Patents
Literature
214results about How to "Protect data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Hermetically sealed electronics arrangement and approach
InactiveUS20050068666A1Reduction of magnetic spacingImprove performanceApparatus modification to store record carriersUndesired vibrations/sounds insulation/absorptionMetallic enclosureCold formed
A hermetic sealing approach involves welding an Aluminum cover onto a low-cost Aluminum housing. According to an example embodiment of the present invention, a metal housing having a base and sidewalls extending upward therefrom is adapted to receive and couple to an HDD arrangement. The metal housing is formed using material and processing (e.g., cold formed or die cast Aluminum) that are relatively inexpensive. A feedthrough arrangement including a plurality of communication pins extends through an opening in the base and is coupled thereto, with the communication pins adapted to pass signals between the inside and the outside of the metal housing. A metal cover is welded to an upper portion of the sidewalls and, with the feedthrough arrangement, hermetically seals the metal housing.
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV
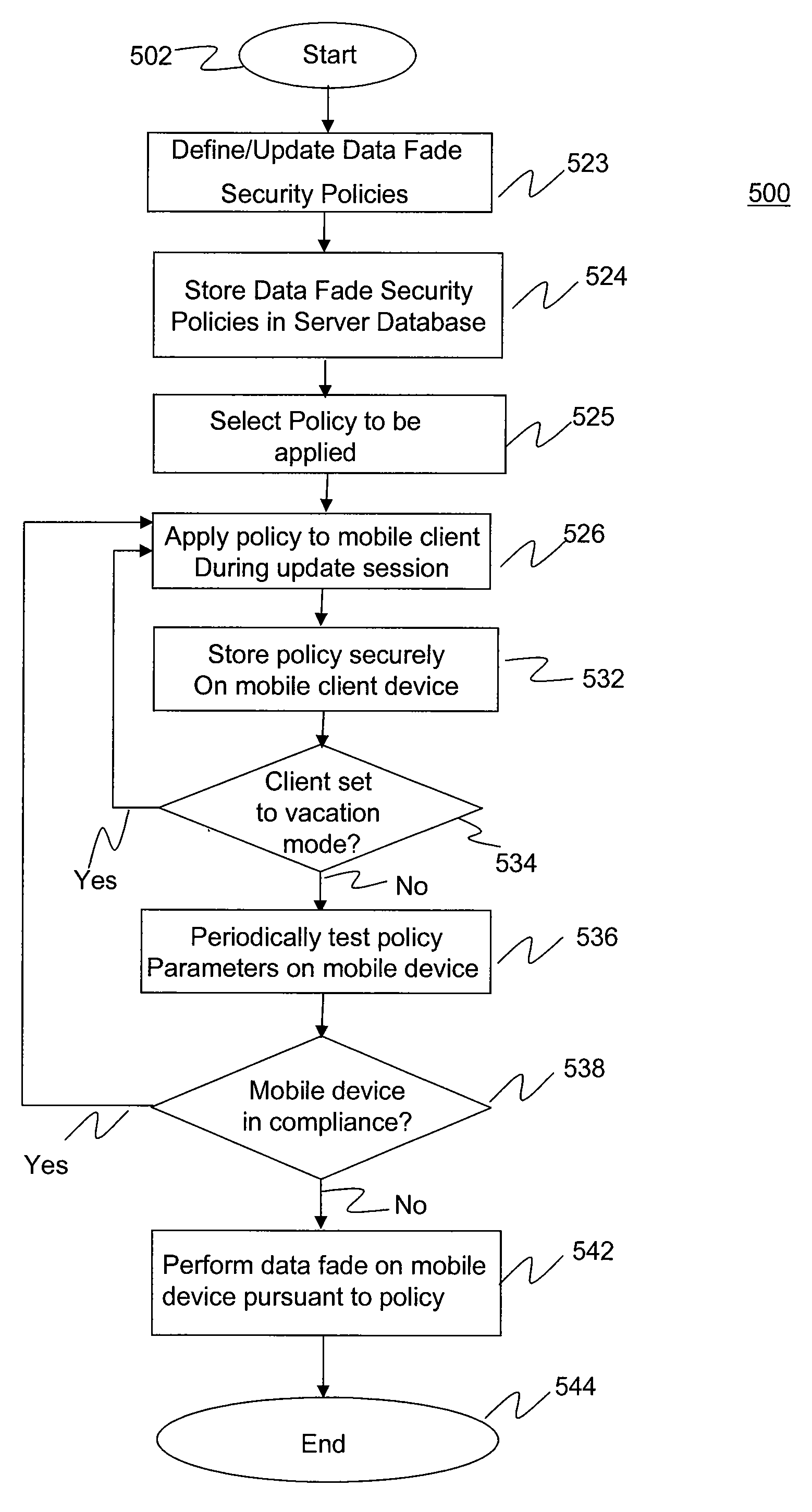
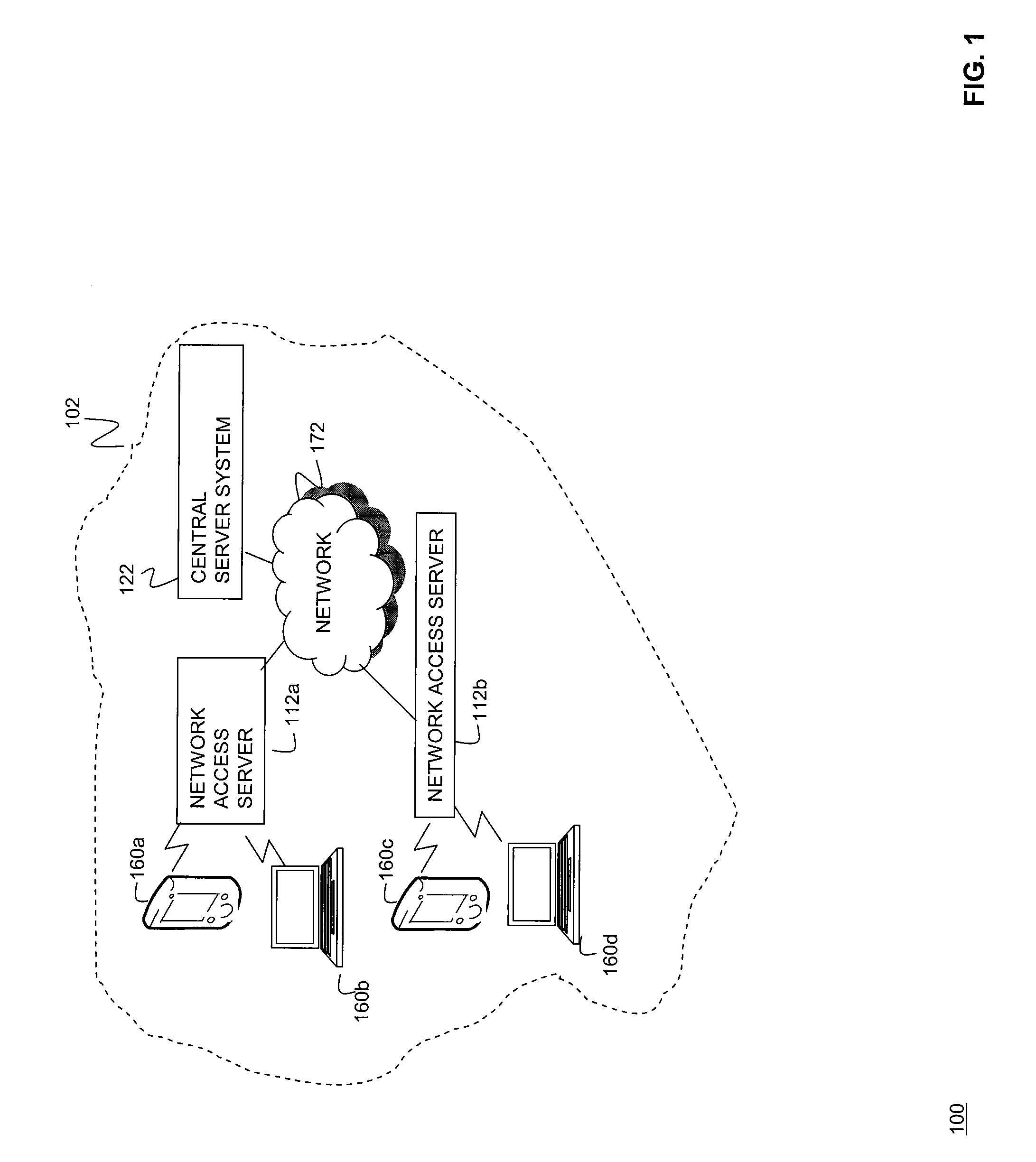
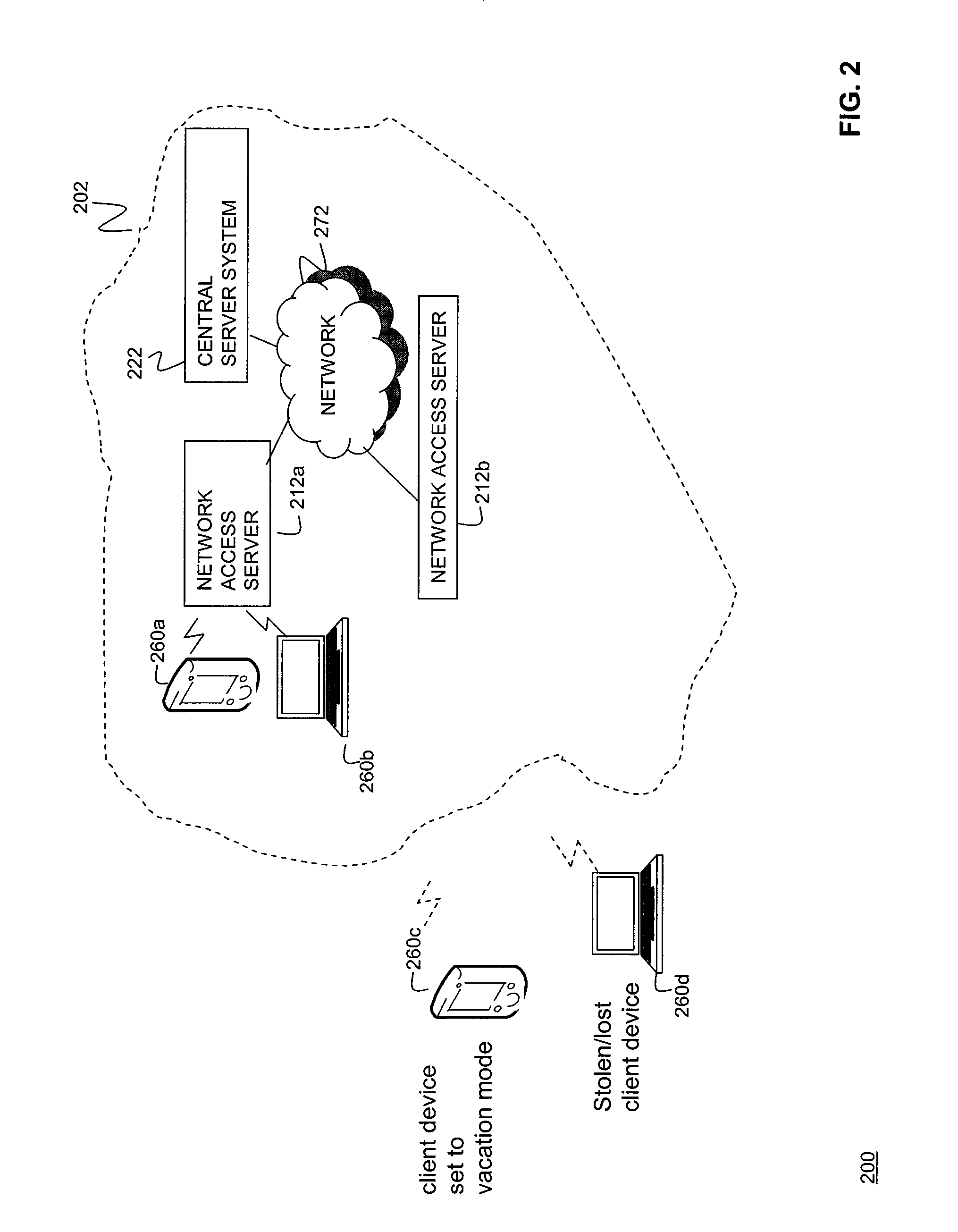
Data Fading to Secure Data on Mobile Client Devices
InactiveUS20090150970A1Protect dataEliminate needInternal/peripheral component protectionTransmissionNetwork security policyClient-side
Methods, systems, and computer program products to secure data stored on mobile client devices are provided. In an embodiment, the method operates by defining one or more security policies. Each security policy comprises a plurality of security policy parameters. The method stores the security policies in a data store, and selects a security policy from among the stored security policies for a mobile client device. The selected security policy is applied to the mobile client device. The mobile client device determines whether it is compliance with parameters of said selected security policy, and performs data fade actions if it is determined that it is out of compliance with said security policy parameters.
Owner:IANYWHERE SOLUTIONS
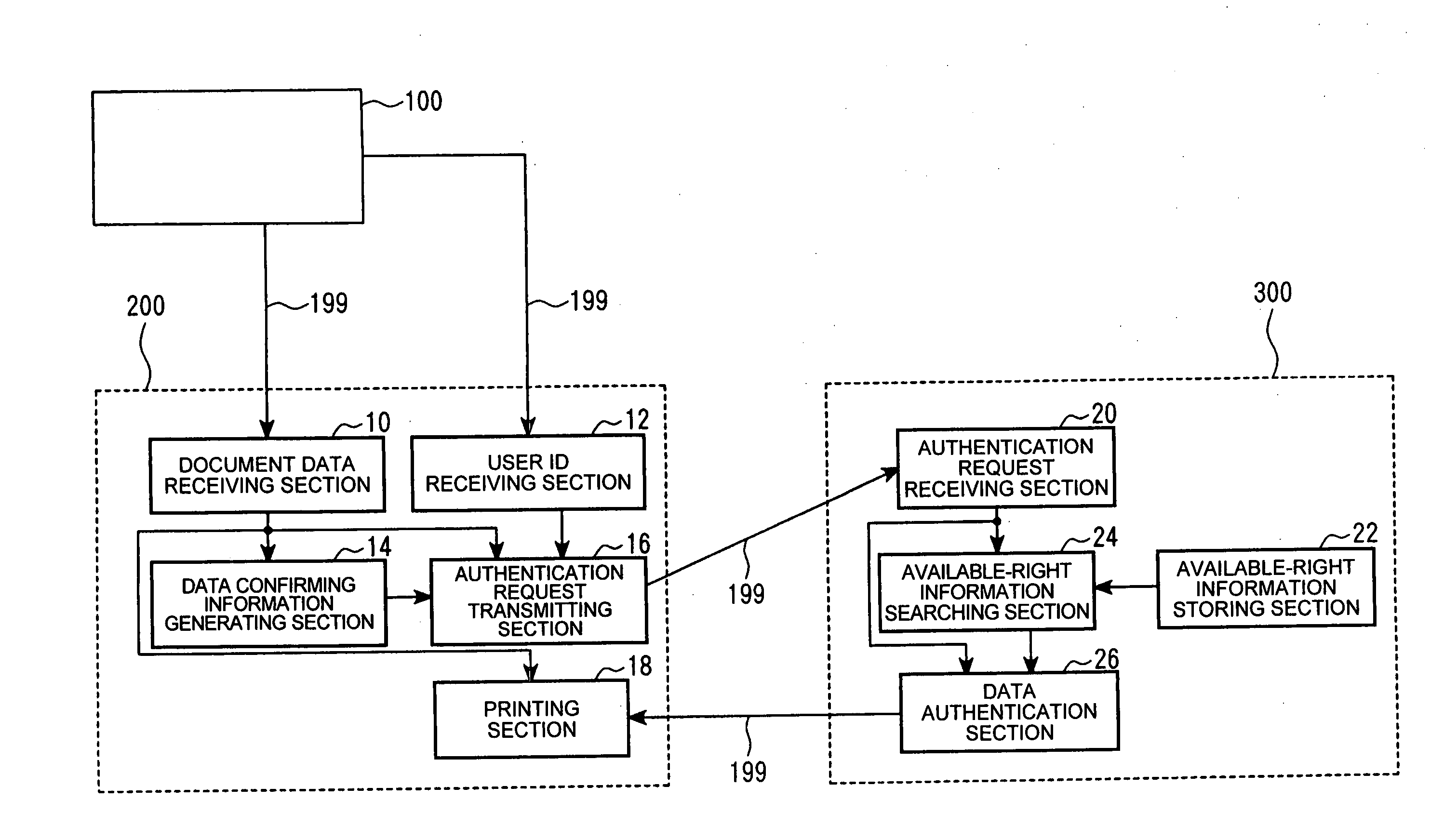
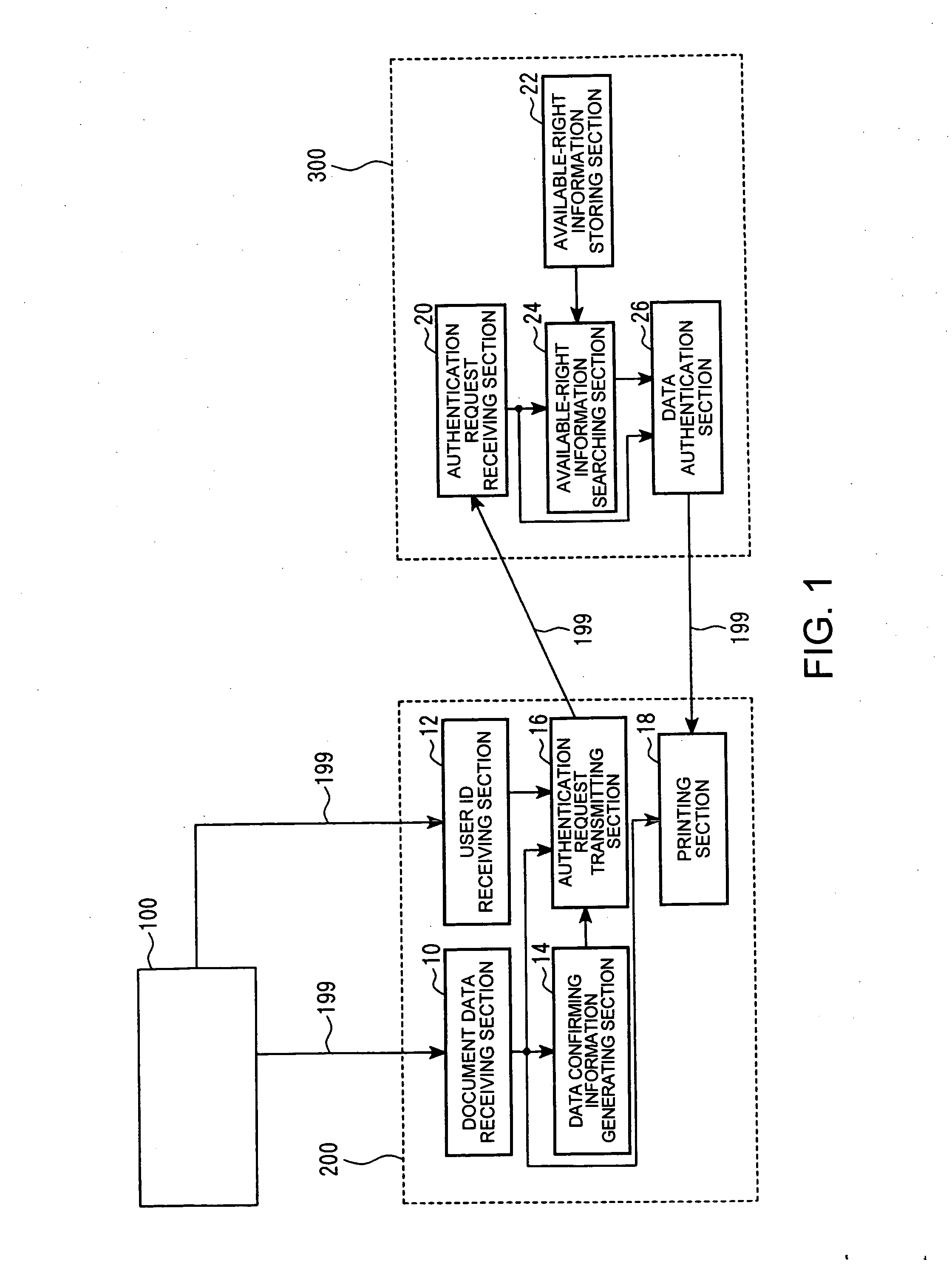
License-authentication functioned output system, output apparatus, data authentication apparatus, design resource output program, data authentication program and license authentication output method
InactiveUS20050114267A1Protect dataImprove convenienceData processing applicationsDigital computer detailsComputer printingPaper document
Exemplary embodiments provide a license-authentication functioned output system which enables data protection positive and enhances and / or improves a user's convenience, further being suited to reduce processing load. A printer receives document data and a user ID and sends design resource-data authentication information and the user ID included in the document data, together with an authentication request, to a data authentication server. When a use-permitting information is received, it prints a design resource within a use-permitted scope depending upon the use-permitting information and design resource data. A data authentication server searches through a license information register table on the basis of the authentication information and reads out license information concerned. The data authentification server decides whether or not the received user ID is included in the license information. When it is decided that the user ID is included, the use-permitting information included in the license information is sent to the printer.
Owner:SEIKO EPSON CORP
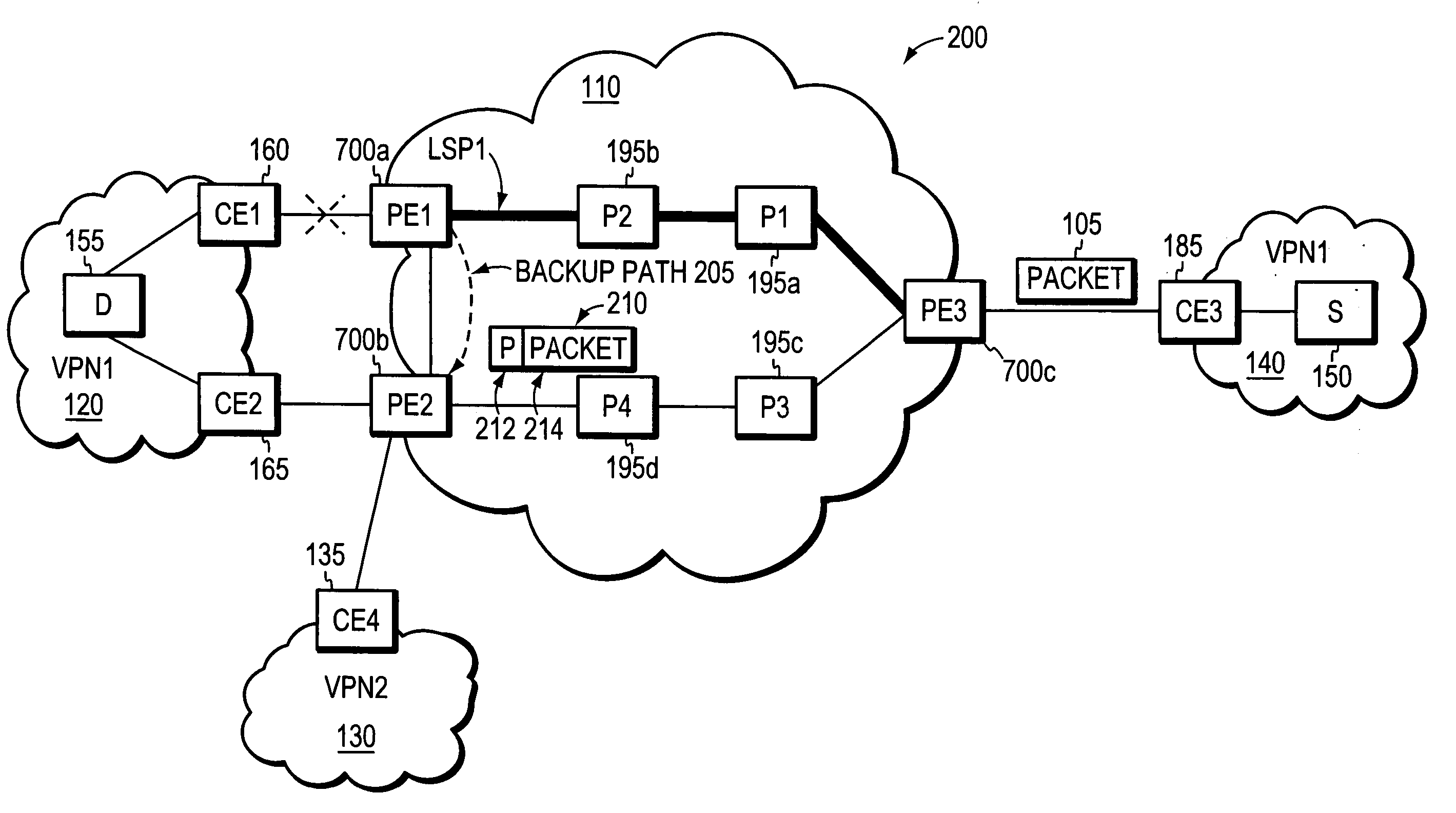
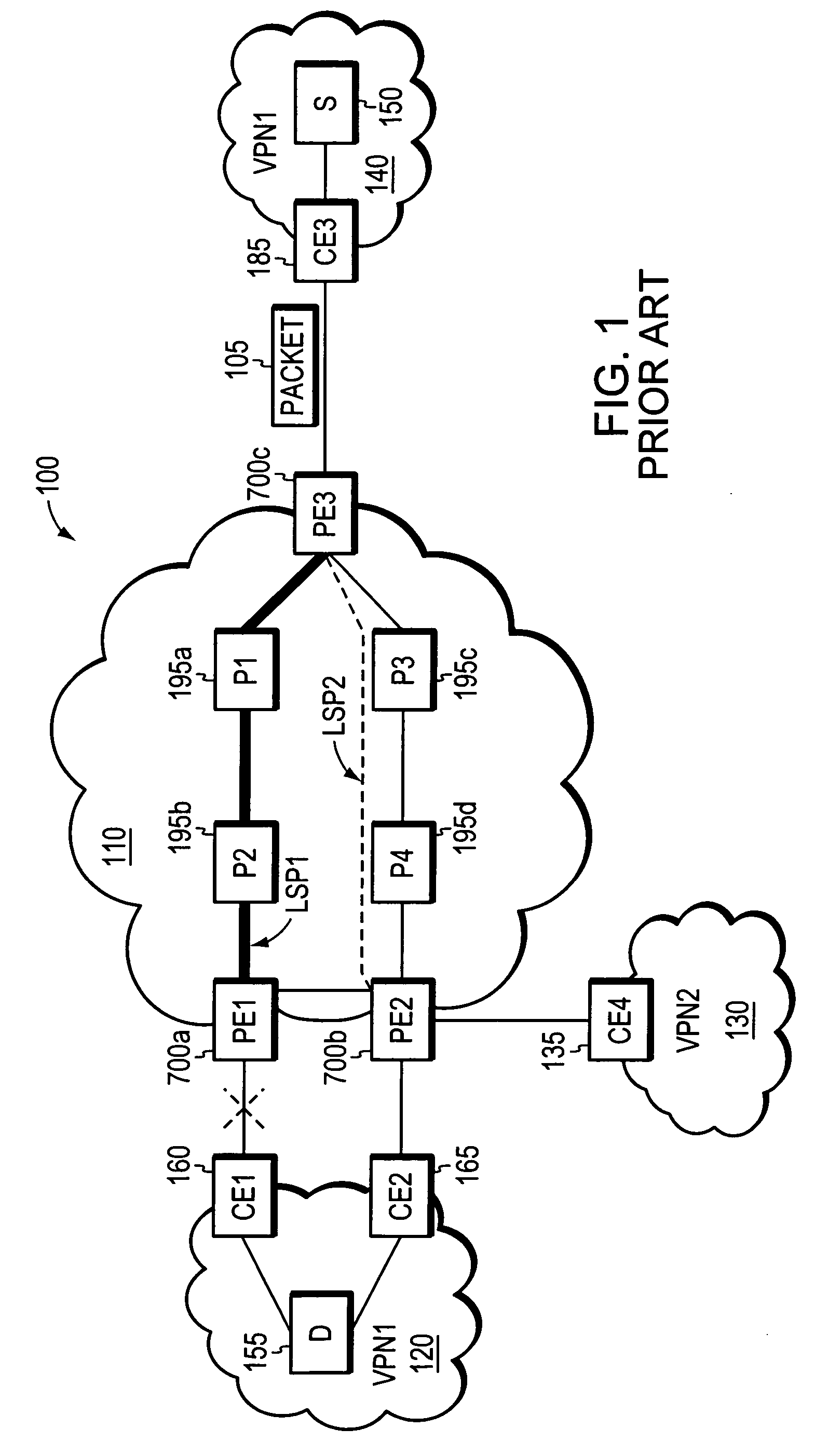
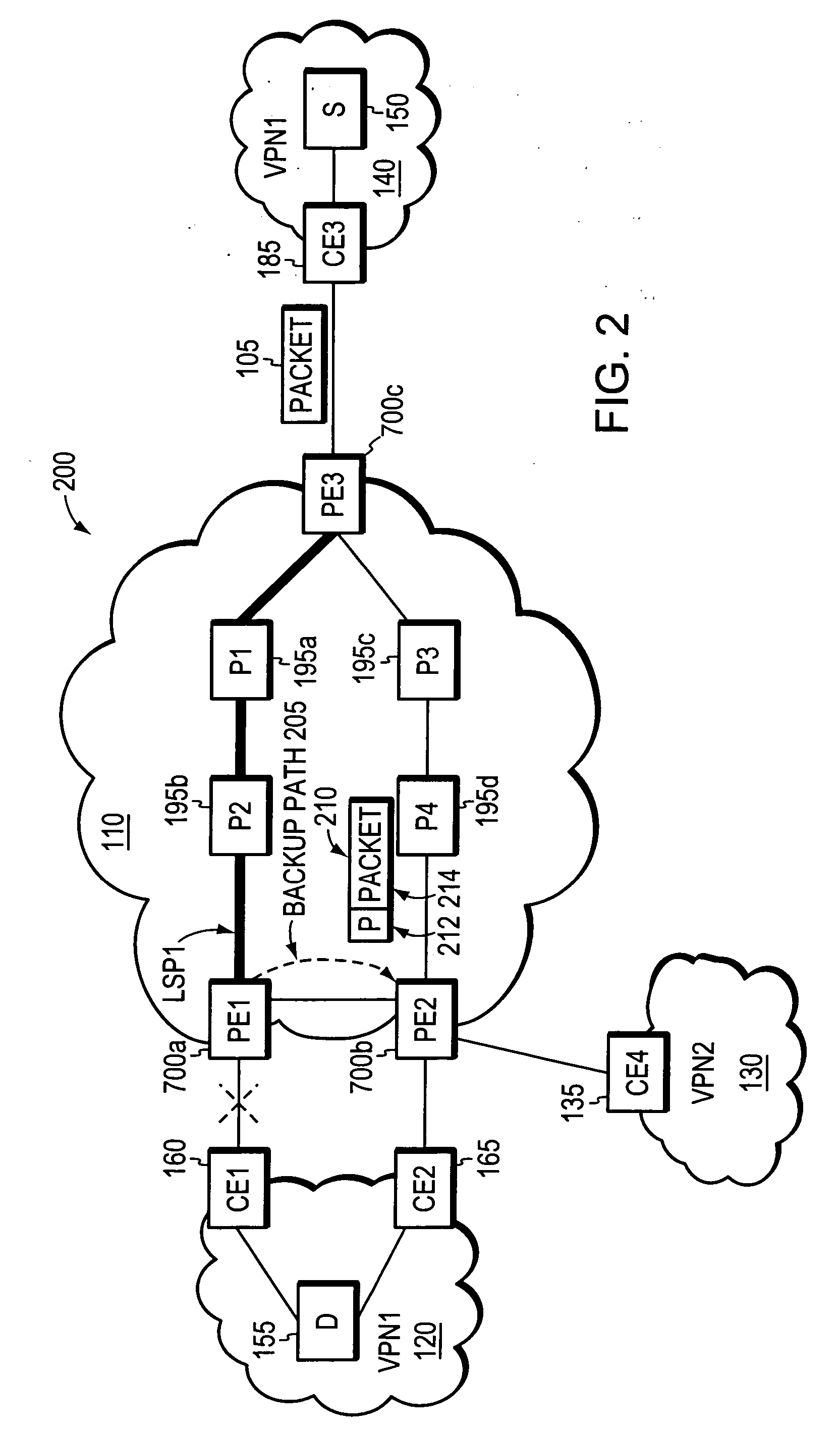
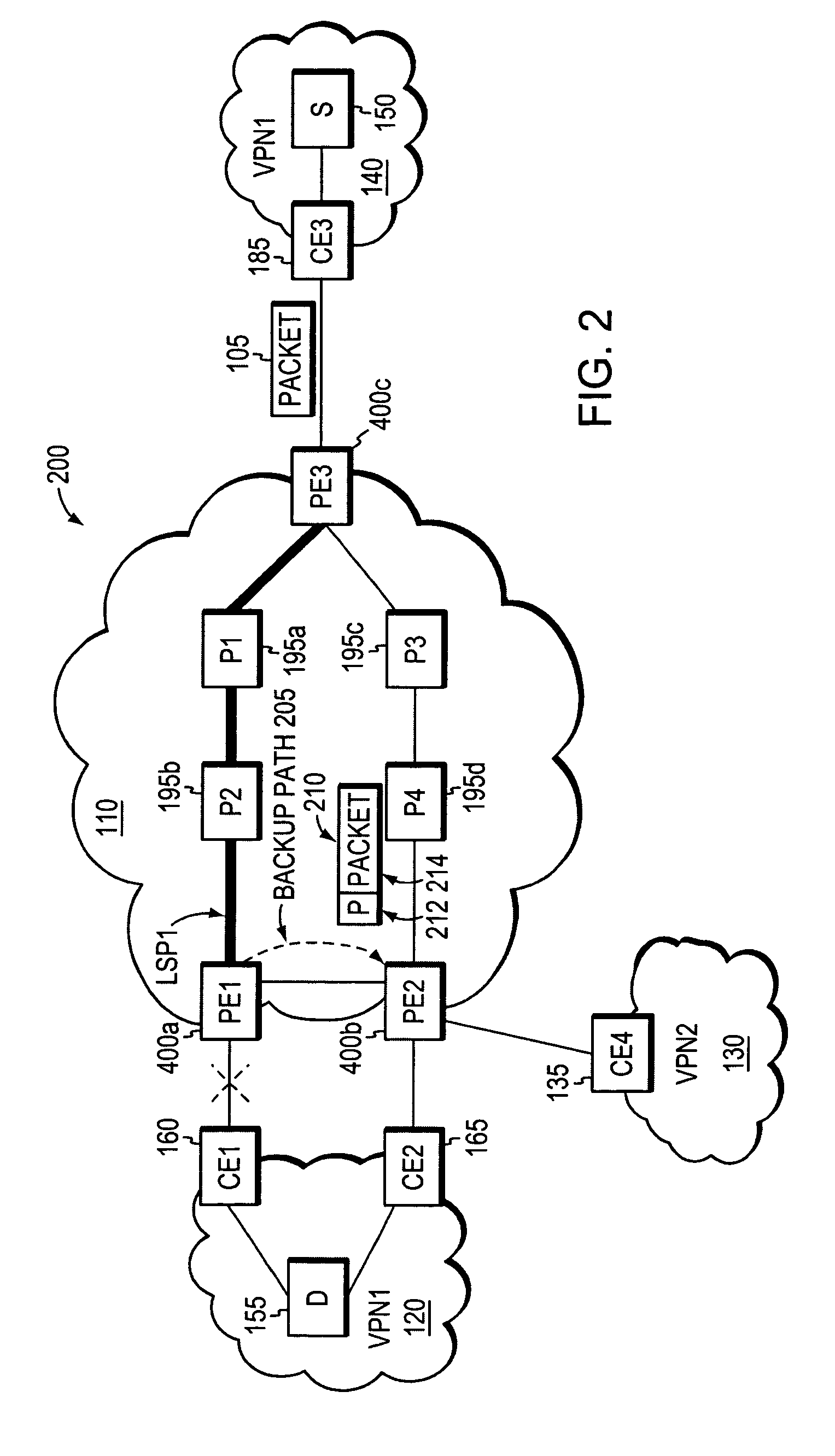
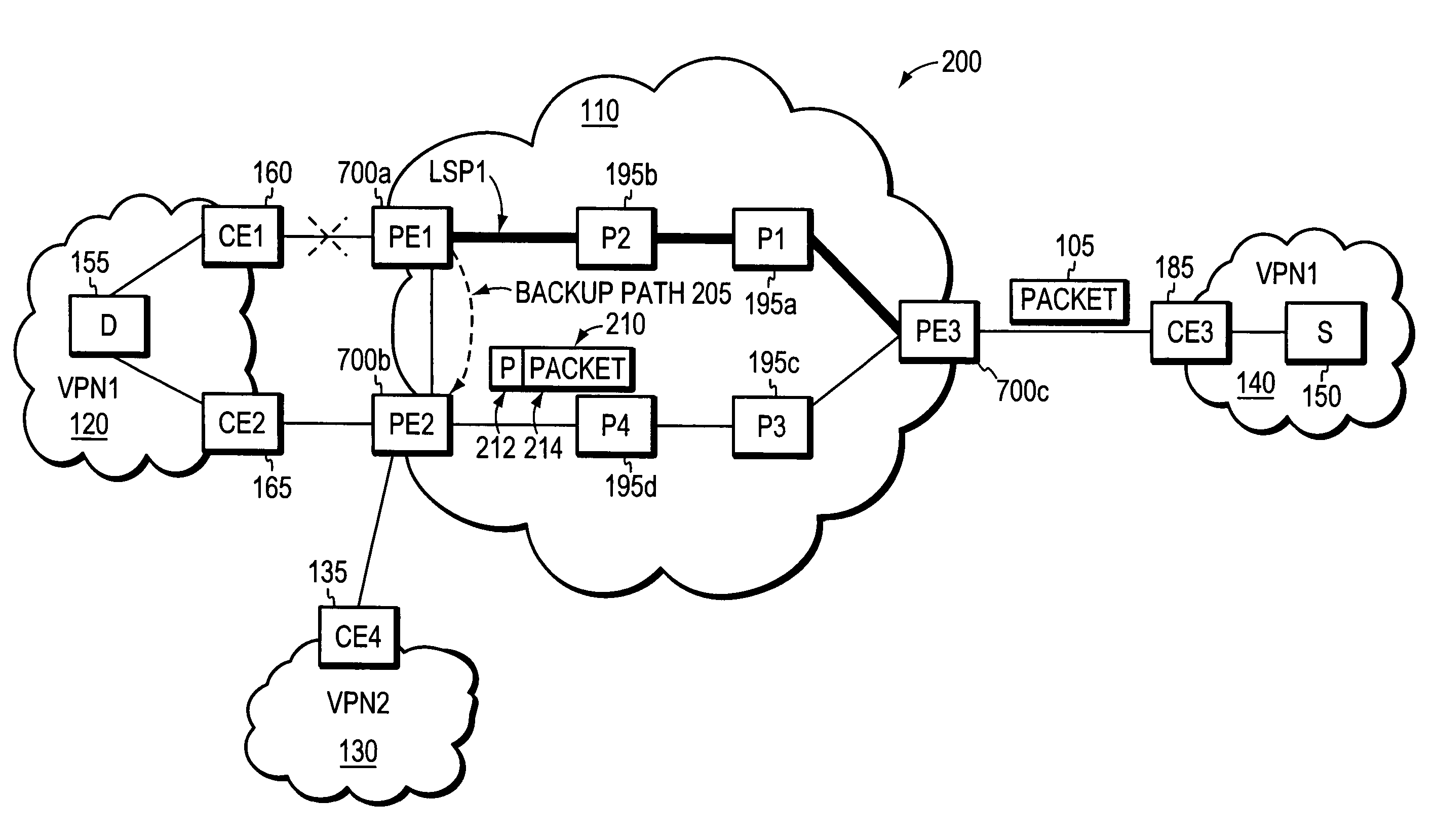
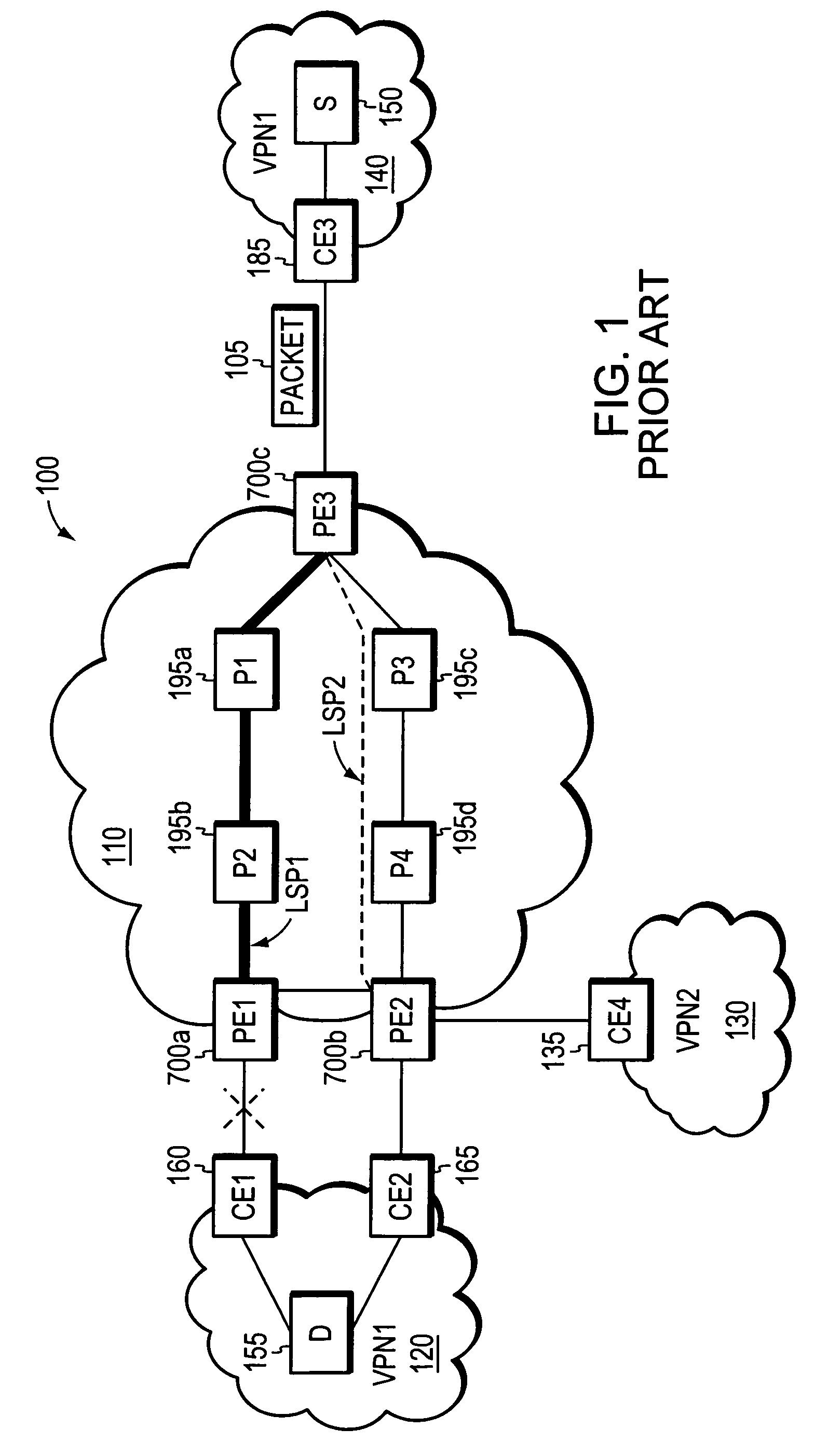
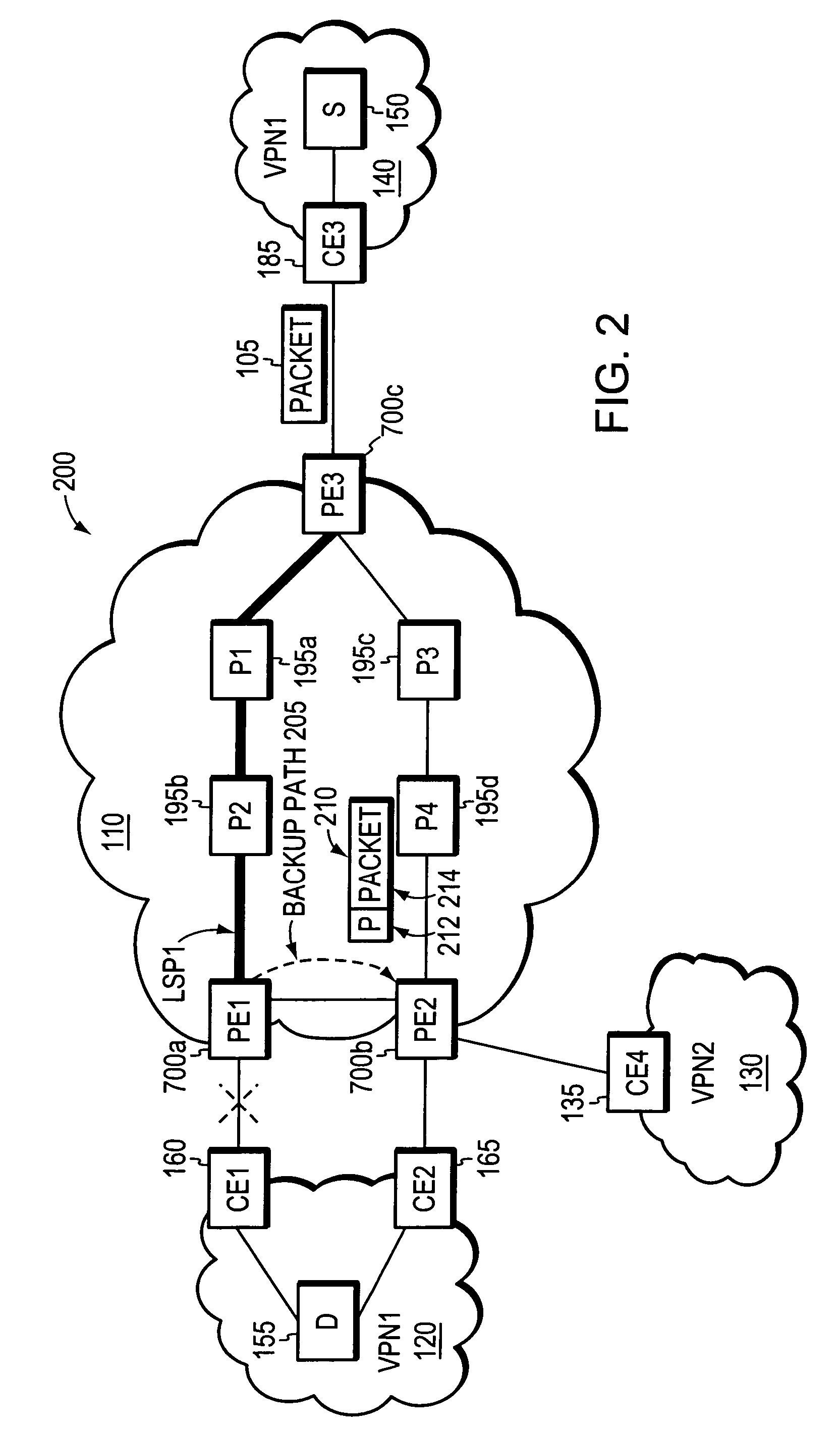
Loop prevention techniques using encapsulation manipulation of IP/MPLS field
ActiveUS20060221813A1Avoid developmentFast reroute (FRR)Error preventionTransmission systemsRouting domainEdge device
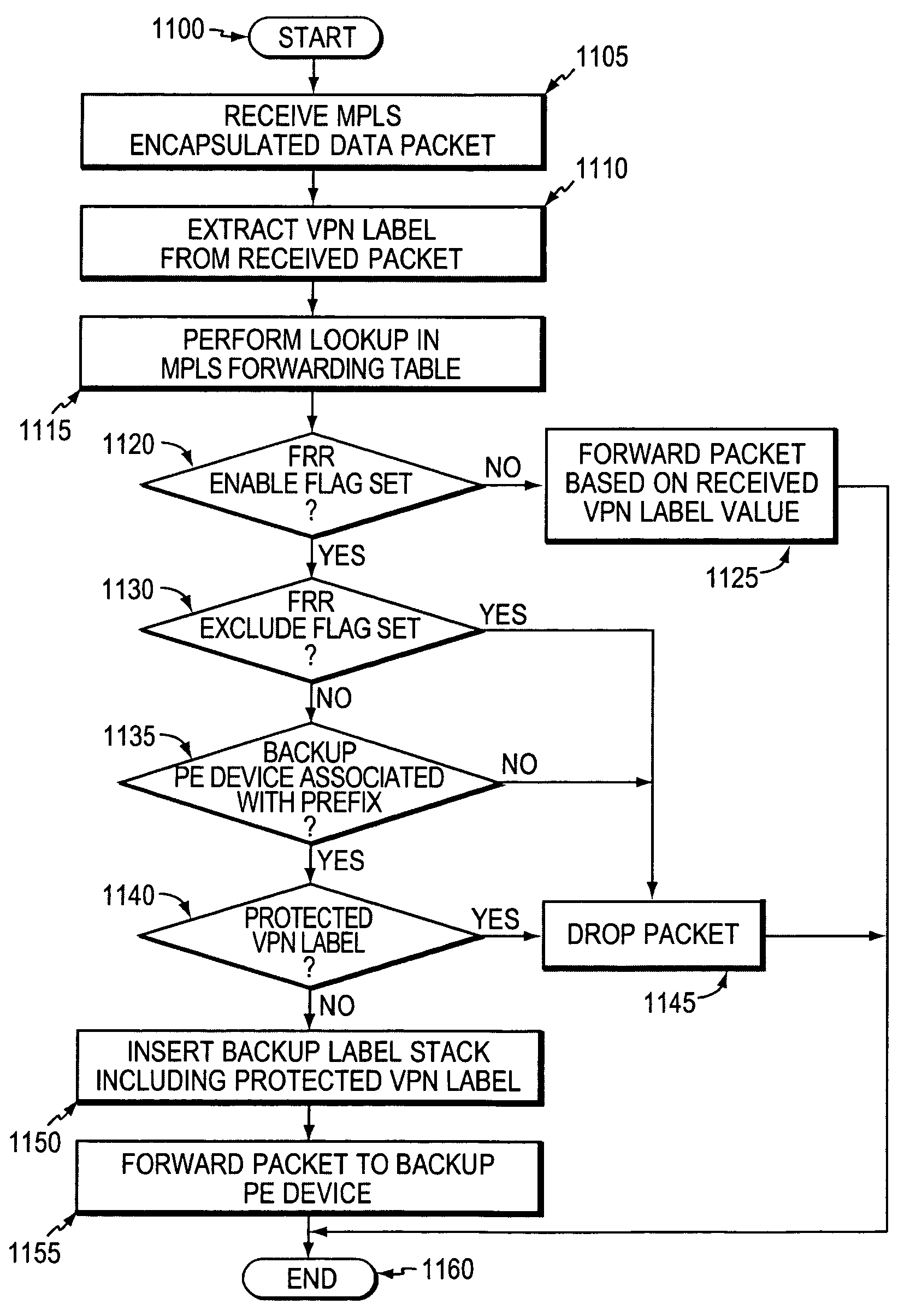
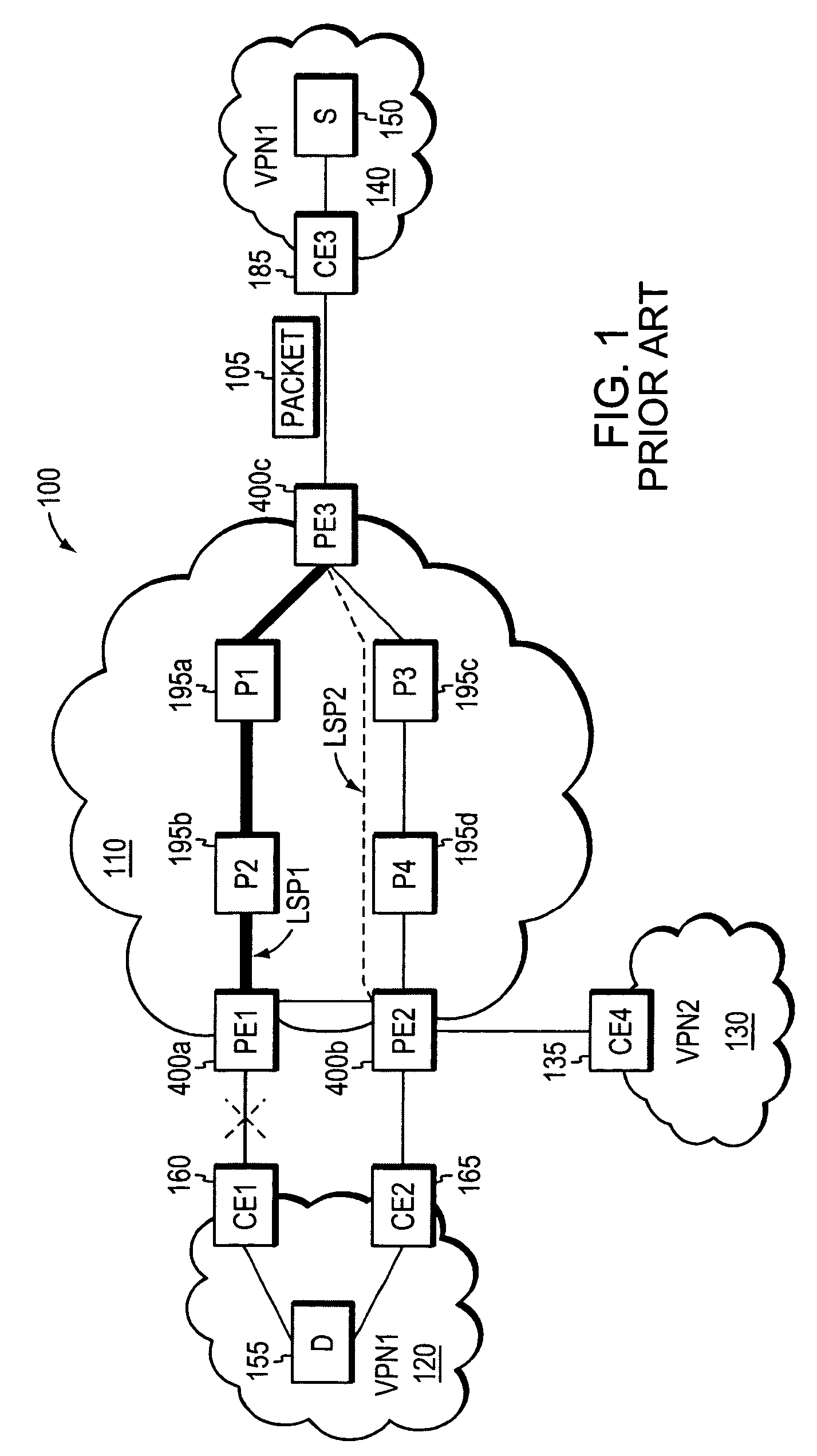
A fast reroute (FRR) technique is implemented at the edge of a computer network. In accordance with the technique, if an edge device detects a node or link failure that prevents it from communicating with a neighboring routing domain, the edge device reroutes at least some data packets addressed to that domain to a backup edge device which, in turn, forwards the packets to the neighboring domain. The rerouted packets are designated as being “protected” (i.e., rerouted) data packets before they are forwarded to the backup edge device. To that end, the edge device incorporates an identifier into the rerouted data packets to indicate that the packets are being FRR rerouted. The identifier may be a predetermined value stored at a known location in the rerouted packets'encapsulation headers, such as in their MPLS or IP headers. Upon receiving a data packet containing the identifier, the backup edge device is not permitted to reroute the packet a second time.
Owner:CISCO TECH INC
Method of authenticating universal serail bus on-the-go device
InactiveUS20050251589A1Improve data securityPrevent unauthorized accessDigital data authenticationInput/output processes for data processingMobile deviceUSB
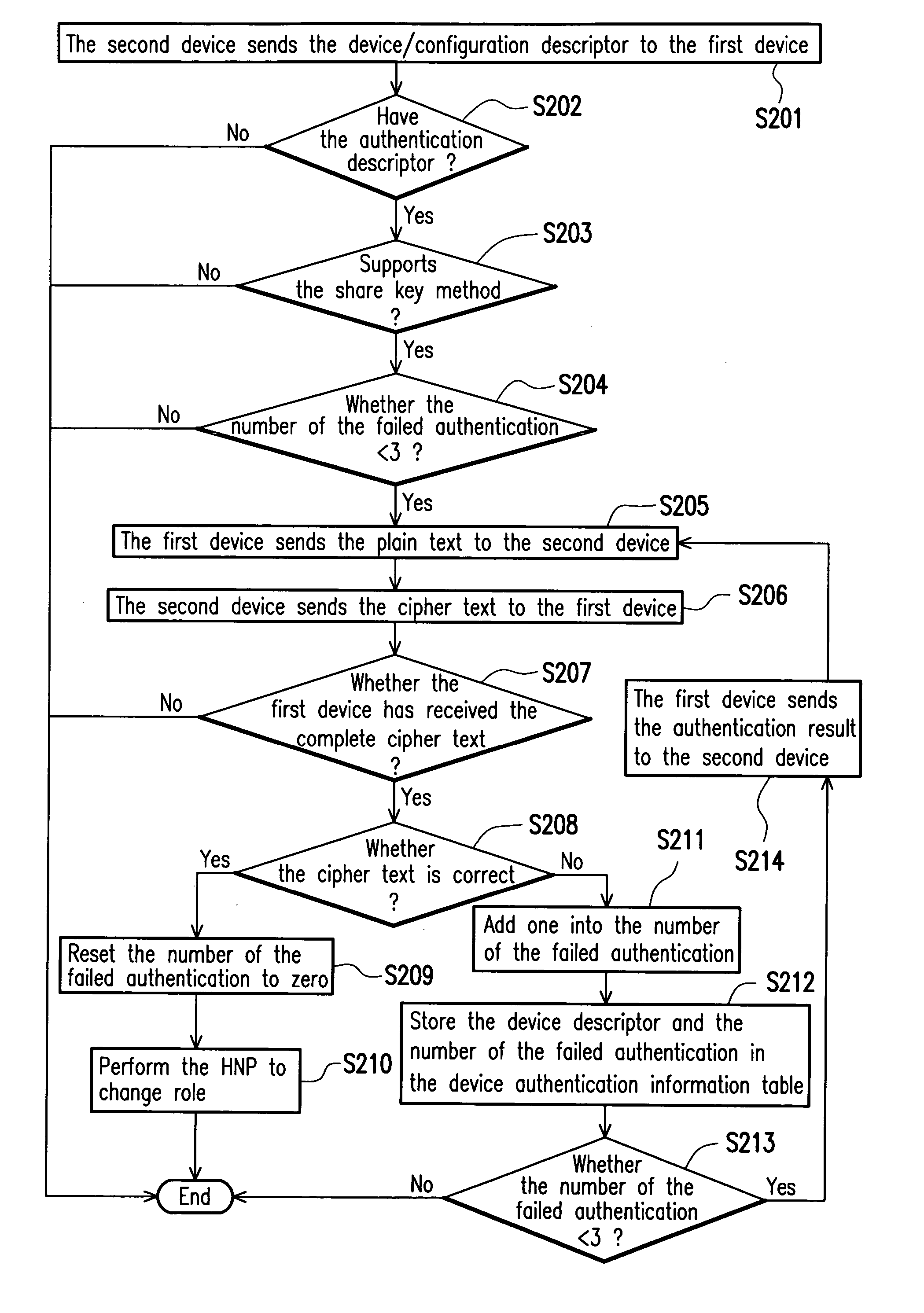
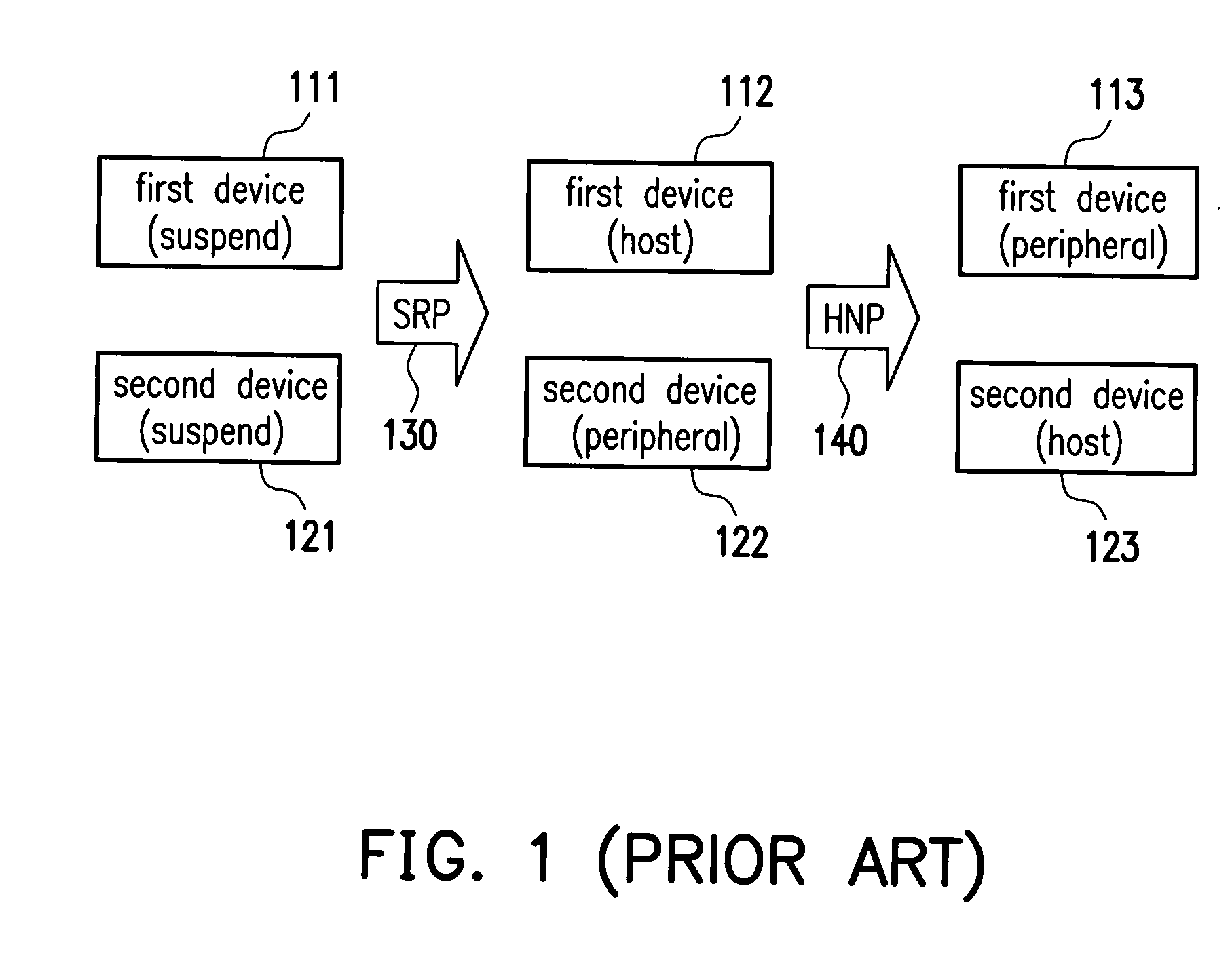
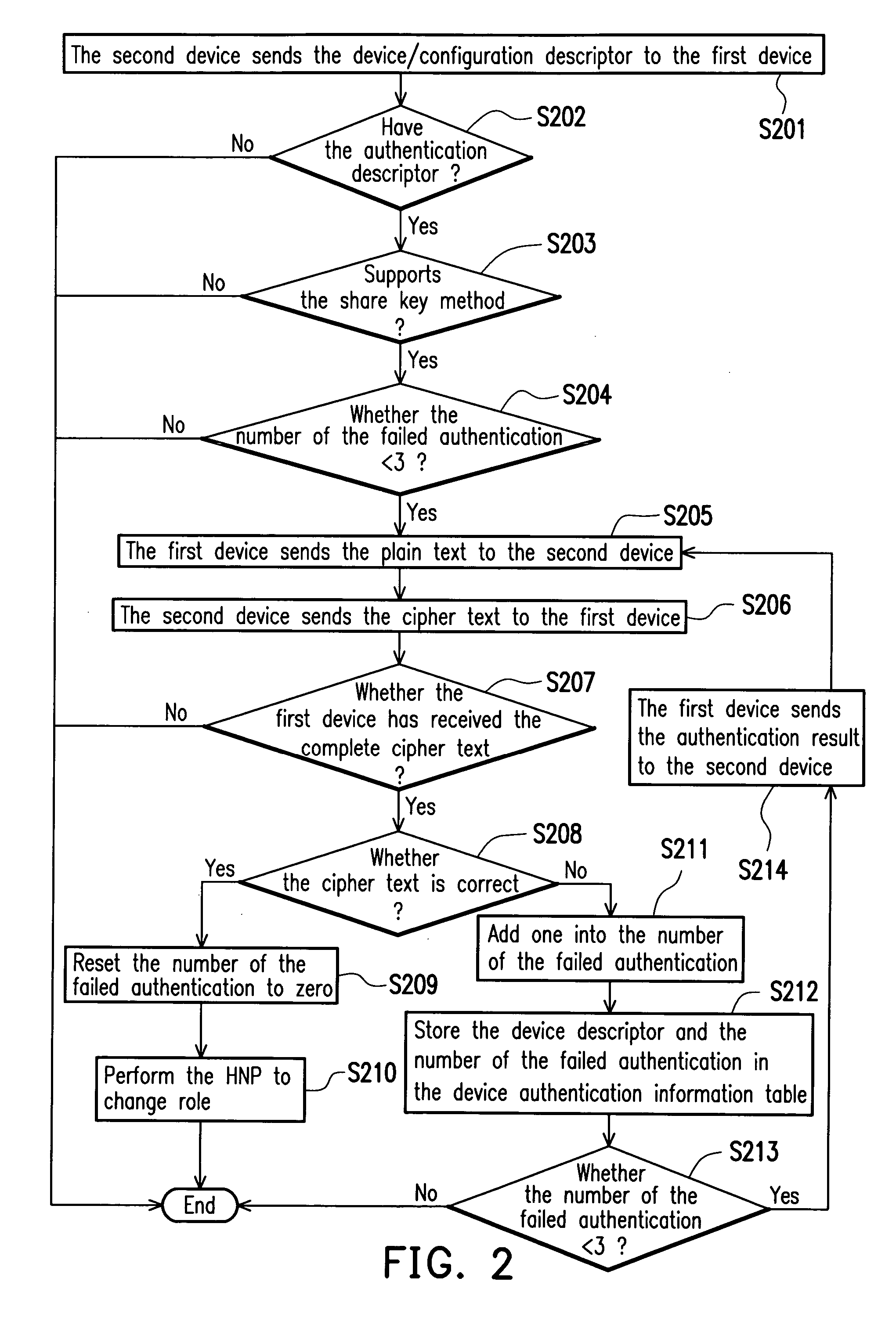
A method for authenticating a universal serial bus on-the-go device is provided. A first device and a second device connected via a universal serial bus supporting an on-the-go protocol are provided. The first device is a host and the second device is a peripheral device. The host uses an authentication rule to determine whether the peripheral device is an authentic device. When the peripheral device is an authentic device, the host sends an enable signal to the peripheral device to perform a host negotiation protocol so that the first device changes role to the peripheral device and the second device changes role to the host; and when the peripheral device is not the authentic device, the host declines to perform the host negotiation protocol with the peripheral device. Hence, the data security of the USB host is enhanced. The data security of the USB peripheral device can also enhanced by providing the authentication mechanism before the USB device (peripheral device) has been accessed by the other devices (e.g., the USB host) in order to prevent the unauthorized user from accessing the data in the USB peripheral device.
Owner:FARADAY TECH CORP
Data tapping system based on Wcb and control method thereof
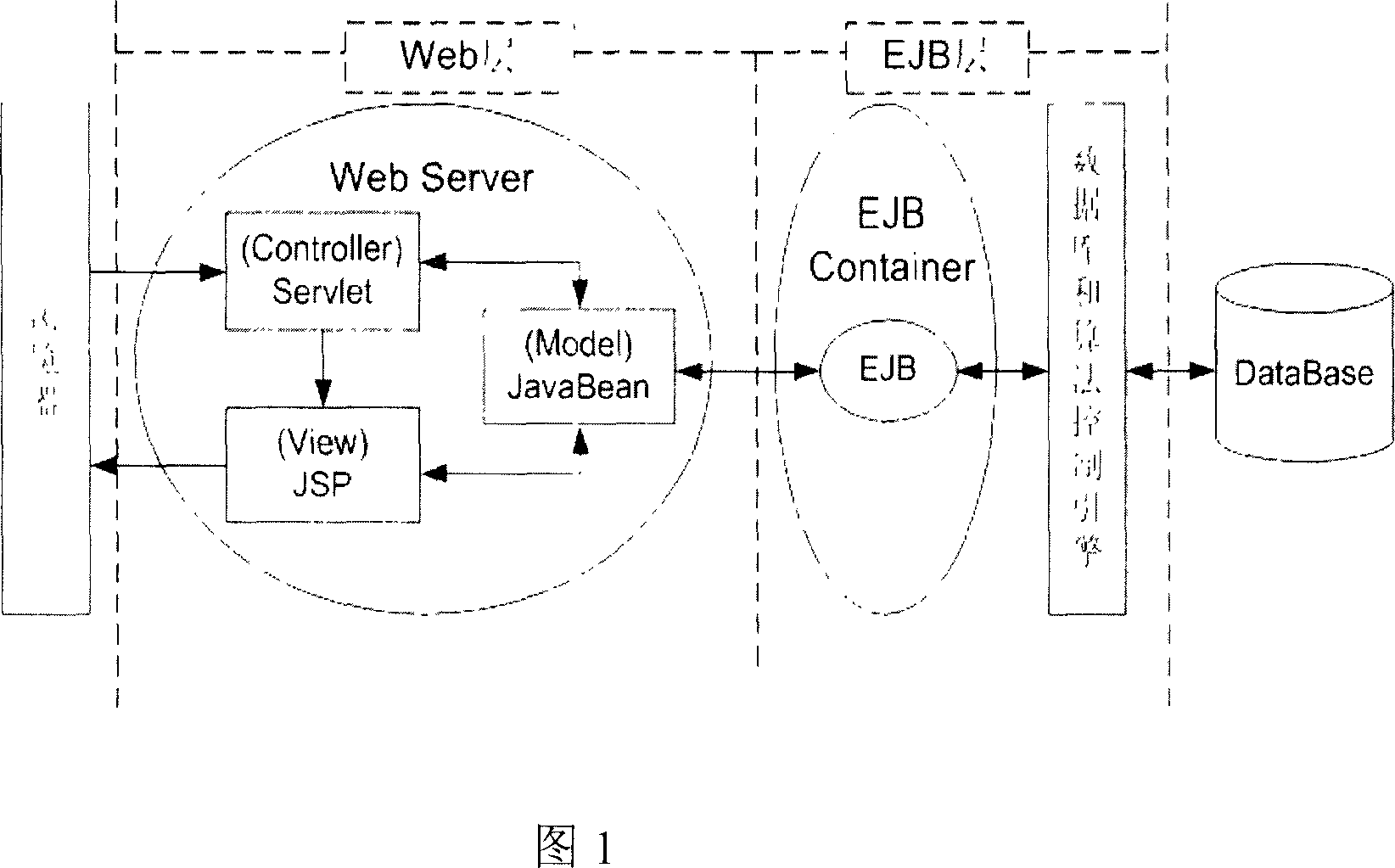
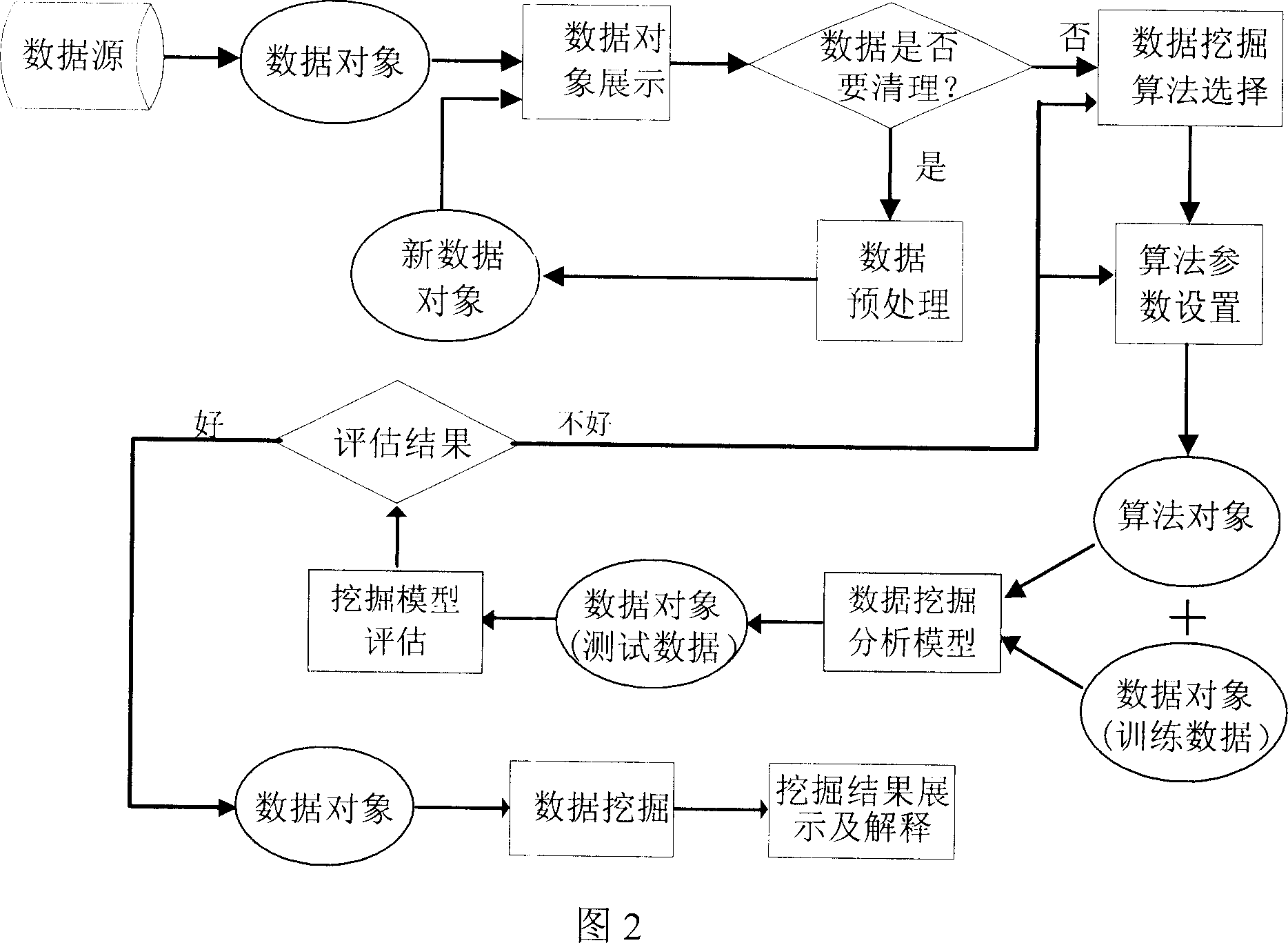
InactiveCN1975720AIntuitive Visual DisplayEasy to understandSpecial data processing applicationsData connectionGraphics
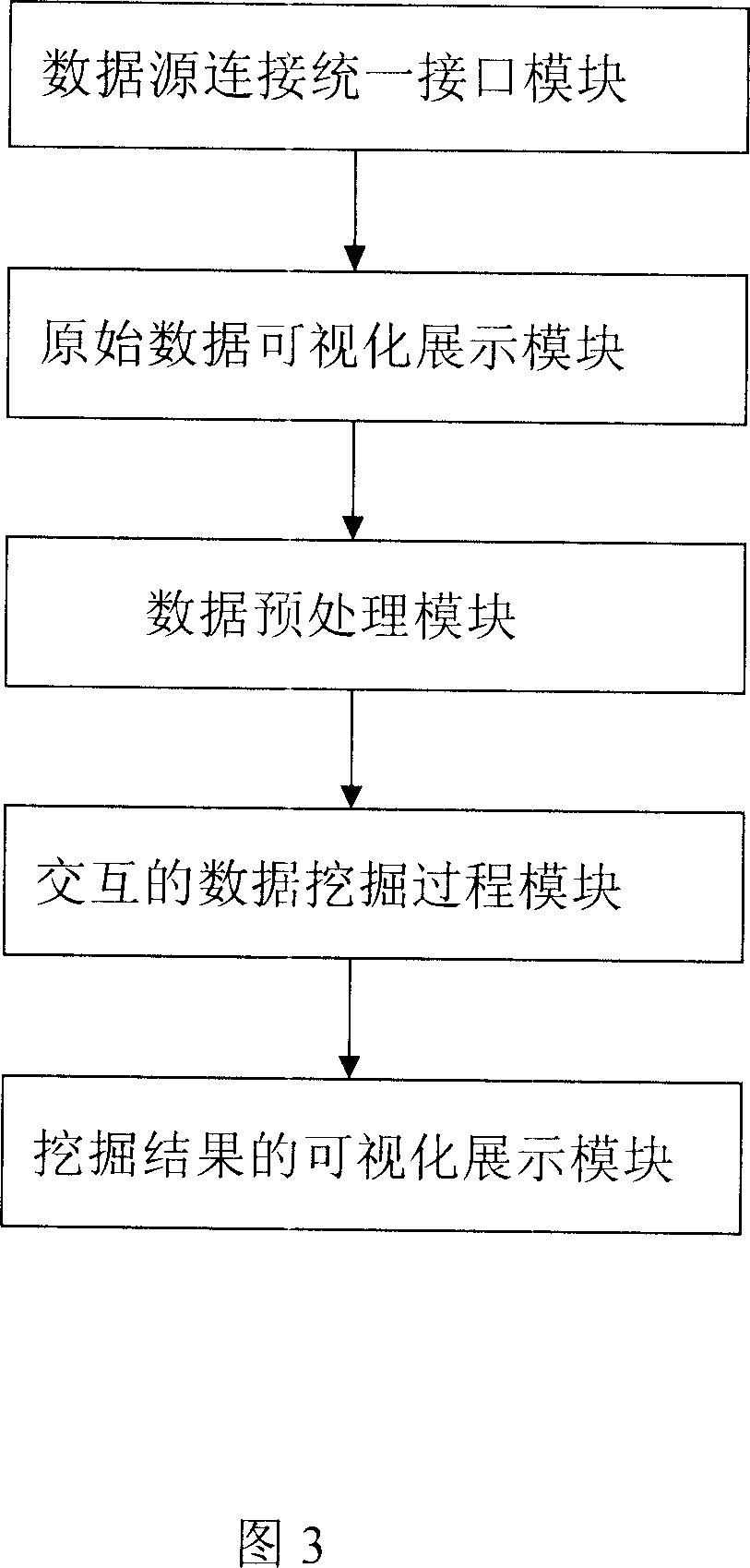
The invention opens a data mining system based on Web, which mainly includes EJB server, Web server and database etc. The EJB server provides the interface between Web server and EJB layer, and implemented various data mining algorithms for different data and data mining tasks. The Web layer provides a user interactive interface to receive user inputs and display results of data mining and analysis. The system consists of several modules: authentication module, initialization module, data connection module, data visualization module, data pre-processing module, mining module, mining data indication module. The system provides on-line internet based data mining and result analysis services.
Owner:章毅 +1
Digital publication system and apparatus
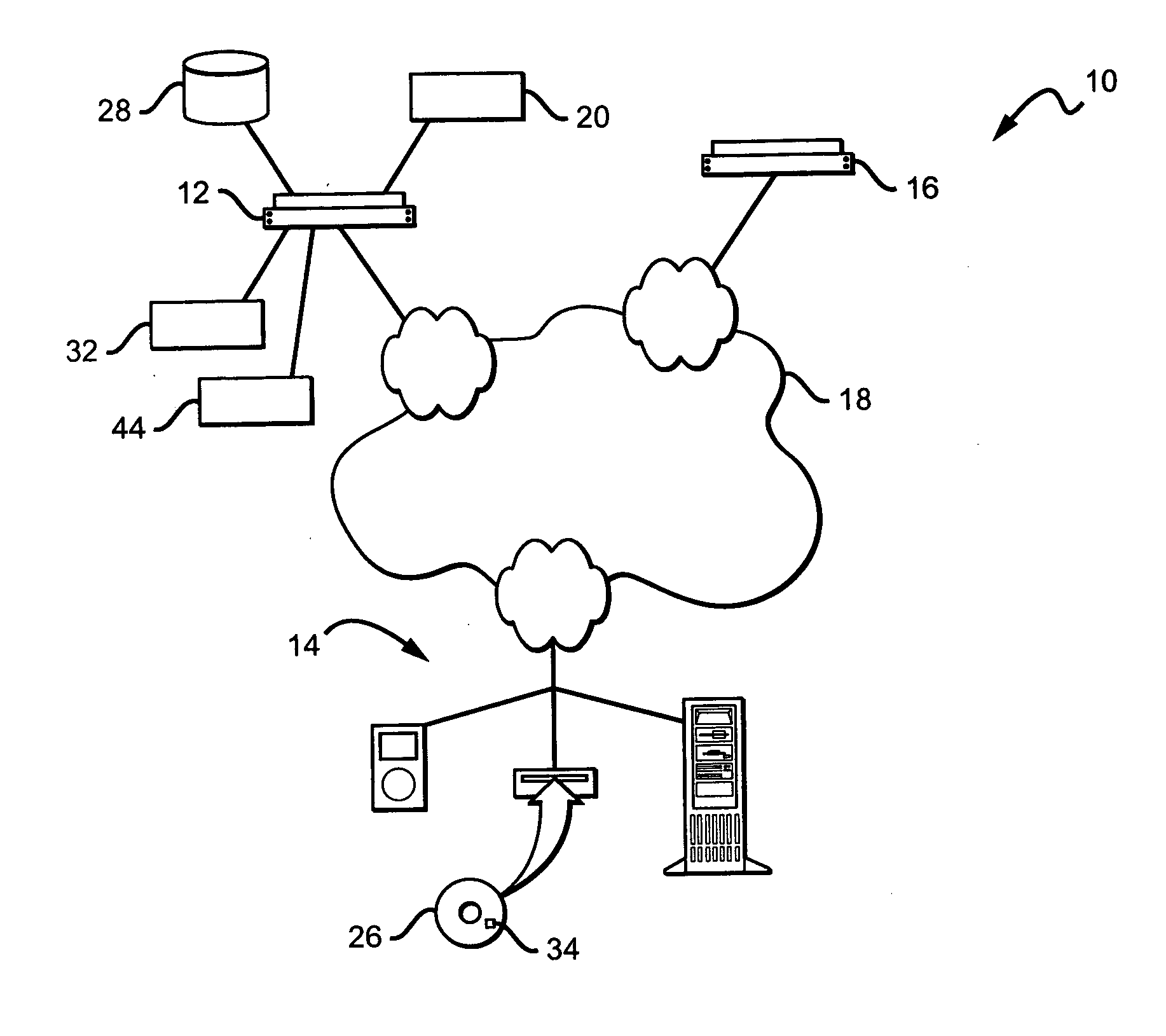
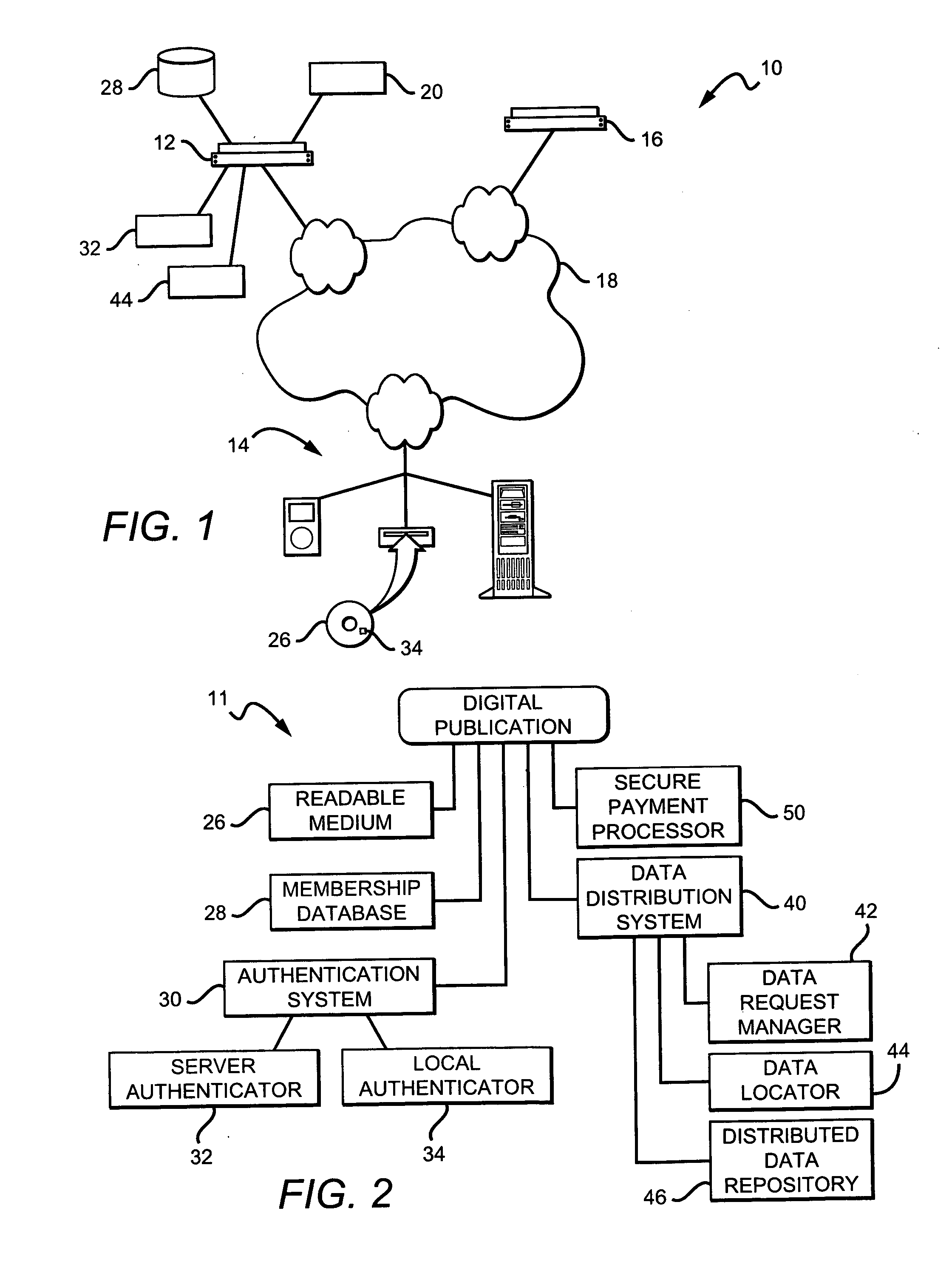
InactiveUS20060271486A1Easy accessEnhanced and dynamic publicationComputer security arrangementsCommerceDistribution systemSafe handling
Embodiments of the present invention are directed to a digital publication system configured to operate in conjunction with a communication network having a content provider system, and a host device operated by a user. The digital publication system comprises an authentication system, a data distribution system and a secure processing system, wherein the authentication system is configured to provide authorization for the user to access the digital publication system. The data distribution system further comprises a data locator and a data request manager, wherein the data locator and data request manager operate in conjunction with each other to provide requested data to the host device. The secure processing system comprises a protocol application for securing the transmission of some user information to and from the host device, wherein securing the transmission.
Owner:CYBERFLOW SOLUTIONS
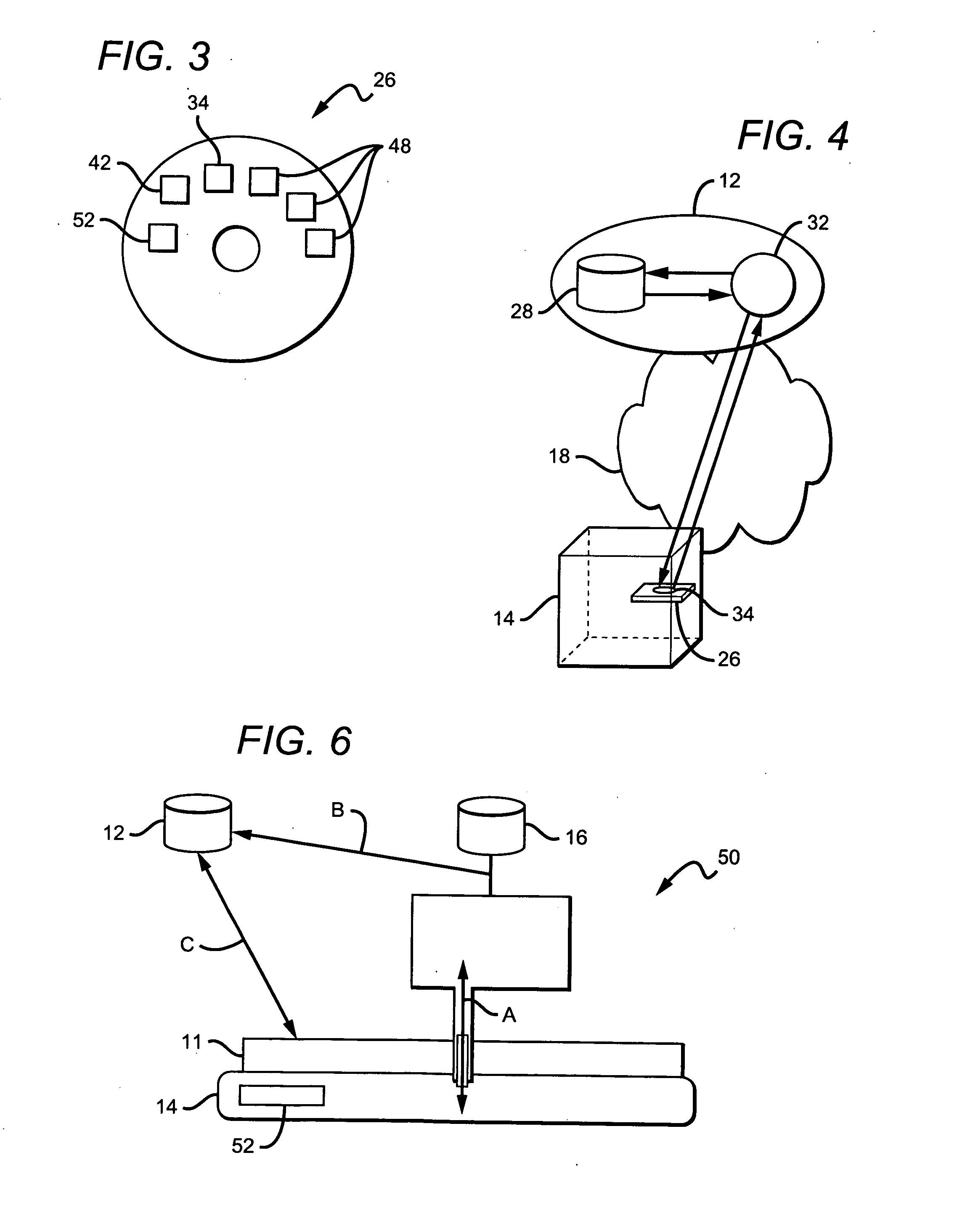
Object oriented apparatus and method for allocating array objects on an invocation stack
InactiveUS6675378B1Improve computing powerImprove performanceSoftware engineeringSpecific program execution arrangementsArray data structureParallel computing
An object oriented mechanism and method allow allocating Java array objects of unknown size at compile time to a method's invocation stack if the array's size is less than a predetermined threshold value. If the array object could typically be allocated to the invocation stack if it were of a known size at compile time, run-time code is generated that examines the actual size of the array object at run-time and that allocates the array object to the invocation stack if the size is less than a predetermined threshold value. In this manner Java array objects that have an unknown size at compile time may still be allocated to an invocation stack at run-time if the size of the object is sufficiently small.
Owner:GOOGLE LLC
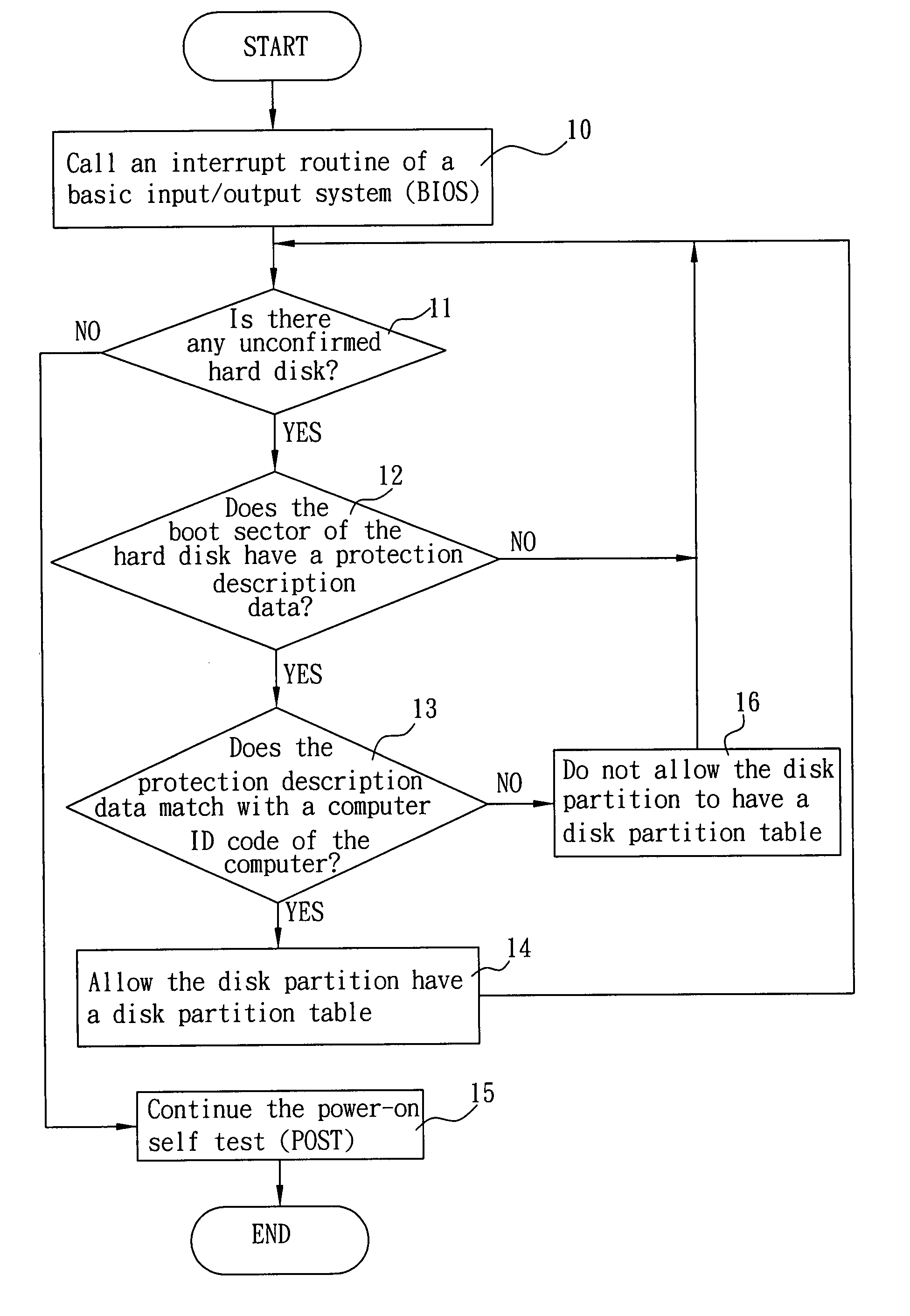
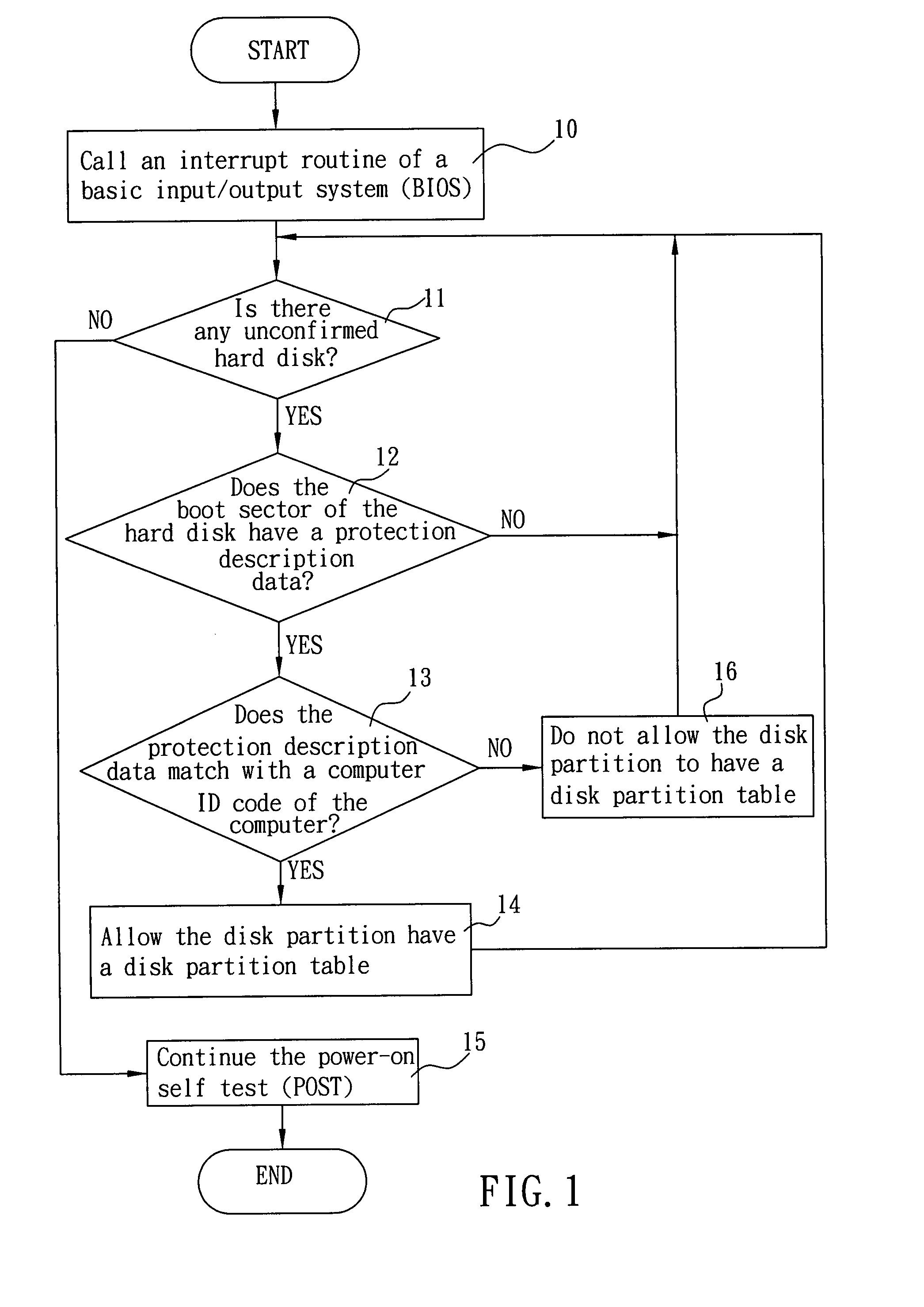
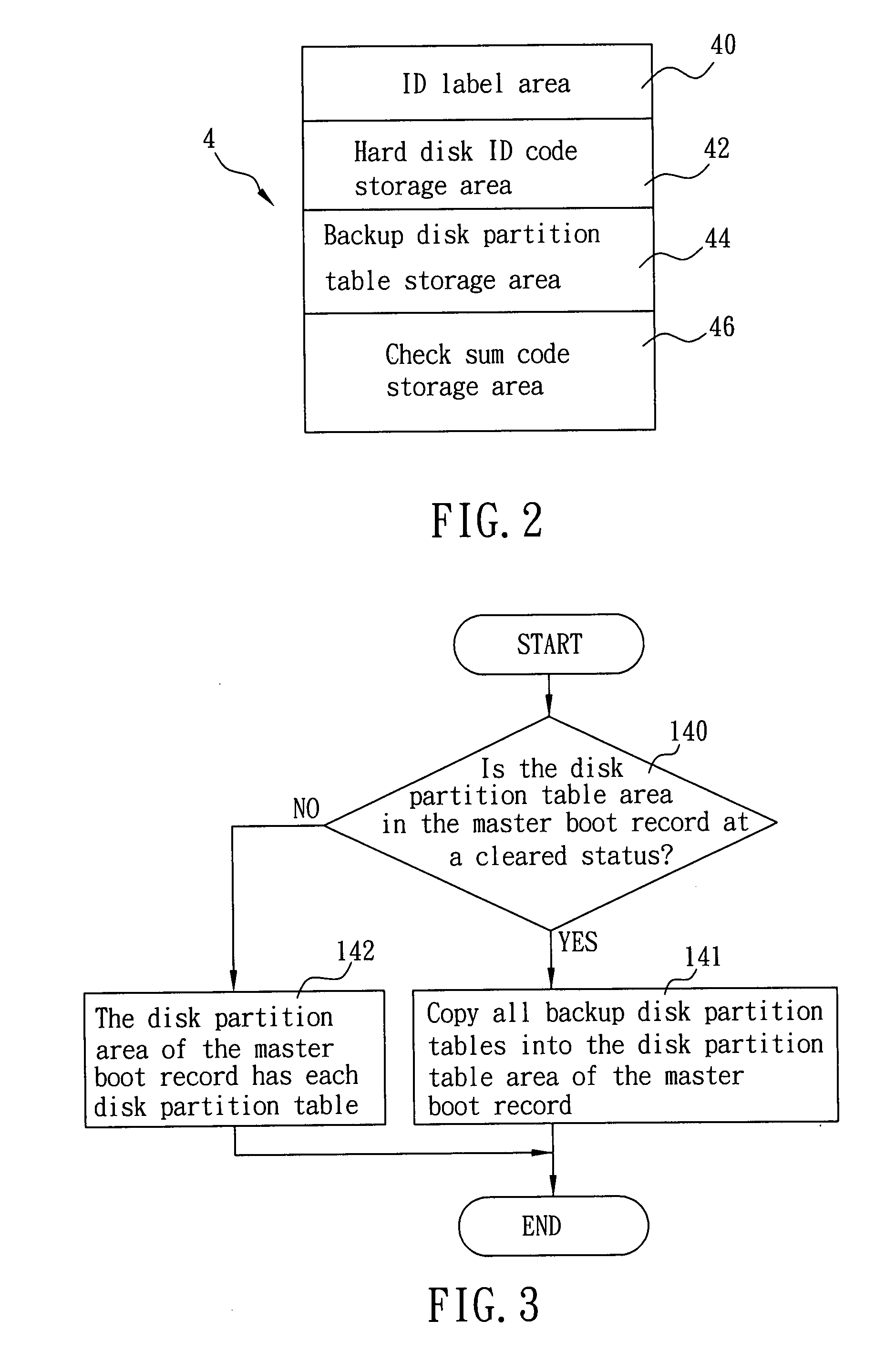
Method for protecting data in a hard disk
ActiveUS20080209553A1Protect dataEasy to understandMemory loss protectionDigital data processing detailsProgram codeComputer engineering
The present invention discloses a method for protecting data in a hard disk, such that when a computer executes a power-on self test (POST) of a basic input / output system (BIOS), completes initialization of memories and calls an interrupt routine of the BIOS to read a hard disk area after initialization program codes of interface devices of all hard disk are executed, the computer will determine whether or not the hard disk has added a protection description data with a portion that matches with a computer identification code of the computer before accessing data in the hard disk.
Owner:INVENTEC CORP
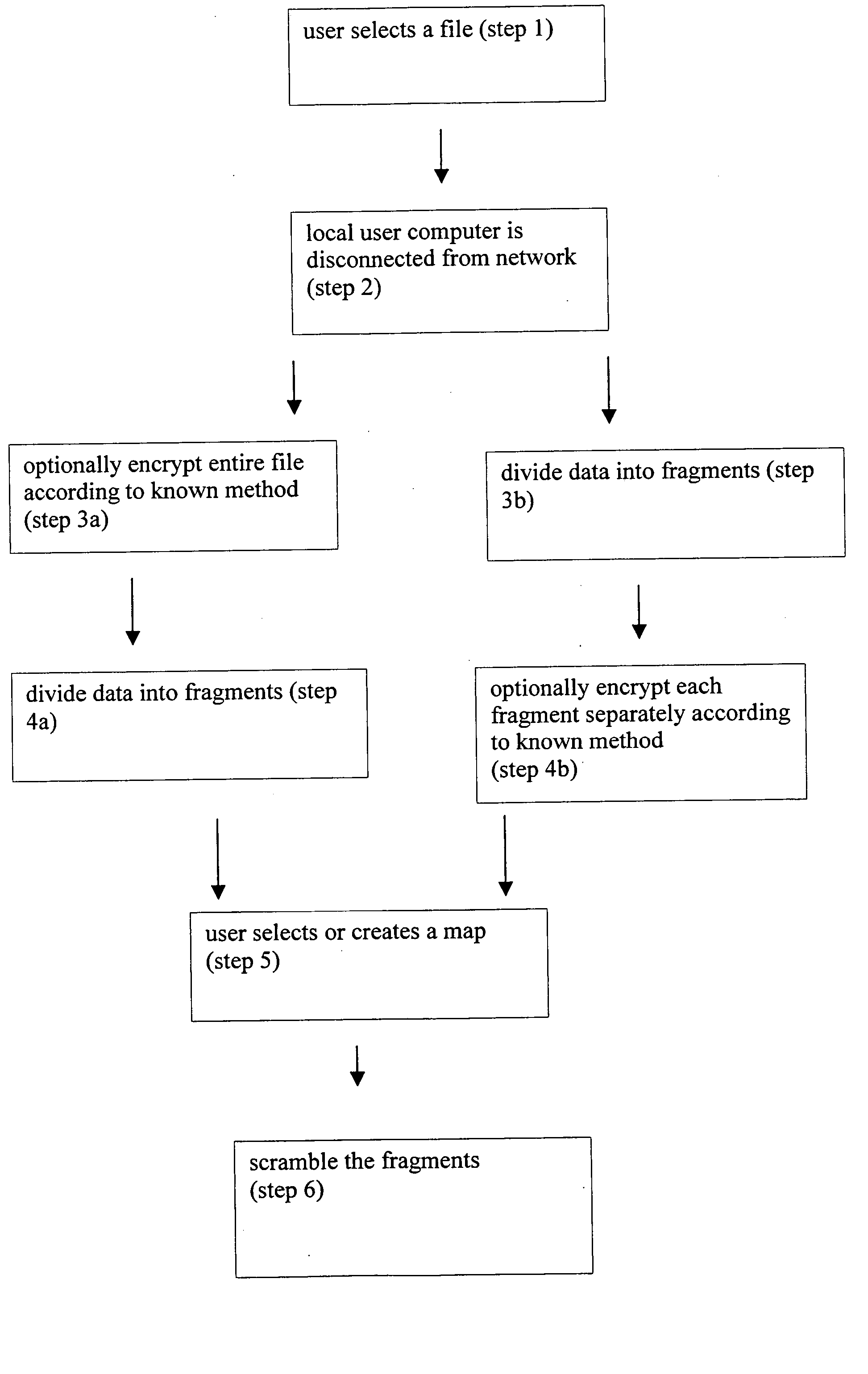
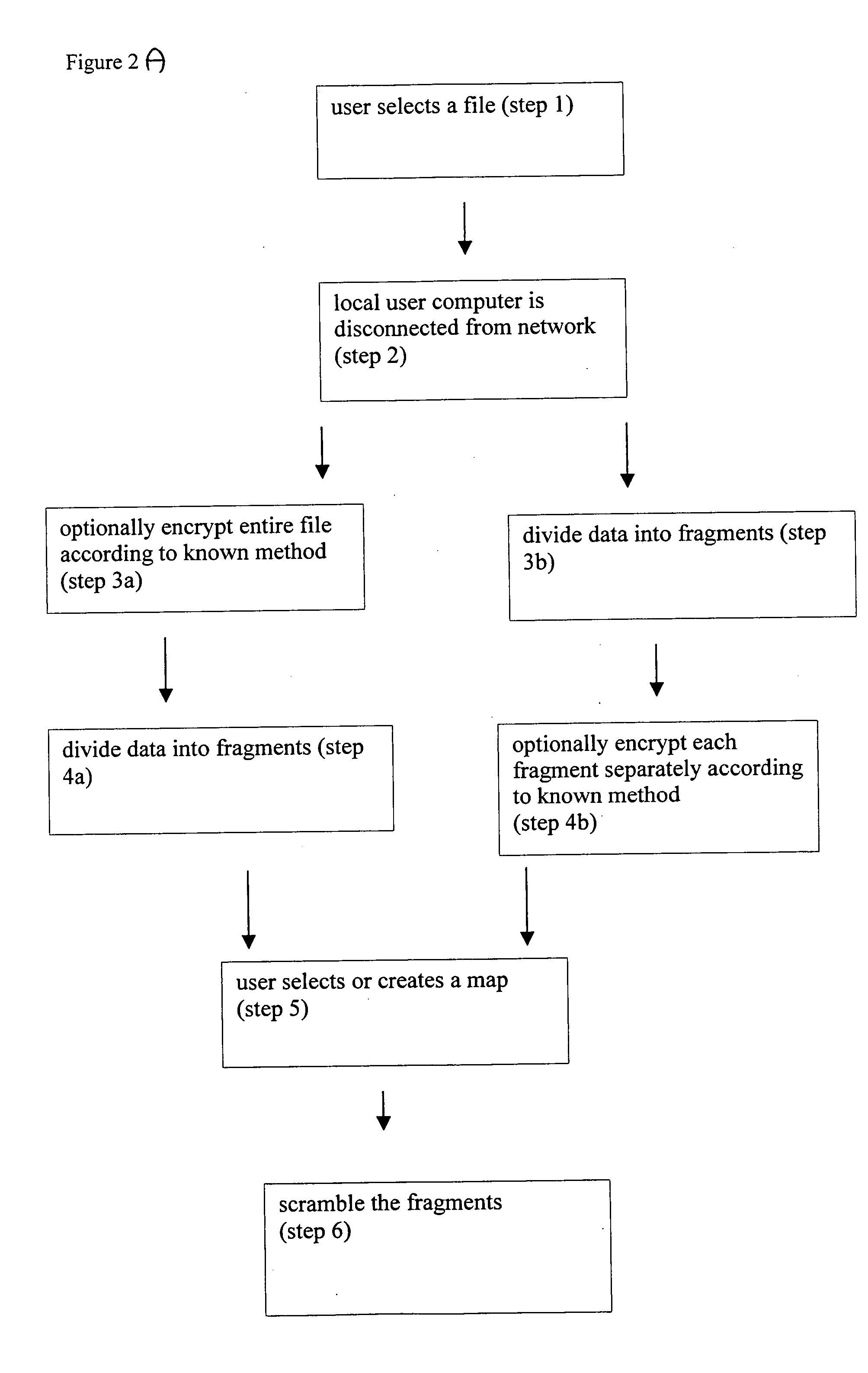
System and method for information protection by navigation and concealment
InactiveUS20060045270A1Increased complexityIncrease the difficultyComputer security arrangementsTelevision systemsTheoretical computer scienceMarine navigation
A system and a method for scrambling data according to a map, which is preferably user-defined, such that the sequential order in which the data must be read is determined by the map. Rather than employing a mathematical formula to scramble the data, the data is separated into a plurality of fragments. A map is then selected for determining the order of the fragments, such that without the map, the fragments cannot be assembled in the correct order. The process of arranging the fragments such that they cannot be correctly read without the map is referred to herein as “scrambling”, as opposed to encryption, as this process does not use a mathematical formula.
Owner:PRIVICY INSIDE
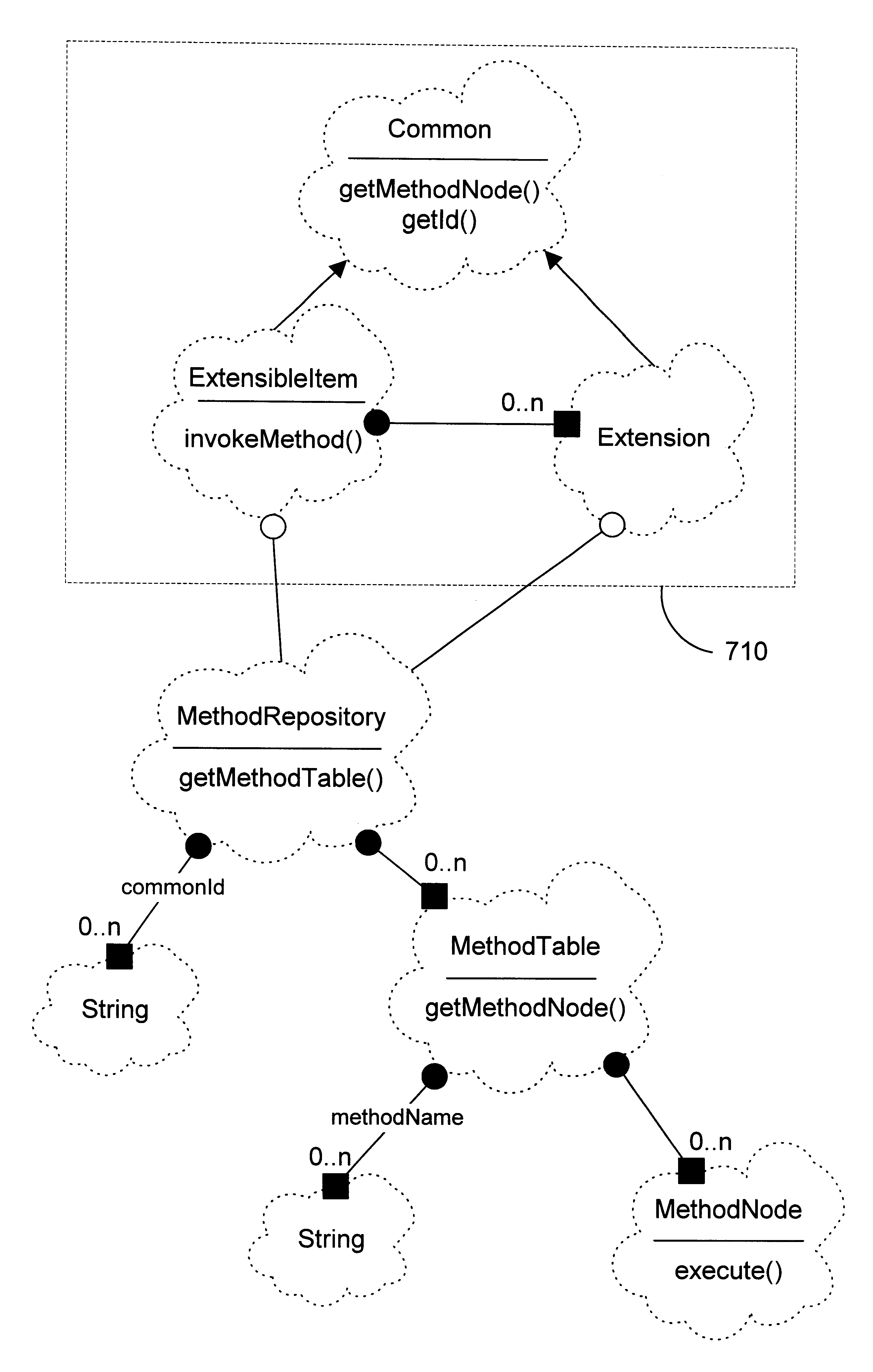
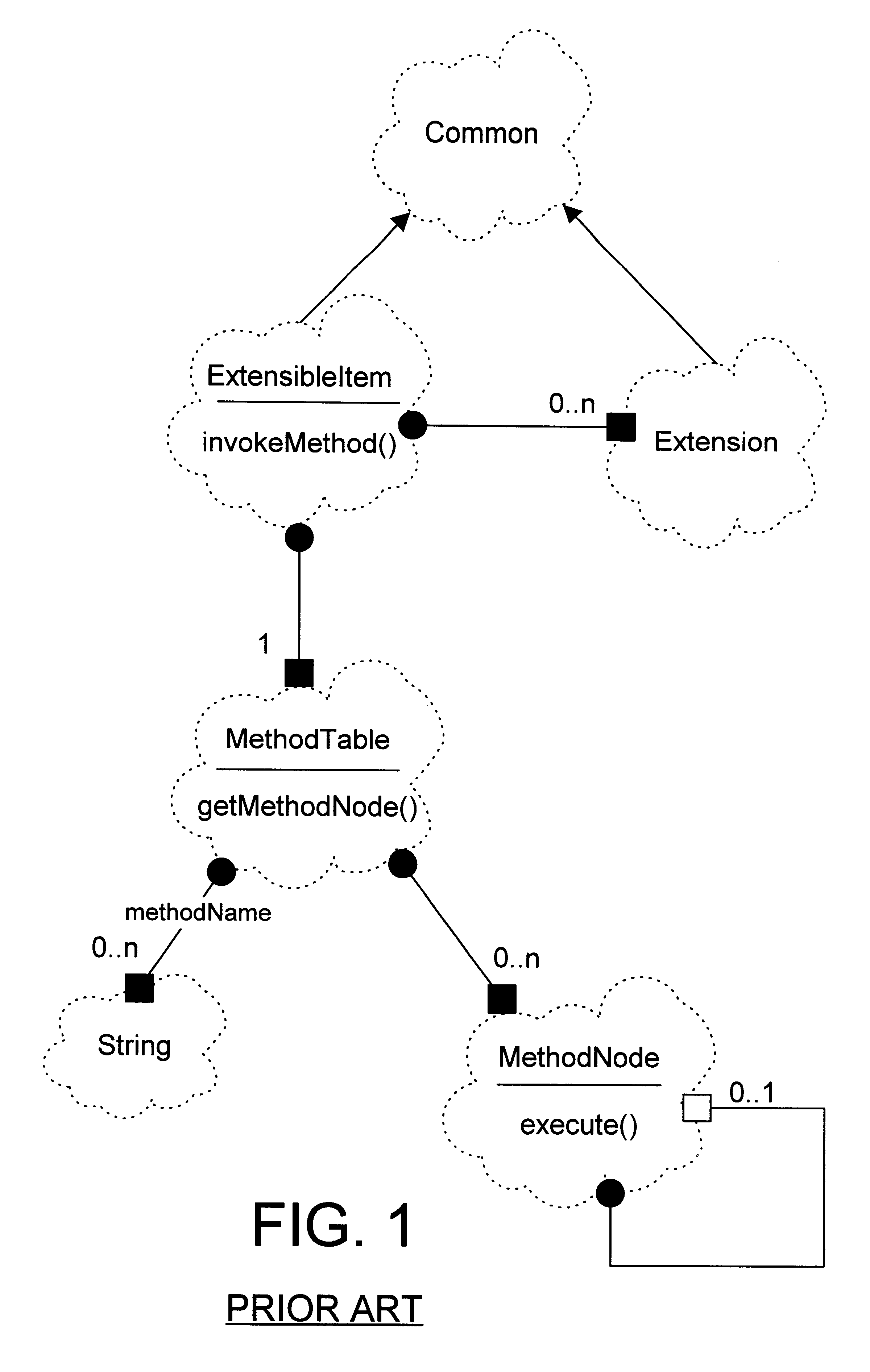
Implementation for an object oriented run-time extensible item
InactiveUS6275979B1Protect dataEasy to customizeData processing applicationsObject oriented databasesProgramming languageComputerized system
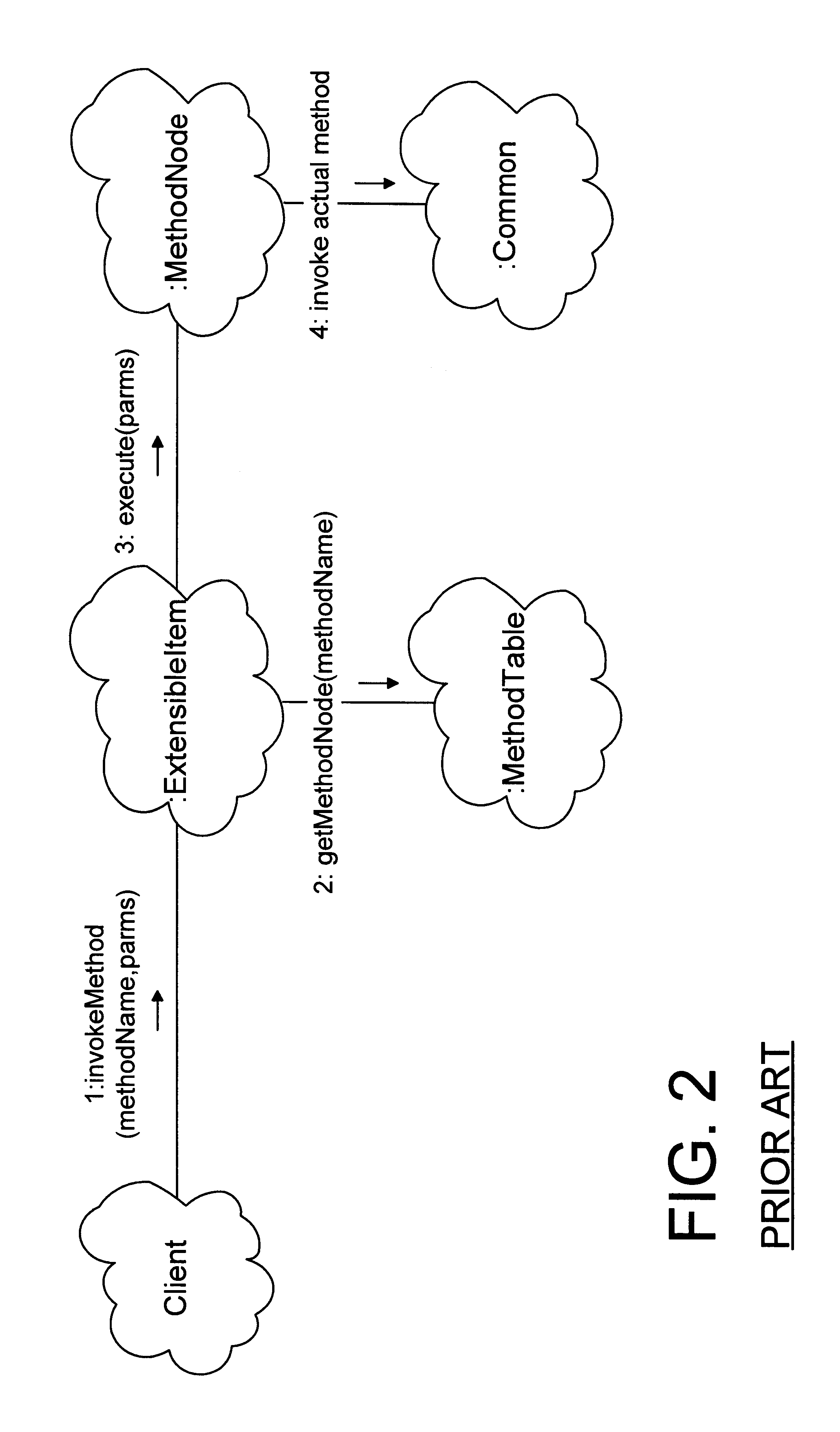
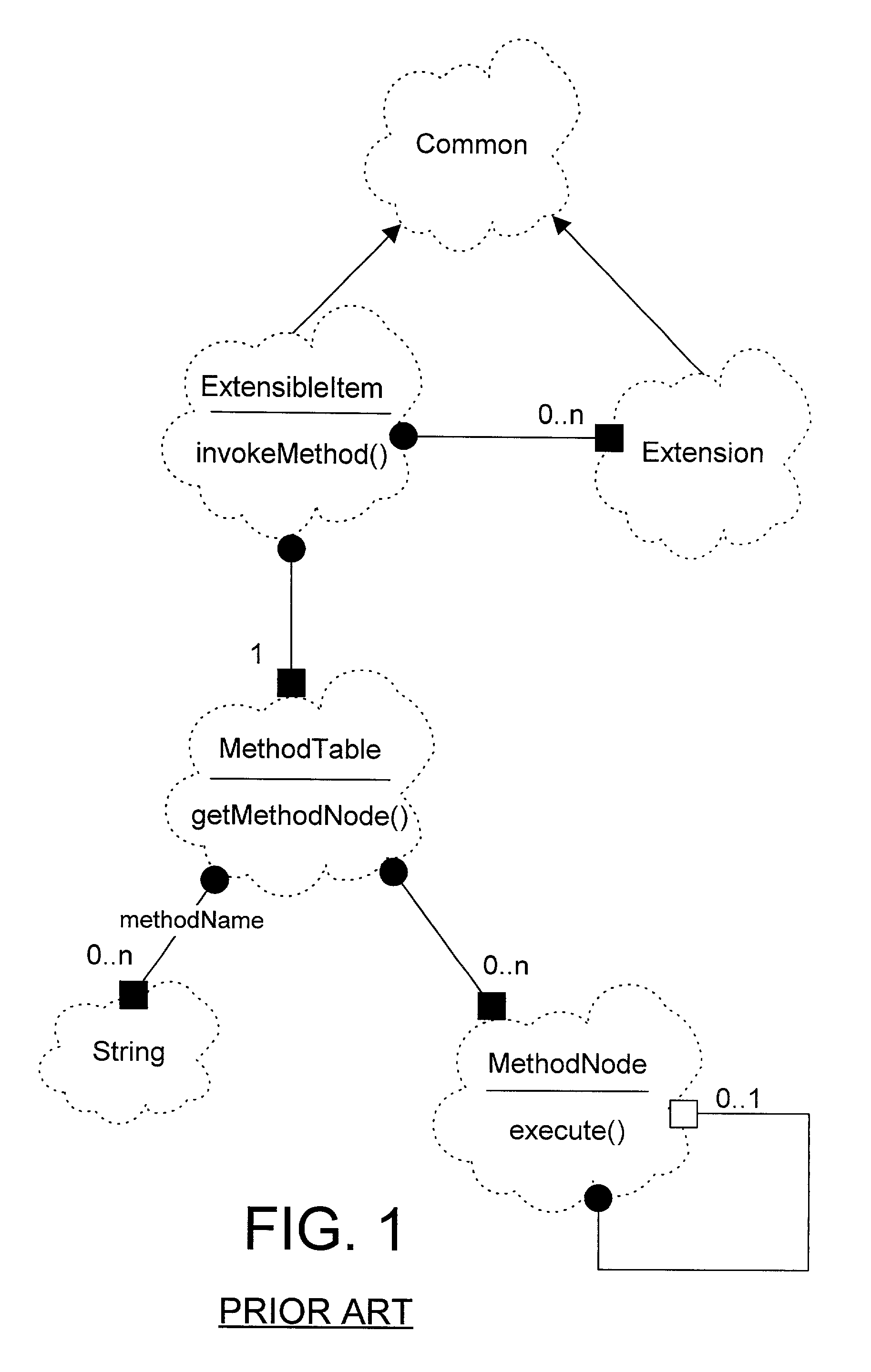
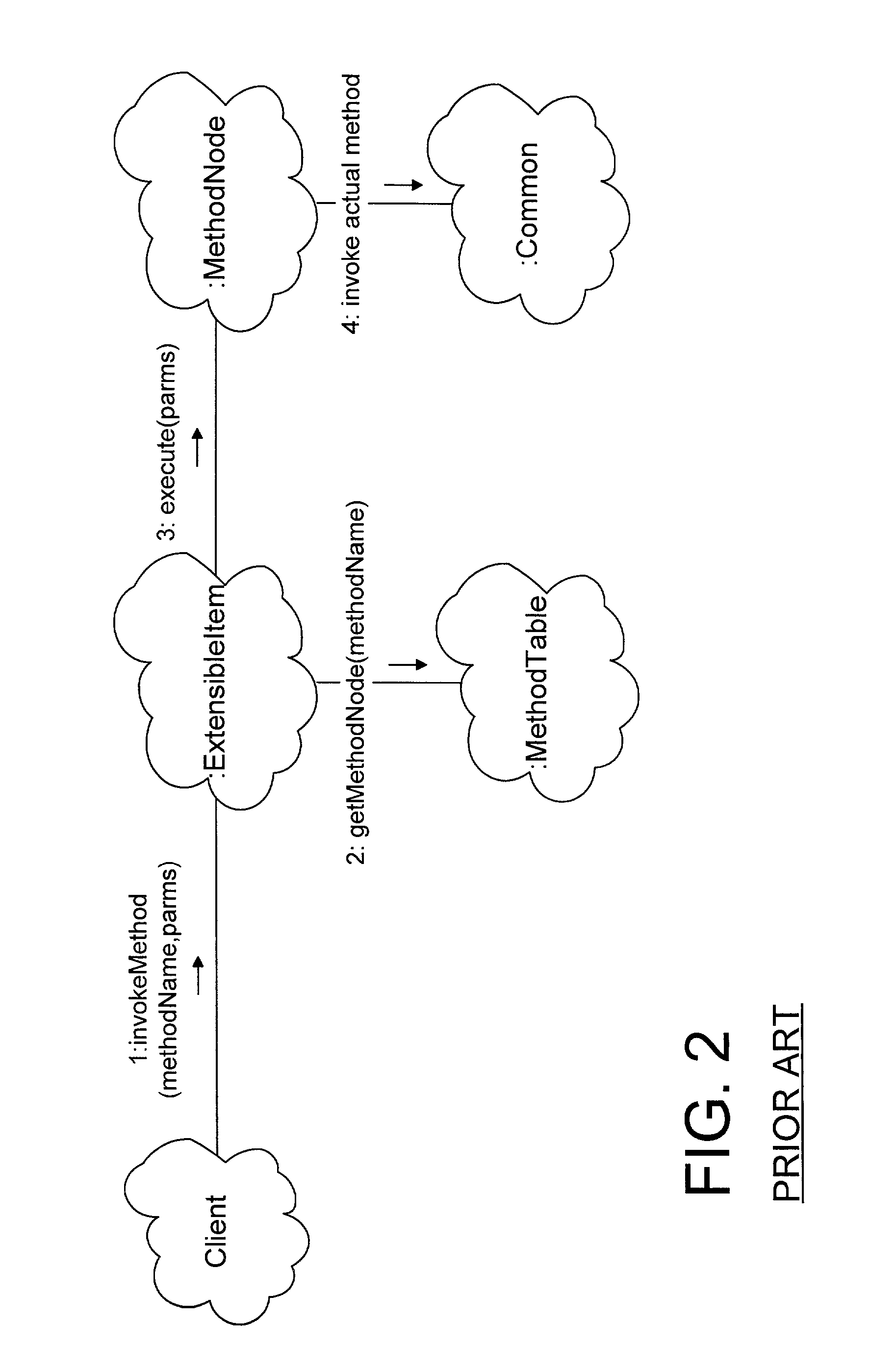
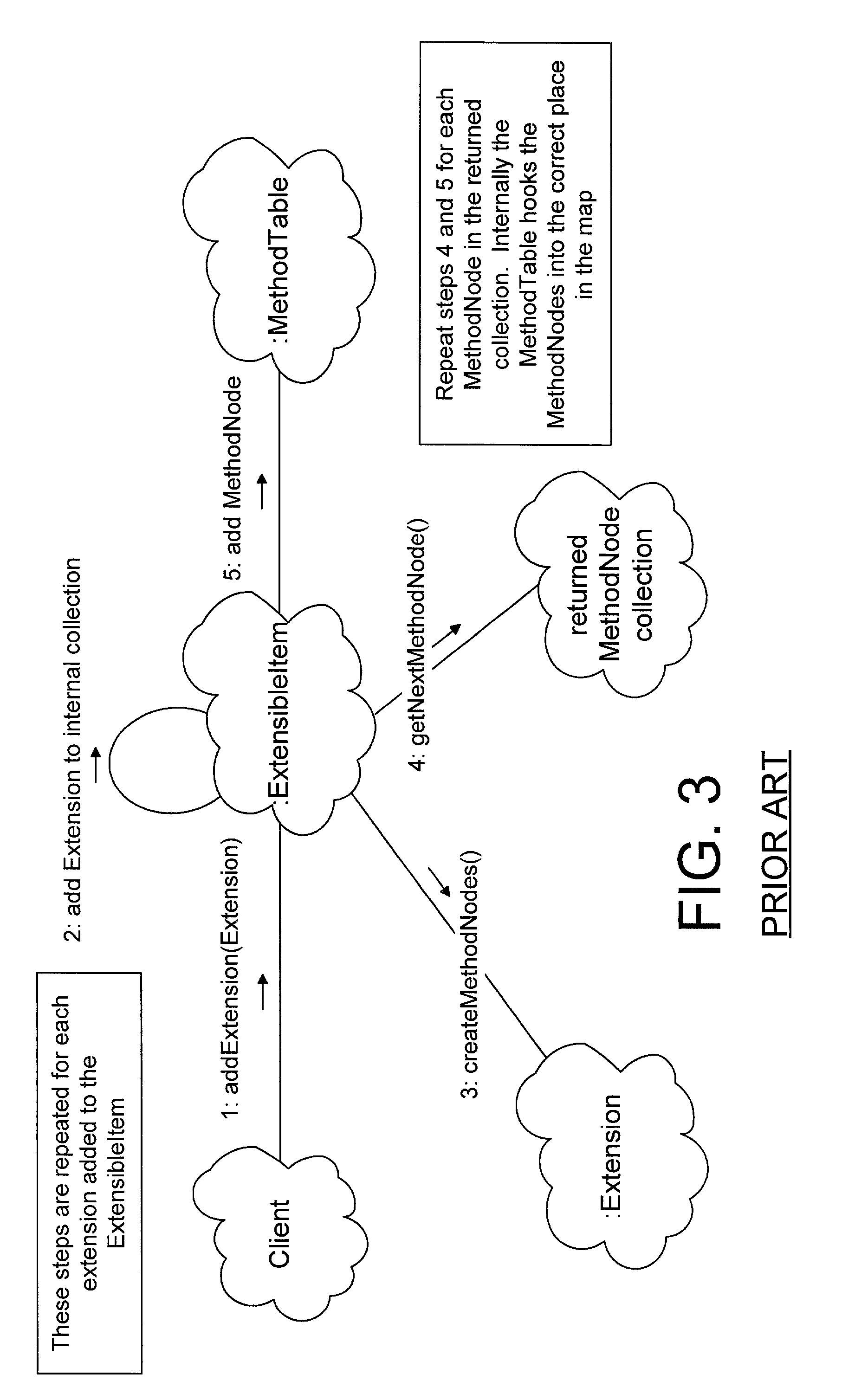
In an object oriented computer system, one or more run-time extensible items are defined that may be dynamically reconfigured as required to support different interfaces at run-time. The behavior associated with these interfaces is supported by one or more extensions owned by the extensible item. Each extension class has a corresponding method table that is shared among instances of the extension class and that correlates the methods defined on the extension class to method node objects that carry out the method. A method repository is a static object that is created at run-time to correlate extensions to their corresponding method tables. When a client invokes an invokeMethod( ) method on an extensible item, specifying the name of the method to be invoked, the extensible item cycles through its extensions, from newest to oldest, looking for an extension that supports the named method. Each extension examines the method repository to see if the method repository contains a method table corresponding to the extension class. If not, a method table corresponding to the extension class is created and placed in the method repository. When an extension is found that supports the named method, a method node that corresponds to the named method is returned. The method node then invokes the named method on the extension.
Owner:IBM CORP
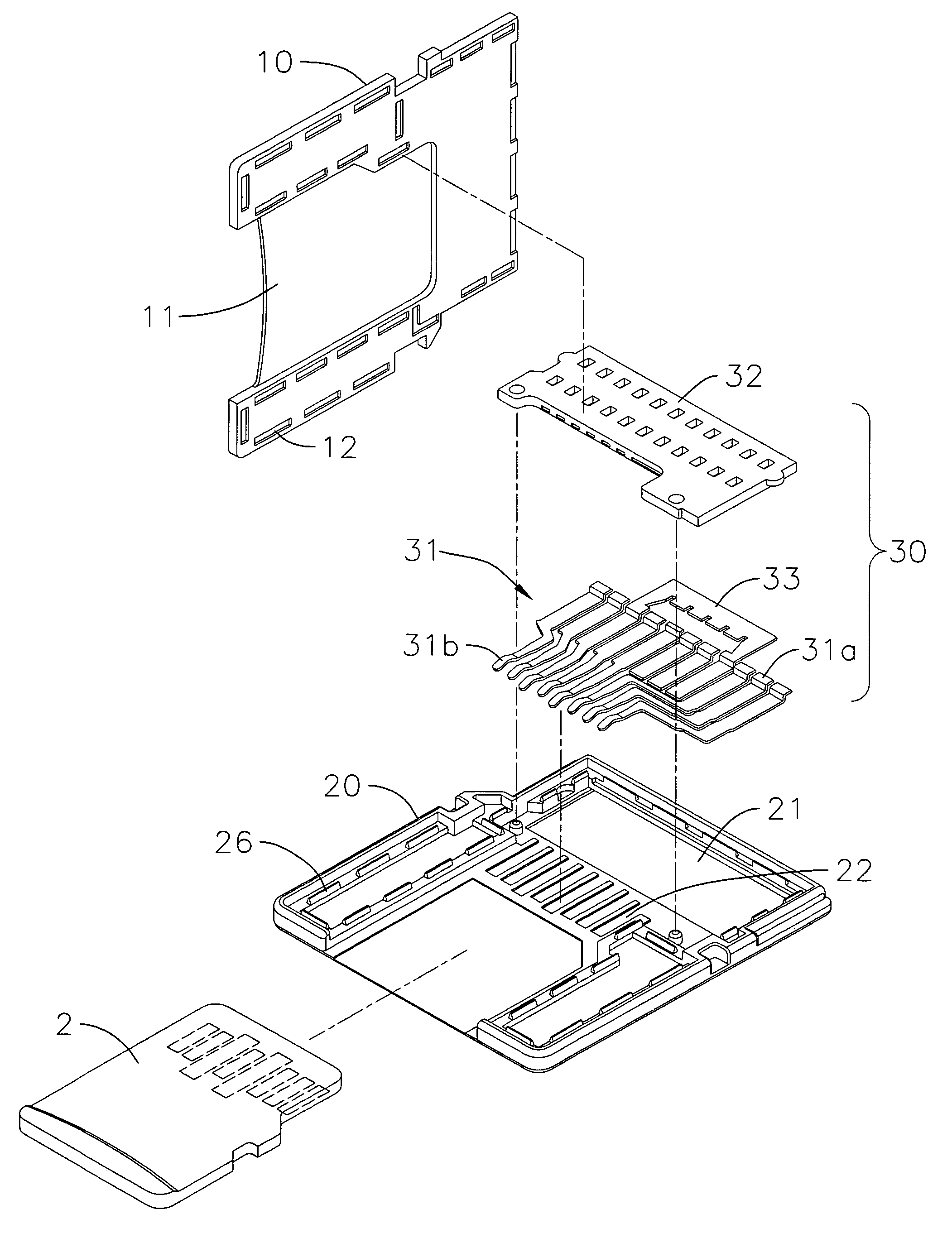
Card adapter structure
InactiveUS7326086B1Increasing practicability and convenienceSimple structureTwo-part coupling devicesRecord carriers used with machinesElectrical resistance and conductanceEngineering
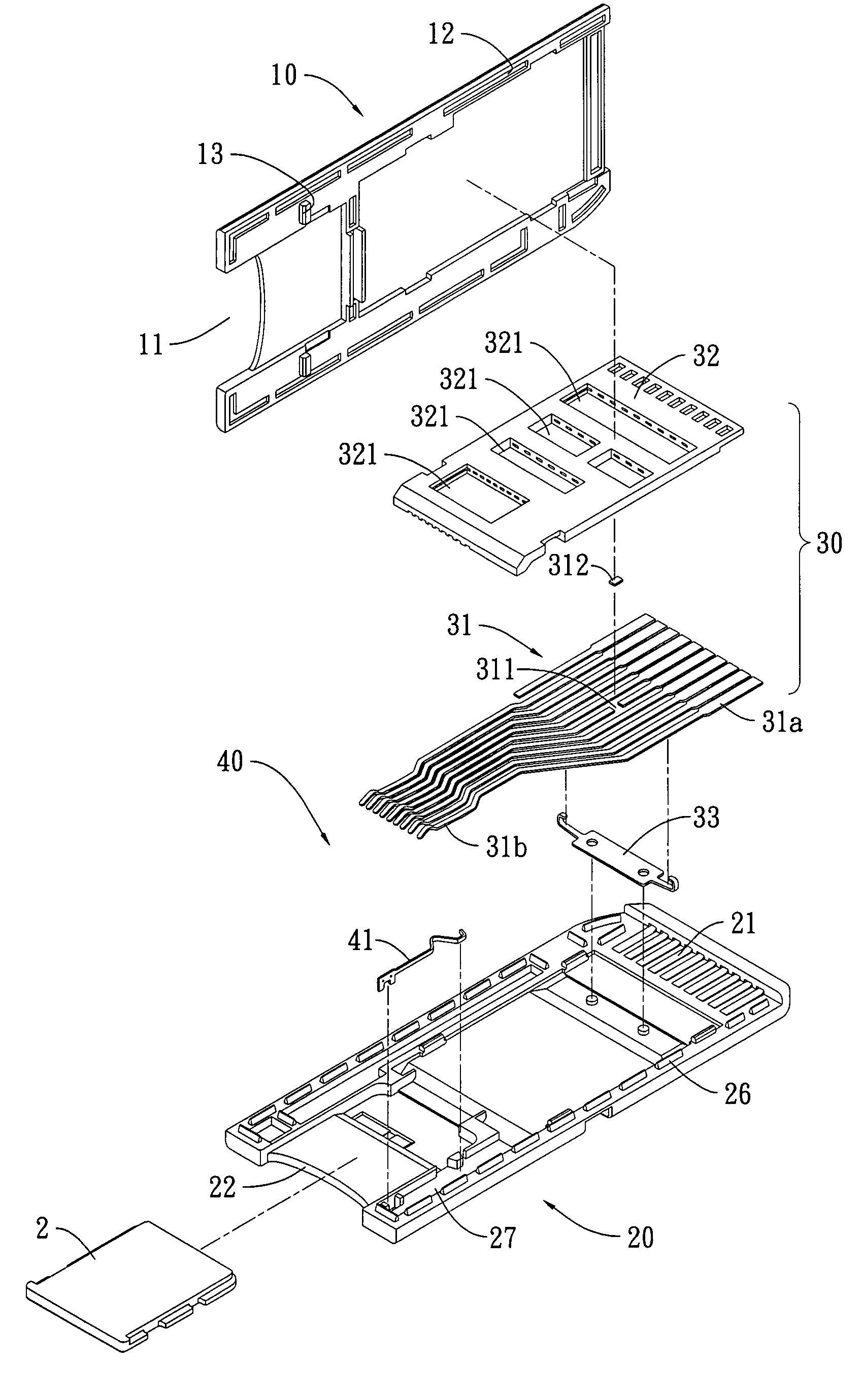
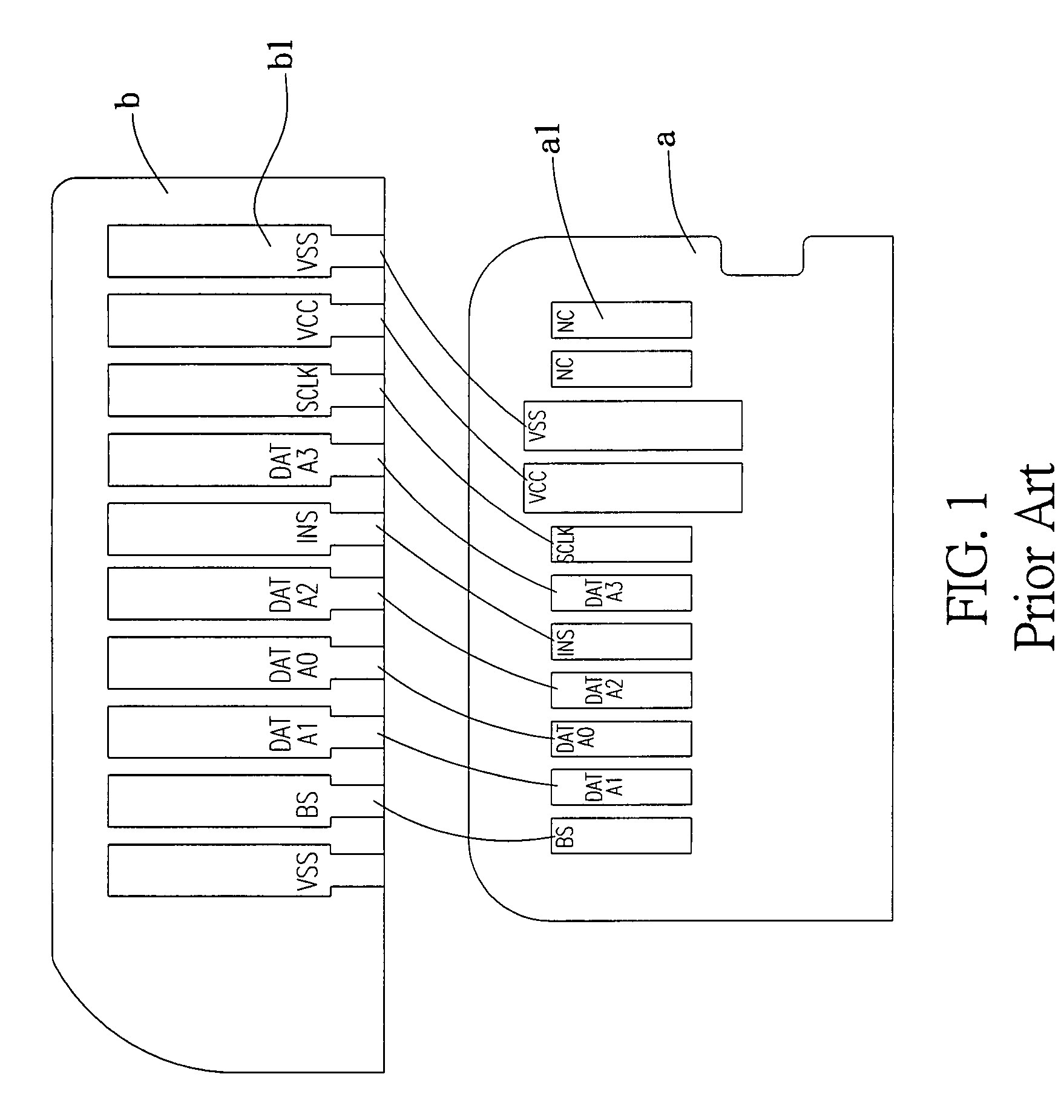
The present invention provides an improved card adapter structure that includes an upper cover, a lower cover, a converter terminal set and a positioning elastic strip set. The upper cover has a structure designed to conform to short memory card (MS) specifications, wherein an insertion slot is defined at the rear of the upper cover corresponding to the shape of a micro memory card (M2). The lower cover has a fixing portions and a positioning structure corresponding to those of the upper cover. Moreover, at least one terminal of the No. four, six, seven and eight terminals of the converter terminal set is configured with a gap that is joined to an electric resistance. The positioning elastic strip set is correspondingly located between both covers. Accordingly, the present invention is able to convert a micro memory card into a short memory card of relatively larger size.
Owner:LEE YUN HSIU
Computer starter and starting method for an ATX computer system
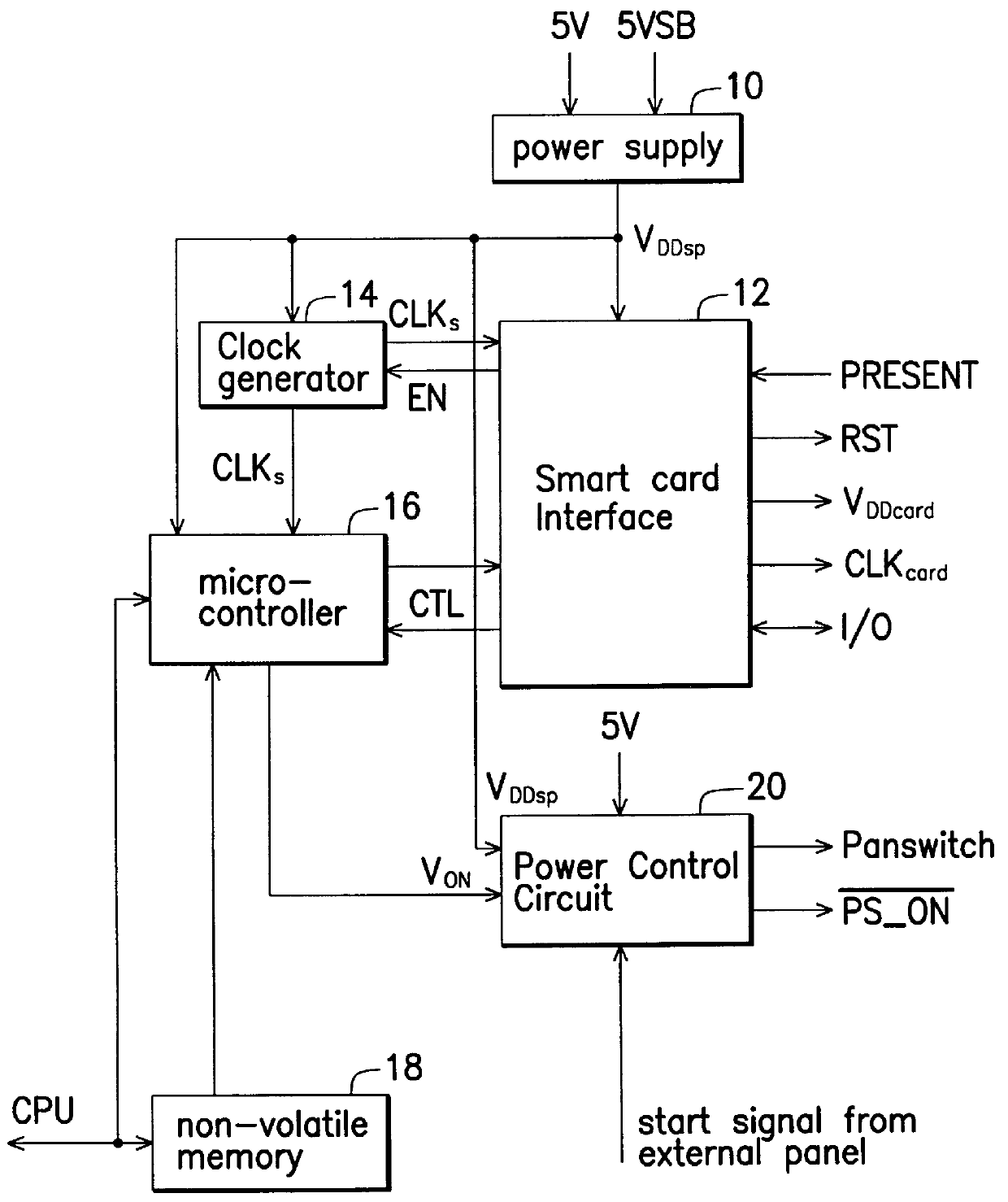
InactiveUS6128744AProtect dataError detection/correctionVolume/mass flow measurementEngineeringSmart card
A computer starter and starting method for an ATX computer system which provides a standby voltage when the computer system is shut down. The computer starter takes the standby signal as its power supply and includes a smart card interface, a clock generator, a non-volatile memory, a micro-controller and a power control circuit. The smart card interface generates an enable signal upon insertion of a smart card. The clock generator generates a reference clock in response to the enable signal. The non-volatile memory stores a computer identification signal. The micro-controller resets the smart card, reads a user identification signal stored in the smart card, and generates a verification signal when the computer identification signal stored in the non-volatile memory matches the user identification signal stored in the smart card. The power control circuit generates a start signal in response to the verification signal so as to start the computer system.
Owner:WINBOND ELECTRONICS CORP
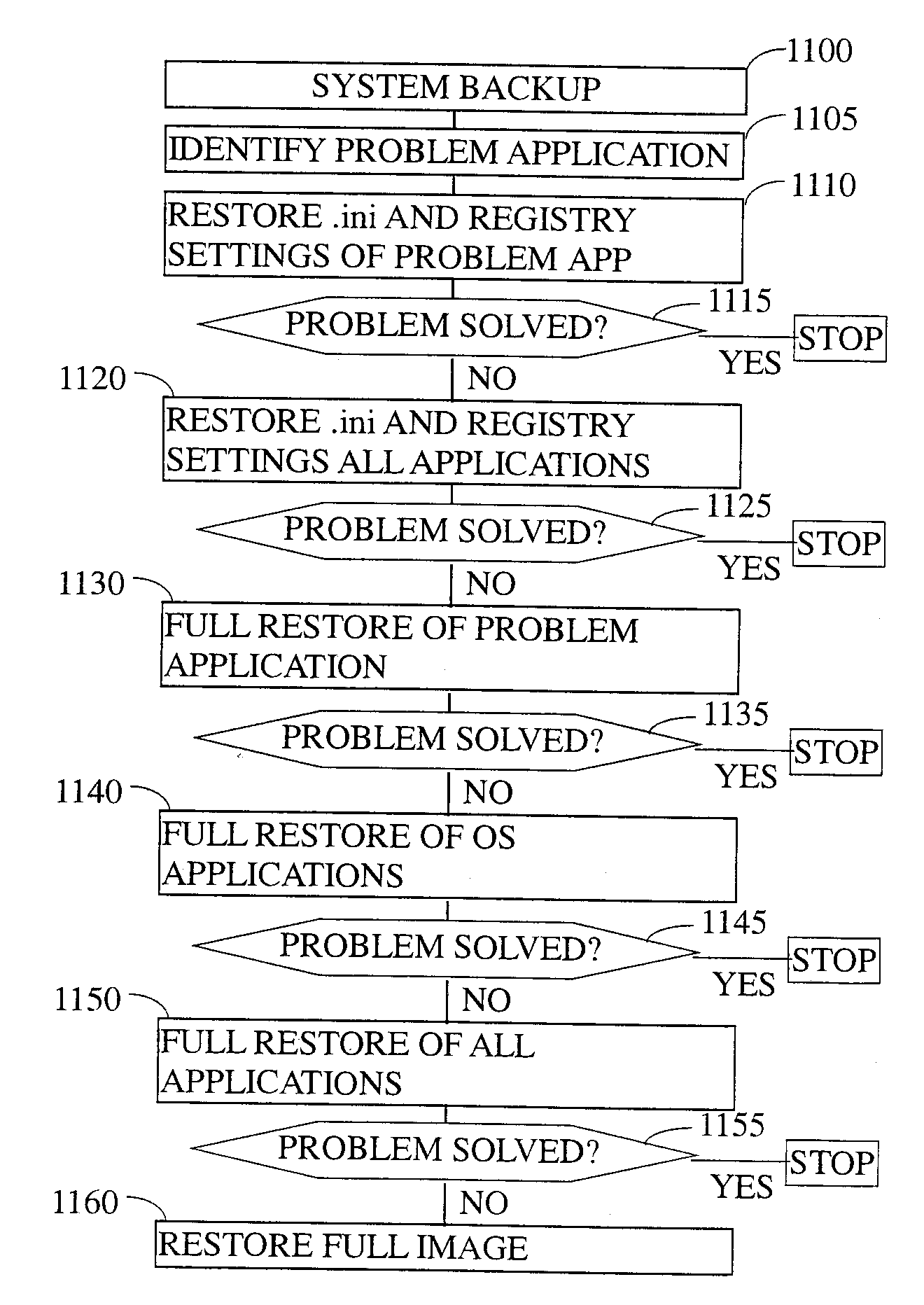
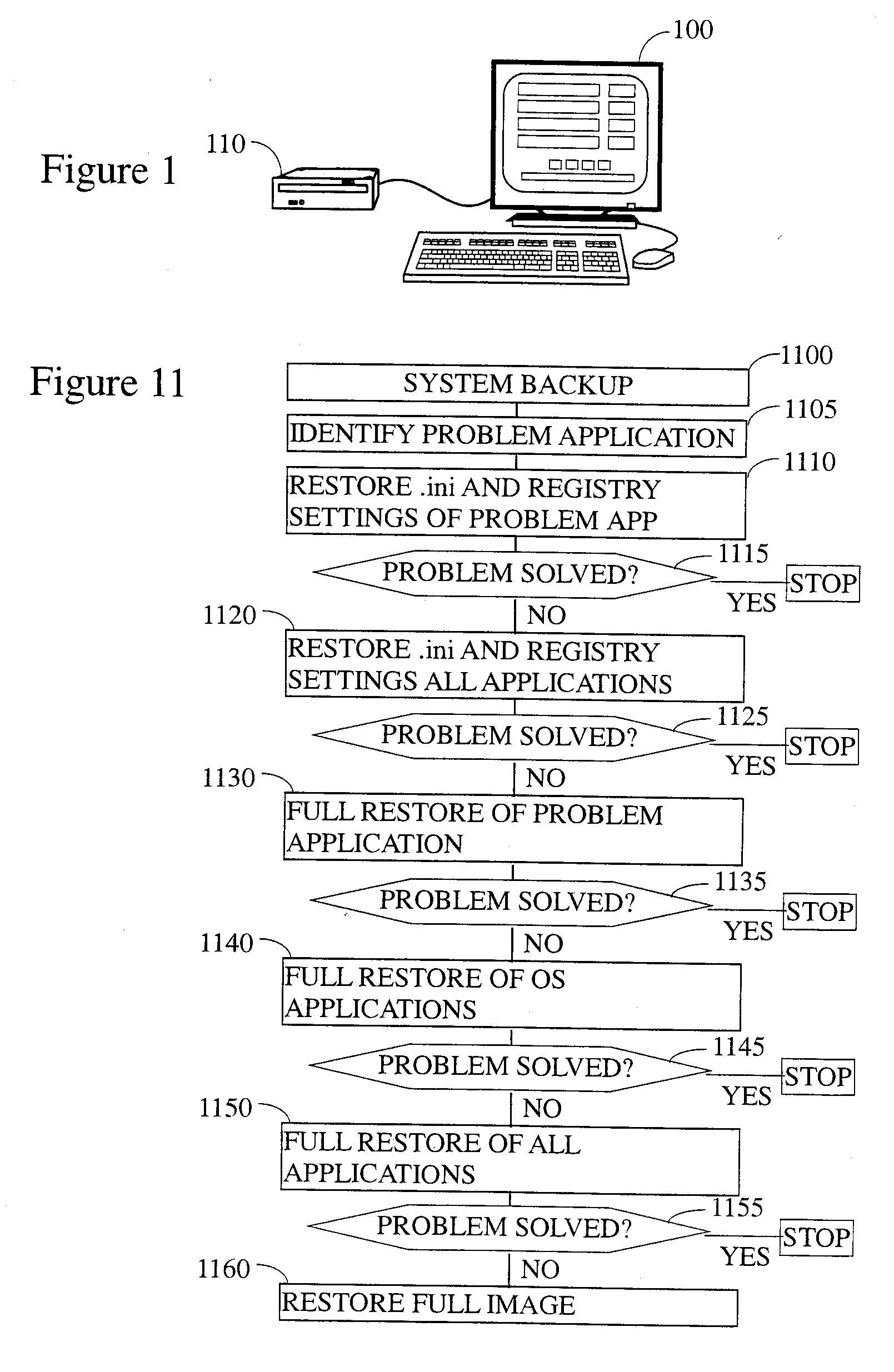
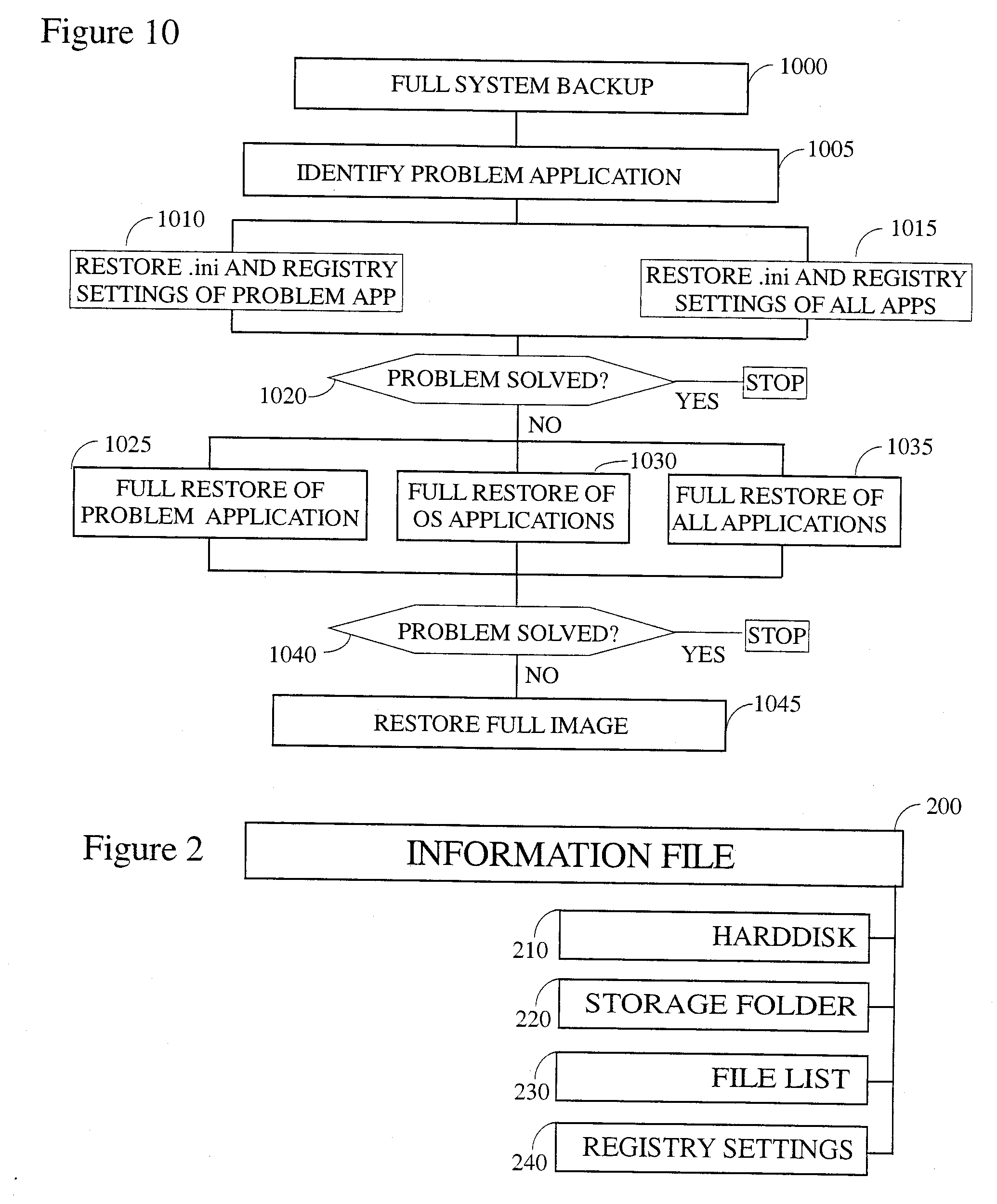
Application-specific intelligent backup and restore system
ActiveUS20080109495A1Reduce amountMaintain securityDigital data processing detailsError detection/correctionPaper documentDocument preparation
There is provided herein an application-oriented backup and restore system, which leads the user through a plurality of different selectable steps to repair specific application errors / problems. The preferred embodiment minimizes the loss of user productivity and because of its easy and accessible layout and presentation it may eliminate the need for tech-support to repair the problem. The average user can initiate the steps, wherein the restore steps are explicitly directed to secure the safe storage of user created documents and files.
Owner:SIMPLITEC
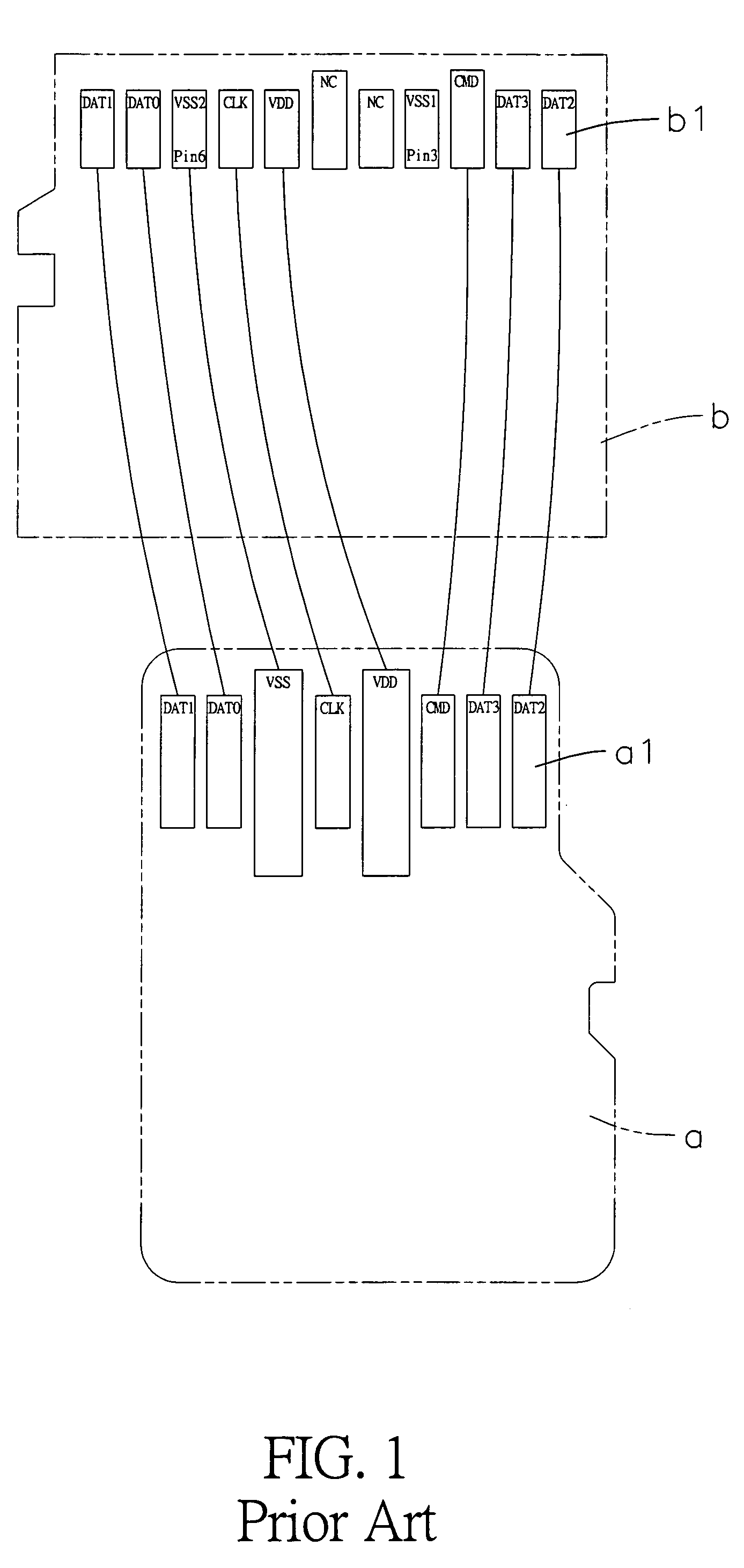
Card adapter structure
InactiveUS7371119B1Large and stable grounding areaAvoid signalingTwo-part coupling devicesSensing record carriersEngineeringMemory cards
The present invention provides an improved card adapter structure which includes an upper cover, a lower cover and a converter terminal set. The upper cover is designed to conform to short memory card specifications, wherein an insertion slot is defined at the rear of the upper cover corresponding to the shape of a micro memory card. A port is configured in a central portion of the lower cover to accommodate a micro memory card. The converter terminal set is configured with eleven terminals, wherein an injection molded fixing mount fixedly covers each pin of the converter terminal set, and eleven pins extend outward towards a short memory card opening. Pin three and pin six are jointly configured with a large grounding area, and eight pins extend outward towards the micro memory card port. Accordingly, the adapter structure conveniently converts a micro memory card into a short memory card.
Owner:LEE YUN HSIU
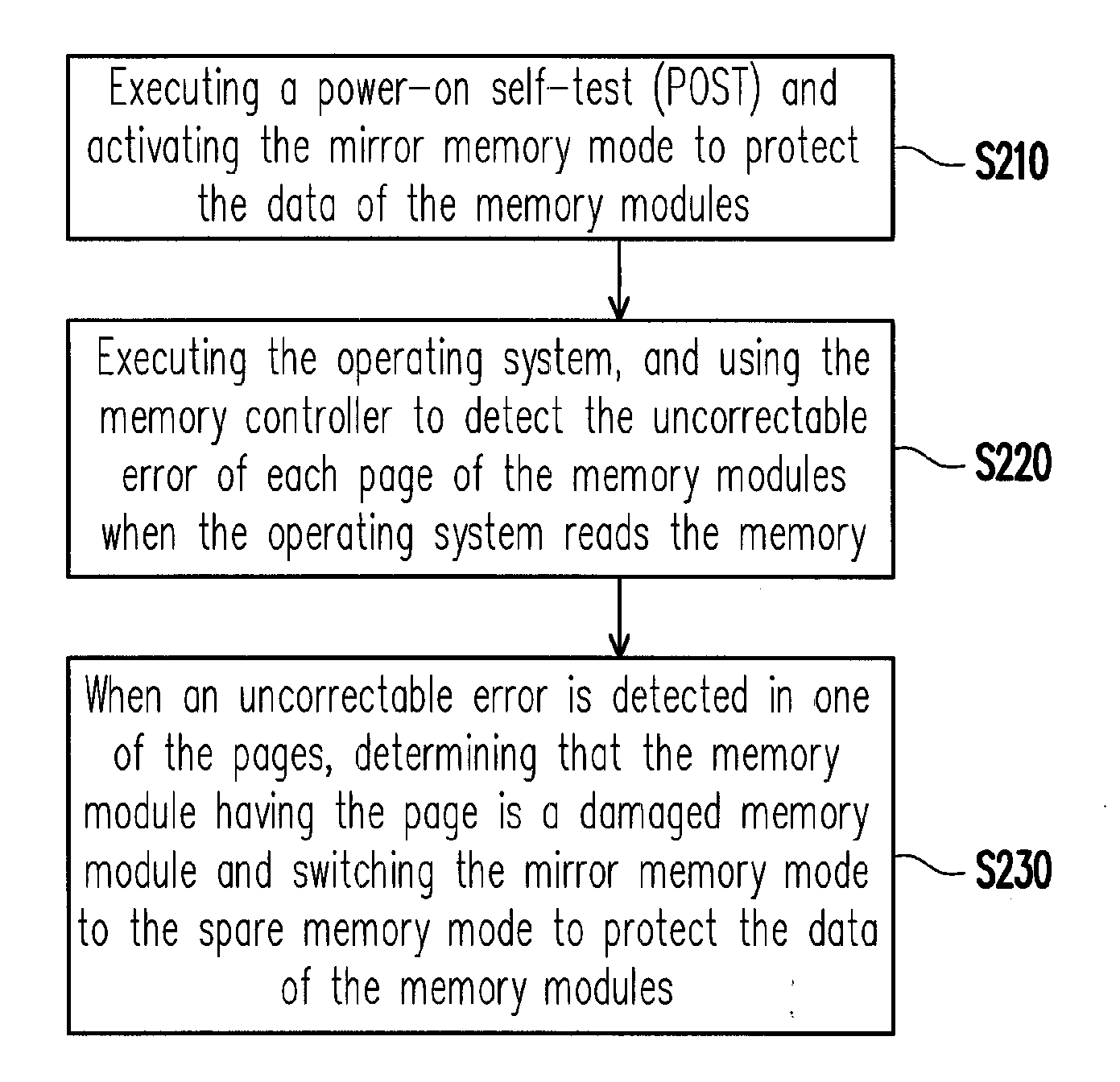
Method for protecting data in damaged memory cells by dynamically switching memory mode
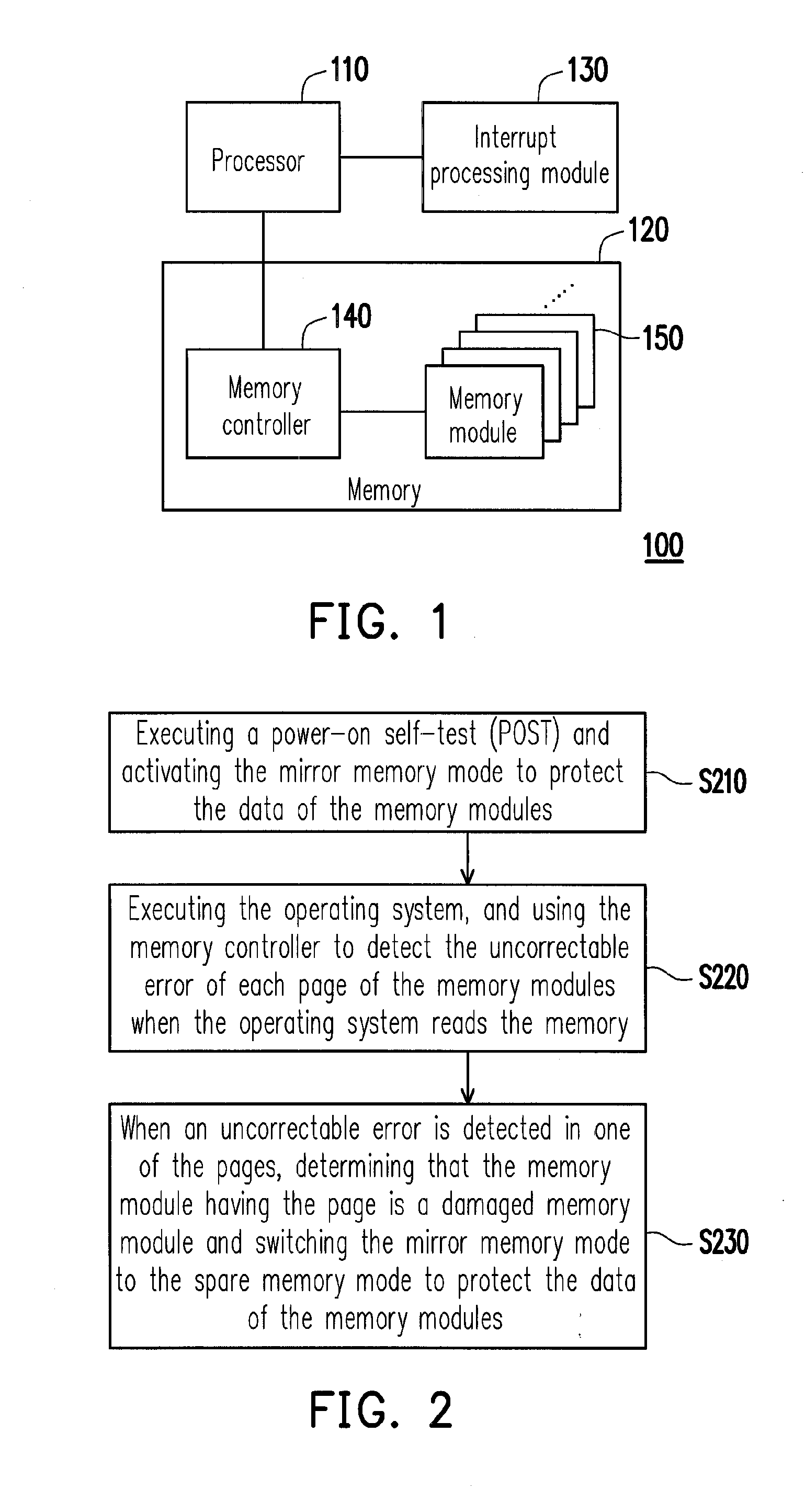
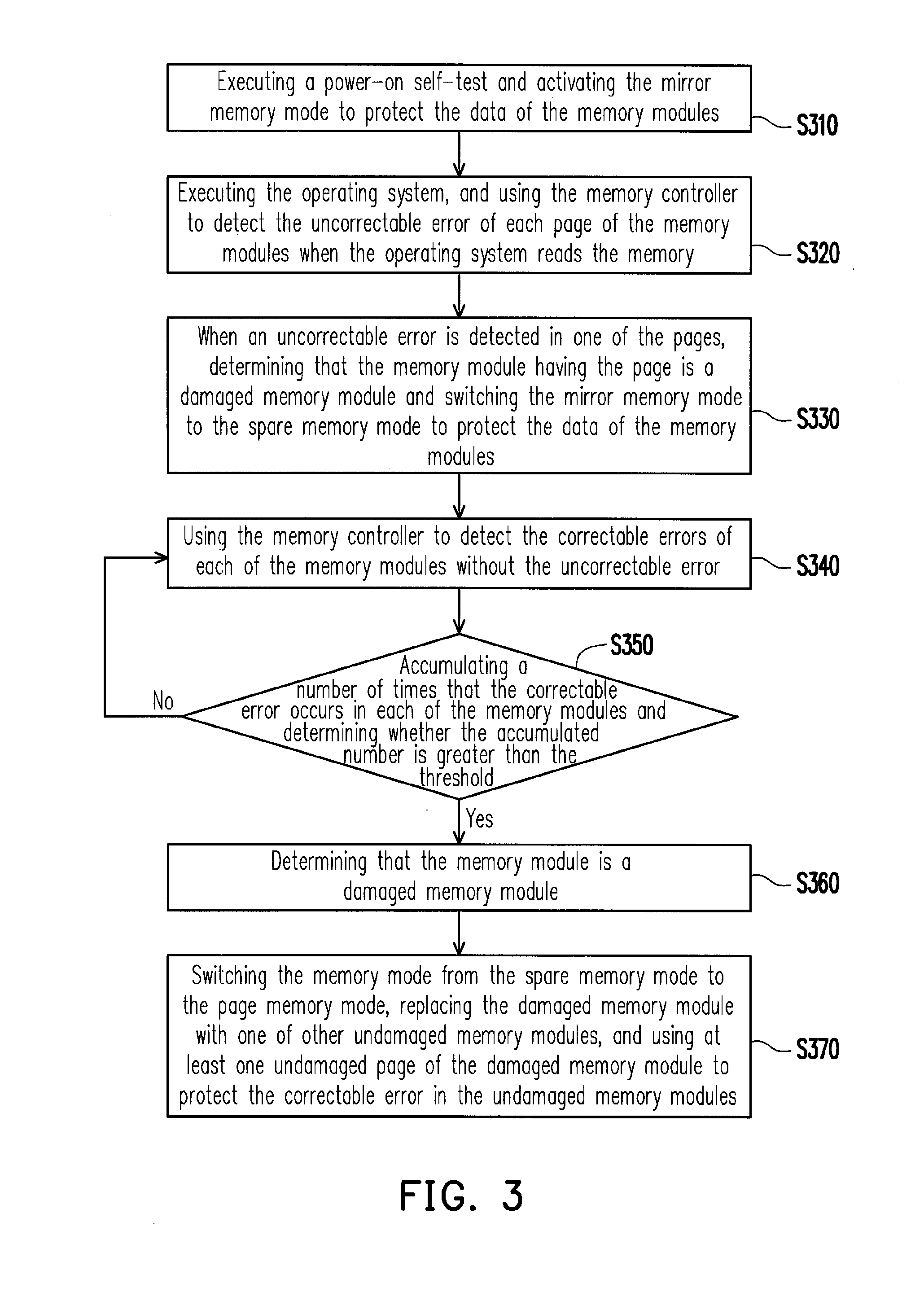
ActiveUS20120137168A1Protecting the correctable error in undamaged memory modulesProtect dataFunctional testingRedundant hardware error correctionComputer moduleMemory controller
A method for protecting data in damaged memory cells by dynamically switching memory mode is provided. The method is adapted to an electronic device having a memory, which has a memory controller and at least one memory module, each of which is consisted of a plurality of memory cells, and the memory cells are divided into a plurality of pages. A power-on self test is executed and a mirror memory mode is activated to protect the data in the memory modules. An uncorrectable error of each page of the memory modules is detected by the memory controller when an operating system reads the memory. If the uncorrectable error in one page is detected, the memory module having the page is determined as a damaged memory module, and the mirror memory mode is switched to a spare memory mode, so as to protect the data in the memory modules.
Owner:INVENTEC CORP
Loop prevention technique for MPLS using two labels
InactiveUS7633859B2Avoid developmentOvercome disadvantagesError preventionTransmission systemsTraffic capacityRouting domain
A fast reroute (FRR) technique is implemented at the edge of a network. In accordance with the technique, if an edge device detects a node or link failure that prevents it from communicating with a neighboring routing domain, the edge device reroutes at least some data packets addressed to that domain to a backup edge device which, in turn, forwards the packets to the neighboring domain. The rerouted packets are designated as being “protected” (i.e., rerouted) data packets before they are forwarded to the backup edge device. To differentiate which data packets are protected and which are not, the backup edge device employs different sets of VPN label values for protected and non-protected network traffic. That is, the backup edge device may allocate two different VPN label values for at least some destination address prefixes that are reachable through the neighboring domain: a first VPN label value for FRR protected traffic and a second VPN label value for non-protected traffic. Upon receiving a data packet containing a protected VPN label value, the backup edge device is not permitted to reroute the packet a second time, e.g., in response to another inter-domain node or link failure, thereby preventing loops from developing at the edge of the network.
Owner:CISCO TECH INC
Loop prevention techniques using encapsulation manipulation of IP/MPLS field
ActiveUS7477593B2Avoid developmentFast reroute (FRR)Error preventionTransmission systemsRouting domainPacket forwarding
A fast reroute (FRR) technique is implemented at the edge of a computer network. In accordance with the technique, if an edge device detects a node or link failure that prevents it from communicating with a neighboring routing domain, the edge device reroutes at least some data packets addressed to that domain to a backup edge device which, in turn, forwards the packets to the neighboring domain. The rerouted packets are designated as being “protected” (i.e., rerouted) data packets before they are forwarded to the backup edge device. To that end, the edge device incorporates an identifier into the rerouted data packets to indicate that the packets are being FRR rerouted. The identifier may be a predetermined value stored at a known location in the rerouted packets'encapsulation headers, such as in their MPLS or IP headers. Upon receiving a data packet containing the identifier, the backup edge device is not permitted to reroute the packet a second time.
Owner:CISCO TECH INC
Implementation for an object oriented run-time extensible item
InactiveUS20010011368A1Protect dataEasy to customizeData processing applicationsObject oriented databasesProgramming languageComputerized system
In an object oriented computer system, one or more run-time extensible items are defined that may be dynamically reconfigured as required to support different interfaces at run-time. The behavior associated with these interfaces is supported by one or more extensions owned by the extensible item. Each extension class has a corresponding method table that is shared among instances of the extension class and that correlates the methods defined on the extension class to method node objects that carry out the method. A method repository is a static object that is created at run-time to correlate extensions to their corresponding method tables. When a client invokes an invokeMethod() method on an extensible item, specifying the name of the method to be invoked, the extensible item cycles through its extensions, from newest to oldest, looking for an extension that supports the named method. Each extension examines the method repository to see if the method repository contains a method table corresponding to the extension class. If not, a method table corresponding to the extension class is created and placed in the method repository. When an extension is found that supports the named method, a method node that corresponds to the named method is returned. The method node then invokes the named method on the extension.
Owner:IBM CORP
Apparatus and method for recording an optical disc identification code
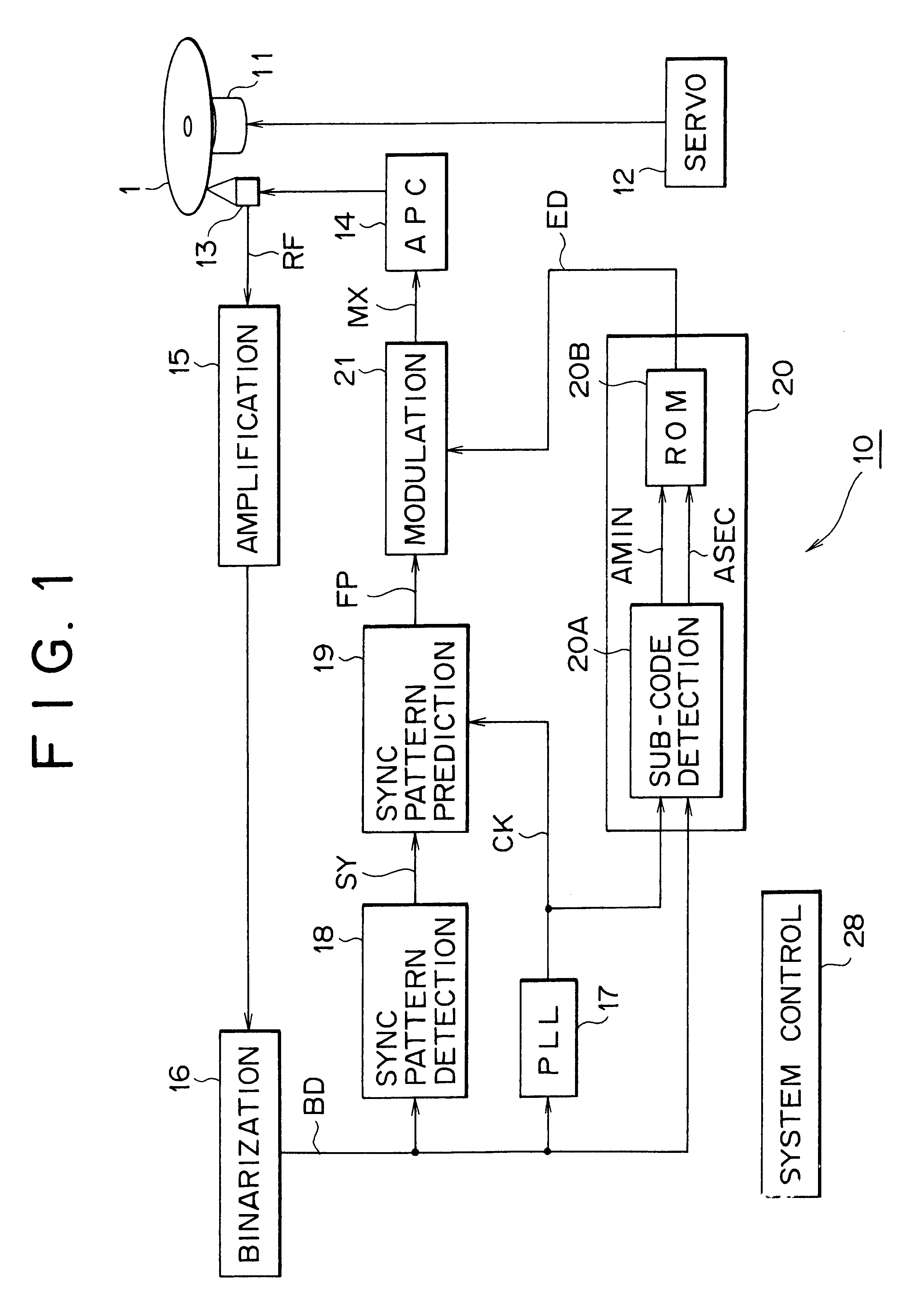
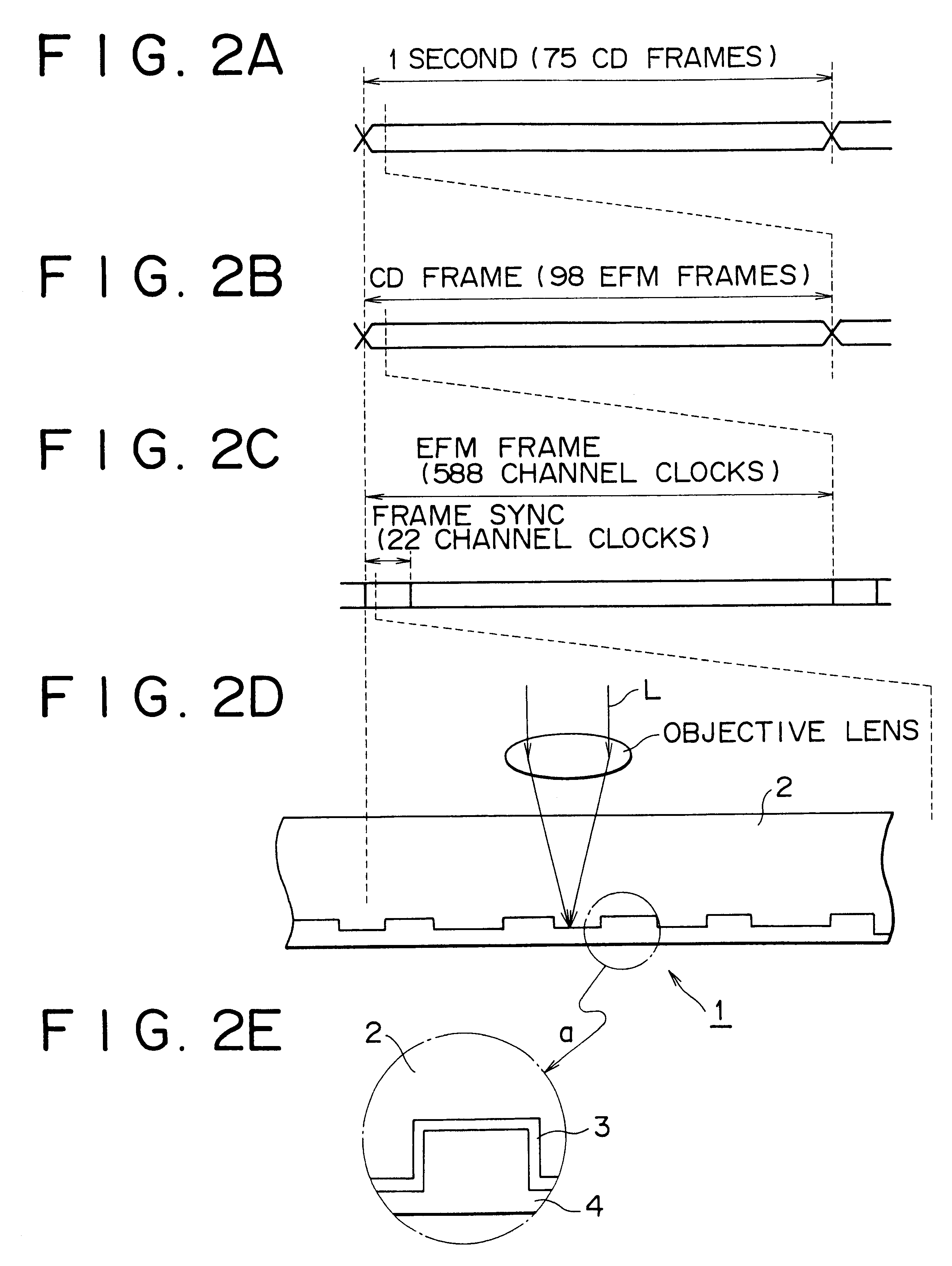
InactiveUS6414913B1Protect dataReduce adverse effectsAccessories for indicating/preventing prior/unwanted useRecord information storageComputer hardwareOptical pickup
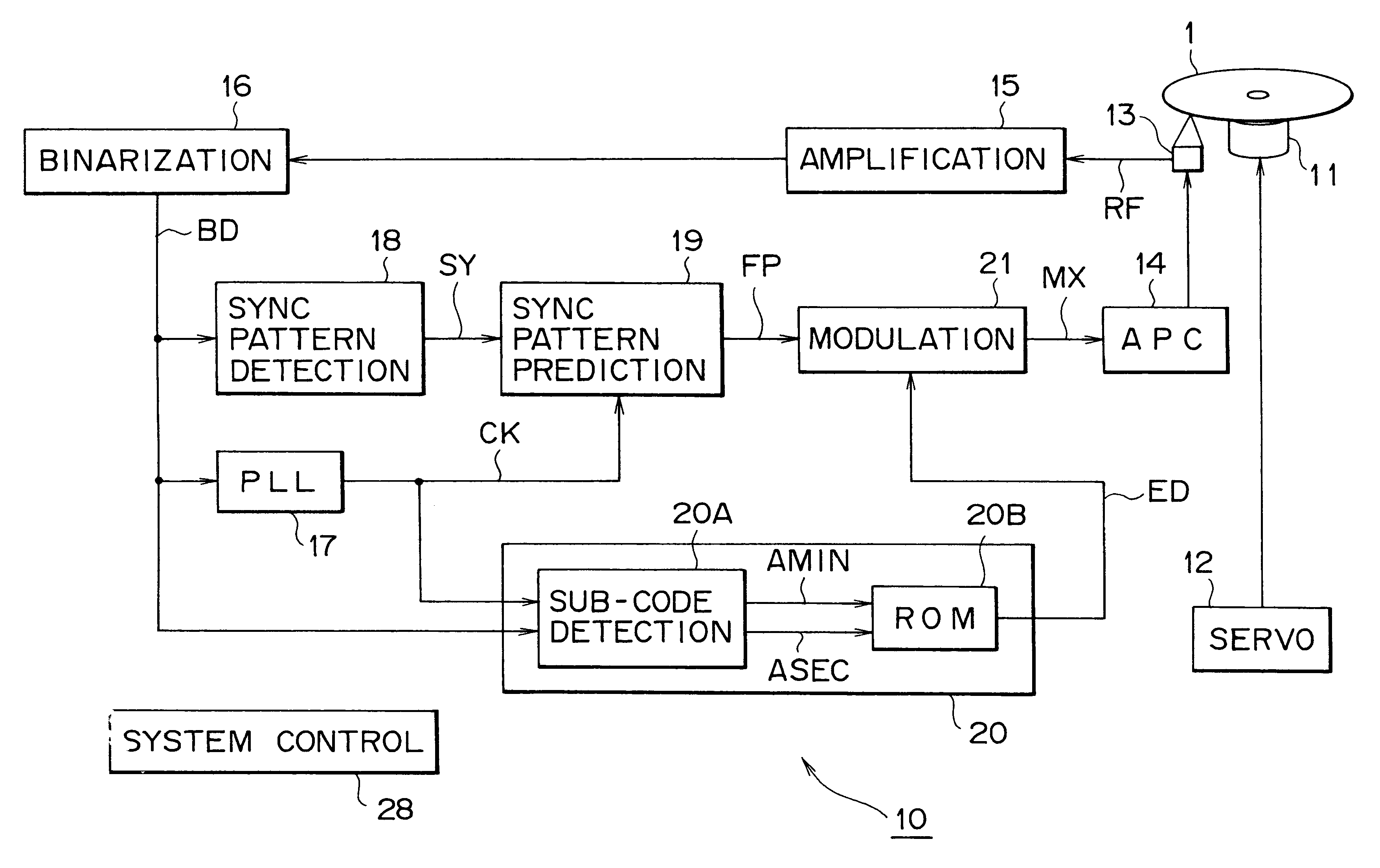
This invention related to an optical disc recording apparatus, an optical disc recording method, and an optical disc, and the present invention is applied to, for example, apparatus for recording on a compact disc, compact discs, and compact disc players, and sub-data strings are recorded so that the main data strings is reproducible by an optical pickup for reproducing the main data string and the main data strings are protected from being copied illegally without any adverse effect on reproduction of the pit-and-land main data strings. The sub-data string ED is recorded by locally changing the reflectance of the reflection film in the form of irregularity such as pit or mark at the timing which does not affect the position information of the edge.
Owner:SONY CORP
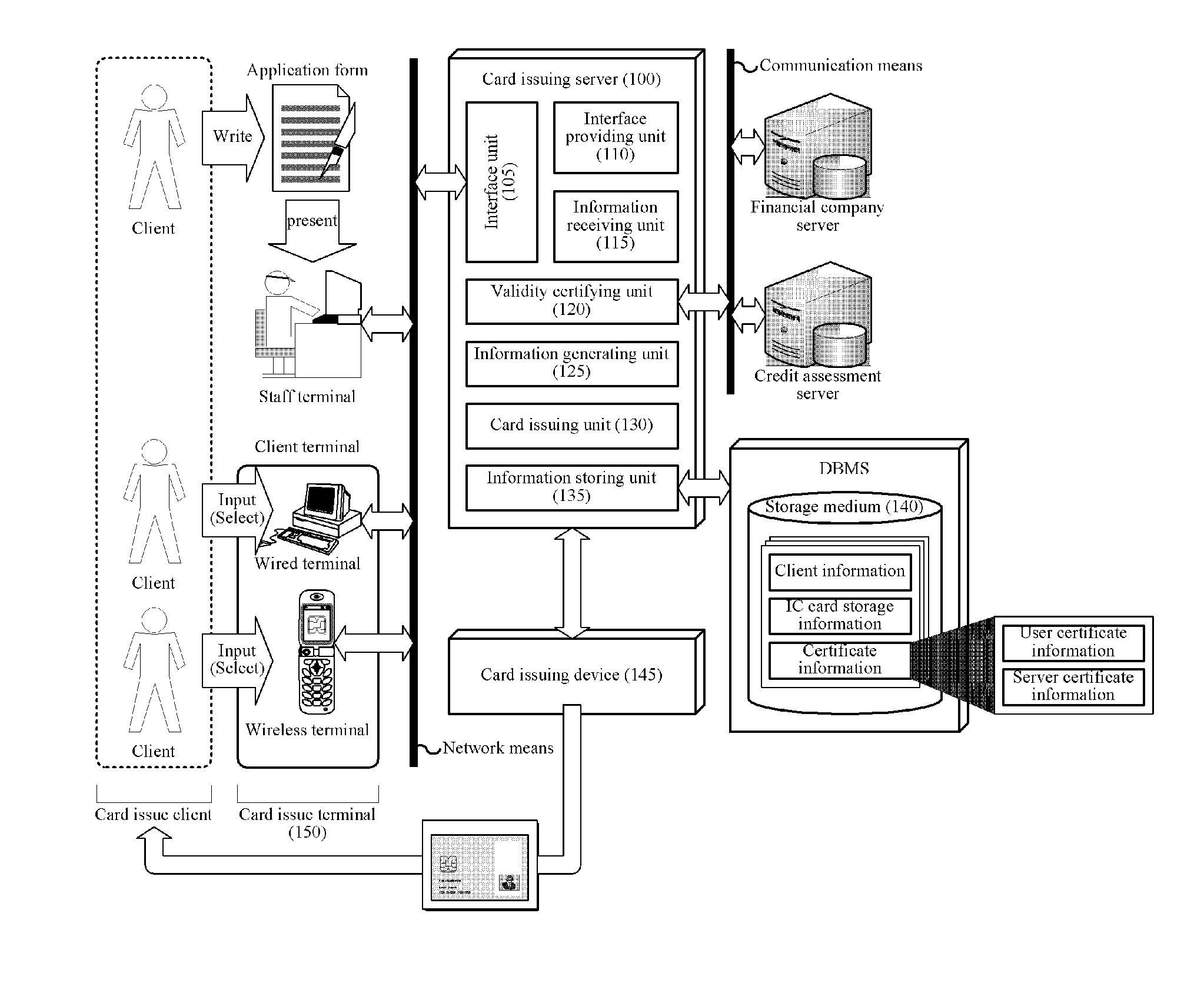
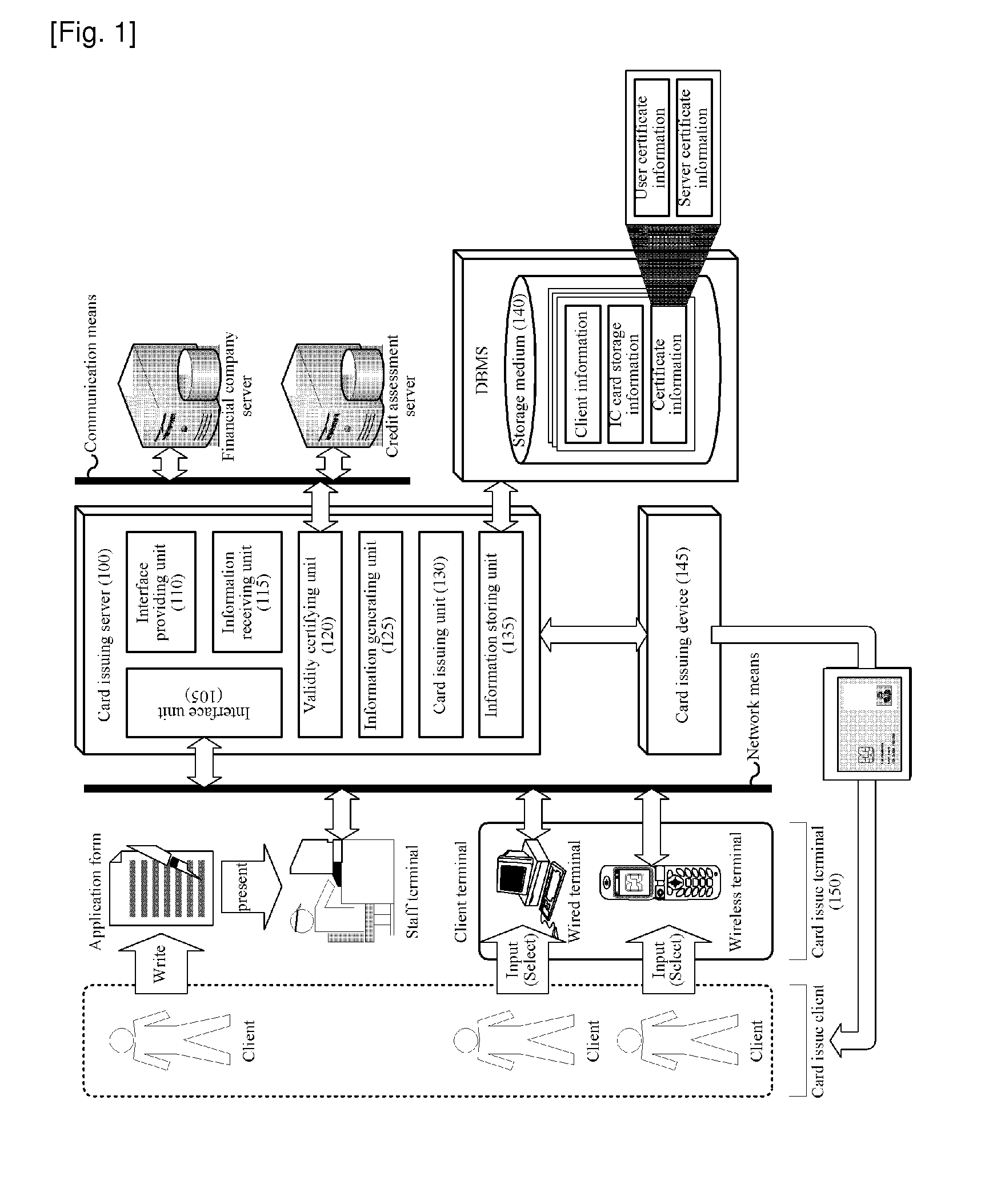
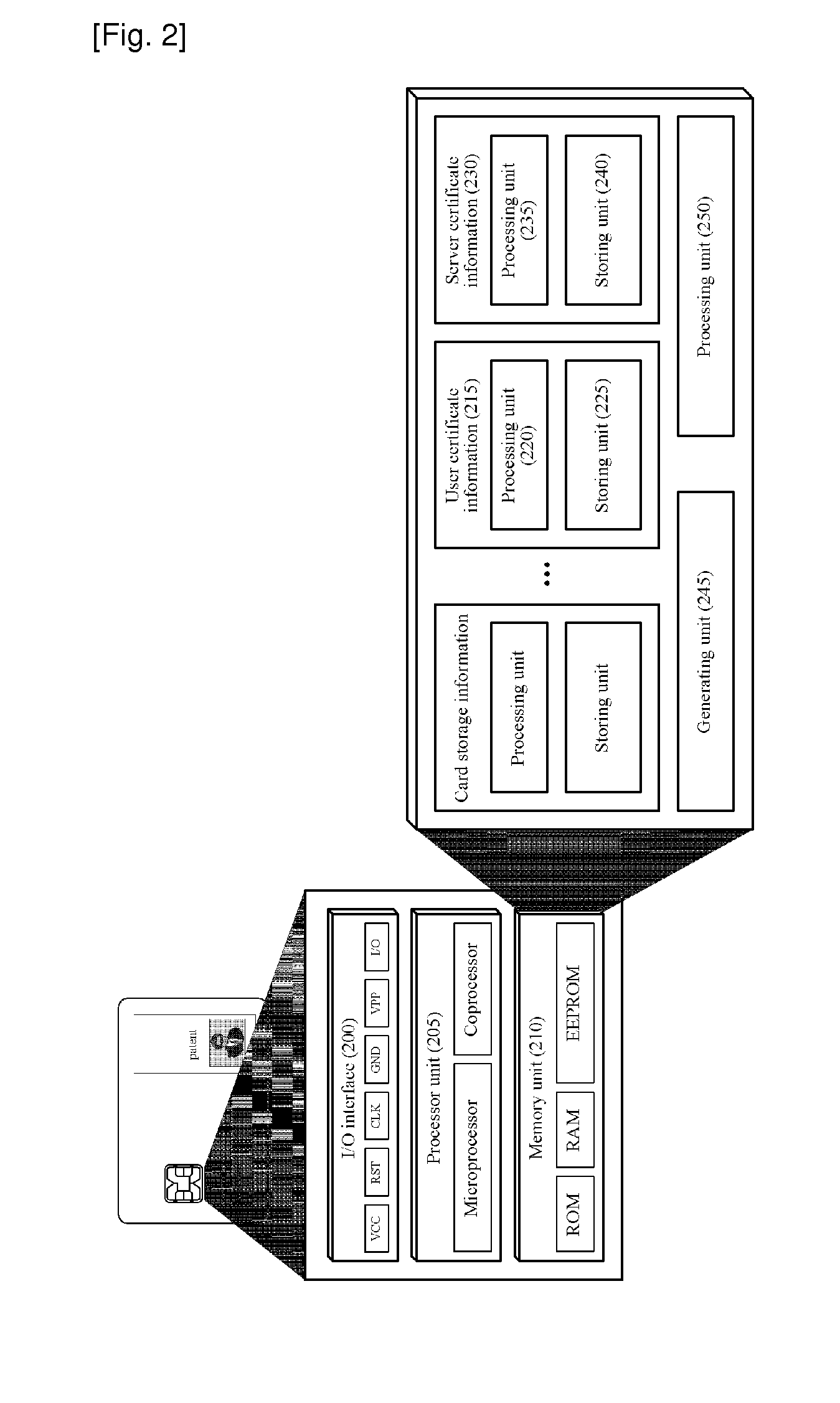
System and Method for Operating End-to-End Security Channel Between Server and IC Card
ActiveUS20100287375A1Avoid dangerPowerful security functionUser identity/authority verificationPayment circuitsComputer hardwareEnd to end security
The present invention relates to a system and method for operating an end-to-end security channel between an IC card and a server on a communication network. A method for connecting an end-to-end security channel between an IC card and a server on a communication network includes the steps of: generating, by the server, a random number Rs for transmission to the IC card, generating an E(Rs) by encrypting the random number Rs by a user public key, and transmitting the E(Rs) to the IC card through the communication network; receiving, by the IC card, the E(Rs) through the communication network and extracting the random number Rs by decrypting the E(Rs) by a user private key; generating, by the IC card, a random number Rc to be transmitted to the server, generating a session key K′ by the random number Rs and the random number Rc, and generating a first card verifier MAC by encrypting the random number Rs by the session key K′; transmitting, by the IC card, the random number Rc and the first card verifier MAC to the server through the communication network; receiving, by the server, the random number Rc and the first card verifier MAC through the communication network, generating a session key K by the random number Rs and the random number Rc, and generating a first server verifier MAC by encrypting the random number Rs by the session key K; and comparing, by the server, the first card verifier MAC and the first server verifier MAC to certify the session key K.
Owner:LEE SUNG MAN
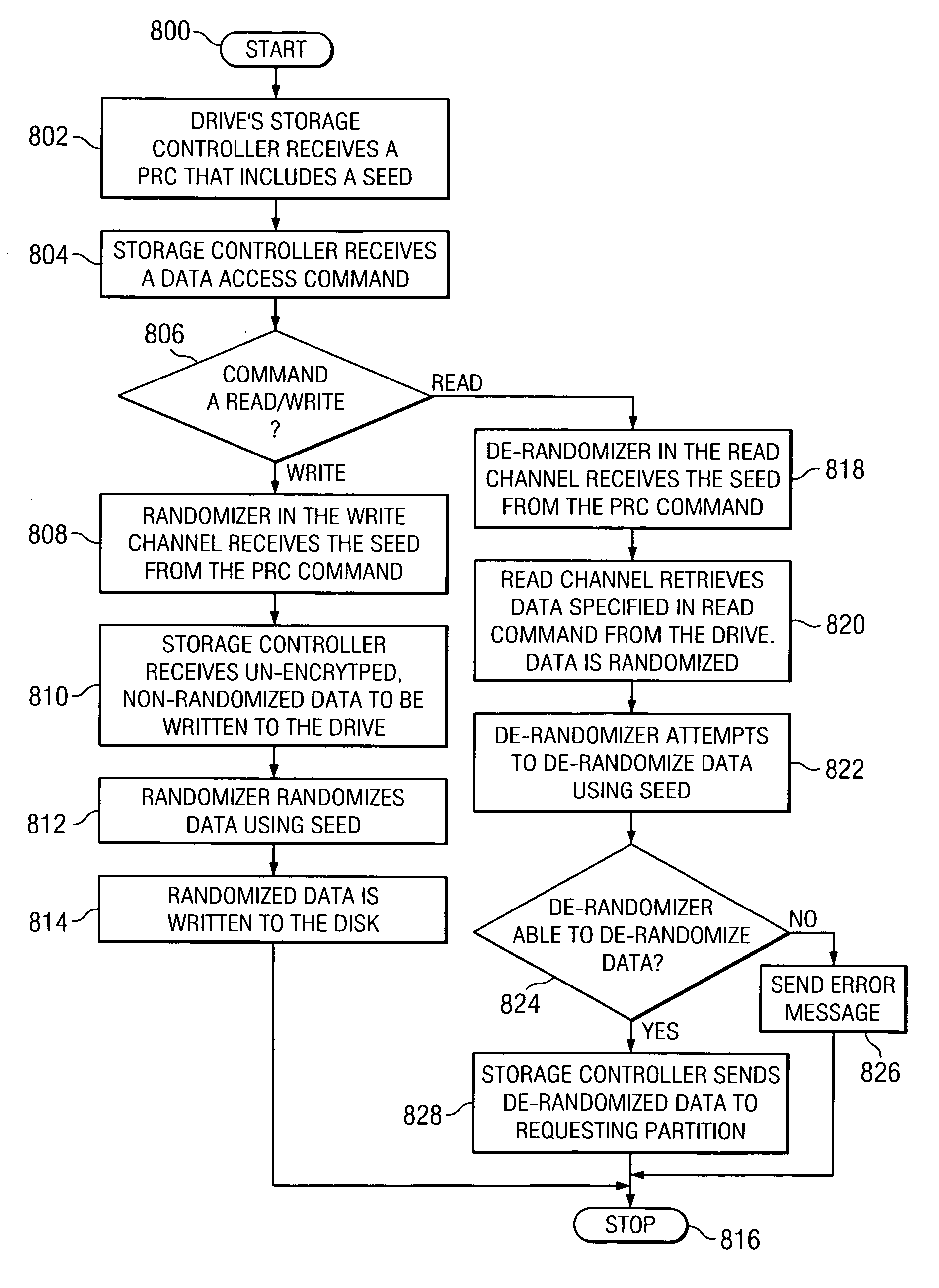
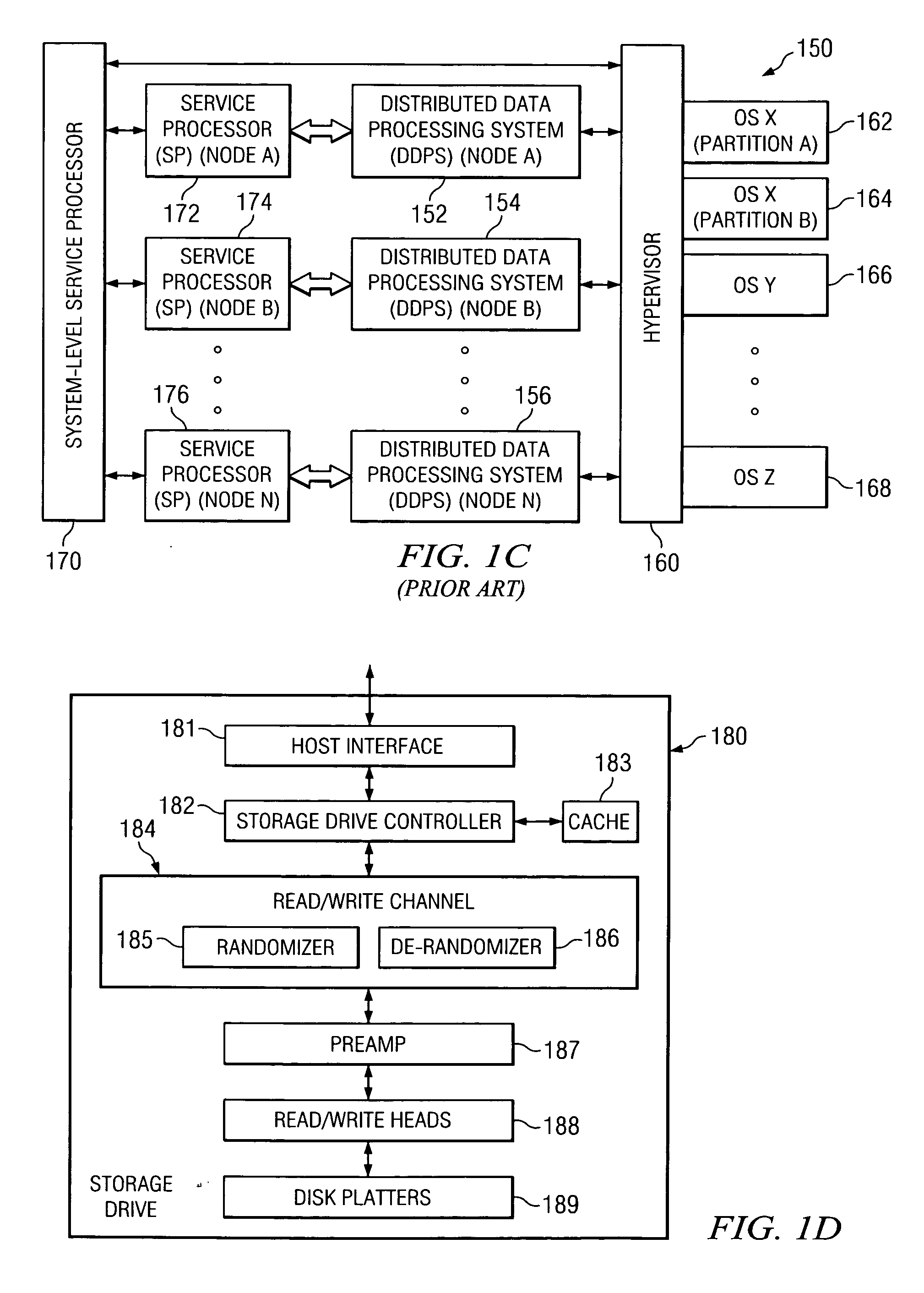
Method, apparatus, and product for prohibiting unauthorized access of data stored on storage drives
InactiveUS20060294331A1Protect dataError detection/correctionVolume/mass flow measurementComputer networkComputer program
A method, apparatus, and computer program product are disclosed in a data processing system for prohibiting unauthorized access of data that is stored on storage drives. Multiple logical partitions are generated. A different unique randomizer seed is associated with each one of the logical partitions. In response to one of the logical partitions needing to access a storage drive, the logical partition transmits a seed to the storage drive. The transmitted seed is associated with the one of the logical partitions. A transmitting one of the logical partitions is unable to transmit a seed that is other than a seed that is associated with the transmitting one of the logical partitions. The storage drive utilizes the transmitted seed to randomize and de-randomize data for the one of the logical partitions. Data randomized for one of the logical partitions cannot be de-randomized for a different one of the logical partitions.
Owner:IBM CORP
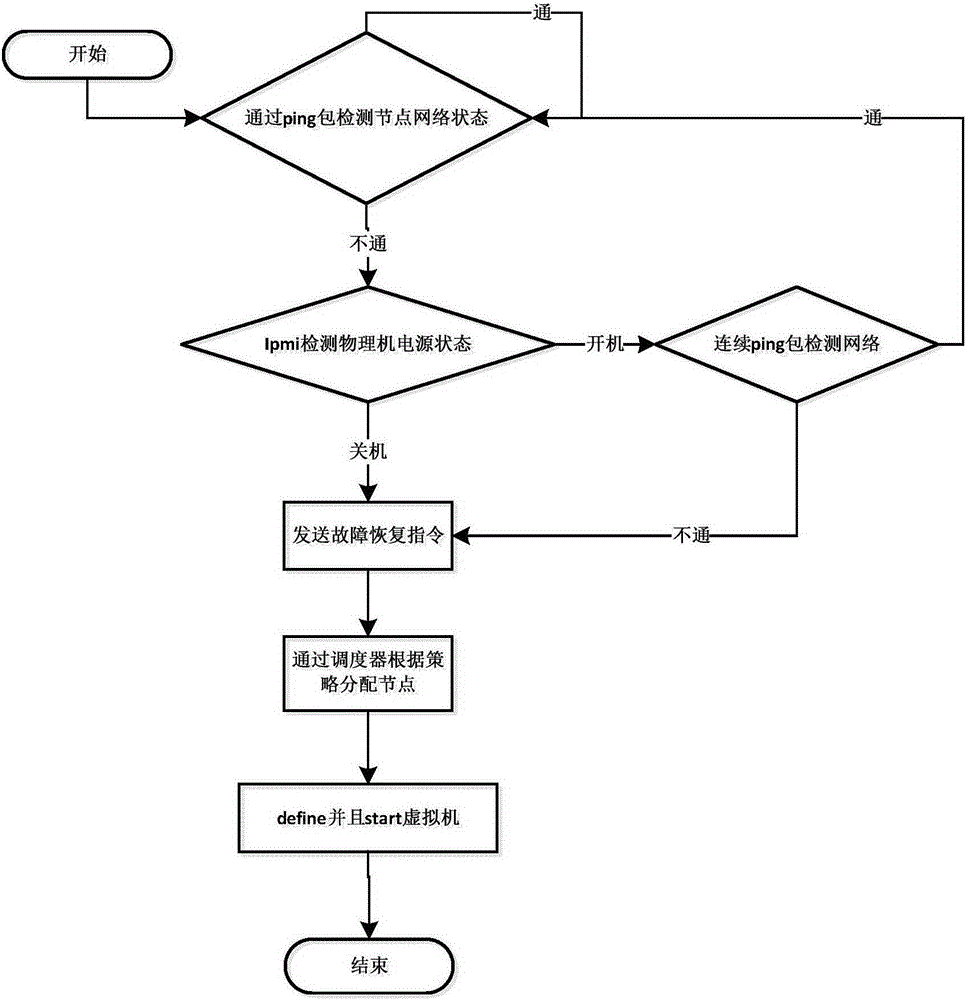
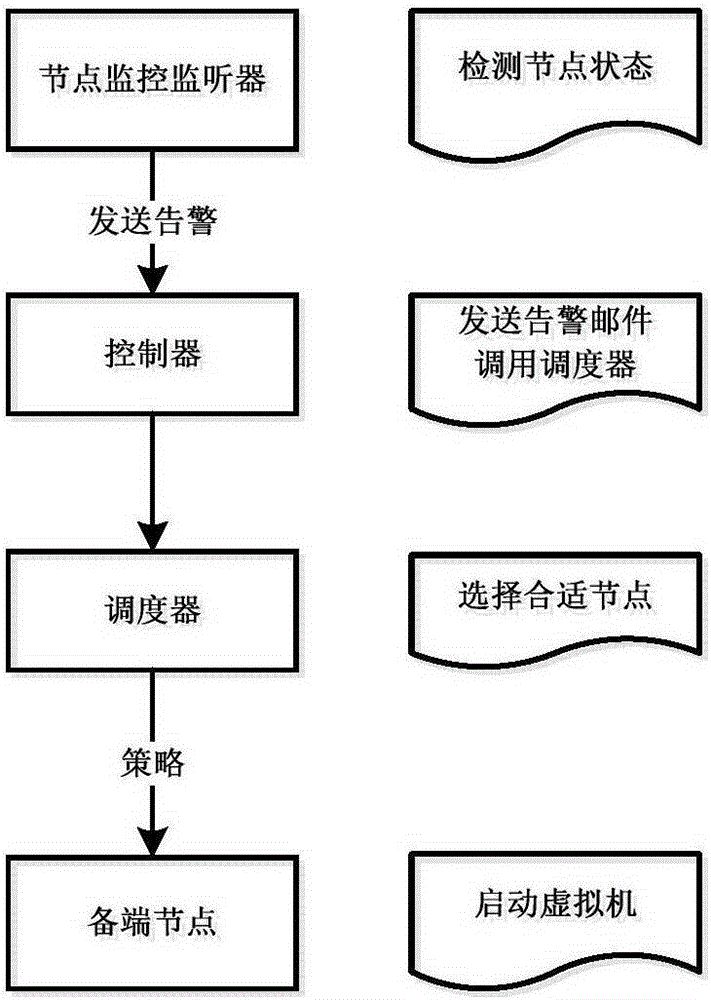
Virtual machine failure detection and recovery method
InactiveCN105335214APrevent wrong migrationGuaranteed uptimeFault responseData switching networksRecovery methodDowntime
The invention relates to the fields of cloud computing and network technique and in particular relates to a virtual machine failure detection and recovery method. The method comprises the following steps: 1, deploying an NFS network file system environment, establishing a mount point on an NFS server, putting a mirror image on the mount point of the NFS server, mounting shared storage on all the nodes, and establishing a virtual machine for the mirror image; 2, starting a detection node timer, detecting whether the network and the power supply are positioned in a normal state, otherwise transmitting a failure recovery instruction to a scheduler; 3, selecting available nodes by virtue of the scheduler according to the preset cpu load strategy and other scheduling rules; 4, regenerating a virtual machine which is the same as the original machine according to a configuration file generated in the process of establishing the virtual machine; and 5, starting the established virtual machine. According to the method disclosed by the invention, the problem that the virtual machine cannot be continuously used after physical node downtime is solved, and the method can be used for virtual machine failure detection and recovery.
Owner:G CLOUD TECH
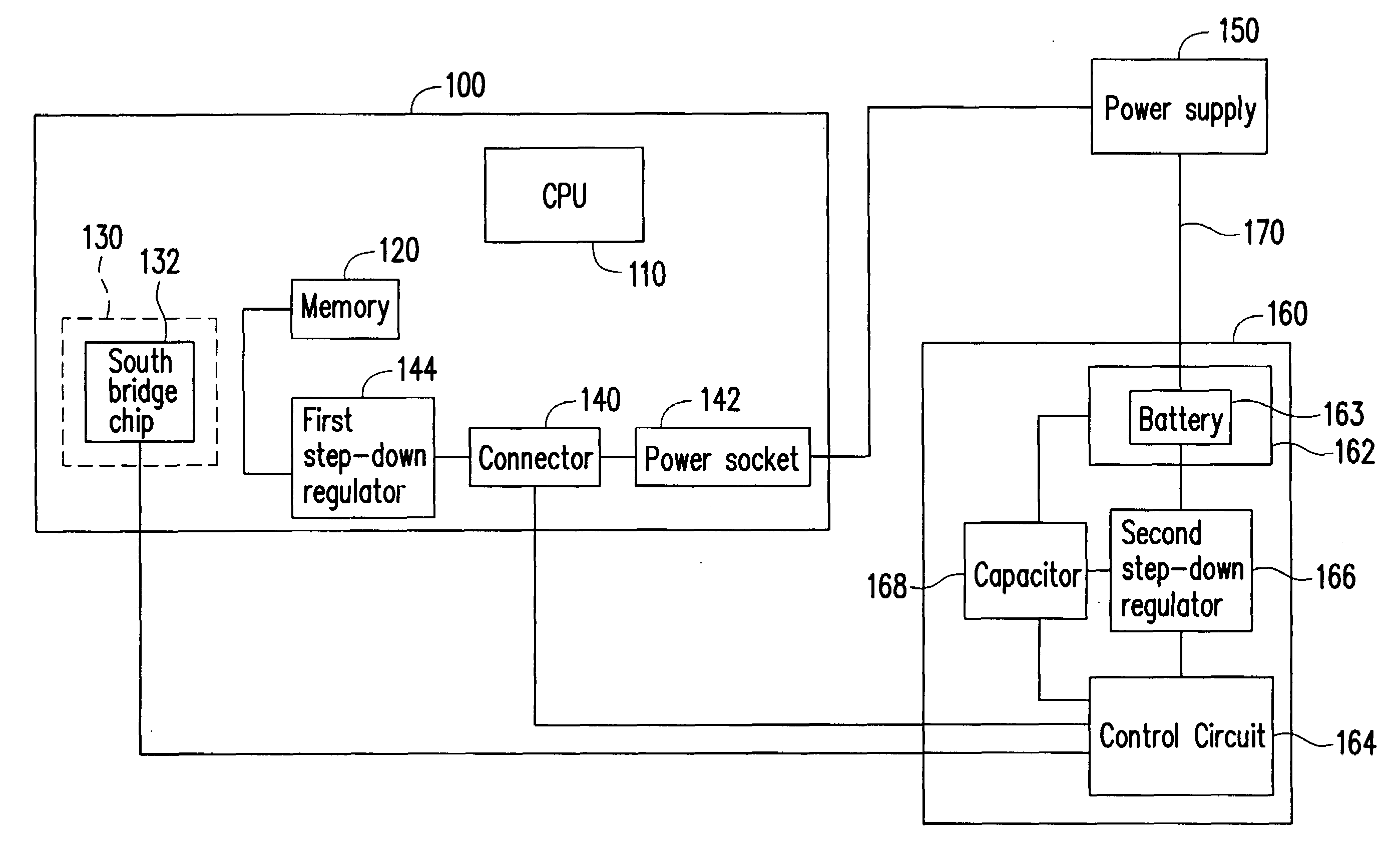
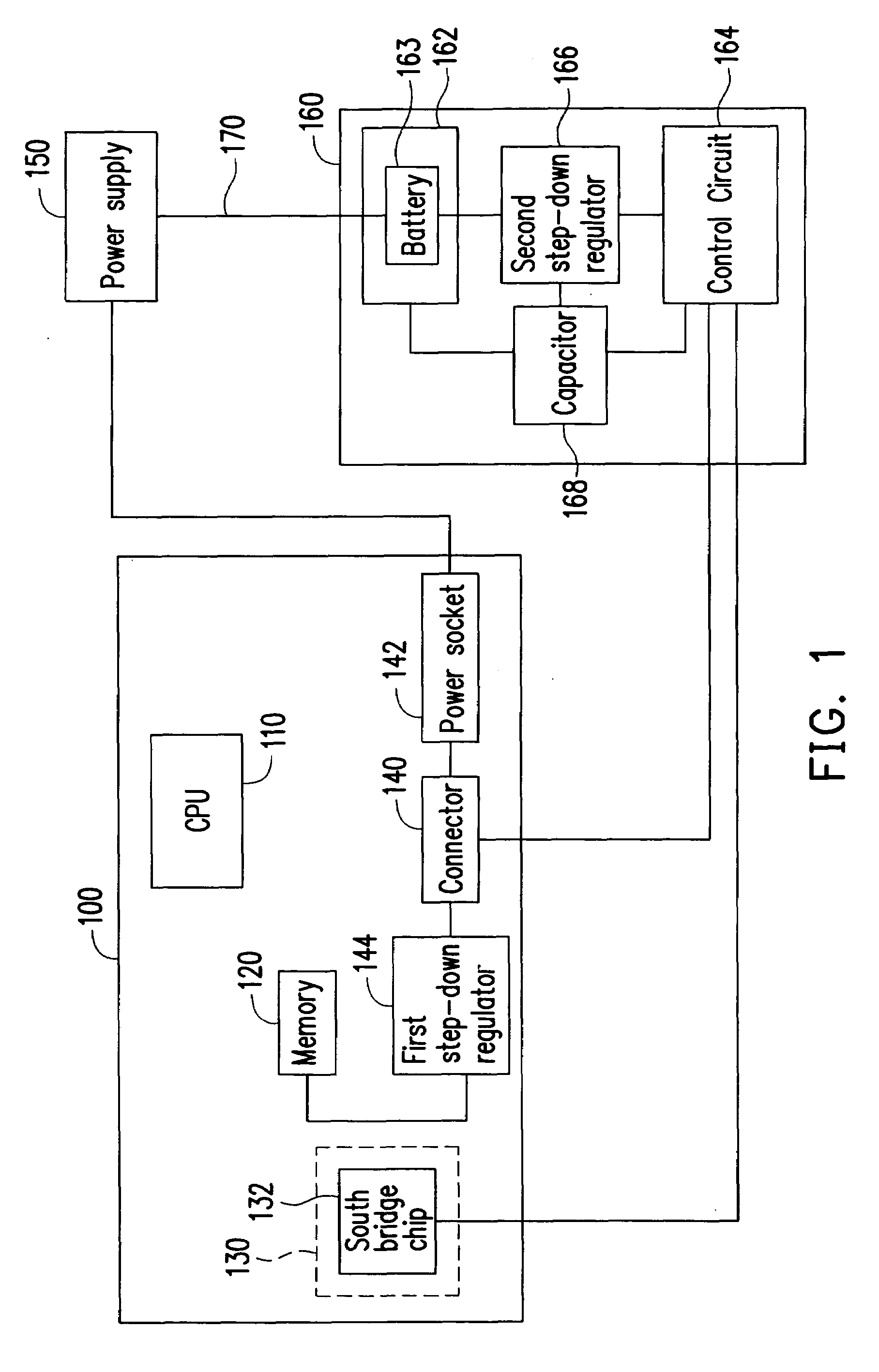
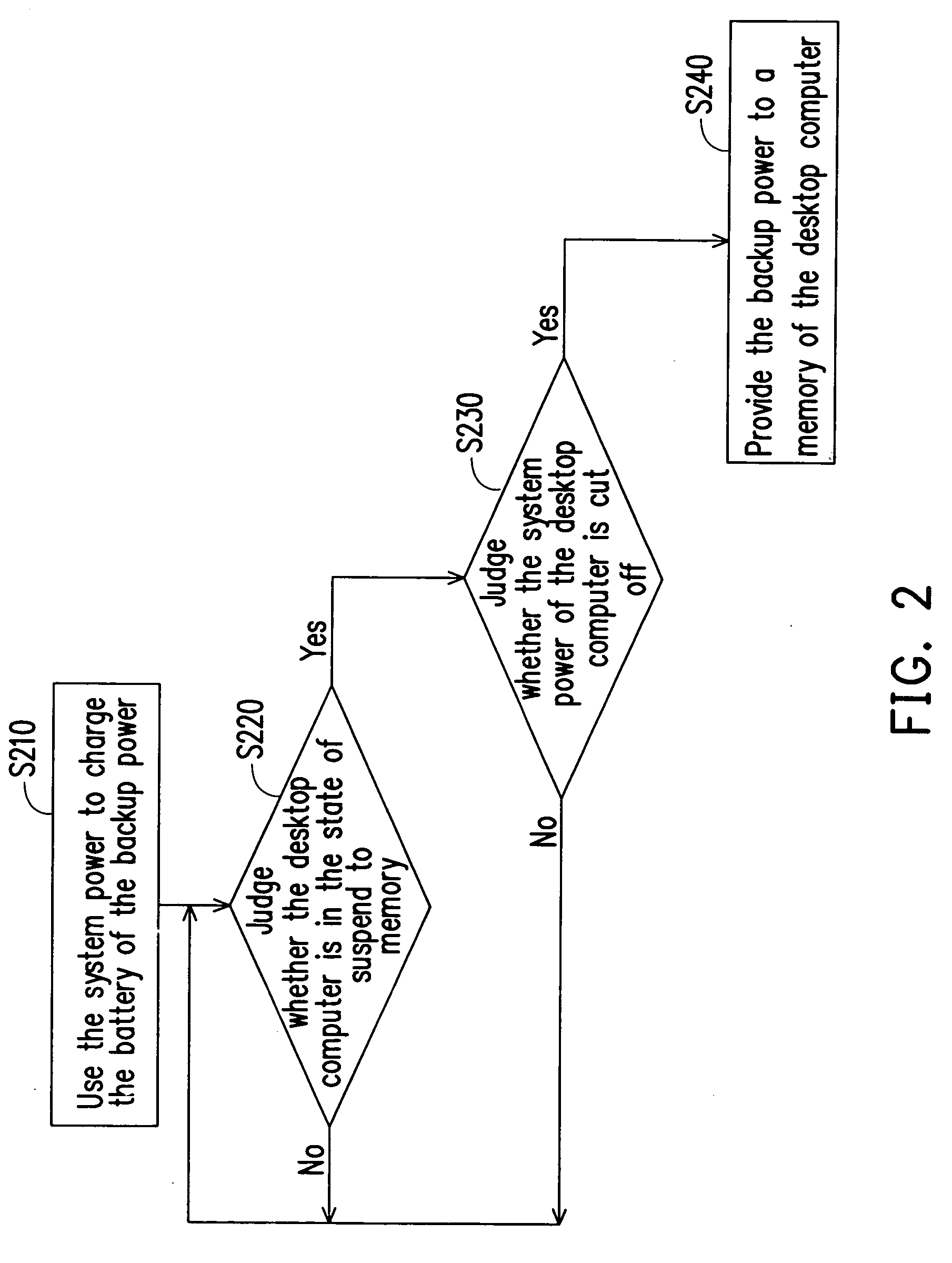
Backup power supply and desktop computer and method for protecting the data thereof
InactiveUS20080010514A1Protect dataAvoid lossError detection/correctionPower supply for data processingStandby power
A backup power supply, a desktop computer and the method for protecting the data thereof are described. The method comprises the steps of judging whether the desktop computer is in the suspend-to-memory mode, judging whether the system power of the desktop computer fails and then providing a backup power to the memory of the desktop computer when the desktop computer is in the suspend-to-memory mode and the system power of the desktop computer fails.
Owner:ELITEGROUP COMPUTER SYSTEMS
Method of protecting privacy data of an application program and apparatus using the same
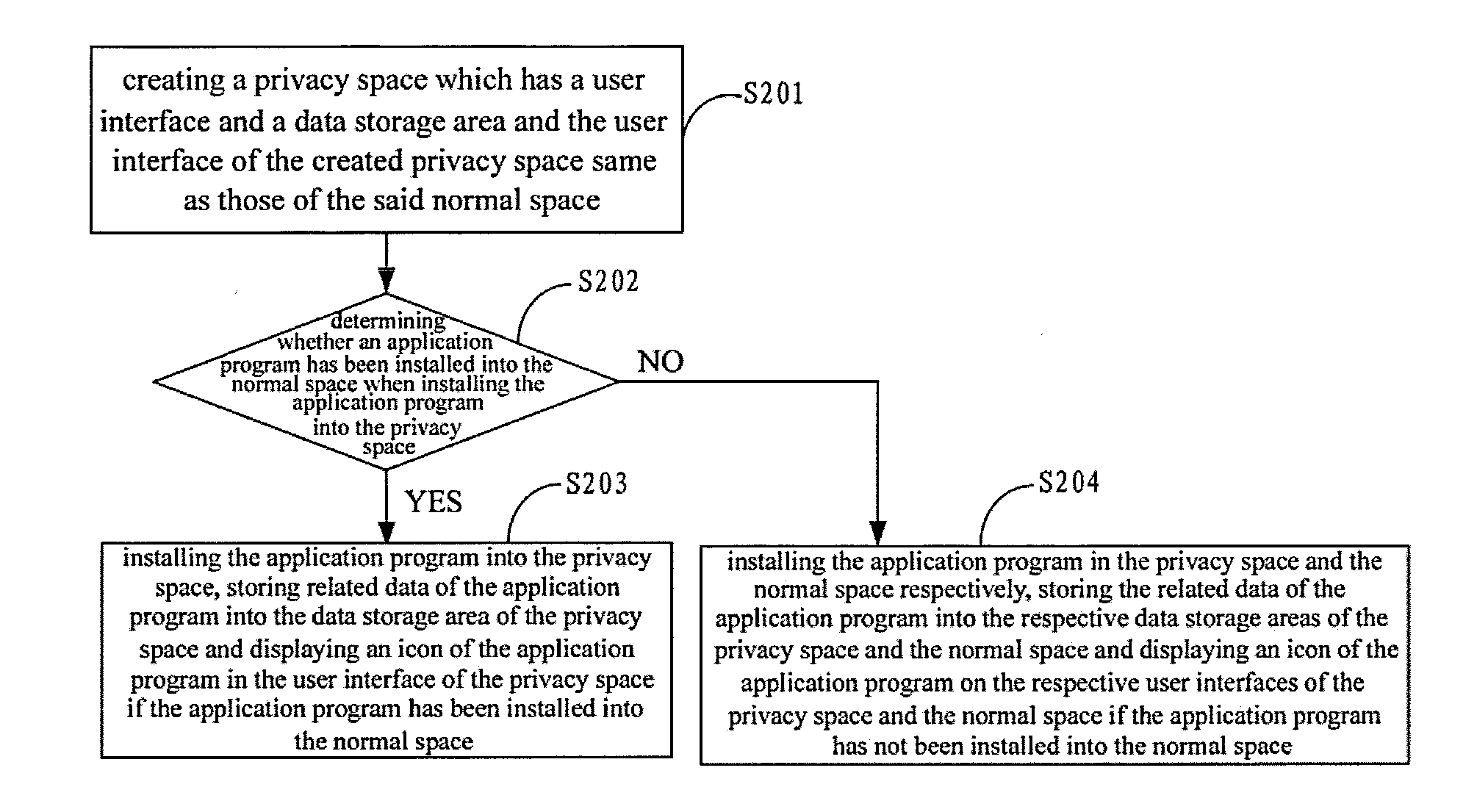
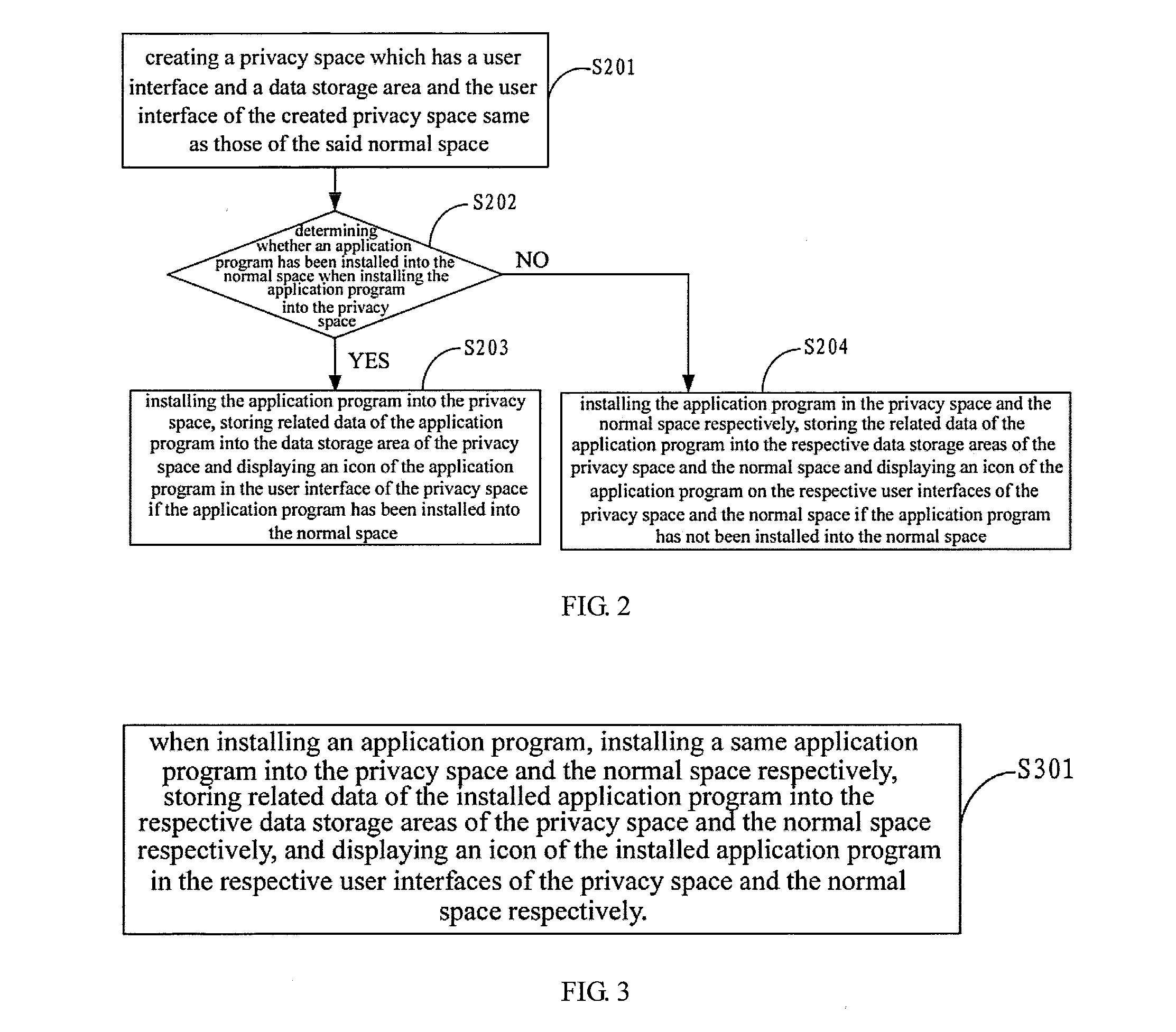
InactiveUS20140373168A1Data incompatibility caused by application program upgrading can be avoided effectivelyEffective protectionDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyComputer terminal
The present application is applied to data processing technique field, providing an application program privacy data protection method and an apparatus. The method includes: creating a privacy space, including creating a user interface and a data storage area that the privacy space corresponds to, the user interface of the created privacy space is the same as the user interface of the normal space; when installing an application program, it is determined whether the application program has been installed into the normal space; if the result of the determination is yes, the application program is installed into the privacy space; if the result of the determination is no, the application program is installed in the privacy space and the normal space respectively. Through the present application, it is possible to protect the privacy data of the application program in the user terminal without any trail.
Owner:TENCENT TECH (SHENZHEN) CO LTD
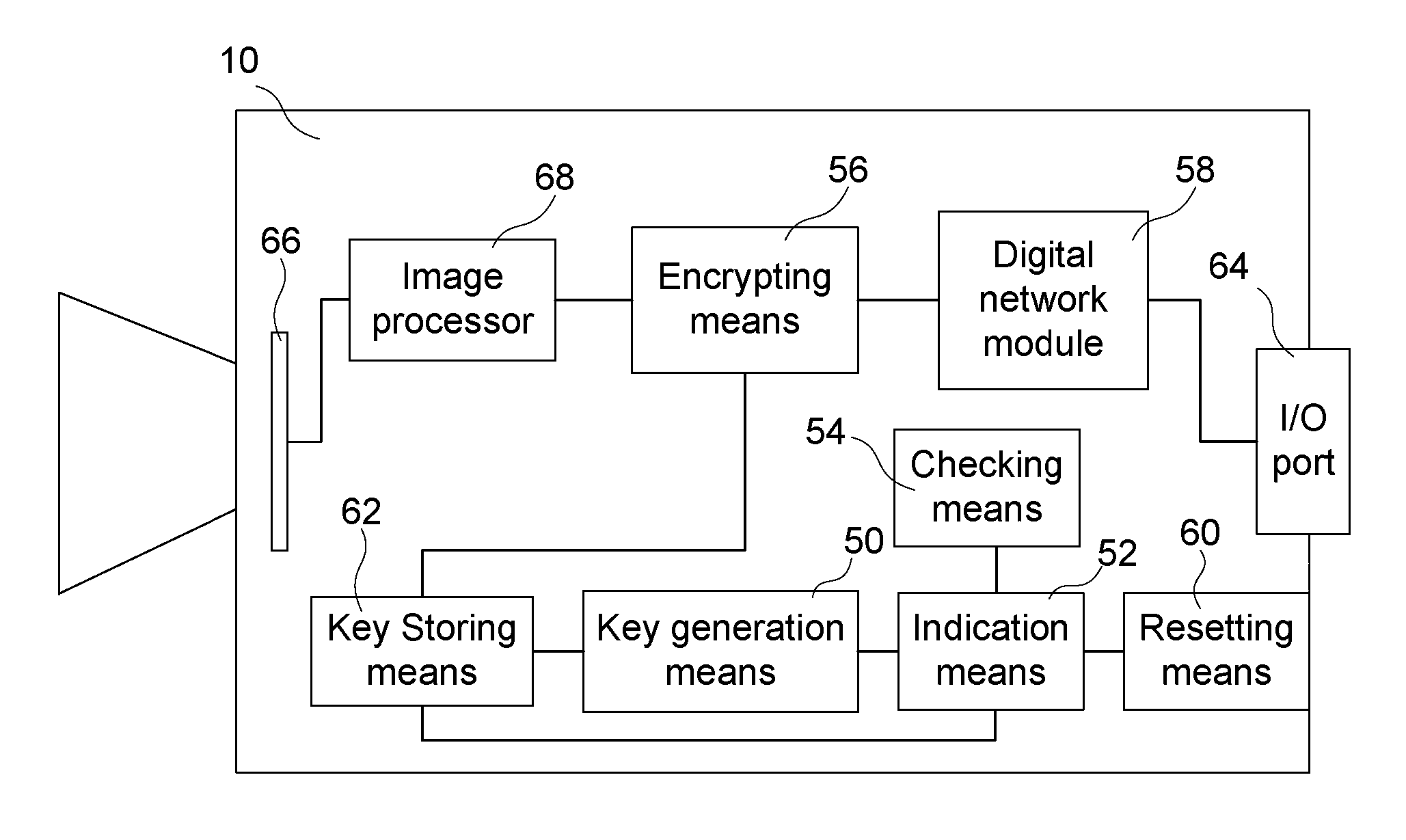
Method for restricting access to media data generated by a camera
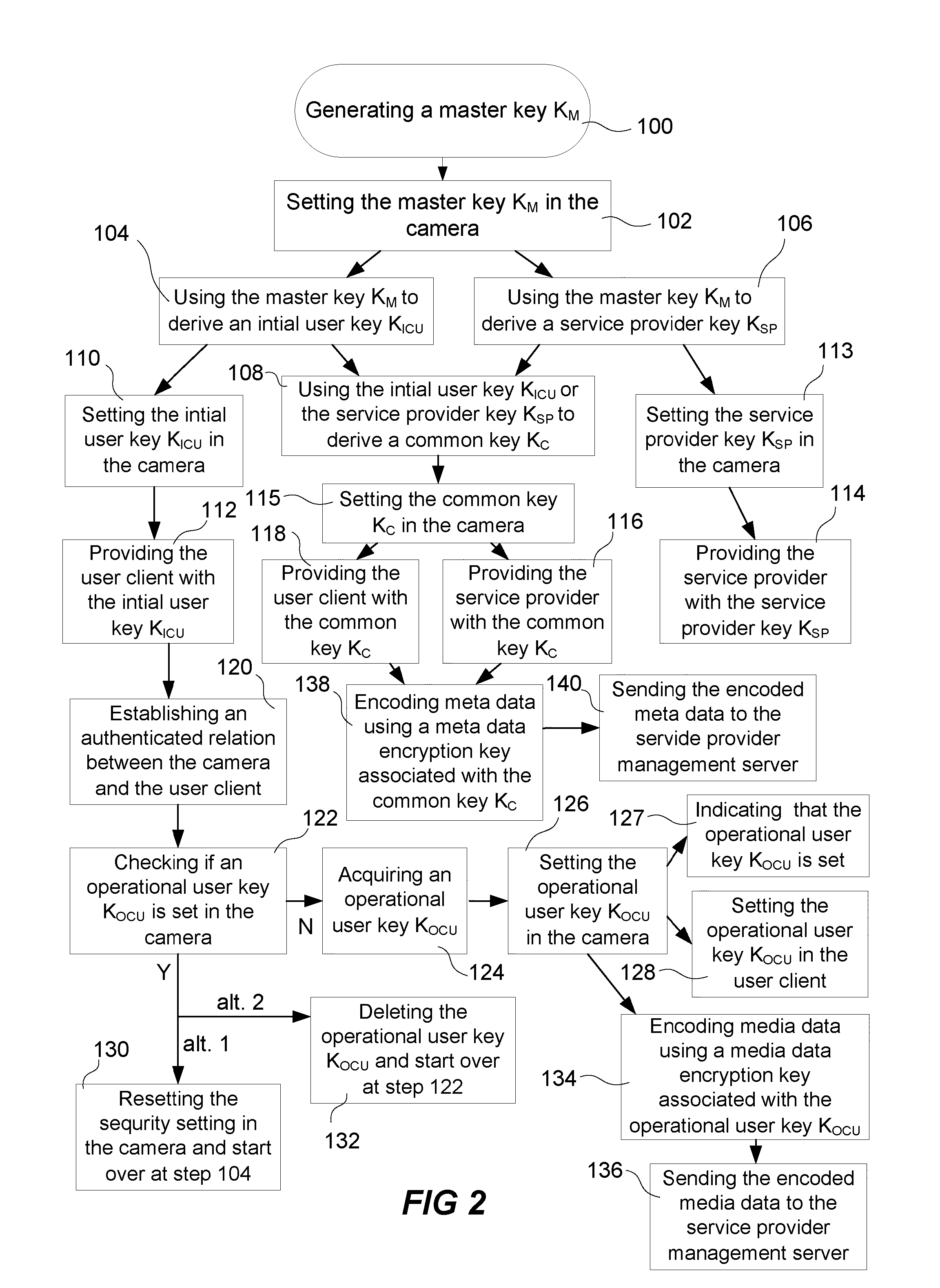
ActiveUS20110016319A1Protect dataSecure distributionDigital data processing detailsUser identity/authority verificationLimited accessClient-side
A method for restricting access to media data generated by a camera comprising: setting a non-public initial user key, KICU, in the camera, providing a user client with the initial user key, KICU, establishing an authenticated relation between the user client and the camera by sending an authentication message including information based on the initial user key, KICU, from the user client to the camera, checking if an operational user key (KOCU) is set in the camera, and performing, in response to the act of checking if the operational user key (KOCU) is set in the camera, the acts a)-d) only if the operational user key (KOCU) is not set: a) acquiring an operational user key (KOCU), b) setting the operational user key (KOCU) in the camera, c) sending the operational user key (KOCU) to the user client, and d) indicating in the camera that the operational user key (KOCU) is set.
Owner:AXIS
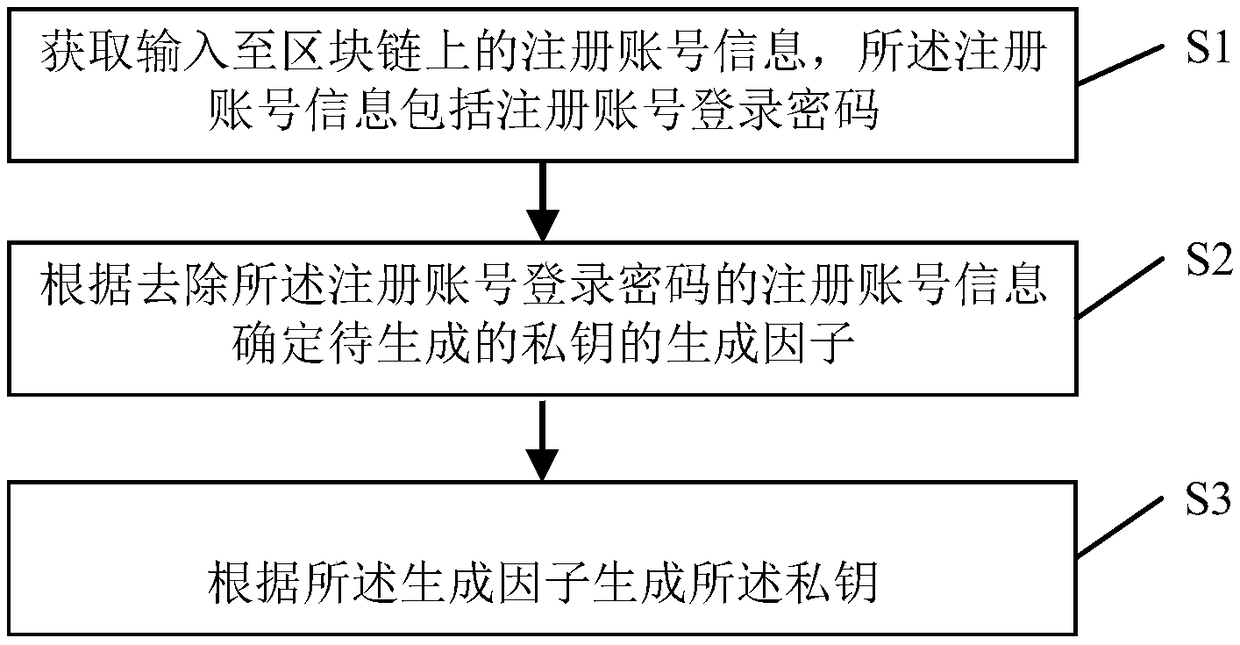
Private key generation and data interaction methods for block chain and systems thereof
InactiveCN109412798AProtection securityAvoid permafrost, costly problemsKey distribution for secure communicationUser identity/authority verificationThird partyPassword
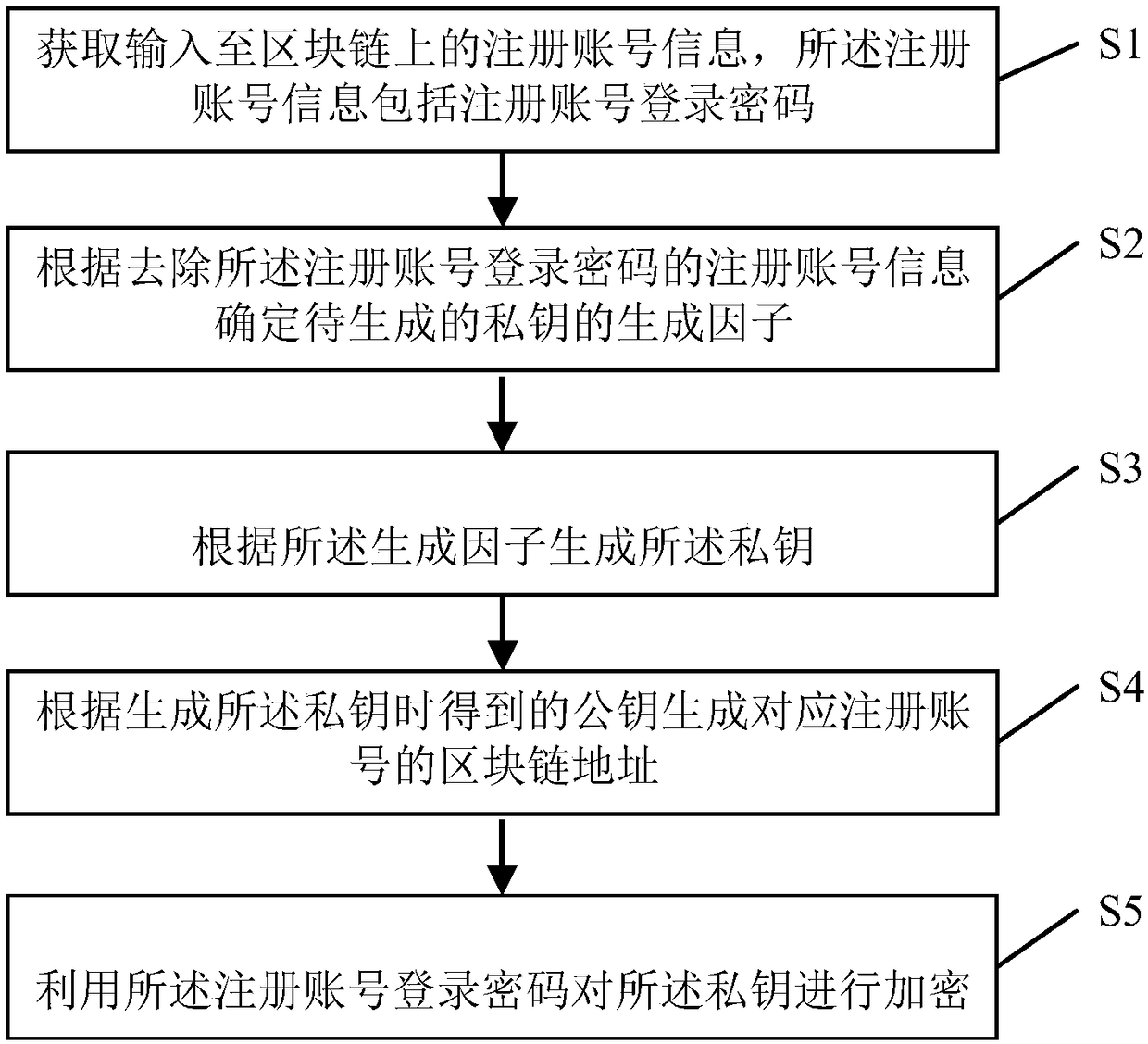
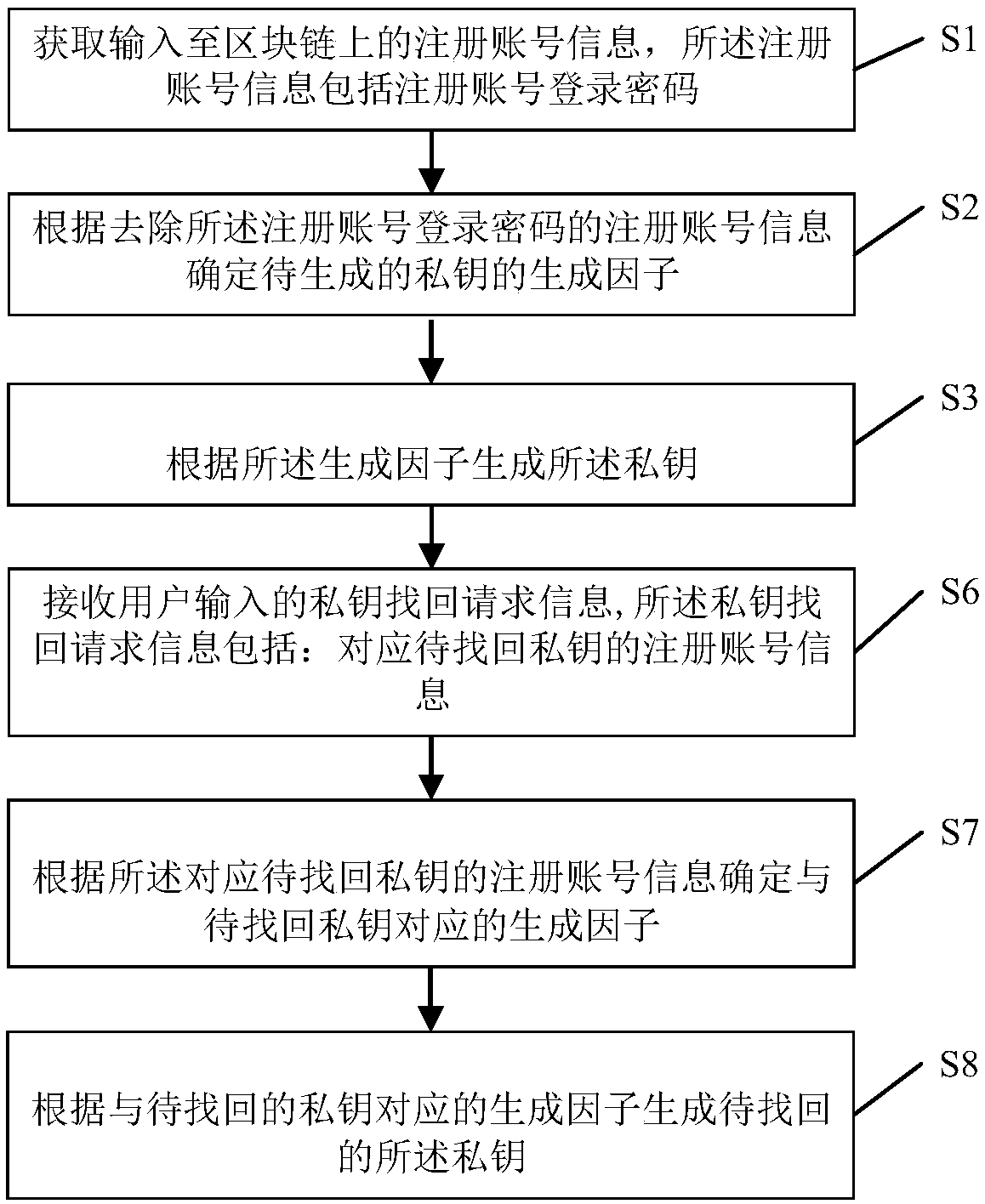
The invention provides private key generation and data interaction methods for a block chain and systems thereof. The generation method comprises steps of acquiring registration account information input into the block chain, wherein the registration account information comprises a login password of the registration account; determining a generation factor of a to-be-generated private key according to the registration account information with the login password of the registration account removed; and generating the private key according to the generation factor. The private key generated through the method can be retrieved, thereby preventing huge loss due to permanent freeze of assets and data in the block chain node resulting from loss of the private key; further, the private key can beretrieved without monitoring or reviewing by a third party, so that the private key is protected and can be retrieved conveniently, and the user data and assets can be protected effectively.
Owner:苏州朗润创新知识产权运营有限公司
Data protection method and device
ActiveCN102411684AProtect dataPrevent illegal useDigital data protectionTerminal equipmentCommunication device
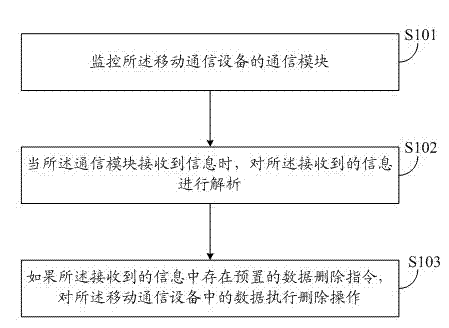
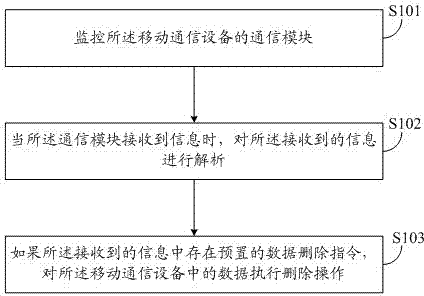
The invention discloses a data protection method and device, applied to mobile communication equipment. The data protection method comprises the following steps that: a communication module of the mobile communication equipment is monitored; when the communication module receives information, the received information is analyzed; and if the received information has a preset data deletion instruction, the data in the mobile communication equipment are deleted. According to the data protection method and device in the invention, when mobile terminal equipment is stolen or lost, the data stored in the mobile terminal equipment can be effectively protected.
Owner:BEIJING QIHOO TECH CO LTD
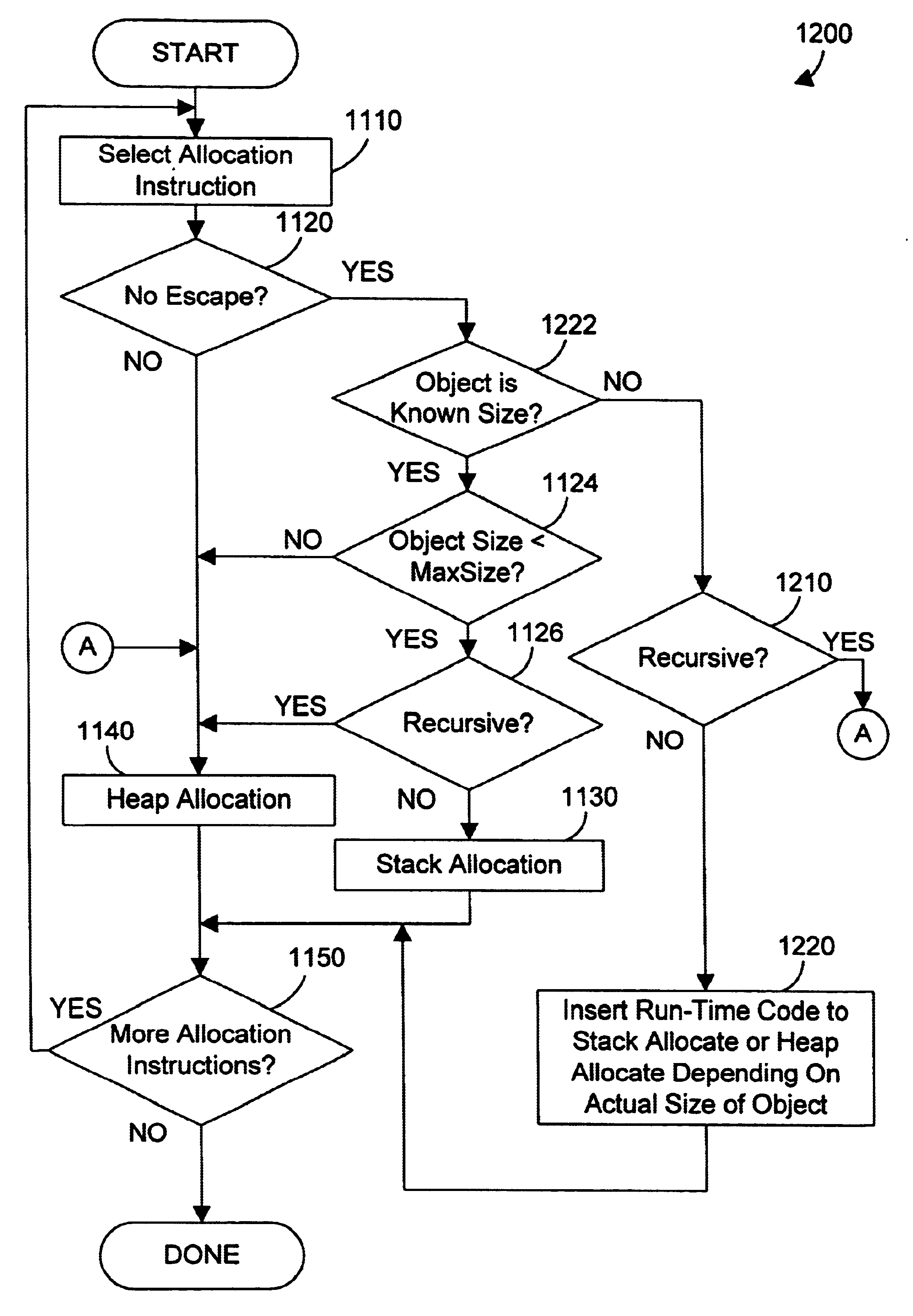
Object oriented apparatus and method for allocating objects on an invocation stack in a partial compilation environment
InactiveUS20020178437A1Protect dataImprove reusabilityExecution paradigmsSoftware simulation/interpretation/emulationProgramming languageEscape analysis
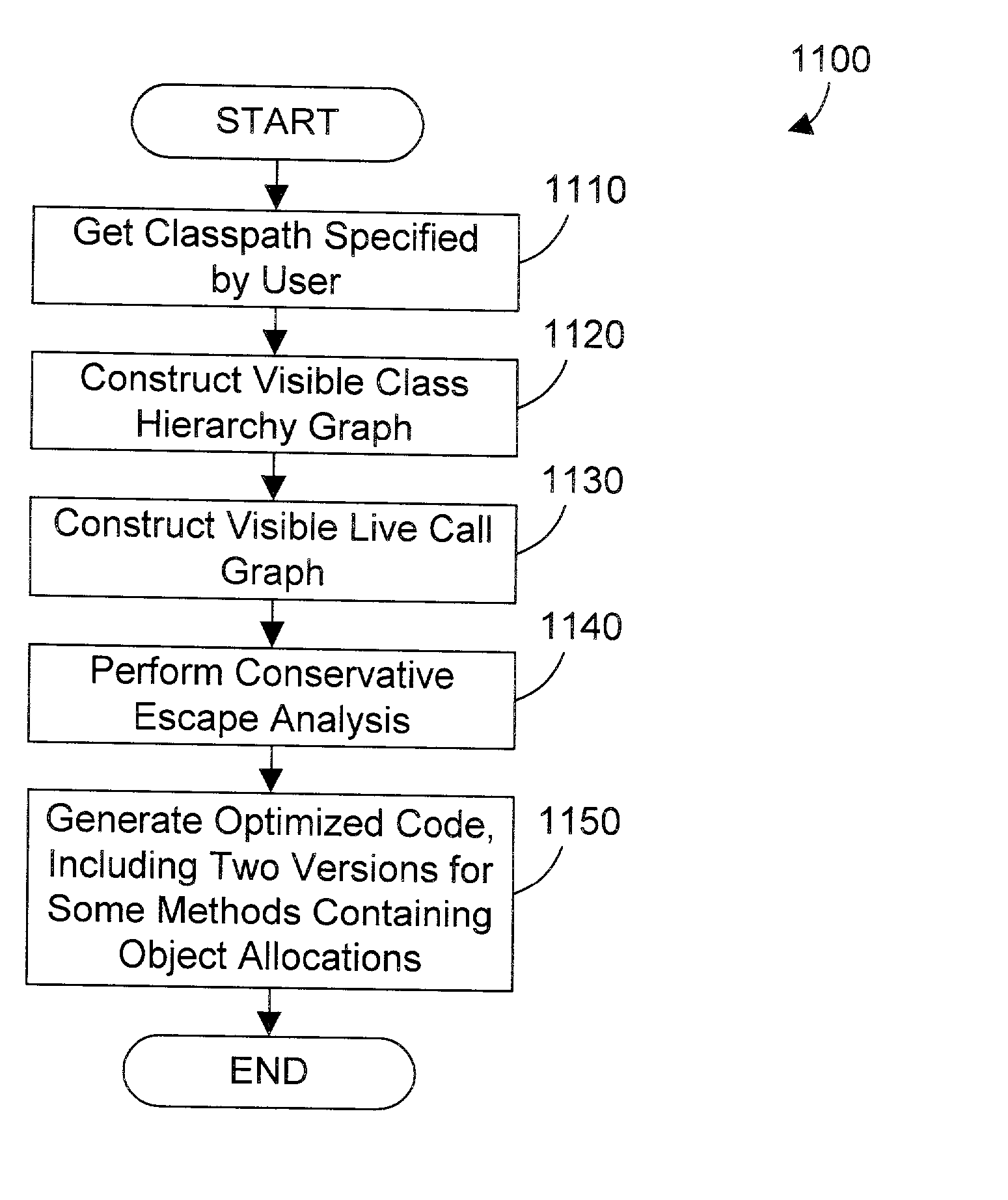
An object oriented mechanism and method allow allocating Java objects on a method's invocation stack in a partial compilation environment under certain conditions. Only the classes that are visible are taken into account when performing escape analysis in accordance with the preferred embodiments. In a first aspect of the invention, conservative assumptions are made to assure that objects are only allocated on an invocation stack when this can be proven safe by examining only those classes in the compilation unit. In a second aspect of the invention, the concept of visible classes is extended to include other classes that may be found from a user-defined classpath that matches the anticipated run-time classpath used to find classes during program execution. When stack allocation decisions for a method depends on such classes that are outside the compilation unit, two versions of run time code for that method are created. One version allocates all objects from the heap, whereas the other allocates some or all objects on the invocation stack. For each class outside the compilation unit that was examined when making stack allocation decisions for a method, information about the requisite class is stored with the method. At run time, the class loader verifies that the run time version of each requisite class matches all stored information about that class. If all information matches for all requisite classes, the version of the method using stack allocation is safe to use at run time. Otherwise, the method using heap allocation must be used.
Owner:IBM CORP
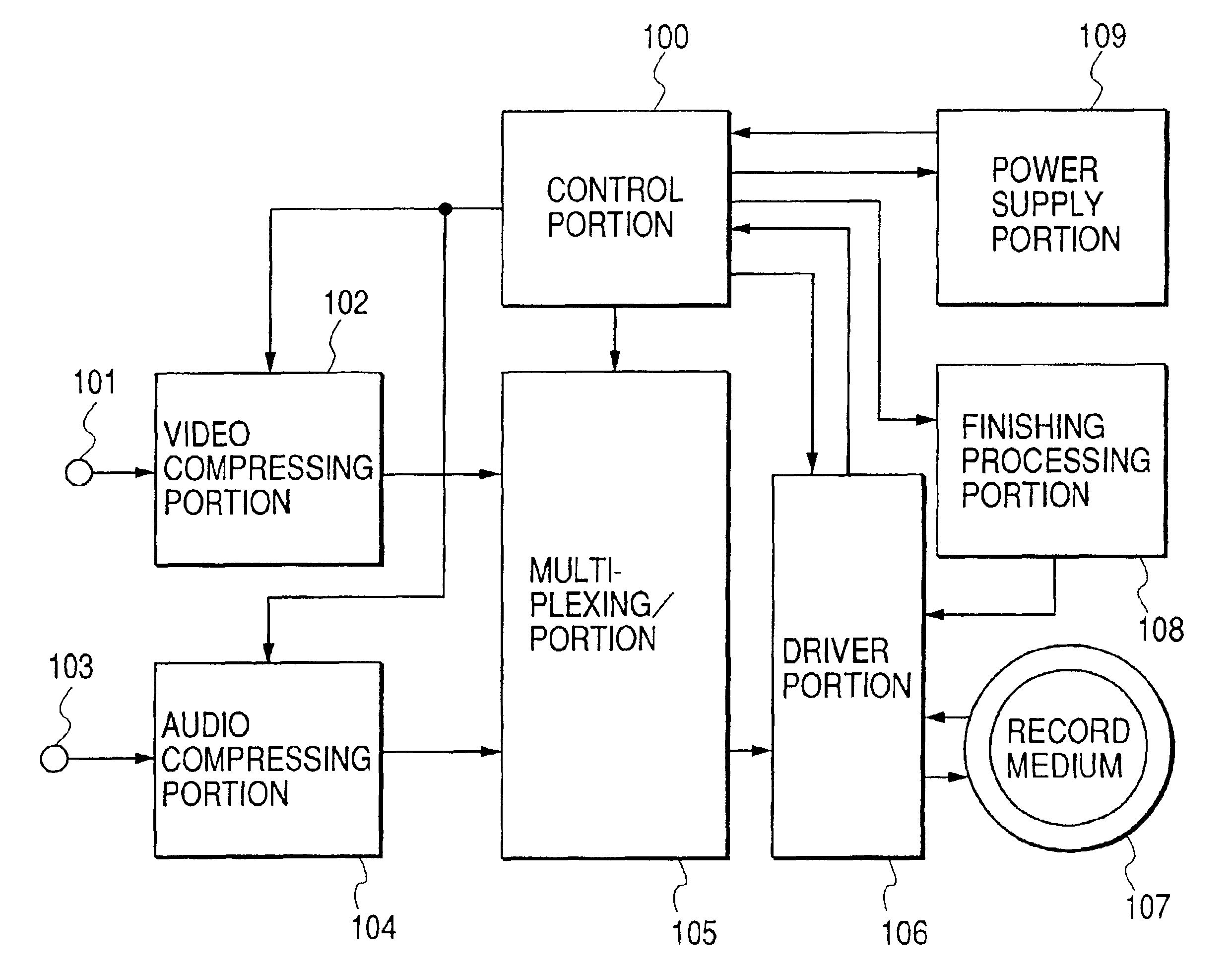
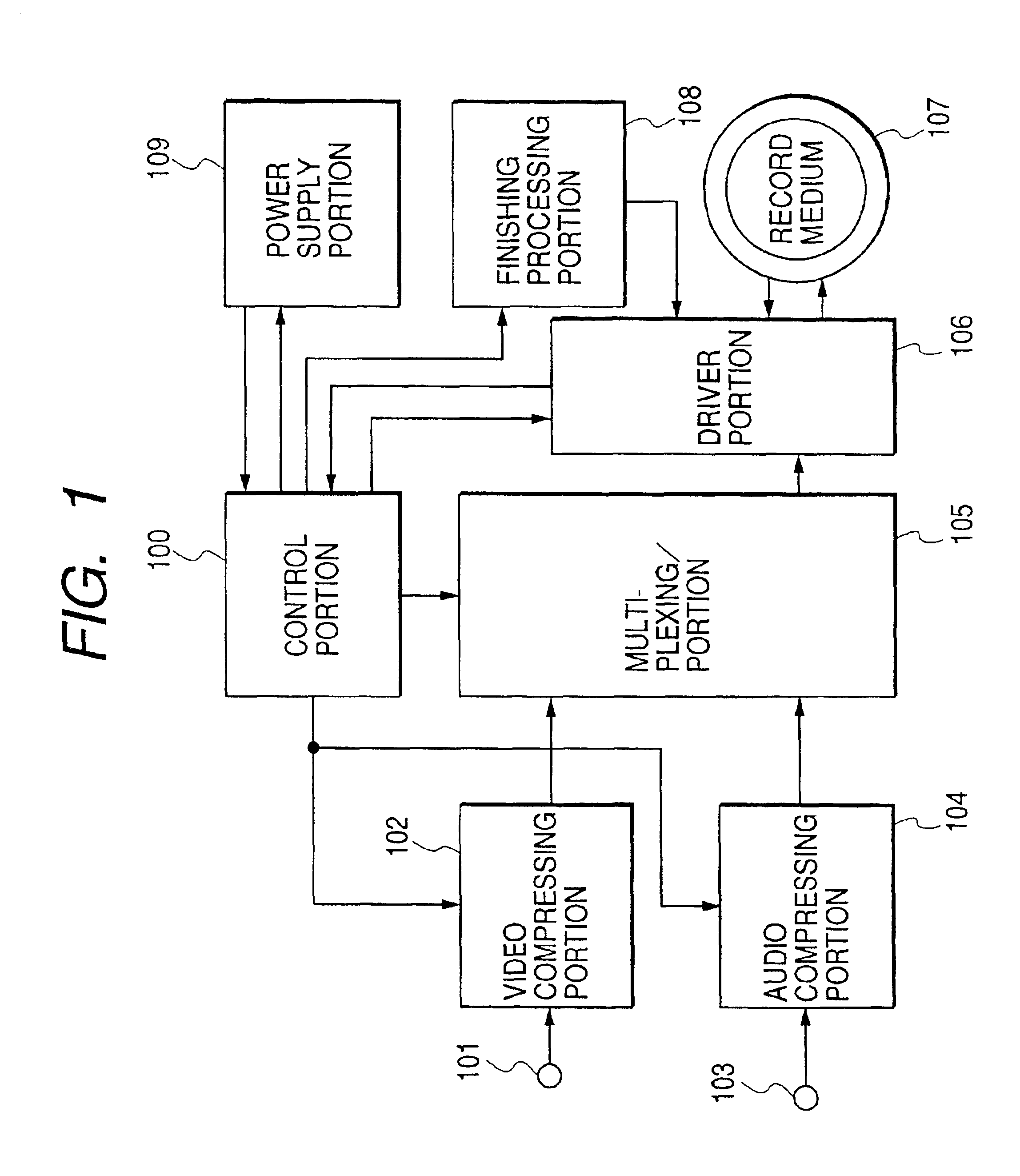
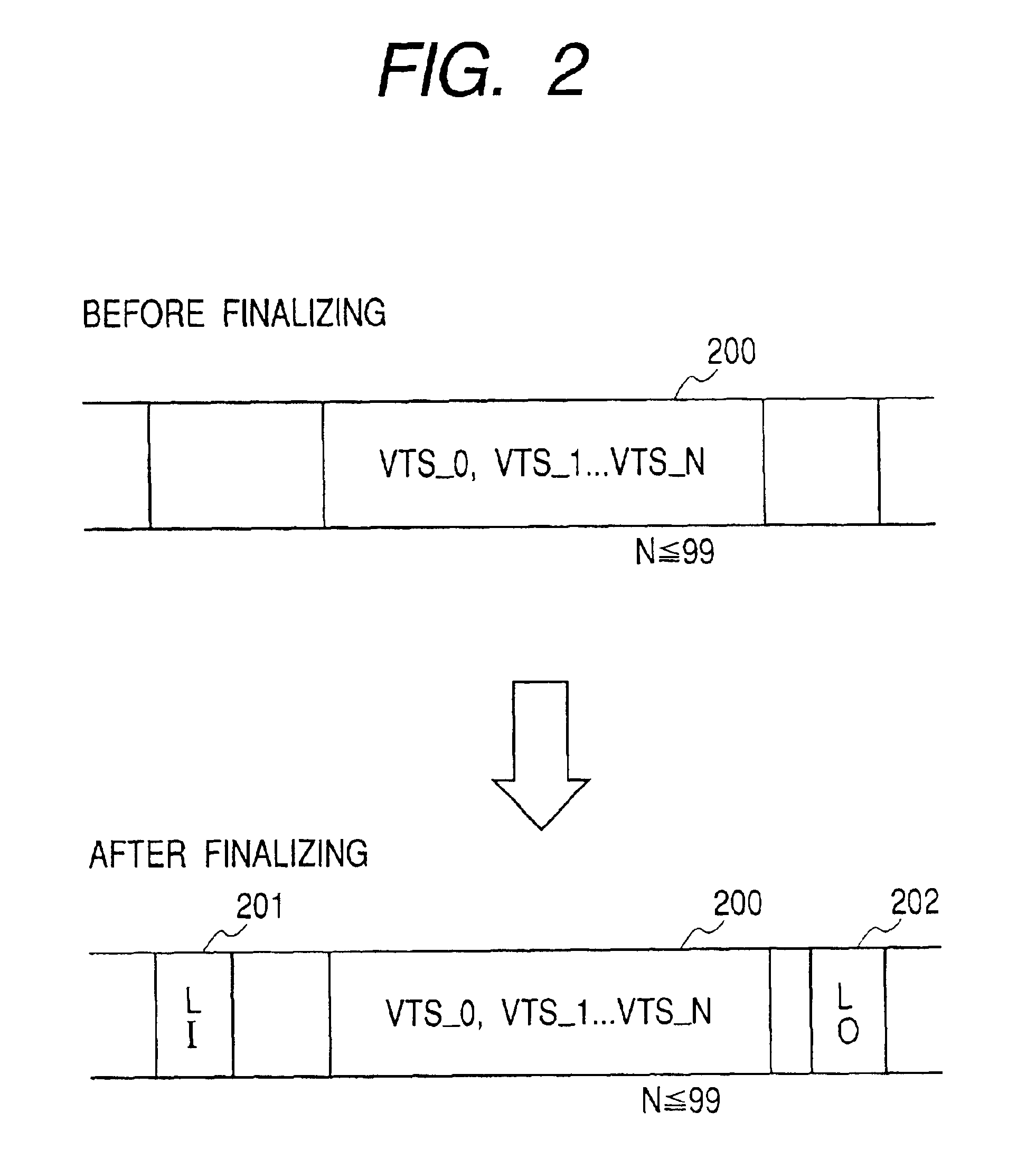
Information recording apparatus for modifying the finishing process based on the power supply
InactiveUS6894960B2Reliability be promoteAvoid failureRecord information storageDigital recordingMachining processComputer engineering
With an object of executing excellent finishing processing when information is recorded to a rewritable type record medium or a write once type record medium, the finishing processing is switched by whether a kind of a medium for recording information is the rewritable type record medium or the write once type record medium and a method of executing the finishing processing is switched based on a state of supplying power.
Owner:MAXELL HLDG LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com