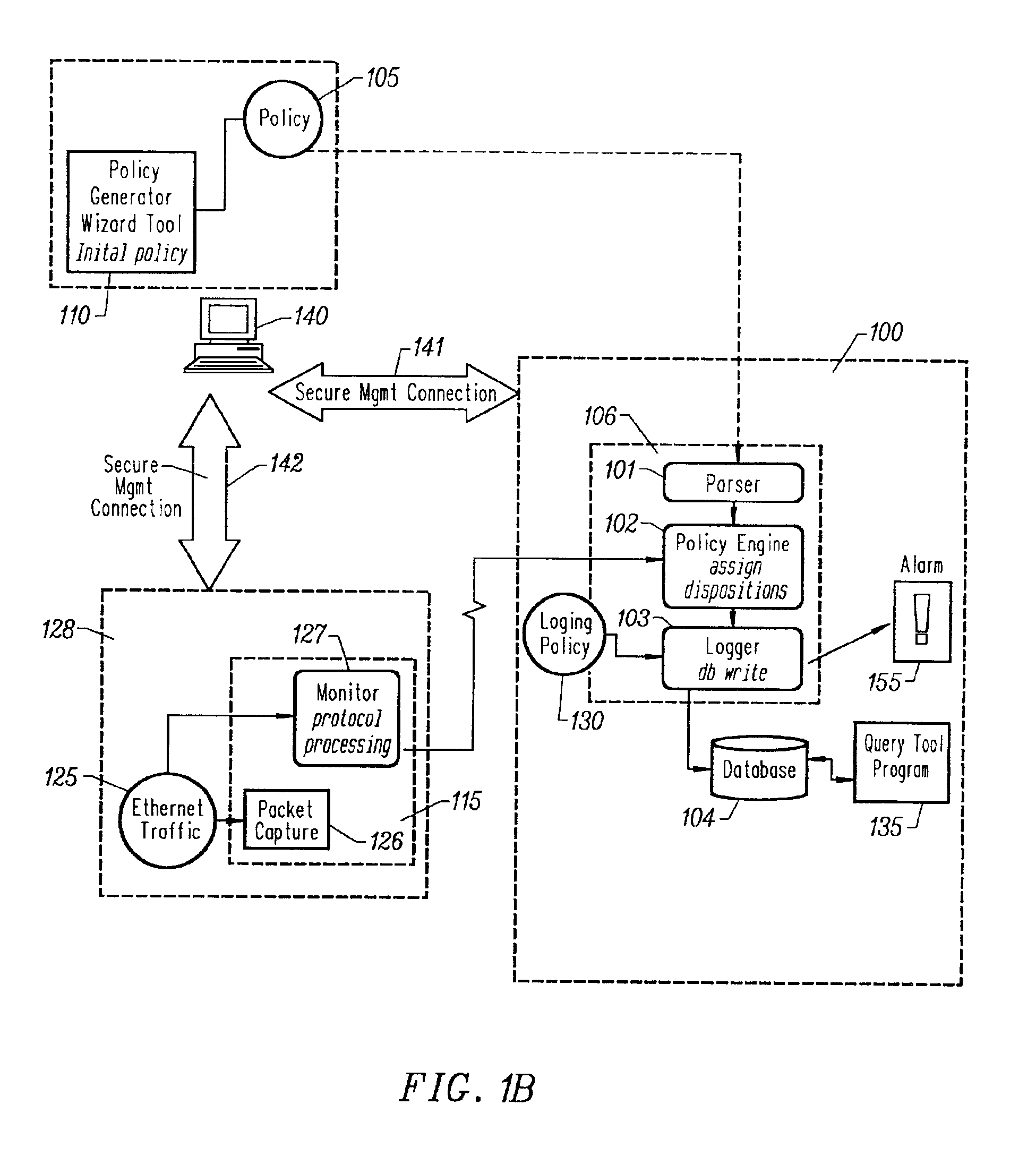
Patents
Literature
716 results about "Network security policy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
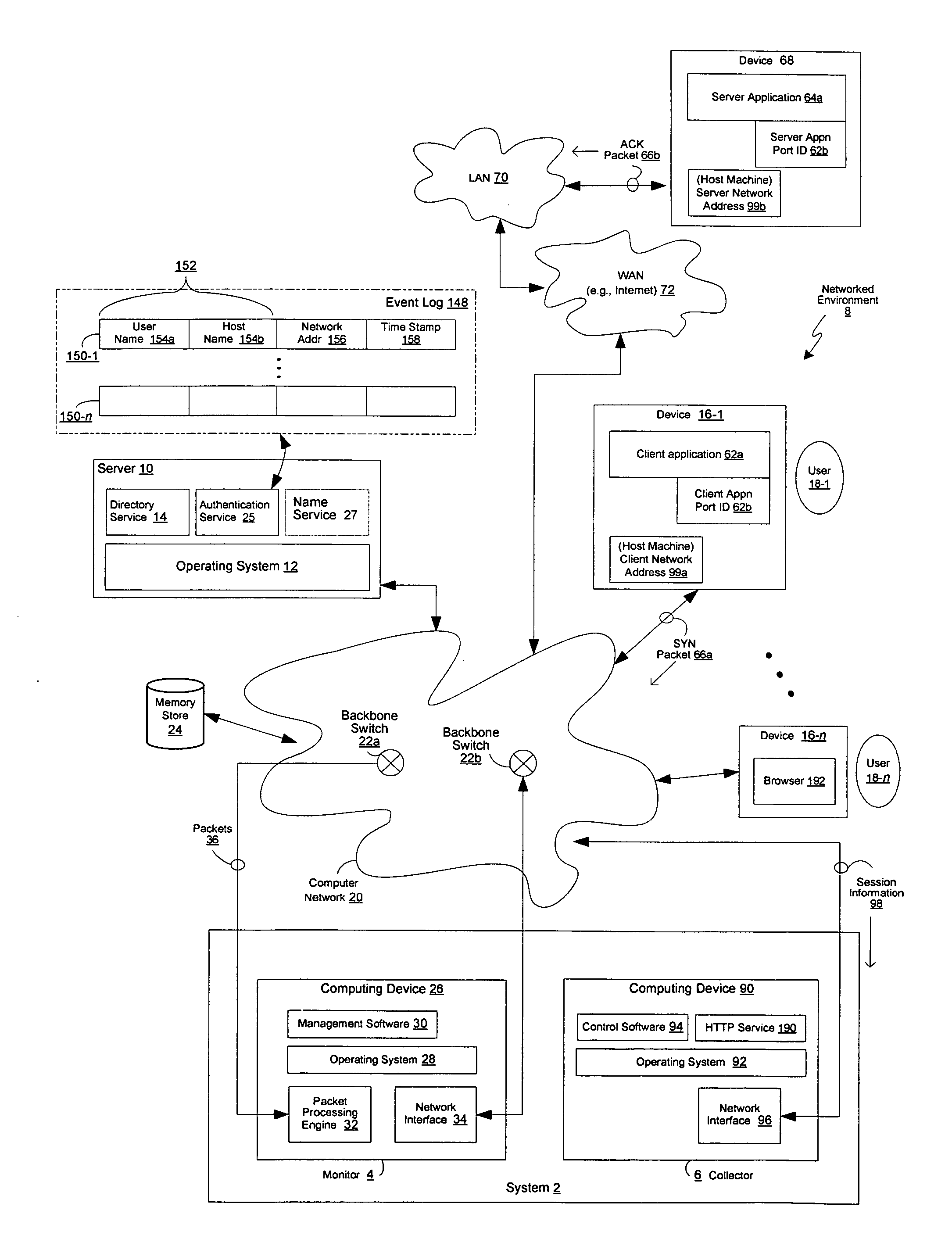
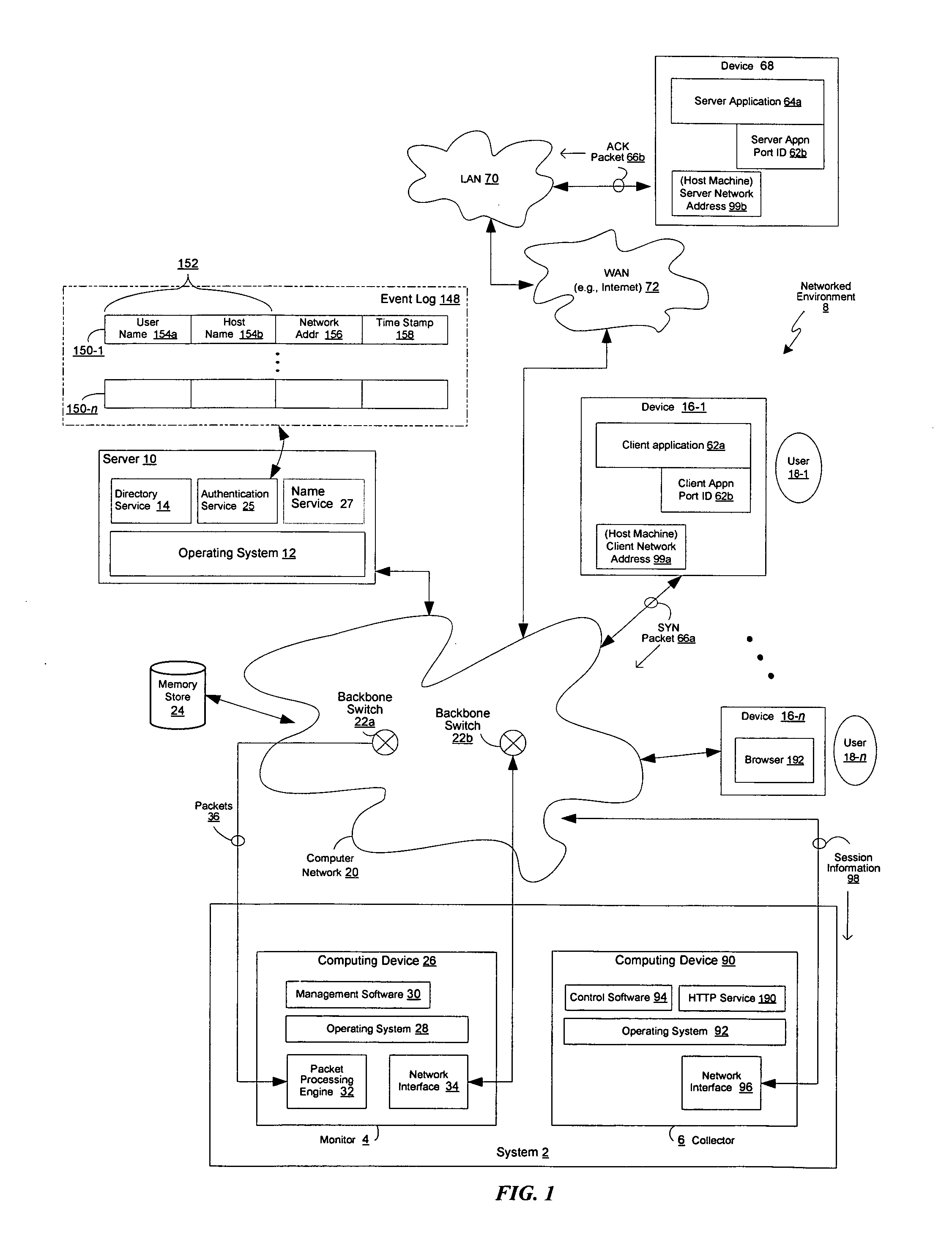
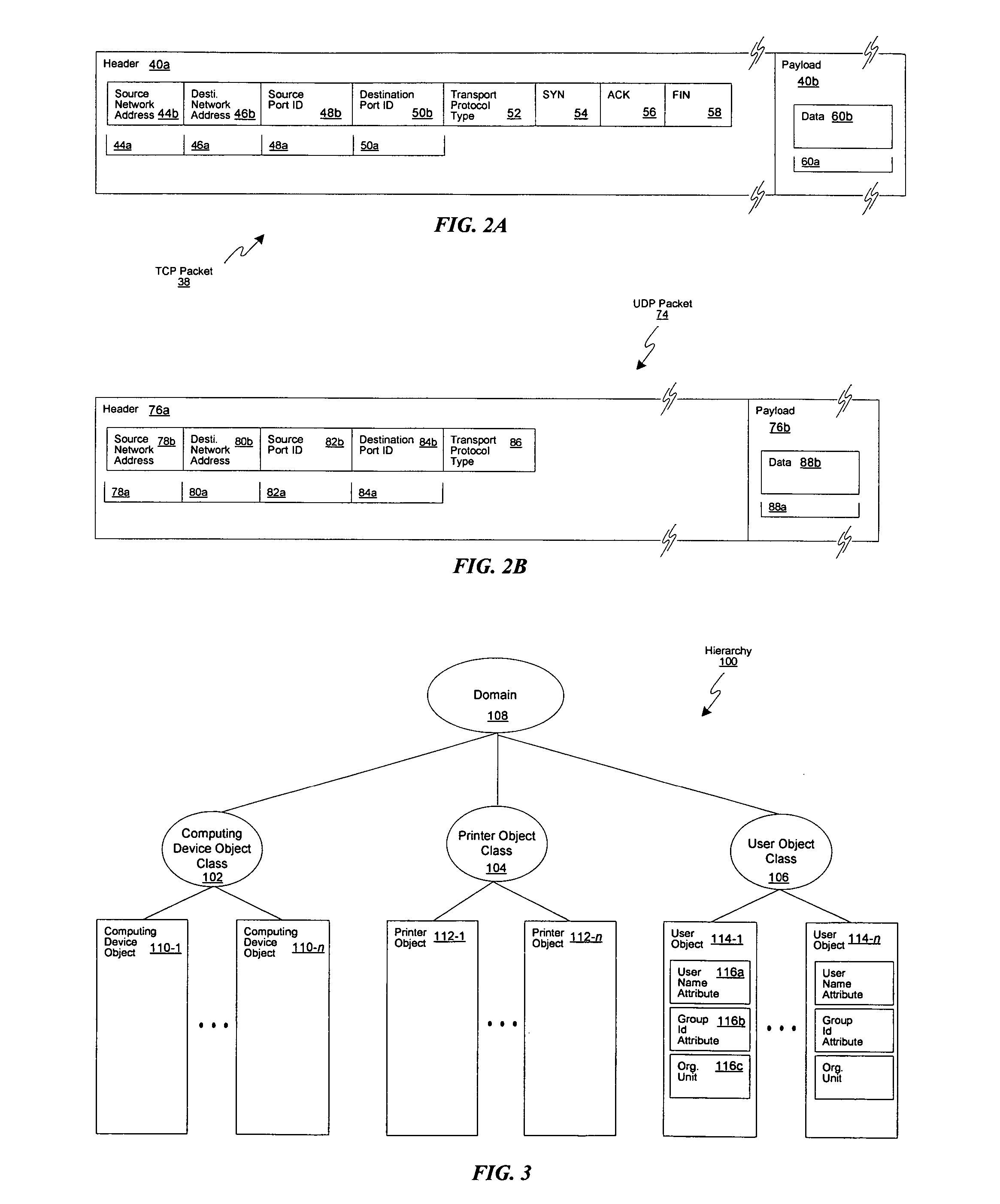
A network security policy (NSP) is a generic document that outlines rules for computer network access, determines how policies are enforced and lays out some of the basic architecture of the company security/ network security environment. The document itself is usually several pages long and written by a committee. A security policy goes far beyond the simple idea of "keep the bad guys out". It's a very complex document, meant to govern data access, web-browsing habits, use of passwords and encryption, email attachments and more. It specifies these rules for individuals or groups of individuals throughout the company.
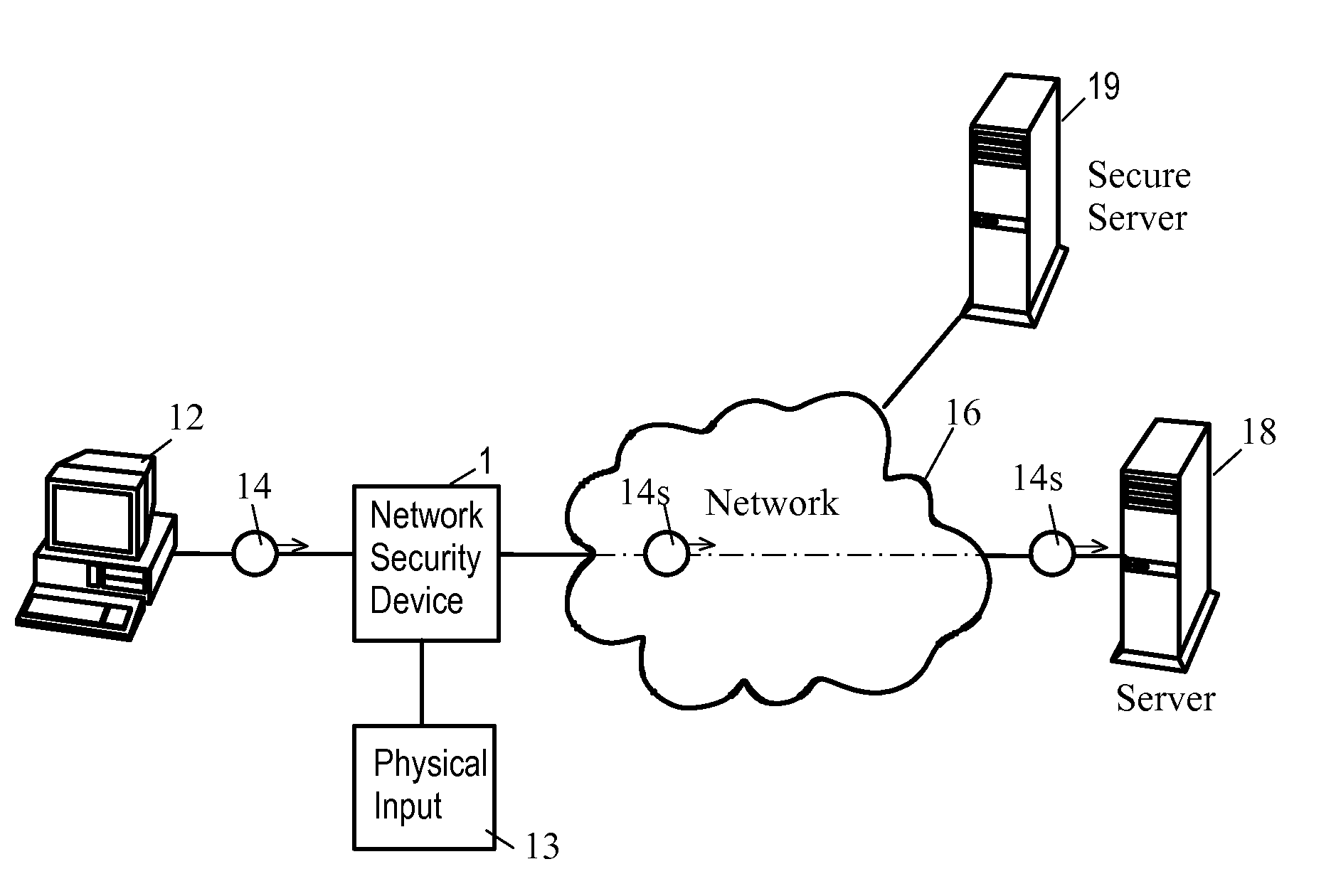
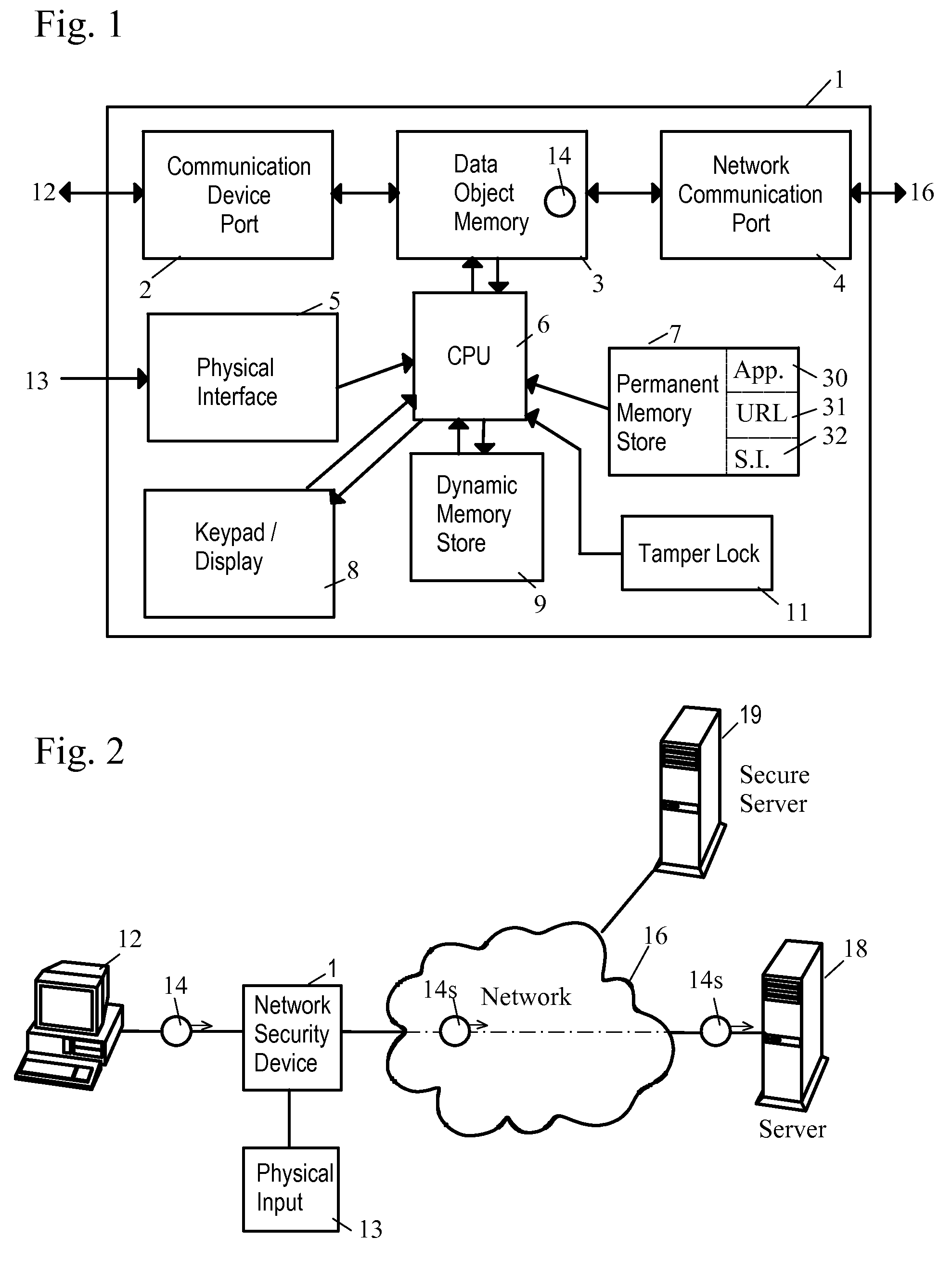
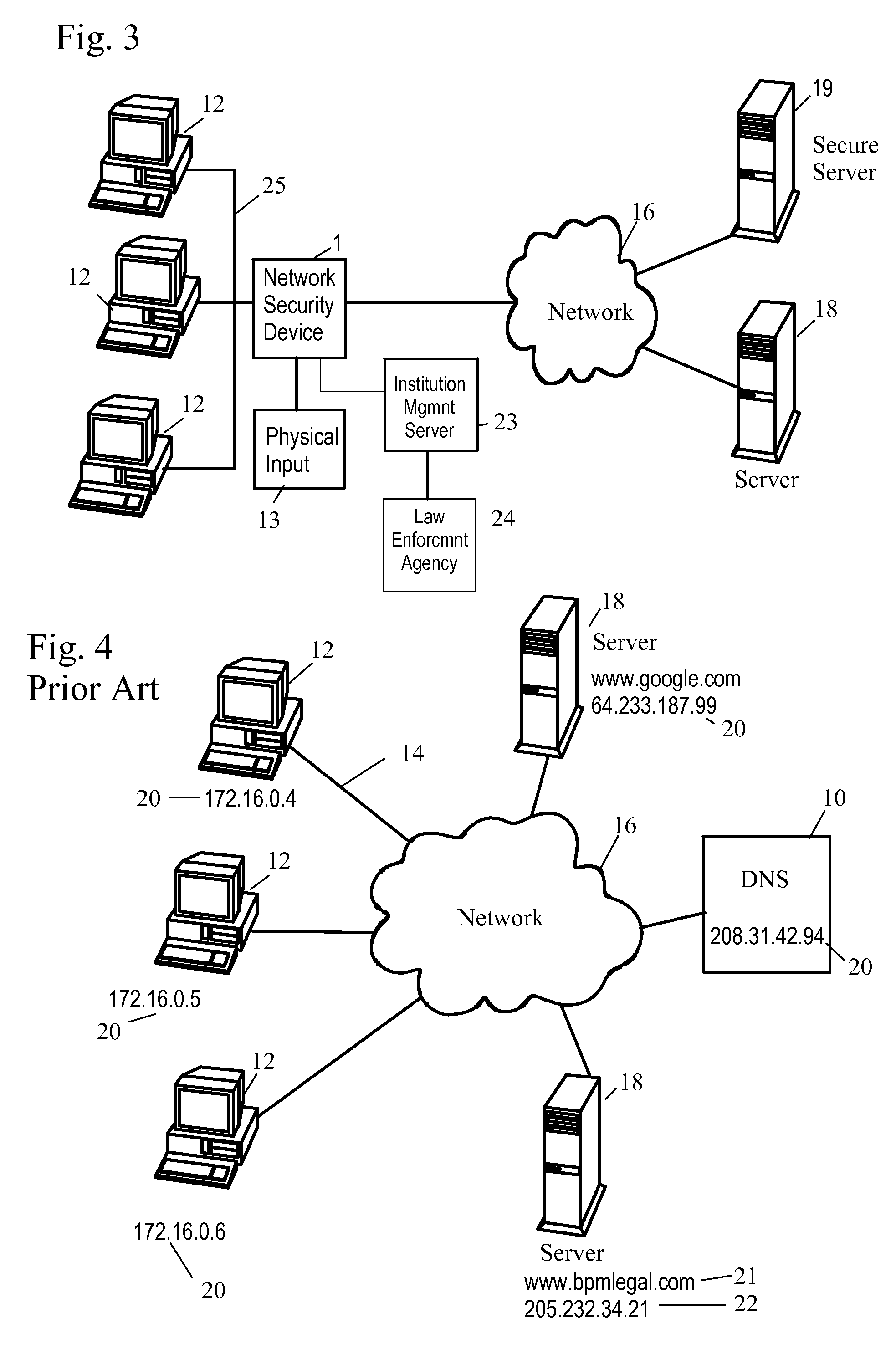
Network Security Device
ActiveUS20070261112A1Function providedFacilitate law enforcement effortDigital data processing detailsUser identity/authority verificationNetwork packetDatapath
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
Apparatus and method for providing trusted network security
InactiveUS6199113B1Digital data processing detailsMultiple digital computer combinationsNetwork packetNetwork security policy
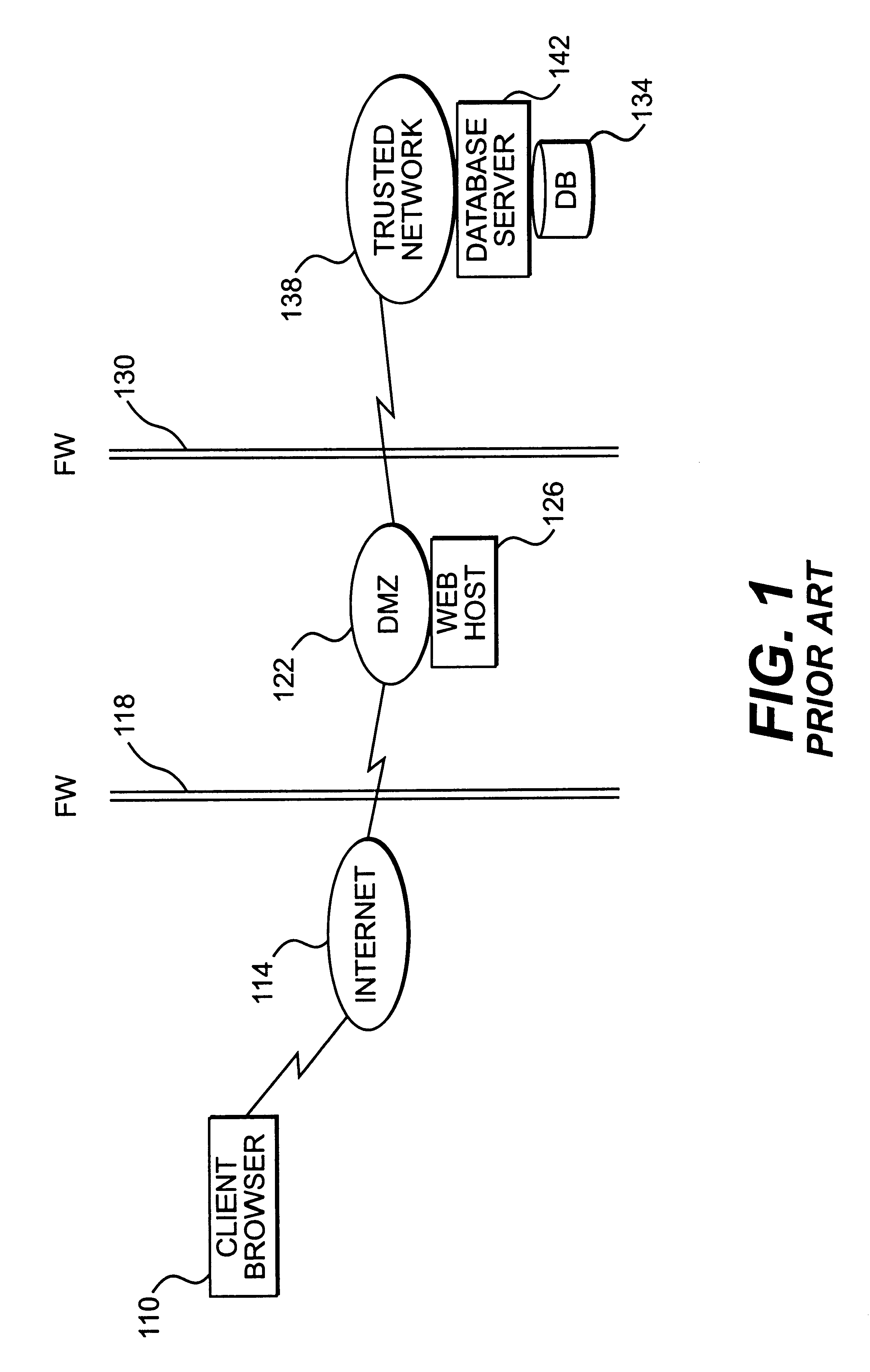
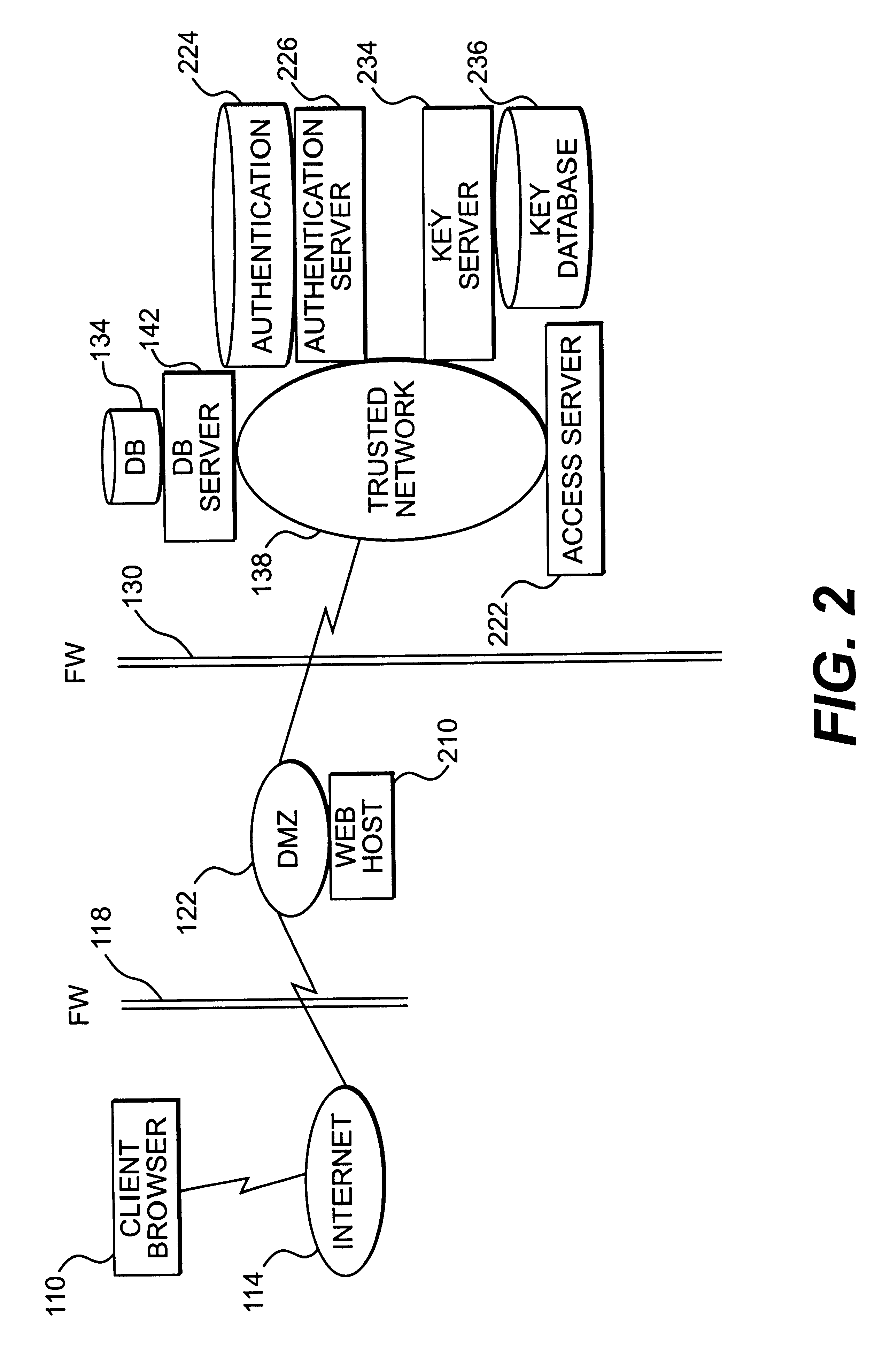
A session key is established for accessing a trusted network from a browser. An authentication process receives identification information from a user at the browser, and authenticates the user by checking the identification information against an authentication database. If the authentication database authenticates the user, a session key is created and stored at the browser. If the user is authenticated, a user profile defining access rights for the user is also retrieved. The user is then presented with access options based on the access rights defined in the user profile. In response to a user selection from the access page, the browser forwards an information request to the trusted network. The request includes a session key. A speaker object processes the information request and session key to form a network request packet. The network request packet is formed in a manner that allows authentication of the speaker object. The session packet is forwarded to a trusted network and processed. The packet is first authenticated to determine if it originated from the speaker object, and then the key is checked for validity at the trusted server. If the key is valid, the information request is processed and the information is returned to the user for display on the browser.
Owner:ORACLE INT CORP
Network security and fraud detection system and method
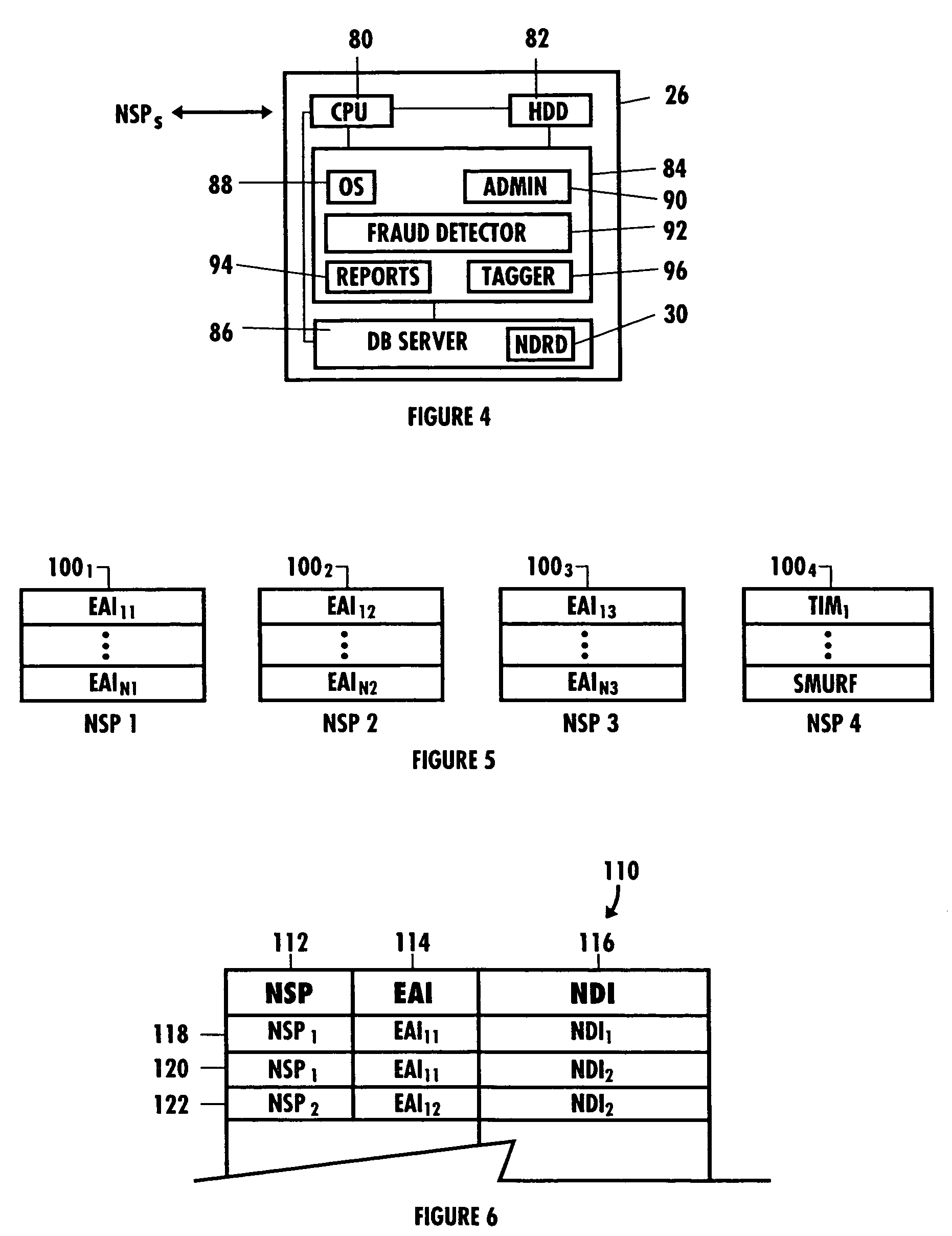
ActiveUS7272728B2Avoid connectionAccess is deniedUser identity/authority verificationUnauthorized memory use protectionNetwork security policyNetwork service
A system and method to detect and prevent fraud in a system is provided. The system may uniquely identify physical devices connecting to a network, register unique devices, track end-user logins, associate end-user accounts with specific devices, and share information with multiple network service providers is described.
Owner:IOVATION
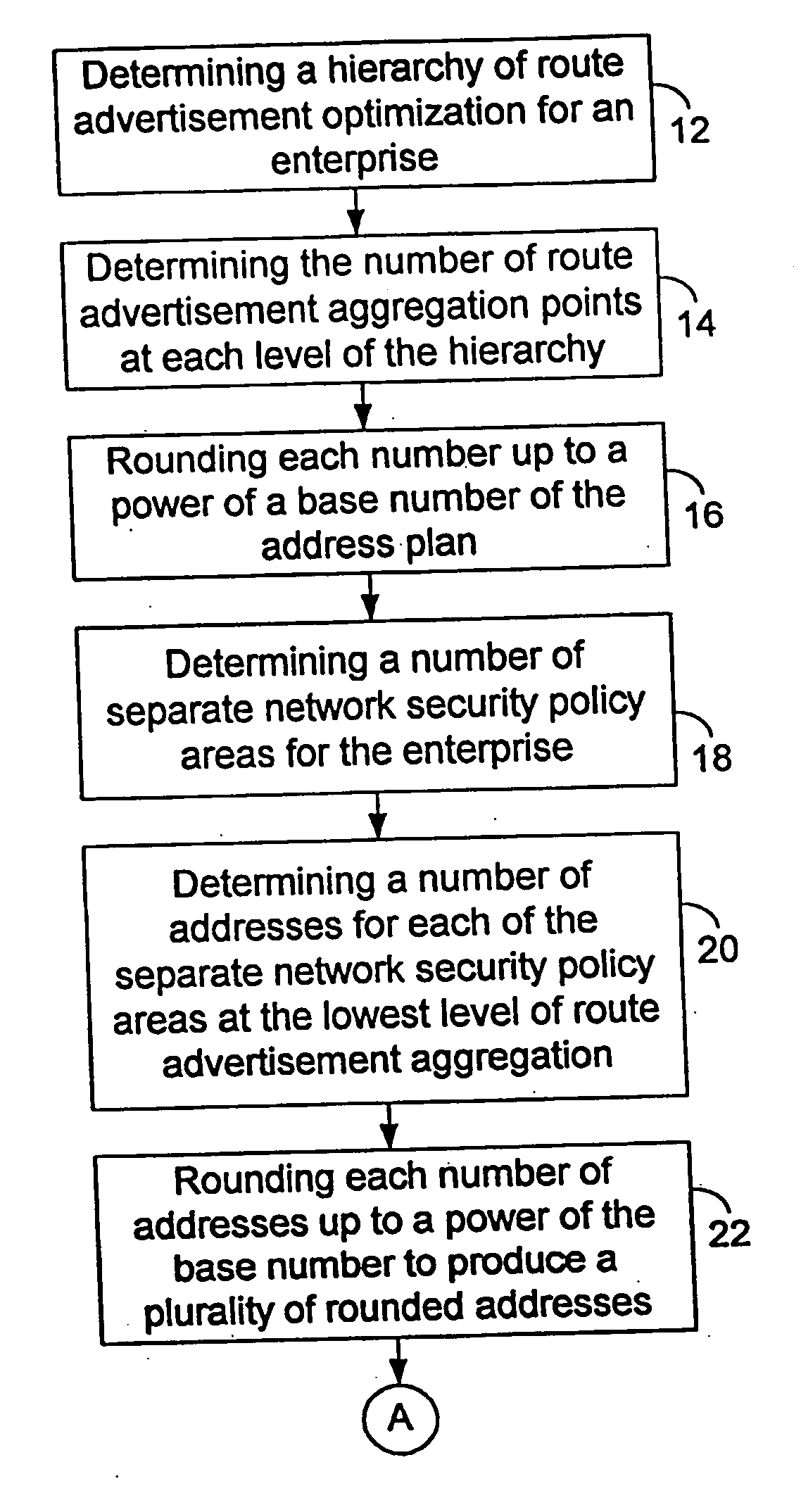
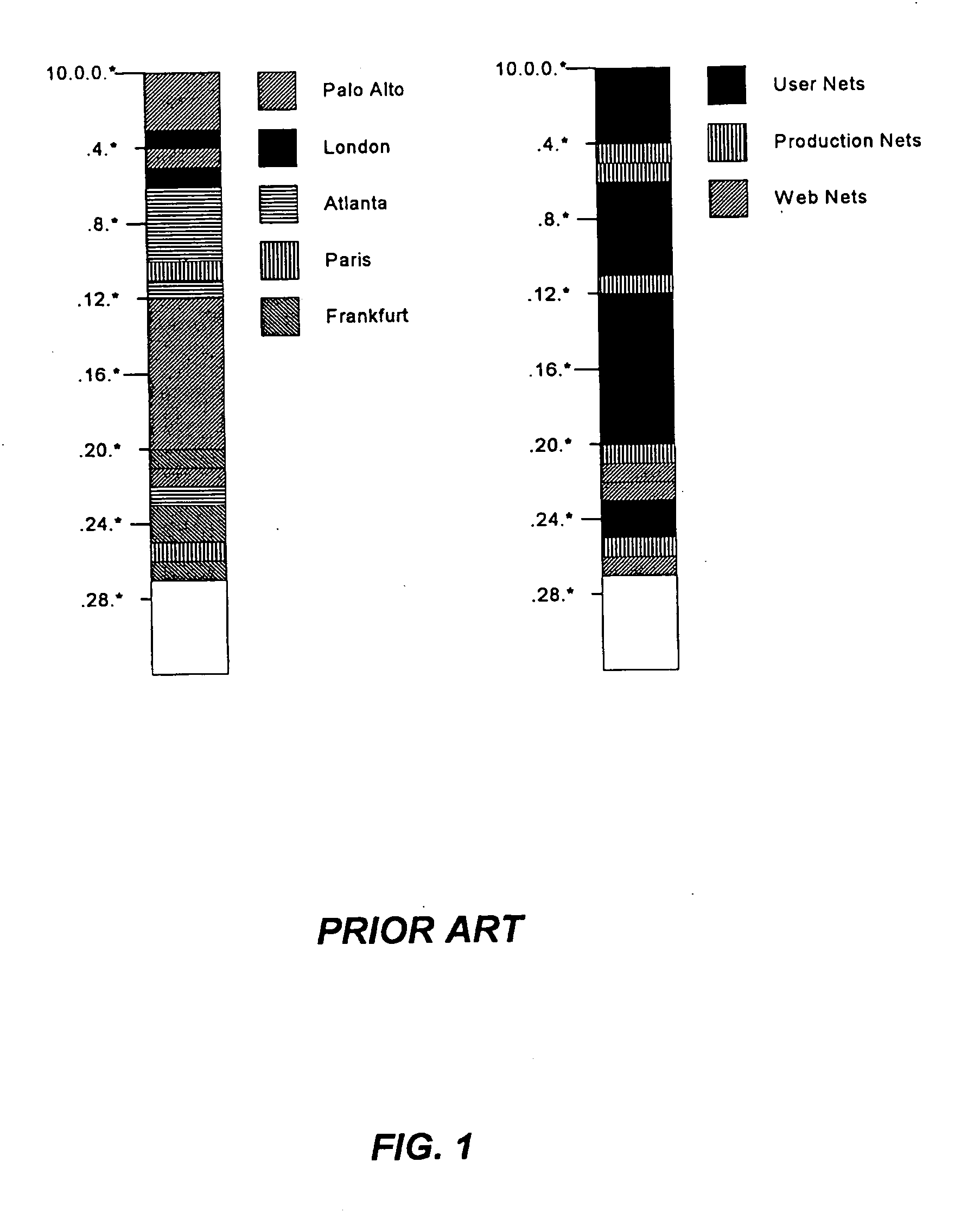
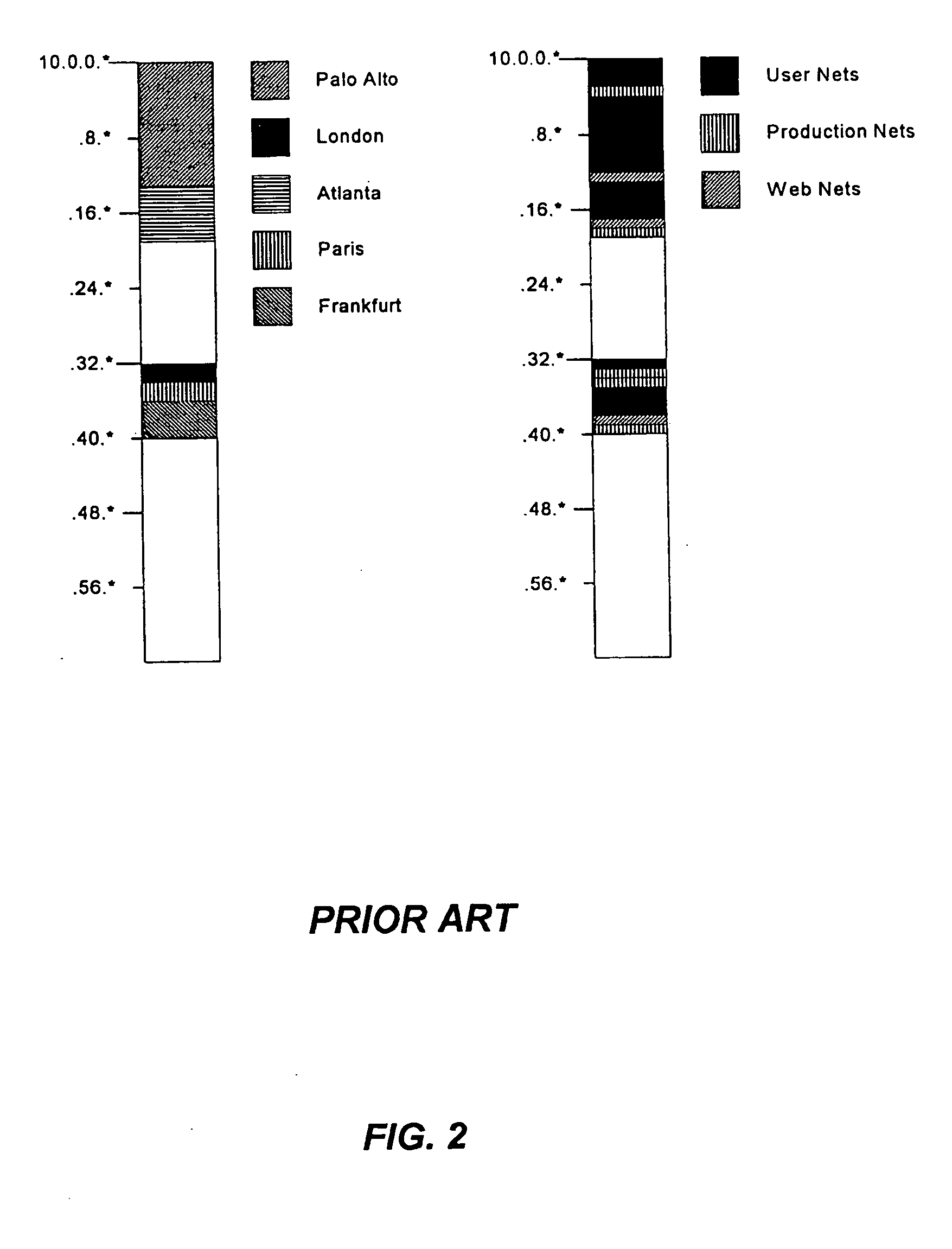
System and method of aggregating discontiguous address ranges into addresses and masks using a plurality of repeating address blocks
A method of creating a discontiguous address plan for an enterprise is provided which includes determining a hierarchy of routing optimization for an enterprise, determining a number of route advertisement aggregation points at each level of the hierarchy, determining a number of network security policy areas for the enterprise, and determining a number of addresses for each of the network security policy areas. The number of addresses is rounded up to a power of the address scheme base number to produce a plurality of rounded addresses. The method further includes allocating an address range for each of the plurality of rounded addresses so that a starting address of the address range begins on a power of the base number and determining a size of the plurality of address ranges. The size of the plurality of address ranges is rounded up to a power of the base number to produce the size of a repeating policy pattern. The method further includes assigning an instance of the repeating policy pattern to each of the route advertisement aggregation points at each hierarchy, and determining an address and a mask for each of the network security policy areas in the repeating policy pattern.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
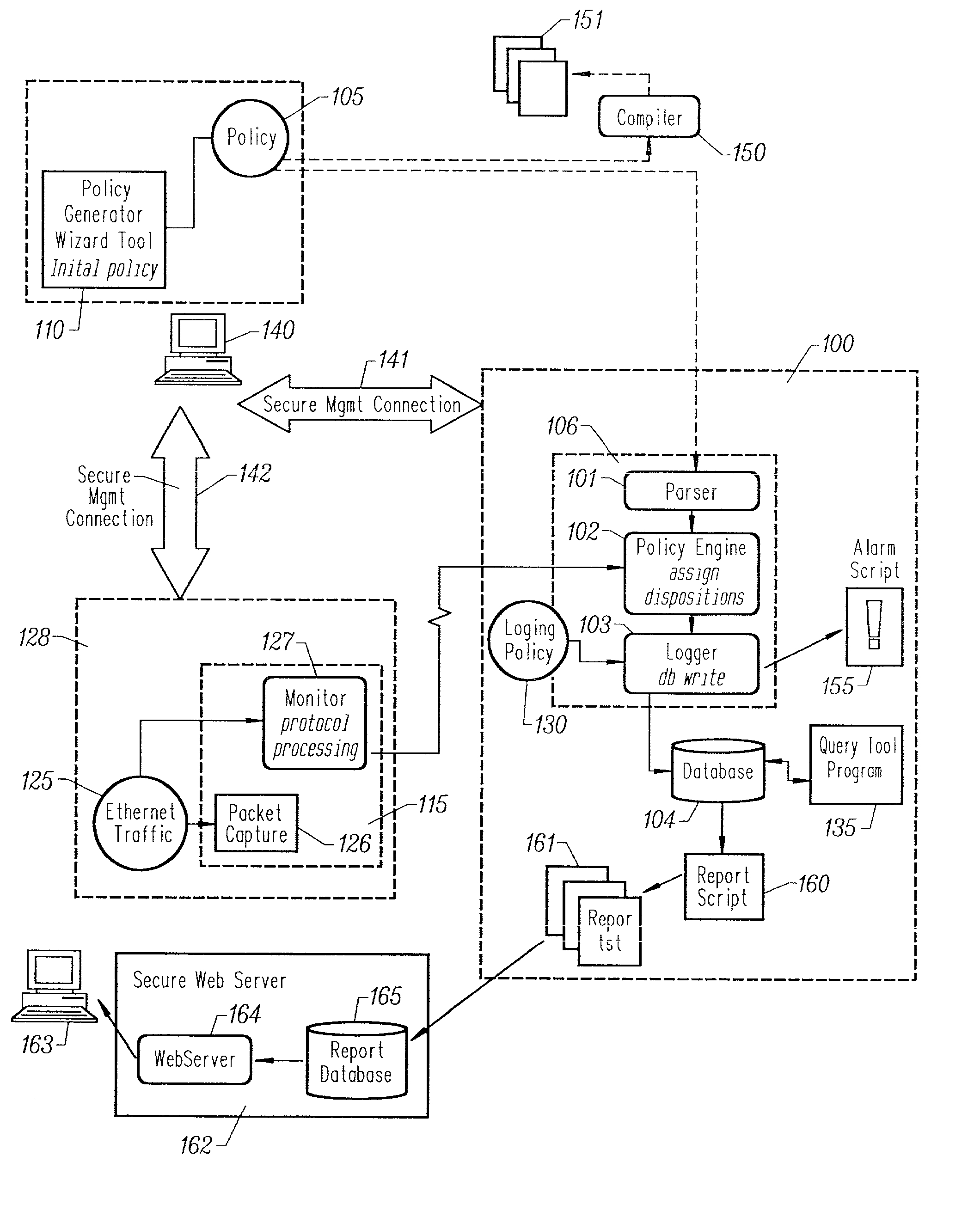
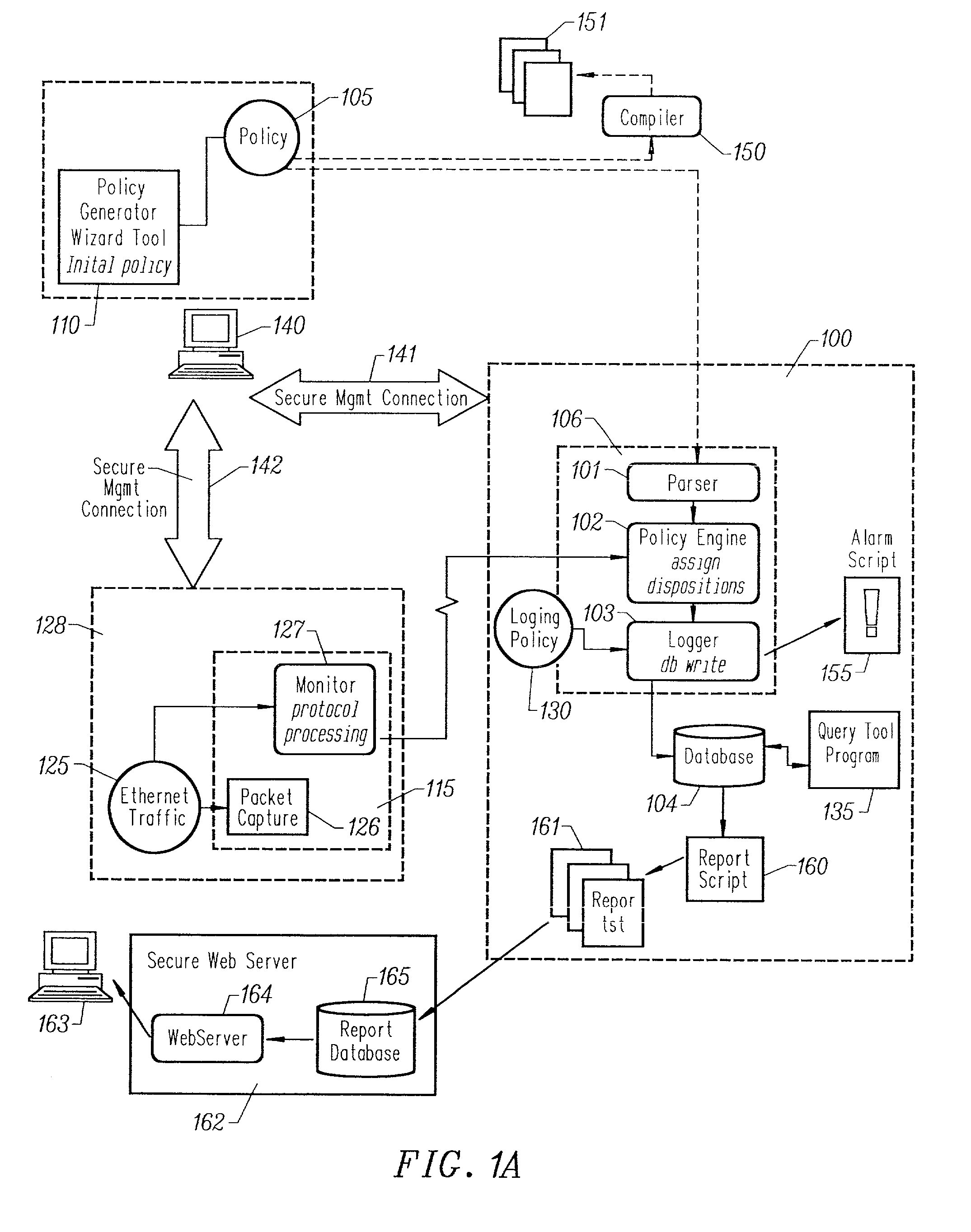
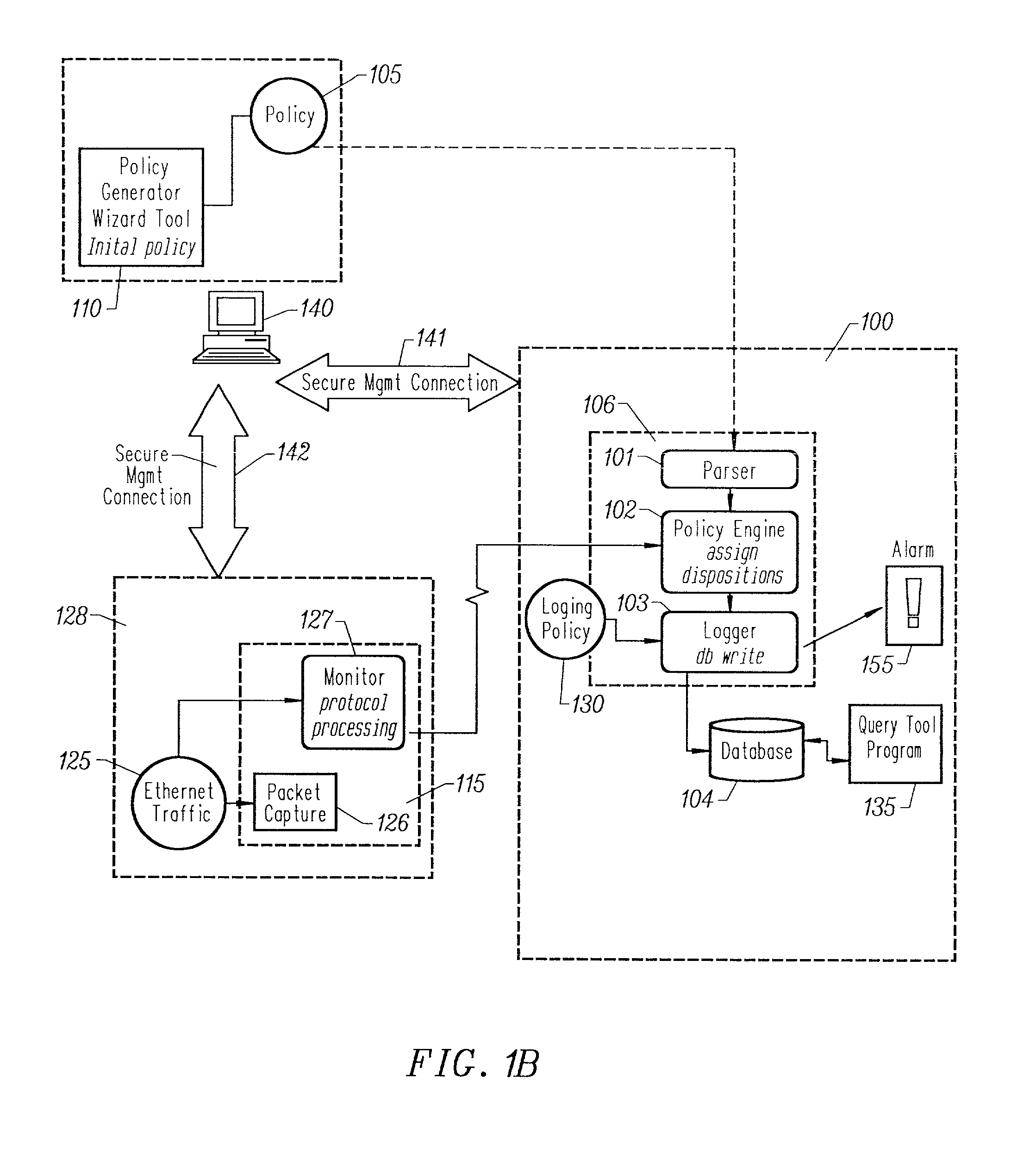
Storing log data efficiently while supporting querying to assist in computer network security
ActiveUS20080162592A1Data processing applicationsError detection/correctionSystem of recordEvent management
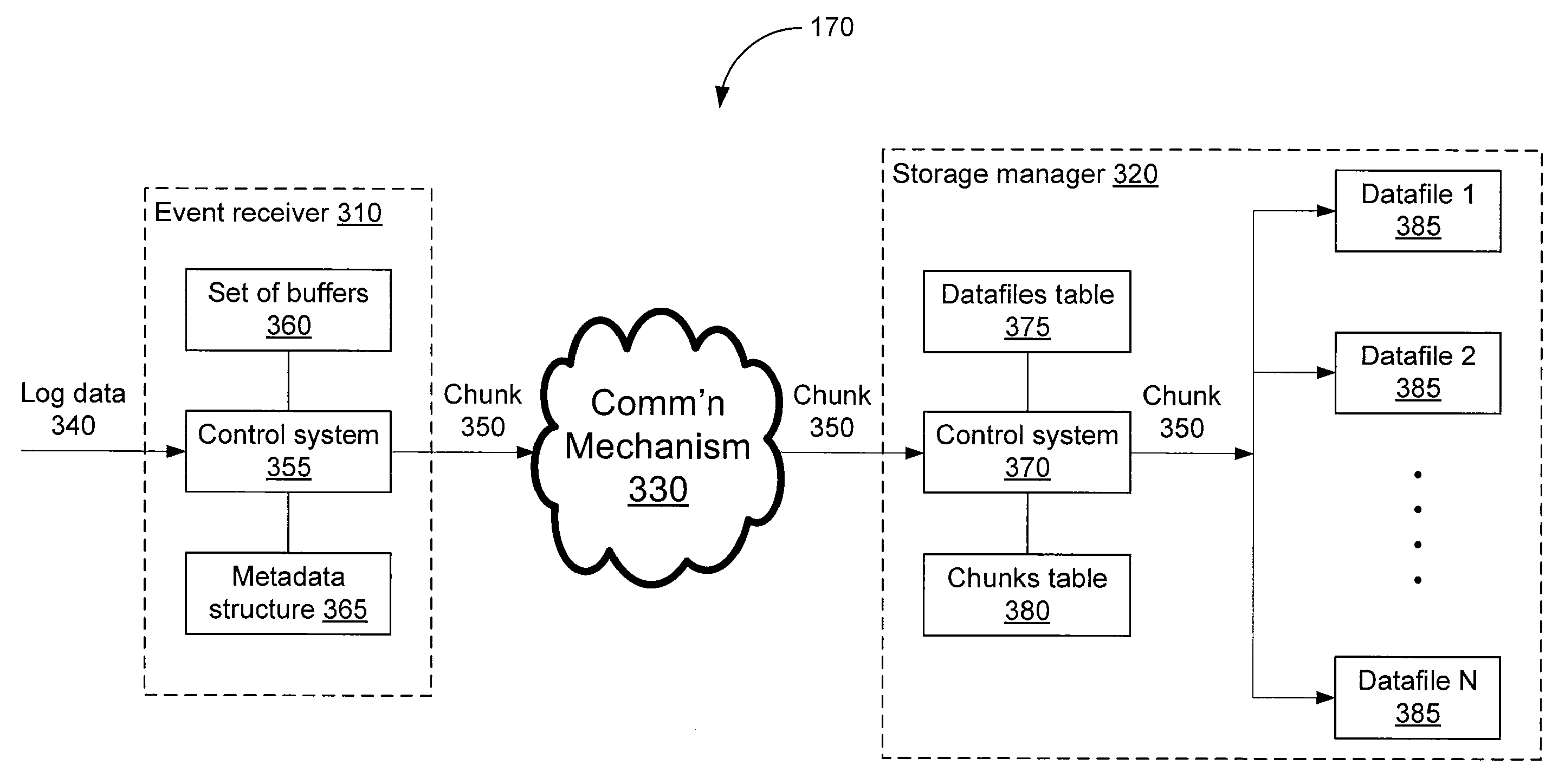
A logging system includes an event receiver and a storage manager. The receiver receives log data, processes it, and outputs a data “chunk.” The manager receives data chunks and stores them so that they can be queried. The receiver includes buffers that store events and a metadata structure that stores metadata about the contents of the buffers. The metadata includes a unique identifier associated with the receiver, the number of events in the buffers, and, for each “field of interest,” a minimum value and a maximum value that reflect the range of values of that field over all of the events in the buffers. A chunk includes the metadata structure and a compressed version of the contents of the buffers. The metadata structure acts as a search index when querying event data. The logging system can be used in conjunction with a security information / event management (SIEM) system.
Owner:MICRO FOCUS LLC
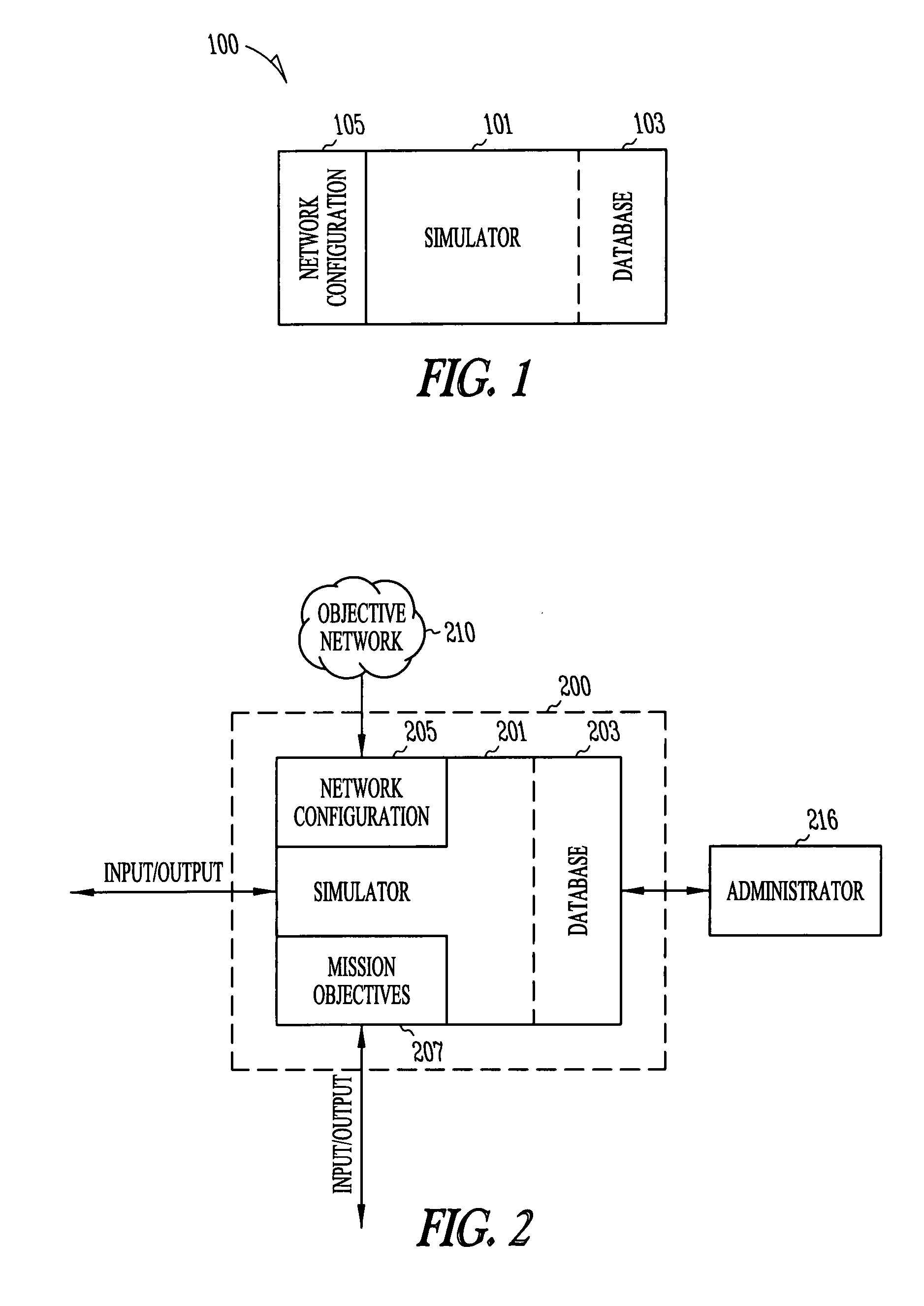
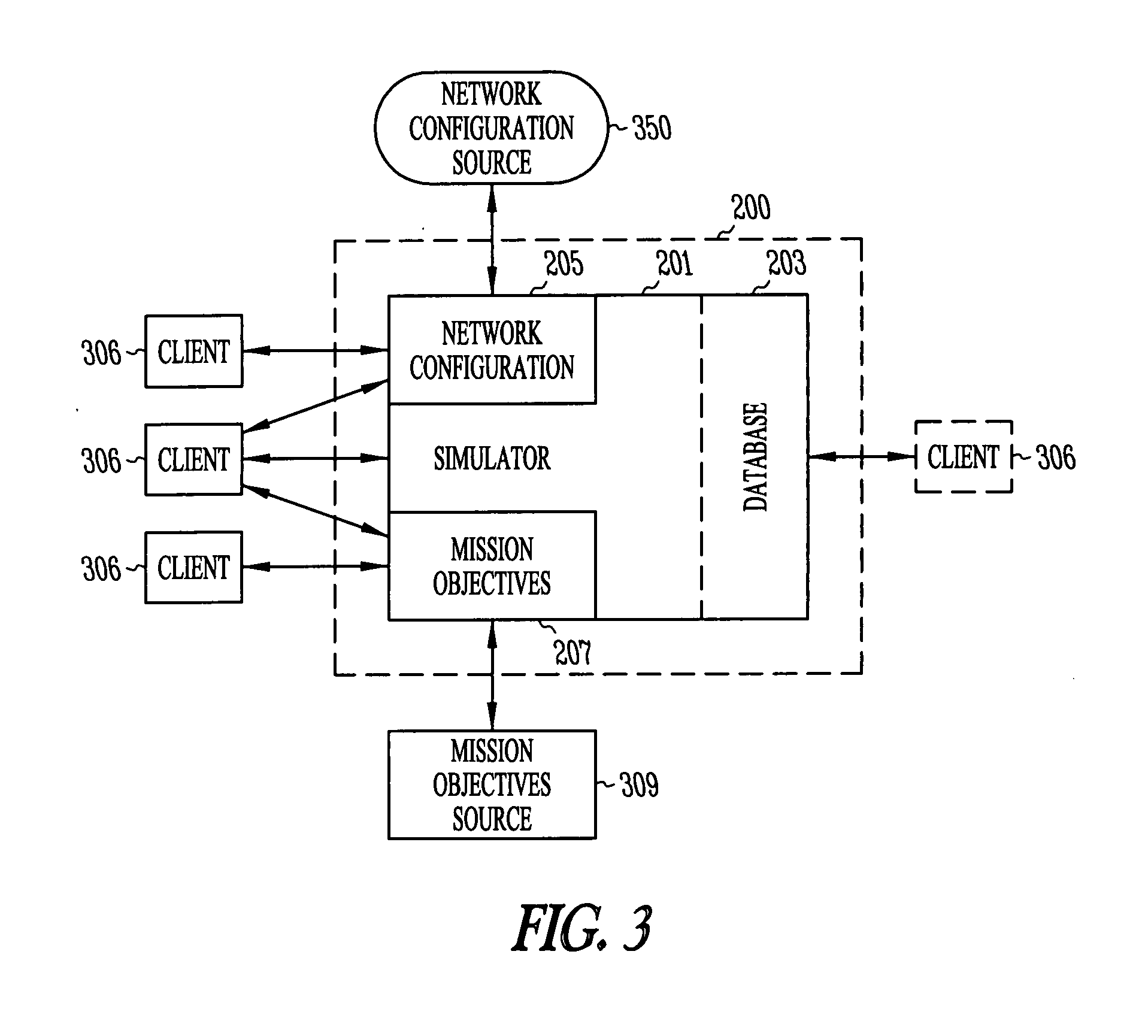
Network security modeling system and method
InactiveUS7315801B1Analogue computers for electric apparatusDigital computer detailsNetwork security policyVulnerability
A network security modeling system which simulates a network and analyzes security vulnerabilities of the network. The system includes a simulator which includes a network vulnerabilities database and a network configuration module having network configuration data. The simulator determines vulnerabilities of the simulated network based on the network configuration data and the vulnerabilities database.
Owner:MCAFEE LLC
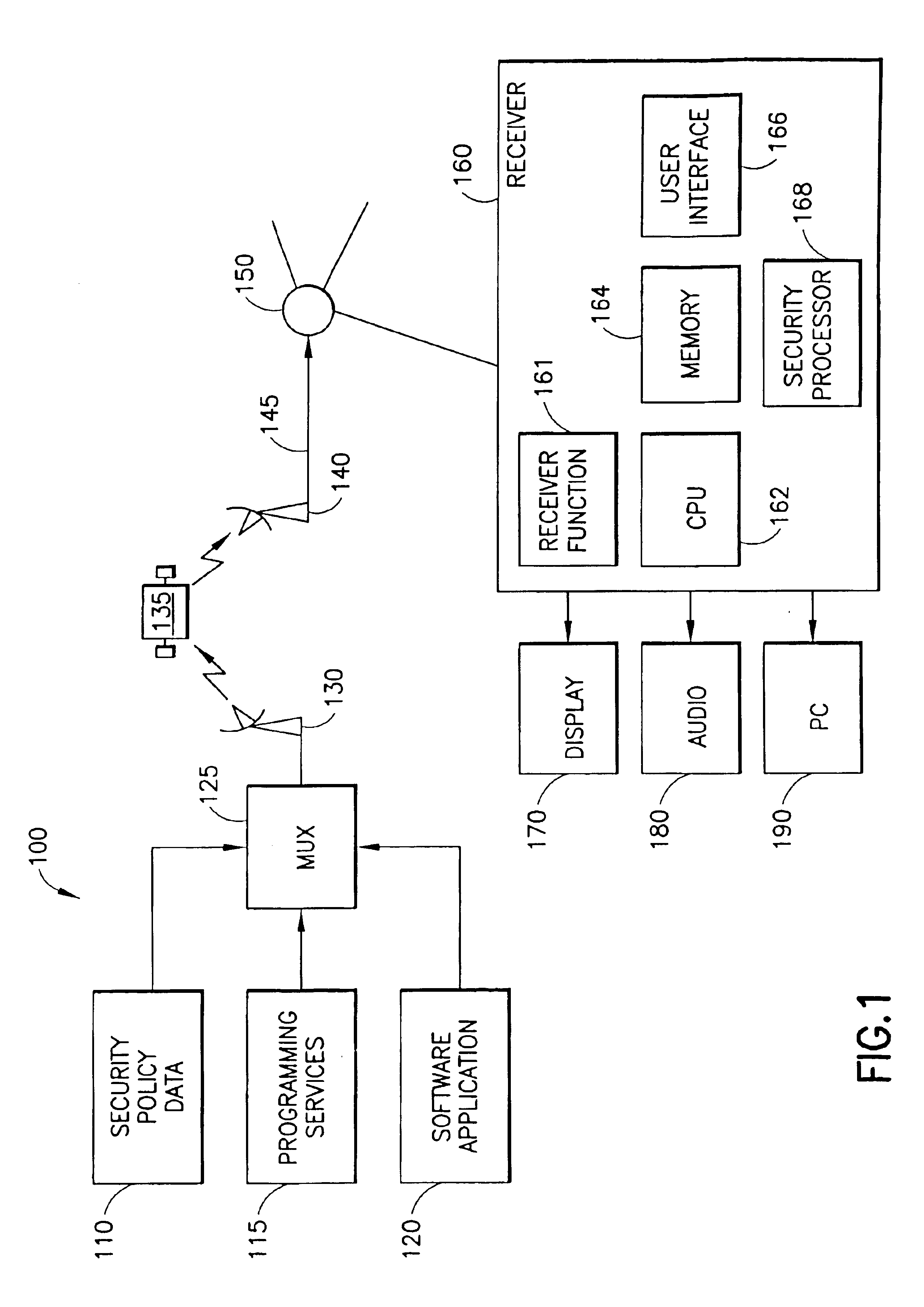
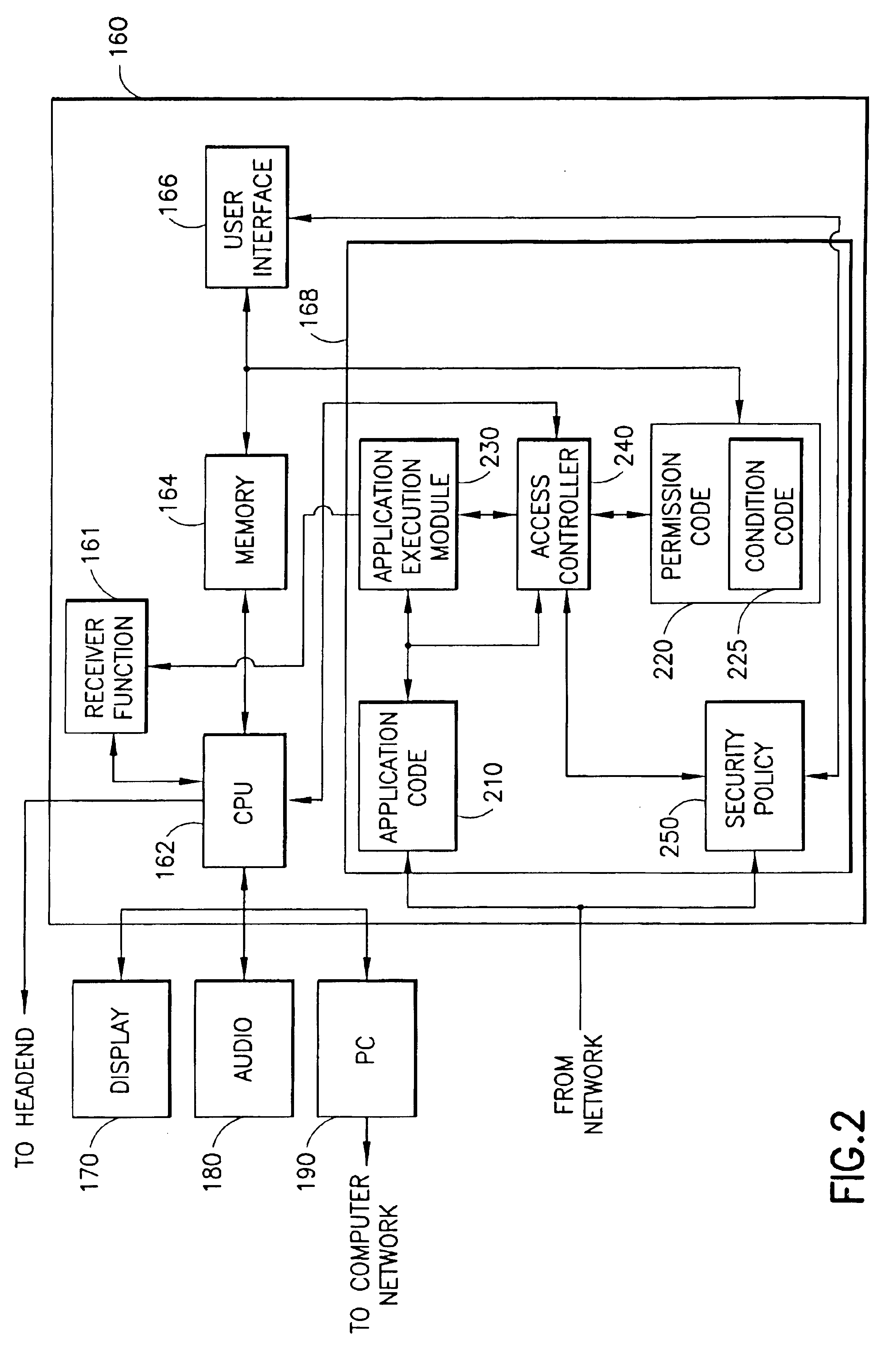
Dynamic security for digital television receivers
InactiveUS6948183B1Digital data processing detailsAnalogue secracy/subscription systemsNetwork security policyReceiver function
A system that allows service providers, consumer electronic (CE) manufacturers or standards bodies to define flexible security policies (110) for the execution of downloaded applications (120) on digital television (DTV) receivers (160). The current receiver environment in which a software application is to be run is evaluated. For example, environmental factors such as time of day, date, channel currently tuned in, parental lockout status, grouping of major and minor virtual channels, and so forth, may be considered. An access controller (168) determines if the receiver's environmental factors satisfy the conditions for granting a permission to a downloadable application to allow access to the receiver functions (161), receiver resources and user private data. The security policy can be modified by installing or downloading a new security policy (110), or modified by a user with the provision of an appropriate interface. A Java code-implemented embodiment is disclosed.
Owner:GOOGLE TECH HLDG LLC
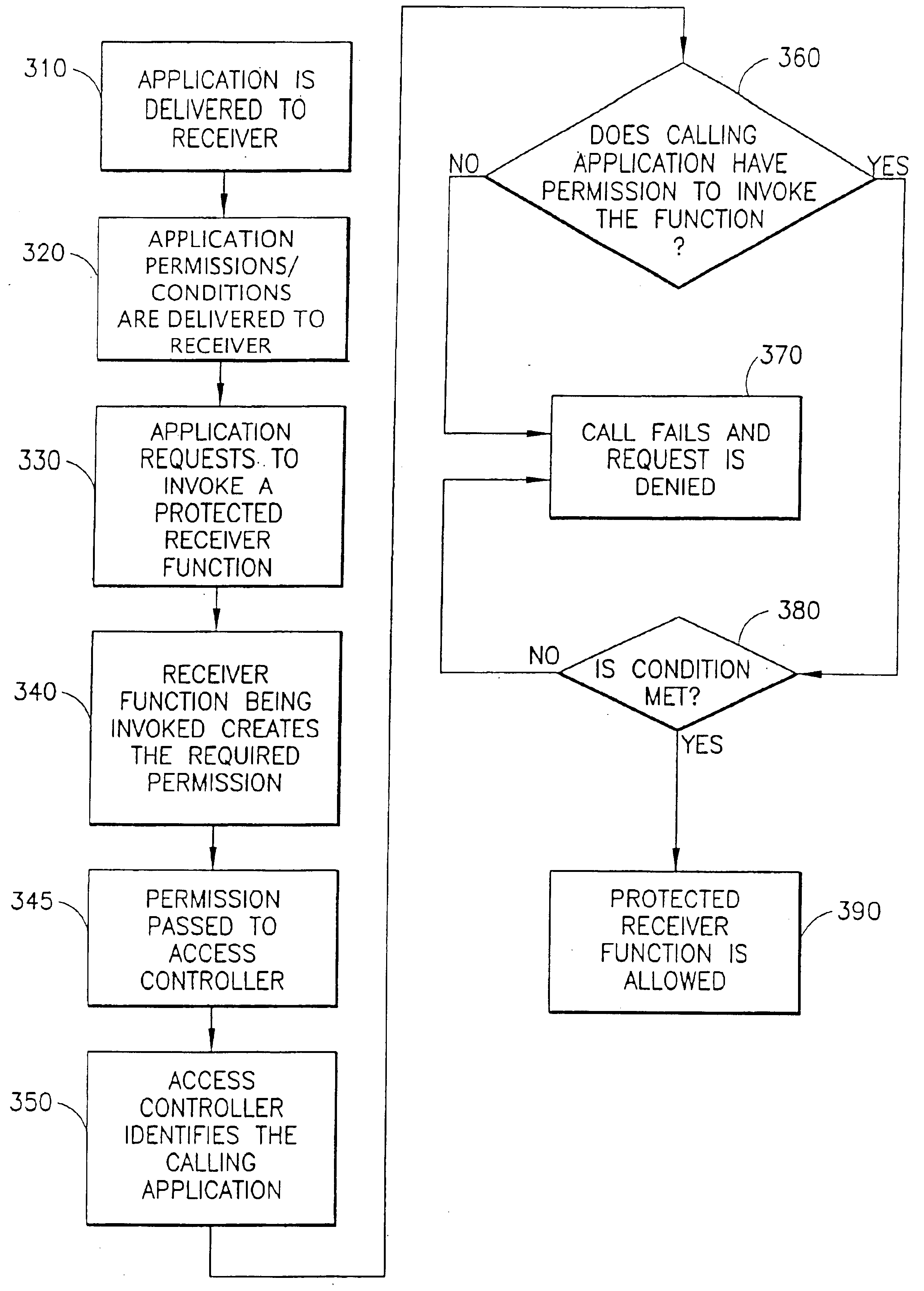
Credential/condition assertion verification optimization
InactiveUS20020053033A1Data taking preventionDigital data processing detailsNetwork security policySecurity policy
A method and apparatus ascertain which credential and which condition both from a network security policy best describe, respectively, information about initiator and target principals involved in an interaction, and tests performed on a state of an associated protocol event.
Owner:MCAFEE LLC
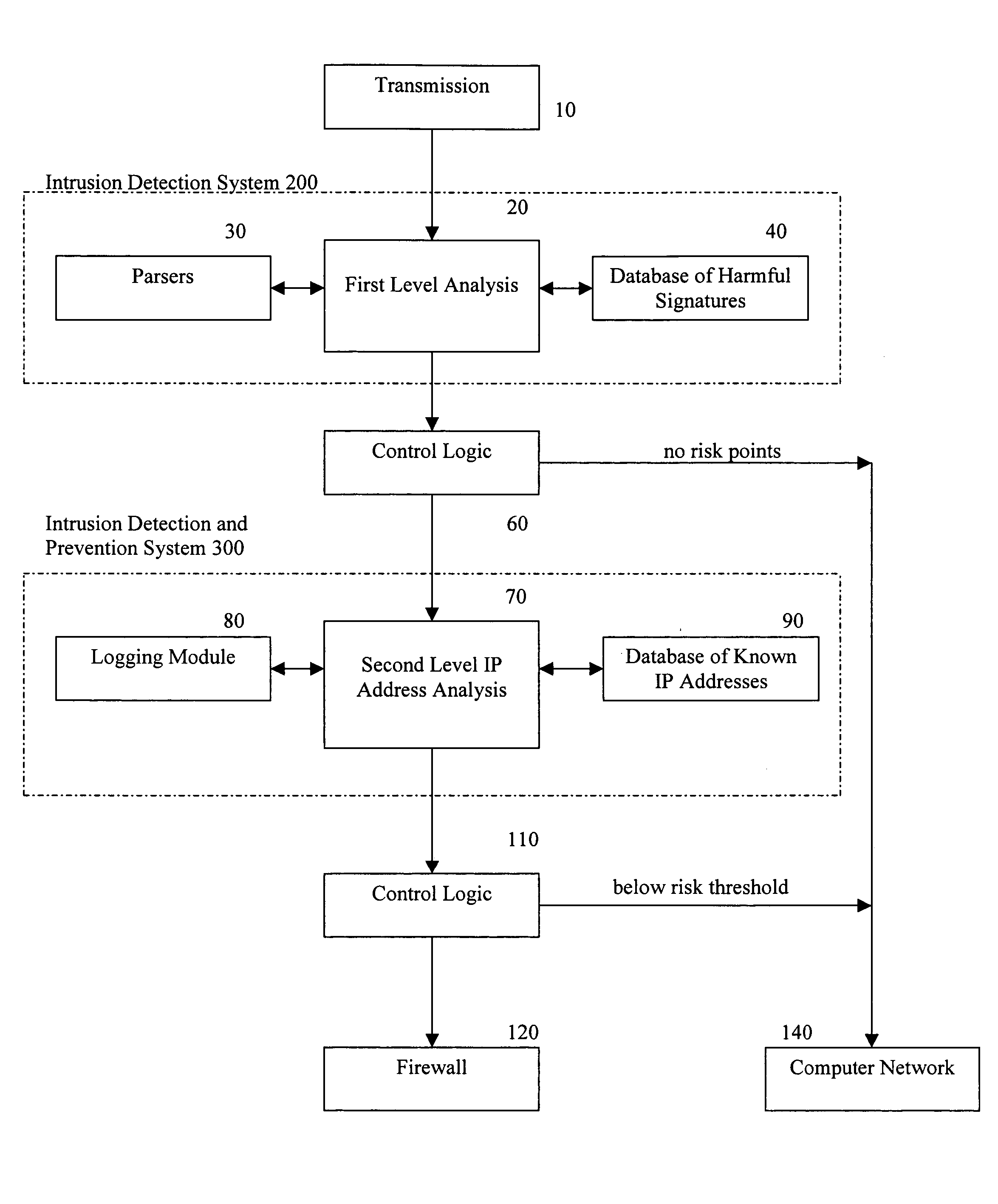
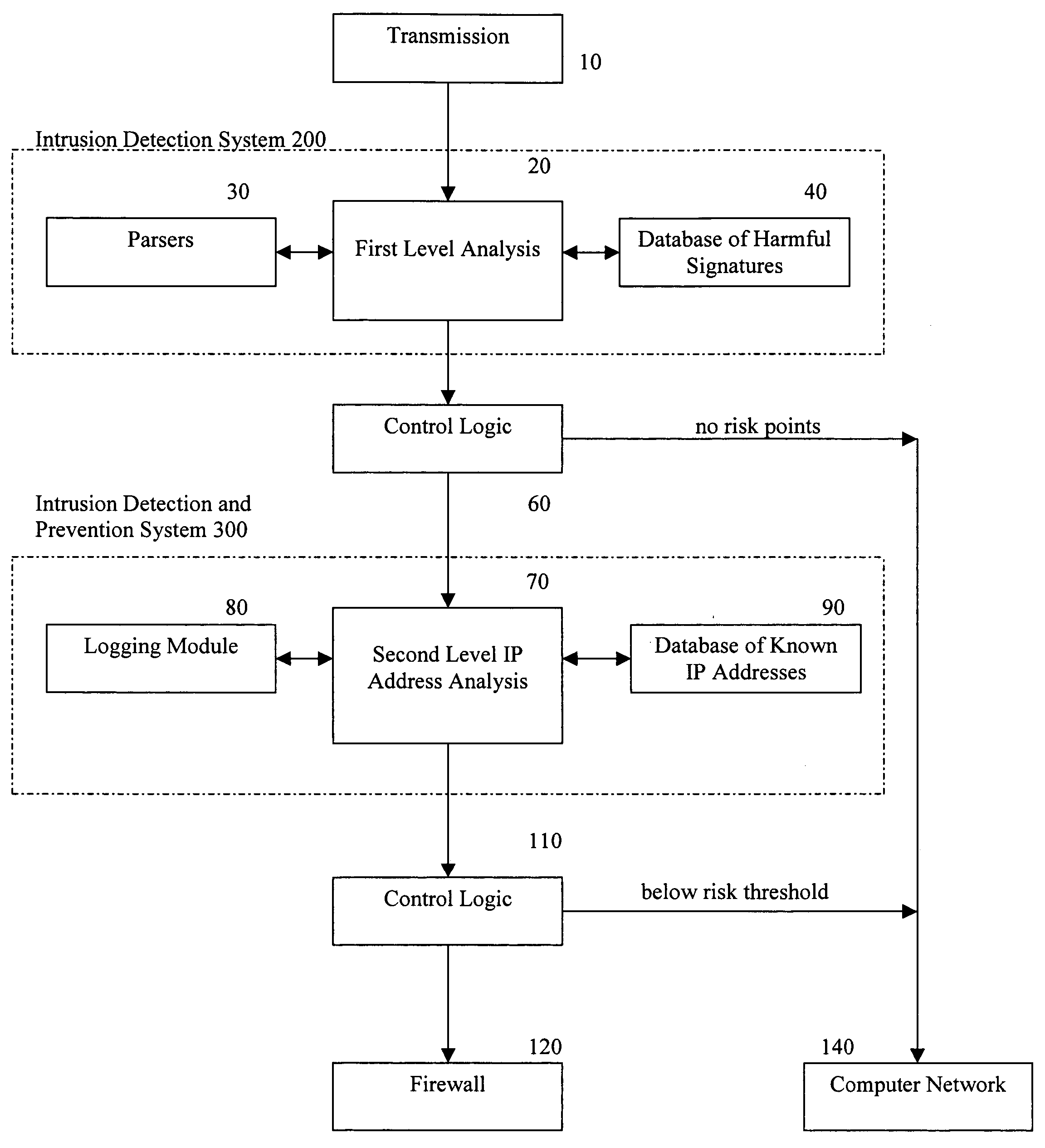
Methods and apparatus for computer network security using intrusion detection and prevention
InactiveUS20050262556A1Overcome disadvantagesMemory loss protectionDigital data processing detailsIp addressIntrusion detection and prevention
A method for providing security to a computer network by selectively blocking network transmissions from selected IP addresses comprising the steps of: establishing a risk threshold whereby transmissions from IP addresses exceeding said risk threshold are selectively blocked; receiving a network transmission having an originating IP address and payload; analyzing the payload of said transmission and assigning a current risk rating to said IP address on the basis of said analysis; comparing the originating IP address of said transmission to a database of known IP addresses, each of said said previous cumulative assigned risk rating being based on at least one previous transmission from a known IP address; known IP addresses having a previous cumulative assigned risk rating, assigning a new cumulative risk rating to said originating IP address, said new cumulative risk rating being the sum of said current risk rating and said previous cumulative assigned risk rating for said originating IP address, with the proviso that where said originating IP address is not contained in said database of known IP addresses, the new cumulative risk rating will equal the current risk rating; logging the new cumulative risk rating for said originating IP address in said database of known IP addresses, with the proviso that where the originating IP address of said transmission is not contained in said database of known IP addresses, a new record is created for the originating IP address and said new cumulative risk rating in said database of known IP addresses; comparing said new cumulative risk rating to said risk threshold; and automatically blocking said transmission if said new cumulative risk rating exceeds said risk threshold.
Owner:DIGITAL SECURITY NETWORK
System and method for secure network connectivity
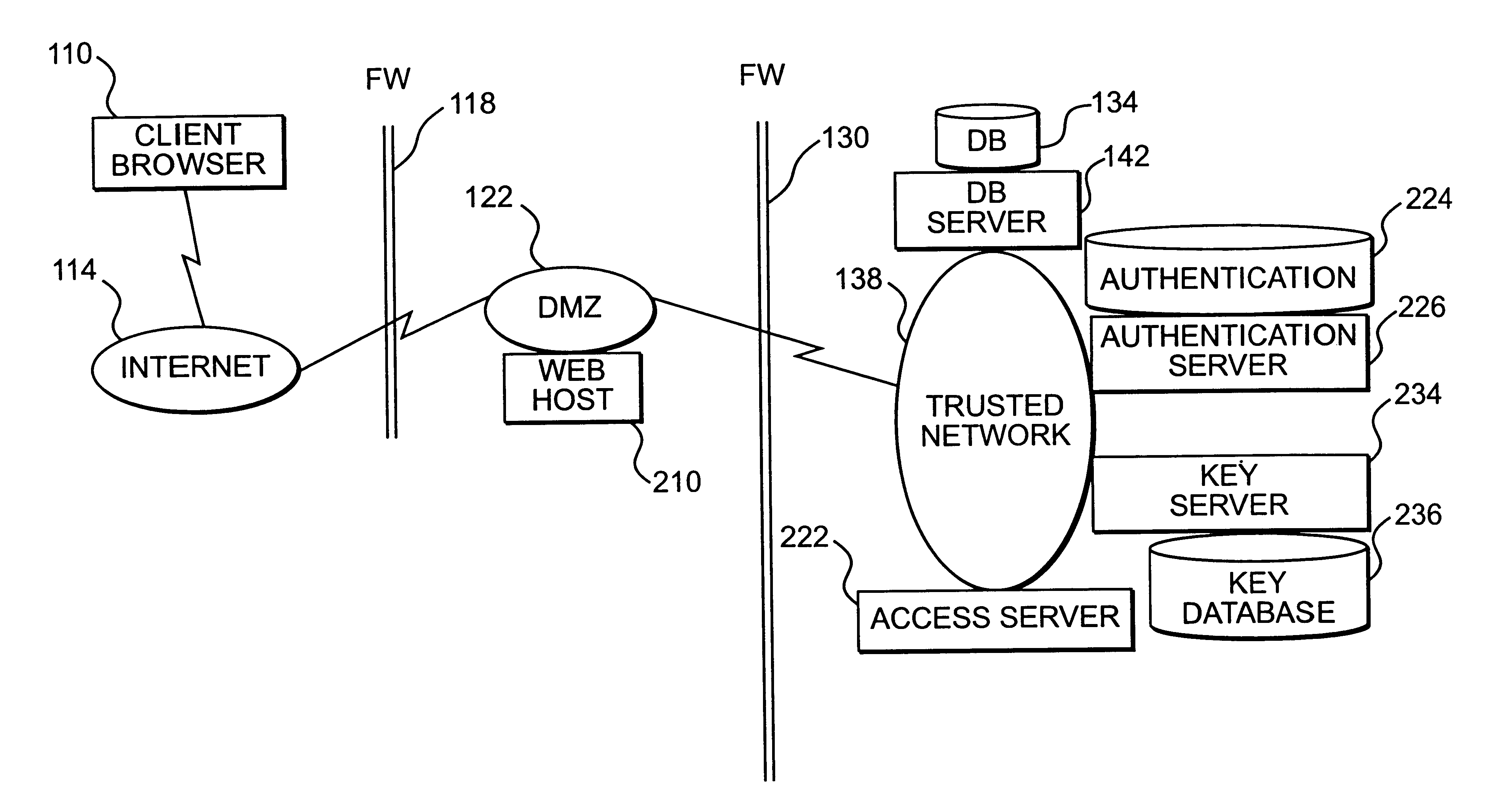
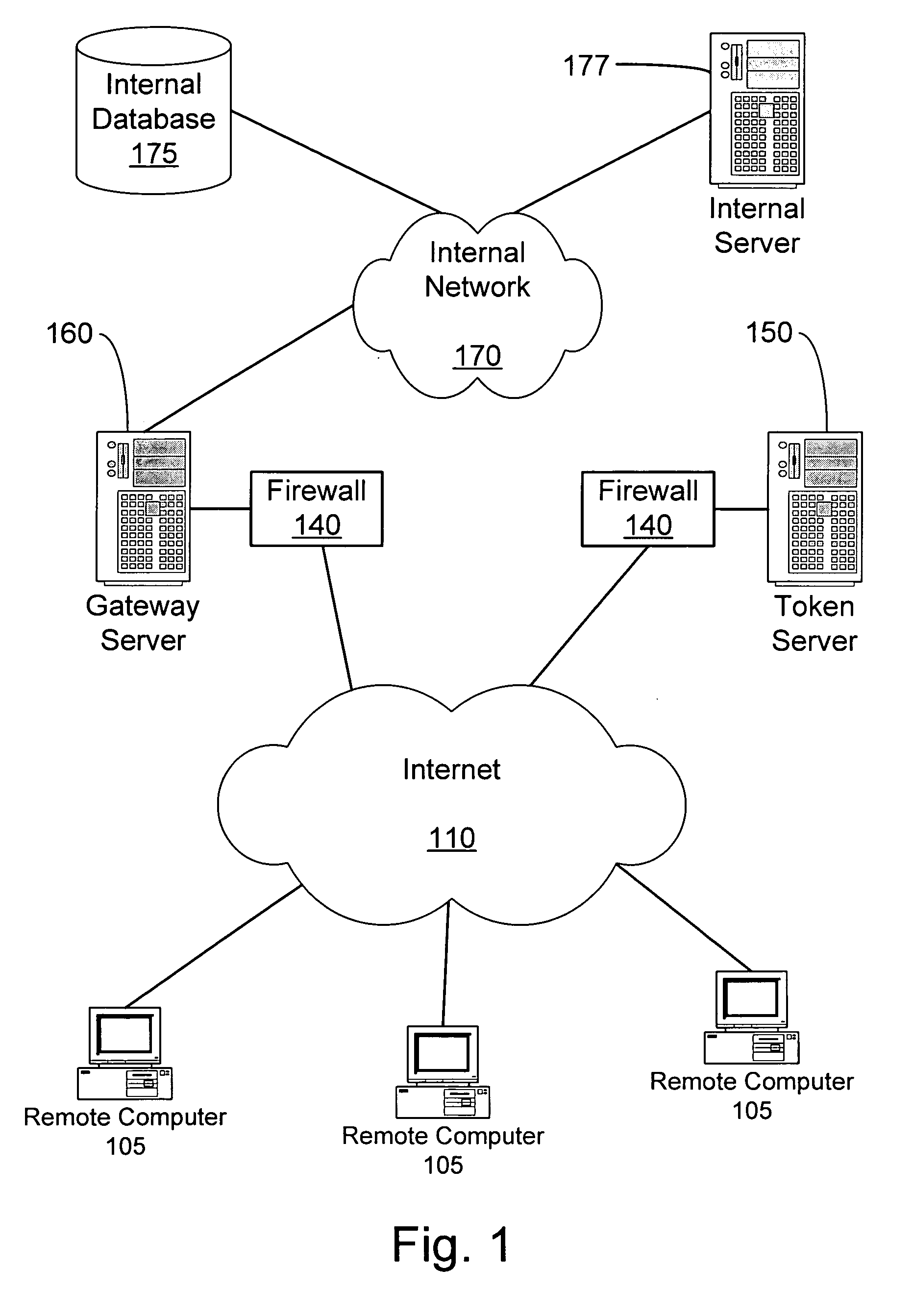
InactiveUS20070101405A1Accurate protectionConnection securityRandom number generatorsMemory loss protectionSecurity checkRemote computer
A system and method to ensure that a remote computer making a VPN connection complies with network security policies. Server-driven security checks may be configured to verify compliance with each access level before access is granted at that level. The security checks may be selected based at least according to the information received from the remote computer. After the server determines that the remote computer complies with the security policy for the requested access level, the server may pass a token to the remote computer, or may grant VPN access to the remote computer. If the remote computer does not comply with the security policy associated with the requested access level but is in compliance with a security policy corresponding to a lower access level, the server may grant the remote computer access to the lower access level.
Owner:BARCLAYS CAPITAL INC
Credential/condition assertion verification optimization
InactiveUS6871284B2Unauthorized memory use protectionHardware monitoringNetwork security policySecurity policy
A method and apparatus ascertain which credential and which condition both from a network security policy best describe, respectively, information about initiator and target principals involved in an interaction, and tests performed on a state of an associated protocol event.
Owner:MCAFEE LLC
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
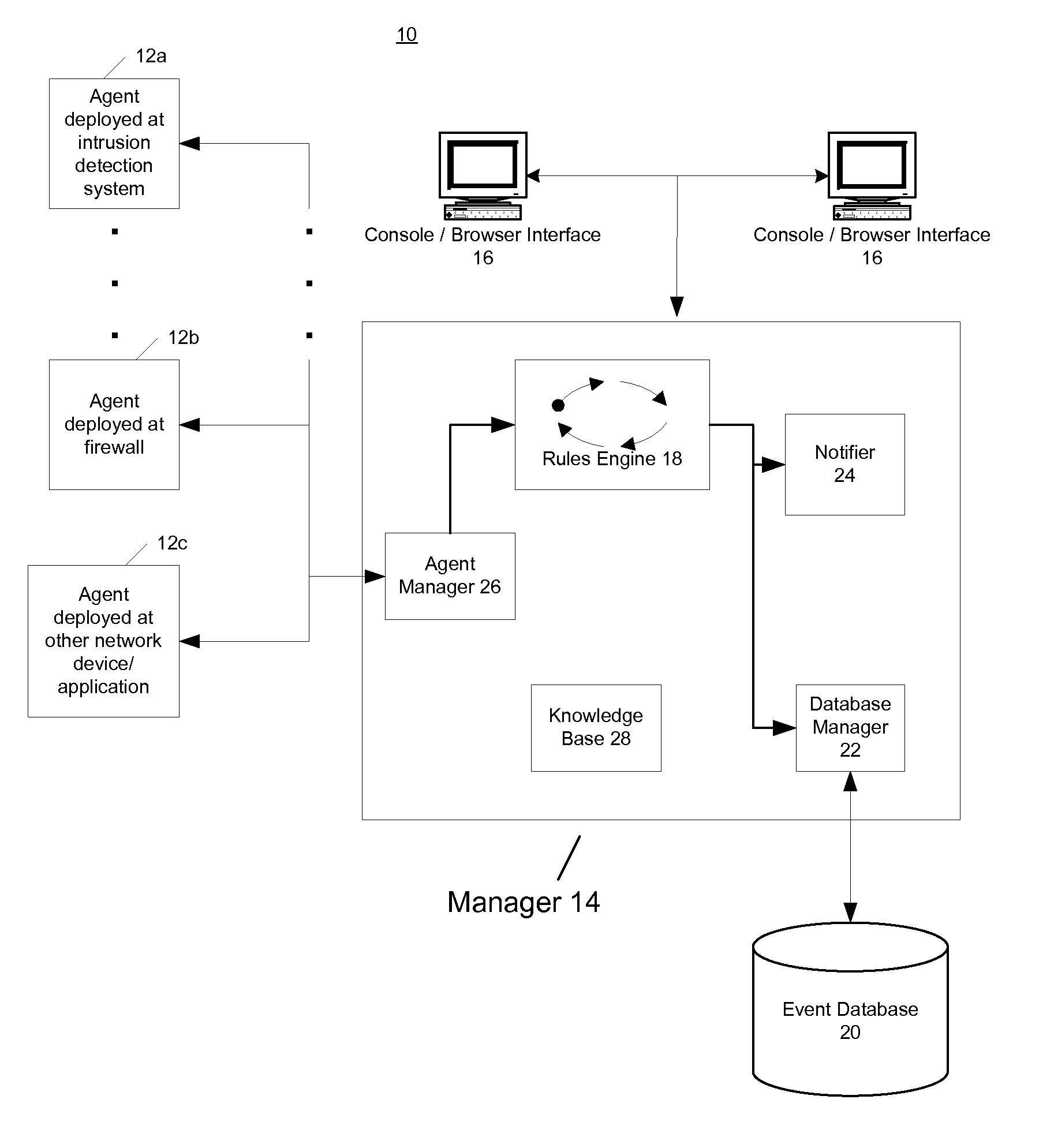
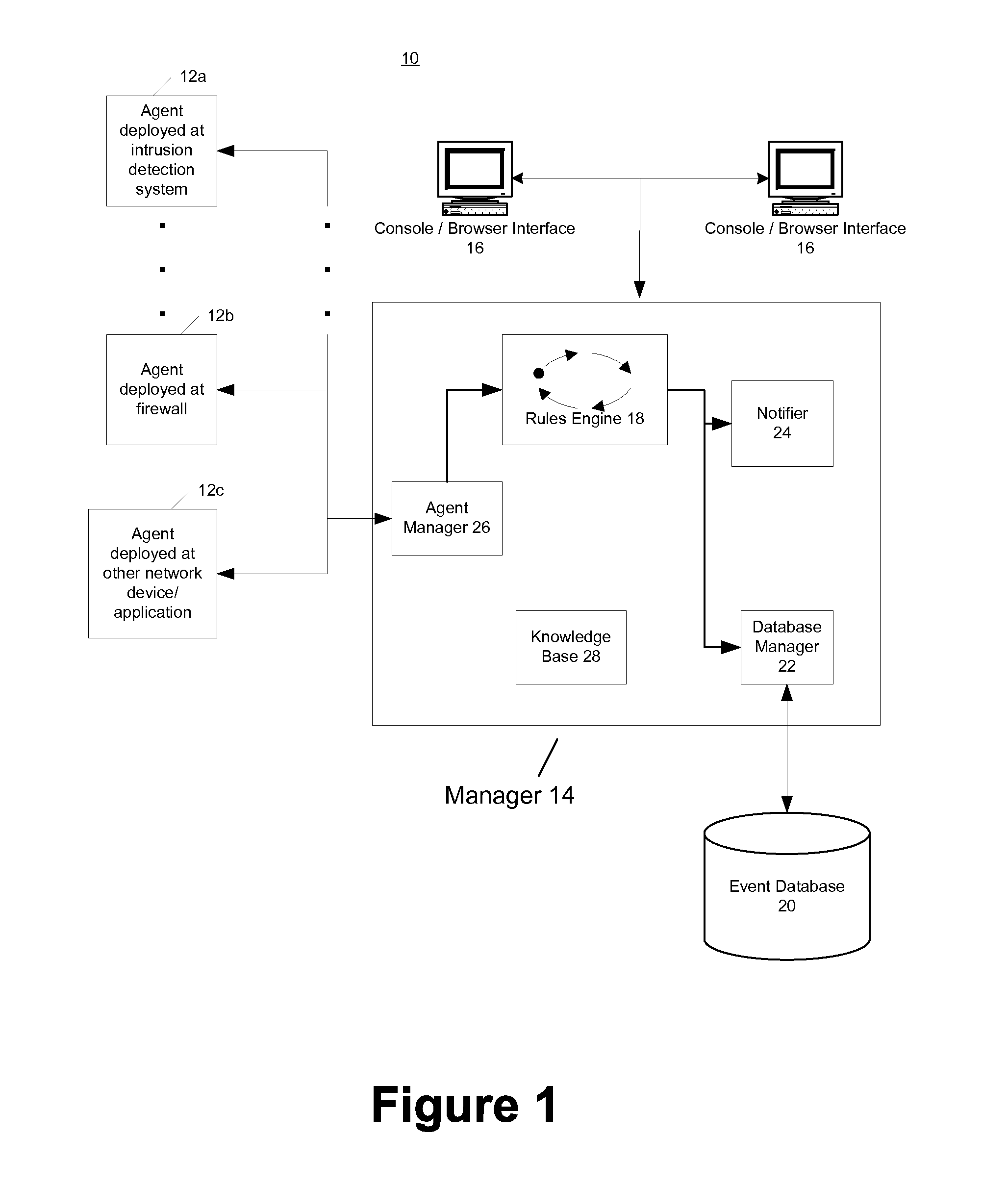
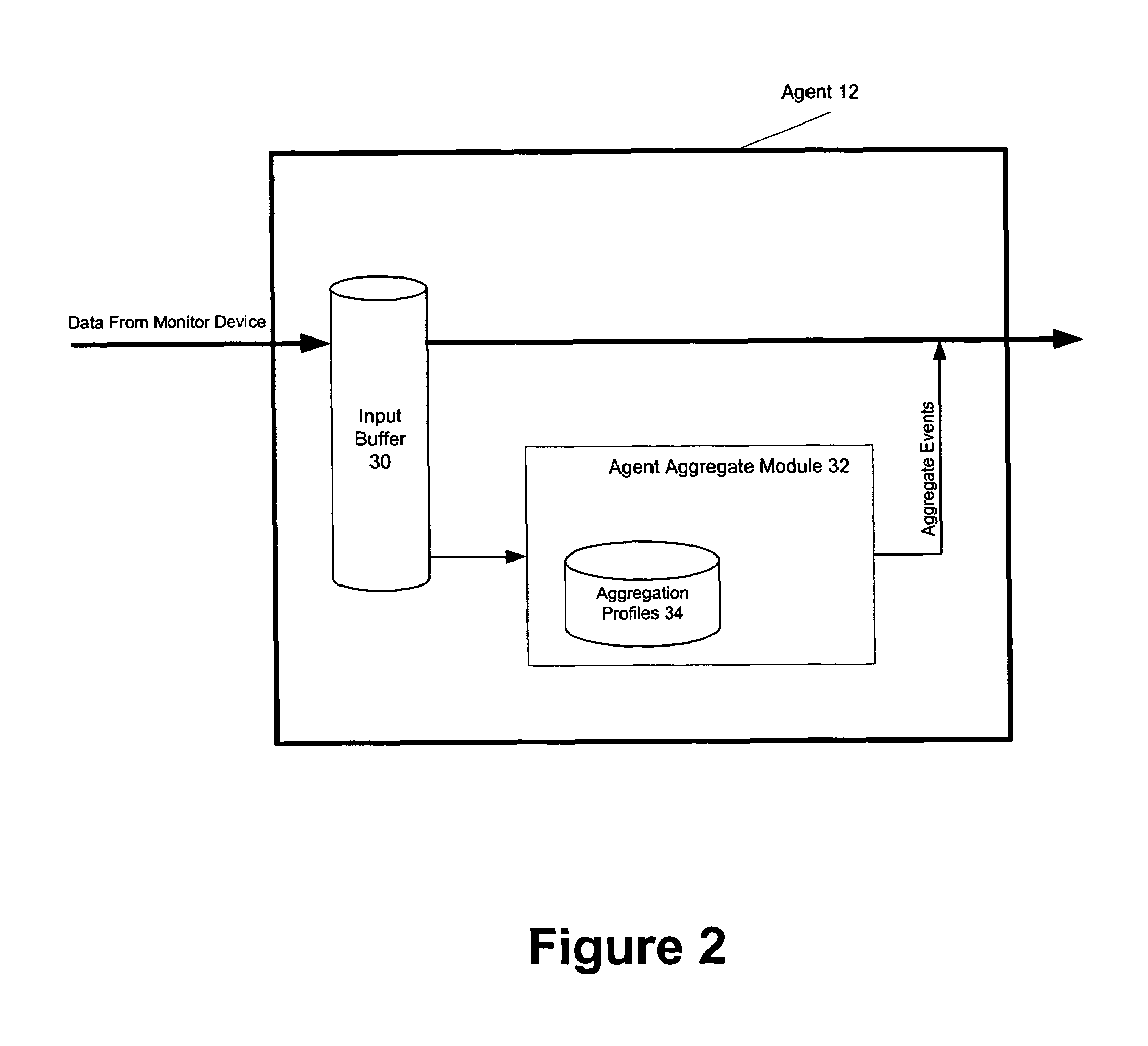
Security event aggregation at software agent
InactiveUS7644438B1Memory loss protectionError detection/correctionNetwork security policySoftware agent
A network security system can have a plurality of distributed software agents configured to collect security events from network devices. In one embodiment, the agents are configured to aggregate the security events. In one embodiment of the present invention, an agent includes a device interface to receive a security event from a network device, a plurality of aggregation profiles, and an agent aggregate module to select one of the plurality of aggregation profiles, and increment an event count of an aggregate event representing the received security event using the selected aggregation profile.
Owner:MICRO FOCUS LLC
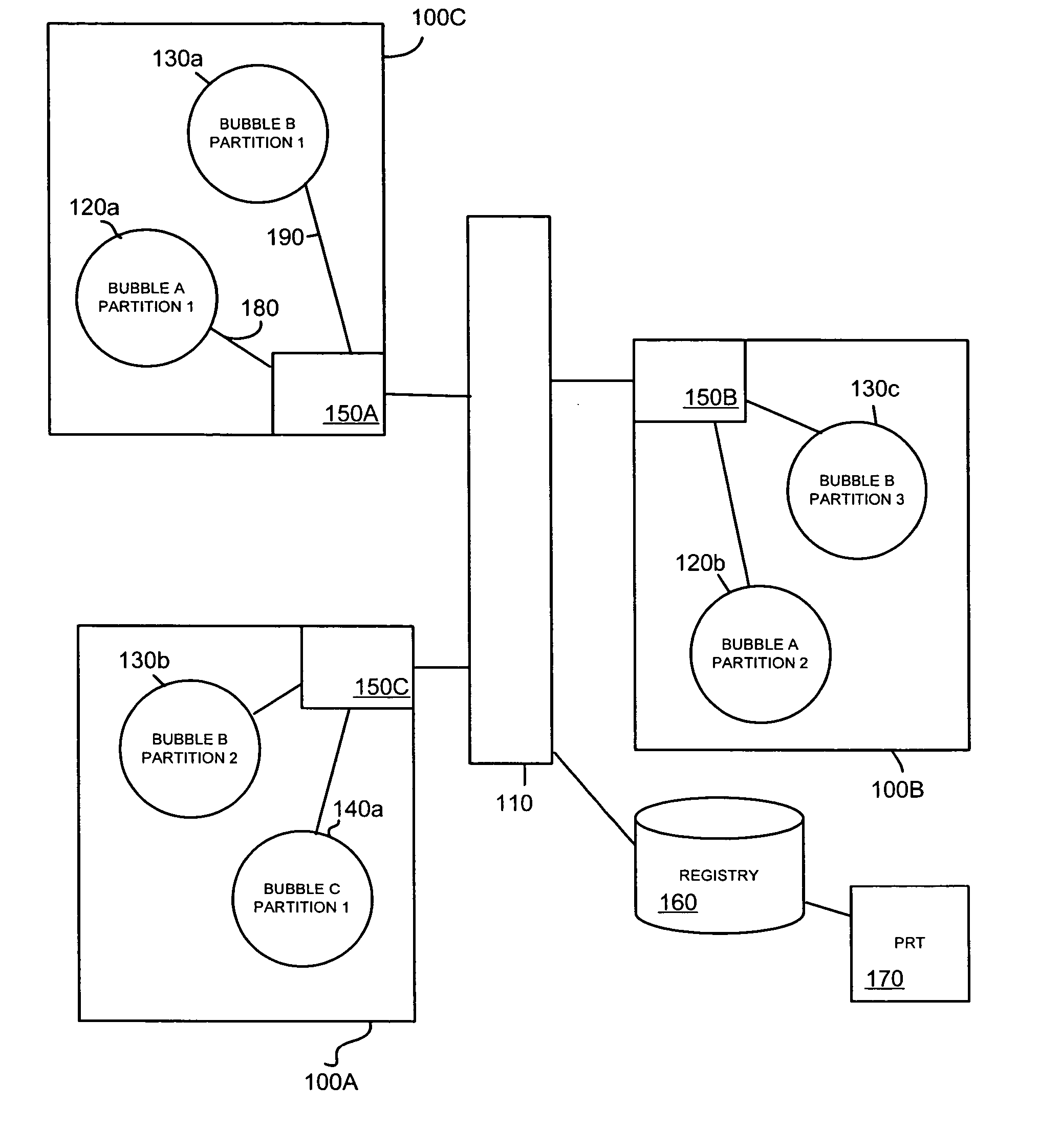
Method and apparatus for implementing security policies in a network
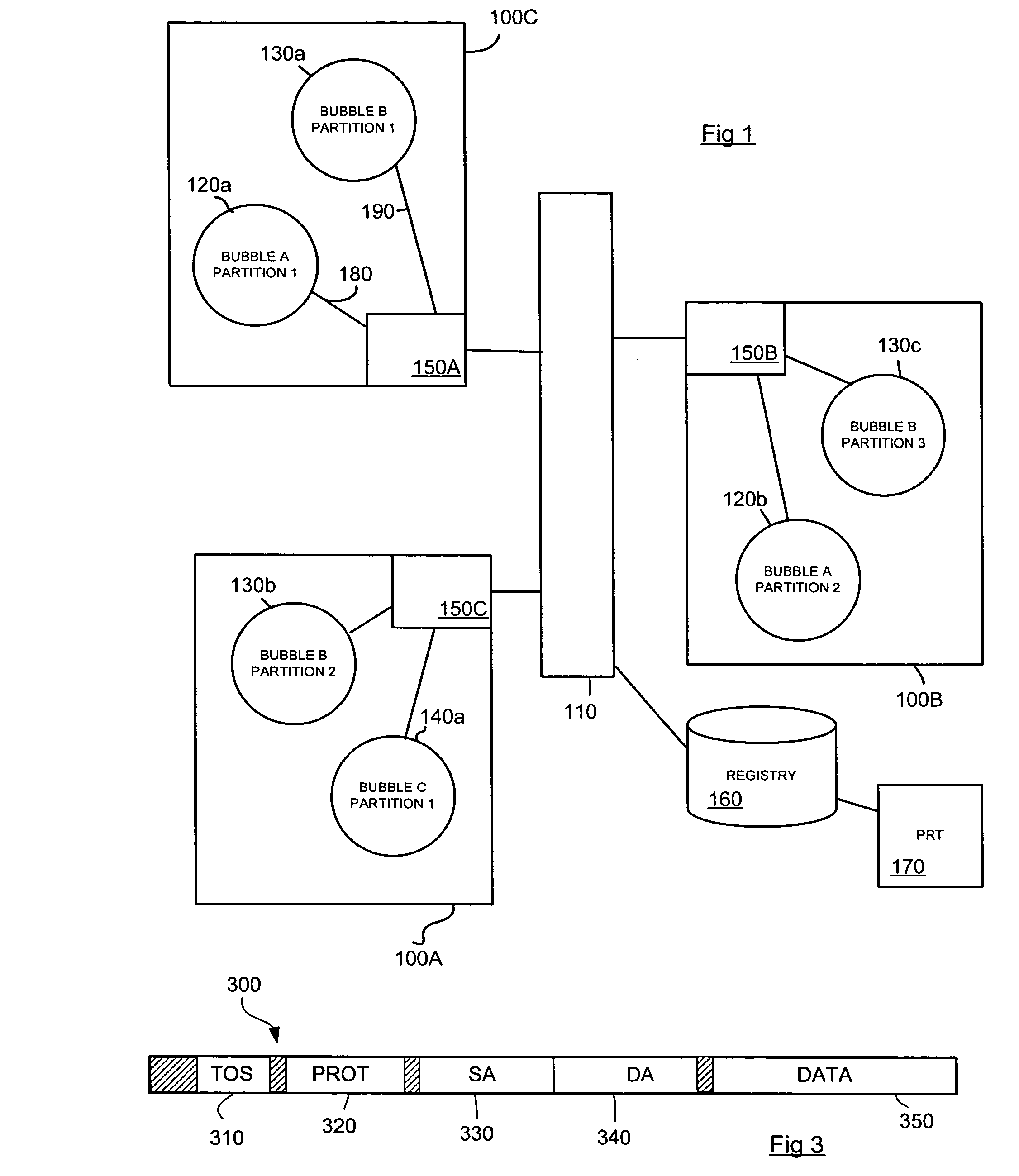
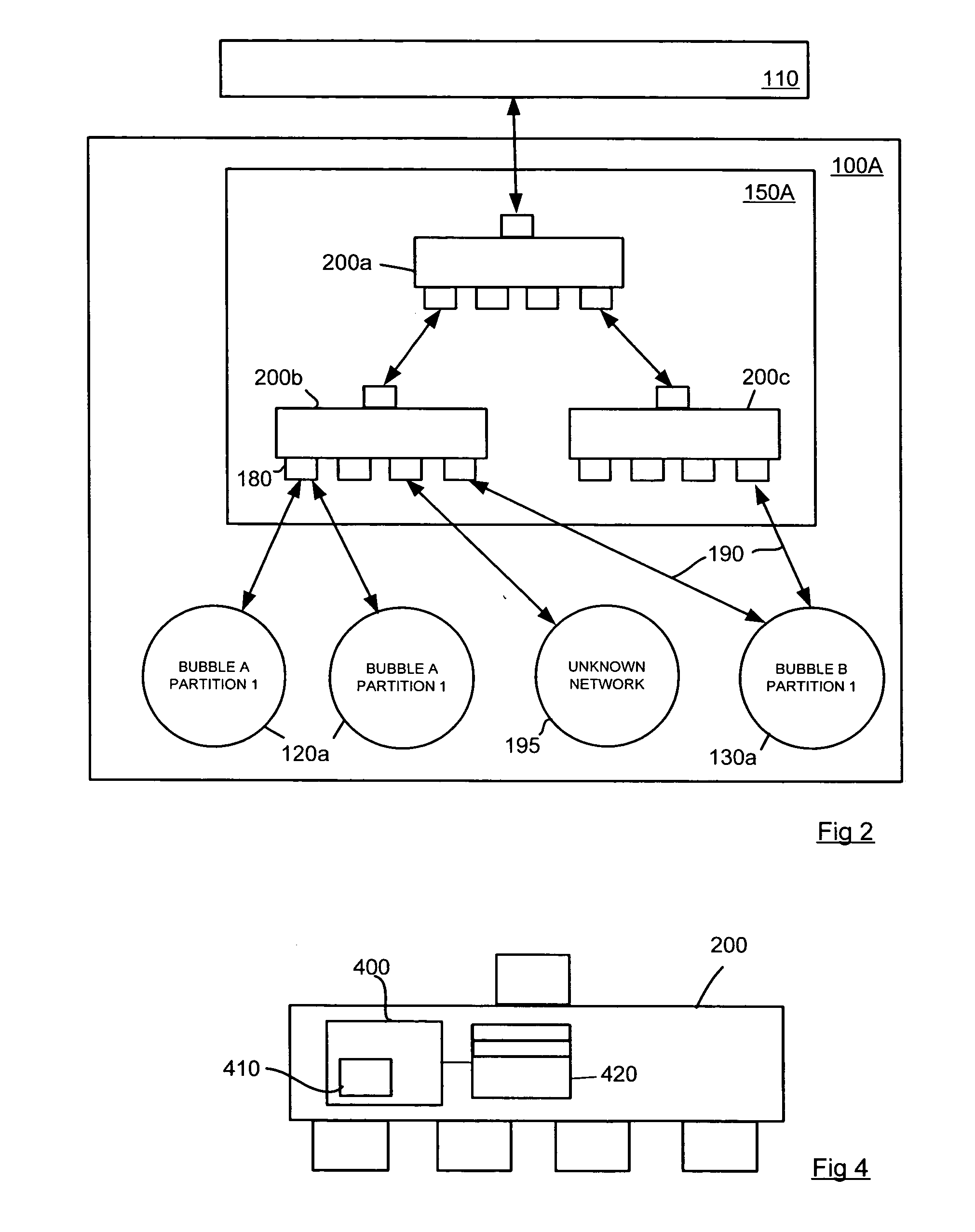
A secured network is disclosed configured to carry data, comprising a plurality of network bubbles and a plurality of network control points, wherein each network bubble comprises one or more bubble partitions and each bubble partition comprises at least one networked device configured to transmit and receive data, and all of the network devices corresponding to at least one of the plurality of network bubbles have a common network security policy. At least one network control point, such as a router, is provided with a marker module arranged to mark outgoing packets with a label corresponding to the network bubble from which the packets originate that can be used to enforce the network security policy of the at least one network bubble.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
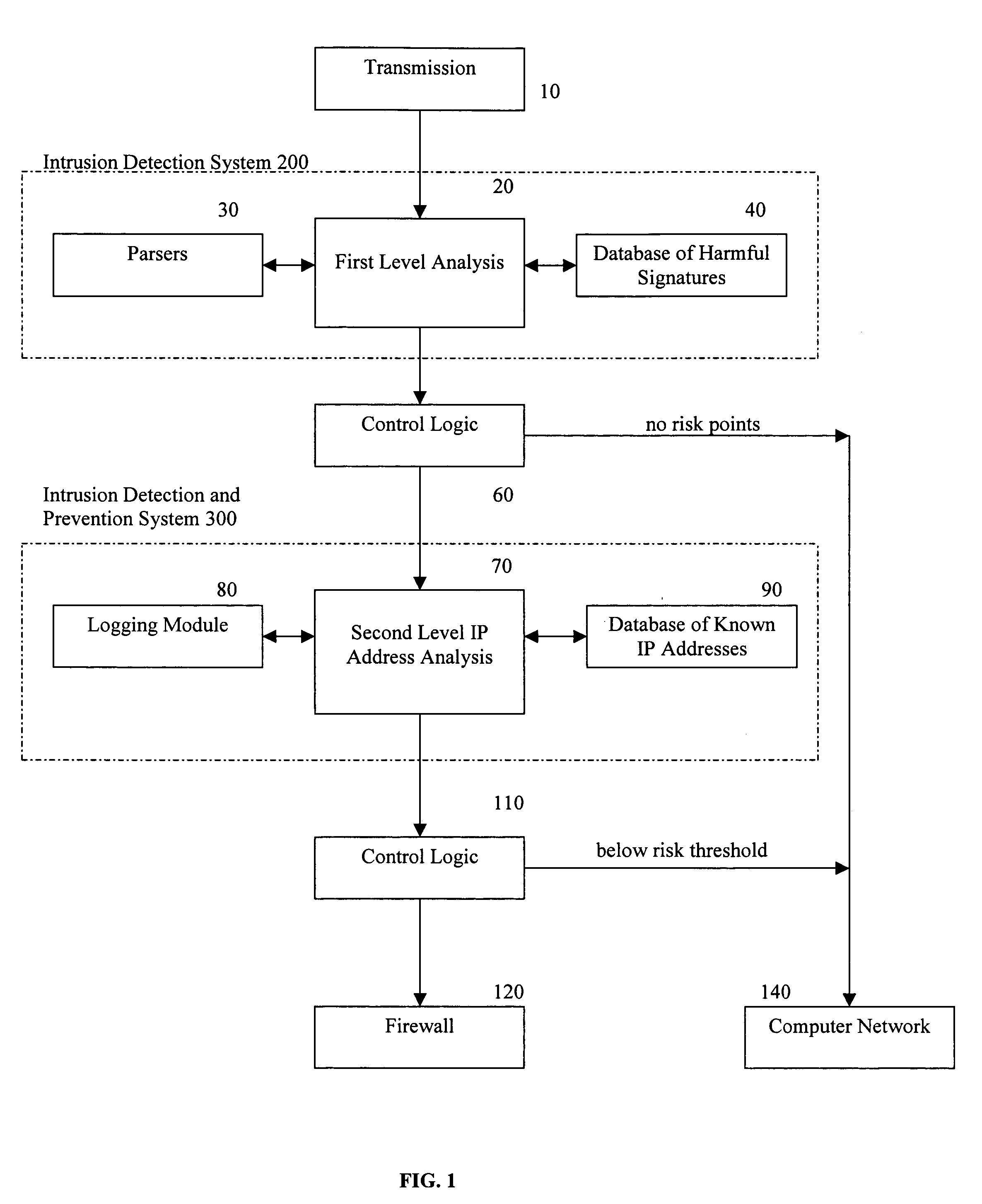
Methods and apparatus for computer network security using intrusion detection and prevention
InactiveUS7225468B2Memory loss protectionDigital data processing detailsIp addressIntrusion detection and prevention
A method provides security to a computer network by selectively blocking network transmissions from selected IP addresses. The method includes the steps of: establishing a risk threshold whereby transmissions from IP addresses exceeding said risk threshold are selectively blocked; receiving a network transmission having an originating IP address and payload; analyzing the payload of said transmission and assigning a current risk rating to said IP address on the basis of said analysis; comparing the originating IP address of said transmission to a database of known IP addresses, each of said known IP addresses having a previous cumulative assigned risk rating, said previous cumulative assigned risk rating being based on at least one previous transmission from a known IP address; assigning a new cumulative risk rating to said originating IP address; logging the new cumulative risk rating for said originating IP address in said database of known IP addresses. The new cumulative risk rating is compared to said risk threshold and the transmission is blocked if said new cumulative risk rating exceeds said risk threshold.
Owner:DIGITAL SECURITY NETWORK
IP network vulnerability and policy compliance assessment by IP device analysis
InactiveUS20080172716A1Reduce vulnerabilityImprove network securityTransmissionSpecial data processing applicationsNetwork security policyCompliance problem
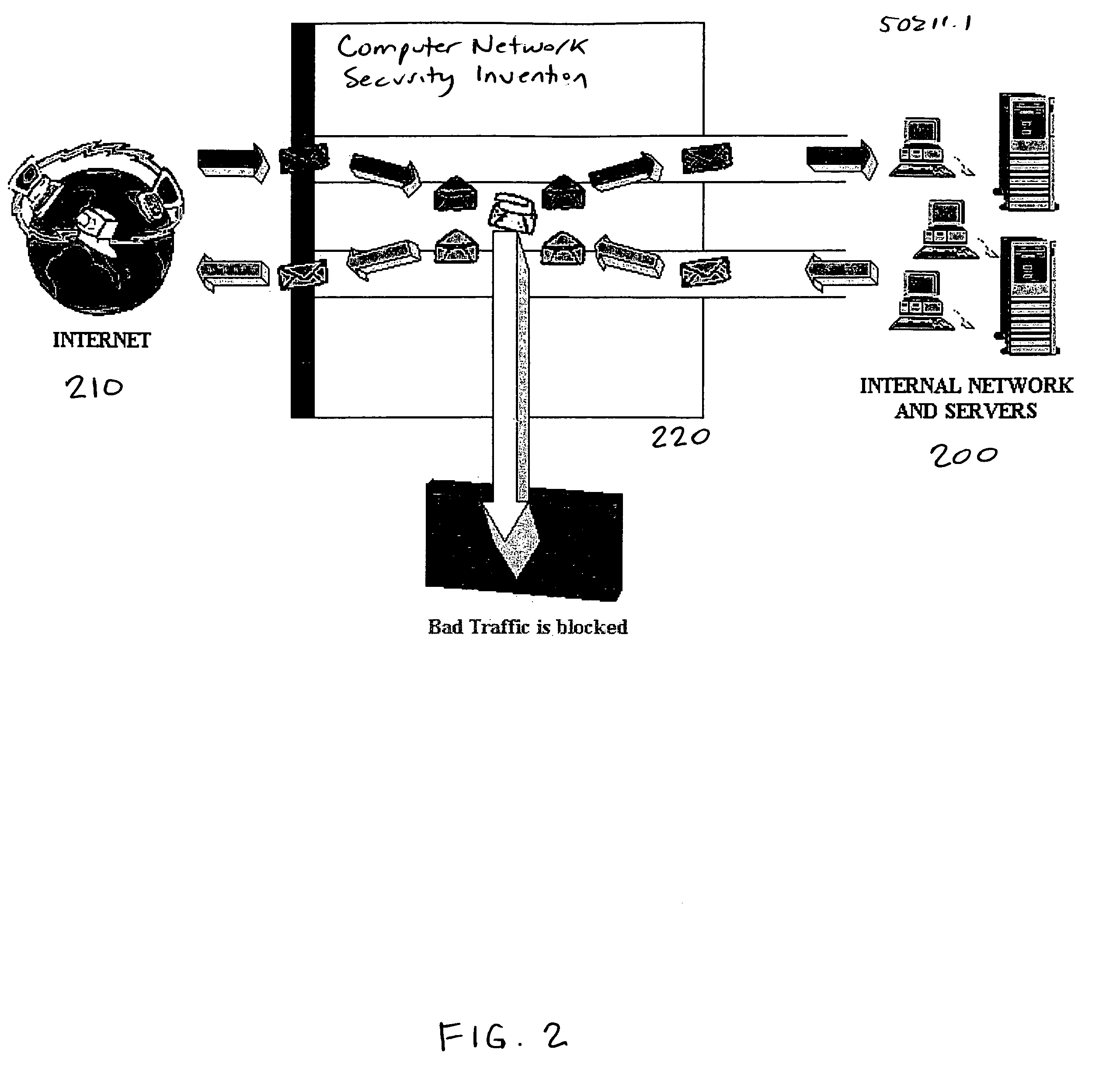
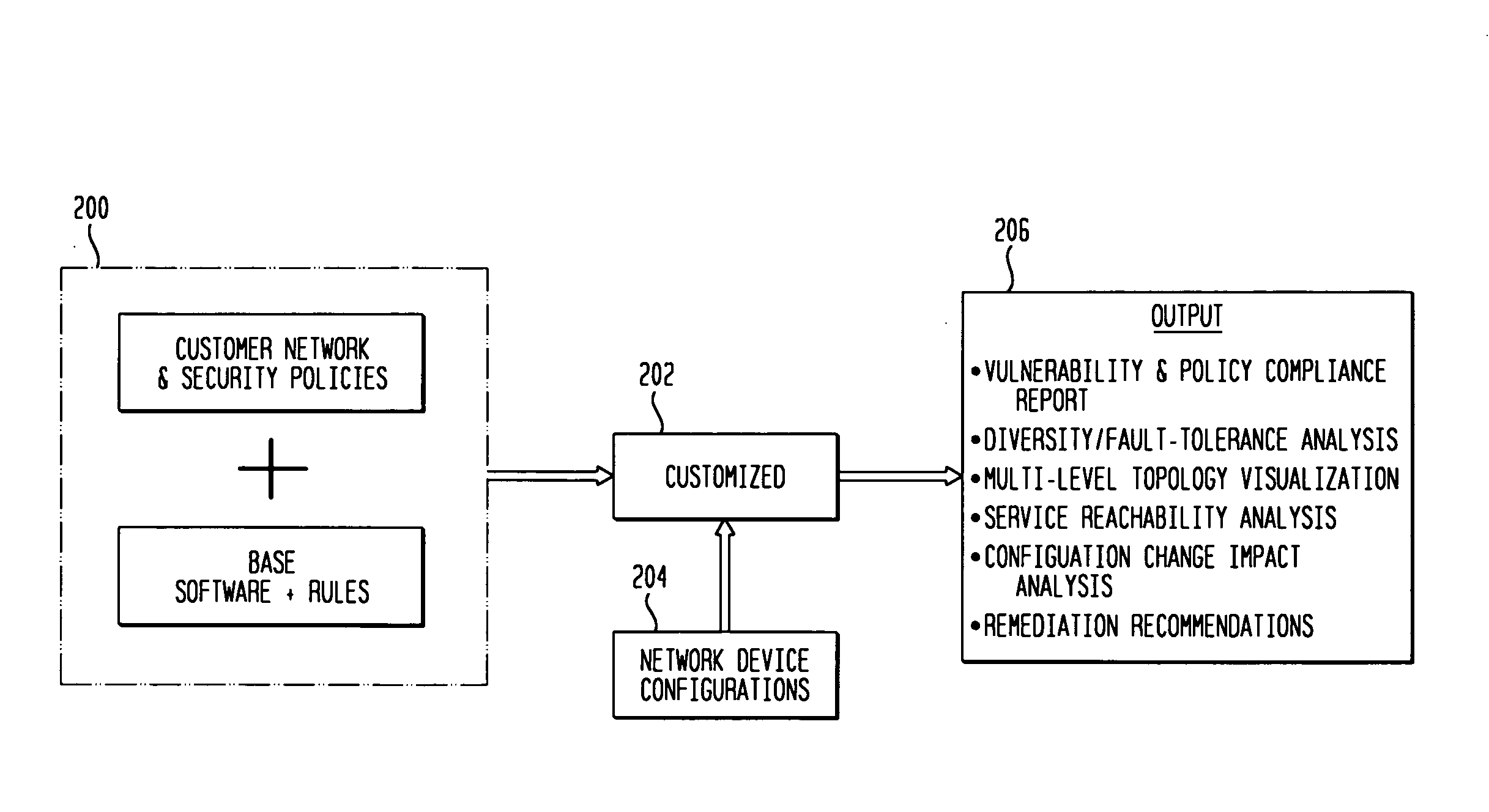
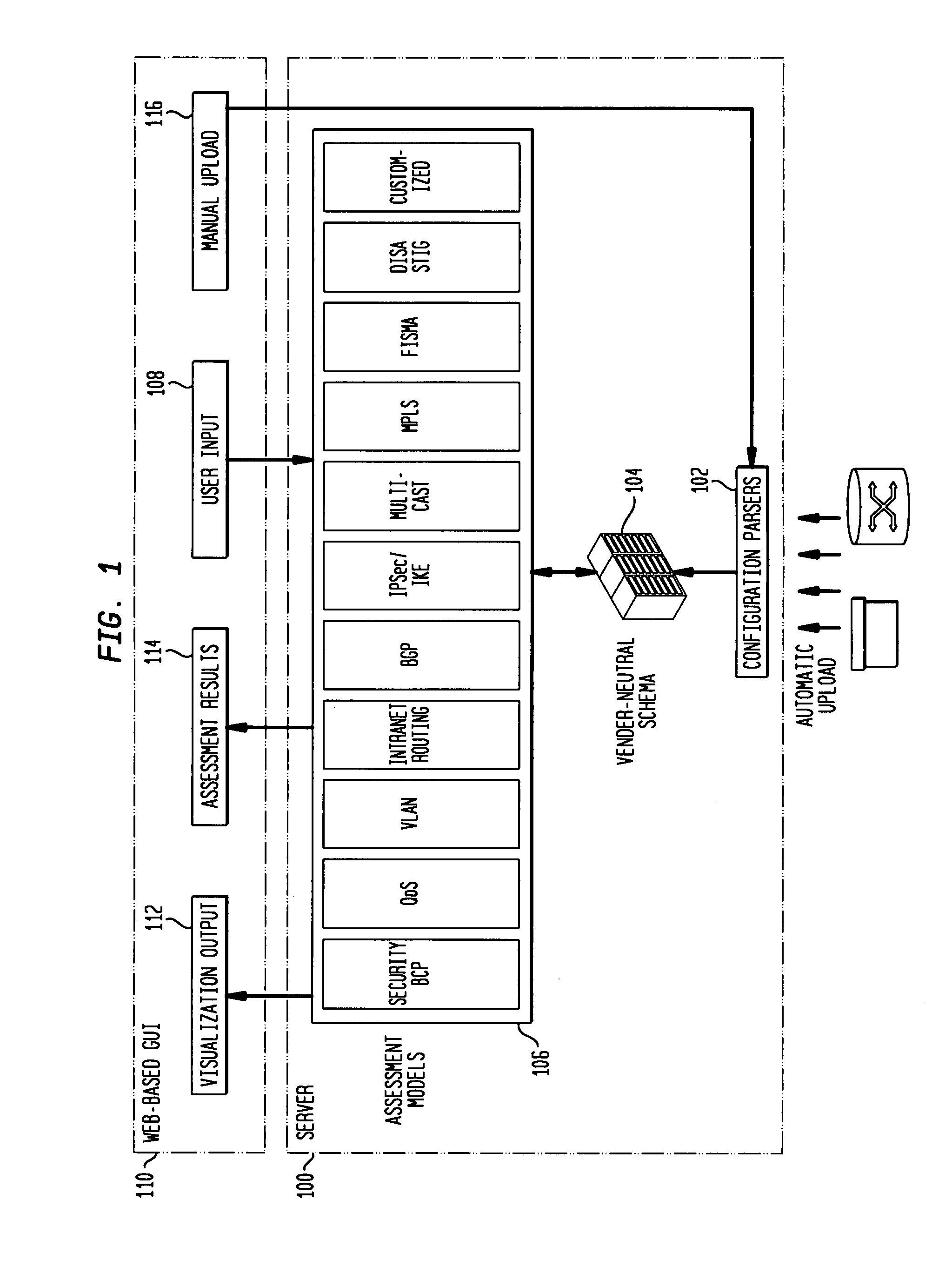
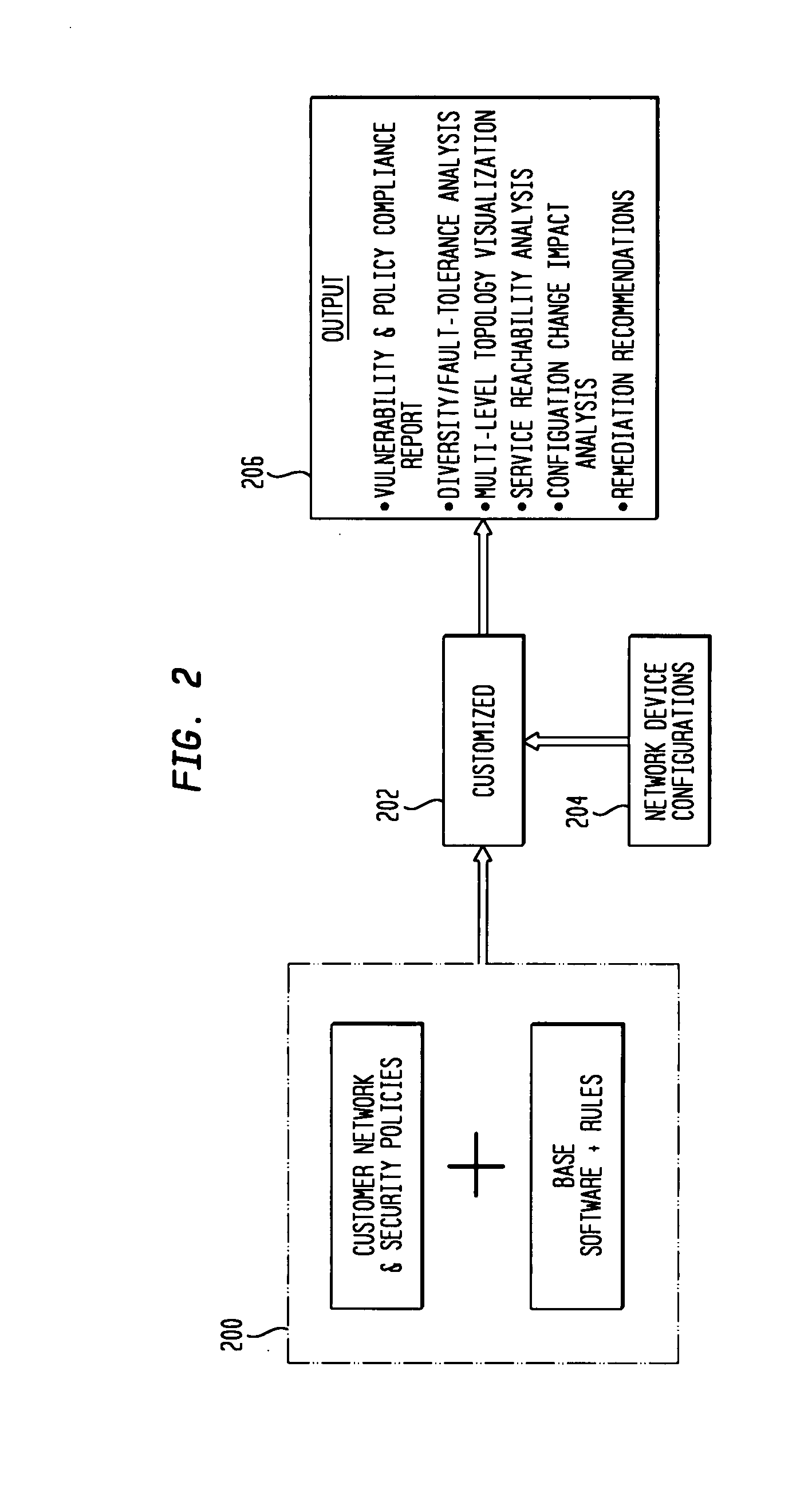
Customizable software provides assurances about the ability of an IP network to satisfy security, regulatory and availability requirements by comprehensive vulnerability and compliance assessment of IP networks through automated analysis of configurations of devices such as routers, switches, and firewalls. The solution comprises three main approaches for testing of IP device configurations to eliminate errors that result in vulnerabilities or requirements compliance issues. The first two fall in to the “static constraint validation” category since they do not change significantly for each IP network, while the last approach involves incorporation of each specific IP network's policies / requirements. These approaches are complementary, and may be used together to satisfy all the properties described above. The first approach involves checking the configurations of devices for conformance to Best-Current-Practices provided by vendors (e.g. Cisco Network Security Policy) and organizations such as the NIST, NSA or CERT. Also this includes checks of compliance with regulations such as FISMA, SOX, HIPPA, PCI, etc. The second approach is where as one reads device configurations, one collects beliefs about network administrator intent. As each belief is collected, an inference engine checks whether the new belief is inconsistent with previously accumulated beliefs. The third approach addresses the multiple device / protocol issue by including an understanding of high-level service and security requirements about the specific IP network under test from the network administrators.
Owner:TT GOVERNMENT SOLUTIONS
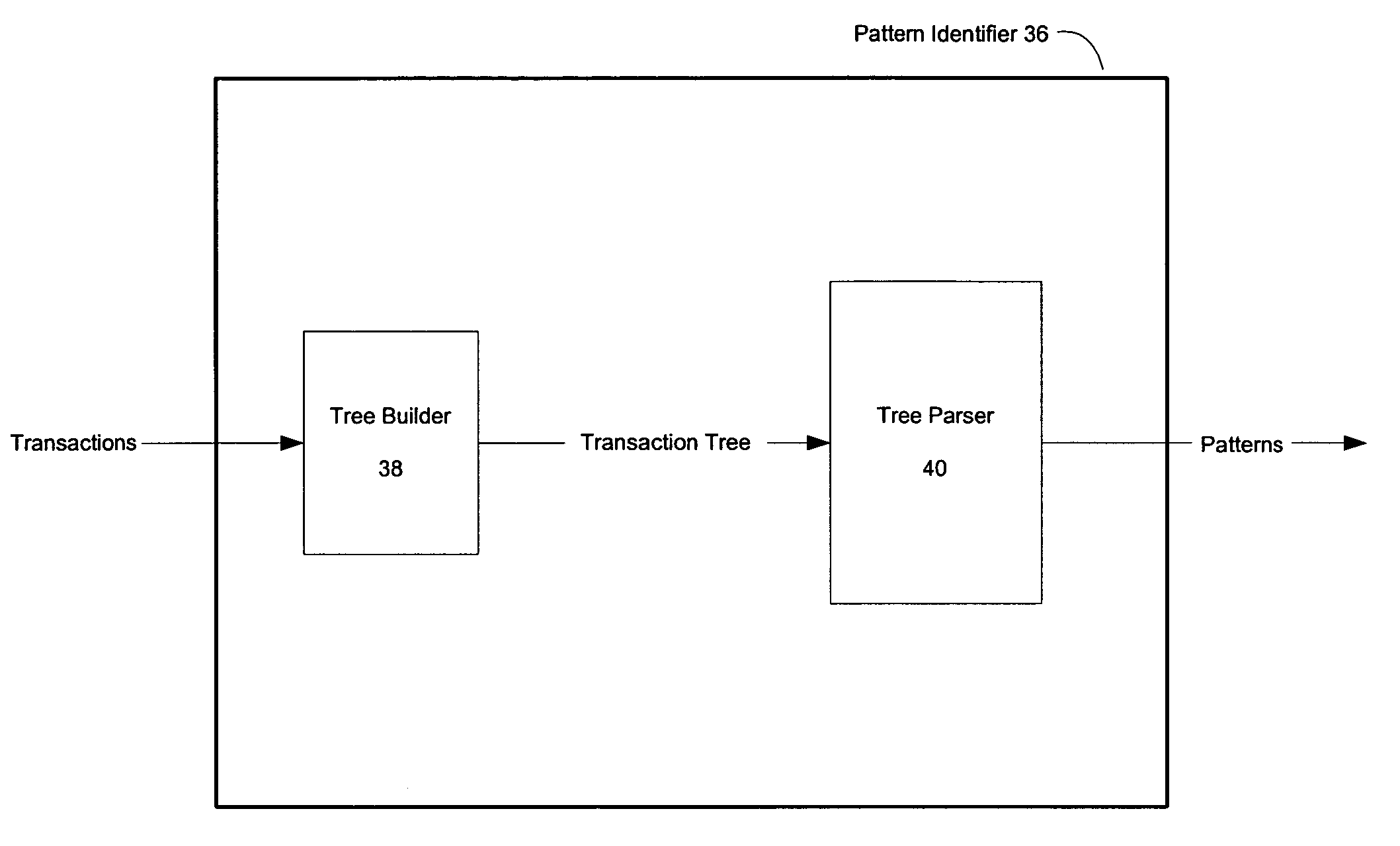
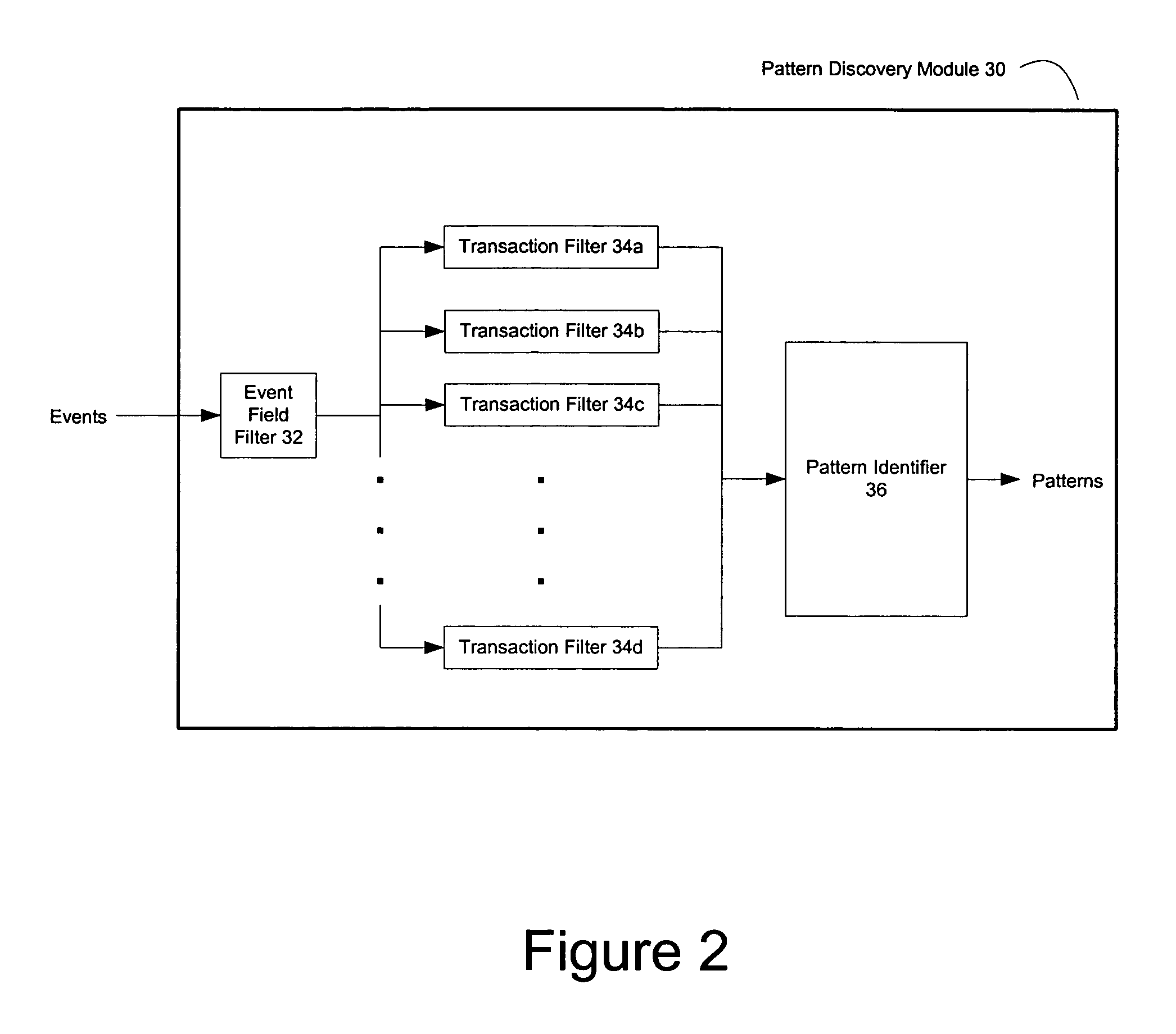
Pattern discovery in a network security system
InactiveUS7509677B2Memory loss protectionDigital data processing detailsNetwork security policyEvent stream
Patterns can be discovered in security events collected by a network security system. In one embodiment, the present invention includes collecting and storing security events from a variety of monitor devices. In one embodiment, a subset of the stored security events is provided to a manager as an event stream. In one embodiment, the present invention further includes the manager discovering one or more previously unknown event patterns in the event stream.
Owner:MICRO FOCUS LLC
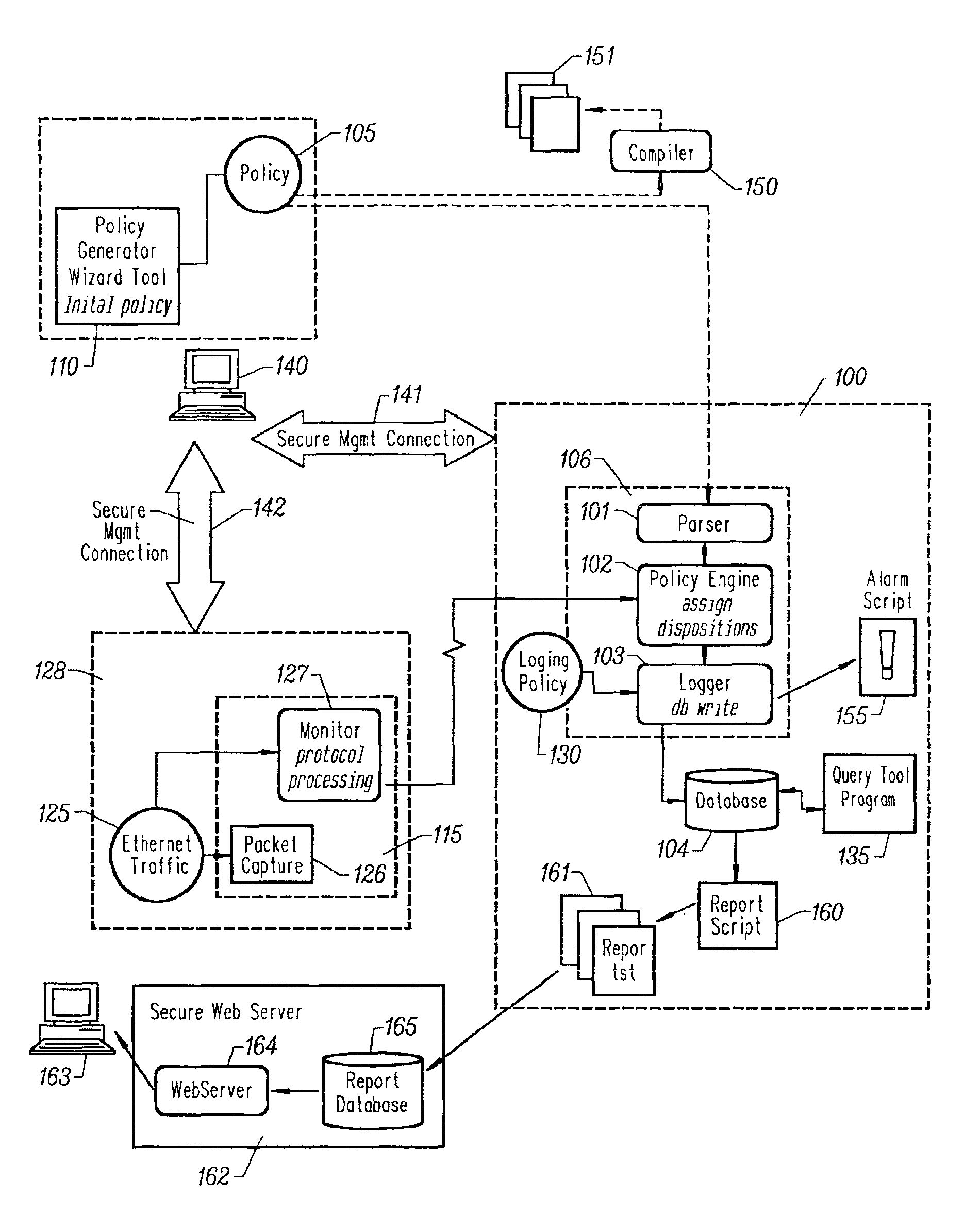
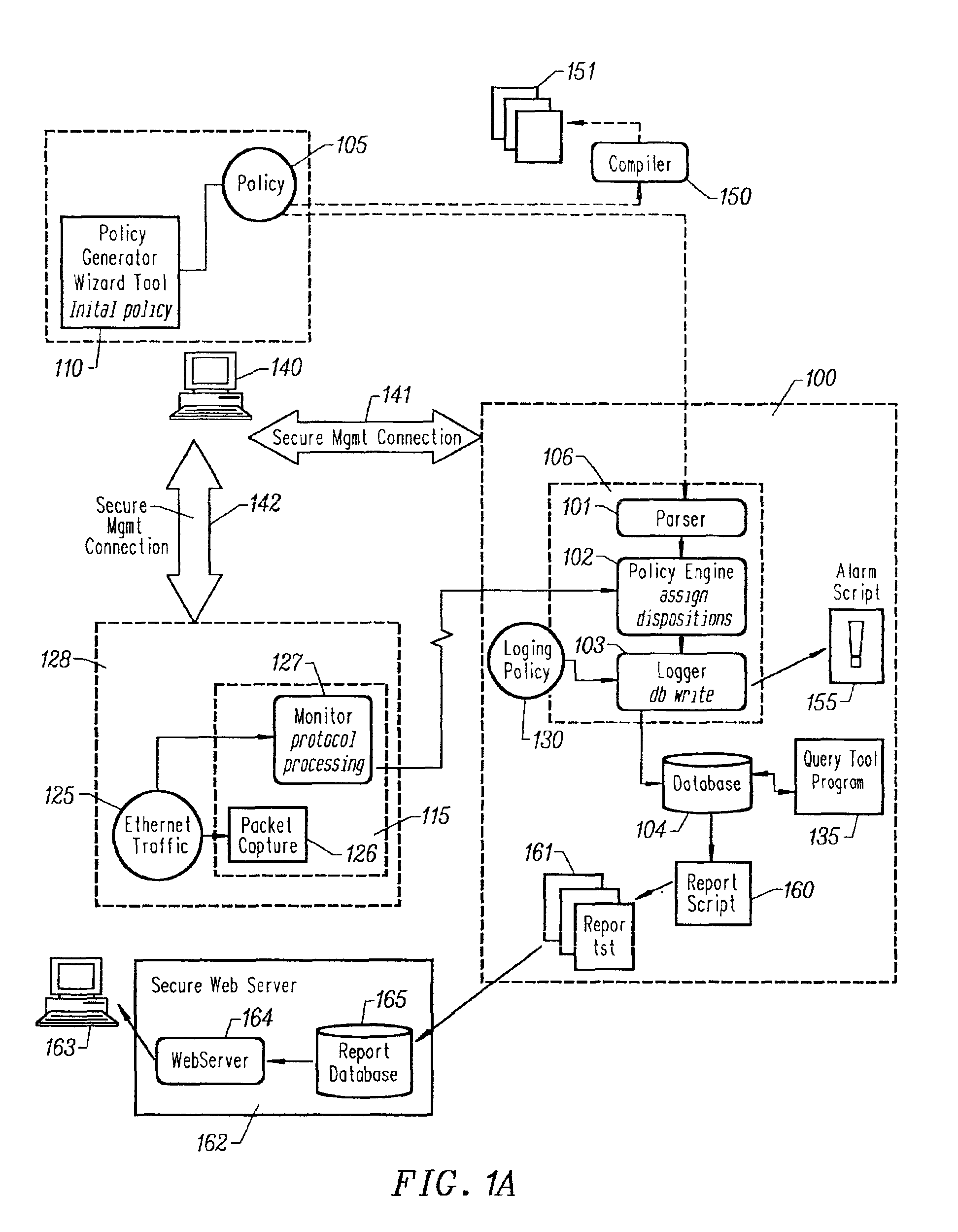
Efficient evaluation of rules
InactiveUS20020069200A1Digital data processing detailsUser identity/authority verificationNetwork security policyDistributed computing
A method and apparatus uses a proprietary algorithm for organizing network security policy rules in a way that minimizes the number of rules considered when determining the set of rules applicable to a given protocol event.
Owner:MCAFEE LLC
Efficient evaluation of rules
InactiveUS7143439B2Minimize the numberMultiple digital computer combinationsProgram controlNetwork security policyDistributed computing
A method and apparatus uses a proprietary algorithm for organizing network security policy rules in a way that minimizes the number of rules considered when determining the set of rules applicable to a given protocol event.
Owner:MCAFEE LLC
System and method for improved network security
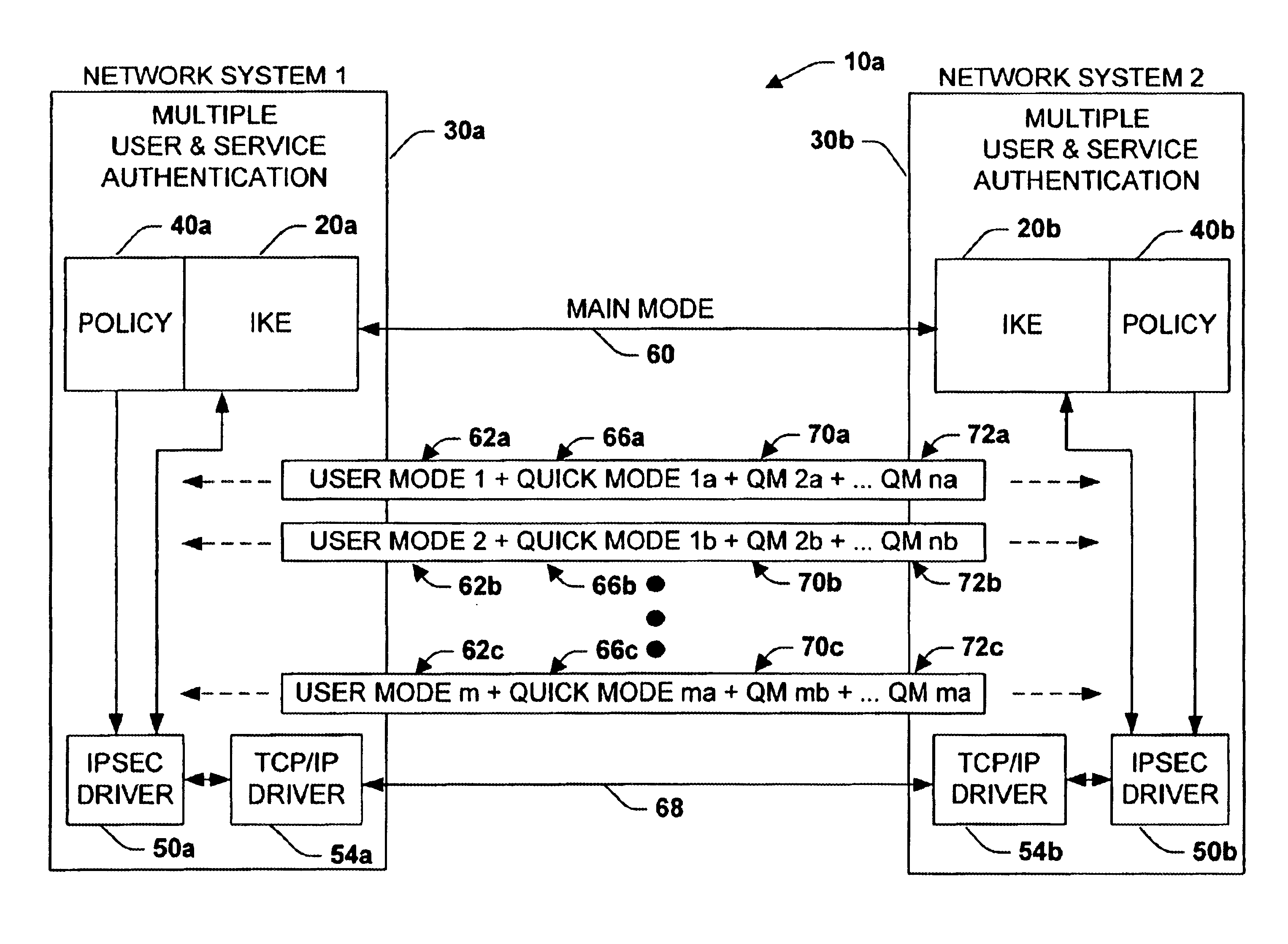
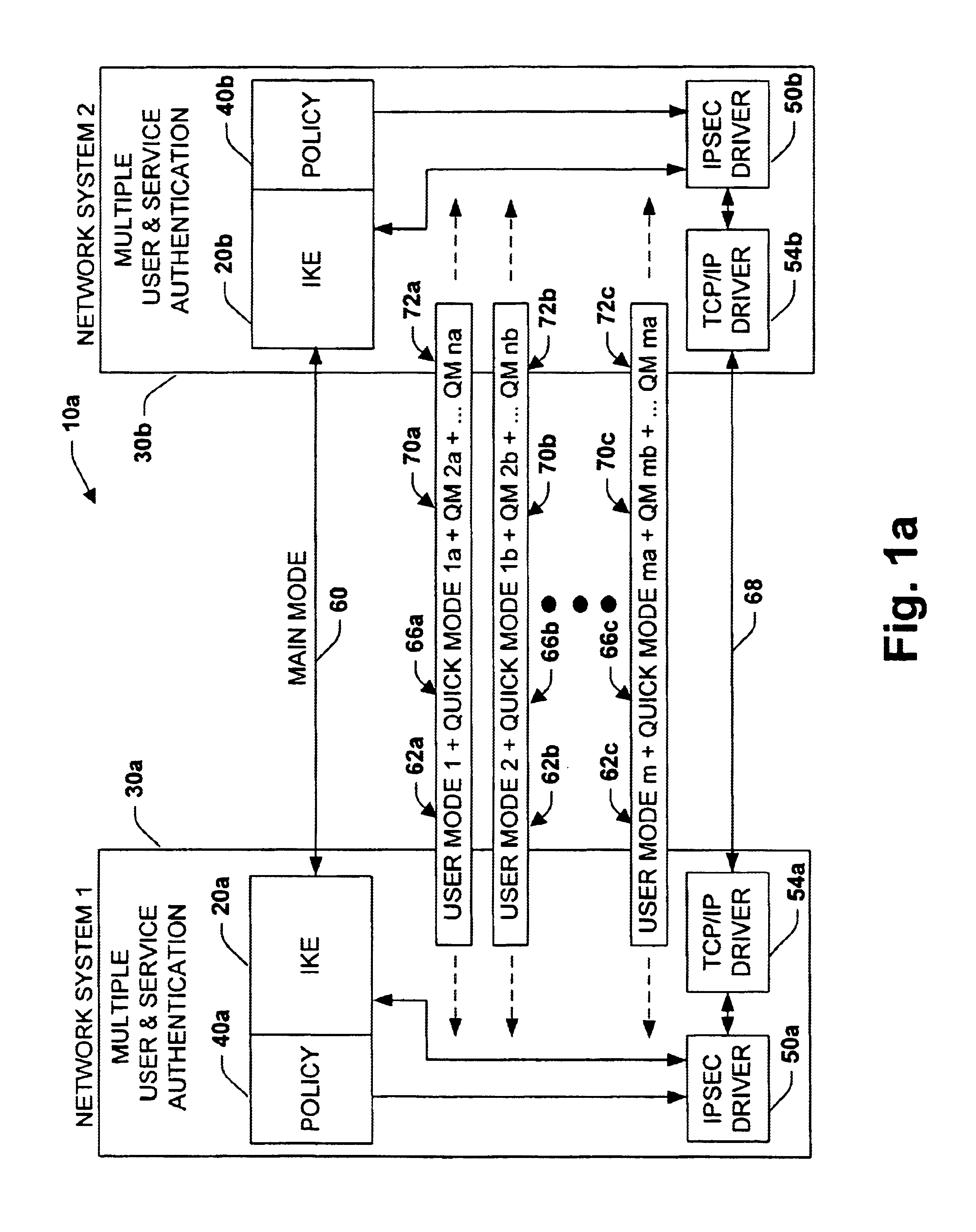
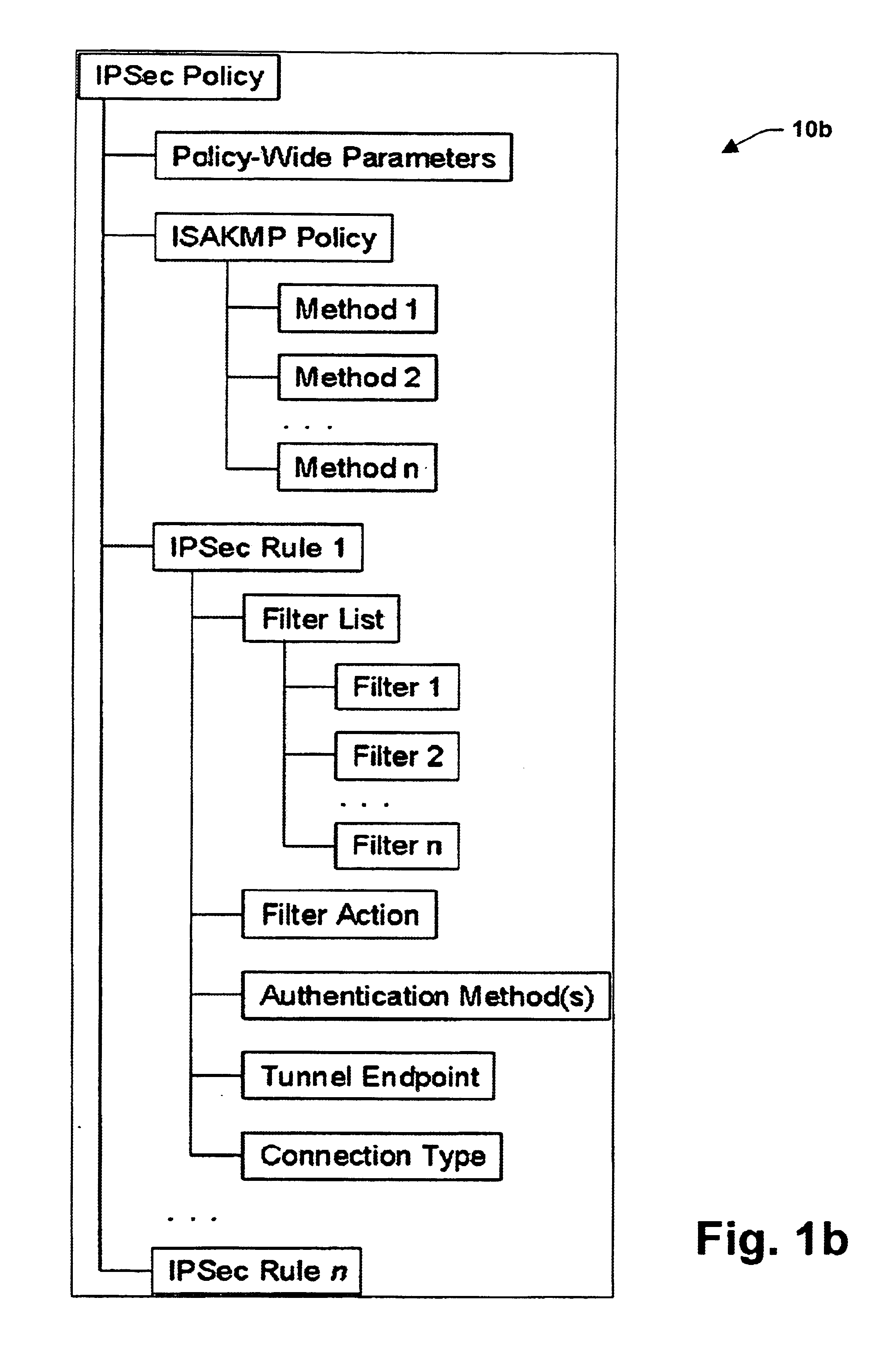
InactiveUS6915437B2Improve performanceImprove securityDigital data processing detailsUser identity/authority verificationTraffic capacityInternet Key Exchange
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for selectively enforcing network security policies using group identifiers
InactiveUS7249374B1Data resettingMultiple digital computer combinationsNetwork packetNetwork addressing
A method and apparatus for selectively enforcing network security policy using group identifiers are disclosed. One or more access controls are created and stored in a policy enforcement point that controls access to the network, wherein each of the access controls specifies that a named group is allowed access to a particular resource. A binding of a network address to an authenticated user of a client, for which the policy enforcement point controls access to the network, is created and stored. The named group is updated to include the network address of the authenticated user at the policy enforcement point. A packet flow originating from the network address is permitted to pass from the policy enforcement point into the network only if the network address is in the named group identified in one of the access controls that specifies that the named group is allowed access to the network. Accordingly, network security may be implemented in the form of abstract groups that include specific network addresses; as a result, users may be allowed or denied access to network addresses by updating membership of the groups to include or delete the network addresses of the users, rather than by creating or deleting access controls that specifically identify the users.
Owner:CISCO TECH INC
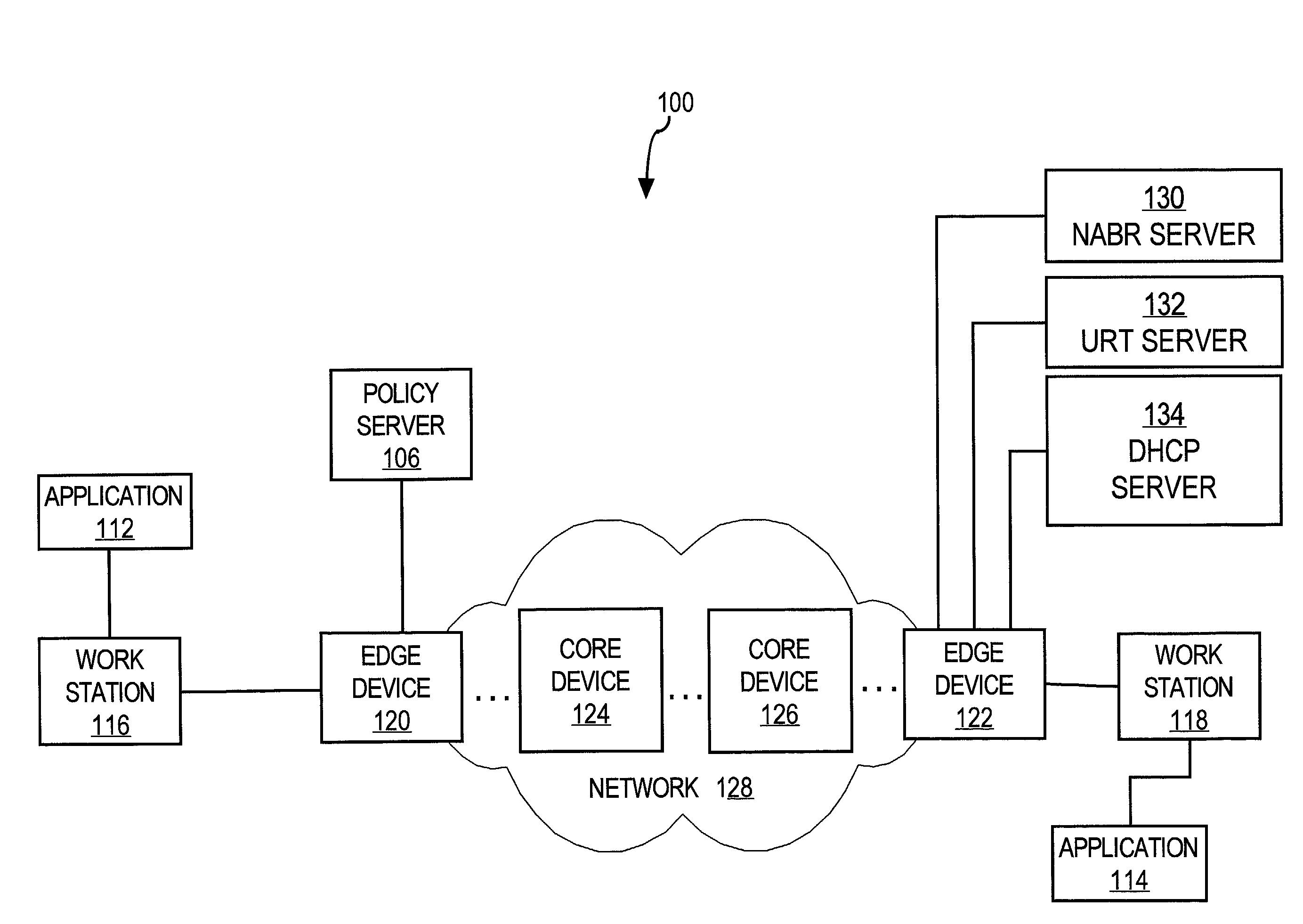
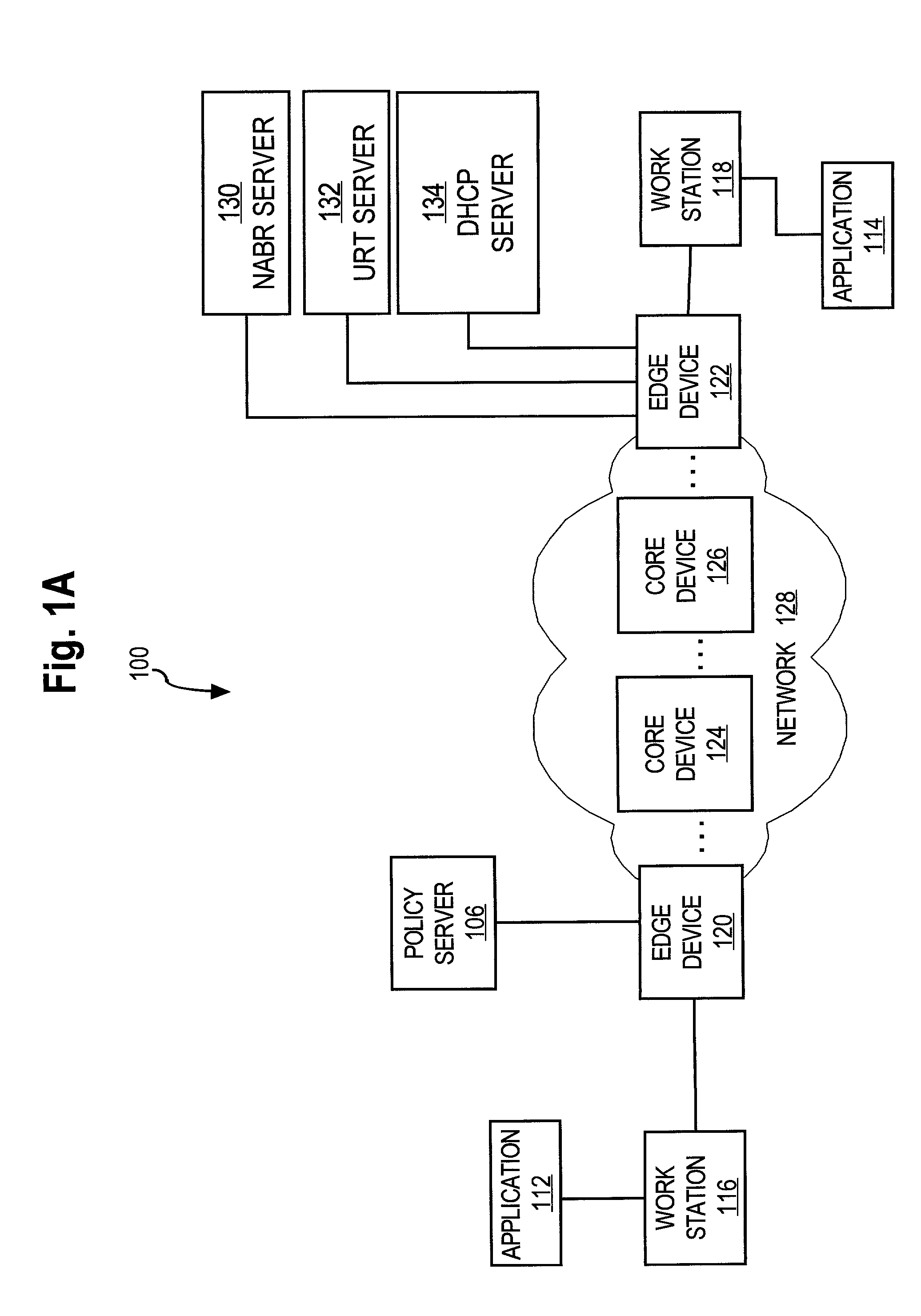
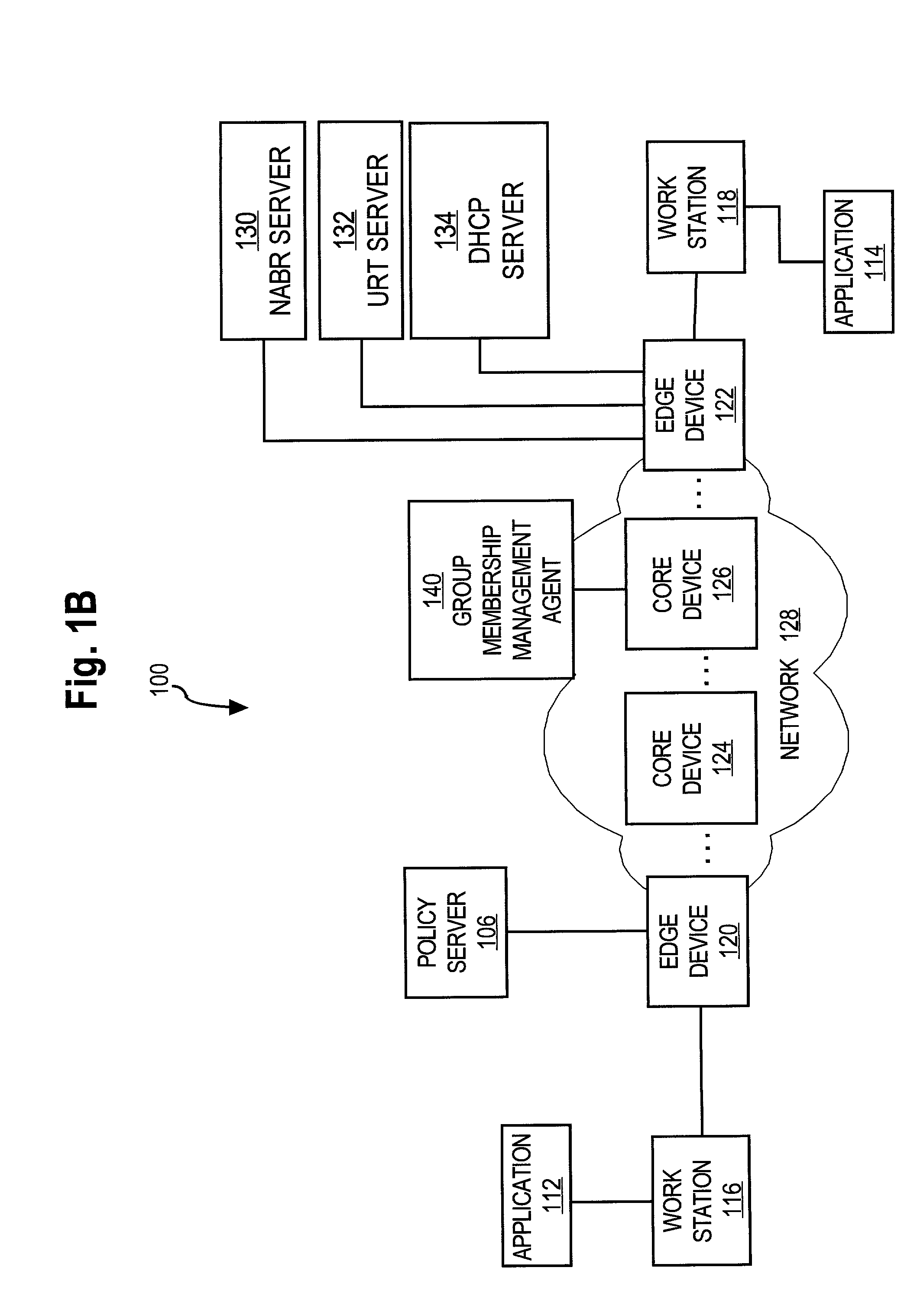
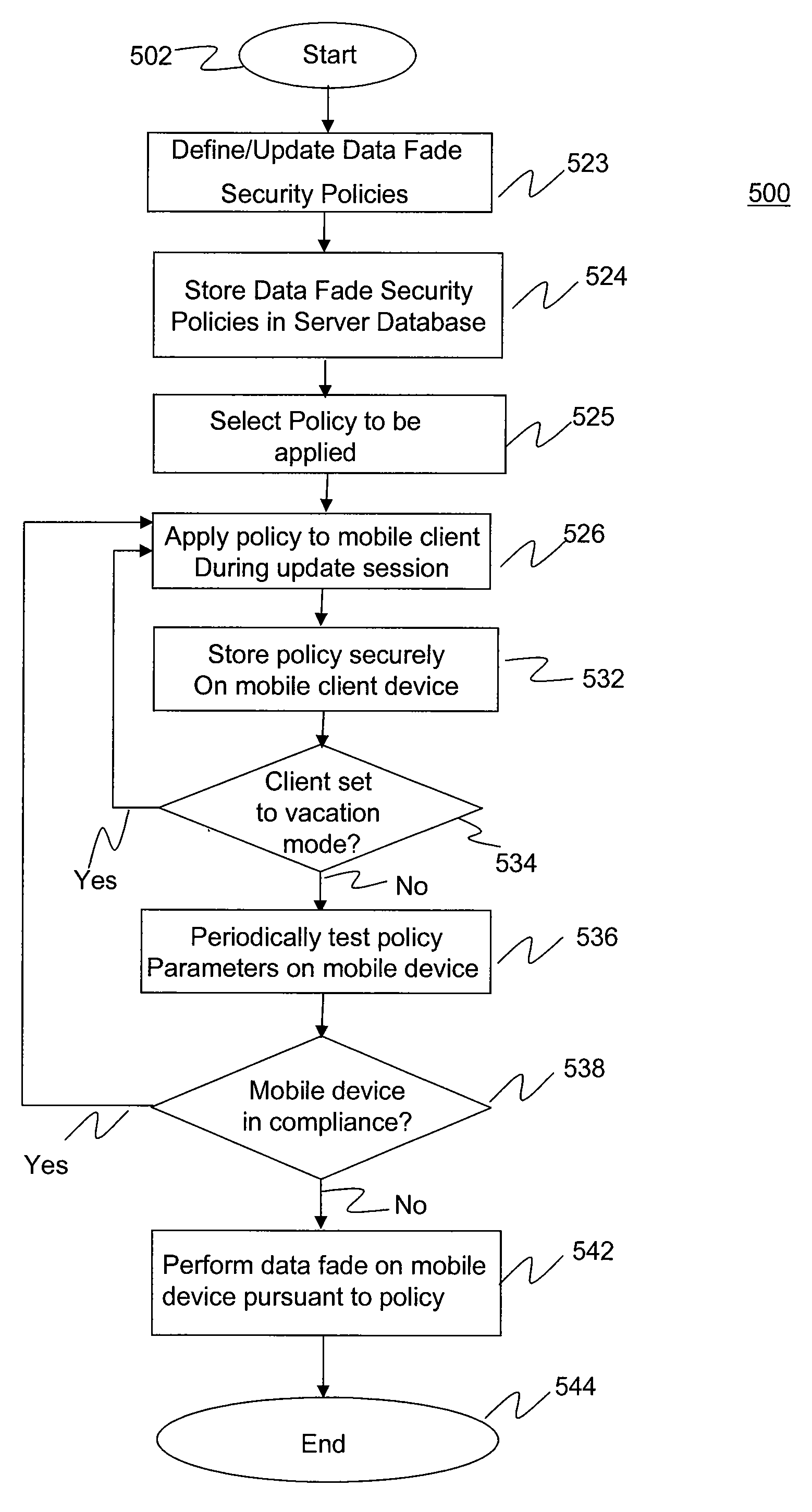
Data Fading to Secure Data on Mobile Client Devices
InactiveUS20090150970A1Protect dataEliminate needInternal/peripheral component protectionTransmissionNetwork security policyClient-side
Methods, systems, and computer program products to secure data stored on mobile client devices are provided. In an embodiment, the method operates by defining one or more security policies. Each security policy comprises a plurality of security policy parameters. The method stores the security policies in a data store, and selects a security policy from among the stored security policies for a mobile client device. The selected security policy is applied to the mobile client device. The mobile client device determines whether it is compliance with parameters of said selected security policy, and performs data fade actions if it is determined that it is out of compliance with said security policy parameters.
Owner:IANYWHERE SOLUTIONS
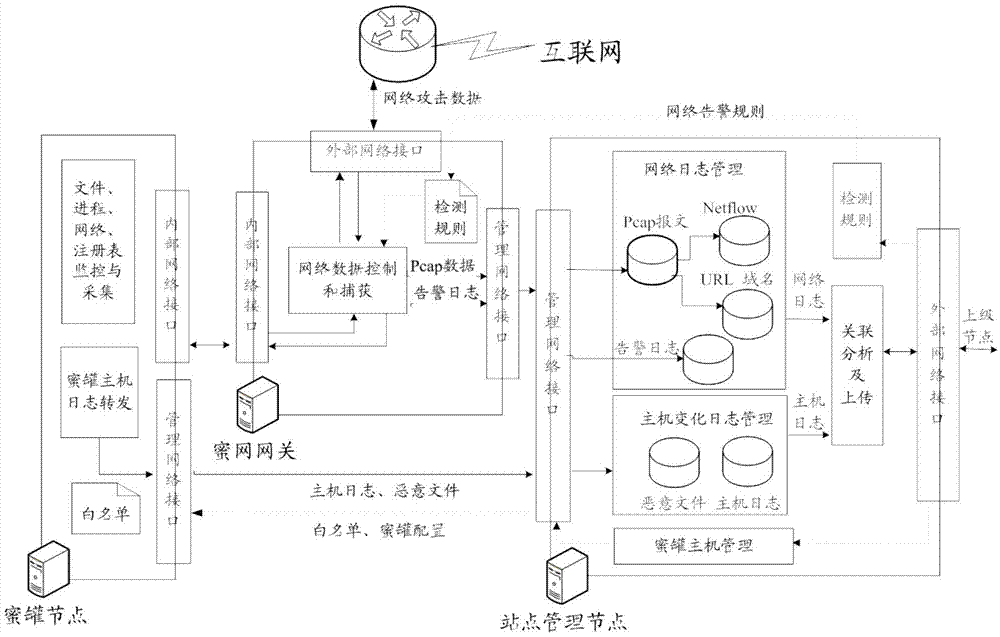
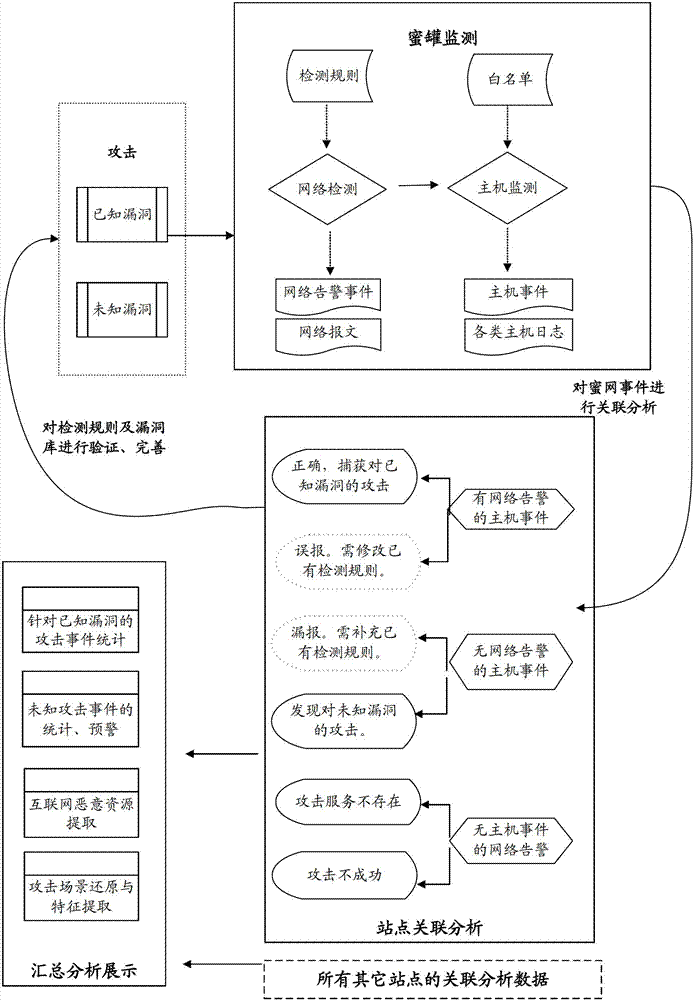
High-interaction honeypot based network security system and implementation method thereof
InactiveCN102739647AImplement auto-discoveryAchieve acquisitionData switching networksResource informationNetwork behavior
The invention discloses a high-interaction honeypot based network security system and an implementation method thereof. The system comprises a honeypot monitoring module, a website correlation analysis module, a summarizing analysis / display module, wherein the honeypot monitoring module is used for carrying out classified acquisition on the attack incidents network behavior logs and host behavior logs; the website correlation analysis module is used for carrying out summarization and automatic correlation analysis on the attack incidents network behavior logs and the host behavior logs, and filtering invalid network alarms, capturing known attack incidents, automatically finding out unknown attack incidents, and extracting concealed Internet malicious resource information according to the automatic correlation analysis results; and the summarizing analysis / display module is used for summarizing and accounting known attack incidents and / or unknown attack incidents captured on all honeypot websites, displaying and reducing selected attack incidents for users, and carrying out automatic detection on concealed Internet malicious resources according to the concealed Internet malicious resource information.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
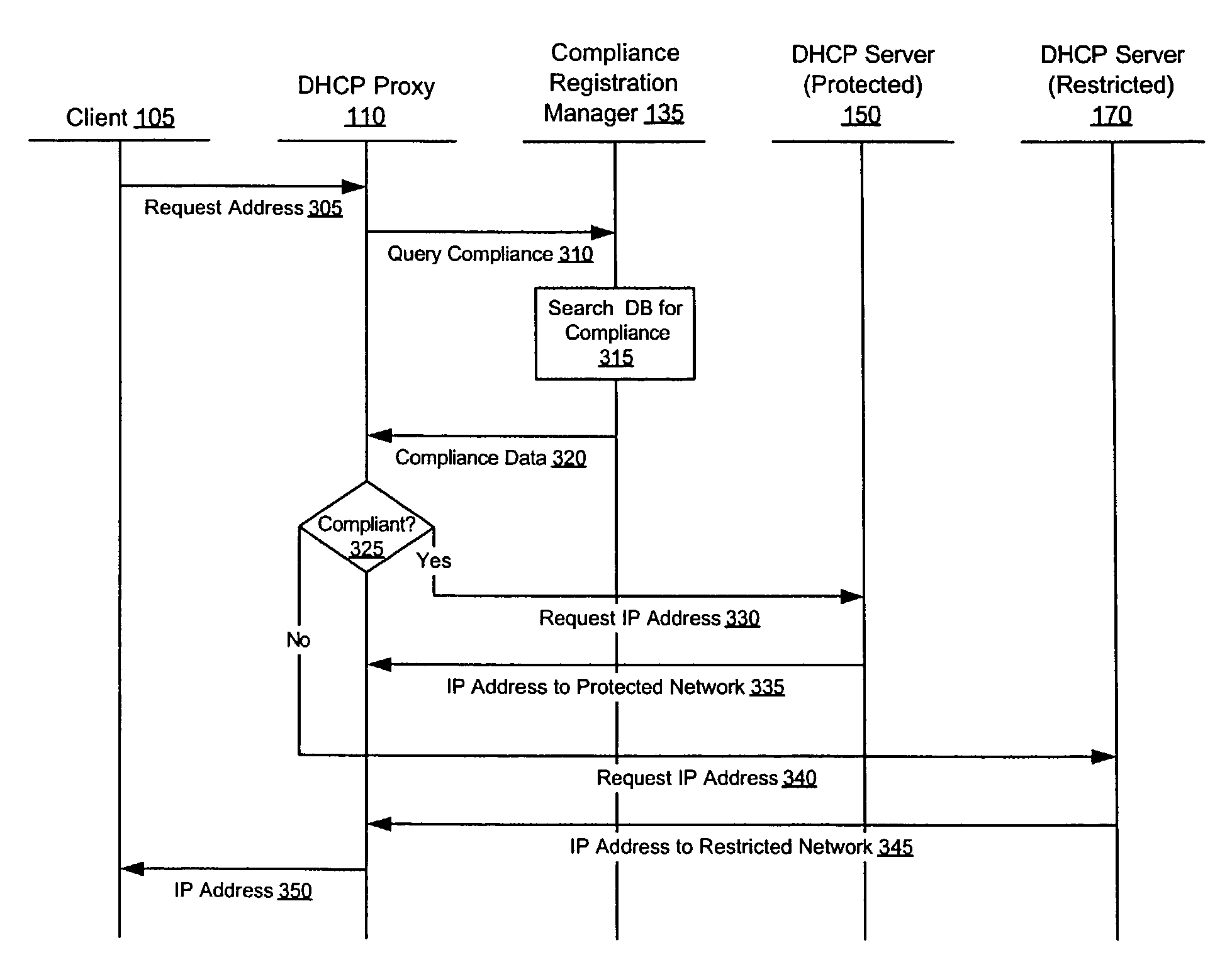
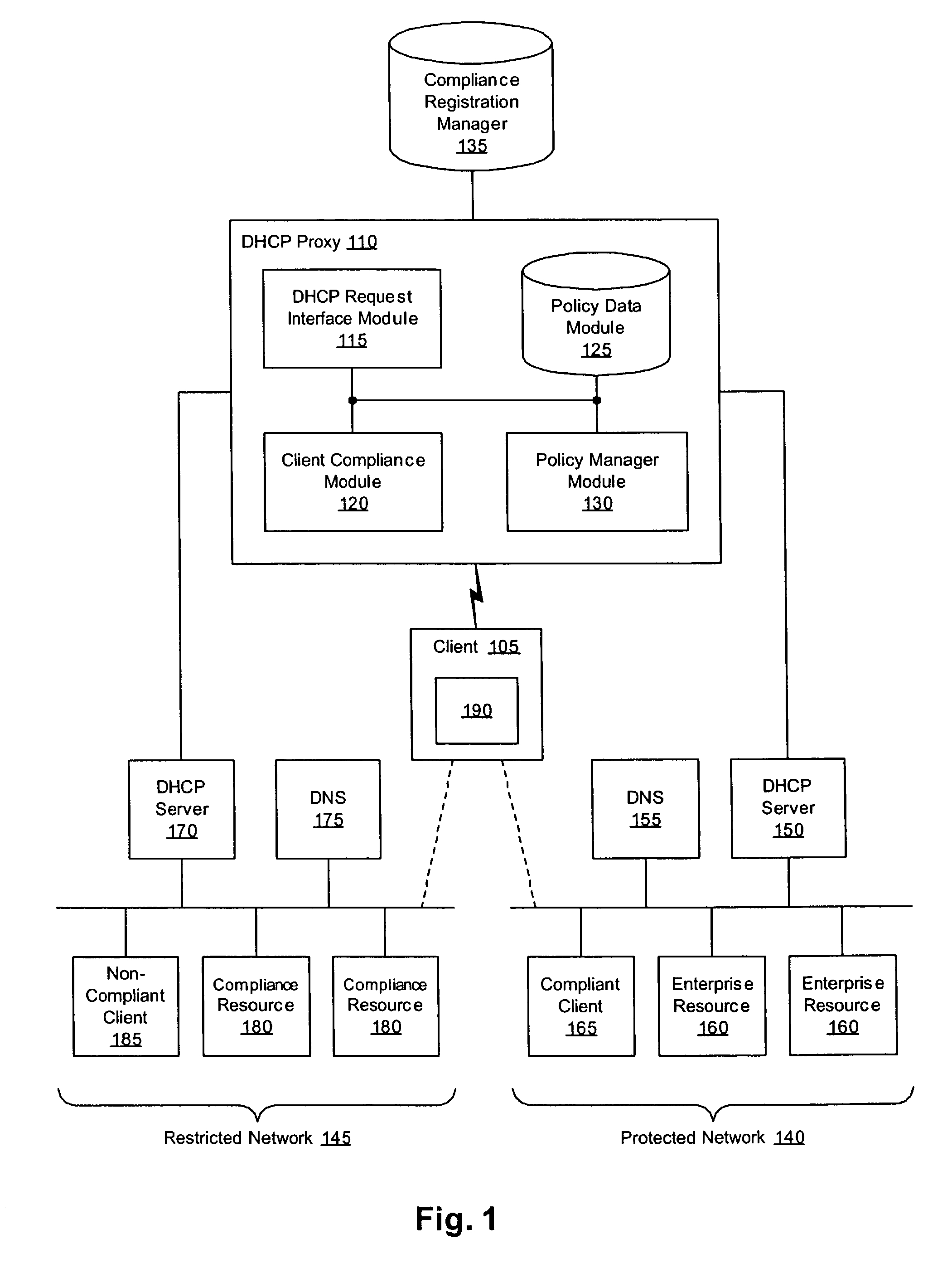
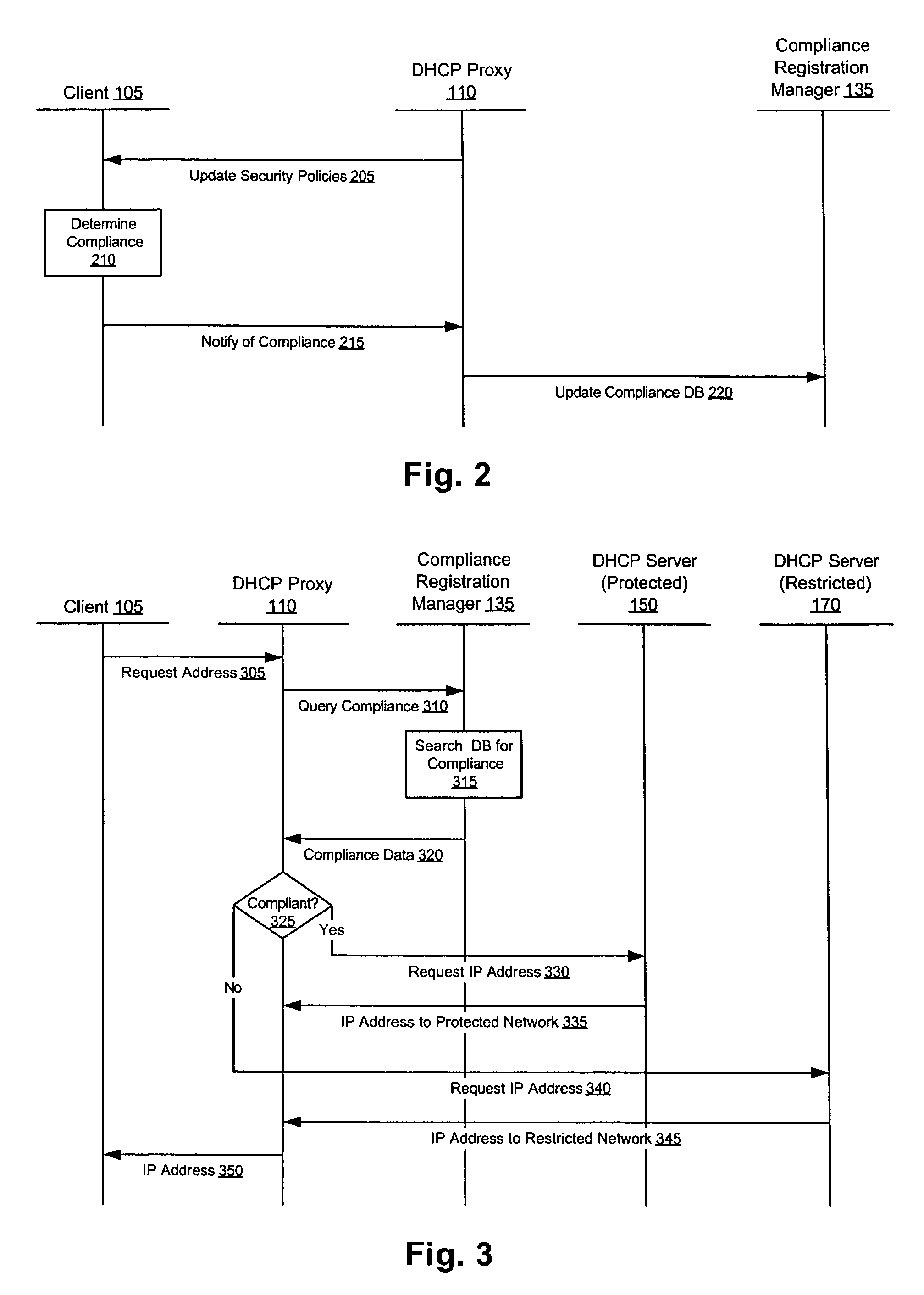
Enforcement of compliance with network security policies
ActiveUS7249187B2Digital data processing detailsMultiple digital computer combinationsNetwork addressingNetwork address
Methods, apparati, and computer program products enforce computer network security policies by assigning network membership to a client (105) based on the client's compliance with the security policies. When a client (105) requests (305) a network address, the DHCP proxy (110) intercepts the request and assigns (350) that client (105) a logical address on the protected network (140) if the client (105) is in compliance with the security policies. If the client (105) is not in compliance with the security policies, in various embodiments, the DHCP proxy (110) assigns (350) the client (105) an address on a restricted network (145) or no network address at all.
Owner:CA TECH INC
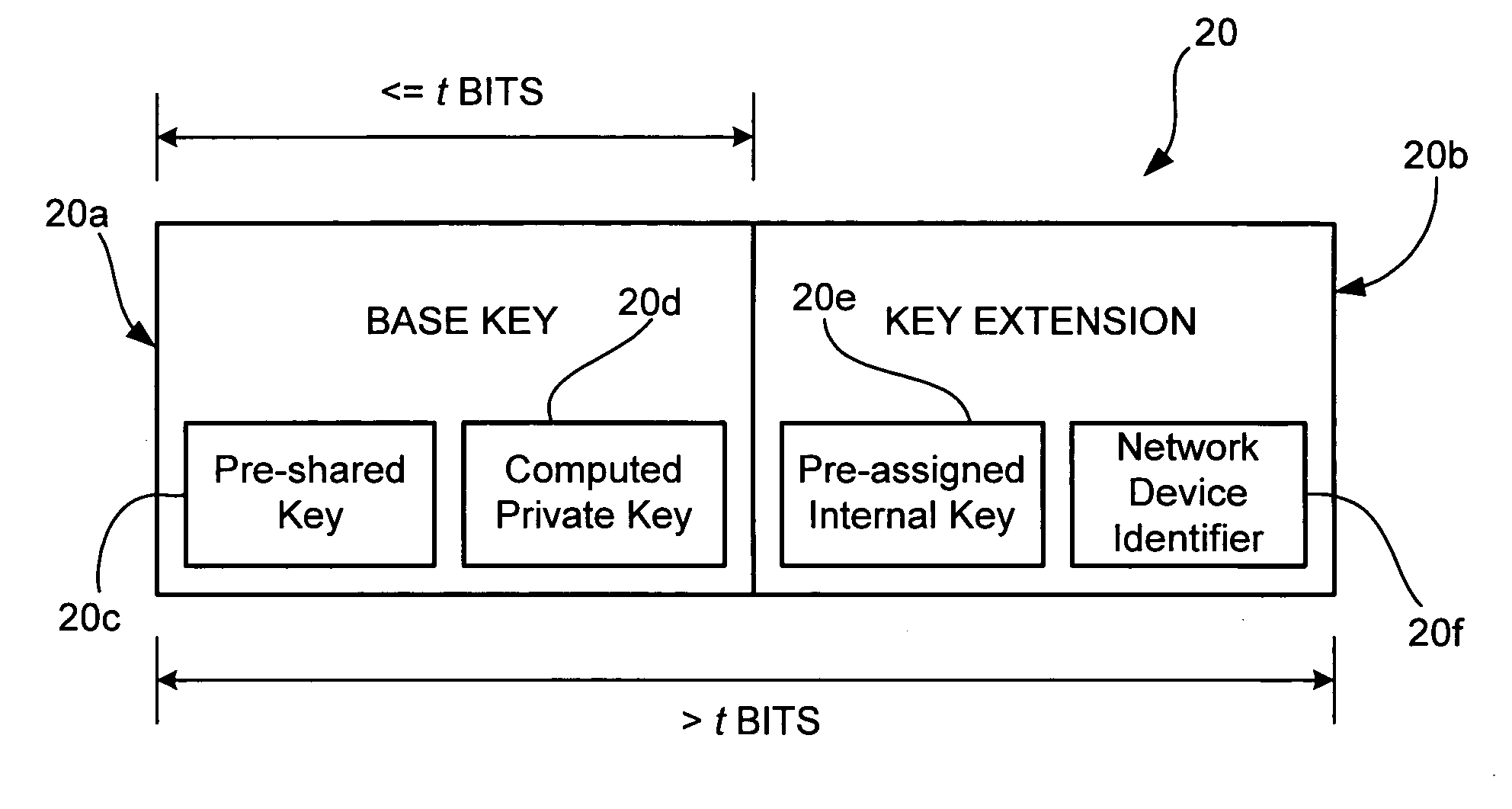
Method and system for network security capable of doing stronger encryption with authorized devices
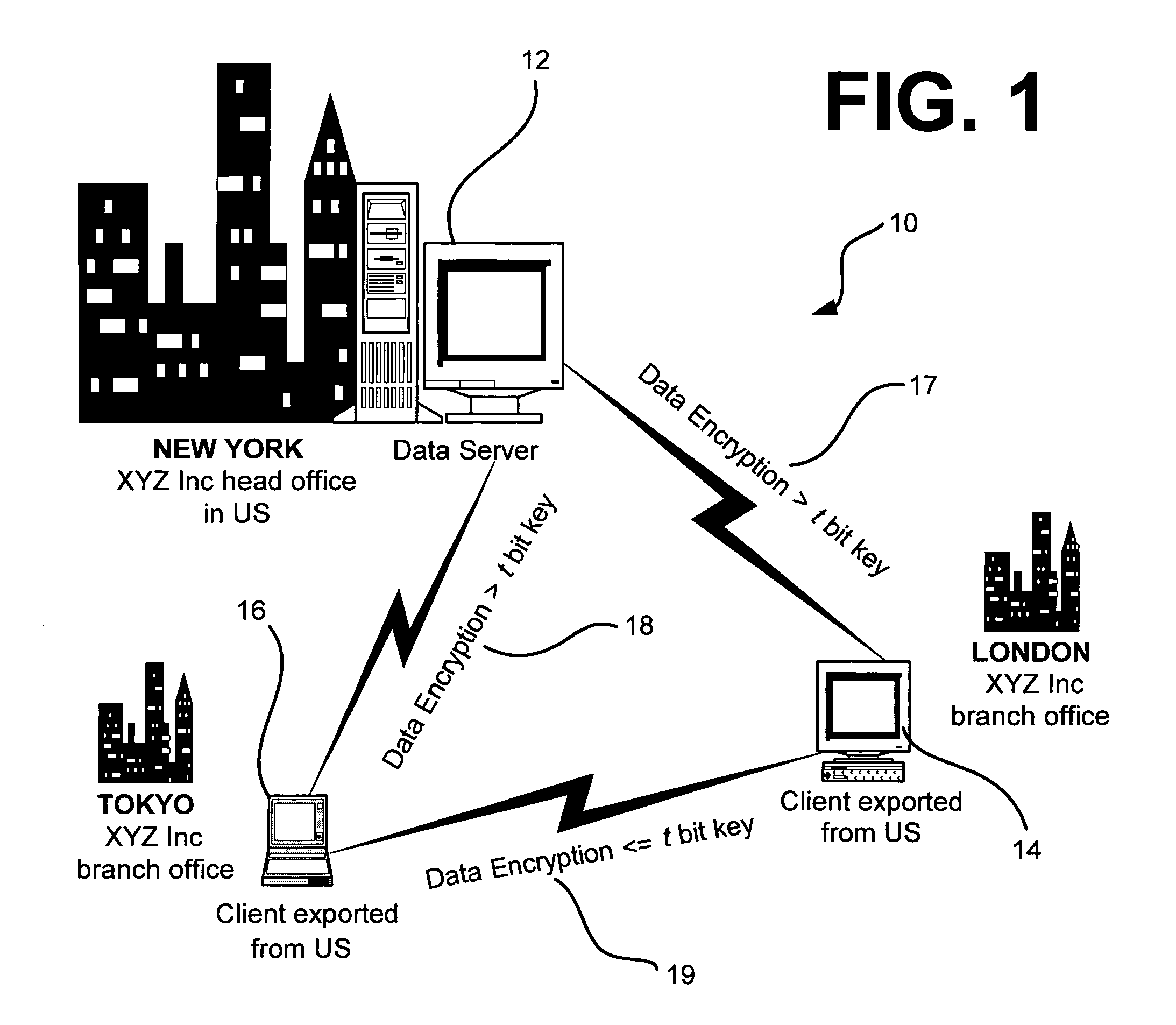
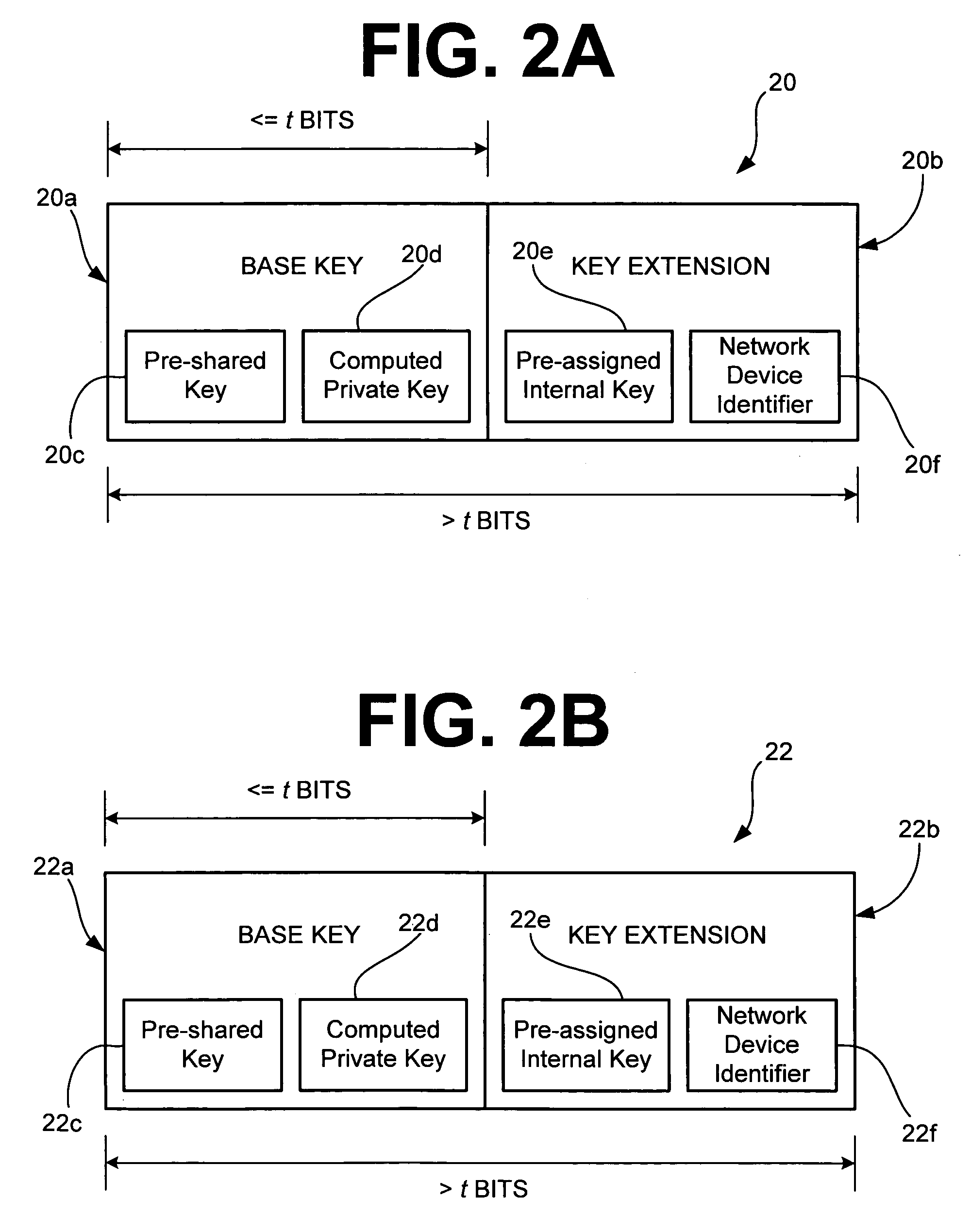
InactiveUS6965992B1Improve securityKey distribution for secure communicationPresent methodNetwork security policy
A method and system for network security includes a first network device having a first set of key material with a base key and a key extension, and a second network device also having the first set of key material and a second set of key material with a second base key. The second network device is capable of communicating with the first network device using security determined by the first set of key material. The method and system for network security may further include a third network device having the second set of key material. The third network device is capable of communicating with the second network device using security determined by the second set of key material. For the present method and system, security determined by the first set of key material is stronger than security determined by the second set of key material.
Owner:HEWLETT PACKARD DEV CO LP
Method, device and system of distributing network safety strategies
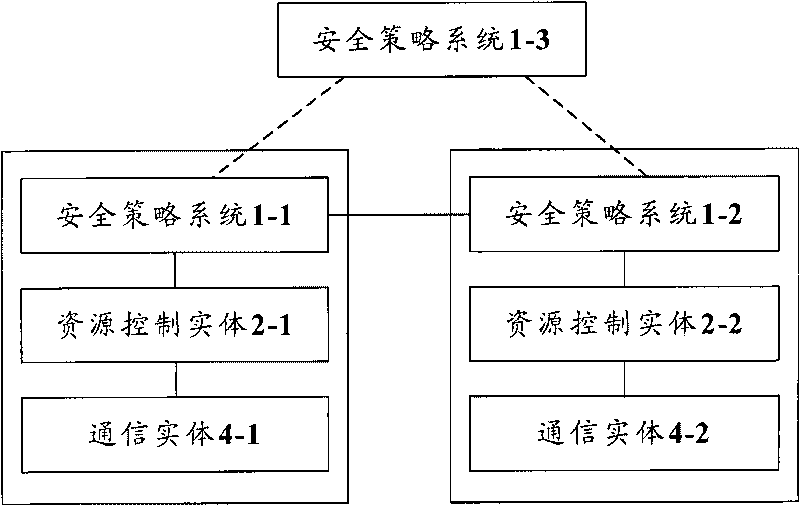
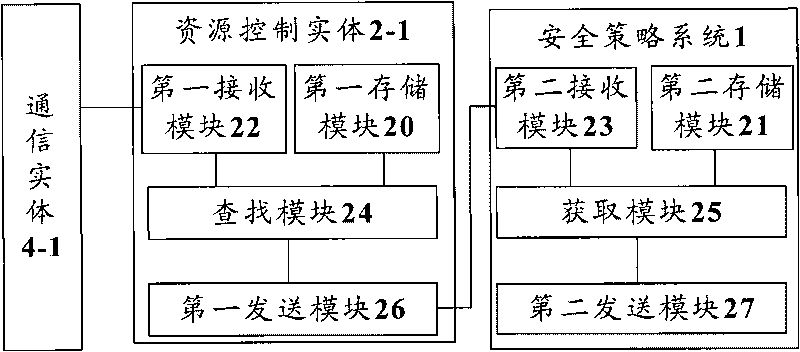
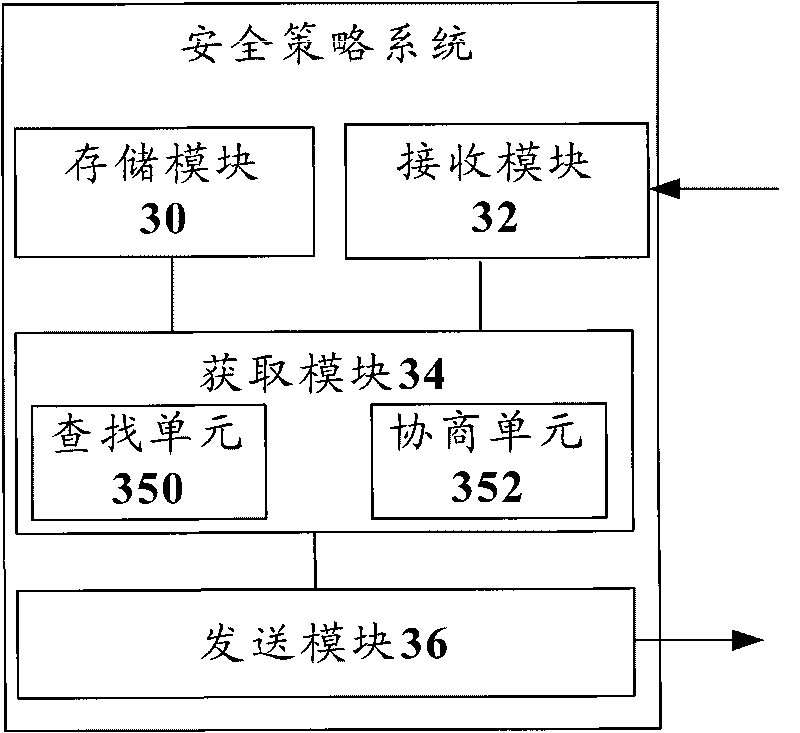
InactiveCN101729531AEliminate security threatsImprove defenseTransmissionNetwork security policySecurity policy
The invention discloses a method, a device and a system of distributing network safety strategies, wherein the system of distributing the network safety strategies comprises a safety strategy system, one or more resource control entities attributed to the safety strategy system and one or more communication entities respectively attributed to each resource control entity, wherein each resource control entity is used for sending a request message to the attributed safety strategy system thereof when receiving a communication request, and the request message is used for requesting a safety strategy related to the communication request; and the safety strategy system is used for obtaining the safety strategy related to the communication request according to the received request message and sending the safety strategy to each resource control entity. Through the invention, the integral defensive effect of a network can be enhanced, and the network safety threat is eliminated.
Owner:ZTE CORP
Apparatus and method for facilitating network security
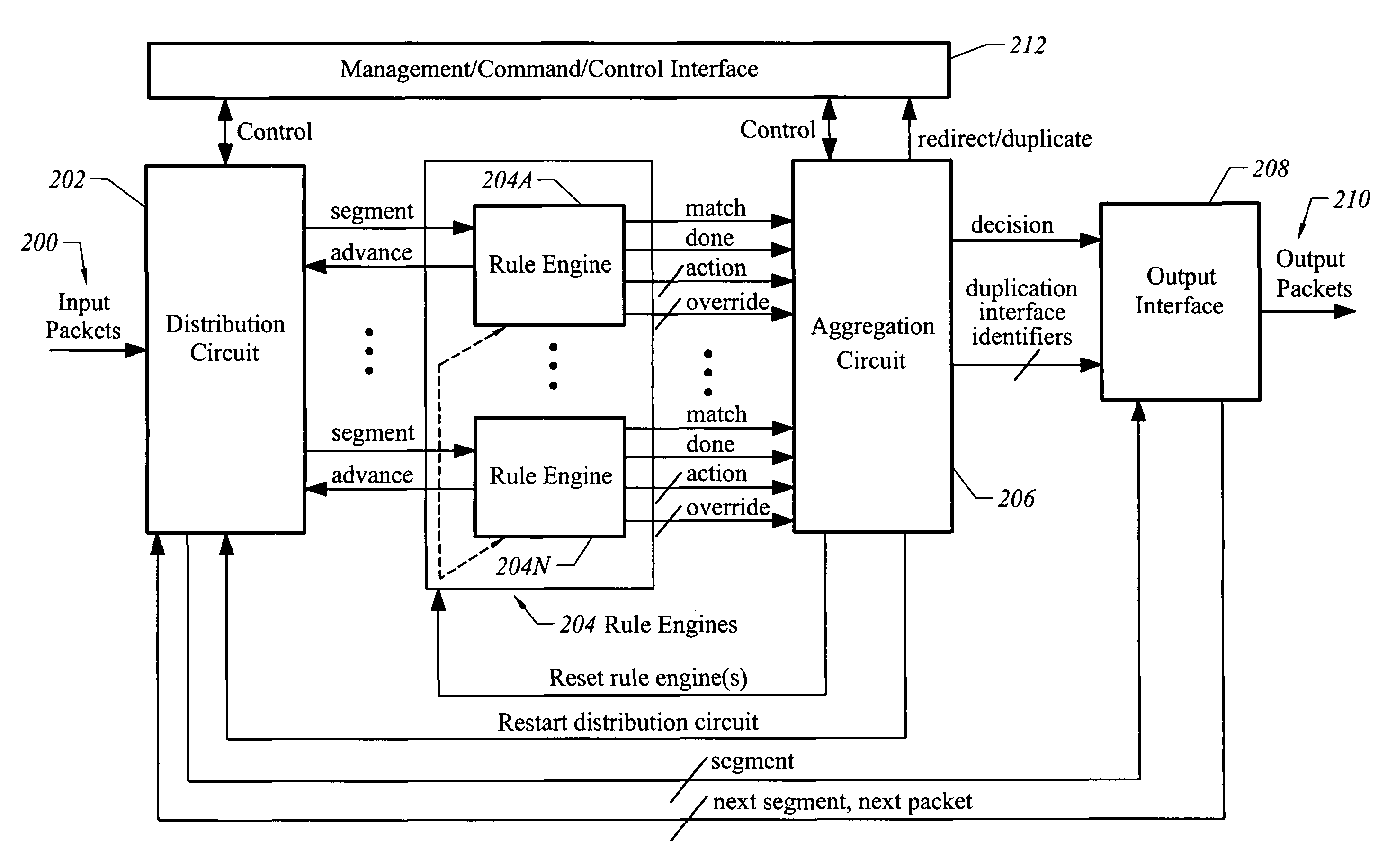
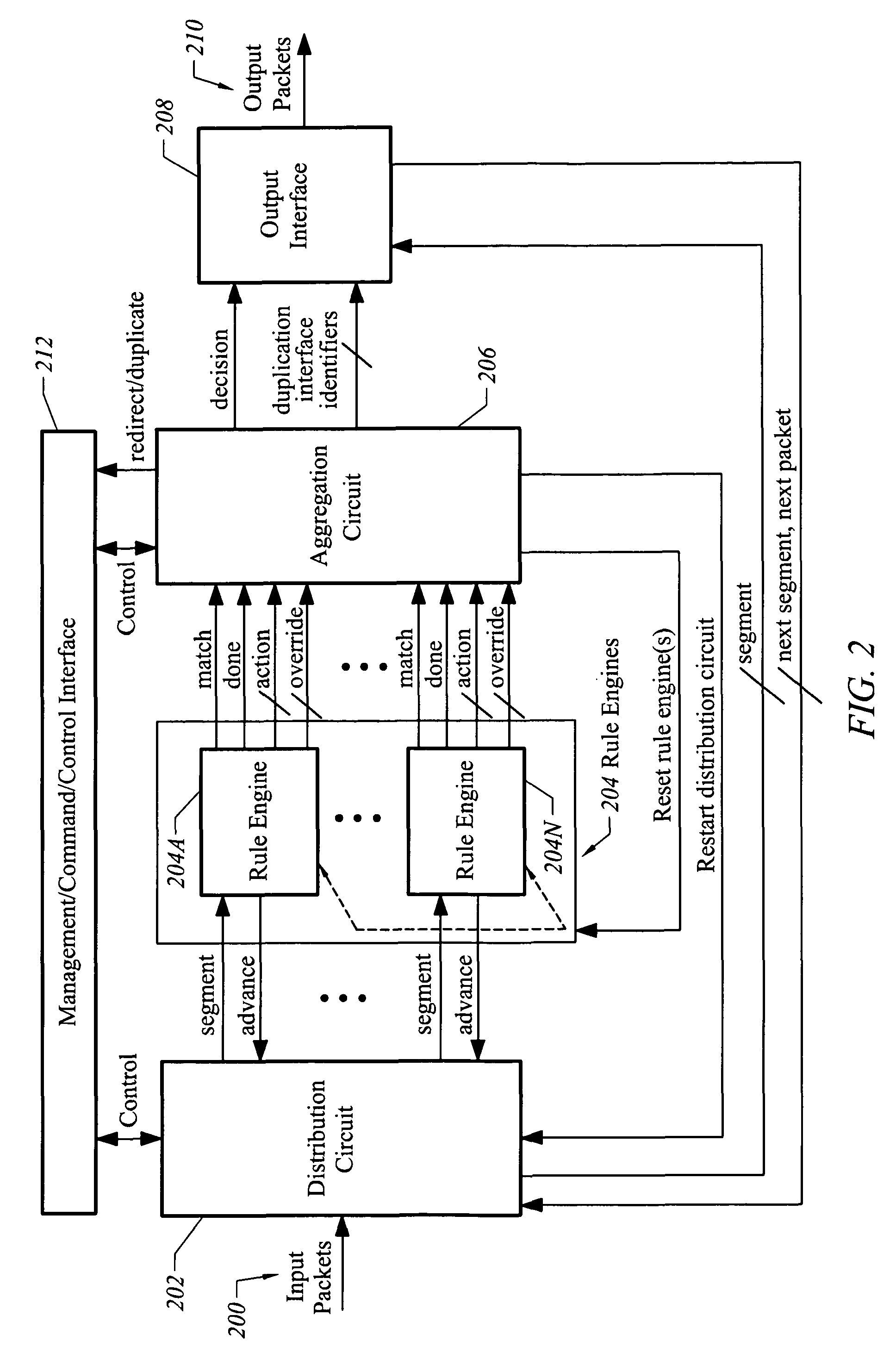
ActiveUS7937756B2Easy networkingImprove securityError preventionFrequency-division multiplex detailsTraffic capacityLogical combination
An embodiment of an apparatus that facilitates network security and traffic monitoring for input network traffic includes a plurality of microcode controlled state machines, each of which includes a computation kernel. A plurality of rules applied to a network traffic segment are distributed across the computation kernels. Each of the computation kernels includes condition logic configured by microcode stored in an associated control store to evaluate a unique configured rule in the microcode to produce an associated output. A distribution circuit routes the network traffic segment to each of the plurality of microcode controlled state machines. An aggregation circuit generates a decision on which forwarding of the network traffic segment is based, where the decision is a logical combination of the associated output of each of the computation kernels.
Owner:CPACKET NETWORKS
Network security policy enforcement using application session information and object attributes
A packet traversing on the computer network is received; session information is generated from the packet with the session information including a client network address and a server network address; the packet is associated with at least one object attribute from the directory by using the session information; and a security policy defined for the network environment is enforced by using the session information and the object attribute(s) to determine whether the packet violates the security policy.
Owner:VMWARE INC
SMTP network security processing in a transparent relay in a computer network
ActiveUS20070204341A1Memory loss protectionError detection/correctionCommunication interfaceNetwork Communication Protocols
In one embodiment, a transparent relay receives diverted e-mail communications between an e-mail client and an e-mail server. The transparent relay may be configured to examine the e-mail communications for network security policy violations. E-mail communications that do not violate a network security policy may be relayed to their intended destination. Policy actions, such as discarding or redirection, may be performed on those that violate one or more network security policies. The transparent relay may include a pair of communications interfaces running in promiscuous mode, one for downstream communications and another for upstream communications. The transparent relay may decompose a network communication protocol to look network security policy violations.
Owner:TREND MICRO INC
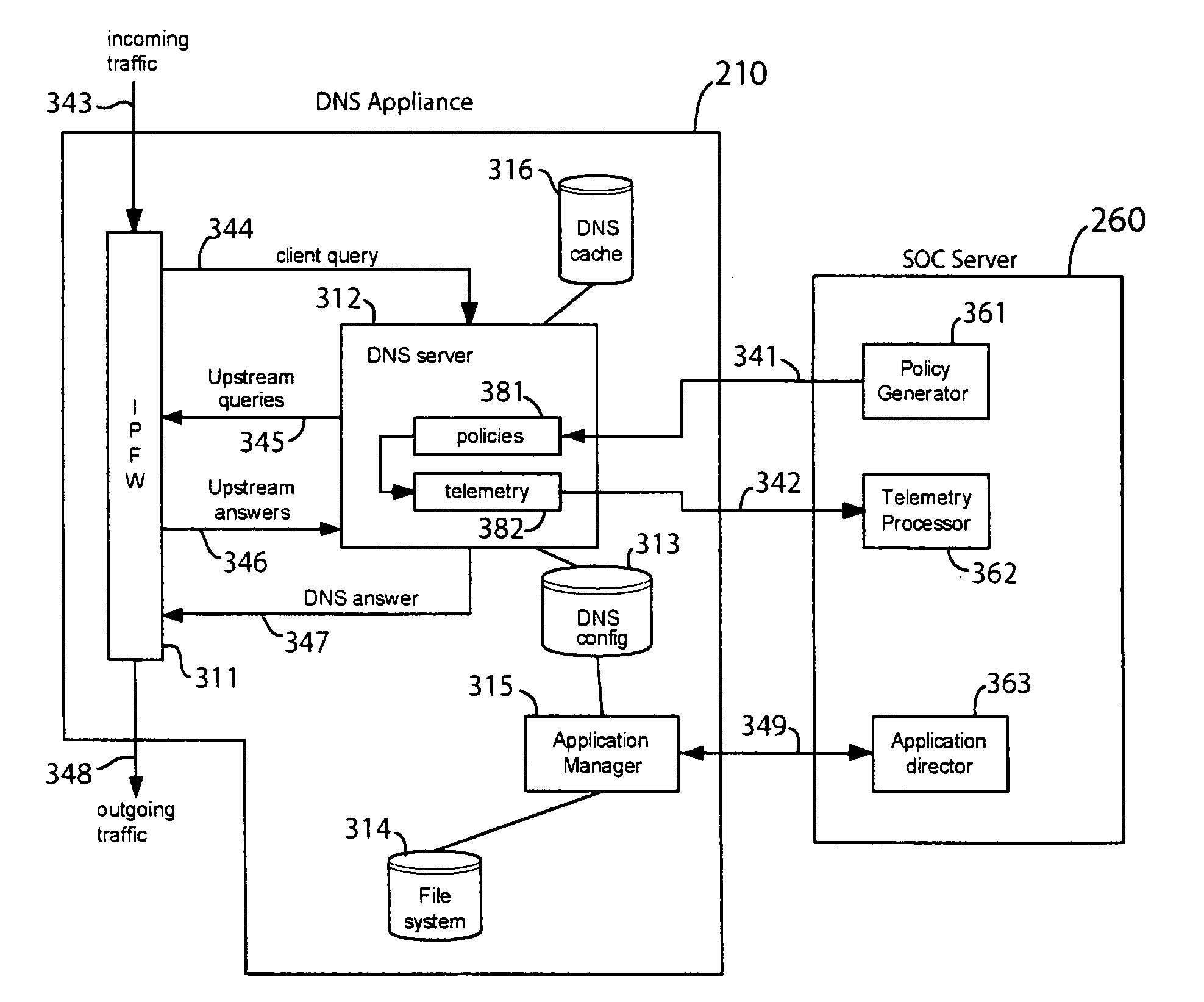
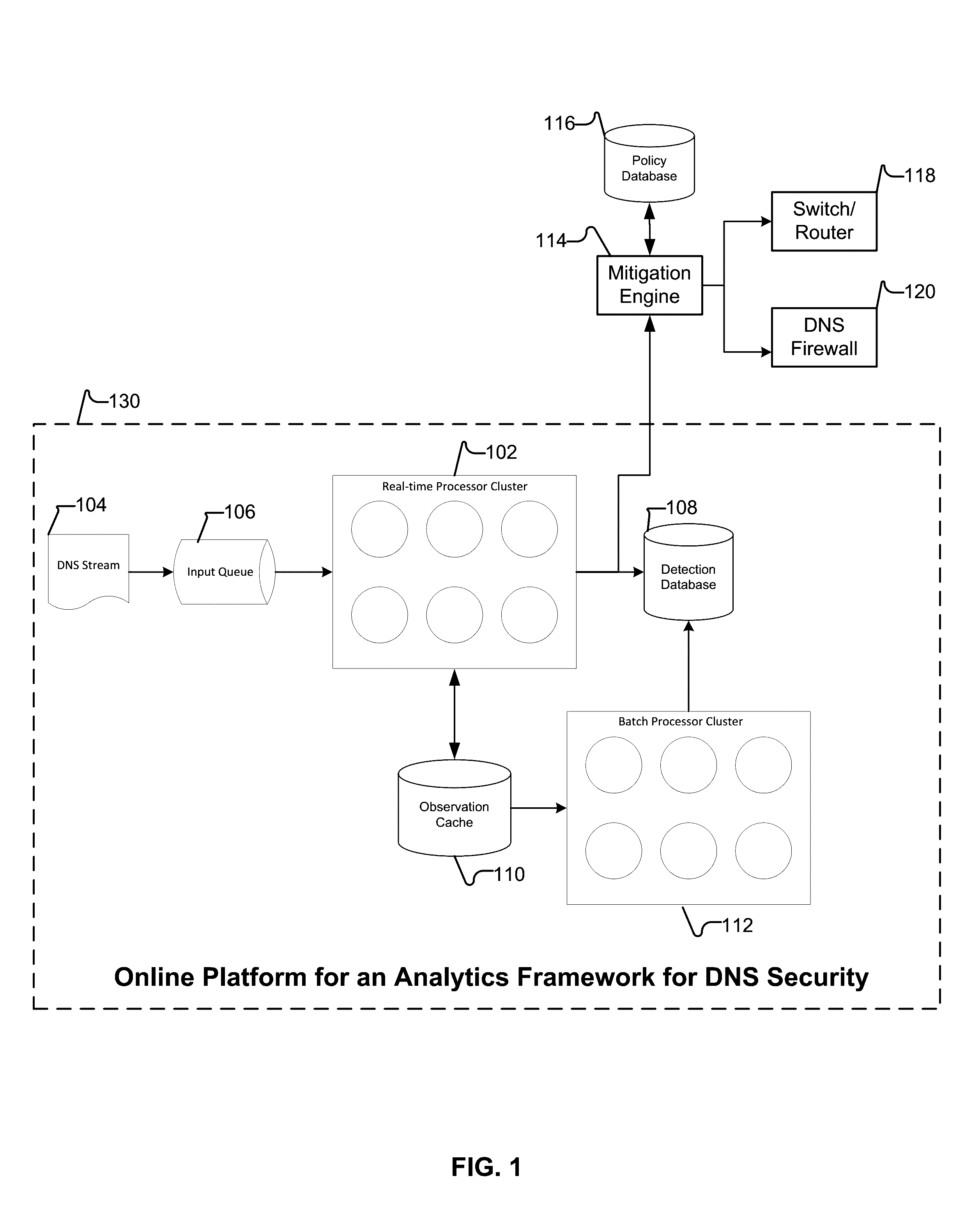
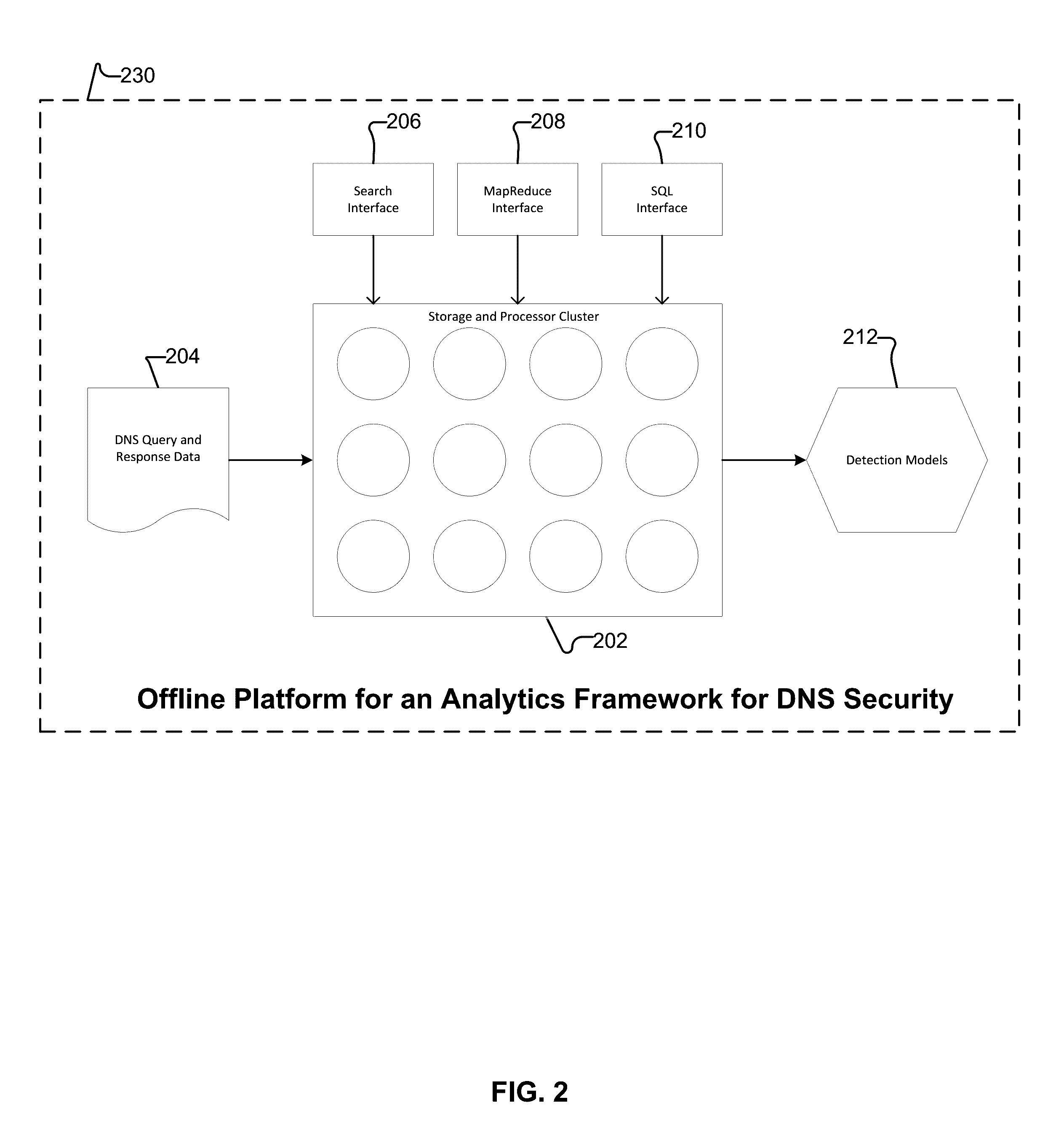
Behavior analysis based DNS tunneling detection and classification framework for network security
New and improved techniques for a behavior analysis based DNS tunneling detection and classification framework for network security are disclosed. In some embodiments, a platform implementing an analytics framework for DNS security is provided for facilitating DNS tunneling detection. For example, an online platform can implement an analytics framework for DNS security based on passive DNS traffic analysis.
Owner:INFOBLOX
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com