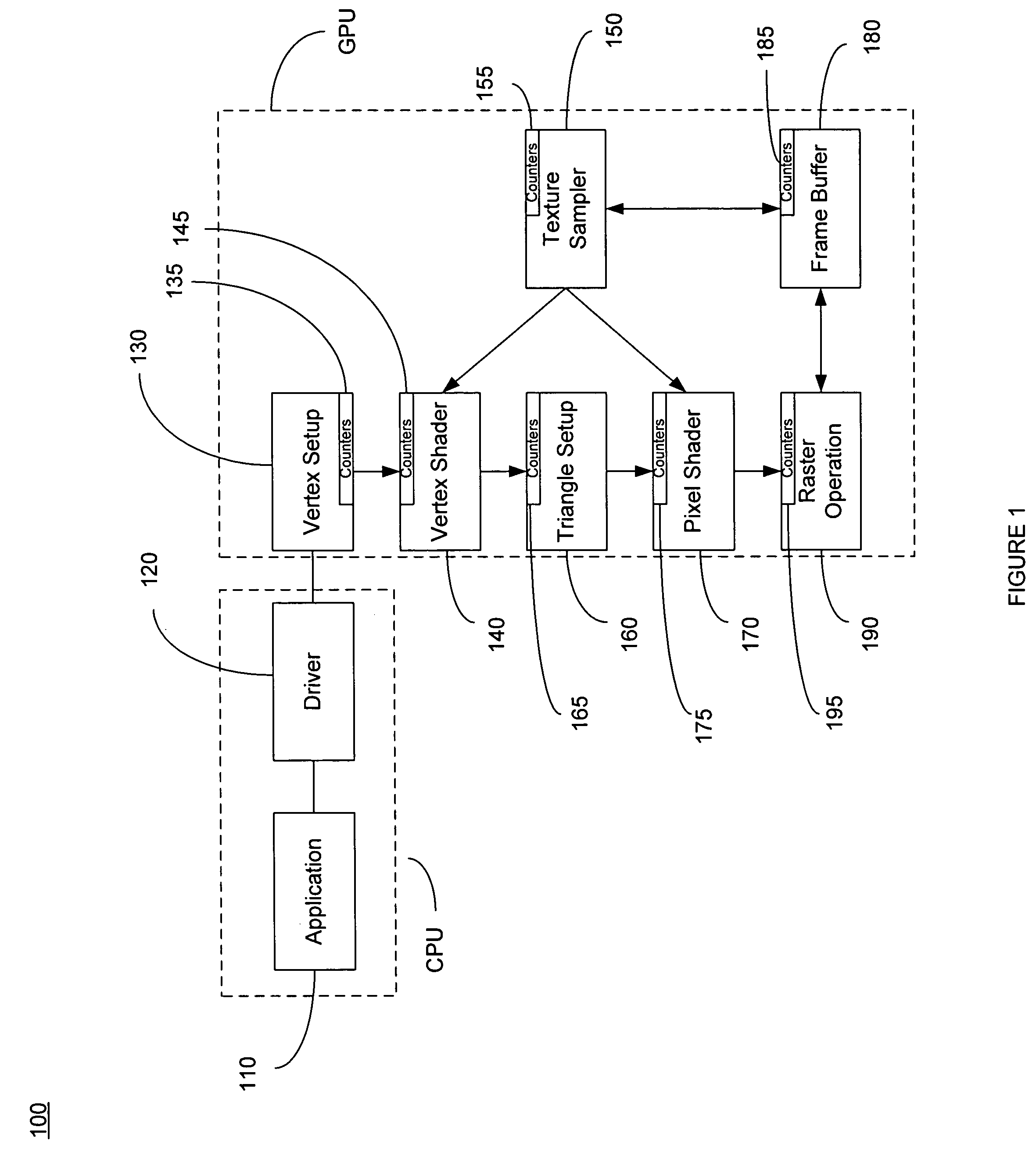
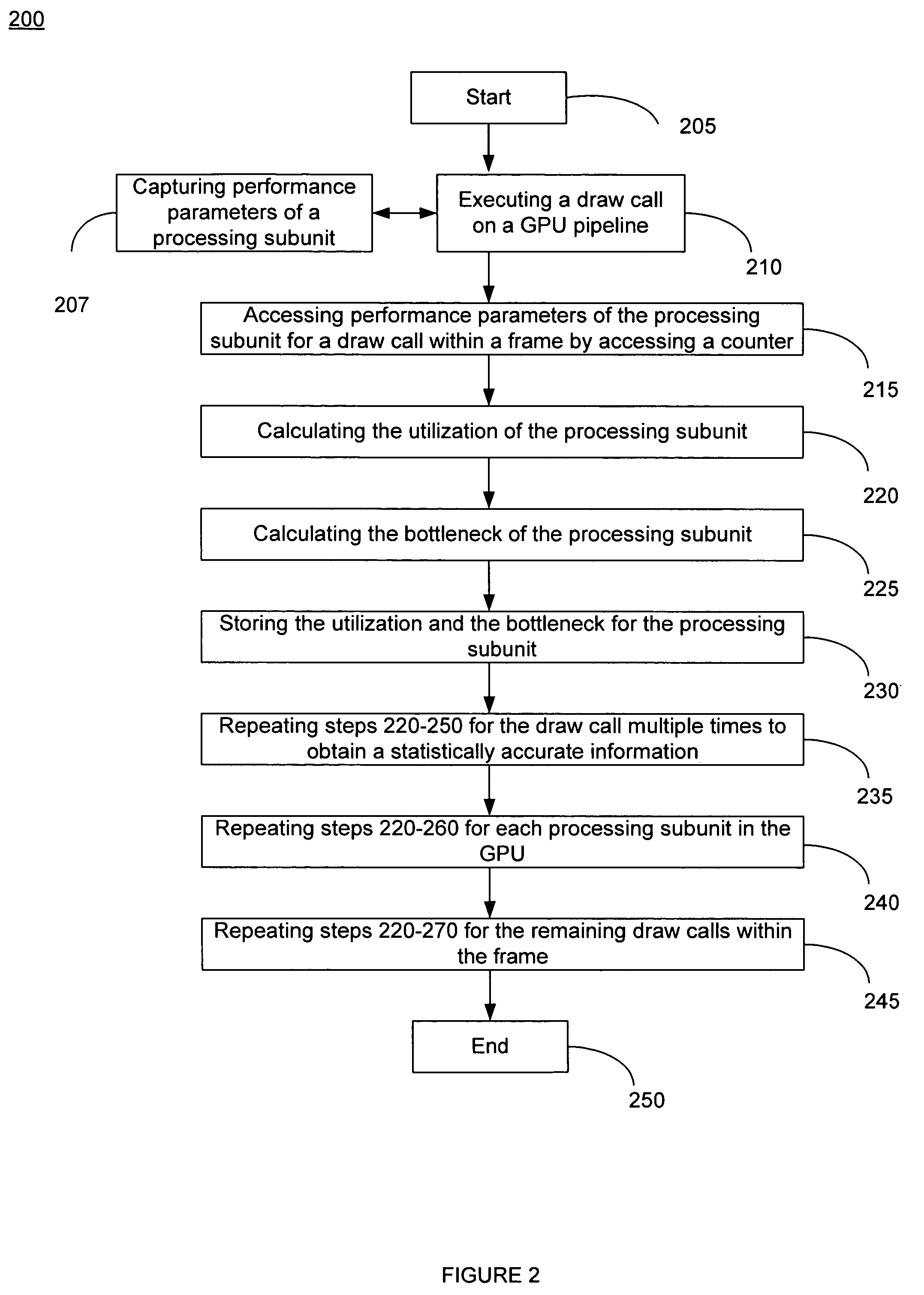
ActiveUS7778800B2Increase frame rateProtect informationDigital computer detailsNuclear monitoringGraphicsDownstream processing
A method of calculating utilization and bottleneck performance parameters of a processing unit within a graphical processing unit (GPU). The utilization is a measure of a percentage that the processing unit is utilized over a draw call execution time. The bottleneck is the sum of the time period that the processing unit is active, the time period that the processing unit is full and does not accept data from an upstream processing unit, minus the time period that the processing unit is paused because the downstream processing unit is busy and cannot accept data, all over the execution time of the draw call. Performance parameters may be determined by sampling the processing unit and incrementing a counter when a condition is true. The method is repeated for the same draw call, for each processing unit of the GPU, and for a plurality of draw calls comprising a frame.
Owner:NVIDIA CORP
Method and system for calculating performance parameters for a processor
ActiveUS20080033696A1Increase frame rateAccurate calculationMeasurement arrangements for variableDigital computer detailsGraphicsDownstream processing
A method of calculating utilization and bottleneck performance parameters of a processing unit within a graphical processing unit (GPU). The utilization is a measure of a percentage that the processing unit is utilized over a draw call execution time. The bottleneck is the sum of the time period that the processing unit is active, the time period that the processing unit is full and does not accept data from an upstream processing unit, minus the time period that the processing unit is paused because the downstream processing unit is busy and cannot accept data, all over the execution time of the draw call. Performance parameters may be determined by sampling the processing unit and incrementing a counter when a condition is true. The method is repeated for the same draw call, for each processing unit of the GPU, and for a plurality of draw calls comprising a frame.
Owner:NVIDIA CORP
Method and devices for distributing media contents and related computer program product
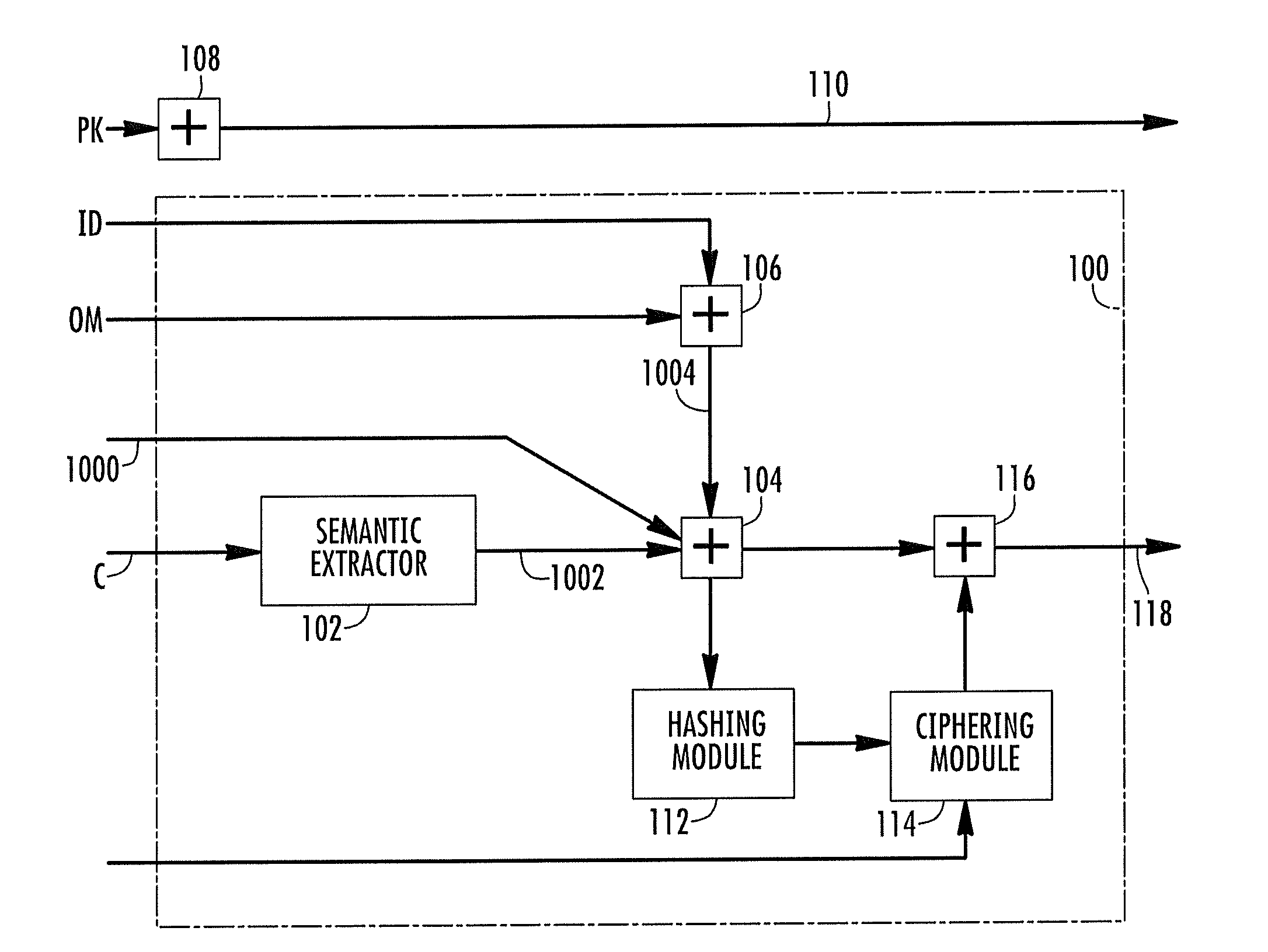
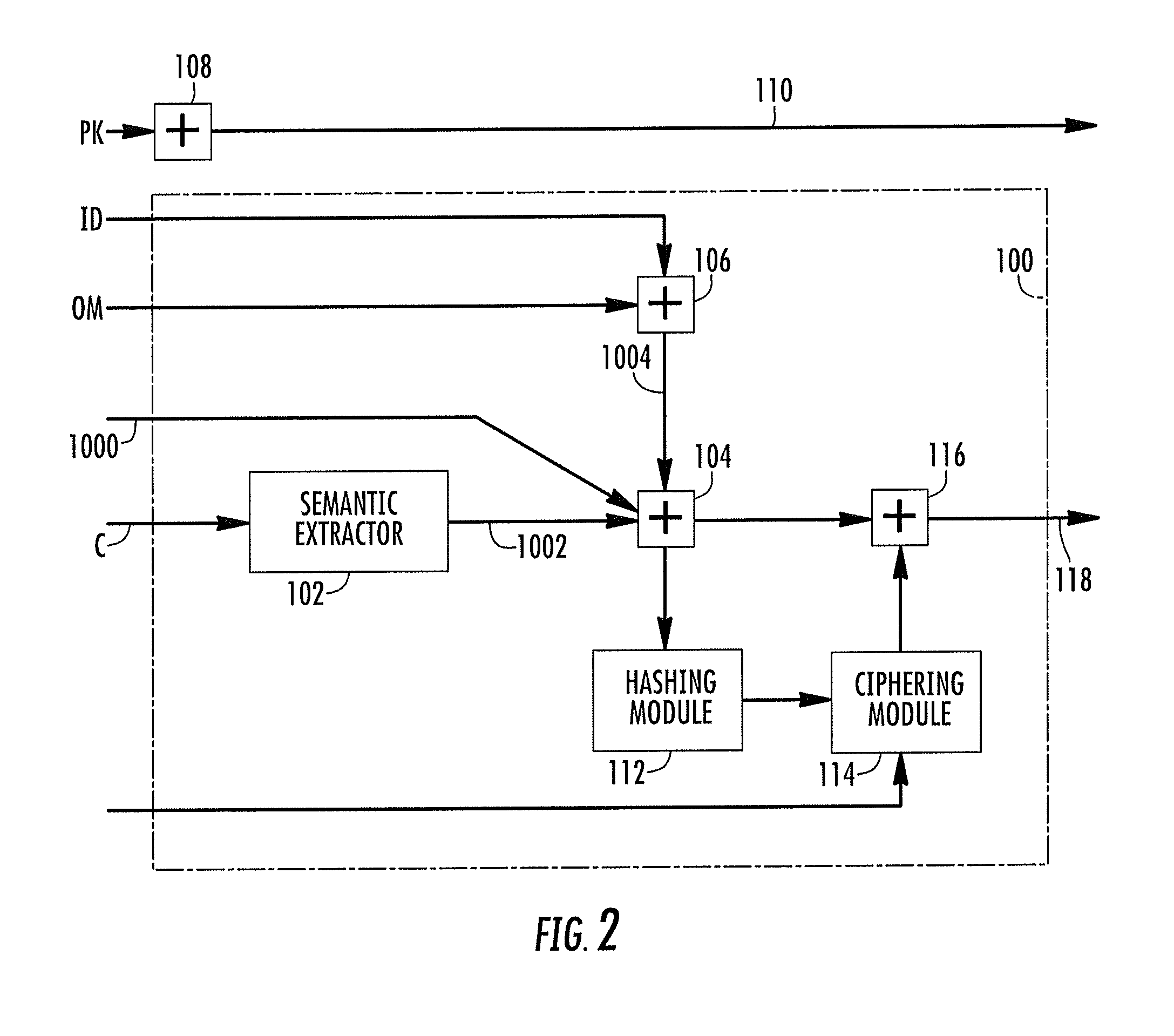
ActiveUS20110161668A1Enriching video browsing experienceDeterring effectUser identity/authority verificationMultiple digital computer combinationsDigital signatureComputer science
A method of distributing media content over networks where content is shared includes coupling downloading metadata, which is accessed to start downloading media contents from the network, with semantic metadata representative of the semantic information associated with at least one of the content, and with source metadata indicative of the source of the media content. At least one of the semantic and the source metadata may be made accessible without downloading, even partially, the media content. A digital signature may also be applied to the metadata to enable the verification that, at reception, the metadata is intact and has not been subjected to malicious tampering.
Owner:STMICROELECTRONICS SRL
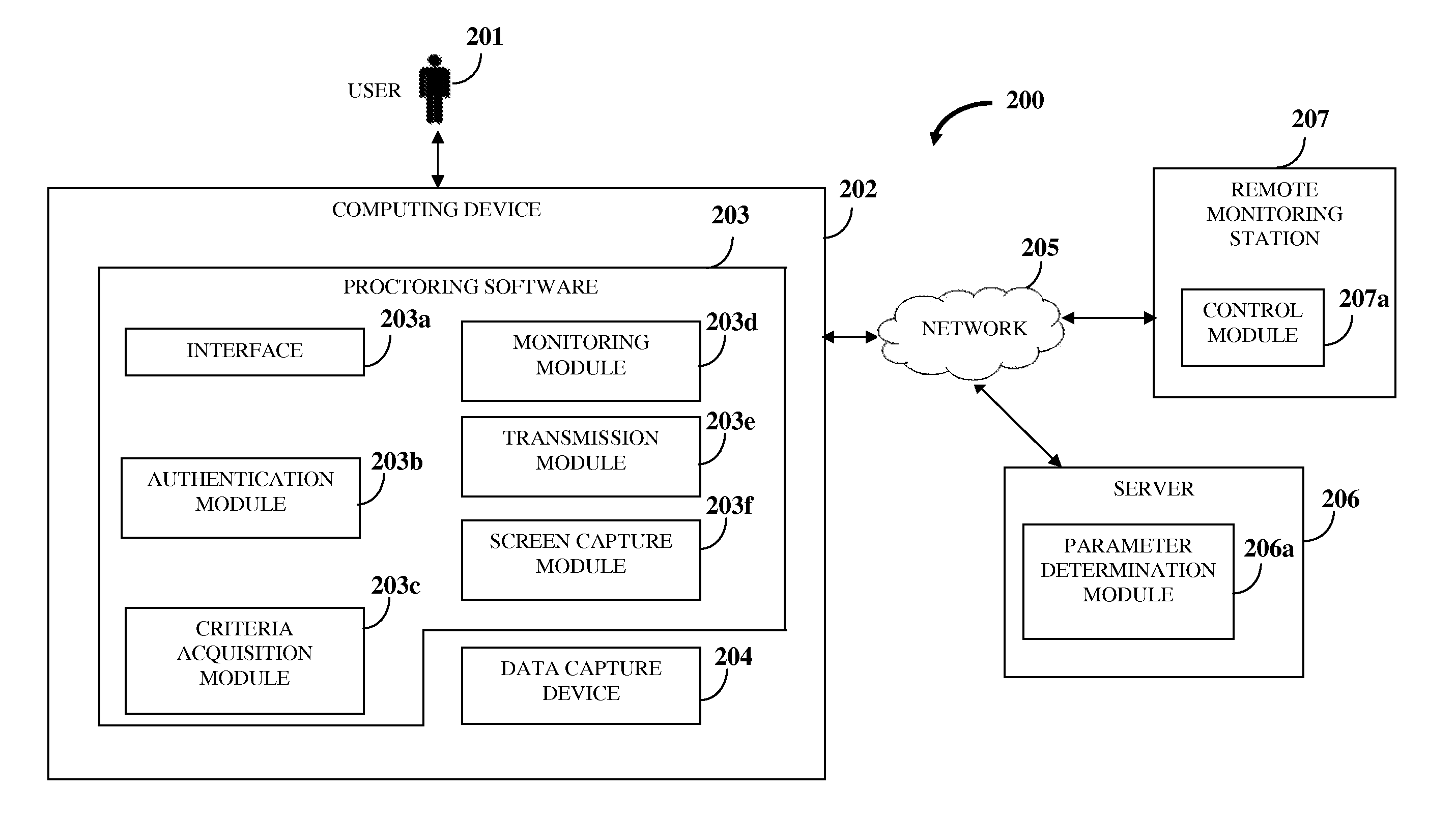
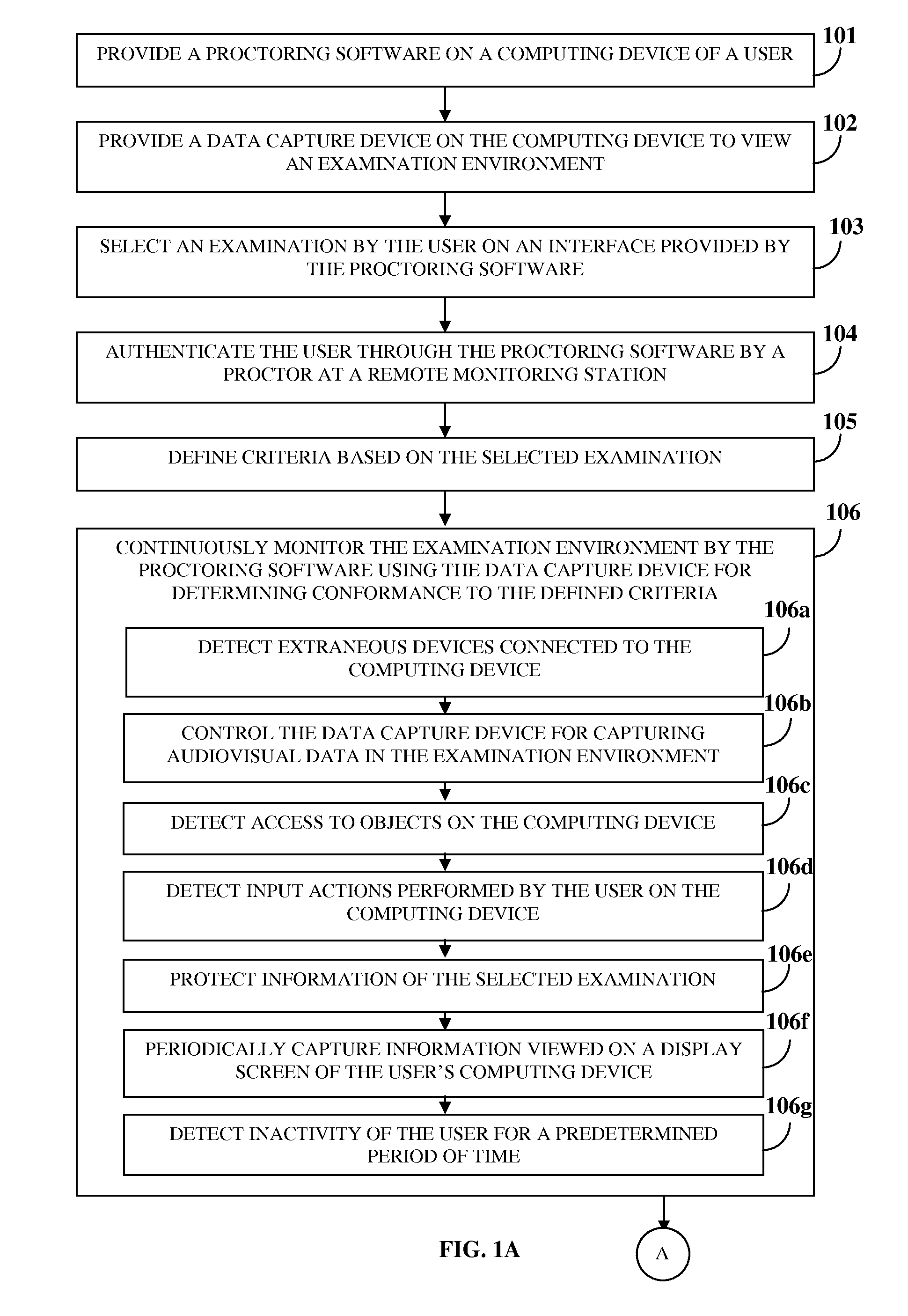
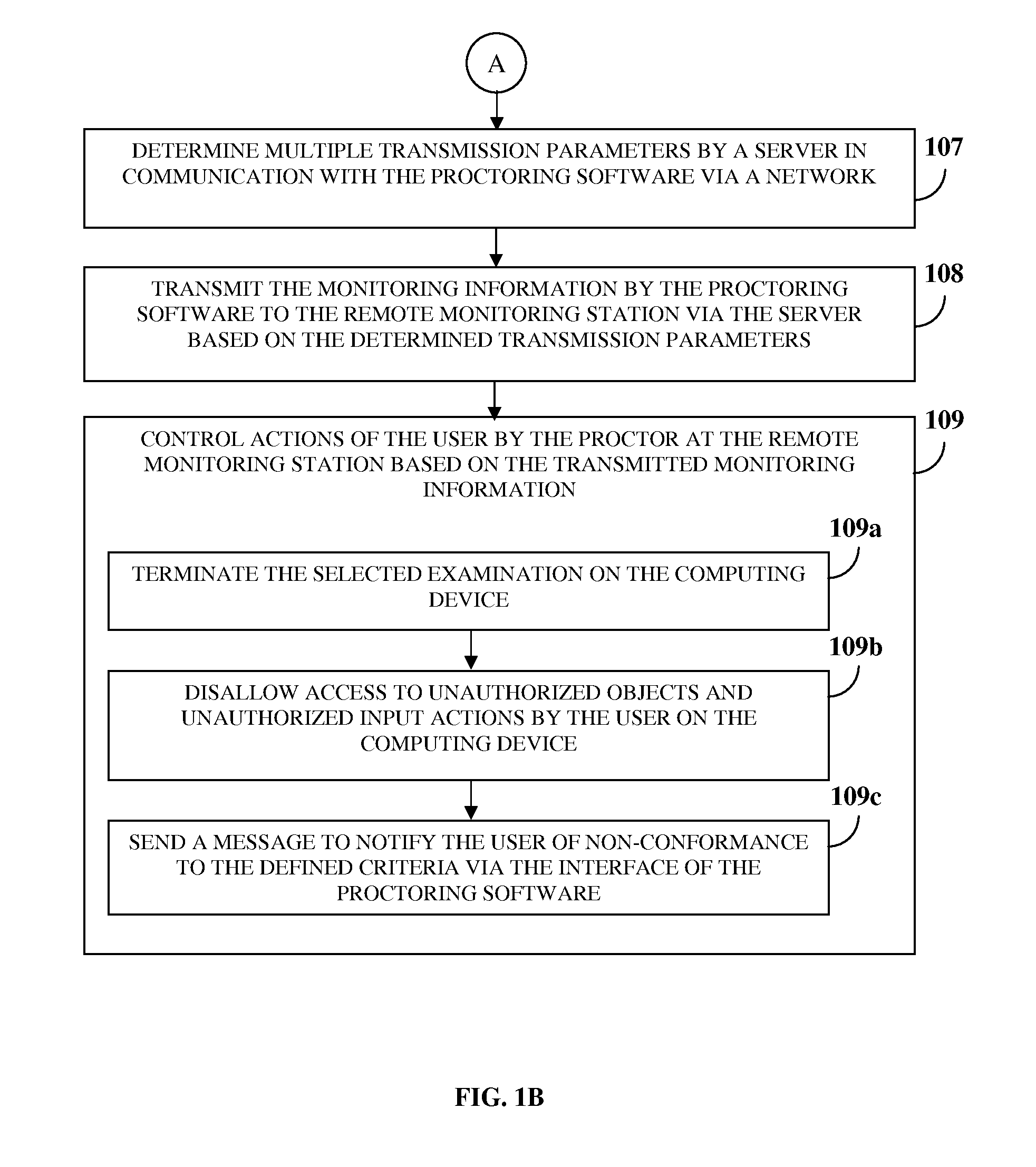
Proctoring System
InactiveUS20120042358A1Protect informationDigital data processing detailsComputer security arrangementsSoftwareComputer science
A computer implemented method and system is provided for authenticating and monitoring an examination environment of a user. A proctoring software provided on a user's computing device communicates with a remote monitoring station via a server over a network. A data capture device provided on the computing device is configured to rotate and tilt to multiple angles to view and capture audiovisual data from the examination environment. A proctor administering the remote monitoring station authenticates the user based on an examination selected by the user. The proctor defines criteria comprising actions allowed for the user while taking the examination. The proctoring software monitors the examination environment for conformance to the defined criteria. The proctoring software transmits the monitoring information to the remote monitoring station based on transmission parameters determined by the server. The proctor controls actions of the user when the user is not in conformance with the defined criteria.
Owner:DEVSQUARE
Out-of-band remote management station
InactiveUS7171467B2Eliminate security concernsProtect informationDigital computer detailsSupervisory/monitoring/testing arrangementsModem deviceDigital interface
A computer network management system with an embedded processor, an analog communication means and a digital interface for network management provides a system for remotely and securely managing a network. Backup power in the form of an uninterrupted power supply, or other power means as appropriate, allows the modem to provide power outage notification to a remote site. The system further provides authentication and authorization capabilities for security purposes.
Owner:INTELLECTUAL VENTURES II
Method and system for routing ioi's and trade orders
InactiveUS20120089502A1Protect informationEasy to useFinanceDigital data processing detailsRegulatory ReportAnonymity
Embodiments of the present invention include systems for linking routed orders to IOI's. Broker / dealers and buyside clients may be connected to the system through system interfaces or via standard FIX protocols. A broker / dealer may submit an order to the system, which verifies and forwards the order to an ATS to be matched with an authorized buyside order. The system constructs an actionable IOI (ATX-IOI) and sends the ATX-IOI to the buyside. The buyside may send responsive orders to the system, which verifies, creates, and submits a buy order to the ATS, preserving the anonymity of the buyside. If a trade is executed, the ATS delivers notice to the system, which may generate and send fill reports to the broker / dealer and buyside, at which point identifying information of the buyside may also be provided. The system may generate compliance and regulatory reports further to the completion of the trade.
Owner:DIX ADAM E +2
Method and devices for distributing media contents and related computer program product
ActiveUS8843744B2Lower performance requirementsIncrease chanceMemory loss protectionDigital data processing detailsDigital signatureMetadata
A method of distributing media content over networks where content is shared includes coupling downloading metadata, which is accessed to start downloading media contents from the network, with semantic metadata representative of the semantic information associated with at least one of the content, and with source metadata indicative of the source of the media content. At least one of the semantic and the source metadata may be made accessible without downloading, even partially, the media content. A digital signature may also be applied to the metadata to enable the verification that, at reception, the metadata is intact and has not been subjected to malicious tampering.
Owner:STMICROELECTRONICS SRL
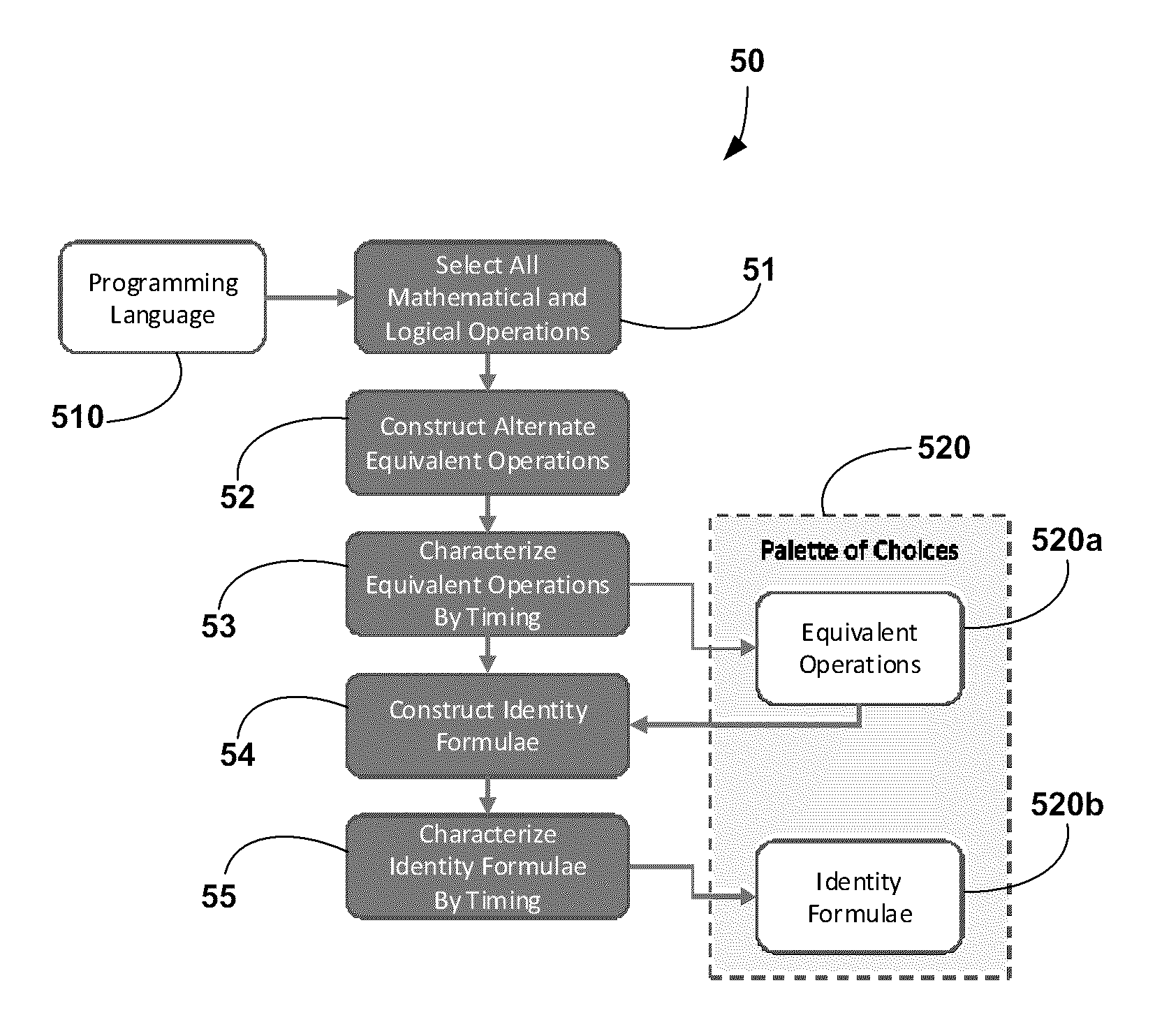
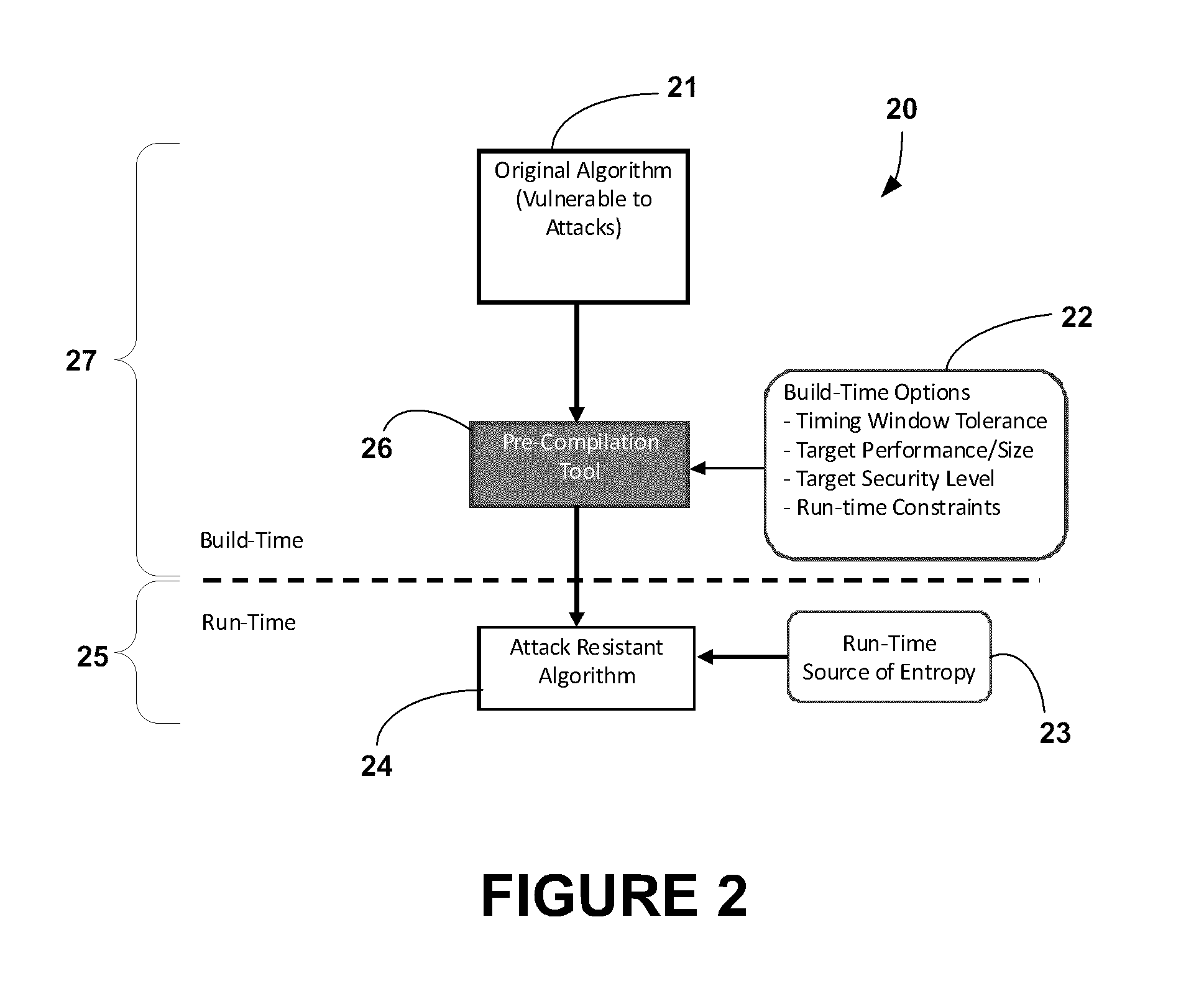
System and Method for Dynamic, Variably-Timed Operation Paths as a Resistance to Side Channel and Repeated Invocation Attacks
InactiveUS20130007881A1Preventing side channel or repeated invocationReduce the amount of solutionMemory loss protectionError detection/correctionComputer scienceSoftware implementation
A system and method for constructing variably-timed operation paths and applying those paths to any algorithm. In particular, the system and method may be applied to cryptography algorithms as a means to resist side-channel, repeated invocation, and any similar attacks based on the physical characteristics of a system for a given software implementation. The method has the benefit of being generally applicable to any algorithm and has the ability to constrain performance to known timing windows.
Owner:IRDETO CANADA CORP
Security system
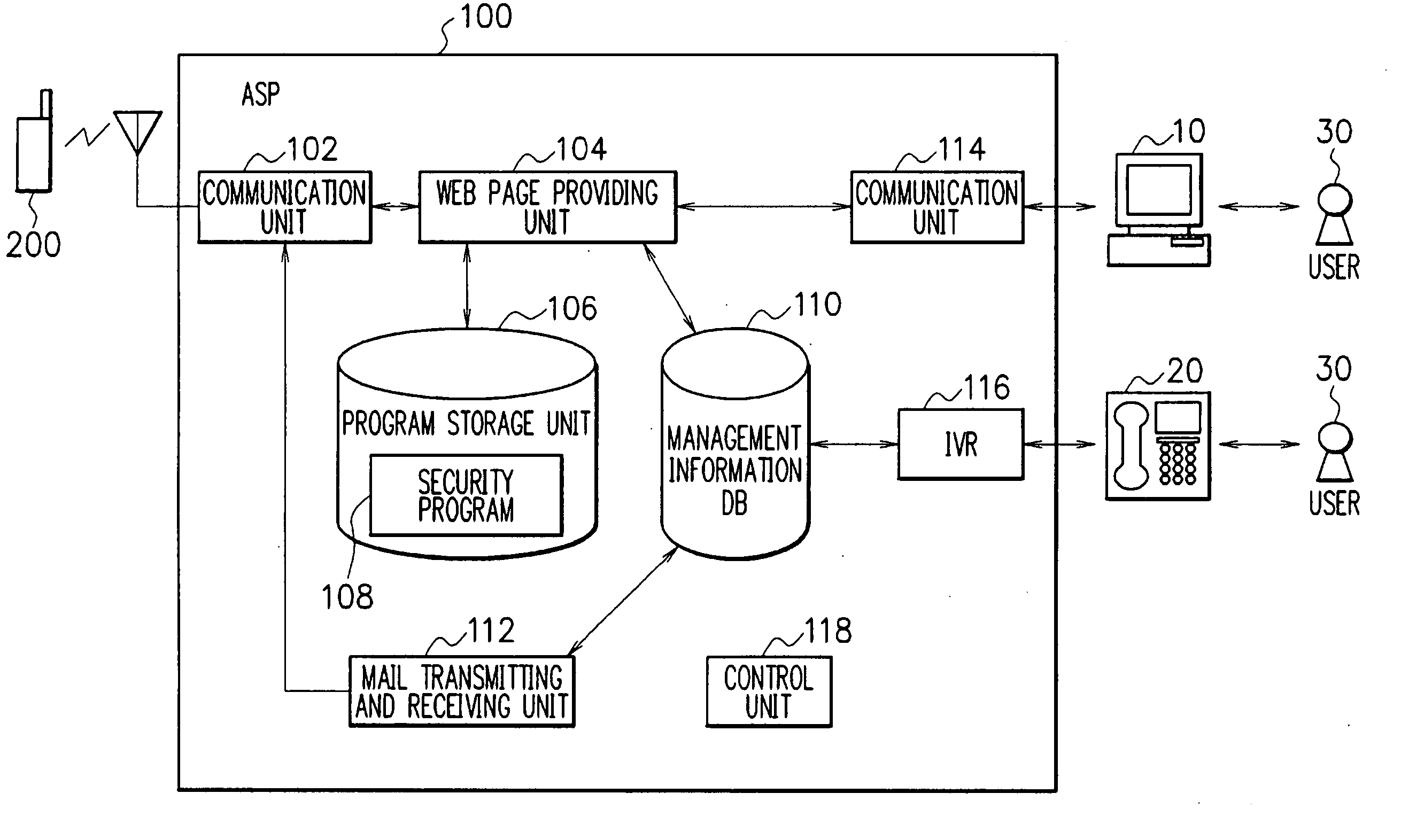
ActiveUS20060109101A1Protect informationFrequency-division multiplex detailsUnauthorised/fraudulent call preventionSafe systemInformation storage
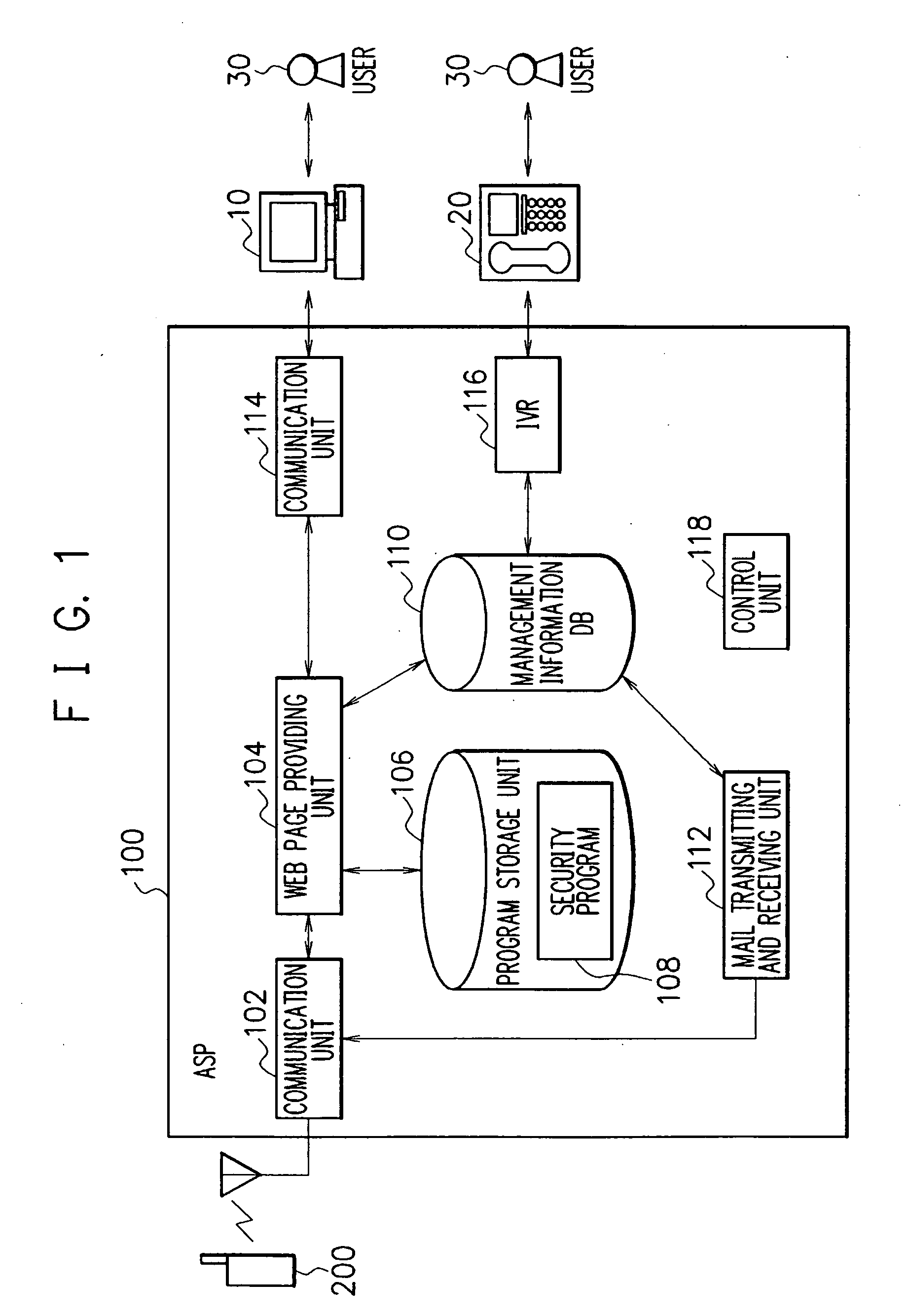
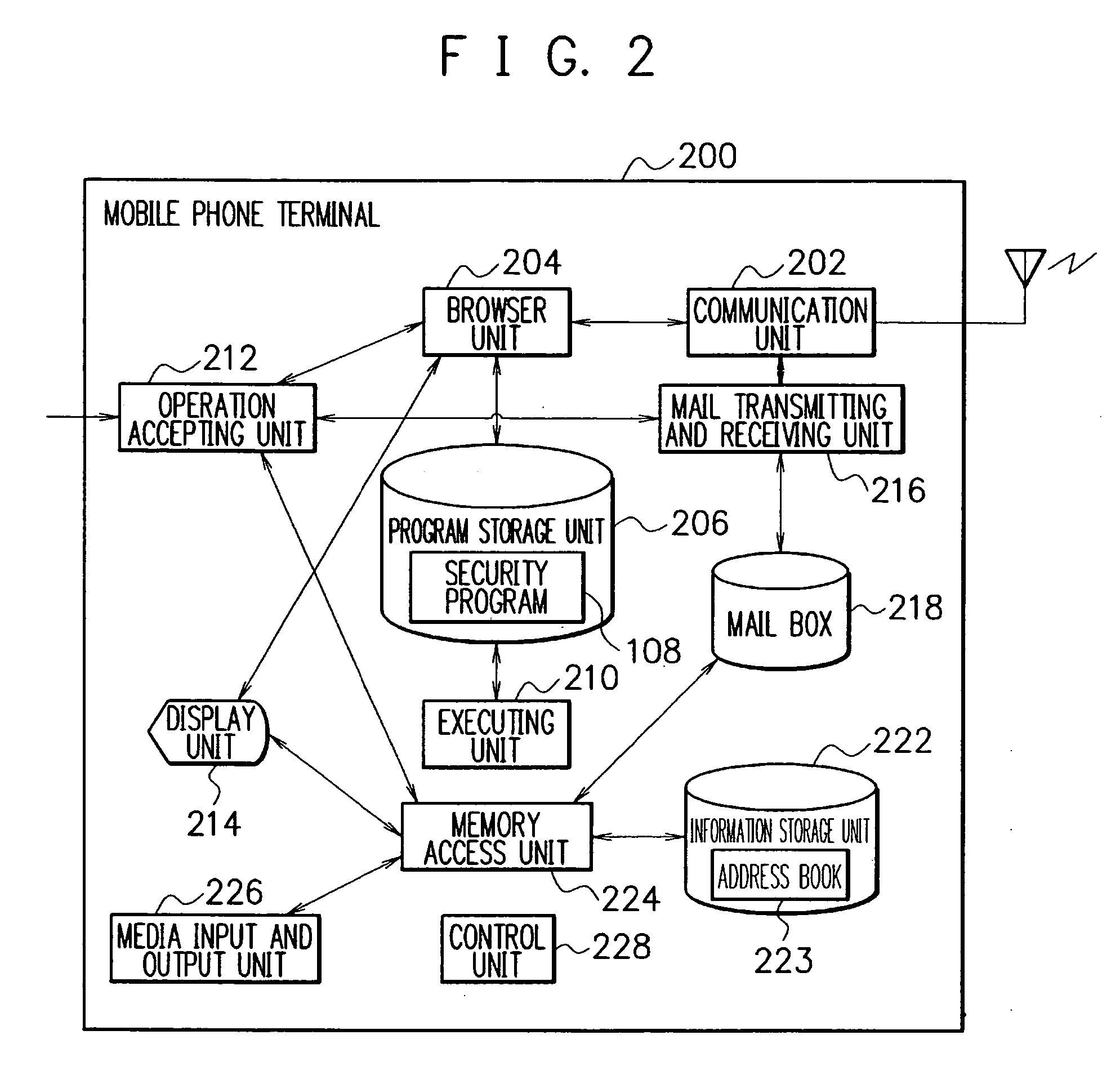
A security system is provided, which can protect information within a mobile phone terminal when the mobile phone terminal is lost or stolen. The security system comprises an ASP to protect information on the mobile phone terminal having information storage unit to store information, and the ASP includes an instruction accepting unit to accept a protection instruction to protect information from a user of the mobile phone terminal and a cancellation instruction to cancel the protection of the information, an authentication unit to certify the user of the mobile phone terminal, and an instruction exhibiting unit to notify a portable communication terminal of the protection instruction and the cancellation instruction when the authentication unit authenticate the user, and the mobile phone terminal includes an instruction referring unit to receive the protection instruction and the cancellation instruction from the ASP, a protecting unit to perform a process of protecting the information according to the protection instruction and a canceling unit to perform a process of canceling the protection of the information according to the cancellation instruction.
Owner:NEC CORP
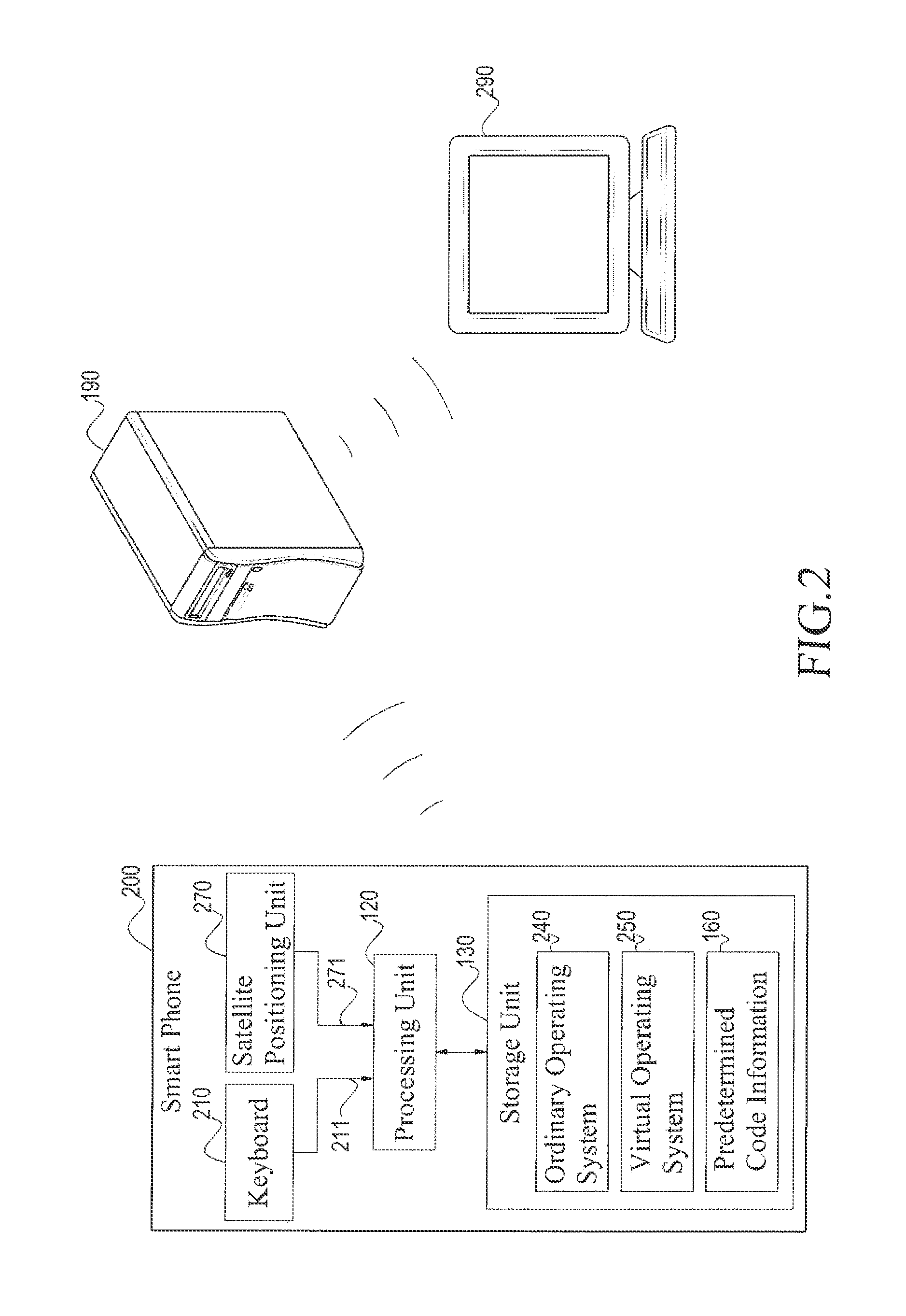
Anti-theft system for mobile electronic device and method thereof
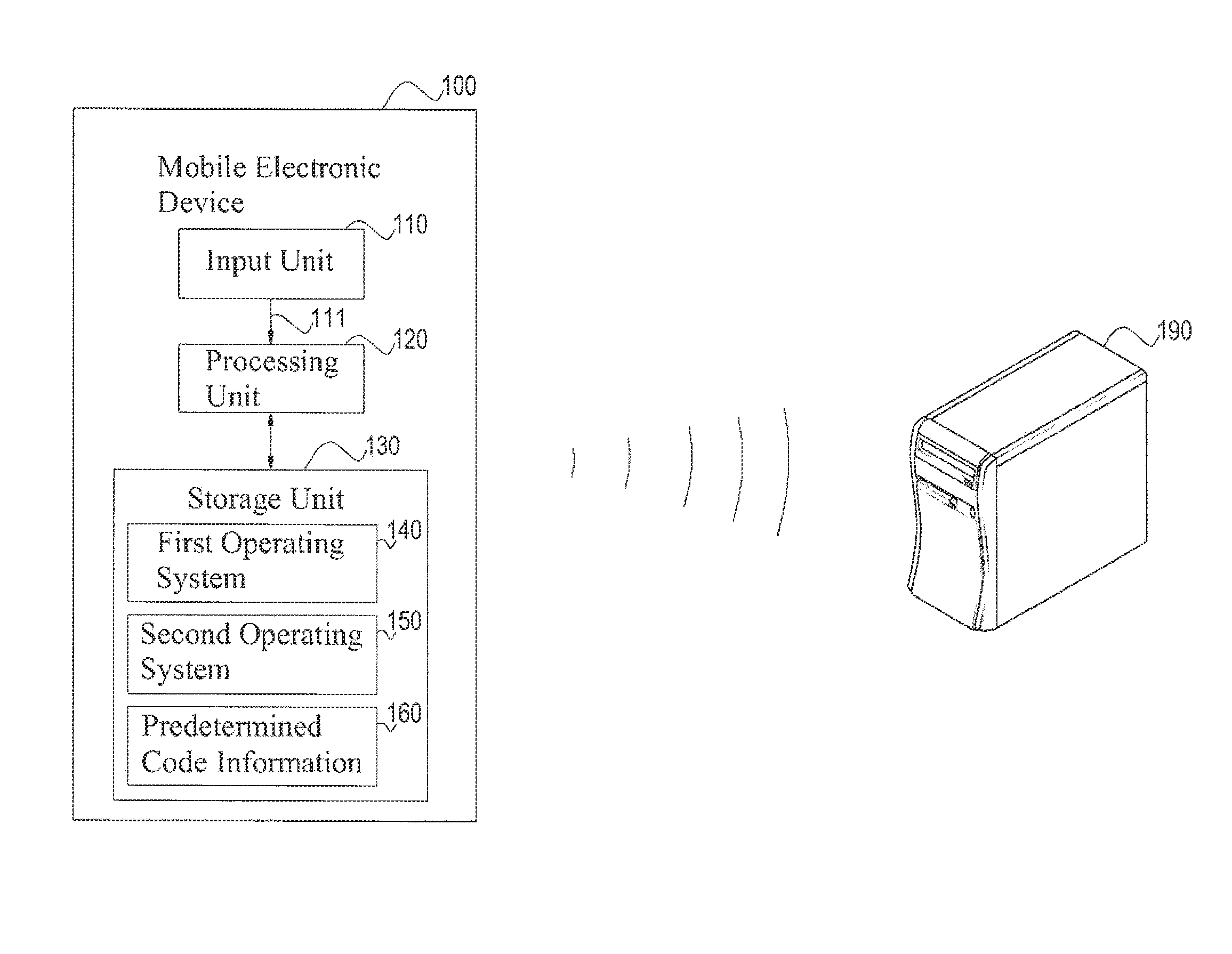
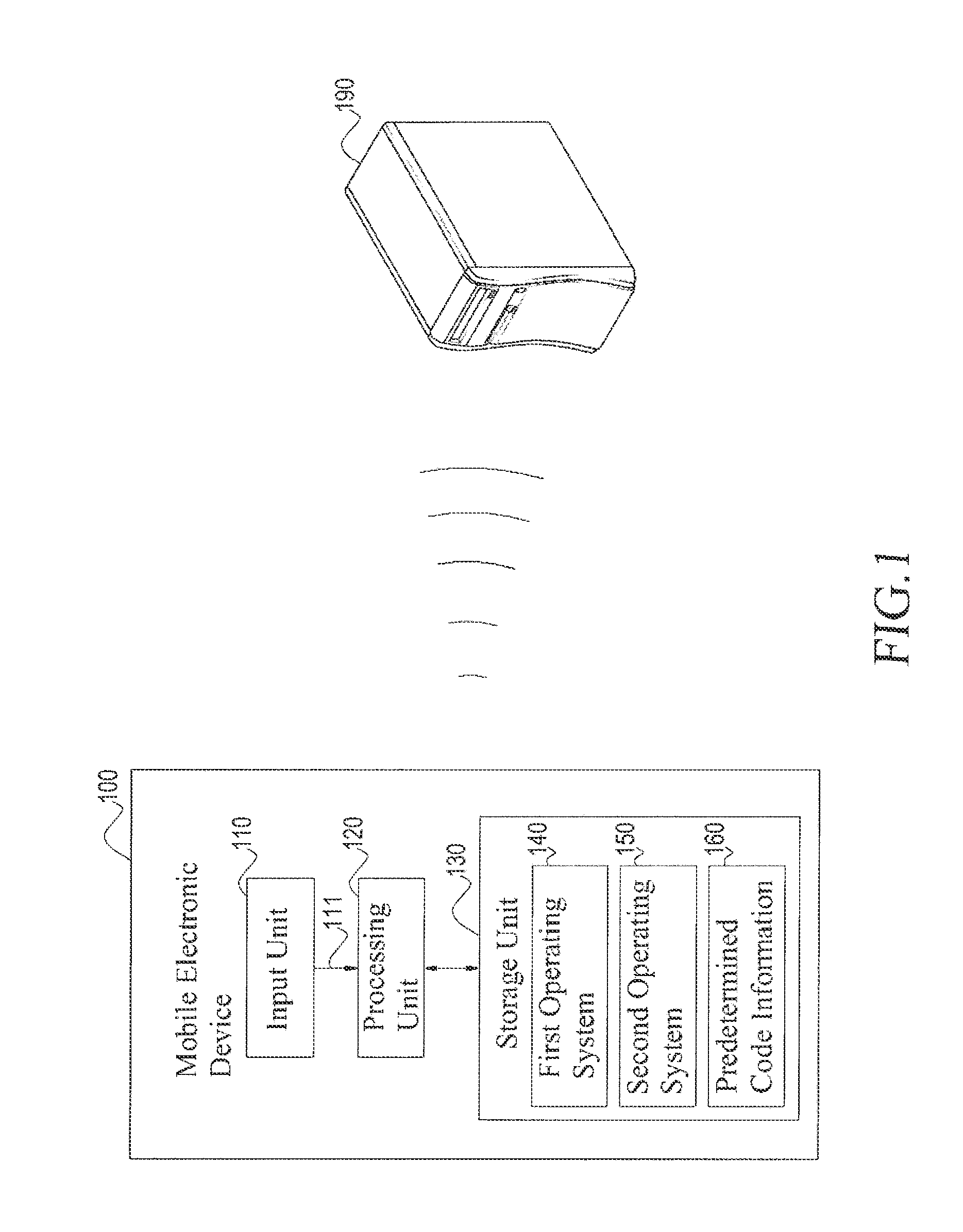
InactiveUS20130260722A1Easy to find outProtect informationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsOperational systemOperating system
An anti-theft system applicable to a portable electronic device is provided in the present invention. The anti-theft system includes an input unit, a storage unit and a processing unit. The input unit is configured to receive code information. The storage unit is configured to store a first operating system, a second operating system and predetermined code information. The processing unit is configured to compare the code information with the predetermined code information. When the code information matches the predetermined code information, the processing unit enables the first operating system. When the code information does not match the predetermined code information, the processing unit enables the second operating system.
Owner:INVENTECSHANGHAI TECH +2
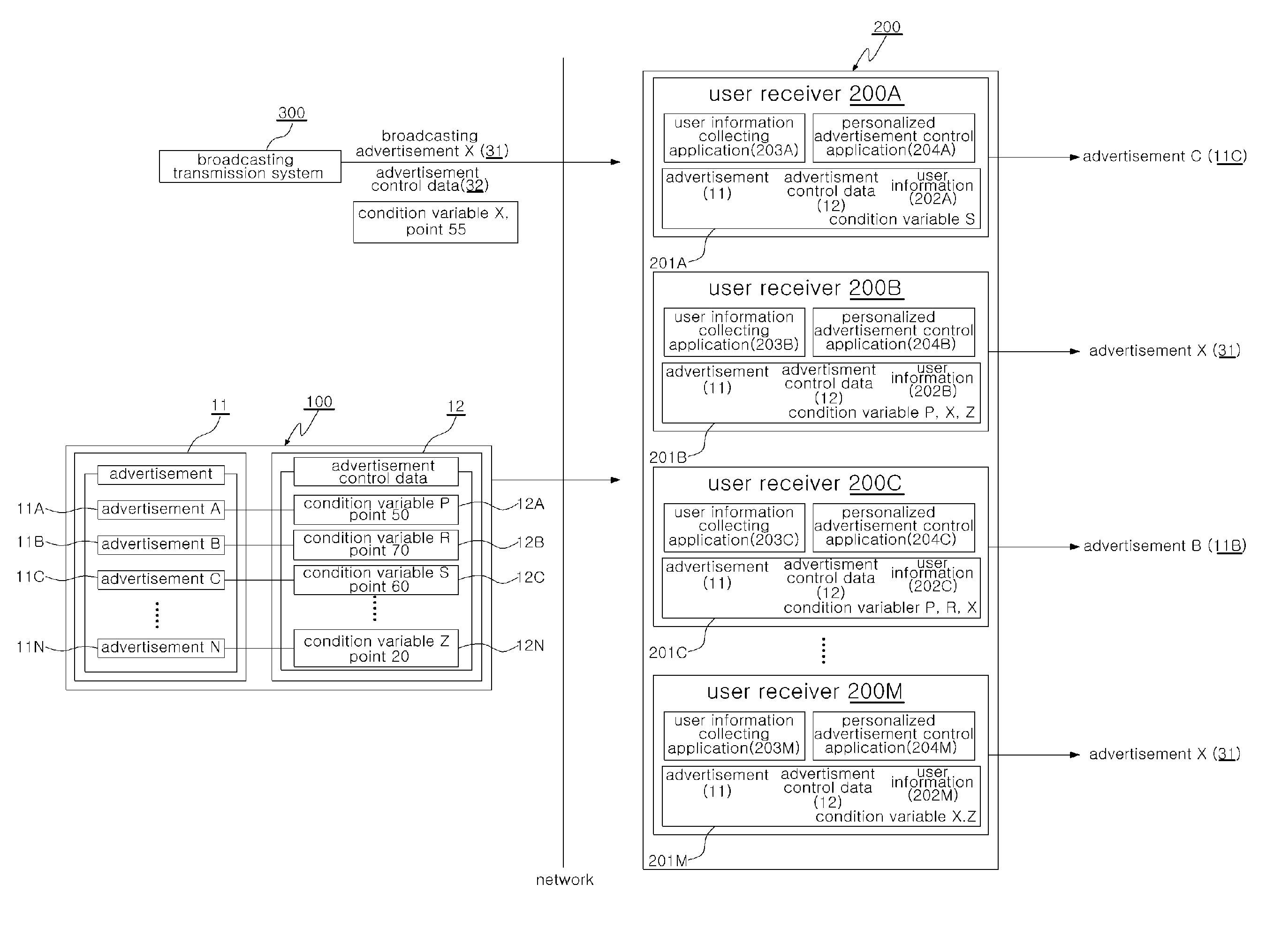
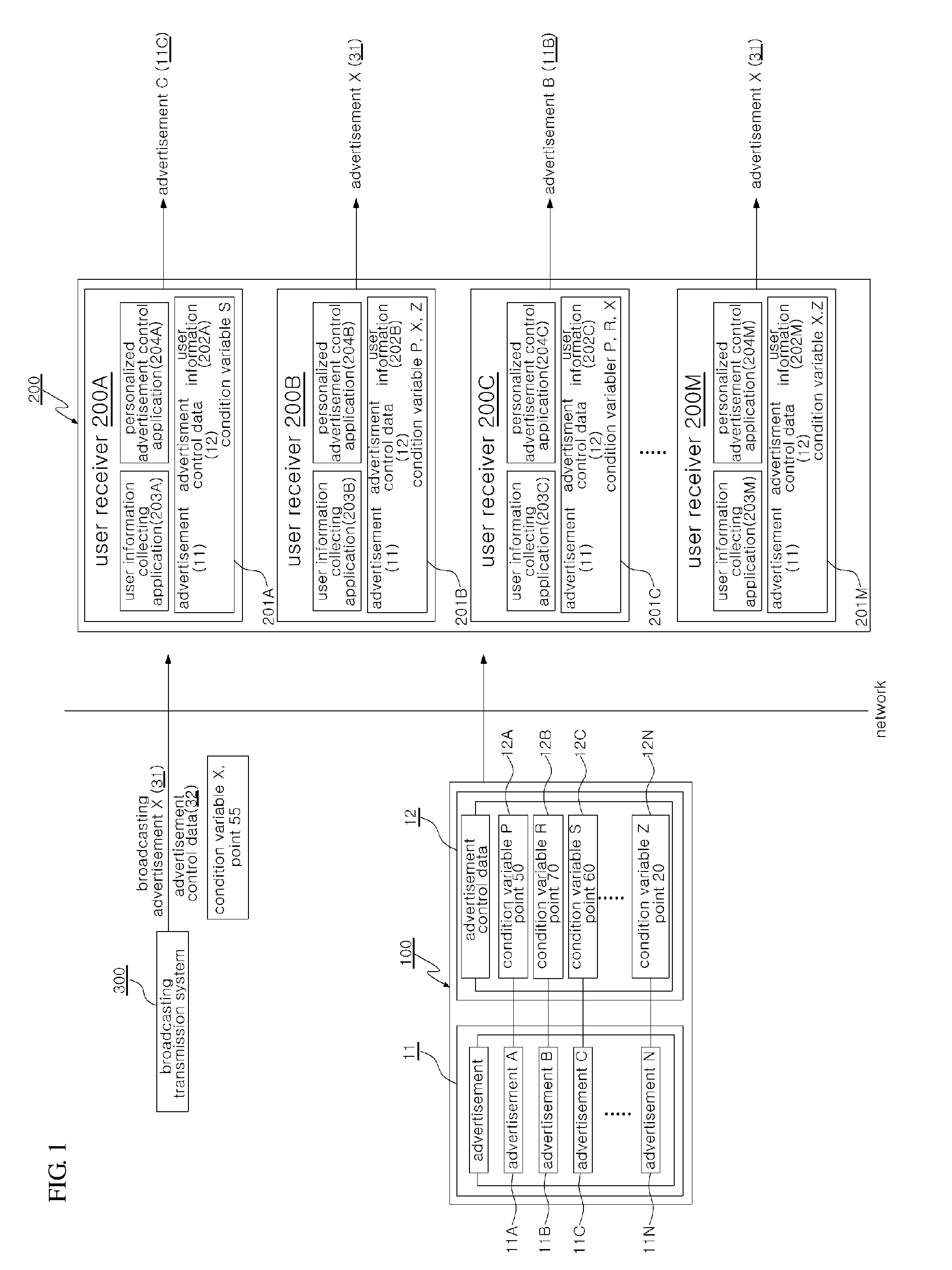
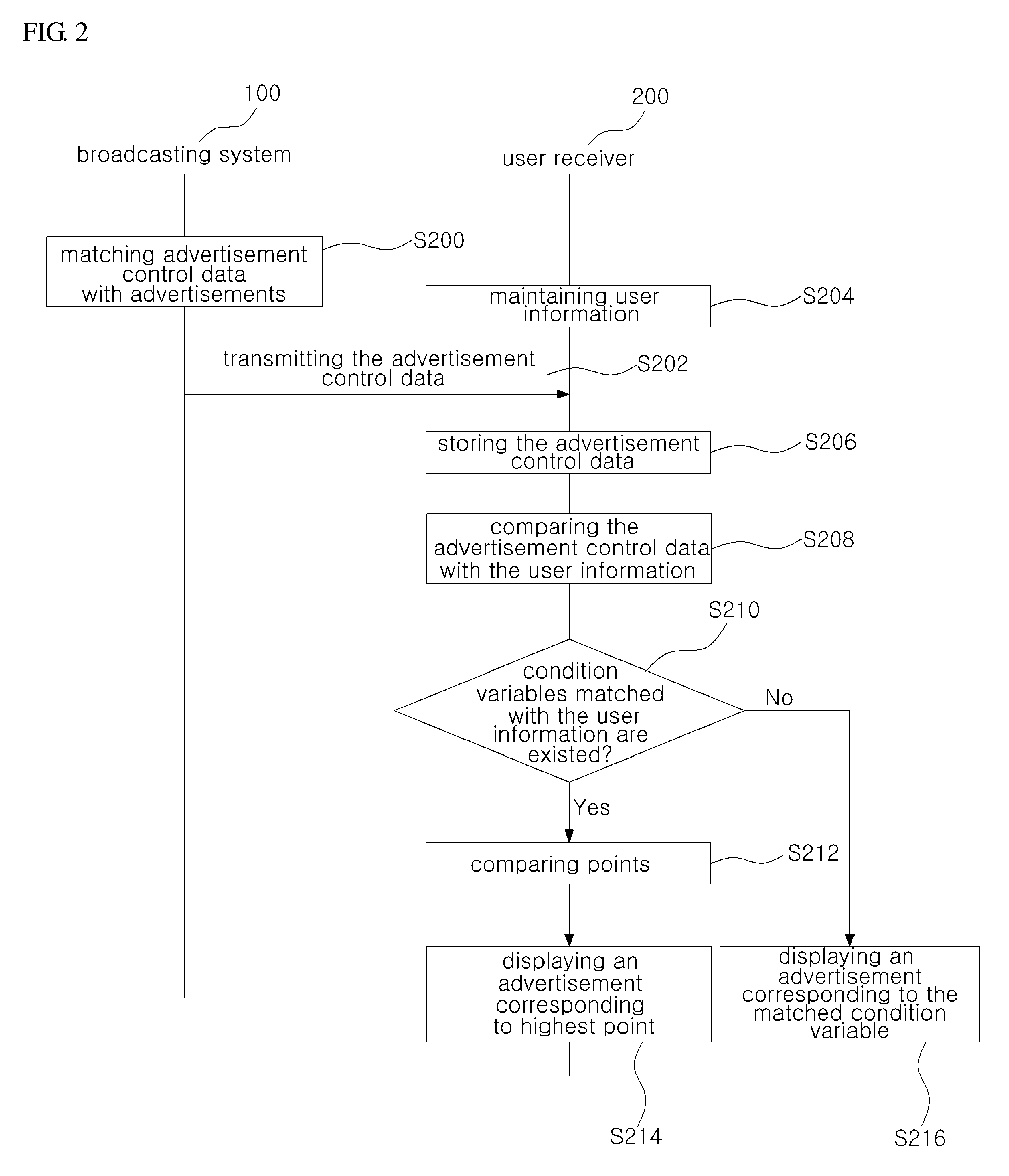
Method of providing personalized advertisements
A user receiver coupled to an advertisement system through a network is used to provide a method of providing a personalized advertisement. The method includes: maintaining user information related to user's video view; receiving from the advertisement system respective first advertisement control data corresponding to a plurality of first advertisements, wherein the respective first advertisement control data includes at least one first condition variable and at least one first point; comparing the user information with the first condition variable or variables; and displaying, when first conditional variables matched with the user information exist, an advertisement corresponding to a first condition variable having the highest first point among the first condition variables matched with the user information.
Owner:ALTICAST
Security device for equipment information and the operation method thereof
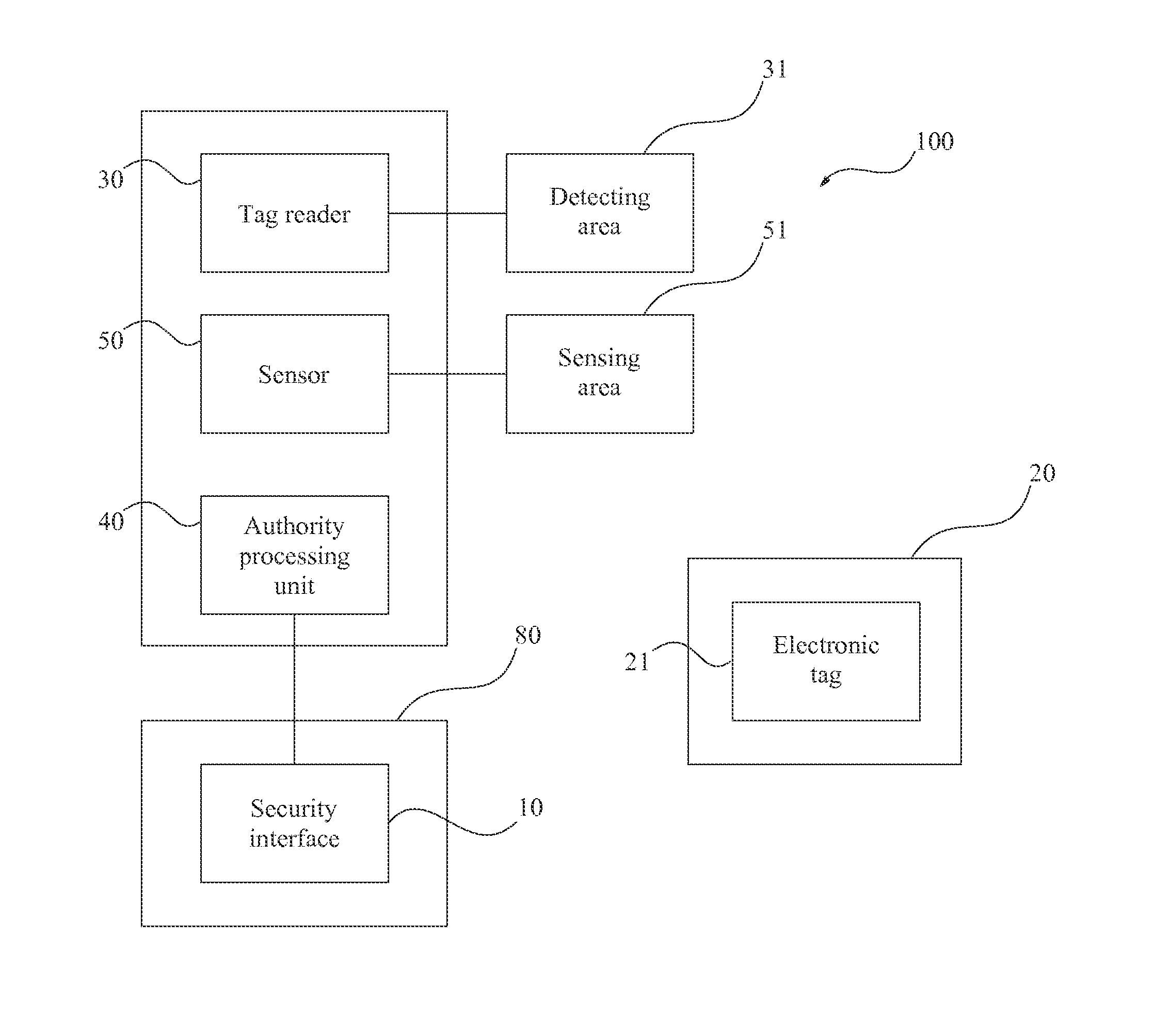
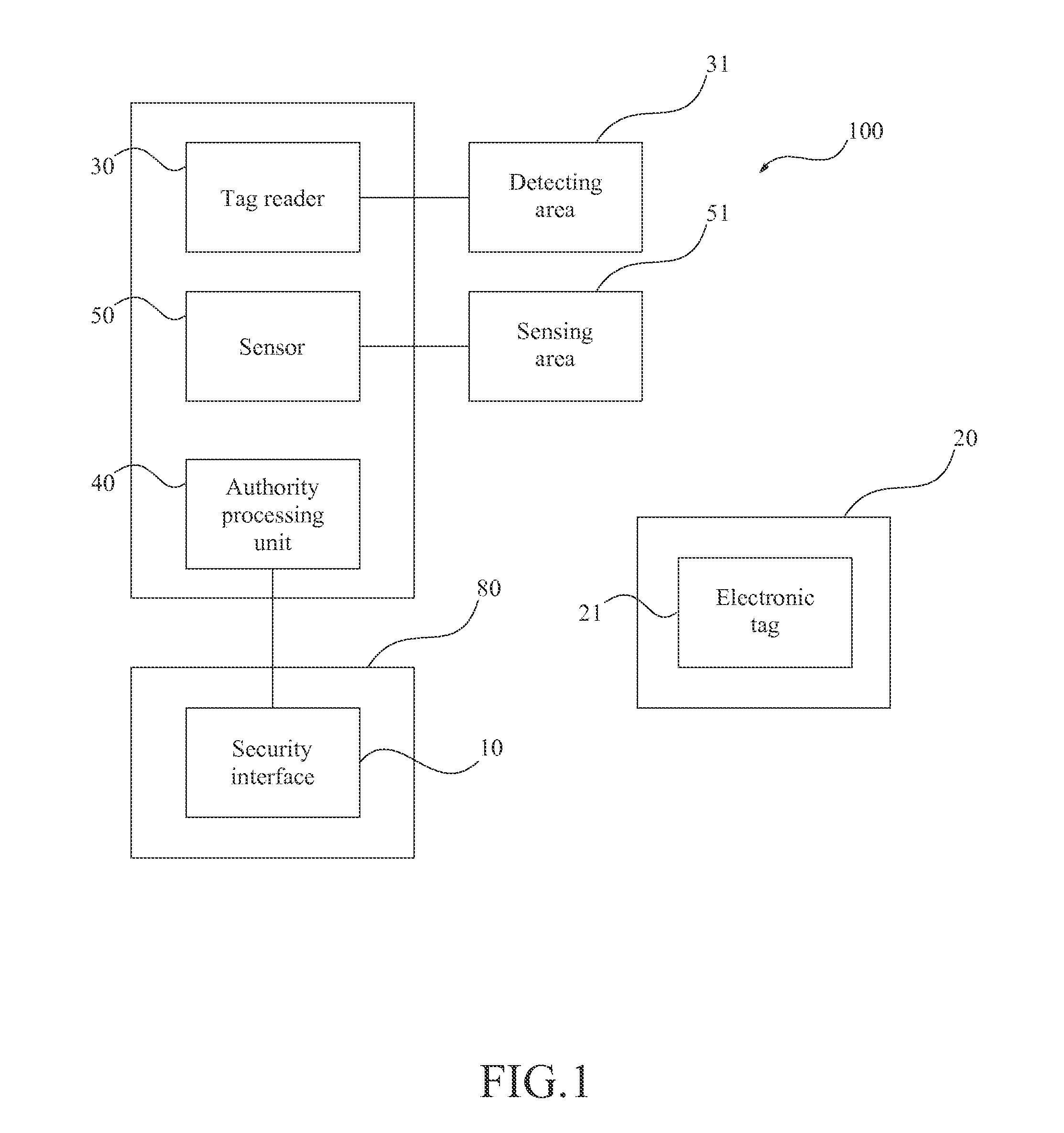
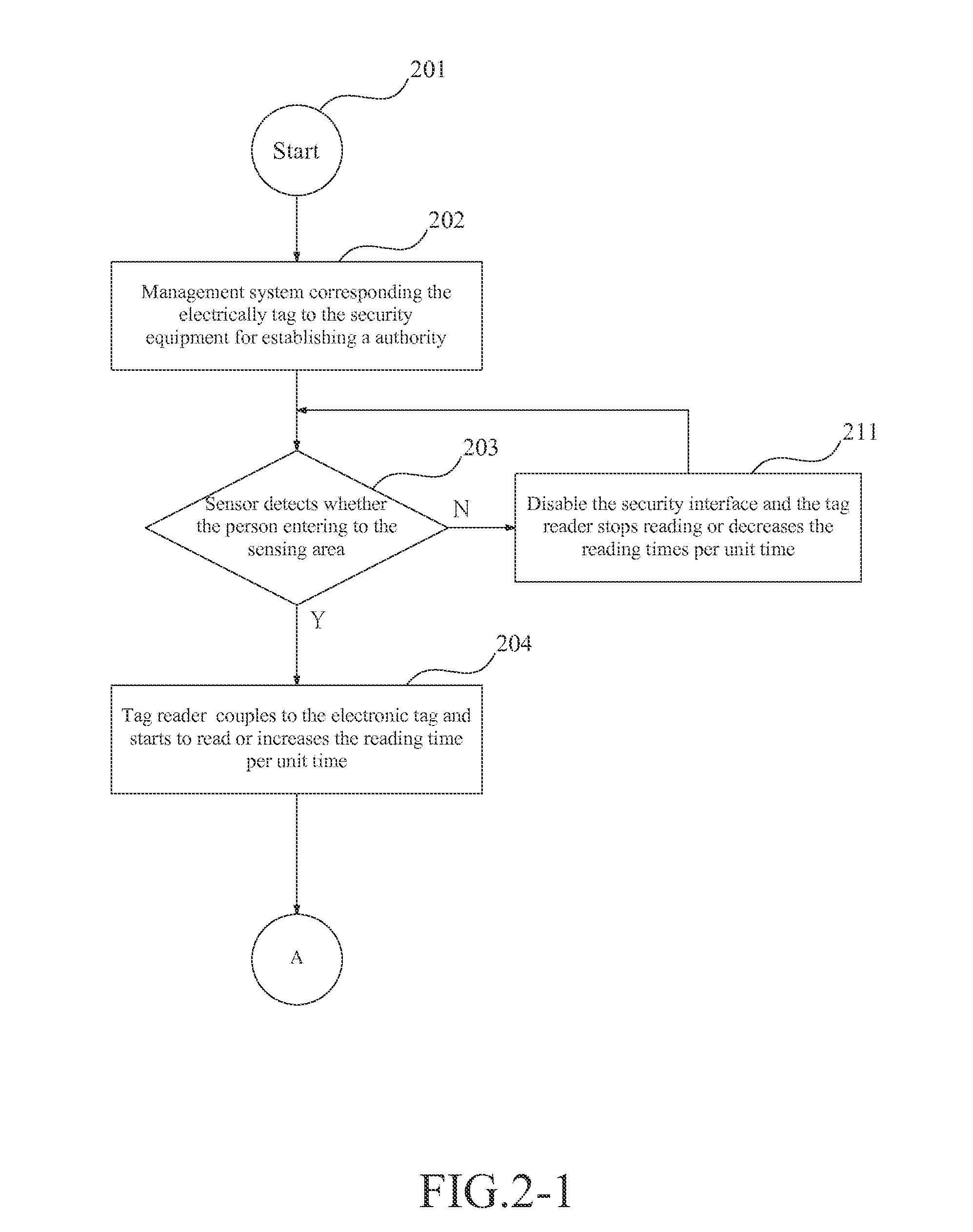
InactiveUS20140218169A1Protect informationInhibition of informationProgramme controlElectric signal transmission systemsElectronic taggingSecure state
An equipment information security device is provided. The equipment information security device is installed on an equipment with confidential information, wherein the equipment or the device has a security interface, the device comprises: a fitting which is worn by a staff and combined with an electronic tag with or without authority to the corresponding equipment; a tag reader, which detects the electronic tag within a detecting area corresponding to the security interface; and an authority processing unit, which links to the tag reader: wherein the authority processing unit sets the security interface to an operation state and enables the security interface when there are only the authorized electronic tags being detected in the detecting area, and the authority processing unit sets the security interface to a security state and disables the security interface when one or more unauthorized electronic tags are detected in the detecting area.
Owner:SOLUTIONS
Information generation device, information reproduction device, and information recording device
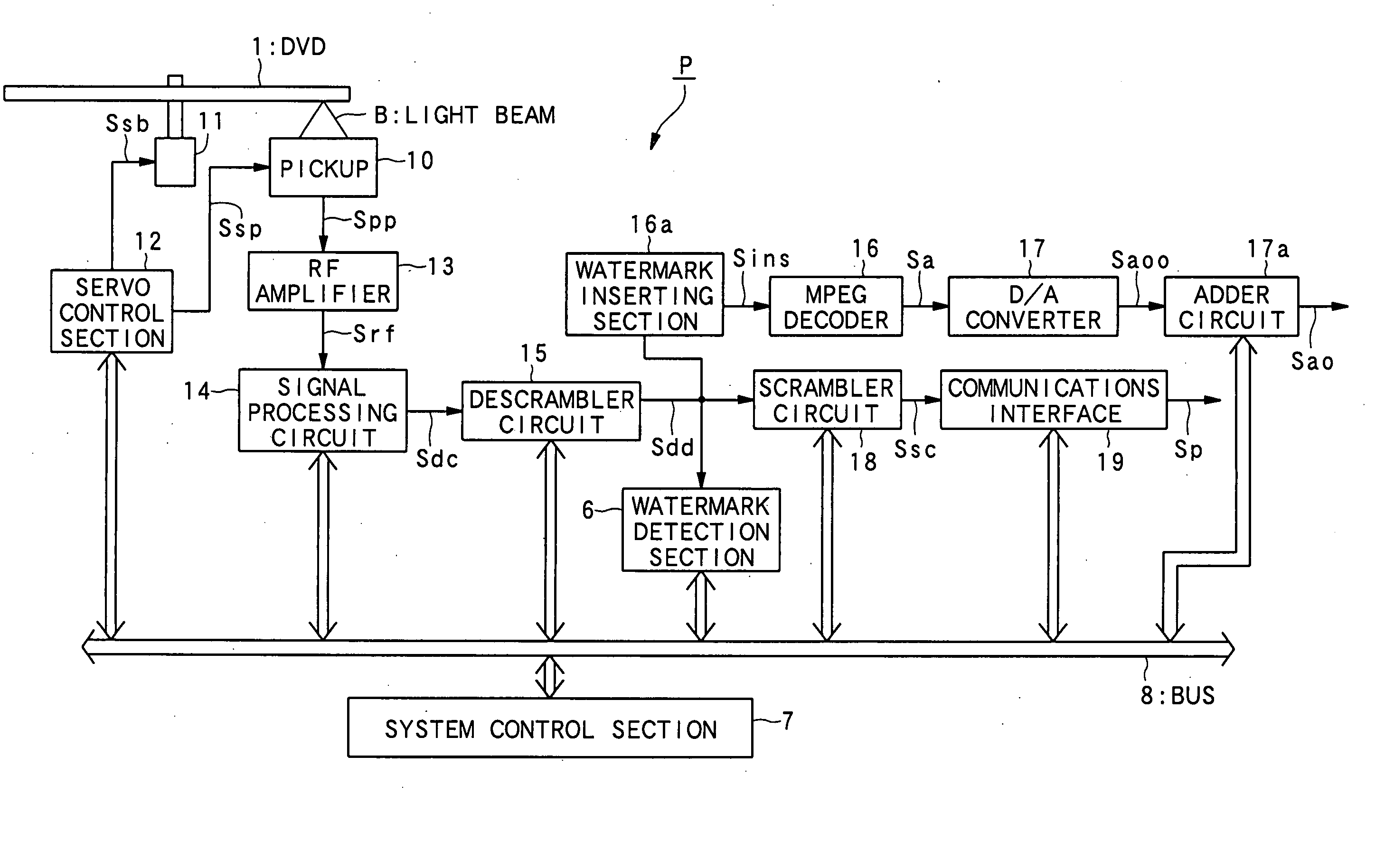
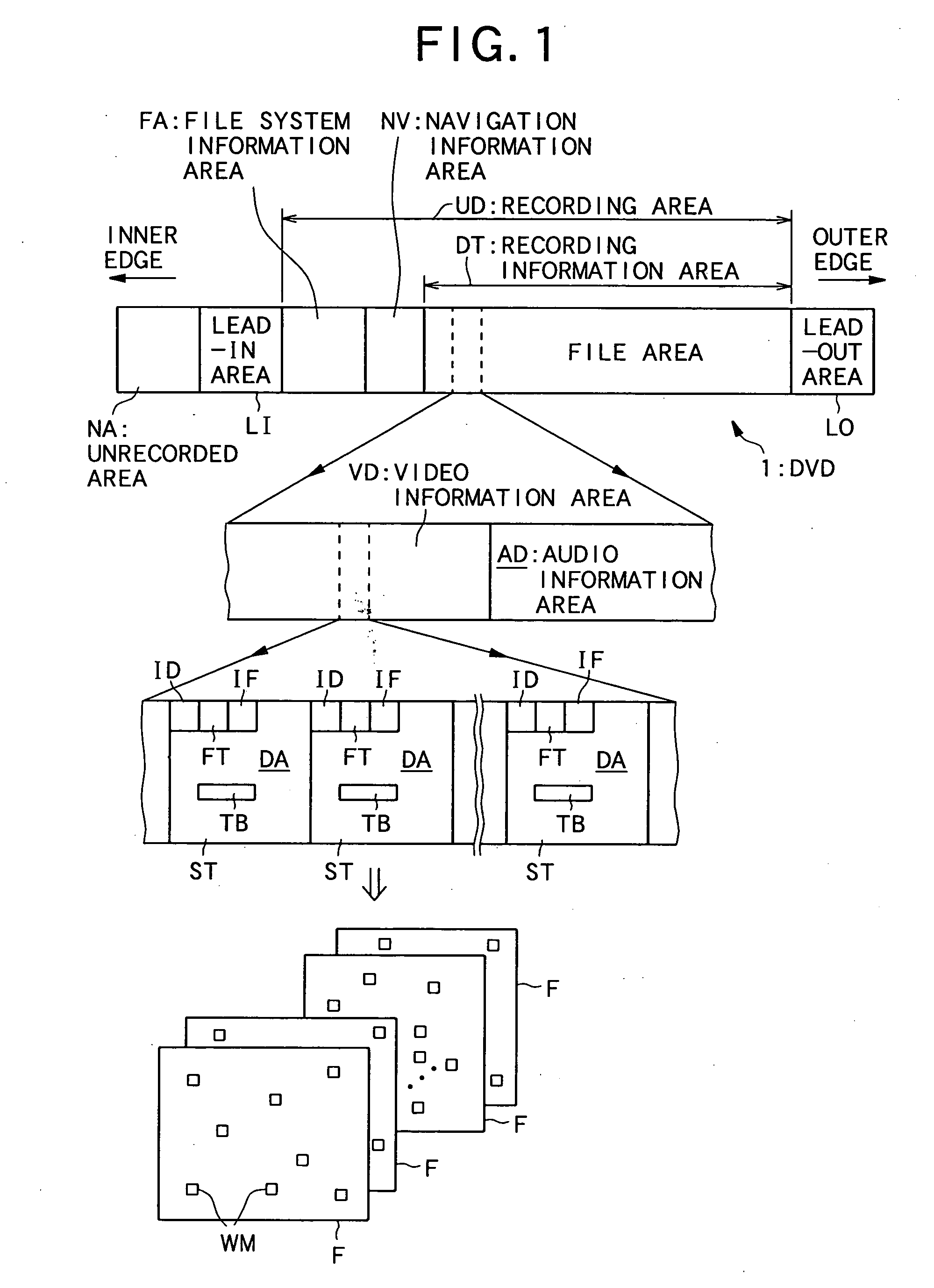
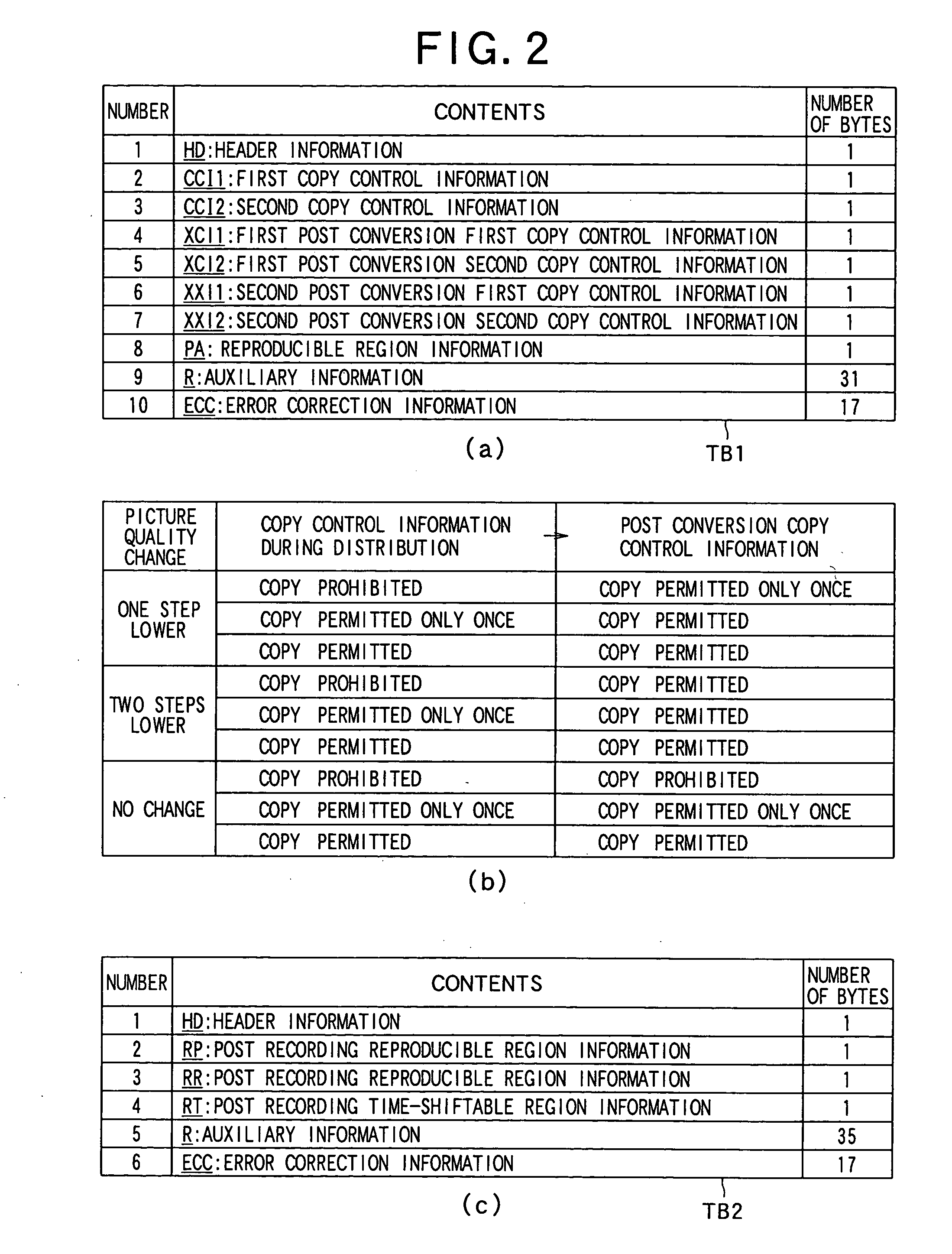
InactiveUS20050254364A1Copyright protectionEffectively protecting copyrightTelevision system detailsFilamentary/web record carriersDistribution systemInformation quality
An information distribution system is provided which can distribute a movie and so on while restricting the copying of information more widely and properly in the case where the information such as a movie is distributed via a network and so on. Change copy control information (XCI1, XCI2, XXI1, and XXI2) and normal copy control information (CCI1 and CCI2) are superimposed on reproduced information and are distributed. The change copy control information is used when a changing operation for changing the quality of reproduced information is performed, and the normal copy control information is used when the changing operation is not performed.
Owner:PIONEER CORP
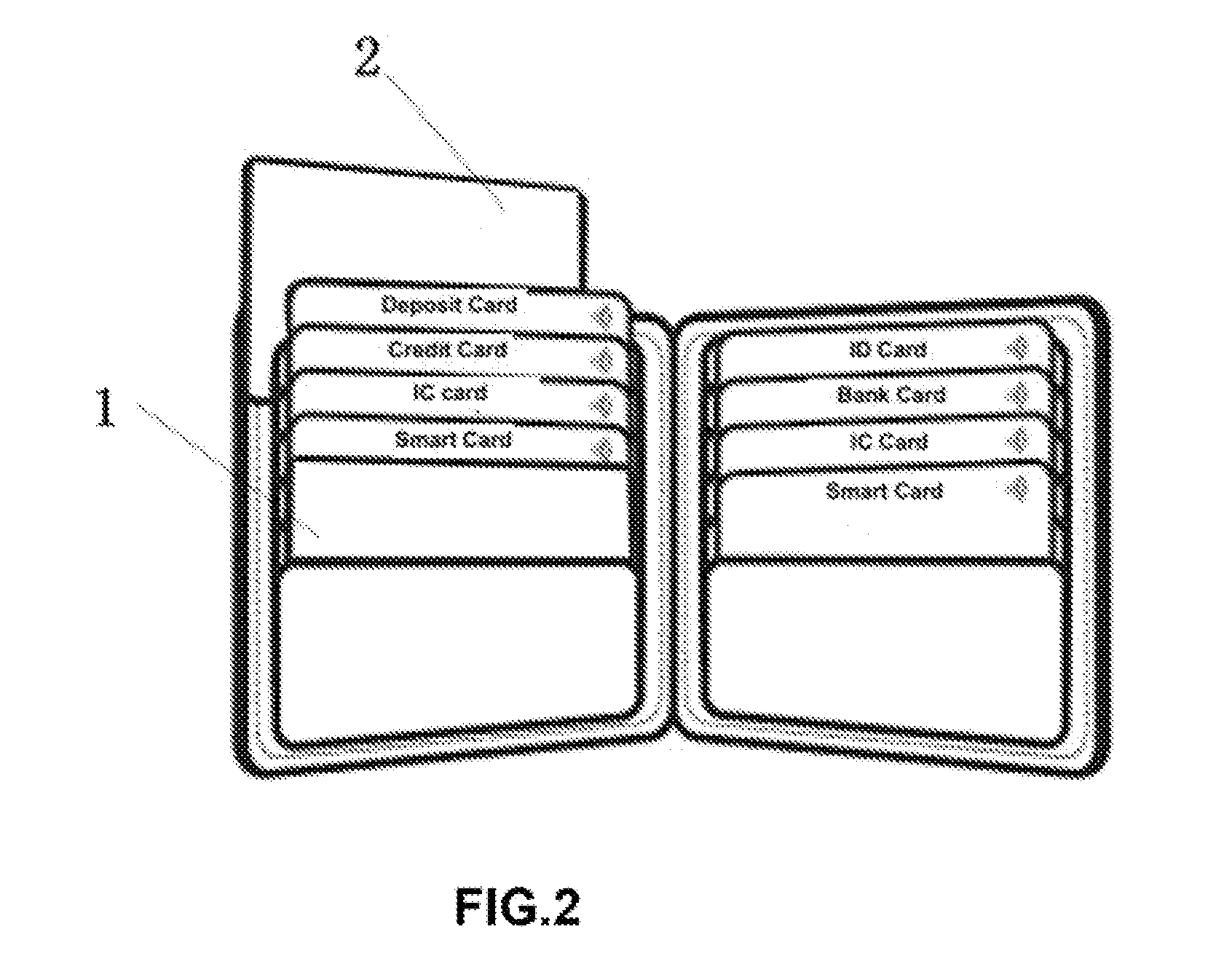
New-type Non-contact information data shielding and anti-theft card sleeve device and Manufacturing Method thereof
InactiveUS20160374442A1Effective protectionBringing unnecessary lossPursesMoney bagsCredit cardSmart card
The present invention refers to the field of shielding card, in particular to A new-type non-contact metallic shielding information data card, which can protect the personal information of credit card, IC card, smart card, identity card, driving license, bank card from being stolen by RFID electronic scanner effectively, and bringing unnecessary loss due to information exposure or other risks. It comprises a first shielding layer, a second shielding layer, and an accommodation space in physical for placing cards composed of the first shielding layer and the second shielding layer. The first shielding layer and the second shielding layer are sheet metal, and the words and / or images can be printed on the front and back side of the sheet metal based on customer's need. It can protect the personal information of credit card, IC card, smart card, identity card, driving license, bank card from being stolen by RFID electronic scanner effectively, and bringing unnecessary loss due to information exposure or other risks.
Owner:HUIZHOU JINCHENG CREATIVE TECH CO LTD
Card information protection device and finance service equipment having the same
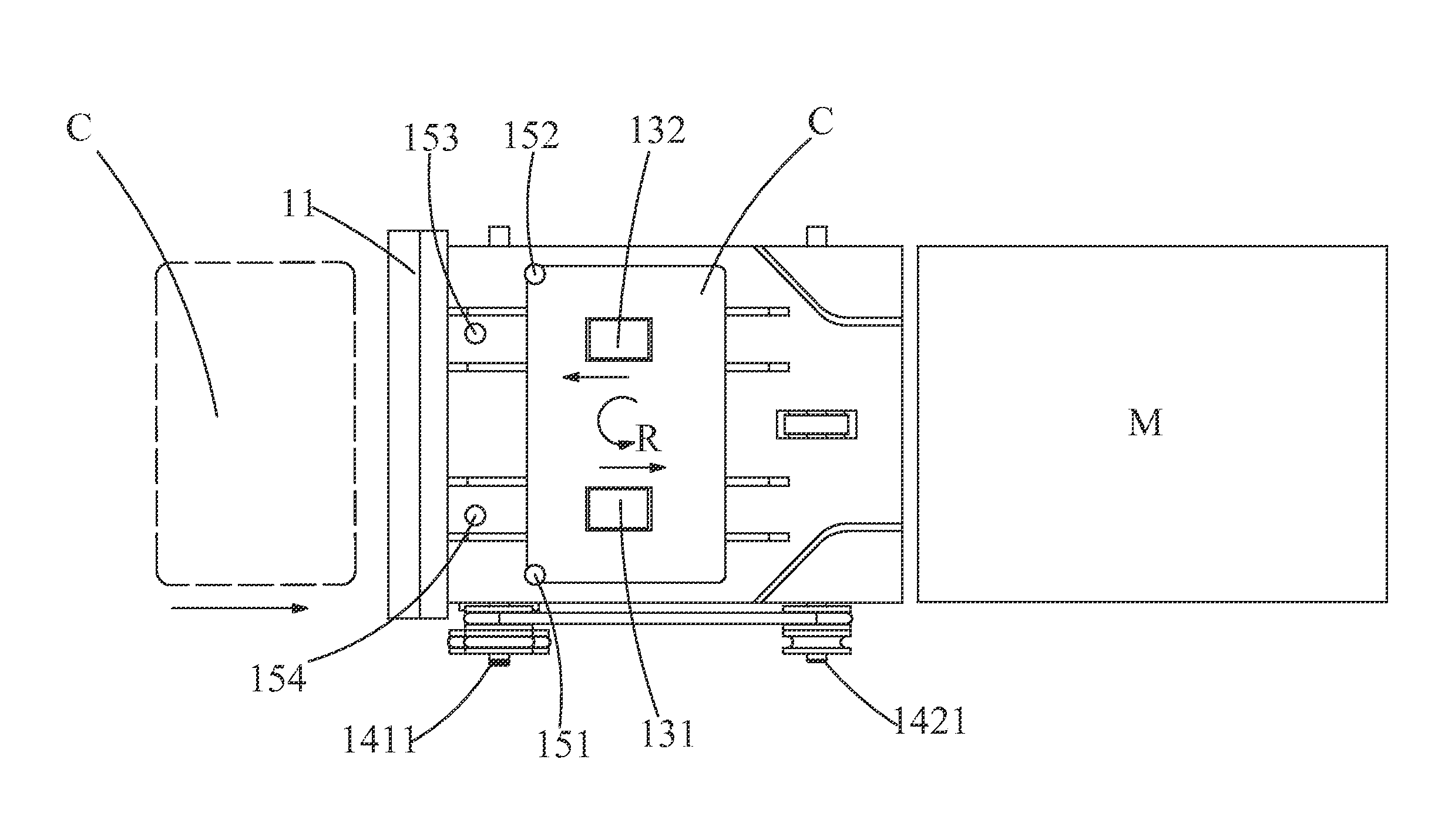
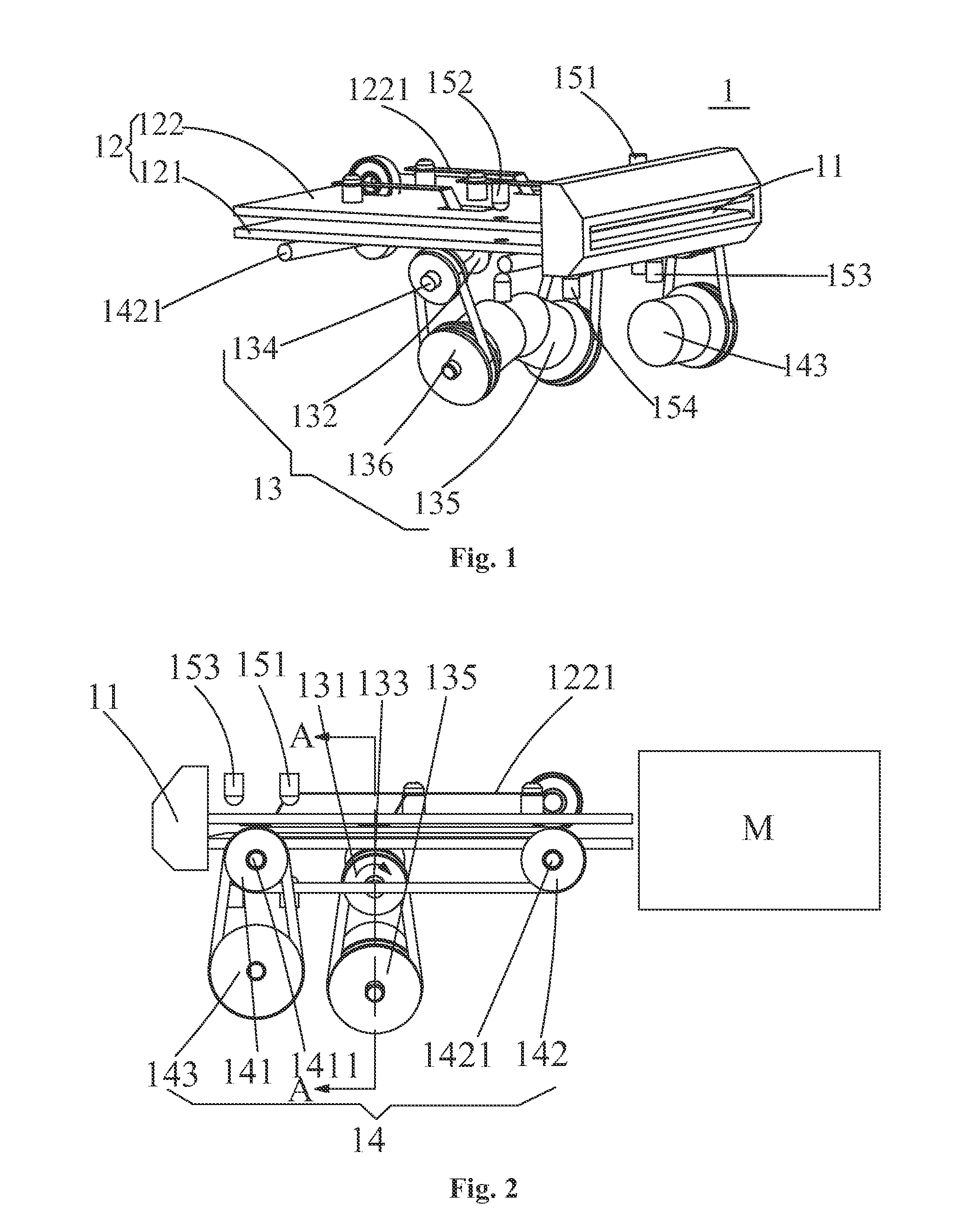
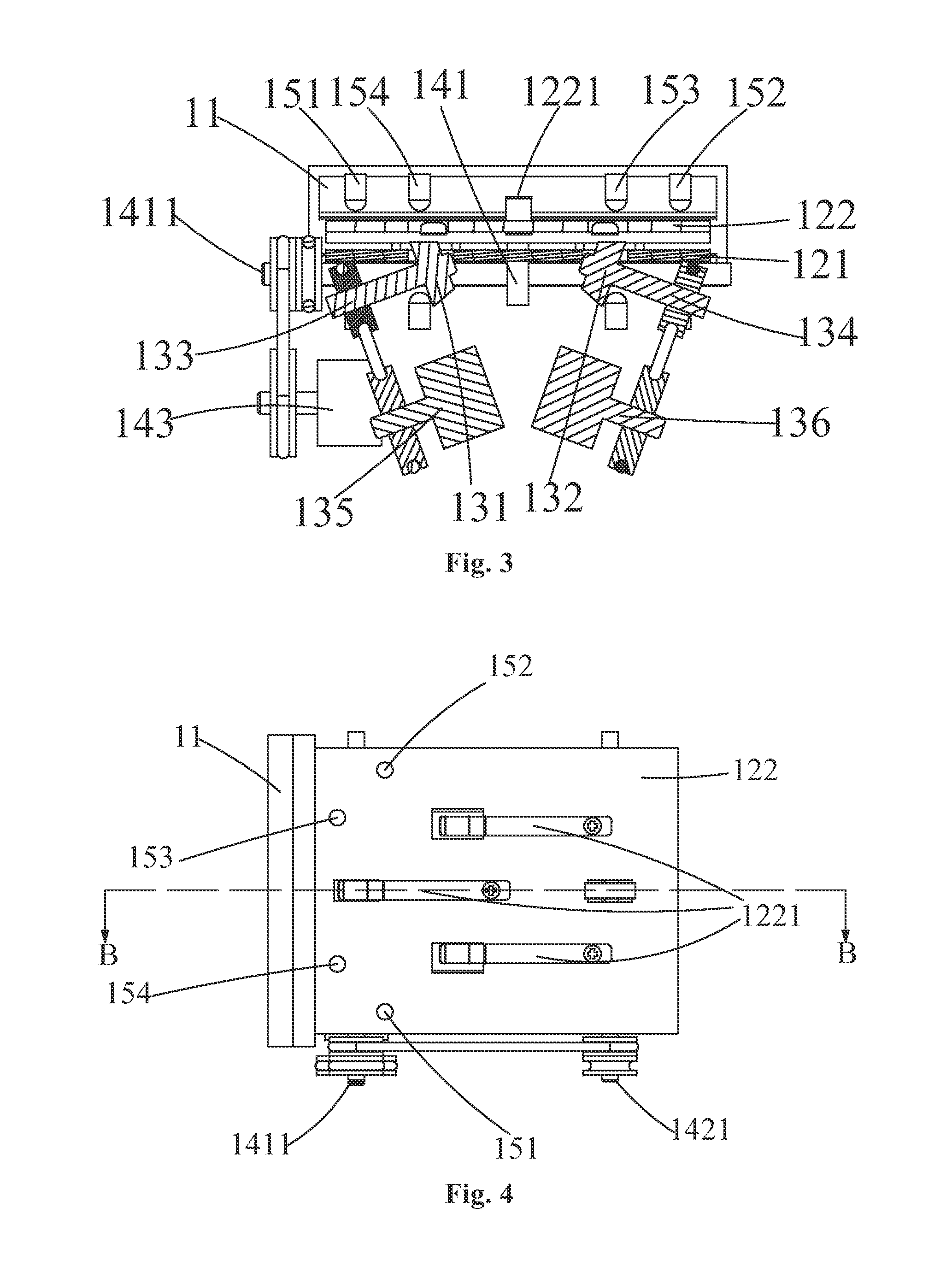
InactiveUS20140054368A1Good effectSolve the real problemComplete banking machinesAcutation objectsMechanical engineeringElectrical and Electronics engineering
A card information protection device and a finance service equipment having the same are provided. The card information protection device is arranged between a transverse card inlet and a longitudinal magnetic card information reader, and comprises a magnetic card transverse admission port. A magnetic card conveying channel is arranged between the magnetic card transverse admission port and the longitudinal magnetic card information reader. A magnetic card rotating mechanism is arranged in the magnetic card channel. The magnetic card rotating mechanism is used for rotating a transversely-inserted magnetic card to longitudinal direction in order to convey the magnetic card into the longitudinal magnetic card information reader, and rotating the longitudinal magnetic card returned by the longitudinal magnetic card information reader to transverse direction in order to convey the transverse magnetic card out. The problem that the whole magnetic strip of the magnetic card information reader which allows a user to plug the magnetic card in the longitudinal direction is completely scanned by a card stealer device illegally arranged in a card plug-in buckle in the process of longitudinally inserting the magnetic card can be effectively solved, and thereby the problem that the magnetic card information is stolen illegally can be thoroughly solved.
Owner:GRG BAKING EQUIP CO LTD
Image composition beautifying method and system based on visual area proportion balance rule
ActiveCN103824259AIn line with visual aesthetic perceptionSimple methodImage enhancementGeometric image transformationSpecific gravityComputer vision
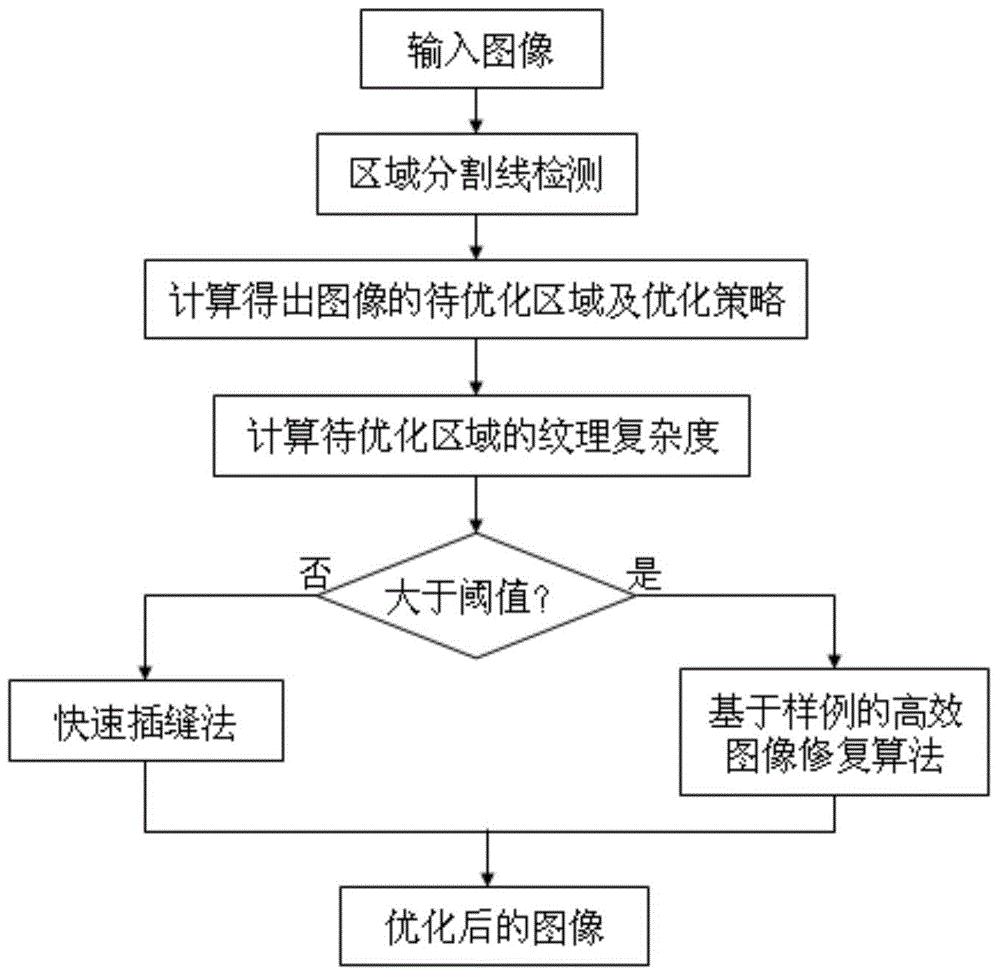
The invention discloses an image composition beautifying method based on a visual area proportion balance rule. The method comprises the following steps: (1) inputting an image; (2) detecting an area segmentation line of the image and dividing the image into two areas; (3) obtaining an area to be optimized and an optimization strategy of the image by utilizing the visual area proportion balance rule and based on the area segmentation line; (4) calculating texture complexity of the area to be optimized; (5) performing optimization on the area to be optimized based on the optimization strategy, utilizing a rapid seam-insertion method to perform stretching or reducing on the area to be optimized when the texture complexity of the image is smaller than a preset threshold value of the texture complexity, and otherwise, utilizing a sample-based high-efficiency image restoration algorithm to perform stretching on the area to be optimized; and (6) outputting the optimized image. The invention further discloses an image composition beautifying system based on the visual area proportion balance rule. According to the image composition beautifying method and system based on the visual area proportion balance rule, the image composition is automatically beautified and the image is allowed to have a better esthetic visual effect.
Owner:SOUTH CHINA UNIV OF TECH
Method of tracking tools
InactiveUS6915952B1More reliably readable by a scannerProtect informationWork tools storageResourcesProgramming languageData Matrix
To track a large number of tools, the tools are kept in sets with each set having a container. A silhouette of each tool stored in the container is printed at the point of storage along with a dat matrix code that has stored in binary code a description of the tool, the part number, and an identification of the kit of which it is a part. The associated tool has etched into the surface thereof a data matrix code containing the same information as the code printed at the point of storage. The data matrix codes are readable by a scanner and a record of all the tools is maintained on a computer.
Owner:UFP TECHNOLOGIES
Adaptive image scaling method based on content
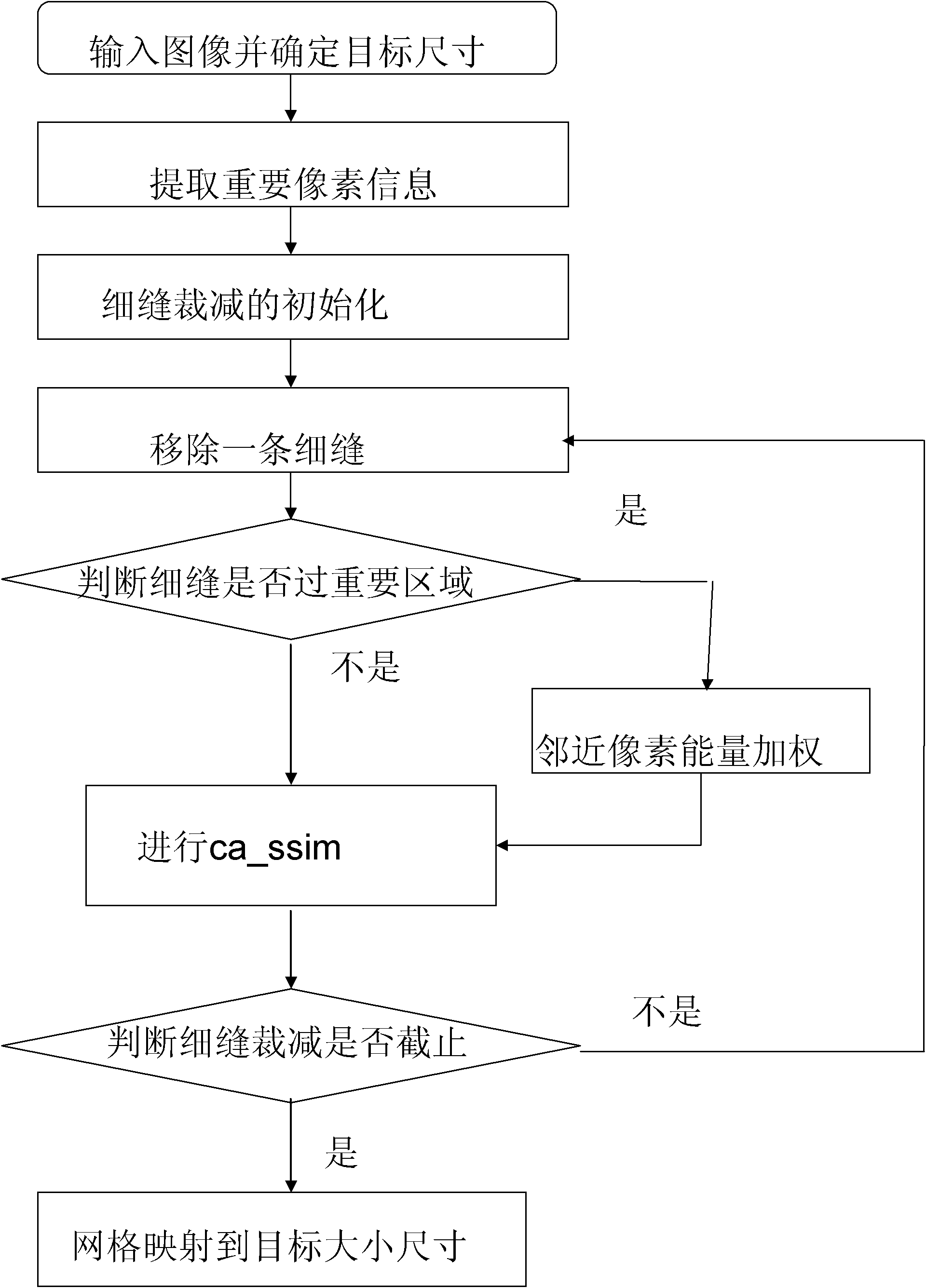
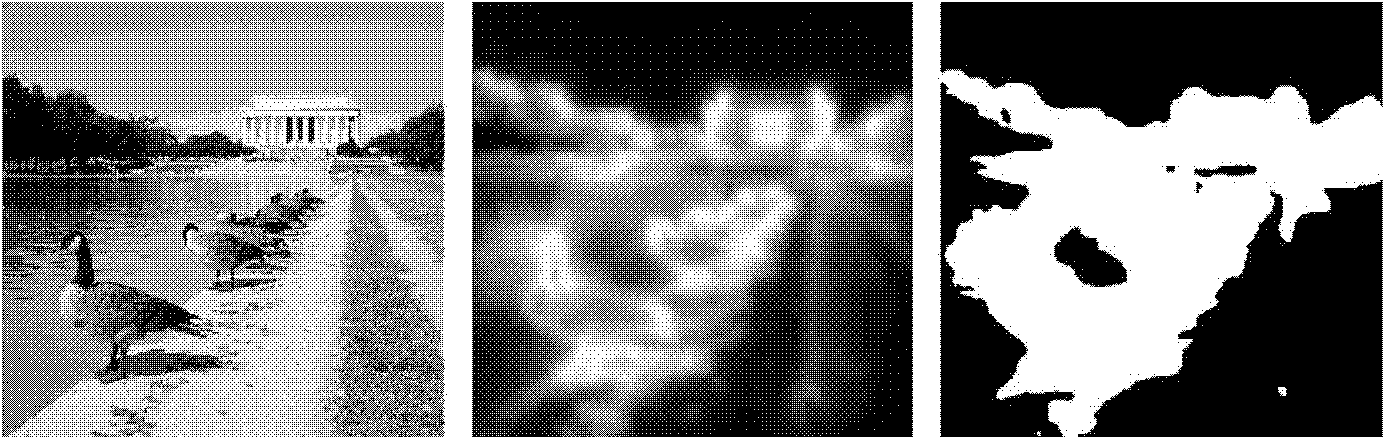
InactiveCN102254300AReduce lossesProtect informationGeometric image transformationImaging processingImage scale
The invention discloses an adaptive image scaling method based on content, belonging to the field of image processing. In the method, the current slit reduction is weighted and then is combined with a mesh mapping process. The method comprises the following steps of: firstly, reducing an image by a slit reduction method, when a slit is in an important region, weighting energy of the important region near the slit to reduce the slit reduction of the important region and increase the slit reduction of a non-important region; and performing a mesh mapping process on the image subjected to the slit reduction process to enable the image to achieve a target size. The method not only scales the image information of the non-important region, but also effectively keeps proportion and detail of important image information after scaling, so that optimization of adaptive property of the image content is implemented.
Owner:BEIJING UNIV OF TECH
Apparatus and method of mirroring firmware and data of embedded system
InactiveUS7996720B2Increase reliability and operabilityProtect informationMemory loss protectionRedundant hardware error correctionOperabilityData loss
Disclosed is an apparatus and method of mirroring firmware and data of an embedded system. The embedded system mirrors a boot loader image, a kernel image, a RAM disk image and data that are stored on a main flash memory to be operated onto a secondary flash memory. Therefore, when a main flash memory does not normally work, the firmware and data that are stored on the main flash memory to be operated is mirrored onto the secondary flash memory, which prevents the loss of data and maintains the operation of the embedded system. As a result, it is possible to secure the reliability and operability of the system.
Owner:ELECTRONICS & TELECOMM RES INST
System and method for implementing operation system separation
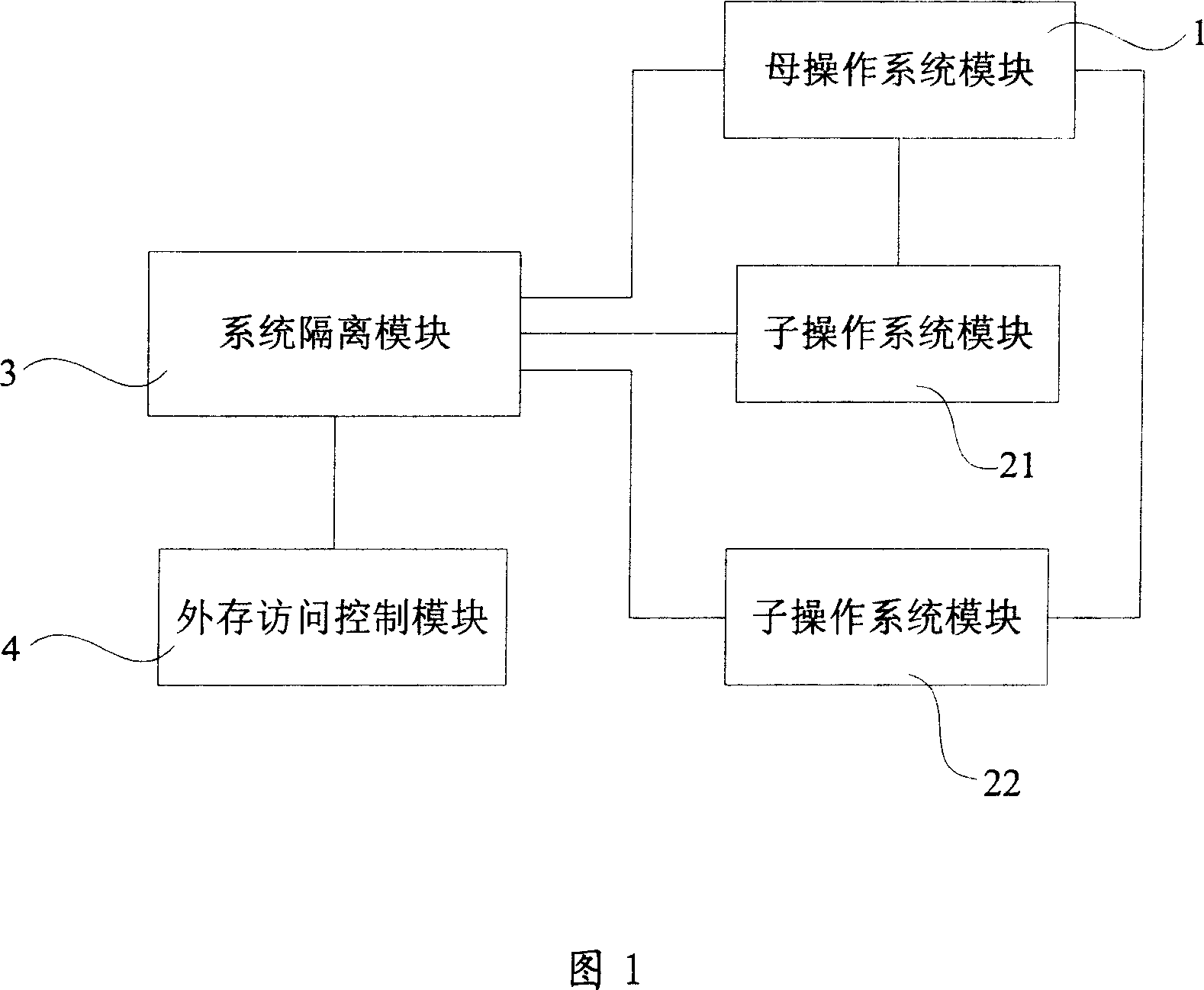
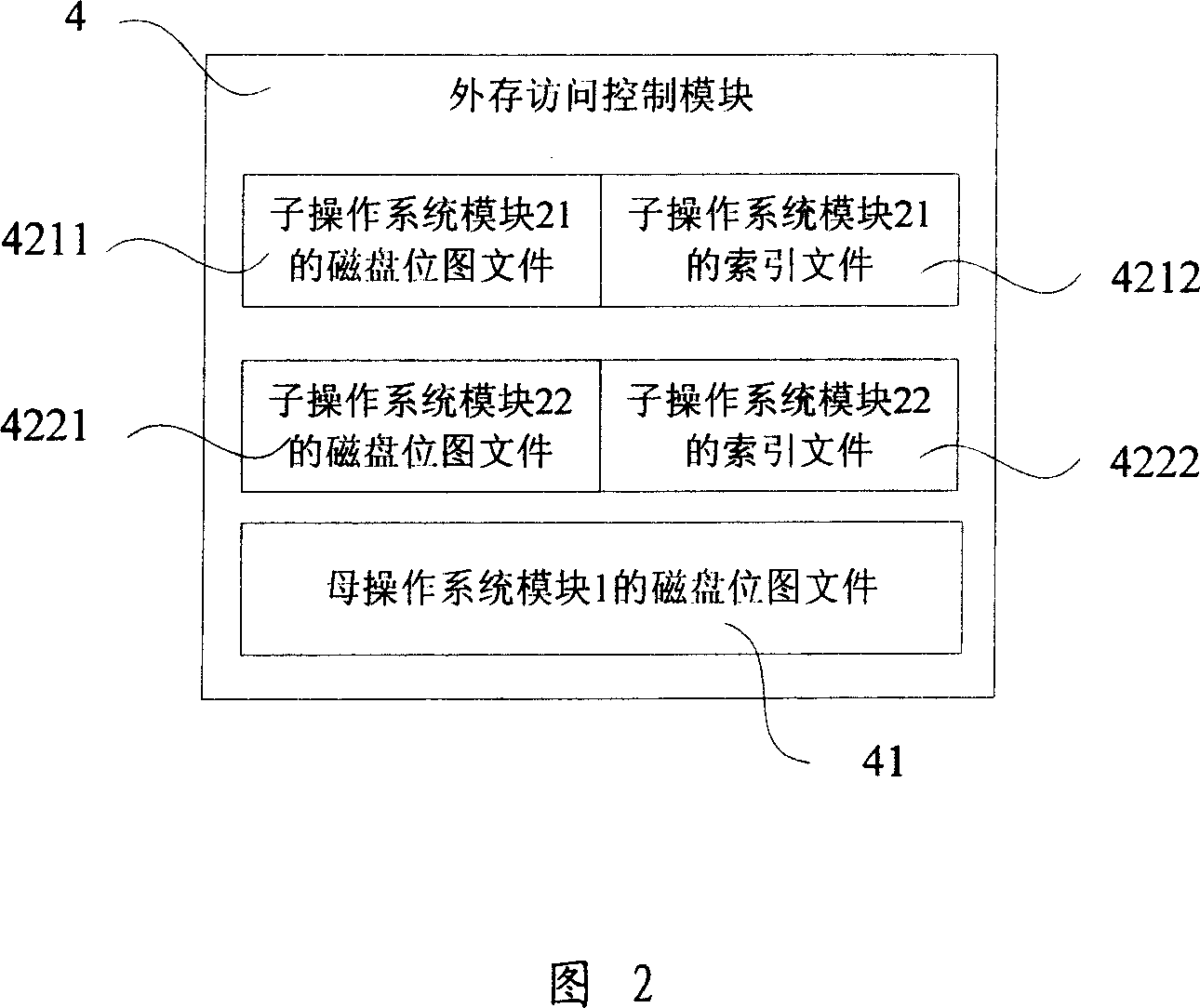
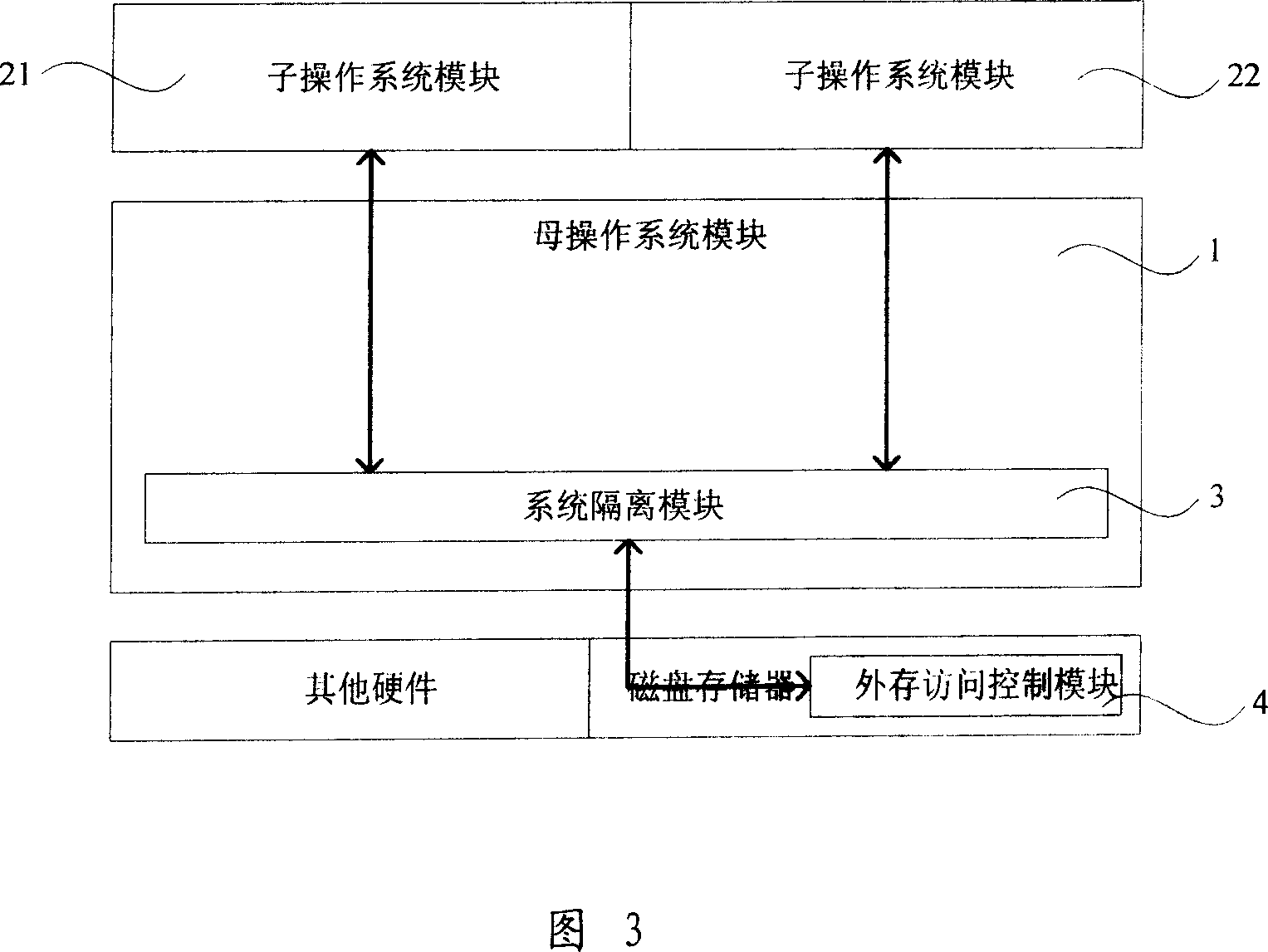
ActiveCN1920731AFlexible useReduce in quantityDigital data processing detailsMultiprogramming arrangementsOperational systemComputer science
The invention relates to a system for separating the operation system and a relative method, wherein it comprises: a mother operation system module, at least one sub operation system module for containing the modify information of user on the mother operation system module, a system separating module and an external memory access control module for recording the disc spaces of mother / sub operation system module; said system separating module via the user command instructs and / or build sub operation system module, to instruct and / or modify the disc space and disc blank space of mother / sub operation system module, and detect the read / write access of mother / sub operation system modules on the disc. The invention can build different operation systems without occupying more space of disc, to separate the operation system and reduce the system abundance, increase the safety and reliability, to protect the user information at different sub operation system modules.
Owner:NANTONG JINGXI INFORMATION TECH CO LTD
Semiconductor memory device, semiconductor system and reading method
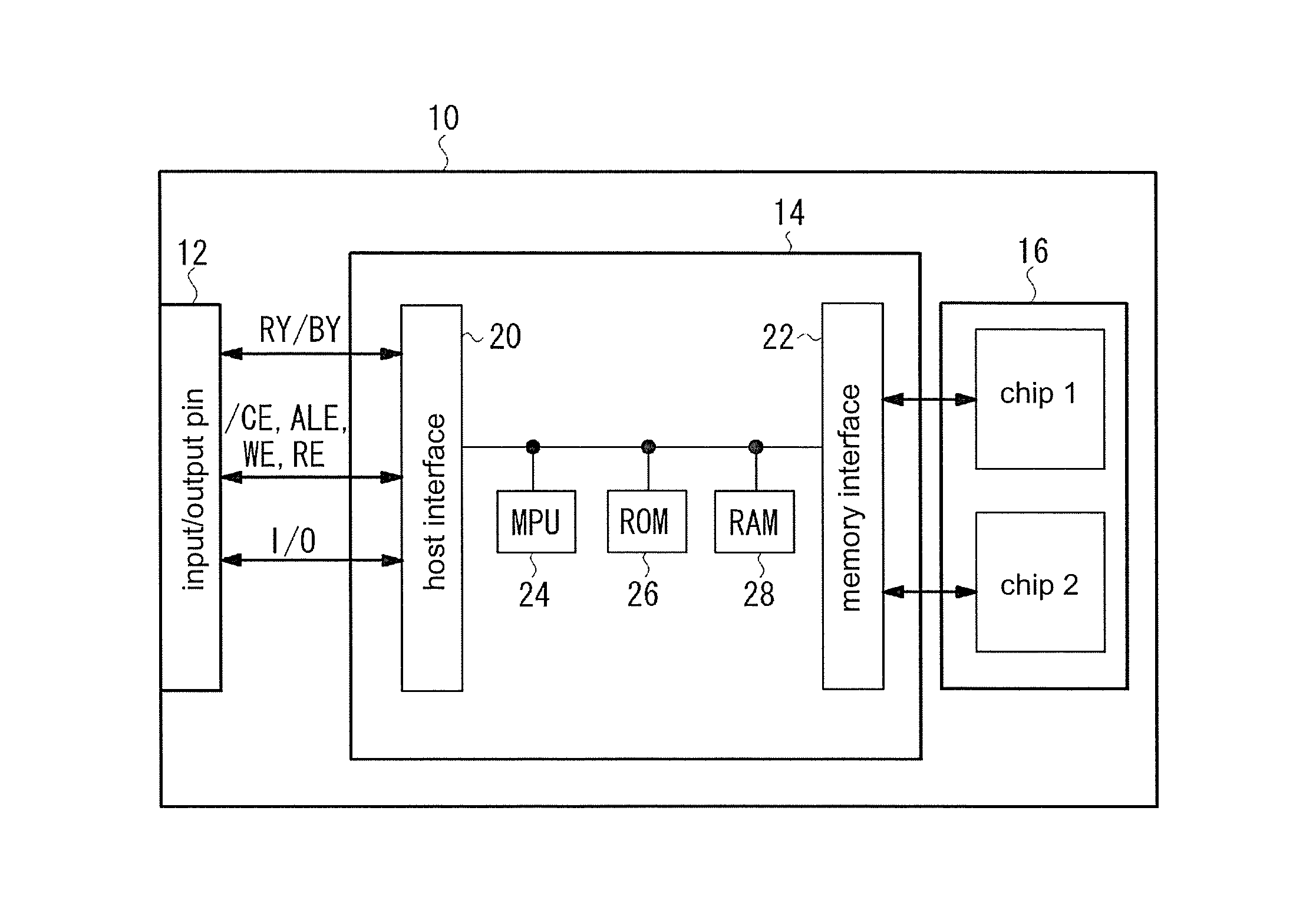
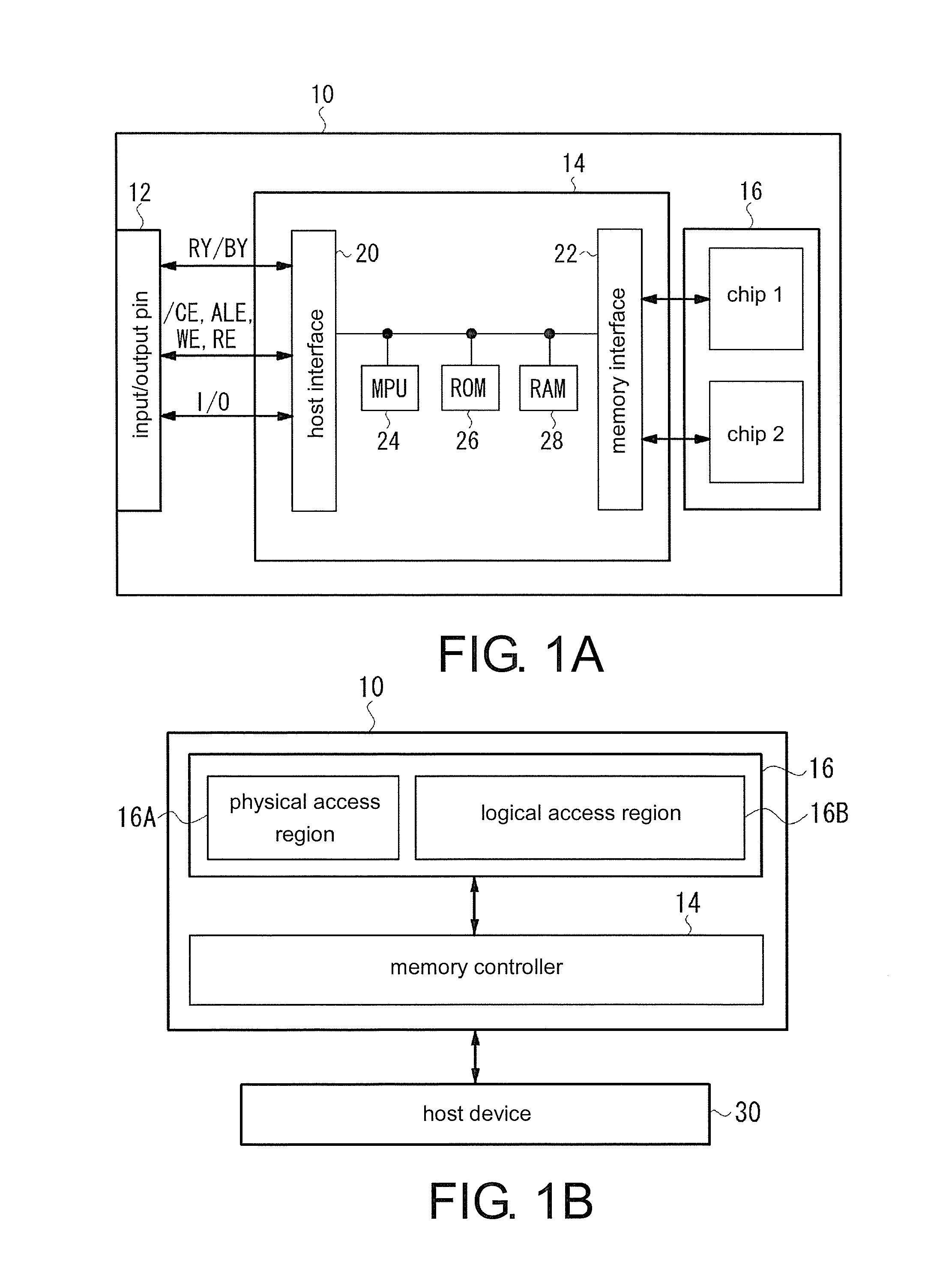
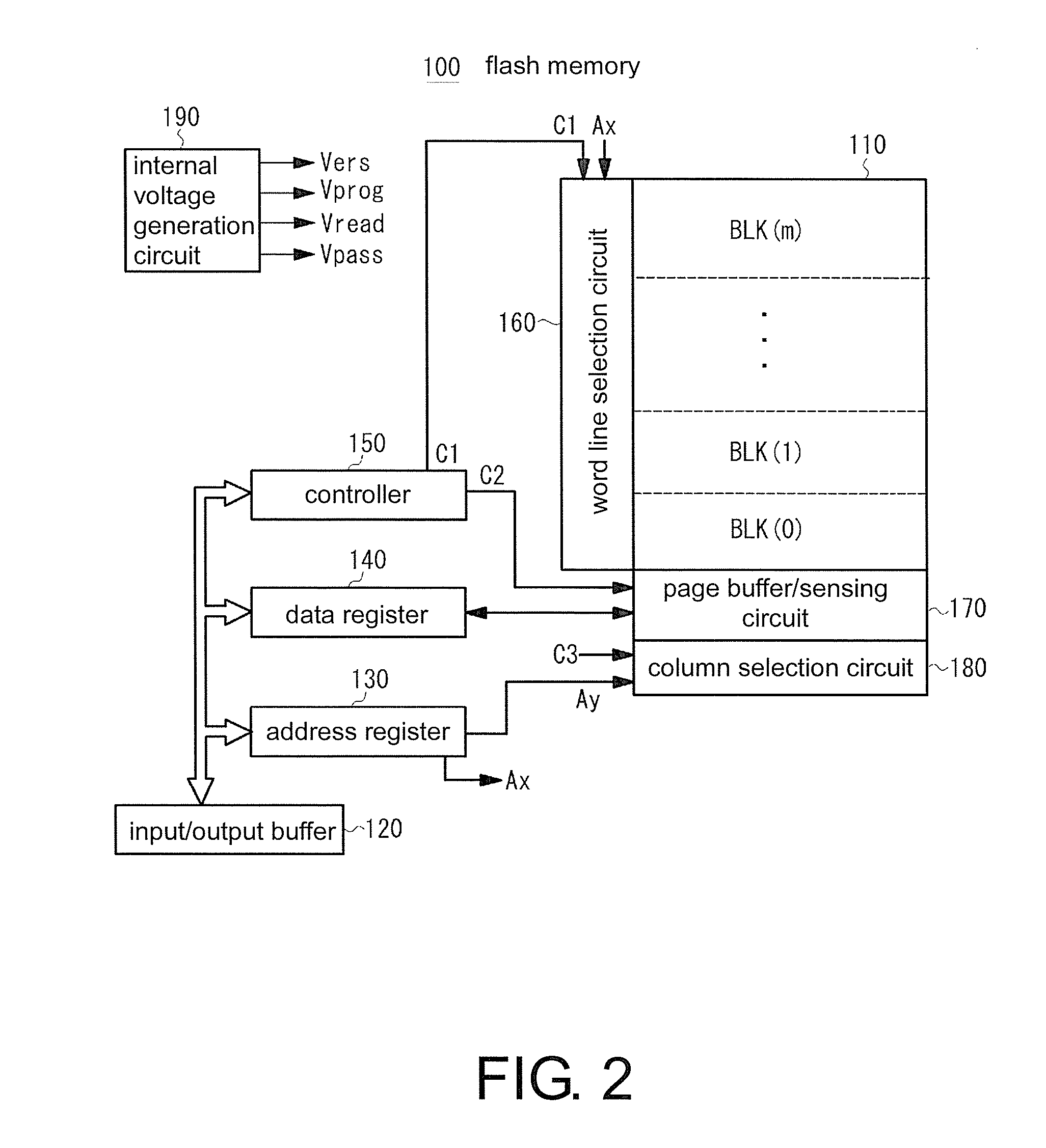
ActiveUS20150324122A1Improve security levelLimited readingInput/output to record carriersRead-only memoriesData setData storing
The invention provides a flash memory which may effectively protect information with a high security level. A flash memory includes a setting part. When the setting part is inputted a specific command, the setting part sets up specific address information to a nonvolatile configuration register, and sets up specific data in a hidden storage region. The flash memory also includes: a comparing part, which compares inputted address information and the specific address information during a reading operation; and a control part, which reads specific data set in the storage region and erases a specific address when two address information are consistent, and reads data stored in a memory array according to the inputted address information when two address information are inconsistent.
Owner:WINBOND ELECTRONICS CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com