Patents
Literature
34 results about "Credentialing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Credentialing is the process of establishing the qualifications of licensed medical professionals and assessing their background and legitimacy. Many health care institutions and provider networks conduct their own credentialing, generally through a credentialing specialist or electronic service, with review by a credentialing committee. It may include granting and reviewing specific clinical privileges, and allied health staff membership.
Method and system for creating and managing multiple subscribers of a content delivery network
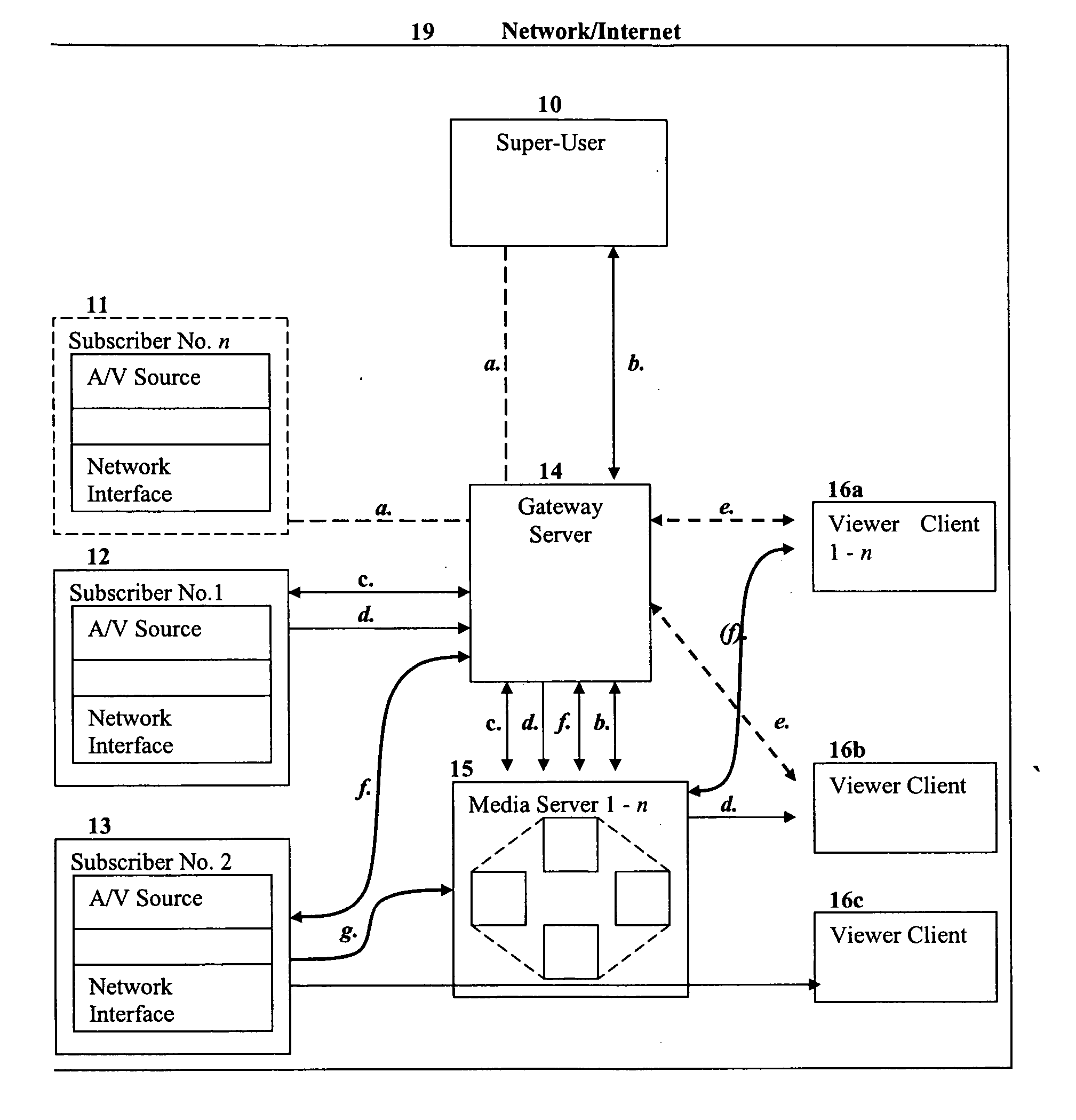
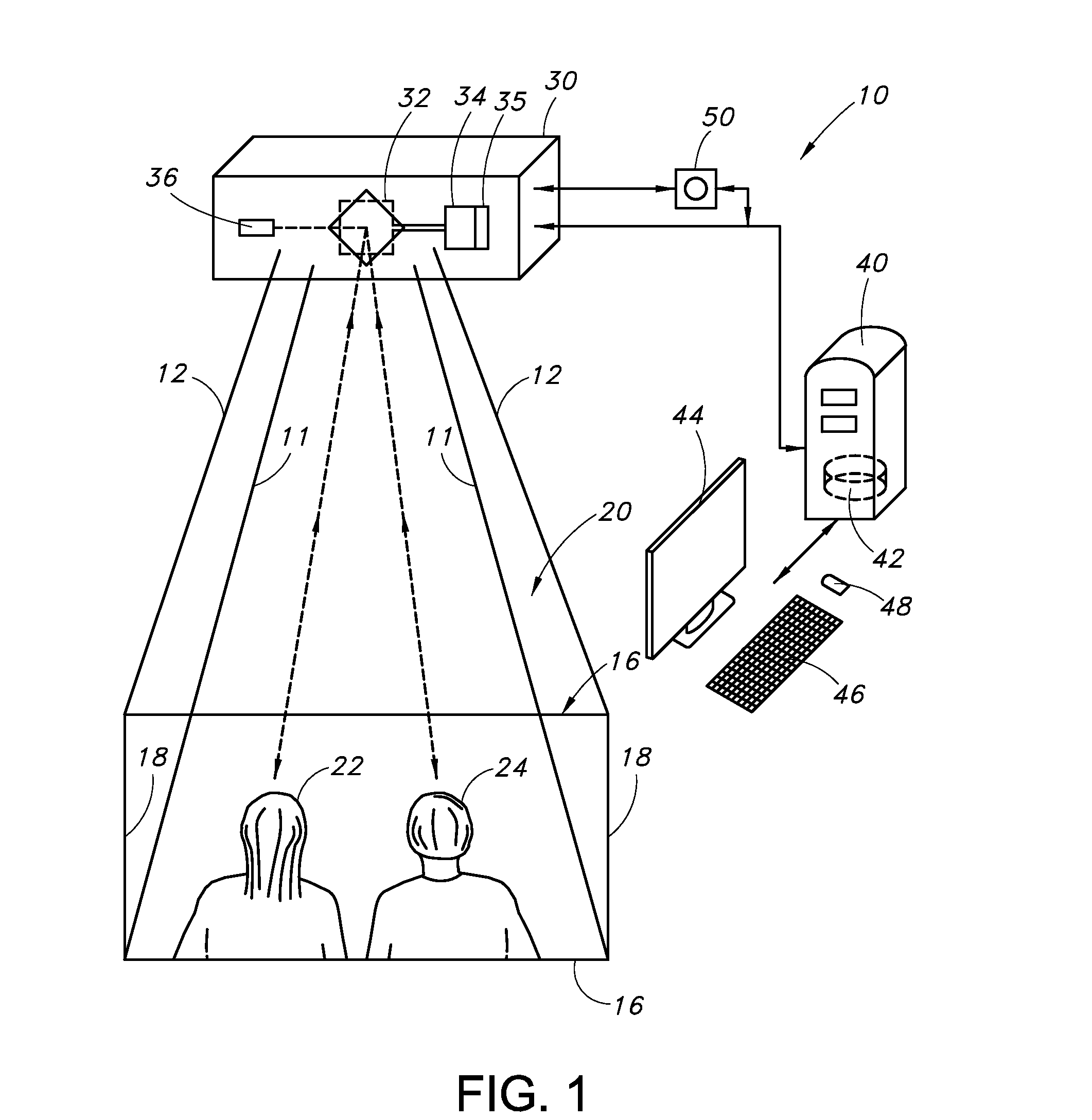
InactiveUS20060120385A1Improve experienceData switching by path configurationTwo-way working systemsCredentialingThe Internet
A system for the real-time transmission, storage, retrieval and credentialing of video (and / or audio) data from a plurality of possible sources (subscribers) is accessible via a network, such as the Internet, to a plurality of authorized viewer clients and the subscriber for the purposes of management, addition or deletion of stored content, changing or creating of the live content location universal resource locator (URL) or the of credentials for viewers.
Owner:ATCHISON DARRELL TODD +1
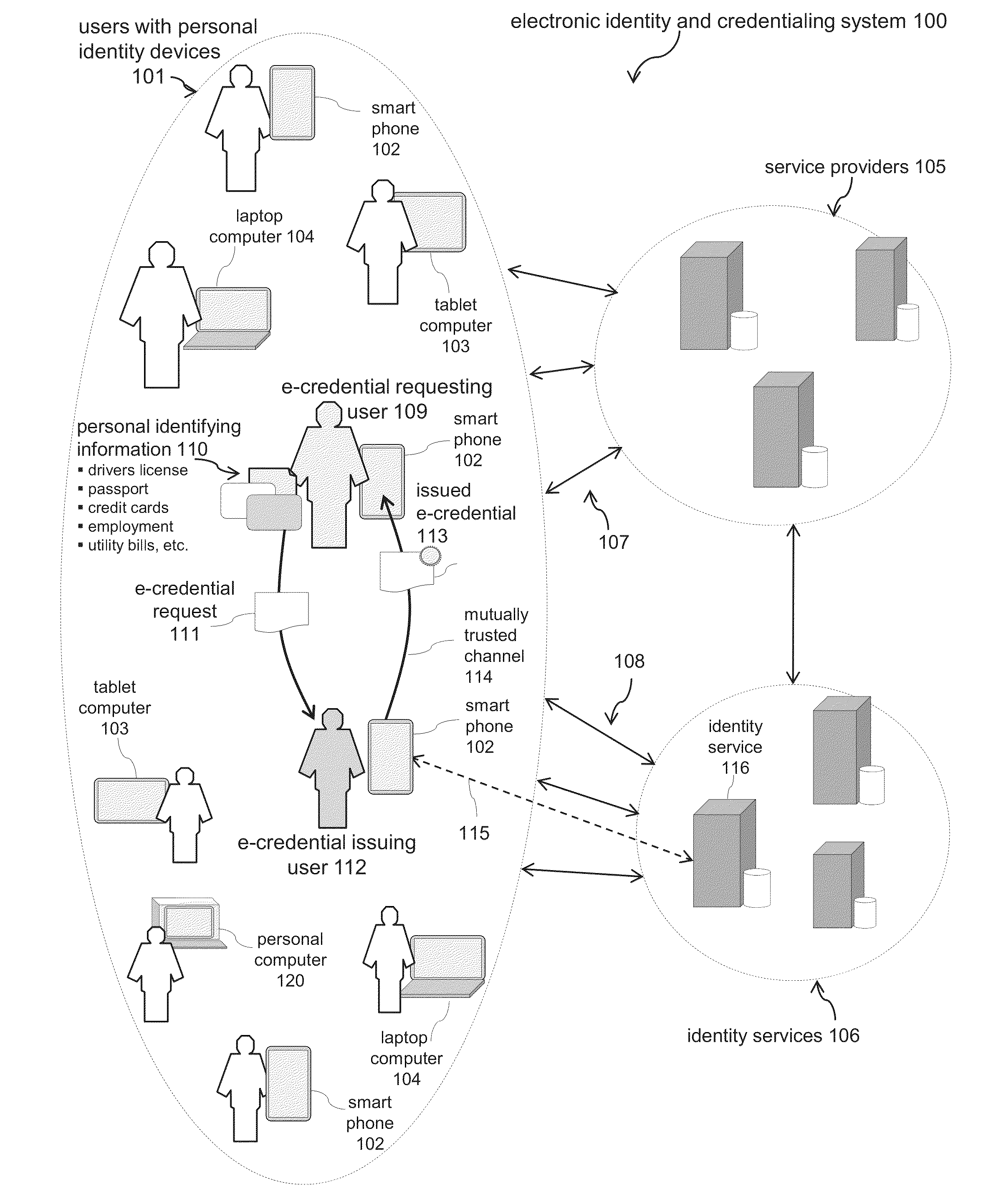
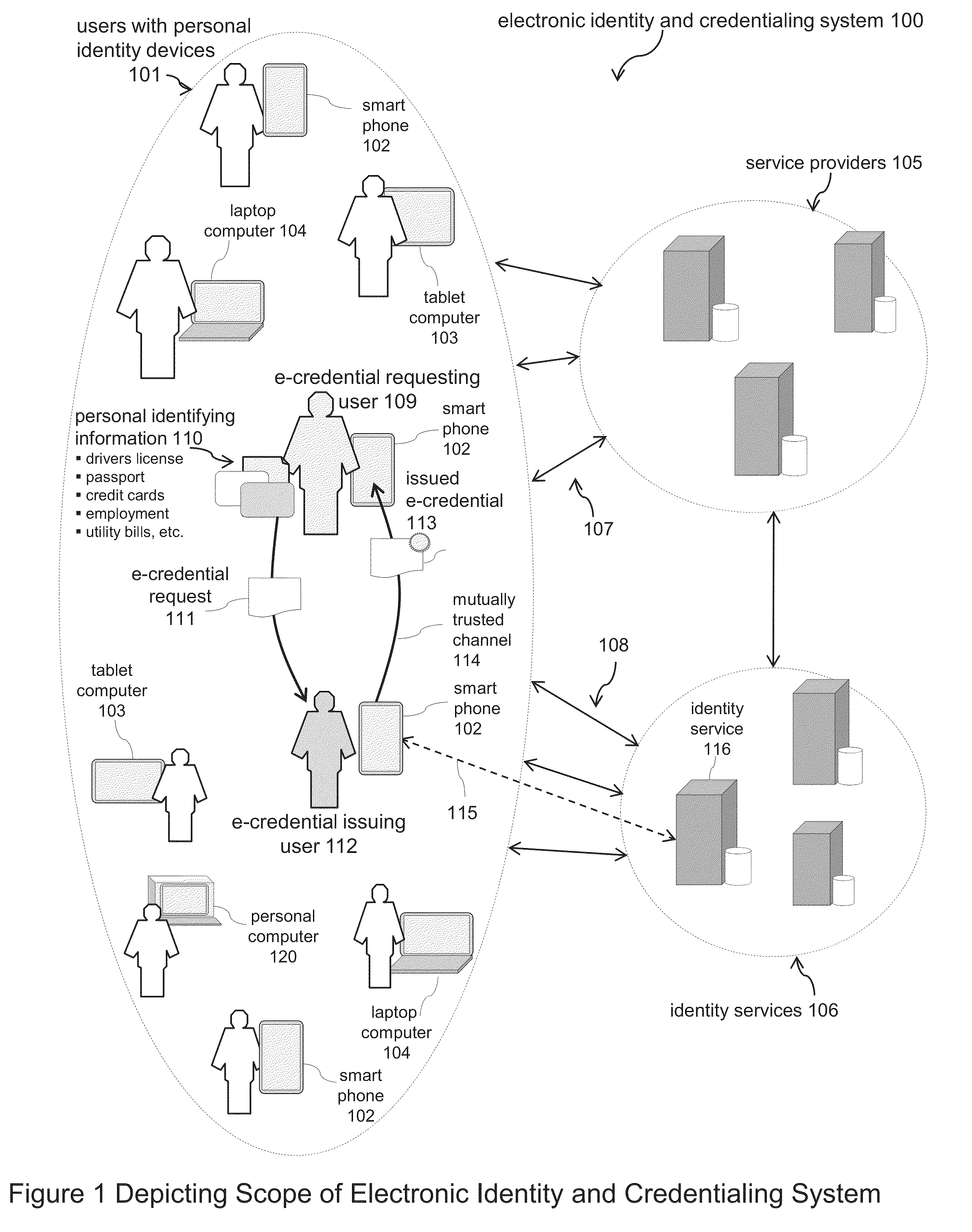
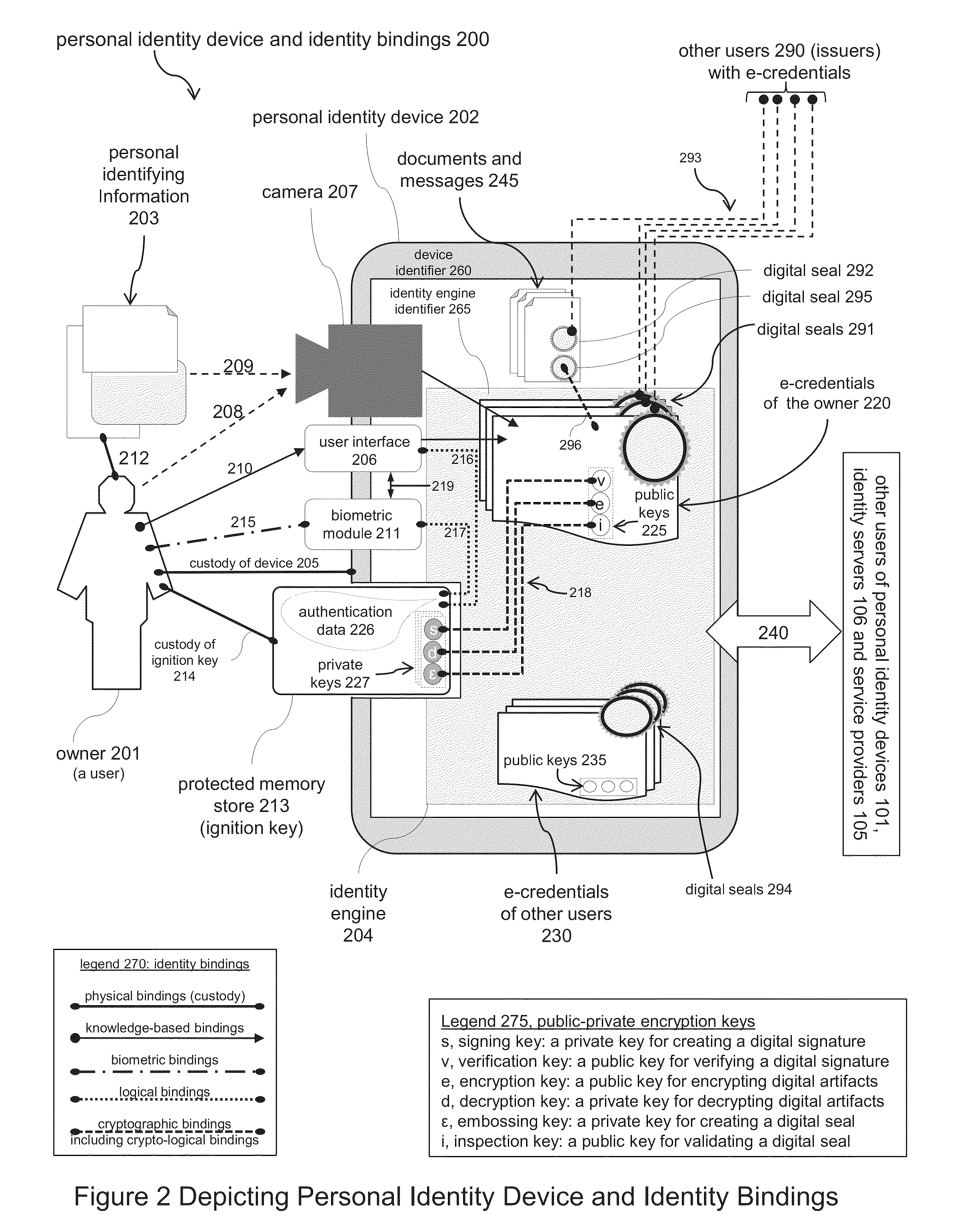
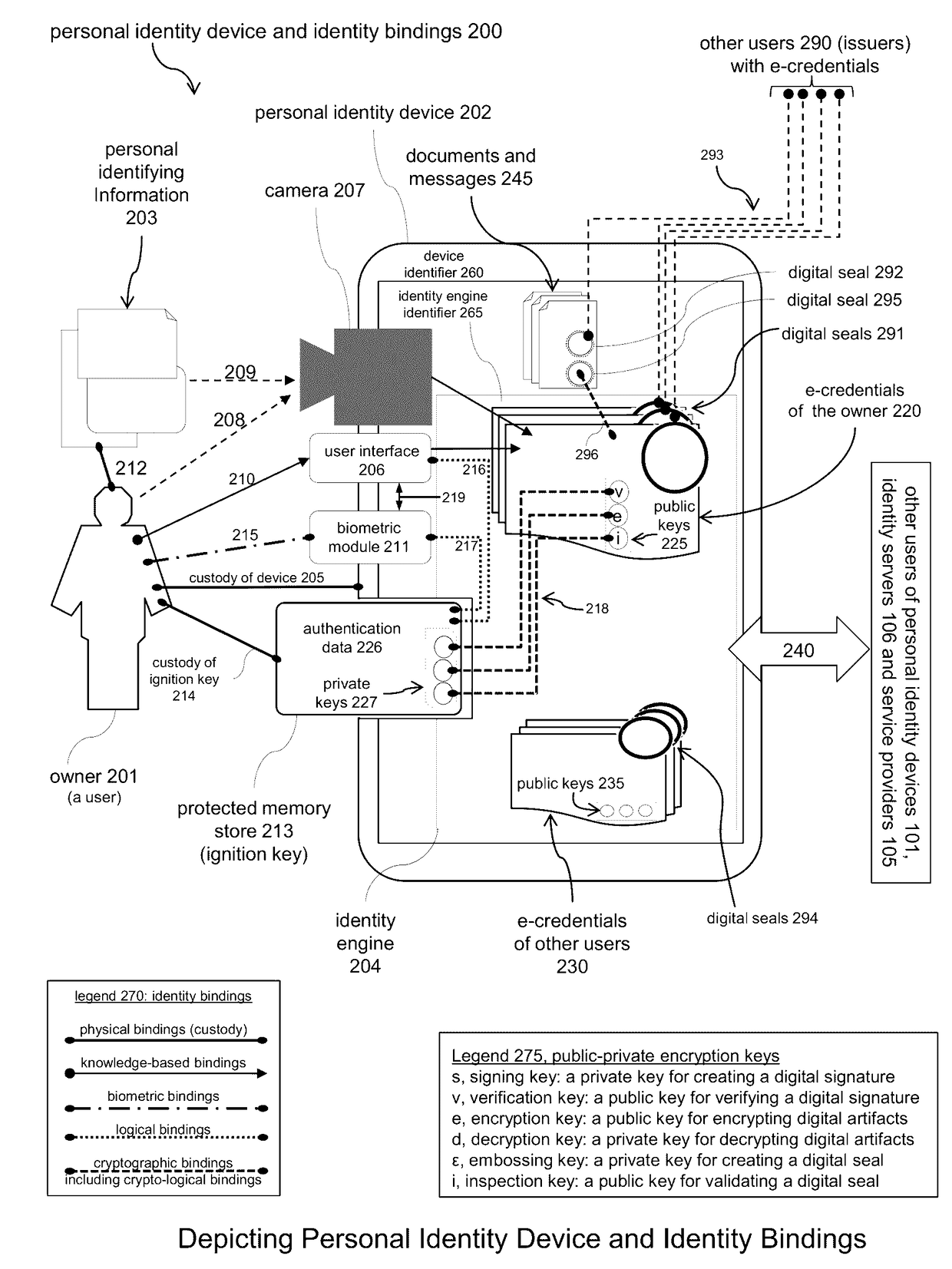
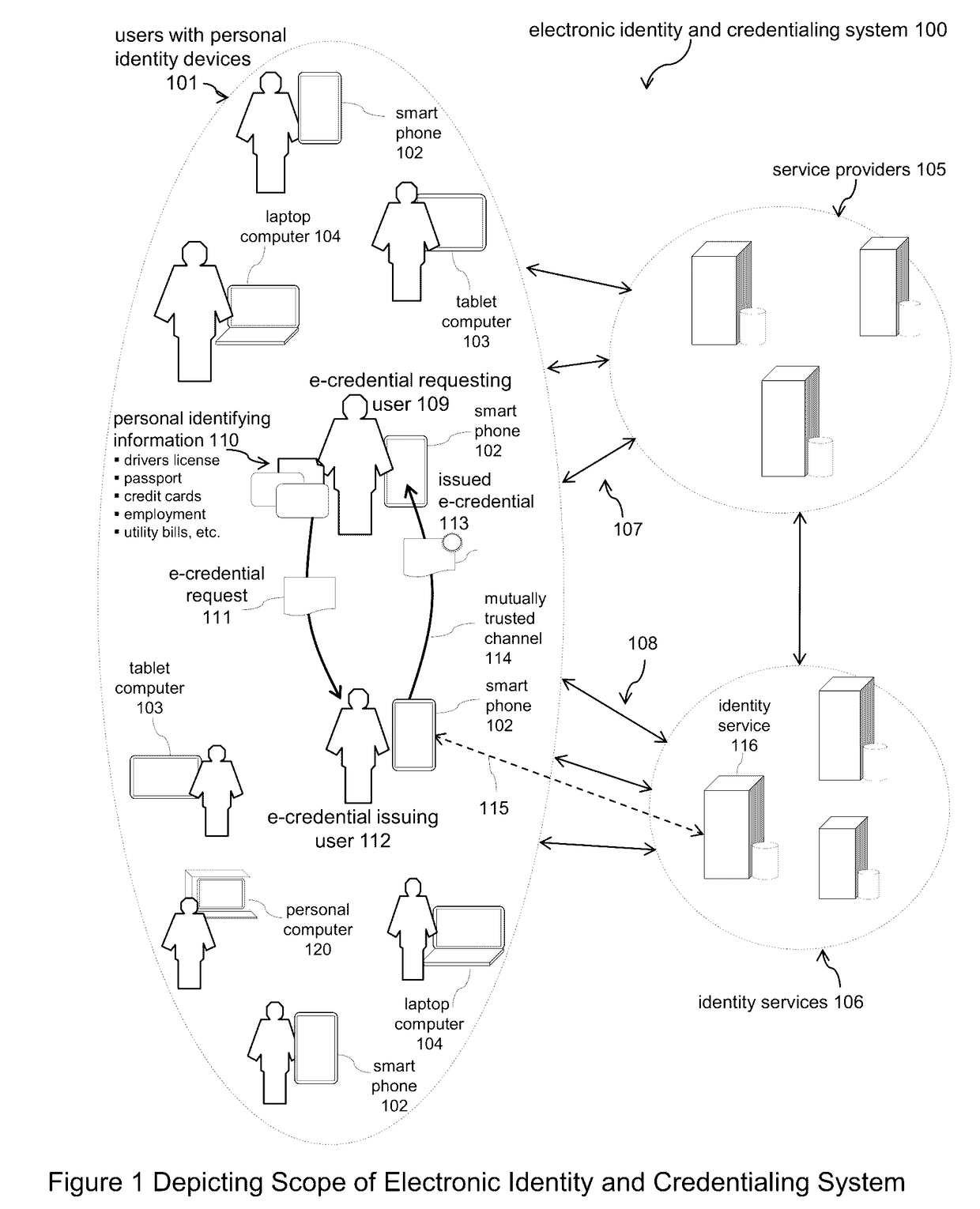
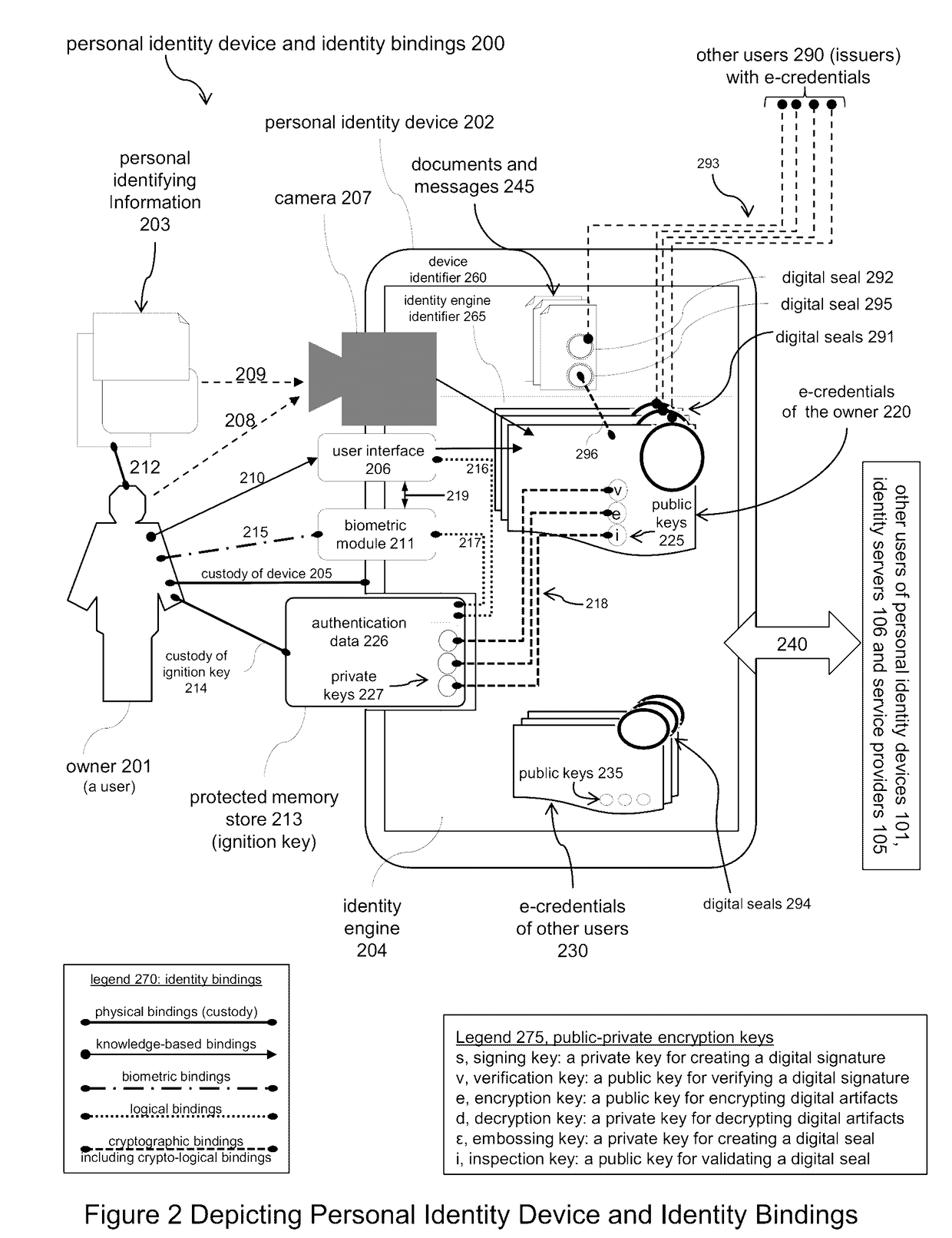
Electronic Identity and Credentialing System
ActiveUS20150095999A1Reduce riskAvoid attenuationDigital data processing detailsUser identity/authority verificationTablet computerCredentialing
Described is an electronic credentialing system that allows personal identity devices to interact; each interacting device has an installed identity engine that acquires, holds, issues and uses electronic credentials (e-credentials), these electronic credentials can be installed on personal identity devices, such as: smart phones, tablets, laptops, embedded systems, and / or personal computers.
Owner:TOTH KALMAN CSABA
Electronic identity and credentialing system
ActiveUS9646150B2Reduce riskAvoid attenuationUser identity/authority verificationDigital data authenticationTablet computerCredentialing
Described is an electronic credentialing system that allows personal identity devices to interact; each interacting device has an installed identity engine that acquires, holds, issues and uses electronic credentials (e-credentials), these electronic credentials can be installed on personal identity devices, such as: smart phones, tablets, laptops, embedded systems, and / or personal computers.
Owner:TOTH KALMAN CSABA
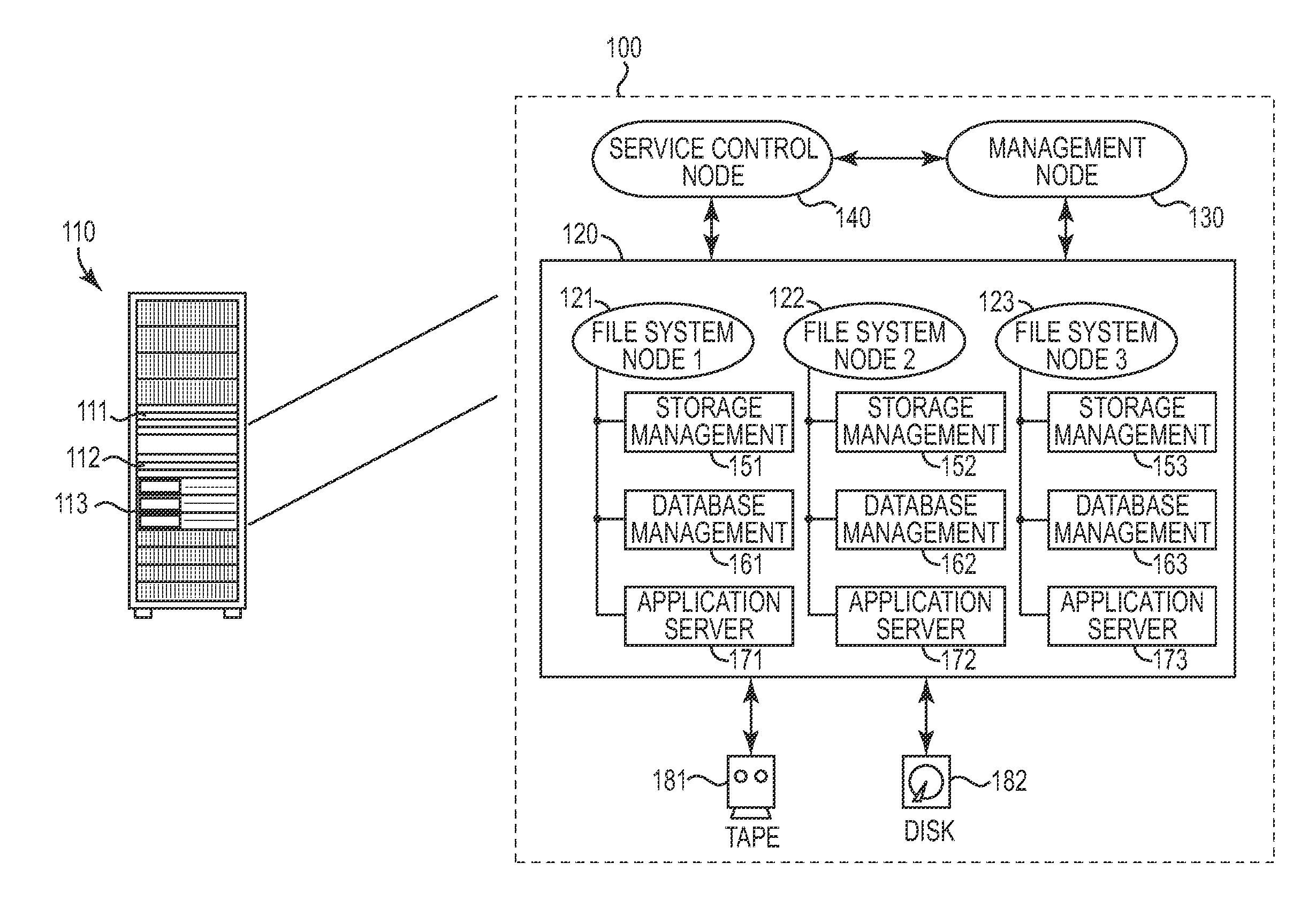
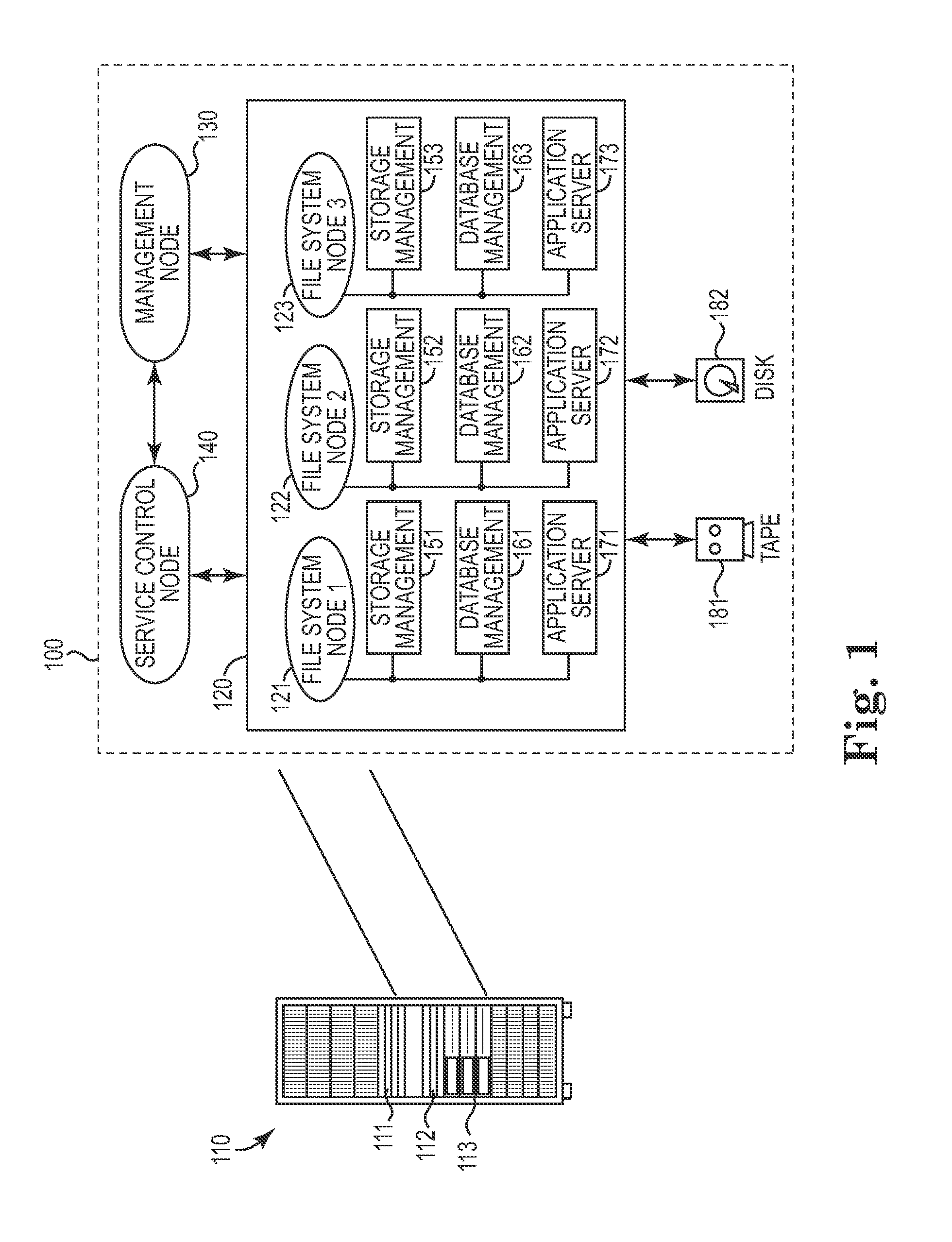
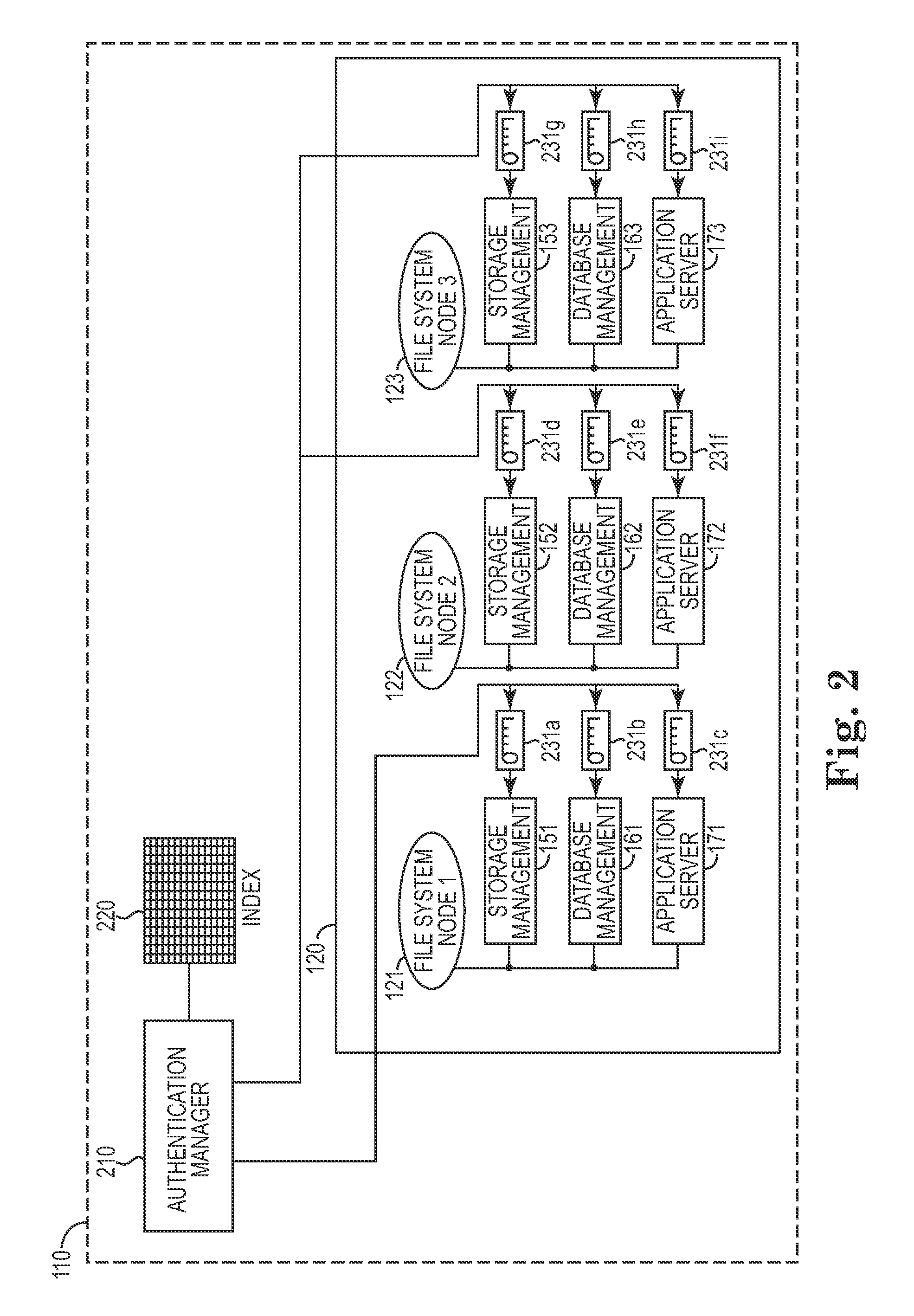
Automated management of system credentials
InactiveUS20120151563A1Facilitate communicationImprove securityDigital data processing detailsMultiple digital computer combinationsCredentialingApplication server
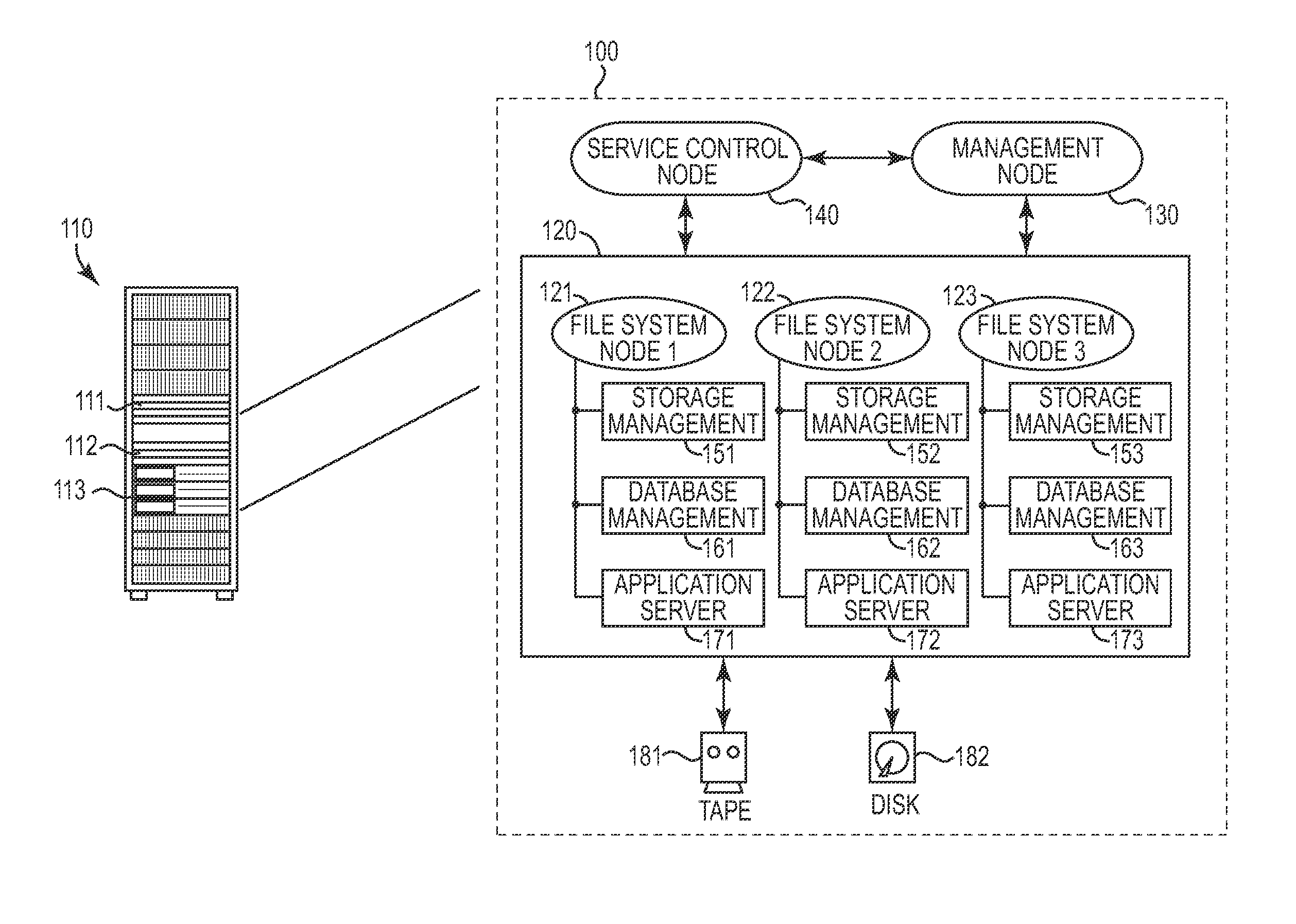
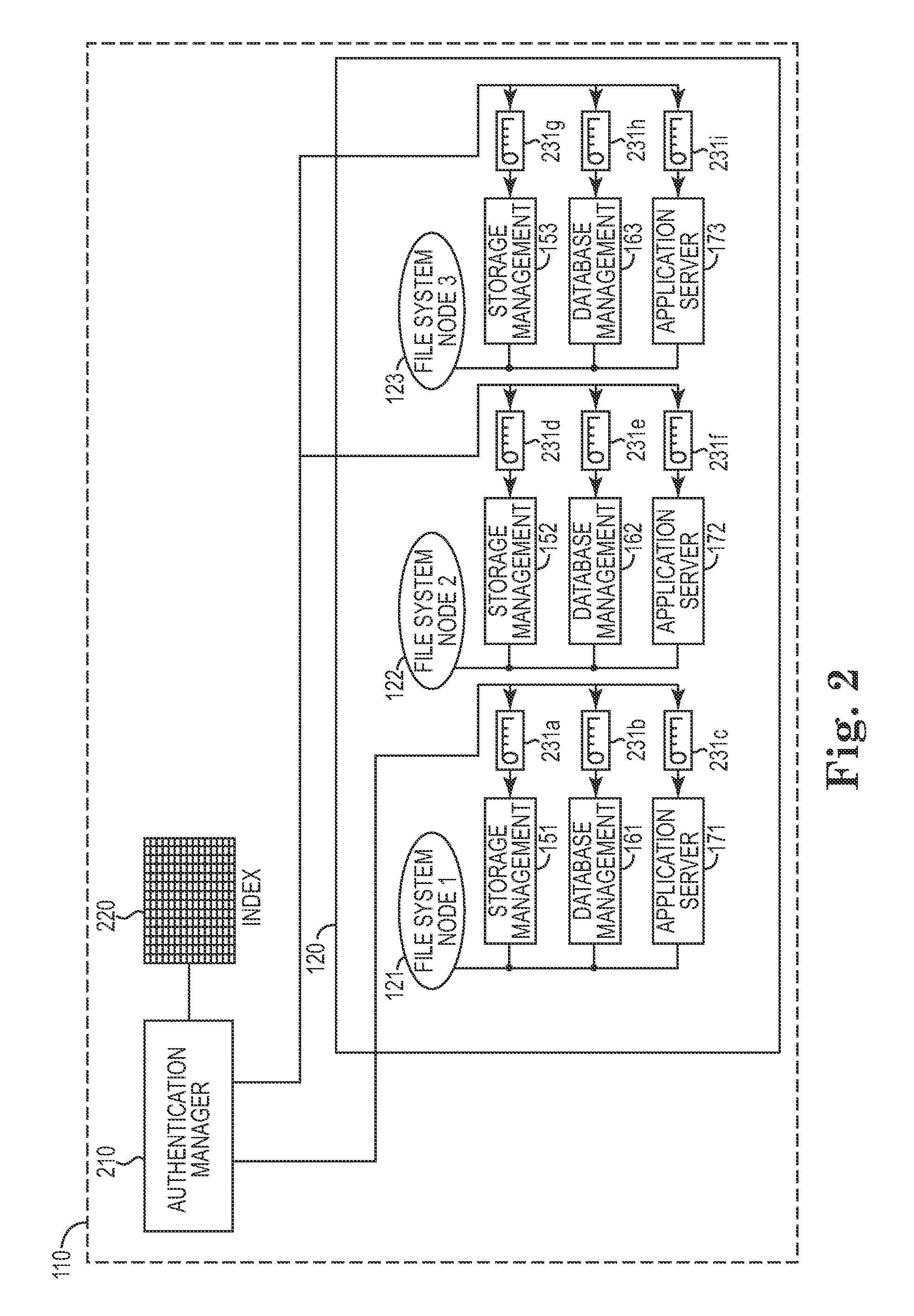
One disclosed aspect of the present invention includes authentication and user account automation within a compute cluster for each cluster node that requires password or other credential administration. For example, a storage appliance computing system may rely on a plurality of subsystems (such as databases, storage management software, and application servers) that each have internal user accounts with associated passwords and credential keys that need to be changed at frequent intervals. Rather than requiring an administrator to manually manage all of these accounts, the presently described invention includes techniques and an authentication manager component to automatically manage, update, and refresh authentication information as required. Further, the authentication manager component may be used to perform and propagate automatic credential changes such as new sets of SSH keys or updated passwords as required within a computing system, and respond to new nodes or out-of-sync credentialing scenarios.
Owner:IBM CORP
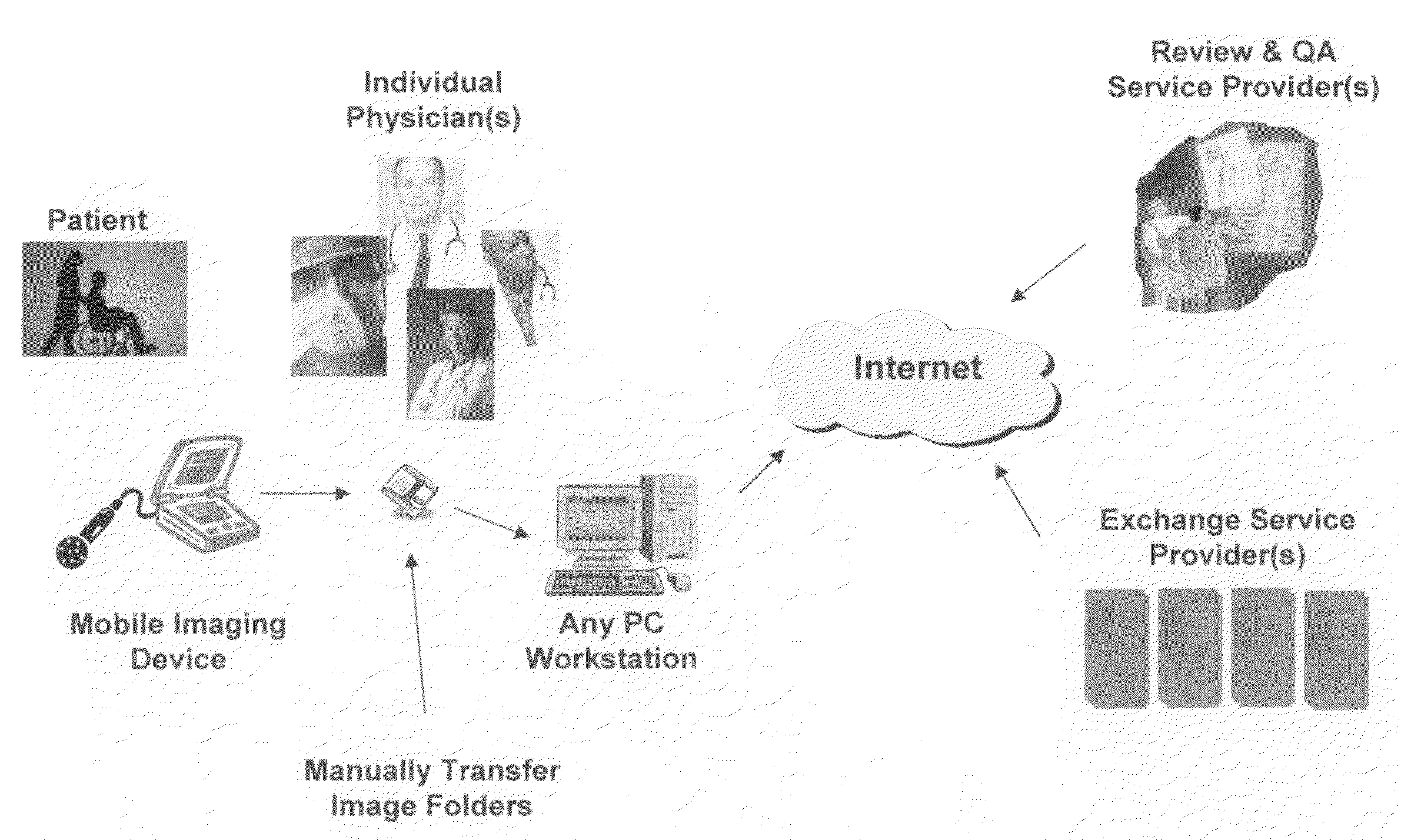
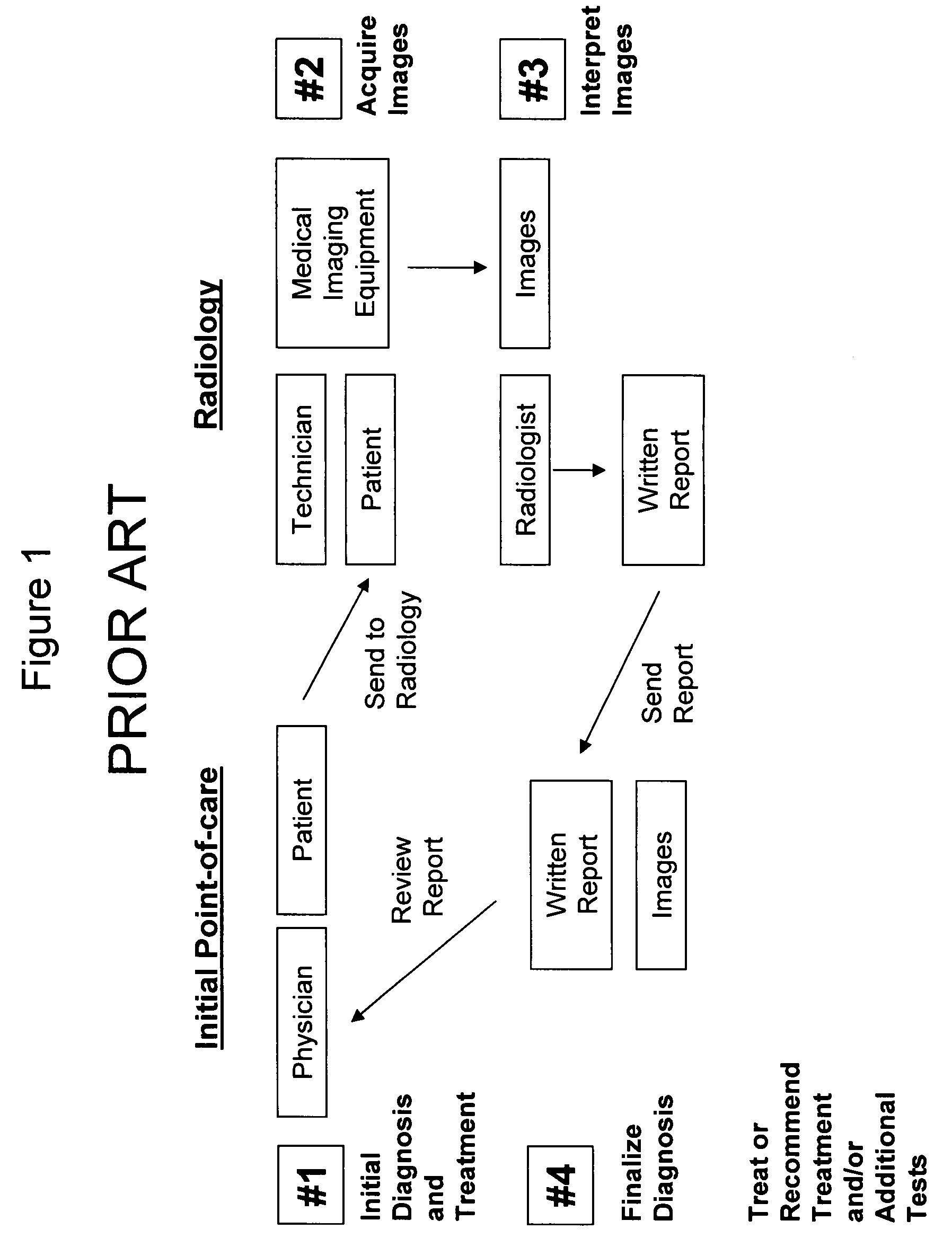
Medical imaging examination review and quality assurance system and method
InactiveUS20070232885A1Authentication is convenientEffectively use and diagnoseMedical communicationDiagnostic recording/measuringPoint of careCredentialing
The present invention is a computer-based review and quality assurance system and method for physicians who use portable imaging technology to diagnose and treat patients at a point of care. The system and method facilitates the credentialing of physicians, provides on-going quality assurance (QA), and integrates medical imaging equipment with software that runs over a network. Such credentialing assists medical institutions by identifying physicians who effectively use and diagnose patients with the imaging equipment.
Owner:COOK THOMAS +2
Systems and devices for real time health status credentialing
Systems and processes are presented for real time health credentialing of individuals seeking entry to a facility requiring health credentialing for access. A system and process for real time detection of a febrile condition comprises providing a heat sensor operable to receive thermal radiation from a person. Optionally, the system provides a controller operable to selectively orient the thermal sensor incident to the facial region of a person within a zone of detection. Further, the system optionally processes the sensor temperature to conditionally determine a febrile condition.
Owner:HELLER ALAN C
Automated management of system credentials
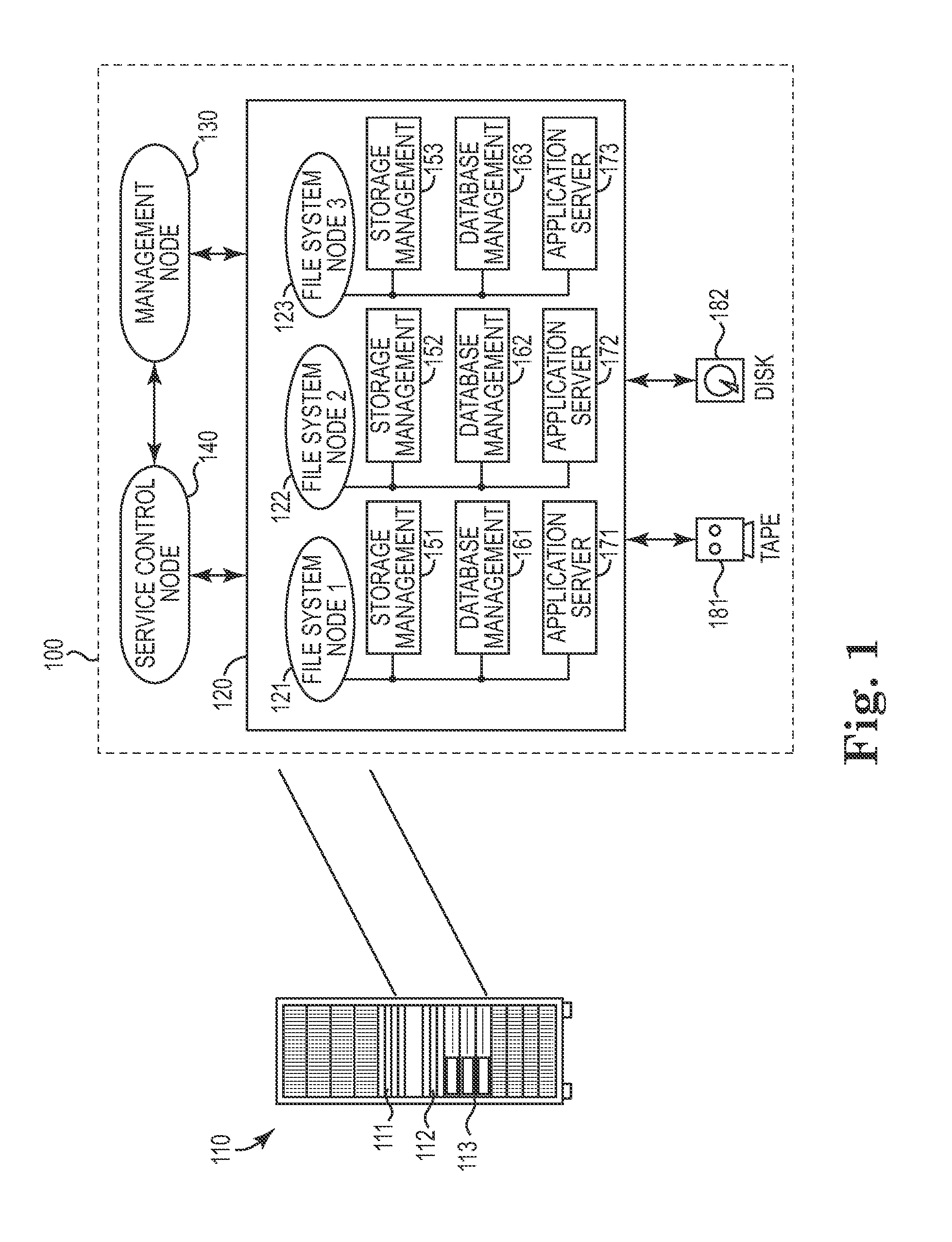
InactiveUS8539562B2Facilitate communicationImprove securityDigital data processing detailsMultiple digital computer combinationsCredentialingApplication server
One disclosed aspect of the present invention includes authentication and user account automation within a compute cluster for each cluster node that requires password or other credential administration. For example, a storage appliance computing system may rely on a plurality of subsystems (such as databases, storage management software, and application servers) that each have internal user accounts with associated passwords and credential keys that need to be changed at frequent intervals. Rather than requiring an administrator to manually manage all of these accounts, the presently described invention includes techniques and an authentication manager component to automatically manage, update, and refresh authentication information as required. Further, the authentication manager component may be used to perform and propagate automatic credential changes such as new sets of SSH keys or updated passwords as required within a computing system, and respond to new nodes or out-of-sync credentialing scenarios.
Owner:IBM CORP
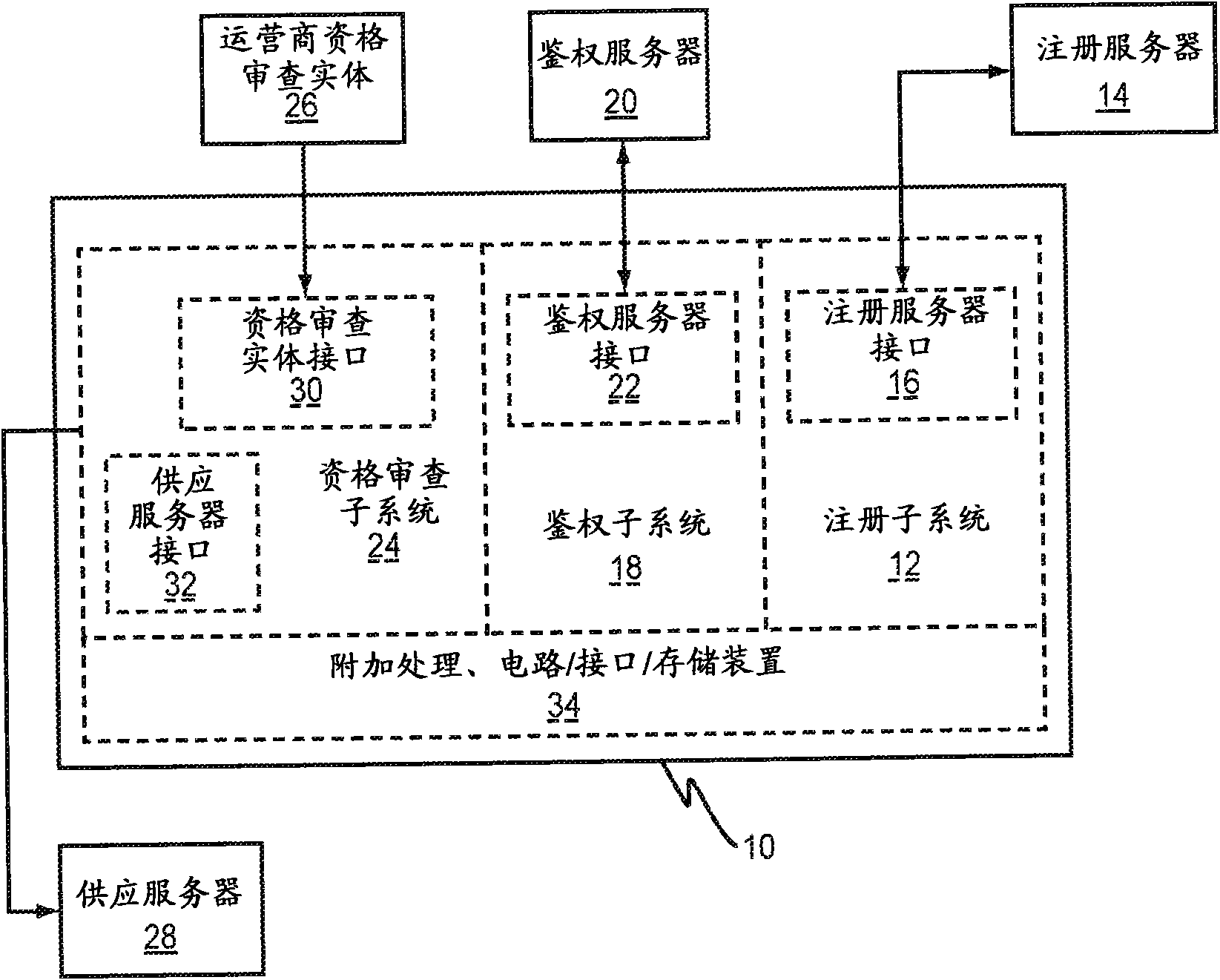
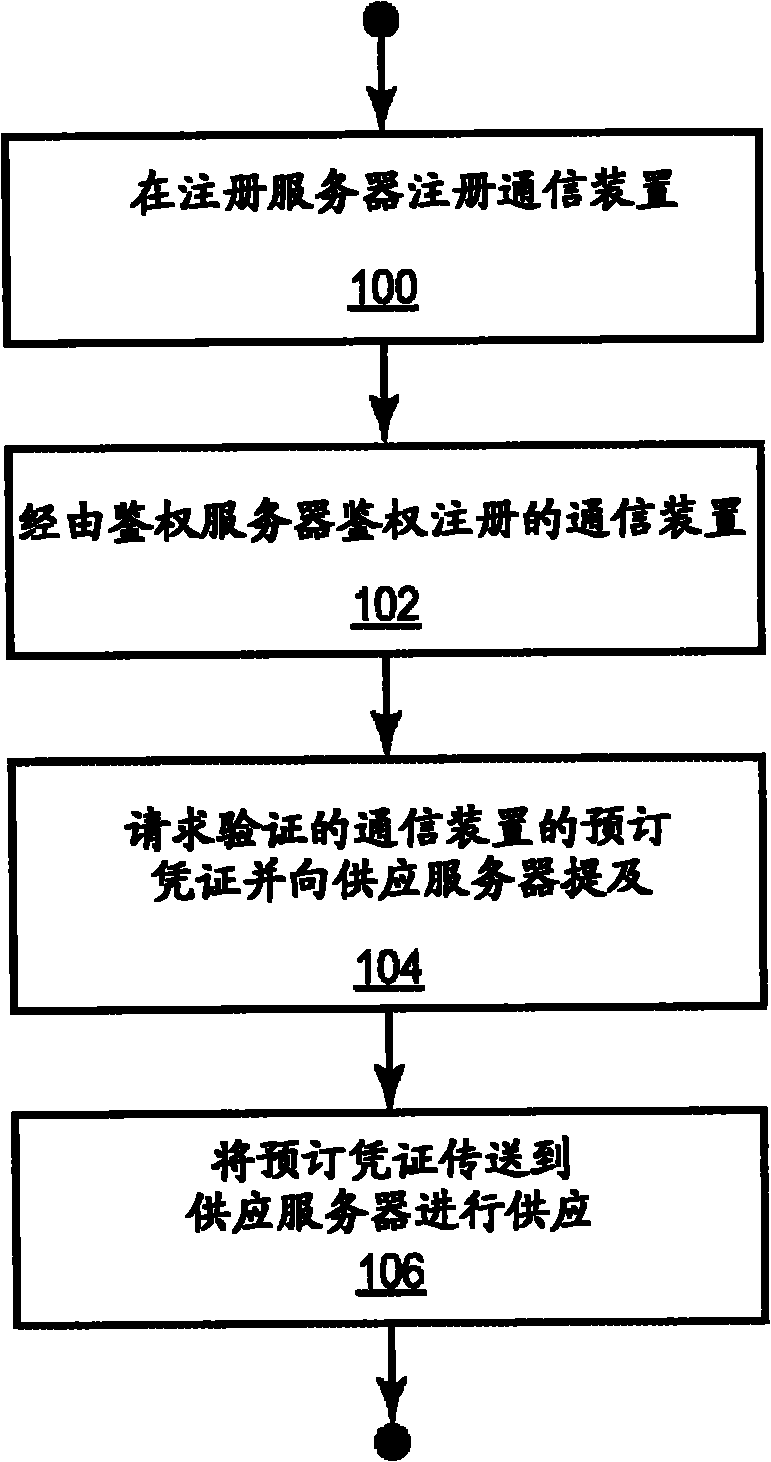
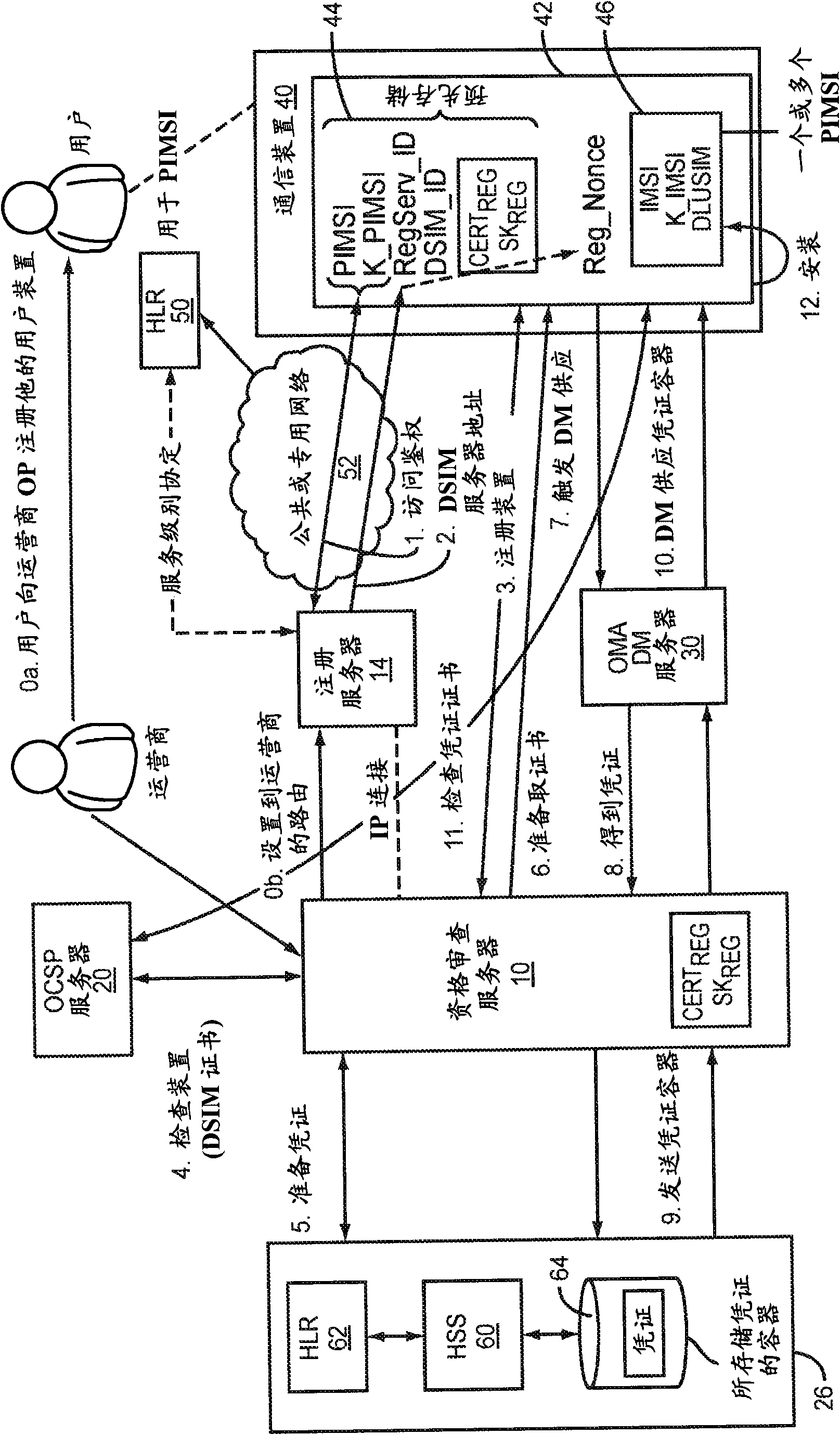
Method and system for mobile device credentialing
ActiveCN101690287ADigital data authenticationElectronic credentialsCredentialingAuthentication server
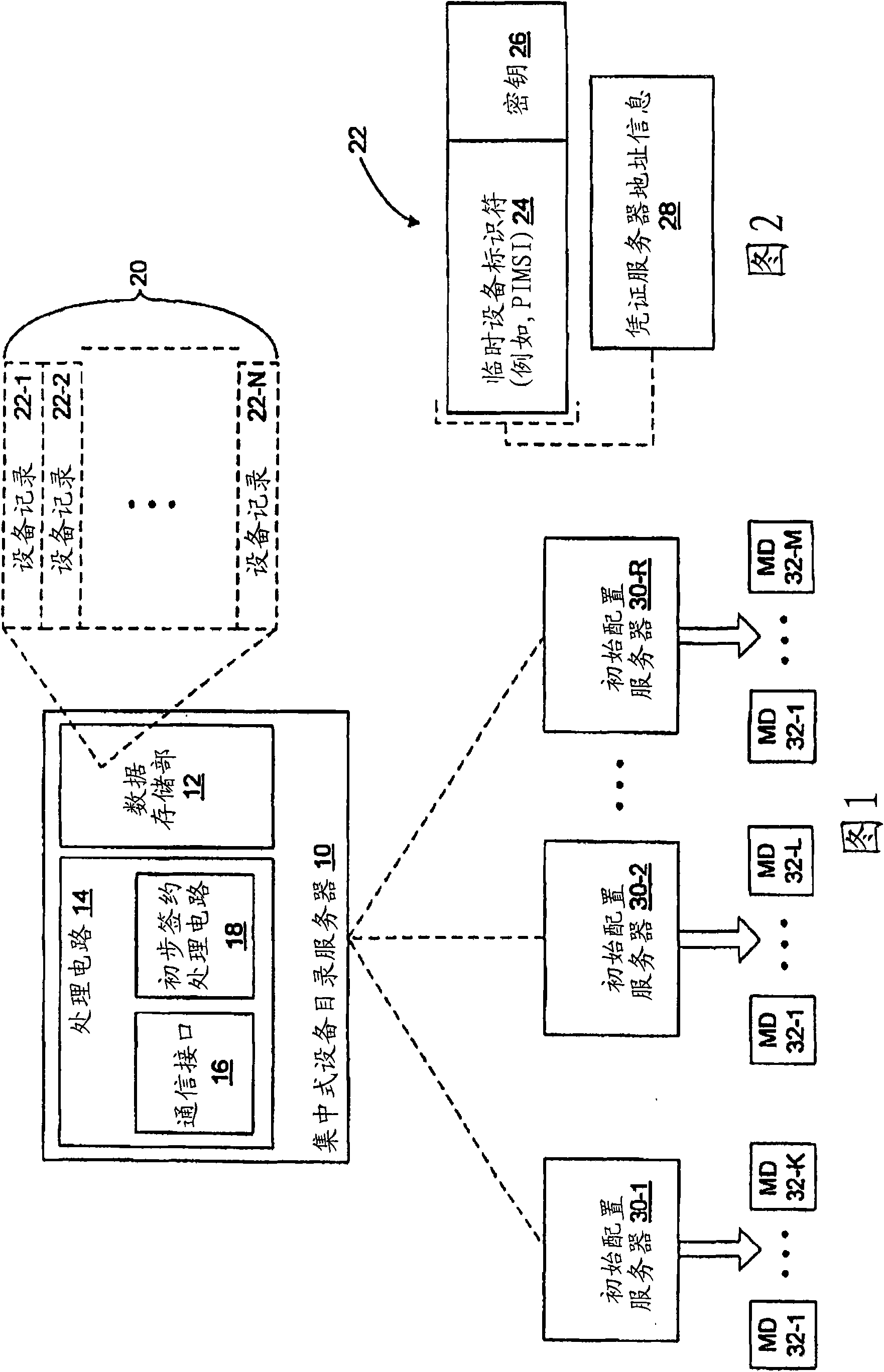
Methods and systems taught herein allow mobile device manufacturers to preconfigure mobile devices for subscription with any network operator having access to a centralized device directory server. The directory server stores device records, each including a preliminary subscription identity. Manufacturers individually provision new mobile devices with these preliminary subscription identities, and network operators preliminarily register subscribers by submitting requests to the directory server that cause it to link individual device records with the appropriate credential server addresses. Mobile devices gain temporary network access by submitting their preliminary subscription identities, which get passed along to the directory server for verification. In turn, the directory server generates authentication vectors giving the mobile devices temporary network access, and returns the appropriate credential server addresses. The mobile devices use the address information to submit secure requests for permanent subscription credentials, and the involved credential servers securely return permanent subscription credentials responsive to valid requests.
Owner:TELEFON AB LM ERICSSON (PUBL)
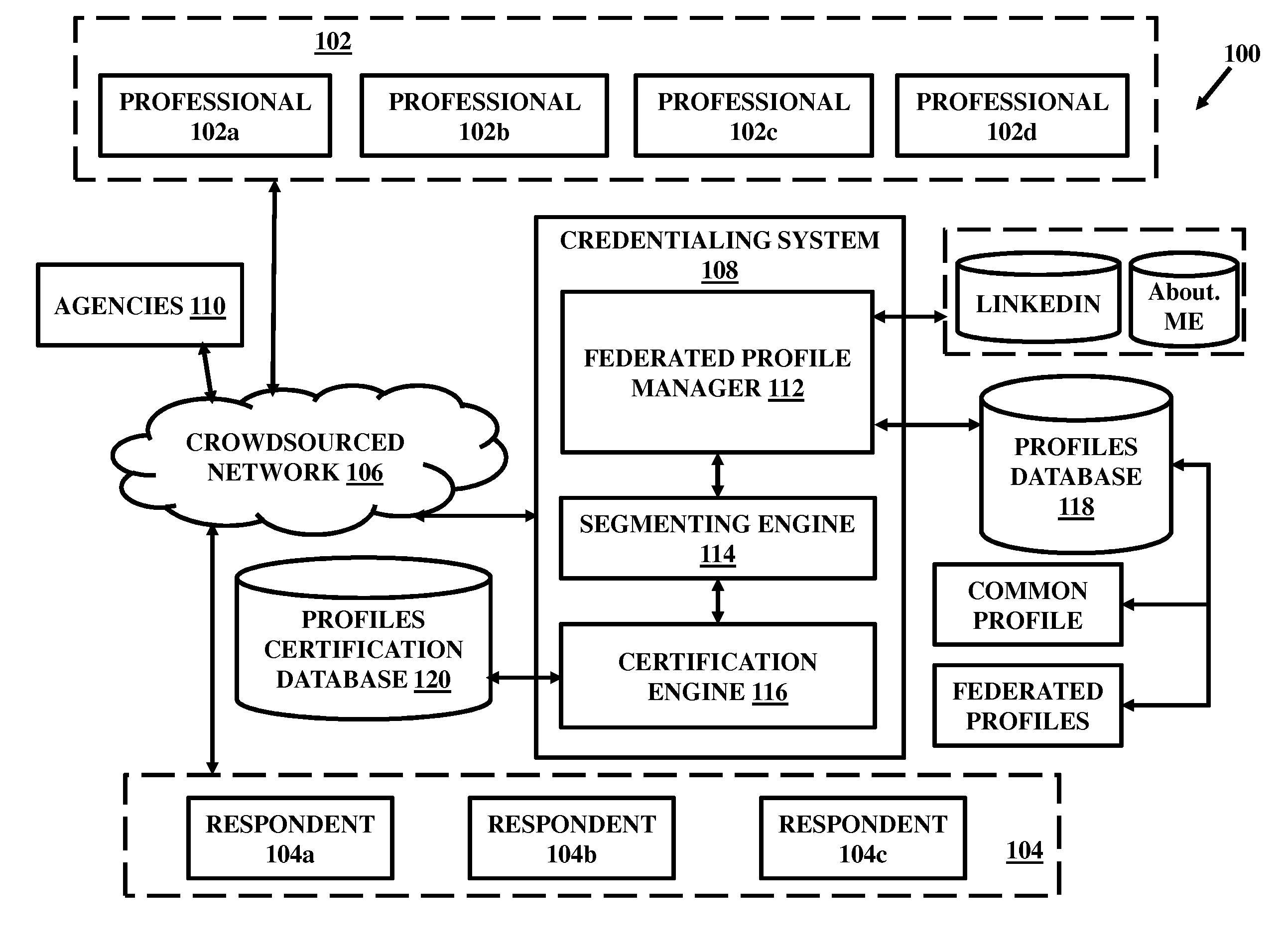
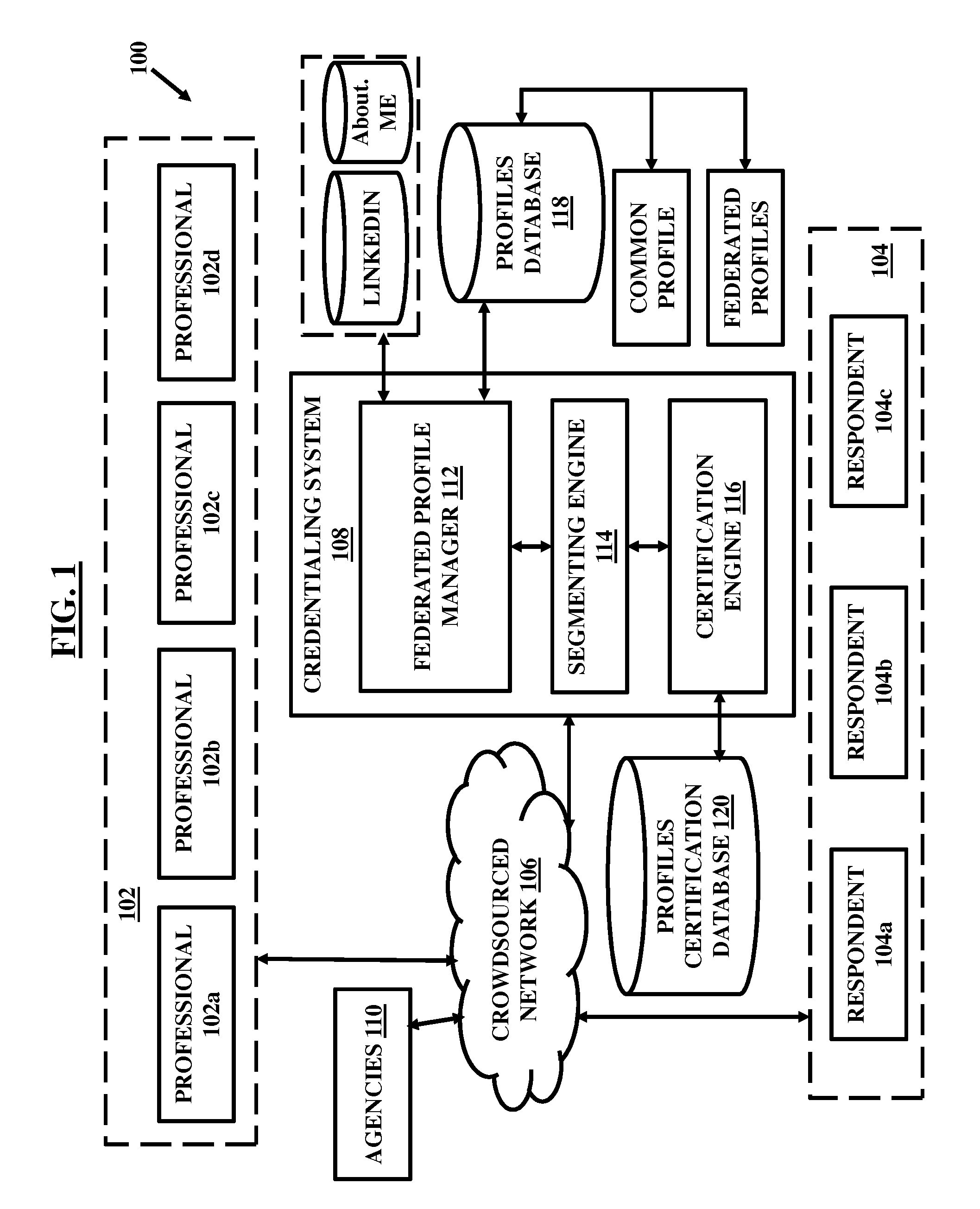
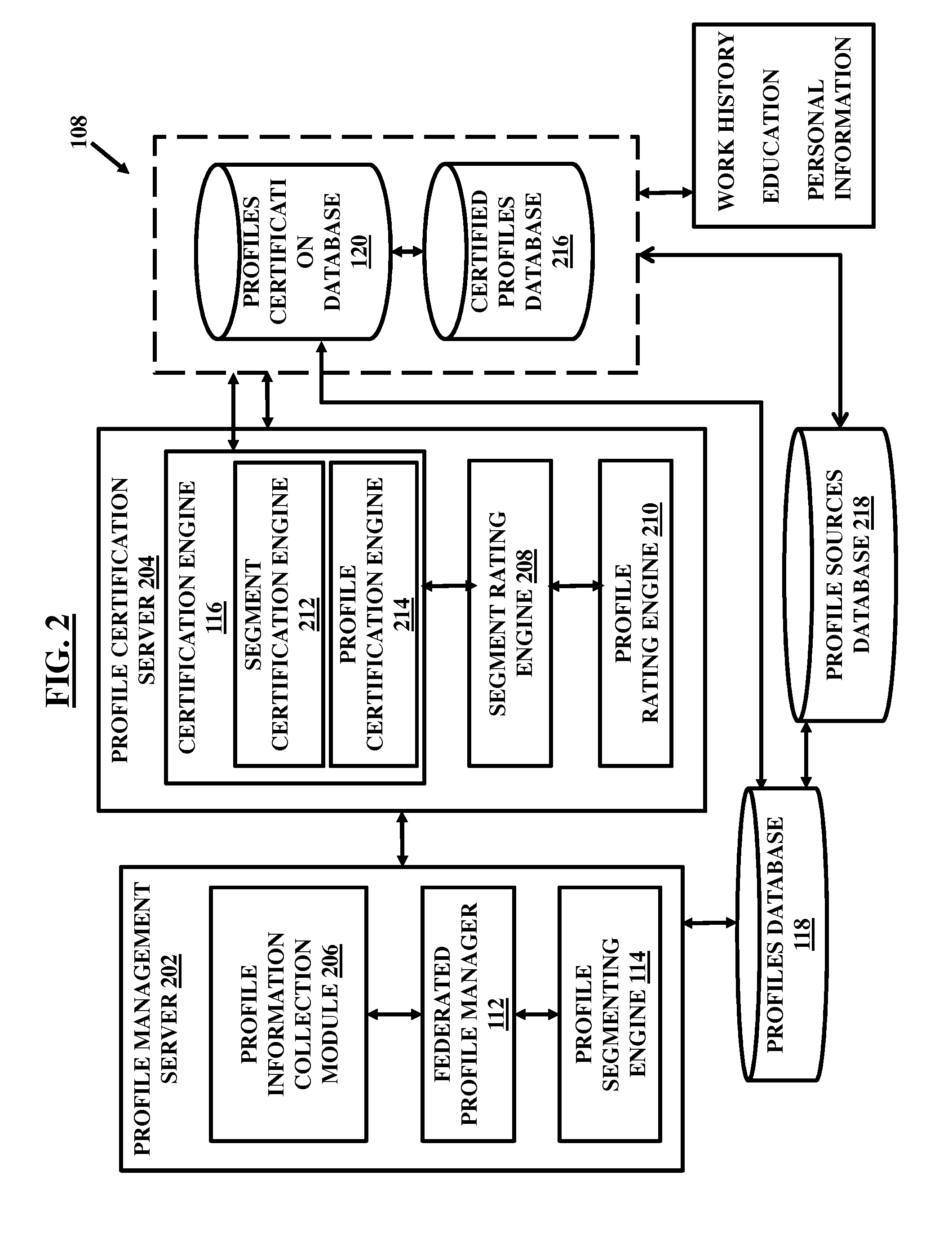
System and method for facilitating crowdsourced credentialing and accreditation
A system and method for facilitating crowdsourced credentialing over a network includes a federated profile manager to maintain profile related information for a plurality of professionals obtained from a plurality of federated sources distributed across the crowdsourced network. The system further includes a profile segmenting engine to segment and classify the profile-related information for each of the professionals into a plurality of federated profiles. The system further includes a certification engine to allow a plurality of crowdsourced respondents to respond to the federated profiles associated with each of the plurality of professionals and credential them.
Owner:NETSPECTIVE COMM
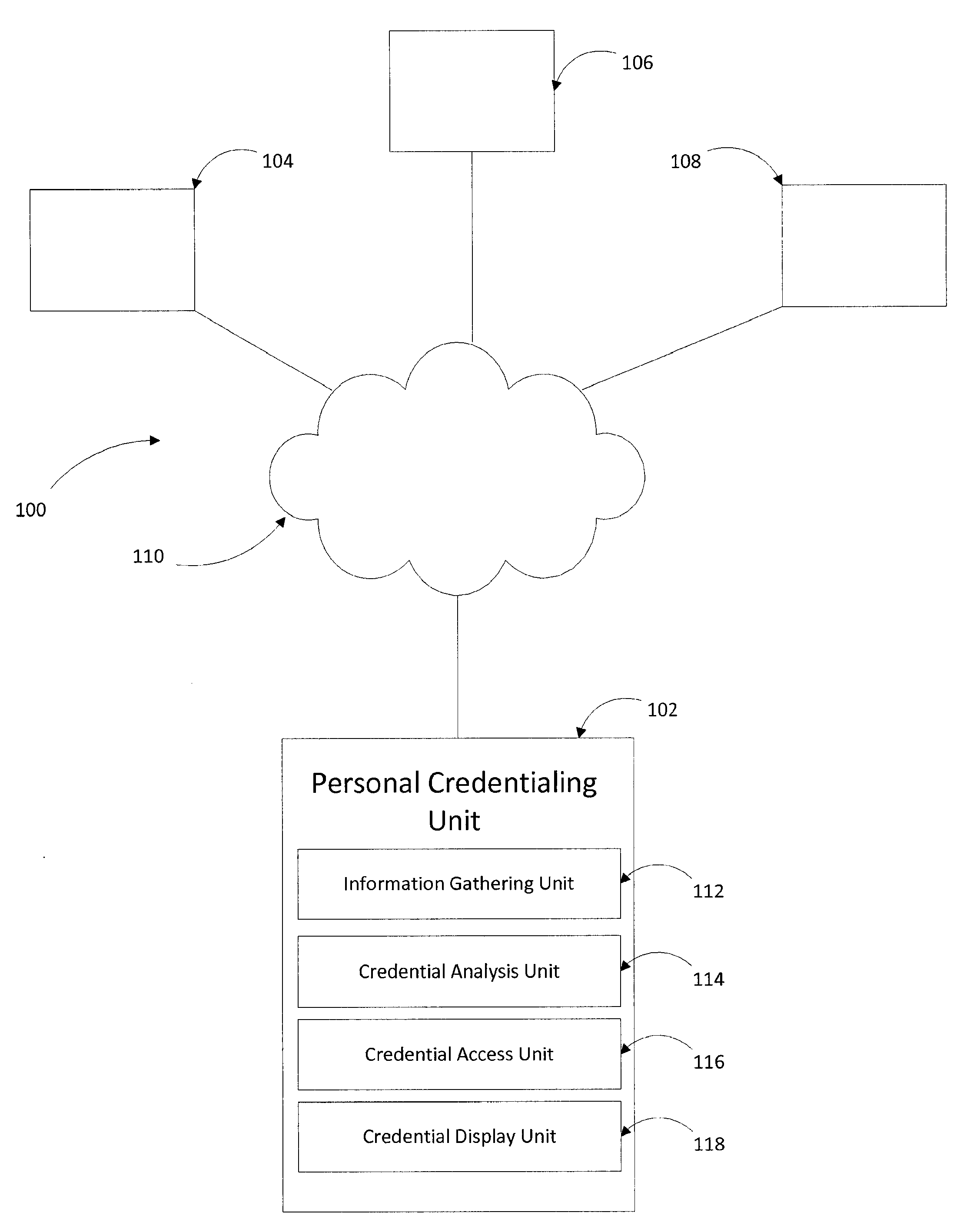
Credential authentication system and methods of performing the same
InactiveUS20140351907A1Avoid normal displayDigital data processing detailsMultiple digital computer combinationsThird partyCredentialing
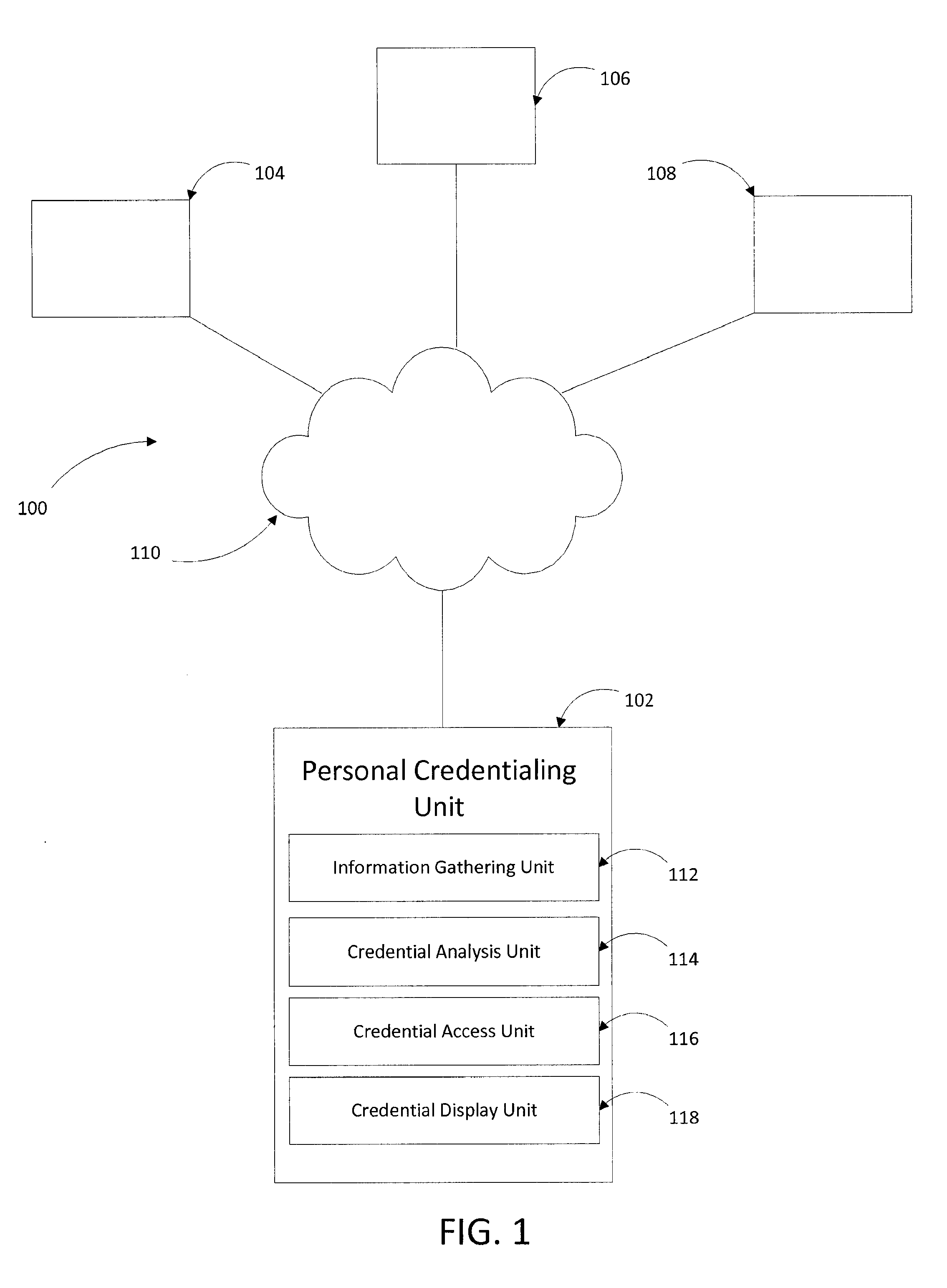
A personal credentialing system including an information gathering unit that gathers information from a subscriber. A credential analysis unit configured to gather additional information pertaining to the subscriber based on the information gathered by the information gathering unit, store the additional information in a storage unit, categorize the additional information based on predefined criteria, assign an indicator to the additional information based on categorization of the additional information, and stores the additional information and indicators. A credential access unit that receives requests for access to view the indicators and stored additional information from a third party. A credential display unit that displays the indicators and stored additional information after the credential access unit authorizes a request to view the stored additional information. Methods of verifying a person's credentials, conveying personal credential information, and preventing fraudulent on-line postings.
Owner:PERSONAL CREDENTIALING GRP
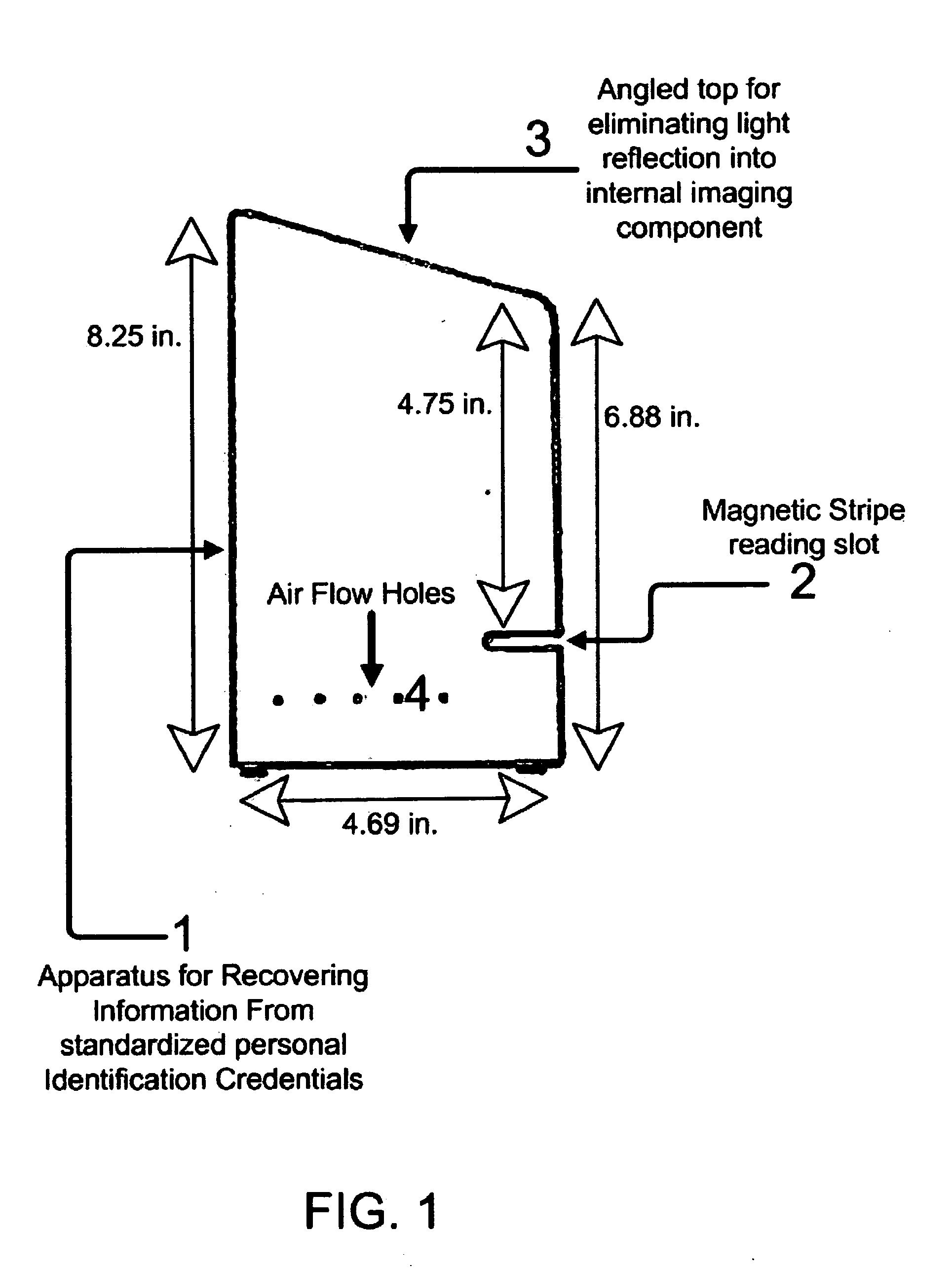
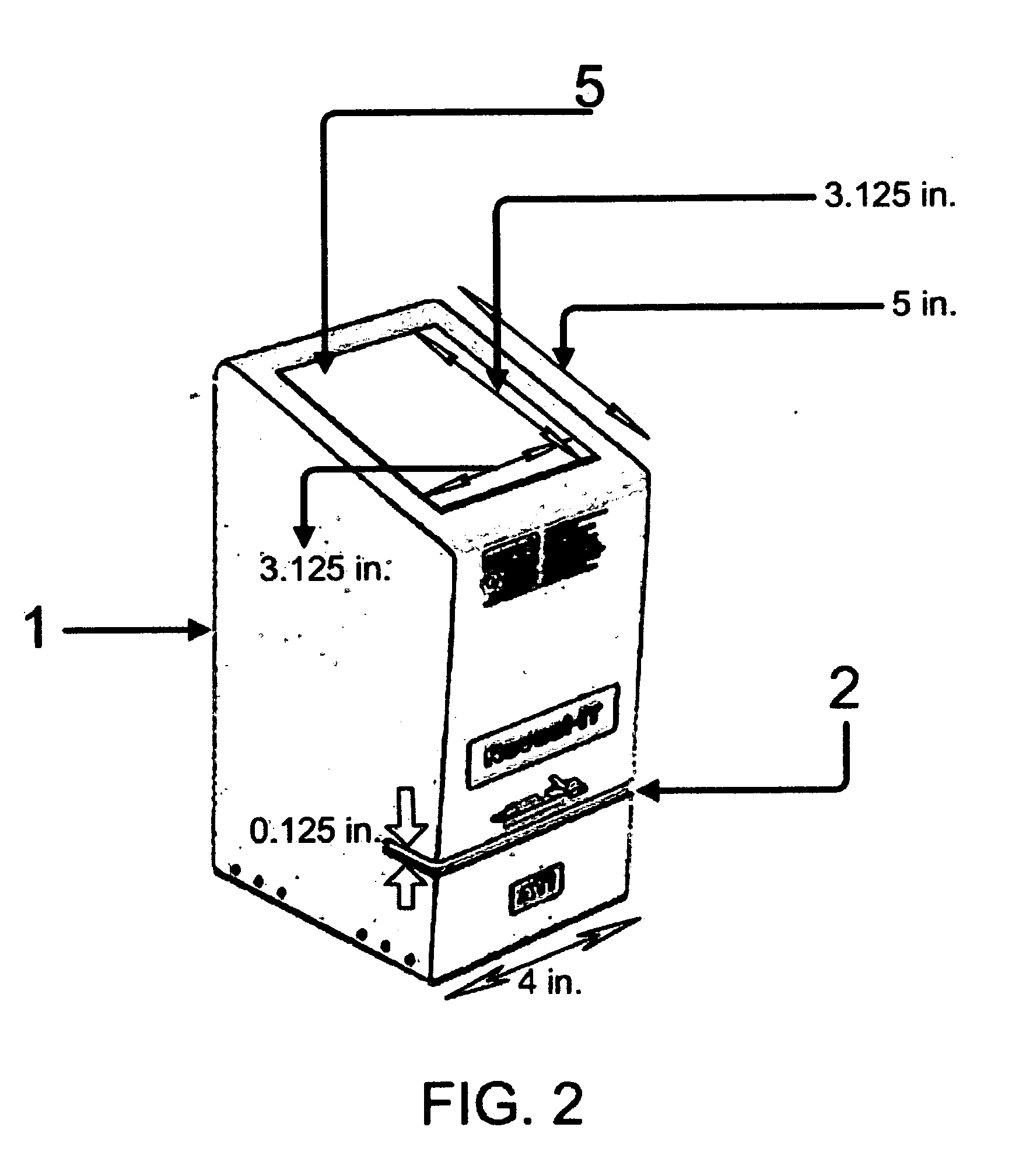
Apparatus for reading standardized personal identification credentials for integration with automated access control systems
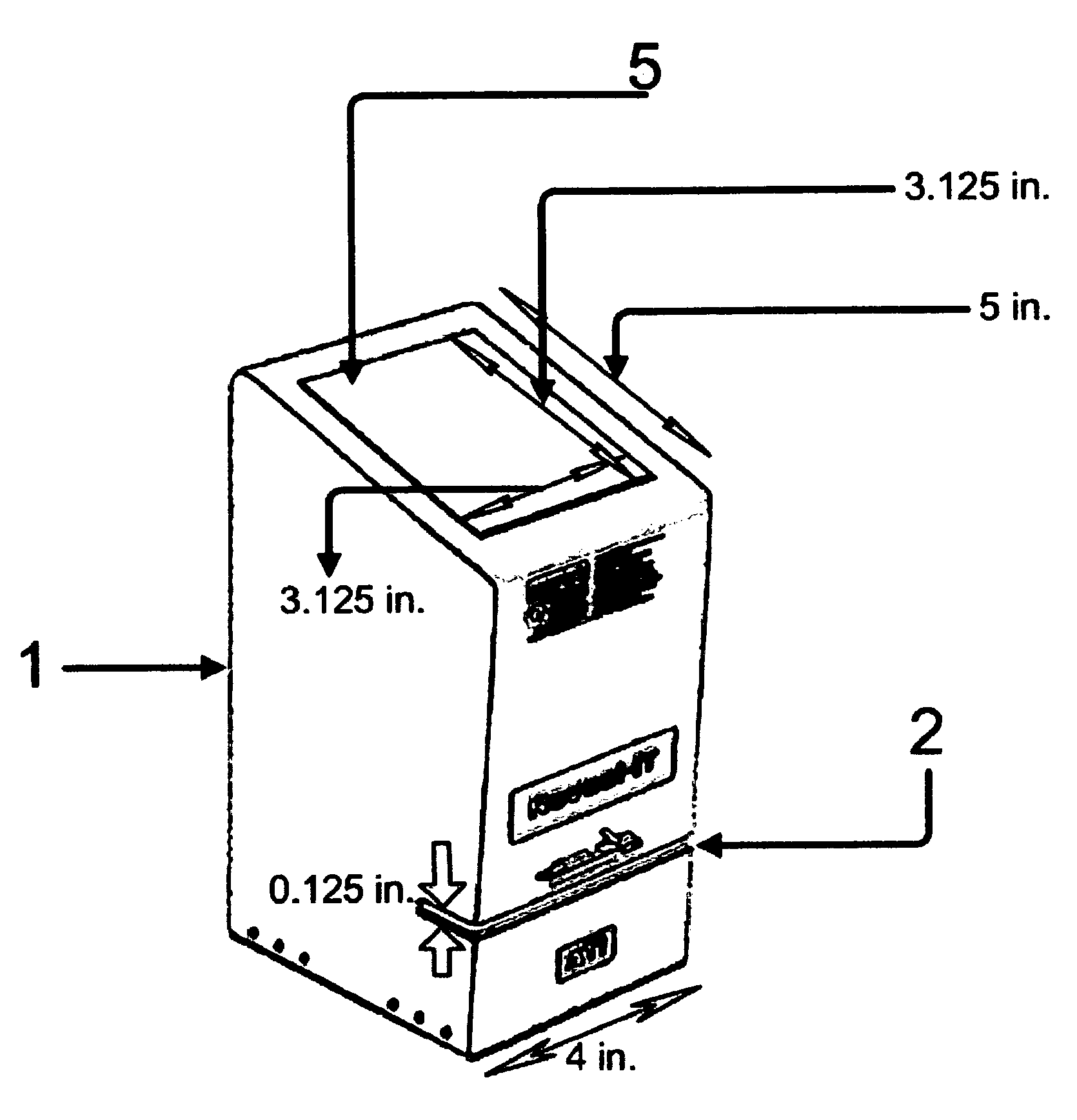
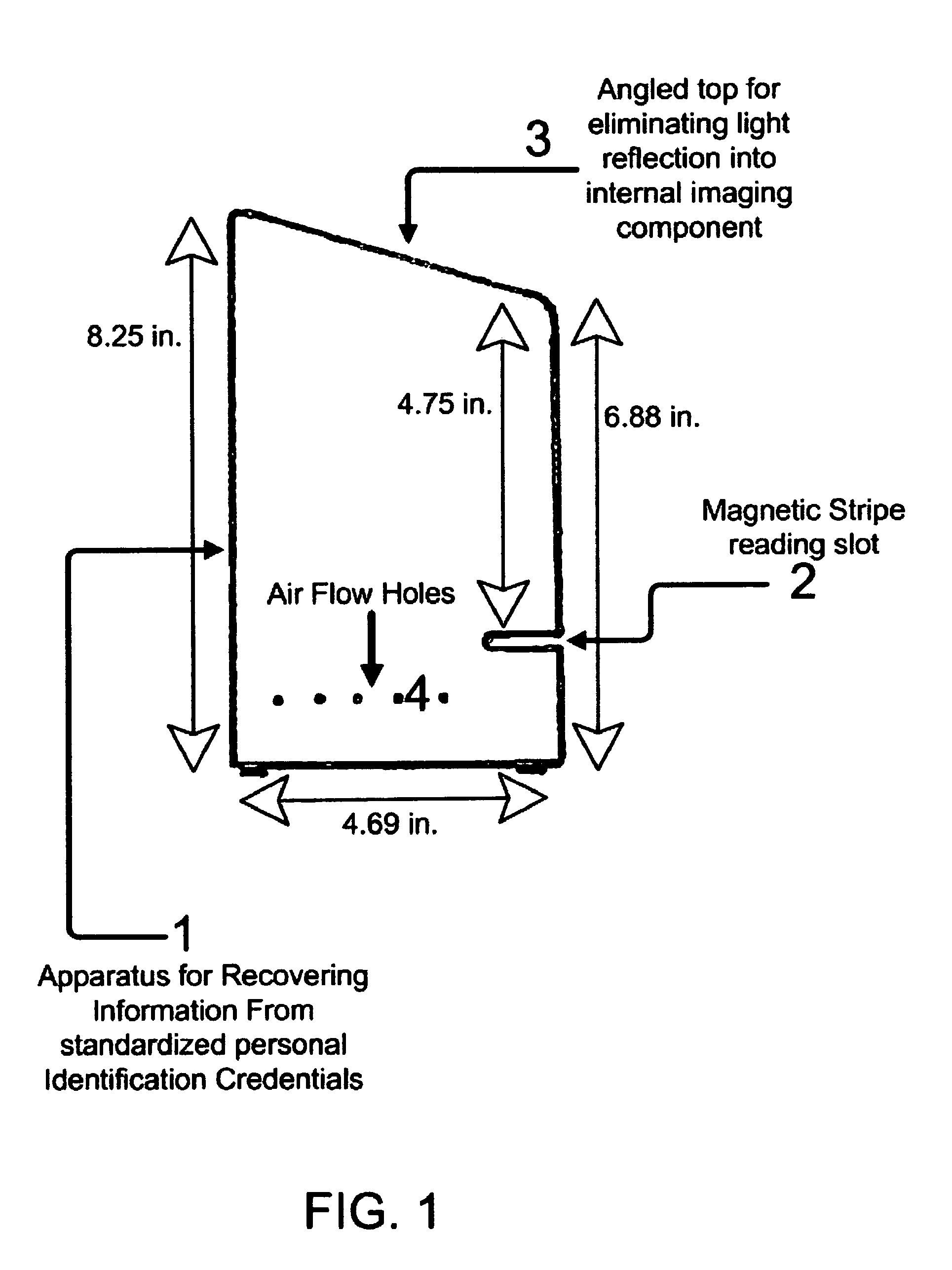
An apparatus for reading information encoded on standardized personal identification credentials includes a reading device that reads information encoded on 3-track magnetic stripes as well as barcodes, and connects to a computer system to allow complete automation of information collection. The software application uses the apparatus to automate the collection of data from individuals entering a secure facility, and includes a credentialing for recognizing employees, contractors and visitors. The software system allows for visitor pre-announcement, specification of visit duration, and printing of time-sensitive access passes. The software application supports an unlimited number of printers. Security is enhanced through an automatic checking of government supplied terrorists lists, and other ENTRY NOT ALLOWED lists. The software application encrypts important visitor personal data for privacy purposes, and includes a device for customizing system security and data collection. The software application includes reporting, and data exporting utilities.
Owner:HADDAD MICHAEL A
Method and system for registering, credentialing, rating, and/or cataloging businesses, organizations, and individuals on a communications network
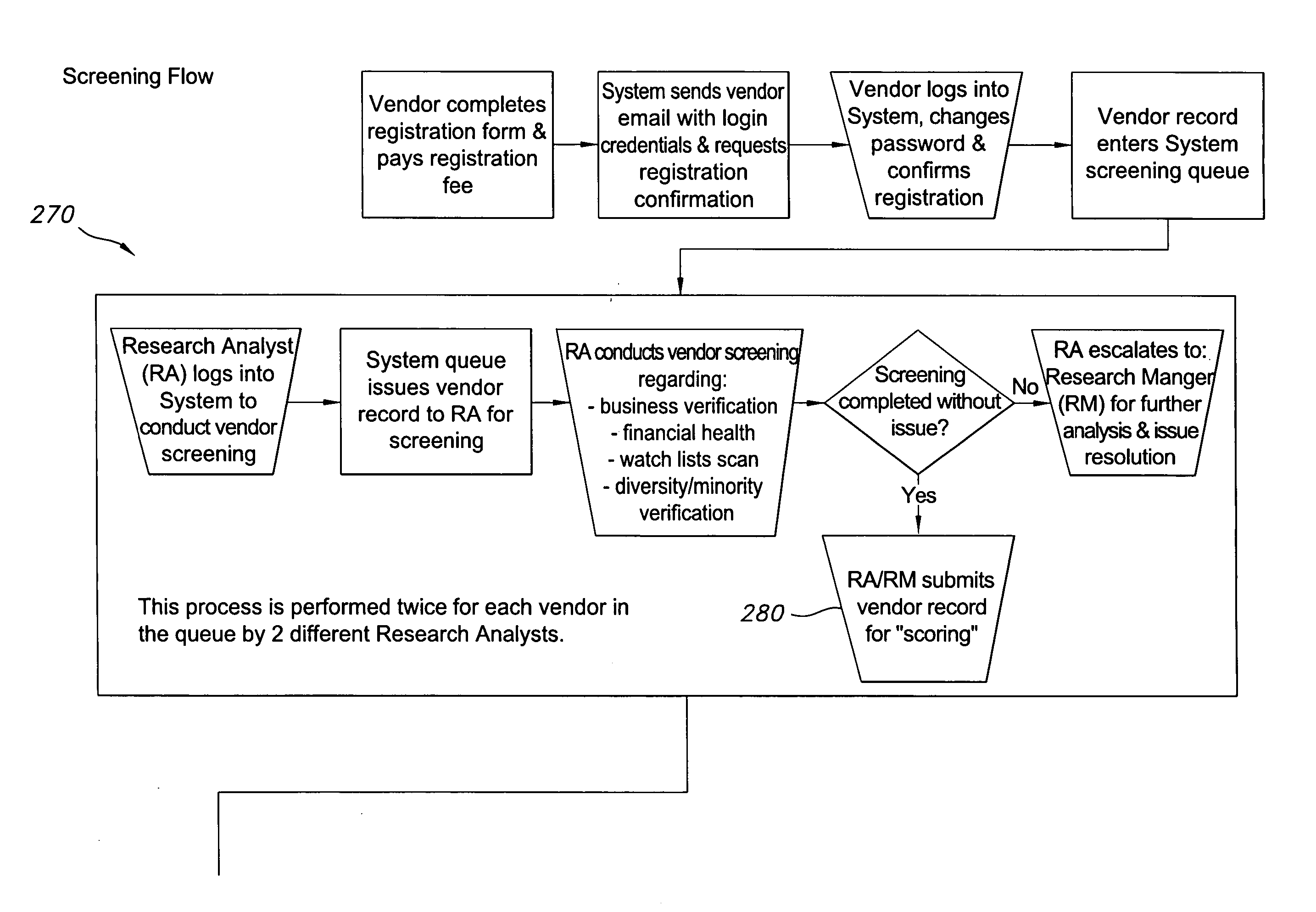
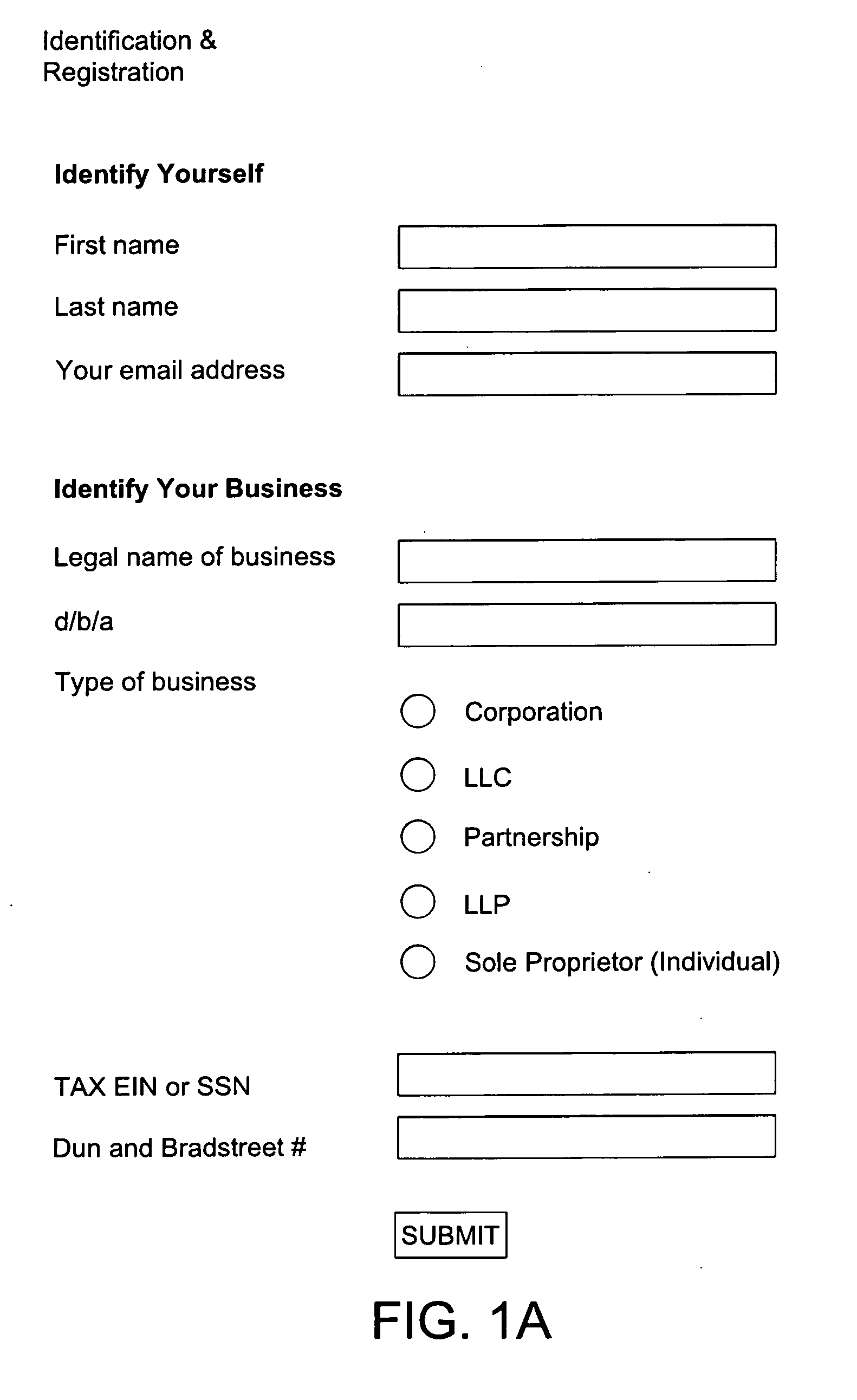
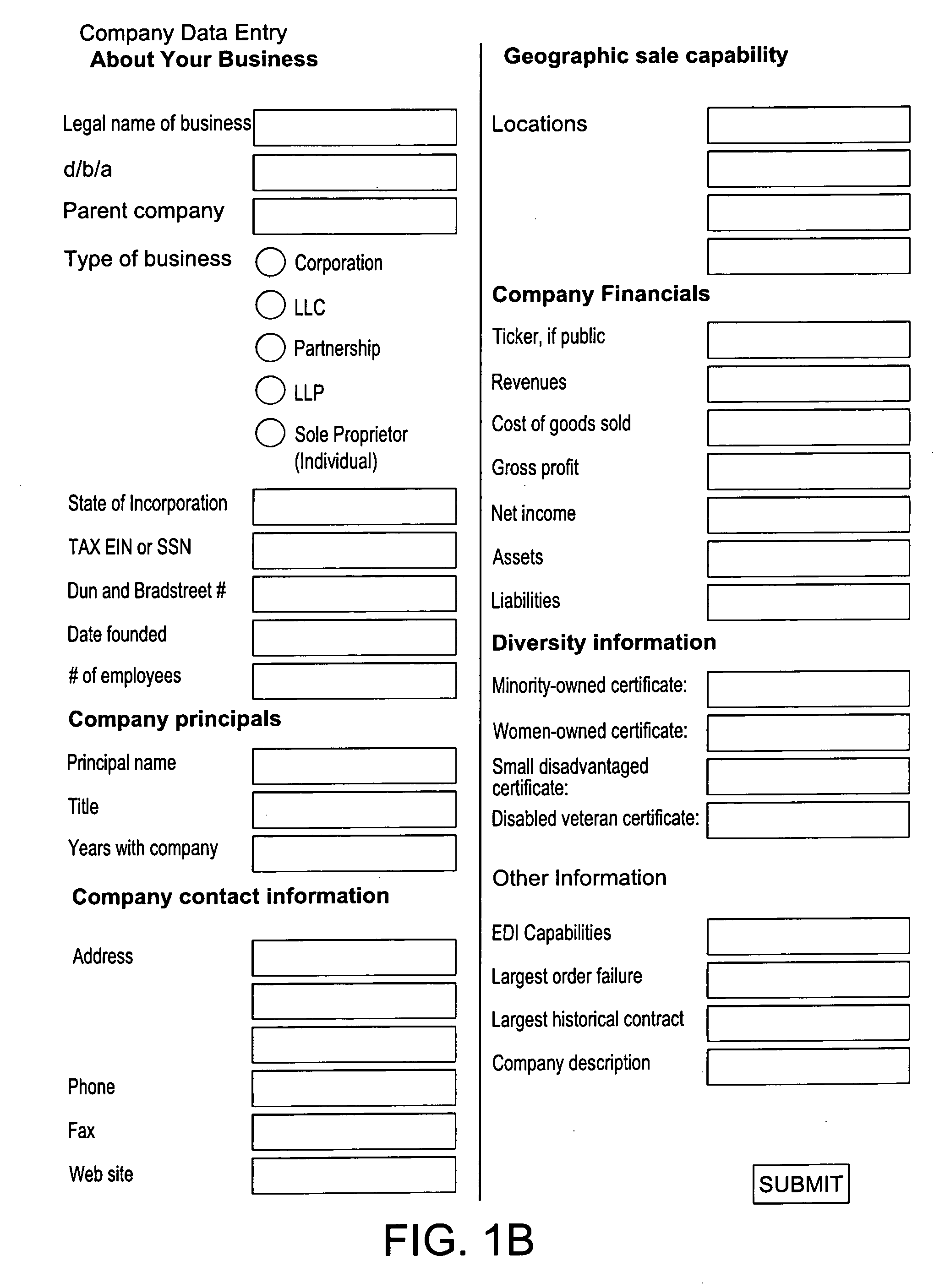
A method and system for registering, credentialing, rating, trending, monitoring and cataloging businesses, organizations, and individuals. The applicant business, organization, or individual clicks to a computer server to begin the registration process for the benefit of the applicant and its customer. The server system receives the request for registration and requests contact information, product category codes, and other details and payment information from the applicant. The applicant's details are then used to aggregate other electronic records to determine applicant's suitability. The details and records are then rated based on predetermined thresholds to provide an acceptability score for the applicant. The applicant may return to the computer server to log-in to view and edit the applicant's details pursuant to a subscription agreement. The customer may then also log-in to view all details of registered vendors, sorted according to various options. In the preferred embodiment of the invention, the internet acts as the computer network described.
Owner:VENDORMATE
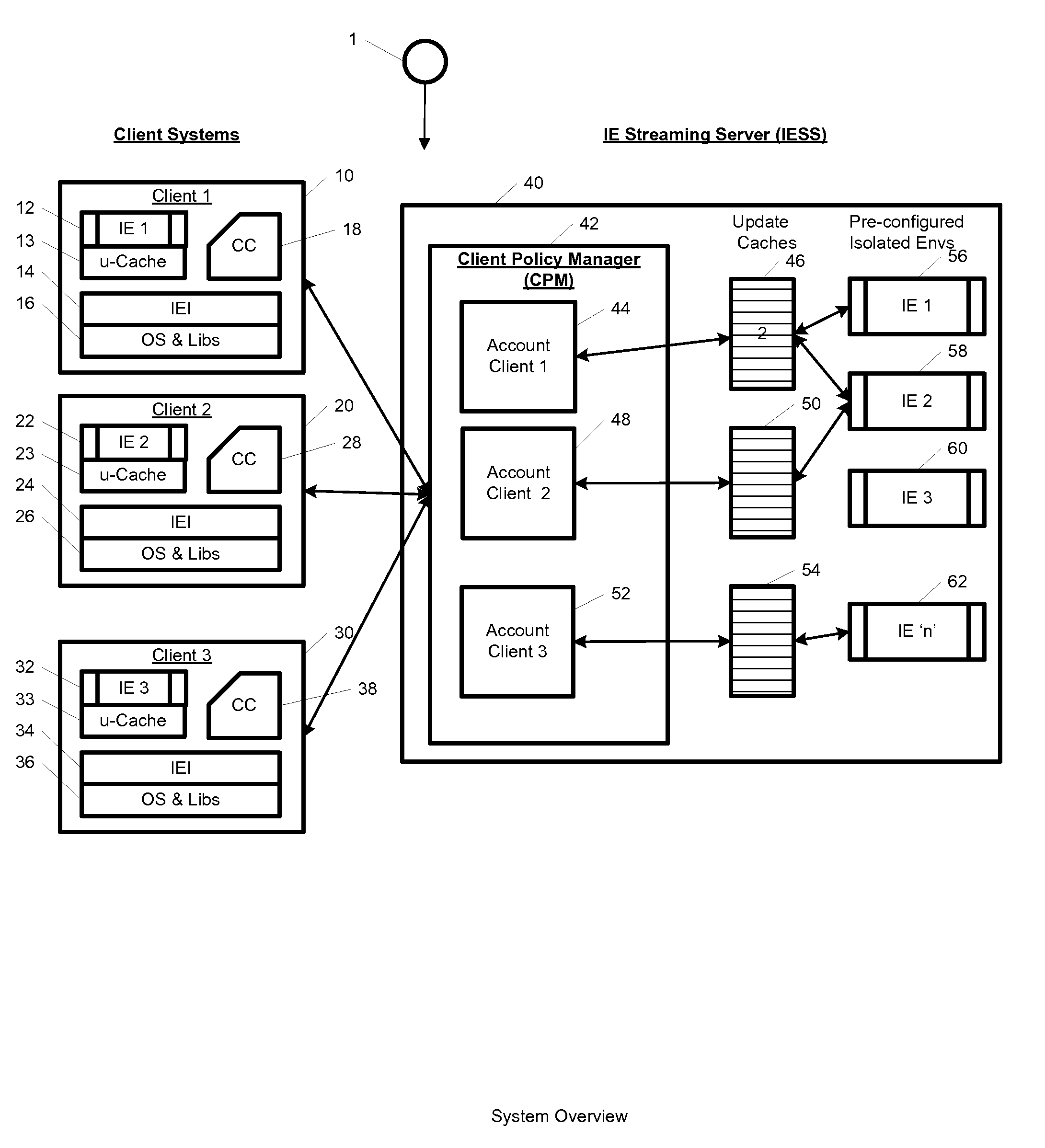
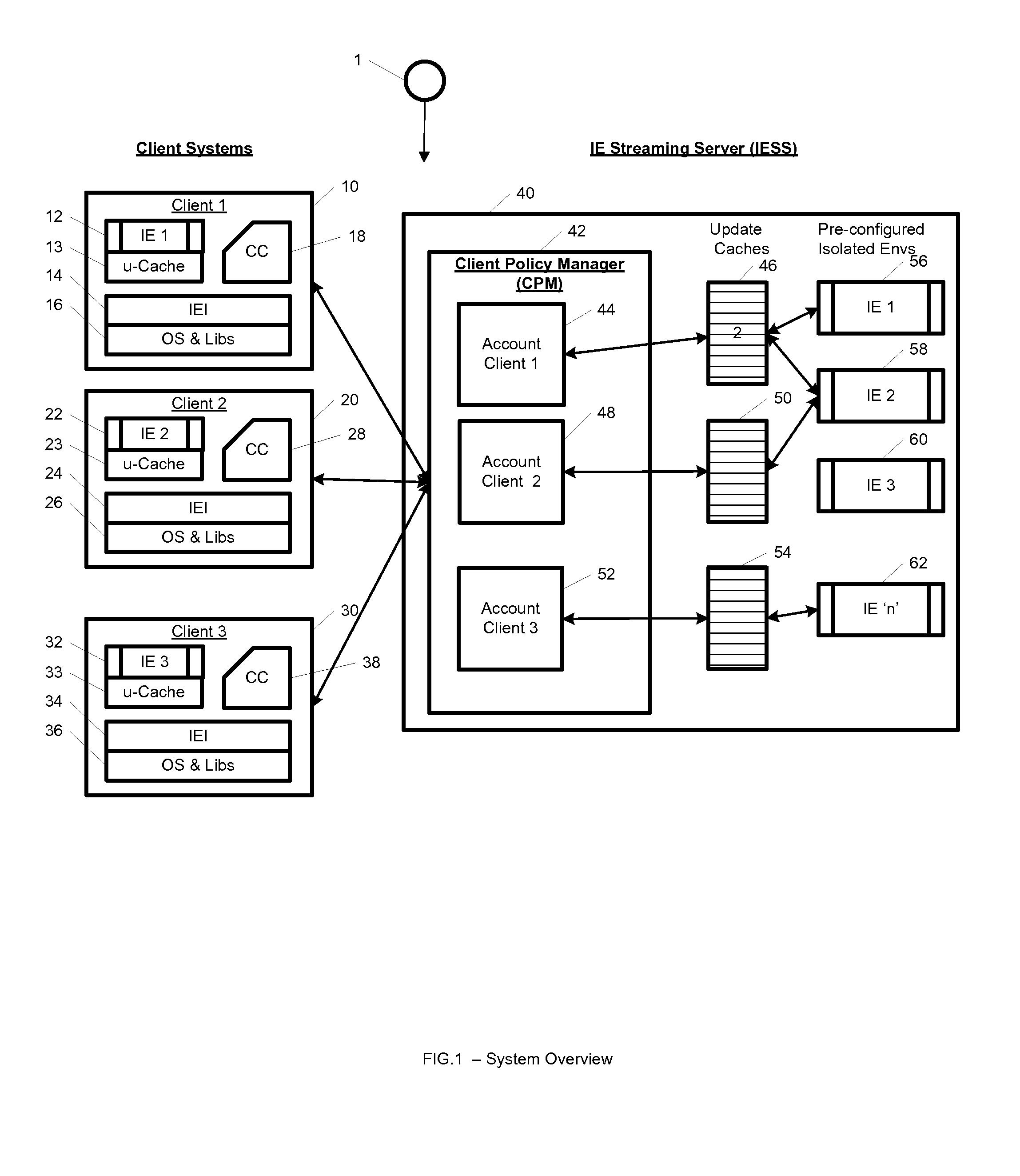
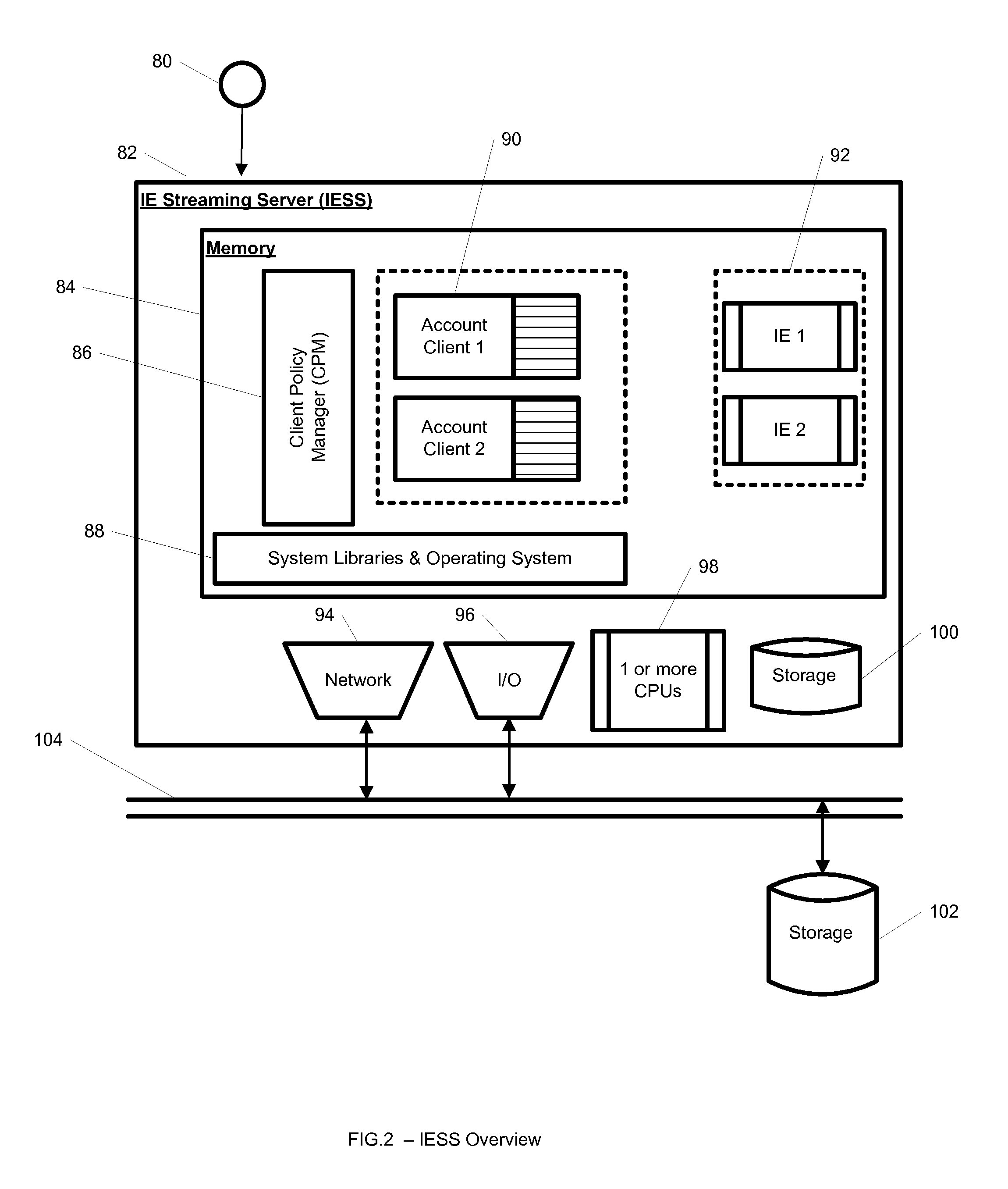
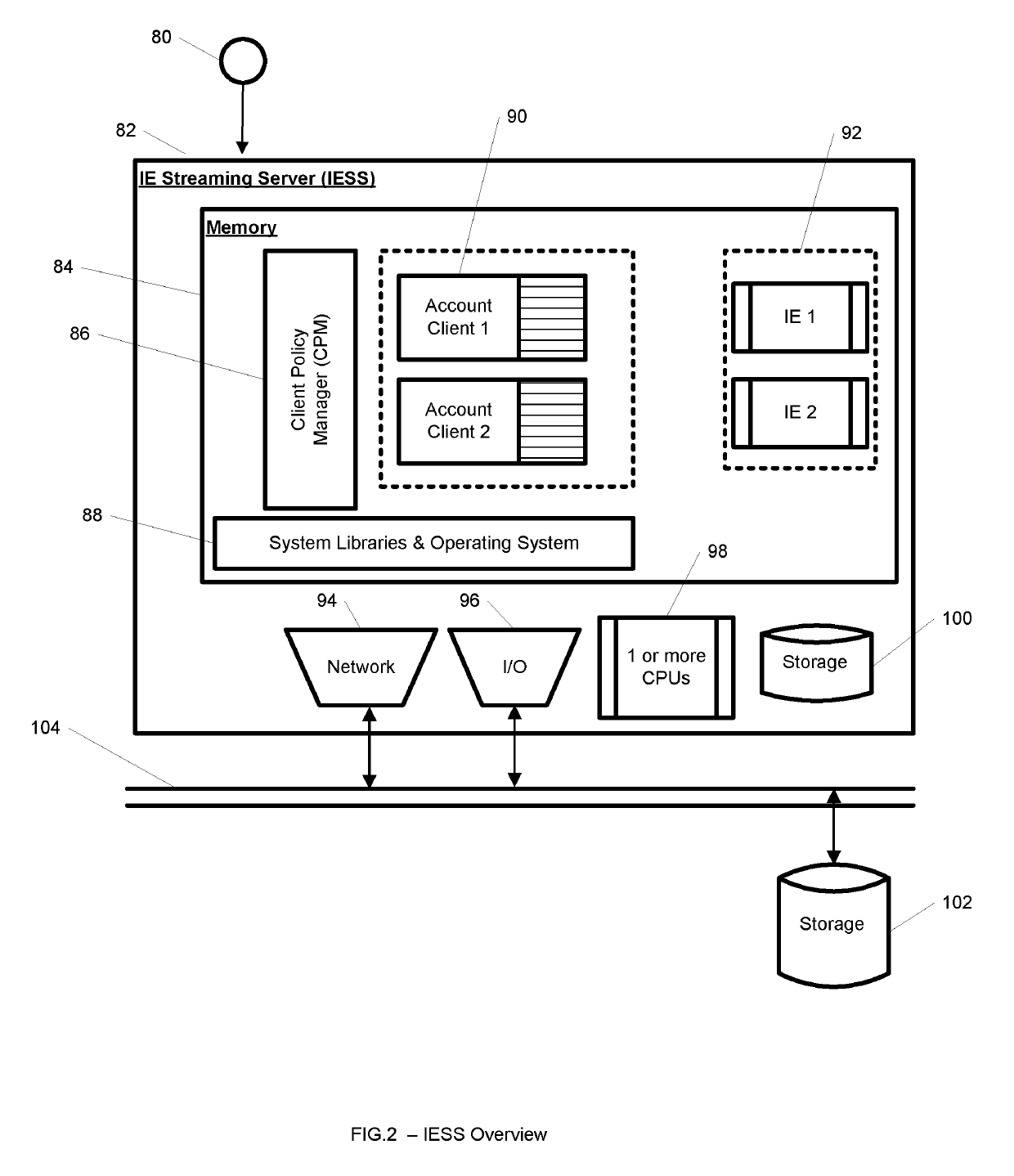
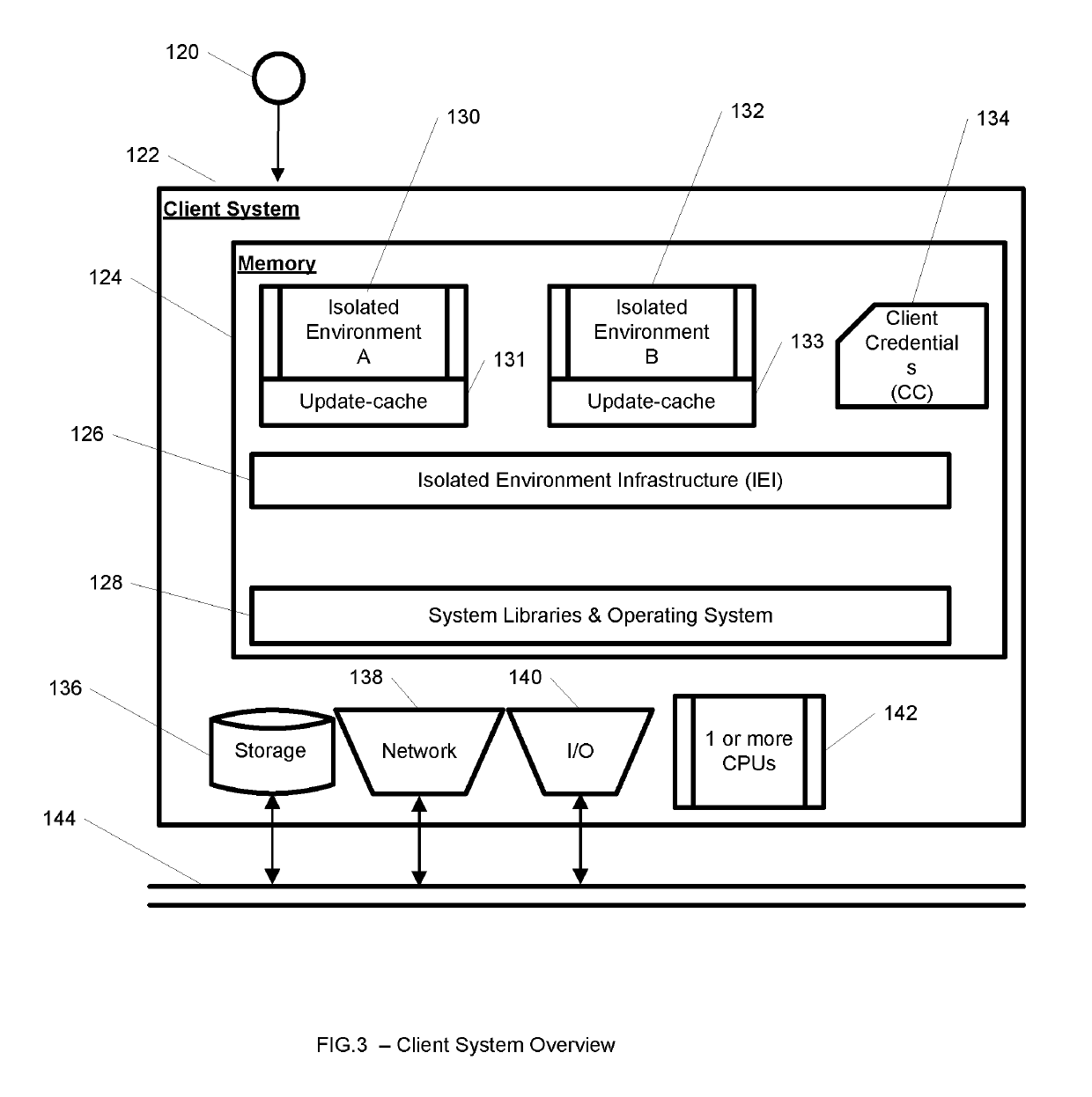
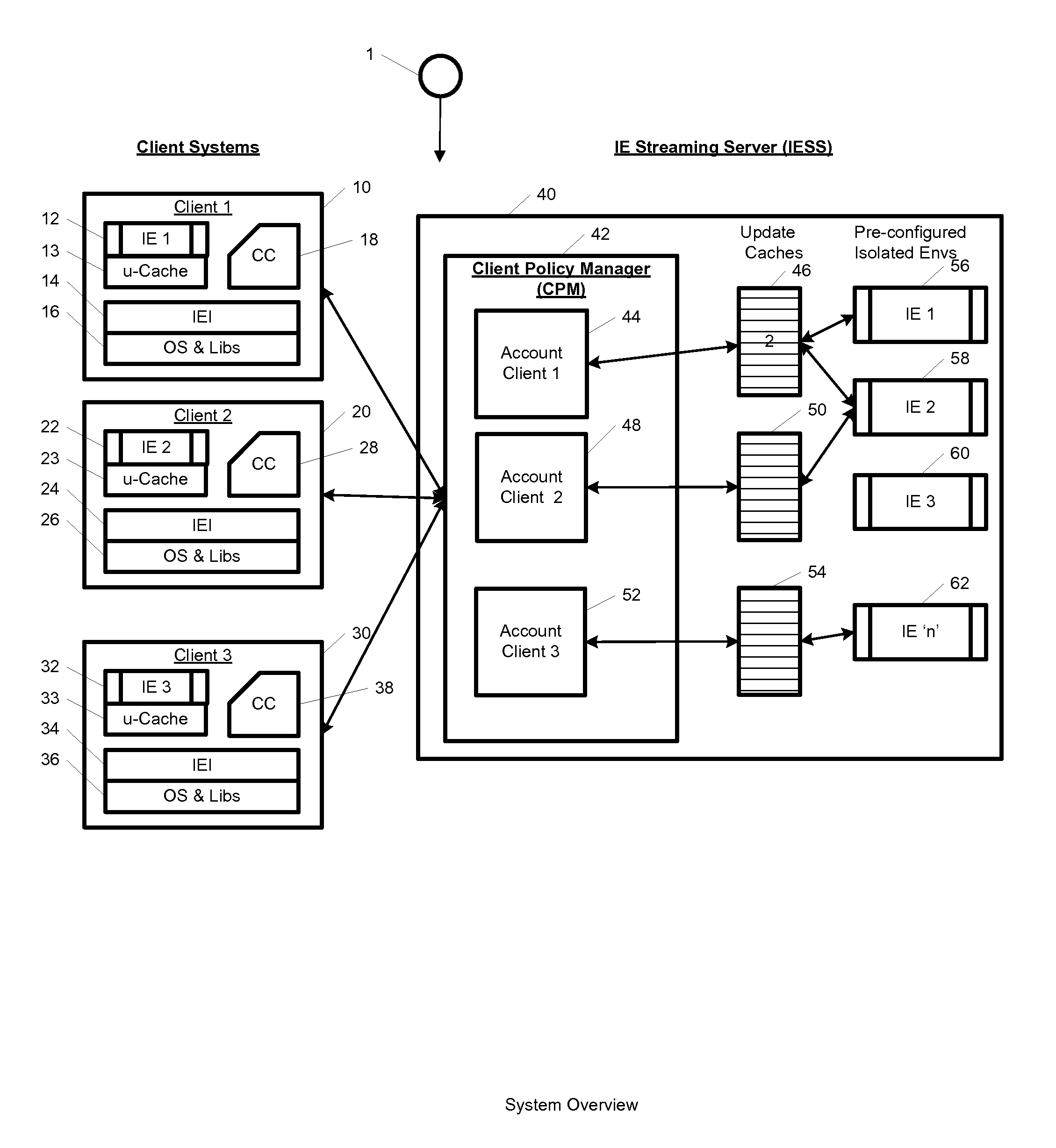
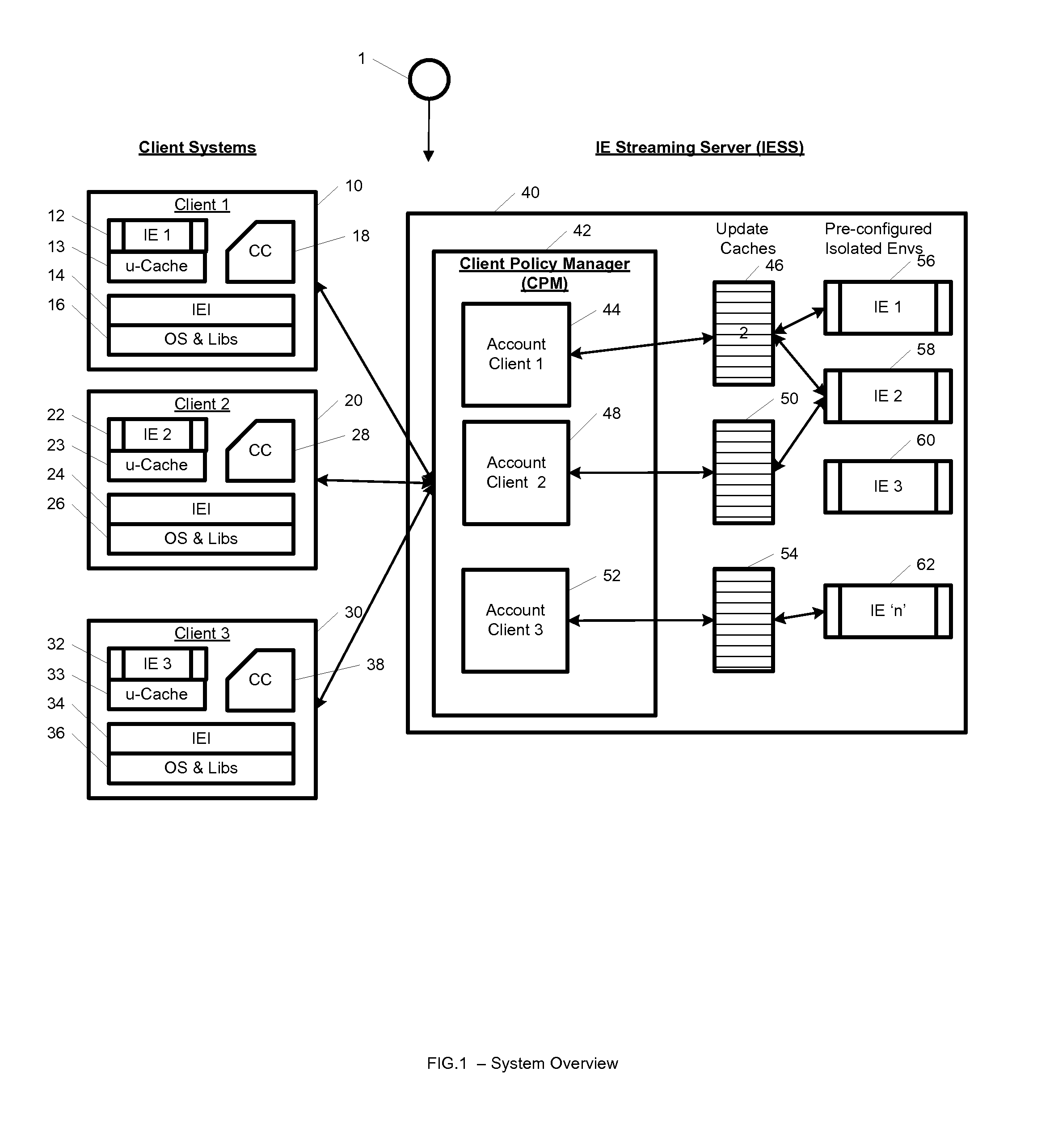
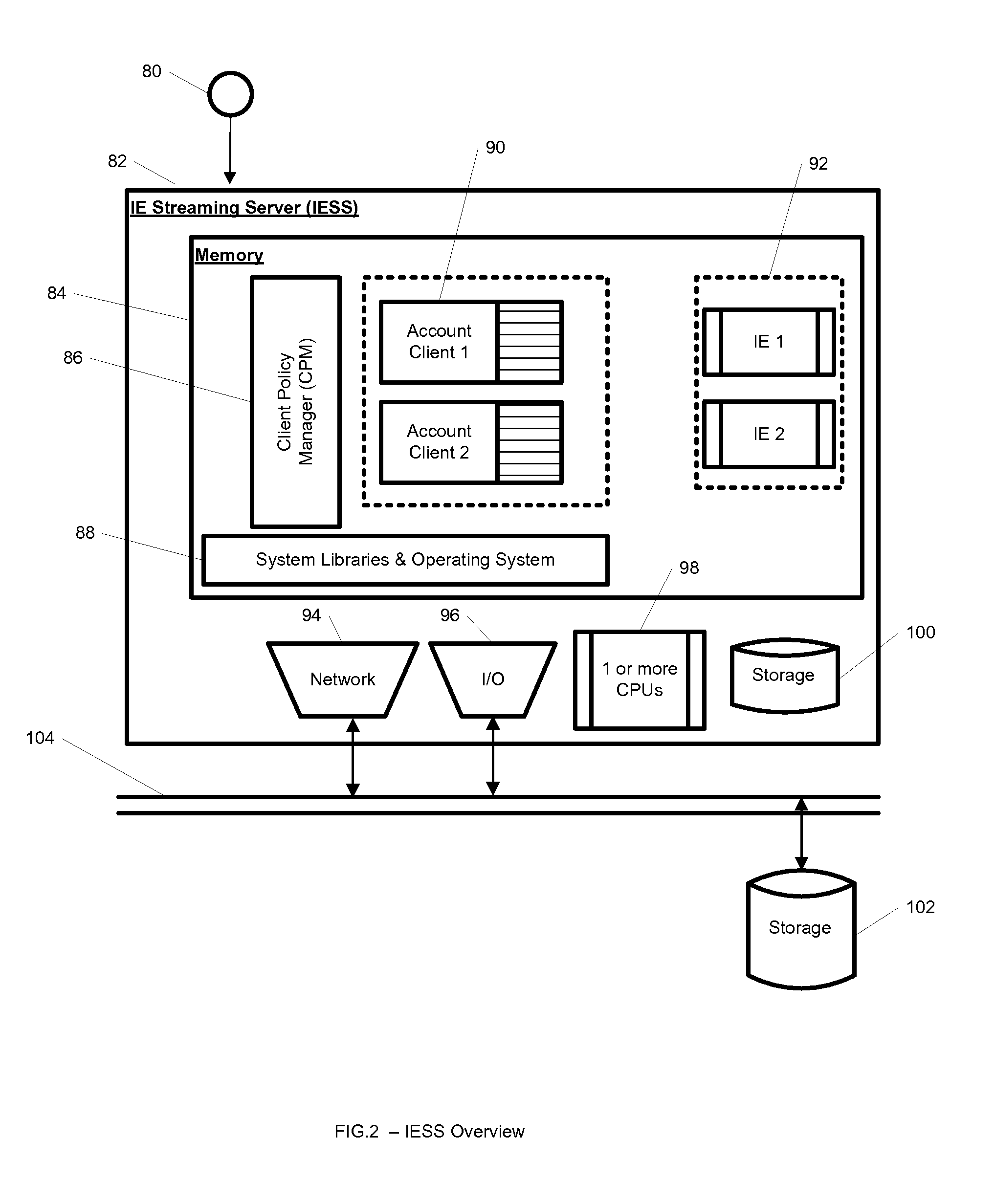
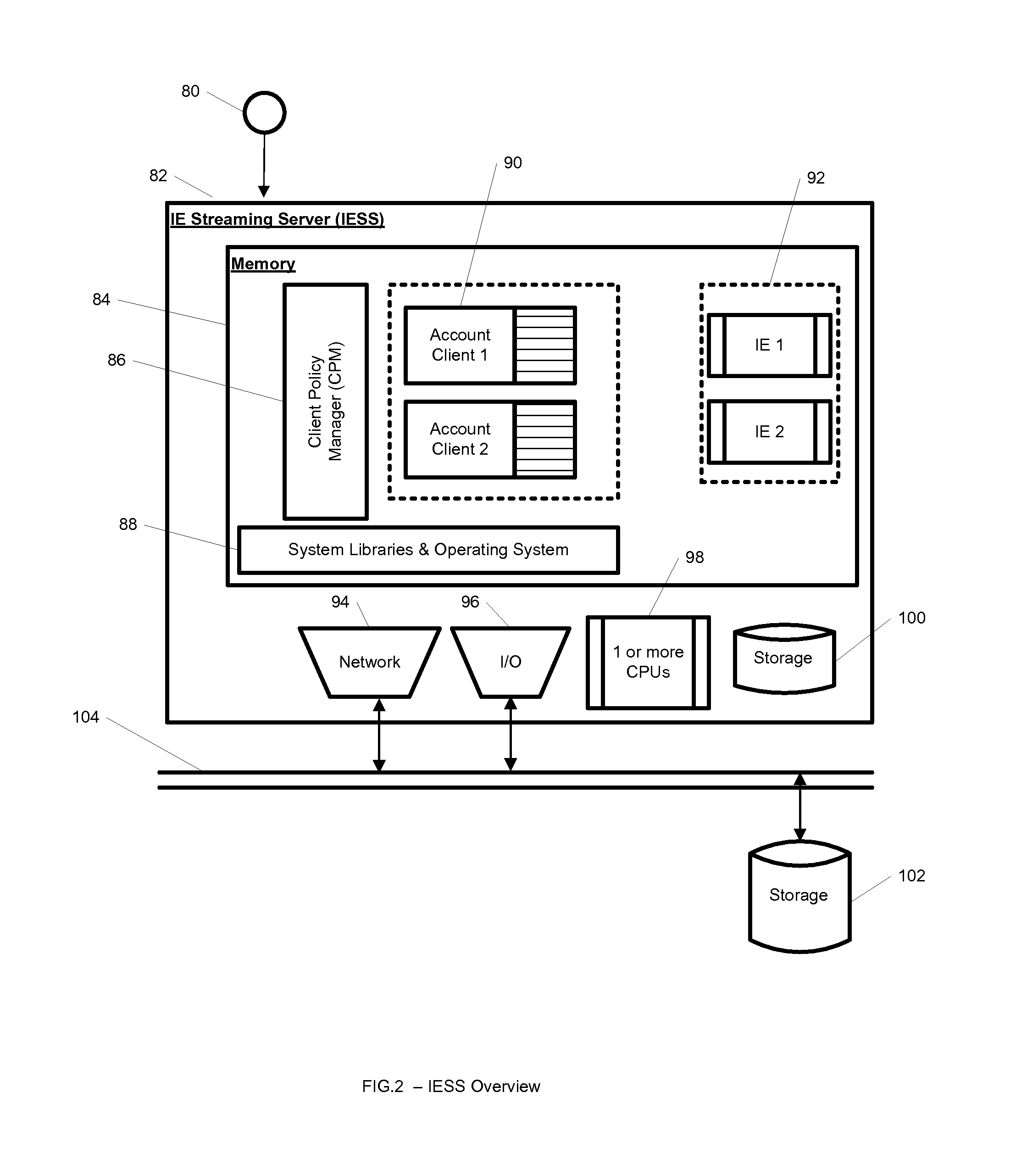
System and method for streaming application isolation
InactiveUS8418236B1Optimizing streamingDigital data processing detailsUser identity/authority verificationCredentialingOperational system
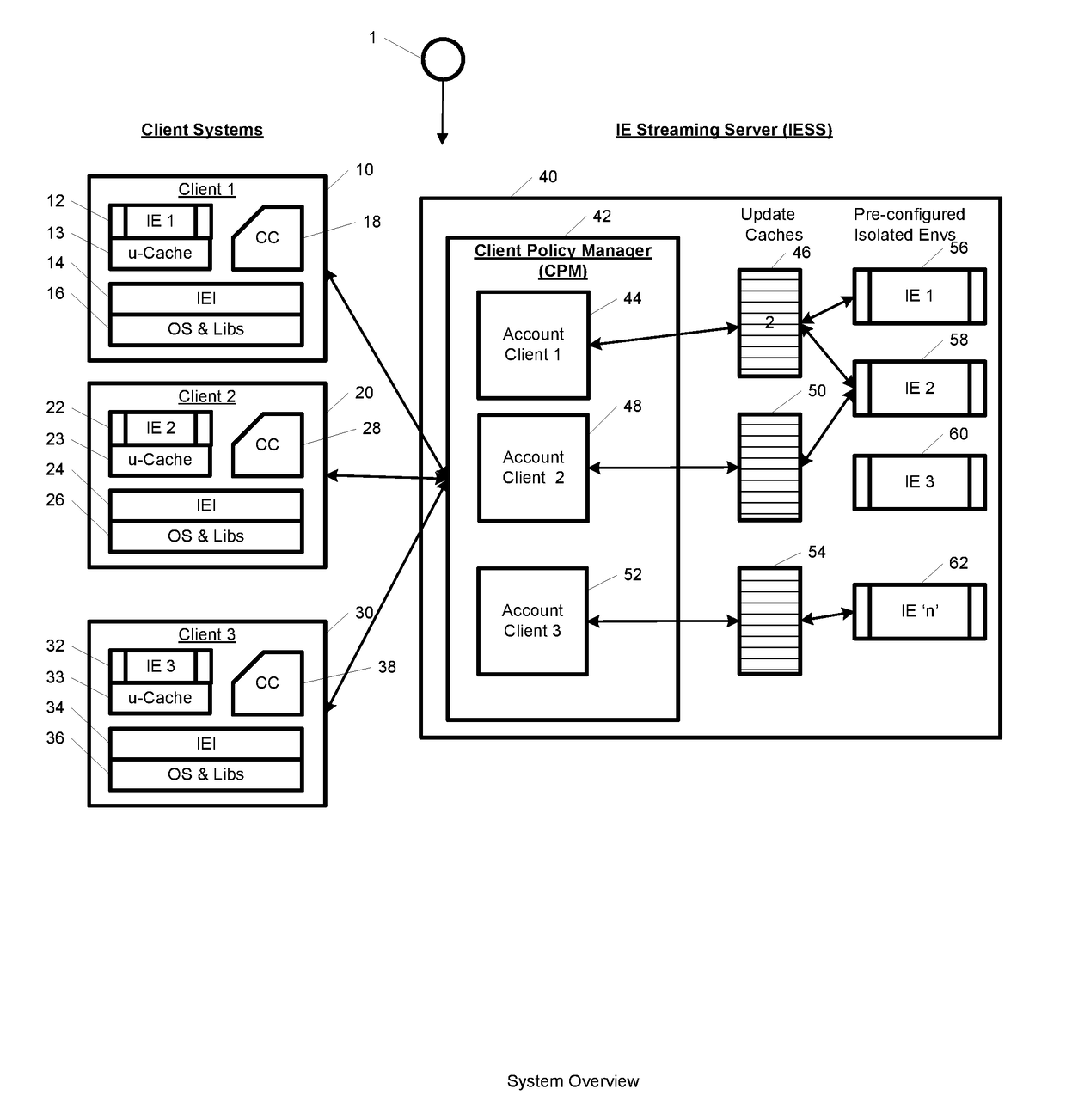
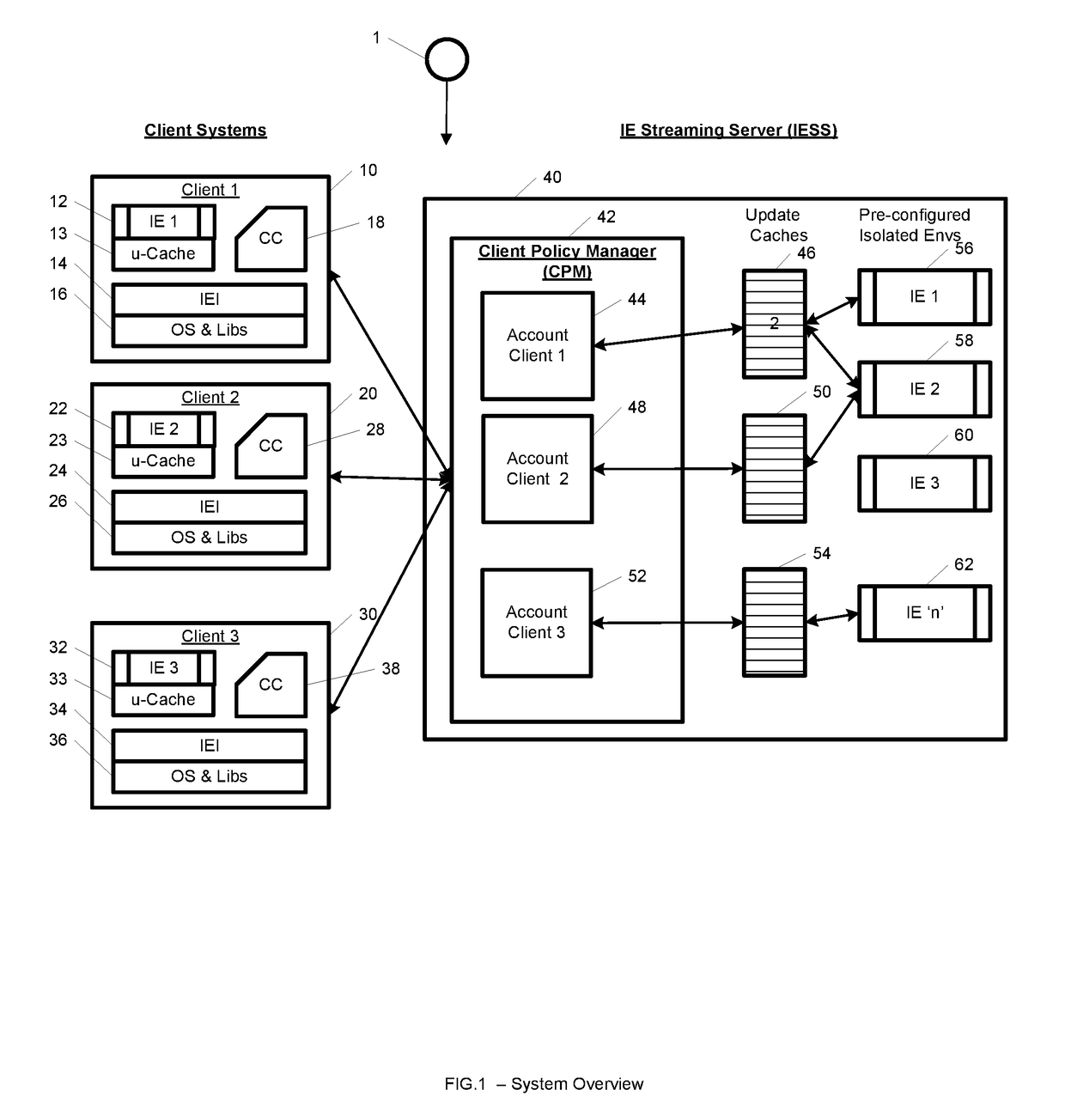
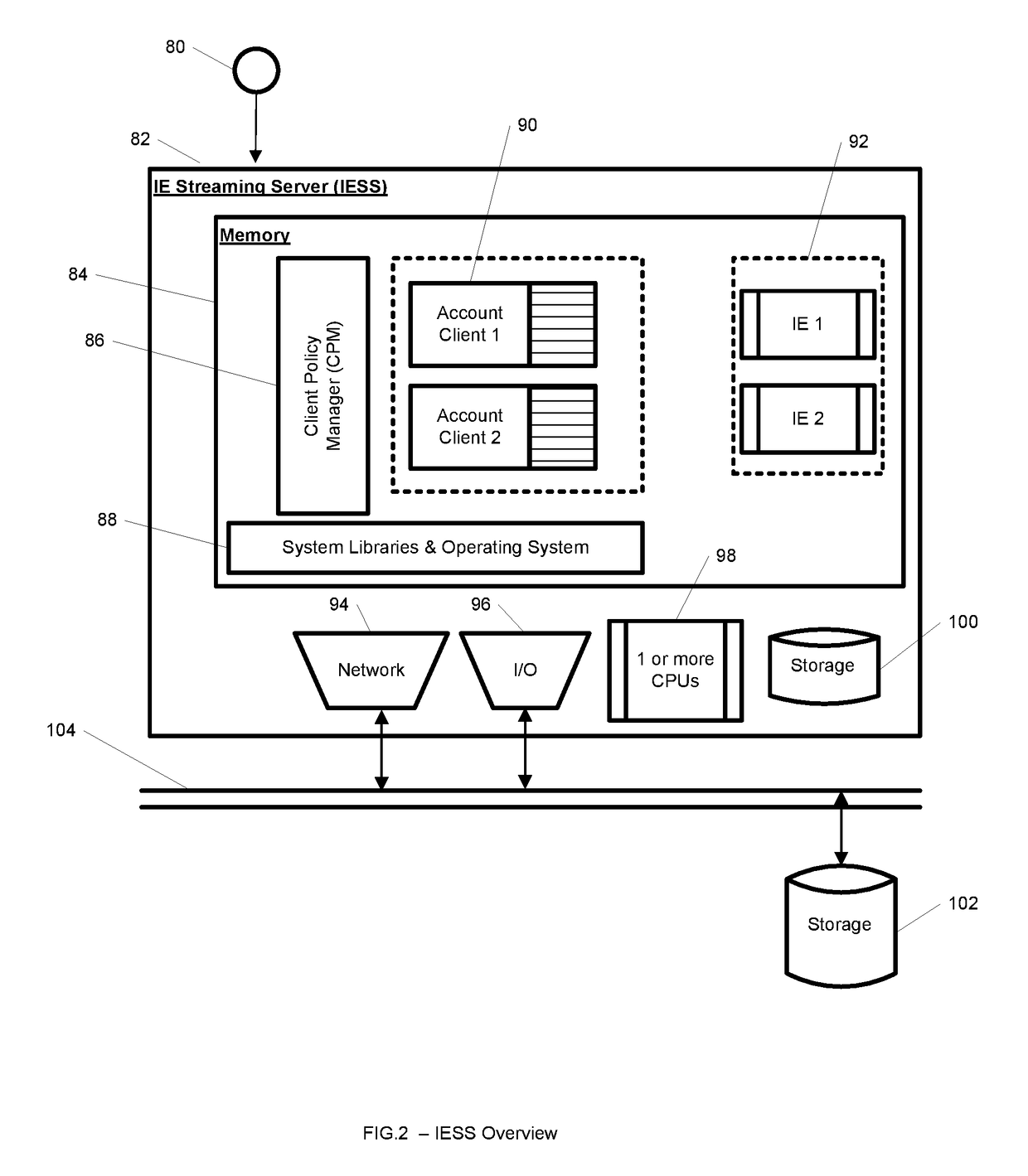
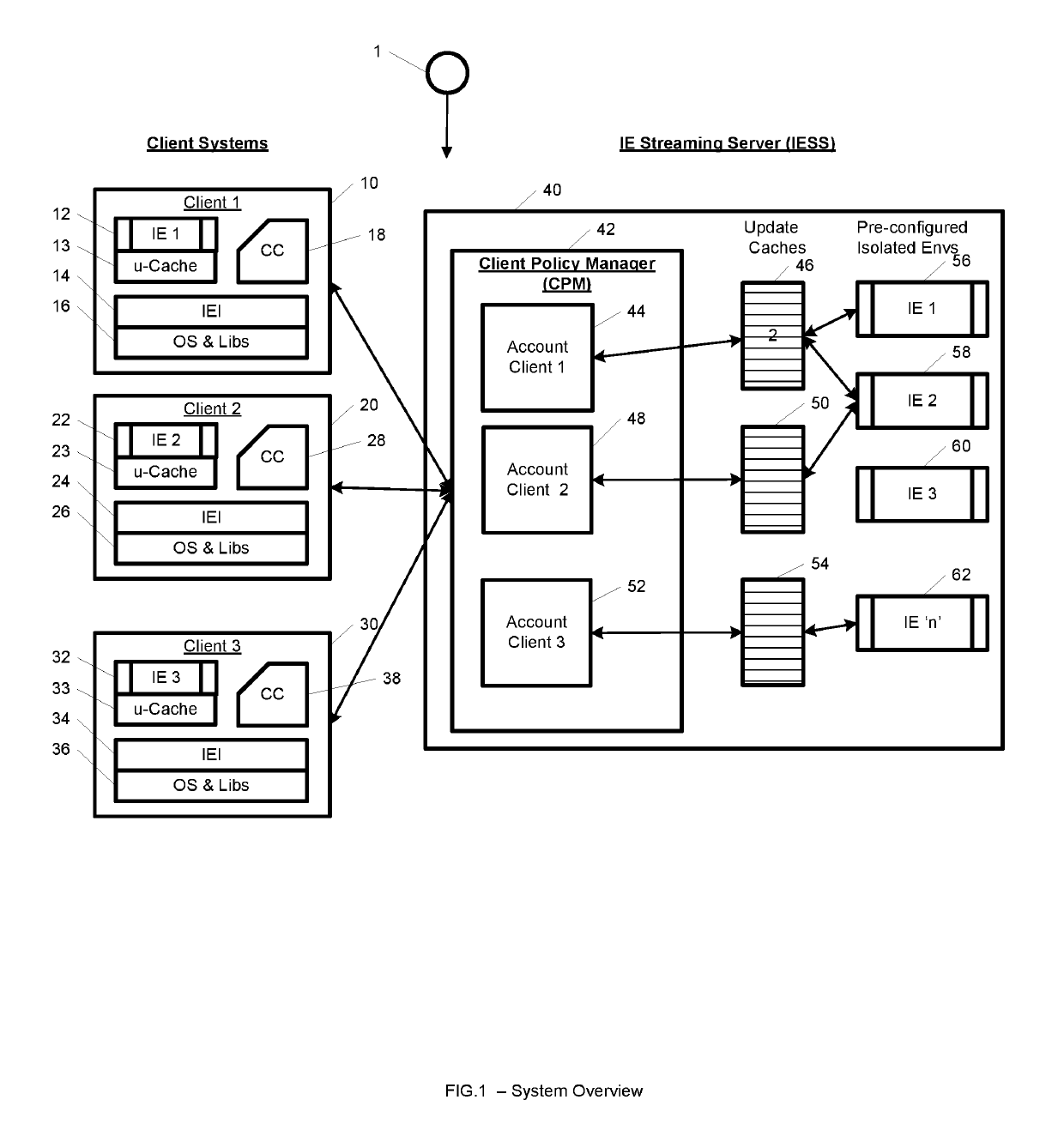
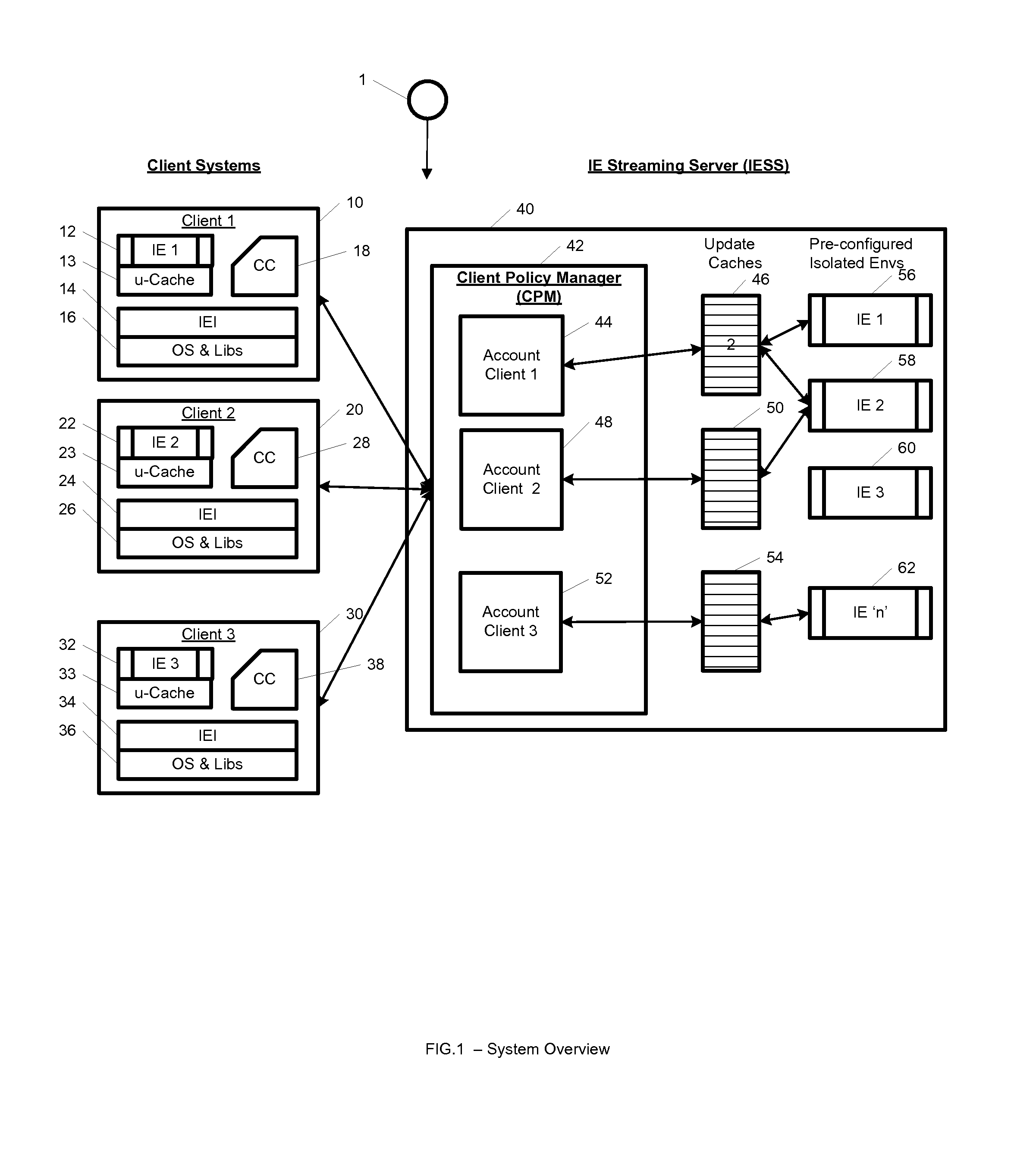
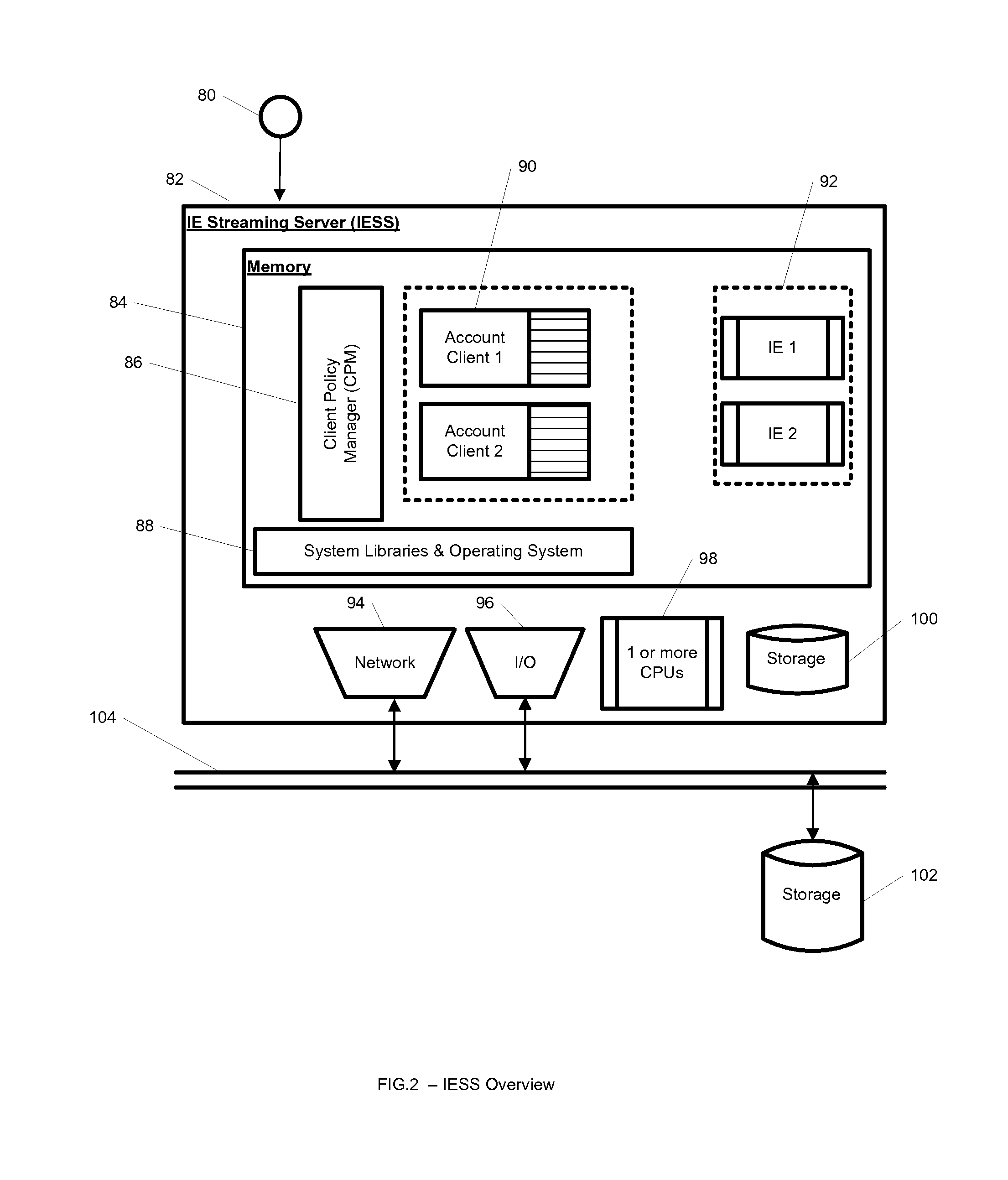
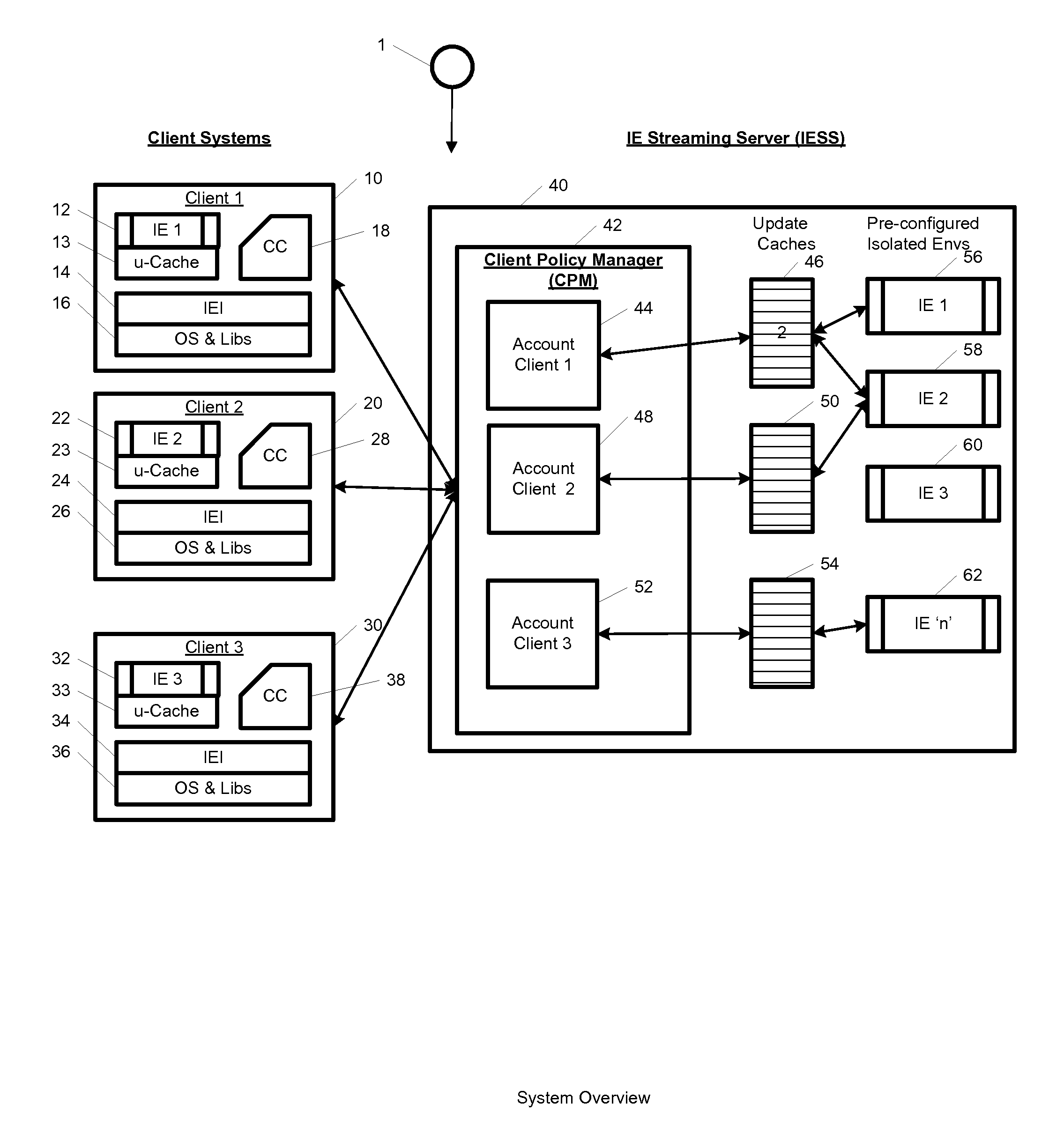
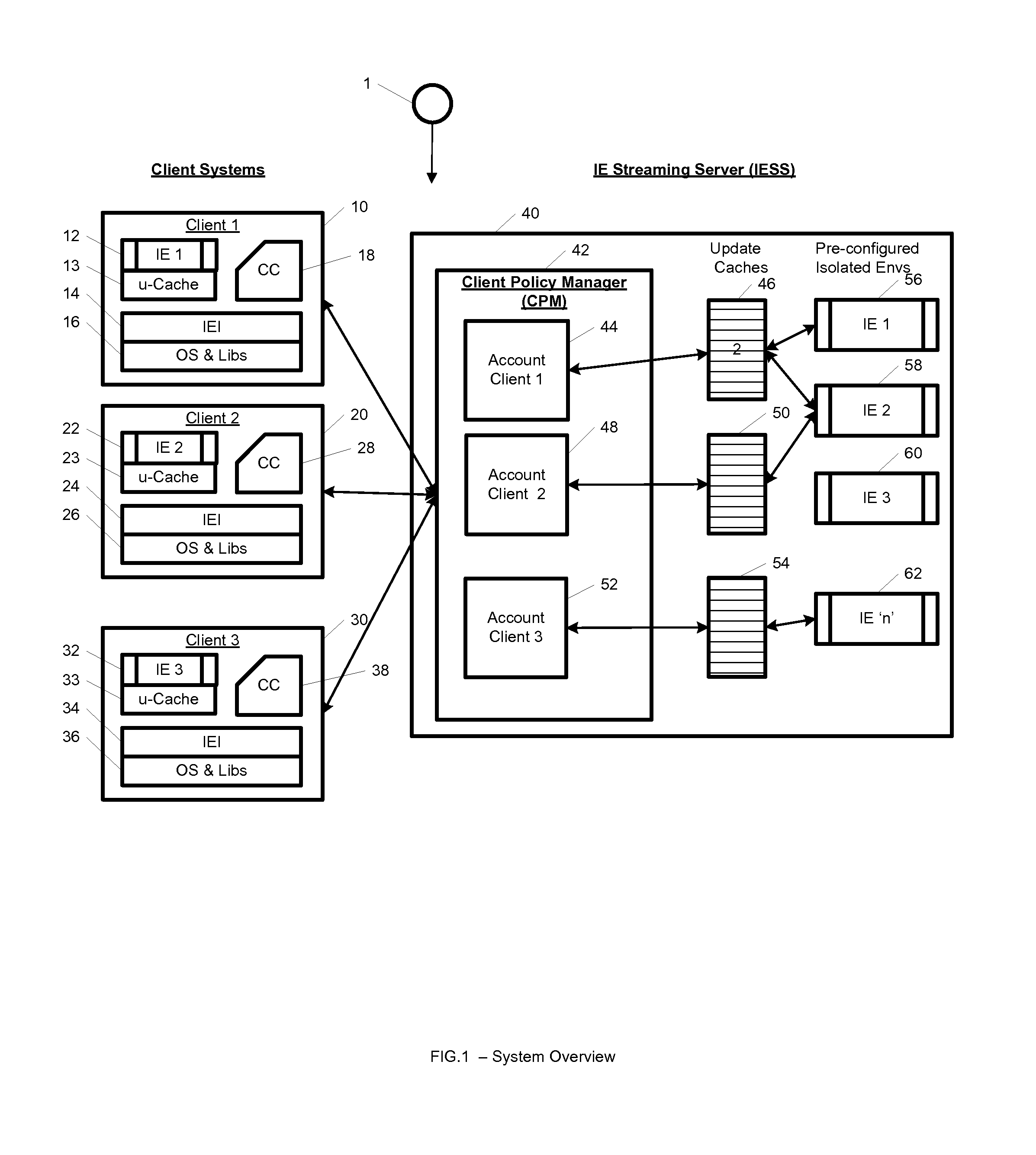
A system, method, computer program and / or computer readable medium for providing streaming of one or more applications from streaming servers onto one or more clients. The computer readable medium includes computer-executable instructions for execution by a processing system. The one or more applications are contained within one or move isolated environments, and the isolated environments are streamed from the servers onto clients. The system may include authentication of the streaming servers and authentication of clients and credentialing of the isolated environments and applications the clients are configured to run. The system may further include encrypted communication between the streaming servers and the clients. The system may further include a management interface where administrators may add, remove and configure isolated environments, configure client policies and credentials, and force upgrades. The streamed isolated environments may be isolated from other applications and the host operating system on the clients and applications within the isolated environments may run without performing an application-installation on the client.
Owner:OPEN INVENTION NEWTORK LLC
Apparatus for reading standardized personal identification credentials for integration with automated access control systems
An apparatus for reading information encoded on standardized personal identification credentials includes a reading device that reads information encoded on 3-track magnetic stripes as well as barcodes, and connects to a computer system to allow complete automation of information collection. The software application uses the apparatus to automate the collection of data from individuals entering a secure facility, and includes a credentialing for recognizing employees, contractors and visitors. The software system allows for visitor pre-announcement, specification of visit duration, and printing of time-sensitive access passes. The software application supports an unlimited number of printers. Security is enhanced through an automatic checking of government supplied terrorists lists, and other ENTRY NOT ALLOWED lists. The software application encrypts important visitor personal data for privacy purposes, and includes a device for customizing system security and data collection. The software application includes reporting, and data exporting utilities.
Owner:HADDAD MICHAEL A
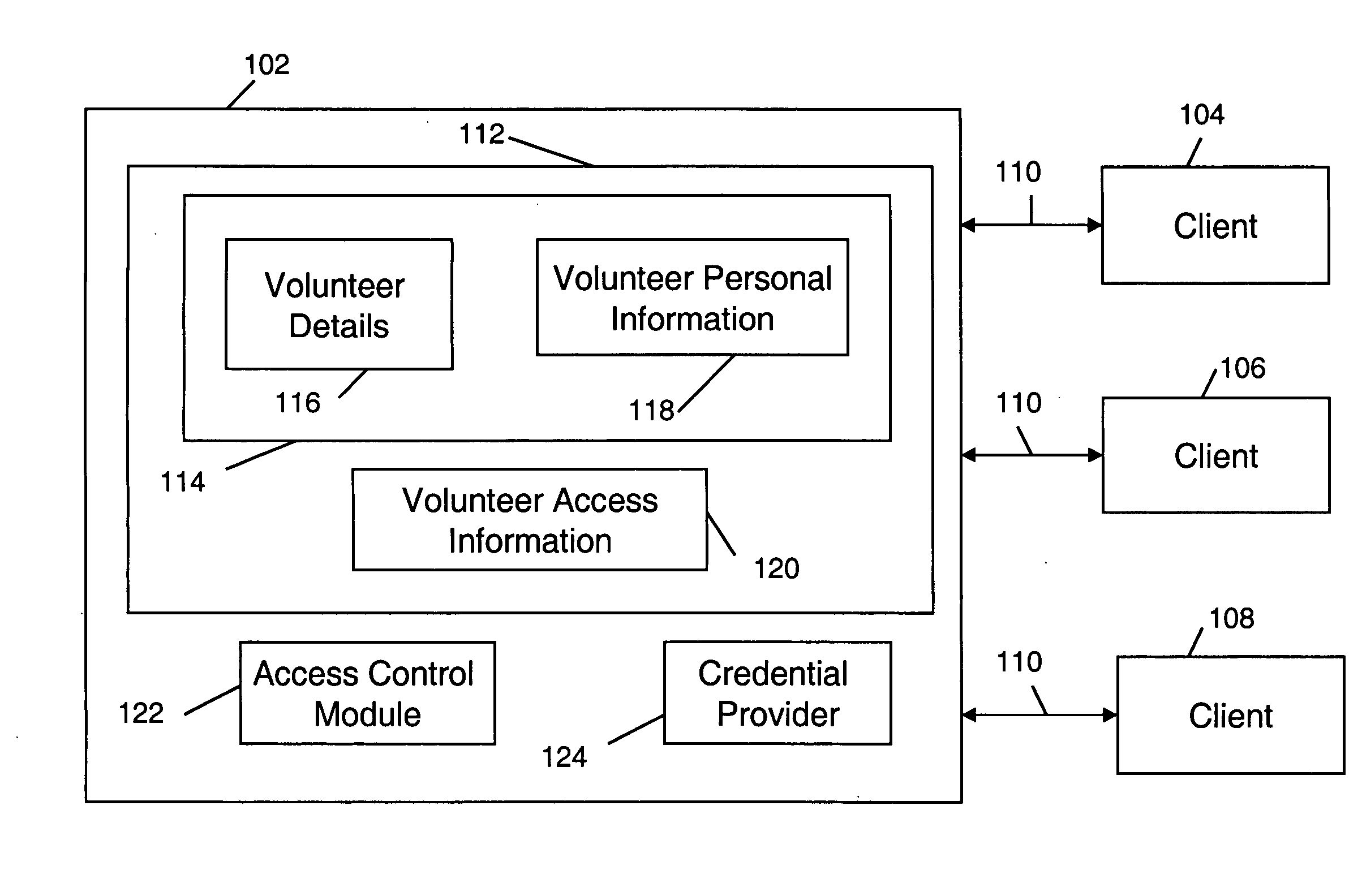
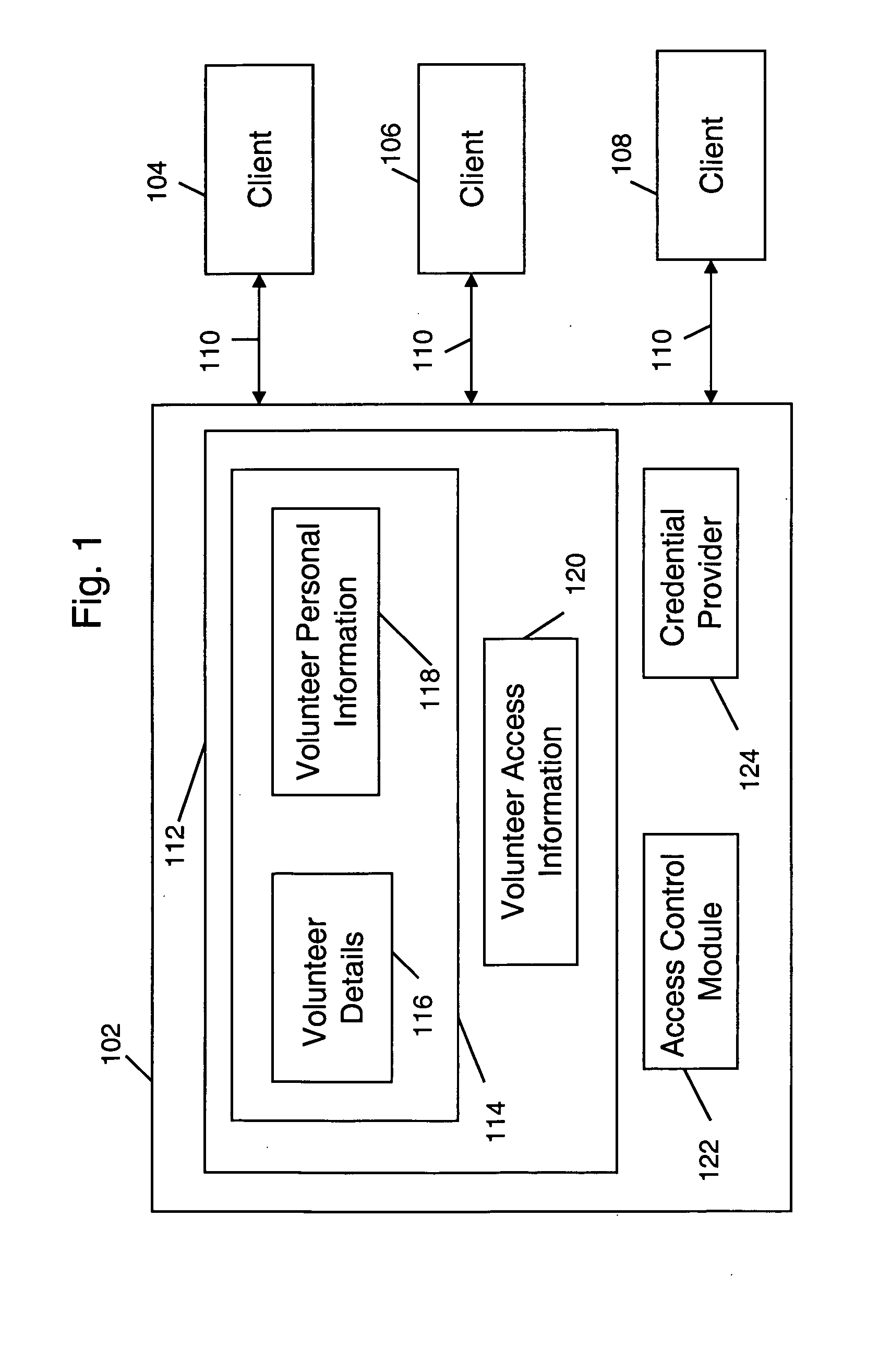
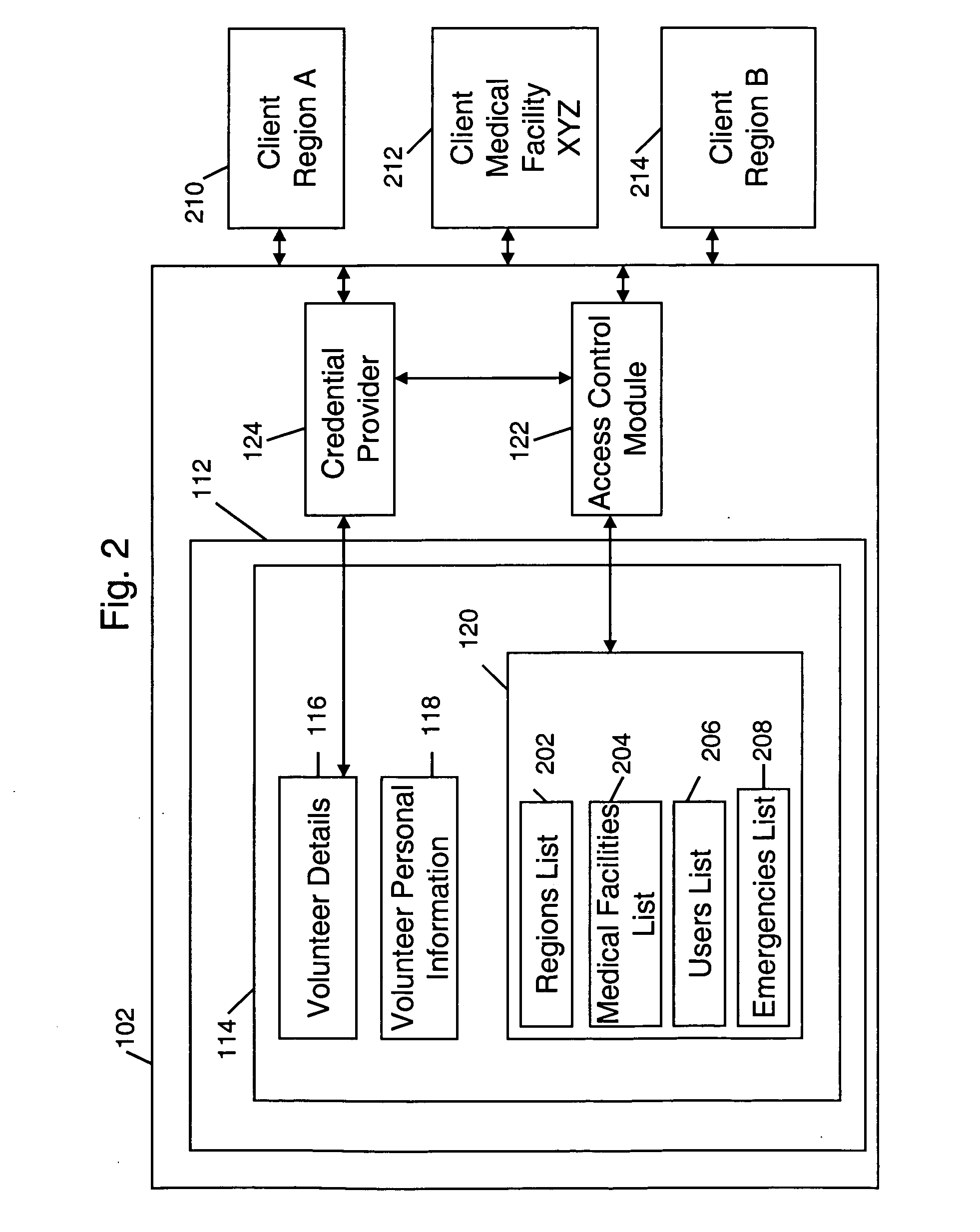
Method and system for advanced credentialing and registration for health care professionals
InactiveUS20080059268A1Data processing applicationsHospital data managementCredentialingComputer science
The present invention provides a method and a system for storing information about volunteers and other medical personnel along with a credential level associated with each volunteer or medical personnel. The credential level is generated on the basis of information provided by the volunteer. The invention also provides for sharing the volunteer information with one or more users that are associated with one or more medical facilities or regions that have a medical emergency. The information is shared on the basis of the access levels that are assigned to the users and to the stored volunteer information.
Owner:ARES CAPITAL +1
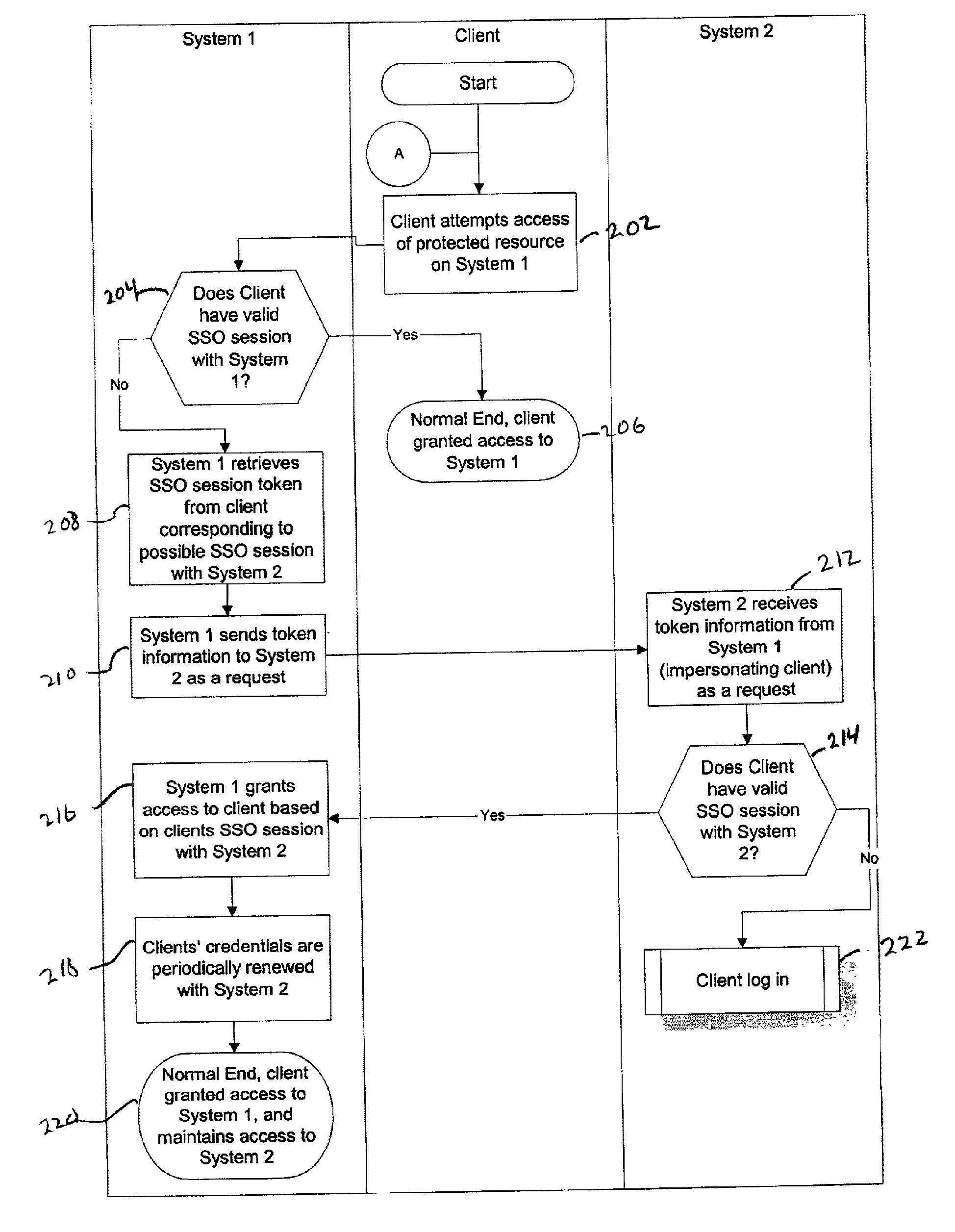
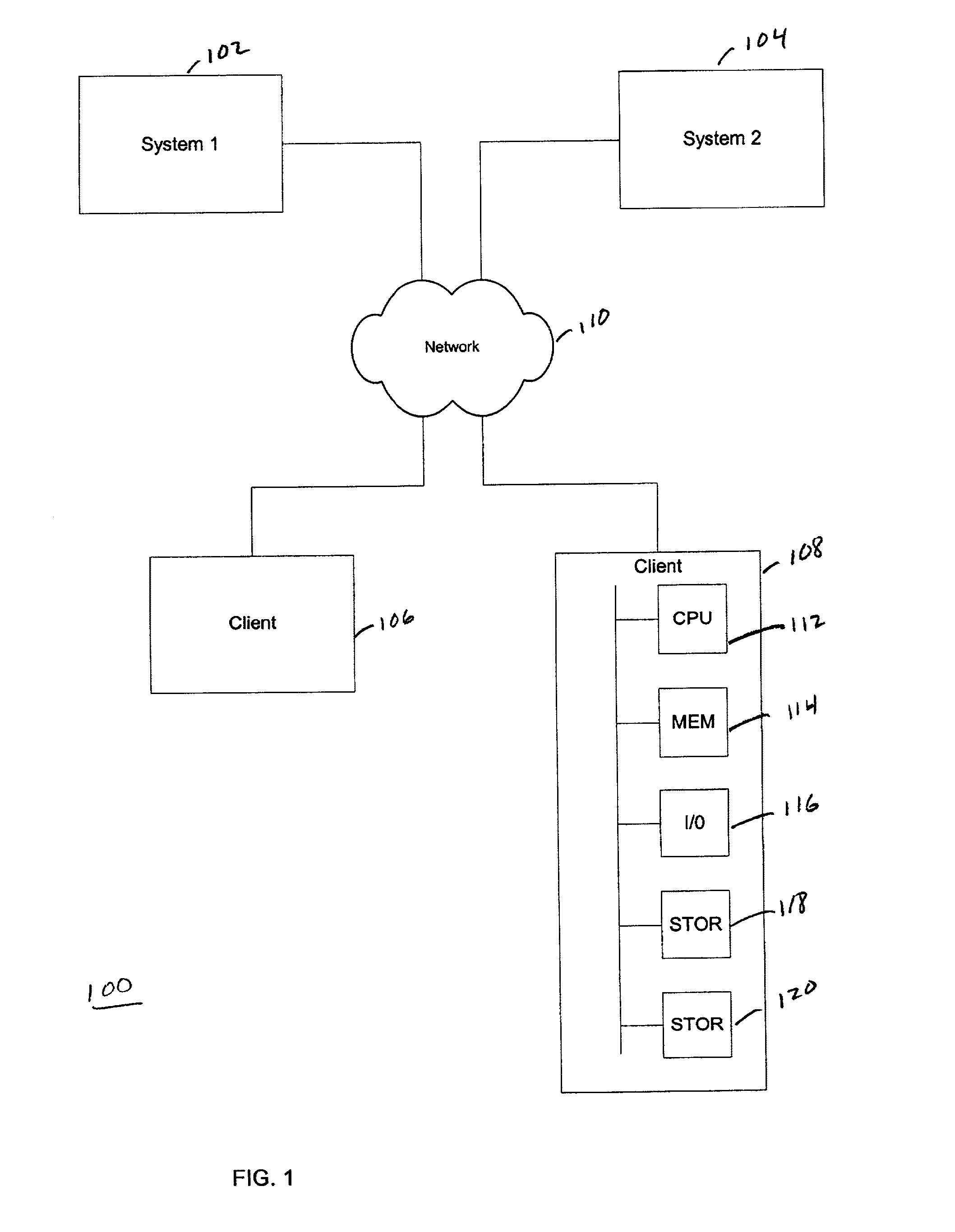
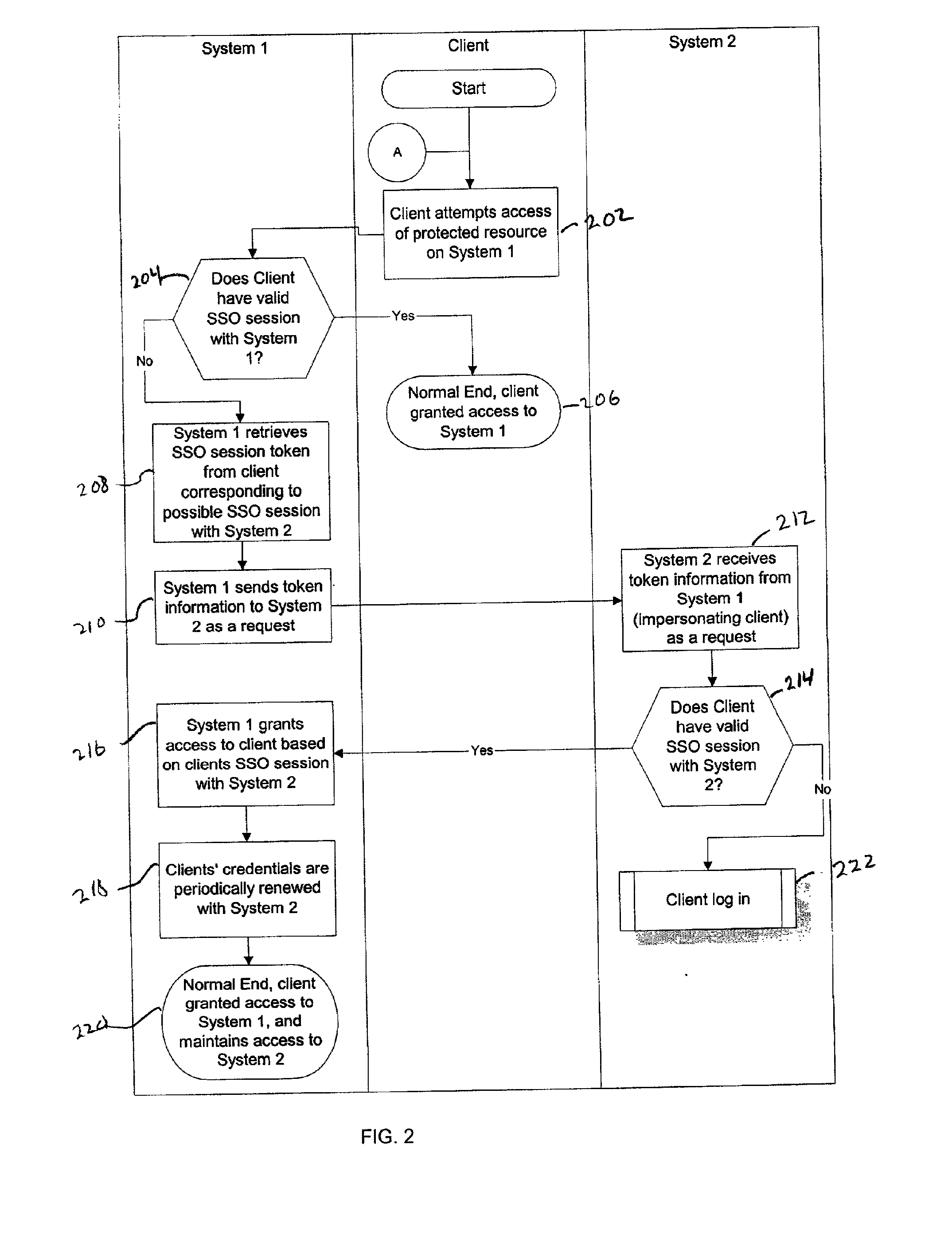
System and Method for Single Session Sign-On
InactiveUS20110252465A1Digital data processing detailsMultiple digital computer combinationsSingle sessionCredentialing
Owner:JPMORGAN CHASE BANK NA
System and method for providing an information platform with credentials validation
InactiveUS20150249661A1Digital data processing detailsMultiple digital computer combinationsCredentialingExternal validation
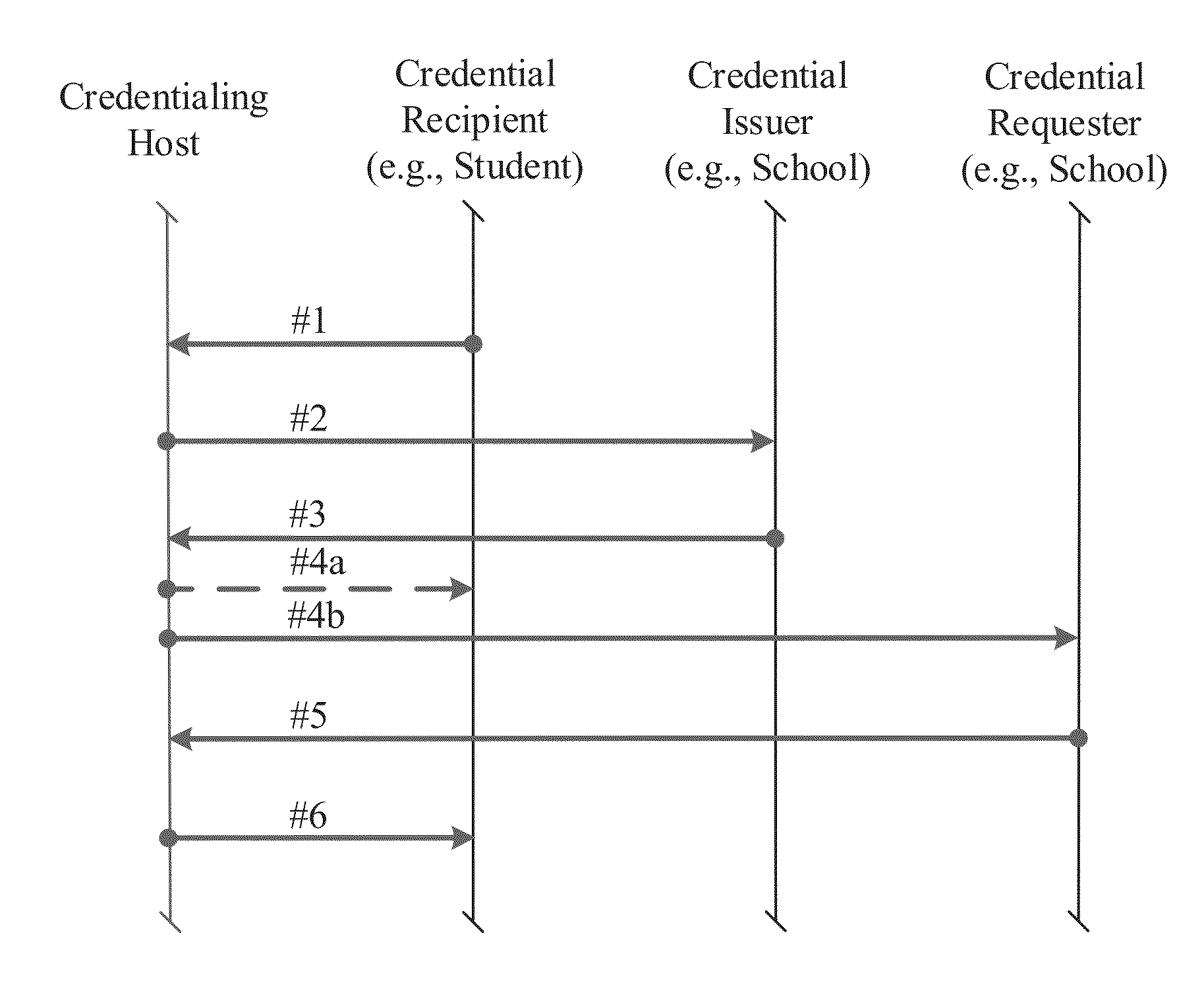
A system and method for providing an information platform with credentials validation are disclosed. A particular embodiment is configured to: receive, from one or more user interface platforms via a data network, a credentialing service request, the credentialing service request including information indicative of an identity of a credential recipient, an identity of a particular credential, and an identity of a credential requester; determine an identity of a credential issuer corresponding to the particular credential and based on the credentialing service request; generate a credential validation request and send the credential validation request to the credential issuer via the data network, the credential validation request including information indicative of the identity of the credential recipient; receive, from the credential issuer via the data network, a credential validation response including information indicative of the credentialing status of the credential recipient relative to the particular credential; and generate a credential certification and send the credential certification to the credential requester via the data network, the credential certification including information indicative of the identity of the credential recipient and information indicative of the credentialing status of the credential recipient relative to the particular credential.
Owner:CAUTHEN LEILANI
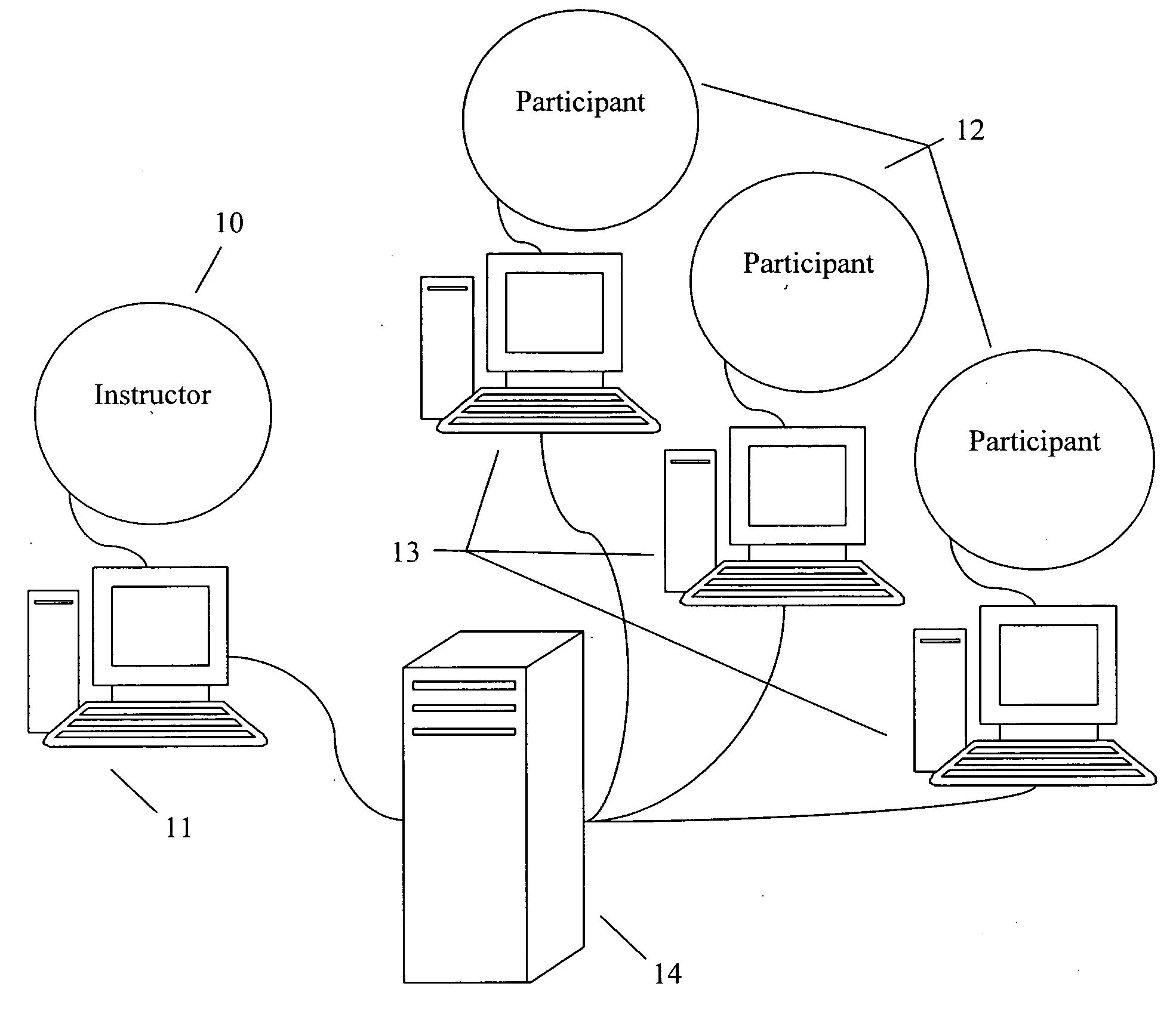
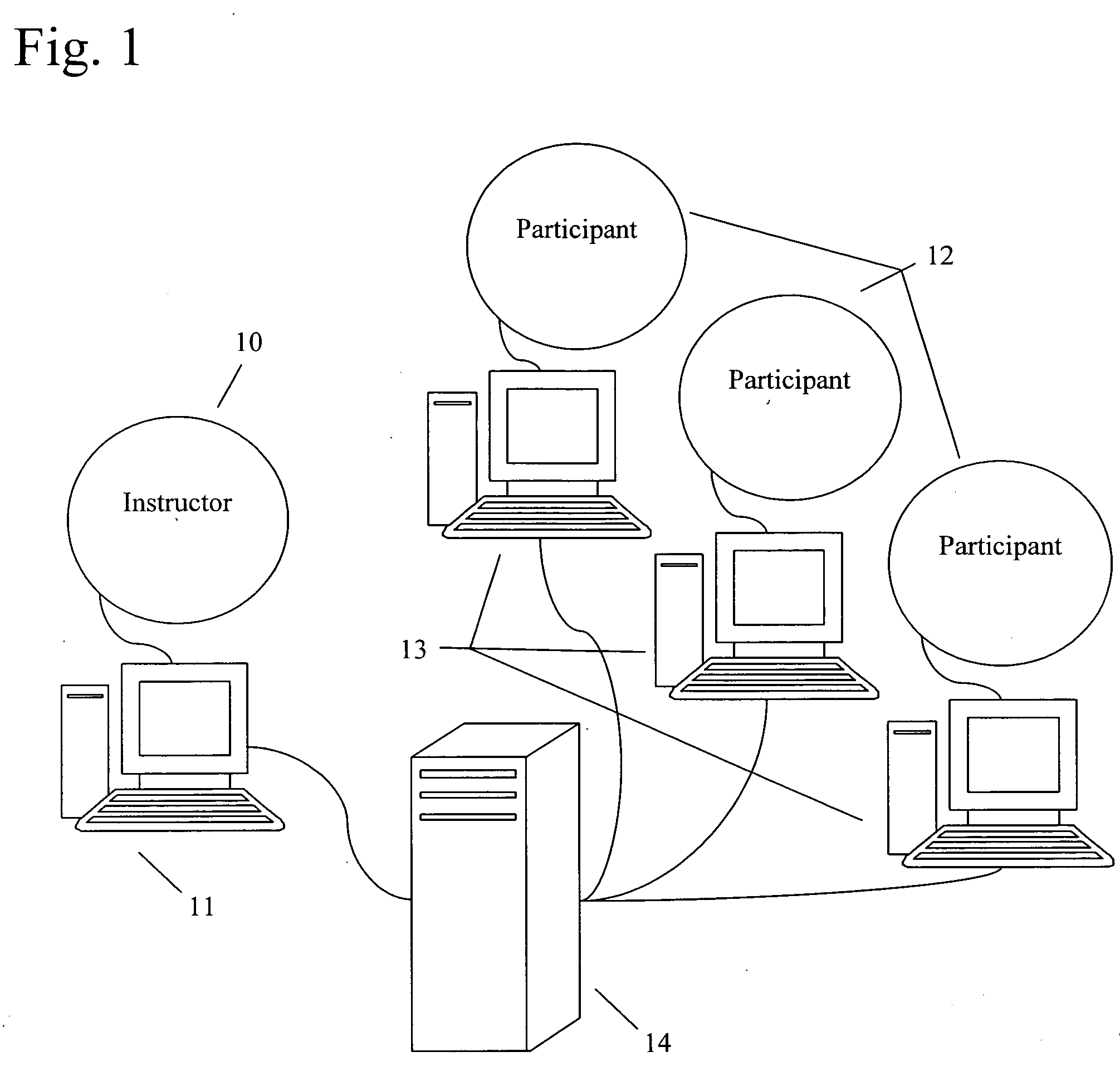
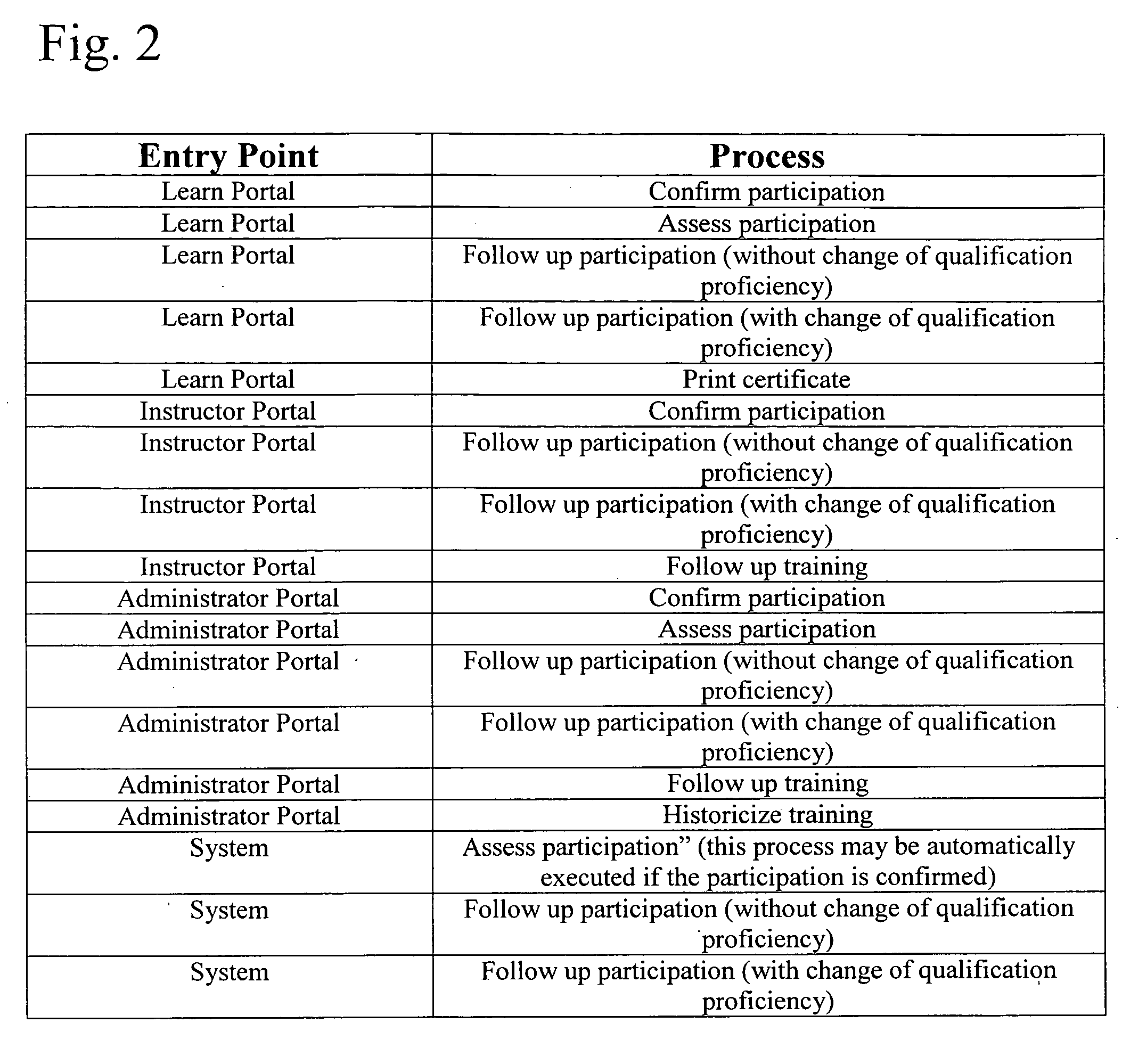
Method and system for computer assisted training and credentialing with follow-up control
A method for computer assisted training and credentialing includes providing a training session, taught by an instructor, or a computer program acting as an instructor, to one or more participants. One or more process steps are executed at corresponding entry points to provide credentialing of those of the one or more participants who are deemed to have satisfactorily participated in the training session.
Owner:SAP AG
Method and system for mobile device credentialing
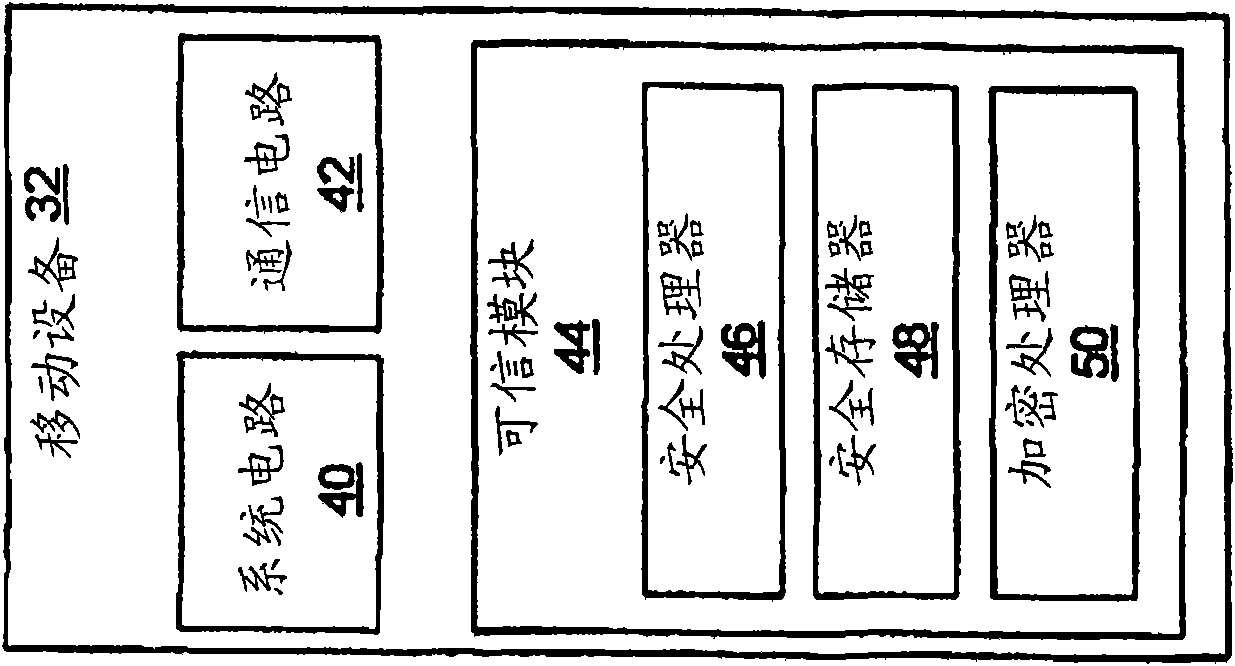
Methods and systems taught herein allow communication device manufacturers to preconfigure communication devices to use preliminary access credentials to gain temporary network access for downloading subscription credentials, and particularly allow the network operator issuing the subscription credentials to verify that individual devices requesting credentials are trusted. In one or more embodiments, a credentialing server is owned or controlled by the network operator, and is used by the network operator to verify that subscription credentials are issued only to trusted communication devices, even though such devices may be referred to the credentialing server by an external registration server and may be provisioned by an external provisioning server. Particularly, the credentialing server interrogates requesting devices for their device certificates and submits these device certificates to an external authorization server, e.g., an independent OCSP server, for verification. A common Public Key Infrastructure (PKI) may be used for operator and device certificates.
Owner:TELEFON AB LM ERICSSON (PUBL)
Systems and devices for real time health status credentialing
Systems and processes are presented for real time health credentialing of individuals seeking entry to a facility requiring health credentialing for access. A system and process for real time detection of a febrile condition comprises providing a heat sensor operable to receive thermal radiation from a person. Optionally, the system provides a controller operable to selectively orient the thermal sensor incident to the facial region of a person within a zone of detection. Further, the system optionally processes the sensor temperature to conditionally determine a febrile condition.
Owner:HELLER ALAN C
System and method for cached streaming application isolation
InactiveUS9762701B1Optimizing streamingDigital data information retrievalProgram initiation/switchingCredentialingOperational system
A system, method, and computer readable medium for providing optimized streaming of one or more applications from streaming servers onto one or more clients. The one or more applications are contained within one or move isolated environments, and the isolated environments are streamed from the servers onto clients. The streaming is optimized using update-caches which are maintained on the streaming server and compared against the client's most recent update-caches. The update-caches are updated when applications are installed, removed or patched inside particular isolated environment and when the operating system is patched or updated. The system may include authentication of the streaming servers and authentication of clients and credentialing of the isolated environments and applications the clients are configured to run. The system may further include encrypted communication between the streaming servers and the clients. The system may further include a management interface where administrators may add, remove and configure isolated environments, configure client policies and credentials, and force upgrades. The streamed isolated environments may be isolated from other applications and the host operating system on the clients and applications within the isolated environments may run without performing an application-installation on the client.
Owner:OPEN INVENTION NEWTORK LLC
System and method for streaming application isolation
ActiveUS10419504B1Internal/peripheral component protectionTransmissionCredentialingOperational system
Providing streaming of one or more applications from streaming servers onto one or more clients. The computer readable medium includes computer-executable instructions for execution by a processing system. The applications are contained within one or more isolated environments, and the isolated environments are streamed from the servers onto clients. The system may include authentication of the streaming servers and authentication of clients and credentialing of the isolated environments and applications the clients are configured to run. The system may include encrypted communication between the streaming servers and the clients. The system may further include a management interface where administrators may add, remove and configure isolated environments, configure client policies and credentials, and force upgrades. The streamed isolated environments may be isolated from other applications and the host operating system on the clients and applications within the isolated environments may run without performing an application-installation on the client.
Owner:IBM CORP
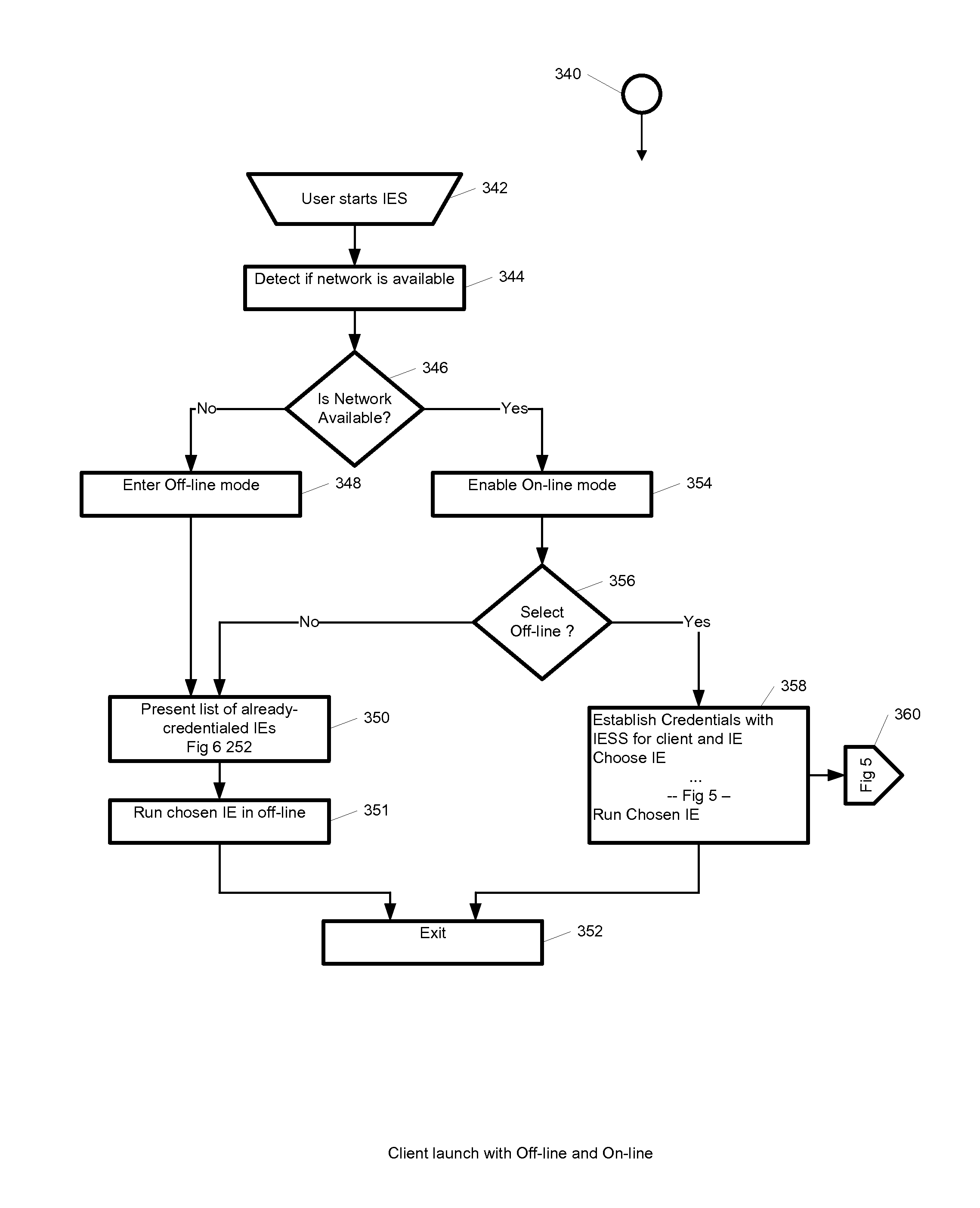
System and method for on-line and off-line streaming application isolation
InactiveUS8555360B1Optimizing streamingDigital data processing detailsMultiple digital computer combinationsCredentialingOperational system
A system, method, and computer readable medium for providing streaming of one or more applications from streaming servers onto one or more clients. The one or more applications are contained within one or move isolated environments, and the isolated environments are streamed from the servers onto clients. The system may include the option of running both in on-line and off-line. When on-line, the system may include authentication of the streaming servers and authentication of clients and credentialing of the isolated environments and applications the clients are configured to run. The system may further include encrypted communication between the streaming servers and the clients. When off-line, the system may include the ability to run already installed isolated environments without requiring credentialing. The system may further include a management interface where administrators may add, remove and configure isolated environments, configure client policies and credentials, and force upgrades. The streamed isolated environments may be isolated from other applications and the host operating system on the clients and applications within the isolated environments may run without performing an application-installation on the client.
Owner:IBM CORP
System and method for assembling and analyzing candidate application for credential
InactiveCN104823403ADigital data processing detailsUser identity/authority verificationCredentialingComputer science
An automated system and method for assembling and analyzing a candidate application to determine a type of credential in a professional credentialing area for the candidate is provided. The automated system may facilitate the receipt of application materials from various sources and may enable review and appraisal of the application by multiple parties. The application may be tailored to a specific type of requested credential.
Owner:AMERICAN NURSES CREDENTIALING CENT
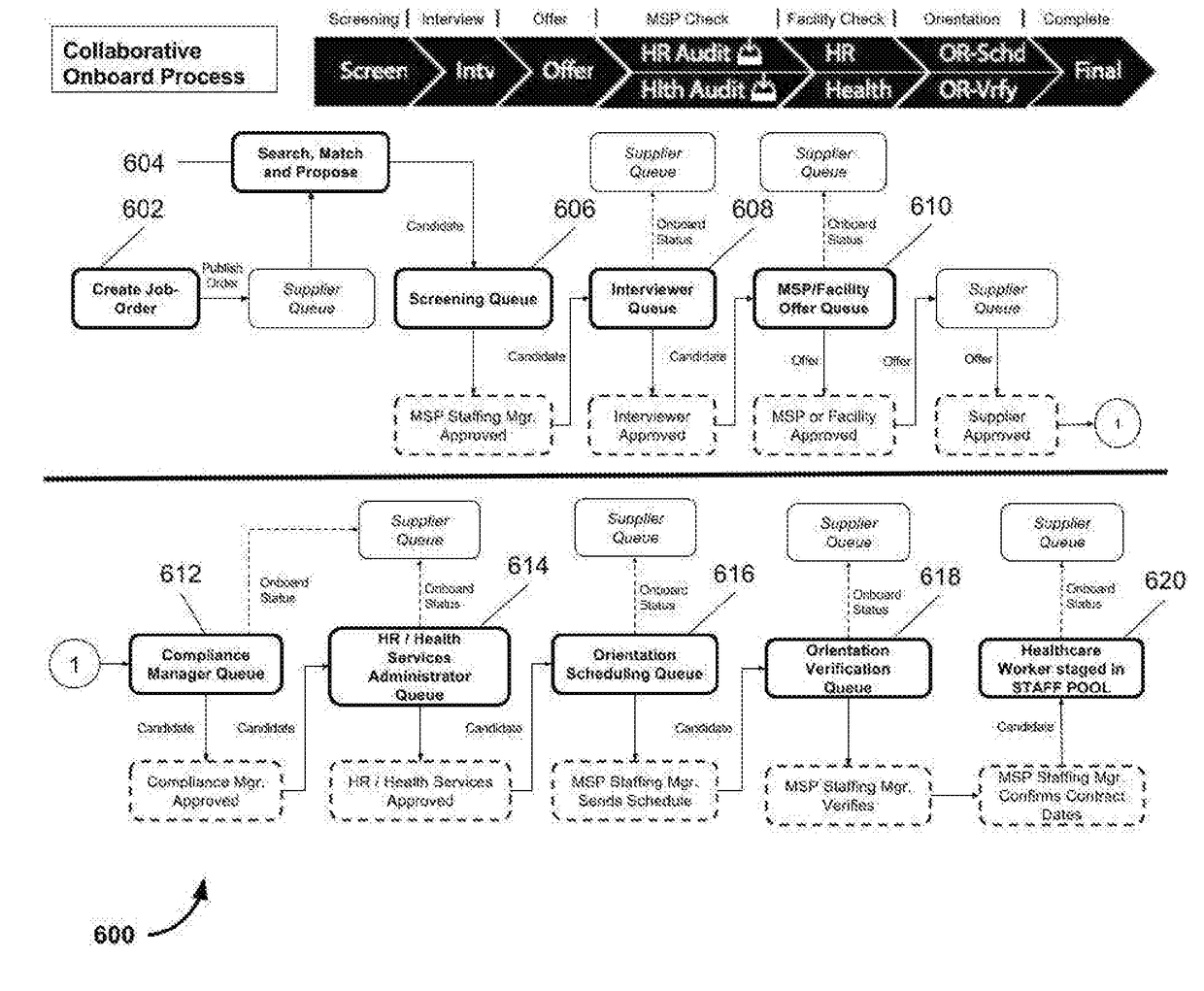
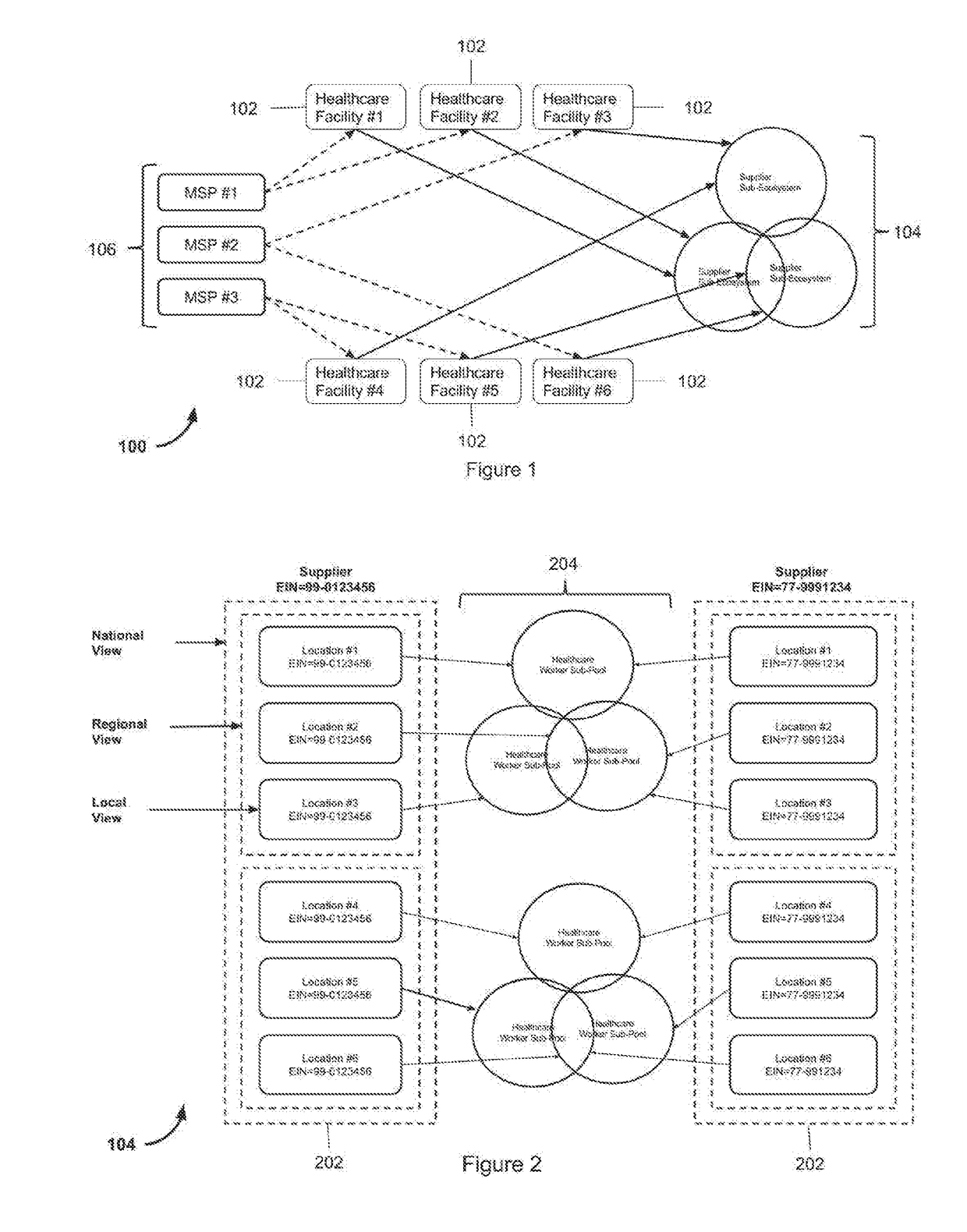
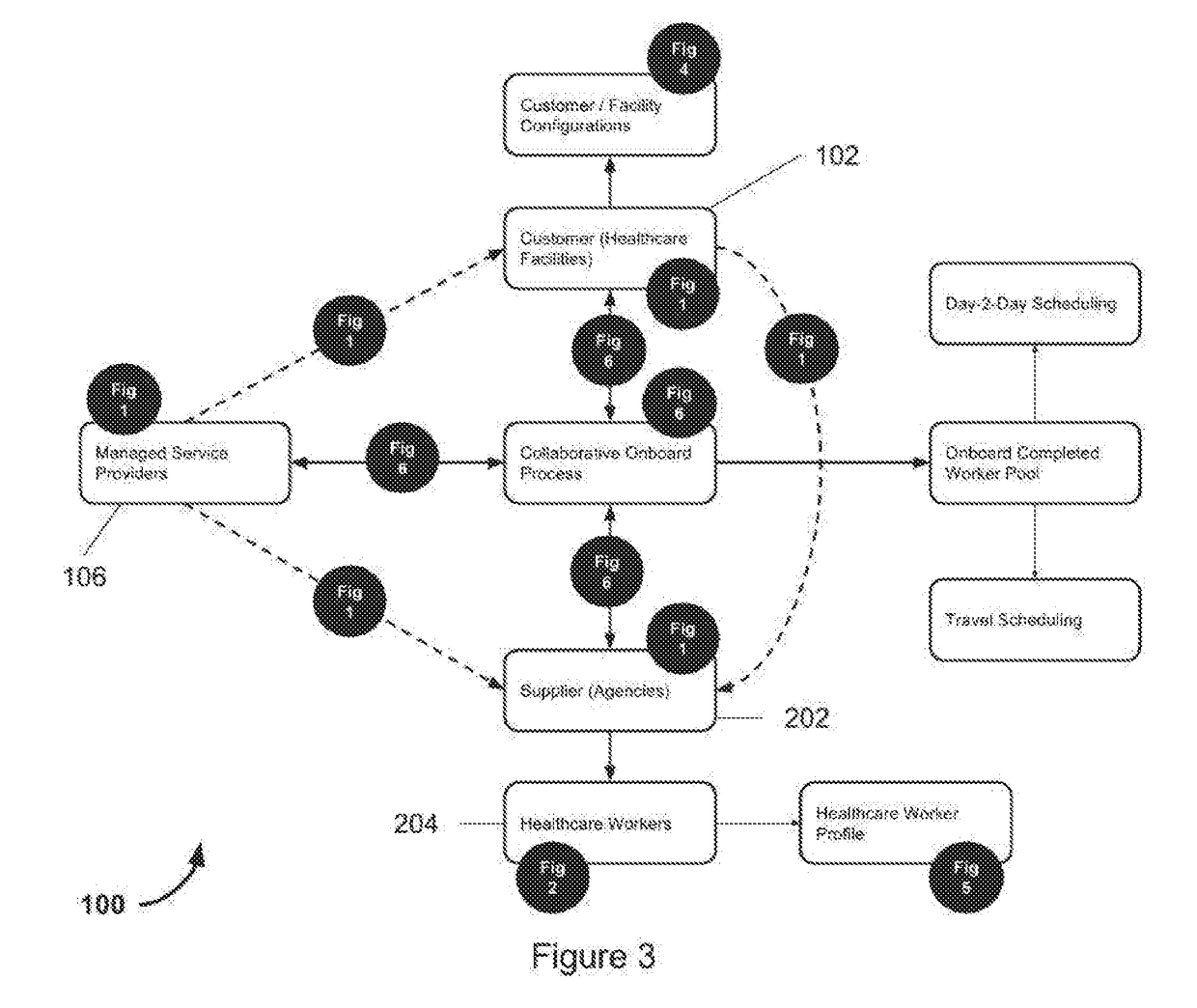
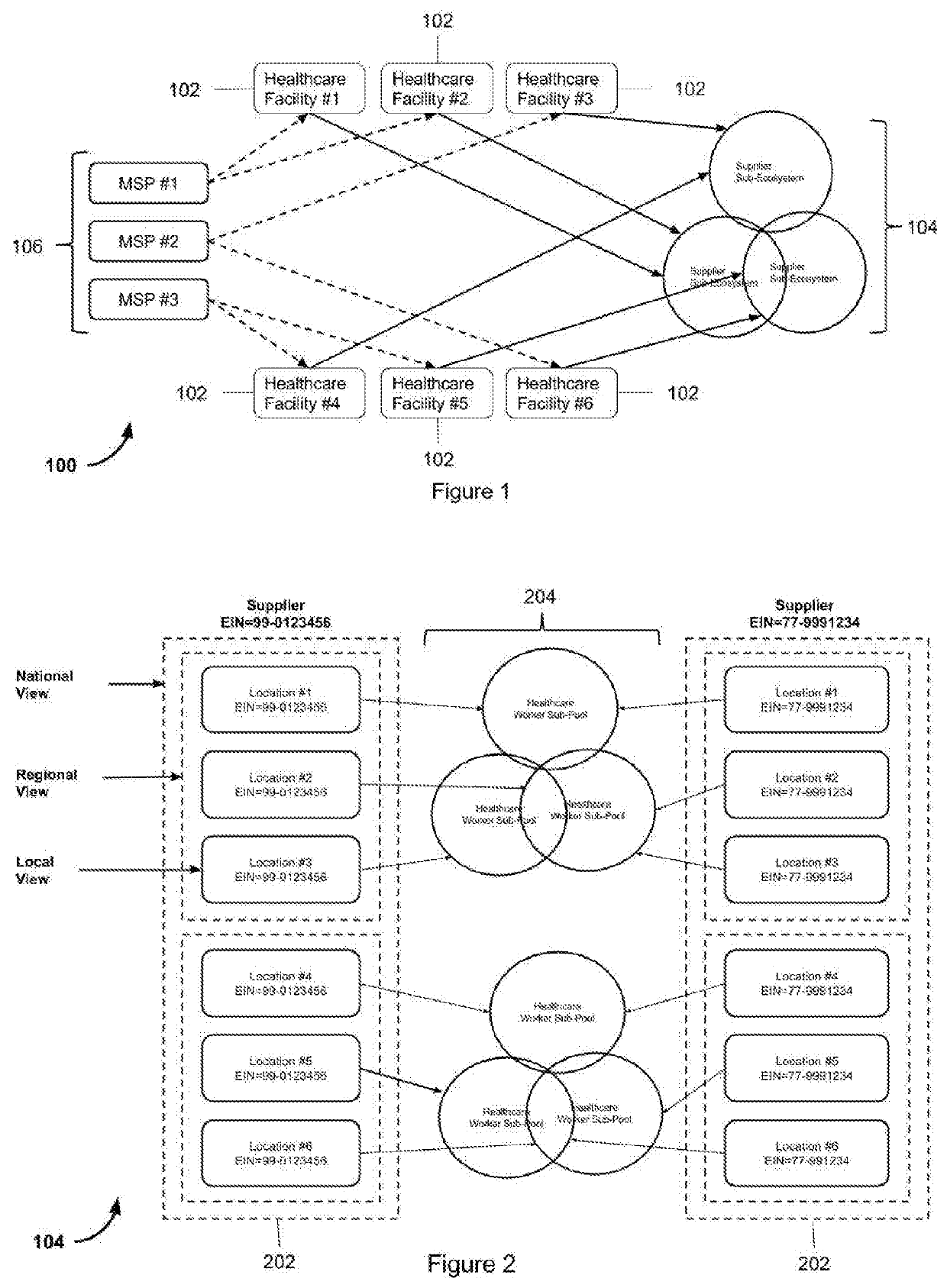
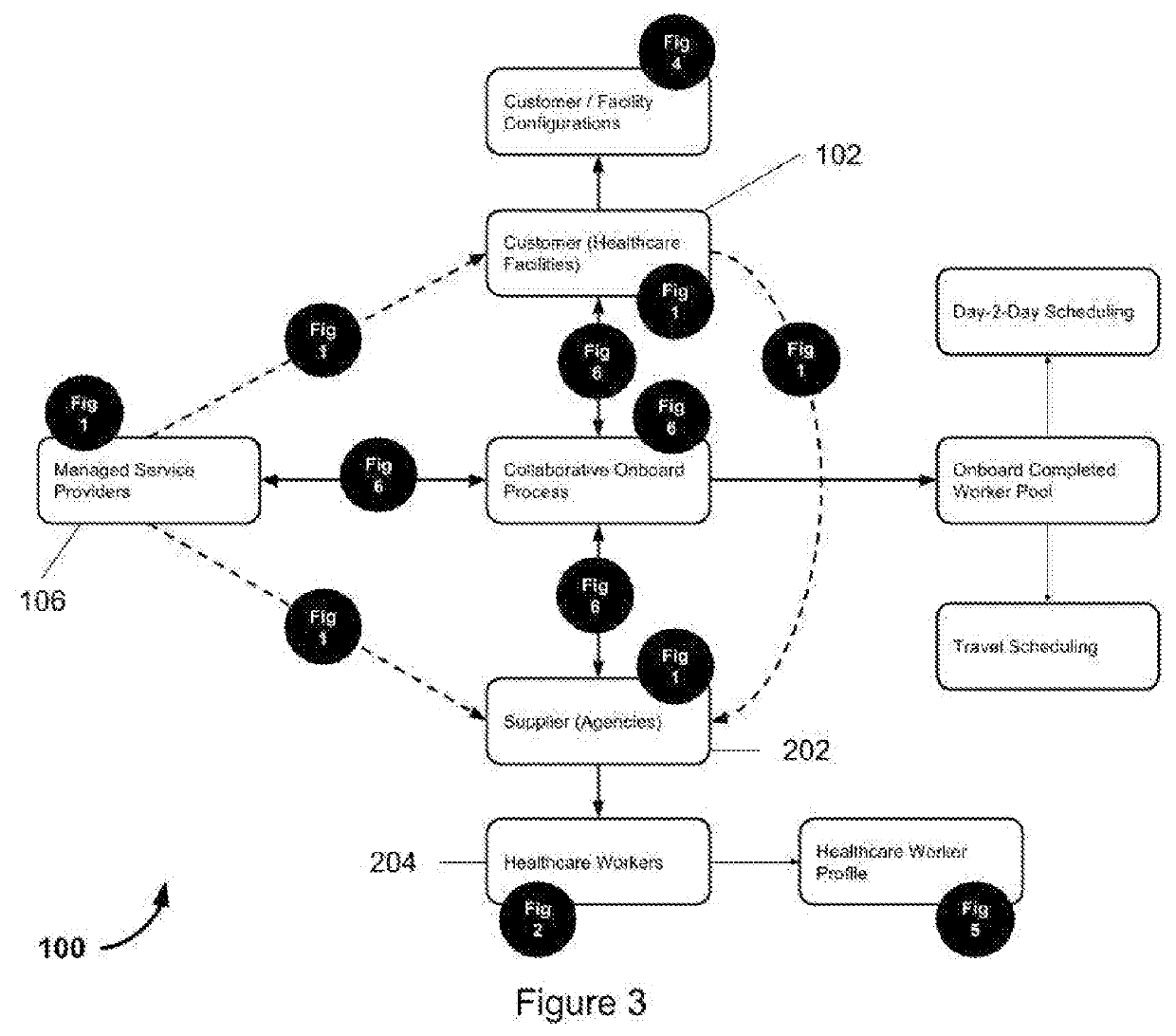
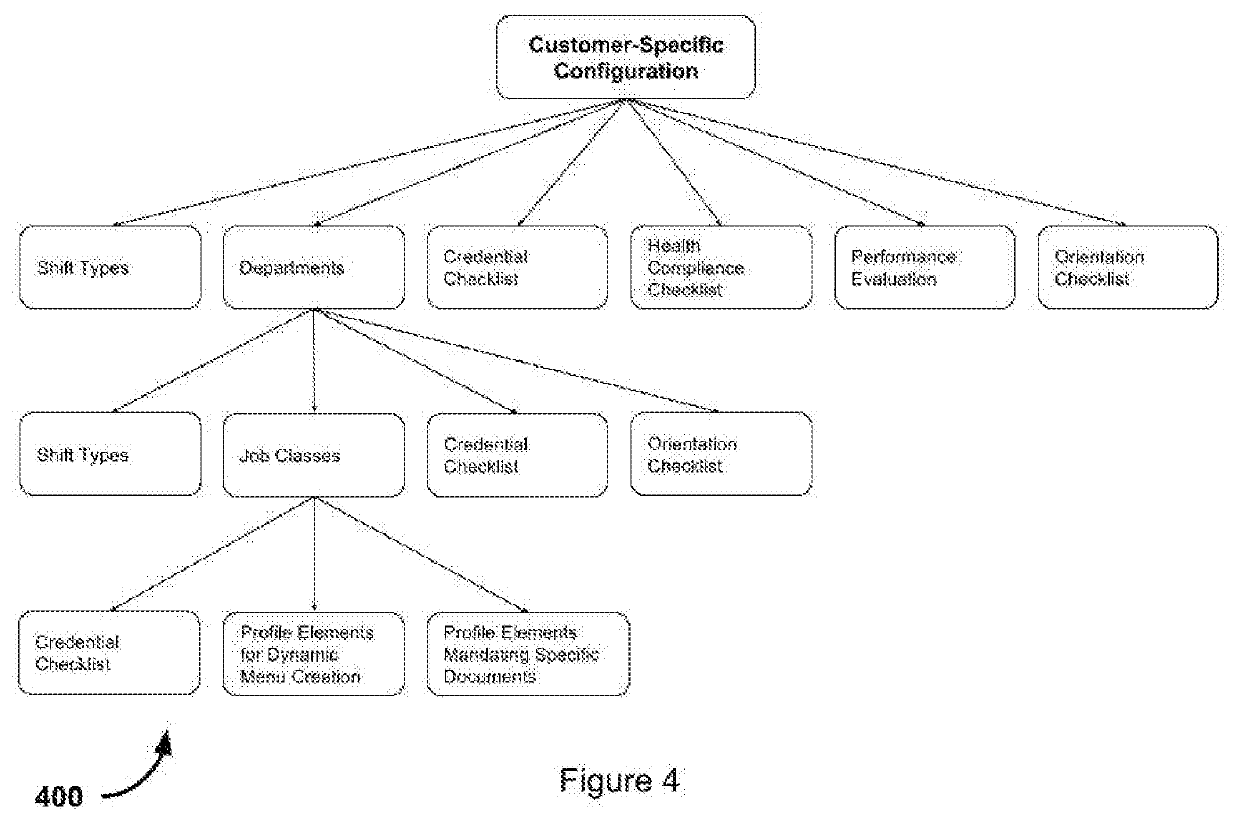
Managed service provider system for collaborative healthcare credentialing, compliance, and scheduling across shared suppliers
ActiveUS20170300640A1Prevents over subscriptionAvoids unnecessary withdrawalOffice automationHospital data managementCredentialingBroadcasting
A MSP platform provides contingent healthcare worker recruiting and shift assignation in a multilayered process of job order broadcasting, competency matching, proposals from healthcare agencies aka vendors, screening, compliance management, and onboard of each candidate. Each staff profile submitted has to go through multilayered review, approval, and orientation process. Additionally, each healthcare worker's calendar, credential, and compliance have to be managed across multiple employers to prevent scheduling conflict and compliance violations, and guaranteeing full visibility of all healthcare workers across the entire supply chain. MSPs (Managed Service Providers) have the ability to service a large number of facilities on whose behalf the MSPs generate job orders for contingent workforce, and manage fulfillment using suppliers (aka vendors) mapped to the facility being serviced. The supplier ecosystem is a cohesive block that may be shared across all MSPs, and several such MSP ecosystems should be allowed to coexist in the system. Suppliers can be tiered by geography allowing a large vendor network to track demand from one or more healthcare facilities across a single location or a group of vendor locations. Additionally, a facility that is part of an MSP should also be able to work directly with all suppliers either in conjunction with or independent of an MSP. Both long term assignments referred to as ‘Travel’ position, and on-demand shift assignments referred to as ‘Day-to-day’ position are serviceable under this centrally available software commonly referred to as ‘Software as a Service’.
Owner:GULZAR NADIR
System and method for streaming application isolation
ActiveUS9253184B1Optimizing streamingTransmissionSecurity arrangementCredentialingOperational system
Providing streaming of one or more applications from streaming servers onto one or more clients. The computer readable medium includes computer-executable instructions for execution by a processing system. The applications are contained within one or more isolated environments, and the isolated environments are streamed from the servers onto clients. The system may include authentication of the streaming servers and authentication of clients and credentialing of the isolated environments and applications the clients are configured to run. The system may include encrypted communication between the streaming servers and the clients. The system may further include a management interface where administrators may add, remove and configure isolated environments, configure client policies and credentials, and force upgrades. The streamed isolated environments may be isolated from other applications and the host operating system on the clients and applications within the isolated environments may run without performing an application-installation on the client.
Owner:IBM CORP
System and method for on-line and off-line streaming application isolation
ActiveUS9369358B1Optimizing streamingPlatform integrity maintainanceData switching networksCredentialingOnline and offline
Owner:INT BUSINESS MASCH CORP
System and method for cached streaming application isolation
InactiveUS9577893B1Optimizing streamingPlatform integrity maintainanceData switching networksOperational systemCredentialing
A system, method, and computer readable medium for providing optimized streaming of one or more applications from streaming servers onto one or more clients. The one or more applications are contained within one or move isolated environments, and the isolated environments are streamed from the servers onto clients. The streaming is optimized using update-caches which are maintained on the streaming server and compared against the client's most recent update-caches. The update-caches are updated when applications are installed, removed or patched inside particular isolated environment and when the operating system is patched or updated. The system may include authentication of the streaming servers and authentication of clients and credentialing of the isolated environments and applications the clients are configured to run. The system may further include encrypted communication between the streaming servers and the clients. The system may further include a management interface where administrators may add, remove and configure isolated environments, configure client policies and credentials, and force upgrades. The streamed isolated environments may be isolated from other applications and the host operating system on the clients and applications within the isolated environments may run without performing an application-installation on the client.
Owner:OPEN INVENTION NEWTORK LLC
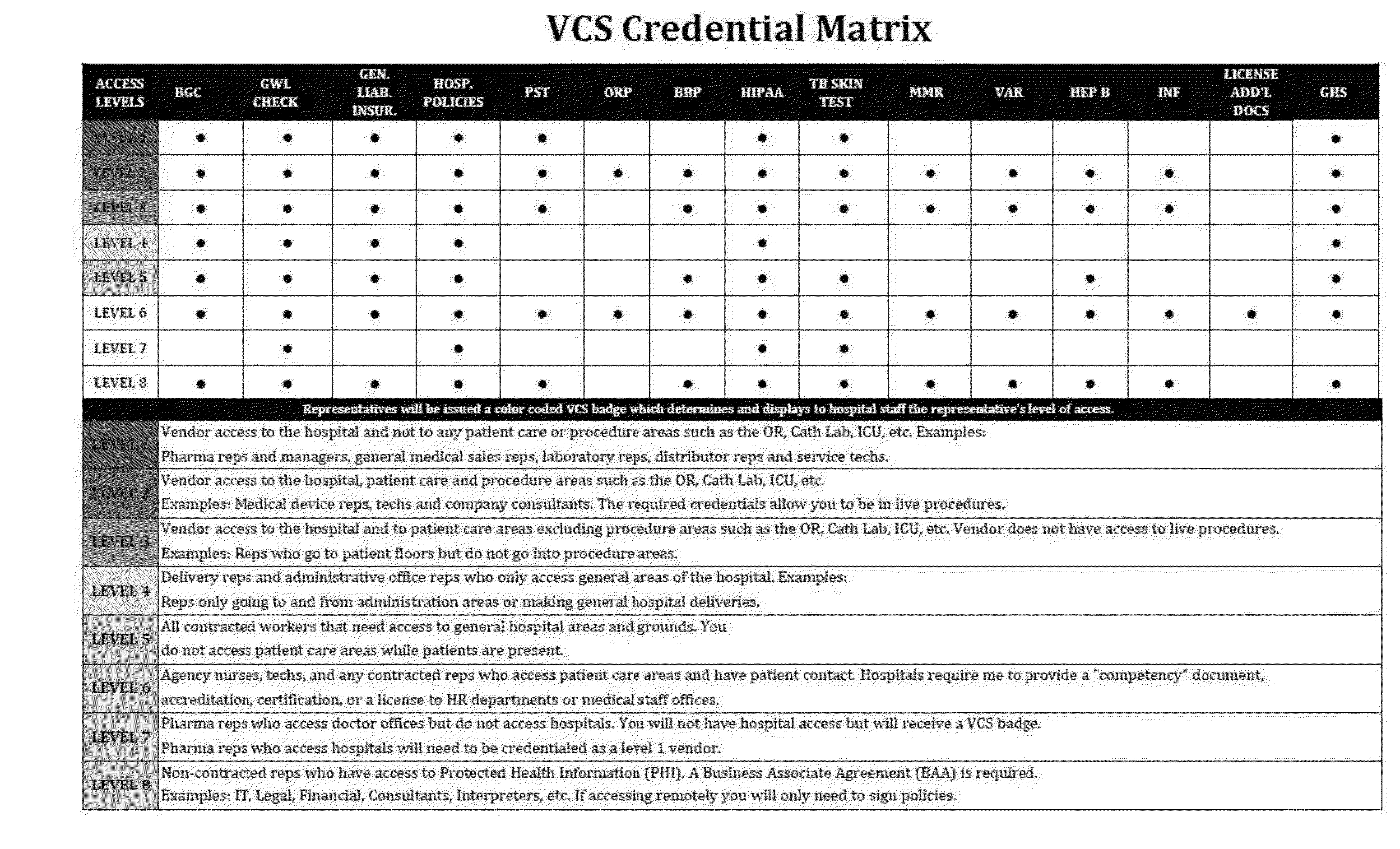
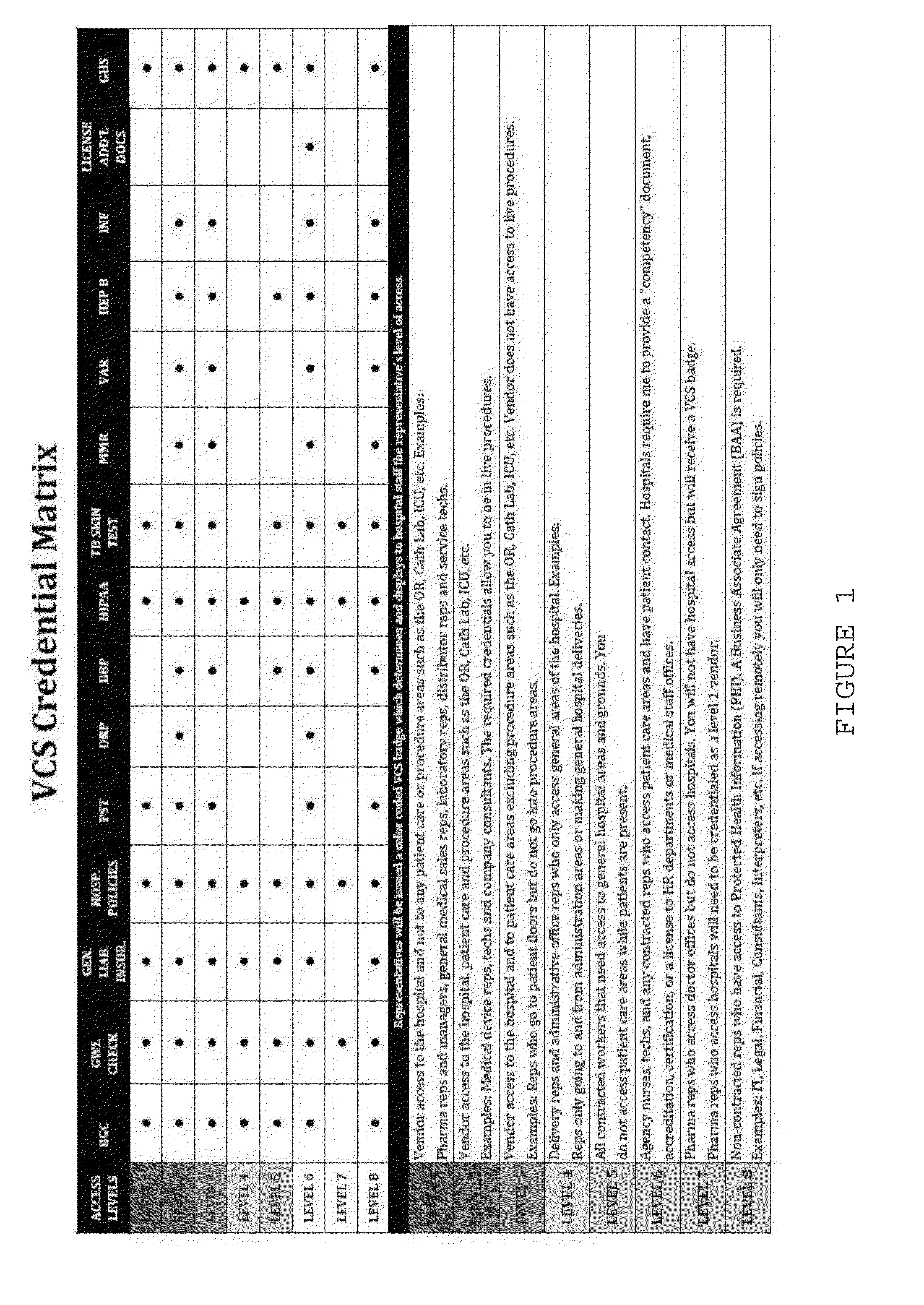
Custom credentialing
InactiveUS20160027227A1Electric signal transmission systemsDigital data processing detailsCredentialingDatabase
In one example, credentialing method involving a credentialing provider and a client comprising the step of establishing one or more custom credential categories for an entity.
Owner:VENDOR CREDENTIALING SERVICE
Managed service provider system for collaborative healthcare scheduling, credentialing, and compliance across shared suppliers
InactiveUS20200005935A1Prevents over subscriptionAvoids unnecessary withdrawalOffice automationHealthcare resources and facilitiesCredentialingService provision
An MSP platform provides contingent healthcare worker recruiting and shift assignation in a multilayered process of job order broadcasting, competency matching, proposals from healthcare agencies aka vendors, screening, compliance management, and onboard of each candidate. Each staff profile submitted has to go through multilayered review, approval, and orientation process. Additionally, each healthcare worker's calendar, credential, and compliance have to be managed across multiple employers to prevent scheduling conflict and compliance violations, and guaranteeing full visibility of all healthcare workers across the entire supply chain. MSPs (Managed Service Providers) have the ability to service a large number of facilities on whose behalf the MSPs generate job orders for contingent workforce, and manage fulfillment using suppliers (aka vendors) mapped to the facility being serviced. The supplier ecosystem is a cohesive block that may be shared across all MSPs, and several such MSP ecosystems should be allowed to coexist in the system. Suppliers can be tiered by geography allowing a large vendor network to track demand from one or more healthcare facilities across a single location or a group of vendor locations. Additionally, a facility that is part of an MSP should also be able to work directly with all suppliers either in conjunction with or independent of an MSP. Both long term assignments referred to as ‘Travel’ position, and on-demand shift assignments referred to as ‘Day-to-day’ position are serviceable under this centrally available software commonly referred to as ‘Software as a Service’.
Owner:GULZAR NADIR
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com