Patents
Literature
1245results about How to "Improve data security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
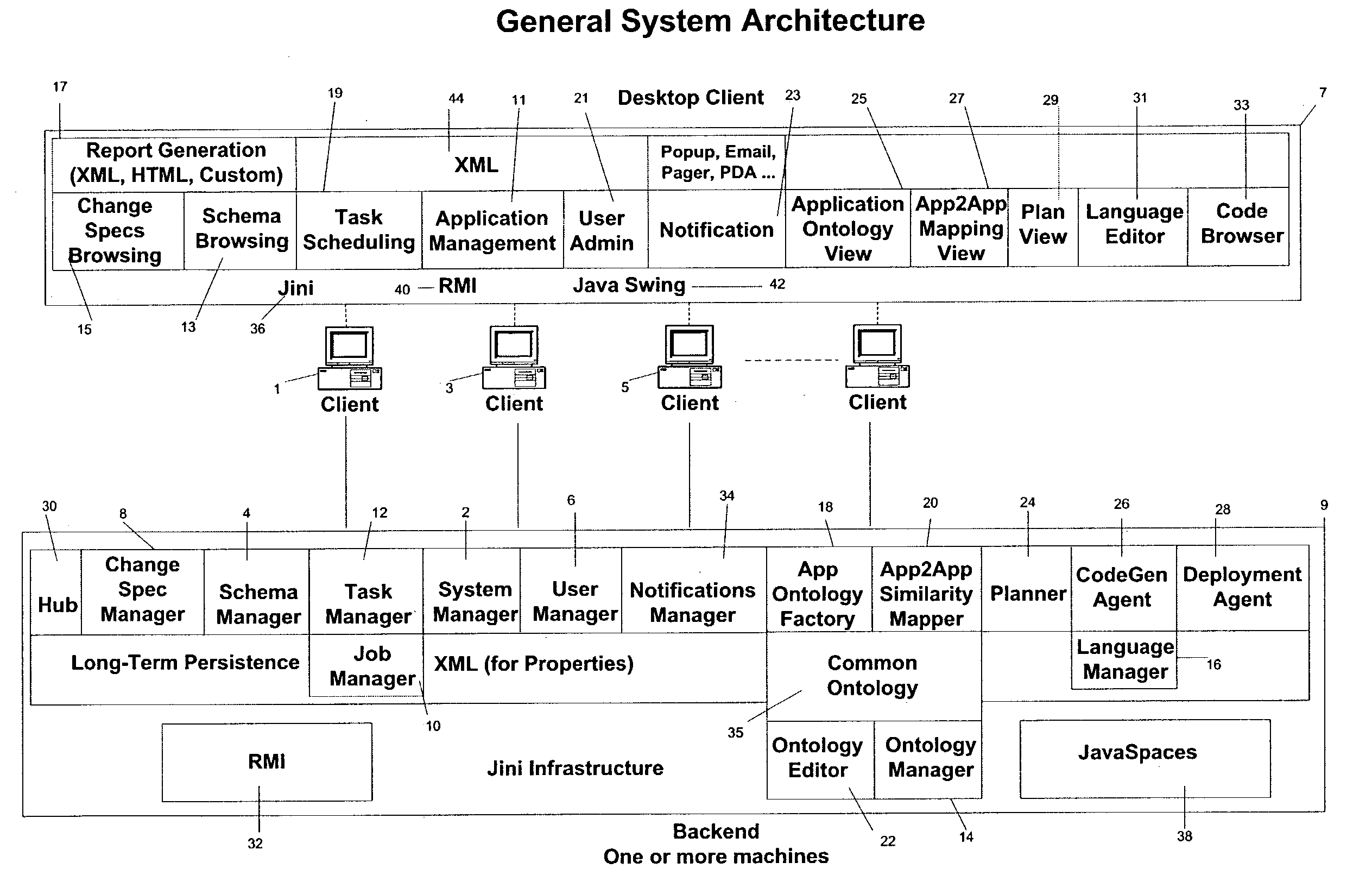
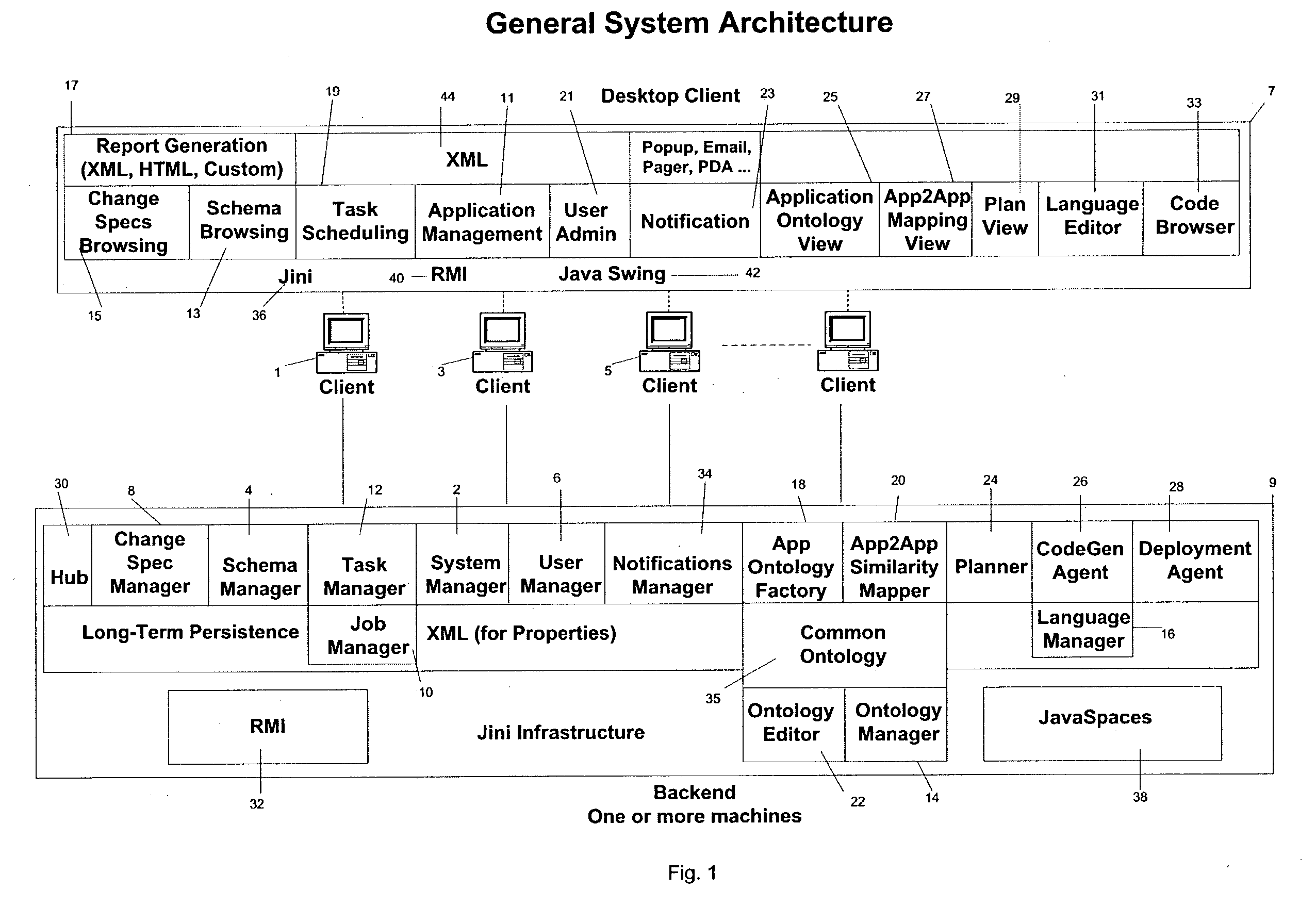
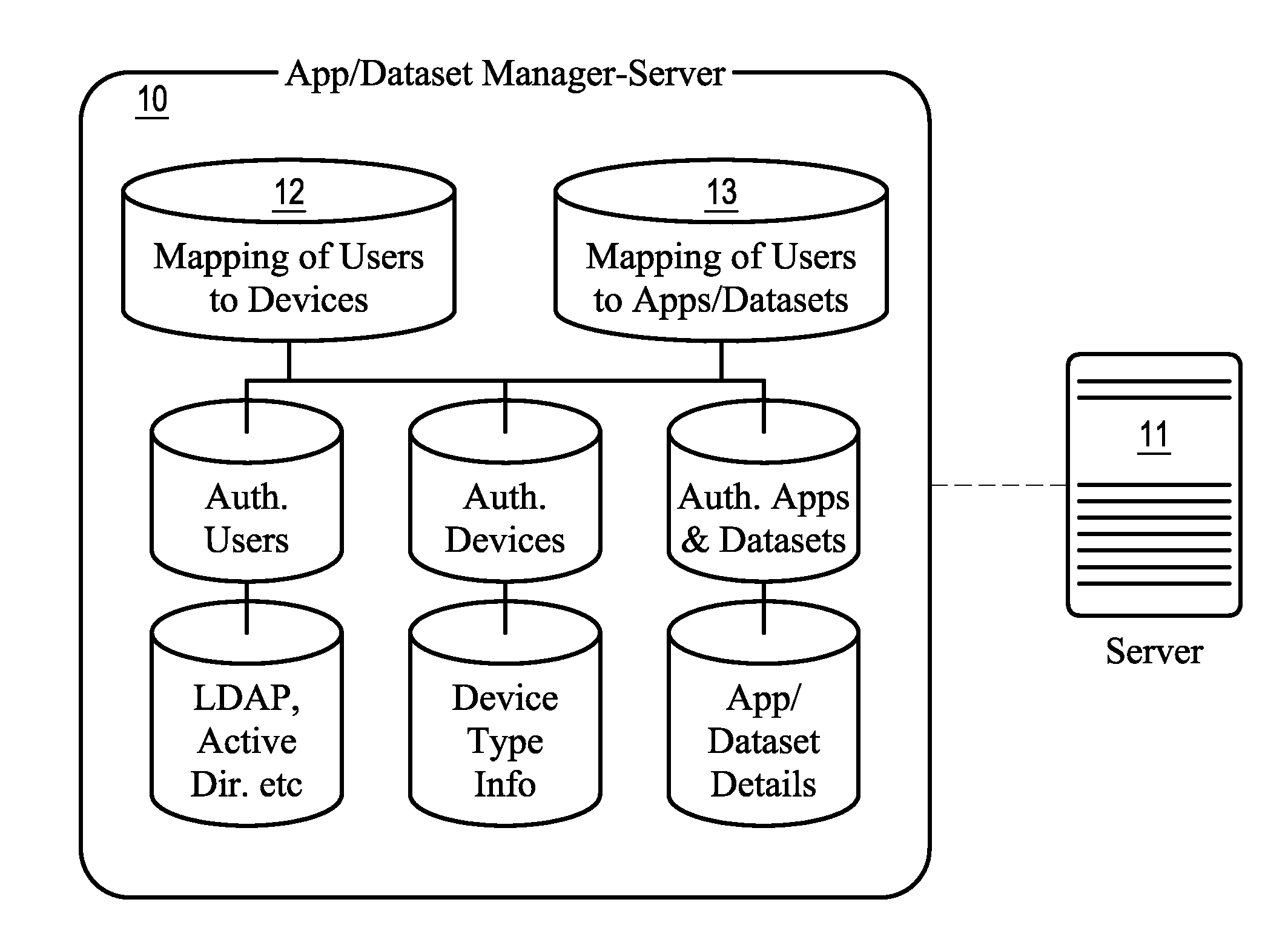
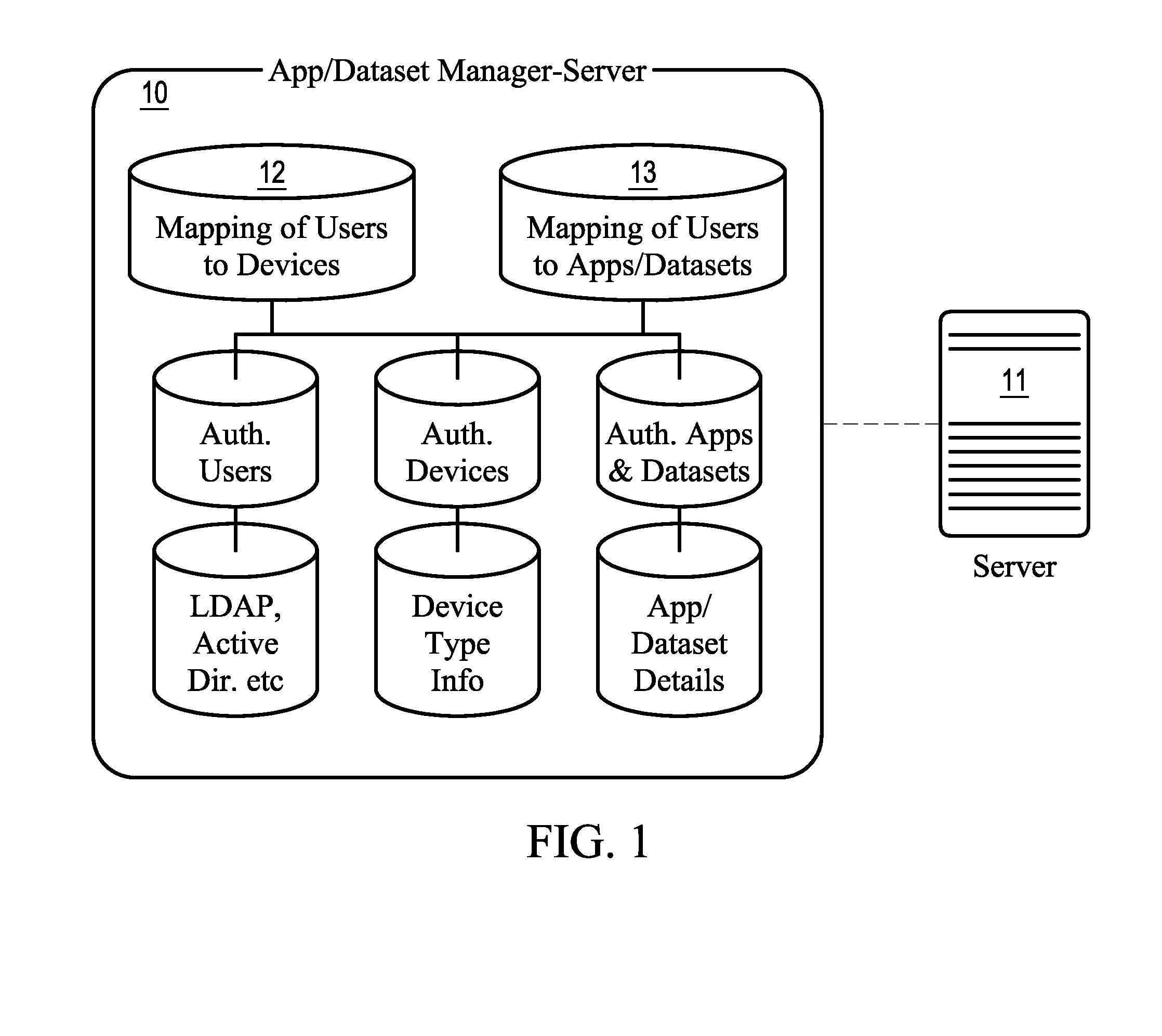
System and method for autonomously generating heterogeneous data source interoperability bridges based on semantic modeling derived from self adapting ontology
InactiveUS20030172368A1Reduce dependenceImprove data securityVersion controlKnowledge representationTime errorData source
A system, including software components, that efficiently and dynamically analyzes changes to data sources, including application programs, within an integration environment and simultaneously re-codes dynamic adapters between the data sources is disclosed. The system also monitors at least two of said data sources to detect similarities within the data structures of said data sources and generates new dynamic adapters to integrate said at least two of said data sources. The system also provides real time error validation of dynamic adapters as well as performance optimization of newly created dynamic adapters that have been generated under changing environmental conditions.
Owner:COMPASS AL INC +1
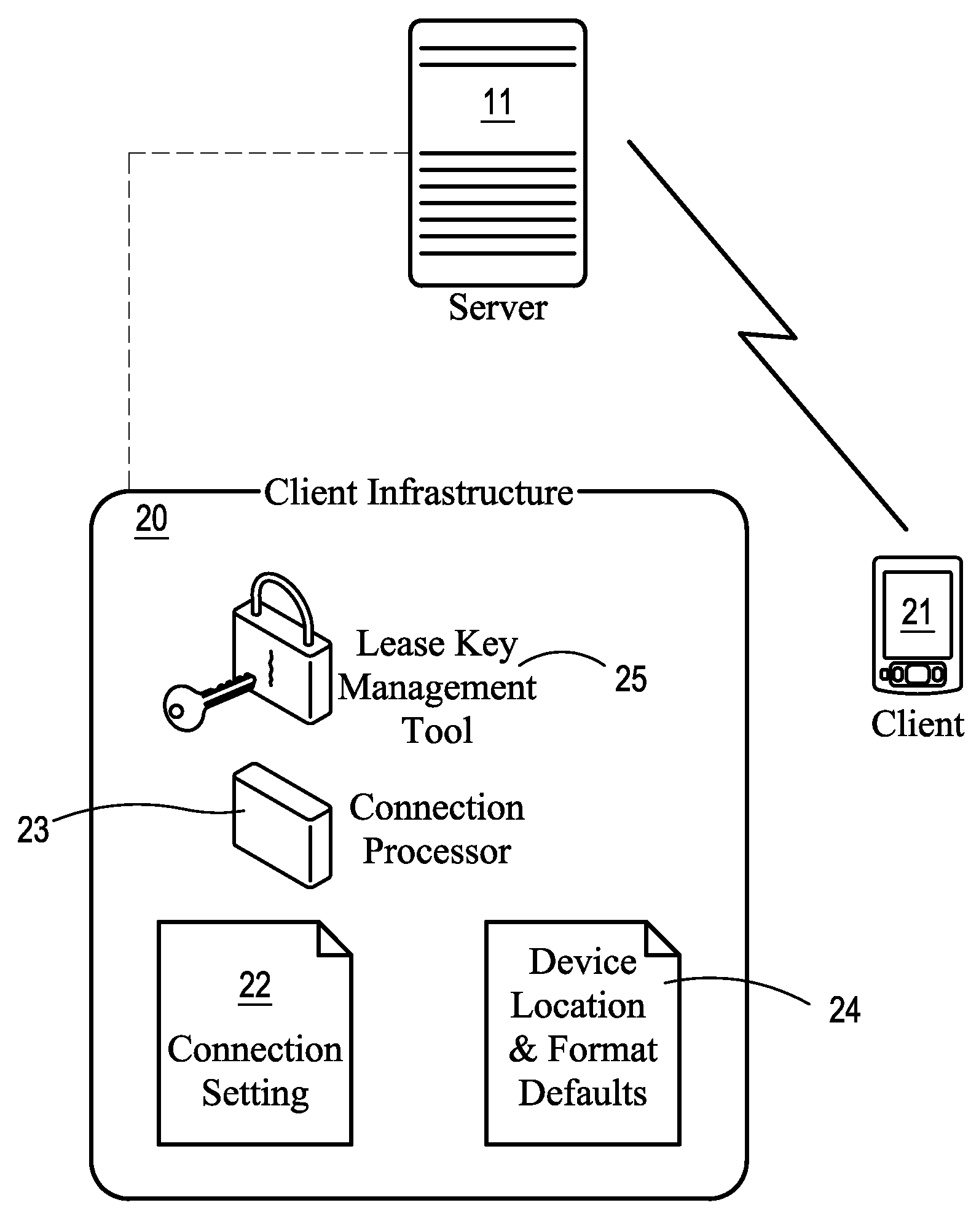
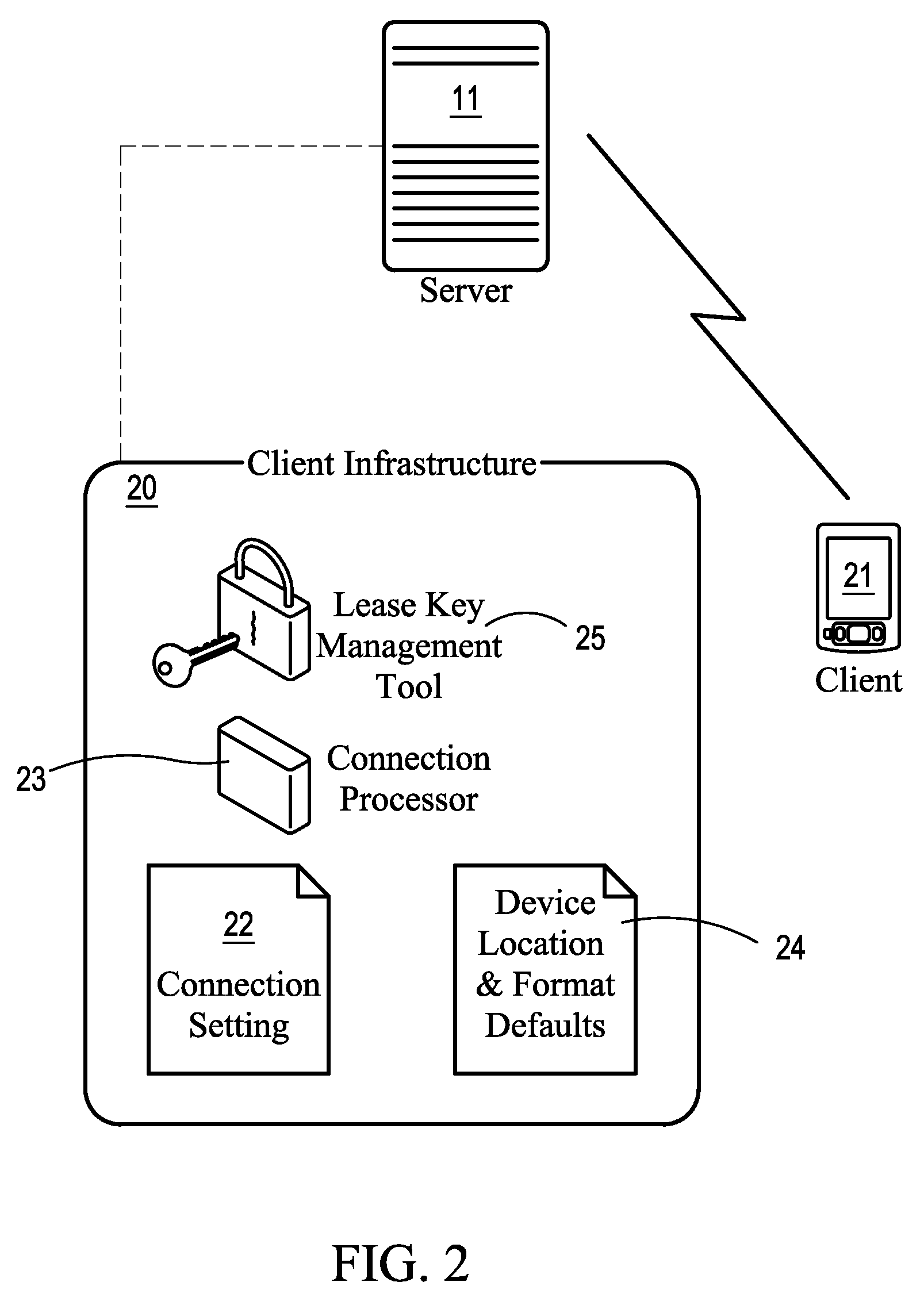
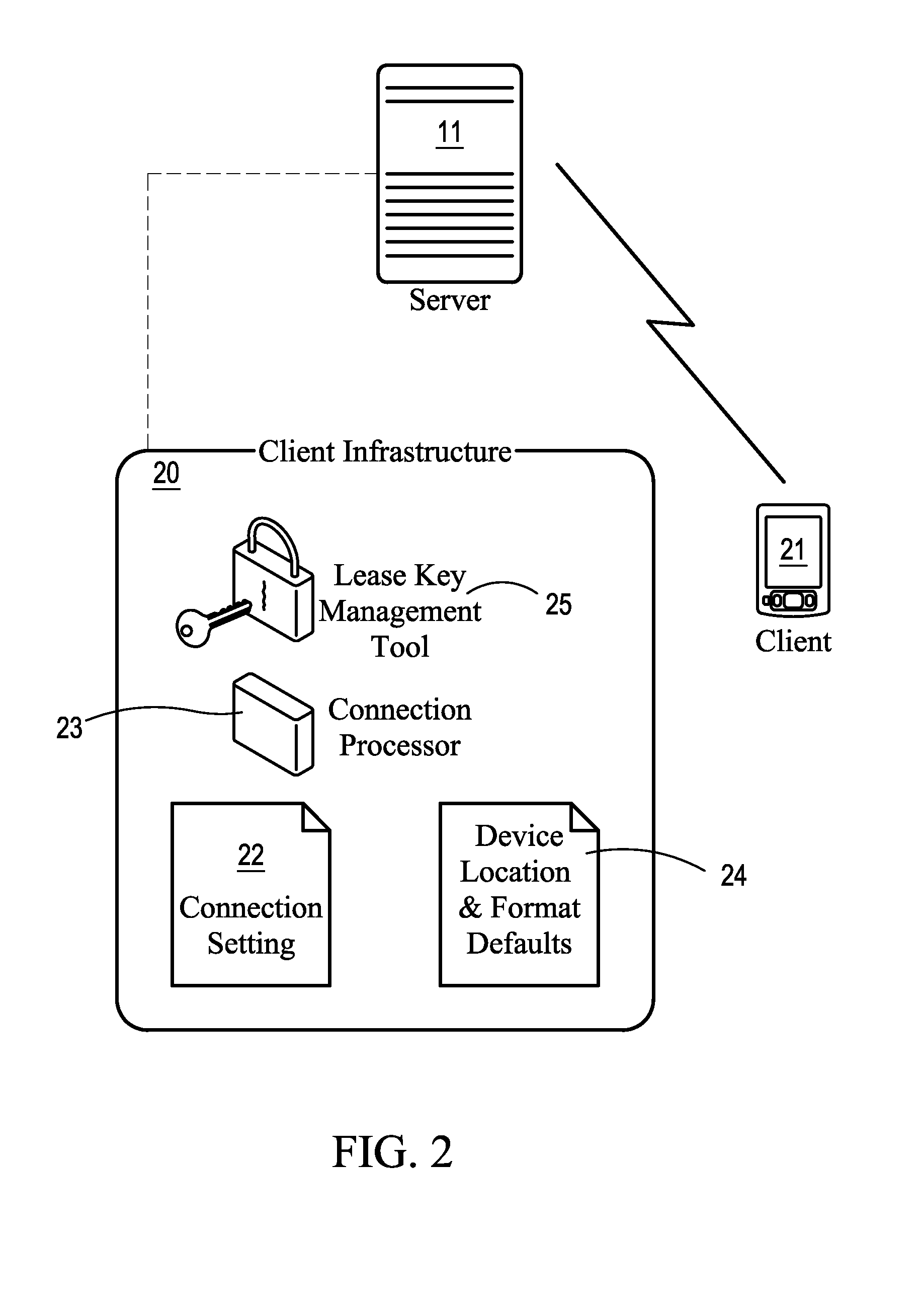
System for providing mobile data security
ActiveUS7917963B2Save bandwidthShorten the timeDigital data processing detailsAnalogue secracy/subscription systemsData setData security
Owner:VAULTUS MOBILE TECH
System for providing mobile data security
ActiveUS20080134347A1Save bandwidthShorten the timeDigital data processing detailsAnalogue secracy/subscription systemsData setClient-side
A system transfers applications and datasets (files) from a server to a client device and assigns to each file a lease key that will expire at a specified time. A file cannot be accessed unless its lease key is validated. Upon expiration of a lease key, the client device will connect to the server to determine if the lease key may be renewed. If the lease key may be renewed, a new lease key is created and access to the associated application or dataset is restored. If the lease key may not be renewed, the file may be deleted or rendered inaccessible. If rendered inaccessible, the file may be restored in the future without having to re-transmit it from the server to the client device. The server may also revoke a lease key before it expires.
Owner:VAULTUS MOBILE TECH
Security method and apparatus for controlling the data exchange on handheld computers
InactiveUS7346778B1Avoid accessTransparent to userDigital data processing detailsUnauthorized memory use protectionData transmissionAuthorization
A method and system for protecting portable computer data from unauthorized transfer or using portable computers to download unauthorized data. The invention is applicable to any computer capable of transferring data, but in one embodiment a portable computer is described. Authorization is enabled by an interface permitting synchronization of the portable computer with a host computer by authentication of the particular portable computer identity. For instance, in one embodiment, when a portable computer is docked with a compatible interface connected to a host desktop computer, it is sensed and identified by the interface. If the particular portable computer identity is authenticated as authorized for that desktop, then synchronization will be enabled by the interface. The computers may then transfer data. However, if the identity is not an authorized one, then authentication will not occur, synchronization is correspondingly disabled, and data transfer is prevented. Various systems can enable the identity authentication.
Owner:ACCESS
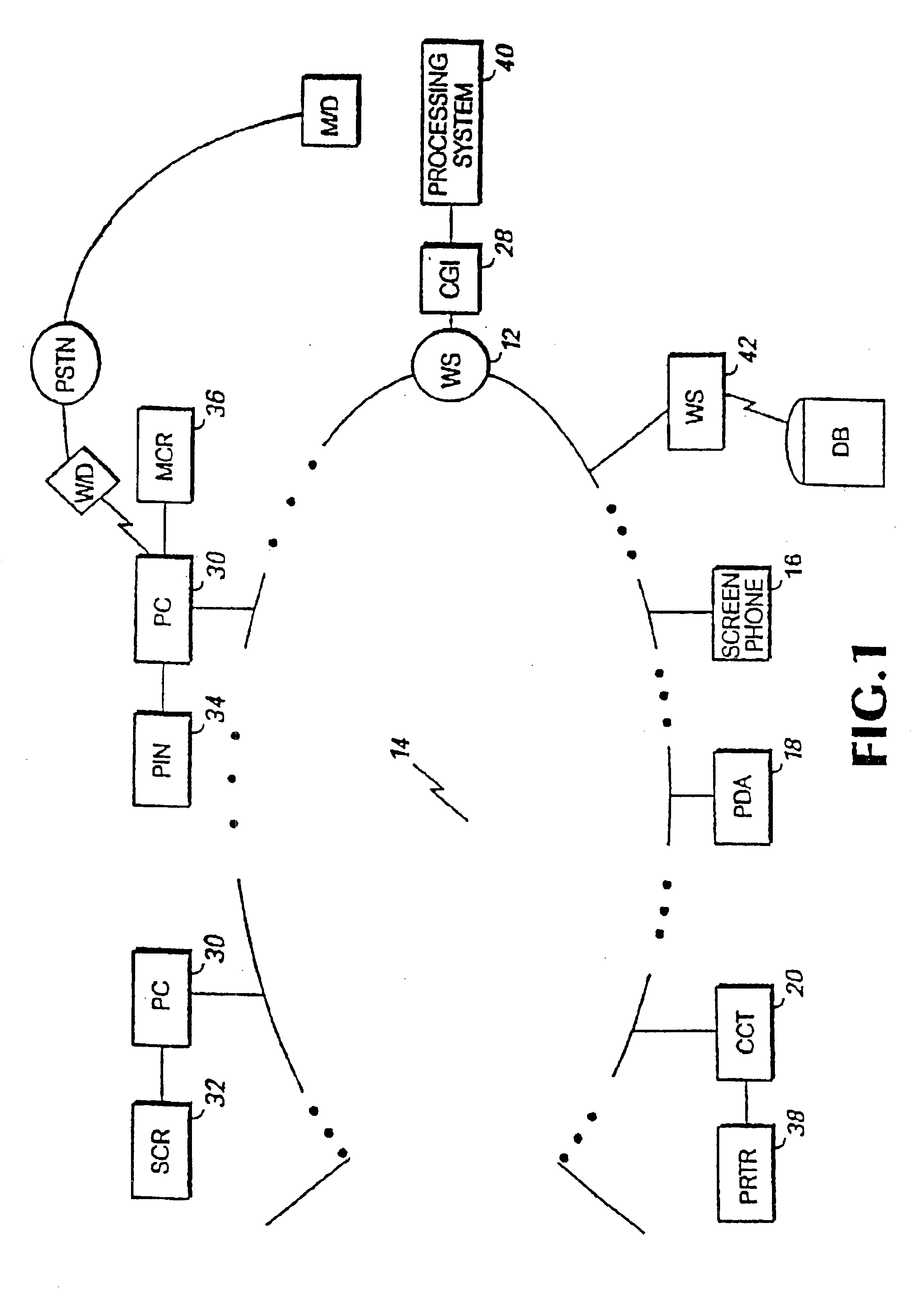
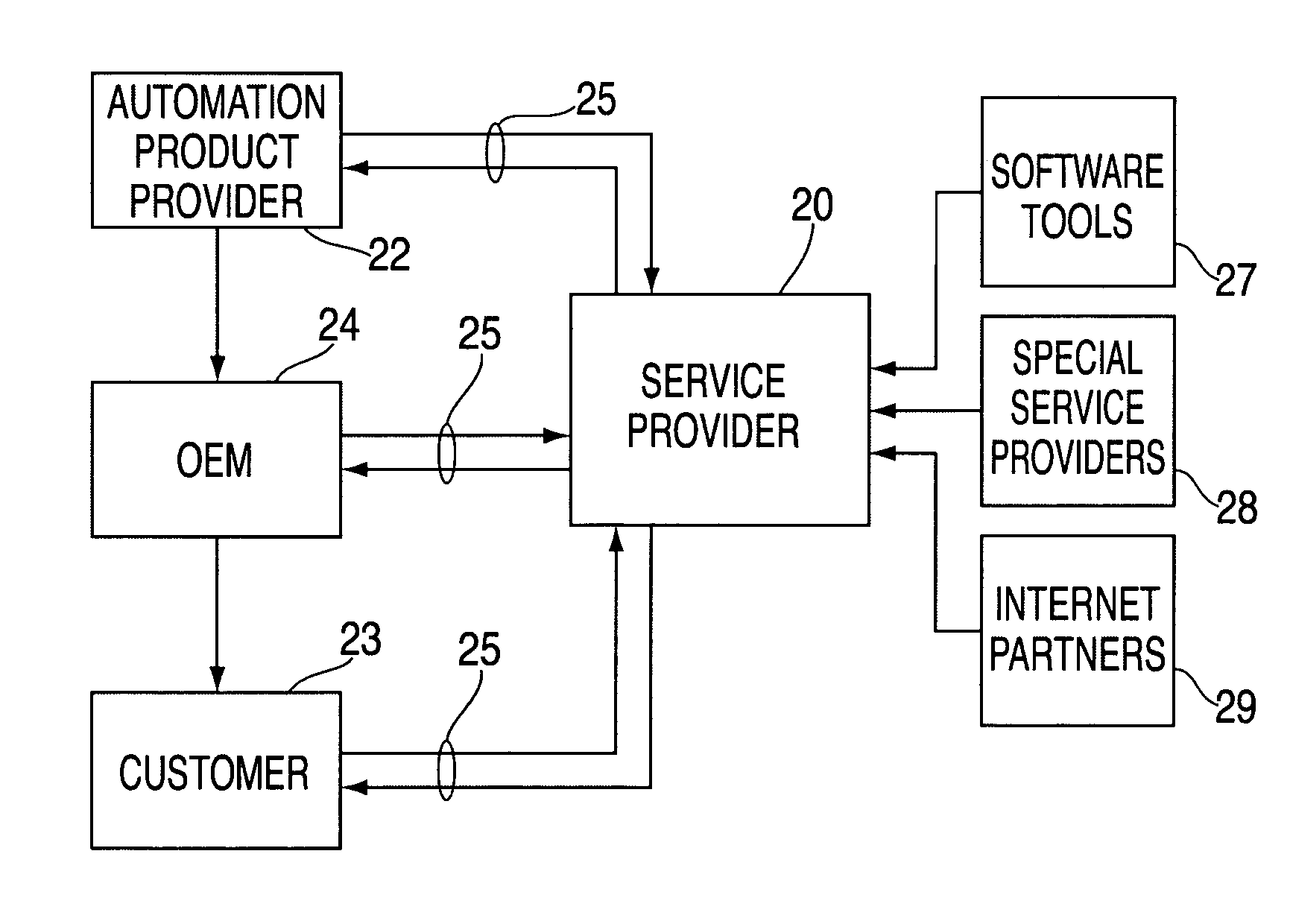
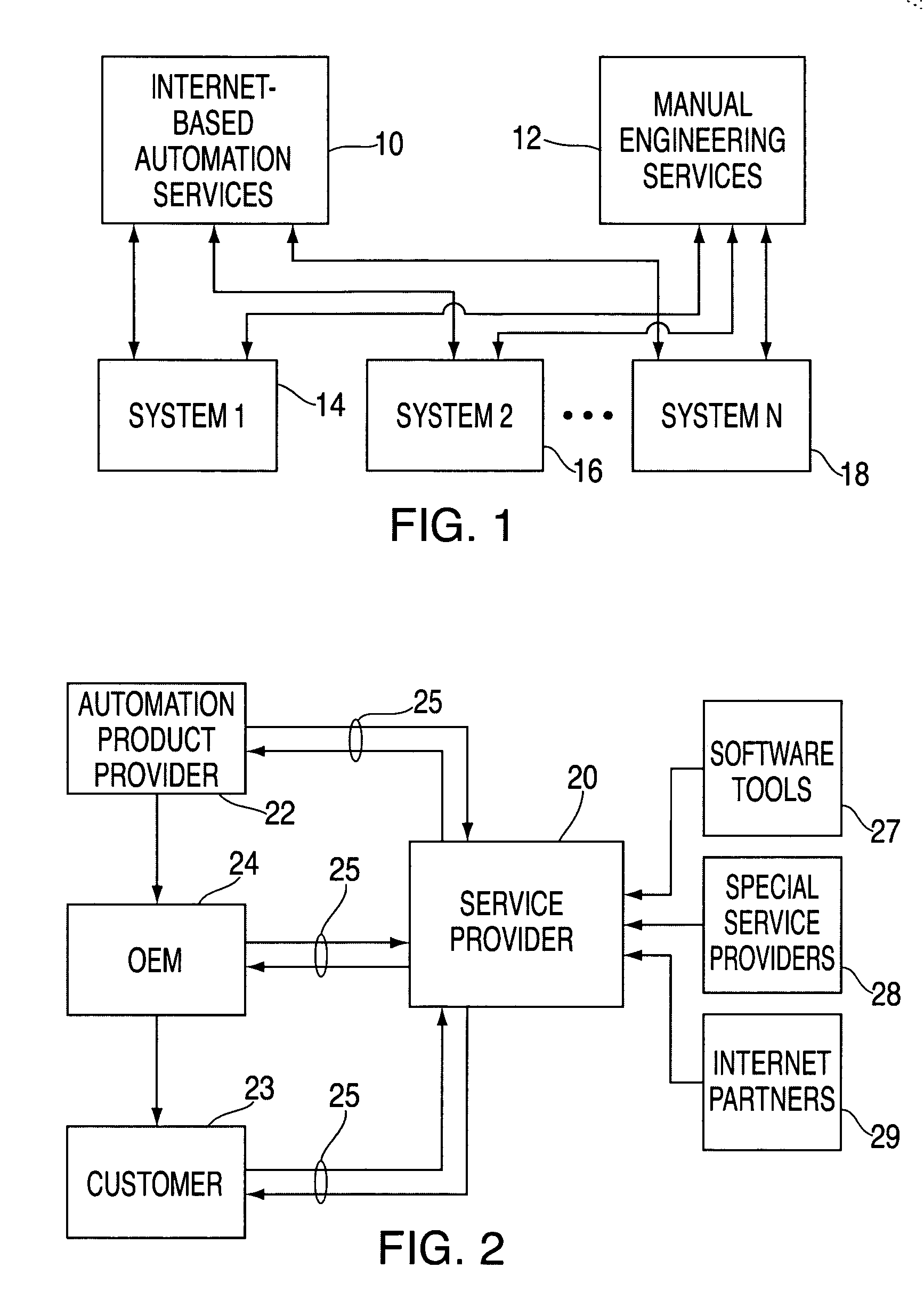
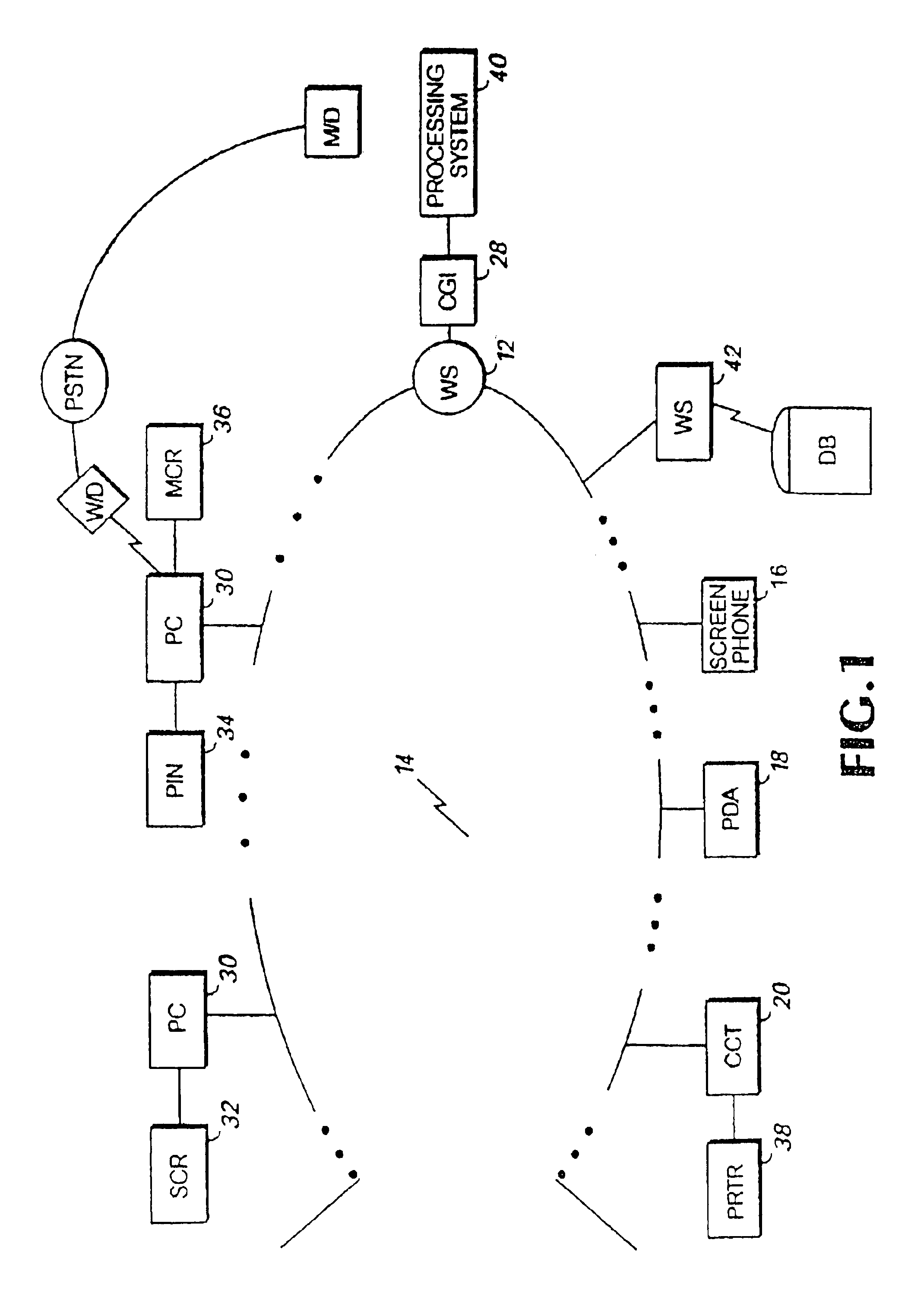
System and method for enabling transactions between a web server and an automated teller machine over the internet
InactiveUS6850996B2Reduce the risk of fraudInformation receivedDigital data processing detailsMultiple digital computer combinationsComputer networkComputer interpretation
An automated teller machine (ATM) implements financial transactions over the Internet. The ATM includes a computer and at least one non-standard I / O device coupled to the computer. The computer of the ATM interprets extended open network protocol statements to control the non-standard I / O device for purposes of implementing a financial transaction.
Owner:WI LAN TECH INC
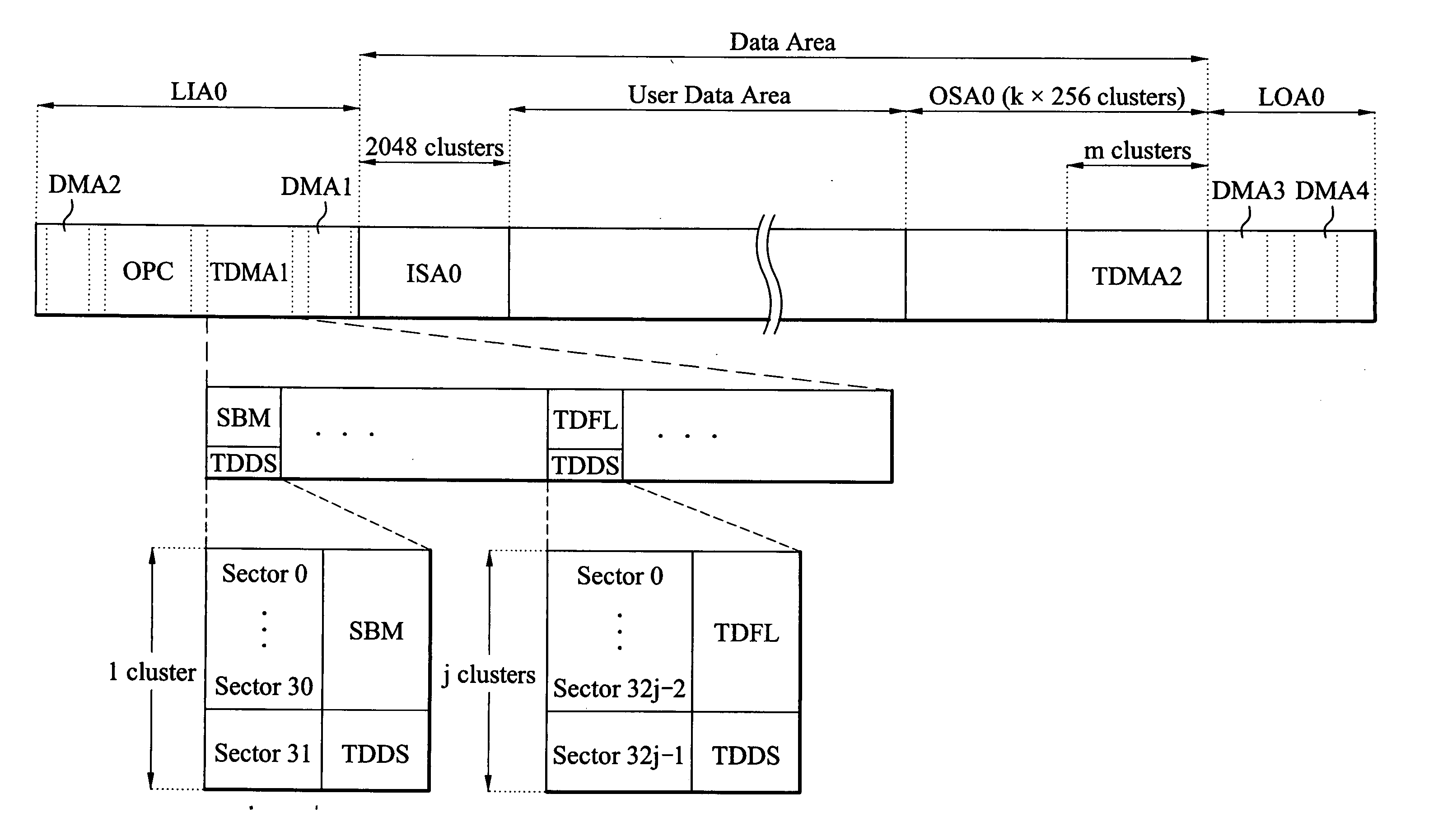
Method for recording on optical recording medium and apparatus using the same
ActiveUS20040174793A1Efficient managementImprove data integrityTelevision system detailsDisc-shaped record carriersInformation controlRecord status
A method and apparatus for recording on an optical recording medium, including the recording of management information, are described as a standard for the write-once Blu-ray disc. The management information is recorded in a management area of the disc, such as a temporary defect management area (TDMA), and includes record status information and update information. The record status information is a space bitmap (SBM) indicating whether a recording operation has been performed for a predetermined area of the disc, and the update information is SBM update information indicating whether the record status information is to be continuously managed. The SBM update information controls the state of an SBM-on / off function for each of a plurality of recording areas and may be in the form of either start position information and length information corresponding to the respective areas or an SBM update flag. The SBM update information is recorded in the TDMA and is stored in a memory of an optical disc recording / reproducing device for use during recording and reproducing operations. At the time of recording in the predetermined area, an SBM-on state enables a logical overwriting operation to be performed as necessary.
Owner:LG ELECTRONICS INC
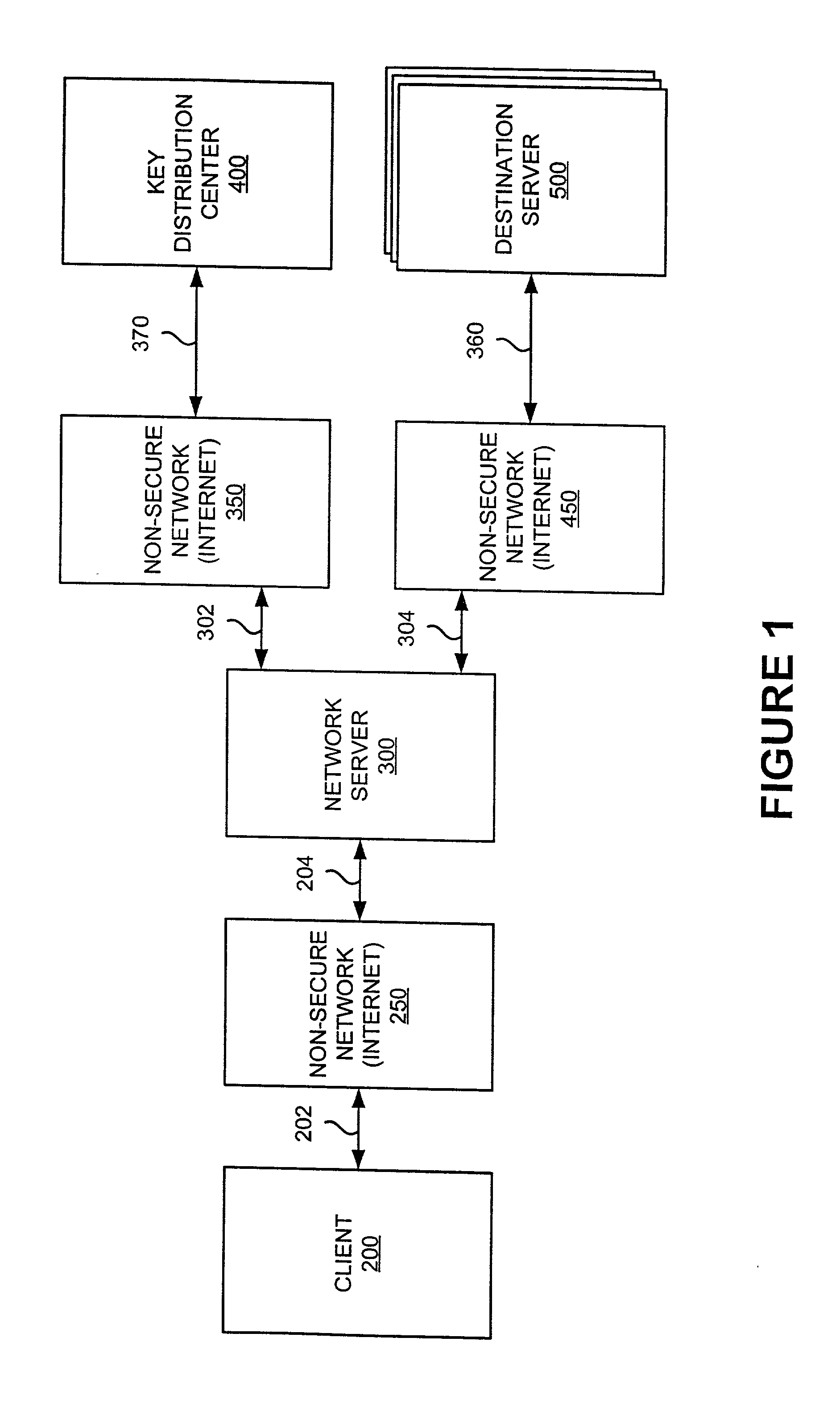
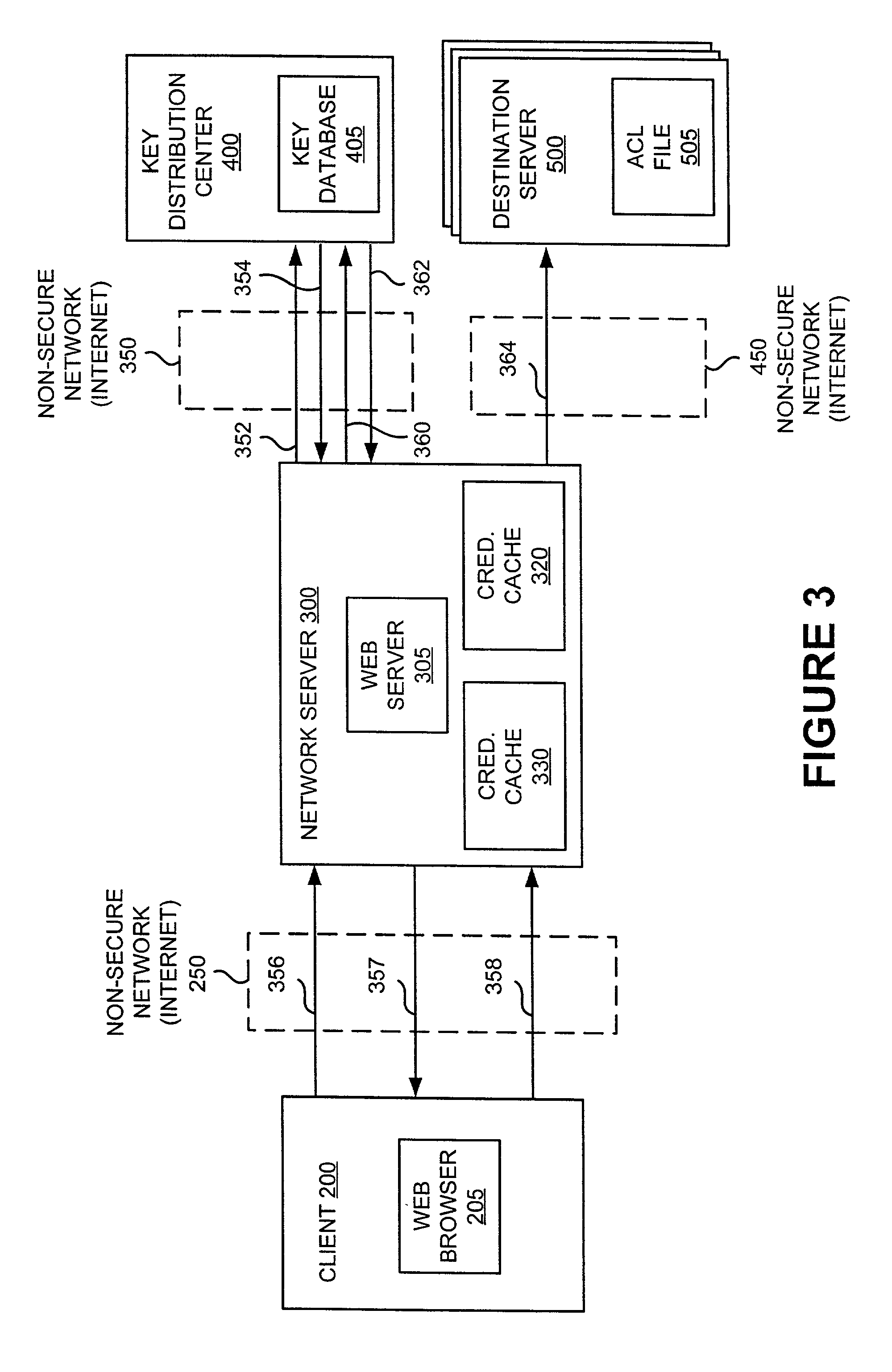
Platform-neutral system and method for providing secure remote operations over an insecure computer network
InactiveUS20010020274A1Improve securityImprove data securityKey distribution for secure communicationDigital data processing detailsClient-sideNetwork service
A method, system and computer program product are disclosed for enhancing the security of a message sent through a network server from a client computer to a destination server running any computer platform. Credentials for authorizing a principal are obtained by the client computer from a validation center. The principal-authentication information is transmitted to the network server. The network server may use the principal-authenticating information to obtain permission data from the validation center for use in accessing the destination server. Also described is a method of providing a remote interactive login connection using the same method.
Owner:HANGER SOLUTIONS LLC
Data protection management apparatus and data protection management method
InactiveUS20060173787A1Improve data securityData can be usedData processing applicationsError detection/correctionComputer securityLicensure
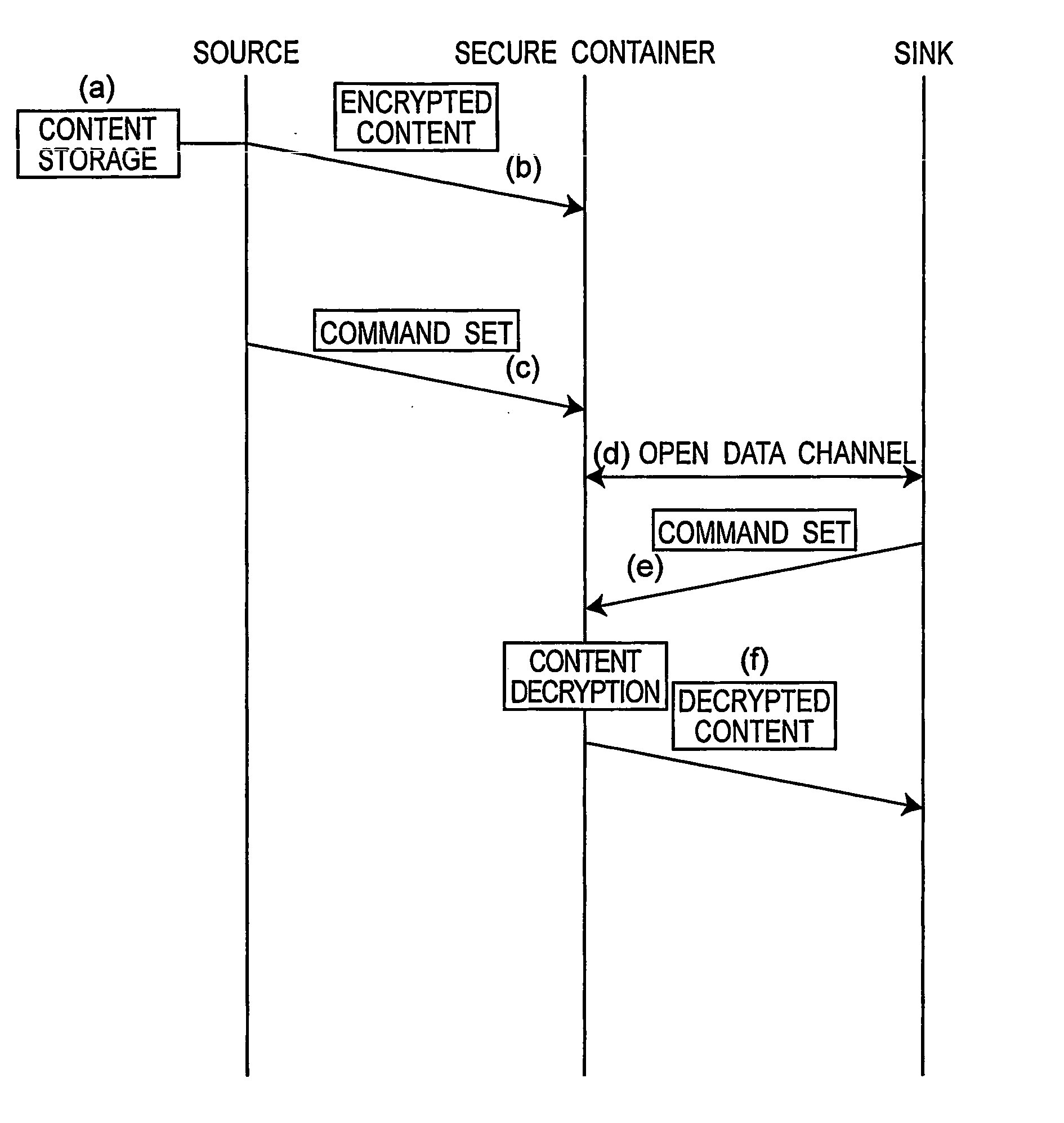
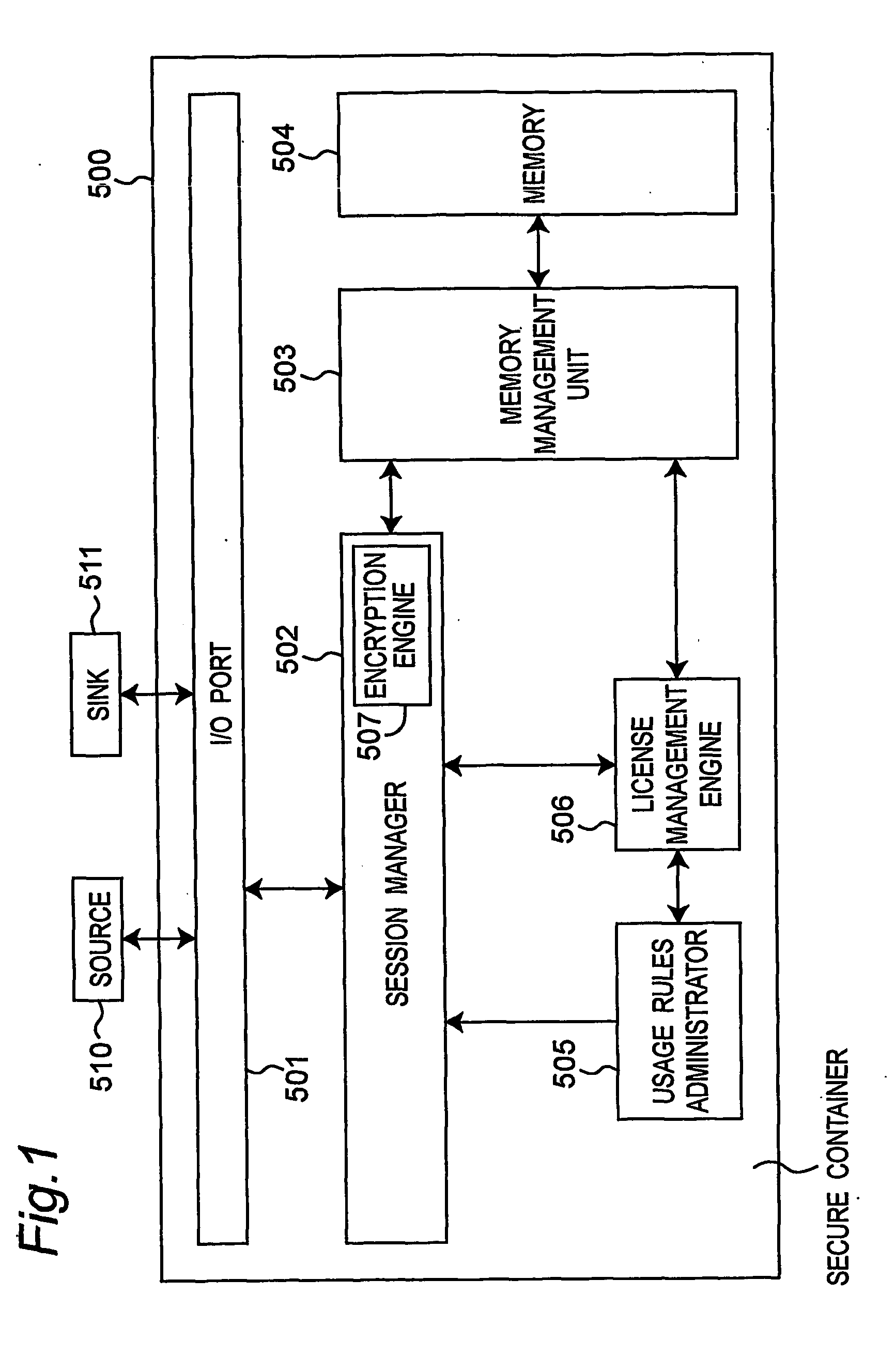
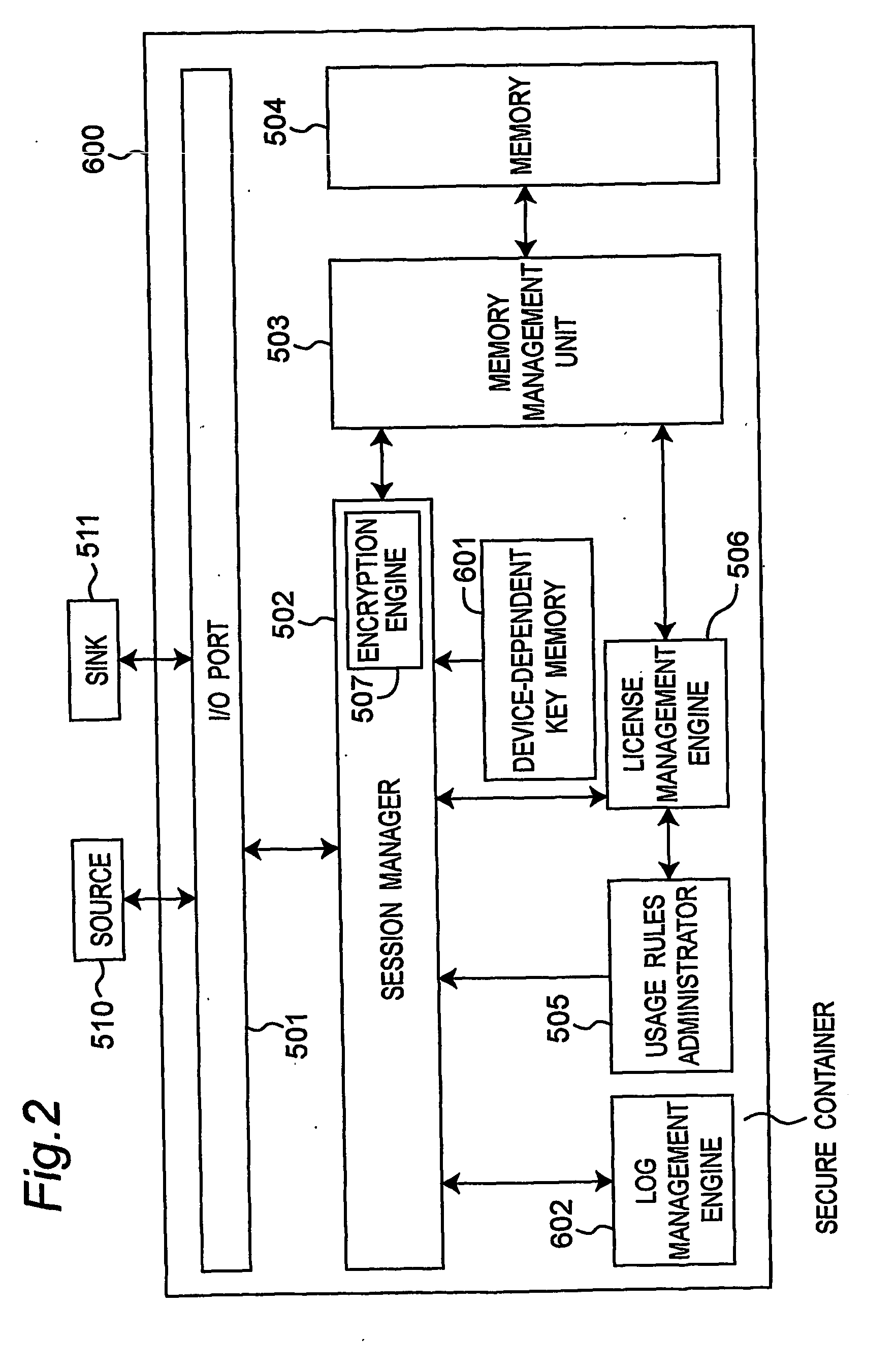
The data protection management apparatus protects digital licenses and digital data, so that the abuse and illegal use of digital data is prevented. The apparatus has an I / O port, session manager, license management engine, usage rules administrator, encryption engine, memory manager, and memory. The license management engine acquires, stores, and manages licenses in sessions opened by the session manager, and the usage rules administrator provides an encryption algorithm and protocol for securely storing and sending digital license data by applying the usage rules to the use of licenses managed by the license management engine.
Owner:PANASONIC CORP
Device for reproducing data
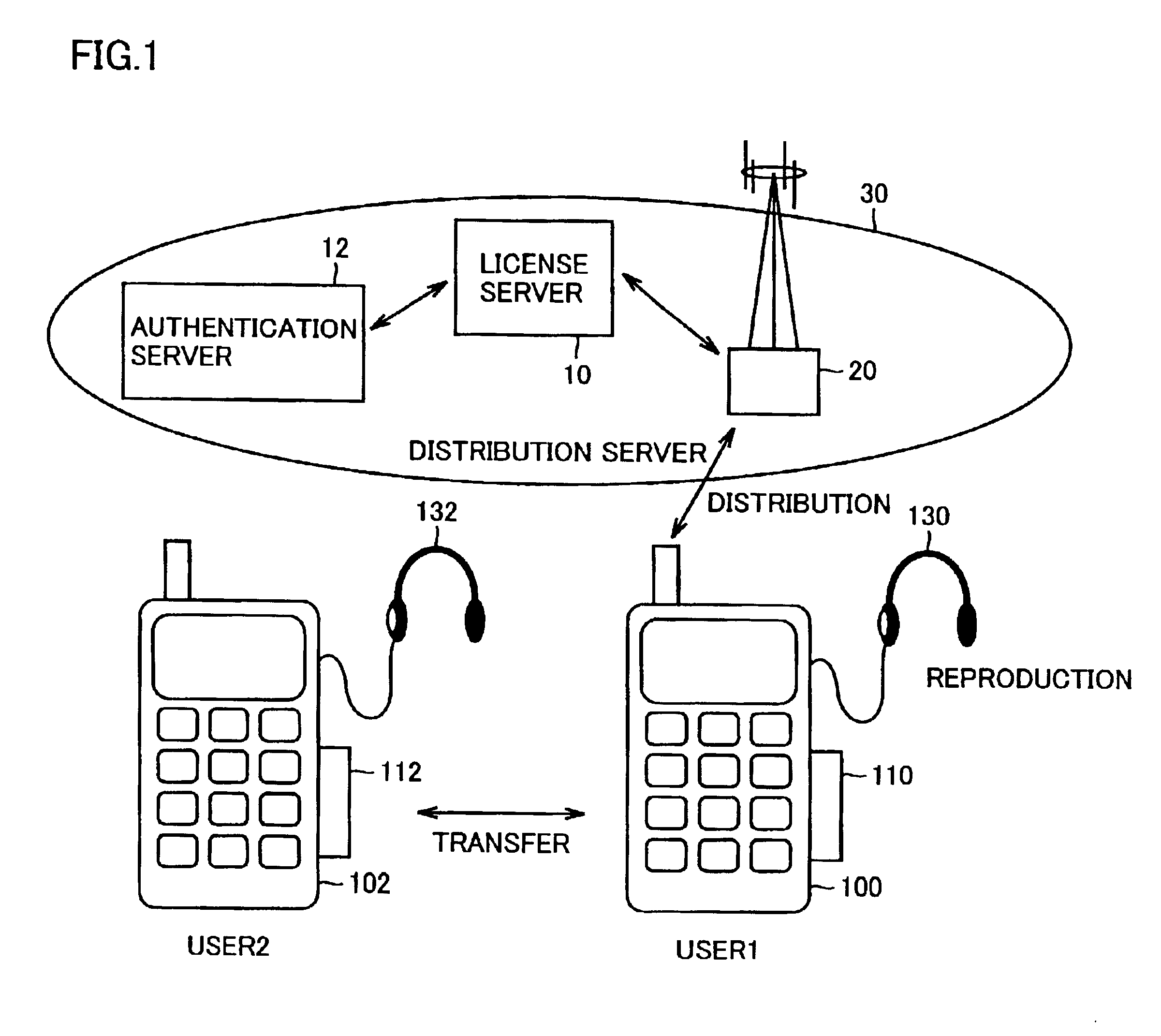
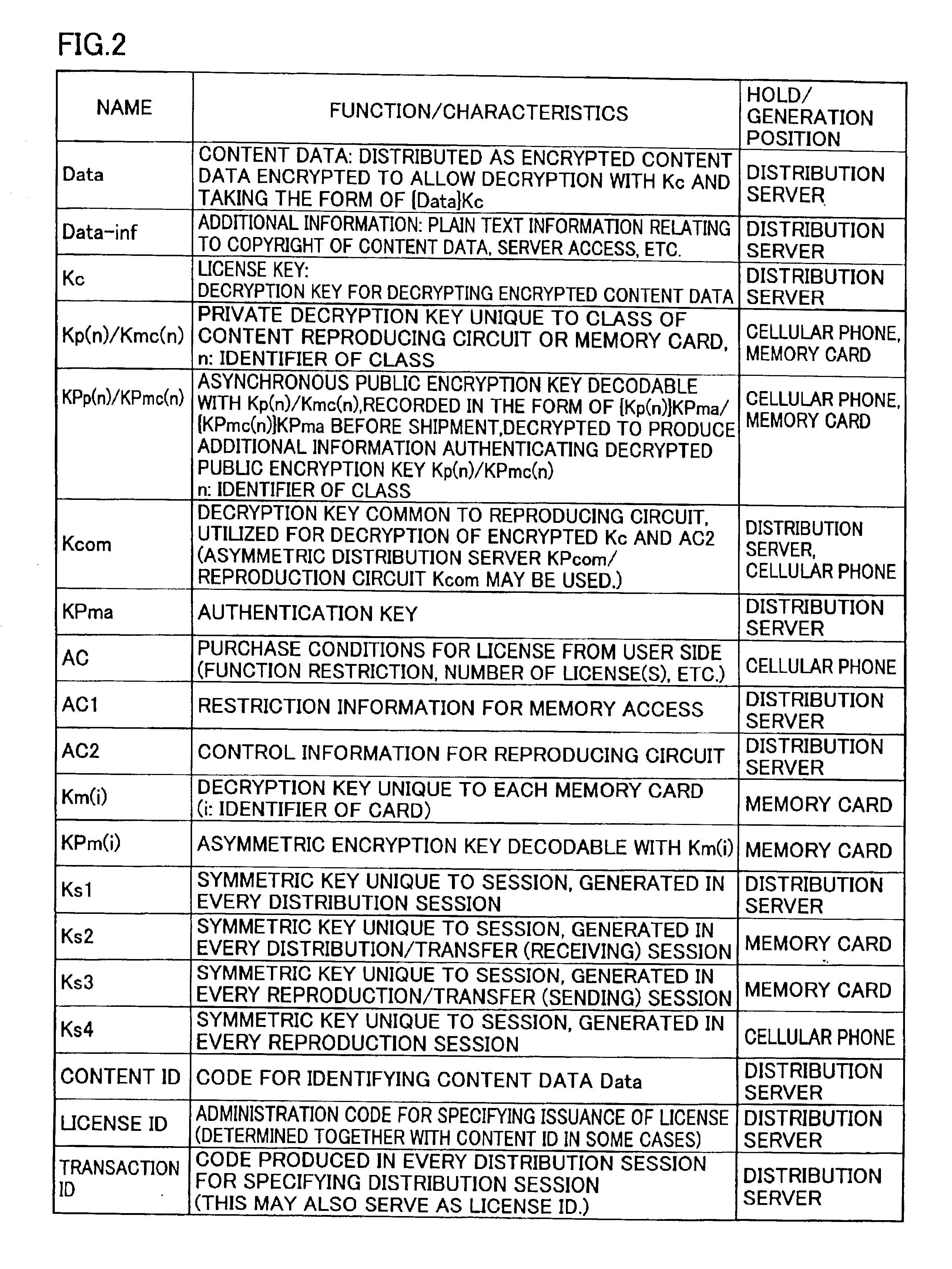
InactiveUS6898708B2Improve data securityEasy to handleCordless telephonesKey distribution for secure communicationMemory cardsLicense
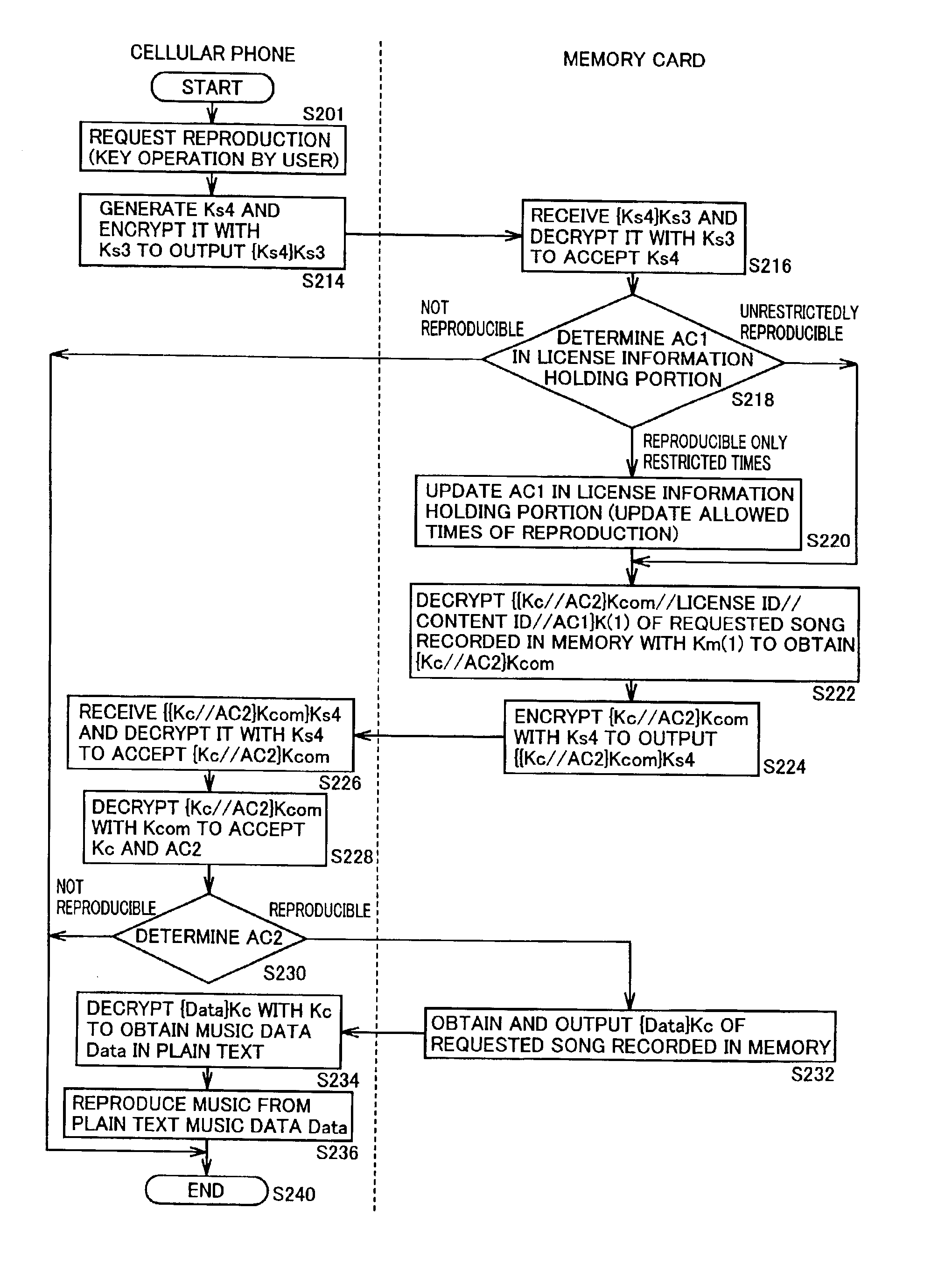
A cellular phone (100) stores encrypted content data and encrypted license key distributed thereto in a memory card (110). The cellular phone (100) and the memory card (110) collectively perform a part of mutual authentication processing upon power-on. The encrypted license key (Kc) read from the memory card (110) is decrypted by a first decryption processing portion (1510) with a session key (Ks4), and is further decrypted by a second decryption processing portion (1514) with a system symmetric key (Kcom) for extraction. A third encryption processing portion (1516) decrypts the encrypted content data read from memory card (110) with the license key (Kc) to reproduce content data (Data).
Owner:SANYO ELECTRIC CO LTD +1
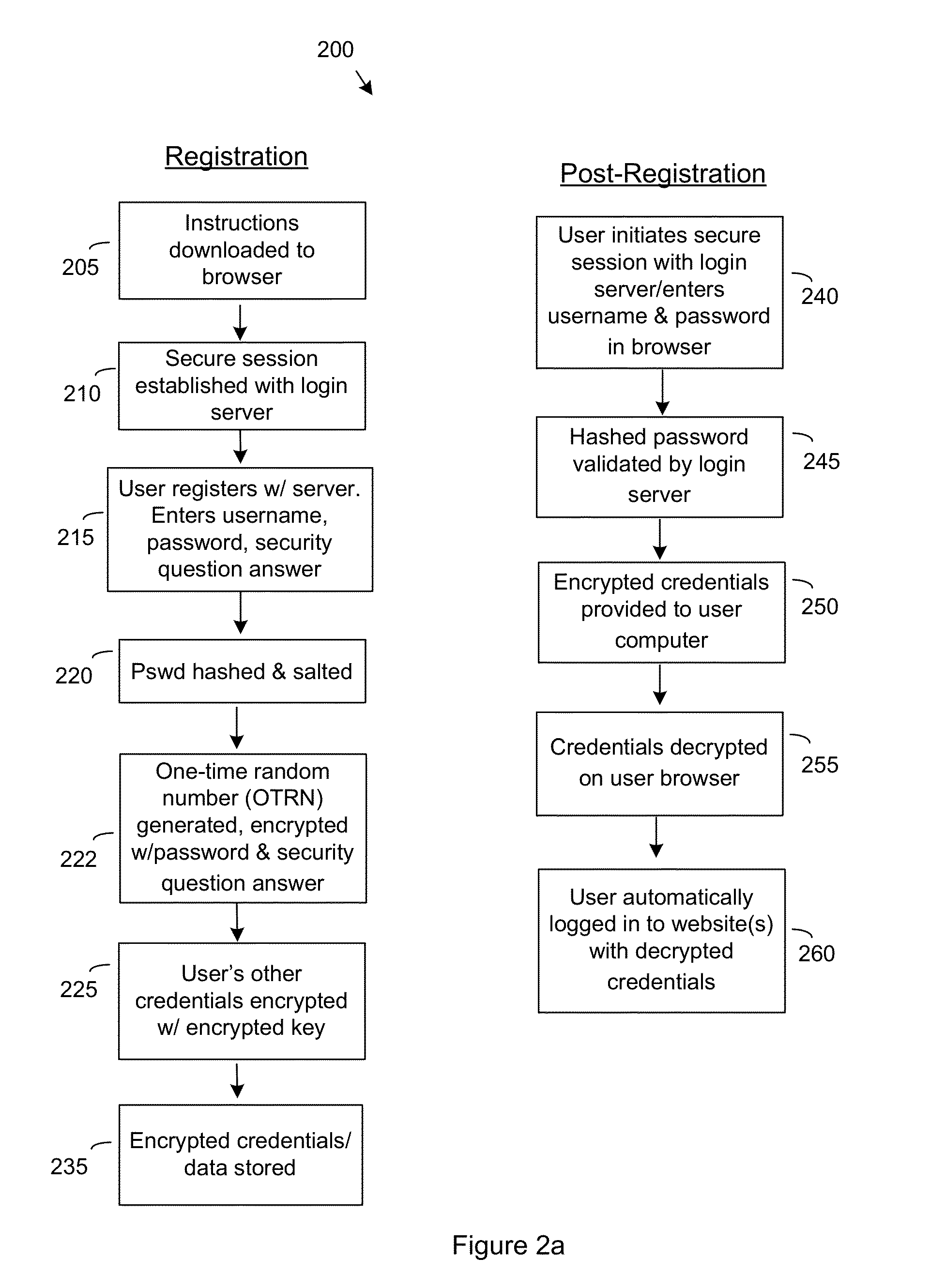
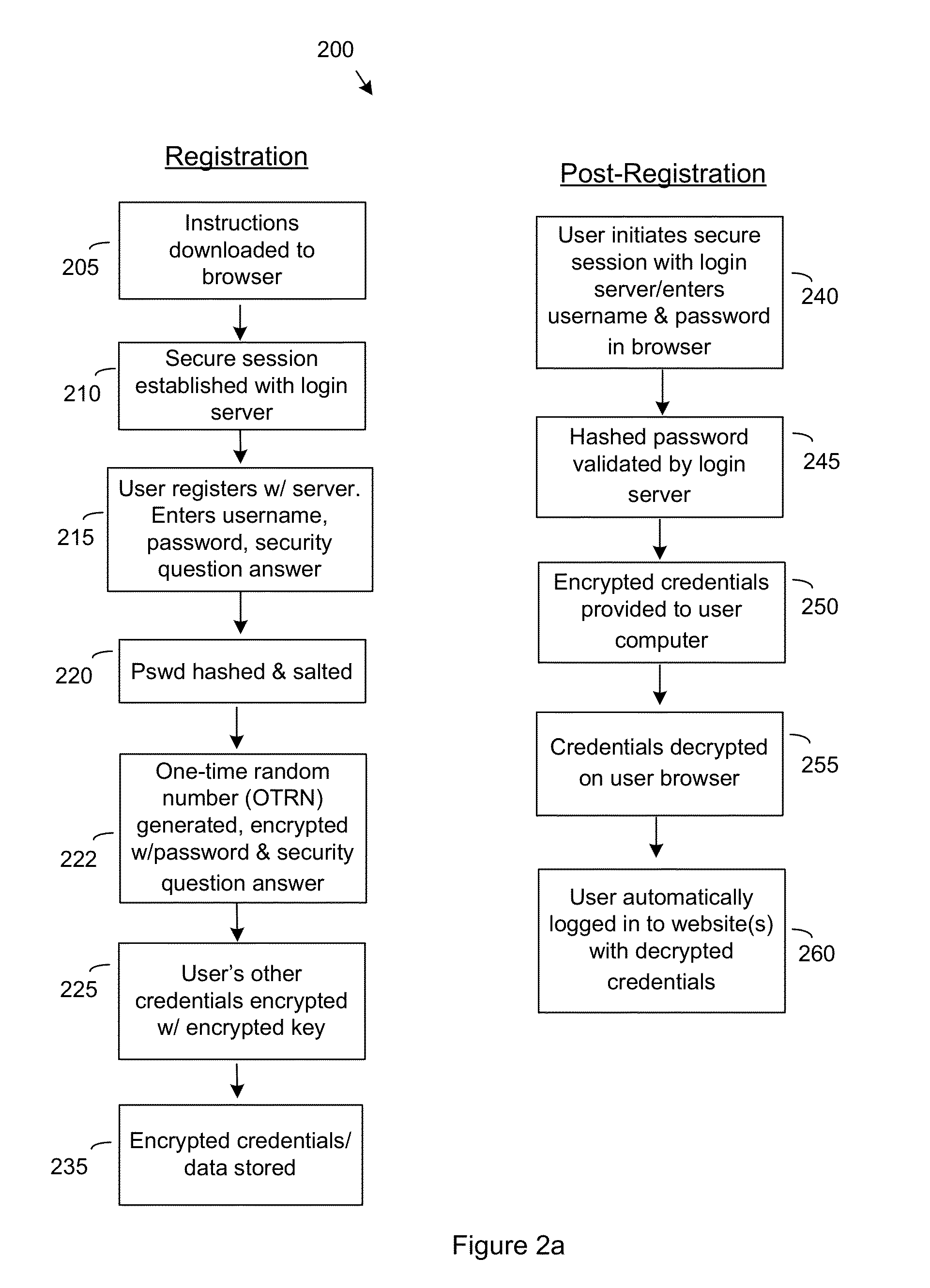
Methods for Single Signon (SSO) Using Decentralized Password and Credential Management
ActiveUS20130166918A1Information be quite largeImprove safetyUser identity/authority verificationComputer security arrangementsDistributed serversEnd to end security
A method for single sign-on (SSO) that provides decentralized credential management using end-to-end security. Credential (and other personal user information) management is decentralized in that encryption is performed locally on the user's computer. The user's encrypted credentials may be stored by the login server and / or a plurality of distributed servers / databases (such as a cloud). The login server never has access to the user's credentials or other personal information. When the user wants to use single sign-on, he enters his password into his browser and the browser submits the encrypted / hashed password to the login server for validation. Upon validation, the browser receives the user's encrypted credentials. The credentials are decrypted by the browser and provided to relevant websites to automatically log the user in.
Owner:SHAHBAZI MAJID +1
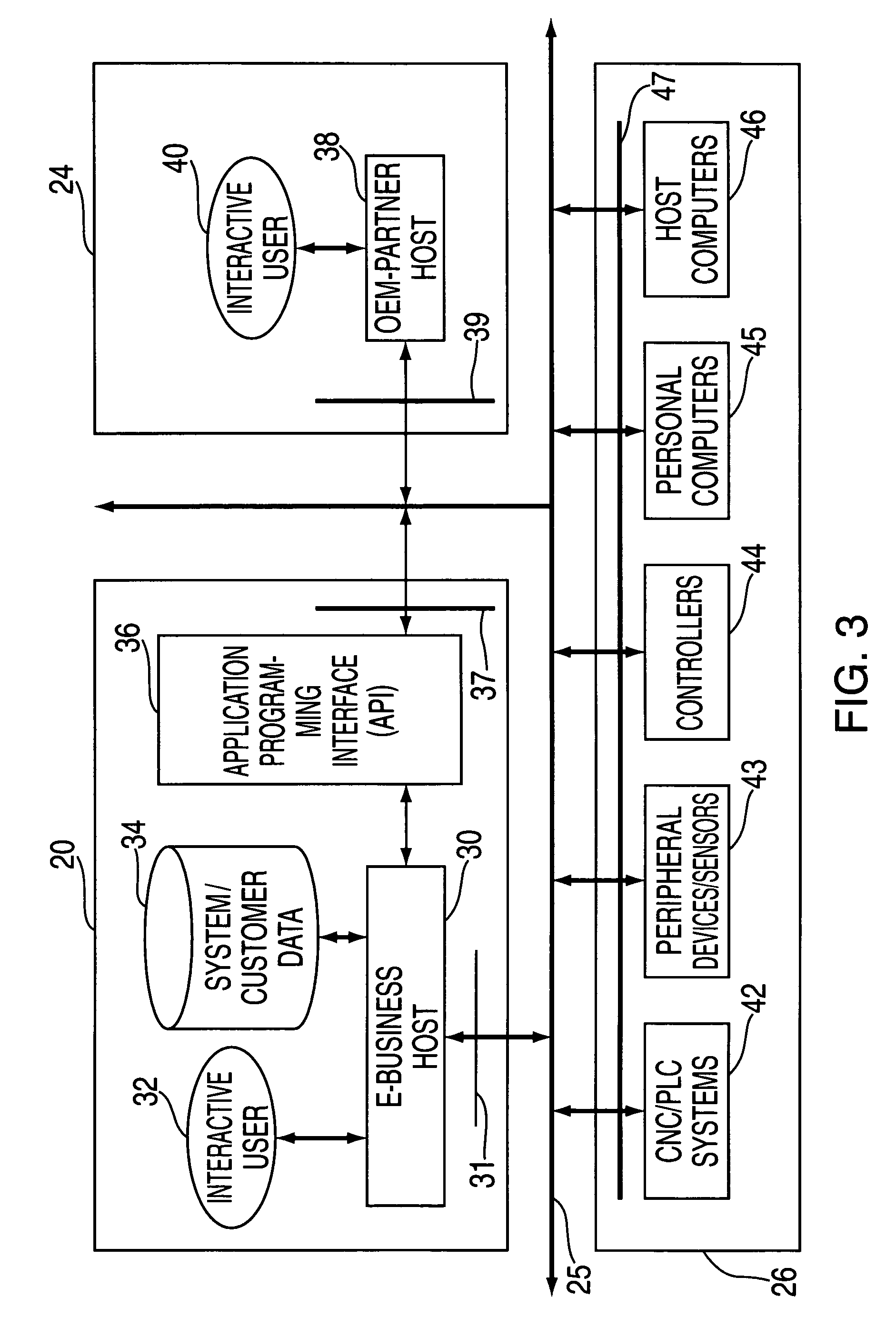
Data capture for electronically delivered automation services
InactiveUS7395122B2Improve data securityImprove securityProgramme controlComputer controlReal-time dataControl system
Content is generated on a host system based on real-time data from a controlled process collected over an internet from a customer's client machine tool control system. The real-time data is captured from the client machine tool by downloading software that manipulates controller functionality to perform a data capture trace predefined events and triggers. The captured data is retrieved by the host, which may generate content based on the data, or provide selective, authorized access to the data by others.
Owner:SIEMENS AG
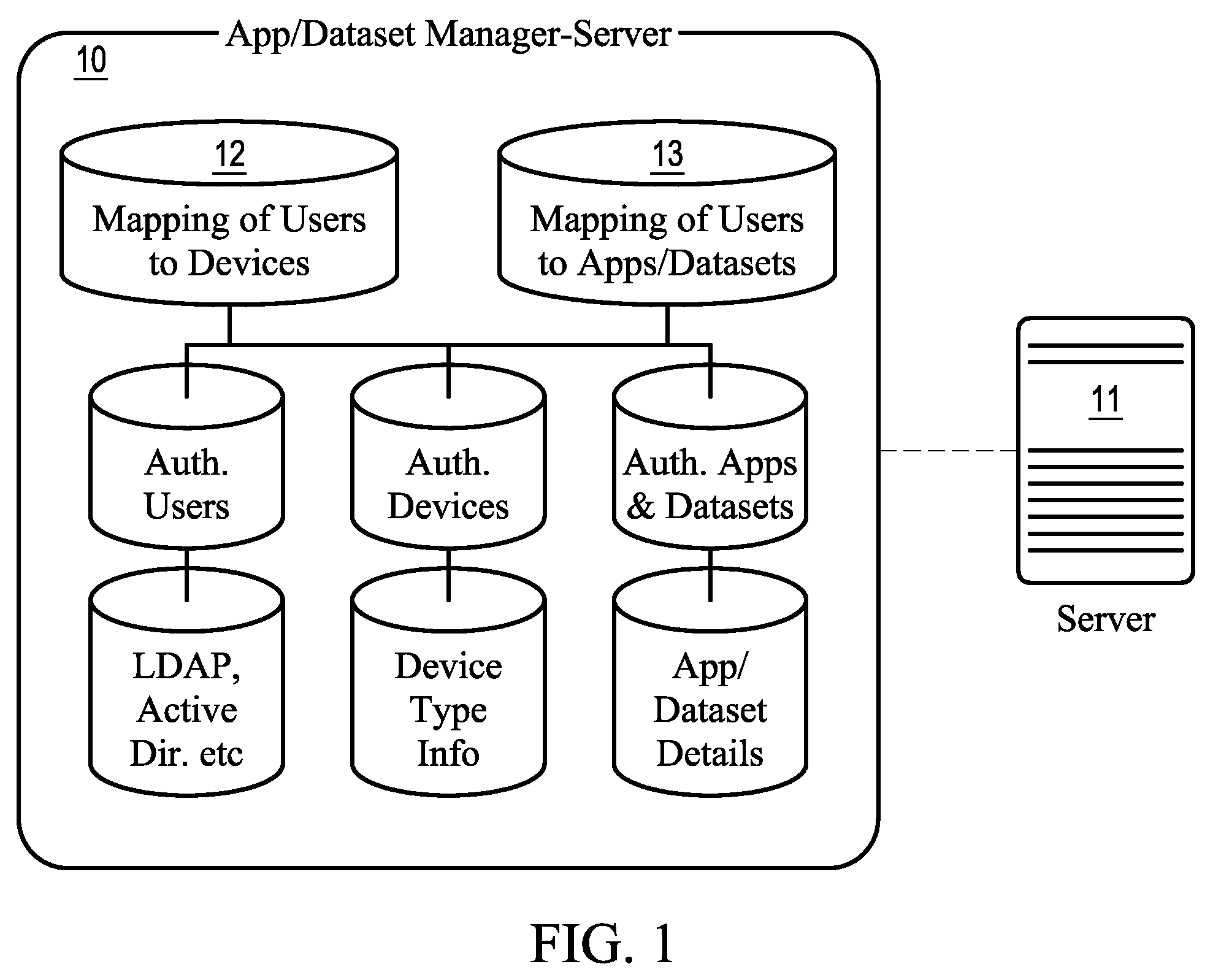
Method and apparatus for improving security in a data processing system
ActiveUS8200761B1Improve data securityPrivacy protectionMemory loss protectionDigital data processing detailsData processing systemSubject matter
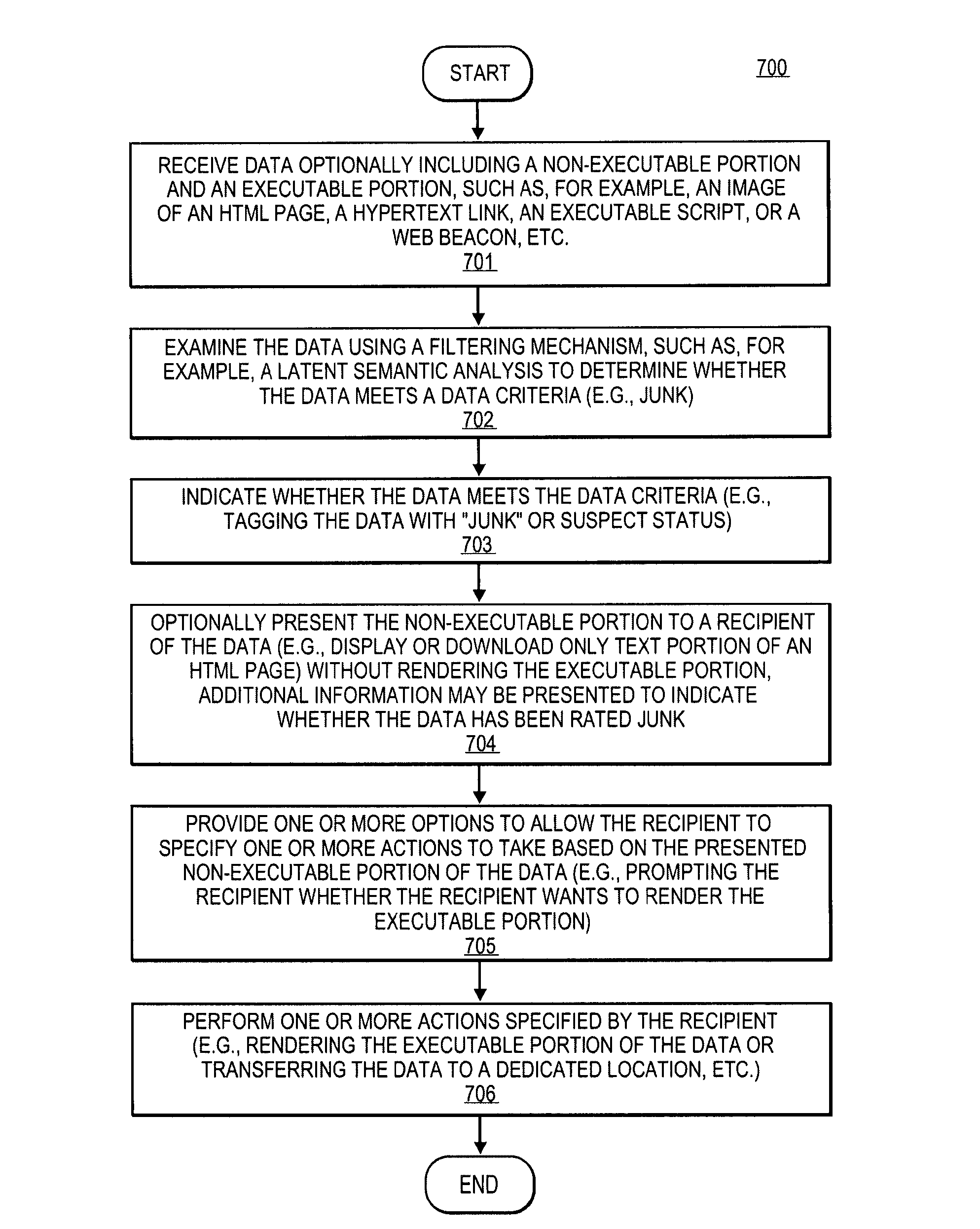
Methods and Apparatuses for processing data are described herein. In one aspect of the invention, an exemplary method receives data which may include an executable portion and a non-executable portion. The non-executable portion of the data may be presented to a user without rendering the executable portion. The non-executable portion of data presented may also include information regarding the executable portion (e.g., subject matter or source of the data). The executable portion of the data is rendered or executed only when a request from a user is specifically received. Other methods and apparatuses are also described.
Owner:APPLE INC
Open network system and method for I/O operations with non-standard I/O devices using an extended open network protocol
InactiveUS6907476B2Reduce the risk of fraudInformation receivedMultiple digital computer combinationsPayment architectureNetworking protocolApplication procedure
An open network system supports input / output (I / O) operations for non-standard I / O devices coupled to an open network. The system includes a server coupled to a plurality of I / O devices through an open network, at least some of the I / O devices being non-standard I / O devices. The non-standard I / O devices communicate with a client program that processes extended open network protocol statements. The extended open network protocol statements communicated between the server and the non-standard I / O devices are processed by the server and the client program to support I / O operations between the non-standard I / O devices and the server or application programs coupled to the server.
Owner:WI LAN TECH INC
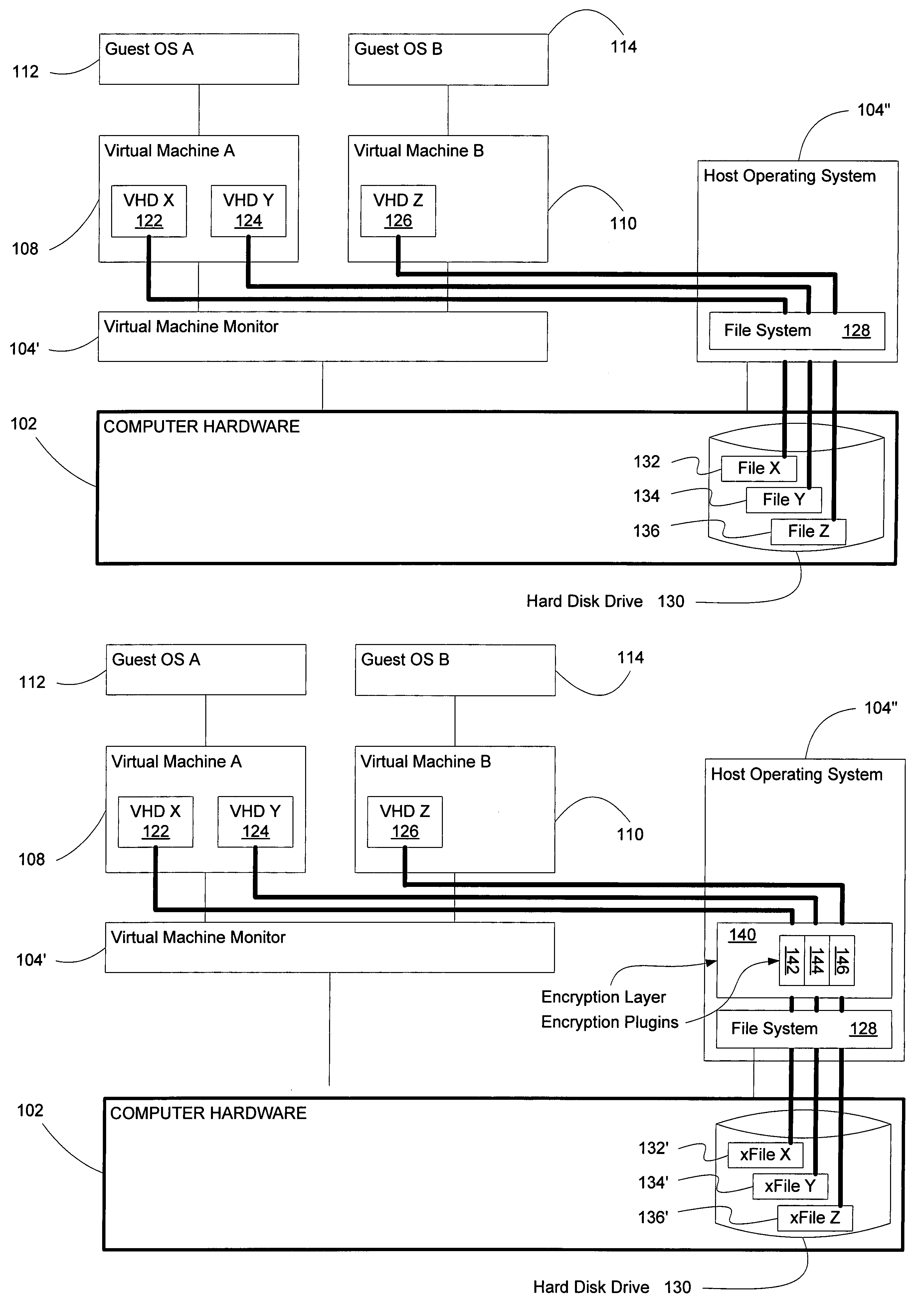
Systems and methods for data encryption using plugins within virtual systems and subsystems
ActiveUS7987497B1Improving data access securityImproved data access securityDigital data processing detailsUnauthorized memory use protectionHard disc driveData access
Several embodiments of the present invention provide a means for improving data access security in computer systems to support high-security applications, and certain of these embodiments are specifically directed to providing sector-level encryption of a virtual hard disk in a virtual machine environment. More specifically, certain embodiments are directed to providing sector-level encryption by using plug-ins in a virtual machine environment, thereby providing improved data access security in a computer system that supports high-security applications. Certain embodiments also use encryption plug-ins associated with standard encryption software for exchanging data between a virtual machine (VM) and its associated virtual hard drive(s) (VHDs). Moreover, several embodiments of the present invention are directed to the use of plug-in encryption services that interface with, and provide services for, a VM via a VM Encryption API (or its equivalent).
Owner:MICROSOFT TECH LICENSING LLC
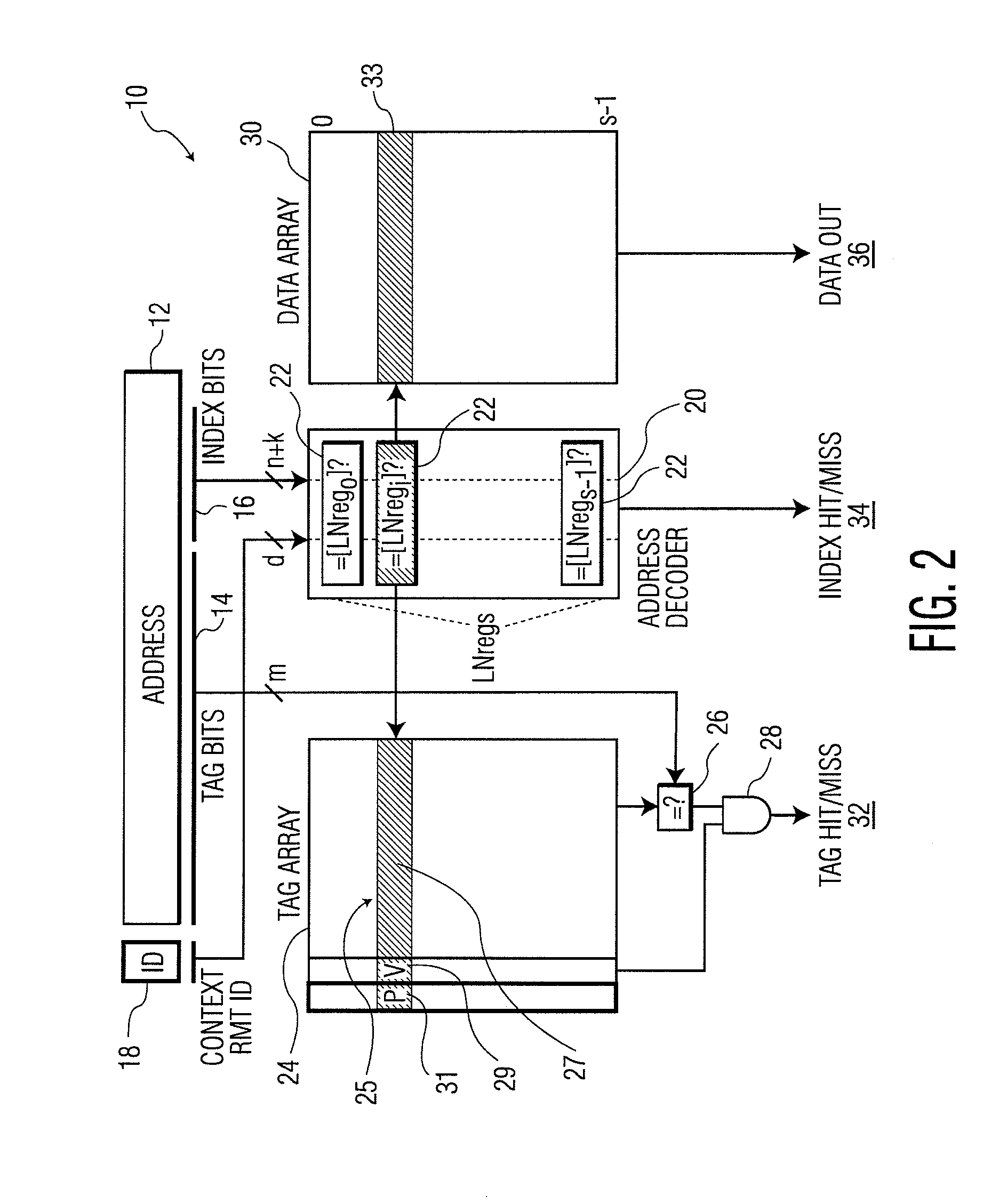
Cache Memory Having Enhanced Performance and Security Features
ActiveUS20100180083A1Enhance performance and security featureEnhance performanceMemory architecture accessing/allocationEnergy efficient ICTSecurity functionAddress decoder
A cache memory having enhanced performance and security feature is provided. The cache memory includes a data array storing a plurality of data elements, a tag array storing a plurality of tags corresponding to the plurality of data elements, and an address decoder which permits dynamic memory-to-cache mapping to provide enhanced security of the data elements, as well as enhanced performance. The address decoder receives a context identifier and a plurality of index bits of an address passed to the cache memory, and determines whether a matching value in a line number register exists. The line number registers allow for dynamic memory-to-cache mapping, and their contents can be modified as desired. Methods for accessing and replacing data in a cache memory are also provided, wherein a plurality of index bits and a plurality of tag bits at the cache memory are received. The plurality of index bits are processed to determine whether a matching index exists in the cache memory and the plurality of tag bits are processed to determine whether a matching tag exists in the cache memory, and a data line is retrieved from the cache memory if both a matching tag and a matching index exist in the cache memory. A random line in the cache memory can be replaced with a data line from a main memory, or evicted without replacement, based on the combination of index and tag misses, security contexts and protection bits. User-defined and / or vendor-defined replacement procedures can be utilized to replace data lines in the cache memory.
Owner:CORESECURE TECH LLC
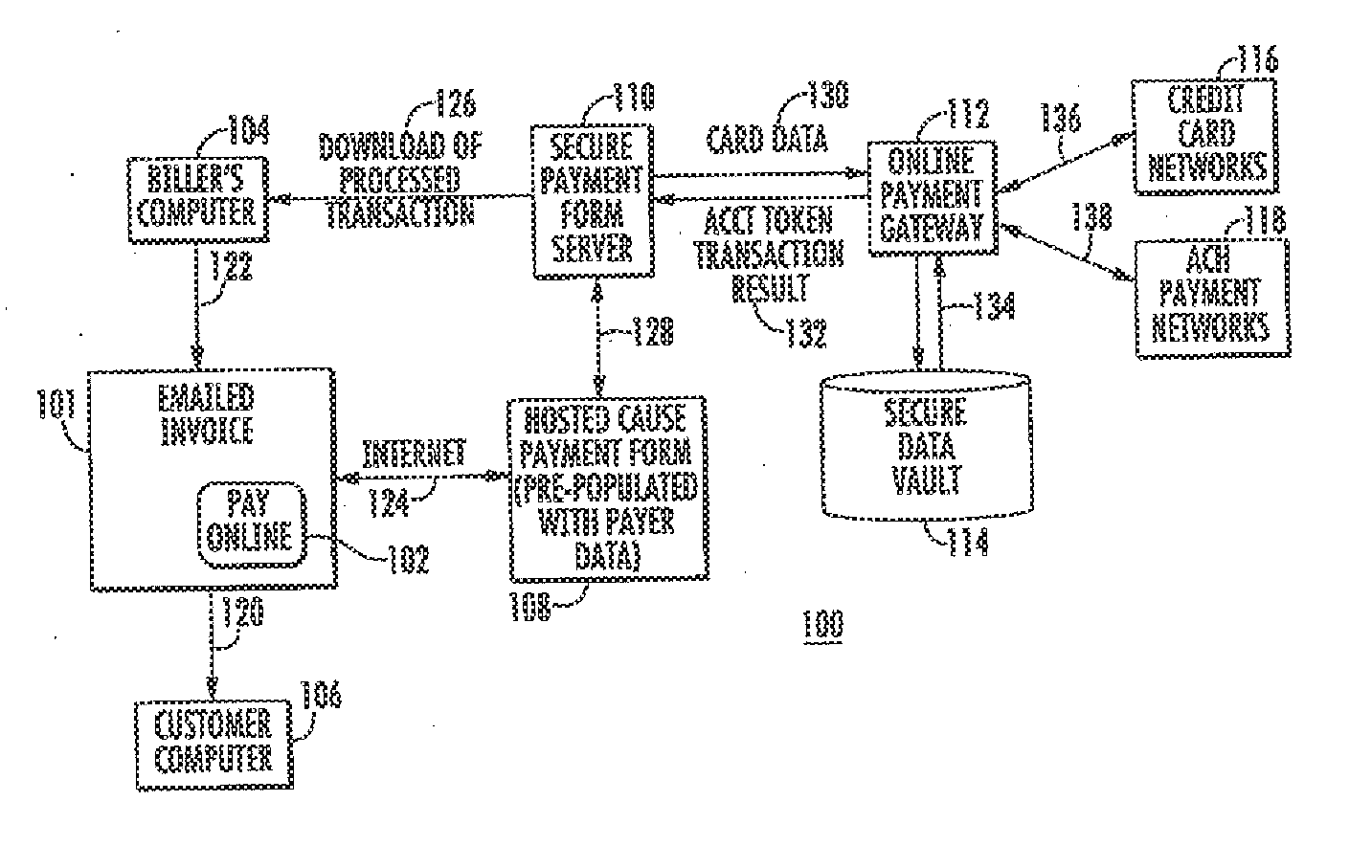
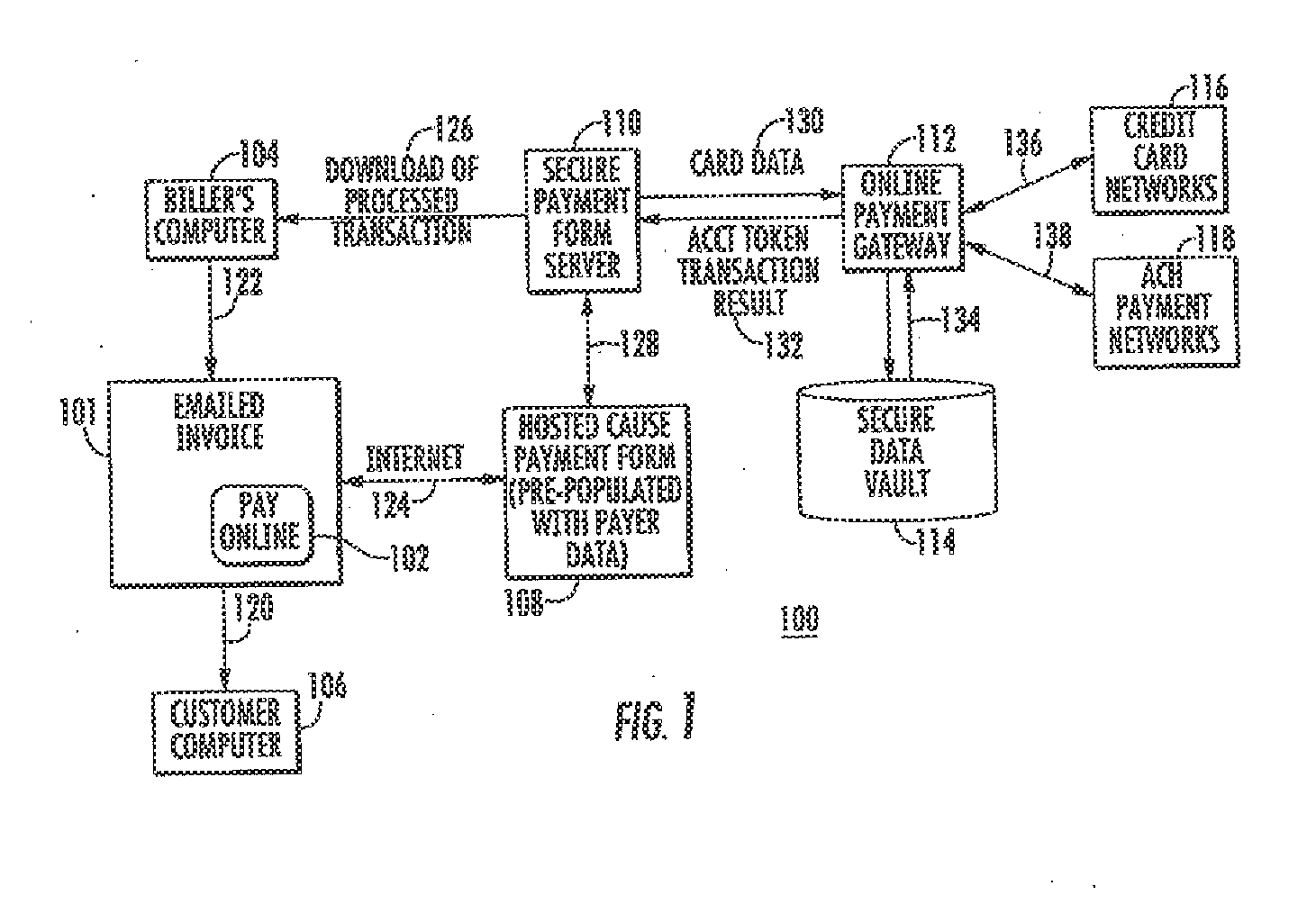
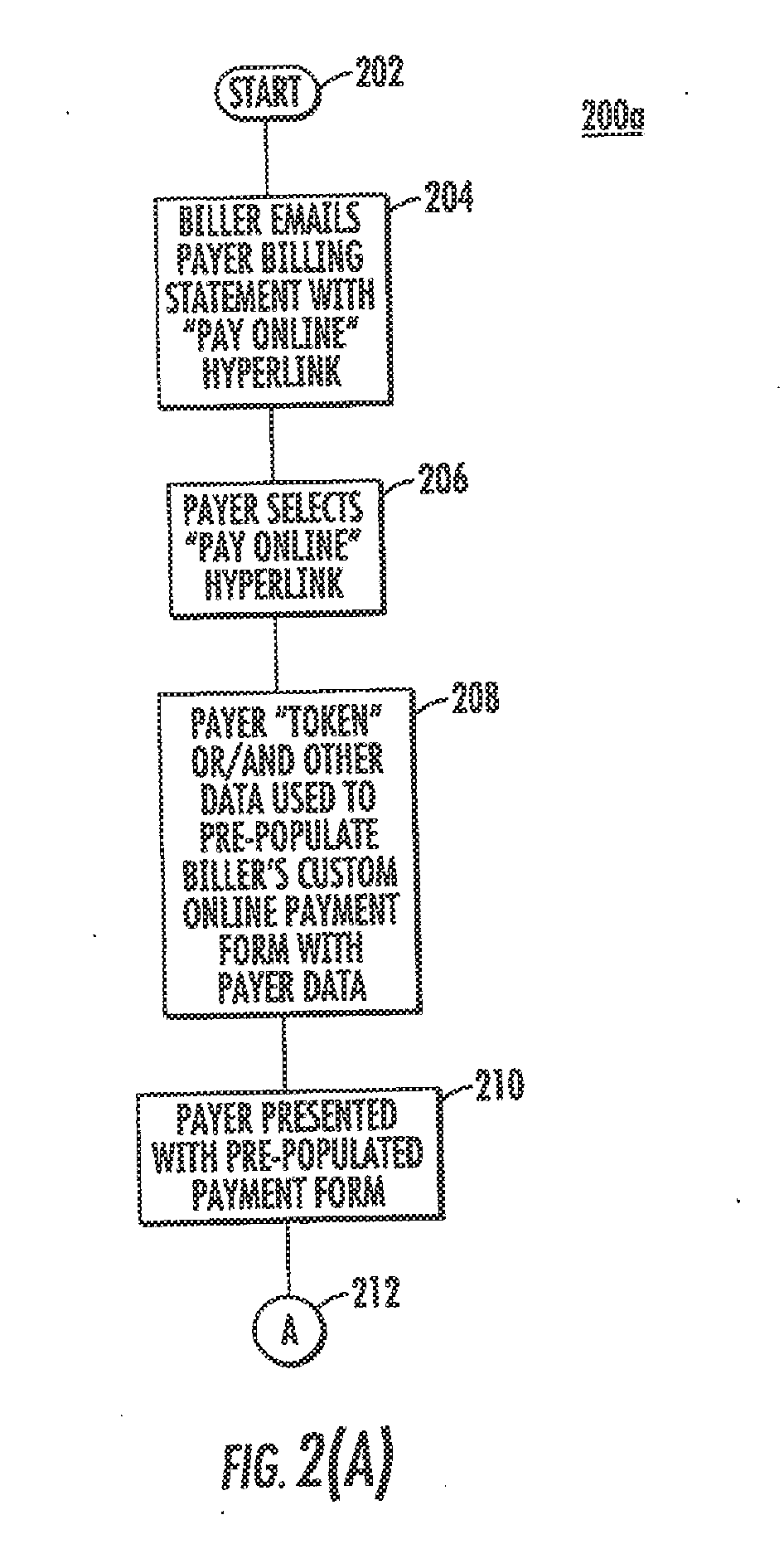
Method and system to process payment using URL shortening and/or qr codes
ActiveUS20120078782A1Optimize data processingEasy to customizeFinancePayment architectureHyperlinkPersonalization
Provided is a method and system for payment processing, including emailing a billing statement to a payer by a biller, the billing statement including an online payment hyperlink having a shortened URL personalized for the payer and a token uniquely identifying the payer. The payer may select the online payment hyperlink, at which point they are presented with the biller's online payment form without the payer logging in or preregistering. The online payment form includes data fields pre-populated with available payer information derived from the personalized shortened URL and token, which may be reviewed, completed and / or corrected by the payer and sent to a secure payment form server. Also provided is the use of Quick response (QR) codes incorporating the shortened URL in a printed format, particularly for use with a mobile communication device.
Owner:SOFTERWARE
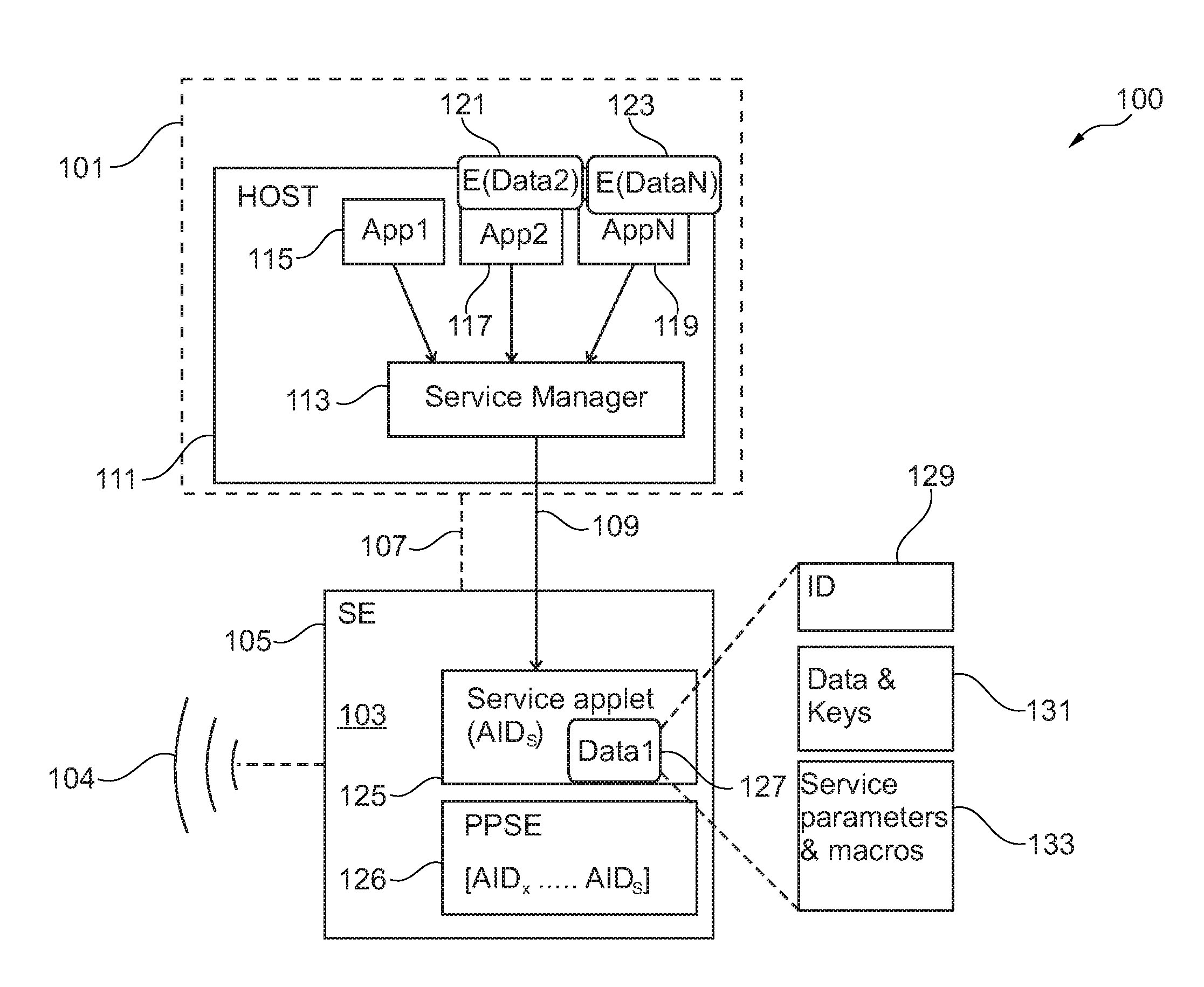
Method for accessing a secure storage, secure storage and system comprising the secure storage
InactiveUS20130145455A1Reduce complexityFree secure storageDigital data processing detailsUnauthorized memory use protectionMobile deviceComputer security
It is described a method for accessing a secure storage of a mobile device, the method comprising: providing a generic interface for accessing the secure storage; accessing the secure storage using the generic interface by a first application of the mobile device; accessing the secure storage using the generic interface by a second application of the mobile device. Further, a corresponding secure electronic storage and a system is described.
Owner:NXP BV
Secure memory device for smart cards
InactiveUS7395435B2Improve data securityDigital data processing detailsUser identity/authority verificationPasswordSecret code
A secure memory device which can be used for multi-application smart cards for secure identification in data transfer, or for component verification in a computer system, without the requirement of an internal microprocessor. The secure memory device features a dual authentication protocol in which the memory and host authenticate each other. The secure memory device also includes an encrypted password feature, as well as using stream encryption to encrypt the data.
Owner:ATMEL CORP
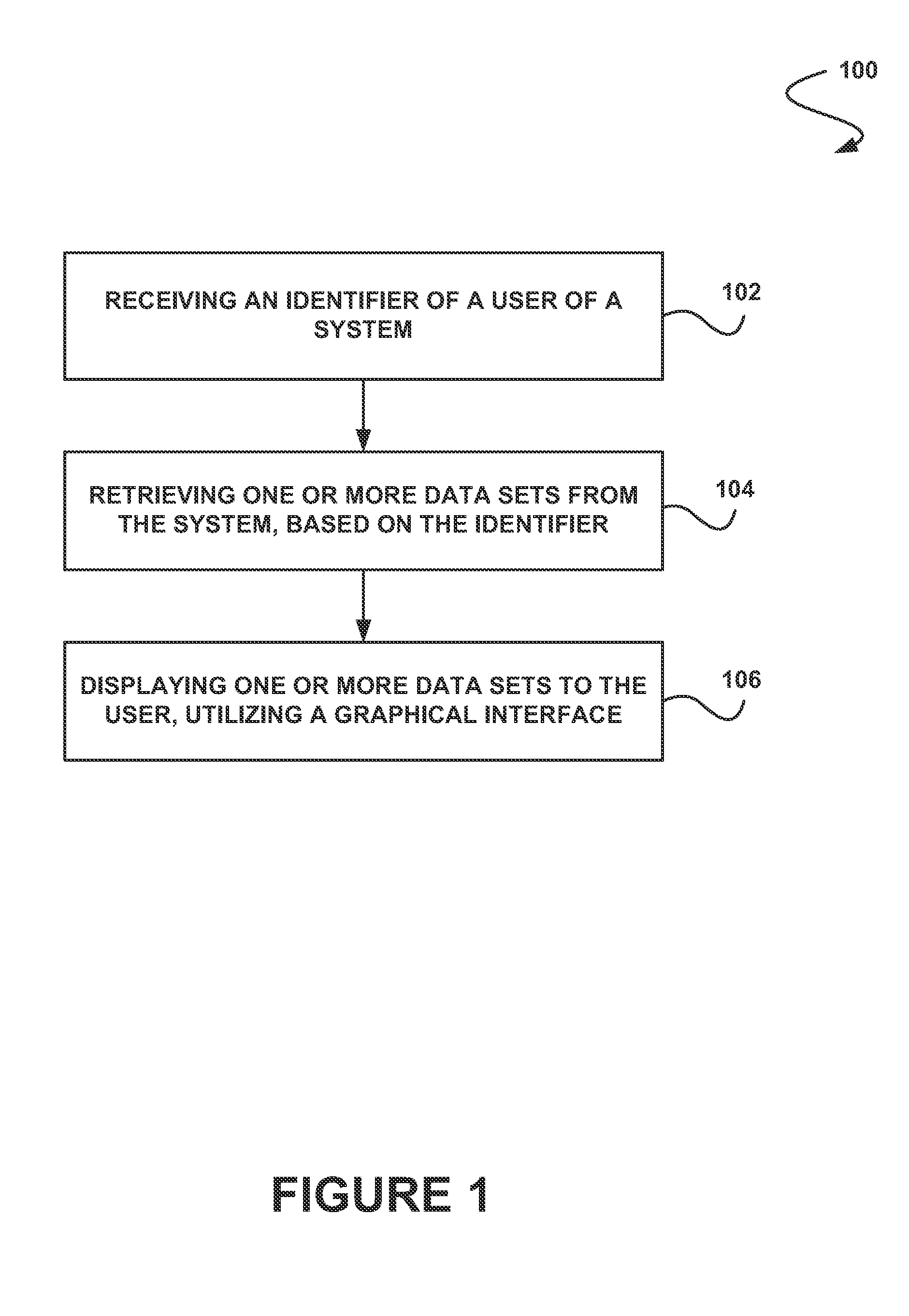
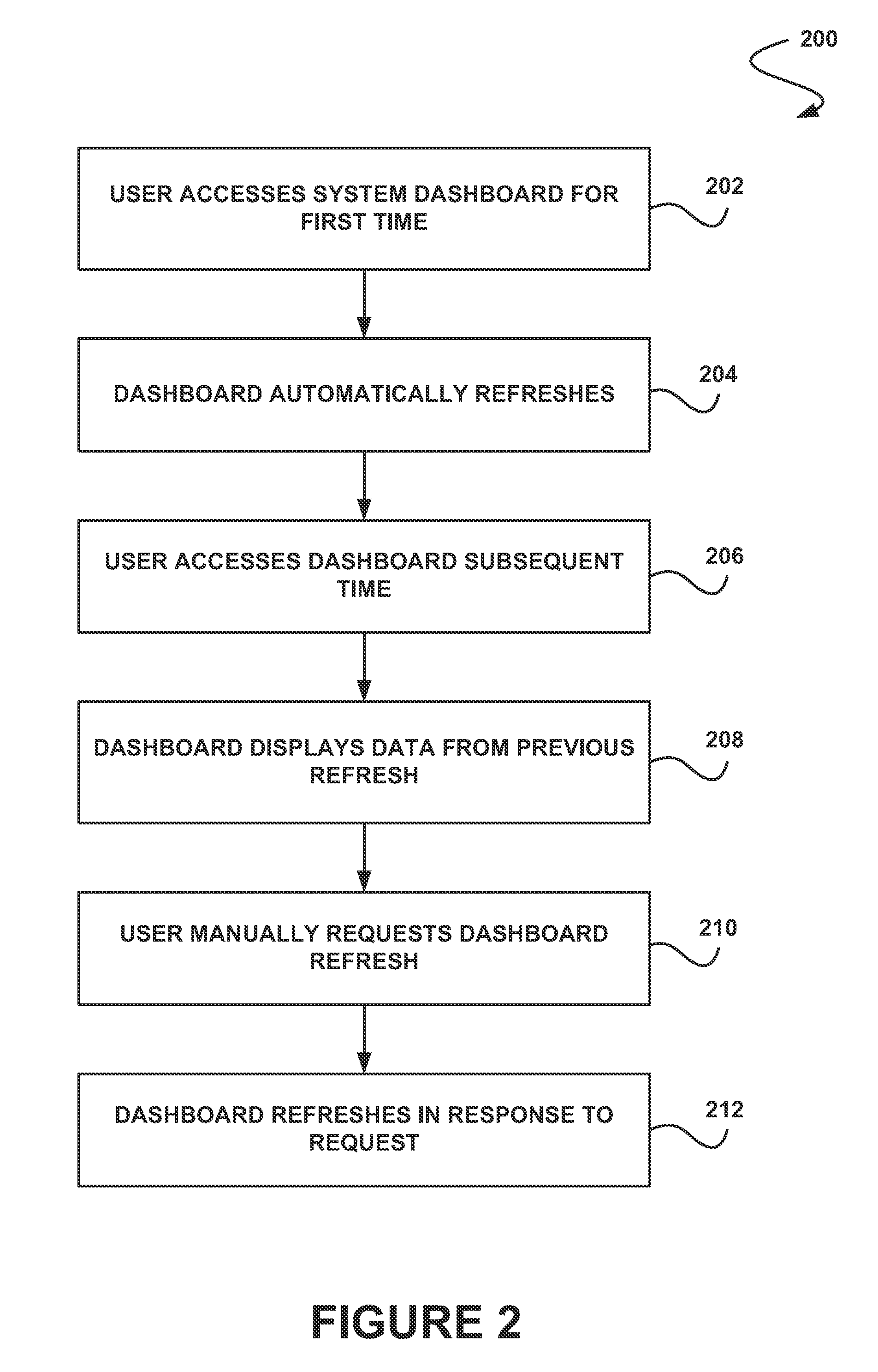
System, method and computer program product for displaying one or more data sets to a user
ActiveUS20130246399A1Improve data securityDisplay moreDigital data information retrievalDigital data processing detailsData displayData set
In accordance with embodiments, there are provided mechanisms and methods for displaying one or more data sets to a user. These mechanisms and methods for displaying one or more data sets to a user can enable enhanced data security, more relevant data display, reduced processing, etc.
Owner:SALESFORCE COM INC
Solid-state flash memory write cache system and method based on dynamic non-covering RAID technology
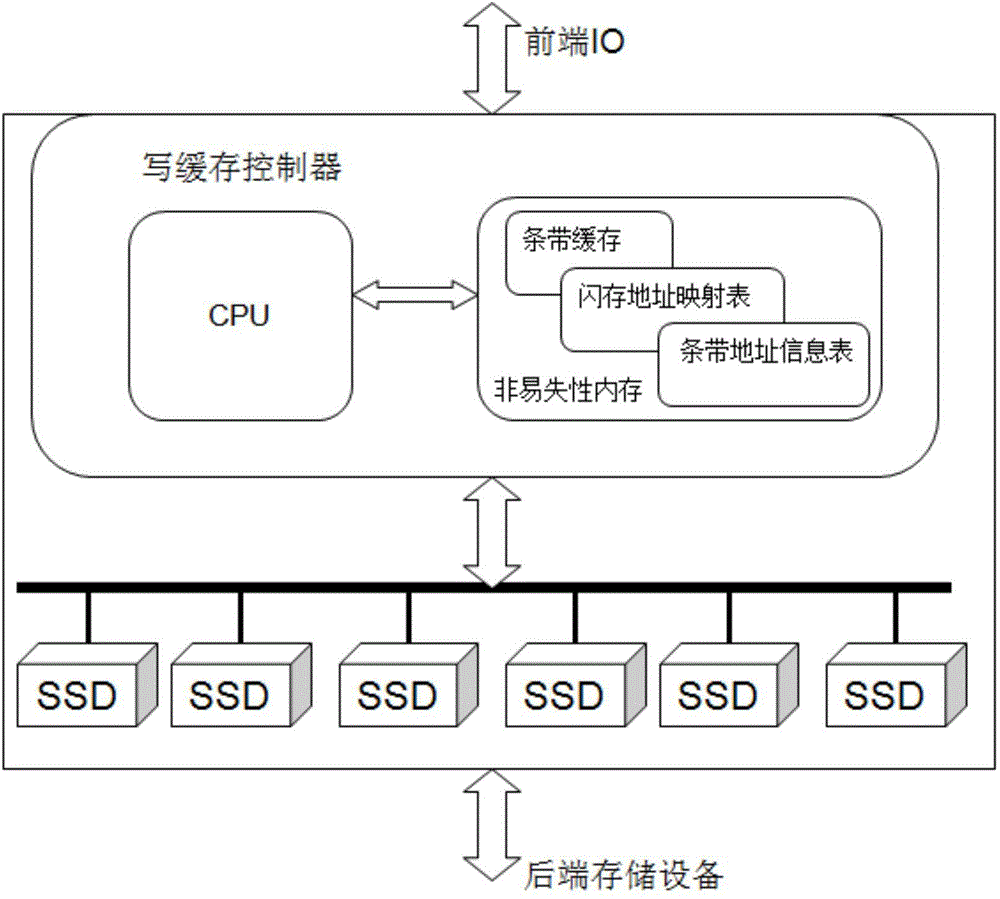
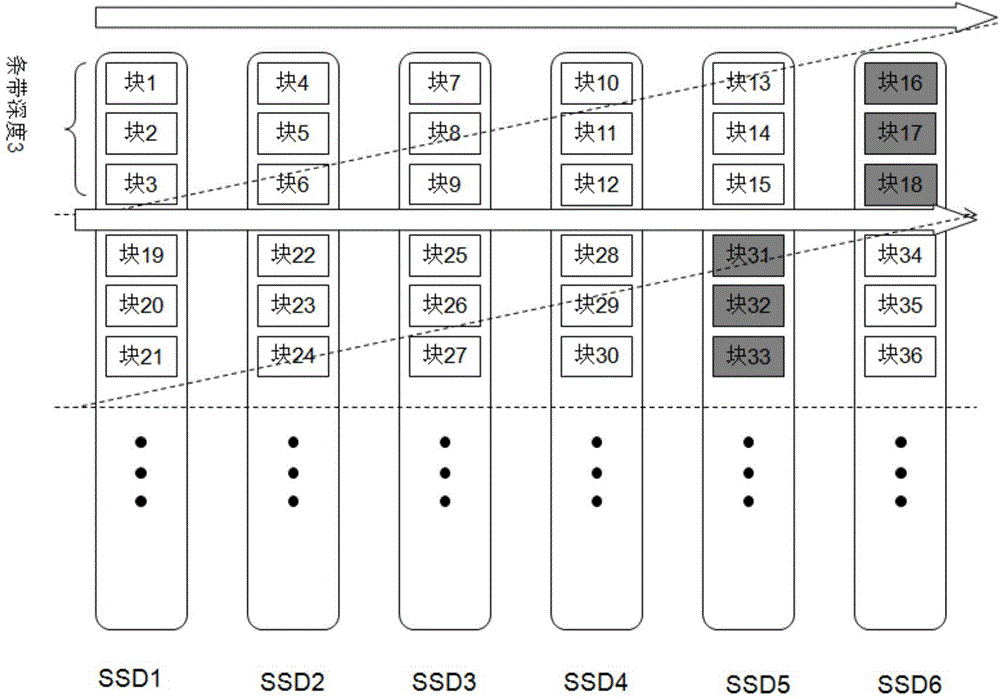
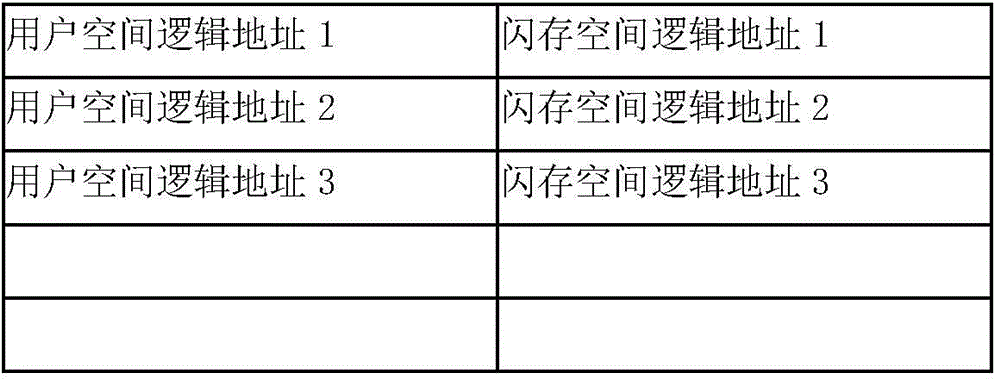
ActiveCN104794070ALarge capacityReduce power consumptionInput/output to record carriersMemory adressing/allocation/relocationSolid-stateMemory module
The invention discloses a solid-state flash memory write cache system and method based on the dynamic non-covering RAID technology. According to the system, multiple solid-state flash memory hard disks form an RAID to serve as memory space of write cache, and the solid-state flash memory hard disks are connected with a write cache controller; the controller is connected with a front-end IO and back-end storage data, comprises a CPU and a nonvolatile memory module and is used for receiving front-end read requests, reading data from the solid-state flash memory hard disks or back-end storage equipment and receiving front-end write requests, the data are assembled into RAID strips in the nonvolatile memory module and then written in newly distributed strips in the solid-state flash memory hard disks in a non-covering mode, active data in solid-state flash memory strips are written in the back-end storage equipment, and the recovery of the solid-state flash memory strips is achieved. According to the solid-state flash memory write cache system and method based on the dynamic non-covering RAID technology, the strips are assembled dynamically, the phenomenon that the strips are updated frequently is avoided, the system write-in bandwidth is effectively improved, the wear of Flash chips is reduced, and the advantages of being large in capacity and high in property and reliability and the like are achieved.
Owner:南京道熵信息技术有限公司
Method of authenticating universal serail bus on-the-go device
InactiveUS20050251589A1Improve data securityPrevent unauthorized accessDigital data authenticationInput/output processes for data processingMobile deviceUSB
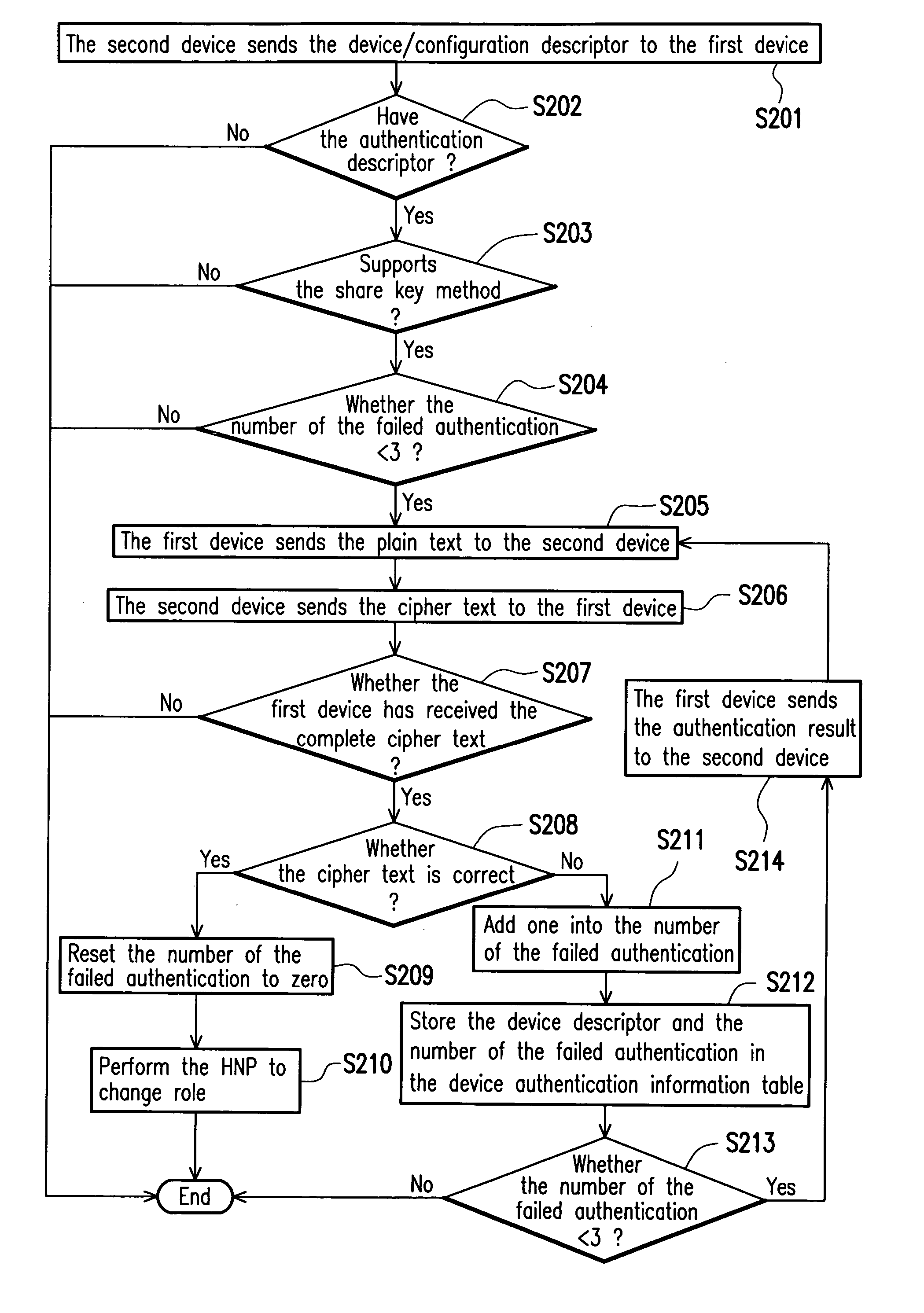
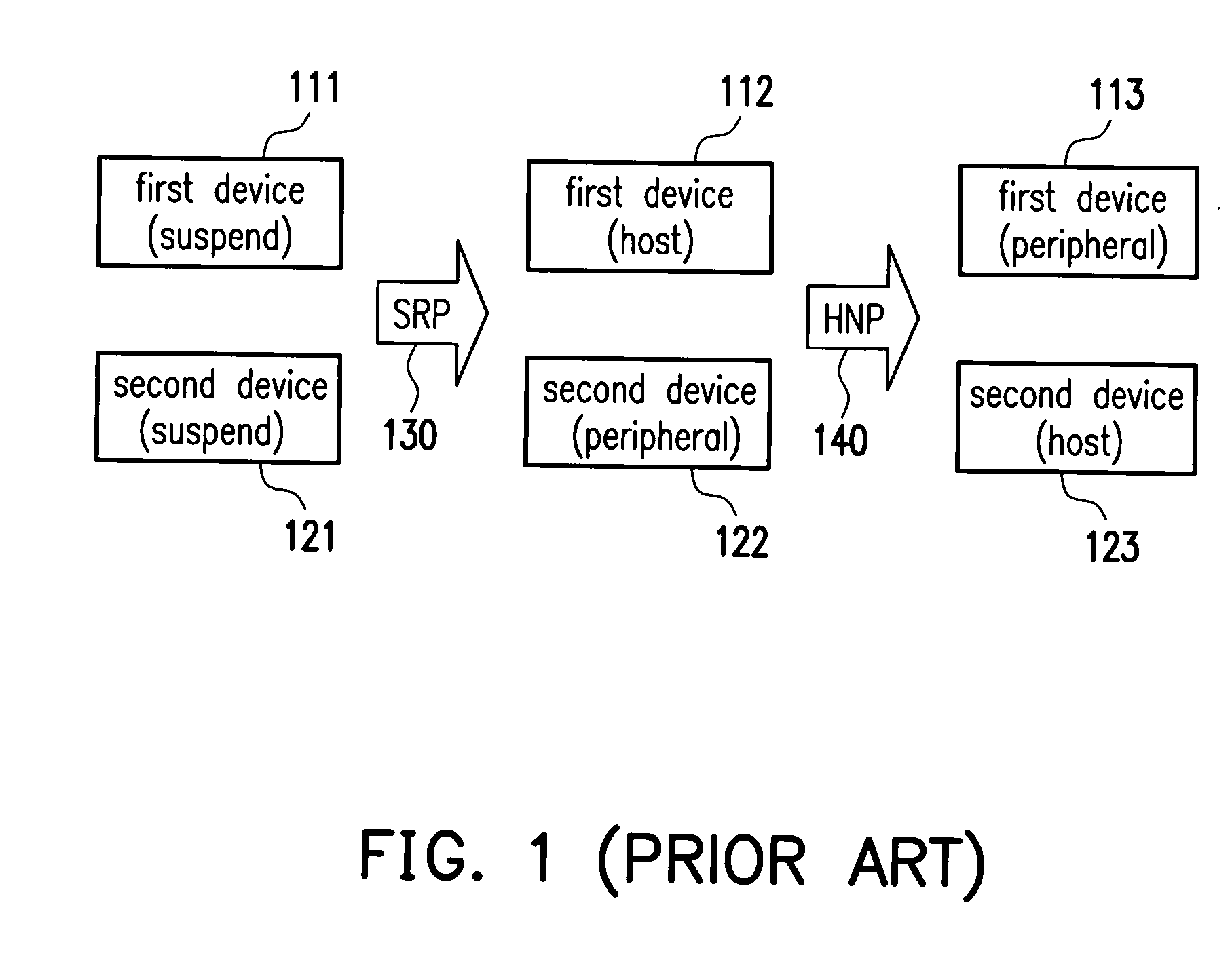
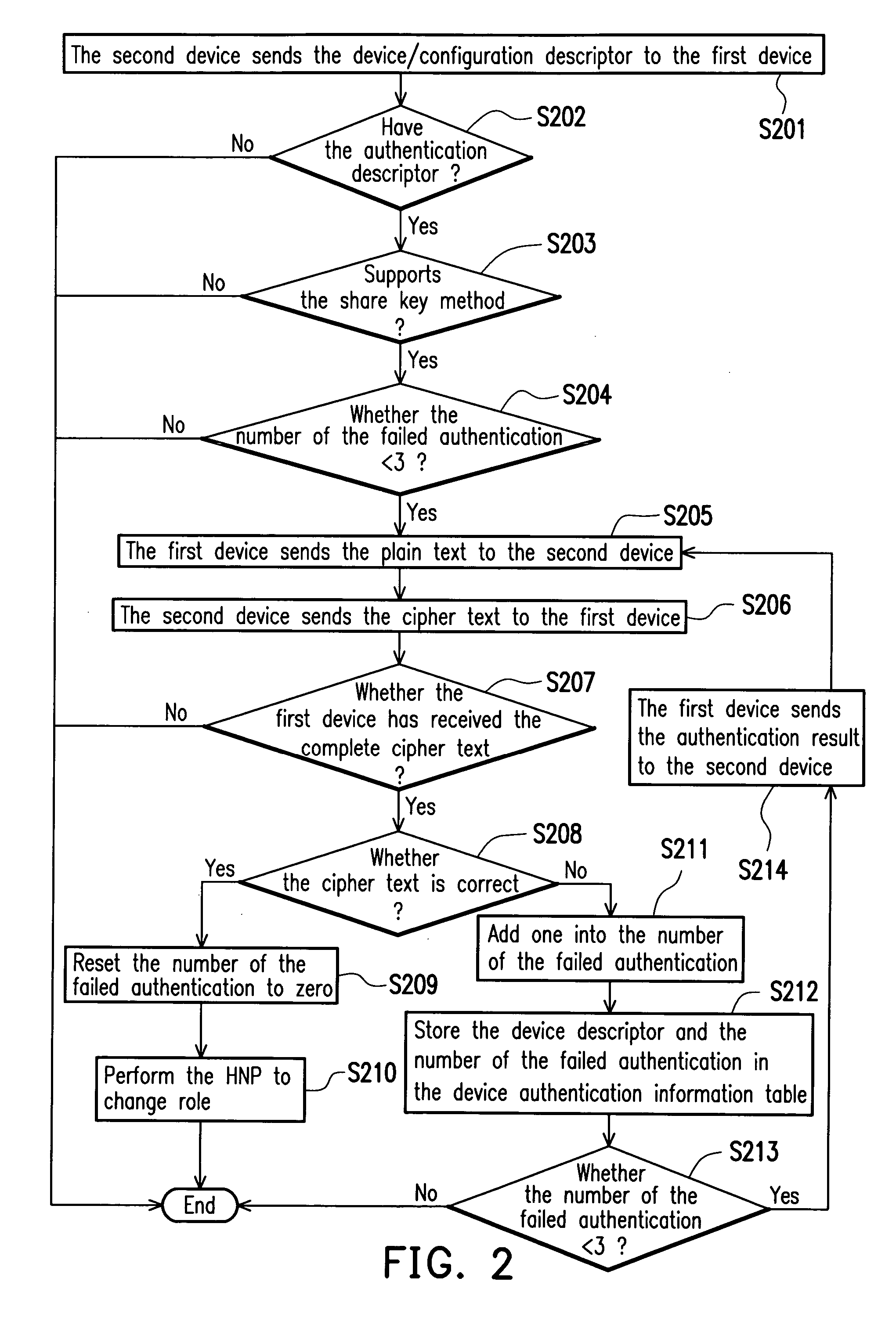
A method for authenticating a universal serial bus on-the-go device is provided. A first device and a second device connected via a universal serial bus supporting an on-the-go protocol are provided. The first device is a host and the second device is a peripheral device. The host uses an authentication rule to determine whether the peripheral device is an authentic device. When the peripheral device is an authentic device, the host sends an enable signal to the peripheral device to perform a host negotiation protocol so that the first device changes role to the peripheral device and the second device changes role to the host; and when the peripheral device is not the authentic device, the host declines to perform the host negotiation protocol with the peripheral device. Hence, the data security of the USB host is enhanced. The data security of the USB peripheral device can also enhanced by providing the authentication mechanism before the USB device (peripheral device) has been accessed by the other devices (e.g., the USB host) in order to prevent the unauthorized user from accessing the data in the USB peripheral device.
Owner:FARADAY TECH CORP
Secure searchable and shareable remote storage system and method
ActiveUS20190087432A1Improve data securityLimited expressivenessDigital data protectionFile access structuresPlaintextRelevant information
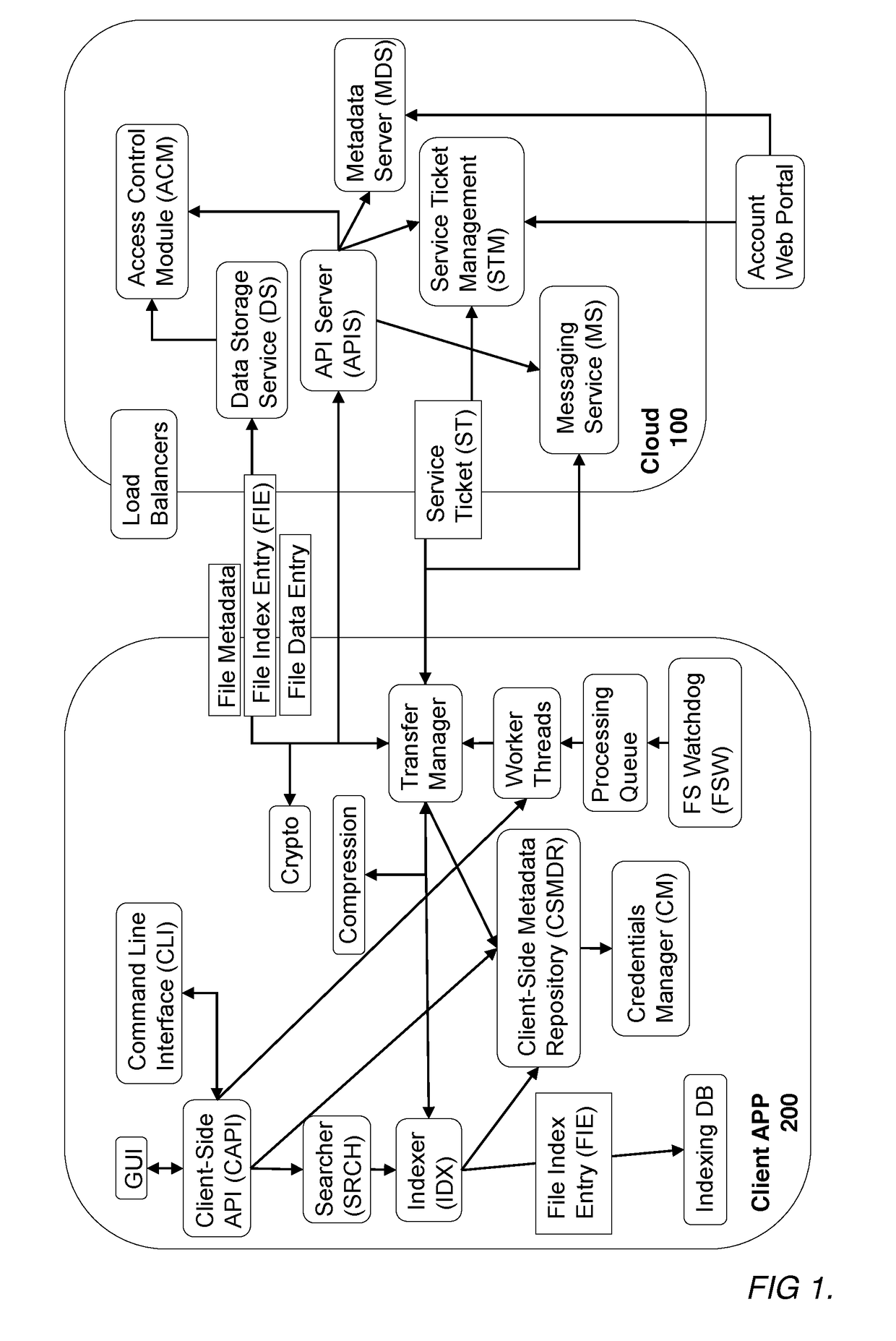
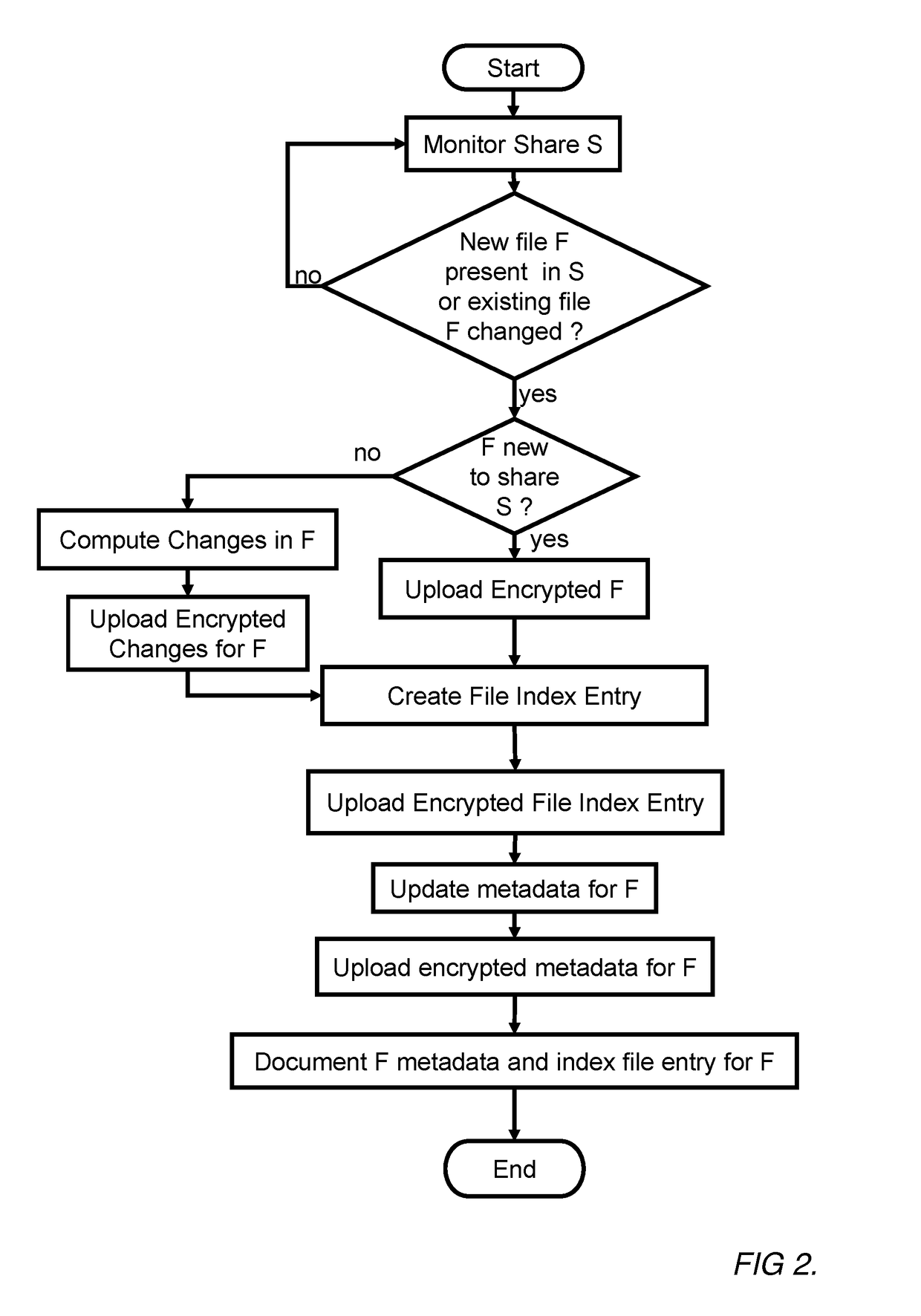
A secure searchable and shareable remote storage system and method which utilizes client side processing to enable search capability of the stored data, allow the synchronizing of stored data between multiple discrete devices, and allow sharing of stored data between multiple discrete users. Such a remote storage system and method includes a networked remote computer server which receives and stores encrypted data and manages access thereto and a client device configured to index data to be stored, upload secured data and related information, perform searches on the stored data and related information locally, and implement cryptographic protocols which allow the stored data and related information to be synchronized with other desired client devices. Advantageously, since trusted client-side search code may directly access mostly plaintext data, it may operate orders of magnitude faster than the equivalent server code which may access encrypted data only.
Owner:PRIVATE MACHINES INC
IC card and IC chip module
InactiveUS20050023361A1Improve data securityLow costDigital data processing detailsSolid-state devicesVolatile memory
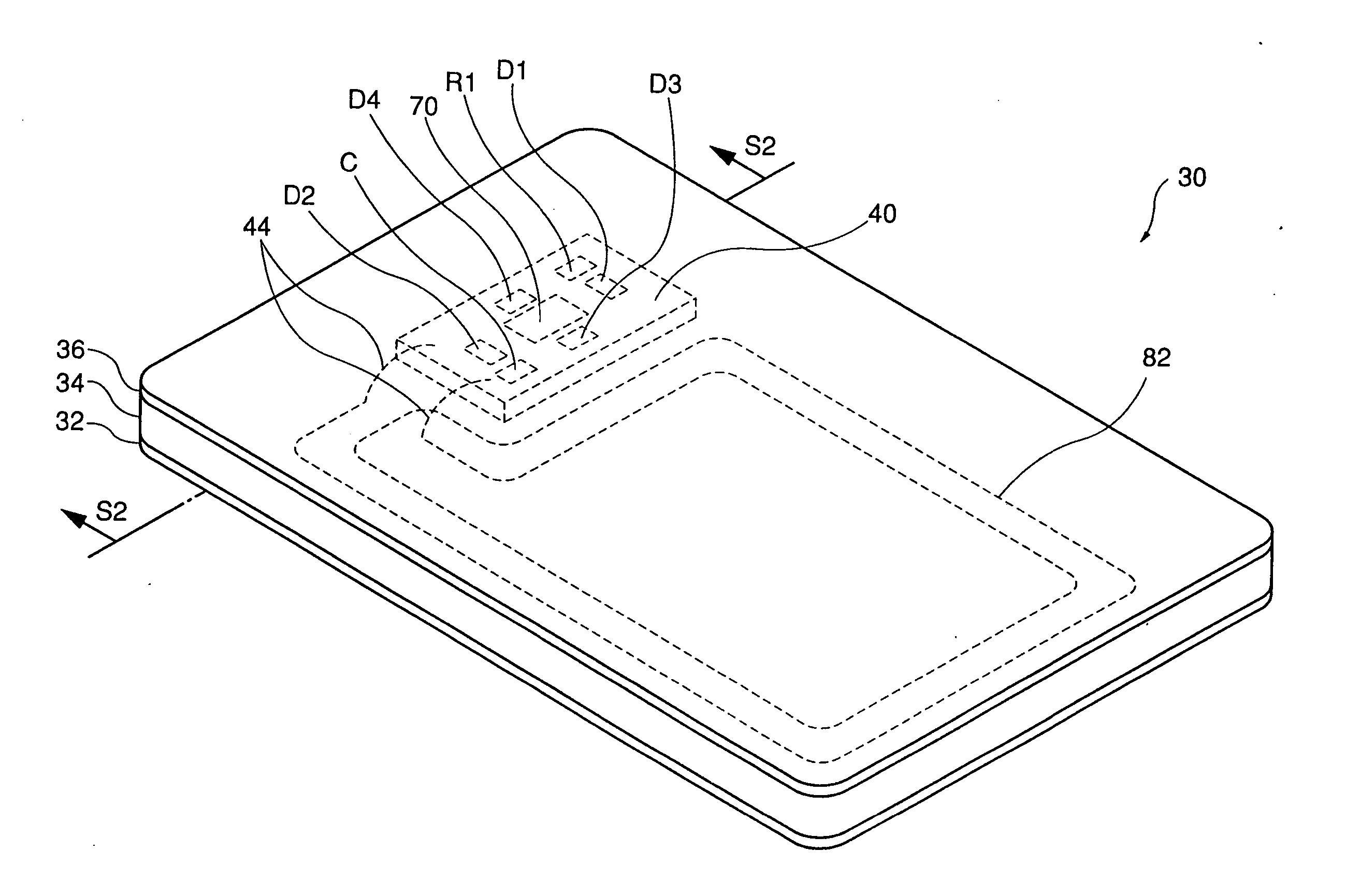
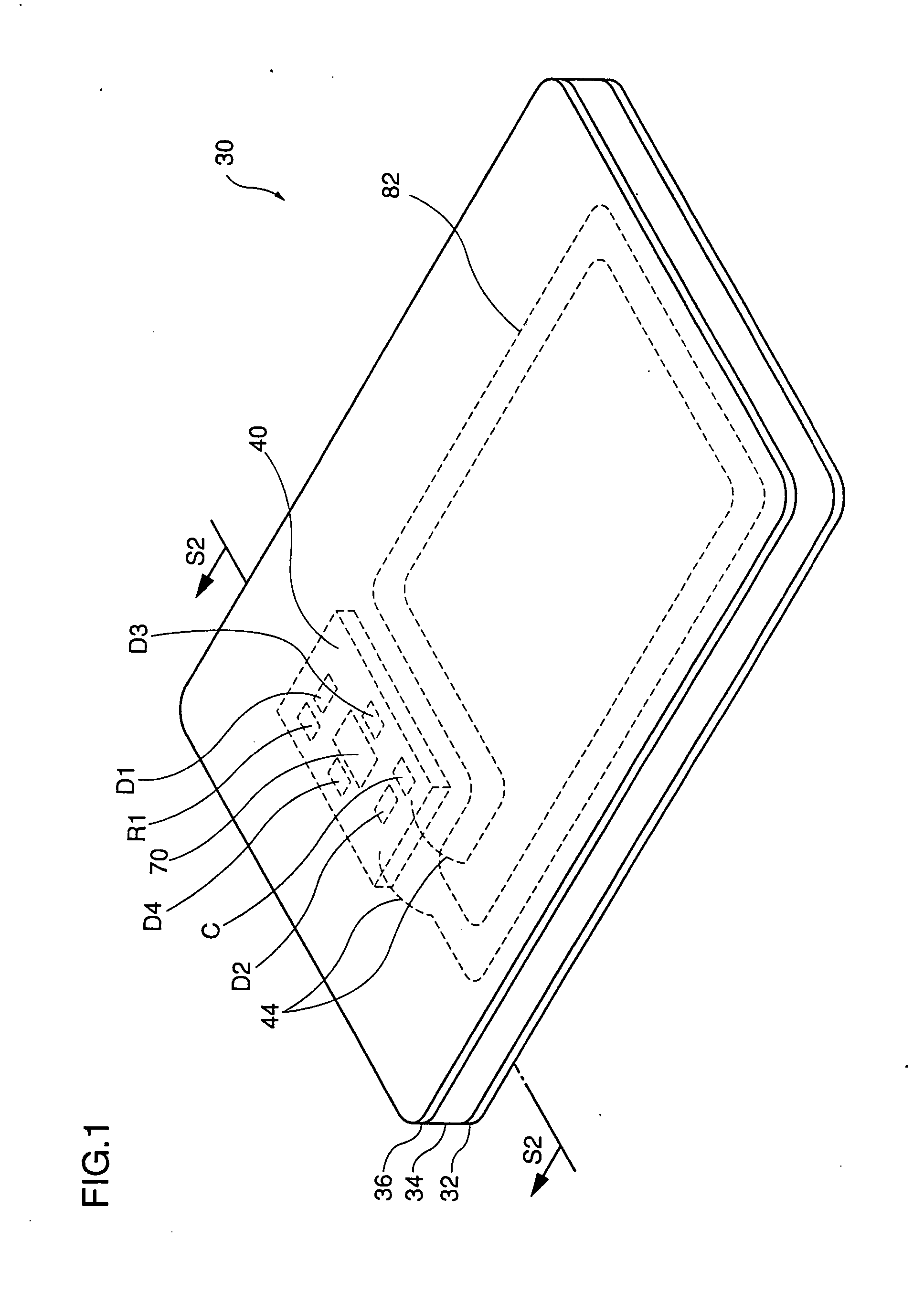
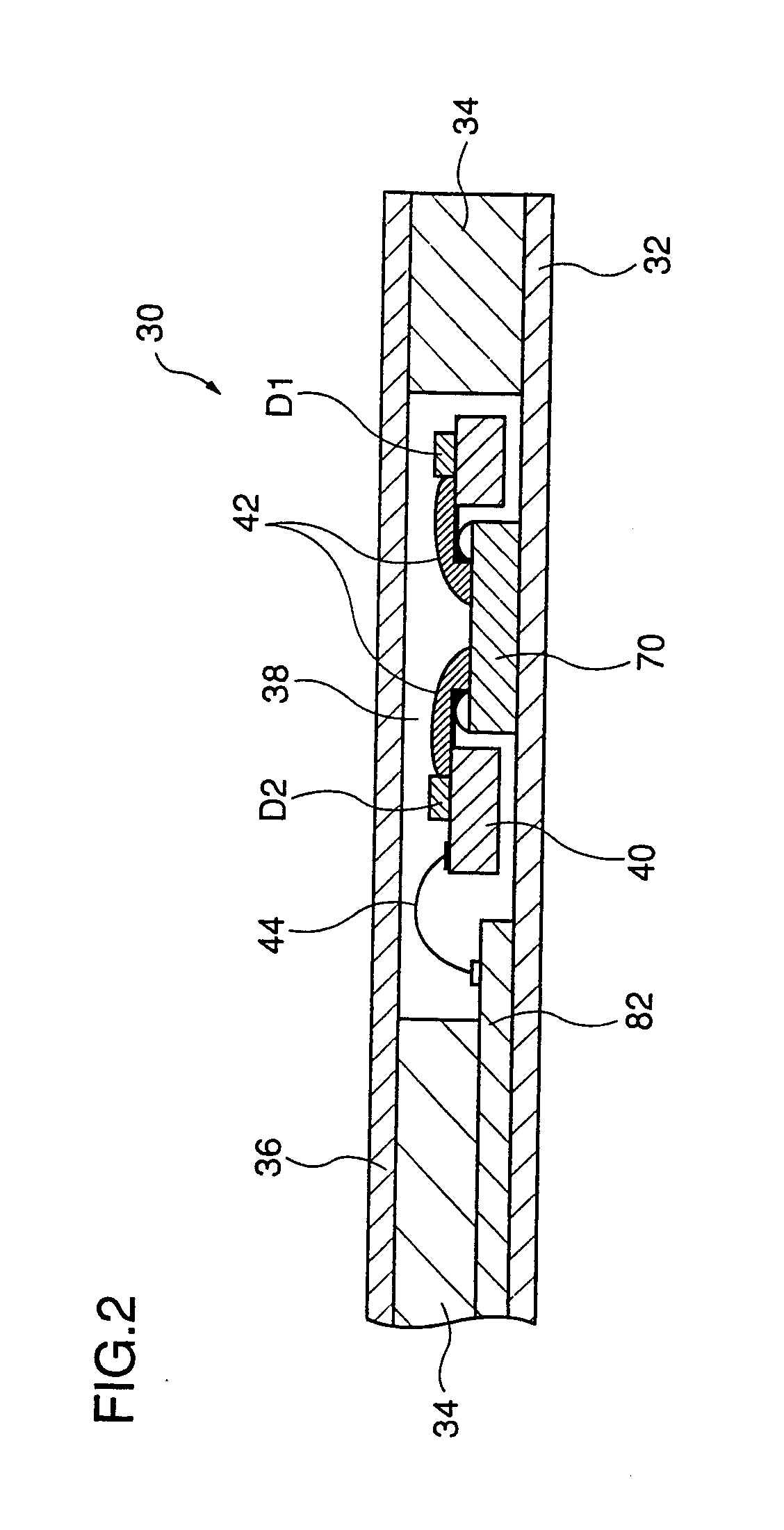
In an IC card 30 is sealed an IC chip 70 provided with an exposure sensor 84. When exposure sensor 84 detects that IC card 30 has been opened, exposure sensor 84 outputs an exposure detection signal to a CPU 76. In response to the exposure detection signal, CPU 76 provides a predetermined operation, such as erasure of data in a non-volatile memory 78. As such, the data in non-volatile memory 78 cannot be obtained if IC card 30 is improperly opened to check the data in non-volatile memory 78. Thus the IC card can obtain an enhanced data security.
Owner:ROHM CO LTD
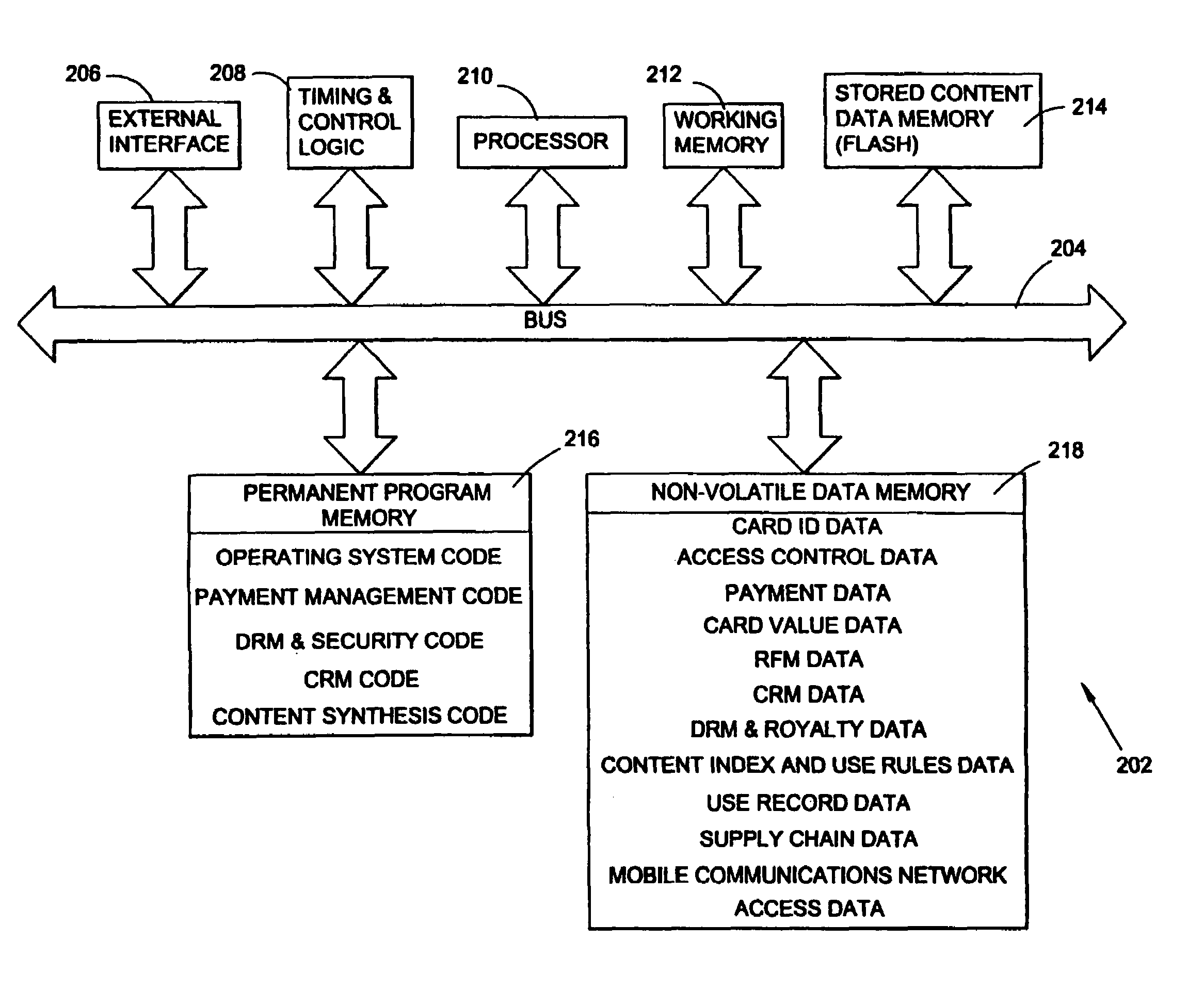
Data storage and access systems
InactiveUS7334720B2Improve data securityAvoiding long delayTelevision system detailsColor television detailsPaymentWeb site
Data storage and access systems are described for downloading and paying for data such as audio and video data, text, software, games and other types of data. A portable data carrier has an interface for sending and receiving data, non-volatile data memory for storing received content data and non-volatile payment validation memory for providing payment validation data to an external device. The carrier may also store a record of access made to the stored content, and content use rules for controlling access to the stored content. Preferred embodiments store further access control data and supplementary data such as hot links to web sites and / or advertising data. A complementary data access terminal, data supply computer system and data access device are also described. The combination of payment data and stored content data and, in preferred embodiments, use rule data, helps reduce the risk of unauthorized access to data such as compressed music and video data, especially over the Internet.
Owner:SMARTFLASH
Methods for single signon (SSO) using decentralized password and credential management
ActiveUS8819444B2Decentralized credential managementShorten the timeComputer security arrangementsSecuring communicationEnd to end securityPassword
A method for single sign-on (SSO) that provides decentralized credential management using end-to-end security. Credential (and other personal user information) management is decentralized in that encryption is performed locally on the user's computer. The user's encrypted credentials may be stored by the login server and / or a plurality of distributed servers / databases (such as a cloud). The login server never has access to the user's credentials or other personal information. When the user wants to use single sign-on, he enters his password into his browser and the browser submits the encrypted / hashed password to the login server for validation. Upon validation, the browser receives the user's encrypted credentials. The credentials are decrypted by the browser and provided to relevant websites to automatically log the user in.
Owner:SHAHBAZI MAJID +1
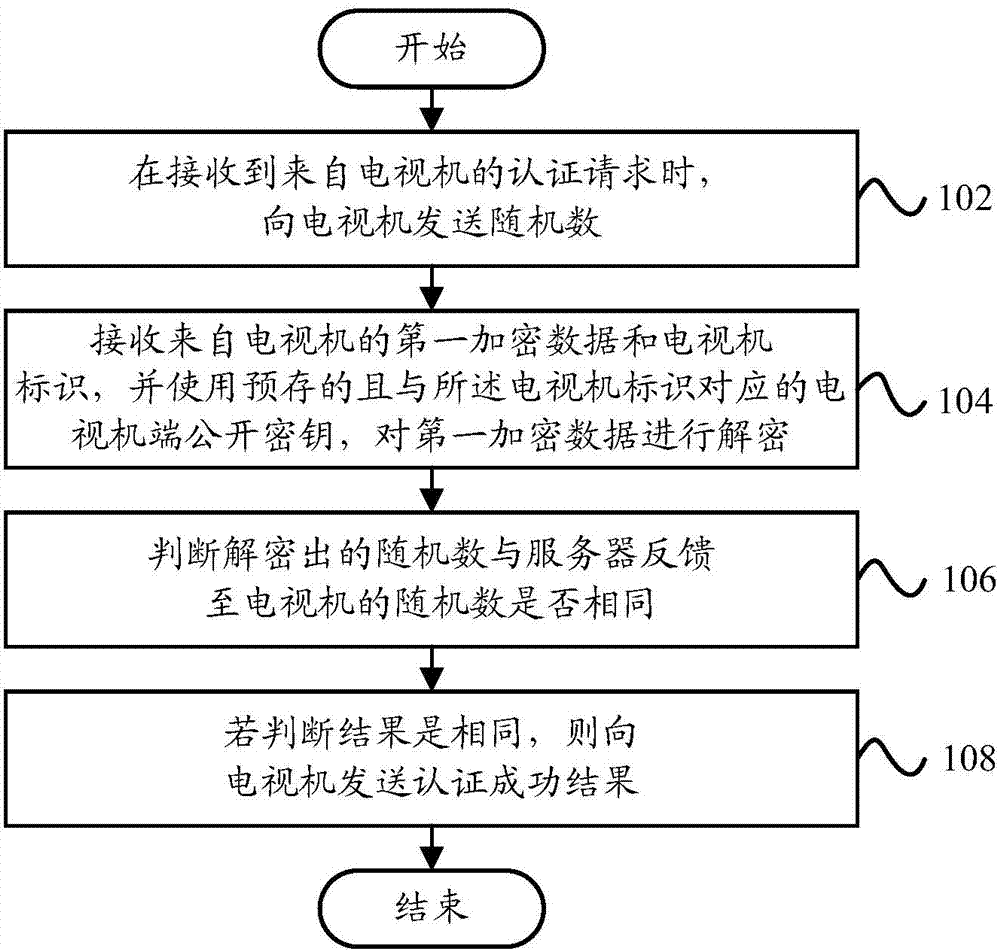
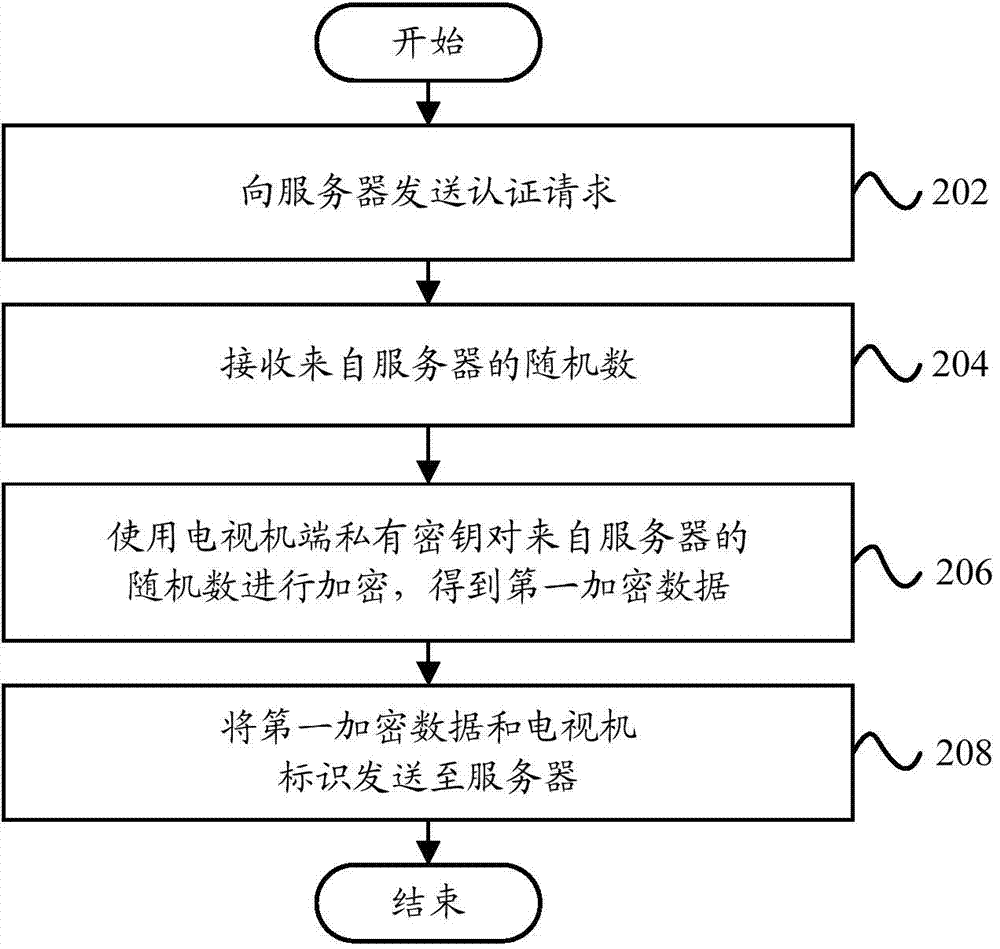
Authentication method, server and television
ActiveCN103763631APrevent theftPrevent authorizationSelective content distributionAuthentication systemEncryption
The invention provides an authentication method, a server and a television. The authentication method comprises the steps that when an authentication request from the television is received, a random number is sent to the television; first encrypted data and television identification from the television are received and a pre-stored television side public key corresponding to the television identification is used for conducting decryption on the first encrypted data, wherein the first encrypted data are data generated through the method that encryption is conducted on the random number by a television side private key used by the television and the television side public key and the television side private key are a pair of matched keys; whether a decrypted random number is identical to the random number fed back to the television is judged; if the judged result shows that the two random numbers are identical, a successful authentication result is sent to the television. According to the technical scheme, bidirectional authentication of the server and the television is achieved, an external device is not needed, the authentication process is simple, the random numbers are involved in the authentication process, and the safety of the authentication system is improved.
Owner:HISENSE VISUAL TECH CO LTD
Method for transmitting data apparatus for recording data medium for recording data and apparatus for reproducing data
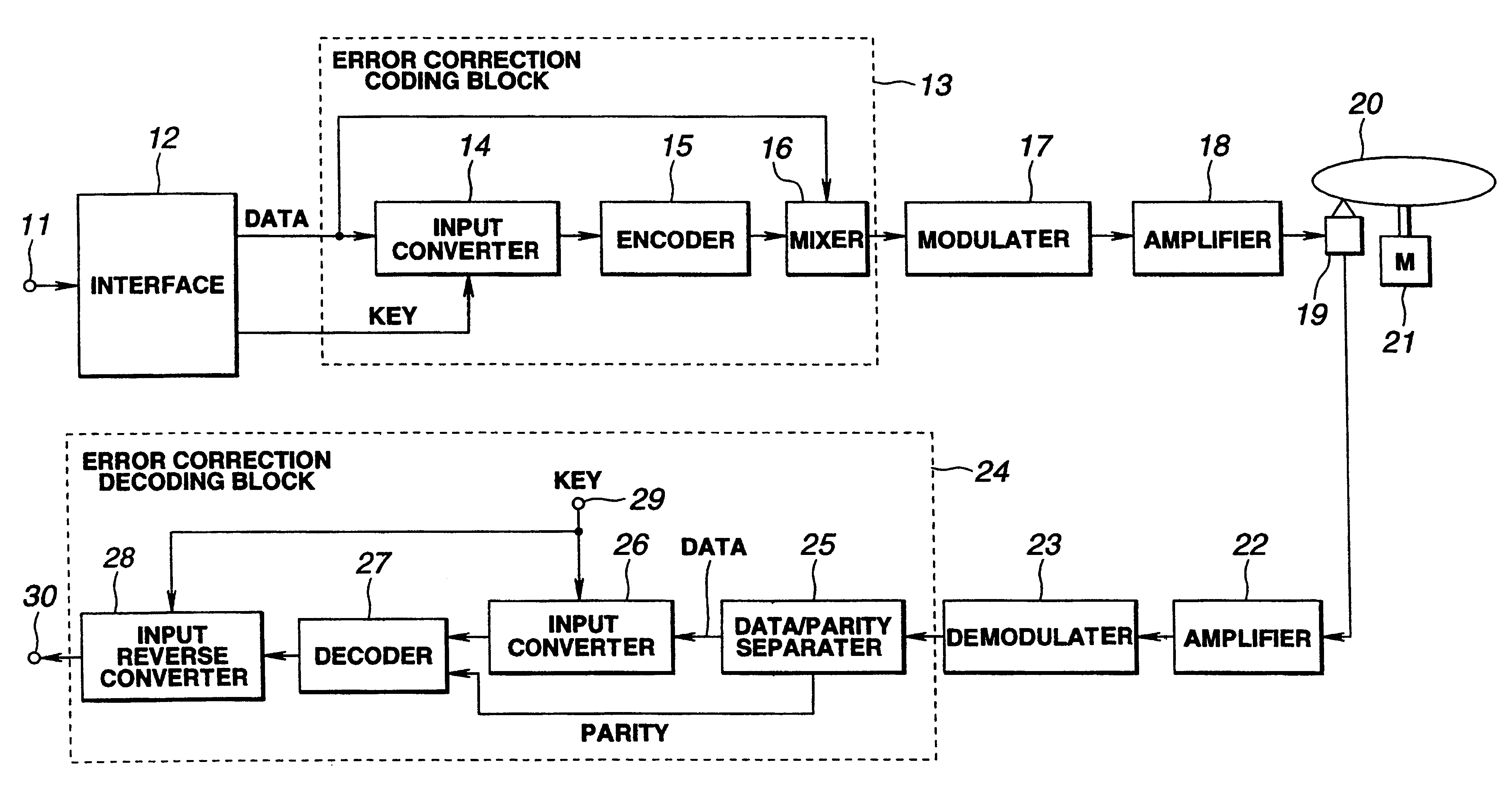
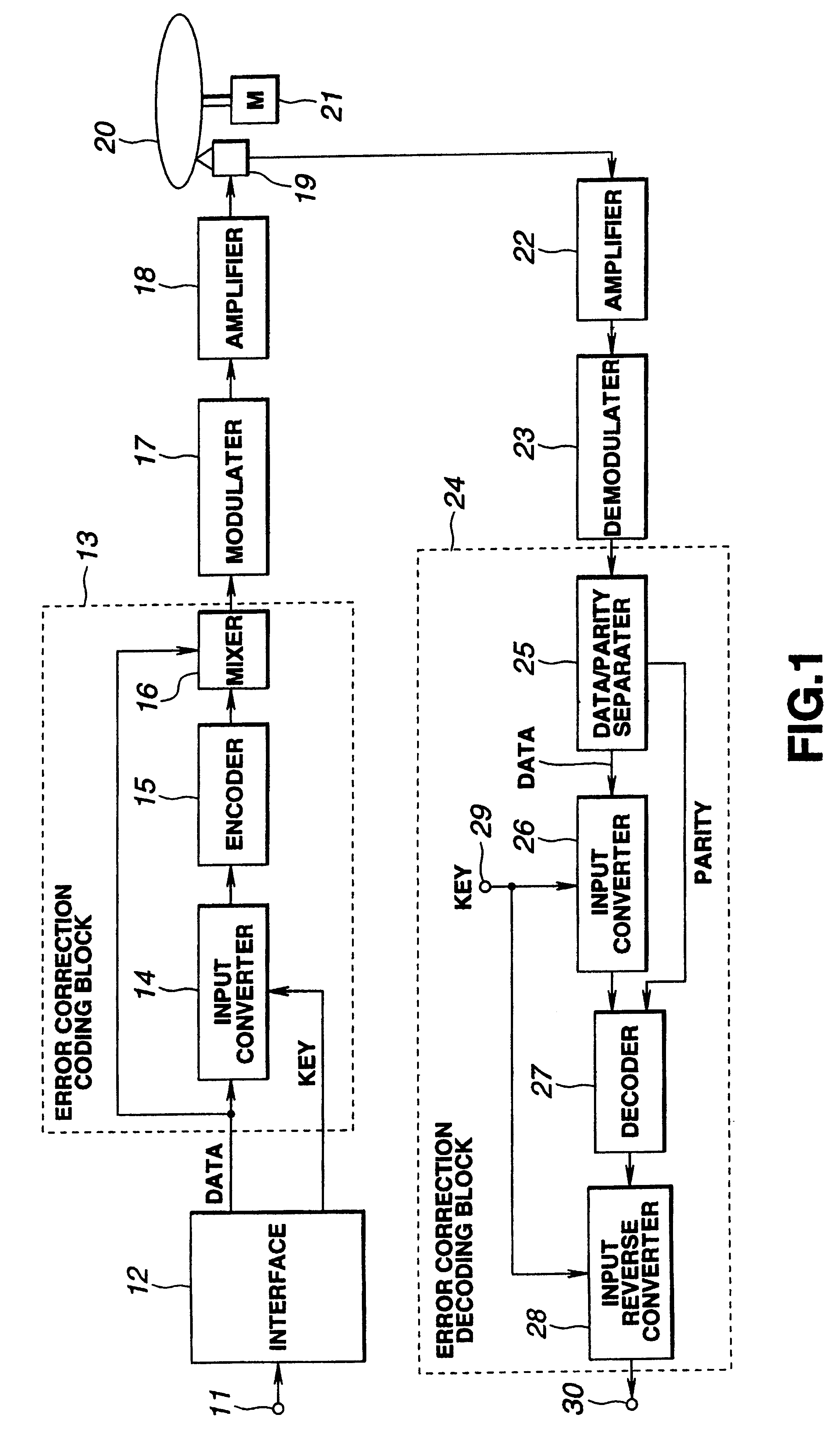
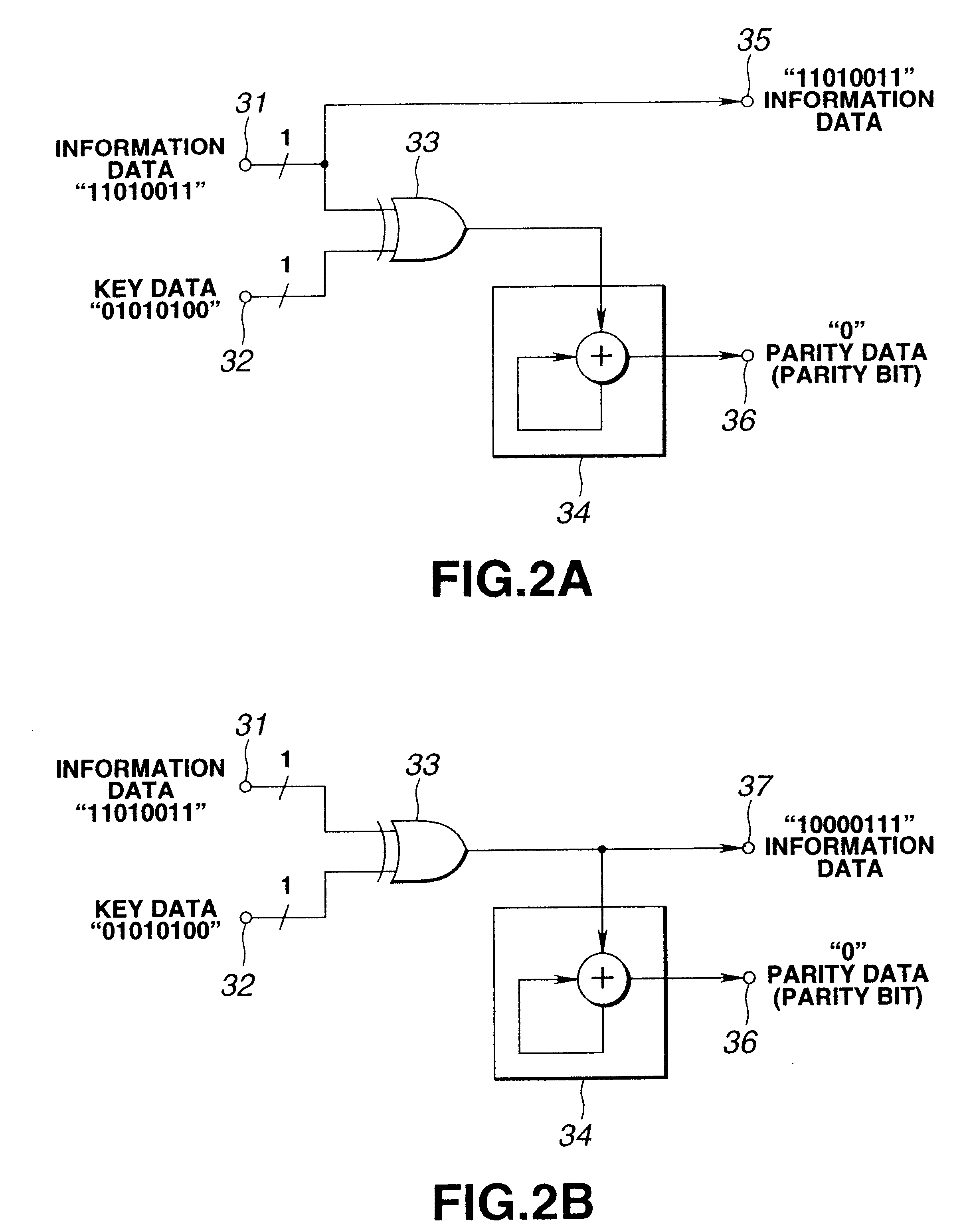
InactiveUS6463153B1Improve data securityDigital data processing detailsUnauthorized memory use protectionInterface circuitsCoding block
A data transmitting method, a data recording apparatus, a data record medium and a data reproducing apparatus are provided to disallow the encryption to be easily decoded and keep the secrecy of key information higher. The data transmitting apparatus includes an error correction coding process block. In the block, an input converting circuit operates to perform a logic operation with respect to the information data from an interface circuit according to the key data. The converted information data is sent to an encoder for generating parity data. This parity data is mixed in a mixing circuit with information data before conversion. The error correction coding block operates to send the resulting data to a modulating circuit for modulating the data. The modulated data is recorded on a disk record medium.
Owner:SONY CORP
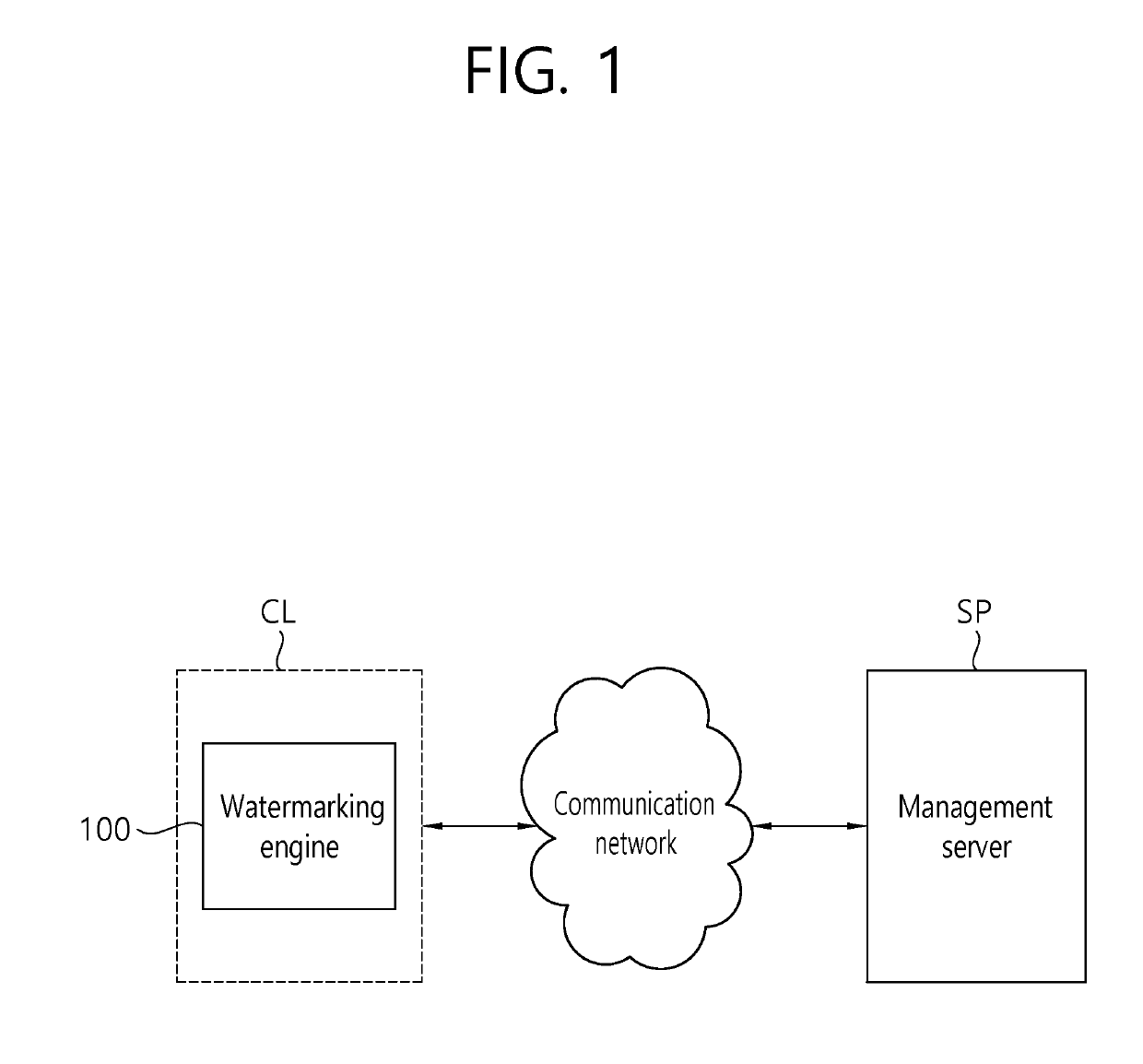
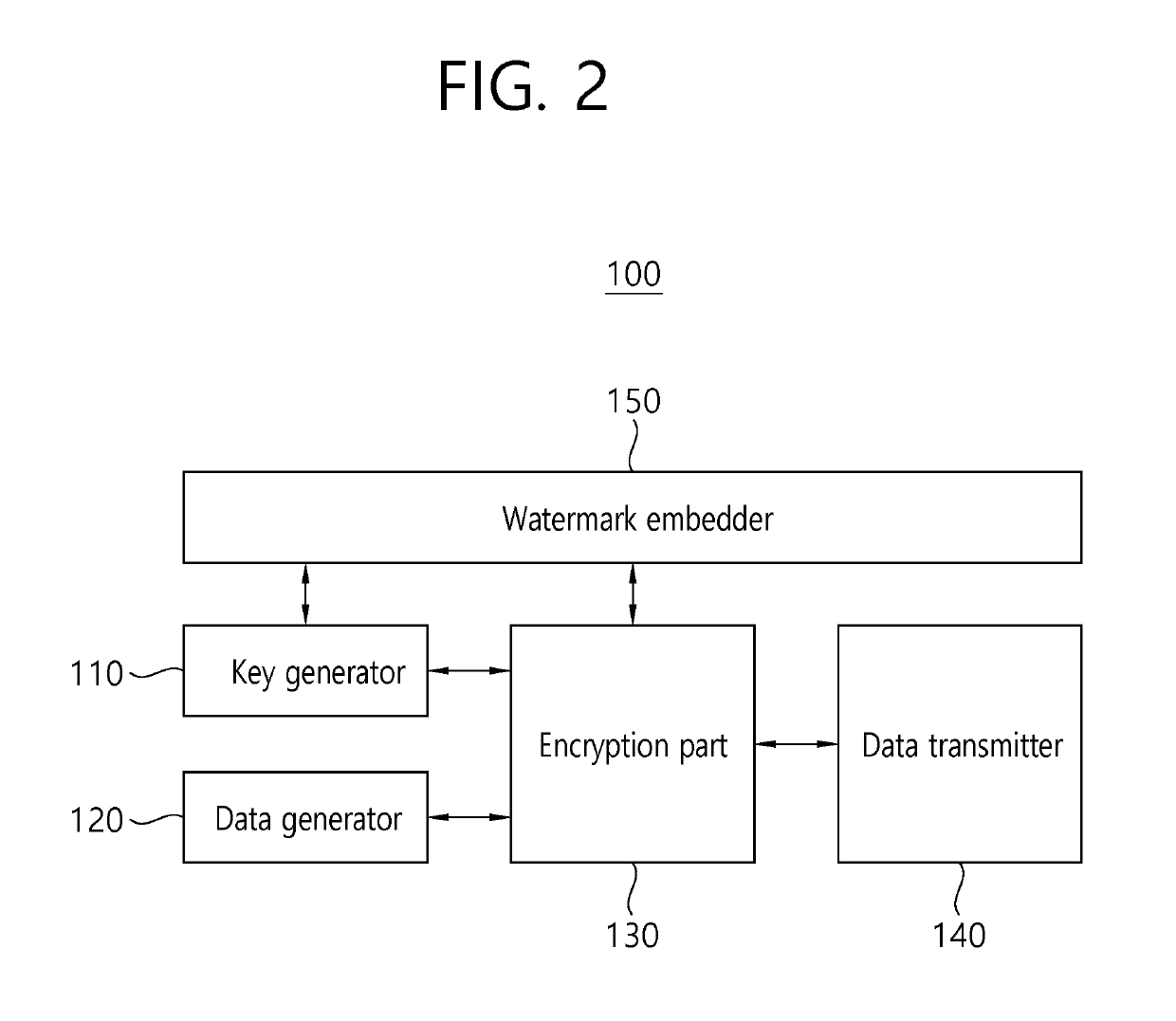
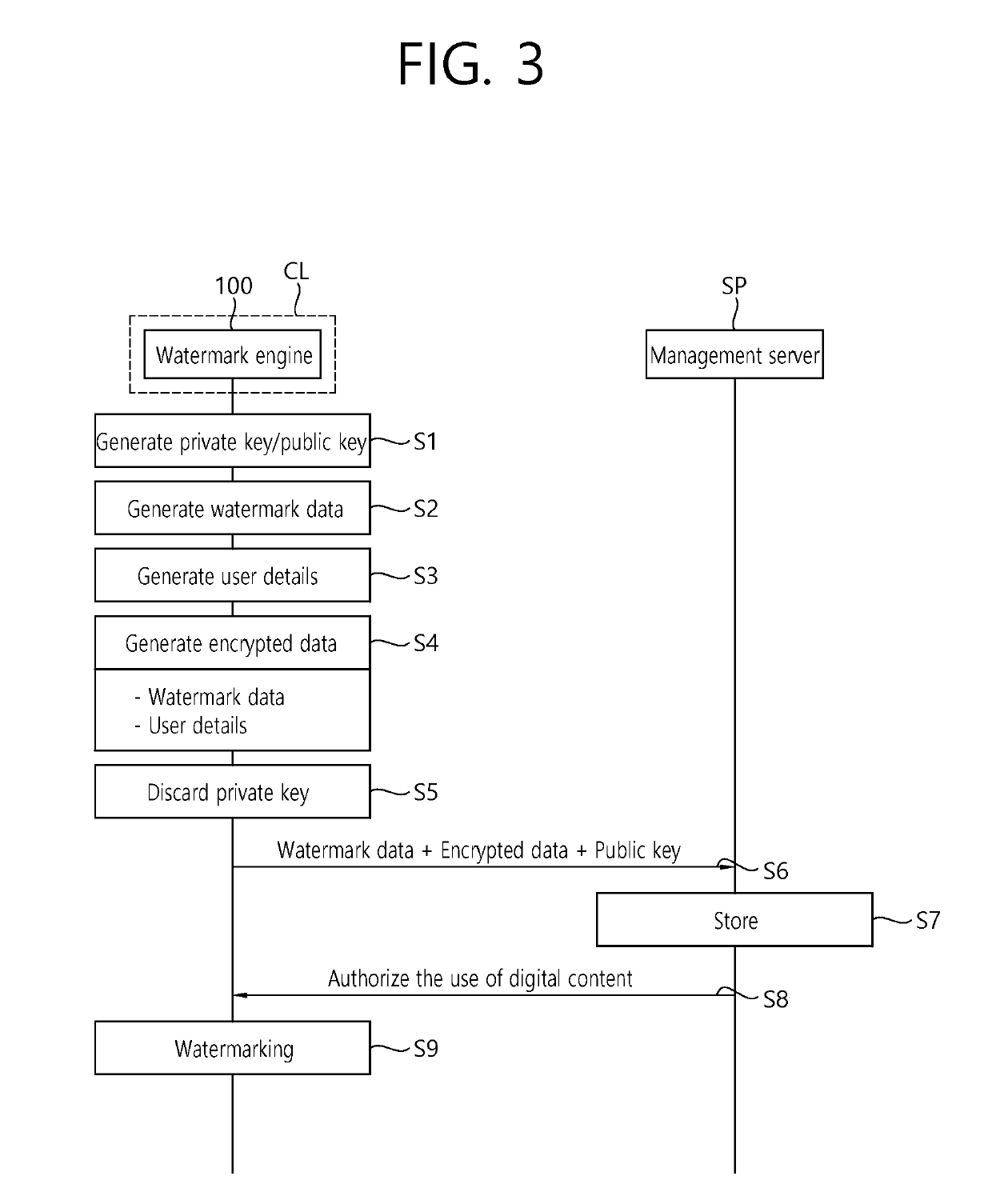
Method and apparatus for watermarking of digital content, method for extracting information
ActiveUS20190294761A1Reducing watermarking timeEnsure safetyKey distribution for secure communicationProgram/content distribution protectionDigital contentComputer terminal
A method and apparatus for watermarking digital content and a data extraction method are disclosed. The digital content watermarking method includes: generating private and public keys corresponding to the user terminal; generating watermark data containing user identity information corresponding to the user terminal and user details associated with the watermark data; generating encrypted data by encrypting the watermark data and the user details with the private key; transmitting the watermark data, the encrypted data, and the public key to a server; receiving digital content when authorized by the server; and watermarking the digital content with the watermark data.
Owner:MARKANY
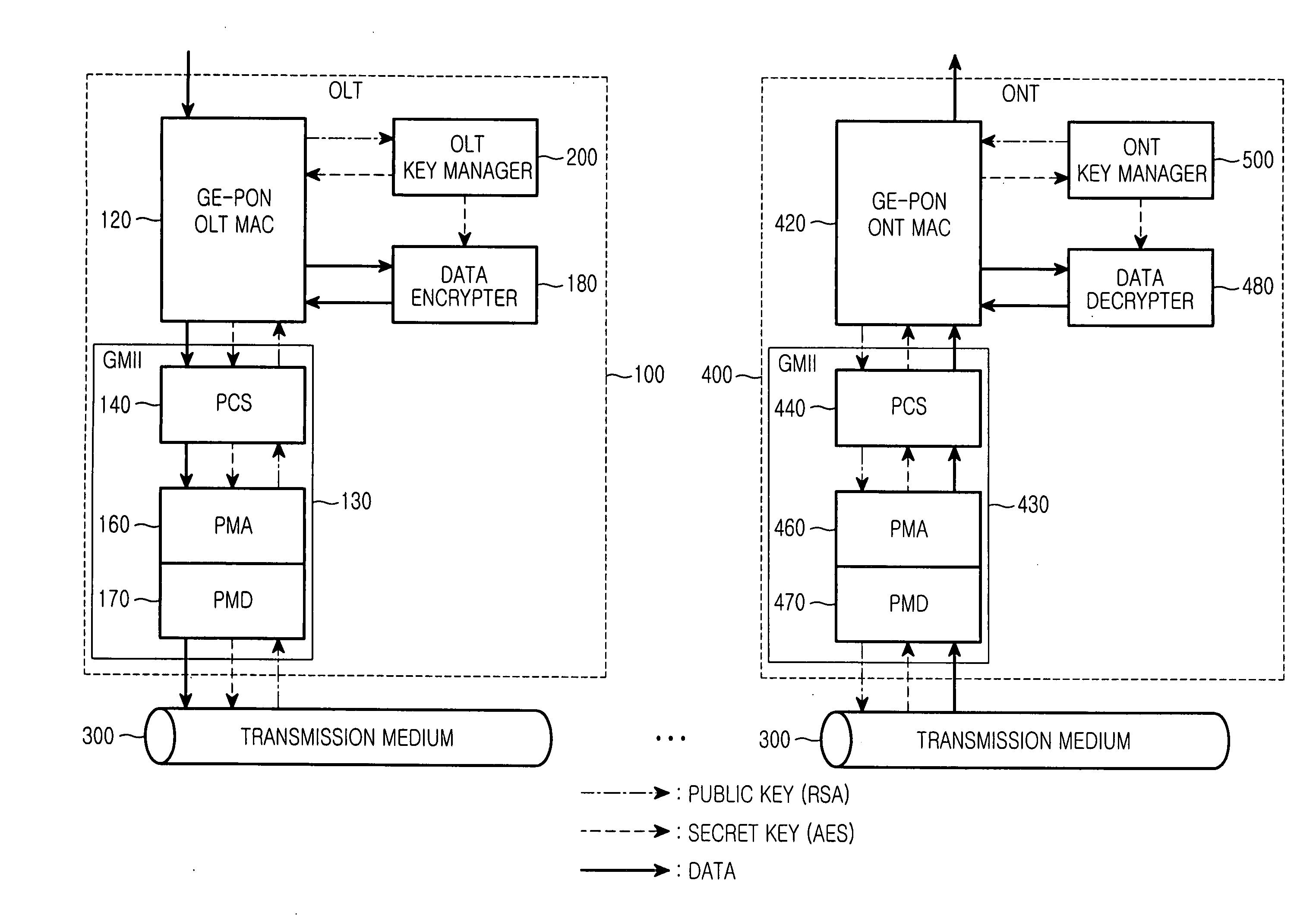
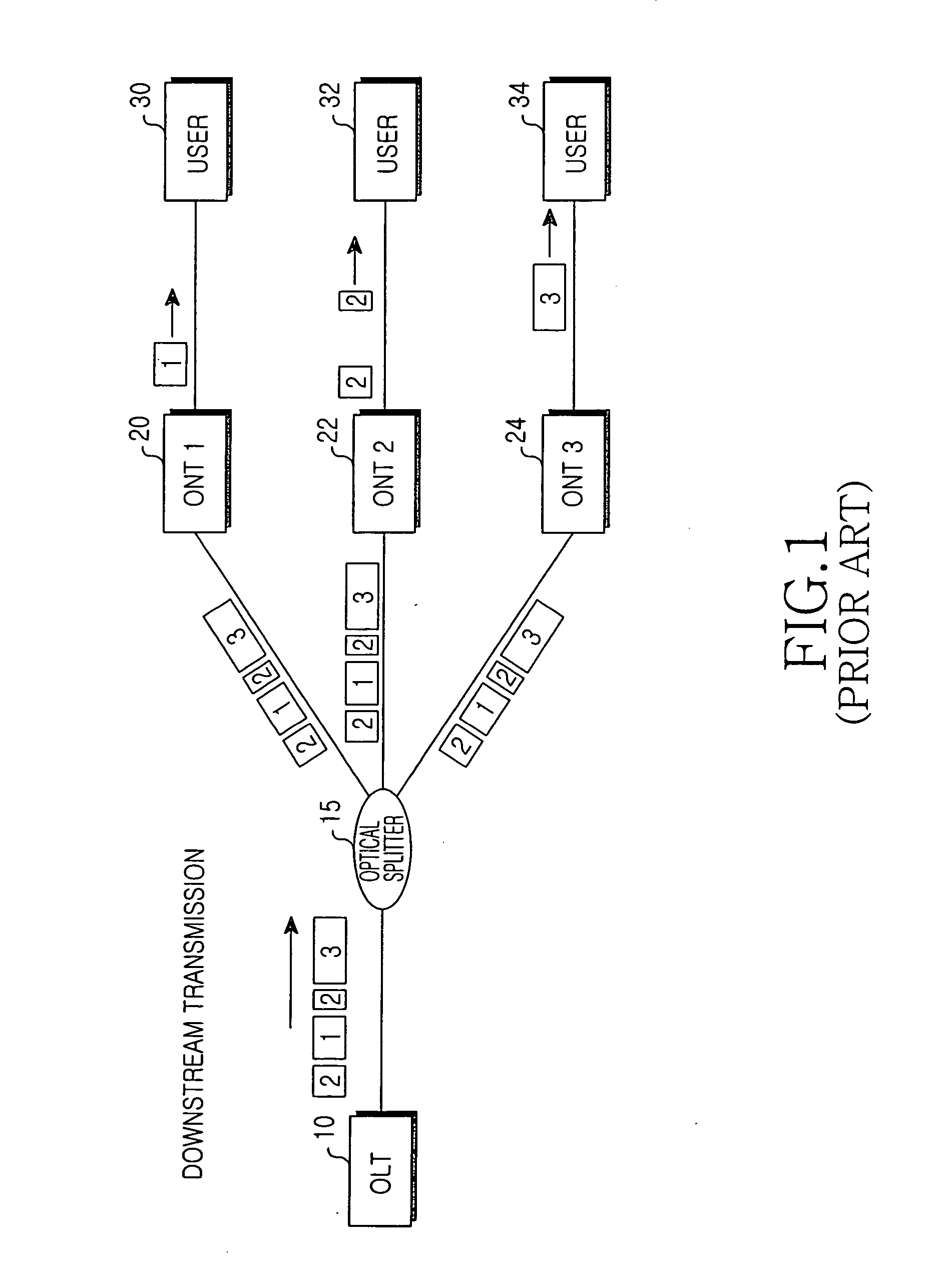
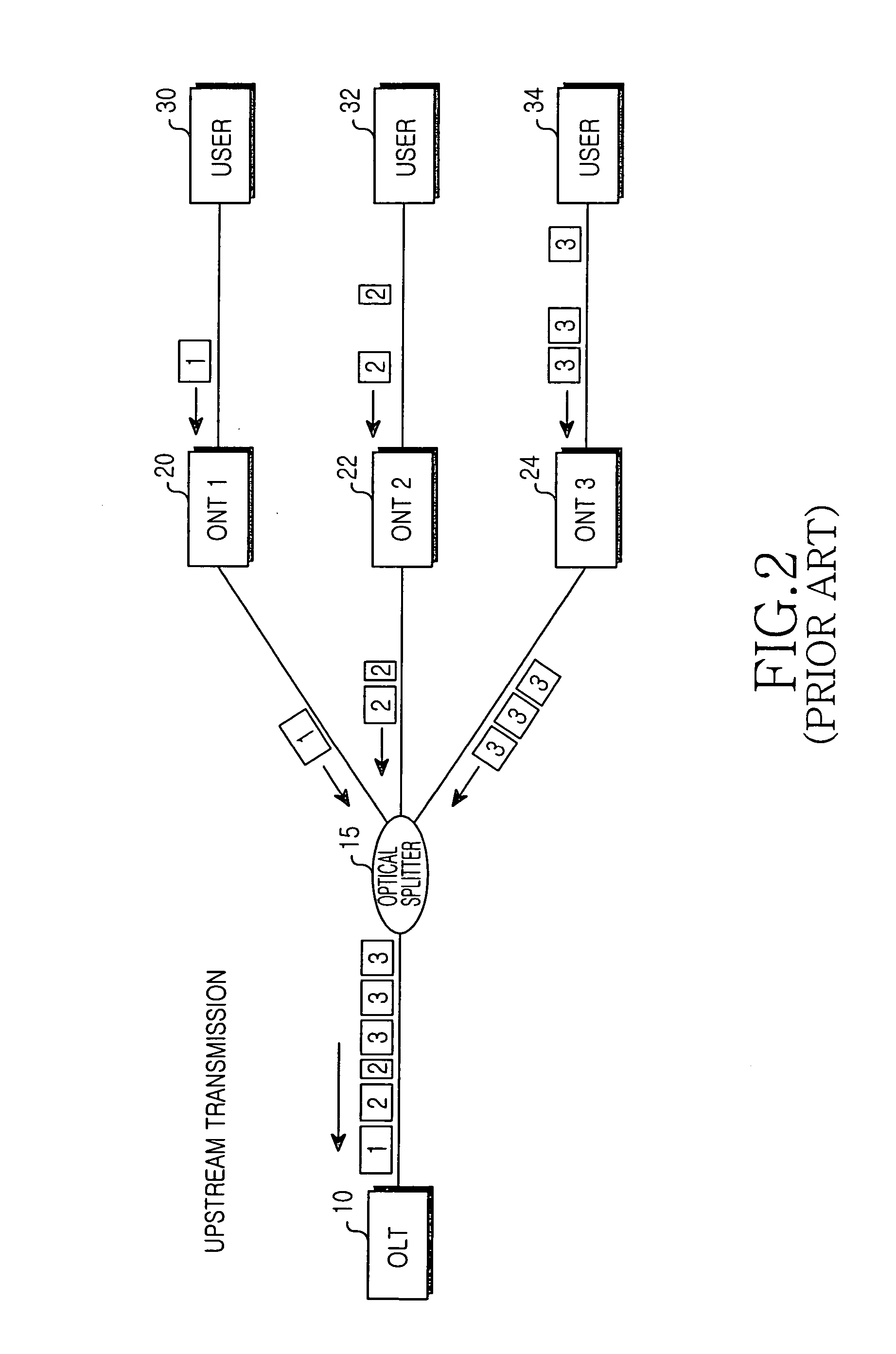
Gigabit Ethernet passive optical network for securely transferring data through exchange of encryption key and data encryption method using the same
InactiveUS20050135609A1Improve data securityEffective encryptionKey distribution for secure communicationMultiple keys/algorithms usageOptical line terminationEncryption
A Gigabit Ethernet passive optical network (GE-PON) for securely transferring data through exchange of an encryption key comprises an optical line terminal (OLT) for encrypting a secret key using a public key received through a transmission medium, transmitting the encrypted secret key, encrypting data using the encrypted secret key, and transmitting the encrypted data, and at least one optical network terminal (ONT) for transmitting the public key to the OLT, decrypting the encrypted secret key transmitted from the OLT using a private key, and decrypting the data encrypted with the encrypted secret key, transmitted from the OLT, using the decrypted secret key.
Owner:SAMSUNG ELECTRONICS CO LTD
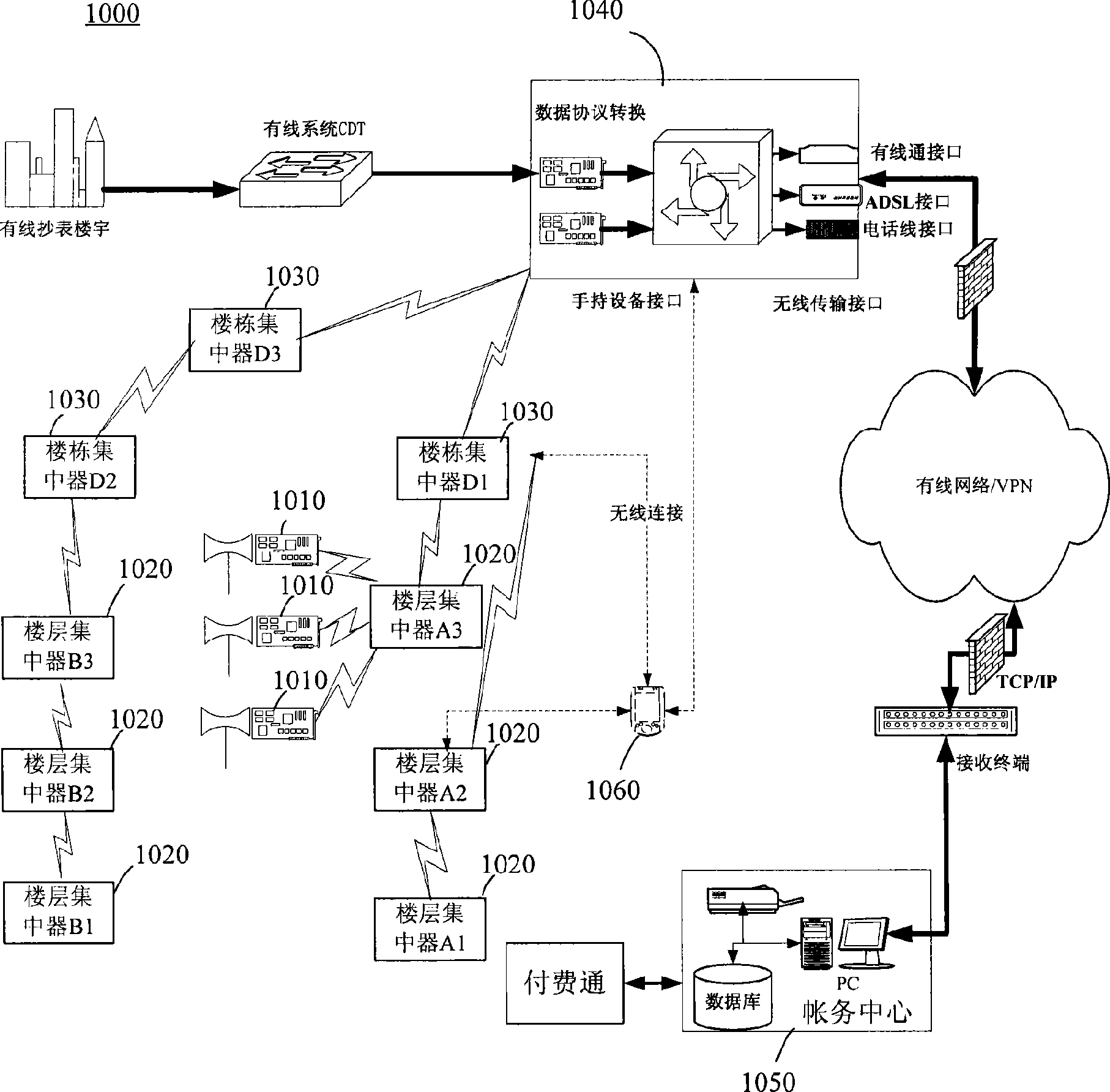
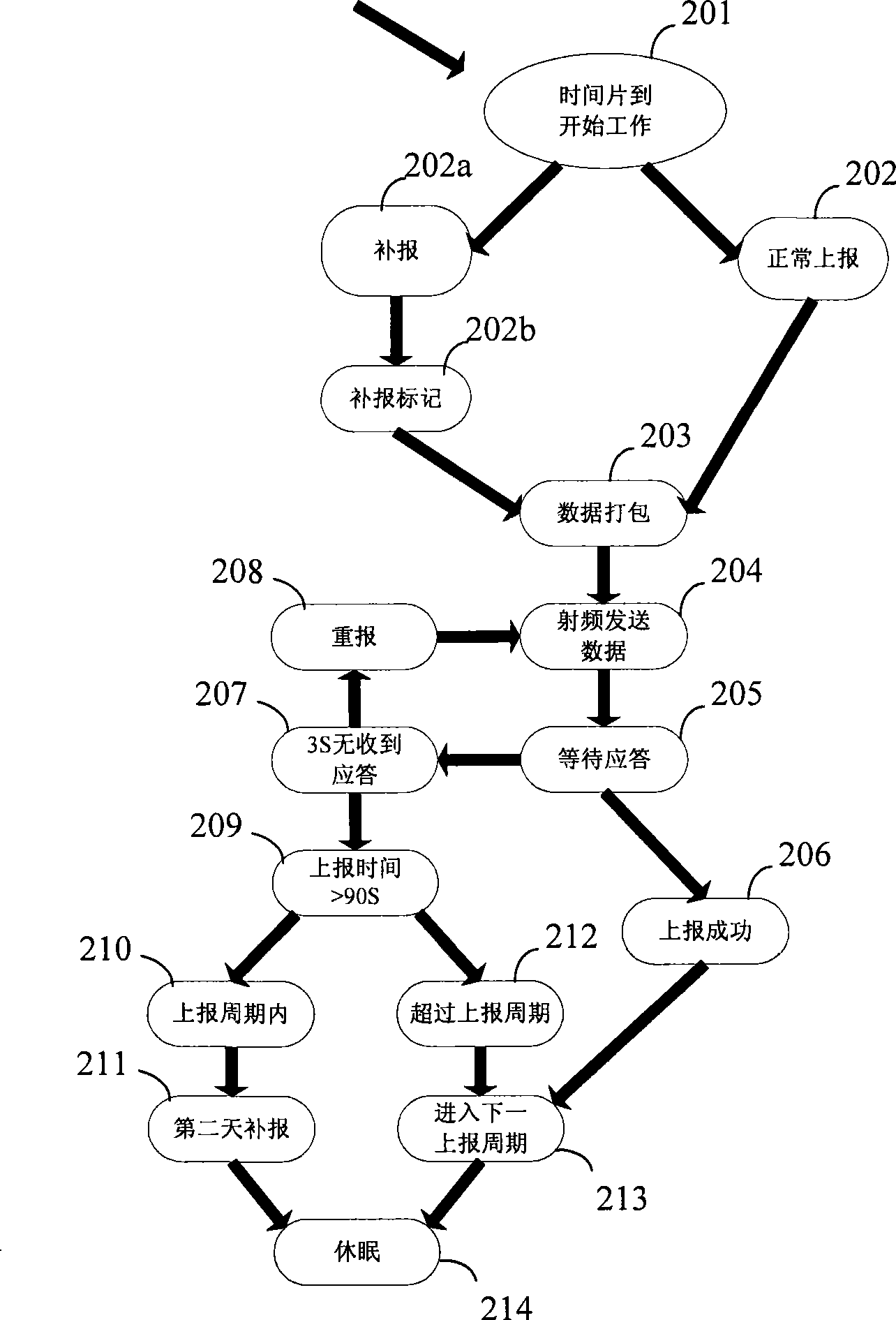
Data collection method used for remote wireless meter reading system
InactiveCN101458868AImprove data securityImprove stabilityElectric signal transmission systemsData terminalComputer terminal
The invention relates to a data collection method for remote wireless meter reading system. The remote wireless meter reading system comprises a wireless meter reading terminal for sending data, a data terminal for receiving data and accessing a front computer of an accounting center, and a concentrator for relaying data between the wireless meter copying terminal and the data terminal. The data collection method comprises that: the wireless meter reading module uploads data at fixed time in each day and backups data, and after the failure of data upload, uploads data again in a time interval; the concentrator automatically generates a meter data index list according to a preset meter ID list, searches and stores the data of the meter according to the index list, manages and maintains the storage device; the data terminal obtains the meter reading data of each day, collects and backups the data, and periodically reports the meter reading data to the front computer.
Owner:SHANGHAI MUNICIPAL WATER RESOURCES DEV & UTILIZATION NAT ENG CENT +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com