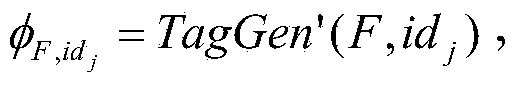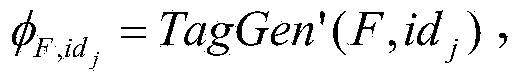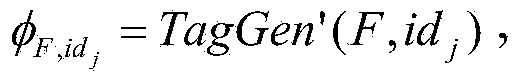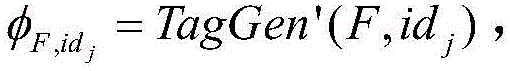Patents
Literature
40results about How to "Protection of confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safe distributed duplicated data deletion method
ActiveCN103763362AProtection of confidentialitySatisfy deduplicationTransmissionShort ValueComputer hardware
The invention discloses a safe distributed duplicated data deletion method. According to the method, a file is segmented into fragments through a secret sharing technology without any encryption mechanism. The shared fragments are distributed in a plurality of independent storage servers. In addition, in order to support reduplication removing, a different short value is calculated and sent to the storage servers as the indicator of one fragment. Only possessors uploading data for the first time need to carry out such calculation and distribution of secrete sharing, and then people possessing the same data copies do not need to calculate and store the sharing any longer. When the data copies are restored, users must access the storage servers with the minimum quantity to reconstruct the data through authentication and acquisition of the secret sharing. In other words, the secret sharing of the data can only be accessed by the users who possess the same copies and are authorized.
Owner:XIDIAN UNIV
Intelligent secret keyboard with key values being changed randomly
InactiveCN1431575ARealize the designImprove confidentialityInput/output processes for data processingComputer hardwareCryptogram
The display position of the N key value of N key position (N represents the number of part or alloy key buttons on the keyboard) on the keyboard can be changed randomly so as to assure the security and the right of privacy of the user's input data in maximum, keeping the input data from robbing. The intelligent secret keyboard is applicable to financial plate in banks, stock exchange, ATM, market... etc. has the vast market foreground.
Owner:王洋
Intelligent identification system for an exhibition hall and an exhibition hall
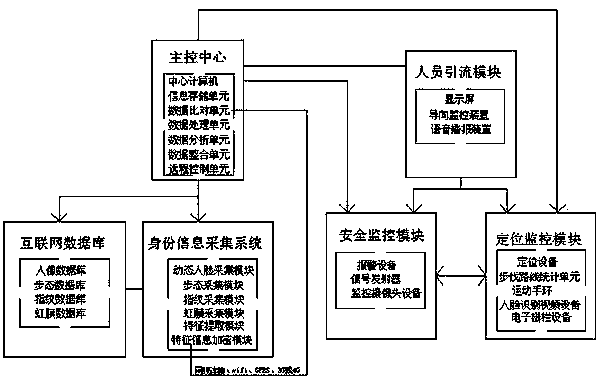
InactiveCN109658310AImprove the effect of early warningAvoid emergenciesForecastingDigital data protectionThe InternetGait
The invention provides an intelligent identification system for an exhibition hall and an exhibition hall, the intelligent identification system comprises an identity information acquisition system, an internet database, a personnel drainage module, a safety monitoring module, a positioning monitoring module and a main control center, and the identity information acquisition system comprises a dynamic face acquisition module, a gait acquisition module, a fingerprint acquisition module and an iris acquisition module; According to the invention, the identity information acquisition system is used; Internet database, Personnel drainage module, Safety monitoring module, the positioning monitoring module can effectively carry out multiple effective identification on the identities of visitors entering the exhibition hall and the exhibition hall; the management personnel can effectively manage and control visitors entering the exhibition hall and the exhibition hall; Compared with the priorart, the system has the advantages that emergency situations are avoided, meanwhile, the early warning capability of the emergency situations is improved, an optimized visiting route can be rapidly provided for visitors through the personnel drainage module, crowding caused by the fact that most people visit the same partition is avoided, and exhibition hall exhibition hall personnel distributionis reasonably planned.
Owner:振伟博展科技股份有限公司
Printer
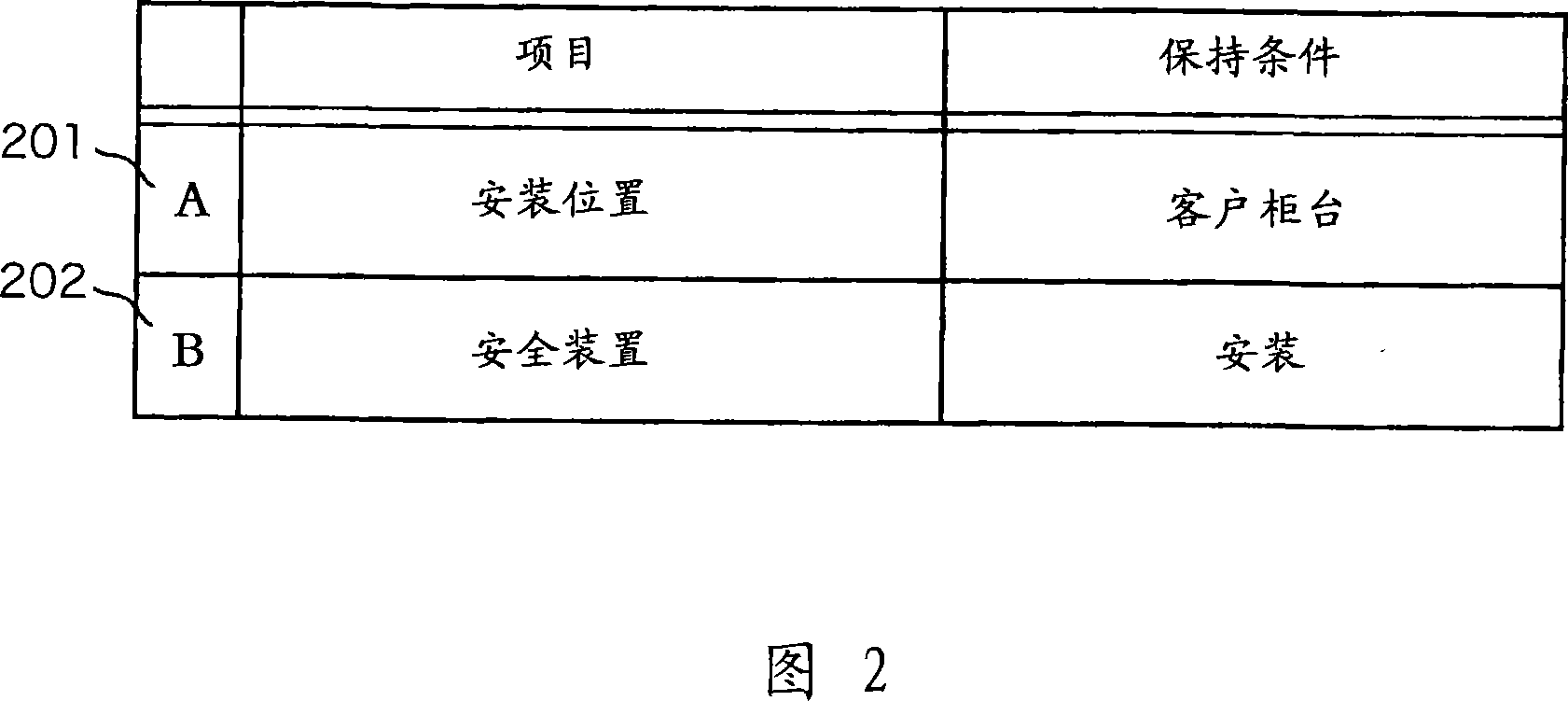
InactiveCN101098383AGuaranteed confidentialityMeasuring Confidentiality LevelsComputer security arrangementsElectrographic process apparatusConfidentialityData storing
A printer includes an obtaining section for obtaining printing data, a storage section for storing the printing data obtained by the obtaining section, a printing section for printing the printing data stored in the storage section, an receiving section for receiving information about the printer, and a control section for extracting predetermined information about the printing data from the printing data and protecting the confidentiality of the printing data on the basis of the extracted information and the information received by the receiving section.
Owner:SHARP KK
Conference control system
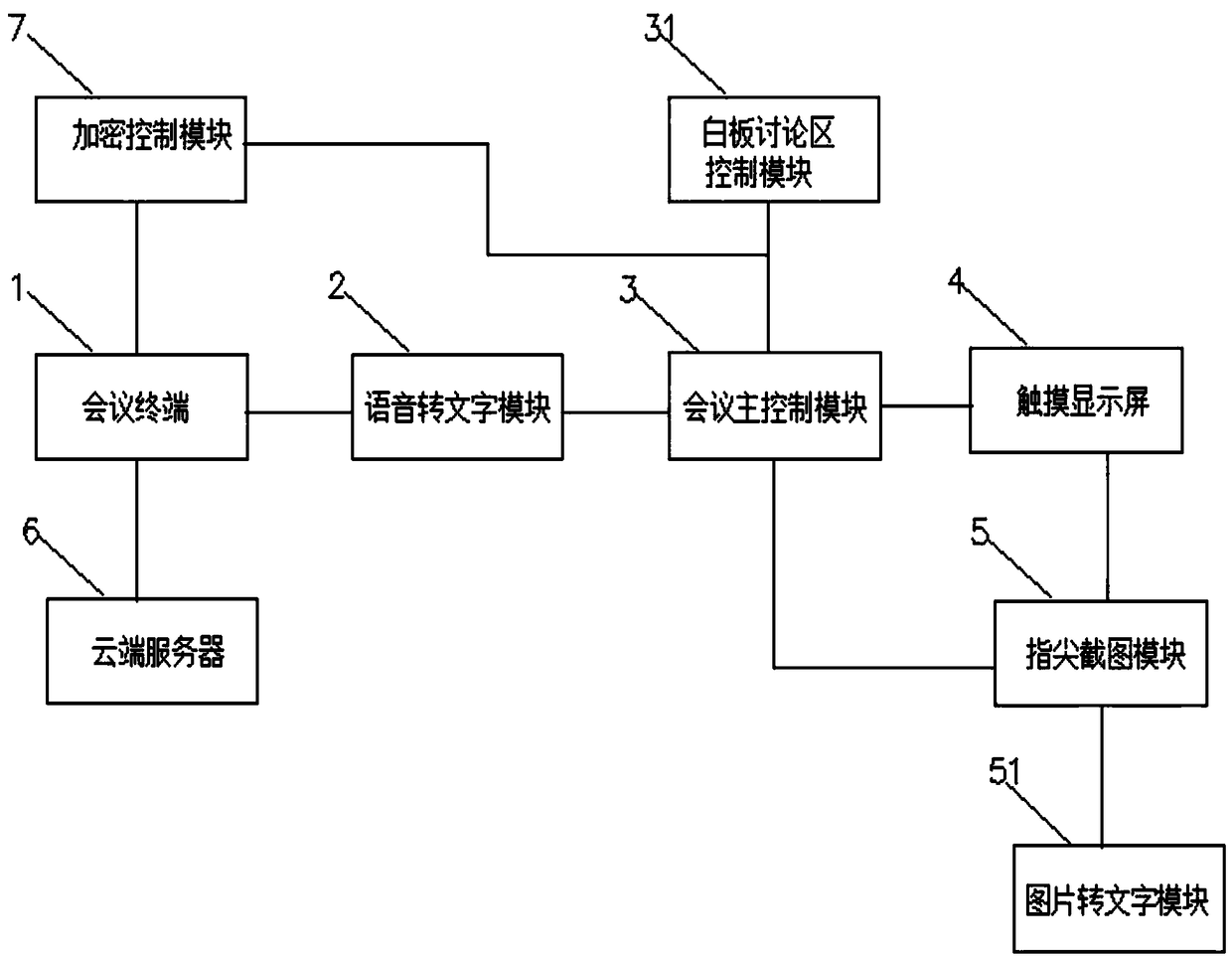
InactiveCN109327674AImprove time and efficiencyProtection of confidentialityTelevision conference systemsTwo-way working systemsData transmissionData information
The invention discloses a conference control system comprising a conference terminal, a voice-to-text module, a conference main control module, a touch display screen, a fingertip screen capturing module, a cloud server and an encryption control module; the conference terminal transmits conference audio and video data to the conference main control module via the voice-to-text module; the conference main control module controls the touch display screen to display conference content; the fingertip screen capturing module does a screenshot via the touch display screen, and transmits picture information to the conference main control module; the conference main control module controls the encryption control module to encrypt, the encryption control module transmits encrypted data informationto the conference terminal, and the conference terminal transmits the data information to the cloud server for storing. The invention aims at providing the conference control system that is simple andconvenient to operate, diverse in function and high in intelligence degree.
Owner:武汉立信通达科技有限公司
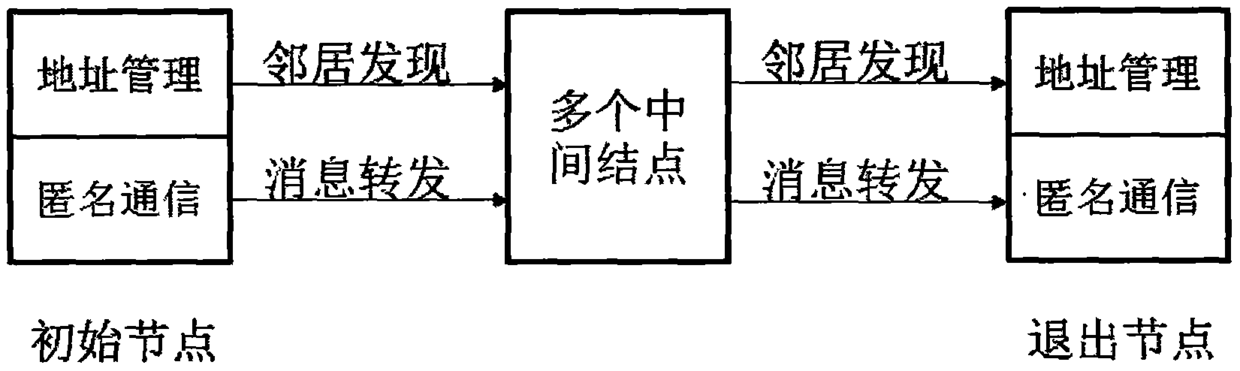
Point-to-point anonymous communication method based on random stateless address distributing policies in IPv6 network
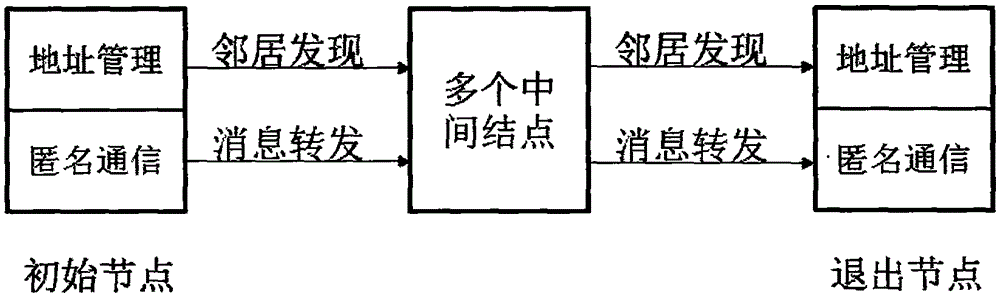
InactiveCN105282161AEnhanced anonymityPrivacy protectionTransmissionExtensibilitySecure communication
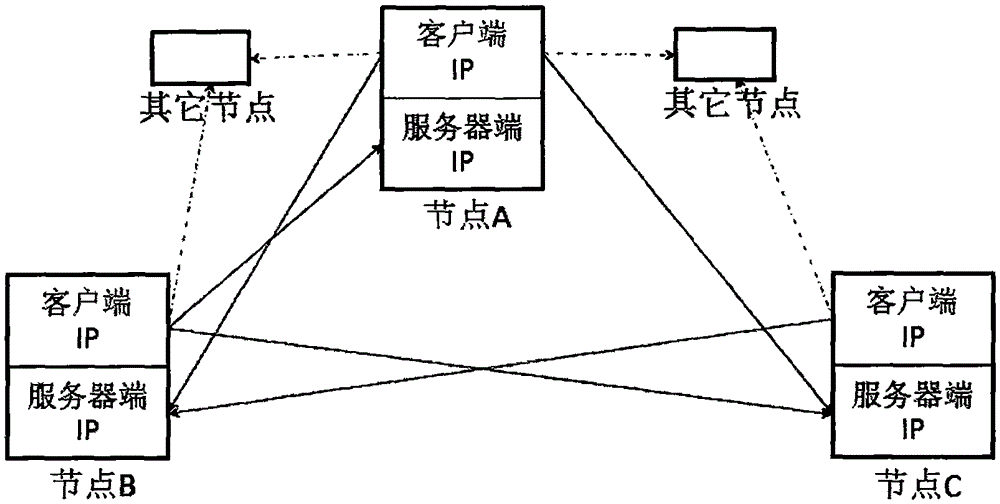
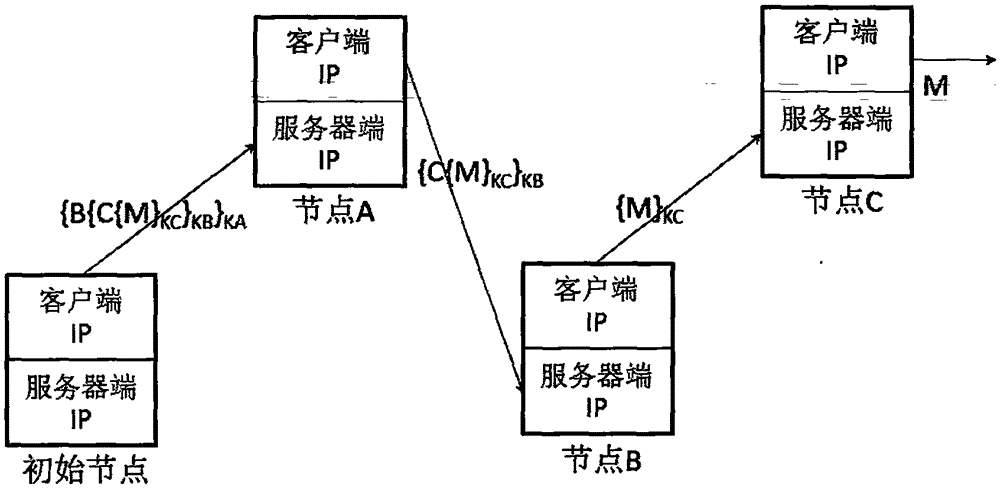
The invention relates to a point-to-point anonymous communication method based on random stateless address distributing policies in an IPv6 network and belongs to the Internet technical field. Based on an onion routing anonymous communication mechanism, the IPv6 address of a node is changed periodically through an improved IPv6 address algorithm and by means of a huge IPv6 address space, and therefore, privacy leakage caused by an IPv6 address identifier can be avoided; and cross-network segment hiding and data encryption of the IPv6 address can be ensured through the onion routing mechanism. With the method adopted, the anonymous performance of an anonymous communication system can be obviously improved; the communication efficiency and the compatibility of the system are not weakened; and various kinds of effective safe communication technologies can be provided for future Internet applications. The method has high universality and excellent expansibility, and can meet the requirements of the development of the future Internet applications.
Owner:MIANYANG TEACHERS COLLEGE
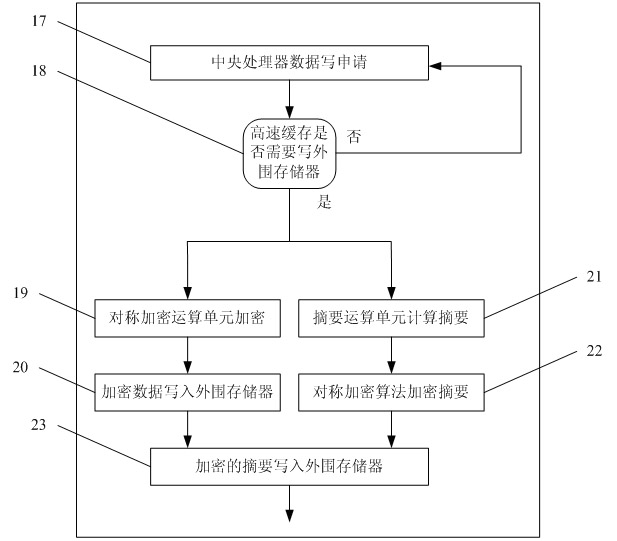
Data protection unit applicable to embedded system
ActiveCN102004880AImprove securityReasonable designDigital data protectionIntegrated circuitSoftware
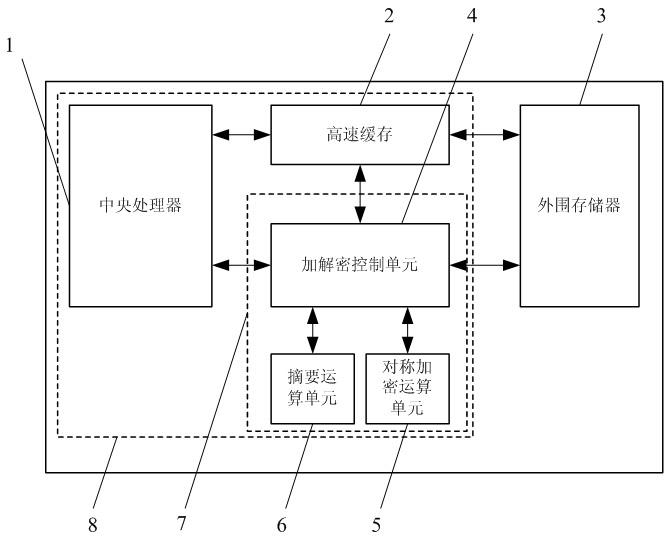
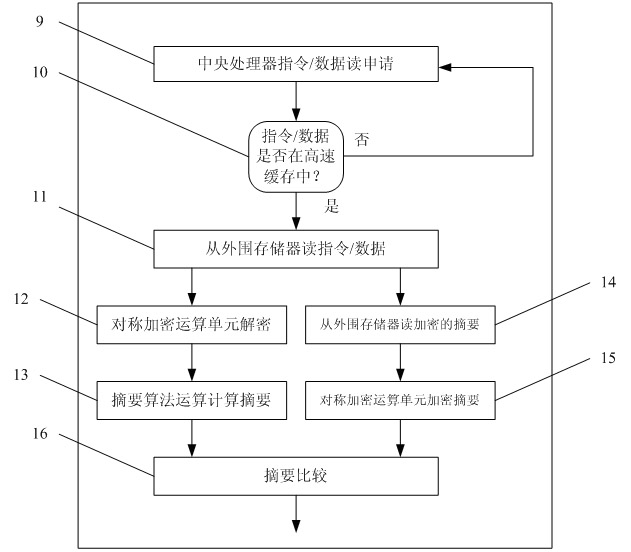
The invention belongs to the technical field of design of integrated circuits, in particular to a data protection unit applicable to an embedded system. The embedded system comprises a central process, a high-speed cache and a chip memory. The system also has a decryption control unit, a symmetric encryption operation unit and an abstract operation unit for protecting the security and integrity of data. In an operation process, the system flexibly configures different operation modes according to requirements on security level and performance. The data protection unit is easy to expand and has a high promotion value. By introducing the data protection unit, the security of the embedded system is improved considerably enough to prevent software pirating by software copying and effectively prevent vicious software tamper.
Owner:FUDAN UNIV
Content security at service layer
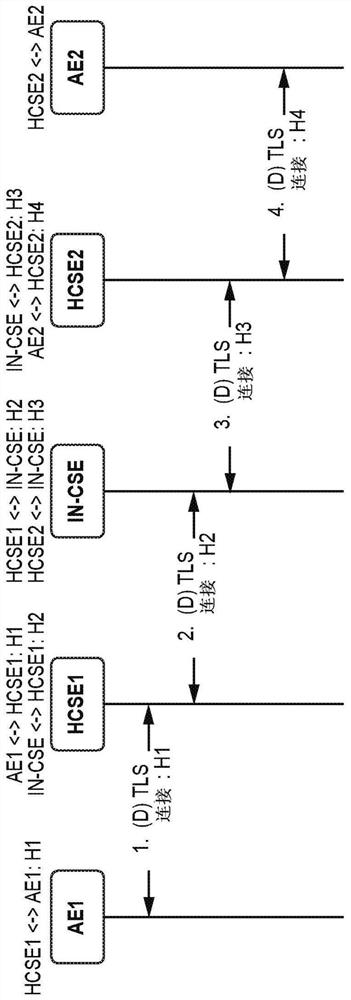
ActiveCN107852405AImprove integrityProtection of confidentialityTransmissionSecurity arrangementConfidentialityContent security
Existing approaches to security within network, for instance one M2M networks, are limited. For example, content might only be protected while the content is in transit between entities that trust each other. Here, the integrity and the confidentiality of content in an M2M network are protected. Such content may be "at rest," such that the content is stored at a hosting node. Only authorized entities may store and retrieve the data that is stored at the hosting node, and the data may be protected from a confidentiality perspective and an integrity perspective.
Owner:CONVIDA WIRELESS LLC
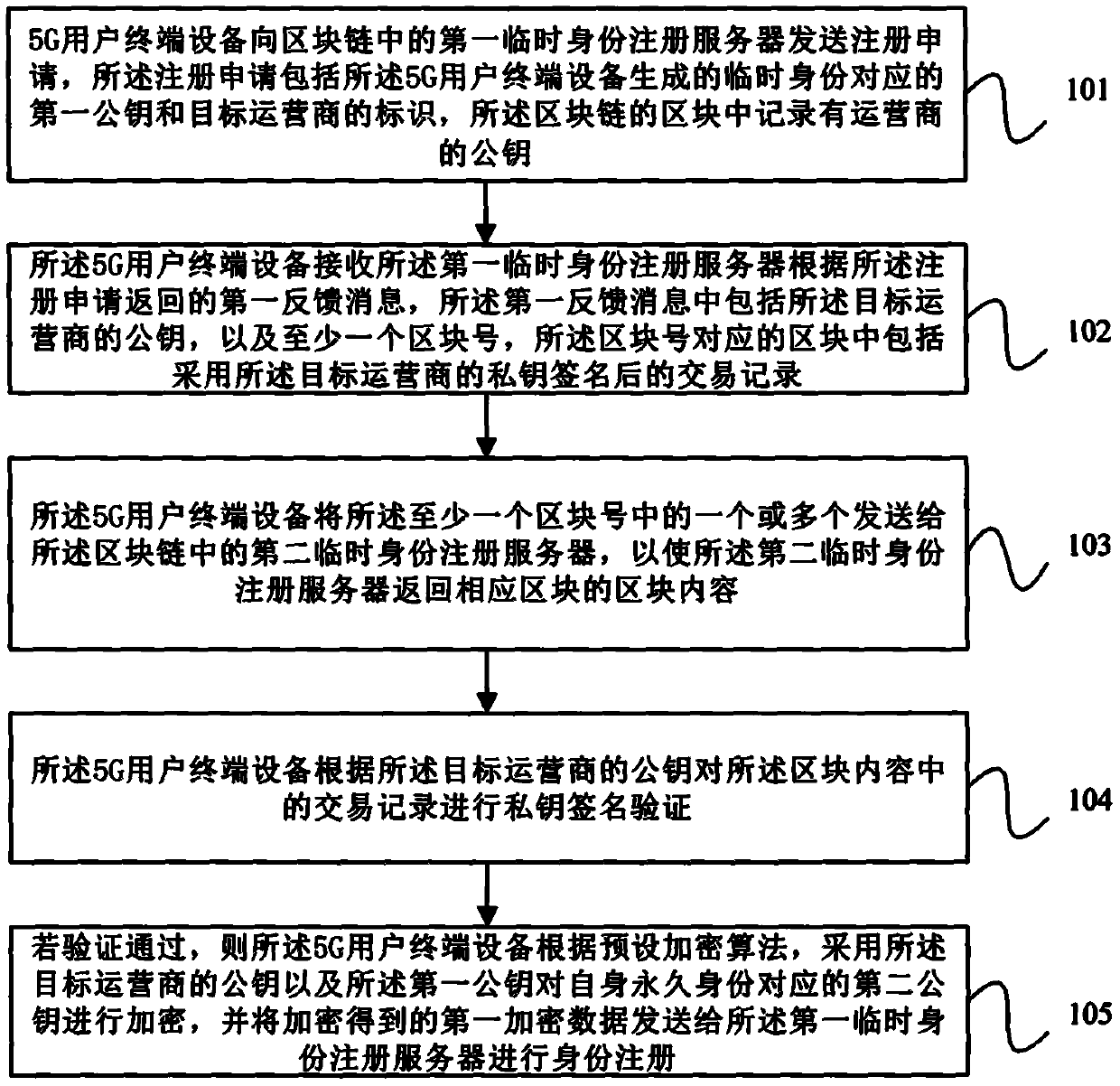
Registration method of 5G user terminal, user terminal equipment and medium
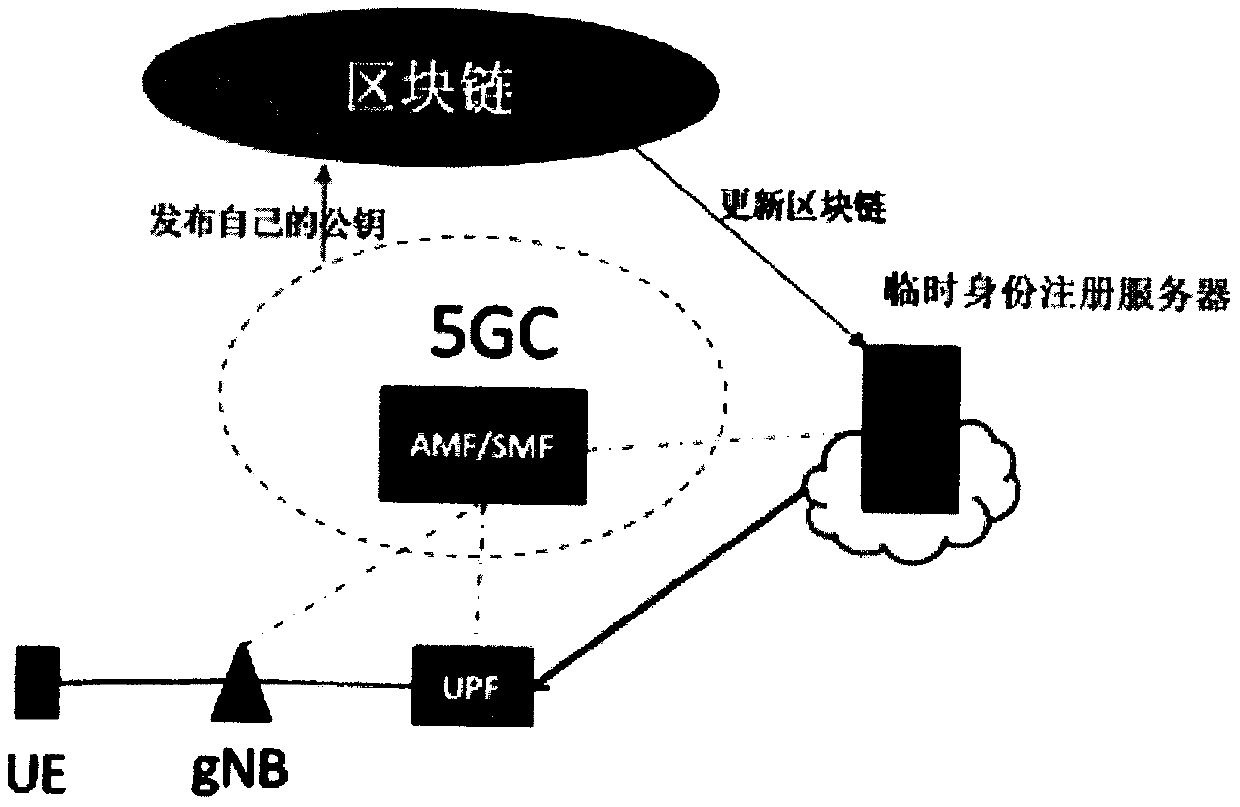
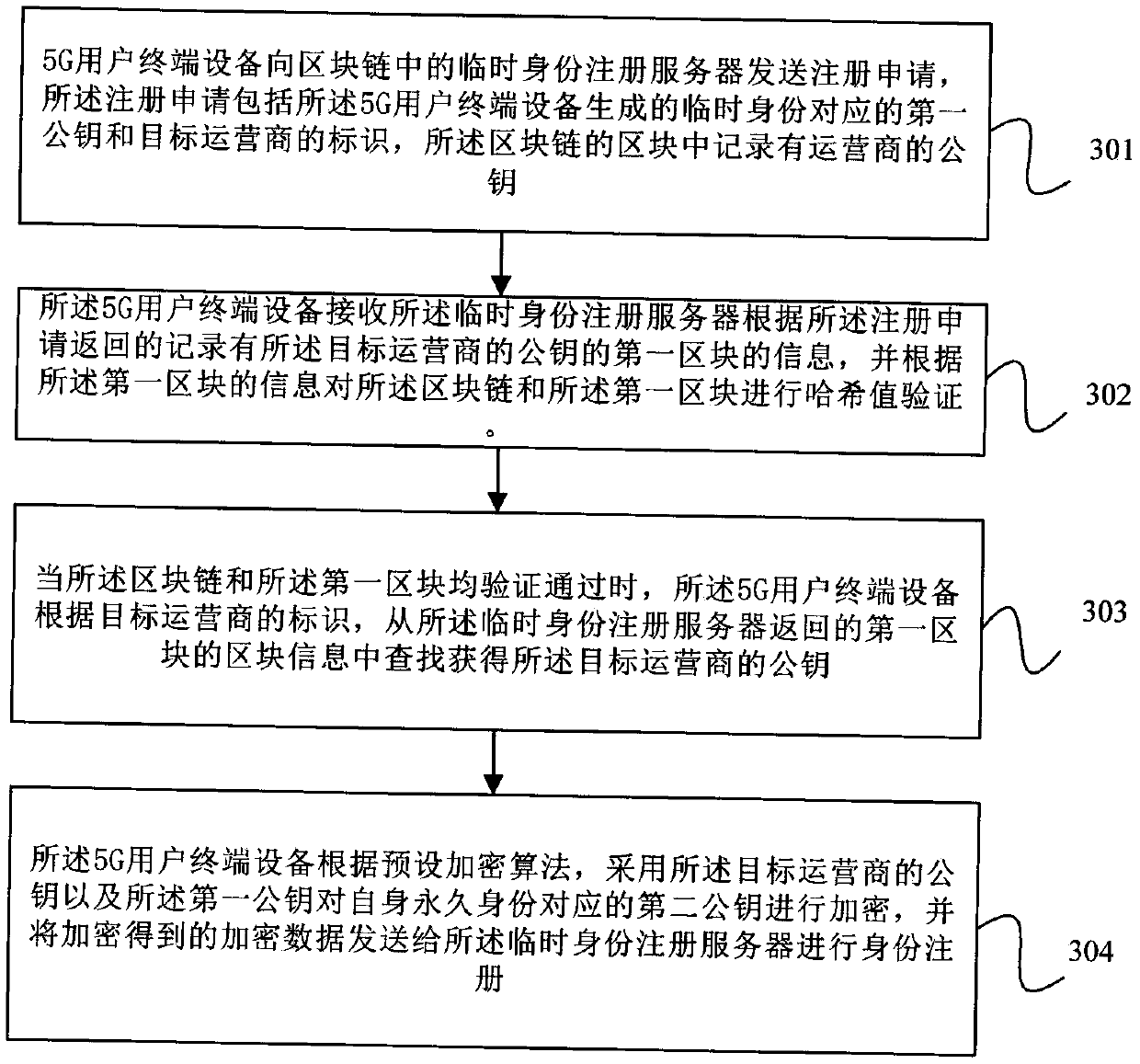
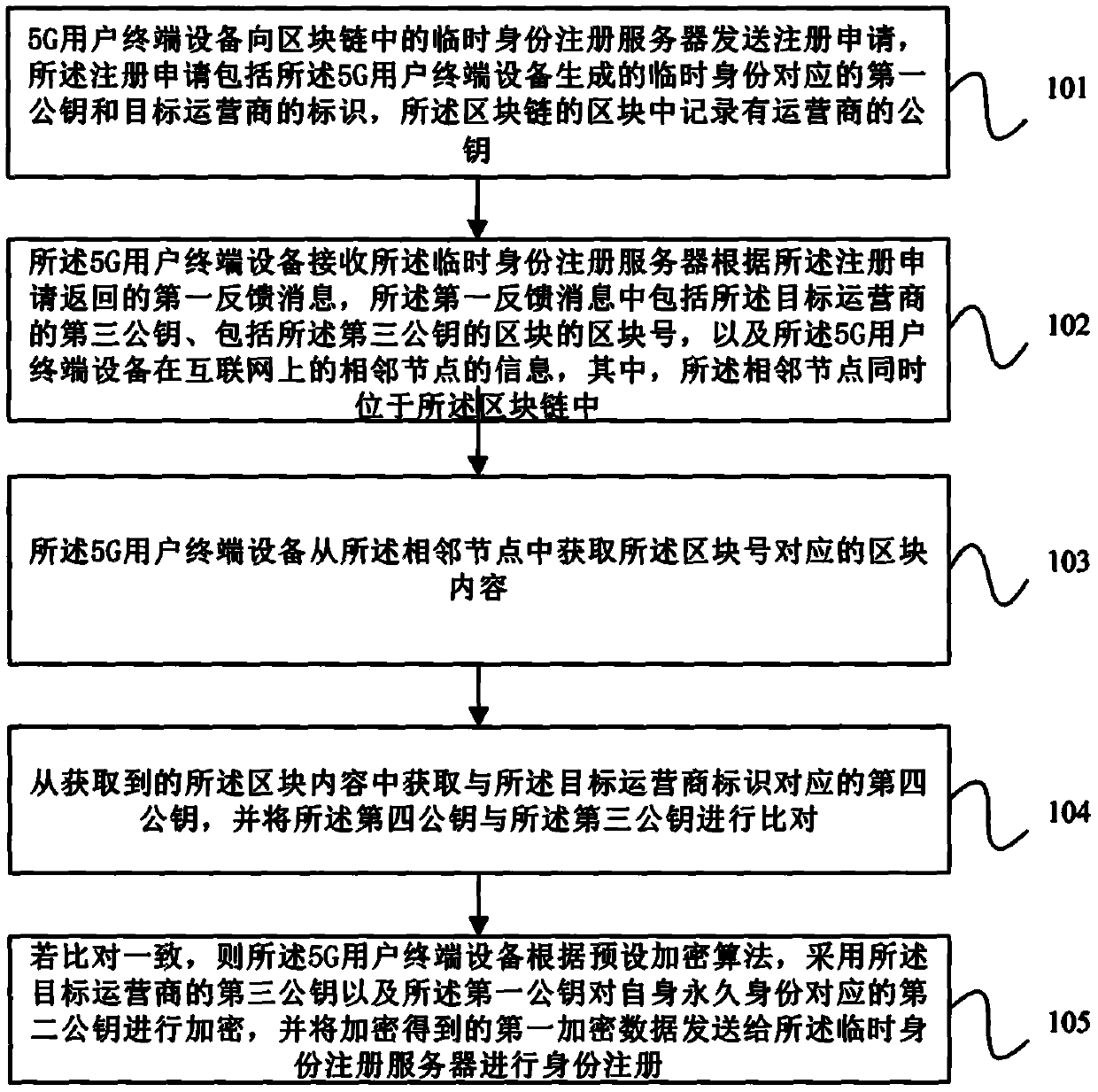
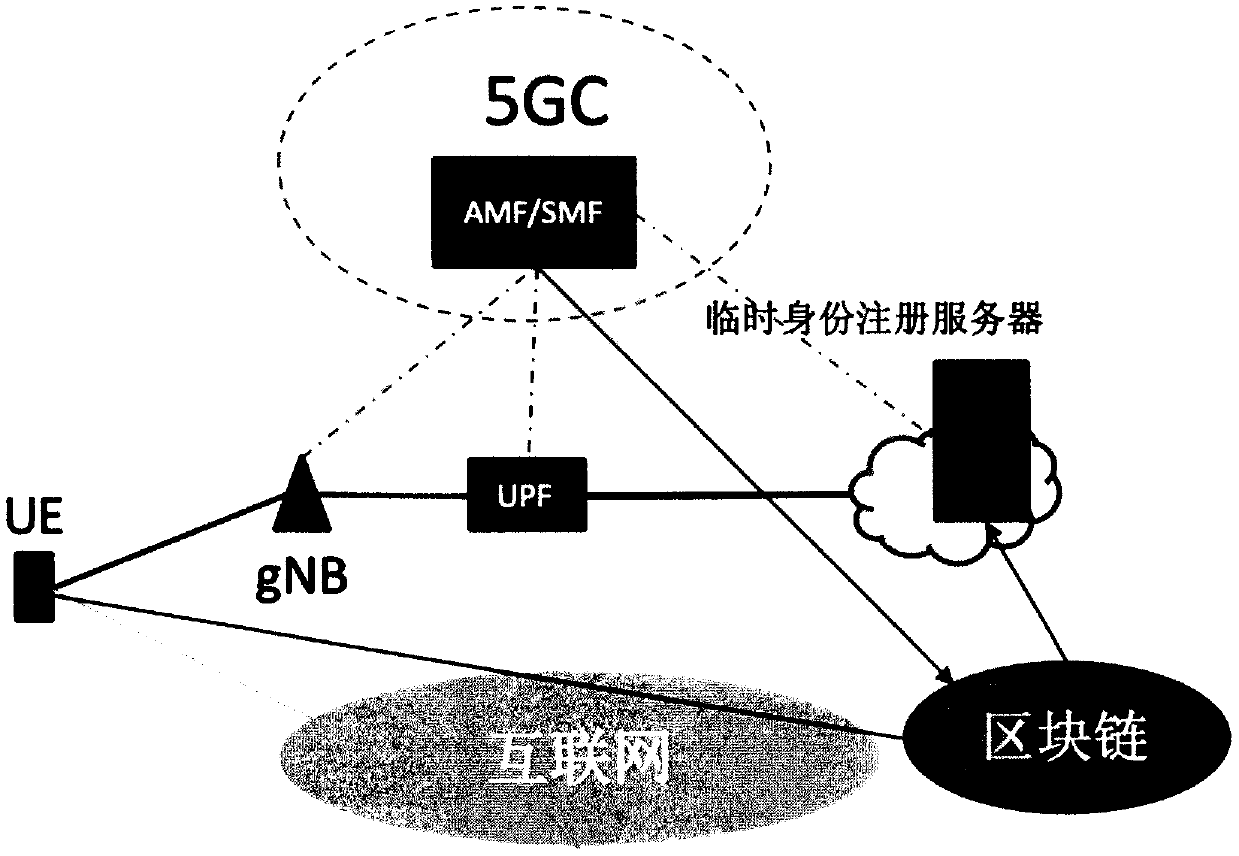
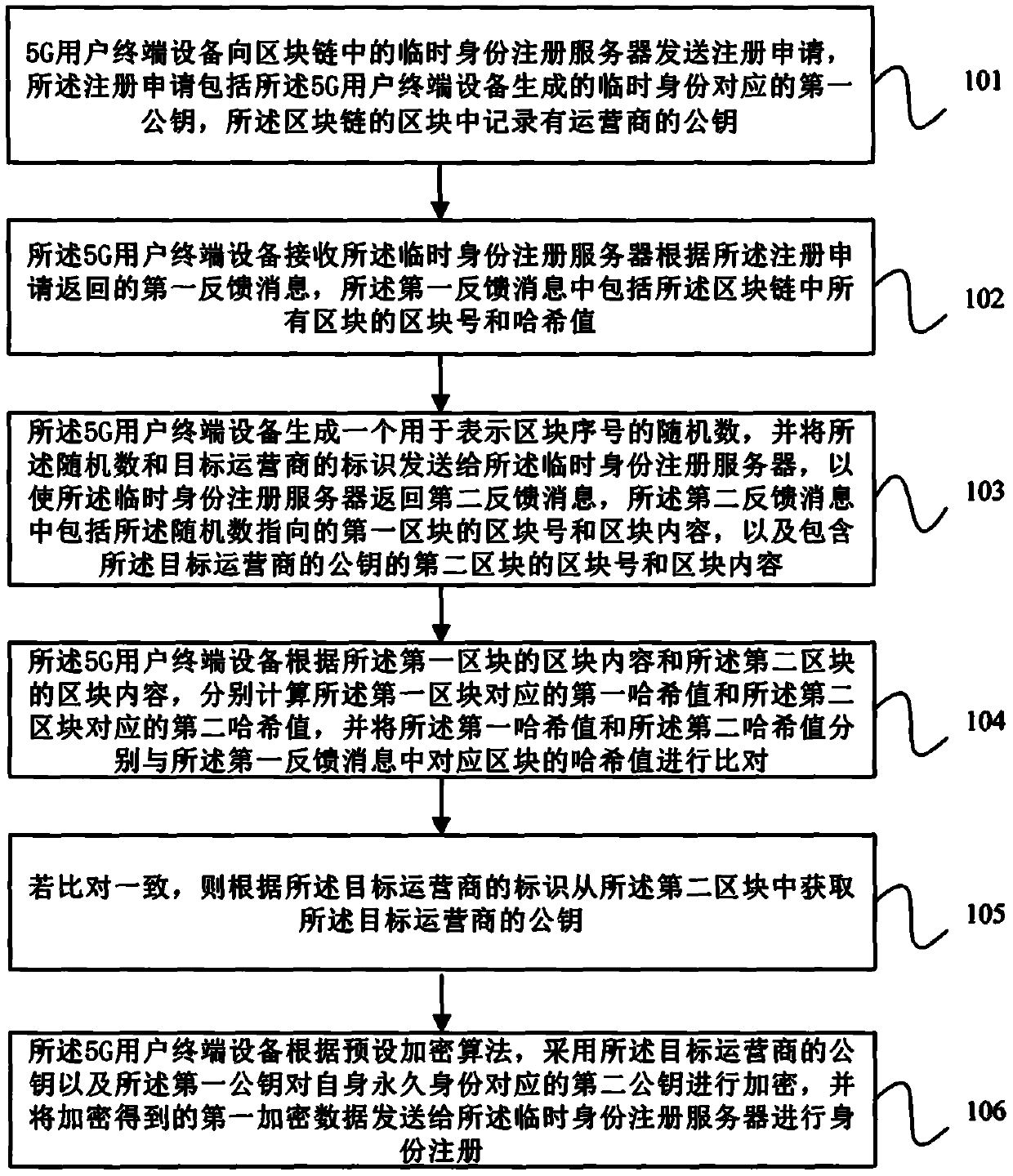
PendingCN111148094AImprove securityImprove confidentialityUser identity/authority verificationSecurity arrangementConfidentialityTerminal equipment
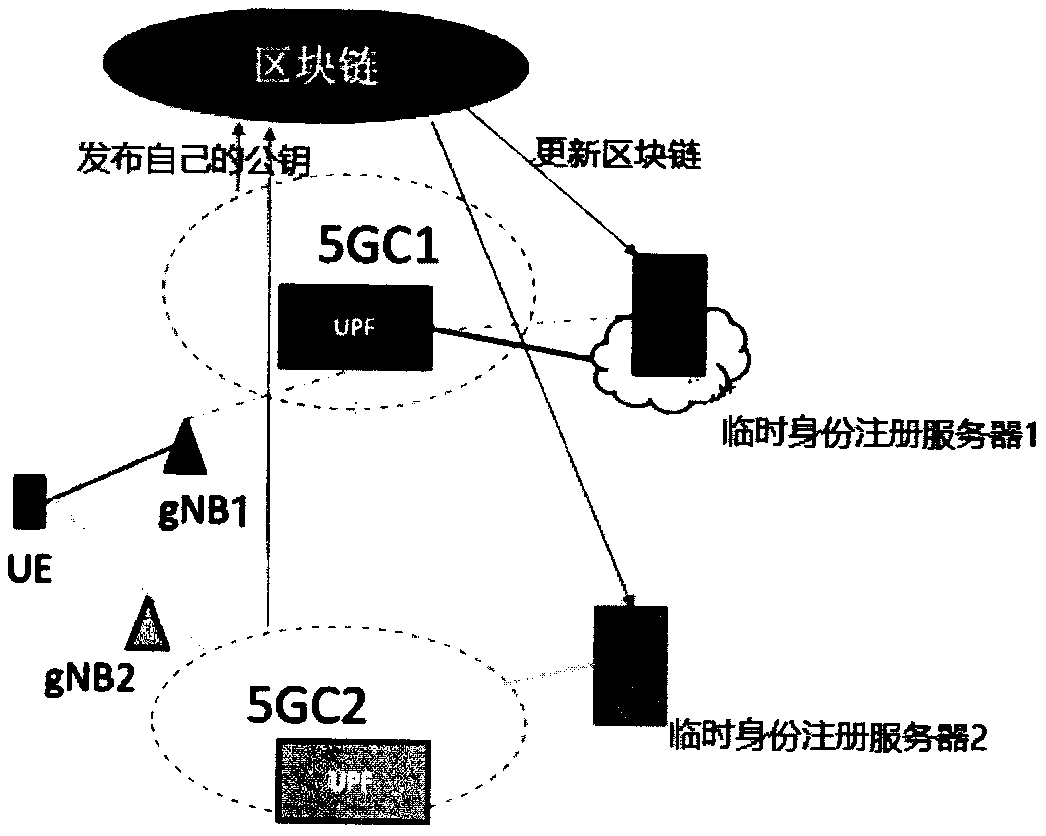
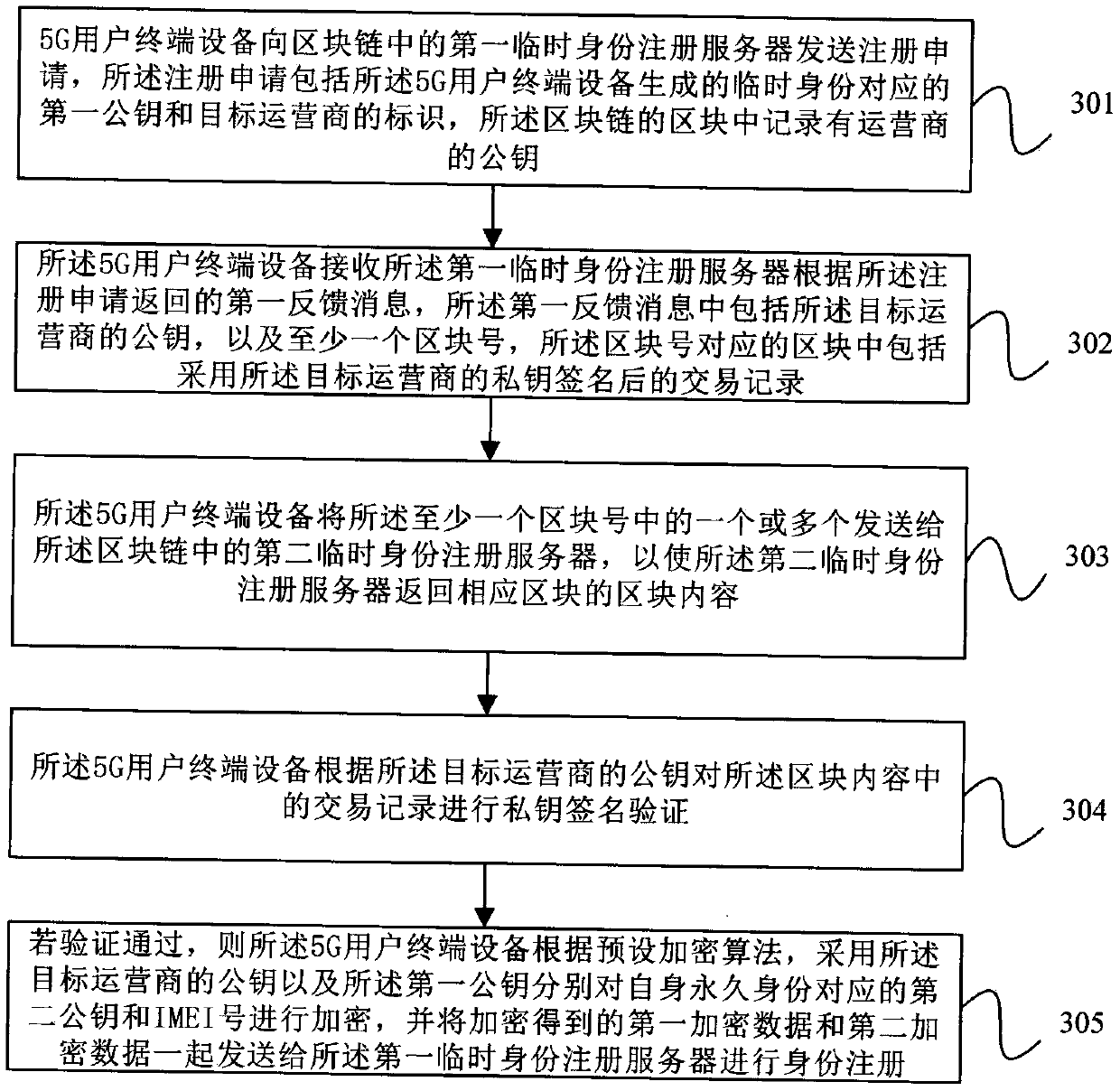
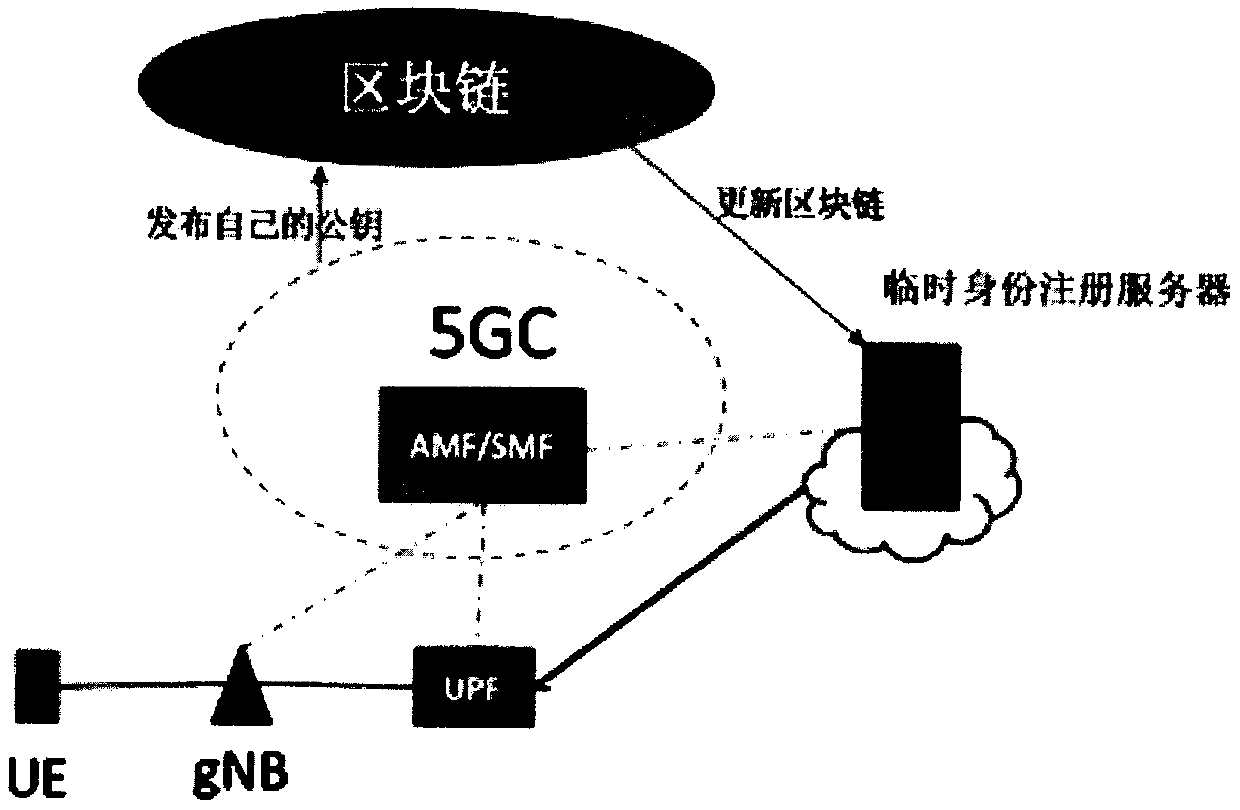
The embodiment of the invention provides a registration method of a 5G user terminal, user terminal equipment and a medium, and the method comprises the steps of enabling the 5G user terminal equipment to send a registration application to a temporary identity registration server in a block chain, wherein the registration application comprises a first public key corresponding to a temporary identity generated by the equipment; receiving block information returned by the temporary identity registration server, and performing hash value verification on the block chain and blocks in the block chain according to the block information; when the verification is passed, searching for a public key of the target operator from the block information returned by the temporary identity registration server according to the identifier of the target operator; and according to a preset encryption algorithm, encrypting a second public key of the target operator by adopting the public key of the target operator and the first public key, and sending encrypted data obtained by encryption to a temporary identity registration server for identity registration. According to the scheme provided by the embodiment of the invention, the data security and confidentiality of the 5G user terminal equipment during identity registration are improved.
Owner:全链通有限公司
System and method of realizing dual logic channels of smart element
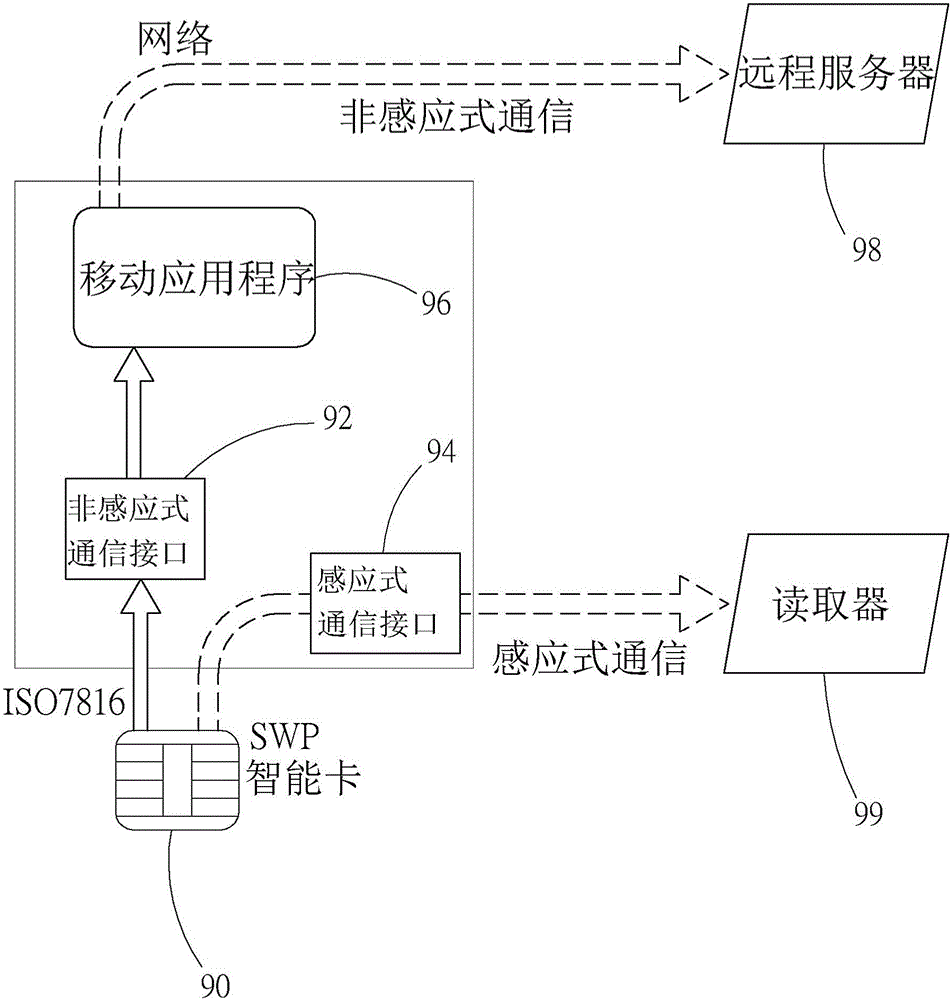
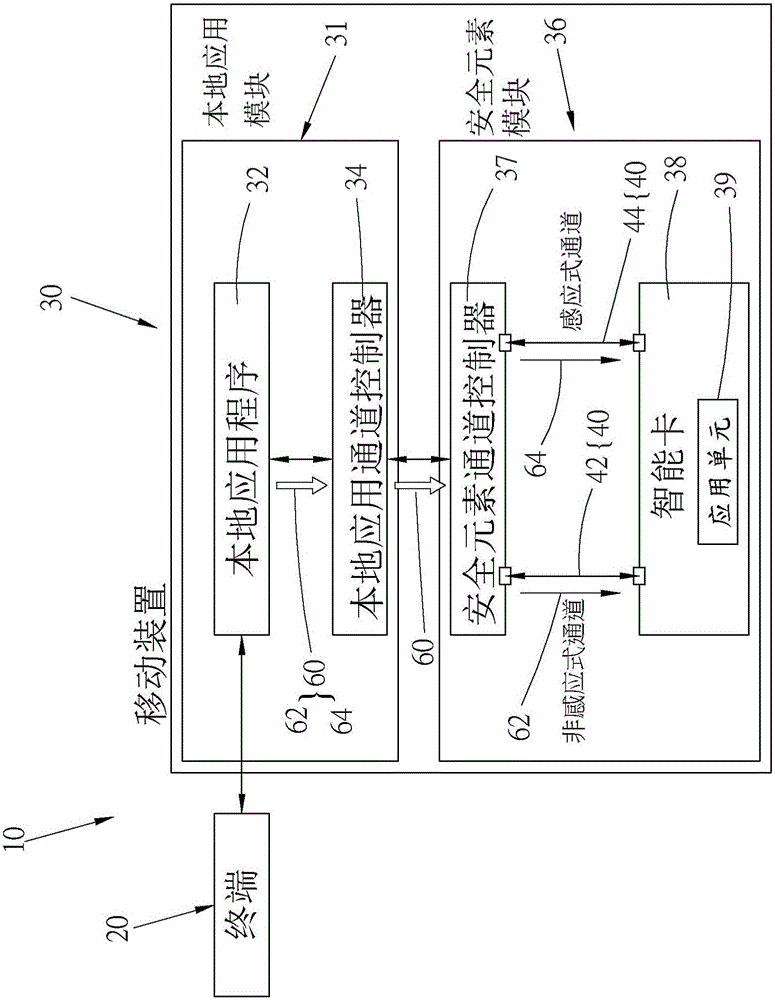
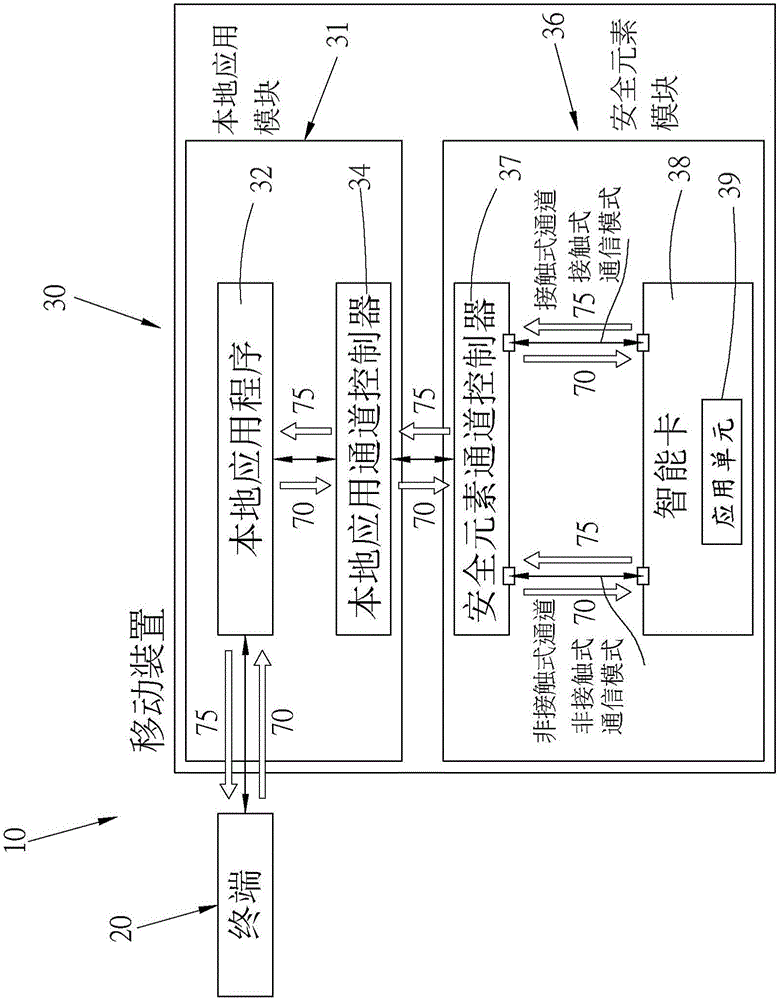
InactiveCN105938598AWide compatibilityProtection of confidentialityTransmissionProtocol authorisationComputer moduleComputer terminal
The invention provides a system and method of realizing dual logic channels of a smart element. The system includes a terminal; a mobile device; a local application module mounted in the mobile device for setting the mobile device as non-contactless or contactless communication; a secure element module mounted in the mobile device and having a smart element; and at least one channel mounted in the secure element module and connected with the smart element. The local application module emits a communication mode request to the smart element through the channel and then the smart element returns a signal to the terminal, completing a trading or an identification. The system also provides a method of realizing dual logic channels of a mart element.
Owner:GOTRUSTID INC
Registration method of 5G user terminal, user terminal equipment and medium
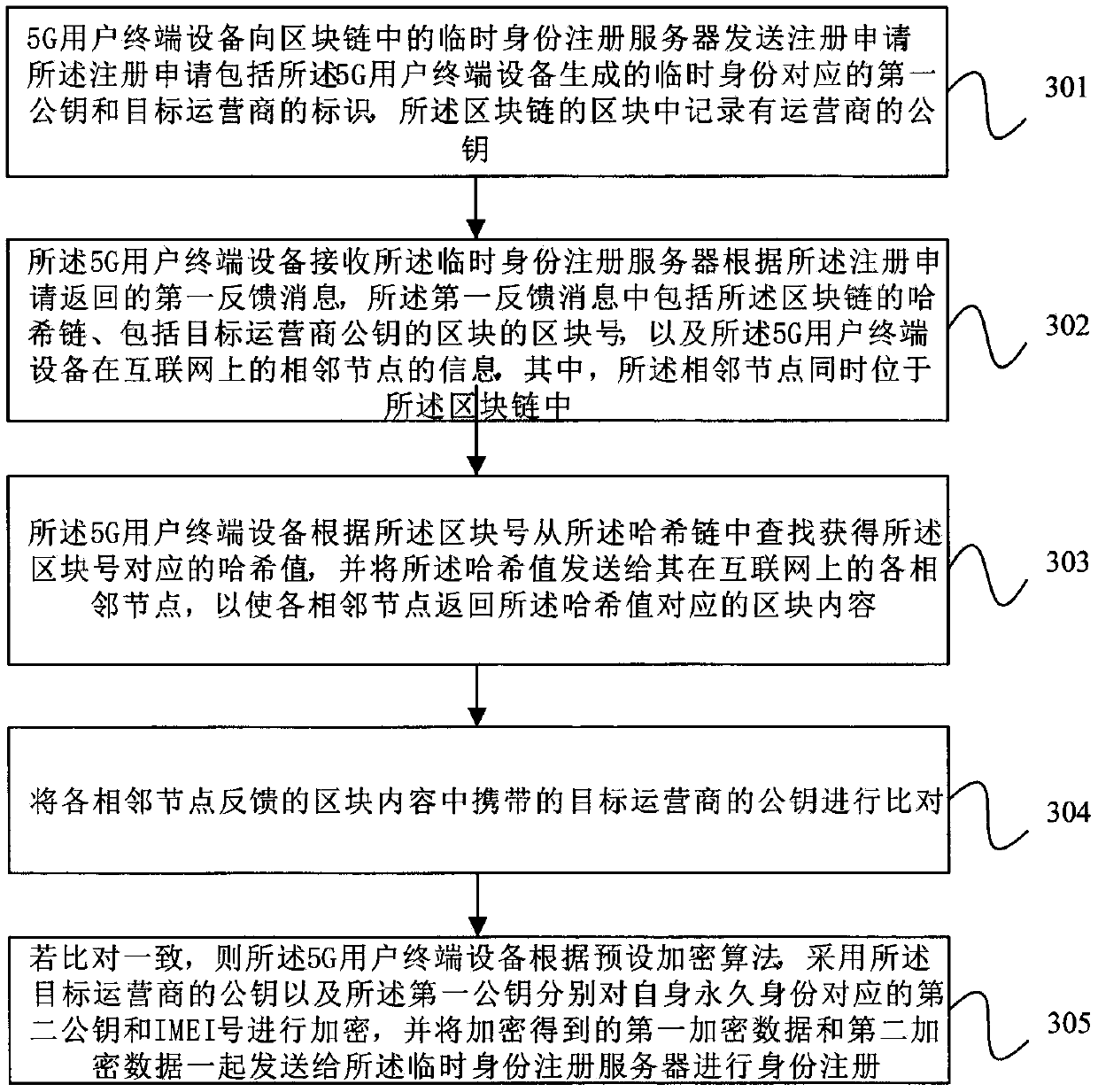
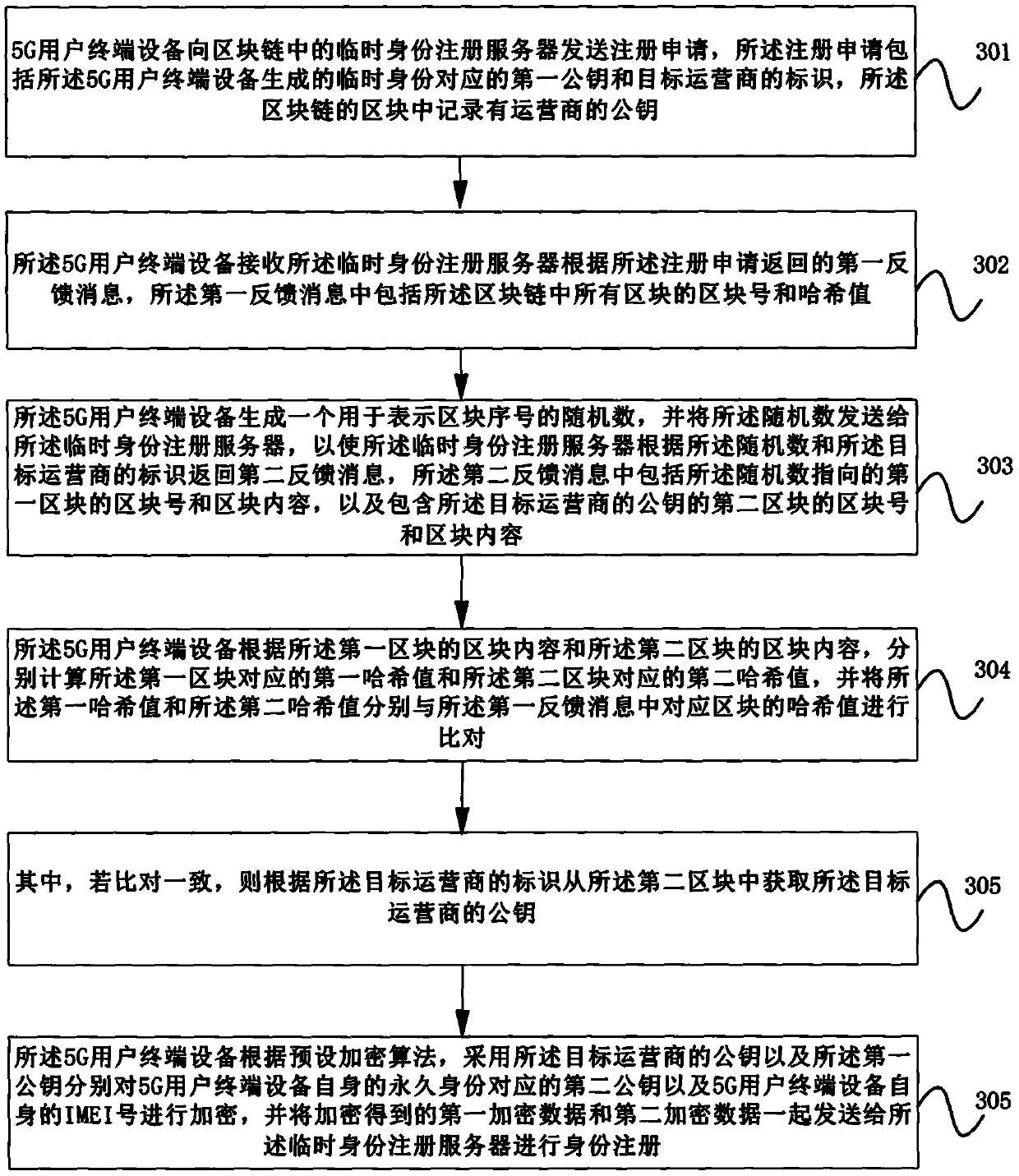
PendingCN111132149AImprove securityAvoid substitutionSecurity arrangementConfidentialityThe Internet
The embodiment of the invention provides a registration method of a 5G user terminal, user terminal equipment and a medium. A third public key of a target operator, a block number of a block includingthe third public key and information of an adjacent node of the 5G user terminal equipment on the Internet are acquired from a temporary identity registration server, the block content correspondingto the block number is obtained from the adjacent node, and the third public key fed back by the temporary identity registration server is verified through the obtained block content, so that the third public key is prevented from being tampered or replaced, and the data security and confidentiality in the 5G UE registration process are improved.
Owner:全链通有限公司
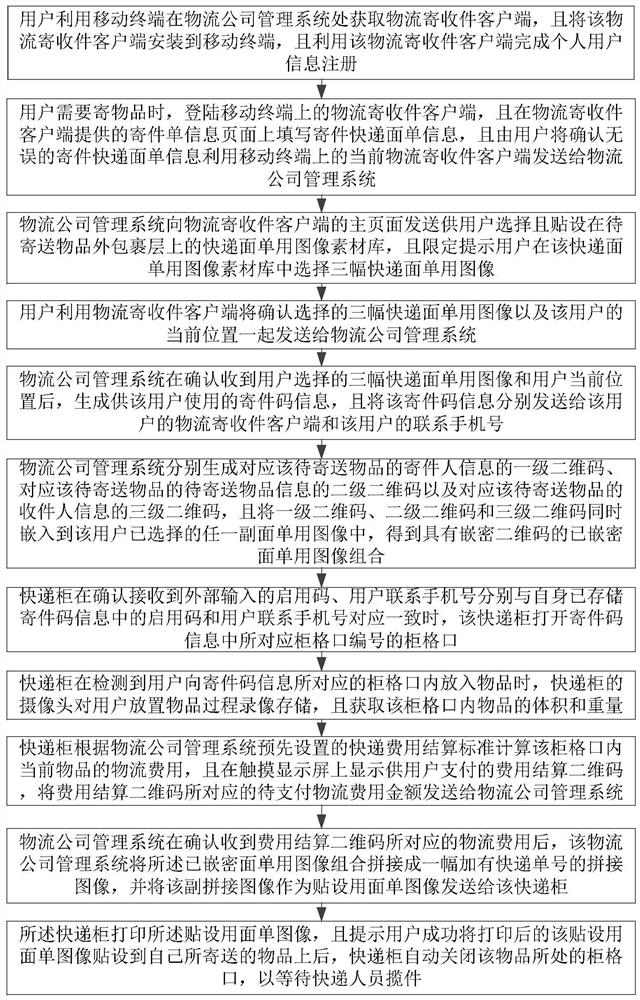
Modern logistics cost intelligent settlement method
PendingCN112668955AEasy to sendEasy to payPayment architectureFranking apparatusManagement systemOperating system
The invention relates to a modern logistics cost intelligent settlement method, and the method comprises the steps that a user fills in the information of a sending express sheet for sending through a logistics sending and receiving client installed at a mobile terminal; a logistics company management system allocates an express cabinet suitable for the distance position of a current user and express sending code information used when the user places articles to cabinet cells of the express cabinet, and then generates an embedded secret express sheet image combination embedded with express sending and receiving information two-dimensional codes according to three express sheet images selected by the user. Under the condition that the user does not need to go to a logistics company website, the to-be-sent object can be placed in the cabinet grid opening of the corresponding express cabinet, the express cabinet accurately calculates the logistics cost needing to be paid by the user, and finally, after the user successfully pays the logistics cost, an express sheet image for pasting corresponding to the current to-be-sent object is printed. In this way, the logistics cost needing to be paid by the user is intelligently obtained, and the user can conveniently complete sending and cost payment of the to-be-sent object nearby.
Owner:ZHEJIANG WANLI UNIV
Registration method of 5G user terminal, user terminal equipment and medium
ActiveCN111132156AAvoid substitutionPrevent tamperingUser identity/authority verificationSecurity arrangementConfidentialityTerminal equipment
The embodiment of the invention provides a registration method of a 5G user terminal, user terminal equipment and a medium. A public key of a target operator is obtained through a first path between the 5G user terminal equipment and a first temporary identity registration server, and the public key of the target operator acquired by the first path is verified through a second path between the 5Guser terminal equipment and a second temporary identity registration server, so that the public key of the target operator can be prevented from being replaced or tampered in the issuing process. Furthermore, a second public key corresponding to the permanent identity of the target operator is encrypted by adopting the public key of the target operator and a first public key corresponding to the temporary identity of the target operator through a preset encryption algorithm after the public key of the target operator is obtained, and the encrypted data is sent to the temporary identity registration server for identity registration, so that the security and confidentiality of sending the permanent identity public key to the temporary identity registration server by the 5G user terminal equipment can be improved.
Owner:全链通有限公司
A Safe Distributed Data Deduplication Method
ActiveCN103763362BProtection of confidentialitySatisfy deduplicationTransmissionShort ValueComputer hardware
The invention discloses a safe distributed duplicated data deletion method. According to the method, a file is segmented into fragments through a secret sharing technology without any encryption mechanism. The shared fragments are distributed in a plurality of independent storage servers. In addition, in order to support reduplication removing, a different short value is calculated and sent to the storage servers as the indicator of one fragment. Only possessors uploading data for the first time need to carry out such calculation and distribution of secrete sharing, and then people possessing the same data copies do not need to calculate and store the sharing any longer. When the data copies are restored, users must access the storage servers with the minimum quantity to reconstruct the data through authentication and acquisition of the secret sharing. In other words, the secret sharing of the data can only be accessed by the users who possess the same copies and are authorized.
Owner:XIDIAN UNIV
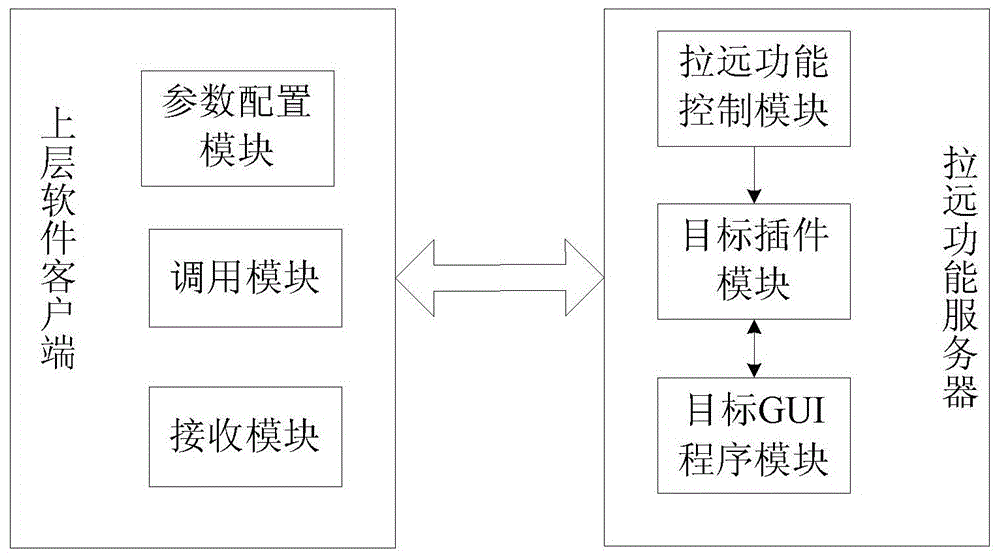
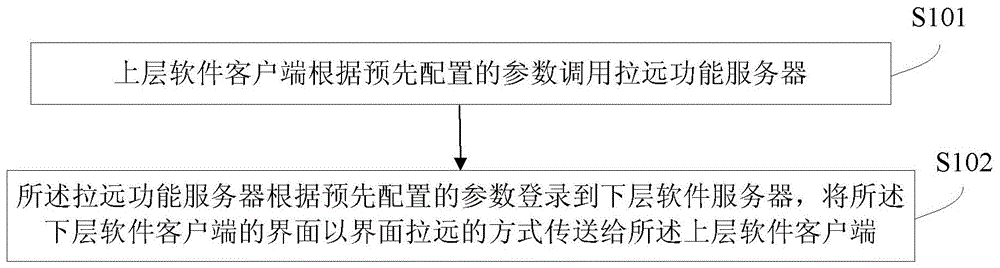
Method for extending software functions, upper-layer software client and remote function server
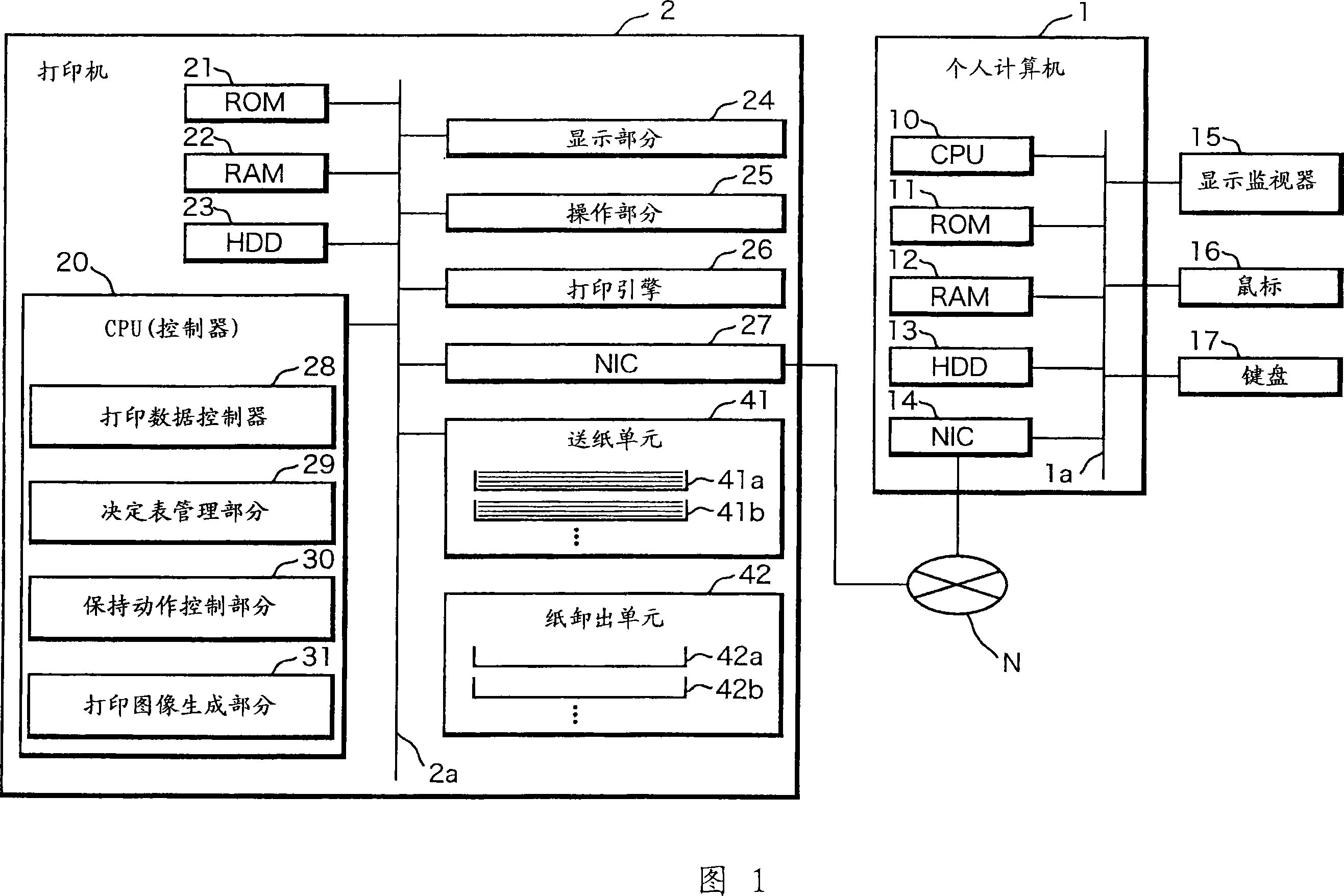
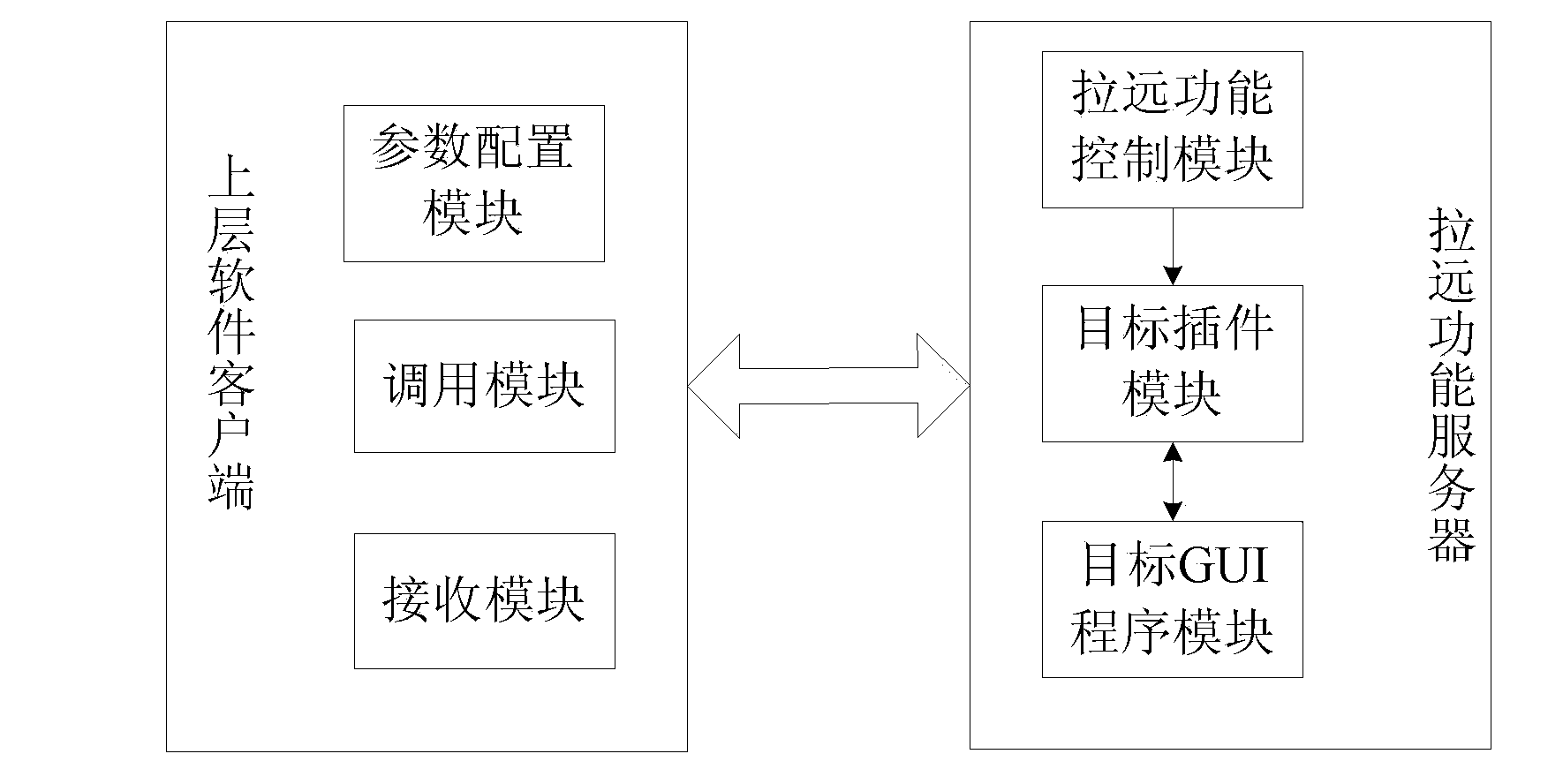
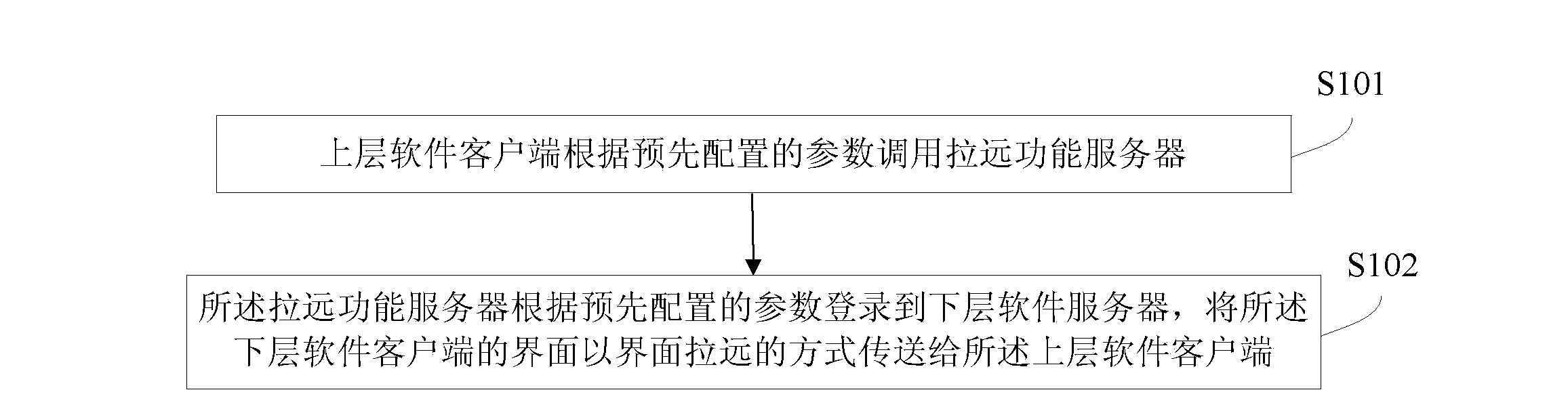
ActiveCN103425517AFunction increaseImprove functional requirementsMultiprogramming arrangementsTransmissionServer logGraphics
The invention discloses a method and a system for extending software functions, an upper-layer software client and a remote function server. The method includes that the upper-layer software client calls the remote function server according to parameters configured in advance; the remote function server logs in a lower-layer software server according to the parameters configured in advance, and an interface of a lower-layer software client is transmitted to the upper-layer software client in an interface remote mode. The system comprises the upper-layer software client and the remote function server. The upper-layer software client comprises a parameter configuring module, a calling module and a receiving module. The remote function server comprises a target plug-in module and a target graphical user interface (GUI) program module. The method, the system, the upper-layer software client and the remote function server have the advantages that the software functions are extended in the interface remote mode under the condition that original software function codes are not changed, and the safety and the confidentiality of lower-layer software are protected.
Owner:ZTE CORP
Card distributing user terminer, paying center, and method and system for protecting repaid card data
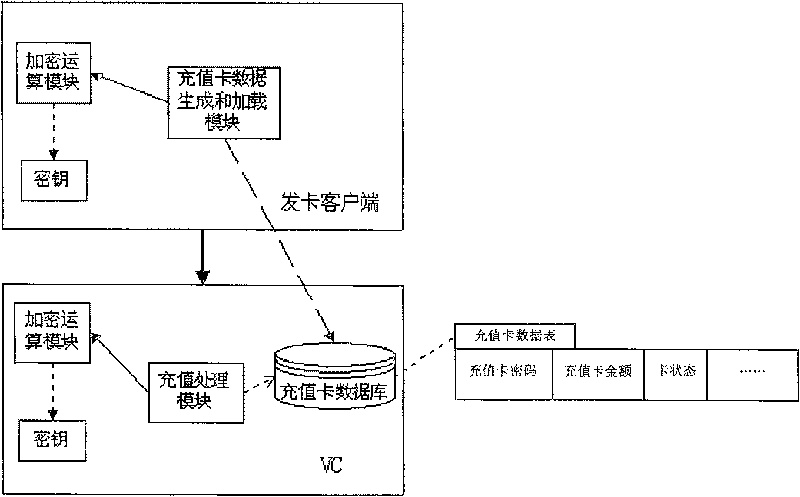
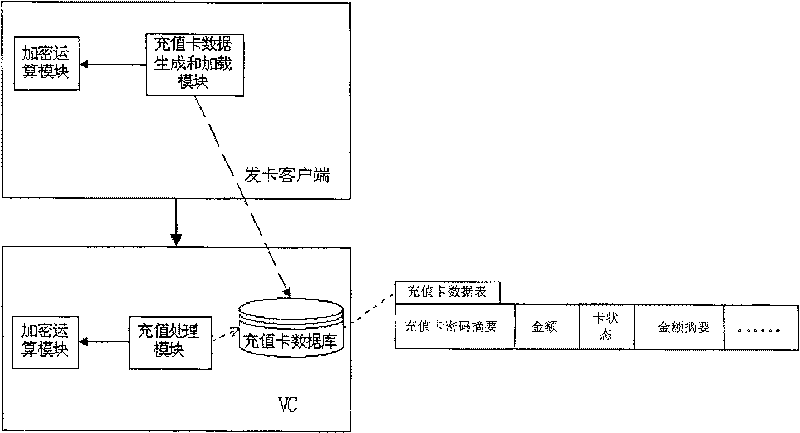
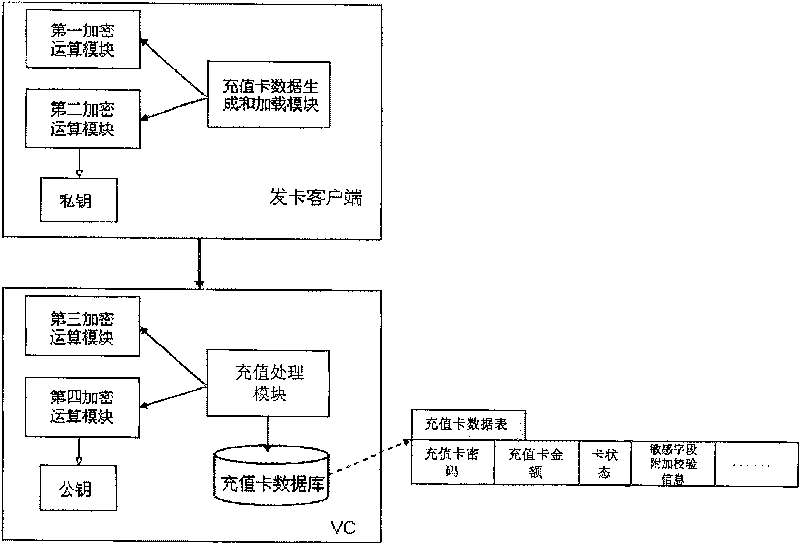
InactiveCN1913547BImprove securityPrevent forgeryPrepayment telephone systemsIntelligent NetworkData bank
This invention discloses a method for protecting data of charge cards of a charge center in an intelligent network including: applying an encrypted cryptographic key in the public key system to encrypt information in the charge card data to generate attached verification information and loading recordings of charge cards containing said attached check information, when a user is charged, the intelligent network charge center applies a de-ciphered cryptographic key corresponding to the key to de-cipher the attached verification information corresponding to the charge center. This invention alsodiscloses a data encrypting method, a de-ciphering method to charge card data, a system for protecting the charge card data, a card-issuing customer end and a charge center of an intelligent network.
Owner:HUAWEI TECH CO LTD
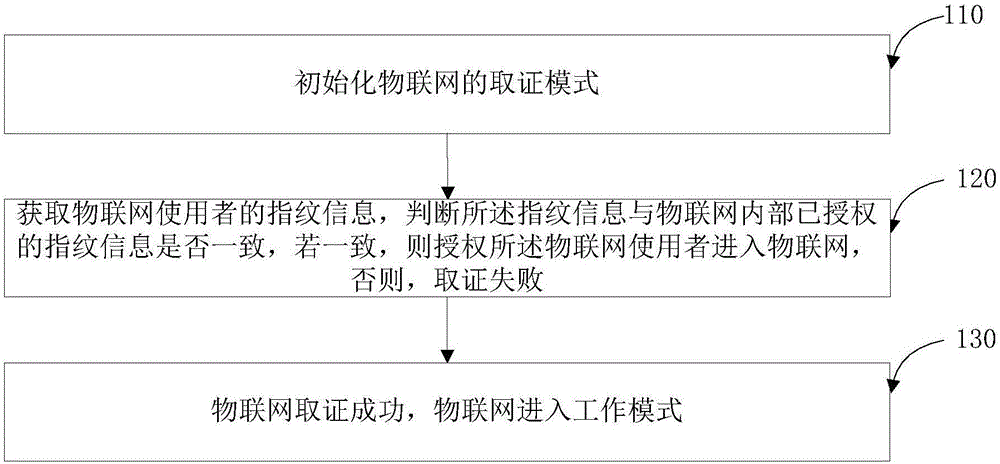
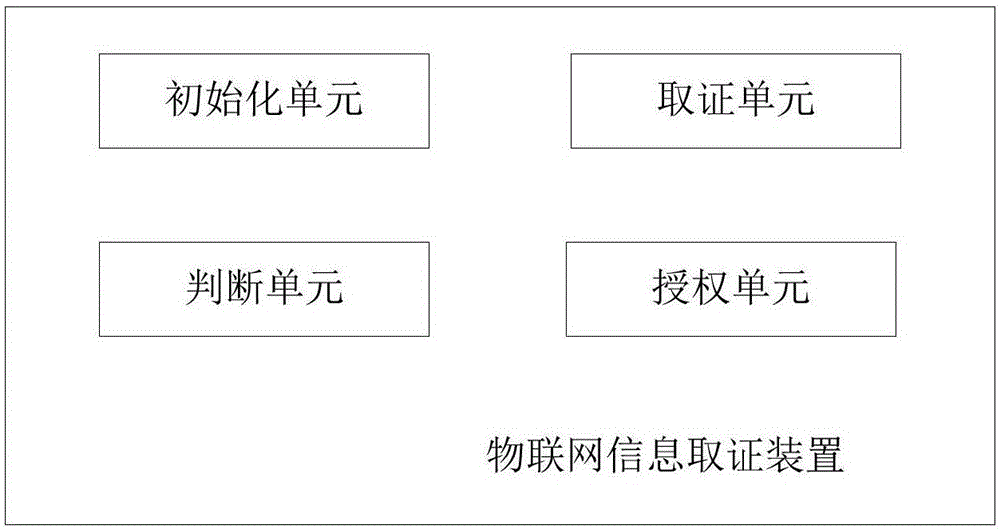
Information evidence obtaining method and device for Internet of Things
InactiveCN106650489AProtection securityProtection of confidentialityDigital data protectionDigital data authenticationConfidentialityThe Internet
The invention relates to the field of Internet of Things, in particular to an information evidence obtaining method and device for the Internet of Things. The method includes the steps that an Internet of Things evidence obtaining mode is initialized; fingerprint information of an Internet of Things user is acquired; whether the fingerprint information is consistent with authorized fingerprint information in the Internet of Things or not is judged, if yes, the Internet of Things user is authorized to has access to the Internet of Things, and otherwise, evidence obtaining fails; after Internet of Things evidence obtaining succeeds, the Internet of Things enters a working mode. By means of the method and device, information evidence obtaining is provided for the Internet of Things, it can be guaranteed that all operators are qualified, specific user information can be traced in each time of operation, valid evidence can be collected, and the security and confidentiality of the Internet of Things are protected.
Owner:过冬
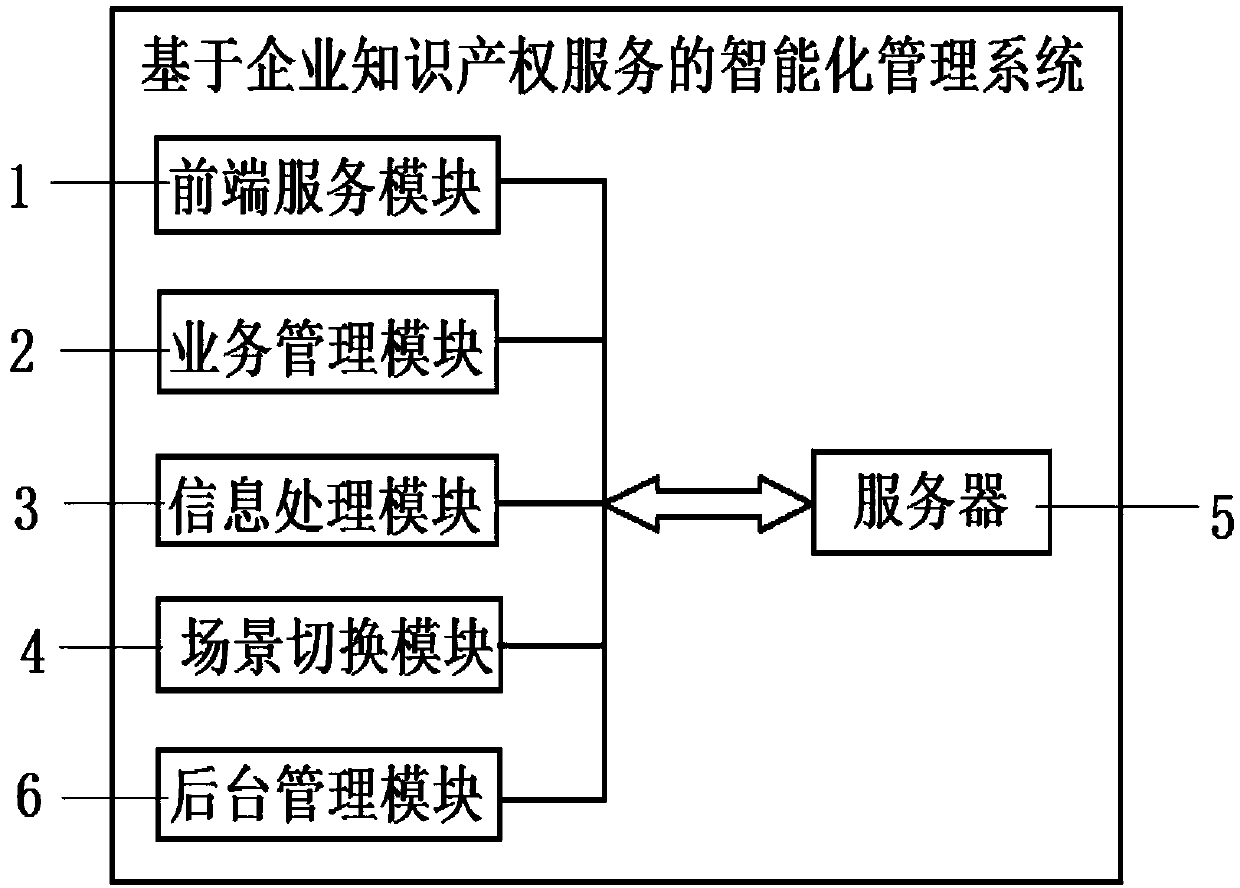
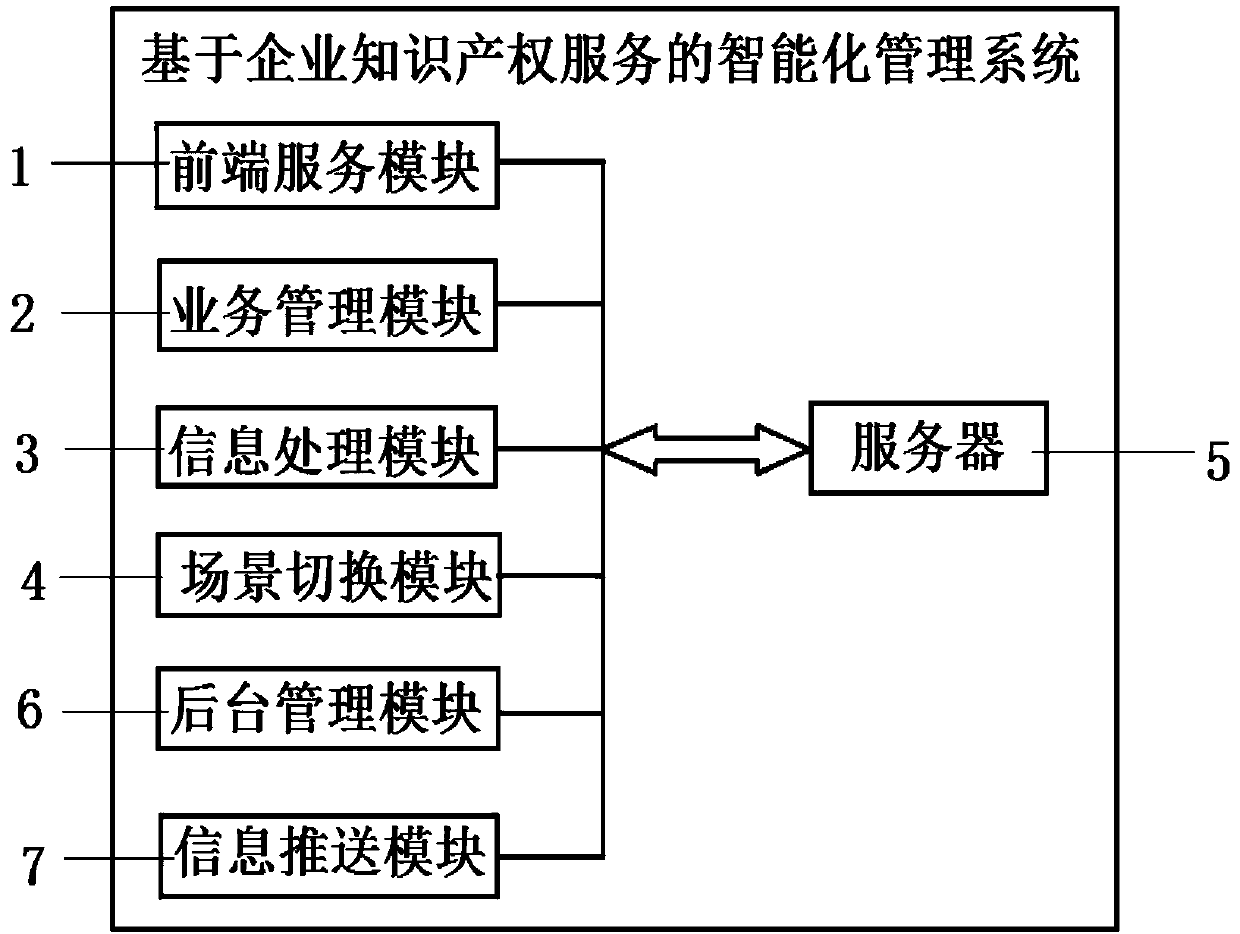
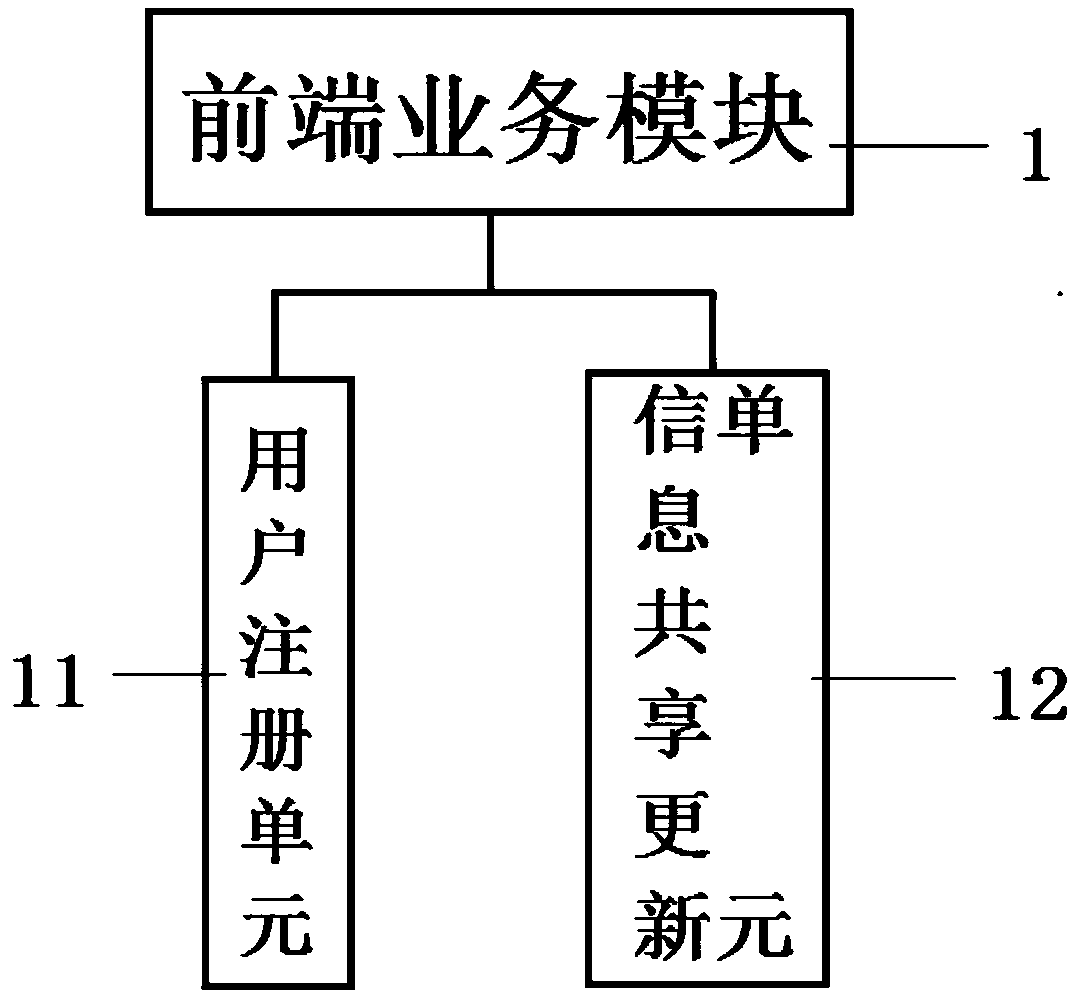
Intelligent management system based on enterprise intellectual property service
InactiveCN110866727AImprove work efficiencyEfficient processingOffice automationManagement systemEngineering management
The invention discloses an intelligent management system based on enterprise intellectual property service. The system comprises a front-end service module, a service management module, an informationprocessing module, a scene switching module, a server and a background management module, and the front-end service module, the service management module, the information processing module, the sceneswitching module and the background management module are electrically connected with the server; on one hand, an alarm subunit in the information processing module sends out prompt early warning information when the work progress lags behind, managers are prompted to carry out corresponding processing in time, and the effectiveness of enterprise intellectual property service management is improved; on the other hand, the managers with different authorities can be clearly distinguished by selecting a personal scene or an enterprise scene, so that the confidentiality of enterprise intellectual property rights is protected; in addition, the system uses the background management module to filter invalid data, and the work efficiency of intellectual property data management is improved.
Owner:苏州绿诚企业管理有限公司
Registration method of 5G user terminal, user terminal equipment and medium
ActiveCN111148213AImprove securityImprove confidentialitySecurity arrangementConfidentialityTerminal equipment
The embodiment of the invention provides a registration method of a 5G user terminal, user terminal equipment and a medium. The method comprises the following steps: firstly, sending block numbers andhash values of all blocks to 5G UE; according to a random number sent by the 5G UE, sending the block contents of the first block pointed by the random number and the second block containing the public key of the target operator to 5G UE, so that the 5G UE can obtain the hash value of the block based on the received block numbers and hash values of all blocks; verifying the contents of the firstblock and the second block; after the verification is passed, obtaining a public key of a target operator from the second block. The second public key corresponding to the permanent identity of the target operator is encrypted through the preset encryption algorithm, the public key of the target operator and the first public key of the target operator, and the encrypted data is sent to the temporary identity registration server for identity registration, so that the data security and confidentiality in the 5G UE registration process are improved.
Owner:全链通有限公司
Scientific research big data closed-loop information management method
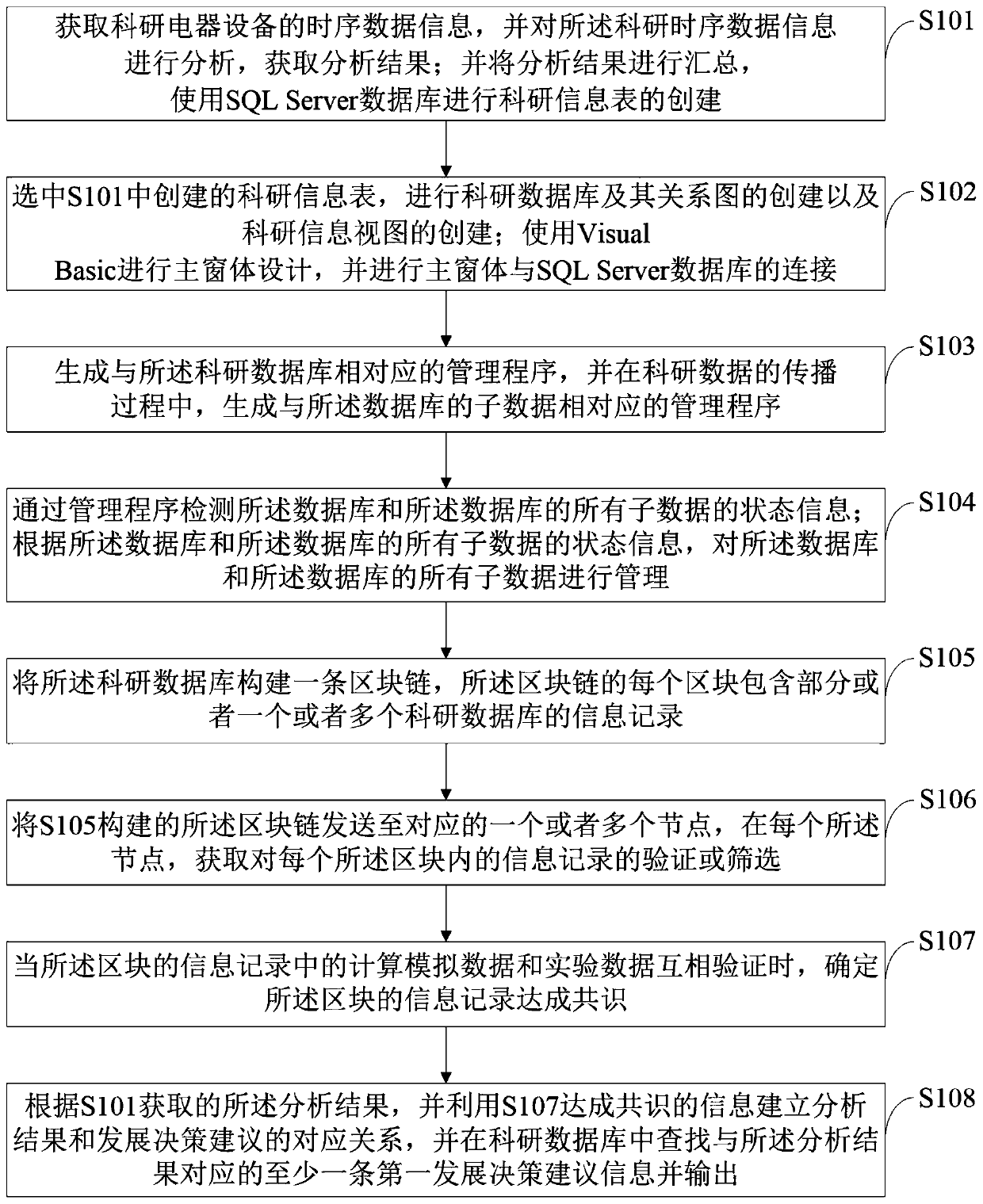
PendingCN111259080AGood combination consistencyImprove accuracyDatabase distribution/replicationSpecial data processing applicationsData informationSql server
The invention belongs to the technical field of information management, and discloses a scientific research big data closed-loop information management method, which comprises the following steps: acquiring data information of scientific research equipment, analyzing and summarizing the data information, creating a scientific research database, and managing the scientific research database througha management program; constructing a block chain for the scientific research database, verifying or screening the information record in the block, and determining that the information record of the block reaches a consensus; and establishing a corresponding relationship between the analysis result and the development decision suggestions, searching at least one piece of first development decisionsuggestion information corresponding to the analysis result in a scientific research database, and outputting the first development decision suggestion information. According to the invention, the scientific research information table is created through the SQL Server database, the operation is simple, the combination coherence and integration of information are good, and the connection method issimple. The data management and analysis flexibility can be improved, the scientific research big data closed-loop information management efficiency is high, the accuracy is good, and policy guidanceand suggestions are provided for scientific research risk avoidance.
Owner:DALIAN JIAOTONG UNIVERSITY
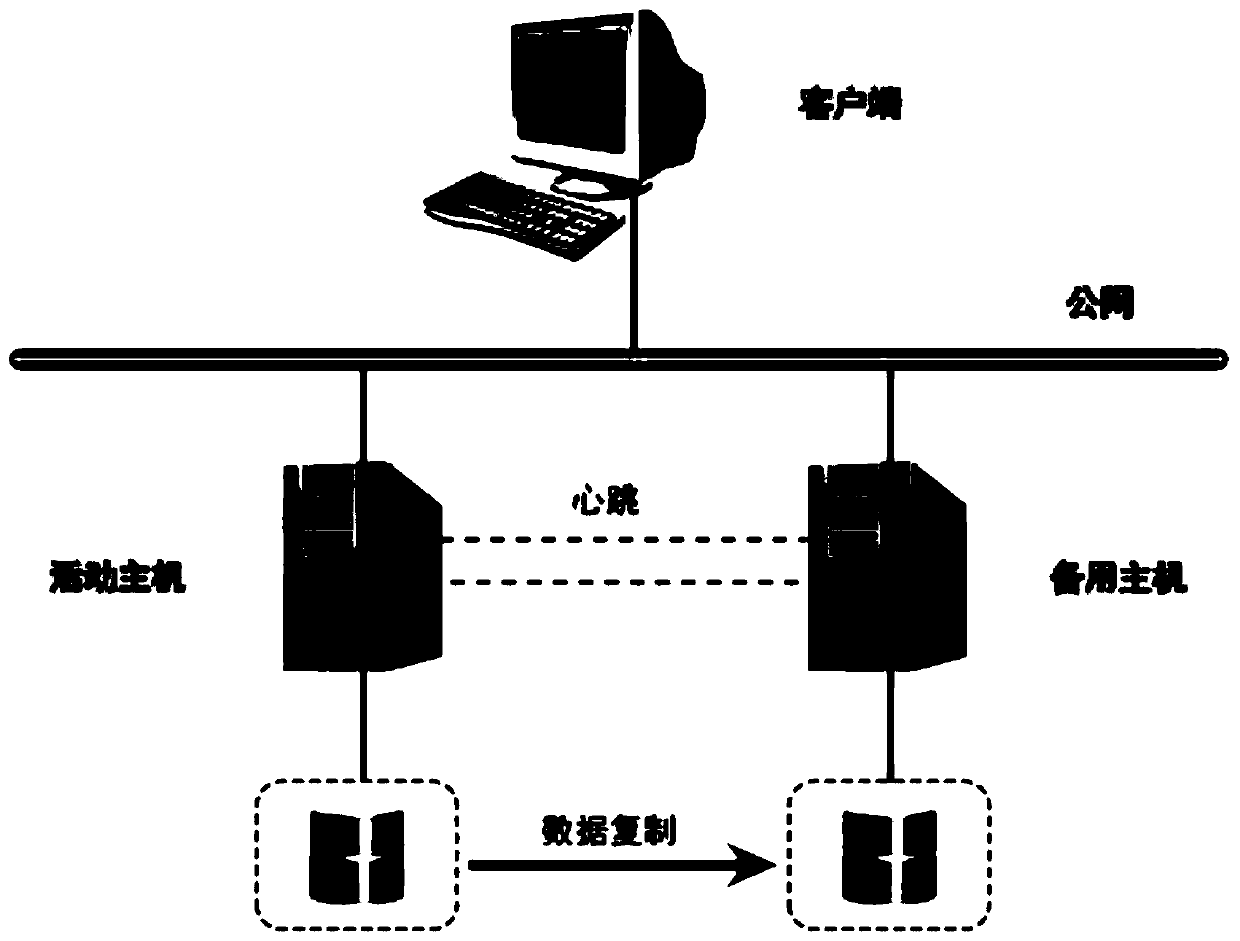
Data security backup system and method
PendingCN111078474AProtection securityProtection of confidentialityRedundant hardware error correctionConfidentialityServer
The invention provides a data security backup system and a method, and the system comprises a main server and a backup server, and the main server and the backup server employ a dual hot standby deployment mode. The method comprises the steps of copying the data in the main server to a backup server in real time by using a data real-time mirroring method, and monitoring the running state of the application resources in real time; according to the monitored running state of the application resources, intelligent early warning and strategy switching are carried out; according to the system, databackup, data transfer and even system switching can be completed in a very short time, so that the service is not influenced, and the security and confidentiality of data can be greatly protected.
Owner:SHAANXI NANLIANG MINING
Method for extending software functions, upper layer software client and remote function server
ActiveCN103425517BFunction increaseImprove functional requirementsMultiprogramming arrangementsTransmissionGraphicsServer log
Owner:ZTE CORP
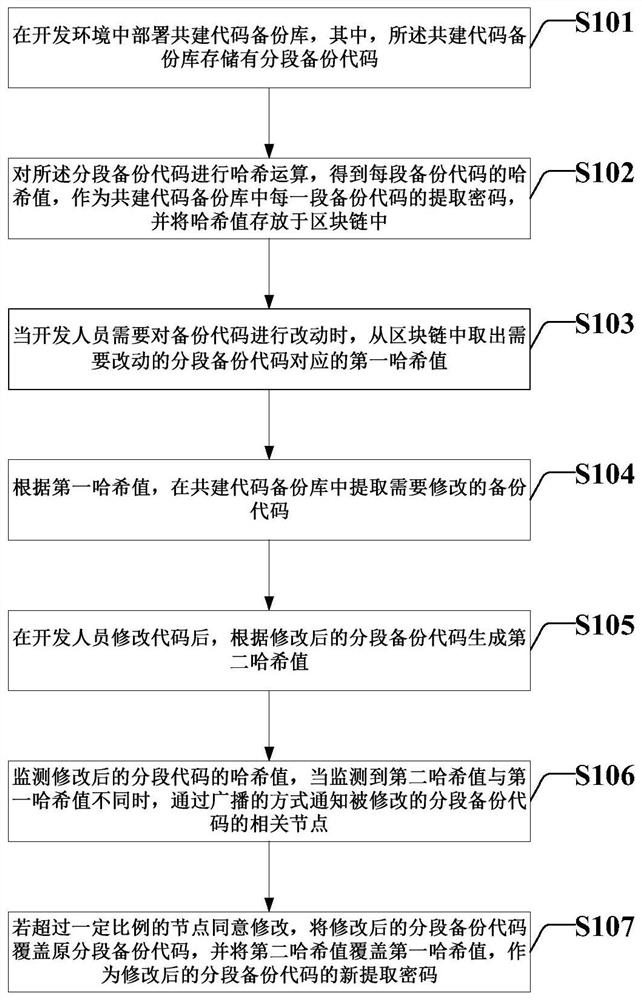
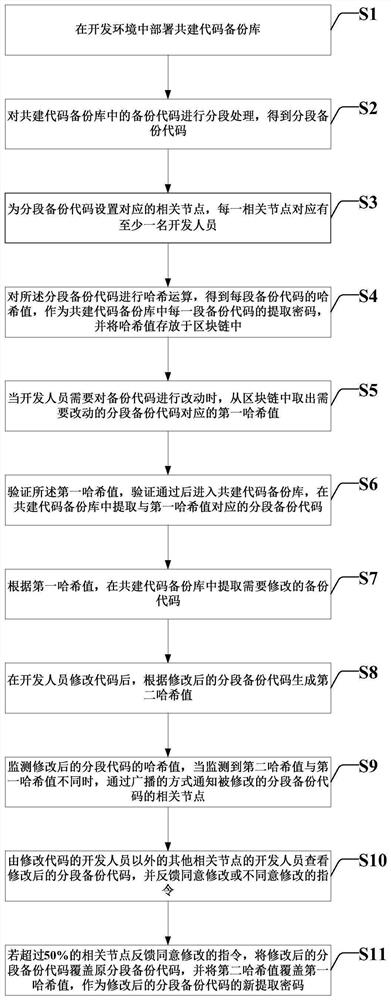
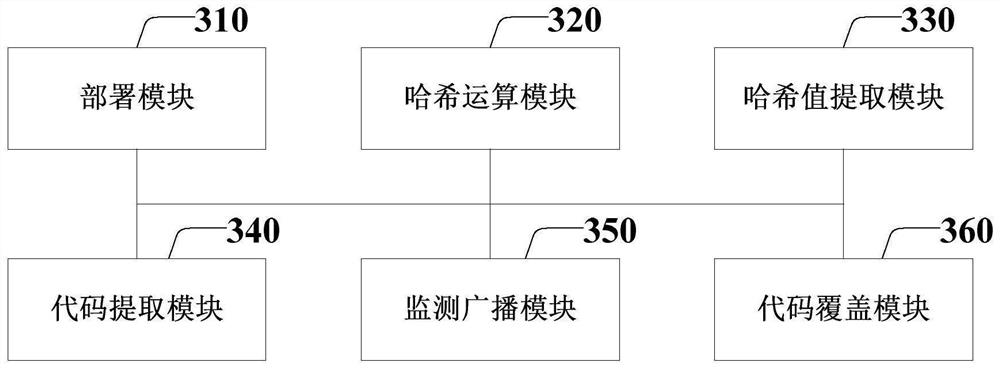
Block chain-based co-construction code backup library processing method and system
PendingCN113220503AProtection of confidentialityPrevent illegal tamperingDigital data protectionDigital data authenticationBlockchainDevelopment environment
The invention discloses a block chain-based co-construction code backup library processing method and system, and relates to the technical field of block chains. The method comprises the steps of deploying a co-construction code backup library in a development environment; performing Hash operation on the segmented backup code to obtain a Hash value, and storing the Hash value in a block chain; when a developer needs to change the backup code, extracting a first hash value corresponding to the segmented backup code needing to be changed from the block chain; according to the first hash value, extracting backup codes needing to be modified from a co-construction code backup library; after the developer modifies the code, generating a second hash value according to the modified segmented backup code; when the hash values are different, notifying related nodes of the modified segmented backup codes in a broadcast mode; and if the nodes exceeding a certain proportion agree to modify, covering the original segmented backup code with the modified segmented backup code, and covering the first hash value with the second hash value to serve as a new extraction password of the modified segmented backup code.
Owner:BANK OF CHINA
Method of generating a monitoring datagram
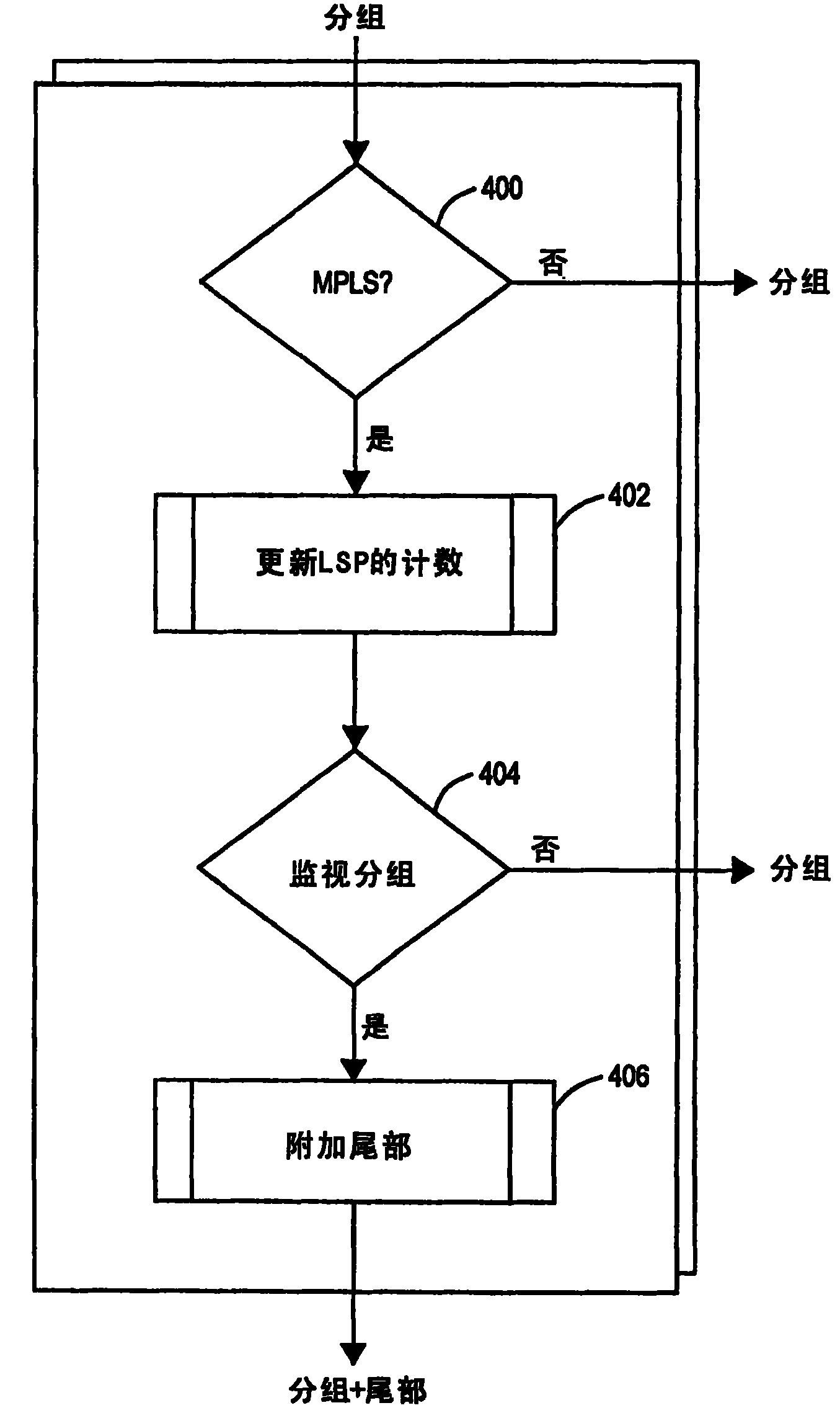
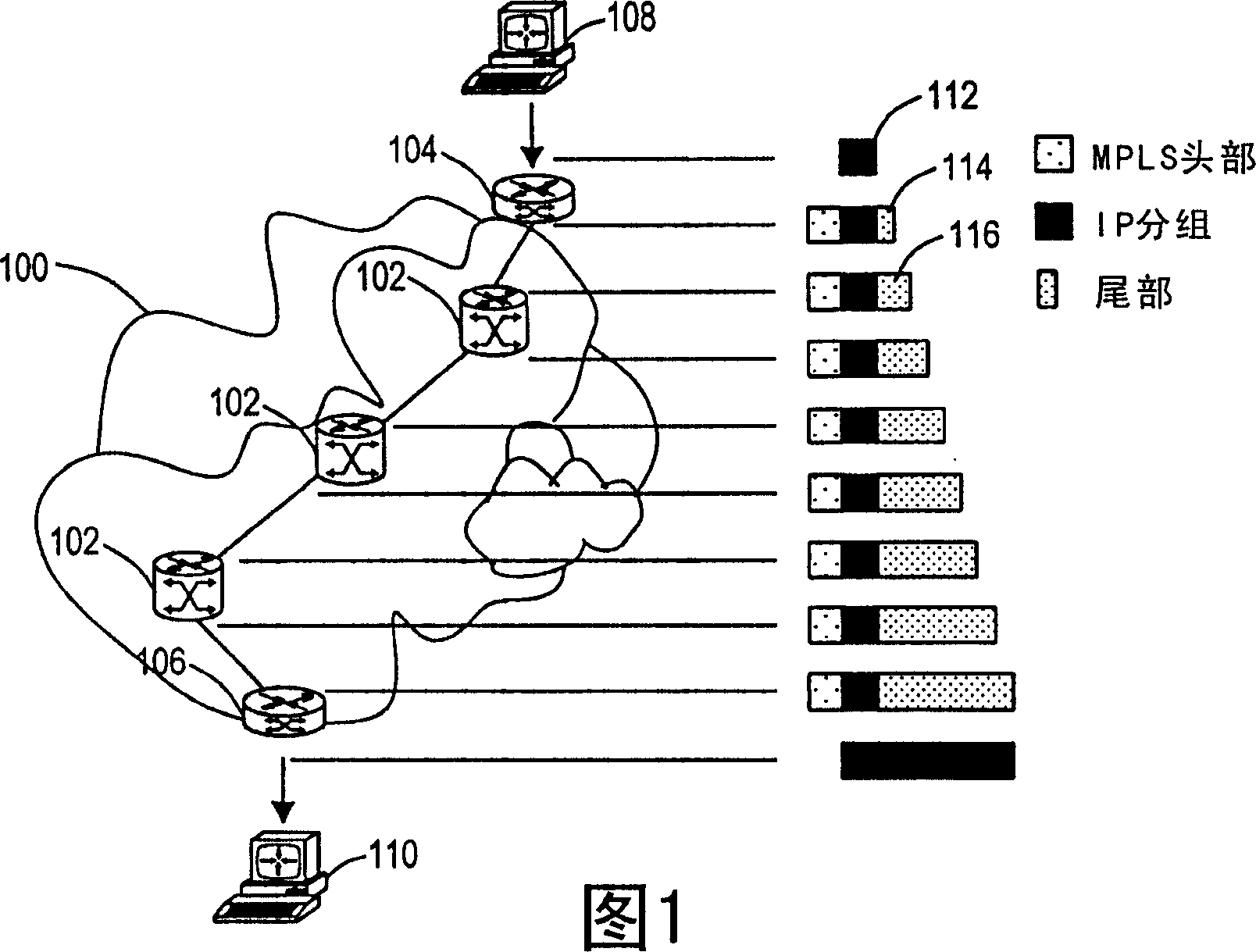
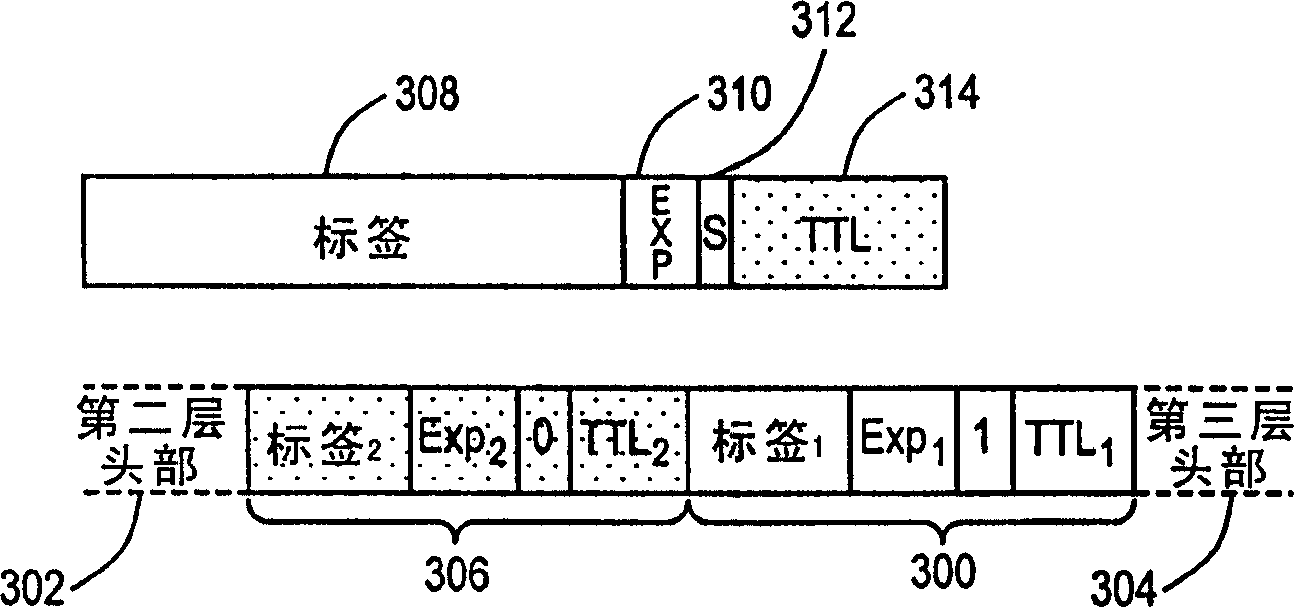
ActiveCN1710888BHigh precisionProtection of confidentialityData switching networksMonitoring statusPacket loss
In packet switched communications systems, a number of techniques exist for measuring packet loss, but each of these has respective disadvantages, each of varying degree. Consequently, the present invention provides a method of generating a test packet for measuring packet loss, where an initial packet is encapsulated with a first shim header (300), the encapsulated initial packet being encapsulated with a second shim header (306). The first shim header (300) has a label (308), the label (308) being indicative of a monitoring status of the test packet and used to identify the monitoring status of the packet as the test packet traverses a Label Switched Path of a Multi-Protocol Label Switched network. An advantage of using this technique is that the trailers of the test packet can be easily forwarded to an Internet Protocol (IP) address of a monitoring station, when the initial packet is an IP packet.
Owner:VIAVISOLUTIONS INC
Means for content security at the service level
ActiveCN107852405BImprove integrityProtection of confidentialityTransmissionSecurity arrangementConfidentialityData storing
Existing approaches to security in networks such as the oneM2M network are limited. For example, content may only be protected if it is transmitted between mutually trusted entities. Here, the integrity and confidentiality of the content in the M2M network is protected. Such content may be "stationary" such that the content is stored at the hosting node. Only authorized entities can store and retrieve data stored at the hosting node, and the data can be protected from a confidentiality and integrity perspective.
Owner:CONVIDA WIRELESS LLC
A mobile e-commerce security protection system based on a trusted computing platform
ActiveCN108462722BAvoid security issuesEnhance business securityTransmissionApplication serverTrusted Computing
Owner:上海黎德信息科技有限公司
A digital fingerprinting system and method for preventing pre-release game piracy
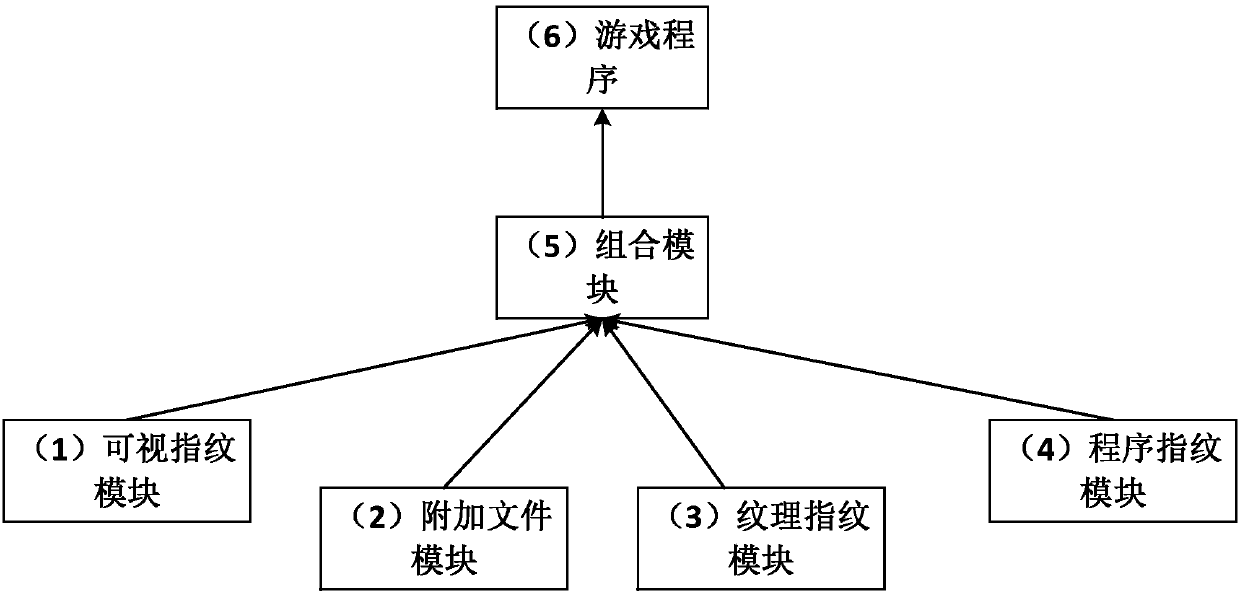
ActiveCN106126983BEasy to findEasy to operateProgram/content distribution protectionPre-Release VersionDigital fingerprint
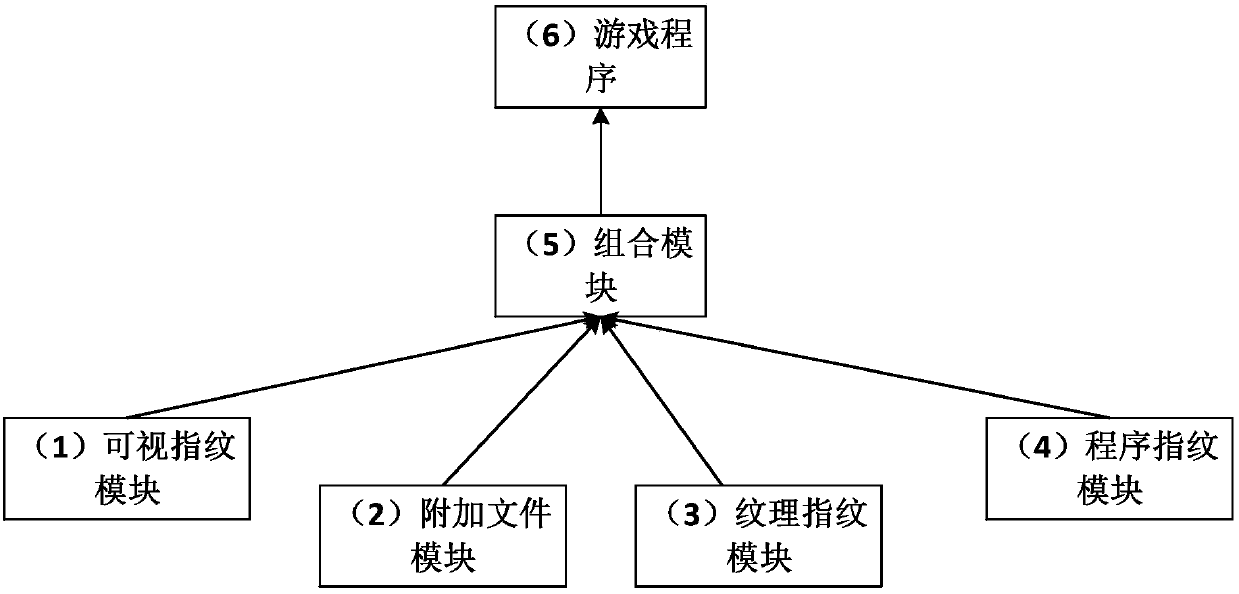
The invention comprises a digital fingerprint system and method for preventing piracy of a pre-release game. The system comprises a visual fingerprint module, an attached file module, a texture fingerprint module, a program fingerprint module and a combination module; the visual fingerprint module is used for adding digital fingerprints in significant pictures and / or characters of the game; the attached file module is used for adding fingerprint files for storing the digital fingerprints, wherein the fingerprint files can be set at user-defined positions; the texture fingerprint module is used for selecting at least one texture file in the game and adding the digital fingerprints in the texture files; the program fingerprint module is used for adding the digital fingerprints in at least one executable program file in the game; the combination module is used for selecting at least one of the visual fingerprint module, the attached file module, the texture fingerprint module and the program fingerprint module in a user-defined mode to add the digital fingerprints in game programs. The system and method have the advantages that a responsible person is conveniently found out after the pre-release version is leaked, therefore, all related personnel are warned to pay attention to protect the product privacy, the product security is improved, and the commercial benefits of the product are maintained; multiple security techniques are combined to be used, automated operations are achieved through tools, the operation procedures are convenient, and no influence is generated on game experience.
Owner:ZHUHAI KINGSOFT ONLINE GAME TECH CO LTD +1
A value-added service system and a value-added service method based on a mobile communication network
InactiveCN109359088AFull potentialImprove intelligenceFile access structuresWireless commuication servicesValue-added serviceMobile service
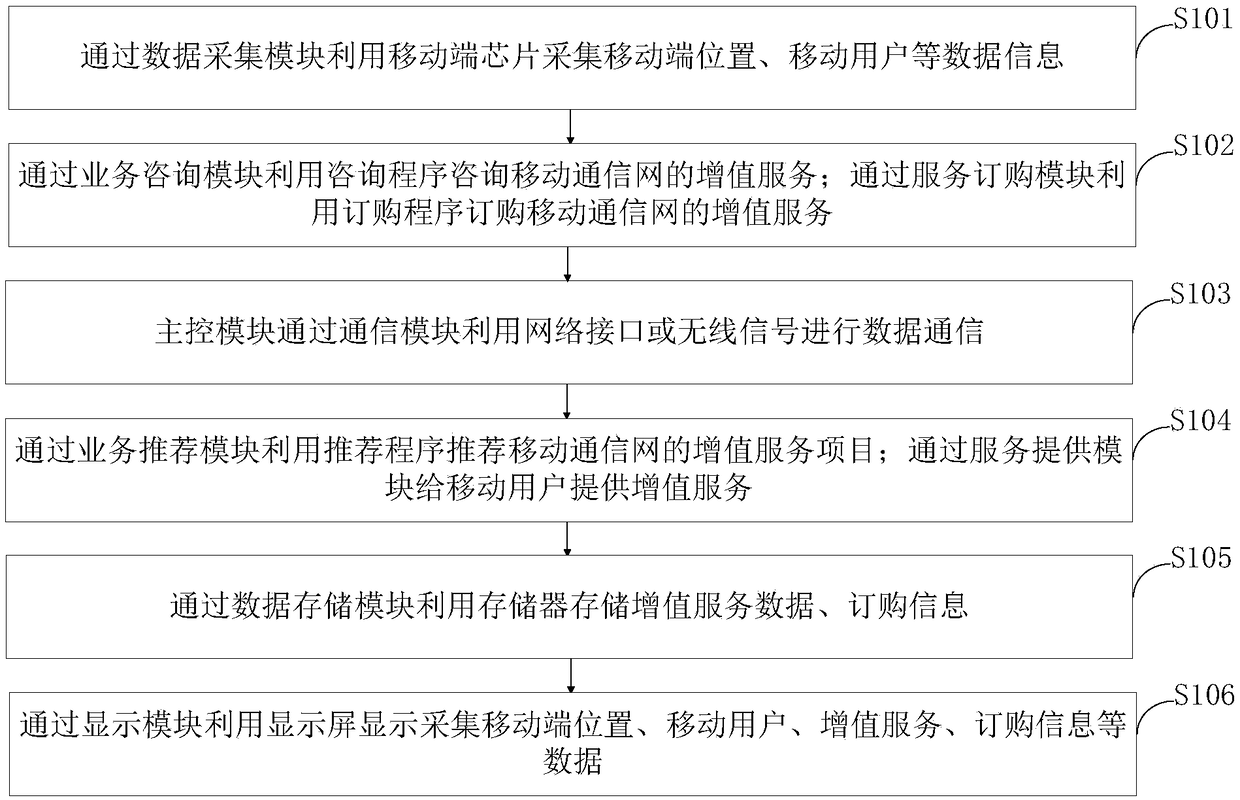
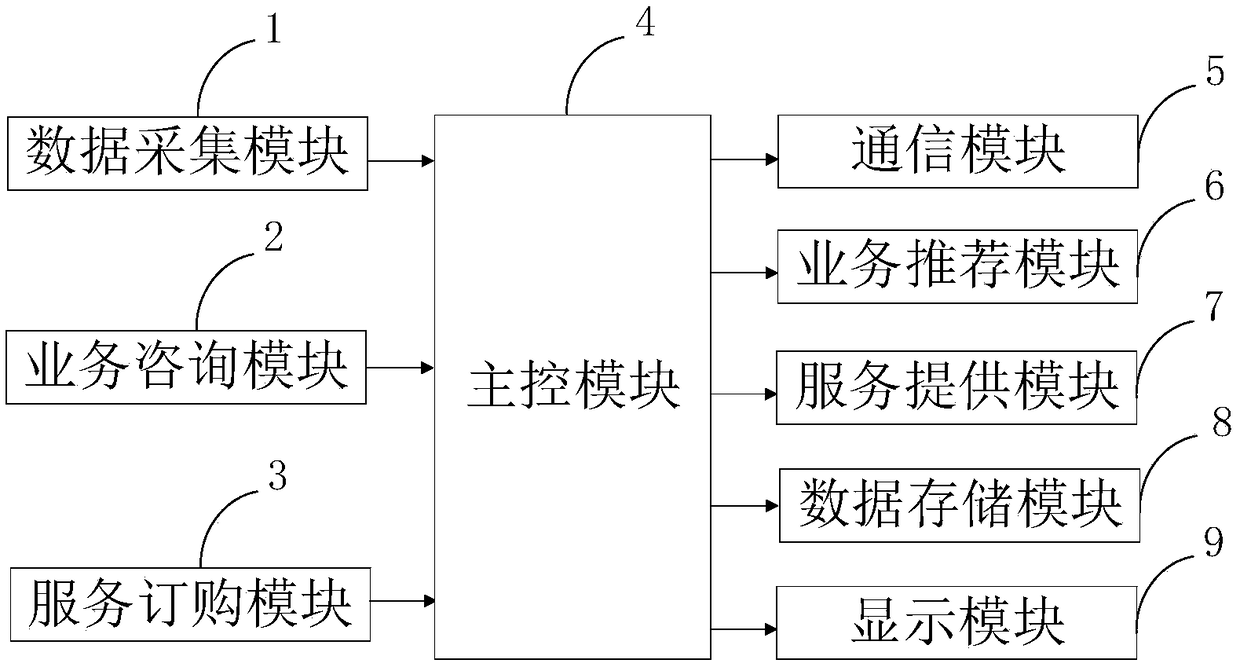
The invention belongs to the technical field of mobile communication and discloses a value-added service system and a value-added service method based on a mobile communication network. The system comprises a data acquisition module, a service consultation module, a service ordering module, a main control module, a communication module, a service recommendation module, a service providing module,a data storage module and a display module. The invention fully excavates the potential of HeNB in the mobile service recommendation through the service recommendation module, increases the intelligence and ease of use provided by the mobile service, and improves the value of the communication network. At that same time, the service provide module provides value-added service to users by using a virtual mobile phone number, bypass the problem of user range limitation brought about by providing value-added service by a real mobile phone number, and can help virtual operators to provide diversified value-added services to a wider user group, so as to give full play to their specialties of providing value-added services.
Owner:武汉市快讯通信息技术有限公司
Technology for engineering positioning and monitoring based on satellite navigation high-precision positioning and lora communication
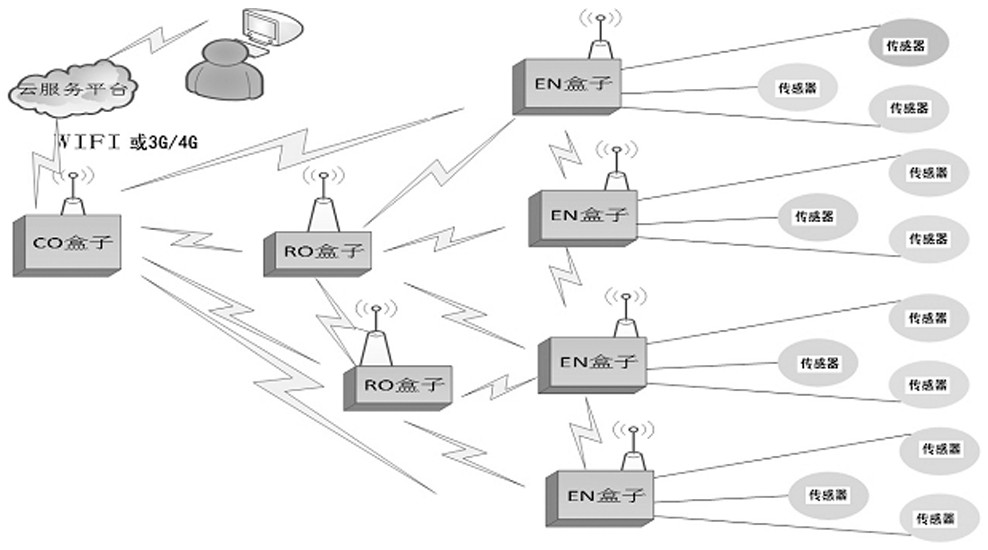
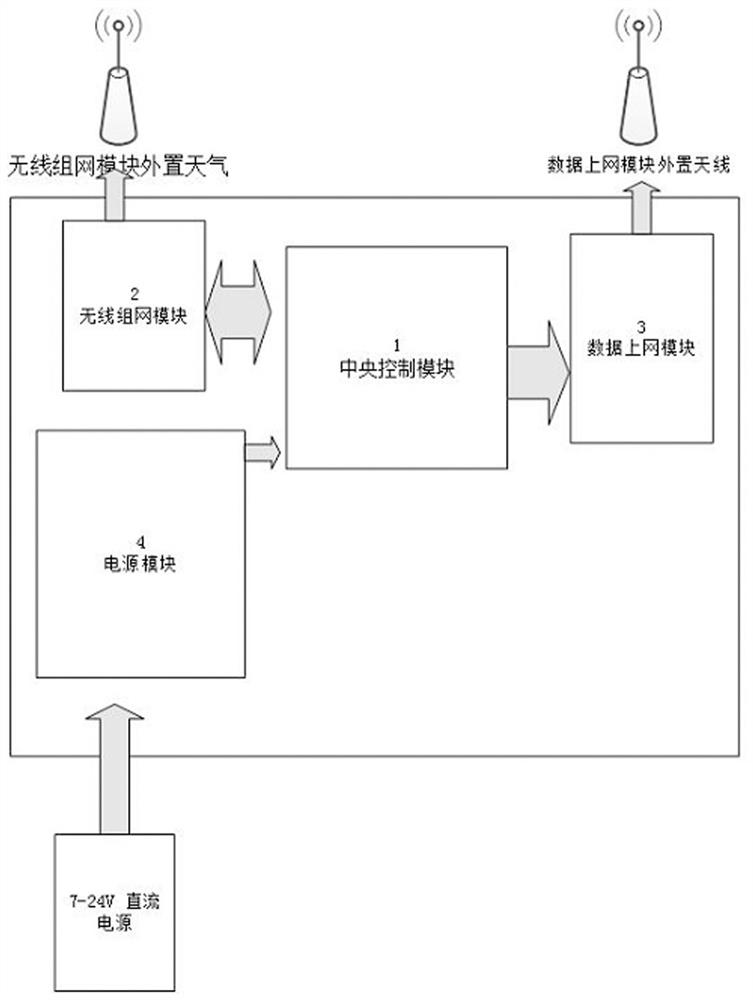
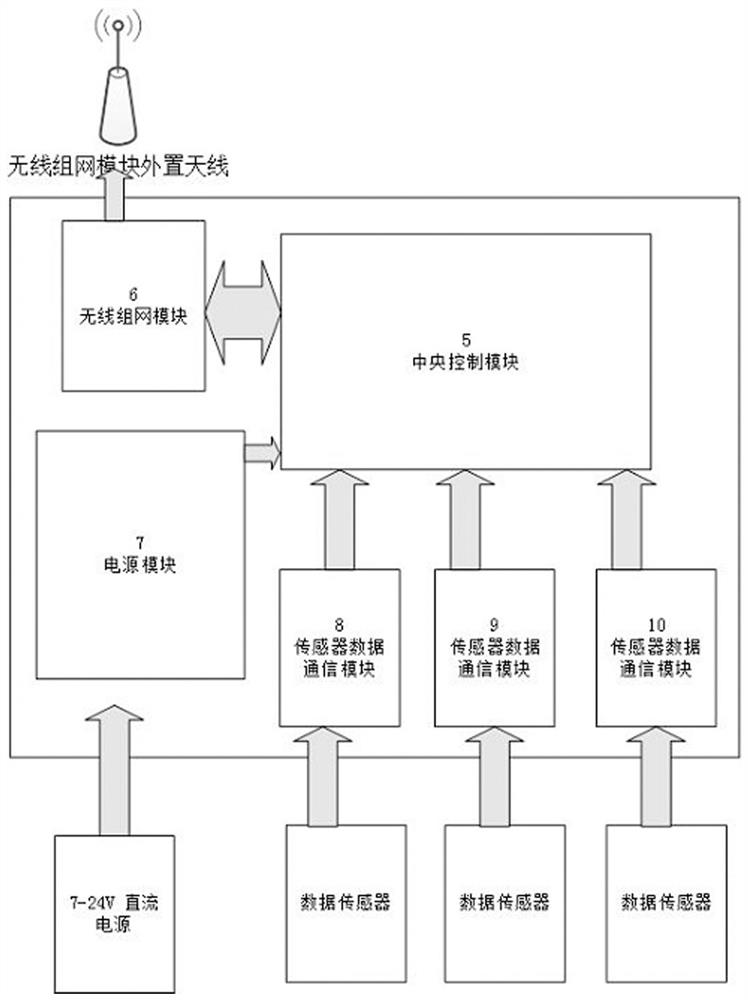
InactiveCN113359163ASufficient monitoring capabilityRealize high-precision monitoringSatellite radio beaconingTransmissionData acquisitionEngineering
The invention belongs to the technical field of engineering monitoring, and particularly relates to a technology for engineering positioning and monitoring based on satellite navigation high-precision positioning and lora communication. An engineering positioning and monitoring system comprises a central communication box (CO box), wherein the CO box comprises a central control module, a wireless networking module, a data internet access module and a power supply module; a terminal control box (EN box), wherein the EN box comprises a central control module, a wireless networking module, a power supply module and three sensor data communication modules; a transfer box (RO box), wherein the RO box comprises a central control module, a wireless networking module and a power supply module 13; and a cloud service platform which is used for receiving, processing, analyzing and calculating all the uploaded data, carrying out data statistics and providing background data service. According to the design of the invention, a high-precision satellite positioning technology and a Lora wireless networking technology applied to an unmanned aerial vehicle are originally integrated and introduced into the field of engineering monitoring, and long-distance free networking, high-precision real-time data acquisition and cloud uploading are realized.
Owner:深圳市慧达工程科技有限公司
Point-to-point anonymous communication method based on random stateless address allocation strategy in IPv6 network
InactiveCN105282161BEnhanced anonymityPrivacy protectionTransmissionExtensibilitySecure communication
The invention discloses a point-to-point anonymous communication method based on a random stateless address allocation strategy in an IPv6 network, belonging to the technical field of the Internet. The present invention is based on the onion routing anonymous communication mechanism, by improving the IPv6 address generation algorithm, using the huge IPv6 address space, periodically changing the node IPv6 address, avoiding the privacy leakage caused by the IPv6 address identification; using the onion routing mechanism to ensure the IPv6 address Cross-network segment hiding and data encryption. The method can obviously improve the anonymity of the anonymous communication system, and the communication efficiency and compatibility of the system are not weakened. The invention has the advantages of: (1) significantly improving the anonymity of the anonymous communication system; (2) the communication efficiency and compatibility of the system are not weakened; (3) strong universality. The present invention can provide multiple effective security communication technologies for the application of the Internet in the future, has good expansibility, and can adapt to the requirements brought about by the development of the application of the Internet in the future.
Owner:MIANYANG TEACHERS COLLEGE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com