Patents
Literature
1343results about How to "Increase resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
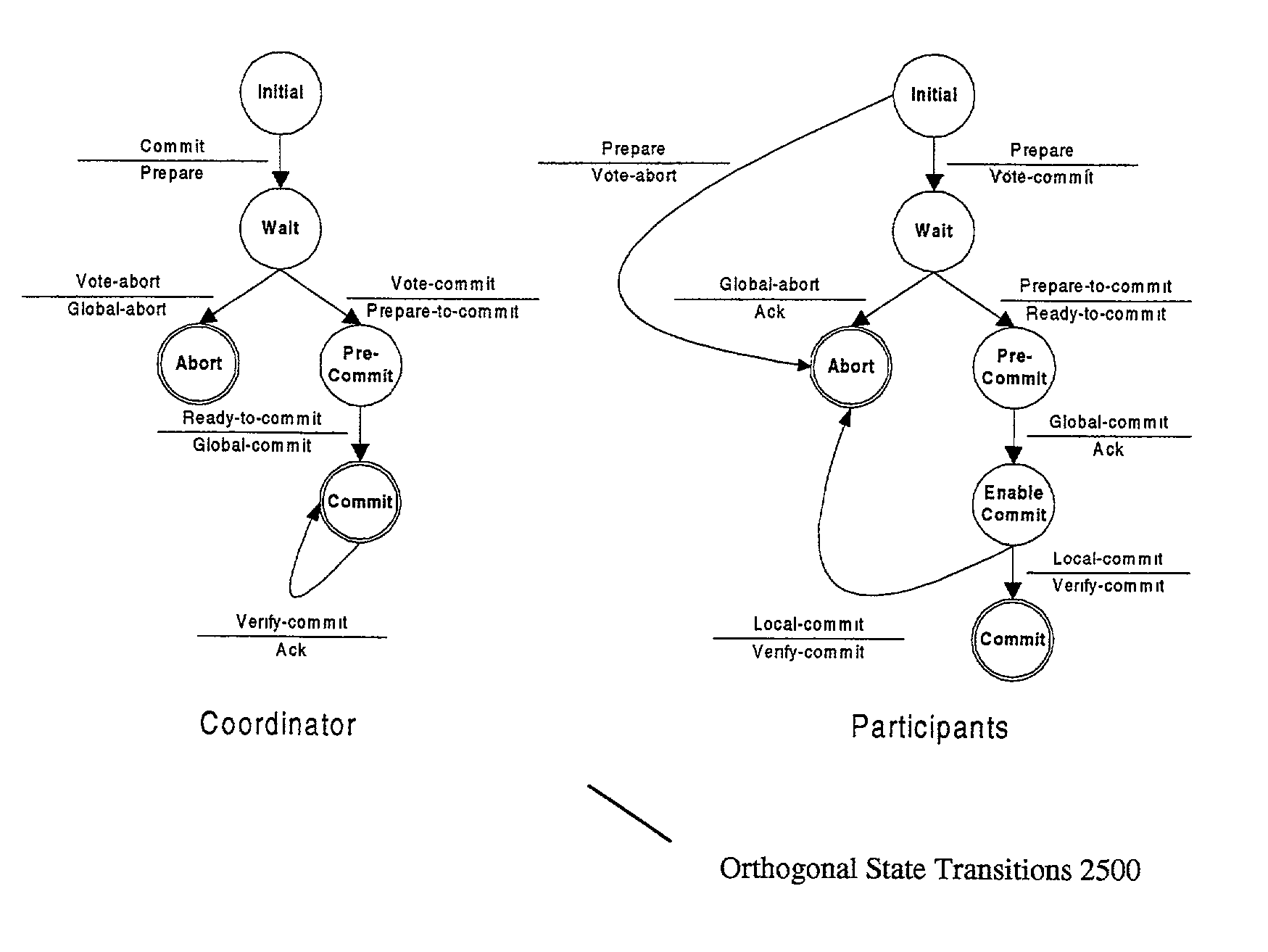
Asynchronous transcription object management system
ActiveUS7206805B1Avoid modificationReduce in quantityData processing applicationsMultiple digital computer combinationsManagement systemDistributed computing
Described herein is a system for executing distributed transactions. A coordinator and one or more participants cooperate to execute a distributed transaction, the distributed transaction including for each participant a transaction executed by the participant. To manage the transaction, the coordinator and the participant communicate over a network using, for example, a stateless protocol. Before each participant commits the transaction, the participants determine that the coordinator has committed the transaction. The coordinator commits the transaction after receiving acknowledgment from all the participants that they will commit the transaction. To determine whether the coordinator has committed the transaction, a participant transmits a message to the coordinator to acknowledge that it will commit the distributed transaction. The participant commits its respective transaction if it receives an acknowledgement from the coordinator. For the particular transaction being executed by a participant, the participant prevents other transactions from modifying a data item affected by the particular transaction. The participant will prevent such modifications until termination criteria for the particular transaction is satisfied, in which case the participant terminates the transaction.
Owner:ORACLE INT CORP
Monitoring latency of a network to manage termination of distributed transactions
InactiveUS7290056B1Reduce in quantityReduce the numberMultiple digital computer combinationsTransmissionStateless protocolFinancial transaction
Described herein is a system for executing distributed transactions. A participant and a coordinator cooperate to execute a distributed transaction, the distributed transaction including a transaction executed by the participant. To manage the transaction, the coordinator and the participant communicate over a network using, for example, a stateless protocol. The distributed transaction may be terminated when communication between the participant and coordinator regarding the transaction does not occur within a time period. The time period may reflect the time required for a coordinator to send a message and a participant to acknowledge receipt of the message, and the time for the participant to perform operations executed for the transaction. The latency of network traffic between the participant and the coordinator is monitored, and the time periods adjusted accordingly. In addition, the amount of time required for the participant to execute operations for the transaction is monitored, and the time periods adjusted accordingly.
Owner:ORACLE INT CORP
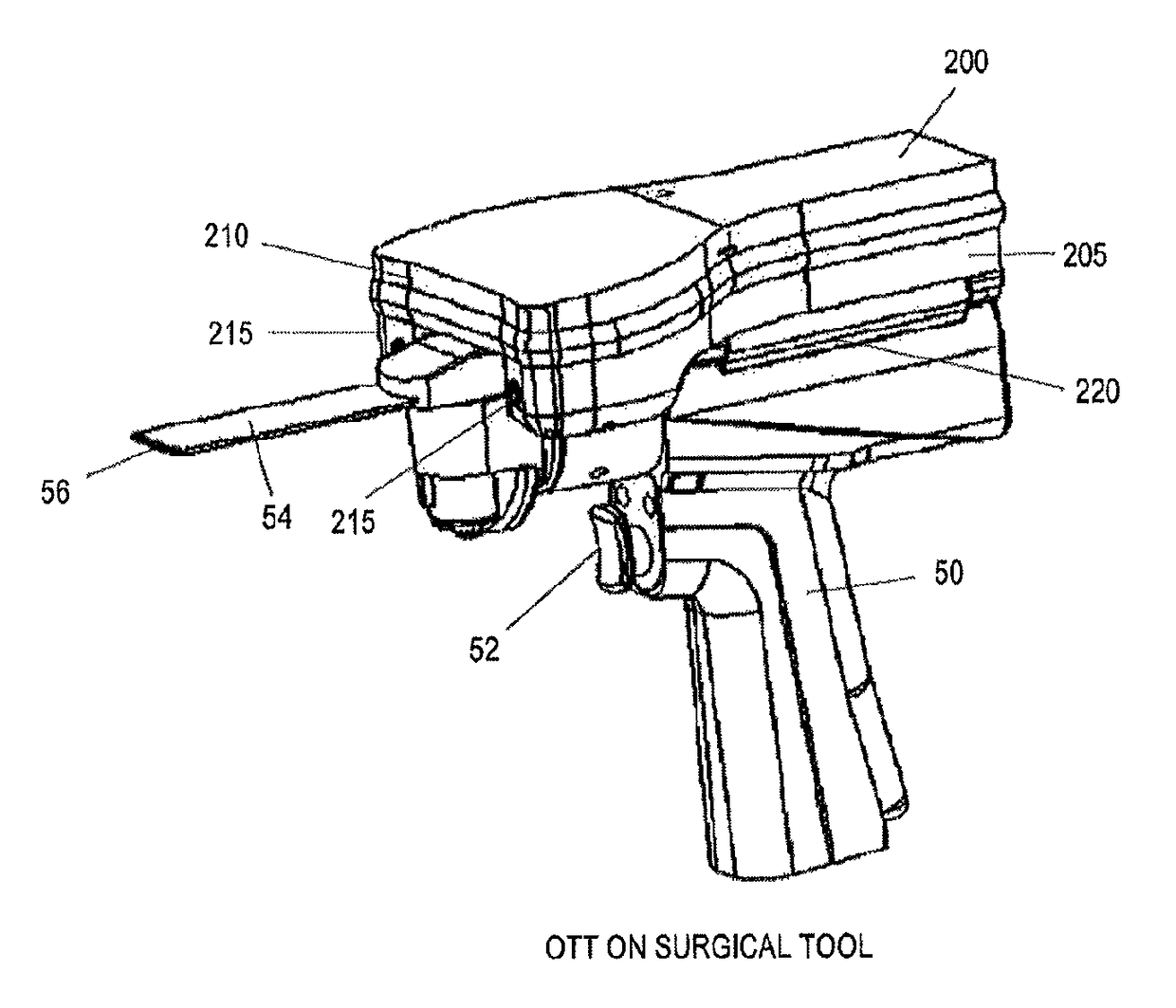
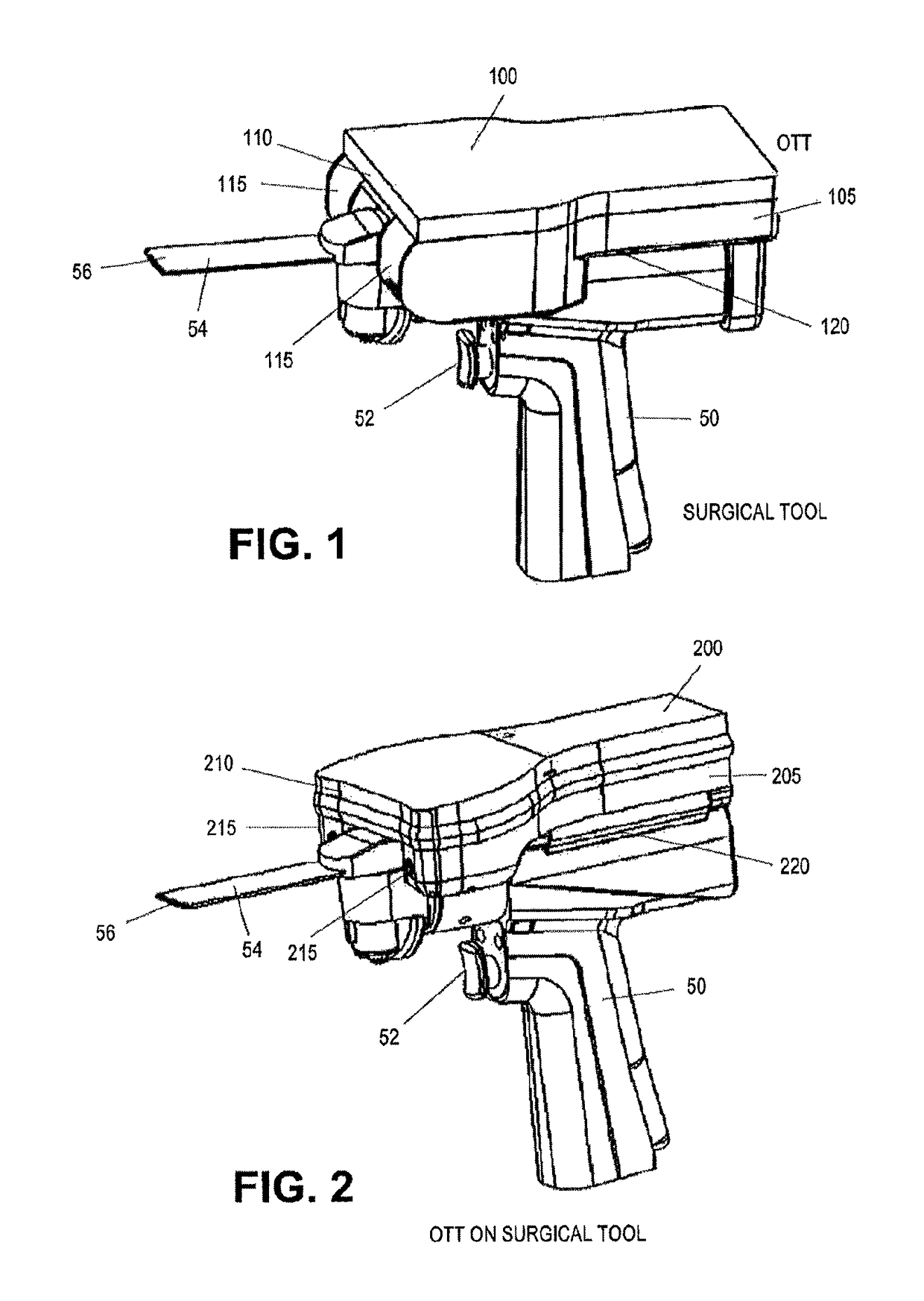
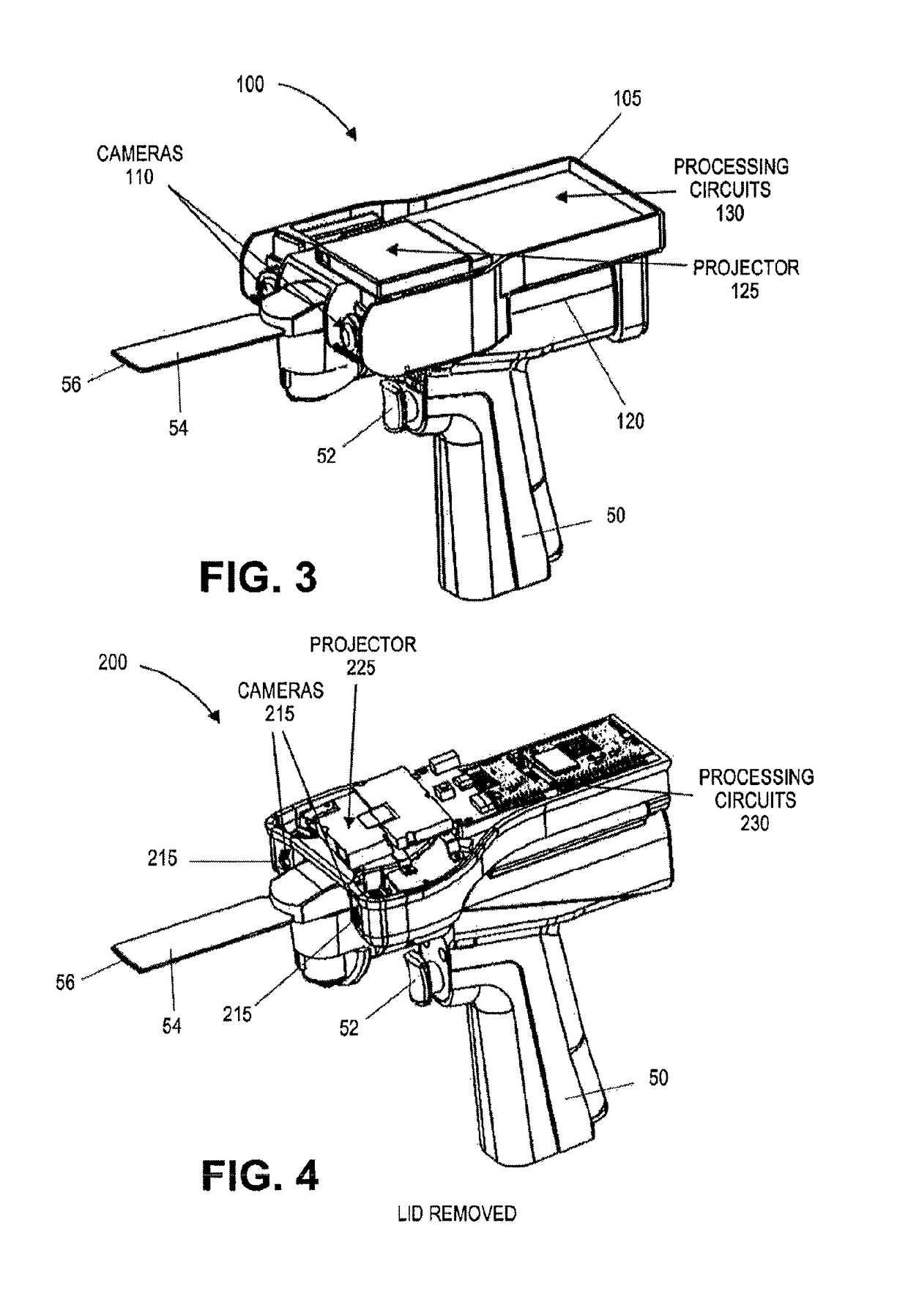
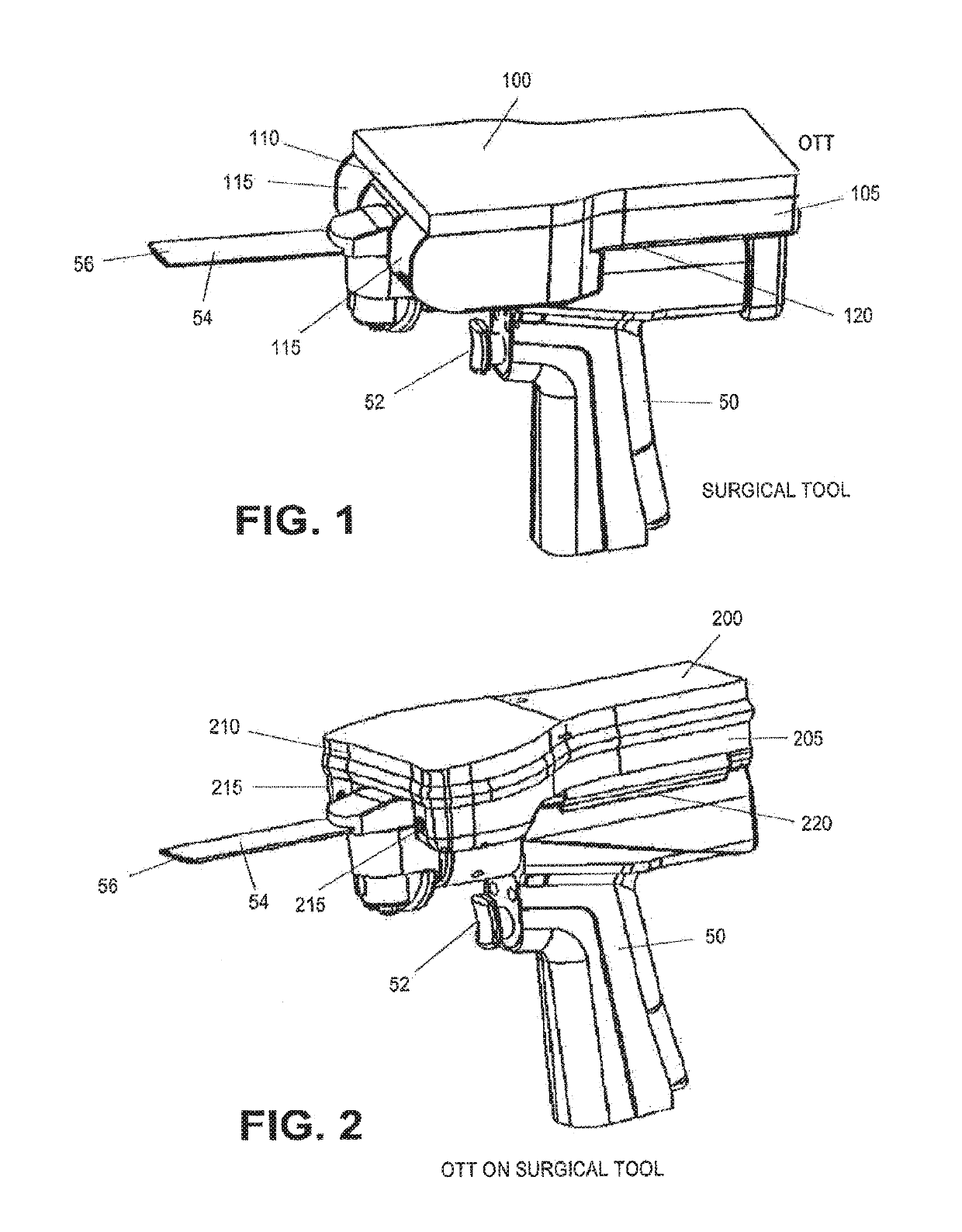
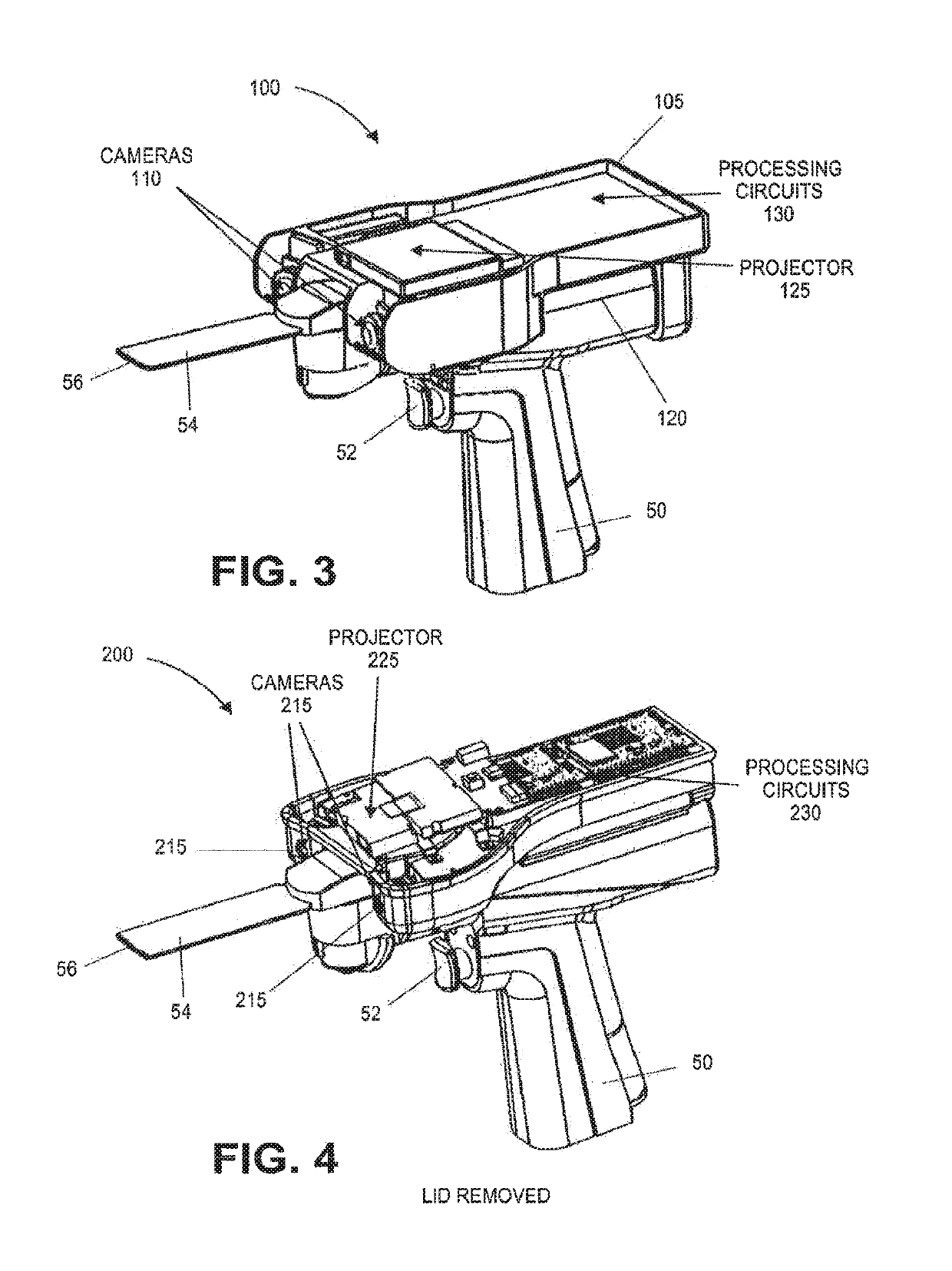
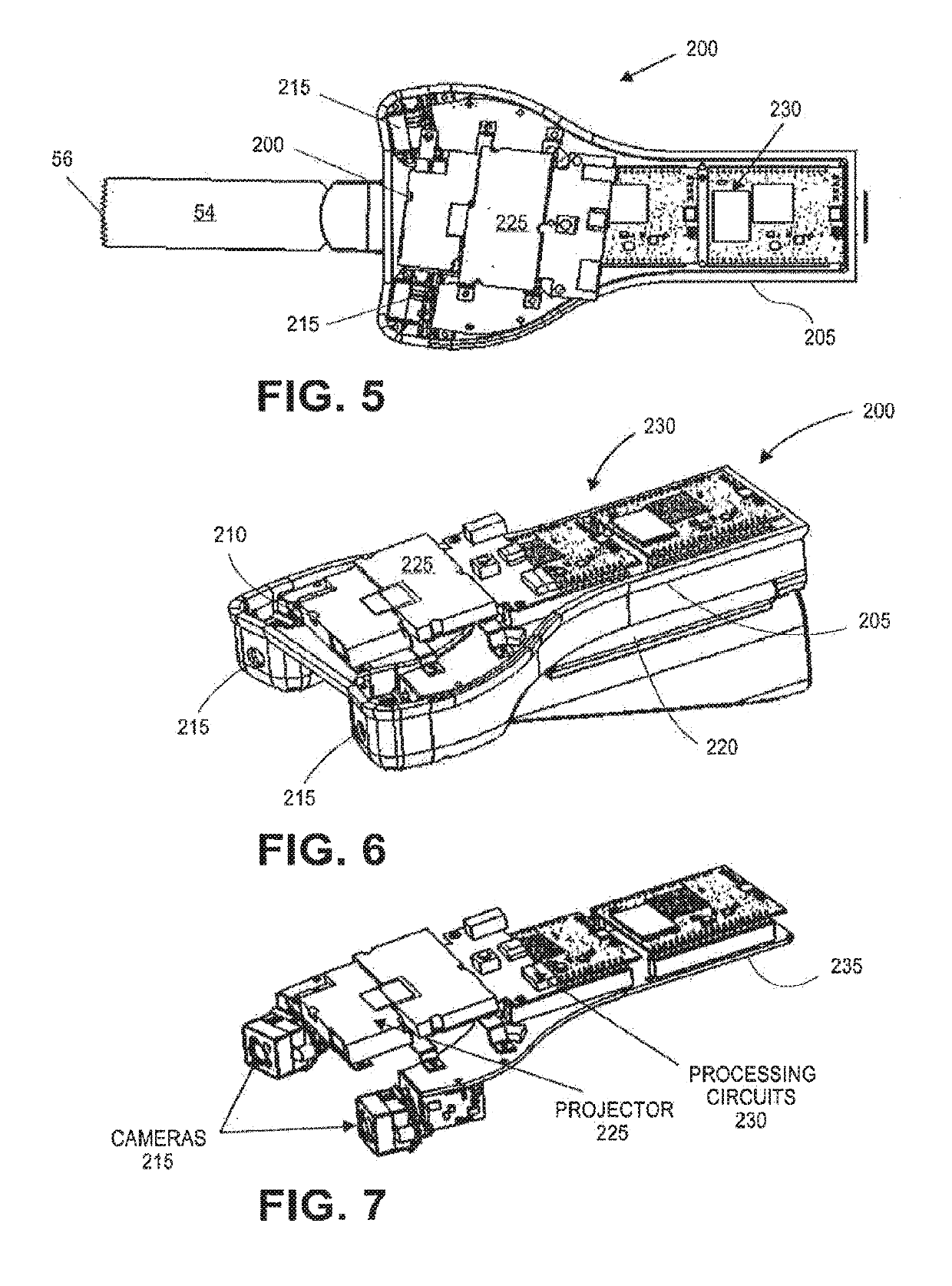
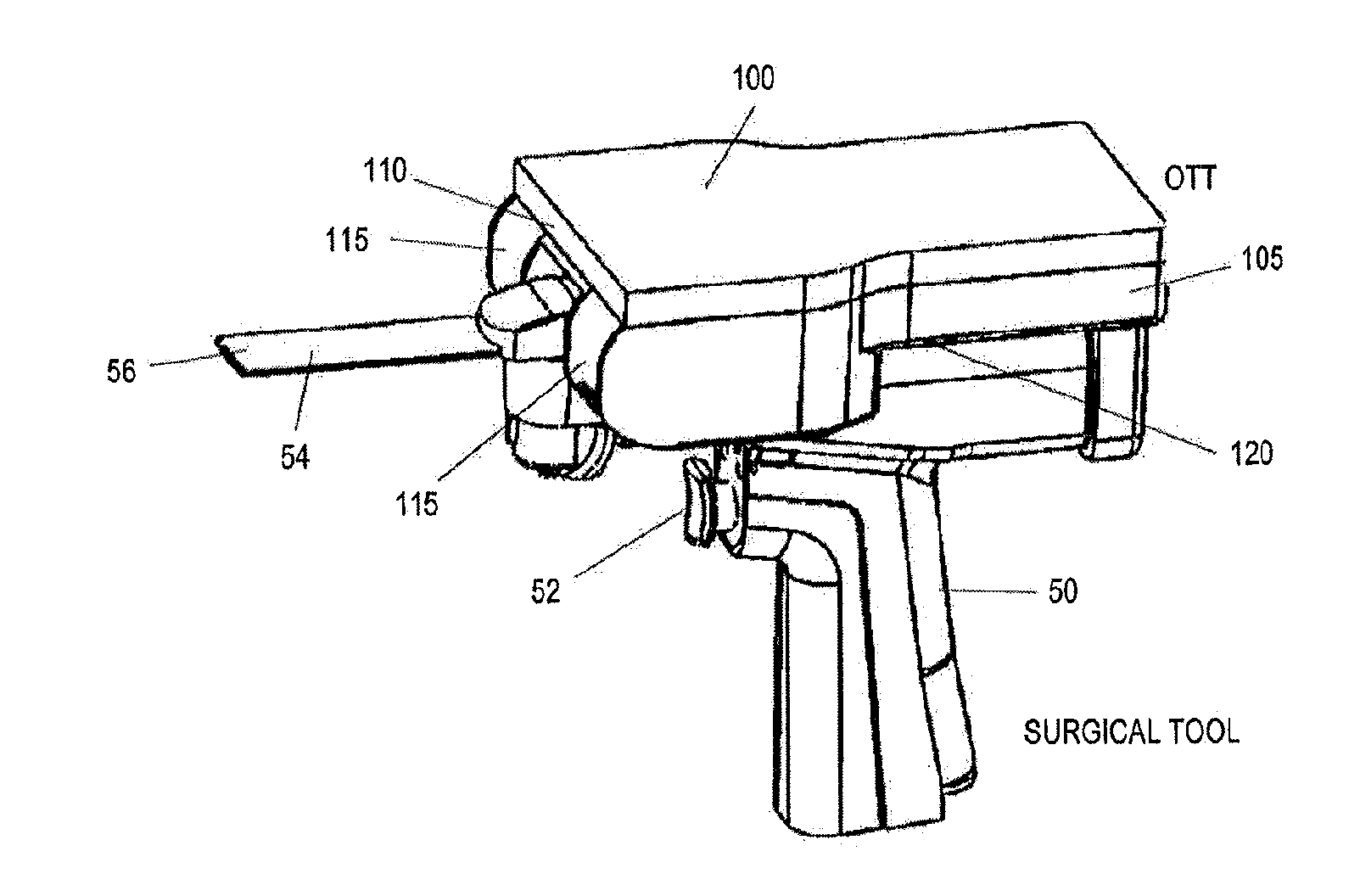
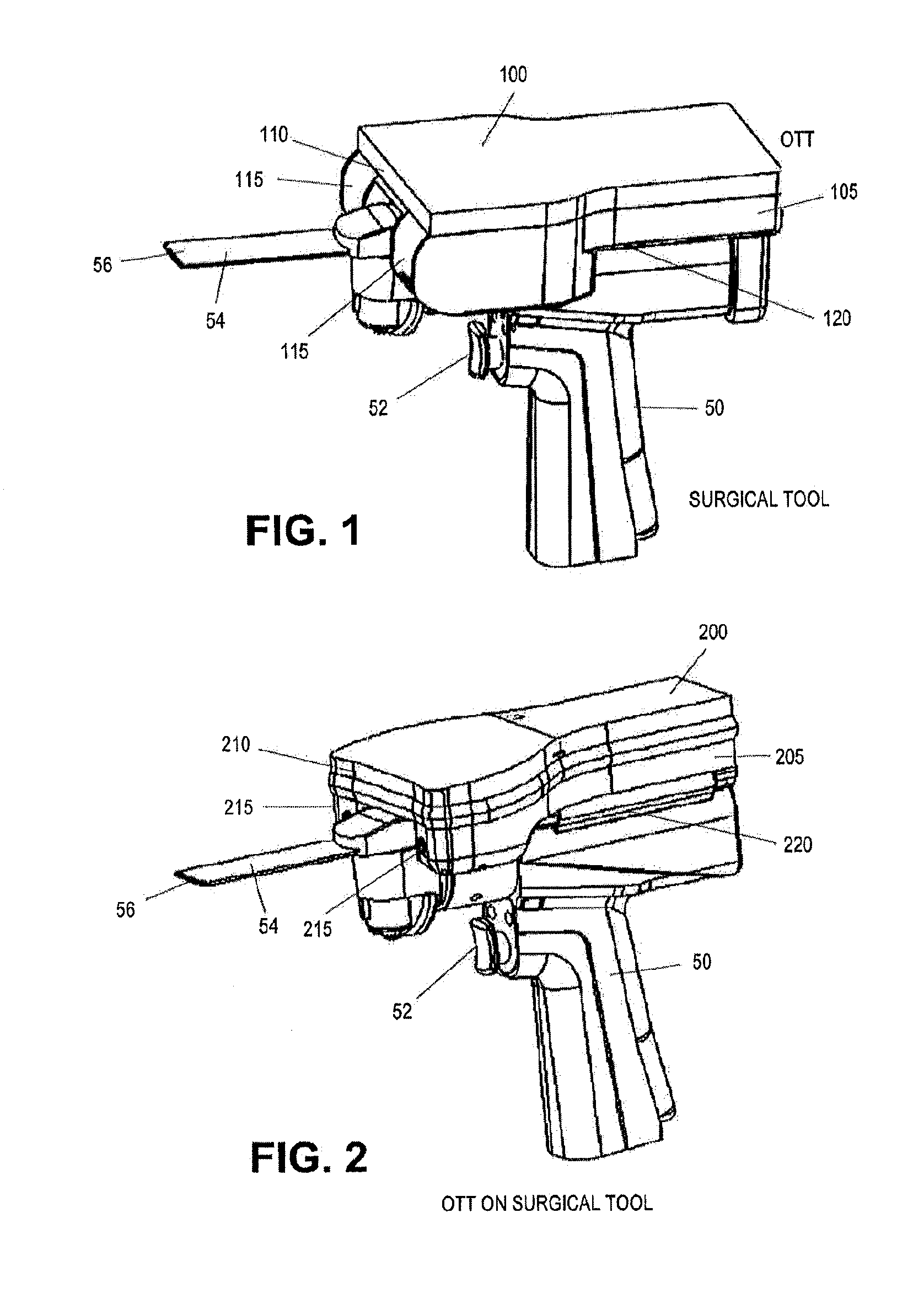
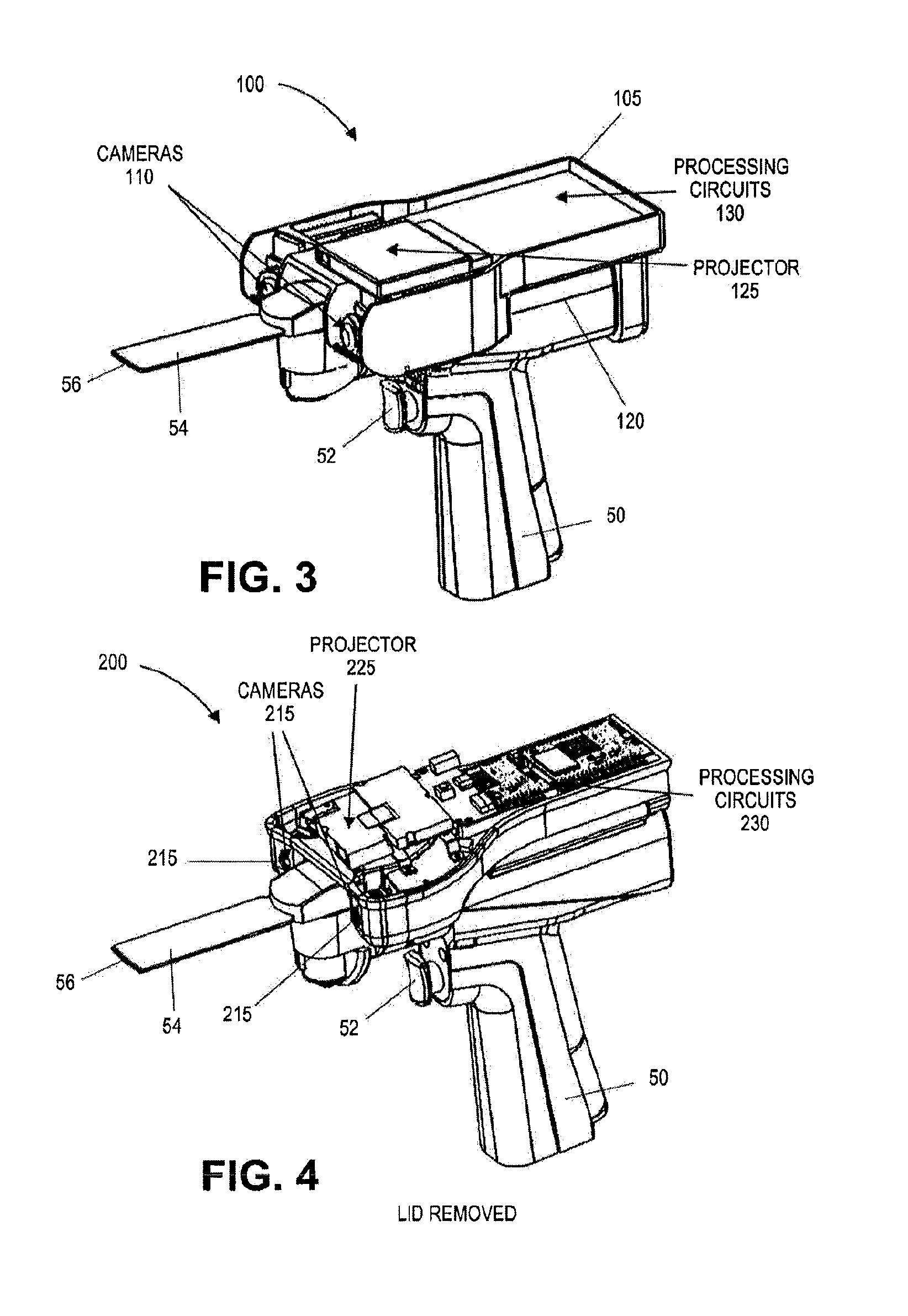
On-board tool tracking system and methods of computer assisted surgery
InactiveUS10105149B2Increase resourcesSurgical navigation systemsComputer-aided planning/modellingComputer-assisted surgeryOn board
A number of improvements are provided relating to computer aided surgery utilizing an on tool tracking system. The various improvements relate generally to both the methods used during computer aided surgery and the devices used during such procedures. Other improvements relate to the structure of the tools used during a procedure and how the tools can be controlled using the OTT device. Still other improvements relate to methods of providing feedback during a procedure to improve either the efficiency or quality, or both, for a procedure including the rate of and type of data processed depending upon a CAS mode.
Owner:TRAK SURGICAL +1
On-board tool tracking system and methods of computer assisted surgery
InactiveUS20190290297A1Increase resourcesDiagnosticsSurgical navigation systemsSurgical operationComputer-assisted surgery
A number of improvements are provided relating to computer aided surgery utilizing an on tool tracking system. The various improvements relate generally to both the methods used during computer aided surgery and the devices used during such procedures. Other improvements relate to the structure of the tools used during a procedure and how the tools can be controlled using the OTT device. Still other improvements relate to methods of providing feedback during a procedure to improve either the efficiency or quality, or both, for a procedure including the rate of and type of data processed depending upon a CAS mode.
Owner:BOARD OF RGT UNIV OF NEBRASKA +1
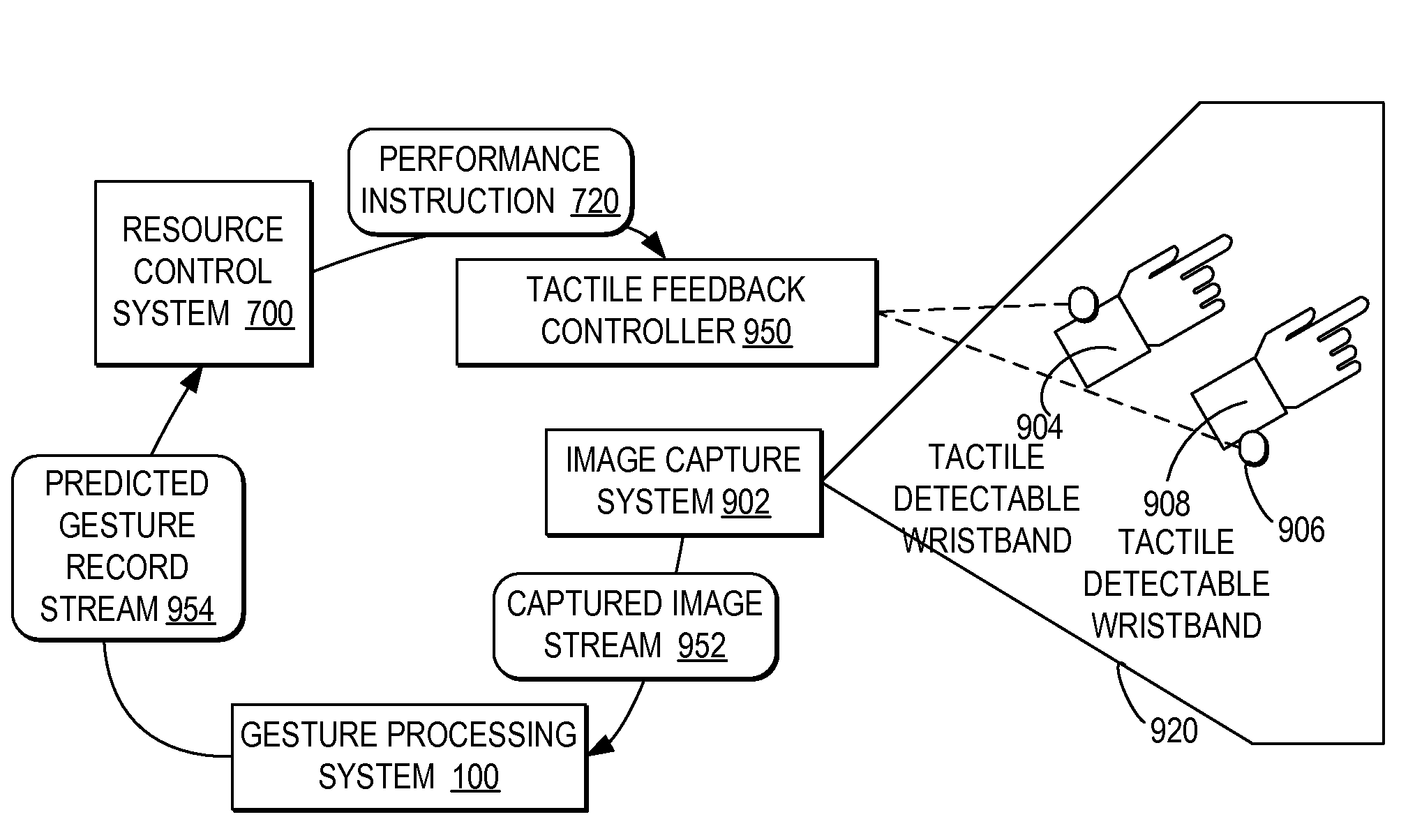
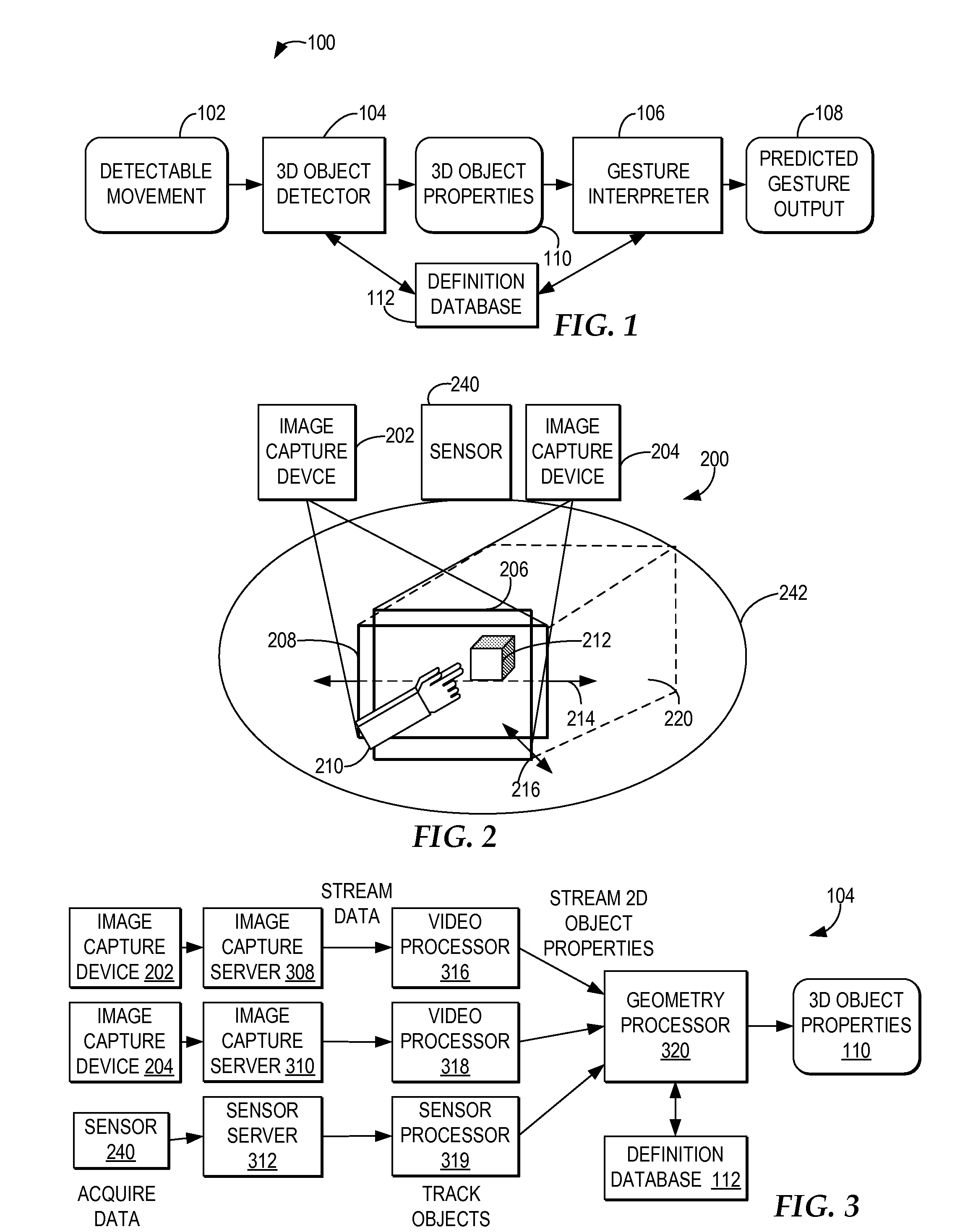
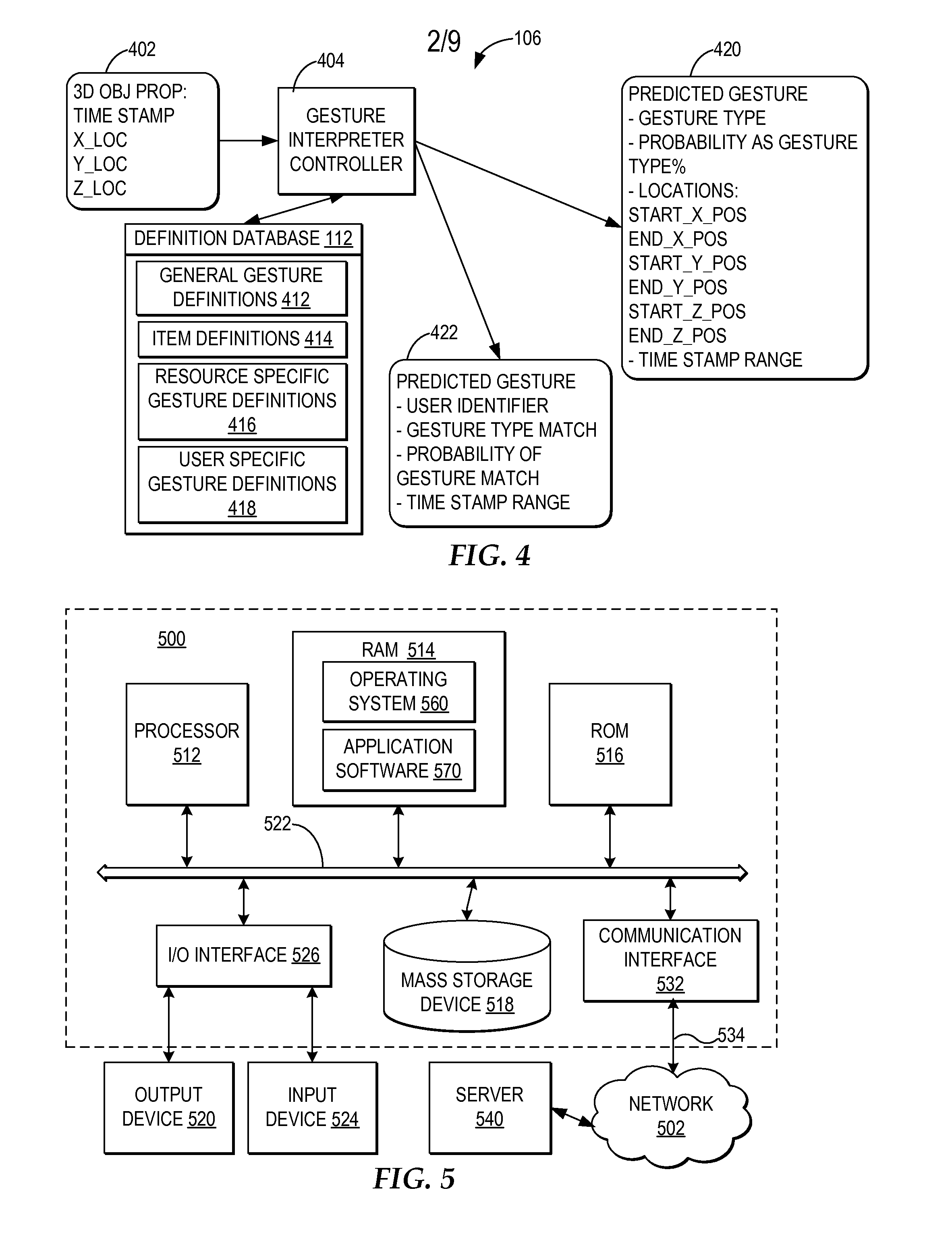
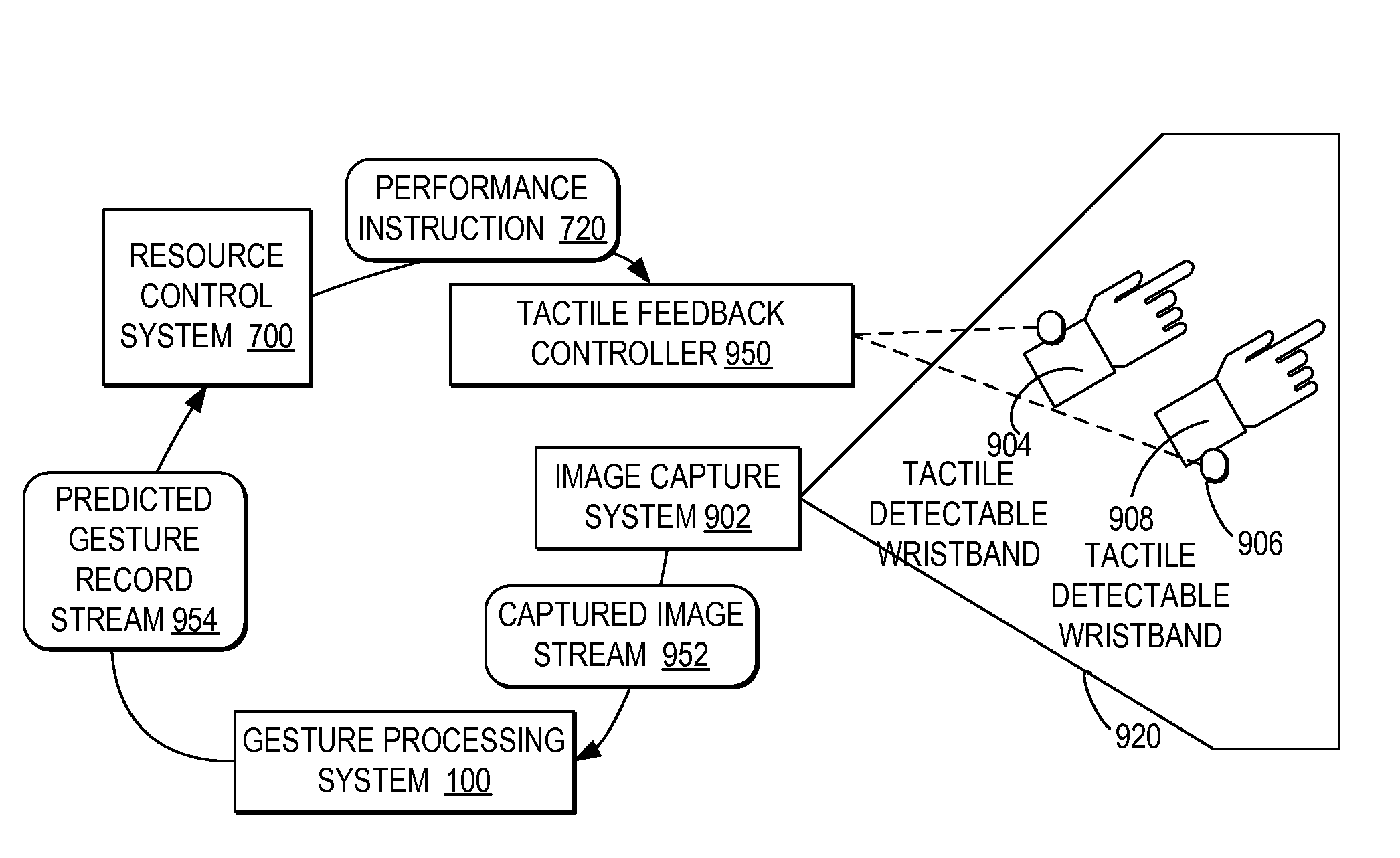
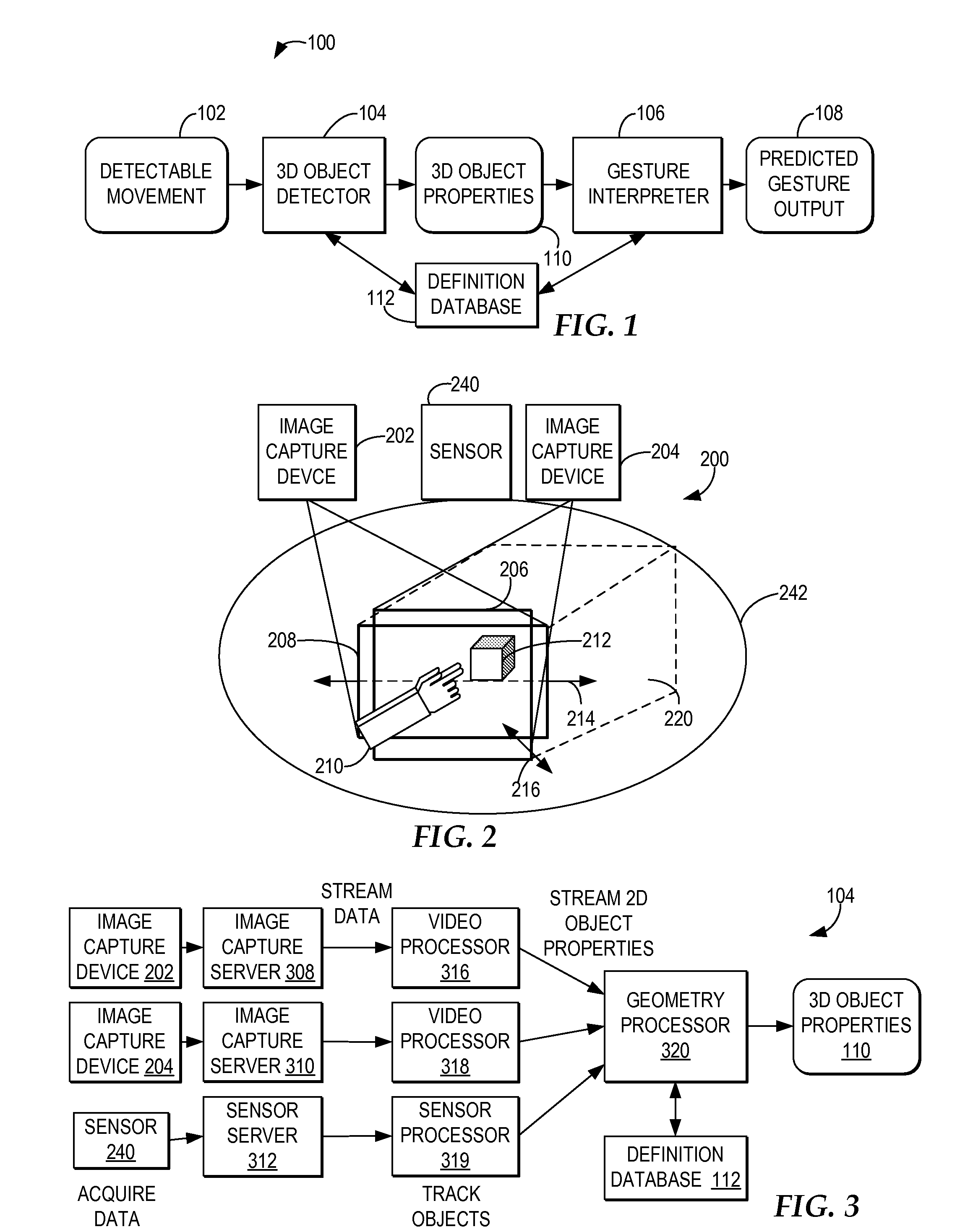
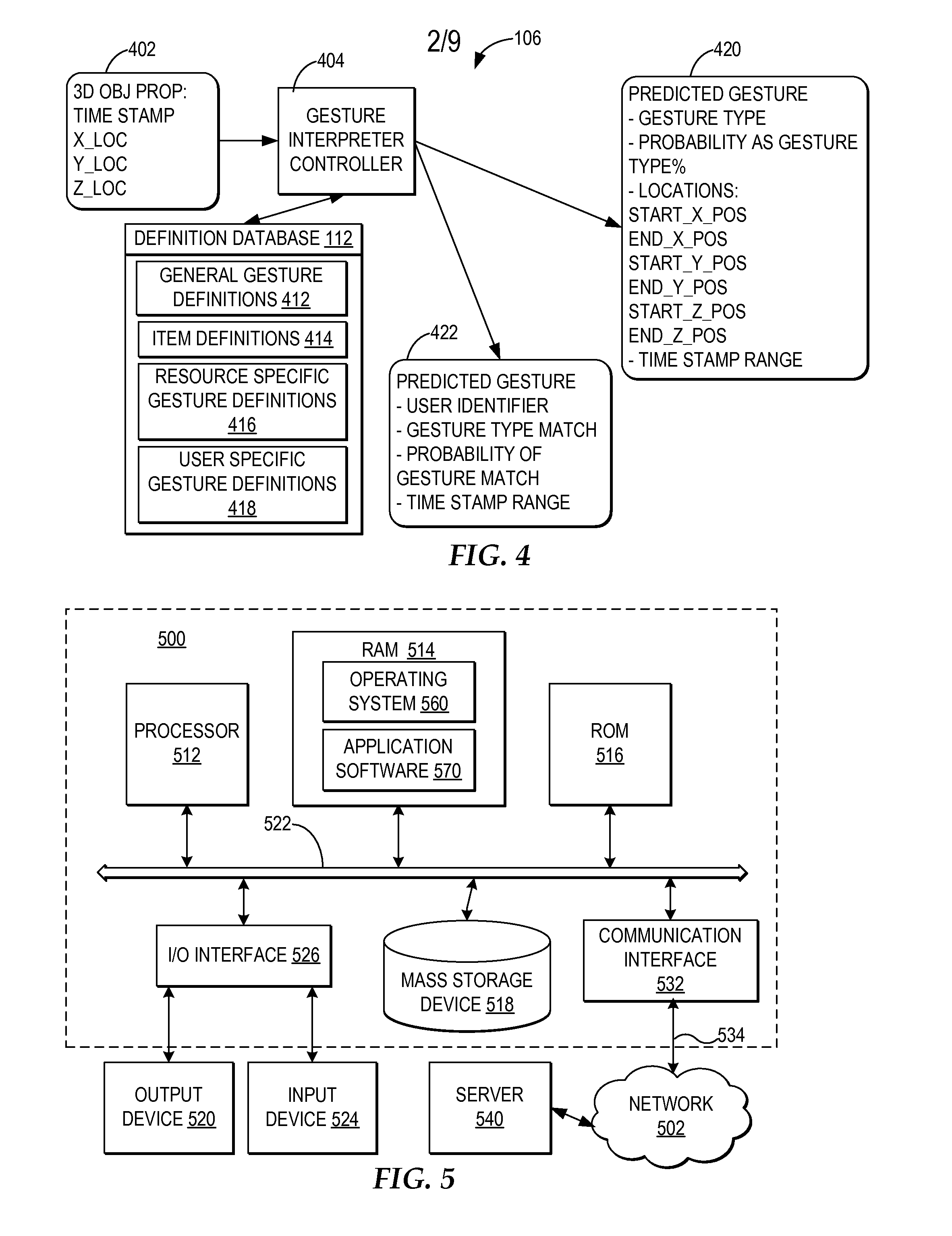
Controlling resource access based on user gesturing in a 3D captured image stream of the user
ActiveUS20080170776A1Improved resource securityIncrease resourcesCharacter and pattern recognitionMultiple digital computer combinationsControl systemResource based
A computer-implemented method, system, and program product comprises a gesture processing system for capturing a three-dimensional movement of a user, wherein the three-dimensional movement is determined using at least one stereoscopic image device aimed at the user to identify and track at least one particular three-dimensional movement of the user. The gesture processing system predicts at least one defined movement within the captured three-dimensional movement matching at least one gesture definition of at least one gesture type from among a plurality of gesture definitions. A resource control system receives a request to access a resource based on the predicted at least one gesture type. The resource control system only allows user access to the resource by matching the predicted at least one gesture type with at least one required gesture type.
Owner:SNAP INC
Controlling resource access based on user gesturing in a 3D captured image stream of the user
ActiveUS7971156B2Increase resourcesCharacter and pattern recognitionMultiple digital computer combinationsControl systemResource based
A computer-implemented method, system, and program product comprises a gesture processing system for capturing a three-dimensional movement of a user, wherein the three-dimensional movement is determined using at least one stereoscopic image device aimed at the user to identify and track at least one particular three-dimensional movement of the user. The gesture processing system predicts at least one defined movement within the captured three-dimensional movement matching at least one gesture definition of at least one gesture type from among a plurality of gesture definitions. A resource control system receives a request to access a resource based on the predicted at least one gesture type. The resource control system only allows user access to the resource by matching the predicted at least one gesture type with at least one required gesture type.
Owner:SNAP INC
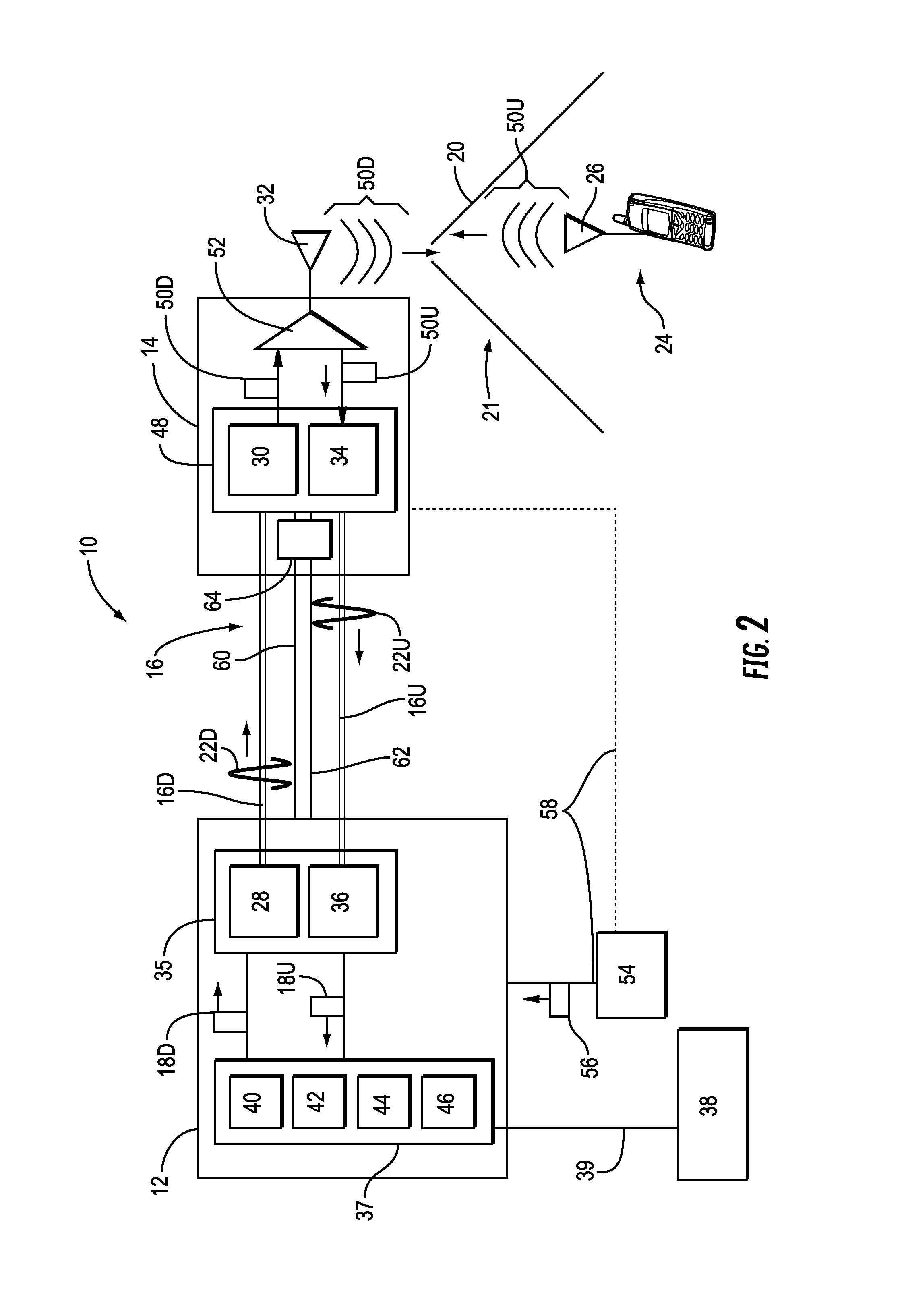
Optical fiber-based distributed radio frequency (RF) antenna systems supporting multiple-input, multiple-output (MIMO) configurations, and related components and methods
InactiveUS20140126914A1Improve communication performanceFacilitate data communicationSpatial transmit diversityRadio-over-fibreDistributed antenna systemFrequency conversion
Optical fiber-based distributed antenna systems that support multiple-input, multiple-output (MIMO) antenna configurations and communications. Embodiments disclosed herein include optical fiber-based distributed antenna system that can be flexibly configured to support or not support MIMO communications configurations. In one embodiment, first and second MIMO communication paths are shared on the same optical fiber using frequency conversion to avoid interference issues, wherein the second communication path is provide to a remote extension unit to remote antenna unit. In another embodiment, the optical fiber-based distributed antenna systems may be configured to allow to provide MIMO communication configurations with existing components. Existing capacity of system components are employed to create second communication paths for MIMO configurations, thereby reducing overall capacity, but allowing avoidance of frequency conversion components and remote extension units.
Owner:CORNING OPTICAL COMM LLC
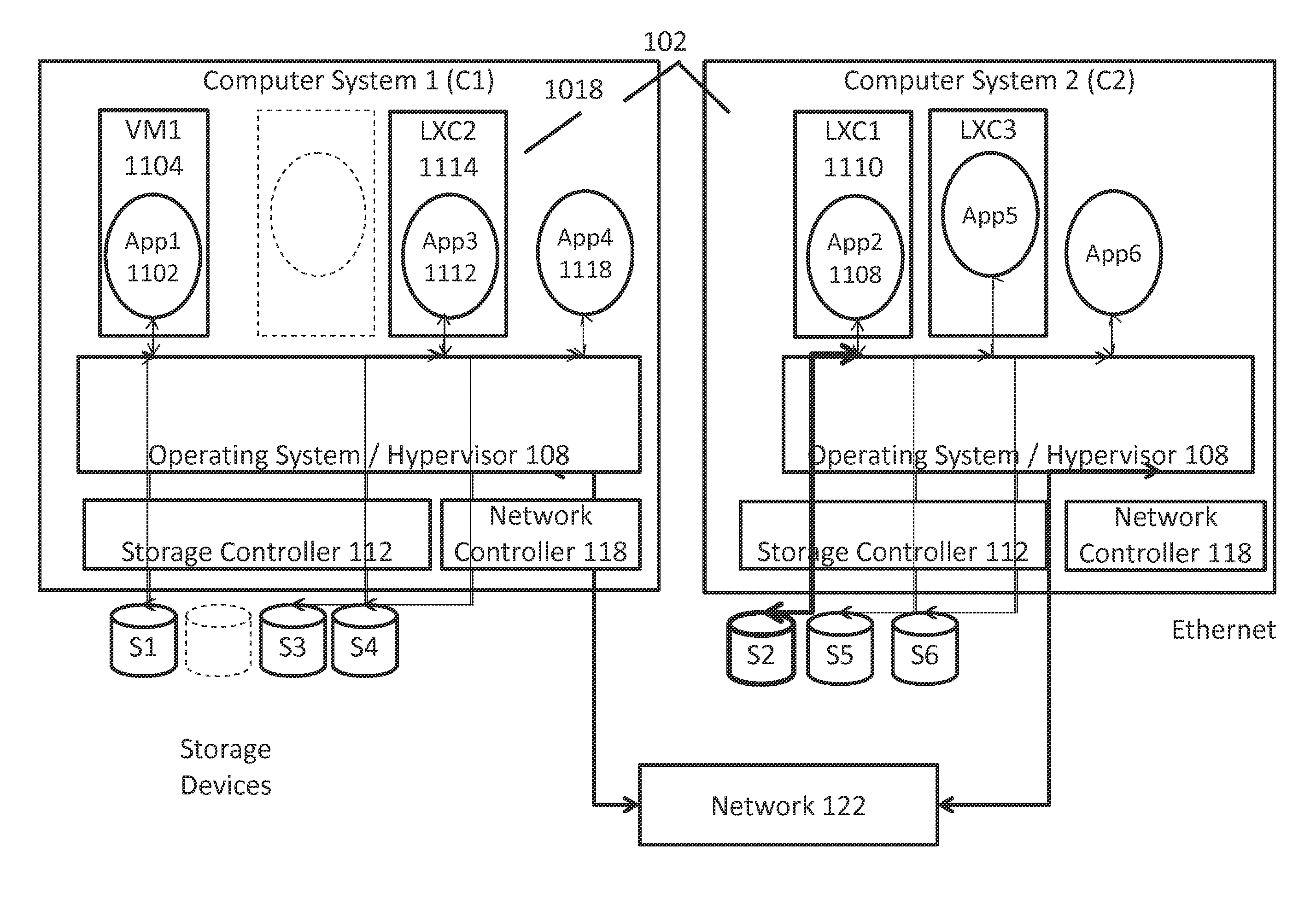
Methods and systems for converged networking and storage
InactiveUS20150254088A1Easy programmingImprove performanceResource allocationDigital computer detailsTraffic capacityNetwork interface controller
A device includes a converged input / output controller that includes a physical target storage media controller, a physical network interface controller and a gateway between the storage media controller and the network interface controller, wherein gateway provides a direct connection for storage traffic and network traffic between the storage media controller and the network interface controller.
Owner:DIAMANTI INC
On-board tool tracking system and methods of computer assisted surgery
InactiveUS20160022374A1The process is feasibleImprove efficiencyDiagnosticsSurgical navigation systemsComputer-assisted surgeryMedicine
A number of improvements are provided relating to computer aided surgery utilizing an on tool tracking system. The various improvements relate generally to both the methods used during computer aided surgery and the devices used during such procedures. Other improvements relate to the structure of the tools used during a procedure and how the tools can be controlled using the OTT device. Still other improvements relate to methods of providing feedback during a procedure to improve either the efficiency or quality, or both, for a procedure including the rate of and type of data processed depending upon a CAS mode.
Owner:TRAK SURGICAL +1
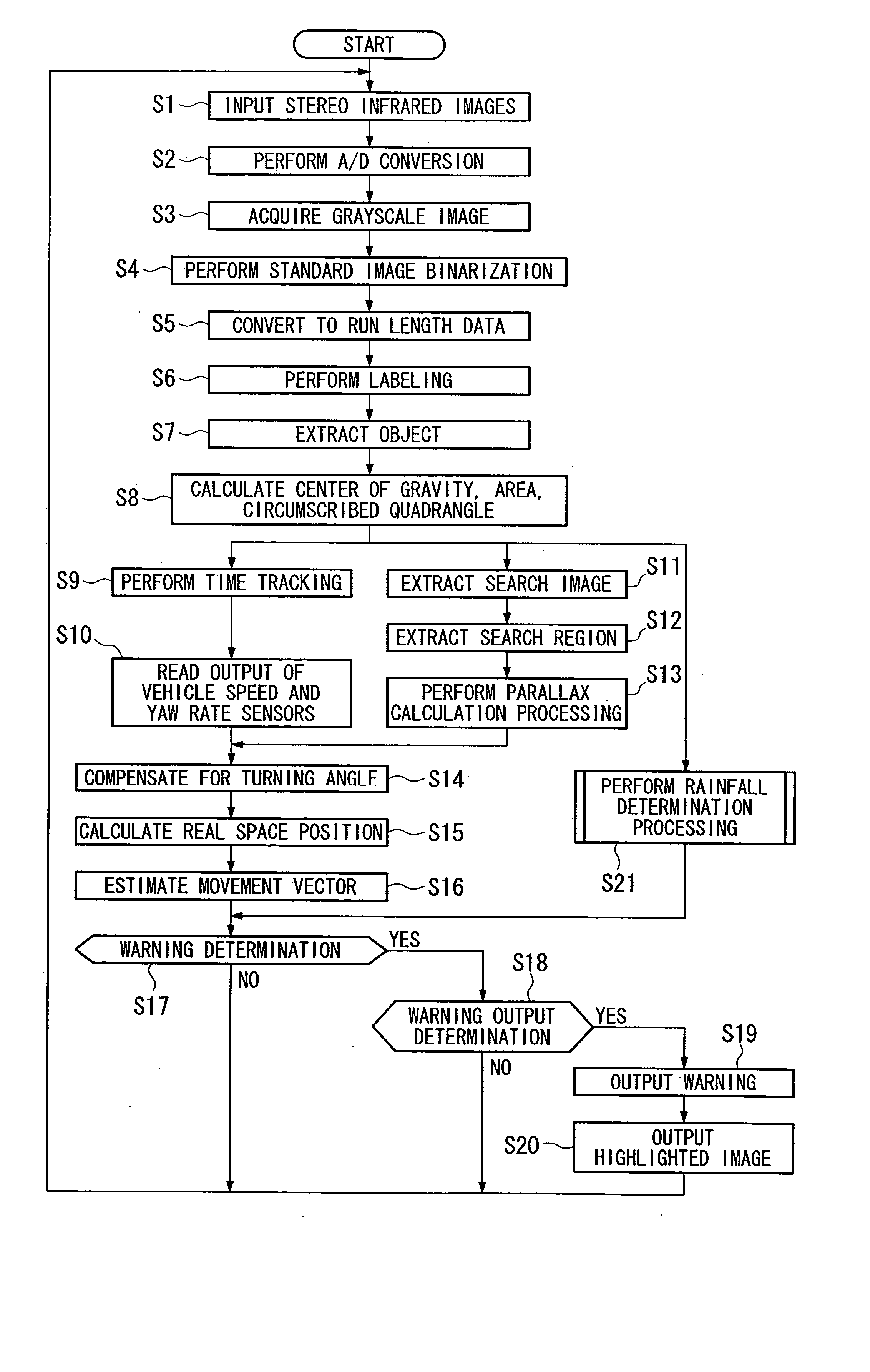
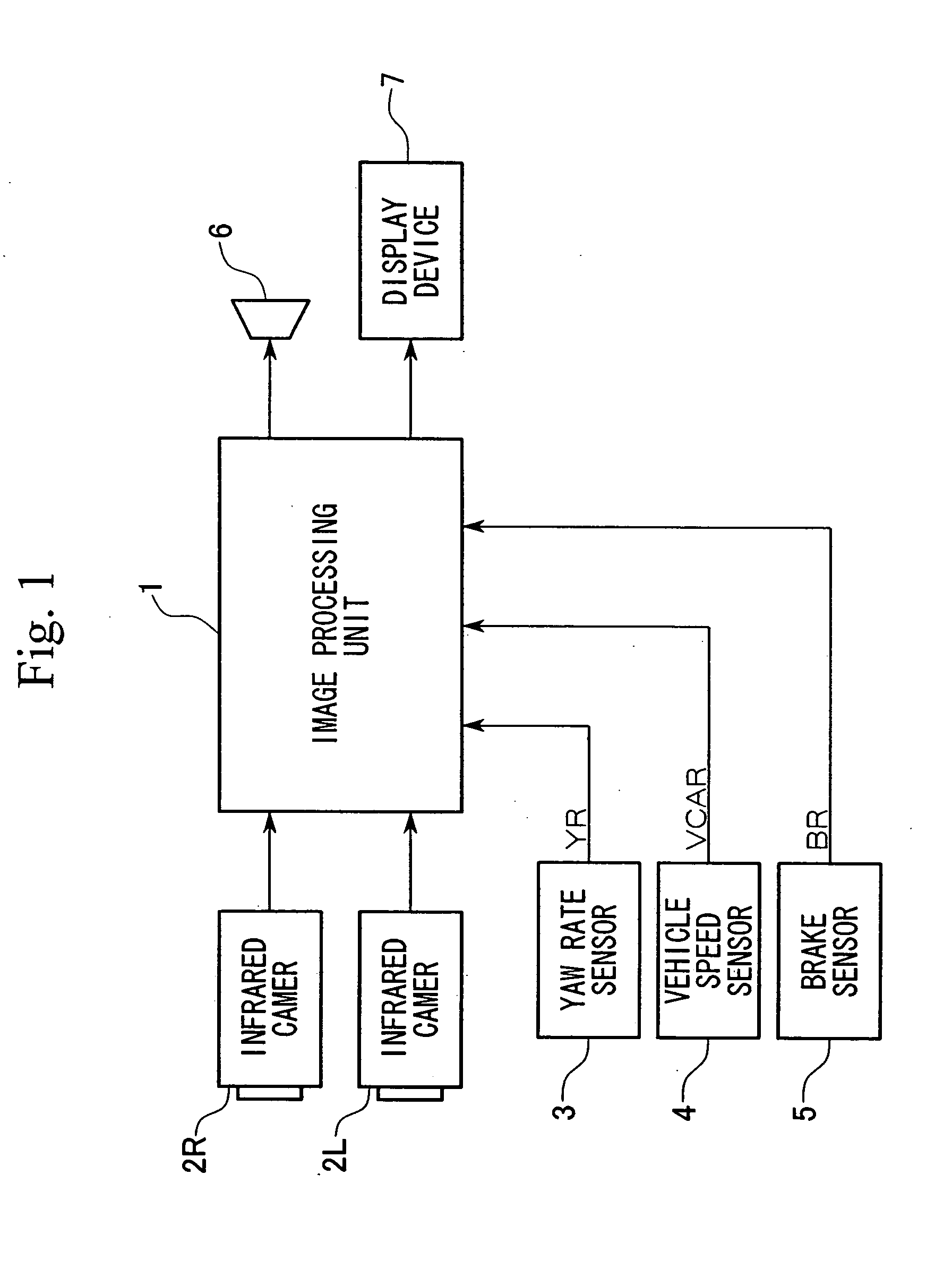
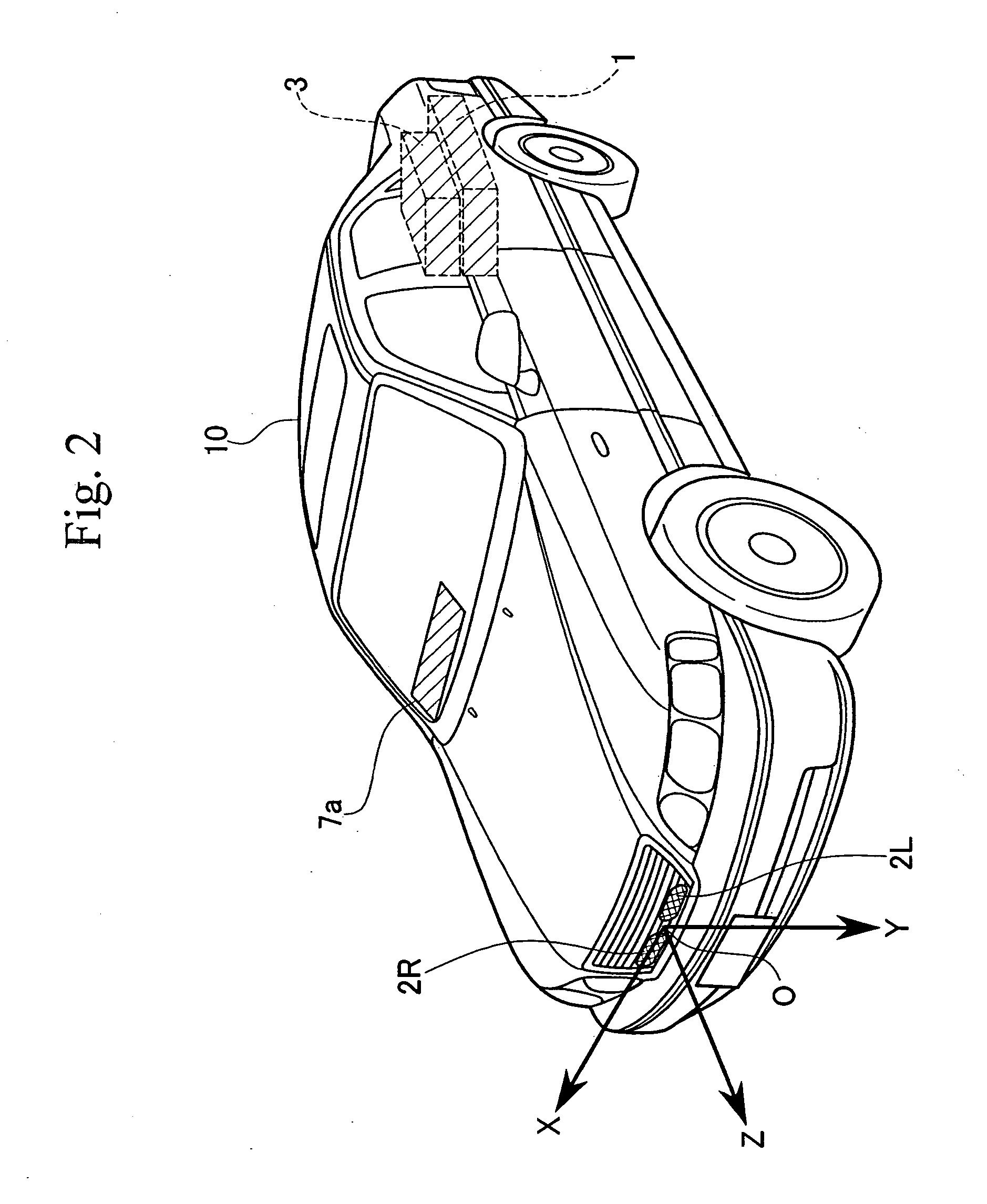
Vehicle environment monitoring device
ActiveUS20050063565A1Improve resource utilizationAccurate judgmentImage enhancementImage analysisHeight differenceState of the Environment
A vehicle environment monitoring device identifies objects from an image taken by an infrared camera. Object extraction from images is performed in accordance with the state of the environment as determined by measurements extracted from the images as follows: N1 binarized objects are extracted from a single frame. Height of a grayscale objects corresponding to one of the binarized objects are calculated. If a ratio of the number of binarized objects C, where the absolute value of the height difference is less than the predetermined value ΔH, to the total number N1 of binarized objects, is greater than a predetermined value X1, the image frame is determined to be rainfall-affected. If the ratio is less than the predetermined value X1, the image frame is determined to be a normal frame. A warning is provided if it is determined that the object is a pedestrian and if a collision is likely.
Owner:ARRIVER SOFTWARE AB
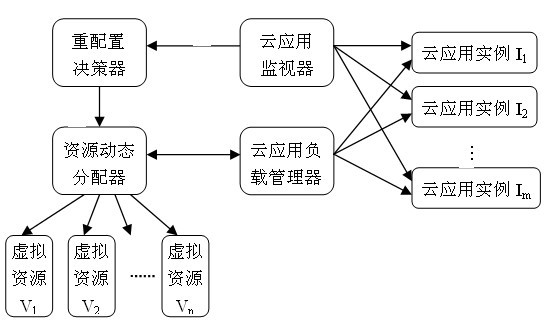
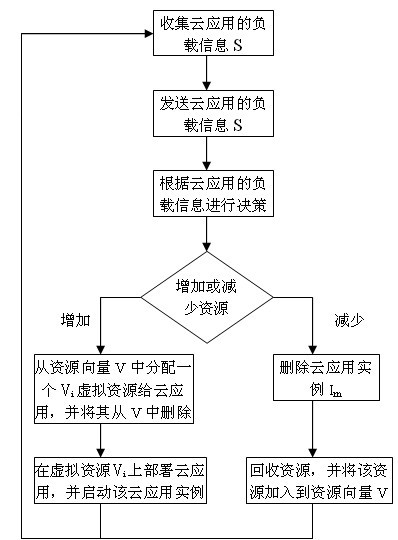
Cloud computing resource scheduling method based on dynamic reconfiguration virtual resources
InactiveCN101938416ADynamic Allocation OptimizationMeeting the Need for Dynamic ScalabilityData switching networksCurrent loadDecision taking
The invention relates to a cloud computing resource scheduling method based on dynamic reconfiguration virtual resources. The method comprises the steps of: using cloud application load information collected by a cloud application monitor as a basis; making a dynamic decision based on the load capacity of the virtual resources for running cloud application and the current load of the cloud application; and dynamically reconfiguring virtual resources for cloud application based on the decision result. Dynamic adjustment of resources is realized by a method for reconfiguring virtual resources for cloud application, without needing dynamic redistribution of physical resources or stopping executing cloud application. The method can dynamically reconfigure the virtual resources according to the load variation of the cloud application, optimize allocation of the cloud computing resources, realize effective use of the cloud computing resources, and meet the requirements on dynamic scalability of cloud application. In addition, the method can avoid waste of the cloud computing resources, and save the cost for using resources for cloud application users.
Owner:SOUTH CHINA UNIV OF TECH
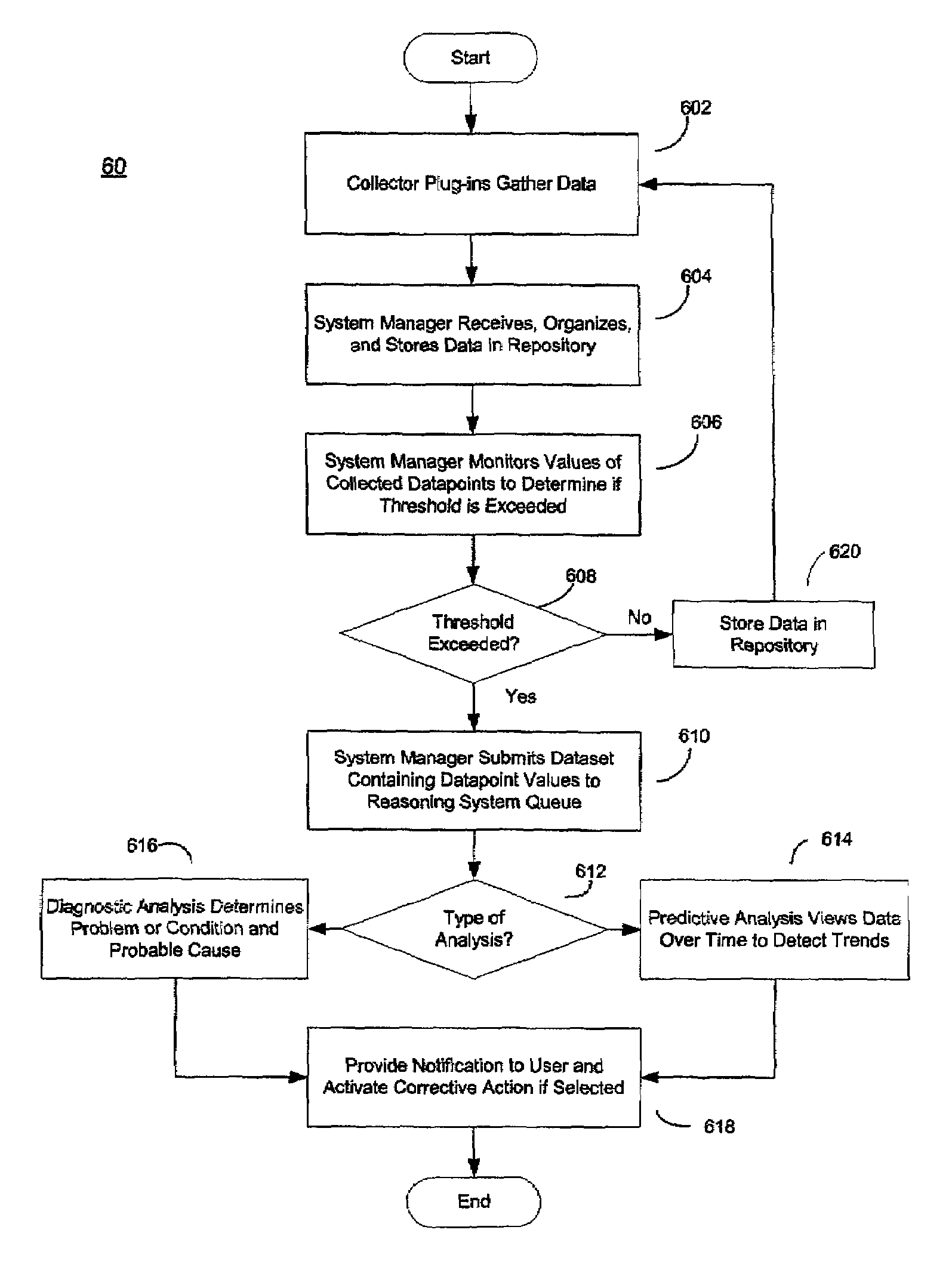
System and method for business systems transactions and infrastructure management
InactiveUS7065566B2Increase costImprove performanceDigital computer detailsBuying/selling/leasing transactionsSecure communicationCollection system
The system and method for business systems transactions and infrastructure management includes a client side collection system and a server side system having the capability to communicate with the other over a secure communication path. The collection system extracts transaction and infrastructure data from a business system and transmits the extracted data to the management server over a secure communication path. The management server receives the extracted data over the secure communication path, compares it to threshold analyzes the data that exceed threshold values, and notifies a user of the results of the analysis. The management server also has the capability to activate corrective scripts in the client business system and to reconfigure the client business system.
Owner:CA TECH INC
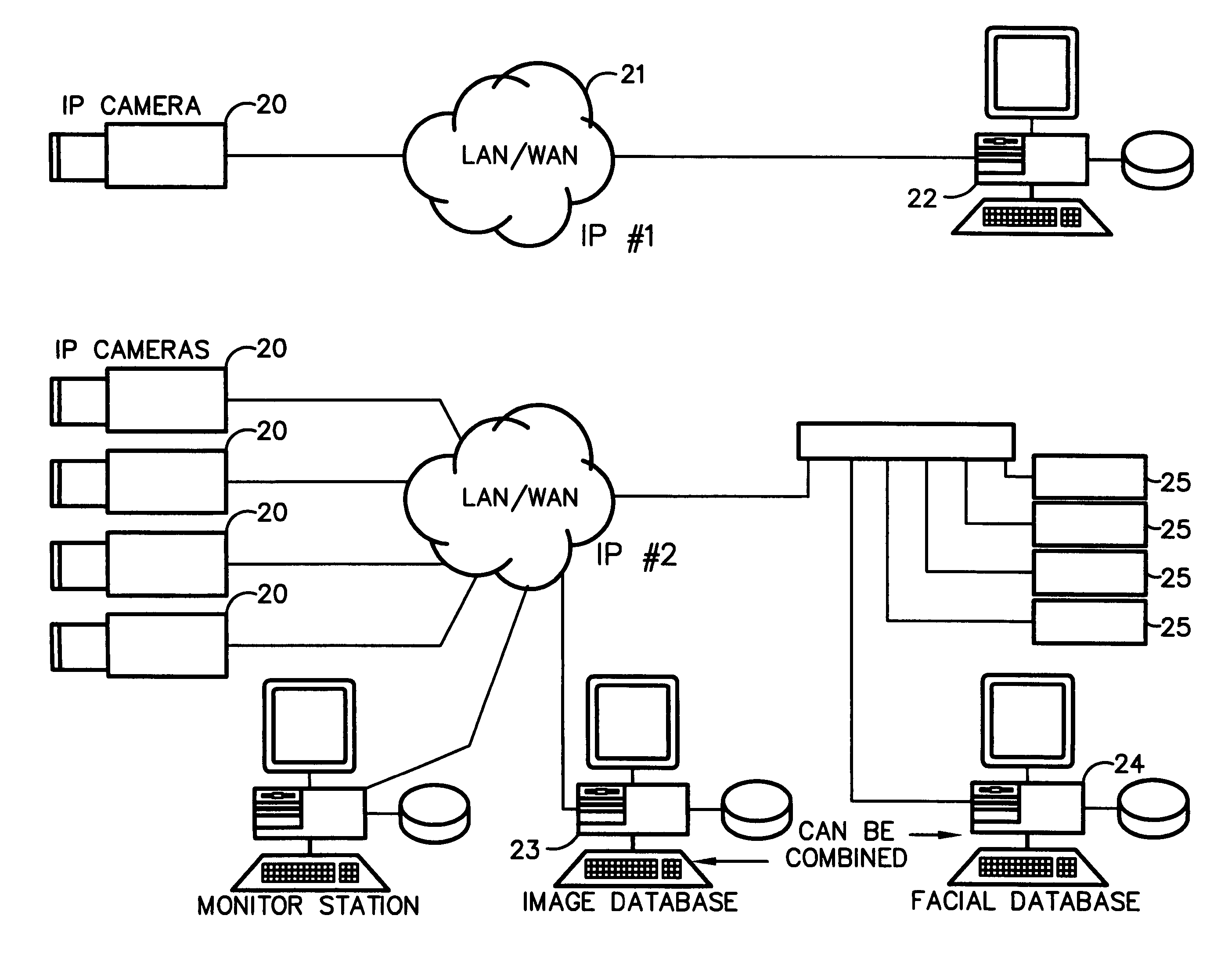
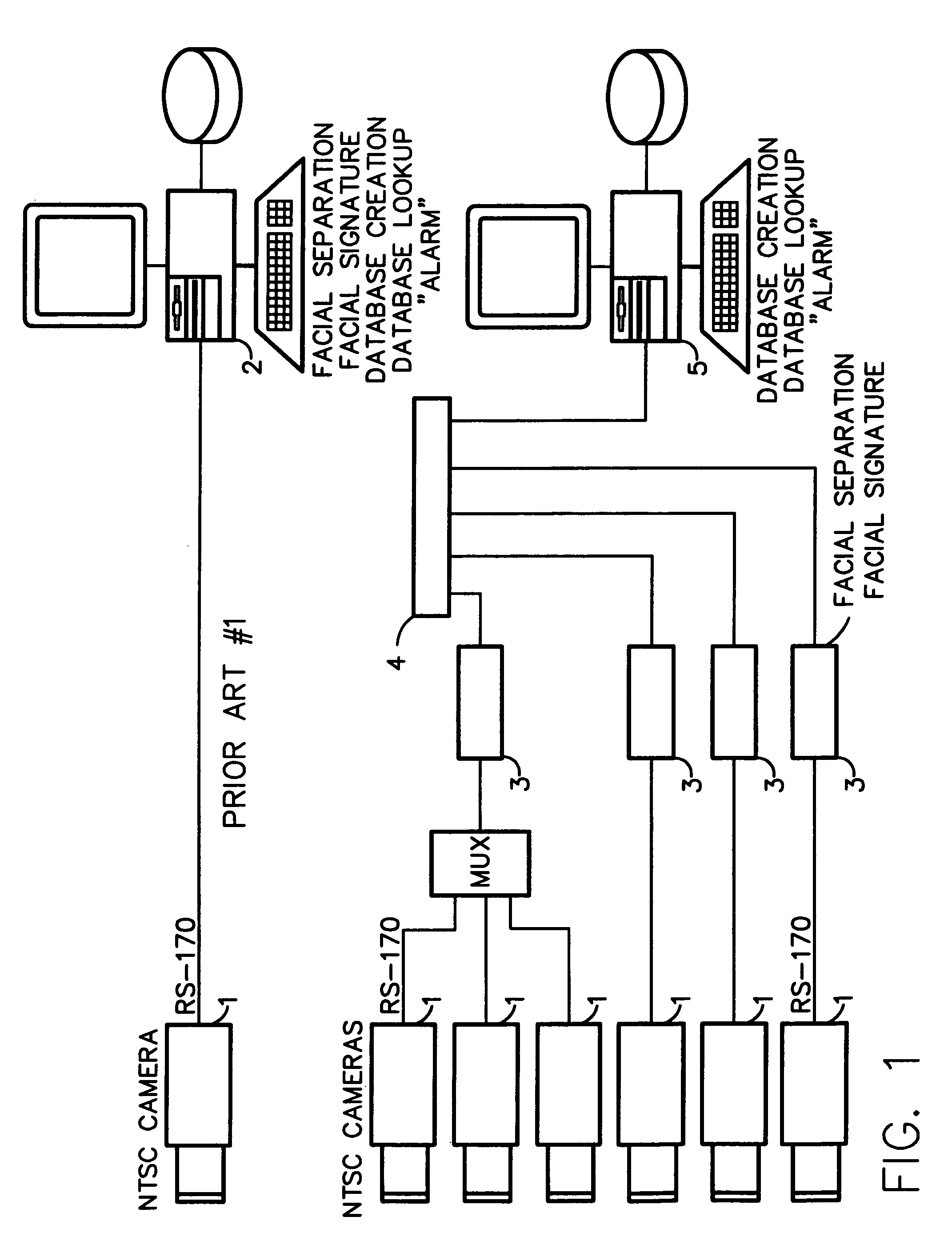
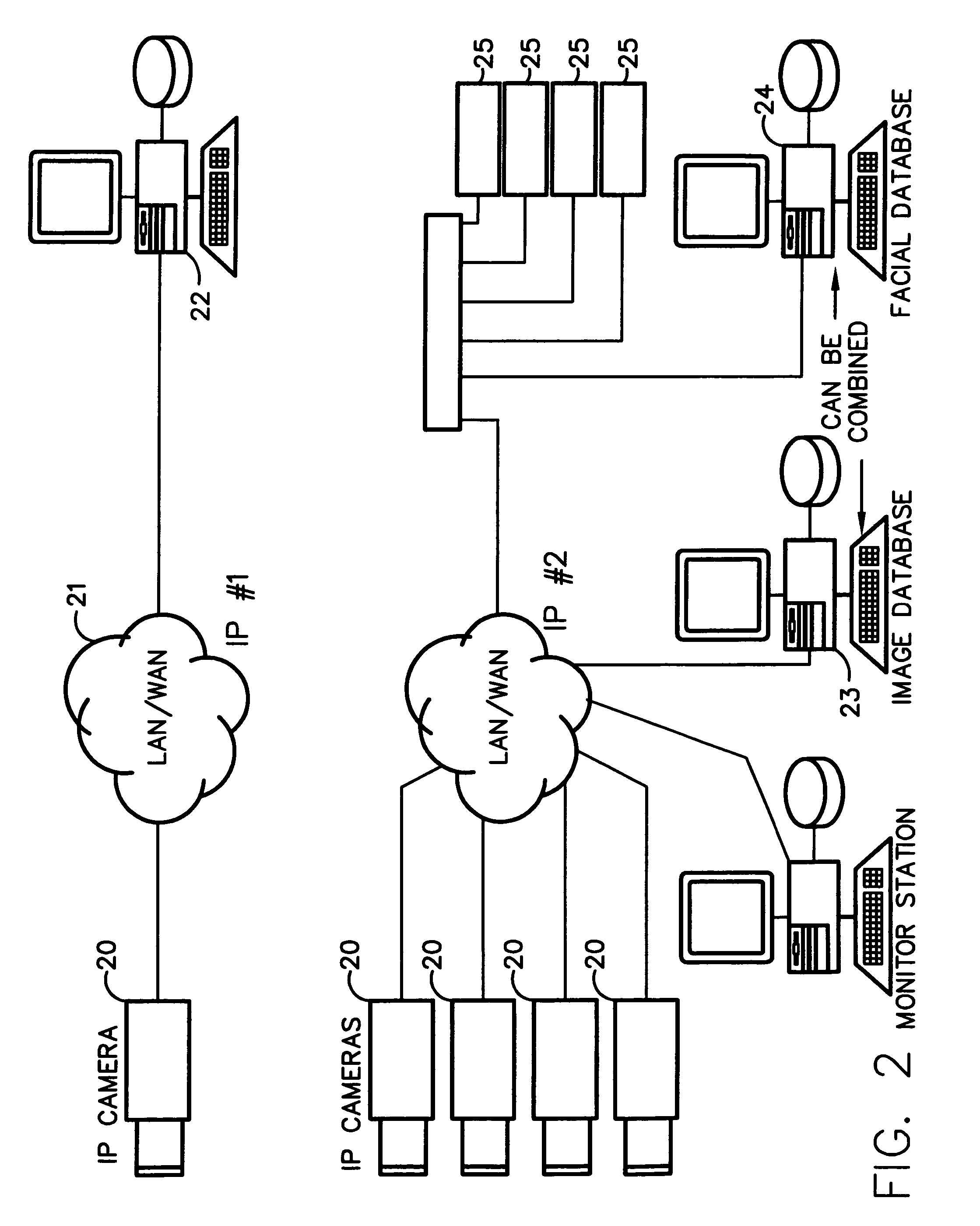
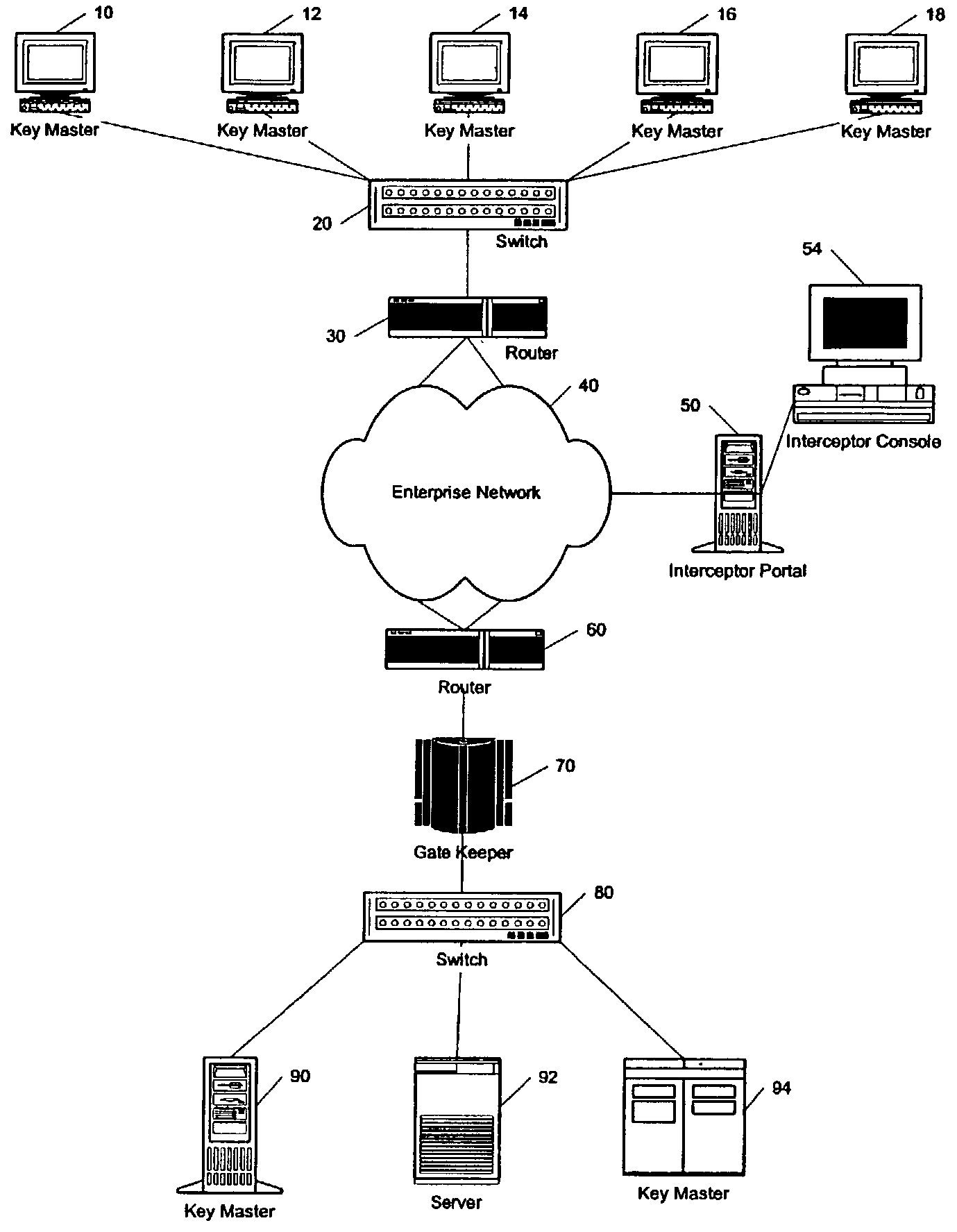
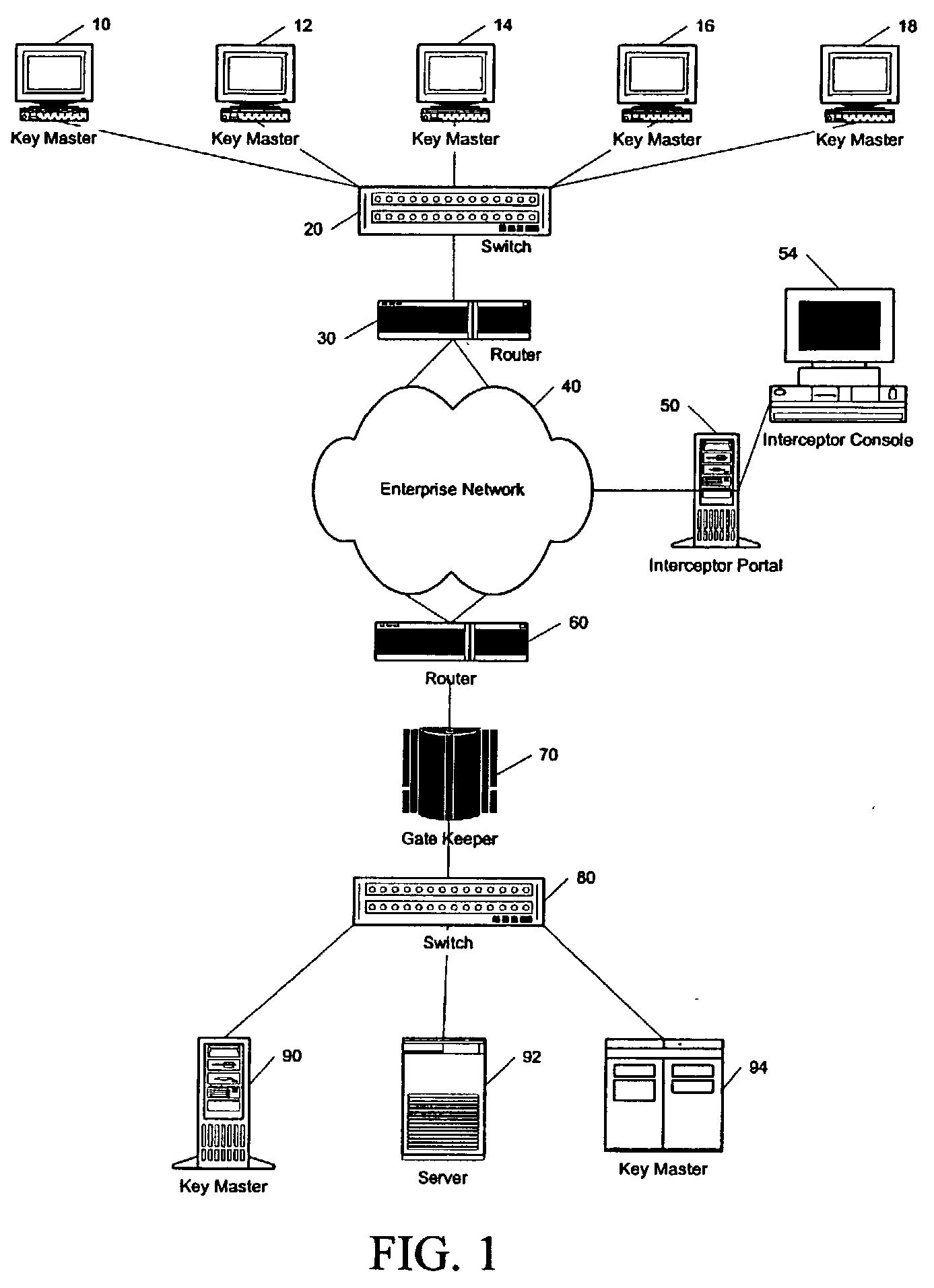
Method for incorporating facial recognition technology in a multimedia surveillance system
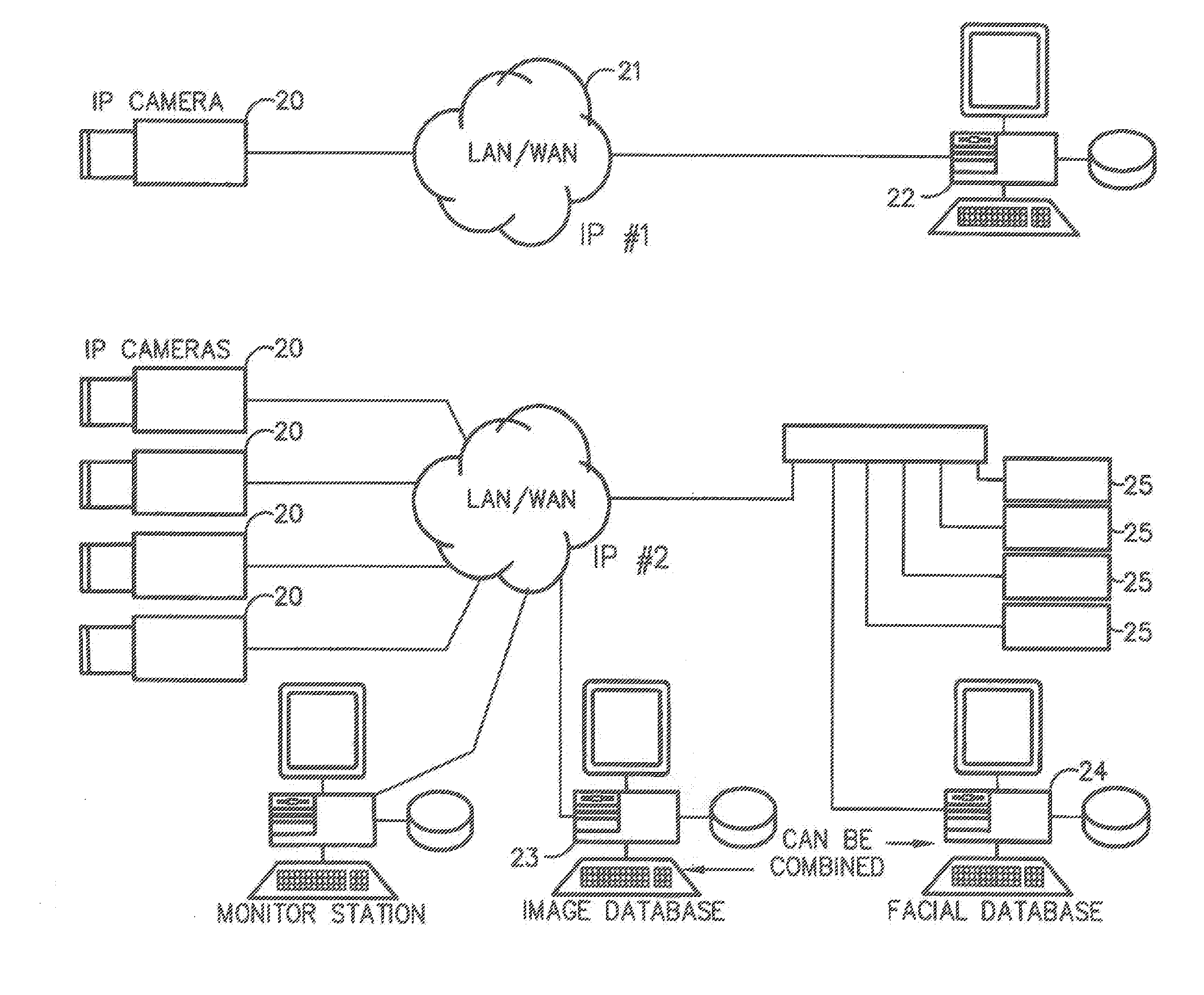
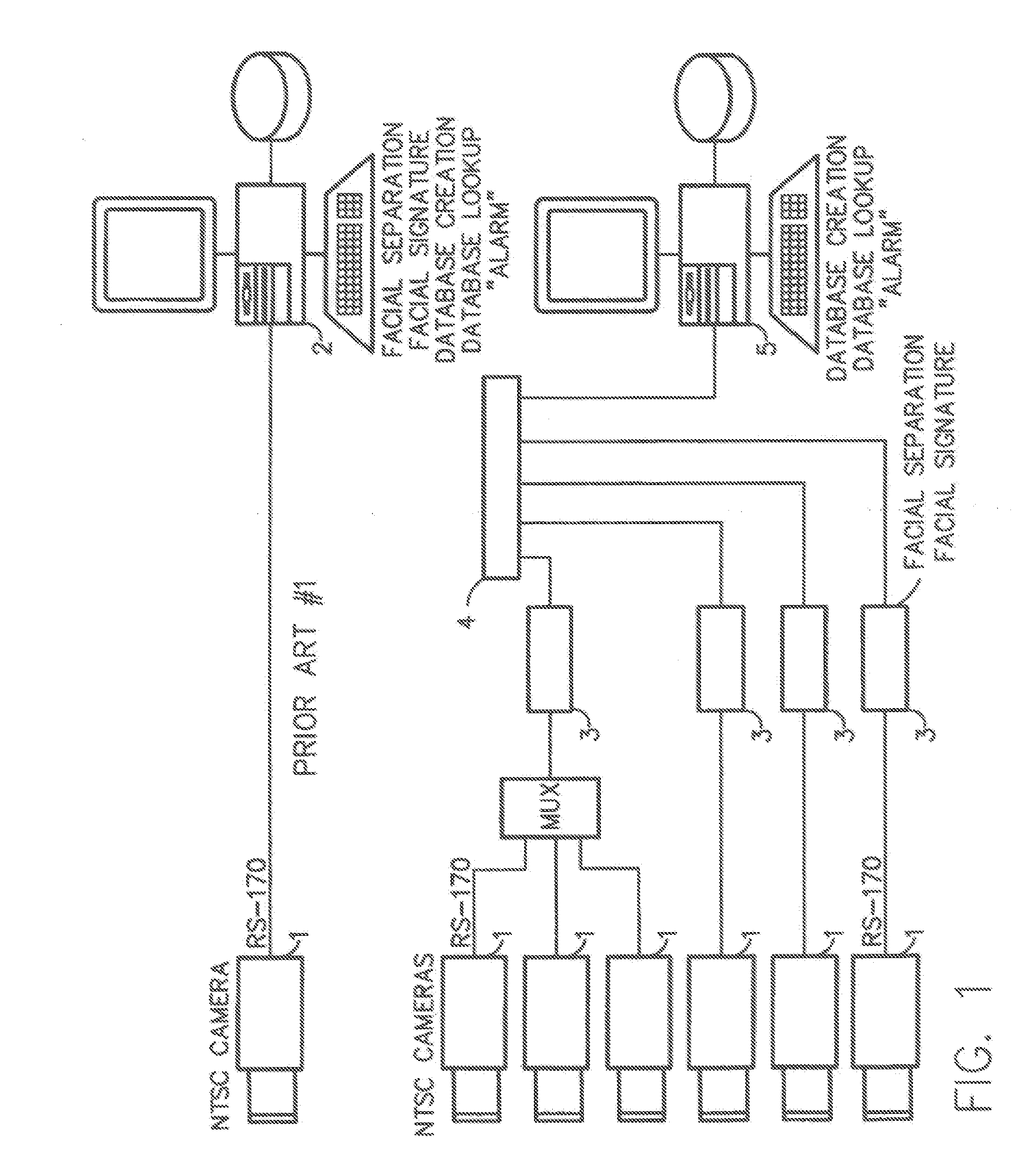
InactiveUS7634662B2Function increaseImprove economyChecking time patrolsCharacter and pattern recognitionSurveillance cameraRecognition algorithm
Embodiment provide a surveillance camera adapted to be connected to an internet protocol network, the surveillance camera including at least one facial processor, at least one facial recognition algorithm embodied in suitable media, at least one facial recognition algorithm executable with digital format image data by at least one facial processor detecting faces, execution of at least one facial recognition algorithm producing unique facial image data, execution of at least one facial separation algorithm producing facial separation data, at least one facial processor in communication with at least one facial signature database to obtain reference data, execution of at least one facial signature algorithm comparing facial separation data and reference data to identify correlations, at least one compression algorithm producing compressed image data, and a network stack configured to transmit to the network unique facial image data for each detected face and compressed image data.
Owner:PR NEWSWIRE
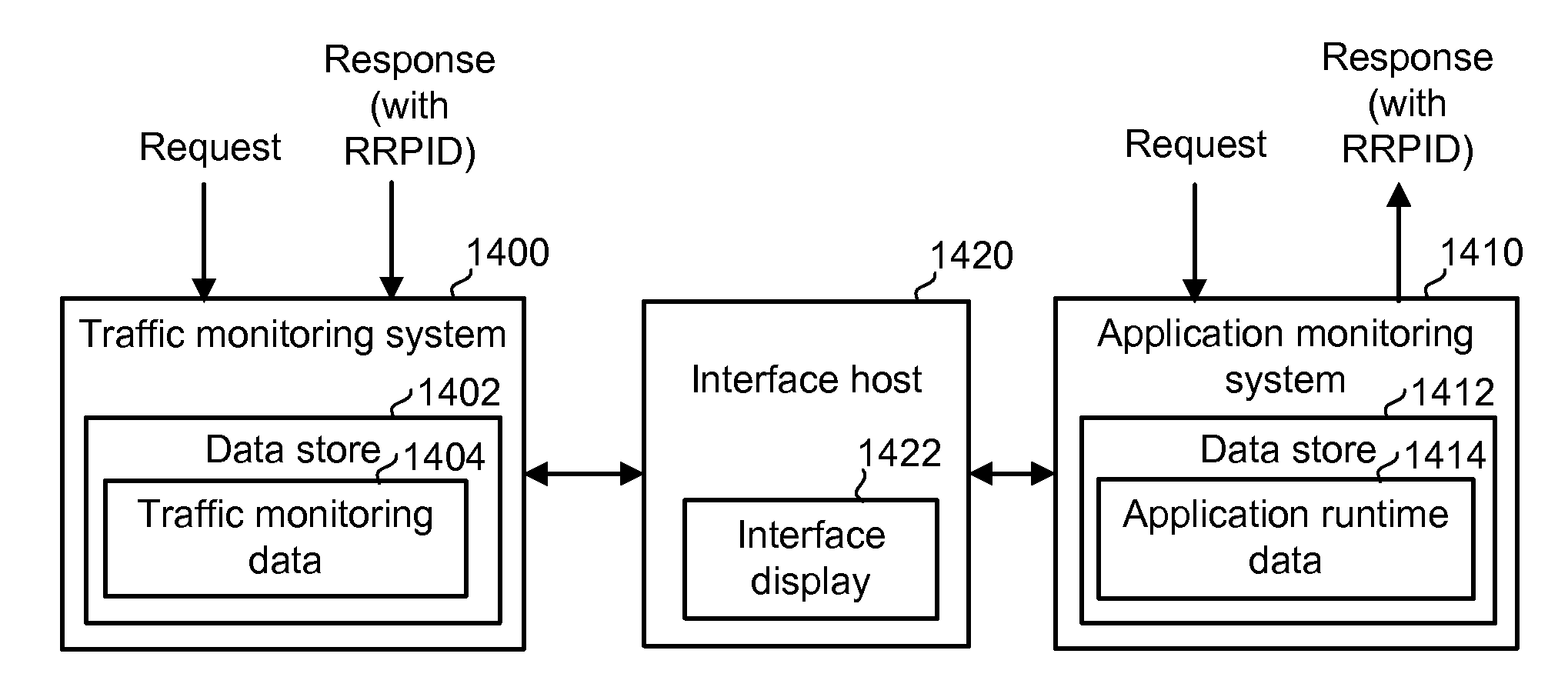
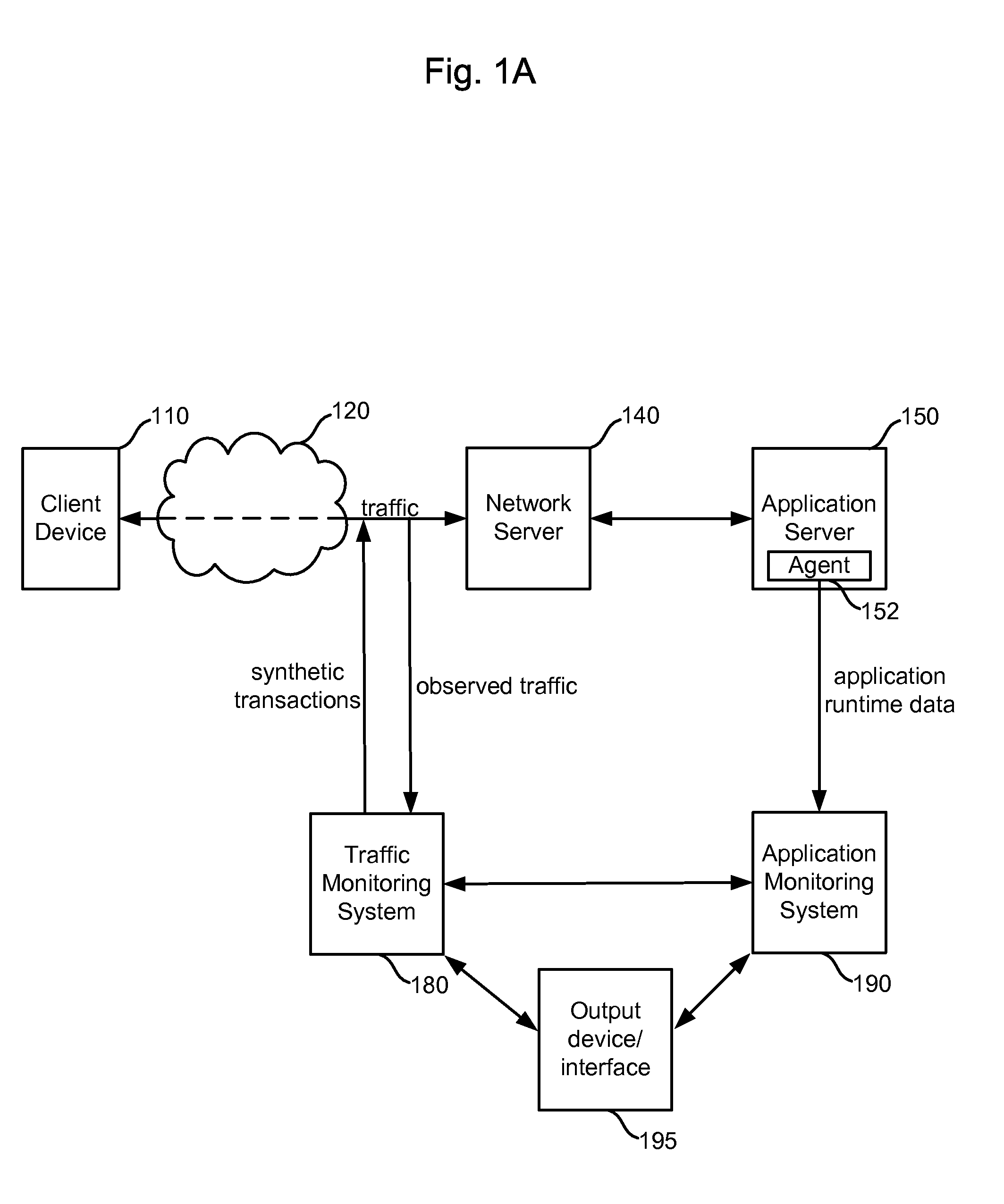
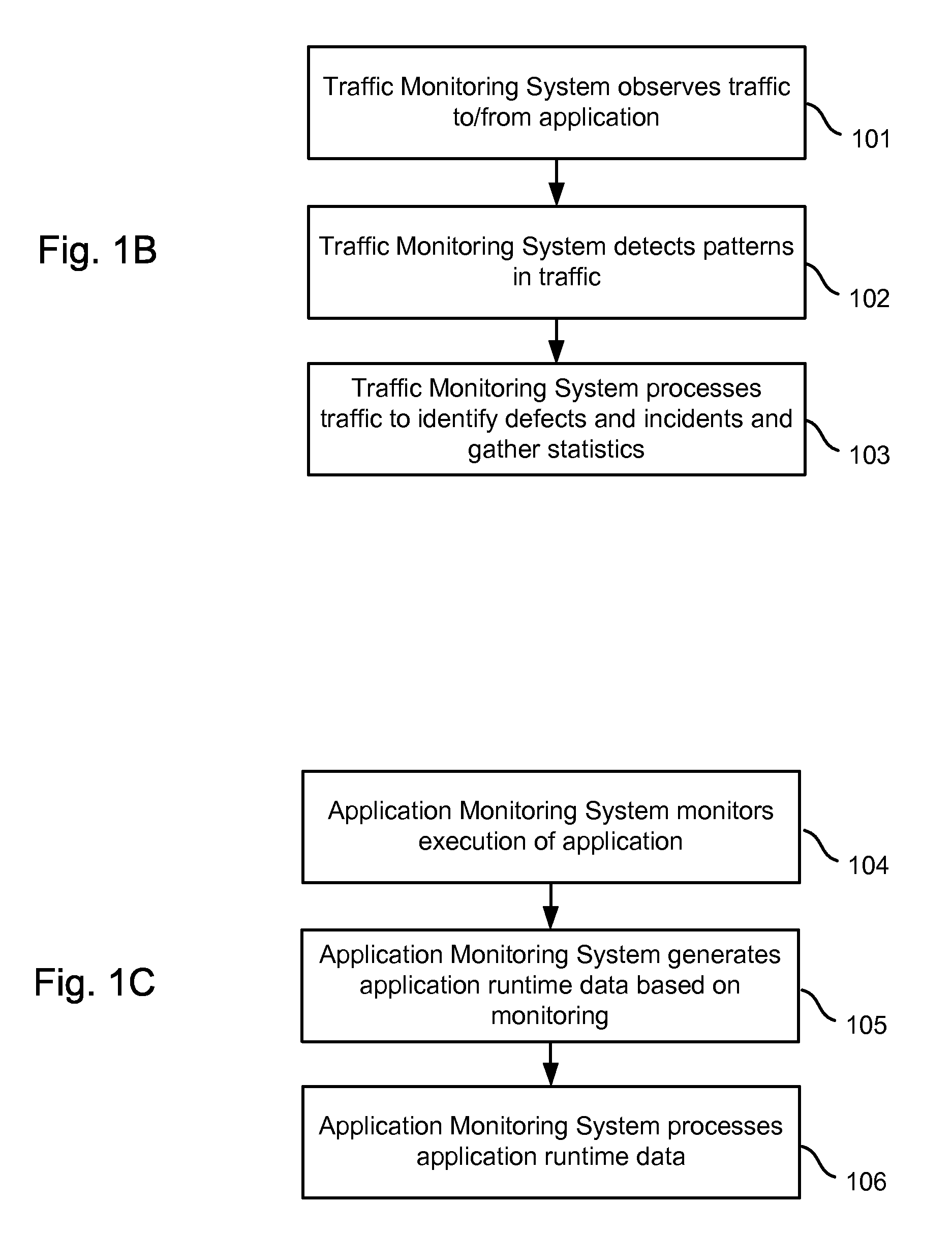
Integrating traffic monitoring data and application runtime data
ActiveUS20070266149A1Enhance capacity planningImprove rendering capabilitiesDigital computer detailsTransmissionTraffic capacityData information
Information is obtained from an application monitoring system which monitors the execution of an application and a traffic monitoring system which monitors traffic between clients and the application. The clients interact with the application to perform transactions or other tasks. Traffic monitoring data, such as information regarding defects and incidents, and application runtime data, such as traces of invoked application components, can be integrated in an output such as an interface to provide an enhanced understanding of system performance. Related traffic monitoring data and application runtime data can be linked by a request-response pair identifier associated with a request provided to the application and a response provided by the application.
Owner:CA TECH INC
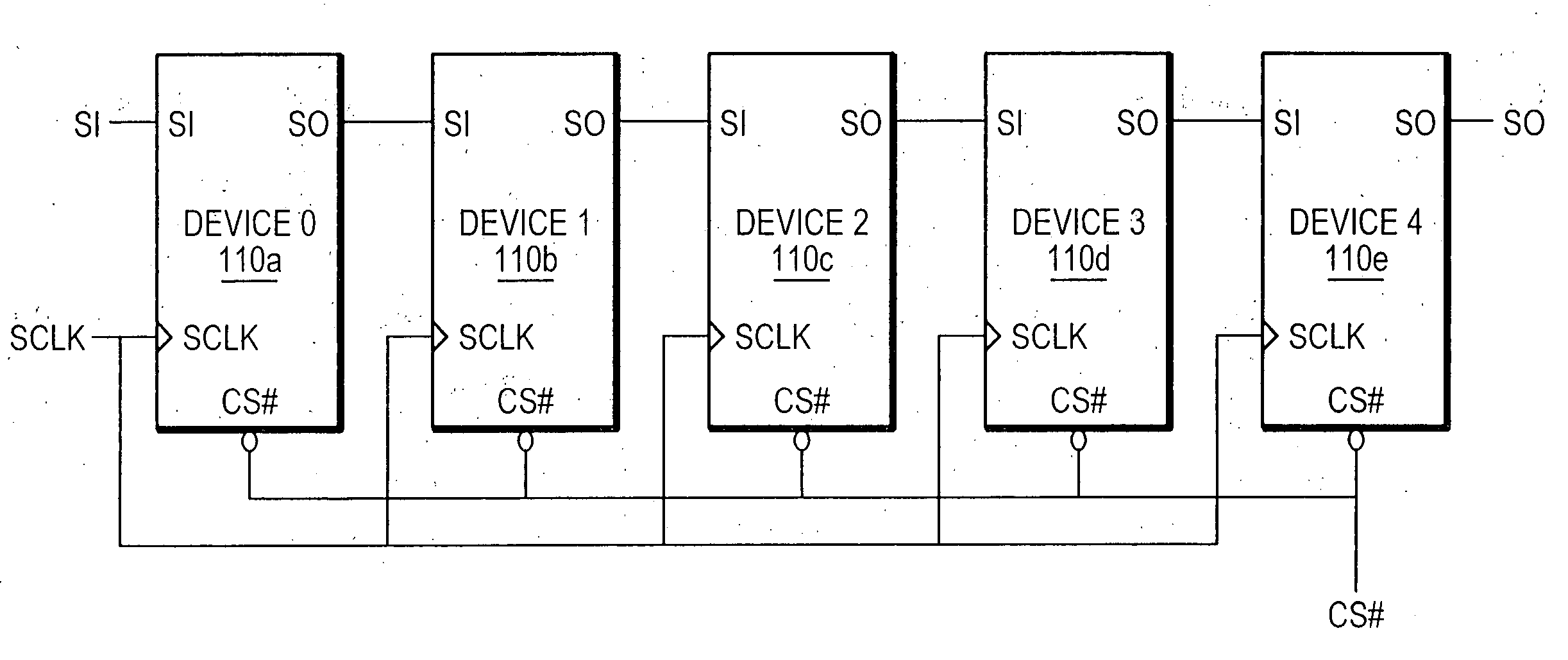
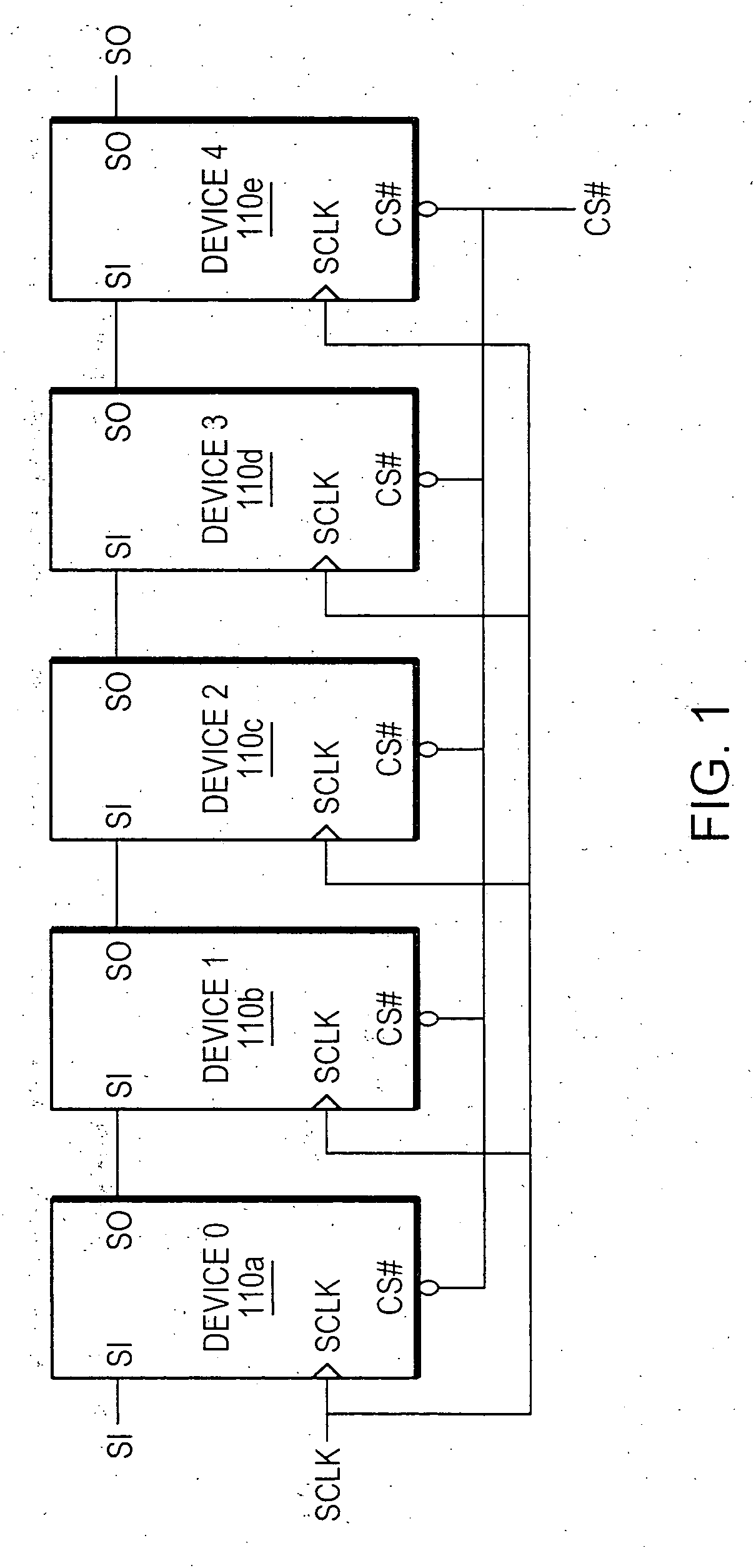
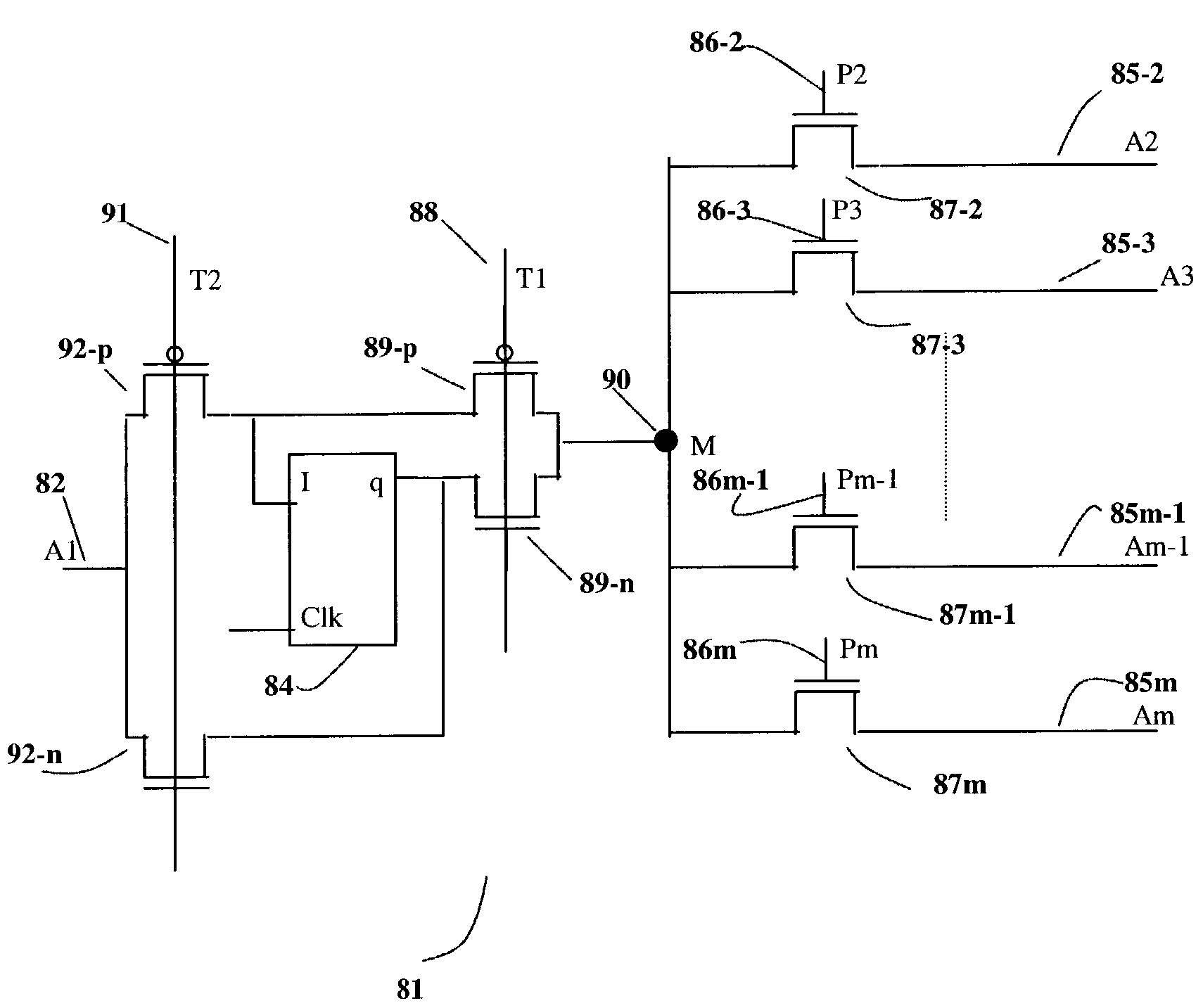
Daisy chain cascading devices
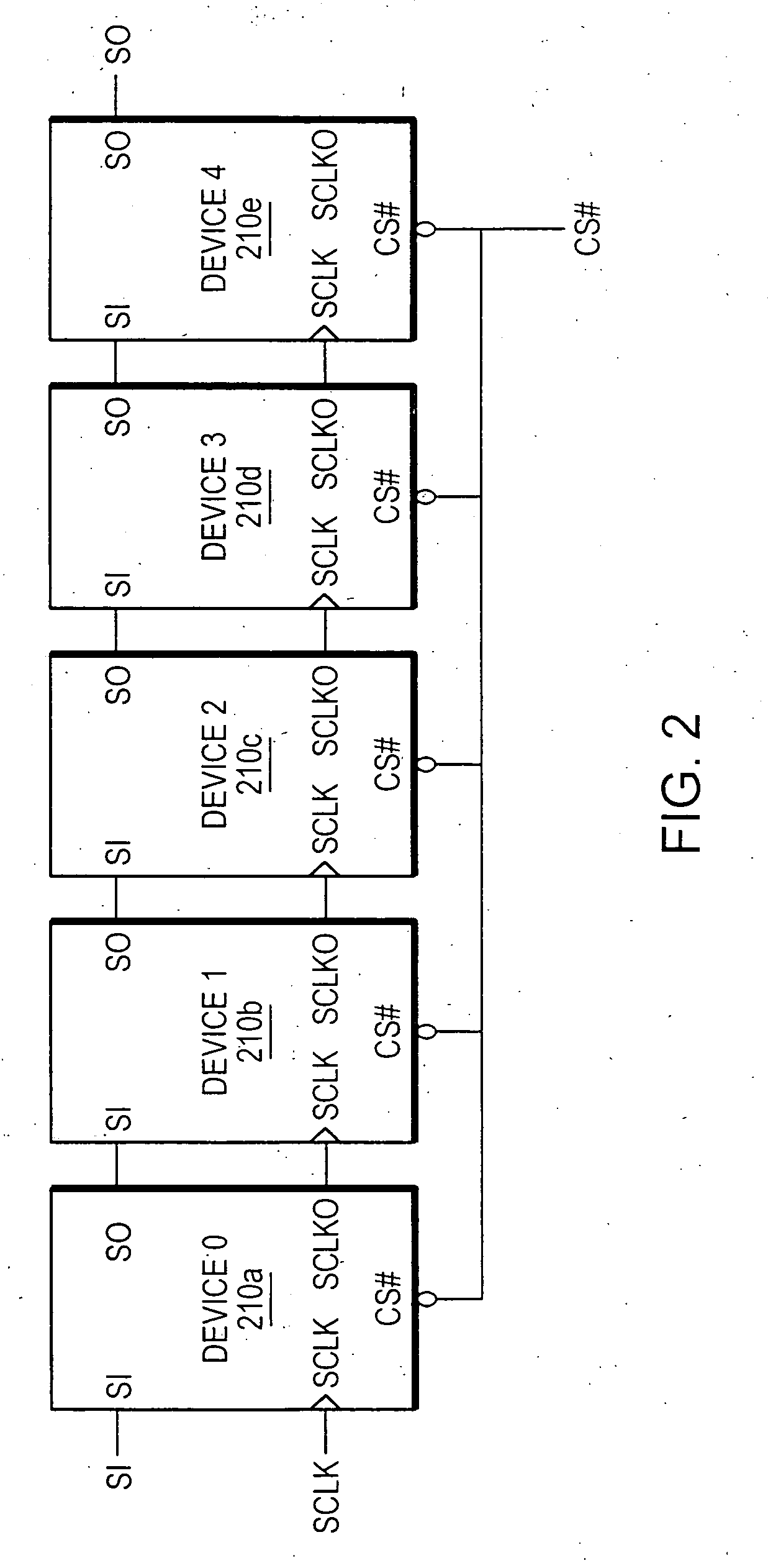
ActiveUS20070109833A1Few and short connectionIncrease speedRead-only memoriesDigital storageComputer hardwareControl signal
A technique for serially coupling devices in a daisy chain cascading arrangement. Devices are coupled in a daisy chain cascade arrangement such that outputs of a first device are coupled to inputs of a second device later in the daisy chain to accommodate the transfer of information, such as data, address and command information, and control signals to the second device from the first device. The devices coupled in the daisy chain comprise a serial input (SI) and a serial output (SO). Information is input to a device via the SI. The information is output from the device via the SO. The SO of an earlier device in the daisy chain cascade is coupled to the SI of a device later in the daisy chain cascade. Information input to the earlier device via the device's SI is passed through the device and output from the device via the device's SO. The information is then transferred to the later device's SI via the connection from the earlier device's SO and the later device's SI.
Owner:MOSAID TECH
Method for Incorporating Facial Recognition Technology in a Multimedia Surveillance System
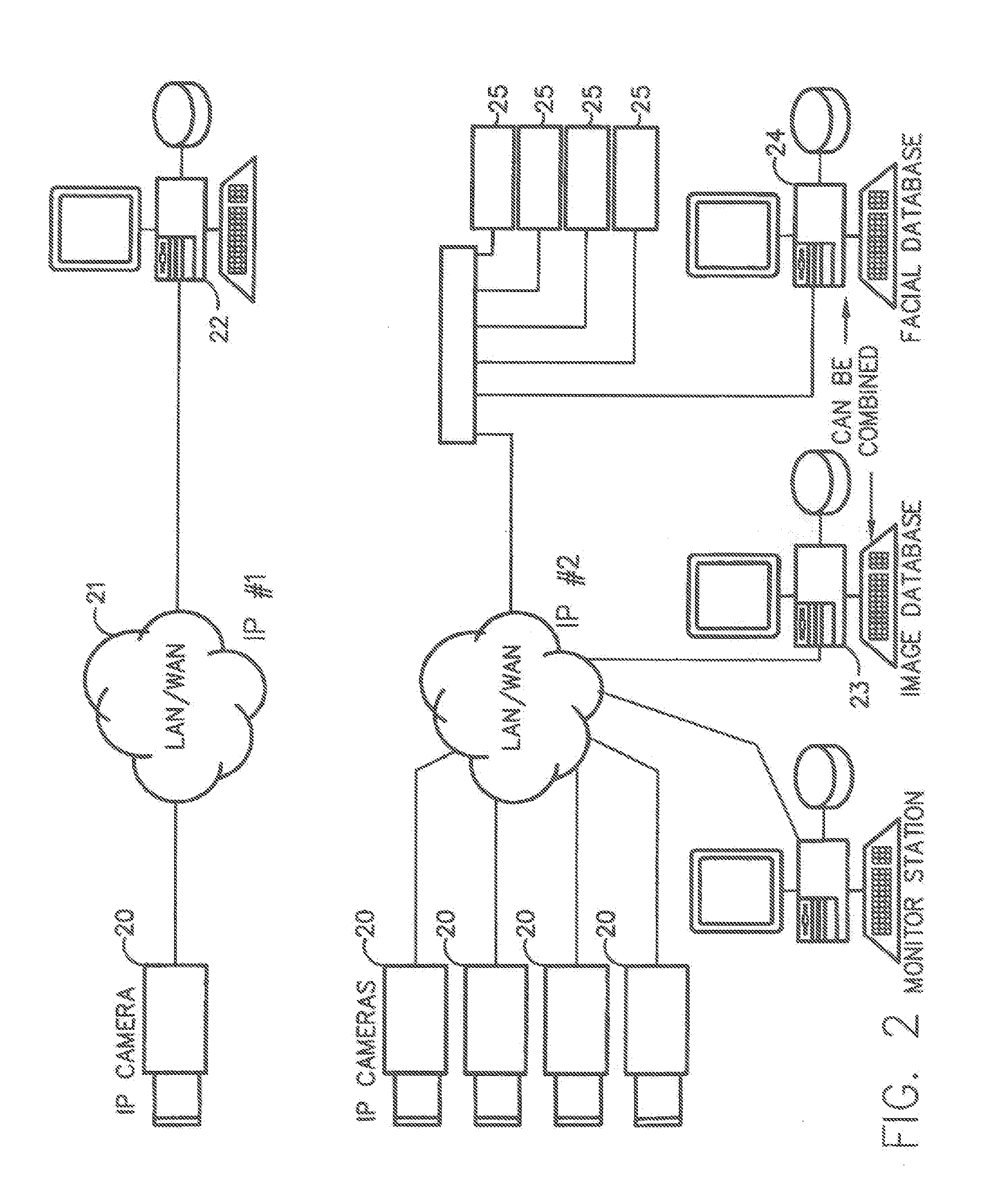
InactiveUS20100111377A1Function increaseImprove economyChecking time patrolsChecking apparatusMonitoring systemRecognition algorithm
Embodiments provide a surveillance system having at least one camera adapted to produce an IP signal, the at least one camera having an image collection device configured for collecting image data, the at least one camera having at least one facial processor configured to execute with digital format image data at least one facial recognition algorithm, execution of the at least one facial recognition algorithm with the digital format image data detecting faces when present in the digital format image data, execution of the at least onefacial recognition algorithm providing for each detected face at least one set of unique facial image data.
Owner:MONROE DAVID A
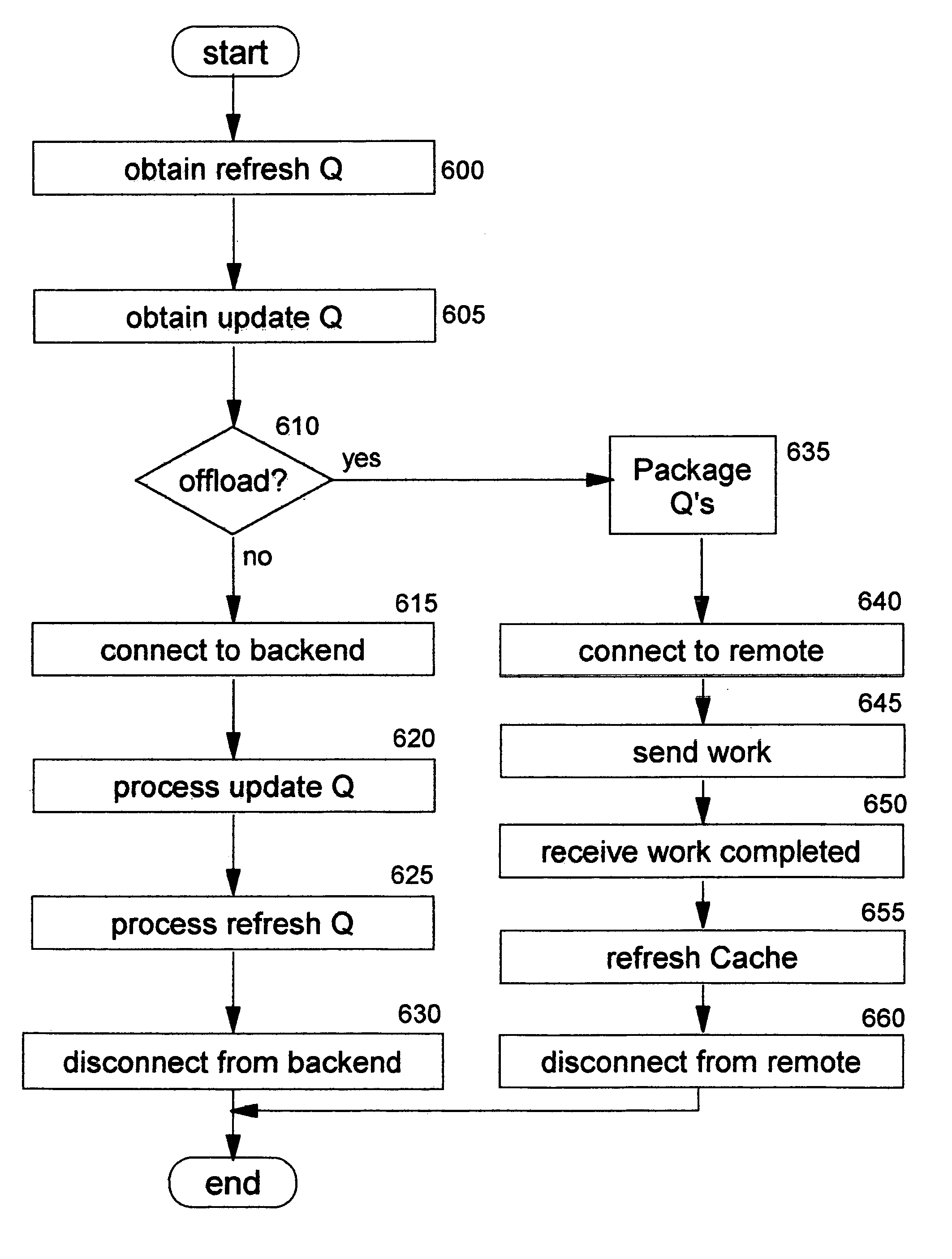
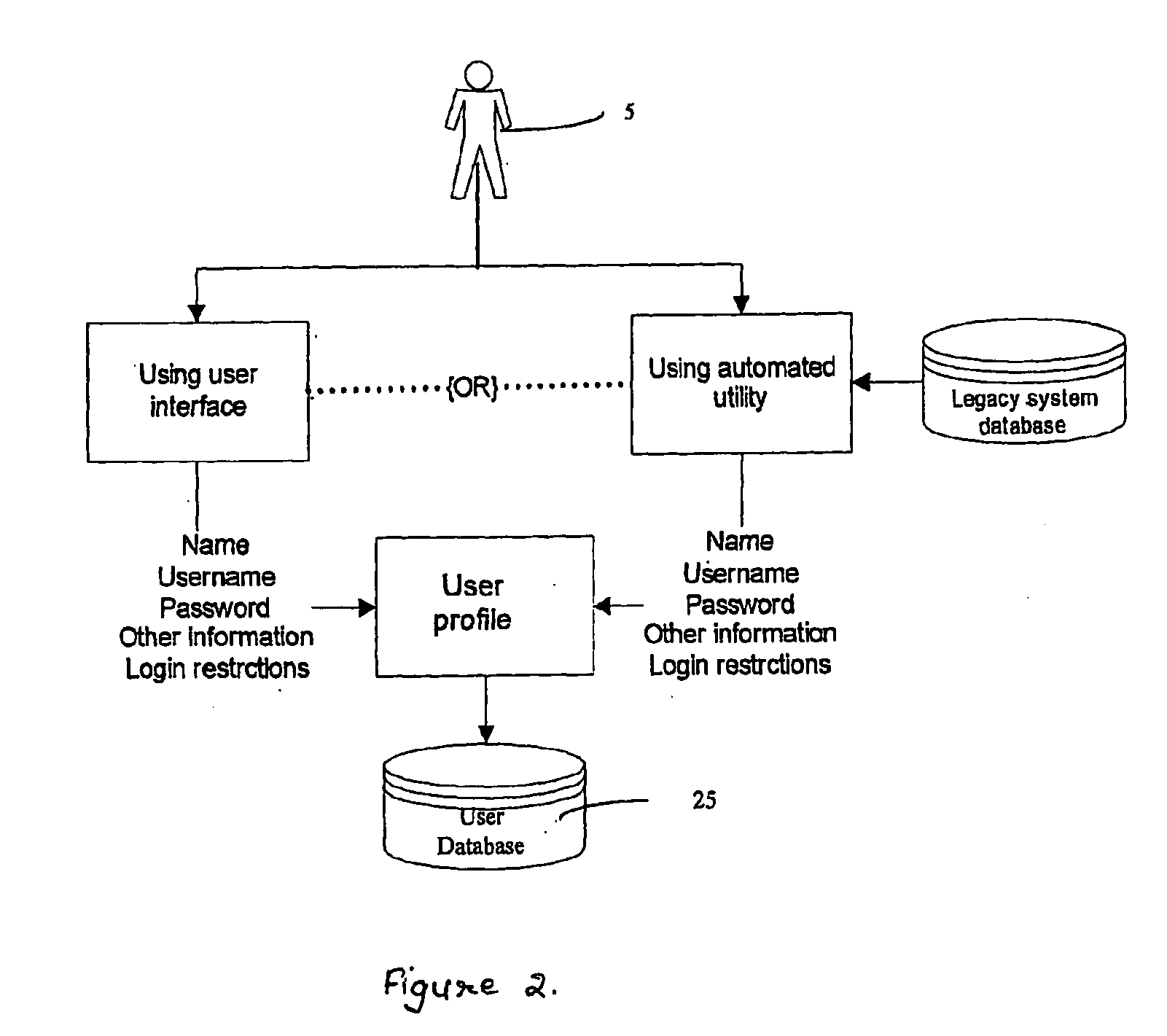
Object caching and update queuing technique to improve performance and resource utilization
InactiveUS7099926B1Improve performanceIncrease resourcesData processing applicationsDigital data information retrievalResource utilizationData source
The present invention provides a method, system, and computer program product for caching objects to improve performance and resource utilization of software applications which interact with a back-end data source, such as a legacy host application and / or legacy host data store or database. Read-only requests for information are satisfied from the cache, avoiding the overhead of a network round-trip and the computing overhead of repeating an interaction with the back-end data source. Refreshes of cached objects and update requests to objects may be queued for delayed processing (for example, at a time when the system is lightly loaded), thereby improving system resource utilization. A sequence of actions that may be required to initiate, and interact with, the refresh and update processes is also preferably stored in the cached objects. This technique is applicant-independent, and may therefore be used for objects having an arbitrary format.
Owner:IBM CORP
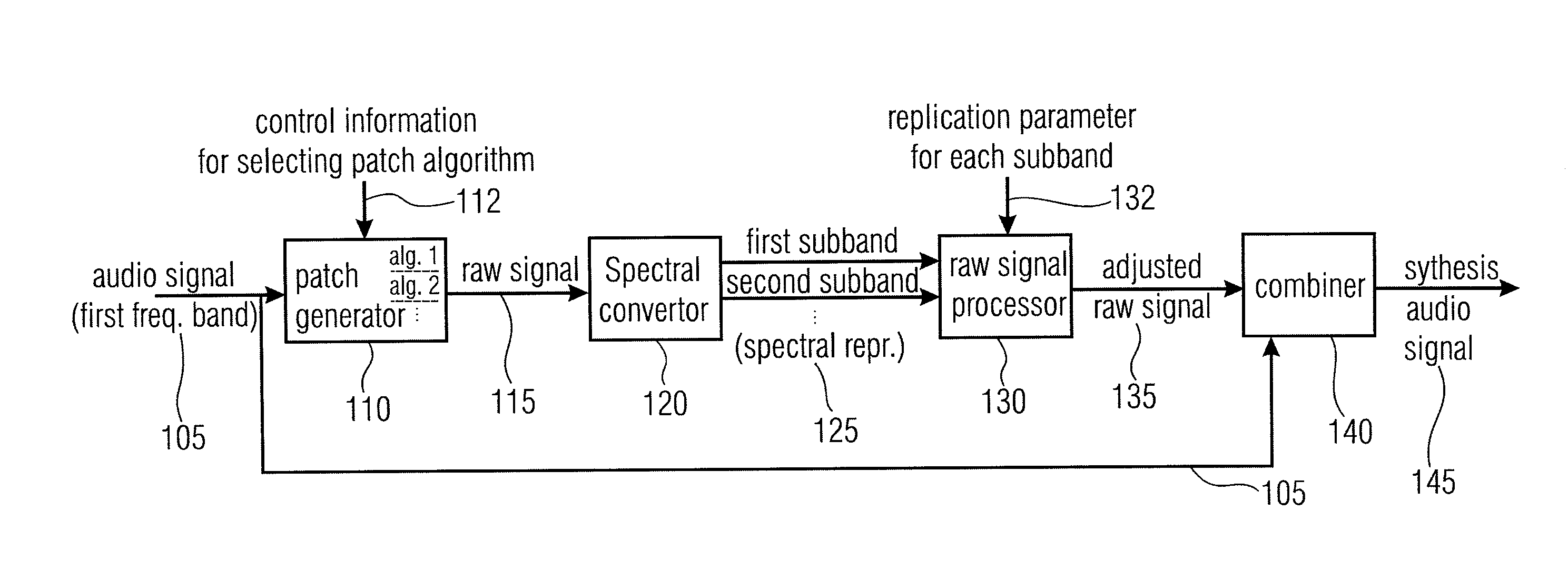
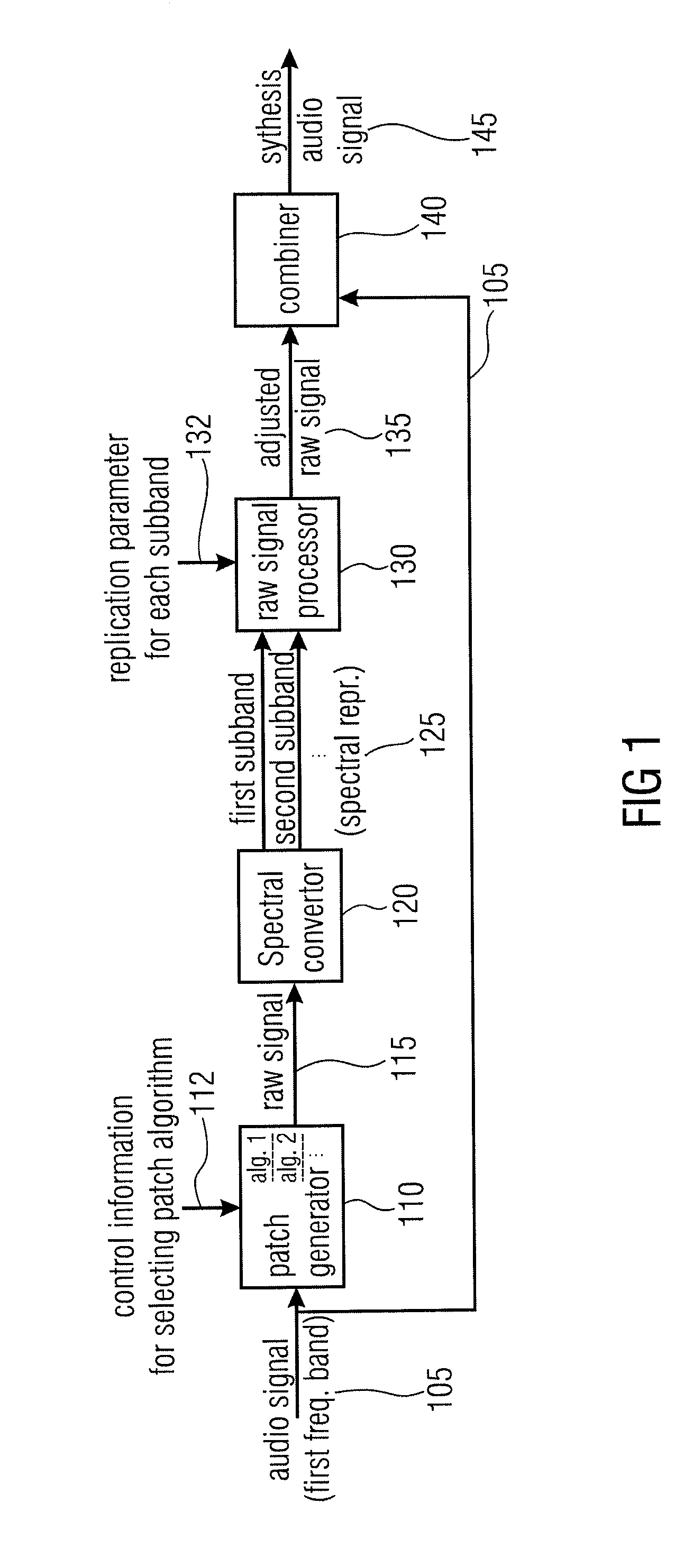
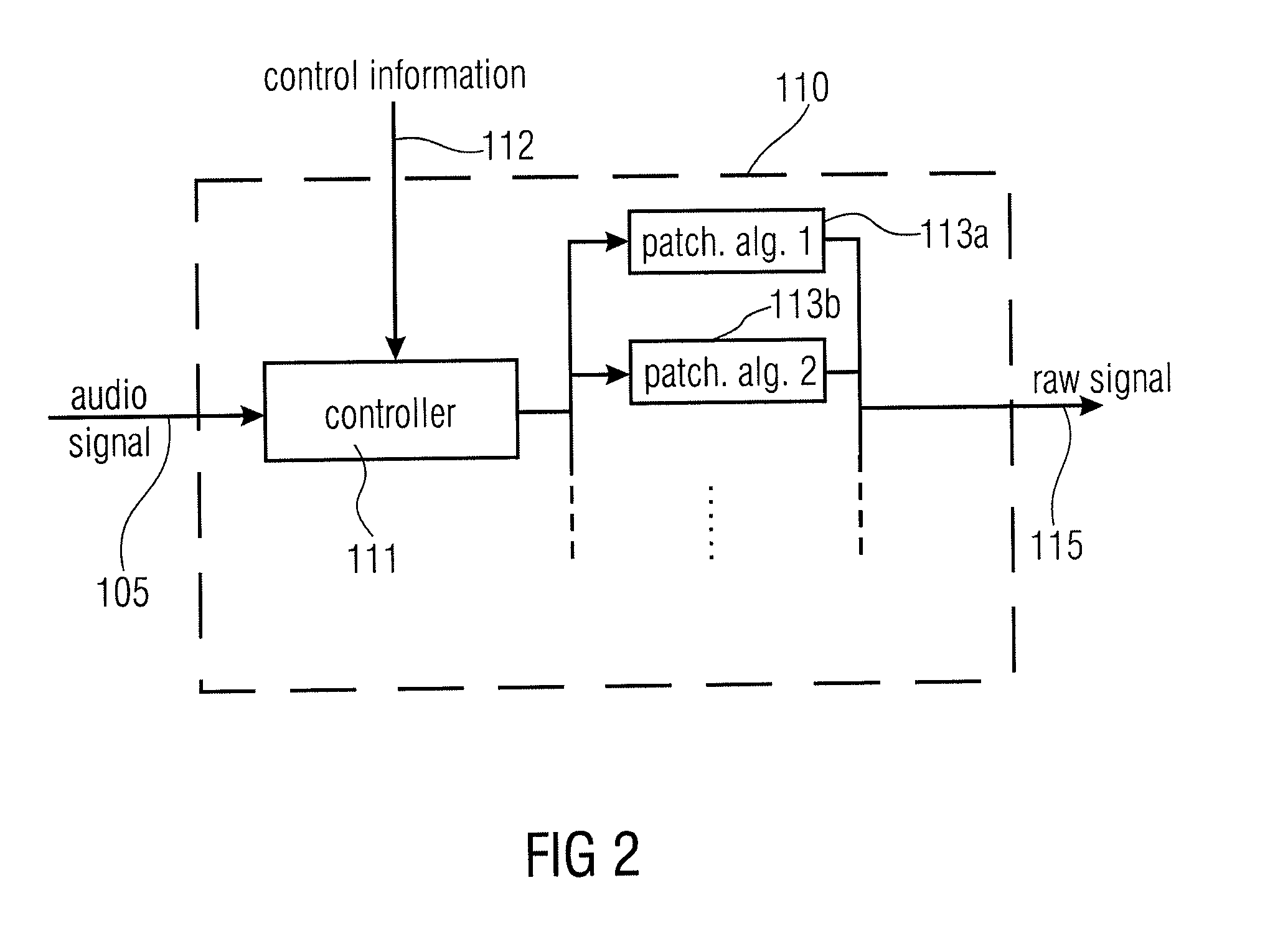
Audio Signal Synthesizer and Audio Signal Encoder
ActiveUS20110173006A1Quality improvementAvoid artifactsSpeech analysisCode conversionFrequency spectrumSpectral domain
An audio signal synthesizer generates a synthesis audio signal having a first frequency band and a second synthesized frequency band derived from the first frequency band and comprises a patch generator, a spectral converter, a raw signal processor and a combiner. The patch generator performs at least two different patching algorithms, each patching algorithm generating a raw signal. The patch generator is adapted to select one of the at least two different patching algorithms in response to a control information. The spectral converter converts the raw signal into a raw signal spectral representation. The raw signal processor processes the raw signal spectral representation in response to spectral domain spectral band replication parameters to obtain an adjusted raw signal spectral representation.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
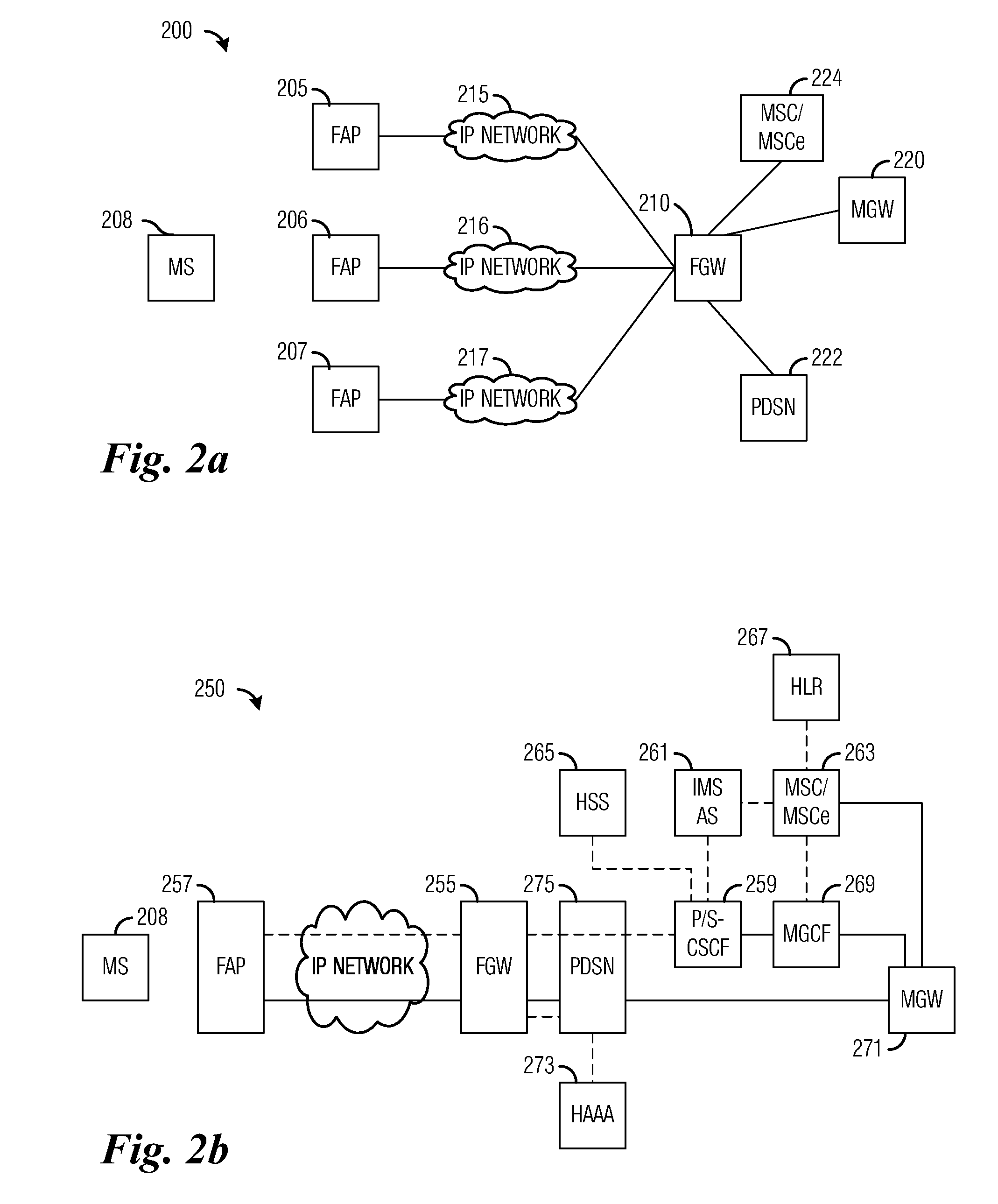
System and Method for Providing Connection Handoffs in Wireless Networks
InactiveUS20090219888A1Overcome size limitationsIncrease resourcesBroadcast service distributionWireless commuication servicesTelecommunicationsMacrocell
System and method for providing connection handoffs from macrocell to femtocell in wireless networks. A method comprises determining a group identifier from a received pseudorandom number sequence, determining a list of access points from a plurality of access points, wherein the access points in the list of access points are all identified by a group identifier, transmitting a request for detecting an identifier of the communications device to each access point in the list of access points, receiving a positive acknowledgement from a locating access point in the list of access points, and locating the communications device in a coverage area of the locating access point. The acknowledgement indicates that the locating access point successfully detected the identifier.
Owner:FUTUREWEI TECH INC
System and method for intrusion prevention in a communications network
InactiveUS20050160289A1Prevents unwanted connectionIncrease resourcesDigital data processing detailsAnalogue secracy/subscription systemsDatabase accessWeb resource
A method, system and program for preventing intrusion in a communications network. A source node initiates a request for network services, such as session establishment, database access, or application access. Known network resources and authorized user information is stored in a database at a network portal along with access policy rules that are device and user dependent. Identification of the source node is required before the source node can construct a transformed packet header that is included with a synchronization packet before transmission to a destination node. An appliance or firewall in the communications network receives and authenticates the synchronization packet before releasing the packet to its, intended destination. The authentication process includes verification of the access policy associated with the source node. Once received at the destination node, the transformed packet header is reformed by extracting a key index value. The extracted key index is subsequently used to transform the packet header in the response transmitted to the source node.
Owner:LIQUIDWARE LABS
Method and apparatus for discovering edge-disjoint shortest path pairs during shortest path tree computation
InactiveUS6928484B1Improve efficiencyReduced computing resourceError preventionFrequency-division multiplex detailsMethod selectionPath protection
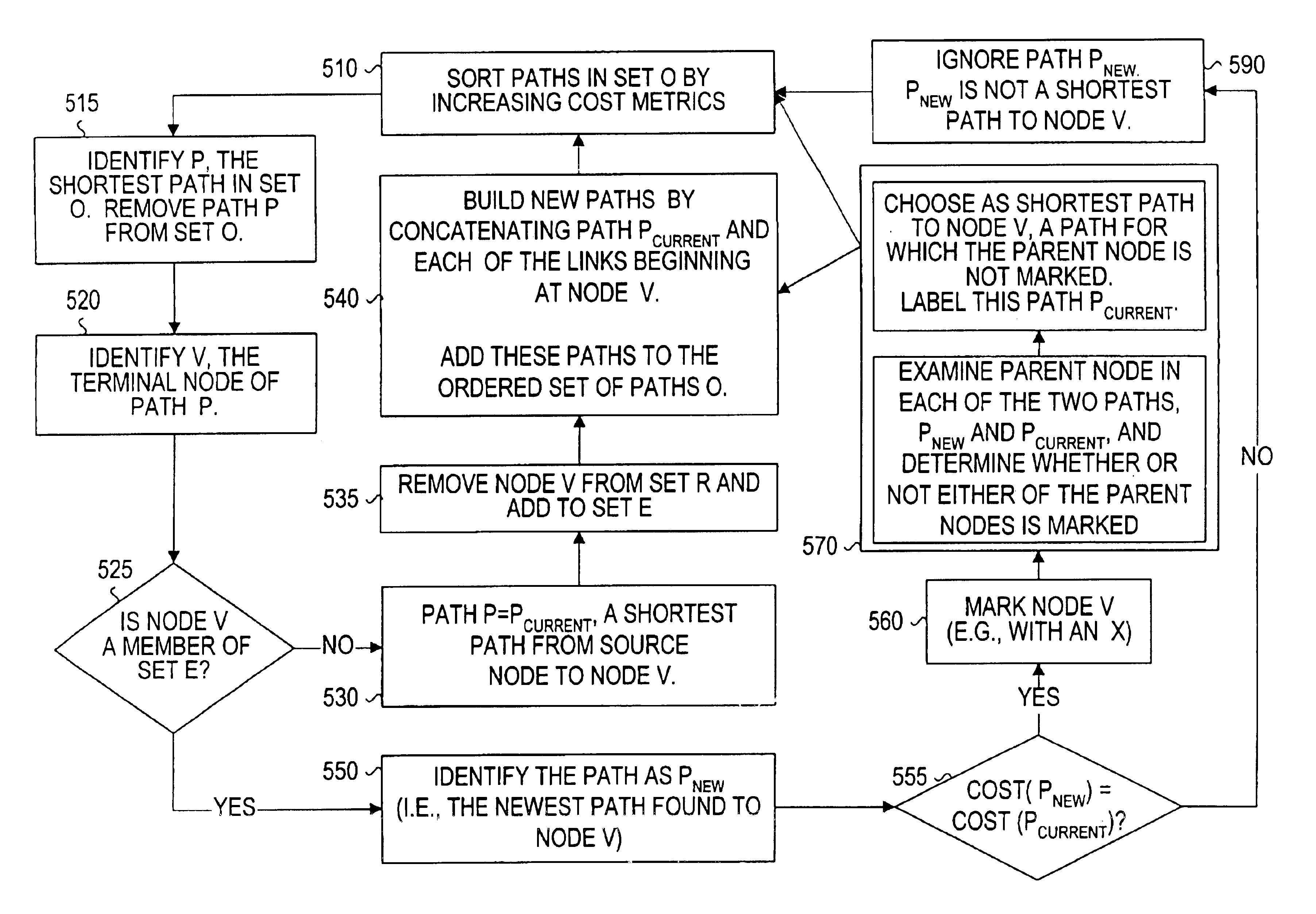
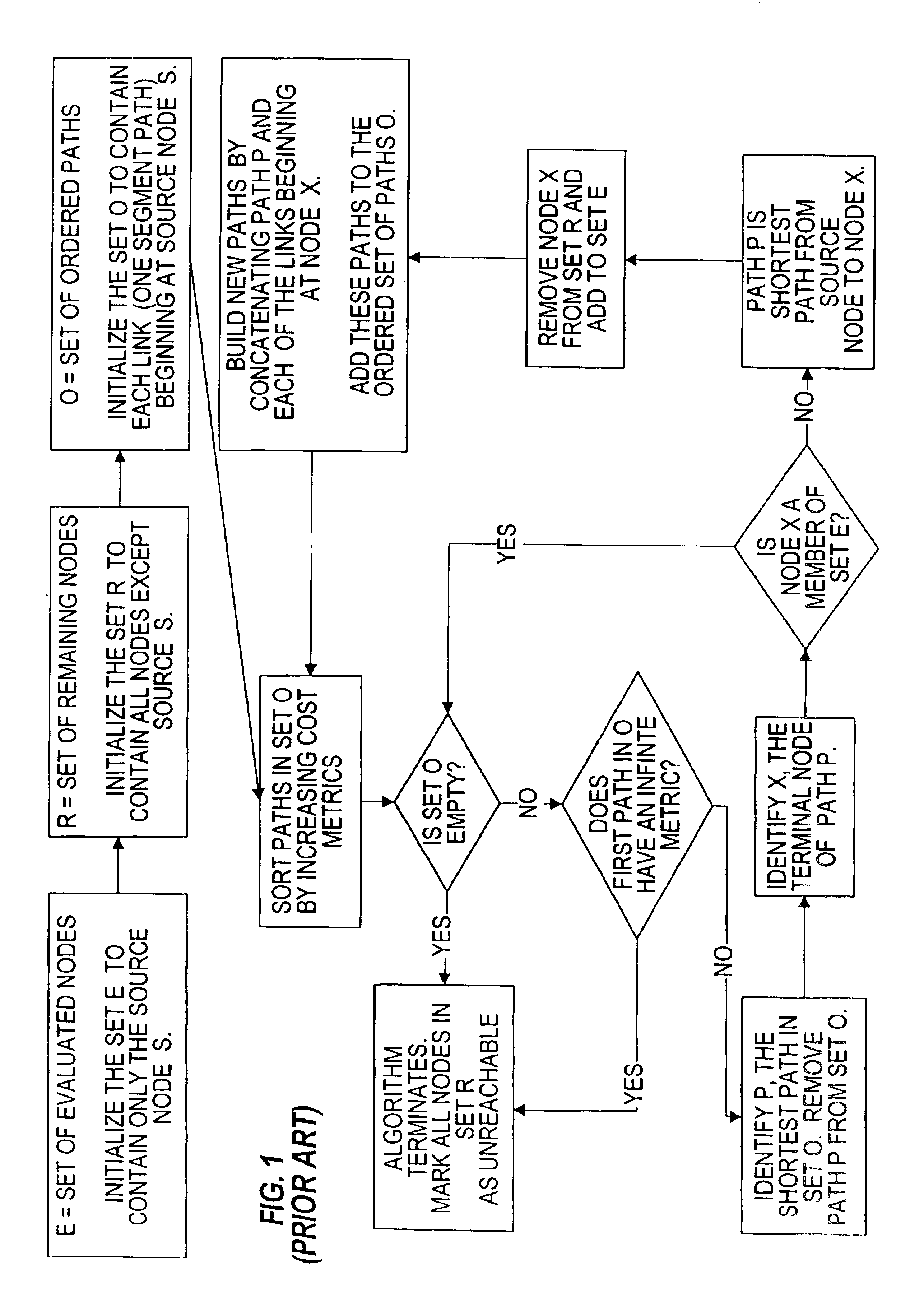
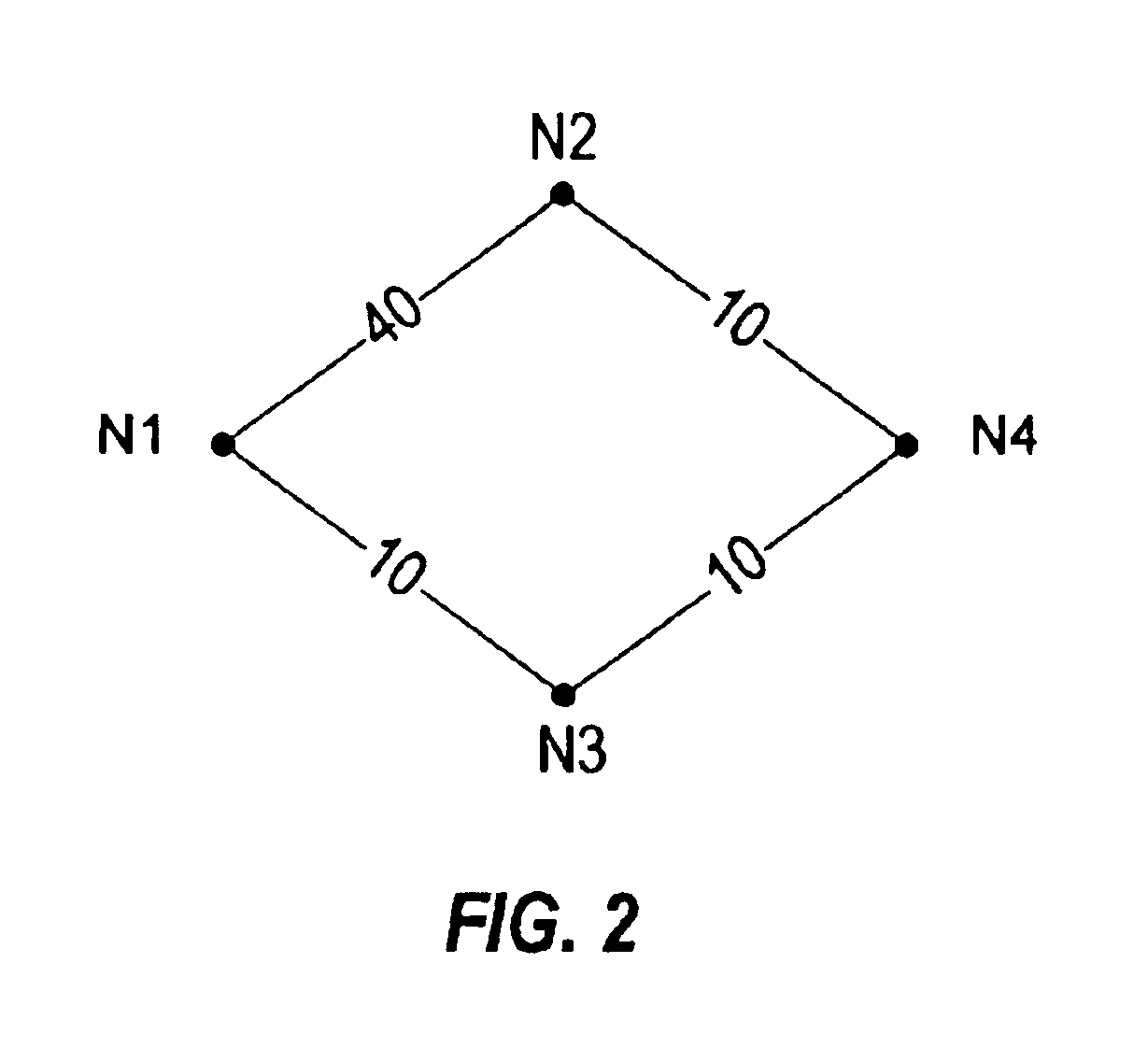
A method for identifying and choosing a shortest path segment that has an alternate edge disjoint path segment. While routing Unidirectional Path Switched Ring (UPSR) path segments in a graph, there may be several equal distance paths to choose the shortest path from. Choosing a certain path as the shortest path may minimize or eliminate the chance of finding an alternative path segment. A method is provided such that if multiple shortest paths from the source node to a particular destination node exist, the method selects the shortest path which has an alternate edge disjoint path, and which can be used for path protection. The particular shortest path chosen by the method is not necessarily the first shortest path constructed.
Owner:CISCO TECH INC
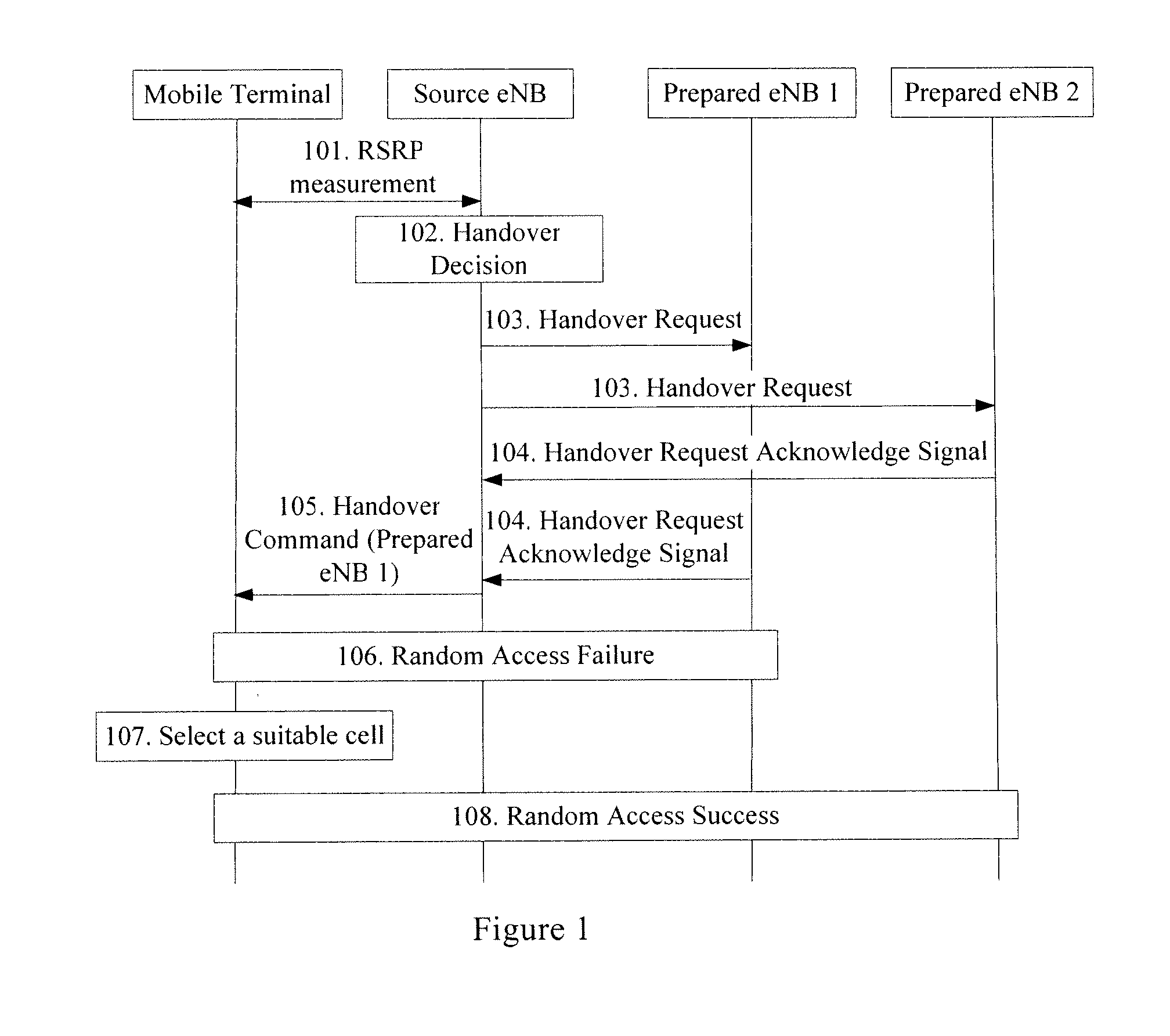
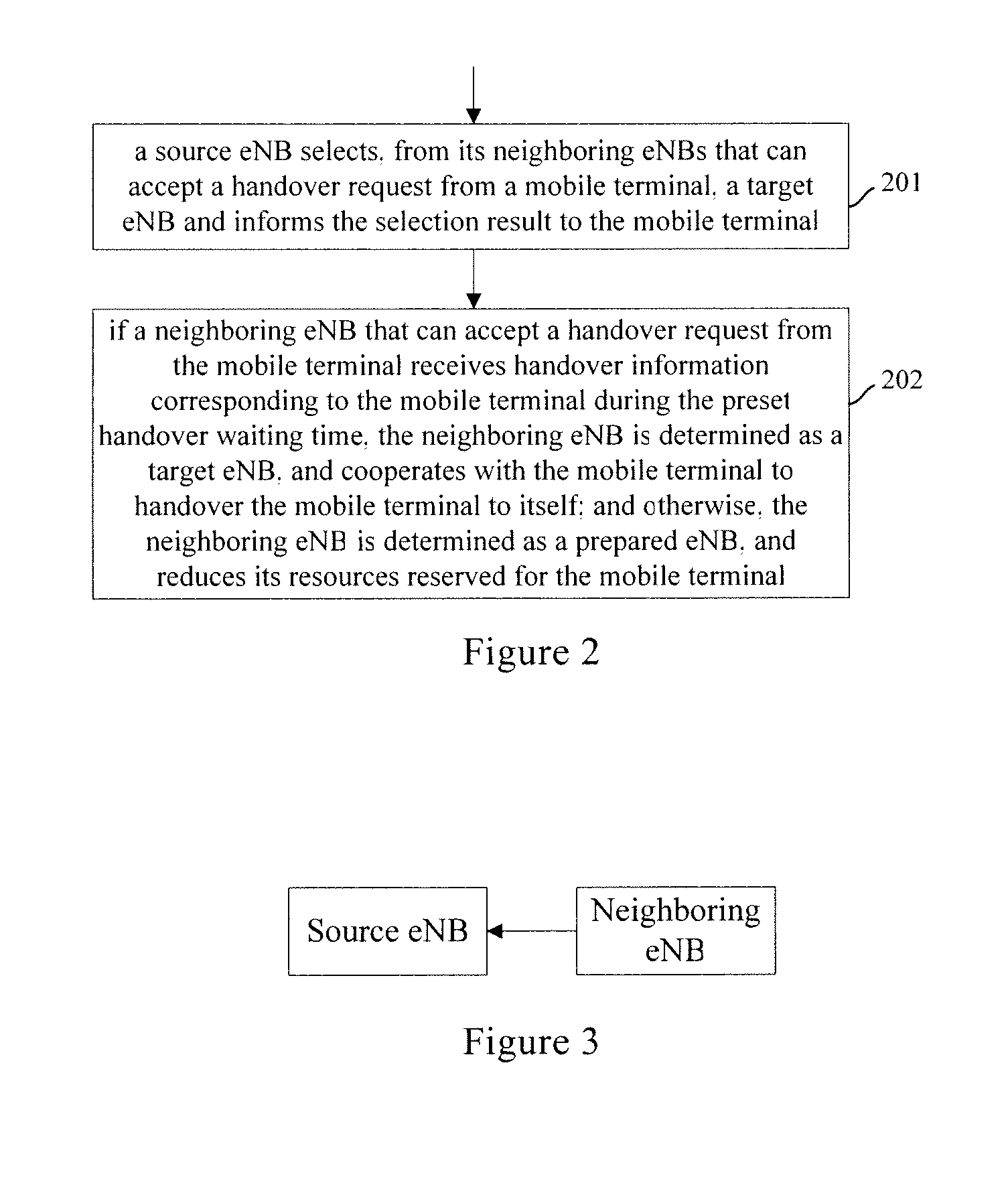
Handover processing method, enb and network communication system thereof
InactiveUS20100027507A1Reduced resourceReduce the amount requiredWireless commuication servicesCommunications systemNetwork communication
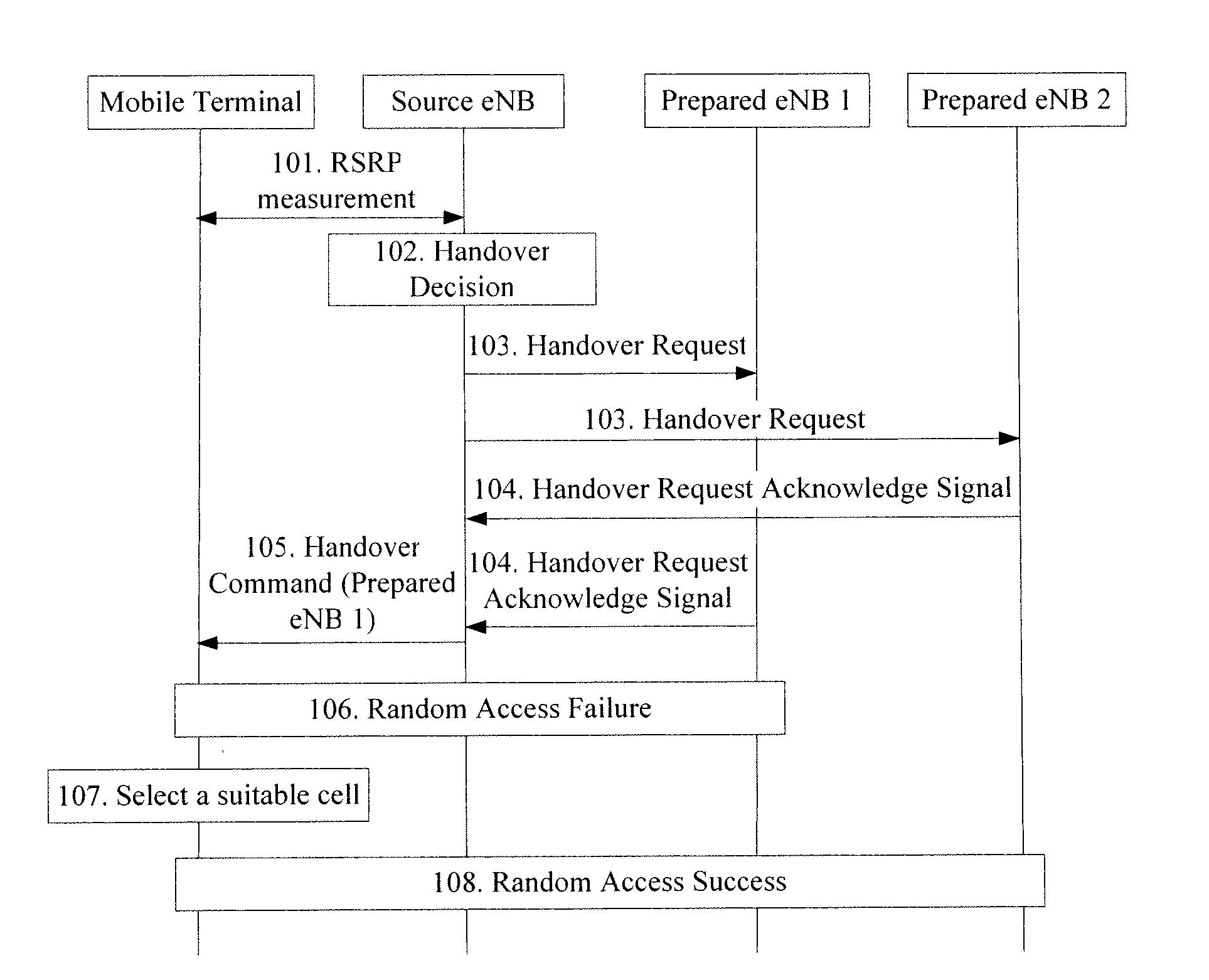
Embodiments of the present invention includes a handover processing method, a source eNB, a neighboring eNB and a network communication system. In one embodiment of the handover processing method, a source eNB selects a target eNB from neighboring eNBs that can accept a handover request from a mobile terminal, and notifies a selection result to the mobile terminal; if handover information corresponding to the mobile terminal is received by an neighboring eNB that can accept the handover request of the mobile terminal within a preset handover waiting time, the neighboring eNB determines that it is a target eNB and cooperates with the mobile terminal to perform a handover; otherwise, the neighboring eNB determines that it is a prepared eNB and reduces its resources reserved for the mobile terminal. The present invention can effectively improve the successful handover probability.
Owner:GOOGLE LLC
System and Method for Controlling Autonomous Vehicles
ActiveUS20170168485A1Great motionIncrease resourcesInstruments for road network navigationAutonomous decision making processMethod selectionEngineering
Owner:MITSUBISHI ELECTRIC RES LAB INC
Systems and methods for determining placement of virtual machines
ActiveUS8099487B1Improve balanceImprove efficiencyEnergy efficient ICTError detection/correctionVirtualizationVirtual machine
Systems and methods are provided for determining an optimized placement for a virtual machine in a virtualized environment on the basis of available performance metrics, in which the virtualized environment includes at least two virtual machines, each hosting at least one application, and at least one virtualized hardware system managed by at least one virtualization server.
Owner:AKORRI NETWORKS
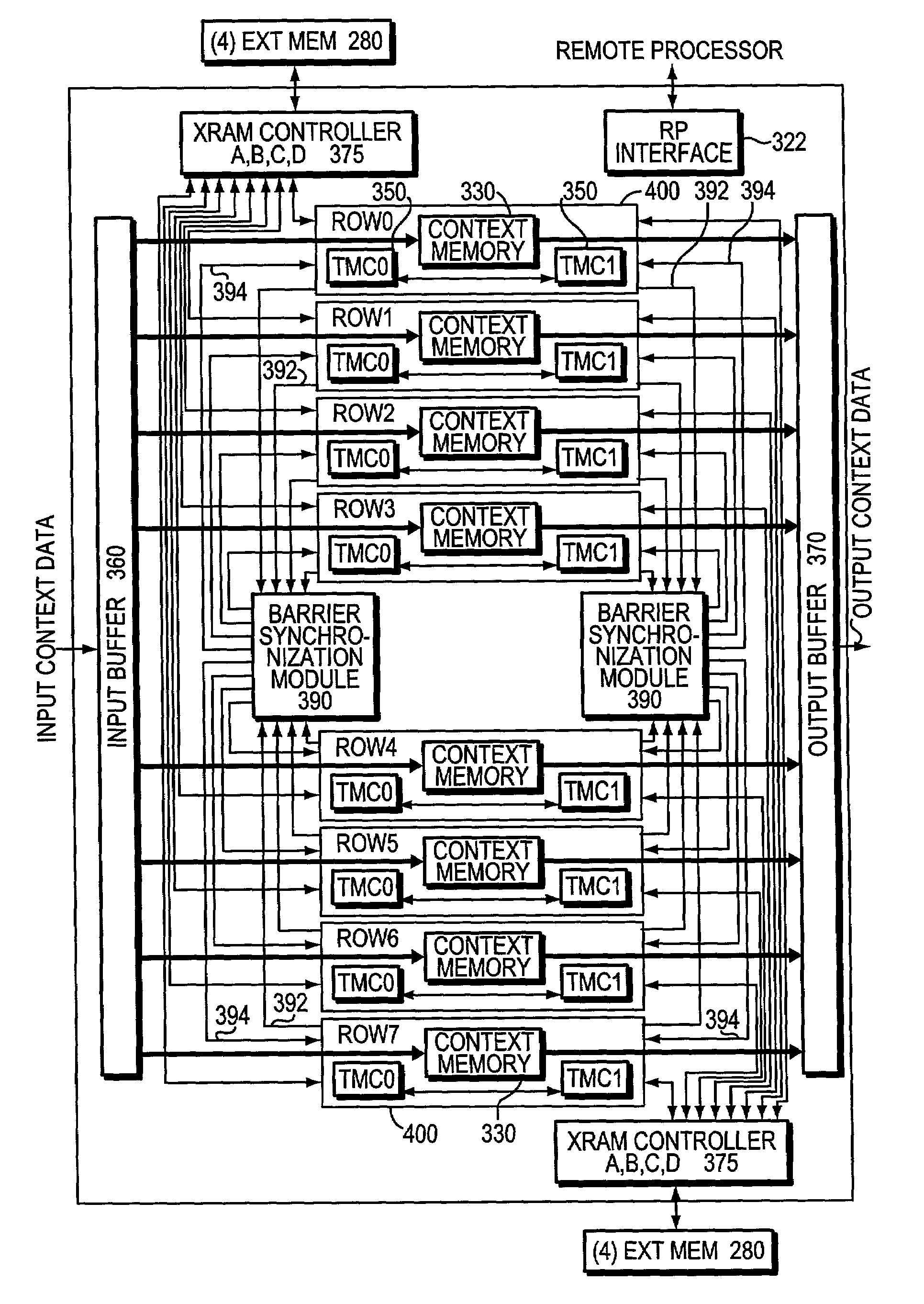
Barrier synchronization mechanism for processors of a systolic array
InactiveUS7100021B1Without consuming substantial memory resourceImprove latencyProgram synchronisationGeneral purpose stored program computerSystolic arrayCommon point
A mechanism synchronizes among processors of a processing engine in an intermediate network station. The processing engine is configured as a systolic array having a plurality of processors arrayed as rows and columns. The mechanism comprises a barrier synchronization mechanism that enables synchronization among processors of a column (i.e., different rows) of the systolic array. That is, the barrier synchronization function allows all participating processors within a column to reach a common point within their instruction code sequences before any of the processors proceed.
Owner:CISCO TECH INC
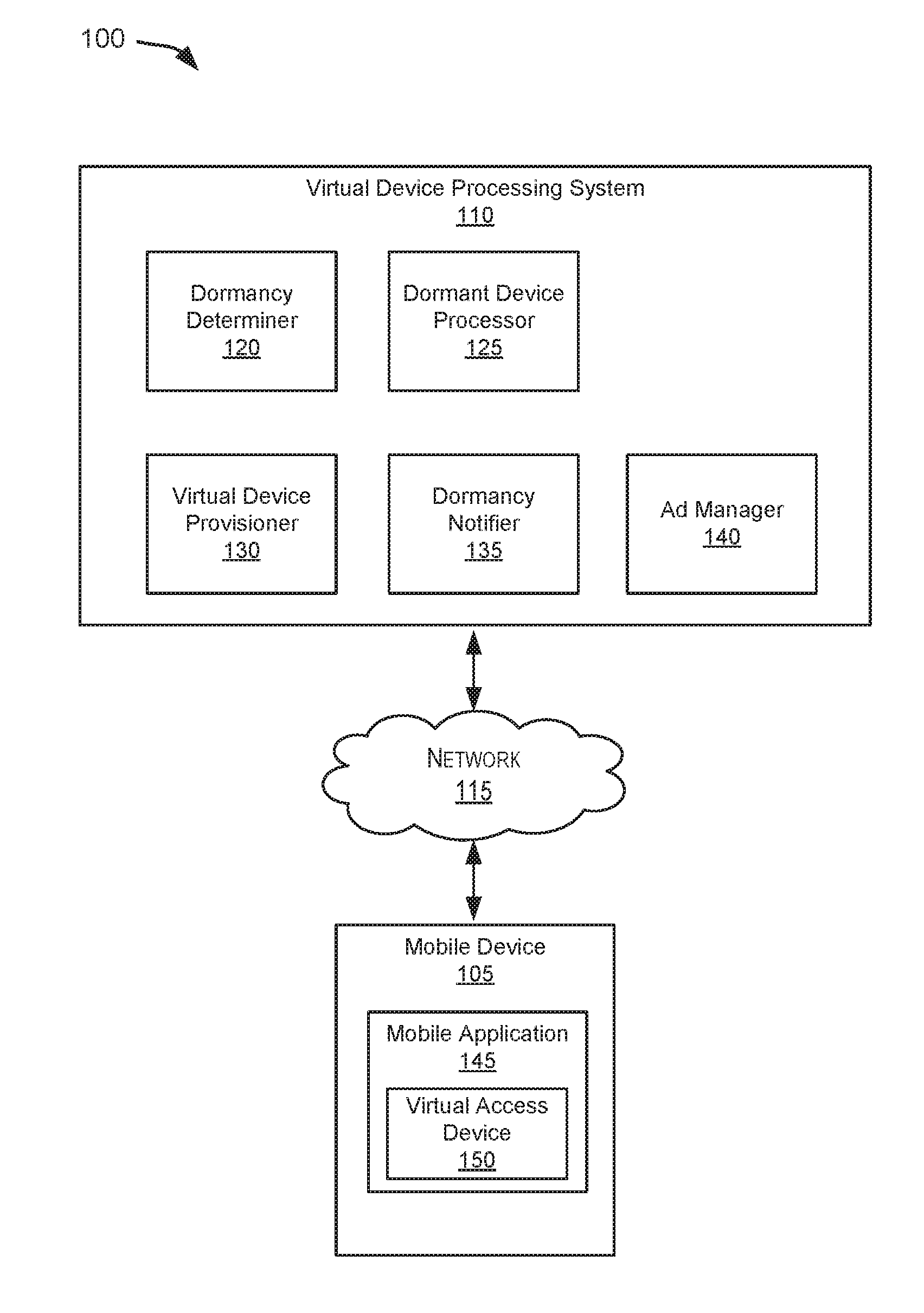
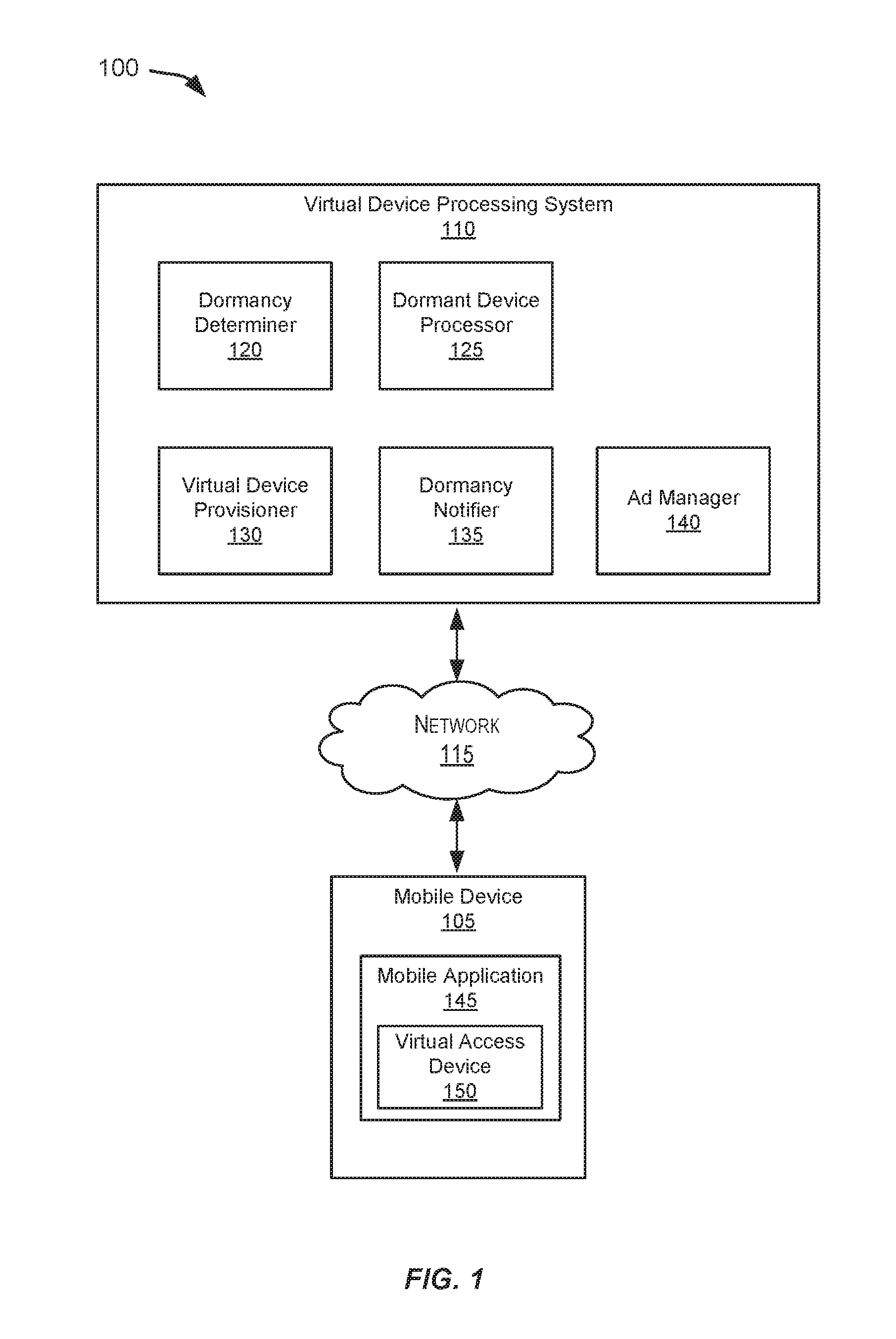
Systems and methods for processing dormant virtual access devices
ActiveUS20160308995A1Improve usage and allocationMinimizing unnecessary reprovisioning attemptService provisioningAssess restrictionAuthorizationMobile device
Embodiments of the invention are directed to ceasing the renewal of a virtual access device that is dormant. Some embodiments may receive a dormancy request from an authorization server, where the dormancy request includes information identifying a virtual access device. Embodiments may determine that the virtual access device is dormant based at least on previous transactions involving the virtual access device and at least one dormancy rule. Certain embodiments may send a dormancy response to the authorization server indicating that the virtual access device is dormant. An authorization server may determine not to renew a virtual access device based at least upon the dormancy response. As such, the authorization server need not provision a mobile device with an updated virtual access device.
Owner:VISA INT SERVICE ASSOC
System and method for intrusion prevention in a communications network
InactiveUS7386889B2Avoid connectionIncrease resourcesDigital data processing detailsAnalogue secracy/subscription systemsIntrusion prevention systemNetwork service
A method, system and program for preventing intrusion in a communications network. A source node initiates a request for network services, such as session establishment, database access, or application access. Known network resources and authorized user information is stored in a database at a network portal along with access policy rules that are device and user dependent. Identification of the source node is required before the source node can construct a transformed packet header that is included with a synchronization packet before transmission to a destination node. An appliance or firewall in the communications network receives and authenticates the synchronization packet before releasing the packet to its, intended destination. The authentication process includes verification of the access policy associated with the source node. Once received at the destination node, the transformed packet header is reformed by extracting a key index value. The extracted key index is subsequently used to transform the packet header in the response transmitted to the source node.
Owner:LIQUIDWARE LABS
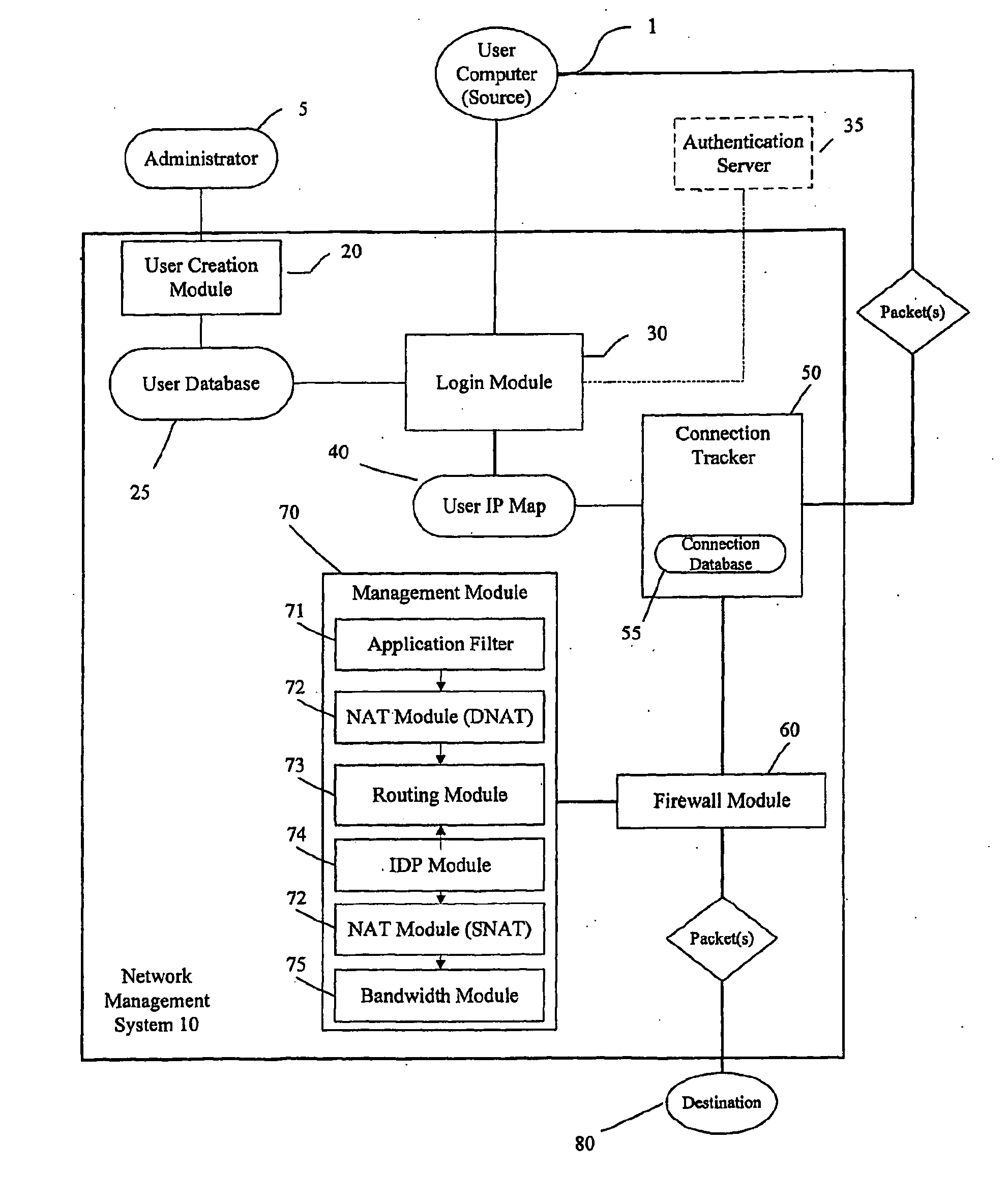
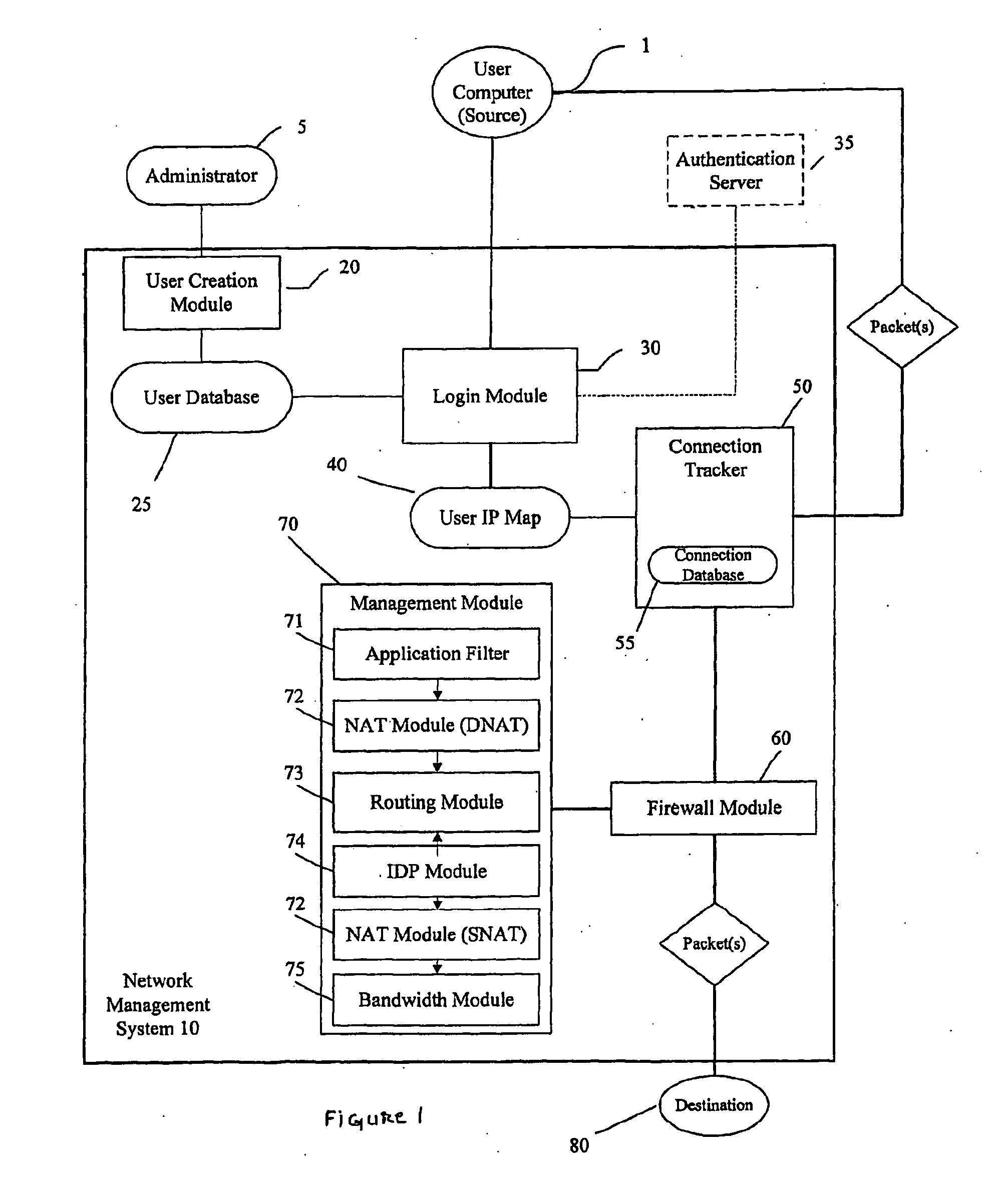
Identity and policy-based network security and management system and method
ActiveUS20100100949A1Improve network securityEnhanced resource optimizationDigital data processing detailsUser identity/authority verificationNetwork security policyManagement system
A system and method for providing security for a network connecting a source and a destination. The system and method provide a security and management system between the source and the destination which is configured to apply rules and policies which are specific to the user to the connection between the source and the destination. The user-specific policies are used to govern.
Owner:SOPHOS
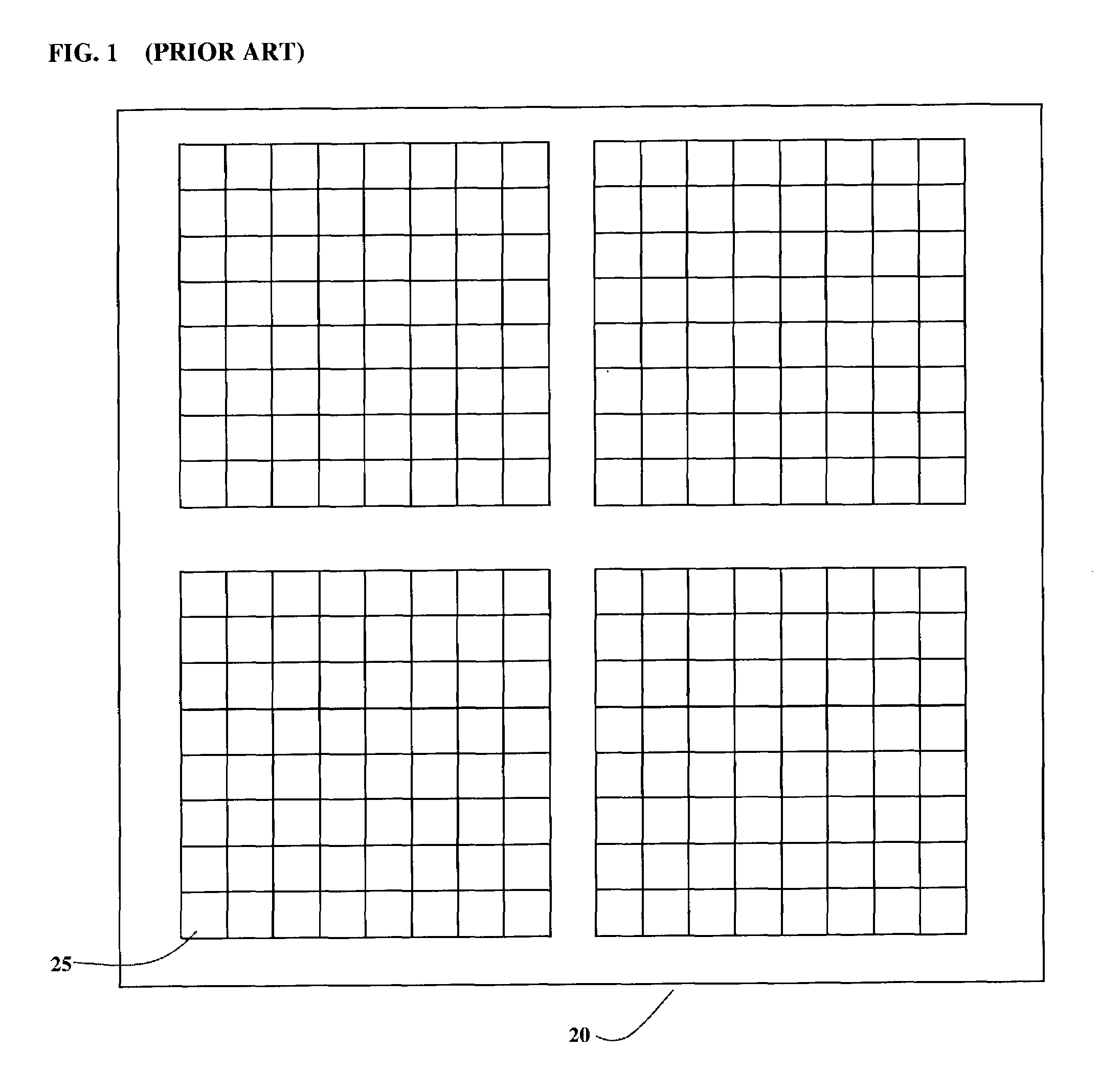
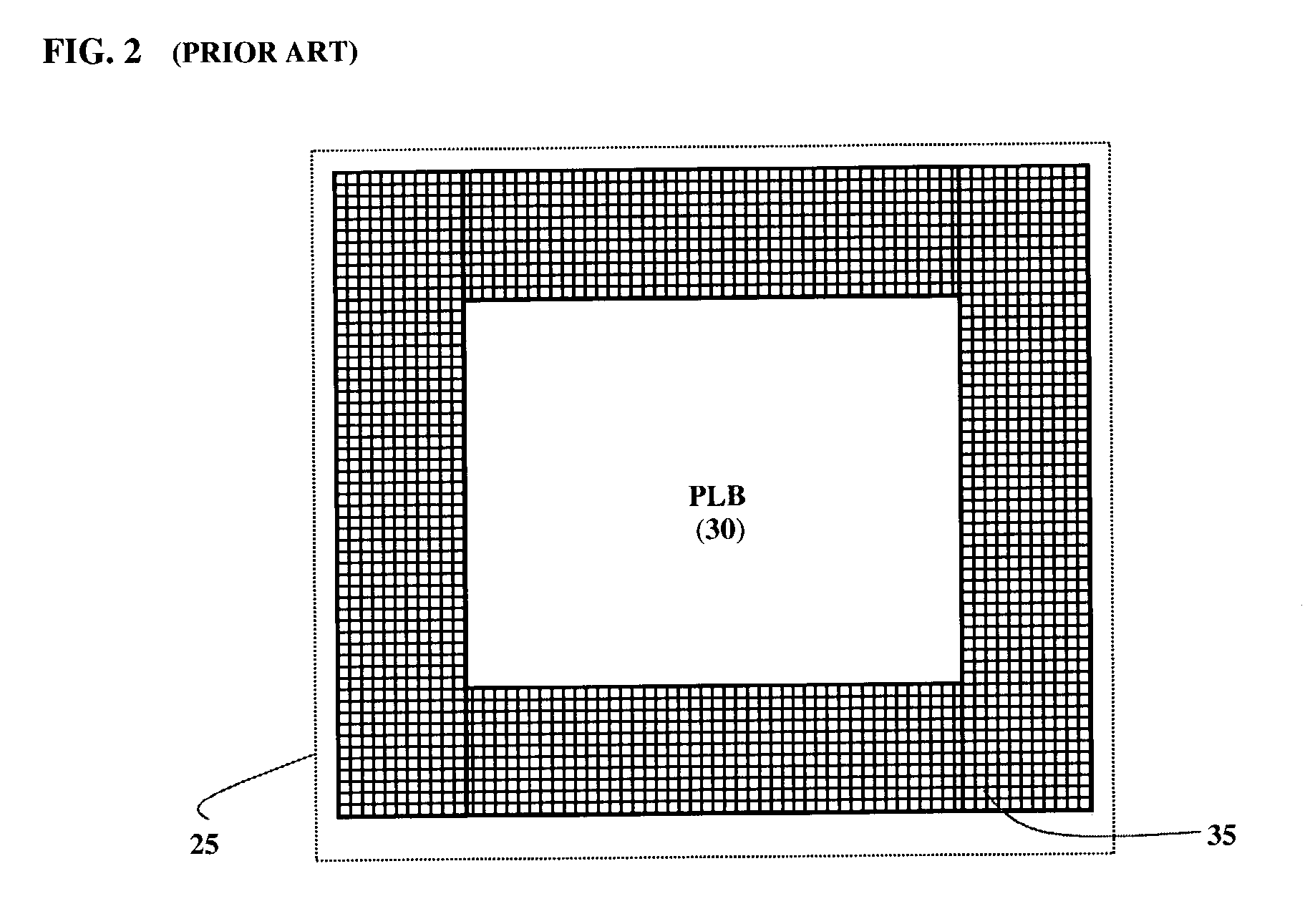
Architecture for programmable logic device
InactiveUS7154299B2Efficient use ofEfficient use of resourcesLogic circuits characterised by logic functionSolid-state devicesComputer architectureProgrammable logic device
An improved Programmable Logic Device architecture that provides more efficient utilization of resources by enabling access to defined circuit elements in the domain of any Programmable Logic Block (PLB) from any other PLB in the device, by incorporating a connecting means in the routing structure for selectively connecting the input or output of the circuit element in the domain of the PLB to the common interconnect matrix connecting all the PLBs together.
Owner:HD SILICON SOLUTIONS LLC
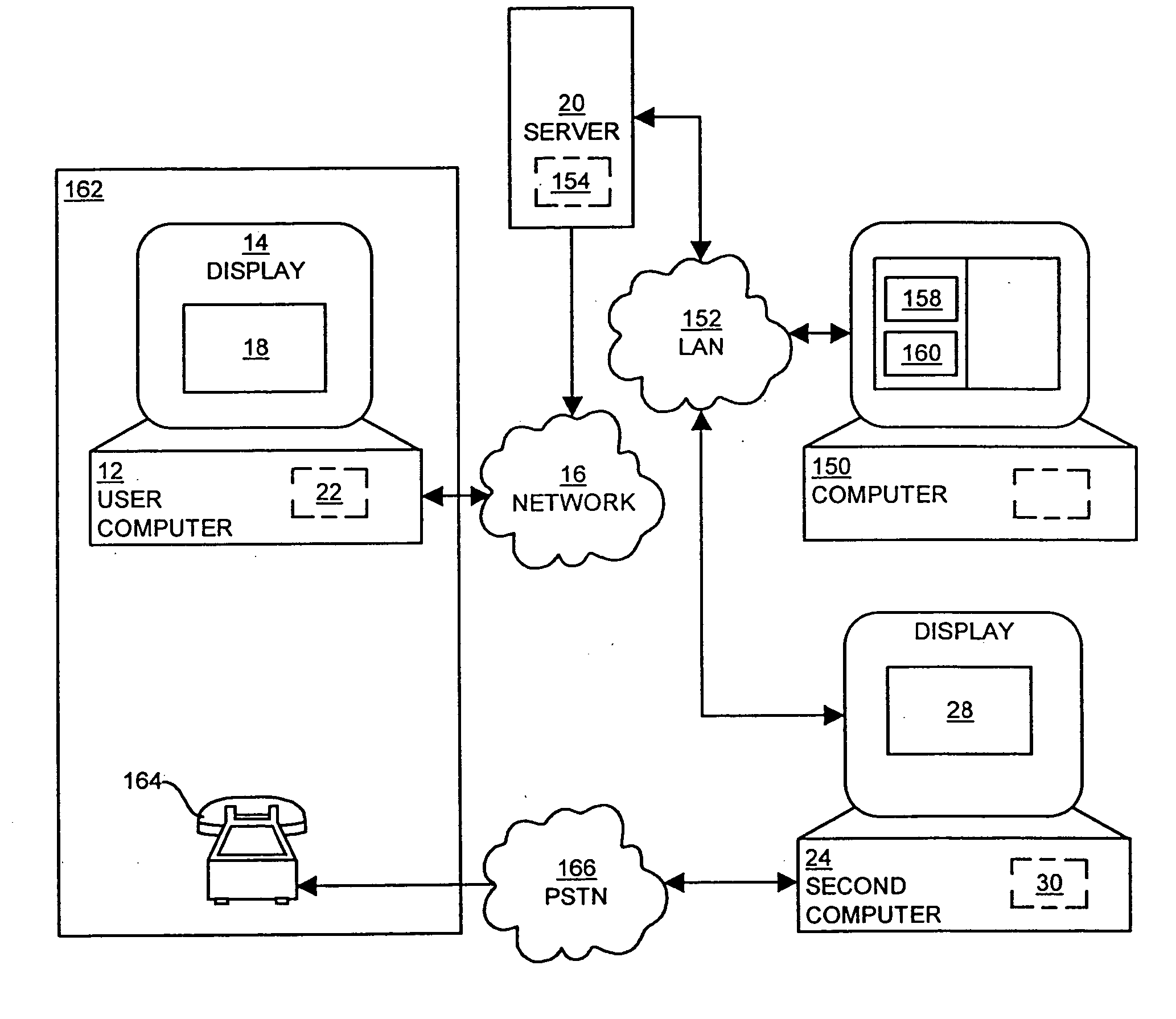
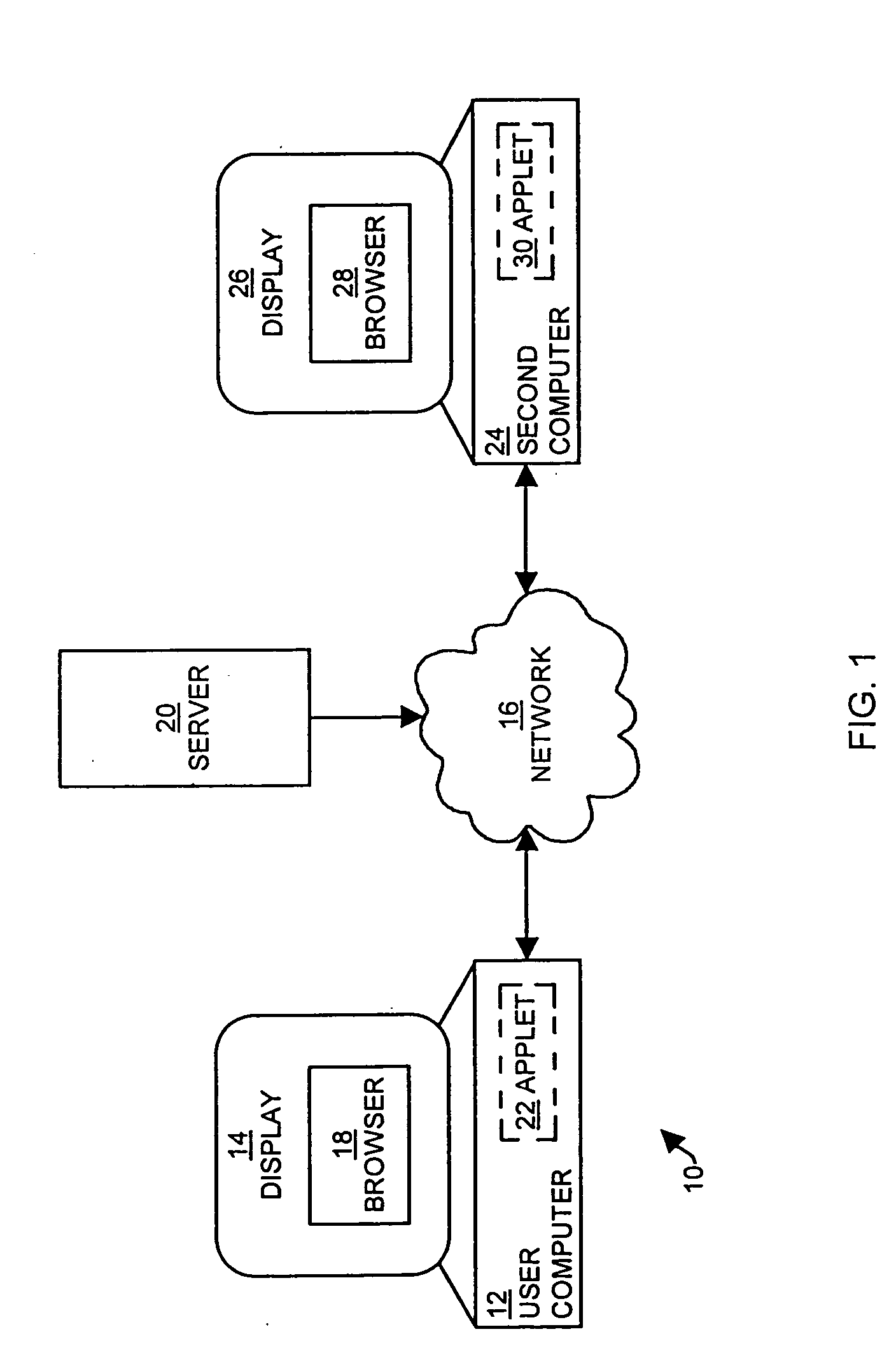
Method and apparatus for coordinating internet multi-media content with telephone and audio communications
InactiveUS20050004977A1Add collection functionDecreases resource collectionTelephone data network interconnectionsSpecial service for subscribersInternet contentDisplay device
Internet content is coordinated with audio communications, such that two or more parties can view the same media content on the Internet while simultaneously communicating over a traditional telephony network or via voice over network. A user computer displays shared content that corresponds to a second computer's display, such that both parties view the same content on their browsers. Either of the parties is allowed to update the visual content of their browsers. Updates in the visual content are transmitted to the other parties so that all parties view the same, shared content. The shared content can include web pages, forms, applications, images, conferences, and files among other information.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com