Patents
Literature
356results about How to "Data Security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
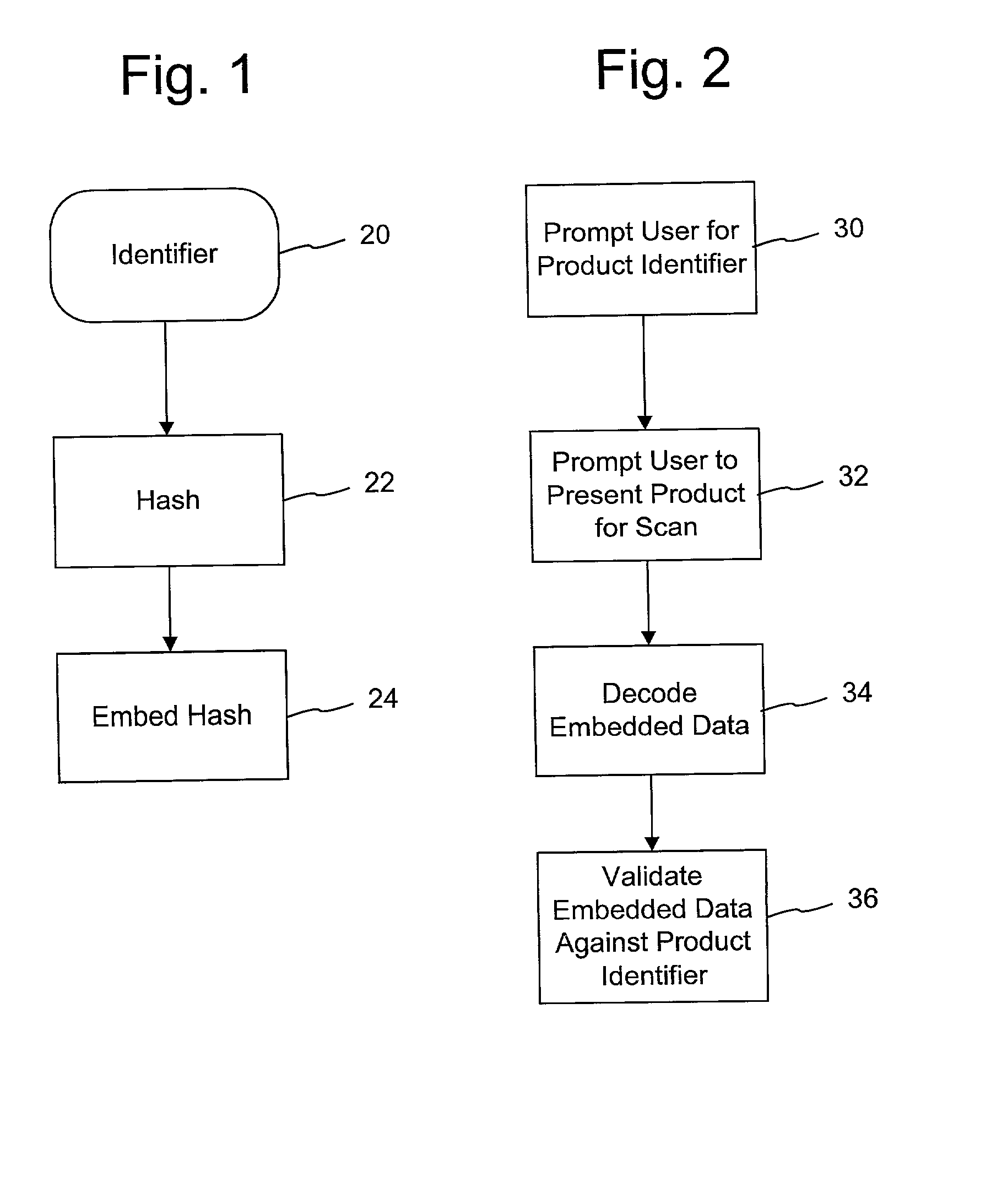
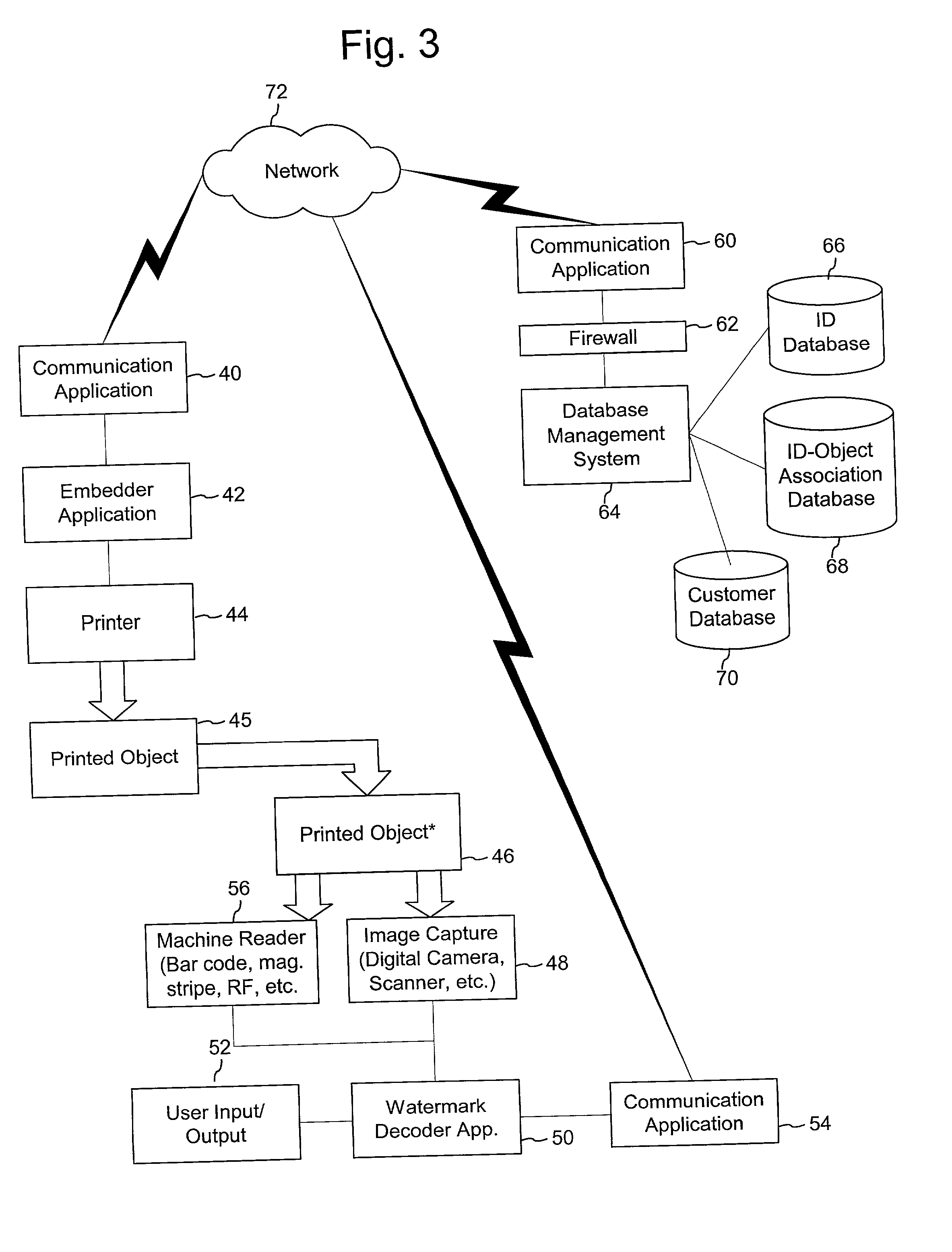
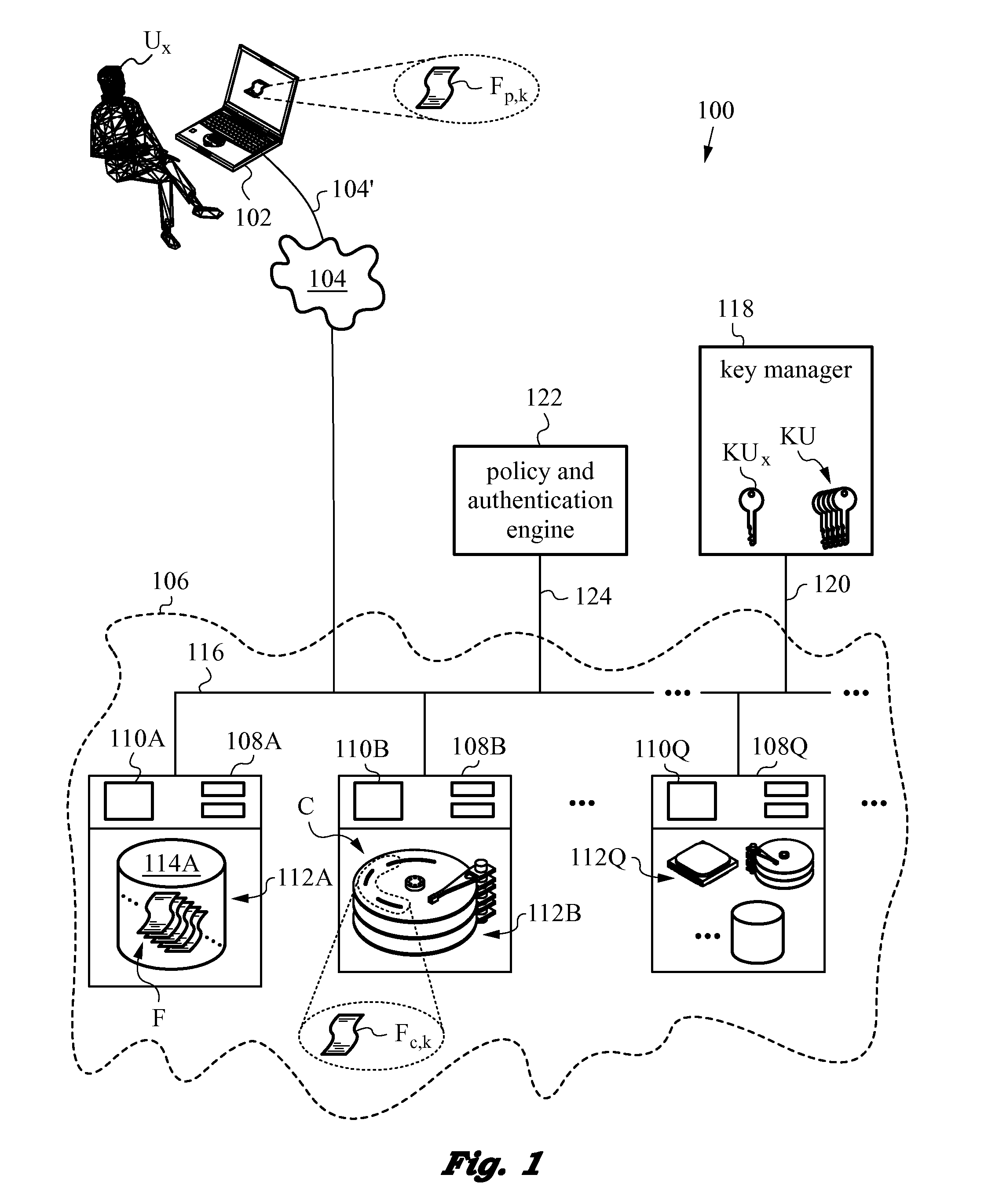
Digital authentication with digital and analog documents
InactiveUS20040153649A1More dataCompact formDigitally marking record carriersDigital data processing detailsAuthentication information
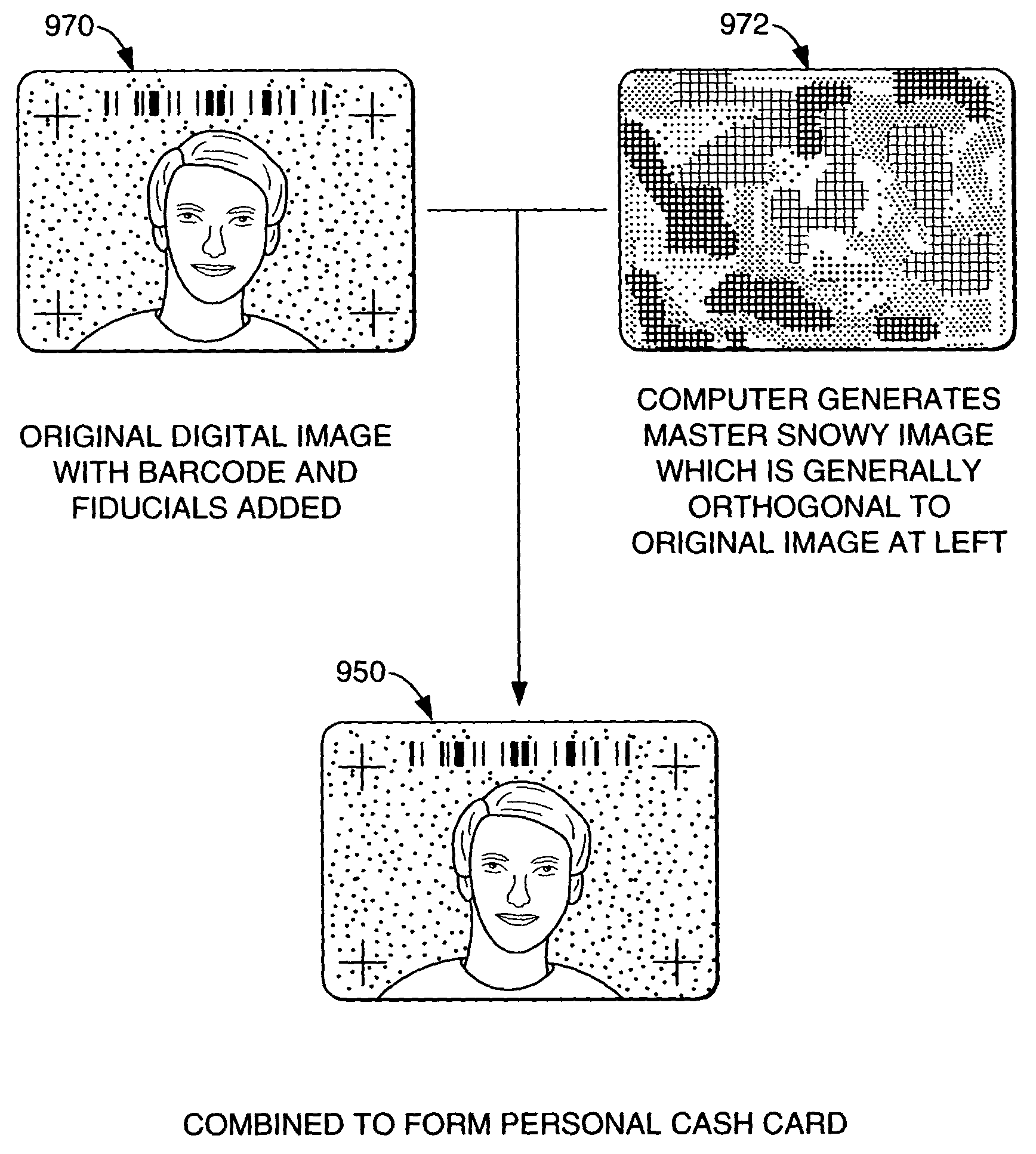
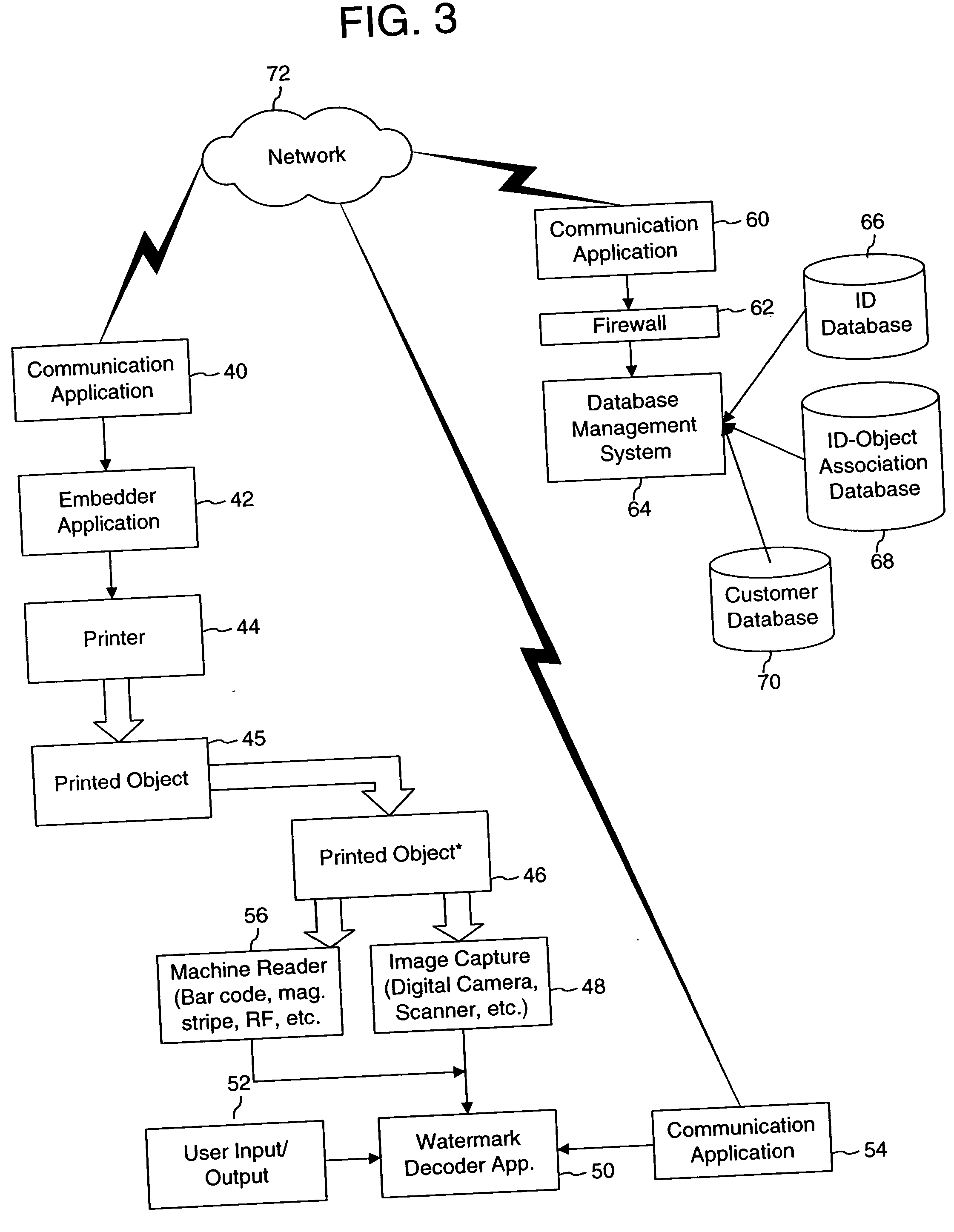
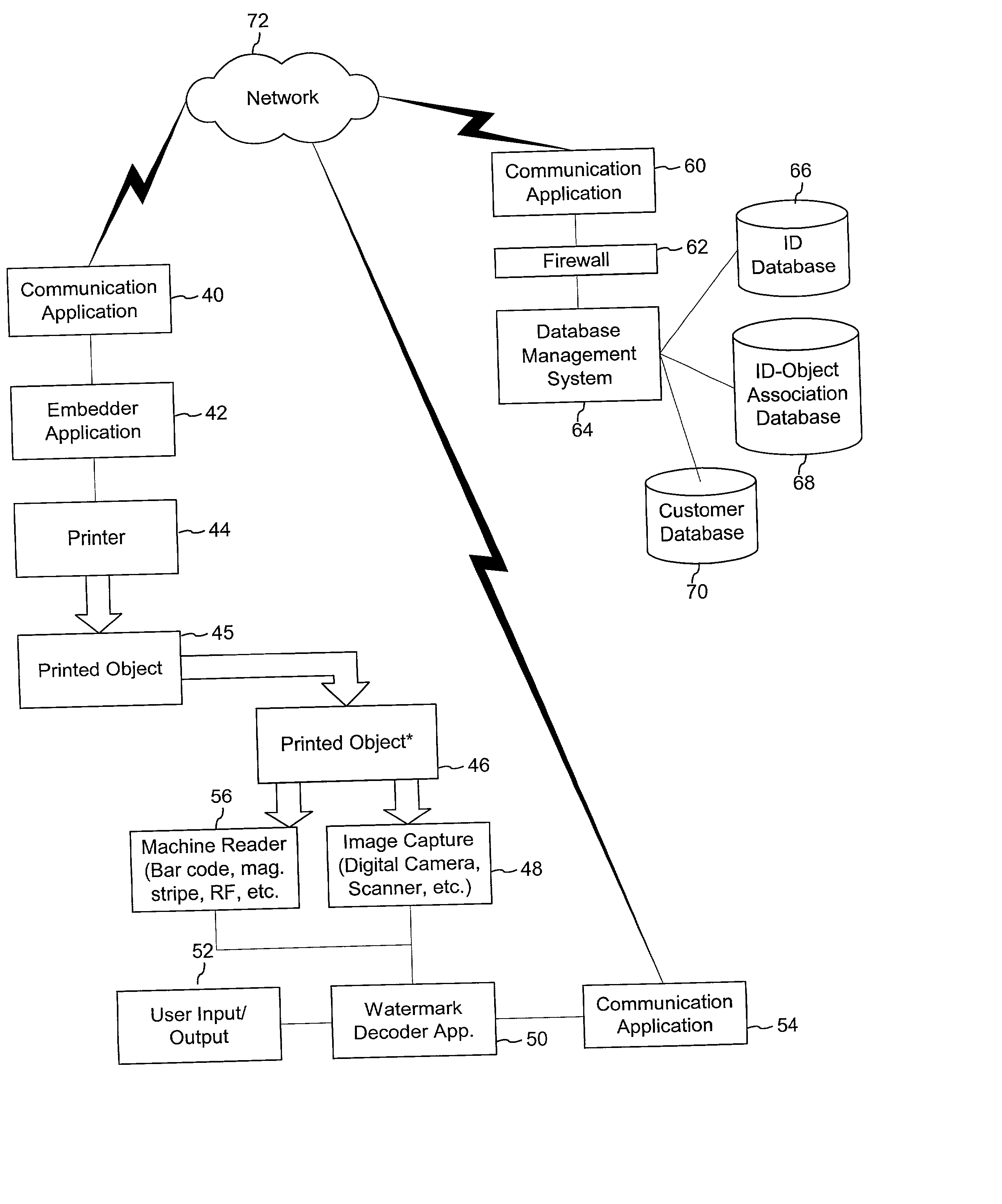
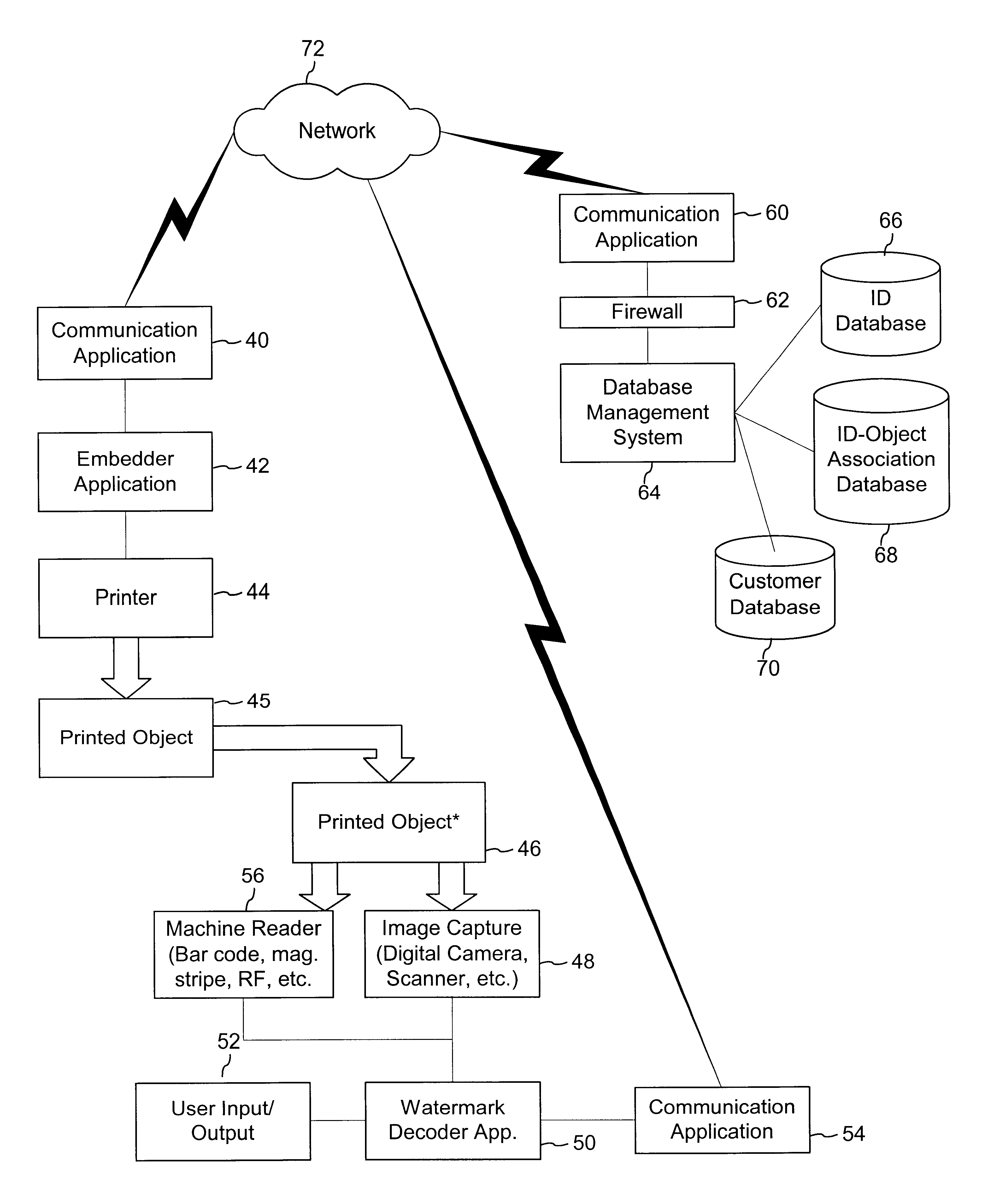
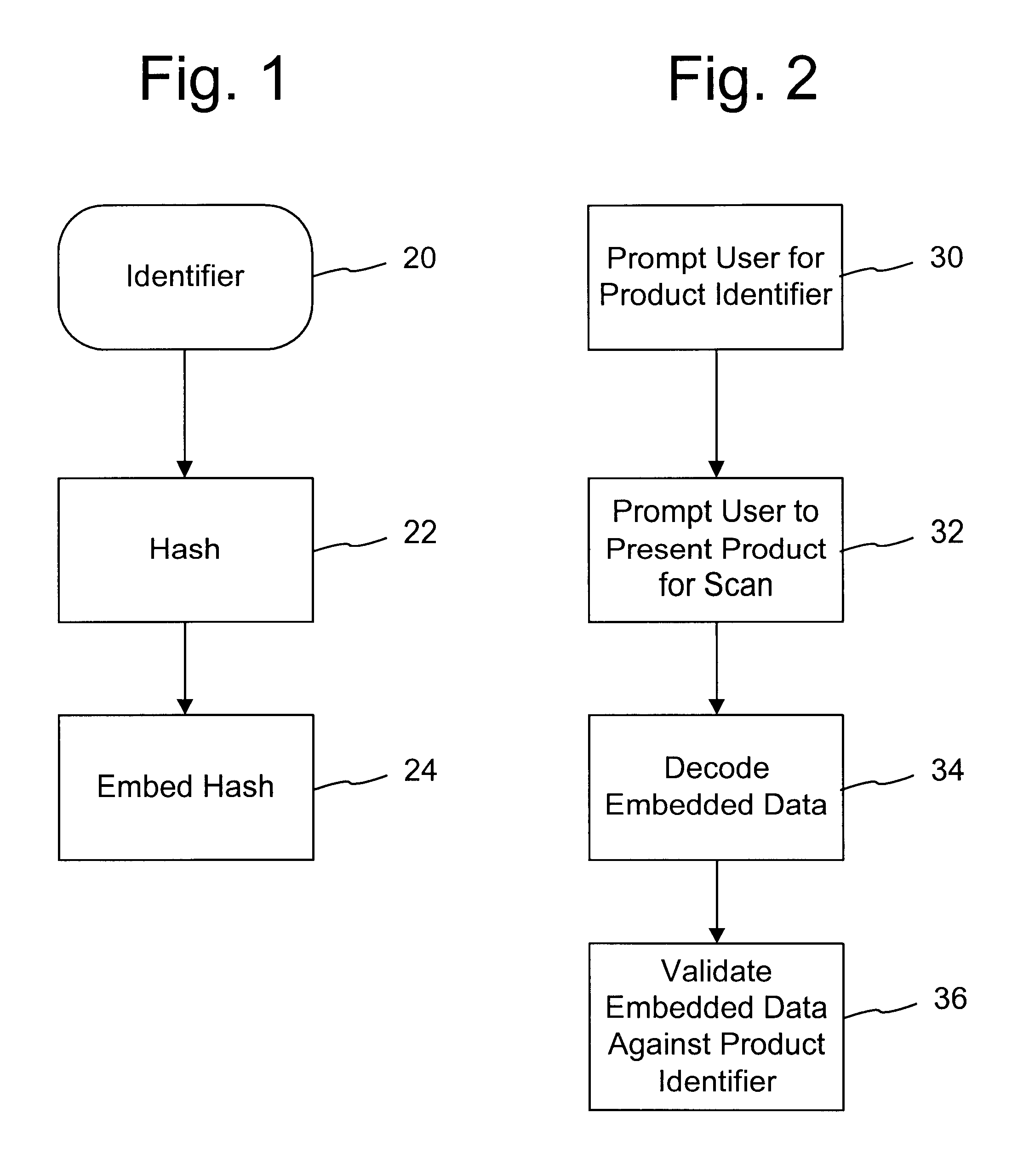
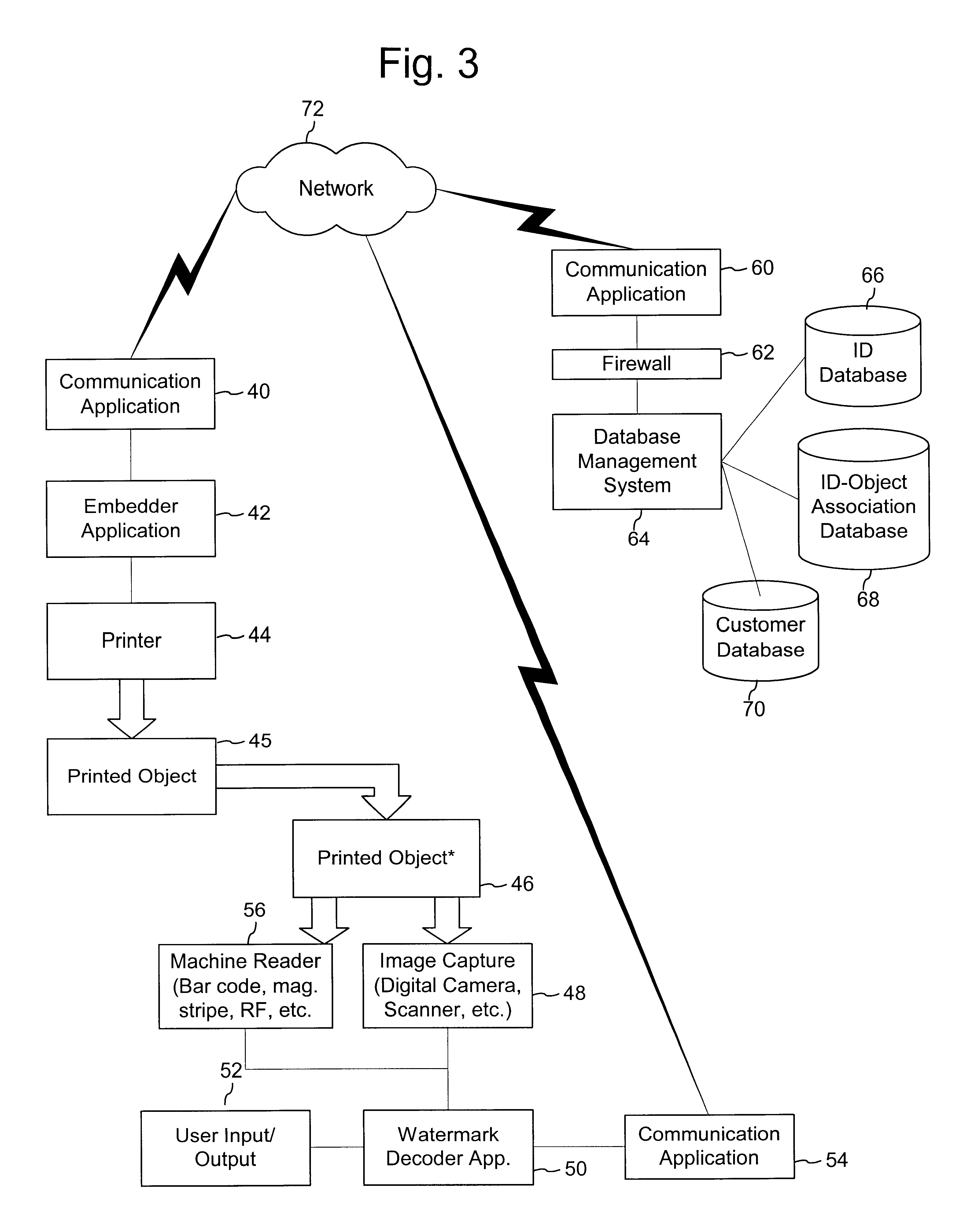
The disclosure describes systems for creating and authenticating printed objects using authentication information. Techniques for incorporating authentication information into digital representations of objects and using the authentication information to authenticate the objects are also provided.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
Authentication watermarks for printed objects and related applications
InactiveUS20020012445A1Correct Geometric DistortionMore dataOther printing matterPaper-money testing devicesRelevant informationCopy detection
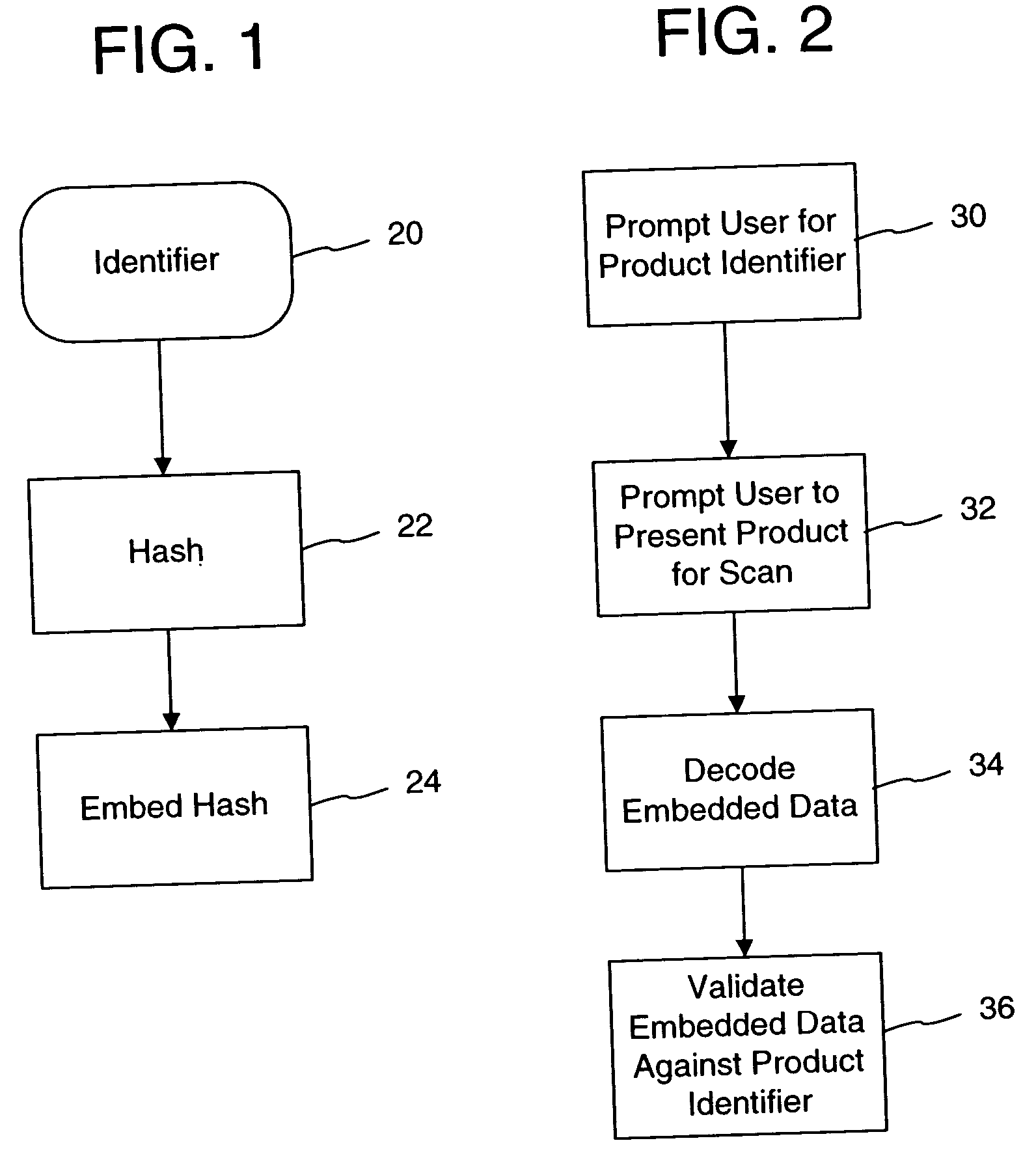
The disclosure describes systems for creating and authenticating printed objects using authentication and copy detection watermarks. For example, one verification system includes a watermark decoder and a verification module. The watermark decoder detects a copy detection watermark in a printed object to determine whether the printed object has been reproduced. The verification module processes a message decoded from an authentication watermark on the printed object to authenticate the printed object or bearer of the printed object. The authentication and copy detection watermarks may be implemented as the same or different watermarks. For example, the copy detection watermark may be a fragile watermark that carries the message and that degrades in response to a reproduction operation, such as photocopying or scanning and then reprinting the object. Alternatively, the authentication and copy detection watermarks may be separate watermarks embedded in an image that is printed on the object. The authentication watermark, in some applications, includes an identifier that links the object to a database entry with related information about the object. This related information can be used to check the bearer of the object by comparing it with attributes of the bearer (such as a user ID or photo) or the validity of the object by comparing it with attributes that are visible or machine readable on the object.
Owner:INTUIT INC
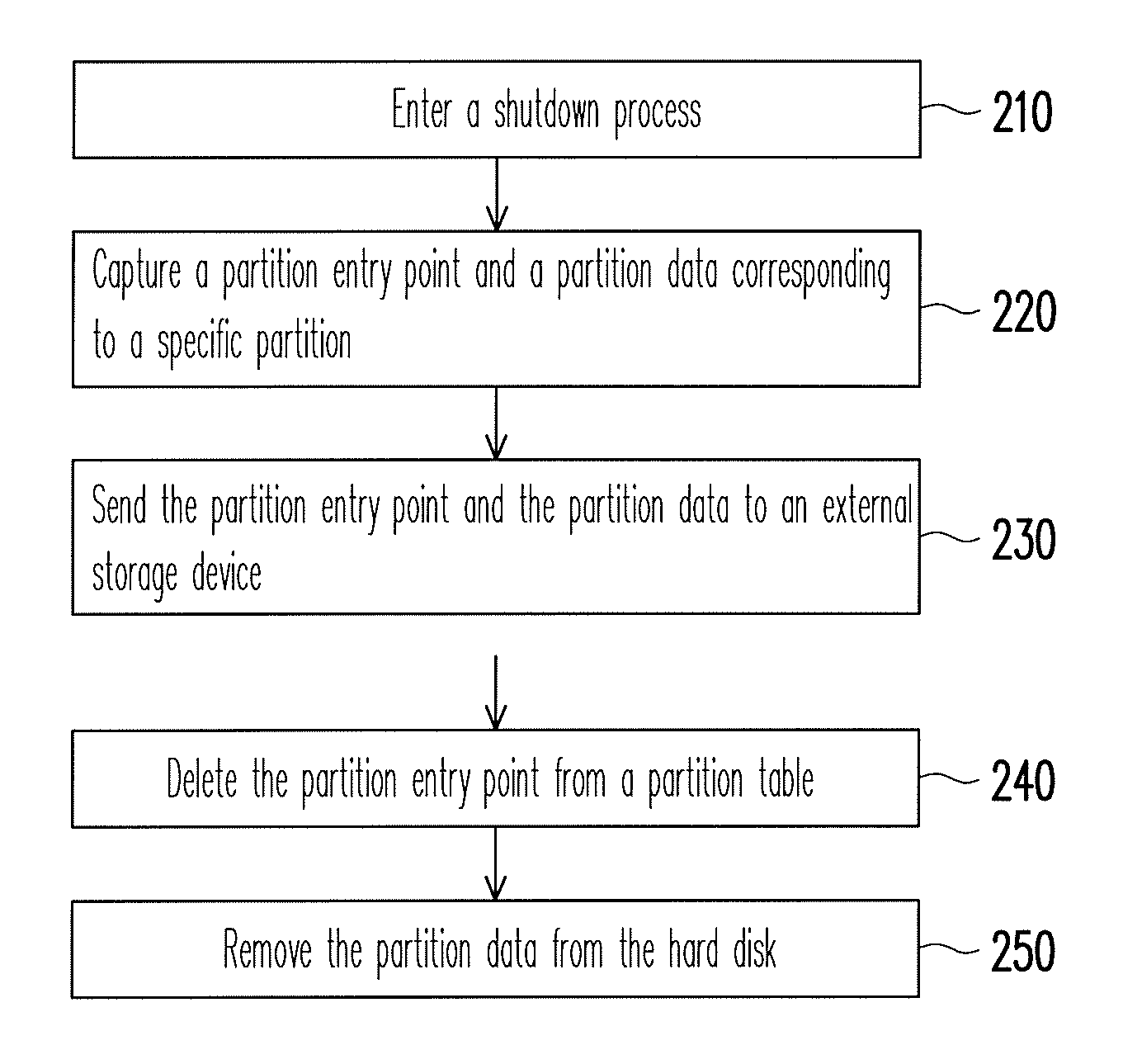
Data protection method
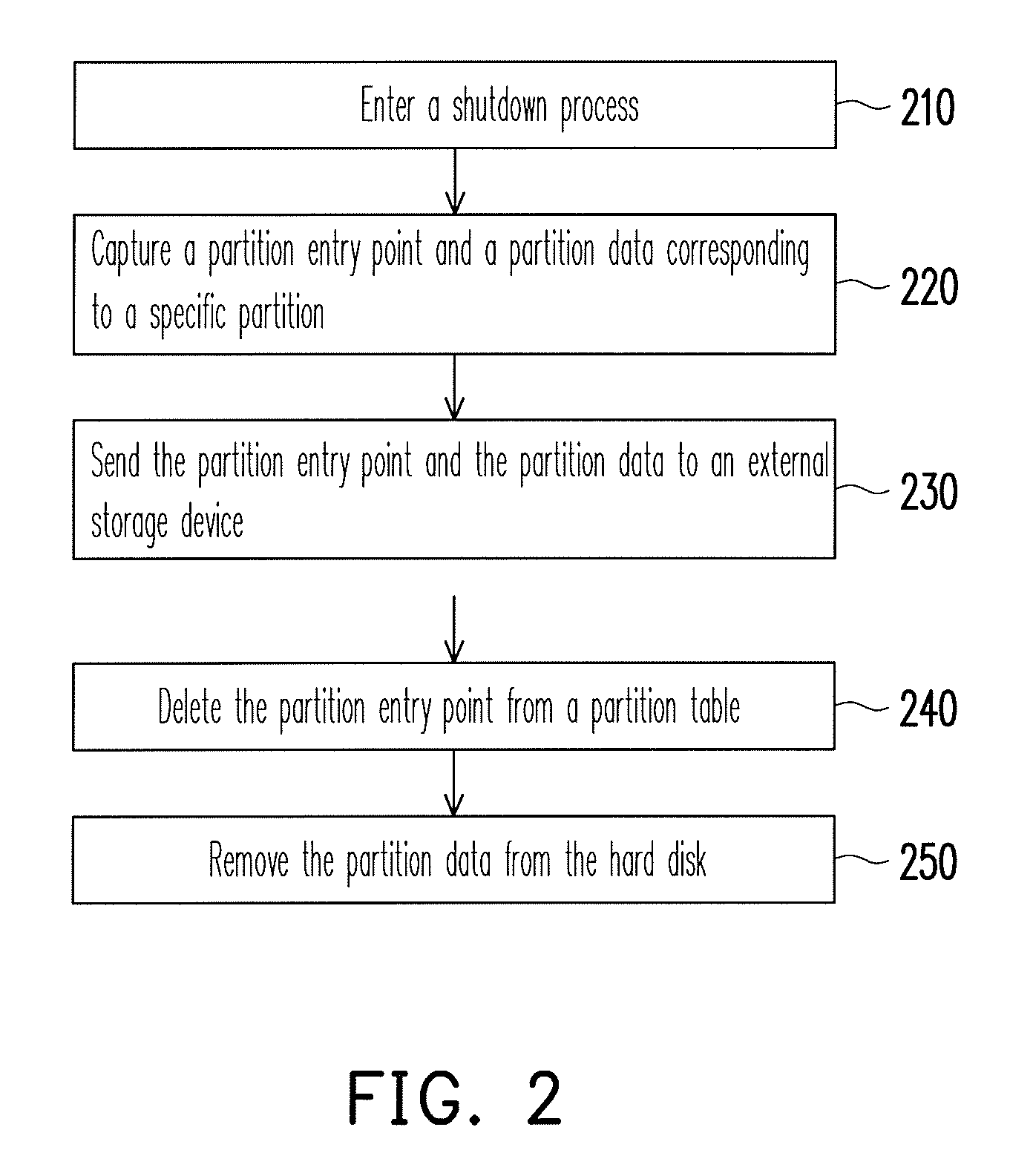
ActiveUS8041913B2Data SecurityEnsure safetyDigital data processing detailsUnauthorized memory use protectionExternal storageEntry point
A data protection method for an electronic device having a storage medium is provided, wherein the storage medium includes a plurality of partitions and a partition table. In the data protection method, a partition entry point and a partition data corresponding to the specific partition are captured and sent to an external storage device when the electronic device enters a shutdown process. Then, the partition entry point is deleted from the partition table and the partition data is removed from the storage medium. When the electronic device is turned on, a user has to provide the corresponding external storage device to restore the partition entry point and the partition data back to the storage medium. Thereby, personal data stored in the storage medium is protected and accordingly data security is ensured.
Owner:ASUSTEK COMPUTER INC
Authentication watermarks for printed objects and related applications
InactiveUS6823075B2More dataCompact formOther printing matterPaper-money testing devicesRelevant informationCopy detection
Owner:INTUIT INC
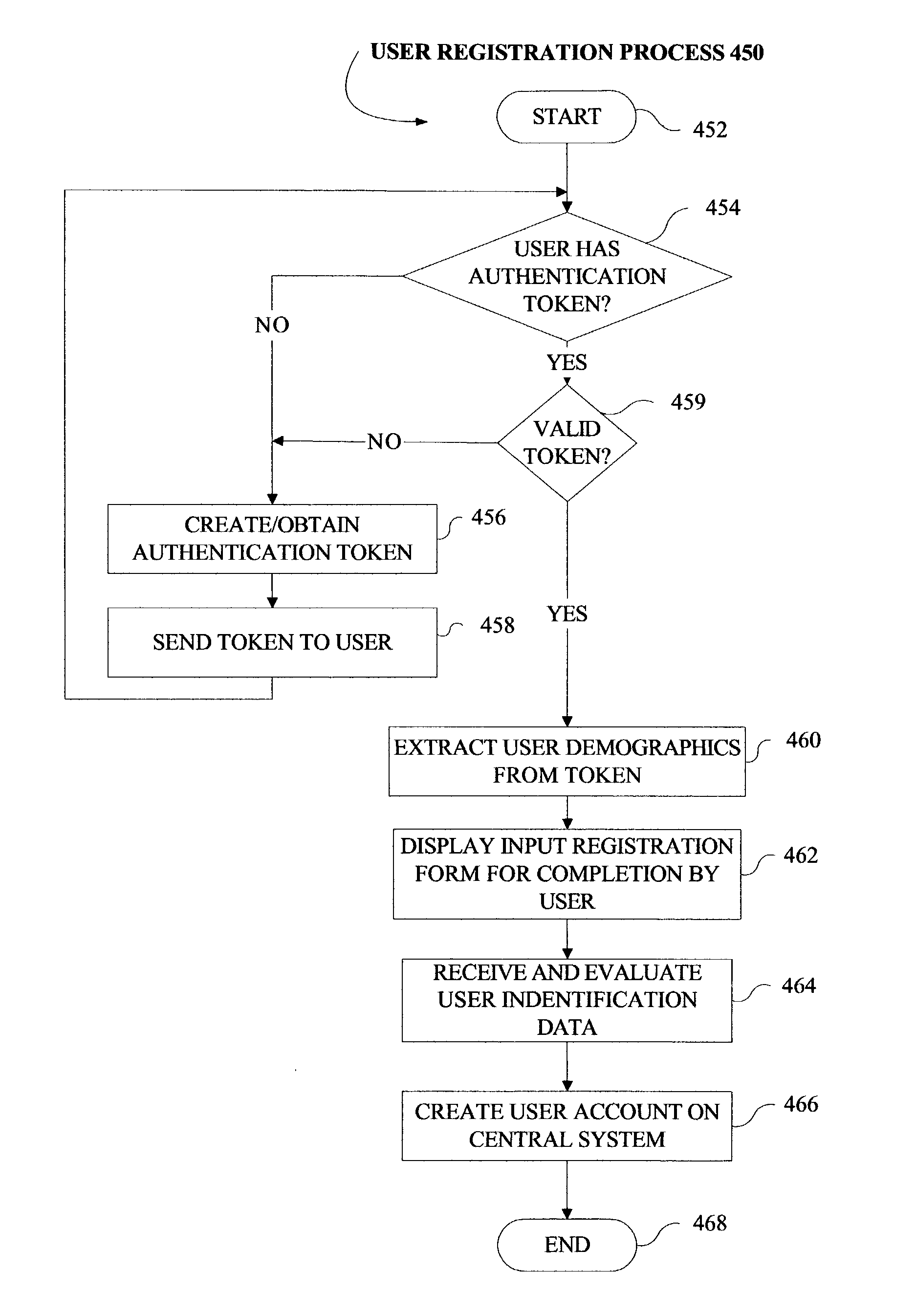
Methods and systems for managing patient authorizations relating to digital medical data
ActiveUS20050027995A1Improve reliabilityData SecurityData processing applicationsUser identity/authority verificationUnique identifierMetadata
A network for mediating the peer-to-peer transfer of digital patient medical data includes a plurality of distributed agents each associated with a health care provider and connected to a central system. Periodically the agents collect local information relating to patient medical files and / or data streams, for example diagnostic images and associated reports, and process that information into metadata files acting as pointers to the original files. The metadata files are transmitted to the central system where they are parsed and the attributes are stored on the central system in patient records with records from the same patient grouped together whenever possible. Registered users can search the central system, even in the absence of a unique identifier, to identify patient records pointing to the remote patient medical files. Upon finding a patient medical file, the invention provides a streamlined process for communicating access authorization from the patient to the hospital or facility storing the medical files. Once patient authorization is received, secure processes are provided for transferring the data in its entirety to or for viewing by the user in a peer-to-peer fashion.
Owner:HX TECH
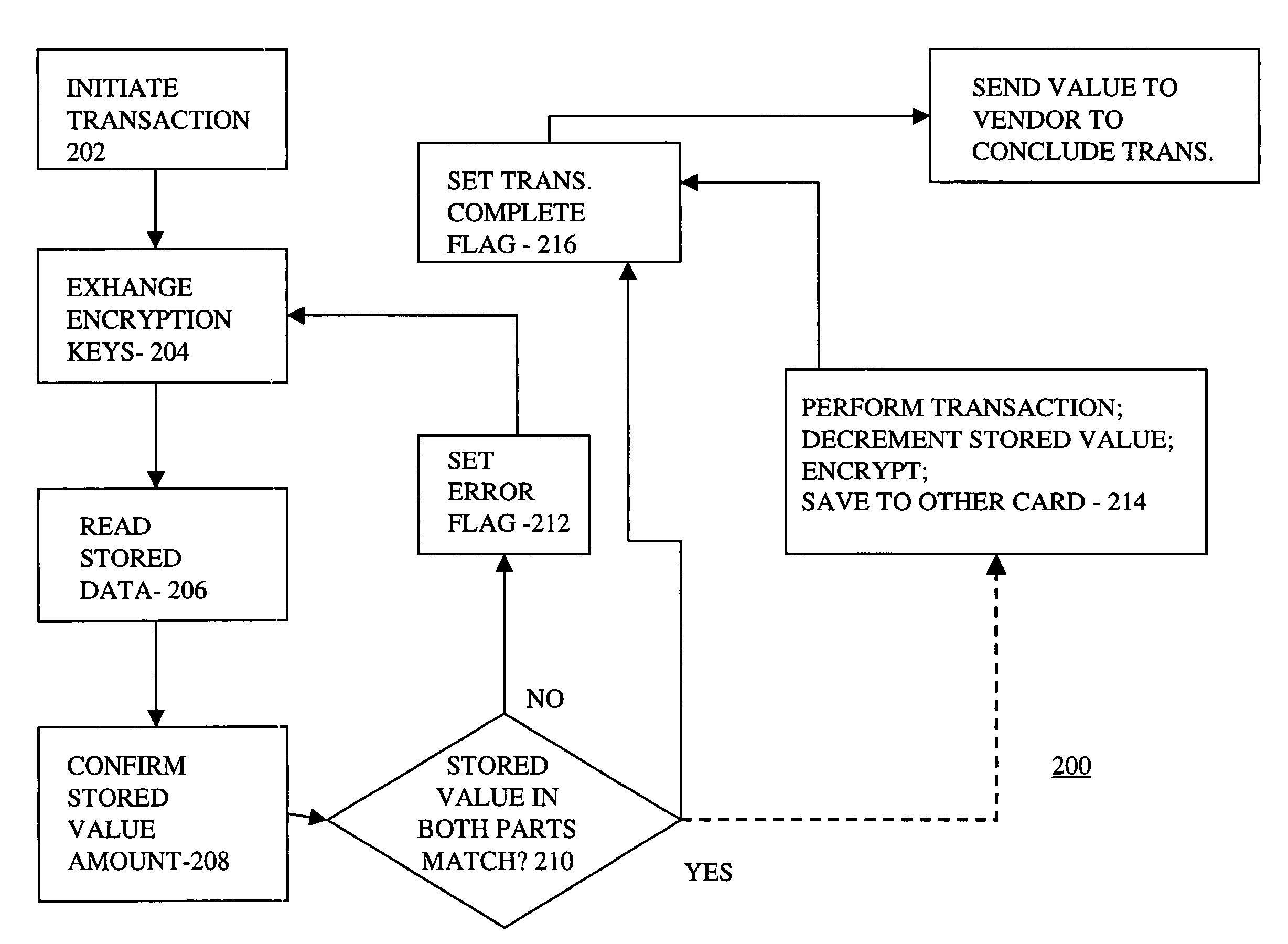
Smart card with back up
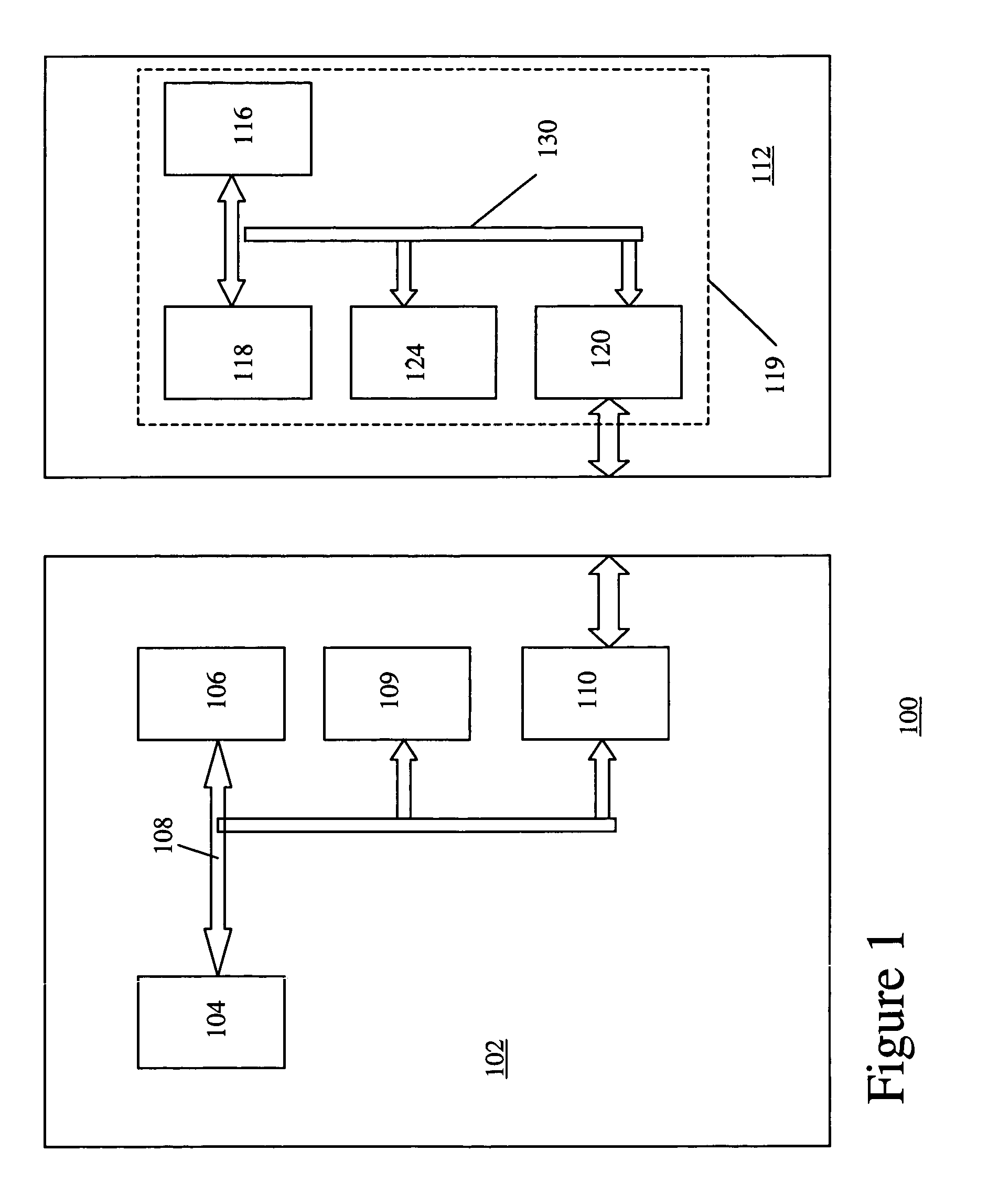
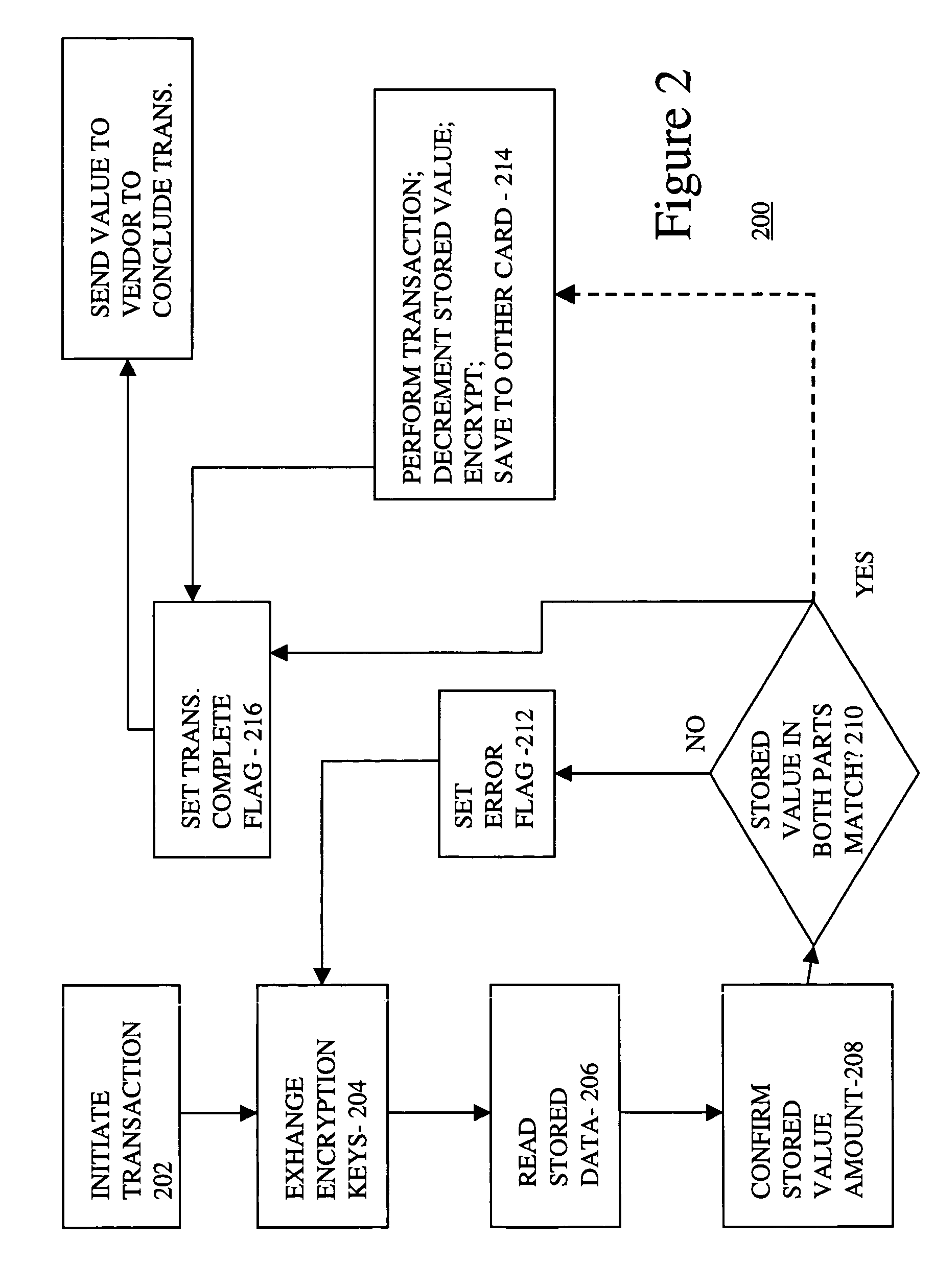
InactiveUS7206847B1Data SecurityImprove securityComplete banking machinesAcutation objectsProgram instructionSmart card security
Smart card security is enhanced by making the smart card a two-piece device. Both parts of the smart card contain copies of user data and a processor, which executes program instructions stored in the smart card half so as to give each part of the two-part smart card security and intelligence. Both parts must be in communication with each other for the data in either card to be accessible and useable. By separating the two pieces, data compromise is virtually impossible.
Owner:GOOGLE TECH HLDG LLC
Cloud Storage Data Access Method, Apparatus and System Based on OTP
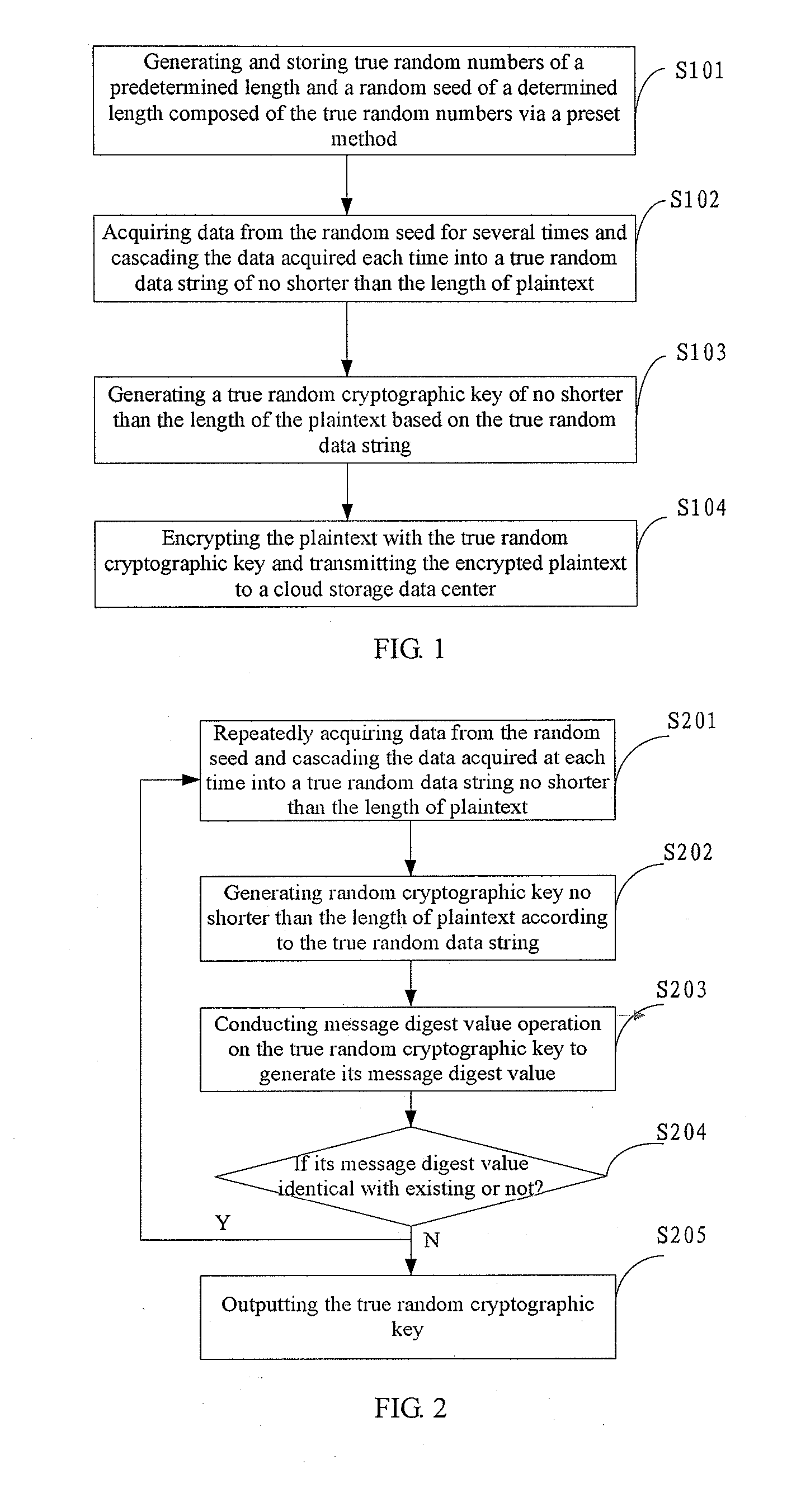
InactiveUS20120134495A1Small storage space occupancyStrengthens cloud storage data securityMemory loss protectionDigital data processing detailsPlaintextComputer hardware
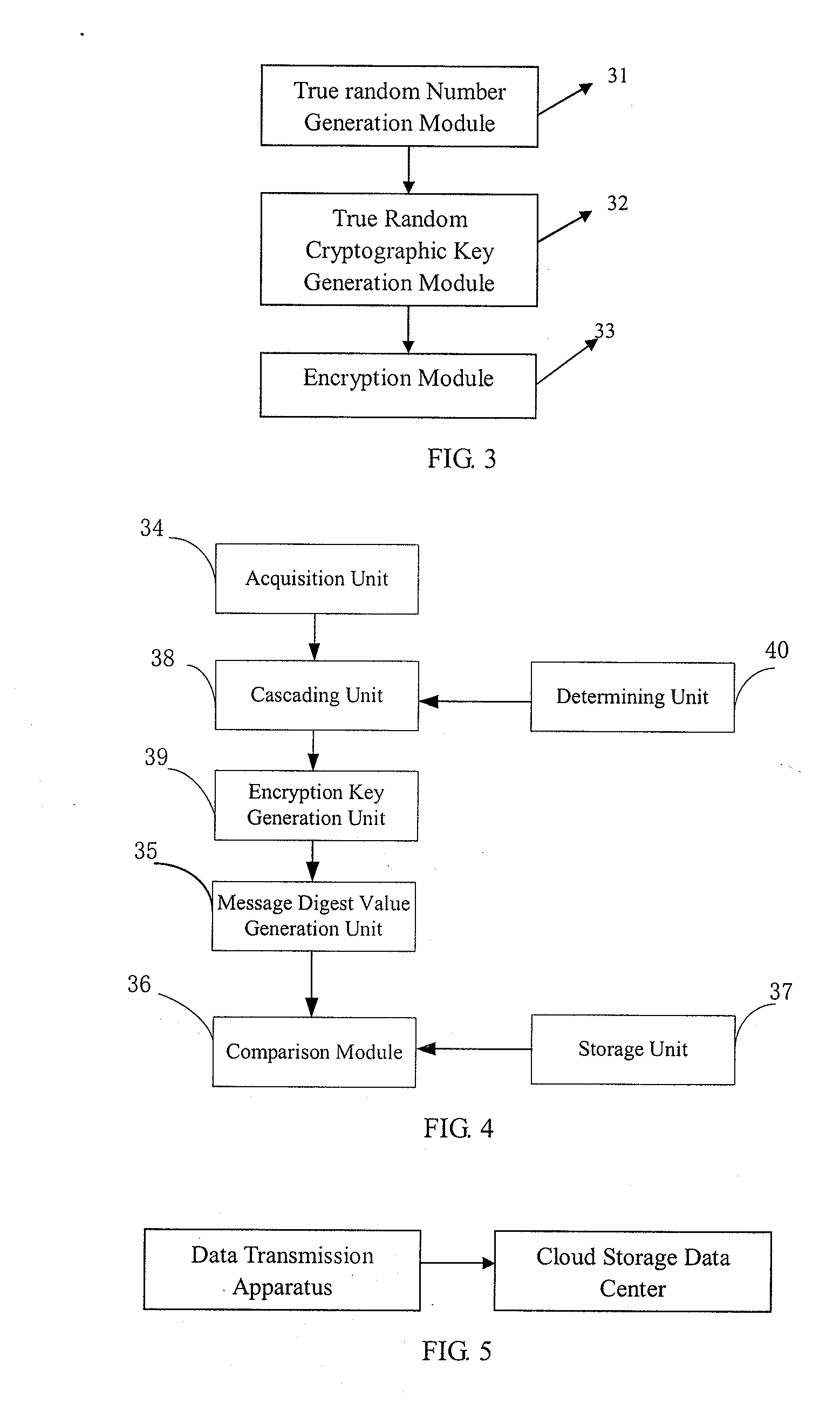
The present application relates to cloud storage technology and especially relates to a cloud storage data access method, apparatus and system based on OTP. This method includes: generating and storing true random numbers of a predetermined length and a random seed of a predetermined length composed of the true random numbers via a preset method; acquiring data from the random seed for several times and cascading the data acquired each time into a true random data string of no shorter than the length of plaintext; based on the true random data string, generating a true random cryptographic key of no shorter than the length of the plaintext, encrypting the plaintext using this cryptographic key and transmitting ciphertext to a cloud storage data center. This application also provides a cloud storage data access apparatus and system based on OTP. The method, apparatus and system introduced by this invention can generate and store sufficient true random cryptographic key with relatively small physical space occupancy in comparison with that of plaintext, thereby enabling OTP to be applied into cloud storage data security protection.
Owner:BEIJING Z & W TECH CONSULTING
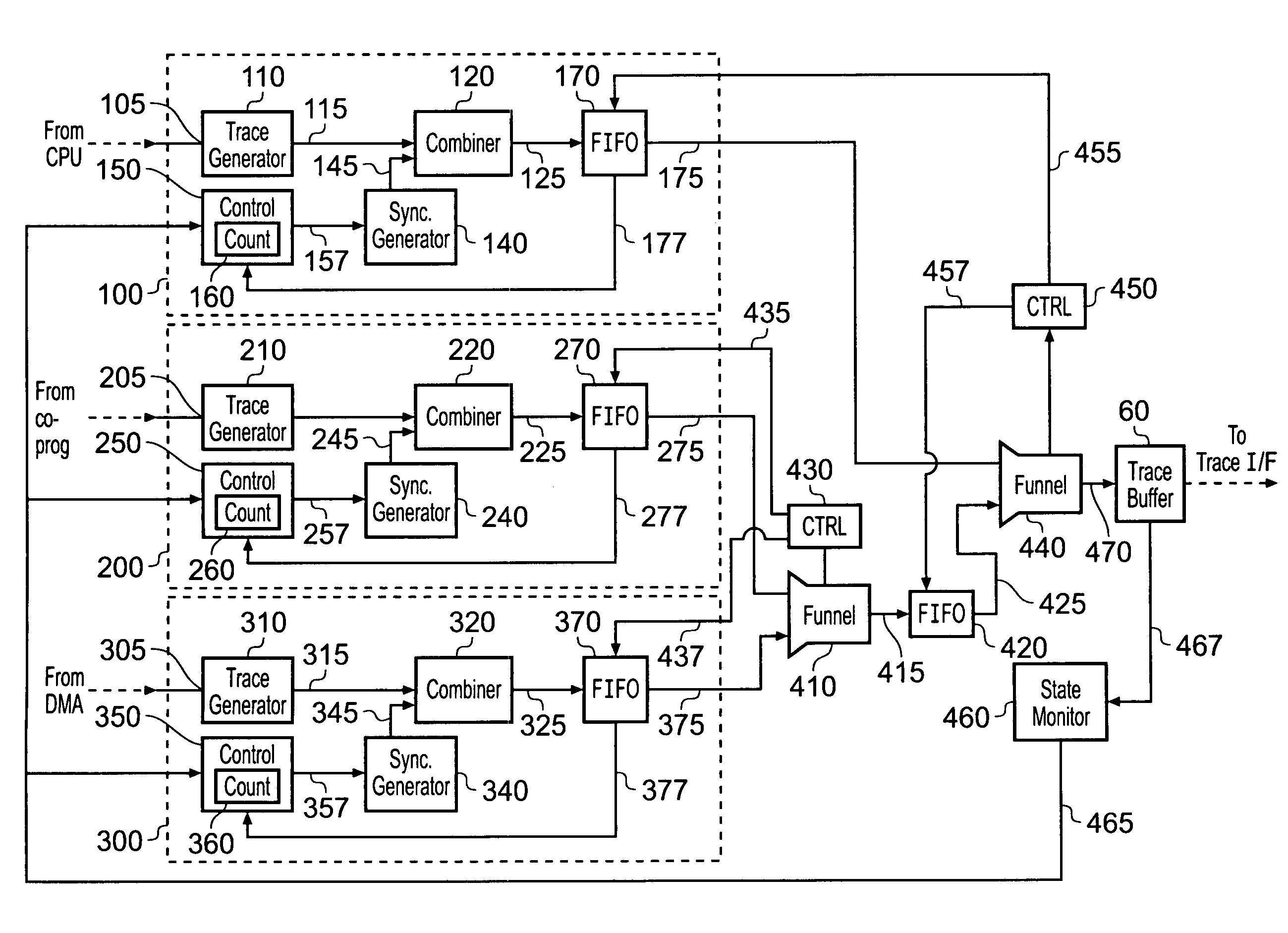
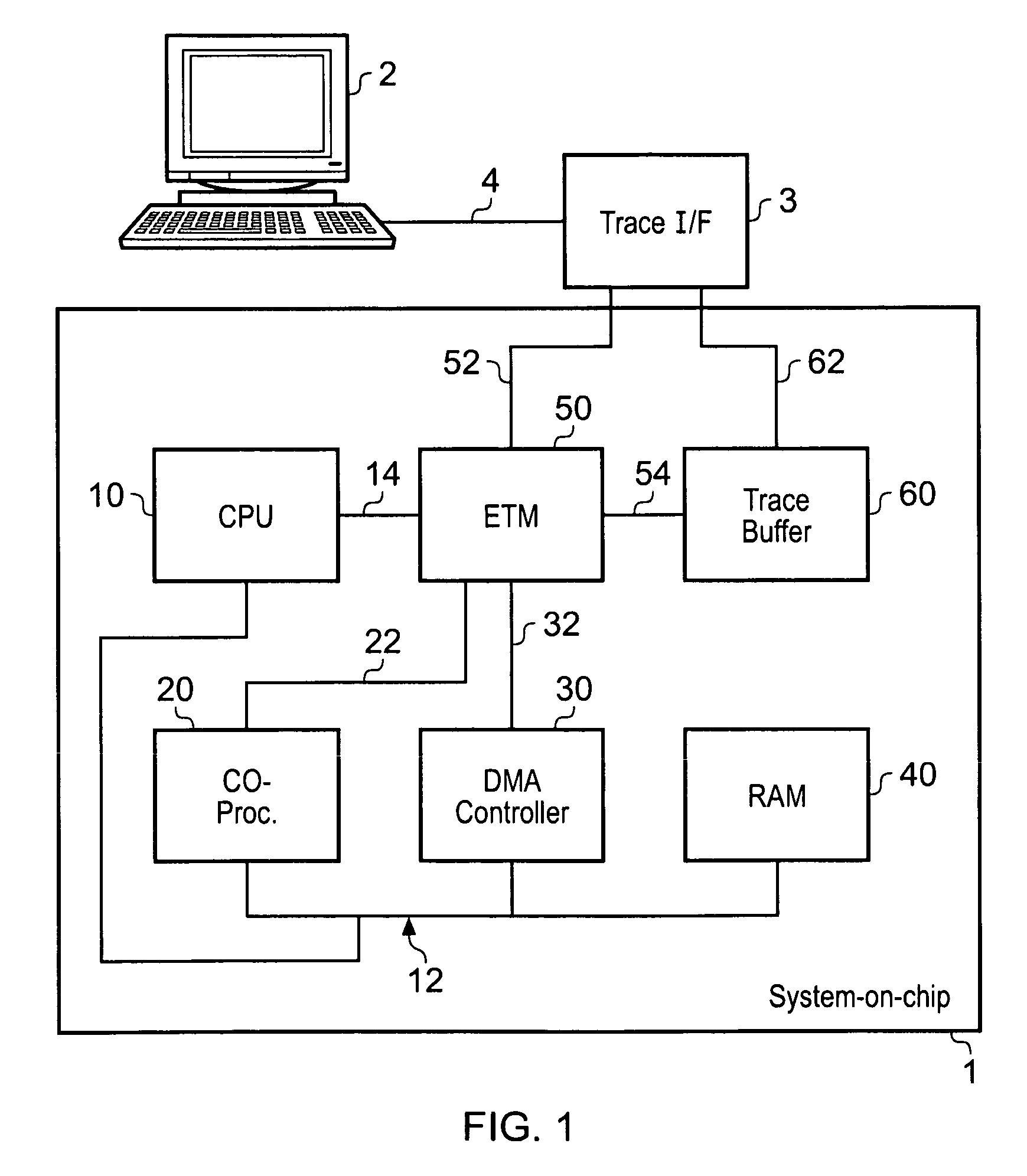
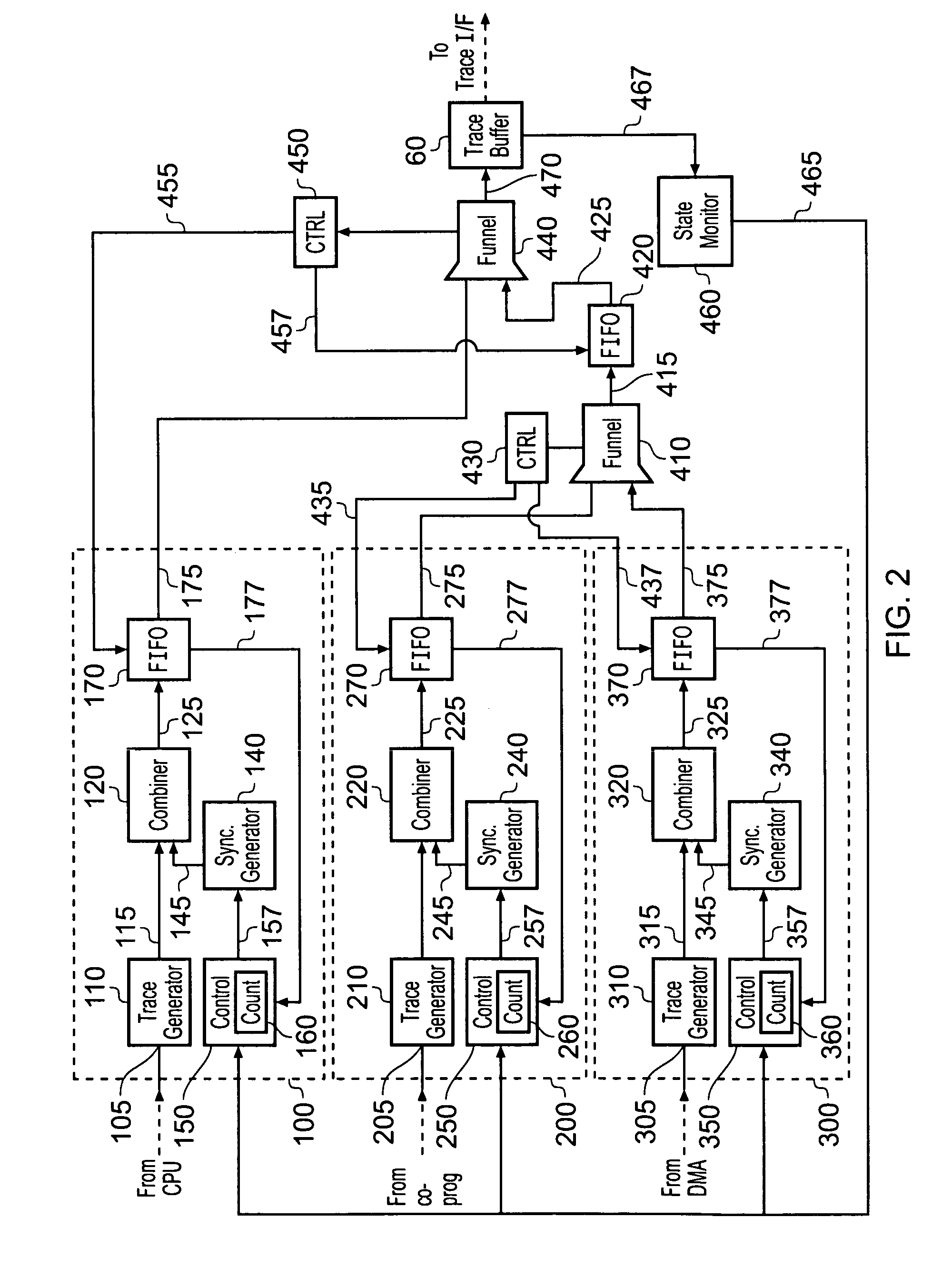
Trace synchronization
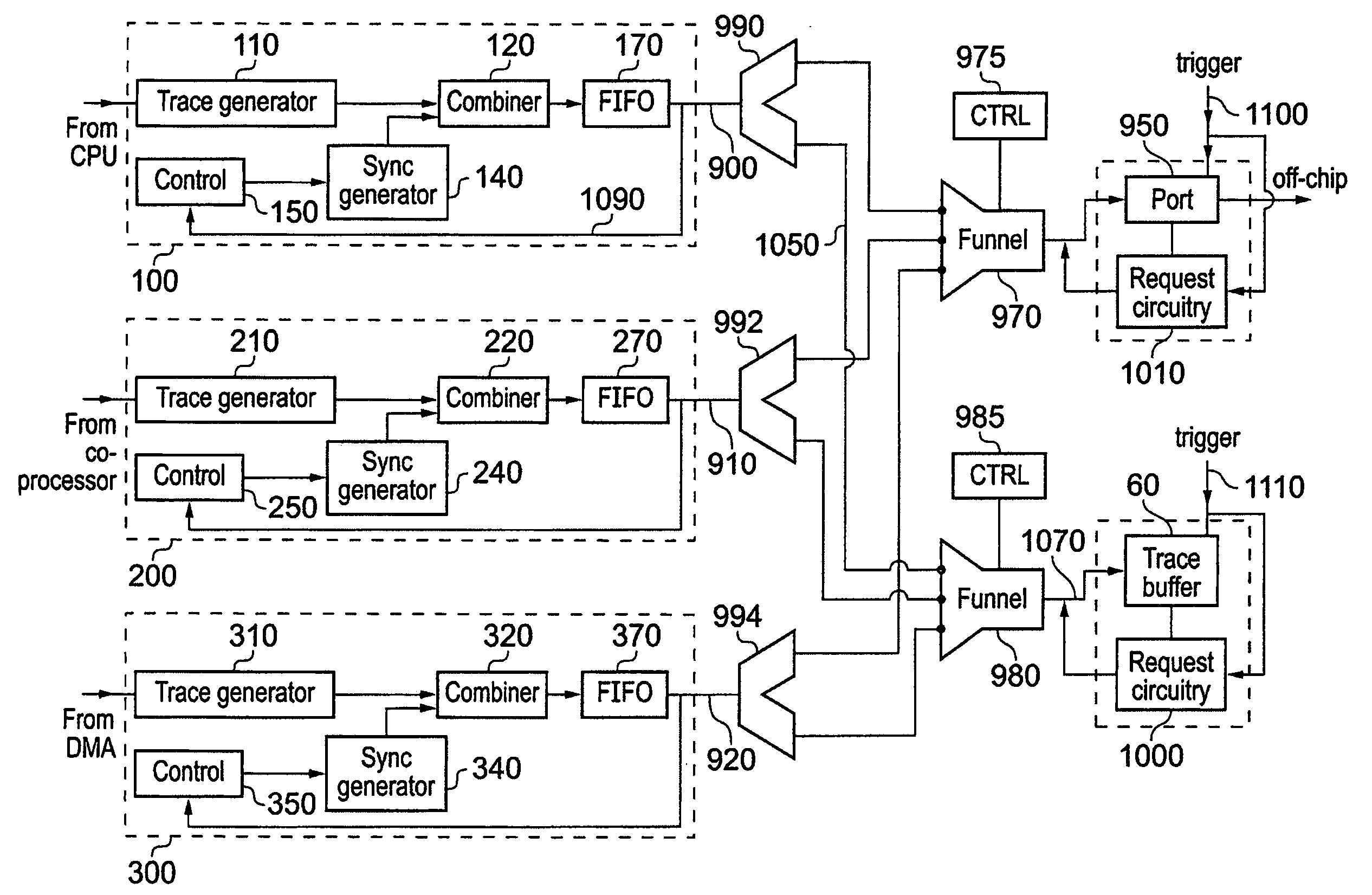
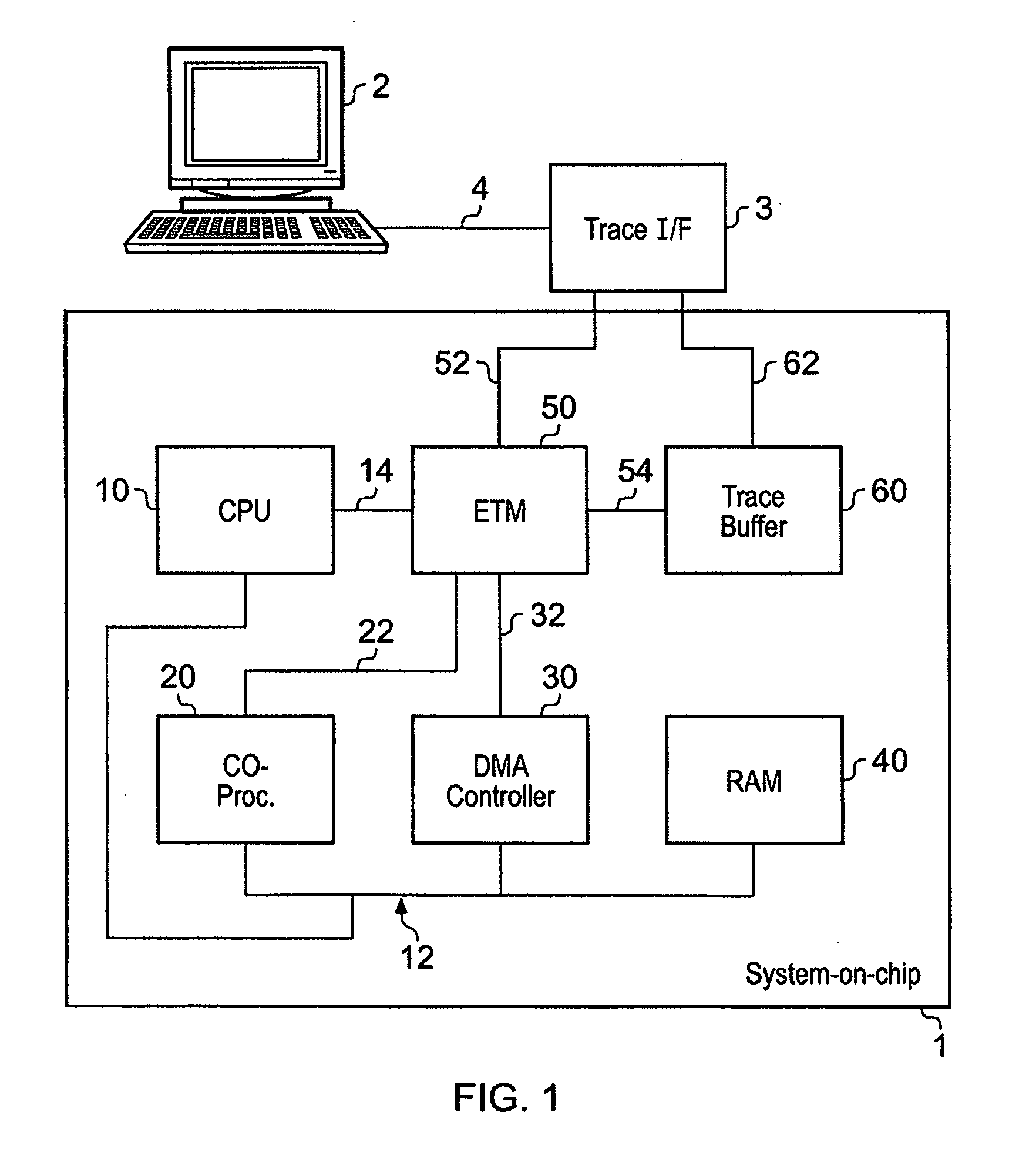
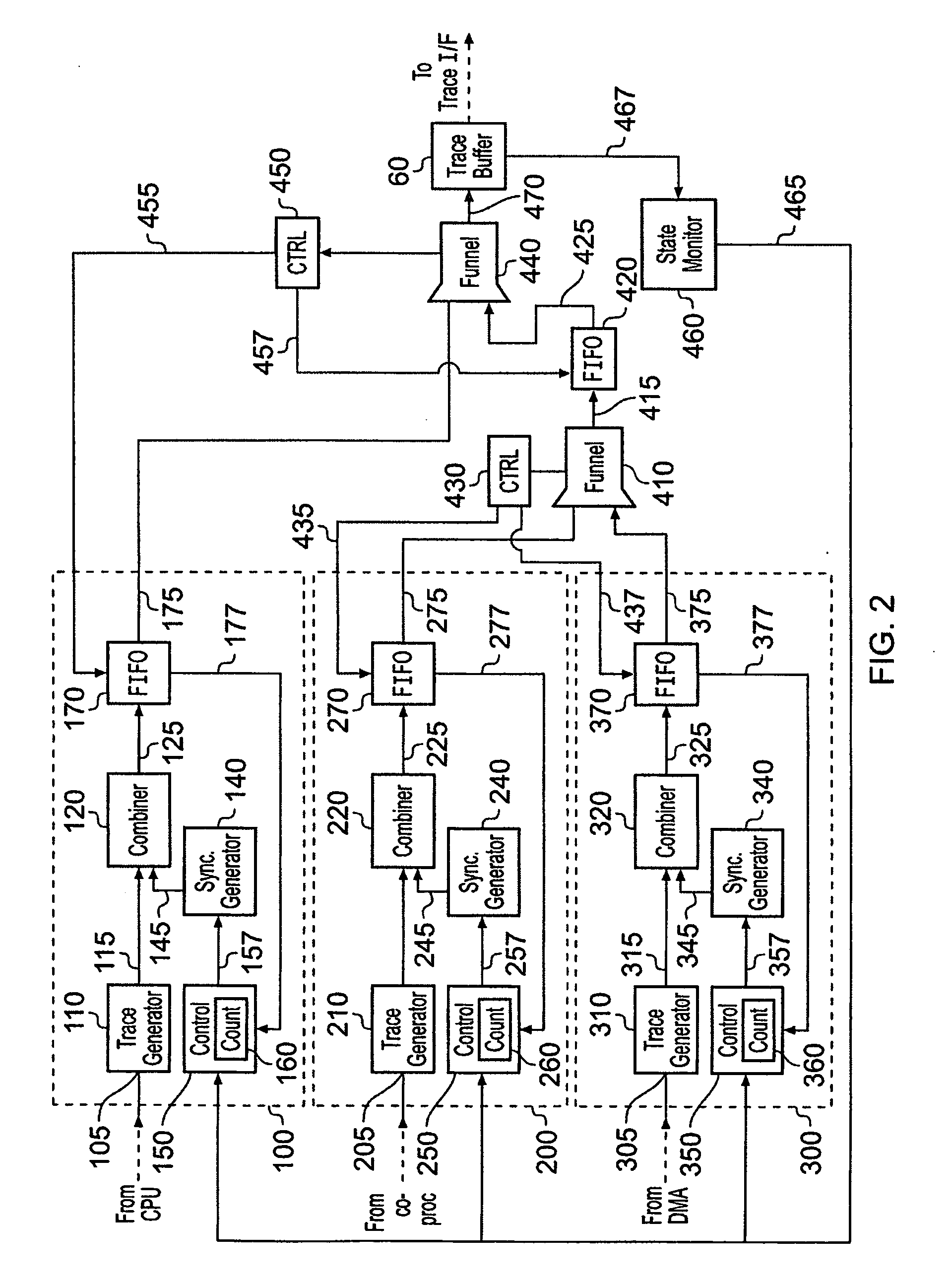
ActiveUS20100257510A1Little additional hardware costGuaranteed usageError detection/correctionDigital computer detailsData synchronizationData stream
A data processing apparatus having one or more trace data sources is provided in which the trace data sources operate to generate respective streams of trace data. At least one of said trace data sources comprises a trace data generator responsive to activity in monitored circuitry to generate trace data representing said activity. A synchronization marker generator is coupled to the trace data generator and operates to generate a synchronization marker and insert the synchronization marker into the trace data stream. The synchronization marker identifies a synchronization position in the trace data stream. A controller is coupled to the synchronization marker generator, and operates to initiate the synchronization marker generator to generate and insert a synchronization marker into the trace data stream. The controller controls initiation in dependence on behavior of the data processing apparatus downstream of the trace data generator with respect to trace data flow. In this way, the downstream behavior of the data processing apparatus can be made to influence the rate and timing of insertion of synchronization markers into a trace data stream, thereby reducing the likelihood of the volume of trace data resulting in an overflow condition in the downstream circuitry.
Owner:ARM LTD
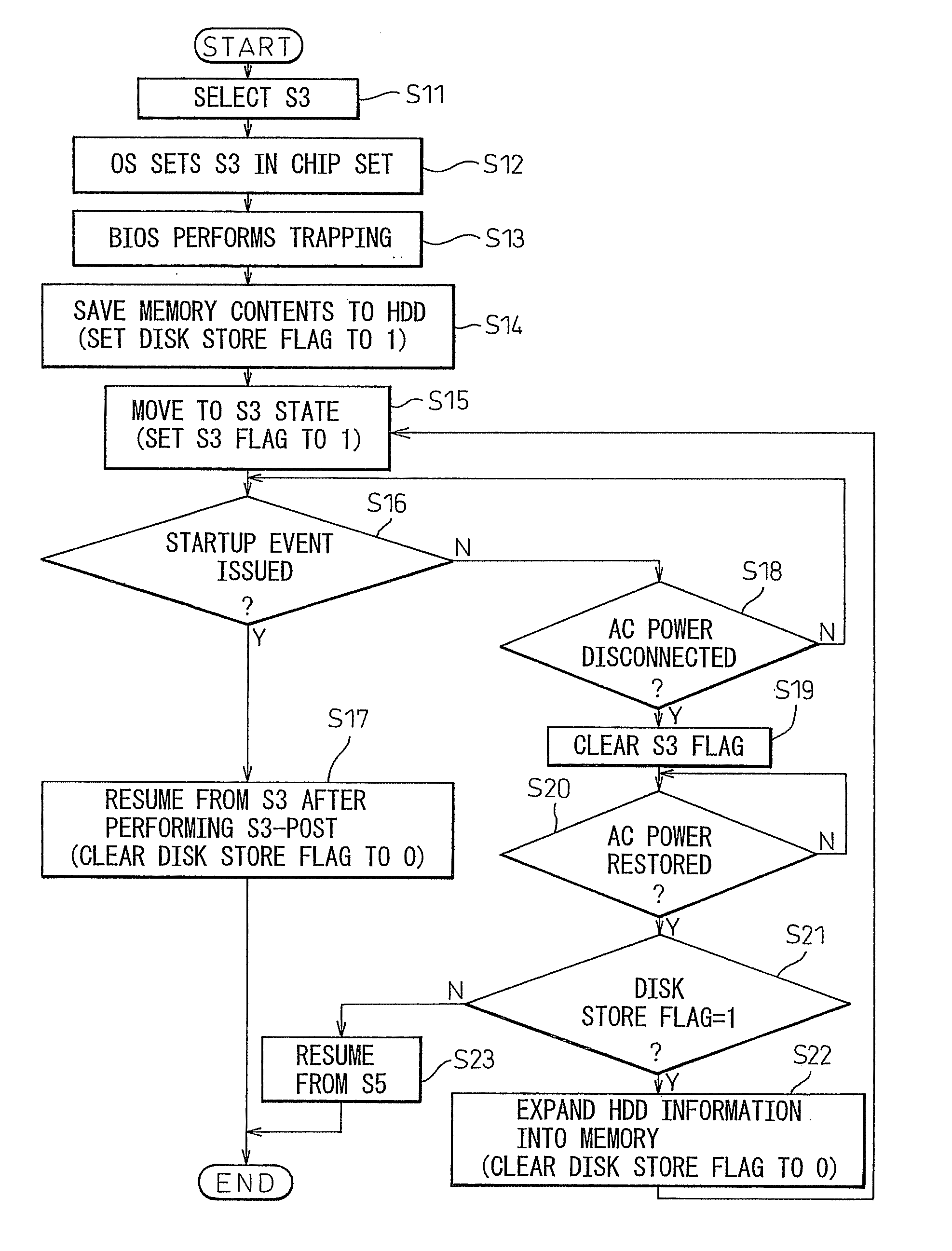
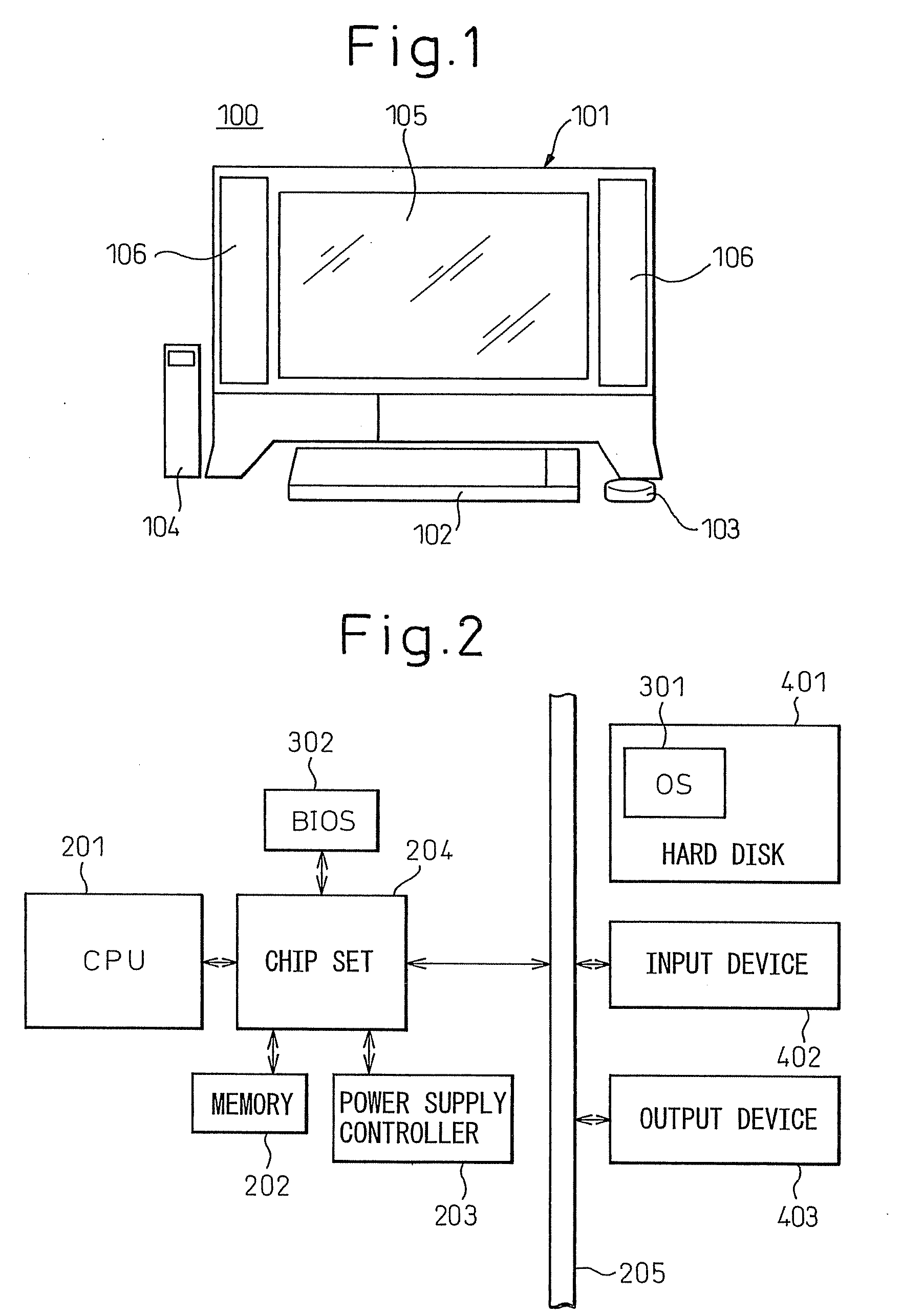
Information processing apparatus and power supply control method
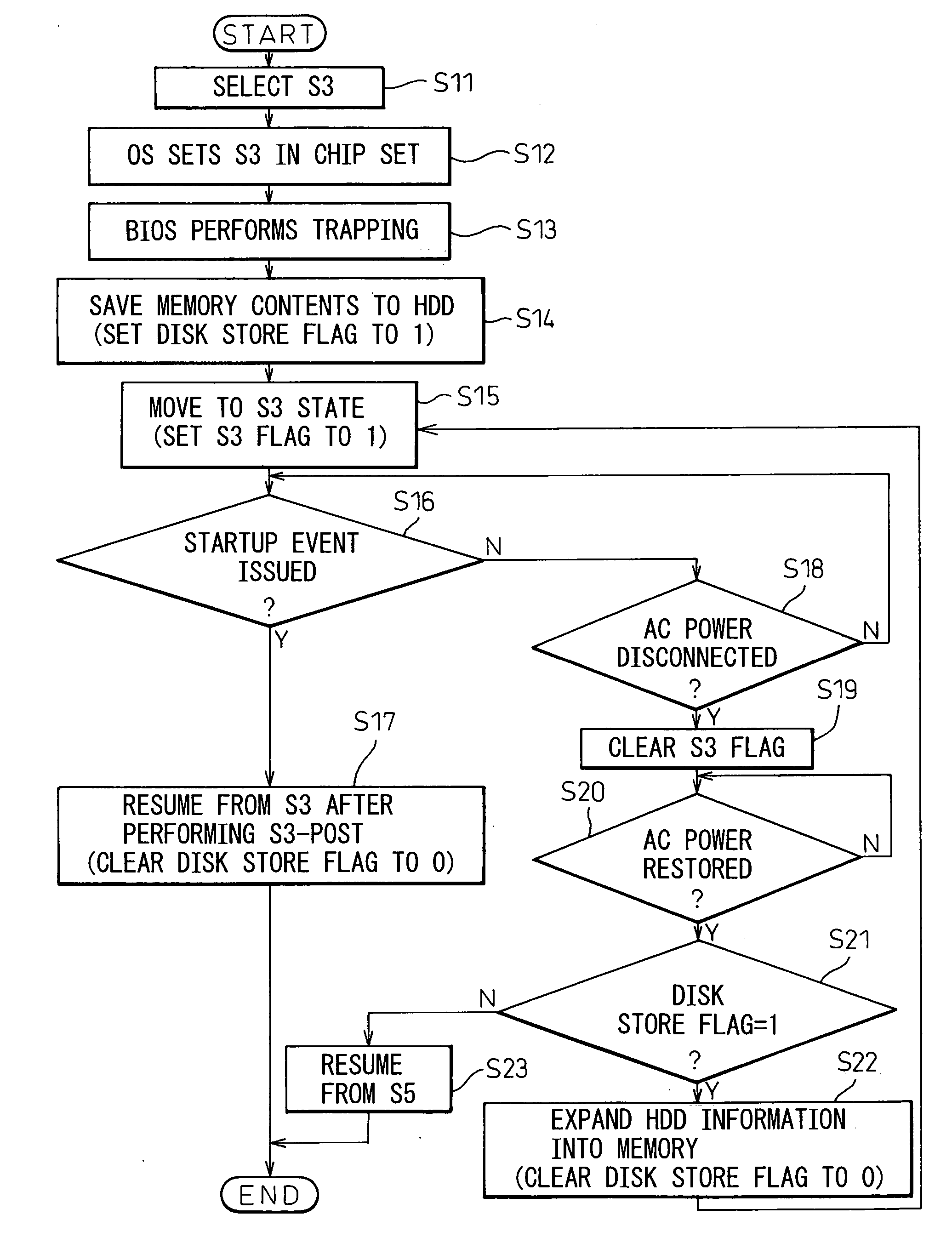
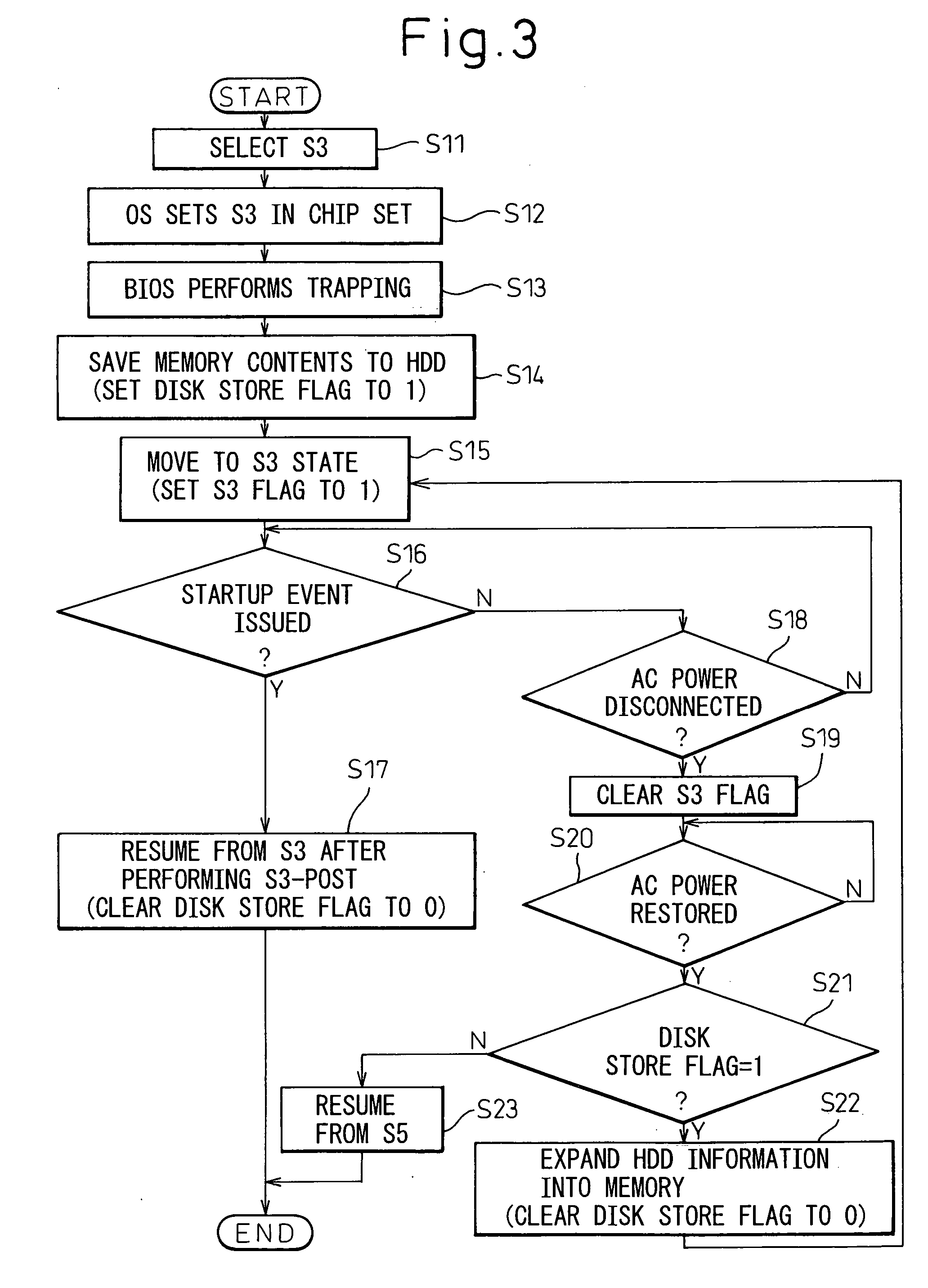
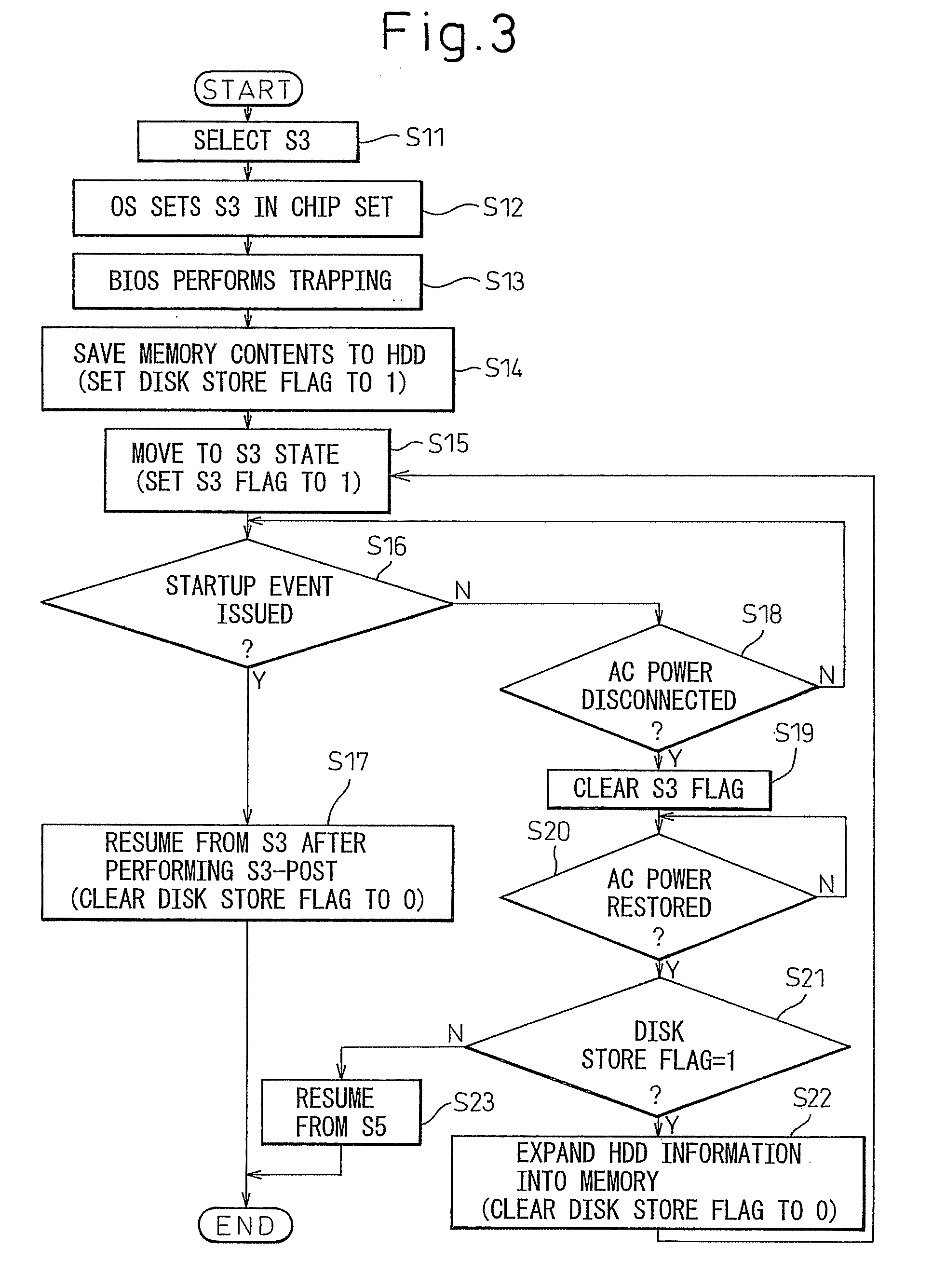
InactiveUS20060059380A1Reduce the required powerShorten the timeTelevision system detailsVolume/mass flow measurementInformation processingElectricity
In standby mode, memory contents are saved to a hard disk. After AC power has been removed by disconnecting the AC plug, when the AC power is restored the data saved on the hard disk is automatically restored into memory to set the power-saving mode back to the standby mode. When the power is turned on next, quick resumption from standby mode can be accomplished.
Owner:FUJITSU CLIENT COMPUTING LTD
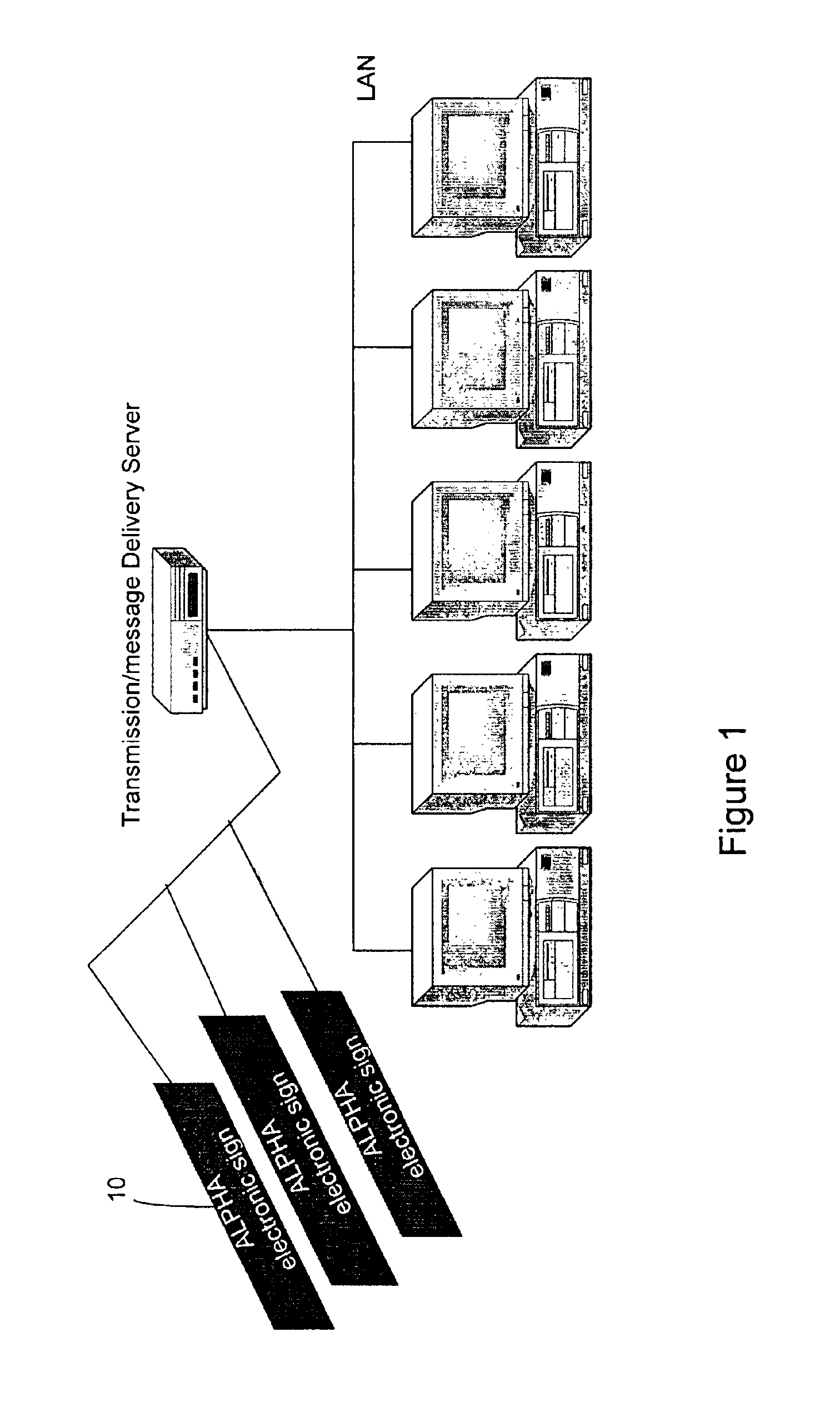
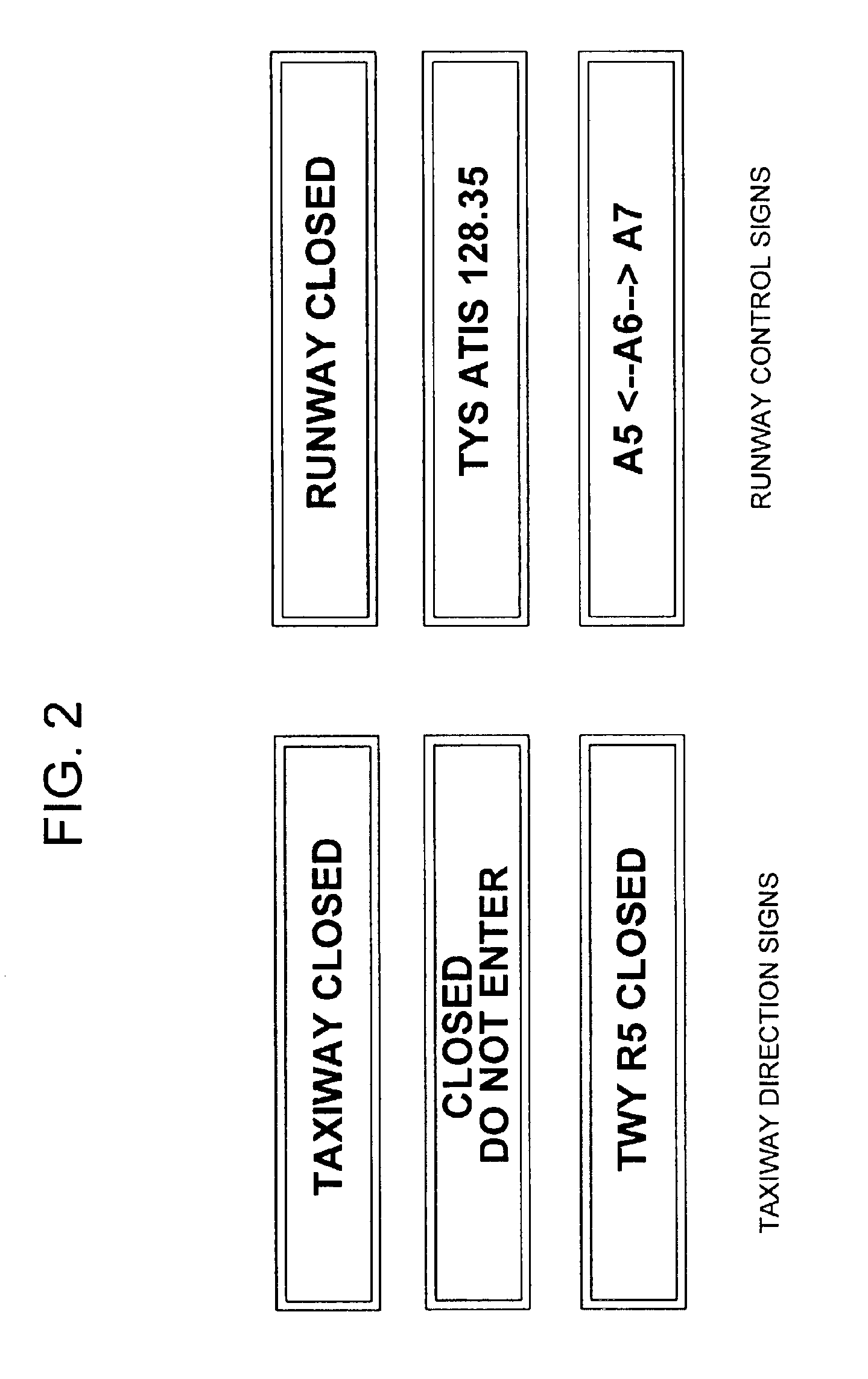
Surface traffic movement system and method
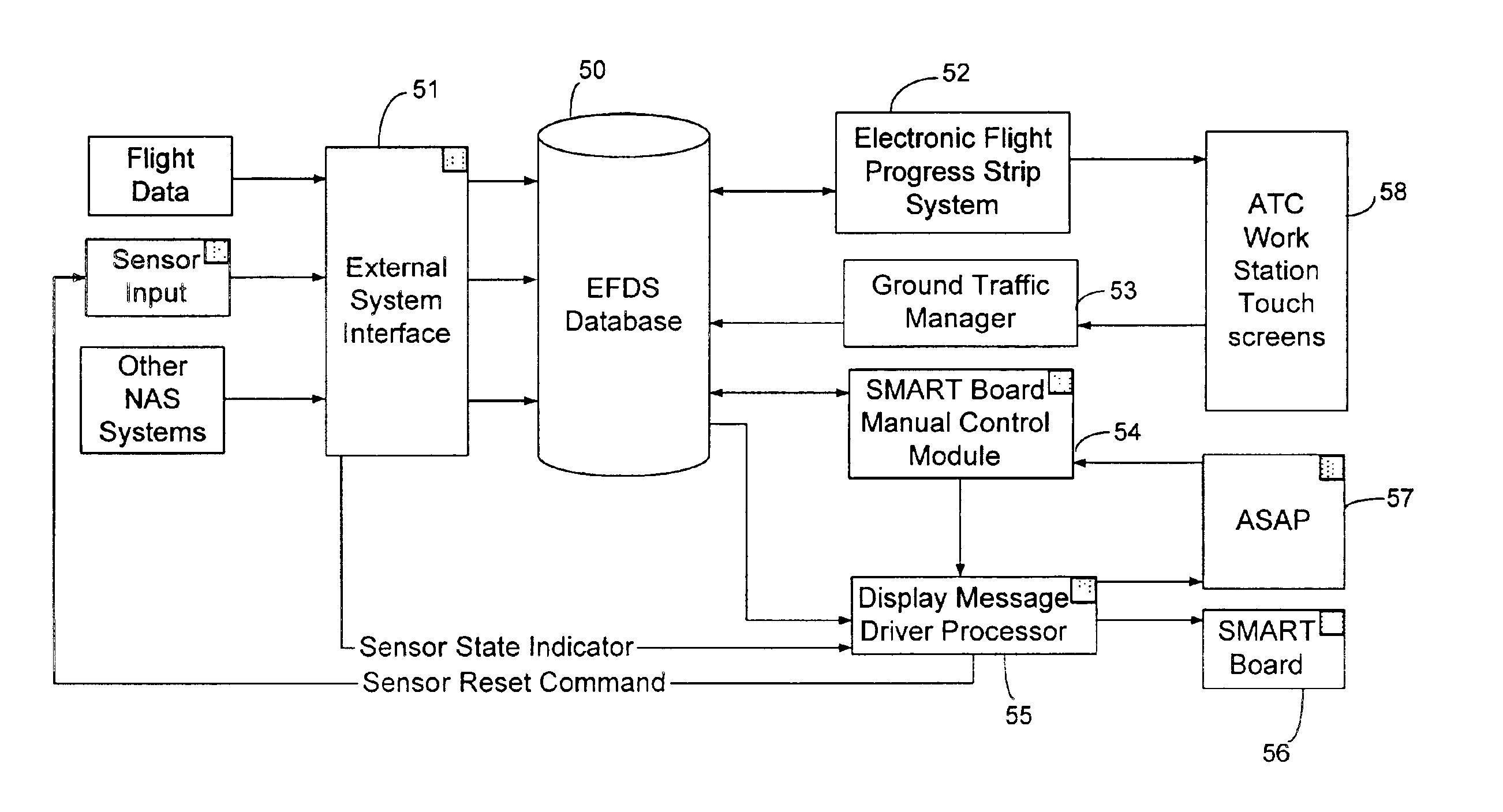
InactiveUS6920390B2Curtailing runway incursionIncrease collisionAnalogue computers for vehiclesInstruments for road network navigationSurface displayTransit system
A Surface Movement Area / Runway Traffic and Surface Area Flow Tool with Runway Incursion Protection System reduces runway incursions due to lost or disoriented aircraft, navigation in low visibility conditions, unfamiliarity with local procedures and airport layouts, and truncated or misunderstood clearances or other frequency congestion related communication and workload problems. SMART Board surface displays are used to provide route guidance instructions to aircraft at ramp and taxiway intersections, confirm to for pilots that their aircraft is at the correct location and is in the assigned queue and sequence before entering active runways, visual confirmation of runway clearances to aircraft and vehicles at all runway entrances, and lessening frequency congestion on Ground and Local communications channels. The system includes an Electronic Flight Data System to generate messages. Sensors and a wireless LAN are used to provide data from the system to all aircraft and vehicles on the surface movement area of an airport.
Owner:TECH PLANNING
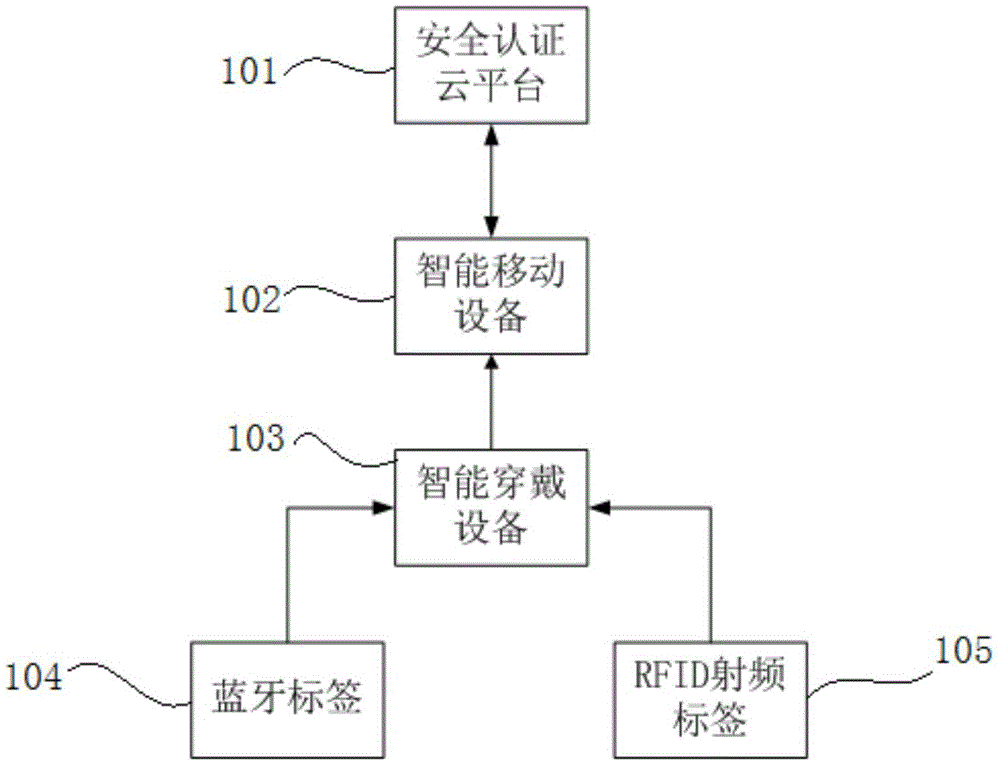
Intelligent wearable terminal based child behavior monitoring and developing method and system
InactiveCN105608654AAchieve recordIncrease the database of dynamic behavior habitsCo-operative working arrangementsOffice automationWi-FiData information
The present invention discloses an intelligent wearable terminal based child behavior monitoring and developing system and method. The system comprises an intelligent wearable device, a Bluetooth tag, an RFID radio-frequency tag, an intelligent mobile device, a security authentication cloud platform and a data cloud platform. The method comprises: based on a position relationship, establishing a Bluetooth tag based on a Bluetooth Ad Hoc network, and a radio-frequency tag, and according to the Bluetooth tag and the radio-frequency tag, monitoring a behavior of a child wearing an intelligent wearable terminal; uploading a monitoring result to a cloud-end server; establishing a classifiable dynamic behavior habit database according to child basic data information and child daily behavior data; and comparing child behavior data in the dynamic behavior habit database with behavior data in a preset standard behavior database, and outputting early-warning and prompting information. According to the method and system disclosed by the present invention, by integrating technologies such as Bluetooth, RFID and Wi-fi, child behavior monitoring and development are implemented.
Owner:刘国正
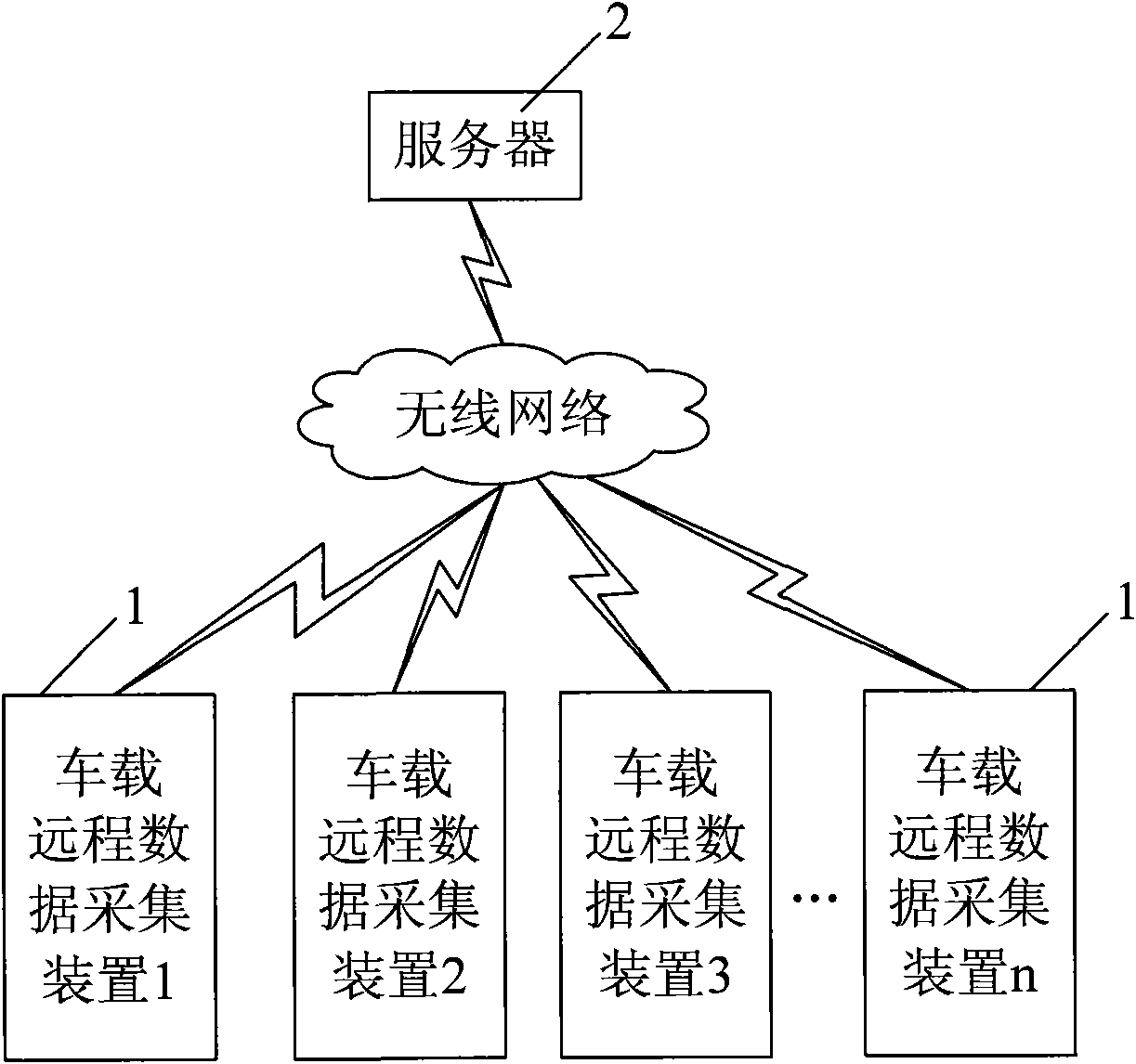
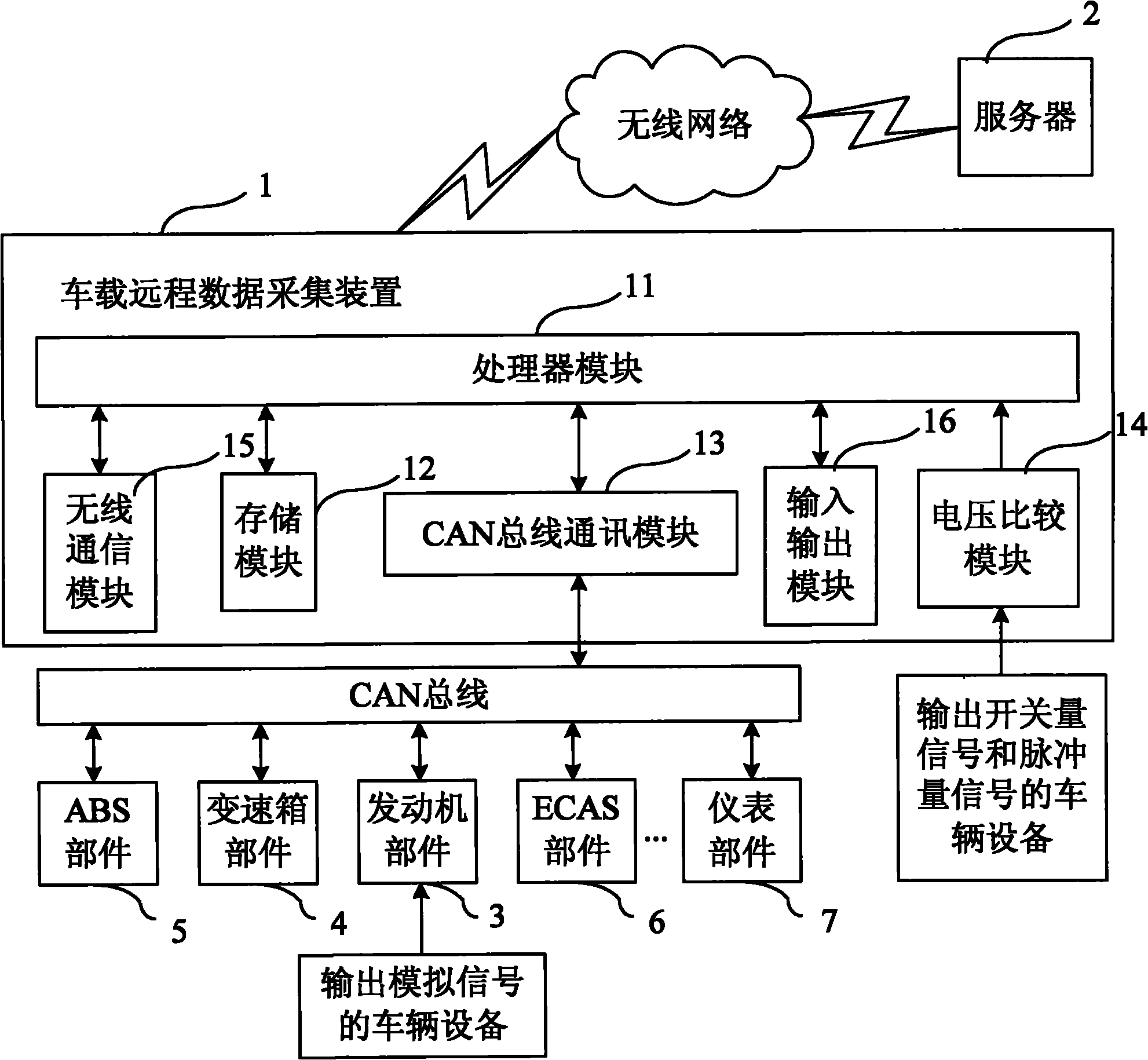
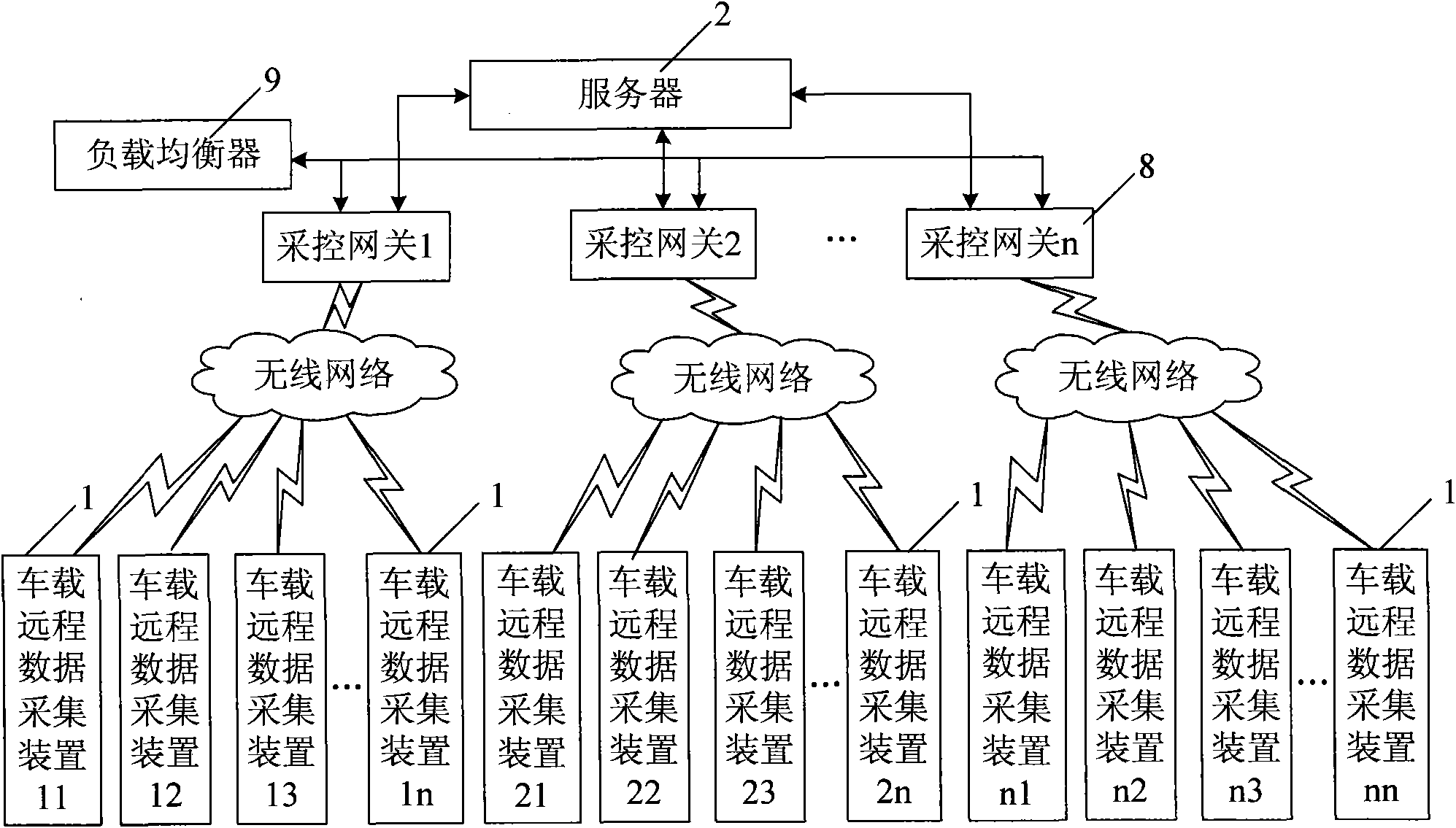
Vehicle remote data acquisition system based on CAN (Controller Area Network) bus
InactiveCN101853021AEasy to collectComprehensive dataTransmissionTotal factory controlArea networkData acquisition
The invention discloses a vehicle remote data acquisition system based on a CAN (Controller Area Network) bus, comprising a remote server and at least one vehicle-mounted remote data acquisition device, wherein each vehicle-mounted remote data acquisition device comprises a processor module, a CAN bus communication module, a voltage comparison module and a radio communication module; input signals of the voltage comparison modules are switching value signals and pulse value signals which are output by vehicle equipment; analog value signals output by the vehicle equipment are processed by an engine ECU (Electronic Control Unit), then transmitted to the CAN bus and received by the CAN bus communication modules; the CAN bus communication module are also used for receiving equipment signals hung on the CAN bus, and the output ends of the CAN bus communication modules are connected with the processor modules through an SPI (Serial Peripheral Interface) bus; and the radio communication modules are used for carrying out radio communication with the server. The system can acquire various information of the vehicle equipment on a plurality of vehicles, data is transmitted to the server for storing through radio communication, and reliable references are provided for the maintenance and the management of the vehicles according to acquired data.
Owner:HIGER
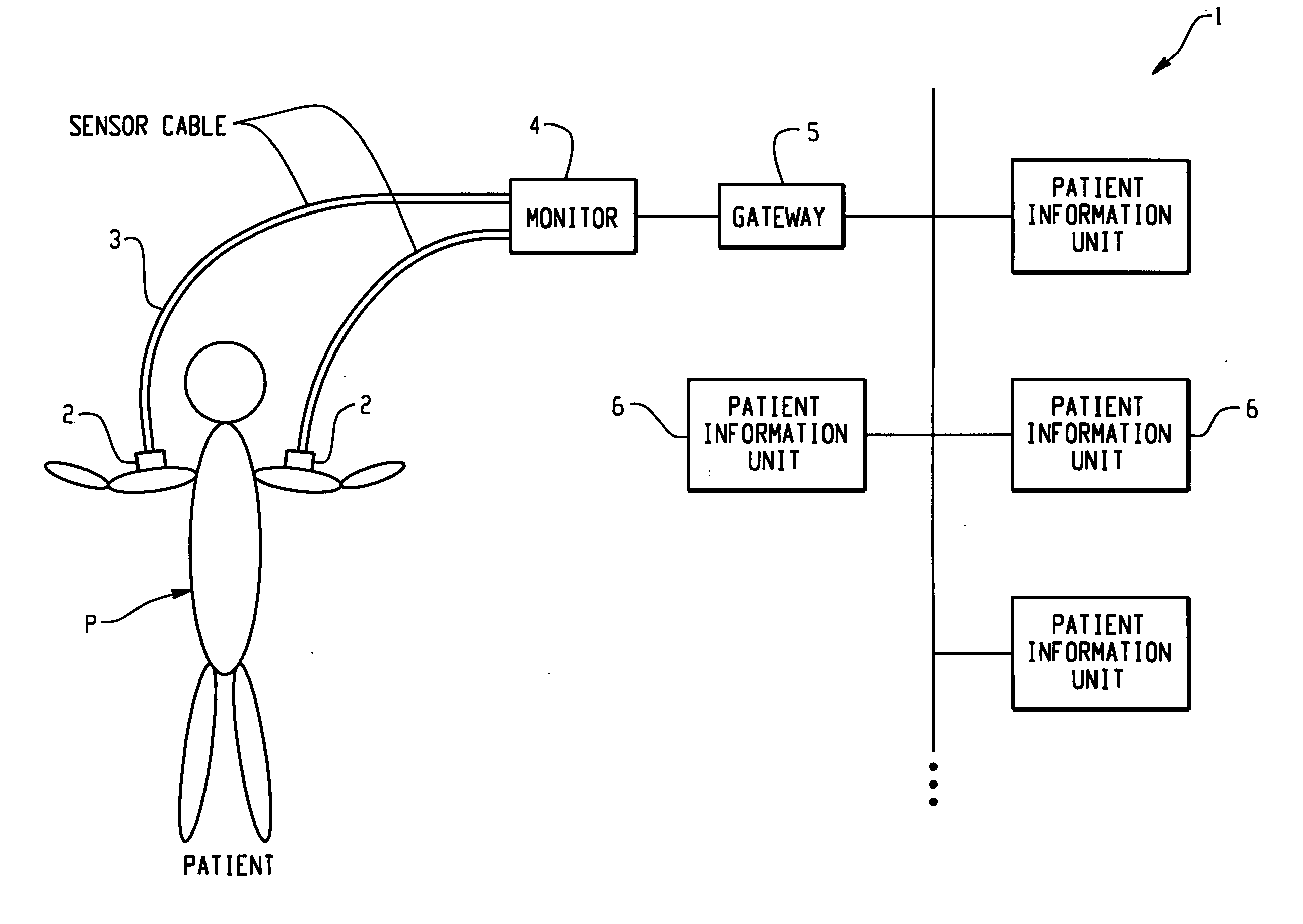
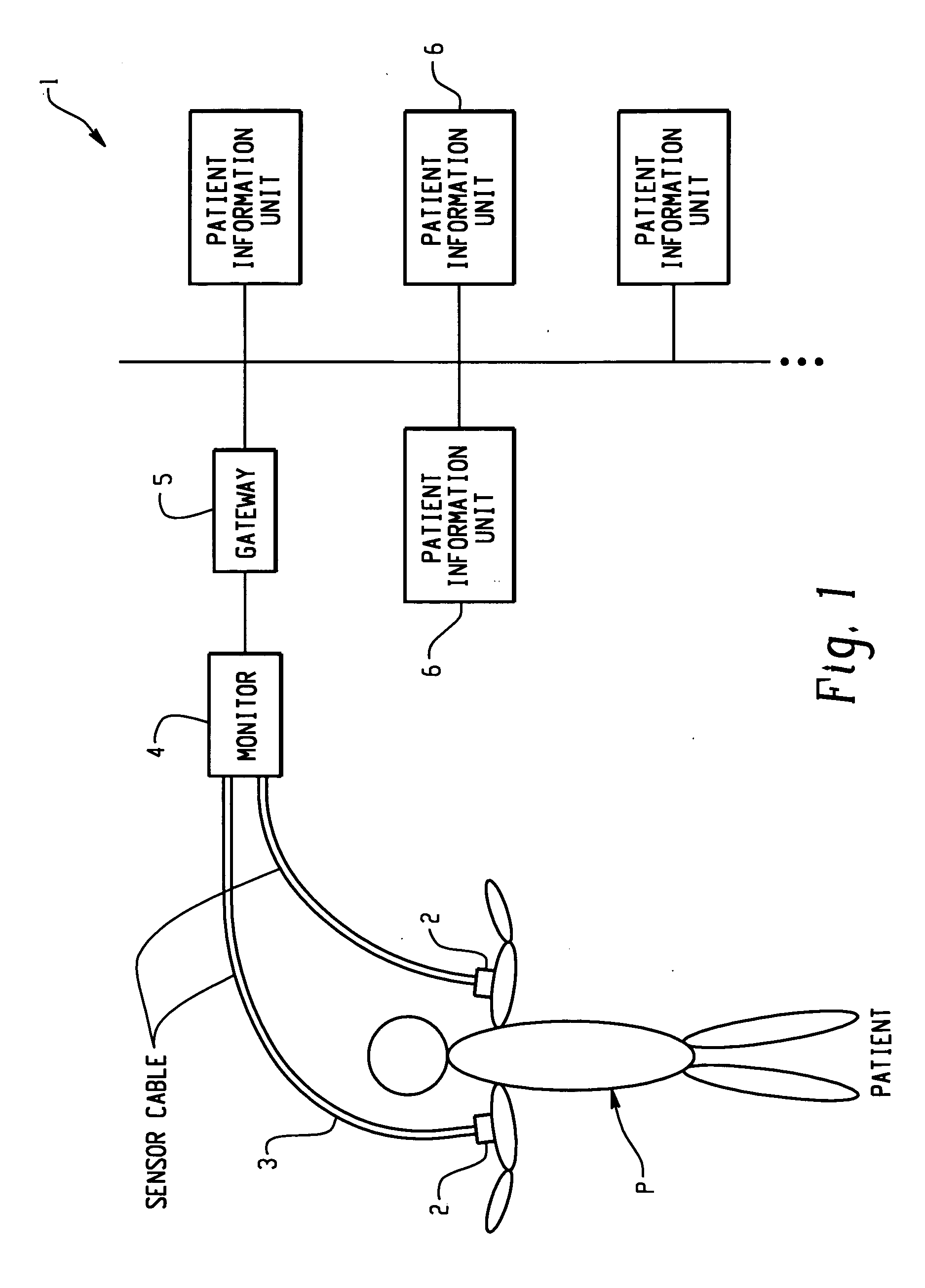
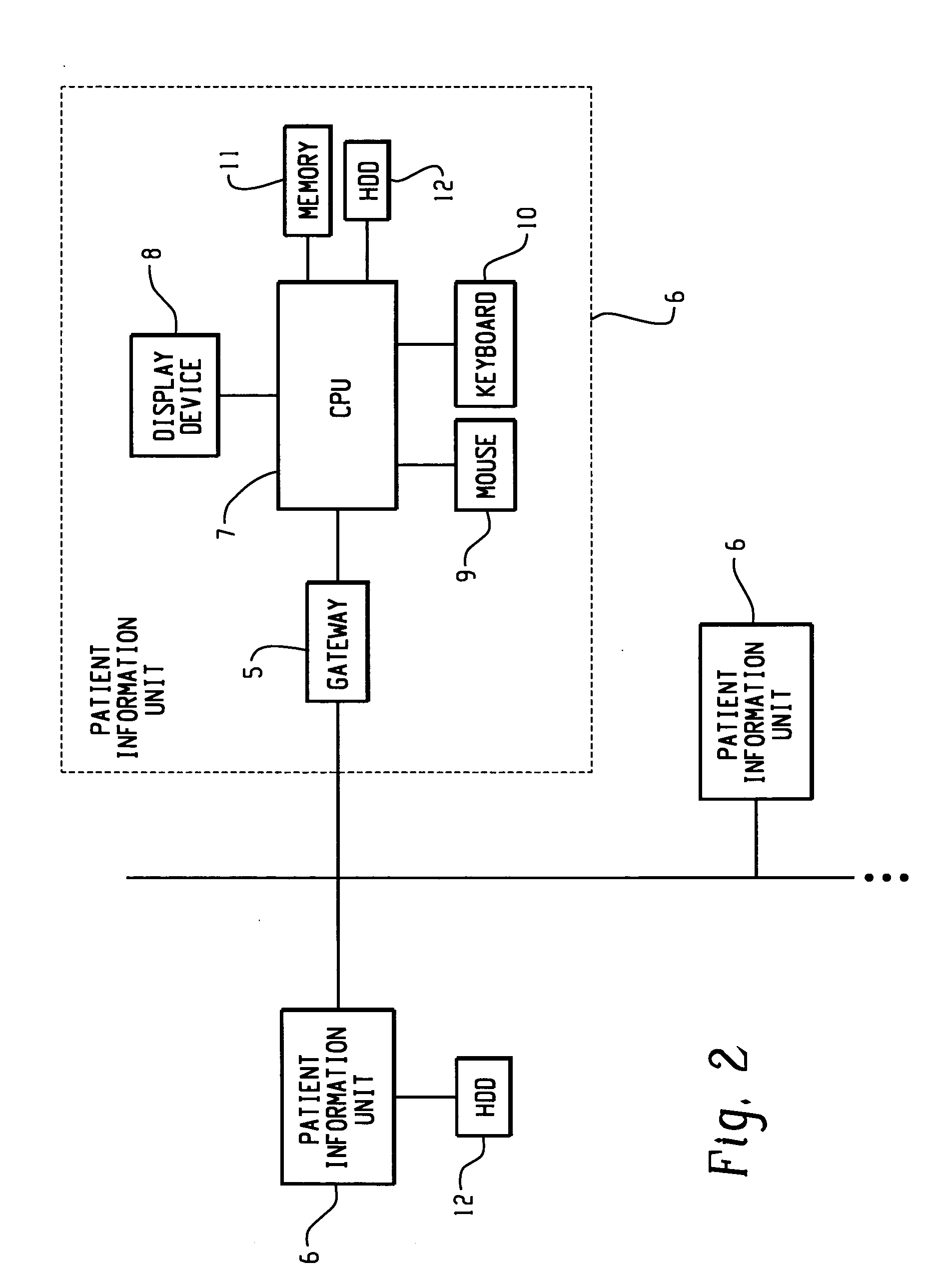
Patient information management apparatus and method
InactiveUS20050010447A1Easy to checkPrecision therapyData processing applicationsTherapiesGraphicsComputer science
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
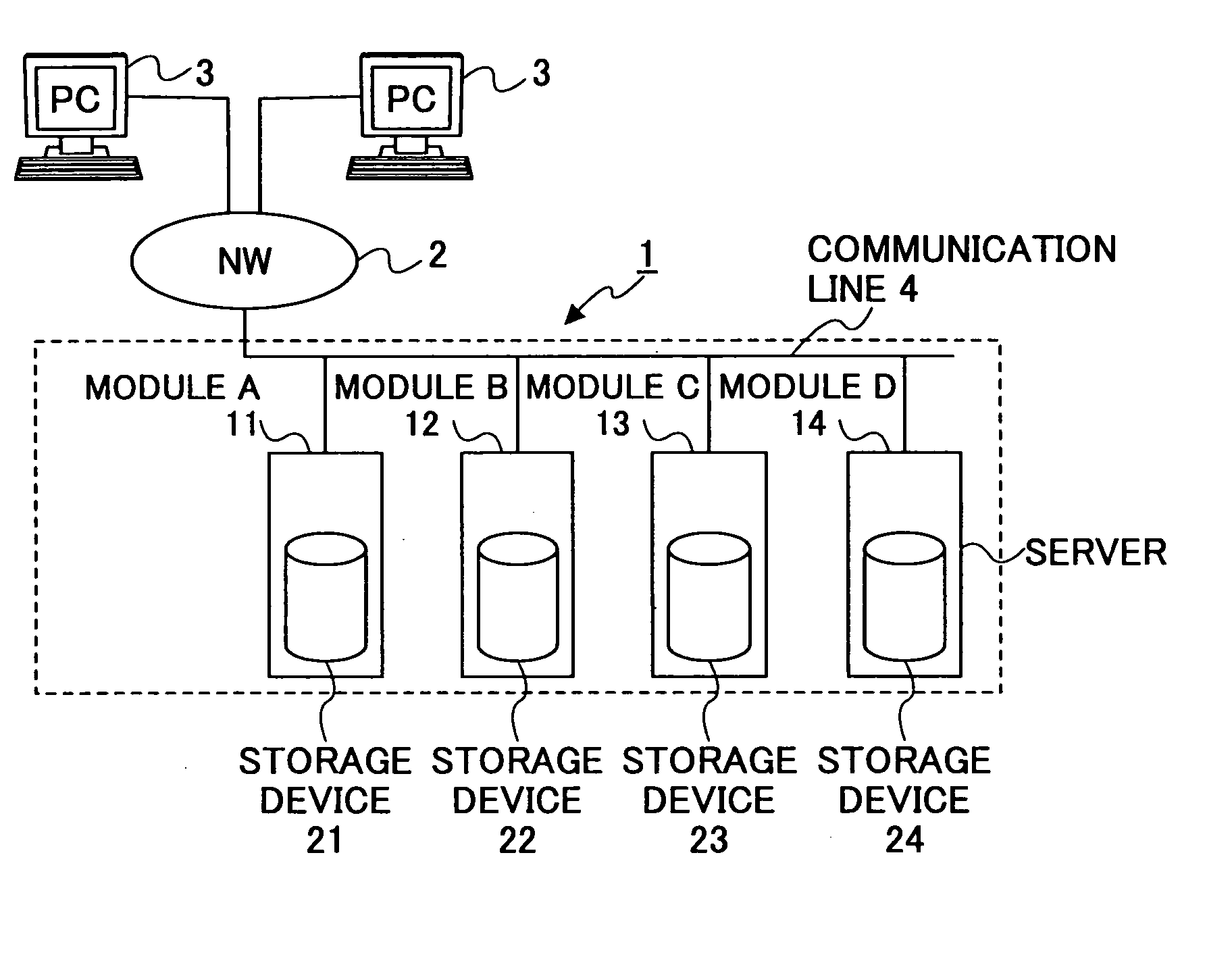
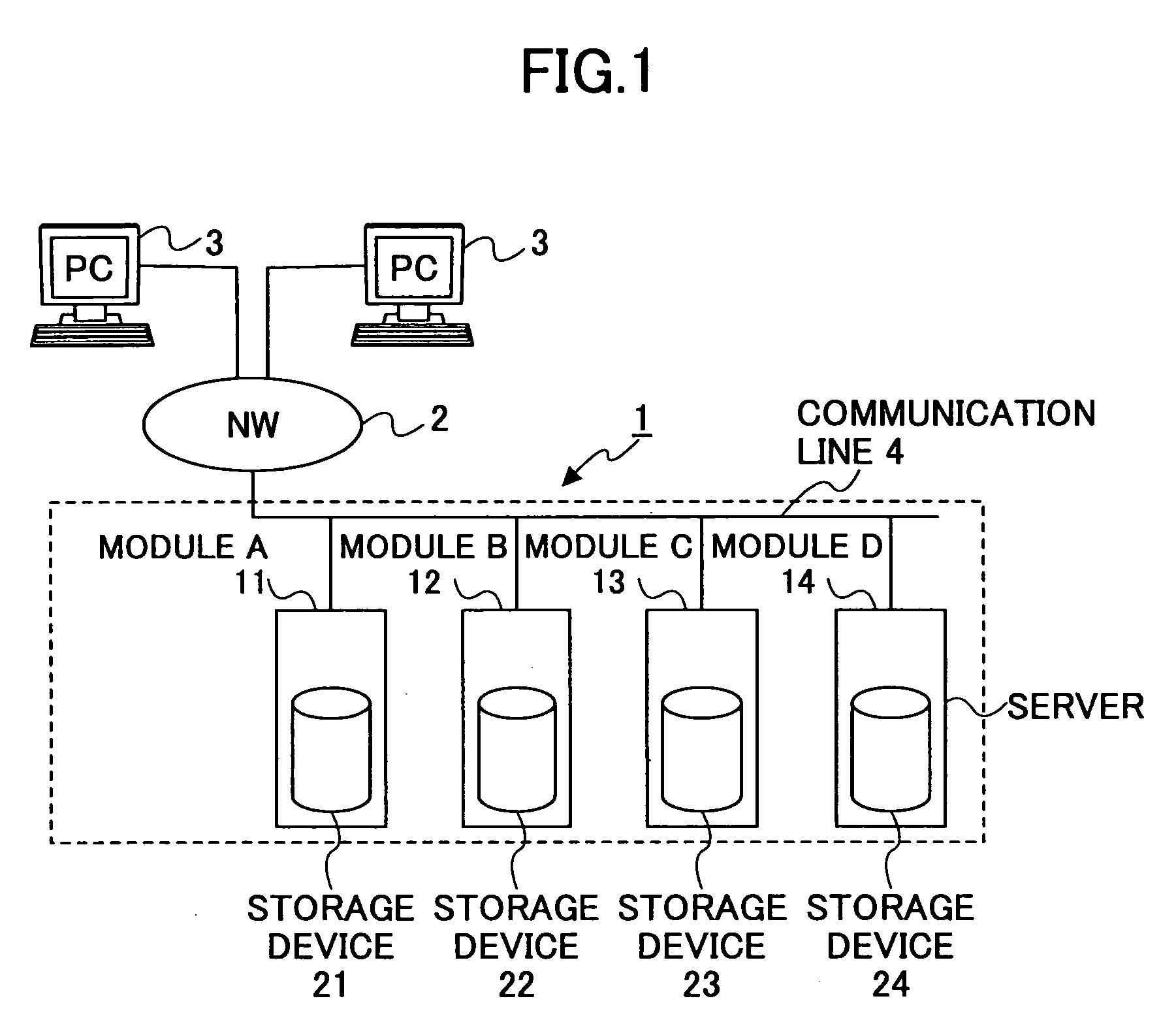
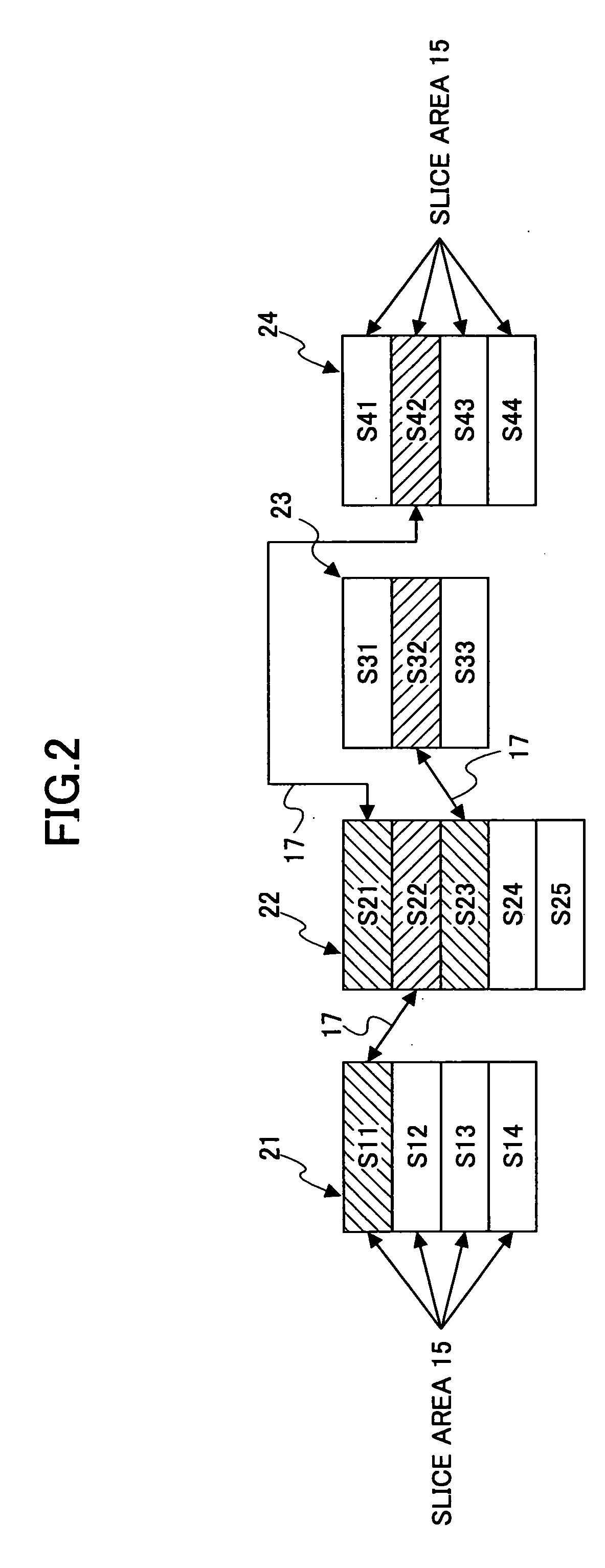
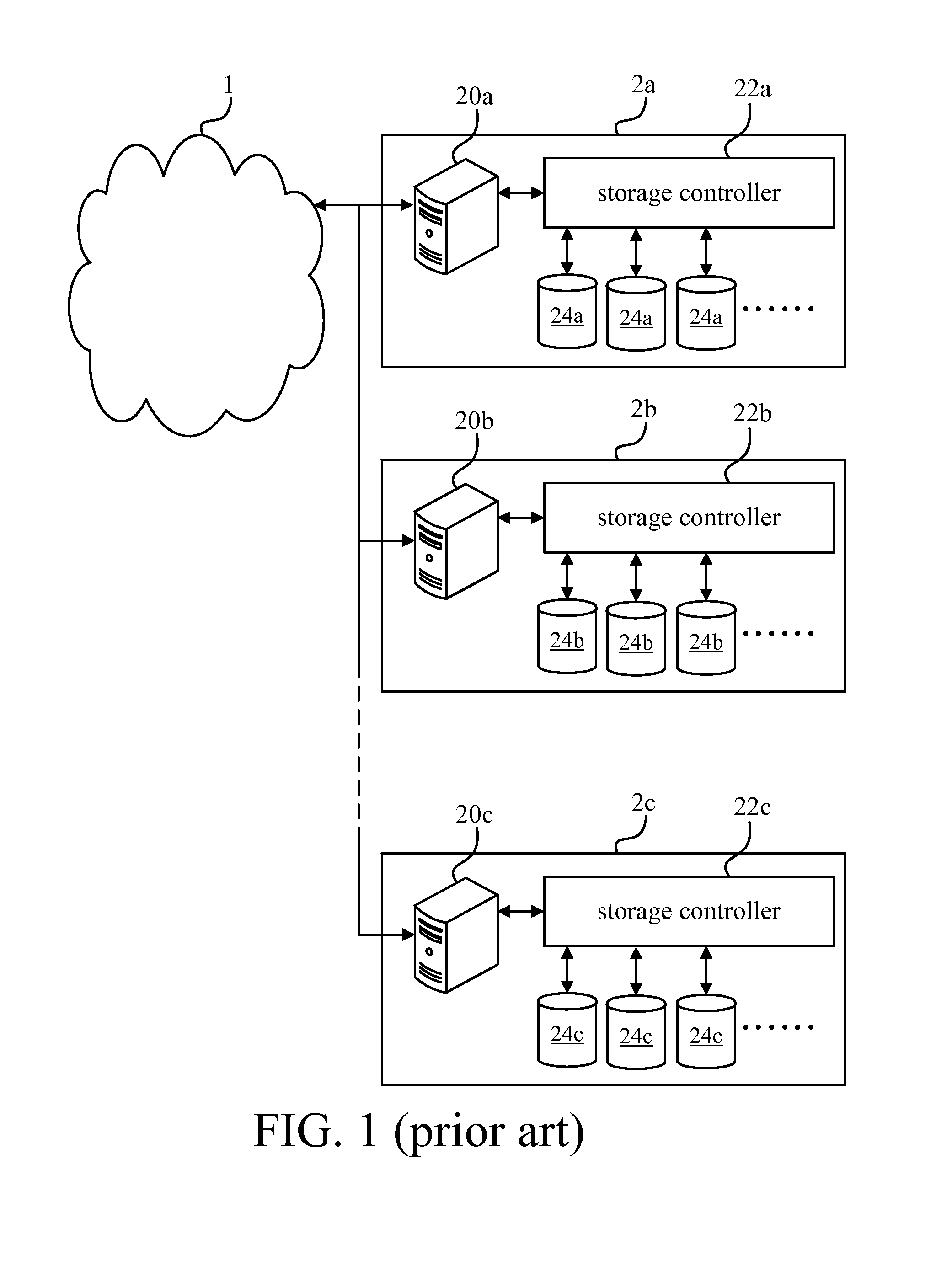
Storage system
InactiveUS20050235109A1High use efficiencySafety be assureInput/output to record carriersMemory adressing/allocation/relocationInformation storageFunctional module
A storage system is disclosed that stores data across plural storage devices. The storage system includes plural modules. Each of the modules includes a storage device including a data storage section that has plural slice areas to store data elements one in each, and a control-information storage section that stores control information of the plural slice areas, a communications-function section having a function of sending and receiving the data elements stored in the slice areas in the data storage section. The modules communicate with each other to replicate the data element stored in the slice area into an unused slice area in another module so as to have data redundancy.
Owner:FUJITSU LTD
Trace synchronization
ActiveUS20090183034A1Reduce the possibilityEasy loadingHardware monitoringData synchronizationData stream
A data processing apparatus having one or more trace data sources is provided in which the trace data sources operate to generate respective streams of trace data. At least one of said trace data sources comprises a trace data generator responsive to activity in monitored circuitry to generate trace data representing said activity. A synchronization marker generator is coupled to the trace data generator and operates to generate a synchronization marker and insert the synchronization marker into the trace data stream. The synchronization marker identifies a synchronization position in the trace data stream. A controller is coupled to the synchronization marker generator, and operates to initiate the synchronization marker generator to generate and insert a synchronization marker into the trace data stream. The controller controls initiation in dependence on behaviour of the data processing apparatus downstream of the trace data generator with respect to trace data flow. In this way, the downstream behaviour of the data processing apparatus can be made to influence the rate and timing of insertion of synchronization markers into a trace data stream, thereby reducing the likelihood of the volume of trace data resulting in an overflow condition in the downstream circuitry.
Owner:ARM LTD
Safe distributed duplicated data deletion method
ActiveCN103763362AProtection of confidentialitySatisfy deduplicationTransmissionShort ValueComputer hardware
The invention discloses a safe distributed duplicated data deletion method. According to the method, a file is segmented into fragments through a secret sharing technology without any encryption mechanism. The shared fragments are distributed in a plurality of independent storage servers. In addition, in order to support reduplication removing, a different short value is calculated and sent to the storage servers as the indicator of one fragment. Only possessors uploading data for the first time need to carry out such calculation and distribution of secrete sharing, and then people possessing the same data copies do not need to calculate and store the sharing any longer. When the data copies are restored, users must access the storage servers with the minimum quantity to reconstruct the data through authentication and acquisition of the secret sharing. In other words, the secret sharing of the data can only be accessed by the users who possess the same copies and are authorized.
Owner:XIDIAN UNIV
Methods and sysems for improving the security of secret authentication data during authentication transactions
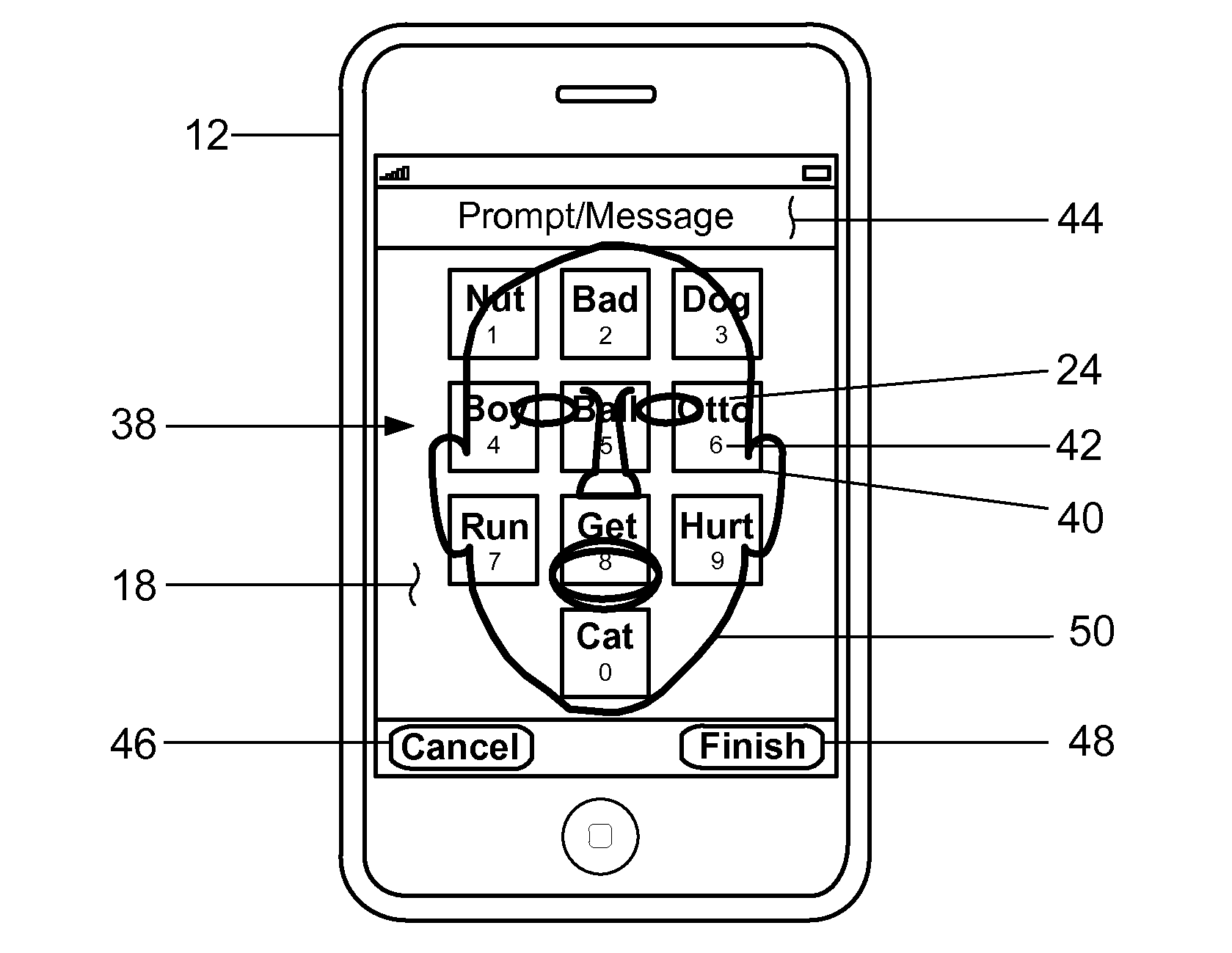
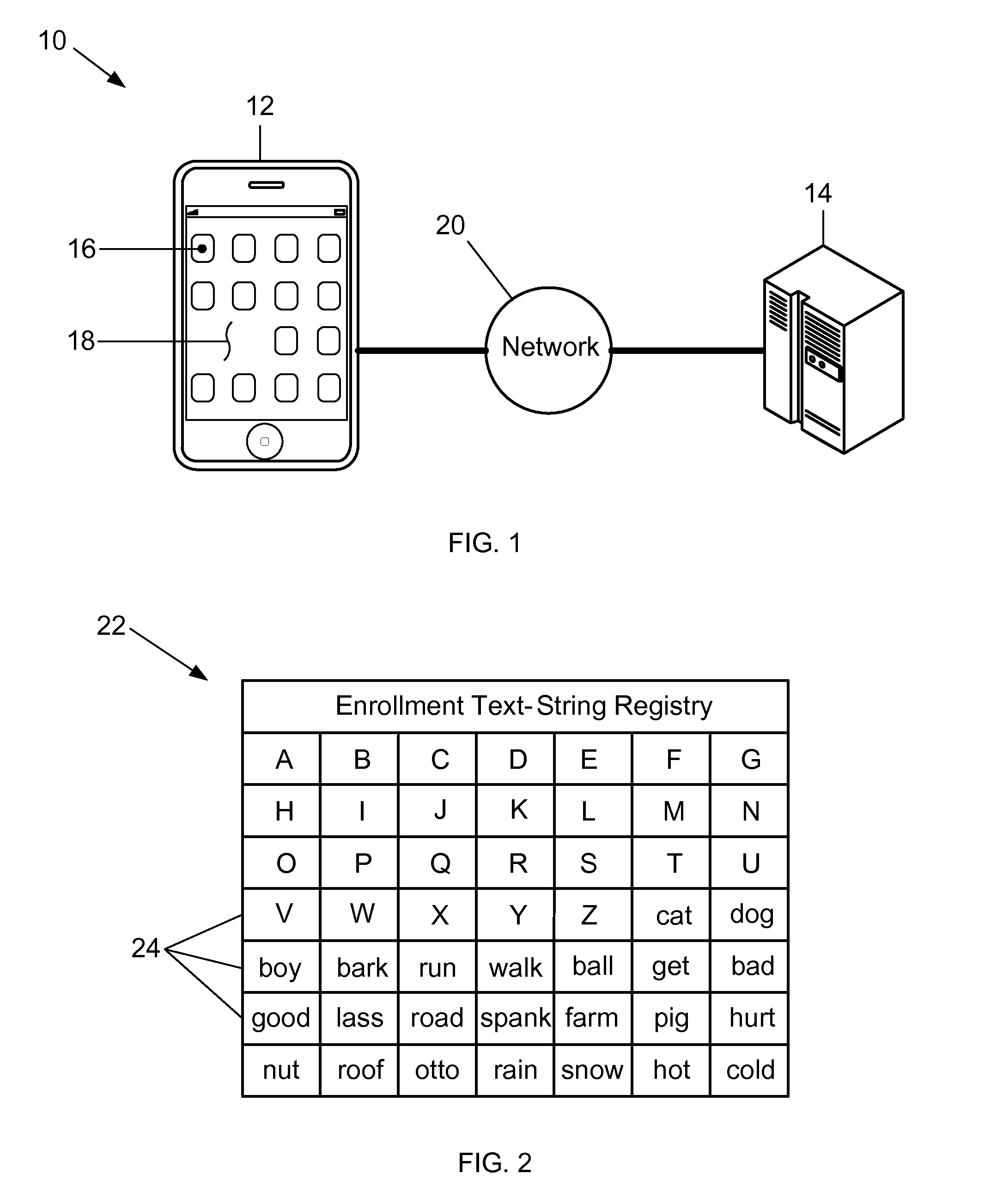
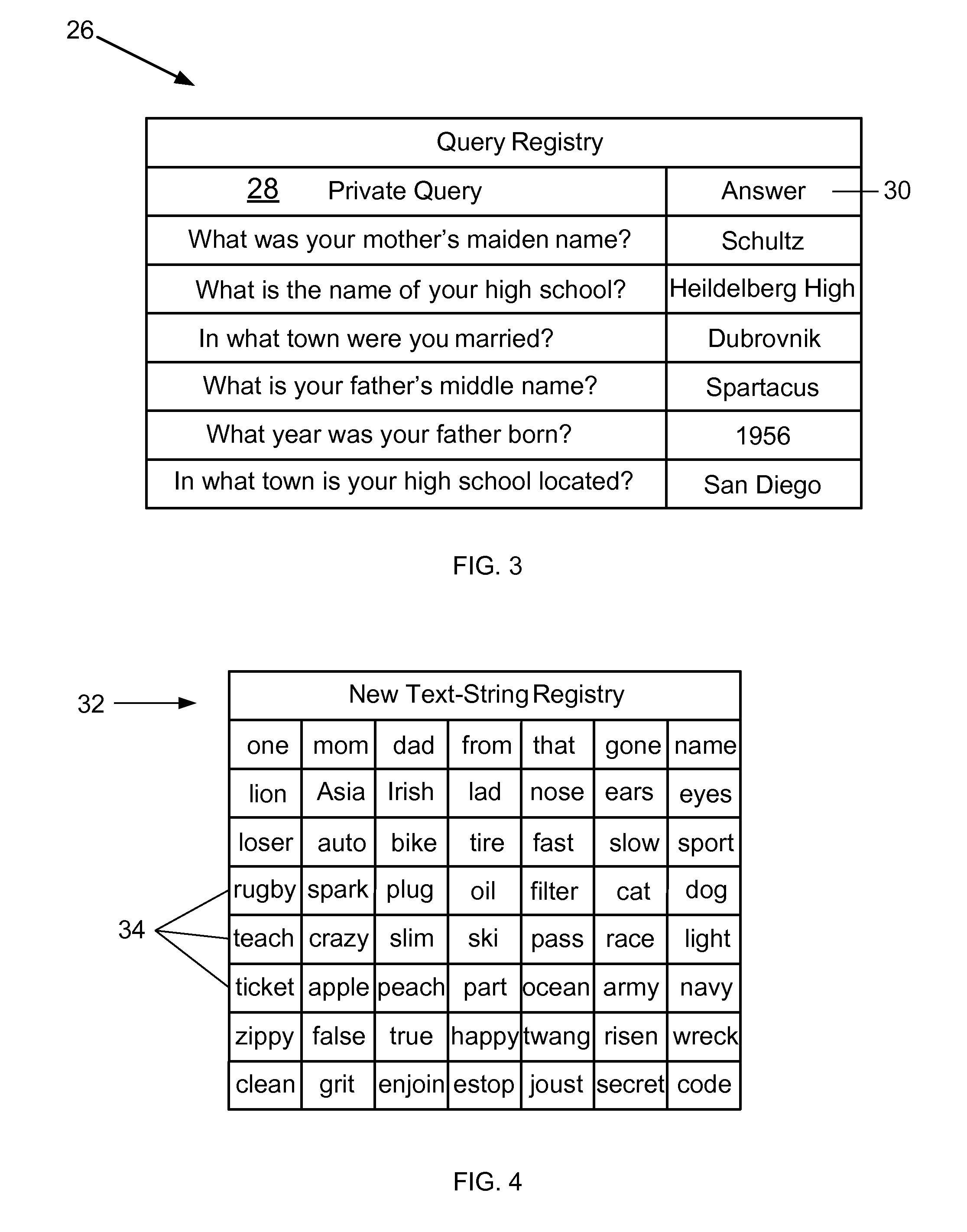
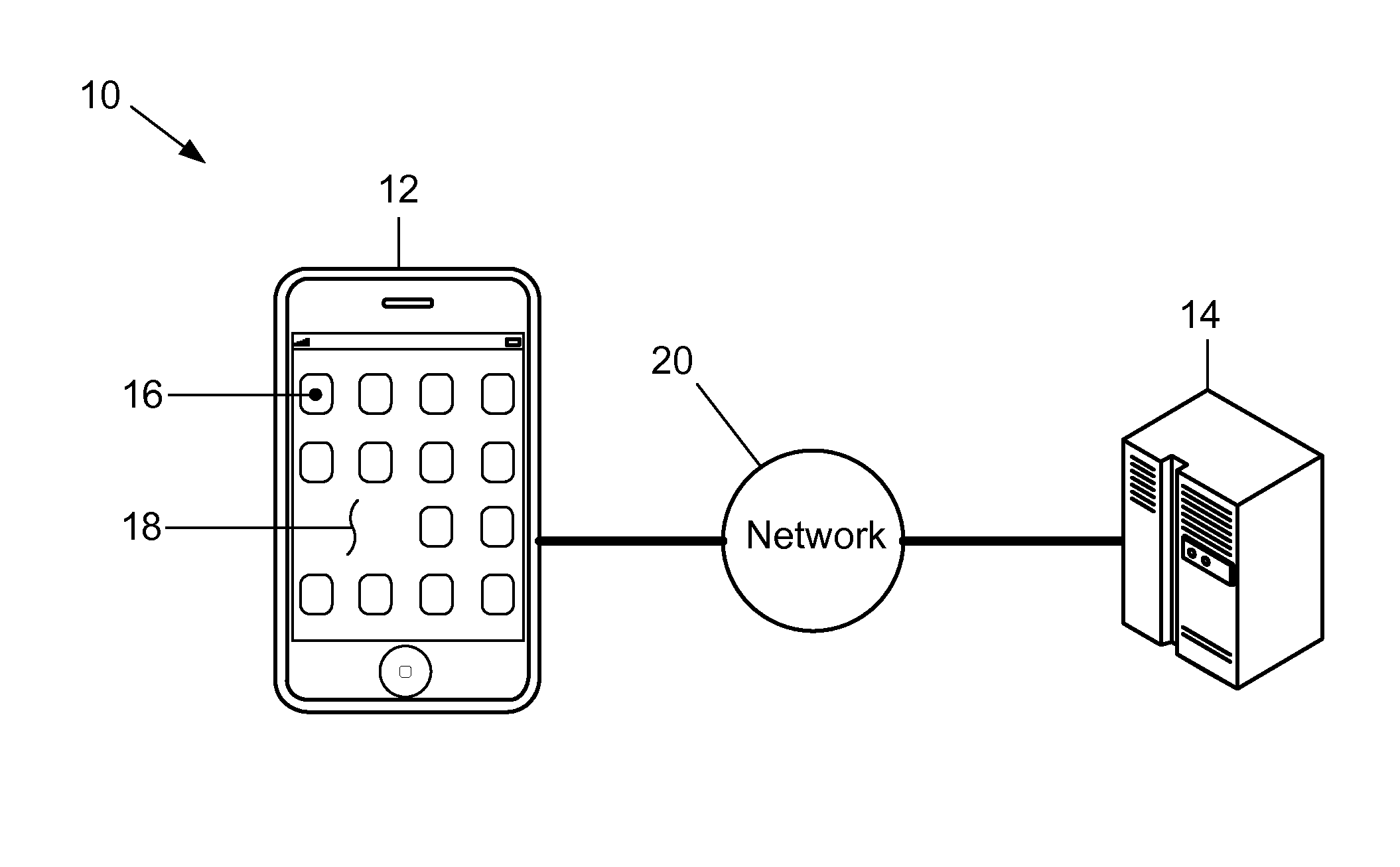
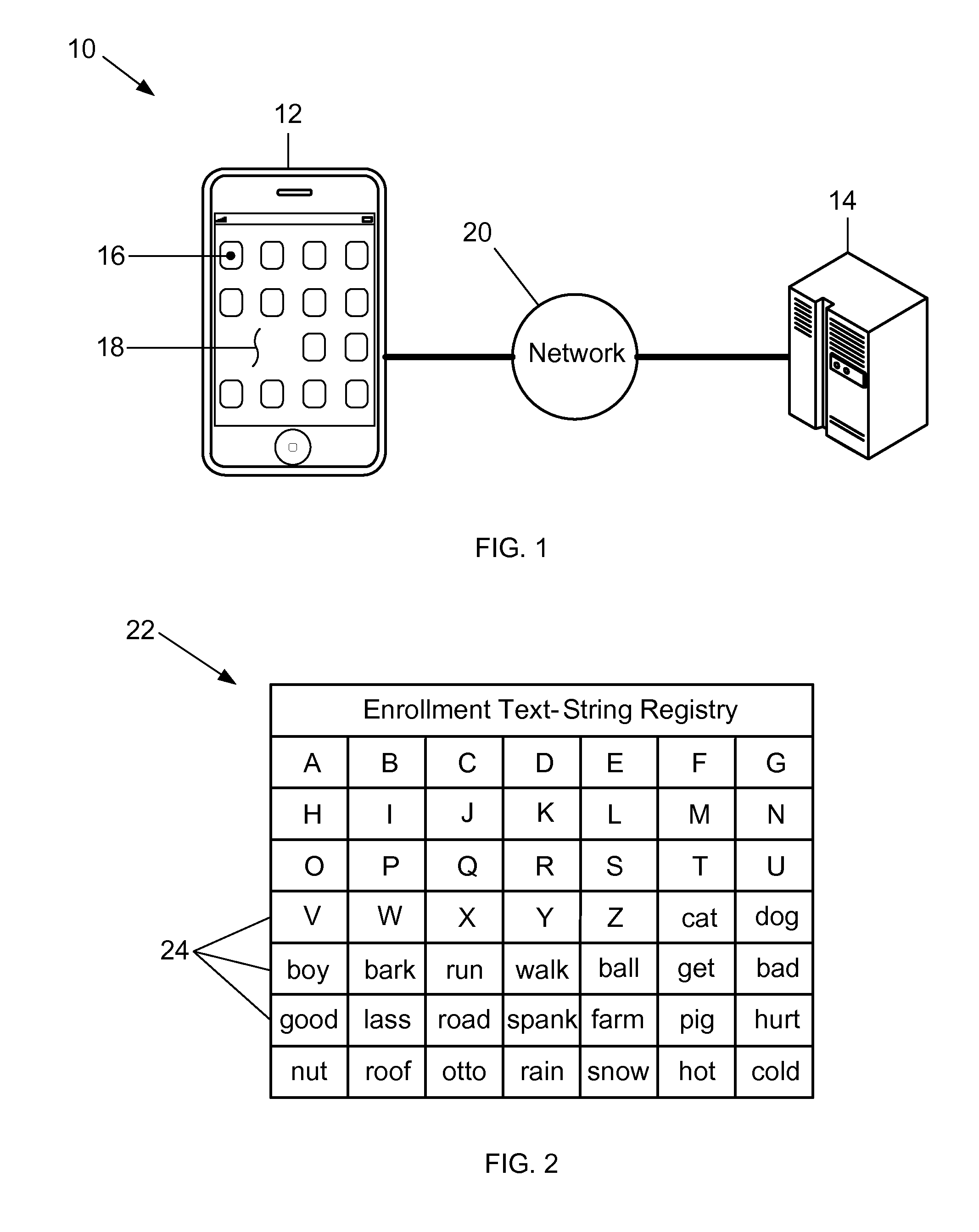
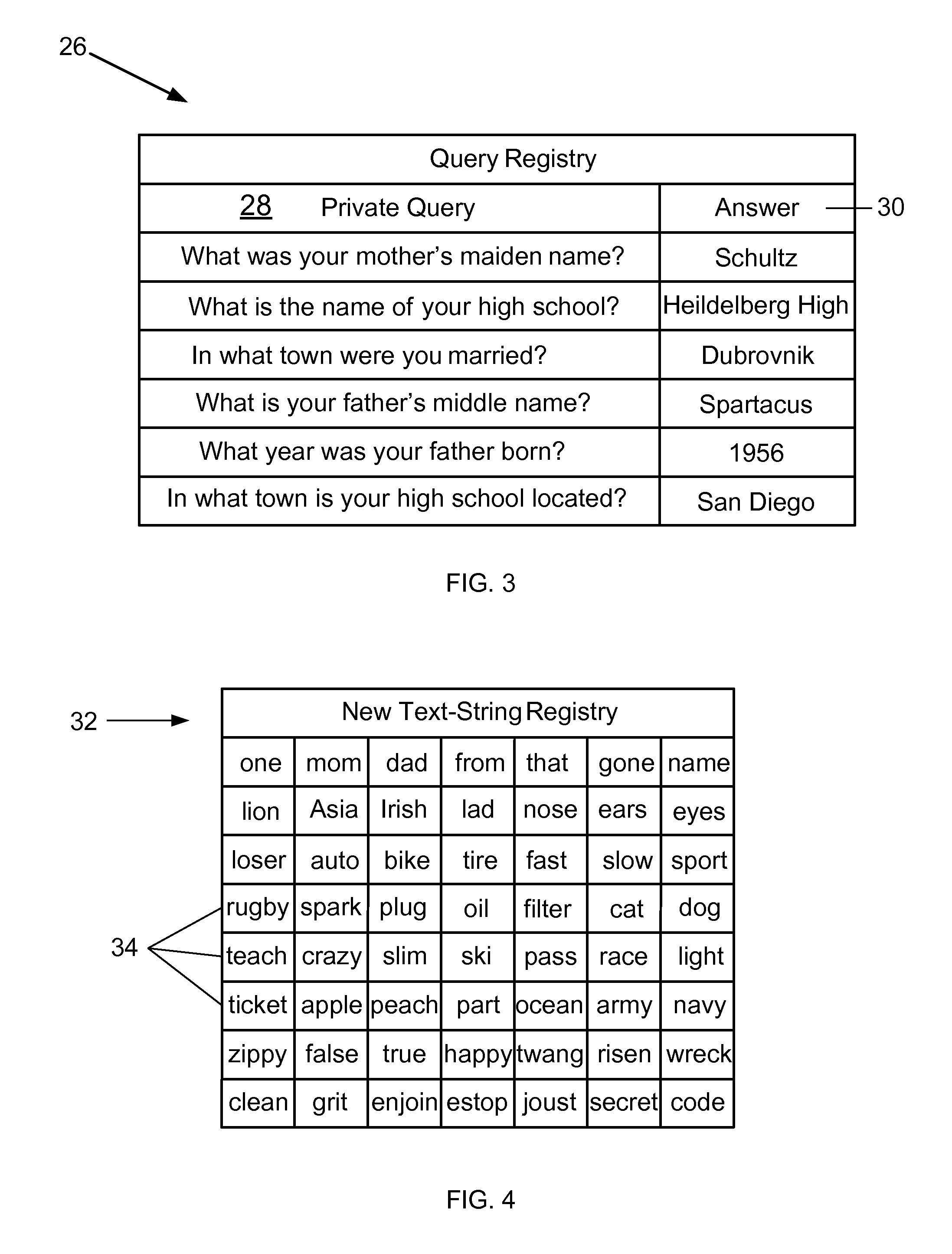
ActiveUS20140283022A1Improve securityData SecurityDigital data processing detailsUnauthorized memory use protectionText stringCommunication device
A method for improving the security of secret authentication data during authentication transactions is provided that includes converting the secret authentication data of a user into scrambled secret authentication data by associating a different text-string with each item of information included in the secret authentication data. The method also includes capturing the scrambled secret authentication data with a communications device, and conducting an authentication transaction with the captured authentication data.
Owner:DAON TECH
Online monitoring system of water quality
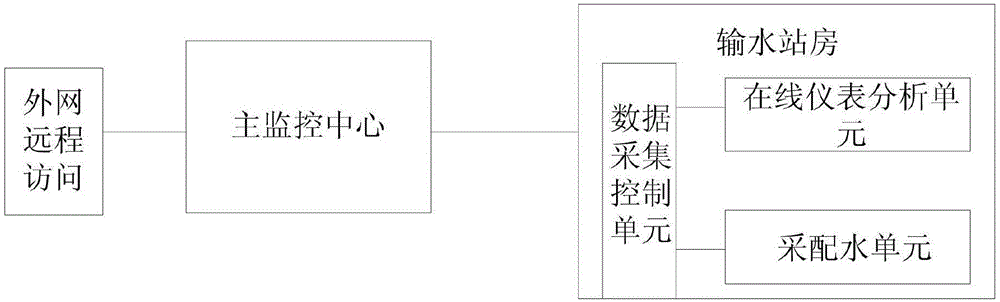
InactiveCN106530140AImprove access speedData SecurityData processing applicationsGeneral water supply conservationStatistical ReportWater quality
The invention discloses an online monitoring system of water quality. The online monitoring system comprises an external network remote access module, a main monitoring center module and a water transporting station house module. The main monitoring center module is connected with the external network remote access module and the water transporting station house module. The external network remote access module carries out identity authentication on users for accessing through internet, and achieves grading access control for monitoring data and statistical reports. The main monitoring center module is used for data acquisition, communication transmission, data management, information issuing, novel monitoring and public configuration. The water transporting station house module is used for data acquisition, online analysis and acquisition configuration. According to the invention, access speed, data safety and convenient management and maintenance can be improved.
Owner:SHANGHAI XINZHENG INTELLIGENT TECH CO LTD
Big dipper and 4G-based unmanned aerial vehicle
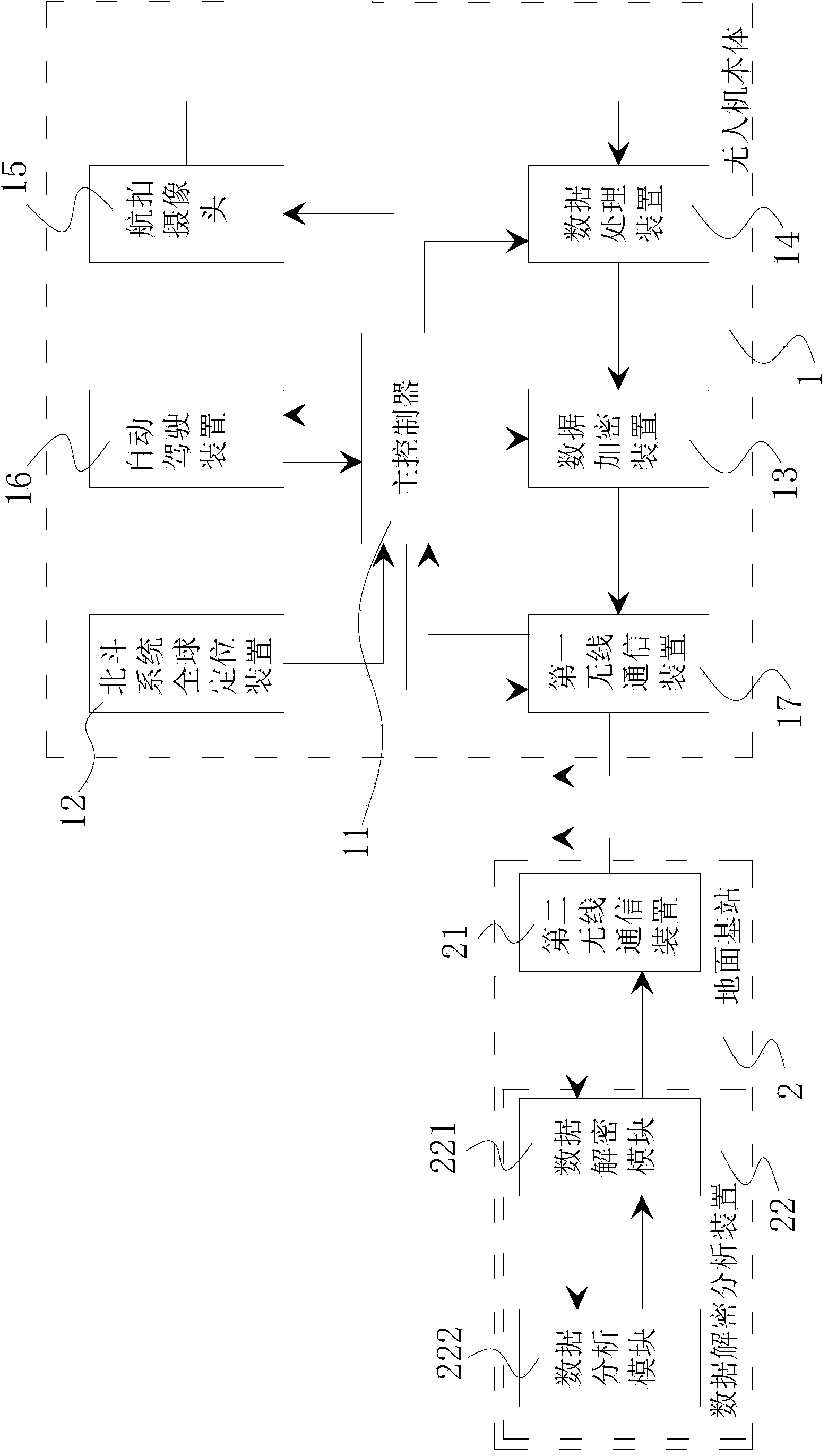
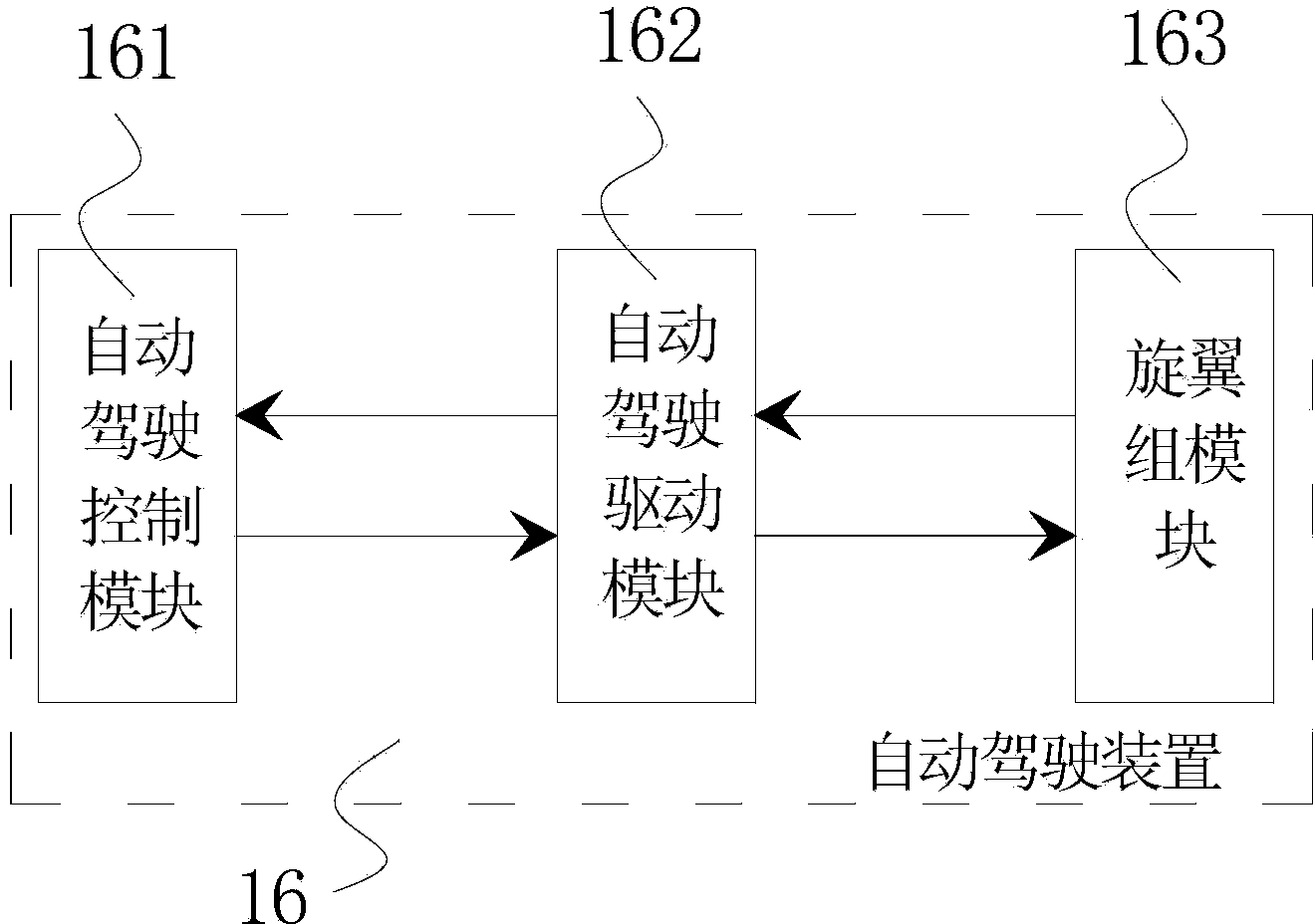
InactiveCN104071333AAchieve vertical takeoff and landingData SecurityClosed circuit television systemsPosition/course control in three dimensionsUncrewed vehicleData treatment
The invention discloses a big dipper and 4G-based unmanned aerial vehicle which comprises an unmanned aerial vehicle body, wherein a main controller, a big dipper system global positioning device, a data encrypting device, a data processing device, an aerial photo camera, an automatic driving device and a first wireless communication device are arranged on the unmanned aerial vehicle body, and the main controller is respectively connected with the big dipper system global positioning device, the data encrypting device, the data processing device, the aerial photo camera, the automatic driving device and the first wireless communication device. The big dipper and 4G-based unmanned aerial vehicle further comprises a ground base station, wherein the ground base station is provided with a second wireless communication device and a data decryption and analysis device, the data decryption and analysis device is connected with the second wireless communication device, and the first wireless communication device is wirelessly connected with the second wireless communication device through a 4G network. The big dipper and 4G-based unmanned aerial vehicle disclosed by the invention has the characteristics of safety data, immediate monitoring, wide use range and the like.
Owner:WUZHOU UNIV
Methods and systems for improving the security of secret authentication data during authentication transactions
ActiveUS8453207B1Improve securityData SecurityDigital data processing detailsUser identity/authority verificationCommunication deviceAuthentication
A method for improving the security of secret authentication data during authentication transactions is provided that includes converting the secret authentication data of a user into scrambled secret authentication data by associating a different text-string with each item of information included in the secret authentication data. The method also includes capturing the scrambled secret authentication data with a communications device, and conducting an authentication transaction with the captured authentication data.
Owner:DAON TECH
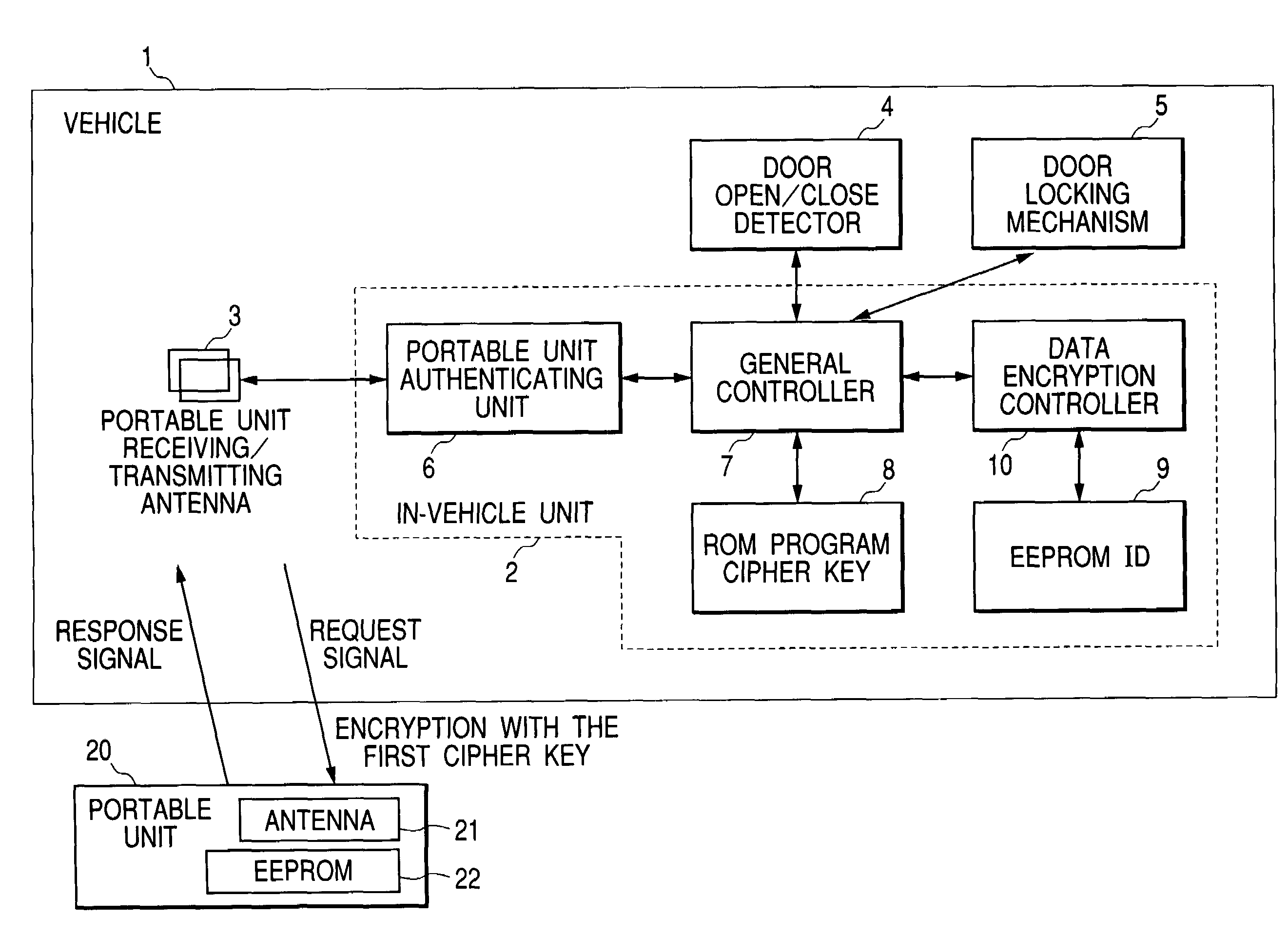
Handling device and method of security data
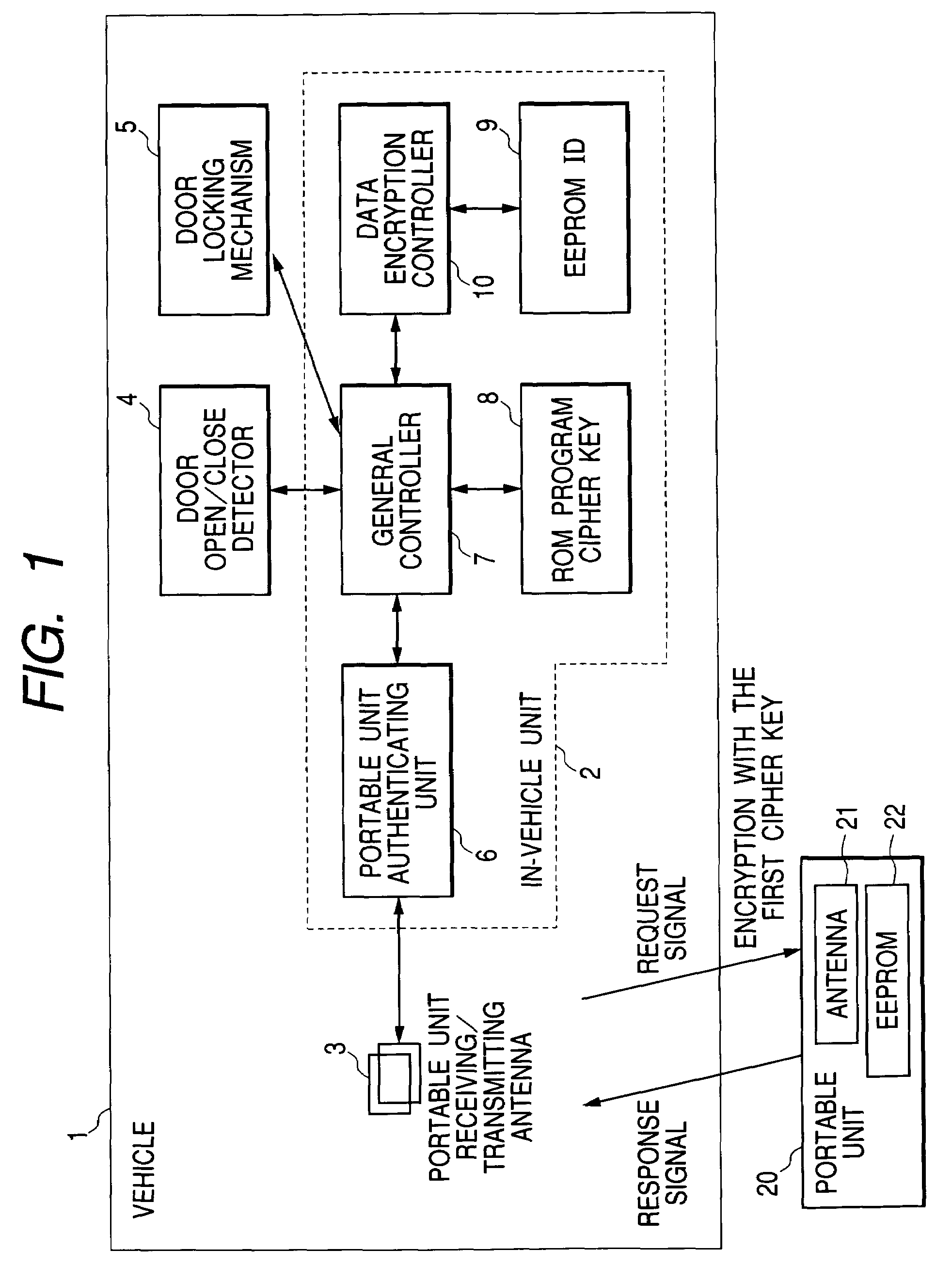
ActiveUS7426275B2Data SecurityElectric signal transmission systemsDigital data processing detailsCommunication unitLocking mechanism
A handling device of security data of a vehicle includes: an in-vehicle unit having a portable unit authenticating unit, an EEPROM, a ROM, and a controller; a vehicle having the in-vehicle unit, a door locking mechanism, and a communication unit; and a portable unit for locking or unlocking the door locking mechanism of the vehicle. In the above device, an encryption unit for encrypting the security data with a cipher key is interposed between the controller and the EEPROM, the security data is encrypted with the cipher key and stored into the EEPROM, according to the instruction from the controller based on the authentication result of the portable unit authenticating unit, and the cipher key is stored into the ROM.
Owner:ALPS ALPINE CO LTD
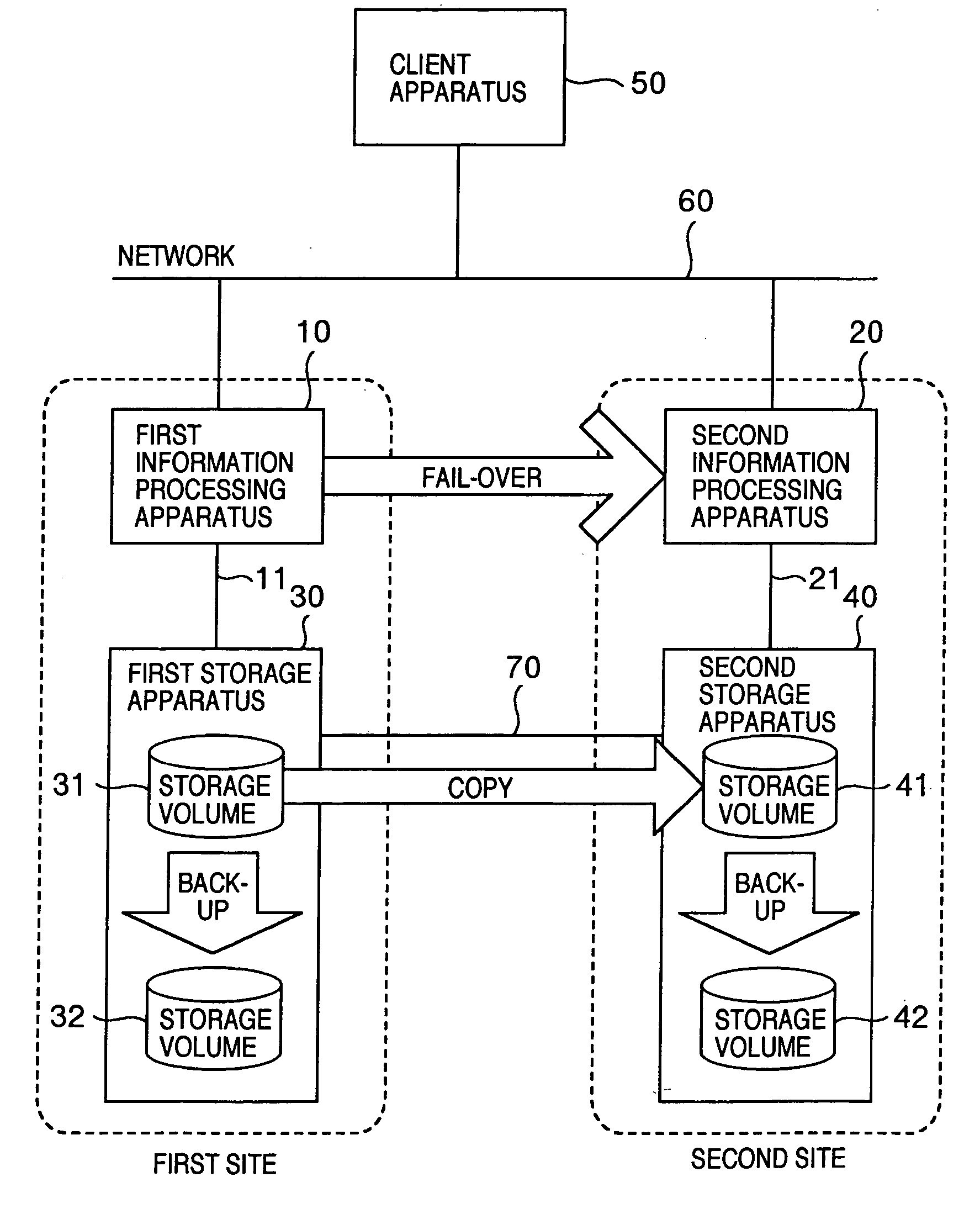
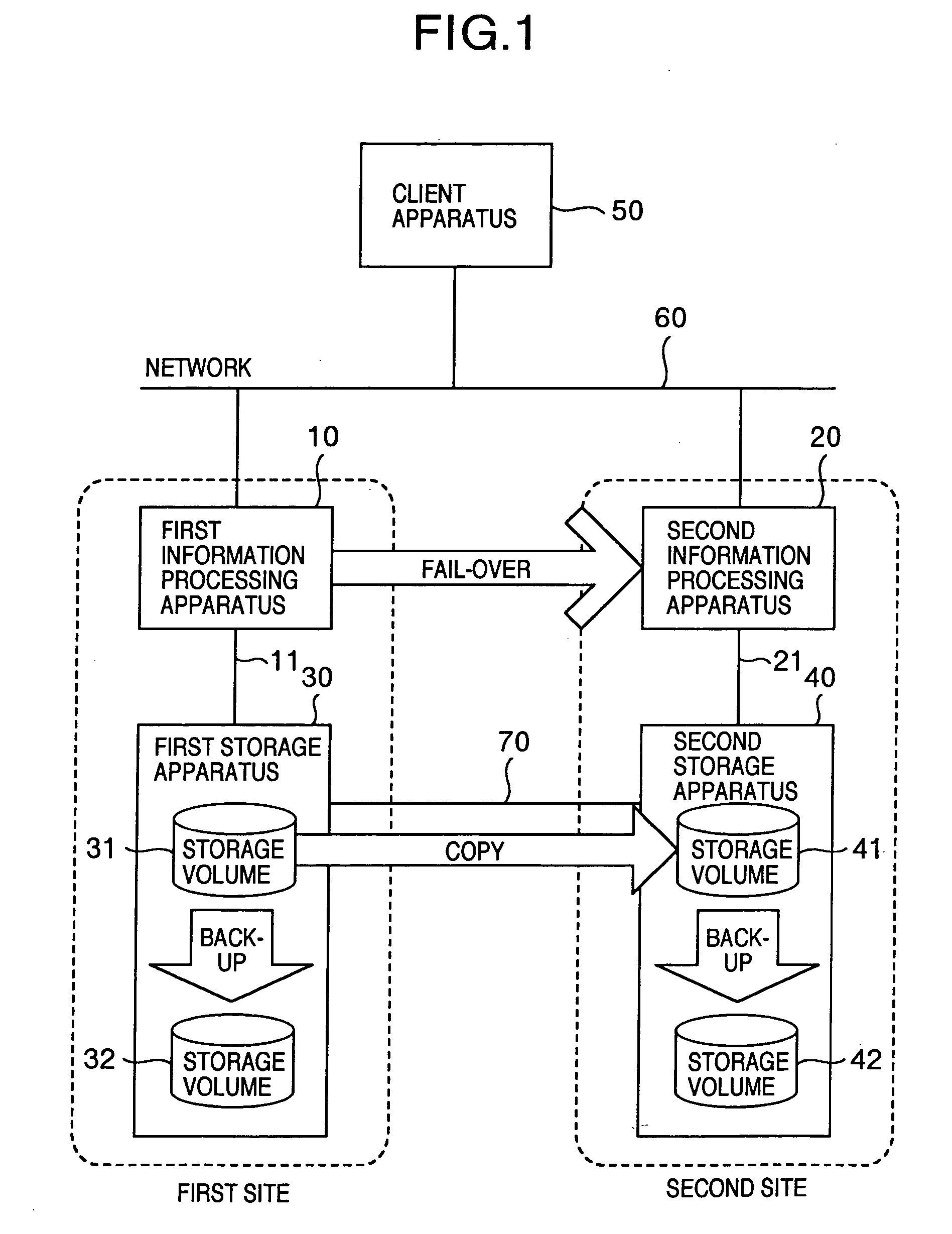
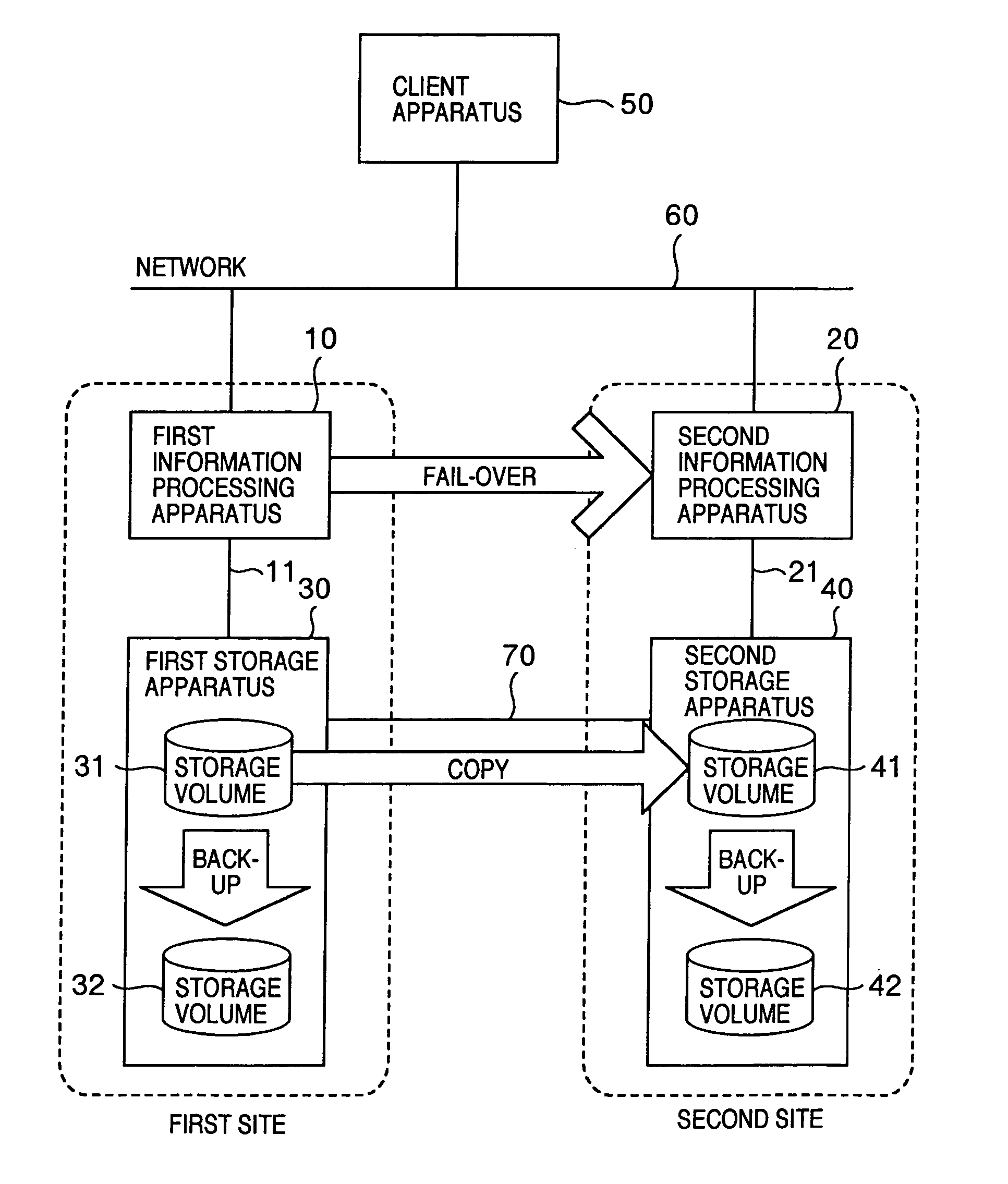
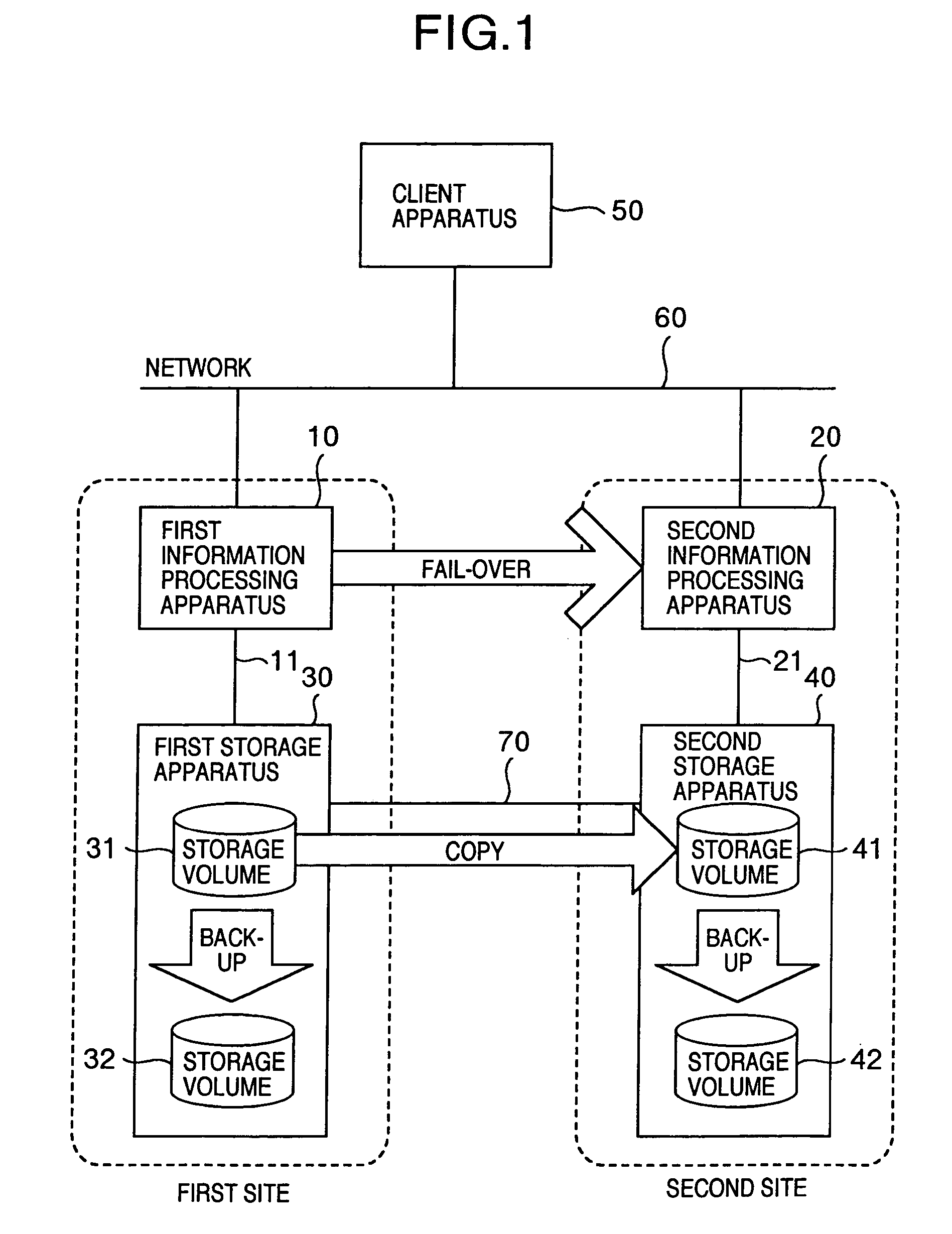
Information processing system, information processing apparatus, and control method for information processing system
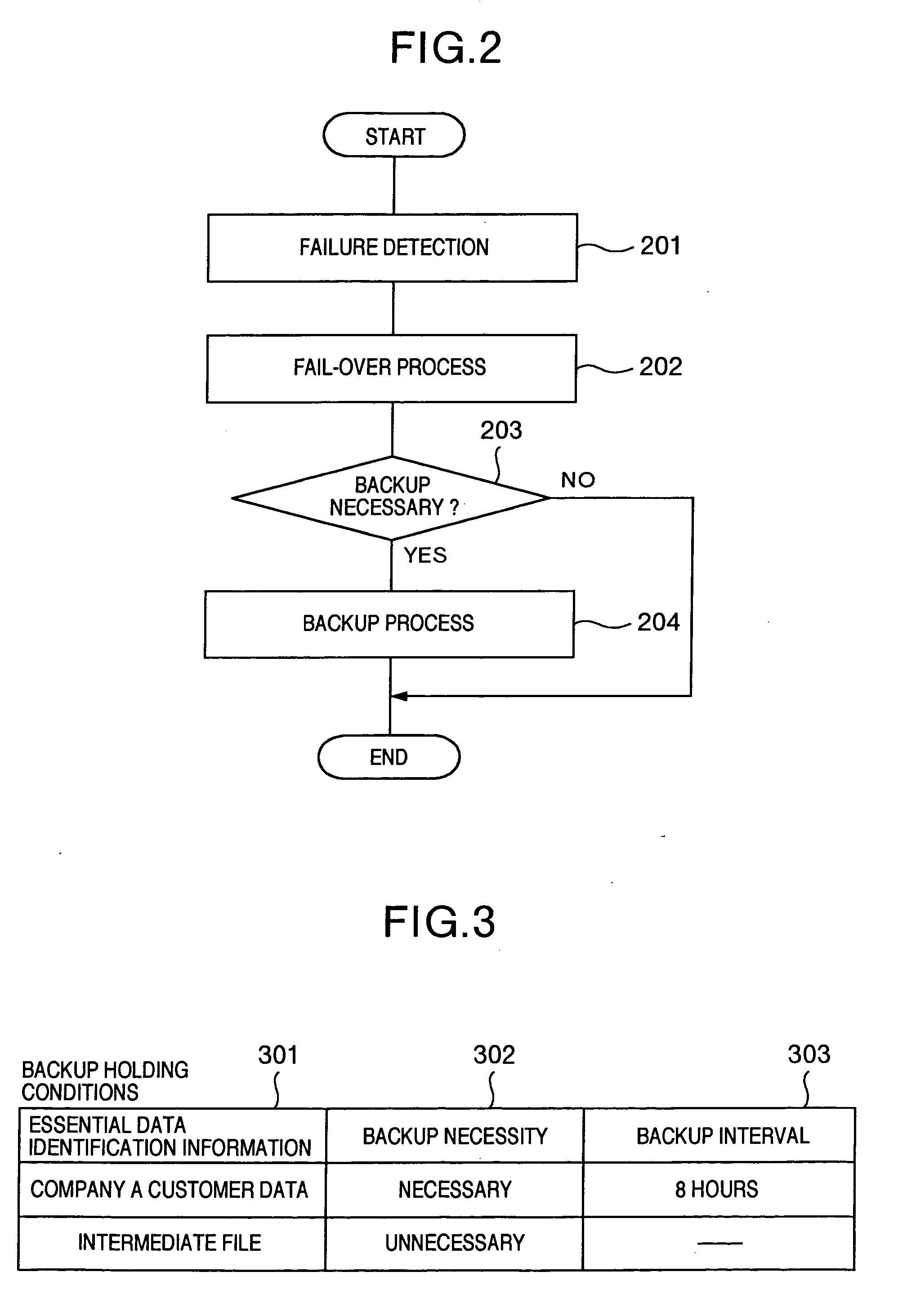
InactiveUS20050160305A1Shorten the durationSafe storageMemory systemsRedundant hardware error correctionInformation processingFailover
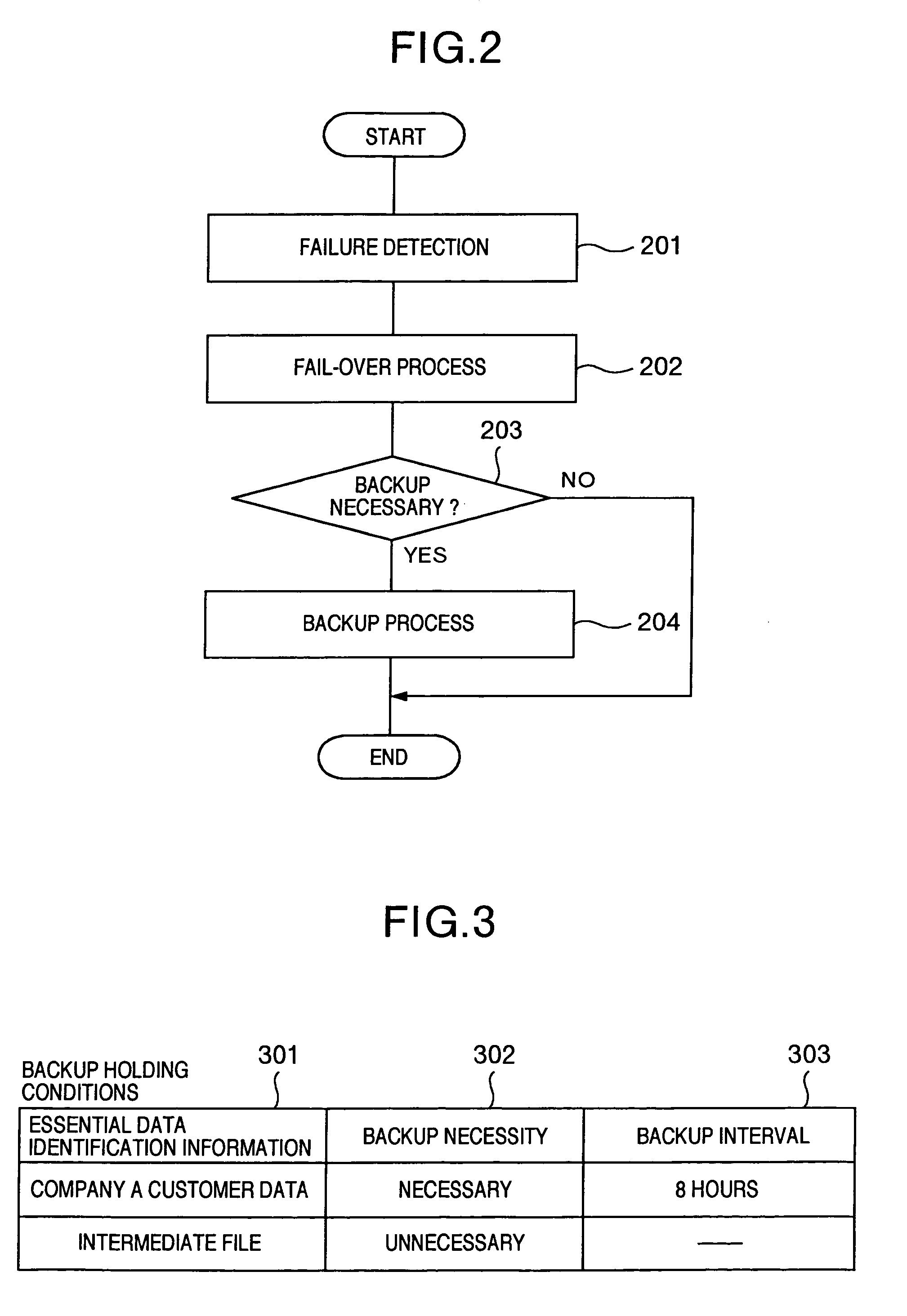
An information processing system has: information processing apparatus installed at each site, the apparatuses being interconnected with each other; fail-over processor realized by program executed by a processing apparatus, wherein when failure occurs, the fail-over processor performs to fail-over of making another different from the processing apparatus hit by the failure inherit processes executed by the processing apparatus hit by the failure; a recovery capability judge for judging whether essential data is managed in recoverable state at any processing apparatus excepting the processing apparatus hit by the failure, when the fail-over is executed passing from the processing apparatus hit by the failure to the other, the essential data necessary for performing fail-over; and backup data generator for generating backup data necessary for recovering the essential data if the data is not managed in recoverable state.
Owner:GOOGLE LLC
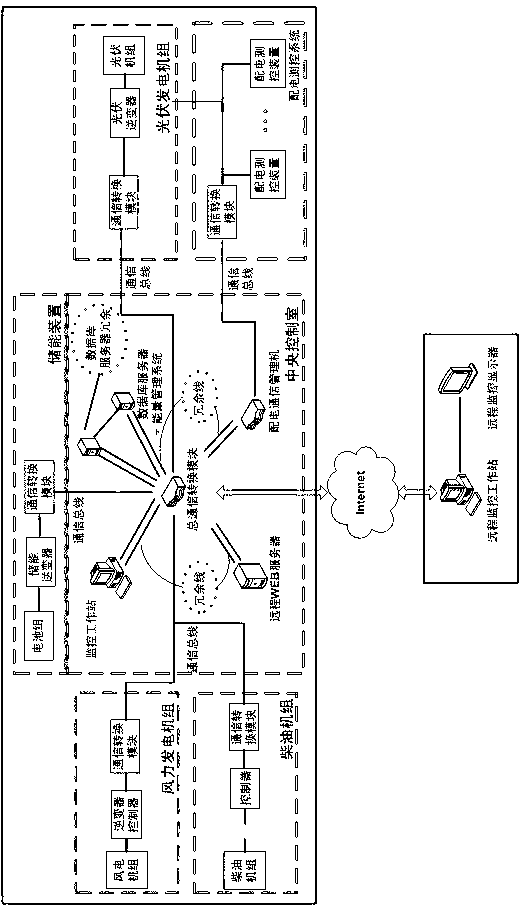
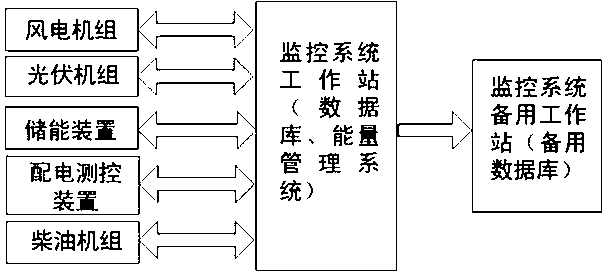
Monitoring system applicable to different types of wind photovoltaic storage microgrid systems
ActiveCN102710023AGuaranteed uptimeTake controlCircuit arrangementsSustainable buildingsMicrogridIslanding
The invention relates to a distributed generation microgrid system, in particular to a monitoring system applicable to different types of wind photovoltaic storage microgrid systems. The monitoring system comprises a communication conversion module, a communication bus, total communication conversion modules, a monitoring work station, a database server and a remote Web server, wherein the controller of each subsystem of the wind photovoltaic storage microgrid system is connected with different communication conversion modules in a one-to-one correspondence mode; the communication conversion modules are connected with the total communication conversion module through the communication bus; and the total communication conversion module is connected with the monitoring work station, the database server and the remote Web server. The monitoring system has the effects of controlling, monitoring and detecting a wind generating set, a diesel engine unit, a photovoltaic generating set, an energy storage device, a power distribution measuring and control device, a protective device and the like of the whole wind photovoltaic storage microgrid system, so that the microgrid system can stably operate under a grid mode and an island mode. The monitoring system can control each subsystem of the microgrid and detect the operation parameters of the microgrid.
Owner:东方电气集团国际合作有限公司
Encapsulated security tokens for electronic transactions
ActiveUS20130318619A1Improve securityDifficult to forgeDigital data processing detailsAnalogue secracy/subscription systemsDigital dataDigital signature
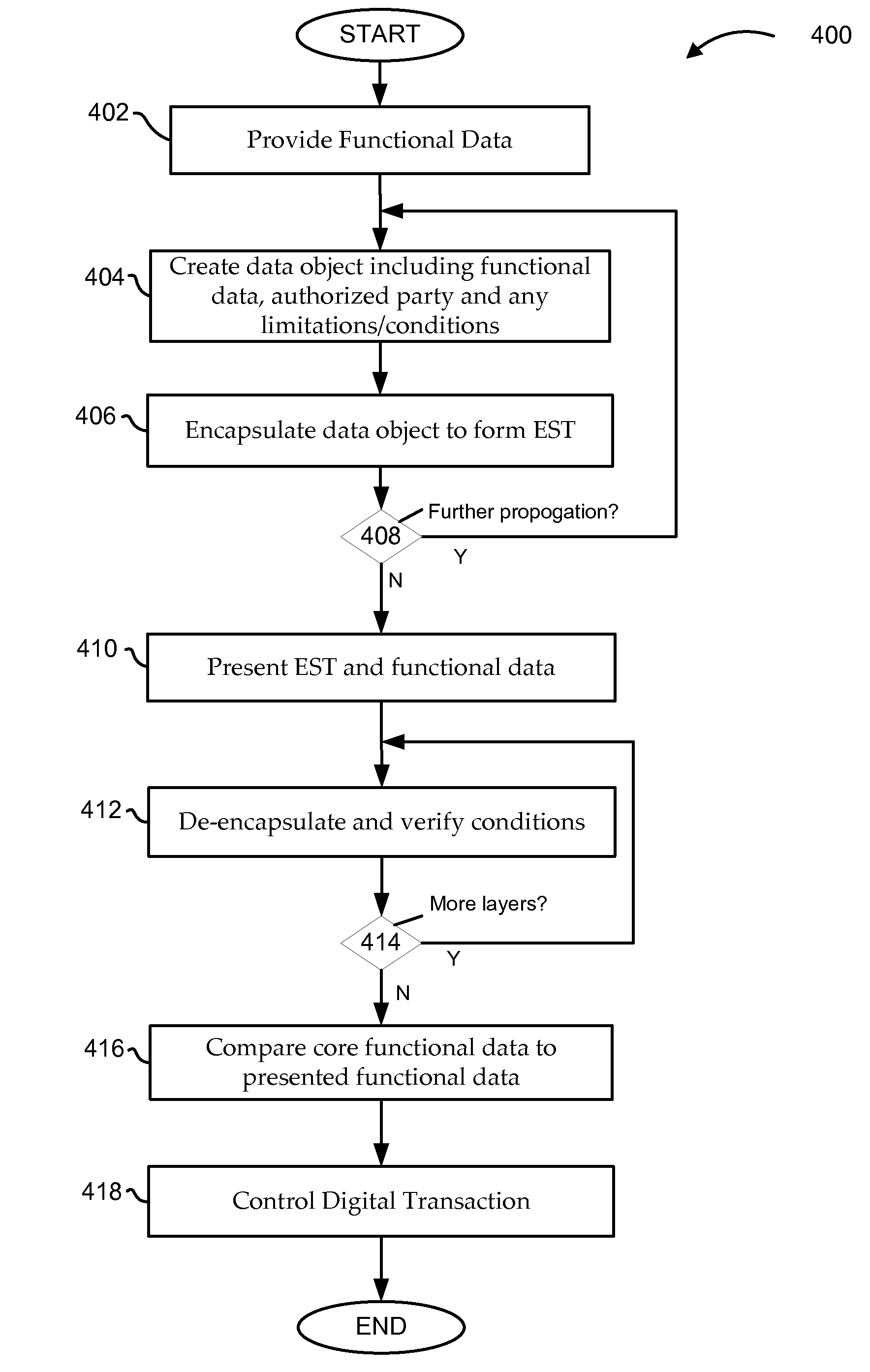
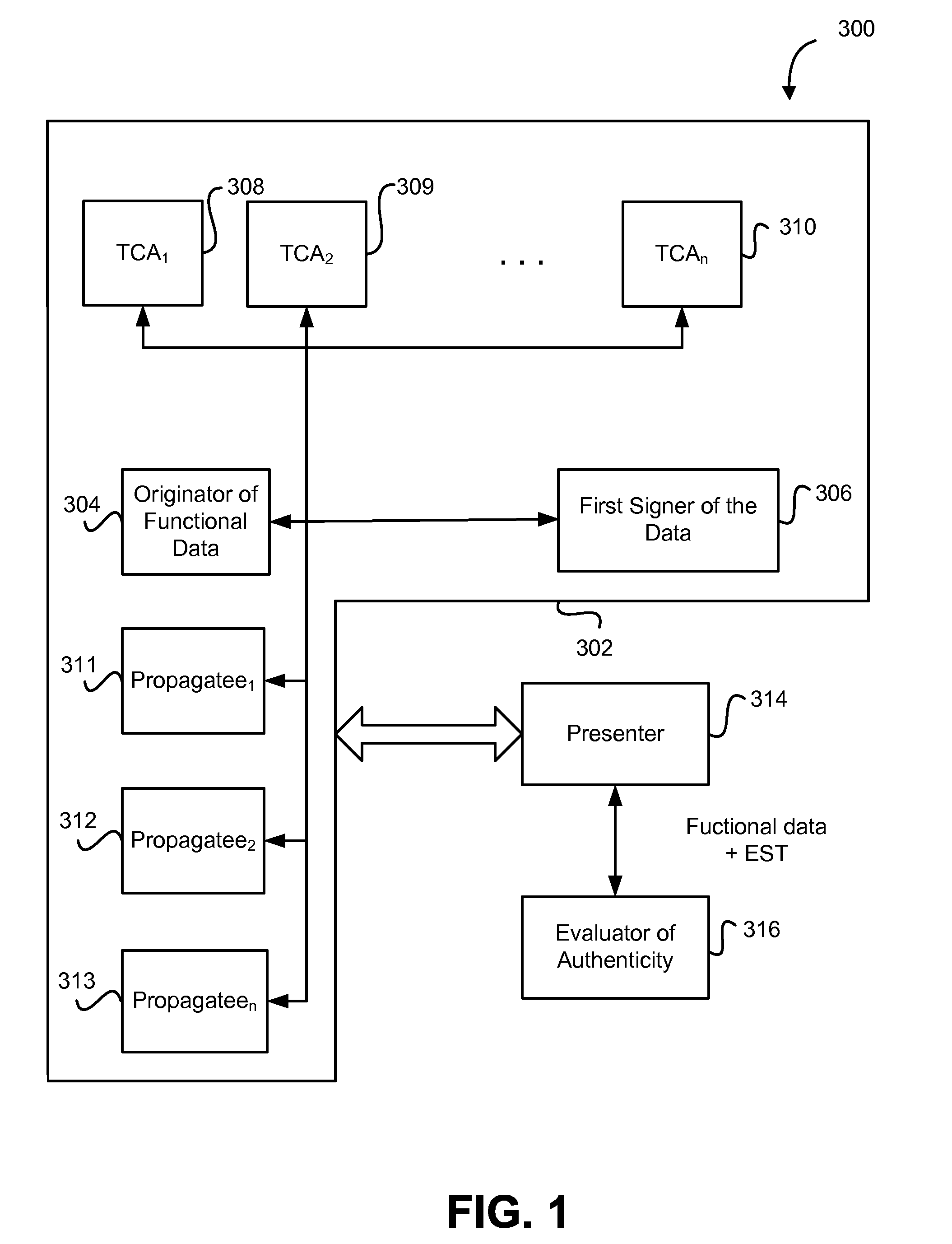
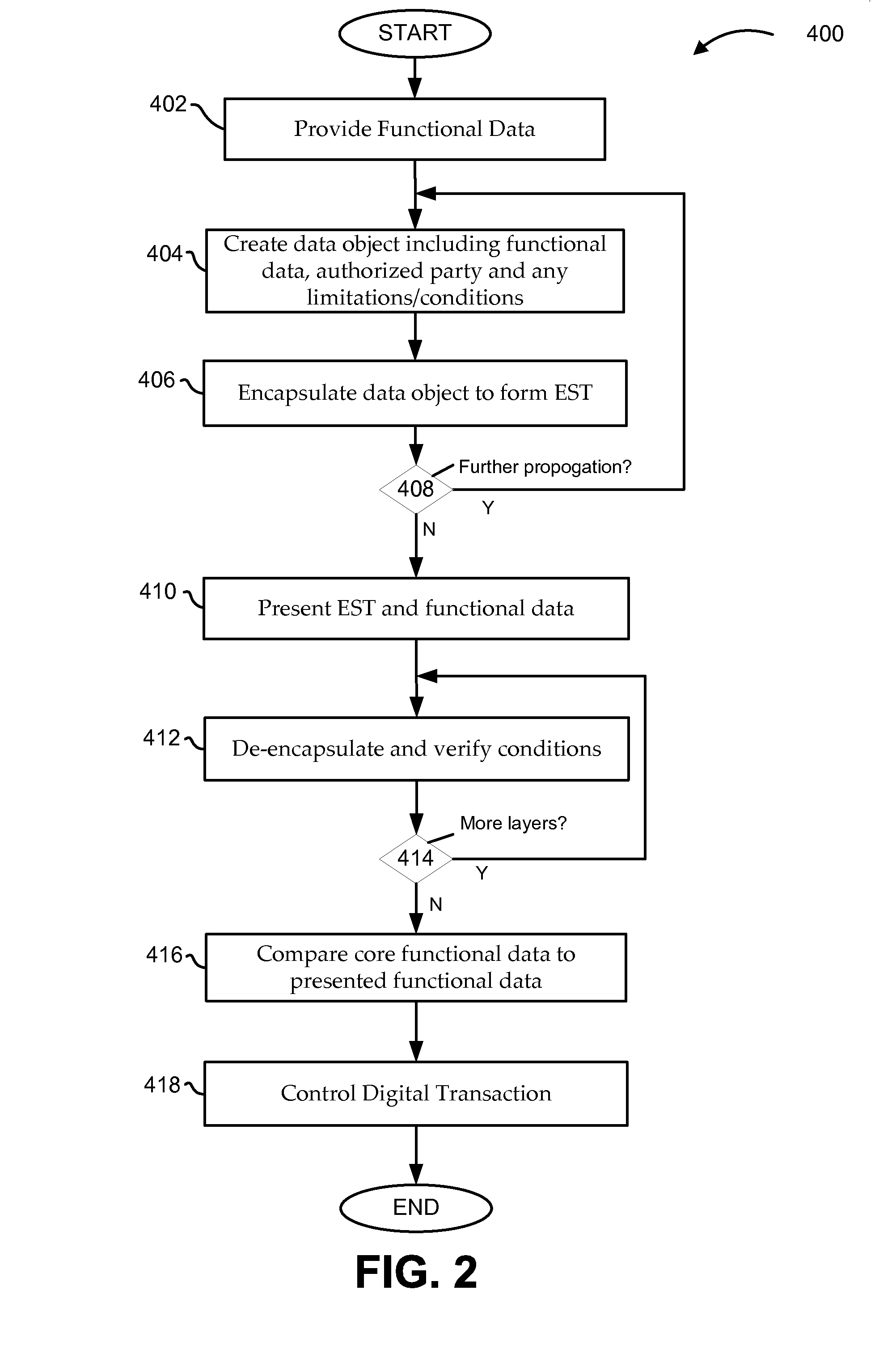
Functional data for use in one or more digital transactions is secured by using an encapsulated security token (EST). In certain embodiments, the EST is created by encapsulating digital data including the functional data using at least two digital signature systems of two parties. The encapsulation and subsequent de-encapsulation can utilize digital signature systems of the parties that involve a private key for encapsulation and a public key for de-encapsulation. If constructed carefully over a series of rigorous events, the resulting EST can be practically impossible to counterfeit. In addition, a propagation of rights can be tracked for auditing and rights can be easily terminated or modified.
Owner:INSTITUTIONAL CASH DISTRIBUTORS TECH
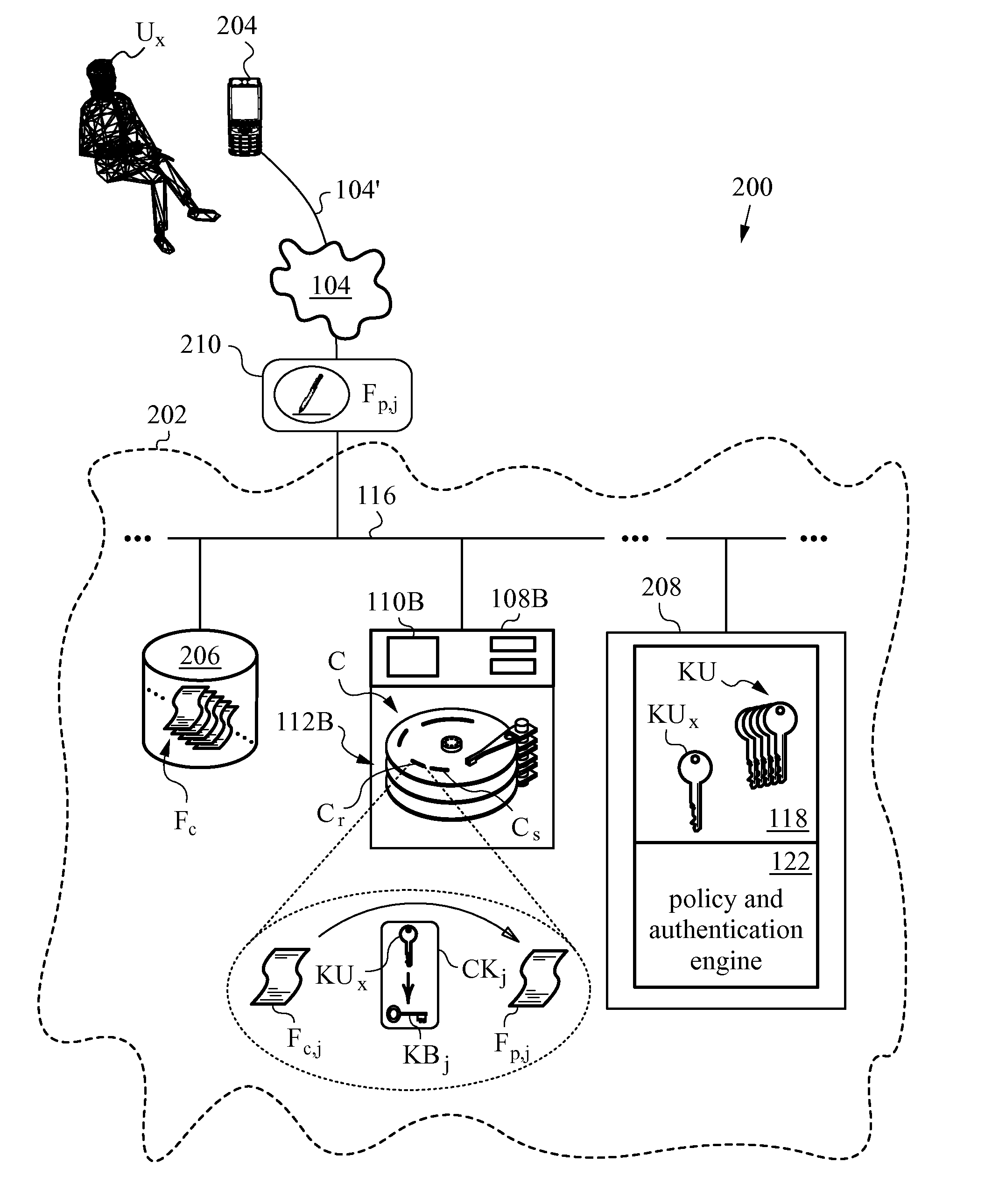
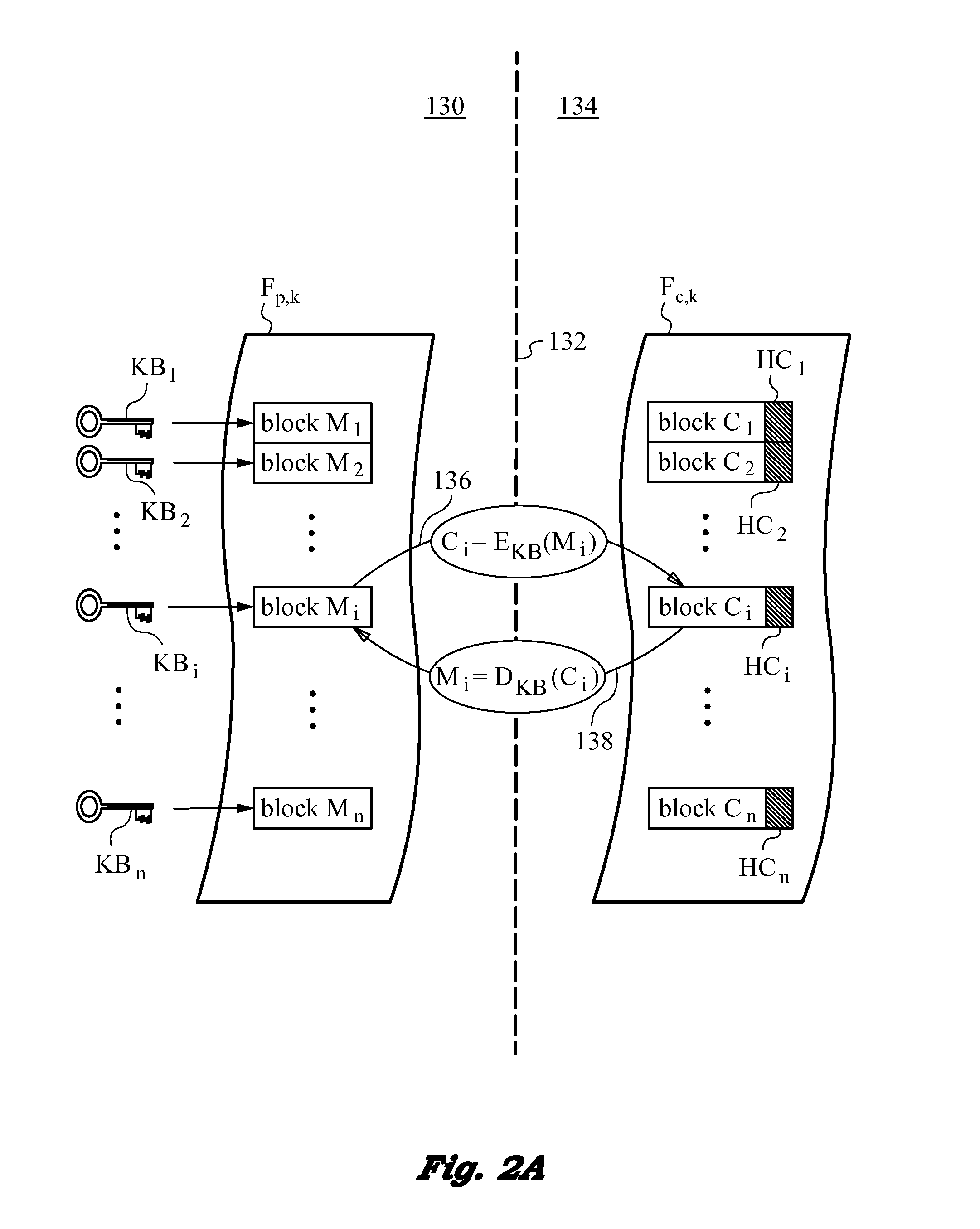
Method of securing files under the semi-trusted user threat model using symmetric keys and per-block key encryption
ActiveUS20150288664A1Rapid and efficientImprove security levelKey distribution for secure communicationMultiple keys/algorithms usageFile systemTrusted client
A computer system and method for securing files in a file system equipped with storage resources that are accessible to an authenticable user operating with an untrusted client device under the semi-trusted client threat model. The file to be secured is stored in one or more blocks belonging to the storage resources along with symmetric per-block key(s) KBi assigned to each of the blocks in the file. The blocks are encrypted with the symmetric per-block keys to obtain encrypted blocks. The user is assigned user key(s) and each per-block key that was used for encryption is in turn encrypted with one of the user's keys to derive wrapped key(s) for each encrypted block. Wrapped key(s) are placed in encrypted block headers and introduce a level of indirection to encrypted file(s) that is appropriate for the semi-trusted client threat model.
Owner:ZETTASET
Information processing system for judging if backup at secondary site is necessary upon failover
InactiveUS7114094B2Shorten the durationSafe storageMemory systemsRedundant hardware error correctionFailoverInformation processing
Owner:GOOGLE LLC
Computer power backup system and device
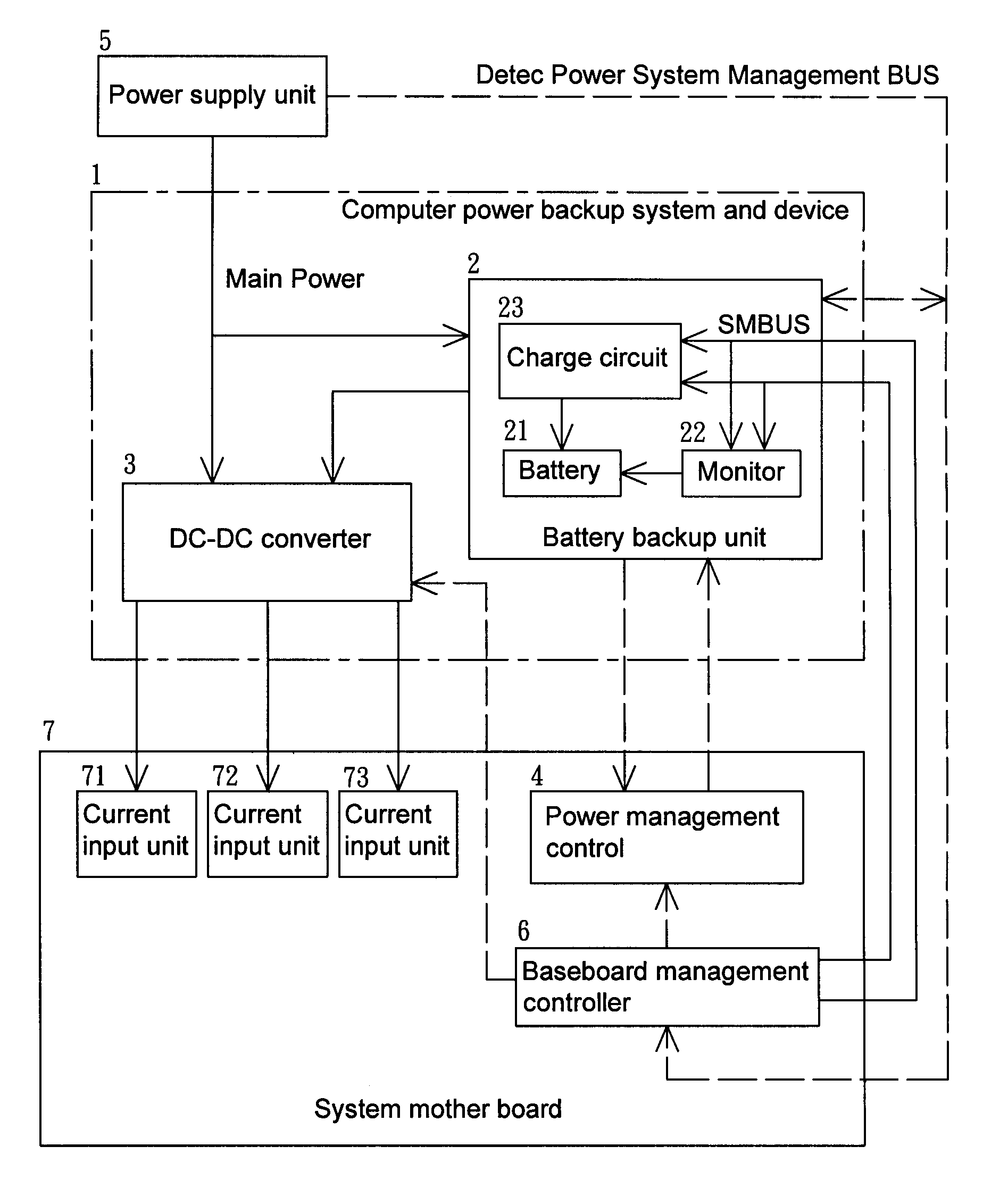
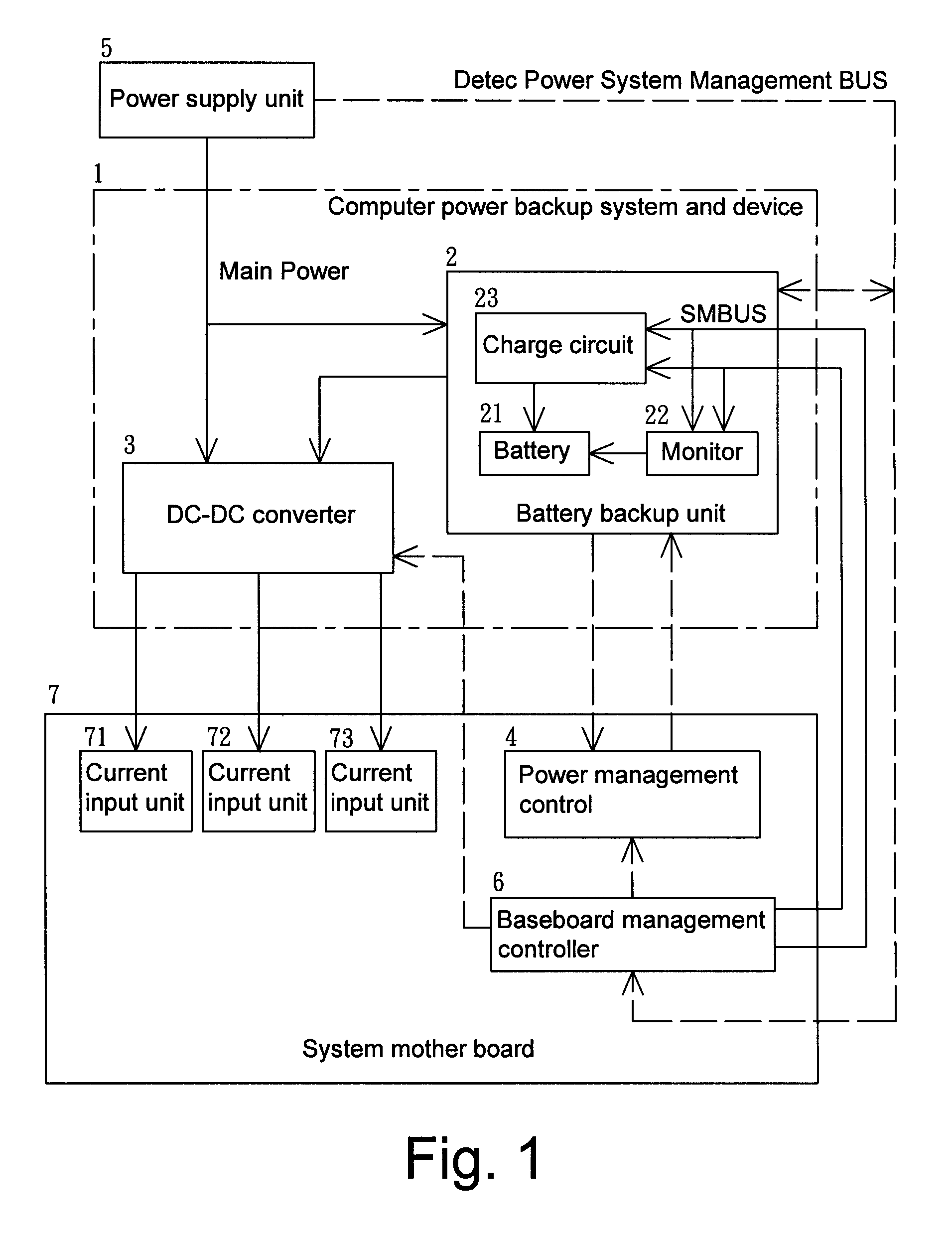
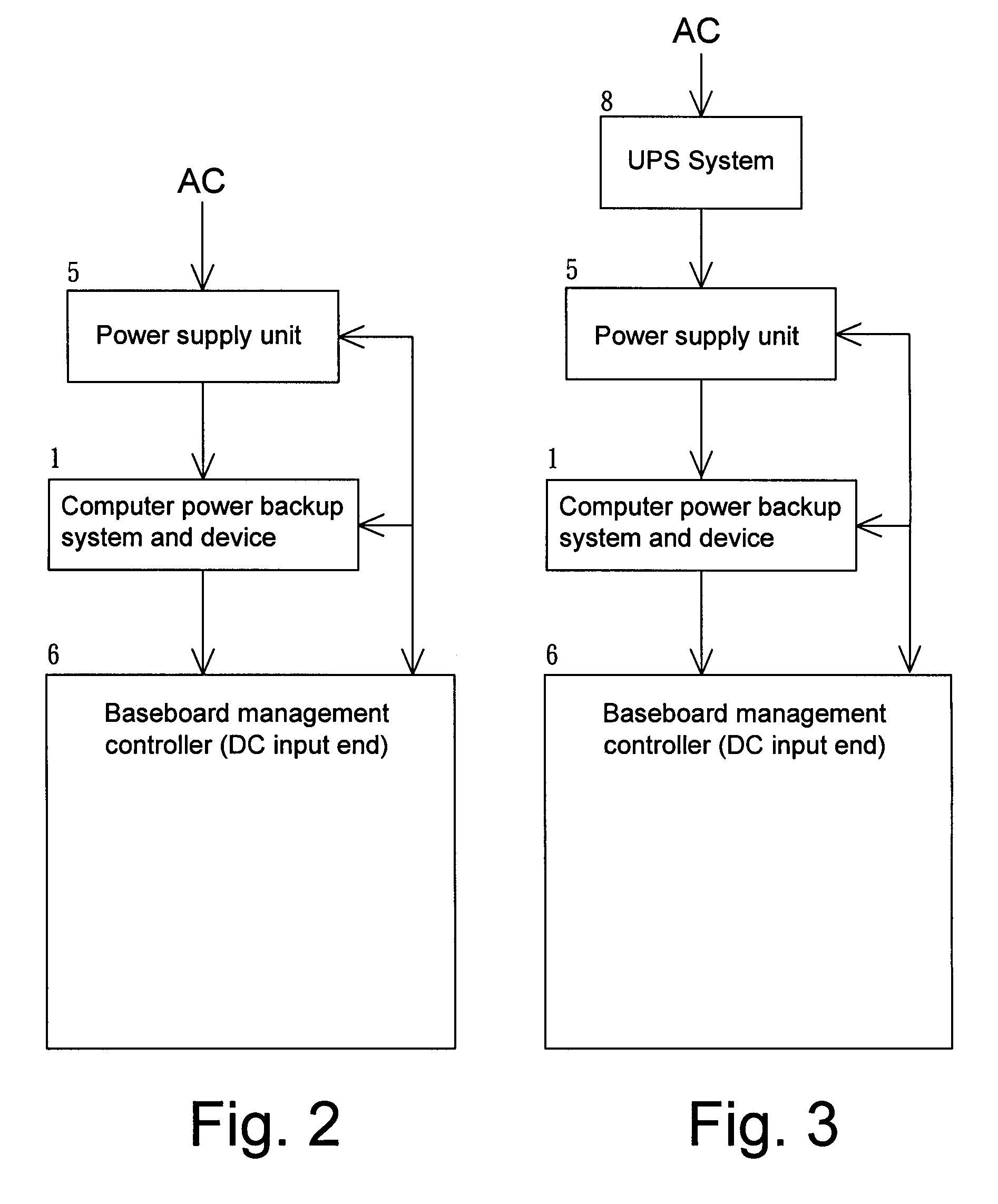
ActiveUS20110016340A1Easy to useStore data safelyVolume/mass flow measurementHardware monitoringEmbedded systemPower management
A computer power backup system and device are provided. When power to a computer system is lost, a battery backup unit provides power to the computer system for a while, allowing a power management control to send out an alert to an enterprise client so as to urge immediate action. If the power outage persists without being solved, and the power management control detects insufficient power in a battery of the battery backup unit, the power management control will store data in a storage device automatically and safely and then shut down the computer system. When power is restored, the power management control turns on the computer system automatically and begins charging the battery of the battery backup unit. Through the above operation, the integrity and safety of data in the computer system are secured.
Owner:AIC INC
Handheld computer for emergency responders
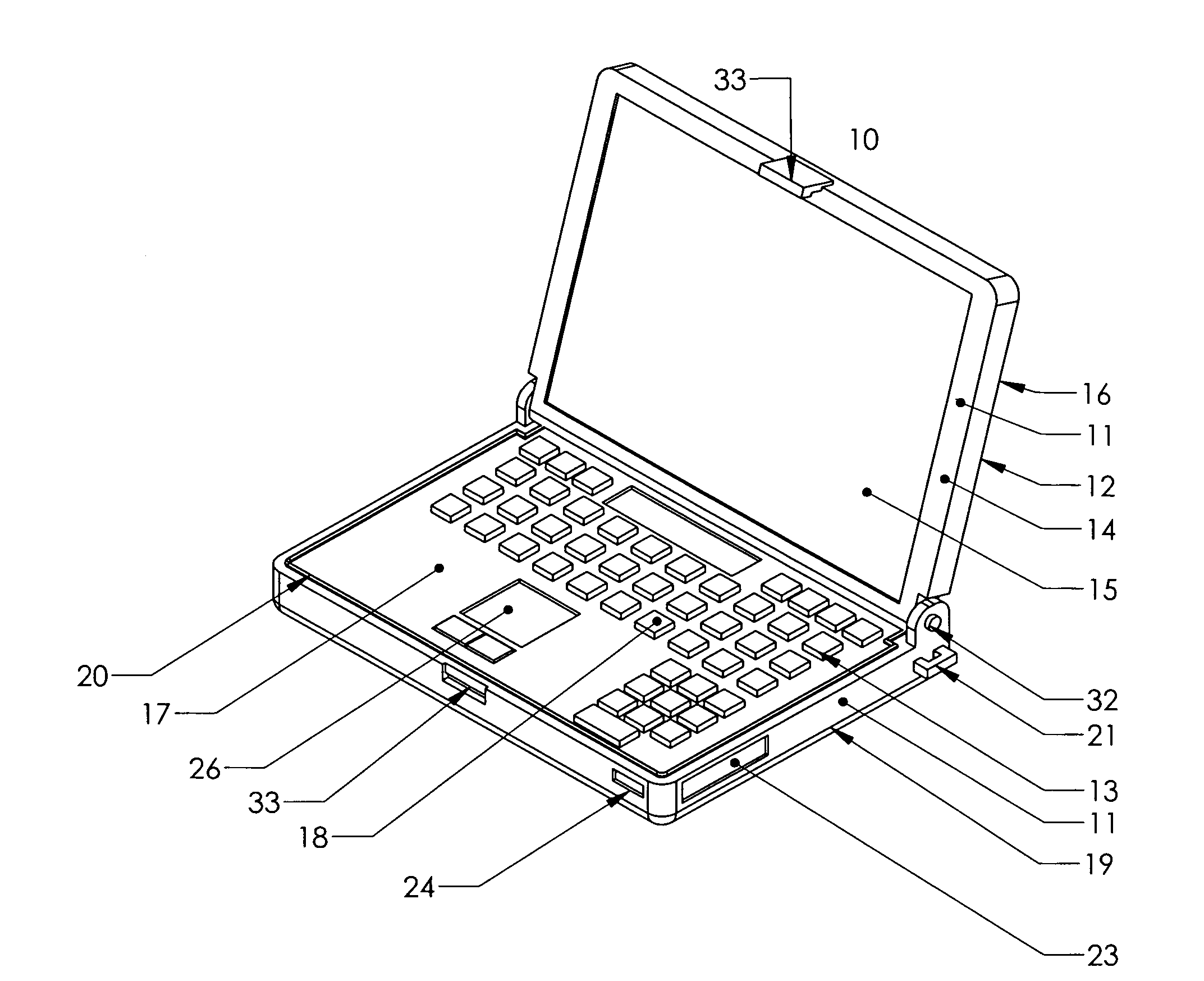
InactiveUS20090186647A1Economical to useEasy to useDetails for portable computersRadio transmissionDisplay deviceComputer science
A compact handheld notebook computer using flash memory to store, retrieve and display information needed by emergency responders is designed for prolonged use under severe conditions and utilizes an electrophoretic display to conserve energy and provide a high resolution display more readable than LCD displays.
Owner:SMART DAVID A +1
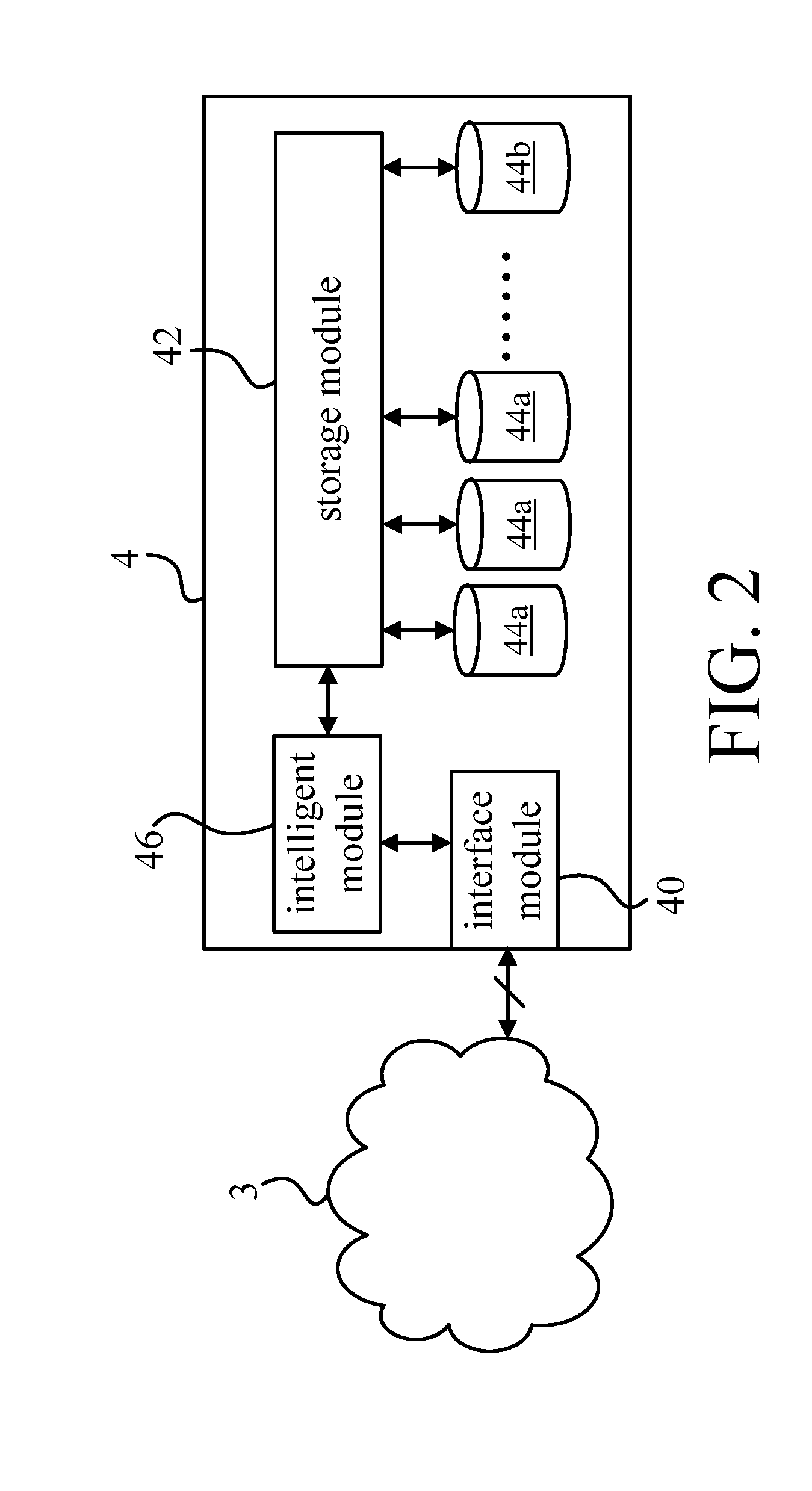
Network-attached storage system
InactiveUS20120131275A1Data SecuritySave power consumptionEnergy efficient ICTMemory loss protectionTransmission protocolThrough transmission
The invention discloses a network-attached storage system including an interface module, a plurality of storage devices and a storage module. The interface module is configured to be attached to a network. The interface module is for receiving a transmission protocol information transmitted over the network, and processing the information into storage data and access instructions. The storage module is for receiving the storage data and the access instructions, and controlling, according to the access instructions, access of the storage data to the primary storage devices through a transmission interface.
Owner:PROMISE TECHNOLOGY
Information processing apparatus and power supply control method
InactiveUS20100131789A1Promote recoveryData SecurityTelevision system detailsError detection/correctionInformation processingAC power
In standby mode, memory contents are saved to a hard disk. After AC power has been removed by disconnecting the AC plug, when the AC power is restored the data saved on the hard disk is automatically restored into memory to set the power-saving mode back to the standby mode. When the power is turned on next, quick resumption from standby mode can be accomplished.
Owner:FUJITSU LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com