Patents
Literature
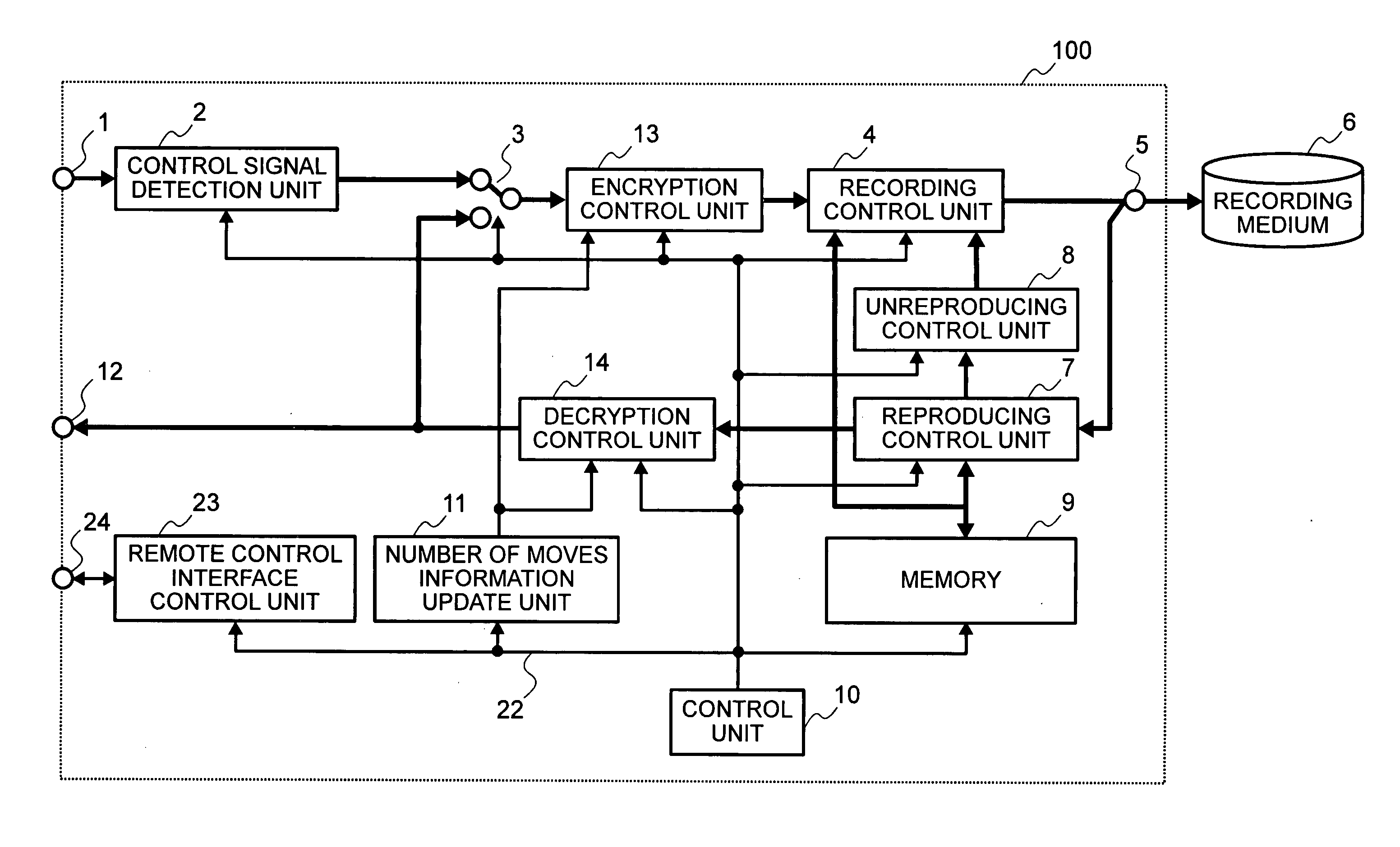
410 results about "Copy control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Copy Control is defined as a process in which important transactions in a sales document are copied from one document to other. It consists of routines, which determine the system on how the data is to be copied from a source document to a target document.
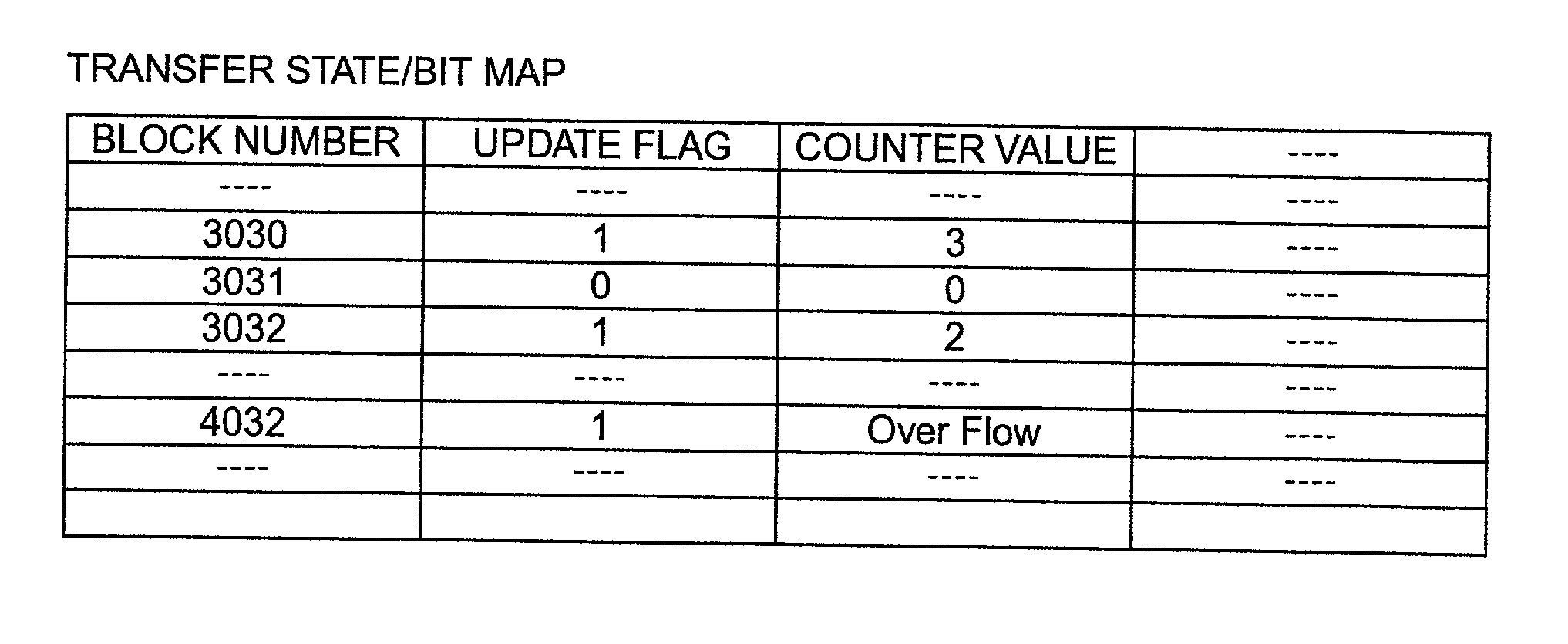
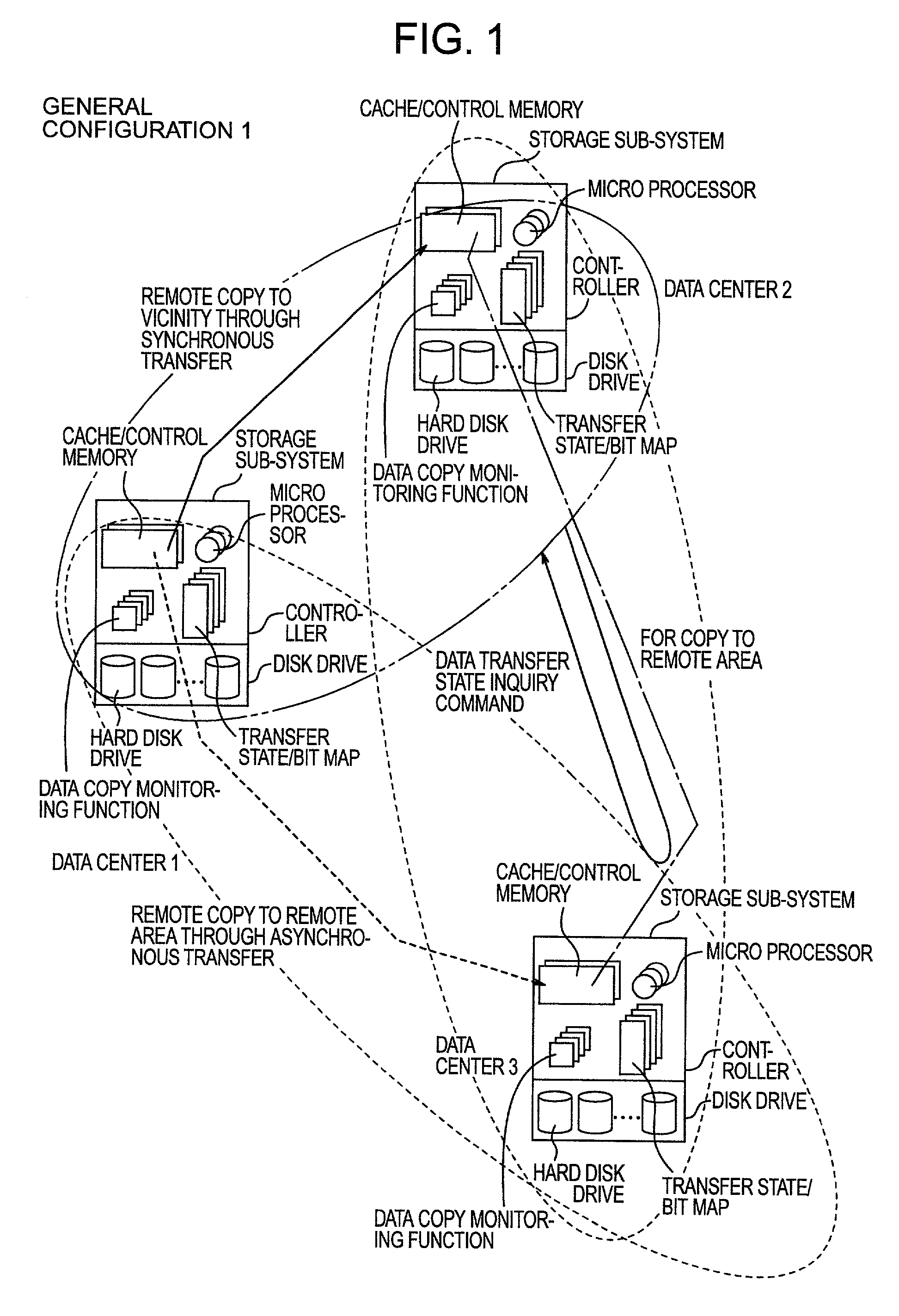
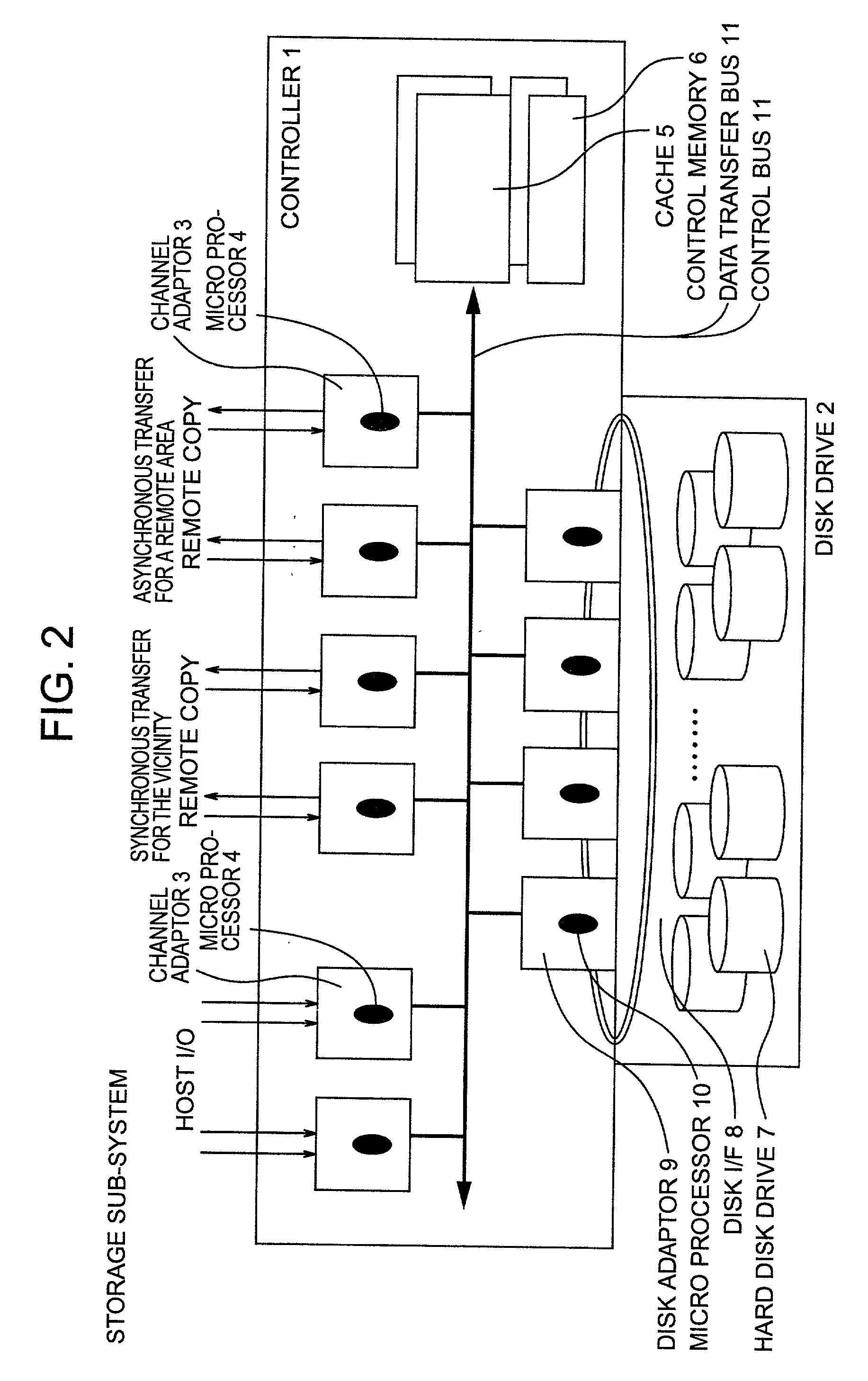
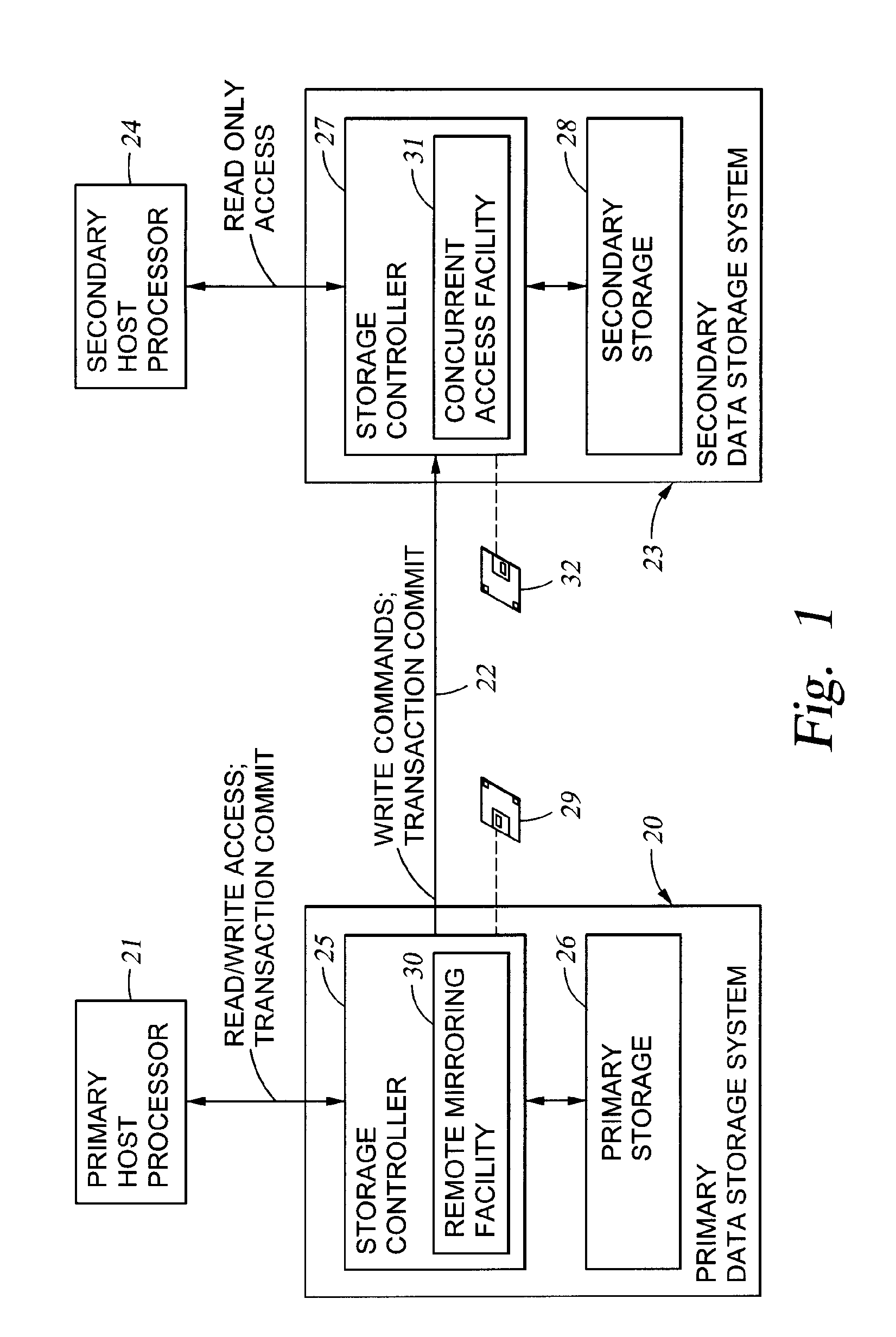
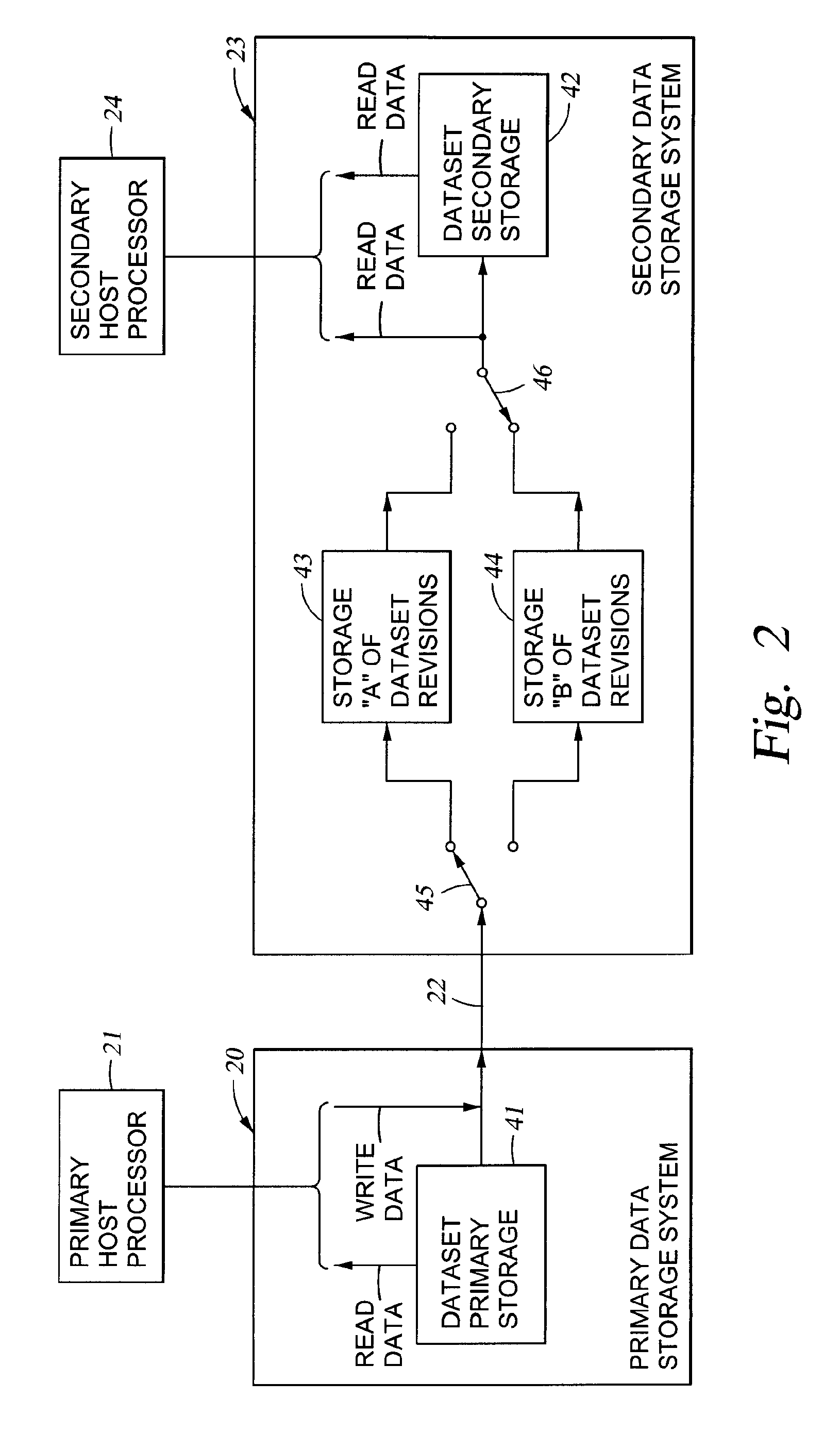
Remote copy control method, storage sub-system with the method, and large area data storage system using them
InactiveUS20030051111A1Data augmentationExtension of timeData processing applicationsInput/output to record carriersData centerData transmission
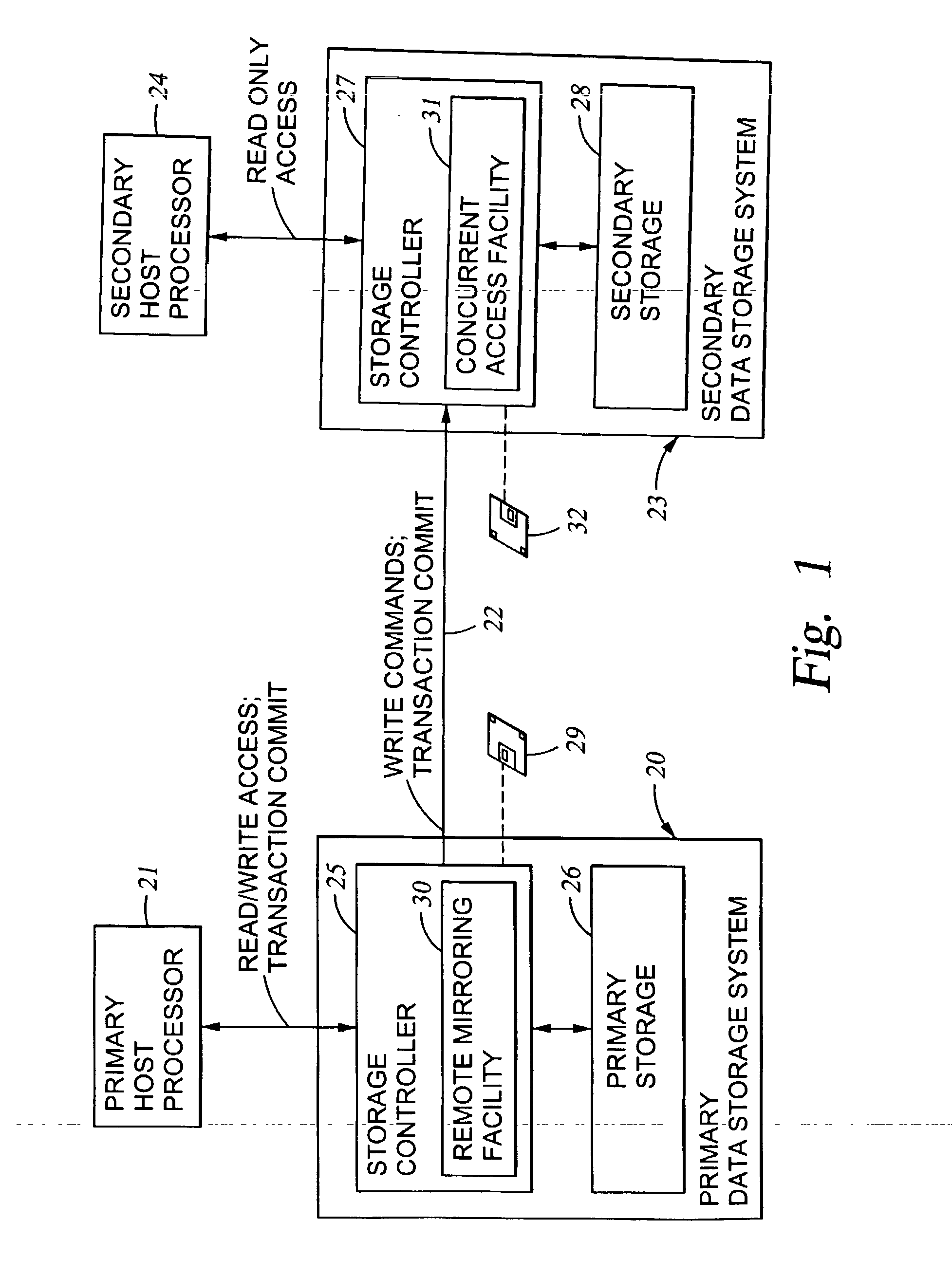
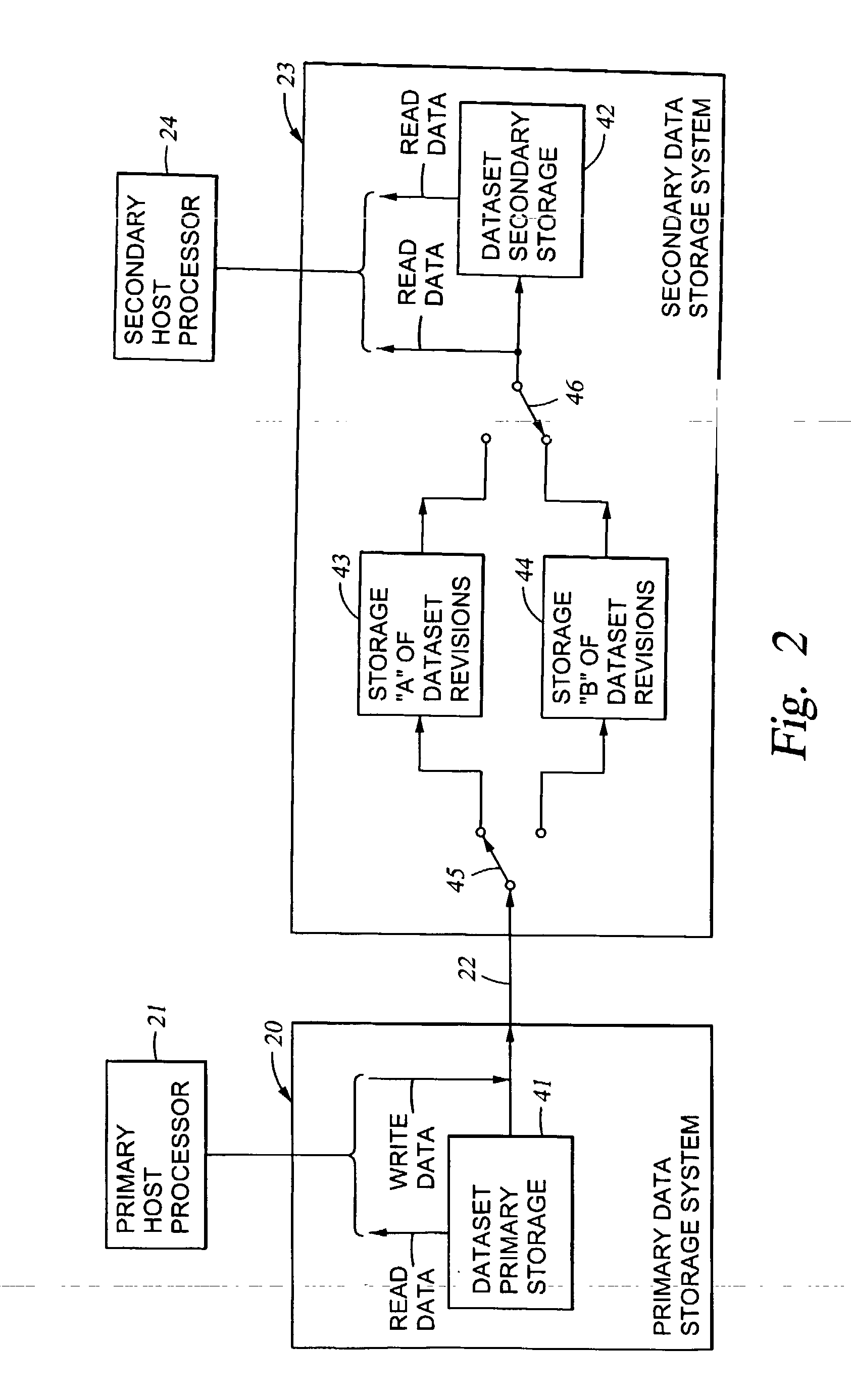
Two data centers located in the vicinity are connected using a synchronous transfer copy function, and one of the data centers is coupled with a third data center disposed at a remote location by an asynchronous remote copying function. The order whereat a storage sub-system located in the vicinity has received data from a host is consistently guaranteed, and the third data center holds the data. Further, each storage sub-system includes a function whereby, during normal operation, data can be exchanged and the data update state can be obtained by the storage sub-systems located in the two data centers that do not directly engage in data transmission.
Owner:HITACHI LTD
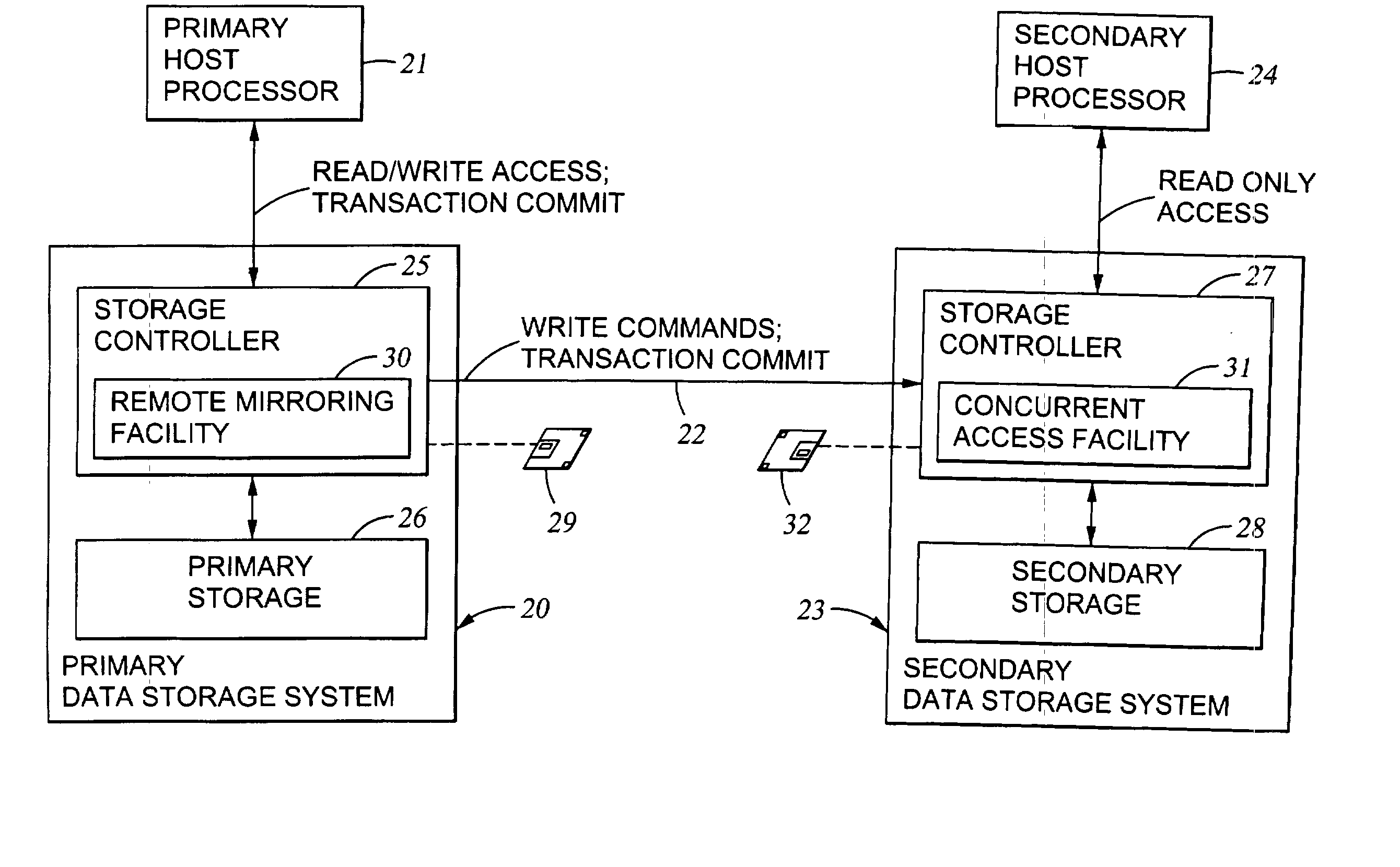
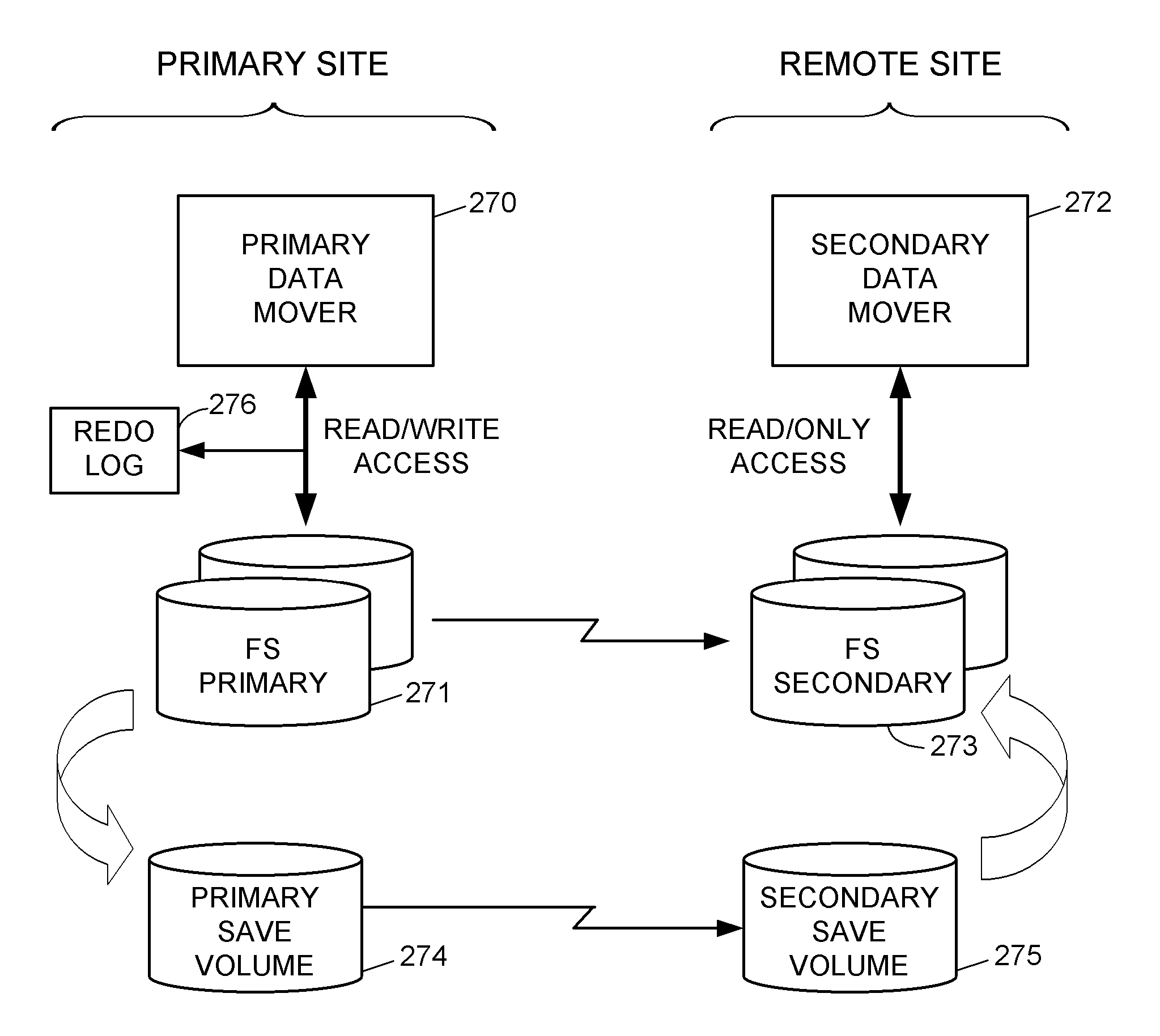
Replication of remote copy data for internet protocol (IP) transmission
ActiveUS20030217119A1Special service provision for substationError detection/correctionInternet protocol suiteRouting table
Consistent updates are made automatically over a wide-area IP network, concurrently with read-only access to the remote copies. A replication control protocol (RCP) is layered over TCP / IP providing the capability for a remote site to replicate and rebroadcast blocks of the remote copy data to specified groups of destinations, as configured in a routing table. A volume multicast layer over RCP provides for multicasting to specified volume extents of the blocks. The blocks are copied at the logical level, so that it does not matter what physical structure is used for storing the remote copies. Save volumes buffer the remote copy data transmitted between the primary or secondary file system volume and the IP network, in order to ensure independence between the replication process, the IP transport method, and the primary file system being replicated.
Owner:EMC IP HLDG CO LLC
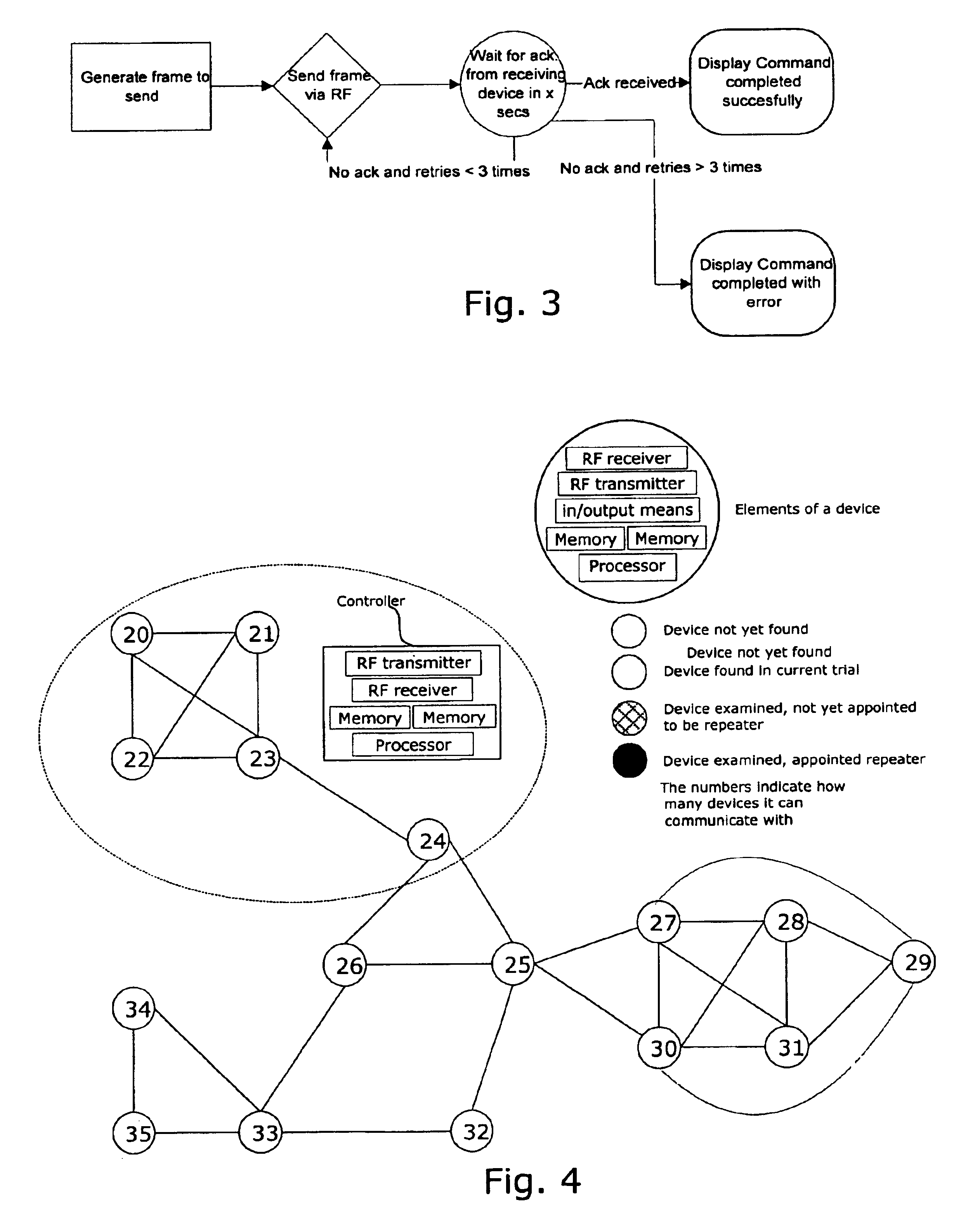
RF home automation system with replicable controllers
InactiveUS6980080B2Low priceQuality improvementElectric signal transmission systemsSafety arrangmentsEmbedded systemCopy control
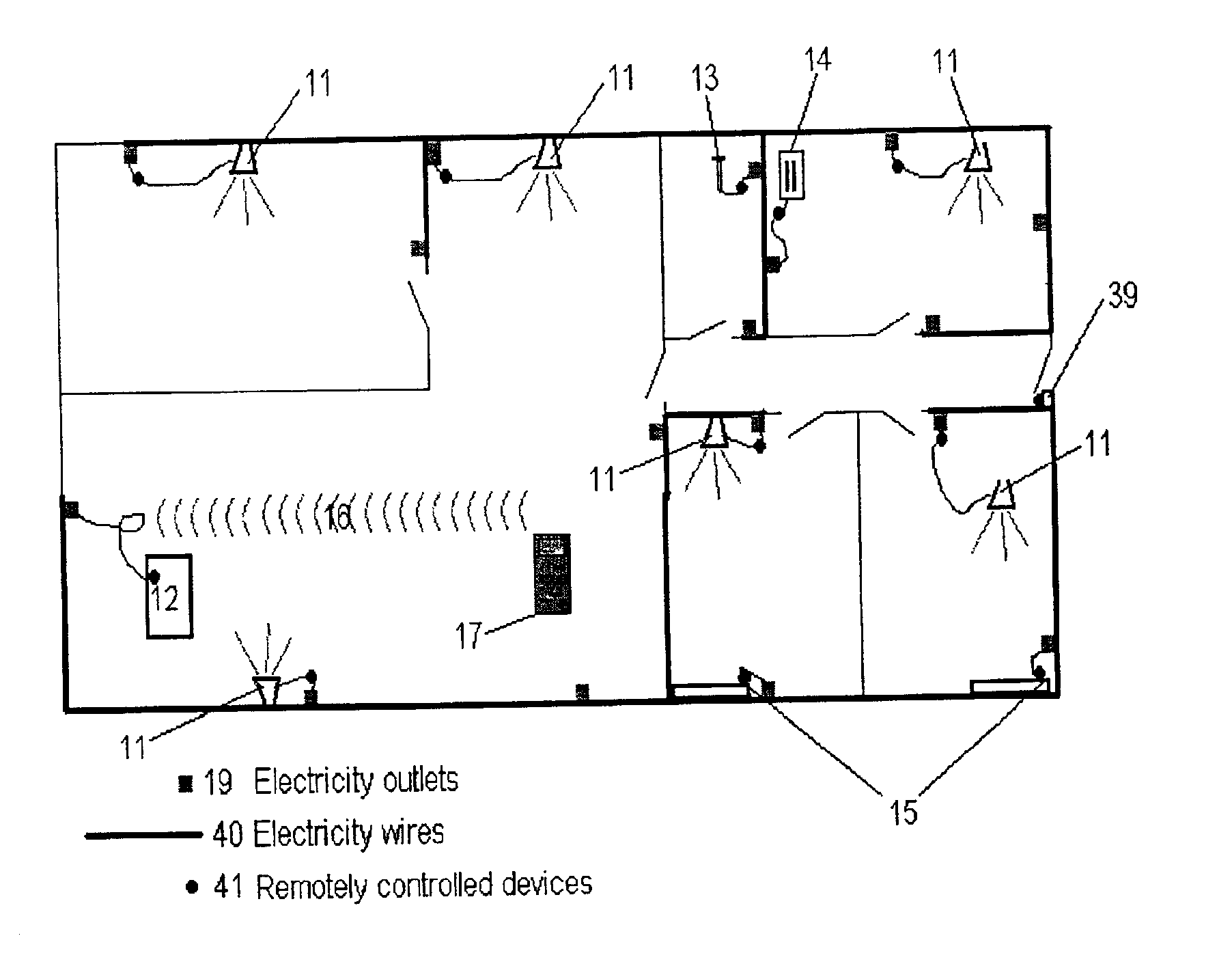
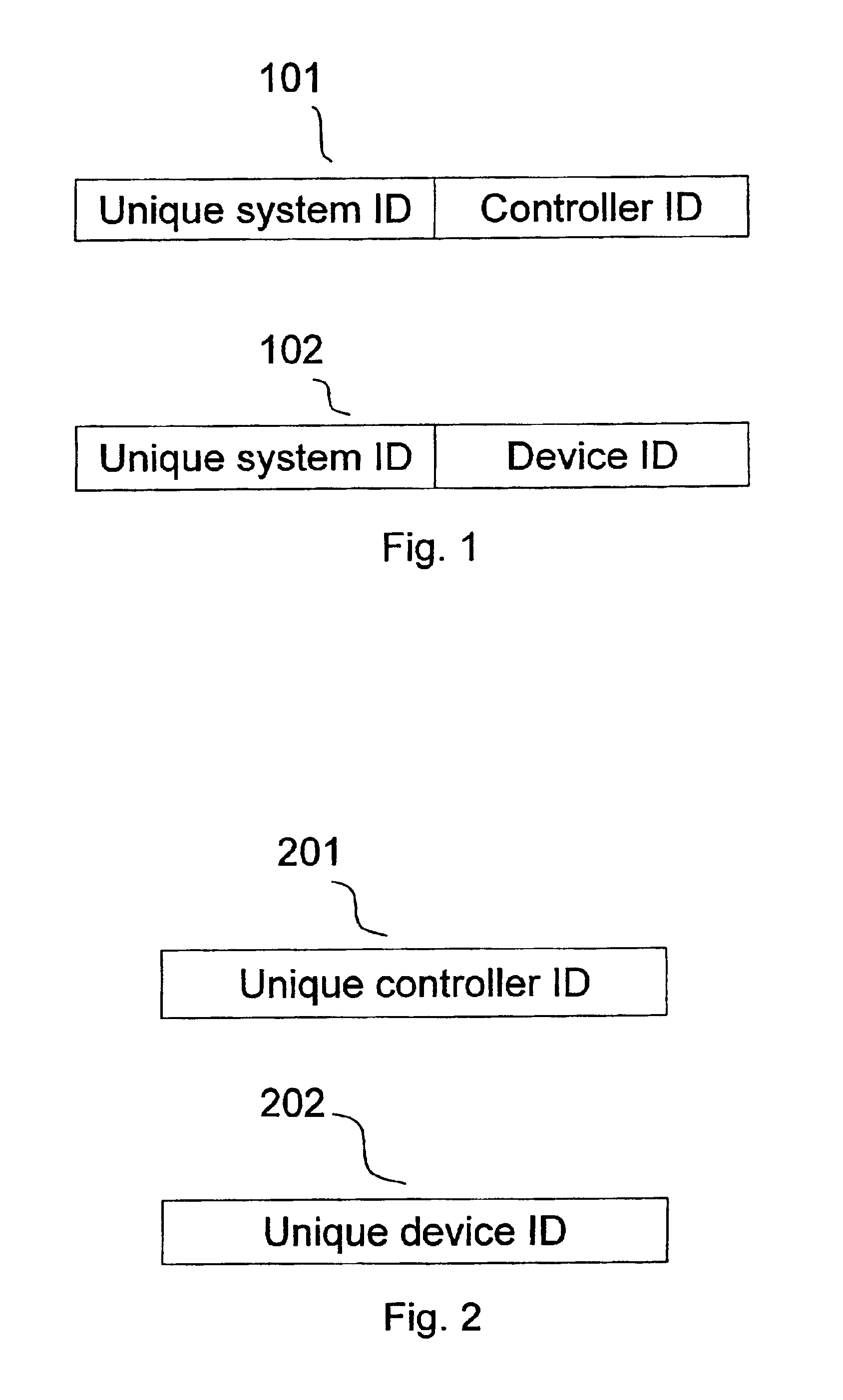
The present invention relates to a wireless home automation system having controllers for controlling a broad variety of functions via two-way communication with a plurality of devices. More specifically, the invention relates to sharing information related to the system between controllers, e.g. by updating a second controller with the newly learned information of a first controller, or by replicating a controller by making a second controller a complete copy of a first controller. The information can be shared by generating and transmitting, with a first controller, a list of device identifiers of devices controlled by the first controller to a second controller. The list is received by the second controller and stored in a memory of the second controller dedicated to store device identifiers of devices controlled by the second controller. This function proves advantageous when new controllers are introduced or if a controller is lost, worn out, or destroyed.
Owner:SILICON LAB INC
Methods for audio watermarking and decoding
InactiveUS6983051B1Widen meansEasy to obtainTelevision system detailsError preventionAudio watermarkCarrier signal
An identification code signal is hidden in a carrier signal (such as an electronic data signal or a physical medium) in a manner that permits the identification signal later to be discerned. The carrier signal can thereby be identified, or some machine responsive action can thereby be taken. The technique can be applied in video imagery embodiments to control associated video equipment, e.g. to serve as a copy control signal.
Owner:DIGIMARC CORP
File replication system, replication control method, and storage medium
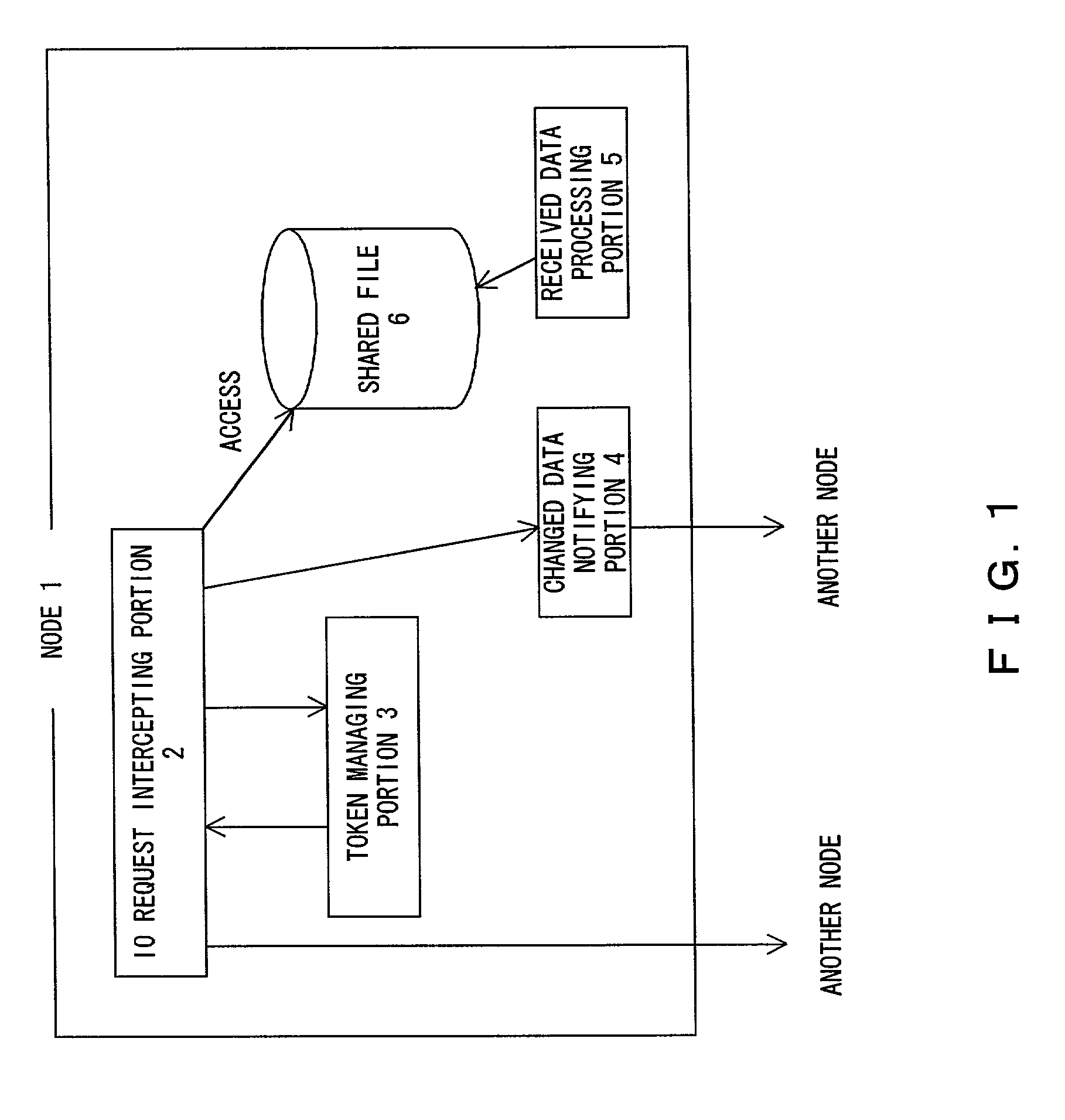
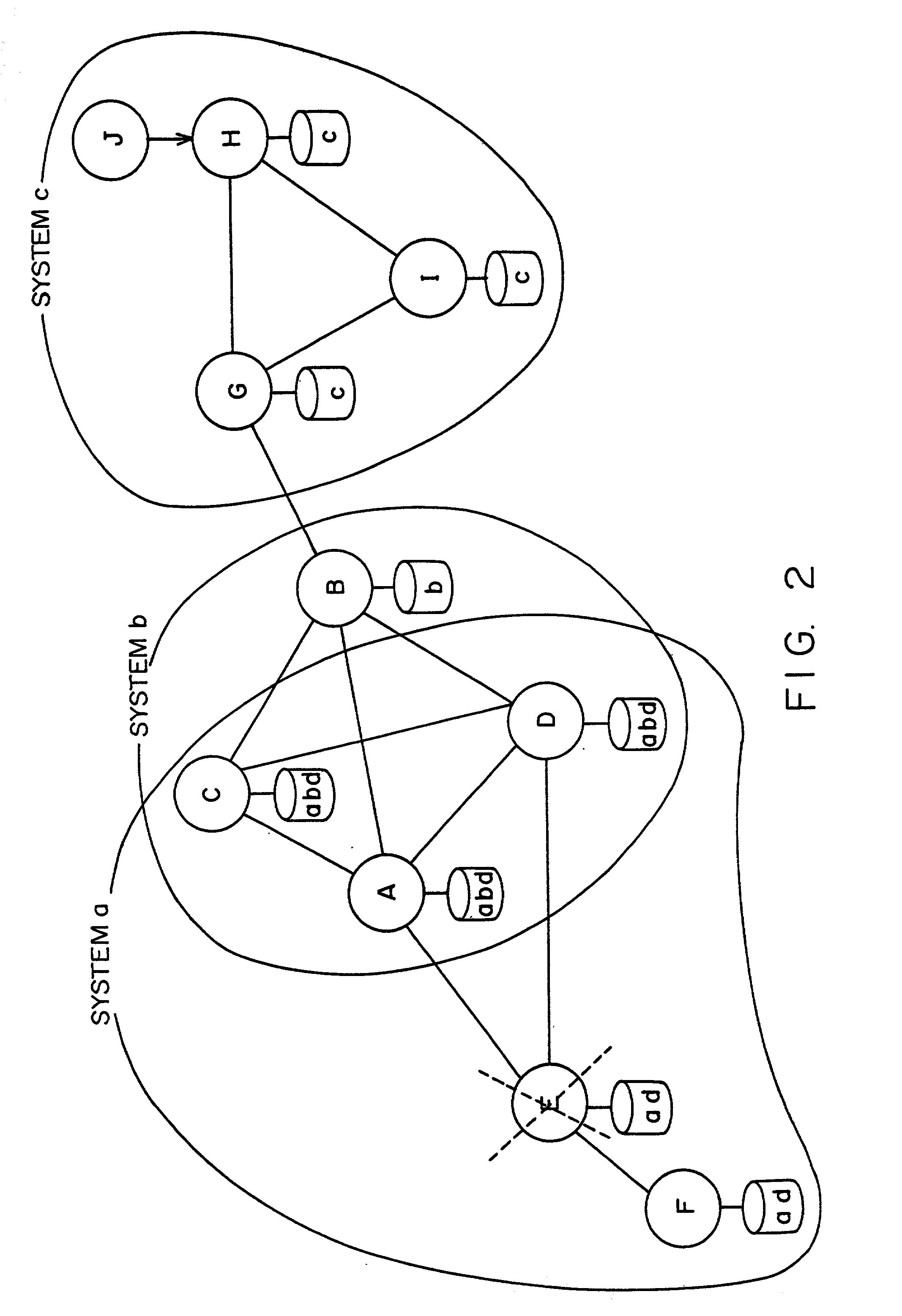
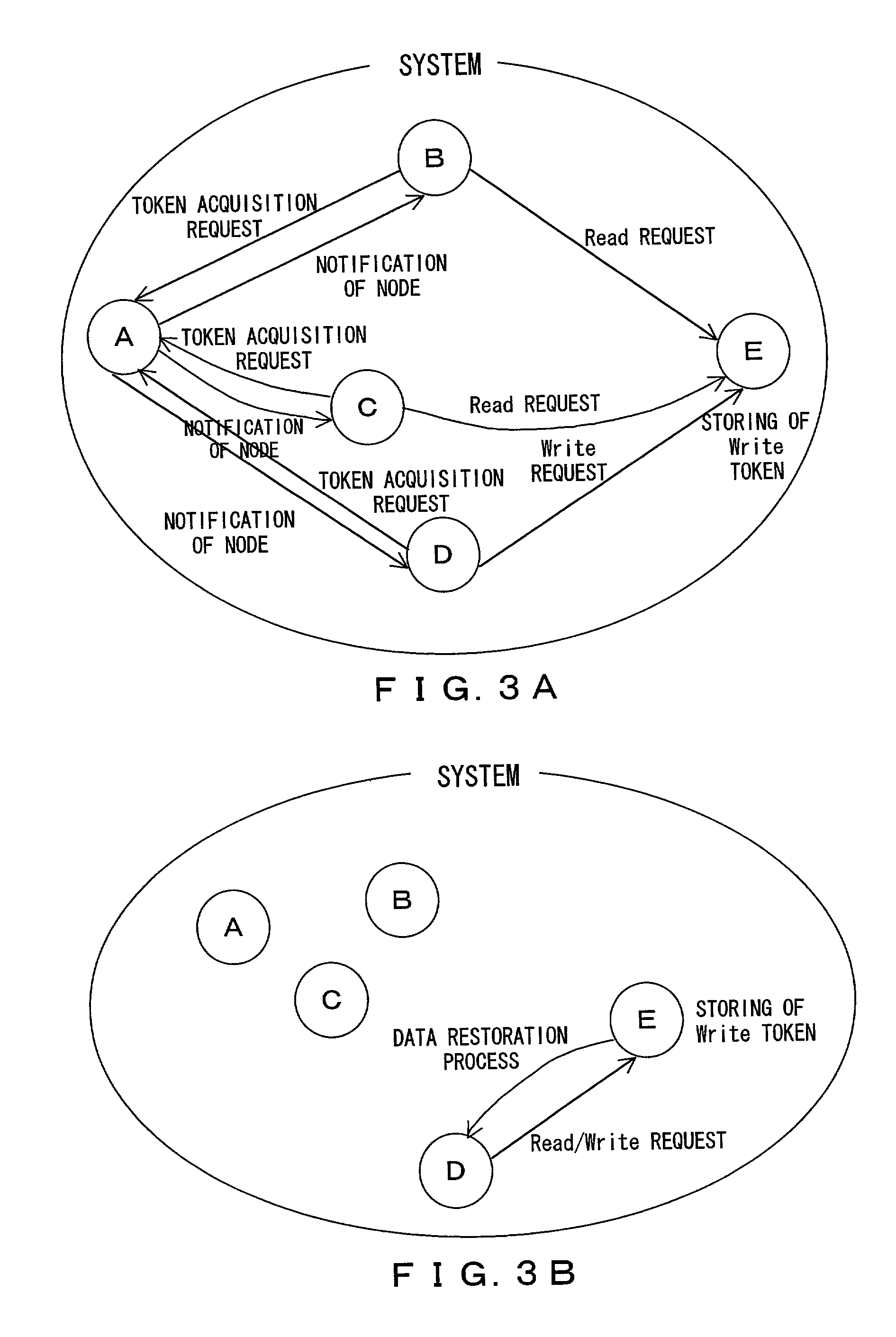
InactiveUS20010039548A1Input/output to record carriersDigital data information retrievalFile replicationCopy control
A token managing portion manages an access request for a shared file. An IO request intercepting portion asks the token managing portion to acquire access permission for the shared file in response to an access request for the shared file in the node itself. The token managing portion notifies the IO request intercepting portion of a node that has update permission in response to the access request of the IO request intercepting portion. The IO request intercepting portion asks the node that has the update permission to access the shared file when the IO request intercepting portion is not capable of acquiring the access permission. Thus, with a file consistent assurance control, a file replication system as an improved application of a file replication can be accomplished.
Owner:FUJITSU LTD
Replication of remote copy data for internet protocol (IP) transmission
ActiveUS7546364B2Special service provision for substationDigital computer detailsInternet protocol suiteRouting table
Owner:EMC IP HLDG CO LLC
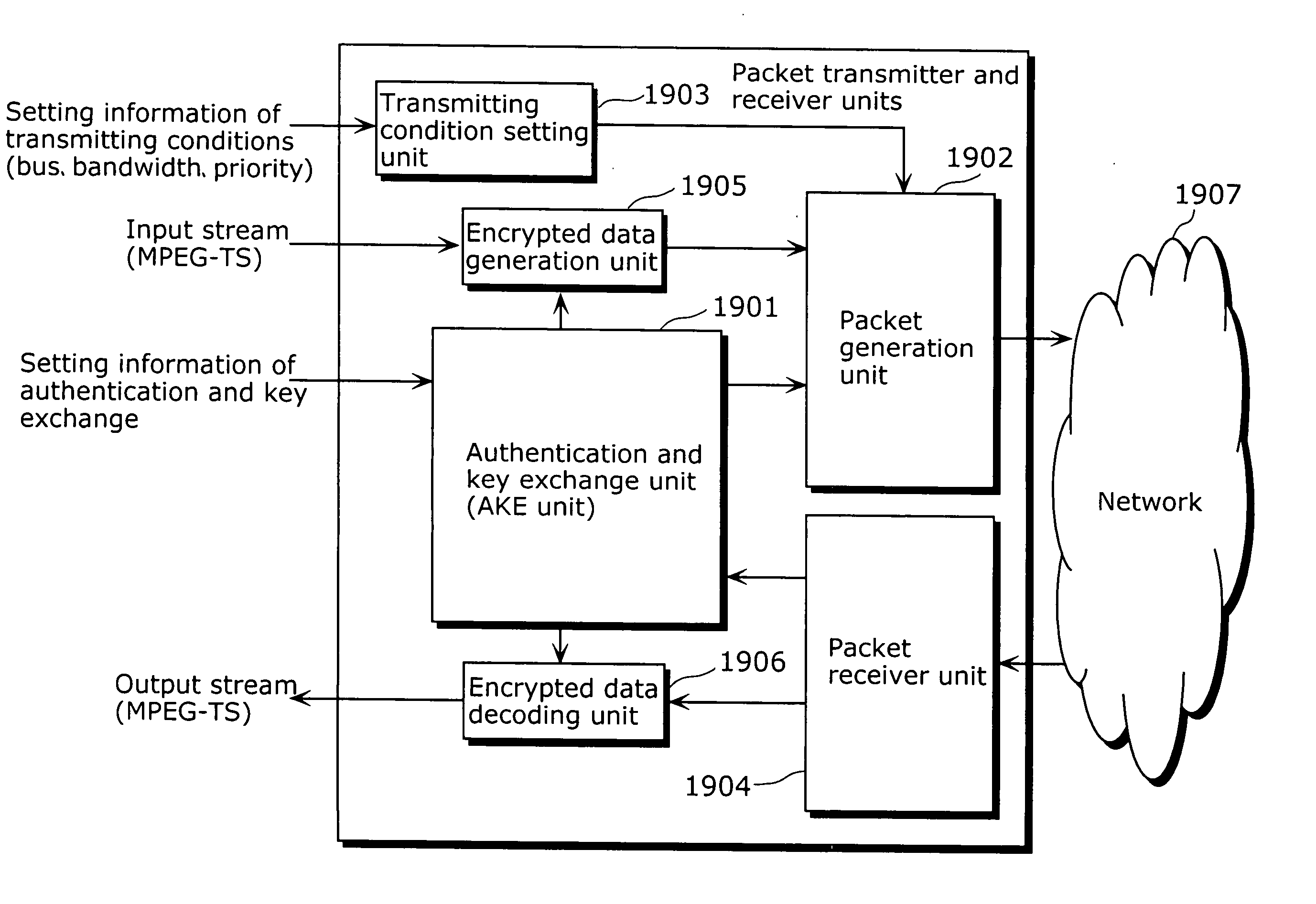
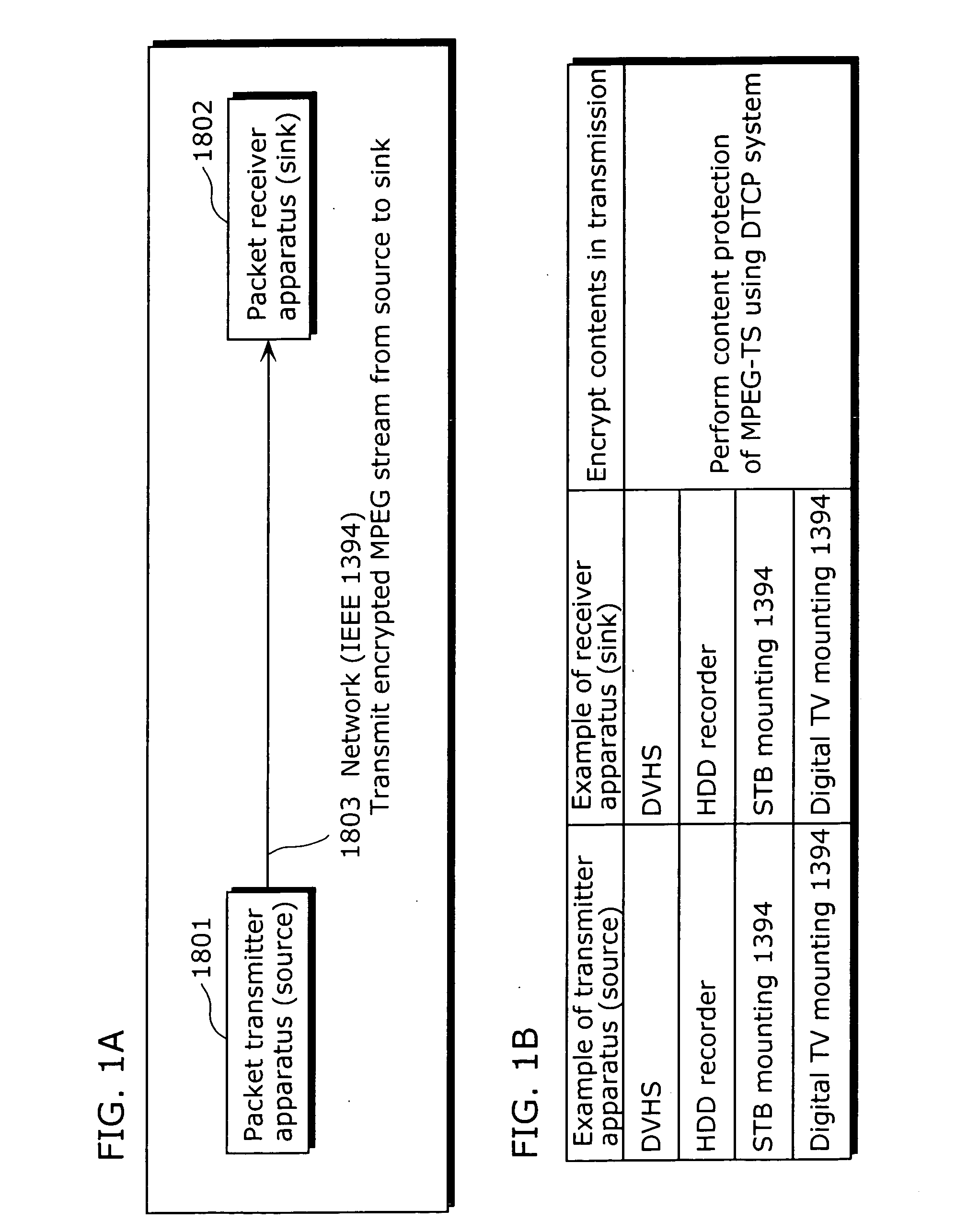
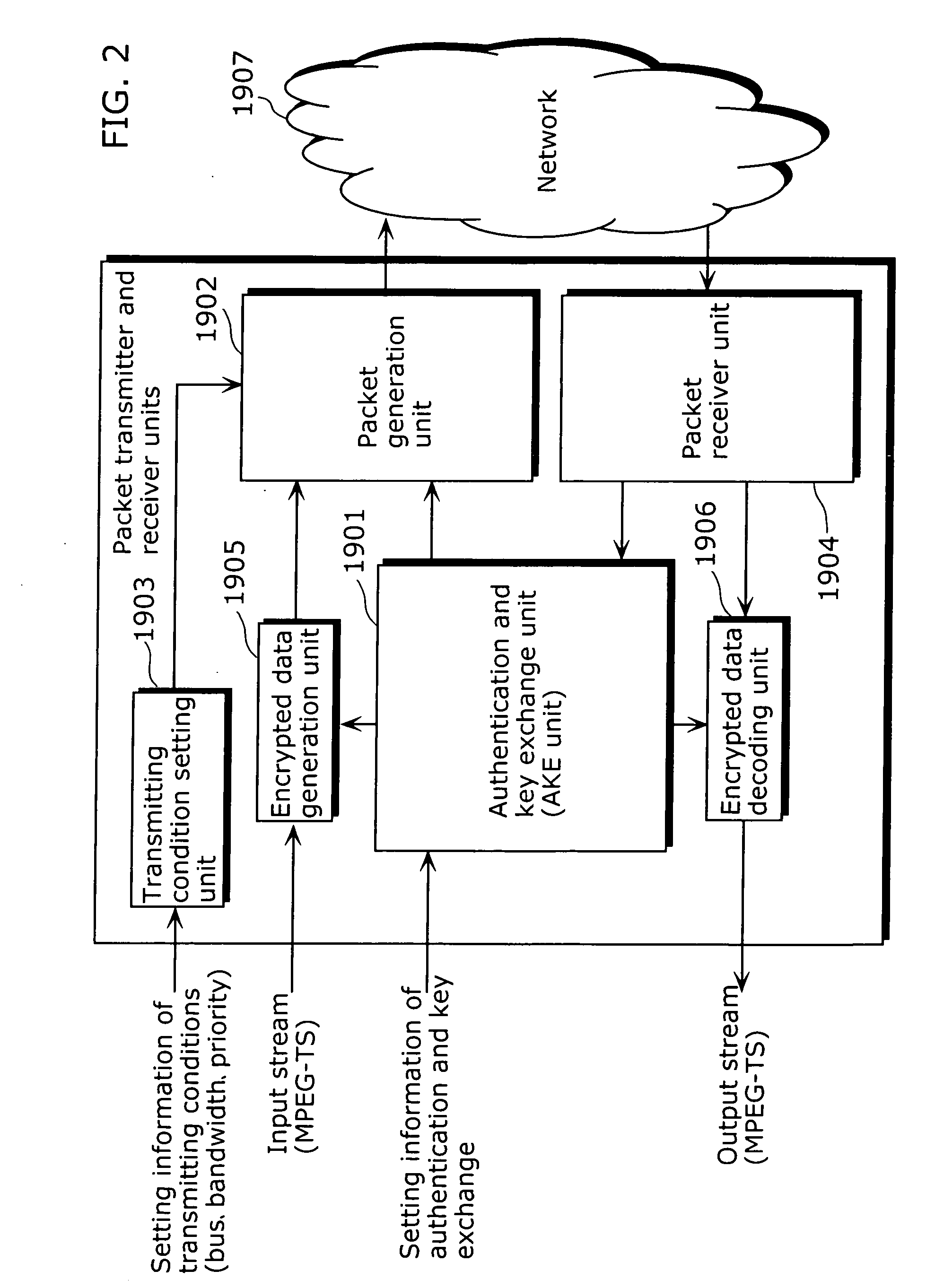
Packet transmitter apparatus
ActiveUS20070162981A1Maintain compatibilityMaintain confidentialityData taking preventionDigital data processing detailsData packManagement unit
To provide a packet transmitter apparatus which can transmit contents protected by a content protection technique such as DTCP or the like, using packets such as IP packets which have become widespread. The packet transmitter apparatus includes a transmitting condition setting management unit (404) which extracts at least one of charge information, playback control information and copy control information of AV data from the inputted non-AV data or AV data and generates, based on the extracted information, encryption mode information indicating an encryption mode which becomes a condition at the time of transmitting the AV data; an encrypted data generation unit (406) which generates encrypted data by encrypting, based on the transmitting condition, the inputted AV data and adding encryption information headers based on the encryption mode information to the encrypted AV data; and a packet generation unit (403) which generates packets by adding packet headers to the generated encrypted data. The transmitting condition is to be determined as a combination of input terminal information, data format information and attribute information.
Owner:PANASONIC CORP
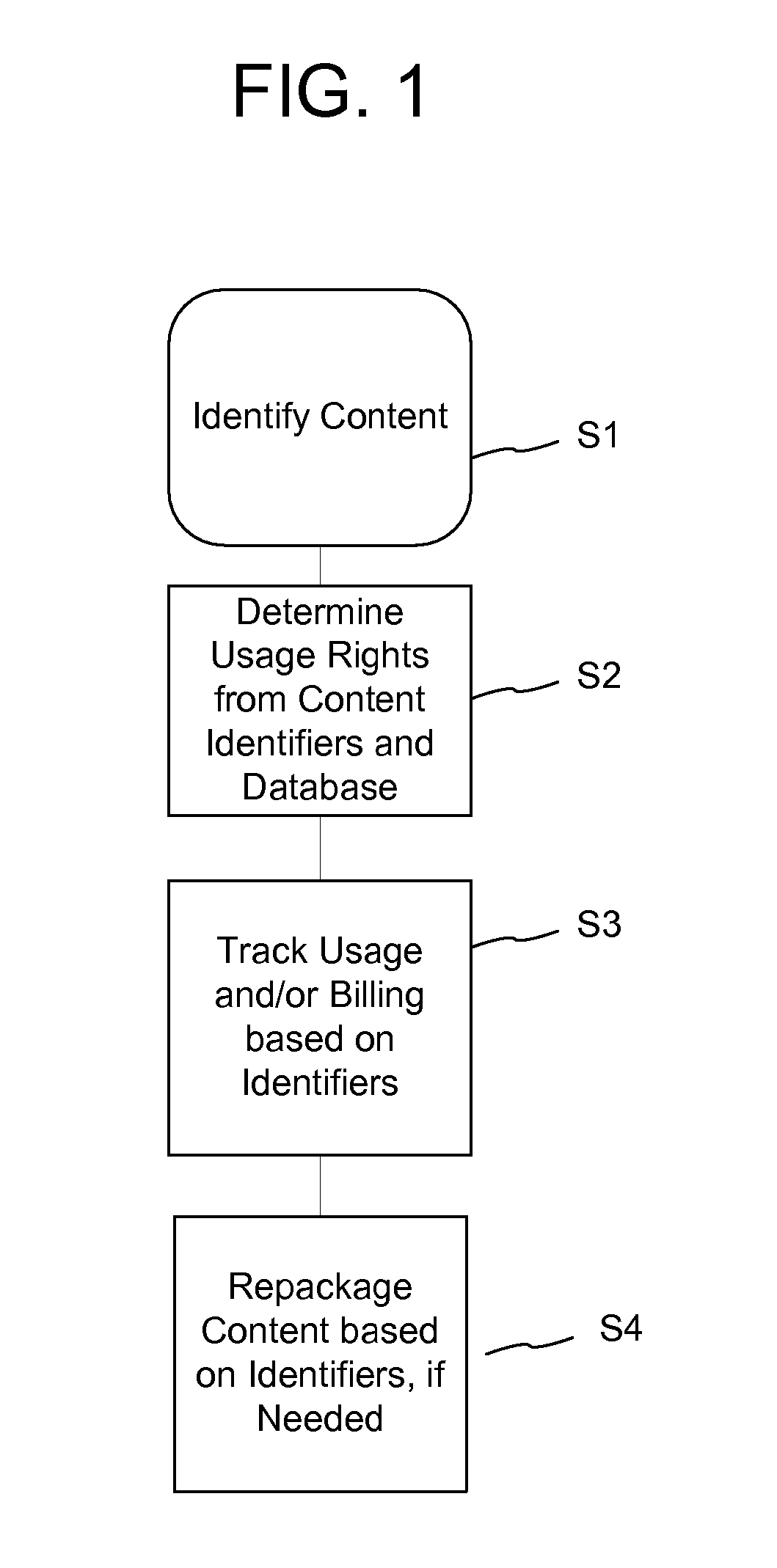
Rights Management System and Methods
ActiveUS20070294173A1Difficult to controlDifficult to trackDigital data processing detailsRecord information storageContent IdentifierRights management
A method of performing digital asset management of content is provided. The content is identified with an identifier. The identifier can be identified with a digital watermark, header file, or both. The identifier is linked to usage rules to regulate usage and protect the content. The usage rules can be maintained on a remote or local database or server. Once extracted, an identifier is used to index the database to locate a corresponding usage rule, and can be used to override copy control information with proper purchase and subsequent protection. Content can be managed from such. In another embodiment, an identifier is used to track usage, such as amount of content viewed, time played, and copies made. In yet another embodiment, a content identifier is used to regulate content throughout a distribution chain, and a distributed set of databases with information relevant only to the owner of the database act as one database due to a central router.
Owner:DIGIMARC CORP
Hiding encrypted messages in information carriers
InactiveUS6959386B2ExpandedEasy to copyTelevision system detailsError preventionCarrier signalVideo equipment
An identification code signal is hidden in a carrier signal (such as an electronic data signal or a physical medium) in a manner that permits the identification signal later to be discerned. The carrier signal can thereby be identified, or some machine responsive action can thereby be taken. The technique can be applied in video imagery embodiments to control associated video equipment, e.g. to serve as a copy control signal.
Owner:DIGIMARC CORP
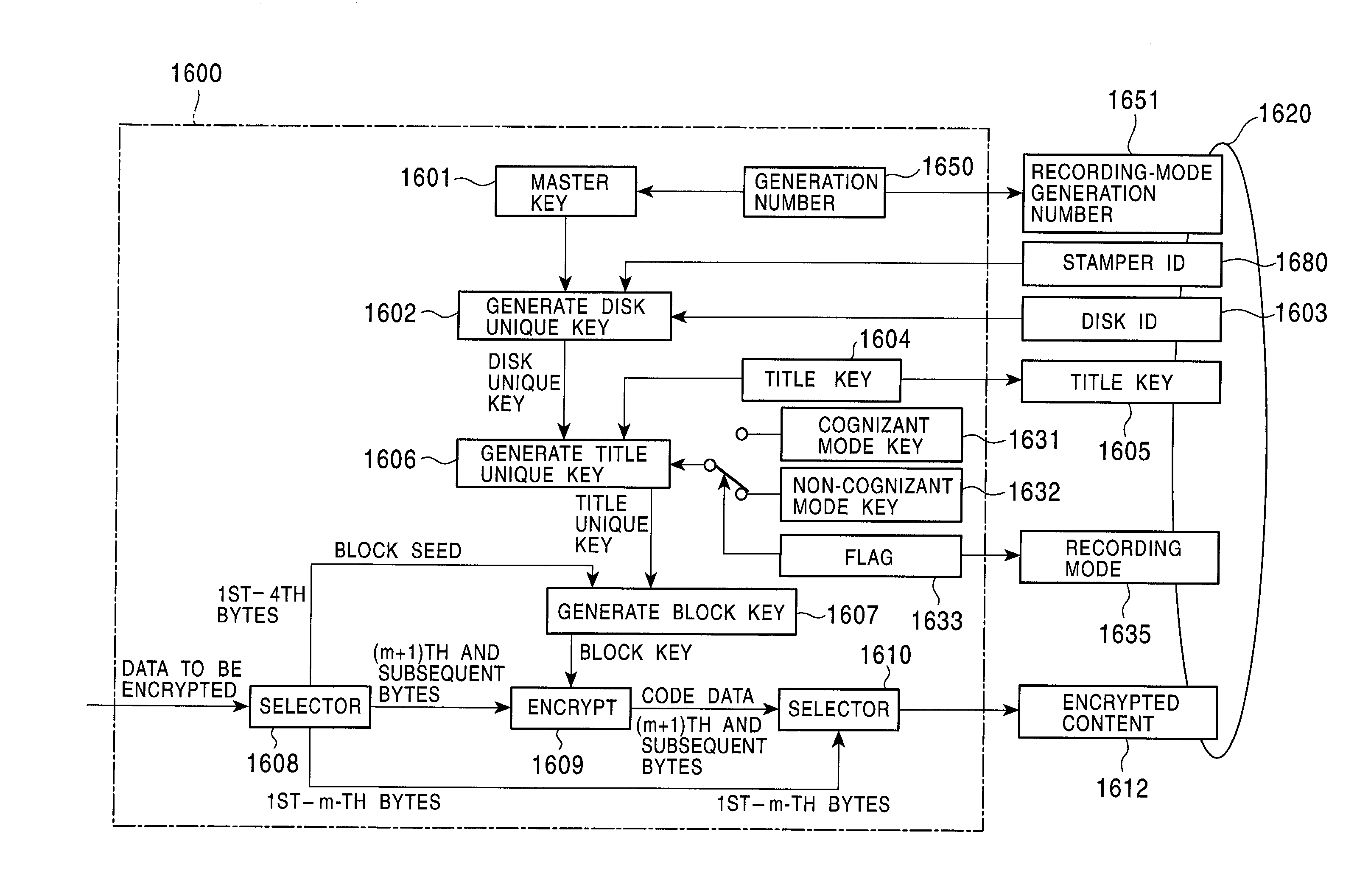
Method and apparatus for selectively executing information recording using a cognizant mode and a non-cognizant mode
InactiveUS7203968B2Reduce usagePreventing executionTelevision system detailsKey distribution for secure communicationCryptographic key generationPattern selection
When the recording mode of an information recording / playback device is a cognizant mode which analyzes embedded copy control information, the information recording / playback device performs content encryption using a content-encryption key generated by using a cognizant key as a content-encryption-key generating key in the cognizant mode. When the recording mode of the information recording / playback device is a non-cognizant mode which does not analyze the embedded copy control information, the information recording / playback device performs content encryption using a content-encryption key generated by using a cognizant key as a content-encryption-key generating key in the non-cognizant mode. By using these techniques, the above two recording modes are clearly distinguished and separately executed. This prevents an encryption mode indicator as copy control information and embedded copy control information from being mismatched.
Owner:SONY CORP
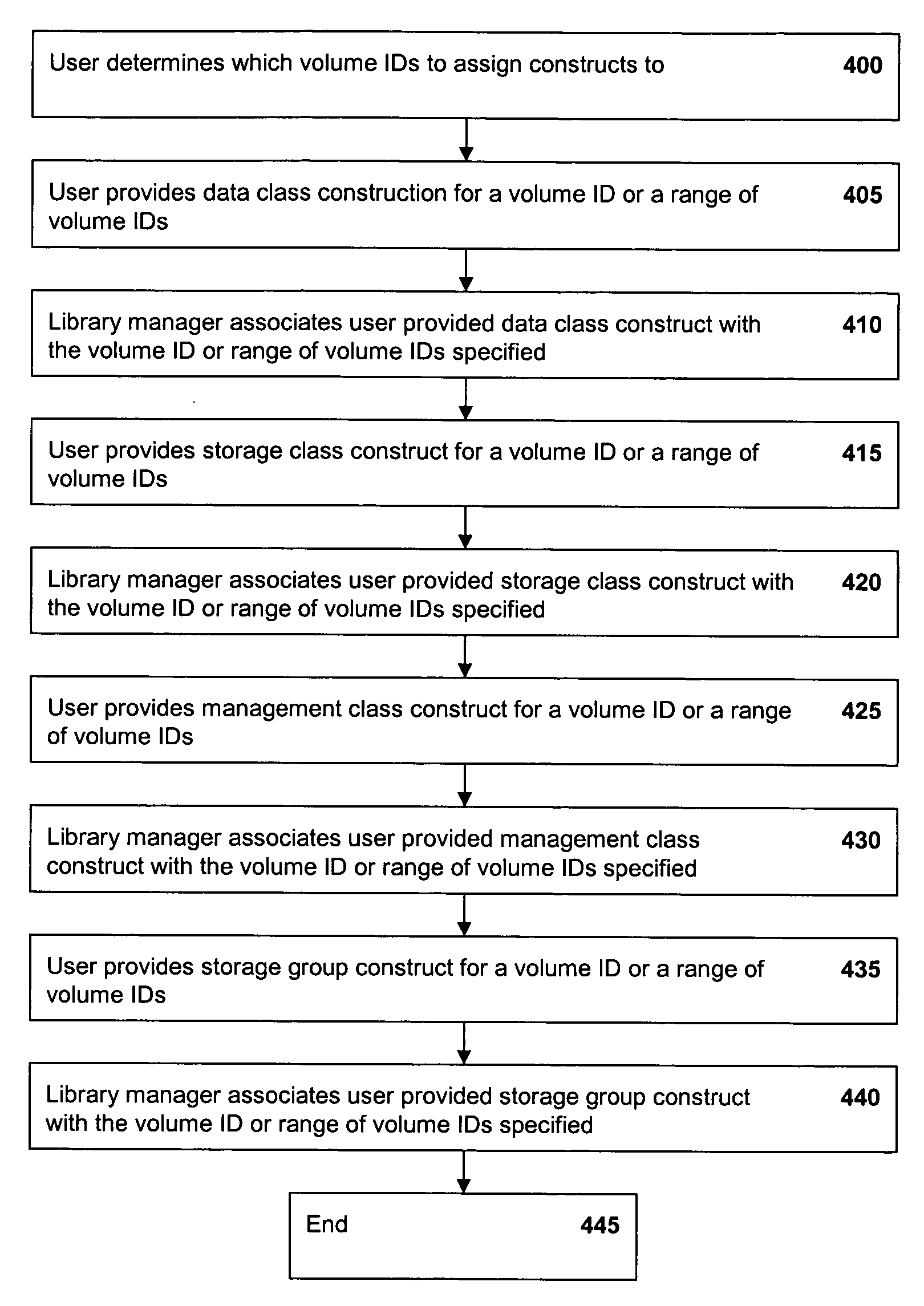
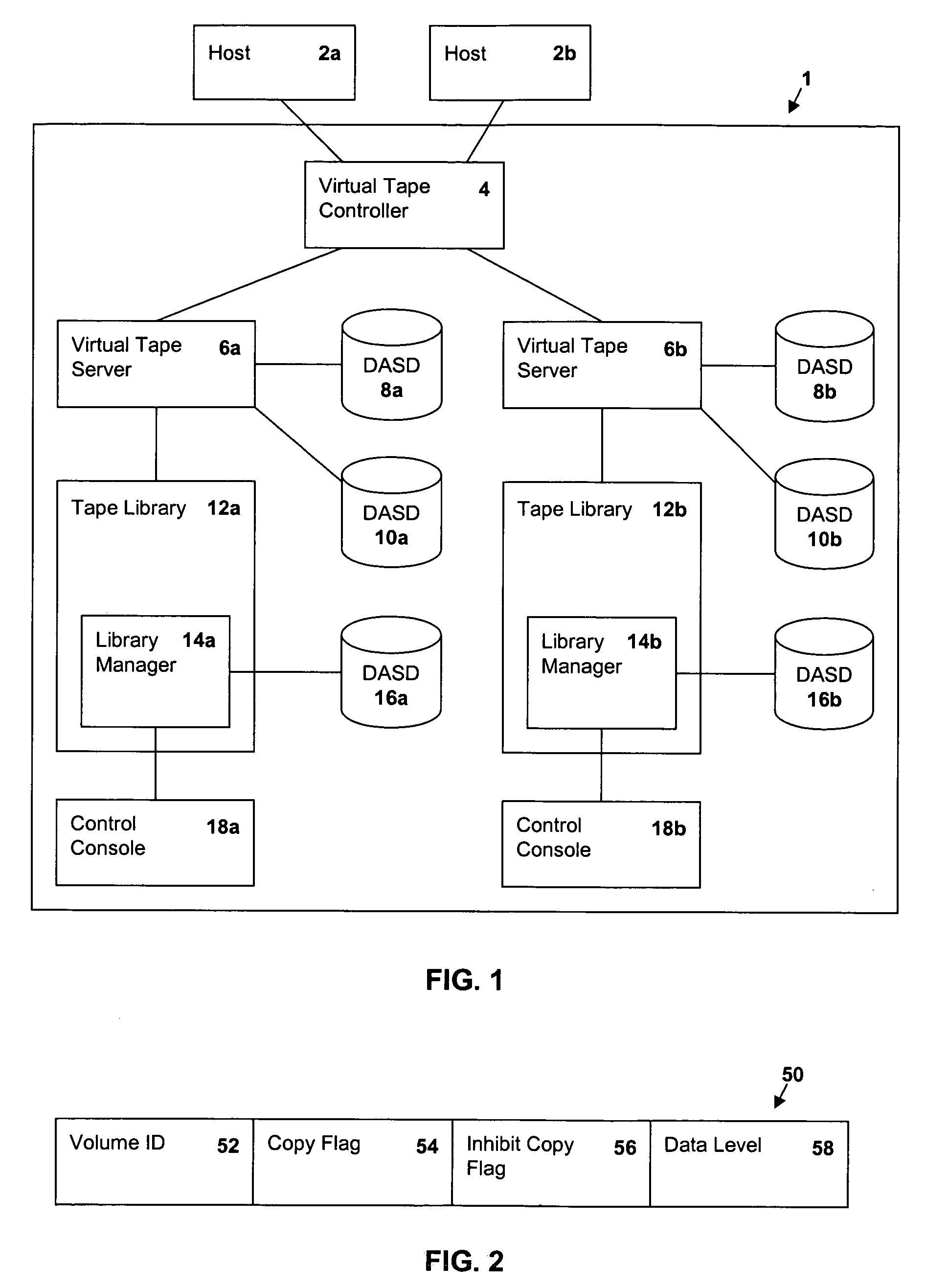
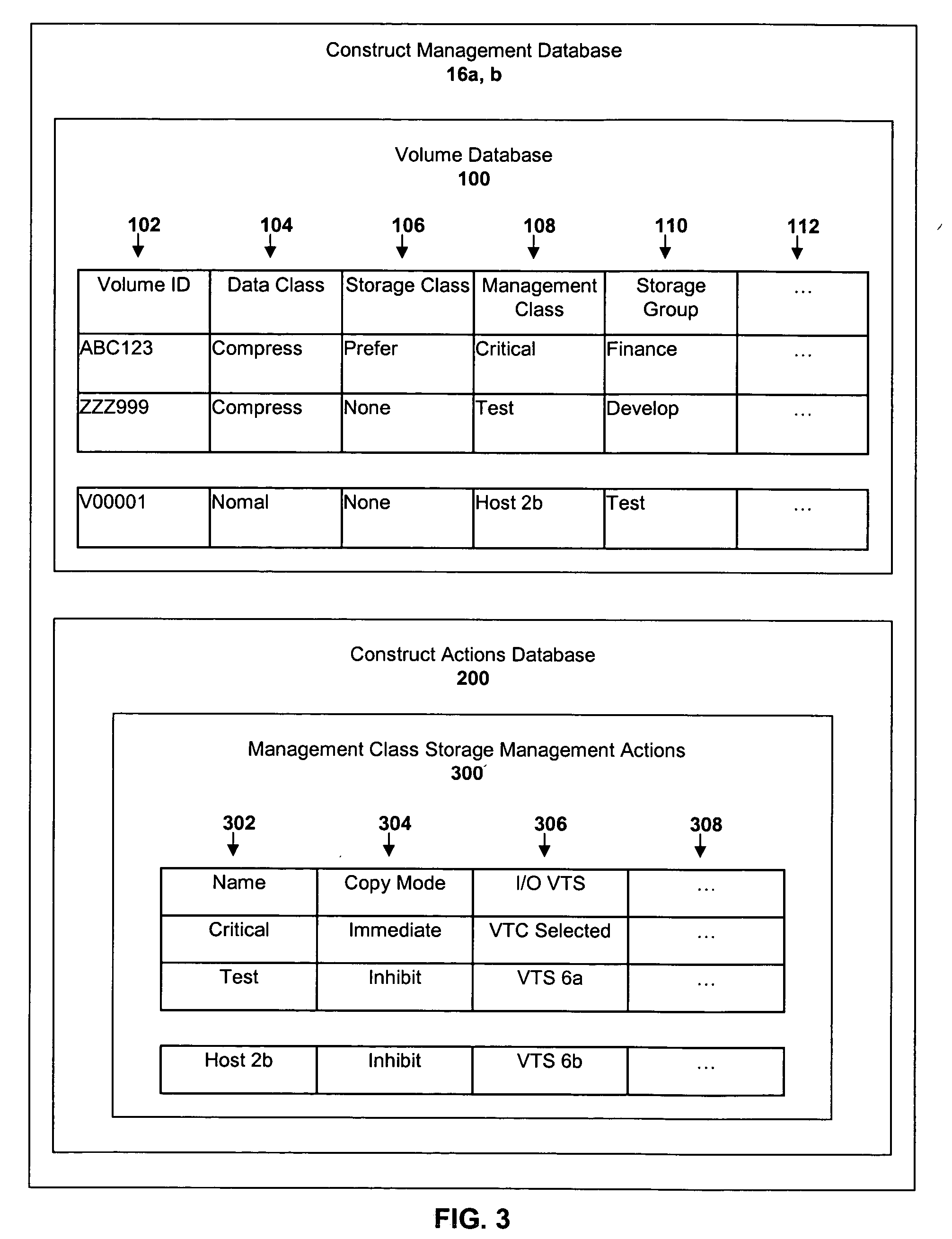
Selective dual copy control of data storage and copying in a peer-to-peer virtual tape server system
InactiveUS20050262296A1Memory systemsInput/output processes for data processingMagnetic tapeData storing
A method of storing data to one of a first or second storage device associated with a data storage system where each storage device provides for the redundant access to and storage of data within the same logical data volumes. The method of storing data consists of defining a storage construct which will direct the performance of a specific storage function. The storage construct is then associated with a logical data volume. The method further consists of mounting the logical data volume residing on one of the two storage devices and executing a storage function in accordance with the storage construct. The storage construct may be defined by a command issued by a host associated with the data storage system. Alternatively, the storage construct may be defined by a user of the data storage system through a user interface. The storage function which is directed by the defined storage construct may consist of selecting which one of the first and second storage devices will execute input / output (I / O) commands received from the data storage system for a particular logical data volume mount. Alternatively, the storage function may consist of determining whether data stored to a logical data volume physically associated with one of the storage devices will be copied to the other storage device. Other storage functions can be directed by a storage construct.
Owner:IBM CORP
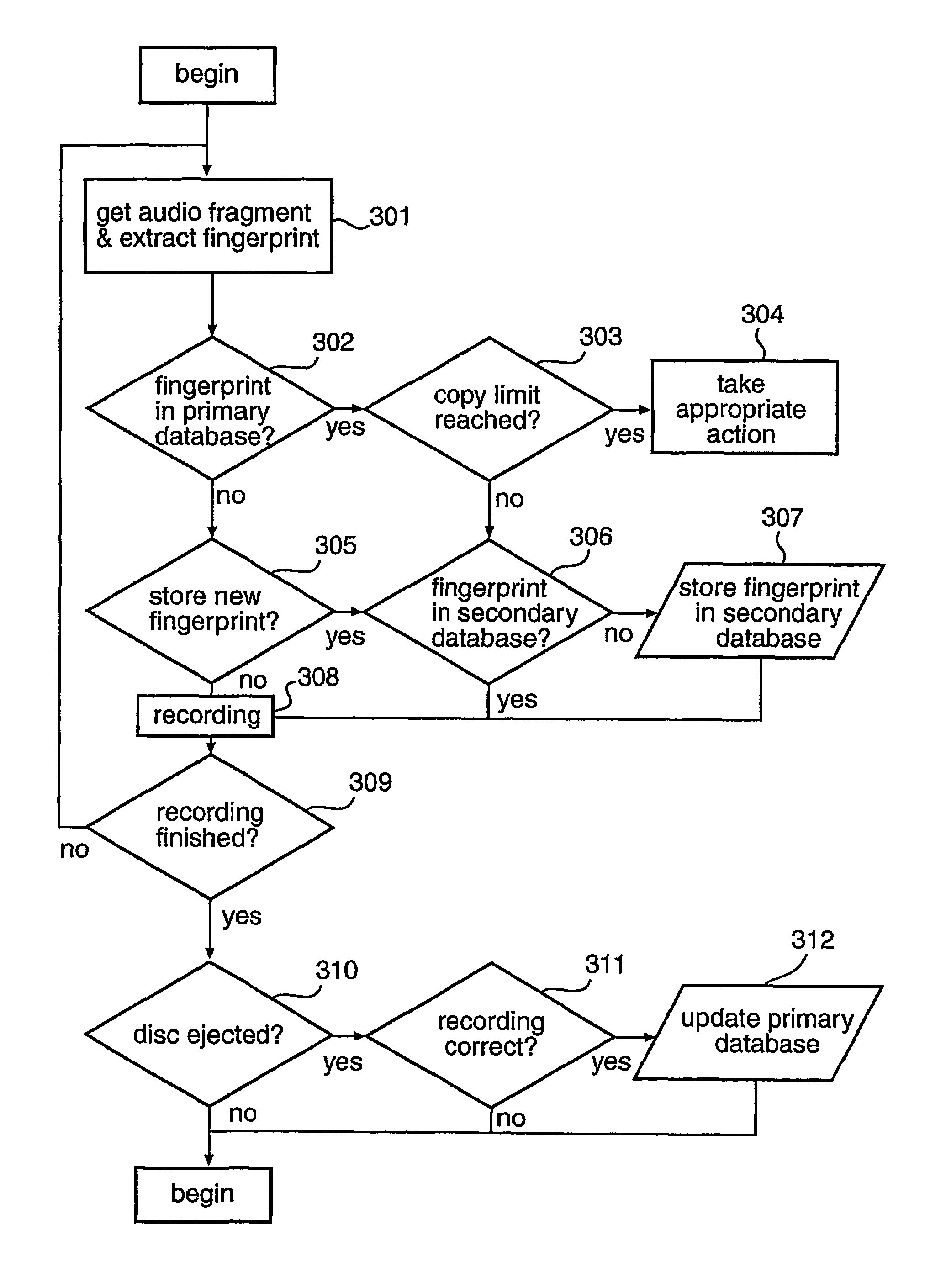
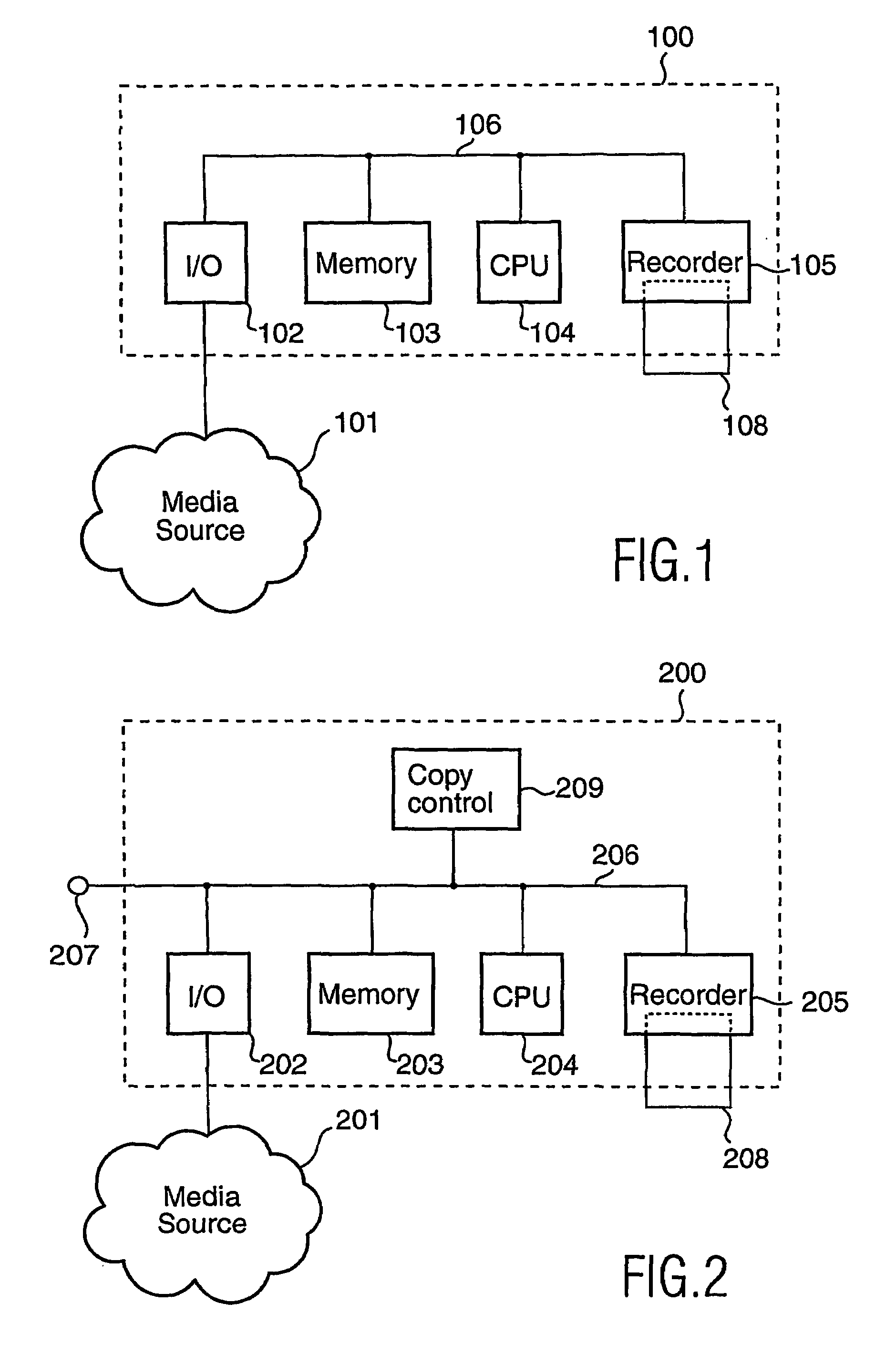
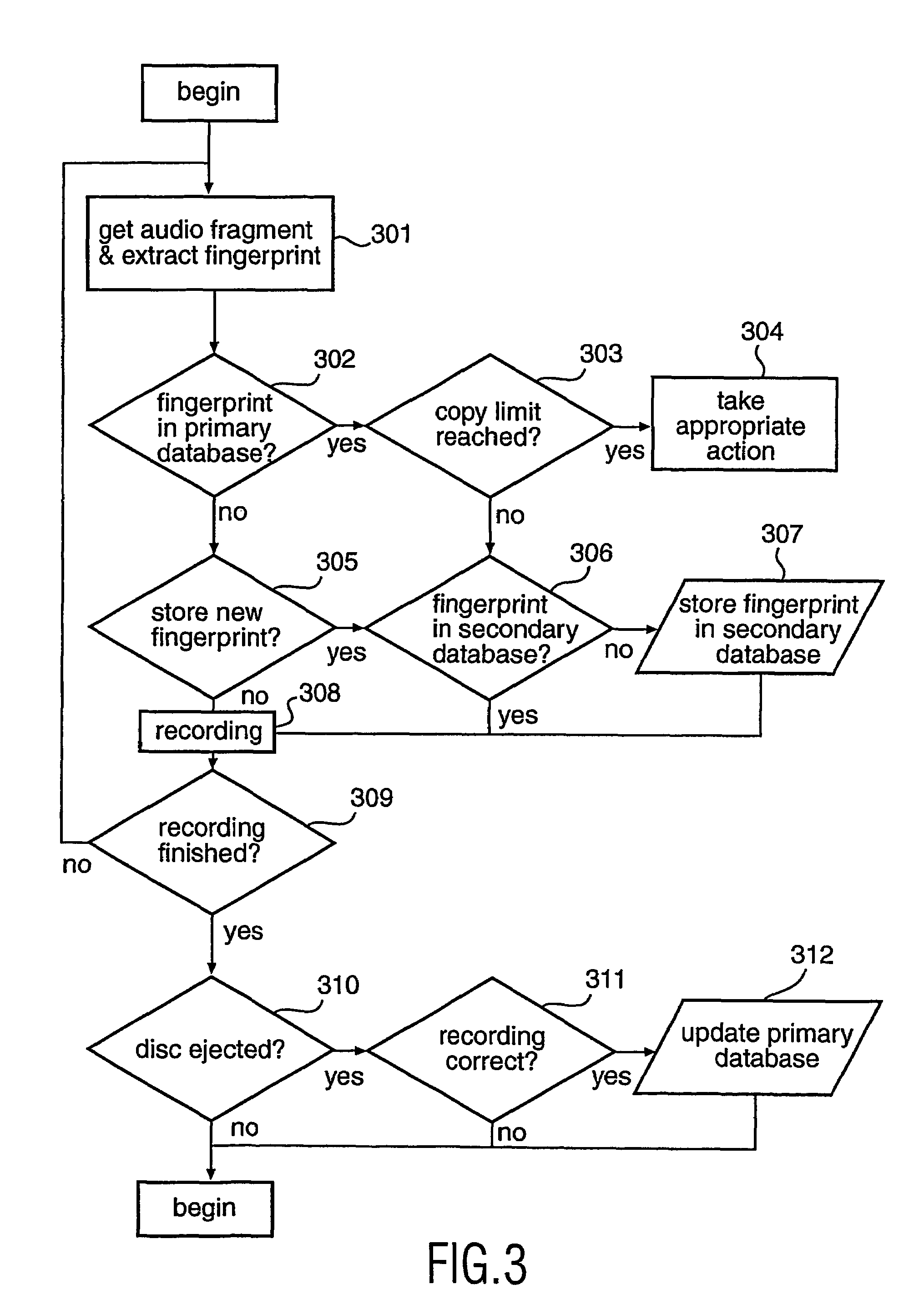
Copy control using digital speed bumps
A digital media recorder and a method of controlling such are provided. During attempts to copy media content, sub-sequences are extracted from an input media sequence. A digital fingerprint of the sub-sequence is calculated and compared with at least one first reference fingerprint from a database. The outcome of the comparison determines the action to take in the further processing. Recording of the input media sequence on a media carrier is either allowed or obstructed, e.g. disallowed. In the case recording of the sequence is allowed, the database is updated with information that the digital media sequence has been recorded.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
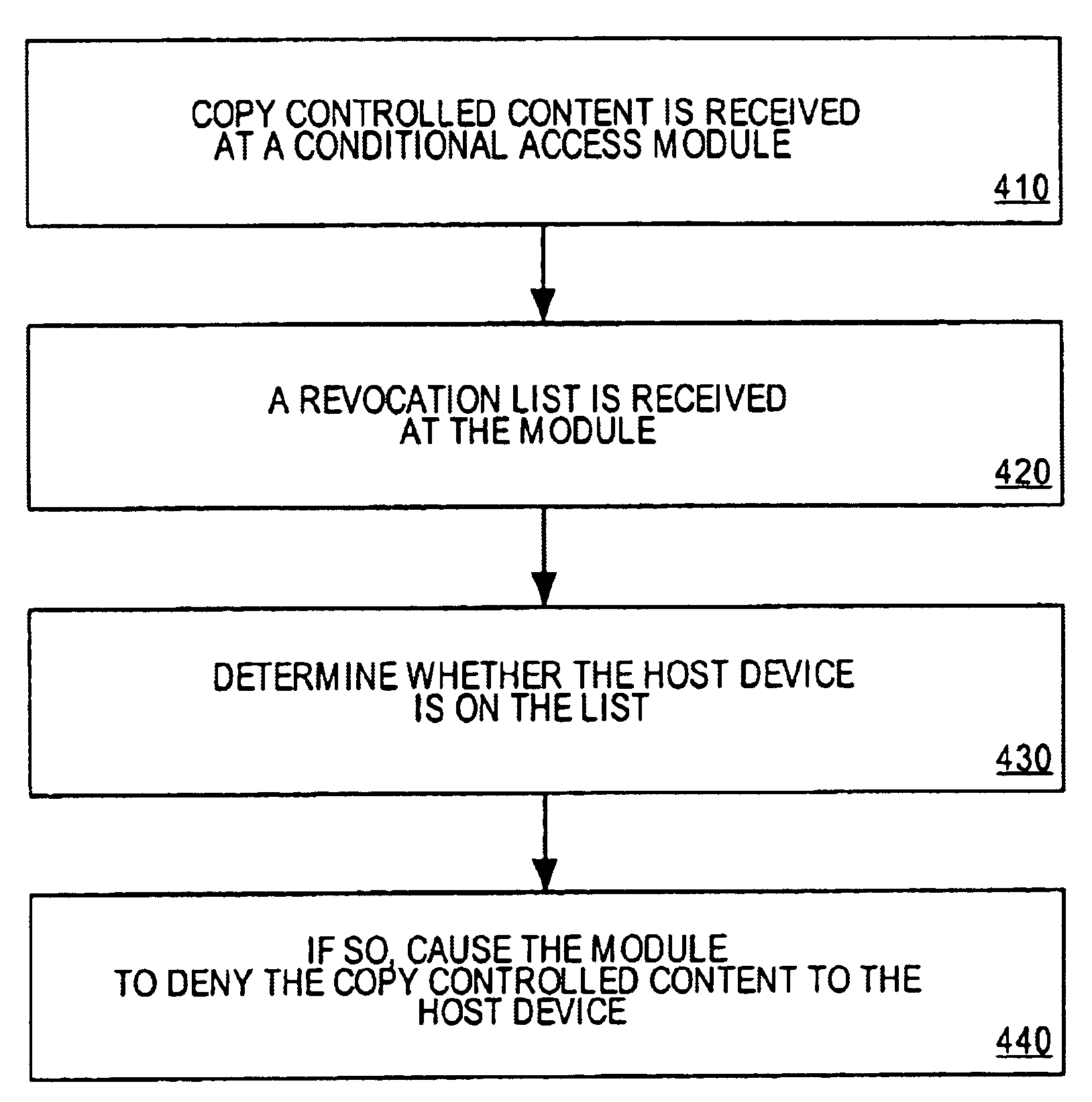
Method and apparatus for implementing revocation in broadcast networks
InactiveUS7225164B1Analogue secracy/subscription systemsRecord information storageComputer moduleConditional access
A method of revoking a descrambling privilege for copy controlled content to a host device is provided. The method includes receiving copy controlled content at a conditional access module. A revocation list is also received at the module. The method includes determining whether the host device associated with the module is on the list. If so, the conditional access module will not descramble the content.
Owner:SONY CORP +1
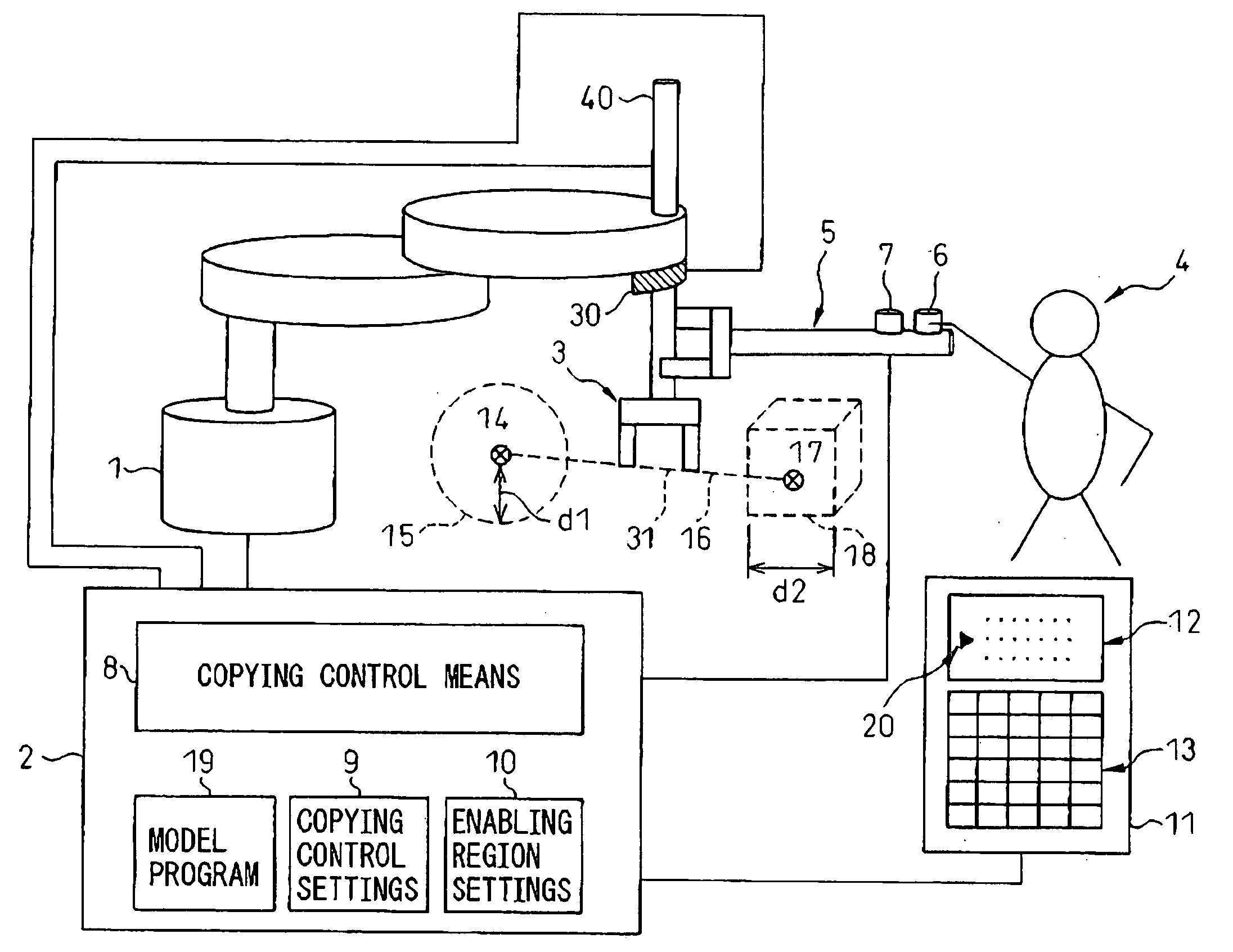
Robot teaching apparatus
InactiveUS20050222714A1Simplification of program adjustmentReduce stepsProgramme-controlled manipulatorComputer controlEngineeringRobot control
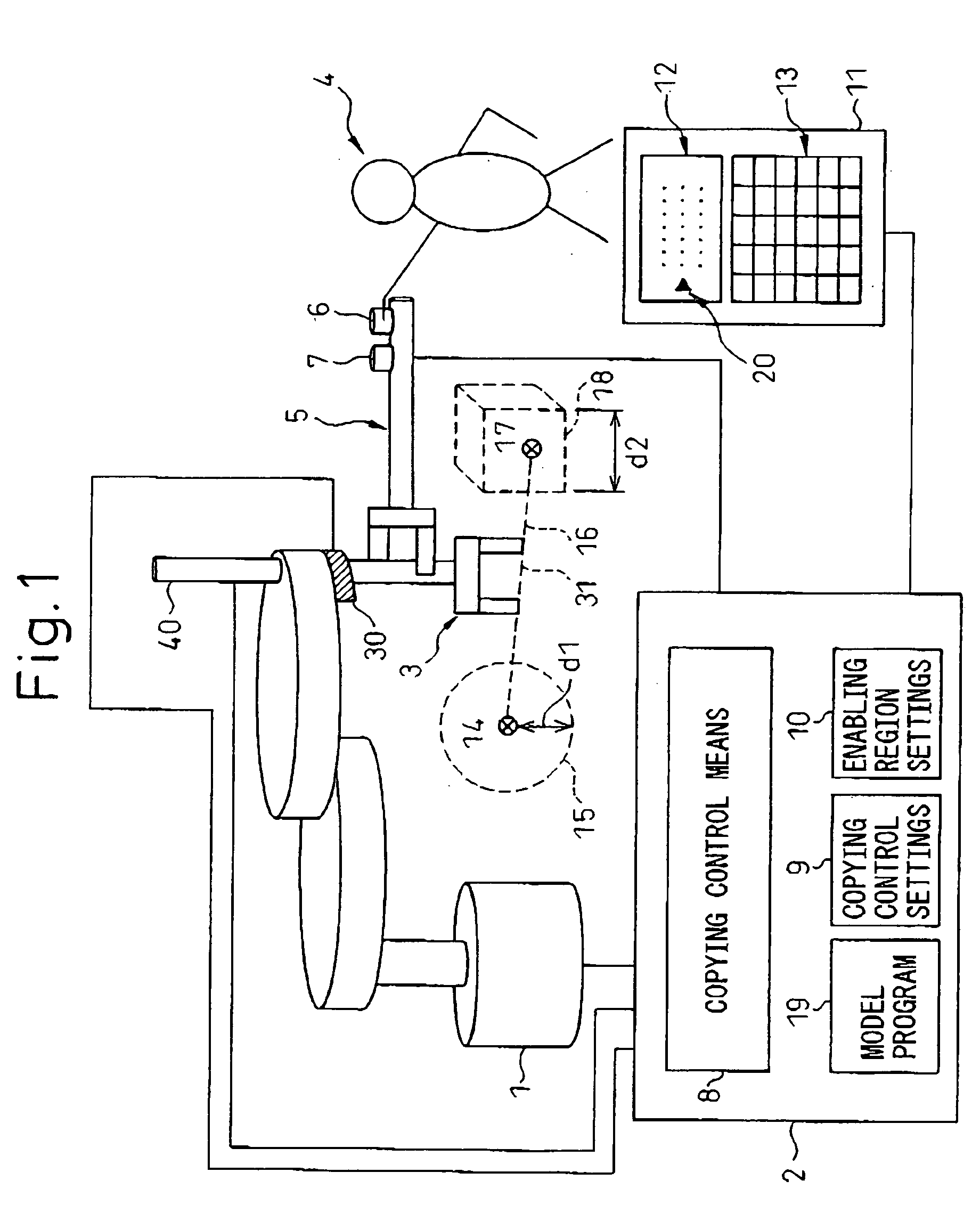
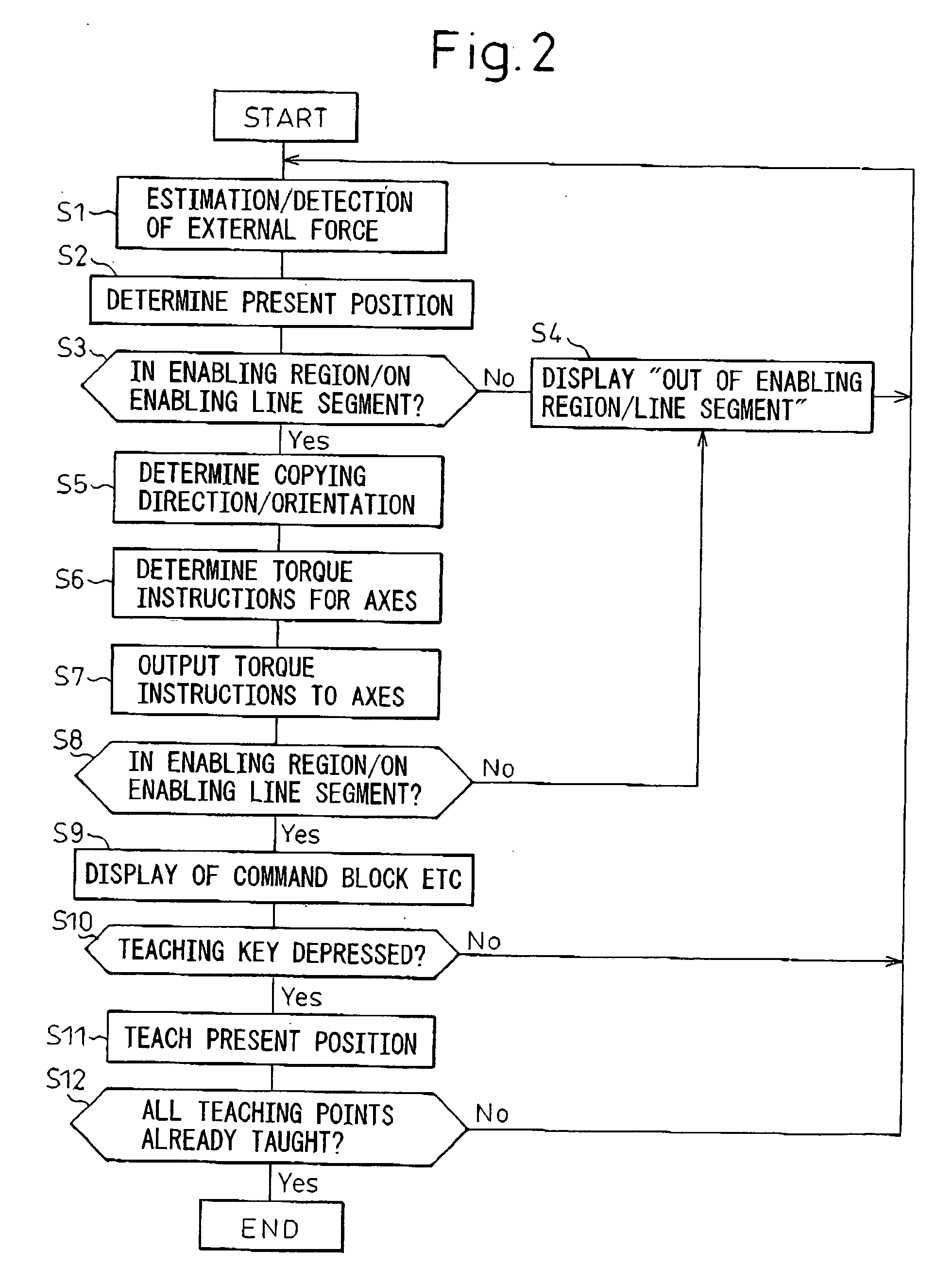
When an operator (4) applies an external force to a robot (1) via a handle (5) attached to an end portion of an arm of the robot (1), the external force is estimated or detected by a force sensor (30) or an acceleration sensor (40). A copying control means (8) of a robot control unit (2) determines the position of the tool top point (31). When the robot (1) is located in a copying control enabling region (15, 18) or a copying control enabling line segment (16) defined in a block (10) of enabling region settings, the copying control is carried out. The directions of the movement and change of orientation to be followed are determined with reference to the content of the copying control settings in the region where the robot is located at present in the block (9) of the copying control settings, and the copying control is carried out for only the movement and change of orientation in the determined directions, to thereby move the robot (1).
Owner:FANUC LTD
Method and apparatus for block based volume backup
InactiveUS20100306174A1Memory loss protectionDigital data processing detailsFile serverCloud storage
Embodiments of the invention provide methods and apparatuses for block based storage subsystem to have backup ability to a file based storage service such as HTTP or cloud storage service. In one embodiment, a storage system is coupled via a network to a storage service which has one or more file servers. The storage system comprises a processor; a memory; a volume-based snapshot control module configured to create a snapshot volume of data at a certain time, the snapshot volume being a block-based volume which is divided into a plurality of portions; and a copy control module configured to read each portion of the snapshot volume and send said each portion as file data to the storage service via the network, and to generate mapping information between an address of said each portion in the storage system and a file identifier of the file data of said each portion in the storage service.
Owner:HITACHI LTD
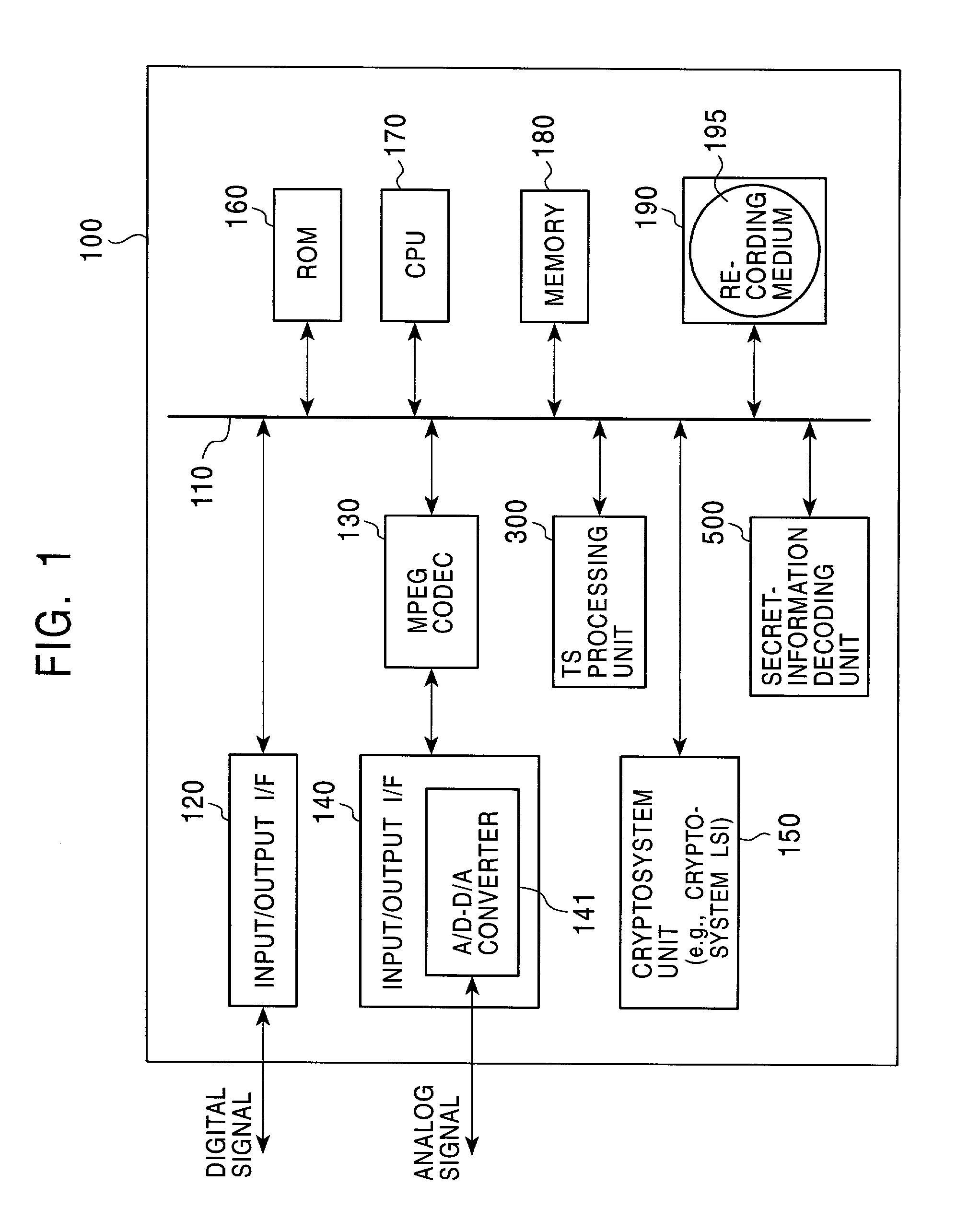
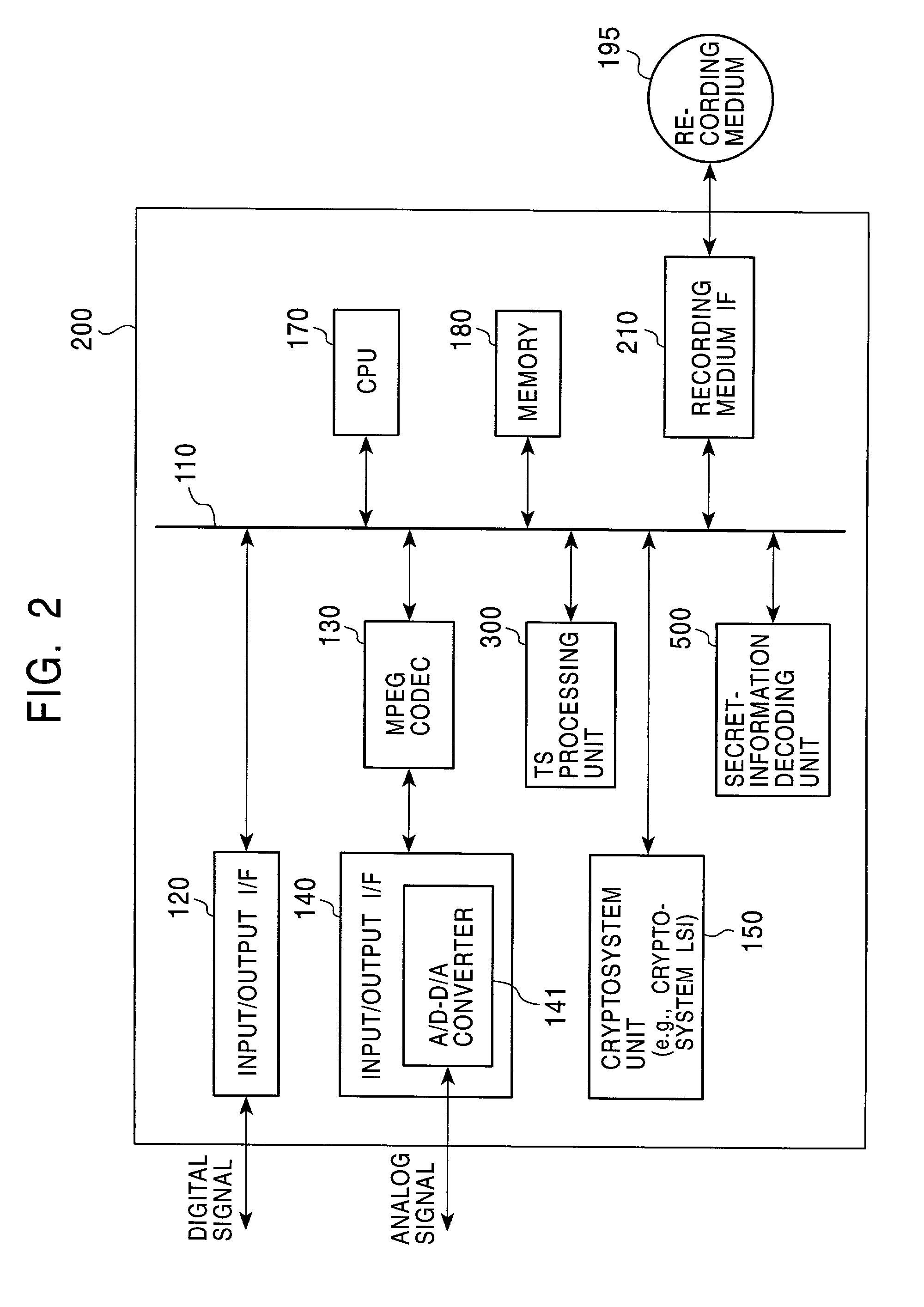
MPEG data recorder having IEEE 1394 interface
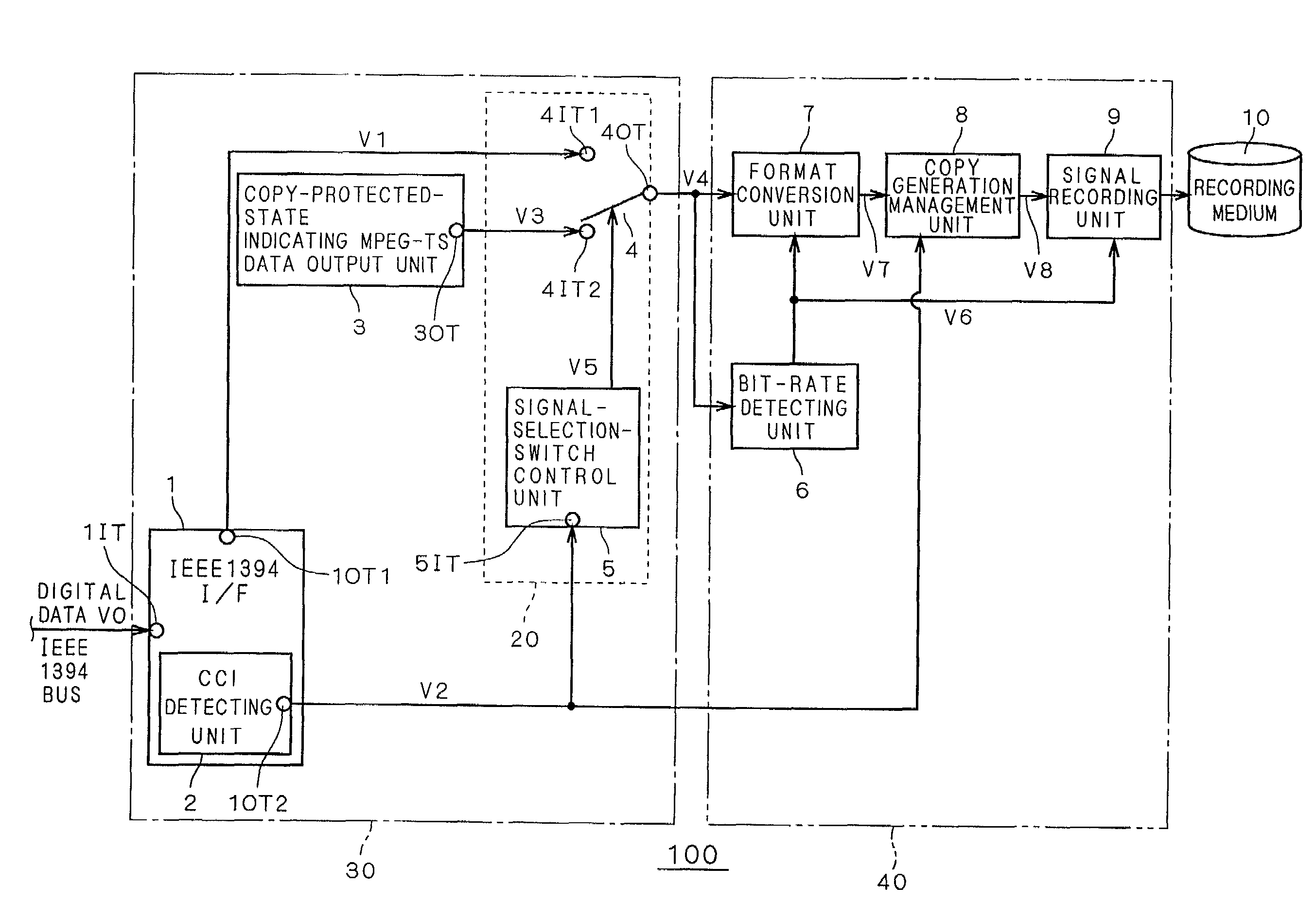
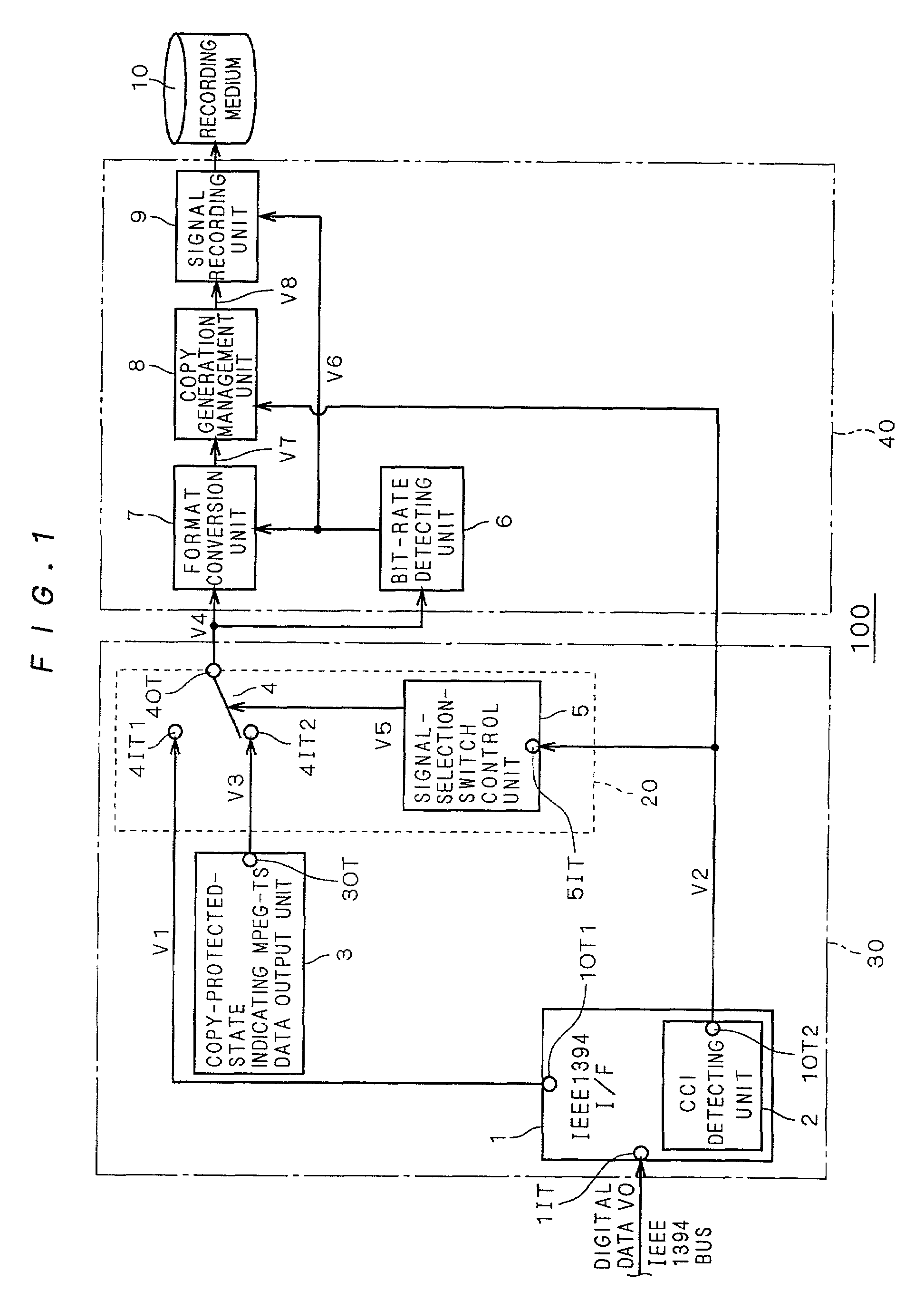
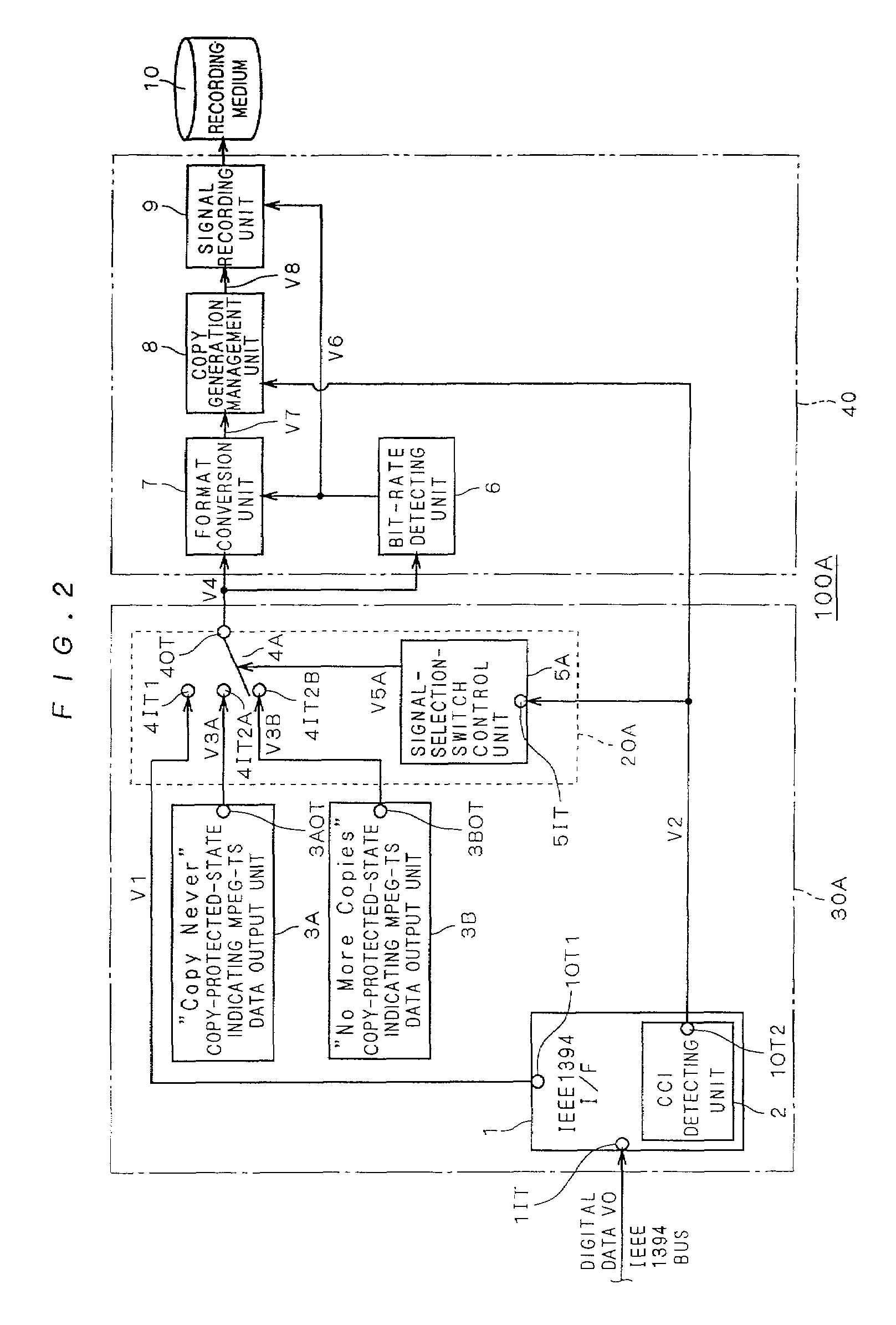
InactiveUS7227953B2Easily find outSimple circuit configurationTelevision system detailsDigital data processing detailsCopy controlIEEE 1394
A copy-protected-state indicating MPEG-TS data output unit (3) holds a bit stream obtained by previously compressing and encoding image and / or audio data representing that recording desired by the user has ended in failure because the contents is copy-protected. When copy control information (V2) outputted from an IEEE 1394 interface (1) indicates a copy-protected state, a selecting unit (20) selects copy-protected-state indicating MPEG-TS data (V3) outputted from the copy-protected-state indicating MPEG-TS data output unit (3) and outputs it as to-be-recorded MPEG-TS data (V4). Thereby, the data (V3) is recorded.
Owner:MITSUBISHI ELECTRIC CORP
Digital information recording and reproducing method and apparatus therefor
InactiveUS20060077825A1Improve user friendlinessHigh precisionOptical re-recordingDigital data processing detailsCopy controlBit rate
To solve the problem inhibiting the copyright protection caused by reason that there are no means for restricting the number of backups to other media, which makes it impossible for a copyright owner to specify the allowable number of backups for the content of “Copy One Generation”, disclosed herein is a digital information recording and reproducing method. The method is so configured that: a first piece of digital information and copy control information of the first piece of digital information is received, wherein the copy control information is for controlling the recording of the first piece of digital information on a recording medium; and when the received copy control information is Copy One Generation indicating that only one generation copy of digital information is allowed, a plurality of the first pieces of digital information are recorded on a first recording medium as the first piece of digital information and a second piece of digital information, wherein the first piece of digital information is different in format or in bit rate from the second piece of digital information.
Owner:MAXELL HLDG LTD
Watermarking technique for scaled image
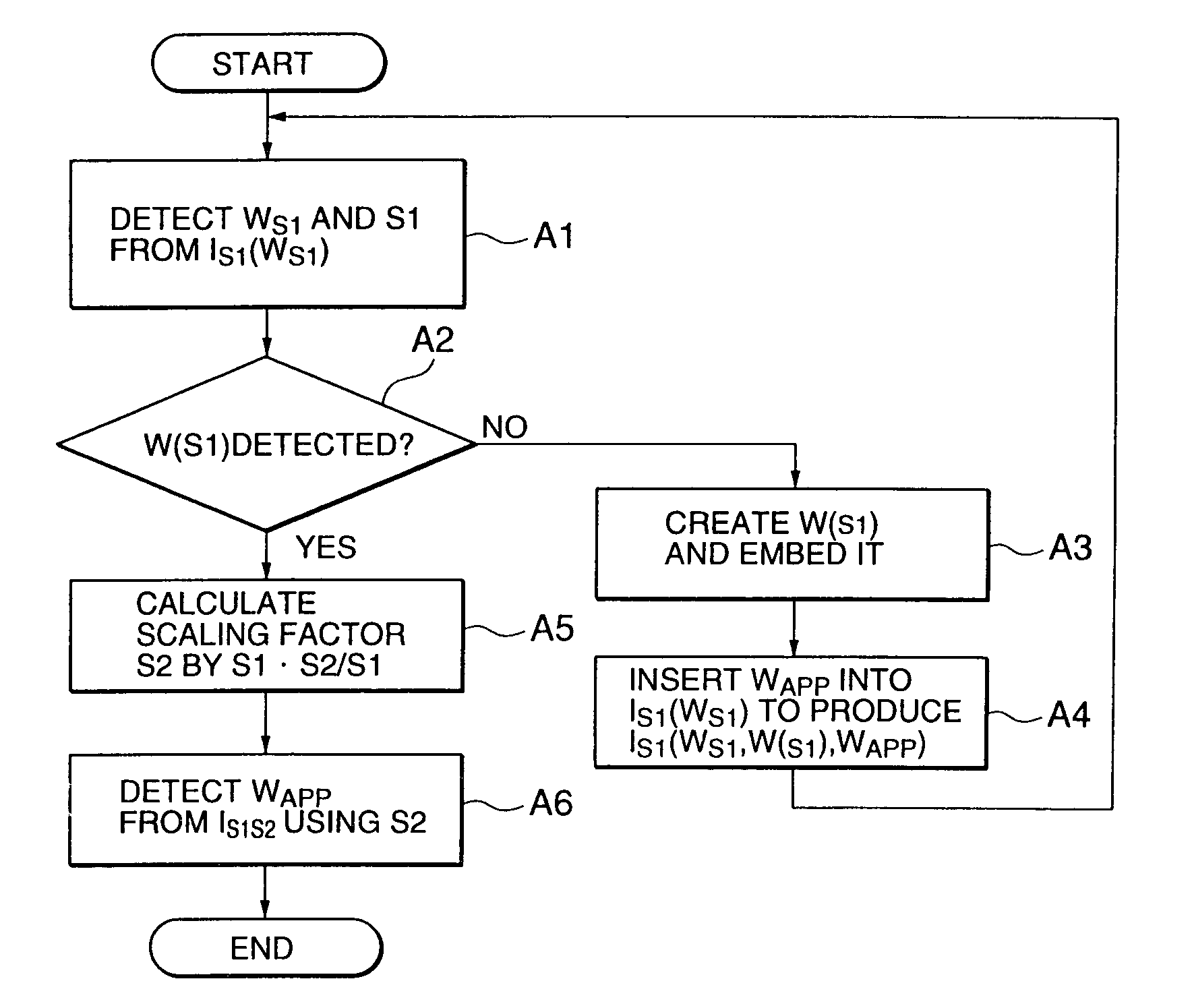
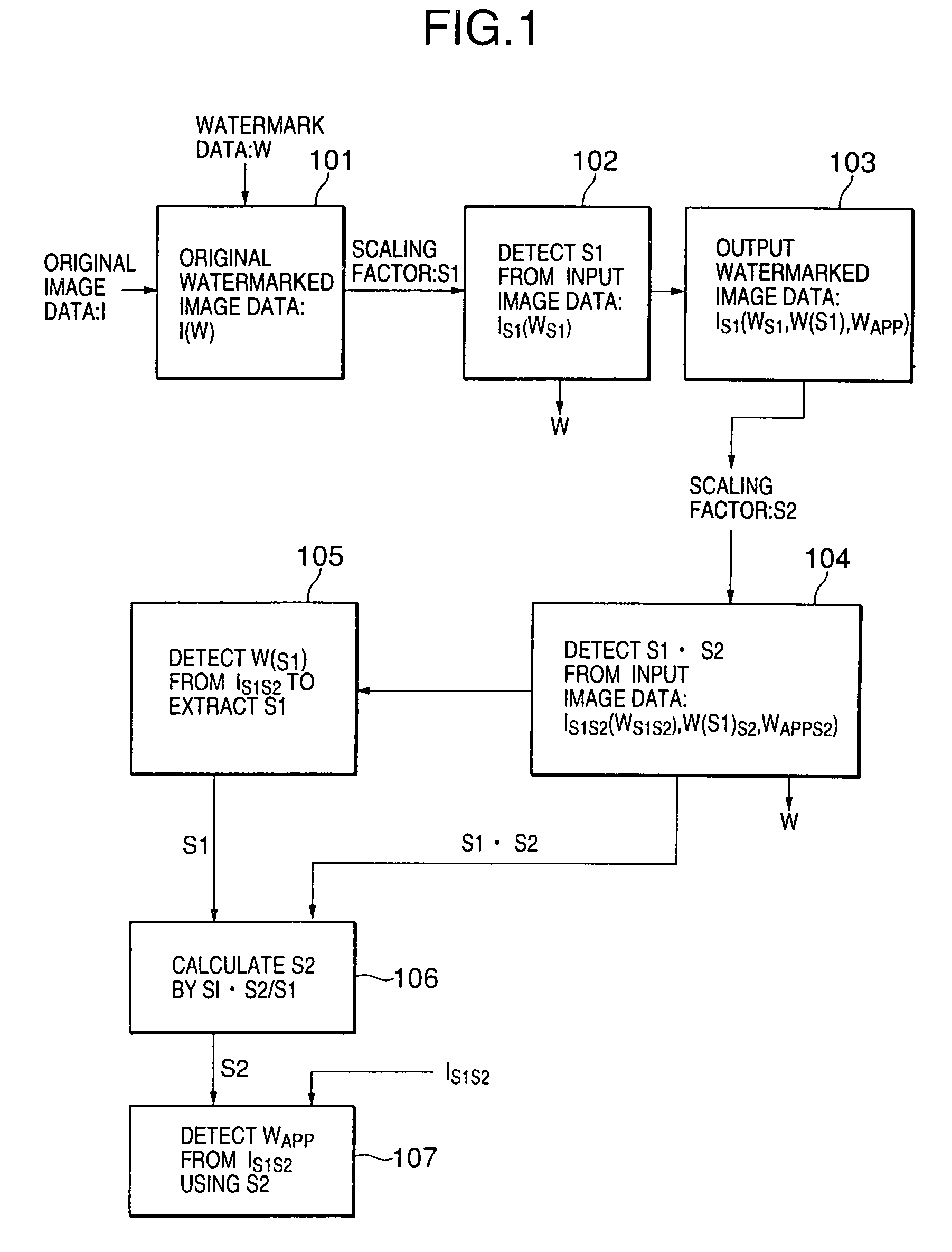
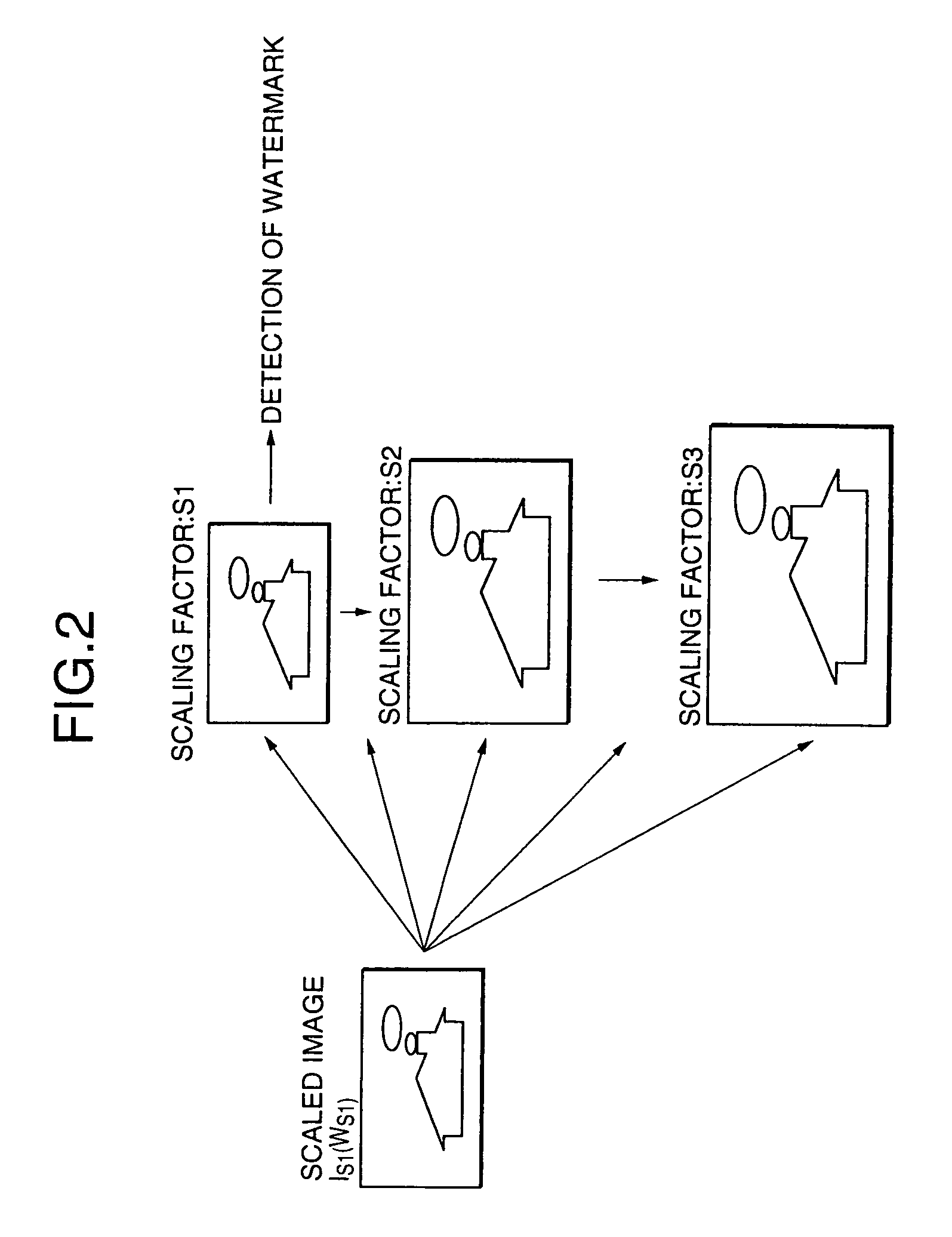
ActiveUS7007167B2Easy to detectEasy to insertTelevision system detailsUser identity/authority verificationComputer visionComputer science
A watermarking system allowing an appended-type watermark to be easily inserted into a scaled-up / down image without deteriorating the detection accuracy of the appended-type watermark is disclosed. A first scaling factor of an input watermarked image is detected by detecting a copy control watermark from the input watermarked image. It is determined whether a watermark including a second scaling factor is detected from the input watermarked image. When the watermark including the second scaling factor fails to be detected, a second watermark including the first scaling factor is created and embedded into the input watermarked image and further an appended-type watermark is inserted into the input watermarked image. When the watermark including the second scaling factor is detected, the first and second scaling factors are used to calculate a third scaling factor, which is used to detect the appended-type watermark.
Owner:NEC PERSONAL COMPUTERS LTD
Scheduled-recording method that schedules recording of copy-protected content
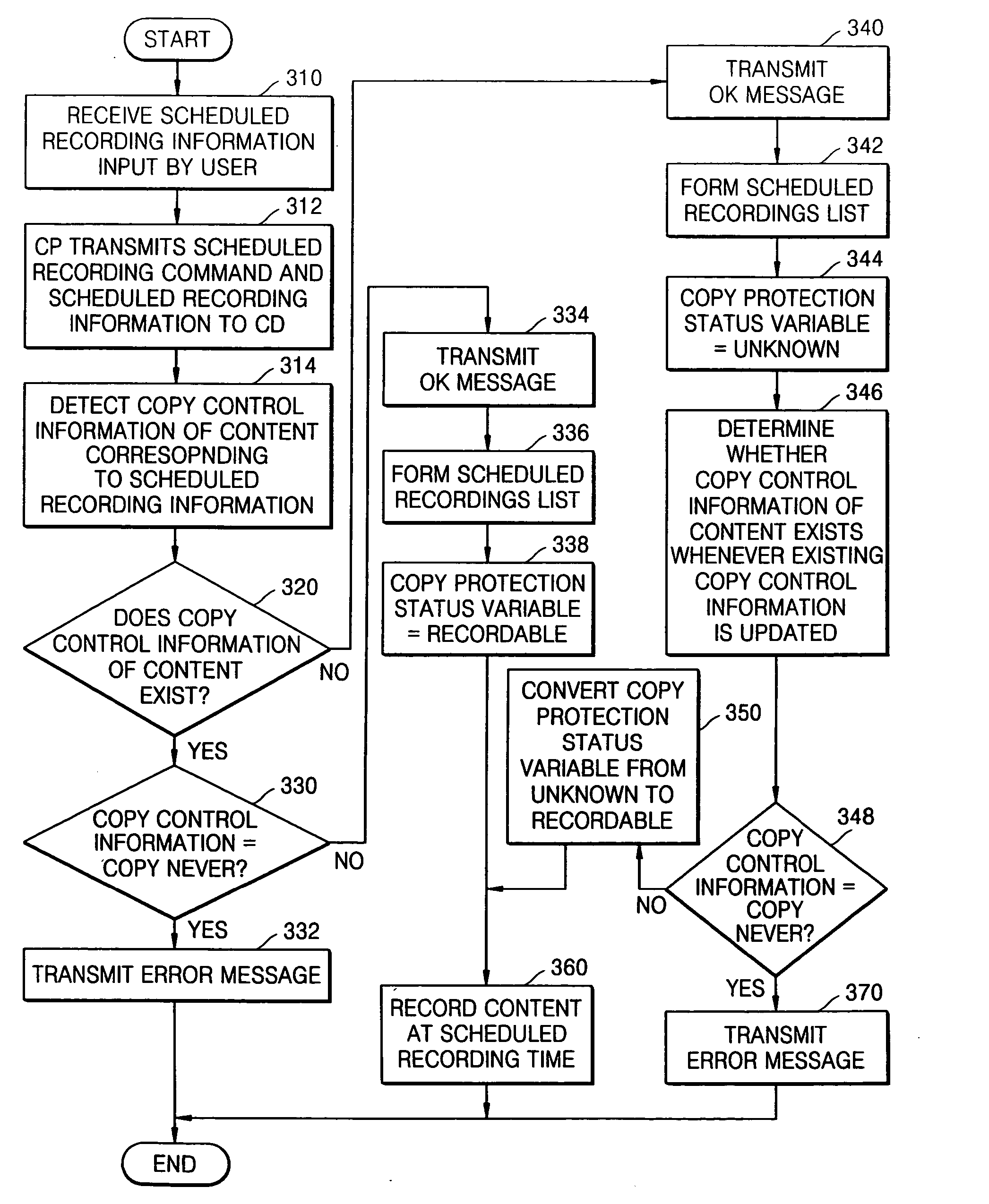
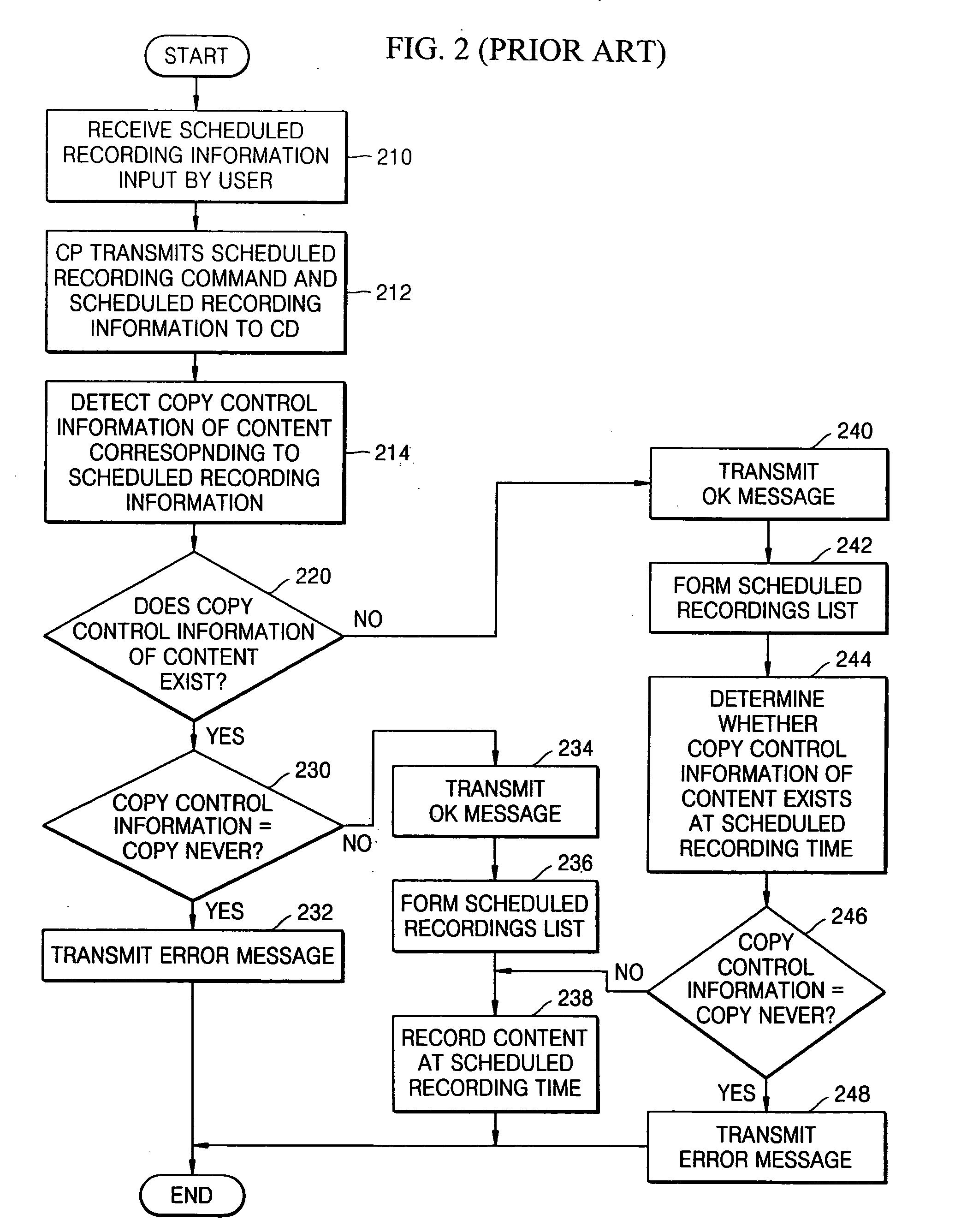
InactiveUS20050238168A1Special service provision for substationTelevision system detailsCopy protectionCopy control
A scheduled recording method, which schedules recording of copy-protected content, is provided. The scheduled recording method involves determining whether copy control information of content of interest exists in a recording device storing various copy control information; if the copy control information does not exist in the recording device, newly receiving copy control information and then determining whether the copy control information exists among the newly received information; if the copy control information of the content exists in the recording device, determining whether the copy control information “copy never”; and if the copy control information of the content is “copy never”, transmitting an error message to a user indicating that the content of interest is not recordable to a user. Accordingly, it is possible to let a user know about whether content is recordable by defining a copy protection status variable and determining whether the content is recordable whenever new copy control information is received.
Owner:SAMSUNG ELECTRONICS CO LTD
Secure optical media storage
ActiveUS20060104190A1Secure distributionDigital data processing detailsAnalogue secracy/subscription systemsOptical recordingCopy control
An optical recording medium is provided for distributing content through a portable medium which can be transported by hand from one media player to another media player. The optical recording medium includes a read-only zone and a writable area. Copy control information is stored in the read-only zone. The copy control information specifies (a) an authorized content source and (b) content which is authorized to be downloaded from the authorized content source and recorded in the writable area of the optical recording medium.
Owner:MAGNOLIA LICENSING LLC +1
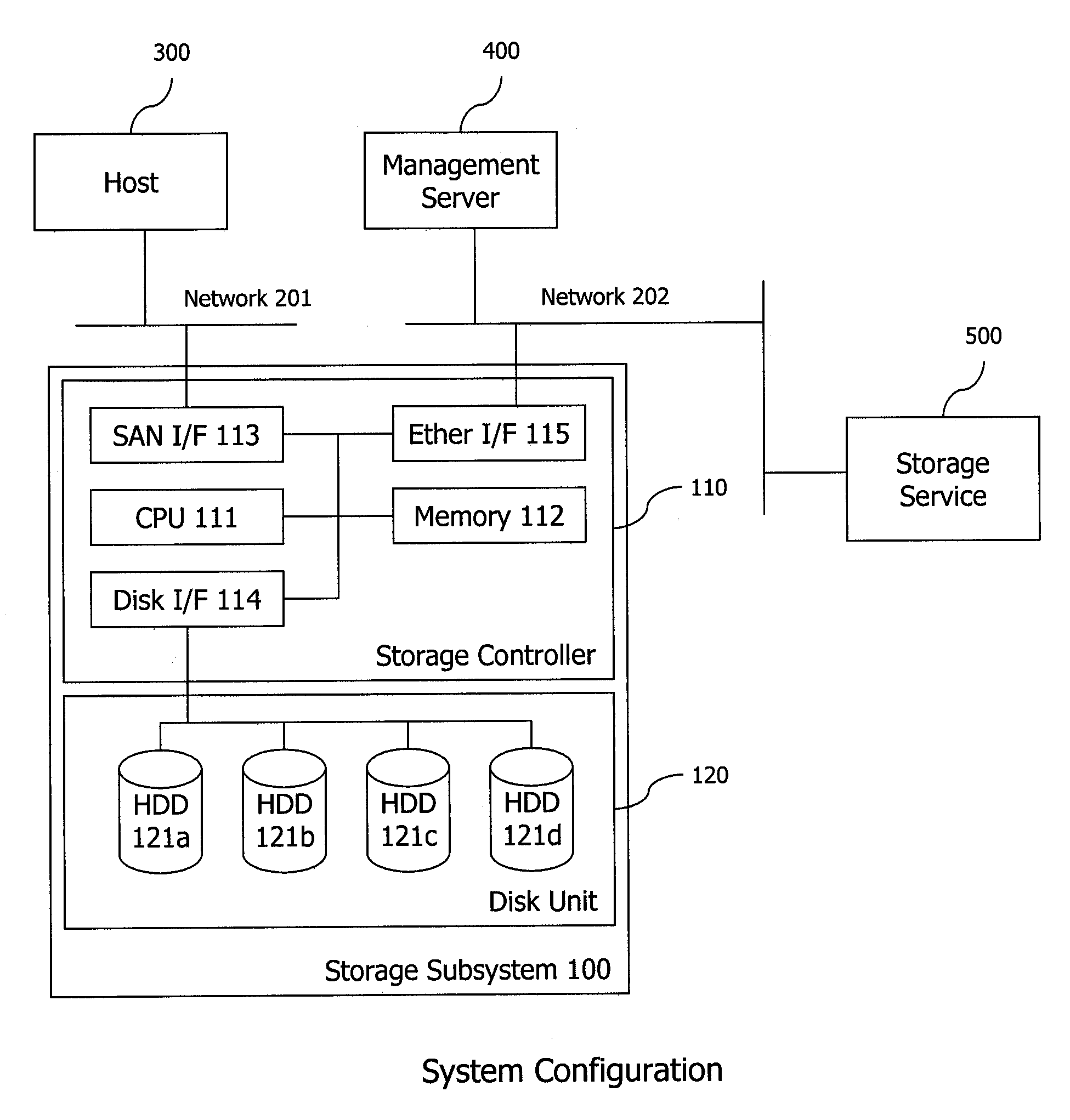
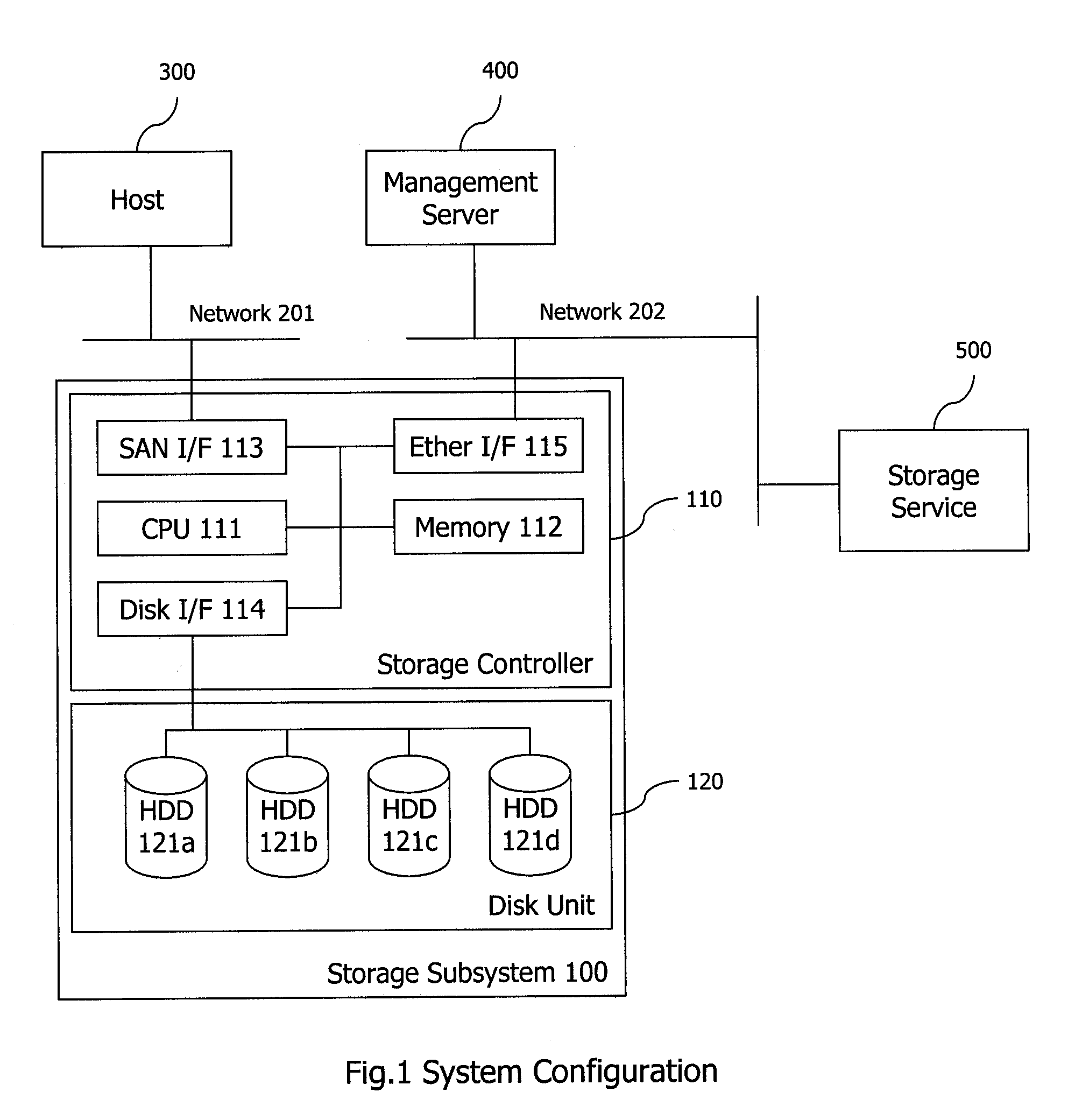
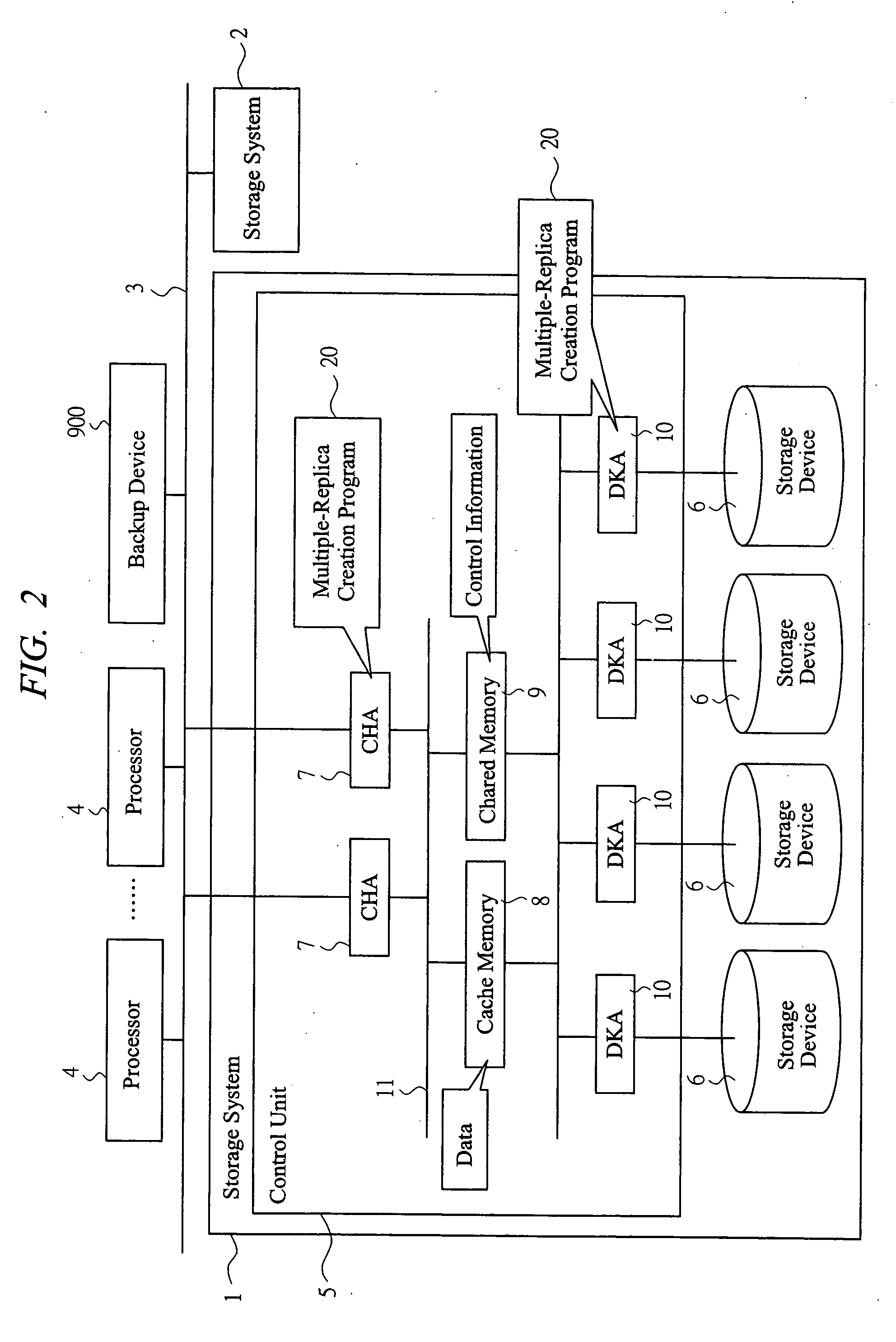
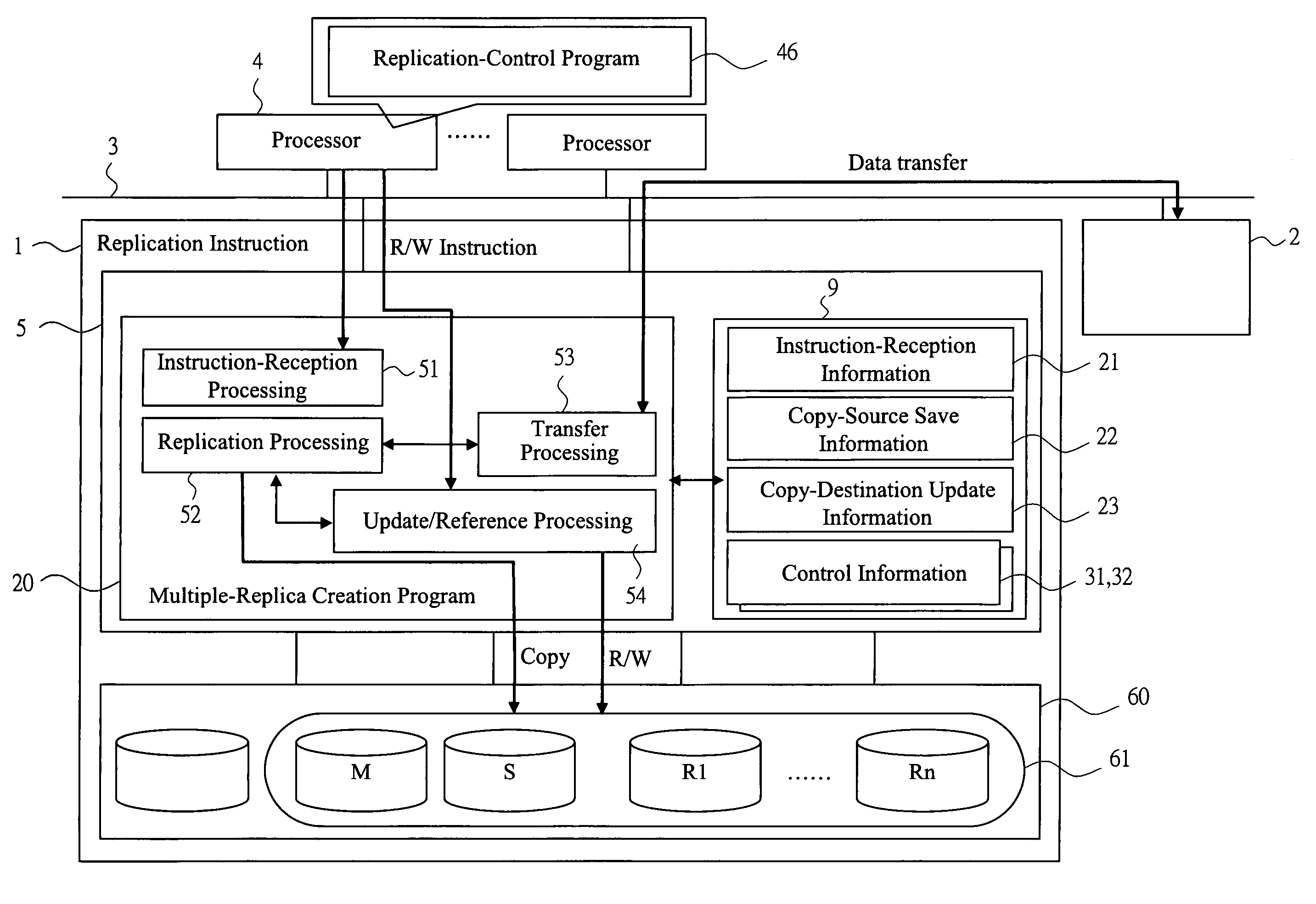
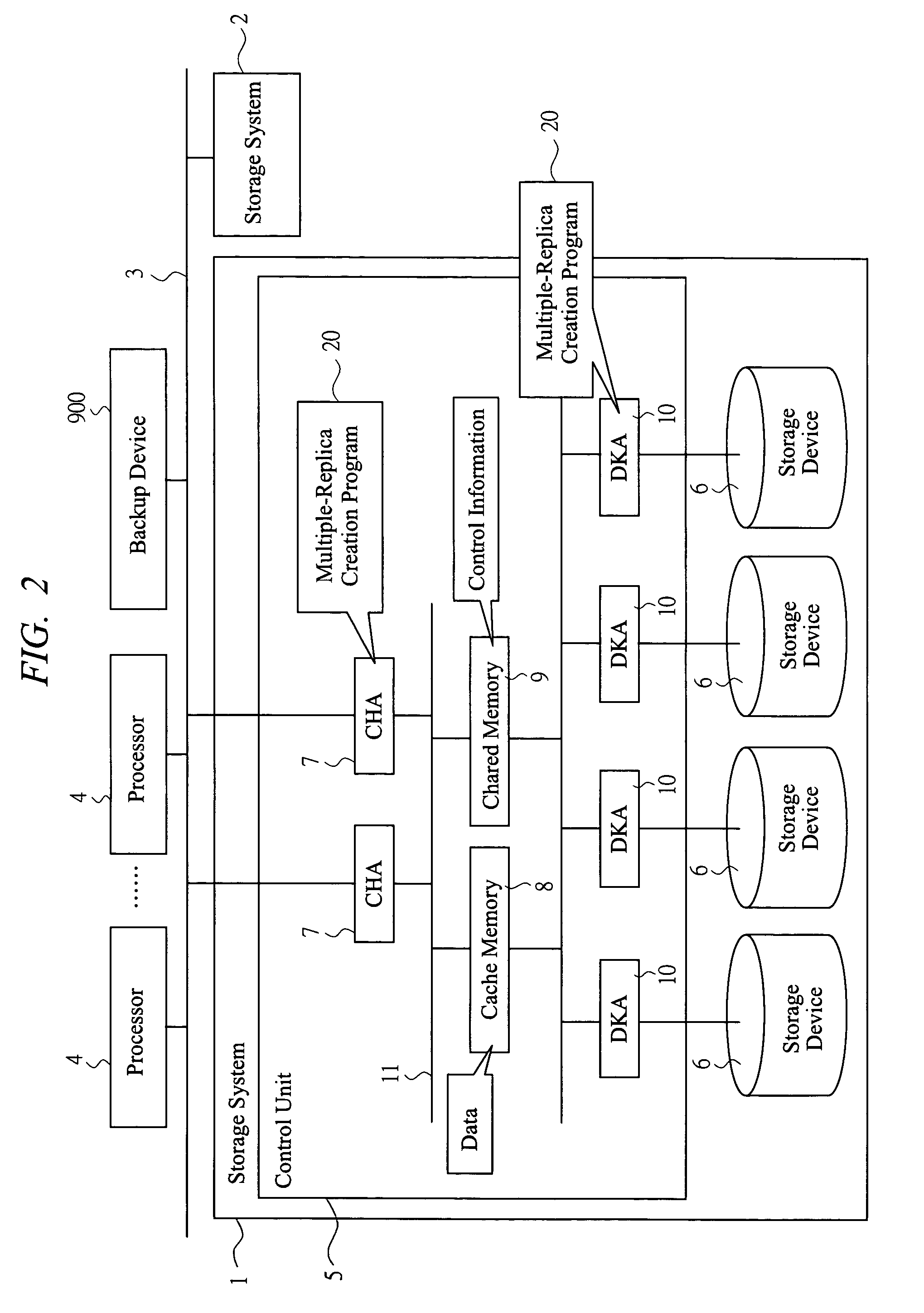
Storage system
InactiveUS20060020754A1PluralityEnsure data consistencyData processing applicationsMemory loss protectionLogic cellControl data
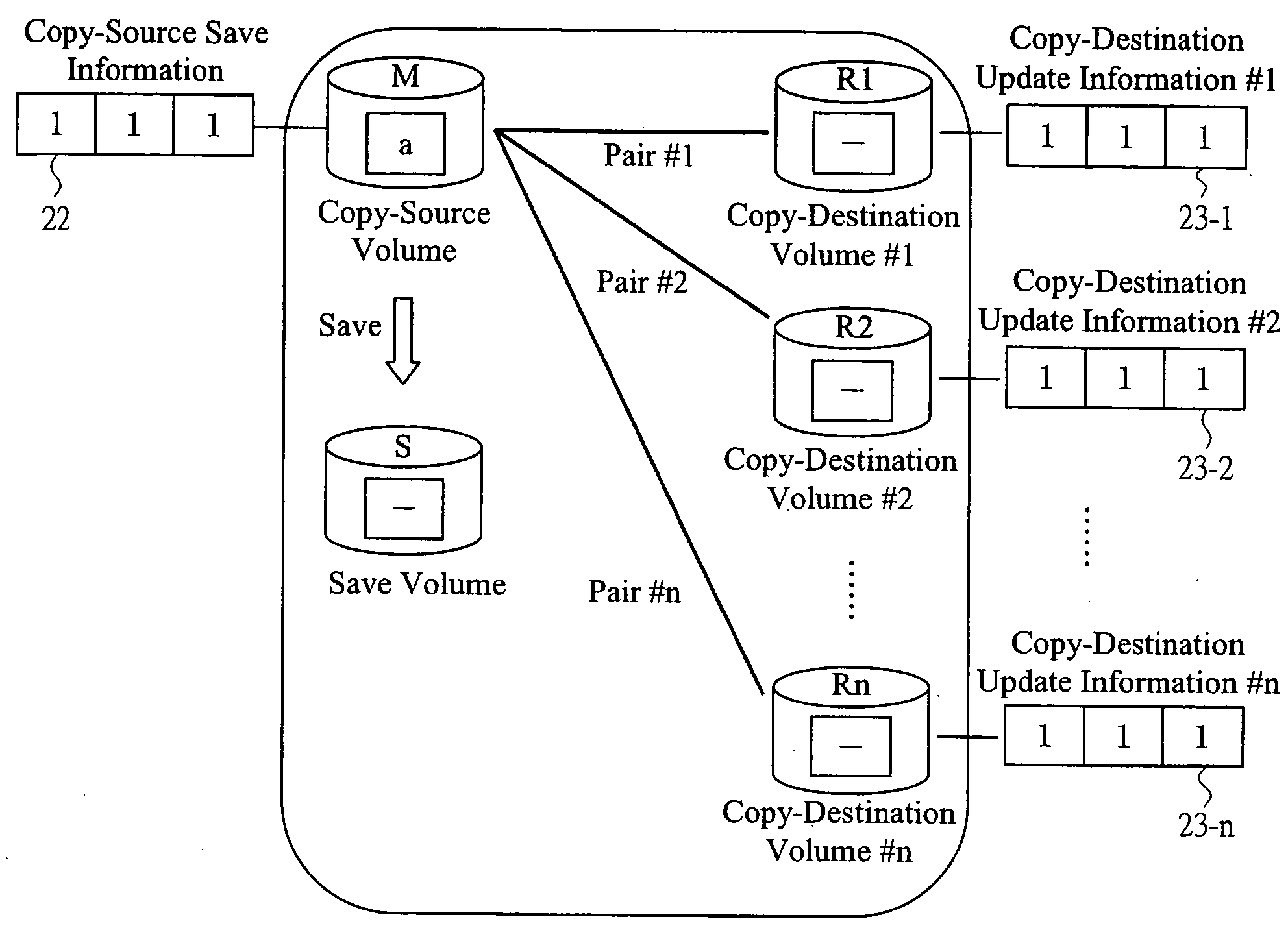
In creating replicas to data of a storage volume in a storage system, a technique in which labor for issuing instructions from a processor can be reduced and then data consistency of related volumes can be secured is provided. A single replication instruction including designated information is issued for data of a logical unit serving as a copy source and a copy destination from a replication-control program of the processor. A control unit of the storage system possesses a multiple-replica creation program which enables a processing for creating replicas while securing the data consistency when an access such as a update or reference occurs for a group including a plurality of pairs of copy-source volume and copy-destination volume based on reception of the instruction. A save volume is provided to identify and control data save and update state by copy-source save information and copy-destination update information at the shared memory.
Owner:HITACHI LTD
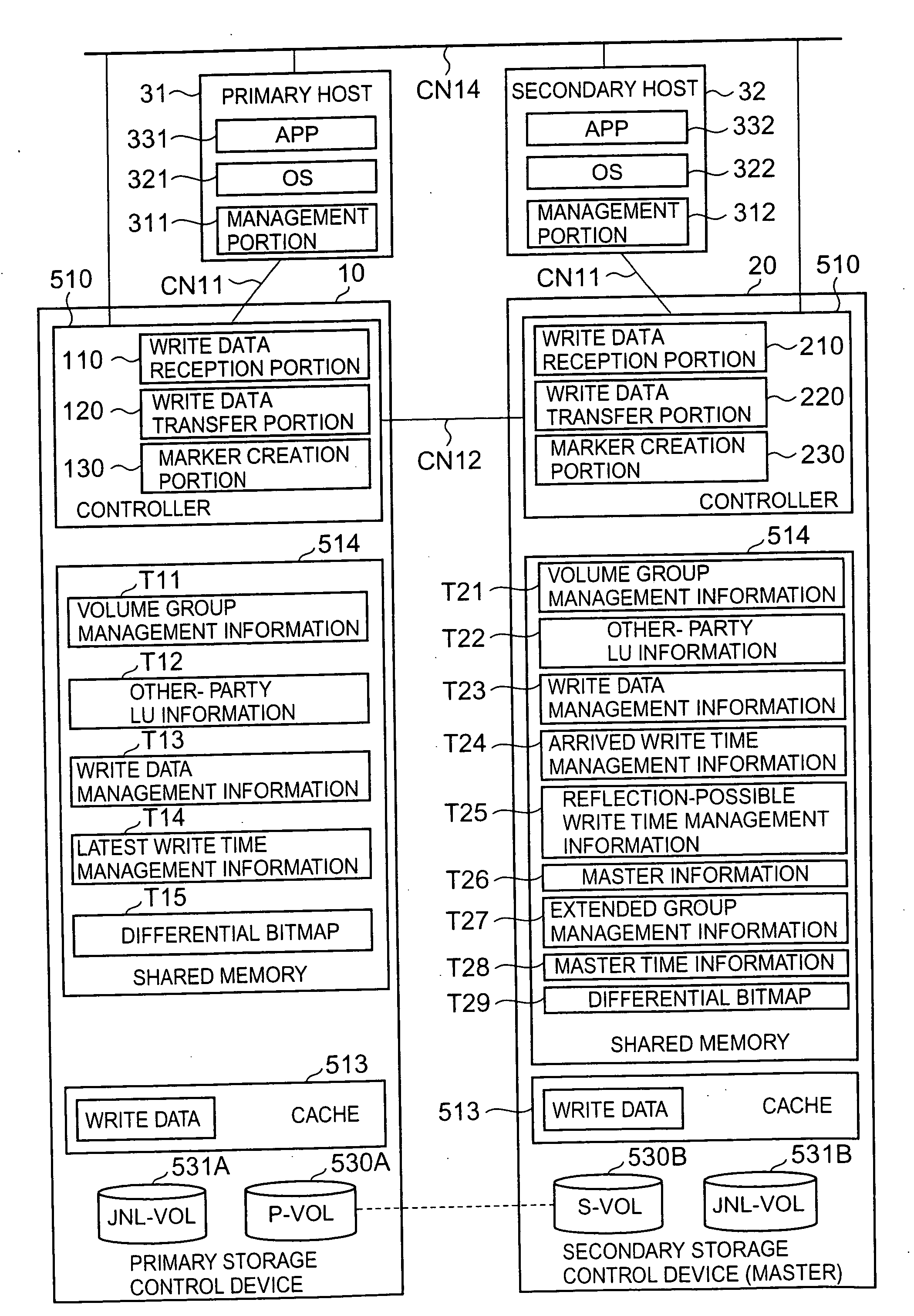
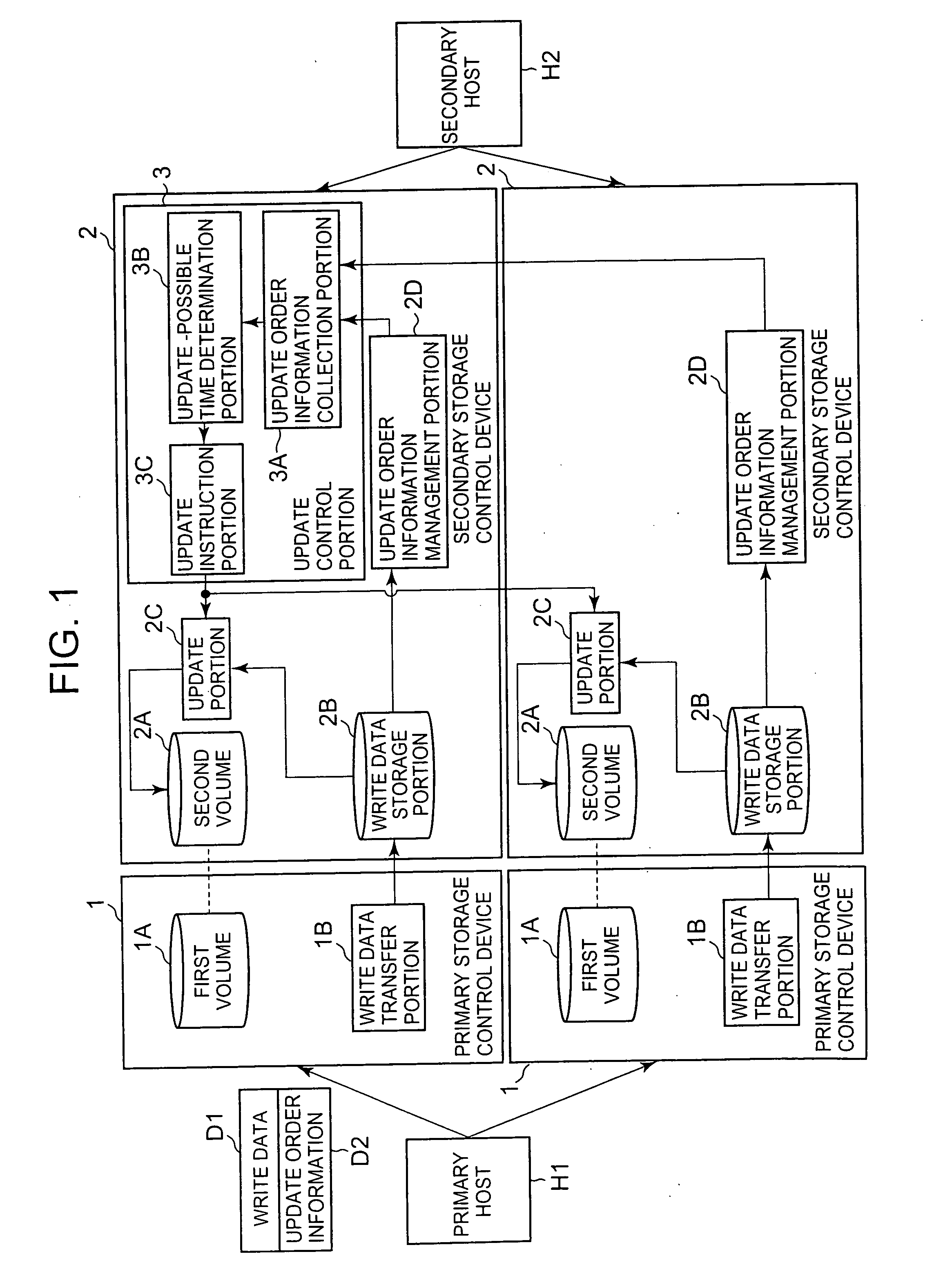
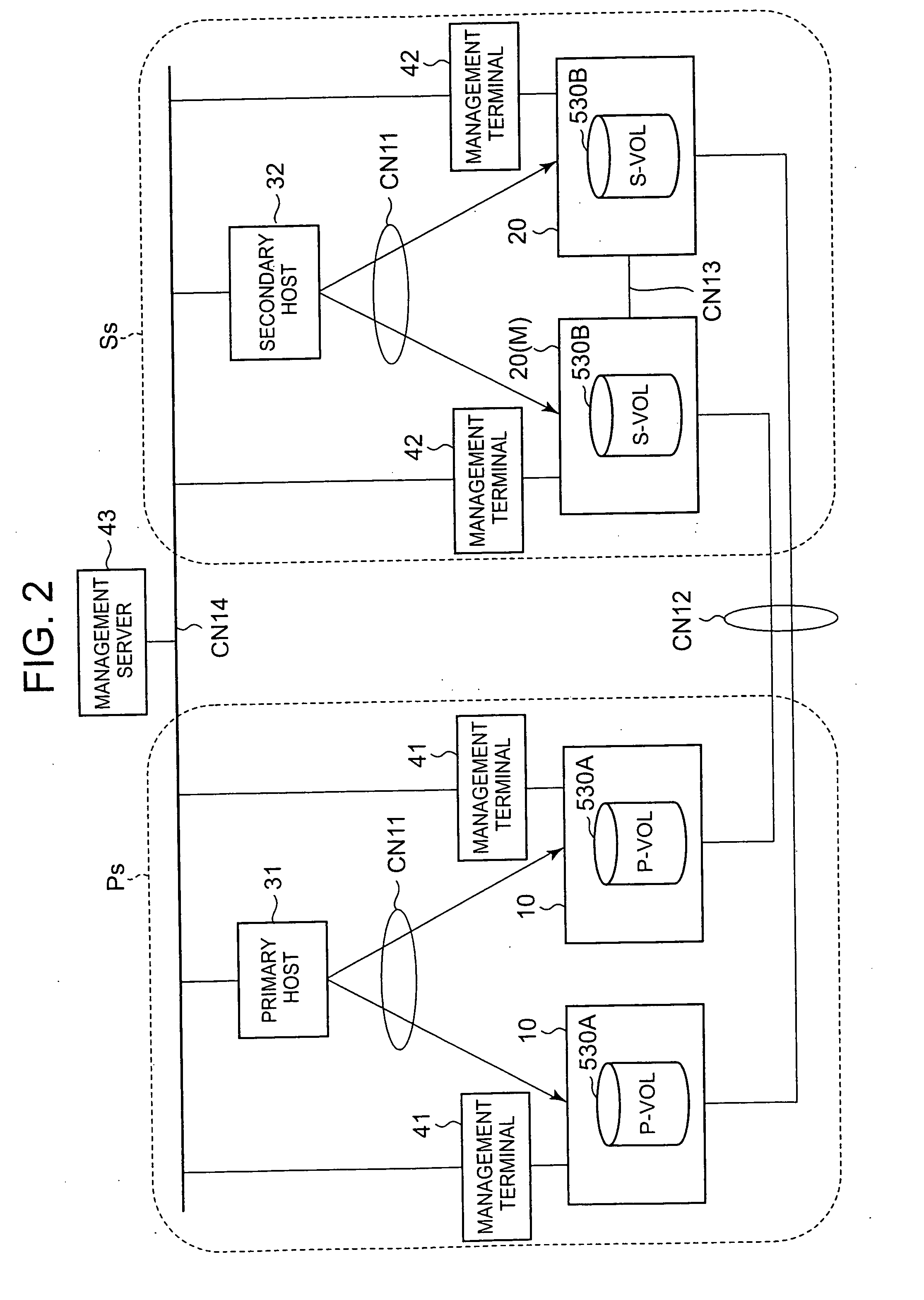
Storage system and remote copy control method for storage system
InactiveUS20070233981A1Maintain data consistencyMaintain consistencyMemory loss protectionError detection/correctionData storeOperating system
A storage system of this invention maintains consistency of the stored contents between volumes even when a plurality of remote copying operations are executed asynchronously. A plurality of primary storage control devices and a plurality of secondary storage control devices are connected by a plurality of paths, and remote copying is performed asynchronously between respective first volumes and second volumes. Write data transferred from the primary storage control device to the secondary storage control device is held in a write data storage portion. Update order information, including write times and sequential numbers, is managed by update order information management portions. An update control portion collects update order information from each update order information management portion, determines the time at which update of each second volume is possible, and notifies each-update portion. By this means, the stored contents of each second volume can be updated up to the time at which update is possible.
Owner:HITACHI LTD
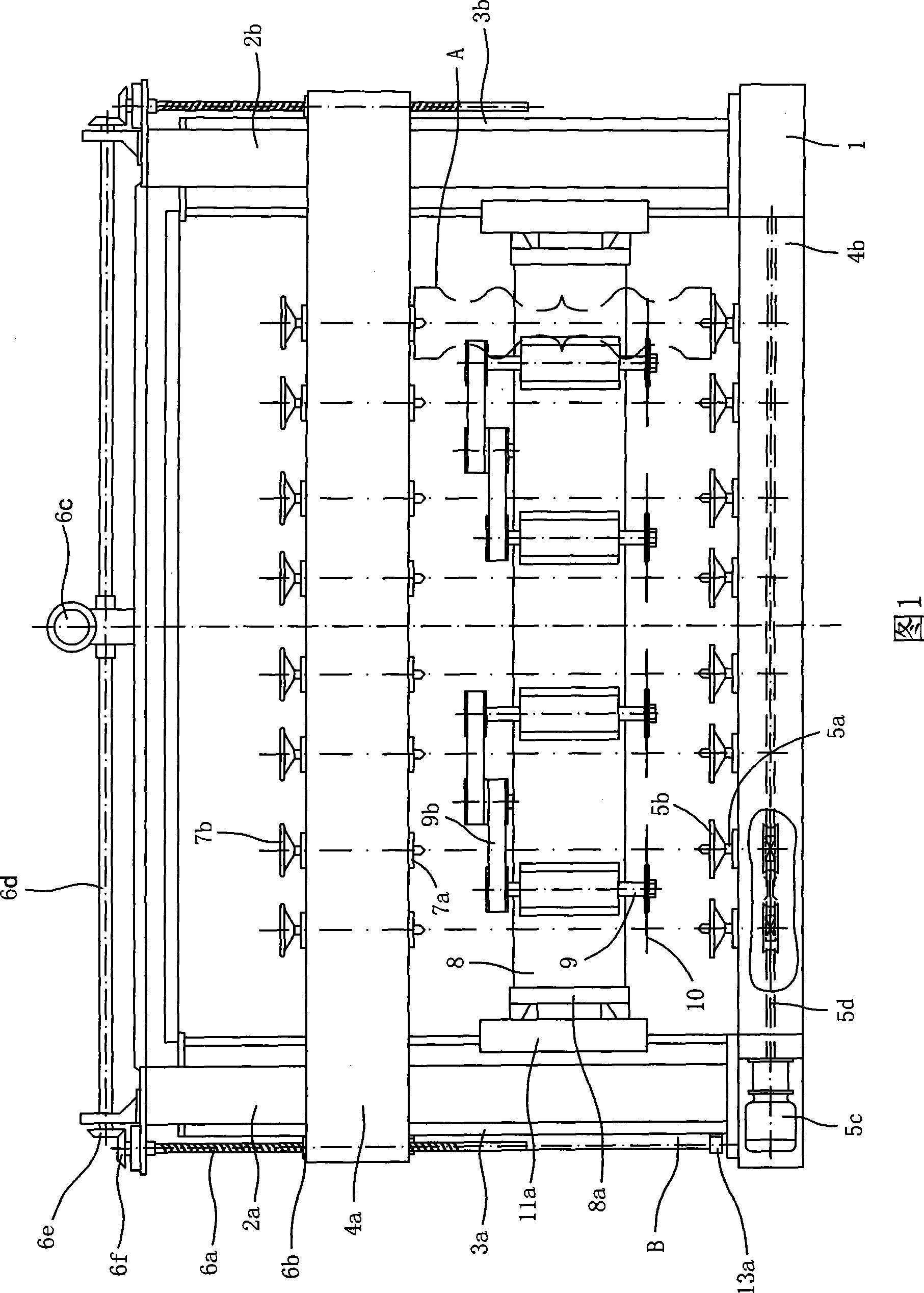
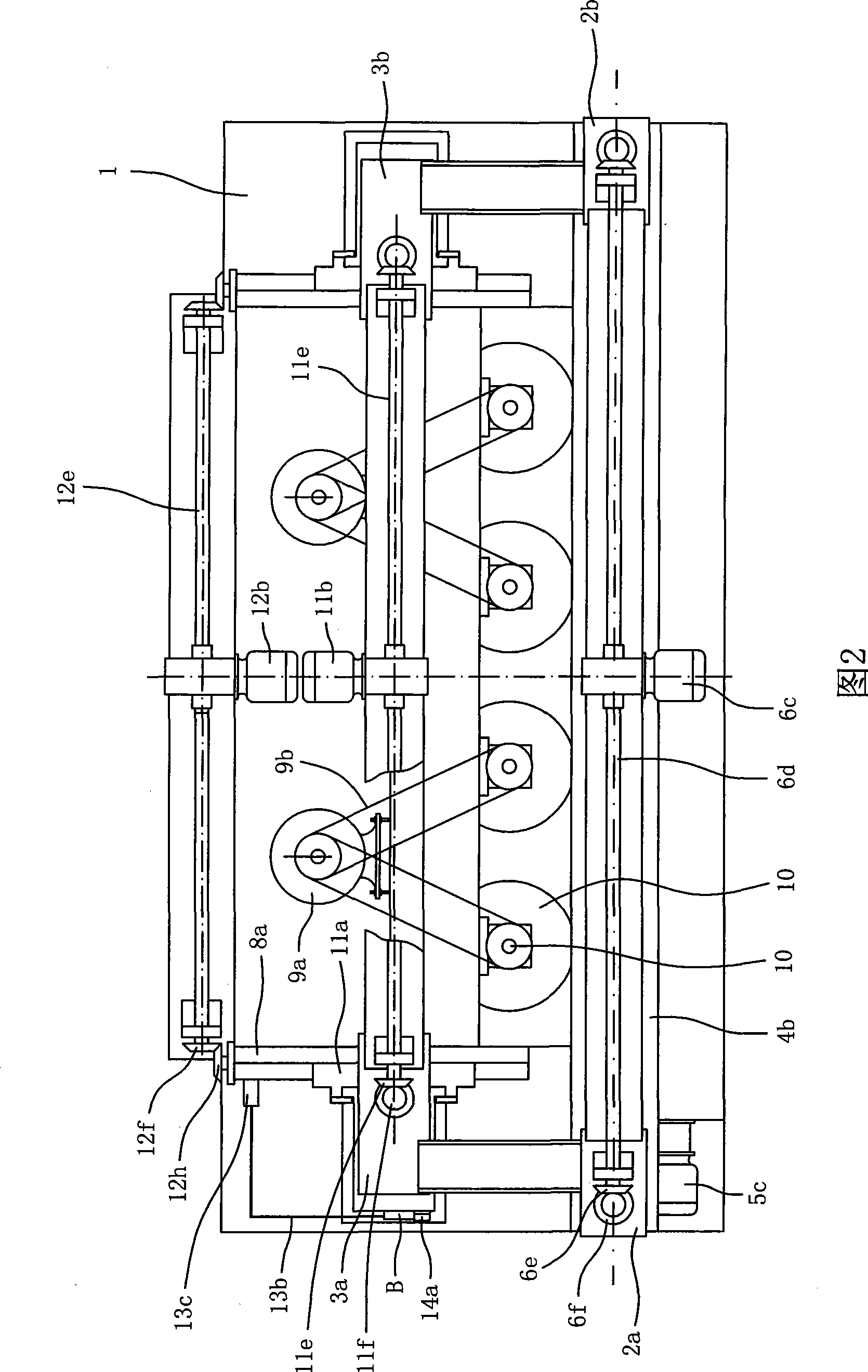
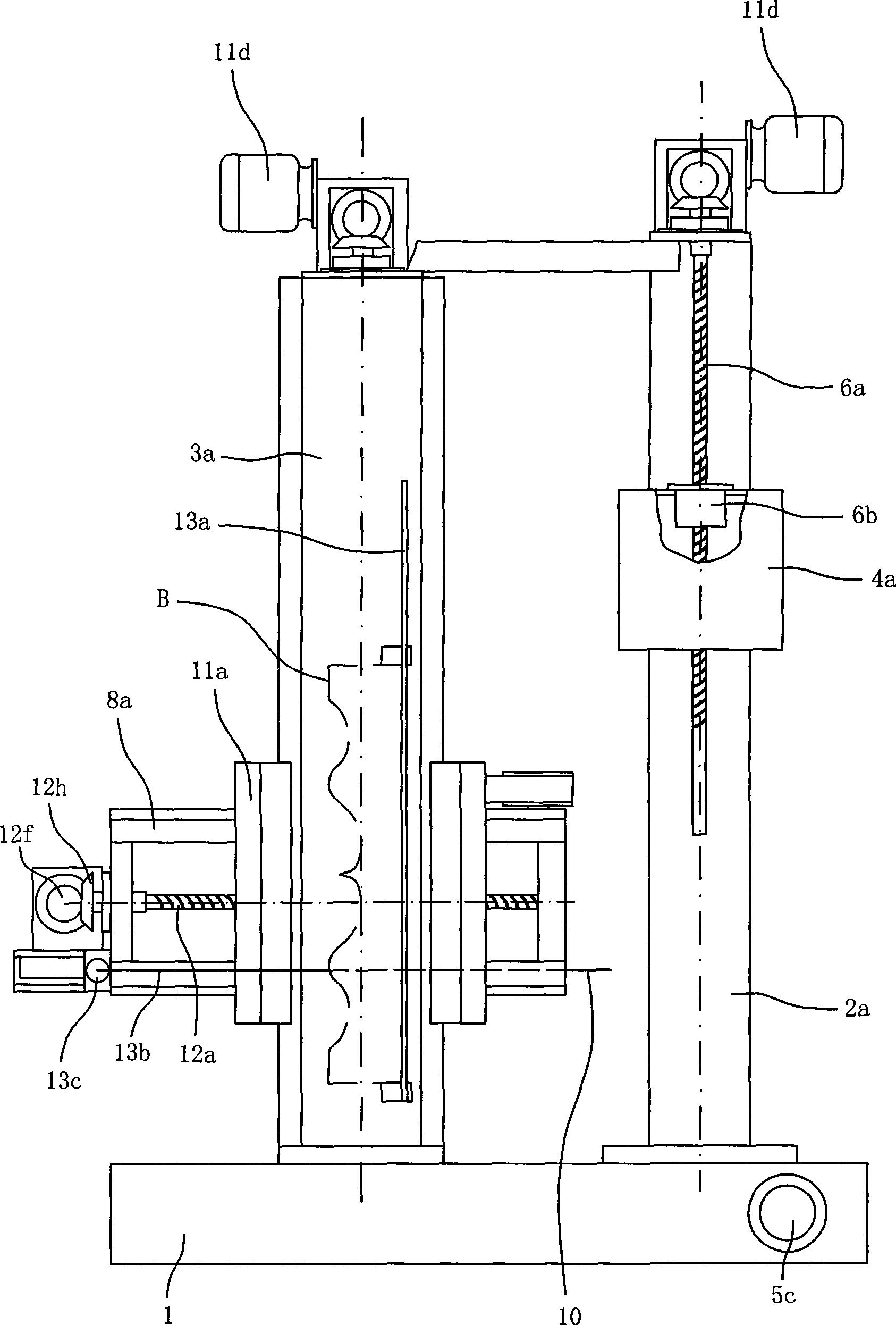
Multiheaded cylinder type stone profiling machine
ActiveCN101367253AGood shape identityEasy to operateStone-like material working toolsEngineeringMechanical engineering
The invention provides a multi-head cylindrical stone copying machine. Front upright columns and back upright columns are correspondingly and vertically fixed on a base; The front upright columns and the back upright columns respectively comprise two upright columns symmetrically arranged on two sides of the base; a workpiece clamping mechanism is arranged on the front upright columns; the workpiece clamping mechanism can simultaneously clamp a plurality of machined workpieces and drive all the workpieces to synchronously rotate; and a workpiece cutting device is arranged on the back upright columns. The workpiece cutting device comprises a beam, a plurality of cutting cutter heads and a copying control device, wherein the beam which can move up and down as well as back and forth through a vertical-lifting and horizontal-shift drive mechanism is horizontally arranged between an back-left upright column and a back-right upright column; the cutting cutter heads are driven by a main shaft which is vertically supported on the beam along the longitudinal direction to synchronously cut the workpieces; and the copying control device tracks a copying template curved surface through photoelectric induction so as to control cutting drive mechanisms. The copying machine has the advantages that the copying machine can simultaneously machine a plurality of workpieces at a time, is simple to operate, reduces labor intensity, has high work efficiency and reduces production cost, and machined products are good in shape identity.
Owner:QUANZHOU JIANENG MACHINERY MFG
Storage system
InactiveUS7243116B2PluralityEnsure data consistencyData processing applicationsInput/output to record carriersLogic cellControl data
In creating replicas to data of a storage volume in a storage system, a technique in which labor for issuing instructions from a processor can be reduced and then data consistency of related volumes can be secured is provided. A single replication instruction including designated information is issued for data of a logical unit serving as a copy source and a copy destination from a replication-control program of the processor. A control unit of the storage system possesses a multiple-replica creation program which enables a processing for creating replicas while securing the data consistency when an access such as a update or reference occurs for a group including a plurality of pairs of copy-source volume and copy-destination volume based on reception of the instruction. A save volume is provided to identify and control data save and update state by copy-source save information and copy-destination update information at the shared memory.
Owner:HITACHI LTD
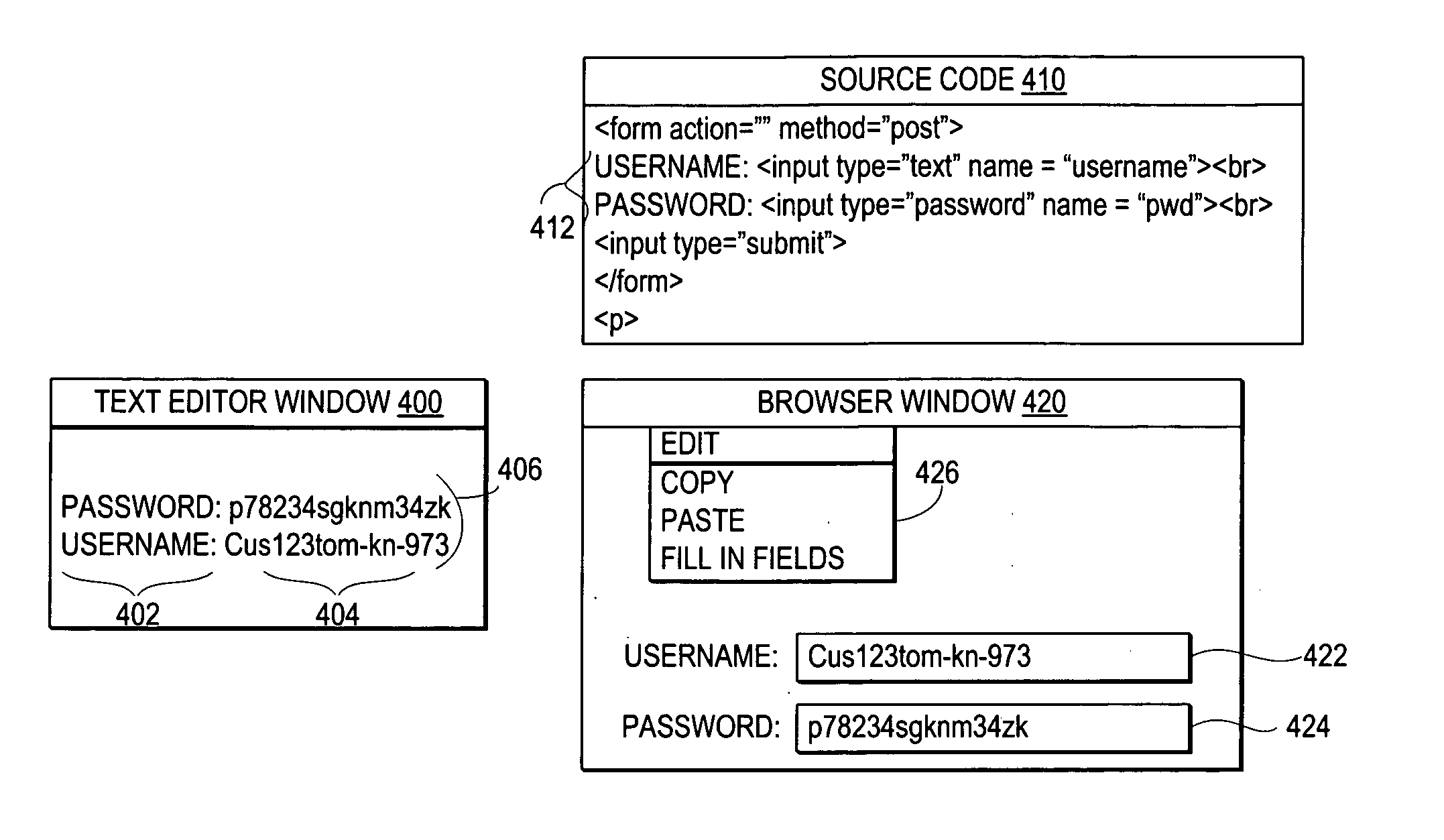
Automatic simultaneous entry of values in multiple web page fields
InactiveUS20060059247A1Improved copyingImproved pastingNatural language data processingMultiple digital computer combinationsWeb browserSegment descriptor
A method, system, and program for automatic simultaneous entry of values in multiple web page fields are provided. Responsive to detecting a single action selection by a user to fill multiple fields of a web page, wherein each of the fields is associated with one from among multiple field descriptors within a source code for the web page, a field copy controller scans multiple lines of text copied into a local memory to identify text tags that match the field descriptors. Then, the field copy controller automatically fills in the fields within the web browser with the values from the lines of text, wherein each of the values is associated with one from among multiple text tags matching the field descriptors associated with the fields, such that multiple fields of a web page are automatically filled in responsive to only a single action by a user.
Owner:IBM CORP
Methods for audio watermarking and decoding
An identification code signal is hidden in a carrier signal (such as an electronic data signal or a physical medium) in a manner that permits the identification signal later to be discerned. The carrier signal can thereby be identified, or some machine responsive action can thereby be taken. The technique can be applied in audio and video embodiments to control associated consumer electronic equipment, e.g. to serve as a copy control signal.
Owner:DIGIMARC CORP
Video copy detection method based on multi-feature Hash
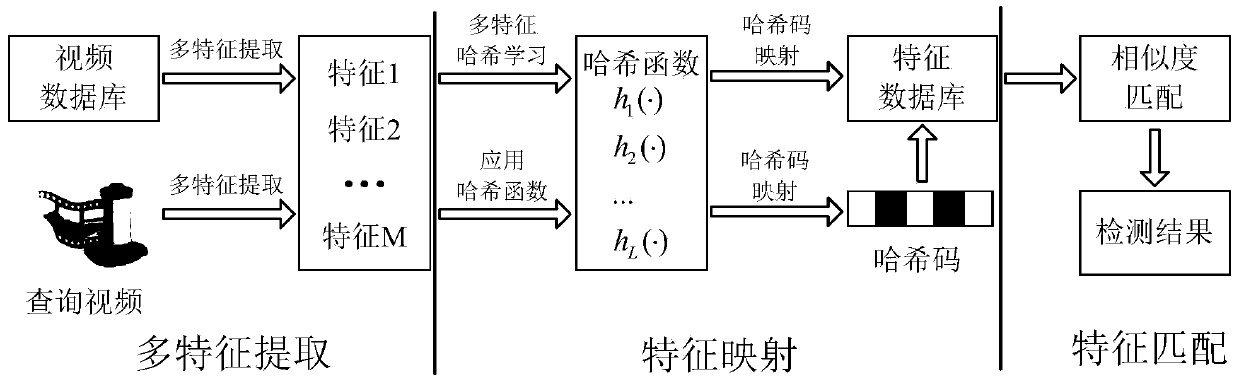
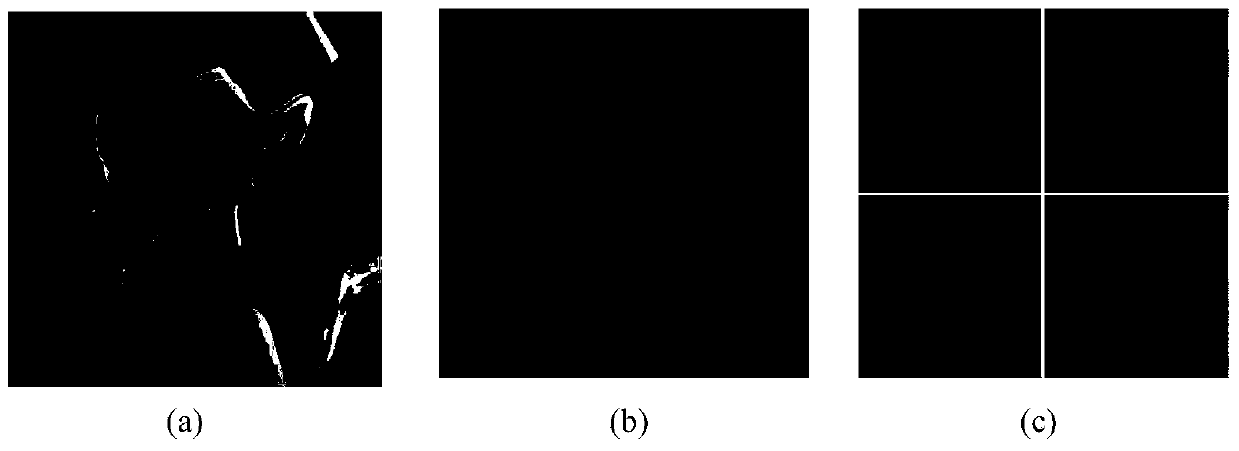
InactiveCN103744973AHigh precisionImprove robustnessCharacter and pattern recognitionSpecial data processing applicationsDigital videoHash function
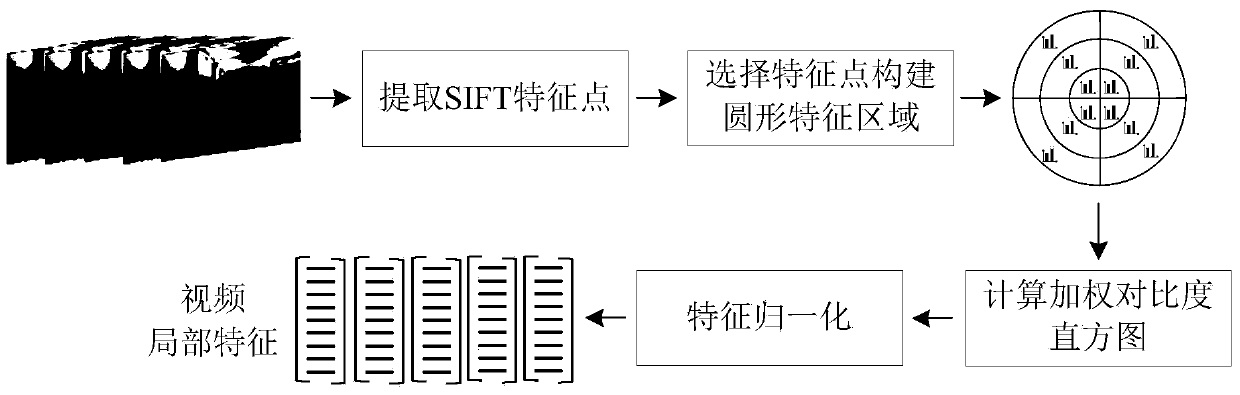
The invention discloses a video copy detection method based on multi-feature Hash, which mainly solves the problem that detection efficiency and detection accuracy cannot be effectively balanced in the exiting video copy detection algorithm. The video copy detection method based on multi-feature Hash comprises the following realization steps of: (1) extracting the pyramid histogram of oriented gradients (PHOG) of a key frame as the global feature of the key frame; (2) extracting a weighted contrast histogram based on scale invariant feature transform (SIFT) of the key frame as the local feature of the key frame; (3) establishing a target function by a similarity-preserving multi-feature Hash learning SPM2H algorithm, and obtaining L Hash functions by optimization solution; (4) mapping the key frame of a database video and the key frame of an inquired video into an L-dimensional Hash code by virtue of the L Hash functions; (5) judging whether the inquired video is the copied video or not through feature matching. The video copy detection method based on multi-feature Hash disclosed by the invention is good in robustness for multiple attacks, and capable of being used for copyright protection, copy control and data mining for digital videos on the Internet.
Owner:XIDIAN UNIV
Load balancing method and device, storage medium and electronic equipment
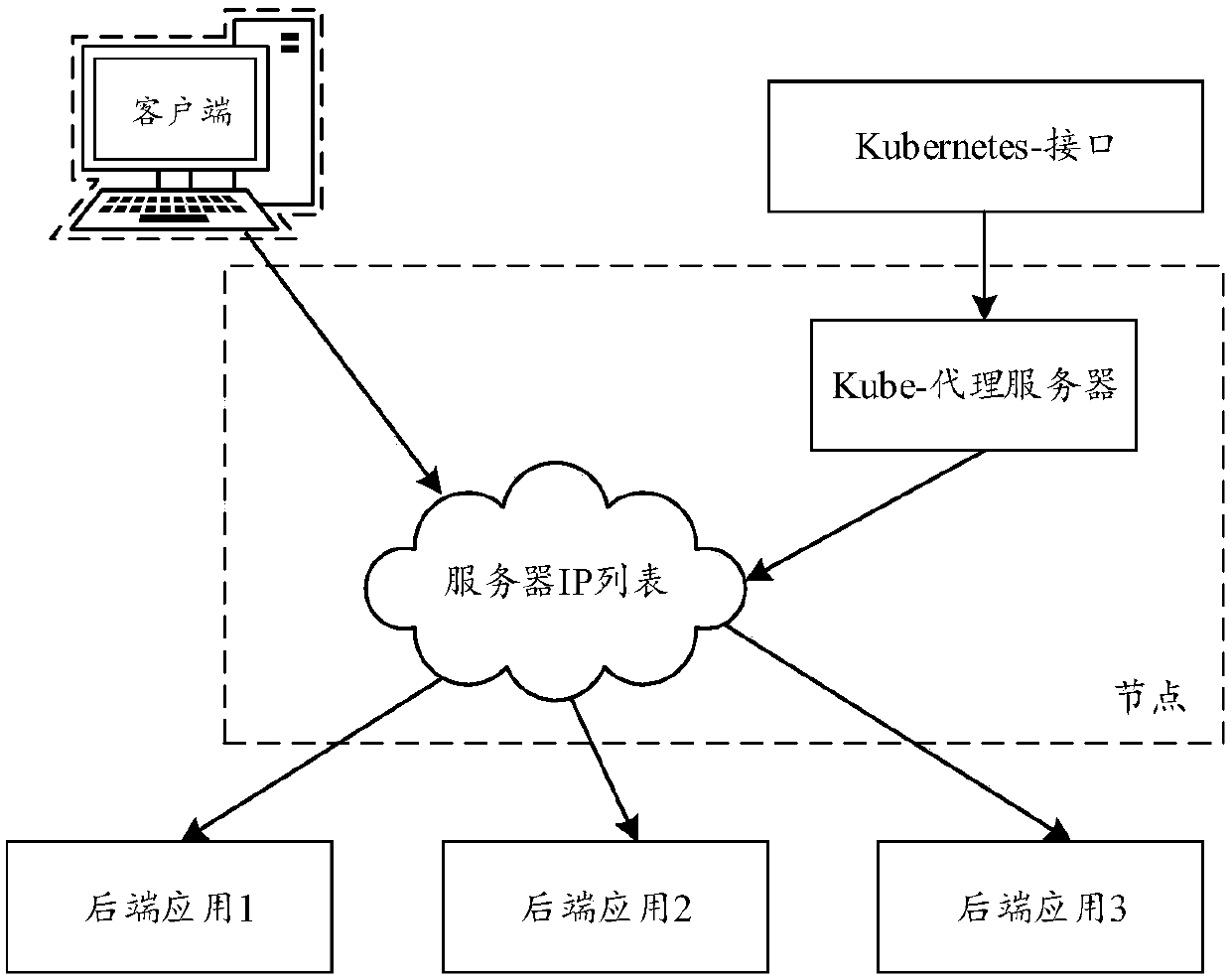
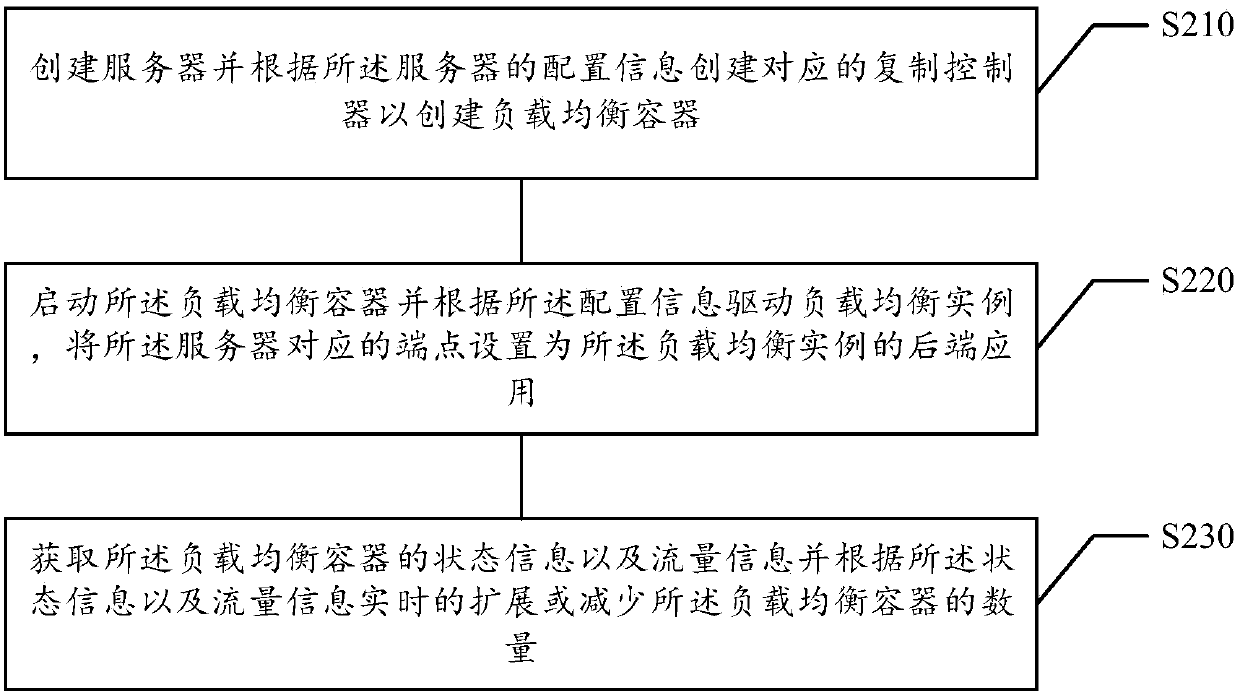
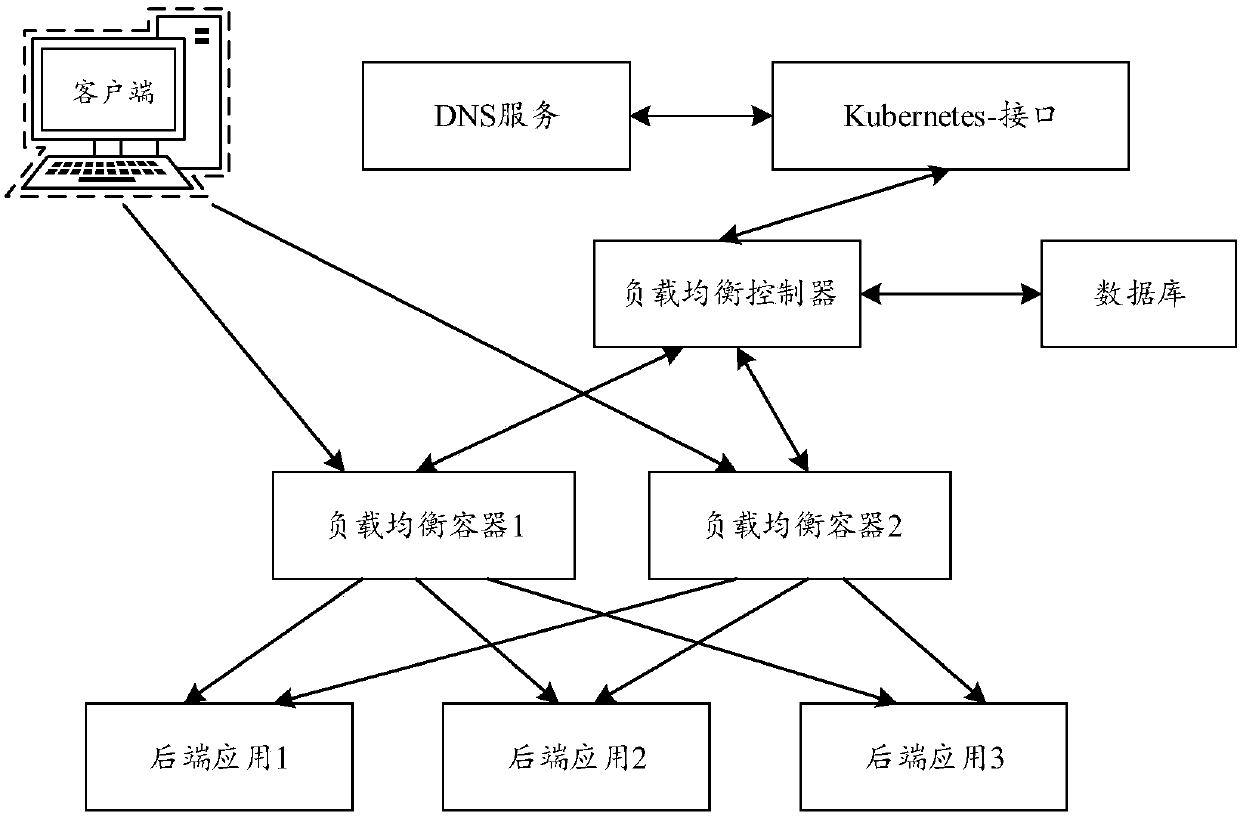
ActiveCN107590001AReduce in quantitySolve the problem of too slow speed caused by high utilizationResource allocationTraffic capacityResource isolation
The invention relates to a load balancing method and device, and relates to the technical field of Internet applications. The method comprises the following steps that: creating a server, and creatinga corresponding replication controller according to the configuration information of the server to create load balancing containers; starting the load balancing containers, and driving a load balancing living example according to the configuration information, and setting an end point corresponding to the server as the rear-end application of the load balancing living example; and obtaining the state information and the traffic information of the rear-end application, and expanding or reducing the amount of the load balancing containers in real time according to the state information and thetraffic information. By use of the method, the resource isolation characteristics of the container can be utilized to deploy the load balancing living example in the container so as to avoid resourcecompetition among different load balancing living examples on the same server.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
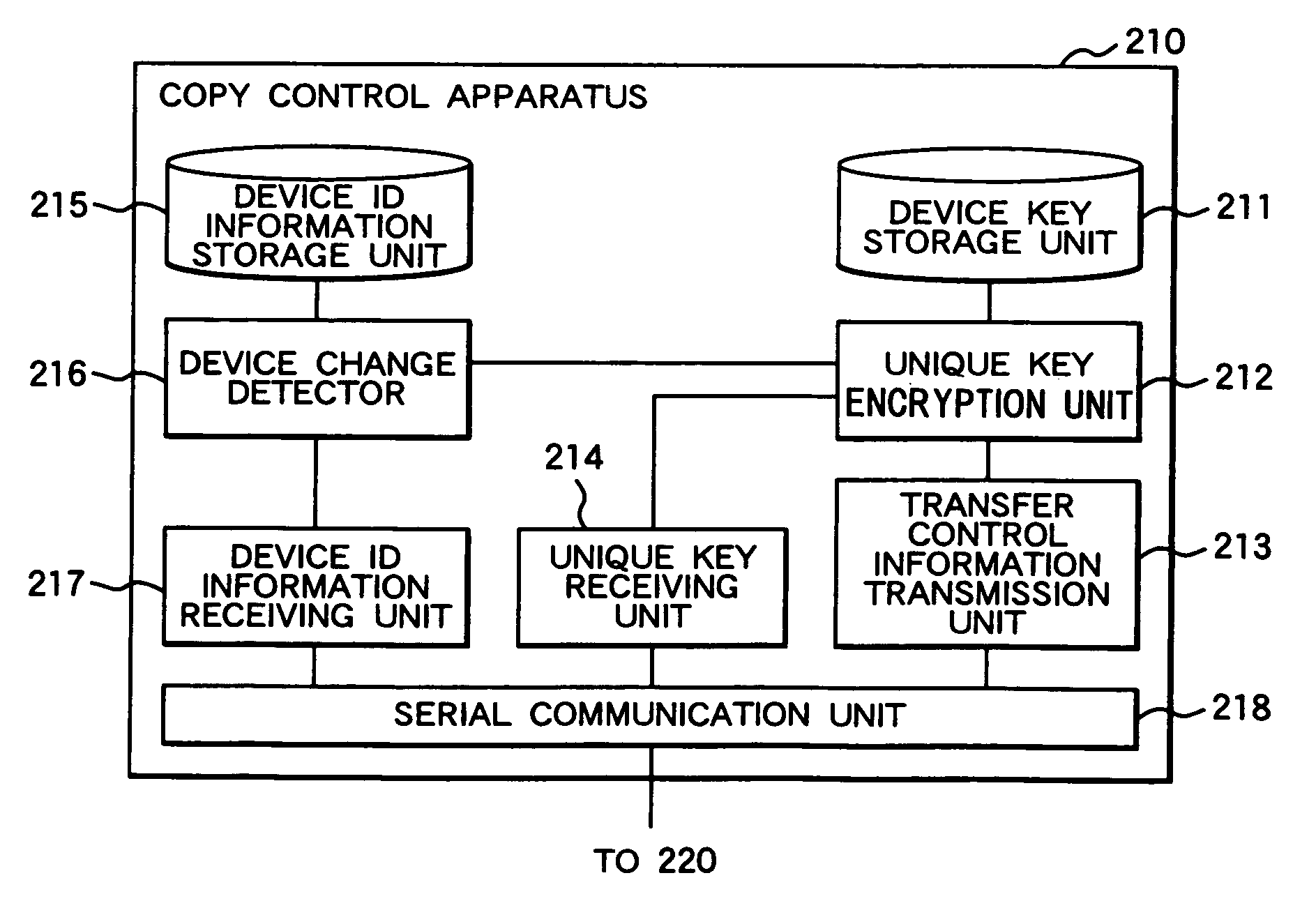
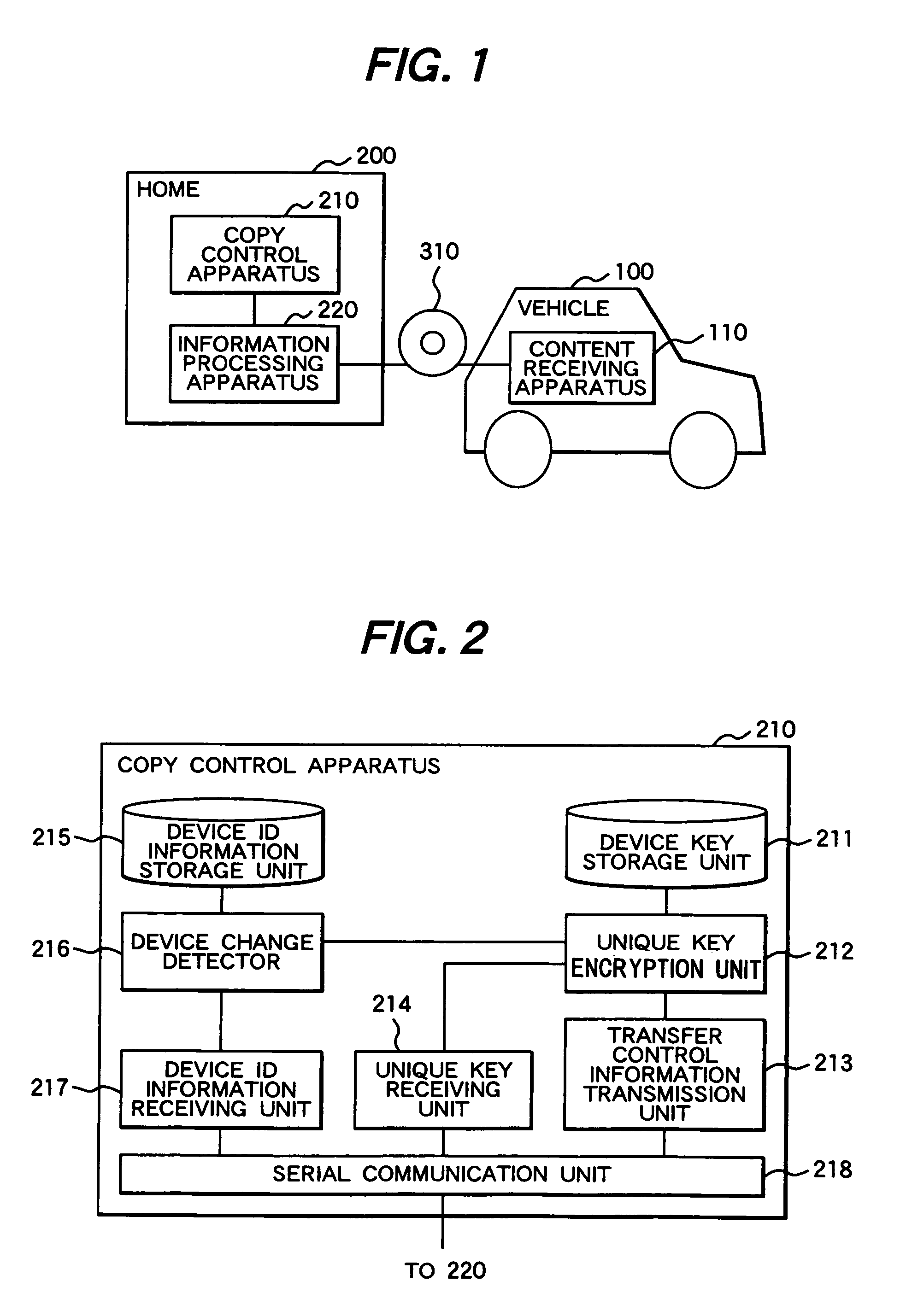
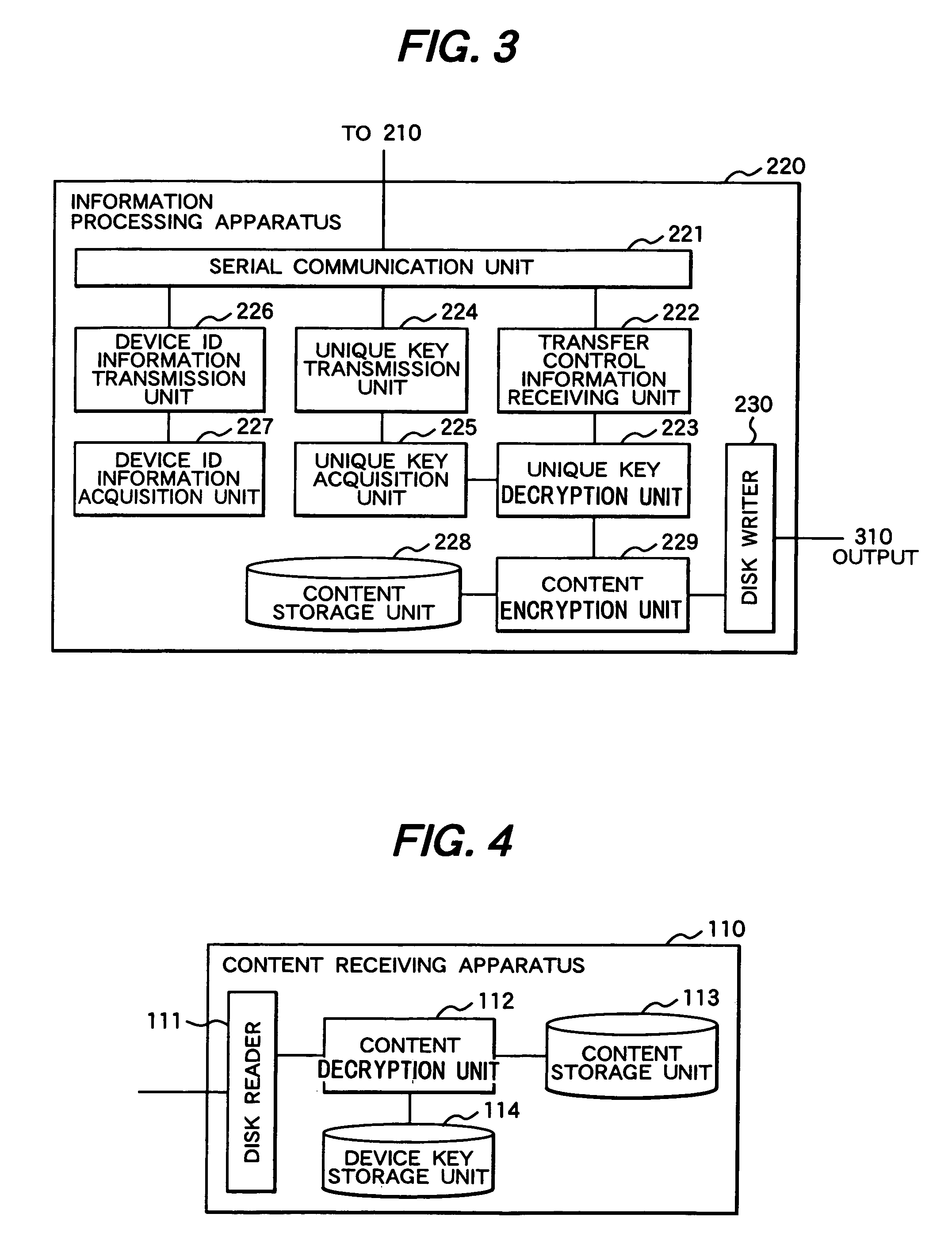
Copy control apparatus and method thereof, information processing apparatus and method thereof, and content receiving apparatus
InactiveUS20070160199A1RestrictControl contentDigital data protectionSecret communicationInformation processingCopy control
A copy control apparatus is provided in one-to-one correspondence with a car navigation system. Connection of the copy control apparatus with an information processing apparatus such as a PC enables to transmit content only from the information processing apparatus to which the copy control apparatus is connected to the car navigation system. With this configuration, the copy control apparatus stores a device key used to encrypt the content, and encrypts the device key with another encryption key to transmit the encrypted device key to the information processing apparatus. The information processing apparatus encrypts a copy of the content by use of the received device key, and then sends the encrypted copy to a content receiving apparatus. The content receiving apparatus decrypts the received copy of the content by use of a stored device key, and then stores the decrypted copy of the content in a storage unit.
Owner:XANAVI INFORMATICS
Correction data checking system for rebots
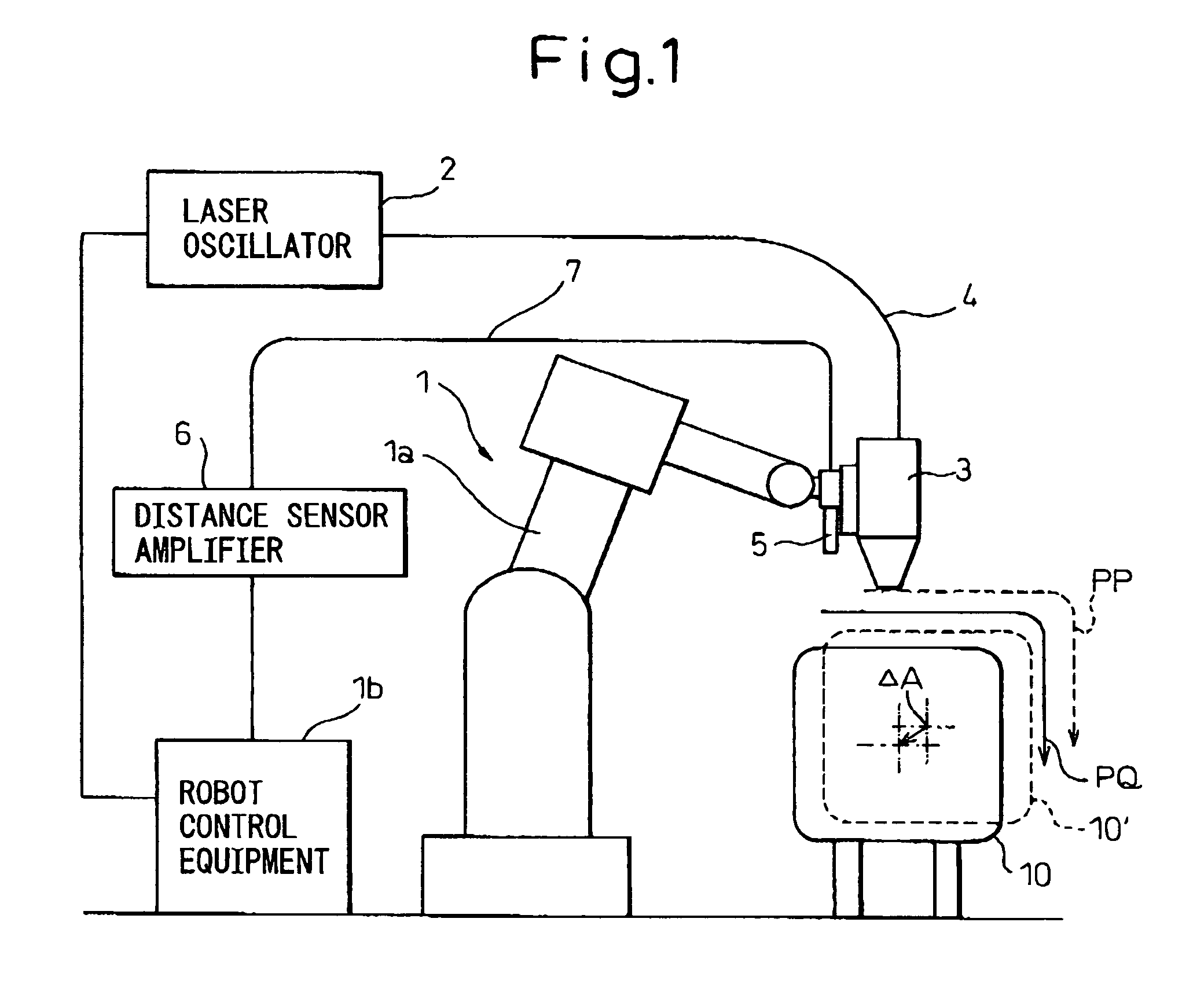
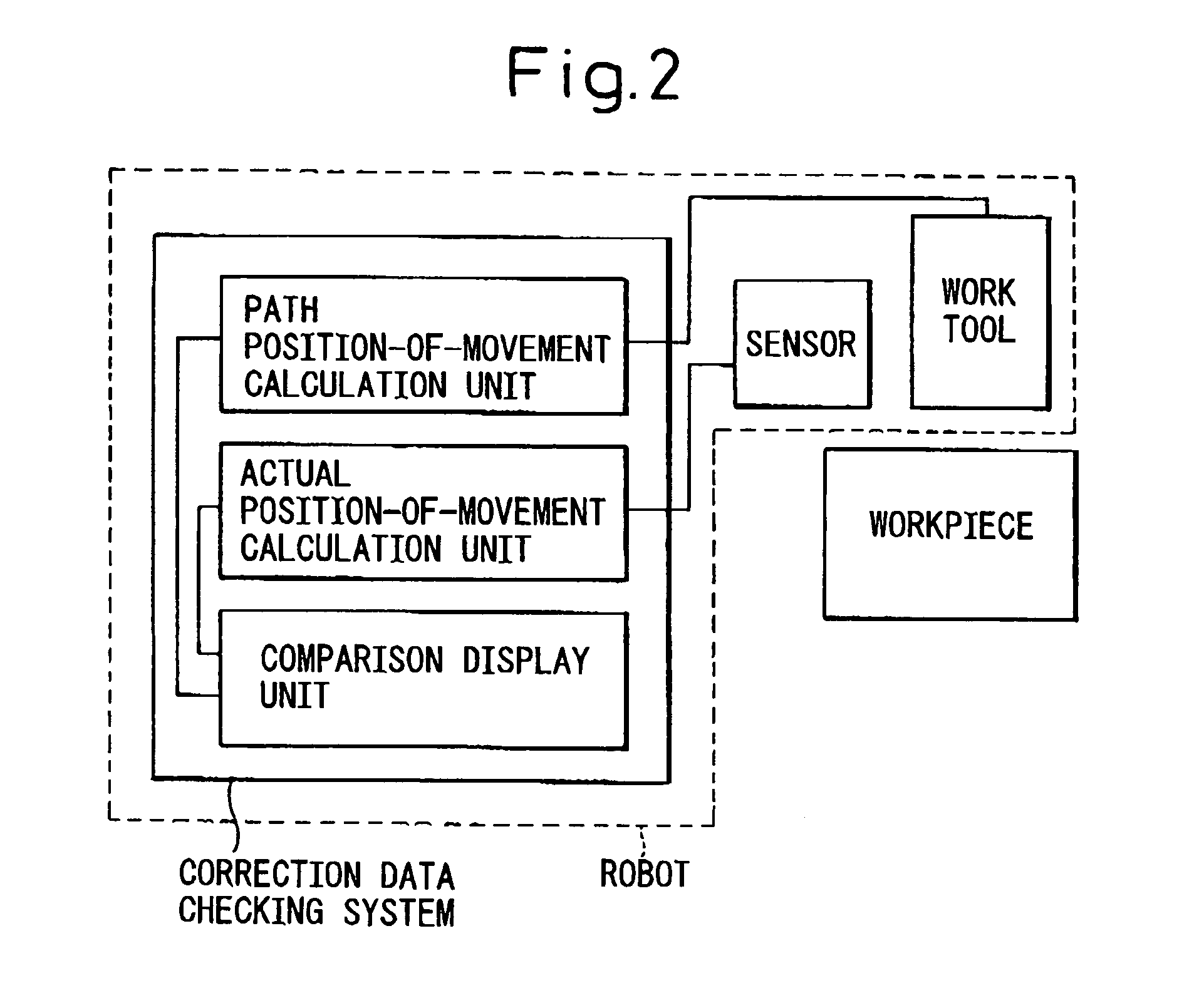
InactiveUS7149602B2Easily exposedProgramme controlProgramme-controlled manipulatorDisplay deviceTeaching program
Provided is a correction data checking system, for robots, which makes it easy to reveal the cause of a machining defect. A laser machining head and a distance sensor or a sensor for detecting a work line are attached to the distal end of a robot arm. A robot is driven based on a teaching program, and a copying control technique is implemented based on information sent from the sensor so that the distance between the laser machining head and a workpiece will be equal to a set value. A path of taught positions of the laser machining head and a path of actual positions thereof are displayed in comparison with each other on a display of a teaching console or the like. Moreover, the difference between the taught position and actual position is calculated and displayed. As both the position commanded by the teaching program and the actual position derived from the copying control technique are displayed, if a machining defect occurs, the machining defect is checked to see if it is a problem attributable to the sensor or a problem attributable to the workpiece or a jig. The cause of the machining defect is then revealed. Consequently, the cause of a machining defect can be quickly revealed and dealt with at a working site.
Owner:FANUC LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com