Flow detection method for cloud environment and resource pool system
A traffic detection and cloud environment technology, applied in the transmission system, electrical components, etc., can solve the problems of binding network cards, resource pool network element allocation, complex security system structure, and large resource consumption, etc., to achieve flexibility and performance, Efficient effect of security resource isolation
Active Publication Date: 2019-07-05
BEIJING VENUS INFORMATION SECURITY TECH +1
View PDF6 Cites 7 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
For detection products, two methods are mainly used for offload processing. One is to implement traffic arrangement through hardware SDN switches and network card pass-through technology, so as to improve hardware processing performance. However, this method is difficult to handle when the cloud platform has multiple user networks. , it is necessary to write a complex flow table, which consumes a lot of resources. At the same time, this technology of binding network cards is difficult to allocate network elements inside the resource pool, and cannot guarantee dynamic flexibility.
Another way is to design a virtual splitter
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
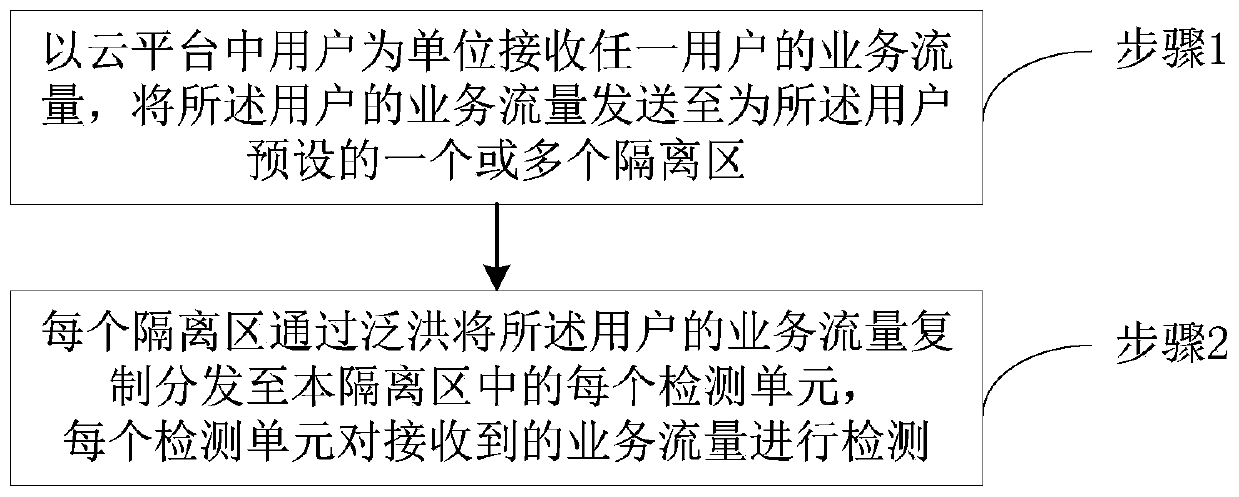
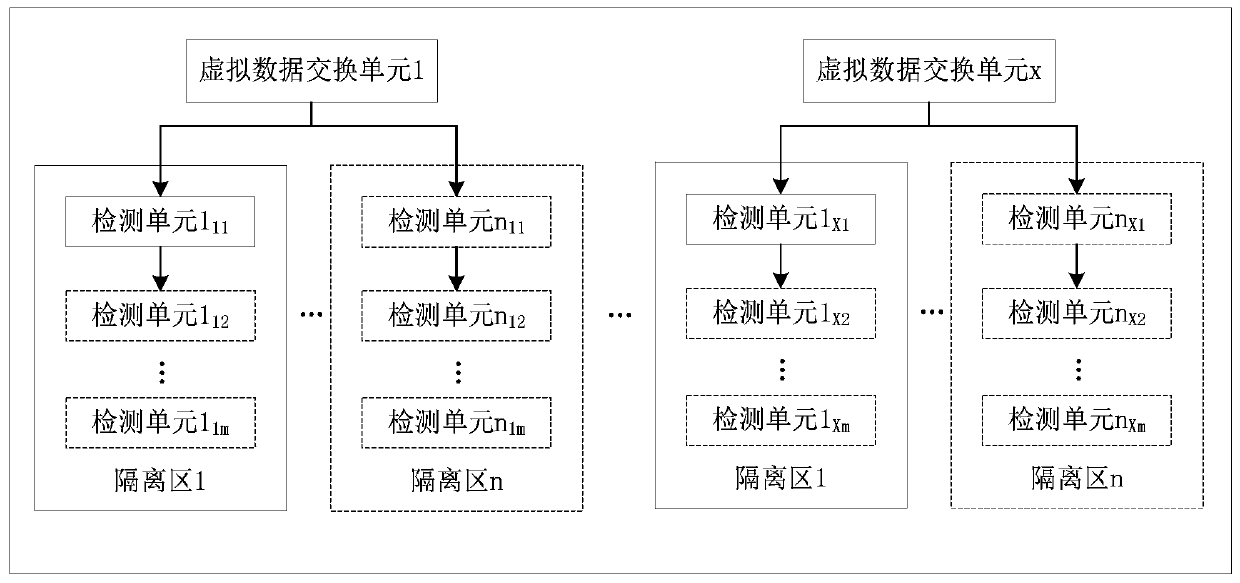
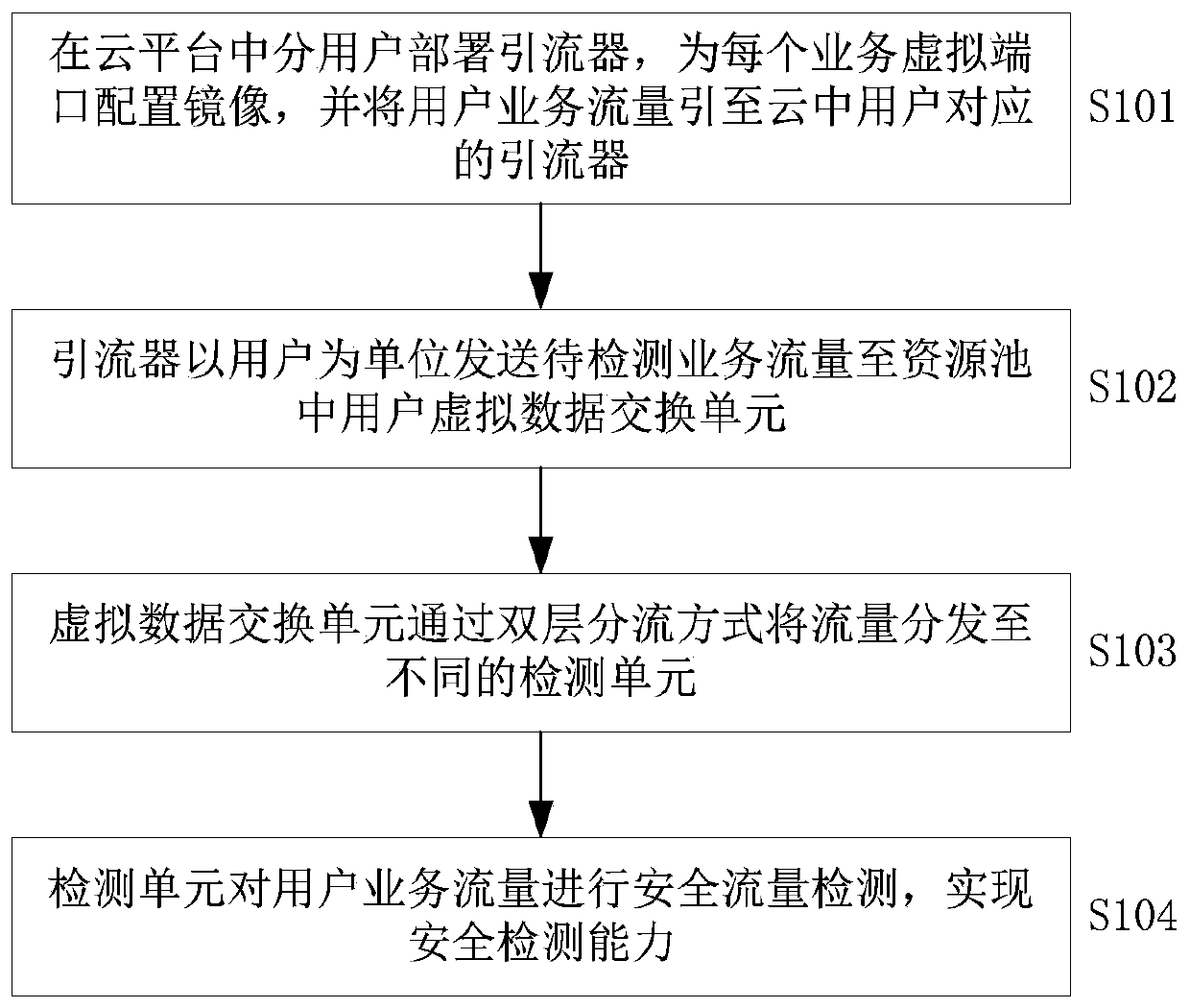
The embodiment of the invention discloses a flow detection method for a cloud environment and a resource pool system. The method comprises the following steps of: receiving the service flow of any user by taking the user in the cloud platform as a unit; sending the service flow of the user to one or more isolation regions preset for the user, wherein each isolation region comprises one or more detection units, each isolation region copies and distributes the service flow of the user to each detection unit in the isolation region through flooding, and each detection unit detects the received service flow. According to the embodiment of the invention, multi-user security resource isolation and high-efficiency forwarding performance can be realized, so that the flexibility and the performanceare both realized.
Description
technical field [0001] The invention relates to the field of computer information security, in particular to a traffic detection method and a resource pool system used in a cloud environment. Background technique [0002] With the rapid development of computer communication and information technology, cloud computing has gradually become the mainstream deployment method for various industries and businesses. However, after businesses go to the cloud, traditional security problems will not only be magnified, but also new security risks will be brought. [0003] In the face of these problems, the mainstream manufacturers' approach is to deploy virtual security network elements in the external security resource pool in a side-mounted manner, and divert traffic to the external resource pool in the cloud to realize the virtualization function. For example, some existing technical solutions are to virtualize physical resources to provide system environment services for the applica...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06
CPCH04L63/0272H04L63/1408
Inventor 胡毅勋郭春梅
Owner BEIJING VENUS INFORMATION SECURITY TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com