Self-recovery image encryption and decryption method combining zero watermarks and block classification fusion
An encryption method and zero-watermark technology, applied in the field of self-recovery image encryption and decryption, can solve the problems of limited ability to resist attacks, limited attention to the ability of encrypted images to resist attacks, and lack of ability to repair after attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
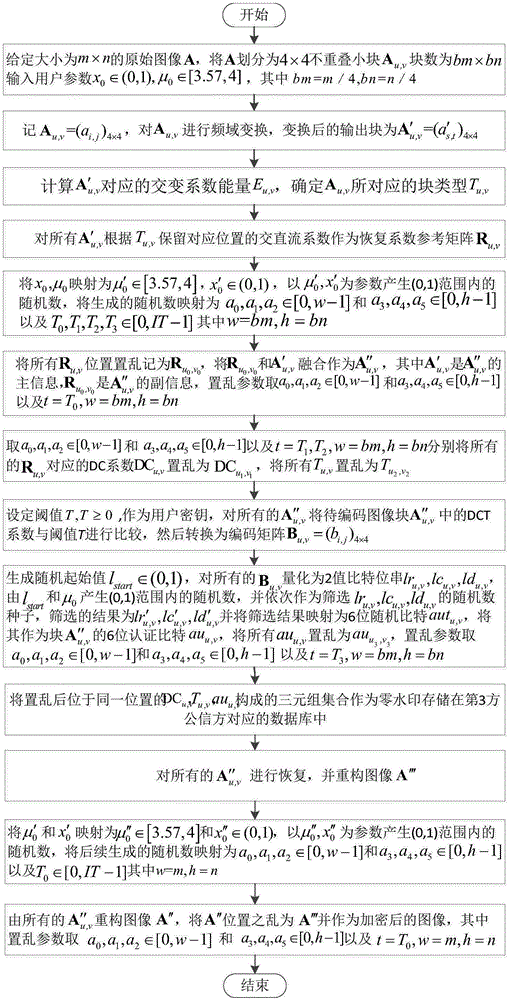
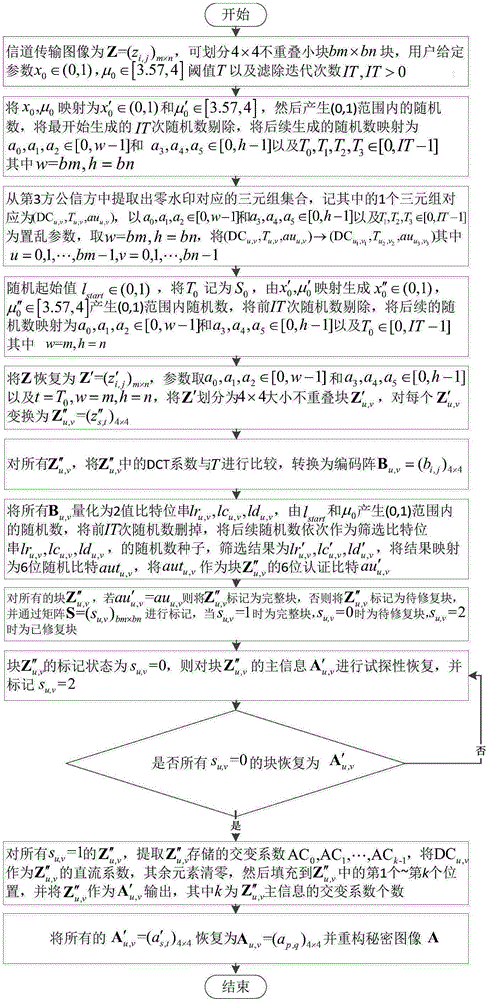
[0165] The experimental test environment is Windows 10 operating system, the CPU is Inter(R)Core(TM)i5-6600, the main frequency is 3.31GHz, the memory is 8.00GB, and the experimental coding language is Java jdk1.8.0_65. The embodiment of the invention is described in detail, but not limited to this implementation case, where figure 1 is the encryption flow chart, figure 2 is the recovery flow chart. The specific implementation steps of the embedding method are as follows:
[0166] Step 1: Note that the resolution is m×n original image A, and satisfy (m)mod4=0, (n)mod4=0, divide A into 4×4 non-overlapping small blocks A u,v , u=0,1,...,(m / 4)-1, v=0,1,...,(n / 4)-1, and the number of subdivided blocks is bm×bn, then bm=m / 4 ,bn=n / 4, input user given parameter x 0 ∈(0,1) and μ 0 ∈[3.57,4]; for example: take image 3 is the original image, the original image is an 8-bit grayscale image Lena with a resolution of 512×512, where m=512, n=512, bm=m / 4=128, bn=n / 4=128, input user gi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com