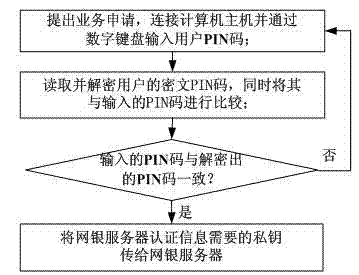
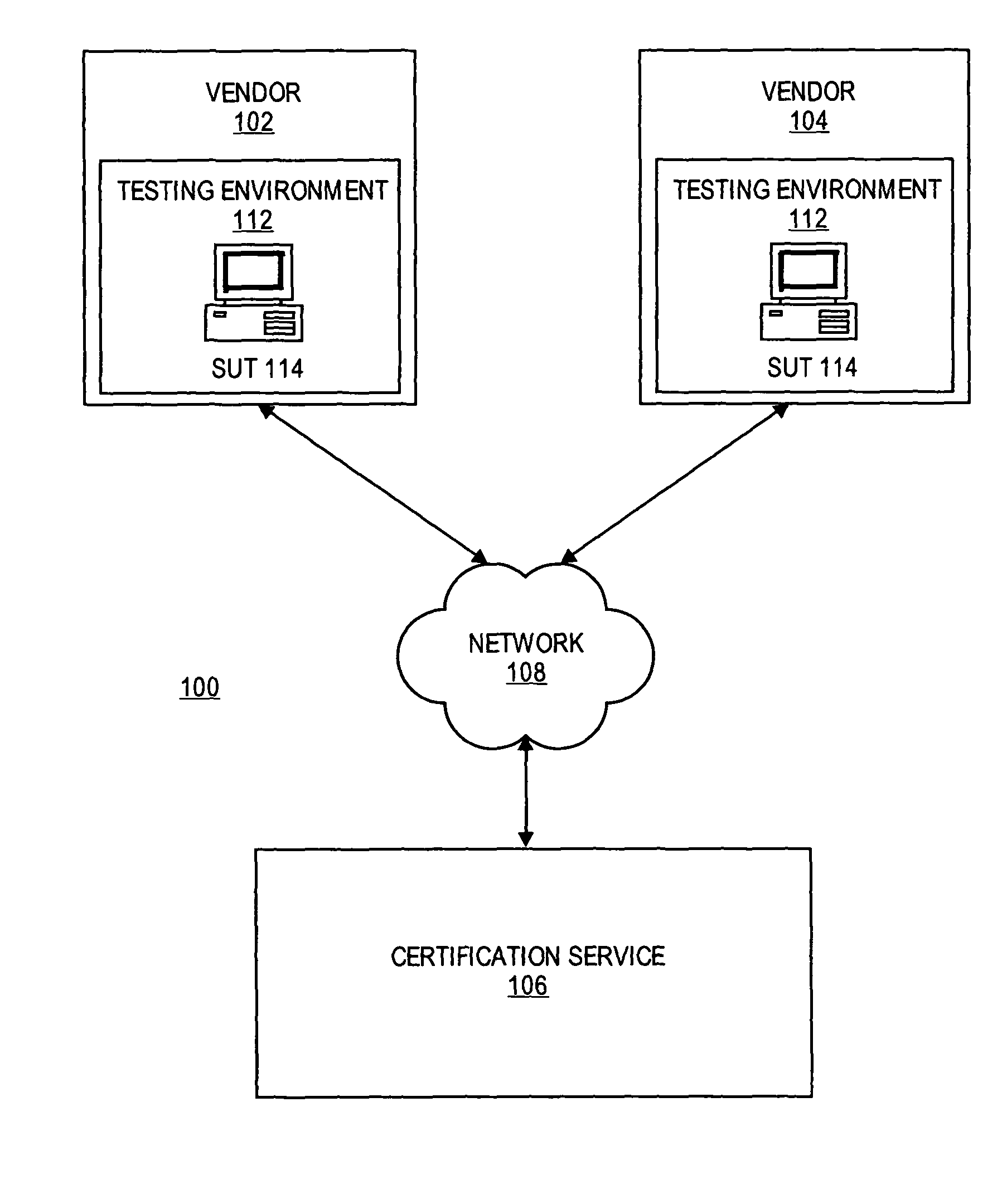
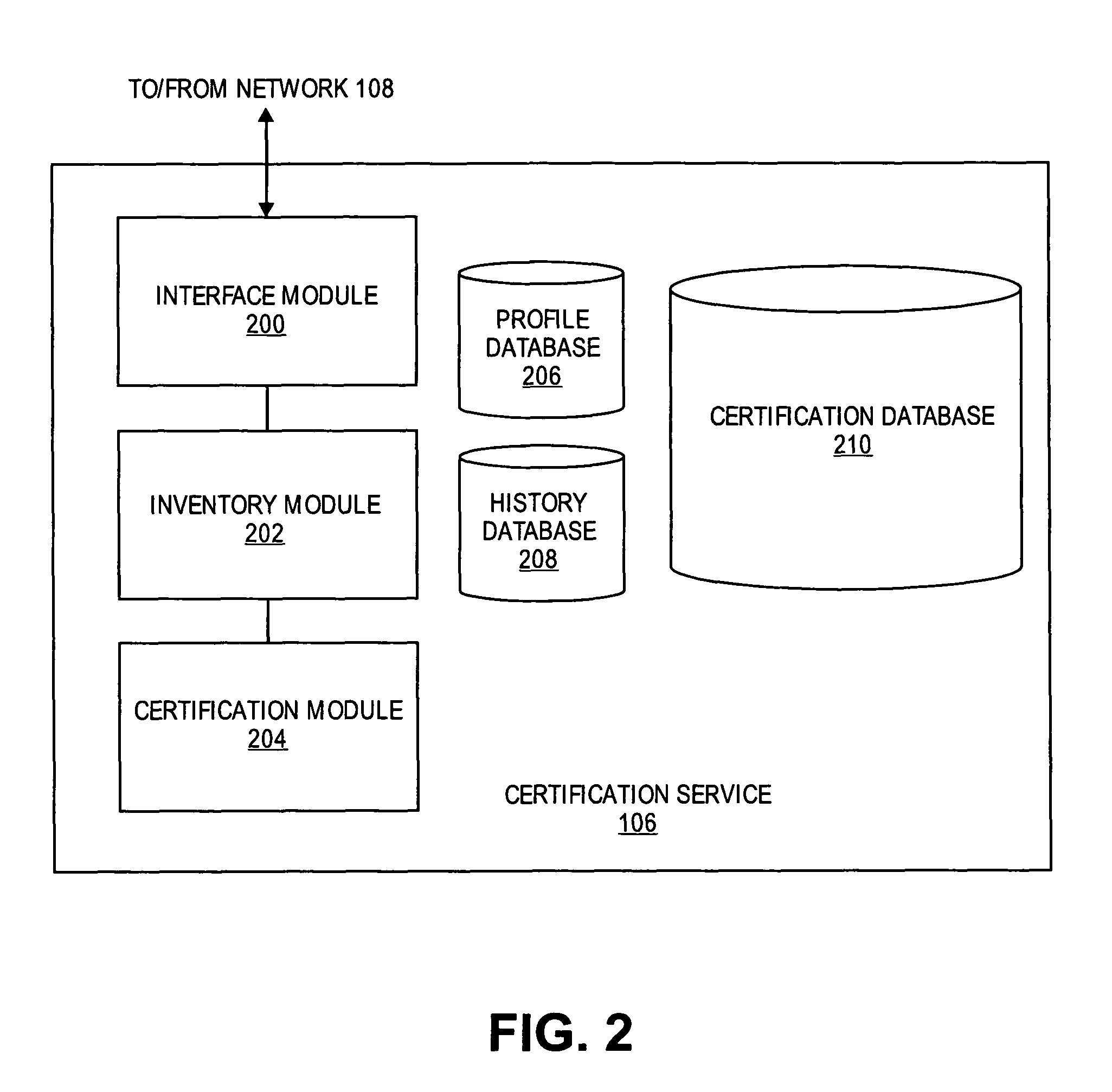
Patents
Literature
61 results about "Hardware authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The term "hardware authentication" refers to a security system that uses a hardware device to grant access to users. Hardware authentication is used most commonly for computer systems and networks to protect sensitive data.
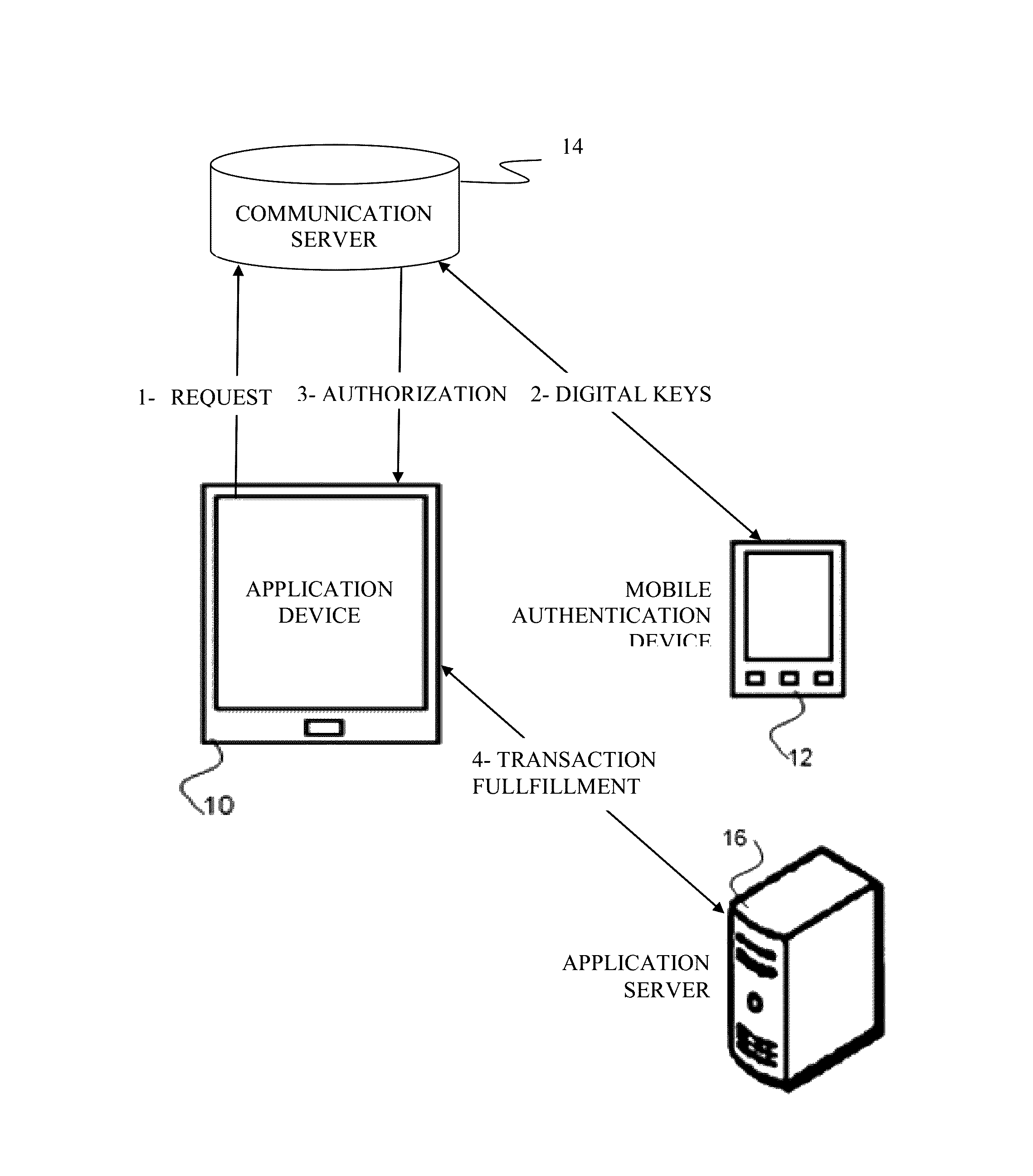
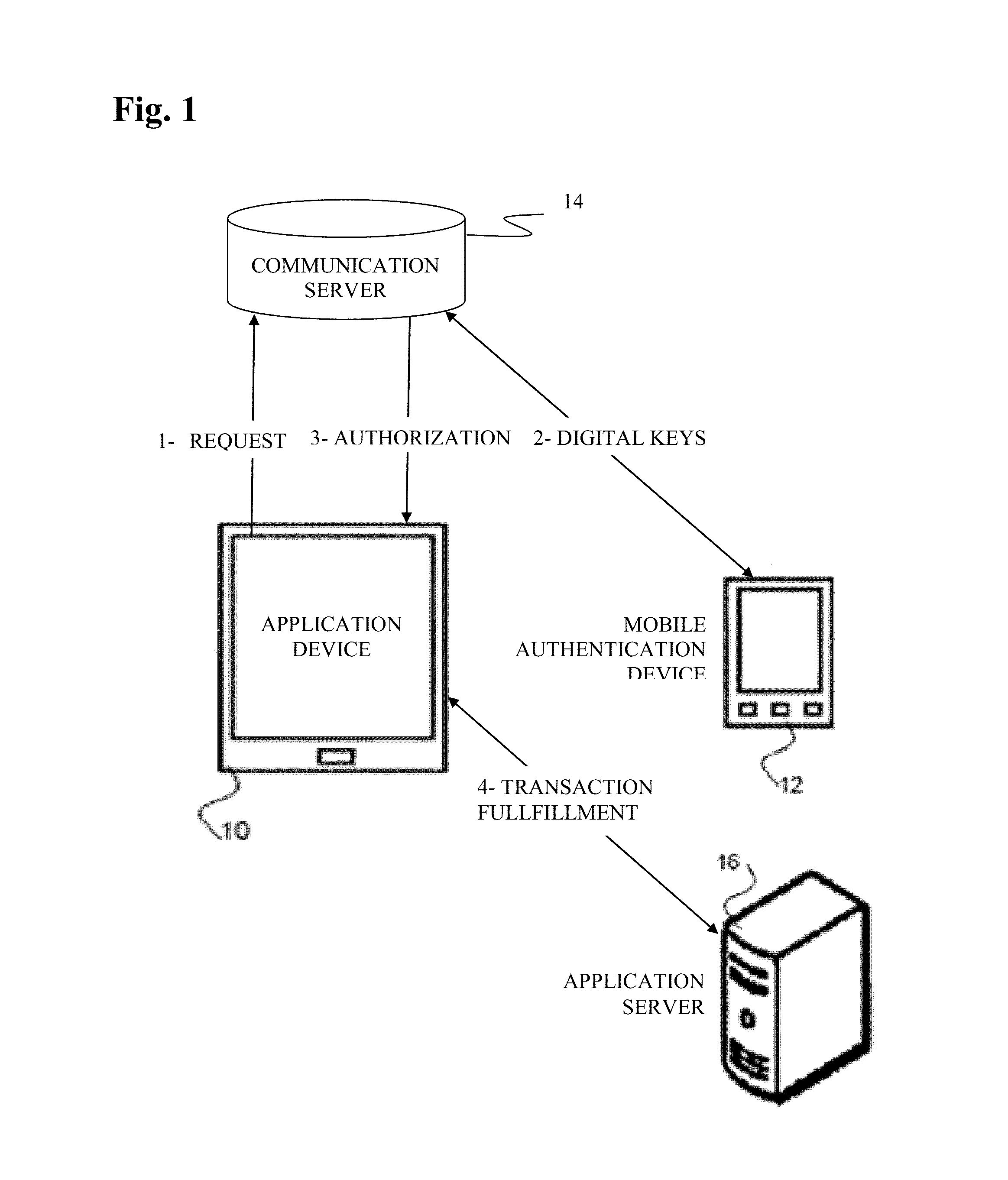
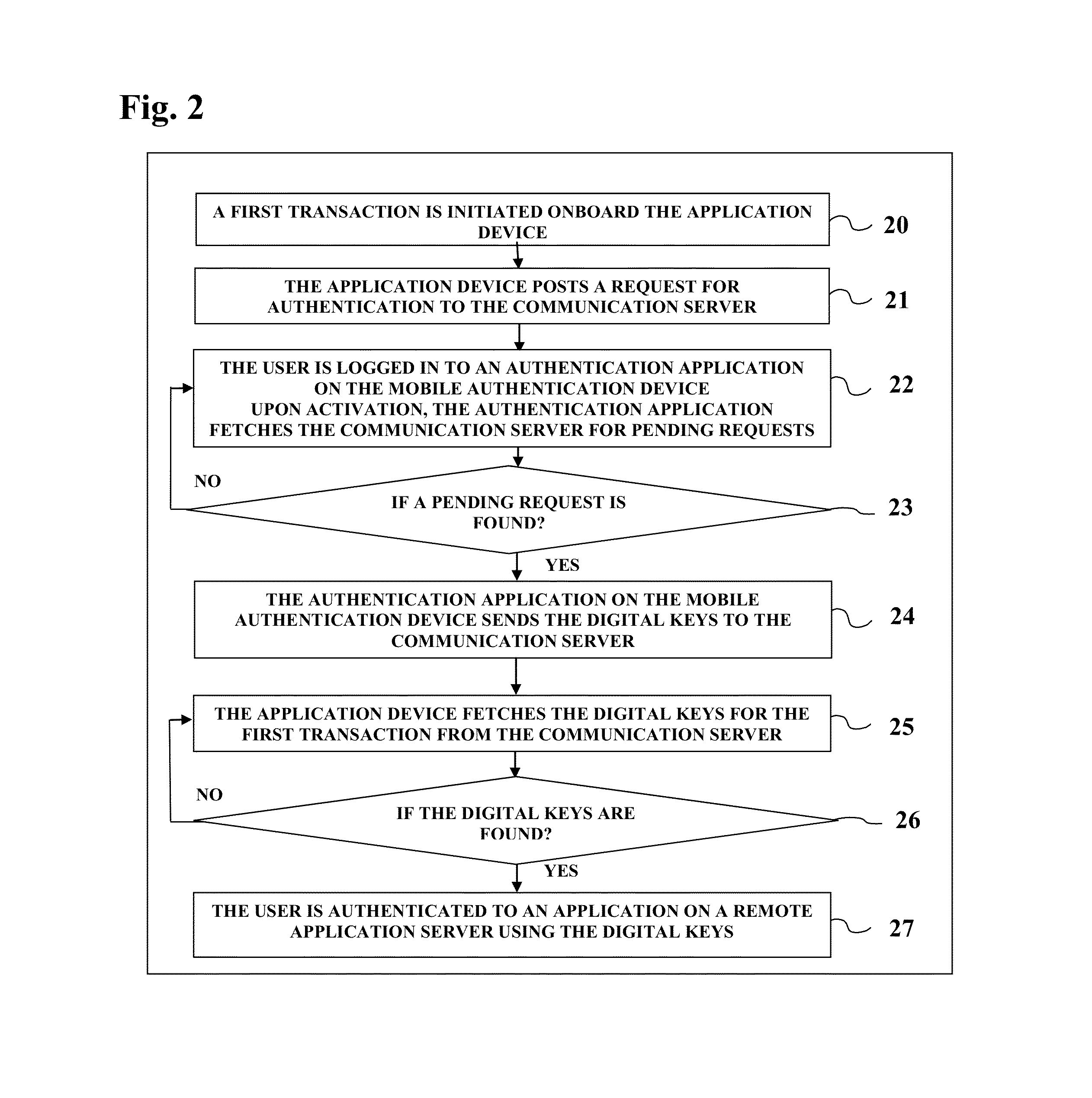
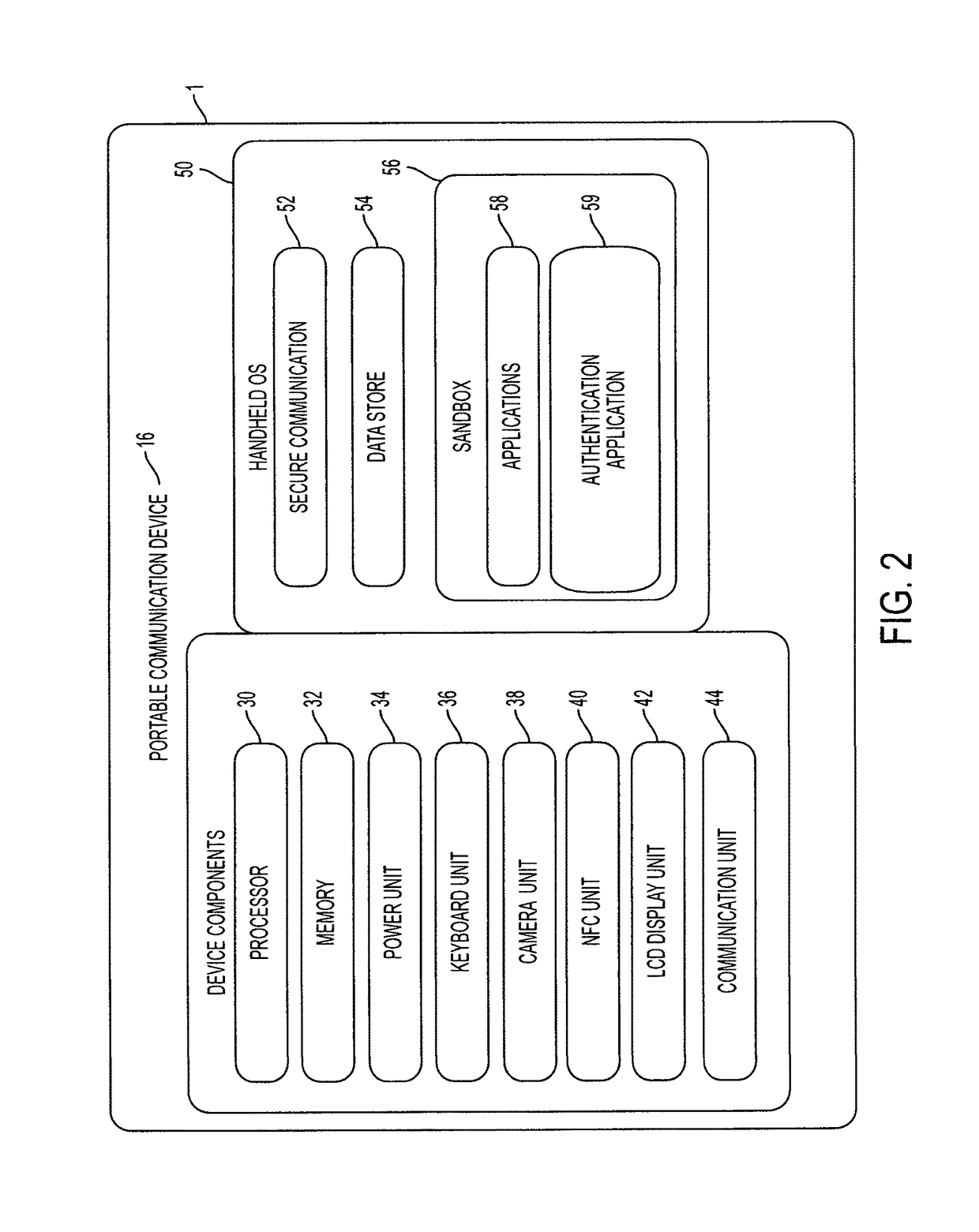
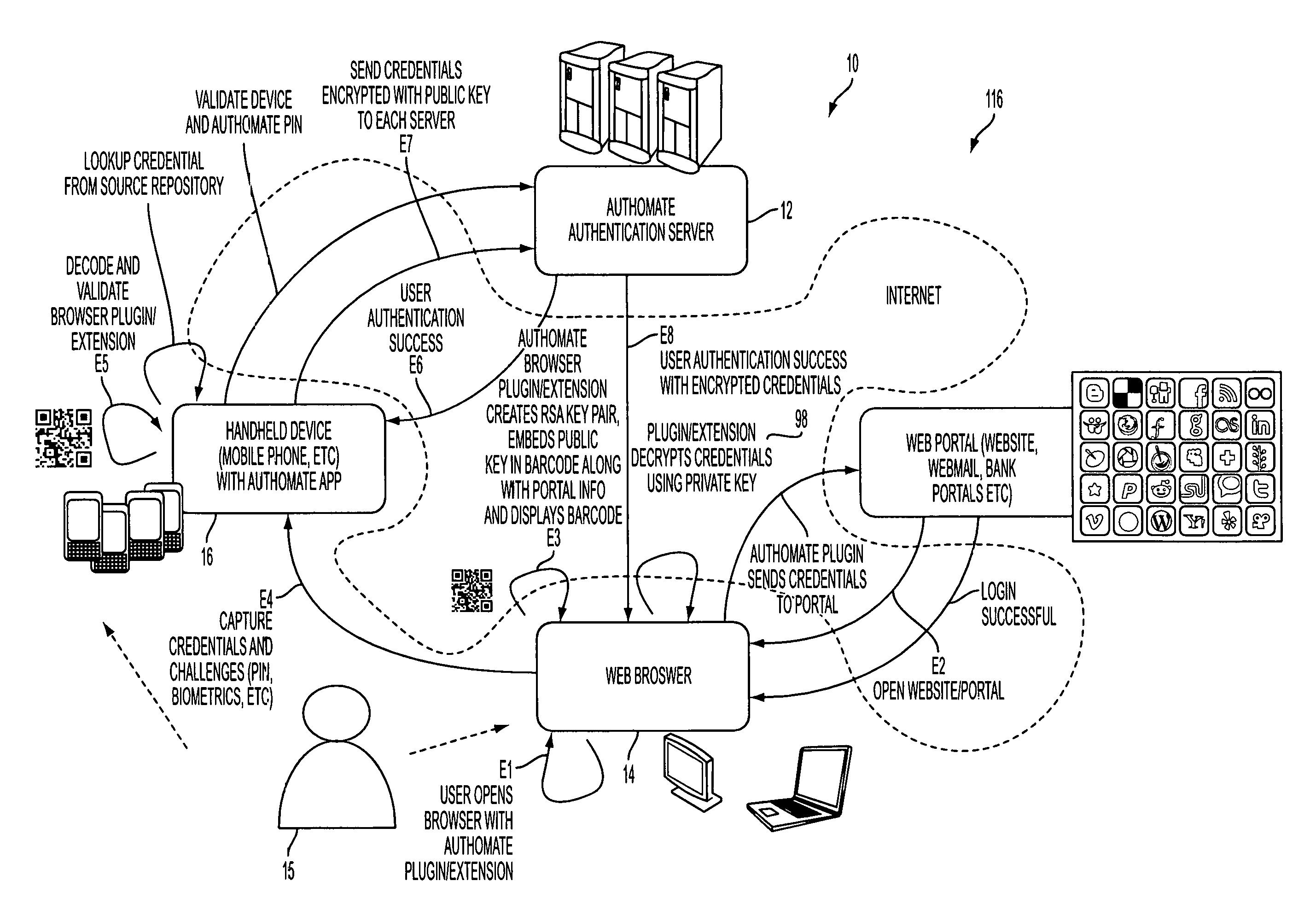
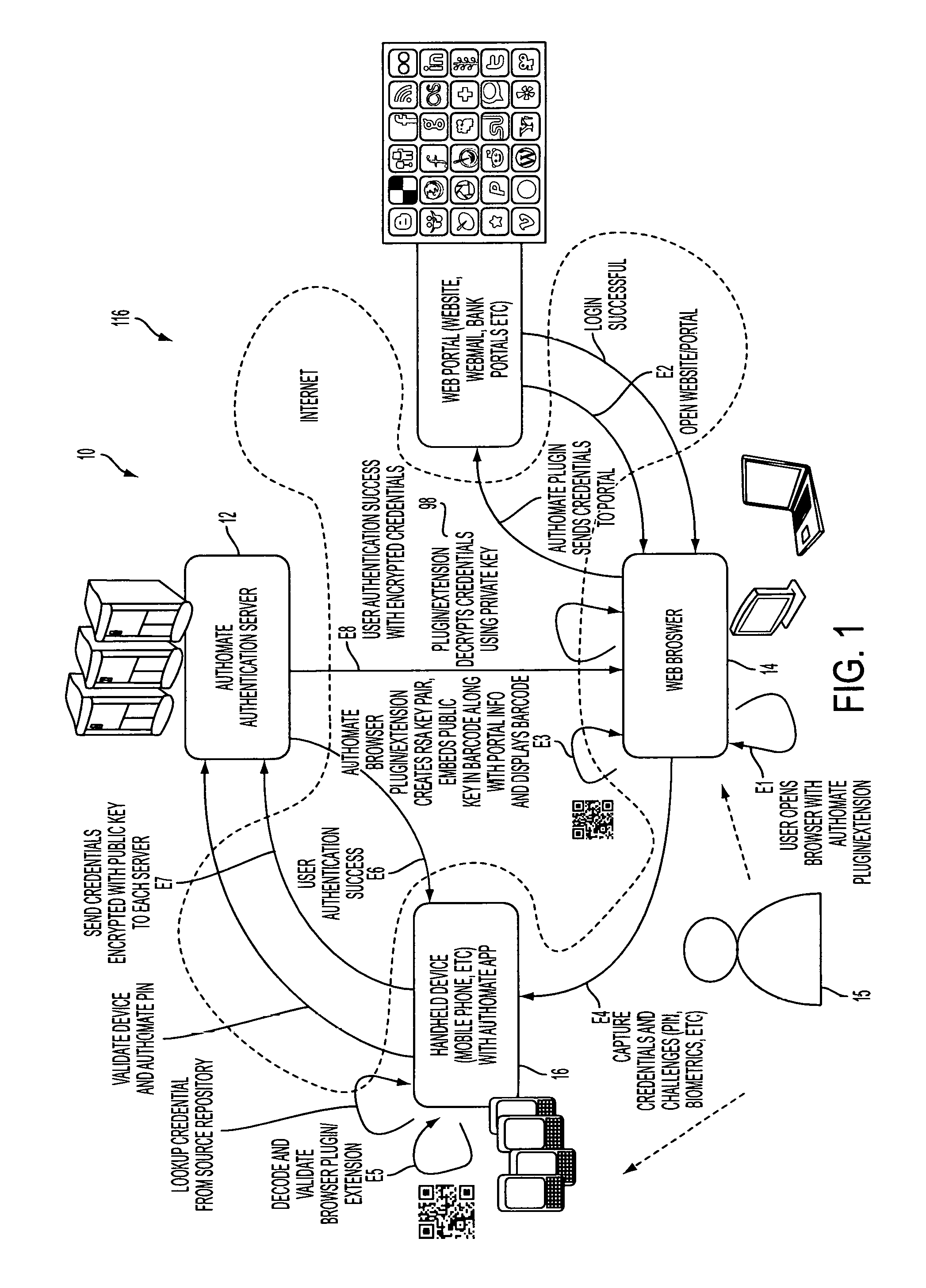
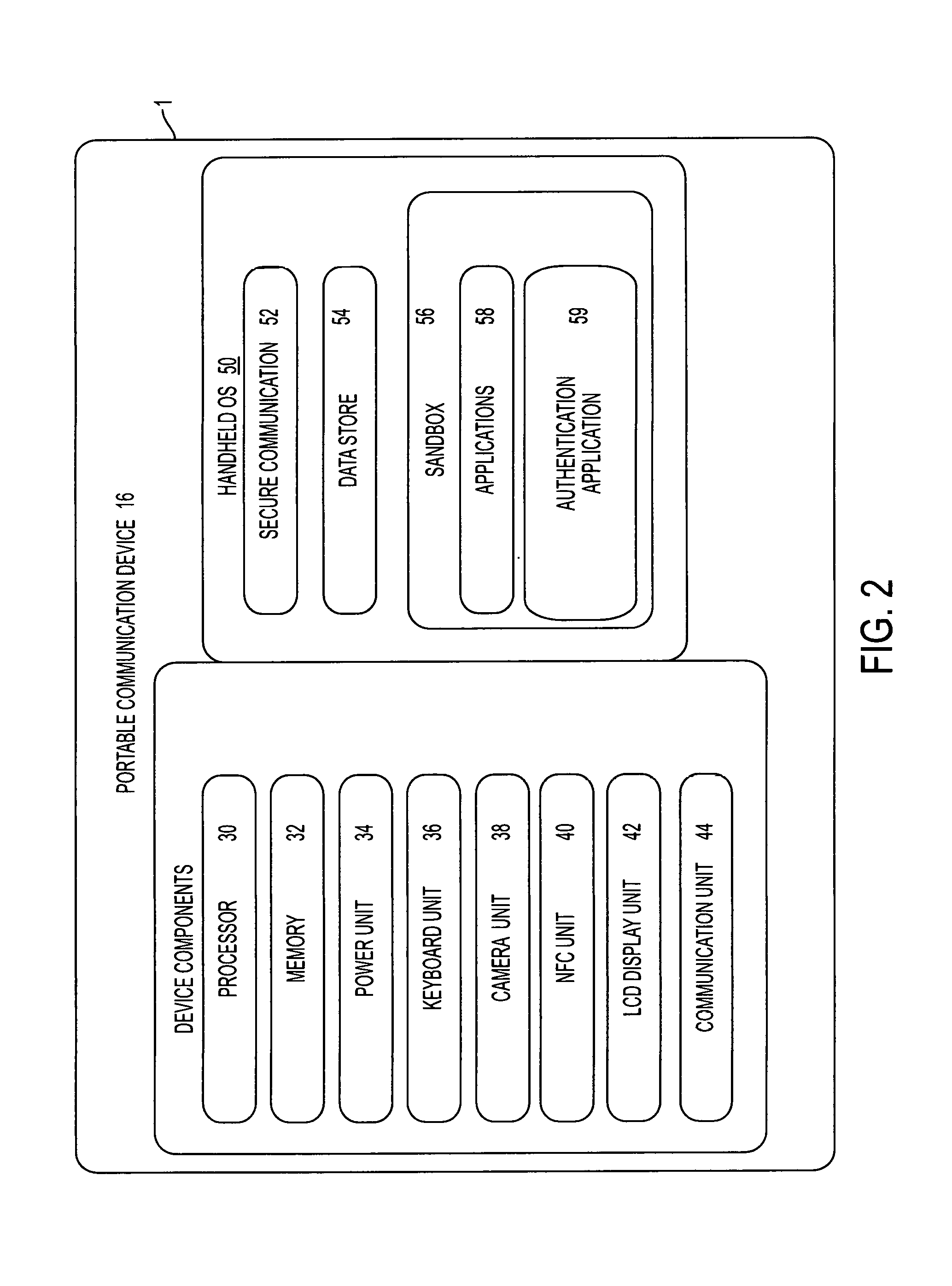
Method for adaptive authentication using a mobile device
ActiveUS8646060B1Digital data processing detailsServices signallingNetwork availabilityHardware authentication
A method for facilitating login using adaptive authentication. The method uses different authentication methods and different data protection methods depending on the user location, availability of network, importance of the data.
Owner:OPTIMA DIRECT LLC
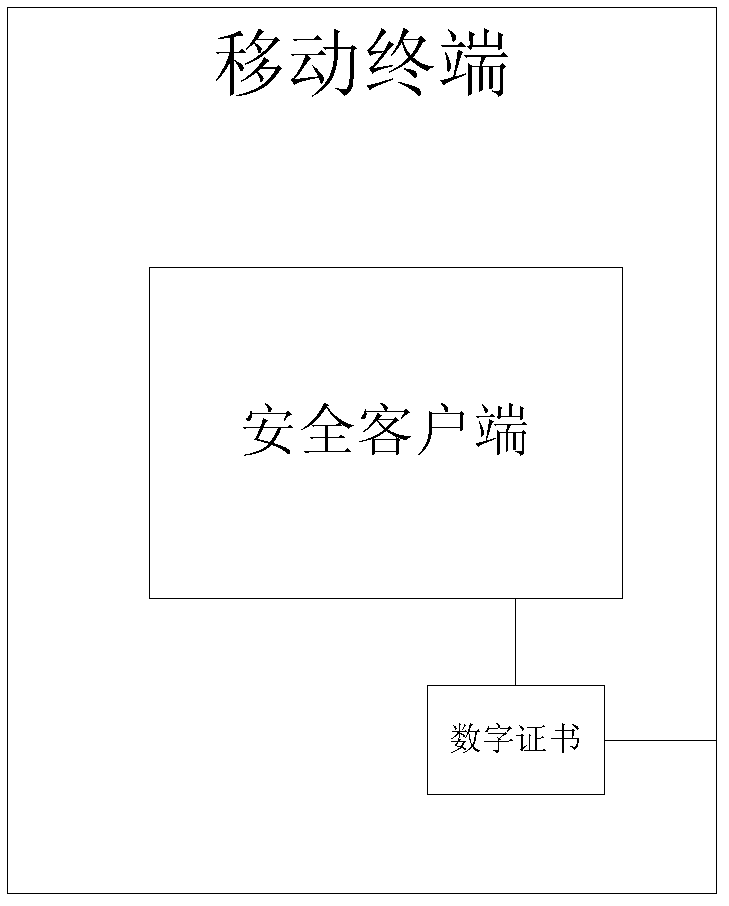
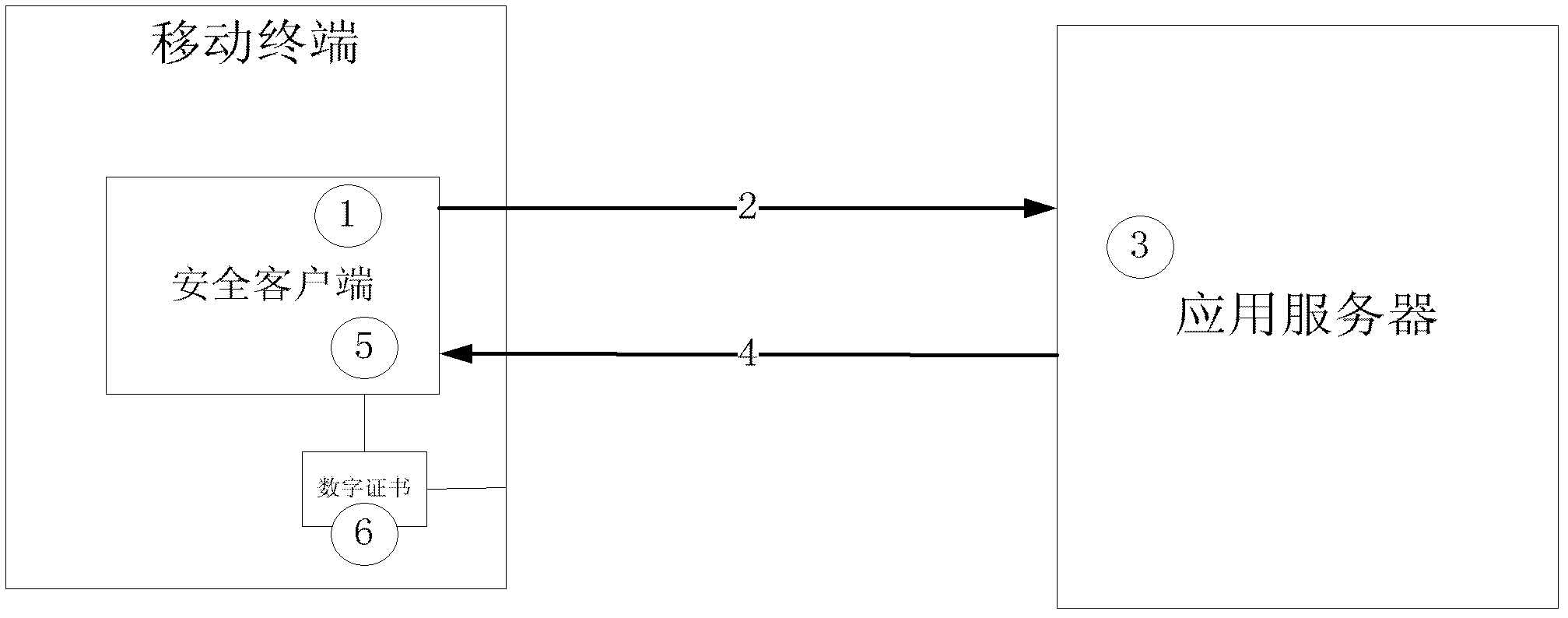
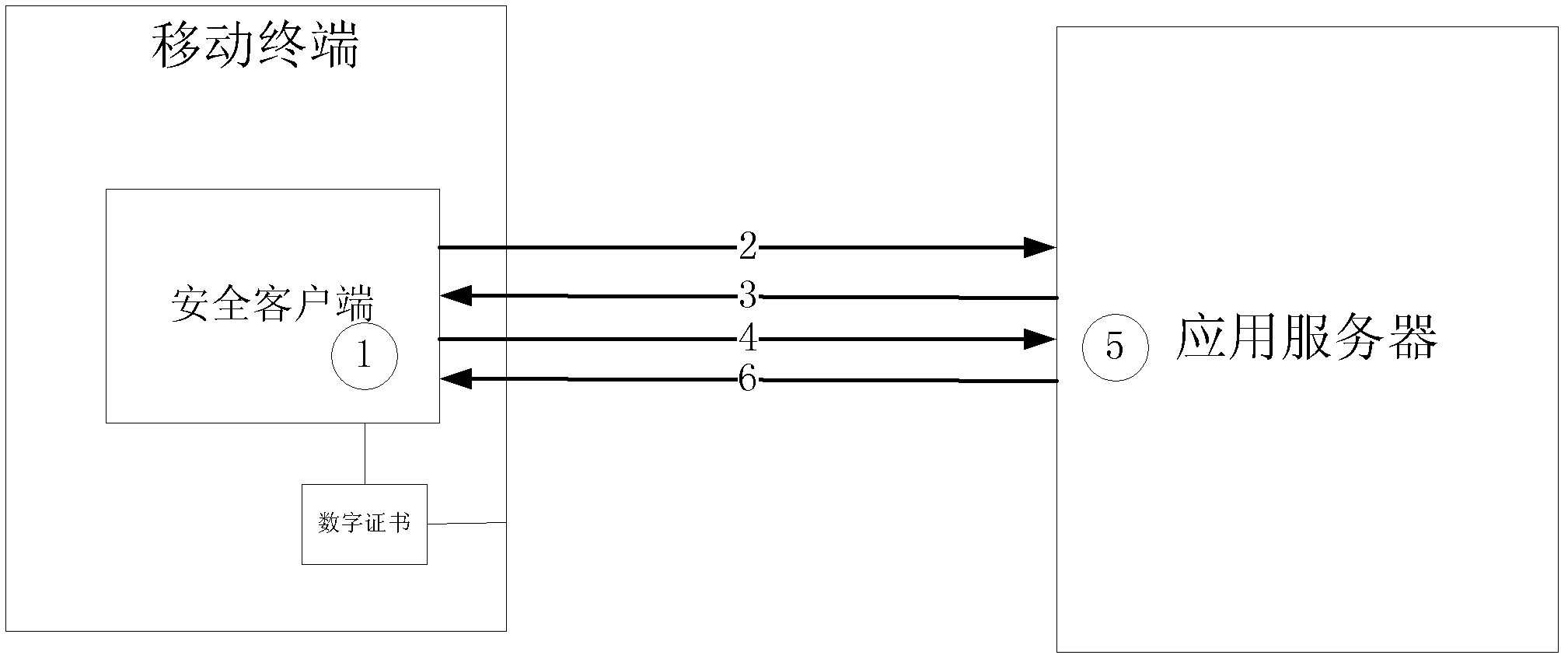
Authentication method of mobile terminal uniqueness based on software digital certificate
ActiveCN103167491AImprove authentication strengthNot afraid to stealUser identity/authority verificationSecurity arrangementApplication serverComputer terminal
The invention discloses an authentication method of mobile terminal uniqueness based on a software digital certificate, and belongs to the technical field of computers and information safety. The method specifically comprises the following steps: (1), a safe client side is installed on a mobile terminal, a certificate request relevant to equipment information is generated so as to be registered by a server side; a digital certificate is issued to the mobile terminal by the server side, and relevance between the digital certificate and the equipment is achieved. (2), when the method is used, random information is sent to the mobile terminal by the server side, the information is received by the safe client side, the random information is signed by using a private key of the digital certificate of the equipment, and the signing data are sent to the server side. The signature is verified by a public key of the digital certificate by an application server, and a communication opposite terminal identity is confirmed. The method is capable of verifying the mobile terminal commendably and enhancing intensity of authentication on the basis that hardware authentication equipment is not added.
Owner:KOAL SOFTWARE CO LTD
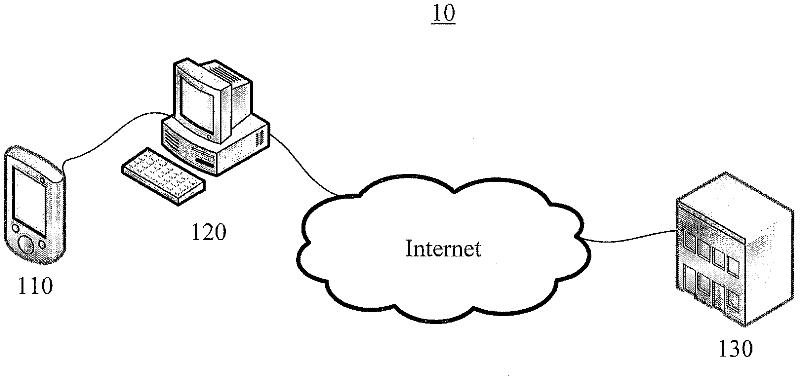
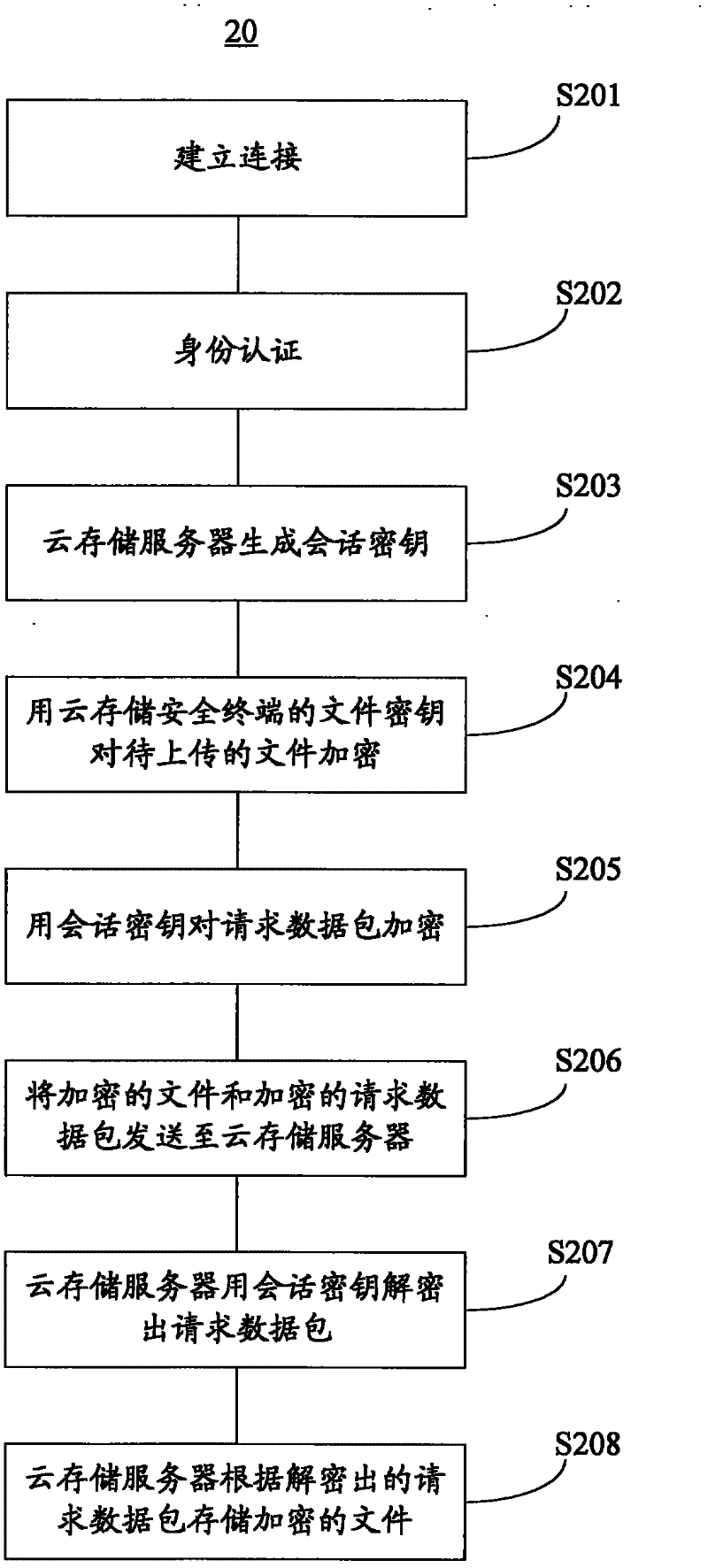
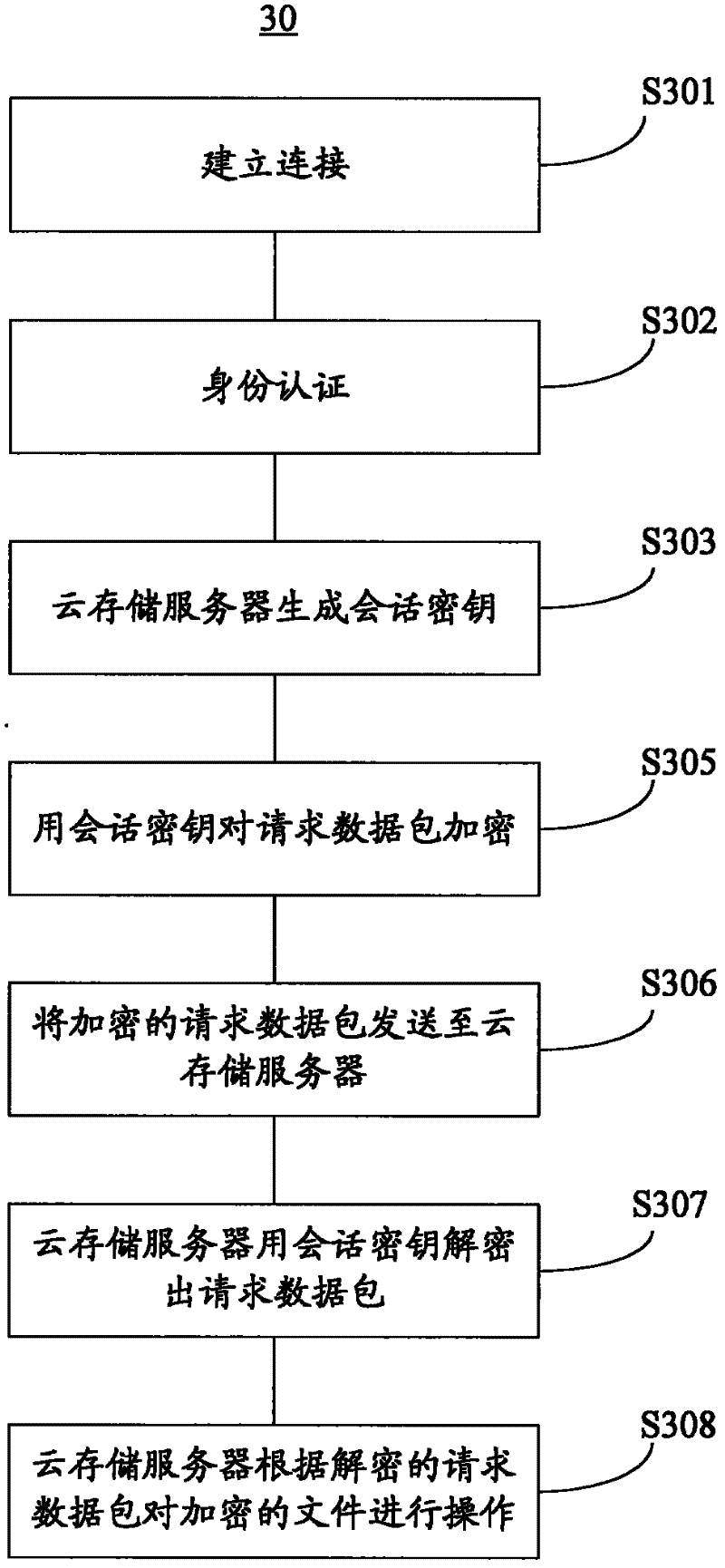
Cloud storage system and data management method thereof
ActiveCN102638568AEnsure safetyUser identity/authority verificationCloud storage securityData management
The invention discloses a cloud storage system and a data management method thereof. The cloud storage system comprises a cloud storage server, a client side and a cloud storage safety terminal, wherein the cloud storage server is configured to store file data of multiple users; the client side is configured to be capable of operating client side software so as to establish connection with the cloud storage server; and the cloud storage safety terminal with a file encryption key is configured to be capable of establishing connection with the client side. The file data stored in the cloud storage server are the data encrypted with the file encryption key of the cloud storage safety terminal. According to the scheme, safety of the data is guaranteed by hardware certification of the cloud storage safety terminal.
Owner:NETAK TECH KO LTD
Hardware certification based on certifying development processes
ActiveUS20070226487A1Error detection/correctionSecuring communicationSoftware development processSoftware engineering
Owner:RED HAT
Identity authentication method, equipment and system
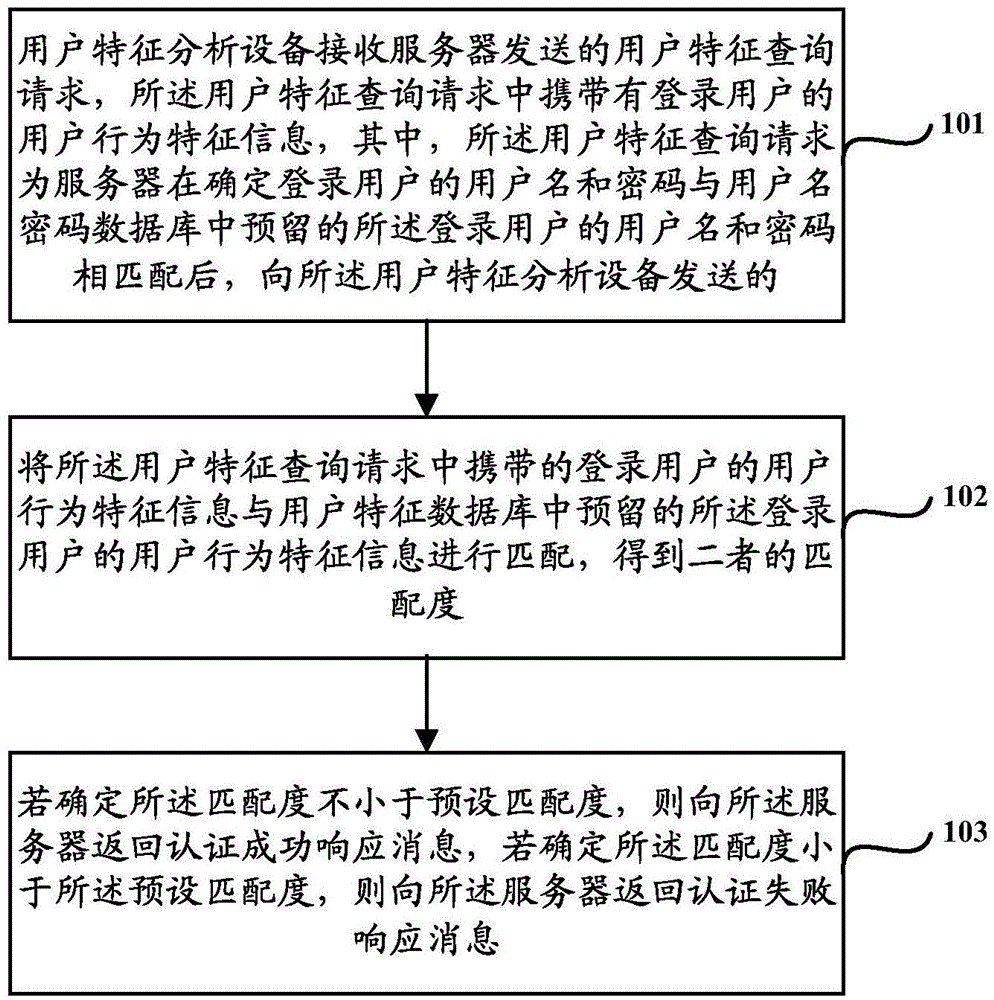
InactiveCN105991281AFree yourself from the dilemma of remembering complex passwordsImprove experienceUser identity/authority verificationPasswordHardware authentication
The invention discloses an identity authentication method, equipment and system. The identity authentication method comprises the steps: user characteristic analysis equipment receives a user characteristic query request which is sent from a server when the server determines that the user name and the password of a login user are matched with the reserved user name and password of the login user, wherein the user characteristic query request carries the user behavior characteristic information of the login user; and the user characteristic analysis equipment matches the carried user behavior characteristic information of the login user with the reserved user behavior characteristic information of the login user so as to return an authentication response message to the server according to the matching degree between the carried user behavior characteristic information of the login user and the reserved user behavior characteristic information of the login user. In other words, for the scheme of the identity authentication method, equipment and system, based on traditional user-name+password authentication, the user behavior characteristic information is introduced to perform further authentication on the user identity, so that the dilemma of memorizing complicated passwords for the user is avoided; the difficulty in managing the passwords by the user is reduced; and the account number safety is improved. Besides, relative to the traditional authentication mode which requires hardware authentication equipment and the like, the scheme of the identity authentication method, equipment and system also has the advantage of reducing the identity authentication cost.
Owner:CHINA MOBILE COMM GRP CO LTD
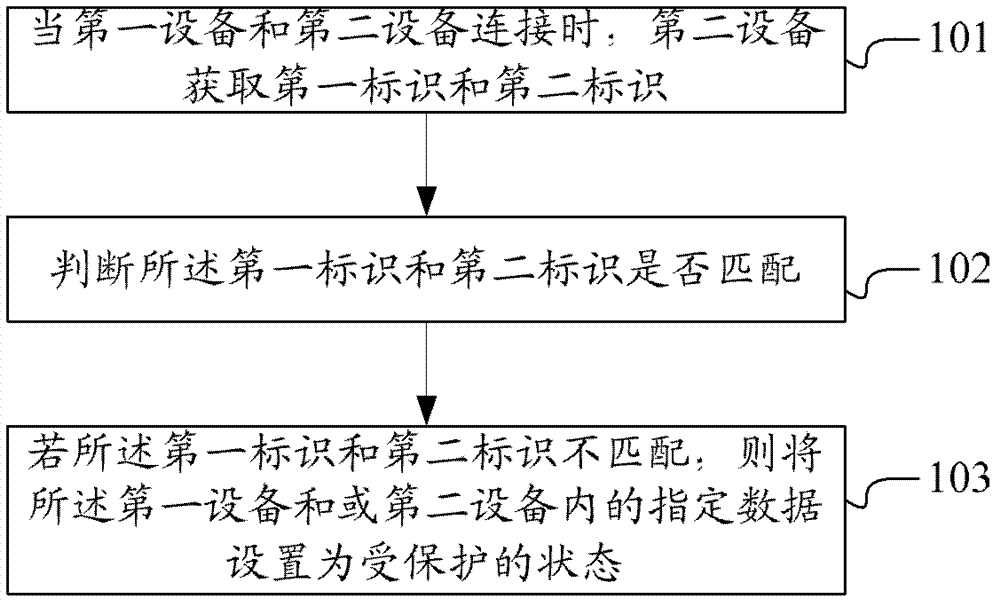
Method, device and equipment for protecting data
The invention discloses a method, a device and equipment for protecting data. The method is applied to second equipment, and specifically comprises the following steps that: in the case that first equipment is connected with the second equipment, the second equipment obtains a first identification and a second identification, wherein the first identification is the unique identification of the first equipment, and the second identification is the unique identification of the second equipment; and whether the first identification is matched with the second identification is judged, if the first identification is not matched with the second identification, then specified data in the first equipment and / or the second equipment are set to be in a protected state. Special hardware peripherals have no need to be added during an application for the method, the device and the equipment for protecting data disclosed by the invention, and the specified data in the first equipment and the second equipment are protected via hardware authentication according to the identifications (ID) of the equipment; and therefore, the method, the device and the equipment for protecting data are low in cost and high in safety.
Owner:LENOVO (BEIJING) CO LTD
System and method for point of sale payment data credentials management using out-of-band authentication
ActiveUS9741033B2Easy to usePromote disseminationKey distribution for secure communicationCryptography processingApplication softwareMulti dimensional
The invention provides an easy to use credential management mechanism for multi-factor out-of-band multi-channel authentication process to protect payment credentials without the risk of malware and skimming attacks. When opened, the secure payment application generates a multi-dimensional transitory key. The user authenticates the multi-dimensional transitory key and validates the secure payment application, triggering an out-of-band outbound mechanism. The portable mobile device invokes the authentication server and the authentication server authenticates the user based on the authenticated transitory key. After authentication, the merchant is allowed access to the payment credentials to complete the transaction. The process of the invention includes an authentication server, a secure payment application to generate an authentication vehicle or an embodiment (i.e. multi-dimensional transitory key) and handle incoming requests, and a portable communication device with a smartphone application.
Owner:GCOM IP LLC
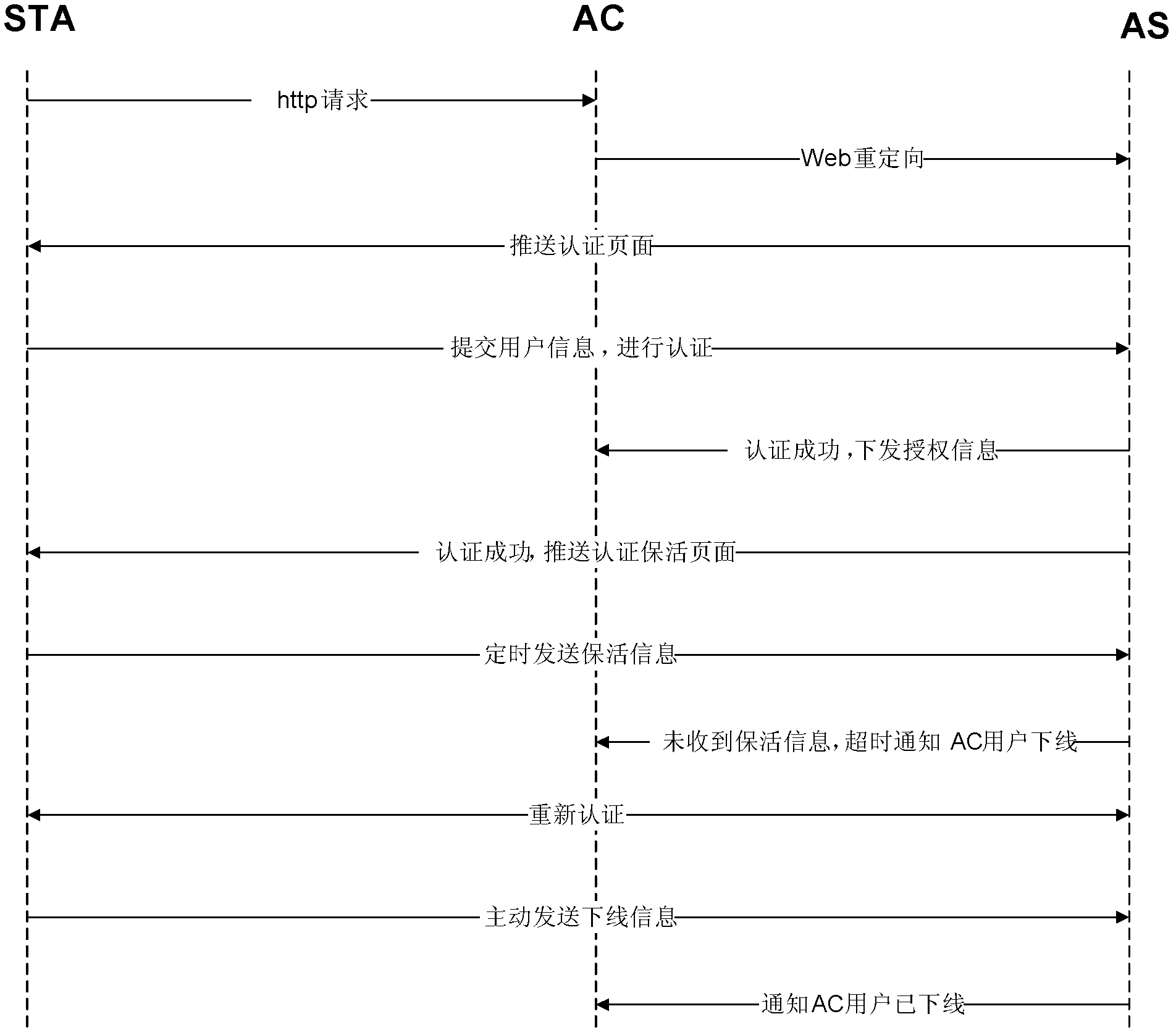
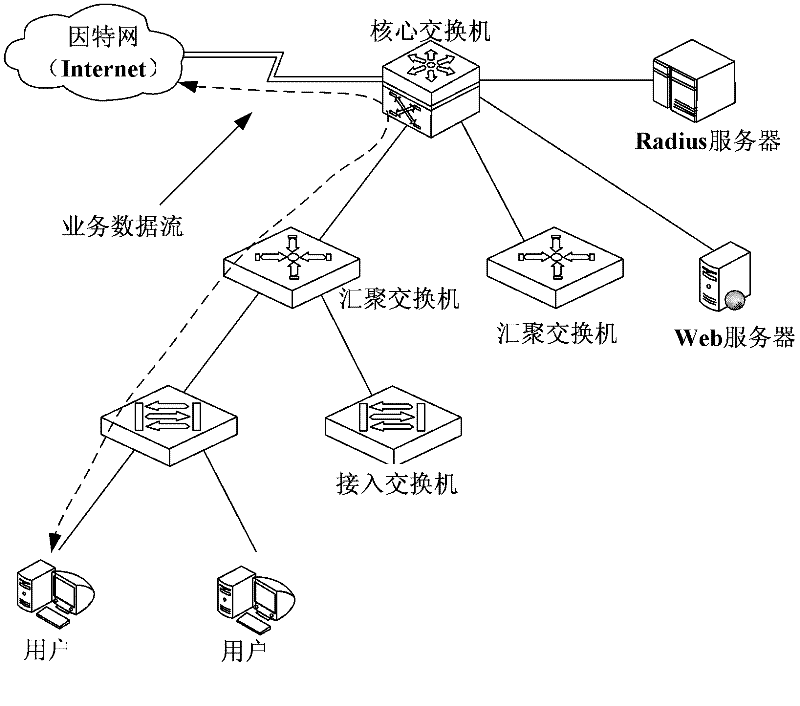
Web authentication method, network equipment and Web authentication system
ActiveCN102148838ASolve the problem of forced offlineTransmissionWeb authenticationNetwork connection
The invention provides a Web authentication method, network equipment and a Web authentication system. The Web authentication method comprises the following steps: after a user terminal passes Web authentication, access equipment records authentication information of the user terminal; and if the access equipment knows that an authentication keep-alive page of the user terminal does not send keep-alive information in a preset keep-alive information sending period by detection and knows that the user terminal is accessed to a wireless network covered by the access equipment or detects the flow of the user terminal, the access equipment sends the keep-alive information to an authentication server according to the recorded authentication information of the user terminal, so that the authentication server keeps network connection of the user terminal. By adopting the Web authentication method, the network equipment and the Web authentication system, which are provided by the invention, the user terminal can still be ensured to normally use the network when the user terminal and the Web authentication are not compatible.
Owner:RUIJIE NETWORKS CO LTD
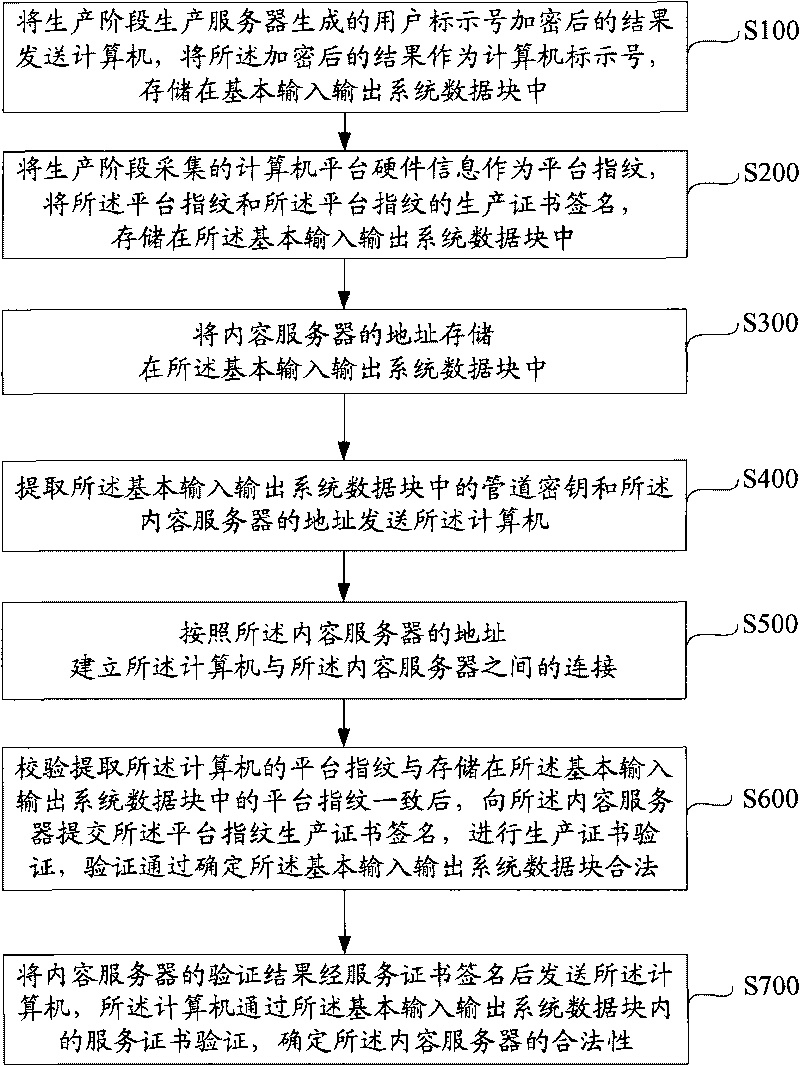
Method and system for authenticating two-way hardware
ActiveCN101741561AImprove securityAchieve authenticationUser identity/authority verificationHardware authenticationFingerprint
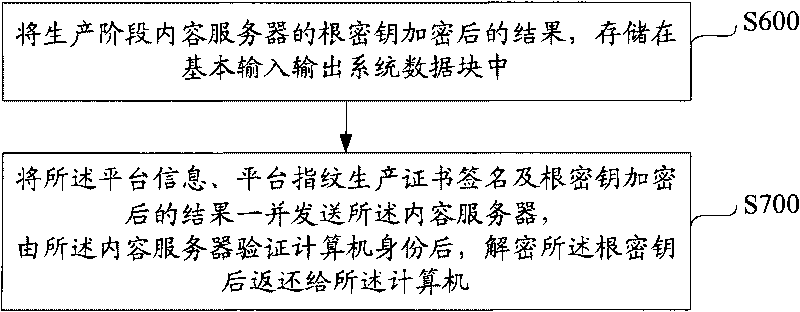
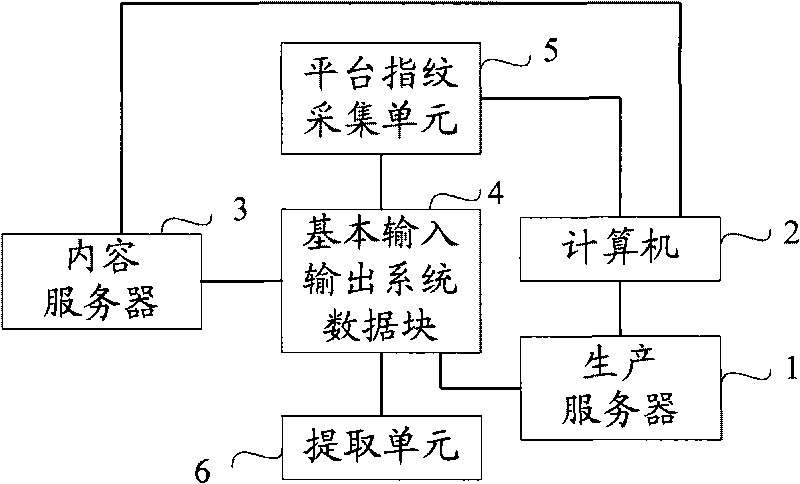
The invention relates a method for authenticating two-way hardware. The method comprises the following steps of: storing a computer mark number, a platform fingerprint, a platform fingerprint production certificate signature, and an address of a content server in a data block of a basic input / output system; extracting the address of the content server in the data block of the basic input / output system, and sending the address to a computer; building a connection between the computer and the content server according to the address of the content server; extracting a computer platform fingerprint, and verifying that the computer platform fingerprint is consistent with the platform fingerprint stored in the data block of the basic input / output system; and submitting the platform fingerprint production certificate signature to the content server to verify a production certificate; confirming that the data block of the basic input / output system is legal after passing the verification; sending a verification result of the content server to the computer through the service certificate signature; and confirming that the content server is legal after the computer passes the service certificate verification in the data block of the basic input / output system. The method and system for authenticating the two-way hardware realize two-way authentication between the content server and the computer.
Owner:LENOVO (BEIJING) CO LTD
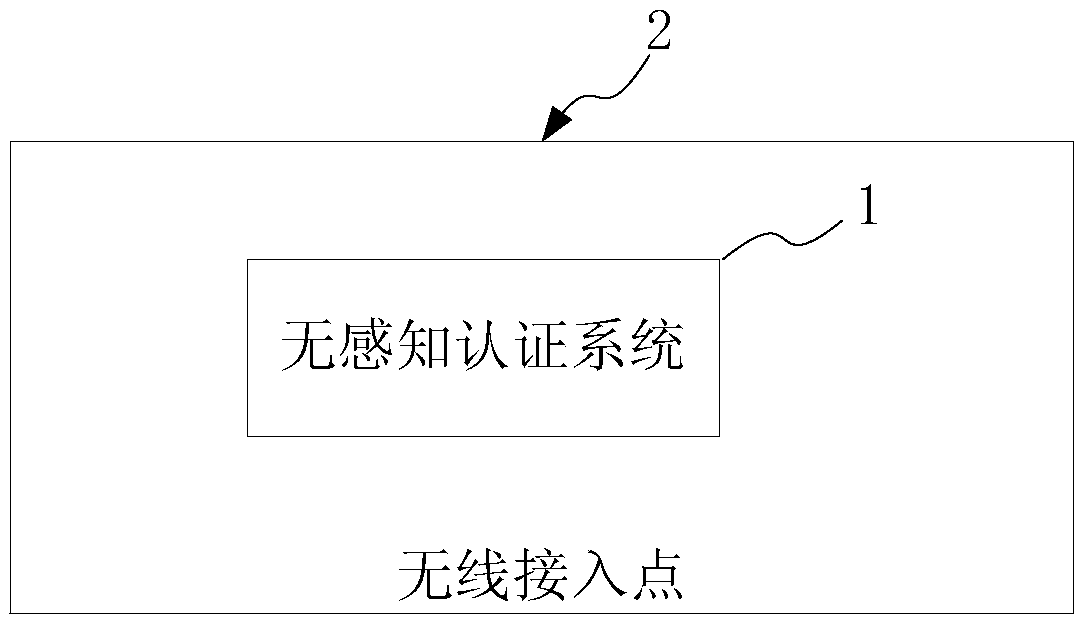
Perception-free authentication method and system, control method and system based on same
ActiveCN105516961AAvoid gettingReduce authentication requestsNetwork topologiesTransmissionThe InternetTerminal equipment
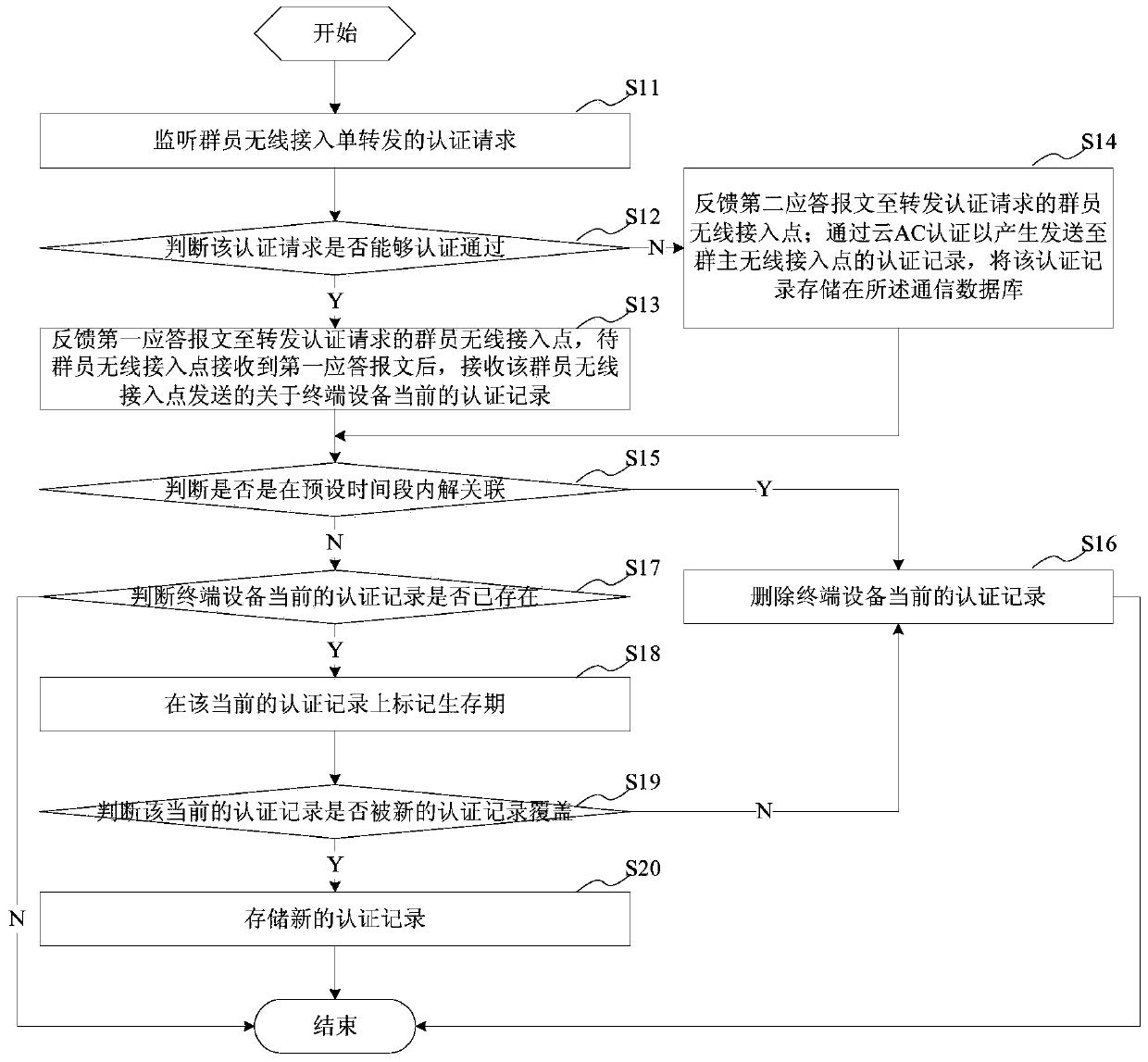
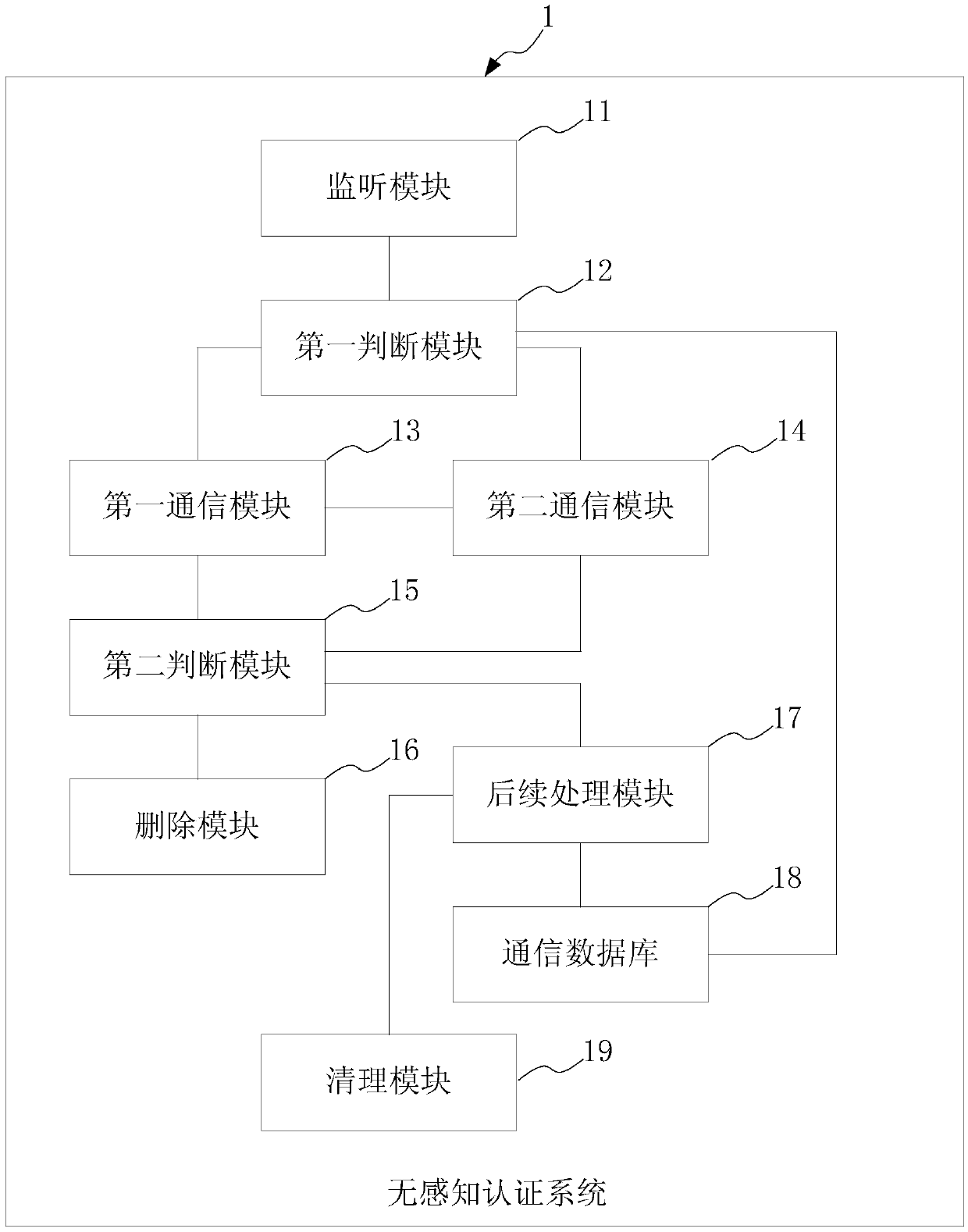
The invention provides a perception-free authentication method, comprising the following steps of after a cloud AC establishes communication links with a plurality of wireless access points, monitoring an authentication request forwarded by a member wireless access point from a terminal device; judging whether the authentication request is passed, if yes, feeding a first response message back to the member wireless access point forwarding the authentication request to allow the terminal device to directly access the Internet; if no, feeding a second response message back to the member wireless access point forwarding the authentication request, wherein the second response message indicates the member wireless access point to send the authentication request to the cloud AC, and an authentication record sending to a leader wireless access point is generated through the authentication of the cloud AC. According to the method, acquiring the authentication information from the remote cloud AC is avoided, the cross public network authentication request process is reduced, the authentication efficiency is improved, and thereby the perception-free authentication of user roaming can achieve good experience.
Owner:台州市吉吉知识产权运营有限公司
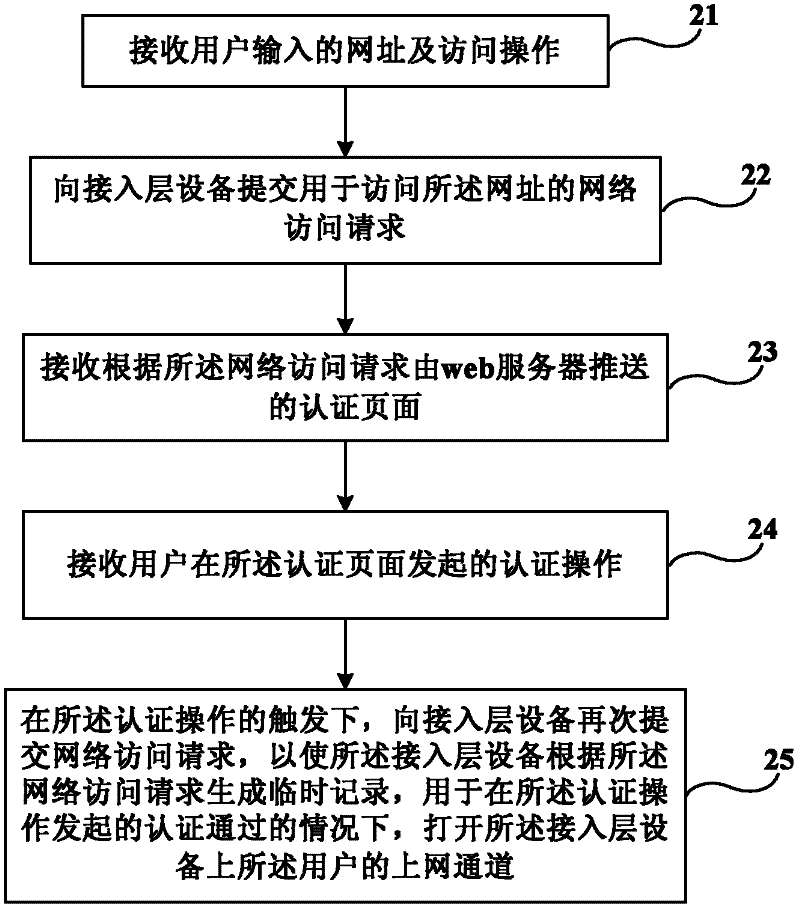
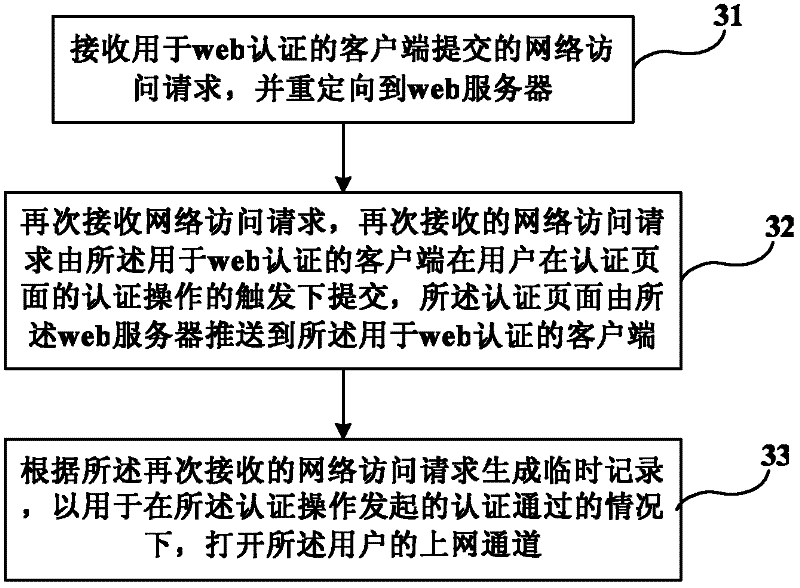
Web authentication method, and client and access layer device used for web authentication
ActiveCN102523220APrevent agingOnline implementationTransmissionRelevant informationWeb authentication
The invention provides a web authentication method, and a client and an access layer device used for web authentication. Through carrying out triggering to submit a network access request in user click authentication, when a temporary record is deleted, the access layer device can carry out redirection on the network access request again and collect related information anew such as IP, MAC and the like to generate a temporary record, thus when the authentication is passed, the web server can open a networking channel, an aged problem of authentication information such as the temporary record in the access layer device is solved, and when a user carries out an authentication operation after an authentication page is pushed for a long time, networking still can be realized.
Owner:上海锐山网络有限公司
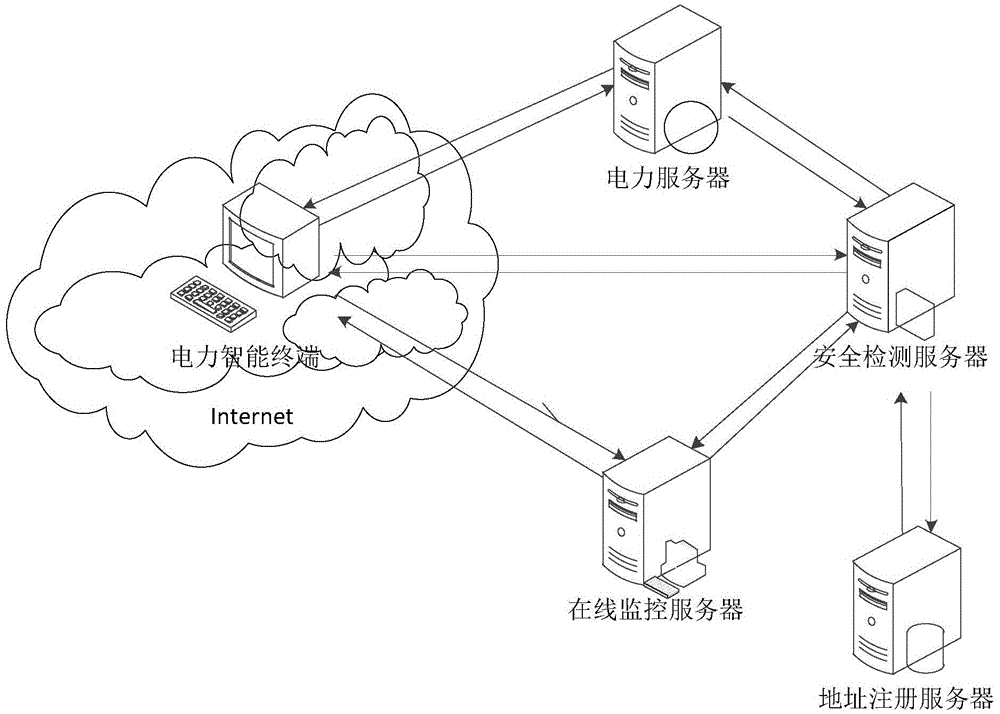
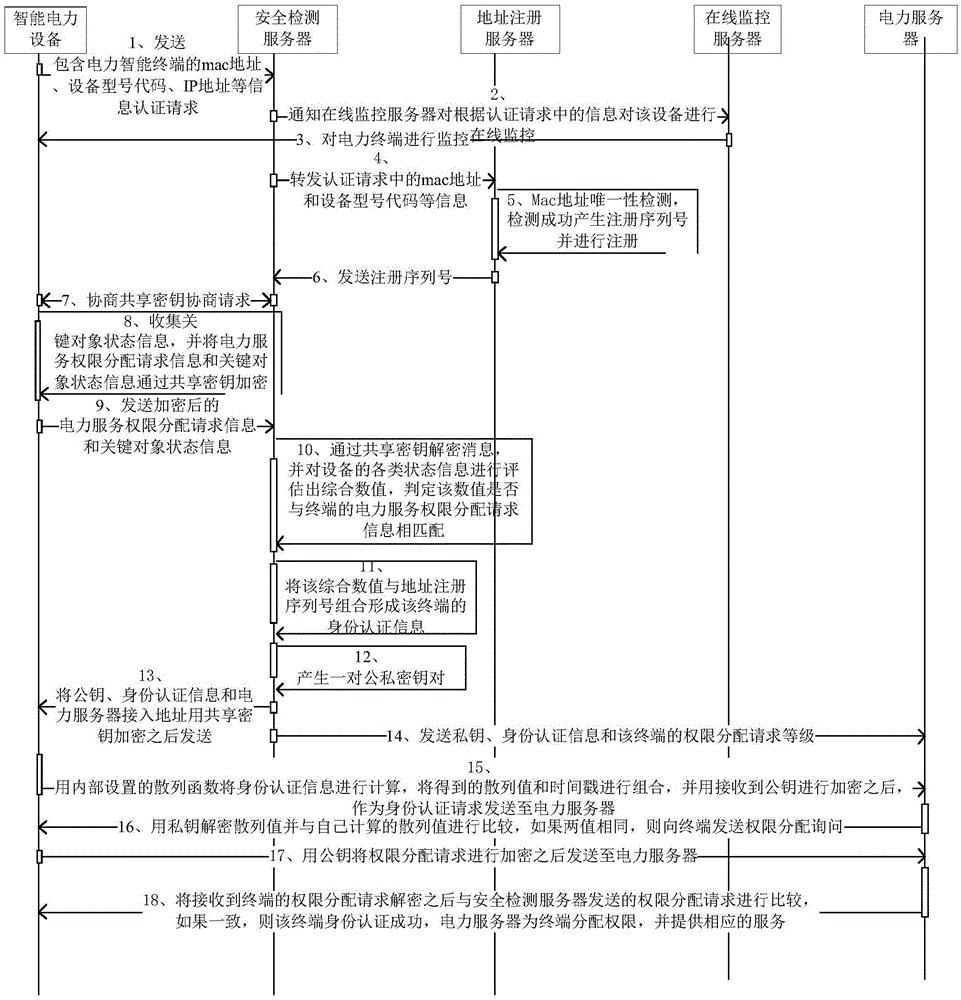
Security authentication system and method for smart power terminal
ActiveCN105553666AGuaranteed uptimePrevent theftUser identity/authority verificationSmart gridThe Internet
The invention provides a security authentication system and method for a smart power terminal. The system comprises a security detection server, a power server, an online monitoring server and an address registration server. The method comprises the following steps that: firstly, the address registration server performs uniqueness detection on the terminal, and generates a registration serial number and transmits the generated registration serial number to the security detection server if the terminal is legal; the security detection server judges whether terminal key object information is matched with power service permission allocation request information of the terminal or not, and generates unique terminal identity authentication information; and the terminal performs authentication and registration on the power server to obtain corresponding services. The system and the method provided by the invention are flexible and effective. Reliable authentication of software is realized without hardware authentication. Meanwhile, the terminal identity authentication information is protected from being stolen. A security detection method which is more efficient and economical than an existing hardware authentication method is provided for the power terminal, so that secure and efficient running of a smart power grid into which an Internet technology is introduced is ensured.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
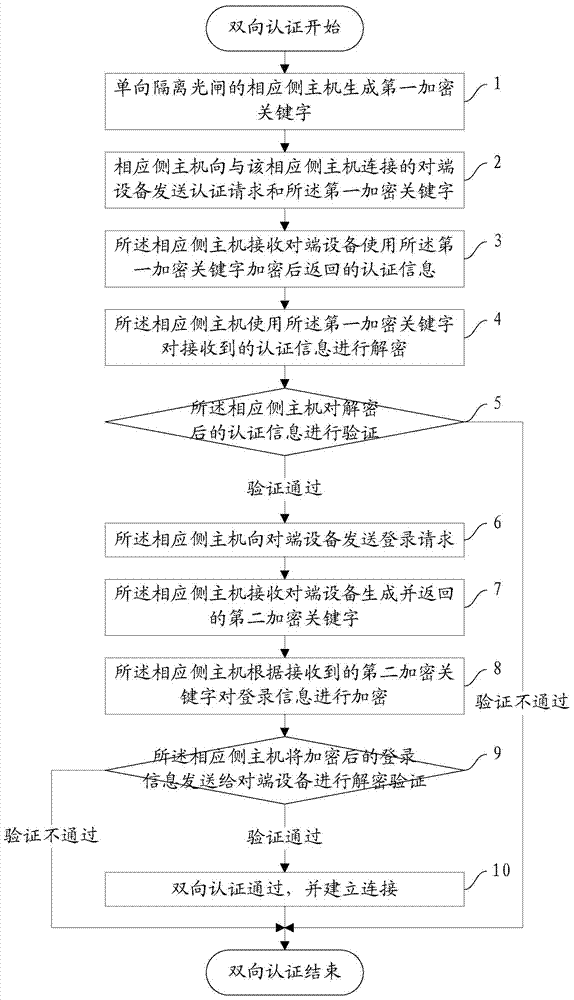
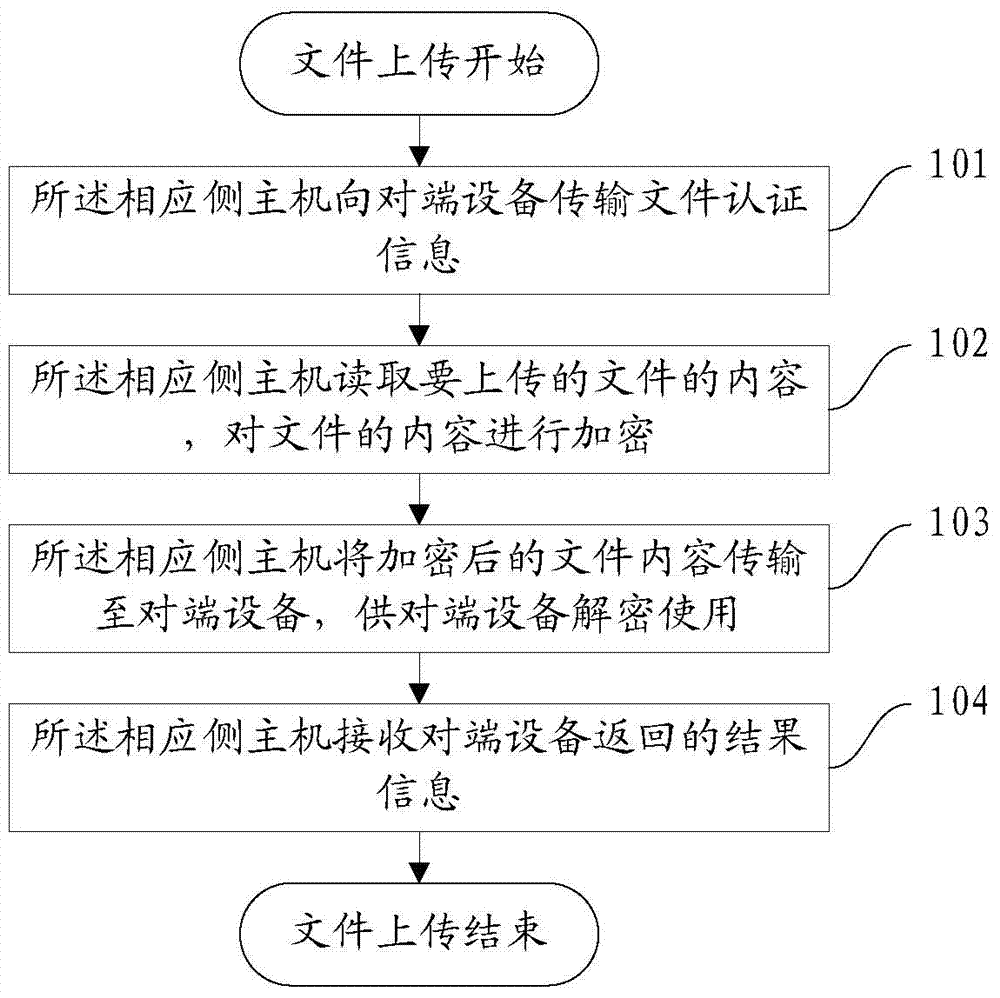
Bidirectional authentication method, device and system
ActiveCN104270346AEnsure safetyAvoid connection spoofingUser identity/authority verificationComputer hardwareInformation transmission
The invention discloses a bidirectional authentication method, device and system and belongs to the technical field of network safety. The bidirectional authentication method comprises the steps that firstly, a first encryption key word is generated; secondly, an authentication request and the first encryption key word are sent; thirdly, authentication information is received; fourthly, decryption is conducted on the authentication information; fifthly, the authentication information is verified; sixthly, a logging-in request is sent; seventhly, a second encryption key word is received; eighthly, logging-in information is encrypted; ninthly, the logging-in information is sent so that decryption verification can be conducted; tenthly, bidirectional authentication is passed, and connection is established. By the adoption of the bidirectional authentication method, device and system, bidirectional hardware authentication of the host of a corresponding side and an opposite-end device of unidirectional isolation optical gate can be achieved, connection cheating is avoided, the safety of the information transmission process is guaranteed, and therefore the safety of a unidirectional importing system is guaranteed.
Owner:BEIJING TOPWALK INFORMATION TECH
System encryption-based data protection method and device
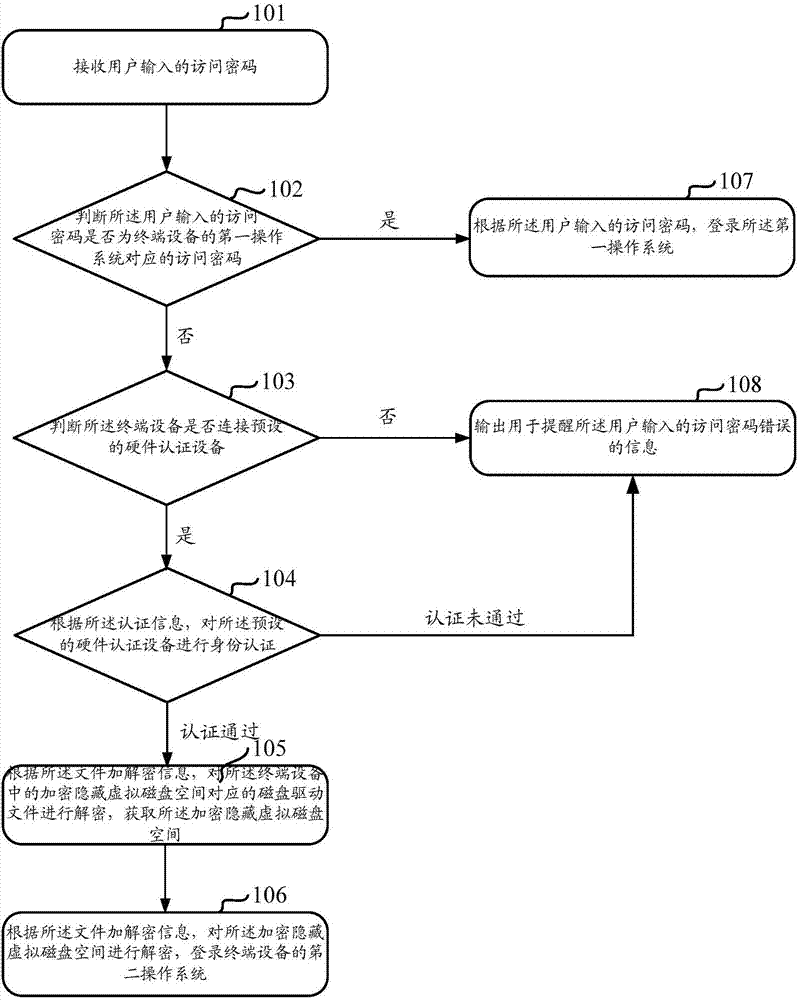
InactiveCN107092836AImprove securityDigital data protectionDigital data authenticationOperational systemPassword
The invention discloses a system encryption-based data protection method and device, and aims at solving the problem that data protection method in the prior art is relatively bad in safety. The method comprises the following steps of: receiving an access password input by a user; judging whether the access password corresponds to a first operation system or not; if the access password does not correspond to the first operation system, judging whether terminal equipment is connected with preset hardware authentication equipment or not; if the terminal equipment is connected with the preset hardware authentication equipment, carrying out identity authentication on the preset hardware authentication equipment according to authentication information; if the authentication passes, decrypting a disk driving file corresponding to an encrypted hidden virtual disk space in the terminal equipment according to file encryption / decryption information, so as to obtain the encrypted hidden virtual disk space; and decrypting the encrypted hidden virtual disk space according to the file encryption information, and logging in a second operation system, wherein the second operation system is installed in the encrypted hidden virtual disk space, and local data needing protection is stored in the second operation system.
Owner:BEIJING BANGCLE TECH CO LTD
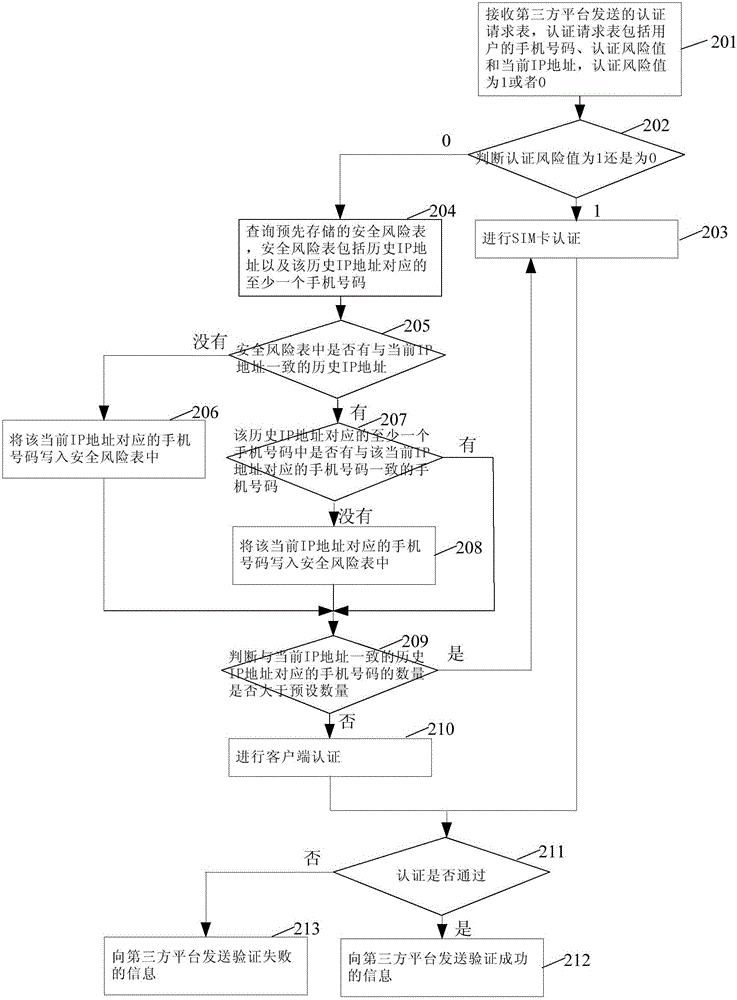
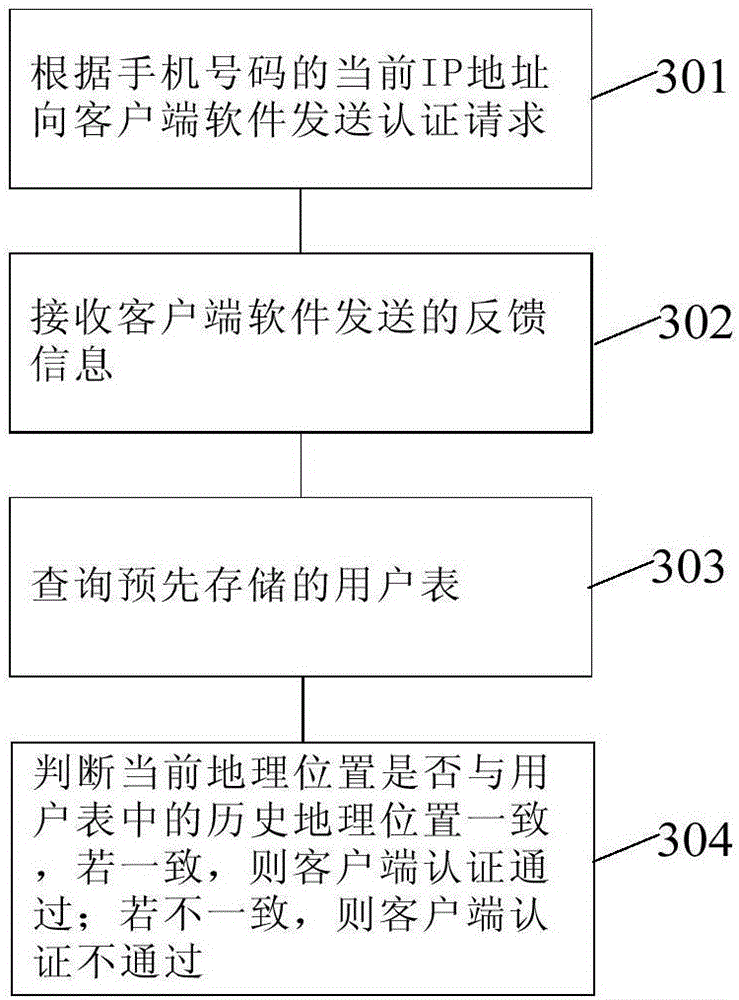
Identity authentication method, authentication server and third-party platform
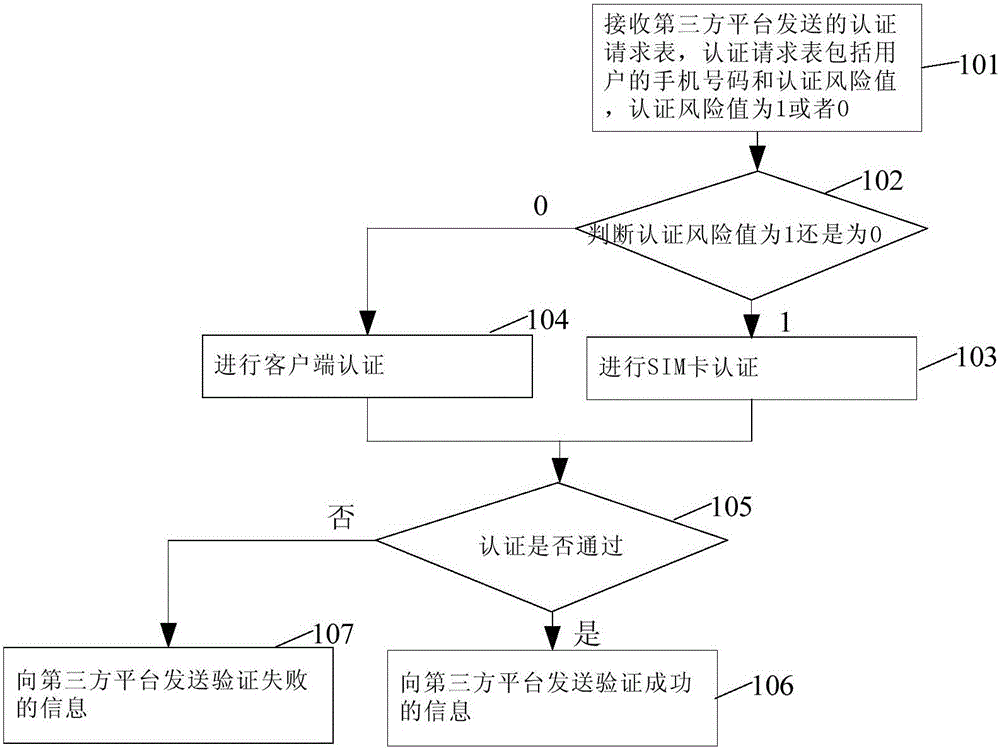
ActiveCN105897771AReduce the number of timesProcessing power limitMessaging/mailboxes/announcementsTransmissionThird partyAuthentication server
The invention provides an identity authentication method, an authentication server and a third-party platform. The method comprises the steps of receiving an authentication request table sent by the third-party platform, wherein the authentication request table comprises a mobile phone number of a user and an authentication risk value, and the authentication risk value is equal to 1 or 0; judging whether the authentication risk value is equal to 1 or 0; if the authentication risk value is equal to 1, carrying out SIM (Subscriber Identity Module) card authentication; if the authentication risk value is equal to 0, carrying out client authentication; if SIM card authentication or client authentication is passed, sending information that authentication is successful to the third-party platform; and if SIM card authentication or client authentication is not passed, sending information that authentication is failed to the third-party platform. In the technical scheme of the identity authentication method, the authentication server and the third-party platform which are provided by the invention, times of short message communication between an SIM card and the authentication server of an operator can be reduced, so that the condition that due to limitation of processing capacity of a short message gateway of the operator, large-scale authentication cannot be supported can be reduced.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
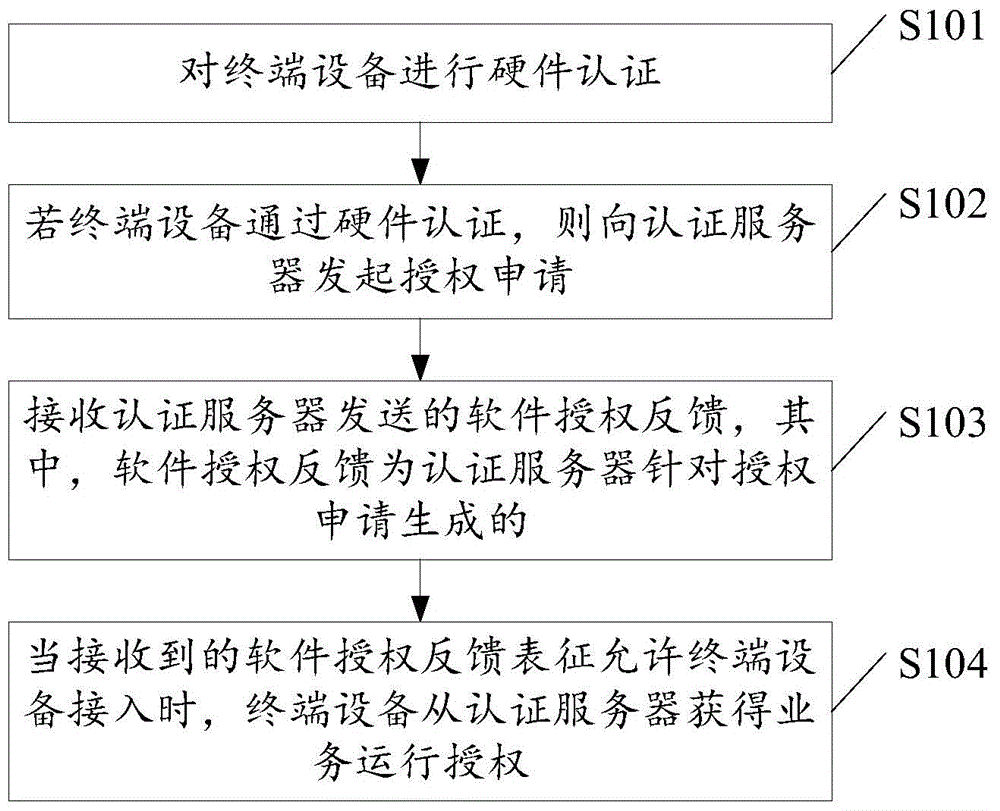
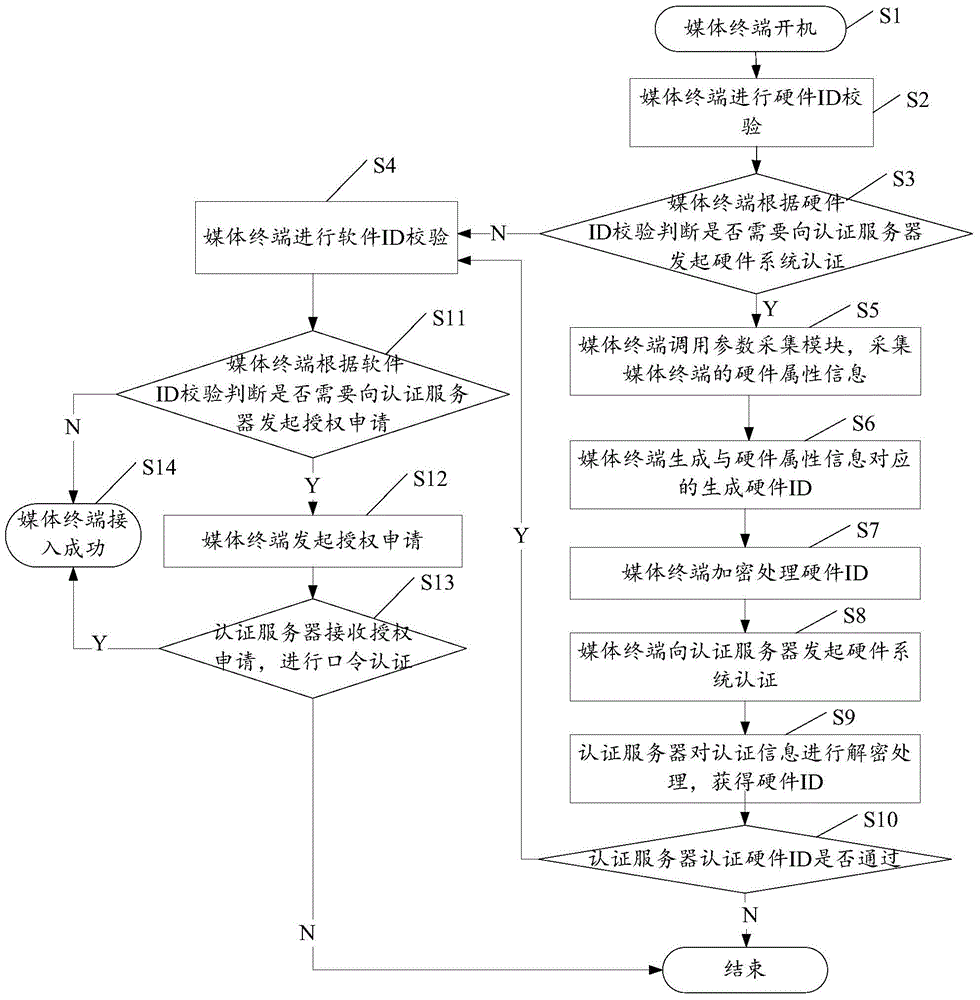
Terminal access authentication authorization method and terminal access authentication authorization system
ActiveCN104486322AEnsure safetyAvoid aggressive behaviorTransmissionTerminal equipmentHardware authentication
The invention discloses a terminal access authentication authorization method and a terminal access authentication authorization system, which are applied to terminal equipment. The method comprises the following steps of carrying out hardware authentication on the terminal equipment; if the terminal equipment is authenticated by the hardware authentication, sending an authorization application to an authentication server; receiving a software authentication feedback sent by the authentication server, wherein the software authentication feedback is generated aiming at the authorization application by the authentication server and the terminal equipment obtains business operation authorization from the authentication server when the received software authentication feedback shows that the terminal equipment is allowed to access.
Owner:WUHAN OPTICS VALLEY INFORMATION TECH
Security processing method, device and processing chip, network equipment
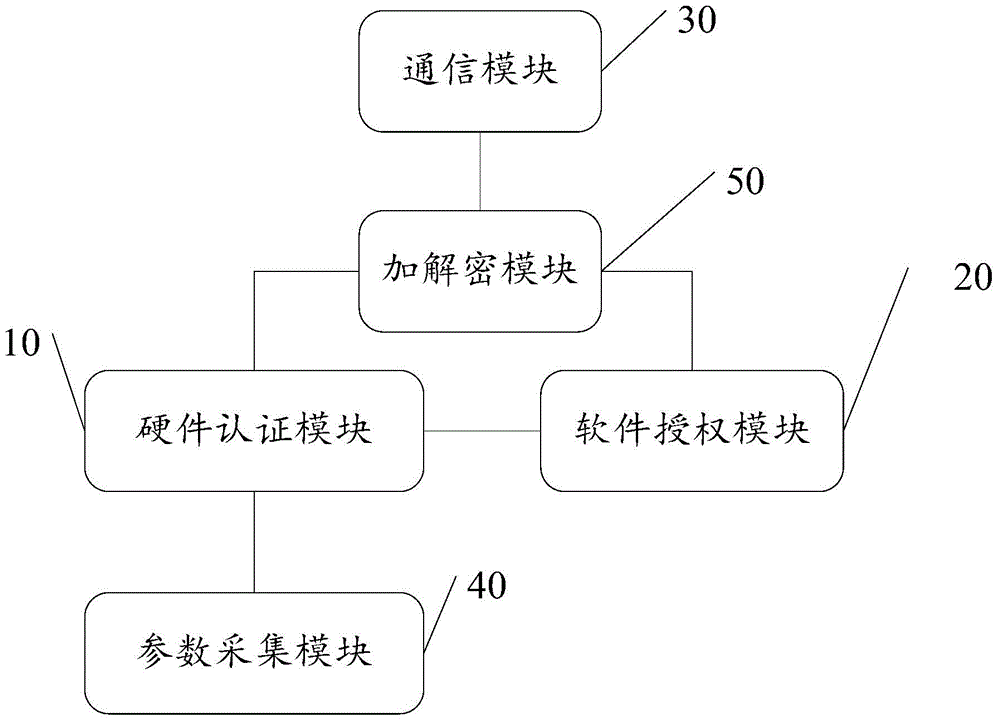
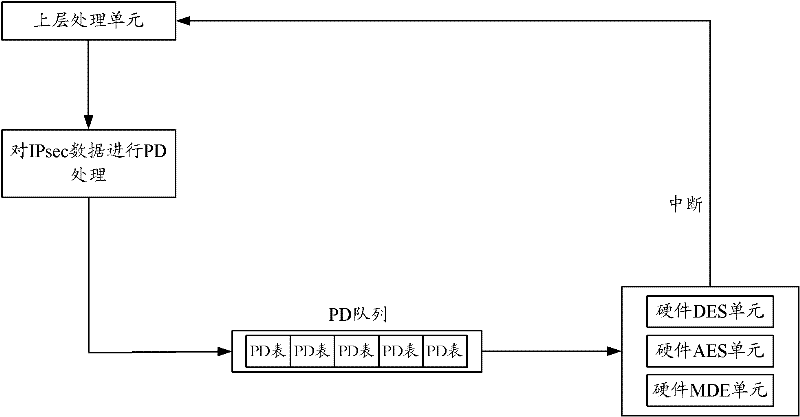
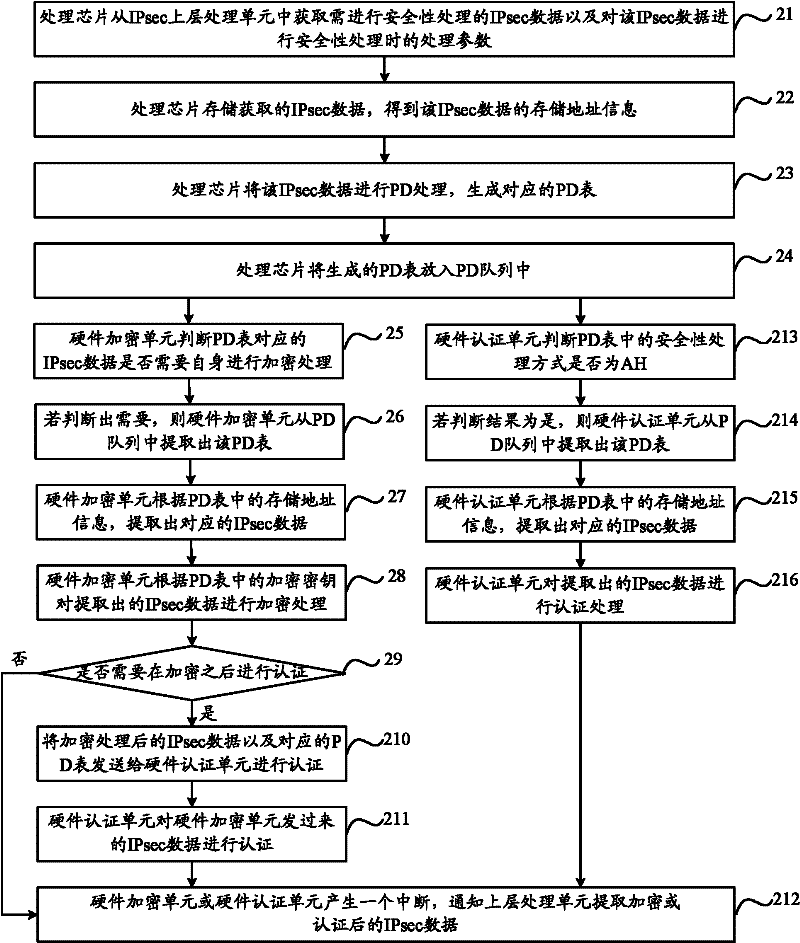
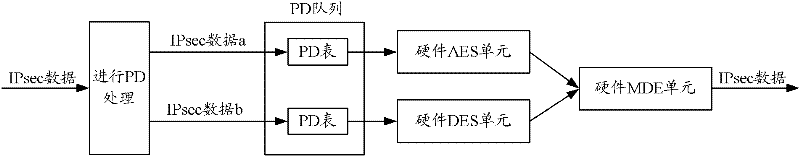
ActiveCN102263794AIntegrity guaranteedNo tamperingEncryption apparatus with shift registers/memoriesIPsecHardware authentication
The invention discloses a security processing method, a security processing device, a processing chip and network equipment. The method comprises the following steps of: obtaining a security processing way for Internet protocol security (IPsec) data requiring security processing; if authentication processing is determined to be required after encryption processing is performed on the IPsec data according to the security processing way, obtaining an encryption algorithm for the encryption processing of the IPsec data; determining an authentication processing way for the authentication processing of the IPsec data according to the obtained encryption algorithm, wherein the authentication processing way comprises a software authentication processing way and a hardware authentication processing way; performing hardware encryption processing on the IPsec data according to the obtained encryption algorithm; and performing the authentication processing on the hardware-encrypted IPsec data according to the determined authentication processing way. By the technical scheme provided by the invention, the problem of relatively lower processing efficiency in the authentication processing of the IPsec data in the prior art is solved.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
System, design and process for easy to use credentials management for online accounts using out-of-band authentication
ActiveUS9412283B2Easy to useProtection attackUser identity/authority verificationCoding/ciphering apparatusApplication softwareMulti dimensional
Owner:GCOM IP LLC
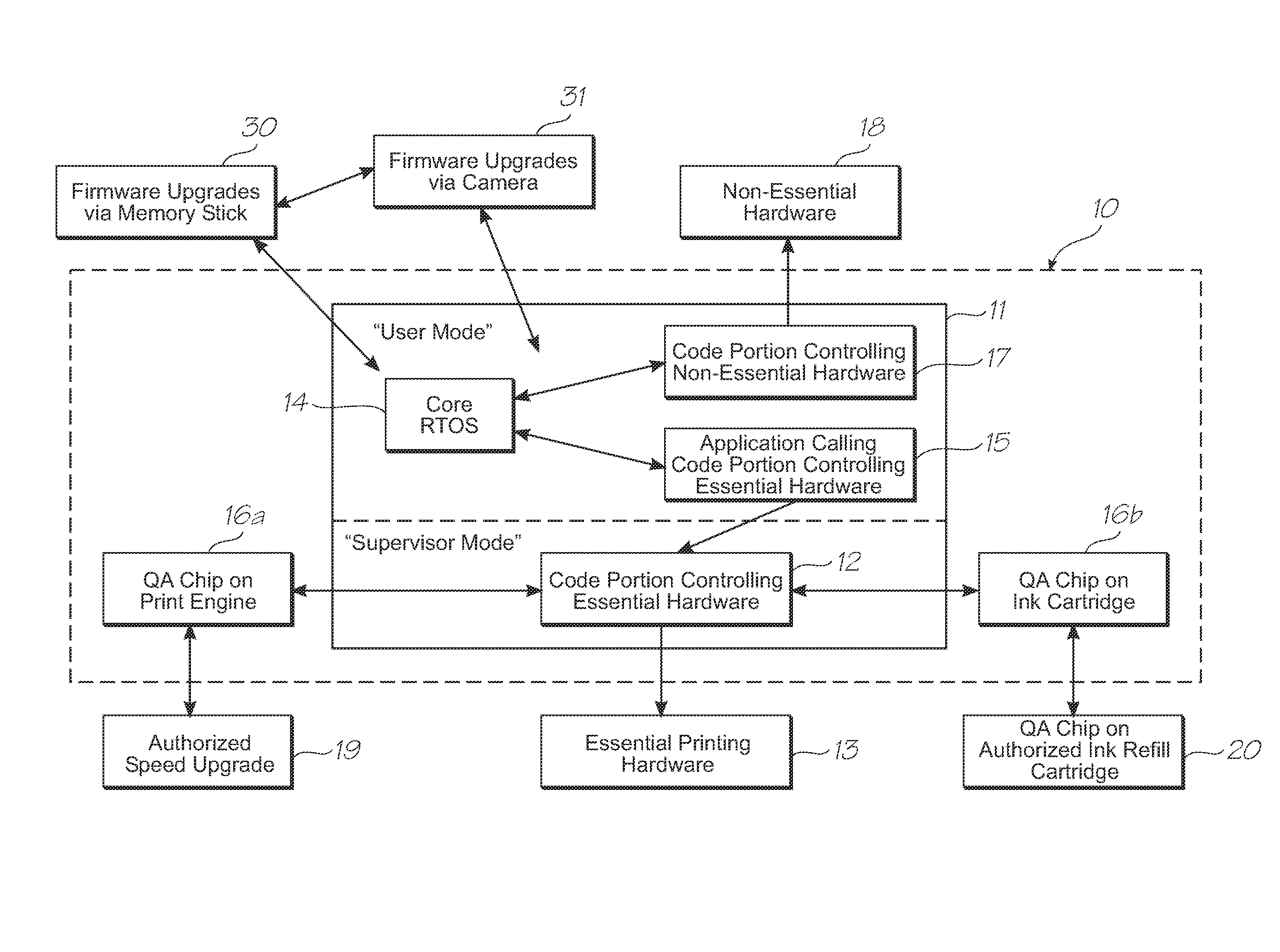
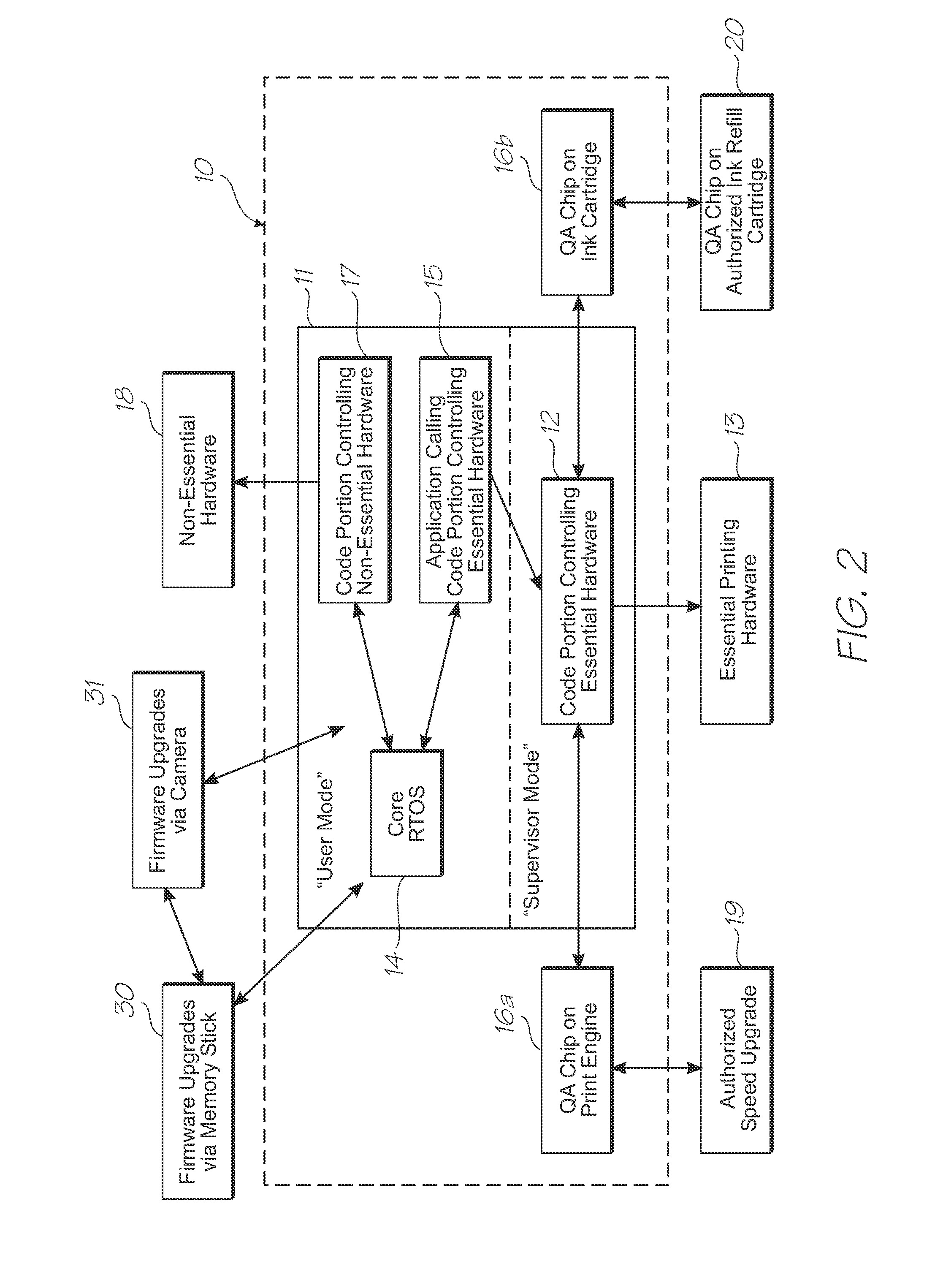
Electronic device having essential hardware authentication
InactiveUS20100277536A1Simple processDigital data processing detailsUnauthorized memory use protectionComputer hardwareOperational system
An electronic device having an embedded computer system is provided. The device has a processor supporting a real-time operating system (RTOS). The processor further supports user and supervisor modes. The computer system is programmed such that only code portions directly controlling essential hardware in the device are run in supervisor mode. The code portion directly controlling essential hardware communicates with at least one authentication chip in the device before an operation of the hardware, the authentication chip authorizing the operation
Owner:ZAMTEC
Server login authentication system based on zero knowledge proof
InactiveCN111585762AAccess request deniedUser identity/authority verificationEngineeringNetwork communication
The invention relates to the technical field of server login authentication based on zero knowledge proof. The invention further discloses a server login authentication system based on zero knowledgeproof. The system comprises a cloud server Sf in which a server login authentication system runs, and an intelligent terminal Ui or a PC terminal Uj in which the server login authentication system runs, wherein the intelligent terminal Ui or the PC terminal Uj is in communication connection with the cloud server Sf on the server login authentication system through network communication equipment;the server login authentication system verifies the user identity of the intelligent terminal Ui or the PC terminal Uj by adopting a verification method based on zero knowledge proof; only when the user identity of the intelligent terminal Ui or the PC terminal Uj passes the verification of the server login authentication system, the cloud server Sf accepts the access request of the intelligent terminal Ui or the PC terminal Uj. Under the condition that a hardware USB Key authentication mode is not adopted, the technical effect of safely authenticating the identity of the user is achieved.
Owner:谢广钦
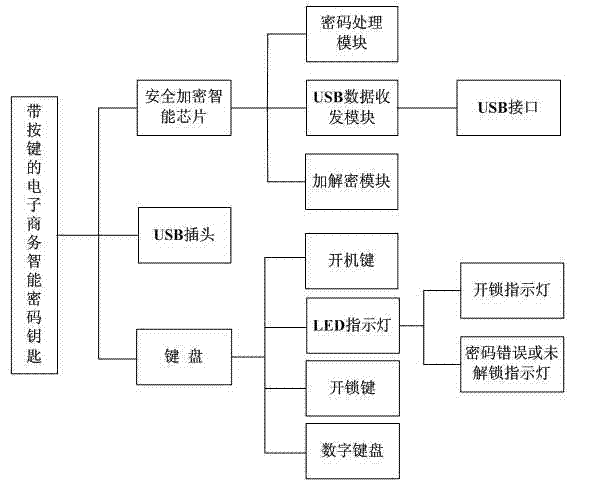
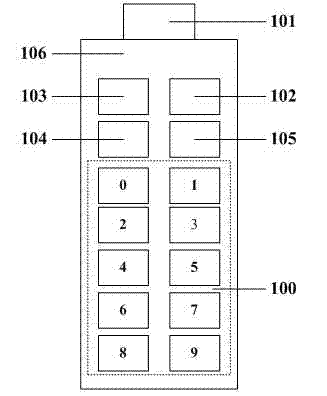
Electronic commerce intelligent password key with button and implementation method for electronic commerce intelligent password key
ActiveCN102902903AReduce risk of leakageAvoid Record LeakageDigital data authenticationProtocol authorisationPersonal identification numberPassword
The invention relates to the technical field of information security, and provides an electronic commerce intelligent password key with a button and an implementation method for the electronic commerce intelligent password key. The intelligent password key comprises a universal serial bus (USB) plug, a keyboard and a built-in security encryption intelligent chip, wherein a digital keyboard, a power button, an unlocking button and a light emitting diode (LED) indicating lamp are arranged on the keyboard; the intelligent chip comprises a password processing module for processing the buttons, initializing a user personal identification number (PIN) code, modifying the user PIN code and checking the user PIN code, a USB data transmitting and receiving module for transmitting authentication information and confirming work of equipment, and an encryption and decryption module for encrypting and decrypting user authentication information. By an encryption storage mode, the user authentication information is prevented from being violently cracked; by a digital keyboard hardware authentication mode, the potential security hazards of keyboard Trojan horses and 'screen shot' password stealing Trojan horses are avoided; and therefore, the risk that the PIN code is stolen by the Trojan horse during authentication is reduced, and the intelligent password key is secure and reliable and is low in cost.
Owner:SHANDONG ZHONGFU INFORMATION IND
Hardware certification based on certifying development processes
ActiveUS8266426B2Error detection/correctionTransmissionSoftware development processSoftware engineering
Owner:RED HAT
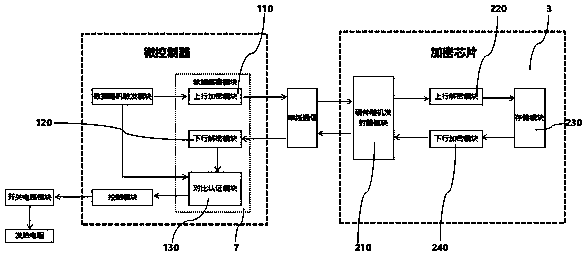
Encryption chip based on hardware random encryption authentication and electronic cigarette comprising chip
PendingCN111064582AIt is difficult to crackImprove anti-counterfeiting performanceKey distribution for secure communicationUser identity/authority verificationMicrocontrollerComputer architecture
The invention relates to the technical field of electronic cigarettes, and discloses an encryption chip based on hardware random encryption authentication and an electronic cigarette comprising the chip. An encryption authentication chip comprises a soft encryption and decryption module arranged in a microcontroller and an encryption chip arranged in an atomizer. The soft encryption and decryptionmodule comprises an uplink encryption module, a downlink decryption module and a comparison authentication module, the encryption chip comprises a hardware random transmitter module, an uplink decryption module, a storage module and a downlink encryption module, and the uplink encryption module, the downlink decryption module and the hardware random transmitter module carry out data transmissionthrough single-wire communication. According to the invention, the encryption chip is arranged in the atomizer to carry out hardware authentication anti-counterfeiting identification, and bidirectional random processing is carried out on the ciphertext based on the hardware random emitter in the encryption and decryption process, so that the encryption and decryption process of the chip is more complex, the cracking difficulty is higher, the anti-counterfeiting capability of the encryption chip is improved, and the benefits of merchants and users are effectively protected.
Owner:深圳市艾迪科泰电子有限公司
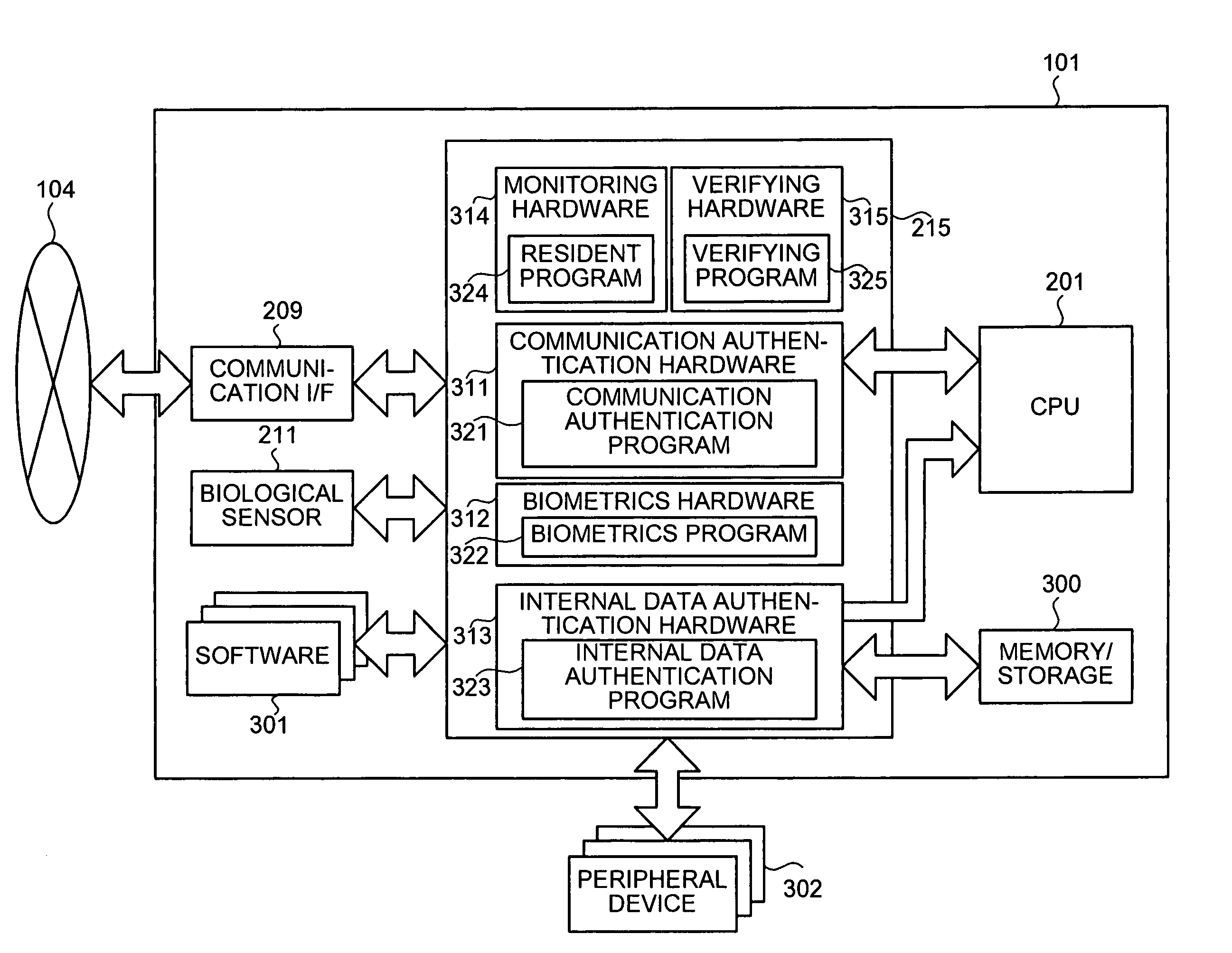
Data managing device equipped with various authentication functions
InactiveUS8272050B2Digital data processing detailsUnauthorized memory use protectionComputer hardwareData management
A data managing device with a single chip that includes: first hardware that authenticates security of communication performed by a data processing apparatus that houses the data managing device; second hardware that performs different processing from processing performed by the first hardware; and third hardware that receives an update program for a program executed by any one of the first hardware and the second hardware, from a data providing apparatus with which security of communication is authenticated by the first hardware, and updates the program by the update program.
Owner:SOCIONEXT INC
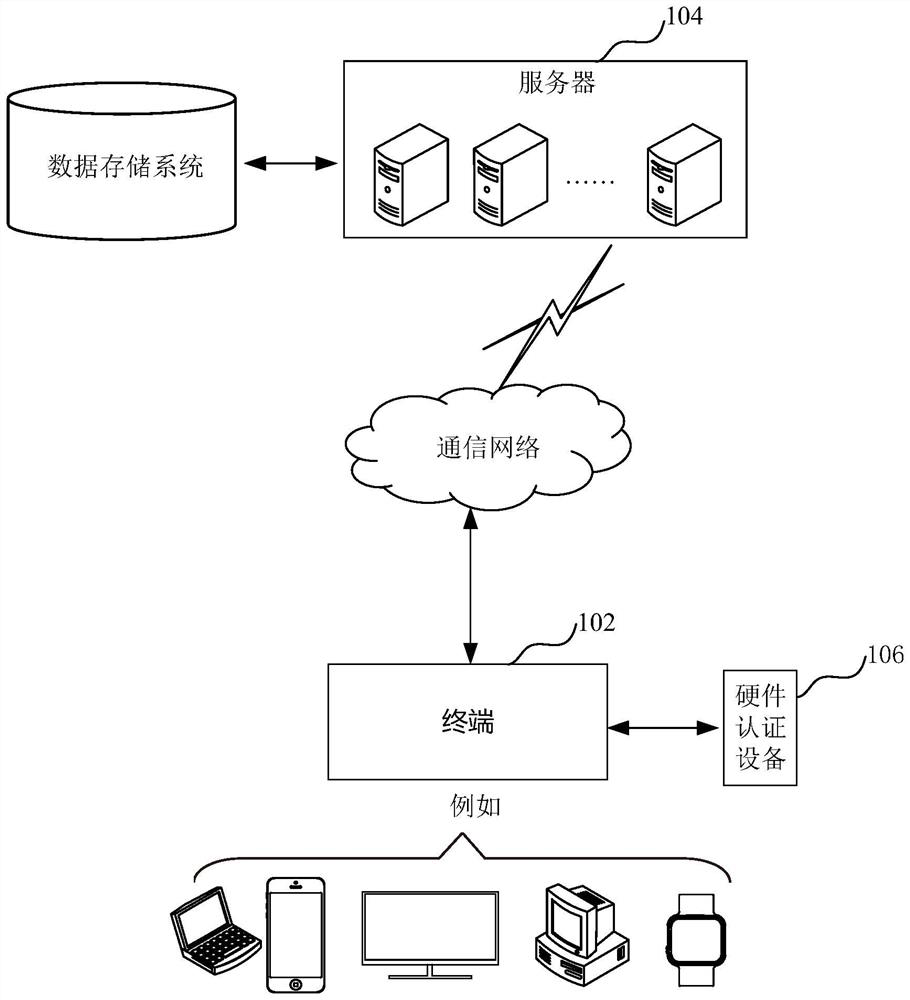
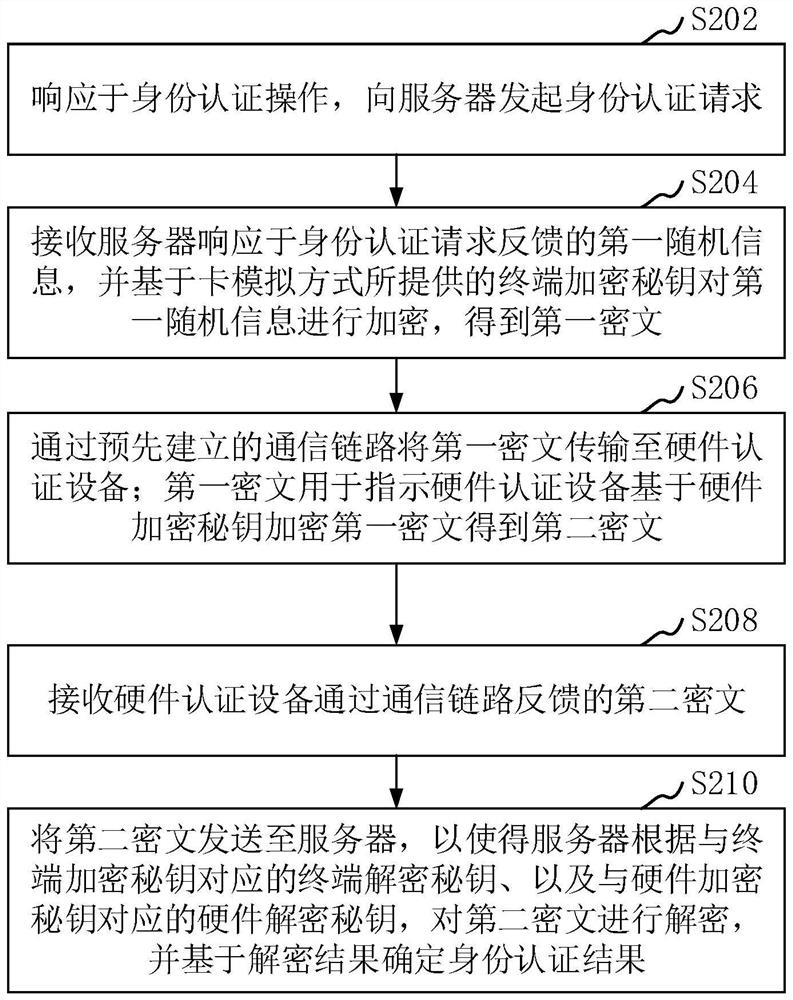
Identity authentication method and device, equipment, storage medium and computer program product
PendingCN114070614AImprove securityDoes not pose a security problemKey distribution for secure communicationDigital data protectionTelecommunications linkCiphertext
The invention relates to an identity authentication method and device, equipment, a storage medium and a computer program product for use in the field of information security. The method comprises the following steps: in response to an identity authentication operation, initiating an identity authentication request to a server; receiving first random information fed back by the server in response to the identity authentication request, and encrypting the first random information based on a terminal encryption key provided in a card simulation mode to obtain a first ciphertext; transmitting the first ciphertext to hardware authentication equipment through a communication link, so as to enable the hardware authentication equipment to encrypt the first ciphertext based on the hardware encryption key to obtain a second ciphertext; receiving the second ciphertext fed back by the hardware authentication equipment through the communication link; and sending the second ciphertext to the server, so as to enable the server to decrypt the second ciphertext according to a terminal decryption key corresponding to the terminal encryption key and a hardware decryption key corresponding to the hardware encryption key, and determining an identity authentication result based on a decryption result. By adopting the method, the security of identity authentication can be improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Acquired information sharing method and system based on dual authentication and multiple protection measures
InactiveCN110611661ASolve potential safety hazardsSolve untraceable problemsTransmissionInternet Authentication ServiceInformation sharing
The invention discloses an acquired information sharing method and a system based on dual authentication multiple protection measures, and relates to an acquired information sharing method. In the prior art, head information is used for transmitting user identity verification information, and user information is easy to intercept in the method. The method comprises the following steps: a client initiates an account authentication request; if the authentication is passed, randomly generating a temporary token, and returning the temporary token to the receiver; initiating the data request againafter obtaining the temporary token by the receiver, and decrypting the token by the sender after receiving the request and judging the validity of the token and the timeliness of the token; if the verification is passed, entering links of extracting data and assembling the data; the server extracts the acquired data and performs data desensitization; signing the data and encrypting the data; andsending the original text and the encrypted abstract to a receiver together. According to the method, an authentication method combining account authentication and token authentication is used, identity authentication service and data providing service are separated, and the security of interface interaction is greatly improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO MARKETING SERVICE CENT +4
Cloud platform authentication method, system and device based on blockchain, and medium
ActiveCN112468301AGuaranteed validityGuaranteed to completeUser identity/authority verificationDatabase distribution/replicationTimestampPassword
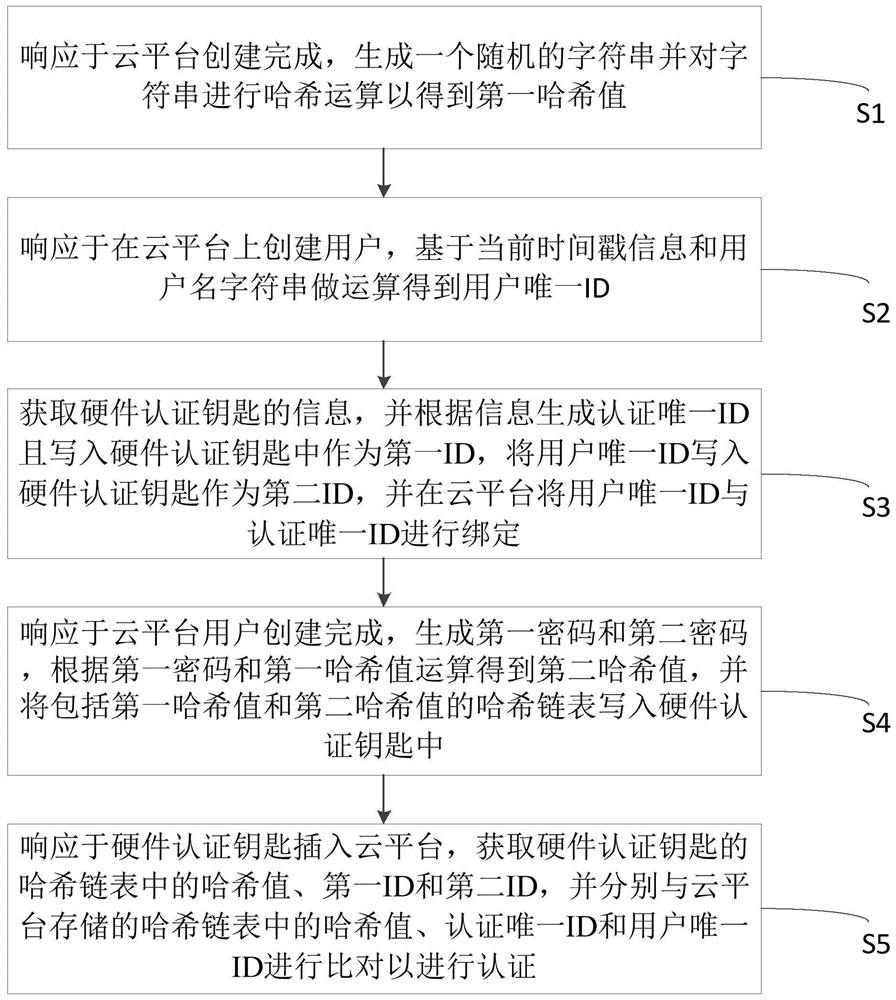
The invention discloses a cloud platform authentication method based on a block chain, which comprises the following steps: generating a random character string in response to completion of creation of a cloud platform, and performing hash operation on the character string to obtain a first hash value; in response to creation of a user on the cloud platform, performing operation based on the current timestamp information and the user name character string to obtain a unique user ID; acquiring information of the hardware authentication key, generating an authentication unique ID according to the information, writing the authentication unique ID and the user unique ID into the hardware authentication key, and binding the user unique ID with the authentication unique ID; in response to completion of creation of the cloud platform user, generating a first password and a second password, performing operation according to the first password and the first hash value to obtain a second hash value, and writing the second hash value into the hardware authentication key as a final hash value; and in response to the fact that the hardware authentication key is inserted into the cloud platform,comparing the obtained information with a hash chain table, an authentication unique ID and a user unique ID stored in the cloud platform to perform authentication.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Hardware authentication token with remote validation
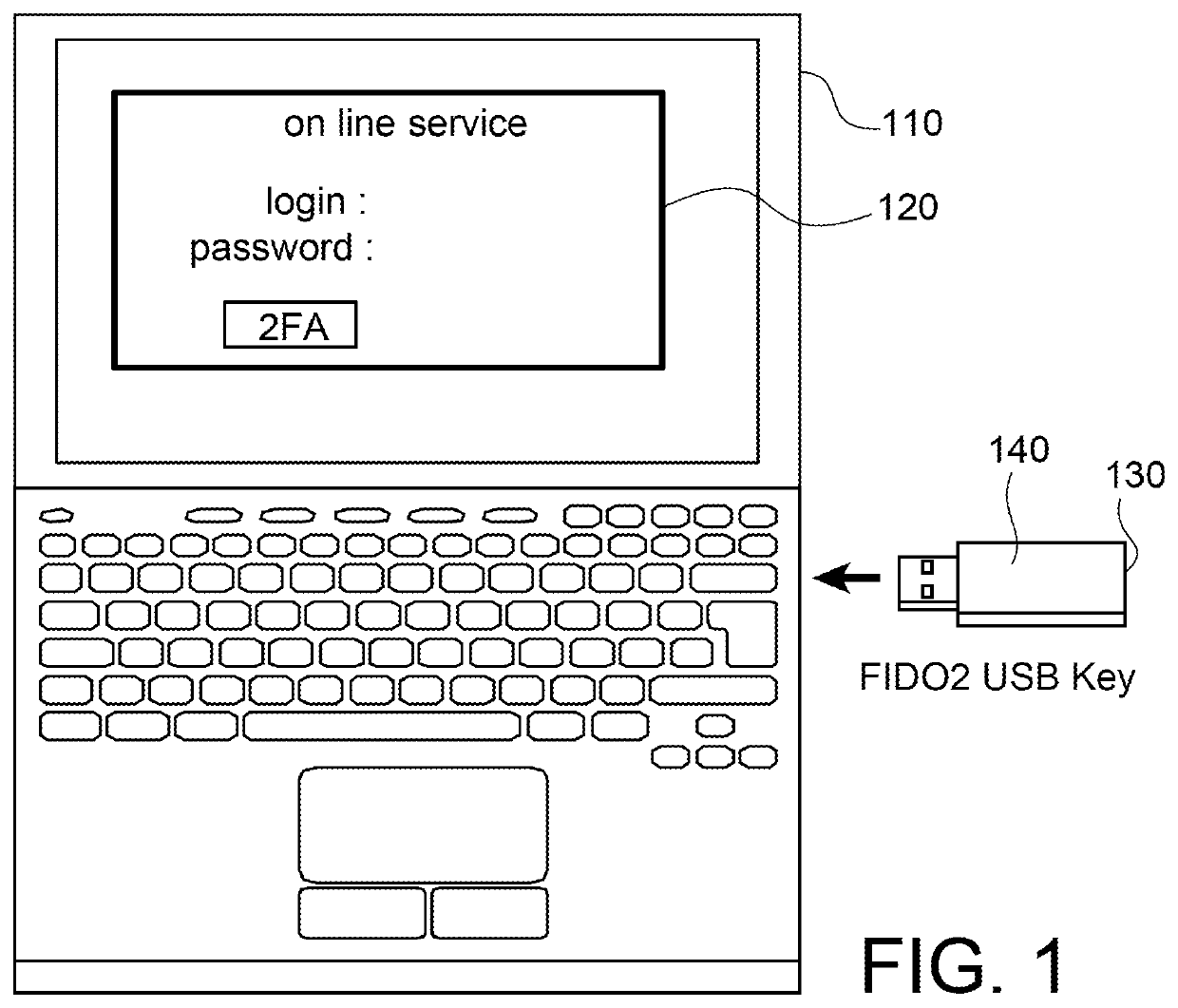
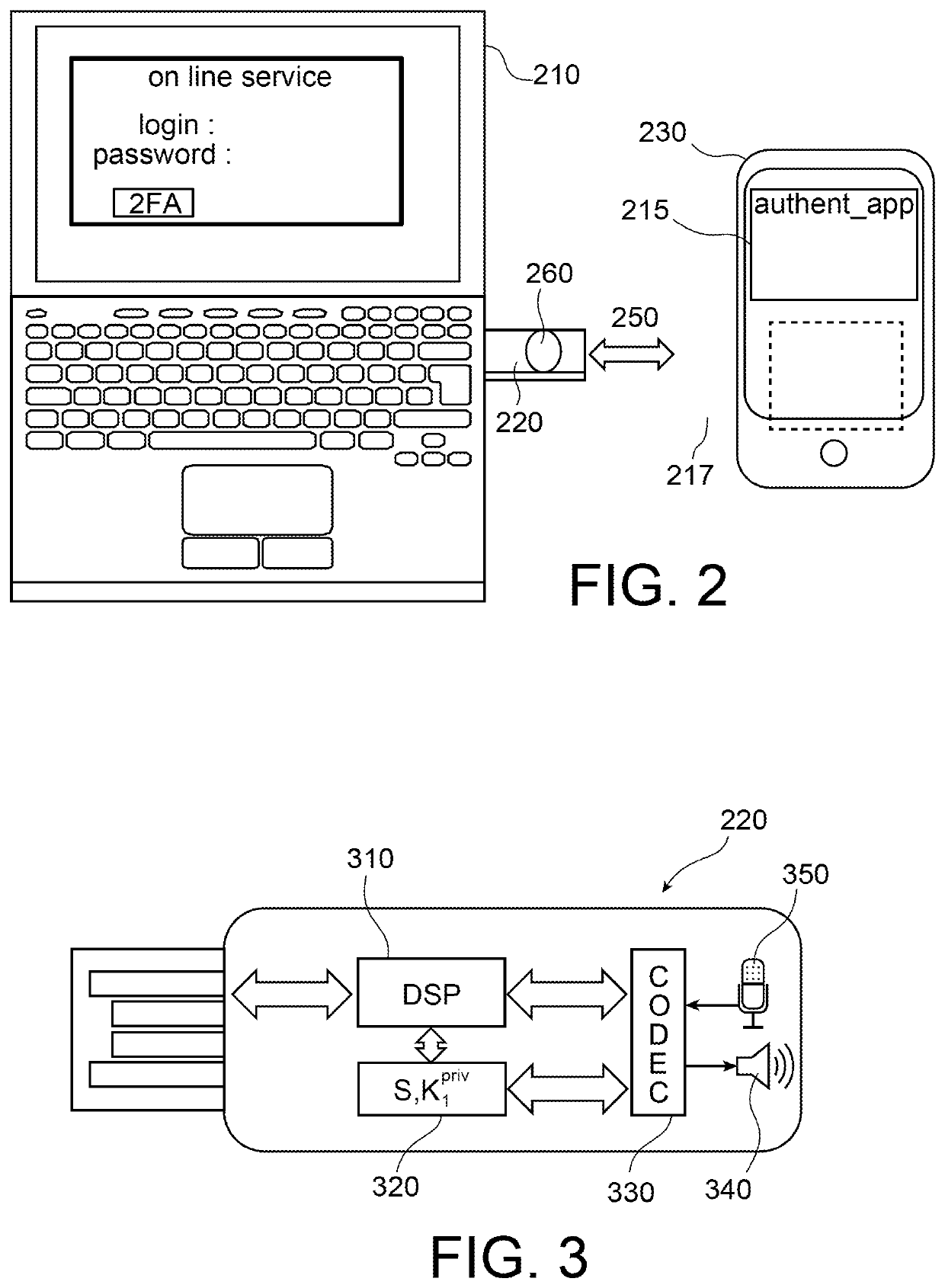
PendingUS20220166623A1Key distribution for secure communicationPublic key for secure communicationEngineeringHardware authentication
A hardware authentication token is intended for being connected to a computer terminal. This token includes a confirmation button, a processor and a secure memory area where a first private key is stored. The terminal can ask the user to authenticate using the token by transmitting a first nonce to the user. After the confirmation button has been pressed, the token generates a second nonce, encodes it using ultrasonic signals and transmits it, via an acoustic channel, to the user's smartphone. The token determines from the response whether the second nonce has been signed with a second private key belonging to the user and, if so, returns the first nonce encrypted by the first private key to the computer terminal in order to authenticate the user.
Owner:COPSONIC
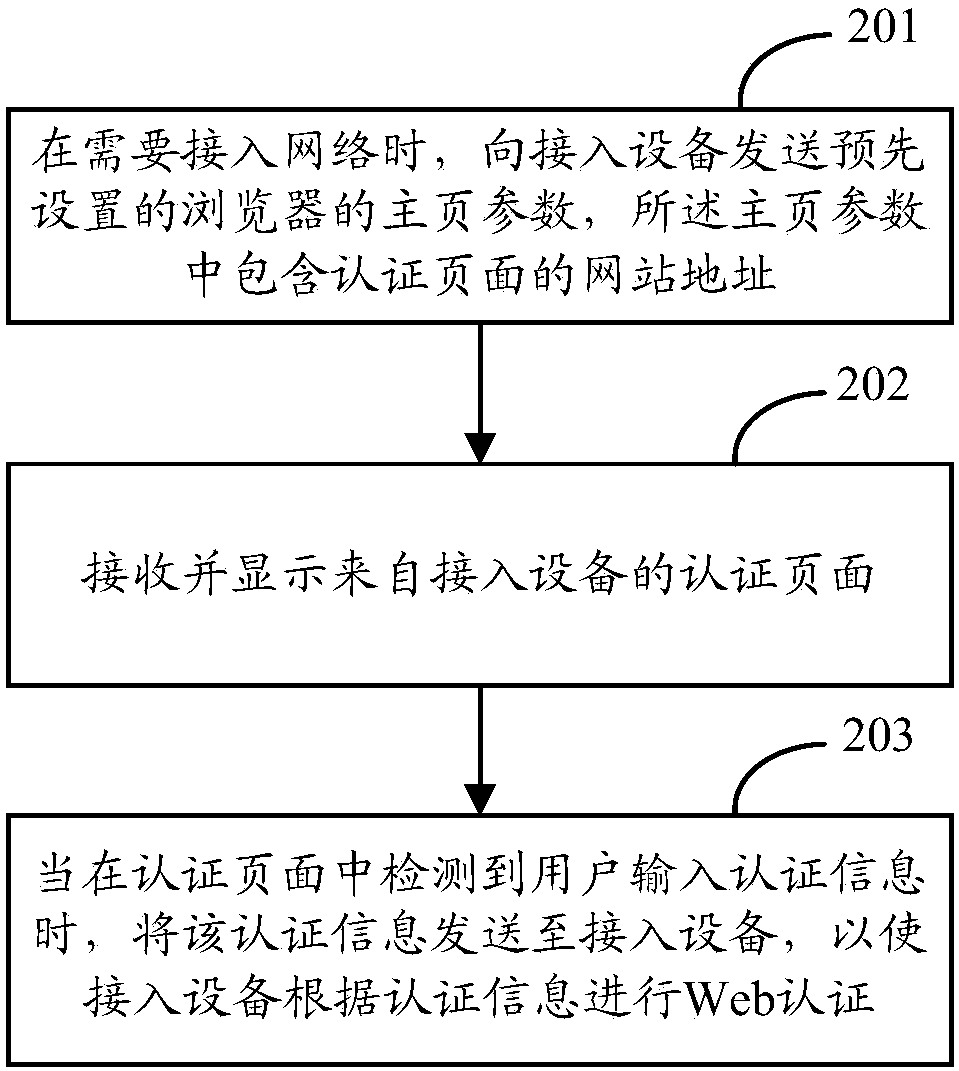
Internet surfing authentication method and device
The application provides an Internet surfing authentication method and device. The Internet surfing authentication method comprises the following steps: sending preset home page parameters of the browser to an access device when requiring to access the network, wherein the home page parameters include the website address of an authentication page; receiving and displaying the authentication page from the access device; and sending the authentication information to the access device when the user input authentication information is detected in the authentication page, so that the access deviceperforms Web authentication according to the authentication information. According to the Internet surfing authentication method and device, the website address of the authentication page is set in the home page parameters to show that the authentication page is trusted, therefore, the warning that the certificate is unsafe is not popped up when the user terminal accesses the network, and the authentication page is displayed directly, therefore, the use experience is improved; and the website address used for authentication is included in the home page parameters when performing the Web authentication, therefore, the access device can directly return to the authentication page without intercepting the Web request and then the website address of the authentication page is pushed, therefore,the device processing performance is improved.
Owner:HANGZHOU DPTECH TECH
Database multiple authentication method and system, terminal and storage medium
ActiveCN112491843AMulti-factor authentication implementationImprove securityKey distribution for secure communicationUser identity/authority verificationConfidentialityHardware authentication
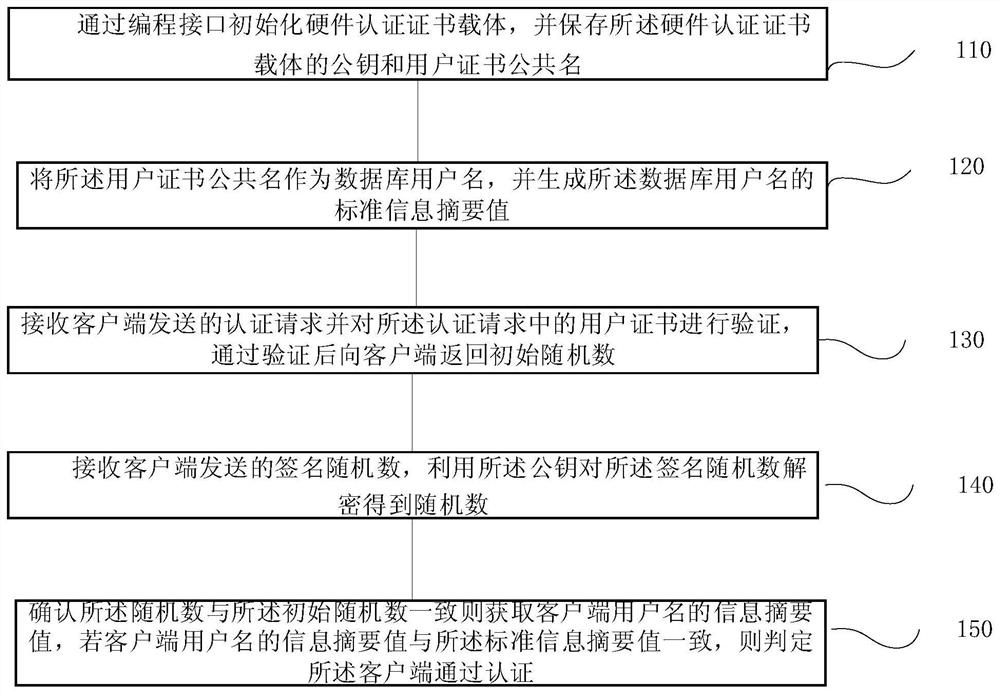
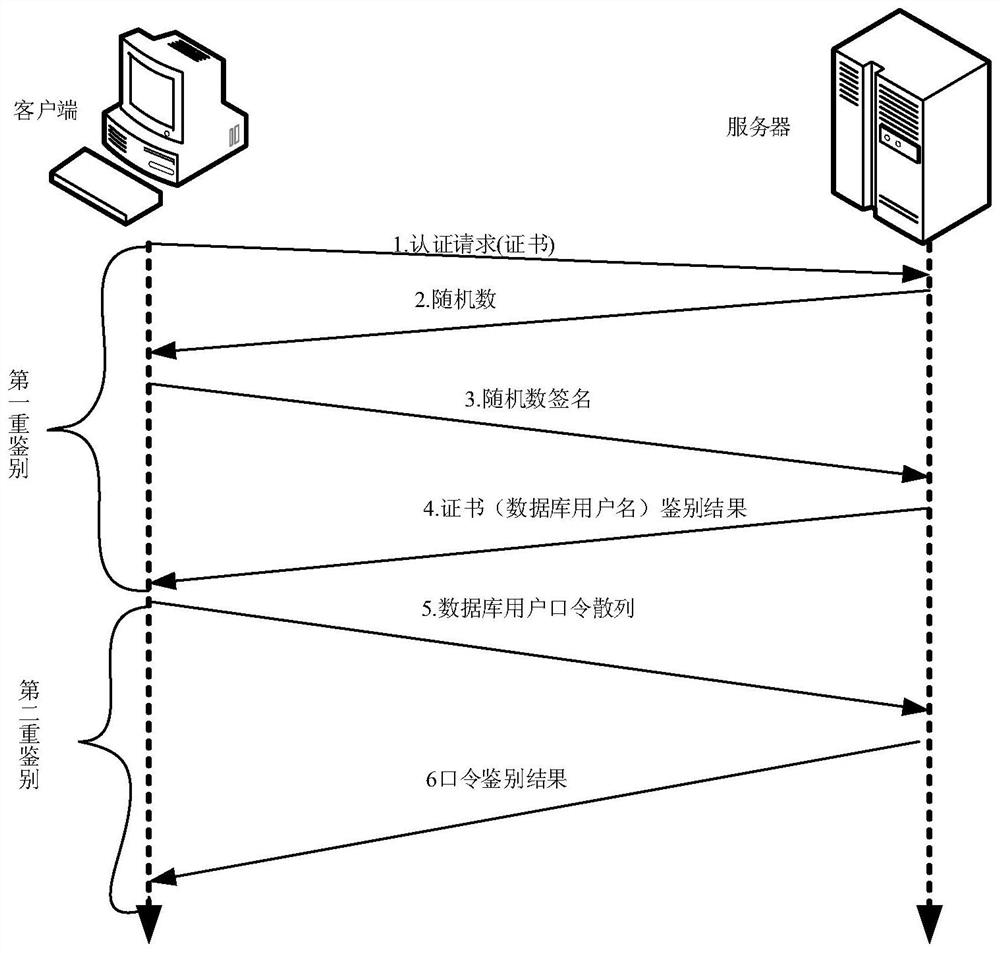
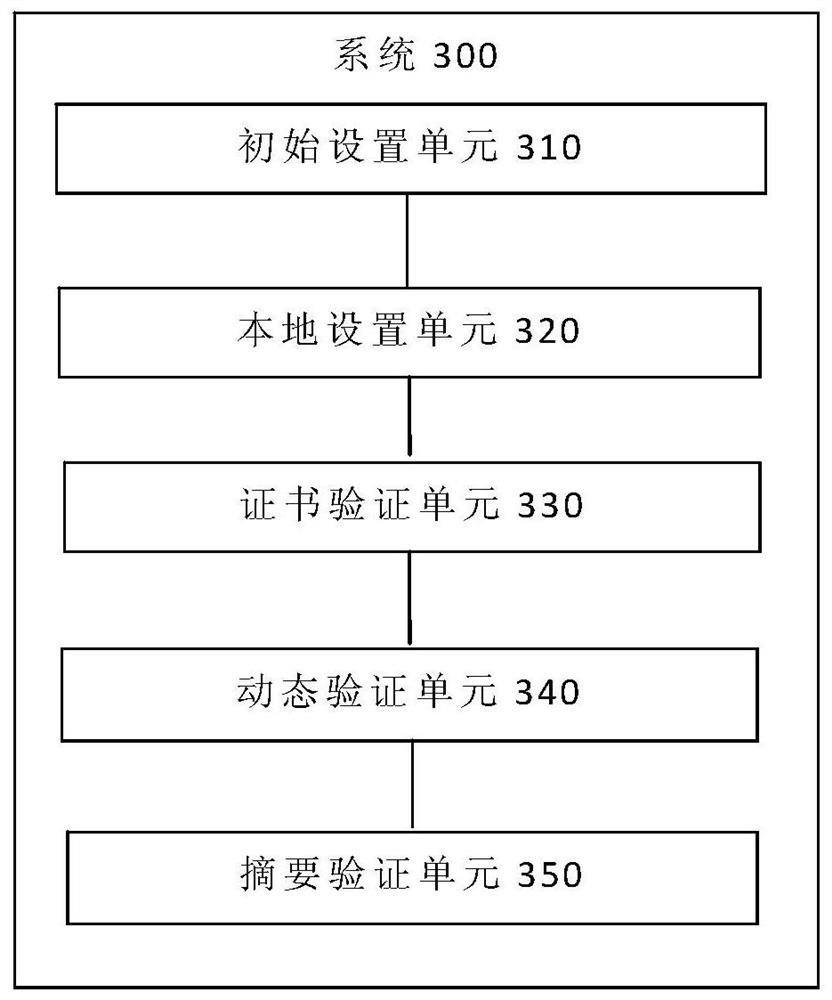
The invention provides a database multiple authentication method and system, a terminal and a storage medium, and the method comprises the steps: initializing a hardware authentication certificate carrier through a programming interface, and storing a public key and a user certificate public name of the hardware authentication certificate carrier; taking the user certificate public name as a database user name, and generating a standard information abstract value of the database user name; receiving an authentication request sent by the client, verifying a user certificate in the authentication request, and returning an initial random number to the client after the verification is passed; receiving a signature random number sent by a client, and decrypting the signature random number by using the public key to obtain a random number; and if the random number is consistent with the initial random number, obtaining an information abstract value of a client user name, and if the information abstract value of the client user name is consistent with the standard information abstract value, determining that the client passes the authentication. According to the invention, the security ofthe database and the confidentiality of the user are improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com