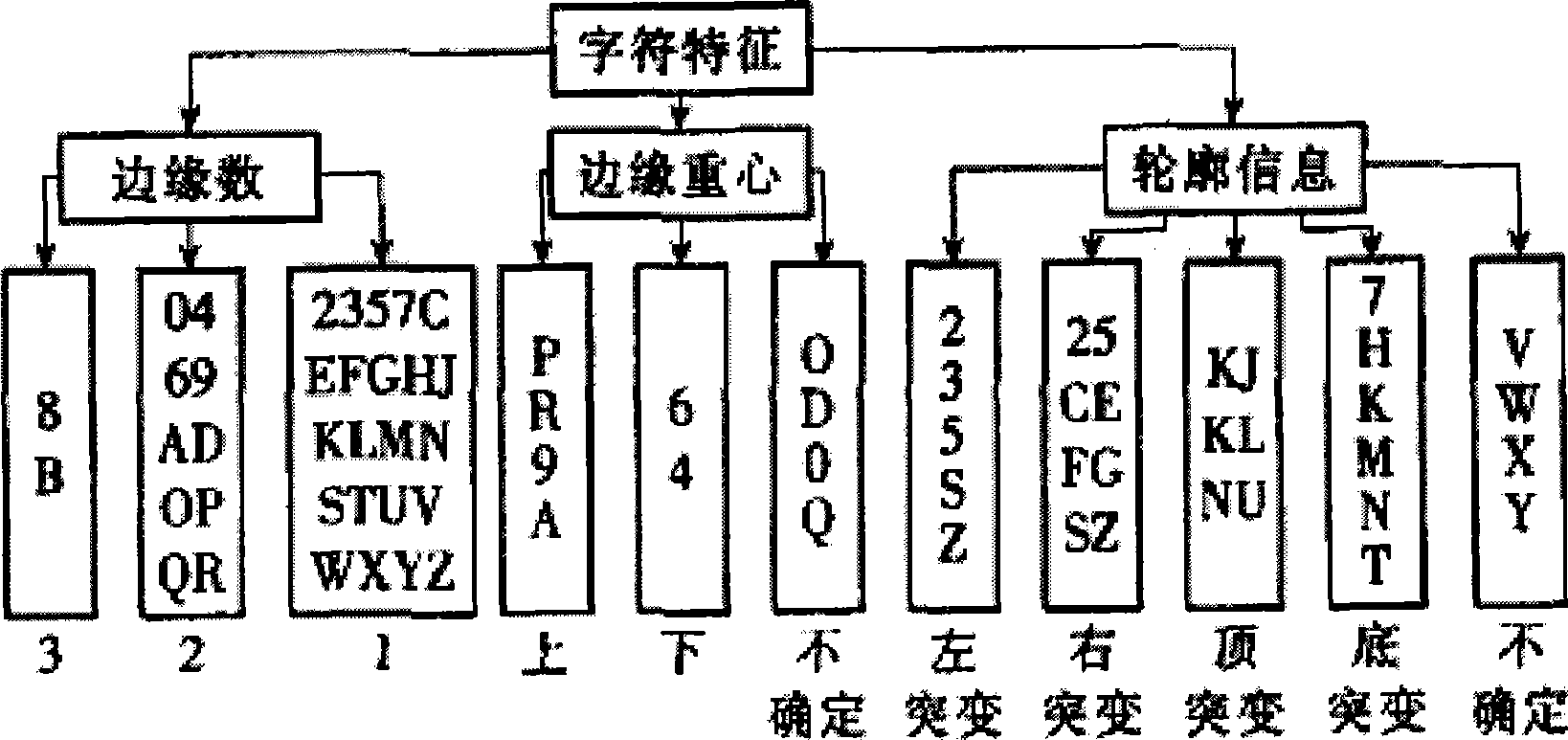
Patents
Literature
552 results about "Certificate verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The online certificate verification process can be used to verify that a certificate of filing or a certificate of fact has, in fact, been issued by the Corporations Section of the Texas Secretary of State. Enter the document number that appears at the bottom of the document you wish to verify,...
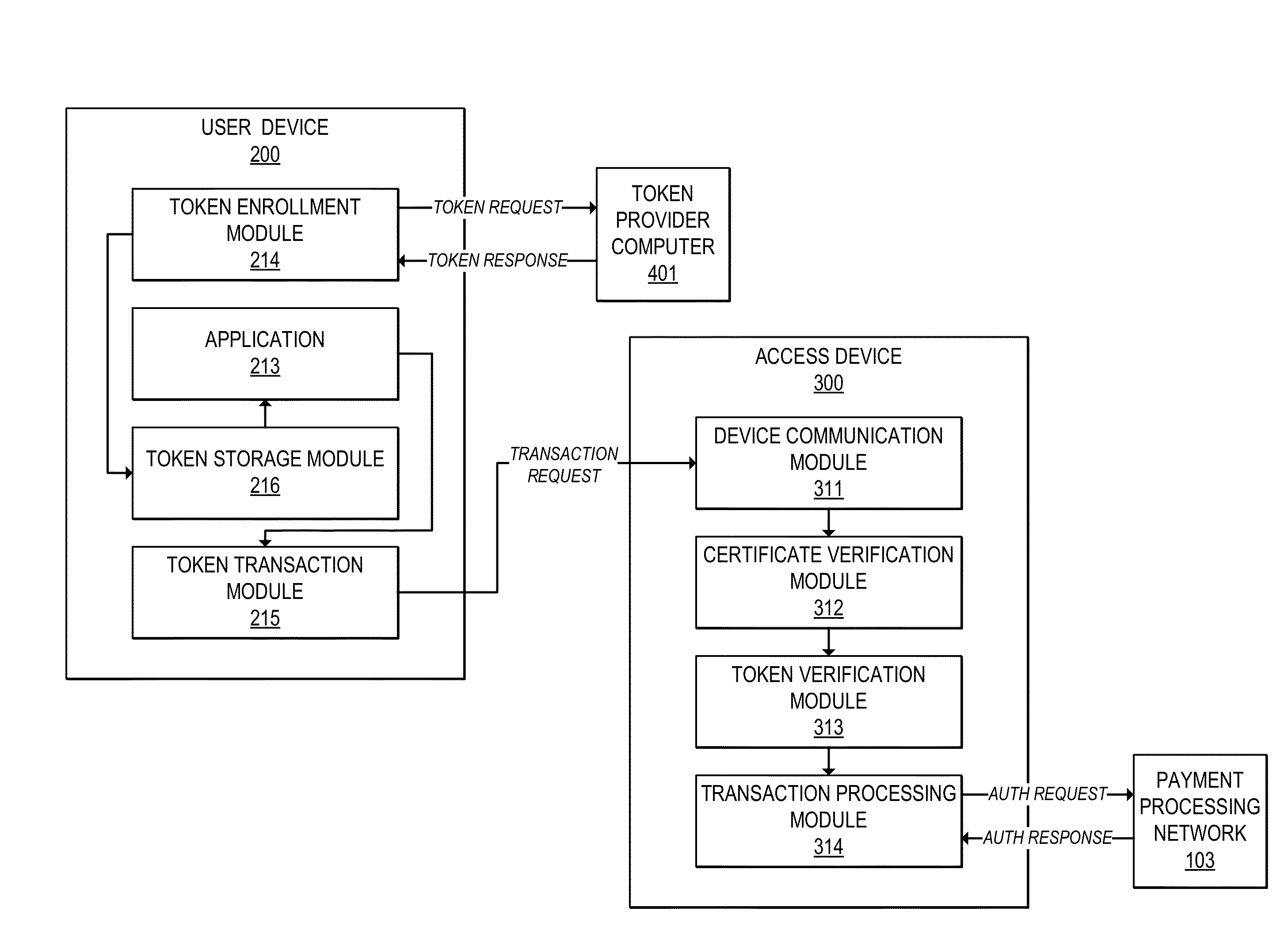
Token verification using limited use certificates
InactiveUS20150220917A1User identity/authority verificationPayment protocolsUser deviceDigital signature
Methods, devices, and systems are provided for verifying tokens using limited-use certificates. For example, a user device can send a token request to a token provider computer, and receive in response a token and a token certificate associated with the token. The token certificate may include, for example, a hash of the token and a digital signature by the token provider computer or another trusted entity. The user device can provide the token and the token certificate to an access device. The access device can verify the token using the token certificate, and verify the token certificate using a digital signature. In some cases, the token and token certificate may be verified offline. The access device can then conduct a transaction using the token.
Owner:VISA INT SERVICE ASSOC
Methods and systems for remote password reset using an authentication credential managed by a third party
ActiveUS20080046982A1Digital data processing detailsUser identity/authority verificationThird partyPassword
Embodiments of the present invention provide a secure remote password reset capability. In some embodiments, an exemplary method provides a remote reset of a password associated with a token in a computer system having a security server. A token-based authentication process is activated by connecting the token to the security server. A server-based authentication process is initiated in the security server by activating a password reset process in a security client. The server-based authentication process communicates with the token-based authentication process over a secure channel. An authentication credential is managed by a third party agent that supplies a query and the authentication credential as a correct response to the query to the security server. A prompt provided by the password reset process collects the authentication credential and a new password. After the authentication credential is validated mutually authentication is performed between the security server and the token. The token is updated with the new password based on a successful result of the mutual authentication.
Owner:RED HAT
Physical access control
InactiveUS7353396B2Digital data processing detailsUser identity/authority verificationHash functionGranularity
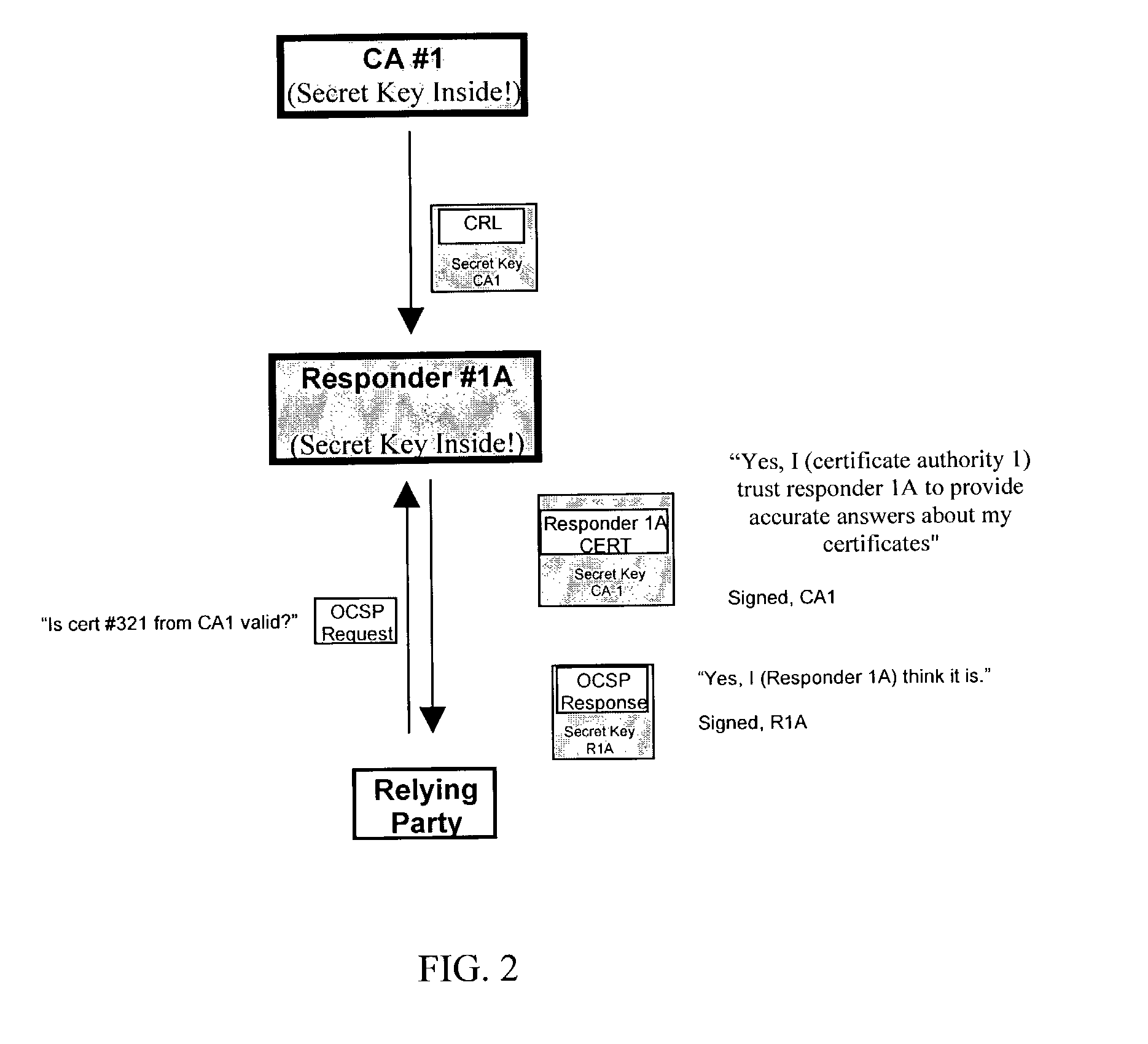
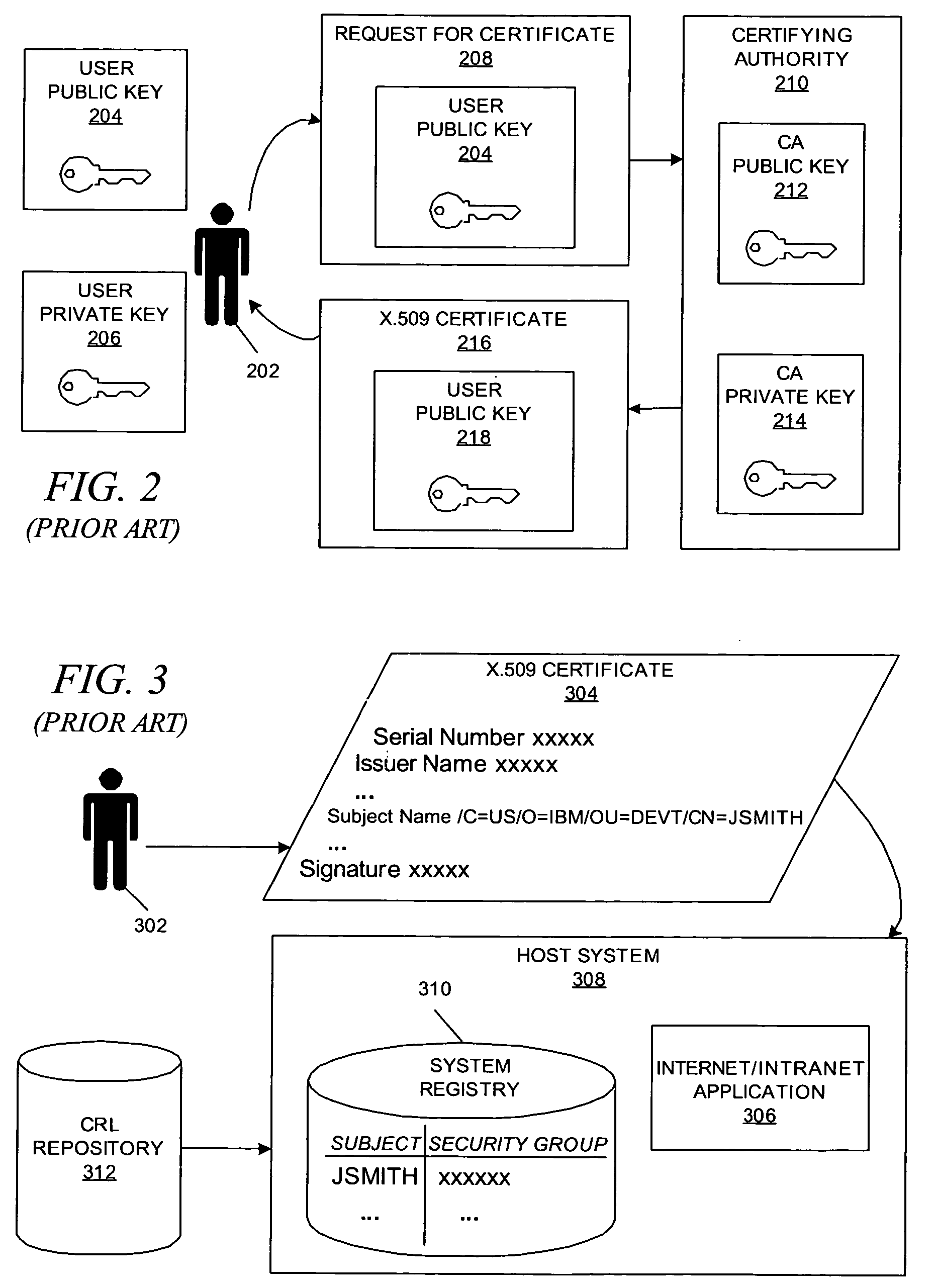
A system and method are disclosed for controlling physical access through a digital certificate validation process that works with standard certificate formats and that enables a certifying authority (CA) to prove the validity status of each certificate C at any time interval (e.g., every day, hour, or minute) starting with C's issue date, D1. C's time granularity may be specified within the certificate itself, unless it is the same for all certificates. For example, all certificates may have a one-day granularity with each certificate expires 365 days after issuance. Given certain initial inputs provided by the CA, a one-way hash function is utilized to compute values of a specified byte size that are included on the digital certificate and to compute other values that are kept secret and used in the validation process.
Owner:ASSA ABLOY AB
Method and system for certification path processing
InactiveUS20050278534A1Improve service efficiencyUser identity/authority verificationData processing systemRoot certificate
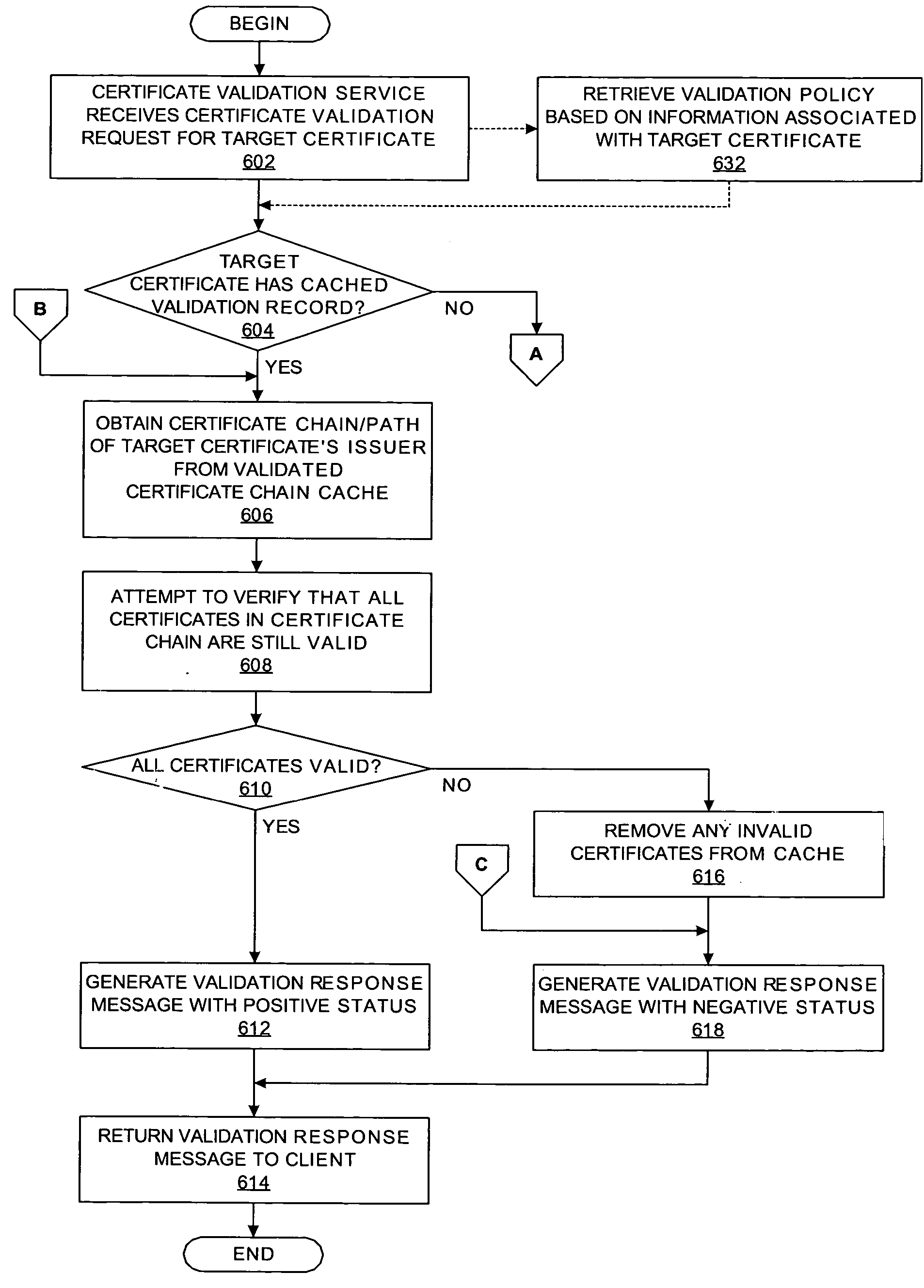
A method, an apparatus, a system, and a computer program product are presented for validating certificates. A certificate validation service receives a certificate validation request for a target certificate from a client, thereby allowing the client to offload certificate validation tasks into an online certificate validation service that is accessible and sharable by multiple components within a data processing system. In response to a determination that the target certificate is valid or invalid, the certificate validation service sends a certificate validation response with an indicating status value that the target certificate is valid or invalid. The certificate validation service is able to cache information about previously validated certificates and the associated certificate chains, thereby enhancing the efficiency of the service. Different certificate validation policies may be applied against target certificates based upon information associated with the target certificates.
Owner:IBM CORP
Attribute Certificate Verification Method and System
InactiveUS20080016335A1Data processing applicationsUser identity/authority verificationService provisionOperating system
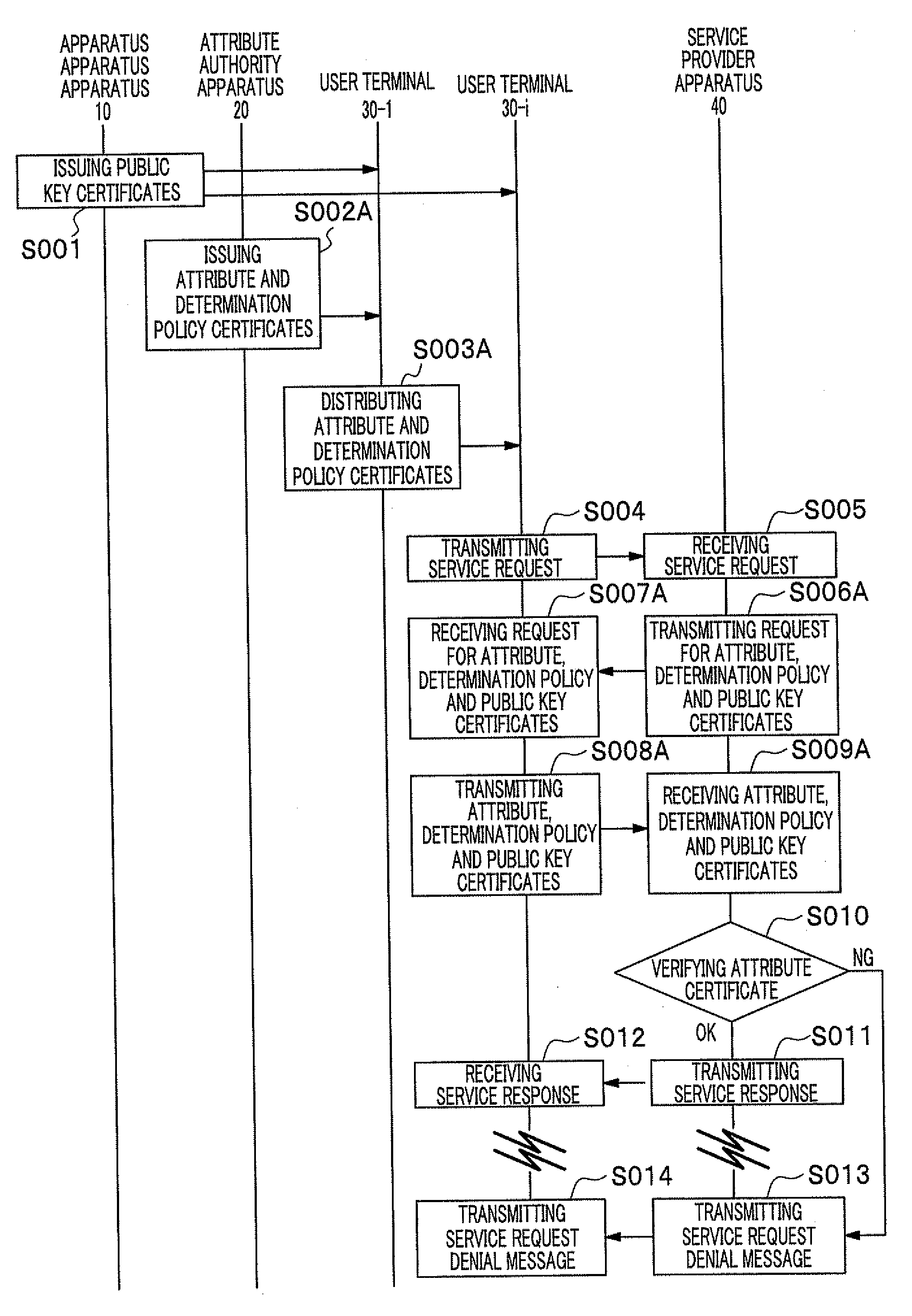
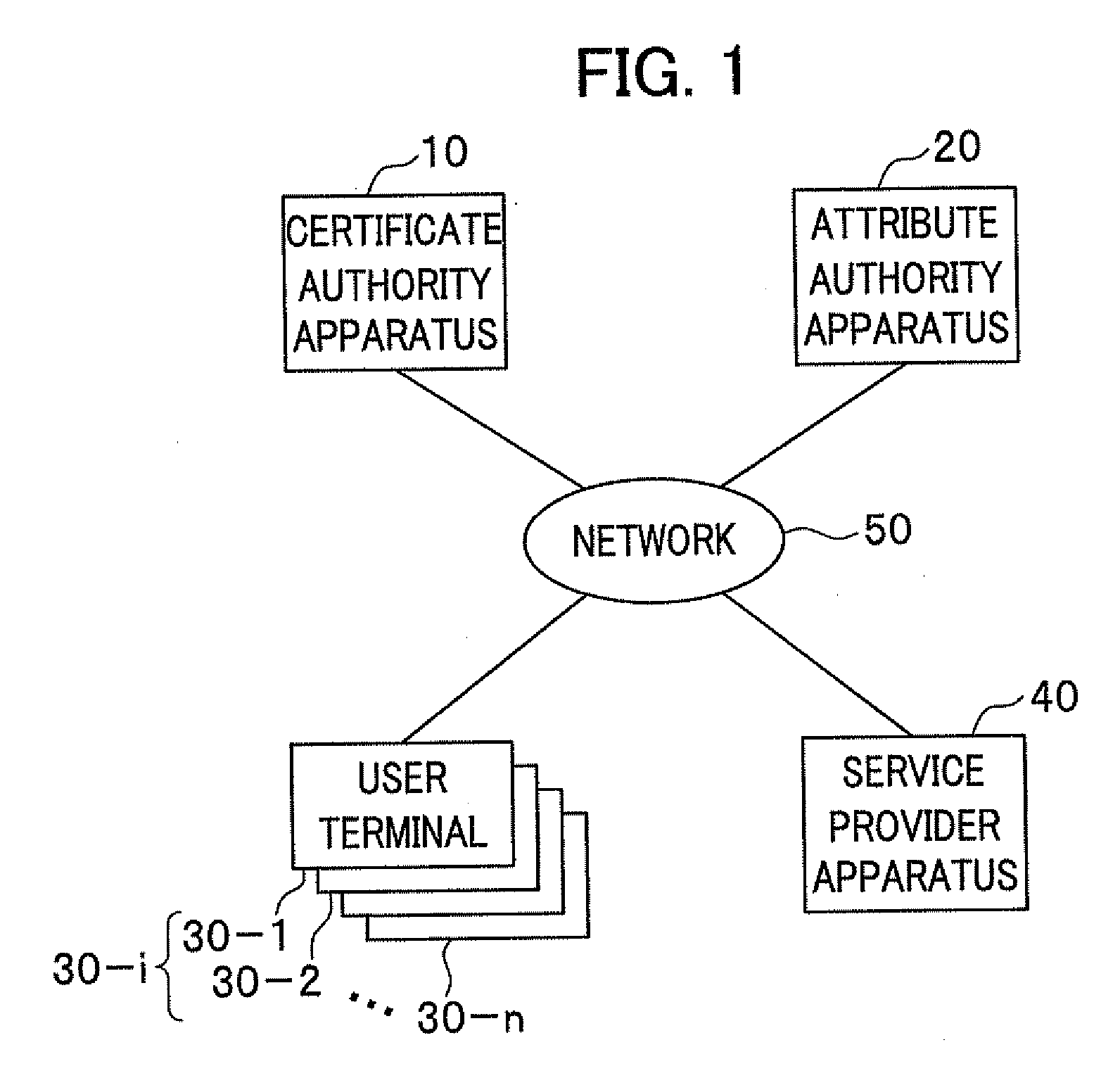
Upon issuance of an attribute certificate, an attribute authority apparatus makes a determination policy available. The determination policy includes information designating at least one item to be checked by a service provider apparatus for determination to be made to verify the attribute certificate, and a criterion for the determination. The determination policy may be recorded in the attribute certificate, or released to public, or made available by issuing a determination policy certificate released to public. Information for obtaining the determination policy certificate may be recorded in or outside the attribute certificate and furnished to the service provider apparatus. In order to verify an attribute certificate transmitted from a user terminal, a service provider apparatus obtains the determination policy, and determines whether data in the at least one item designated in the determination policy fulfill the criterion recorded in the determination policy.
Owner:HITACHI LTD
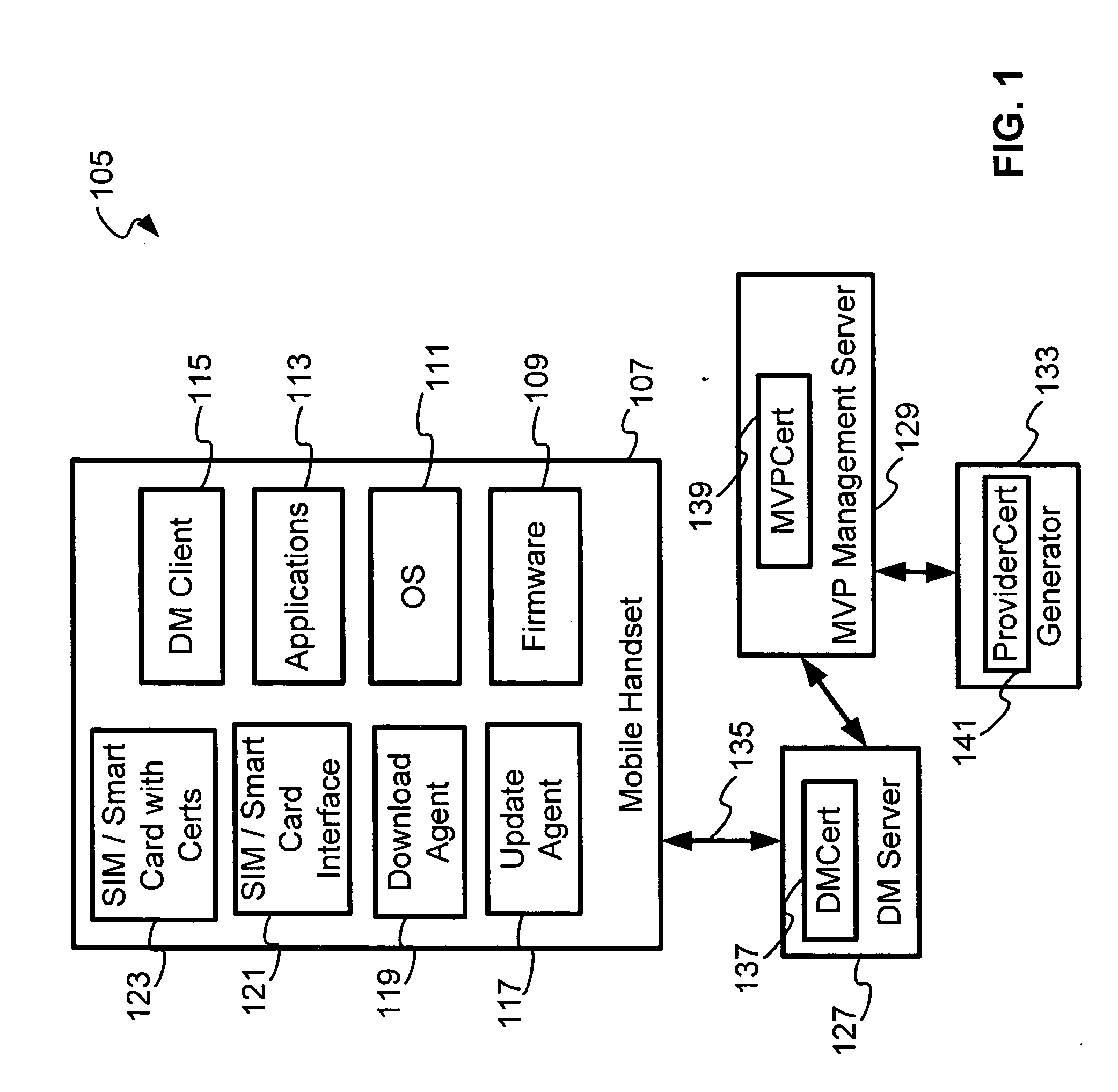
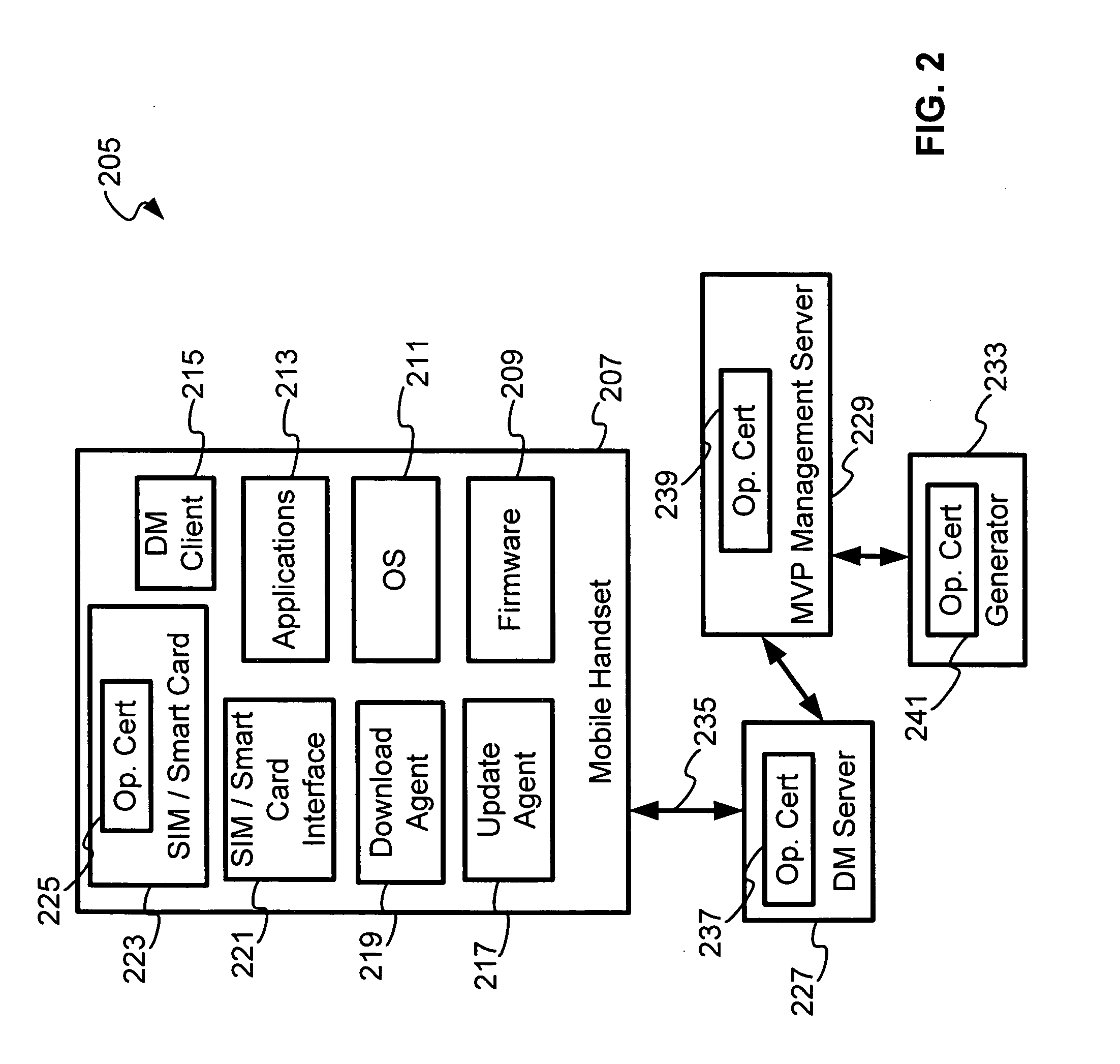
Security for device management and firmware updates in an operator network
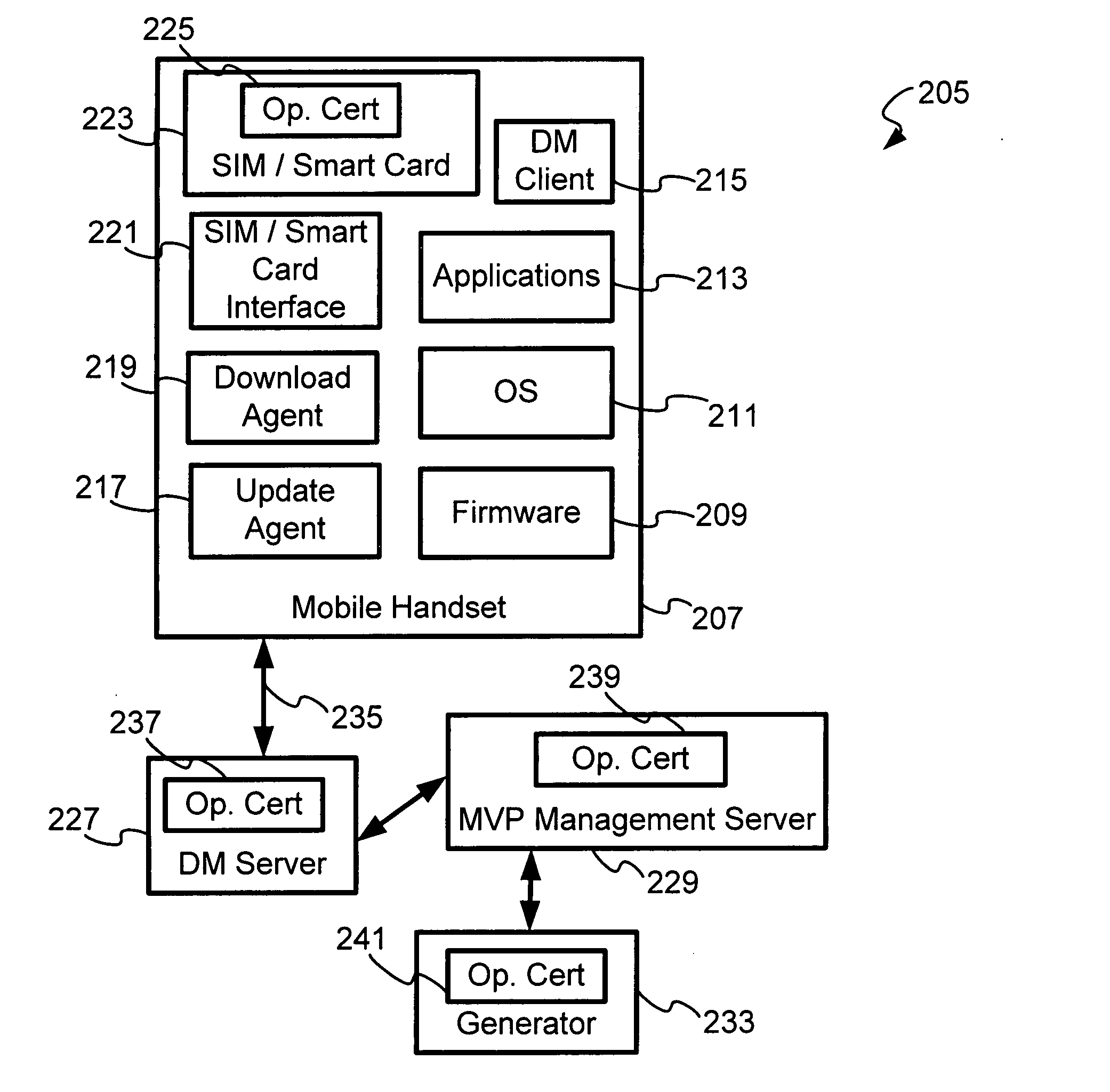
InactiveUS20060039564A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsRoot certificateSmart card
A SIM / Smartcards based approach to security within an operator's network (OMA device management system), by providing certificates to mobile devices as a way of authenticating the servers. A root certificate is stored in the SIM / Smartcard of each mobile device and accessed by the electronic device when the SIM / Smartcard is inserted into programmed card reader. Typically, in a OMA device management system, there are device management (DM) servers, mobile variance platform (MVP) server and generator; each are provisioned with a unique certificate that refers to a root certificate issued or associated with the operator, device management certificate (DMCert), mobile variance platform certificate (MVPCert) and provider certificate (ProviderCert), respectively. The mobile device authenticates each server session for Bootstrap provisioning and update package sessions originated by the servers, by verifying the root certificate with the certificates of the servers that accompany Bootstrap provisioning and update package messages.
Owner:HEWLETT PACKARD DEV CO LP
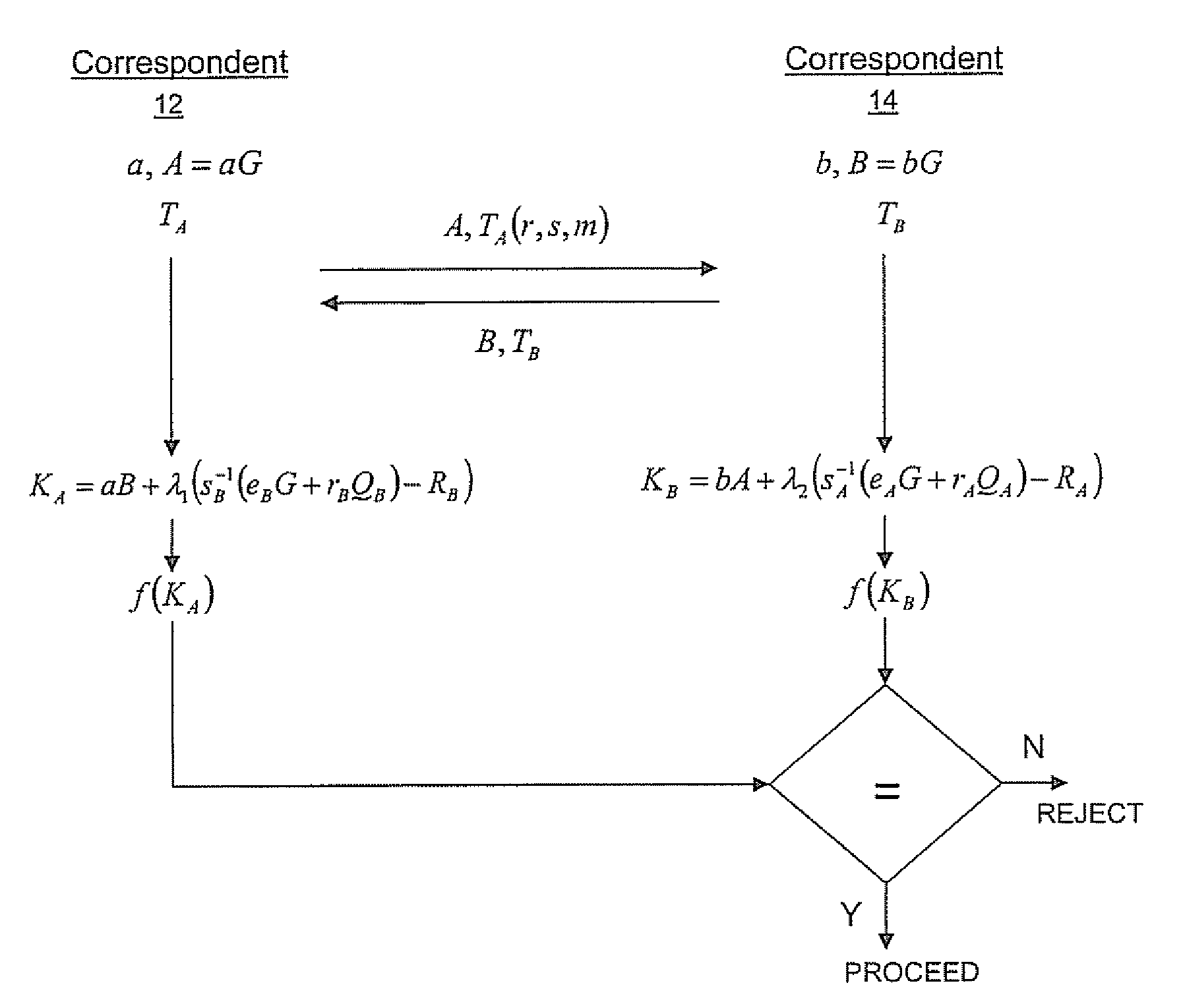
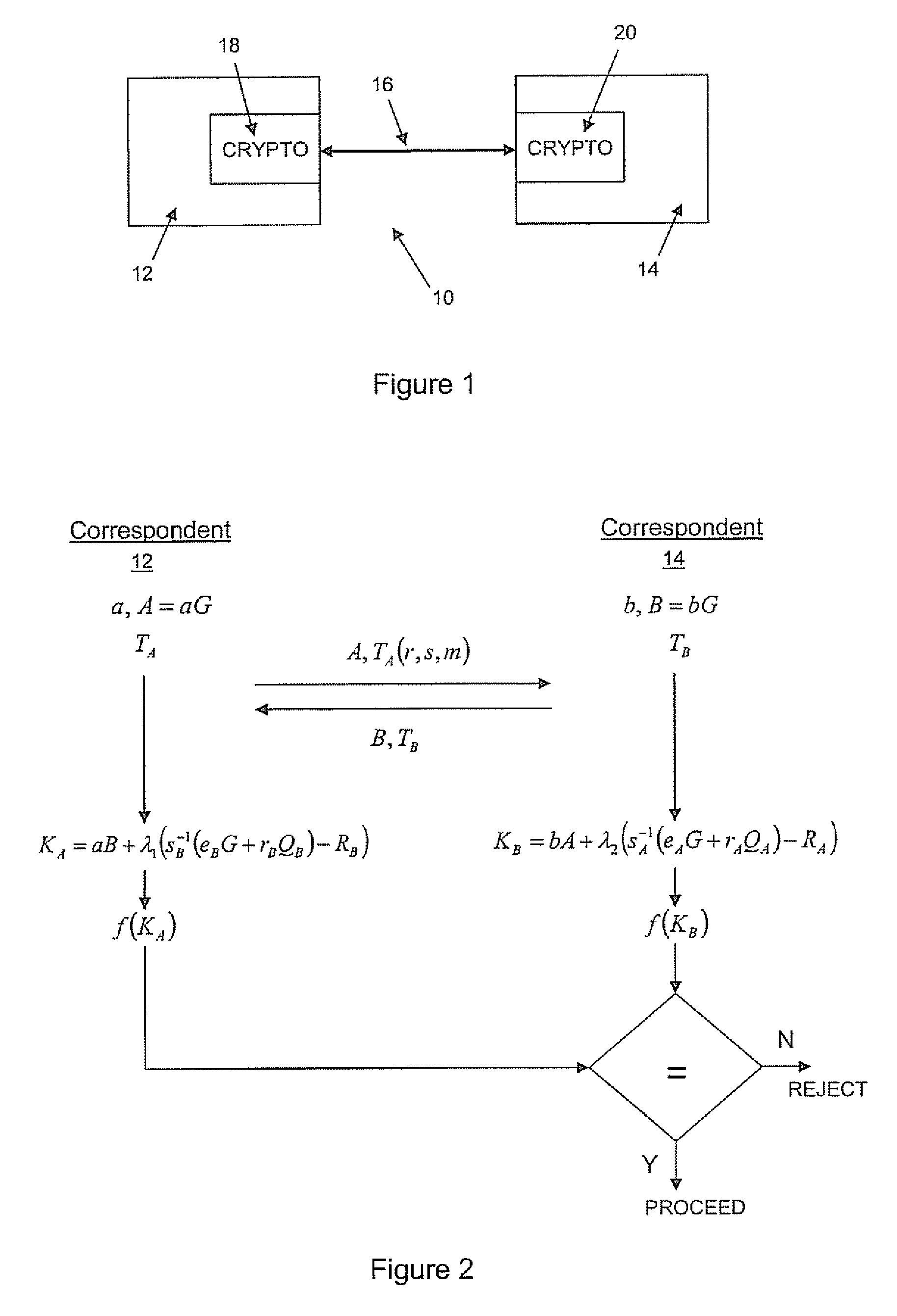
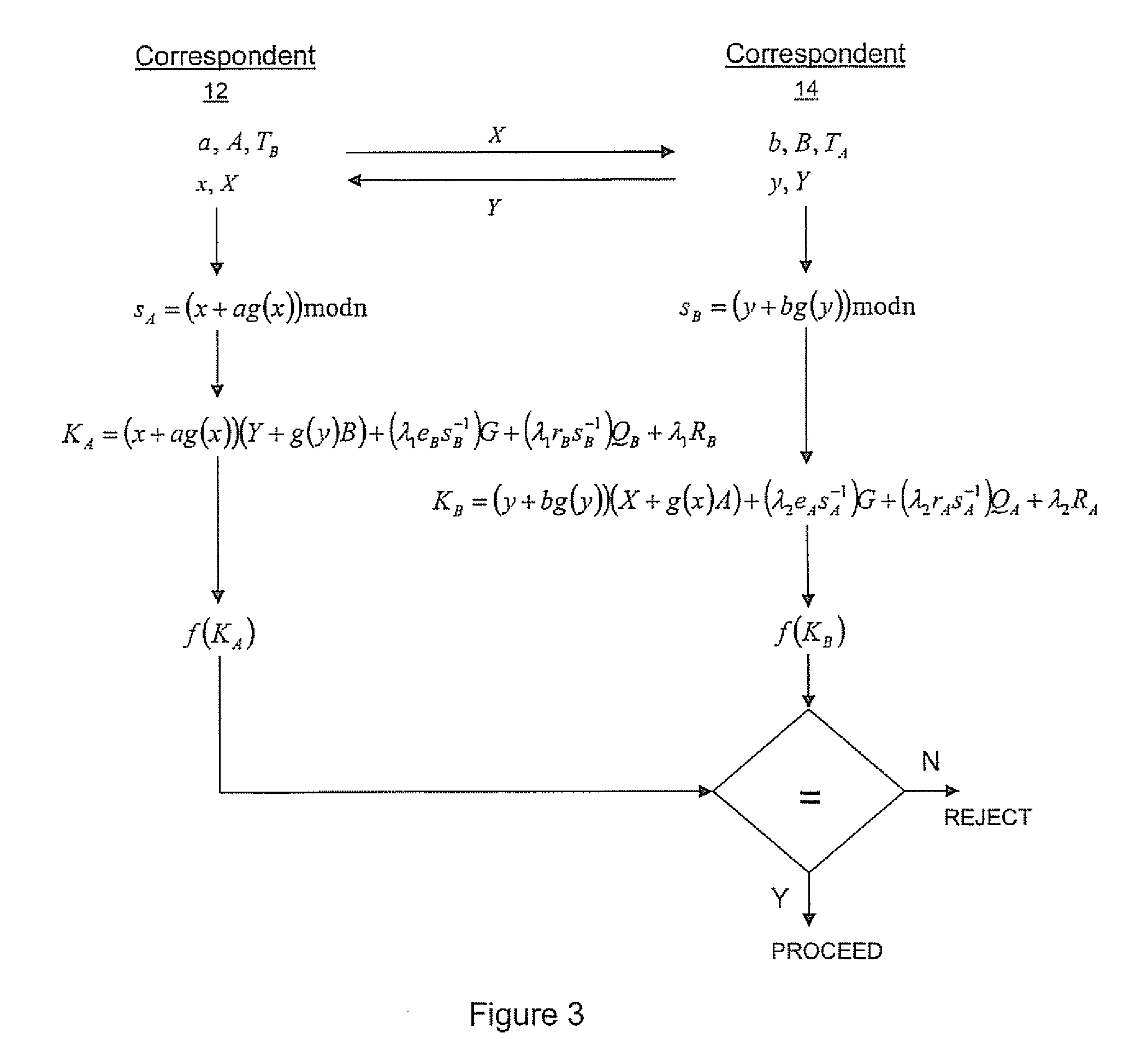
Implicit certificate verification
ActiveUS20100023771A1Heavy calculationPublic key for secure communicationDigital data processing detailsCryptographic key typesCryptographic nonce
A method of computing a cryptographic key to be shared between a pair of correspondents communicating with one another through a cryptographic system is provided, where one of the correspondents receives a certificate of the other correspondents public key information to be combined with private key information of the one correspondent to generate the key. The method comprises the steps of computing the key by combining the public key information and the private key information and including in the computation a component corresponding to verification of the certificate, such that failure of the certificate to verify results in a key at the one corespondent that is different to the key computed at the other correspondent.
Owner:MALIKIE INNOVATIONS LTD
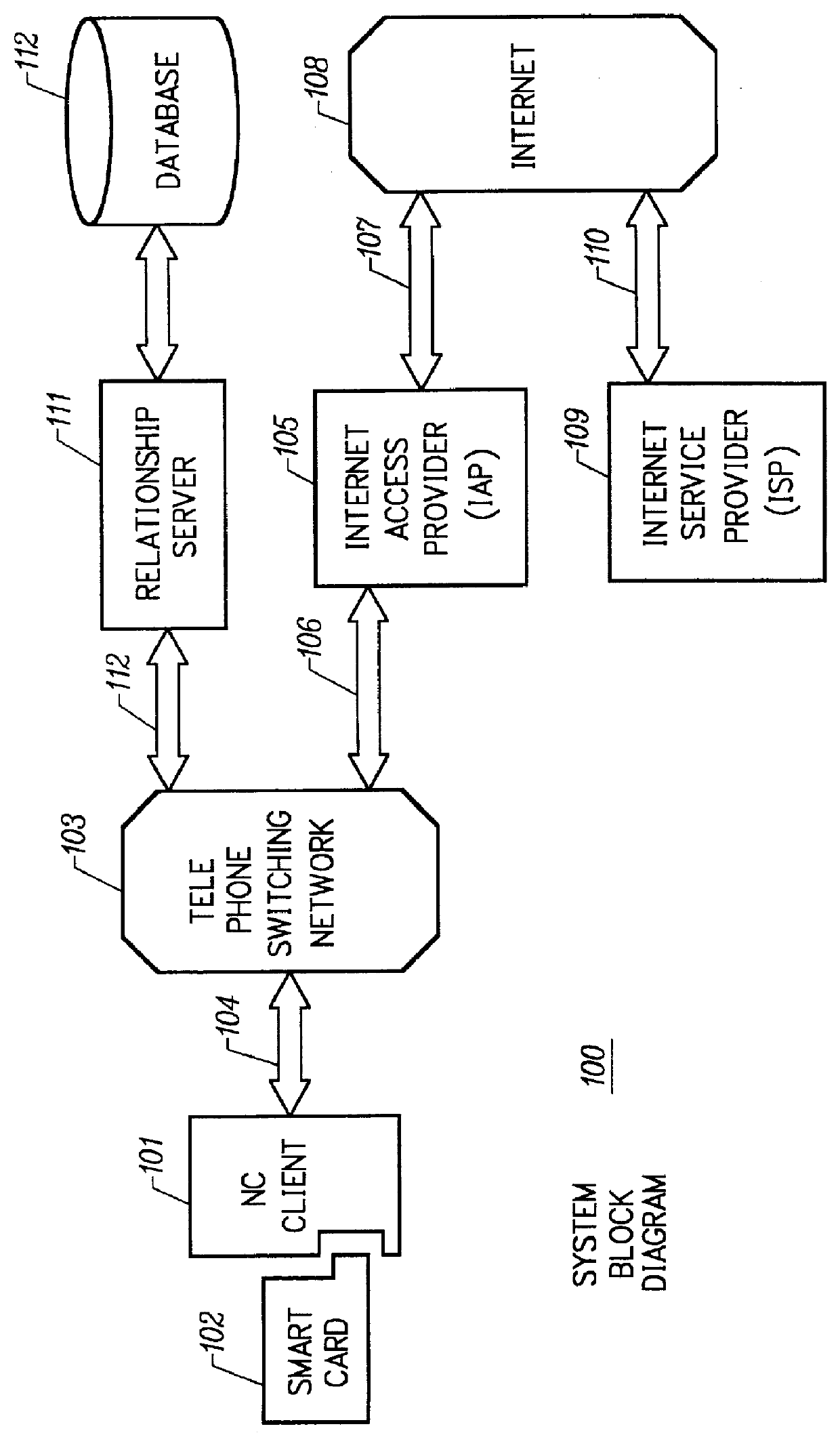
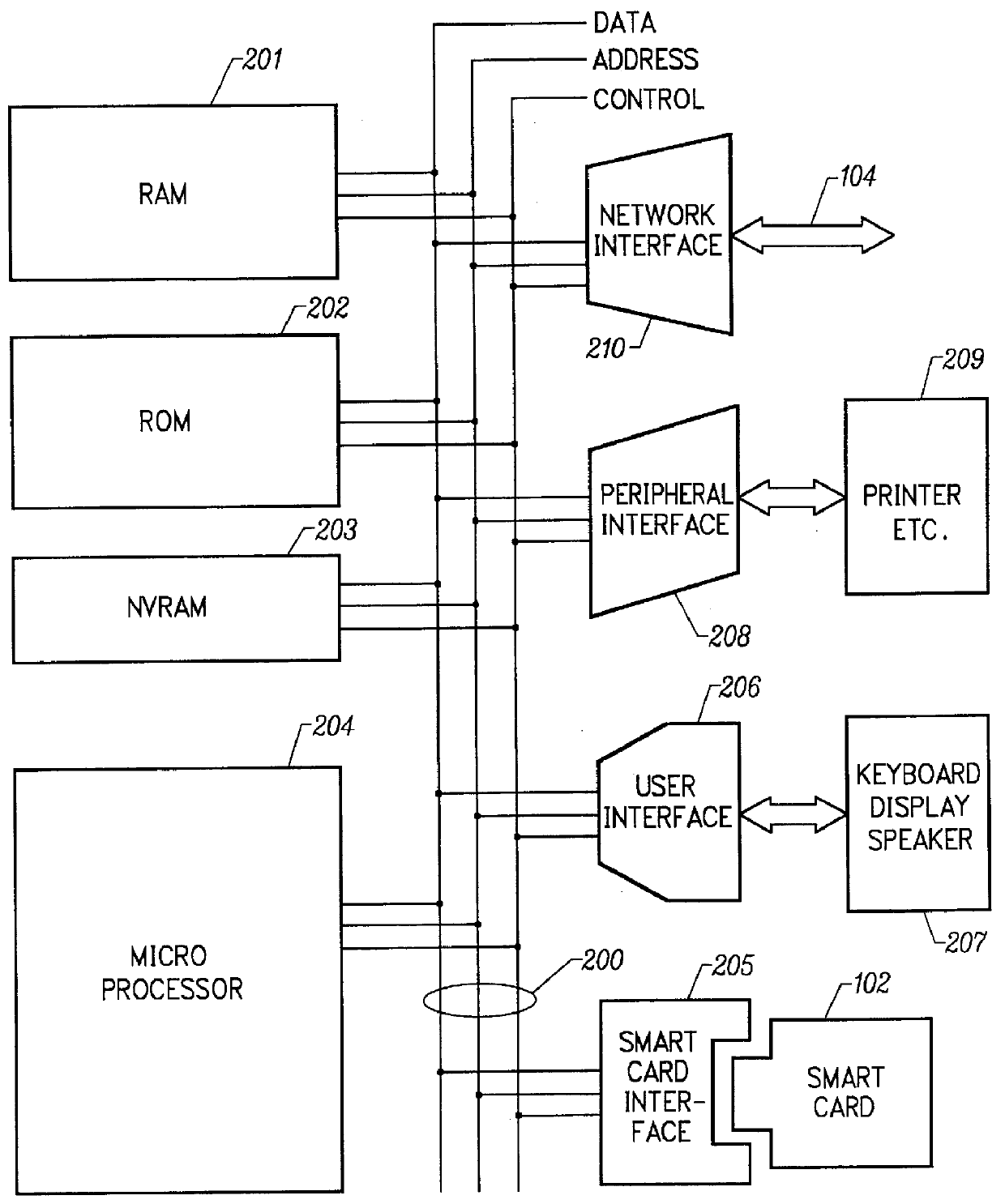
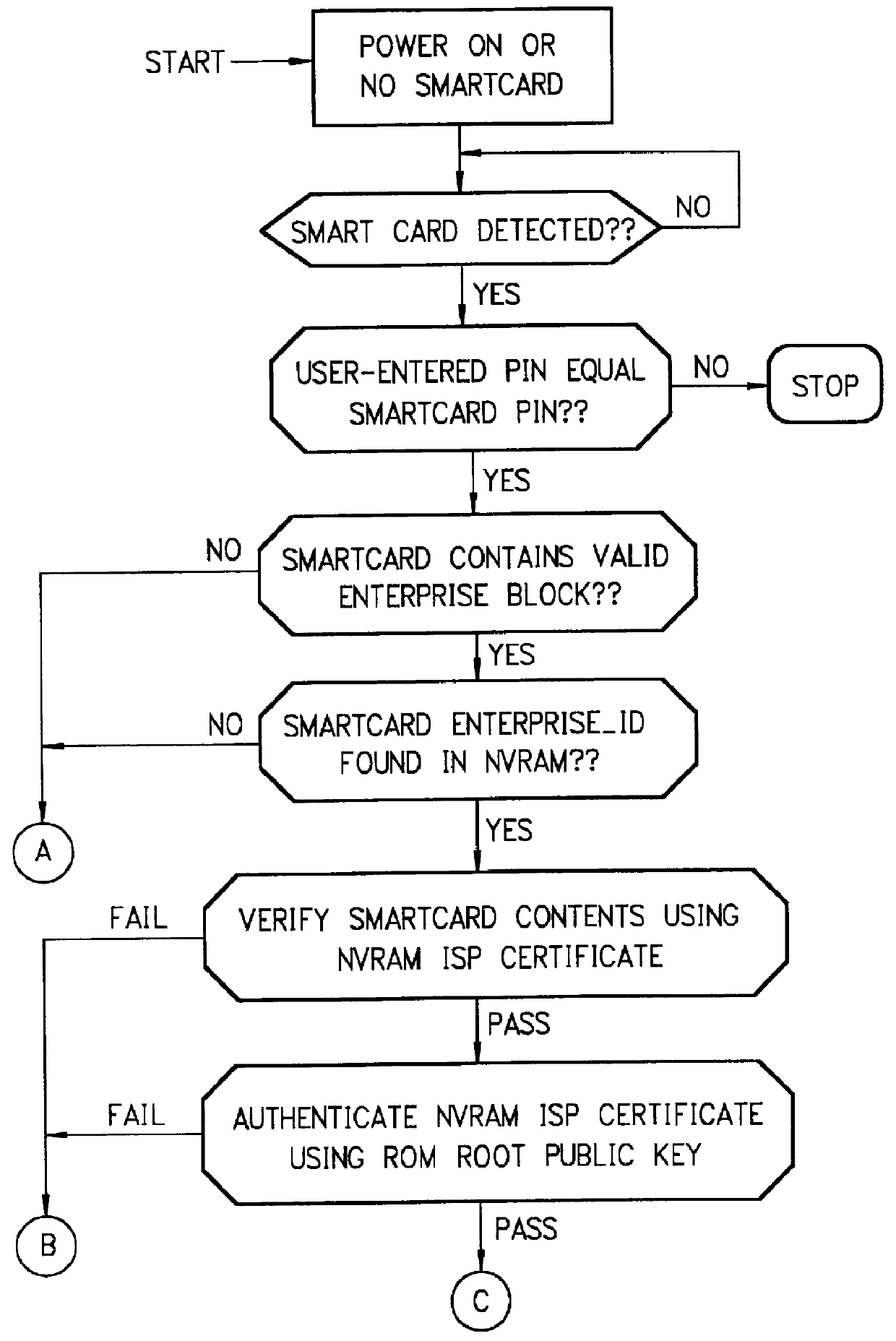
Mechanism for dynamically binding a network computer client device to an approved internet service provider
InactiveUS6112305AUser identity/authority verificationSecret communicationDigital signatureSmart card
All network computer client device (NC) manufacturers' authorizations to connect to specific internet service providers (ISPs) are maintained in a central database associated with a relationship server. The relationship server issues digital certificates which associate various ISPs to their respective public keys. Each ISP is assigned a unique enterprise identification number by the relationship server. To authorize a specific ISP, the manufacturer begins with the relationship server's ISP certificate. The manufacturer computes and appends its own digital signature for the relationship server's ISP certificate, thereby creating an ISP usage certificate valid for its NCs which it sends back to the relationship server. Upon first powering on, each NC dials the relationship server and transmits its manufacturer identification number. The relationship server uses the manufacturer identification number to find the ISP usage certificates corresponding to the NC manufacturer. The relationship server then sends to the NC the ISP usage certificate corresponding to the enterprise identification number, or corresponding to the user's selection if no enterprise identification number on the smart card is established. The NC performs a cryptographic verification of the ISP usage certificate using the manufacturer's public key which is permanently stored in the NC in read only memory. Only if the verification of the ISP usage certificate is successful, thus indicating that the ISP usage certificate is signed by the manufacturer does the NC then attempts to connect to the ISP. When an ISP and manufacturer terminate an agreement, the relationship server disables the ISP's managed access software; when the NC's attempt to connect to the ISP fails, the NC then dials the relationship server to receive a new ISP usage certificate.
Owner:COMCAST CABLE COMM MANAGEMENT LLC
System and method for distributed group management
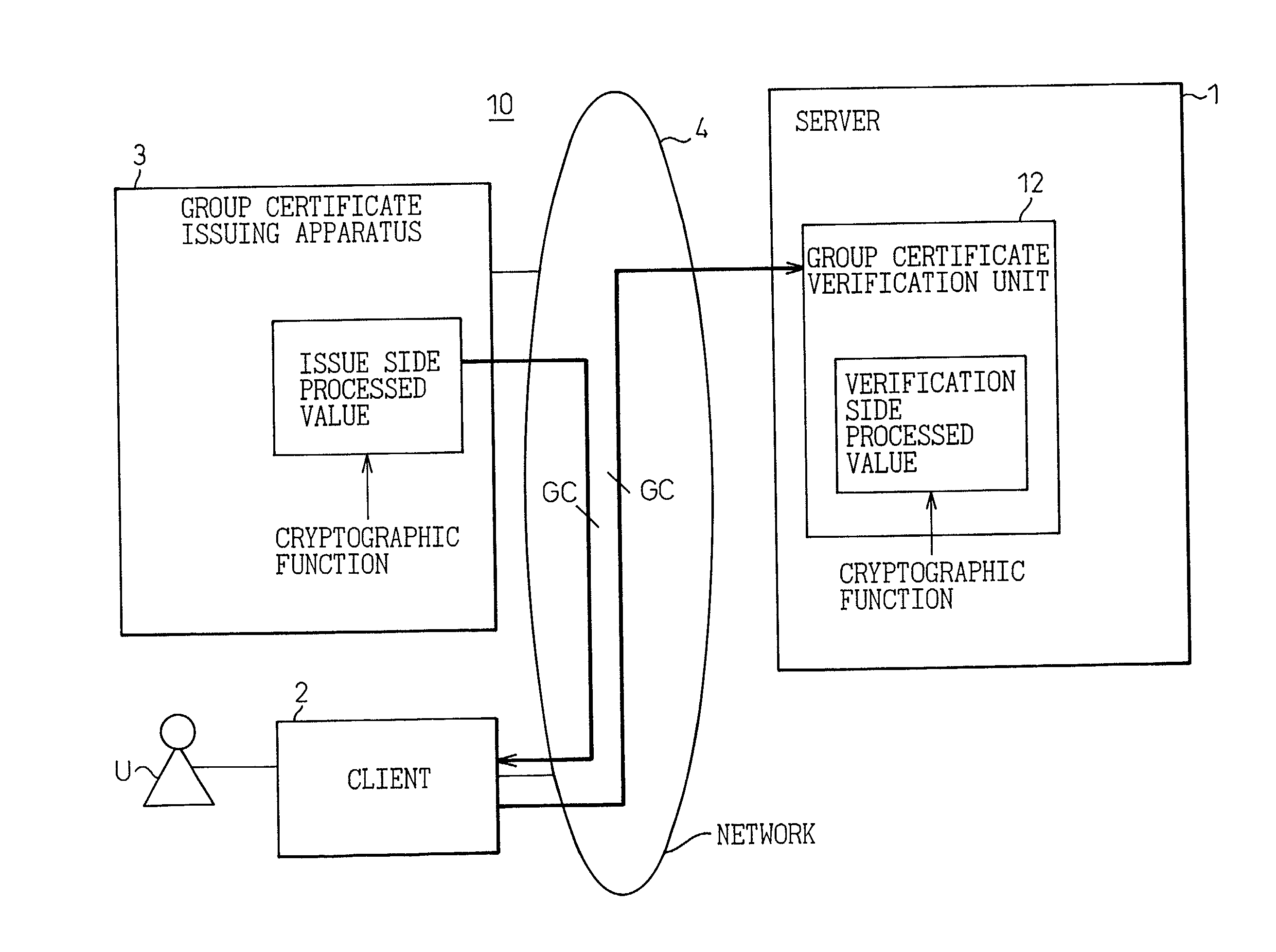
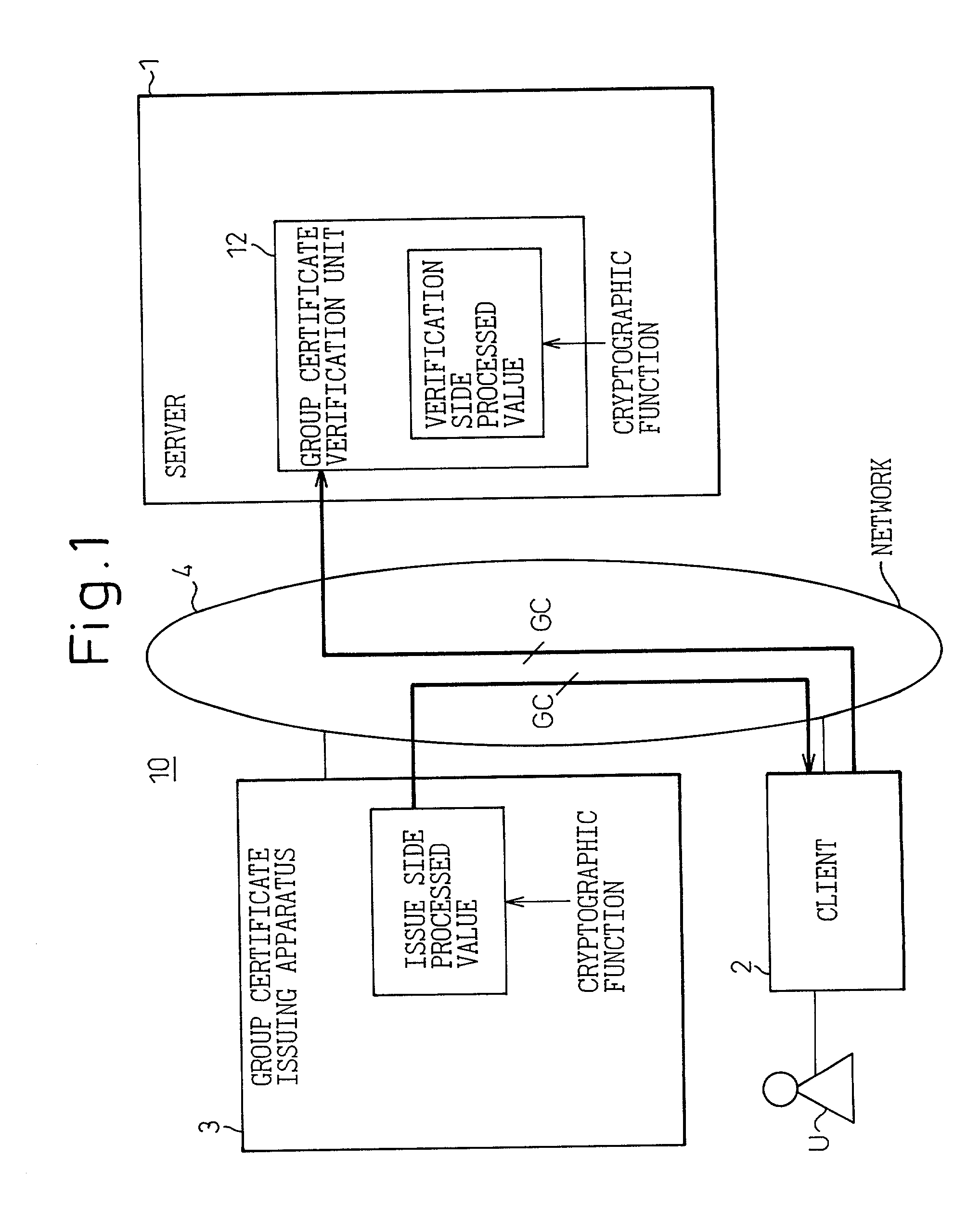
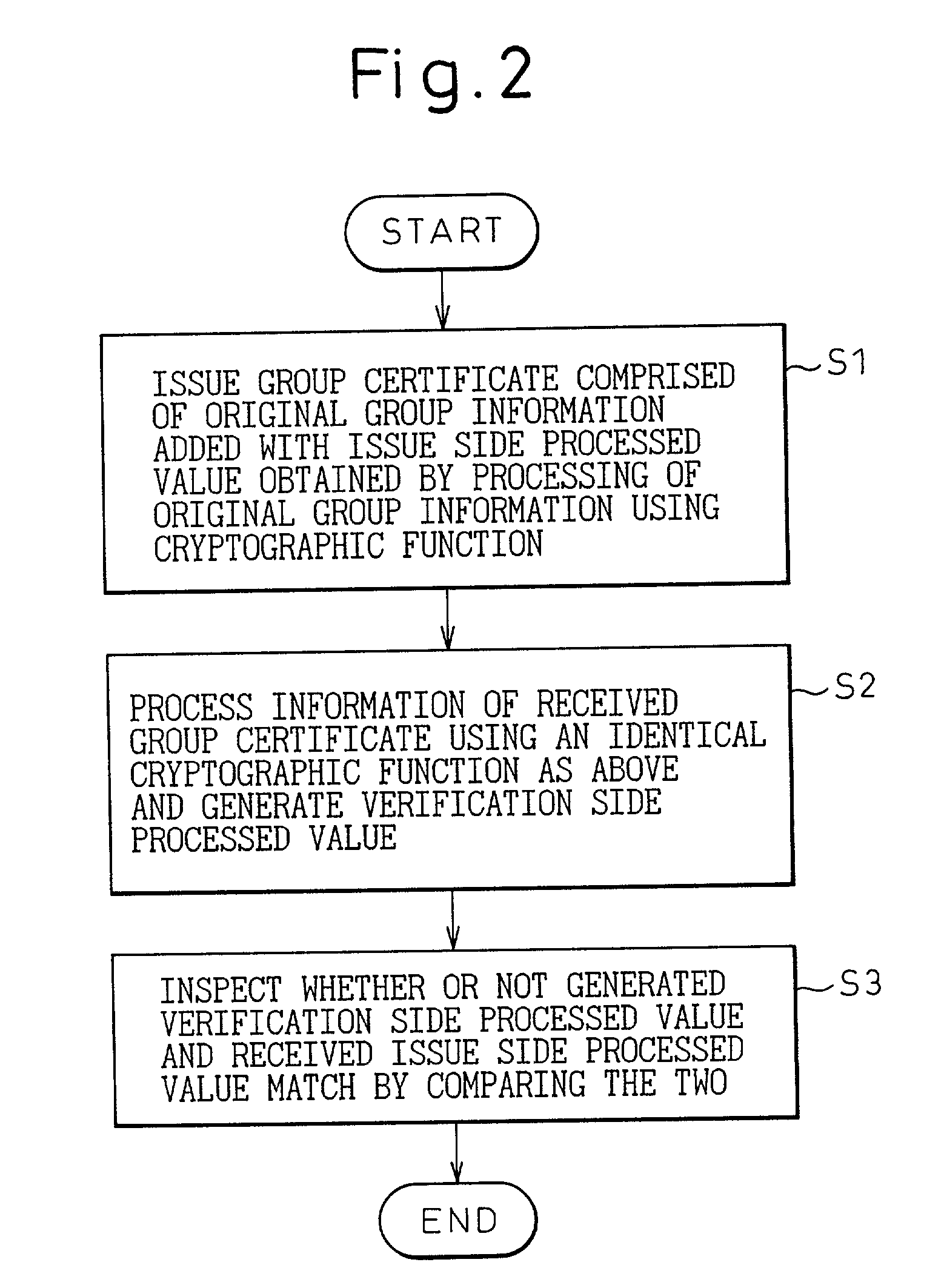
InactiveUS7185194B2Increase speedUser identity/authority verificationDigital data authenticationClient-sideManagement system
A system of distributed group management for generating authentication information relating to a group to which users belong at a high speed on a client side and, at the same time, wherein a server side can verify this at a high speed. This system provides a group certificate issuing apparatus for issuing a group certificate on a client side based on original group information including the name of the group to which the users belong and a group certificate verification unit for verifying a legitimacy of the certificate transmitted from the client side in a server. Here, the group certificate issuing apparatus adds an issuance side processed value obtained by processing the information of the original group information by a cryptographic function to this original group information to obtain a group certificate, and the group certificate verification unit processes part of information included in the received certificate by an identical cryptographic function to obtain a verification side processed value and performs an authentication by confirming that the issuance side processed value and the verification side processed value coincide.
Owner:FUJITSU LTD
Method and apparatus for distributing, interpreting, and storing heterogeneous certificates in a homogenous public key infrastructure
InactiveUS6895501B1Avoid less flexibilityUser identity/authority verificationWeb browserDigital signature
A connection is established between a server and a web browser having access to a first, trusted public key. The server downloads a digitally signed archive to the browser, the archive including a second public key. The browser verifies the digitally signed archive using the first public key, and stores the second public key in response to the verification. The browser then uses the stored second public key to authenticate the server and establish a secure connection with the server. The second public key and its chain of trust need not be known by the browser beforehand, and the archive may include program fragments that store the key in an area where the browser (or an applet running under the browser) can access and use it. The archive may also include a program fragment that performs certificate validation for the client—enabling the client to handle certificate types it does not know about. Advantages include allowing the archive to be transmitted over any insecure connection since it is integrity protected and authenticated; and allowing the client to make a direct connection to the server without having to access certificate stores on the platform.
Owner:ATTACHMATE
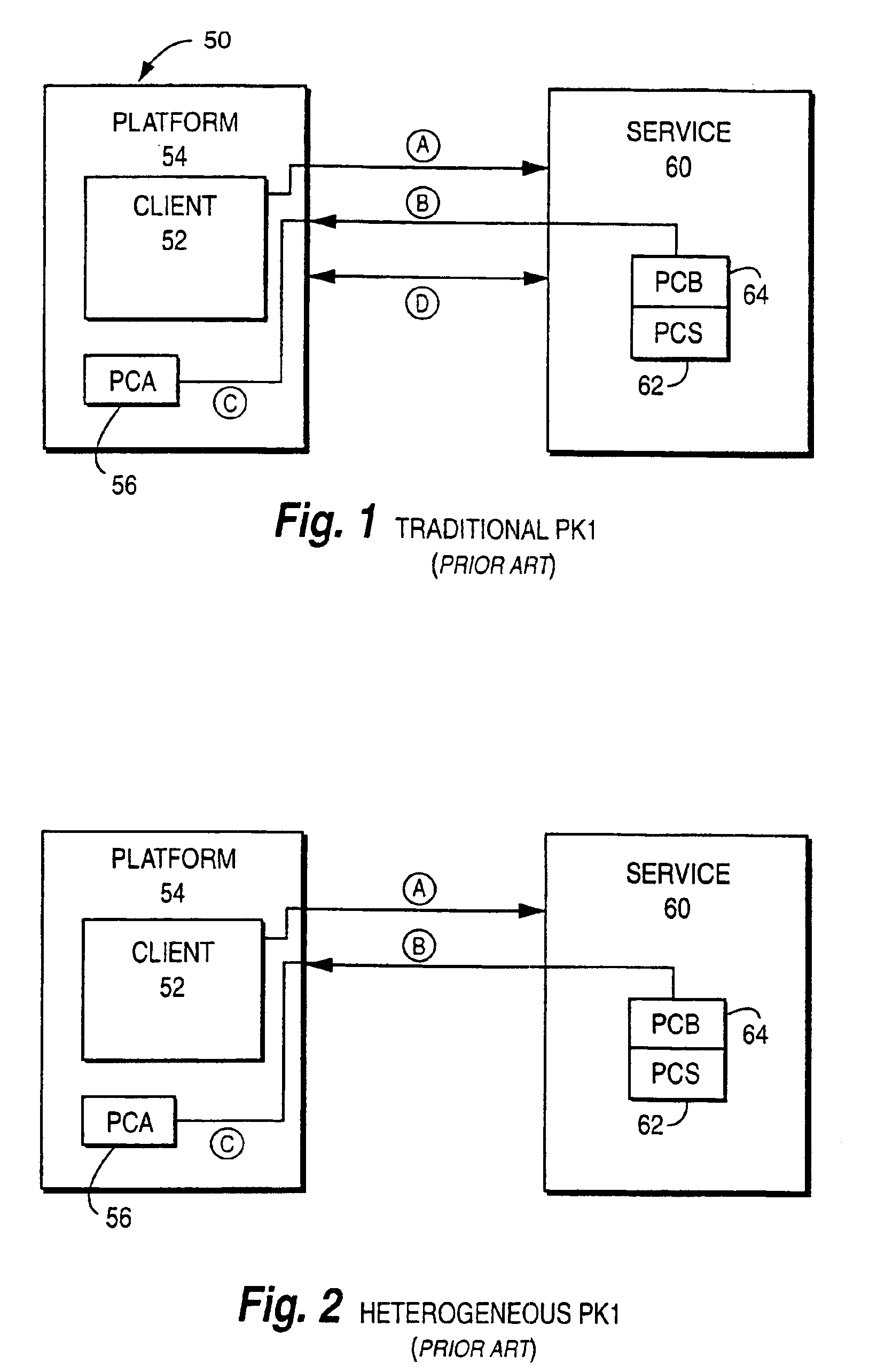
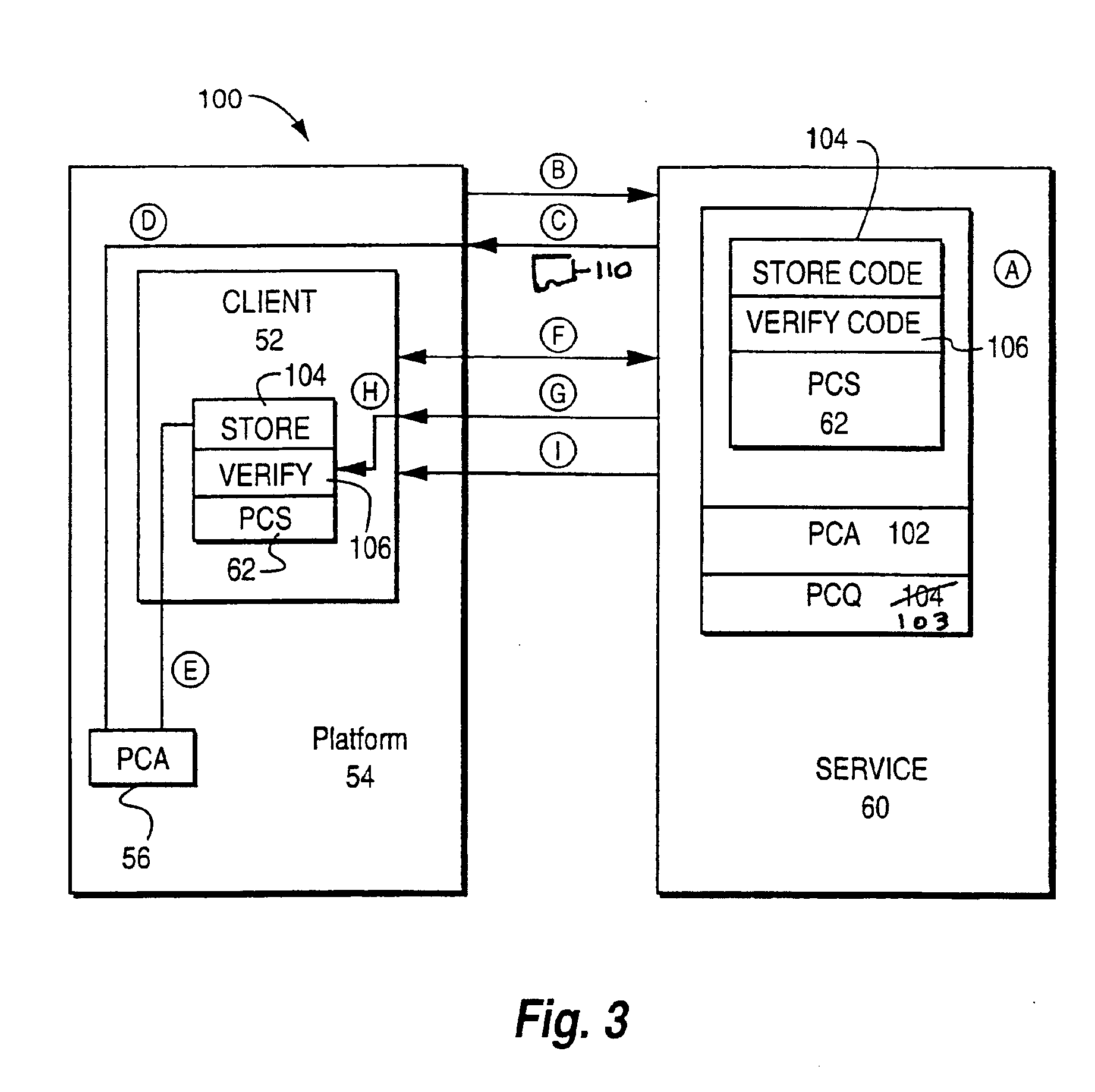
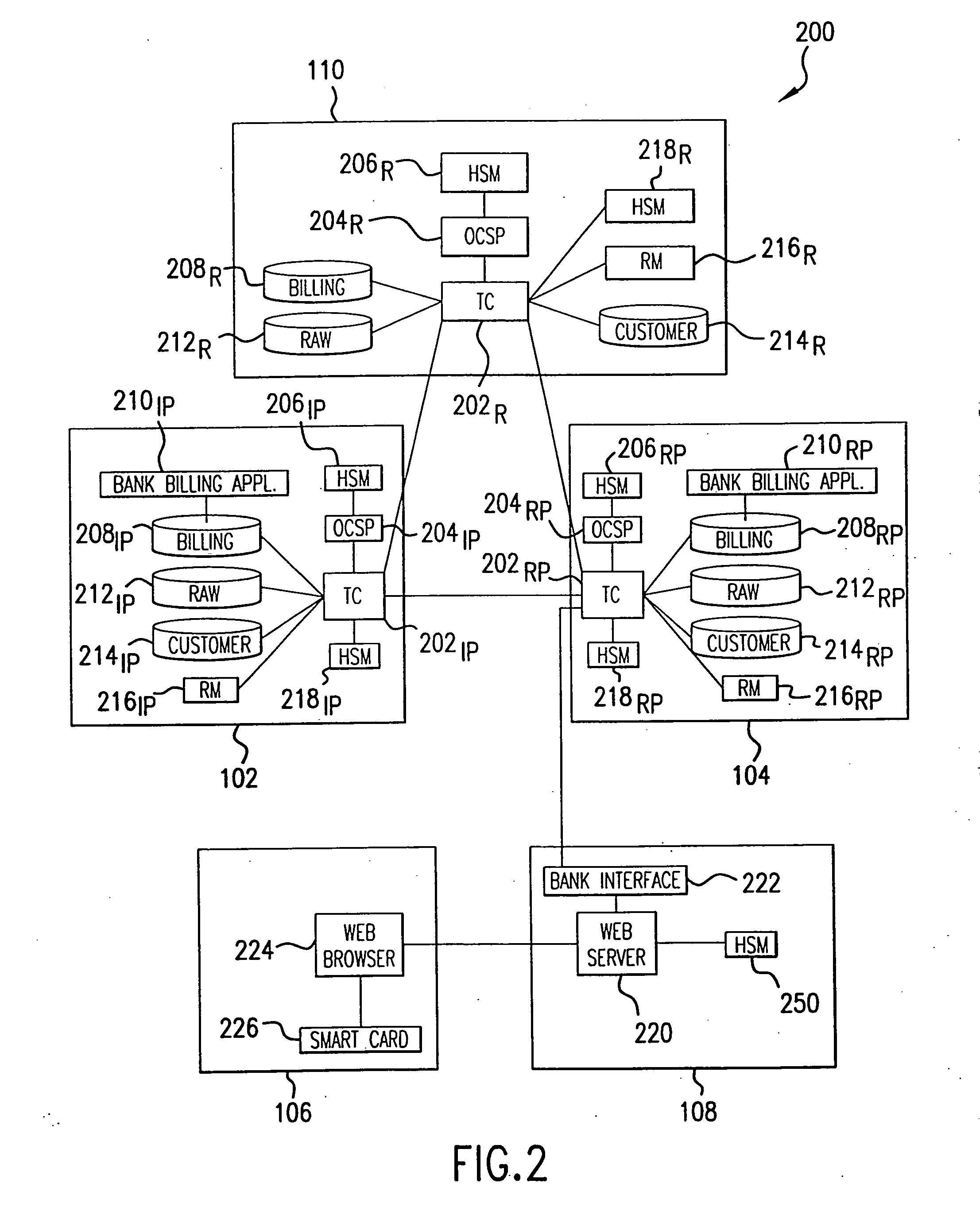
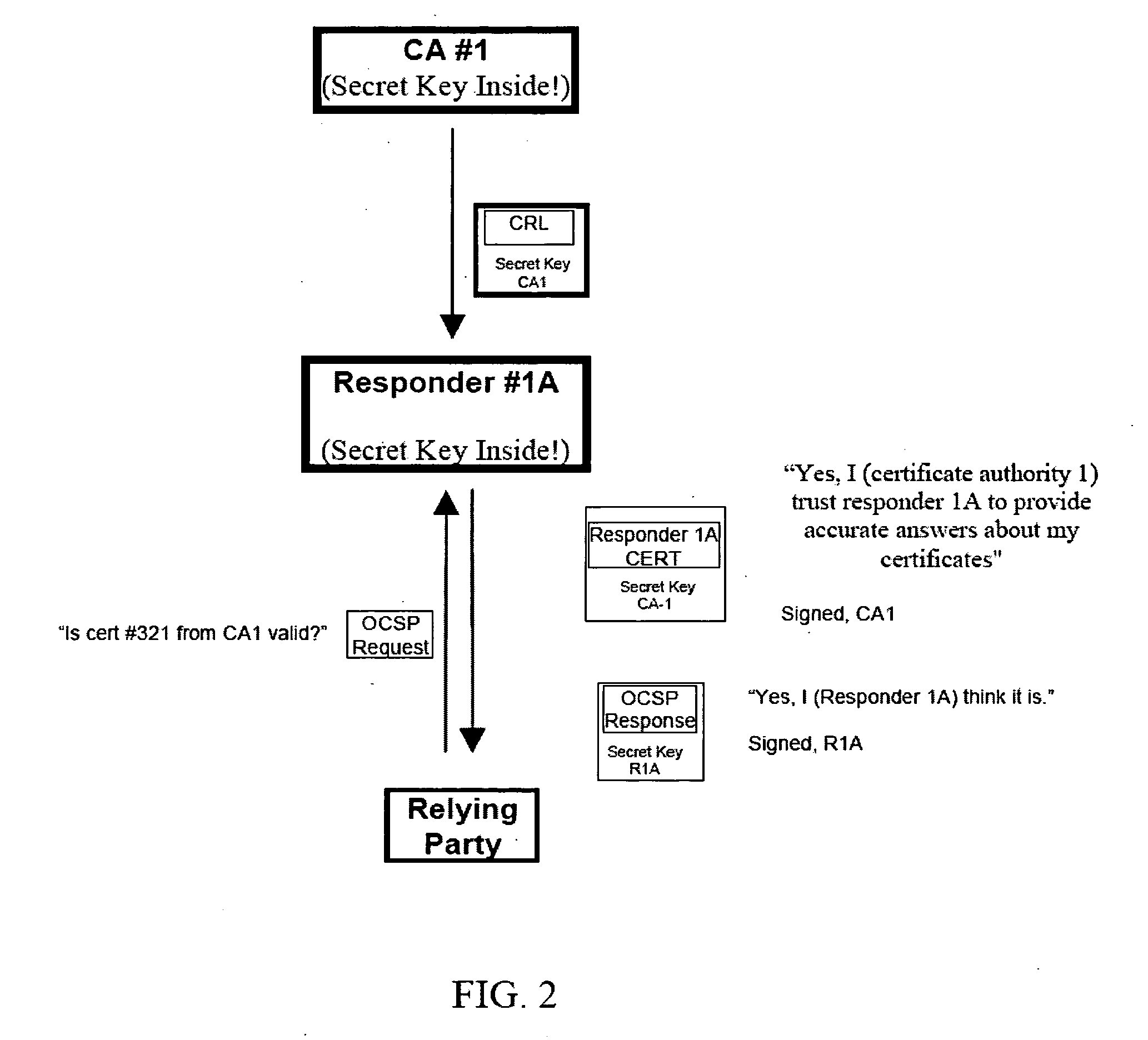
Transaction coordinator for digital certificate validation and other services
InactiveUS20070073621A1Easy to reuseEasy maintenanceCryptography processingPayment protocolsRoot certificateTransaction data
Systems and methods for facilitating electronic commerce by securely providing certificate-related and other services including certificate validation and warranty. In a preferred embodiment, these services are provided within the context of a four-corner trust model. The four-corner model comprises a buyer, or subscribing customer, and a seller, or relying customer, who engage in an on-line transaction. The buyer is a customer of a first financial institution, or issuing participant. The issuing participant operates a certificate authority and issues the buyer a hardware token including a private key and a digital certificate signed by the issuing participant. The seller is a customer of a second financial institution, or relying participant. The relying participant operates a certificate authority and issues the seller a hardware token including a private key and a digital certificate signed by the relying participant. The system also includes a root certificate authority that operates a certificate authority that issues digital certificates to the issuing and relying participants. At the time of a transaction, the buyer creates a hash of the transaction data, signs the hash, and transmits the transaction data, the signature, and its digital certificate to the seller. The seller may then request system services via a connection with its financial institution, the relying participant. The system services may include a certificate status check service and a warranty service. The certificate status check service allows the relying customer to validate the subscribing customer's certificate. The warranty service allows the relying customer to receive a collateral-backed warranty that the subscribing customer's certificate is valid. Each participant and the root entity is provided with a transaction coordinator for combining services and operations into a single transaction having the qualities of atomicity, consistency, isolation, and durability. The transaction coordinator provides a single consistent interface for certificate-status messages and requests, as well as messages and requests relating to other services.
Owner:DULIN CHARLES +4
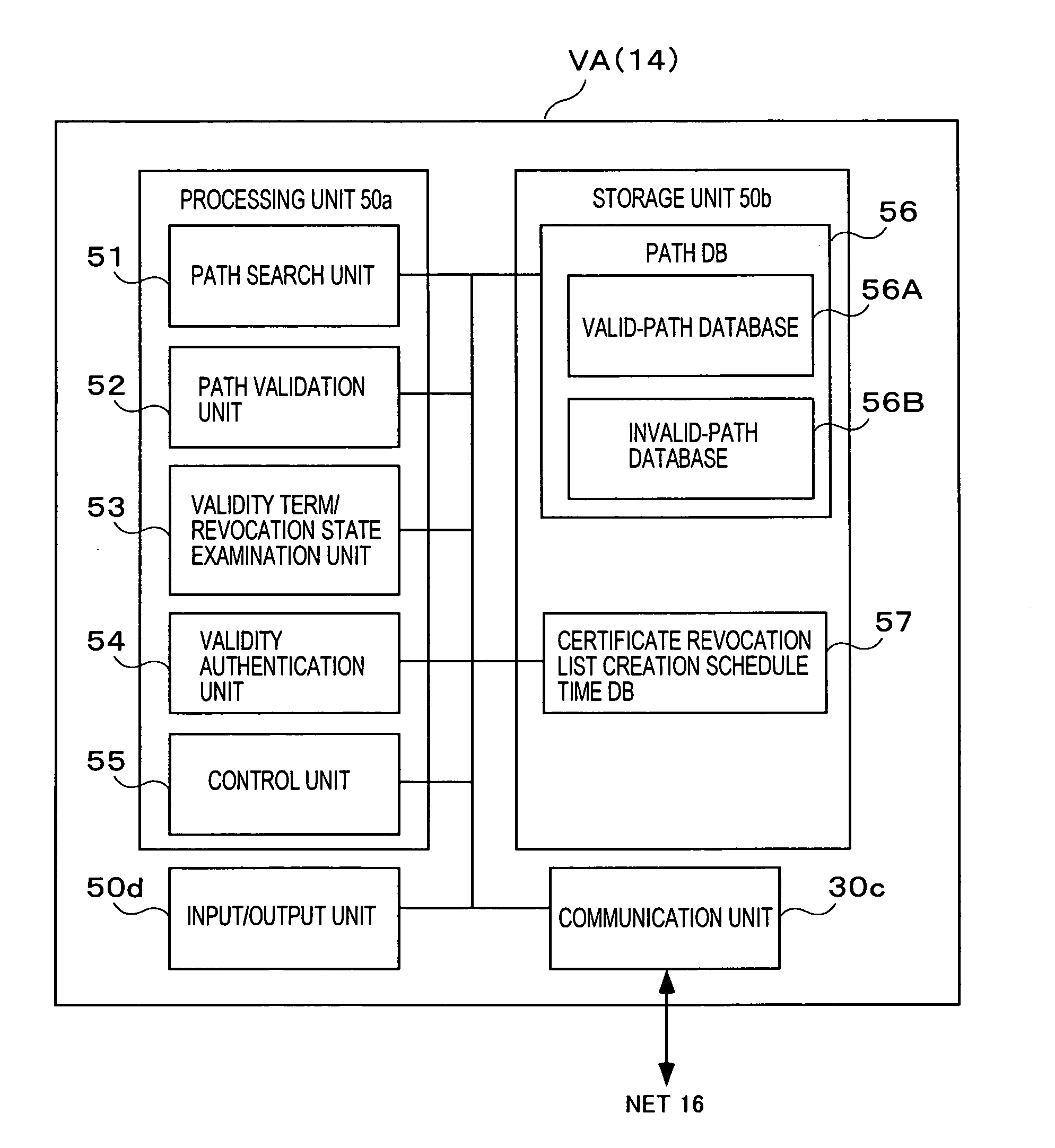
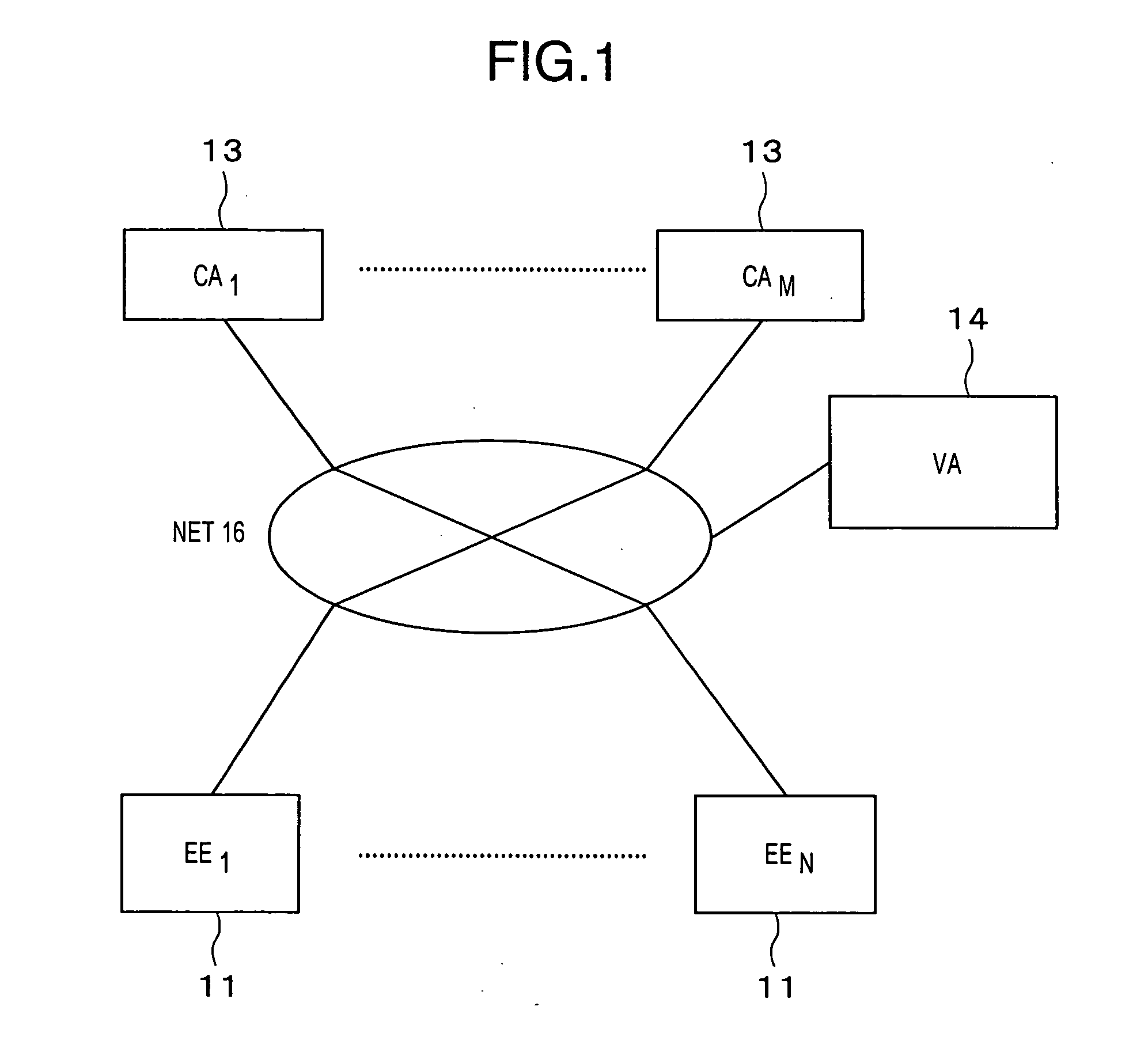
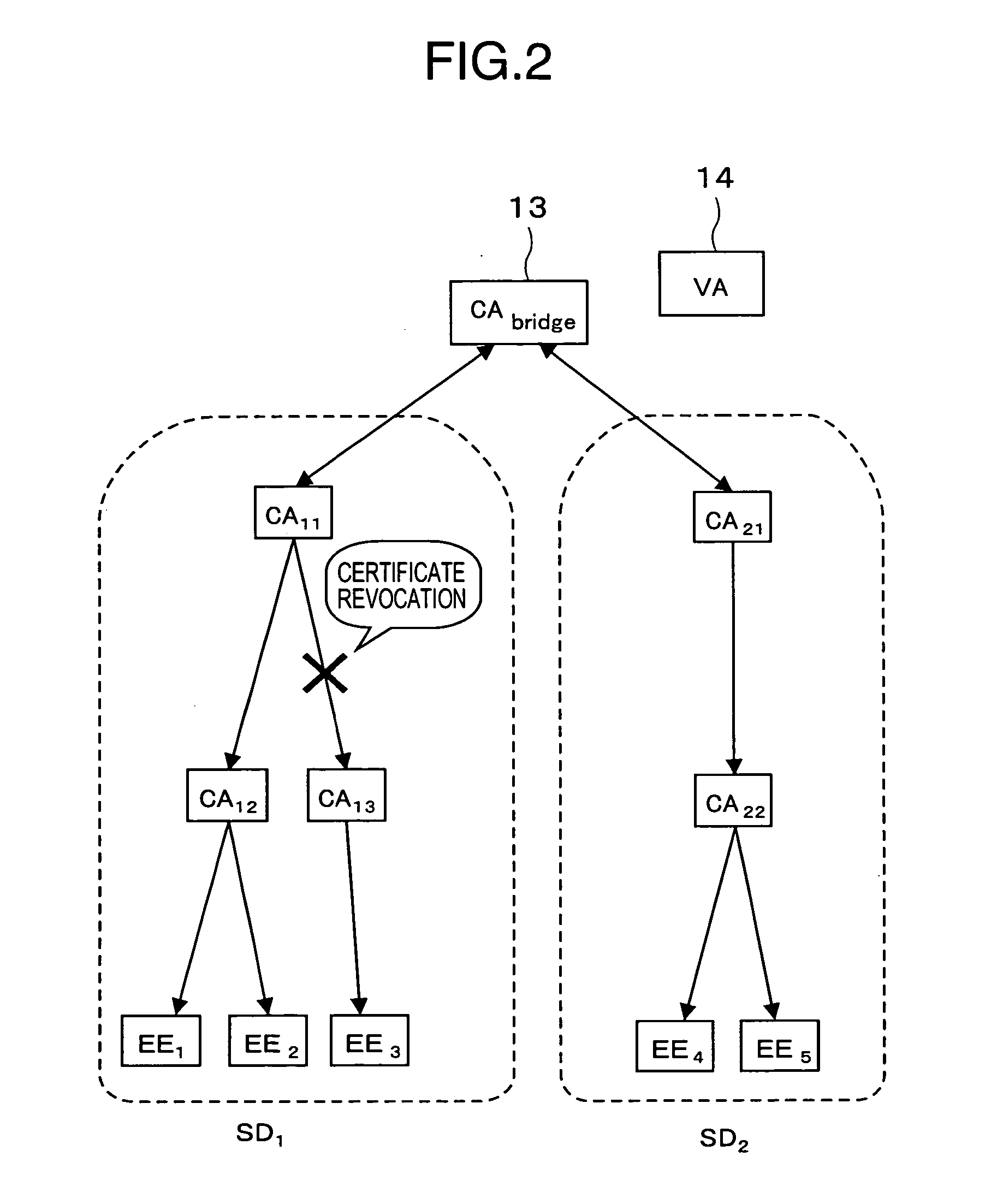
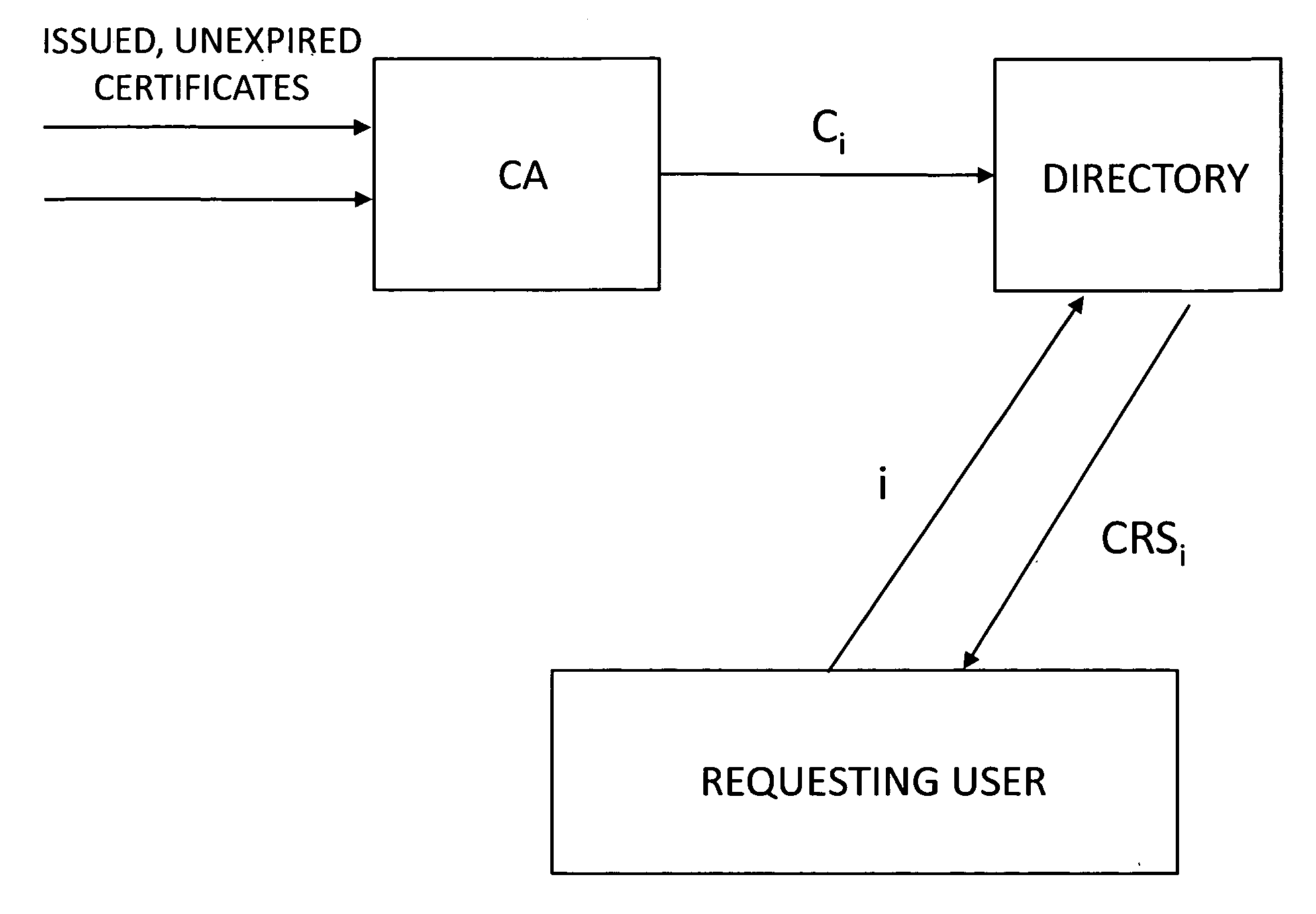
Method and apparatus for accelerating public-key certificate validation
InactiveUS20050081037A1Shorten the time periodKey distribution for secure communicationUser identity/authority verificationDatabaseRevocation list
A validation authority for certificates searches for and verifies paths and certificate revocation lists periodically, and classifies the paths into valid paths and invalid paths in accordance with the results of the validations, so as to register the paths in databases beforehand. Besides, in a case where a request for authenticating the validity of a certificate has been received from an end entity, the validation authority judges the validity of the public key certificate by checking in which of the valid-path database and the invalid-path database a path corresponding to the request is registered. On the other hand, in a case where the path corresponding to the validity authentication request is not registered in either of the databases, the validity of the public key certificate is authenticated by performing path search and validation anew.
Owner:HITACHI LTD
Mobility management in a communication system of at least two communication networks
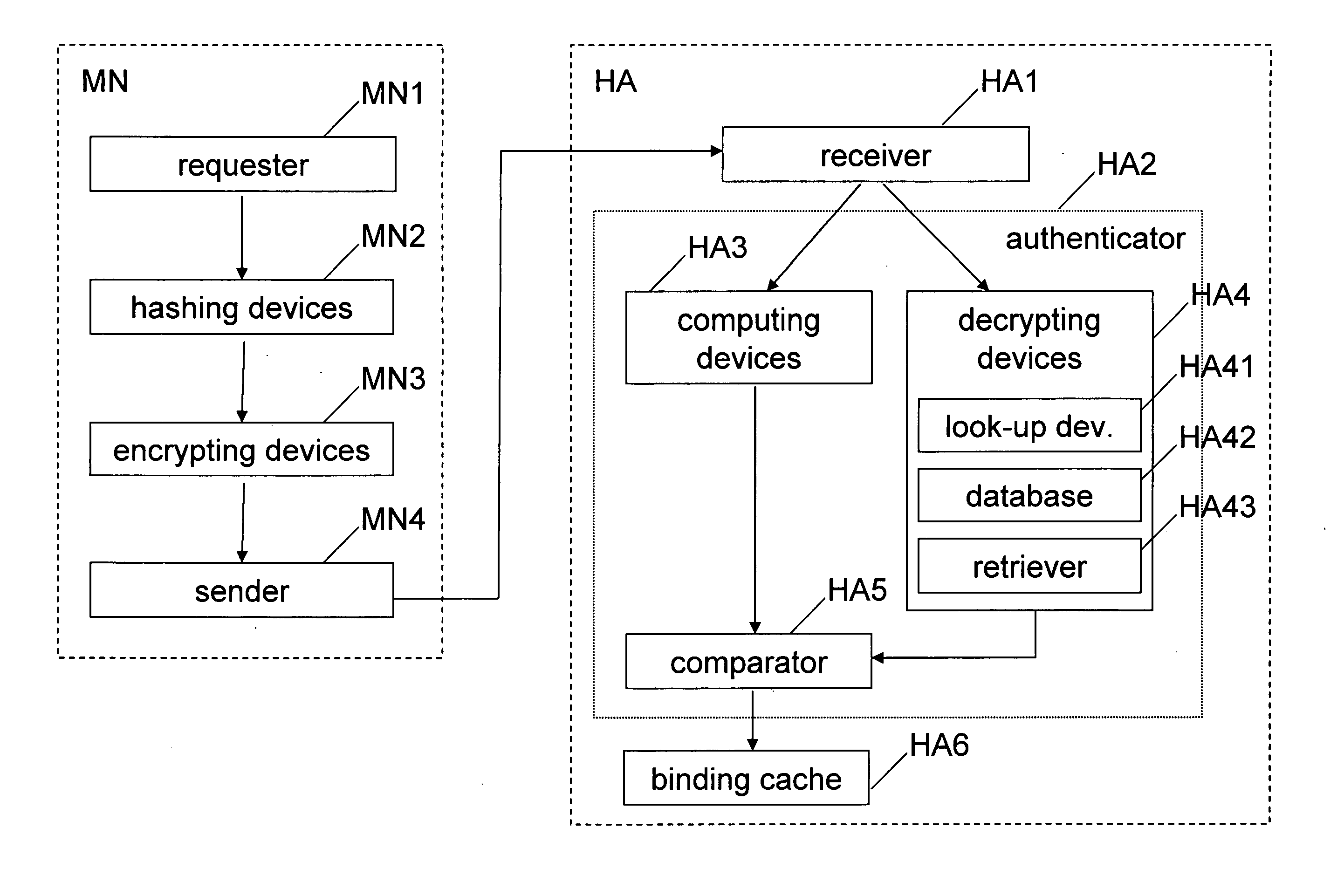
InactiveUS20060291422A1Effective preventionAvoid efficiencyWireless network protocolsRadio/inductive link selection arrangementsCommunications systemDigital signature
A method, network element, mobile node, system and computer program product for mobility management in a communication system comprising at least two communication networks, wherein a mobile node is associated with one of the at least two communication networks as a home network and is allocated a global home address, a certificate and a corresponding private key by a home agent of the home network, and wherein the mobile node, when roaming in a communication network other than the home network, requests a binding operation of a current routing address in the other communication network and the global home address at the home agent of the home network, comprising authenticating, at the home agent, the use of the correct allocated global home address by the mobile node by means of a digital signature and the certificate allocated to the mobile node.
Owner:NOKIA CORP
Certificate validation method and certificate validation server and storage medium
ActiveUS20110004763A1Effectively and safely performingEfficient executionUser identity/authority verificationDigital data protectionValidation methodsCertificate signing request
A certificate validation method for causing a certificate validation server to receive a certificate validation request from a given terminal device, build a certification path of from a first certificate authority (CA) to a second CA, perform validation of the certification path, and send a validation result to the terminal which issued the certificate validation request is disclosed. The validation server detects either a key update of any given CA or a compromise of the given CA, acquires a certificate of relevant CA and first certificate status information and second certificate status information, stores the acquired information in a storage unit or, alternatively, updates the information stored in the storage based on the acquired information, and performs the building of a certification path and validation of the certification path by use of the information of the storage unit.
Owner:HITACHI LTD
Method and apparatus for validating a digital signature
Method and system are described for validating a digital signature. More particularly, a signed message and a corresponding certificate are received. The certificate is checked for validation. A validation statement is generated, and the certificate validation and the signed message provide a status. This status represents a request for validation, and is provided along with a set of validations among which such status is an element. A digest is generated using a Merkle authentication tree corresponding to the set of validations, and this digest is signed with a private key. Accordingly, a notary may provide the signed digest, status and the set of validations for subsequent confirmation of the digital signature.
Owner:PRIVADOR
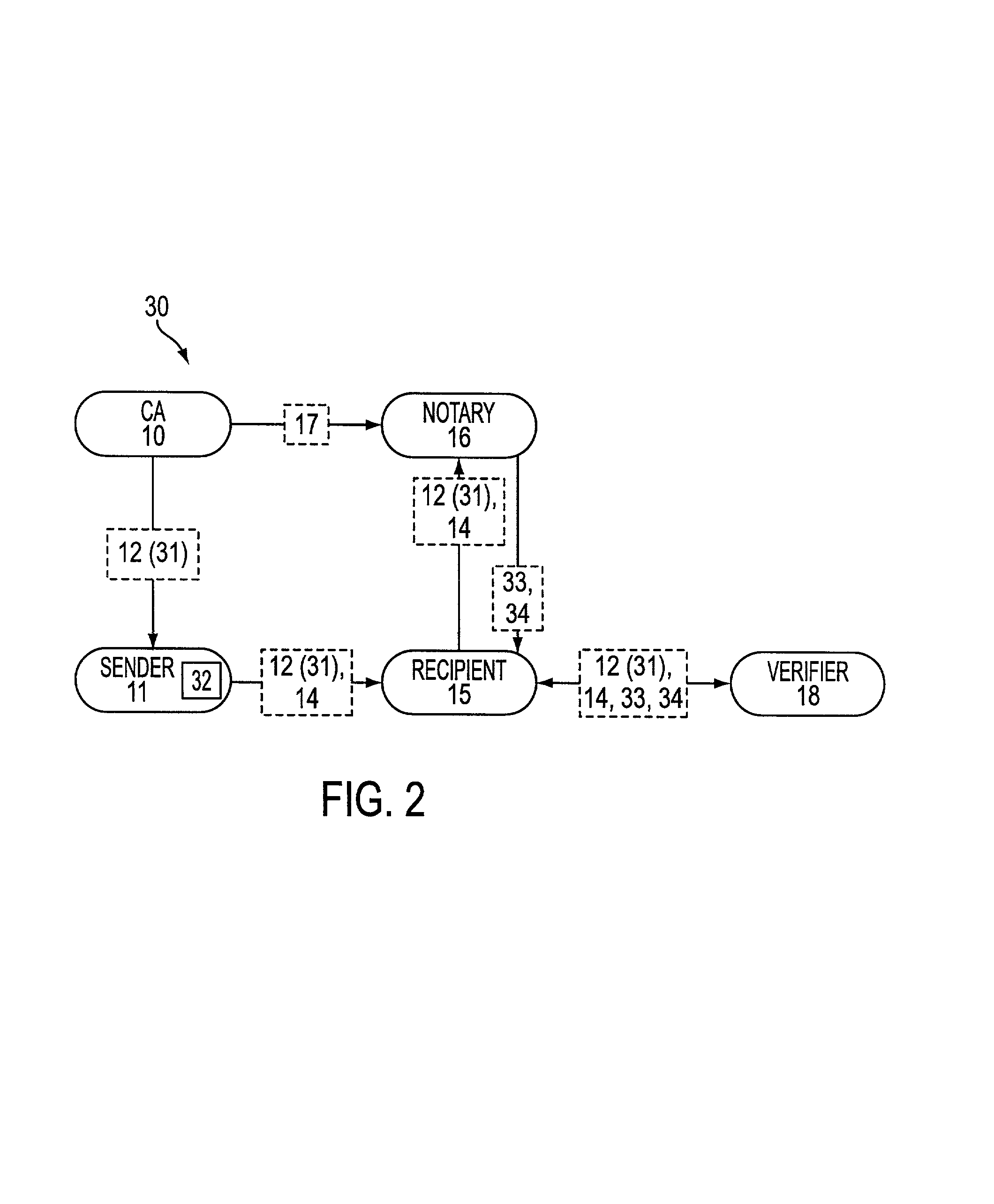
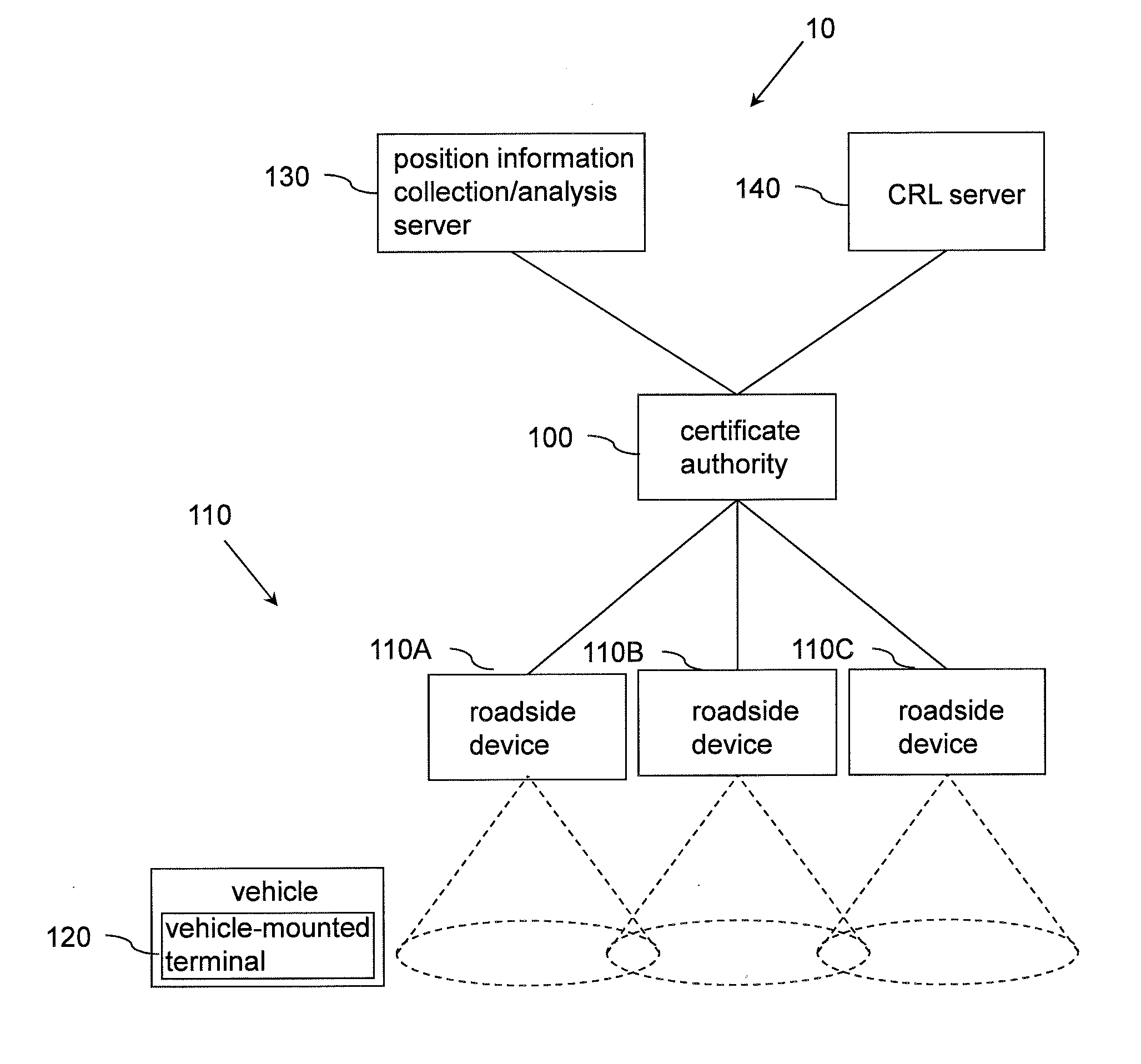
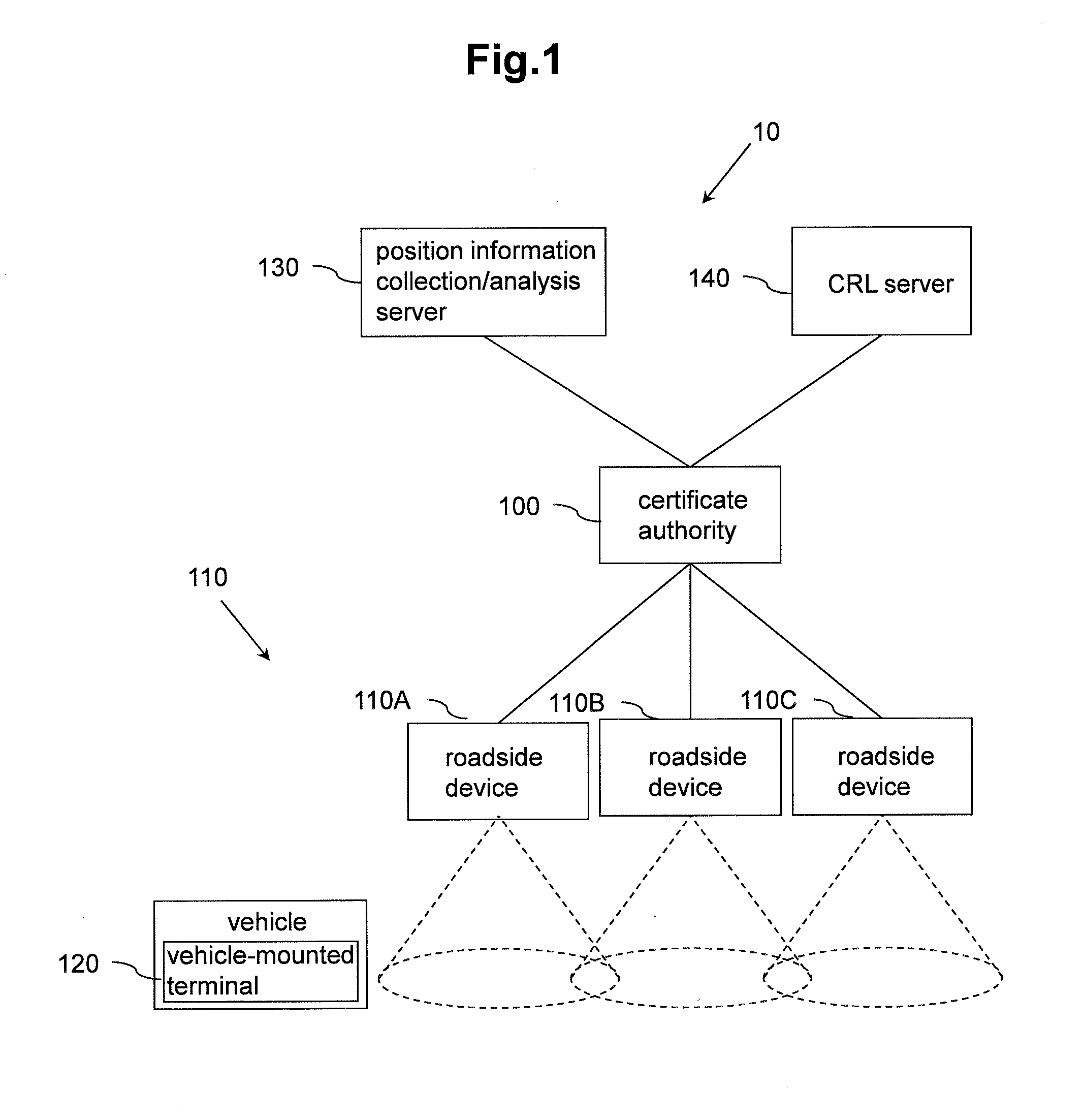
Communication system, vehicle-mounted terminal, roadside device
ActiveUS20130067220A1Key distribution for secure communicationRoad vehicles traffic controlCommunications systemCertificate authority
There is a need to reduce the certificate verification time in a communication system.A communication system (10) includes a certificate authority (100) for performing authentication, a roadside device (110), a vehicle-mounted terminal (120), a first server (130), and a second server (140). The vehicle-mounted terminal transmits its own position information to the first server. The certificate authority acquires information about a vehicle-mounted terminal highly likely to appear according to place and time from the first server. The certificate authority allows the second server to verify validity of a certificate for a vehicle-mounted terminal acquired from the first server. The certificate authority generates a first list of vehicle-mounted terminals having valid certificates and a second list of vehicle-mounted terminals having invalid certificates according to place and time based on a verification result. The certificate authority transmits the first list and the second list to the roadside device and the vehicle-mounted terminal. The roadside device and the vehicle-mounted terminal verify a certificate using the received first and second lists. Thus, the certificate verification time is reduced.
Owner:RENESAS ELECTRONICS CORP
Two-dimensional code processing method, device and system
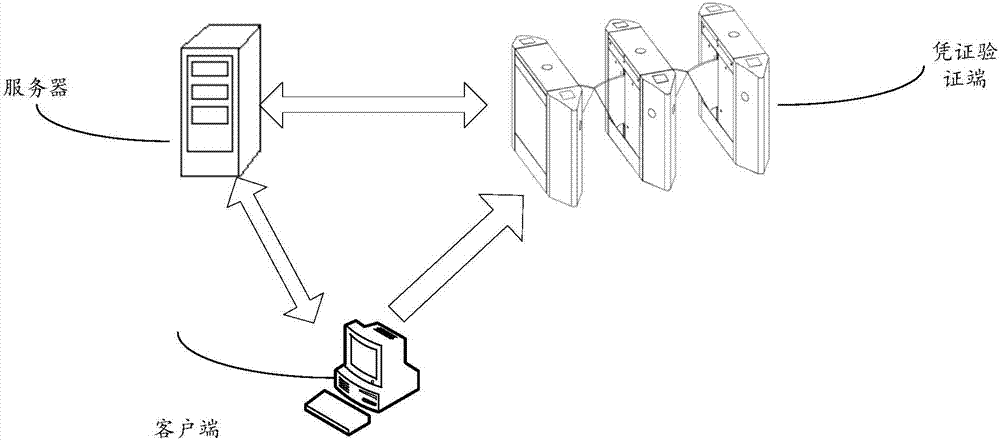
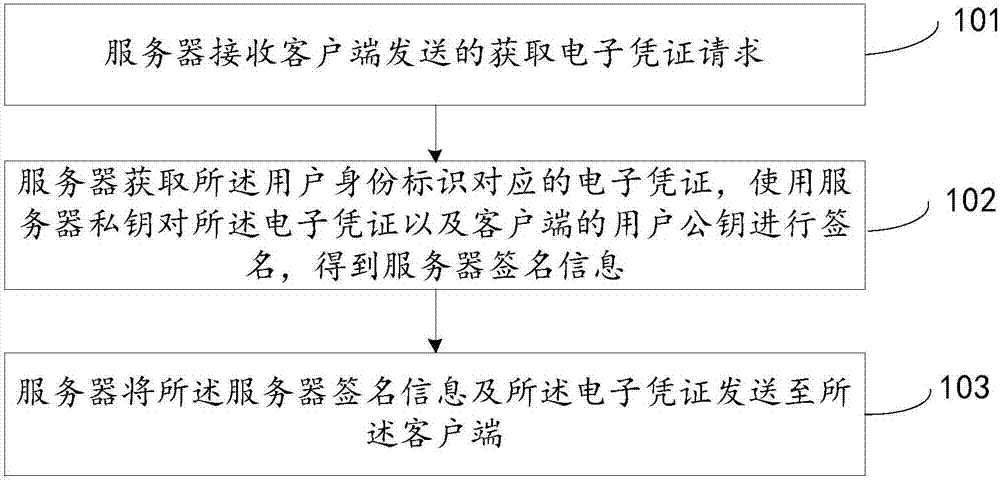
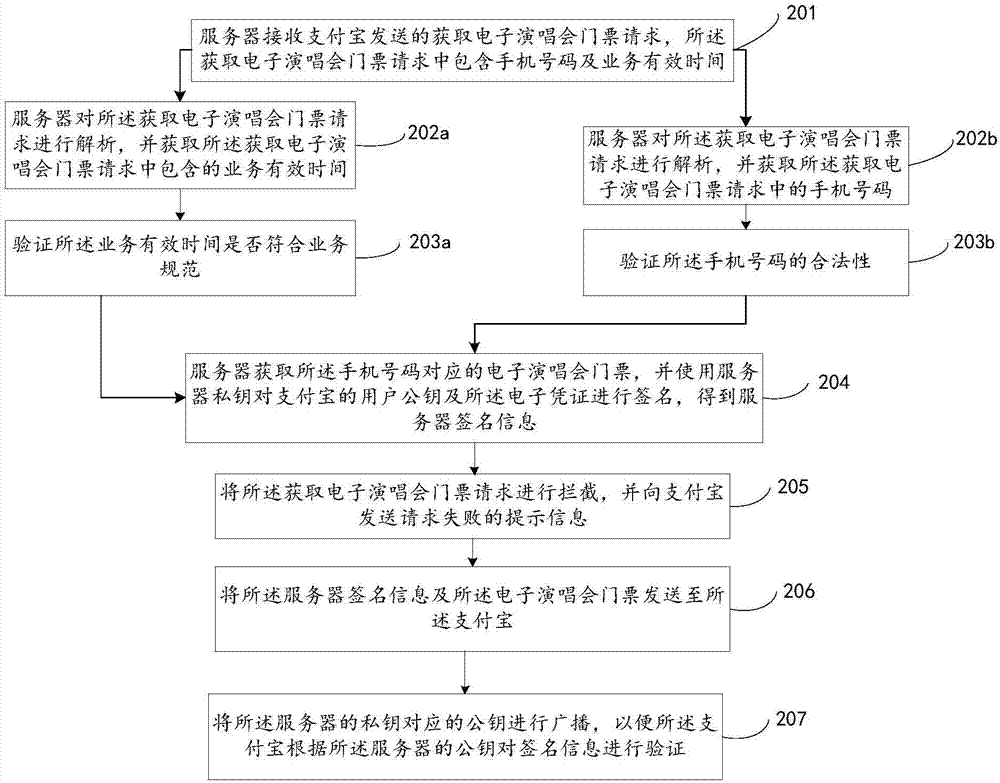
ActiveCN106899570AEnsure safetyDigital data authenticationRecord carriers used with machinesInformation processingClient-side
The invention discloses a two-dimensional code processing method, device and system, and relates to the technical field of information processing. The main purpose is to solve the problem that the electronic certificate security is leaked once an electronic certificate is stolen in a copying or shooting way since the generation of the electronic certificate is dependent on a static random code in the prior art. The technical scheme corresponding to the invention comprises the following steps: a server receives an electronic certification acquisition request sent by a client, and the electronic certificate acquisition request comprises a user identity label; the electronic certificate corresponding to the user identity label is acquired, and a server private key is used for signing the electronic certificate and a user public key of the client, thereby obtaining server signature information; the server signature information and the electronic certificate are sent to the client so that the client can verify the server signature information conveniently, and generates a two-dimensional code according to the electronic certificate, and a certificate verification end verifies the electronic certificate contained in the two-dimensional code, wherein the certificate verification end is used for generating the electronic certificate according to the user identity label.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Physical access control
InactiveUS20080211624A1Electric signal transmission systemsDigital data processing detailsHash functionGranularity
A system and method are disclosed for controlling physical access through a digital certificate validation process that works with standard certificate formats and that enables a certifying authority (CA) to prove the validity status of each certificate C at any time interval (e.g., every day, hour, or minute) starting with C's issue date, D1. C's time granularity may be specified within the certificate itself, unless it is the same for all certificates. For example, all certificates may have a one-day granularity with each certificate expires 365 days after issuance. Given certain initial inputs provided by the CA, a one-way hash function is utilized to compute values of a specified byte size that are included on the digital certificate and to compute other values that are kept secret and used in the validation process.
Owner:ASSA ABLOY AB
Method and apparatus improving efficiency of end-user certificate validation
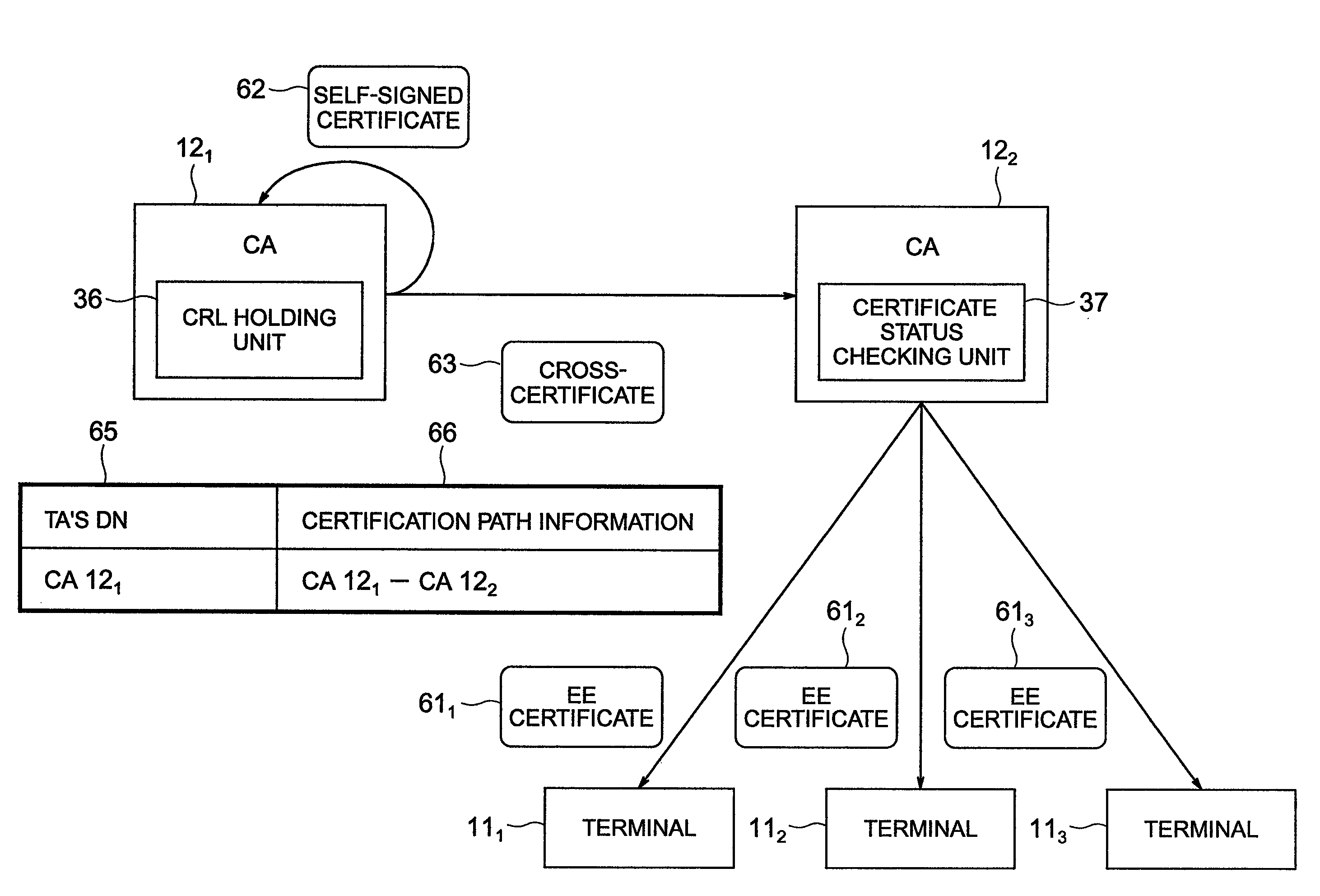
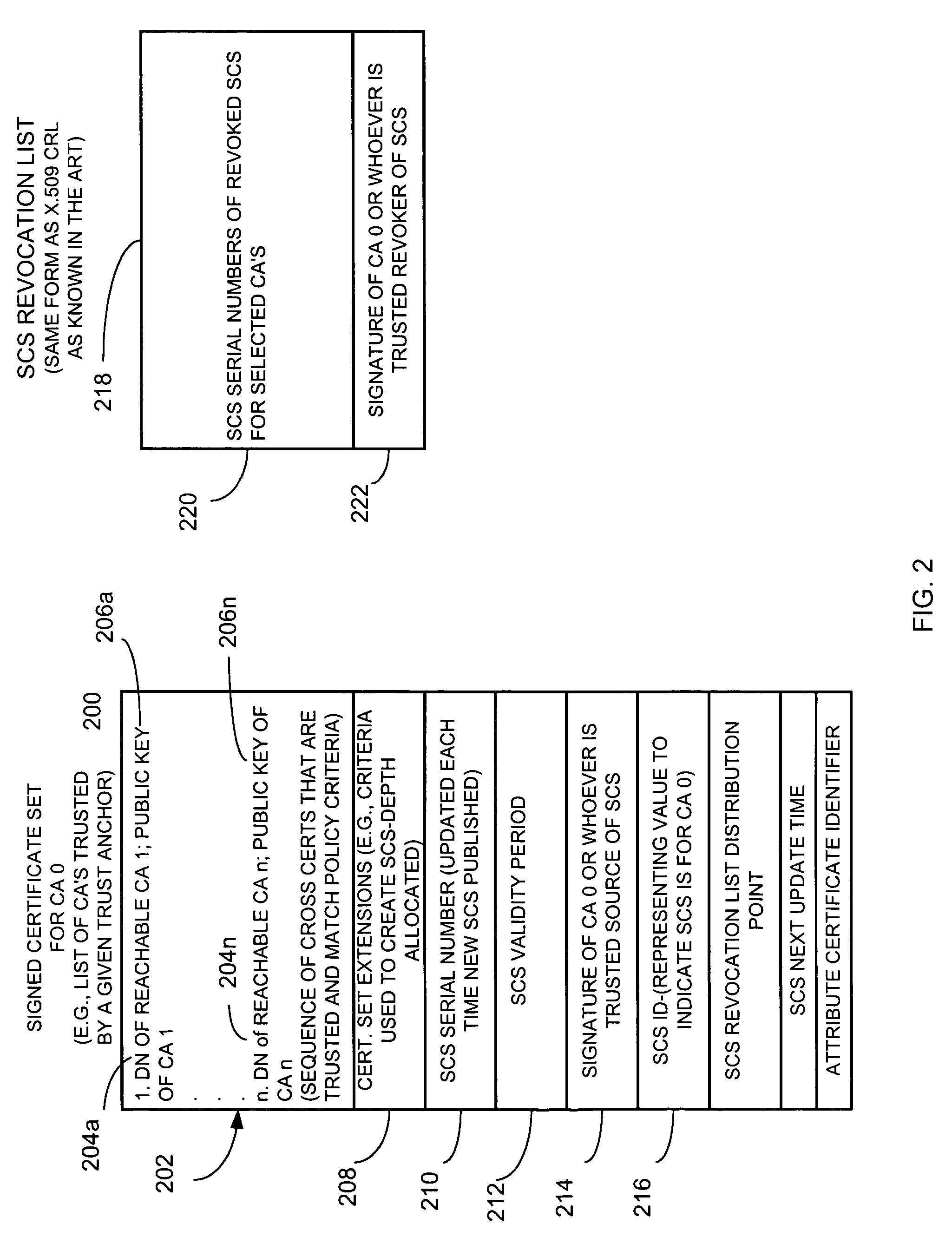
InactiveUS7290133B1User identity/authority verificationMultiple digital computer combinationsPath lengthUnique identifier
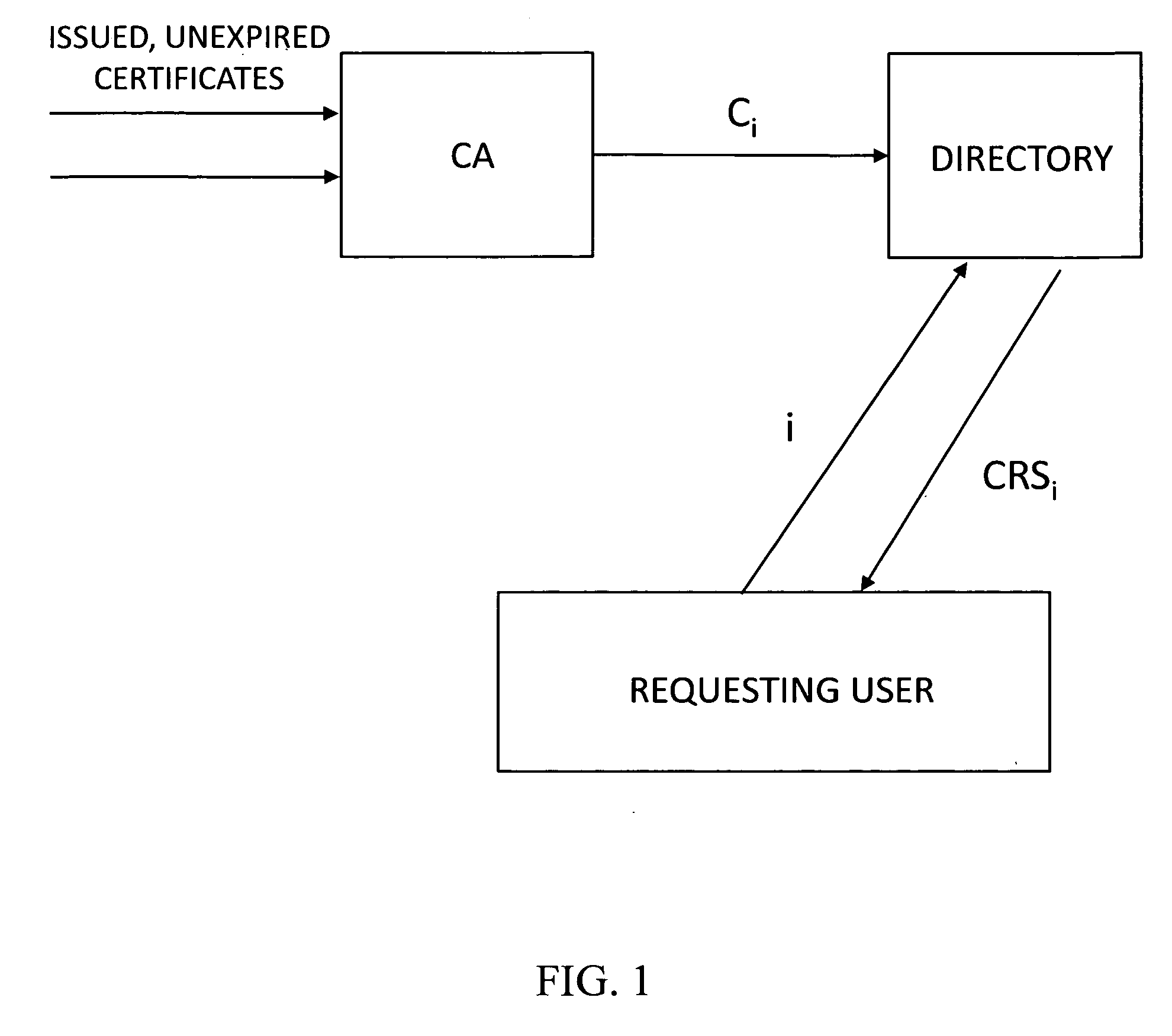
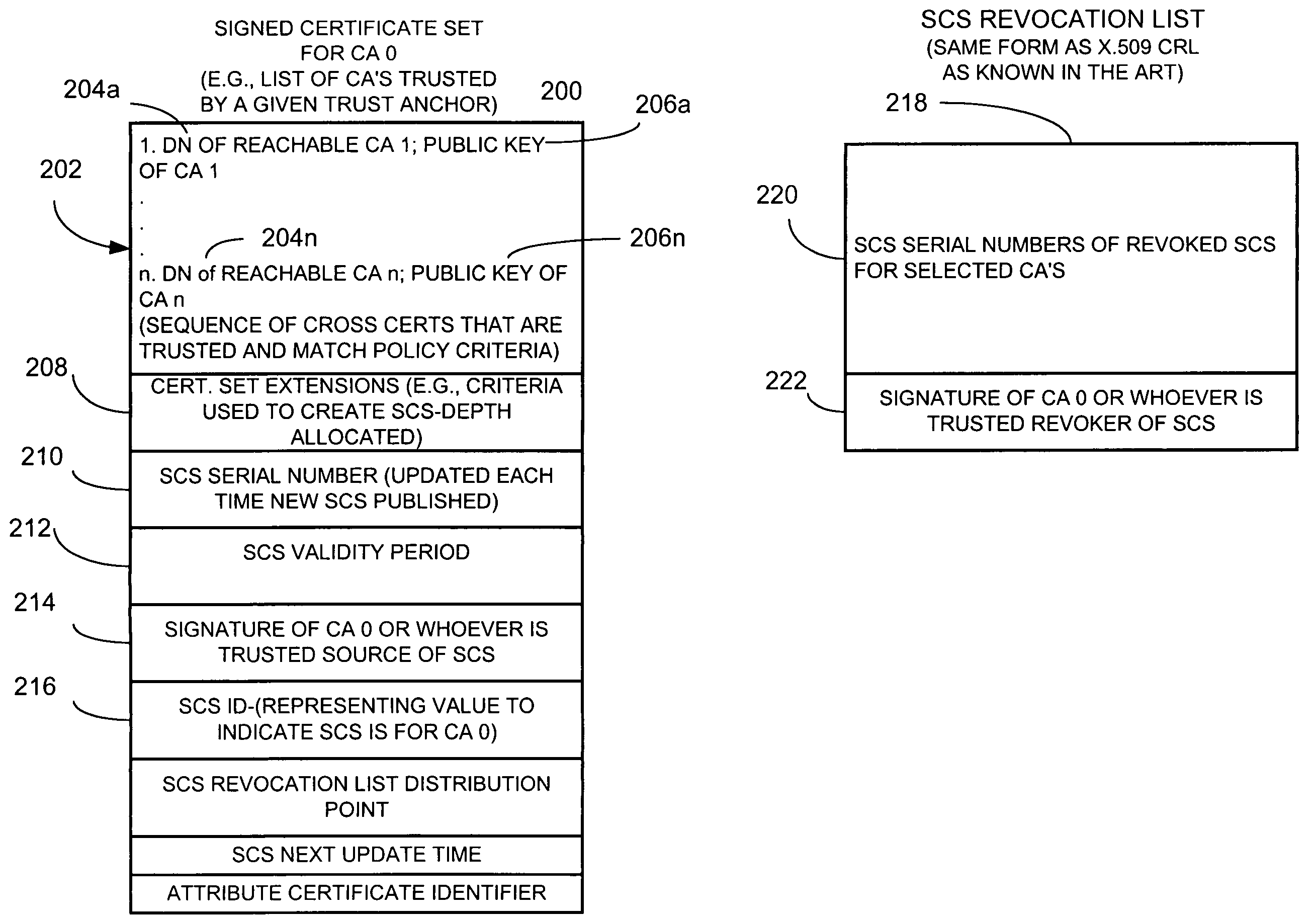
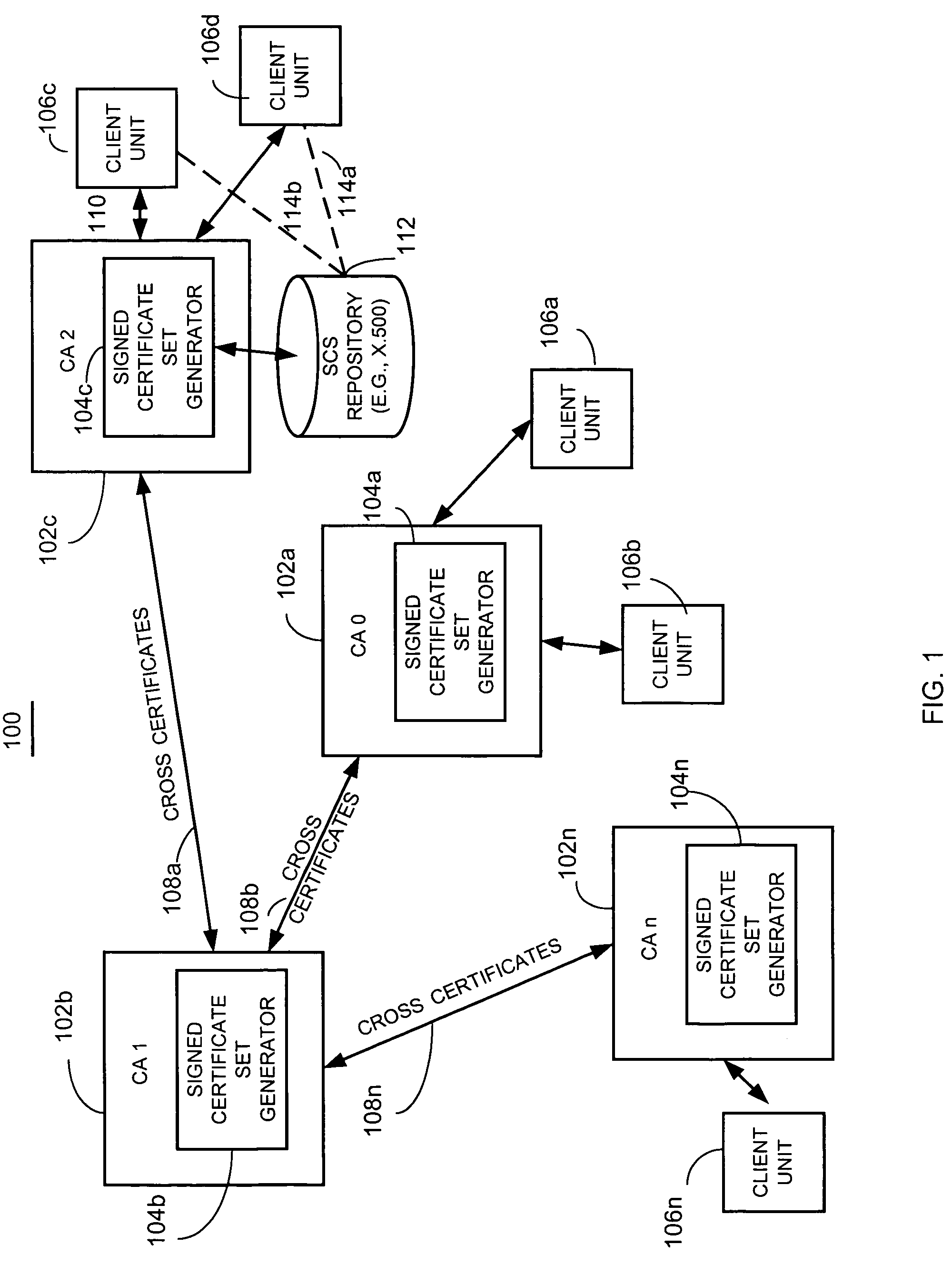
An apparatus and method collects, for a community of interest, at least one cross certificate associated with an anchor certificate issuing unit, and obtains at least one certificate issuing unit public key and an associated unique identifier for a cross-certified certificate issuing unit identified by the at least one cross certificate. For example, a certificate issuing unit, client unit, or other suitable unit, searches for one or up to all certification authorities or certificate issuing units that it can trust based on cross certificate chains. This is done, for example, from a given trust anchor. The apparatus selects those obtained certificates that satisfy, for example, some search criteria, such as what policy must be enforced in each certificate, for example, the allowed path length or depth that the apparatus is allowed to evaluate, and creates a signed certificate set, such as a list of all trusted certificate issuing units from the perspective of a given trust anchor. Accordingly, the apparatus and method creates a signed certificate set identifying certificate issuing units determined to be trusted by the anchor certificate issuing unit based on the cross certificates that the apparatus obtained. The signed certificate set includes at least a unique identifier of each trusted certificate issuing unit, such as the distinguished name (DN) of the certificate issuing unit, and public key of each trusted certificate issuing unit.
Owner:ENTRUST
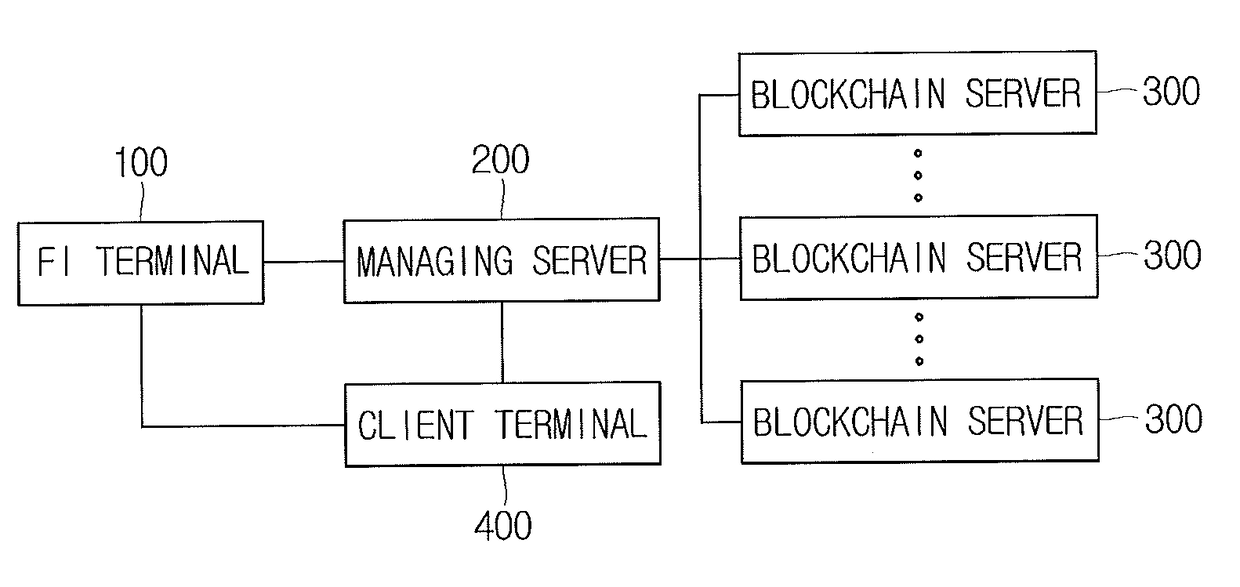
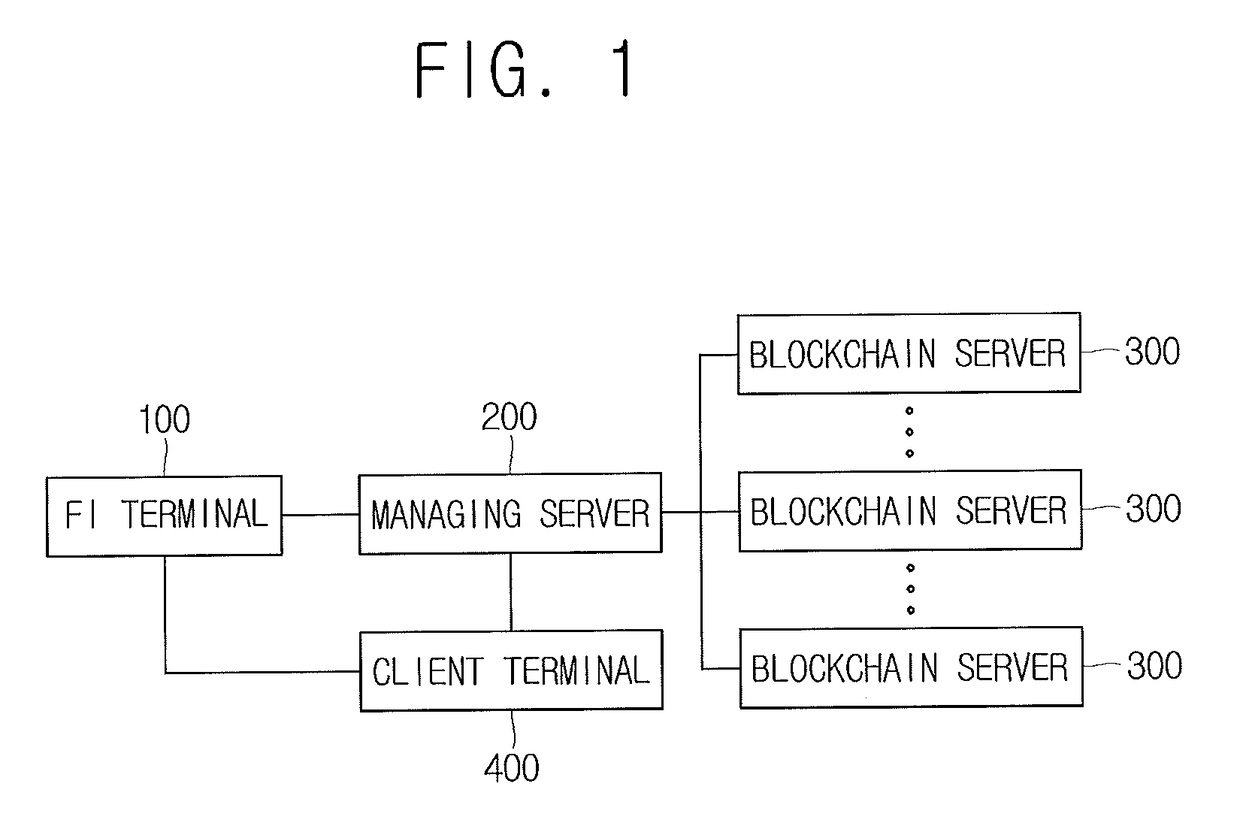
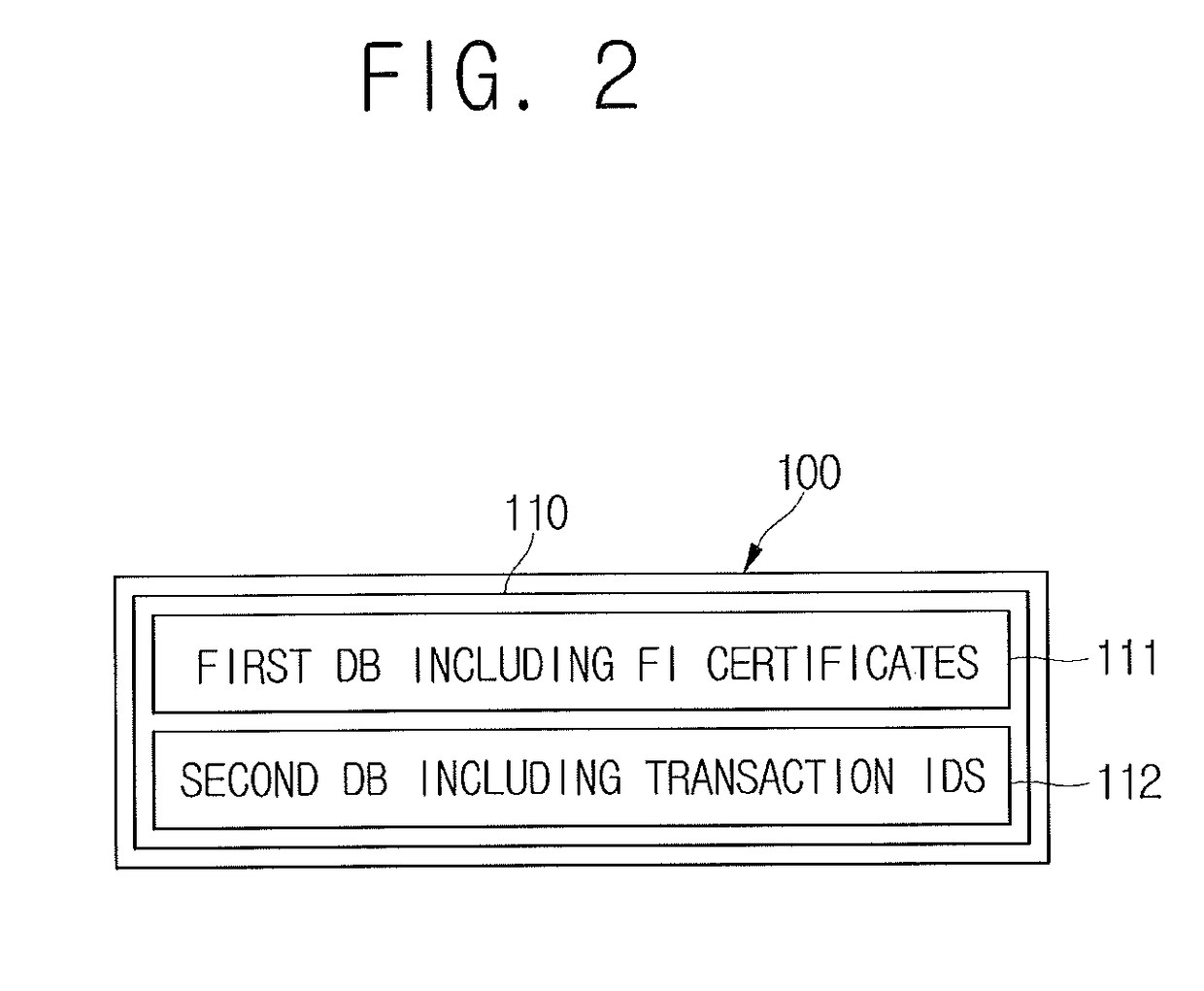
System and method for verifying forgery of financial institution proof documents on basis of block chain
Transaction ID information corresponding to proof certificate-verifying transaction information is transmitted to a block chain retention server if a request for proof certificate information is sensed, when the proof certificate-verifying transaction information generated by using the proof certificate information, to be provided to a customer, is recorded in a block chain retention server and the transaction ID information is managed. The proof certificate-verifying transaction information corresponding to the transaction ID information is acquired from the block chain retention server. A proof certificate index hash value used for comparison, acquired from the proof certificate information to be provided to a customer and corresponding to a request, is compared with a proof certificate-verifying index hash value acquired from the proof certificate verifying-transaction information. Verification information generated with reference to the comparison result of the proof certificate index hash value used for comparison and the proof certificate-verifying index hash value are provided.
Owner:COINPLUG LNC
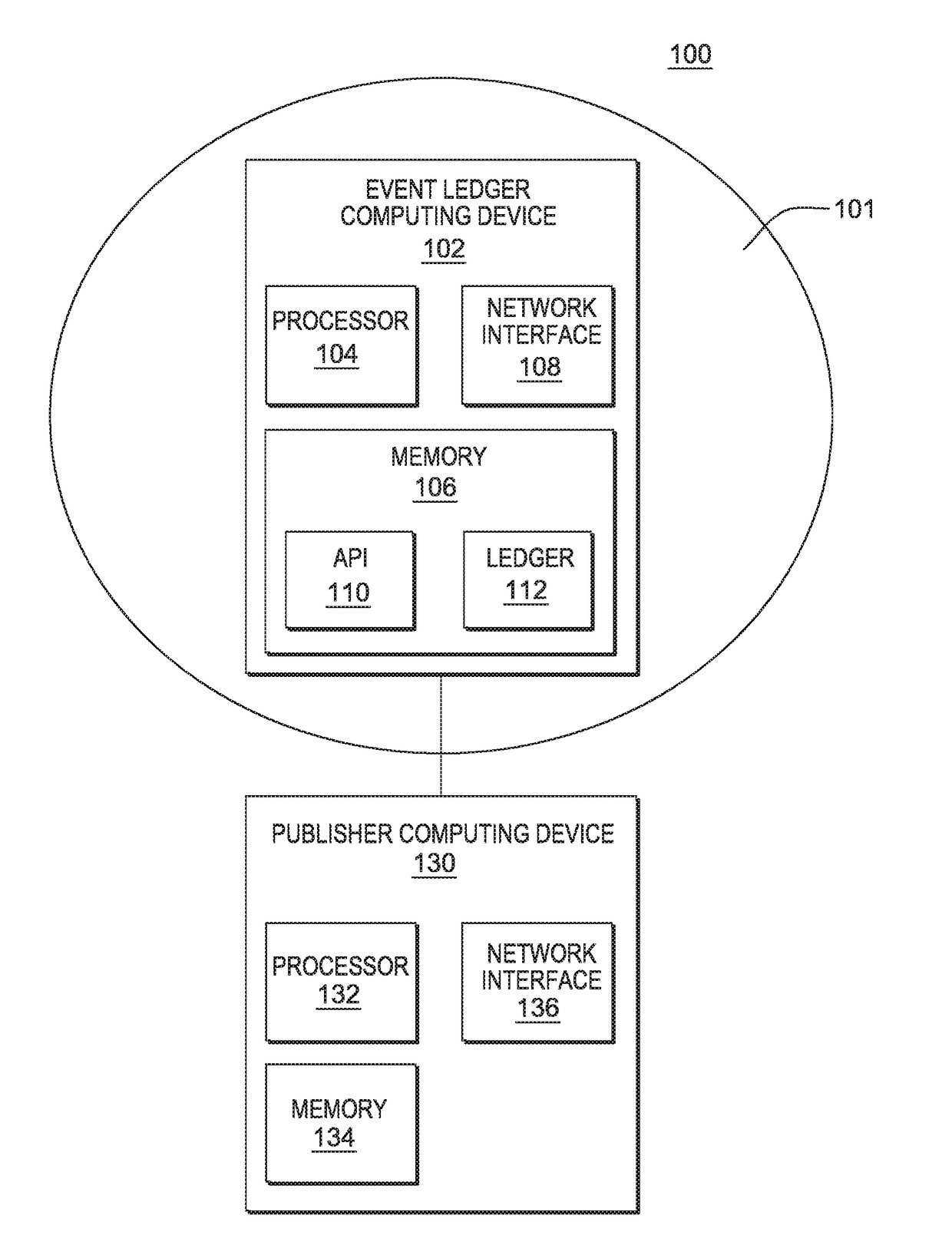
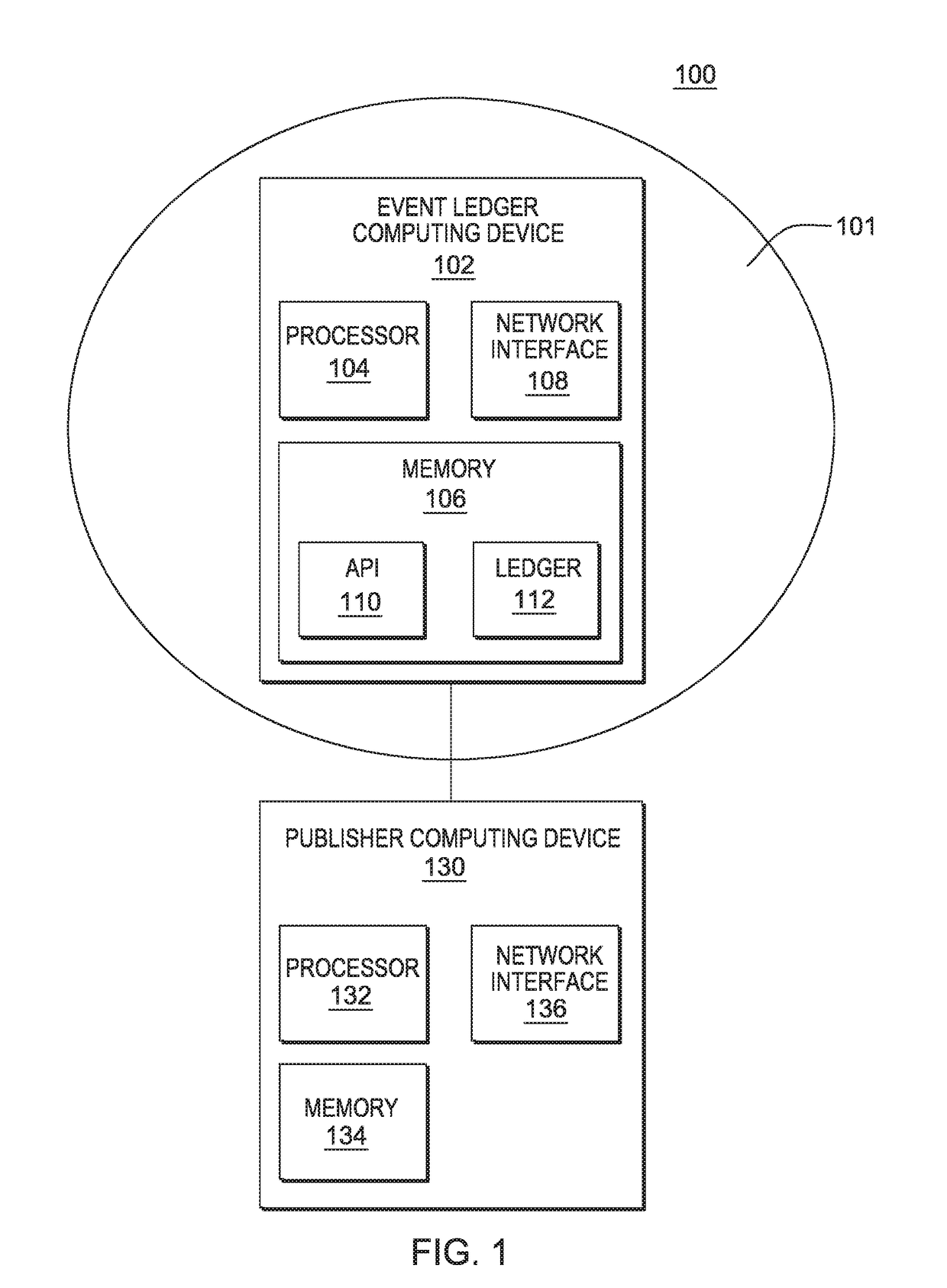
Event ledger
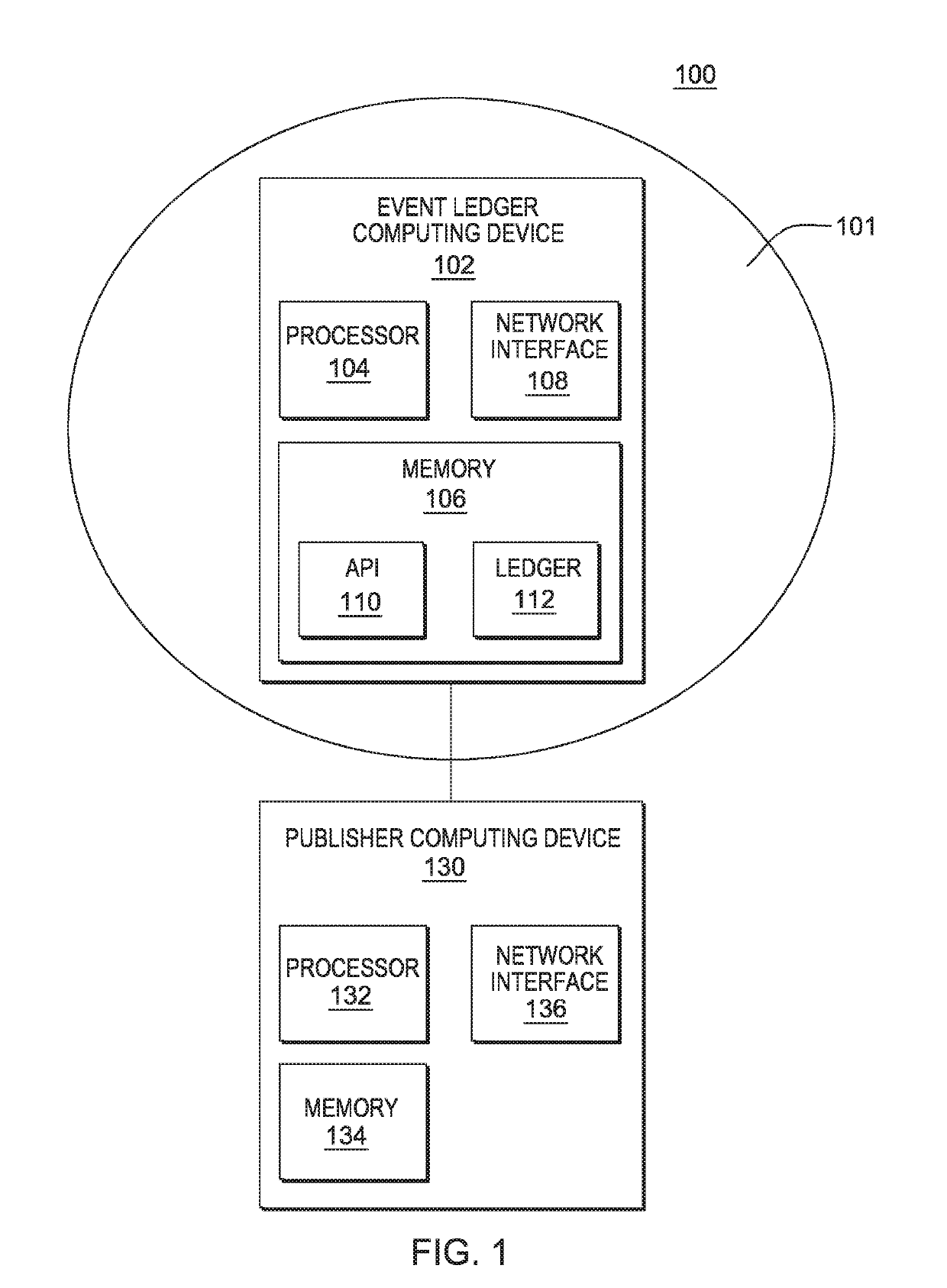
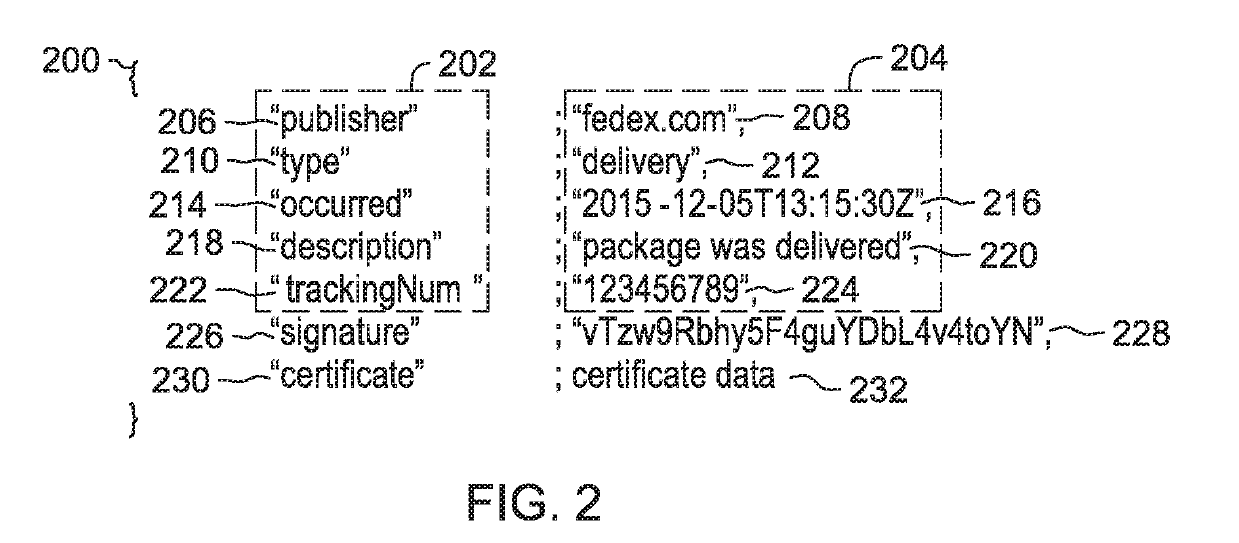
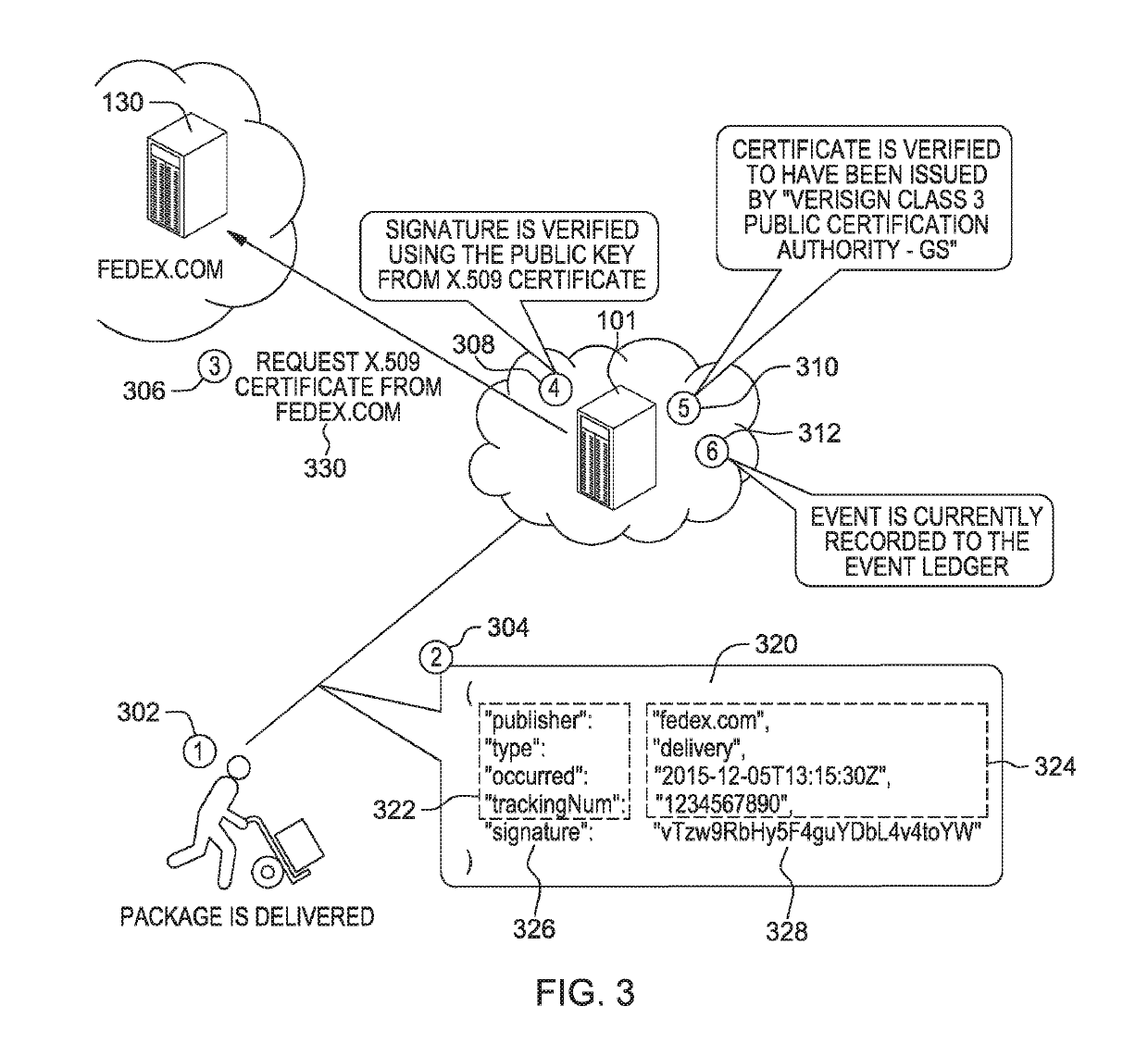
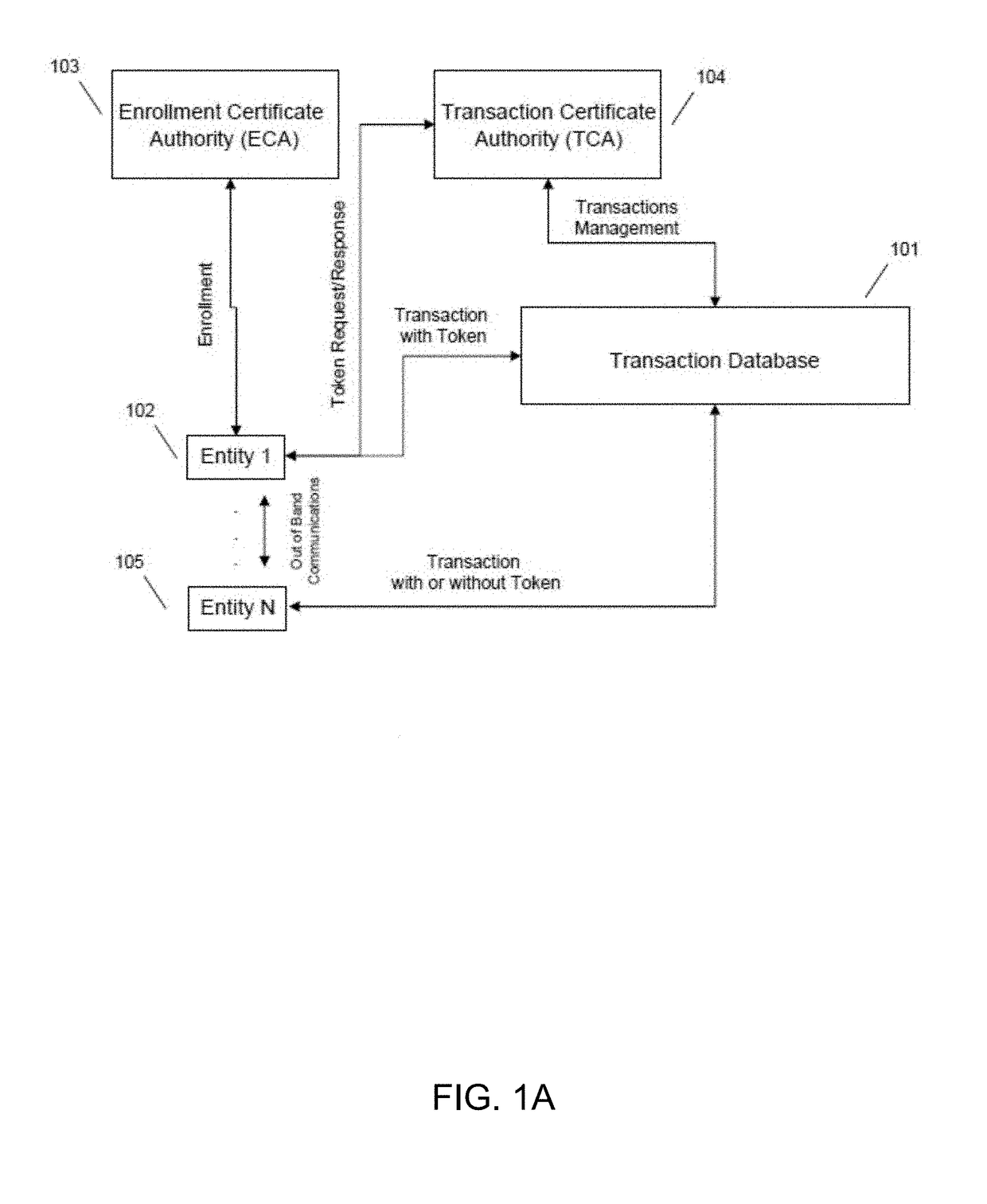
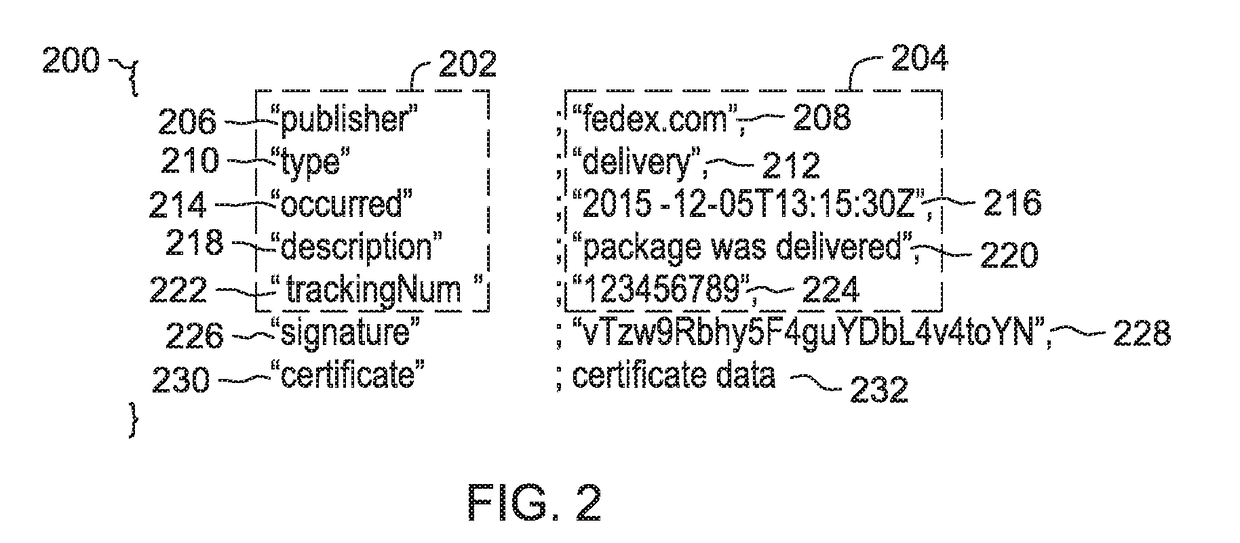
InactiveUS10361869B2Encryption apparatus with shift registers/memoriesUser identity/authority verificationComputer securityCertificate verification
The present disclosure provides a globally accessible, un-forgeable, and permanent repository of published events in the form of an event ledger. A method according to the present disclosure includes receiving a request from a publisher to publish to an event ledger an event including a name of the publisher, a date and time at which the event occurred, a description of the event, and a cryptographic signature of the event signed using a private key of the publisher, receiving a certificate from the publisher including a public key of the publisher, validating the cryptographic signature of the event using the received certificate, and publishing the event to the event ledger.
Owner:INT BUSINESS MASCH CORP
Security mechanism for computer processing modules
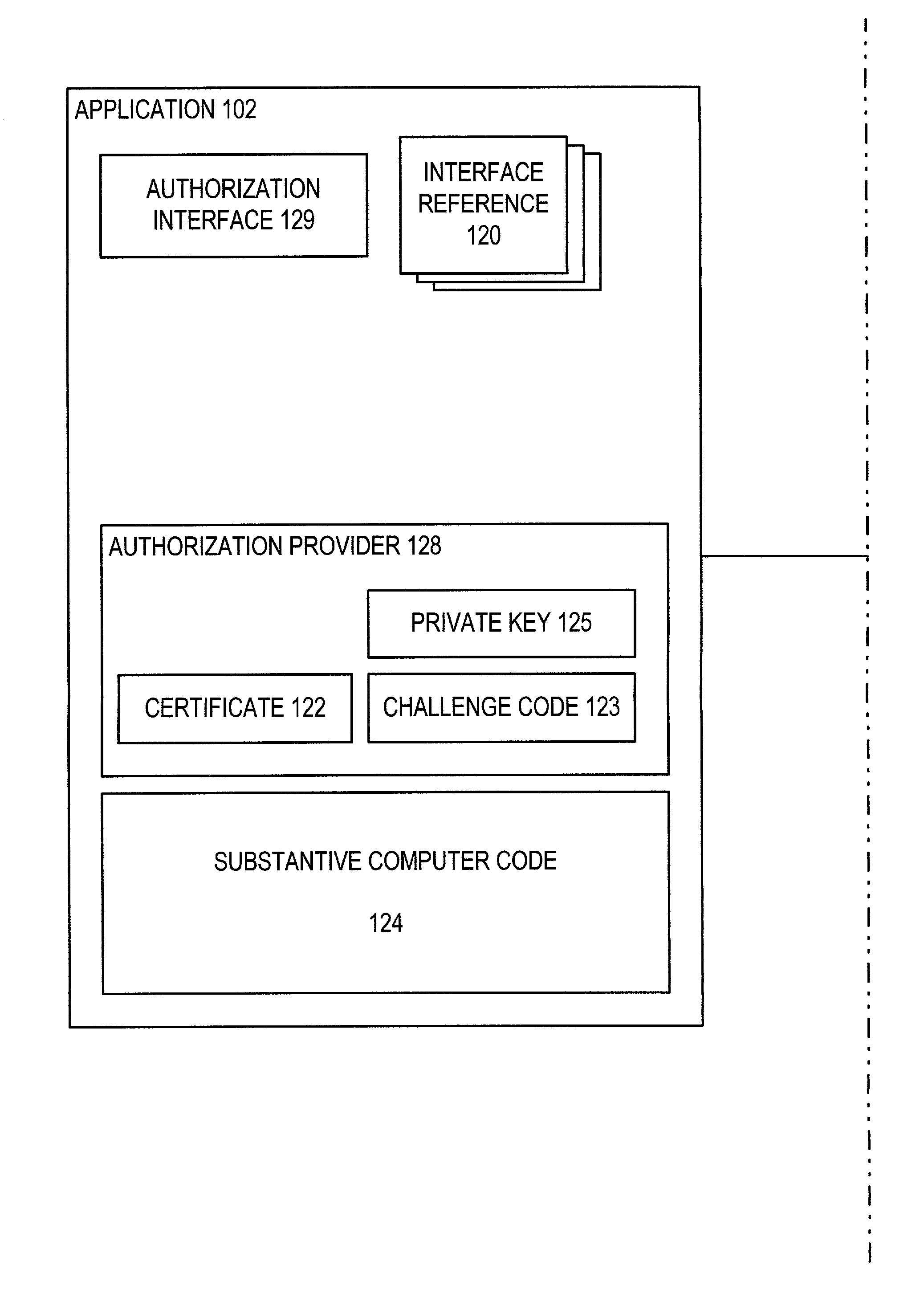
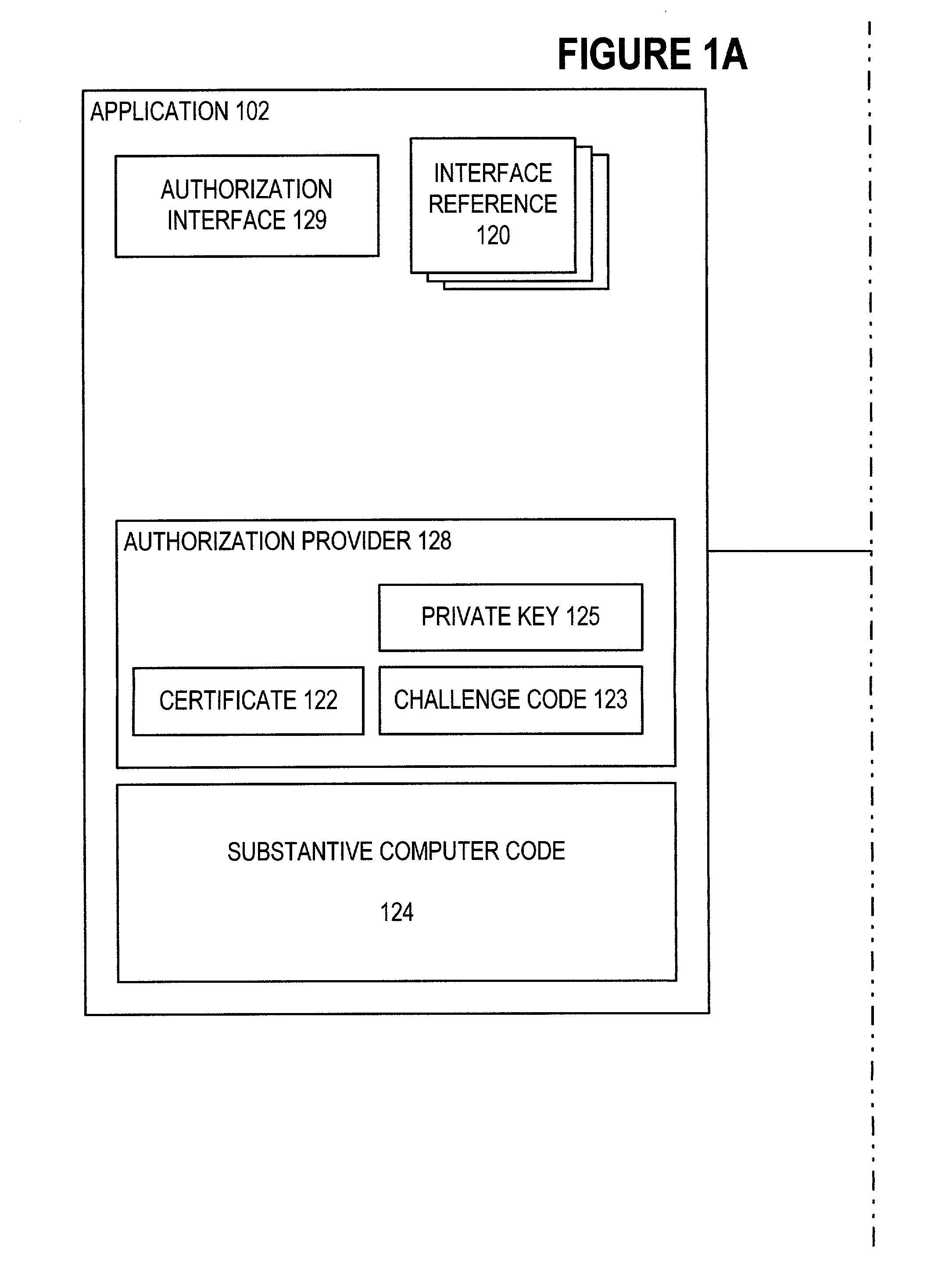
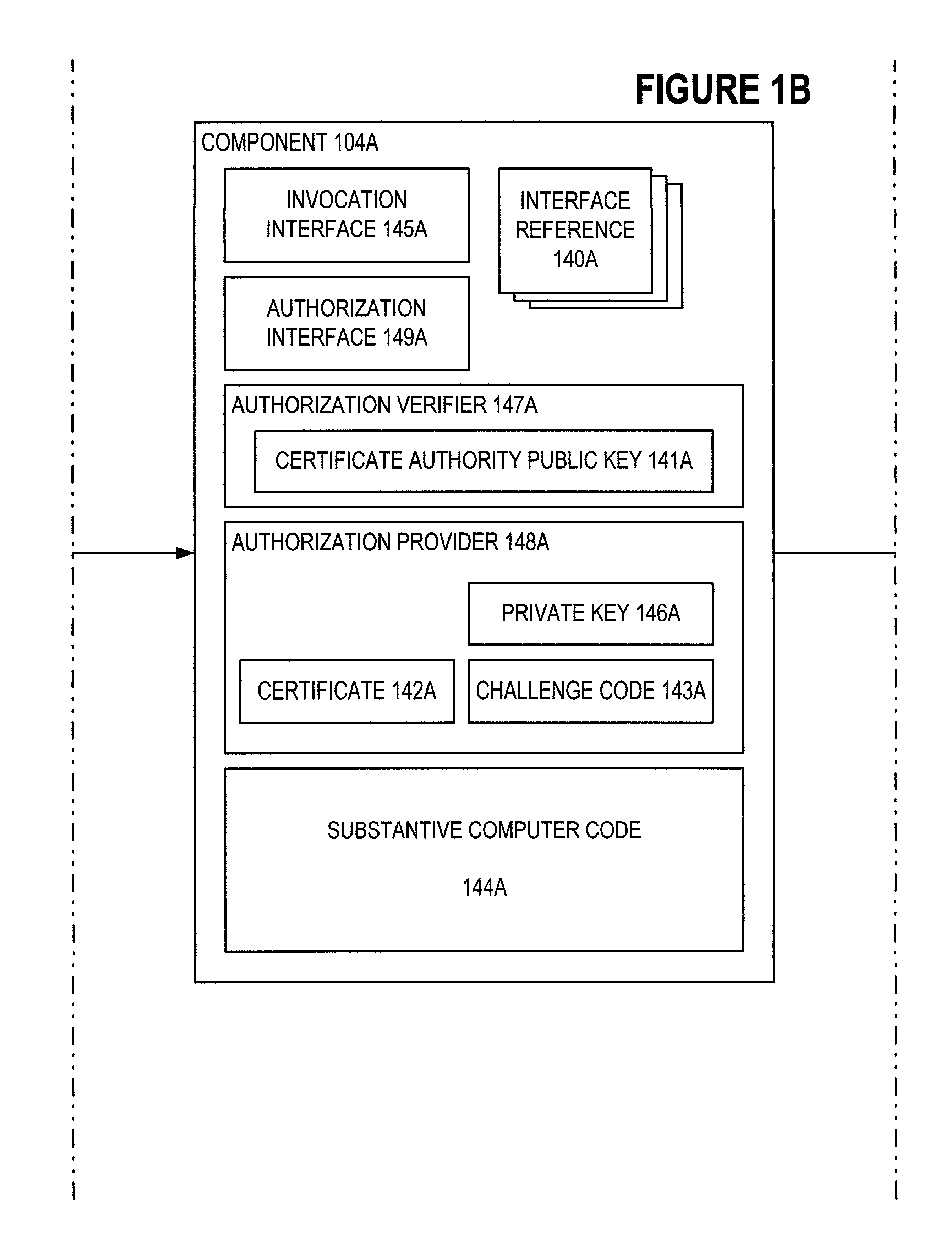
InactiveUS6965994B1Improve securityIncrease flexibilityDigital data processing detailsUser identity/authority verificationProcessingAuthorization
To provide improved security in adjunct program modules such as plug-ins and dynamic link libraries, a requesting module provides an authorization interface to the invoked module such that the invoked module can require a certificate of the requesting module and can also challenge the authority of the requesting module. The certificate can include one or more permissions which are prerequisites for processing by the invoked module. The invoked module can challenge the authority of the requesting module by sending random test data to the requesting module and receiving in response a cryptographic signature of the test data. By verifying the signature of the requesting module using the received certificate, the invoked module confirms that the requesting module is, in fact, the owner of the receive certificate.
Owner:MICROSOFT TECH LICENSING LLC
Software upgrading bag packaging method and software upgrading method
InactiveCN101425114AGuaranteed Safe UpgradesDigital data authenticationProgram loading/initiatingPlaintextDigital signature
The invention relates to a technique for safely updating a software and provides a software update packet packaging method for ensuring the legality and completeness of an updated software, as well as a software updating method. Digital certificates of trustworthy authentication institutes are prearranged in a terminal apparatus, or a server is used for determining the trustworthy authentication institutes; the authentication institutes respectively perform digital signing to the software and transmit an original cleartext software together with all digital signatures and digital certificates to the terminal apparatus; the terminal apparatus verifies whether all digital certificates are legal and judges the authentication institutes working together for updating the software; if all conditions are satisfied, the terminal apparatus verifies all digital signatures and then updates the software after the verification. As the legality of a software update packet is verified according to the digital certificates of the authentication institutes, the completeness of the software update packet is verified according to the digital signatures of the authentication institutes and a plurality of parties participate the concerted signing to the software, the safe update of the software is ensured.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Certificate verification method, system and certificate verification terminal
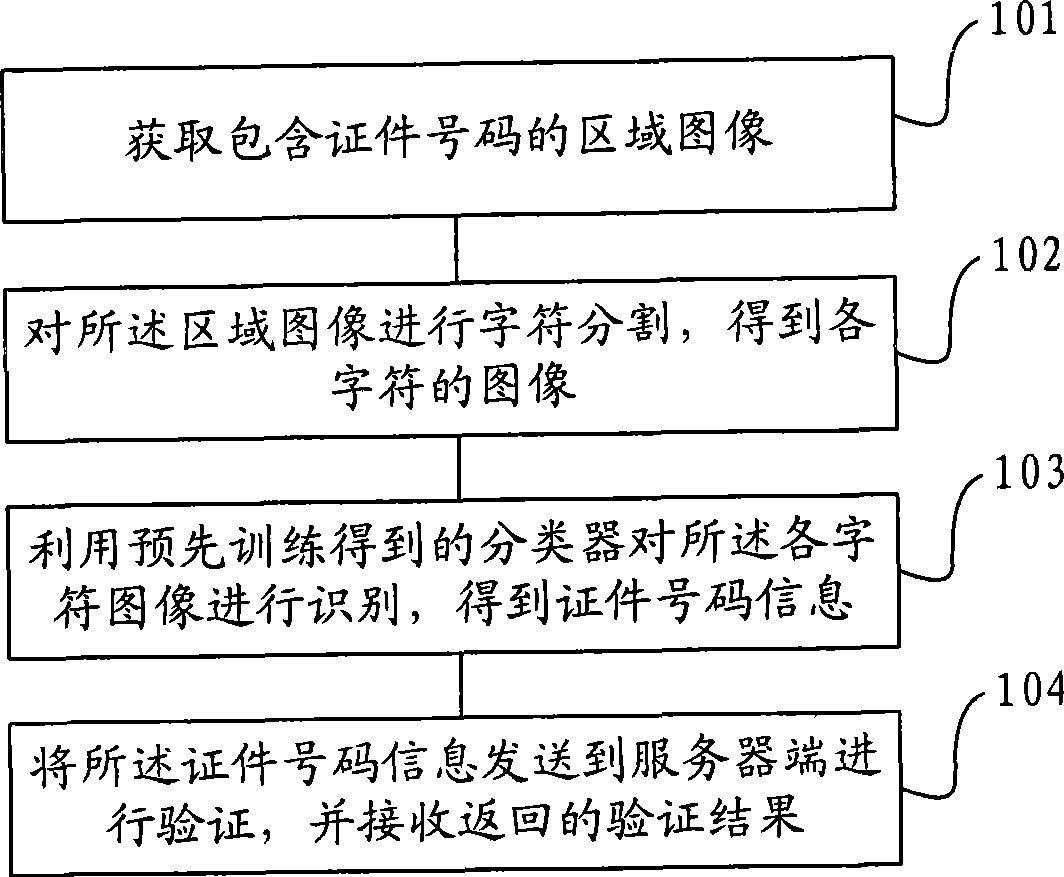
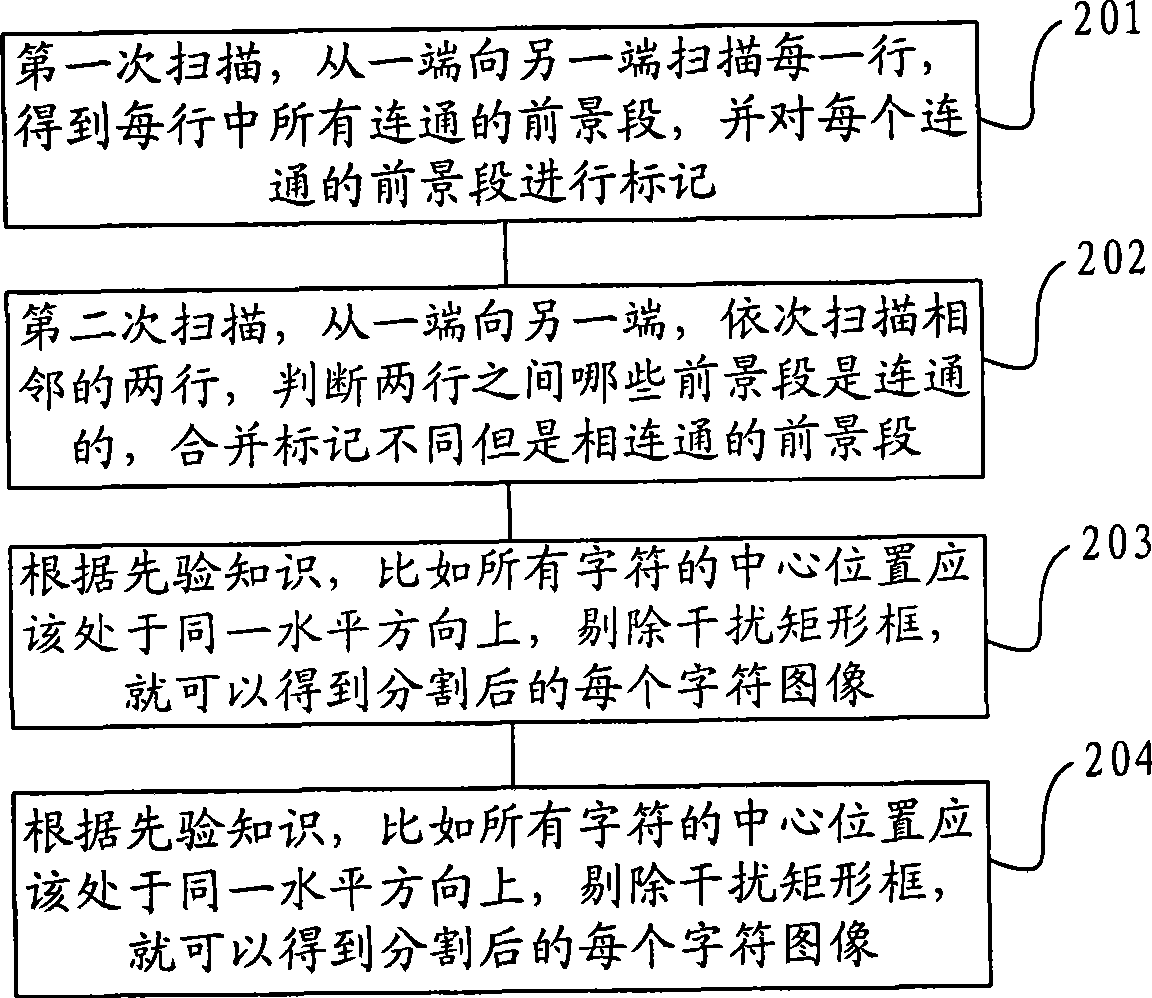
ActiveCN101510258AImprove inspection efficiencyLow costCharacter and pattern recognitionValidation methodsComputer terminal
The invention provides a certificate verification method, a system and a certificate verification terminal, aiming at solving the problem in the traditional checking system which checks the verification of certificates by manually inputting the certificate number and has the disadvantages of wasting time and energy and having high error rate. The method comprises the following steps of: obtainingan area image containing a certificate number; carrying out character segmentation to the area image, thus obtaining images of all the characters; utilizing a classifier obtained by training in advance to carry out identification to the images of all the characters, thus obtaining the certificate number information; and sending the certificate number information to a server side for verification and then receiving the returned checking result. The invention can identify certificate numbers automatically and does not need to input certificate numbers manually, thus greatly raising the efficiency of certificate checking; besides, the identification processing of certificate numbers is carried out in a system terminal, thus occupying little bandwidth and reducing the demand for the performance of network and server terminals.
Owner:GUANGDONG VIMICRO
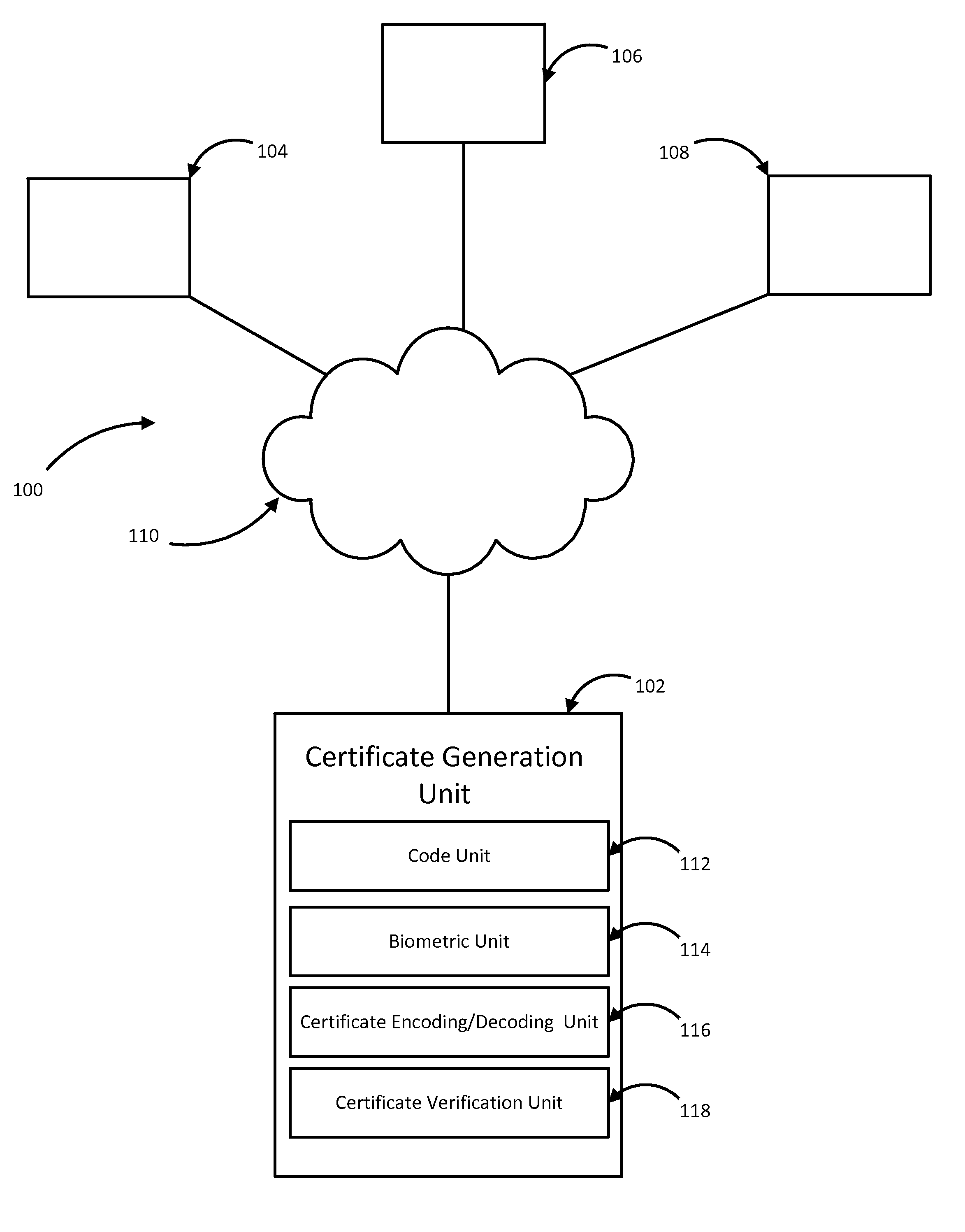
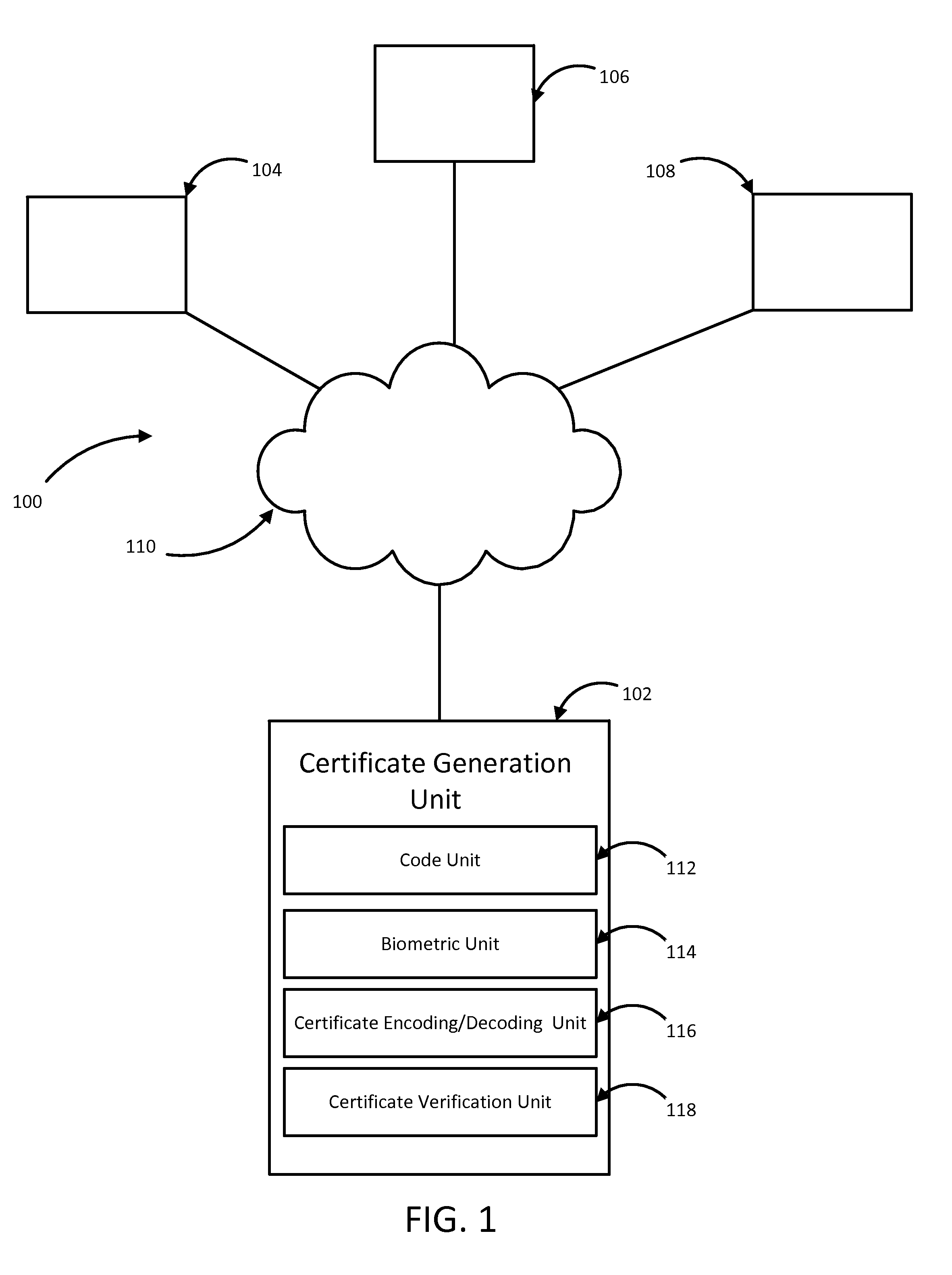
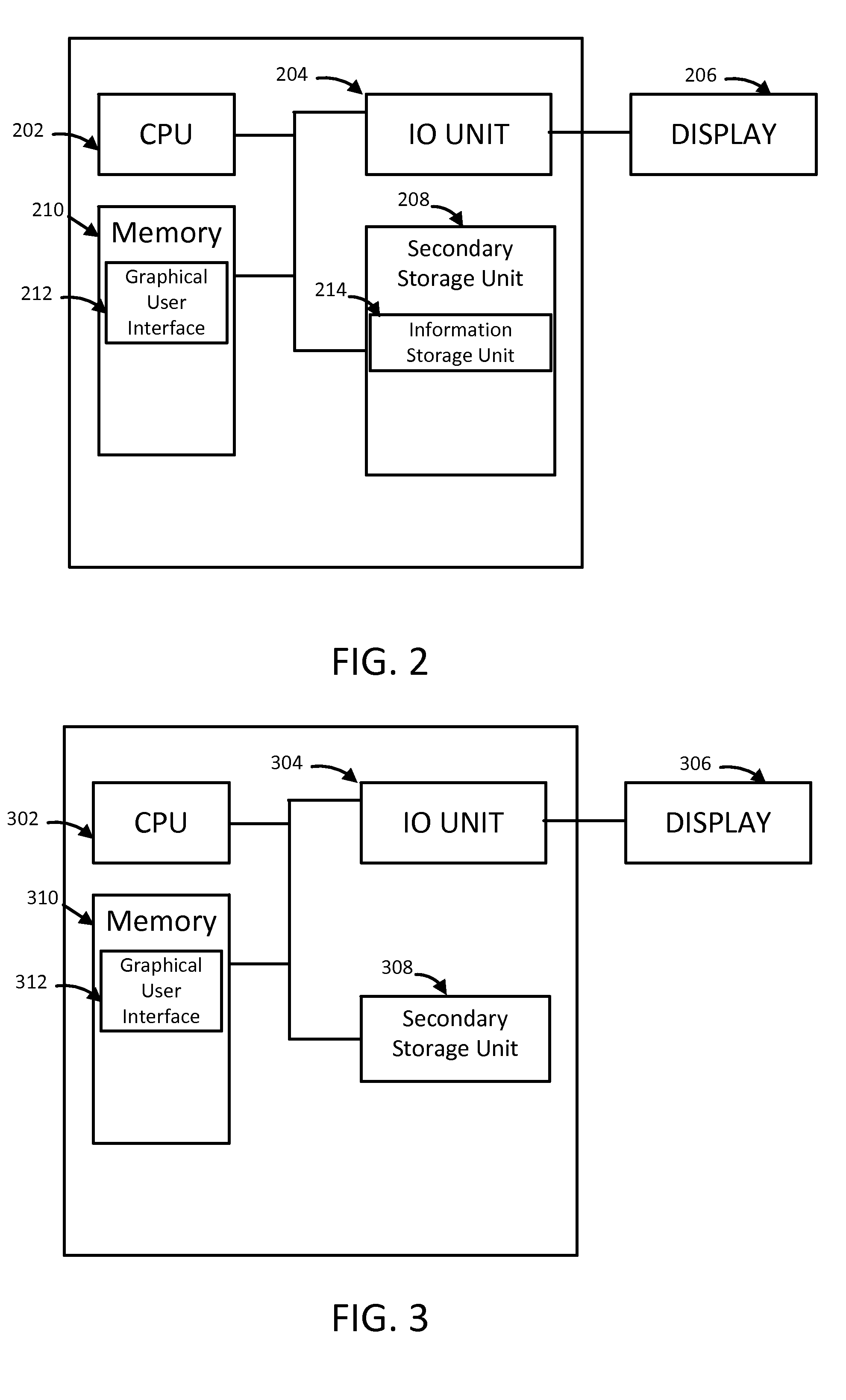
Certificate verification system and methods of performing the same
InactiveUS20150317466A1Digital data processing detailsMultiple digital computer combinationsMetadataComputer security
A system for generating certificates, the system include a certification generation unit having a processor and a memory with an application in the memory executing the steps of generating a digital certificate, retrieving verification information from a user where the verification information are unique to the user, appending a certificate content onto the verification information, appending an issuing authority identifier to the verification information, appending metadata to the verification information, embedding the appended verification information into the digital certificate, encoding the digital certificate with the embedded information, and issuing the encoded digital certificate.
Owner:VERIFICIENT TECH
Vehicle network security authentication method, system and apparatus, vehicle and medium
ActiveCN107919955ANetwork Security GuaranteePrevent intrusionKey distribution for secure communicationUser identity/authority verificationMicrocomputerThe Internet
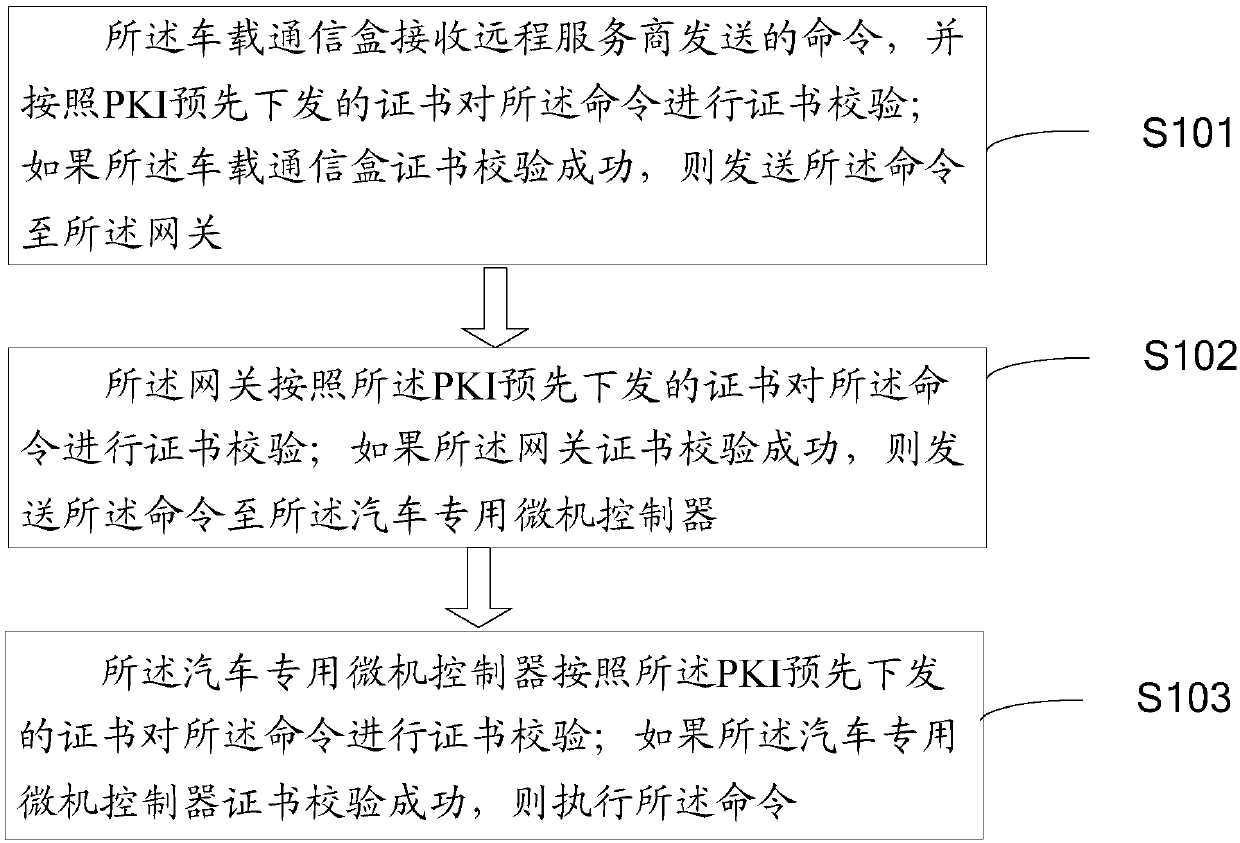
The invention discloses a vehicle network security authentication method, system and apparatus, a vehicle and a medium. The vehicle comprises a vehicle-mounted communication box, a gateway and a special vehicle microcomputer controller. The method comprises the following steps: the vehicle-mounted communication box receives a command sent by a remote service provider, and performs certificate verification on the command according to a certificate issued by PKI in advance; if the certificate verification of the vehicle-mounted communication box is successful, the command is sent to the gateway;the gateway performs certificate verification on the command according to the certificate issued by PKI in advance; if the certificate verification is successful, the command is sent to the vehicle-mounted communication box; the vehicle-mounted communication box performs certificate verification on the command according to the certificate issued by PKI in advance; if the certificate verificationof the special vehicle microcomputer controller is successful, the command is executed. The method and apparatus provided by the invention are used for solving the network security problem of the Internet of Vehicles in the prior art and achieving the technical effect of ensuring the vehicle network security.
Owner:BEIJING QIHOO TECH CO LTD
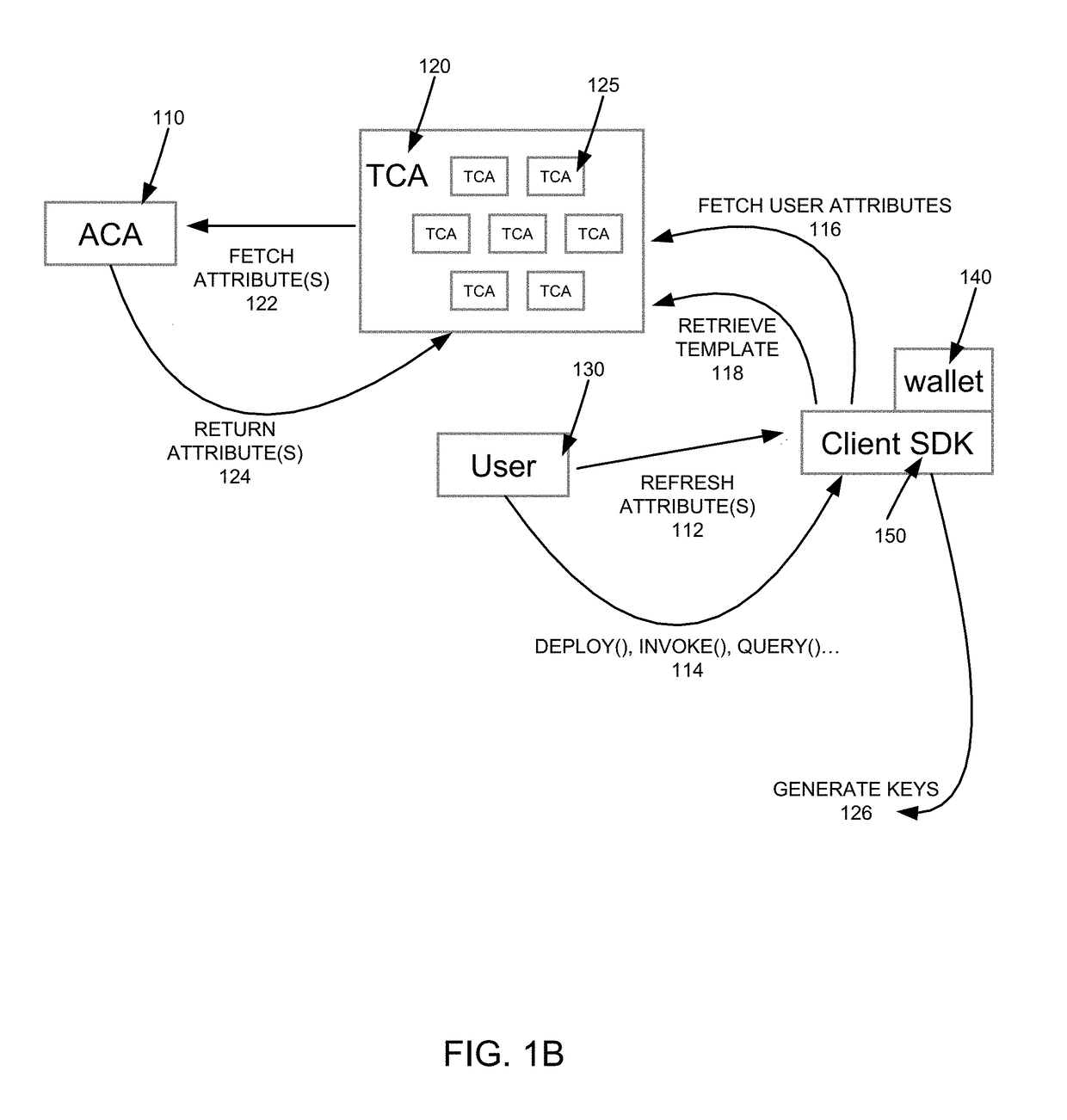
Template-based distributed certificate issuance in a mult-tenant environment
ActiveUS20180019993A1User identity/authority verificationDigital data protectionTemplate basedOperating system
One example method may include generating a template transaction certificate by one or more entities which verify proof of ownership of attributes incorporated into the template transaction certificate, and generating one or more operational transaction certificates by the one or more entities which verified proof of ownership of the template transaction certificate.
Owner:IBM CORP
The event ledger
InactiveUS20180062848A1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesComputer securityCertificate verification
The present disclosure provides a globally accessible, un-forgeable, and permanent repository of published events in the form of an event ledger. A method according to the present disclosure includes receiving a request from a publisher to publish to an event ledger an event including a name of the publisher, a date and time at which the event occurred, a description of the event, and a cryptographic signature of the event signed using a private key of the publisher, receiving a certificate from the publisher including a public key of the publisher, validating the cryptographic signature of the event using the received certificate, and publishing the event to the event ledger.
Owner:IBM CORP
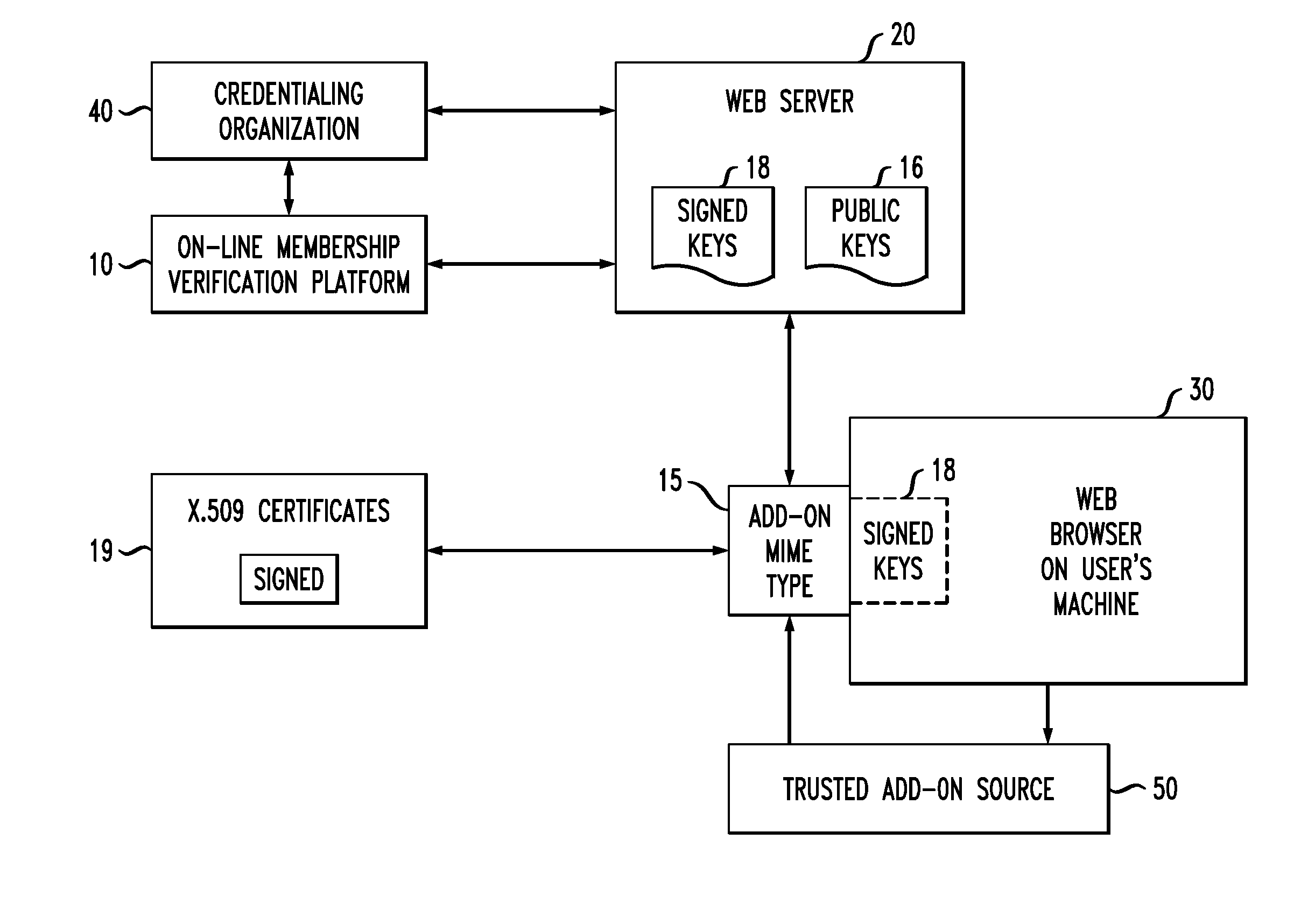
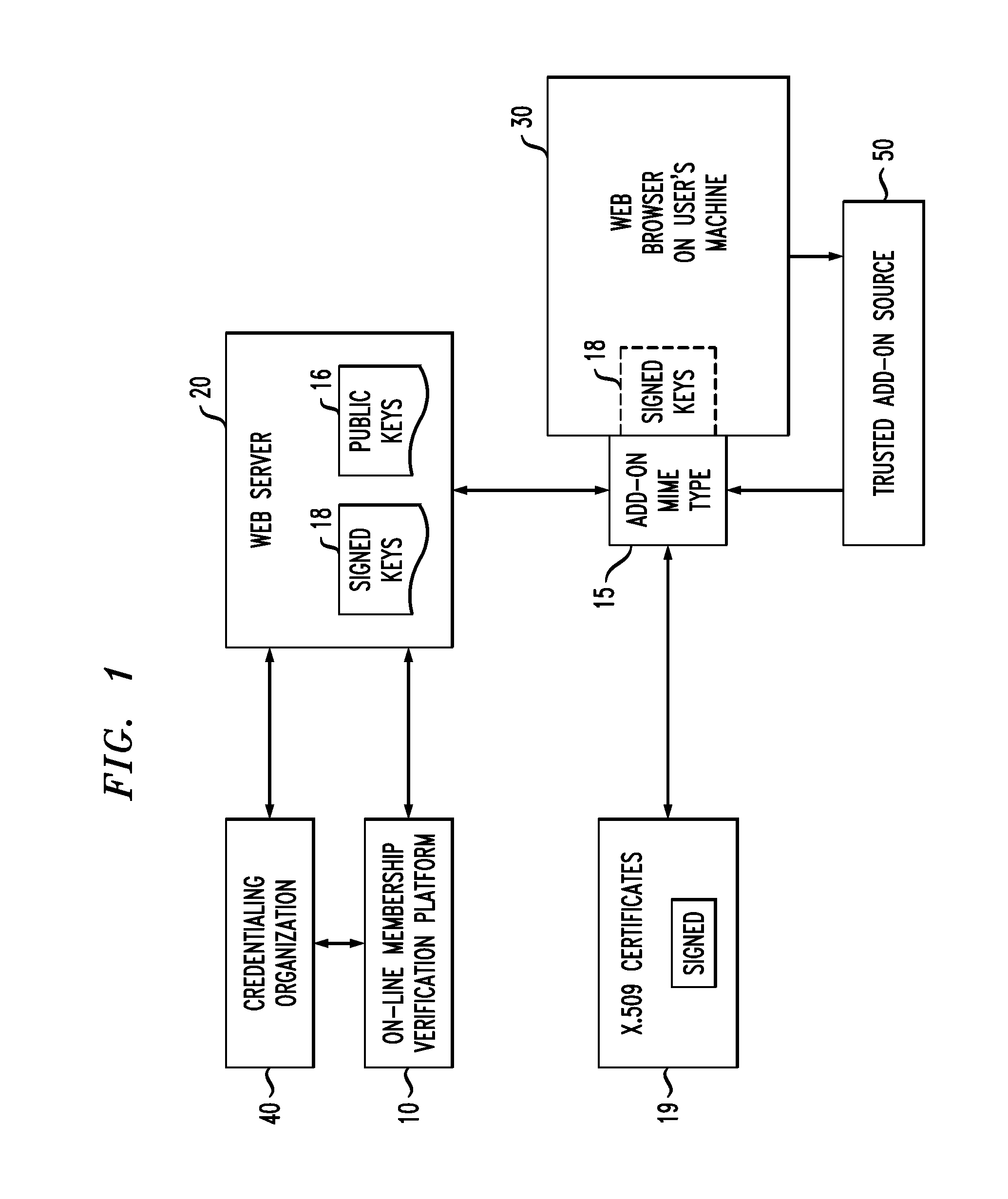
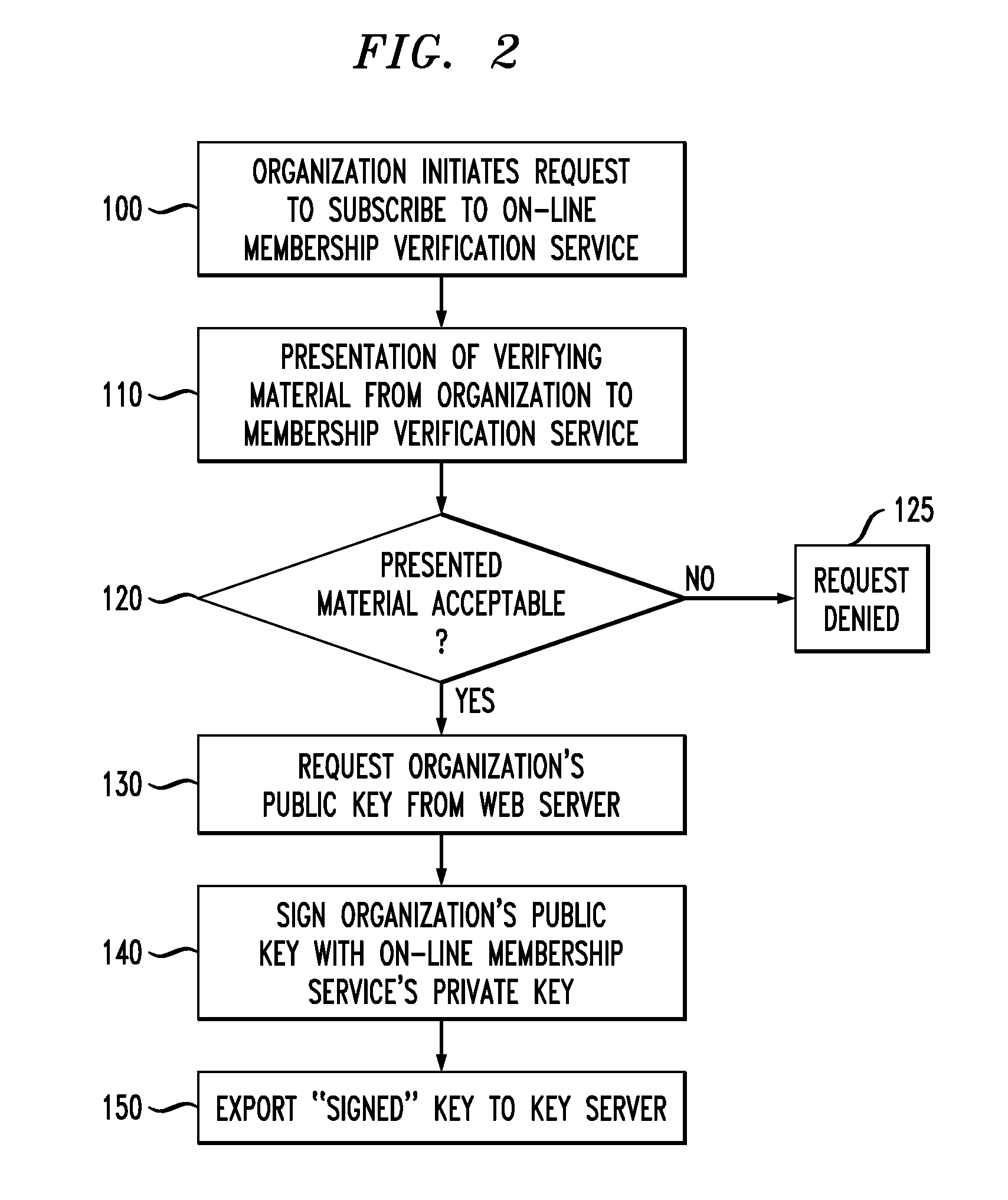
On-Line Membership Verification
ActiveUS20110010553A1Difficult to forgeNot easy to be stolenKey distribution for secure communicationDigital data processing detailsWeb siteNon-repudiation
A system and method of providing on-line verification of various credentials without requiring second site authentication utilizes protocols and cryptography to assure customers (generally referred to hereinafter as “users”) that they are dealing with a person (or organization) that can present multiple, non-repudiable proof of their identification. The system is launched directly from the user's browser such that certificate verification is performed “locally”, without needing to go out and obtain information from a second web site. The system is based upon the creation of a new MIME (i.e. Multipurpose Internet Mail Extensions) type that is employed by the user's browser and utilizes public keys associated with the credentialing organizations in combination with a public key of the verification organization.
Owner:CAHN ROBERT S
Method realizing public key acquiring, certificater verification and bidirectional identification of entity
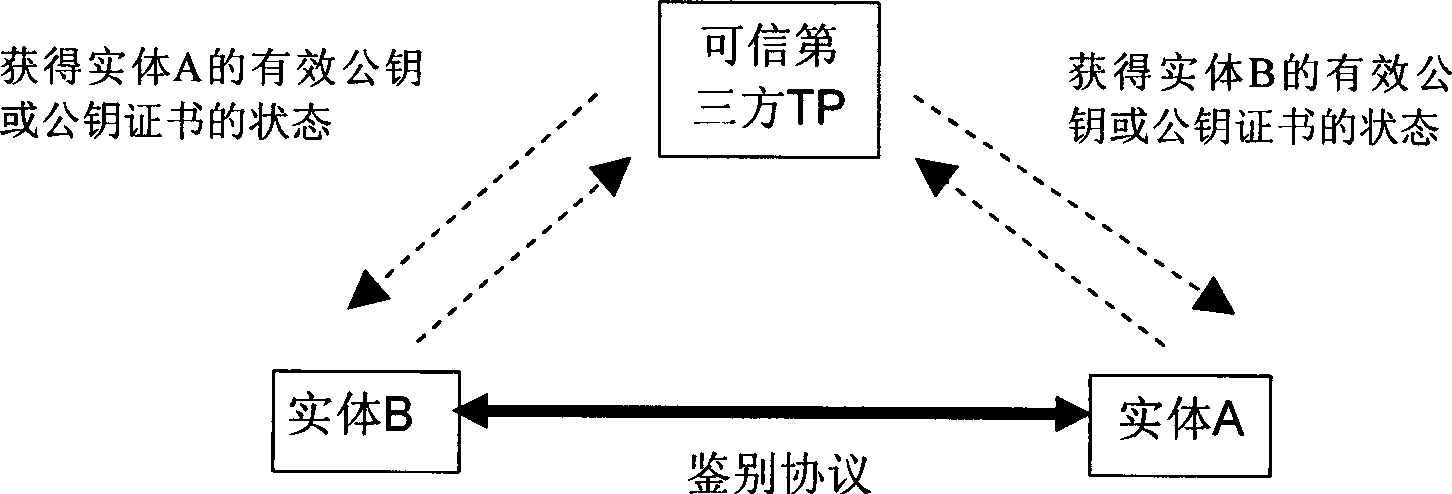
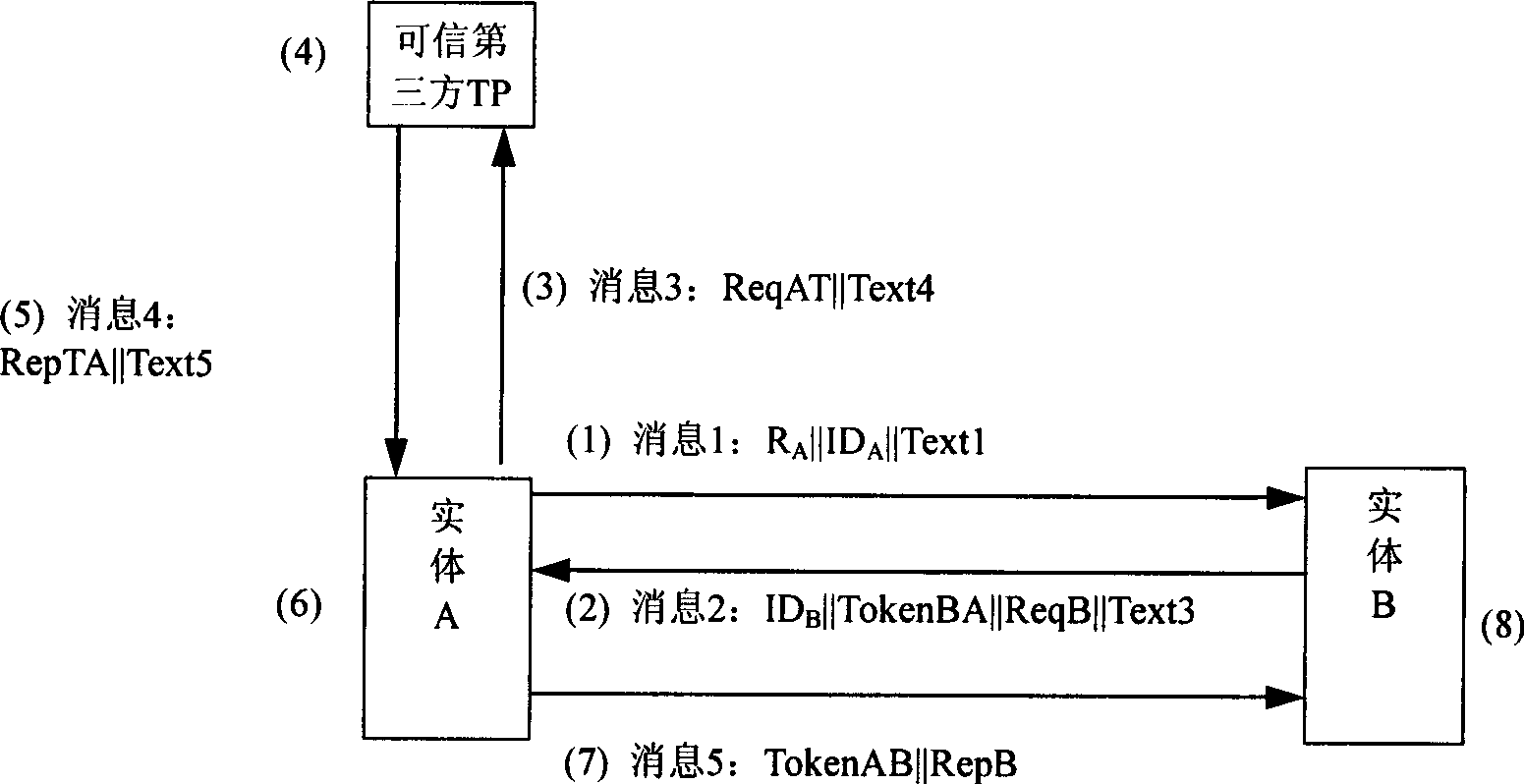
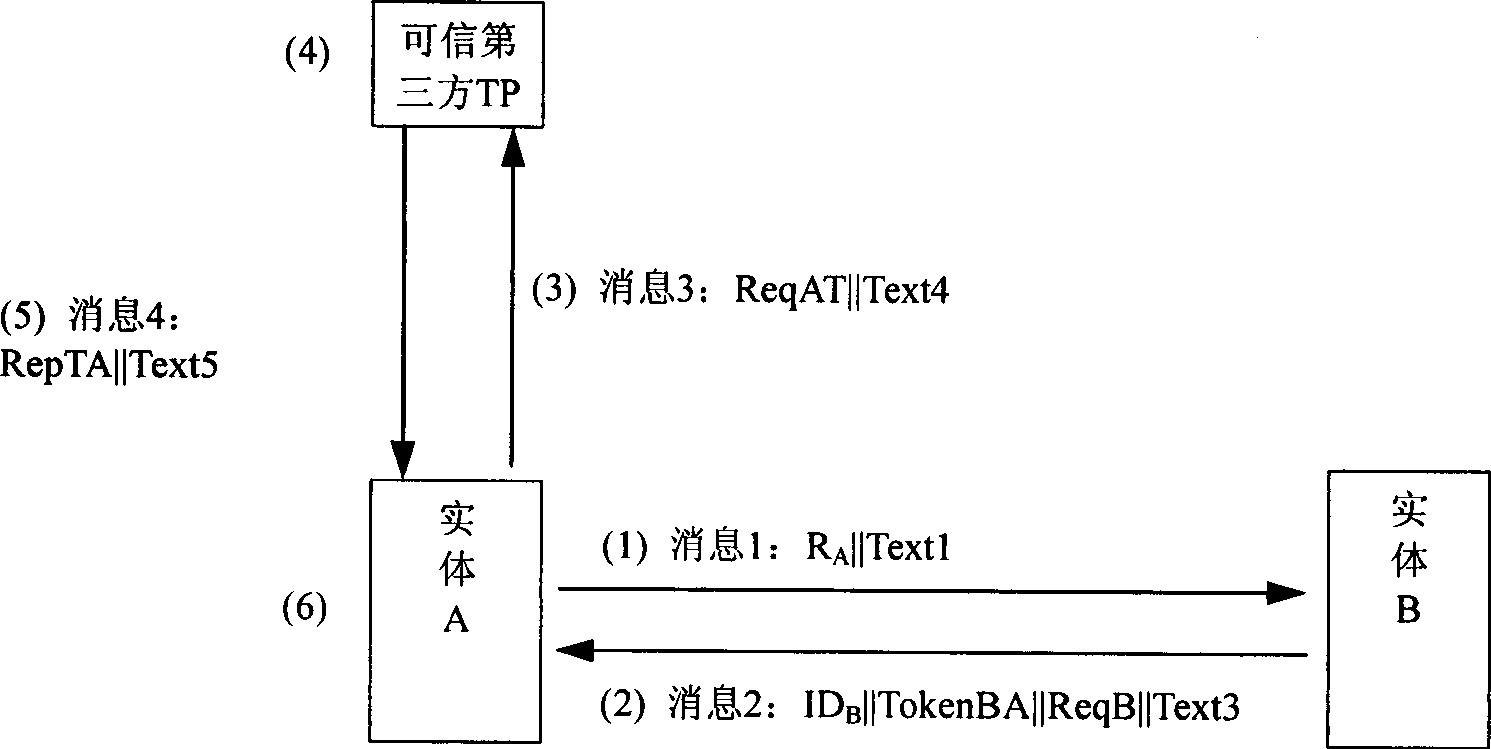
ActiveCN101364876AImprove efficiencyGood effectUser identity/authority verificationThird partyAccess network
The invention relates to a method for achieving public key acquisition, certificate validation and authentication of an entity. The method comprises the following steps: (1) transmitting a message 2 to an entity A by an entity B; (2) transmitting a message 3 to a credible third party TP by the entity A after receiving the message 2; (3) determining response RepTA after the credible third party TP receives the message 3; (4) returning a message 4 to the entity A by the credible third party TP; (5) executing step (6) after the entity A receives the message 4 from the credible third party TP; (6) returning a message 5 to the entity B by the entity A; and (7) processing the message 5 after the entity B receives the message 5 from the entity A to obtain the authentication result of the entity A. The method can achieve public key acquisition, certificate validation and authentication of the entity by fusing in one protocol, thereby facilitating the execution efficiency and the effect of the protocol and facilitating the combination with various public acquisition and public key certificate state enquiry protocols. The method suits with a user-access point-server network structure accessed to the network to meet the authentication requirement of the access network.
Owner:CHINA IWNCOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com