Patents
Literature
1063 results about "Entry point" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, an entry point is where control enters a program or piece of code. In many programming languages, the main function is where a program starts its execution.
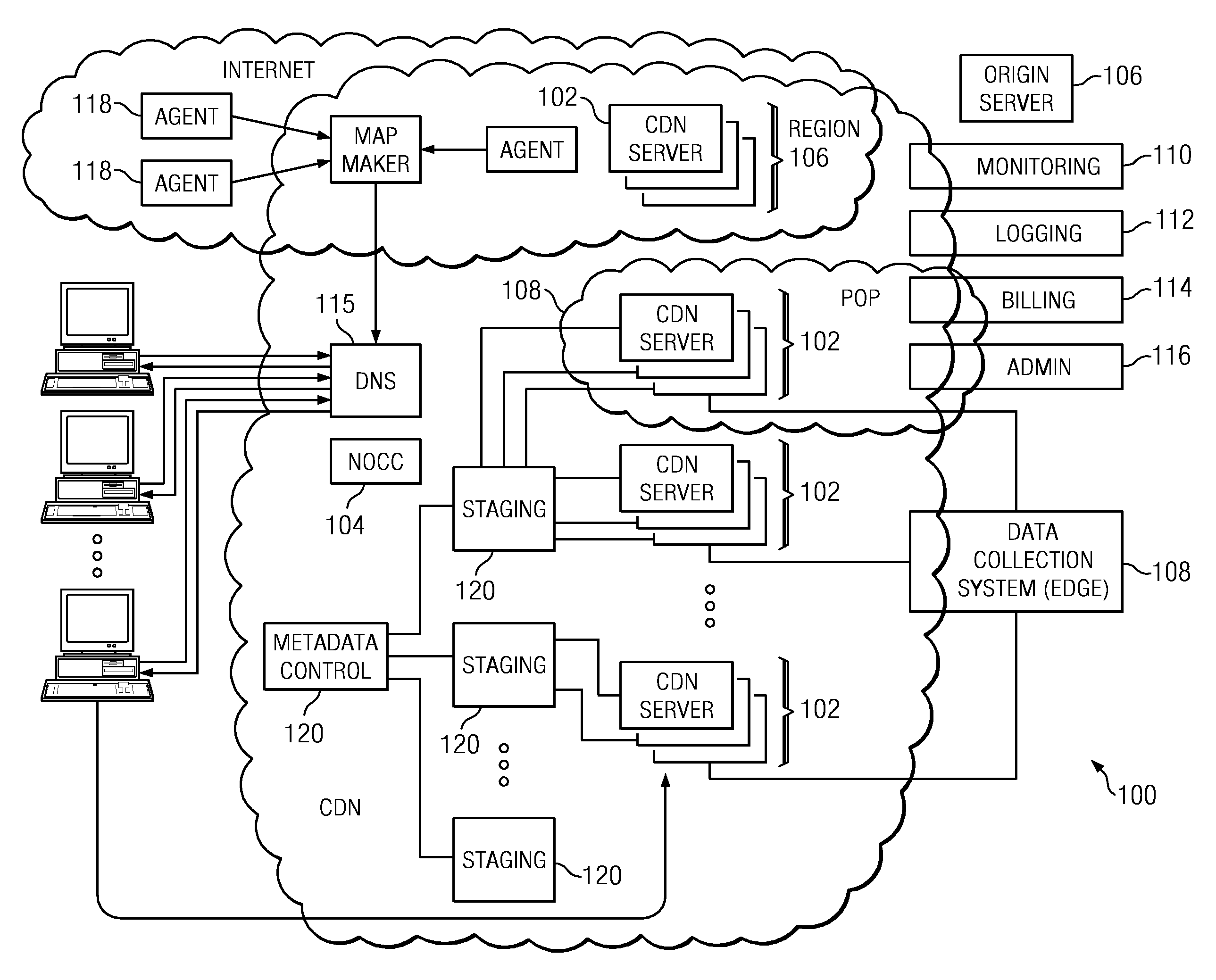
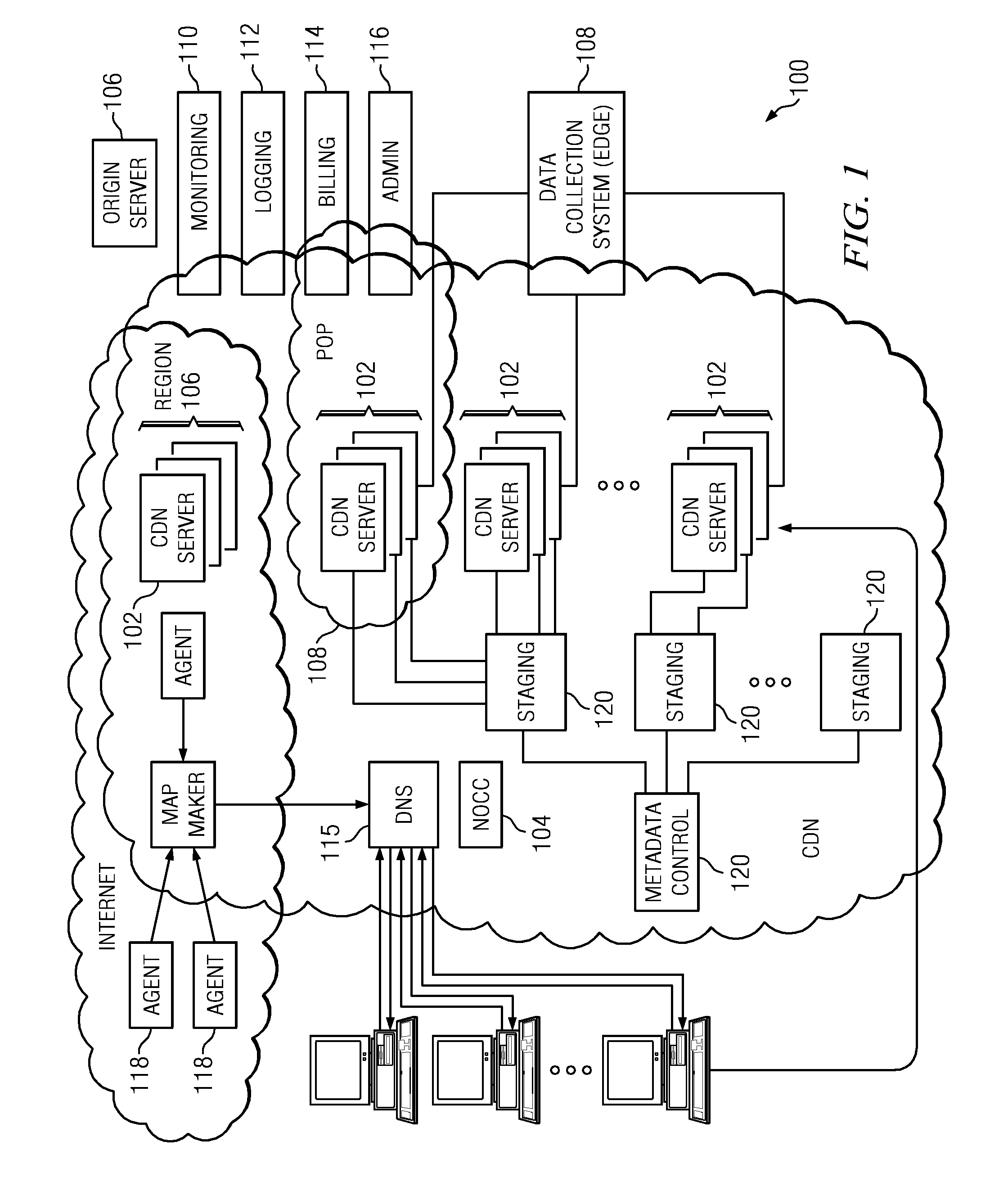
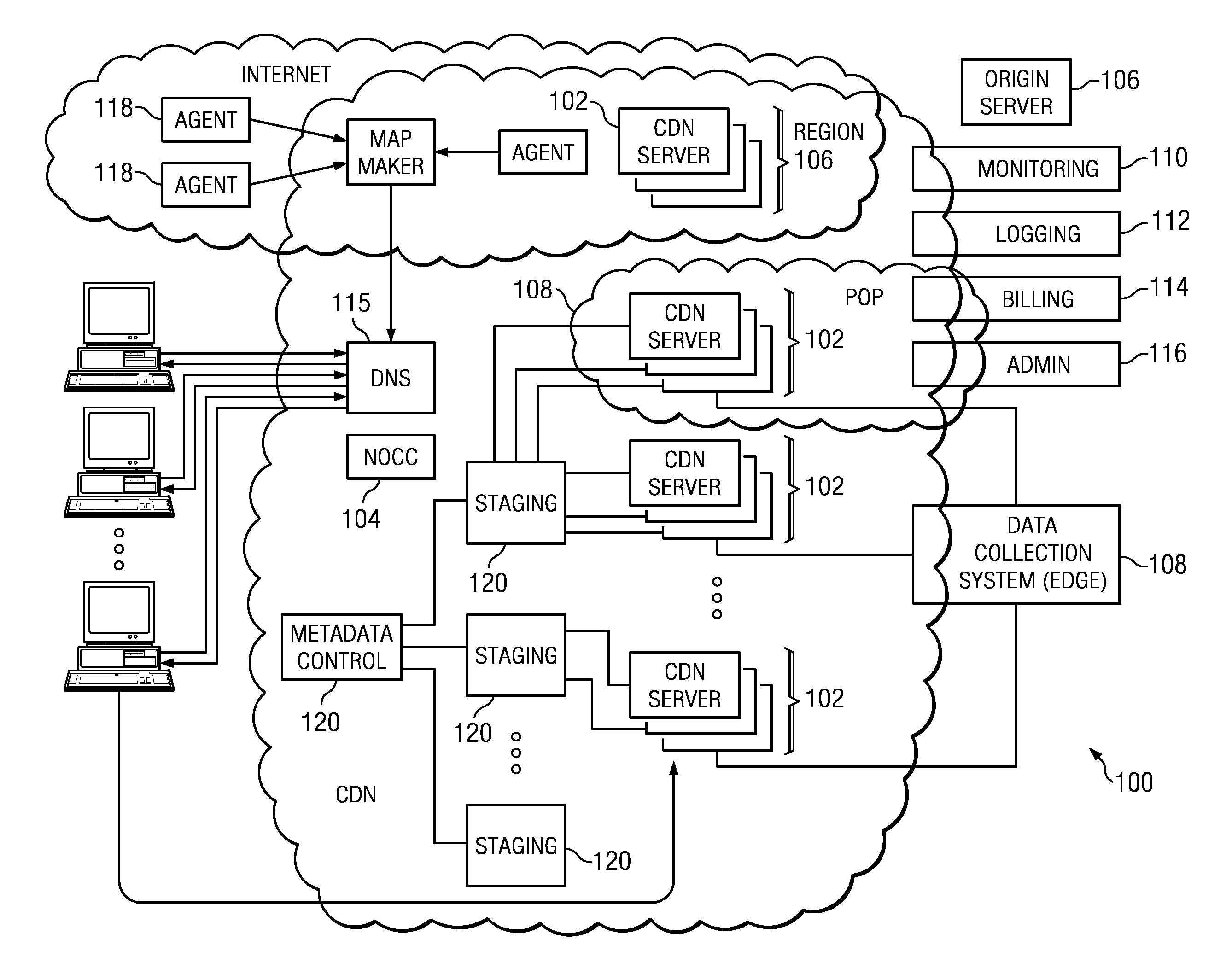
Method and system for HTTP-based stream delivery
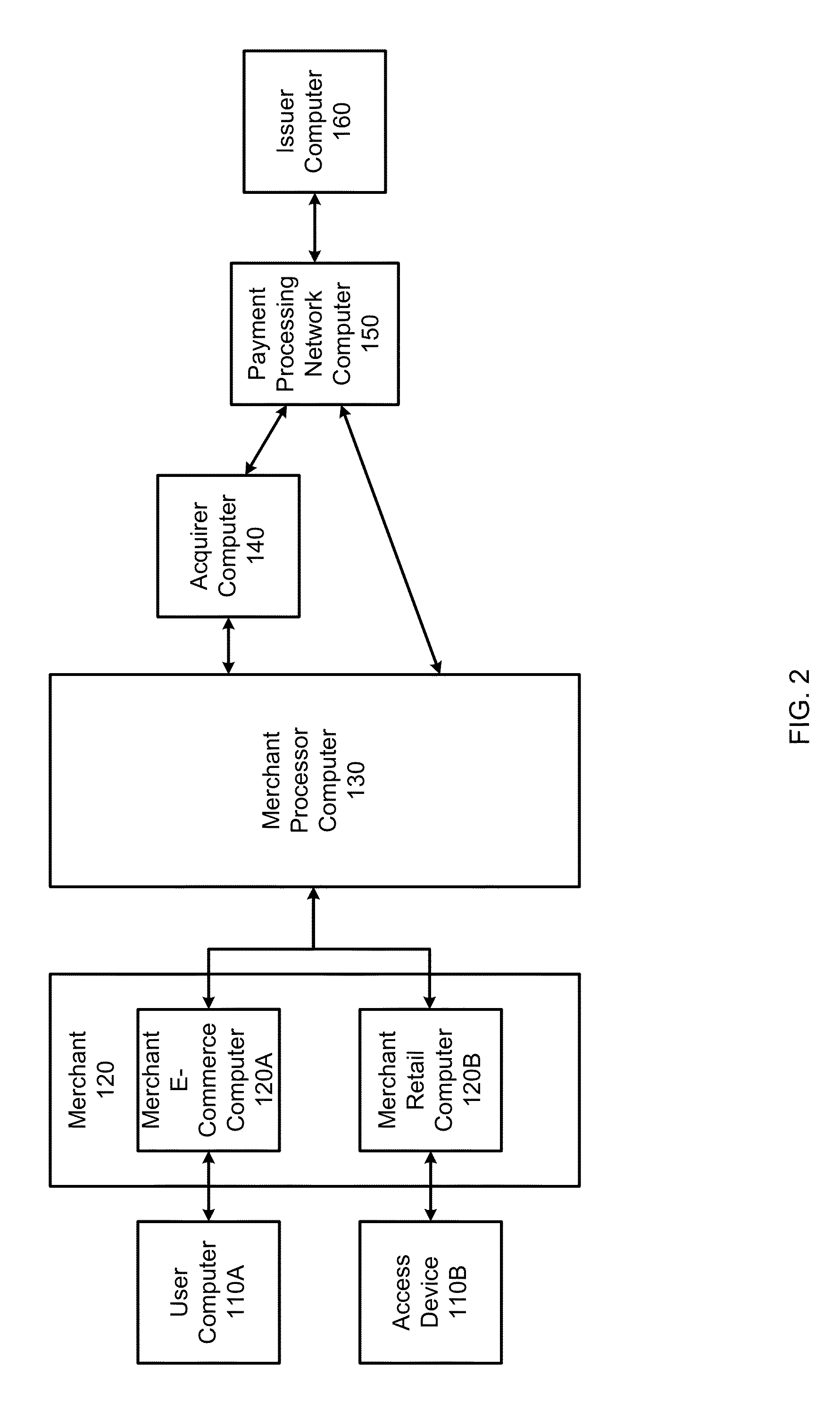
ActiveUS20110173345A1Minimizes downloadMultiple digital computer combinationsTransmissionEntry pointClient-side
A method of delivering a live stream is implemented within a content delivery network (CDN) and includes the high level functions of recording the stream using a recording tier, and playing the stream using a player tier. The step of recording the stream includes a set of sub-steps that begins when the stream is received at a CDN entry point in a source format. The stream is then converted into an intermediate format (IF), which is an internal format for delivering the stream within the CDN and comprises a stream manifest, a set of one or more fragment indexes (FI), and a set of IF fragments. The player process begins when a requesting client is associated with a CDN HTTP proxy. In response to receipt at the HTTP proxy of a request for the stream or a portion thereof, the HTTP proxy retrieves (either from the archive or the data store) the stream manifest and at least one fragment index. Using the fragment index, the IF fragments are retrieved to the HTTP proxy, converted to a target format, and then served in response to the client request. The source format may be the same or different from the target format. Preferably, all fragments are accessed, cached and served by the HTTP proxy via HTTP. In another embodiment, a method of delivering a stream on-demand (VOD) uses a translation tier (in lieu of the recording tier) to manage the creation and / or handling of the IF components.
Owner:AKAMAI TECH INC
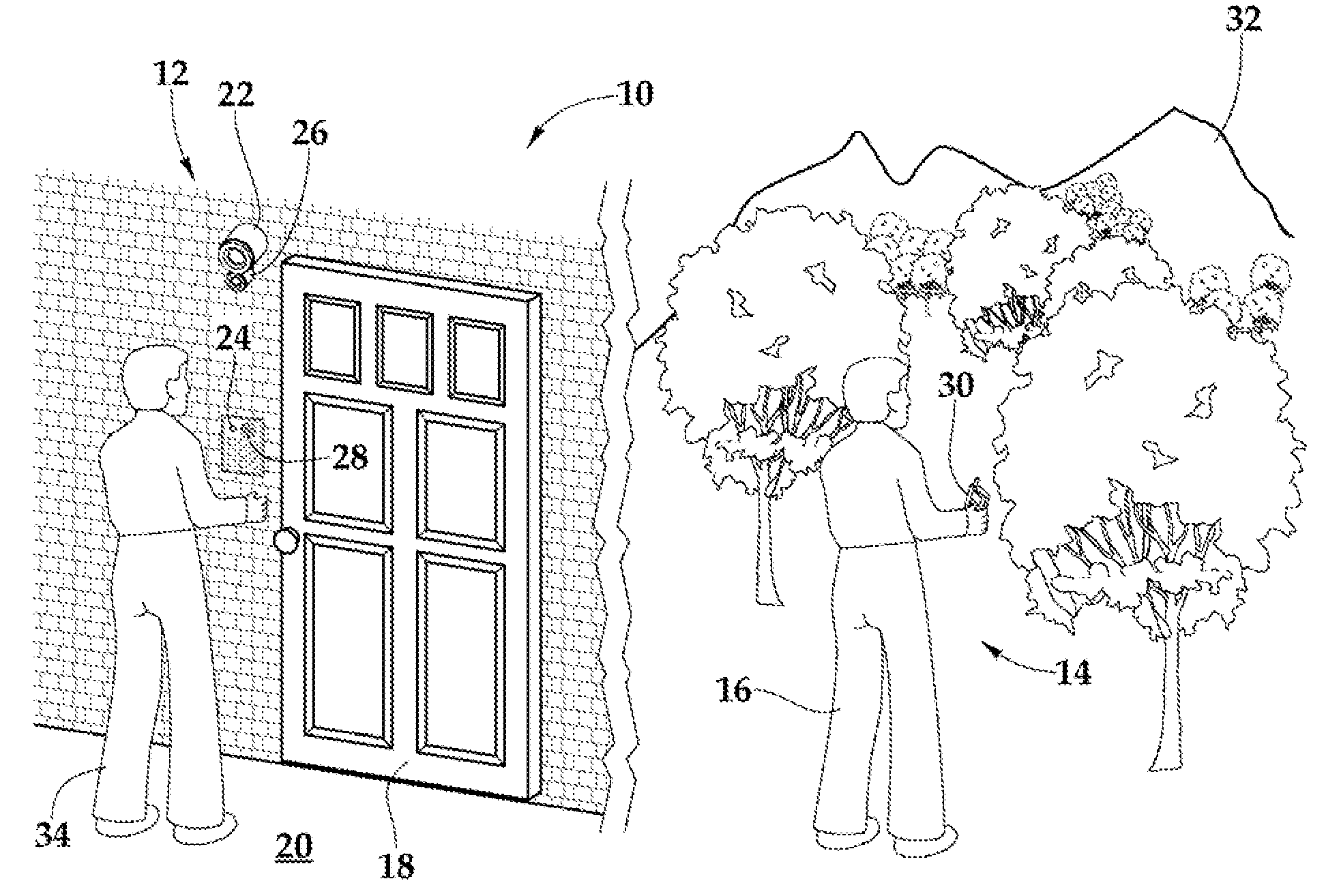
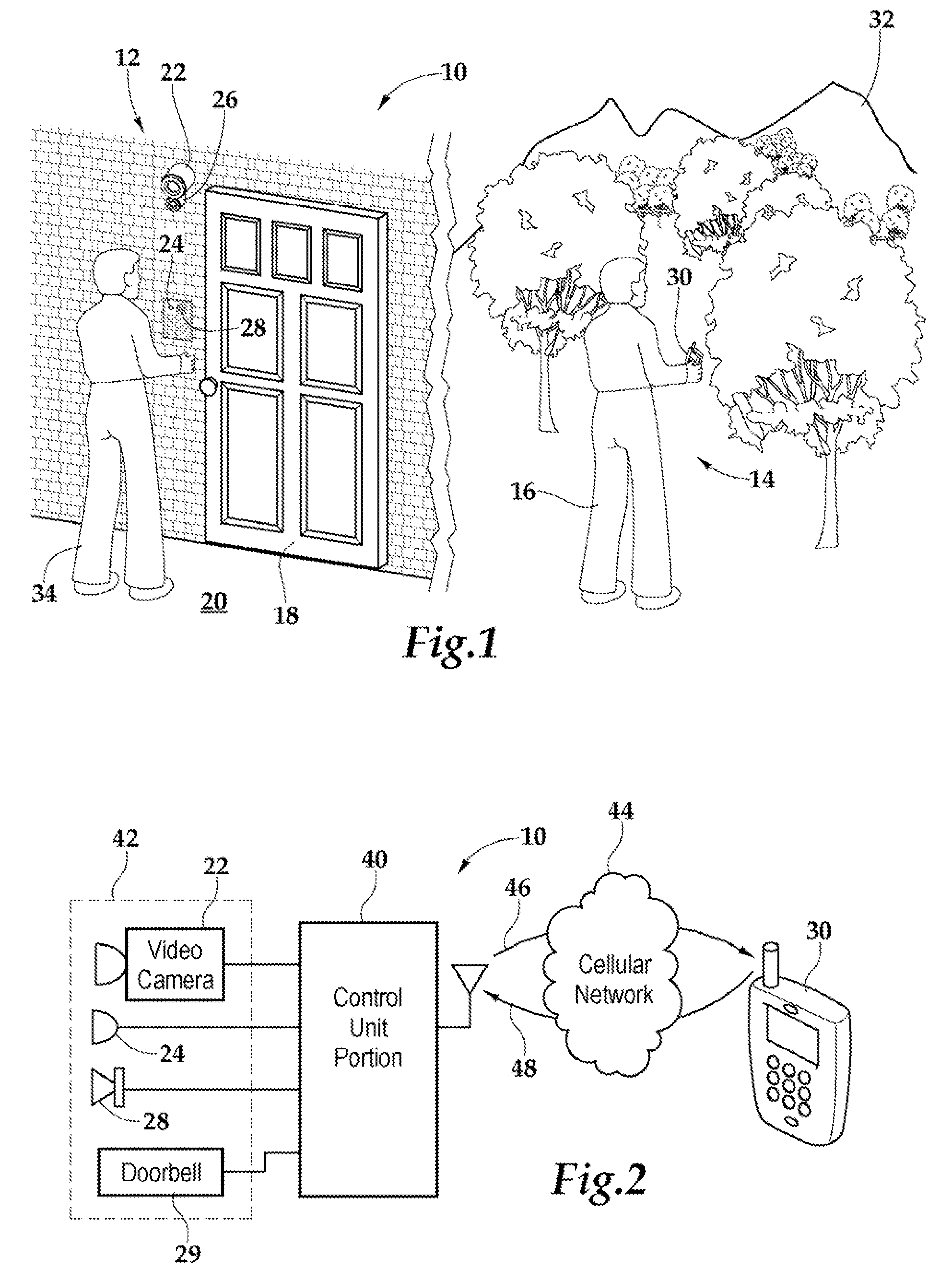
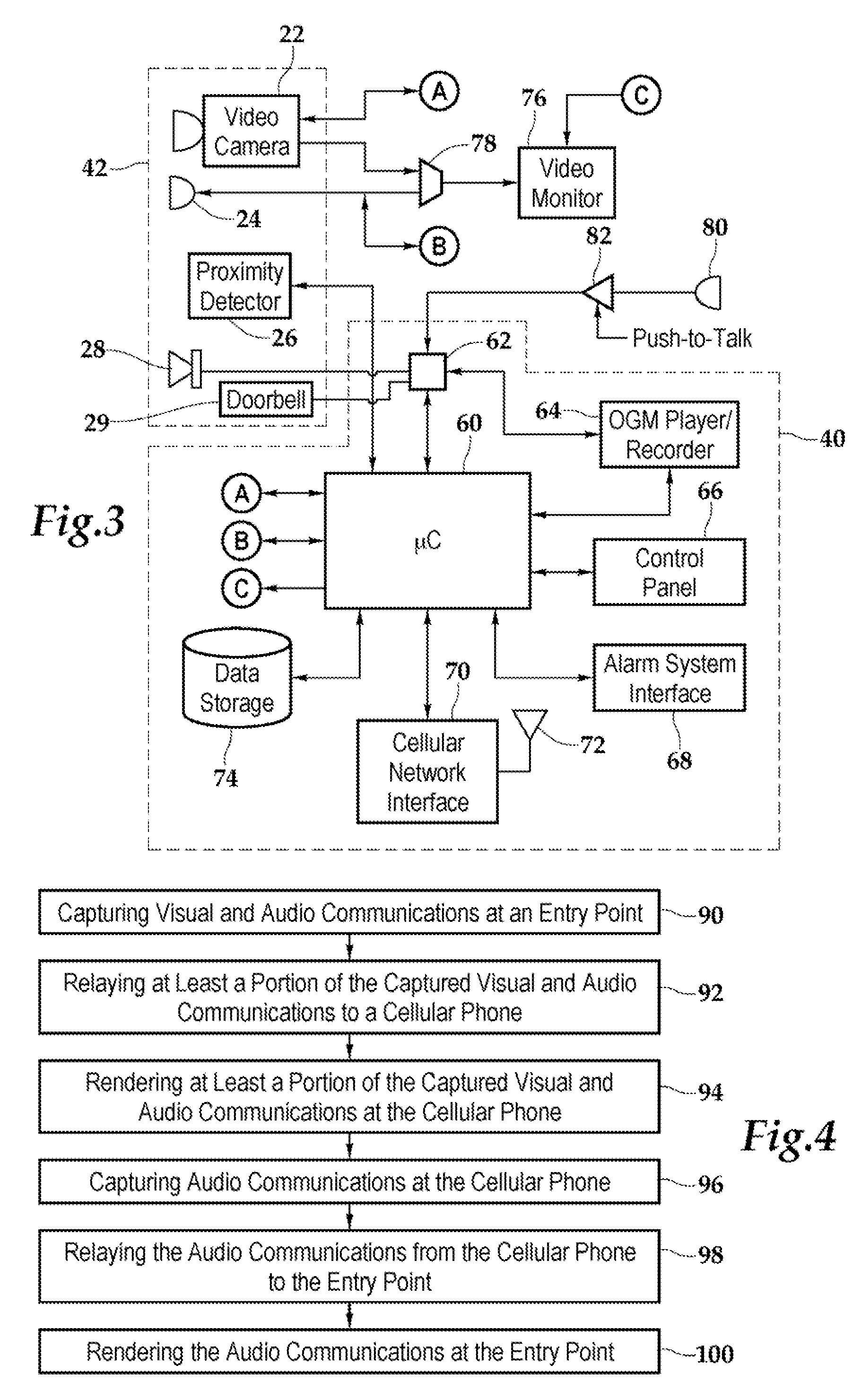
Security system and method for use of same
A security system and method for use of the same are disclosed that provide for remote surveillance. In one embodiment, a property's entry point such as a doorway is equipped with a video camera, an external microphone, and an external speaker. An individual, such as an owner of the property, is away from the property and equipped with a cellular telephone. When a person arrives at the entry point, a control unit relays audio and visual data captured by the video camera and the external microphone to the individual's cellular telephone. Similarly, the control unit relays audio data from the owner to the person at the entry point.
Owner:ZINSER DUKE W
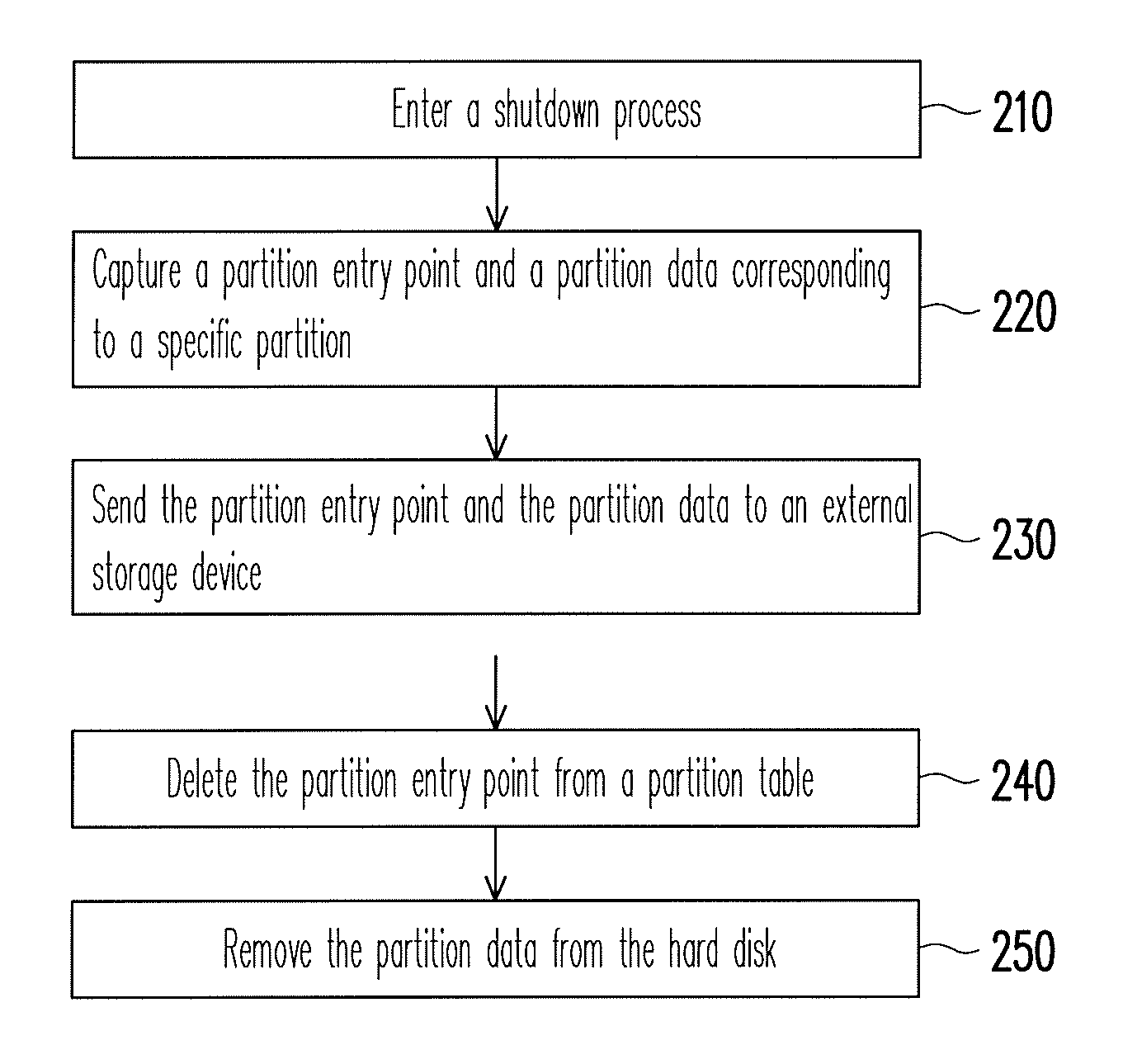
Data protection method
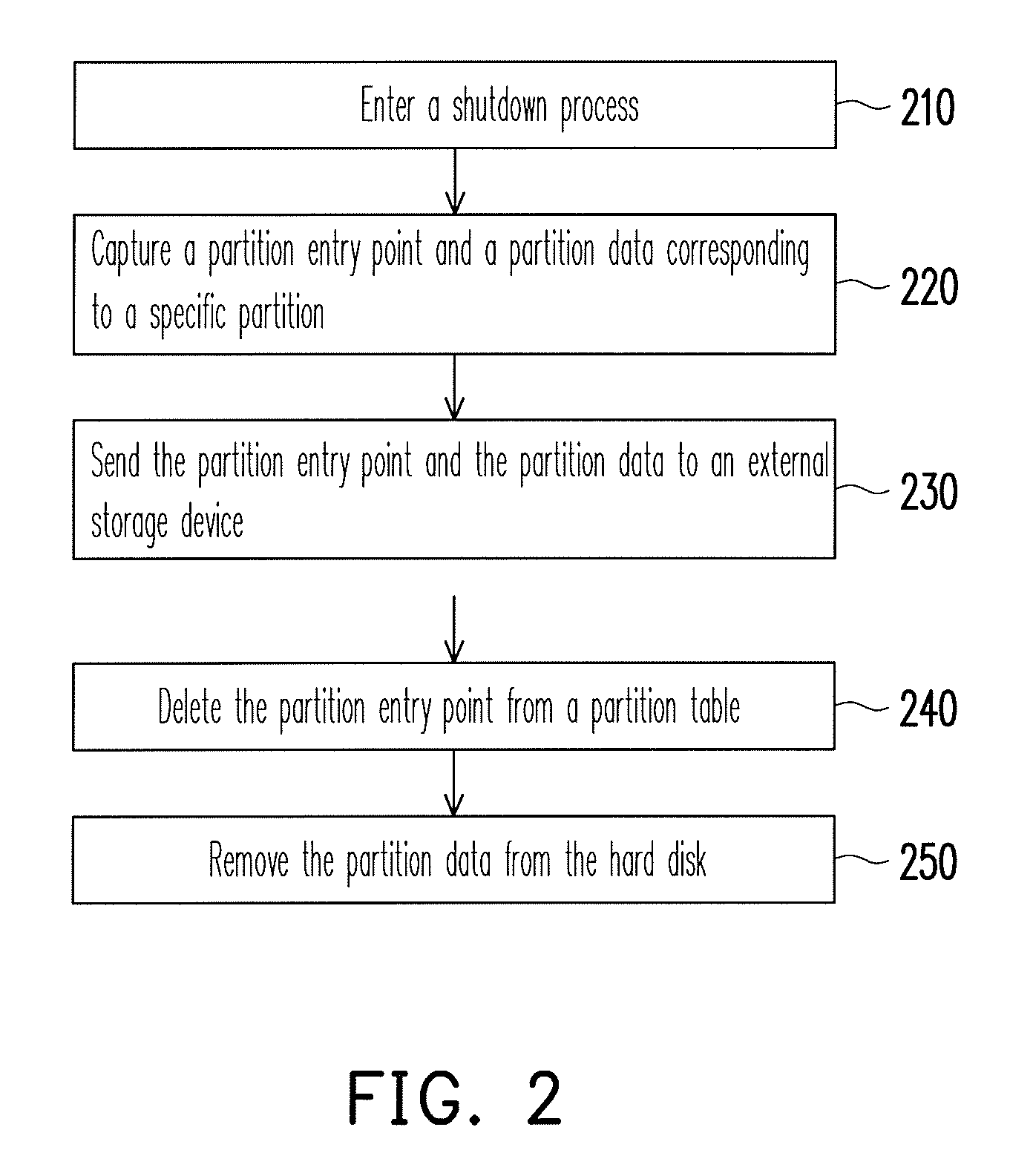
ActiveUS8041913B2Data SecurityEnsure safetyDigital data processing detailsUnauthorized memory use protectionExternal storageEntry point
A data protection method for an electronic device having a storage medium is provided, wherein the storage medium includes a plurality of partitions and a partition table. In the data protection method, a partition entry point and a partition data corresponding to the specific partition are captured and sent to an external storage device when the electronic device enters a shutdown process. Then, the partition entry point is deleted from the partition table and the partition data is removed from the storage medium. When the electronic device is turned on, a user has to provide the corresponding external storage device to restore the partition entry point and the partition data back to the storage medium. Thereby, personal data stored in the storage medium is protected and accordingly data security is ensured.
Owner:ASUSTEK COMPUTER INC
Prioritization of multitasking applications in a mobile device interface
InactiveUS20140013271A1Input/output processes for data processingComputer graphics (images)Entry point
An activity screen or multitasking screen for a mobile device includes a plurality of tiles, each of which corresponds to a different multitasking application on the mobile device. Each of the tiles is allocated to a distinct region on the activity screen, according to a specified layout. The layout may vary according to the number of tiles allocated in the activity screen, and in some examples a region of the activity screen is automatically subdivided to provide additional regions. The content displayed for each tile is selected, at least in part, based on the size of the allocated region, and consequently, of the tile. Content for each possible size of the tile can be pre-defined. Each of the tiles operates as an application entry point for its corresponding application, thus providing a means of access for applications concurrently executing on the device.
Owner:BLACKBERRY LTD
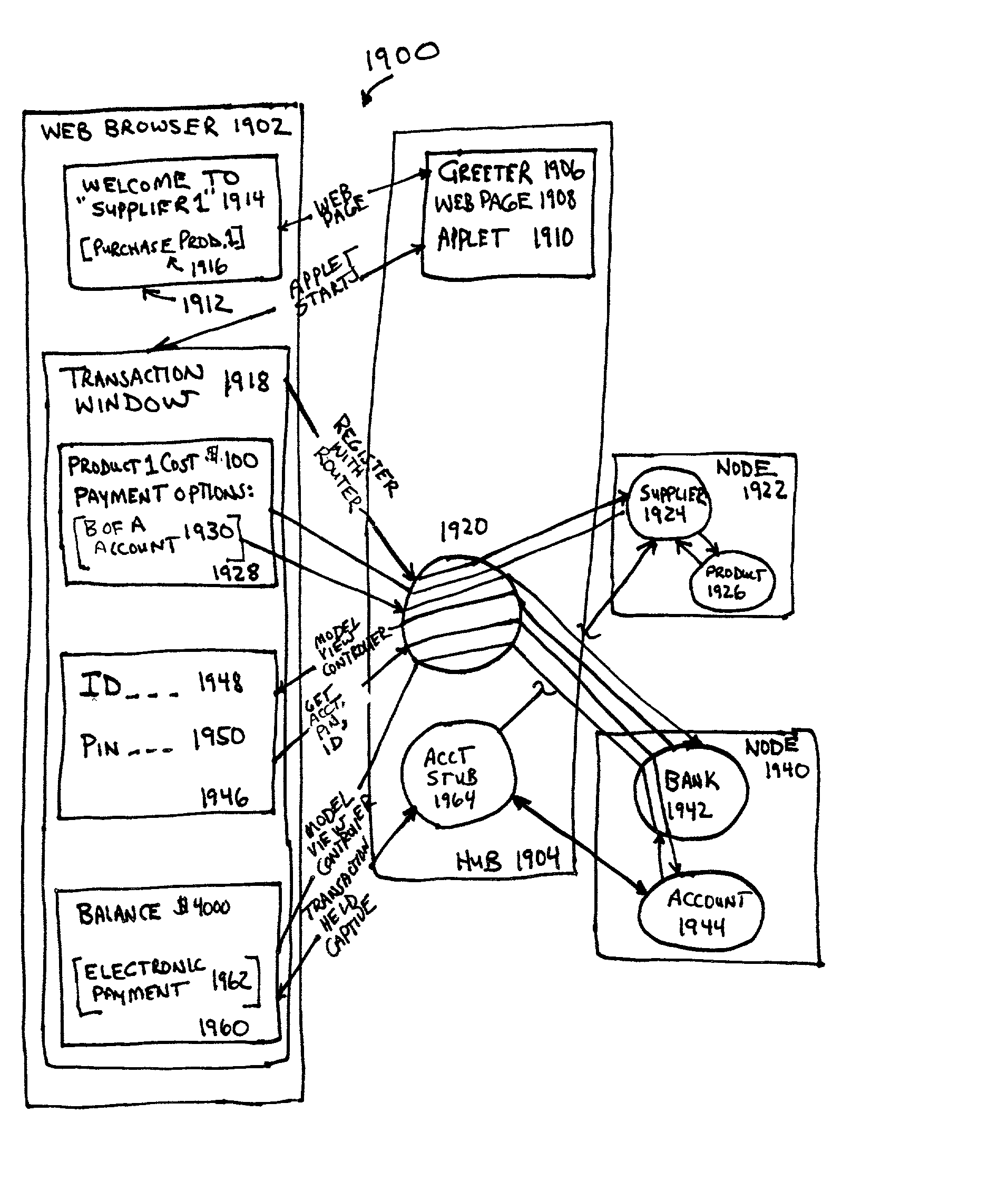
Network transaction portal to control multi-service provider transactions
InactiveUS20030069922A1Multiprogramming arrangementsMultiple digital computer combinationsEntry pointClient-side
The present invention provides a system and method for providing controlled service transactions involving multiple service providers on a service network. A client access device links to the service network via a network entry point and performs the multi-service provider transaction under the control of a network transactional application at a hub that holds the transaction captive and includes a router to route to remote distributed software objects at nodes of the service providers. The software objects include methods that may be remotely executed under the control of the transactional application at the hub.
Owner:ARUNACHALAM LAKSHMI
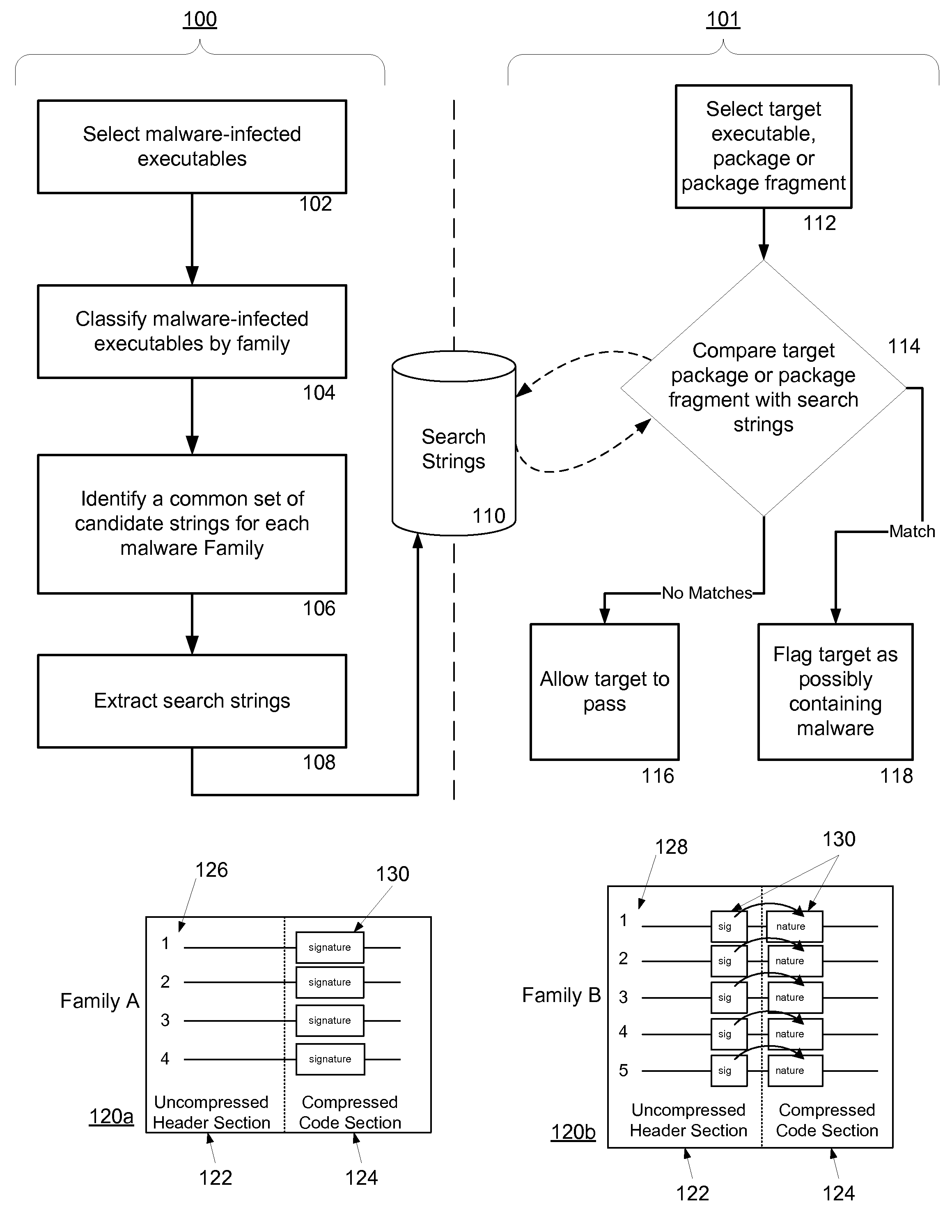
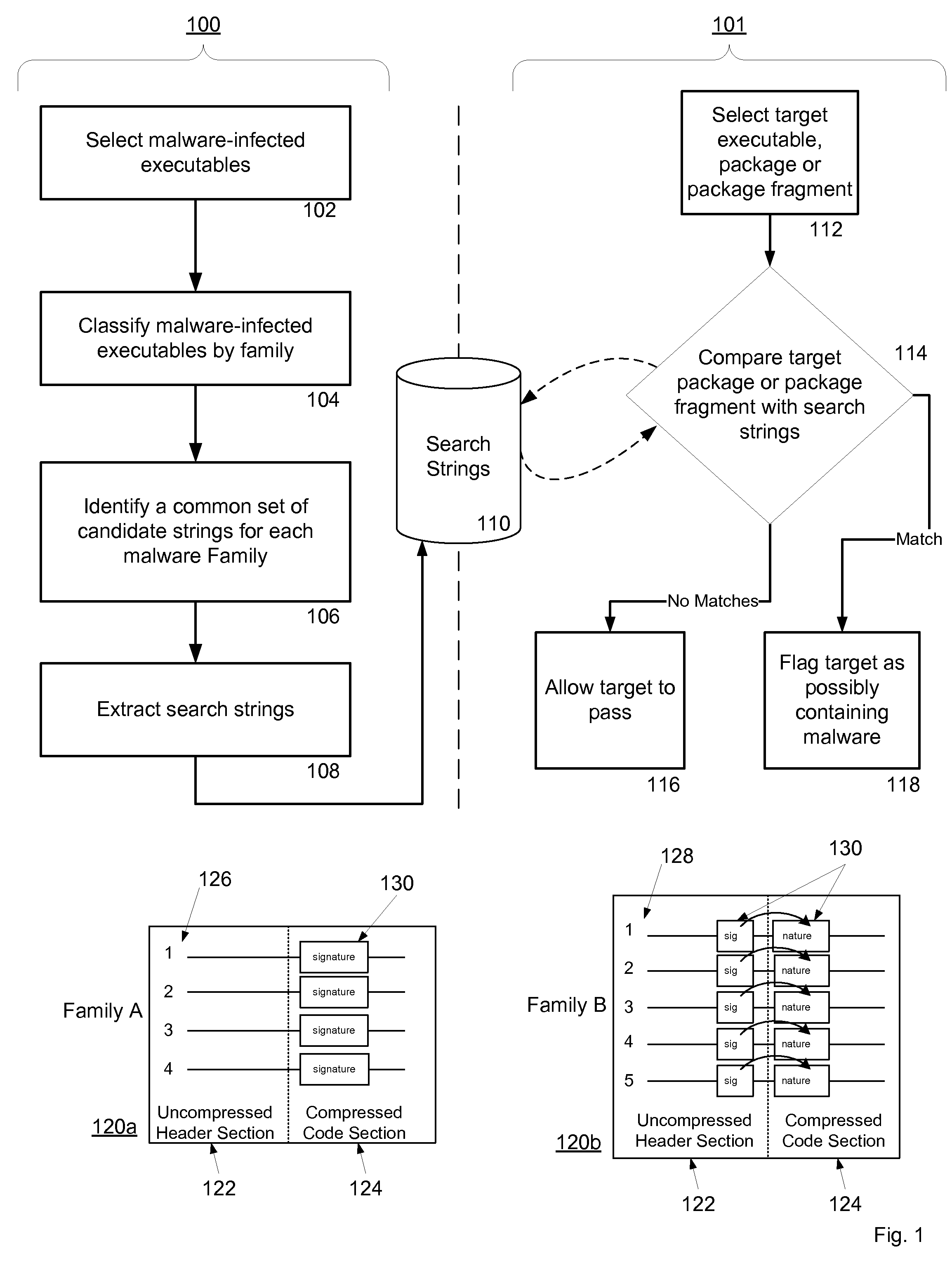
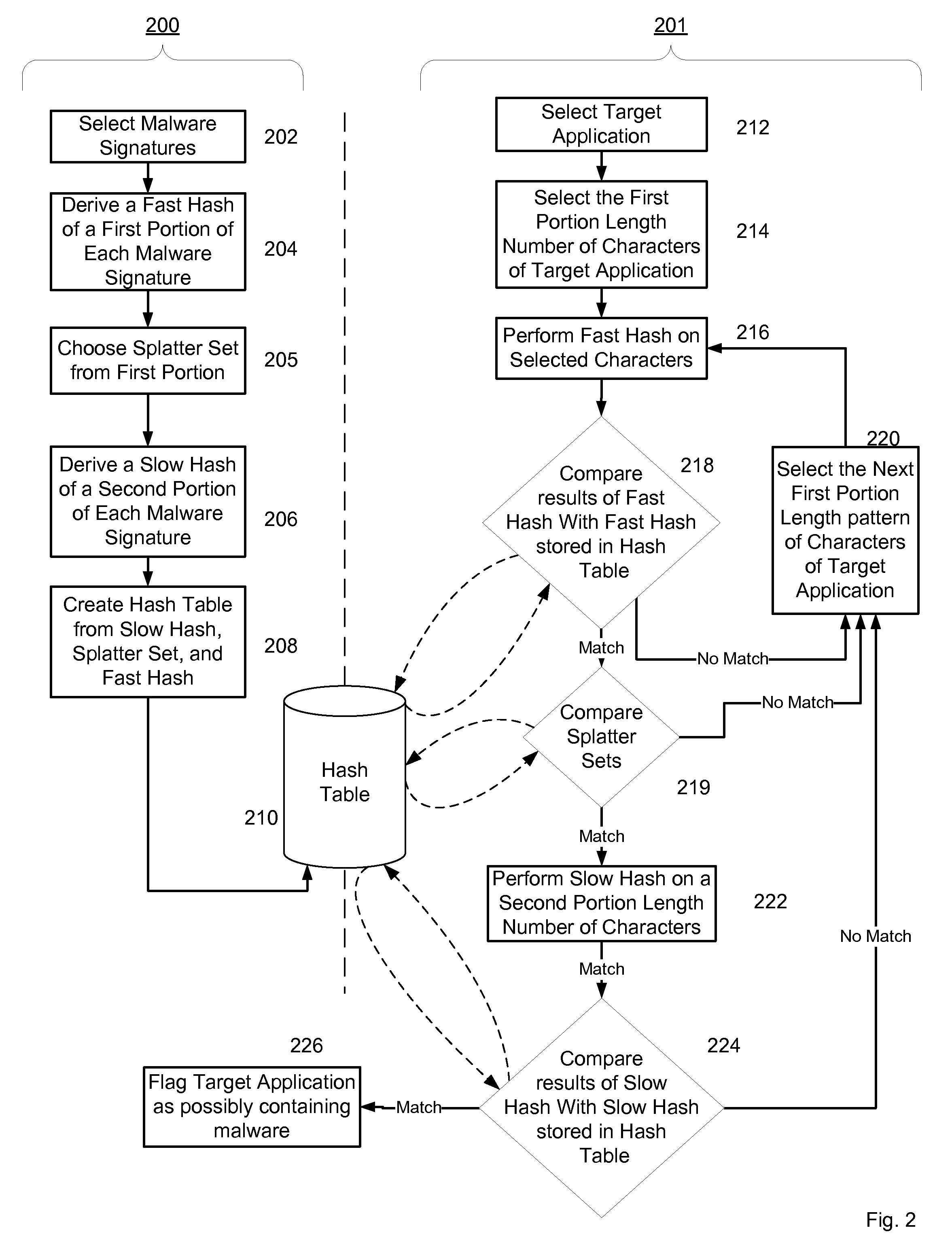
Non-Signature Malware Detection System and Method for Mobile Platforms
ActiveUS20070240221A1Suitable for useReliable detectionMemory loss protectionError detection/correctionEntry pointChecksum
A system and method for detecting malware on a mobile platform in a mobile network. The system and method verifies that an executable is malware-free by computing the checksum of the executable and comparing that checksum with a checksum obtained from a malware-free copy of the executable. The checksum is a sum of all 32-bit values in a code section and an import section of said executable, a byte sequence at an entry point in said executable, a size descriptor of an import table, a size descriptor of said import section, a cyclic redundancy check of said executable, or a combination thereof.
Owner:PULSE SECURE
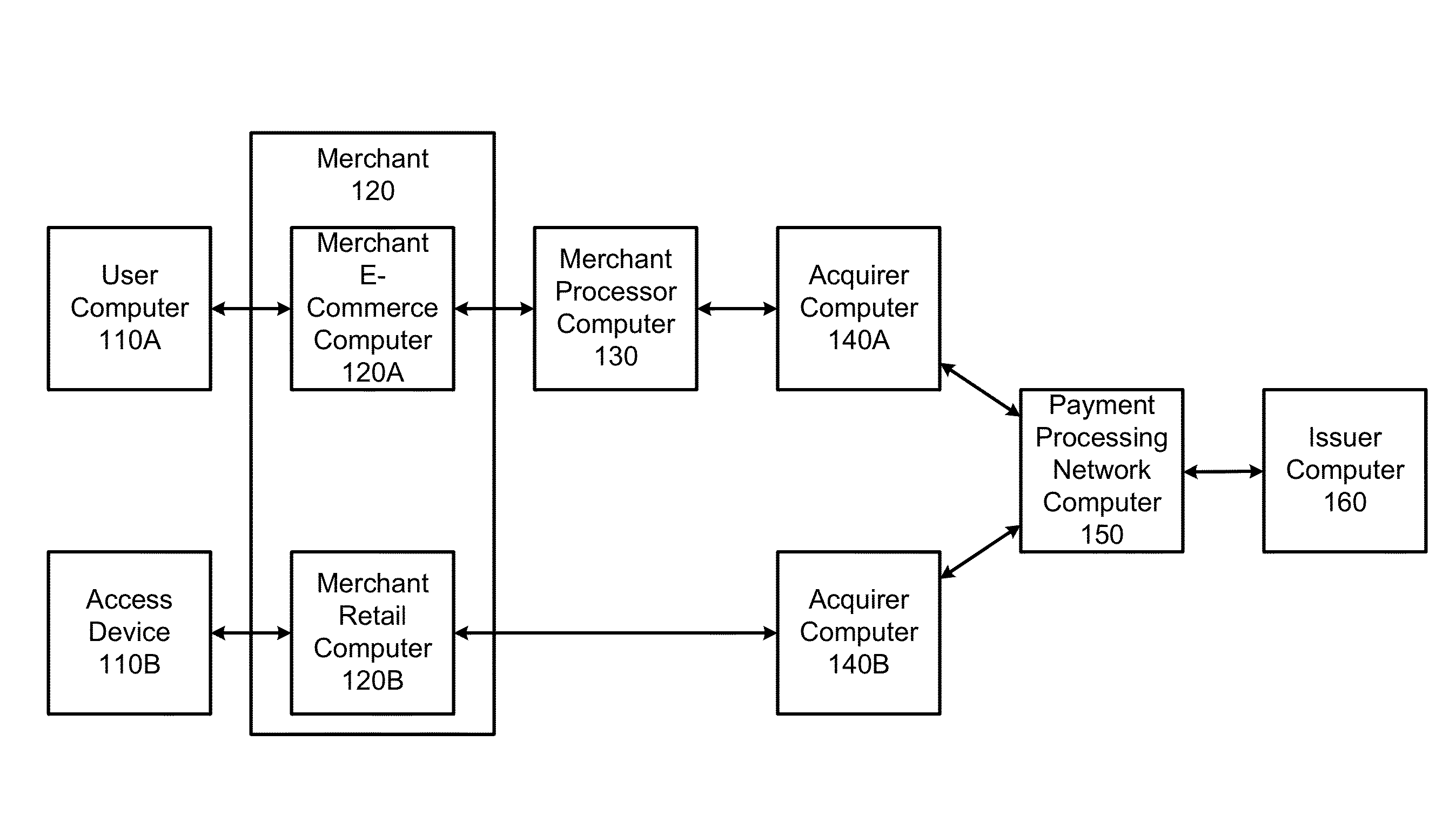
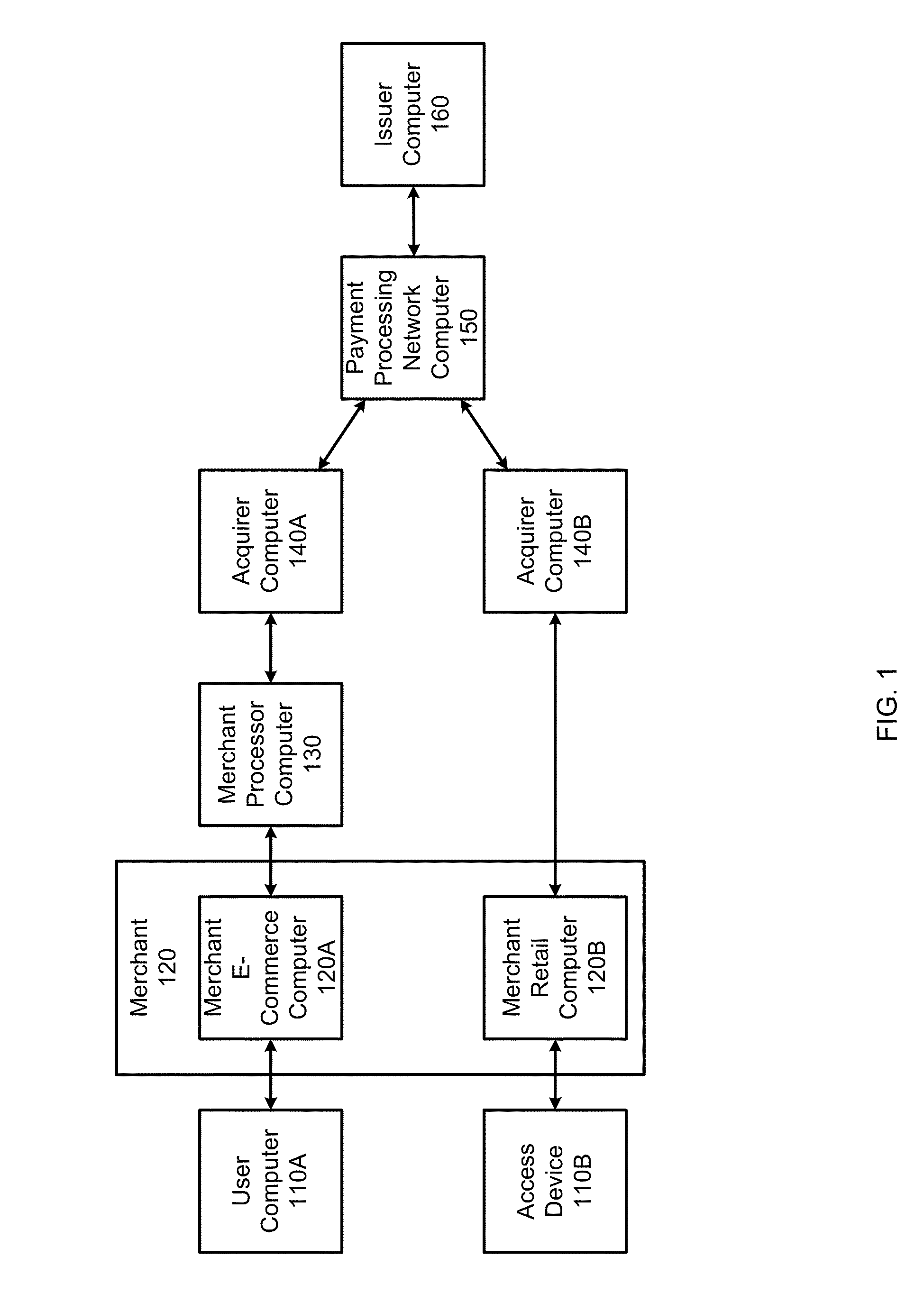
Embedded acceptance system
InactiveUS20140310183A1Reduce management costsImprove securityFinancePayment protocolsEnd-to-end encryptionPayment
Methods and systems can provide for unified processing of merchant transactions over various payment channels over which the transactions originate, such as in-person retail transactions and e-commerce transactions. For example, transactions can be received from payment channels through different payment channel-specific interfaces. The transactions from the various payment channels can then be sent to an entry point module that centrally manages the transactions. An orchestrator can then identify payment channel-agnostic transaction services to be applied to the transactions. This can allow for a unified end-to-end encryption implementation across a merchant's enterprise, reducing management costs and improving overall security. Similarly, universal tokenization services, payment and fraud management can be provided across a merchant's entire enterprise.
Owner:VISA INT SERVICE ASSOC
Targeting method, targeting device, computer readable medium and program element
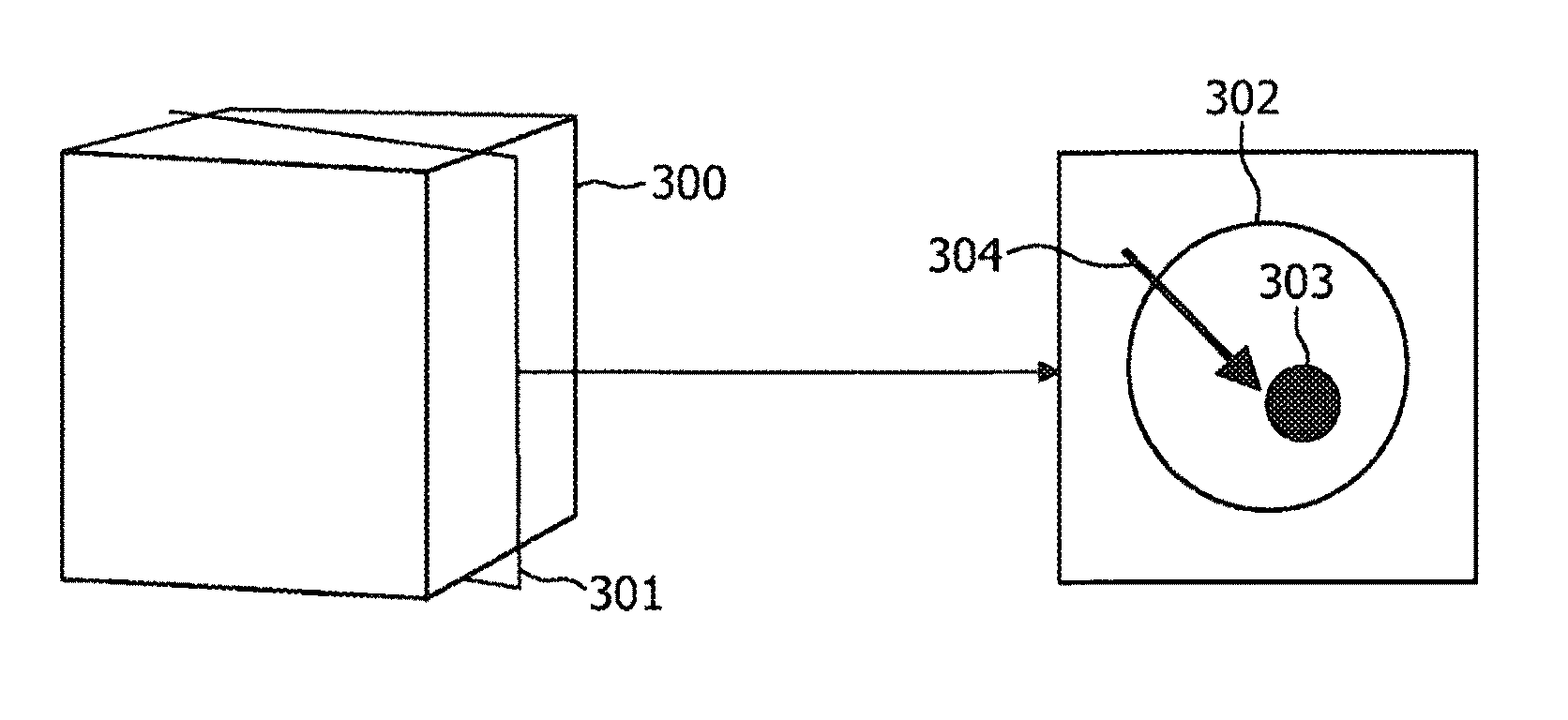
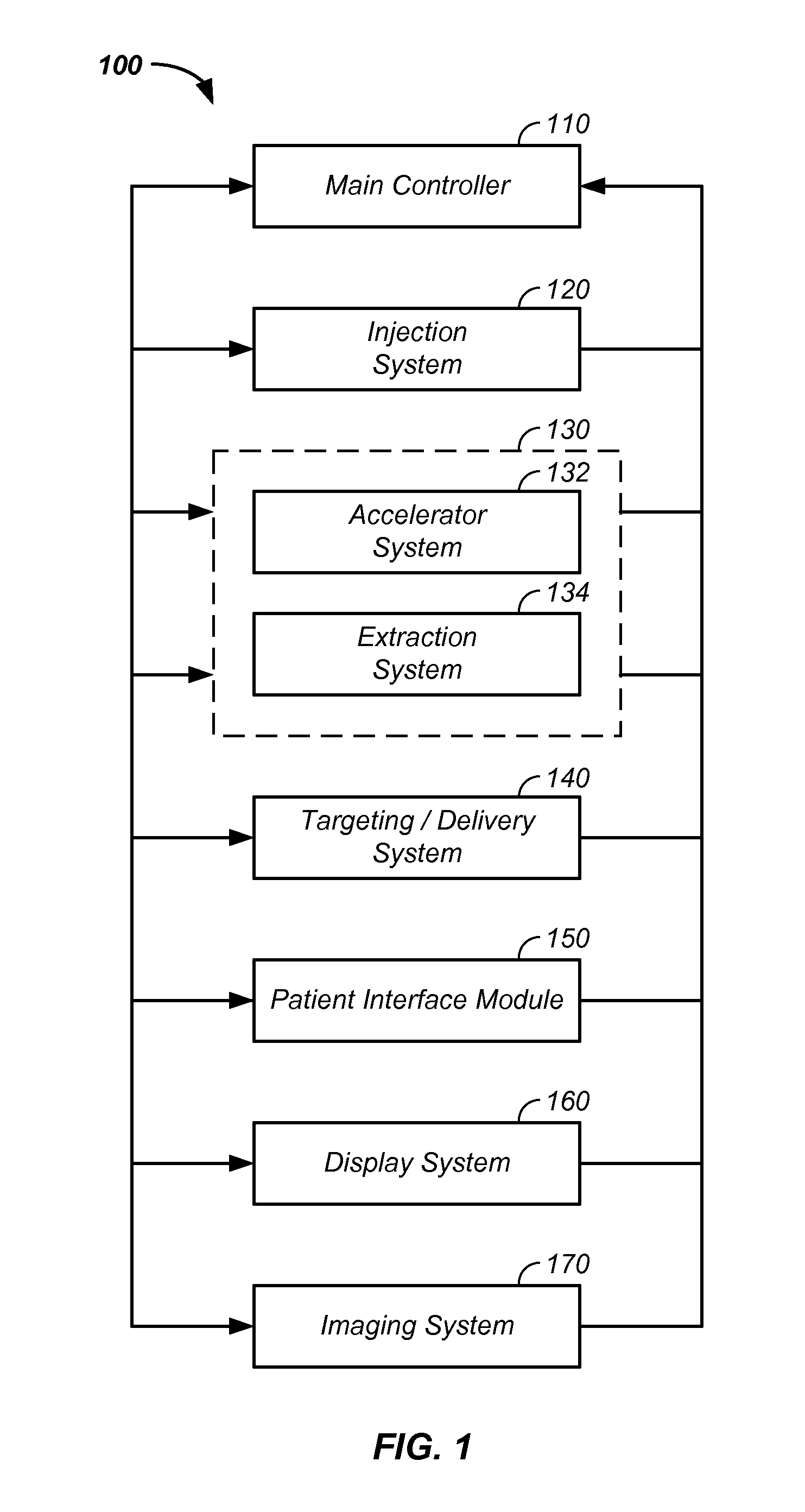
ActiveUS8208708B2Efficient methodReduce doseMaterial analysis using wave/particle radiationRadiation/particle handlingFluoroscopic imageEntry point
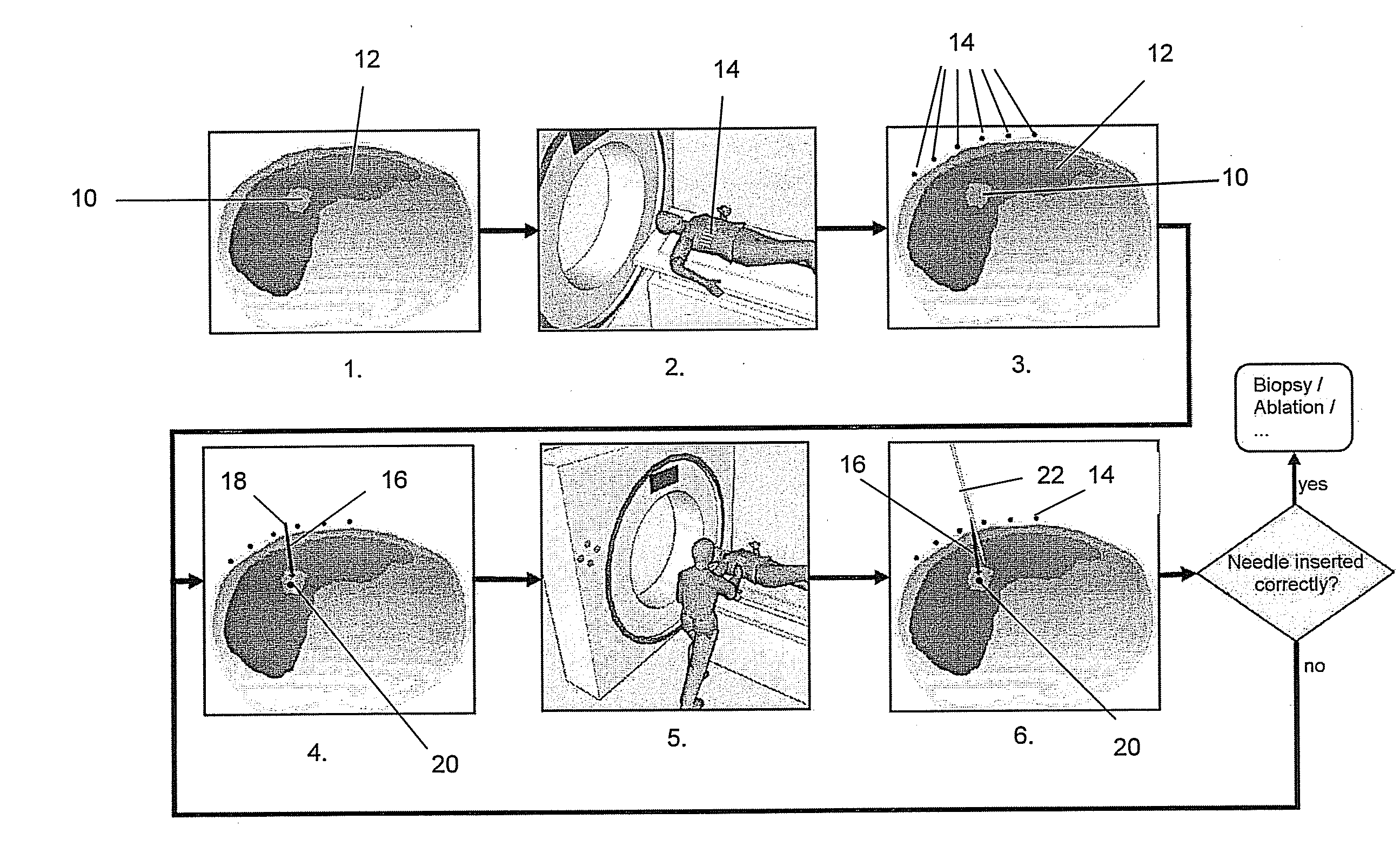
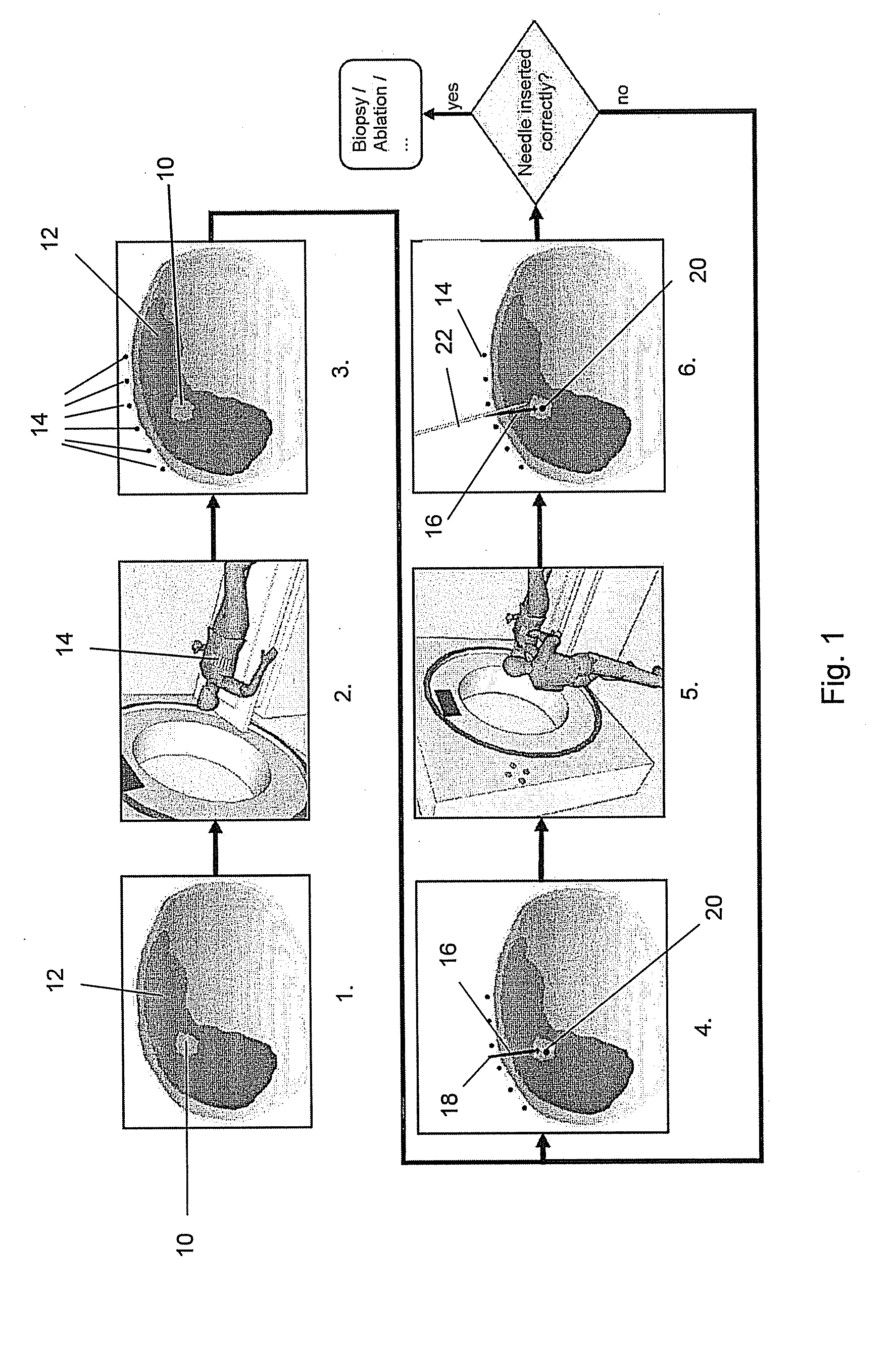
According to an exemplary embodiment a targeting method for targeting a first object from an entry point to a target point in an object (110) under examination is provided, wherein the method comprises selecting a two-dimensional image (301) of the object under examination depicting the entry point (305) and the target point (303) and determining a planned path (304) from the entry point to the target point, wherein the planned path has a first direction. Furthermore, the method comprises recording data representing a fluoroscopic image of the object under examination, wherein the fluoroscopic image is recorded under a second direction so that a normal of the image coincide with the first direction and determining whether the first object is on the determined planned path based on shape and / or position of the projection of the first object in the fluoroscopic image.
Owner:KONINK PHILIPS ELECTRONICS NV
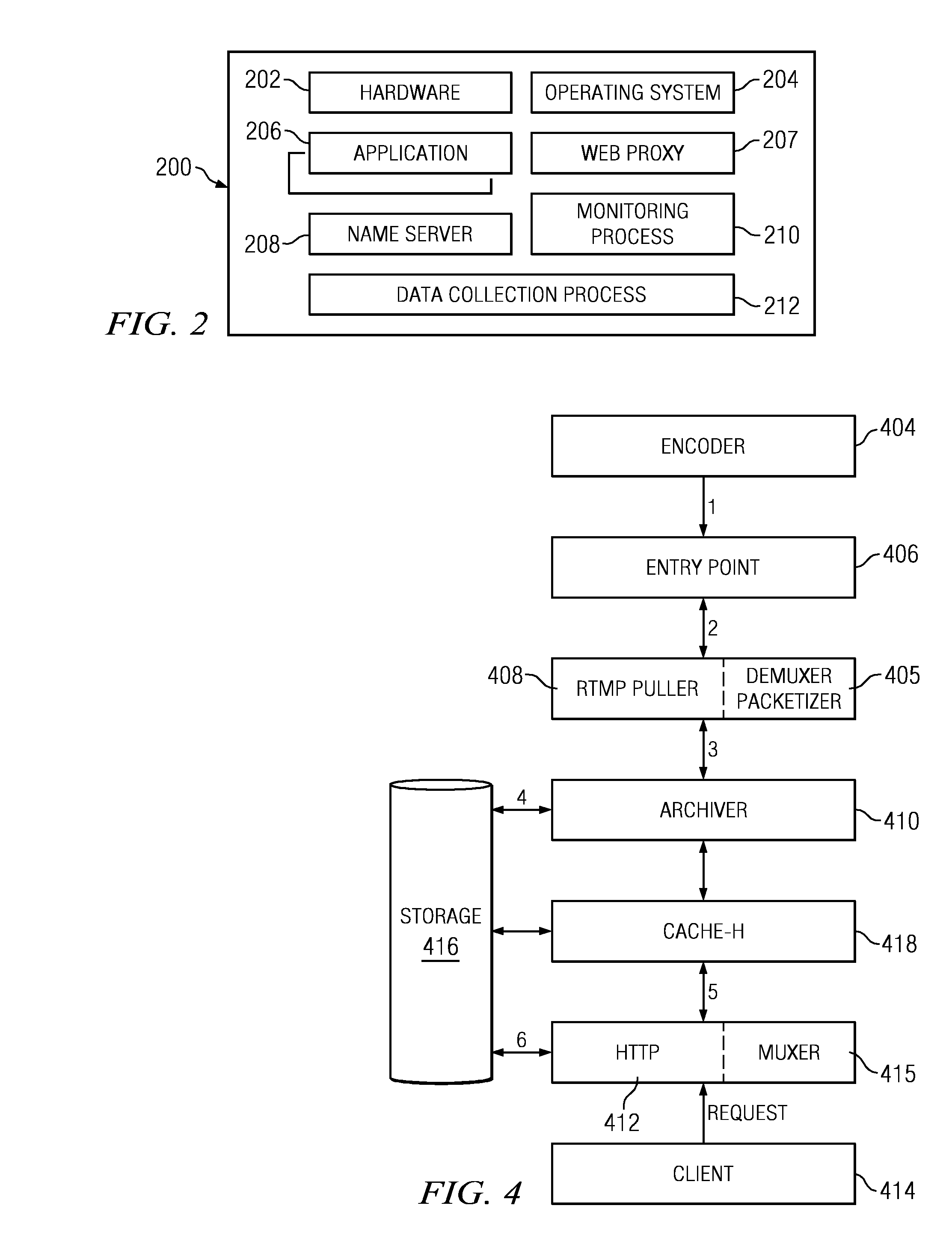
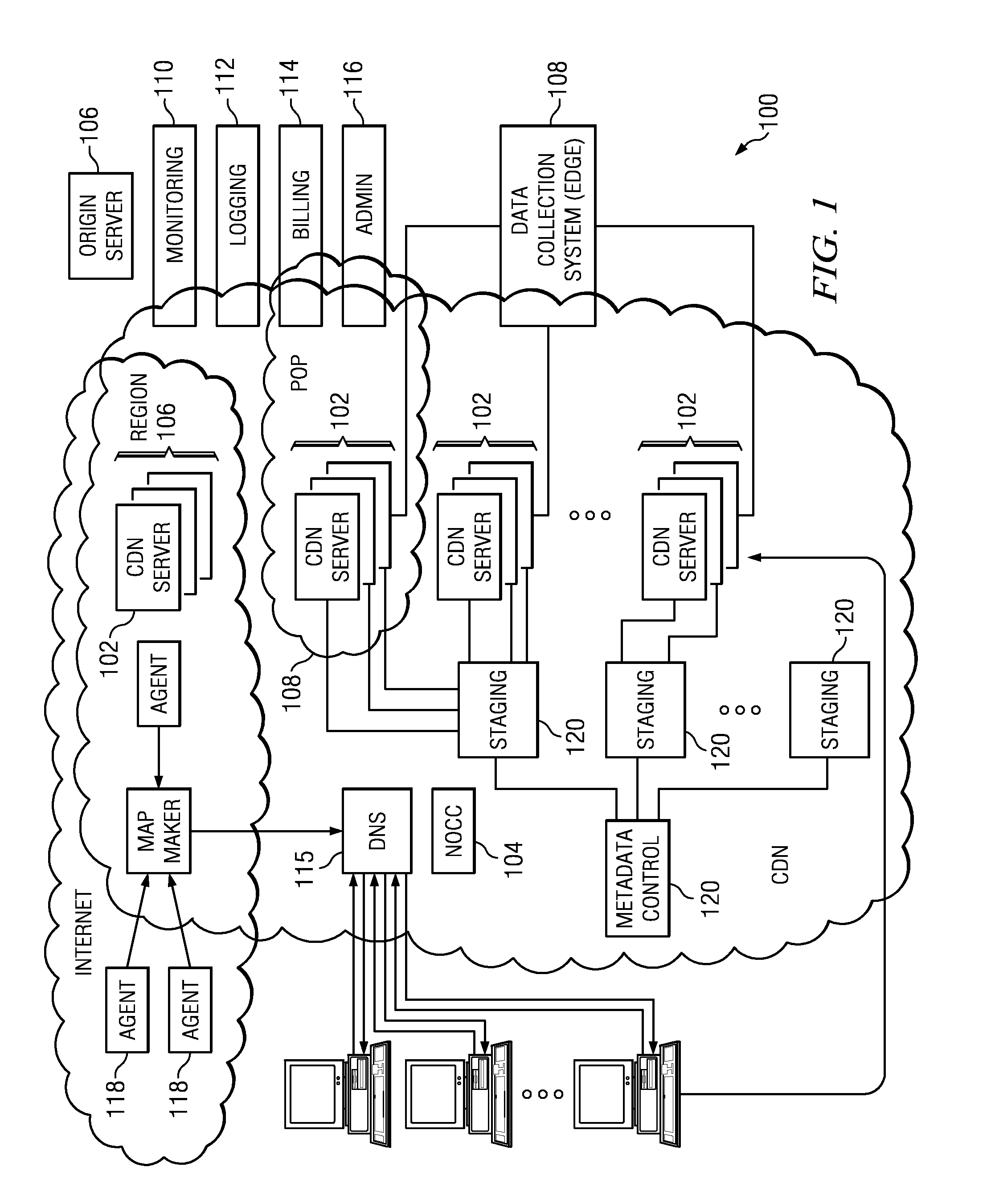
Method and system for stream handling using an intermediate format
InactiveUS20110296048A1Minimizes downloadMultiple digital computer combinationsTransmissionEntry pointClient-side
A method of delivering a live stream is implemented within a content delivery network (CDN) and includes the high level functions of recording the stream using a recording tier, and playing the stream using a player tier. The step of recording the stream includes a set of sub-steps that begins when the stream is received at a CDN entry point in a source format. The stream is then converted into an intermediate format (IF), which is an internal format for delivering the stream within the CDN and comprises a stream manifest, a set of one or more fragment indexes (FI), and a set of IF fragments. The player process begins when a requesting client is associated with a CDN HTTP proxy. In response to receipt at the HTTP proxy of a request for the stream or a portion thereof, the HTTP proxy retrieves (either from the archive or the data store) the stream manifest and at least one fragment index. Using the fragment index, the IF fragments are retrieved to the HTTP proxy, converted to a target format, and then served in response to the client request. The source format may be the same or different from the target format. Preferably, all fragments are accessed, cached and served by the HTTP proxy via HTTP.
Owner:AKAMAI TECH INC
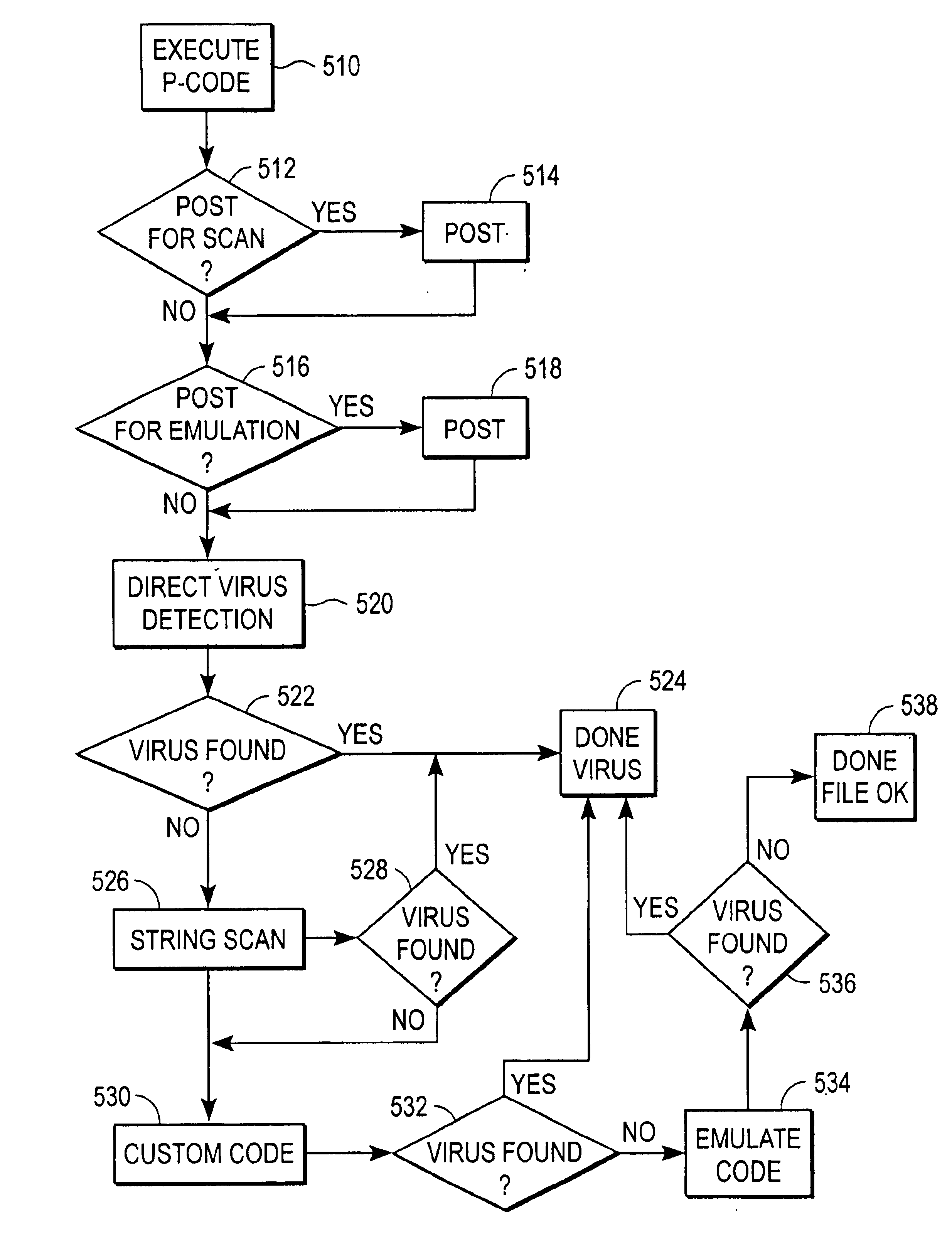
Data driven detection of viruses
InactiveUS6851057B1Easy to detectMemory loss protectionUser identity/authority verificationEntry pointData file
A virus detection system (VDS) (400) operates under the control of P-code to detect the presence of a virus in a file (100) having multiple entry points. P-code is an intermediate instruction format that uses primitives to perform certain functions related to the file (100). The VDS (400) executes the P-code, which provides Turing-equivalent capability to the VDS. The VDS (400) has a P-code data file (410) for holding the P-code, a virus definition file (VDF) (412) for holding signatures of known viruses, and an engine (414) for controlling the VDS. The engine (414) contains a P-code interpreter (418) for interpreting the P-code, a scanning module (424) for scanning regions of the file (100) for the virus signatures in the VDF (412), and an emulating module (426) for emulating entry points of the file. When executed, the P-code examines the file (100), posts (514) regions that may be infected by a virus for scanning, and posts (518) entry points that may be infected by a virus for emulating. The P-code can also detect (520) certain viruses algorithmically. Then, the posted regions and entry points of the file (100) are scanned (526) and emulated (534) to determine if the file is infected with a virus. This technique allows the VDS (400) to perform sophisticated analysis of files having multiple entry points in a relatively brief amount of time. In addition, the functionality of the VDS (400) can be changed by changing the P-code, reducing the need for burdensome engine updates.
Owner:CA TECH INC
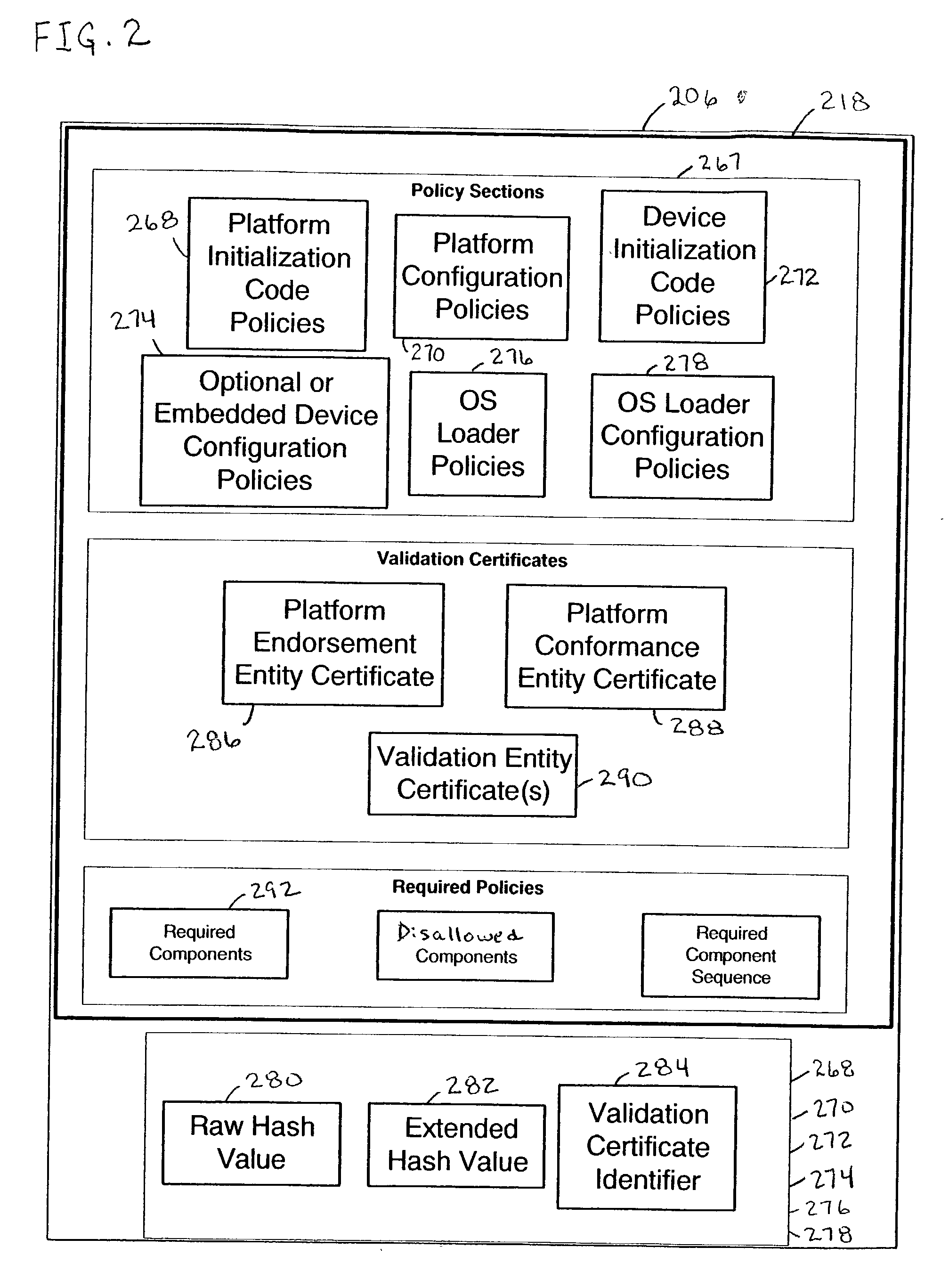
Trusted platform apparatus, system, and method
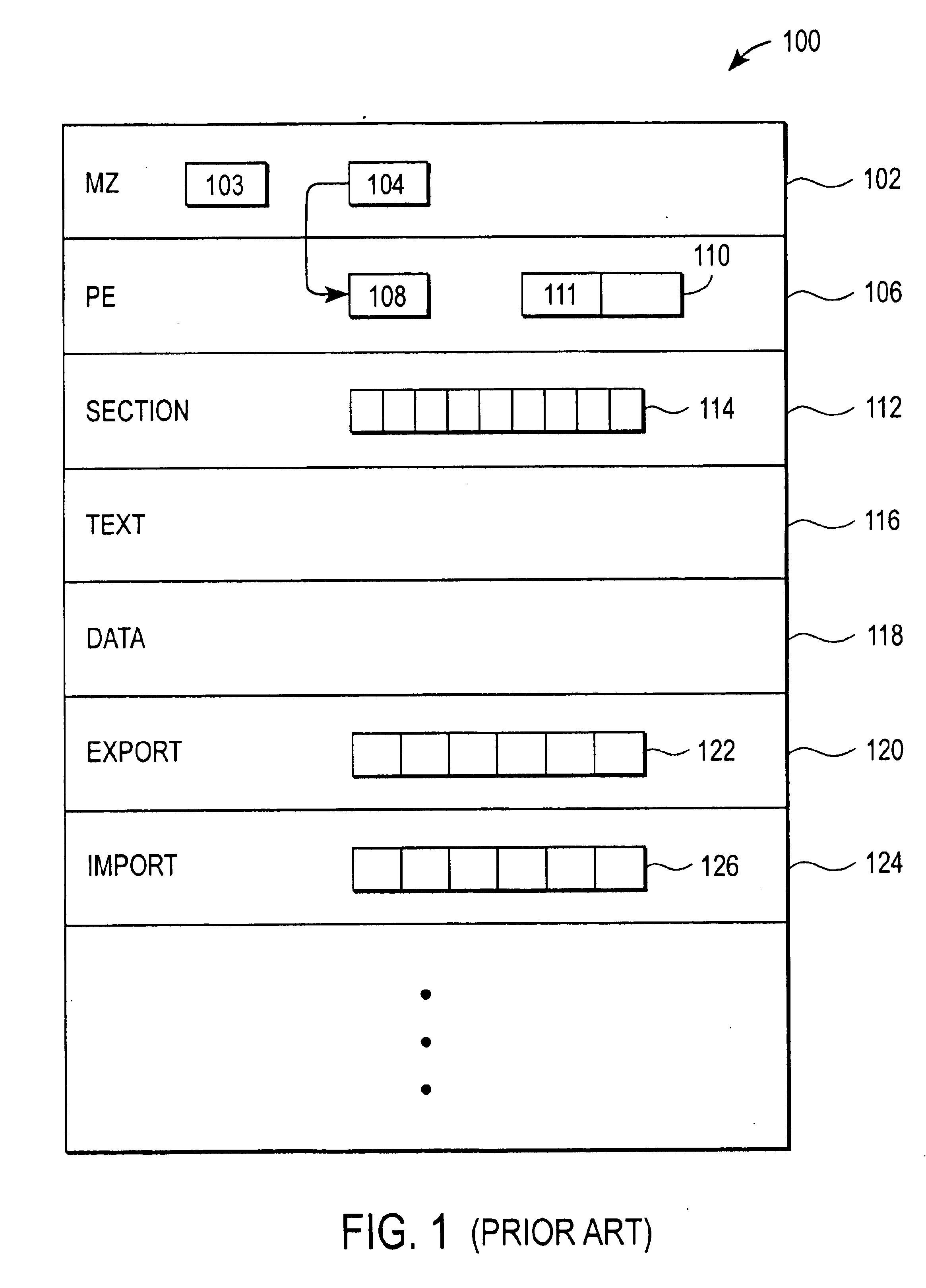
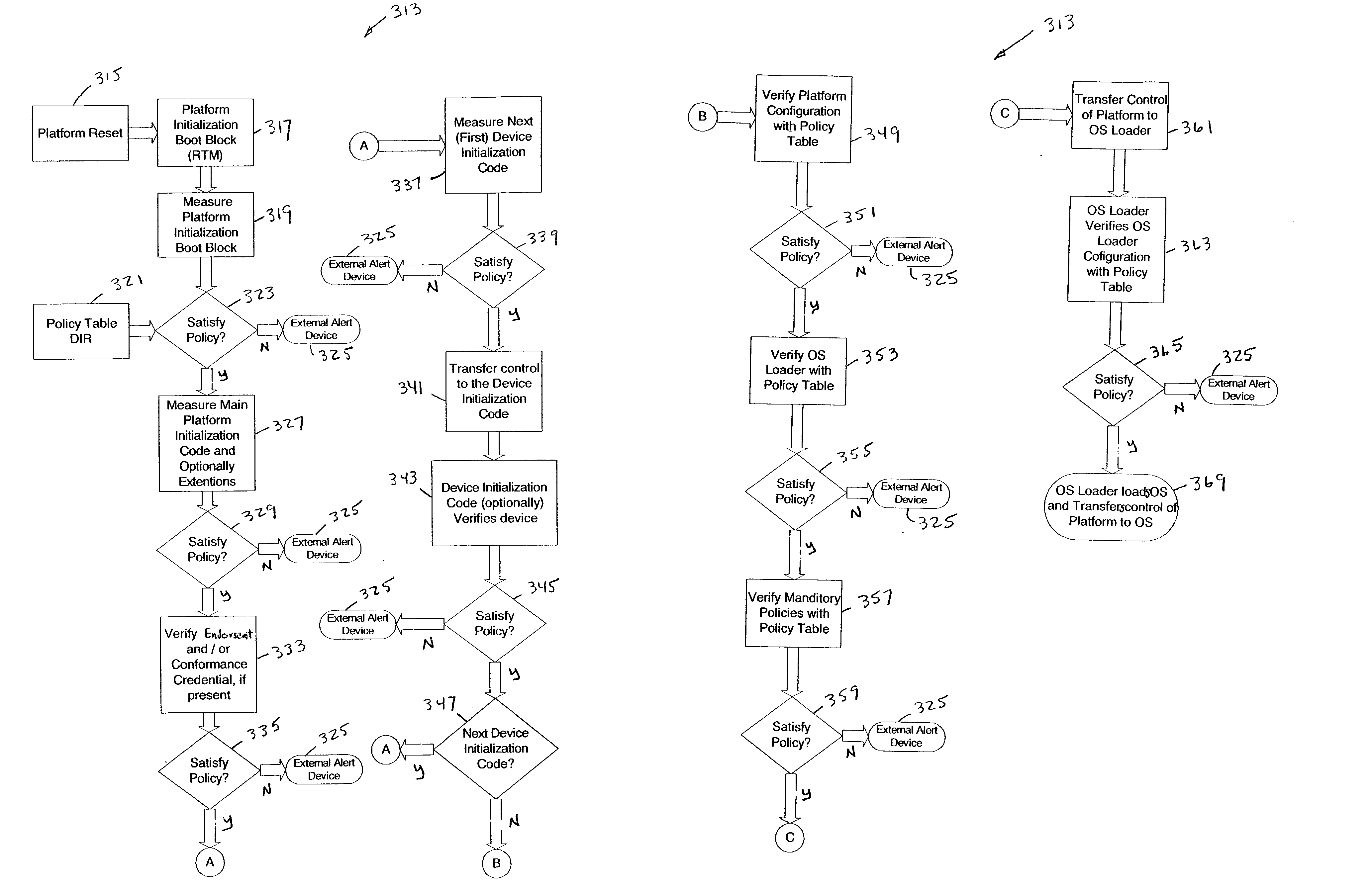
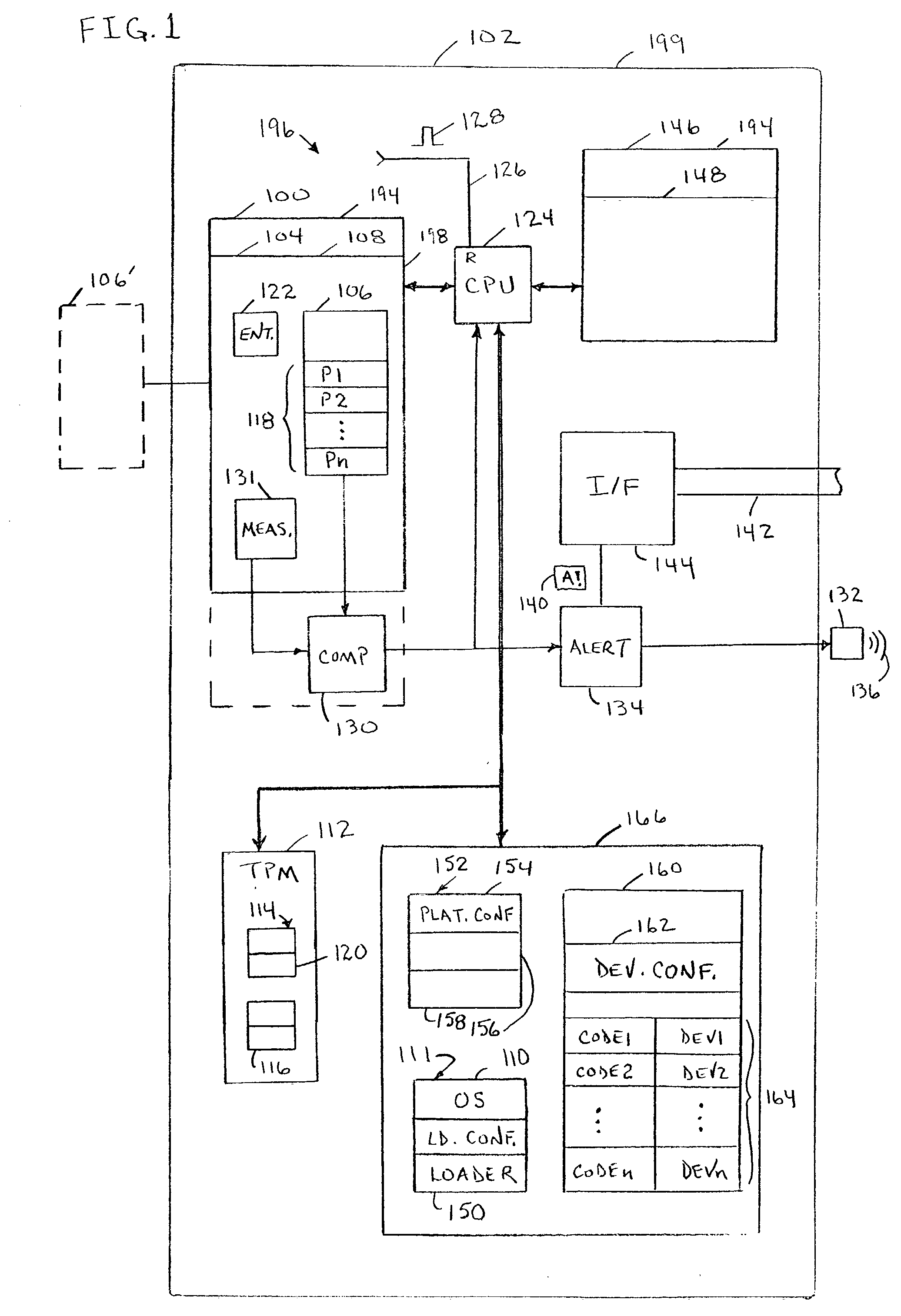
InactiveUS20040003288A1Volume/mass flow measurementDigital computer detailsOperational systemEntry point
An apparatus may include a root of trust for measurement (RTM) module coupled to a verified platform security property policy module and a comparison module. The comparison module may operate to prevent transfer of control to an operating system (and / or halt the boot process) if a policy included in the platform security property policy module is violated. A system may include a memory coupled to a processor, a platform security property policy module, and a comparison module. The memory may include an RTM. A method may include beginning execution at an entry point within an RTM, determining that the RTM is trustworthy, determining that a main initialization code associated with a platform is trustworthy and transferring control to the main initialization code, and otherwise, refraining from transferring control to the main initialization code.
Owner:INTEL CORP
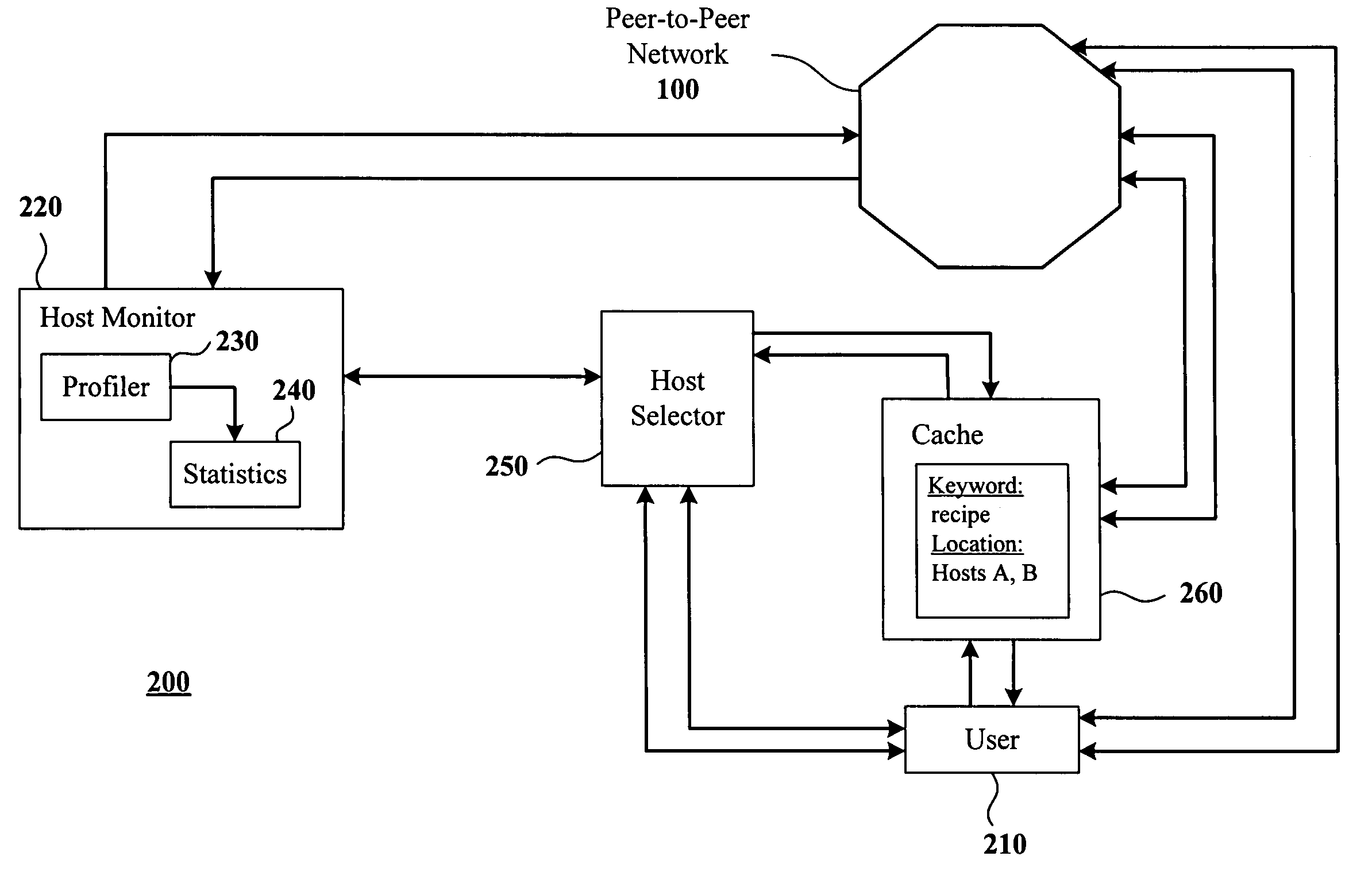
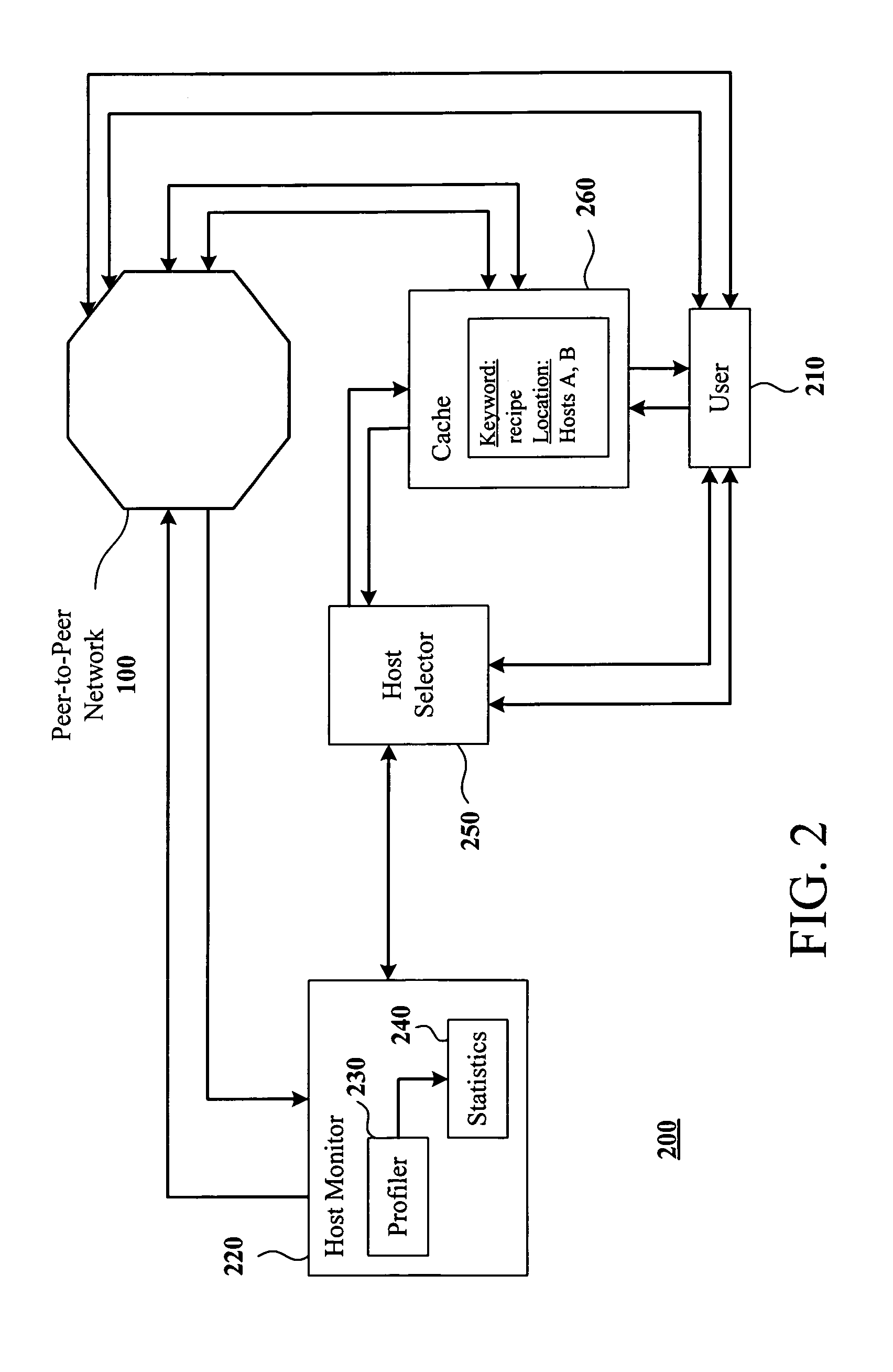
System and method for searching peer-to-peer computer networks by selecting a computer based on at least a number of files shared by the computer
InactiveUS7089301B1Increase opportunitiesStable network environmentData processing applicationsWeb data indexingEntry pointFile sharing
A method and system for intelligently directing a search of a peer-to-peer network, in which a user performing a search is assisted in choosing a host which is likely to return fast, favorable results to the user. A host monitor monitors the peer-to-peer network and collects data on various characteristics of the hosts which make up the network. Thereafter, a host selector ranks the hosts using the data, and passes this information to the user. The user then selects one or more of the highly-ranked hosts as an entry point into the network. Additionally, a cache may collect a list of hosts based on the content on the hosts. In this way, a user may choose to connect to a host which is known to contain information relevant to the user's search. The host selector may be used to select from among the hosts listed in the cache.
Owner:MOON GLOW SERIES 82 OF ALLIED SECURITY TRUST I
Secure and zero knowledge data sharing for cloud applications
Disclosed is a zero-knowledge distributed application configured to securely share information among groups of users having various roles, such as doctors and patients. Confidential information may be encrypted client-side, with private keys that reside solely client side. Encrypted collections of data may be uploaded to, and hosted by, a server that does not have access to keys suitable to decrypt the data. Other users may retrieve encrypted data from the server and decrypt some or all of the data with keys suitable to gain access to at least part of the encrypted data. The system includes a key hierarchy with multiple entry points to a top layer by which access is selectively granted to various users and keys may be recovered.
Owner:MASIMO CORP
Method of processing multiplexed program data using entry points and time units
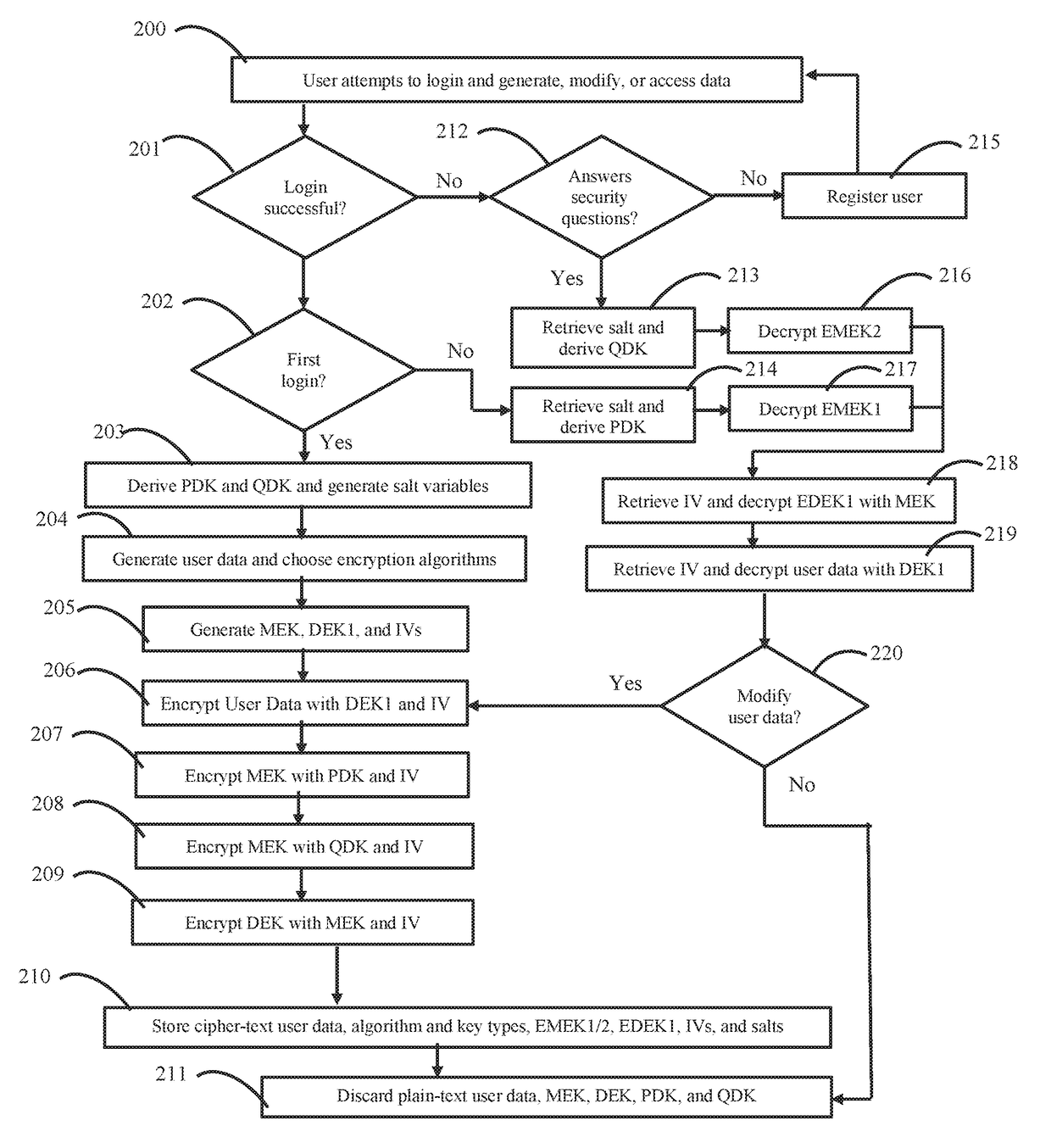
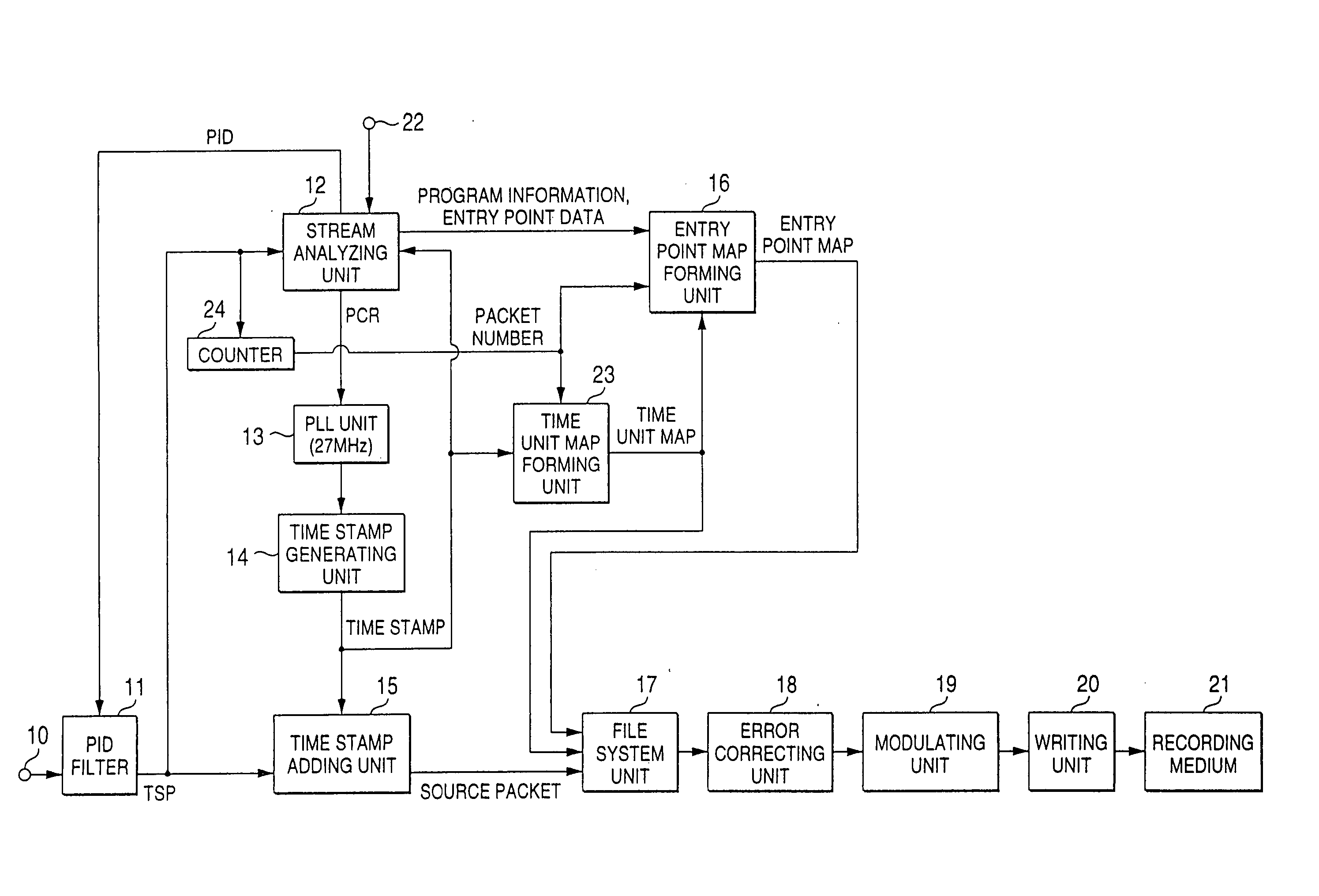
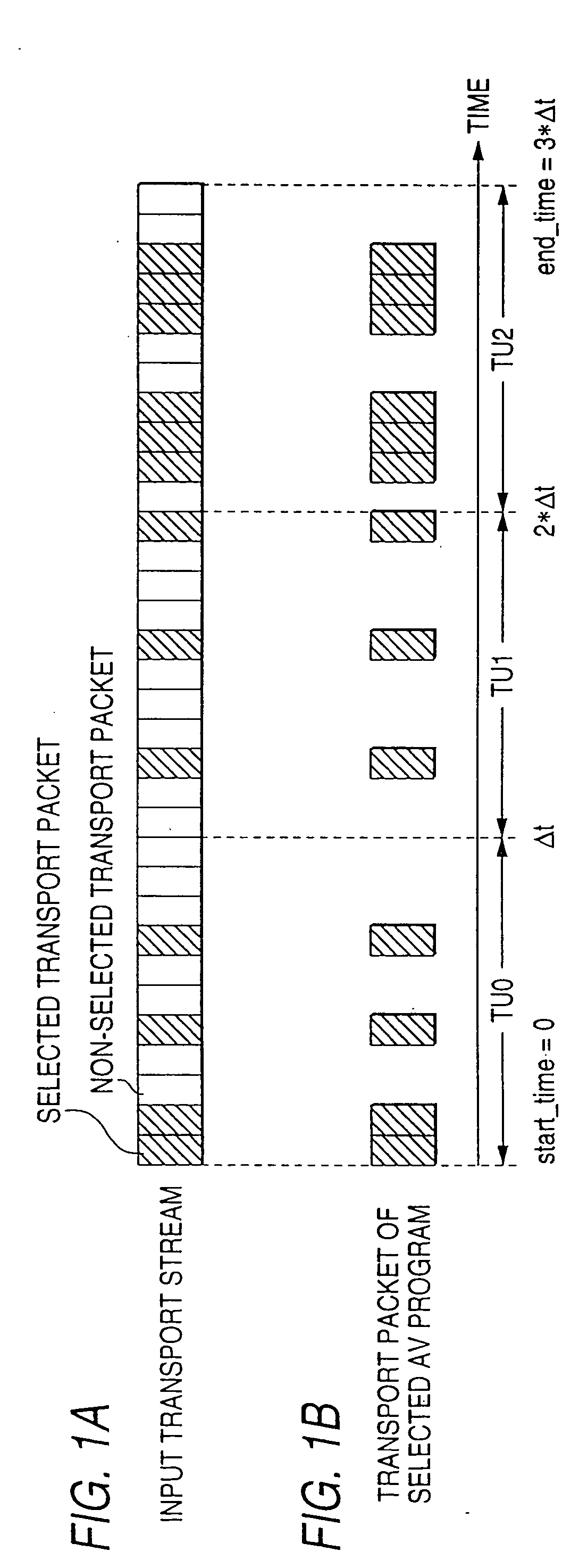
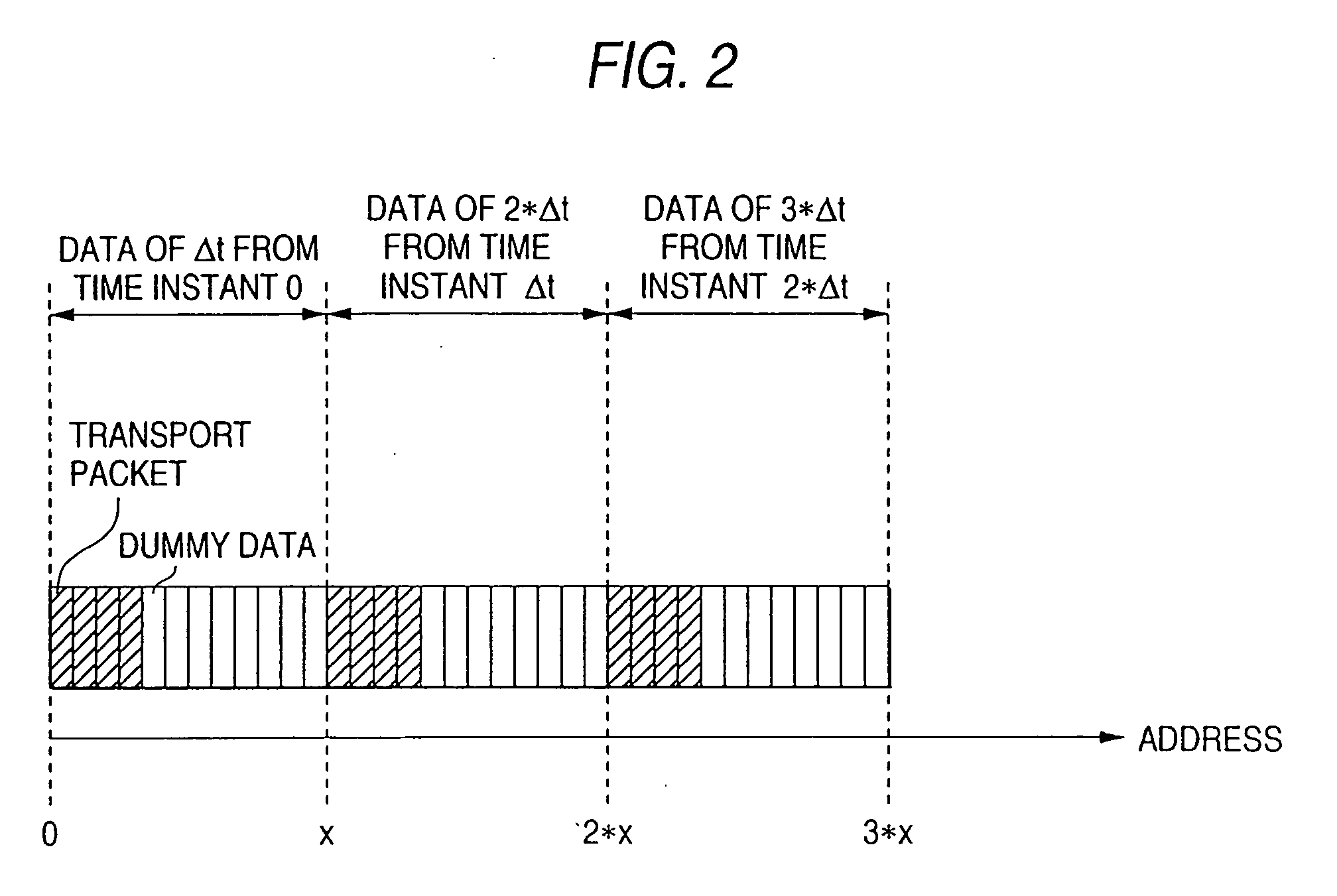
ActiveUS20050036763A1Quickly random-accessingTelevision system detailsDisc-shaped record carriersComputer hardwareEntry point
In a data processing apparatus used for a multi-channel digital television broadcasting system, coded streams are recorded on a recording medium in a high efficiency, and can be random-accessed in a high speed. The data processing apparatus is arranged by segmenting means for segmenting the entered coded stream with respect to a predetermined time unit, and first forming means for forming a time unit map indicative of an address of data every time unit of the coded stream which is segmented by the segmenting means.
Owner:SONY CORP
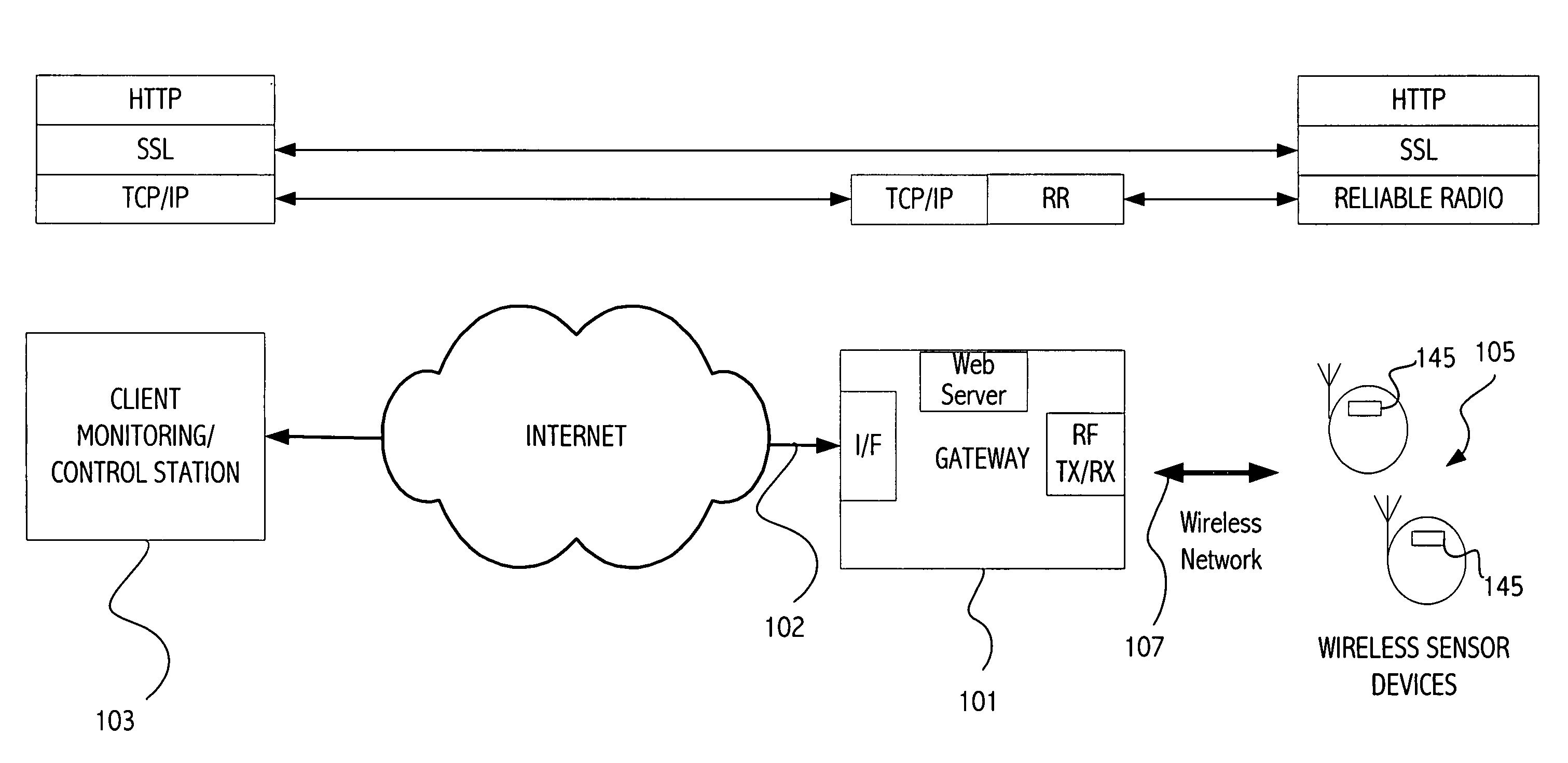
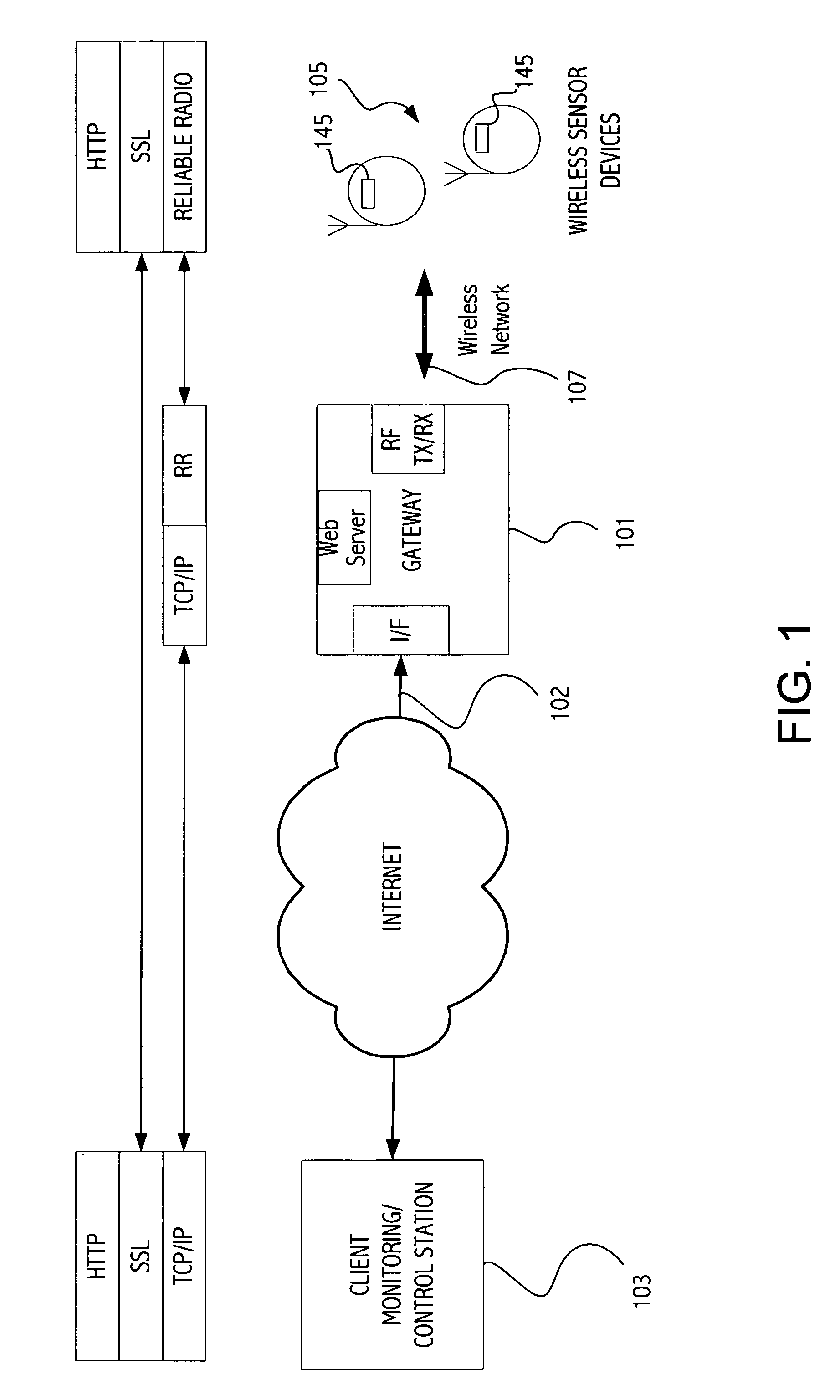
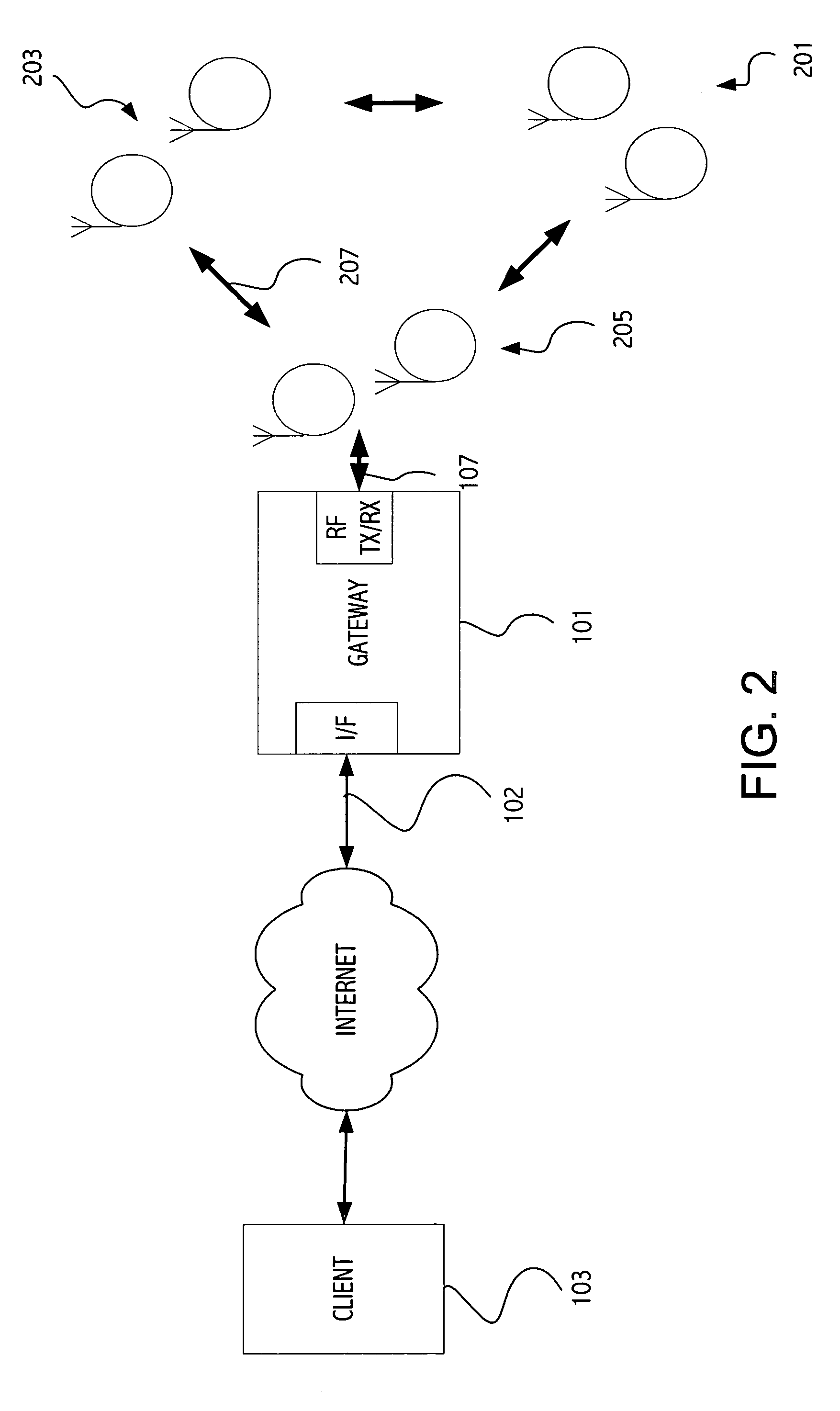
Interaction with wireless sensor devices
InactiveUS20070058634A1Improve interactivityPreserving abilityData switching by path configurationLine sensorEntry point
A client node is communicatively coupled to a gateway node via a TCP / IP network. One or more constrained devices that include a wireless receiver / transmitter circuit communicate with the gateway node via a wireless network. The gateway node includes a web server that provides a dynamic web page accessible by the client node that has a list of the one or more active constrained devices on the wireless network. Each device entry in the list includes a URL that acts as an entry point for the client node to communicate with a web server in a corresponding constrained device. The gateway node automatically discovers a new device on the wireless network and populates the list of the one or more active constrained devices with the newly present constrained device. The new constrained device may be detected based on a periodic message sent by the constrained device indicating the constrained device has turned on its receiver / transmitter circuit for a period of time.
Owner:SUN MICROSYSTEMS INC
Method and system for path identification in packet networks
ActiveUS20050025059A1Simple methodColor television with pulse code modulationError preventionEntry pointSource area
A method and system for extracting and building end-to-end route information in a multi-area Internet protocol (IP) autonomous system (AS) is disclosed. The method and system enable a user, such as a network administrator, to explicitly identify a full set of paths (links and routers) that a given IP packet would potentially traverse from its entry point in the source area of the AS where it originates until its exit point in its intended destination area.
Owner:SONS OF INNOVATION LLC
Multiple insertion point queue to order and select elements to be processed
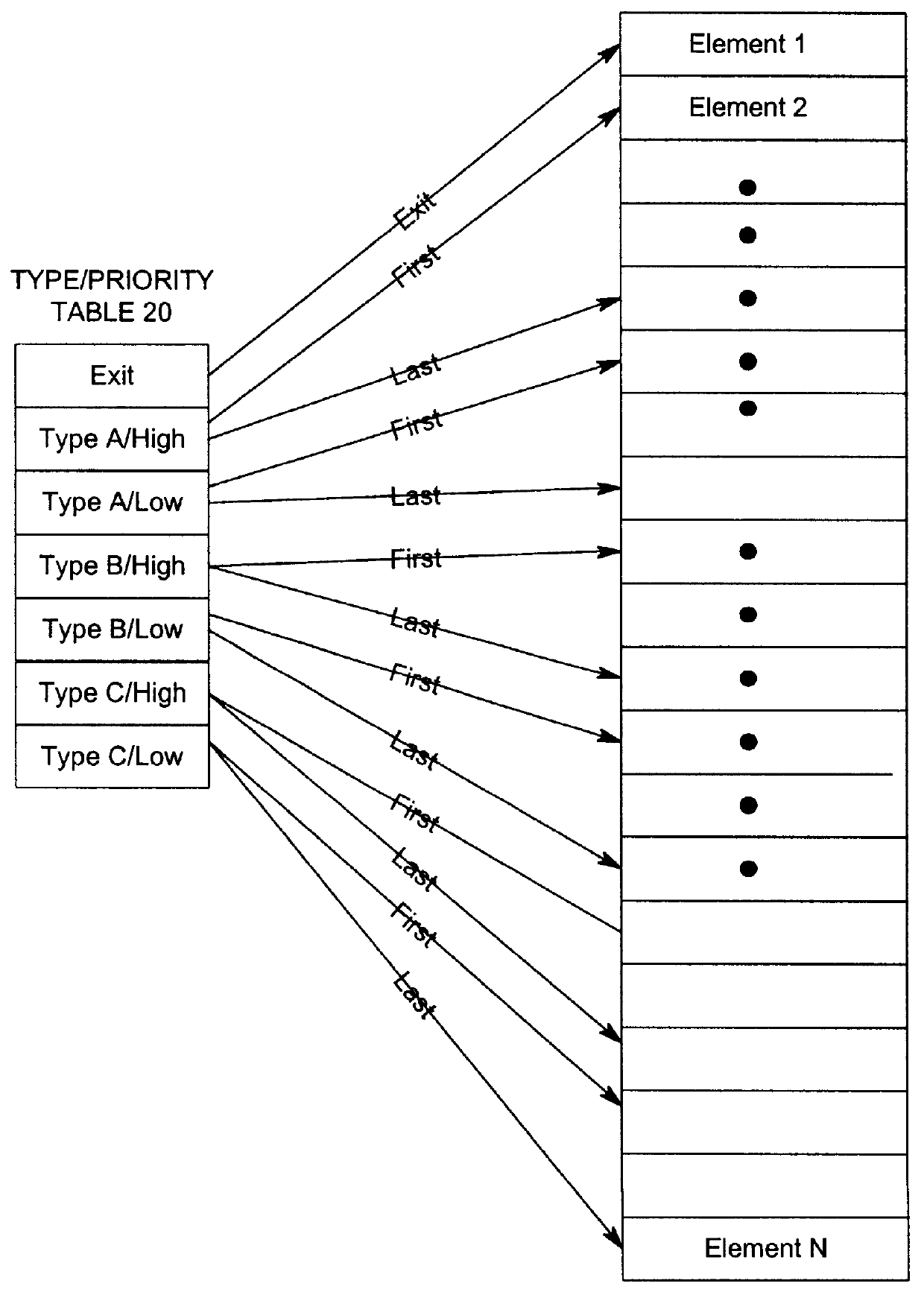
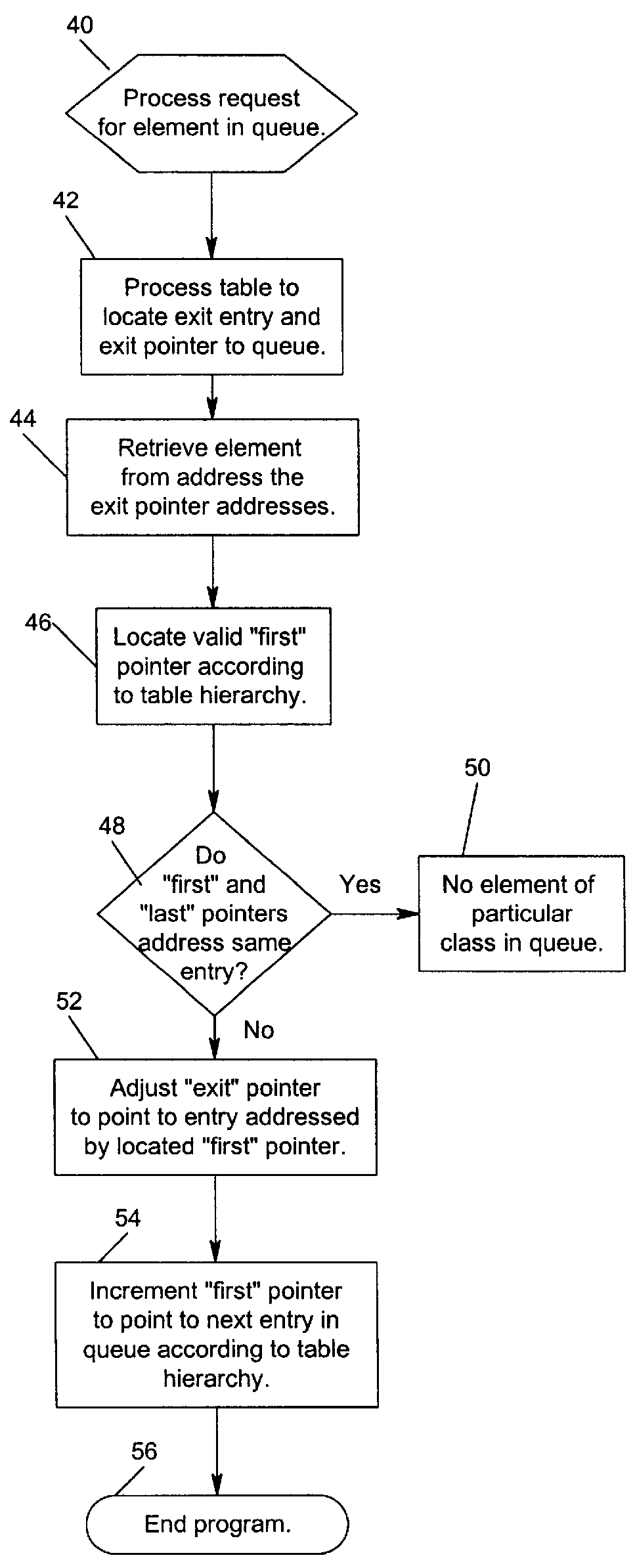
InactiveUS6145031AReduce network trafficDigital output to print unitsData conversionEntry pointInsertion point
Disclosed is a system for queuing elements, such as print jobs. A processing unit receives an element that is associated with a first factor and a second factor, such as data type and a priority within the data type, that indicates a priority of the element. For each first factor and second factor pair, an entry point addresses a point in the queue associated with the first factor and second factor. The processing unit locates an entry point addressing a point in the queue associated with a first factor and second factor that matches the first factor and second factor associated with the received element. The processing unit then inserts the received element in the queue at the entry point.
Owner:RICOH KK
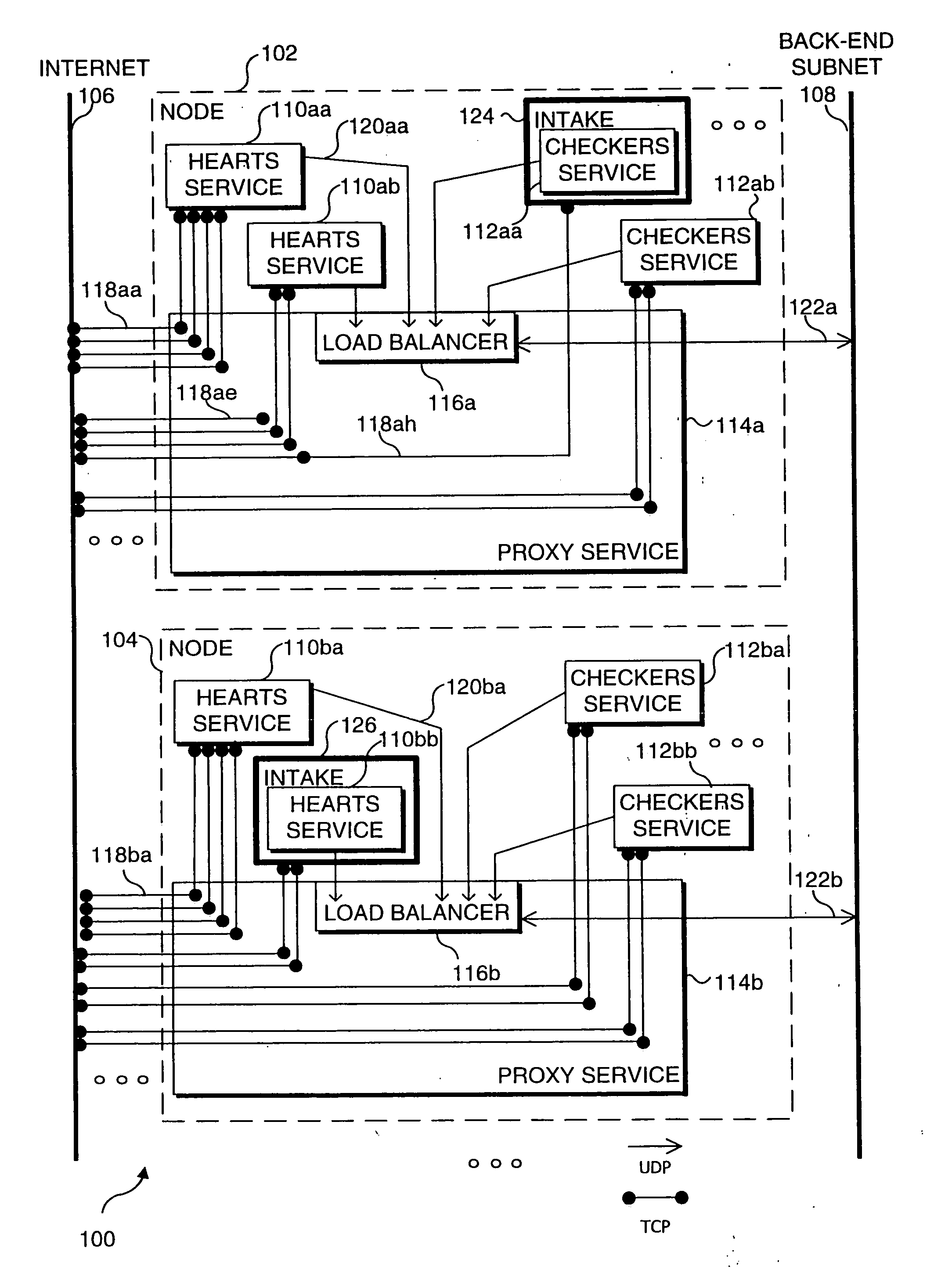
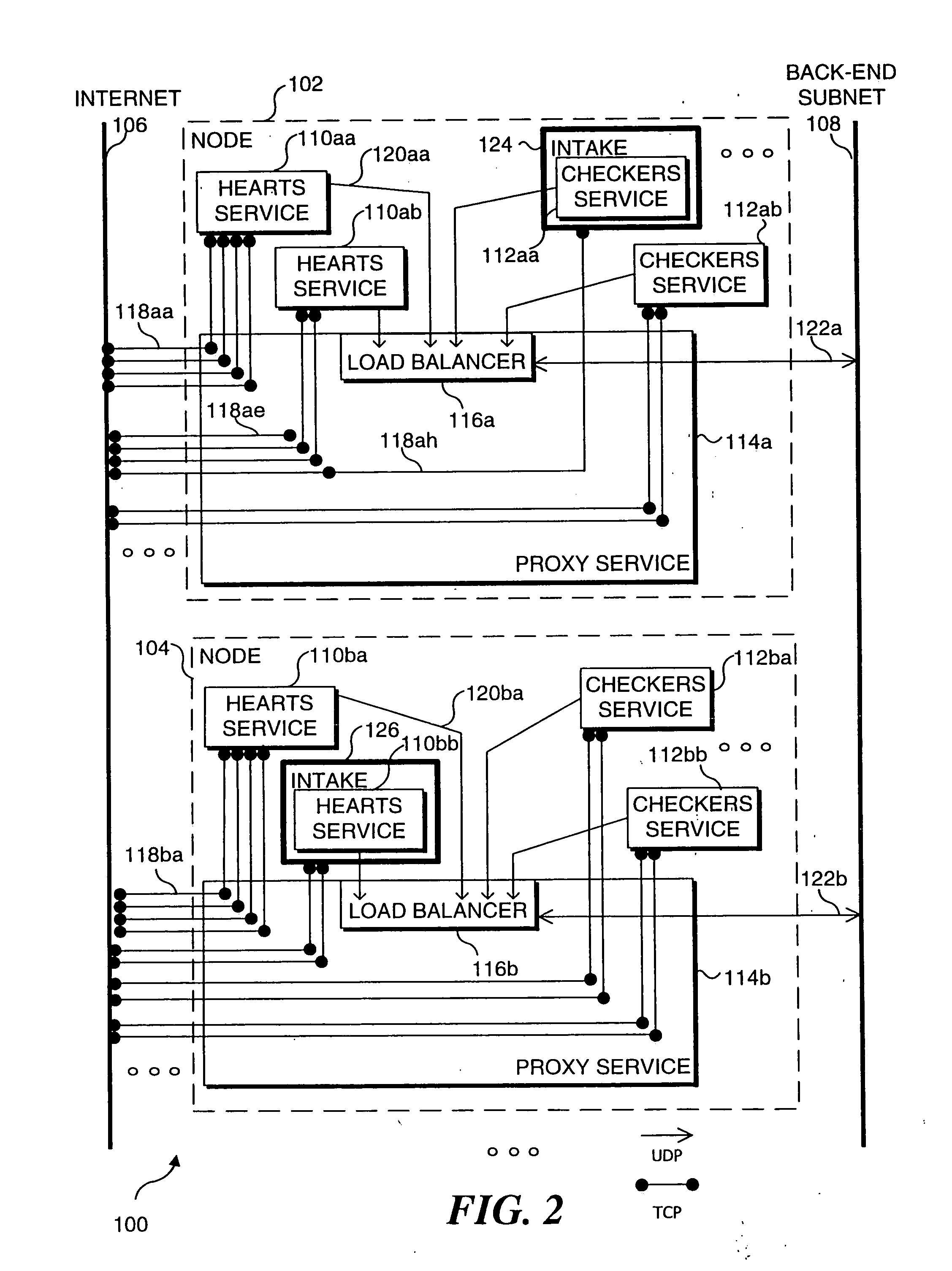
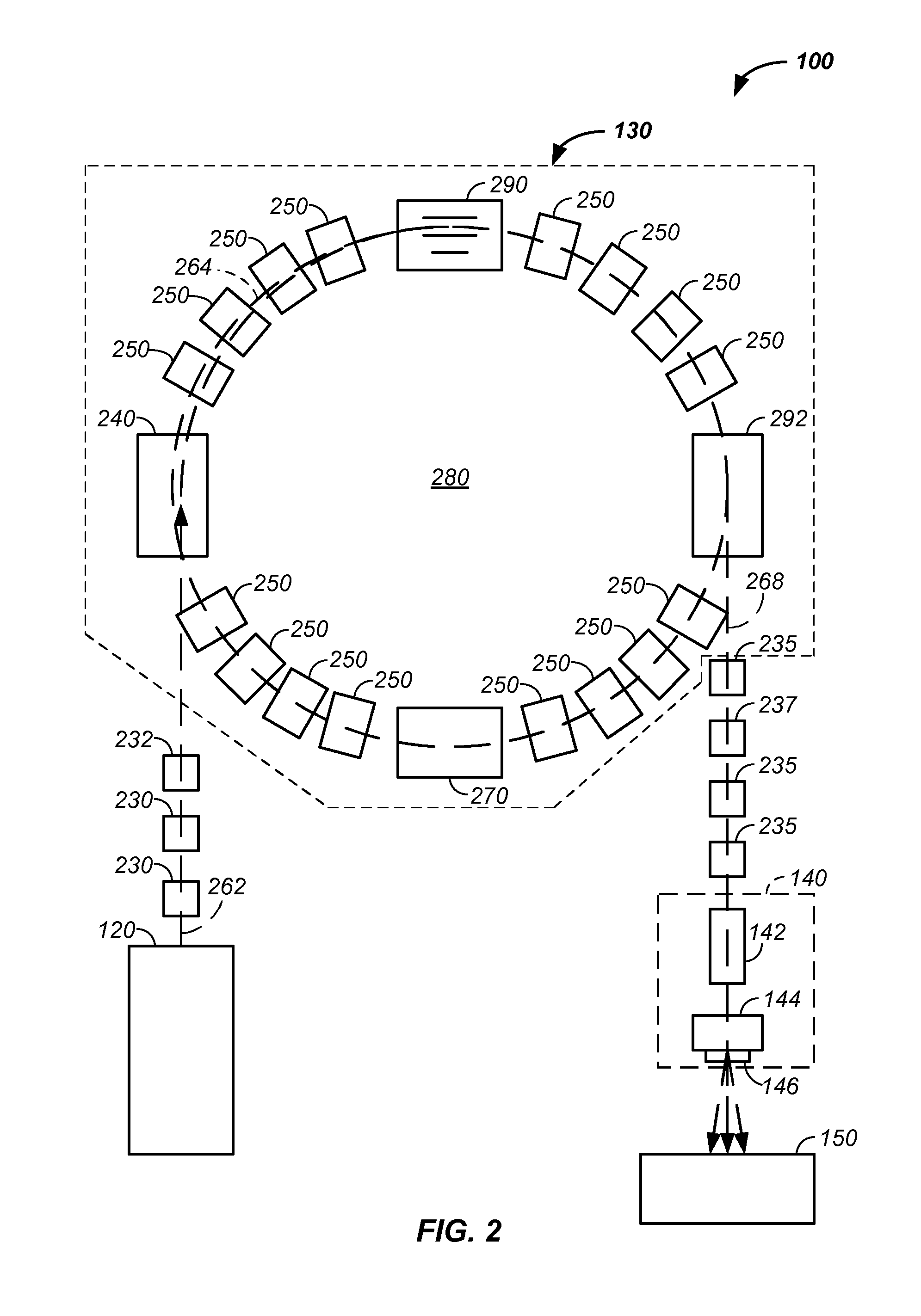
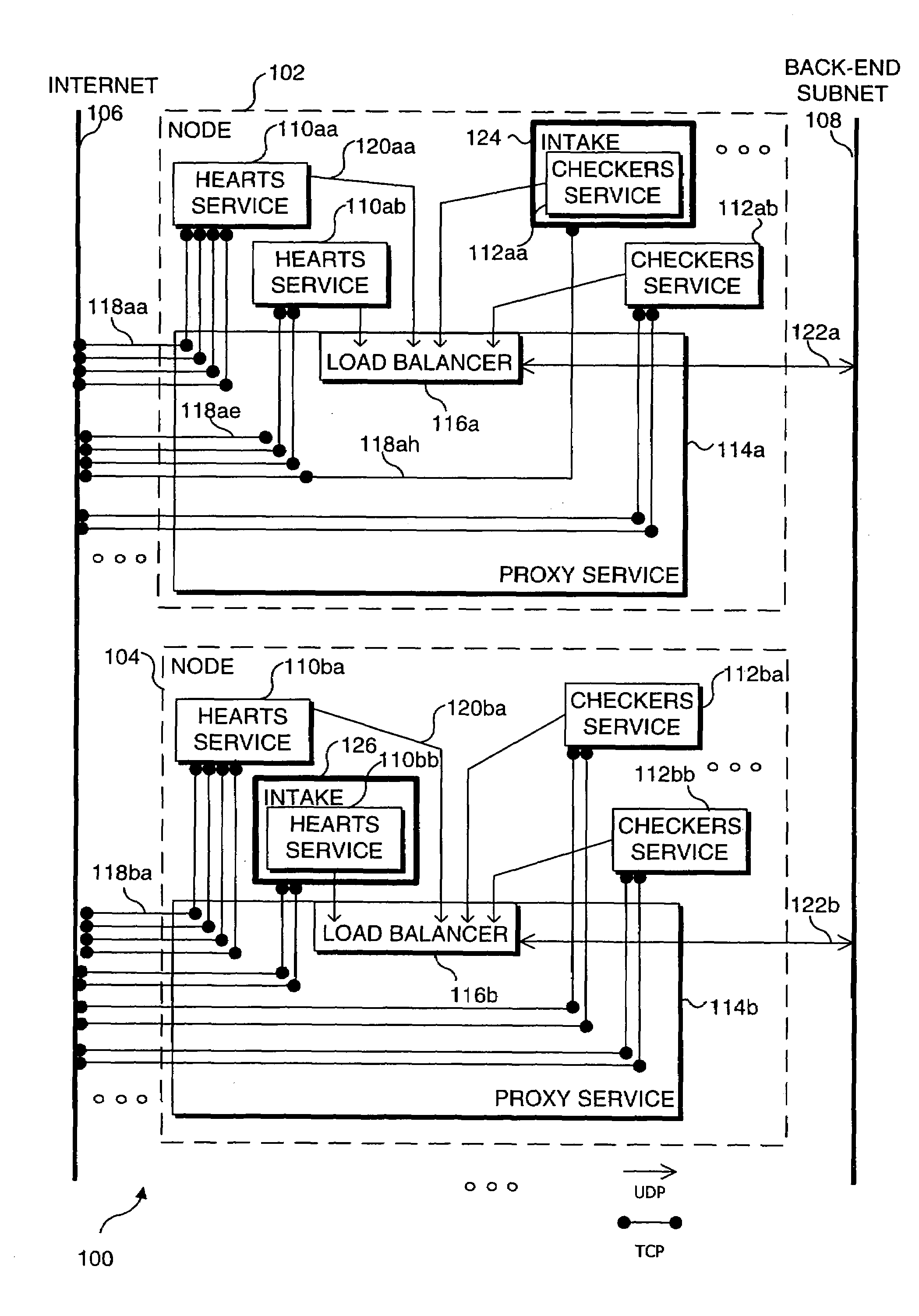
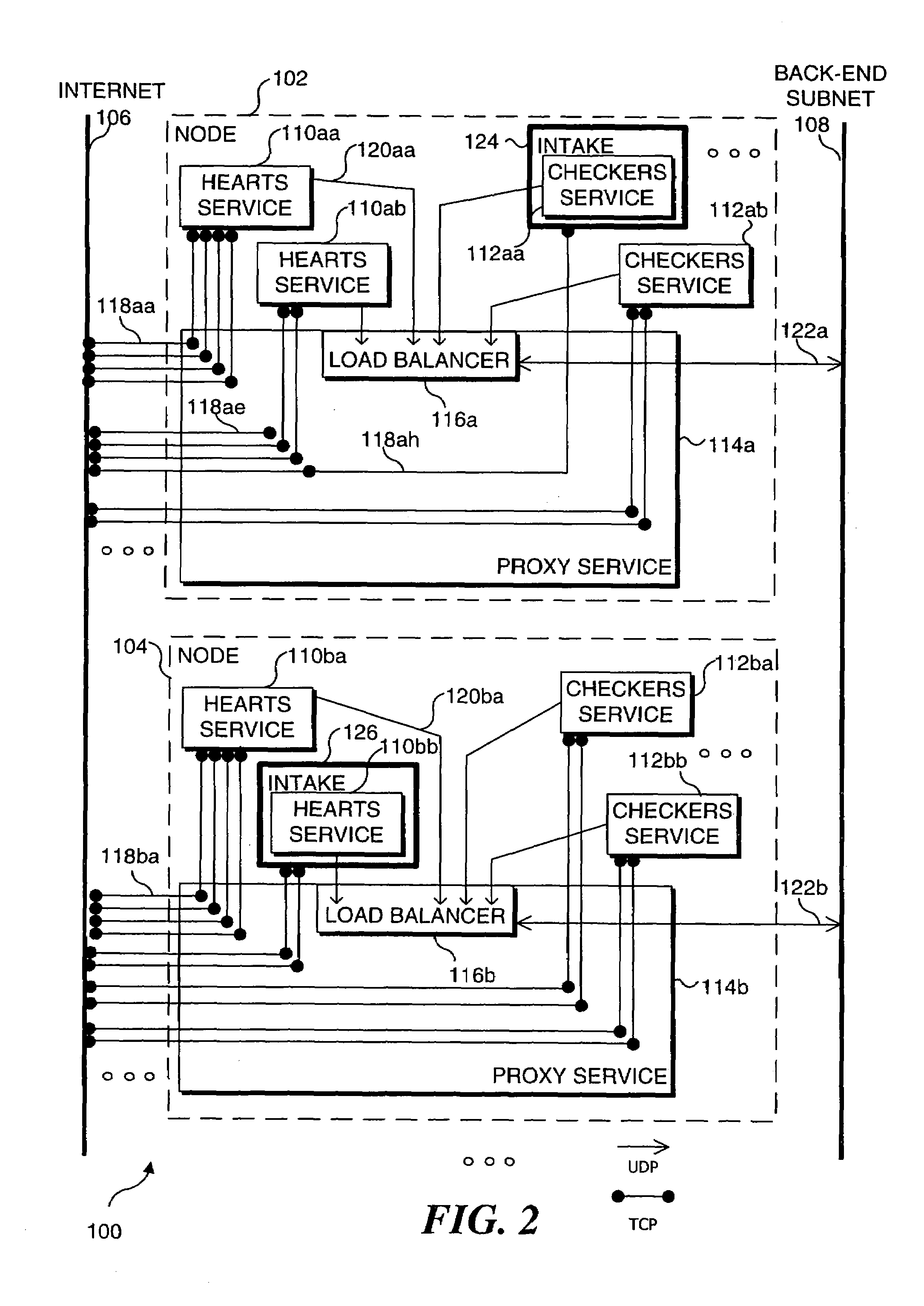
Distributed load balancing for single entry-point systems
InactiveUS20050198335A1Efficient use of resourcesReduce in quantityMultiple digital computer combinationsTransmissionLoad SheddingCurrent load
A method and system for distributing work load in a cluster of at least two service resources. Depending upon the configuration, a service resource may be an individual process, such as a single instance of a computer game, or a node on which multiple processes are executing, such as a Server. Initial connection requests from new clients are directed to a single entry-point service resource in the cluster, called an intake. A separate intake is designated for each type of service provided by the cluster. The clients are processed in a group at the service resource currently designated as the intake to which clients initially connected, for the duration of the session. Based upon its loading, the current intake service resource determines that another service resource in the cluster should become a new intake for subsequent connection requests received from new clients. Selection of another service resource to become the new intake is based on the current work load of each resource in the cluster. All resources in the cluster are periodically informed of the resource for each service being provided that was last designated as the intake, and of the current load on each resource in the cluster. Subsequently, new clients requesting a service are directed to the newly designated intake for that service and processed on that resource for the duration of the session by those clients.
Owner:MICROSOFT TECH LICENSING LLC
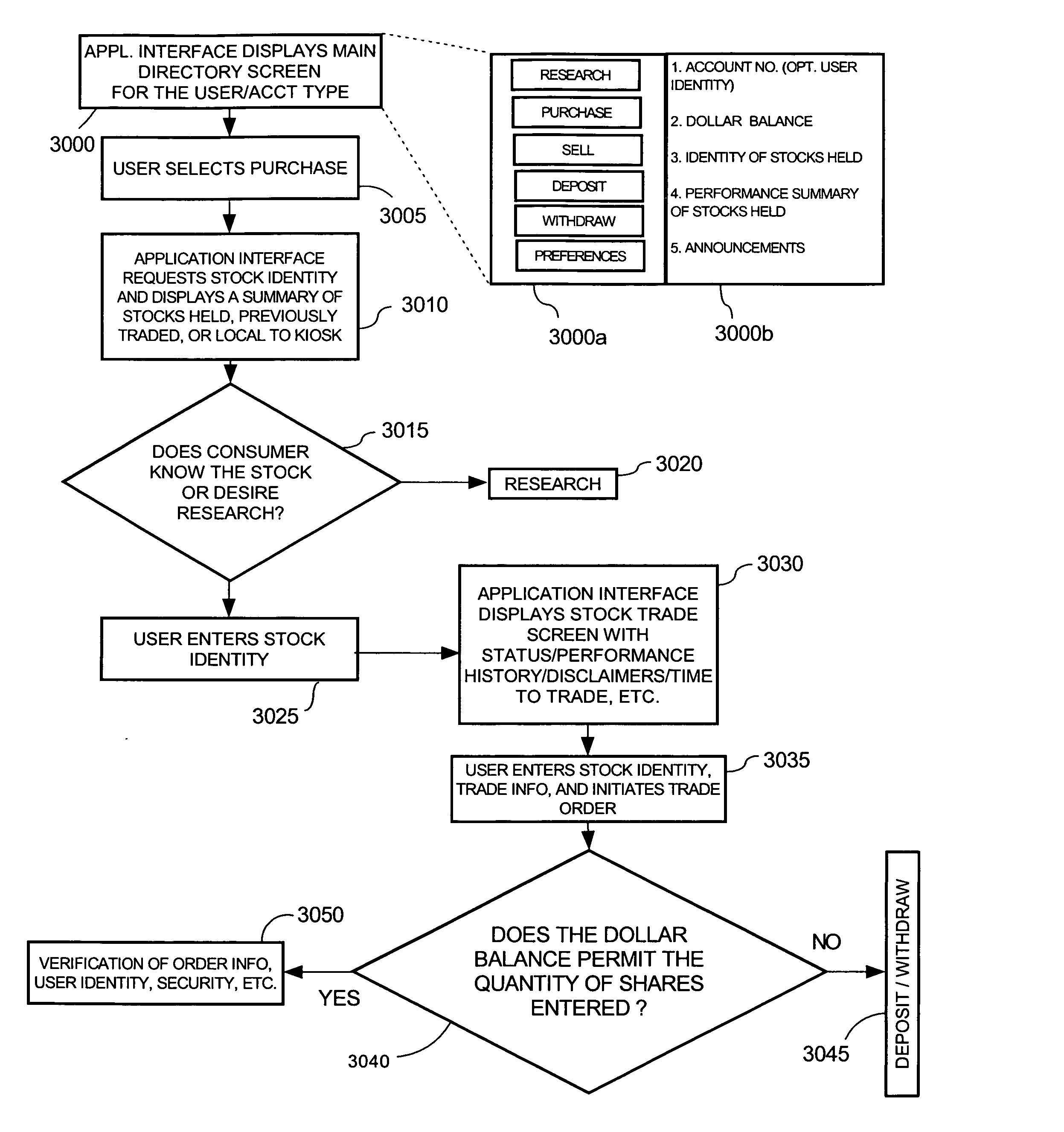
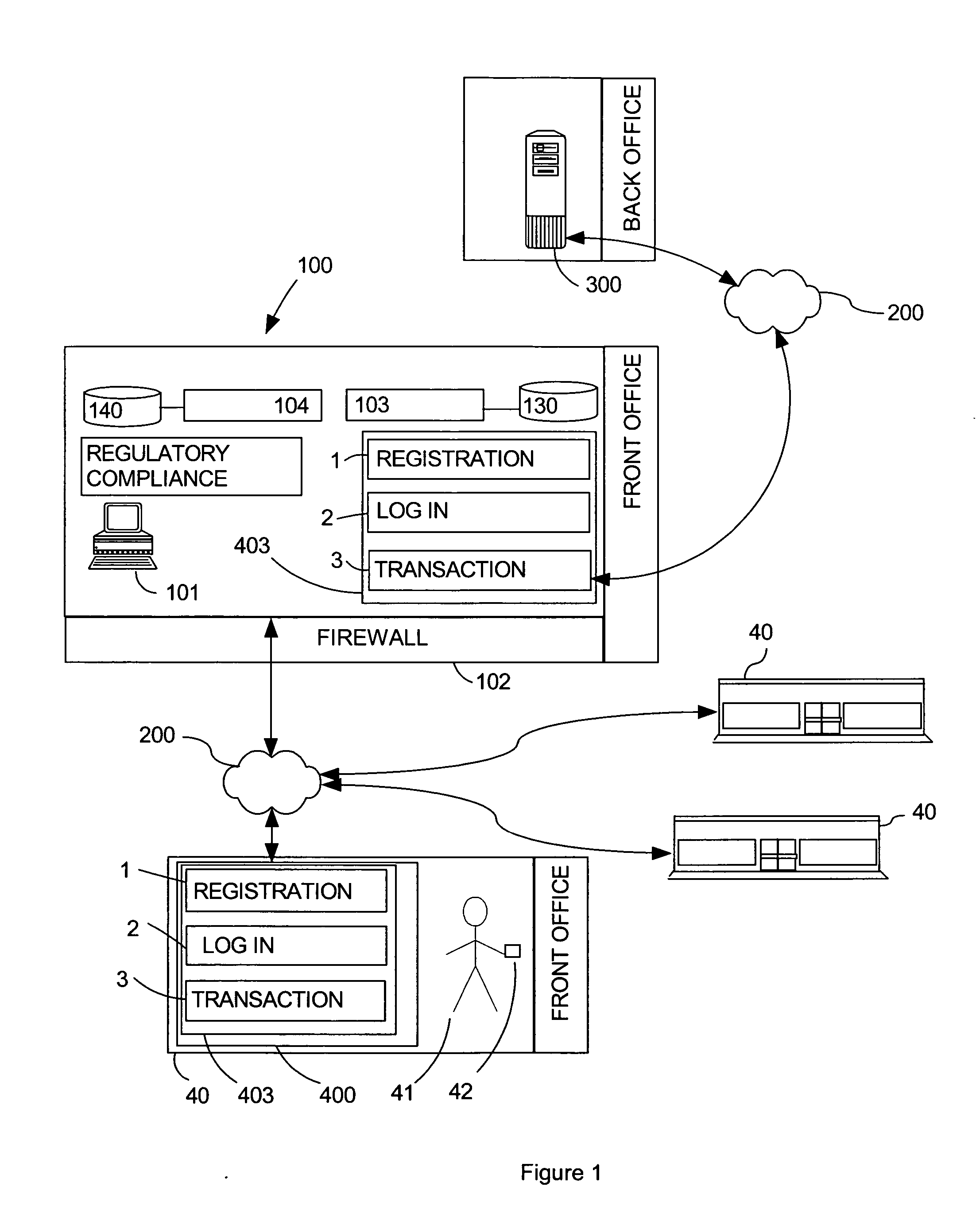
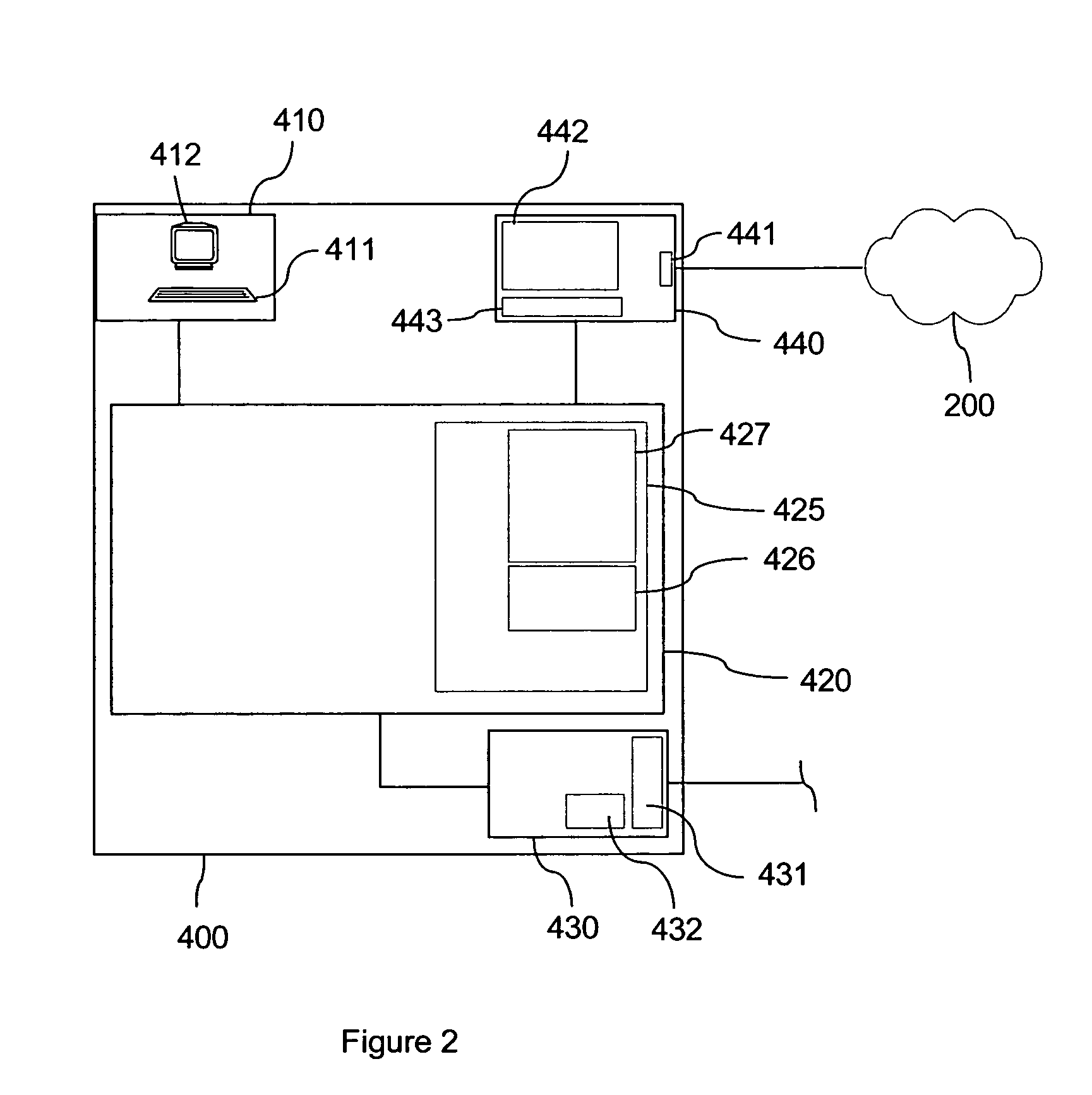
Distributed system for securities transactions
The present invention is a distributed information system that automates the front office function of a traditional stock brokerage, including the ability to register new consumers as clients at an accessible kiosk. Consumers establish cash accounts at the kiosk and undertake securities transactions against a cash account. This system provides a securities trading entry point in the form of user friendly kiosks and the supporting architecture to bring securities trading to a broader segment of the population than traditional brokerages, or direct access trading software applications, which require prior registration and internet access. The kiosks are configured so as to avoid storing personal information of the consumers. The present invention may be used with a computerized back office system, or a traditional back office staff, either in-house or provided by a third party.
Owner:JOHNSON GARRETT
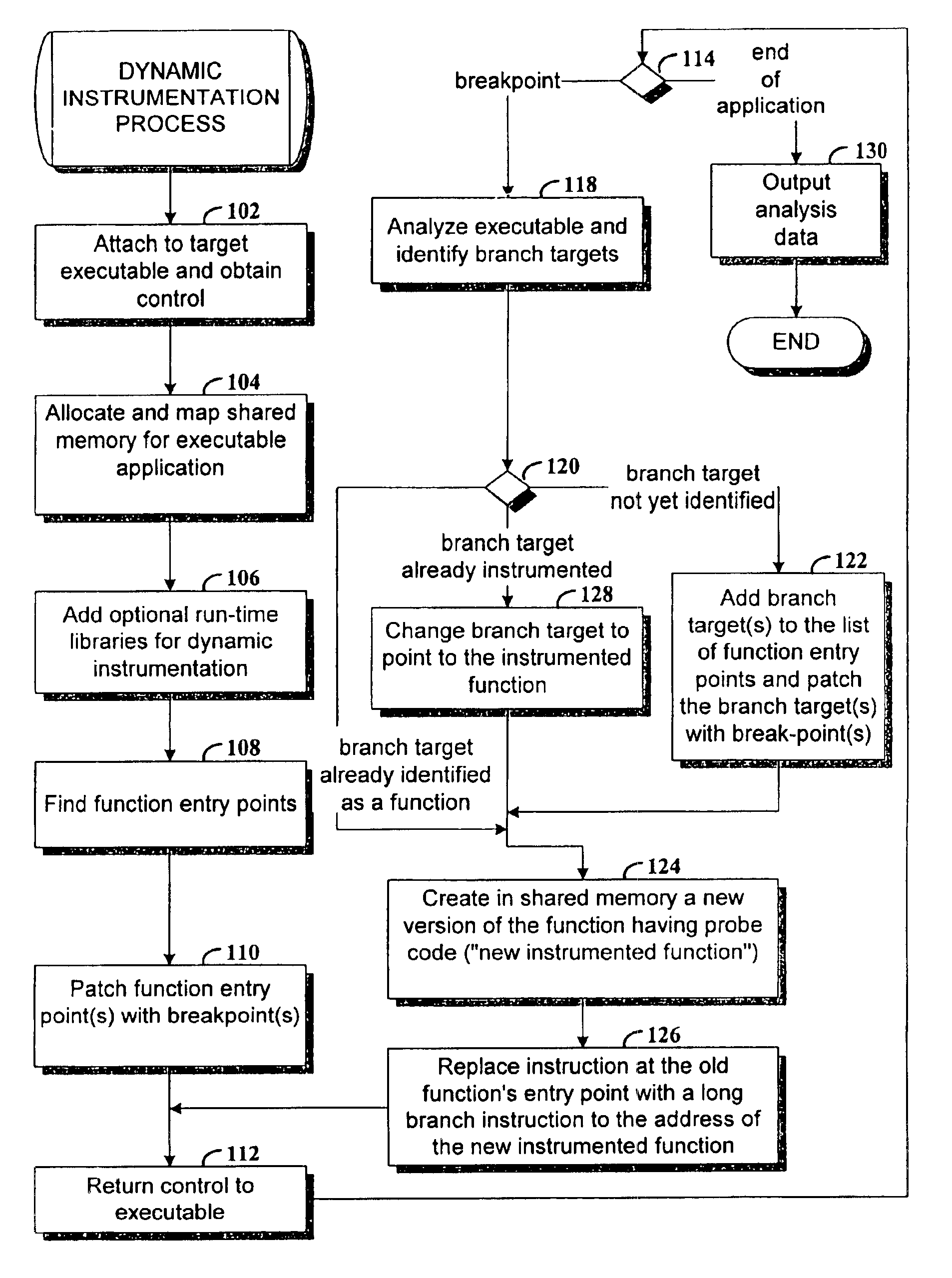
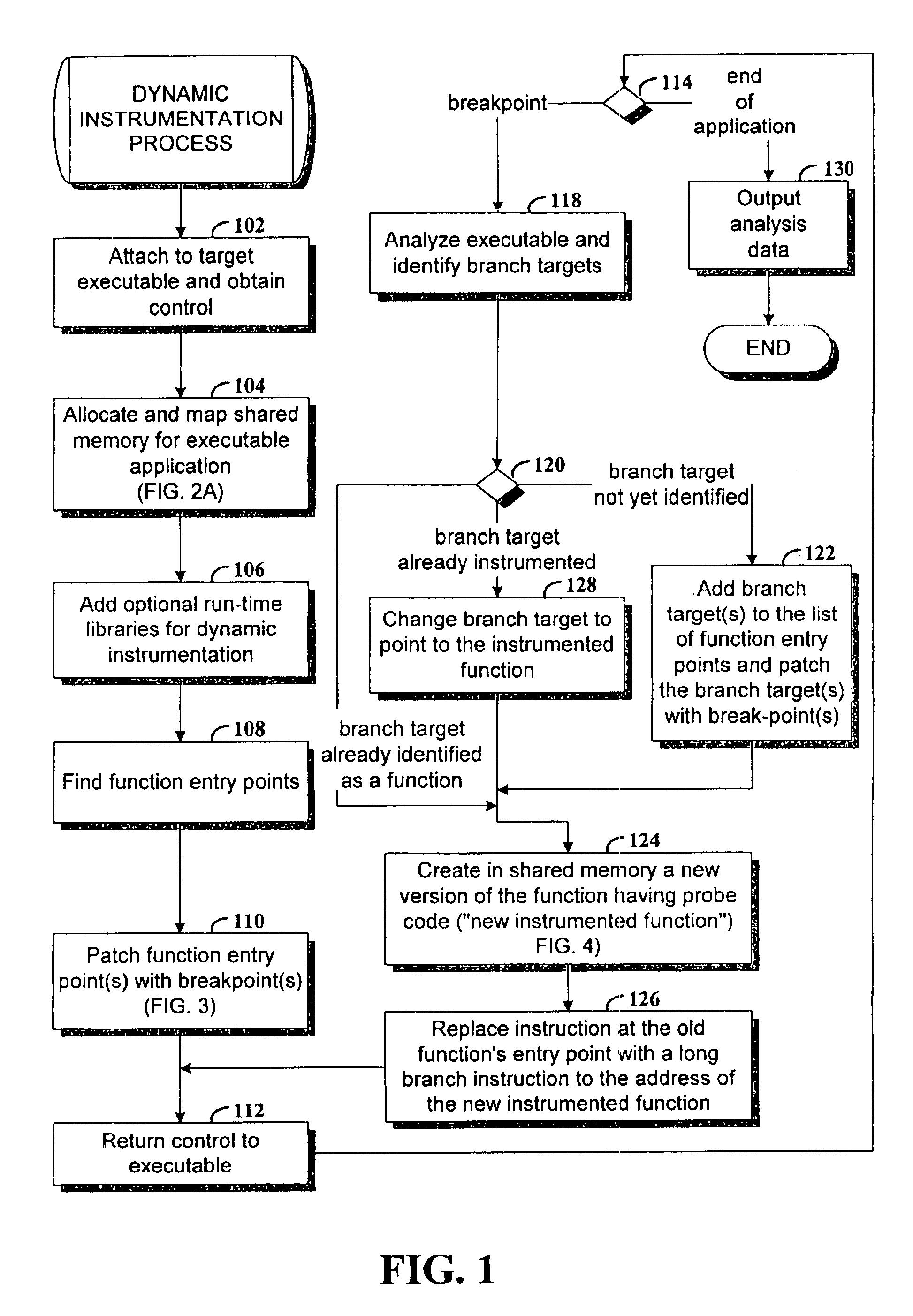
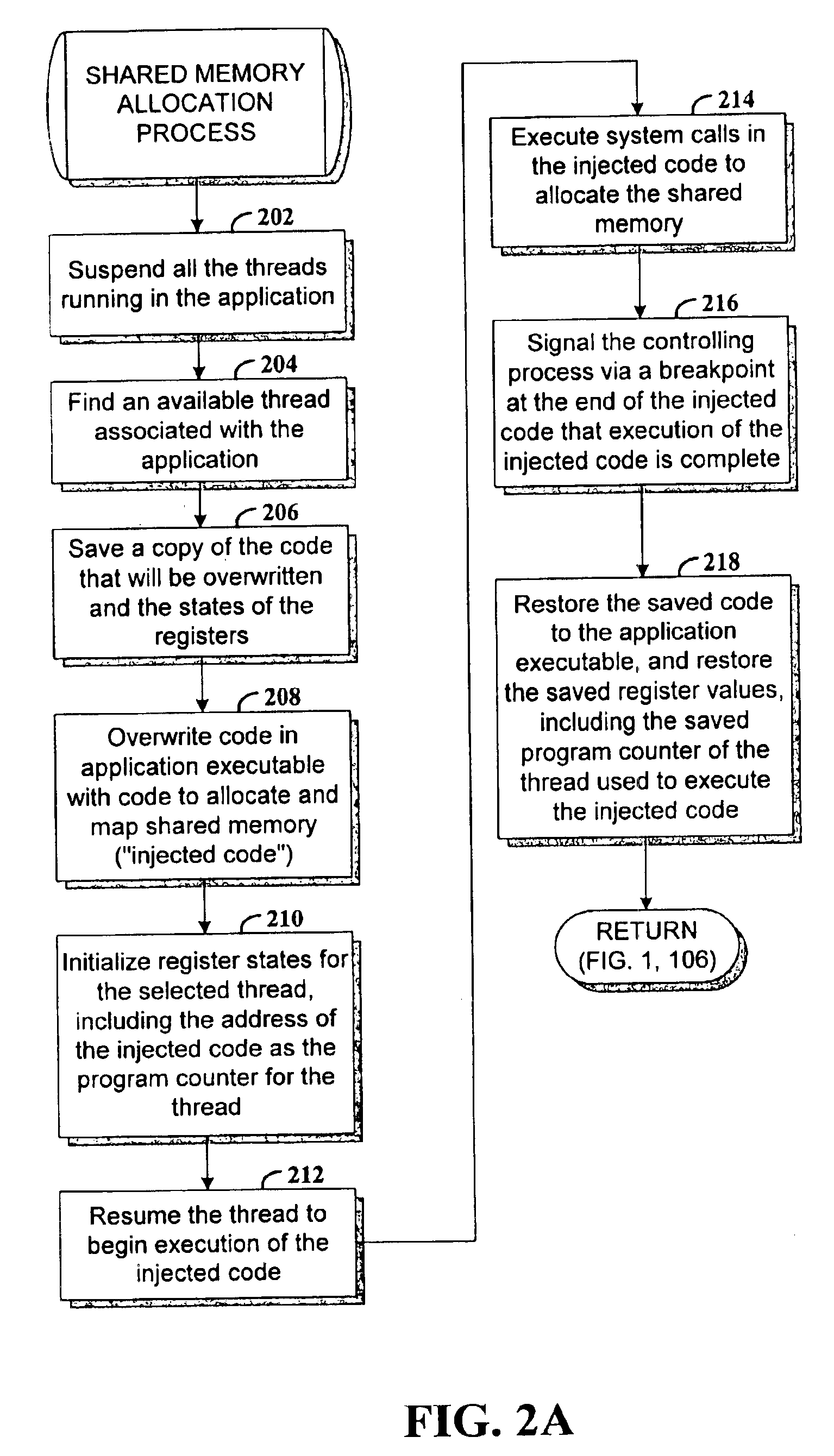
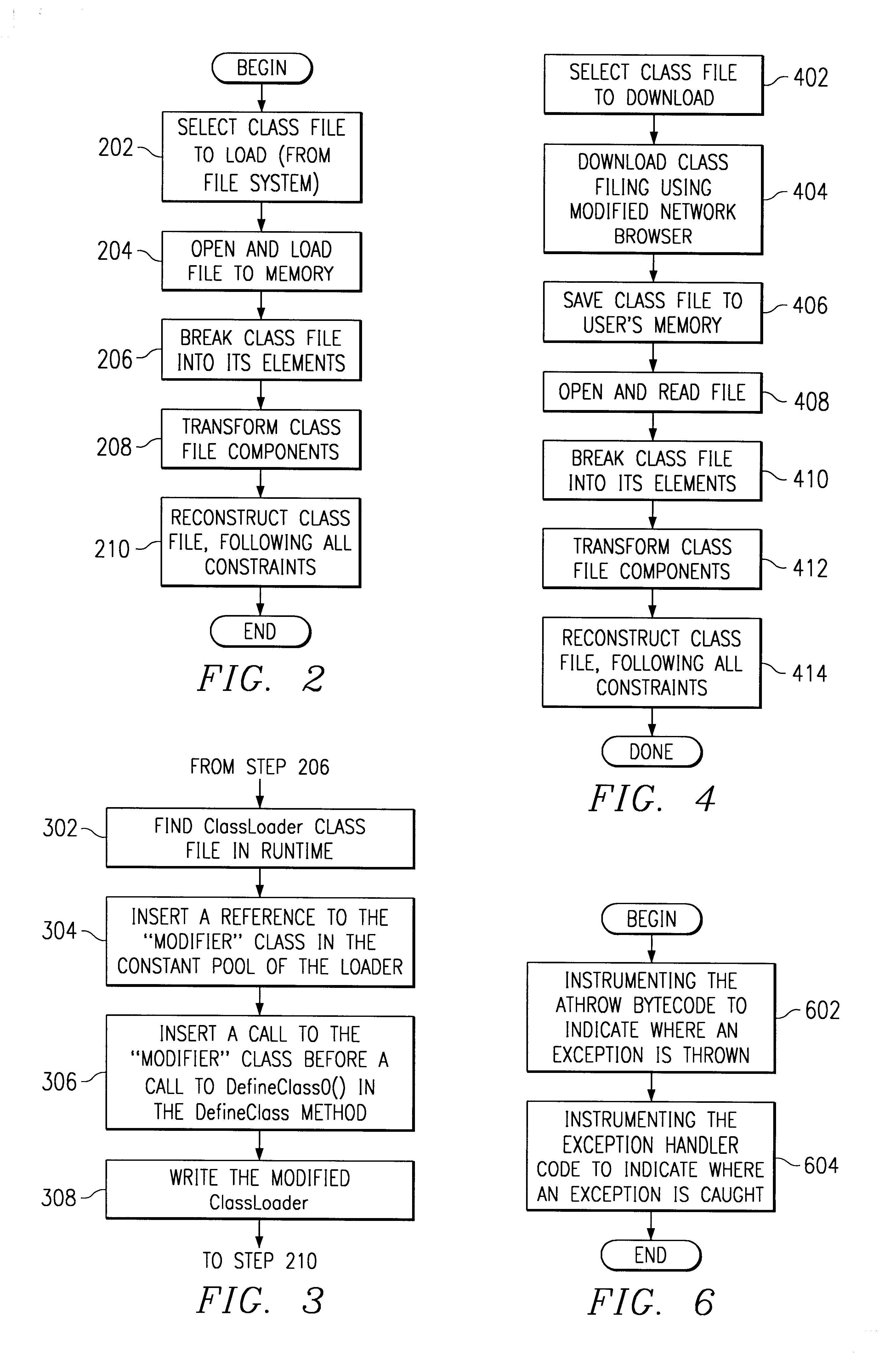
Dynamic instrumentation of an executable program by means of causing a breakpoint at the entry point of a function and providing instrumentation code
InactiveUS6918110B2Software testing/debuggingSpecific program execution arrangementsDynamic instrumentationEntry point
Method and apparatus for dynamic instrumentation of an executable application program. The application program includes a plurality of functions, each function having an entry point and an endpoint. When the application is executed, a shared memory segment is created for an instrumentation program and the application program. Upon initial invocation of the original functions in the application program, corresponding substitute functions are created in the shared memory segment, the substitute versions including instrumentation code. Thereafter, the substitute functions are executed in lieu of the original functions in the application program.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
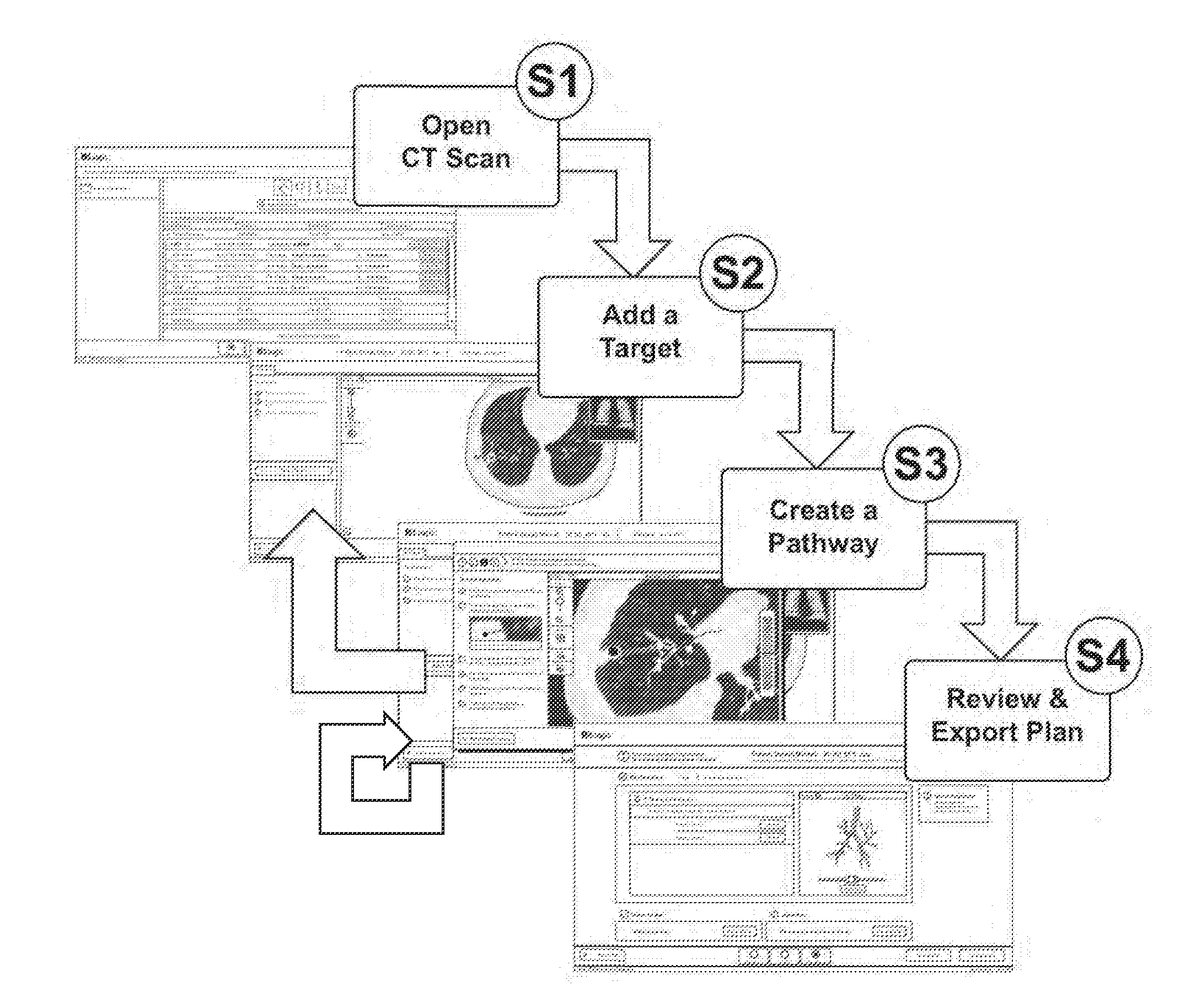
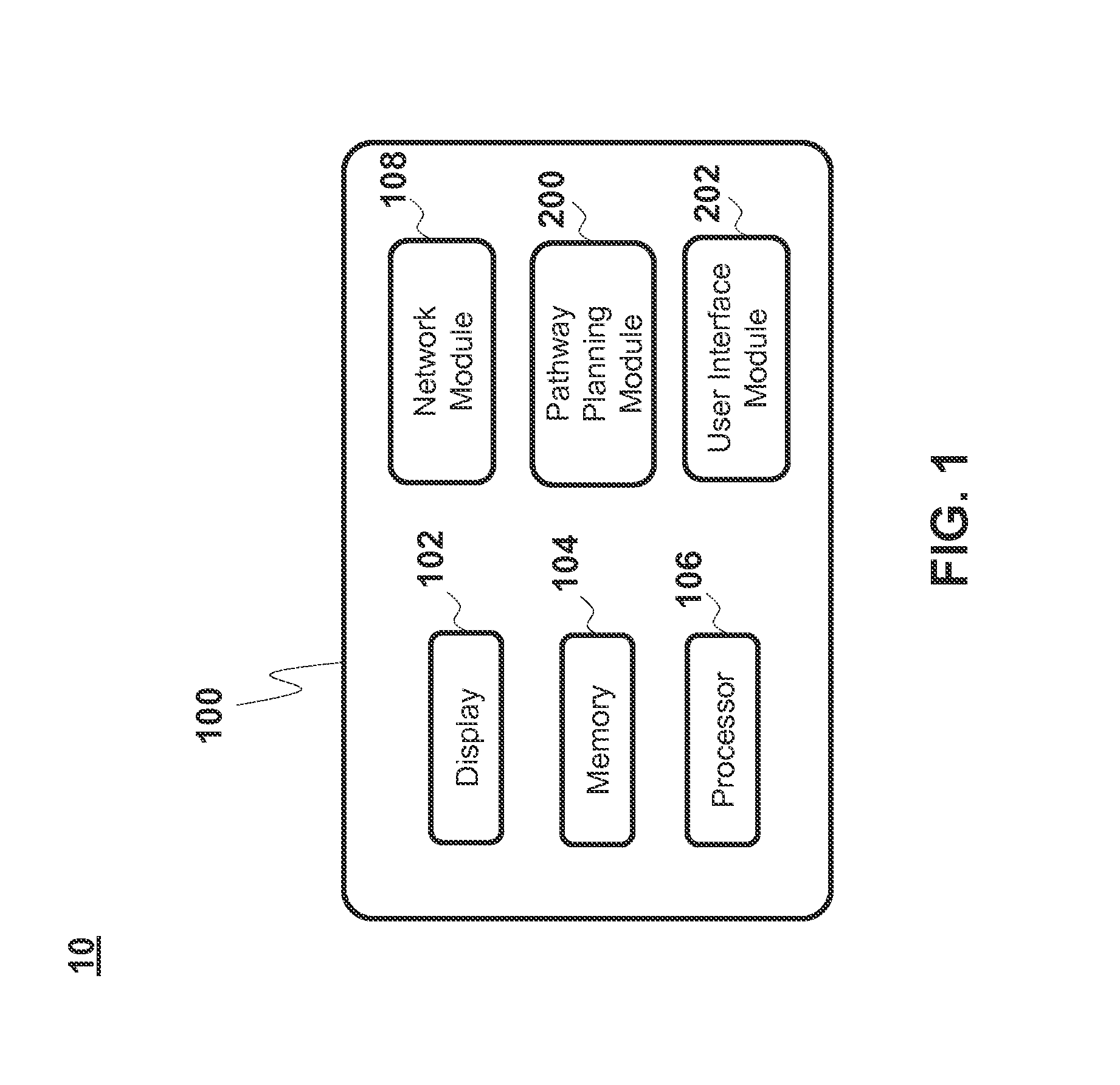
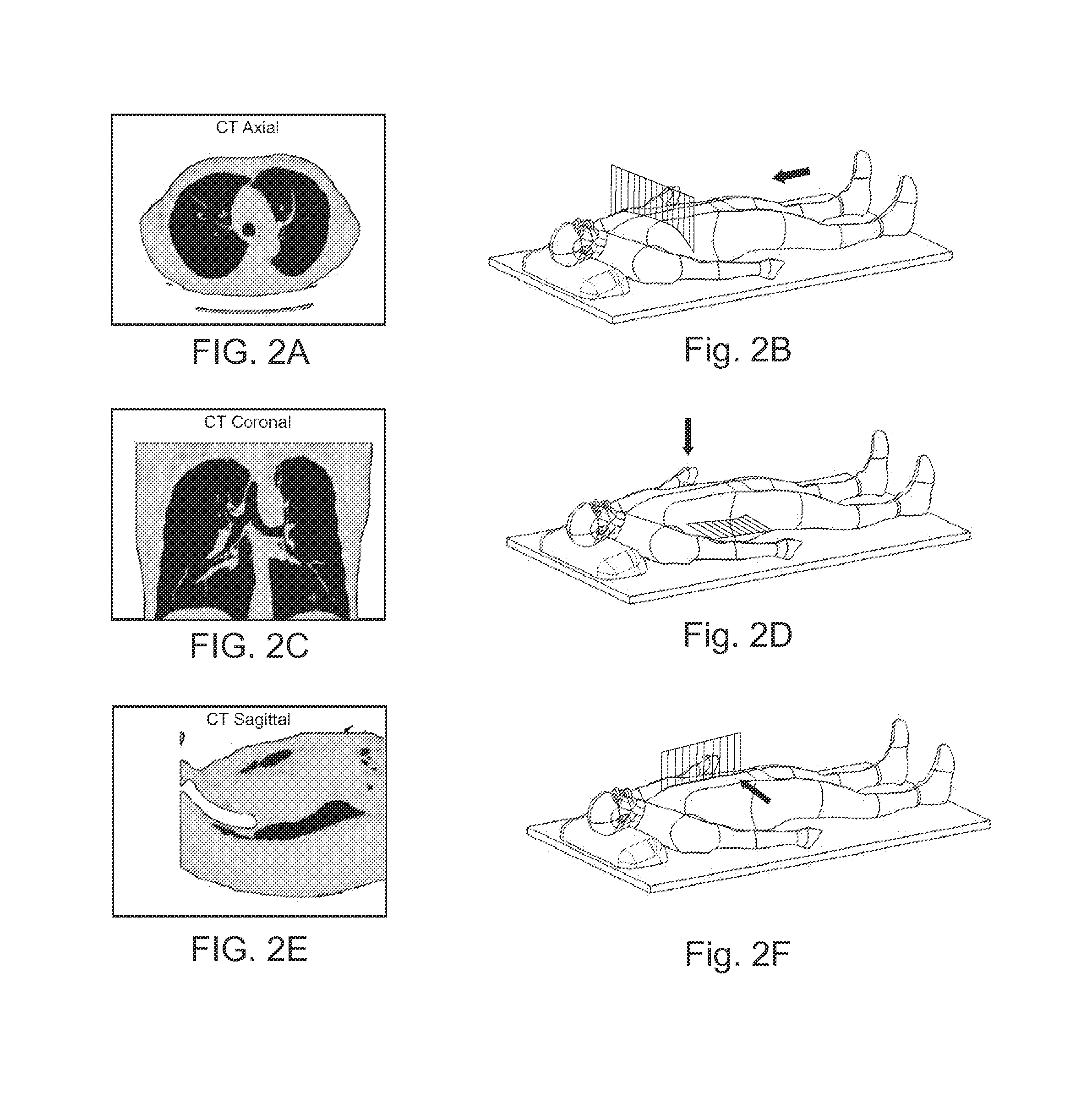
Pathway planning system and method
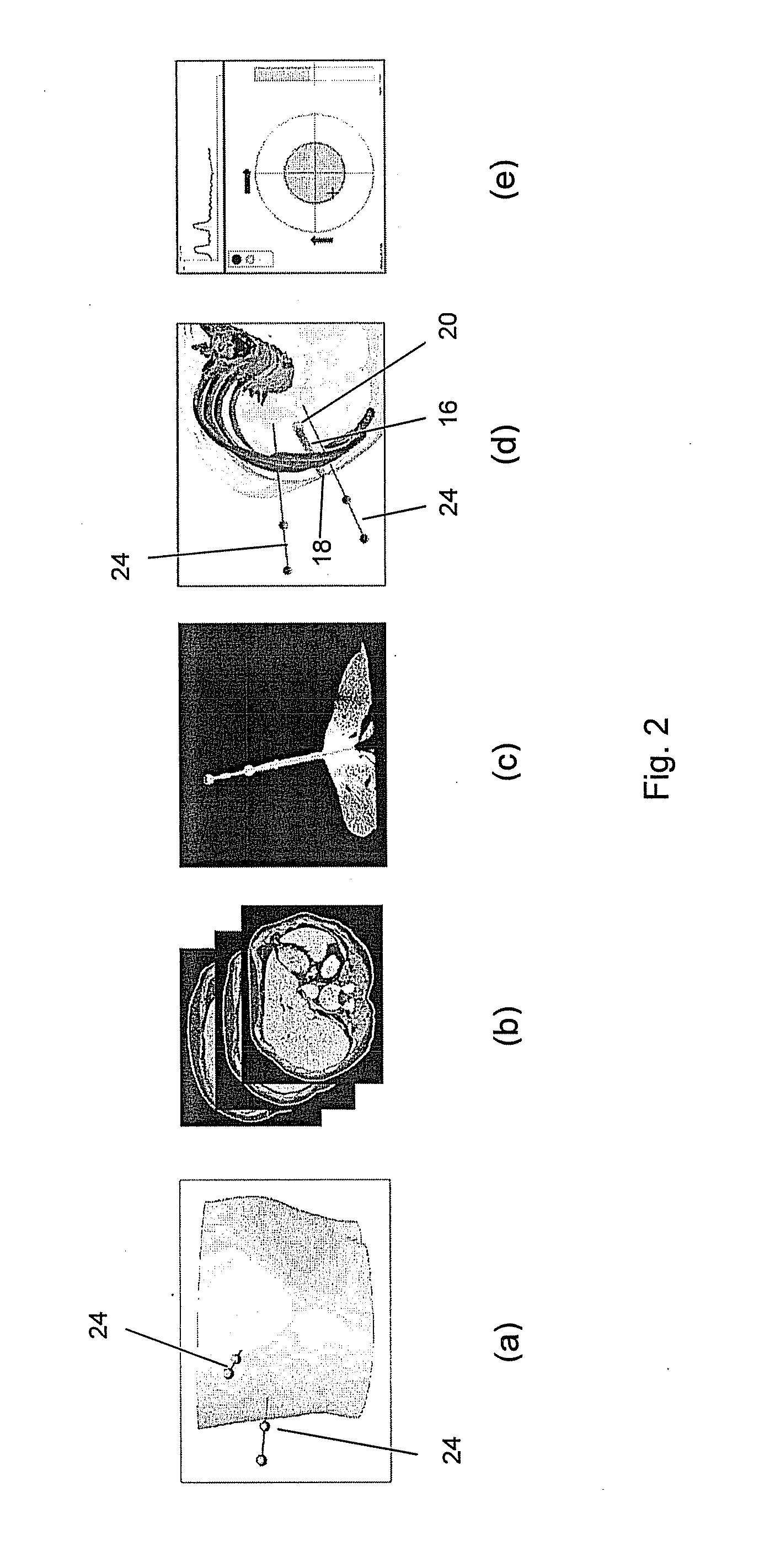
A system and method for planning a pathway through an anatomical luminal network of a patient including a computing device having at least one processor; a display device in communication with the computing device; and a user interface configured for display on the display device and configured to guide a user through a pathway planning procedure. The user interface includes a patient selection window configured to receive a user input to select a patient having CT image data on which to perform pathway planning; a target selection window configured to receive a user input to select at least one target from the CT image data; and an airway finder window configured to generate at least one pathway from the at least one target to an entry point of the anatomical luminal network in response to a user input.
Owner:TYCO HEALTHCARE GRP LP
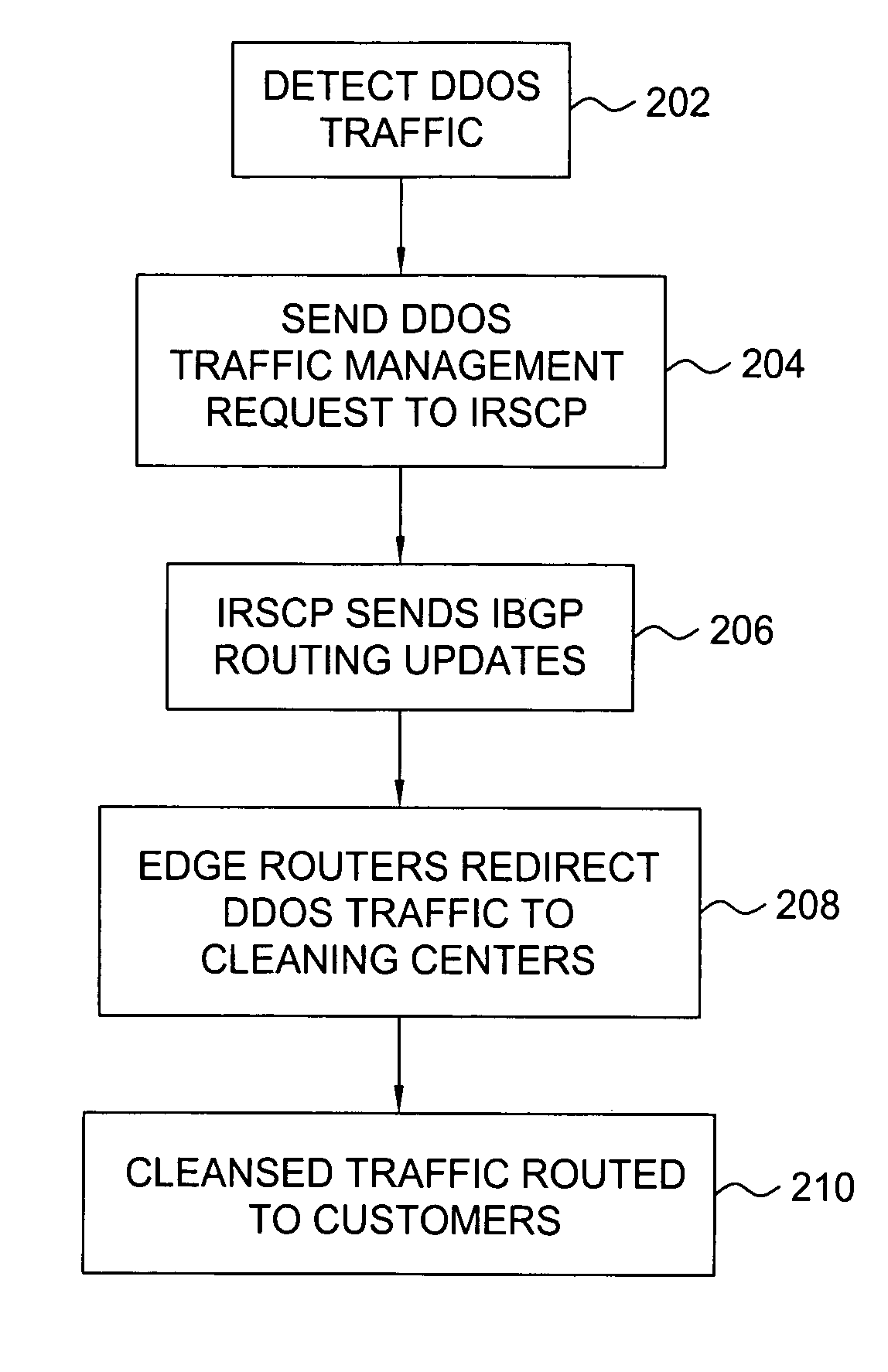
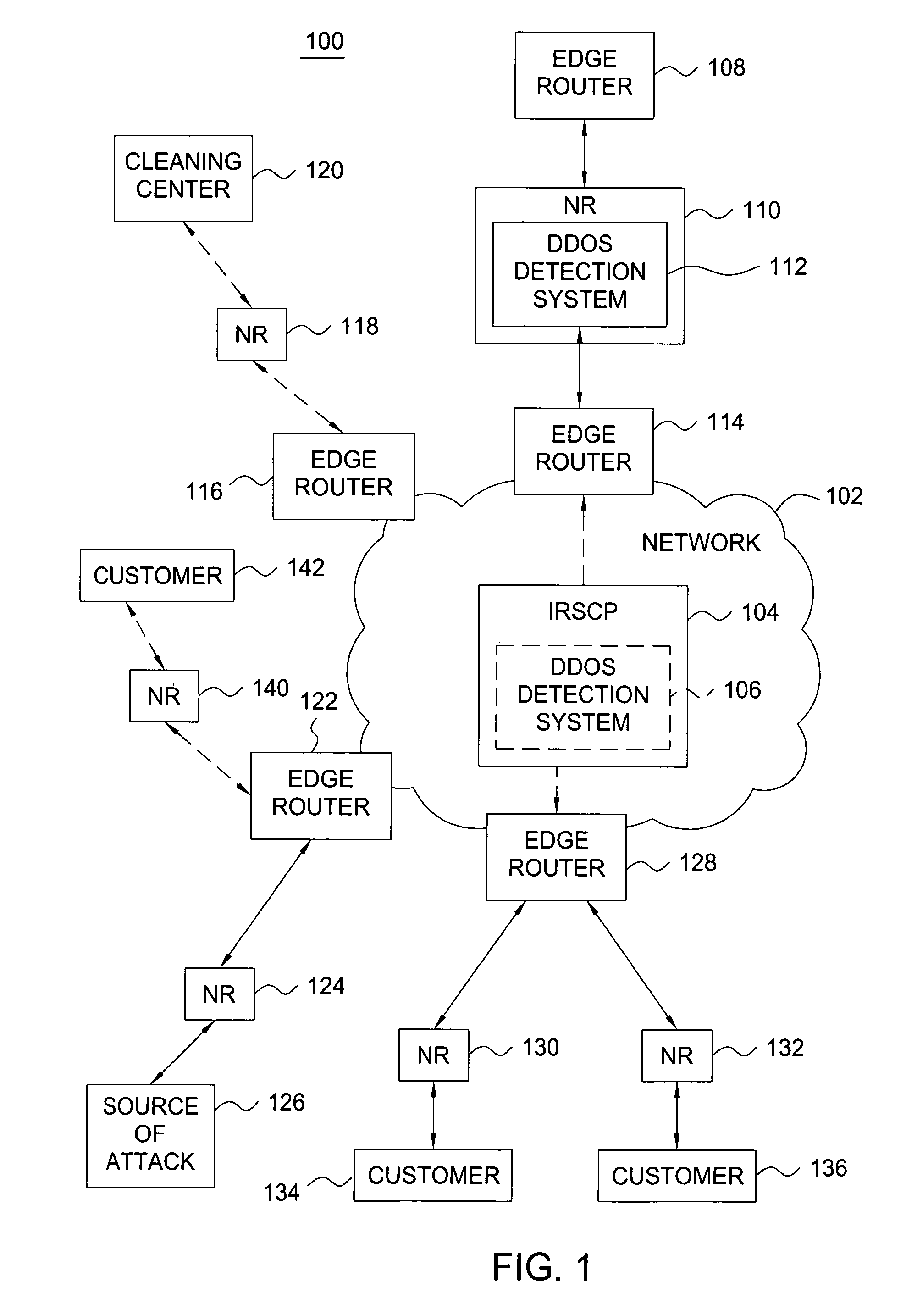
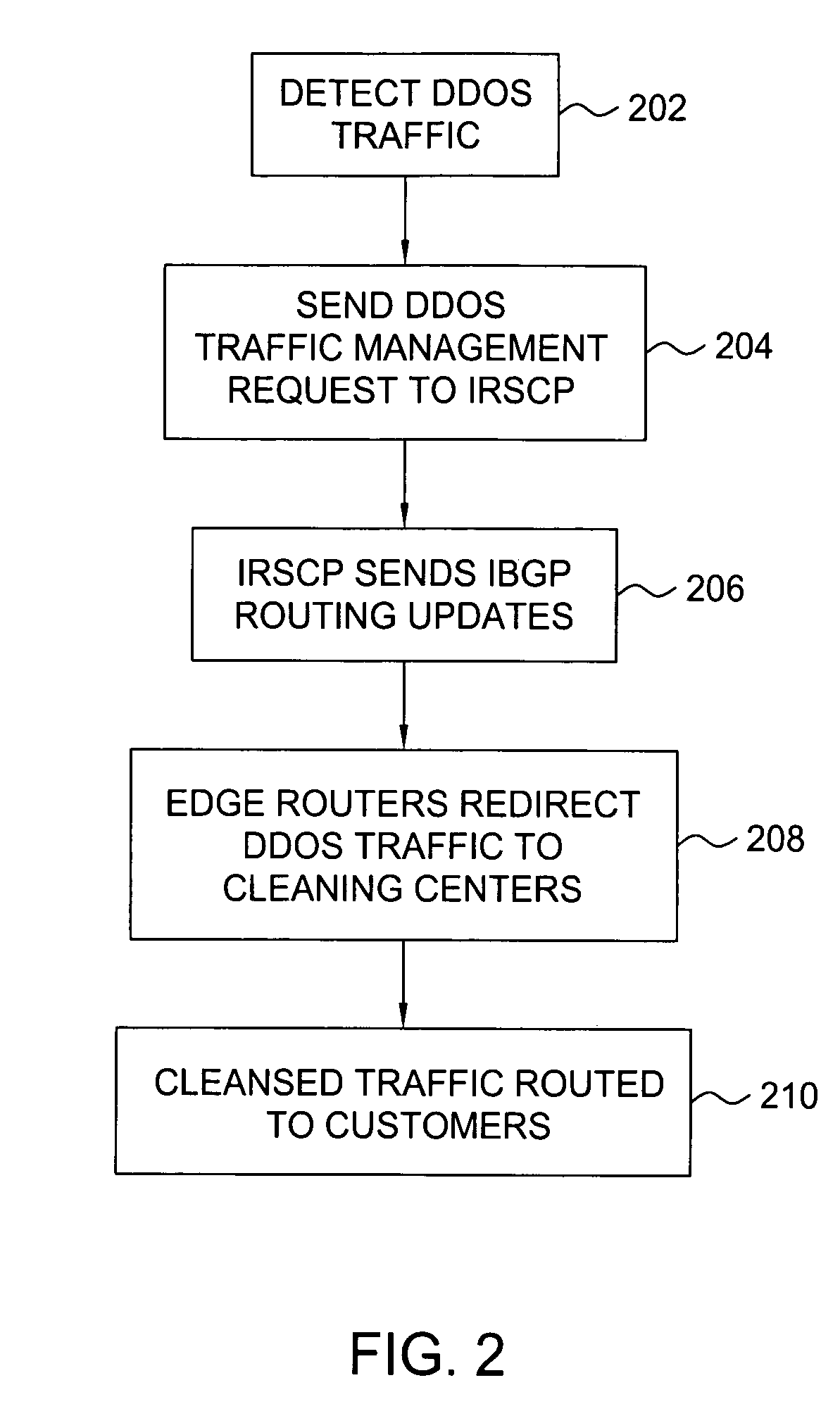
Method and apparatus for traffic control of dynamic denial of service attacks within a communications network
A method and apparatus for providing traffic management for distributed denial of service (DDOS) traffic. Within a communications network, a DDOS detection system monitors network traffic to identify traffic that is designed to attack a particular server within the network and their entry points into the network. A traffic routing control unit is requested to deny service to the DDOS traffic. By selectively manipulating the routing information propagated to network edge routers, the traffic that is denied service is limited to mostly DDOS traffic and is routed to a cleaning center or a null address in the most effective fashion.
Owner:AT&T INTPROP II L P
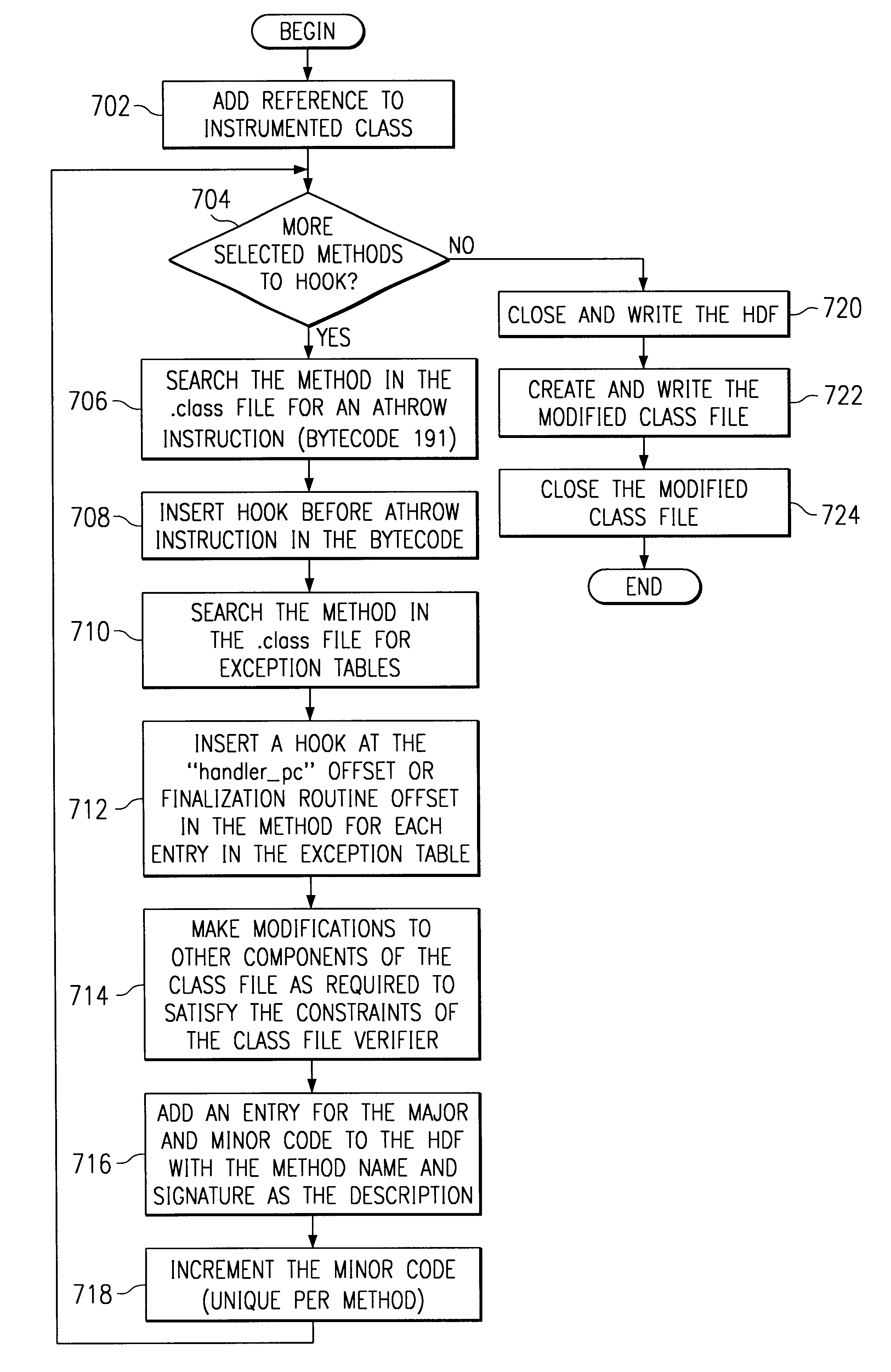
System and method for injecting hooks into Java classes to handle exception and finalization processing
InactiveUS6662359B1Software testing/debuggingSpecific program execution arrangementsEntry pointJava classes
The present invention is directed to a system, method and instructions for handling path flow exception and finalization processing in an object oriented programming language. Initially, each instrumentation method is checked for a code to indicated an exception being thrown. A hook is inserted before the exception code and identifies the method throwing the exception. Methods must also be checked for exception tables. When an exception table is found, then a hook is inserted at the entry point of each exception handler for every entry in the exception table. This hook identifies the method which catches the exception.
Owner:IBM CORP
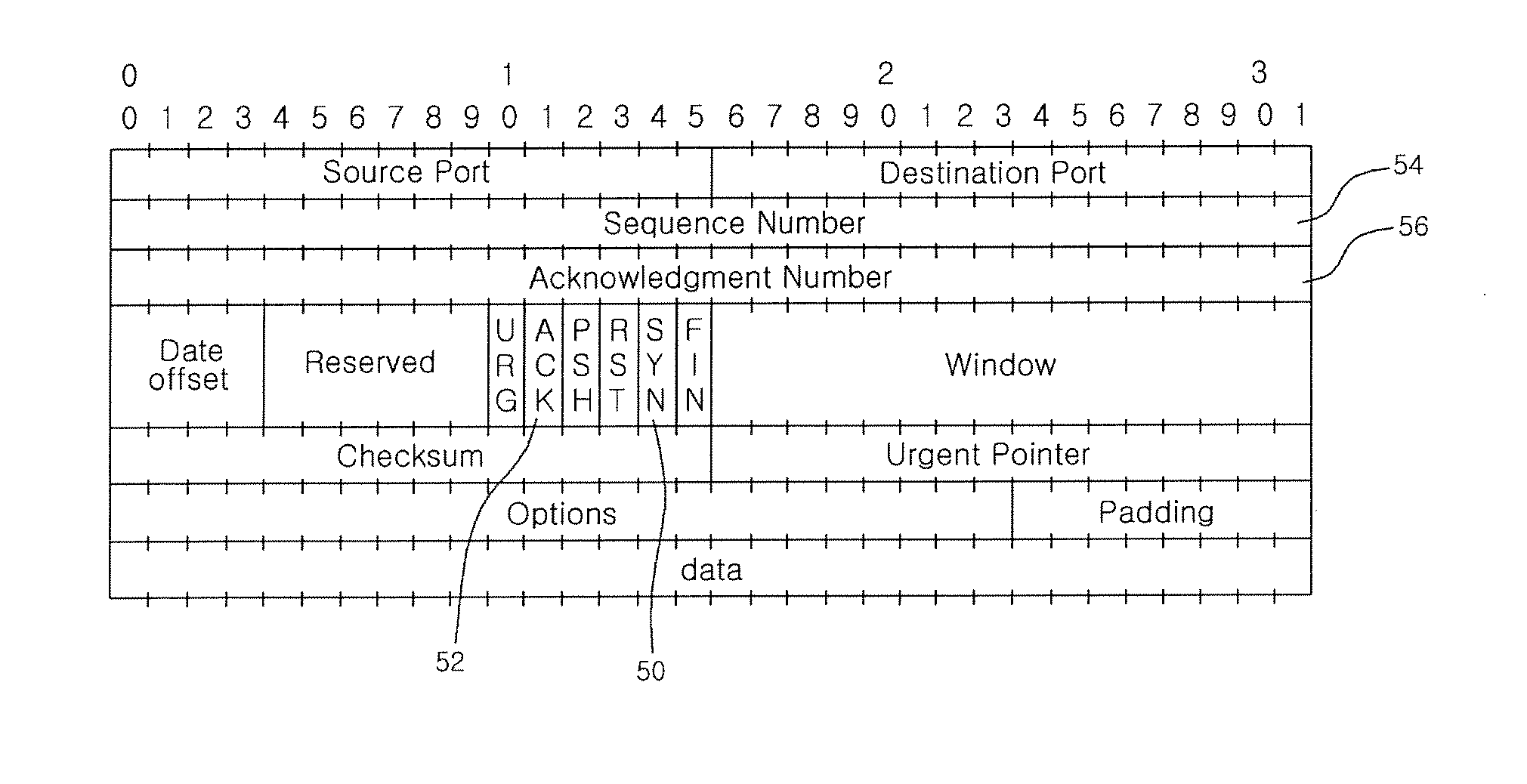
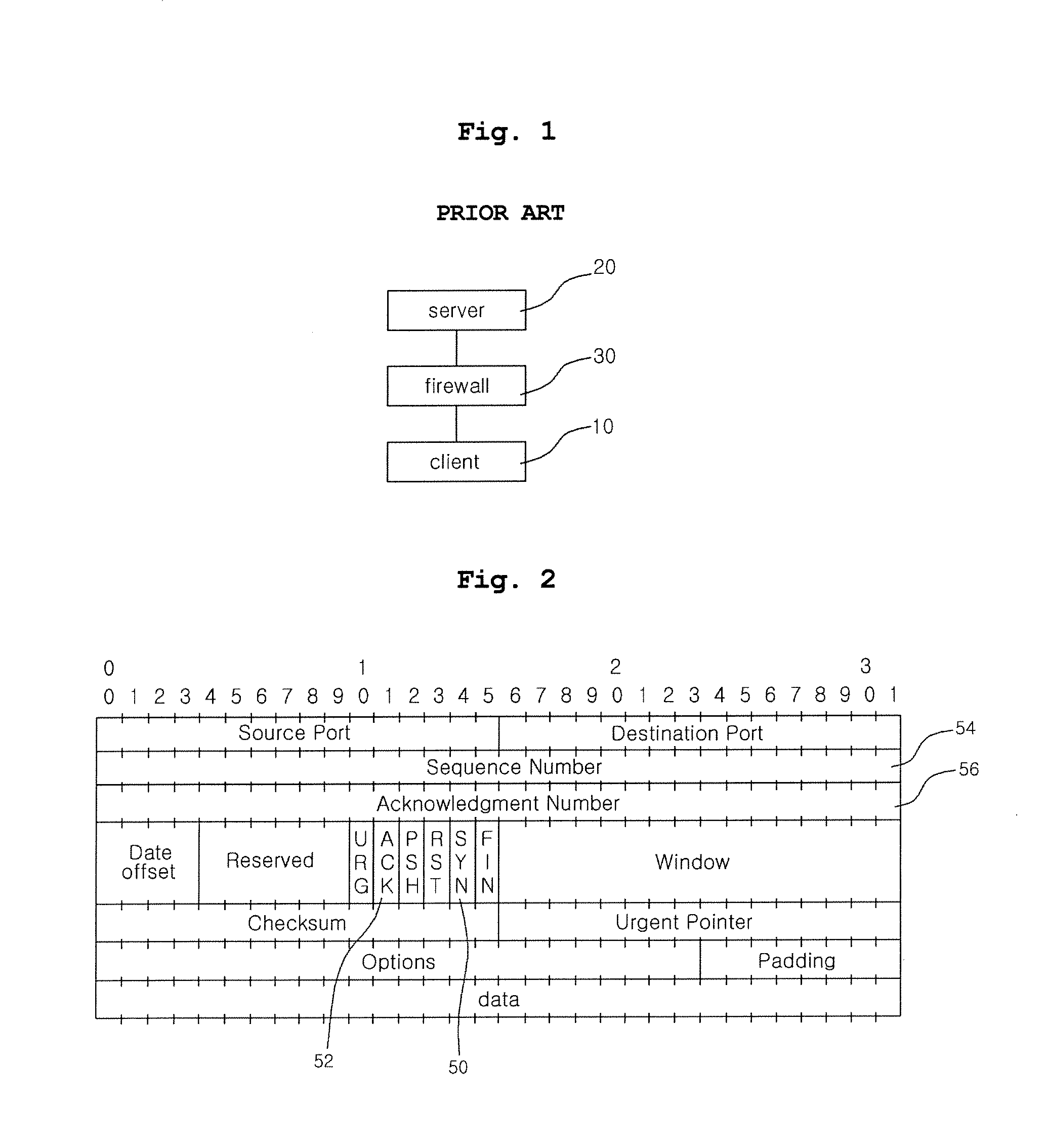
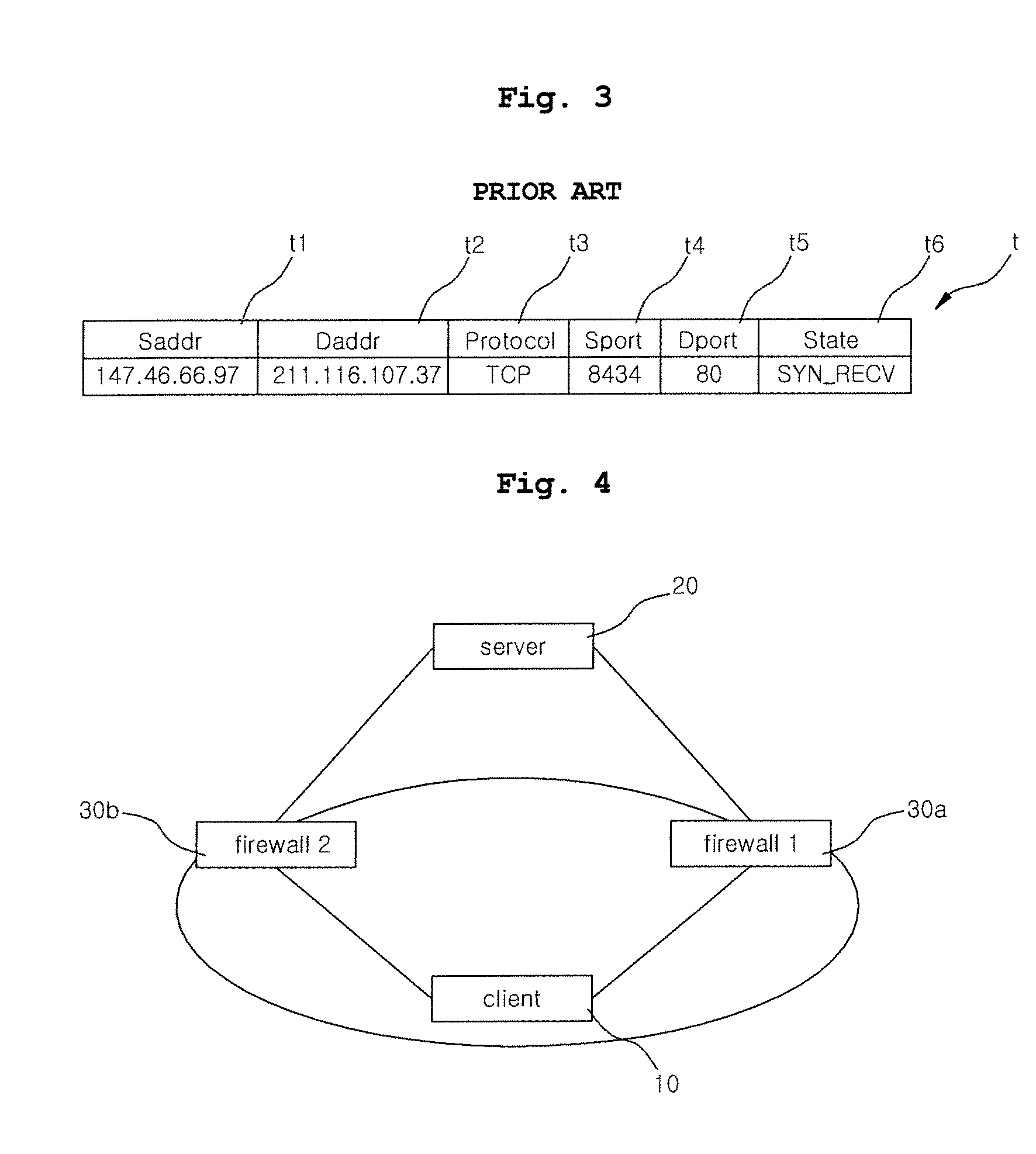
Method of sharing state between stateful inspection firewalls on MEP network
The present invention is devised to solve the problem in which a state cannot be kept track of because an outgoing traffic and an incoming traffic pass through different firewalls on a Multiple Entry / Exit Point (MEP) network having a plurality of entry points. In the present invention, firewalls physically remote from each other can share connection information using a modified SYN cookie, so that stateful inspection firewalls physically remote from each other can be used even on the MEP network.
Owner:SEOUL NAT UNIV R&DB FOUND
Systems and methods for providing a smart group
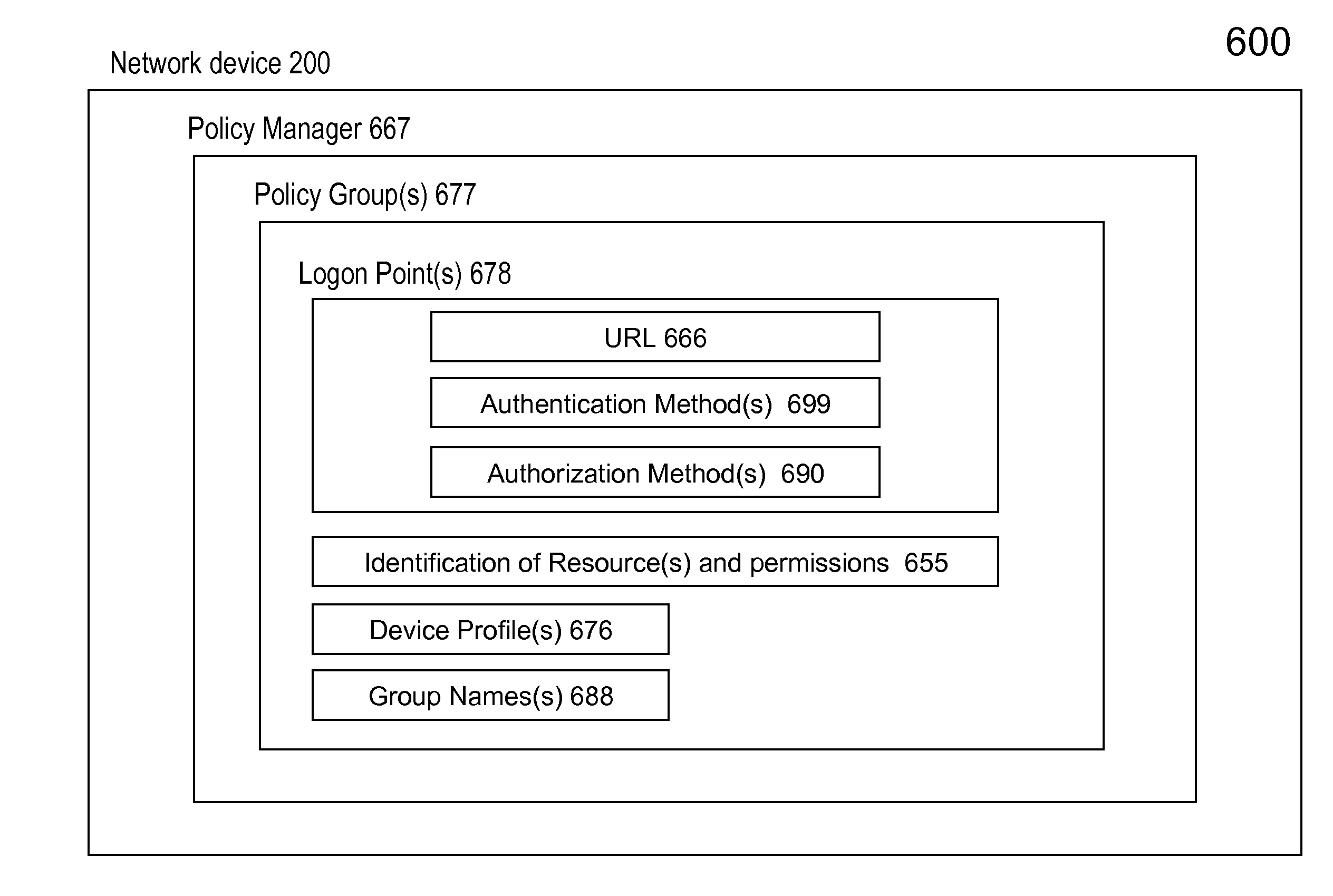
ActiveUS20120023554A1Digital data processing detailsMultiple digital computer combinationsEntry pointUniform resource locator
The present invention is directed towards systems and methods for establishing and applying a policy group to control a user's access to an identified resource. A policy group representing an aggregate of one or more access configurations for a user to access one or more identified resources may be established via a policy manager. The policy group may include a login point component representing an entry point to access the identified resource. The login point may be configured via the policy manager to specify a uniform resource locator for the entry point. One or more authentication and authorization methods may be selected for the login point component. The device may receive a request to access the uniform resource locator. The device may initiate the policy group for evaluation. The device may initiate, with the user, one or more authentication and authorization methods specified by the login point component.
Owner:CITRIX SYST INC
Multi-field charged particle cancer therapy method and apparatus
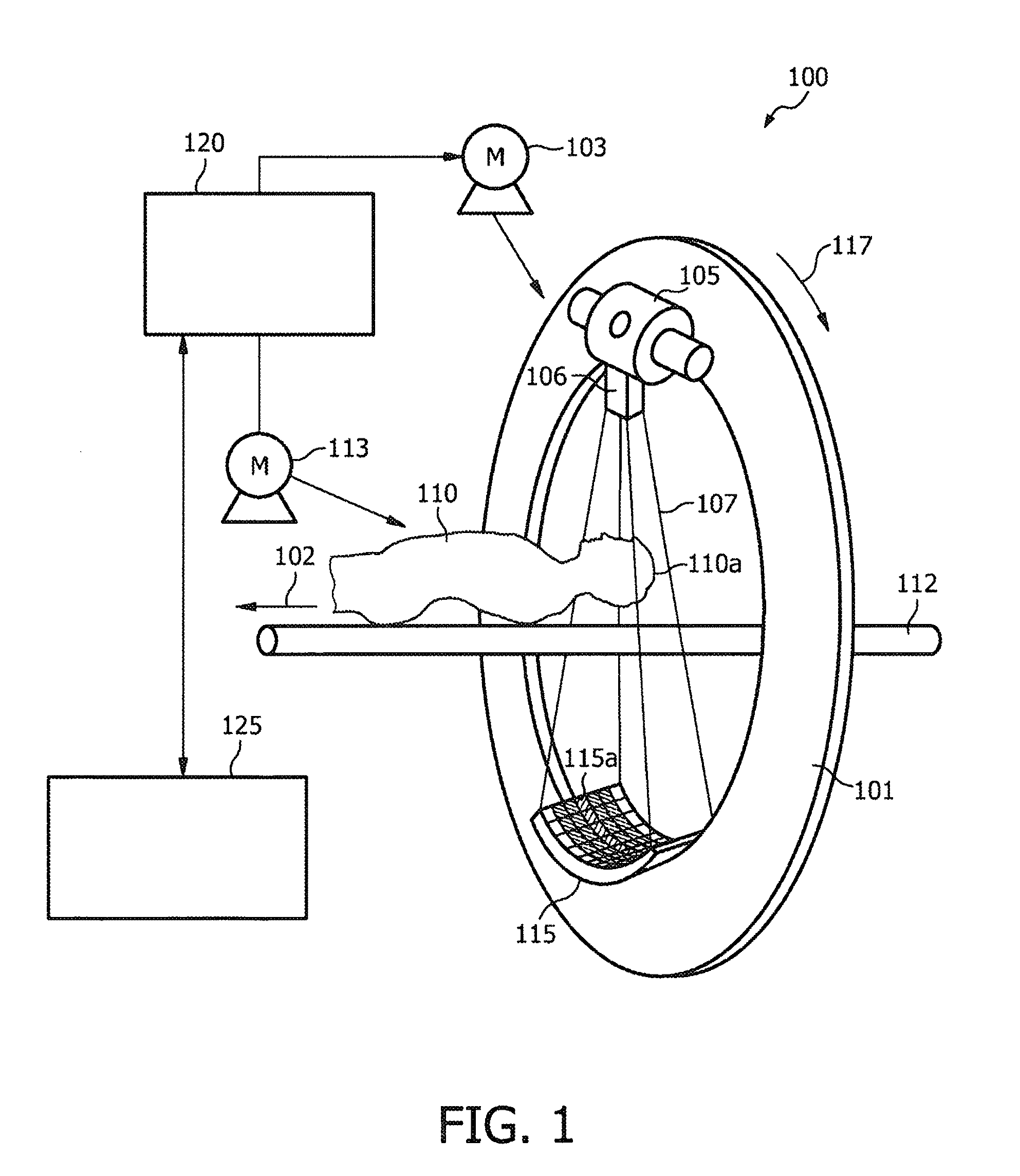
ActiveUS20110233423A1Material analysis by optical meansMagnetic resonance acceleratorsBragg peakMulti field
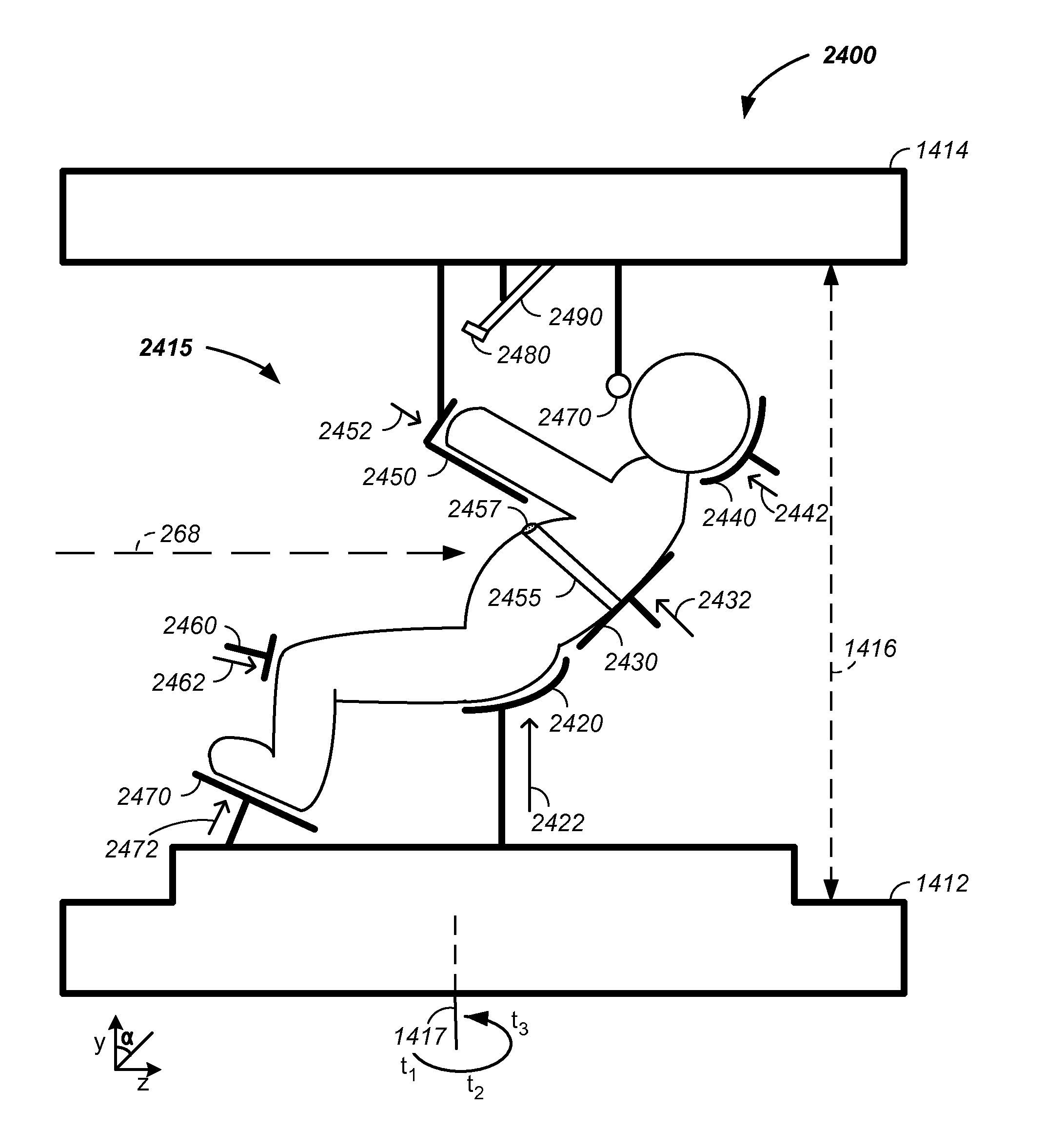
The invention comprises a multi-field charged particle irradiation method and apparatus. Radiation is delivered through an entry point into the tumor and Bragg peak energy is targeted to a distal or far side of the tumor from an ingress point. Delivering Bragg peak energy to the distal side of the tumor from the ingress point is repeated from multiple rotational directions. Preferably, beam intensity is proportional to radiation dose delivery efficiency. Preferably, the charged particle therapy is timed to patient respiration via control of charged particle beam injection, acceleration, extraction, and / or targeting methods and apparatus. Optionally, multi-axis control of the charged particle beam is used simultaneously with the multi-field irradiation. Combined, the system allows multi-field and multi-axis charged particle irradiation of tumors yielding precise and accurate irradiation dosages to a tumor with distribution of harmful irradiation energy about the tumor.
Owner:GEORGIA TECH RES CORP
Distributed load balancing for single entry-point systems
InactiveUS7155515B1Efficient use of resourcesReduce in quantityMultiple digital computer combinationsTransmissionCurrent loadEntry point
A method and system for distributing work load in a cluster of at least two service resources. Depending upon the configuration, a service resource may be an individual process, such as a single instance of a computer game, or a node on which multiple processes are executing, such as a Server. Initial connection requests from new clients are directed to a single entry-point service resource in the cluster, called an intake. A separate intake is designated for each type of service provided by the cluster. The clients are processed in a group at the service resource currently designated as the intake to which clients initially connected, for the duration of the session. Based upon its loading, the current intake service resource determines that another service resource in the cluster should become a new intake for subsequent connection requests received from new clients. Selection of another service resource to become the new intake is based on the current work load of each resource in the cluster. All resources in the cluster are periodically informed of the resource for each service being provided that was last designated as the intake, and of the current load on each resource in the cluster. Subsequently, new clients requesting a service are directed to the newly designated intake for that service and processed on that resource for the duration of the session by those clients.
Owner:MICROSOFT TECH LICENSING LLC
Method, system and computer program product for targeting of a target with an elongate instrument
An embodiment is directed to a method and a system for assisting the targeting of a target with an elongate instrument, wherein the instrument is to be inserted into a living object's body part along a predetermined trajectory extending between an entry point of said instrument into said body part and a target point associated with said target. The method comprises an instrument directing assisting step for generating and displaying an image allowing a user to assess to which extend the longitudinal axis of the instrument is aligned with the vector connecting the target point and the tip portion of said instrument. Also, the method comprises an instrument guiding assisting step of generating and displaying an image allowing a user to assess to which extent the instrument motion during insertion thereof coincides with the predetermined trajectory.
Owner:DEUTES KREBSFORSCHUNGSZENT STIFTUNG DES OFFENTLICHEN RECHTS
Remoting features
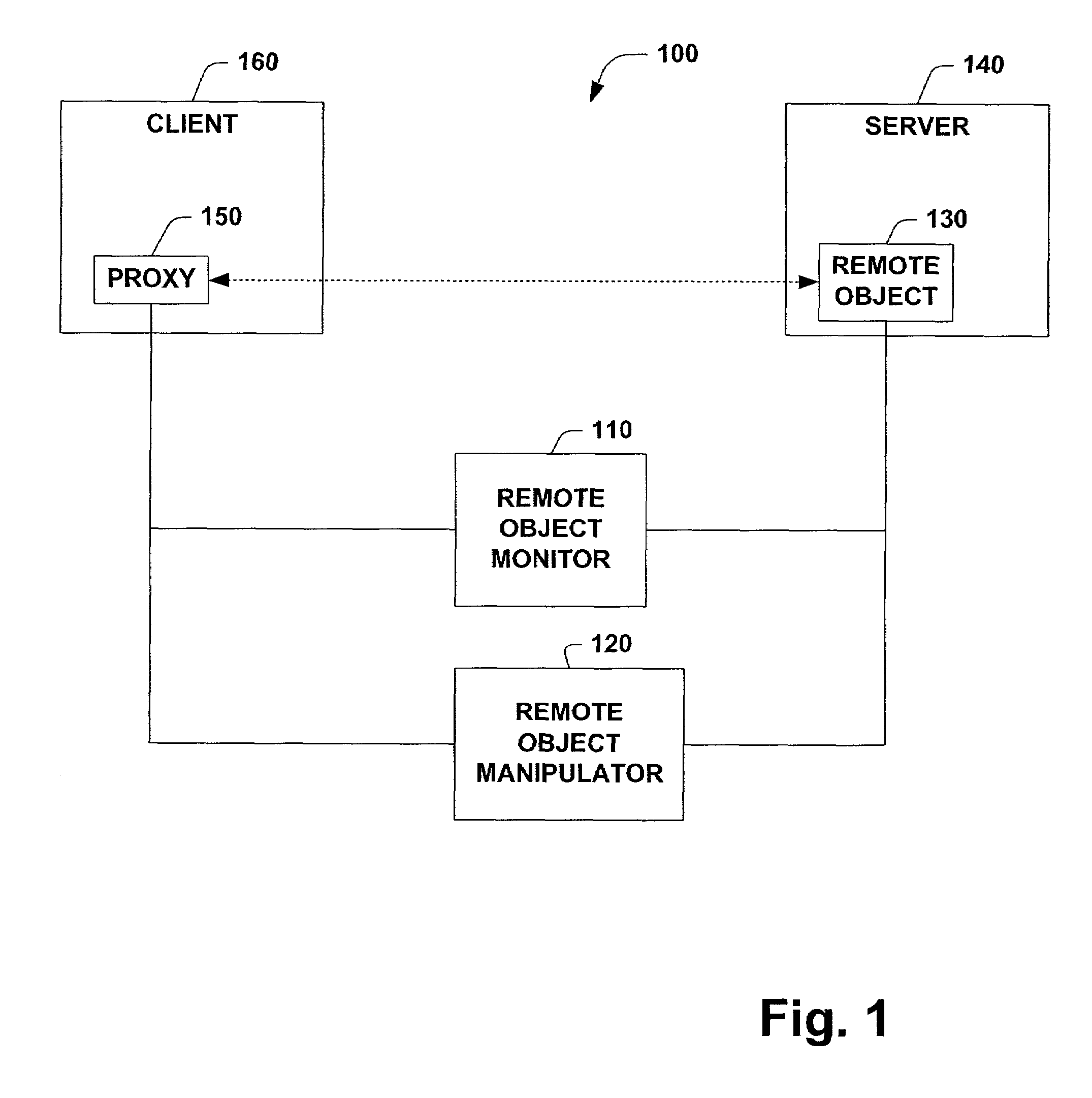
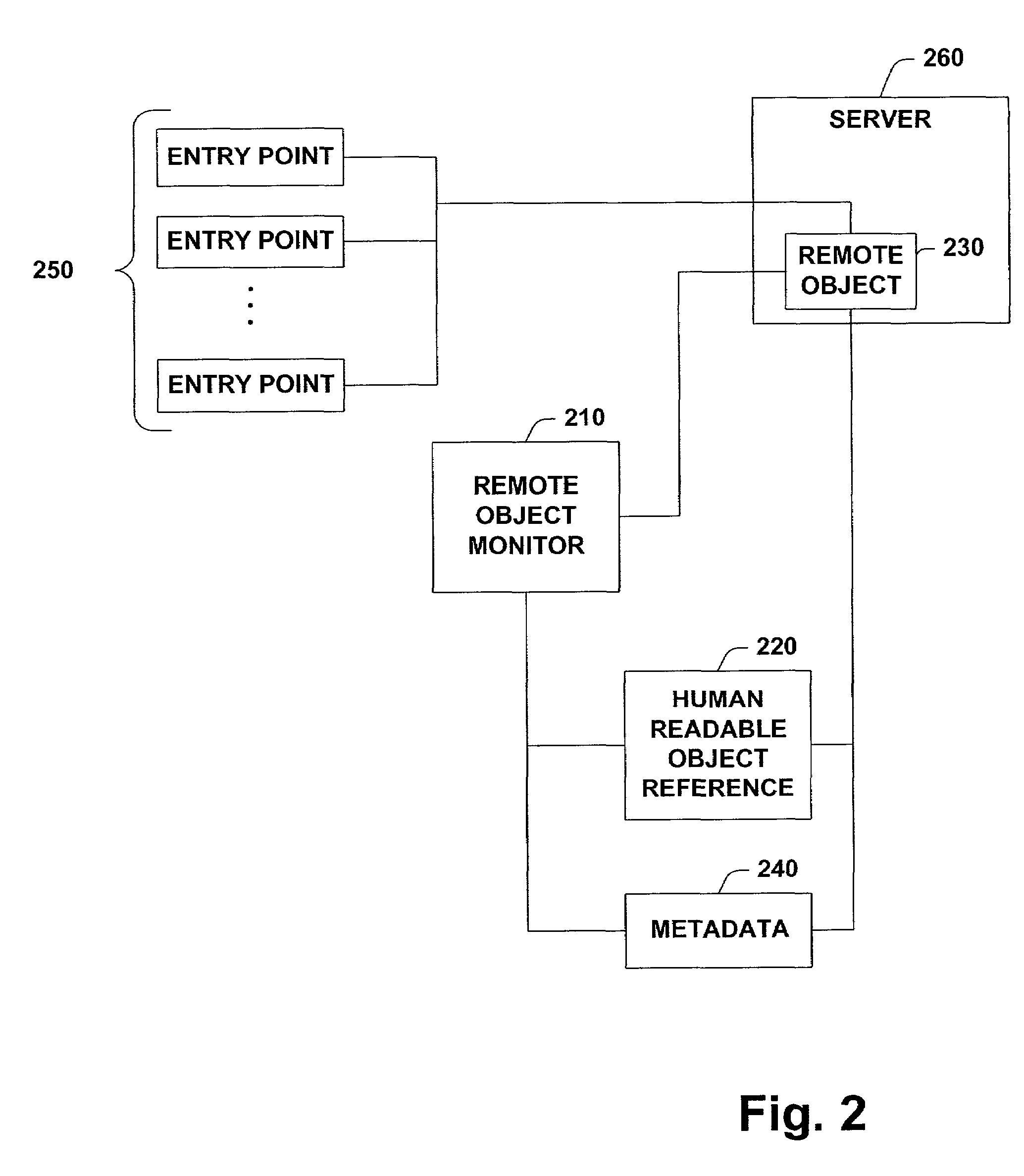
InactiveUS7155728B1To offer comfortEasy to produceProgram controlEntry pointUniform resource identifier
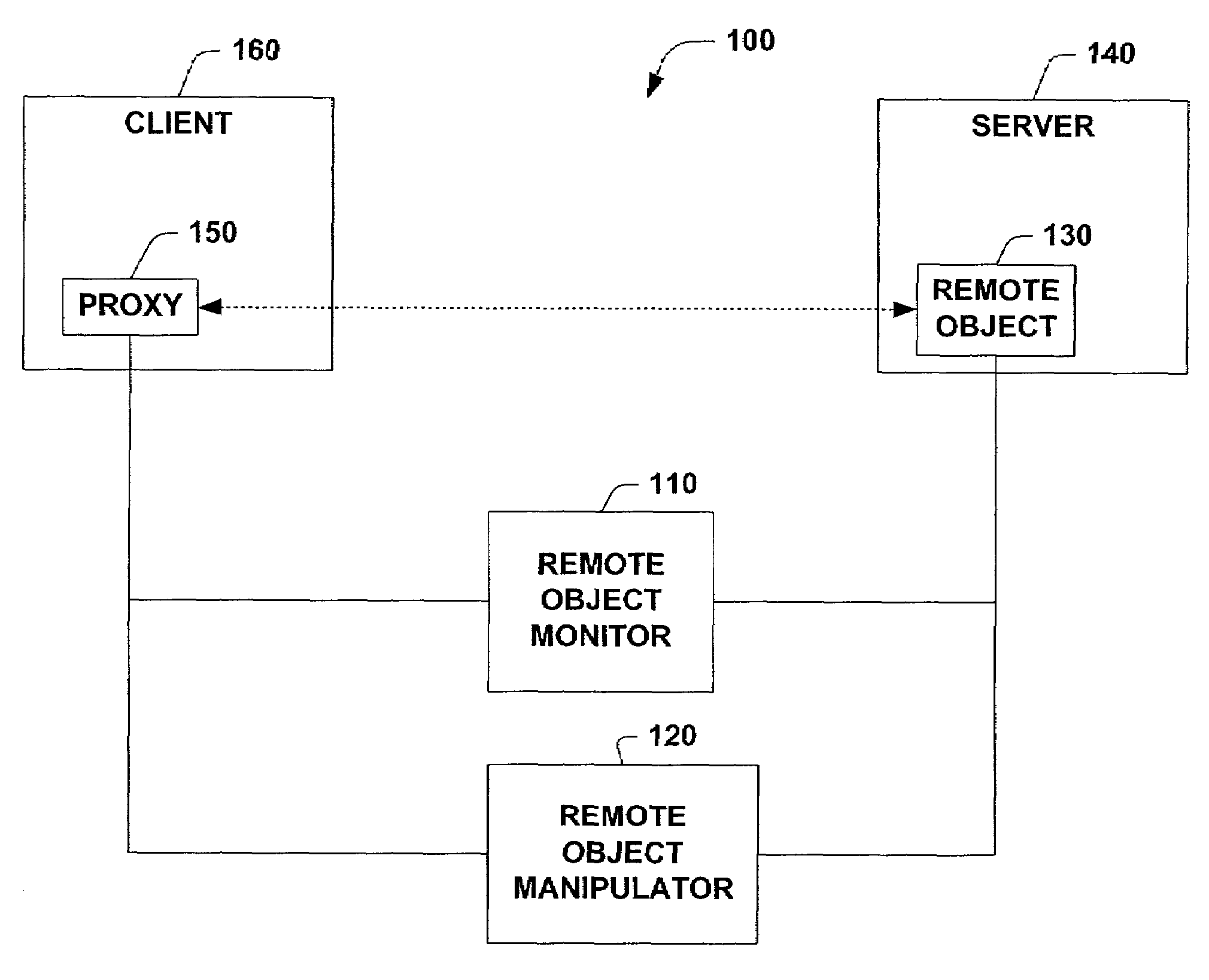
A system and method that provides remoting services in a distributed object system is provided. The system includes a remote object monitor and a remote object manipulator. The remote object monitor can provide a human readable reference to a remote object, where the human readable reference is a URL (Uniform Resource Locator) and can include protocol information, protocol data, an application name and an object URI (Uniform Resource Identifier). The remote object monitor can also provide metadata concerning a remote object, where the metadata can include information concerning interfaces implemented by a remote object, the type of a remote object, the class hierarchy of a remote object, methods implemented by a remote object, properties implemented by a remote object and attributes implemented by a remote object. The remote object monitor can also provide entry points and code interception for custom attribute based activation processing that can be performed before, after and / or substantially in parallel with non-attribute code associated with a remote object. The remote object monitor can also monitor and / or control the lifetime of a remote object, using, for example, a lease manager. The remote object manipulator can also update metadata concerning a remote object and can control the lifetime of a remote object via a lease manager, for example.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for attaching power line communications to customer premises
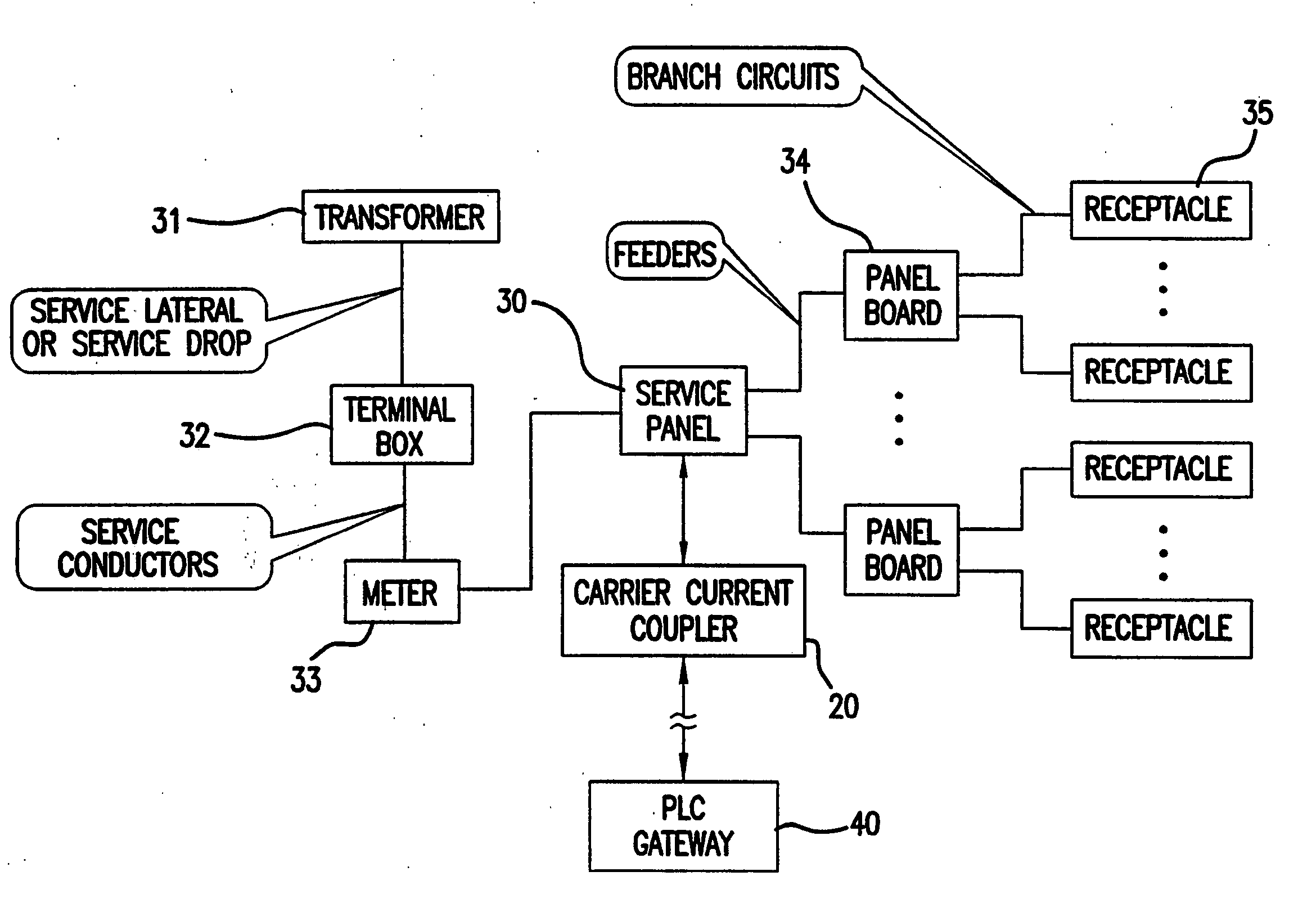
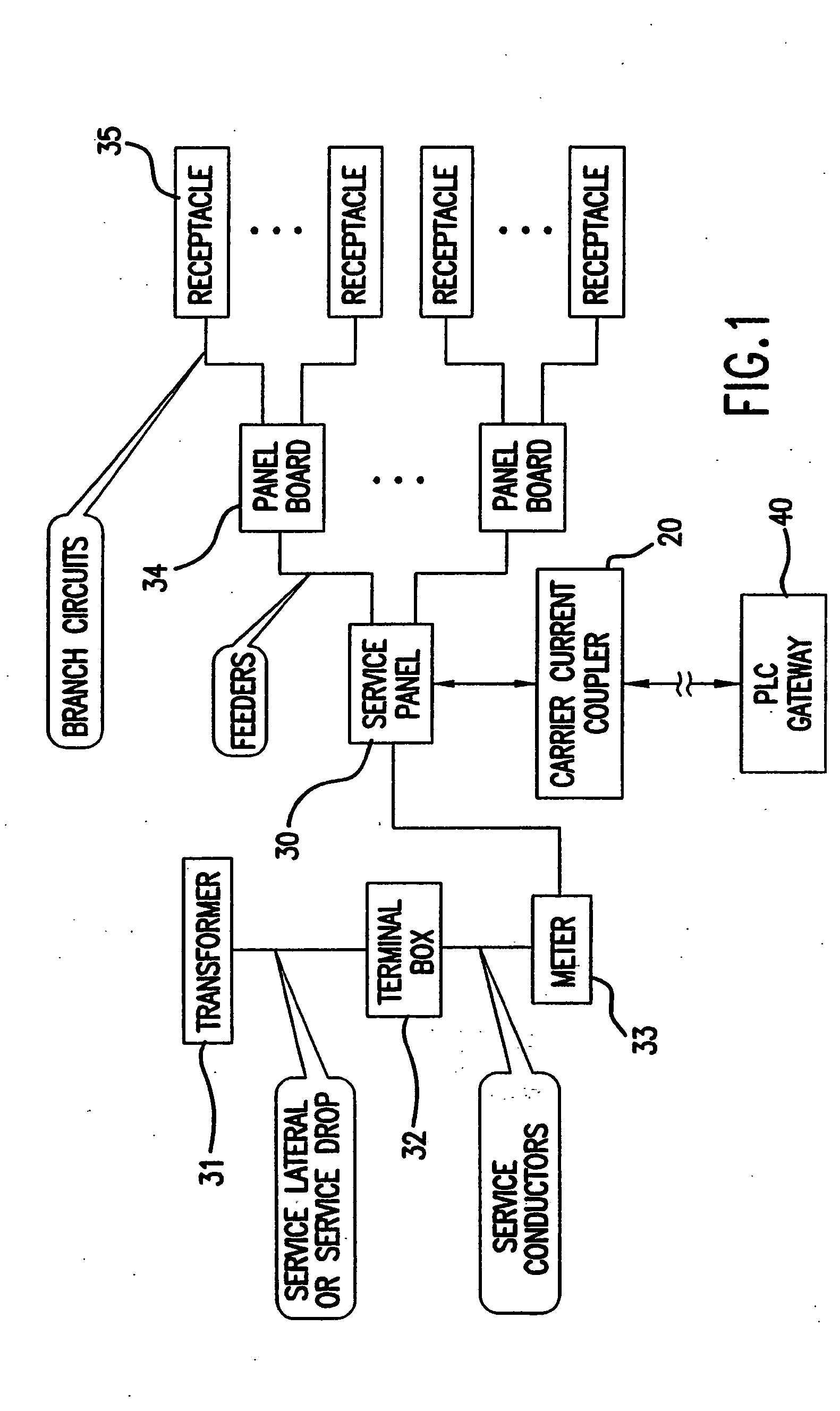
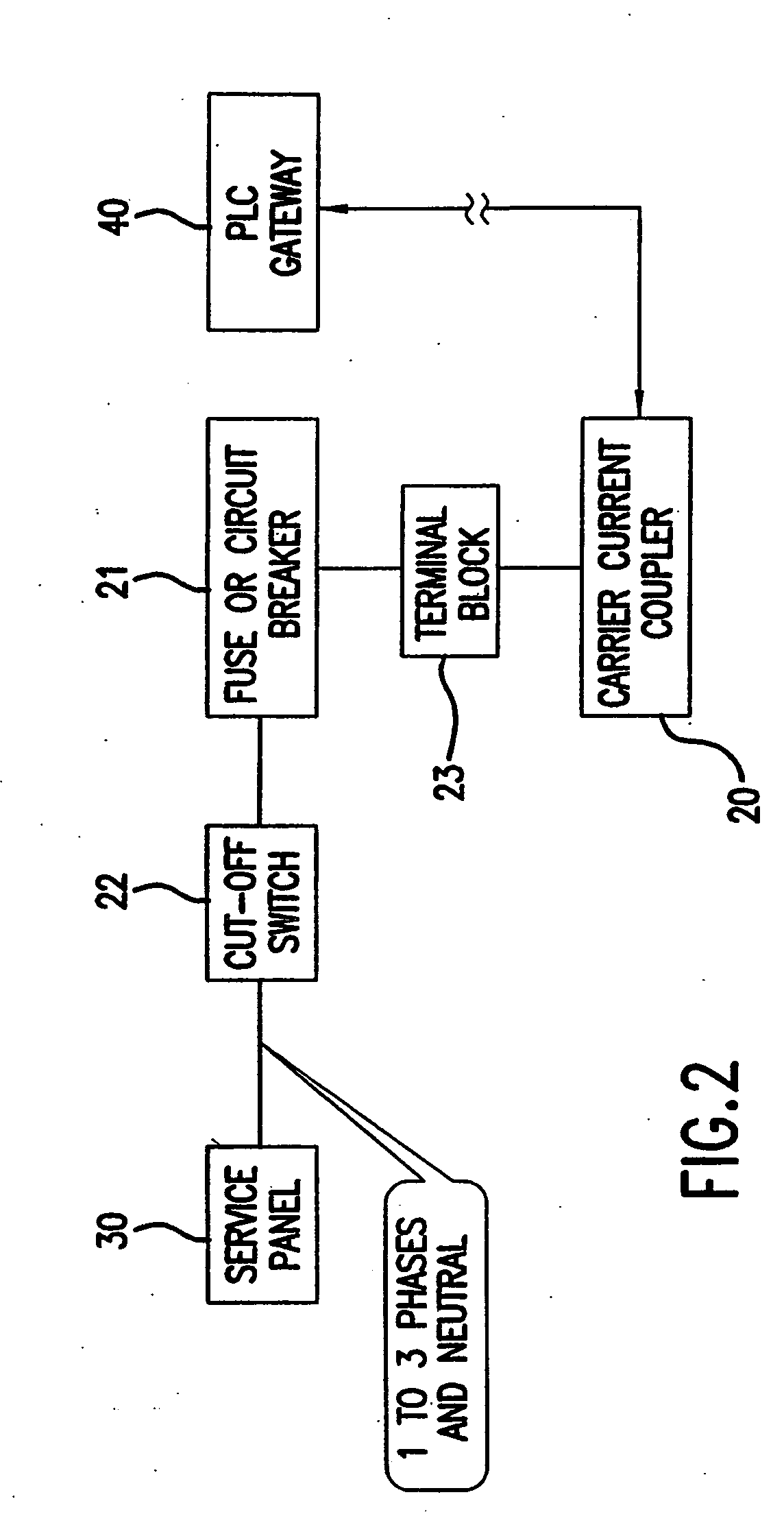
InactiveUS20050046550A1Easy to integrateImprove economyElectric signal transmission systemsPower distribution line transmissionEntry pointOperating energy
A method and apparatus for modifying a power distribution network in a building in order to provide data communication by using a Power Line Carrier (PLC) signal to an approximate electrical central location point of a power distribution system remote from the data entry point of the building. A passive coupler device is attached to a centrally located service panel. The passive coupler receives the Power Line Carrier (PLC) signal from the remote entry point in the building and conditions the signal for entry at the service panel onto each phase of the power distribution network.
Owner:TELKONET COMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com