Patents
Literature
130 results about "Image security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
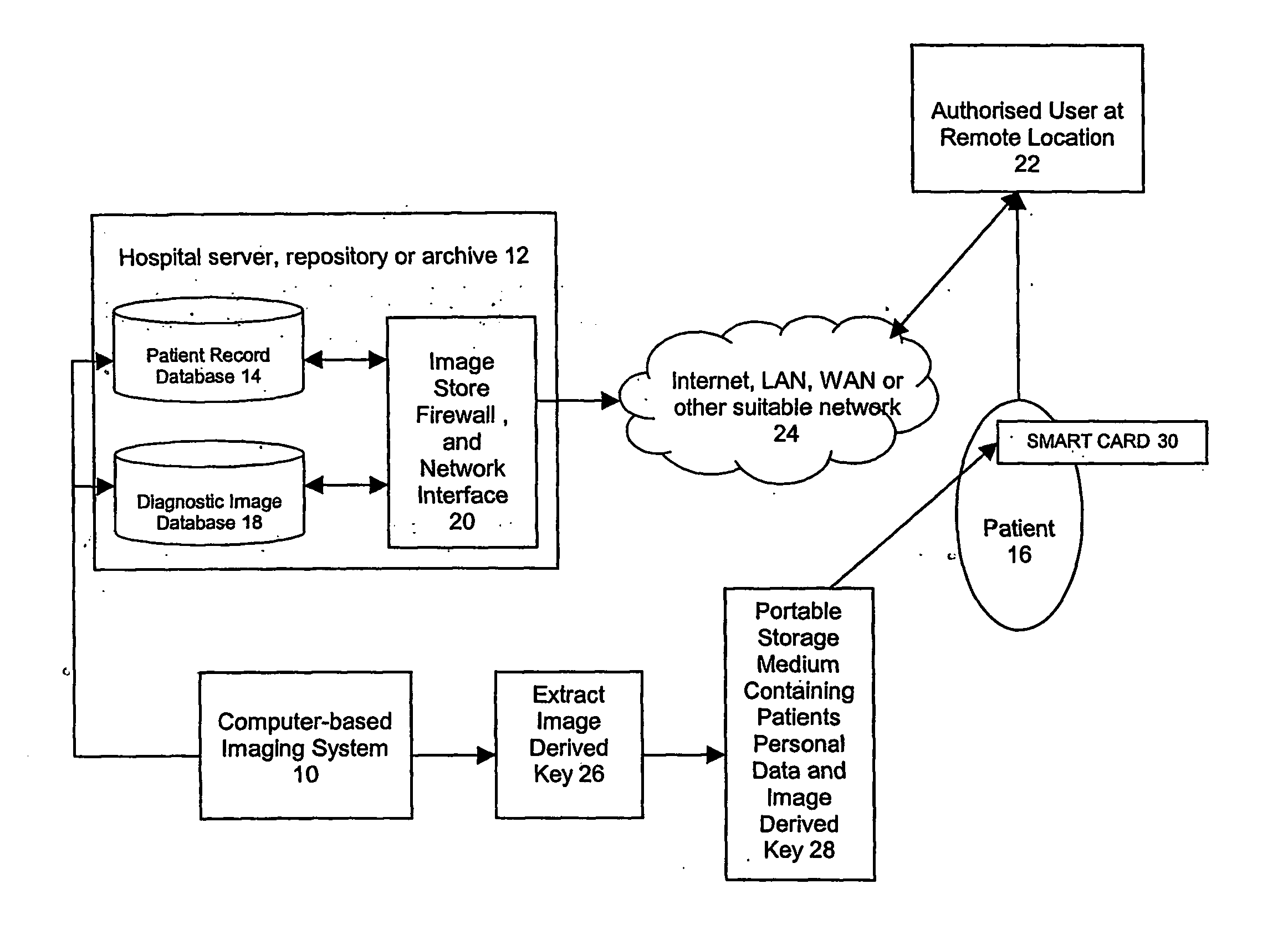
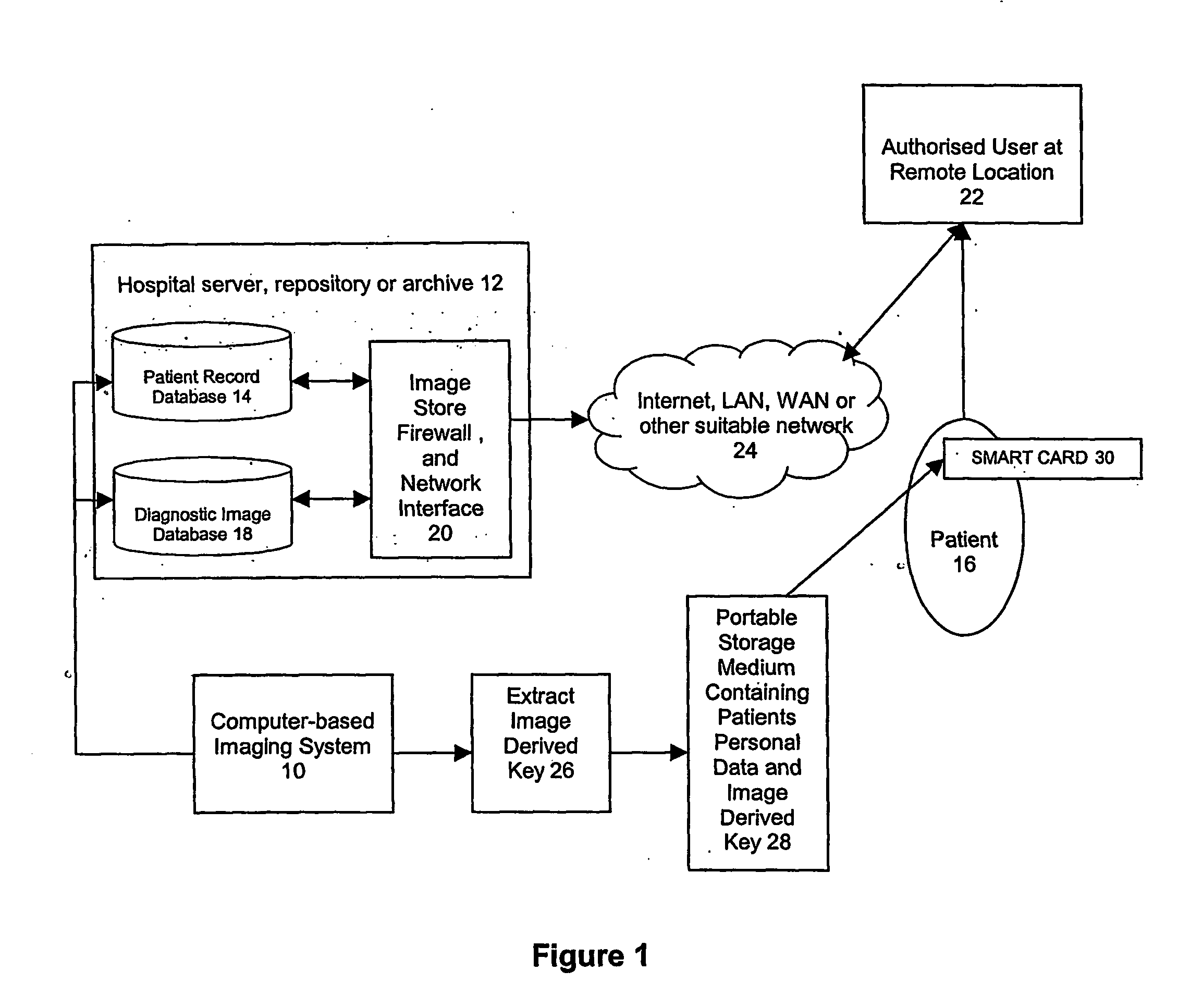
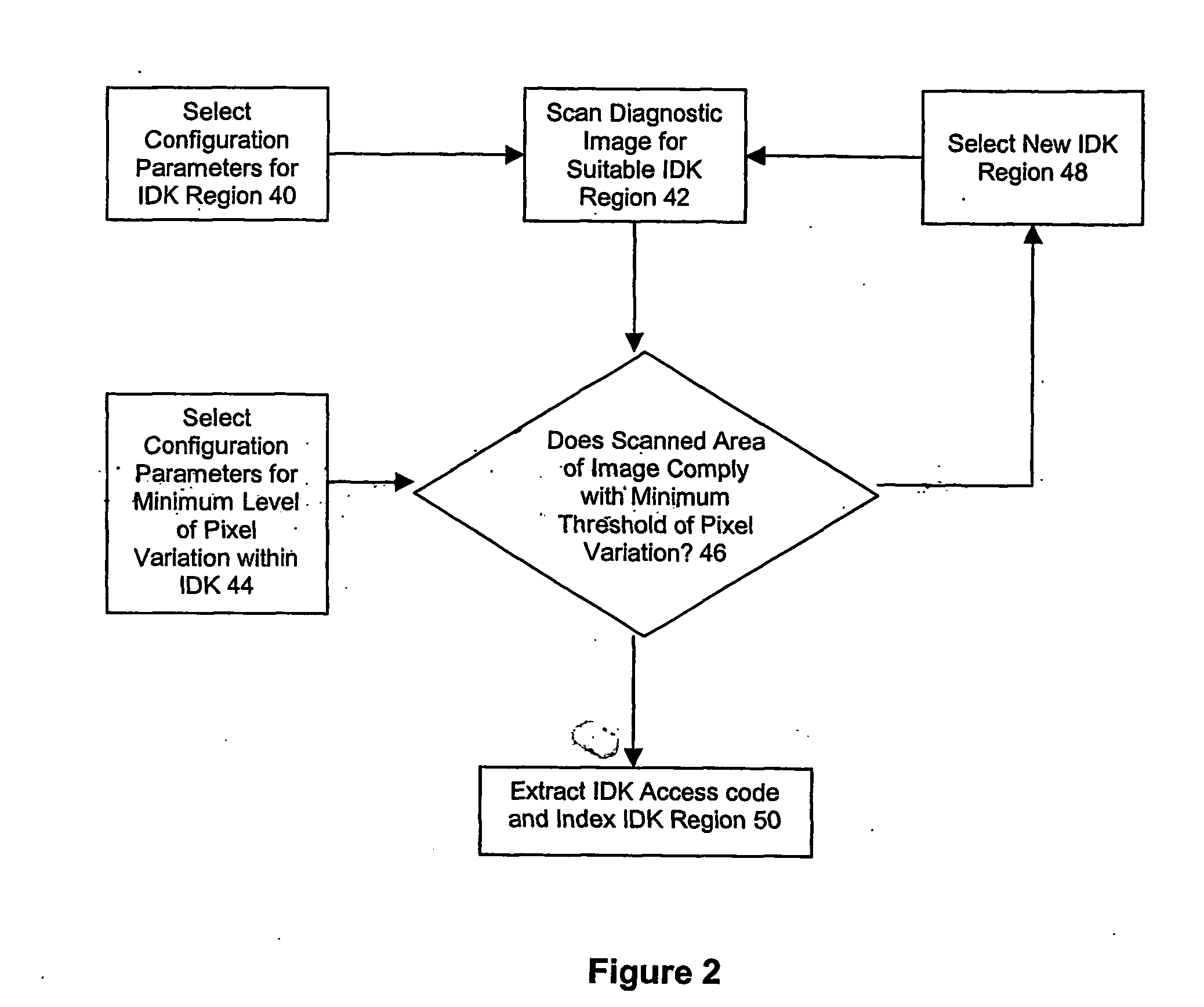
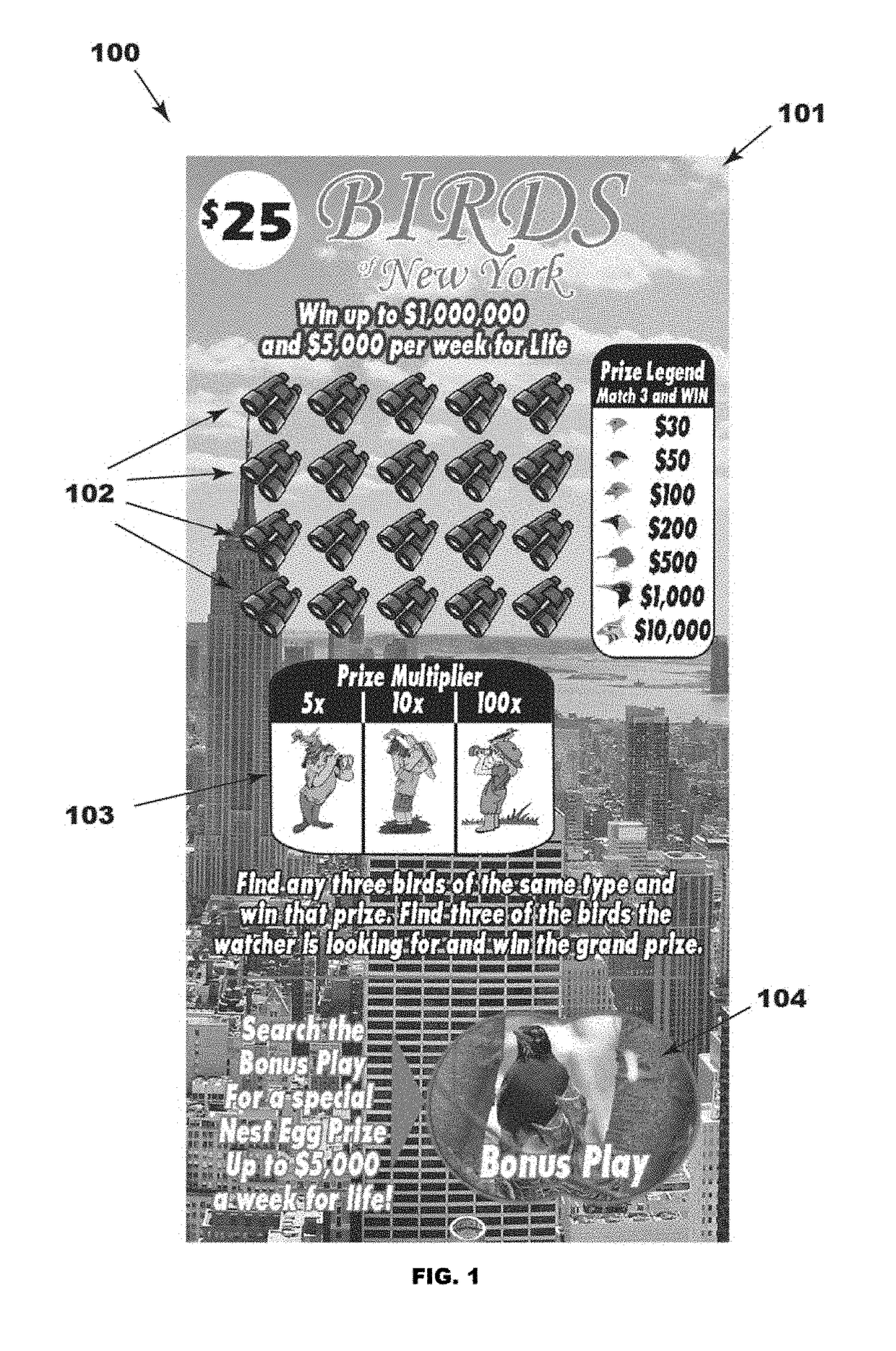
Diagnostic image security system
InactiveUS20070055538A1Data processing applicationsDigital data processing detailsComputer sciencePatient identification data
A method for restricting unauthorised access to a patient's diagnostic images. Patient identification data is stored in a first database and diagnostic images associated with the patient are stored in a remote second database. The patient is issued with an access code which is provided to a user who is authorised by the patient to access the patient's diagnostic image. Use of the access code permits an authorised user to match the patient identification data retrieved from the first database with the associated diagnostic image stored in the second database.
Owner:INTELLIRAD SOLUTIONS
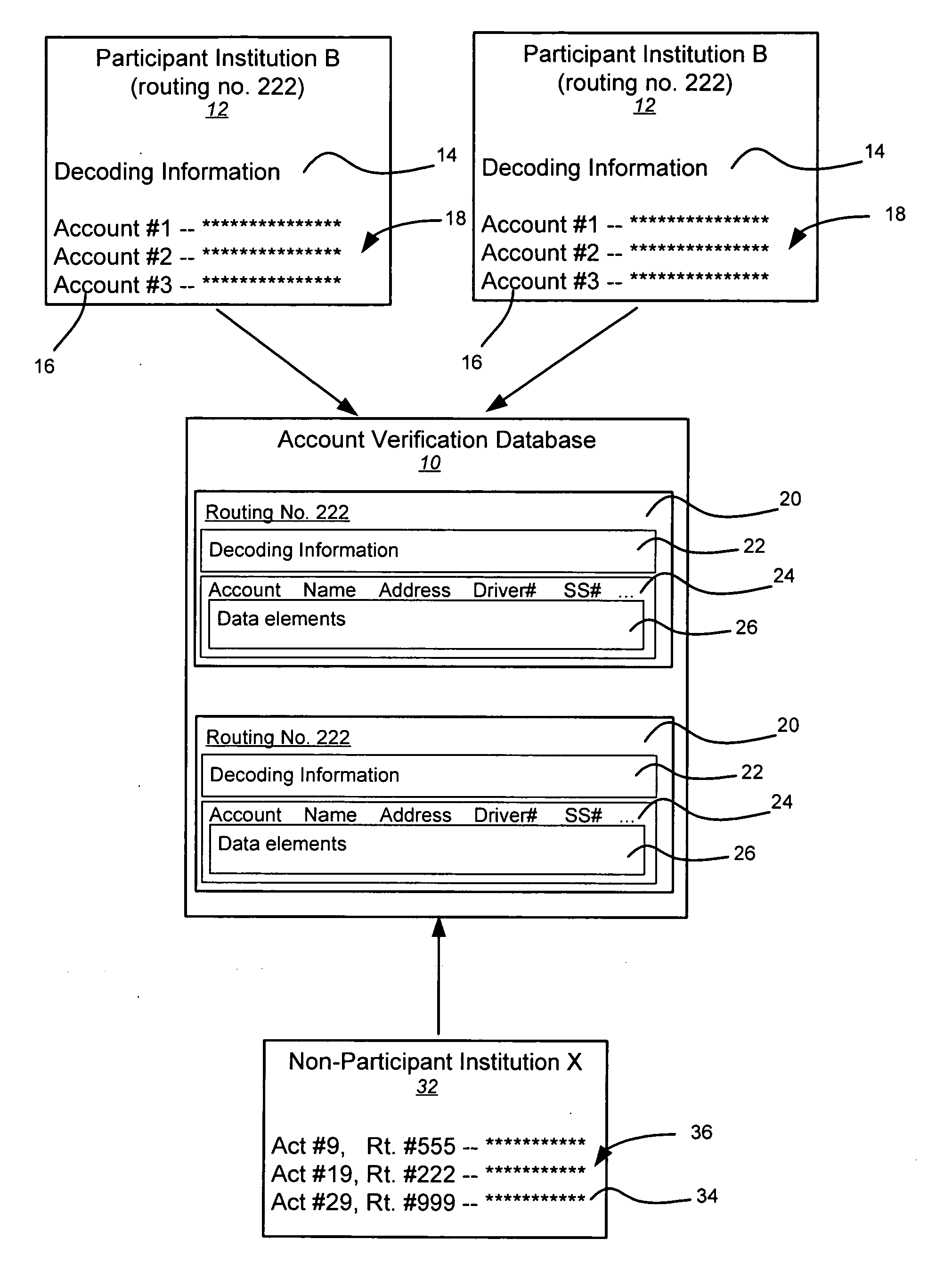
Negotiable instrument authentication systems and methods
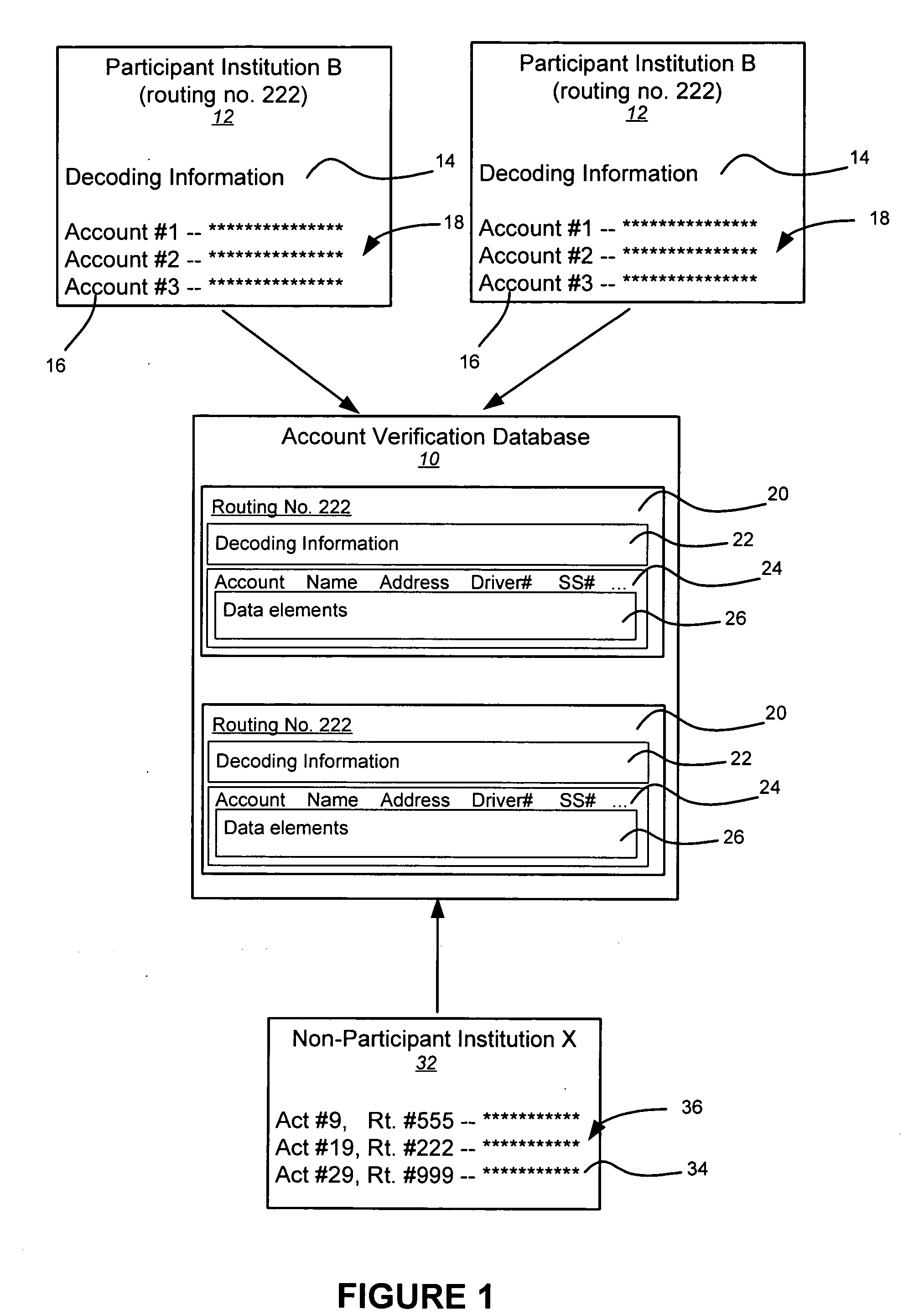
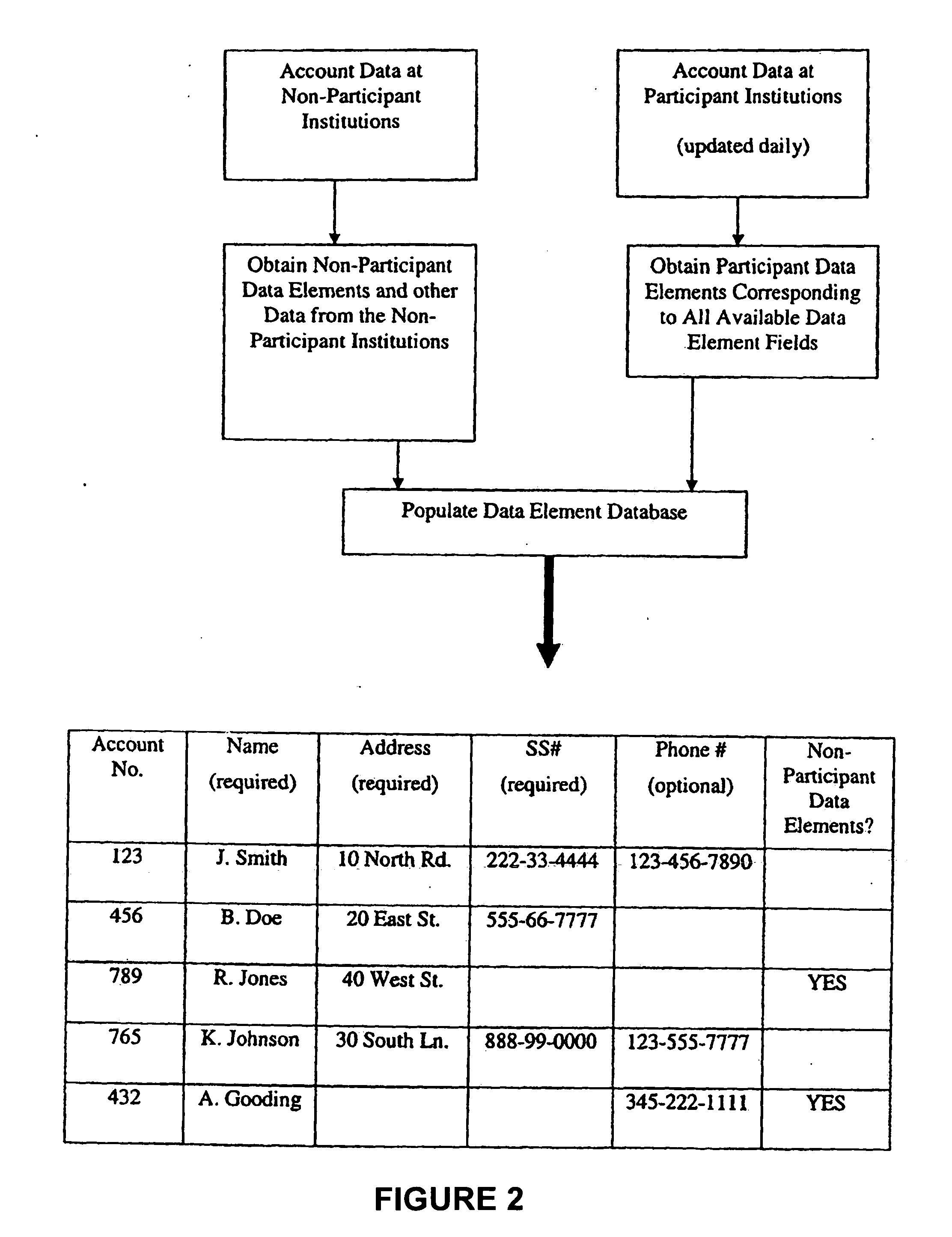
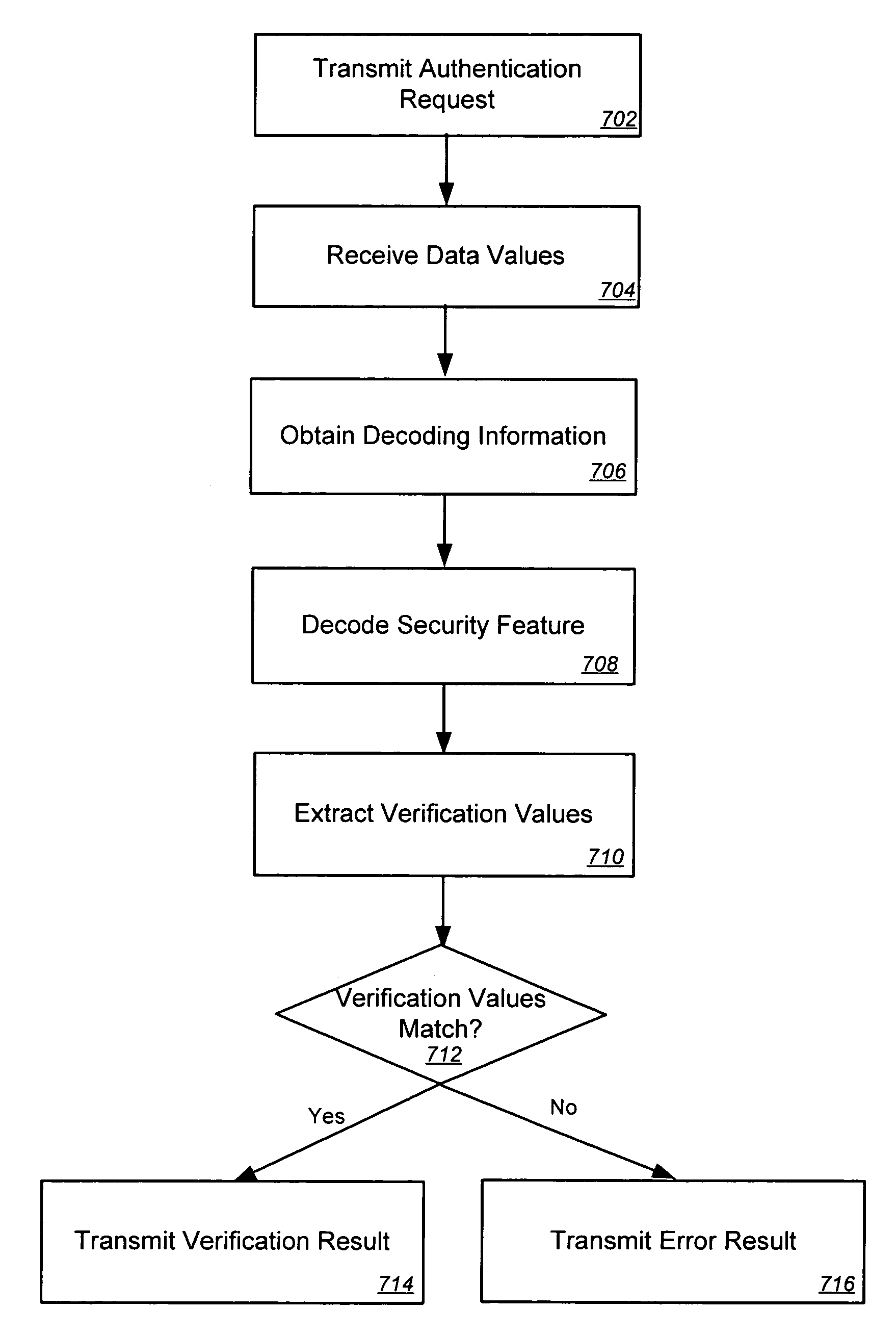
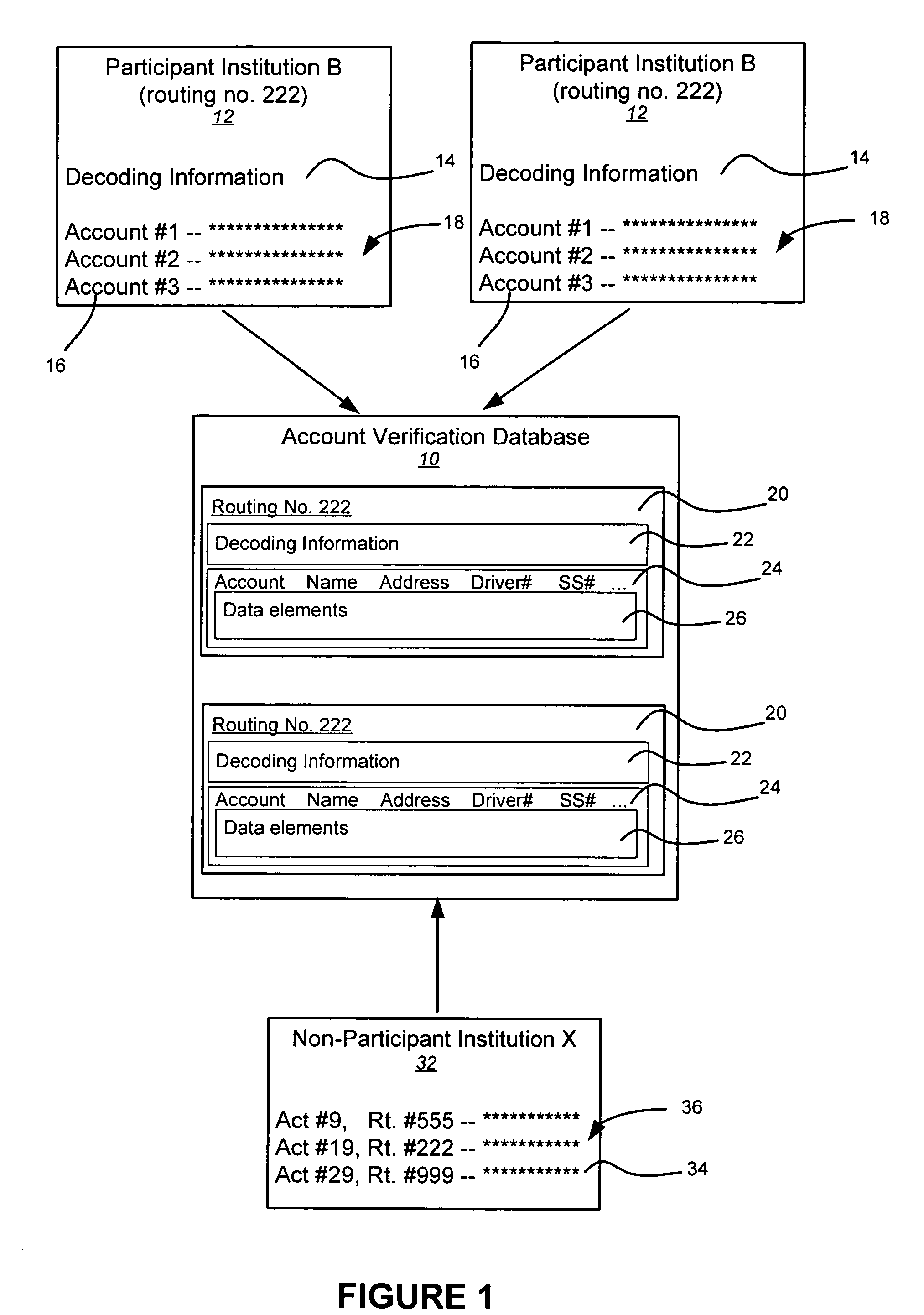
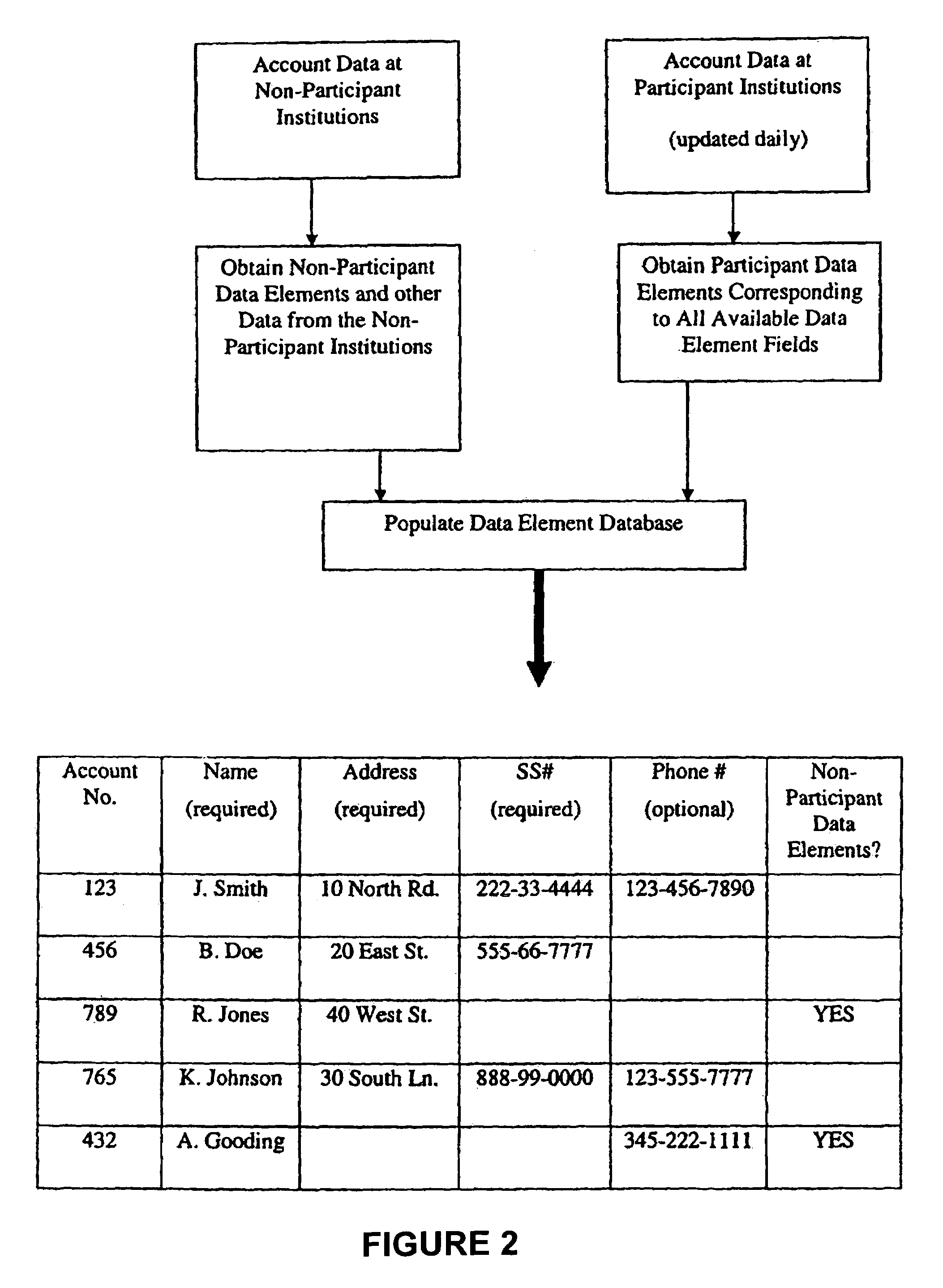
Systems, methods, and databases are disclosed for authenticating negotiable instruments. In one embodiment, the method comprises receiving, at an authentication system, a plurality of data values associated with a negotiable instrument, the plurality of data values including an image security feature and an account. The method further comprises obtaining account decoding information from an account verification databases, the account verification database including decoding information for each of a plurality of financial institutions; decoding the image security feature using the account decoding information; obtaining one or more verification values from the decoded image security feature; comparing each of the verification values to a corresponding one of the data values; and transmitting a result communication indicating a result of the comparison.
Owner:EARLY WARNING SERVICES
Methods and systems for use in security screening, with parallel processing capability
InactiveUS20090175411A1Increase probabilityCharacter and pattern recognitionMaterial analysis by transmitting radiationReference databaseEngineering
A security screening system to determine if an item of luggage carries an object posing a security threat. The security screening system may comprise an input for receiving image data derived from an apparatus that subjects the item of luggage to penetrating radiation, the image data conveying an image of the item of luggage. The security screening system may also comprise a processing module for processing the image data to identify in the image a plurality of regions of interest, the regions of interest manifesting a higher probability of depicting an object posing a security threat than portions of the image outside the regions of interest. The processing module may comprise: a first processing entity for processing a first one of the regions of interest to ascertain if the first region of interest depicts an object posing a security threat; and a second processing entity for processing a second one of the regions of interest to ascertain if the second region of interest depicts an object posing a security threat. The processing of the first and second regions of interest by the first and second processing entity occurs in parallel. Different processing entities may also be used to process in parallel different sets of entries a reference database to determine if an item of luggage carries an object posing a security threat.
Owner:OPTOSECURITY
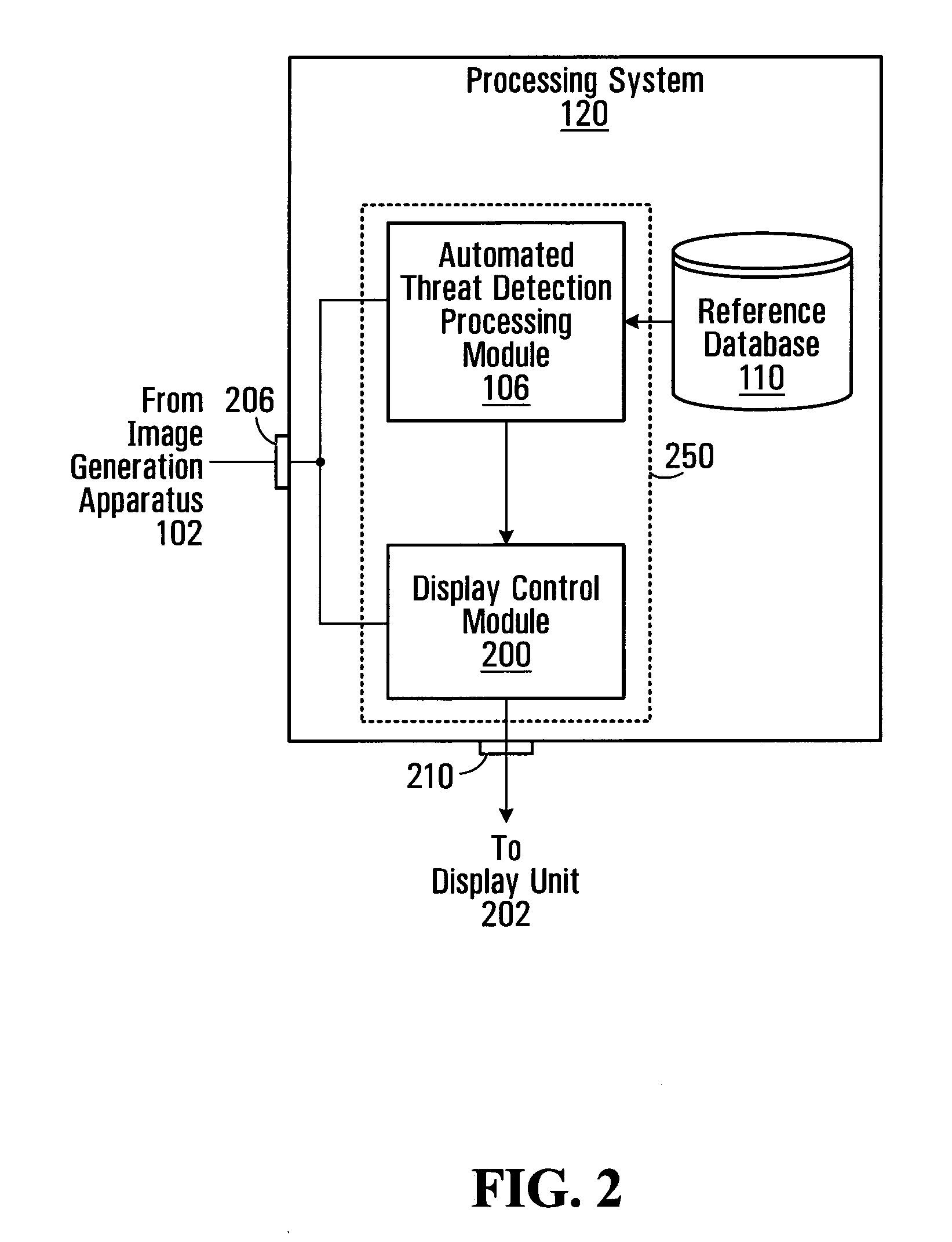
Method and system for online image security
InactiveUS20080209533A1Reduce storage costsSignificantDigital data processing detailsAnalogue secracy/subscription systemsWeb siteDigital image
An online application enables an end user to navigate to a web site, upload digital images, and to combine those images with words in a stylized template to create a user-generated story. A story is a web page, typically a collection of photos and words that are brought together by a stylized template that can be customized by the end user. Preferably, a given story is available from the site at a given location (at a URL) that may be private or public. A given story may be shared with other end users, published to other web sites or web logs, or maintained solely for one's own use. The invention also provides for multiple end users to collaborate to create a “shared” story.
Owner:HEWLETT PACKARD CO
Negotiable instrument authentication systems and methods
Systems, methods, and databases for authenticating negotiable instruments comprise receiving, at an authentication system, a plurality of data values associated with a negotiable instrument, the plurality of data values including an image security feature and an account. The method further comprises obtaining account decoding information from an account verification databases, the account verification database including decoding information for each of a plurality of financial institutions; decoding the image security feature using the account decoding information; obtaining one or more verification values from the decoded image security feature; comparing each of the verification values to a corresponding one of the data values; and transmitting a result communication indicating a result of the comparison.
Owner:EARLY WARNING SERVICES
Gateway-based audit log and method for prevention of data leakage
ActiveUS20150082460A1Avoid data breachesDigital data protectionInternal/peripheral component protectionSecure transmissionServer
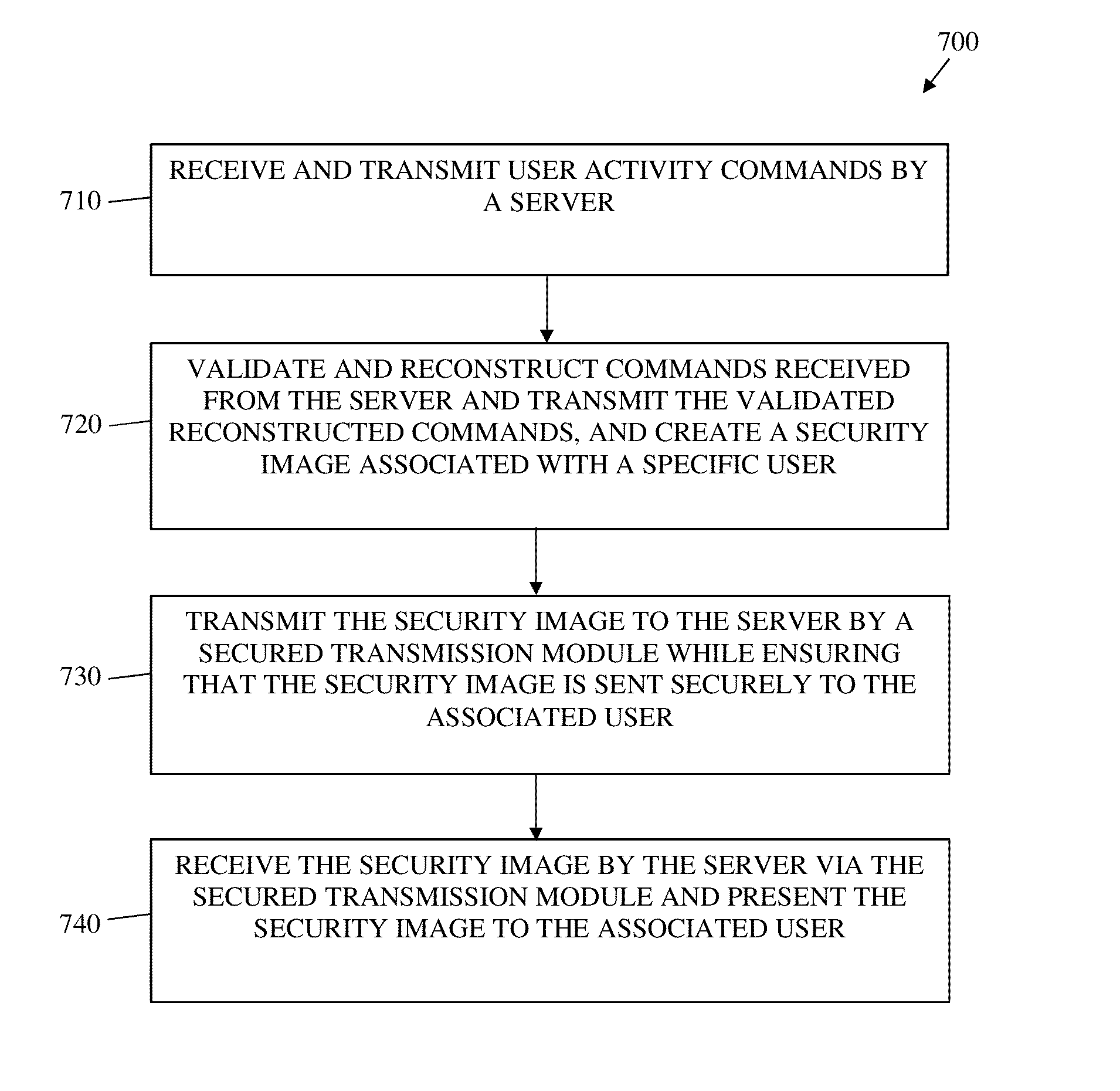
A system and method for prevention of data leakage, the system comprising: a server configured to receive and transmit user activity commands; a protection module configured to validate and reconstruct commands received from the server and to transmit the validated reconstructed commands, the protection module further configured to create a security image associated with a specific user; and a secured transmission module configured to transmit the security image to the server while ensuring that the security image is sent securely to the associated user, wherein the server is further configured to receive the security image via the secured transmission module and to present the security image to the associated user.
Owner:CA TECH INC
Passive millimeter wave imaging security inspection equipment
ActiveCN104076358ARealize detectionNo detectionGeological detection using milimetre wavesRadio wave reradiation/reflectionImaging qualityEngineering
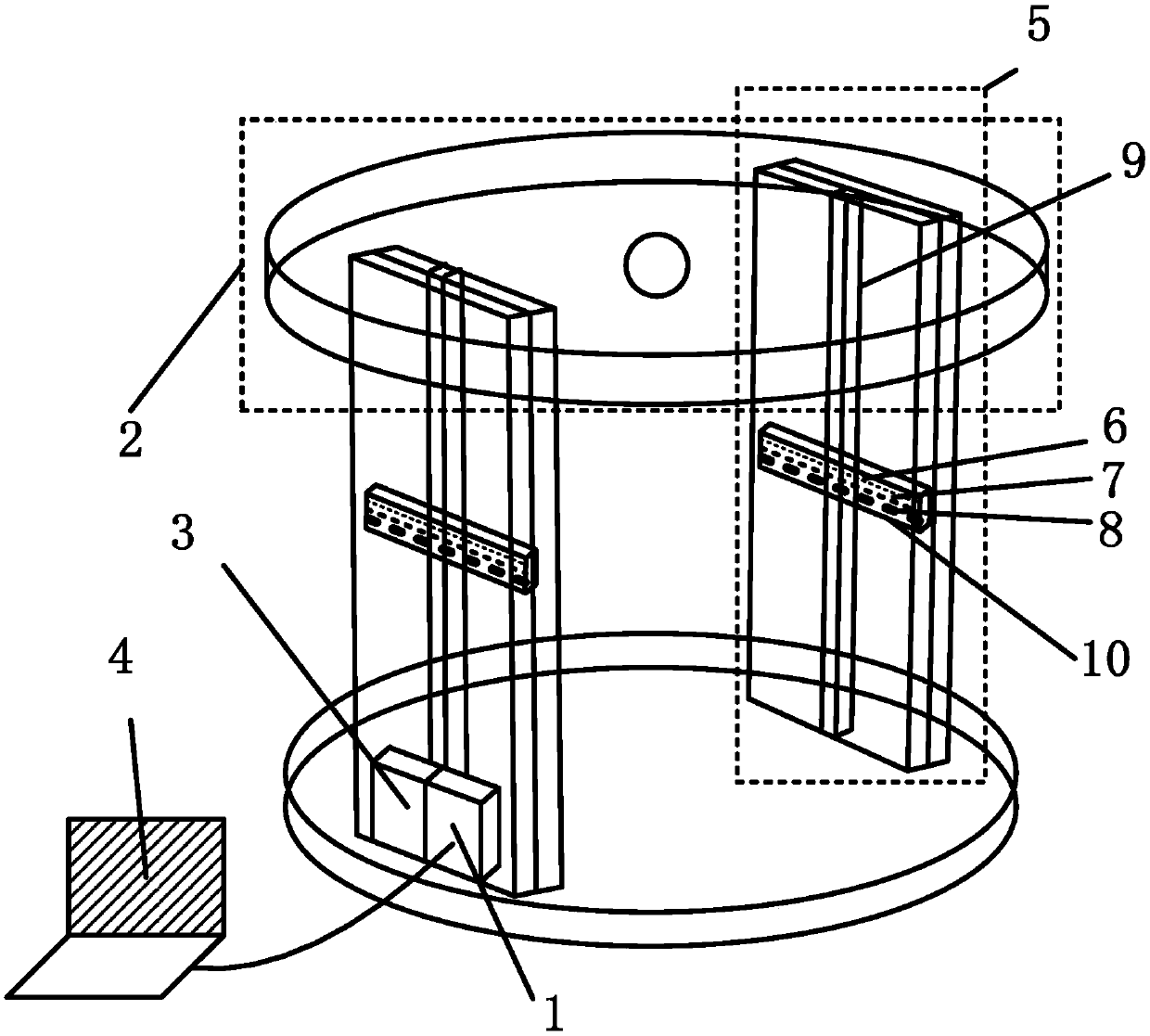
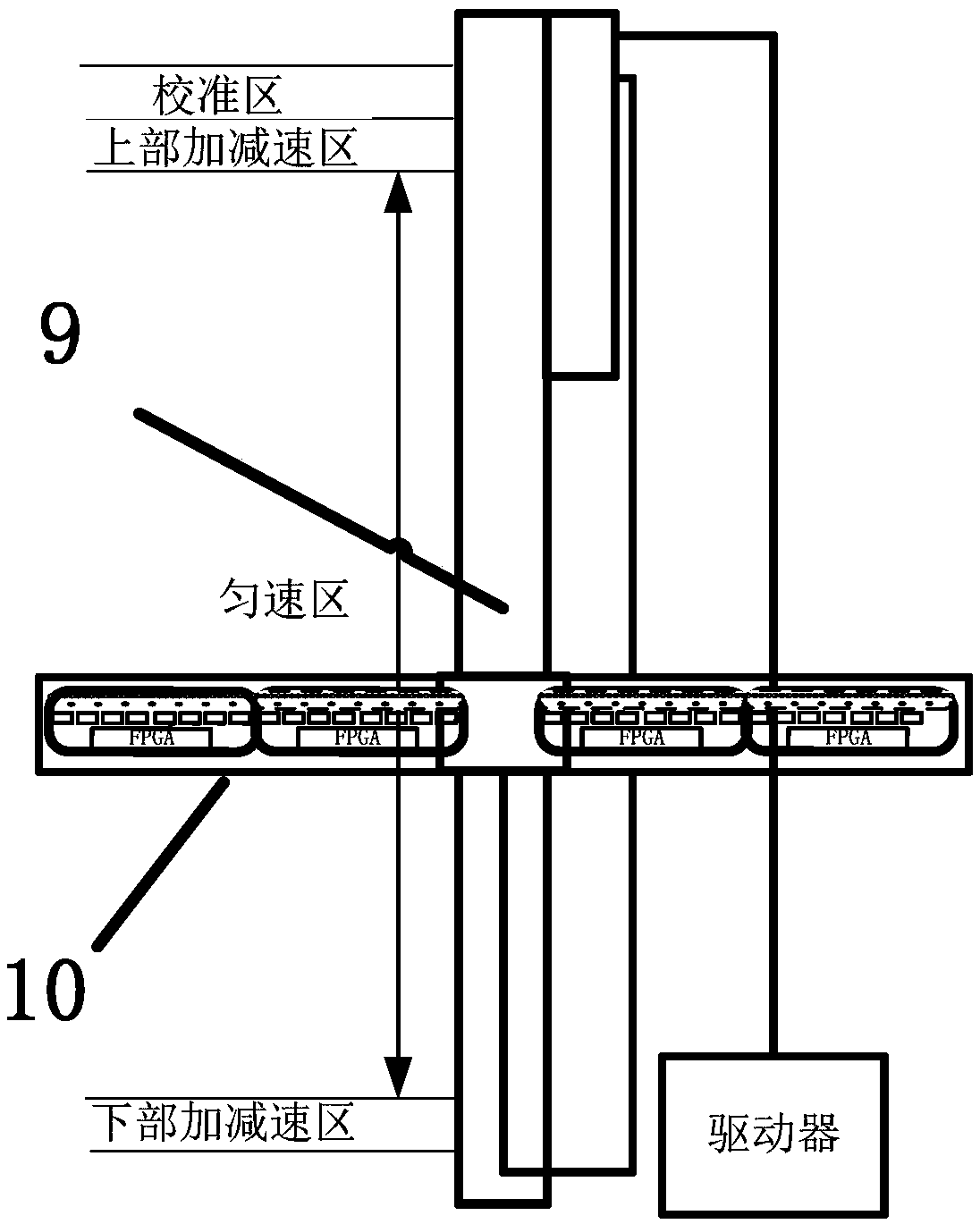
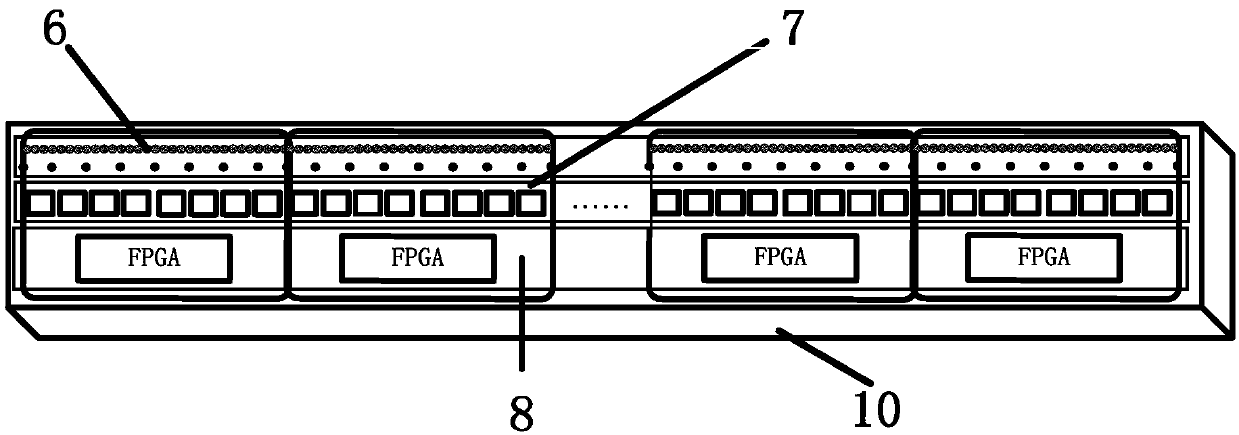
The invention discloses passive millimeter wave imaging security inspection equipment which comprises a one-dimensional focal plane array (1), a reflecting plate (3), a display control sub-system (4), a signal processor (5), an inner calibration combination (6), a reflecting plate rotating mechanism (7), a dielectric panel (8), a rack (9), a detecting table (11), an ellipsoid reflecting surface (2) and an outer calibration combination (10). The ellipsoid reflecting surface (2) focuses electromagnetic waves radiated by a human body, the one-dimensional focal plane array (1) converts the focused electromagnetic waves into voltage signals, the signal processor (5) collects the voltage signals and sends the voltage signals to the display control sub-system (4), and the display control sub-system (4) processes the voltage signals and then outputs two-dimensional grey-scale map. The inner calibration combination (6) and the outer calibration combination (10) are adopted for combined calibration, image quality can be improved, and metal and nonmetal forbidden objects can be detected. The passive millimeter wave imaging security inspection equipment has the advantages of being small in system loss, high in sensitivity and reliability, low in cost, light and the like.
Owner:BEIJING INST OF REMOTE SENSING EQUIP
Salient information guided image irregular mosaic splicing method
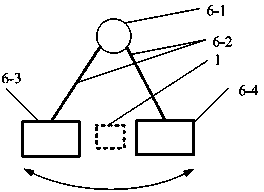
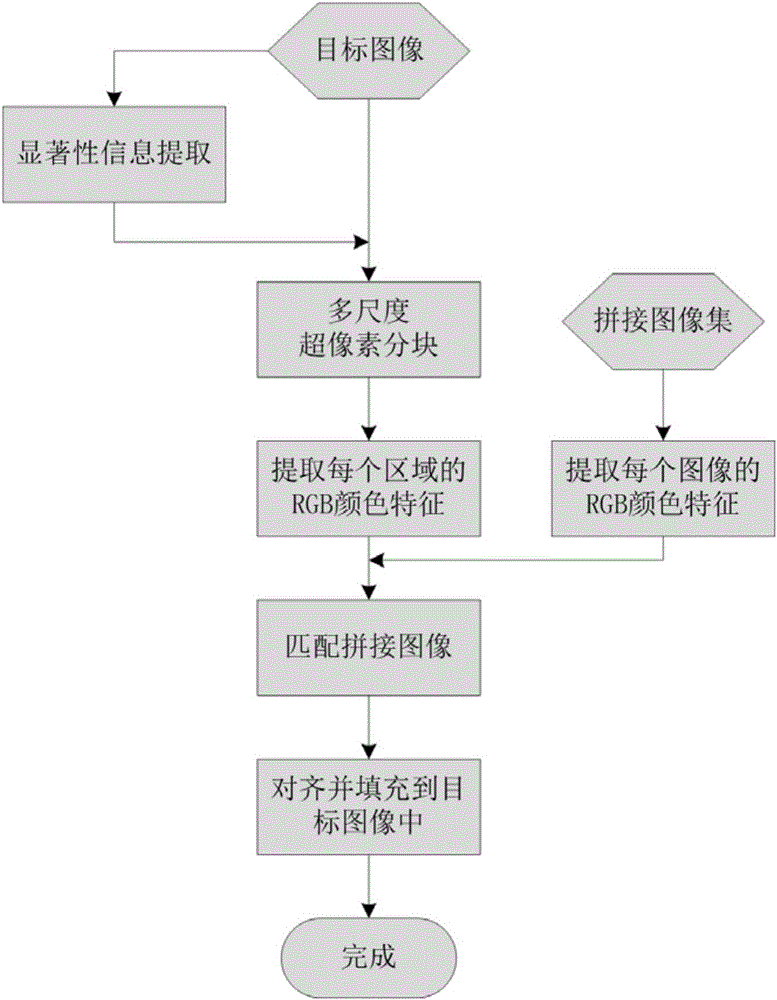
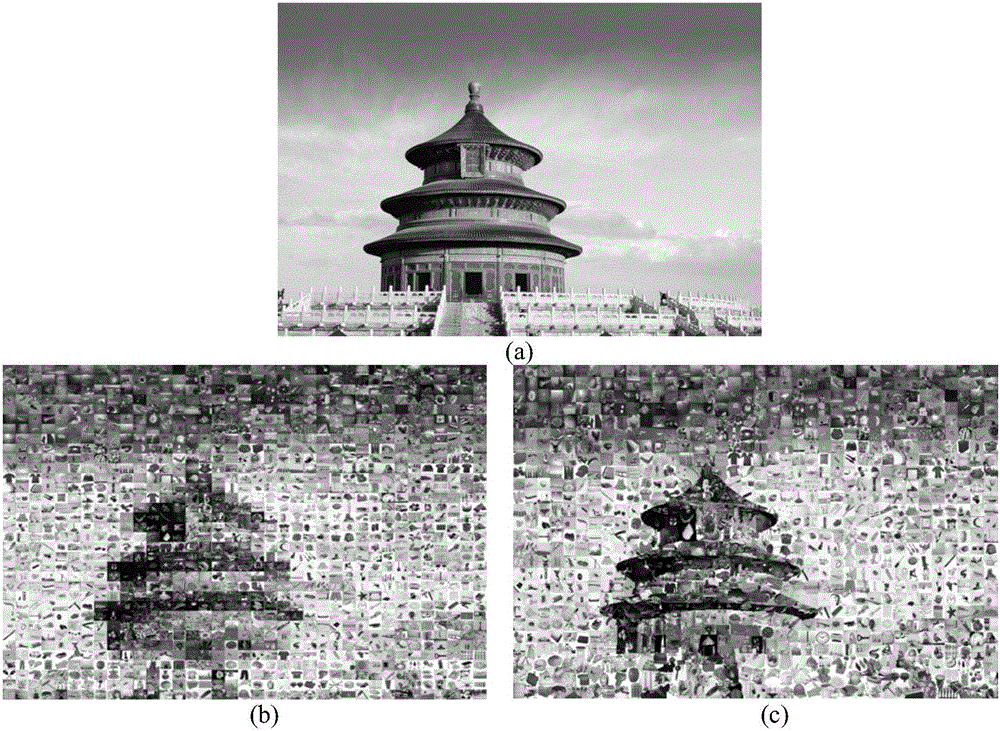
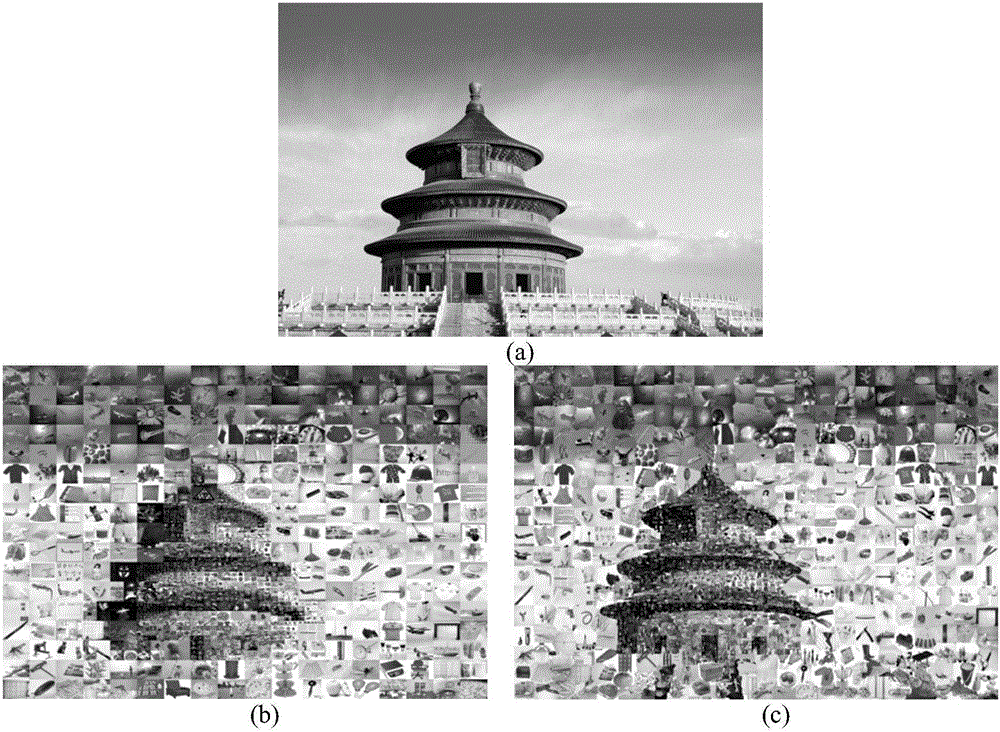
ActiveCN105931180ARealization reservationInhibition lossImage enhancementImage analysisInformation hidingComputer vision
The invention discloses a salient information guided image irregular mosaic splicing method. The main objective of the invention is to solve the problems of large number of jagged structures at the boundary of a target and the lack of detailed information in the prior art. The implementation process of the method includes the following steps that: 1, a target image is inputted, and the salient region of the image is extracted; 2, the target image is segmented into grid images with different densities according to saliency levels; 3, the color mean value characteristics of the images of a splicing image set and the grid regions of the target image are extracted; 4, splicing images of which the color characteristics are most similar to the color characteristics of the grid regions are selected for the grid regions; and 5, the width and height information of the grid regions are extracted, and corresponding splicing images are shrunk and expanded according to the width and height information of the grid regions, and the splicing images are aligned with the grid regions and are trimmed, and the trimmed splicing images are filled in corresponding grids, and mosaic filling of the whole image is completed. With the method of the invention adopted, the ornamental value of a mosaic spliced image can be kept, and the detailed information of the target image can be enhanced. The method of the invention can be applied to image transmission, image security, image information hiding and advertisement design.
Owner:XIDIAN UNIV
Dotted line composite scanning backscattered and stereo transmission imaging device
InactiveCN101655465AQuality improvementMaterial analysis by transmitting radiationImaging qualityTransmission channel
The invention relates to a dotted line composite scanning backscattered and stereo transmission imaging device, belonging to the technical field of radiation imaging security detection equipment. In the device, a dotted line composite scanning generator is sheathed on a radiation source or at the front of the radiation source; a rear or front slit collimator collimates a ray emitted by the dottedline composite scanning generator in a sector scanning surface; the rear or front slit collimator and a backscattered detector are arranged at one side of the radiation source of an detected object, and a line array transmission detector is arranged at the other side thereof; a backscattered channel synchronous switch and a backscattered signal processor are connected between the backscattered detector and an image computer; and a transmission channel synchronous switch and a transmission signal processor are connected between the line array transmission detector and the image computer. In theimaging device, only one radiation source and one scanning generator and primary detection are adopted to obtain a backscattered image and a fine transmission image for highlighting lightweight objects, wherein, the transmission image with fine image quality can be also a stereo image.
Owner:北京睿思厚德辐射信息科技开发有限公司
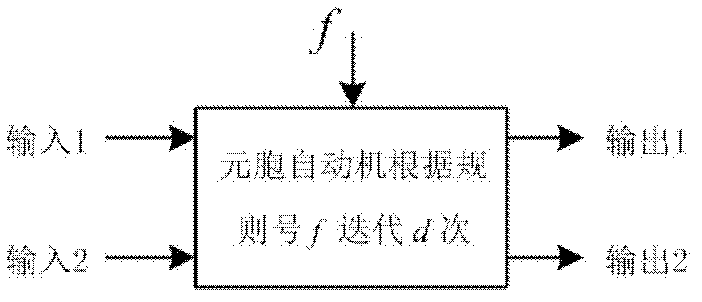
Method for encrypting and decrypting image based on cellular automata
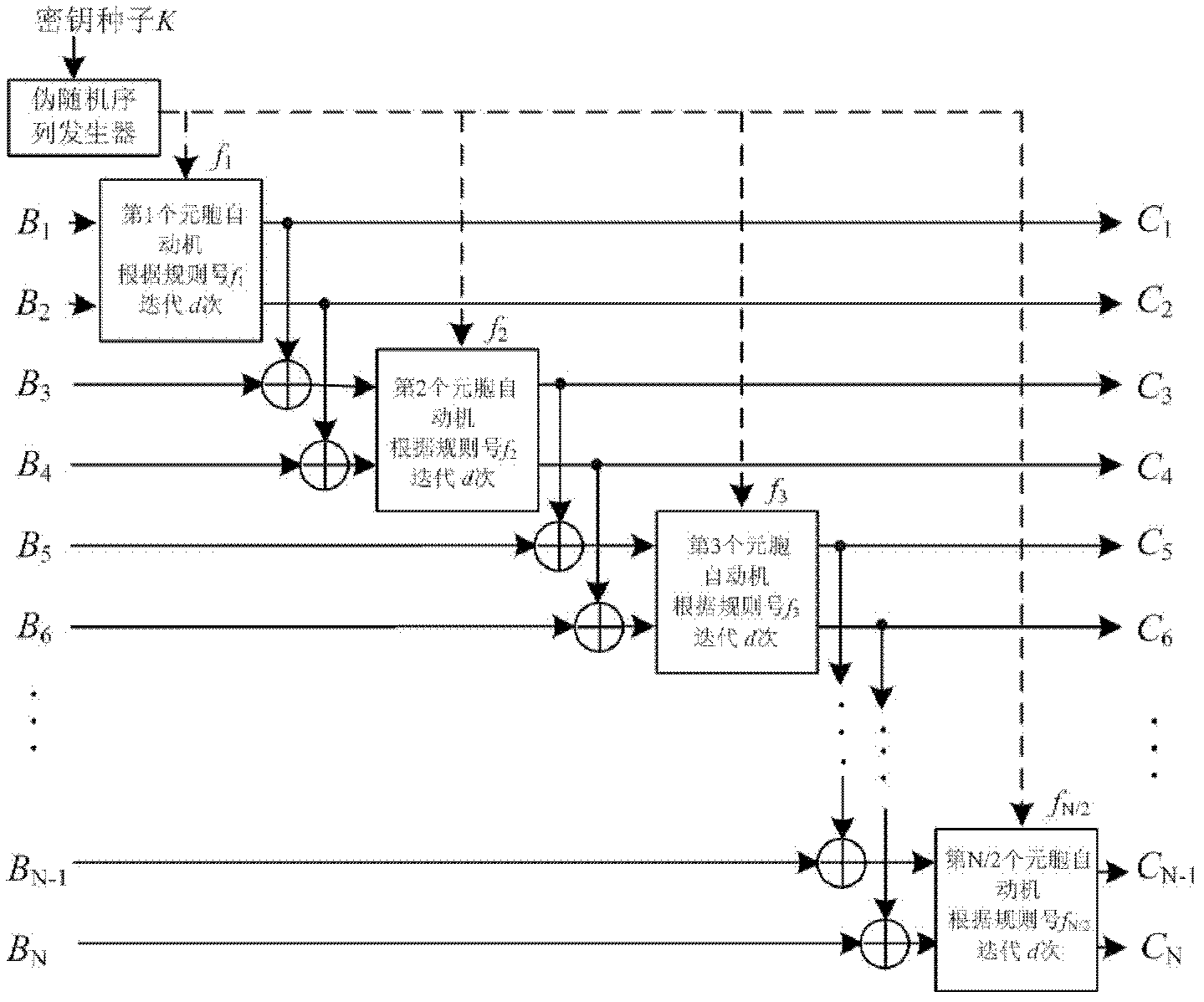
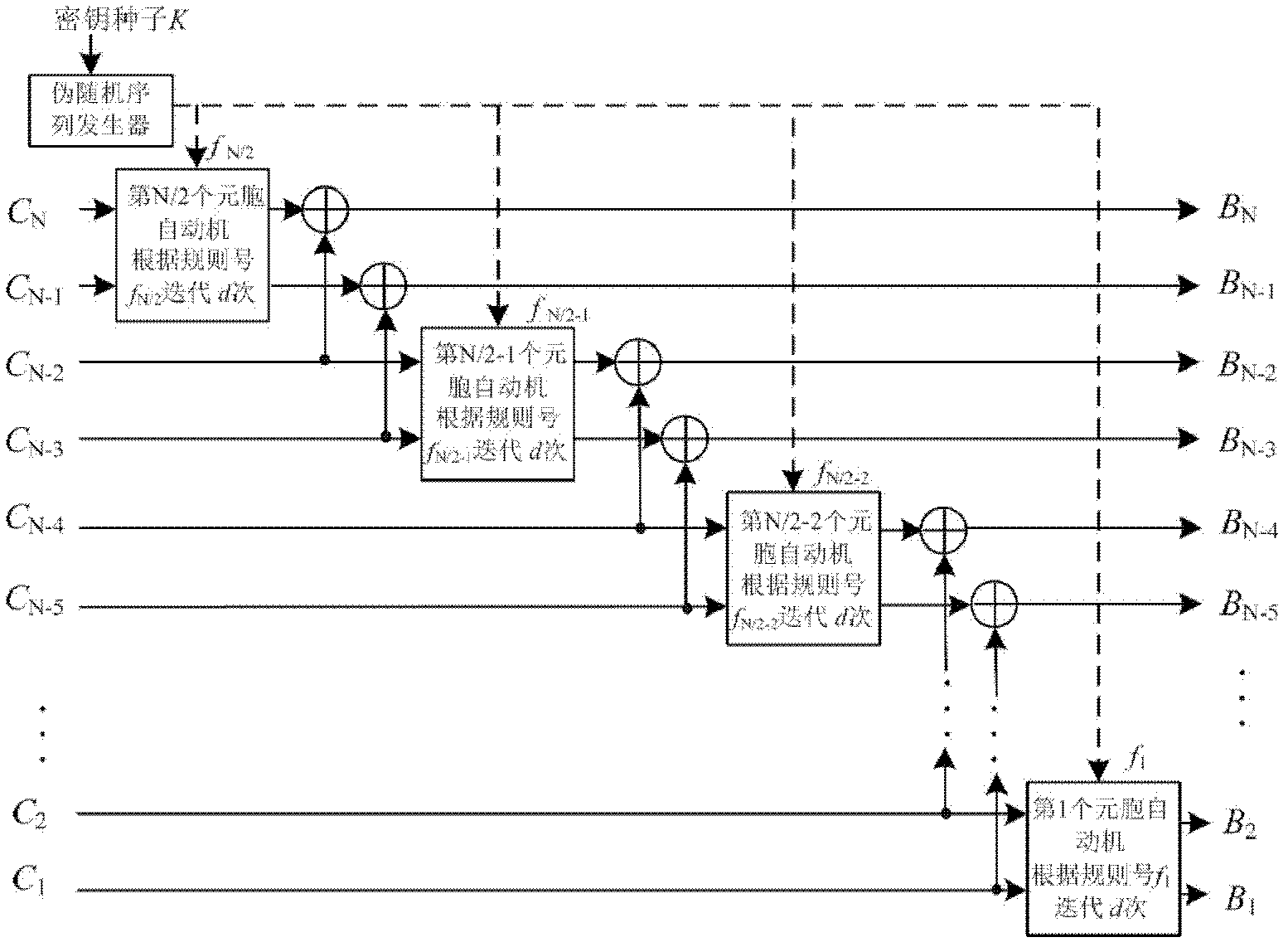
InactiveCN102523365AAvoid rounding errorsGood global diffusion performancePictoral communicationPlaintextPattern recognition
The invention provides a method for encrypting and decrypting an image based on cellular automata, and belongs to an image security technology in the field of information security. The encryption method comprises the following steps of: extracting a pixel matrix of a plaintext image, and converting each line of the pixel matrix into a binary sequence; and performing two round chain cycle iterations on each line of the image by using a plurality of cellular automata, and converting iteration results into corresponding pixel matrixes to obtain a ciphertext image. In each iteration process, iteration frequency is set in advance, and a rule number used in each iteration process is generated by a pseudorandom sequence generator. The decryption process is an inverse process of encryption, and the using sequence of a rule number is reverse to the sequence of the rule number in an encryption process. The method has the advantages that a complex and unpredictable relationship among a plaintext, a secret key and a ciphertext is generated by using the chain cycle iterations of the cellular automata, the image security is ensured in a network transmission process, and the method has certain fault-tolerant capability.
Owner:HOHAI UNIV
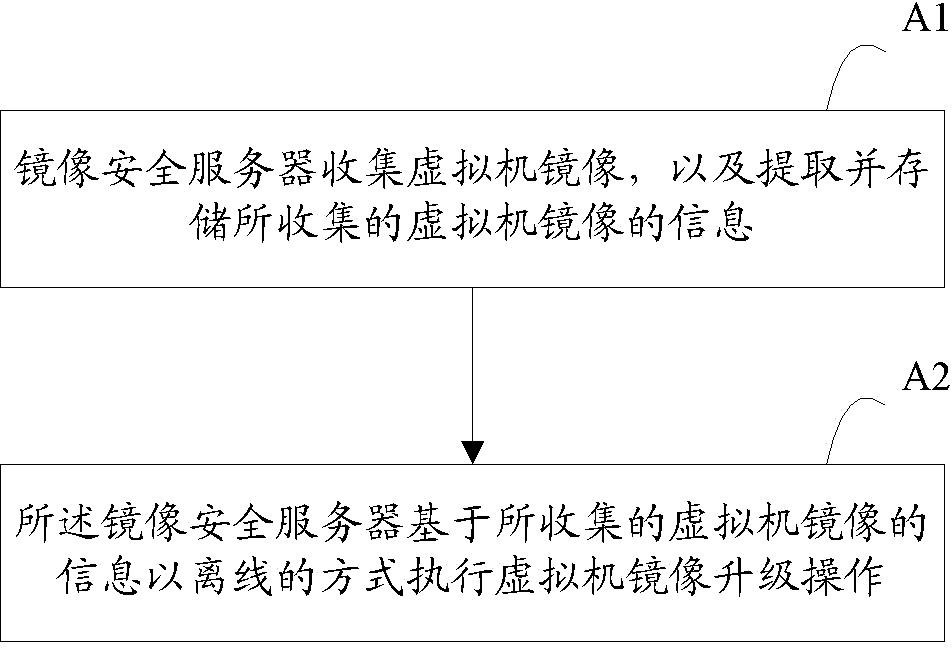
Off-line upgrading method of virtual machine image
ActiveCN104679527AImprove the efficiency of upgrade operationsQuick searchProgram loading/initiatingTransmissionImage securityVirtual machine
A method for offline updating virtual machine images is provided. The method comprises: an image security server collecting virtual machine image, extracting and storing information of the collected virtual machine image; and the image security server updating operation of the virtual machine image in offline mode based on the information of the collected virtual machine image. The method for offline updating virtual machine image disclosed in the present invention is more effective and is capable of updating virtual machine image in offline mode.
Owner:CHINA UNIONPAY
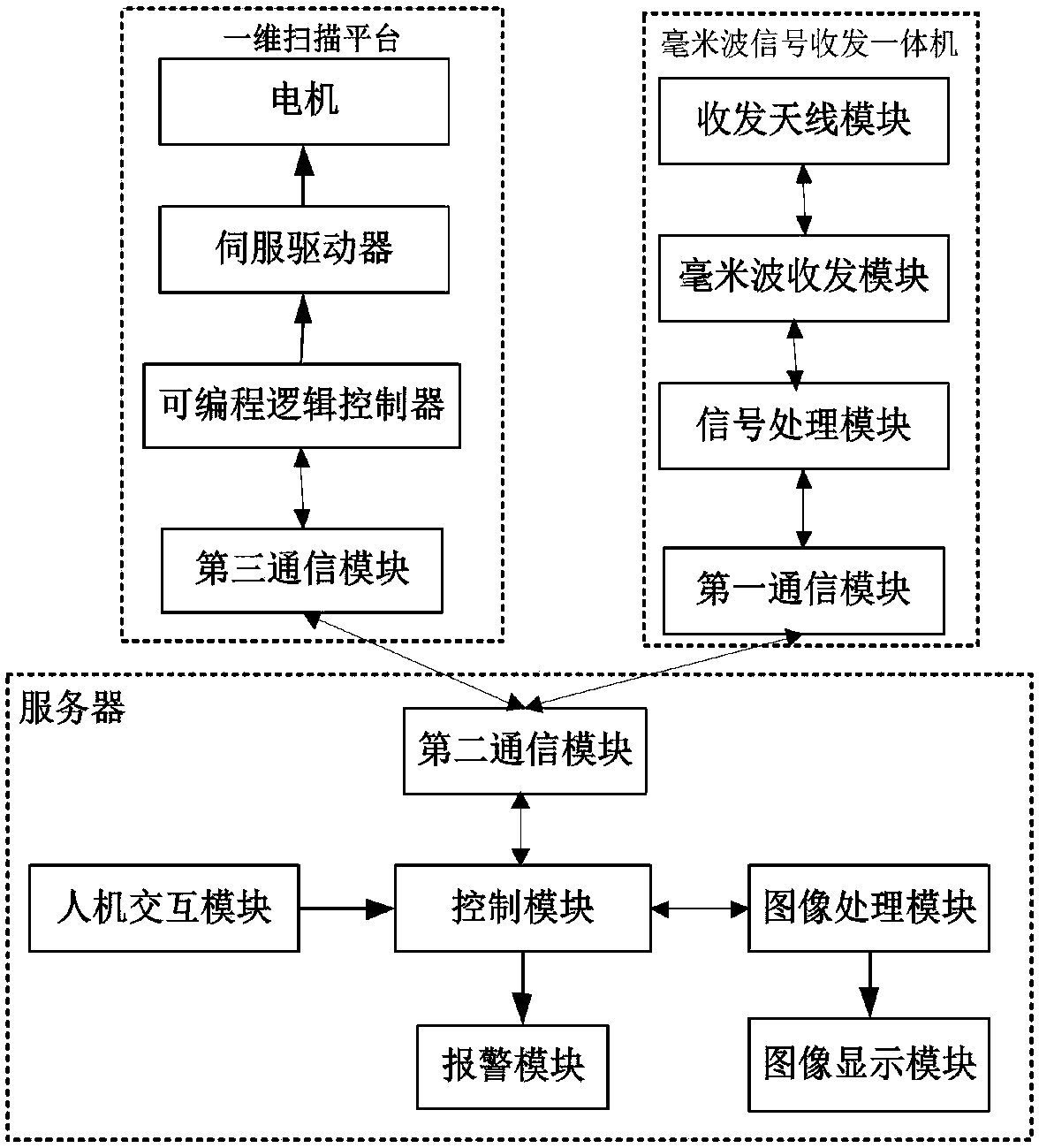
Active millimeter wave imaging security detection system and security detection method
PendingCN108152821AImprove imaging resolutionImprove imaging scan speedRadio wave reradiation/reflectionRadarImage resolution
The invention provides an active millimeter wave imaging security detection system and a security detection method. The security detection system comprises a millimeter wave signal receiving-transmitting integrated machine for generating and sending a millimeter wave signal needed by a detected object and receiving and processing an echo signal returned by the detected object, and a one-dimensional scanning platform for installing and driving the millimeter wave signal receiving-transmitting integrated machine to be moved along a Z-axis direction. The active millimeter wave imaging security detection system uses a synthetic aperture radar imaging principle, the front and back faces of the detected object are rapidly imaged, the imaging resolution ratio is high, and the great convenience isprovided to the detected object and a security person. The detected object only needs to stand in a security detector for 2 seconds, and the security person only needs to detect a suspicious object according to a suspicious object identification result displayed by an image display module, so a problem that the security person uses a security detection device to be backwards and forwards moved ona body of the detected object so as to produce the inconvenience can be solved.
Owner:CHENGDU PHASE LOCK ELECTRONICS TECH
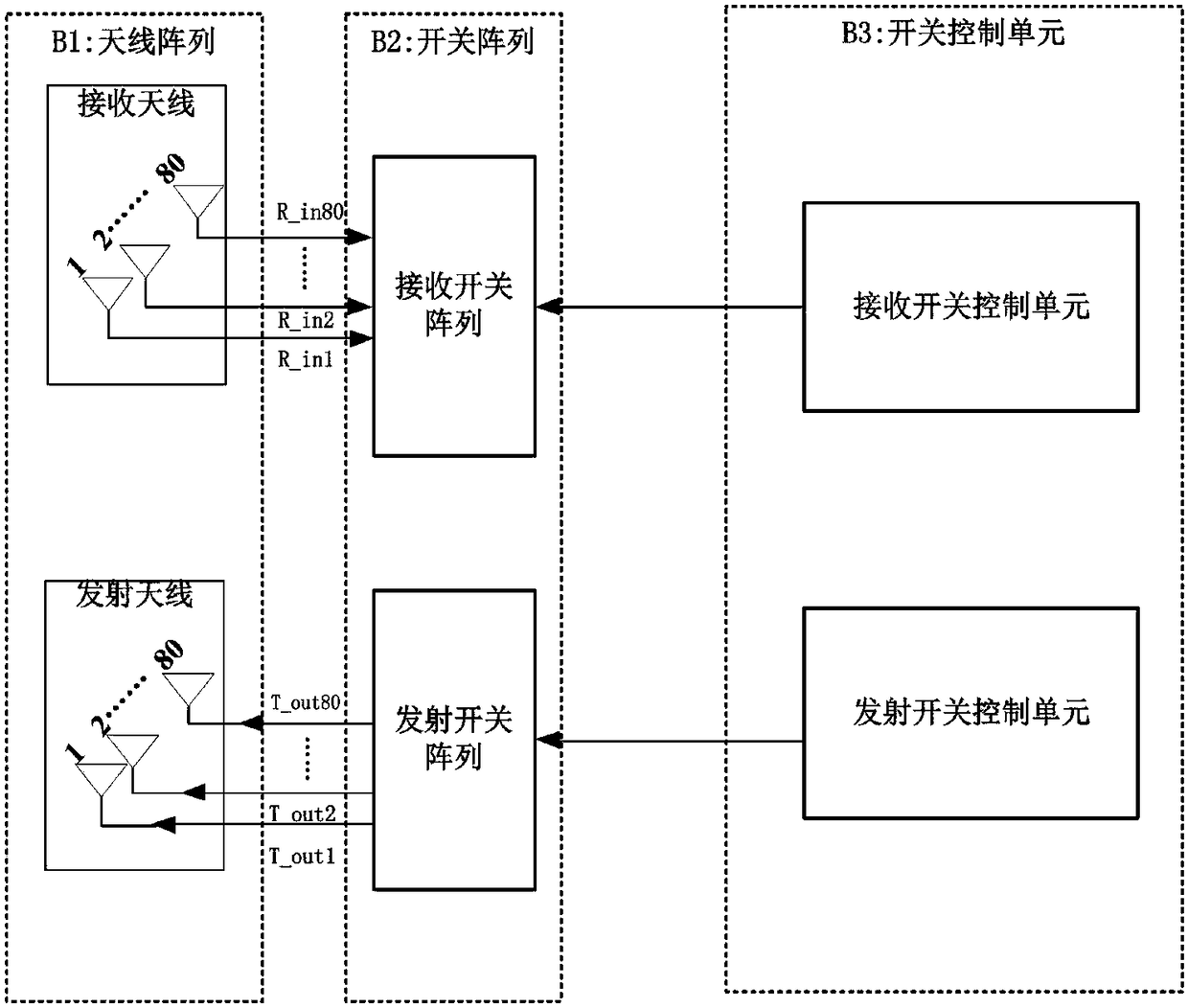
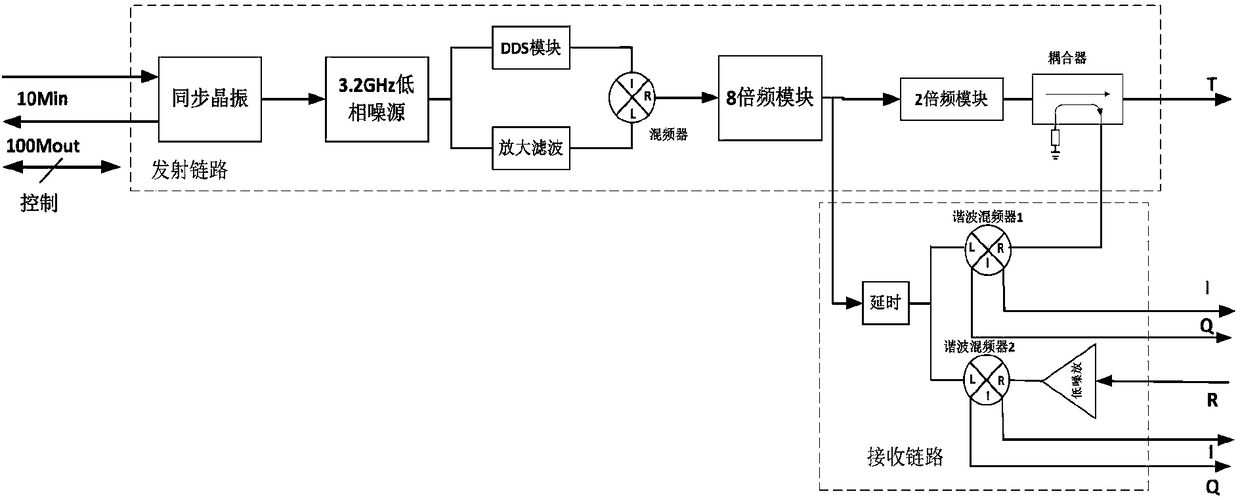
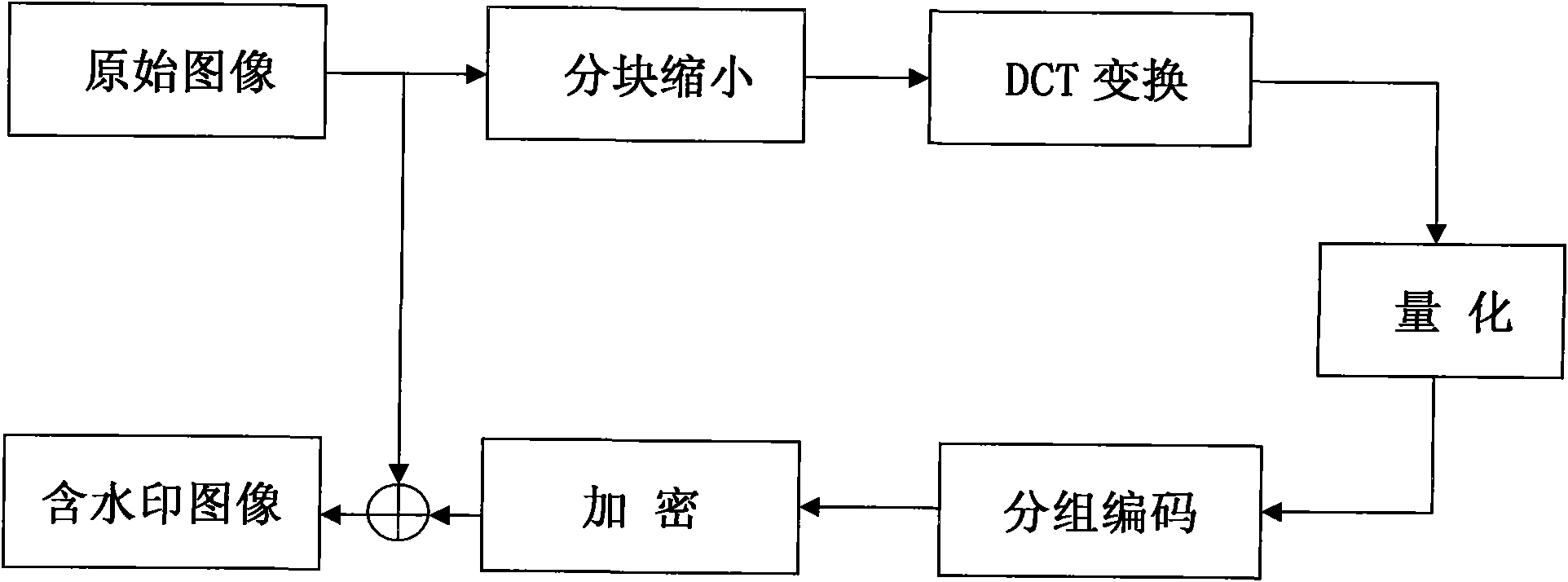
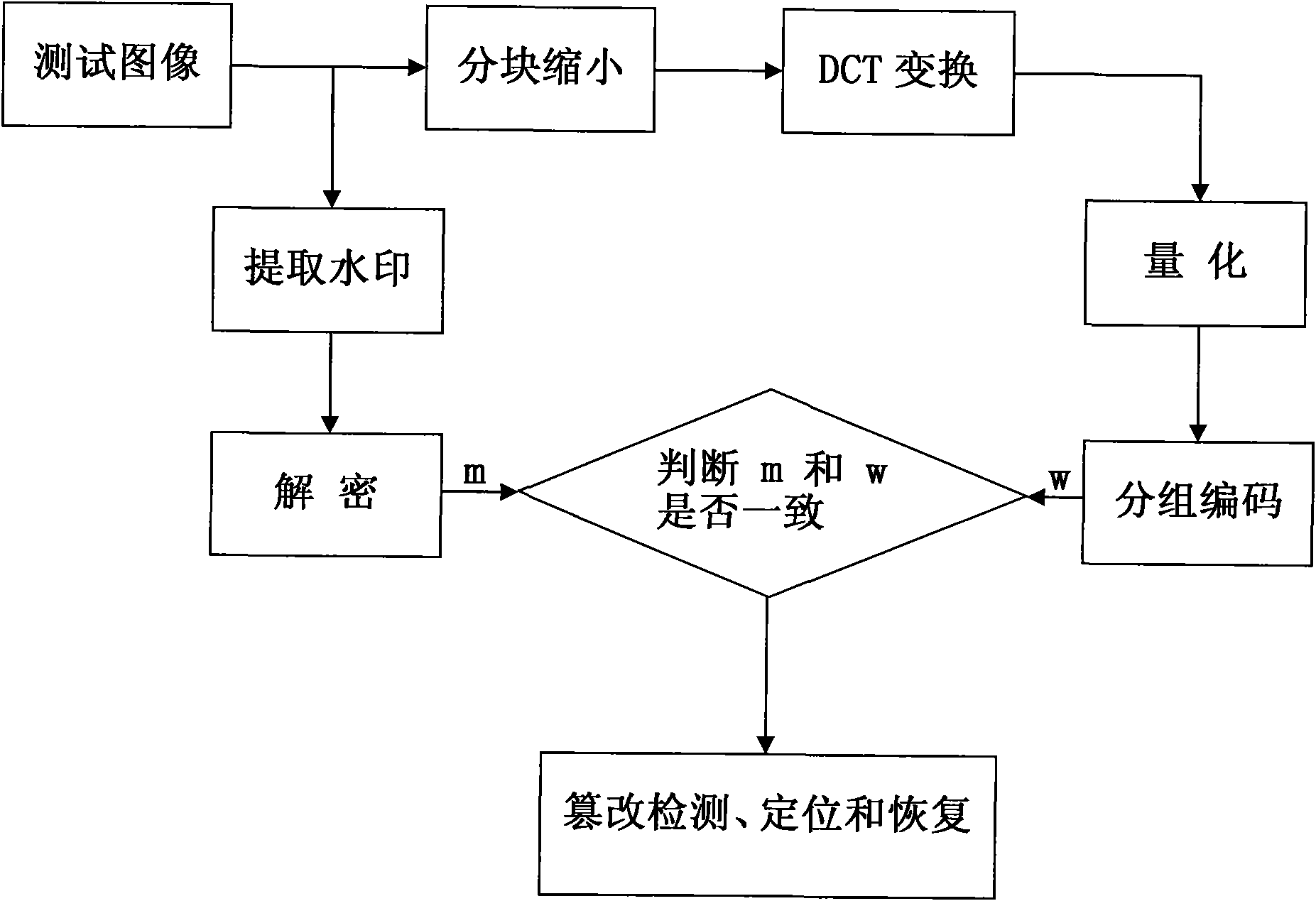
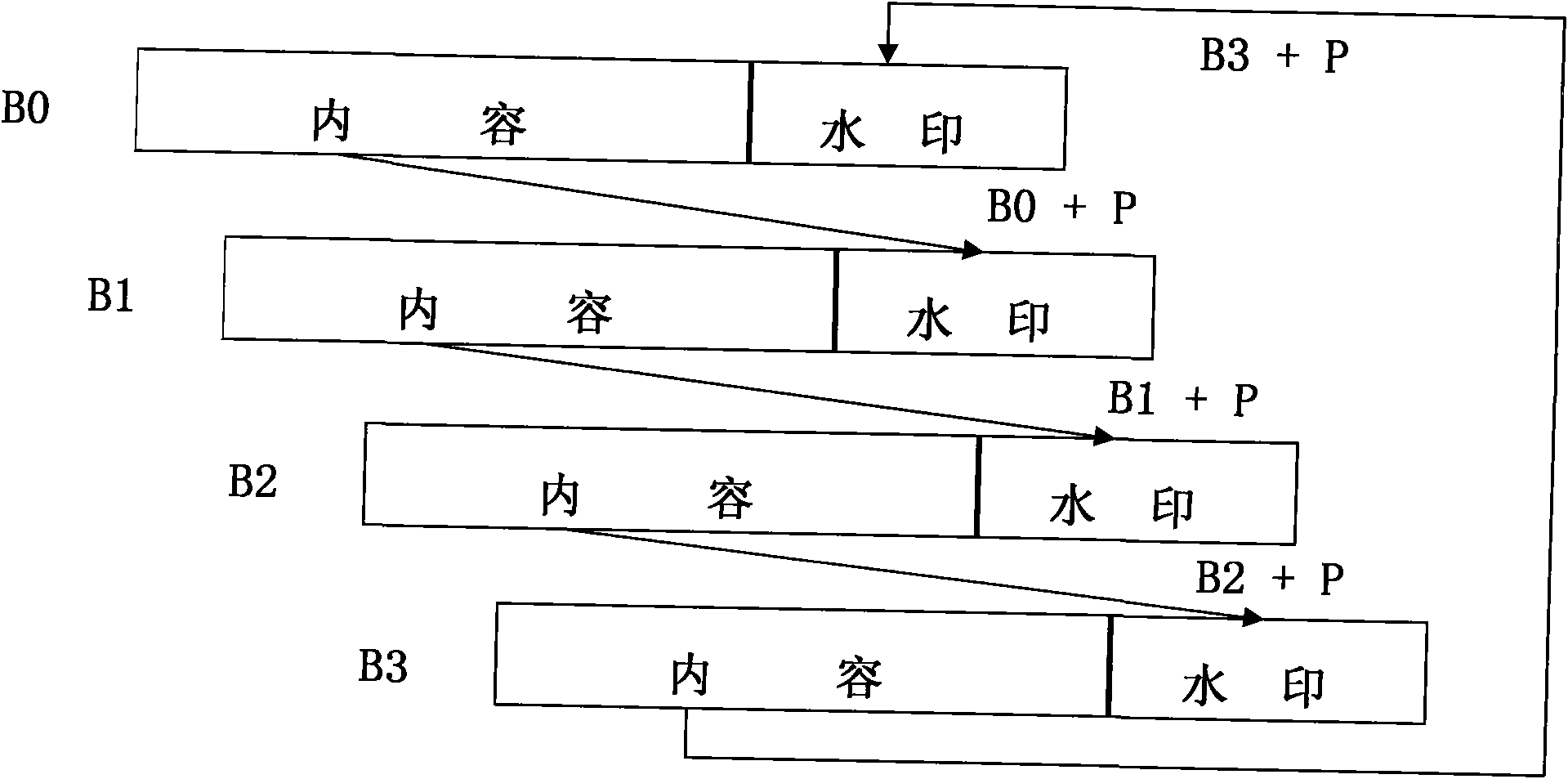
Generating and authenticating method of self-embedded digital watermark of JPEG (Joint Photographic Experts Group) image
InactiveCN101835049APrecise positioningTelevision systemsDigital video signal modificationJPEGBitmap
The invention relates to the technical field of image security certification and discloses a generating and authenticating method of a self-embedded digital watermark of a JPEG (Joint Photographic Experts Group) image. The method comprises the following steps of: reducing a protected JPEG image by 1 / 4; coding the image by applying a fixed length block encoding method; and embedding a code as a watermark onto a DCT (Digital Component Technology) coefficient low frequency component of the protected image. If hostile attacks such as tampering, replacing, and the like are carried out on the JPEG image containing the watermark, a tampered area can be precisely determined by comparing an extracted watermark with the image containing the watermark, the tampered area can be approximately restored, and the restored image is 1 / 4 of the original image. The invention achieves a better coding effect on the basis of analyzing the JPEG parametric statistic characteristics, a limited bitmap matrix is not needed, and any quality factor can be used for quantization.
Owner:SHANGHAI NORMAL UNIVERSITY
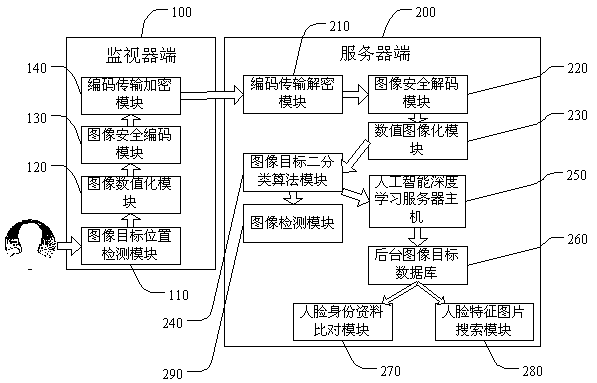
Artificial intelligence image recognition attack defense system
ActiveCN108491785AImprove securityAvoid obfuscation attacksEncryption apparatus with shift registers/memoriesClosed circuit television systemsPattern recognitionGraphics
The invention discloses an artificial intelligence image recognition attack defense system, which comprises a monitor terminal and a server terminal, wherein the monitor terminal and the server terminal are in communication connection; the monitor terminal comprises an image target position detection module, an image numeralization module, an image security coding module and a coding transmissionencryption module; the server terminal comprises a coding transmission decryption module, an image security decoding module, a numeric visualization module, an image target two-category algorithm module, an artificial intelligence depth learning server host and a background image target database. Intelligent human face recognition is carried out through the artificial intelligence image recognition attack defense system, artificial intelligence image recognition confusion attacks can be avoided, the authenticity of the image target can be quickly judged, and the human face recognition securityis improved.
Owner:网御安全技术(深圳)有限公司
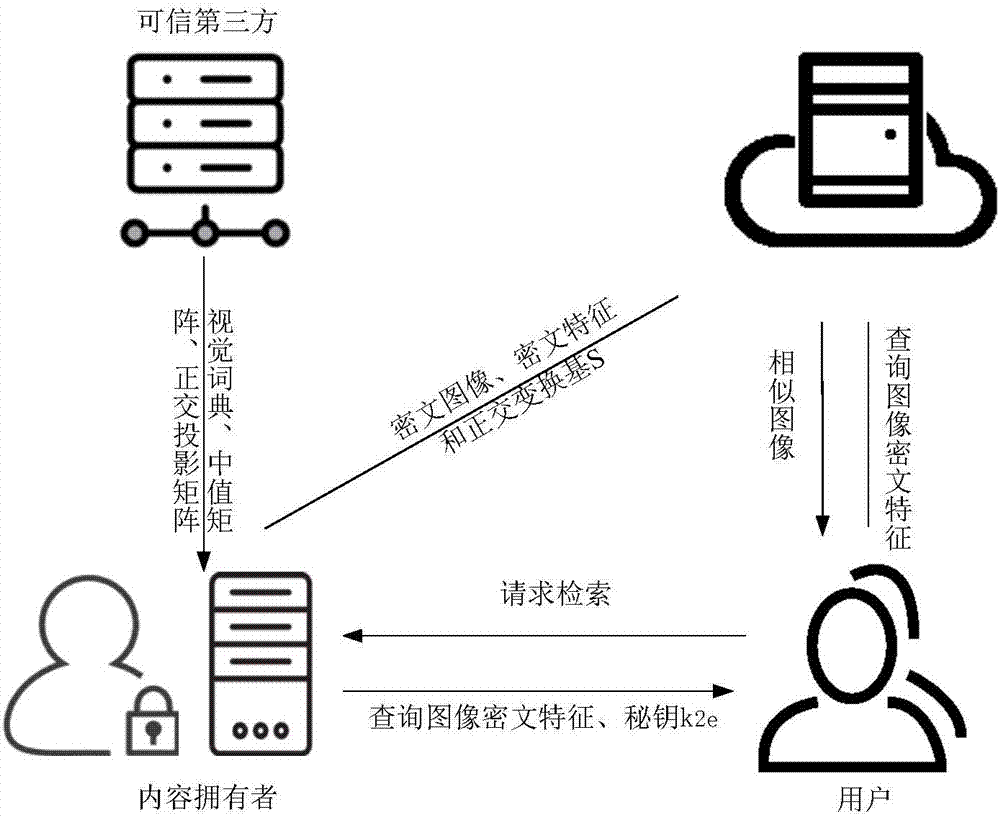
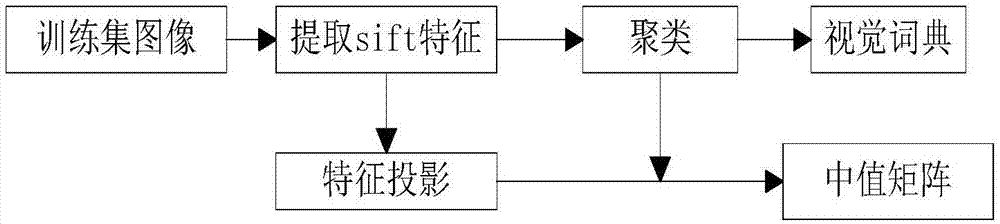
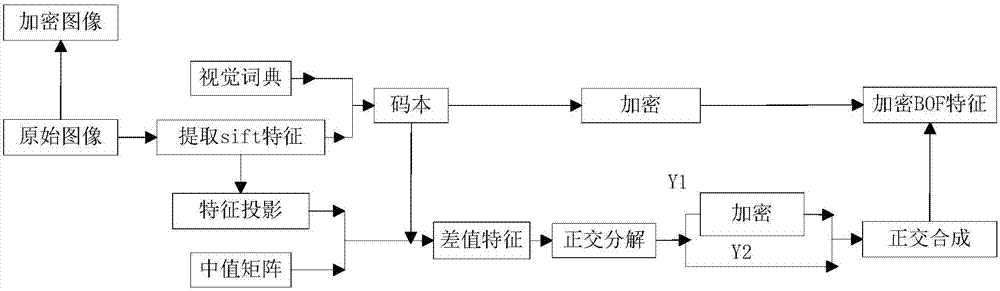
Bag-of-word model-based image security retrieval method for cloud environment
ActiveCN107315812AEnsure safetyImprove securityCharacter and pattern recognitionDigital data protectionCiphertextData domain
The invention belongs to the field of multimedia information security protection and particularly relates to a bag-of-word model-based image security retrieval method for a cloud environment. The method can be used for security retrieval of ciphertext images. A content owner extracts feature operation data of the images based on a bag-of-word model, performs orthogonal decomposition to obtain a password operation domain and a feature extraction operation domain, performs encryption operation and feature extraction operation, superposes operation results in a same data domain through orthogonal inverse transformation to form encrypted features, and uploads the encrypted features to a cloud server. When a user needs to retrieve the images, the cloud server can calculate out the features of the ciphertext images in the data domain of feature extraction by directly performing orthogonal decomposition on ciphertext features without performing decryption; the features of the ciphertext images and the features of the images requested to be retrieved are subjected to similarity measurement; and the images with the highest similarity degree are the to-be-retrieved images. The retrieval method does not depend on a specific encryption method, is high in security and has higher universality; and the bag-of-word model-based retrieval method has very high retrieval precision.
Owner:WUHAN UNIV
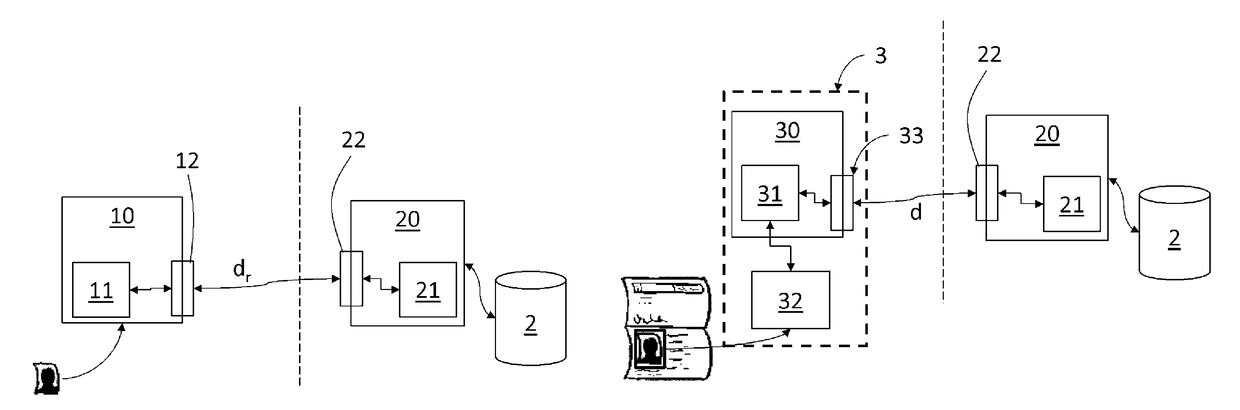
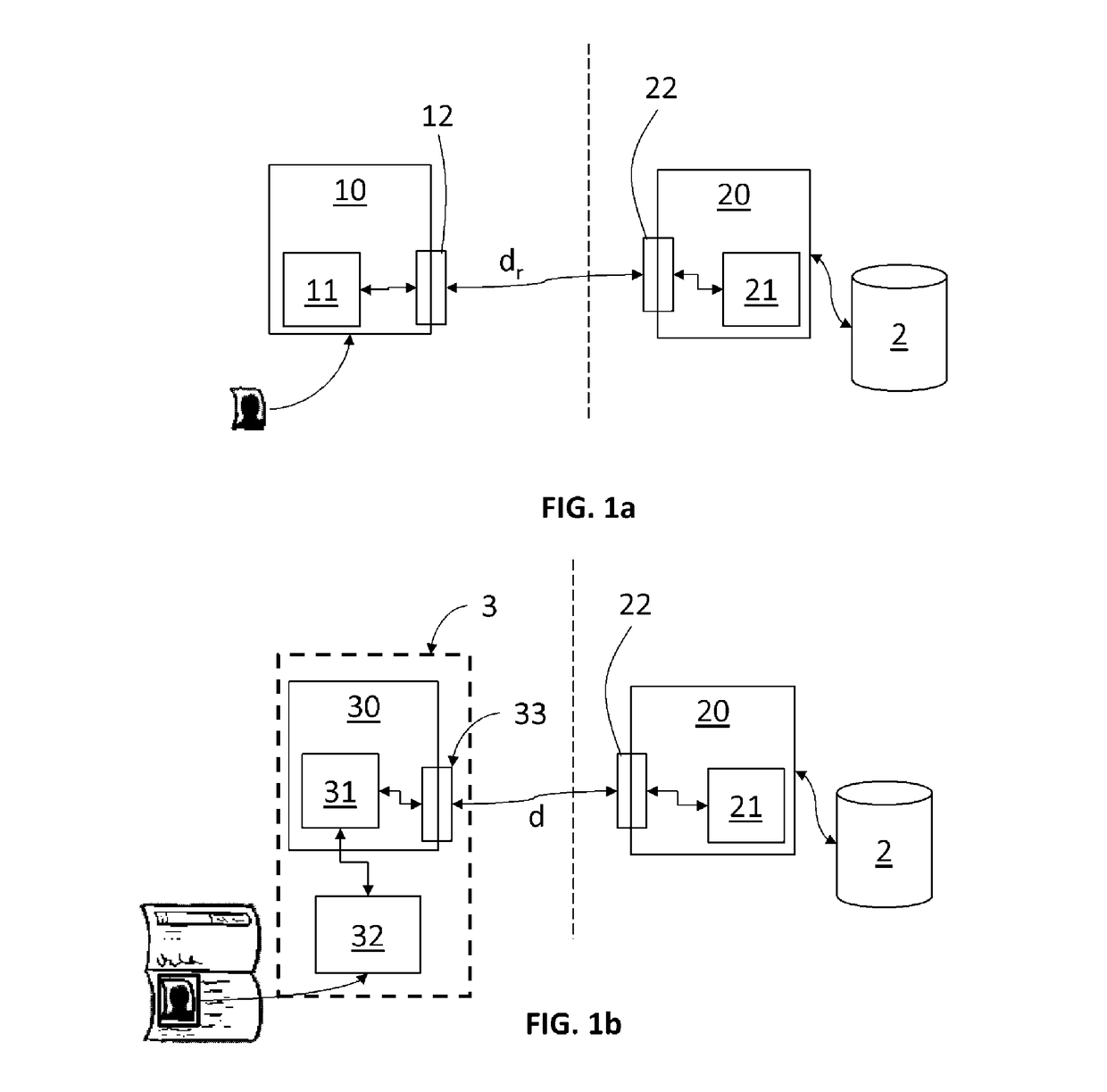
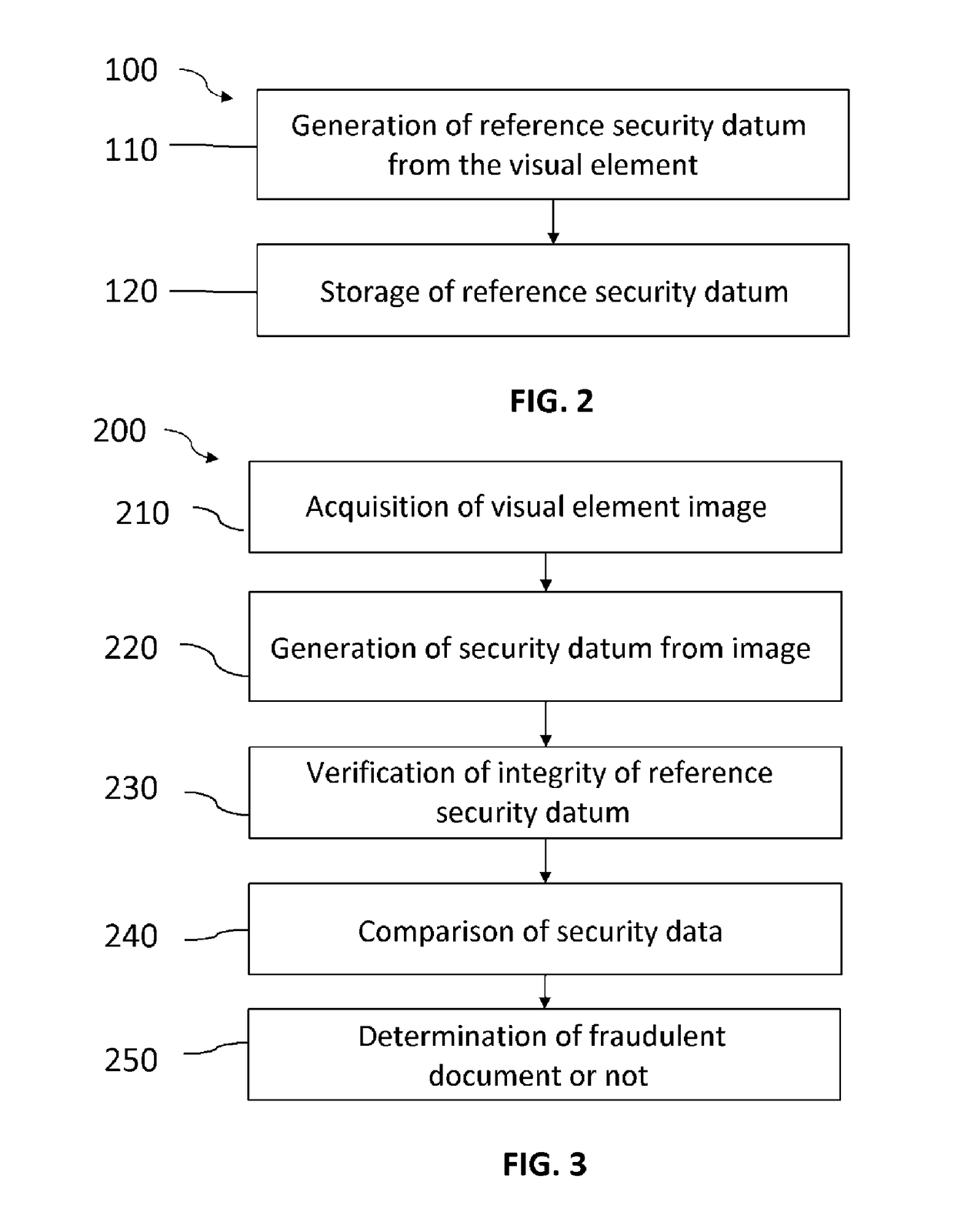
Method for securing and verifying a document
ActiveUS20170236355A1Improve securityIntegrity and SecurityPaper-money testing devicesMaterial analysis by optical meansSoftware engineeringDocumentation
The invention relates to a method for securing a document including a visual element, carried out by a processing unit comprising processing means, the method comprising generation, from the visual element, of a reference security datum, and storage of the reference security datum,wherein the reference security datum is generated by means of an algorithm configured so as to generate:for any image acquired from the visual element, a security datum whereof the differences relative to the reference security datum are less than a determined threshold, andfor any image acquired on a different visual element, a security datum whereof the differences relative to the reference security datum are greater than said threshold.
Owner:IDEMIA IDENTITY & SECURITY FRANCE
System for high-speed scanning and imaging security door channel with terahertz
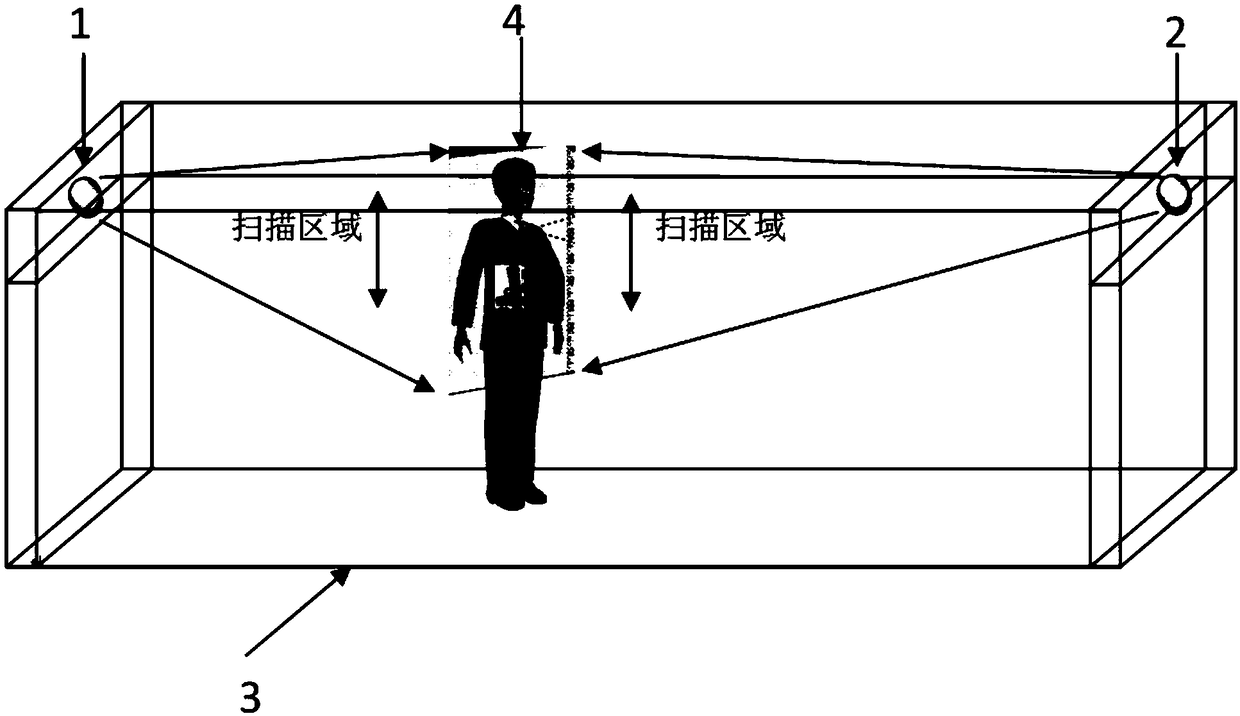
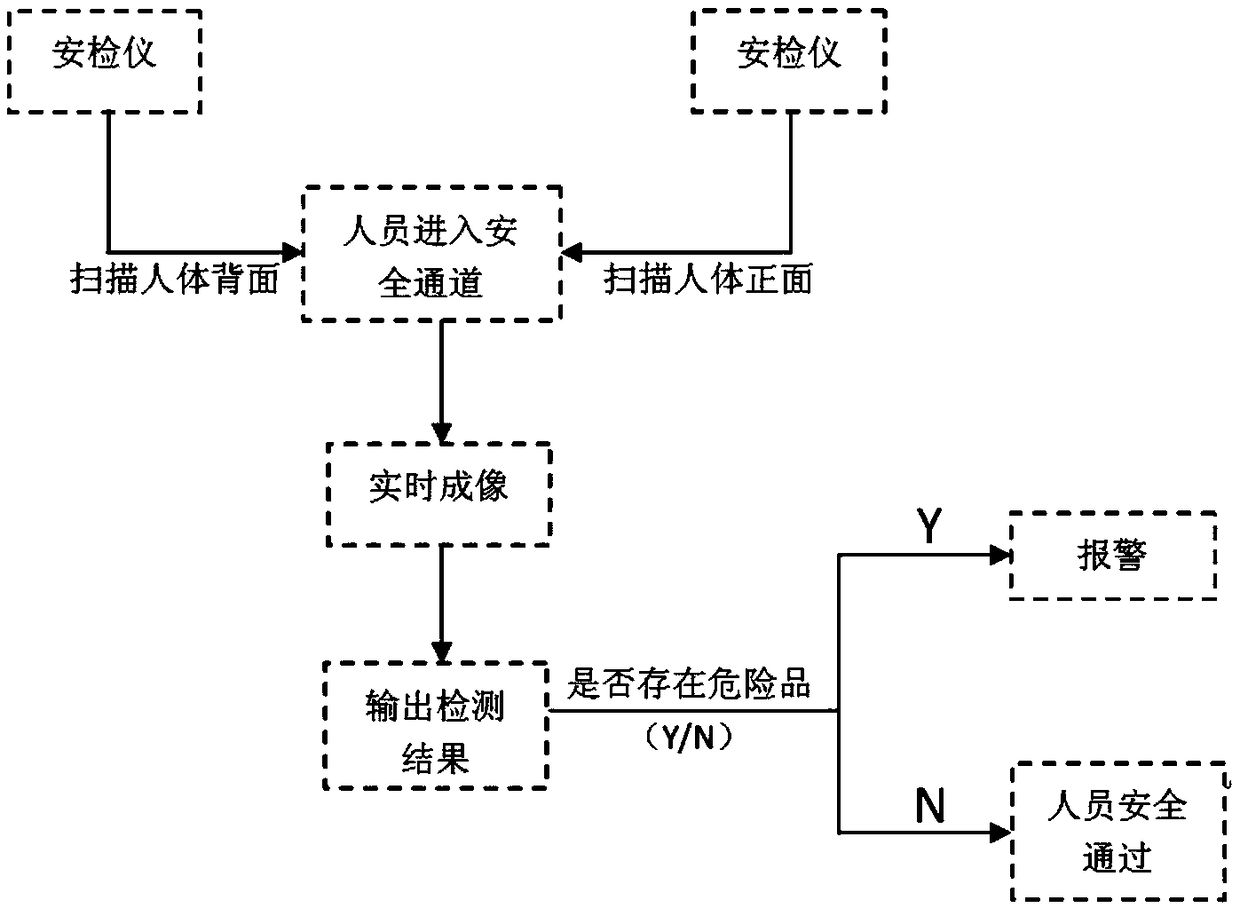
InactiveCN109343142AReduce complexityThe overall structure is simple and reliableOptical detectionSynthetic aperture radarEngineering
The invention discloses a system for high-speed scanning and imaging a security door channel with the terahertz. The purpose of the invention is to provide the system for imaging the security door channel with the terahertz, which has a simple structure, high stability and reliability, and strong resistance to external interference. The invention is realized by the following technical solution, inwhich at least two terahertz security checking devices are symmetrically opposite each other, and are fixed on the detection door frames of the entrance and the exit of the terahertz security door channel through a slot or a screw to form a terahertz security checking channel for the person to be checked (4) to come in and go out, thereby forming an active system for checking the security and imaging with the terahertz, the scanning area of which is greater than the height of the person. The technical solution comprises the steps of: the active system for checking the security and imaging with the terahertz using a terahertz antenna to emit milliwatt-level terahertz waves which can penetrate surface clothes of the person; the system measuring reflected terahertz signals to obtain a surface image of the person; the two terahertz security checking devices simultaneously scanning the front and the back of the person to be checked (4) with an method of interactive overlapping radiation detection of a synthetic aperture radar; and the two terahertz security checking devices transmitting the scan result to an external computer through cables for real-time imaging.
Owner:10TH RES INST OF CETC
Image security retrieval method based on secret sharing in cloud environment
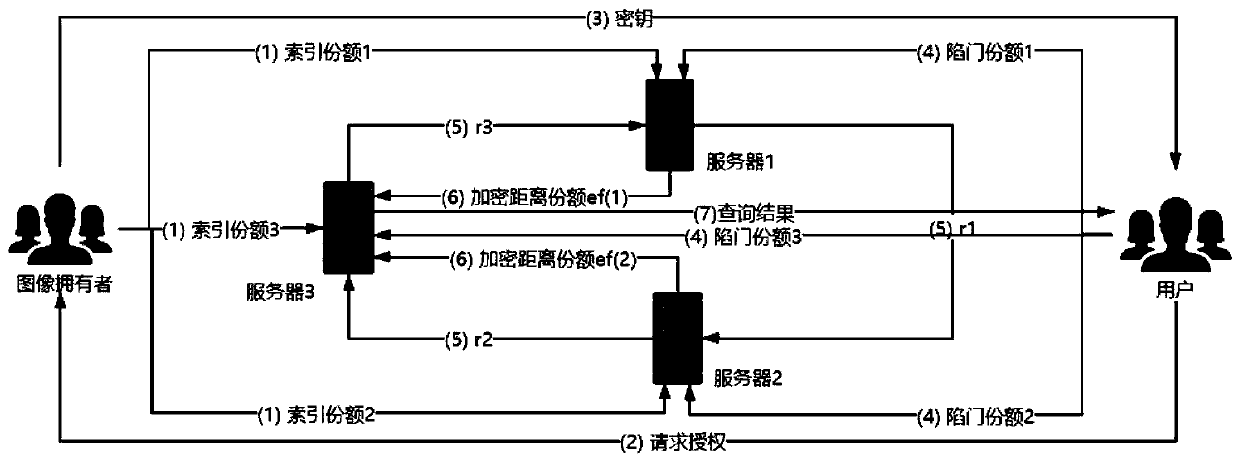
ActiveCN111541679AProtection securityIncrease the difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextEngineering
The invention aims to provide an image security retrieval scheme based on secret sharing in a cloud environment, which realizes security retrieval of a cloud image by constructing an index share and atrap door share. A data owner generates a ciphertext image and an index share and uploads the ciphertext image and the index share to a cloud, during query, a user generates a trap door share and sends the trap door share to the cloud, and the cloud can calculate a distance share and return the ciphertext image closest to the query image, so that the security problem caused by using a unified keyfor encryption in an existing scheme can be solved. In order to prevent an attacker from analyzing image similarity information according to an original Euclidean distance to speculate an image, a random number and a secure multi-party calculation method are used to encrypt a distance share. The security of the scheme depends on a secret sharing technology, the common precision loss problem in image security retrieval is solved, and the retrieval precision is almost consistent with that of plaintext domain image retrieval.
Owner:WUHAN UNIV
Image security identification method based on adversarial sample defense
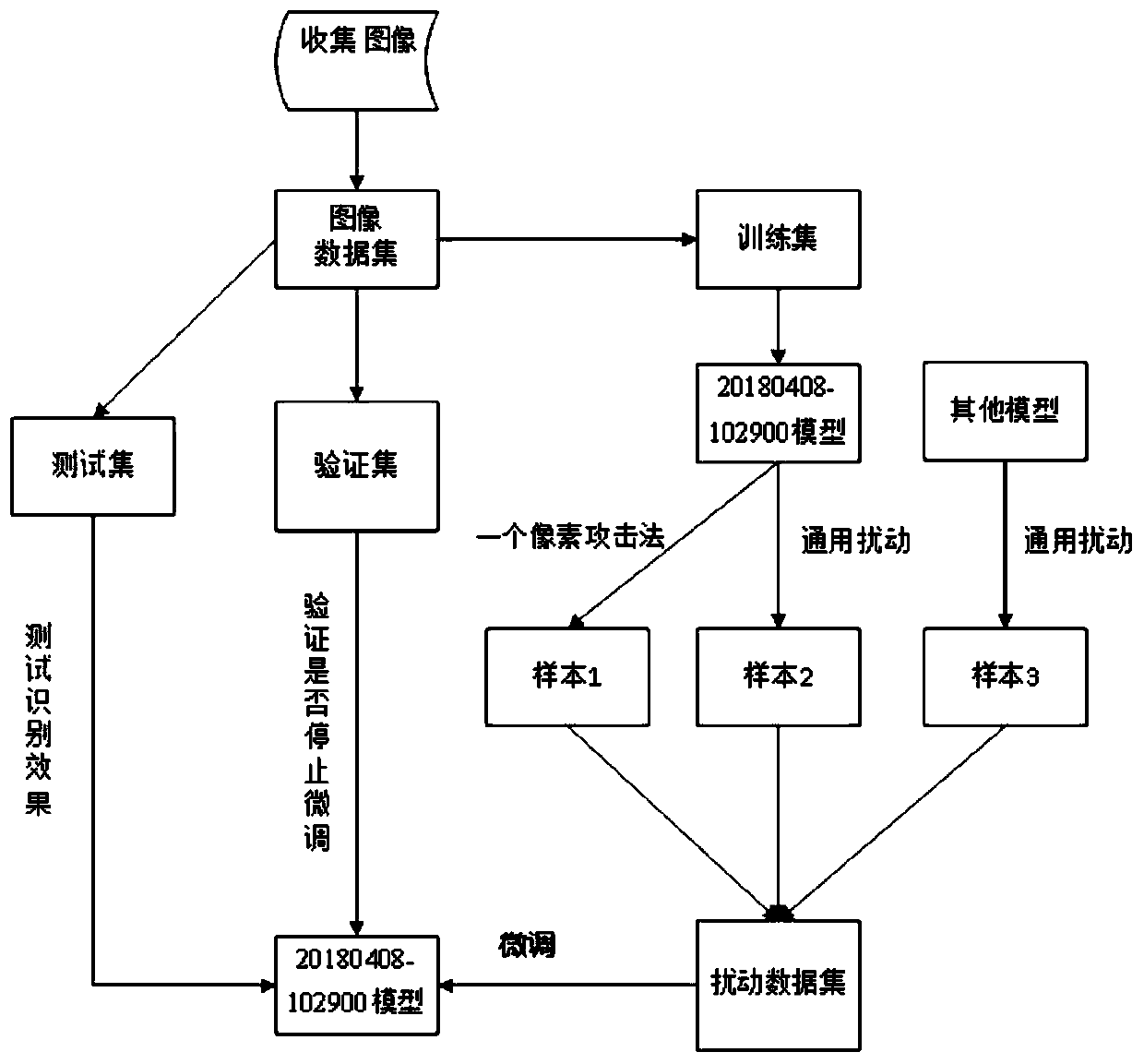
PendingCN111414964AImprove defenseStrong defenseCharacter and pattern recognitionNeural architecturesData setAlgorithm
The invention provides an image security identification method based on adversarial sample defense. The method comprises the following steps: 1, firstly, collecting an image data set; 2, generating anadversarial sample by using a pixel attack method, according to the attack method, utilizing a differential evolution algorithm to iteratively modify each pixel of a test set image to generate a sub-image, then testing the attack effect of each sub-image, and using the sub-image with the best attack effect as an adversarial sample; 3, generating an adversarial sample by using a general disturbance generation method; 4, generating an adversarial test set based on the adversarial sample; 5, taking the image data of the training set as training data, and carrying out the fine adjustment of an original pre-trained model; and 6, performing image recognition on the test set, and checking an image recognition effect. The method has a good defense capability for one pixel generation confrontationdisturbance, has an excellent defense capability for a confrontation sample generated by general disturbance, cannot generate any influence on a generated image recognition model by the general disturbance, and can be used for recognition and classification of electronic files and the like.
Owner:SHANGHAI GOLDEN BRIDGE INFOTECH CO LTD
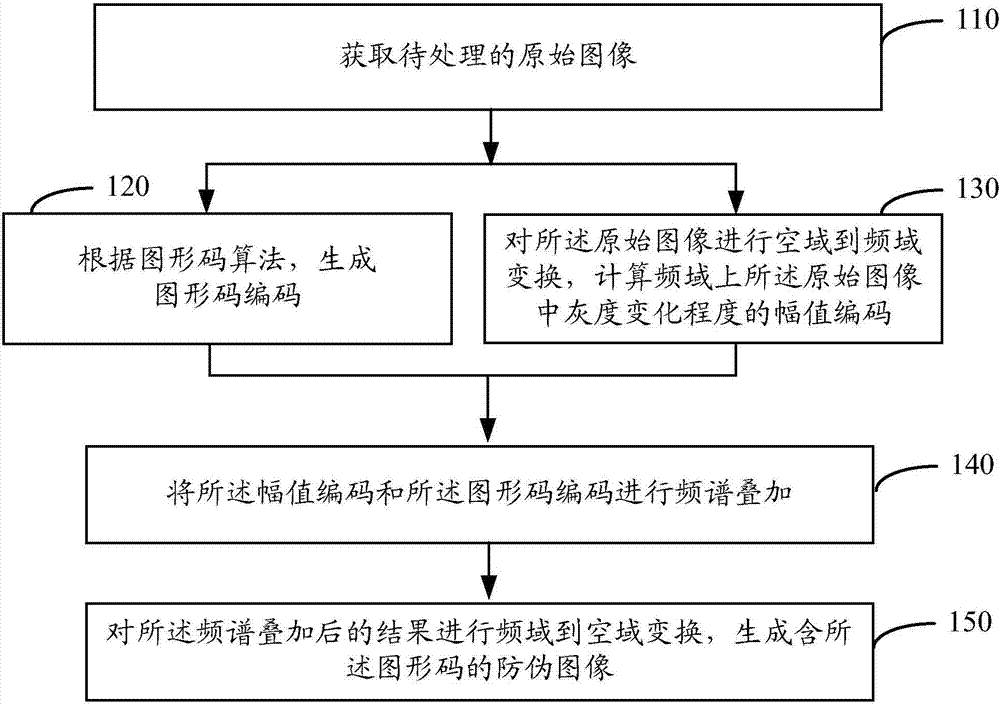
Method and device for generating security image, method and device for identifying security image, and computer storage medium
ActiveCN107248135AHigh degree of anti-counterfeitingIncrease the difficultyTexturing/coloringImage codingGraphicsFrequency spectrum
The embodiments of the invention provide a method and a device for generating a security image. The method includes the following steps: acquiring an original image to be processed; generating a graphic code according to a graphic code algorithm; transforming the original image from the space domain to the frequency domain, and calculating the amplitude code of the gray change of the original image in the frequency domain; superposing the spectrum of the amplitude code and the spectrum of the graphic code; and transforming the result after spectrum superposition from the frequency domain to the space domain, and generating a security image containing the graphic code. According to the embodiment, a security graphic code is added to the frequency domain of the original image through transformation from the space domain to the frequency domain. Although the security image generated through transformation from the frequency domain to the space domain contains the graphic code, the graphic code is invisible to the eye. Therefore, the degree of image security is improved, and the difficulty and cost of security image decoding are increased.
Owner:ADVANCED NEW TECH CO LTD
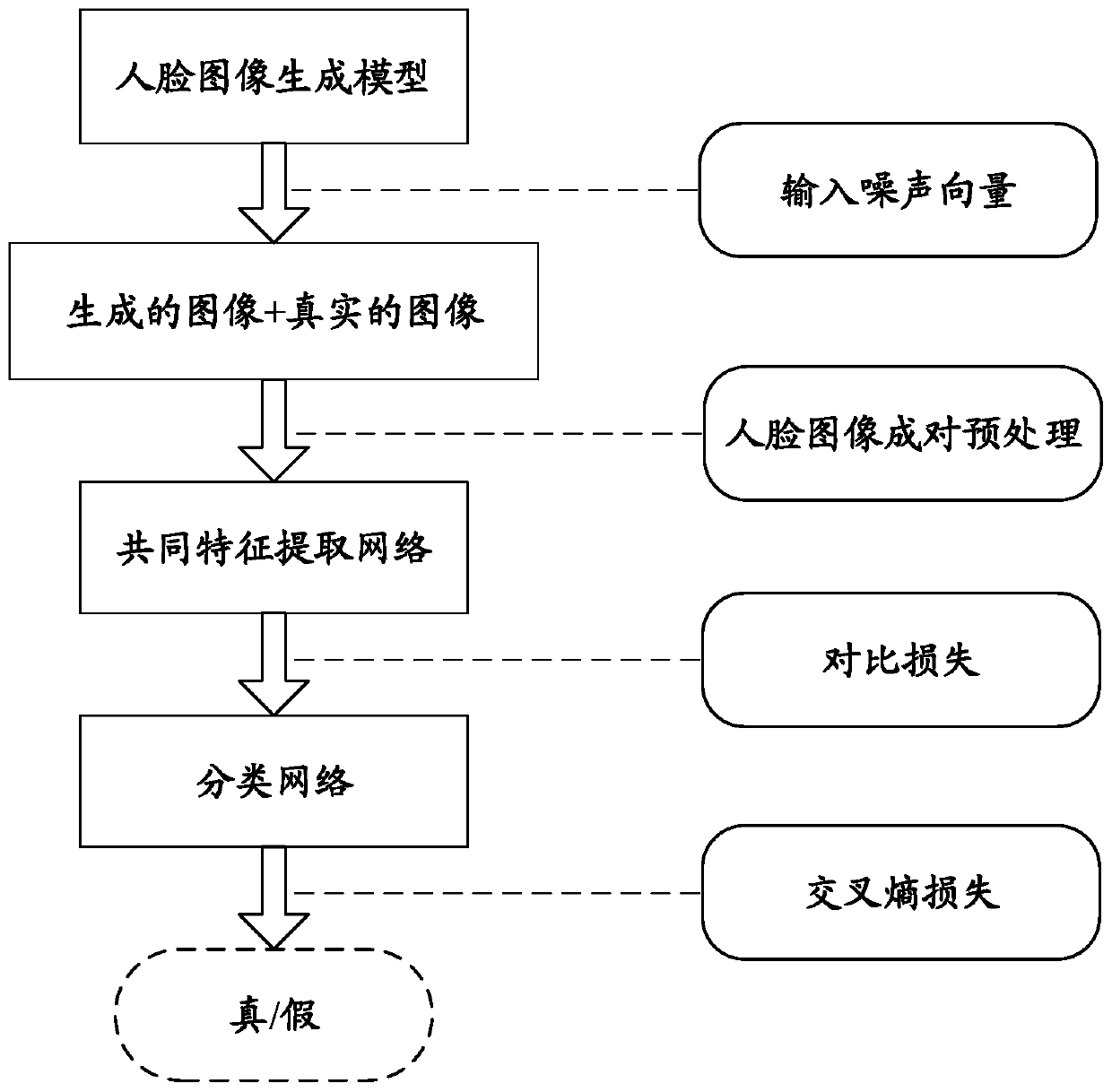
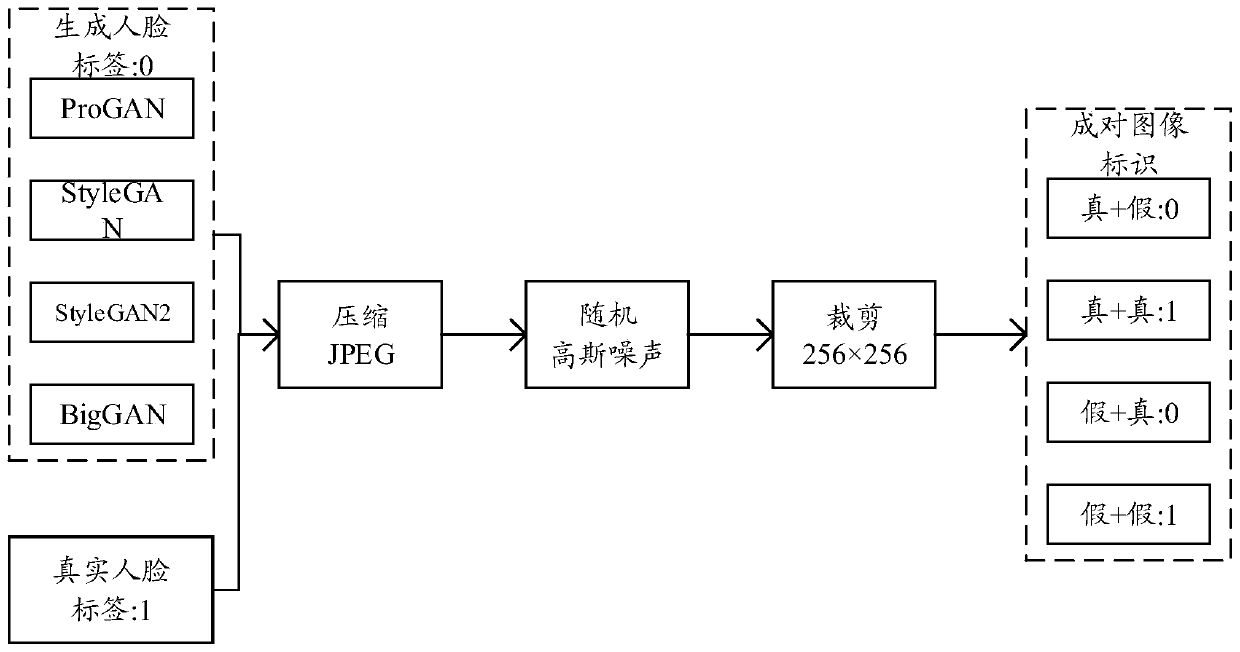
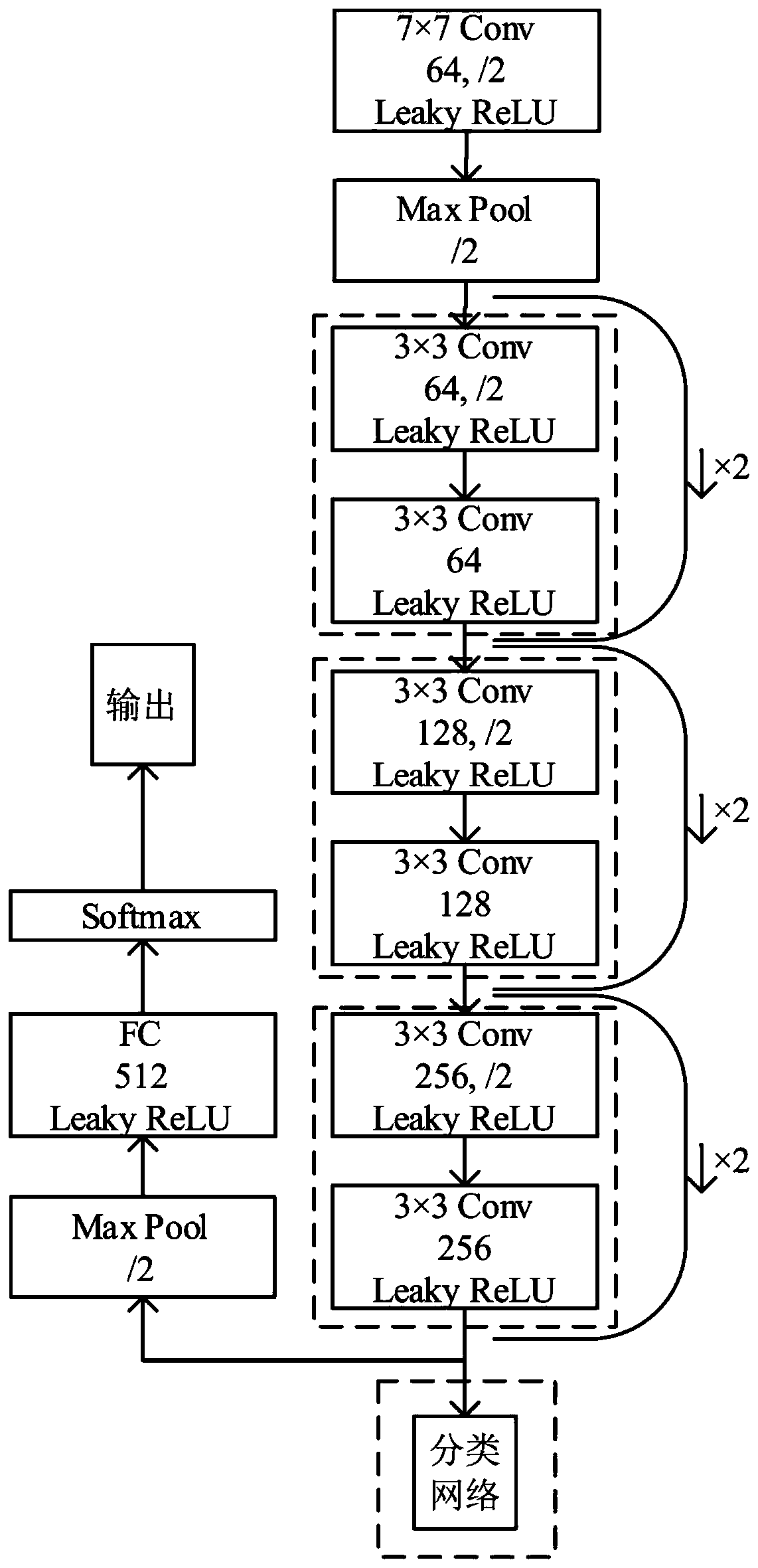
Method for realizing generative false face image identification based on deep convolutional neural network
ActiveCN111597983ASimple structureIdentification speedInternal combustion piston enginesCharacter and pattern recognitionFeature extractionData set
The invention relates to a method for realizing generative false face image identification based on a deep convolutional neural network. The method comprises the following steps: generating a false face by utilizing a mainstream face generation model; performing paired preprocessing on the real face for training and the generated face picture data set, and making a label; constructing a common feature extraction network and a classification network on the basis of the deep convolutional neural network; inputting paired face images for training into the common feature extraction network for training by using the comparison loss; cascading the trained common feature extraction network with a classification network, and inputting a generated or real single face image for training; and carrying out generative false face image identification according to the cascade network model obtained after training. By adopting the method for realizing generative false face image identification based on the deep convolutional neural network, the established network is simple in structure and high in identification speed, and has a wide application prospect in the fields of false biological characteristic image identification and face image security.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
E-waveband millimeter wave imaging security inspection radar system
InactiveCN109633630AHigh-speed and reliable imagingCost-effectiveRadio wave reradiation/reflectionRadar systemsData acquisition
The invention provides an E-waveband millimeter wave imaging security inspection radar system. The system contains a plurality of data acquisition subsystems, comprehensive signal processing subsystems, display and control subsystems, calibration subsystems, and power supply subsystems; the plurality of data acquisition subsystems are arranged around an object to be detected, and are used for generating E-waveband millimeter waves to be transmitted to the object to be detected and acquiring reflection echo data of the object to be detected; the comprehensive signal processing subsystems are electrically connected with the data acquisition subsystems and are used for performing real-time imaging processing on data acquired by the data acquisition subsystems; the display and control subsystems are electrically connected with the comprehensive signal processing subsystems, and are used for performing target detection and identification processing on imaging results of the comprehensive signal processing subsystems, and displaying the results to a user; the calibration subsystems are used for correcting multi-channel amplitude phases of arrays in the data acquisition subsystems; and the power supply subsystems are electrically connected with the data acquisition subsystems, the comprehensive signal processing subsystems and the display and control subsystems and are used for providing electric power. According to the system, high-speed and reliable imaging can be achieved in a high-human-flow-rate and high-density crowd, so that the cost performance of the system is greatly improved, and the system has great advantages in multiple aspects of complexity, cost performance, flexibility and the like.
Owner:SHANGHAI RADIO EQUIP RES INST
Environment security detection method and terminal and computer readable storage medium
InactiveCN107527036AEnsure safetyImprove securityCharacter and pattern recognitionPayment protocolsInternet privacyImage security
The invention discloses an environment security detection method and terminal and a computer readable storage medium, which relate to the technical field of communication. The environment security detection method includes the following steps: determining whether a current application enters a sensitive information input scene; when the current application enters a sensitive information input scene, making a user-oriented camera unit acquire a detection image containing face information in a current environment; comparing the detection image with a standard image to get an image security coefficient; and when the image security coefficient is less than a preset security coefficient, issuing a security warning. According to the environment security detection method and terminal and the computer readable storage medium provided by the invention, a detection image containing face information is taken in a sensitive input scene, the detection image is compared with a standard image to get an image security coefficient, the security of user operation in the sensitive information input scene is ensured through the image security coefficient, and therefore, the security of user's online payment and privacy account login is improved.
Owner:NUBIA TECHNOLOGY CO LTD
A hidden image security device and method
A method for producing an optical device, preferably a security device, including the steps of: forming a planar relief structure on a substantially planar first surface of a substrate, preferably a transparent substrate, the planar relief structure having a first alignment direction and including a plurality of relief structure elements each having the same height; and applying a liquid crystal polymer (LCP) layer onto the planar relief structure such that the LCP layer is aligned with the relief structure, wherein the LCP layer includes at least one or more first LCP regions having a first height and one or more second LCP regions having a second height above the substantially planar first surface of the substrate, wherein the second height is different to the first height, and an optical device formed by such a method.
Owner:CCL SECURE PTY LTD
Mobile back scattering imaging security inspection apparatus and method
ActiveUS9846257B2Reduce mutual interferenceImprove image qualityMaterial analysis using wave/particle radiationNuclear radiation detectionLight beamEngineering
The present disclosure provides a mobile back scattering imaging security inspection apparatus, comprising: a back scattering scanner (2), a detector (3), a controller (4), and a movable stage (1) configured to carry the back scattering scanner, the detector and the controller and being movable with respect to the object to be inspected; wherein the back scattering scanner is a distributed X-ray source comprising a plurality of target points (201), each of which is able to emit the ray beam individually, and wherein the back scattering scanner, the detector and the controller perform an imaging security inspection operation on the object to be inspected during moving along with the movable stage with respect to the object.
Owner:NUCTECH CO LTD +1
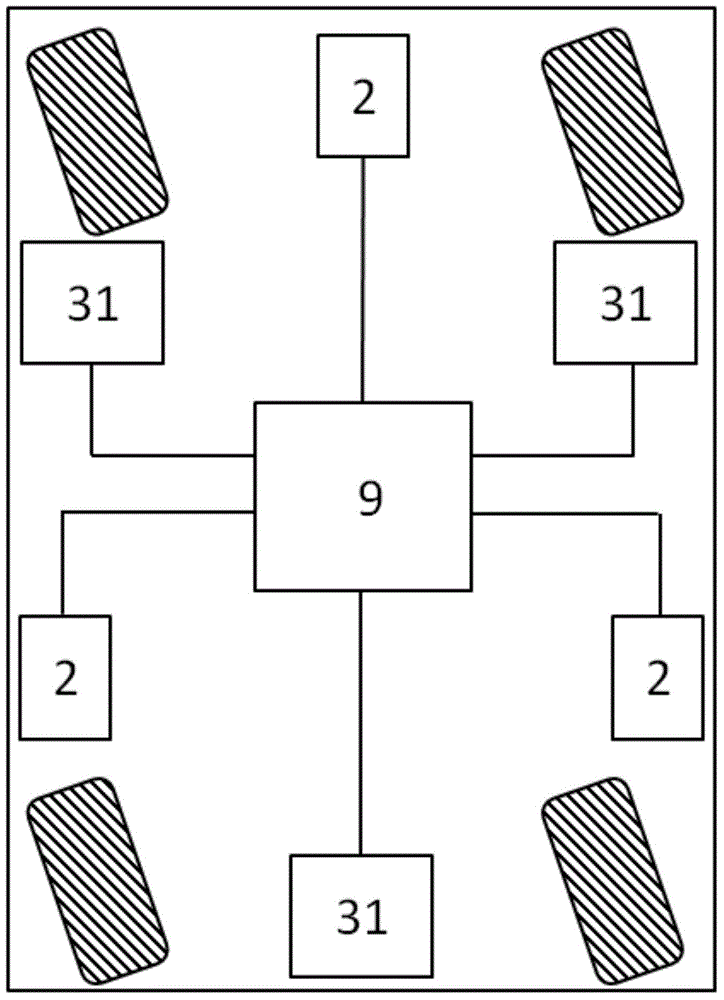
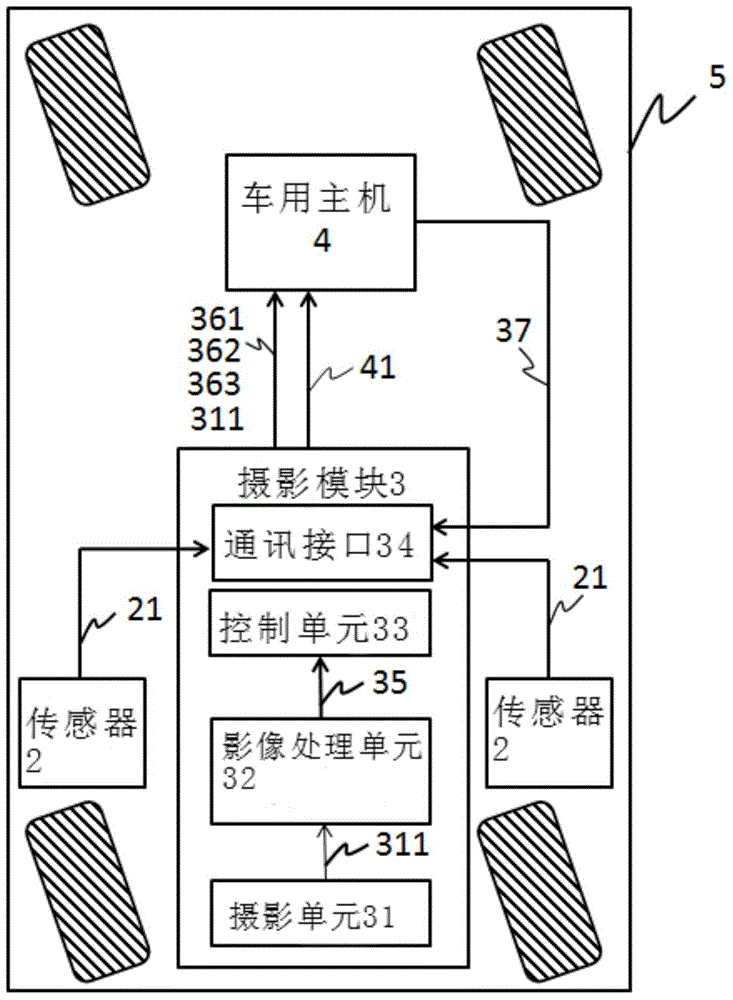
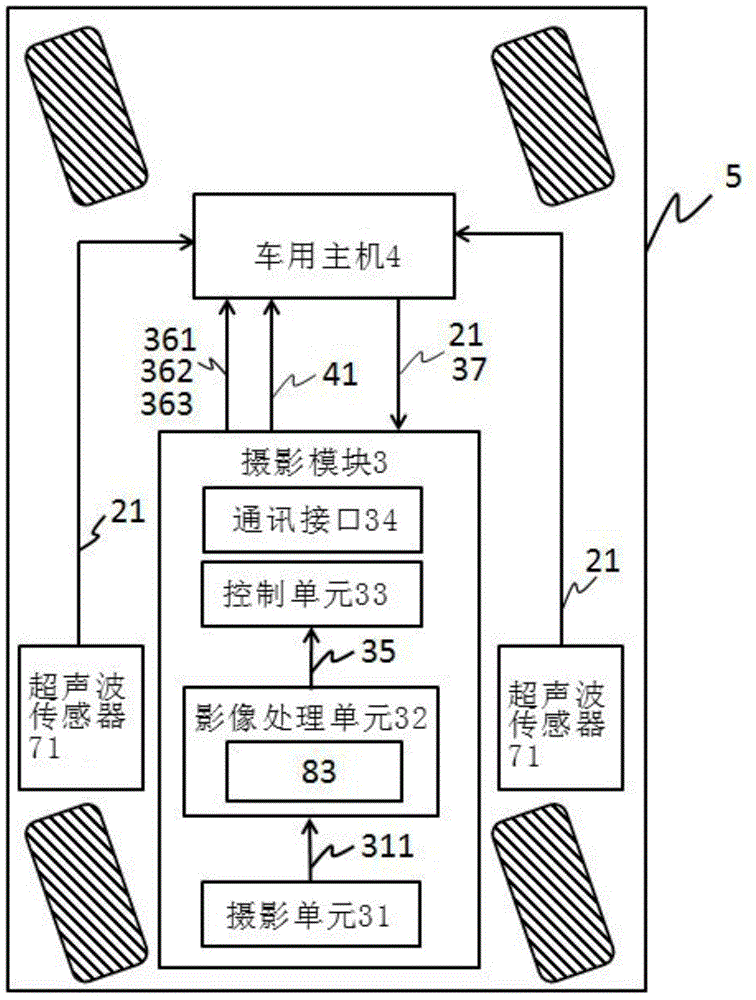
Sensor-integrated vehicle intelligent image security system
ActiveCN105270260AImprove computing powerImprove securityPedestrian/occupant safety arrangementClosed circuit television systemsControl unitDriving safety
The invention provides a sensor-integrated vehicle intelligent image security system applied to a vehicle host and a mobile carrier of a sensor. The system is characterized in that the sensor generates the first detection information and then transmits the first detection information to a capturing module. The image processing unit of the capturing module detects and processes external images to generate the second detection information. The control unit of the capturing module makes out a comprehensive judgment according to the first detection information and the second detection information so as to generate a security warning signal and then transmits the security warning signal to the vehicle host via a communication interface. The vehicle host reminds a driver in the image or audio manner. Therefore, even when the motion carrier is provided with no powerful central computing platform, the auxiliary function of driving safety can be realized based on the above vehicle intelligent image security system.
Owner:OTOBRITE ELECTRONICS
Method of using middleware for generating vector graphics imaged security documents
ActiveUS20180304145A1Reduce bandwidth requirementsLow program costKey distribution for secure communicationLottery apparatusDigital imagingAlgorithm
A method is provided of digitally imaging a secure portion and a non-secure portion of scratch-off-coating protected documents of at least one game using middleware. The method includes: (a) generating the secure variable indicia in non- vector raster format; (b) generating vector graphics to be imaged on physical document locations; (c) assigning the secure variable indicia in a non-vector raster format to documents in and shuffling the documents throughout a print run; and (d) linking via middleware the secure variable indicia in the non-vector raster format to associated vector graphics variable indicia to be digitally imaged on the documents and to generate vector graphics-formatted data for each document in the print run. The secure variable indicia assignment and shuffling are executed by non-vector raster game generation software output that is reinterpreted by the middleware to produce related vector graphic output for the secure variable indicia.
Owner:HYDRAGRAPHIX LLC
Method and system for secure image management
InactiveUS20120328148A1Character and pattern recognitionDigital data protectionText fileManagement system
A method and computer device for managing imagery loaded in an image management system. The method includes analyzing the imagery loaded within the image management system, searching the imagery for one or more images, and displaying images found as a result of searching the imagery. Analyzing includes selecting an image to analyze, authenticating the selected image, and securely uploading an authenticated image into the image management system. Analyzing also includes performing a hashing operation on the selected image. Securely uploading an authenticated image includes, uploading a successfully authenticated into the image management system, including uploading a text file with metadata for the selected image, appending a generated hash for the selected image original to the uploaded text file, uploading the selected image, comparing the generated hash with a hash of the uploaded selected image, and generating an error message if the generated hash does not match the hash of the uploaded selected image.
Owner:UNISYS CORP
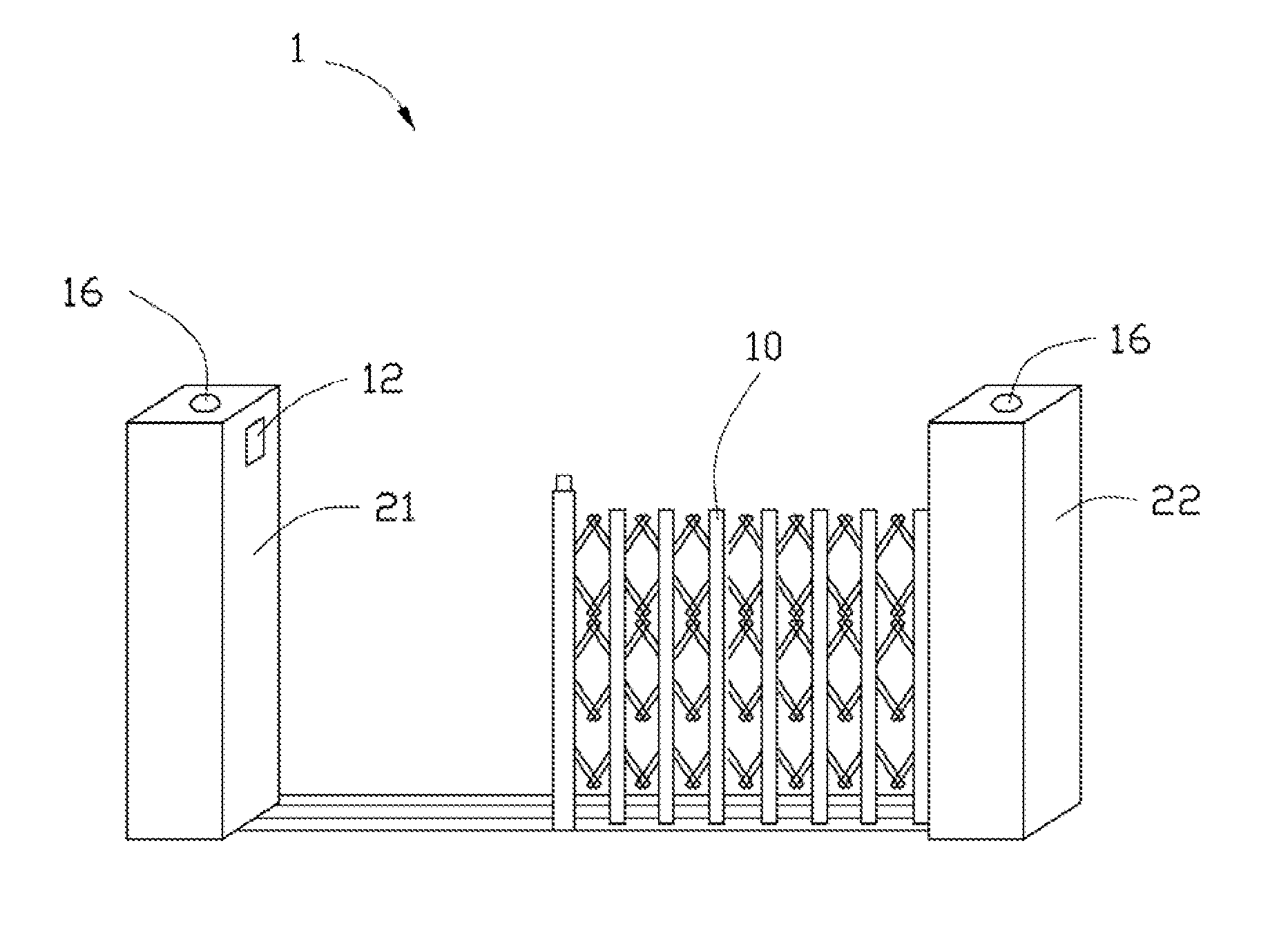
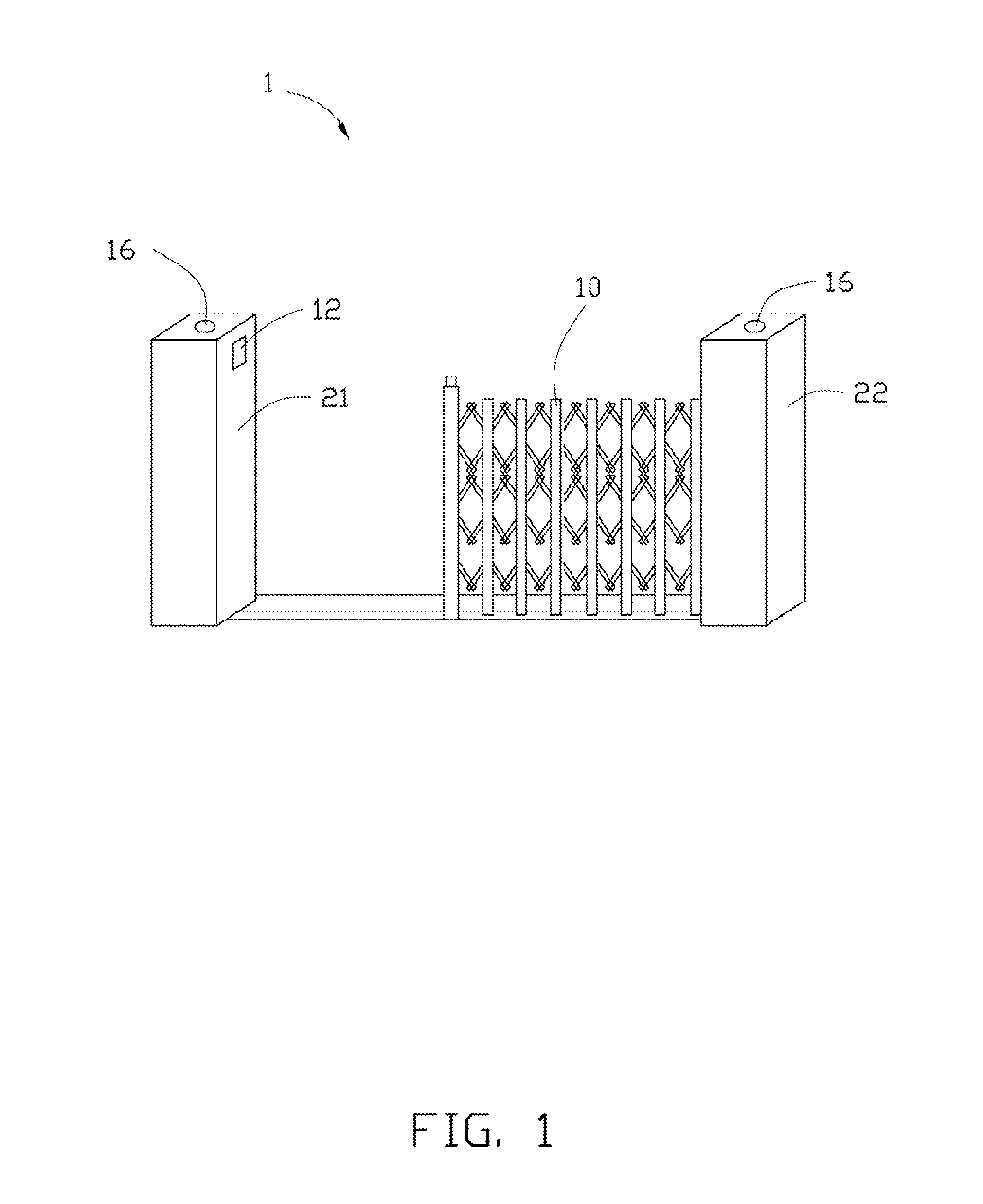
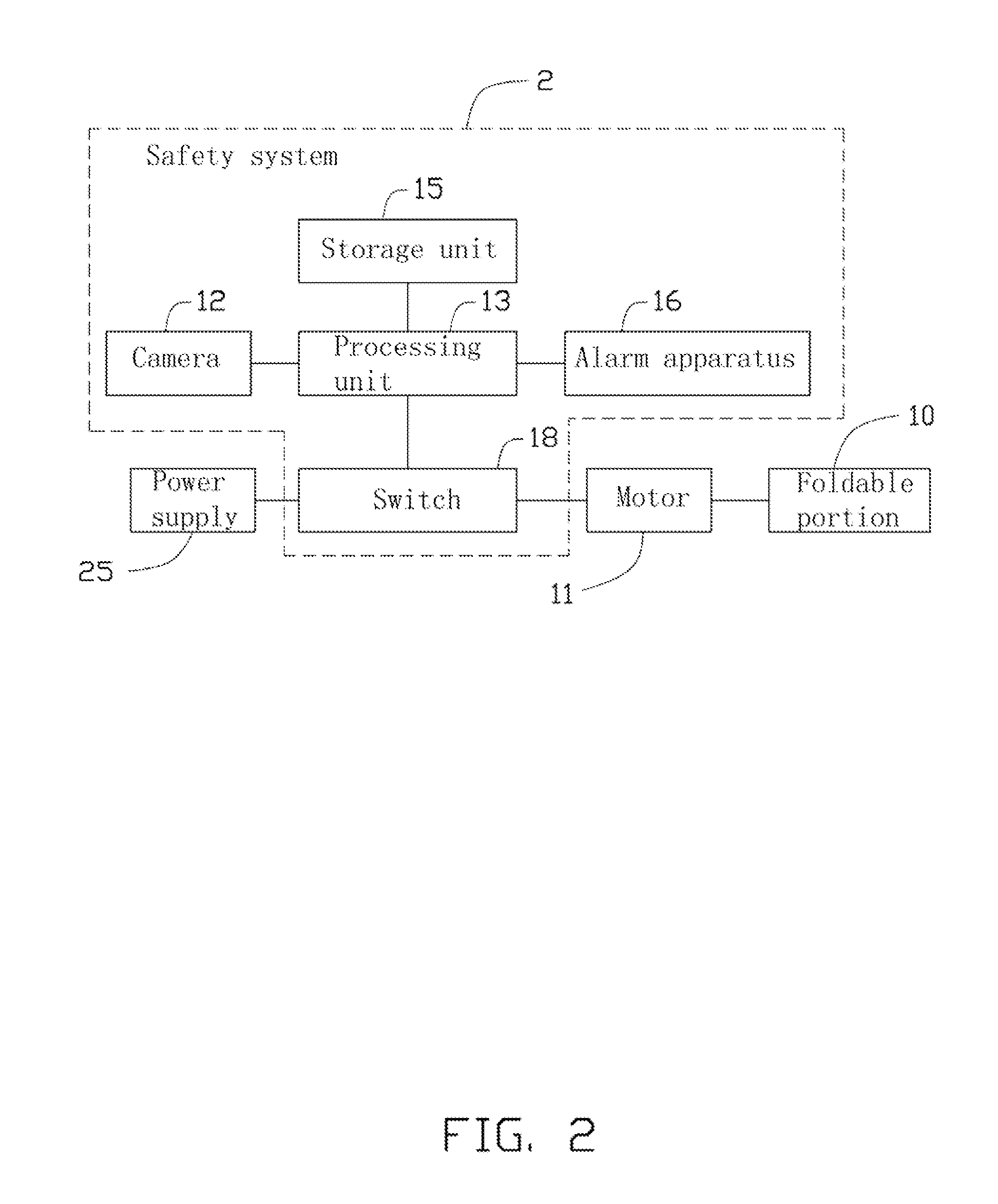
Safety system, method, and electronic gate with the safety system
InactiveUS20120098662A1Programme controlElectric signal transmission systemsEngineeringMotor control
An electronic gate includes a foldable portion, a motor, a camera, a switch, and a safety system. The foldable portion is located between a first support and a second support. The motor controls the foldable portion. The camera captures an image between the first support and the second support. The safety system is to check the image captured by the camera to determine whether there are people between the first support and the second support, and control the switch to cut off a power supply with the motor according to the determination result.
Owner:HON HAI PRECISION IND CO LTD
Self-adaptive feedback correction method and system for image security inspection
ActiveCN102456242AImprove reliabilityIndividual entry/exit registersNuclear radiation detectionUltrasound attenuationEvaluation result
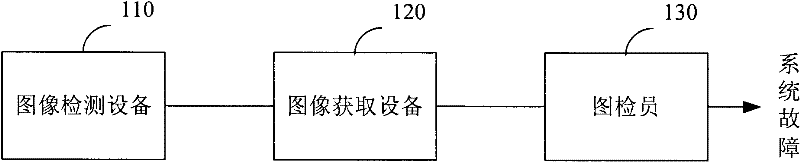
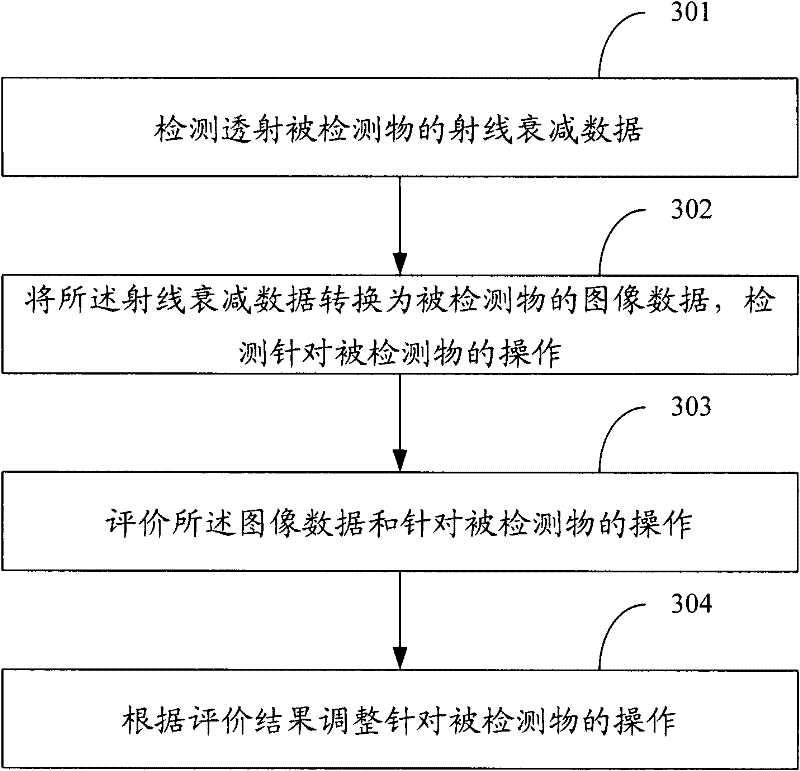
The invention relates to a self-adaptive feedback correction method and a self-adaptive feedback correction system for an image security inspection. The system comprises an image detection device, an image obtaining device connected with the image detection device, an image analysis device connected with the image obtaining device, and an image feedback device connected with the image detection device, the image obtaining device and the image analysis device. The image detection device detects the attenuation data of a ray transmitting a to-be-detected object, and sends the attenuation data of the ray to the image obtaining device. The image obtaining device converts the received attenuation data of the ray to the image data of the to-be-detected object, detects an operation aiming at the to-be-detected object, and sends the conversion and detection results to the image analysis device, wherein the image data comprises the display image of the present to-be-detected object and the substance kinds contained therein. The image analysis device evaluates the image data sent by the image obtaining device and the operation aiming at the to-be-detected object, and notifies the evaluation result to an image feedback device. The image feedback device adjusts the operation aiming at the to-be-detected object according to the evaluation result.
Owner:NUCTECH JIANGSU CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com