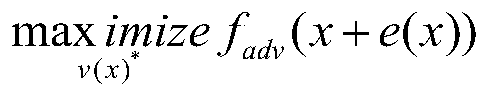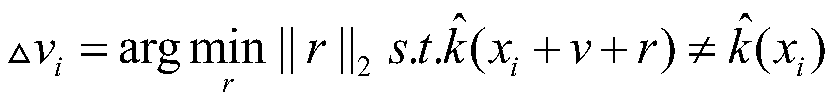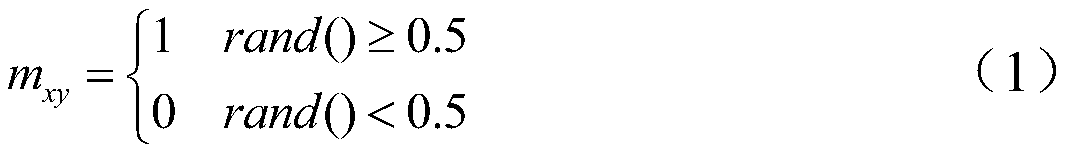Patents
Literature
42results about How to "Strong defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
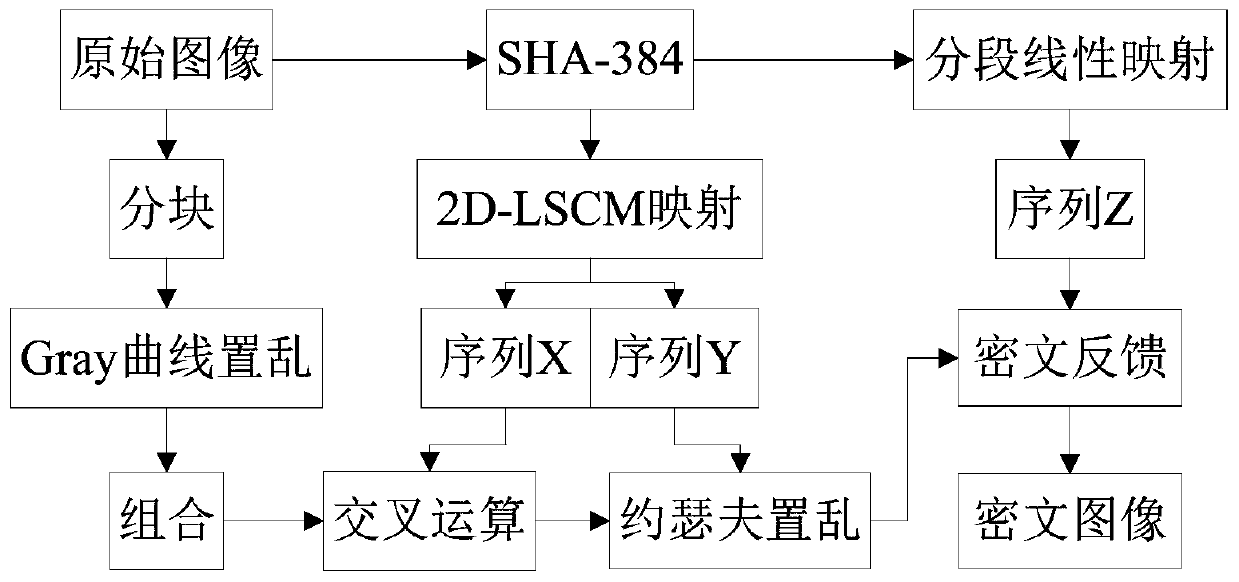
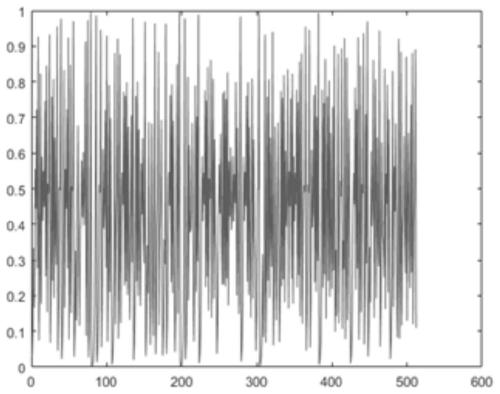
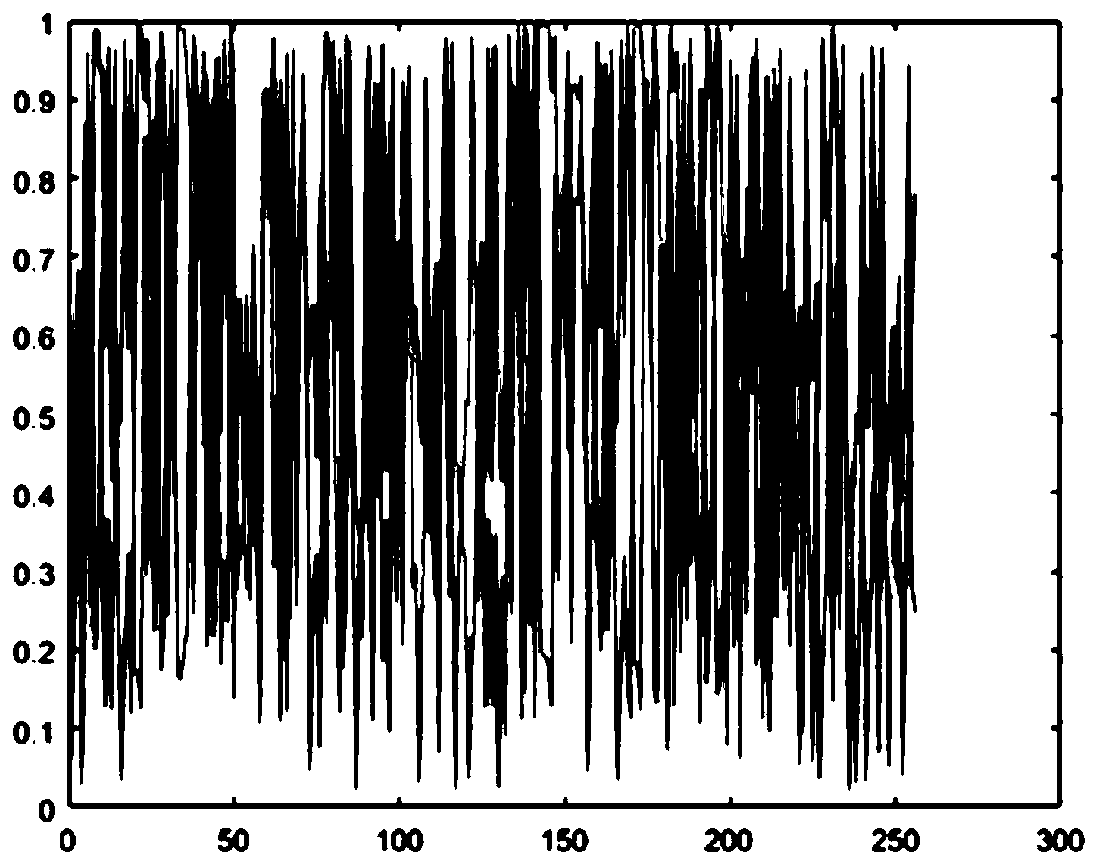
Image encryption method based on multidimensional chaotic system and Josephf scrambling
ActiveCN111105339AAchieve diffusionIncreased sensitivityImage data processing detailsKey spaceAlgorithm
The invention provides an image encryption method based on a multi-dimensional chaotic system and Josephf scrambling, and the method comprises the steps: carrying out the initialization of PWLCM mapping and 2D-LSCM mapping, and obtaining a sequence X, a sequence Y and a sequence Z; uniformly dividing the original image into sub-matrixes according to indexes, carrying out Gray curve scrambling on pixels in the sub-matrixes, and carrying out sequential recombination to obtain a recombined image matrix; taking out elements in the sequence X as a crossover operator, and performing bit crossover operation on the recombined image matrix to obtain an image matrix; taking out a pseudo-random value in the sequence Y as the step value of fixed-step Josephh scrambling, and performing Josephh scrambling operation on the image matrix to obtain a matrix; and taking out the pseudo-random value in the sequence Z and the element pixel value in the matrix to carry out XOR ciphertext feedback to obtain afinal encrypted image. The method can effectively encrypt the image, has a large key space, has high sensitivity to the to-be-encrypted image and the initial key, and has good defense capability whenresisting various attack modes.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
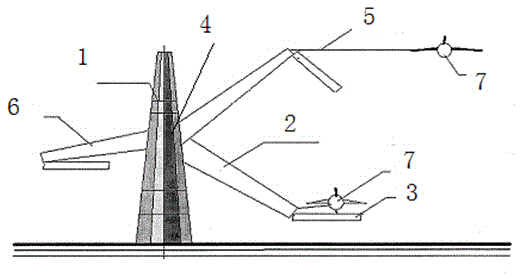
Device for launching and landing aircrafts
InactiveCN104058100AImprove people's livelihoodStrong defenseArresting gearLaunching/towing gearRotational axisFlight vehicle
The invention discloses a device for launching and landing aircrafts. The device comprises a fixedly arranged rotary launching tower, wherein a rotating shaft is arranged at the middle part of the rotary launching tower; a group of rotating arms extending outwards is arranged on the rotating shaft, one end of each rotating arm is hinged to the rotating shaft, and a bearing platform capable of adjusting an angle of inclination is arranged at the extending end of each rotating arm; telescopic flexible elastic ropes matched with the aircrafts are arranged at the extending ends of the rotating arms. The device adopts a brand-new launching and landing manner for the aircrafts, and a large-area runway is not needed, so that a heavy investment is saved; a plurality of aircrafts can be launched at the same during launching, so that the time is reduced compared with the time used during conventionally successive launching; the device is high in controllability and high in reliability, and the requirement for the operant level of navigating mates of the aircrafts is low.
Owner:杨举 +1
Authentication method and system for CAPTCHA Turing test based on static characters
InactiveCN103093138AIncrease the difficultyStrong defenseDigital data authenticationString databaseSemantics
The invention discloses an authentication method and a system for CAPTCHA Turing test based on static characters. The authentication method and the system for the CAPTCHA Turing test based on the static characters include the following steps of establishing a communication connection between a server and a client, selecting randomly a static string in a static string database stored the server in advance, segmenting the static string into single characters, then calling a character image to generate a function which converts single characters into image representation, placing the single characters represented by the image into a region formed by a circular or elliptic boundary to show as a verification code on the client so as to carry out the Turing test CAPTCHA. Utilizing the region formed by the circular or elliptic boundary to place the verification code, the method can effectively prevent the character from being segmented by conventional pixel segmentation, and thus increases the difficulty of attack. The method carries out distortion, mirror image, and increasing interference lines for characters. The method carries out the characters arrangement according to the specific semantics of the characters and increases more human participation and can guarantee the safe man-machine interaction.
Owner:COMMUNICATION UNIVERSITY OF CHINA
Method of designing watermark in consideration of wiener attack and whitening filtered detection
InactiveUS7076081B2Easy to detectEliminate the problemUser identity/authority verificationCharacter and pattern recognitionHypothesisEngineering
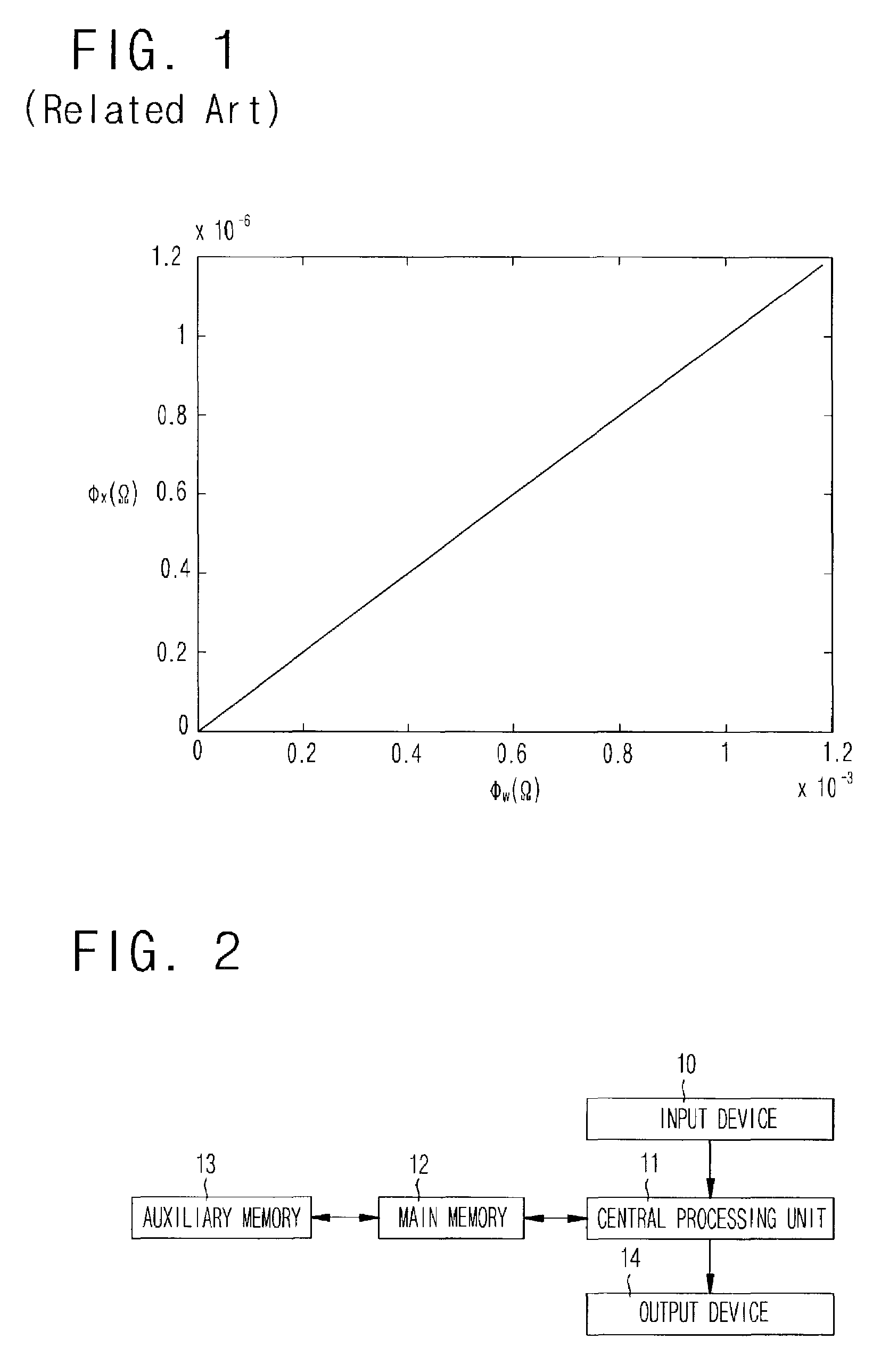
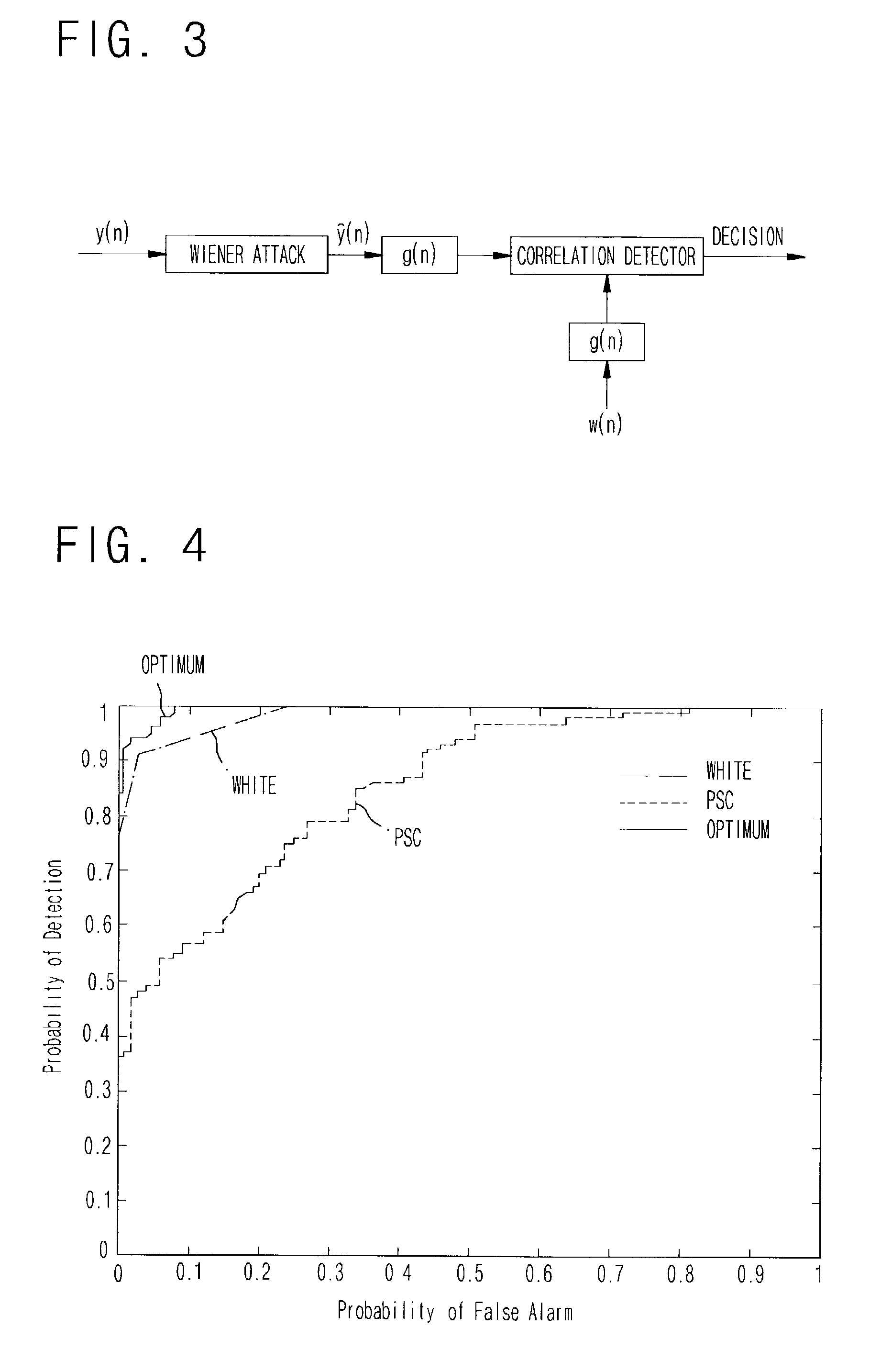
Disclosed a method of designing a watermark having the power spectral density optimized so that the detection performance can be improved by employing the whitening filtered detection after the Wiener attack. The power spectral density of the watermark is designed using an optimization method that can improve the entire detection performance by reflecting the gain of the whitening filter after the Wiener attack. A higher detection gain is obtained using the whitening filter after the Wiener attack, and the expected value of the difference between test statistics of the two hypotheses that the watermark exists and the watermark does not exist, respectively, is maximized to optimize the detection performance. Regarding the expected value of the difference between the test statistics as an objective function, the power spectral density of the watermark, which corresponds to a maximum differentiated value of the power spectral density of the watermark using the Lagrange multiplier method, is obtained.
Owner:ELECTRONICS & TELECOMM RES INST
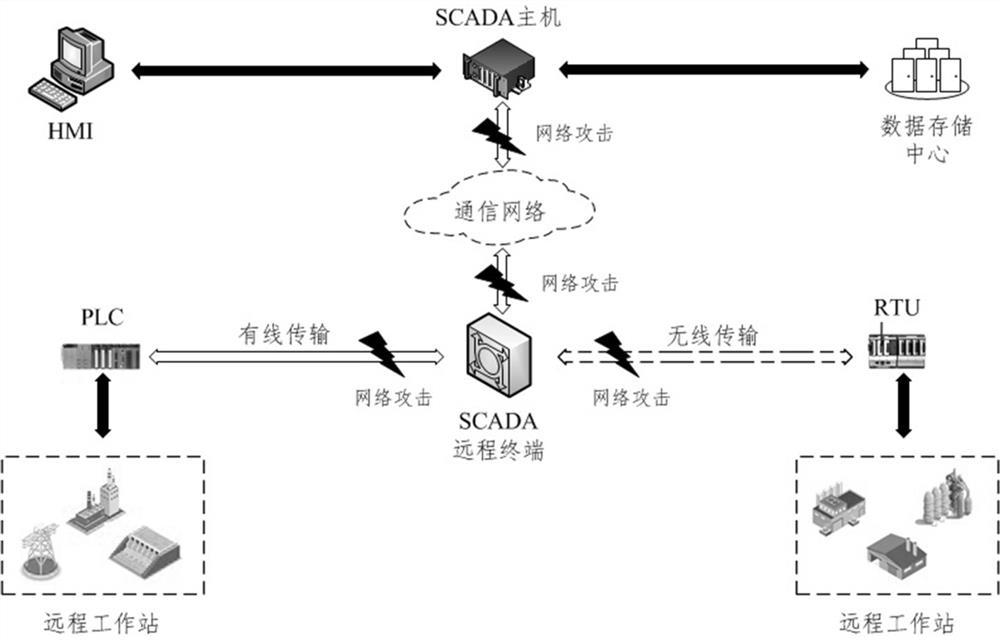
Industrial control system intrusion detection method based on small sample learning
ActiveCN111931175AStrong defenseCharacter and pattern recognitionPlatform integrity maintainanceInternet trafficTraining set
The invention discloses an industrial control system intrusion detection method based on small sample learning. The method comprises the following steps: dividing an original data set extracted from industrial control system network traffic into a detection model training set and a basic model training set; performing dimension reduction on continuous data matrixes in the basic model training setand the detection model training set by using a principal component analysis method; encoding discrete data matrixes in the basic model training set and the detection model training set by using a one-hot encoding method; constructing a small sample training task required by basic model training by using the processed basic model training set; training a basic model based on a convolutional neuralnetwork by means of the constructed small sample training task; based on the trained basic model, using the processed detection model training set for further training, and obtaining a detection model. By means of the center vectors of three different types of samples of the original data set, real-time and effective detection of potential attacks in the network data flow is achieved.
Owner:SICHUAN UNIV
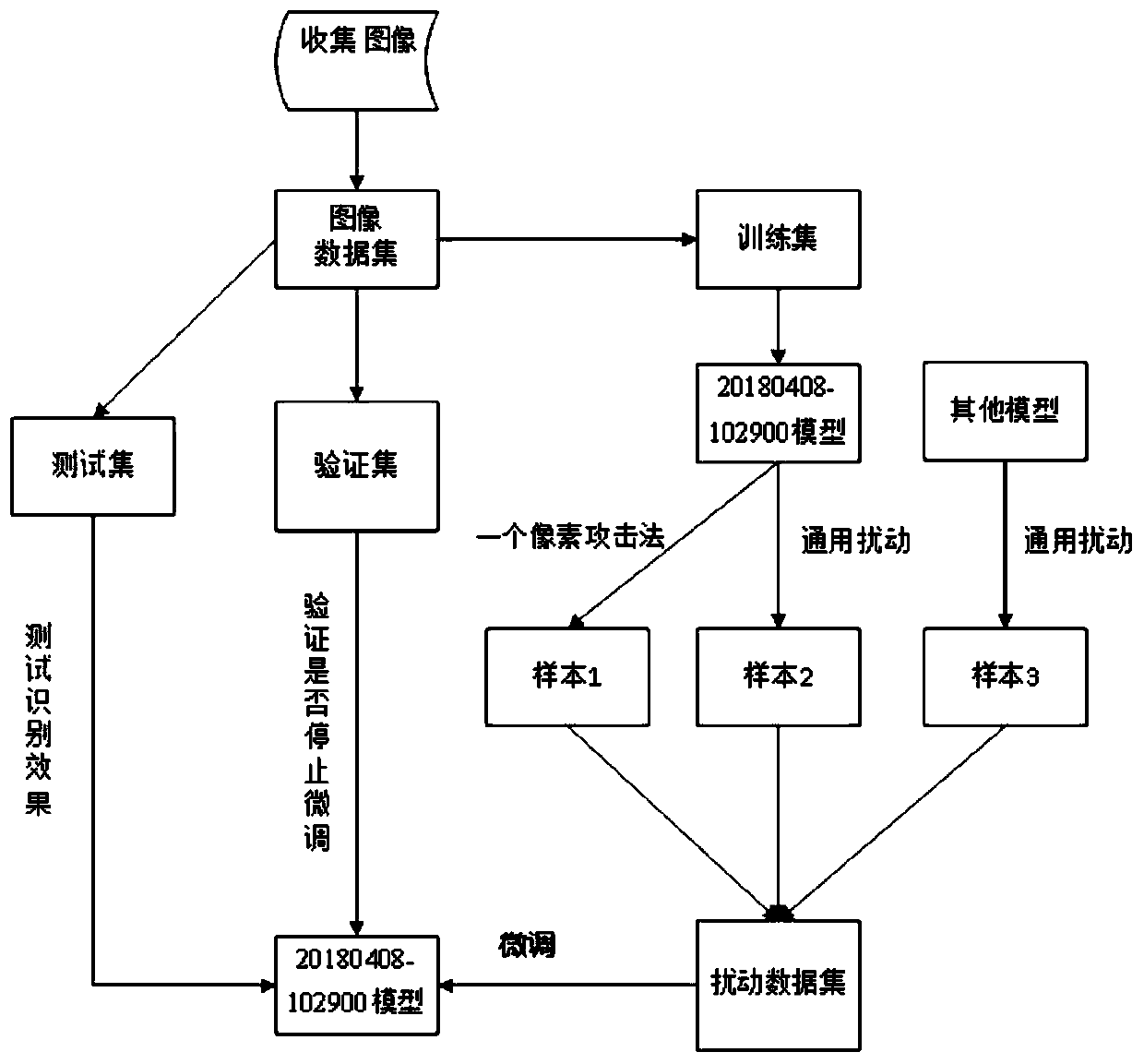
Image security identification method based on adversarial sample defense
PendingCN111414964AImprove defenseStrong defenseCharacter and pattern recognitionNeural architecturesData setAlgorithm
The invention provides an image security identification method based on adversarial sample defense. The method comprises the following steps: 1, firstly, collecting an image data set; 2, generating anadversarial sample by using a pixel attack method, according to the attack method, utilizing a differential evolution algorithm to iteratively modify each pixel of a test set image to generate a sub-image, then testing the attack effect of each sub-image, and using the sub-image with the best attack effect as an adversarial sample; 3, generating an adversarial sample by using a general disturbance generation method; 4, generating an adversarial test set based on the adversarial sample; 5, taking the image data of the training set as training data, and carrying out the fine adjustment of an original pre-trained model; and 6, performing image recognition on the test set, and checking an image recognition effect. The method has a good defense capability for one pixel generation confrontationdisturbance, has an excellent defense capability for a confrontation sample generated by general disturbance, cannot generate any influence on a generated image recognition model by the general disturbance, and can be used for recognition and classification of electronic files and the like.
Owner:SHANGHAI GOLDEN BRIDGE INFOTECH CO LTD
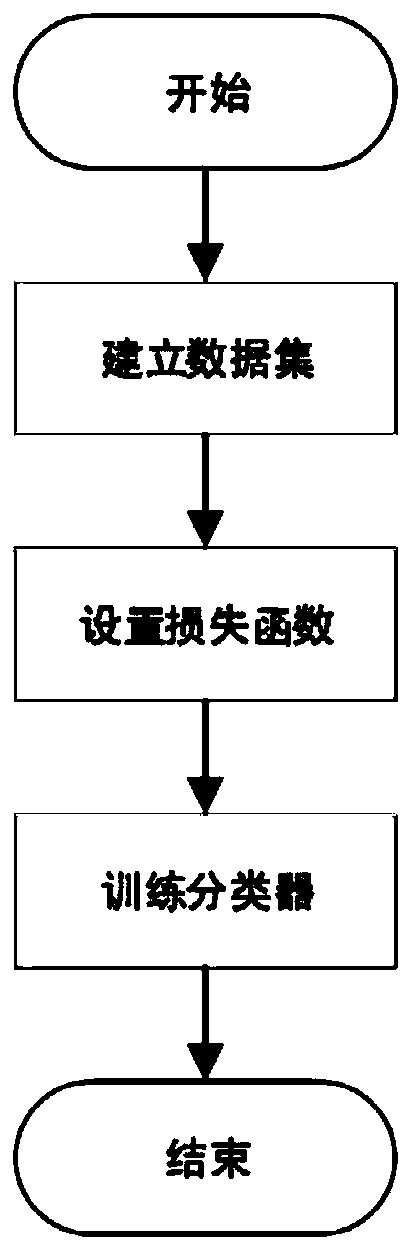
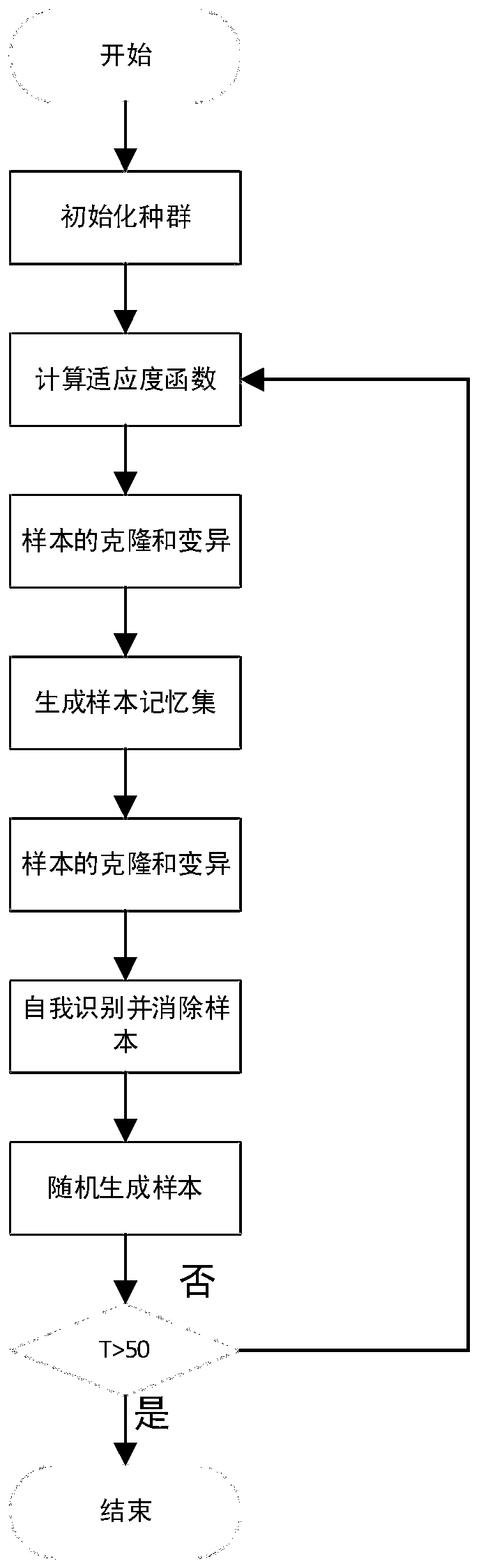
Countermeasure defense method for countermeasure attacks based on artificial immune algorithm
ActiveCN111598210AIncrease diversityEasy to adjustInternal combustion piston enginesCharacter and pattern recognitionAlgorithmArtificial immune algorithm
The invention discloses a confrontation defense method for confrontation attack based on an artificial immune algorithm. The method comprises the following steps: (1) obtaining an original picture sample set; based on the original picture sample, generating an adversarial sample based on an artificial immune algorithm; merging the original picture sample and the adversarial sample, and dividing into a training set and a test set; (2) training a picture classifier by using the training set and the test set to obtain a picture recognition model; and (3) identifying the to-be-identified picture by utilizing the picture identification model to realize confrontation and defense of picture identification. According to the invention, the technical problems of poor defense effect and low classifier identification accuracy in the prior art when attacks are resisted based on an artificial immune algorithm can be solved.
Owner:ZHEJIANG UNIV OF TECH
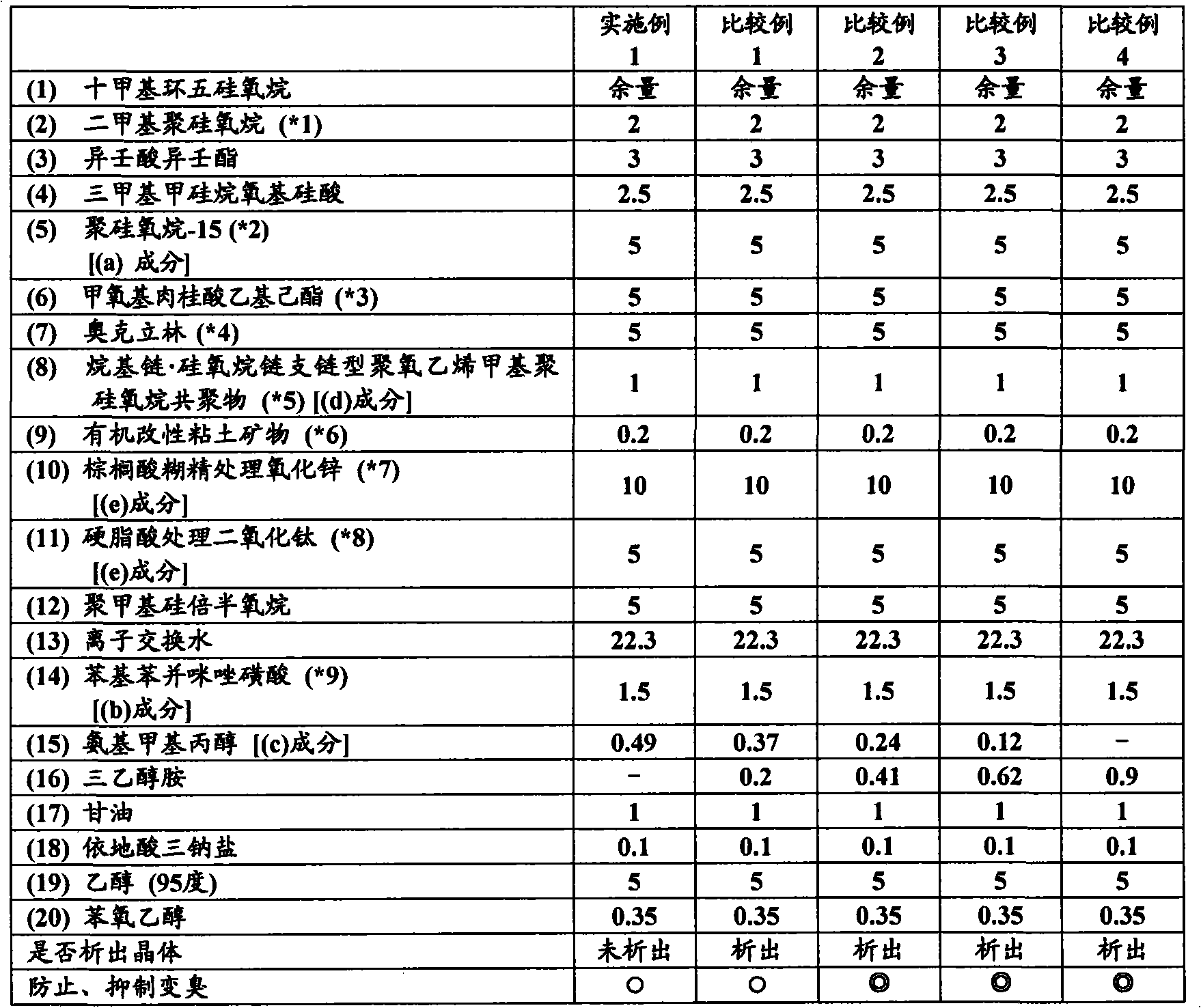
Water-in-oil emulsion type sunscreen cosmetic
ActiveCN101951876AStrong defenseImprove stabilityCosmetic preparationsToilet preparationsWater in oil emulsionNuclear chemistry
Disclosed is a water-in-oil emulsion type sunscreen cosmetic which contains (a) 0.1 to 10 mass% of dimethyl diethyl benzalmalonate, (b) 0.02 to 8 mass% of phenylbenzimidazole sulfonic acid, and (c) a neutralizing agent for the component (b), wherein an aqueous phase makes up 40 mass% or less of the cosmetic. It becomes possible to provide a water-in-oil emulsion type sunscreen cosmetic which comprises (a) dimethyl diethyl benzalmalonate and (b) phenylbenzimidazole sulfonic acid, does not cause the crystallization of phenylbenzimidazole sulfonic acid contained therein, and is extremely stable over time.
Owner:SHISEIDO CO LTD
Active threat detection system
The invention discloses an active threat detection system. Through an Internet outlet deployed at a unit needing monitoring, massive dispersed security information produced by a monitoring host, network equipment and safety equipment is regulated, gathered, filtered and analyzed in a correlation manner. A gateway monitoring system is linked with the virus feature library, the malicious domain library and other national-level network security data centers of the national computer network emergency response technical team / coordination center of China. Various national basis resources are fully utilized to make linkage analysis and intelligent decision so as to accurately find out various complex network security events. Hidden security problems existing in an in-network host are found through comparison of corresponding traffic characteristics, thus achieving the functions of gate traffic monitoring, pre-warning and filtering. The active threat detection system of the invention has the beneficial effect that the system has strong defense capability and can fully guarantee the security of the financial information system.
Owner:国家计算机网络与信息安全管理中心江苏分中心 +1
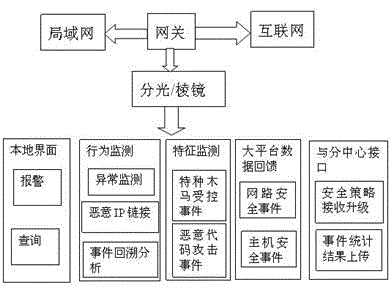
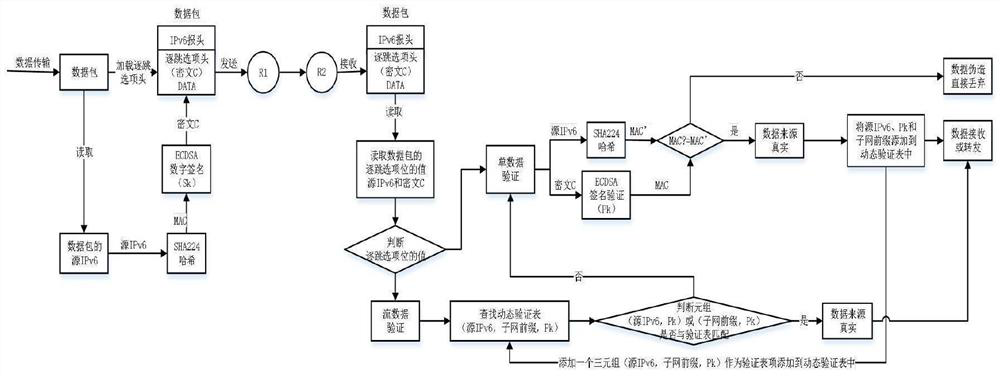
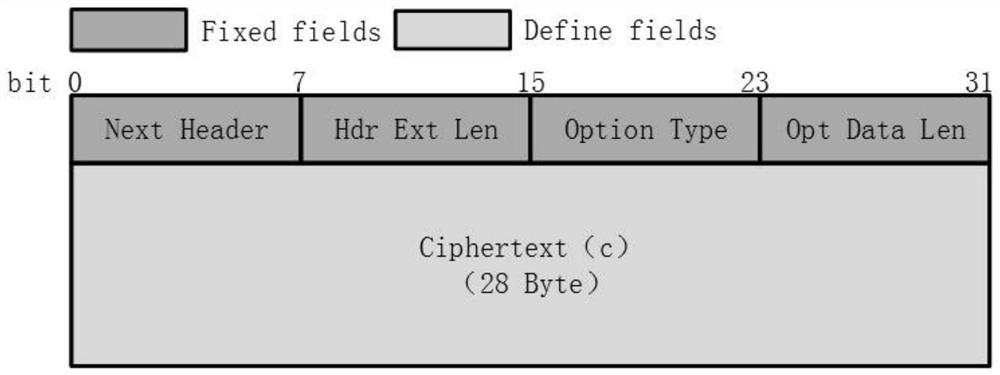
IPv6 option explicit source address encryption security verification gateway and verification method
PendingCN114389835AUniversally applicableRealize integrationUser identity/authority verificationData packCiphertext
The invention discloses an IPv6 option explicit source address encryption security verification gateway, and the security verification gateway comprises a data probability collection module which is used for carrying out the probability collection of a data packet of transmission data, and transmitting the data packet to an encryption function module; the encryption function module is used for encrypting and signing a source IPv6 address in the data packet, loading a ciphertext obtained through signature into a hop-by-hop option header in the data packet and sending the data packet carrying source address verification information to a destination end; and the verification function module is used for verifying the source address information of the received data and the initialized creation and dynamic update of the dynamic verification table. The invention further provides a verification method of the IPv6 option explicit source address encryption security verification gateway, transmitted data can be encrypted, the transmitted data can be verified, and integration of encryption and verification is achieved.
Owner:QINGHAI NORMAL UNIV +1
Synergy-based biocontrol of plant pathogens
Owner:RGT UNIV OF CALIFORNIA
Synergy-based biocontrol of plant pathogens
Owner:RGT UNIV OF CALIFORNIA
Safety isolation method based on firewall system
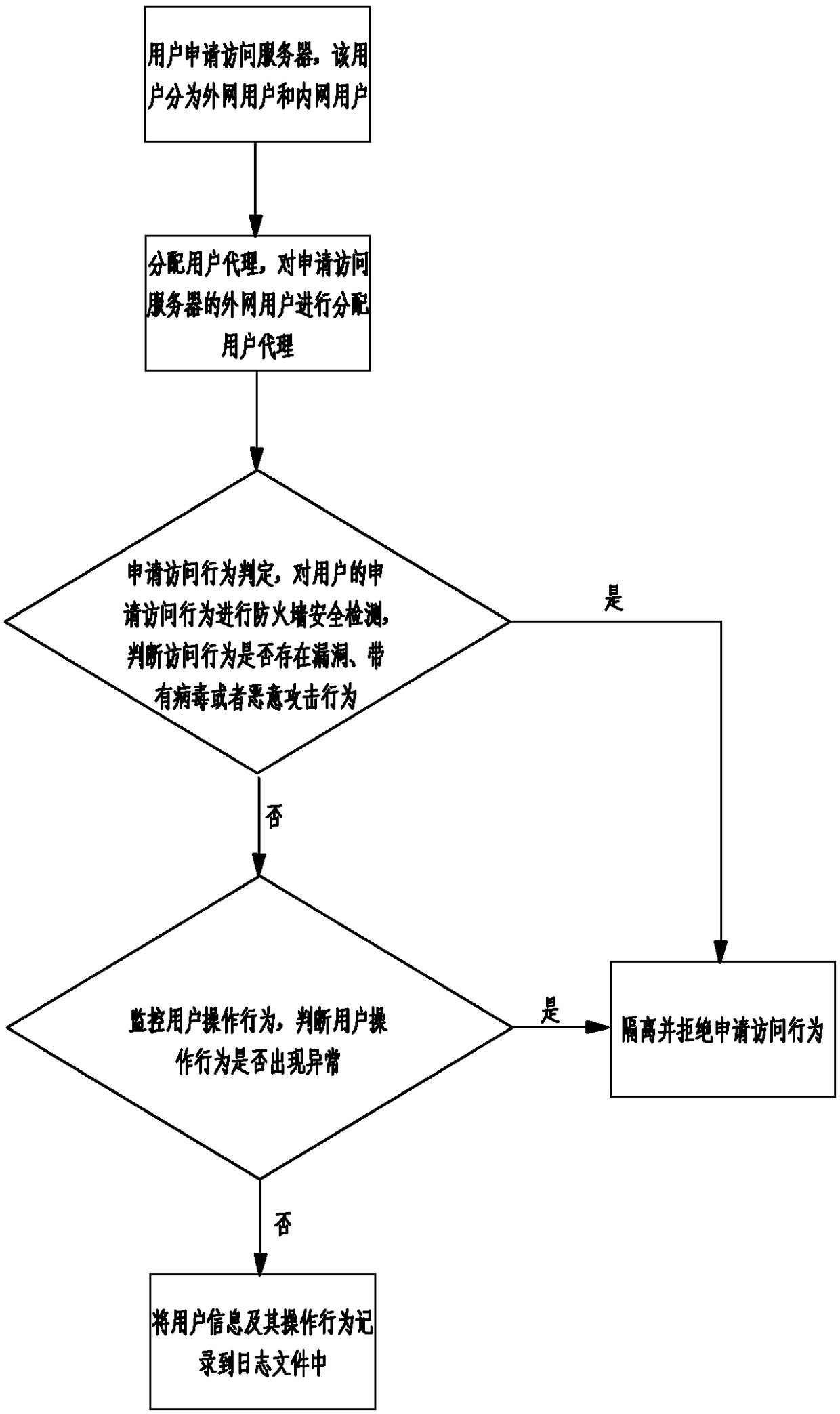
The invention discloses a safety isolation method based on a firewall system, which comprises the steps of: users apply to access a server, wherein the users are divided into internet users and intranet users; allocating user agents, i.e., carrying out allocation of the user agents on the internet users applying to access the server; and carrying out determination of application access behaviors,i.e., carrying out firewall safety detection on the application access behavior of each user, determining whether the access behavior has a bug, or carries viruses or is a malicious attack behavior, if yes, isolating and refusing the application access behavior, and if no, allowing the application access behavior. According to the invention, the intranet users and the internet users are distinguished, and external access is limited by carrying out allocation of the user agents on the internet users, so that the system has higher guarantee and is safer, meanwhile, privacy and safety of the intranet users are improved, and a defense function of the firewall system is better than that of a conventional firewall.
Owner:GUANGDONG NENGLONG EDUCATION
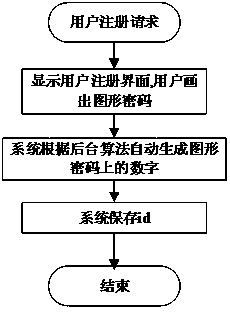
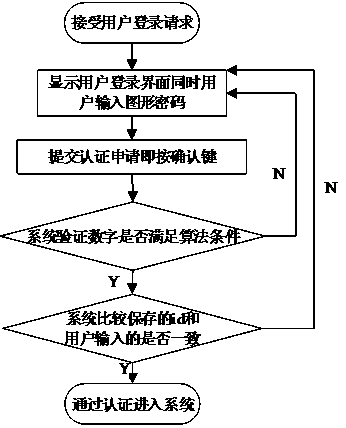
A graphics unlocking cryptographic authentication method based on graphics addition algorithm
ActiveCN108959898AImprove securityIncrease password spaceDigital data authenticationGraphicsUser input
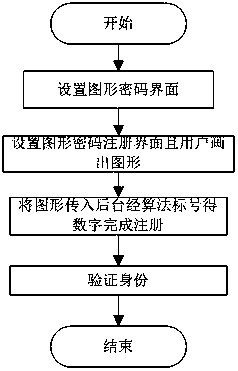
The invention discloses a graphics unlocking password authentication method based on a graphics addition algorithm. The method comprises the following steps: (1) setting a graphic password jiugongge interface; (2) setting a graphic password registration interface user and drawing a graph; (3) passing the graph into a background to obtain a digital password through an algorithm label to complete registration; and (4) a user inputting the graphics to be verified and the digital password to judge whether the graphics and the digital password satisfy the algorithm completion verification. On the basis of a traditional graphic password, the method improves the security of the user password by adding an algorithm, increases the password space, can attack the shoulder peep, the dictionary attackand the violent crack with stronger defensive power, and can be used for the identity authentication of the desktop and the mobile terminal.
Owner:LANZHOU JIAOTONG UNIV
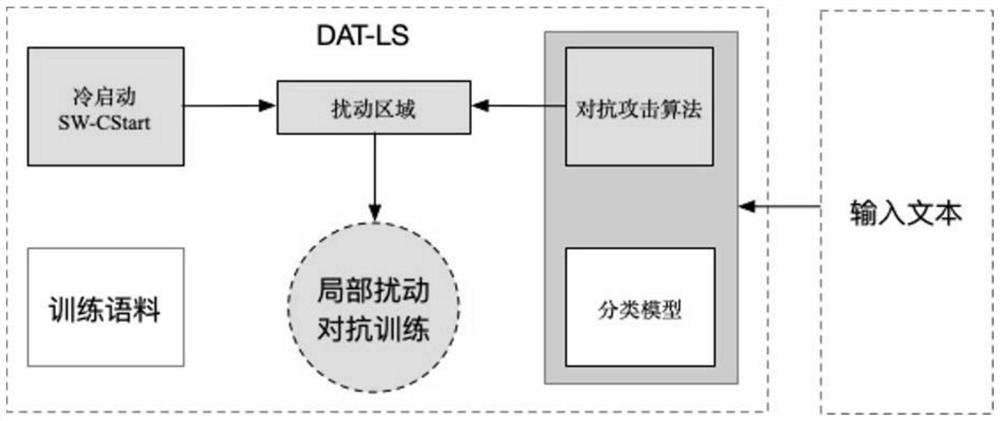
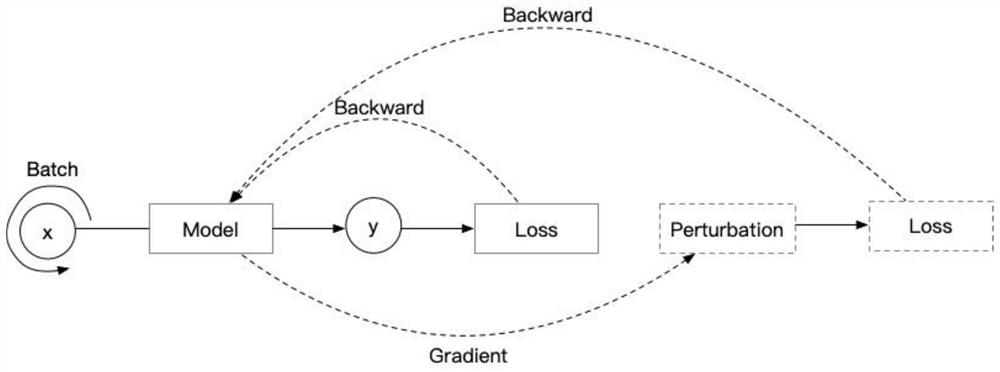
Adversarial sample defense algorithm based on local disturbance
PendingCN112528675AImprove robustnessImprove generalization abilitySemantic analysisNeural learning methodsAlgorithmText categorization
The invention discloses an adversarial sample defense method DATLP based on local disturbance. The algorithm belongs to the type of adversarial training and is used for improving the robustness of themodel to resist attacks of adversarial texts and maintaining credible processing of a text classification model. The algorithm provides improvement and training skills based on adversarial training,and is used for further improving the effect of adversarial training. The method is mainly summarized as follows: global disturbance of a previous adversarial training method is changed into local disturbance, and definition of local region disturbance is to shield vocabularies with obvious classification tendency in training data. The DATLP enables the model to learn more information from the overall semantics of the text, and prevents some vocabularies from playing an overweight role in model training so as not to generate negative effects on the performance of the model.
Owner:成都易书桥科技有限公司
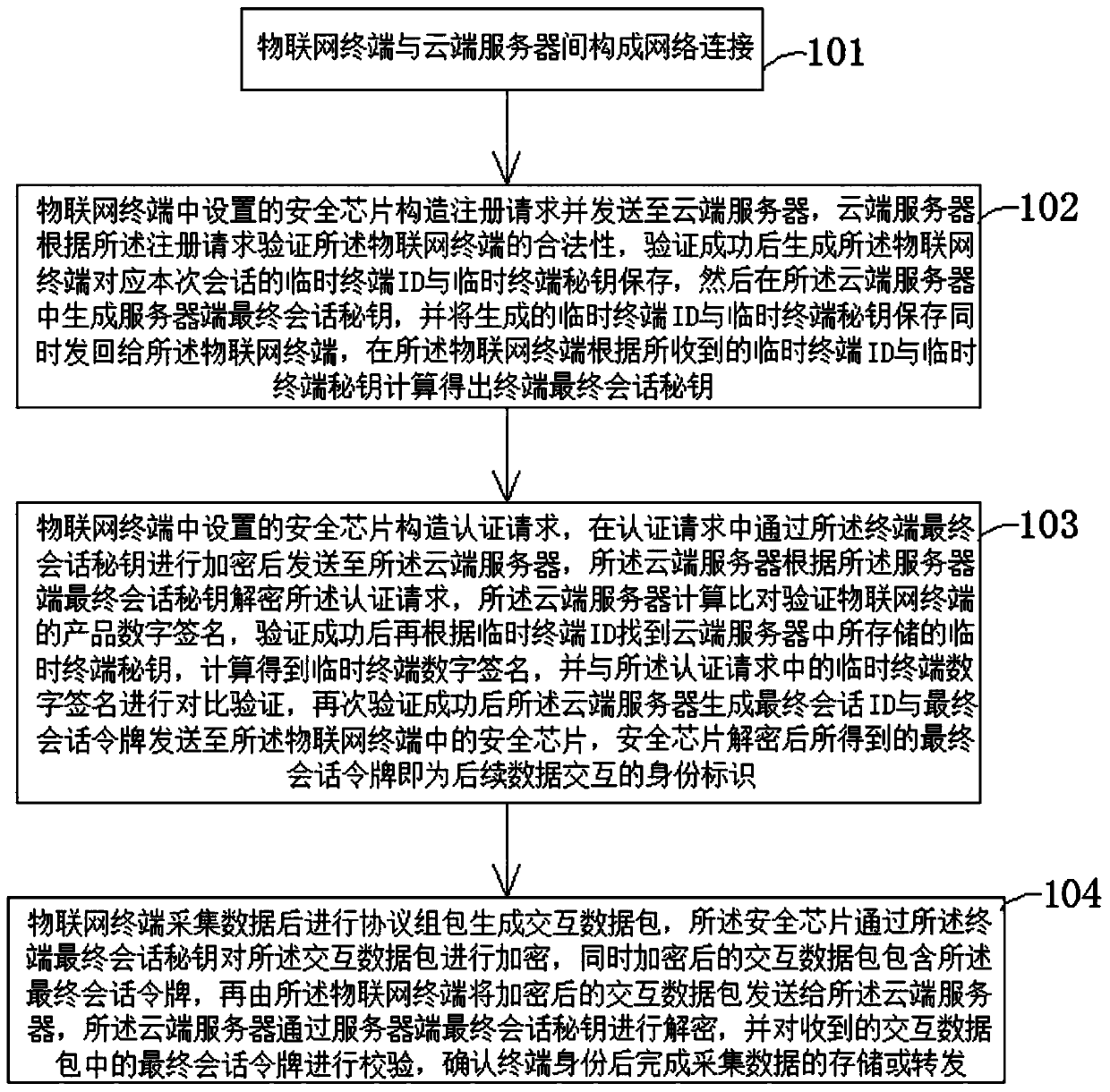
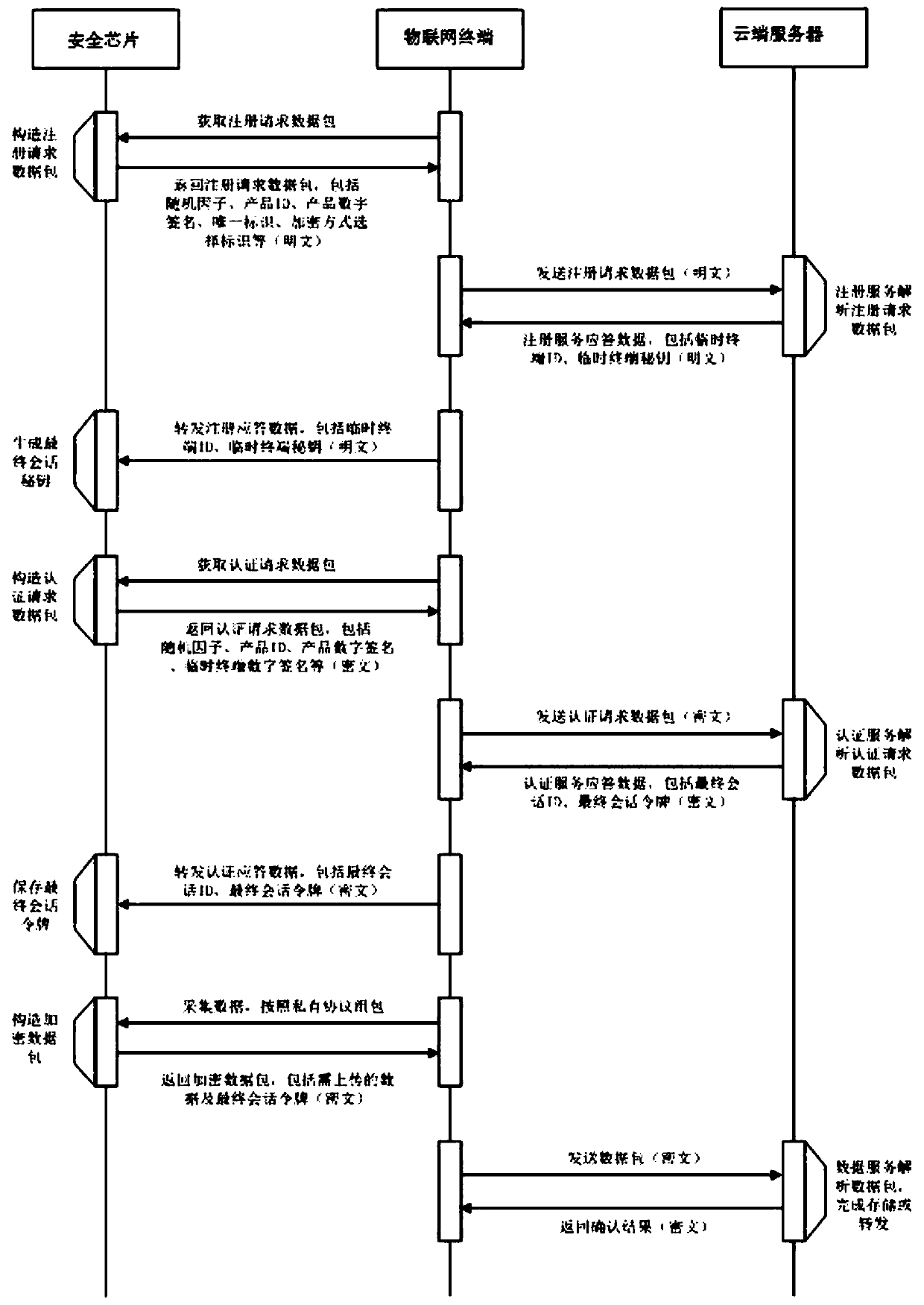
Internet of Things terminal security authentication method based on security chip
ActiveCN110545285AStrong defenseReduce system couplingUser identity/authority verificationEncryptionHardware authentication
The invention discloses an Internet of Things terminal security authentication method based on a security chip. Whole-process safety guarantee of three stages of registration service interaction, authentication service interaction and data service interaction between the Internet of Things terminal and the cloud server is completed. Security authentication is carried out in a mode of combining hardware authentication such as product digital signature authentication and software authentication such as security chip temporary terminal digital signature authentication, and the relatively strong defense capability can be provided for both hardware attacks and software attacks. Besides, all operations related to encryption and decryption are carried out by the cloud and the two ends of the security chip, the communication terminal is transparent, only data acquisition, processing and forwarding are carried out by the communication terminal, and security calculation is not carried out, so that separation of security logic and service logic is realized, the coupling degree of the whole system is reduced, and a higher security level is achieved.
Owner:北京方研矩行科技有限公司
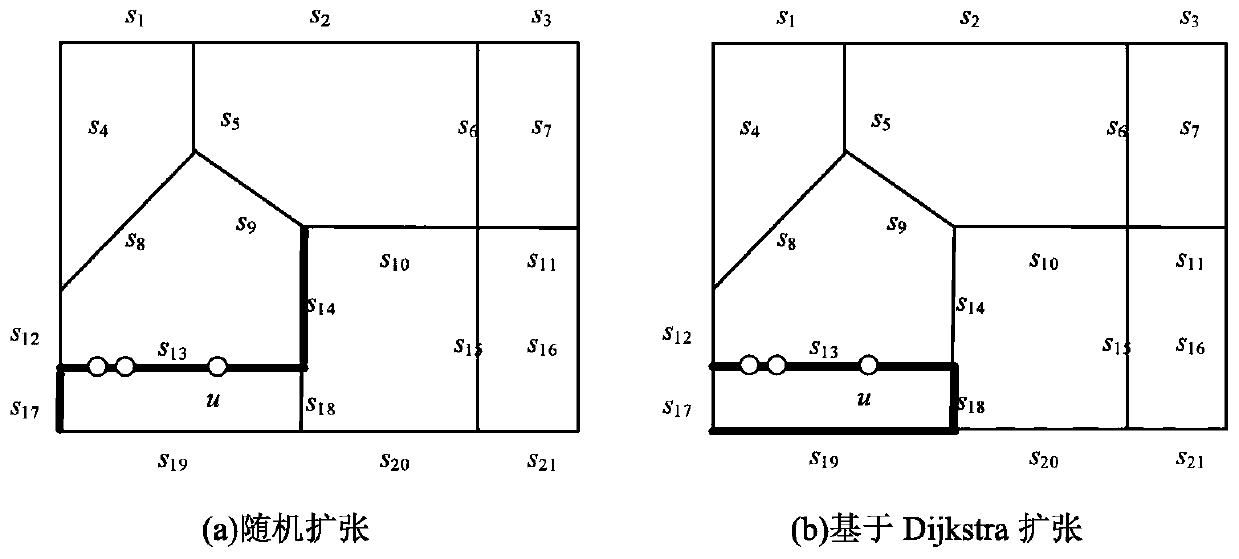
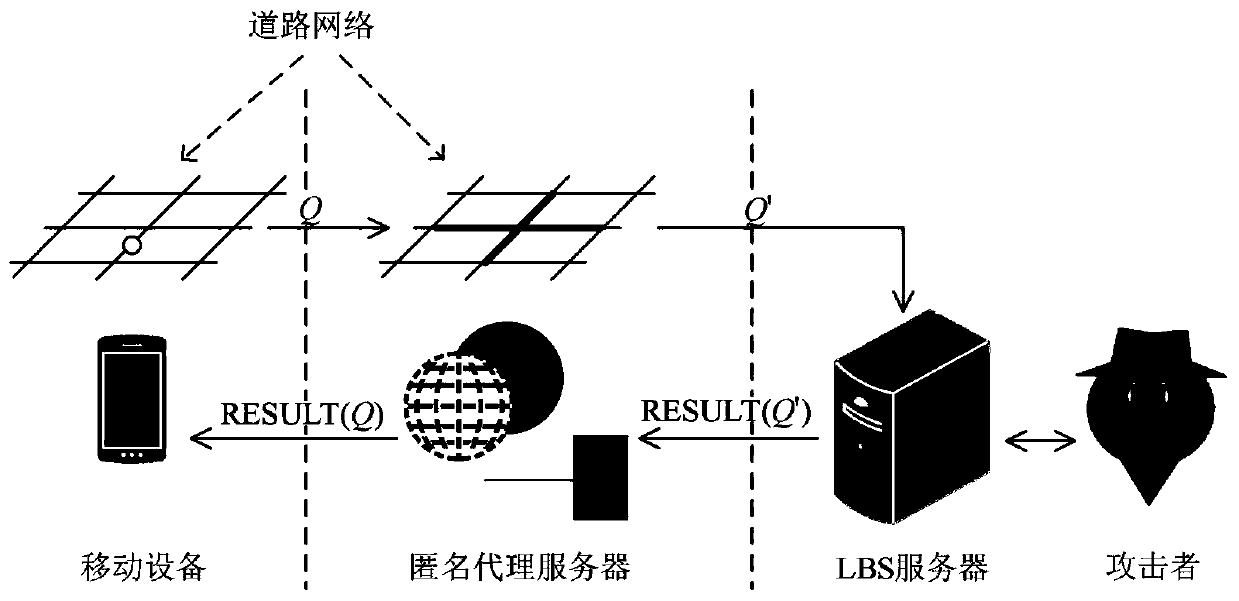
A user privacy protection method for road network continuous query attacks
The invention discloses a user privacy protection method for road network continuous query attacks. The method comprises the following steps: firstly, converting an actual map into an abstract directed weighted graph model, and introducing a position entropy as a privacy measurement standard; secondly, proposing a universal road segment expansion attack algorithm MSARN by combining the constraintcharacteristics of the road network on the action of the user and the maximum moving speed attack idea, and designing a protection algorithm CORE by taking the universal road segment expansion attackalgorithm MSARN as a defense target, so that the probabilities of the user on each road in the anonymous road segment set are as equal as possible; and finally, a moving object is generated on a realmap by using an SUMO tool according to the intelligent driving model in a simulation experiment, the effectiveness of the position entropy measurement is proved, and the superiority of the MSARN compared with a typical attack algorithm and the good resistance of CORE to the MSARN are analyzed. According to the method, the problems that an existing method is easily attacked and a real position hasa high exposure probability are solved, and the user privacy facing the road network is effectively protected.
Owner:NANJING UNIV OF TECH
Pipe leakage monitoring and defense system and method
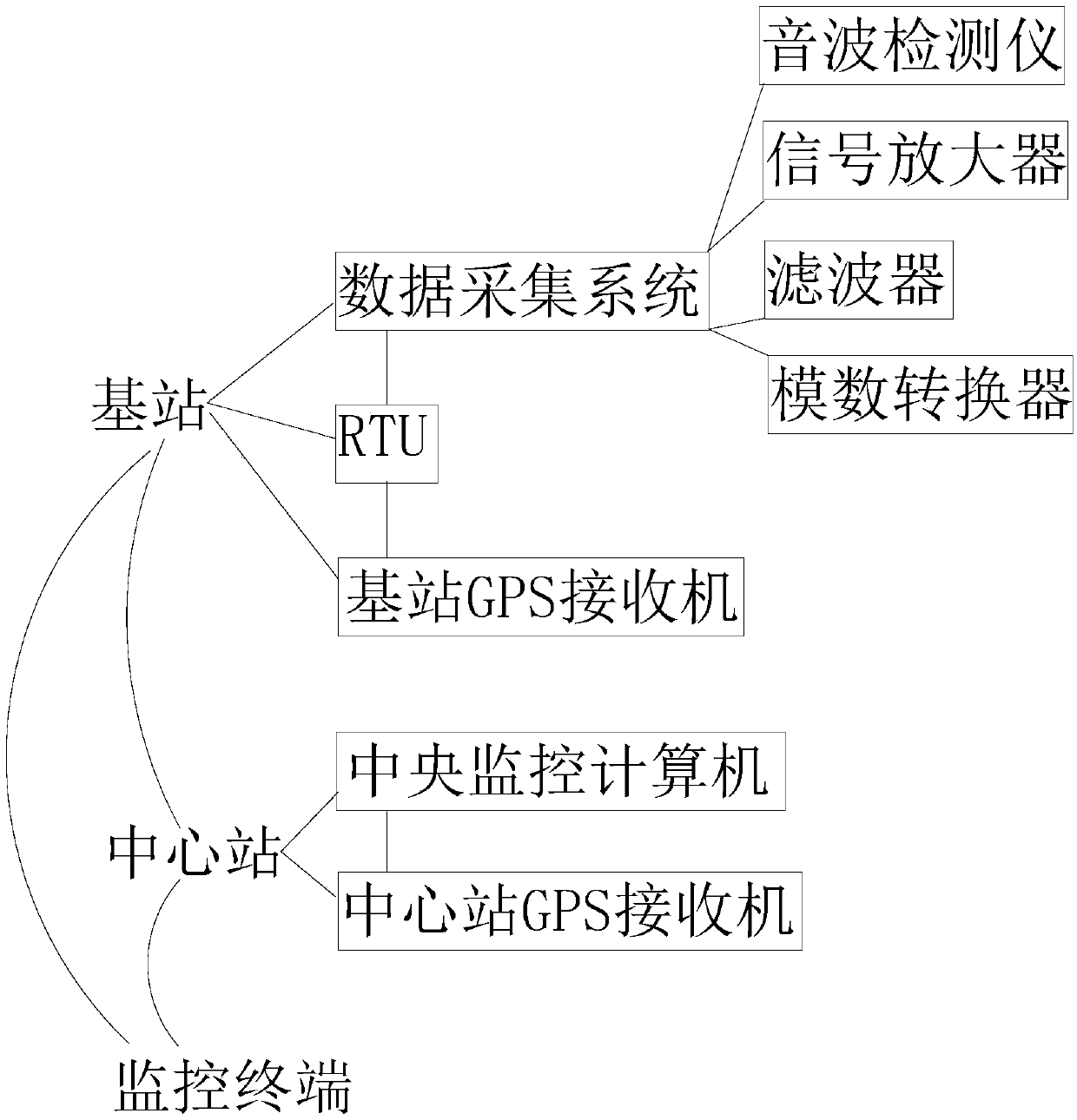
InactiveCN107606494ASuitable for regulationImprove reliabilityPipeline systemsData acquisitionGps receiver
The invention discloses a pipe leakage monitoring and defense system. The system comprises a base station, a center station and a monitoring terminal; the monitoring terminal is equipment used by users; the base station comprises a data acquiring system, a RTU and a base station GPS receiver; the center station comprises a center monitoring computer and a center station GPS receiver; the center monitoring computer is connected with the center station GPS receiver; the data acquiring system is connected with the RTU; the RTU is connected with the base station GPS receiver; the RTU transmits signals to the center station and the monitoring terminal through a network; and the center station and the monitoring terminal communicate through the network. Based on the system, the invention furtherprovides a pipe leakage monitoring and defense method. The system and the method can monitor pipes in real time, and analyze and judge according to detected sound wave signals to give an alarm to terminals and managers. The system and the method are high in reliability, high in defensiveness, low in construction, low in cost, convenient to install and maintain and suitable for national pipe network supervision.
Owner:上海邦芯物联网科技有限公司
Concave bulletproof ceramic plate
The invention discloses a concave bulletproof ceramic plate. The concave bulletproof ceramic plate comprises two parallel arch-shaped surfaces, connecting lines of four vertexes of the arch-shaped surfaces form a square, one of the arch-shaped surfaces protruding outwardly is a bullet-ward surface, a square recess is arranged above the bullet-ward surface, a first cambered surface, a plane and a second cambered surface, which are sequentially connected end to end, are arranged on the side wall of the recess from top to bottom, an extension surface of the plane and the bottom surface of the recess form a 135-degree included angle, and the distance between the upper edge of the side wall of the recess and the end of the arch-shaped surfaces is one ninth of the length of the arch-shaped surfaces. The bullet-ward surface of the ceramic plate is provided with the recess, the center of the recess has good bulletproof function for bullets, and the first cambered surface, the plane and the second cambered surface of the side wall of the recess can change applied force direction of the bullets, thus, a bulletproof plate spliced by a plurality of ceramic plates has higher defense capability.
Owner:ZHEJIANG LIGHT TOUGH COMPOSITE MATERIALS
Anticorrosive, fireproof, heat-insulating and heat-preserving special coating material and preparation method thereof
InactiveCN111793437AAdhesive compatibilityThermally CompatibleFireproof paintsAnti-corrosive paintsAdhesivePotassium feldspar
The invention discloses an anti-corrosion, fireproof, heat-insulation and heat-preservation special coating material and a preparation method thereof. The special coating material comprises a base material, a condensation polymerization raw material, a filler, a flame retardant and a coloring agent, wherein the condensation polymerization raw material adopts modified magnesium ore powder, modifiedaluminum ore powder and potassium feldspar powder, and the filler is prepared from calcium carbonate, barium sulfate, silicon micro powder, mica powder, fly ash hollow micro-beads, carbonized jade powder and bentonite. The preparation method comprises the following steps: mixing a base material and a condensation polymerization raw material, concentrating and polymerizing to generate a binder, uniformly mixing and stirring the binder, a filler and a flame retardant, and uniformly mixing and stirring the obtained mixture and a colorant to obtain the finished product. According to the invention, the adhesive, heat conductivity, flame retardancy, high temperature resistance and the like are compatible with one another, the affinity is outstanding, and the product has very strong defense capability to high temperature and combustion; the materials react and melt at different temperatures, and play a role in a relay manner along with the rise of the temperature, so that a fireproof systemis finally formed, and the stability of the coating in the fireproof process is ensured; and the service life is long.
Owner:营口嘉宸防火科技有限公司
Immunity and memory enhancing health care oral solution preparation method
InactiveCN109259217AImprove immunityCompatibility is scientific and reasonableNatural extract food ingredientsFood ingredient functionsOrange Peel extractHigh pressure
The invention belongs to the technical field of health care beverages and especially relates to an immunity and memory enhancing health care oral solution preparation method. The preparation method specifically comprises the following steps: (1) weighing raw materials; (2) smashing snakehead bone, performing high-pressure steam treatment, roasting, taking out, grinding and smashing in a superfinemode to obtain snakehead bone meal; (3) mixing and pulping fresh dandelion leaf, fresh carrot top and water, boiling by soft fire, continuing to boil by soft fire, adding purple glutinous rice and rhubarb rice while hot, evenly stirring, fermenting, boiling by soft fire, pulping, fermenting, performing hyperfiltration and taking filtrate to obtain fermented rice leaf juice; (4) adding snakehead bone meal, oriental paperbush flower extractive, orange peel extractive and carnation extractive into the fermented rice leaf juice, evenly stirring and homogenizing; (5) obtaining a finished product. The finished product has refreshing and slightly-sweet taste, has refreshing smell, has no stimulation, can effectively enhance the human body immunity, can promote intestinal tract health, can resistcancer, prevent cancer, inhibit tumor cell growth and protect the liver, can effectively relieve cold hands and feet, can enhance memory ability and can improve life quality.
Owner:含山县贝亲生物科技有限公司
Seabed vacuum pipeline defense system
ActiveCN108827082AFast transmissionStrong defenseDefence devicesAmmunition loadingOcean bottomAir tightness
The invention discloses a seabed vacuum pipeline defense system. The seabed vacuum pipeline defense system comprises a main pipeline, branch pipelines, air brake stations, base stations, seabed submarine missile bases, missile transport vehicles and retired submarines. The branch pipelines, the base stations and the seabed submarine missile base are arranged at certain intervals along the main pipeline of the seabed vacuum pipeline. The missile transport vehicles do not need airtight passenger cabins, missiles are directly located on a frame, and missile carriers have automatic loading and unloading functions. The missile bases can be remanufactured and constructed by using abandoned / retired submarines. The invention provides the submarine seabed missile bases which form a three-dimensional active and passive sea strategic defense system together with submarines and aircraft carriers by making full use of the characteristics of wide traffic extension range, high transmission speed andnatural hiding of the seabed vacuum pipeline, so that the security level of territorial waters is improved and meanwhile, the self security of the seabed vacuum pipeline and invasion resistance are protected effectively.
Owner:XIJING UNIV
Method and device for random jumping of network management plane address
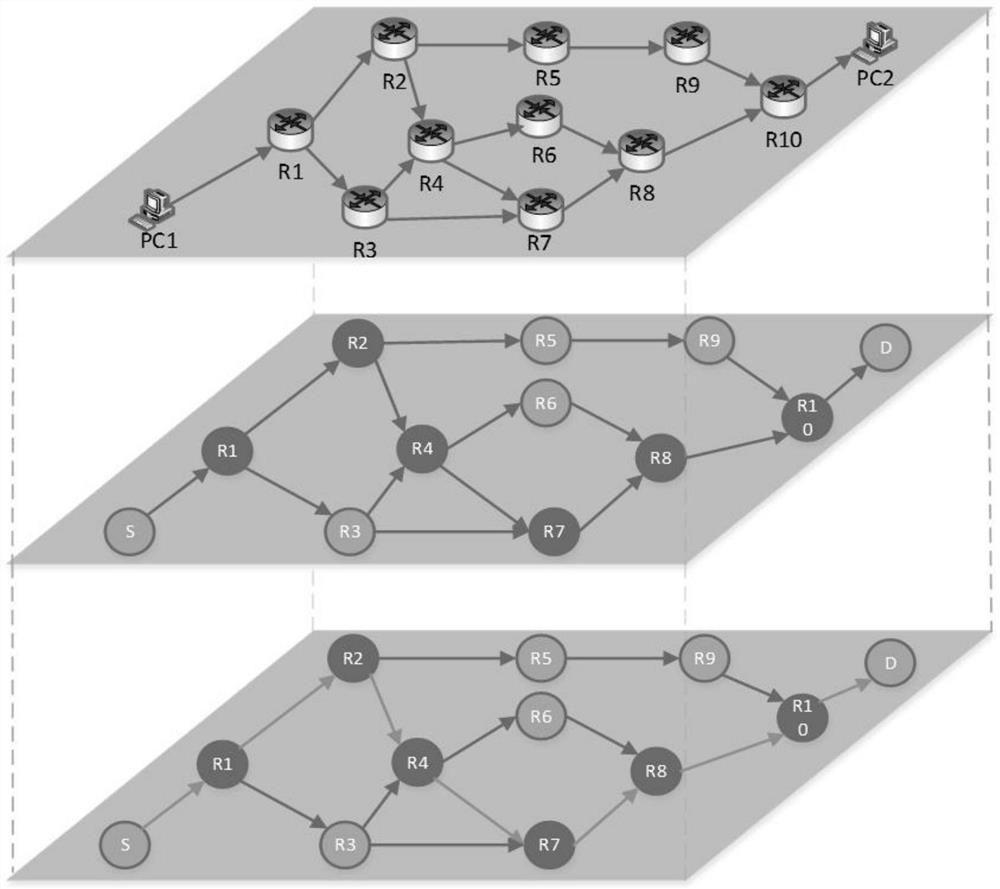
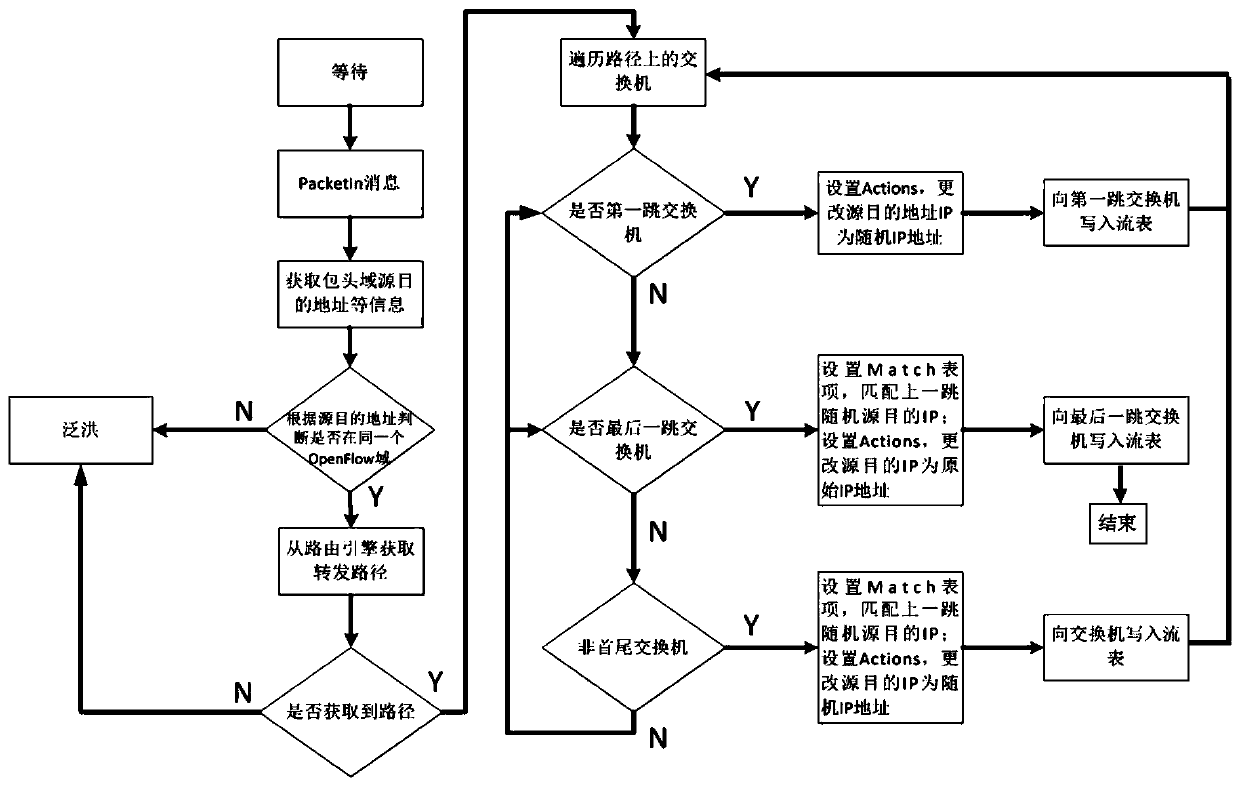
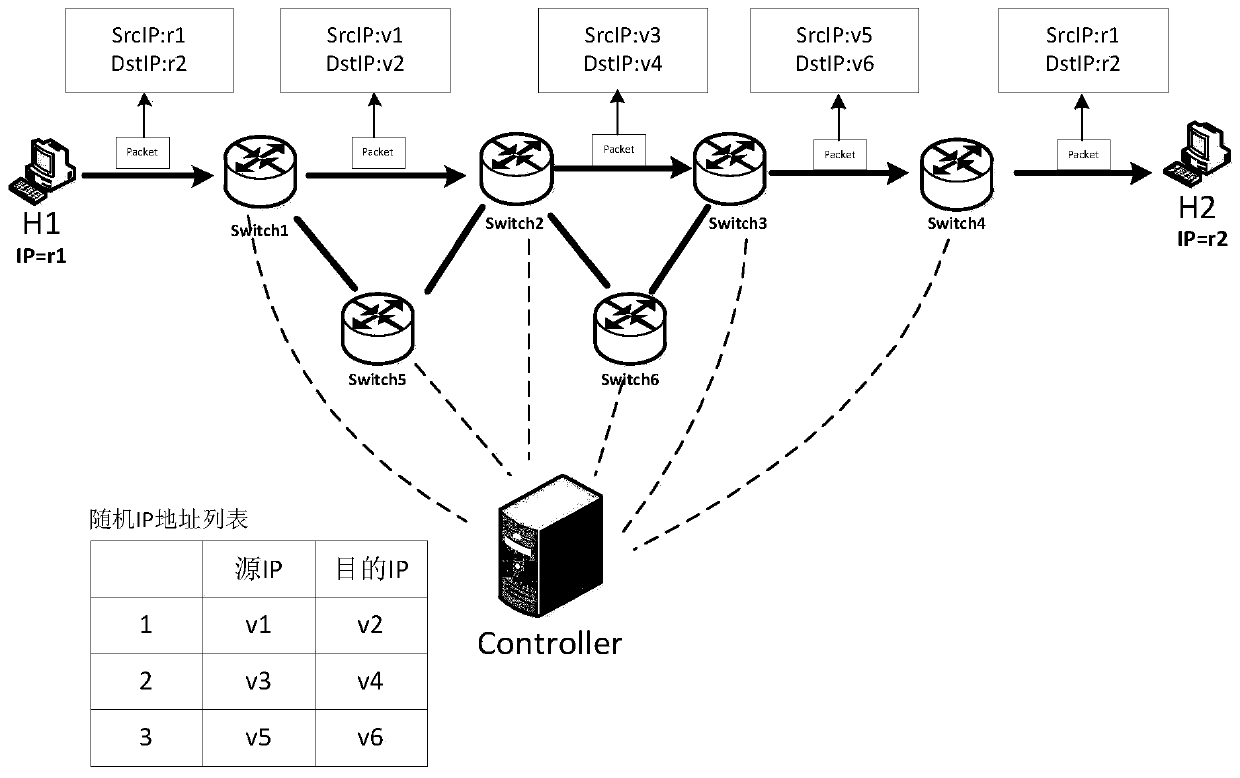
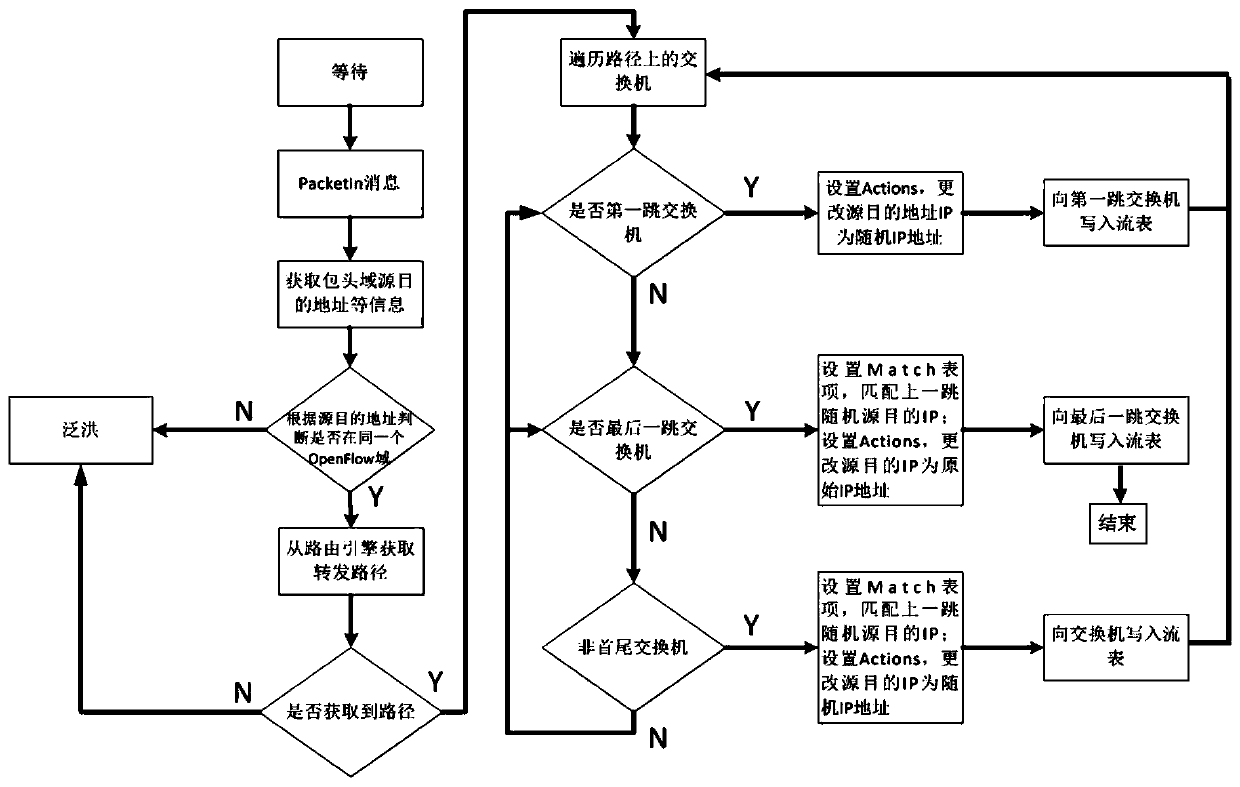
The invention relates to the technical field of prevention of network information eavesdropping, and provides a random jumping method and device for a network management plane address, for solving the problem in the prior art. Inherent IP addresses and ports of source and destination hosts do not need to be re-configured. By means of the method provided by the invention, address jumping has the relatively high frequency; an address is predicted more difficultly; therefore, two attributes including a network node address and port of a network are changed continuously; the network attack complexity and expense are increased; the risk that the network is successfully attacked is reduced; a controller in the invention traverses all switches on a route, and sends a flow table to each switch; according to the sent flow table, the selected switch on the route performs matching of data flows, and changing and forwarding of a header IP address; and data transmission between the source host and the destination host is completed through continuous jump of the IP address on a transmission path.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Combined protective pier for concrete viaduct
PendingCN111705635AReduce casualtiesReduce lossesBridge structural detailsBridge materialsCushioningLarge deformation
The invention provides a combined protective pier for a concrete viaduct and belongs to the field of road-bridge traffic safety facilities. The combined protective pier comprises a soft cushion layer,a protective bent sleeve plate, a cushioning bent sleeve plate, an impact-resistant bent sleeve plate, a protective bent plate base plate, a cushioning bent plate base plate and the like. A pier column and the protective bent sleeve plate are connected through a plurality of supporting connecting rods. A plurality of compressive deformation-resistant energy-absorbing inner-layer assemblies are arranged between the protective bent sleeve plate and the cushioning bent sleeve plate; a plurality of anti-compression-deformation energy-absorbing outer-layer assemblies are arranged between the cushioning bent sleeve plate and the impact-resistant bent sleeve plate, connecting bearing beads are arranged between the soft cushion layer and the impact-resistant bent sleeve plate, cushioning springsare arranged between the soft cushion layer and outer-layer connecting nails, and shear thickening glue filling layers are arranged in the rest spaces of the soft cushion layer and the impact-resistant bent sleeve plate. The damping effect and ductility can be well improved while large deformation can be borne, and impact collision energy can be fully dissipated when a vehicle body collides with apier main body structure.
Owner:沈阳促晋科技有限公司
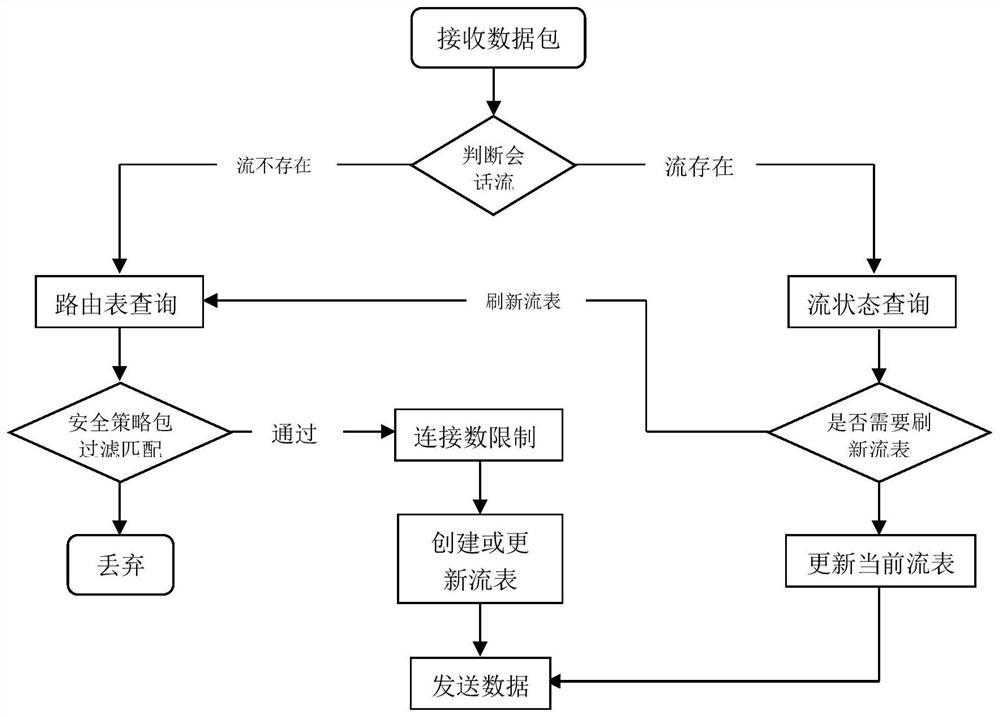
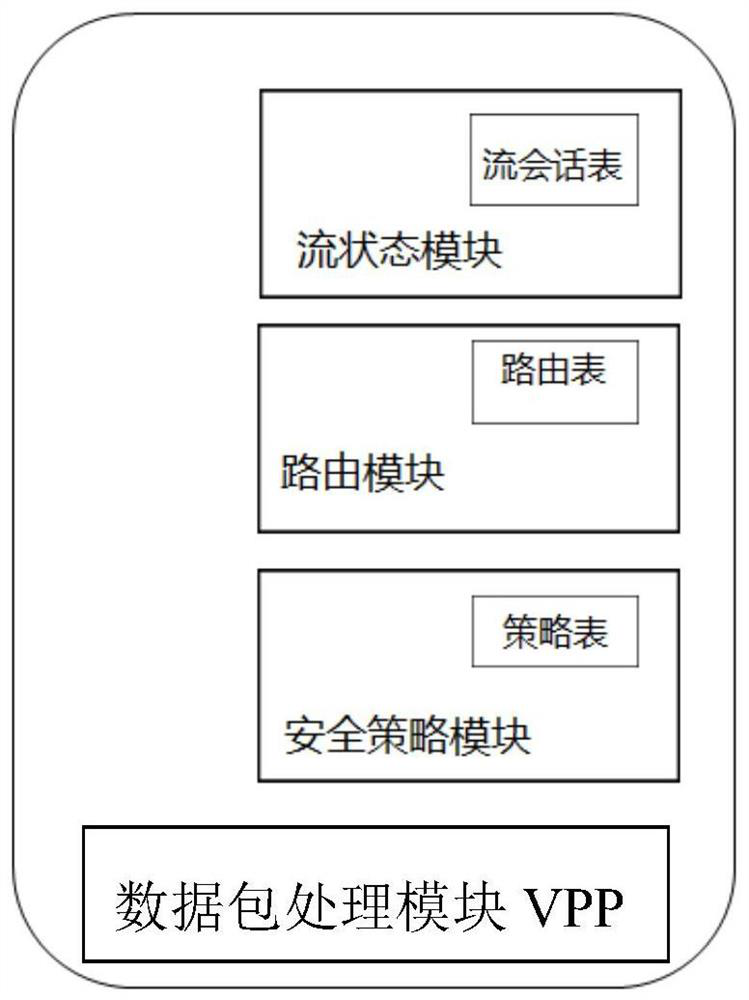
Method and device for realizing high-performance state firewall
PendingCN113765858AImprove throughputImprove the ability to process packetsData switching networksData packData stream
The invention provides a method and a device for realizing a high-performance state firewall. The device comprises a data packet processing module VPP, a routing module, a firewall policy module and a flow state module. The data packet processing module (VPP) is configured to receive transmission data from a network interface. And the routing module queries routing information and forwards data. And the firewall policy module is used for matching a firewall policy issued by a user, and performing security policy matching on the data flow of the session established for the first time according to an IP address, a protocol and a port number. And the flow state module is used for creating a flow session for the data flow successfully passing through the firewall policy, carrying out flow state detection on the flow in which the session is established, refreshing the flow table when the firewall policy is changed and the route is changed, periodically checking the flow table, and deleting the flow of which the state is not updated in a life cycle from the flow table. By reducing the repeated query matching of the firewall security policy table and the query of the routing table, the data packet processing capability of the VPP is improved, the throughput rate of the firewall is improved, and the data forwarding performance of the firewall is effectively improved.
Owner:中创为(成都)量子通信技术有限公司
A submarine vacuum pipeline defense system
ActiveCN108827082BFast transmissionStrong defenseDefence devicesAmmunition loadingSubmarineTerritorial waters
The invention discloses a submarine vacuum pipeline defense system, which comprises a main pipeline, a branch pipeline, an air lock station, a base station, a submarine latent missile base, a missile delivery vehicle, and a decommissioned submarine. Set up branch pipelines, base stations, and submarine latent missile bases. Missile transport vehicles do not need an airtight cabin. The missiles are directly loaded on the vehicle frame. The missile carrier has an automatic loading and unloading function; the abandoned / retired submarine can be used to rebuild the missile base. . The present invention makes full use of the characteristics of wide extension range, fast transmission speed and natural concealment of the submarine vacuum pipeline, and provides a latent submarine missile base, which together with submarines and aircraft carriers forms a three-dimensional, active and passive marine strategic defense system. Improve the security level of territorial waters, while providing effective protection for the submarine vacuum pipeline's own safety and resistance to invasion.
Owner:XIJING UNIV
A strain of Bacillus mohewei cjx-61 and its application
ActiveCN110628661BStrong defenseEnhanced inhibitory effectPlant growth regulatorsBacteriaBiotechnologyAlternaria
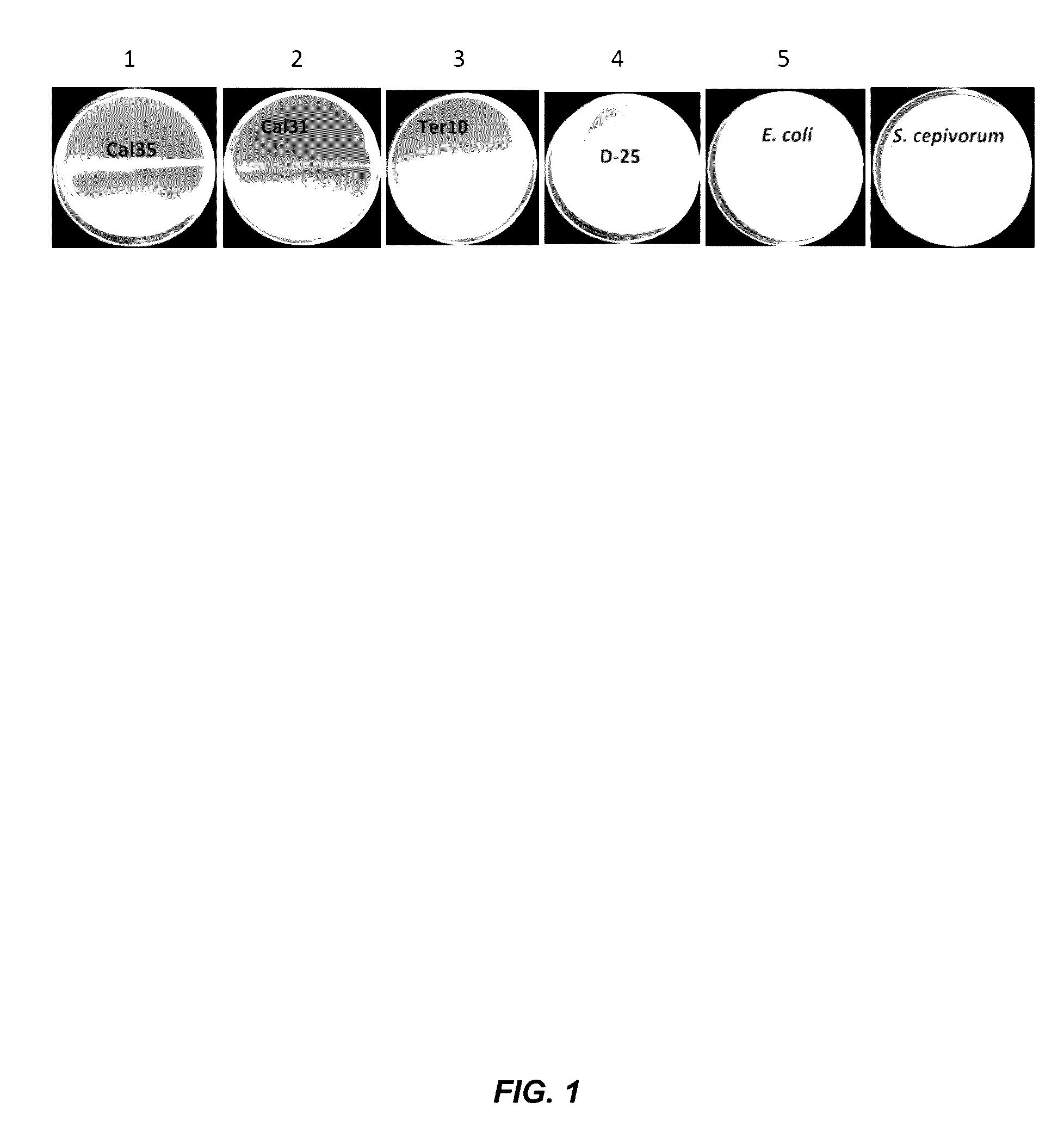
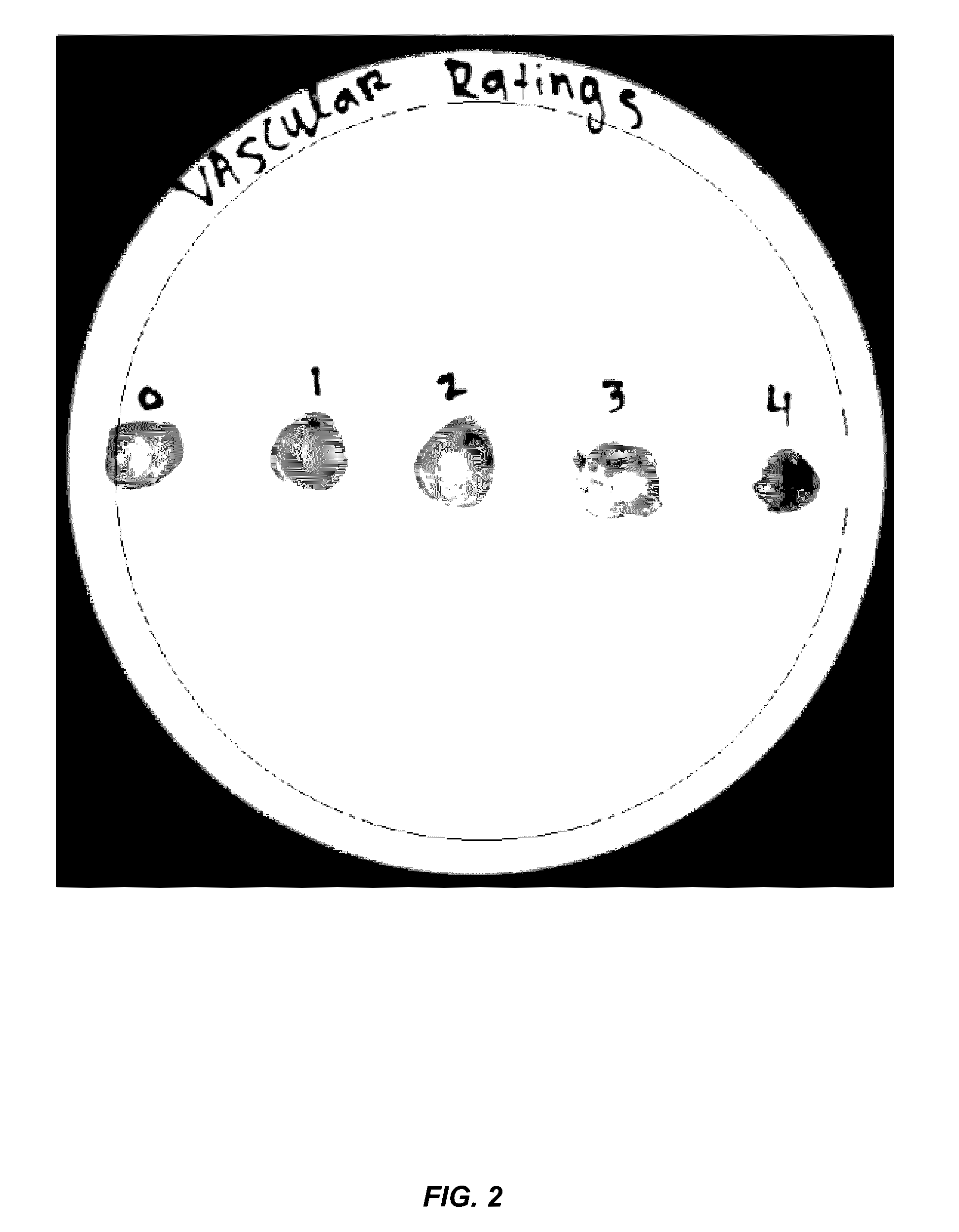
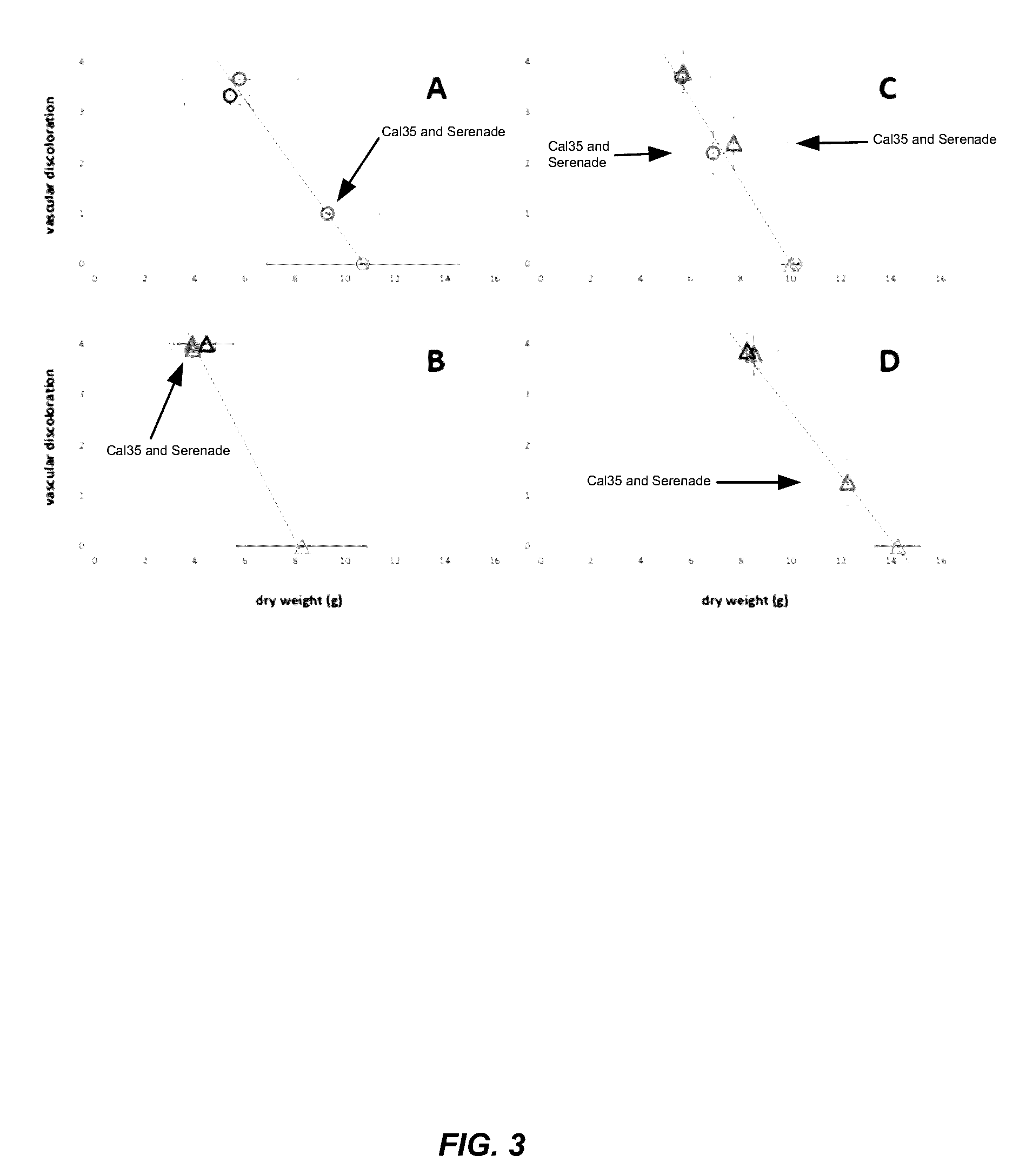
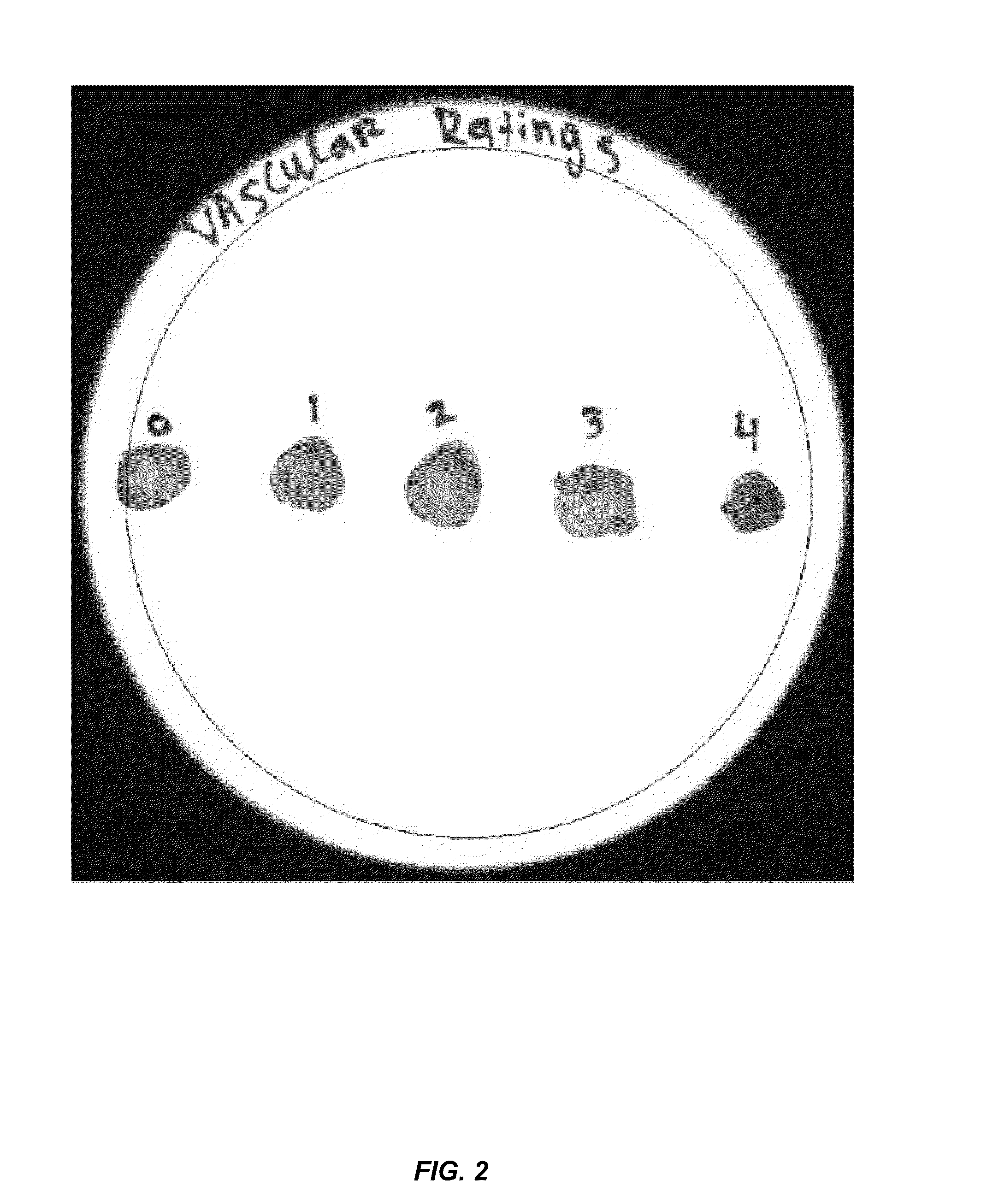
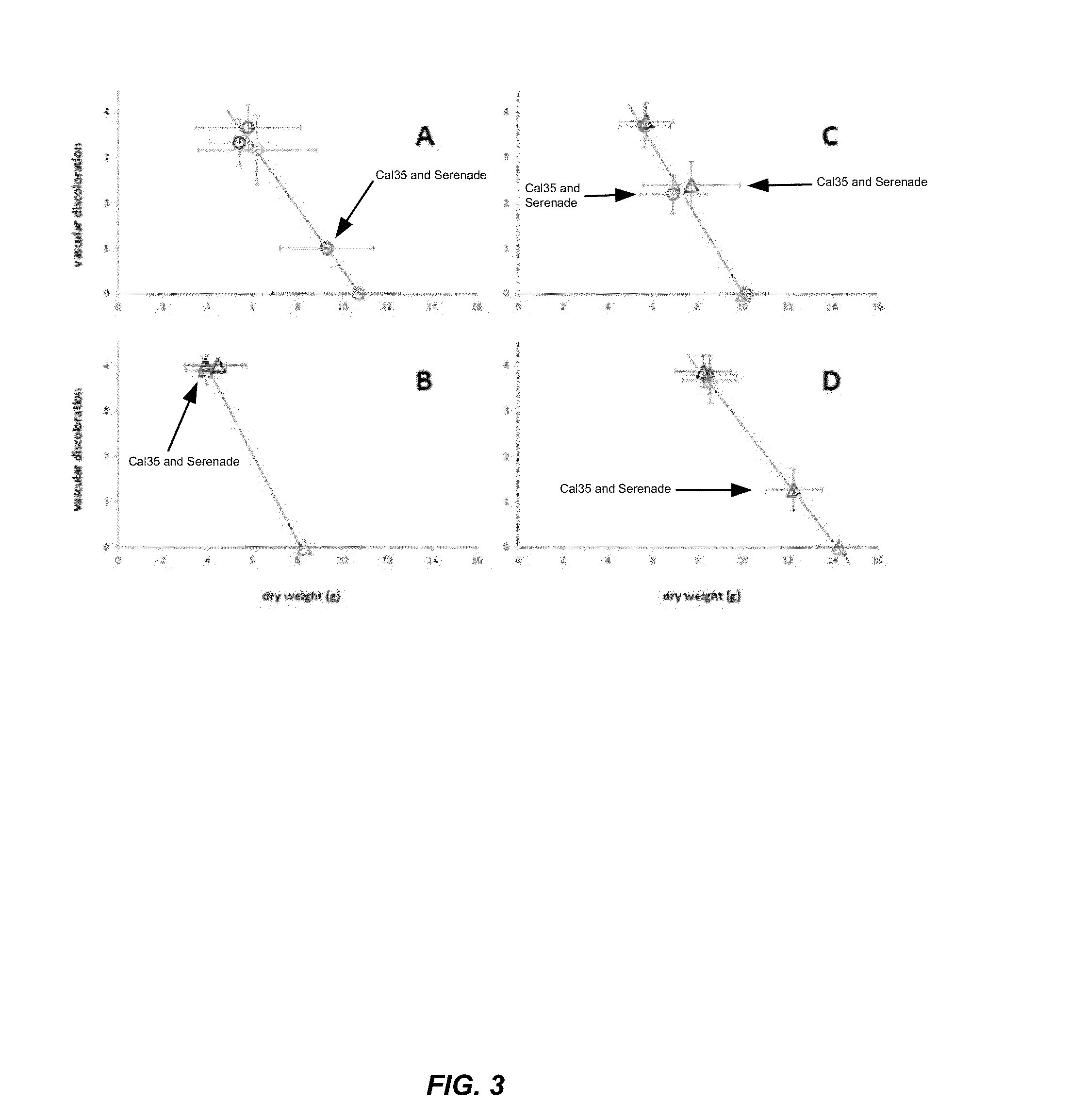
The antagonistic bacteria provided by the present invention is isolated from the potato rhizosphere soil of the disease and obtains a strain of Bacillus mohaiwei CJX-61, and the Bacillus mohaiwei CJX-61 is named as Bacillus mojavensis . It is preserved in the General Microorganism Center of China Microbiological Culture Collection Management Committee, and the preservation number is CGMCC NO.17660. Bacillus mohewei CJX‑61 has the ability to produce chitinase, cellulase, β‑1,3‑glucanase, protease, siderophile, and HCN. CJX‑61 is effective against Fusarium oxysporum, Pyrium oryzae, Sclerotinia sclerotiorum, Fusarium moniliforme, Sclerotinia sclerotiorum, Botrytis cinerea, Fusarium graminearum, Alternaria solani, Fusarium elderberry, etc. All plant pathogenic fungi have a good inhibitory effect. Bacillus mohewei CJX‑61 confers strong defense against potato black mole and increases potato yield under field conditions.
Owner:HARBIN NORMAL UNIVERSITY
Site access response method and device and electronic equipment
The embodiment of the invention provides a site access response method and device and electronic equipment, and the method comprises the steps: presetting a plurality of containers configured into different site assemblies, and selecting at least one part of the containers to form a honeypot site system to respond to a site access request when site access is received. Compared with a honeypot site with a fixed architecture in the prior art, the honeypot site provided by the embodiment of the invention has the advantages that the flexibility of the honeypot site assembly is higher, and the camouflage of the honeypot site and the defense capability to attacks are stronger.
Owner:成都知道创宇信息技术有限公司
A spliced military bunker
Owner:何加圣
Bacillus mojavensis CJX-61 and application thereof
ActiveCN110628661AStrong defenseGood suppression effectPlant growth regulatorsBacteriaLaboratory cultureAlternaria tomato
The antagonistic bacterium provided by the invention is a strain of bacillus mojavensis CJX-61 which is separated from rhizosphere soil of a diseased potato, and the bacillus mojavensis CJX-61 is named as Bacillus mojavensis. The strain is preserved in China General Microbiological Culture Collection Center, and a preservation number is CGMCC NO. 17660. The bacillus mojavensis CJX-61 has the capacity of producing chitinase, cellulase, beta-1, 3-glucanase, protease, siderophore and HCN. The CJX-61 has the relatively good inhibition effect on various plant pathogenic fungi such as fusarium oxysporum, pyricularia oryzae, sclerotinia sclerotiorum, fusarium moniliforme, sclerotinia sclerotiorum, botrytis cinerea, fusarium graminearum, alternaria solani and fusarium sambucinum. The Bacillus mojavensis CJX-61 has very strong defense capability on potato black scurf, and can also improve the potato yield under field conditions.
Owner:HARBIN NORMAL UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com