Patents
Literature
54results about How to "Effective encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
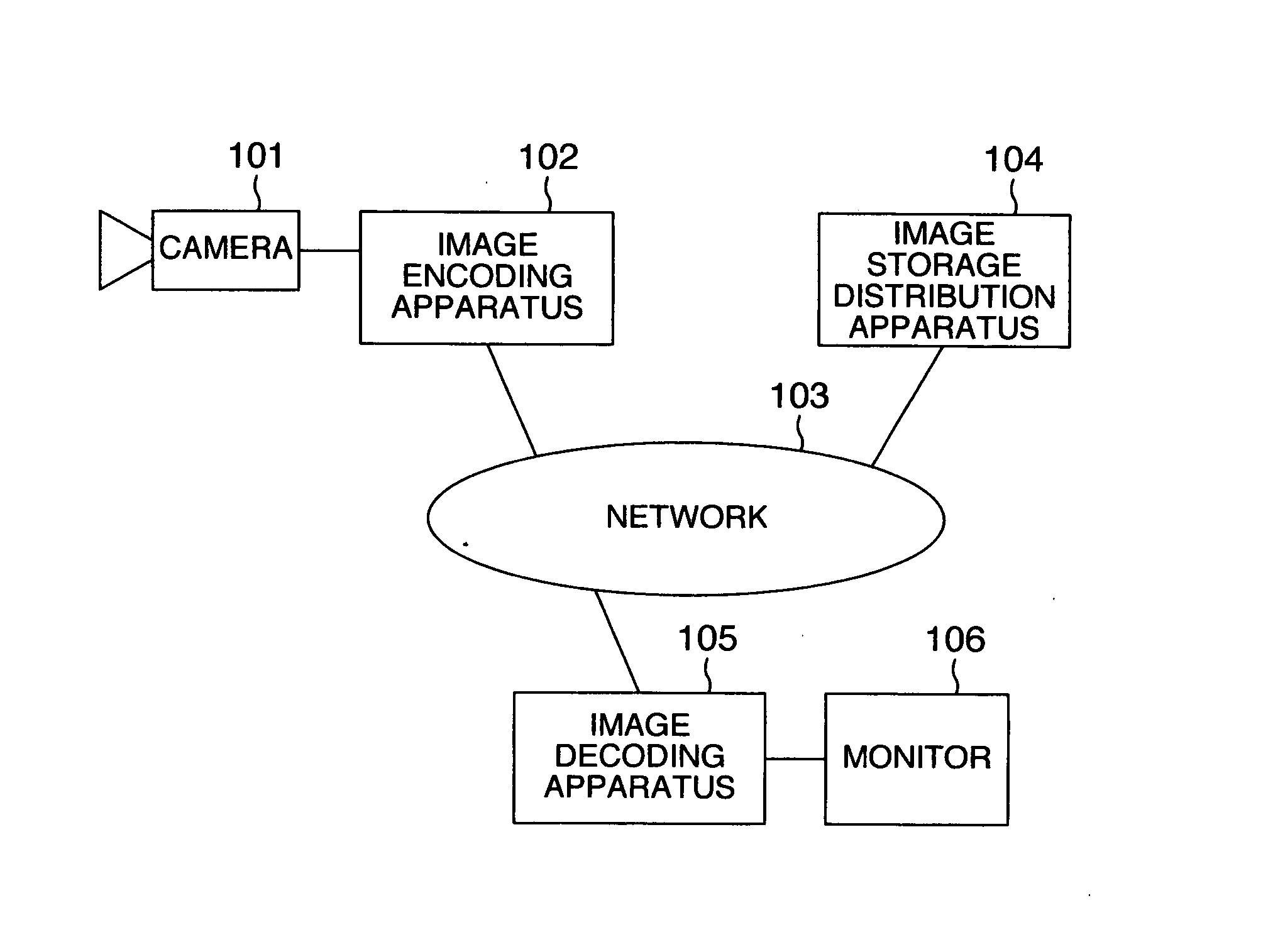
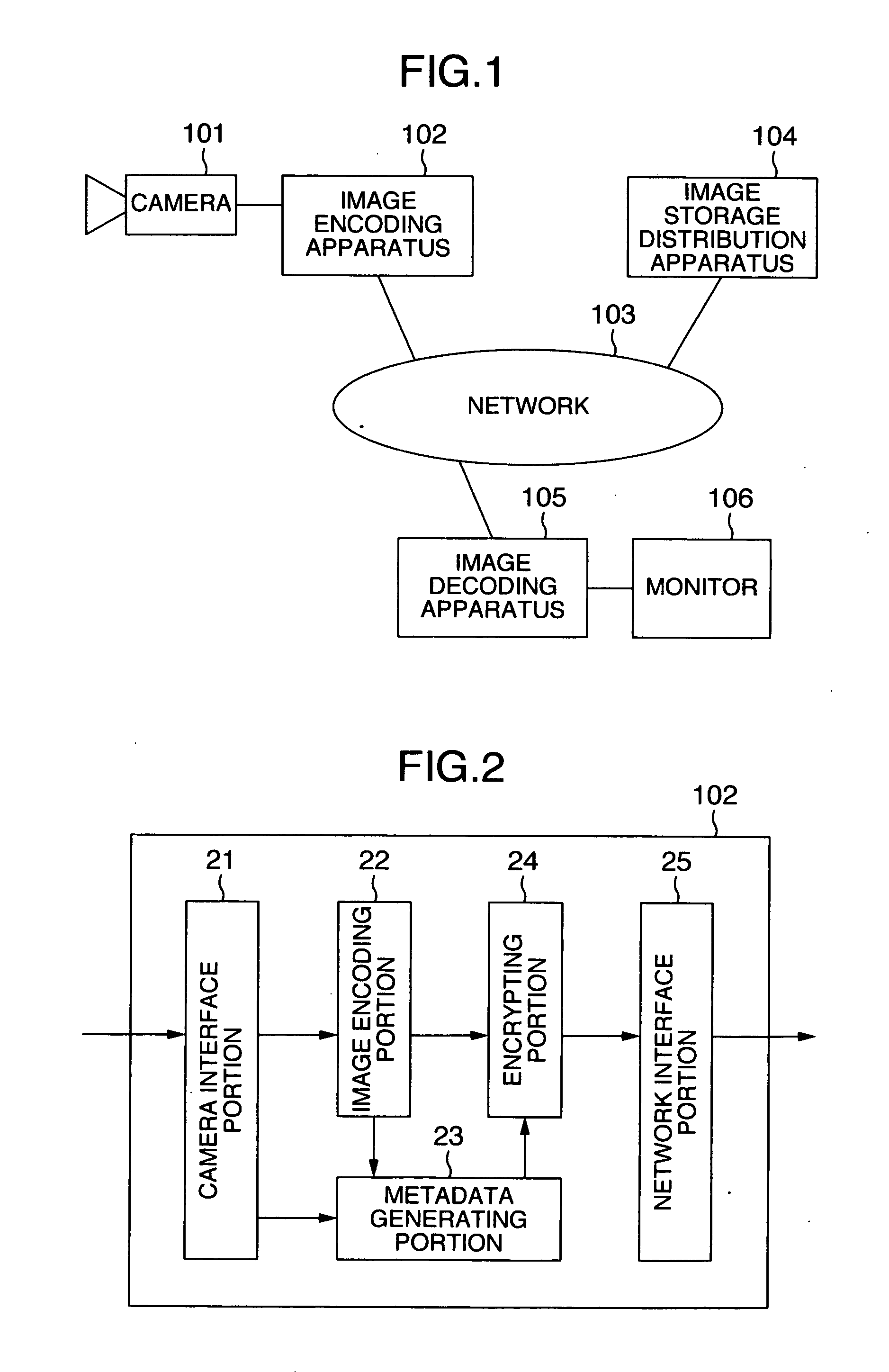
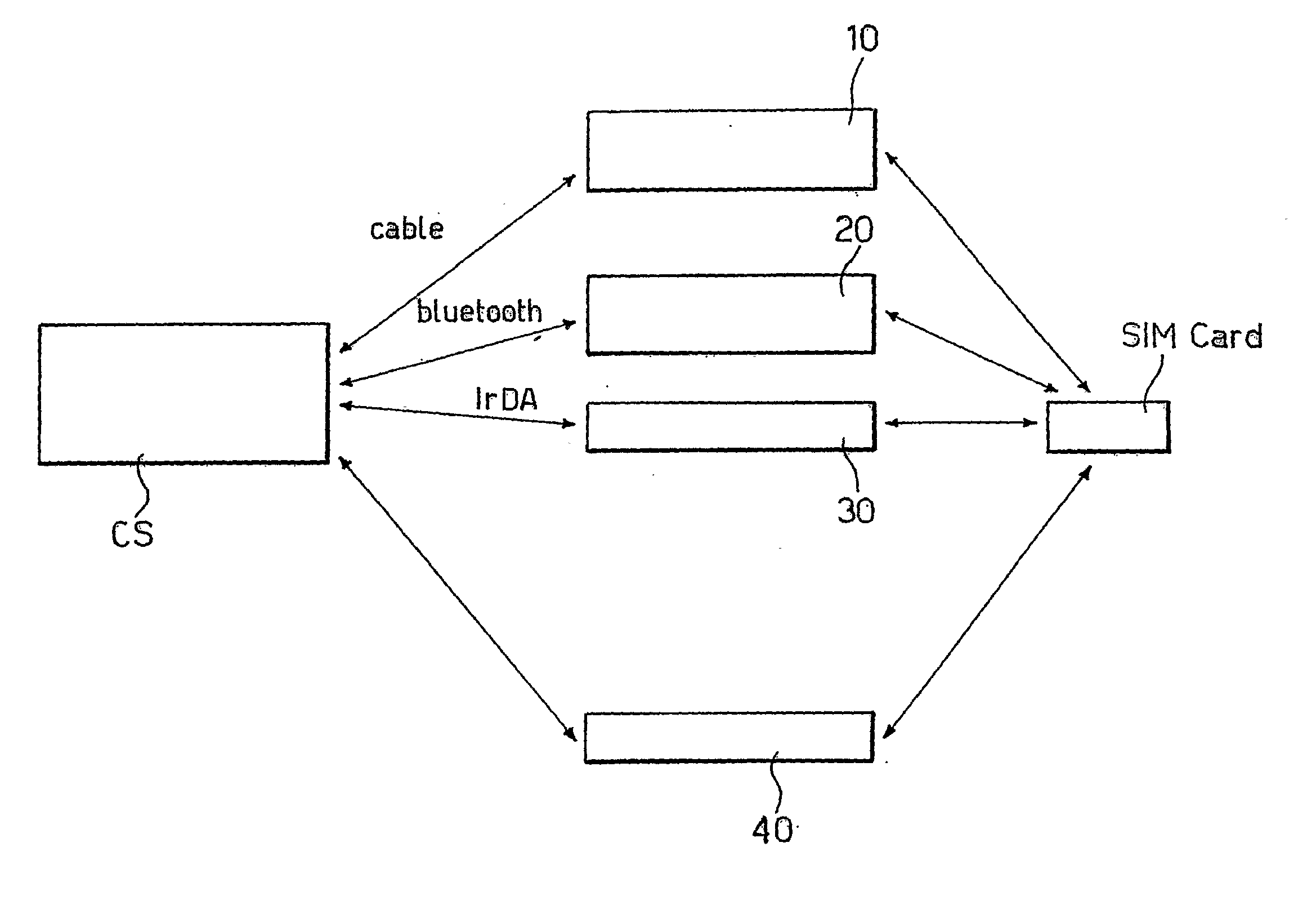
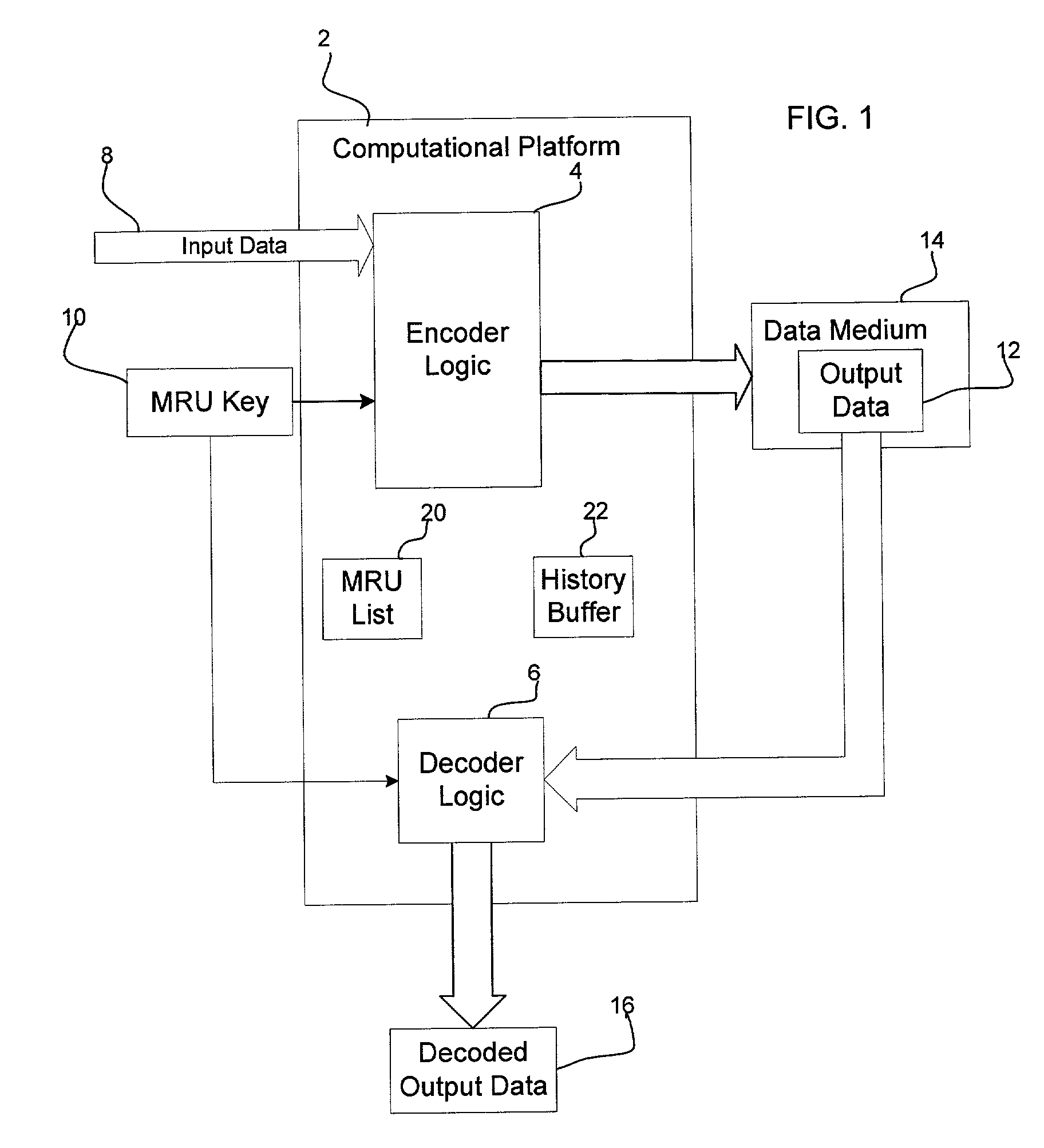
Encryption method, encryption apparatus, data storage distribution apparatus and data delivery system
InactiveUS20060056625A1Effective encryptionKey distribution for secure communicationData taking preventionComputer hardwareData shipping
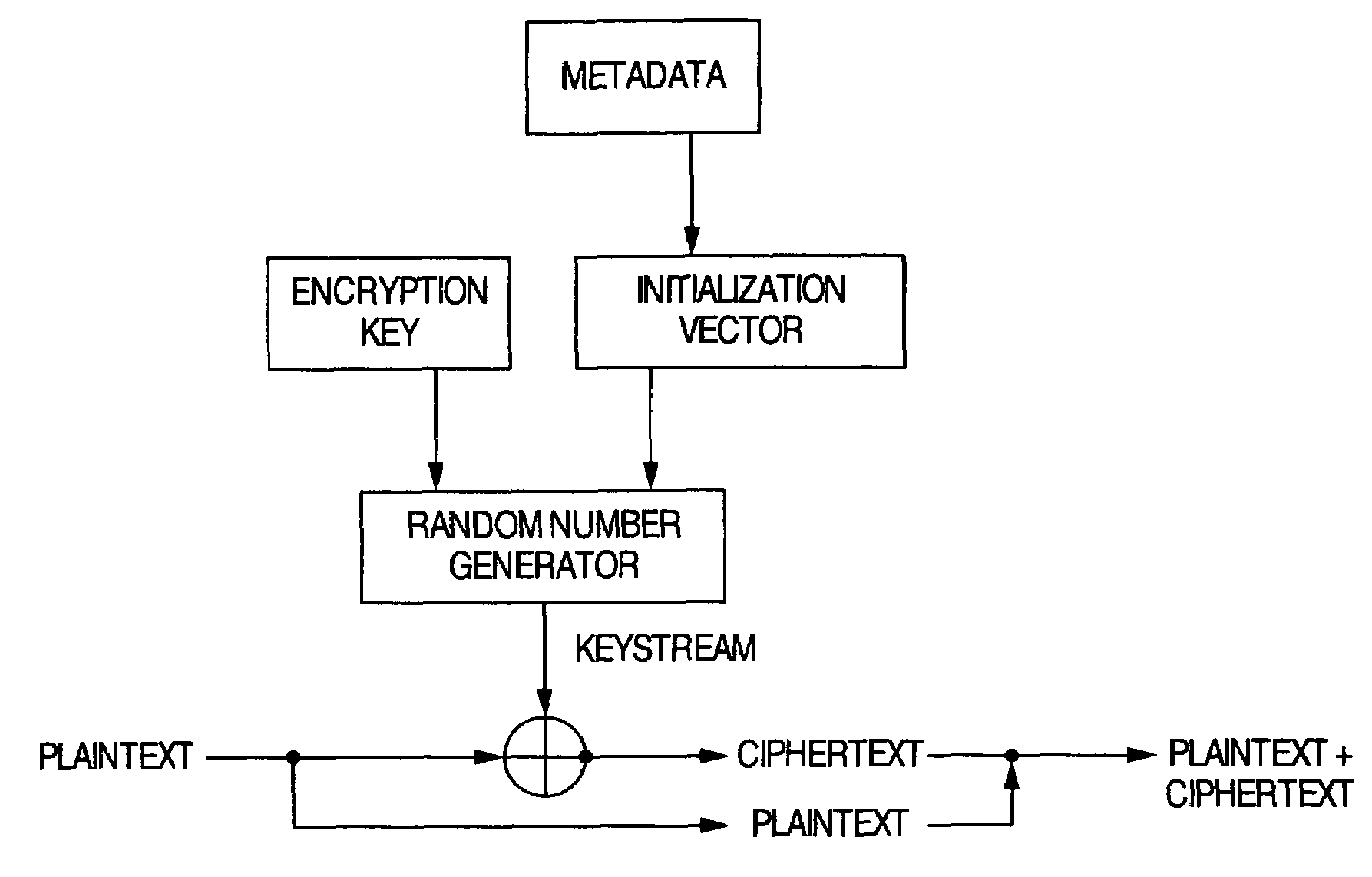
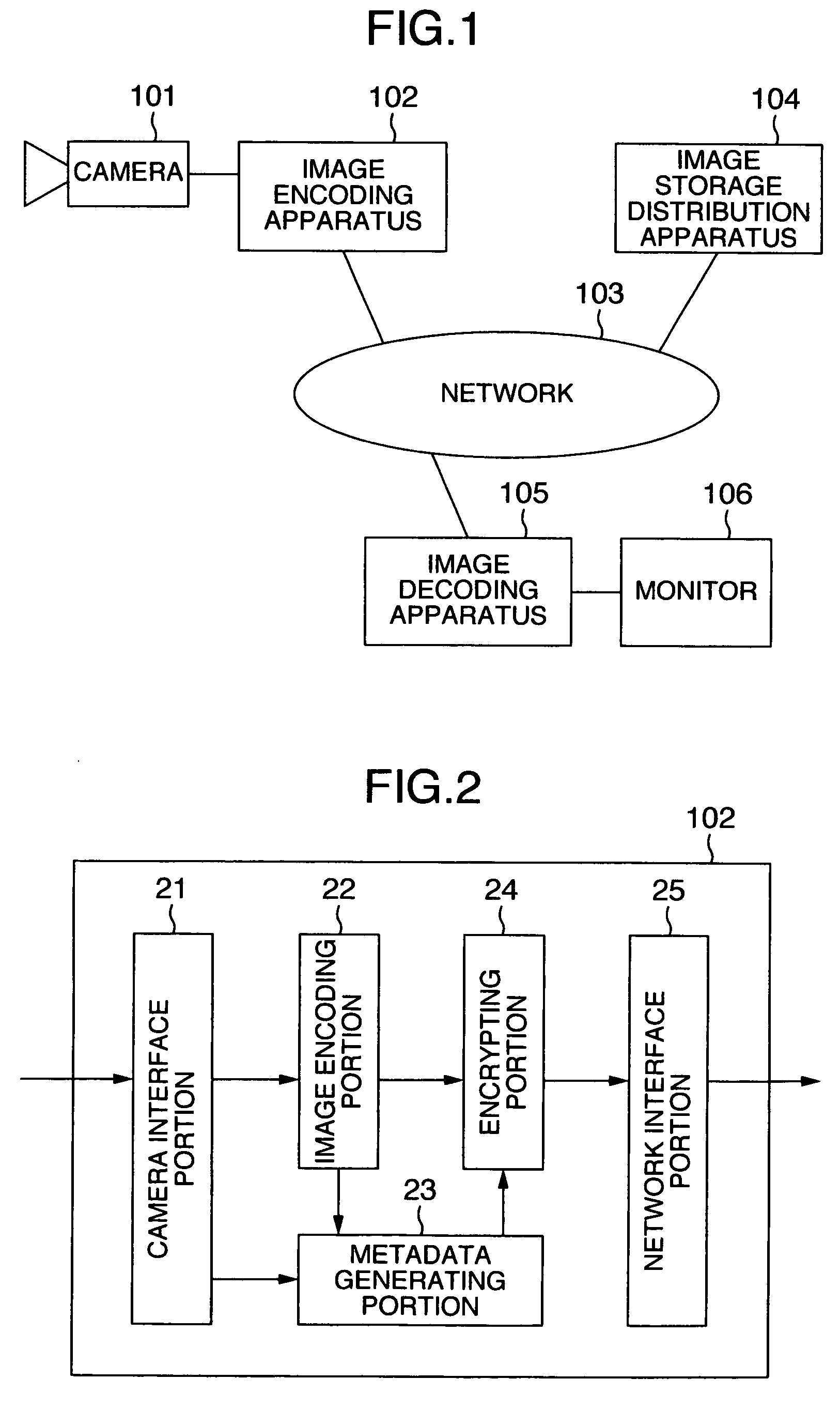
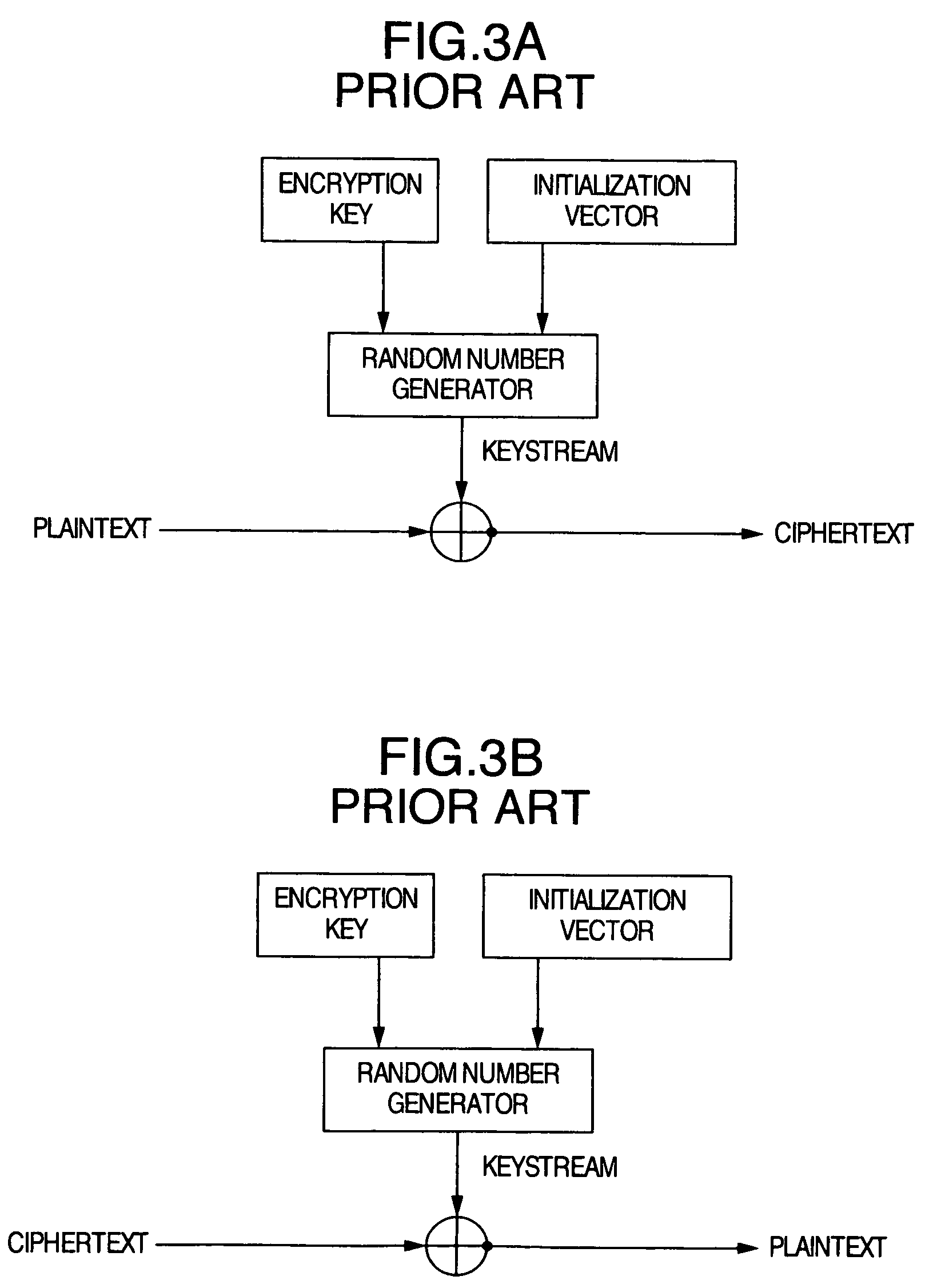
Data to be encrypted is effectively encrypted by a data delivery system for encrypting the data to be encrypted with a transmitting apparatus and decrypting a cipher thereof with a receiving apparatus. In a configuration for encrypting and decrypting the data to be encrypted by using a random number sequence generated by a random number generating portion for generating the random number sequence uniquely decided from an input parameter, the transmitting apparatus generates the input parameter to perform encryption based on metadata of the data to be encrypted while the receiving apparatus generates the input parameter to perform cipher decryption based on the metadata embedded in the data to be encrypted.
Owner:KOKUSA ELECTRIC CO LTD
System and method for digital rights management
InactiveUS20050027991A1Easy to useImprove user experienceUser identity/authority verificationProgram/content distribution protectionRational useDigital content
The invention provides several embodiments of a system and method of securely distributing and using digital content that protects the content owner's copyrights as well as the content user's right of fair use. Digital content may be any work that can be encoded in digital form, e.g. literature, music, software applications, static images, and video, etc. Various embodiments act by implementing public key infrastructure to encrypt digital content in such a way that only a licensed user may access the content. Embodiments enable licensed users to access the content via multiple playback devices and from various locations, regardless of whether they are connected to a publicly accessible, traditional MAN or WAN.
Owner:CONVERGYS CMG UTAH
Pointguard: method and system for protecting programs against pointer corruption attacks
ActiveUS20080060077A1Effective encryptionMemory loss protectionError detection/correctionAddress spaceComputer program
To protect computer programs against security attacks that attempt to corrupt pointers within the address space of the program, the value of a pointer is encrypted each time the pointer is initialized or modified, and then the value is decrypted before use, i.e., each time the pointer is read. Preferably, the encrypting and decrypting steps are effected by instructions generated by a compiler during compilation of the program. One convenient method of implementing the encrypting and decrypting steps is by XOR'ing the pointer with a predetermined encryption key value, which could be specially selected or selected at random.
Owner:APPLE INC
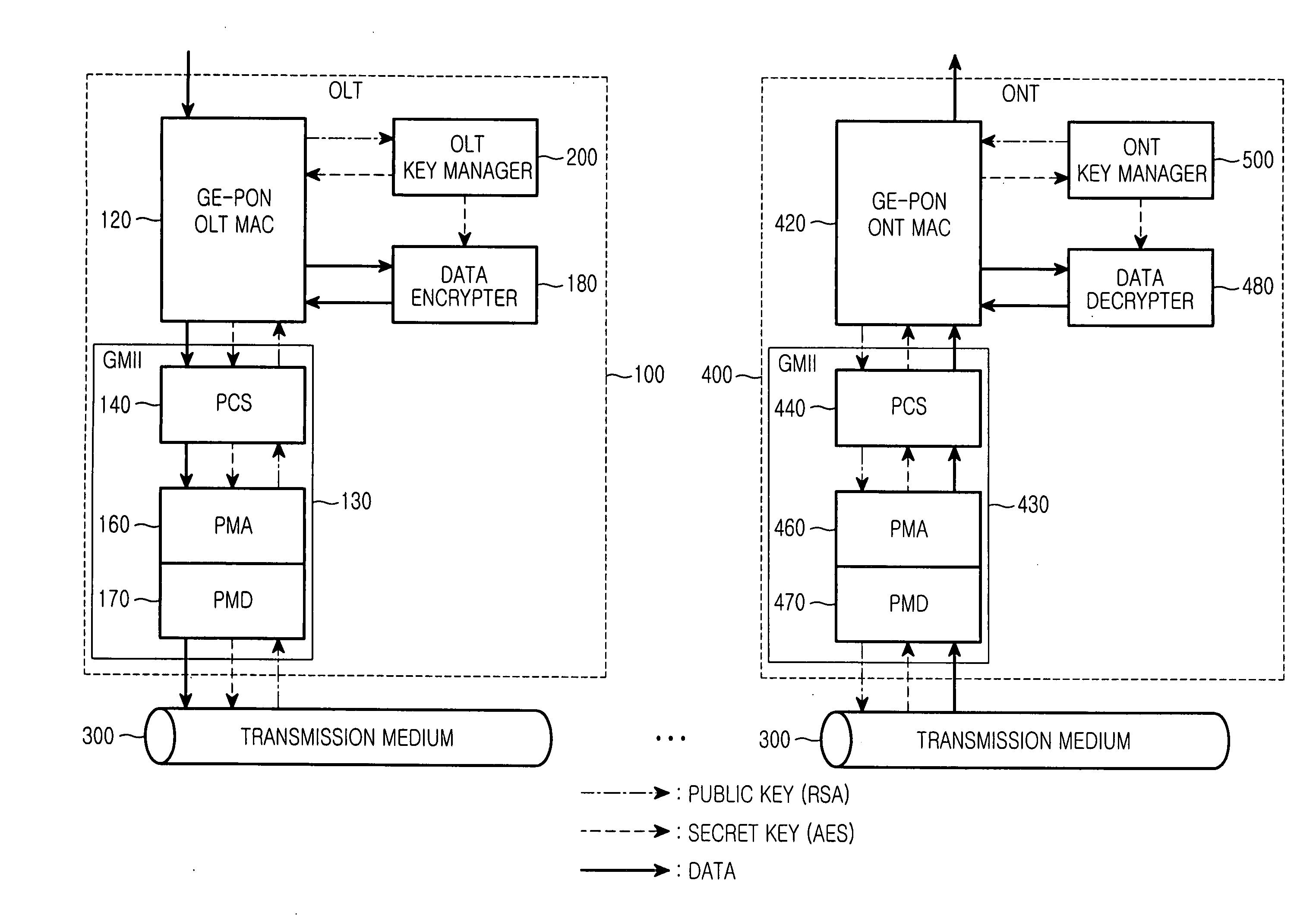
Gigabit Ethernet passive optical network for securely transferring data through exchange of encryption key and data encryption method using the same
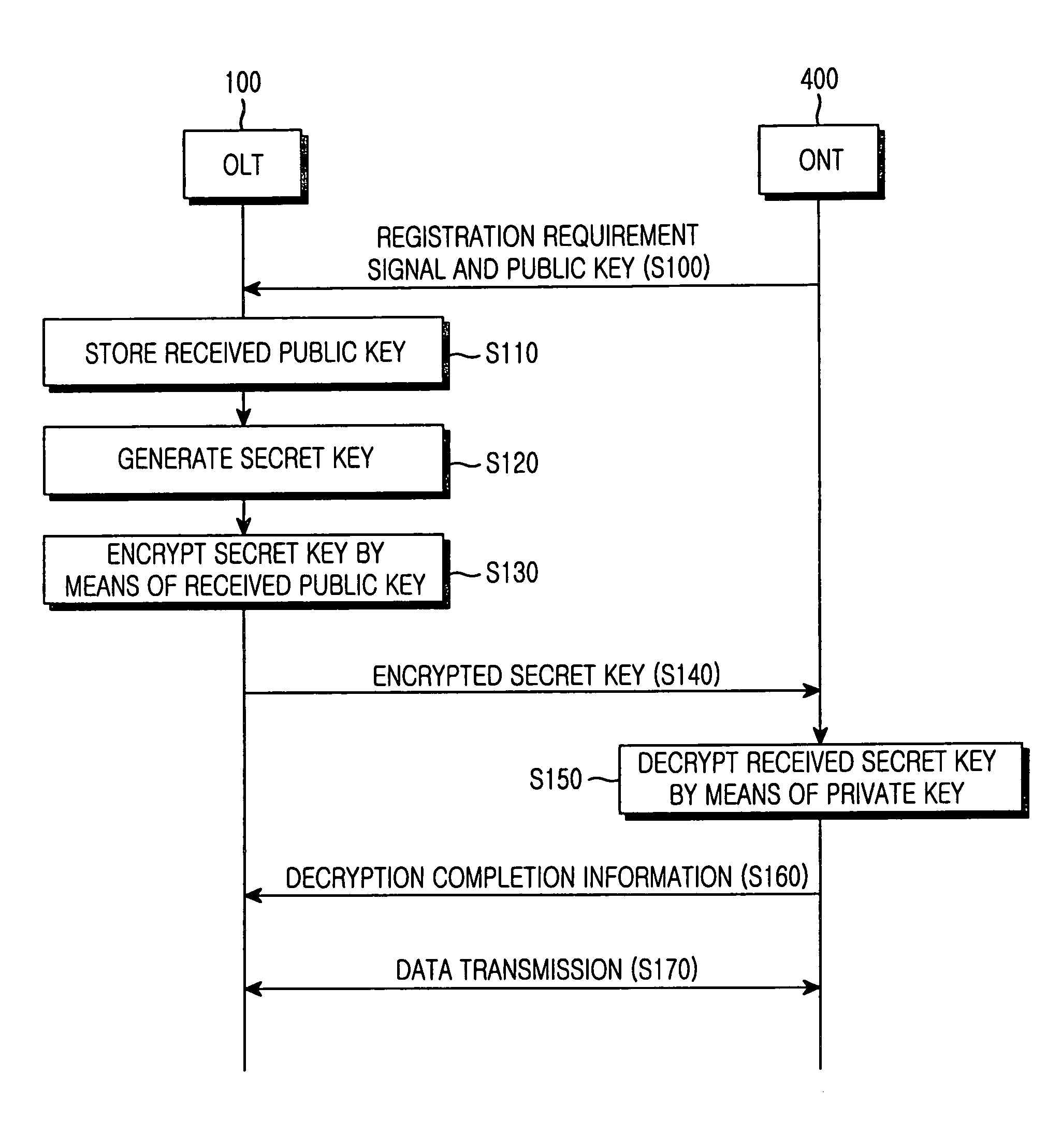
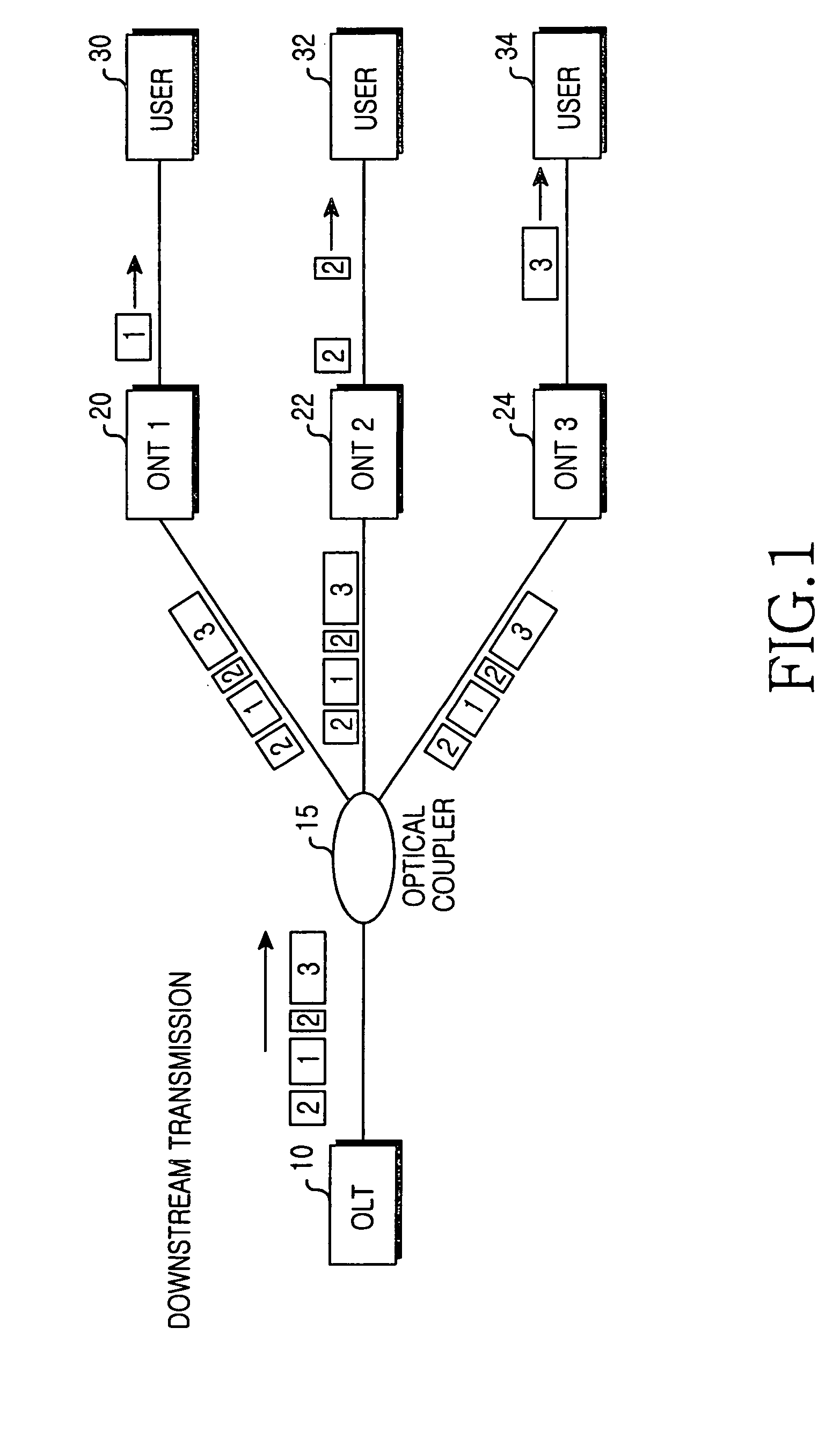
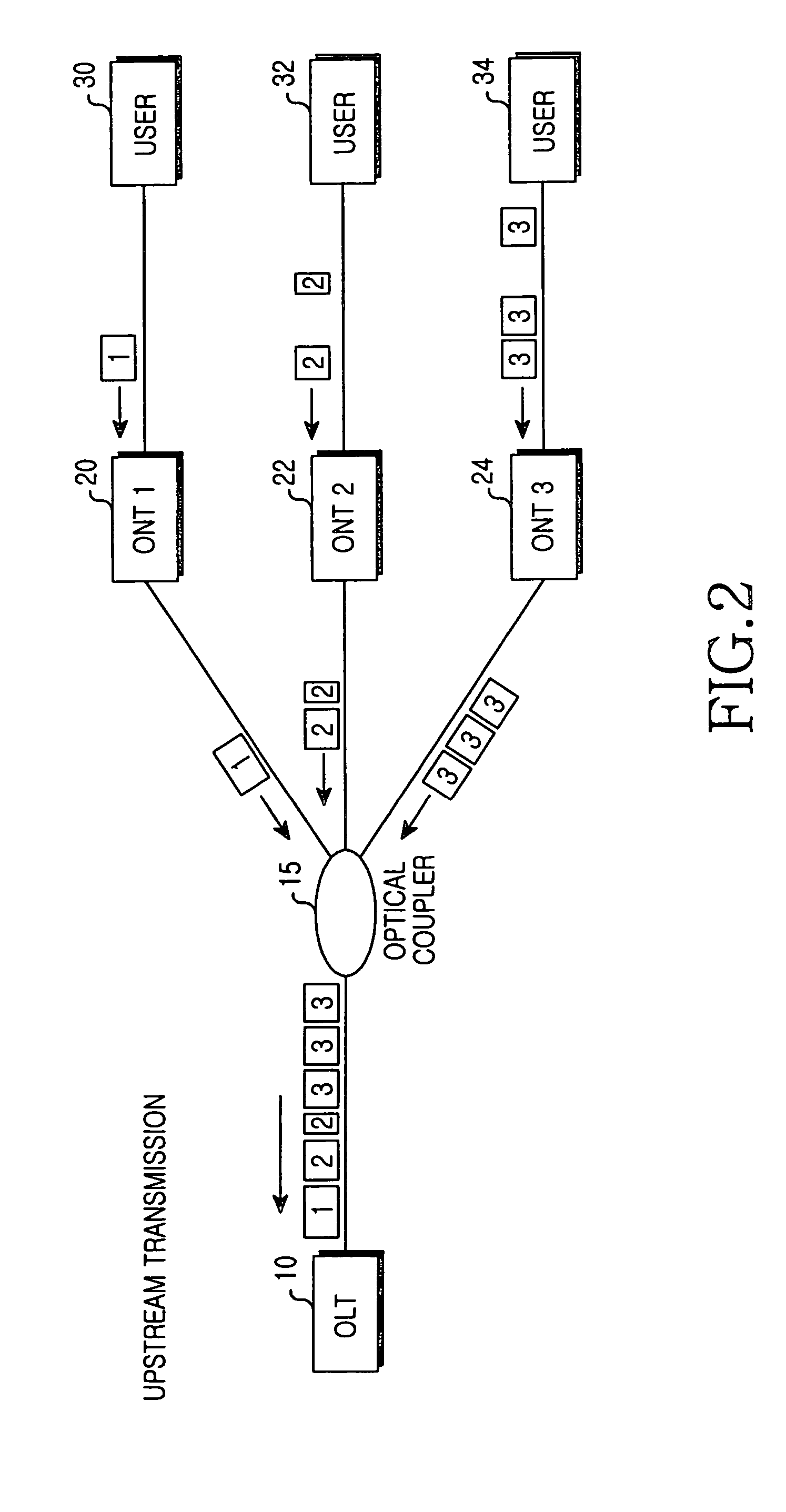
InactiveUS20050135609A1Improve data securityEffective encryptionKey distribution for secure communicationMultiple keys/algorithms usageOptical line terminationEncryption
A Gigabit Ethernet passive optical network (GE-PON) for securely transferring data through exchange of an encryption key comprises an optical line terminal (OLT) for encrypting a secret key using a public key received through a transmission medium, transmitting the encrypted secret key, encrypting data using the encrypted secret key, and transmitting the encrypted data, and at least one optical network terminal (ONT) for transmitting the public key to the OLT, decrypting the encrypted secret key transmitted from the OLT using a private key, and decrypting the data encrypted with the encrypted secret key, transmitted from the OLT, using the decrypted secret key.
Owner:SAMSUNG ELECTRONICS CO LTD
Encryption method, encryption apparatus, data storage distribution apparatus and data delivery system
InactiveUS7636439B2Effective encryptionKey distribution for secure communicationData taking preventionComputer hardwareData shipping
Data to be encrypted is effectively encrypted by a data delivery system for encrypting the data to be encrypted with a transmitting apparatus and decrypting a cipher thereof with a receiving apparatus. In a configuration for encrypting and decrypting the data to be encrypted by using a random number sequence generated by a random number generating portion for generating the random number sequence uniquely decided from an input parameter, the transmitting apparatus generates the input parameter to perform encryption based on metadata of the data to be encrypted while the receiving apparatus generates the input parameter to perform cipher decryption based on the metadata embedded in the data to be encrypted.
Owner:KOKUSA ELECTRIC CO LTD
Hibernating a processing apparatus for processing secure data
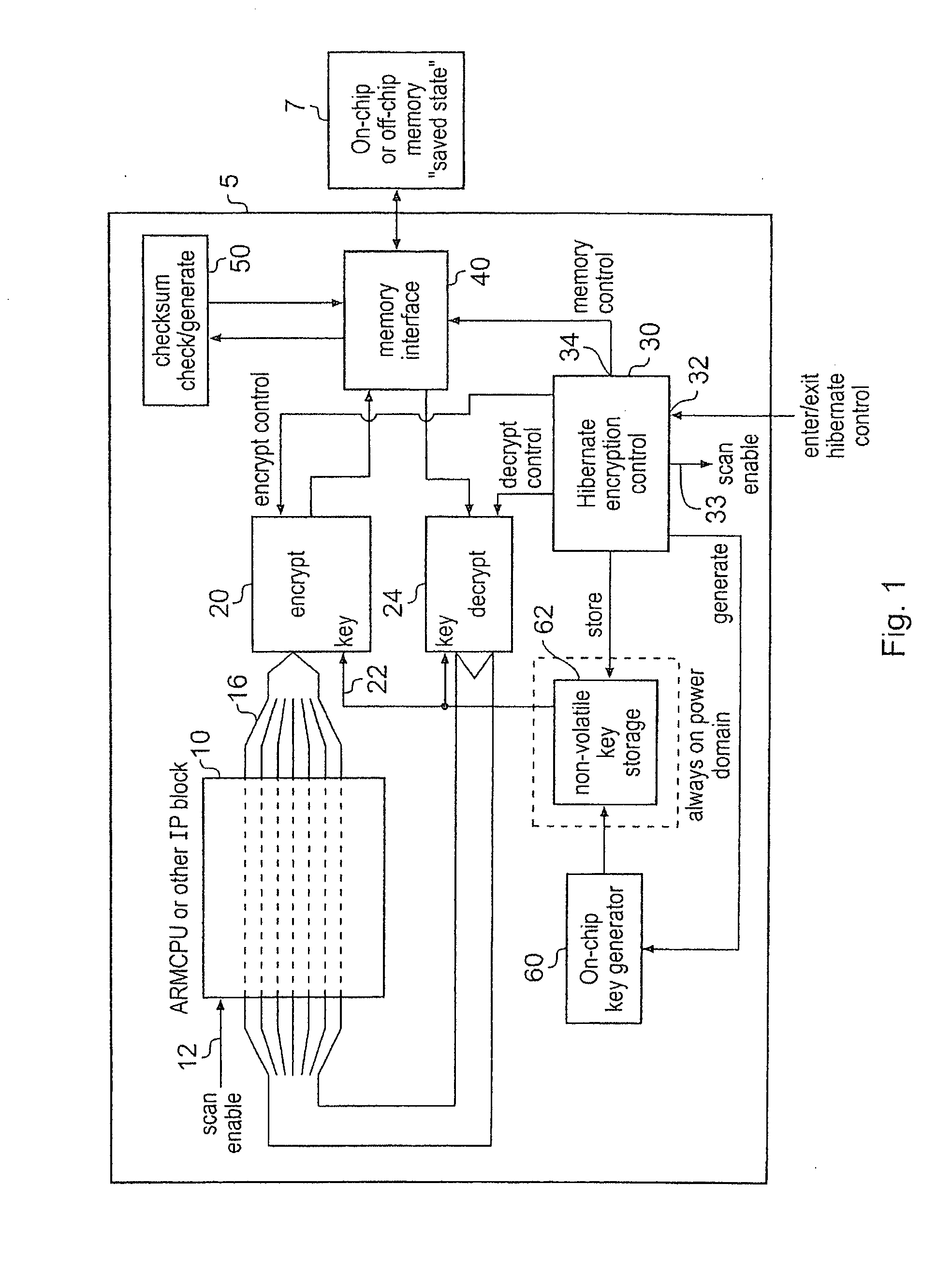
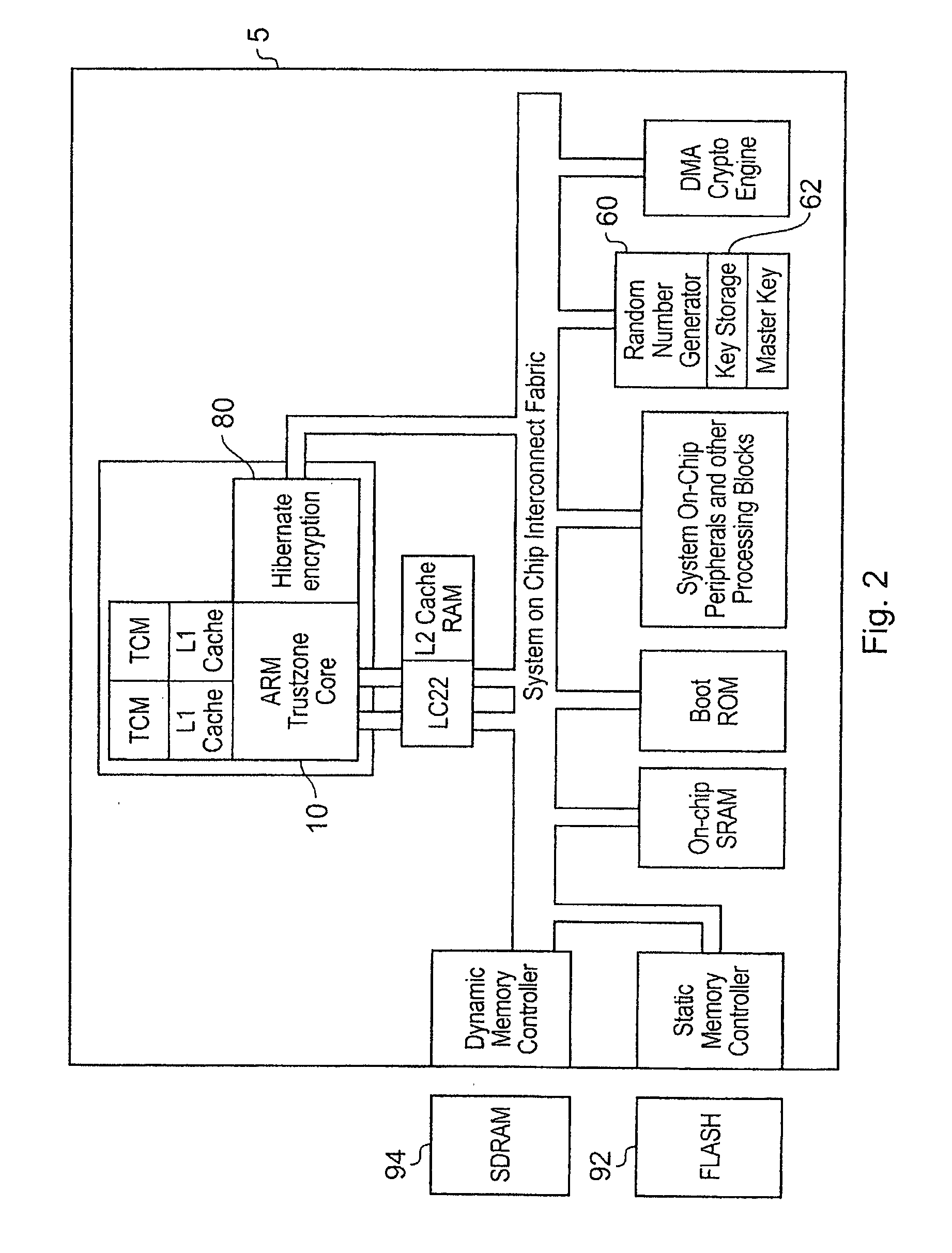
InactiveUS20080201592A1Performed quickly and efficientlyEffective encryptionElectrical testingInternal/peripheral component protectionElectricityComputer hardware
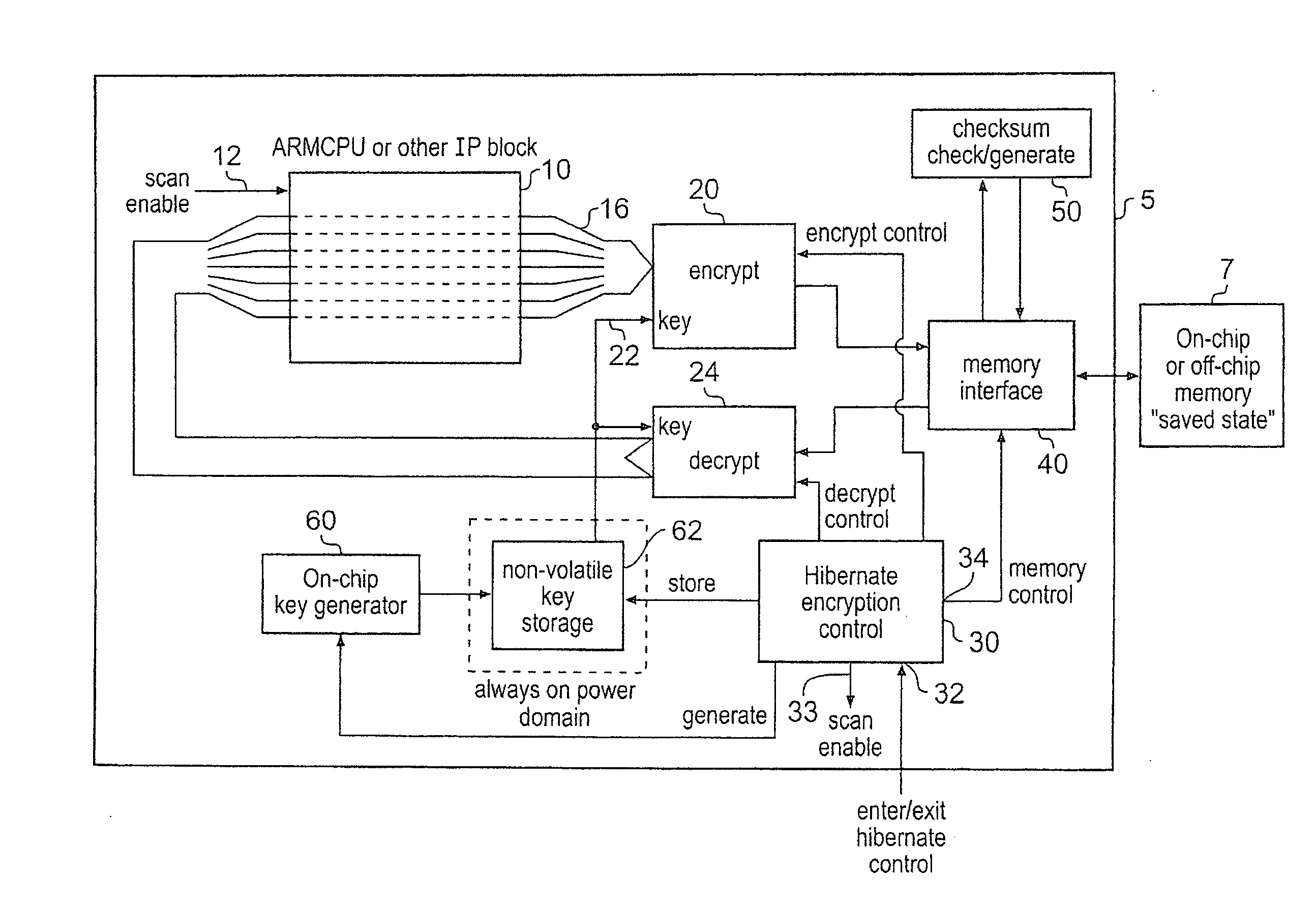
A data processing apparatus for processing secure data is disclosed. The data processing apparatus comprising: processing circuitry comprising a plurality of state retention cells in the form of scan chains for holding a current state of said processing circuitry, at least some of the state retention cells being arranged in series; encryption circuitry; and a hibernate signal input; said data processing apparatus being responsive to receipt of a hibernate signal at said hibernate signal input to switch from an operational mode in which said data processing apparatus is powered up, to a low power mode in which at least said processing circuitry is powered down, said data processing apparatus being operable prior to powering down said processing circuitry, to output a state of said processing circuitry from said plurality of state retention cells and to encrypt said output state using said encryption circuitry and to save said encrypted state to said storage device.
Owner:ARM LTD
Image encryption method based on multidimensional chaotic system and Josephf scrambling
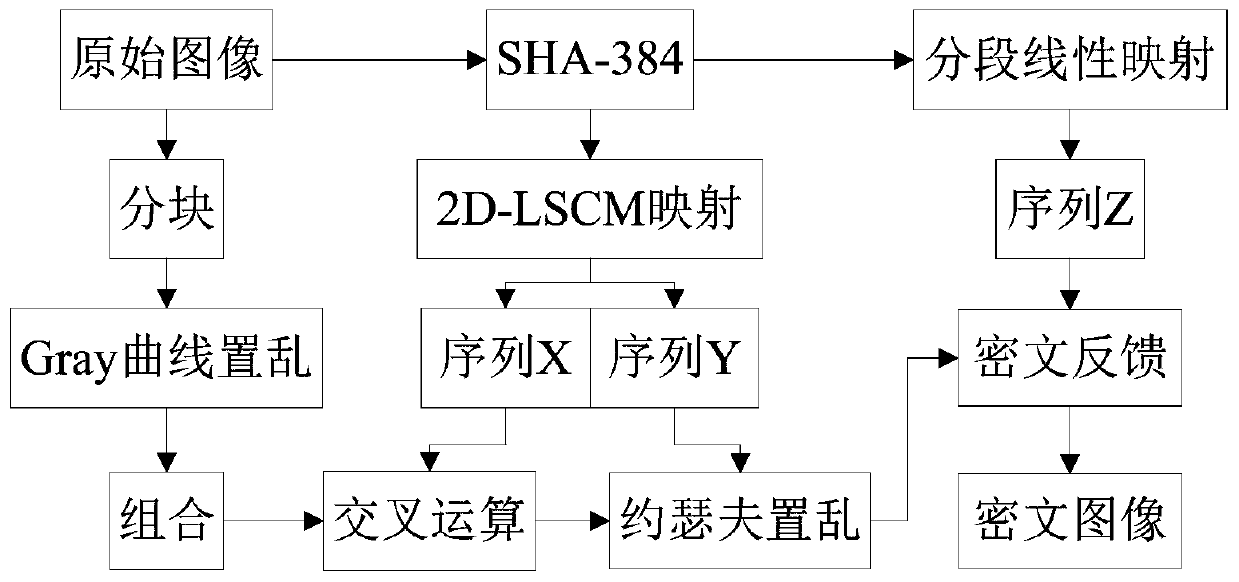
ActiveCN111105339AAchieve diffusionIncreased sensitivityImage data processing detailsKey spaceAlgorithm
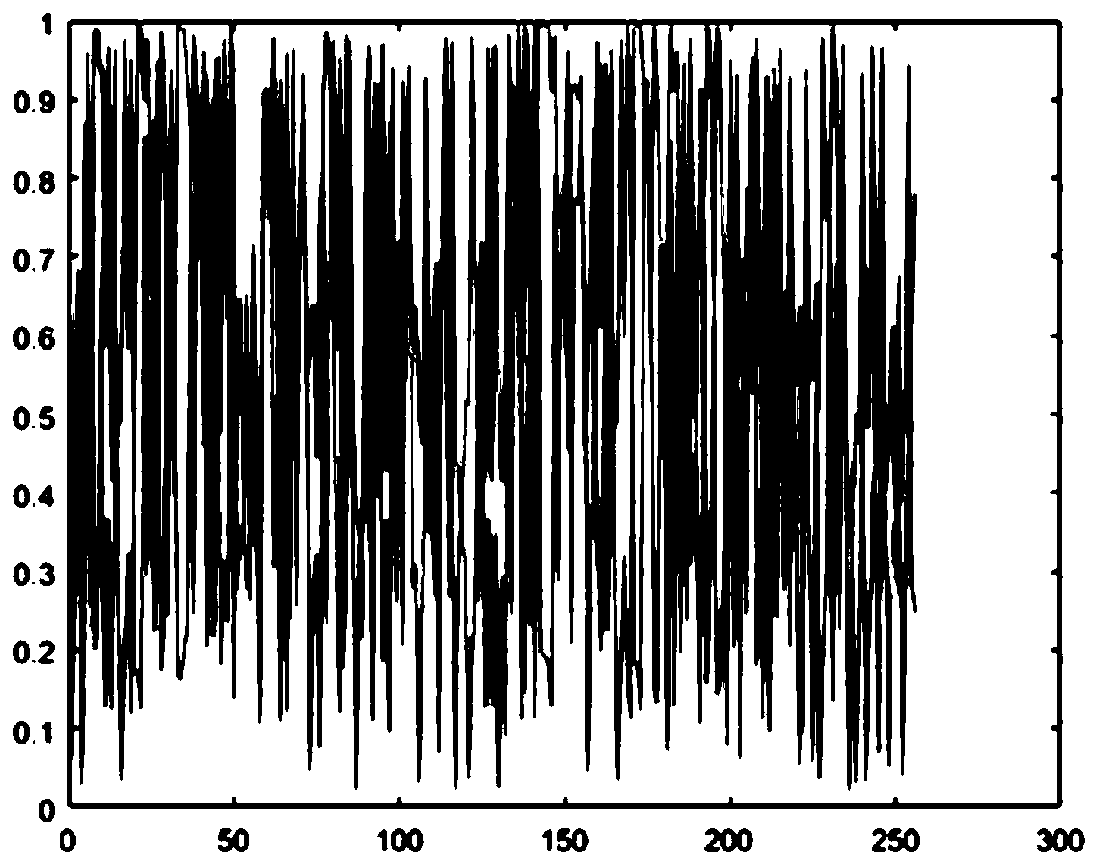
The invention provides an image encryption method based on a multi-dimensional chaotic system and Josephf scrambling, and the method comprises the steps: carrying out the initialization of PWLCM mapping and 2D-LSCM mapping, and obtaining a sequence X, a sequence Y and a sequence Z; uniformly dividing the original image into sub-matrixes according to indexes, carrying out Gray curve scrambling on pixels in the sub-matrixes, and carrying out sequential recombination to obtain a recombined image matrix; taking out elements in the sequence X as a crossover operator, and performing bit crossover operation on the recombined image matrix to obtain an image matrix; taking out a pseudo-random value in the sequence Y as the step value of fixed-step Josephh scrambling, and performing Josephh scrambling operation on the image matrix to obtain a matrix; and taking out the pseudo-random value in the sequence Z and the element pixel value in the matrix to carry out XOR ciphertext feedback to obtain afinal encrypted image. The method can effectively encrypt the image, has a large key space, has high sensitivity to the to-be-encrypted image and the initial key, and has good defense capability whenresisting various attack modes.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Surveillance video transmission apparatus and method and surveillance video receiving apparatus and method
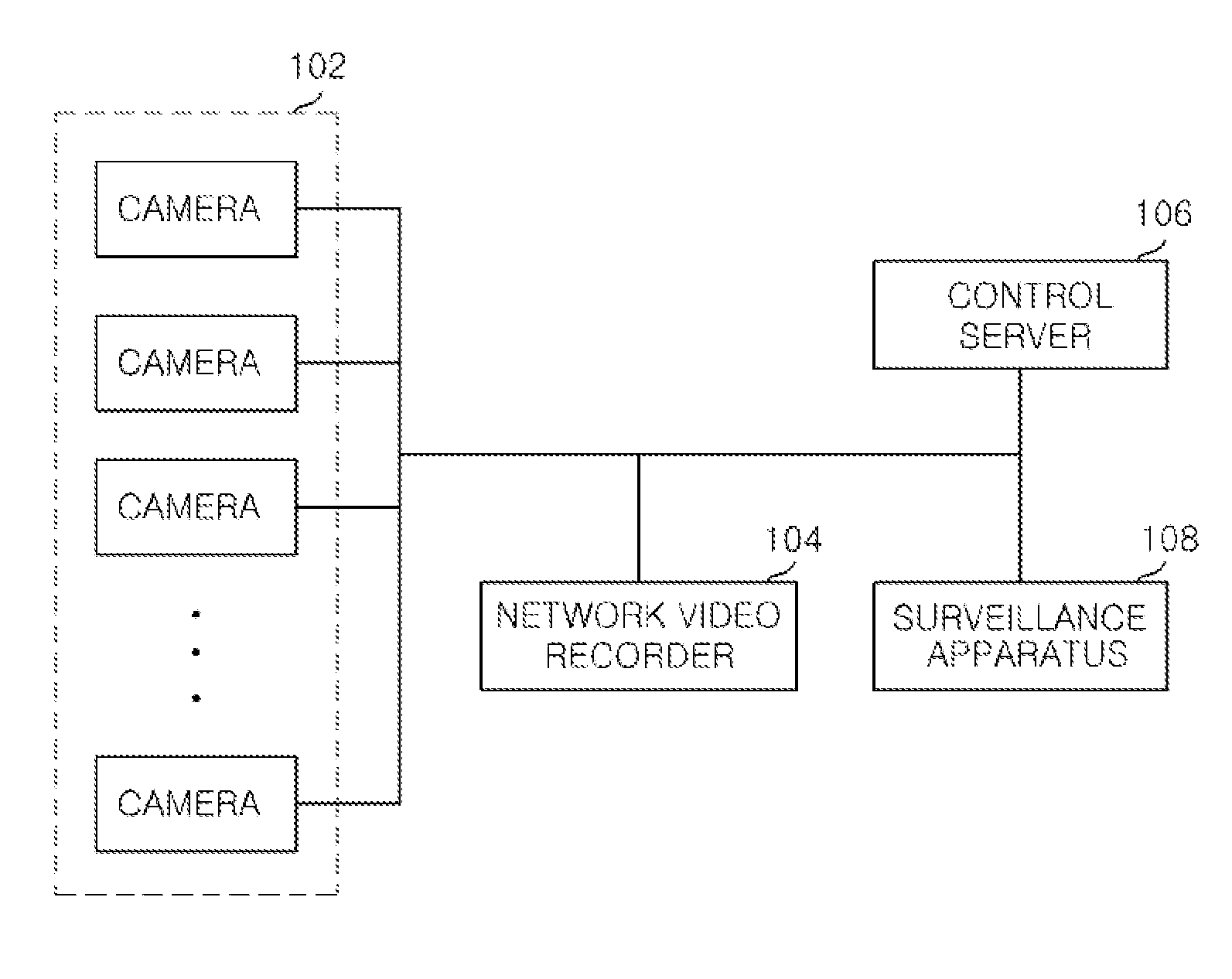
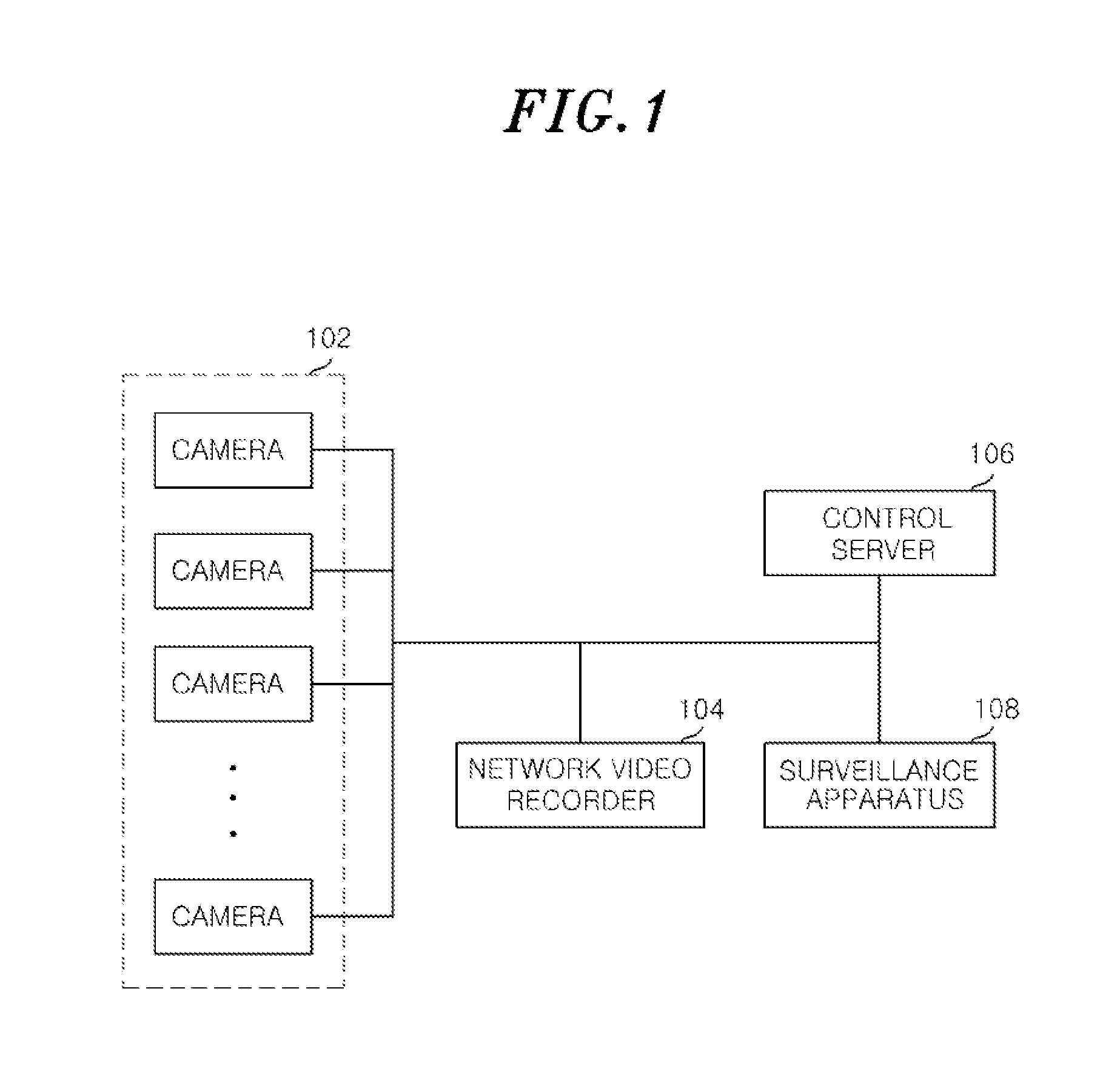
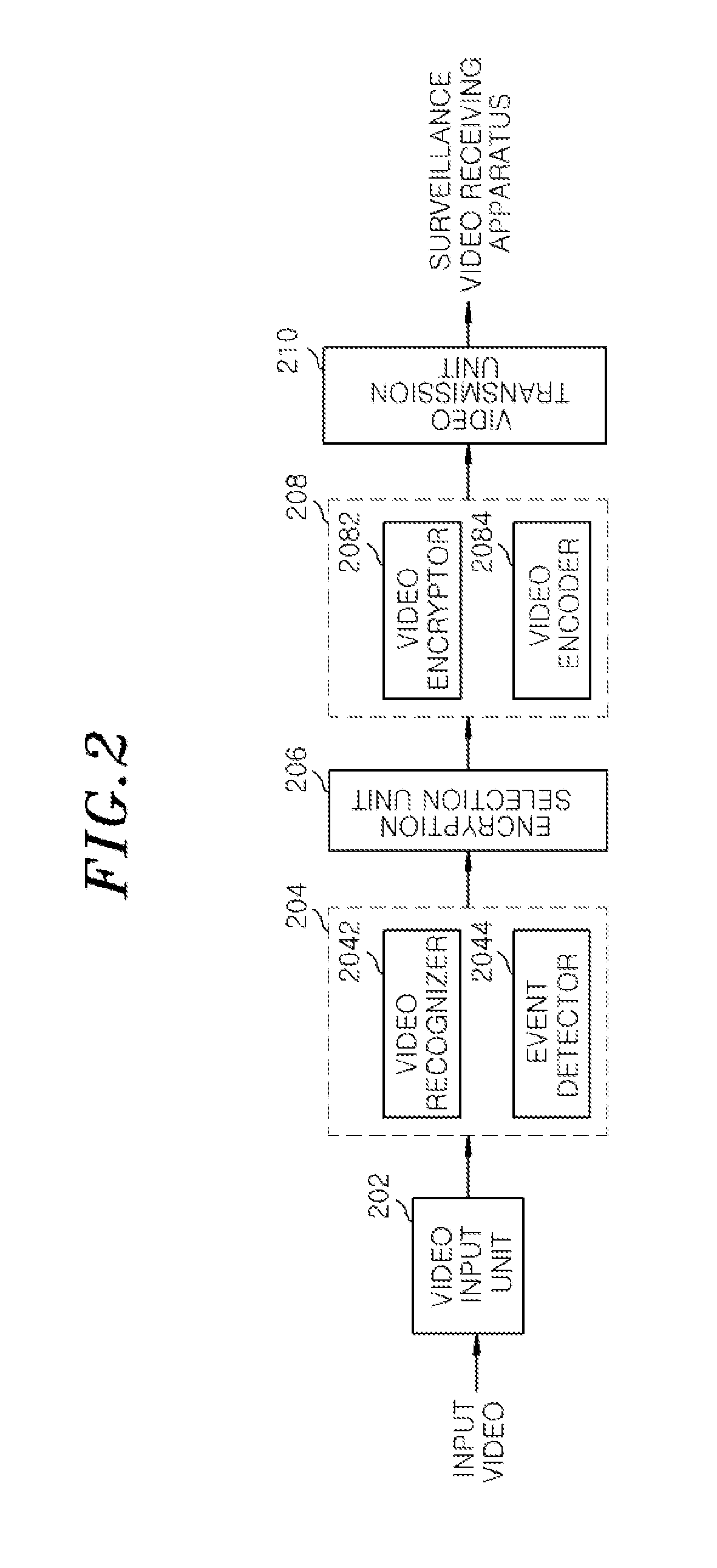
ActiveUS20130156185A1Harmful video information can be preventedProtection of personal informationTelevision system detailsKey distribution for secure communicationVideo transmissionVideo processing
A surveillance video transmission apparatus, includes a video input unit configured to collect physical videos and make the collected physical videos informative; a video analysis unit configured to analyze content of the collected video by recognizing the collected video and detecting an event; and an encryption selection unit configured to select one of a non-encryption mode, a regions-of-interest encryption mode and a full video encryption mode based on the analysis result of the collected video. Further, the surveillance video transmission apparatus includes a video process unit configured to perform one of a non-encryption, a regions-of-interest encryption and a full video encryption and encoding on the collected video according to the selected encryption mode; and a video transmission unit configured to transmit the encoded video and encryption-related information to a surveillance video receiving apparatus.
Owner:ELECTRONICS & TELECOMM RES INST
Method and system for the cipher key controlled exploitation of data resources, related network and computer program products
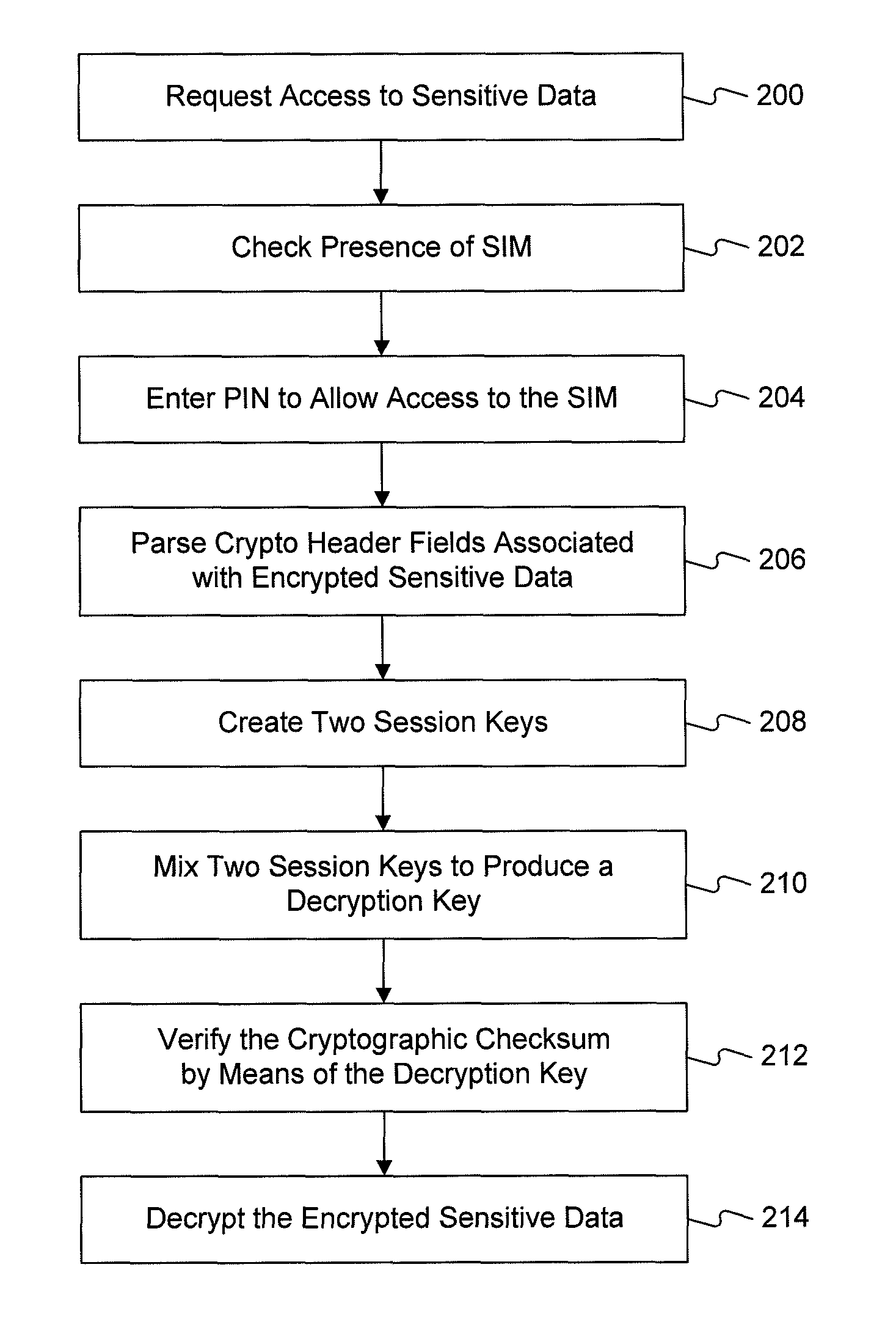
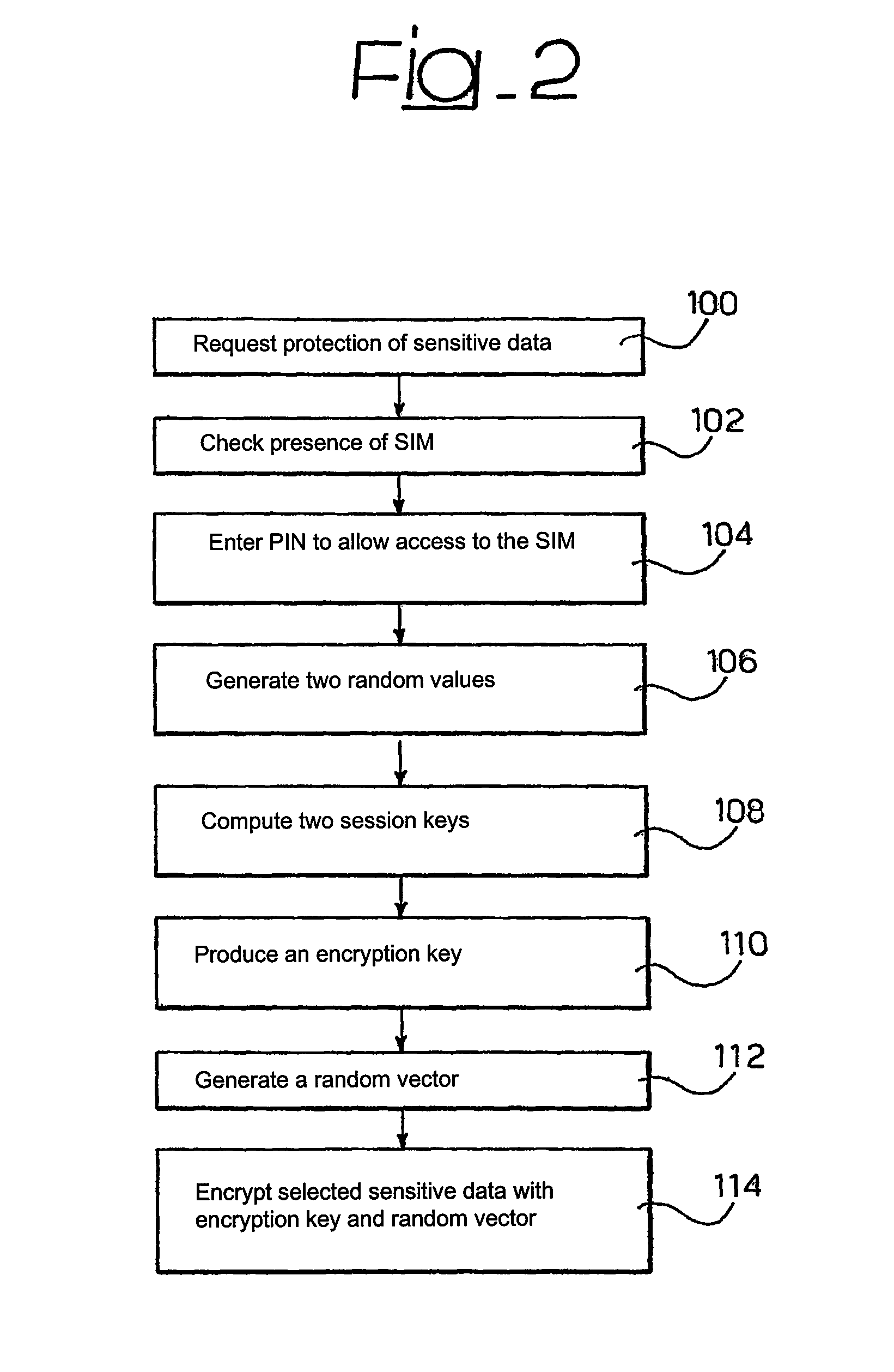
InactiveUS20070079142A1Low costSecurely generateUser identity/authority verificationUnauthorized memory use protectionHash functionSubscriber identity module
An arrangement for the cipher controlled exploitation of data resources (e.g., securely storing and retrieving sensitive data or securely registering and logging on a computer system) includes the steps of providing a subscriber identity module carrying a security algorithm; generating at least one, e.g., two, random values; subjecting the random value to the at least one security algorithm to generate at least one, e.g., two, session keys; processing the session keys via a mixer function such as a hash function to produce a cipher key; and using the cipher key thus produced for exploiting the data resources.
Owner:TELECOM ITALIA SPA
Operation method of multiple network communication based on shared medium
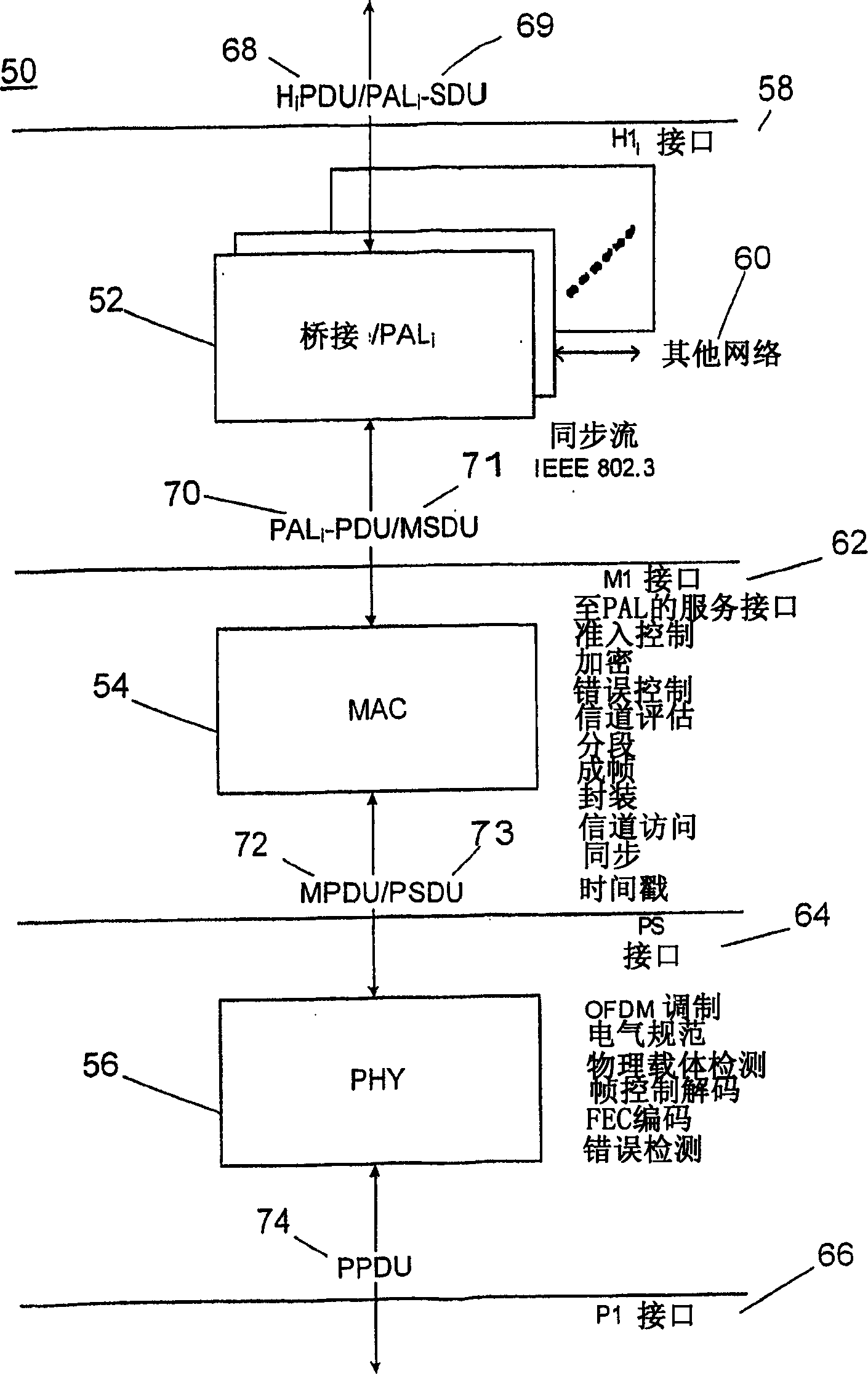
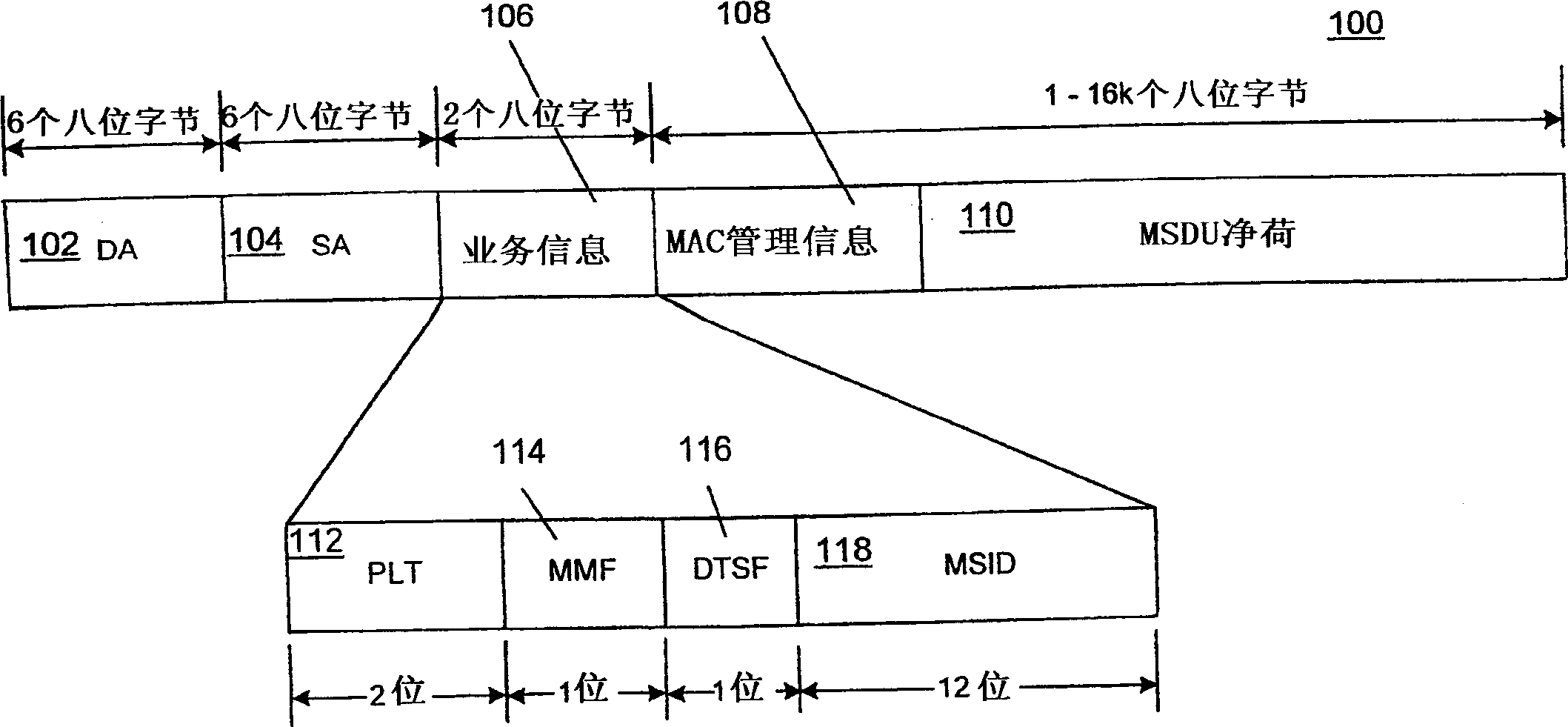
ActiveCN1918558AImprove service qualityAchieve retransmissionError prevention/detection by using return channelDigital computer detailsPALShared medium
A method of operating in a network in which a plurality of stations communicate over a shared medium, comprising providing a physical layer (e.g., PHY) for handling physical communication over the shared medium; providing a high level layer (e.g., PAL) that receives data from the station and supplies high level data units (e.g., MSDUs) for transmission over the medium; providing a MAC layer that receives the high level data units from the high level layer and supplies low level data units (e.g., MPDUs) to the physical layer; at the MAC layer, encapsulating content from a plurality of the high level data units; dividing the encapsulated content into a plurality of pieces (e.g., segments) with each piece capable of being independently retransmitted; and supplying low level data units containing one or more of the plurality of pieces.
Owner:QUALCOMM INC
Encryption method and system of mobile instant message
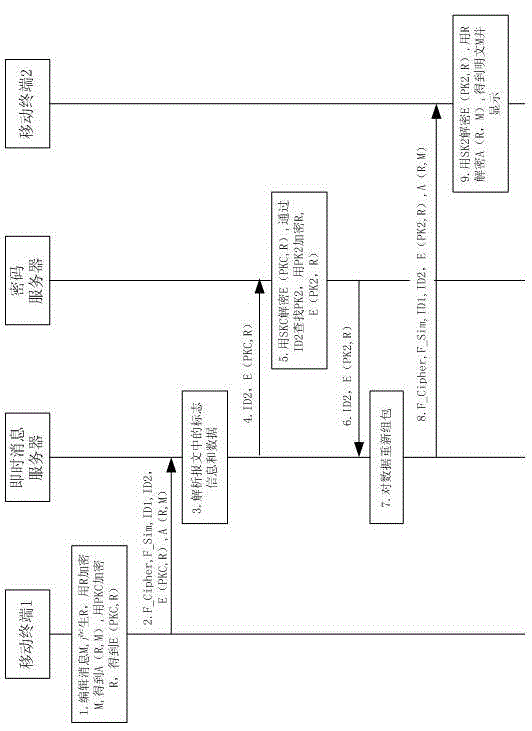
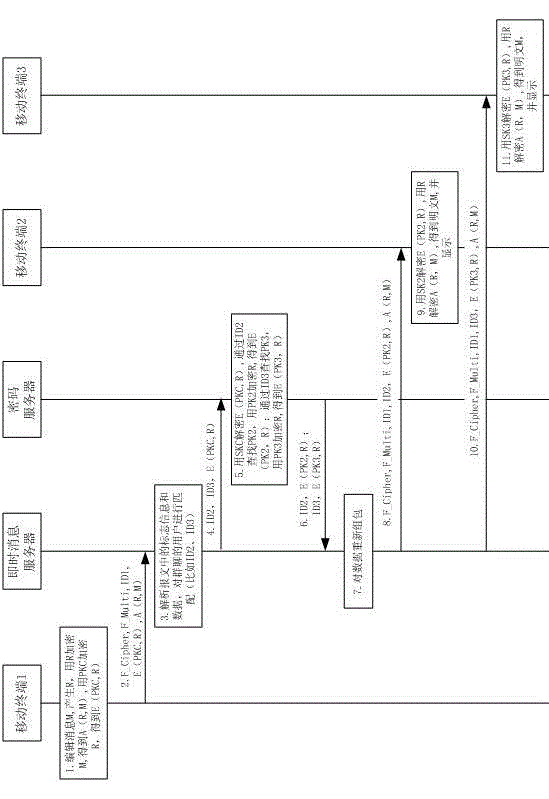
ActiveCN103338437AEffective encryptionNo changes to the communication flowMessaging/mailboxes/announcementsSecurity arrangementPasswordConfidentiality
The invention belongs to the technical field of instant messages and discloses an encryption method of a mobile instant message. The encryption method comprises the steps that the instant message is encrypted by a random number R; the random number R is encrypted by a public key of a password server simultaneously; the password server decrypts the random number R with a private key of the password server and encrypts the random number R with a public key of a mobile terminal of a receiver; the instant message and the random number are sent to the mobile terminal of the receiver; the mobile terminal of the receiver decrypts the random number R with a private key of the mobile terminal, and then decrypts the instant message with R; and the instant message is received and displayed. The instant message is encrypted by the random number R, and the private key R is encrypted during transmission. Confidentiality of the instant message is strengthened. Meanwhile, all password processing such as matching of a user identity with a password, and password conversion are performed on a server with higher processing capacity, so that the terminal burden is reduced, and the purposes of ensuring message transmission security and reducing the computation of the terminal are achieved. In addition, an additional communication flow is not required to be added between the terminal and the server when the encrypted message is transmitted, so that the limited wireless broadband resource is saved.
Owner:成都三零瑞通移动通信有限公司
Gigabit Ethernet-based passive optical network and data encryption method
InactiveUS7450719B2Improve securityEffective encryptionKey distribution for secure communicationPublic key for secure communicationService provisionEncryption
A Gigabit Ethernet-based passive optical network that can reliably transmit data is disclosed. The network includes an OLT for receiving a public key through a transmission medium, encrypting a secret key by means of the received public key, transmitting the encrypted secret key, encrypting data by means of the secret key, and transmitting the encrypted data, the OLT being located in a service provider-side. The network also includes an ONT for transmitting the public key to the OLT, receiving the secret key transmitted from the OLT, decrypting the secret key by means of a private key, receiving the data, and decrypting the received data by means of the decrypted the secret key. The public key is used for encrypting the secret key. The secret key is encrypted by means of the public key. The data is encrypted by the OLT by means of the secret key.
Owner:SAMSUNG ELECTRONICS CO LTD
Format-Preserving Cipher
ActiveUS20170048059A1Improve performanceEffective encryptionData stream serial/continuous modificationMultiple keys/algorithms usagePlaintextCredit card
A format-preserving cipher including encryption and decryption schemes supporting non-linear access to input data by allowing the selection of portions of data from a potentially larger dataset to be encrypted. The cipher first defines a forward mapping from the allowable ciphertext values to an integer set of the number of such allowable ciphertext values, and a corresponding reverse mapping. It also supports exclusion of a certain set of characters from the ciphering process. An encryption algorithm is provided that encrypts the input plaintext data while preserving its original format and length, and a corresponding decryption algorithm is provided. The cipher advantageously embodies the encryption and decryption of multi-byte values, composite datasets, credit card numbers and discontinuous datasets, thus fitting a variety of industrial needs.
Owner:ZETTASET
System and Method for Content Distribution with Broadcast Encryption
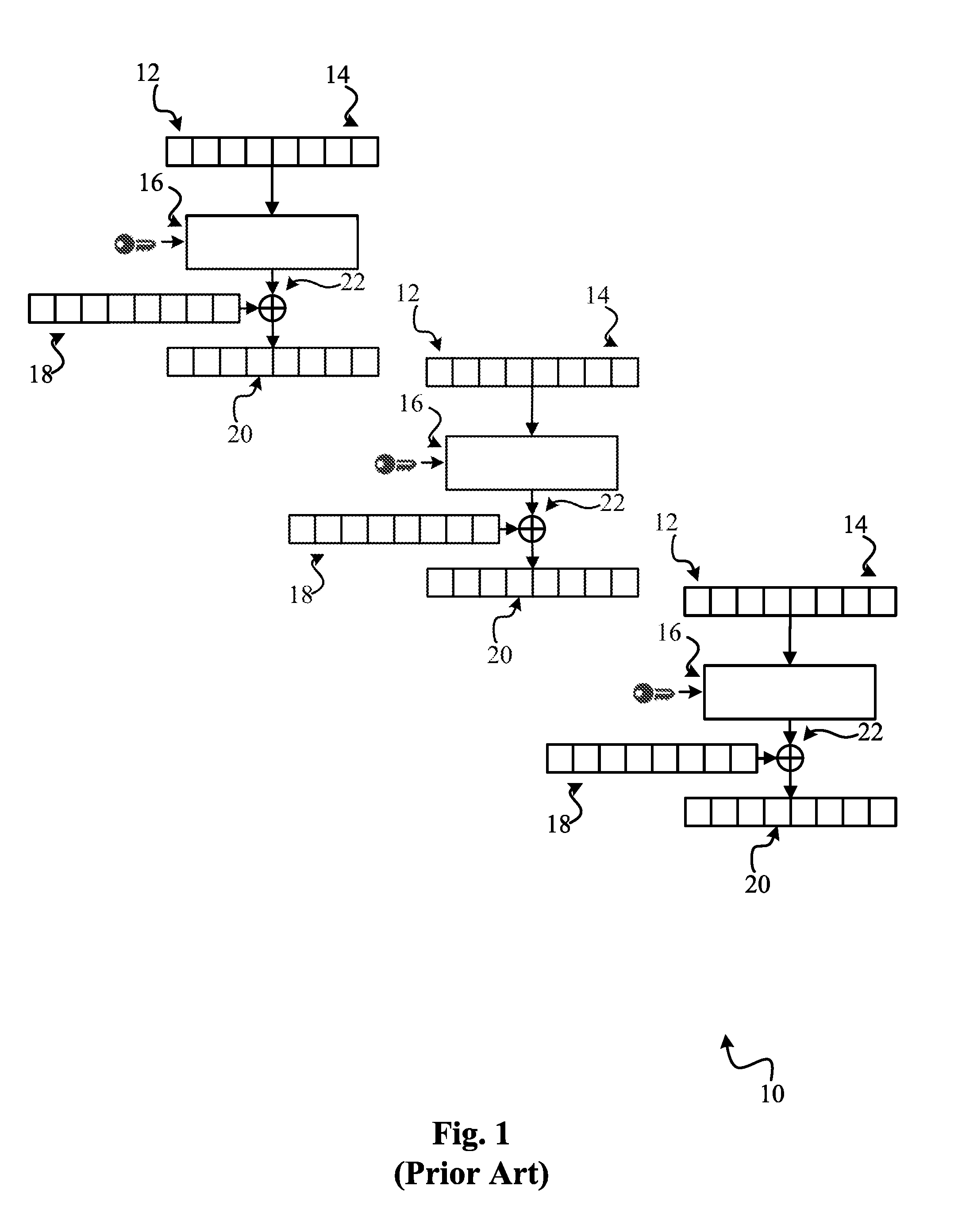
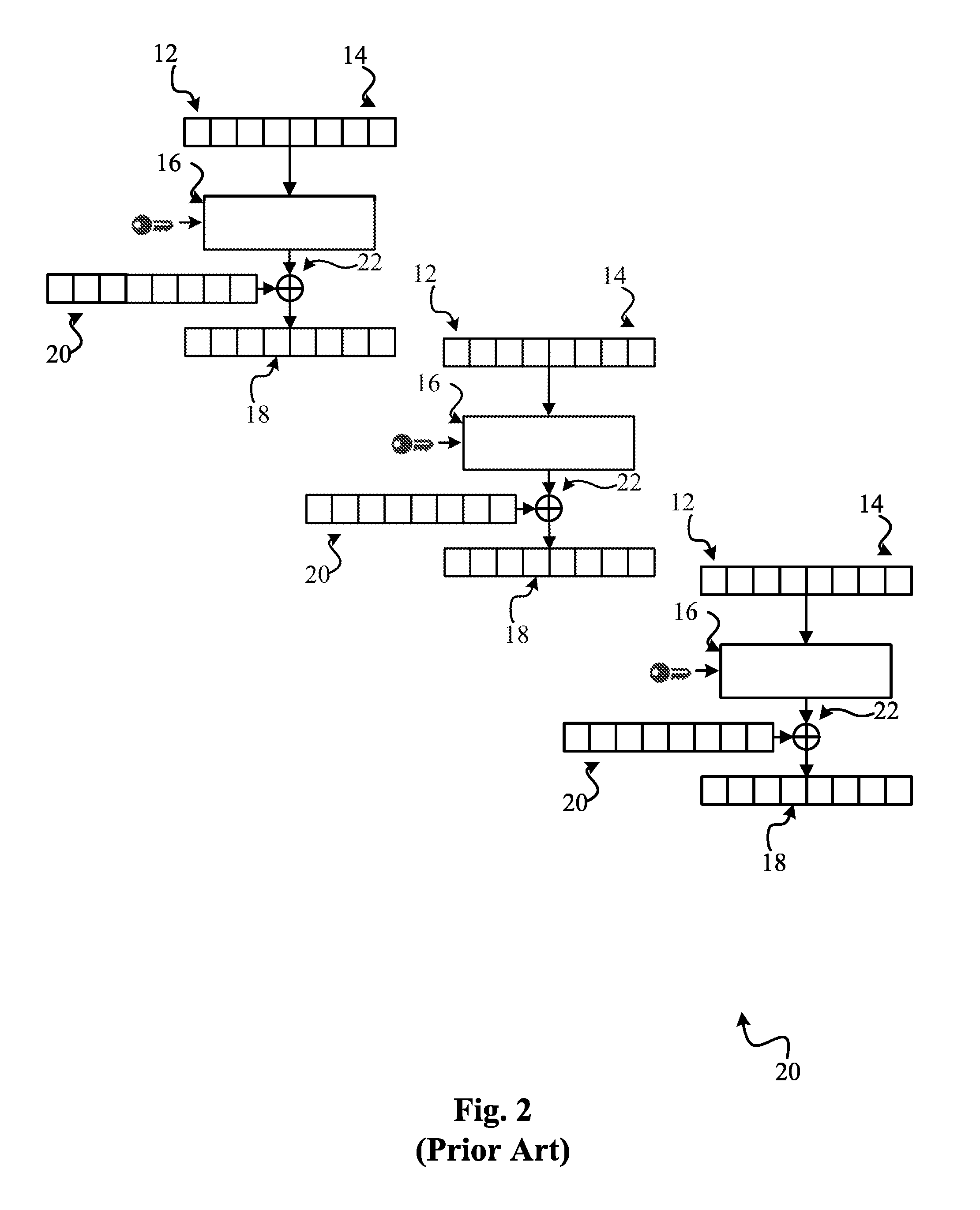
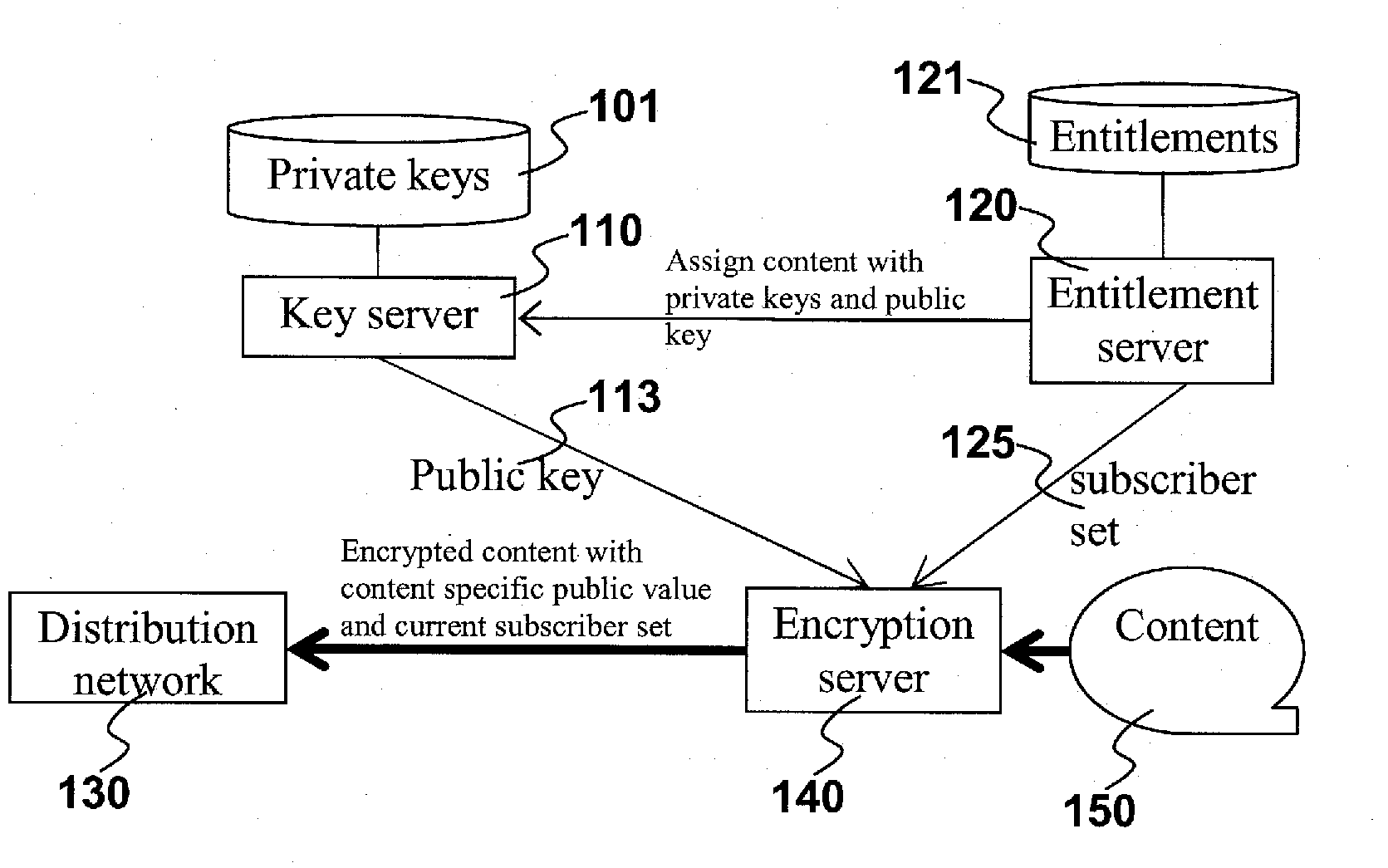
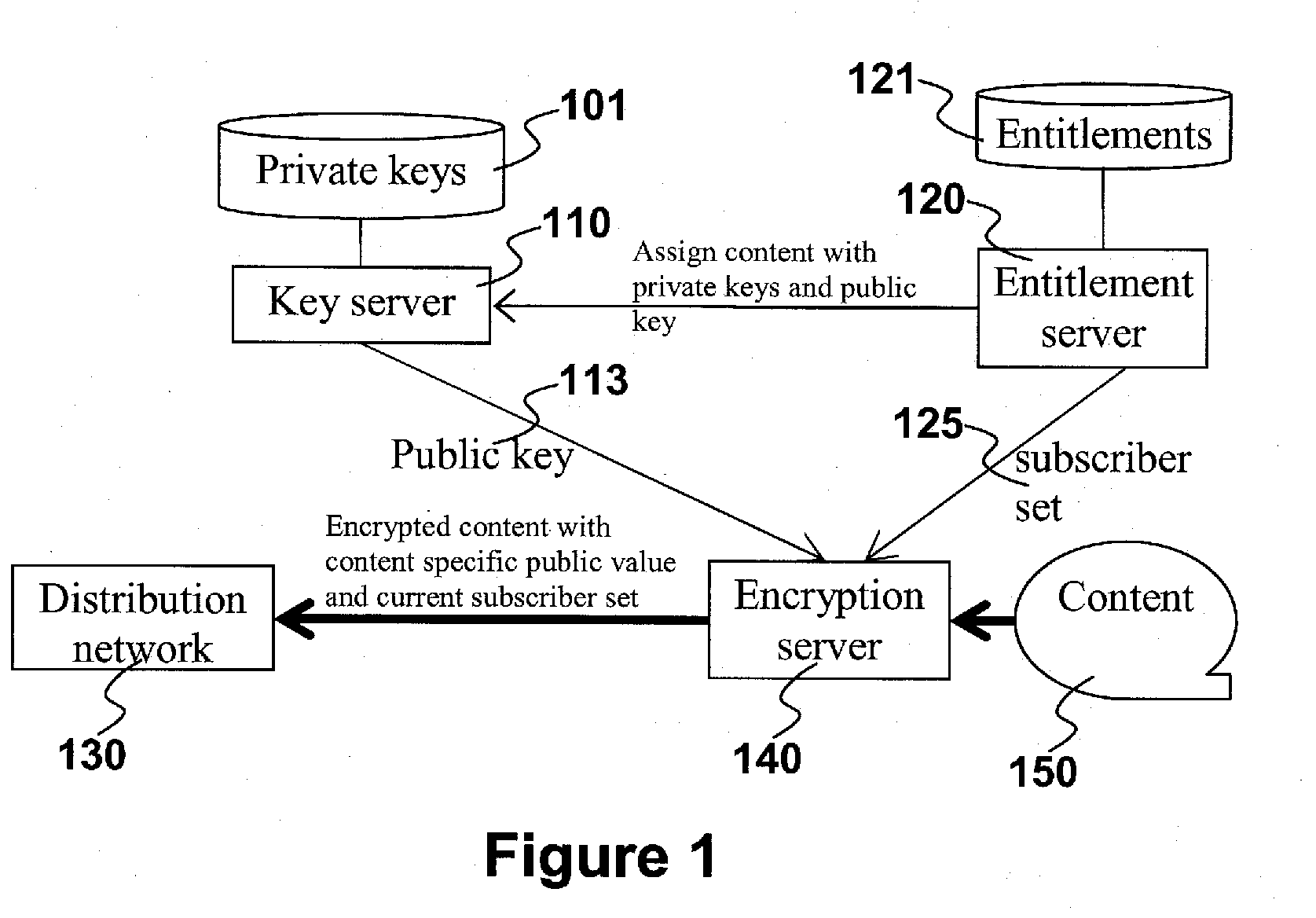
ActiveUS20100228972A1Save computation timeEffective encryptionUser identity/authority verificationComputer security arrangementsContent distributionKey distribution
The claimed invention relates to system and method for providing encrypted content via a distribution network 630 with efficient key distribution and distribution network assignment. The claimed invention assigns users to content-specific distribution network in which the content is broadcast. This makes the content access much more efficient by conducting the authorization at the time of joining the content-specific distribution network and providing the content to entitled users through broadcasting. The claimed invention provides additional security by removing a user from the content-specific distribution network when his entitlement is no longer valid.
Owner:HONG KONG APPLIED SCI & TECH RES INST
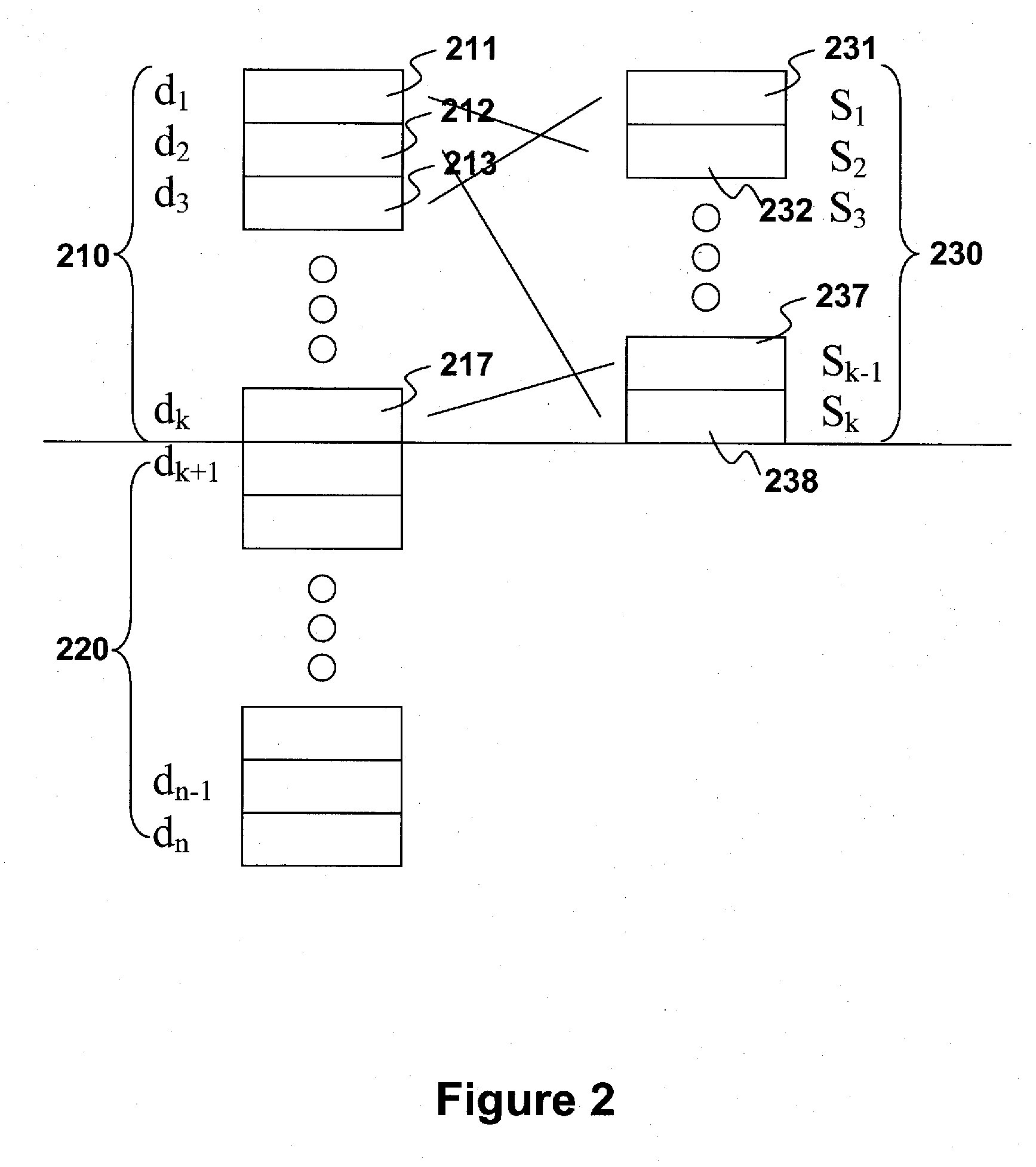
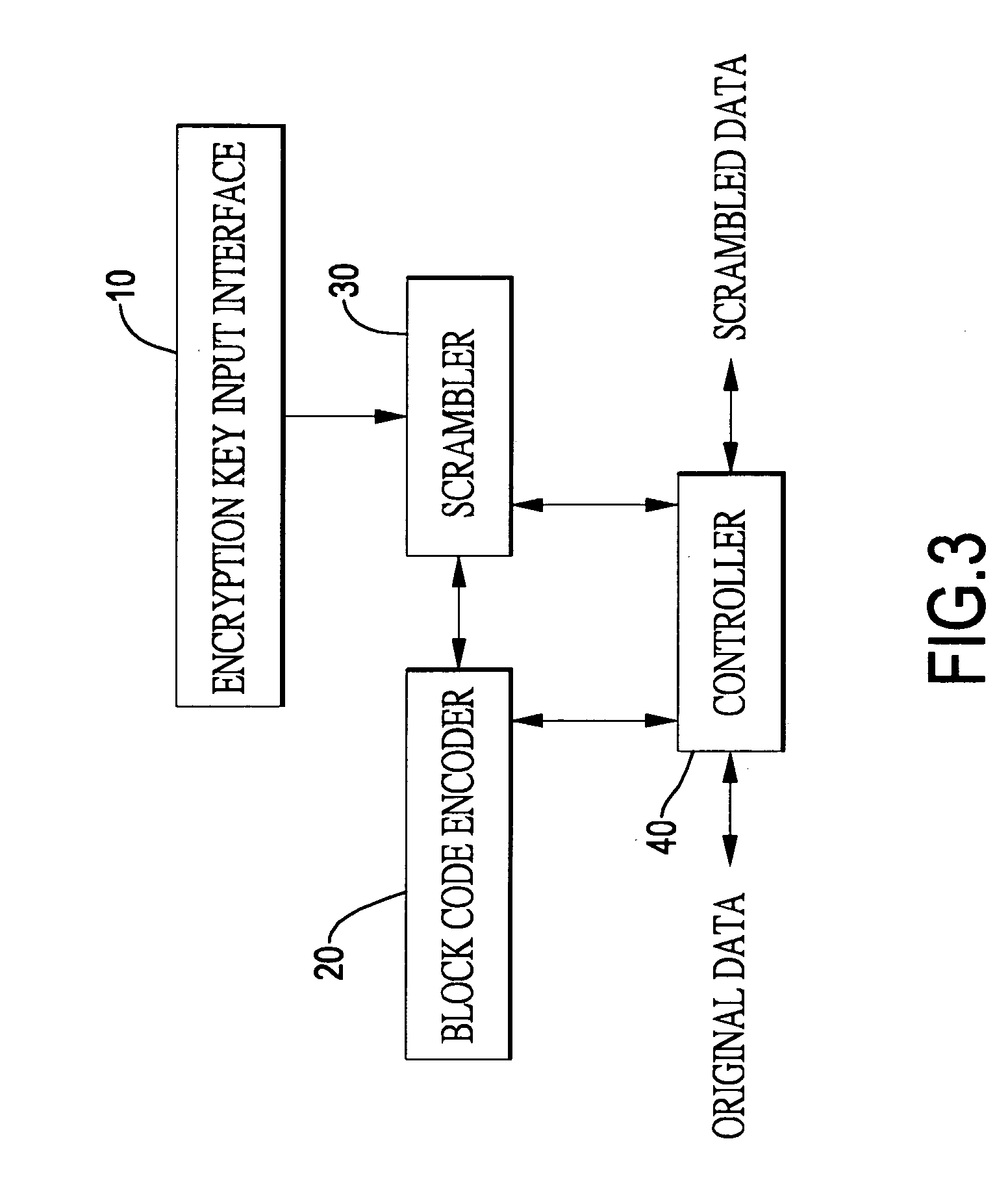
Data encryption device for storage medium
ActiveUS20110289325A1Prevent theftEffective encryptionKey distribution for secure communicationMemory loss protectionComputer hardwareBlock code
A data encryption device for storage medium has an encryption key input interface for acquiring a user encryption key; a block code encoder for encoding and decoding data; a scrambler connected with the encryption key input interface and the block code encoder to scramble and descramble data according to the user encryption keys respectively inputted; and a controller connected with the block code encoder and the scrambler, performing an encryption process transmit original data to the block code encoder for encoding, the encoded data to the scrambler for scrambling, and the scrambled data to a storage medium for storage, and performing a decryption process to transmit the scrambled data to the scrambler for descrambling, the encoded data to the block code encoder for decoding to acquire the original data when the user encryption keys respectively inputted in the encryption process and the decryption process are identical.
Owner:SK HYNIX INC
Remote compelled method and system for mobile terminal equipment and computer
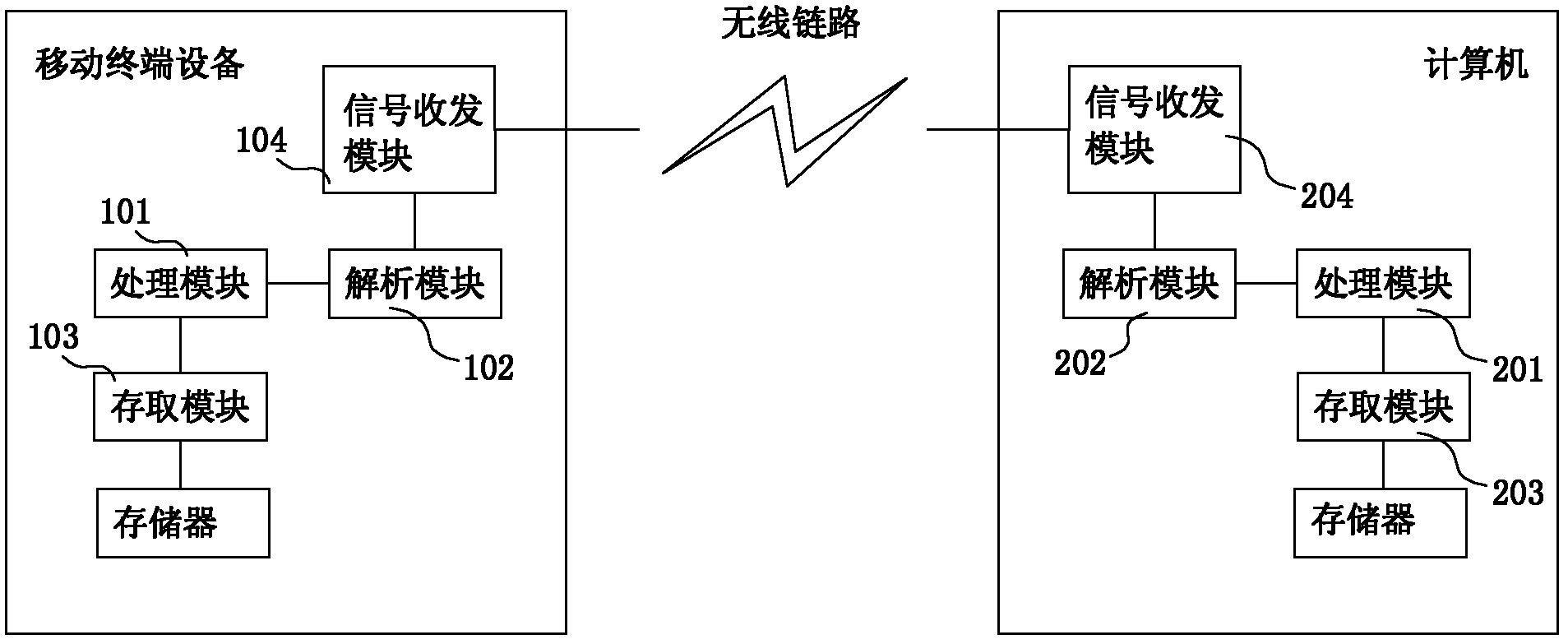
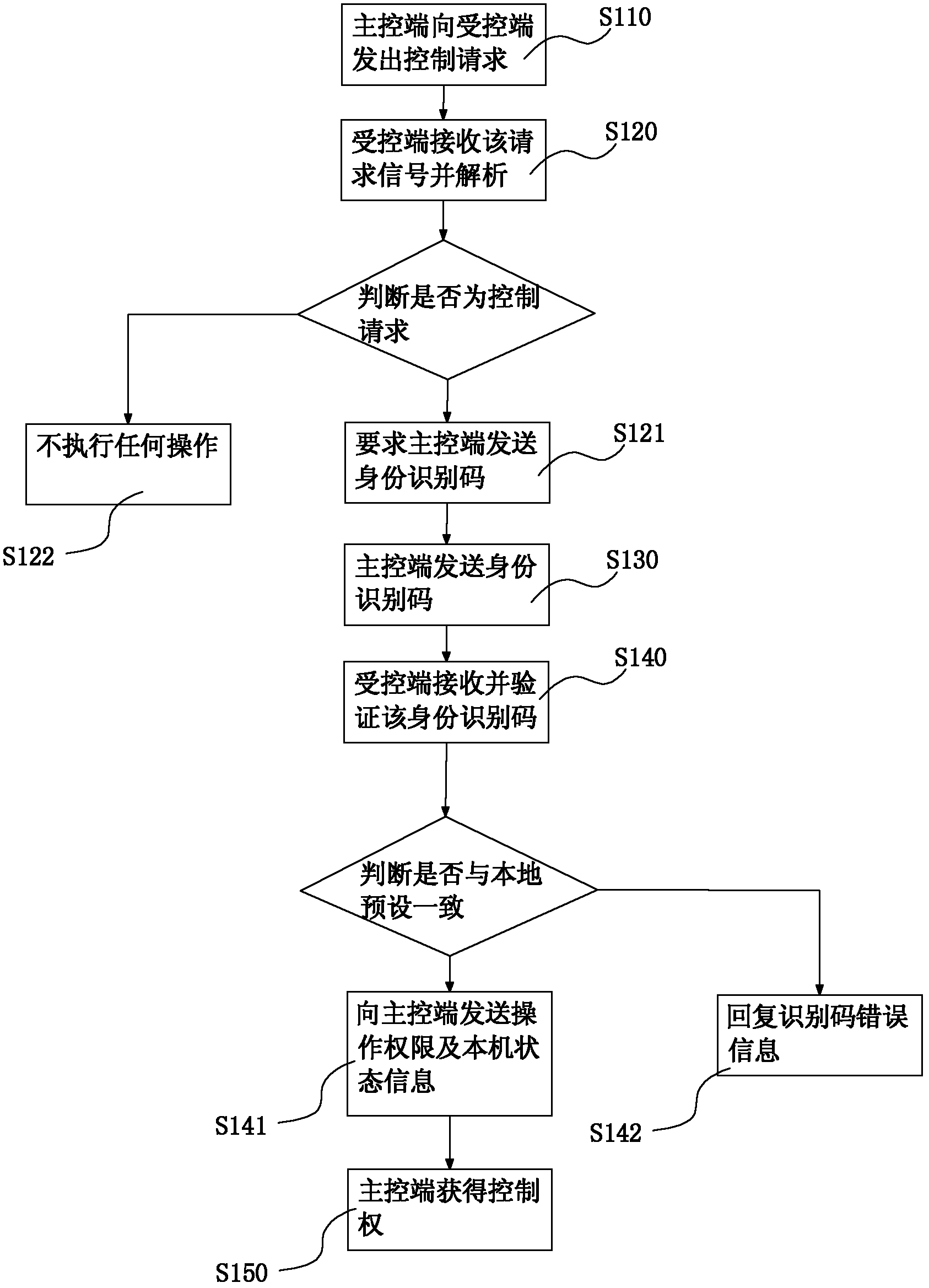
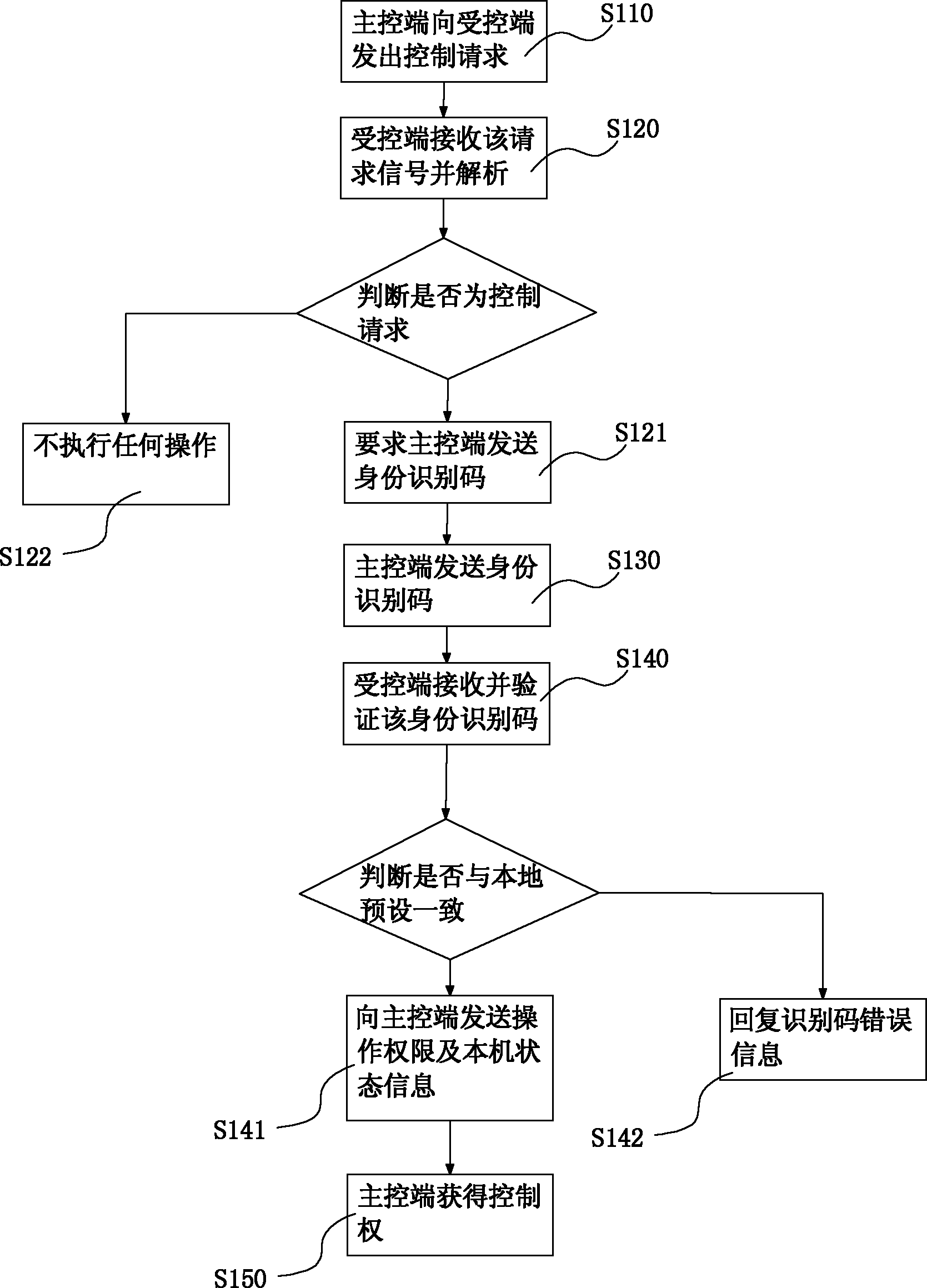
InactiveCN102594893AEasy remote controlEfficient and safe remote controlTransmissionComputer hardwareUser input
The invention provides a remote compelled method for mobile terminal equipment and a computer. The remote compelled method is characterized by comprising the following steps that: the mobile terminal equipment and the computer respectively store a control instruction corresponding to a concrete operation; a user sets an identification code (for identifying a master control end) and an operation authority (corresponding to the identification code) at a controlled end, wherein the operation authority can be implemented by the control instruction stored in the master control end; the user inputs the identification code at the maser control end and sends the identification code to the controlled end; the controlled end carries out verification on the identification code sent by the master control end, and if the sent identification code is not consistent with a local preset identification code according to a verified result, the controlled end sends an error code signal to the maser control end, and waits that the maser control end sends an identification code again; and if the sent identification code is consistent with the local preset identification code according to the verified result, a corresponding control instruction is loaded in the controlled end, and the controlled end sends the operation authority and local state information to the master control end.
Owner:GUANGDONG BUBUGAO ELECTRONICS IND
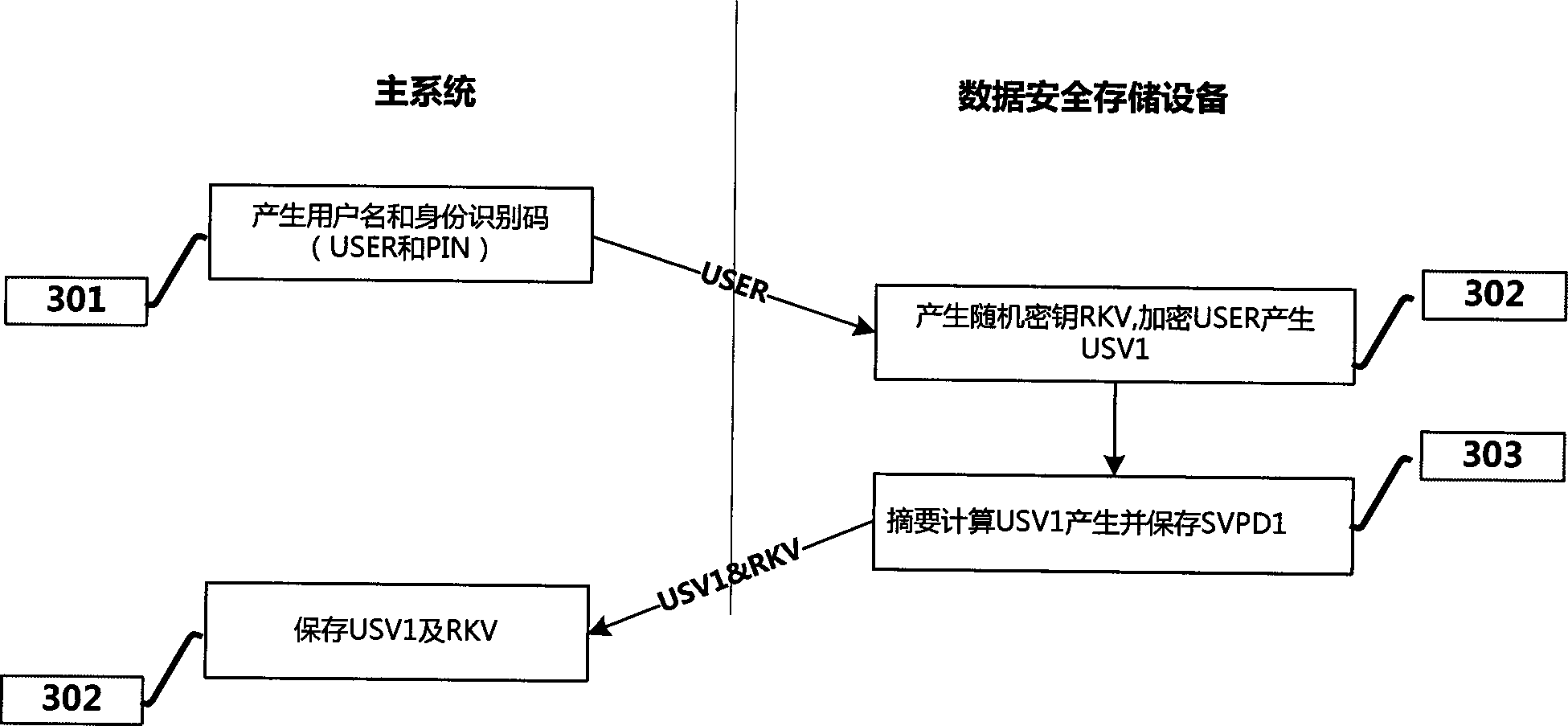
Achieving method of data security storage equipment capable of ensuring data security
InactiveCN103136126AActively and effectively defend against attacksEffective encryptionUser identity/authority verificationUnauthorized memory use protectionProtection mechanismBus mastering
The invention discloses an achieving method of data security storage equipment and relates to the field of data storage and information security. The achieving method includes that a main system is connected with the data security storage equipment by a system bus; data storage medium is connected with the data security storage equipment by a storage bus; the data security storage equipment is composed of a storage bus control unit, a system bus control unit, an encryption processing unit, a central processor unit, a data-caching unit and a nonvolatile storer unit. The invention provides an executing method of the data security storage equipment and further discloses an executing method of a data security protection mechanism. The data security storage equipment and the data security protection mechanism are capable of providing high-strength secure protection for data storage.
Owner:SAGE MICROELECTRONICS CORP
Data processing system and method and storage medium
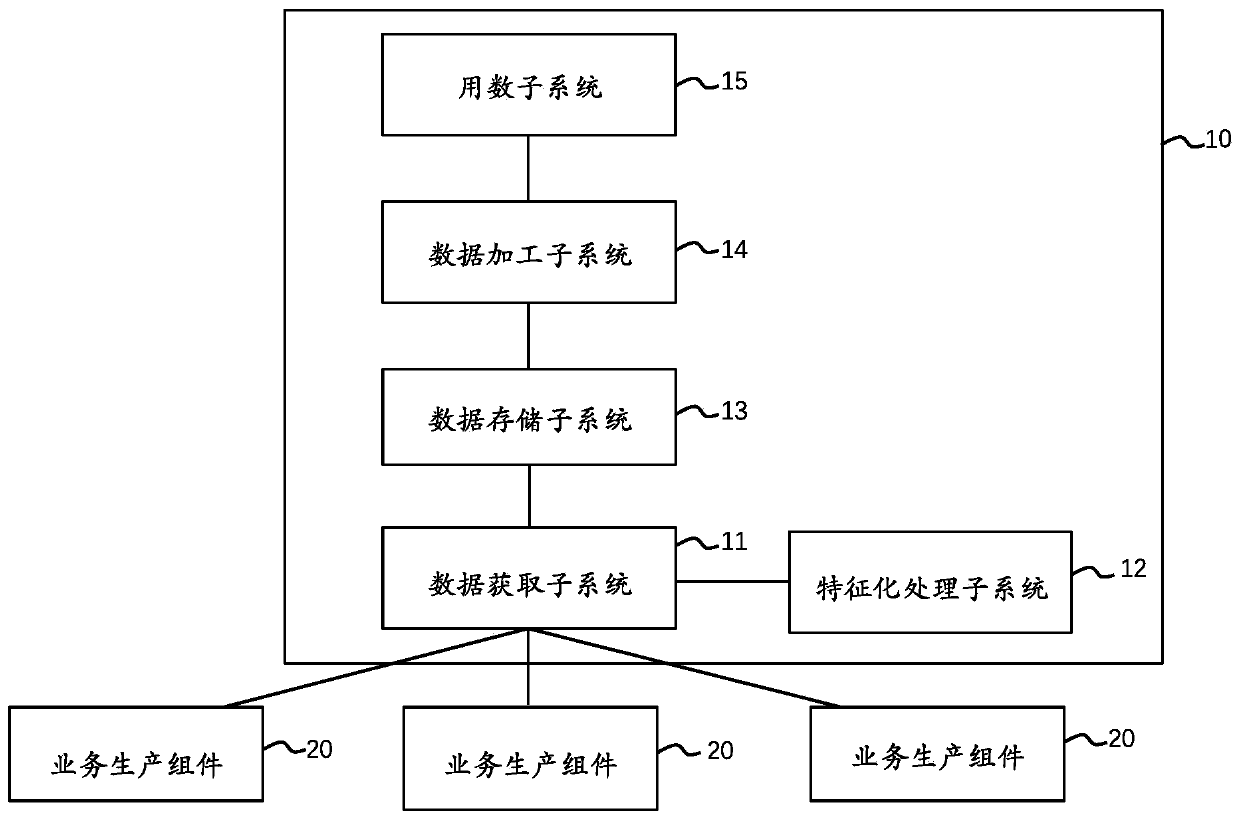
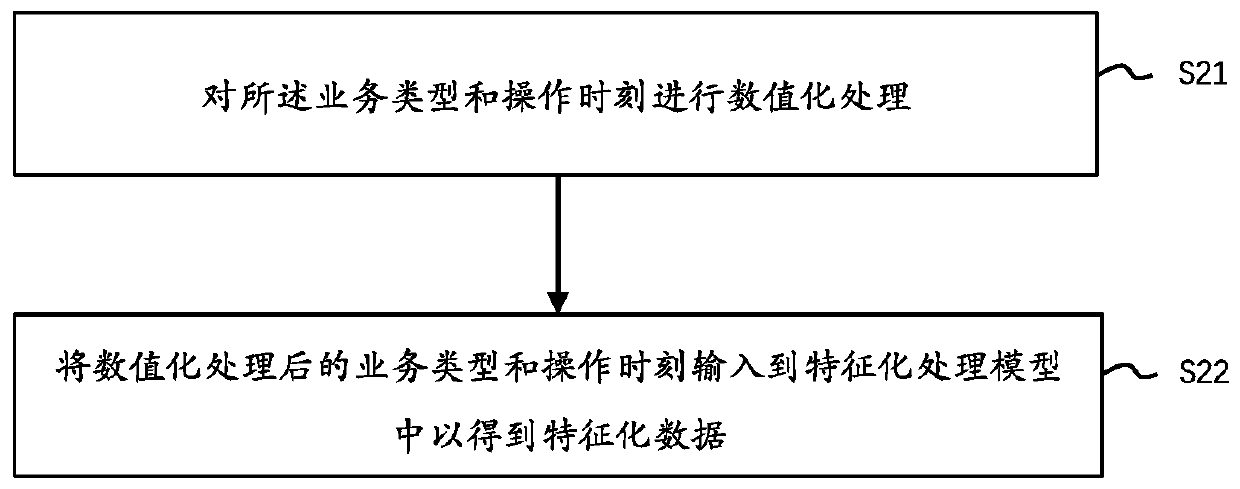
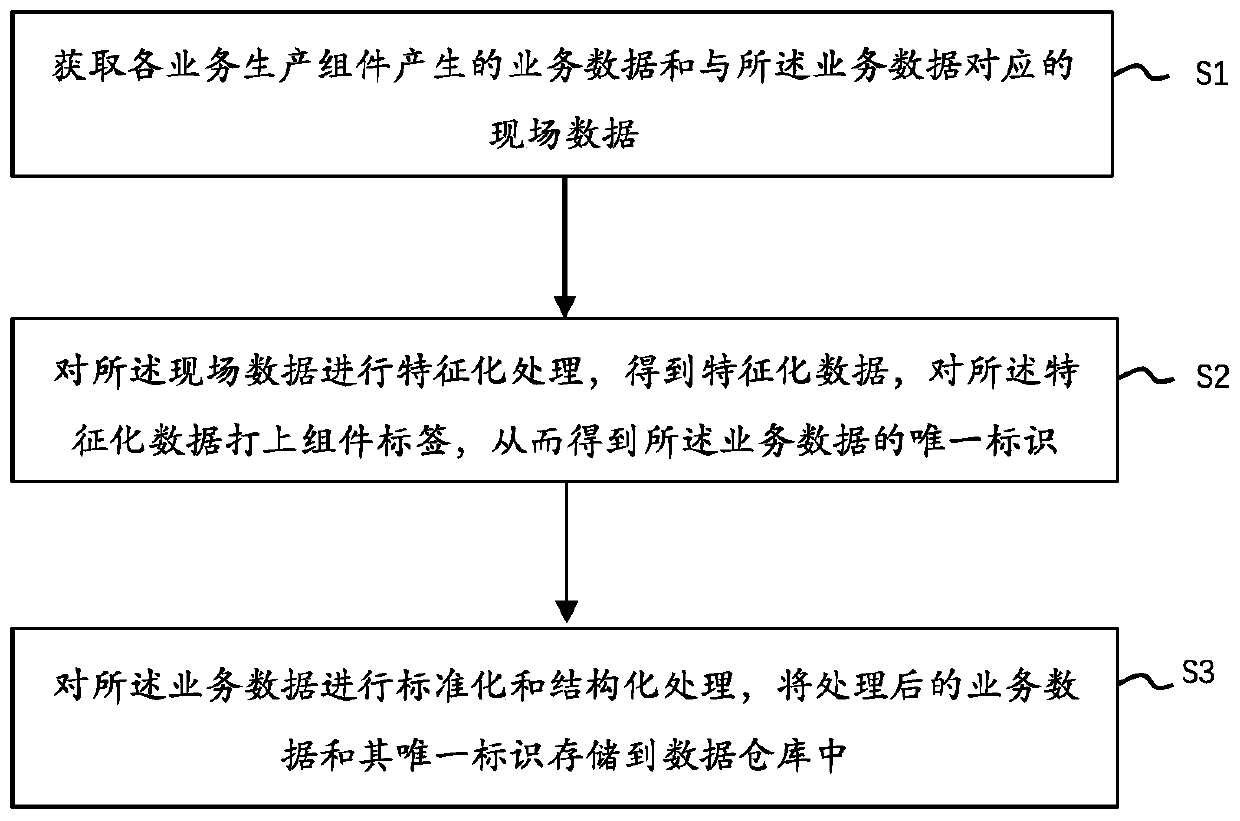
PendingCN111178005AImprove securityEffective encryptionNatural language data processingSpecial data processing applicationsData processing systemData warehouse
The invention provides a data processing system and method and a storage medium, and relates to the field of data processing. The system comprises a data production subsystem which is used for obtaining business data generated by each business production assembly and field data corresponding to the business data, wherein the field data comprises business types and operation moments; a characterization processing subsystem which is used for carrying out characterization processing on the field data to obtain characterization data, and marking a component label on the characterization data to obtain a unique identifier of the service data, wherein the component label comprises a component identifier for generating the on-site business production component and a user identifier for using thebusiness production component; and the data storage subsystem which is used for carrying out standardization and structuralization processing on the business data and storing the processed business data and the unique identifier of the business data into a data warehouse. According to the invention, the data acquisition efficiency and security can be improved.
Owner:CHINA CONSTRUCTION BANK
Secure Personal Medical Process
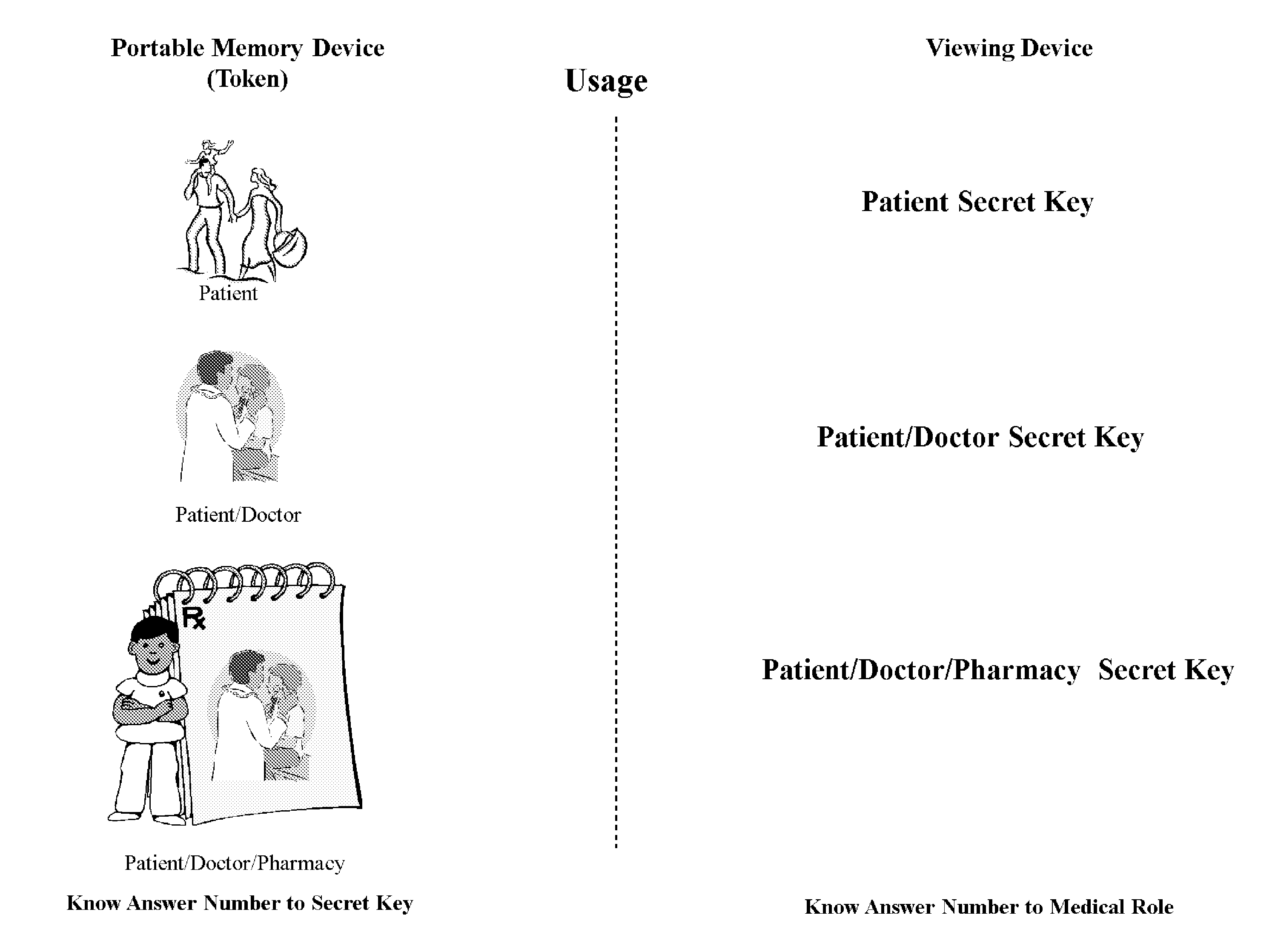
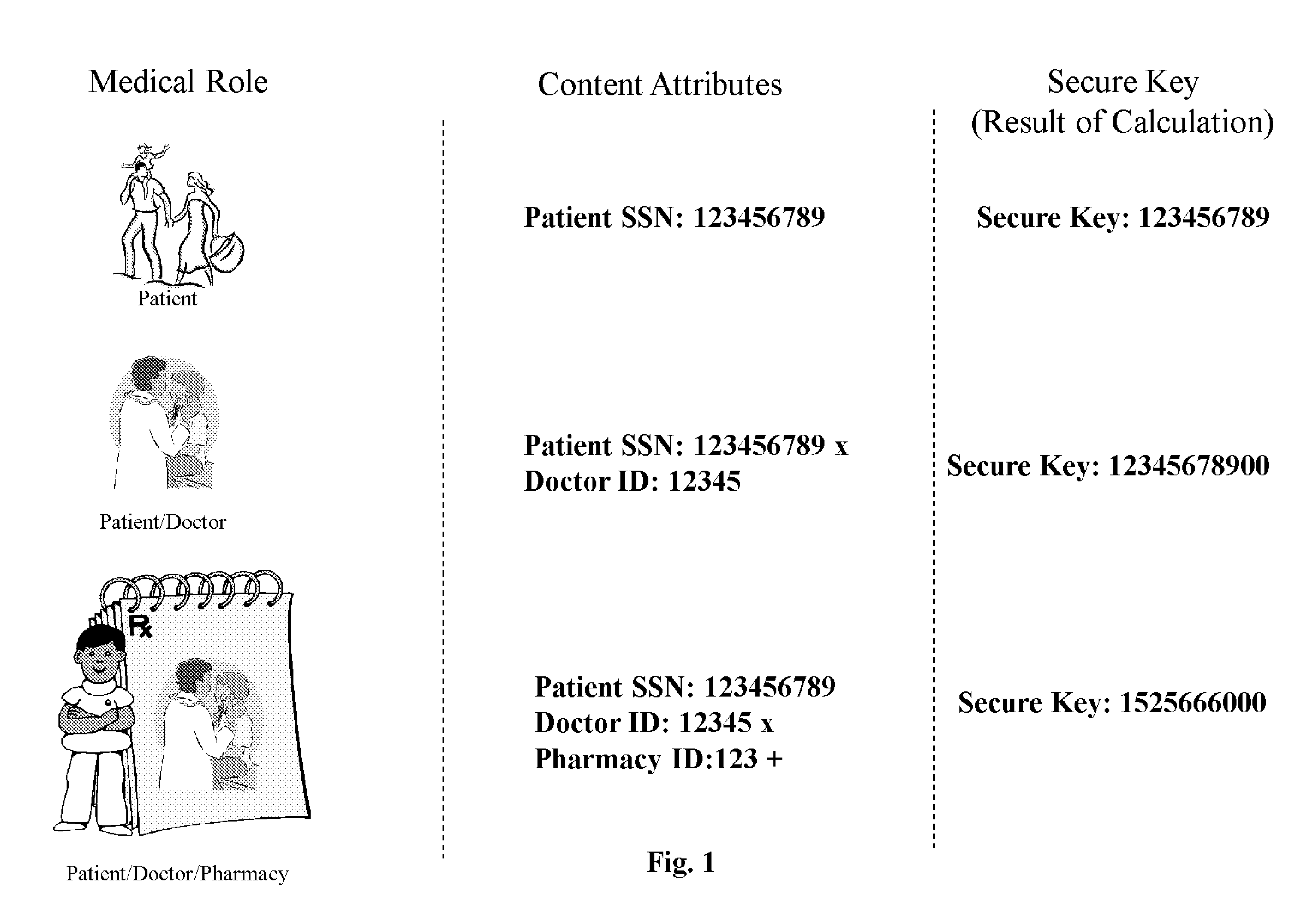
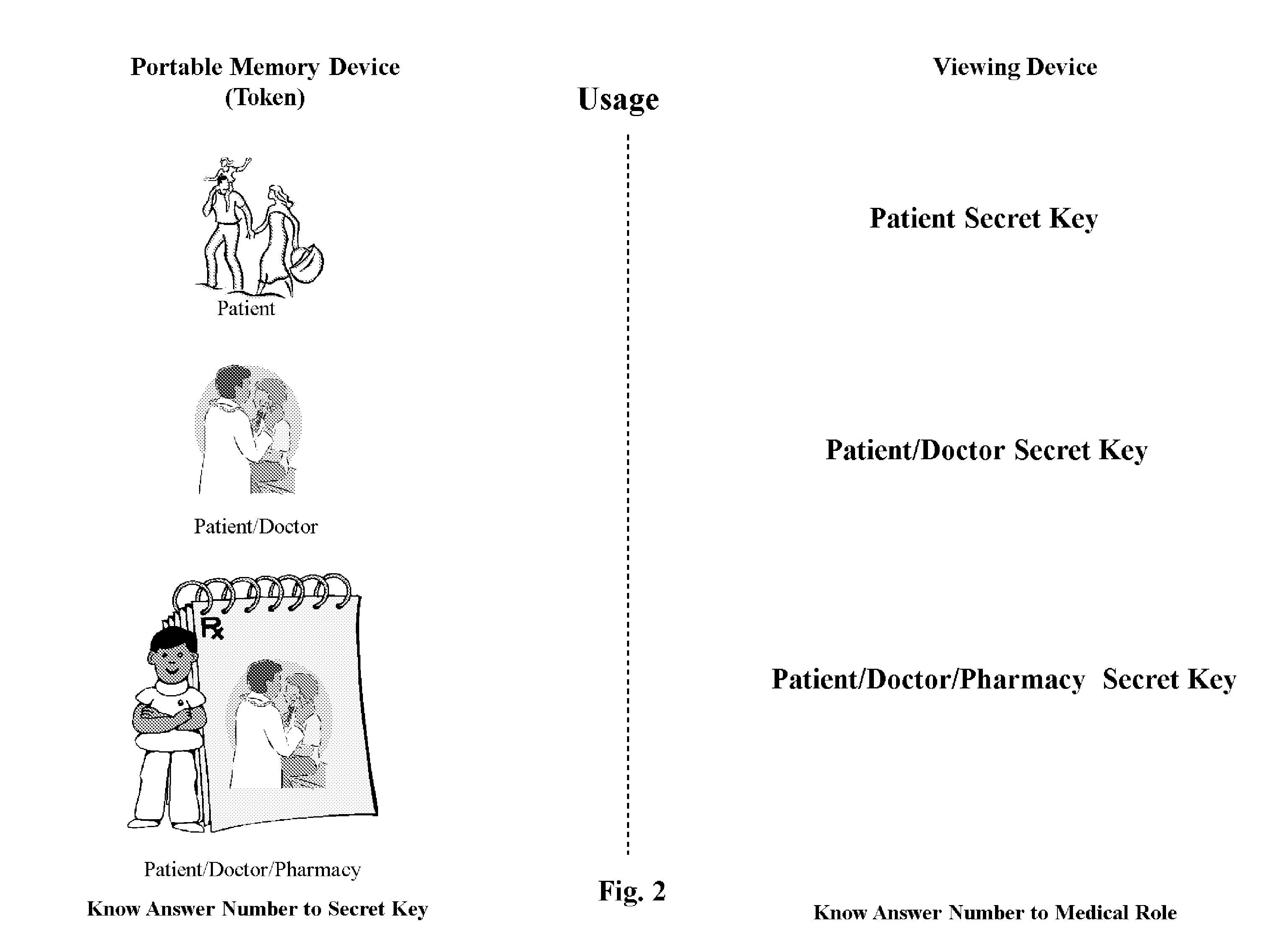
InactiveUS20100235924A1Effective encryptionDigital data processing detailsAnalogue secracy/subscription systemsAccess control matrixInformation access
A process of accessing and controlling medical information data by a Secure Process that includes two schemas—Medical Access Permission Schema (MAPS) information access system and encryption schema. In particular, the invention relates to a secure process for creating an access control and authentication methodology that identifies specific roles found in the medical field, applies these roles to content attributes, and binds those attributes to secret keys associated with an encryption schema.
Owner:KEYFOCUS
Method and system for the cipher key controlled exploitation of data resources, related network and computer program products
InactiveUS7913096B2Securely generateEffective encryptionUser identity/authority verificationUnauthorized memory use protectionHash functionComputer module
An arrangement for the cipher controlled exploitation of data resources (e.g., securely storing and retrieving sensitive data or securely registering and logging on a computer system) includes the steps of providing a subscriber identity module carrying a security algorithm; generating at least one, e.g., two, random values; subjecting the random value to the at least one security algorithm to generate at least one, e.g., two, session keys; processing the session keys via a mixer function such as a hash function to produce a cipher key; and using the cipher key thus produced for exploiting the data resources.
Owner:TELECOM ITALIA SPA
Method, system, and program, for encoding and decoding input data
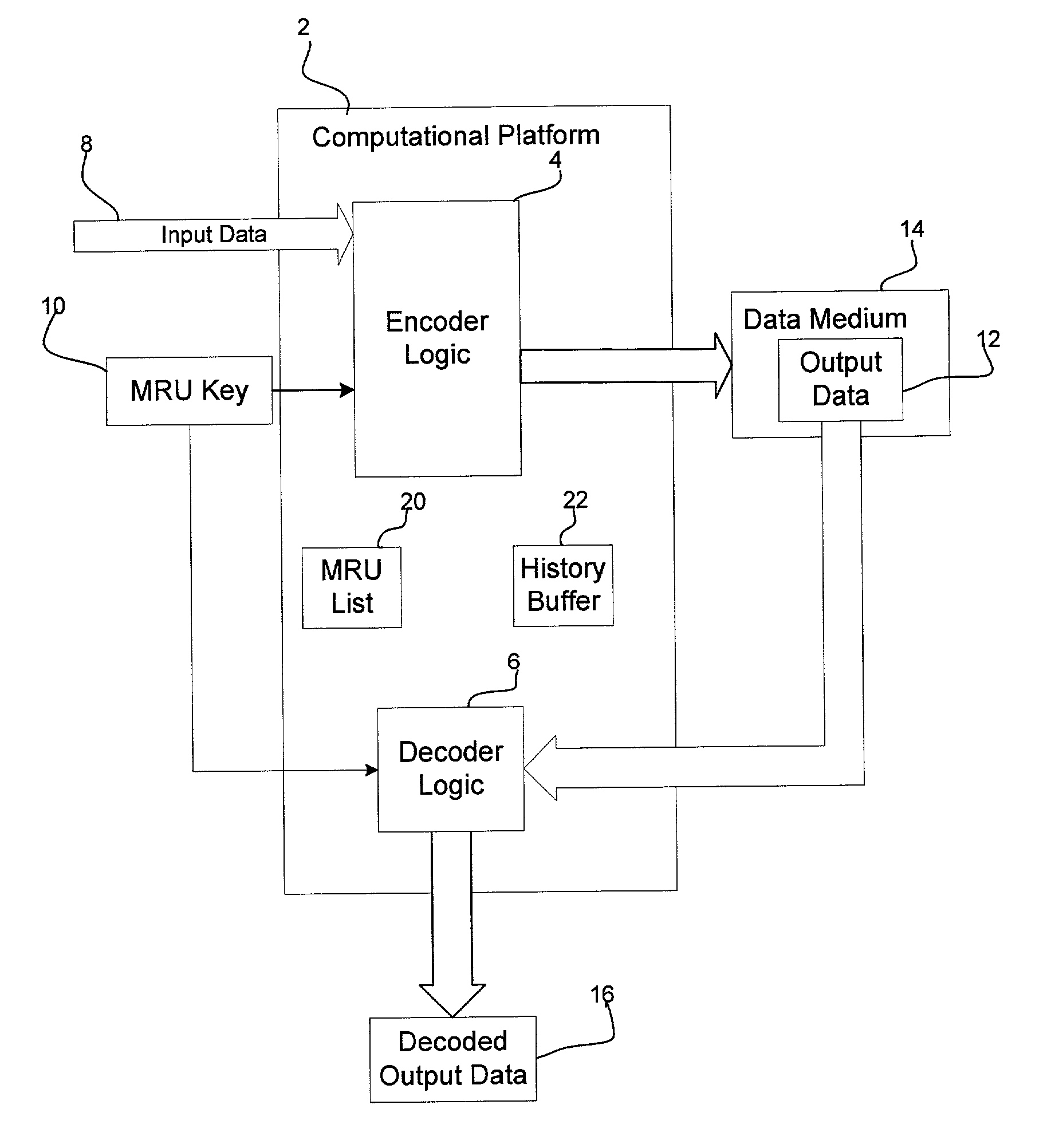
ActiveUS20030072446A1High strengthOptimizes encryption of dataComputer security arrangementsSecuring communicationUser inputTheoretical computer science
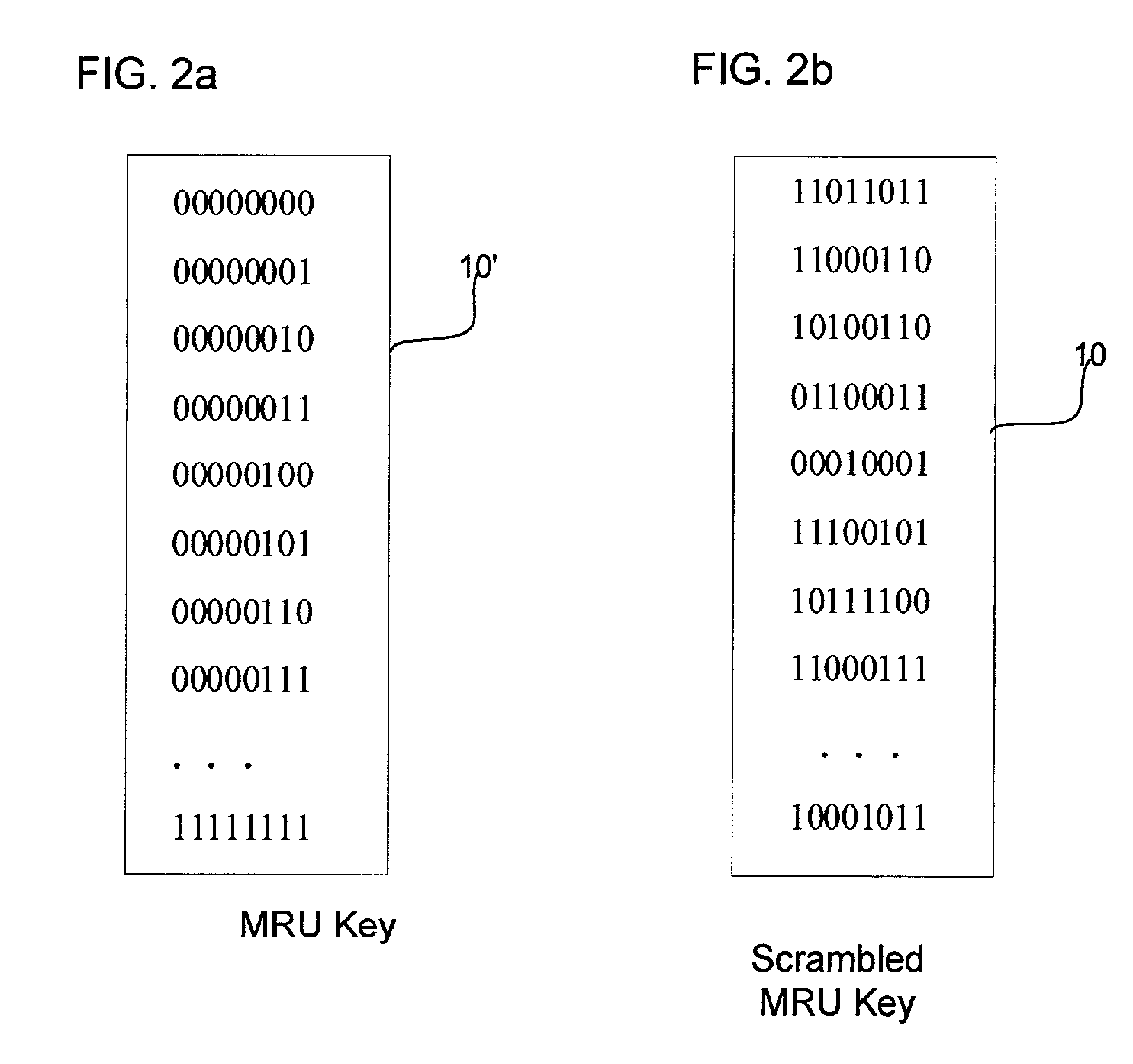
Provided is a method, system, and program for encoding and decoding input data. A key is generated comprising a list of a plurality of binary values, wherein the key is available to a user to provide during decoding. The input data is encoded by using the key to initialize a replacement list. A determination is made whether to replace strings in the input data with a string reference to a matching string value, wherein the input data not replaced with reference to one matching string value comprises one or more literals. Each literal is replaced with a literal reference to one entry in the replacement list matching the literal. The encoded input data is decoded by accessing the generated key in response to user input and using the accessed key to decode the literals replaced with literal references to entries in the replacement list.
Owner:TWITTER INC
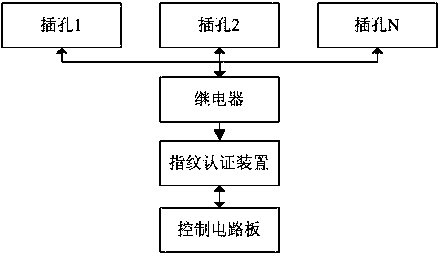
Wiring board power supply system based on fingerprint authentication function
InactiveCN104821470ASolve the problem that user authentication cannot be performedRealize power supply controlCoupling device detailsComputer hardwareControl circuit
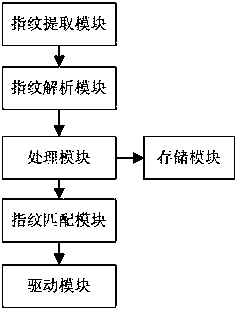
The invention discloses a wiring board power supply system based on a fingerprint authentication function. The system comprises jacks and a control circuit board, and further comprises a fingerprint authentication device and a relay, wherein the input end of the relay is connected with the fingerprint authentication device, and the output end of the relay is connected with the jacks. The fingerprint authentication device comprises a fingerprint extraction module, a fingerprint parsing module, a processing module, a storage module, a fingerprint matching module and a driving module, wherein the fingerprint extraction module is used for registering fingerprints; the fingerprint parsing module is used for parsing obtained fingerprint information; the processing module is used for obtaining user fingerprint images through combination with processing; the storage module is used for storing the user fingerprint images therein; the fingerprint matching module is used for performing matching with the user fingerprint images; and the driving module is used for outputting driving signals for the relay according to match results and supplying power to the jacks in case of closure or cutting off the power of the jacks in case of breaks. The wiring board power supply system based on the fingerprint authentication function can realize power supply control of a wiring board by users, facilitates management and realizes power supply in an intelligent mode.
Owner:WUXI CITY CHONGAN DISTRICT TECH ENTREPRENEURSHIP SERVICE CENT
Intelligent power distribution terminal based on ad-hoc network wireless communication
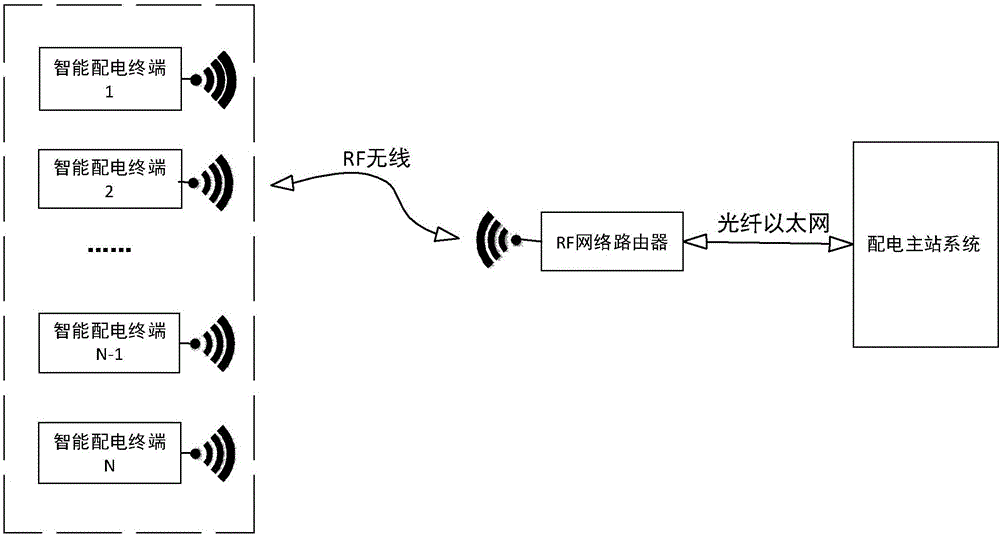
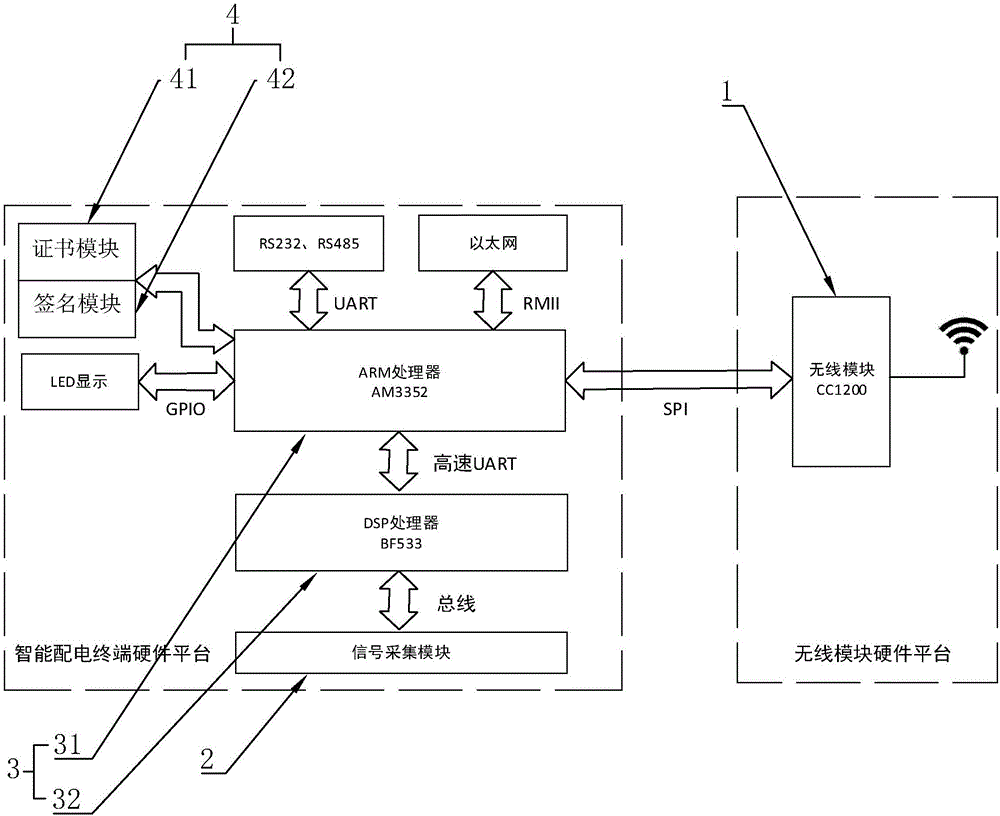
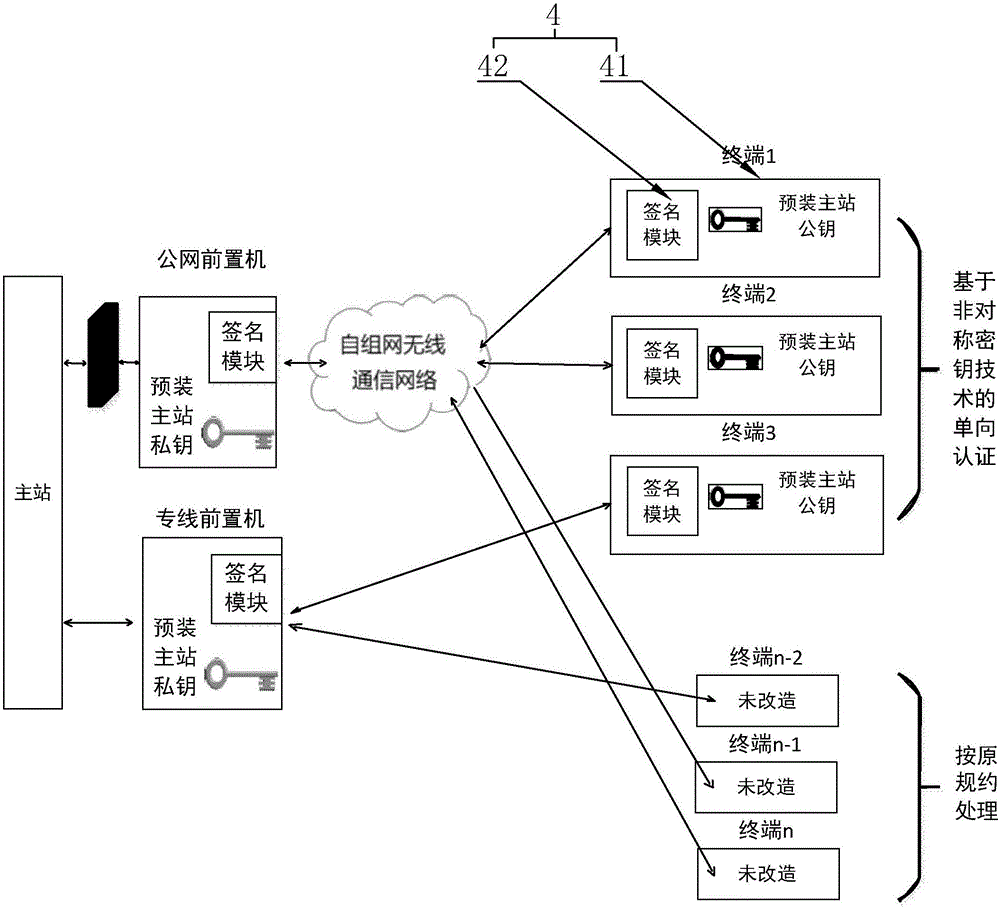
PendingCN106505737AImprove securityEfficient collectionTransmission systemsCircuit arrangementsPower gridSignal acquisition
The invention discloses an intelligent power distribution terminal based on ad-hoc network wireless communication. The terminal is used for connecting an external wireless router in a communication connection mode. The external wireless router is coupled to a power-distribution main station system through an optical fiber Ethernet. The terminal comprises a wireless communication module, a signal acquisition module, a data processing module and a safe access module. The safe access module comprises a certificate module and a signature module. The signature module is coupled to the data processing module and the wireless communication module. A main-station private key is stored in the external wireless router. By using the intelligent power distribution terminal based on the ad-hoc network wireless communication, through arranging the signal acquisition module, the data processing module and the wireless communication module, signals of a power grid can be effectively collected and transmitted into the power-distribution main station system; and through arranging the safe access module, the signal which is transmitted wirelessly is effectively encrypted so that safety of a message of an application layer is effectively increased.
Owner:WENZHOU ELECTRIC POWER BUREAU +2
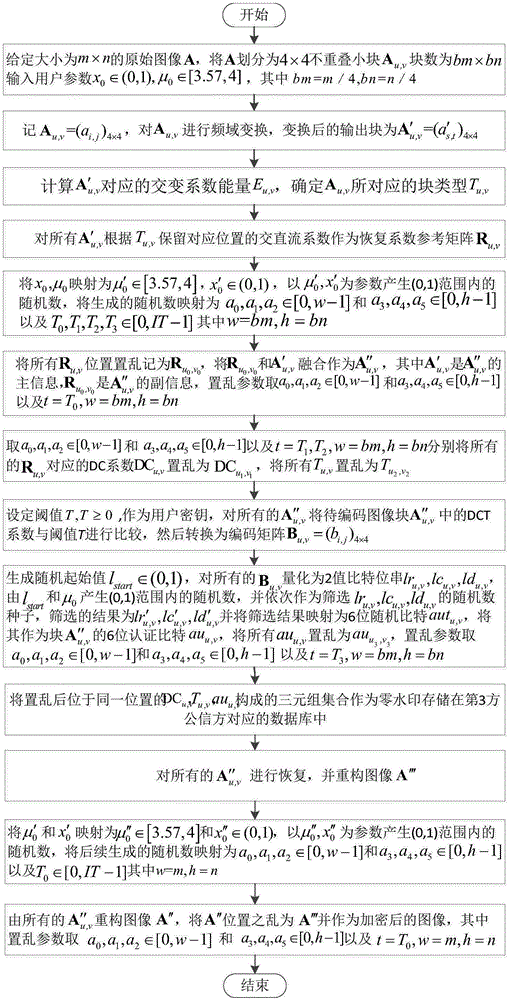
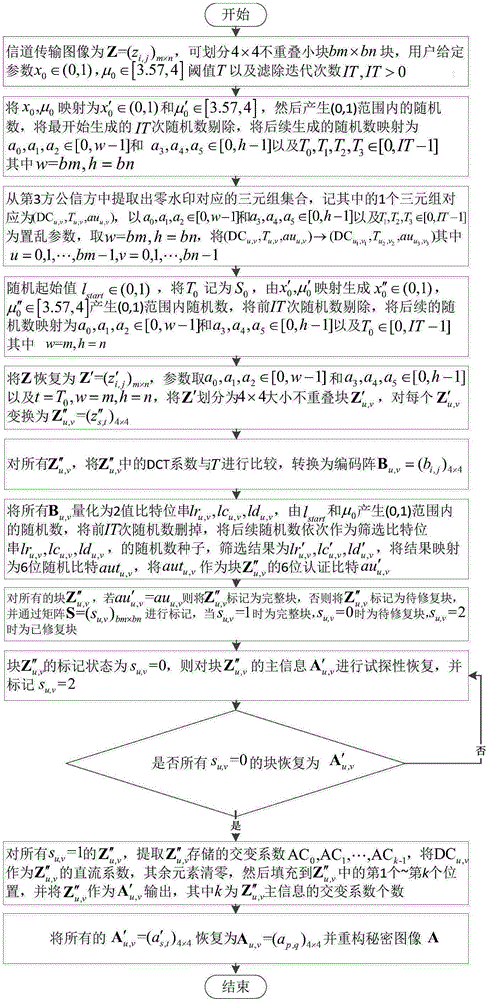
Self-recovery image encryption and decryption method combining zero watermarks and block classification fusion
ActiveCN106780278AImprove resistance to attackEffective encryptionImage data processing detailsComputer hardwareSelf recovery
The invention provides a self-recovery image encryption and decryption method combining zero watermarks and block classification fusion. During encryption, first, small blocks are divided into four types according to a frequency domain alternation coefficient of the small blocks in an image to be encrypted, and corresponding alternating current and direct current coefficients are reserved to serve as a restoration reference matrix; second, main information of the small blocks which are scrambled in position and auxiliary information of an original position reference matrix are fused, and authentication information of the fused small blocks is acquired according to an encoding matrix; third, direct current components and the block types of the scrambled small blocks before fusion and the authentication information of the fused small blocks are used as the zero watermarks stored in a third public trust party; and last, the image is reconstructed from the fused small blocks, and global position scrambling is performed to generate an encrypted image. During recovery, first, the fused small blocks are reconstructed, the main information and auxiliary information authentication relation and zero watermark recovery main information are utilized, and a decrypted image is reconstructed. Compared with existing methods, the method can be used for effectively encrypting the image and performing a certain recovery against a channel attack, thereby having higher application value.
Owner:SHAANXI NORMAL UNIV
Data encryption method based on password book
ActiveCN104518865AEnsure safetyImprove encryption and decryption efficiencyEncryption apparatus with shift registers/memoriesOriginal dataCiphertext
The invention discloses a data encryption method based on a password book and belongs to the technical field of computer data safety. The data encryption method includes that the password book self-defined by a user is utilized for date encryption, a sequence formed by stored data is utilized fully, and extraction of part of bit data or inserting of data among specific bits is not needed to disturb an original data storage sequence; the original data storage sequence is subjected to fixed-length cutting, and fixed length is generally not larger than 8 bit, so that more simplicity and conciseness in ciphertext display are realized, and difficulty in illegal decryption by the user is greatly increased. Compared with the prior art, the data encryption method has the advantages that length of ciphertext is compressed effectively, data encryption speed is increased, and difficulty in illegal decryption of data is increased greatly due to creating of the password book.
Owner:NANJING UNIV OF POSTS & TELECOMM
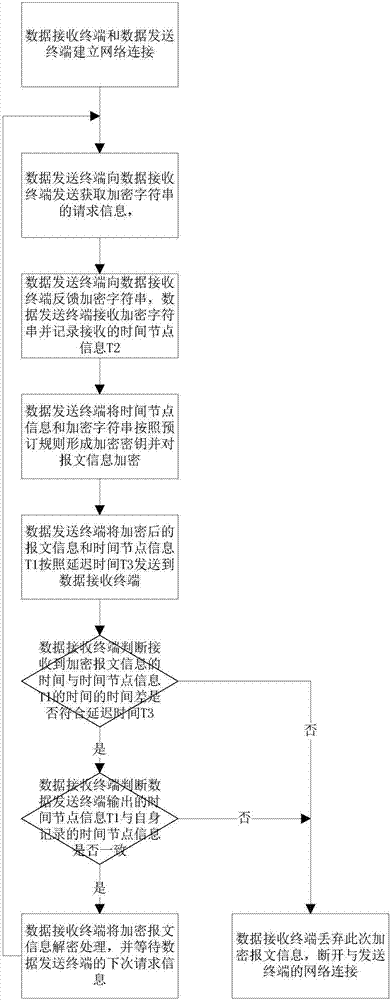
Internet of things data transmission method
ActiveCN106961449AEffective encryptionPrevent interceptionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData transmissionData security
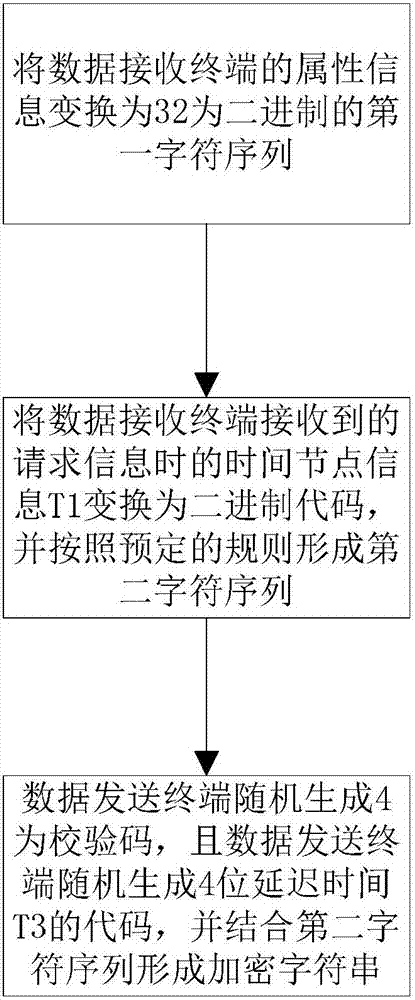
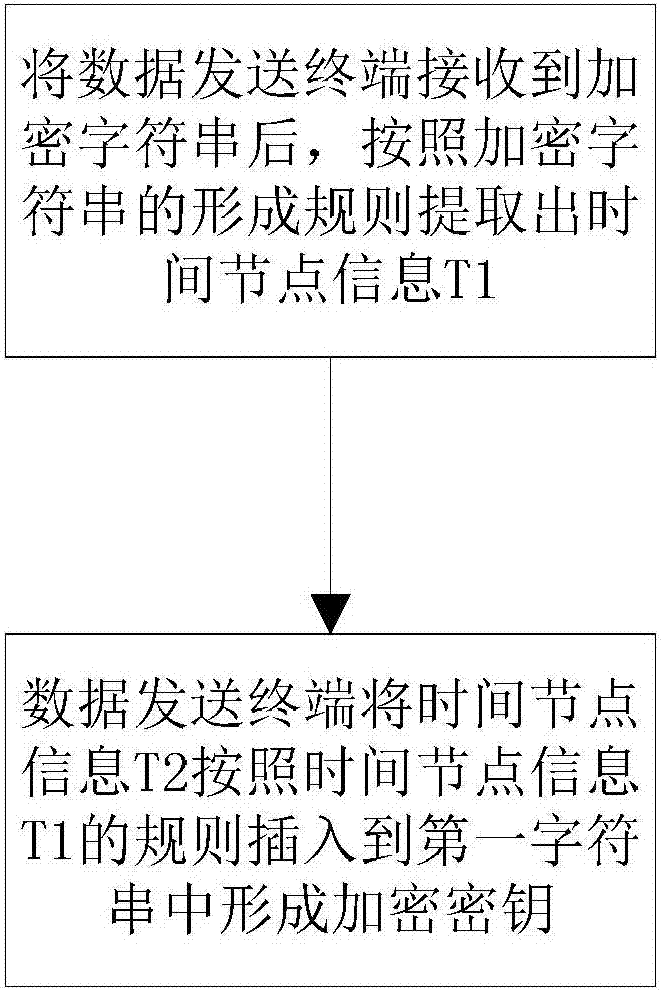
The invention provides an Internet of things data transmission method. The Internet of things data transmission method comprises the following steps: S1, sending request information to a data receiving terminal by a data sending terminal, and feeding back an encrypted character string by the data receiving terminal; S2, receiving the encrypted character string by the data sending terminal, and recording time node information T2 of the received encrypted character string; S3, receiving the time node information T2 of the received encrypted character string by the data sending terminal, and forming an encryption key from the time node information T2 and the encrypted character string according to a predetermined rule; S4, encrypting message information through the encryption key by the data sending terminal, and sending the encrypted message information and the time node information T1 to the data receiving terminal according to predetermined delay time T3; S5, judging whether the received encrypted message information is legal by the data receiving terminal, if so, decrypting data, and otherwise, discarding the received information. By the Internet of things data transmission method, message data in an Internet of things platform can be effectively encrypted so as to ensure data security in an Internet of things system.
Owner:重庆和贯科技有限公司
Method for Encrypting Video Data
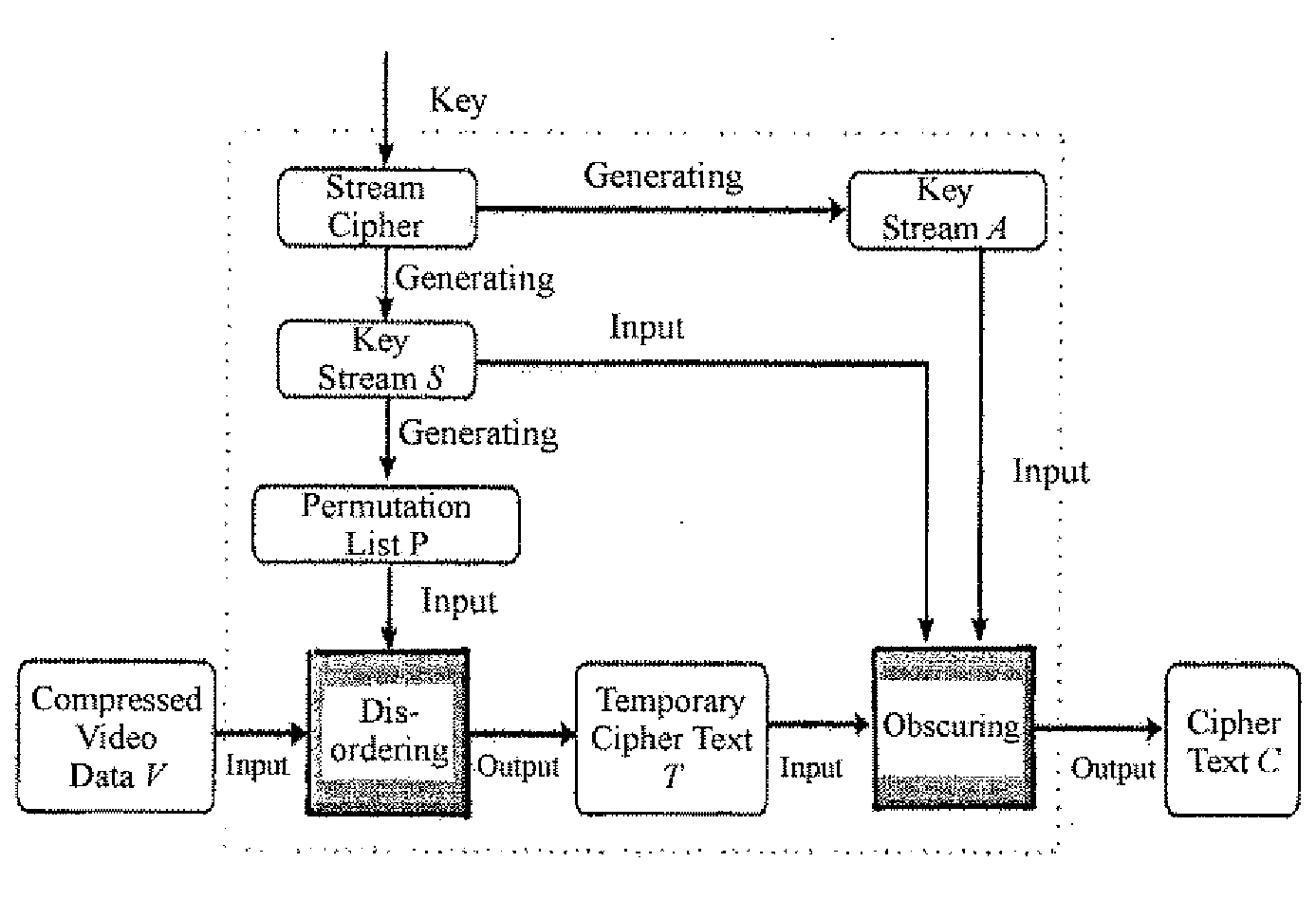
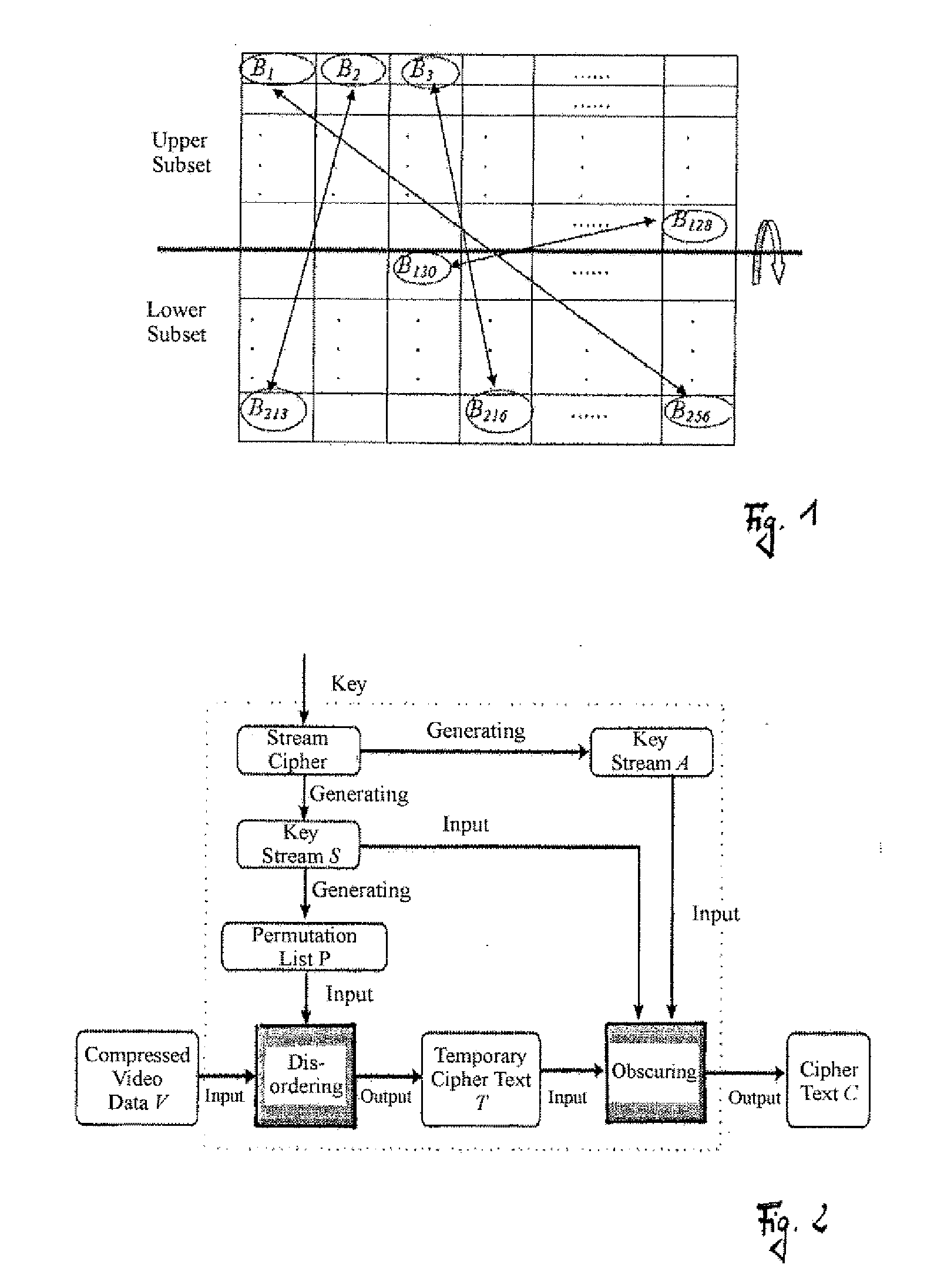
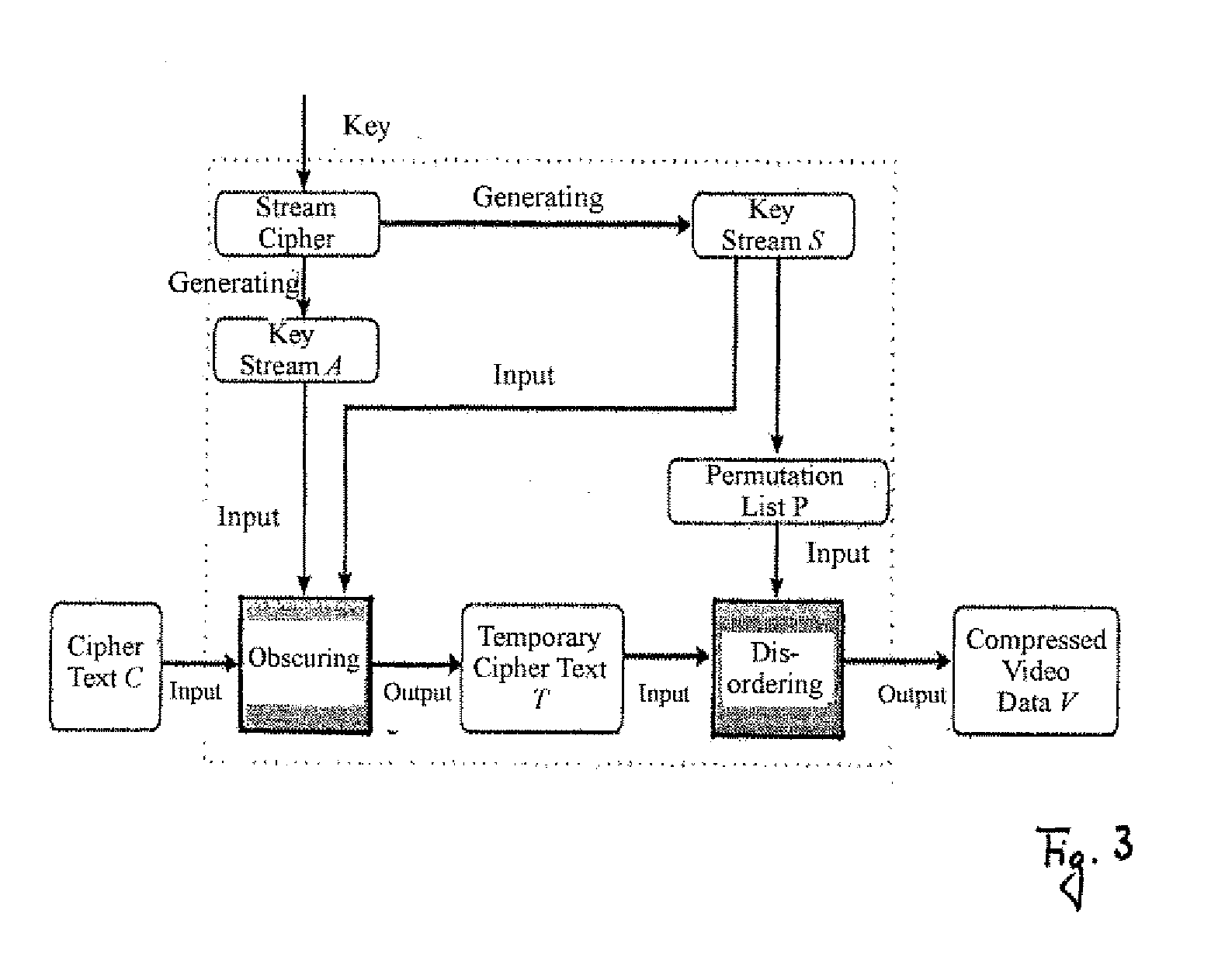
InactiveUS20070237328A1High safety standardsReduce computing costData stream serial/continuous modificationSecret communicationComputer hardwareEncryption
A method for encrypting video data in which the encryption achieves a high standard of security and is carried out at a reduced computation cost. The encryption comprises disordering a set of video data to be encrypted and obscuring the disordered video data.
Owner:BRANDENBURGISCHE TECHN UNIV COTTBUS SENFTENBERG
Storage device with a communications function
InactiveUS20130132715A1Reduce safety concernsReduce riskDigital data processing detailsMultiple digital computer combinationsUSBEmbedded system
The present invention relates to a storage device with a communications function which comprises an integrated circuit module and an application program. The integrated circuit module comprises at least a USB connector, at least a substrate, at least a controller and at least a memory in which there is at least an authentication code; the application program comprises a communications module and a transmission module wherein the communications module is used to receive digital information of at least a data input device in a computer for both the authentication code and the digital information, which has been received by the communications module, transmitted to at least a server or at least a peer by the transmission module.
Owner:WALTON ADVANCED ENG INC
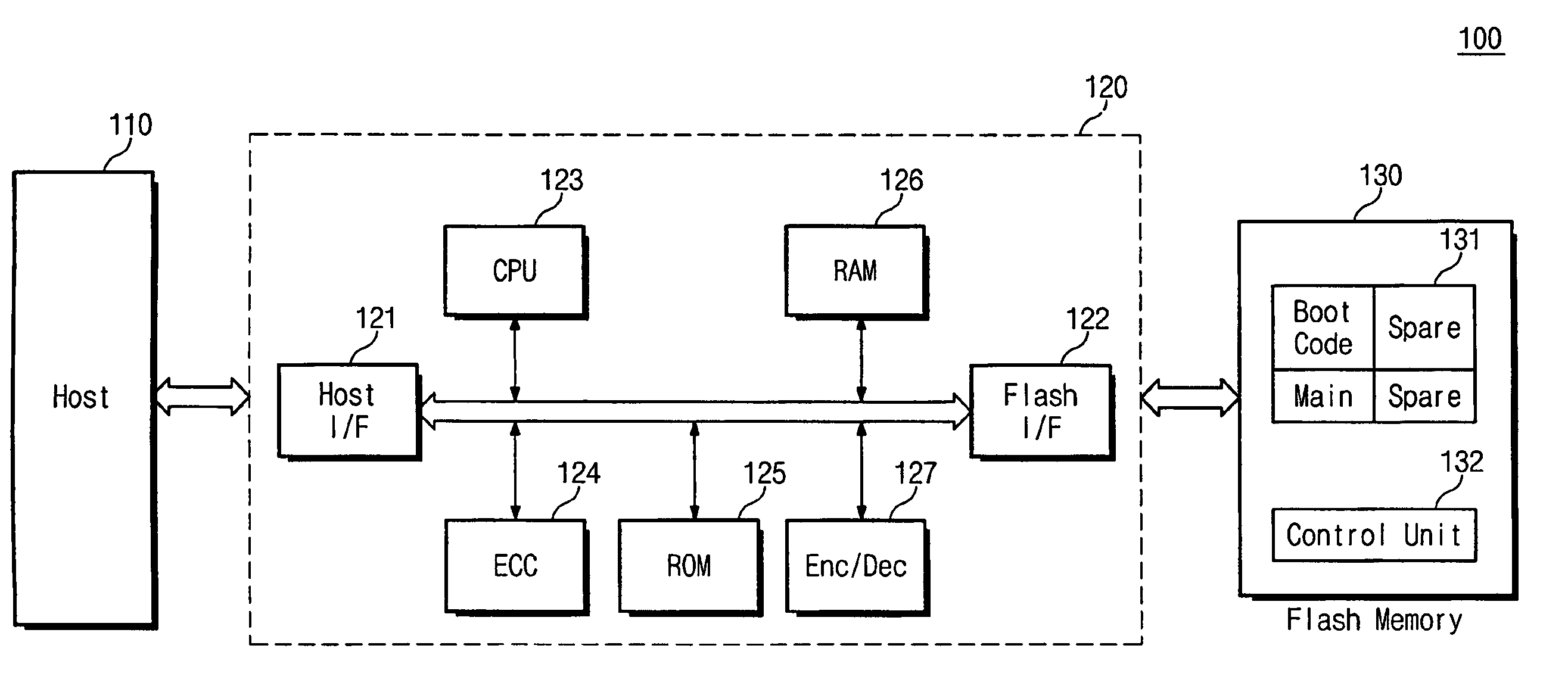
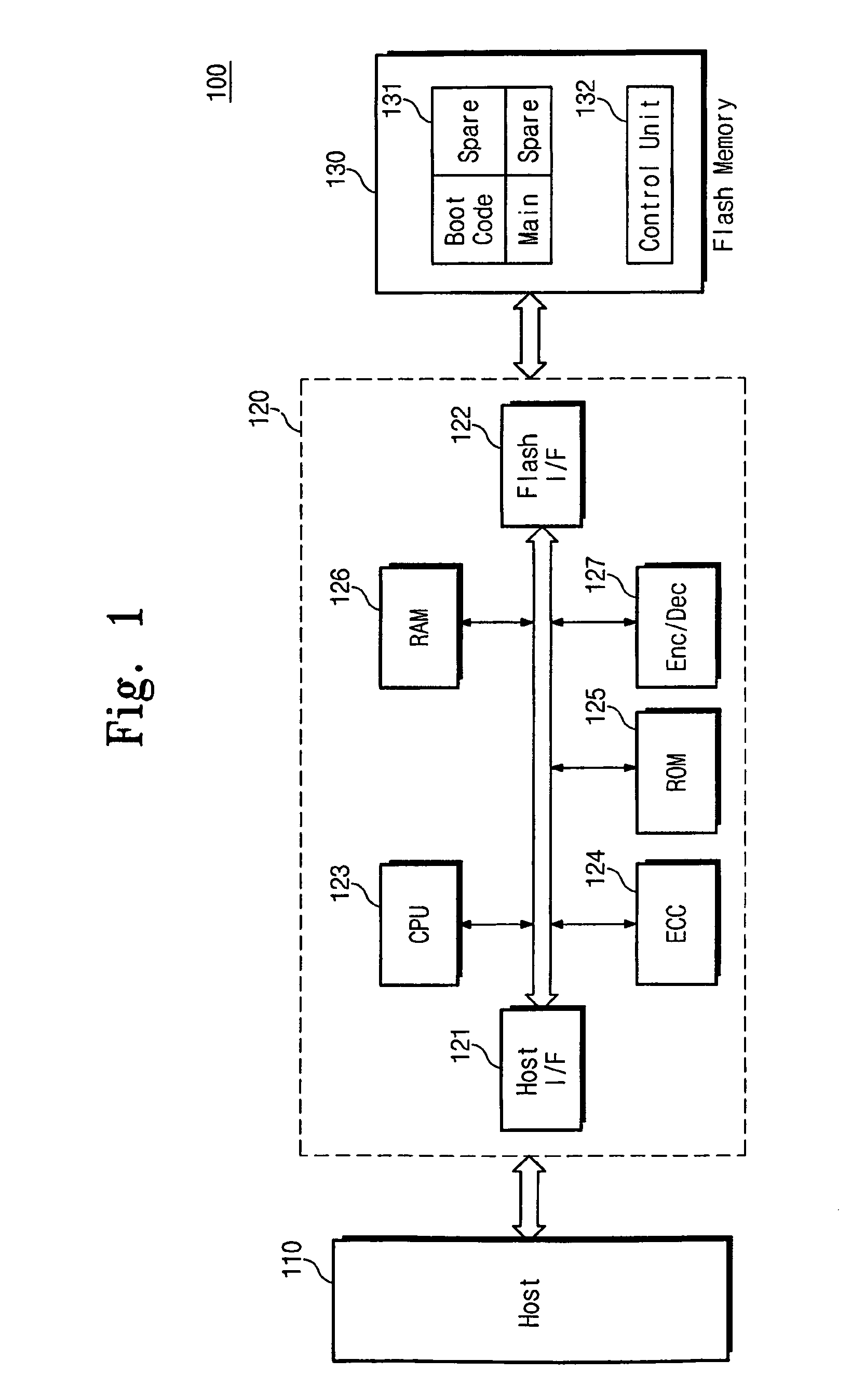
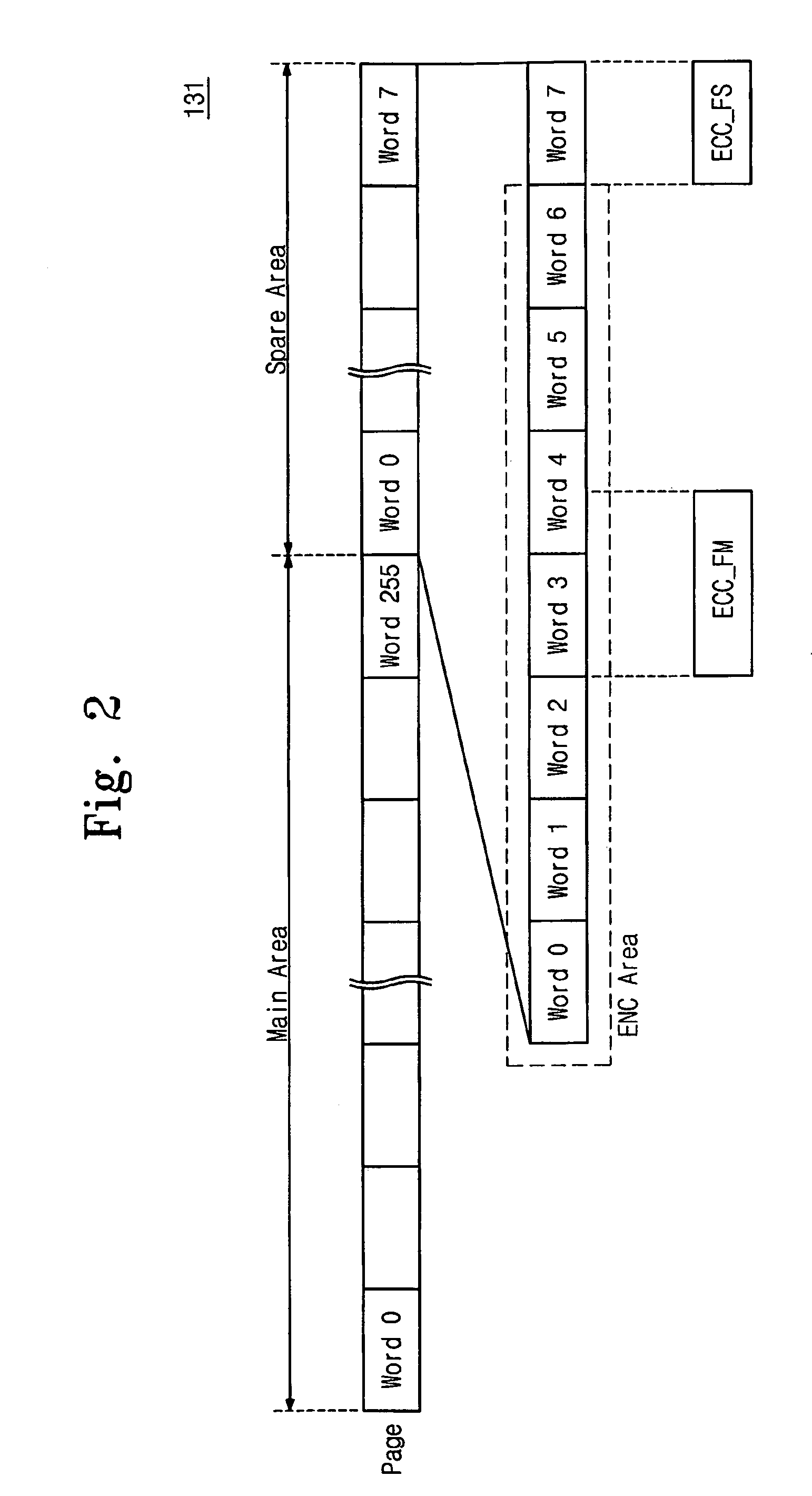
Flash memory system having encrypted error correction code and encryption method for flash memory system
ActiveUS8171378B2Effective encryptionMemory loss protectionCode conversionControl storeMemory controller
A flash memory system includes a flash memory for storing input data, and a memory controller controlling the flash memory, wherein the memory controller generates a first error correction code corresponding to the input data, and encrypts the first error correction code, and the flash memory includes a main area for storing the input data and a spare area for storing the encrypted first error correction code.
Owner:SAMSUNG ELECTRONICS CO LTD
Method of hybrid searchable encryption and system using the same
ActiveUS20190229906A1Low costImprove search efficiencyKey distribution for secure communicationMultiple keys/algorithms usageCiphertextSymmetric-key algorithm
The present invention involves with a method of hybrid searchable encryption, involving using at least one first computing device that has a first processor configured to perform steps of: using a first symmetric key to encrypt data so as to obtain a data first ciphertext, using a second symmetric key to encrypt a keyword related to the data so as to obtain a searchable keyword first ciphertext that is related to the data first ciphertext, and saving the data first ciphertext and the keyword first ciphertext in a first memory of a first computing device; and using the first symmetric key to encrypt the keyword so as to generate a keyword second ciphertext, using a first public key to encrypt the keyword so as to obtain a searchable third keyword ciphertext related to the keyword second ciphertext, and sending the keyword second ciphertext and the searchable third keyword ciphertext to a second computing device; wherein the second computing device has a second processor that is configured to perform steps of: receiving the keyword second ciphertext and the searchable third keyword ciphertext from the first computing device and saving the two together with an identification of the first computing device relationally in a second memory of the second computing device.
Owner:HUAZHONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com