Means for content security at the service level
A technology of content and public service entities, applied in the direction of security devices, machine-to-machine/machine-type communication services, electrical components, etc., can solve problems such as limitations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
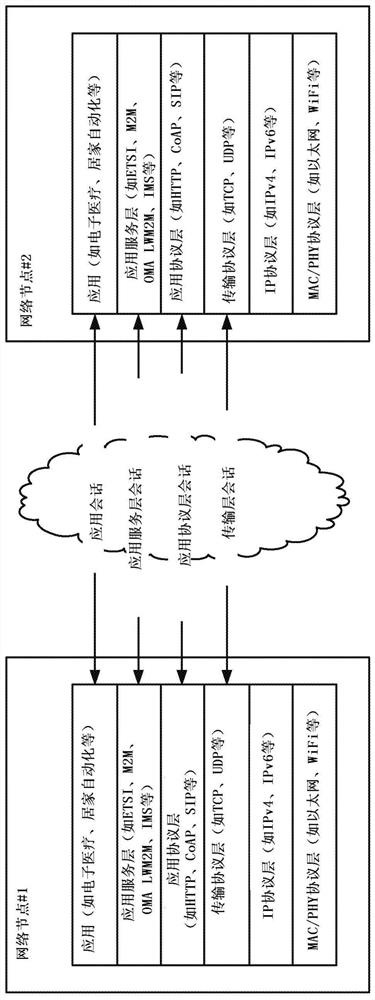
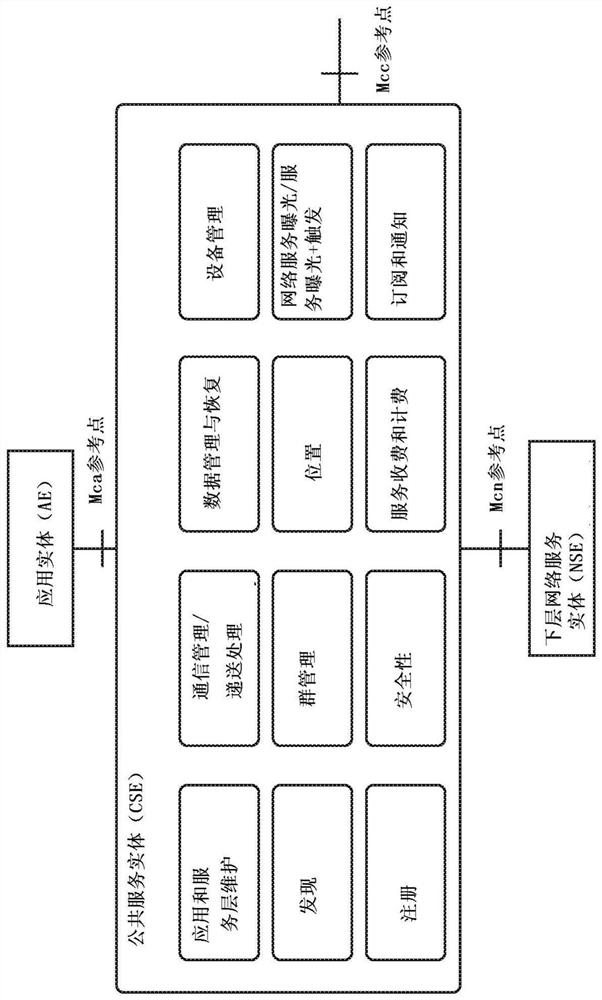
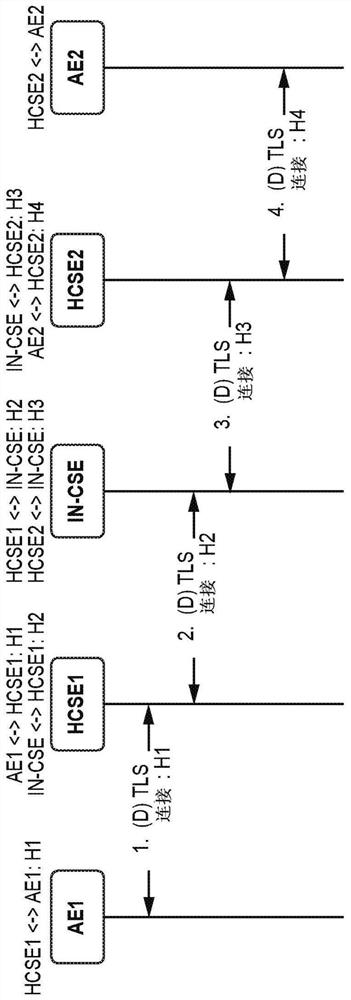
[0058] As mentioned above, existing approaches to security in M2M networks are limited. For example, in oneM2M content may only be protected when "transmitted" between two "trusted" entities by means of a transport layer protocol (eg TLS / DTLS). Therefore, content is not protected while it is hosted at an entity (at rest). The implication is that content (object) protection, if implemented at all, must be done at the application layer. It should be recognized here that there are issues associated with applying content protection methods. For example, the application does not provide a unified mechanism for application content protection. Also, the service layer resources themselves are not protected. Also, if there are application layer protections, they may only provide actual application data protection, not the resources associated with the service layer (SL). It is further recognized herein that a separate application layer protocol for protecting content must be implem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com