Patents
Literature
168 results about "Resource isolation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Enterprise application deployment and management system for multiple tenants
ActiveCN105323282AEasy to addFlexible Service Adaptation EngineData switching networksResource isolationComposite application
The invention relates to an enterprise application deployment and management system for multiple tenants. A container-based multi-tenant isolation mechanism is realized; the integration and migration of enterprise legacy systems are supported; rich enterprise-level services are provided; SOA architecture-based enterprise-level application development is supported; perfect self-service ability is provided; high availability of a platform can be provided; dynamic expansion and demand-based scalability can be realized; and pure asynchronous intelligent routing is realized. The objective of the invention is to solve problems in multi-tenant resource isolation, compatibility with existing applications and composite application construction in cloud computing technologies for enterprise applications. The enterprise application deployment and management system for multiple tenants has the advantages of multi-tenant safe isolation, seamless migration of enterprise applications and the scalability of applications.
Owner:DIGITAL CHINA INFORMATION SYST
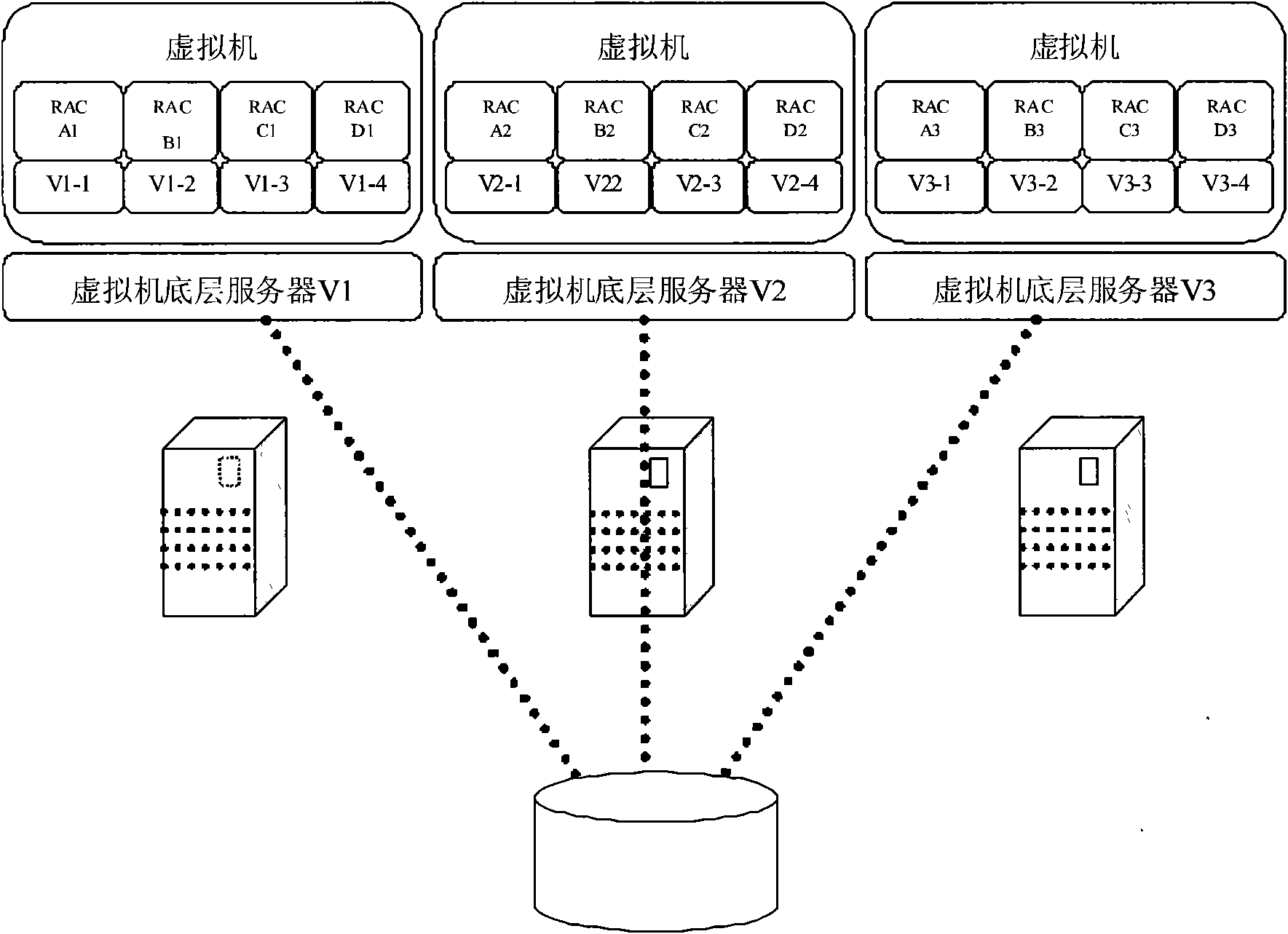
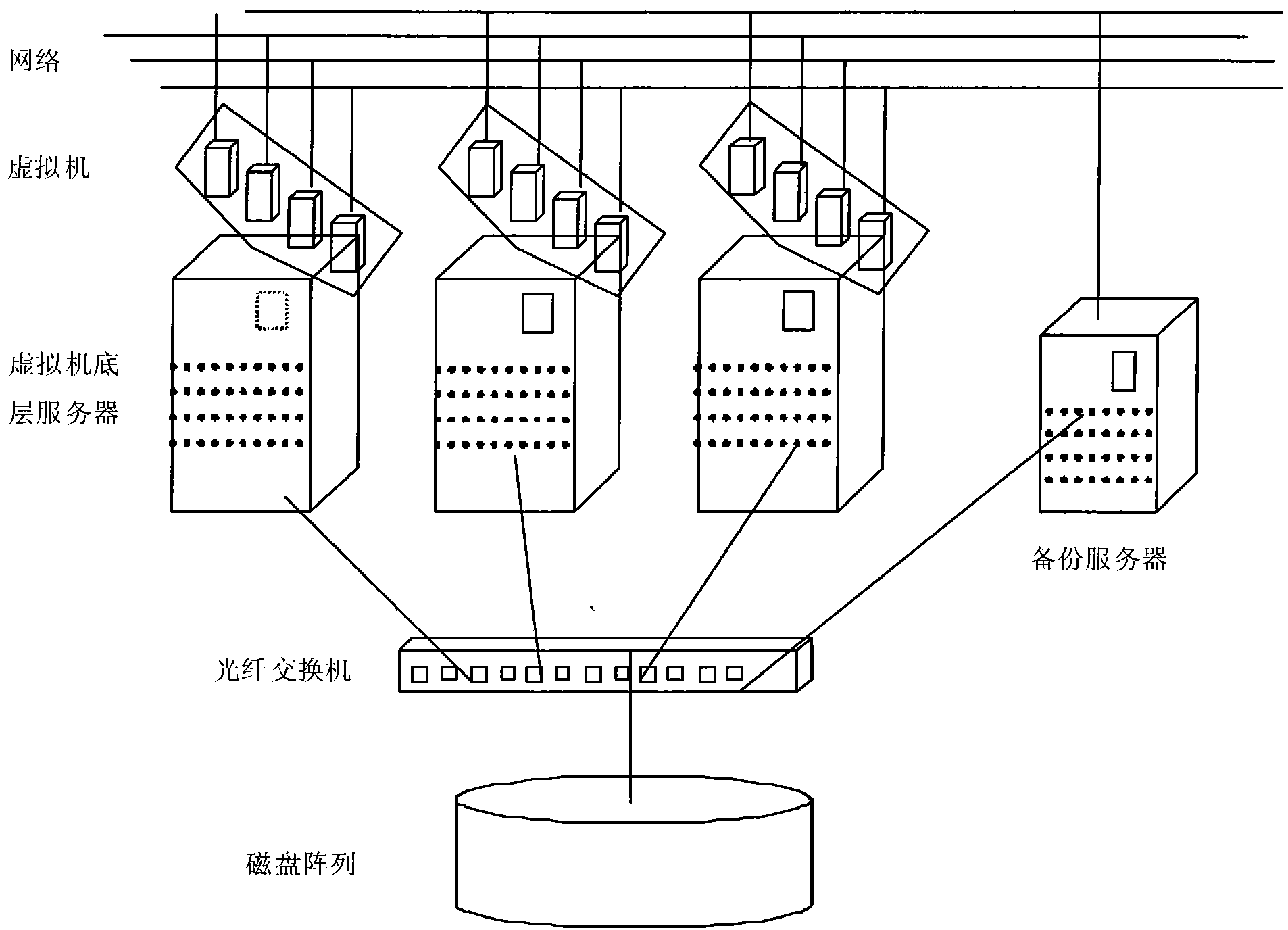
Method for establishing database cluster by utilizing virtualization
The invention provides a method for establishing a database cluster by utilizing virtualization, which utilizes the technical advantages of virtualization, ensures that all processing units in the database cluster obtain optimal resources, simultaneously improves the resource utilization rate of a physical hardware, and realizes the rapid deployment, expansion of the database cluster, the dynamic migration, the resource isolation of a multi-cluster system and the dynamic management of system resources, wherein the all processing units in the database cluster obtain optimal resources, i.e. a CPU, a memory and IO resources are customized and allocated in advance for a virtual machine according to the requirements of the processing unit in the database cluster for the resources in an underlying server system of the virtual machine; the improvement of the utilization rate of system resources means that a plurality of virtual machines are deployed and operated on the underlying server system of the virtual machine so as to improve the resource utilization rate of the underlying server of the virtual machine; the rapid deployment and expansion of the database cluster mean that the rapid expansion of the database cluster is realized through the mirroring replication function of a virtualized software; and the dynamic migration means that the dynamic migration of the virtual machine is realized by utilizing the virtualized software, and the service of the database cluster is not interrupted.
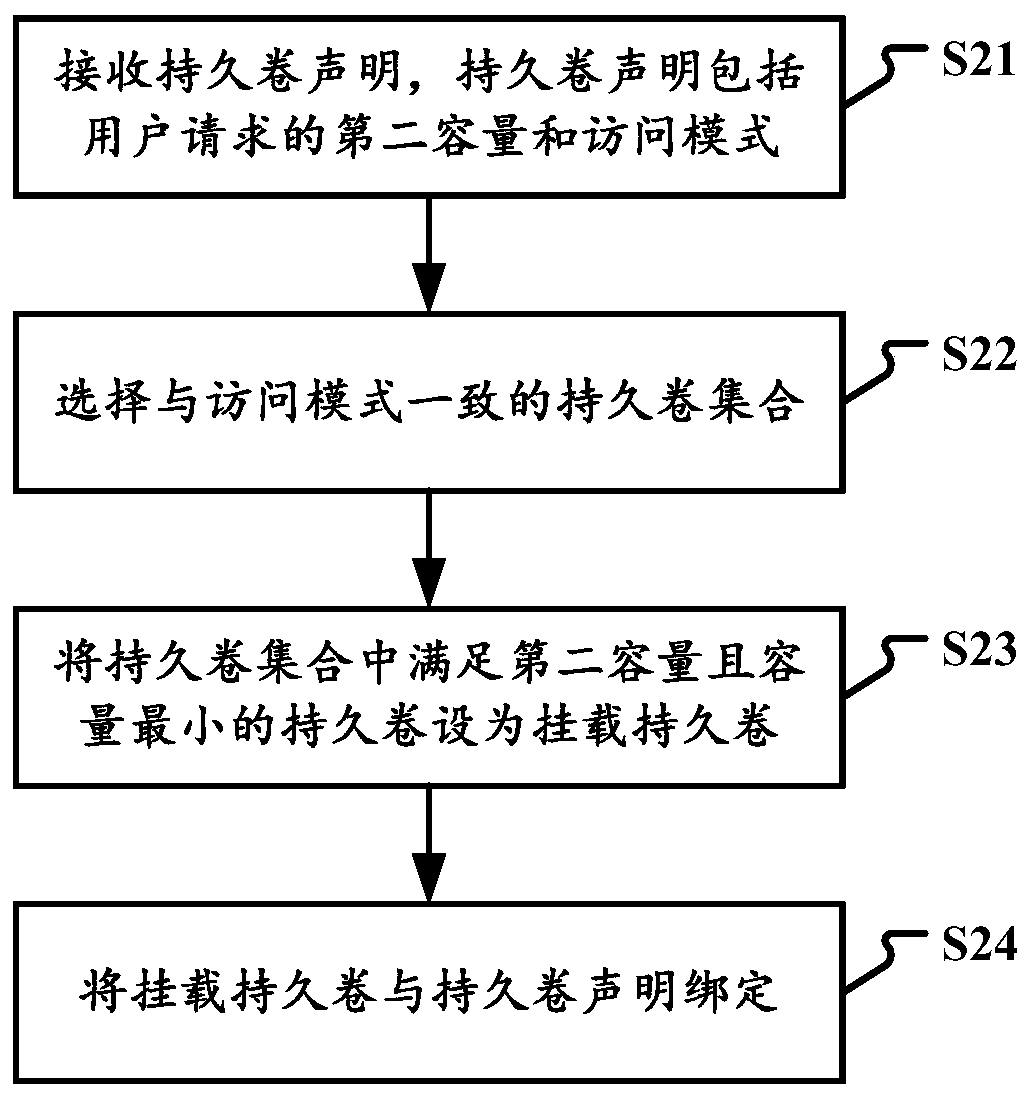
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
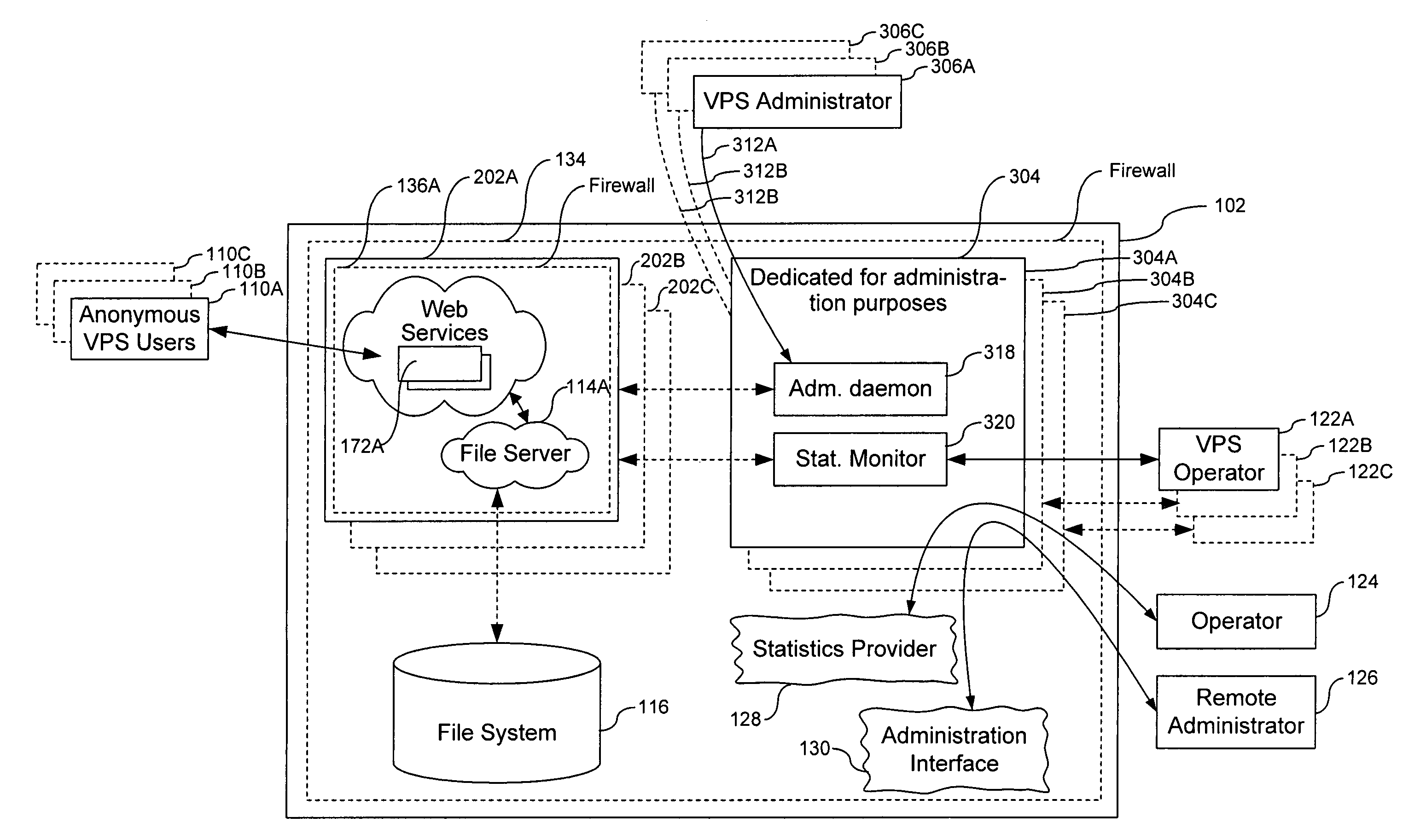
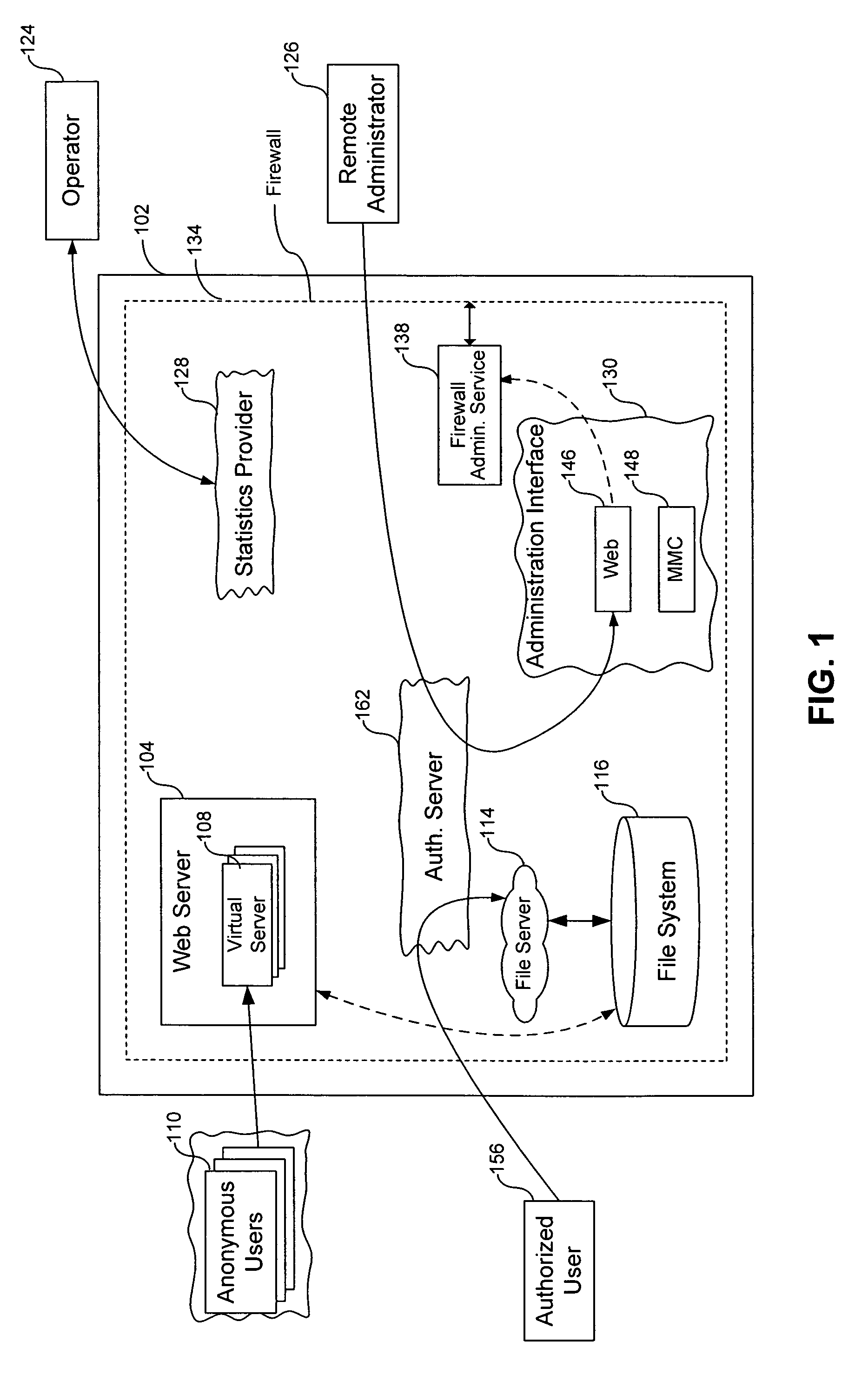
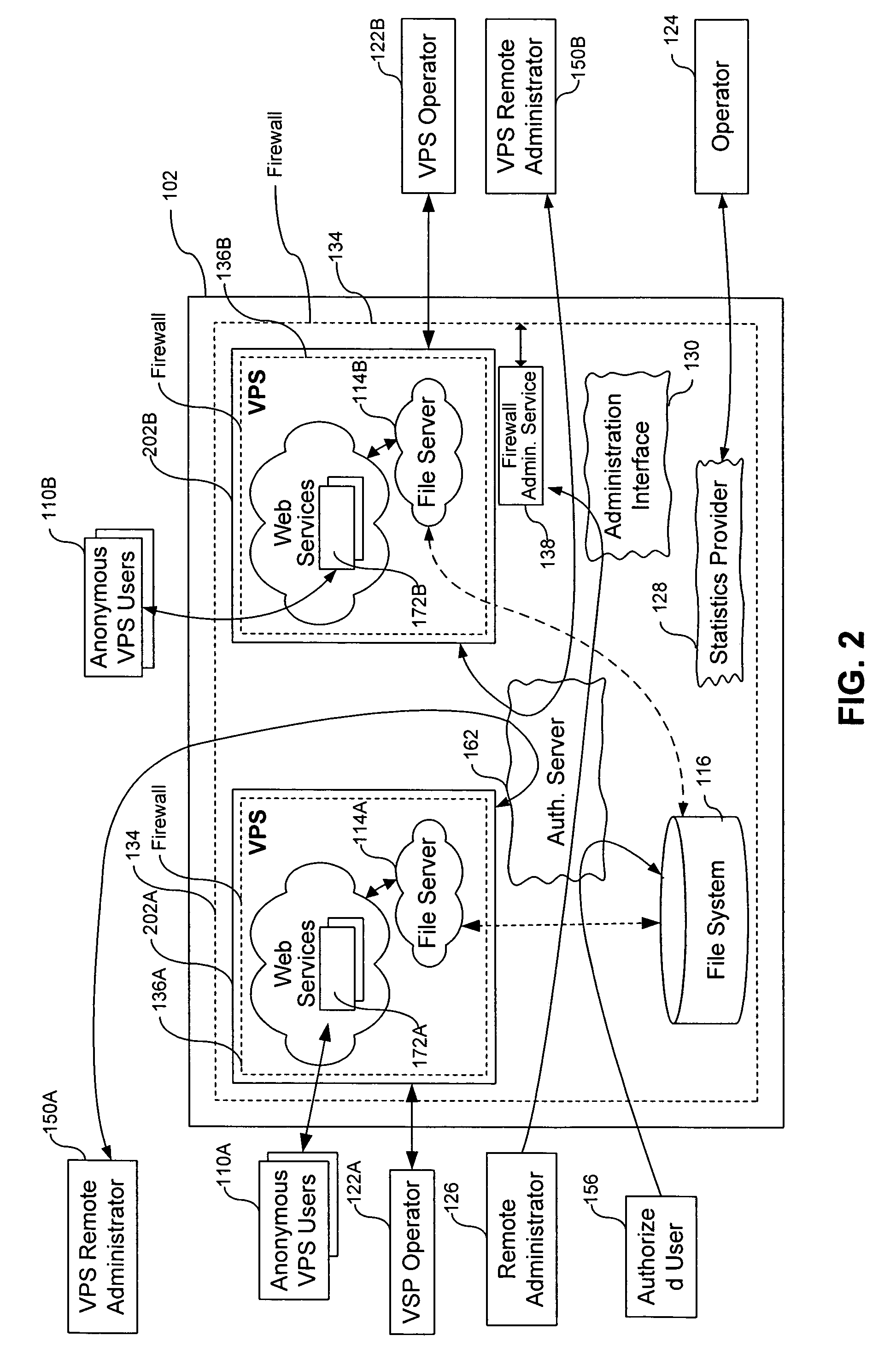
Dedication of administrative servers to management of server functions in a multi-server environment
ActiveUS7698400B1Eliminate disadvantagesMultiple digital computer combinationsData switching networksOperational systemResource isolation
A system for managing administration of computer services provided to users includes a computer system and an operating system running on the computer system. A server process is launched by the computer system for providing services to users. An isolated Virtual Private Server (VPS) has a set of services that perform administrative operations relating to the server process. The server process can be a webserver, a file server, an FTP server, an authentication server, a VPS, a chroot environment, a jail environment, a sand box environment, a print server and a Windows Terminal Service. The administrative operations can include collection of statistics relating to the server process; servicing of requests for management of the server process; servicing of requests for management of operating system functions; servicing of requests for computer system resource allocation; servicing of requests for computer system resource re-allocation; servicing of requests for authorization within the operating system; servicing of requests for authorization within the server process; servicing of requests that the server process is forbidden from executing; servicing of operations that potentially can cause a fault in the server process; and servicing of operations that require multiplexing of server processes. The multiplexing can be based on a network protocol addressing, or on a content of a request directed to the server process. The VPS isolation can include logical isolation of processes, physical isolation of processes, resources isolation, namespace isolation, data isolation, address isolation, fault isolation and performance isolation.
Owner:VIRTUOZZO INT GMBH
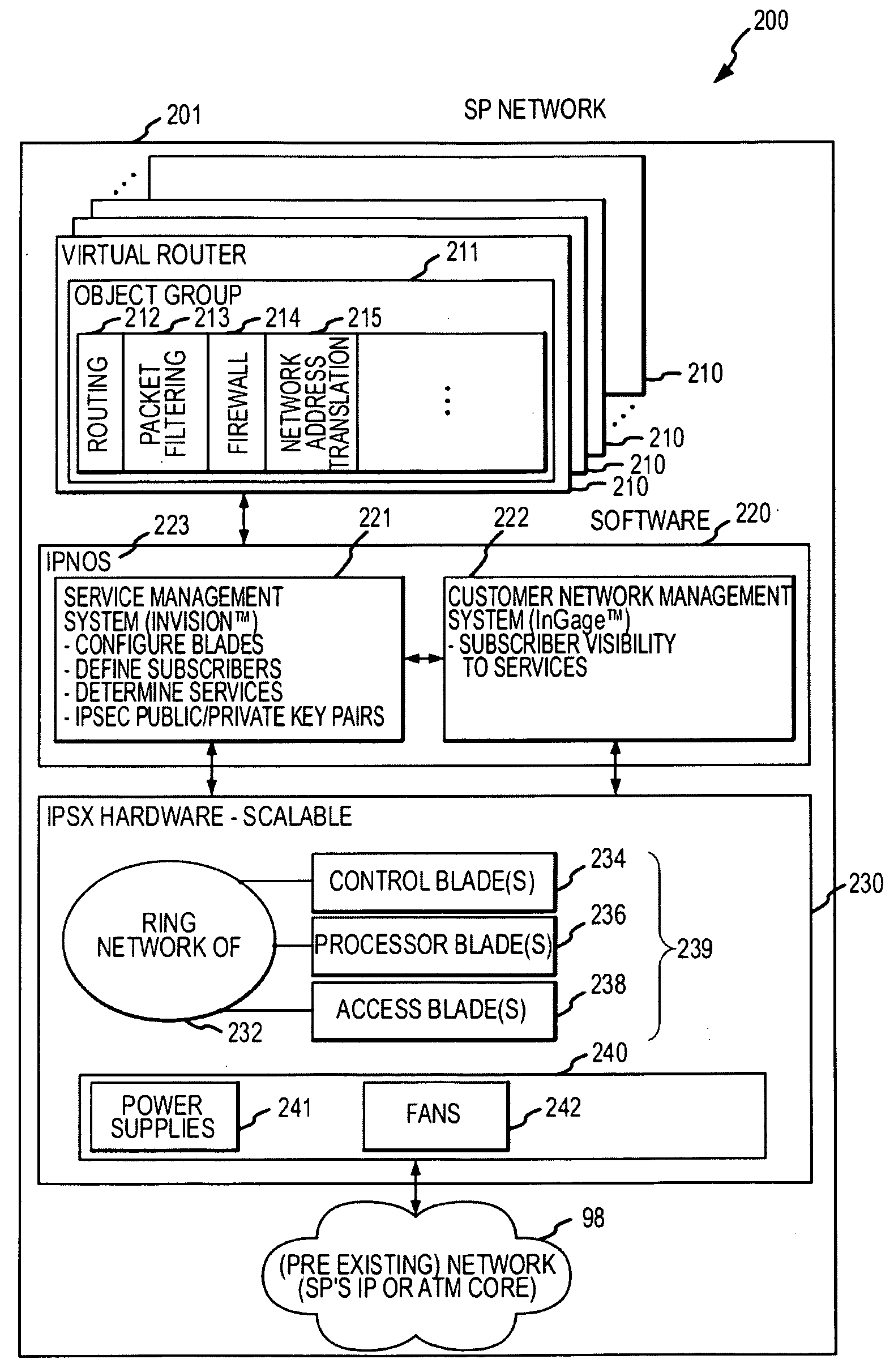
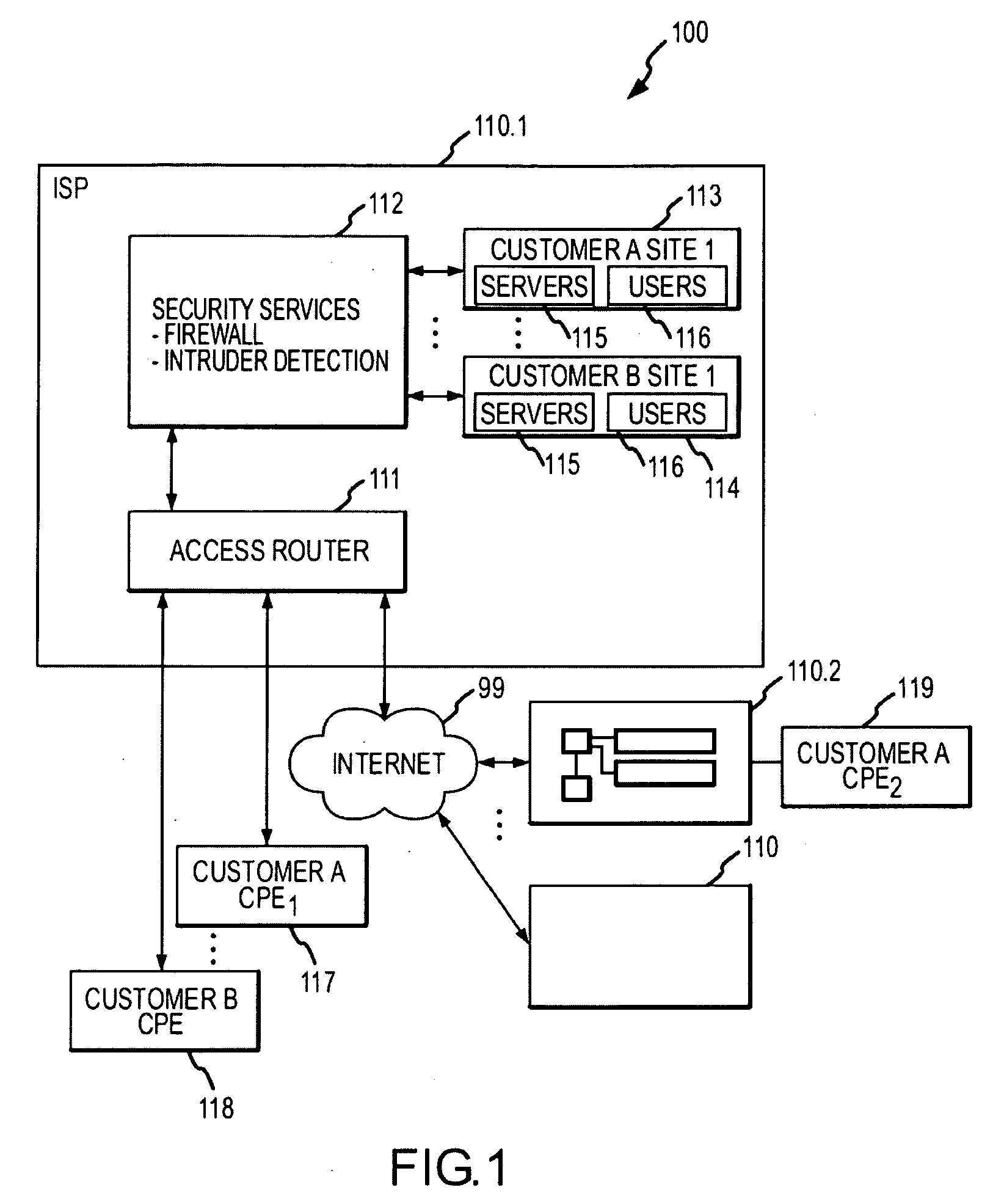
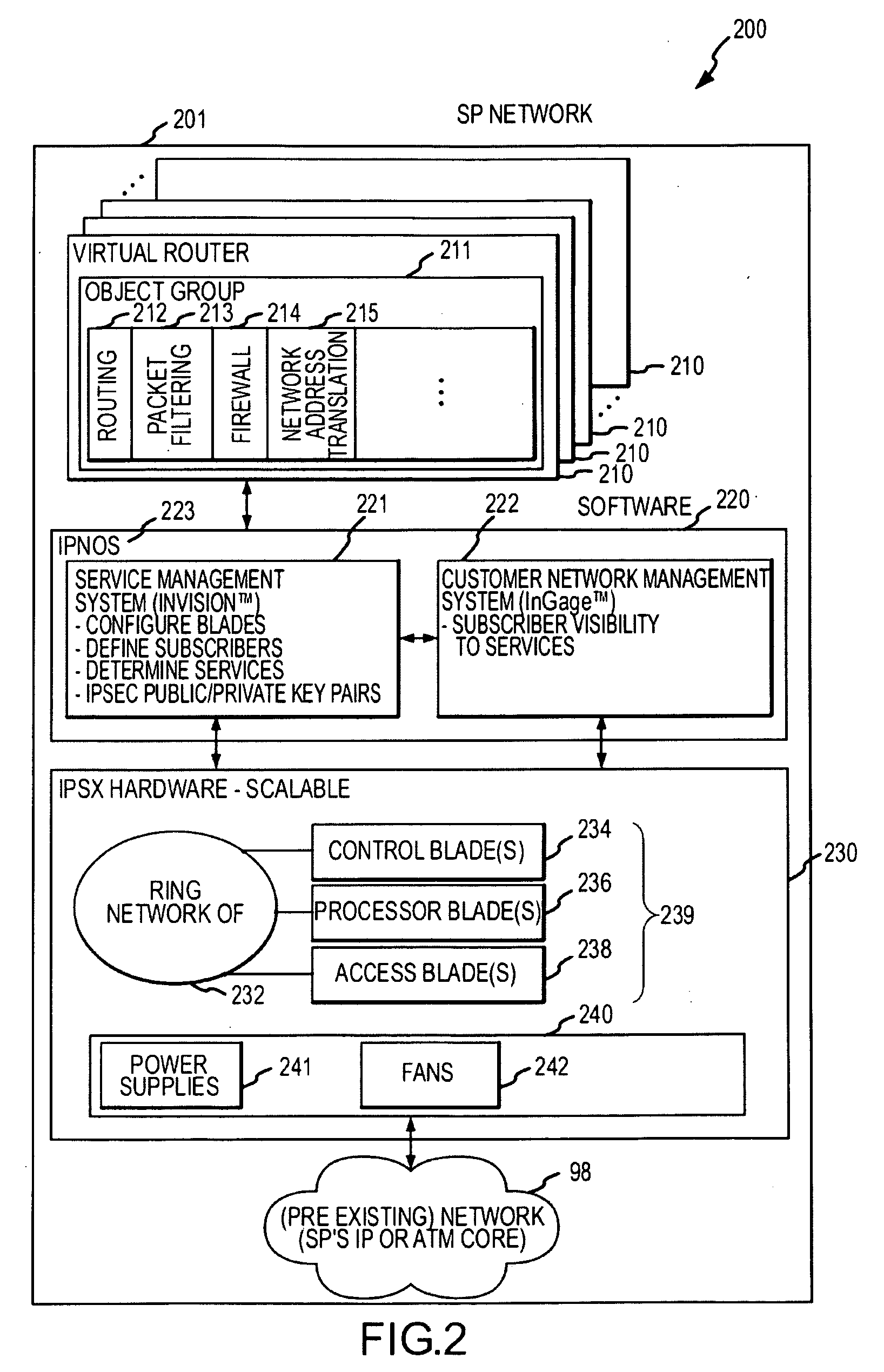
System and method for delivering security services
InactiveUS20090046728A1Data switching by path configurationNetwork connectionsResource isolationEngineering
Systems and methods are provided for delivering security services. According to one embodiment, multiple virtual routers are established within a service processing switch, which is operable to be logically interposed between a public communications network and multiple subscriber sites. Each of the virtual routers has associated therewith a subset of processing and storage resources of the service processing switch. Subscribers are provided with respective sets of customized application layer services. Subscriber resource isolation is provided by partitioning the virtual routers between the subscribers including allocating and configuring partitions, having subsets of the virtual routers, to the subscribers. Changeable provisioning of processing capacity between the subscribers is provided by dynamically reallocating resources of the service processing switch between the partitions based on comparative processing demands of the customized application layer services.
Owner:FORTINET
Cluster resource processing method and system, and resource processing cluster
ActiveCN106708622AAllocation is flexible and efficientFlexible and Efficient DeploymentResource allocationGNU/LinuxResource isolation
The invention relates to a cluster resource processing method and system, and a resource processing cluster. The cluster resource processing method comprises the following steps that: monitoring node calculation resource information, and obtaining current idle calculation resources according to the node calculation resource information; receiving an operation request which carries resource configuration information, wherein the resource configuration information comprises a node label; according to the node label, obtaining a corresponding node queue, and distributing target calculation resources to the operation in the current idle calculation resources of the node in the node queue according to the resource configuration information; and on the node corresponding to the target calculation resources, starting a (User Mode Linux) resource isolation container, and executing the operation in a user space. A cluster use ratio can be improved, and operation throughput in the cluster can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
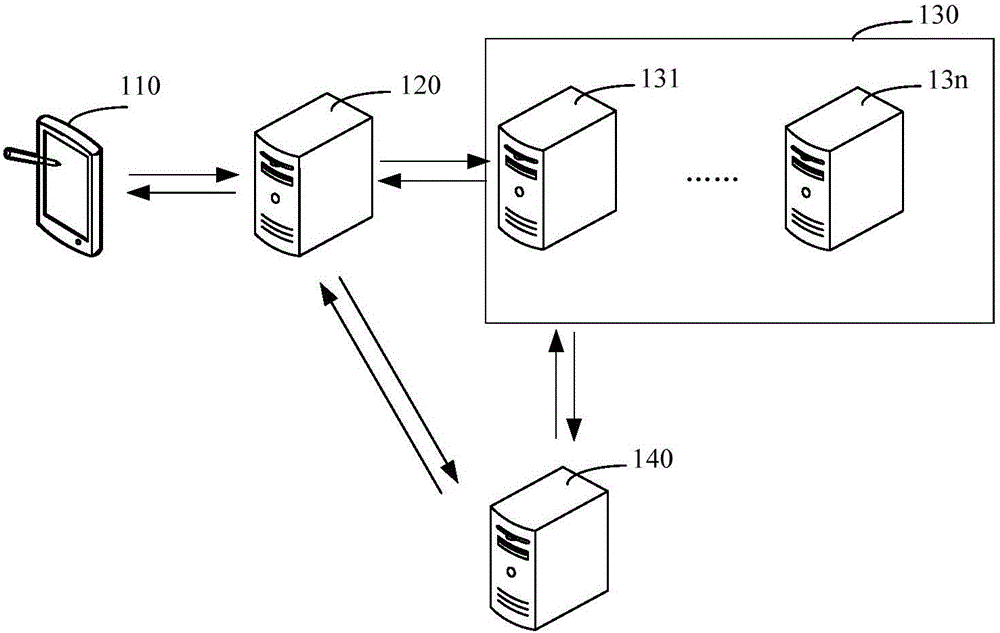
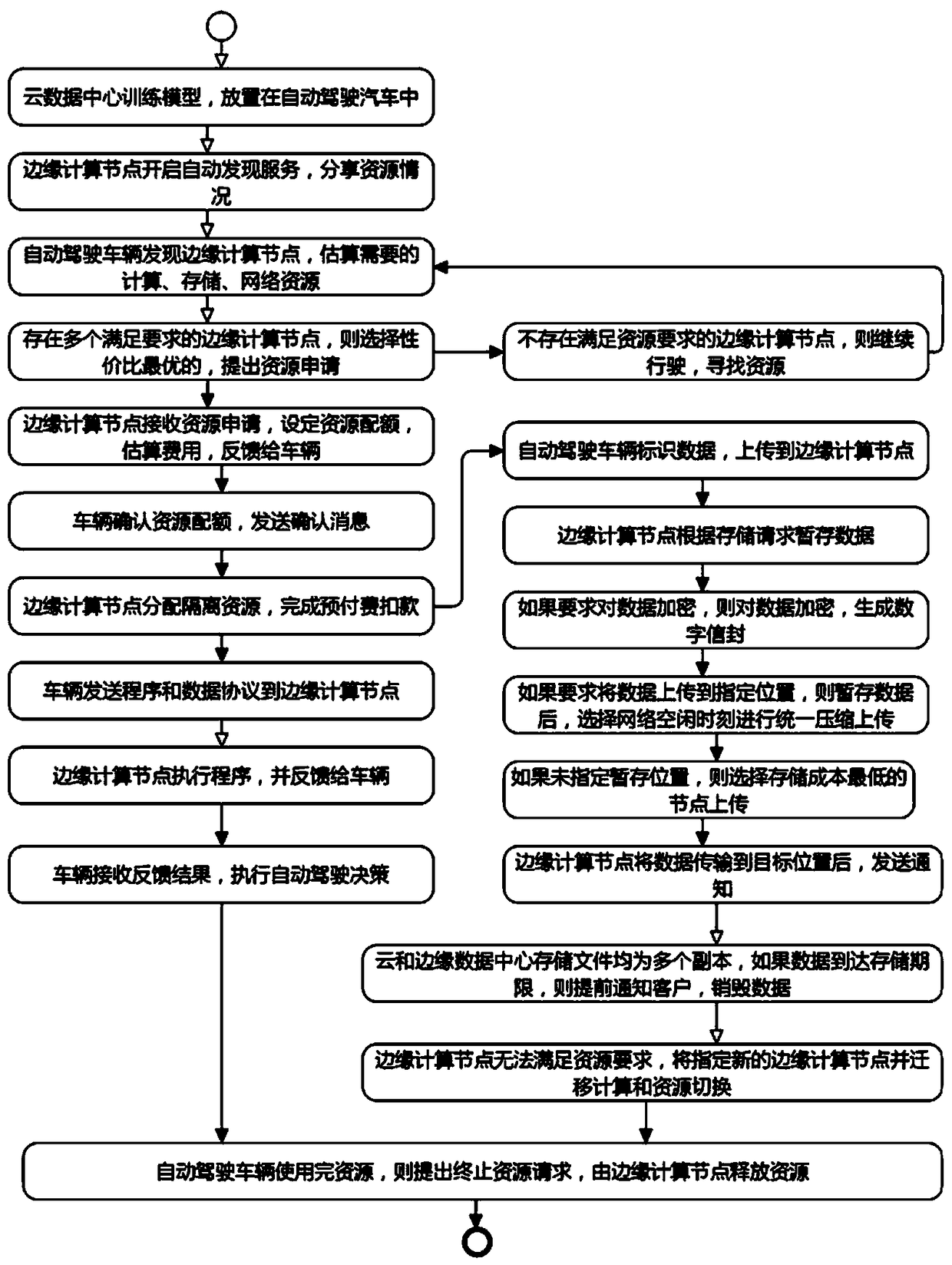
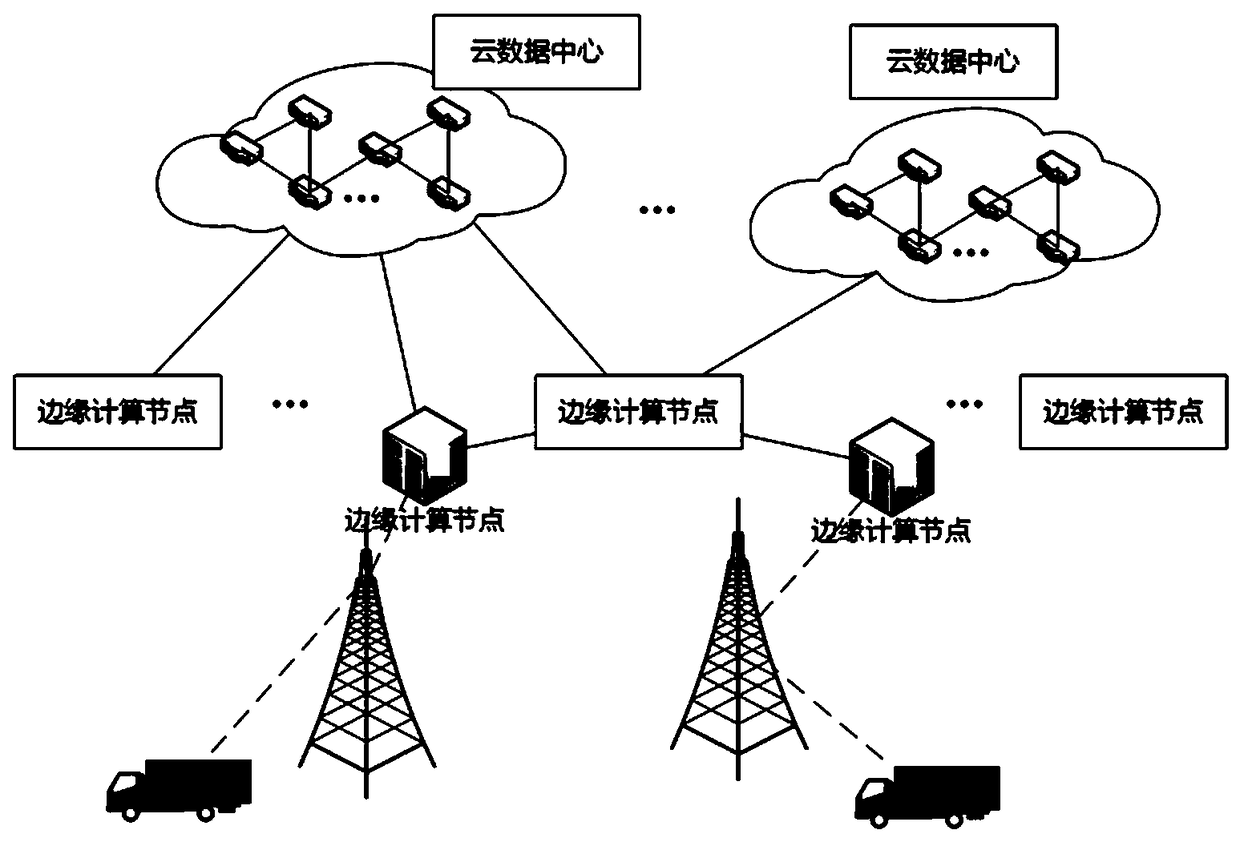
Automatic driving-oriented edge computation resource management method
ActiveCN108845885ARelieve stressReal-time interactionProgram initiation/switchingResource allocationResource isolationHigh availability
The invention discloses an automatic driving-oriented edge computation resource management method. The method comprises the following steps of: carrying out uniform management and dynamic distributionon edge-side resources according to a demand, for computation resources, of an automatic driving business, so as to realize real-time interaction with an autonomous vehicle; migrating the computationto an edge computation node; and storing mass automatic driving data according to a customer demand so as to relieve the pressure, for computation and storage demands, of the vehicle. Compared with the prior art, the method has the advantages that the computation, storage and network resources of edge sides are pooled to form transparent and high-availability resource infrastructure nodes, so that high-availability computation ability is provided for automatic driving businesses, and large-capacity and low-cost storage services and edge side high-speed network services are provided at the same time; resource isolation between businesses and data is realized, and resource switching is dynamically completed, so that the computation, storage and network are respectively charged as required and then the charging is more reasonable; the value maximization of the computation and storage resources is realized; and the automatic driving efficiency is improved.
Owner:山东浪潮创新创业科技有限公司
A method and equipment for generating route
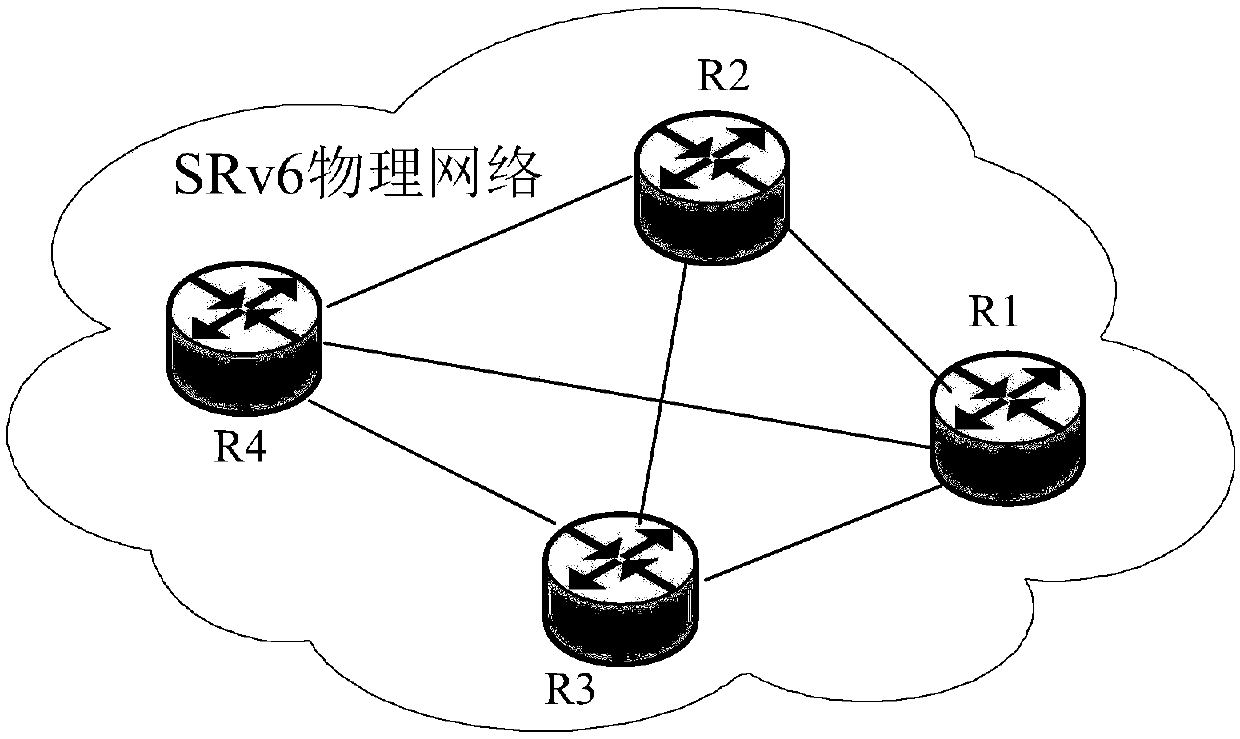
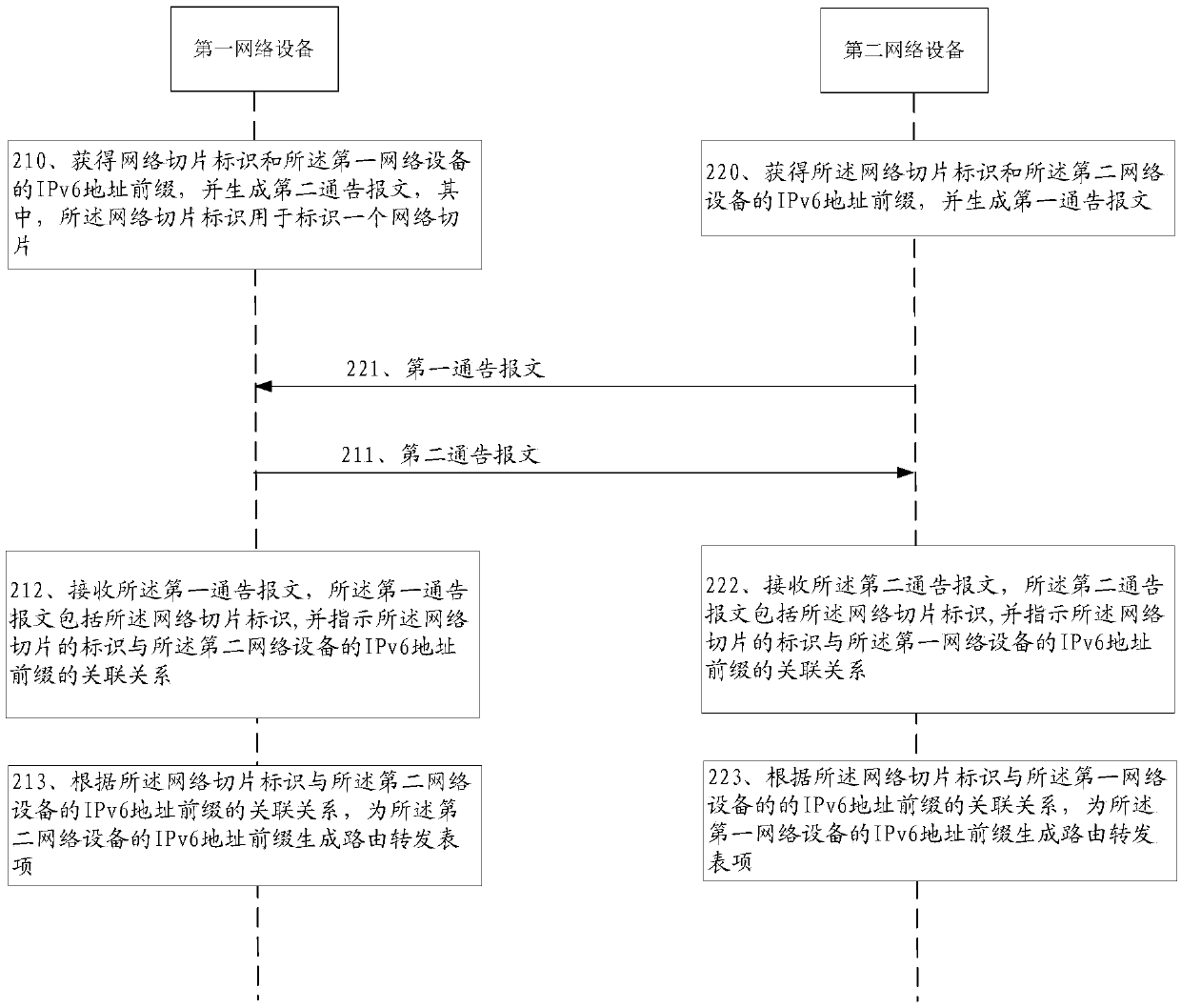
ActiveCN110535766ASlice implementationSolve the problem of generating the corresponding routeData switching networksComputer networkResource isolation
The invention provides a method for generating a route. The method is applied to an SRv6 network. The method comprises the following steps: first network equipment receives a first notification message from second network equipment, wherein the first notification message comprises a network slice identifier, the first notification message indicates an association relationship between identification information of the network slice and an IPv6 address prefix of the second network device, and the network slice identifier is used for identifying one network slice; and the first network equipmentgenerates a routing forwarding entry for the IPv6 address prefix of the second network device according to the association relationship between the network slice identifier and the IPv6 address prefixof the second network device. And network slicing and resource isolation in the SRv6 network can be realized.
Owner:HUAWEI TECH CO LTD
Secure container and design method thereof
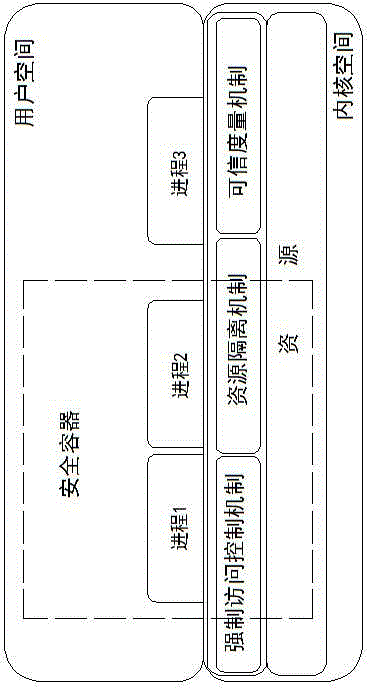
InactiveCN104573507AAvoid security issuesThe use does not affect each otherPlatform integrity maintainanceOperational systemResource isolation
The invention discloses a secure container and a design method thereof, belonging to the technical field of information safety. The secure container disclosed by the invention is characterized in that a secure area is constructed in an operation system; a set of processes is operated in the area by utilizing the three mechanisms including mandatory access control, resource isolation and trusted measurement; the set of processes is only capable of accessing resources in the area and is incapable of accessing resources outside the area; processes outside the area are also incapable of accessing resources in the area; and furthermore, the strategy of the area and application in the area need to be subjected to trusted measurement. Compared with the prior art, the secure container disclosed by the invention is capable of resisting various attacks in a network through the operation system level; therefore, the network information security problem is thoroughly solved; and the secure container and the design method thereof disclosed by the invention have good popularization and application value.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
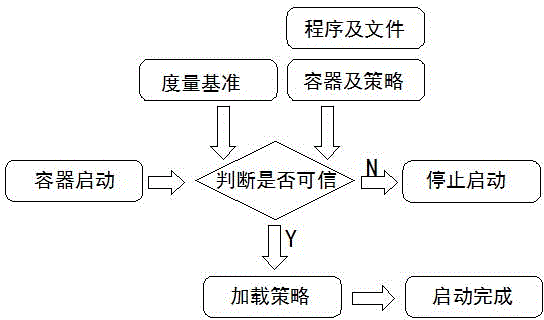
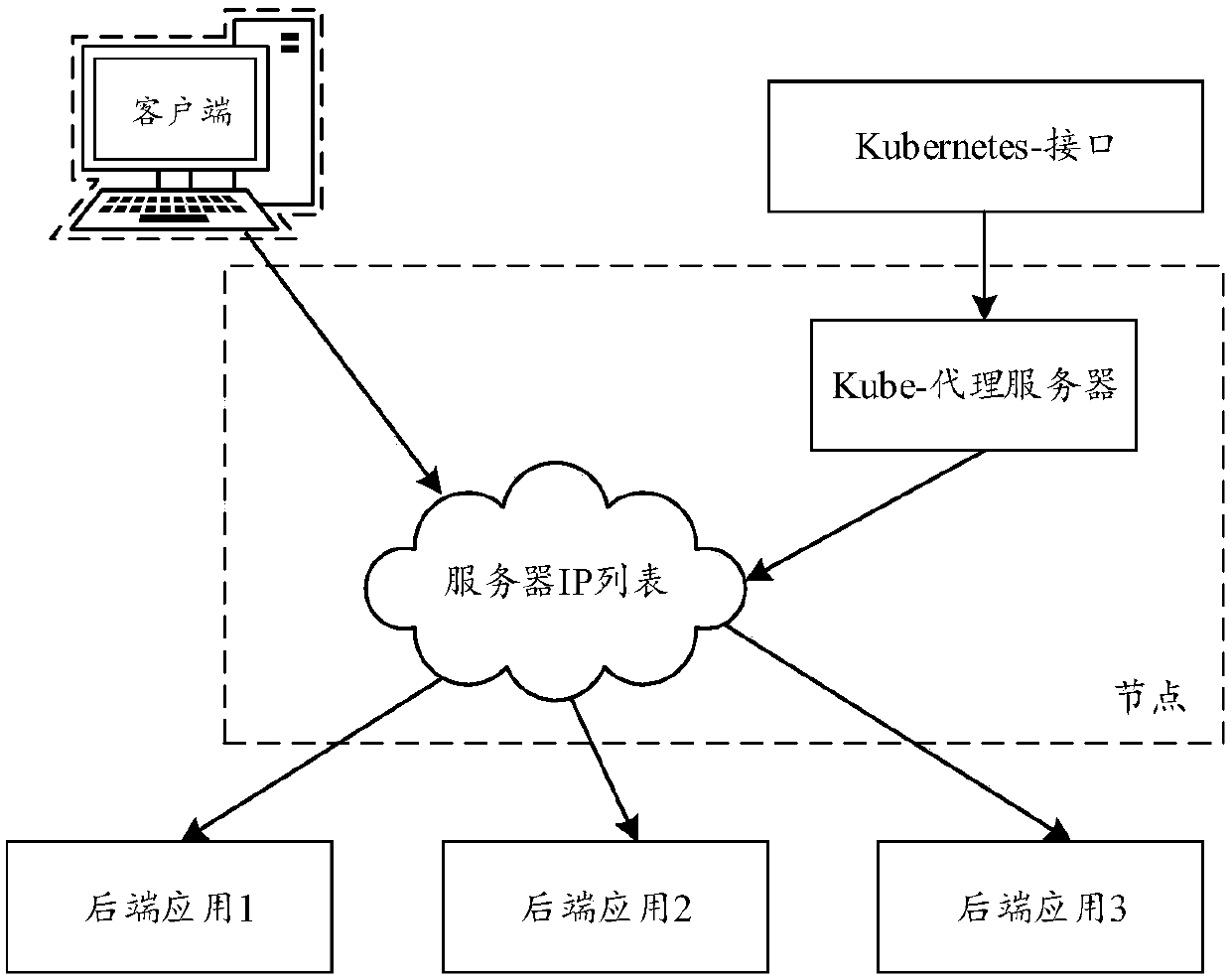
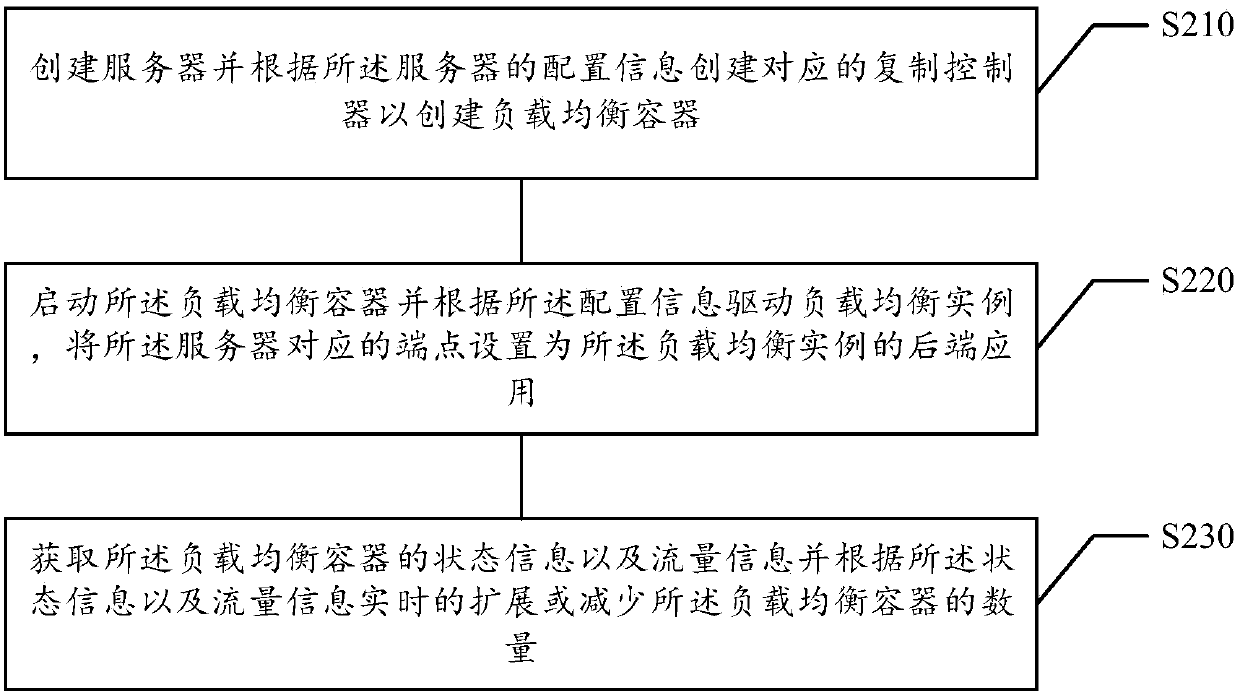
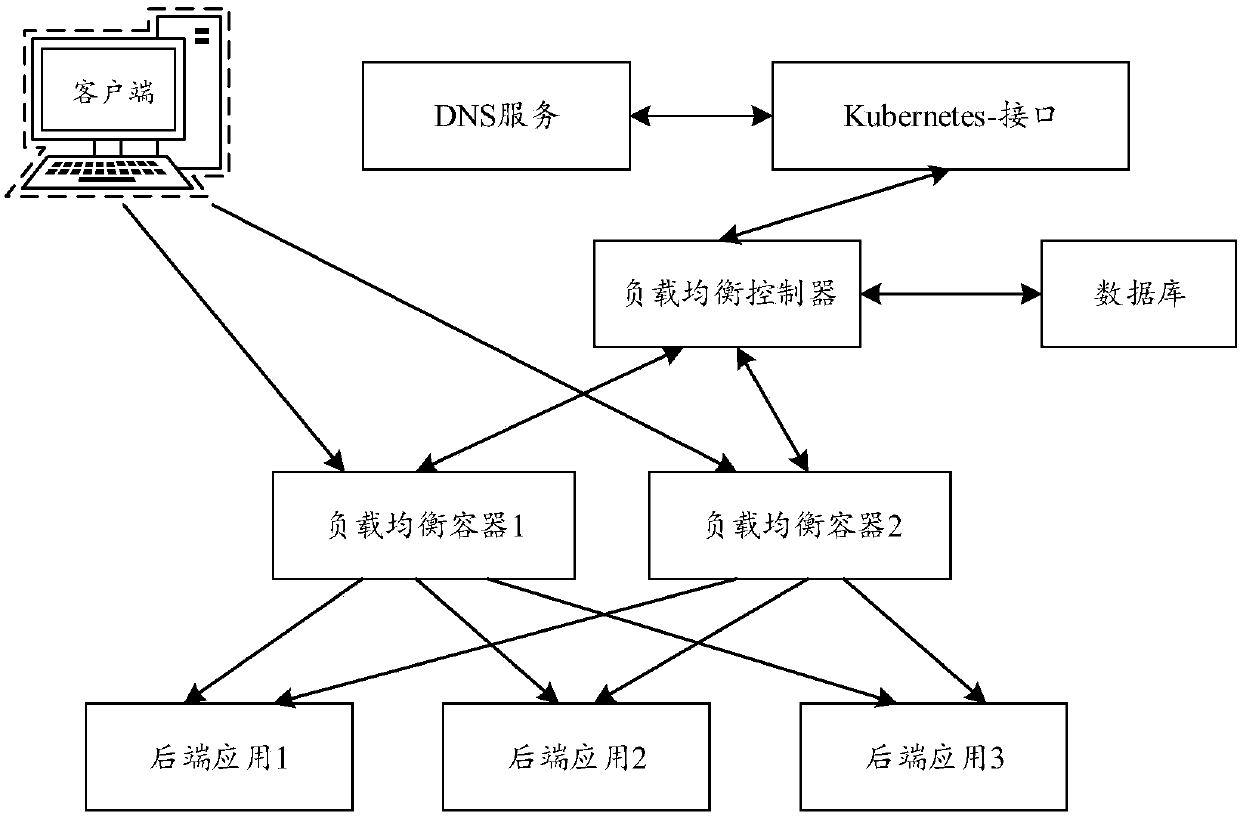
Load balancing method and device, storage medium and electronic equipment
ActiveCN107590001AReduce in quantitySolve the problem of too slow speed caused by high utilizationResource allocationTraffic capacityResource isolation
The invention relates to a load balancing method and device, and relates to the technical field of Internet applications. The method comprises the following steps that: creating a server, and creatinga corresponding replication controller according to the configuration information of the server to create load balancing containers; starting the load balancing containers, and driving a load balancing living example according to the configuration information, and setting an end point corresponding to the server as the rear-end application of the load balancing living example; and obtaining the state information and the traffic information of the rear-end application, and expanding or reducing the amount of the load balancing containers in real time according to the state information and thetraffic information. By use of the method, the resource isolation characteristics of the container can be utilized to deploy the load balancing living example in the container so as to avoid resourcecompetition among different load balancing living examples on the same server.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
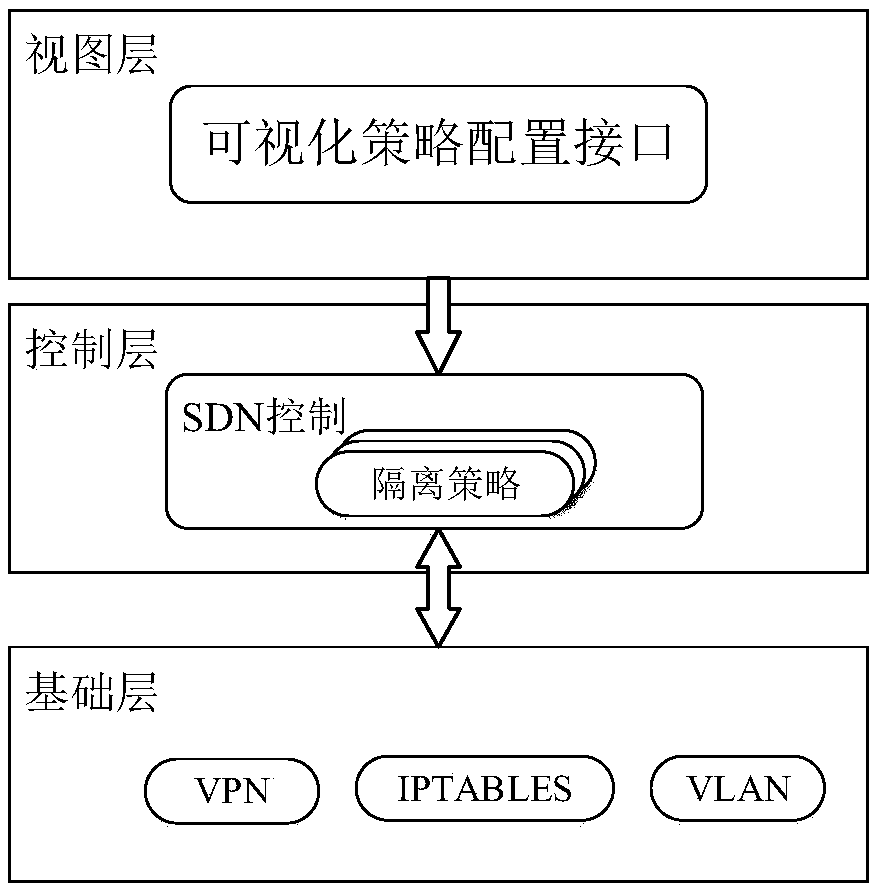
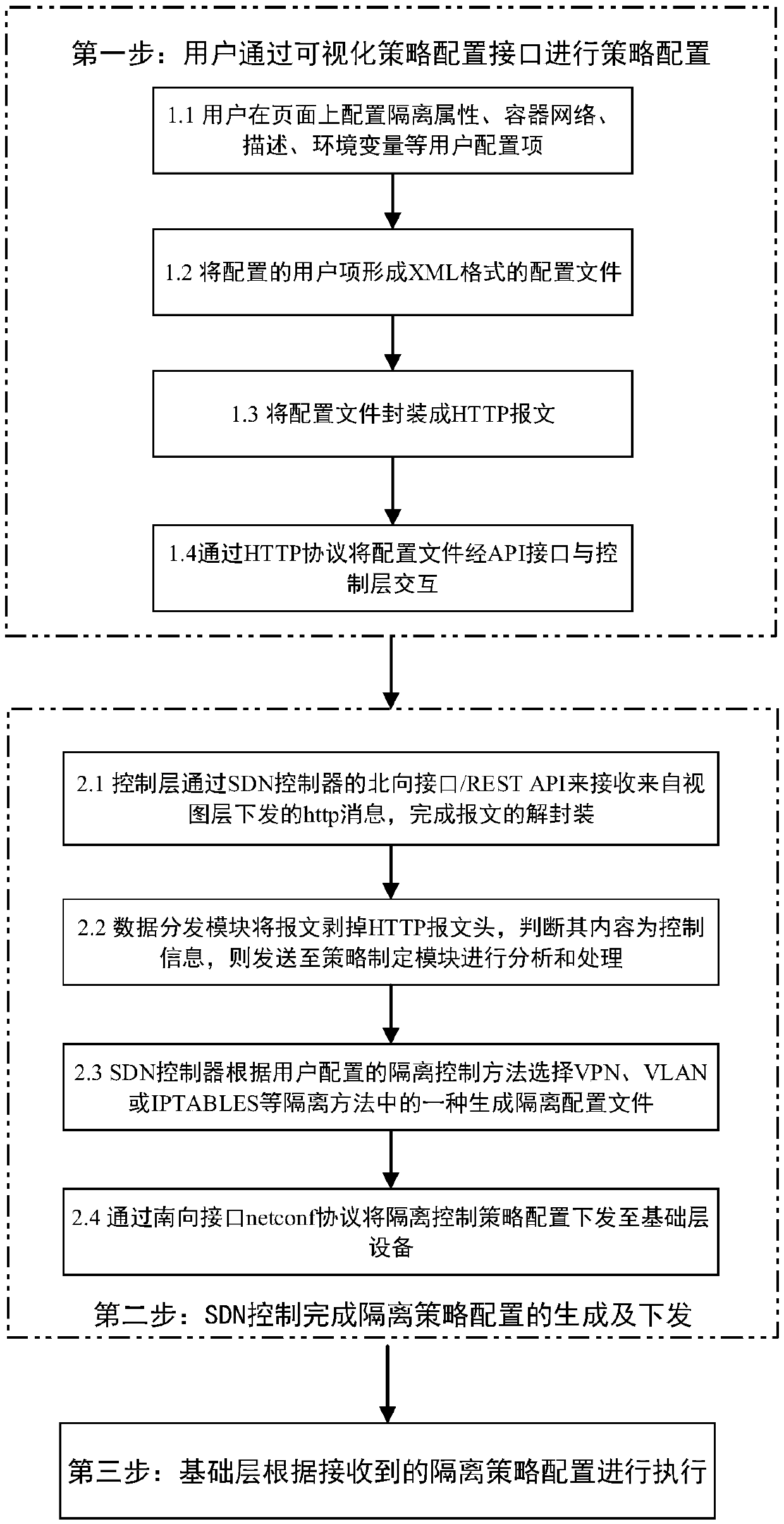
Policy-based container network resource isolation control method
The invention provides a policy-based container network resource isolation control method in allusion to a problem that the container network resource isolation cannot flexibly customize a network access policy according to the task in the prior art. The method comprises the steps that S1, a user actively configures a container network isolation policy scheme through a visual policy configurationinterface according to the service scenario; S2, an SDN (Software Defined Network) controls to generate isolation policy configuration according to the isolation policy scheme configured by the user through the visual policy configuration interface and sends the isolation policy configuration to equipment; and S3, a base layer executes a corresponding isolation and access control mechanism according to the isolation policy configuration sent by the control layer. According to the invention, hierarchical container network isolation is realized in allusion to container network resource isolationcontrol requirements, and the conditions of container network mutual access is flexibly customized according to the service access scenario, thereby realizing the difference of an access relationshipof container network resources under different application scenarios, and ensuring the effective isolation of the network resources.
Owner:NAT UNIV OF DEFENSE TECH
Decentralized storage system based on double-layer network
InactiveCN108282539AReduce processing constraintsSmall amount of calculationTransmissionResource isolationThroughput
Owner:BEIJING QIHOO TECH CO LTD
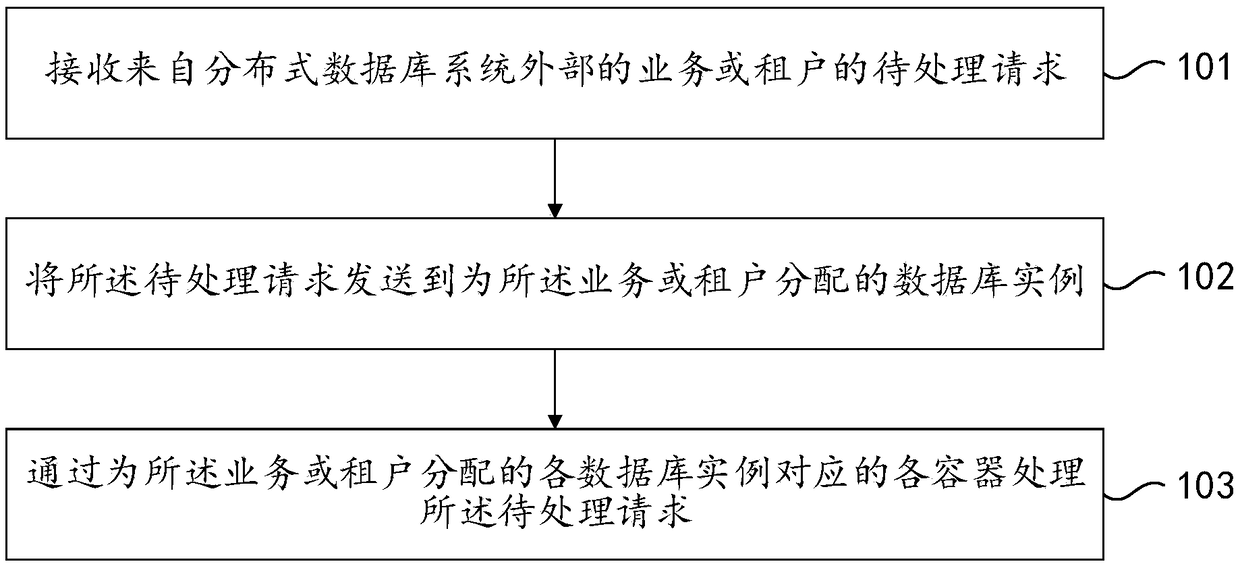
Resource isolation method and device for distributed database system, and server
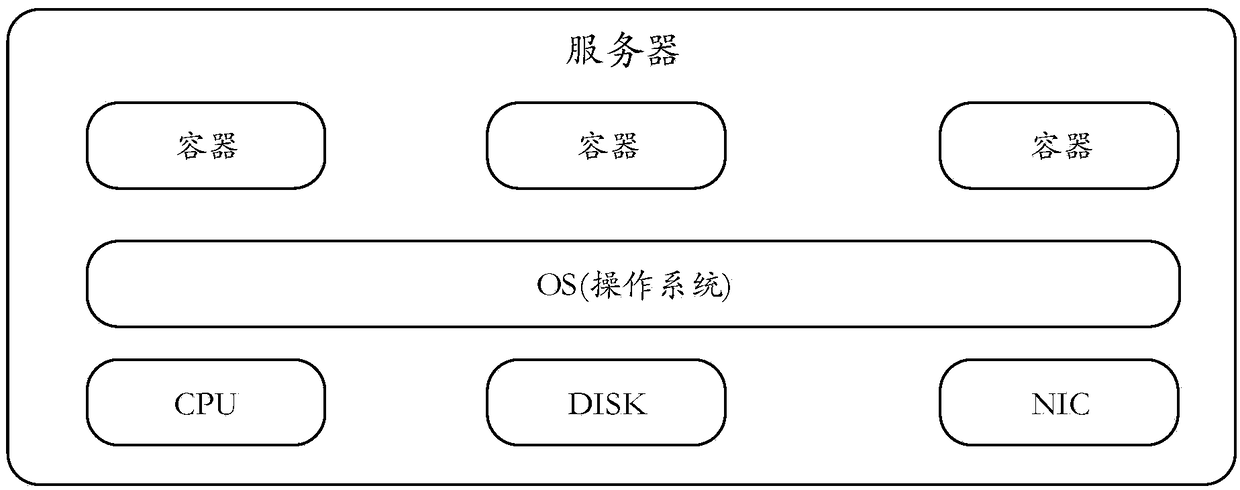
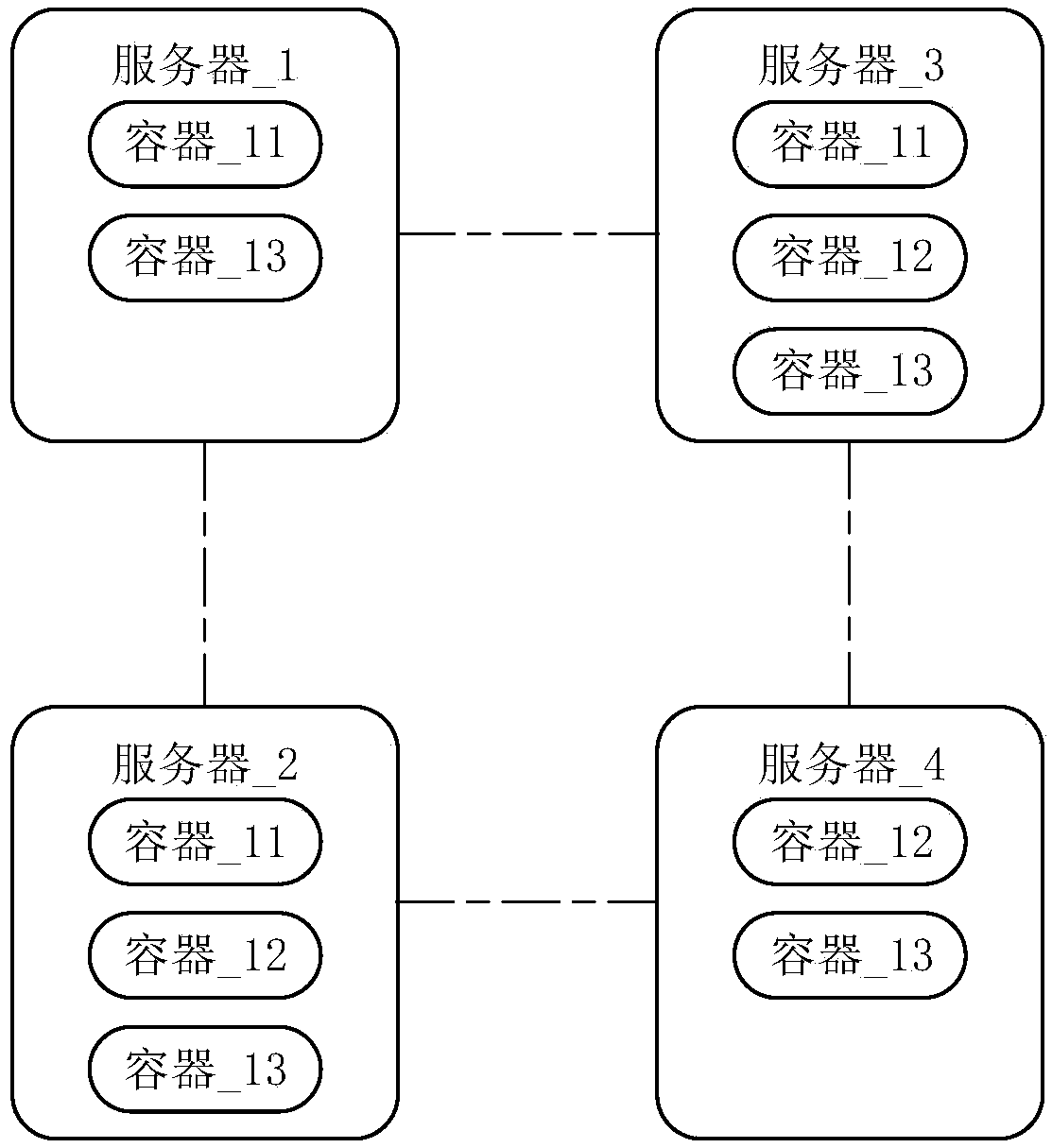
ActiveCN108829507AImplement resource isolationAchieve isolationResource allocationSpecial data processing applicationsResource isolationDistributed database
Embodiments of the invention provide a resource isolation method and device for a distributed database system, and a server. The distributed database system comprises a plurality of servers; a plurality of containers are arranged on each server; each container occupies a pre-allocated resource in the server which the container belongs to; and each container corresponds to a database instance. Themethod comprises the following steps of receiving a service outside the distributed database system or a to-be-processed request of a tenant; sending the to-be-processed request to the database instance allocated to the service or the tenant; and processing the to-be-processed request through each container corresponding to each database instance allocated to the service or the tenant. According to the resource isolation method and device, the service or the request of the tenant can be processed through the container corresponding to each database instance allocated to the service or the tenant, and the request can be processed in a server resource which is allowed to be used by the corresponding container according to the service or the tenant, so that different service or tenant resources are isolated.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
PaaS cloud implementation method based on containers
InactiveCN106445515AAvoid downtimeReduce wasteSpecific program execution arrangementsSoftware deploymentResource isolationResource utilization
The invention discloses a PaaS cloud implementation method based on containers. The method comprises following steps: saving configuration information of all containers and providing disposition; a deployment strategy ensuring that multiple containers under the same APP are scattered across different hosts; performing management on the host and containers and one physical cluster being corresponding to multiple projects, etc.. Therefore, the introduction of containers into the cloud computing basic resource delivery to provide PaaS layer services is realized, reducing waste of resources caused by the traditional PaaS products using virtual machines, increasing disposition efficiency and reducing exploitation and test period for users; the method is a lightweight VM solution scheme based on process containers, realizing a resource isolation and quota of an application program grade; Compared with the traditional cloud infrastructure system implementation, the container-based cloud service system has lower cost of overall ownership, higher resource utilization and is more stable and reliable, which further enhances the virtualization efficiency, improves resource utilization, accelerates enterprise devops process, and provides fast and effective support services for applications.
Owner:深圳市华云中盛科技股份有限公司
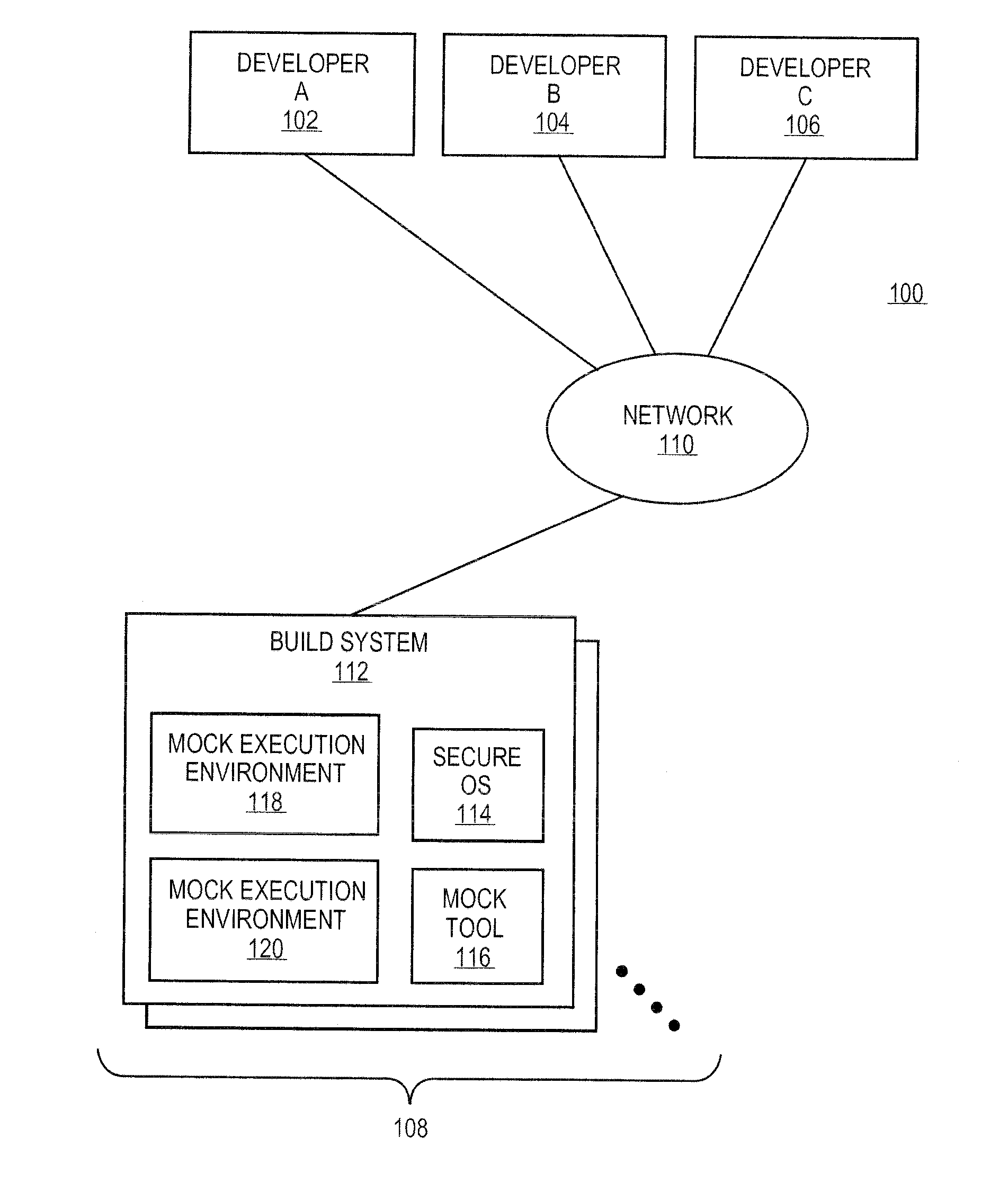
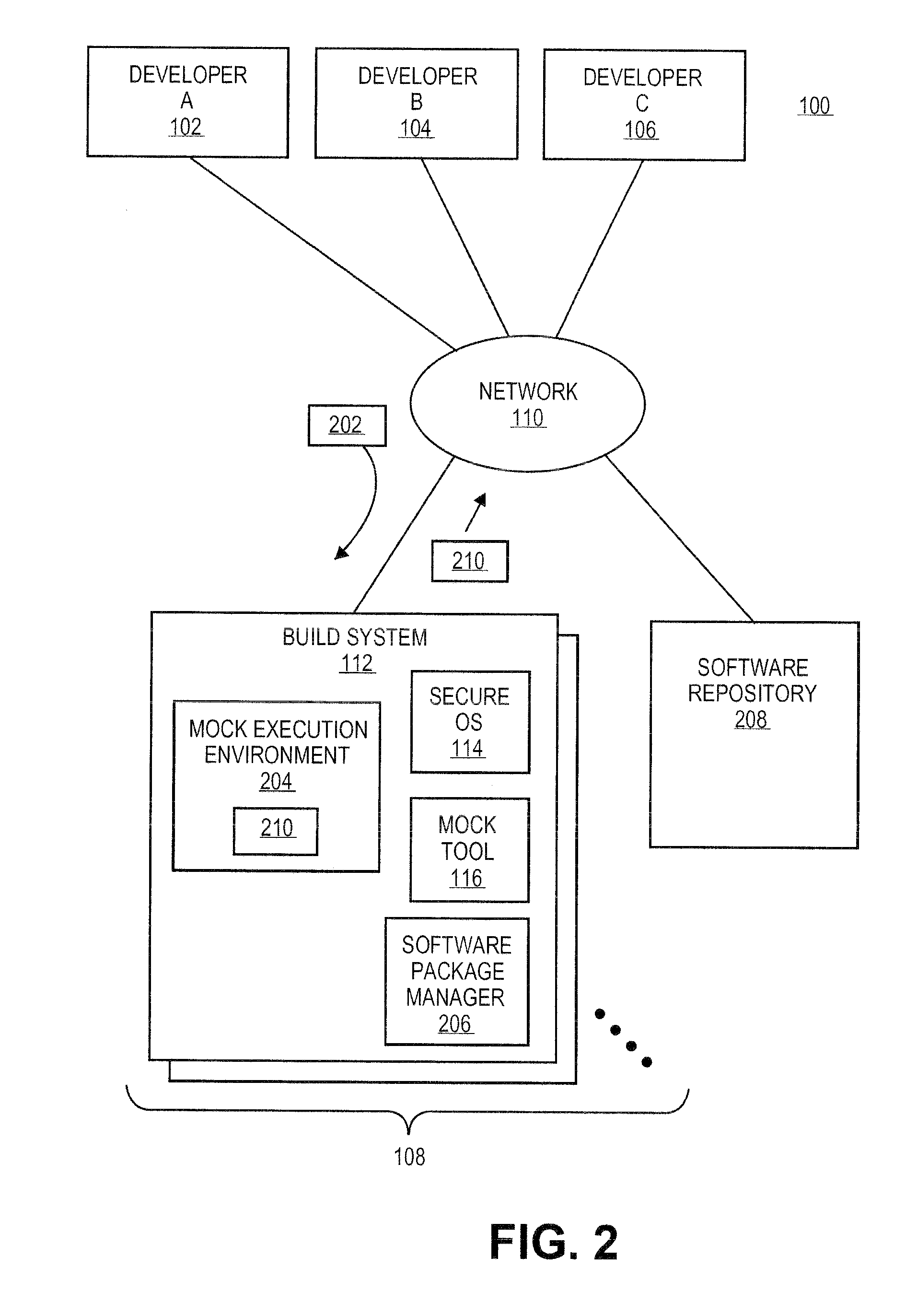
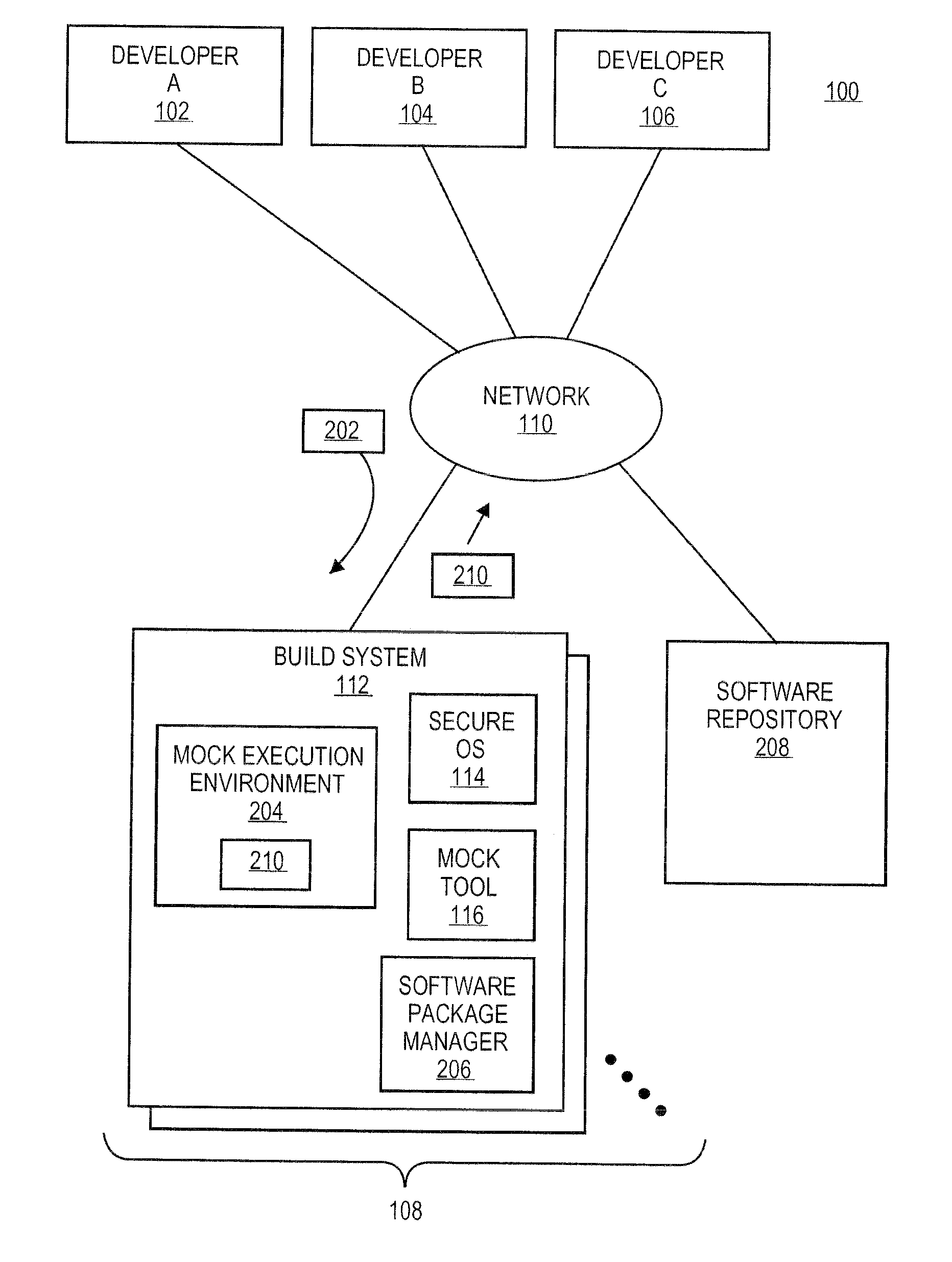
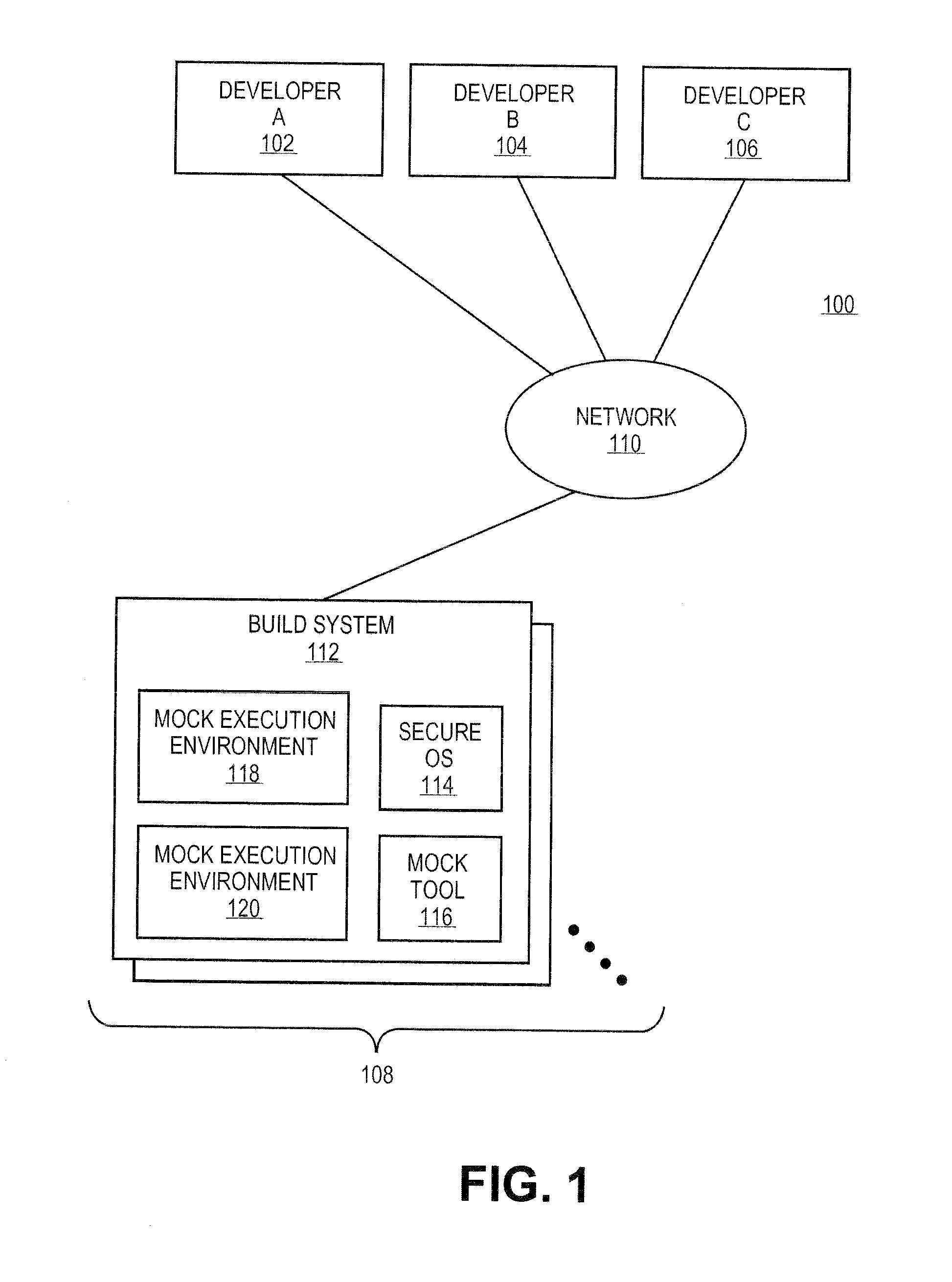
Systems and methods for building software packages in secure development environments
ActiveUS20120167048A1Version controlPlatform integrity maintainanceComputing systemsOperational system
The mock tool can be configured to create a mock execution environment for building software packages. The mock execution environment is isolated from resources of the computing system supporting the mock execution environment and other mock execution environments. Further, the mock execution environment can be created to simulate disabling on any features of the operating system supporting the mock execution environment that could cause problems in the building the software packages.
Owner:RED HAT
Data processing system, method and device
PendingCN110019251AReduce storage costsImprove processing efficiencyDatabase distribution/replicationSpecial data processing applicationsData processing systemResource isolation
The invention discloses a data processing system, method and equipment, and belongs to the technical field of databases. The data processing system comprises a main node and a standby node which are independent of each other, the main node is configured to be used for processing the OLTP service, and the standby node is configured to be used for processing the OLAP service. The main node obtains target data according to the to-be-processed data which is in a row storage format and is subjected to OLTP processing, sends the obtained target data to a standby node; the standby node stores the received target data in a column storage format; carrying out OLAP (On-Line Analytical Processing) on the data; therefore, two different types of services, namely the OLTP and the OLAP, can be concurrently processed in a single database cluster; compared with the prior art, the data storage cost is reduced, the service processing efficiency is improved, the OLTP service and the OLAP service are executed through the two mutually independent database nodes respectively, resource competition can be avoided in a resource isolation mode, and the service processing efficiency is further improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
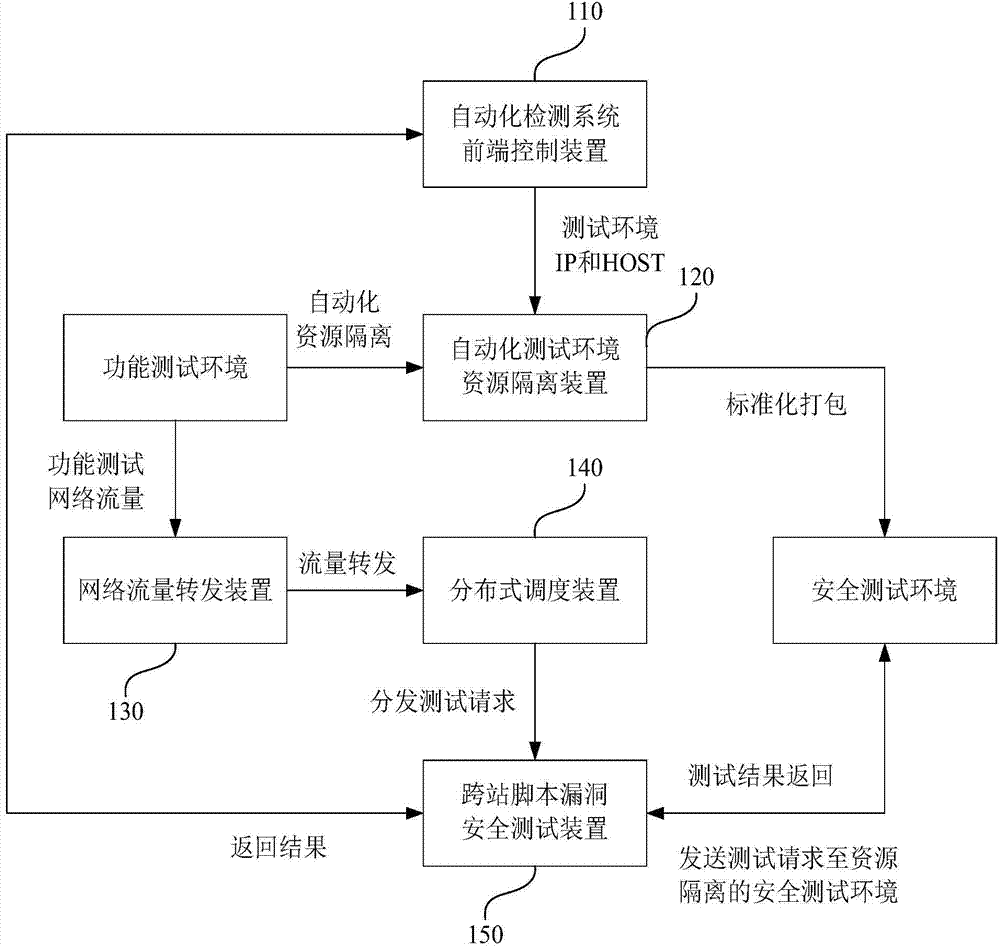
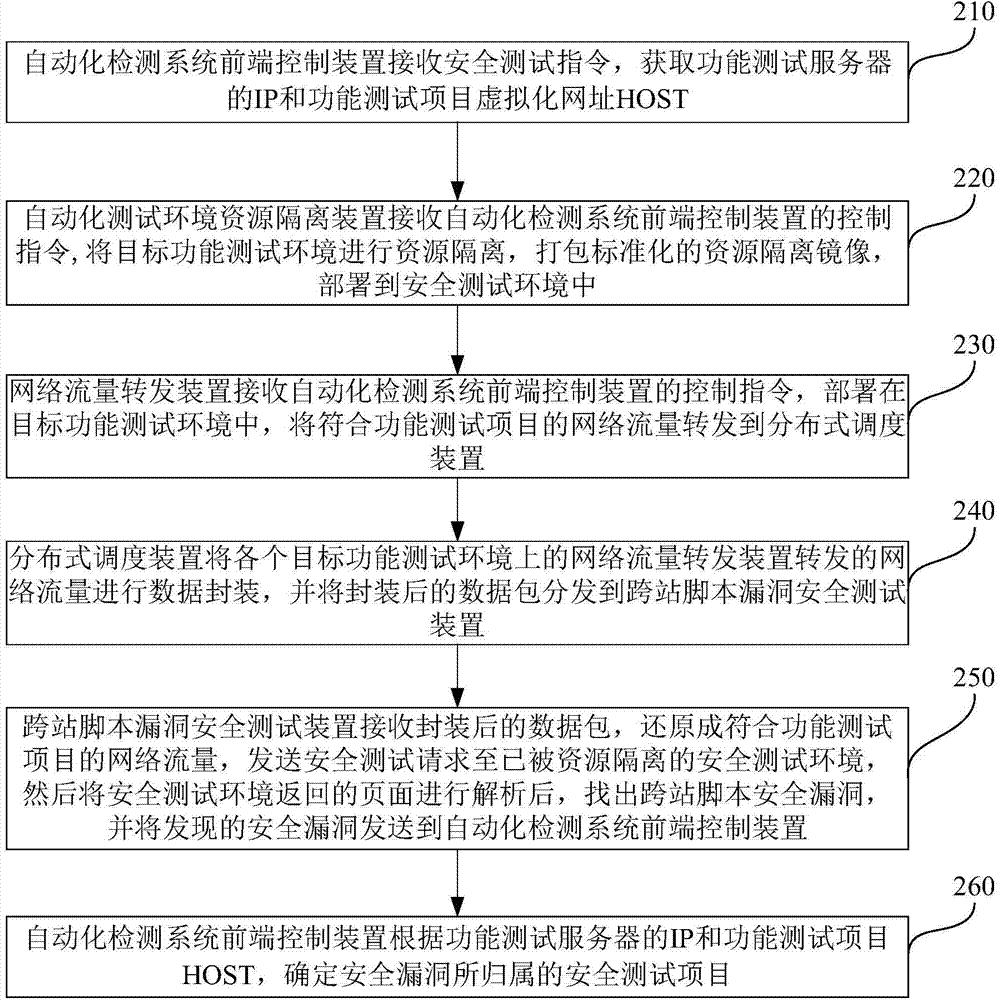
Offline detection method and system for cross-site scripting vulnerability
ActiveCN104765682AIncrease coverageHigh degree of automationSoftware testing/debuggingResource isolationTest fixture
The invention discloses an offline detection method and system for a cross-site scripting vulnerability. The offline detection method includes that a control device acquires the IP of a function test server and a function test project virtualization website HOST; a resource isolating device carries out resource isolation on a target function test environment, packs standard resource isolating mirror images and deploys in a safety test environment; a transmitting device deployed in the target function test environment transmits network flow which conforms to the function test project to a scheduling device; the scheduling device carries out data encapsulation on the transmitted network flow and sends the encapsulated test data to a test device; the test device sends a safety test request to the safety test environment, analyzes the page returned from the safety test environment to find out the cross-site scripting safety vulnerability, and sends to the control device; the control device confirms the safety test project of the safety vulnerability according to the IP of the function test server and the function test project HOST. The offline detection method and system for the cross-site scripting vulnerability enable the coverage and automatic degree of the safety test to be improved.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
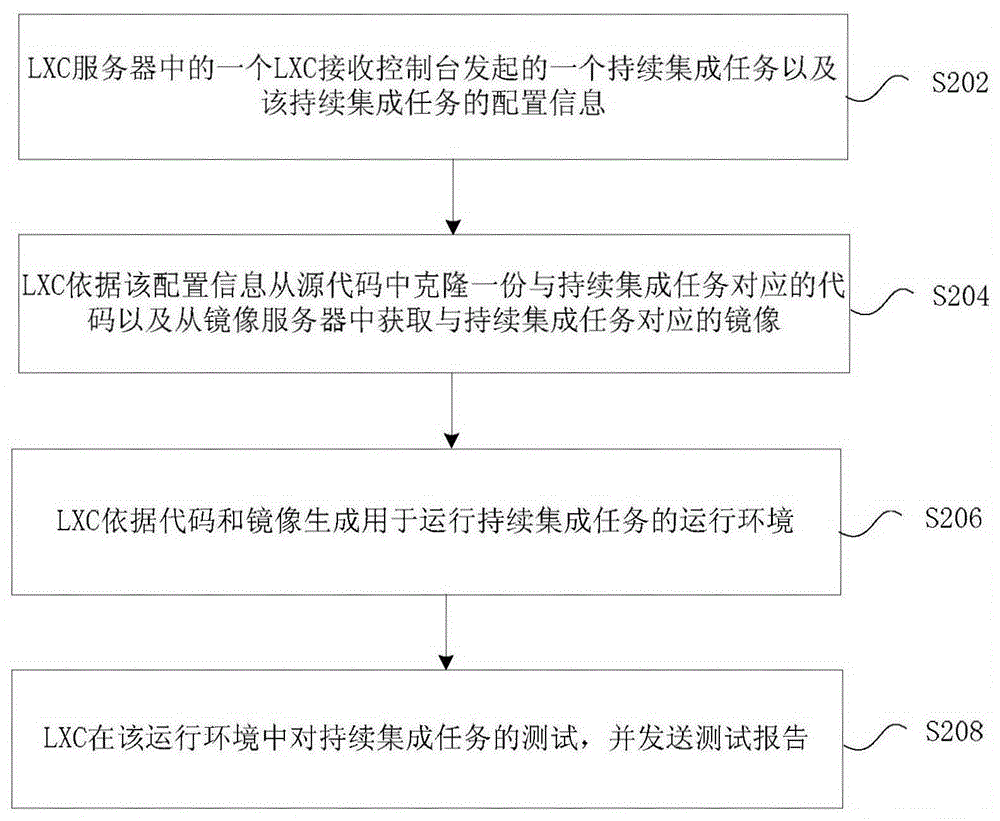
LXC-based continuous integration method and apparatus
ActiveCN106407101AImprove securitySoftware testing/debuggingSoftware simulation/interpretation/emulationContinuous integrationOperational system
The invention provides an LXC-based continuous integration method and apparatus. The method comprises the steps that an LXC in an LXC server receives a continuous integration task initiated by a console and configuration information of the continuous integration task; the LXC clones a code corresponding to the continuous integration task from a source code according to the configuration information and obtains a mirror image corresponding to the continuous integration task from a mirror image server; the LXC generates a running environment used for running the continuous integration task according to the code and the mirror image; and the LXC tests the continuous integration task in the running environment and sends a test report. Through the method and the apparatus, the problems that tasks of Hudson are all executed in one or more task agents and resource isolation cannot be performed for users in related technologies are solved, so that the effect of higher security in operation system level is achieved.
Owner:三亚中兴软件有限责任公司
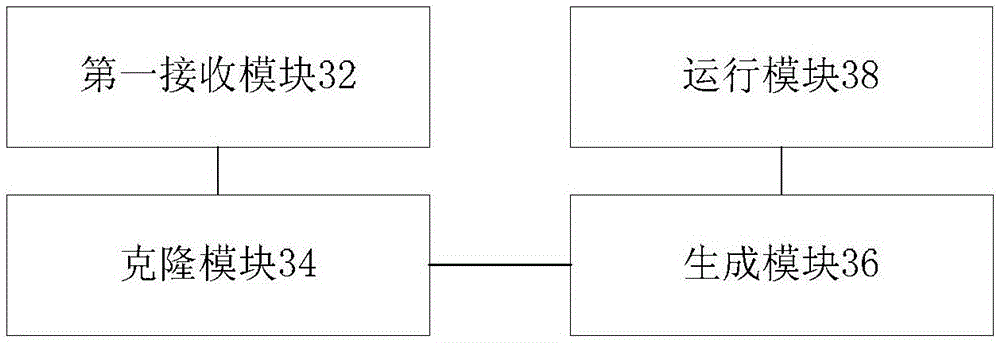
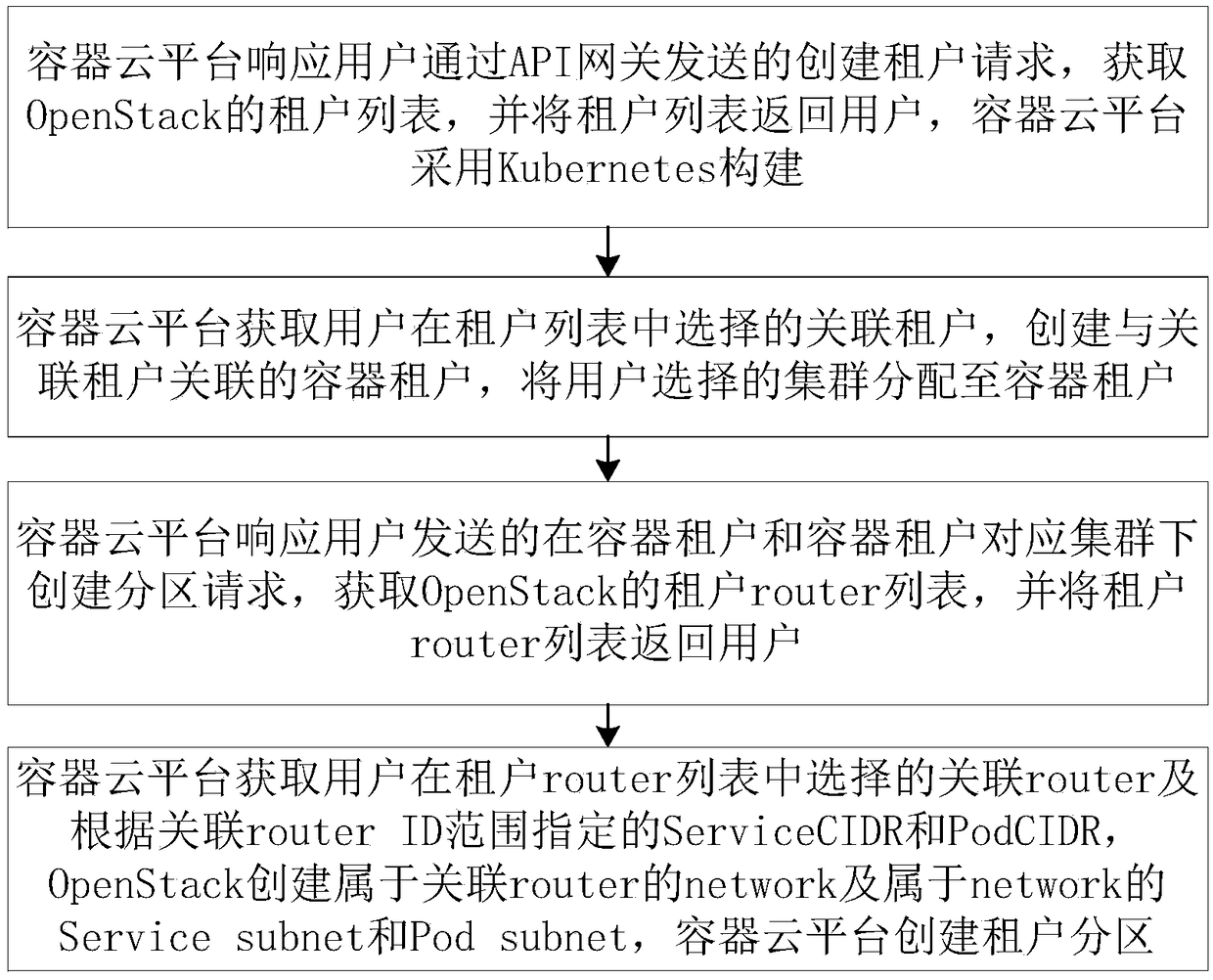
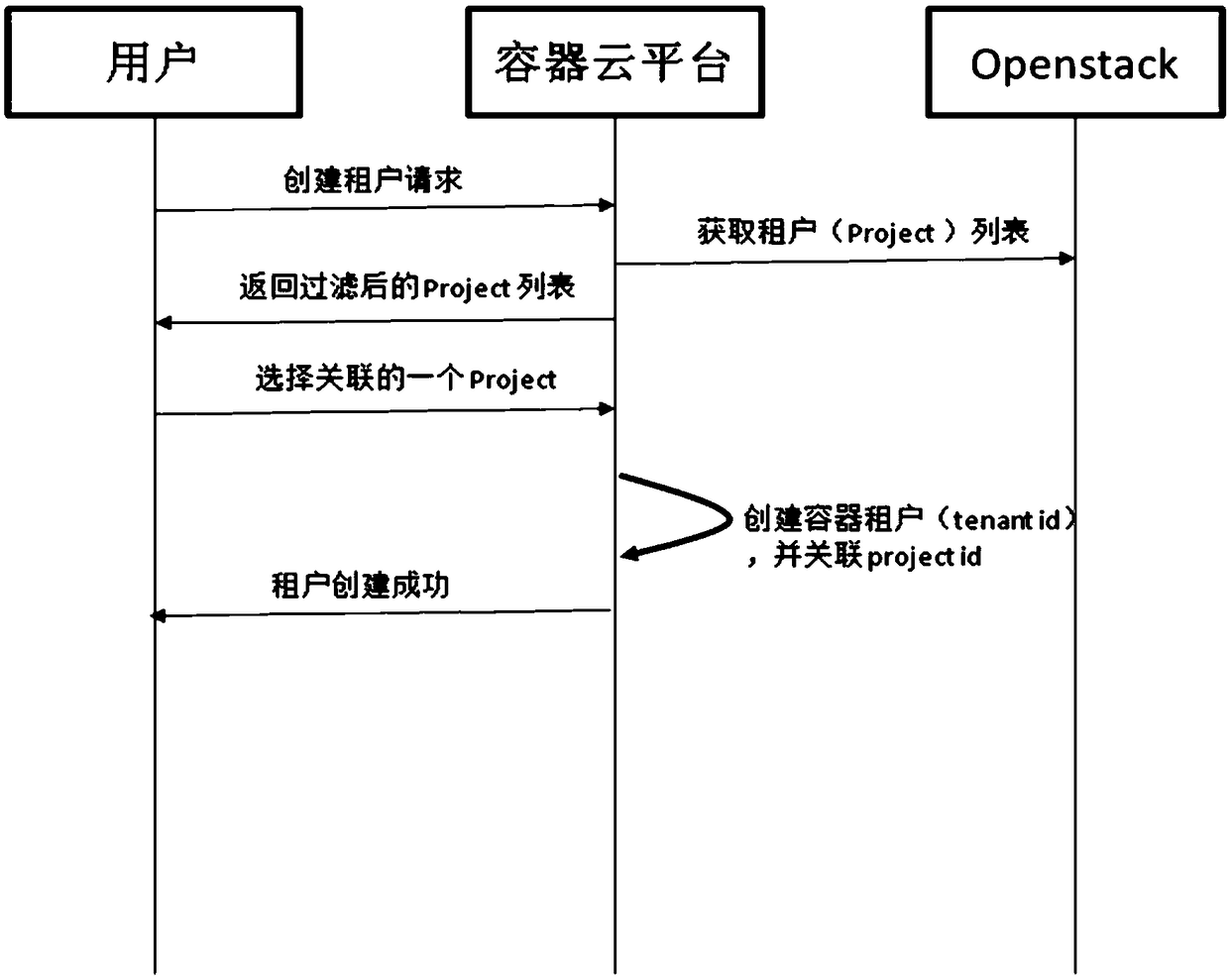
Container cloud platform multi-tenant building method, media, device based on Kubernetes and OpenStack
ActiveCN109067827AAchieve mutual accessGuaranteed resource isolationData switching networksResource isolationDistributed computing
A container cloud platform multi-tenant building method based on Kubernetes and OpenStack includes steps: Container cloud platform responding to requests to create tenant, getting a list of tenants for OpenStack, the associated tenant selected by the user, creating a container tenant associated with the associated tenant, assigning the cluster selected by the user to the container tenant, in response to a request from the user, creating a partition request, getting a list of tenant routers for OpenStack and User-selected associated router, specifying Service CIDR and Pod CIDR according to theID range of the associated router, OpenStack creating a network belonging to the associated router and service subnet and pod subnet belonging to the network, and the container cloud platform creatingtenant partitions. The invention realizes the multi-tenant construction of the container cloud platform, and the tenant can use the corresponding Openstack tenant resources to ensure the resource isolation among different tenants.
Owner:杭州才云科技有限公司
Resource allocation method and network equipment
ActiveCN107153565AAchieve isolationEasy to controlResource allocationTransmissionResource isolationSecurity domain
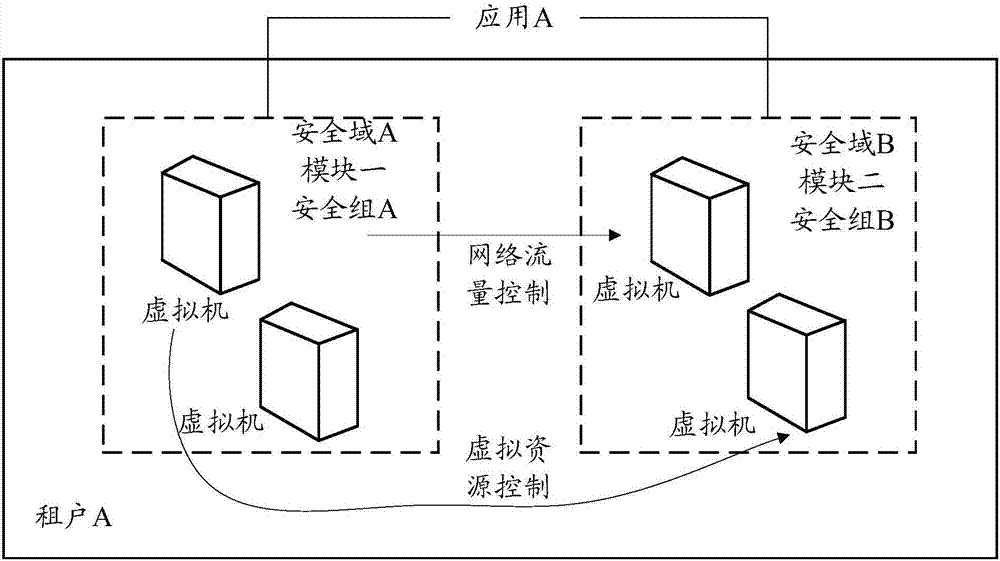
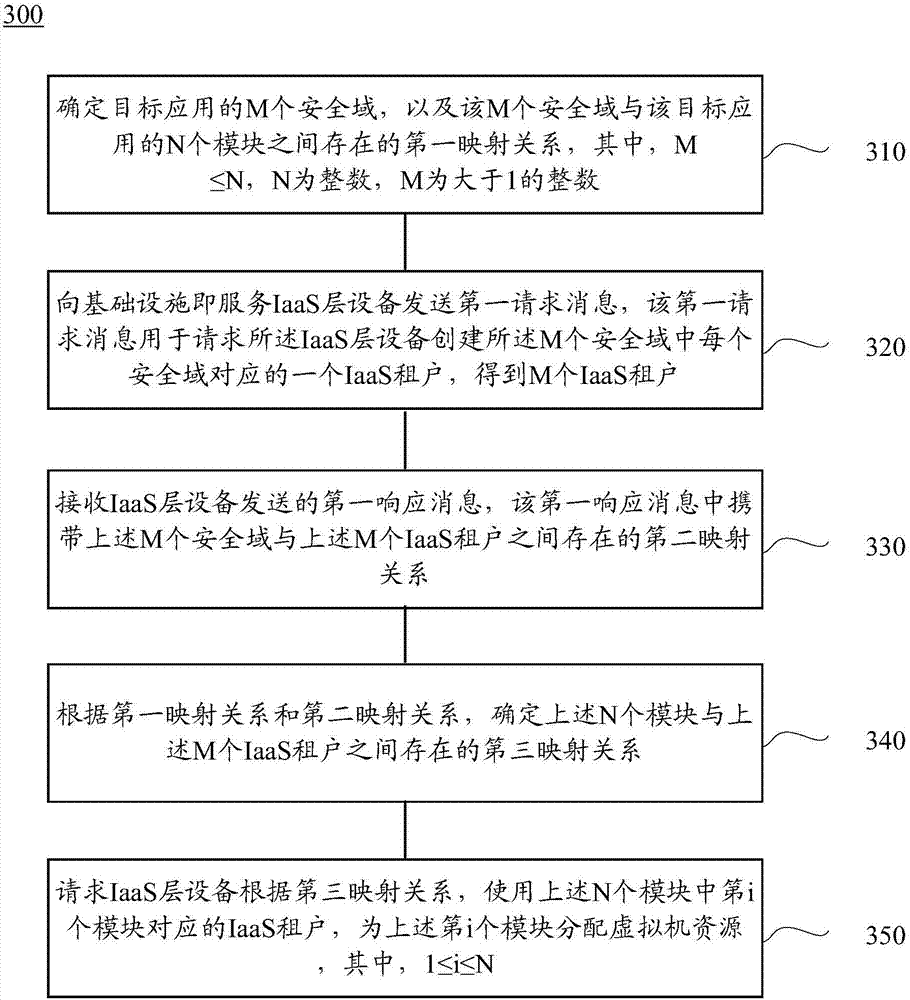
The embodiment of the invention provides a resource allocation method in a cloud environment and network equipment. The method comprises the steps that M security domains of a target application and a first mapping relation of the M security domains and N modules of the target application are determined; a first request message is sent to a basic facility, namely, service IaaS layer equipment, the IaaS layer equipment is requested to create an IaaS tenant corresponding to each security domain in the M security domains, and M IaaS tenants are obtained; a first response message sent by the IaaS layer equipment is received, and the first response message carries a second mapping relation between the M security domains and the M IaaS tenants; a third mapping relation existing between the N modules and the M IaaS tenants is determined, the IaaS layer equipment is requested to use the IaaS tenant corresponding to the i module in the N modules to allocate virtual machine resources for the i module. By means of the method, isolation of the virtual machine resources among different modules of the application can be achieved.
Owner:SUZHOU YUDESHUI ELECTRIC TECH CO LTD
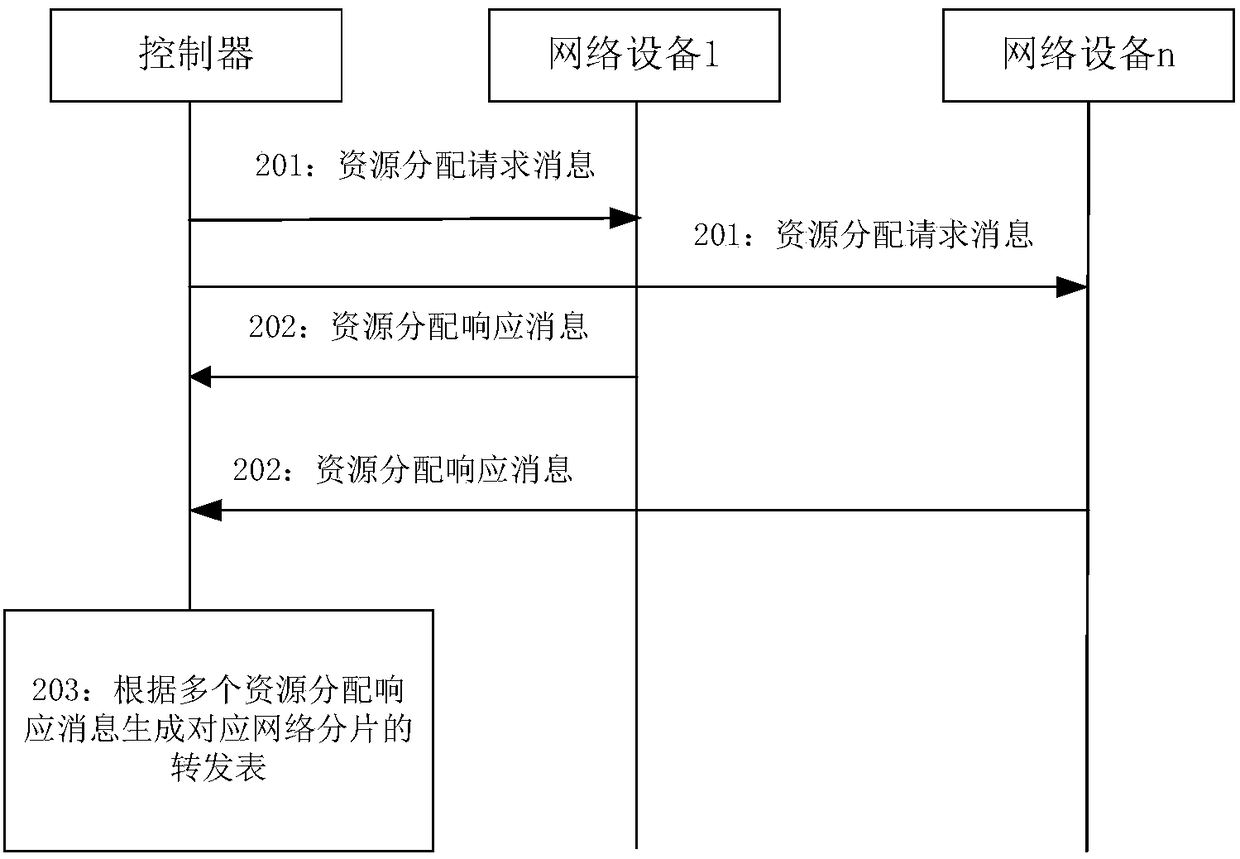
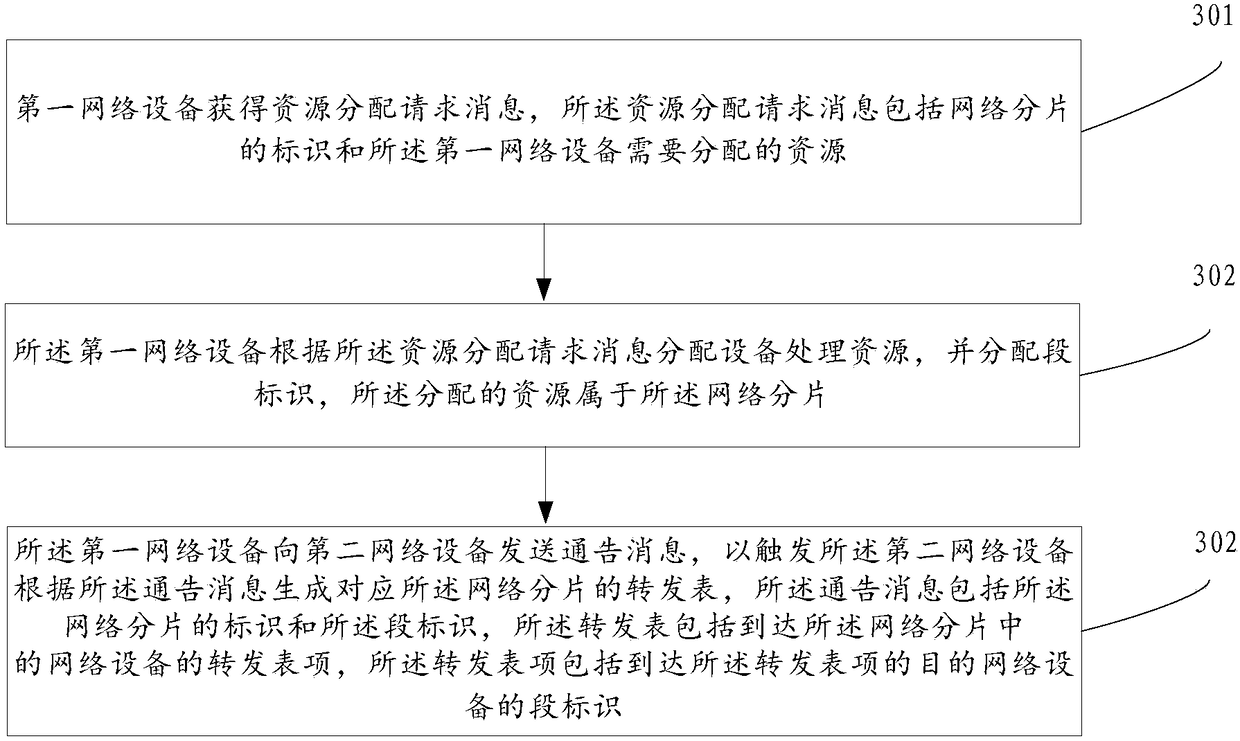
Method for generating forwarding table entry, controller and network device
ActiveCN109218201AFlexible message forwarding modeFlexible forwardingService provisioningNetwork traffic/resource managementResource isolationResource allocation
The present application discloses a method for generating a forwarding table entry and a network device. The method comprises that a controller sends a plurality of resource allocation request messages to a plurality of network devices in a network fragment to trigger the network devices to allocate resources according to the resource allocation request messages, wherein the resource allocation request message include the identifier of the network fragment and a resource required to be allocated to the network fragment by the corresponding network device; the controller receives a plurality ofresource allocation response messages, wherein the resource allocation response message includes the identifier of the network fragment and the segment identifier of the corresponding network device,the resource allocated by each device belongs to the network fragment; the controller generates a forwarding table corresponding to the network fragment according to the resource allocation responsemessages, wherein the forwarding table includes the forwarding table entry reaching the network devices of the network fragment, and the forwarding table entry includes a segment identifier reaching adestination network device. The forwarding table entry helps to provide a user with a flexible message forwarding way based on network fragment resource isolation.
Owner:HUAWEI TECH CO LTD
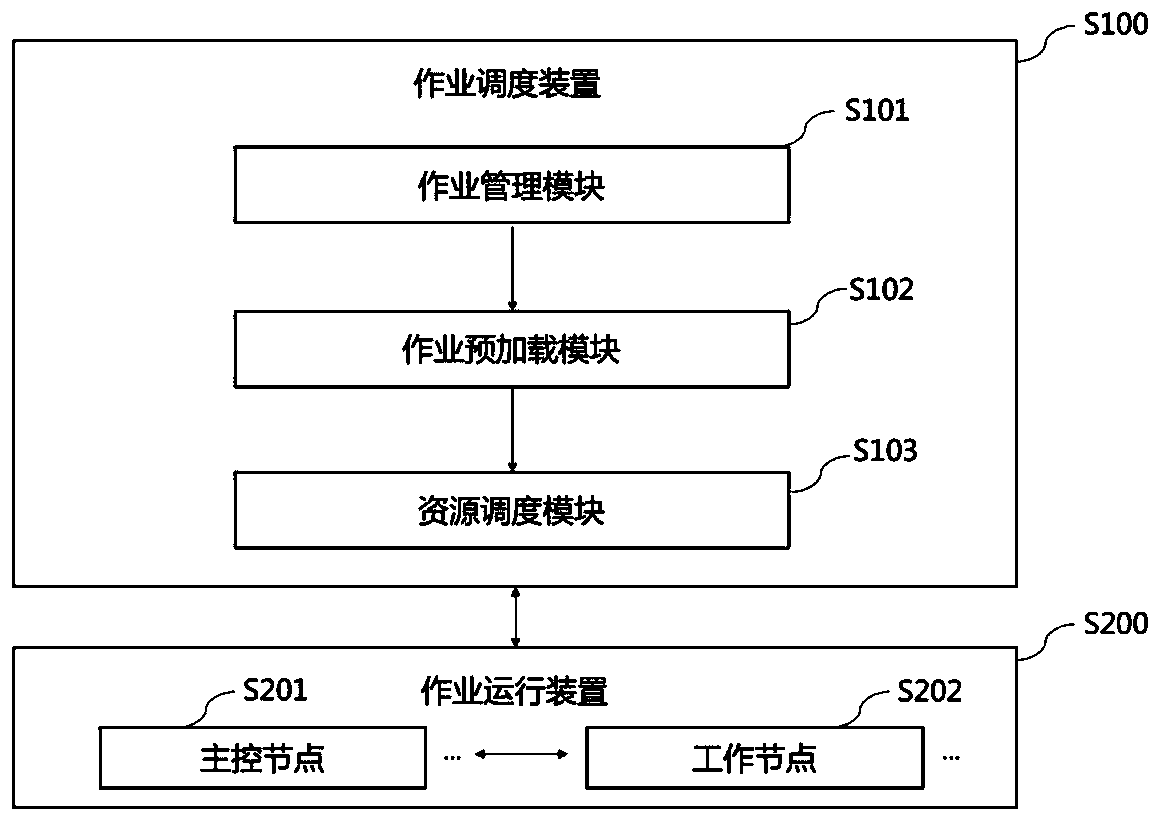
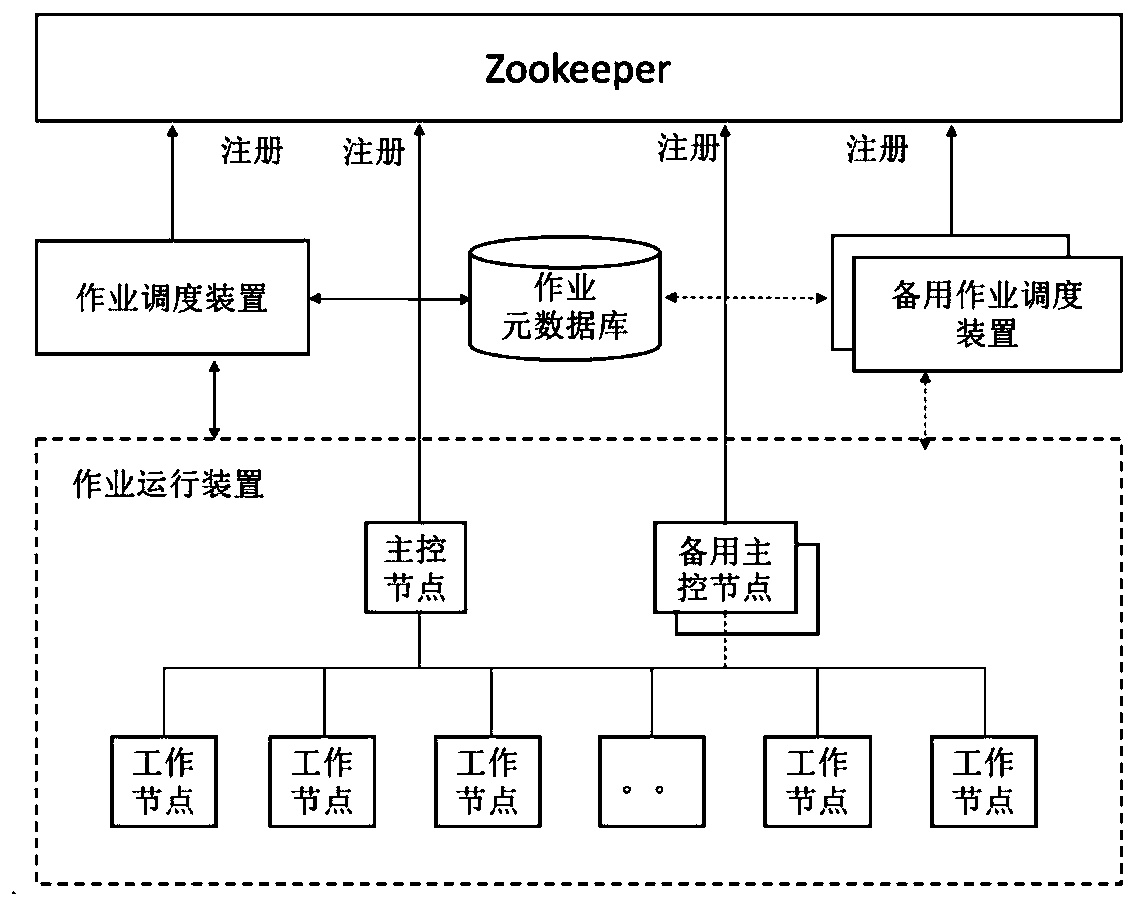
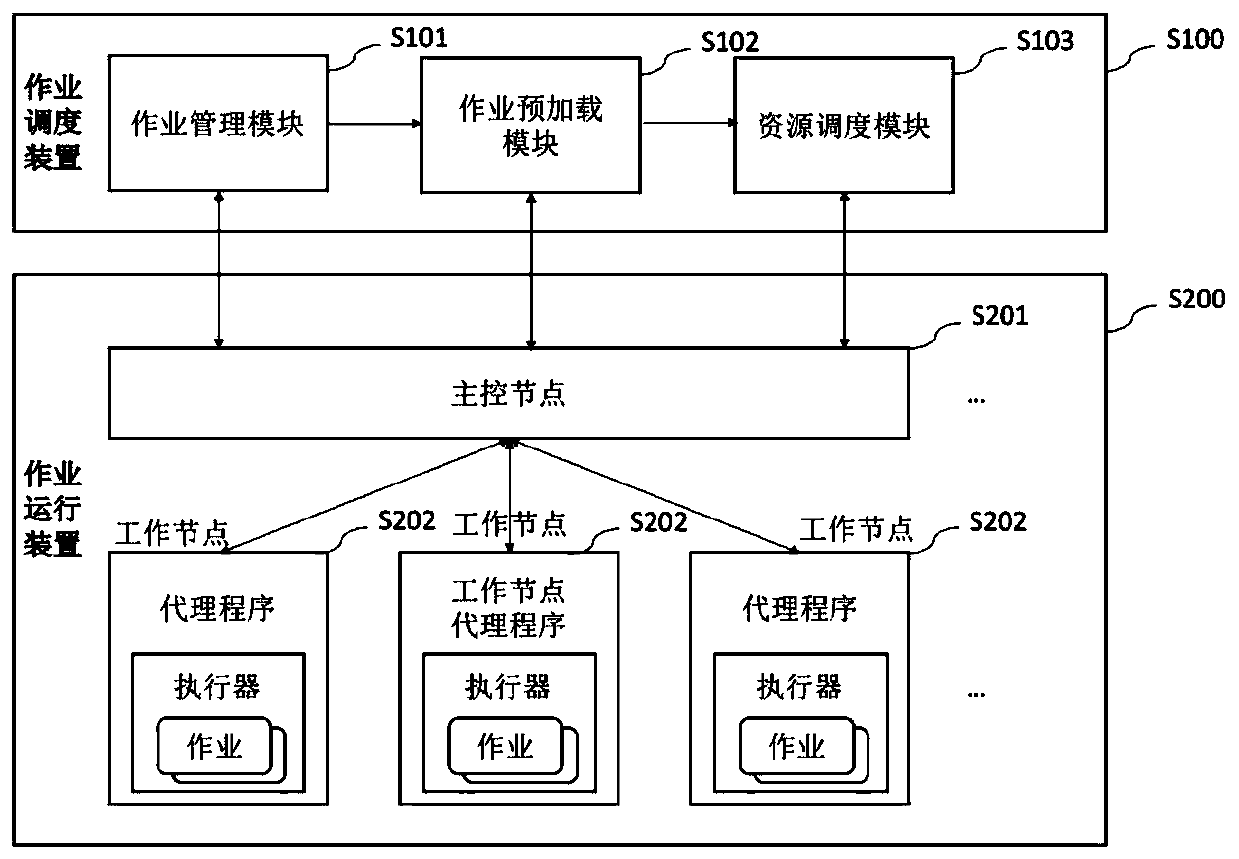
Distributed data integration job scheduling method and device
ActiveCN110362390AEnsure consistencyLower latencyProgram initiation/switchingDatabase distribution/replicationFault toleranceConcurrency control
The invention relates to a distributed data integration job scheduling method and device. The method aims at a special scene possibly faced by data integration. A job scheduling device is responsiblefor issuing the data integration job to the job operation device, and the job operation device receives the scheduling task, starts job execution, feeds back job operation state information to the jobmanagement module, feeds back working node computing resources to the resource scheduling module, and feeds back lost or fault information to the job preloading module. The method has the following comprehensive characteristics: (1) high availability, fault tolerance and weak consistency; (2) a low delay characteristic for quasi-real-time job scheduling; (3) multi-tenant concurrency control oriented to the cloud service application; (4) computing resource isolation and multi-job parallel scheduling; and (5) a priority scheduling mechanism.
Owner:ENJOYOR COMPANY LIMITED
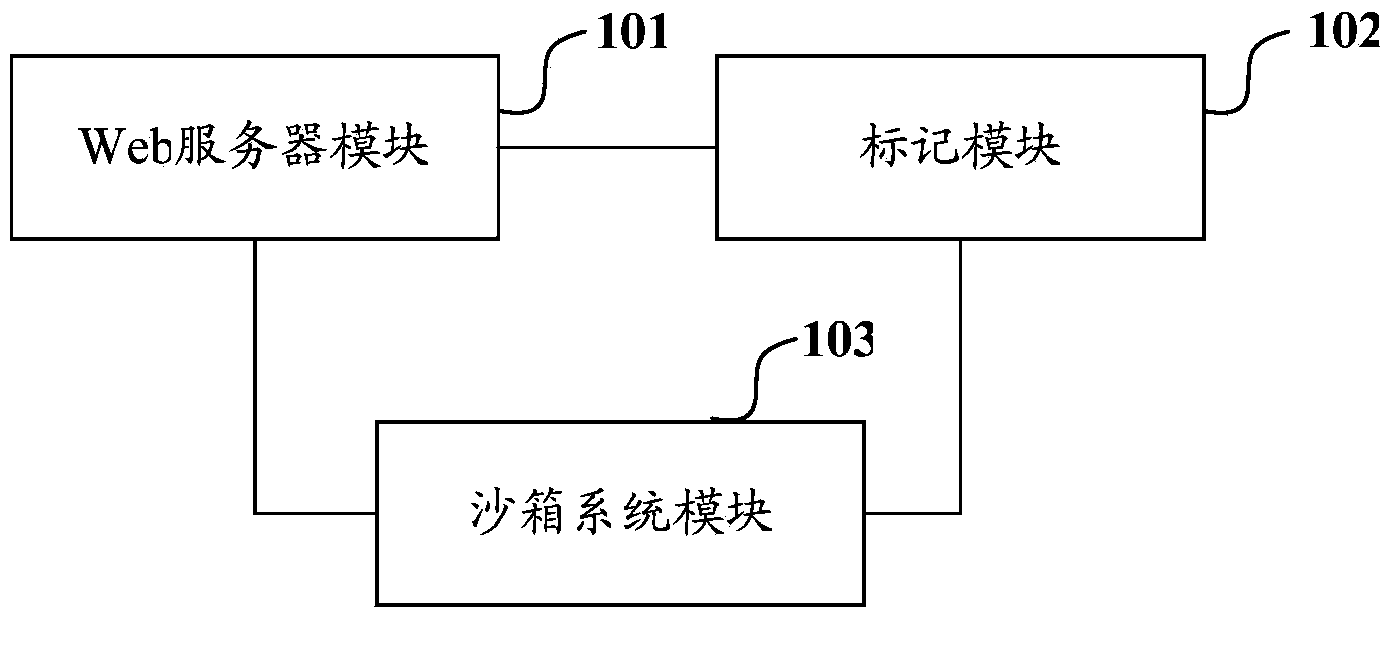
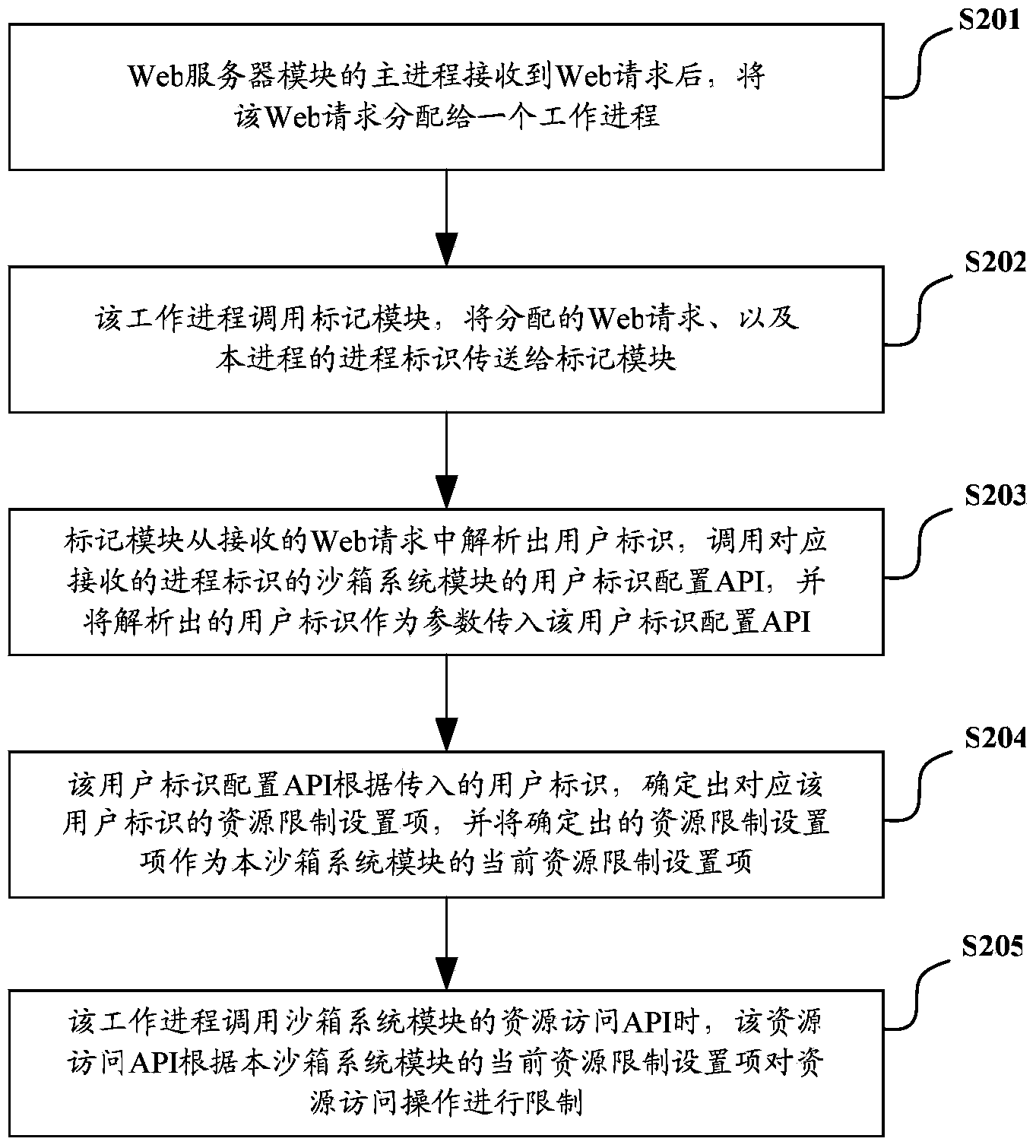
Web server and system resource access control method thereof
The invention discloses a Web server and a system resource access control method thereof. The method comprises the following steps that: after receiving a Web request, a host process allocates the Web request to a work process, and the work process calls a marking module and transmits the allocated Web request to the marking module; the marking module analyzes the received Web request to obtain a user identifier, and transmits the user identifier which is obtained through analysis to a sandbox system module configured for the work process; and when the work process calls a resource access API of the sandbox system module, the resource access API limits resource access operation according to a resource limitation setting item of the user identifier. With the Web server and the system resource access control method thereof of the invention adopted, server resources can be saved under the premise that user resource isolation is realized.
Owner:新浪技术(中国)有限公司
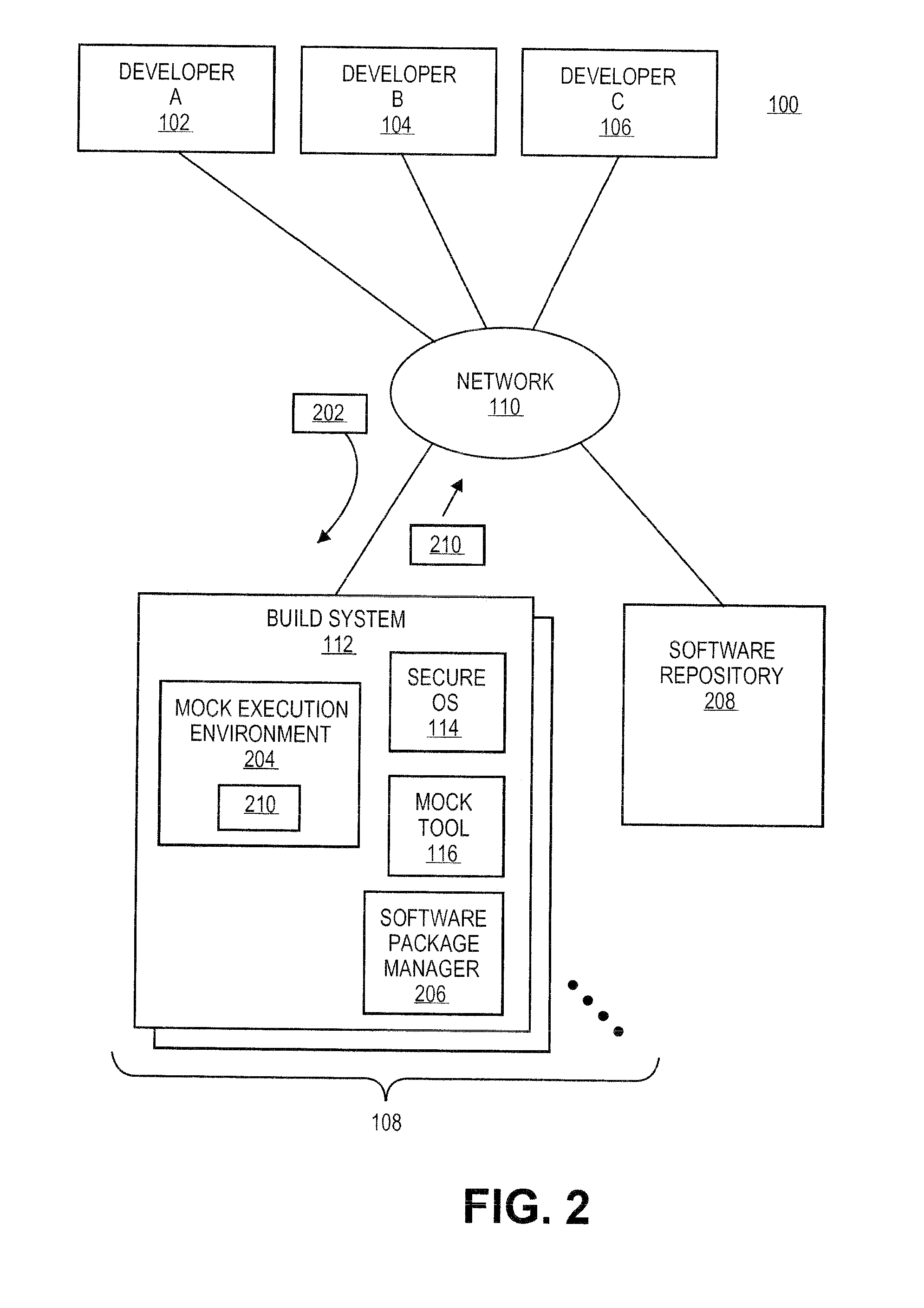
Systems and methods for secure software development environments
ActiveUS20120167157A1Version controlPlatform integrity maintainanceSoftware development processOperational system
The mock tool can be configured to create a mock execution environment for supporting software development processes. The mock execution environment is isolated from resources of the computing system supporting the mock execution environment and other mock execution environments. Further, the mock execution environment can be created to simulate disabling on any features of the operating system supporting the mock execution environment that could cause problems in the software development process.
Owner:RED HAT
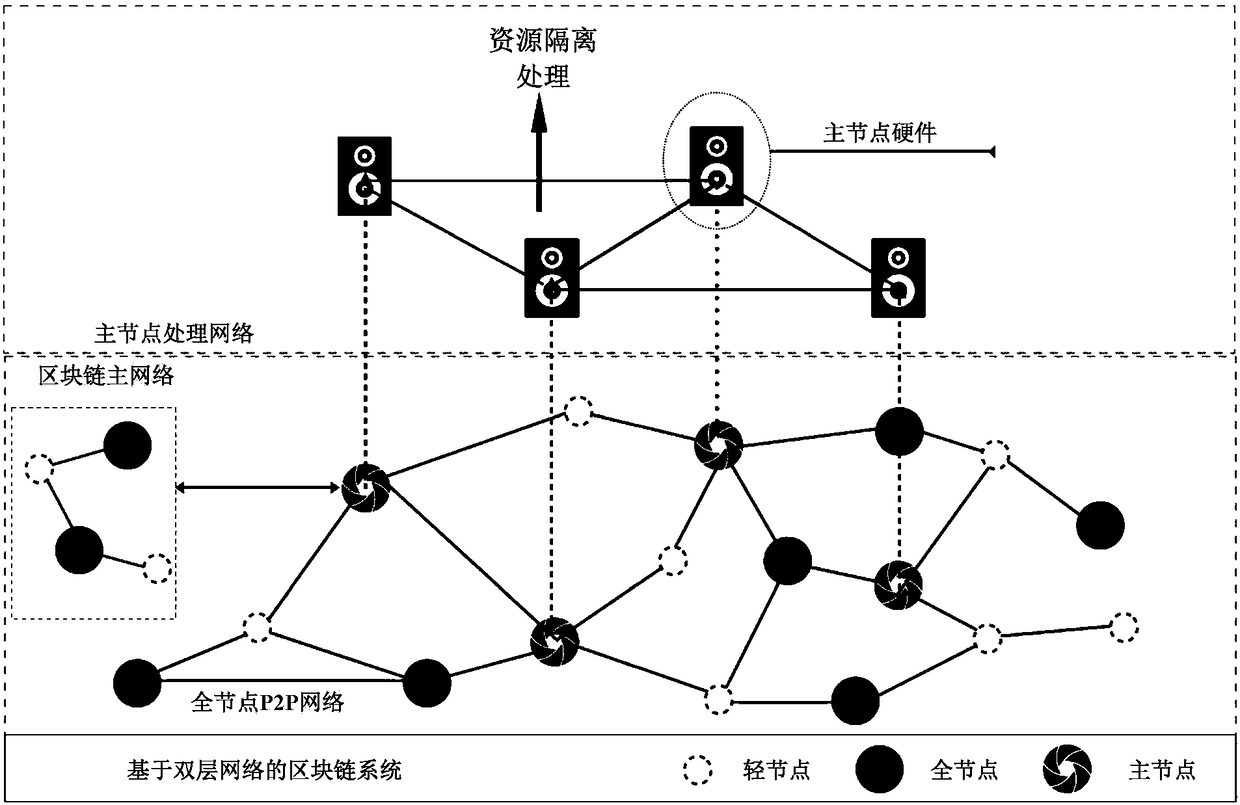
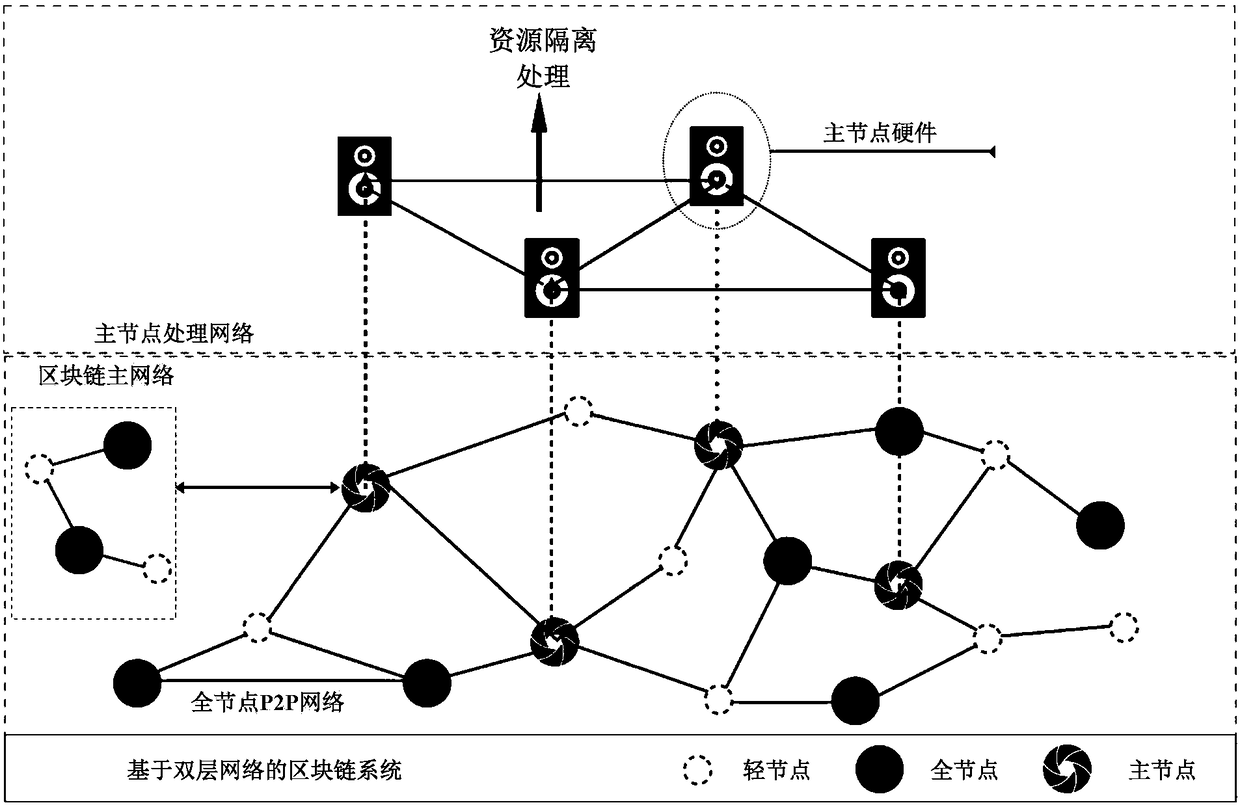
Decentration computation system based on double-layer network
ActiveCN108347483AReduce processing constraintsSmall amount of calculationPayment circuitsTransmissionResource isolationChain network
The invention discloses a decentration computation system based on a double-layer network. The system is constituted by a plurality of light nodes, a plurality of full nodes, and a plurality of mainnodes. A plurality of light nodes, a plurality of full nodes, and a plurality of main nodes are used to form a block chain main network, and a plurality of main nodes are used to form a main node processing network. A plurality of light nodes are used to store user specific data in the block chain network. A plurality of full nodes and a plurality of main nodes are used for a consensus mechanism to store a complete block chain. In the main node processing network, a plurality of main nodes comprise computation nodes having computation functions, which are used to carry out off-chain data computation tasks to acquire computation results. According to the technical scheme provided by the invention, a plurality of main nodes are used for resource isolation, and high expandability is provided,data processing constraints are reduced, and the data throughout of the system is effectively improved.
Owner:BEIJING QIHOO TECH CO LTD
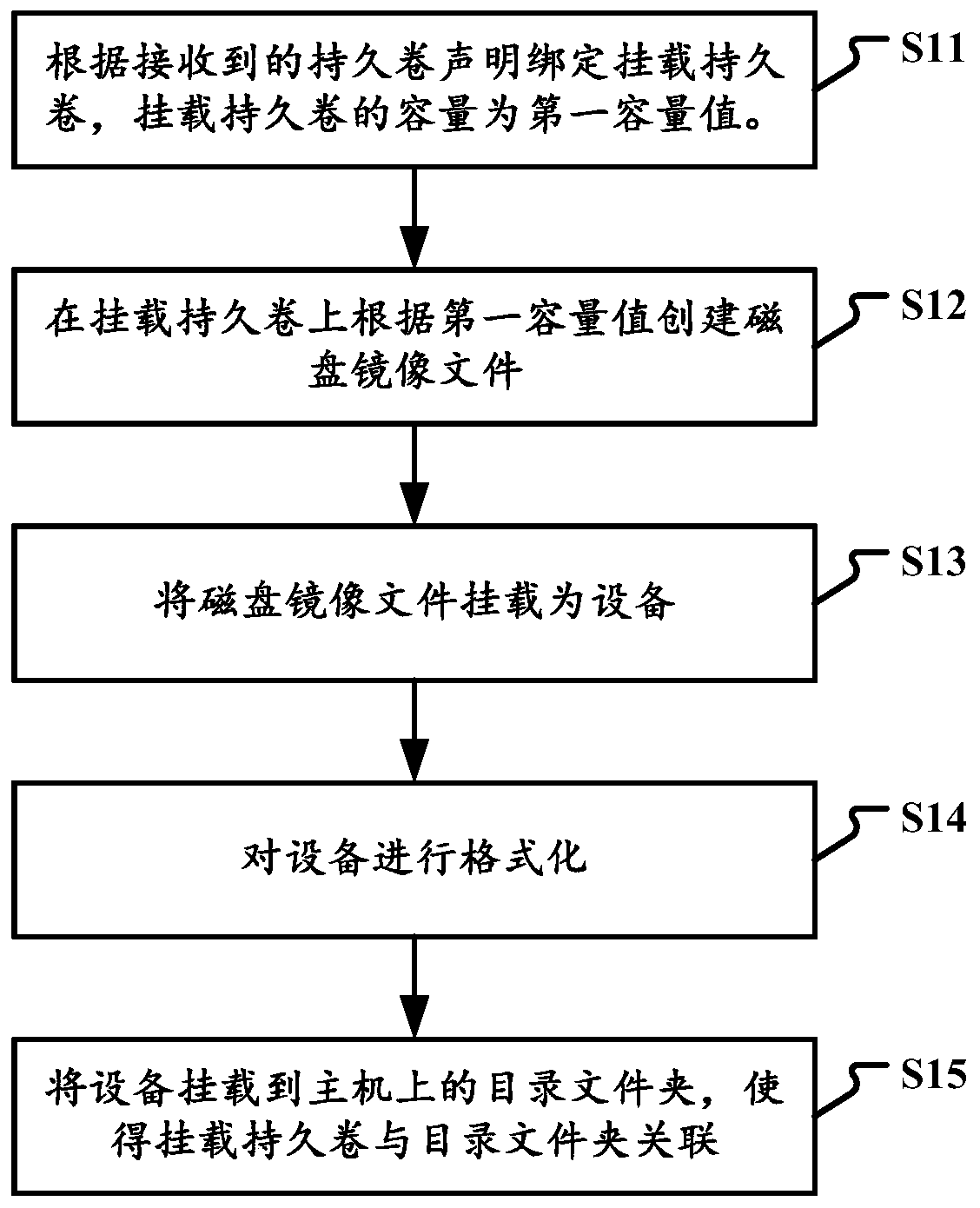
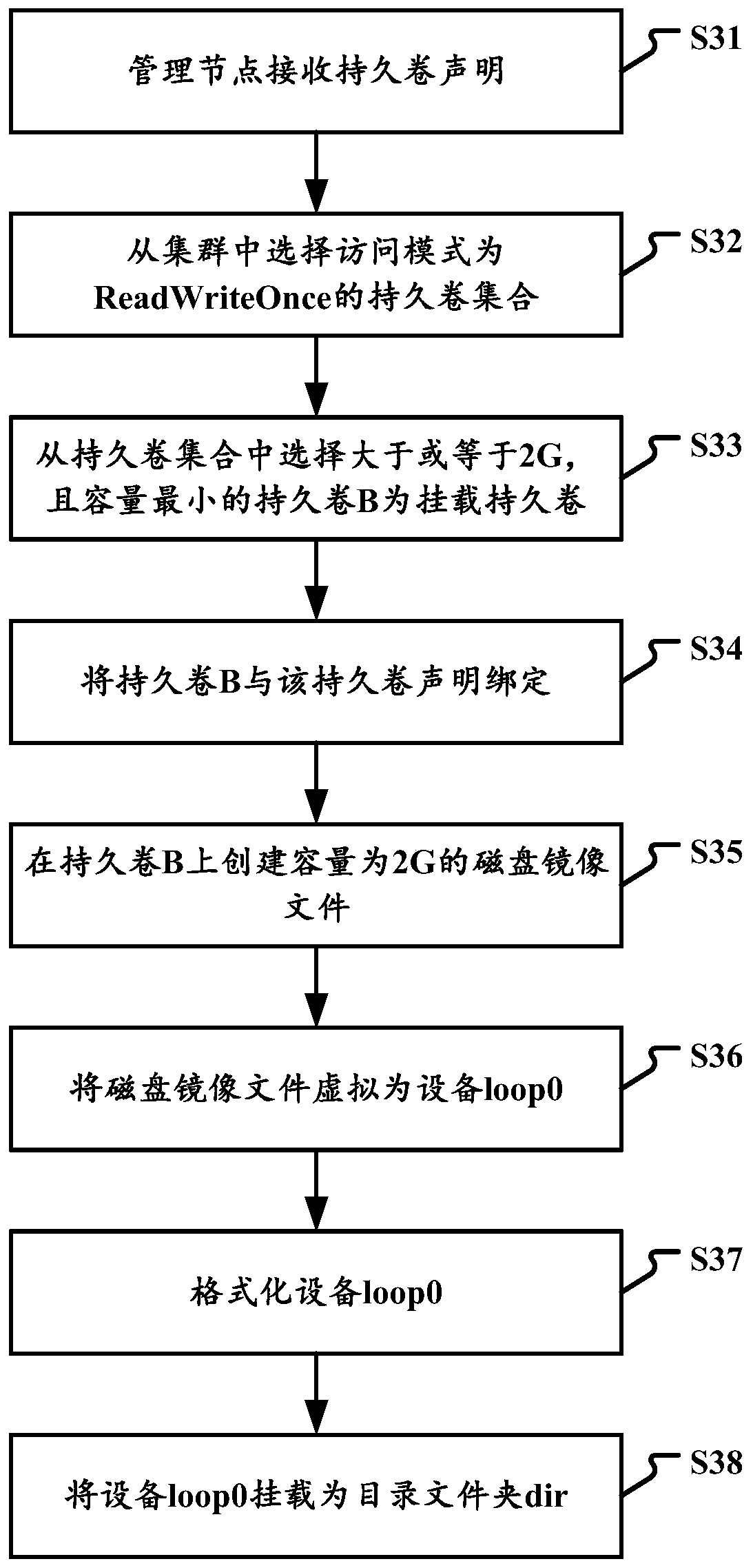
Resource allocation method, device, electronic equipment and storage medium
InactiveCN110362384AGuaranteed uptimeAvoid over-occupancyResource allocationSoftware simulation/interpretation/emulationCapacity valueResource isolation
The invention relates to a resource allocation method, a resource allocation device, electronic equipment and a storage medium. The method comprises the steps of binding a mounted persistent volume according to a received persistent volume declaration, and enabling the capacity of the mounted persistent volume to be a first capacity value; creating a disk mirror image file on the mount persistentvolume according to the first capacity value; mounting the disk mirror image file to a device; formatting the equipment; and mounting the equipment to a directory folder on a host, so that the mountedpersistent volume is associated with the directory folder. According to the technical scheme, the excessive occupation of a host disk due to increase of application log files is effectively avoided.The problem that other application programs cannot be normally started due to too large log files or output files is avoided. The physical resource isolation between different applications on the samehost is fully achieved, and normal operation of all the application programs is guaranteed.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
File system resource isolation method for Docker container
ActiveCN110120940AImprove the isolation effectAchieve isolationDigital data protectionProgram controlGranularityFile system
The invention relates to a file system resource isolation method for a Docker container. The method includes: allocating host file system resources according to the access request of the container anddetermining a lock resource corresponding to the access request, the file system resource isolation method at least comprises the following steps: dividing a lock resource into a first lock capable of being refined and a second lock incapable of being refined based on the granularity of the lock resource, and creating a plurality of new containers in a manner of configuring refined copies of thefirst lock to form independent locks; allocating the host file system resources according to the file resource request parameters required by the new containers, and dividing the plurality of new containers into a first marking container and a second marking container based on the allocation result; and controlling the execution of the file system operation according to the use amount of the filesystem resources allocated to the first marking container or the second marking container under the condition that the lock competition exists or the file system resources need to be used when the first marking container or the second marking container executes the file system operation.
Owner:HUAZHONG UNIV OF SCI & TECH
Design method of real-time available cluster management system
ActiveCN110784350AAchieve synchronizationRealize unbundlingData switching networksDistributed memoryResource isolation
The invention relates to a design method of a real-time high-availability cluster management system, and relates to the technical field of high-availability cluster management. The real-time high-availability cluster management system designed by the invention runs in a real-time operating system, supports visual configuration, and realizes resource isolation, dynamic reconstruction and application migration; high availability guarantee support is provided, and high availability of applications of the computing nodes is realized; distributed memory data management is internally integrated, andsynchronization of key data is achieved through a multi-copy redundancy mechanism. According to the system, unbinding of software and hardware is achieved, the hardware resource utilization rate is increased, when software and hardware faults occur, service applications are automatically migrated to available equipment, fault self-shielding is achieved, and uninterrupted service is guaranteed.
Owner:BEIJING INST OF COMP TECH & APPL
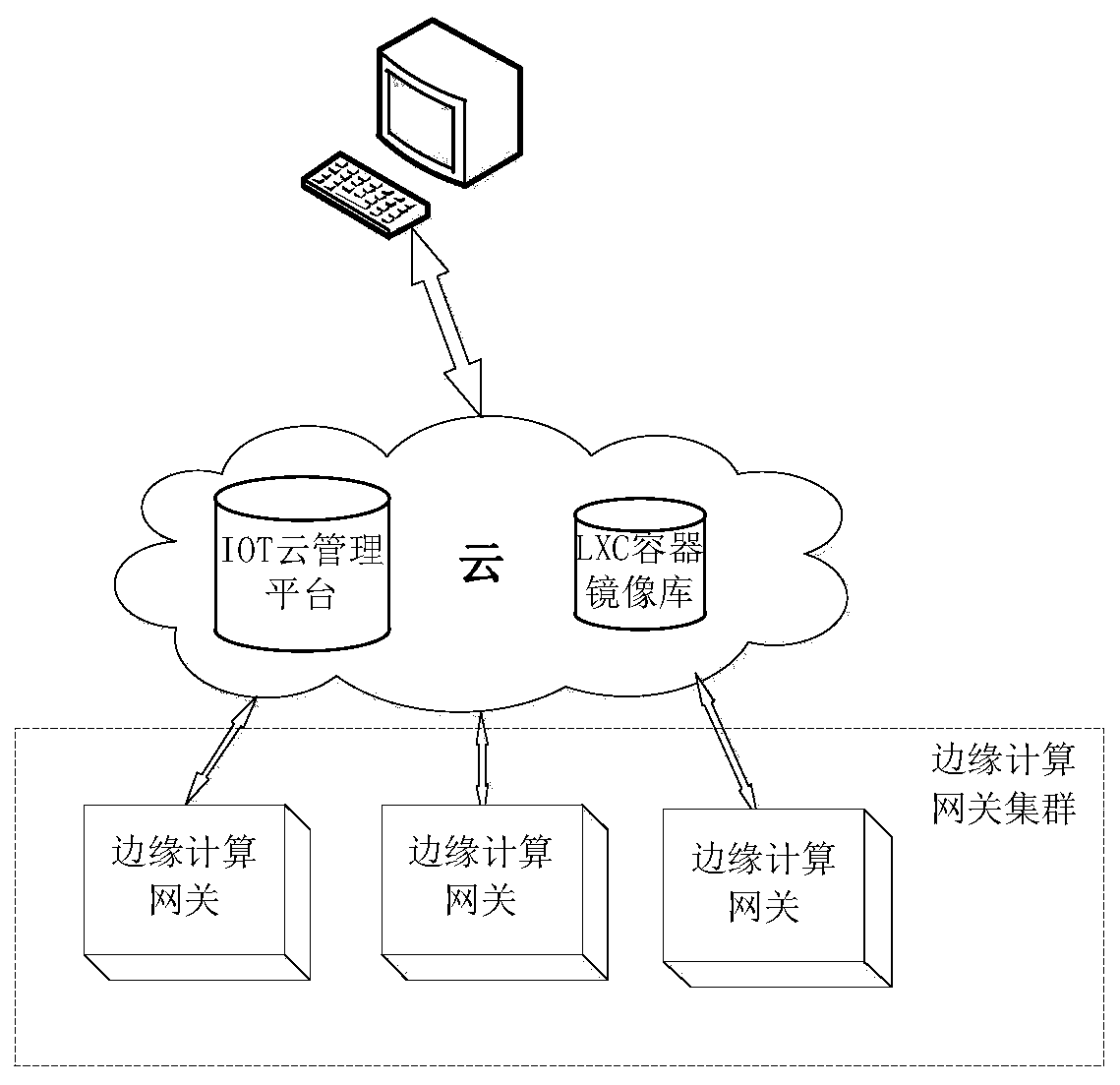
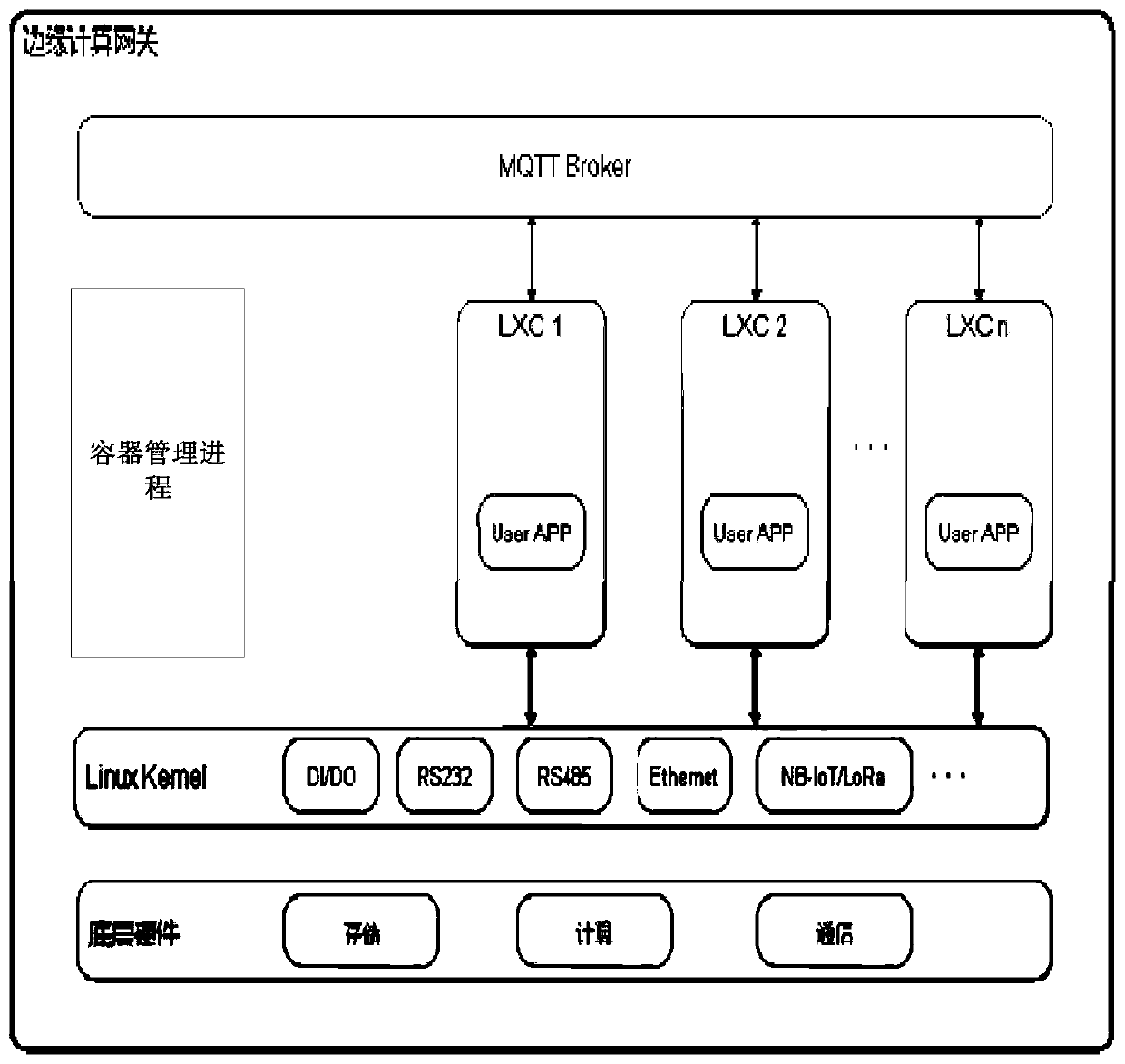
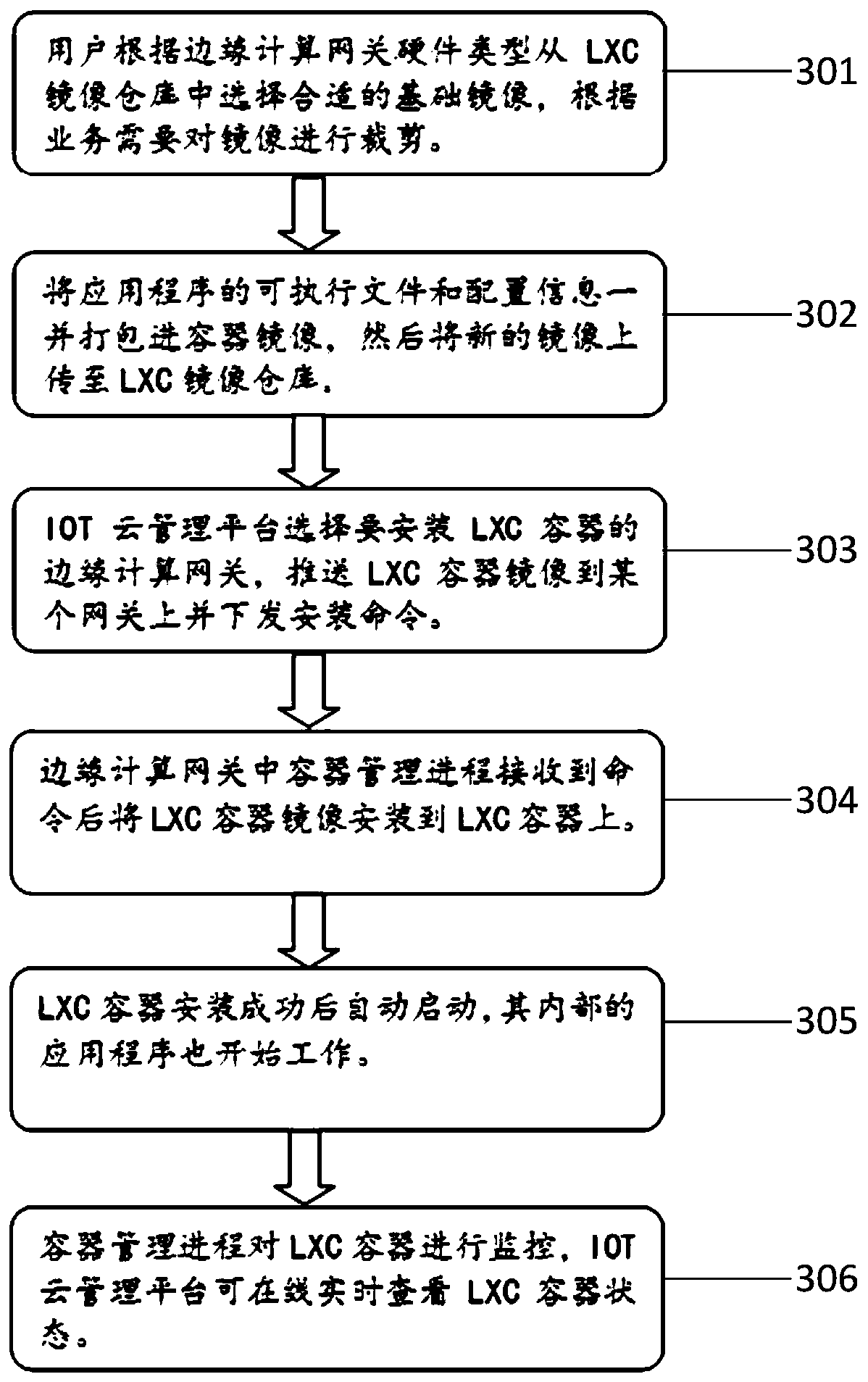
Edge computing gateway management system and method based on LXC container technology
PendingCN111061491AImprove resource utilizationIncrease resourcesResource allocationSoftware simulation/interpretation/emulationEdge computingResource isolation
The invention relates to the field of edge computing, in particular to an edge computing gateway management system based on an LXC container technology. The edge computing gateway management system provided by the invention comprises an edge computing gateway cluster and a cloud server; the edge computing gateway cluster comprises a plurality of edge computing gateways, and a plurality of LXC containers are deployed in the edge computing gateways; an IoT cloud management platform and an LXC container mirror image library are arranged in the cloud server, the IoT cloud management platform is responsible for unified management and monitoring of the whole gateway cluster, and an LXC container basic mirror image is stored in the LXC container mirror image library; and each edge computing gateway in the edge computing gateway cluster establishes communication connection with the cloud server to jointly form a lightweight, flexible and customizable containerized platform. The invention further discloses an edge computing gateway management method applying the system, based on the method, a user can rapidly deploy applications in batches, resource isolation between the applications is achieved, and various Internet of Things application scenes can be met.
Owner:青岛海洋科技中心
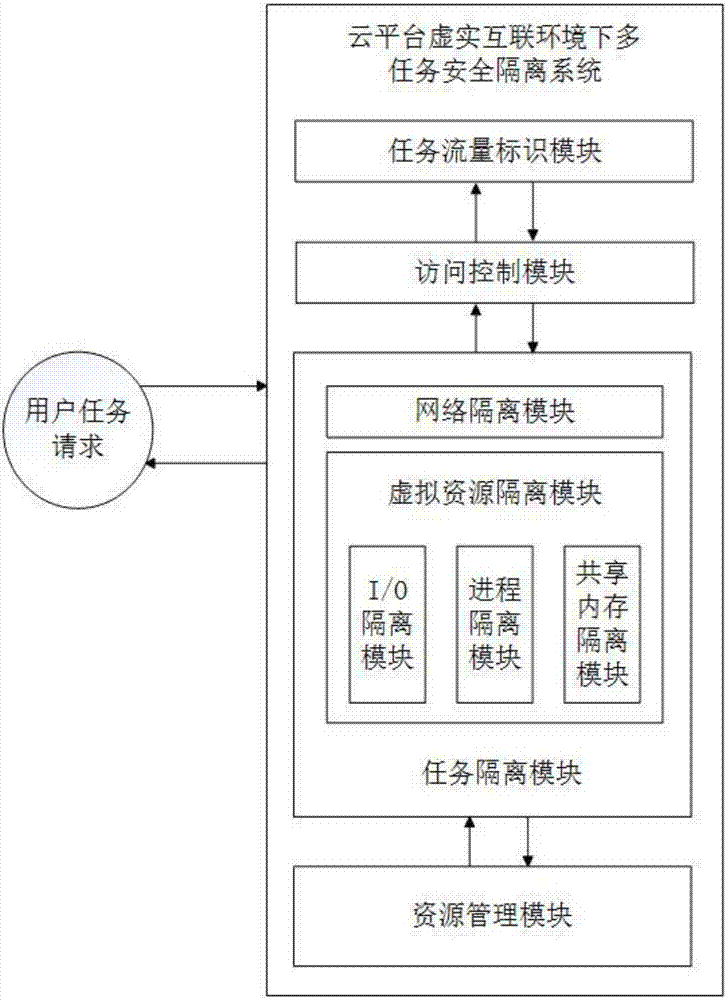
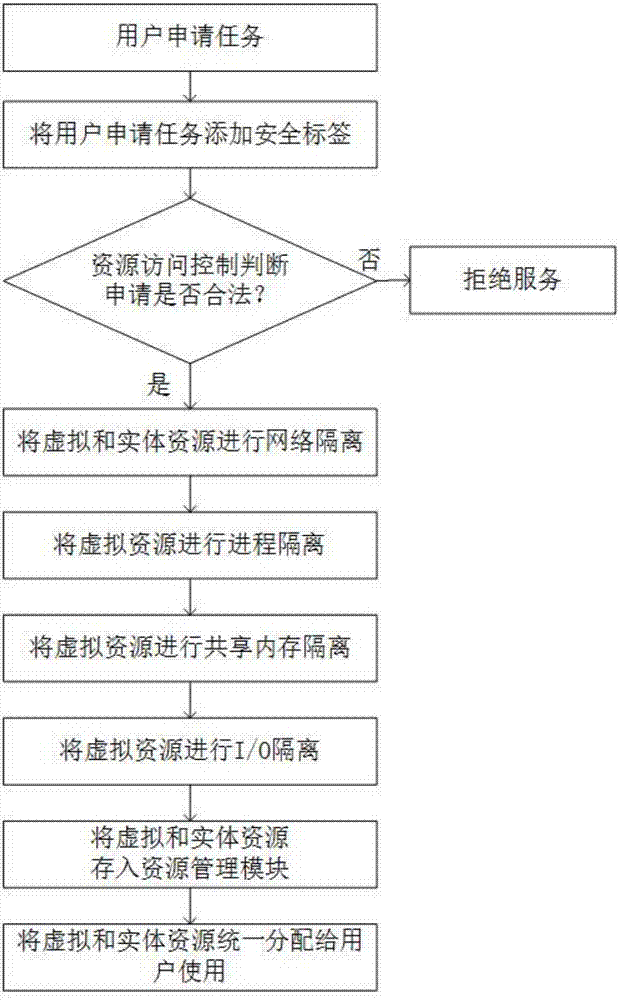
Multitask security isolation system and method under virtual-real interconnected environment of cloud platform
The invention provides a multitask security isolation system and method under a virtual-real interconnected environment of a cloud platform to solve the technical problem existing in the prior art that the unified management of multiple virtual and physical resources and the task security isolation cannot be implemented at the same time. The system comprises a task flow identification module for identifying different tasks, an access control module creating task resources according to the task identification, a task isolation module for security isolation between the tasks and between the resources, and a resource management module for unified management of the securely isolated resources. The implementing steps are as follows: the task flow label module adds a security label to a task and required resources thereof; the access control module verifies user identity and authority information and applies for the virtual and physical resources required by the task; the access control module performs network isolation and virtual resource isolation on the resources applied for the task; and the resource management module performs unified management on the securely isolated virtual and physical resources in the cloud platform and assigns the resources required by the task to the task.
Owner:XIDIAN UNIV
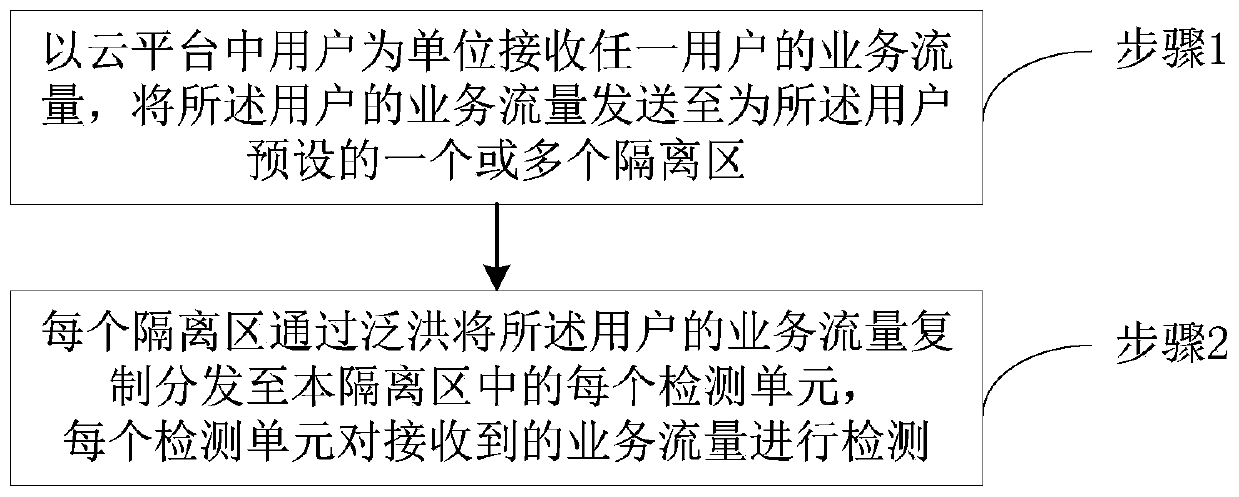
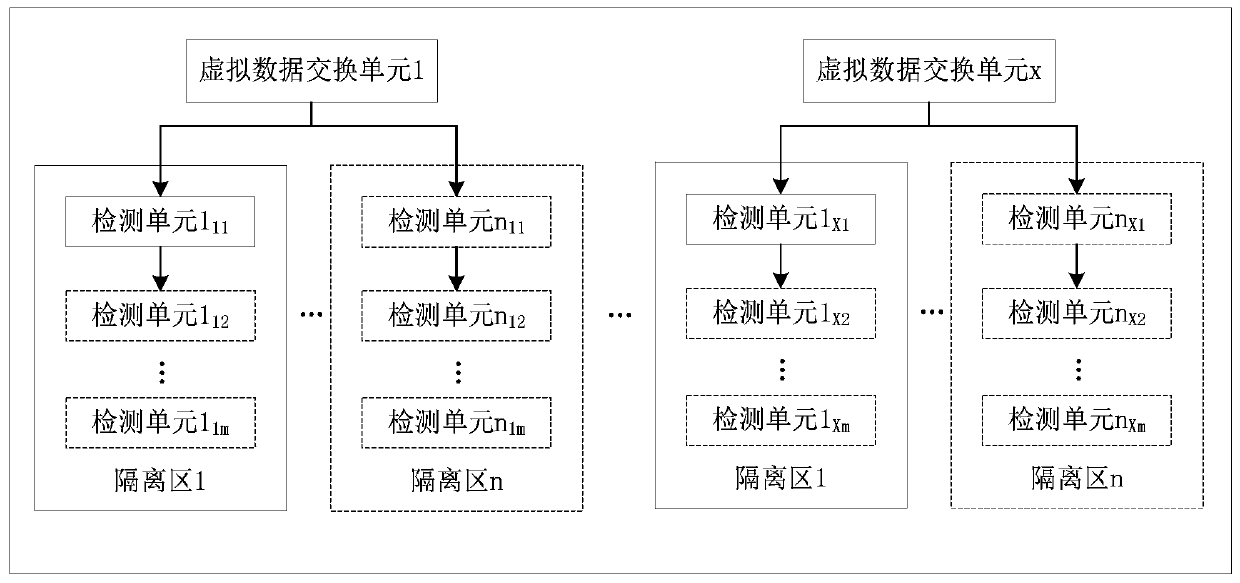
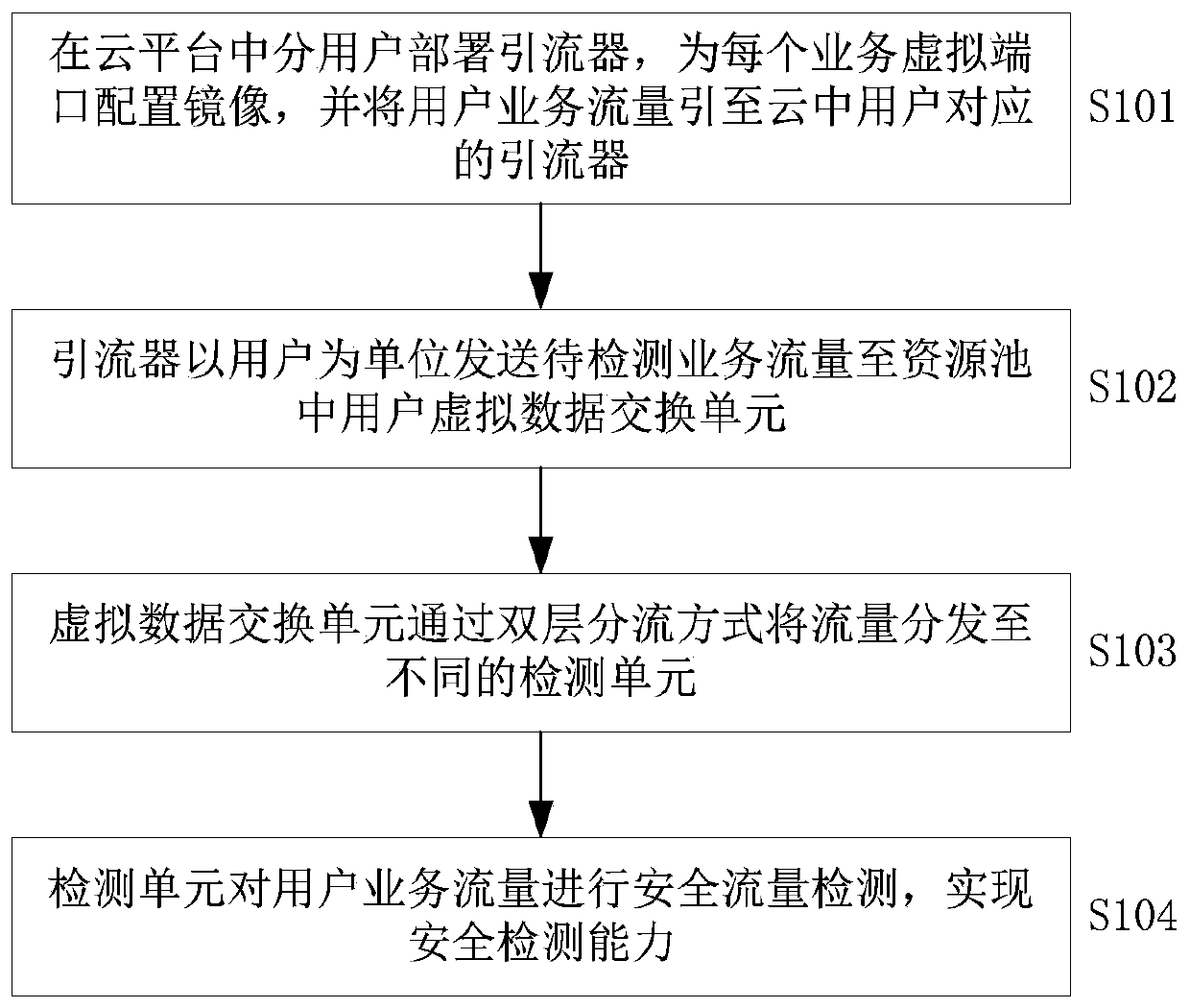
Flow detection method for cloud environment and resource pool system
ActiveCN109981613AImplement security resource isolationEfficient Forwarding PerformanceTransmissionTraffic volumeResource isolation
Owner:BEIJING VENUS INFORMATION SECURITY TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com