Patents
Literature
258 results about "Exchange of information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In the area of tax policy, Exchange of Information is a critical tool in assuring compliance with tax codes. As the economy becomes increasingly globalized taxpayers gain greater freedom to move between countries and regions. Tax authorities, however, are restrained by national borders. In order for governments to ensure the proper application of their tax laws, the free and accurate exchange of information is critical. The OECD Centre for Tax Policy and Administration works to improve flow of information in this area and establish a legal framework to facilitate it.
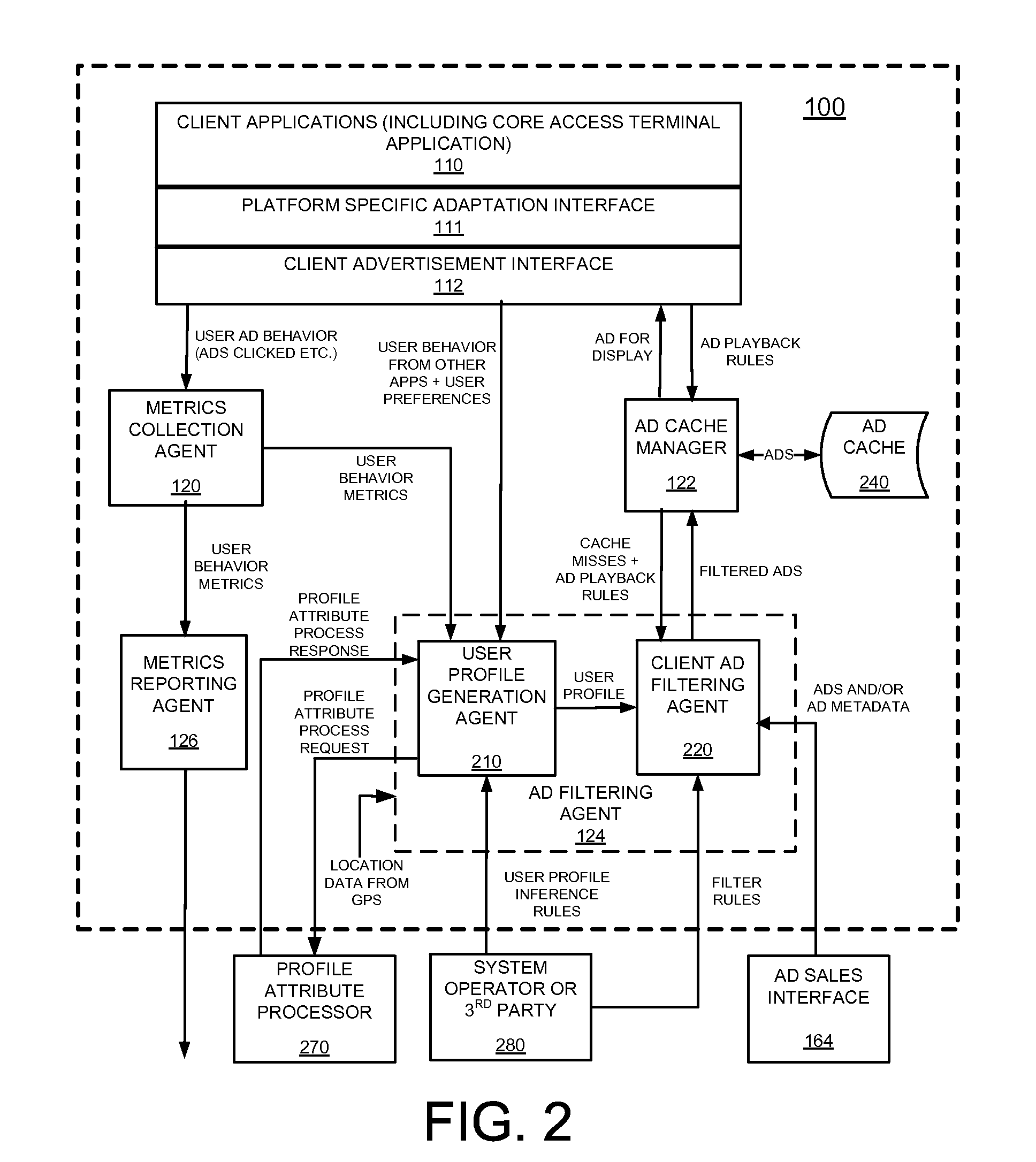
System and method for delivering expert information by computer
InactiveUS6026148AAutomatic call-answering/message-recording/conversation-recordingManual exchangesModem devicePersonal computer
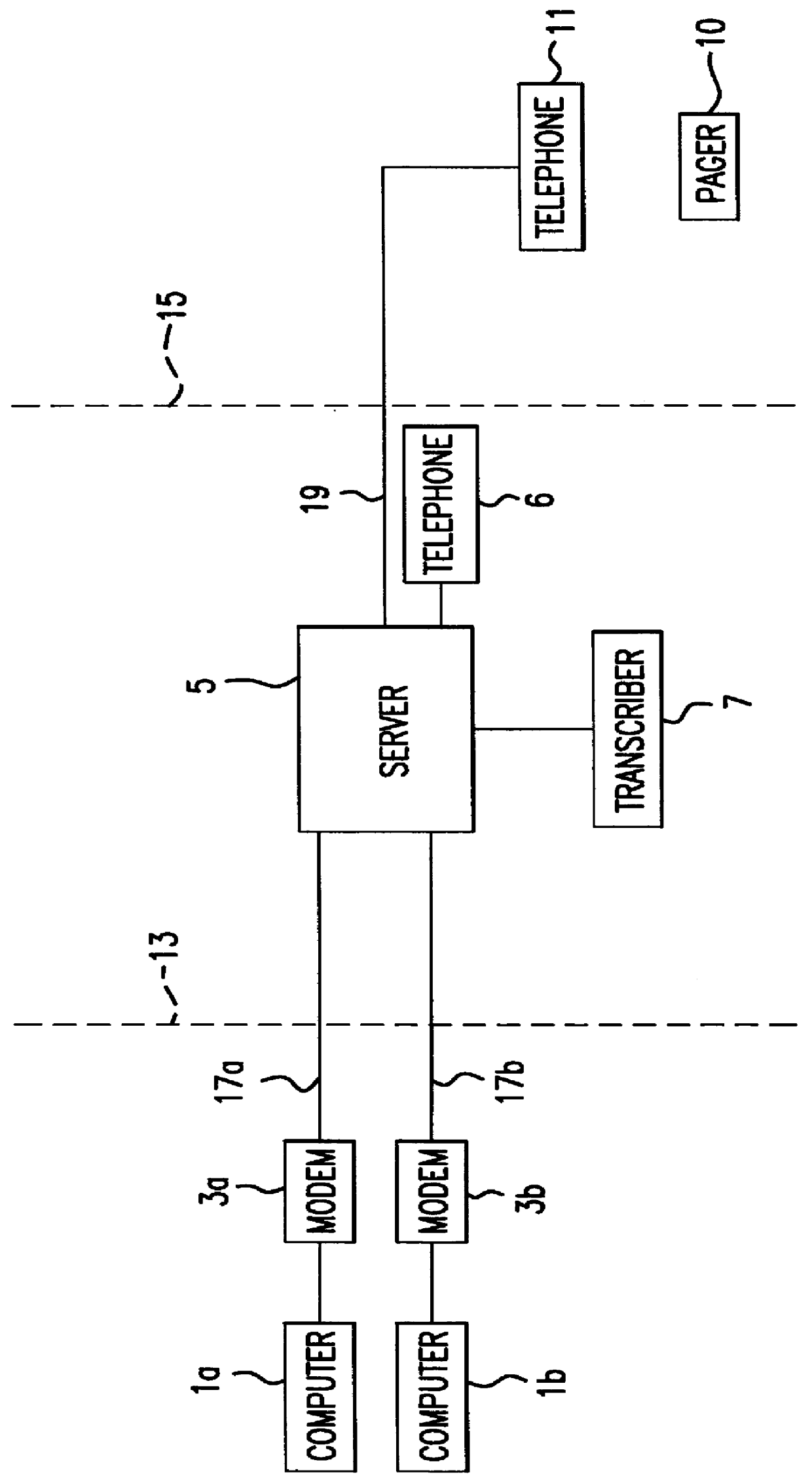
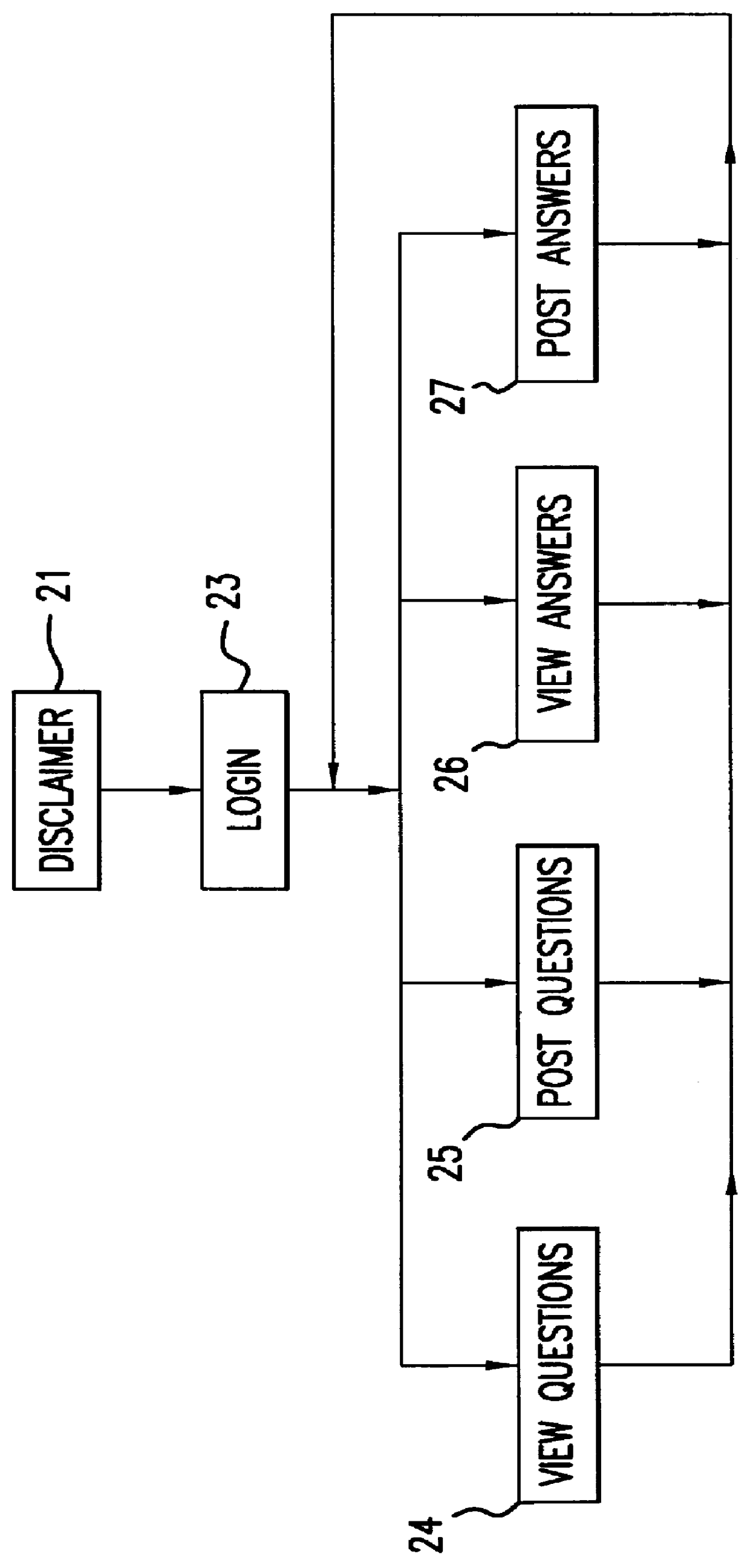
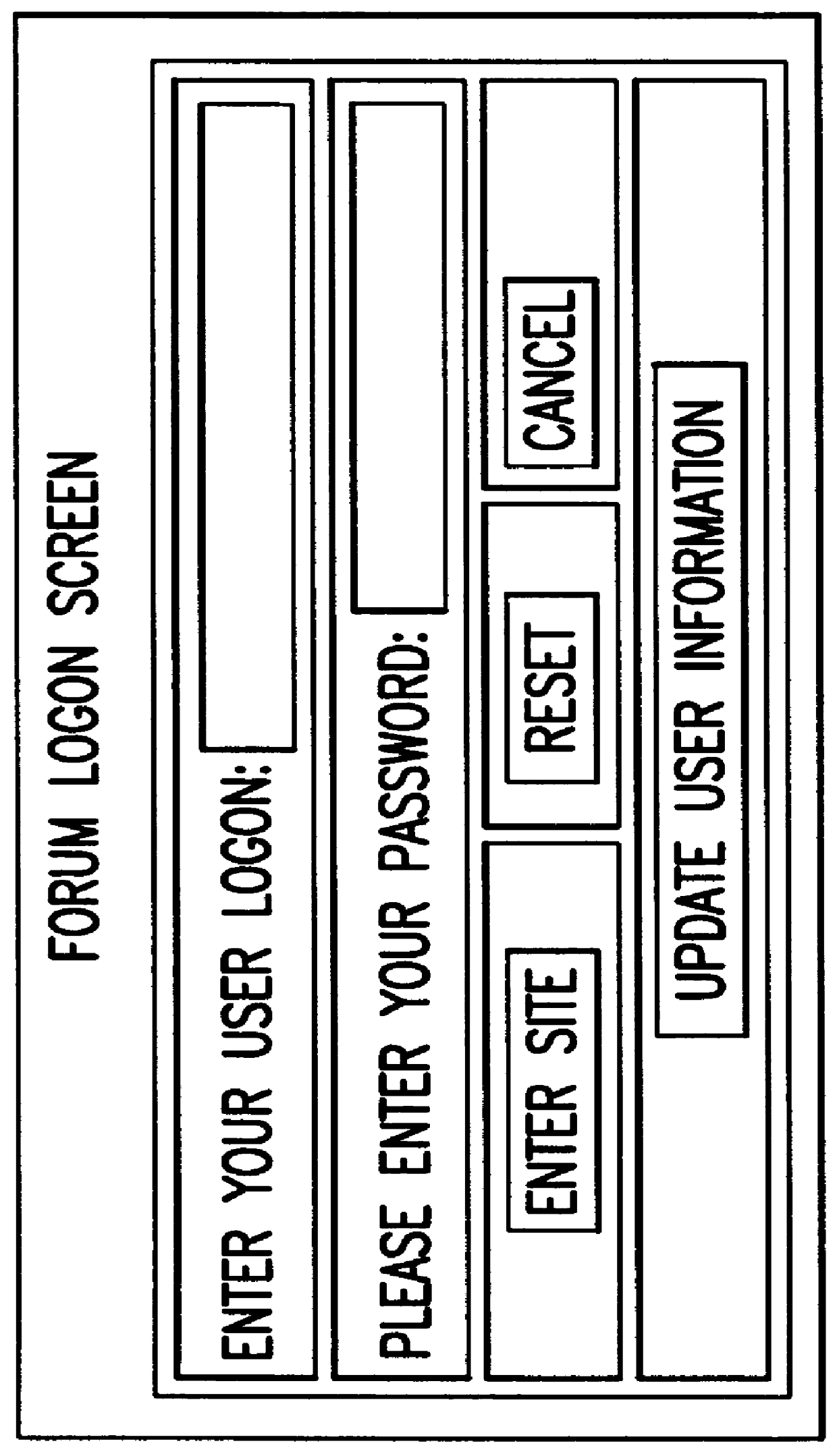
A computer-based system facilitates exchange of information between users and expert respondents. The users post questions on a topic to a computer bulletin board or forum, using a telephone and modem connection to a remote server. The respondents contact the server by telephone, and receive a list of questions that have been posted. The respondents then dictate answers orally, by telephone, and the answers are recorded and stored by the server as sound files. The stored answers can later be played back by users who connect to the server through their personal computers. The answers can also be transcribed into text files for viewing by the users. Thus, a user can both hear the recorded voice of the respondent and see the stored text of the respondent's answer. The system makes it easy for respondents to answer questions, or provide comments, especially in cases where a respondent is not familiar with computer technology, or where a respondent is not conveniently located near a computer.
Owner:HANGER SOLUTIONS LLC
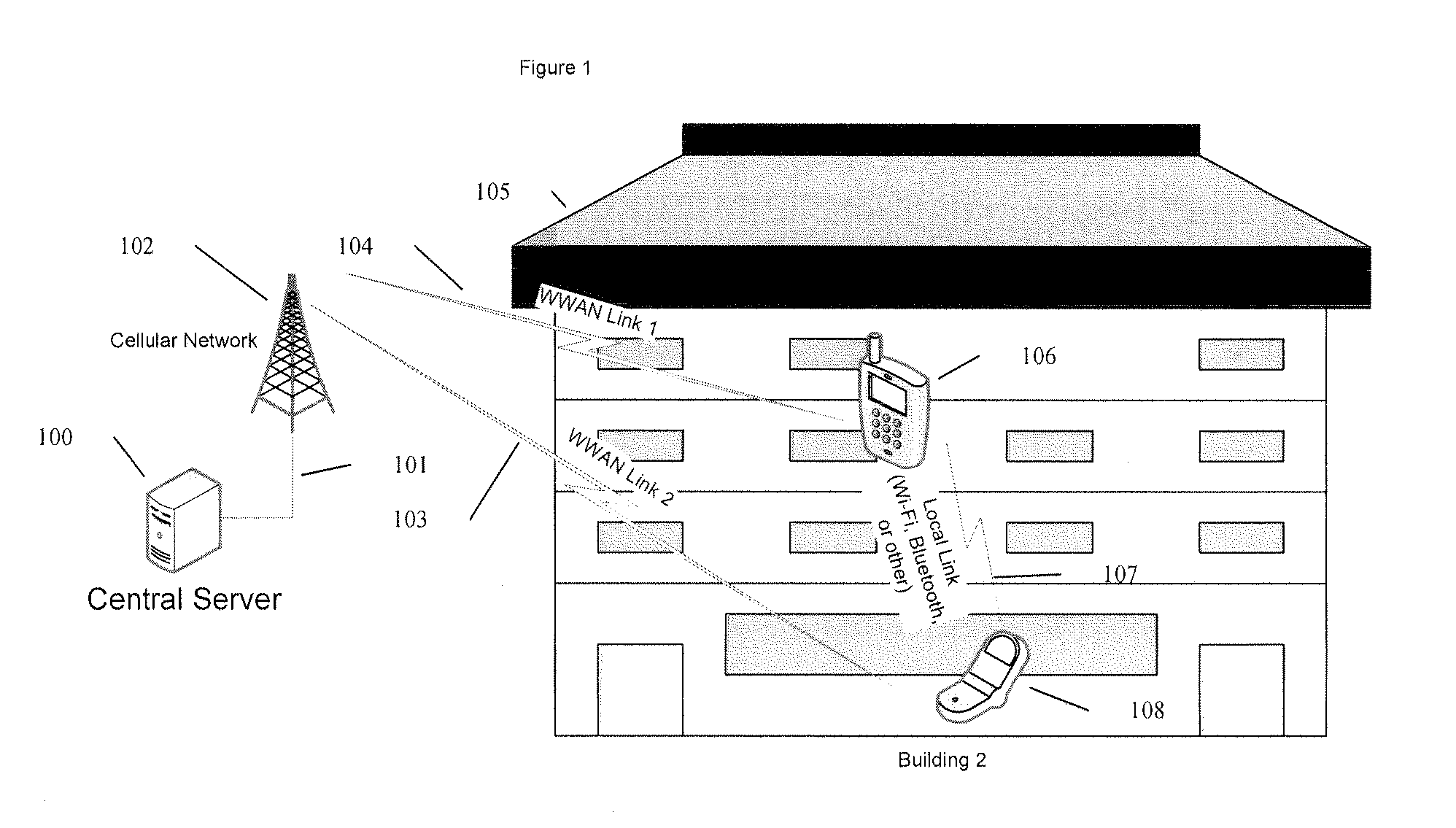
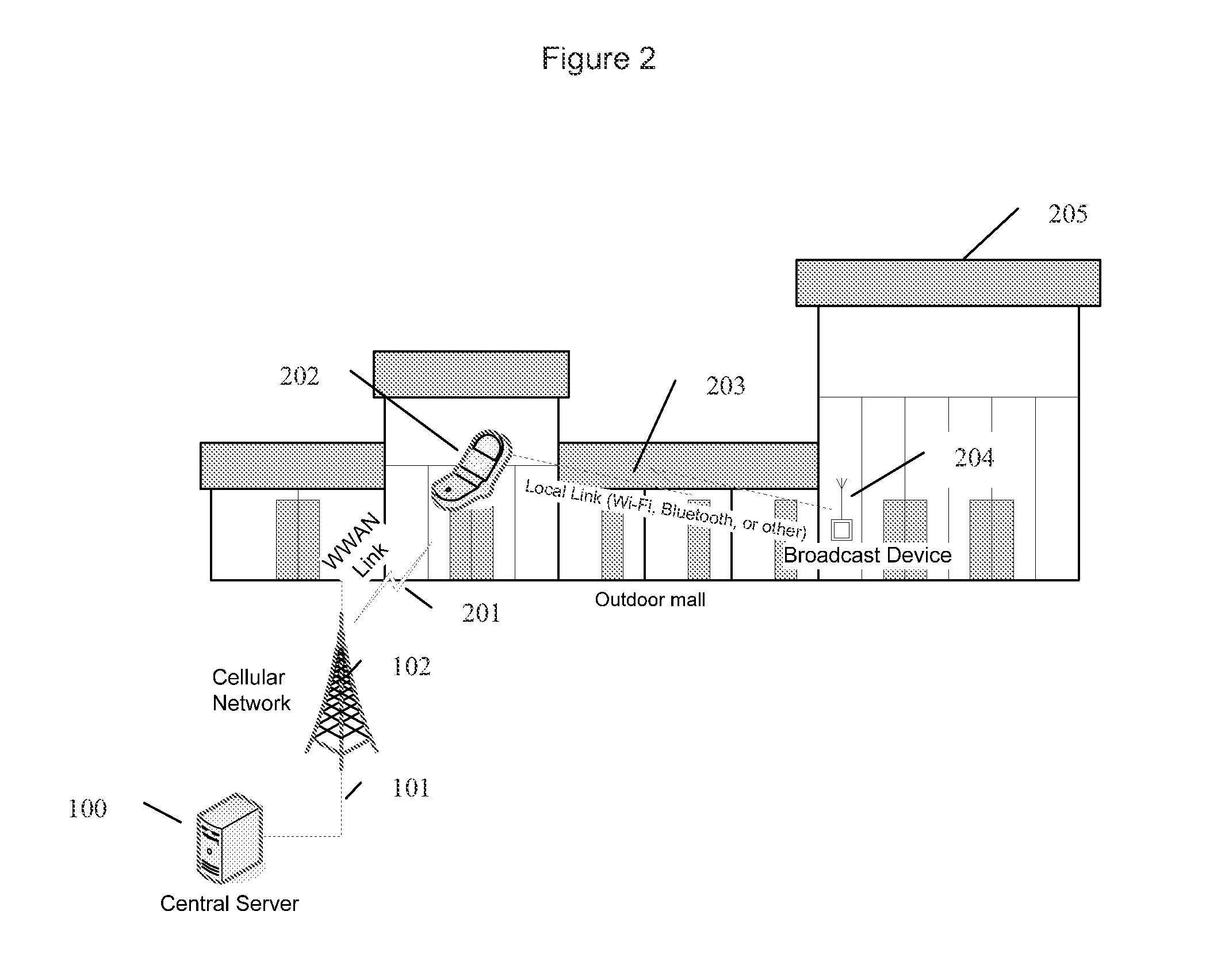
Enforcing policies in wireless communication using exchanged identities
ActiveUS7936736B2Facilitating exchange of information and transactionShort capabilityDiscounts/incentivesServices signallingWi-FiComputer network
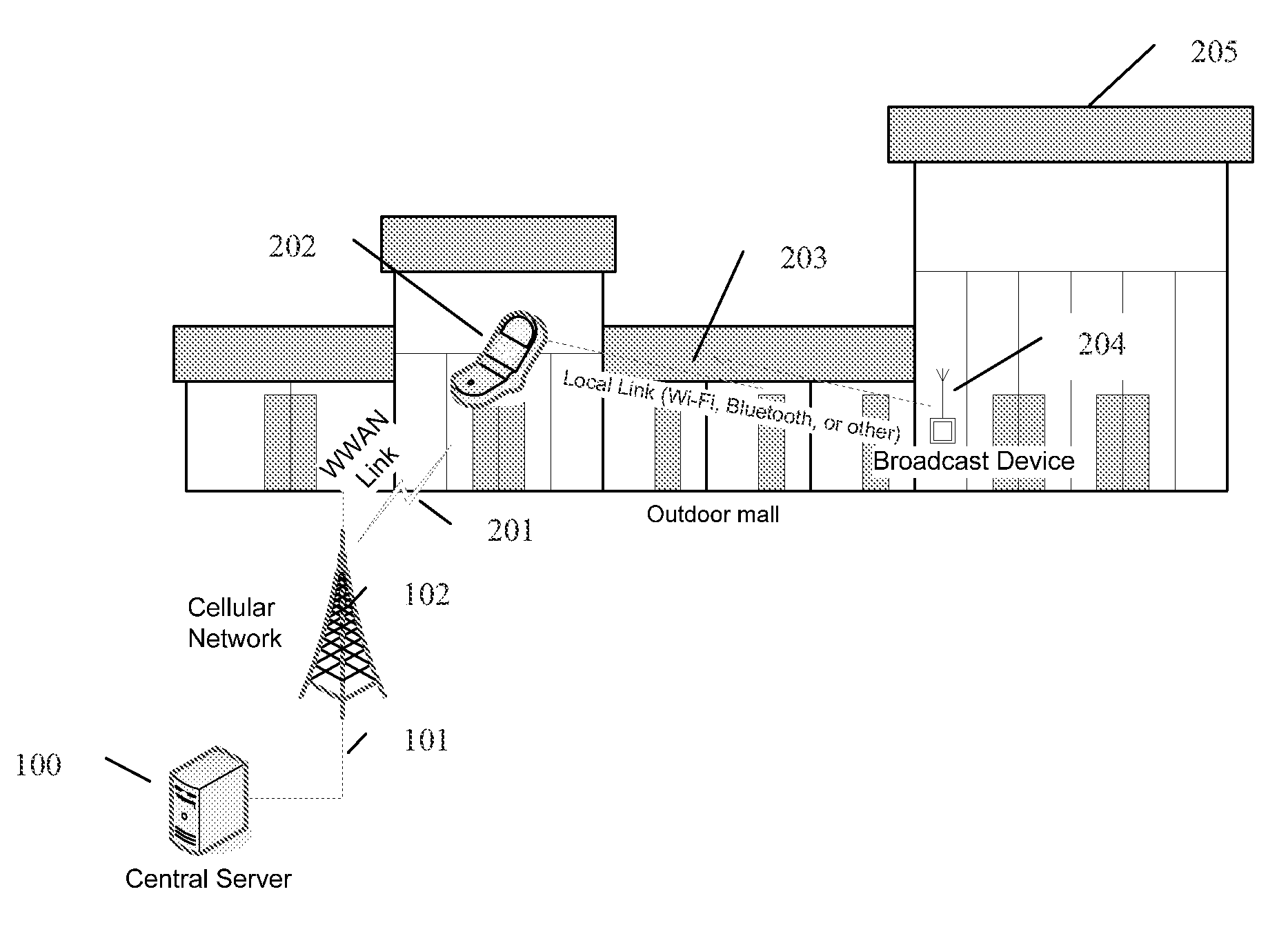
Techniques for facilitating the exchange of information and transactions between two entities associated with two wireless devices when the devices are in close proximity to each other. A first device uses a first short range wireless capability to detect an identifier transmitted from a second device in proximity, ideally using existing radio capabilities such as Bluetooth (IEEE802.15.1-2002) or Wi-Fi (IEEE802.11). The detected identifier, being associated with the device, is also associated with an entity. Rather than directly exchanging application data flow between the two devices using the short range wireless capability, a second wireless capability allows for one or more of the devices to communicate with a central server via the internet, and perform the exchange of application data flow. By using a central server to draw on stored information and content associated with the entities the server can broker the exchange of information between the entities and the devices.
Owner:PROXICOM WIRELESS
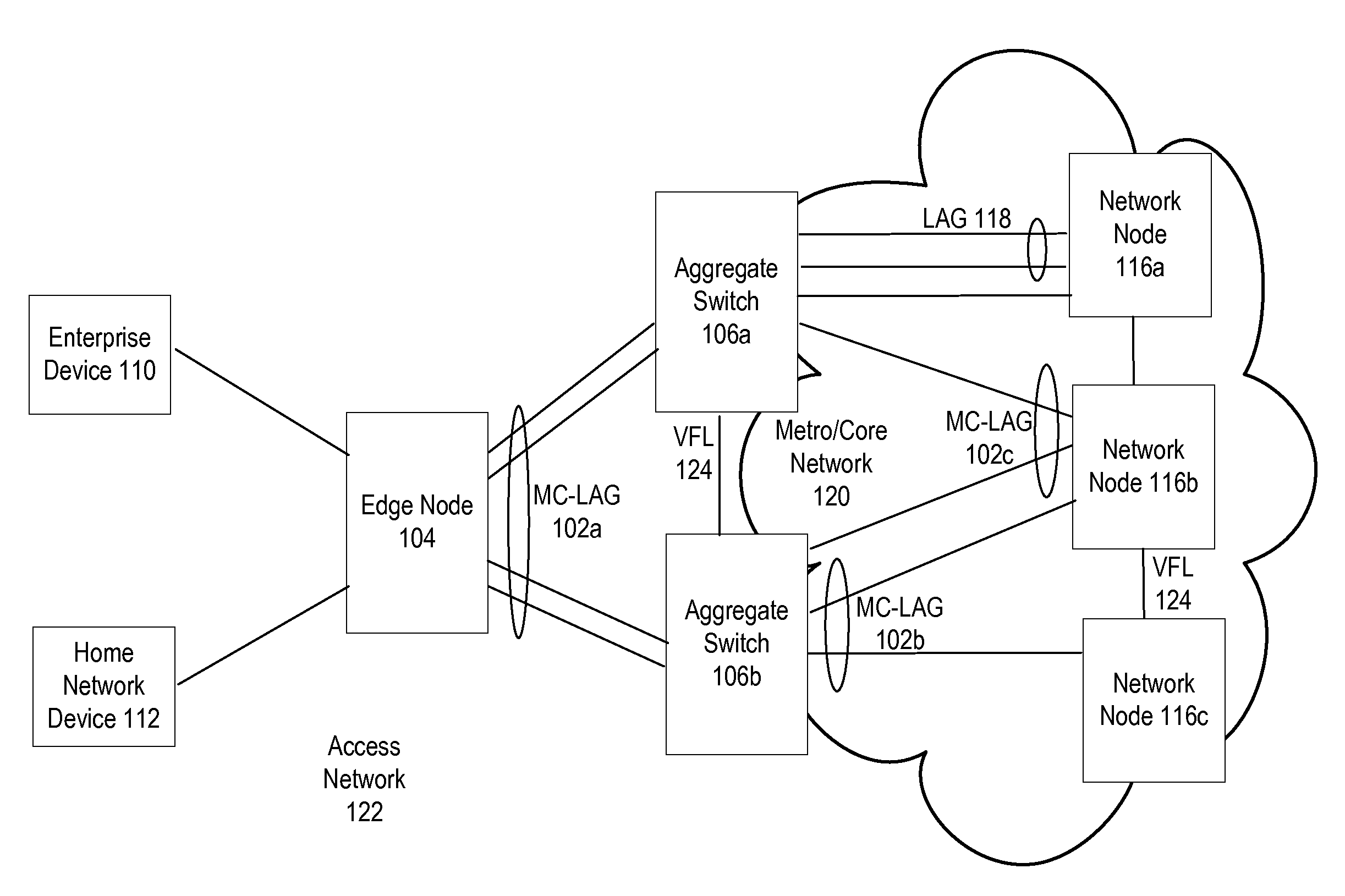
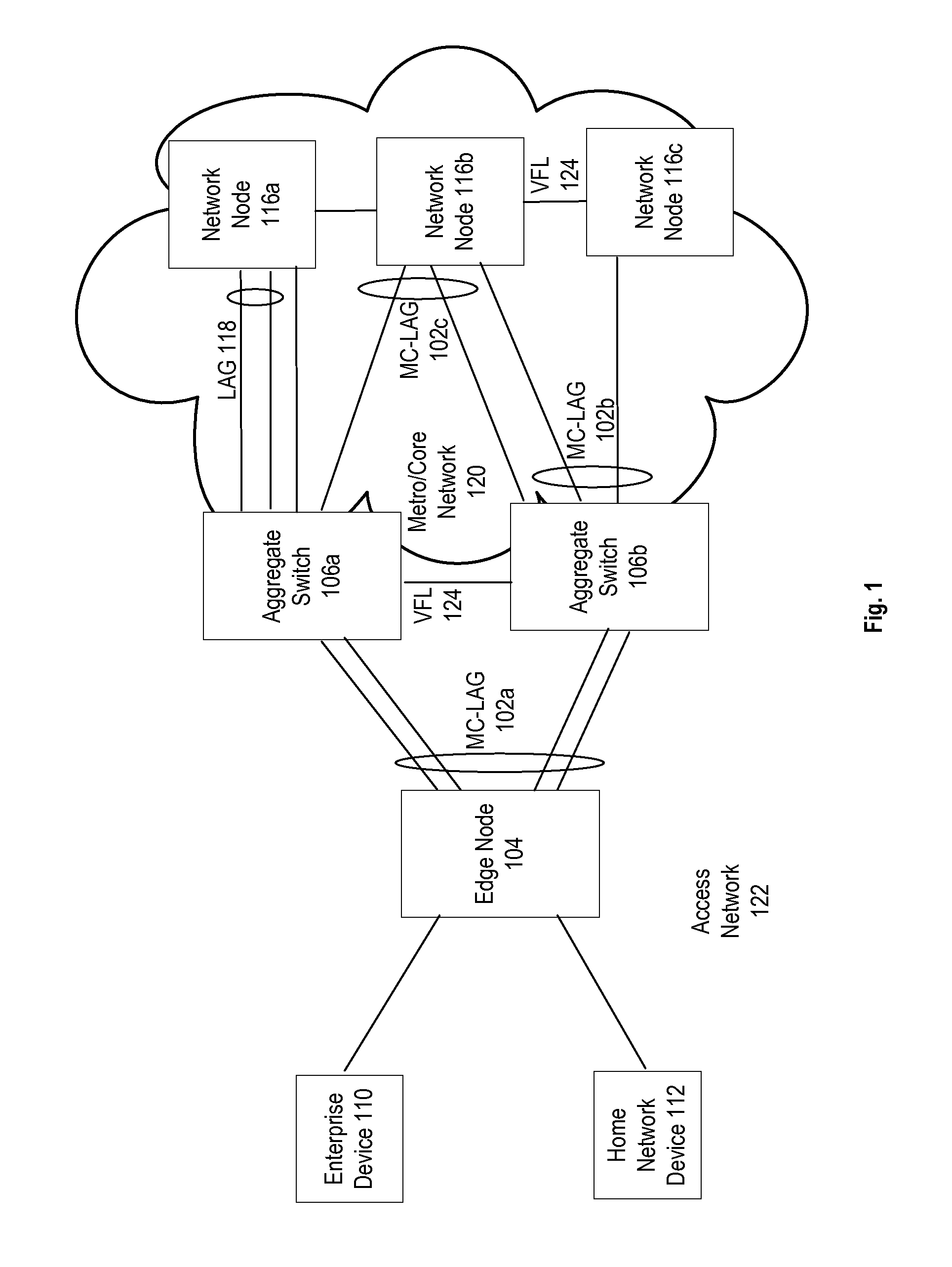
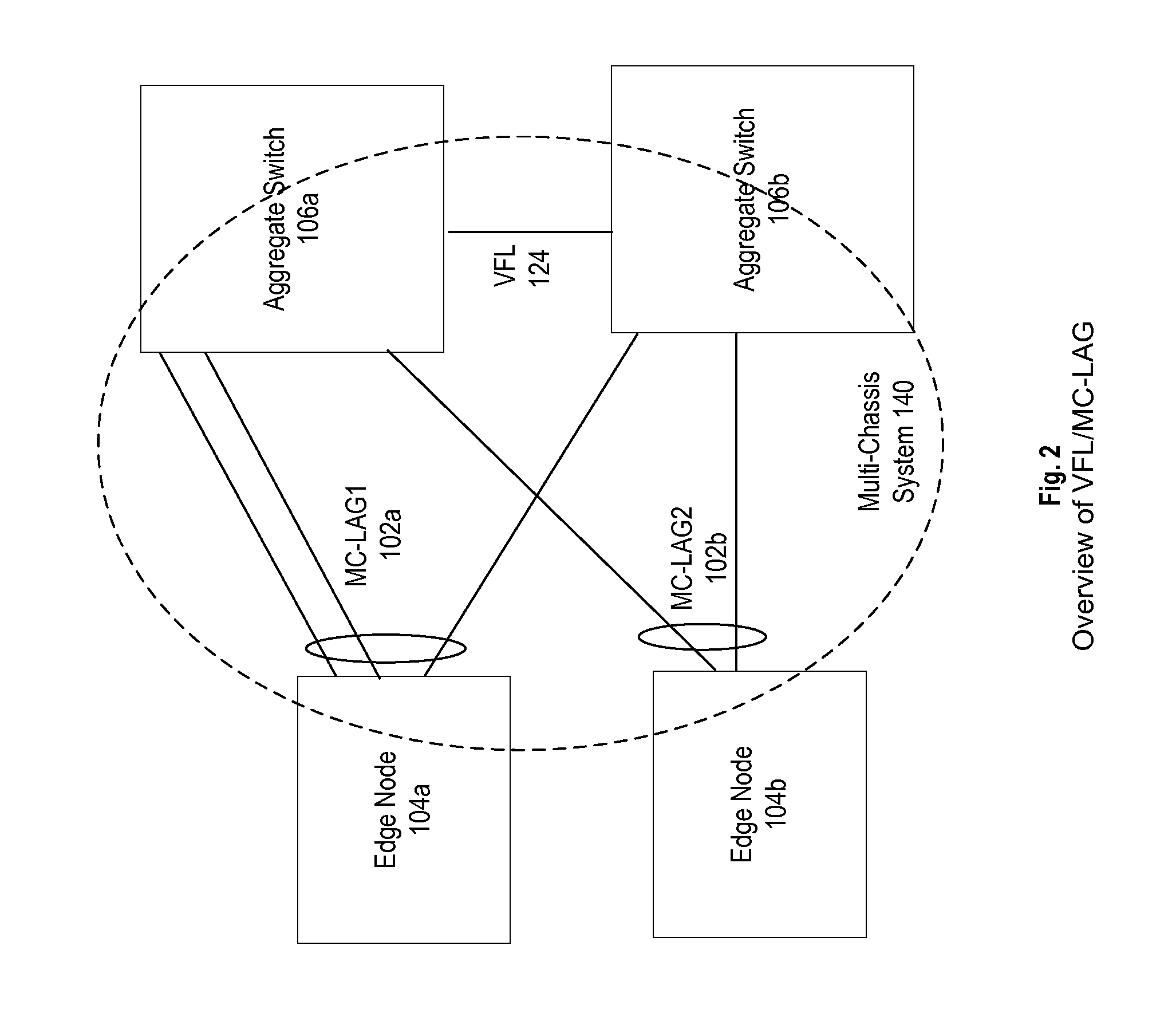
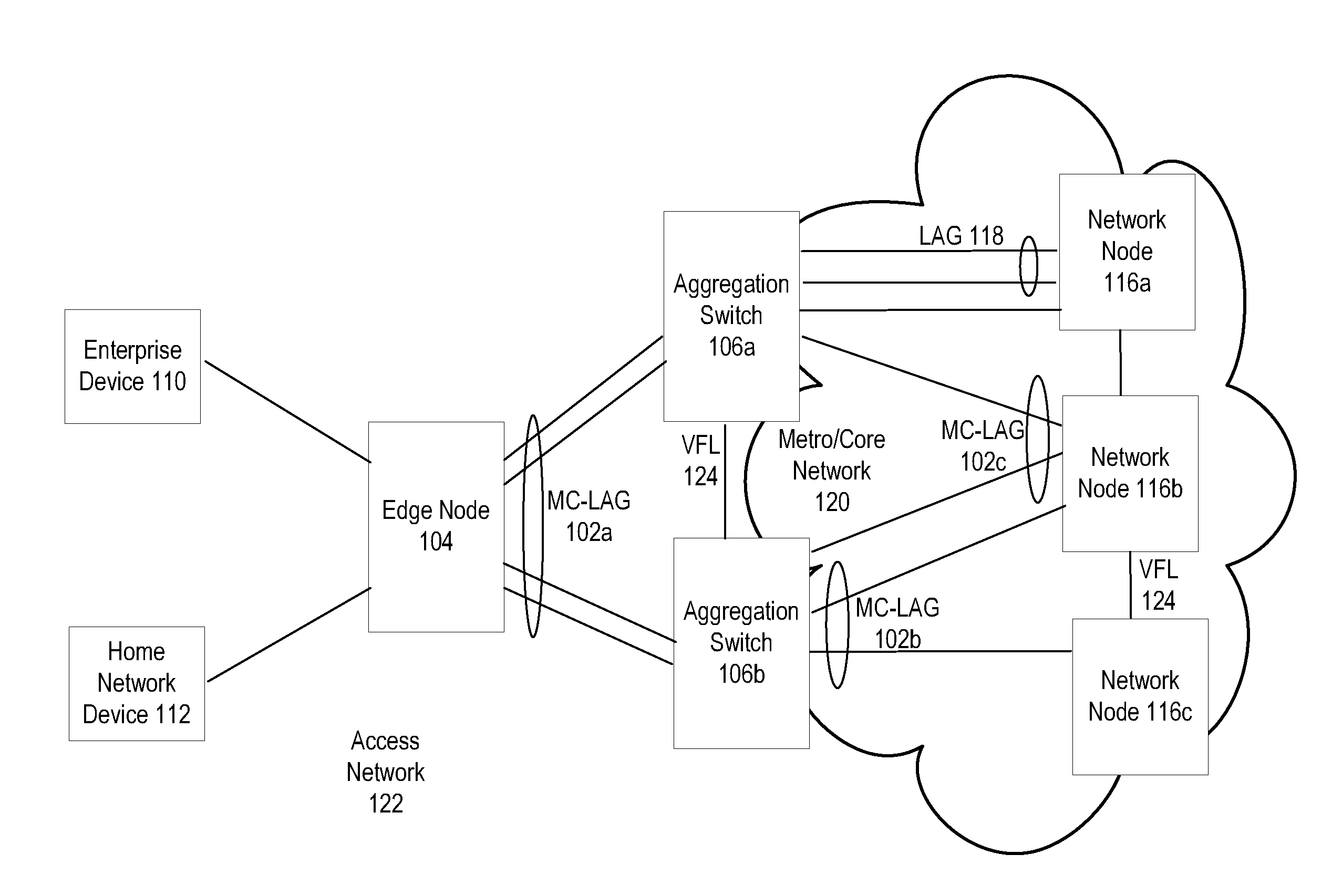
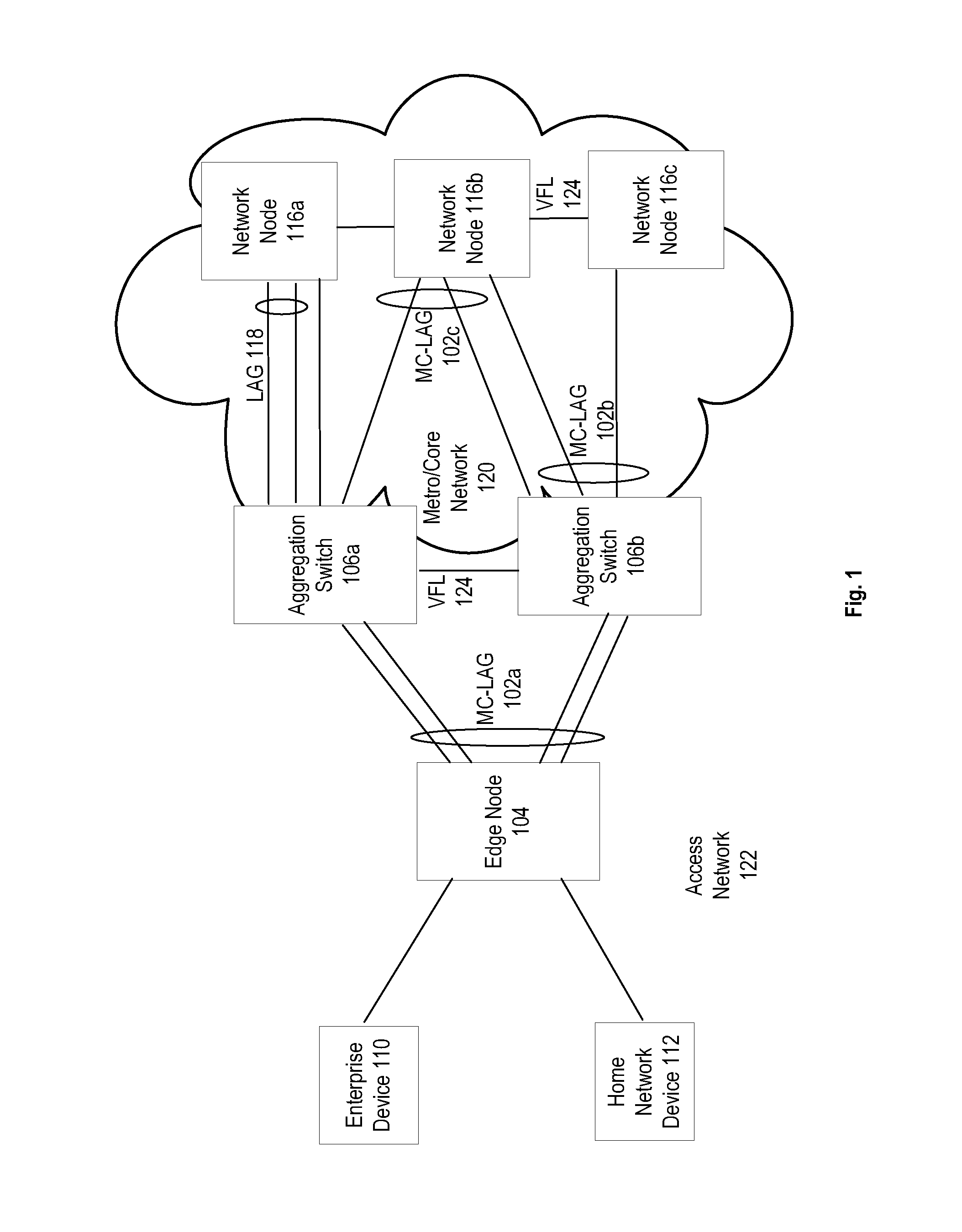
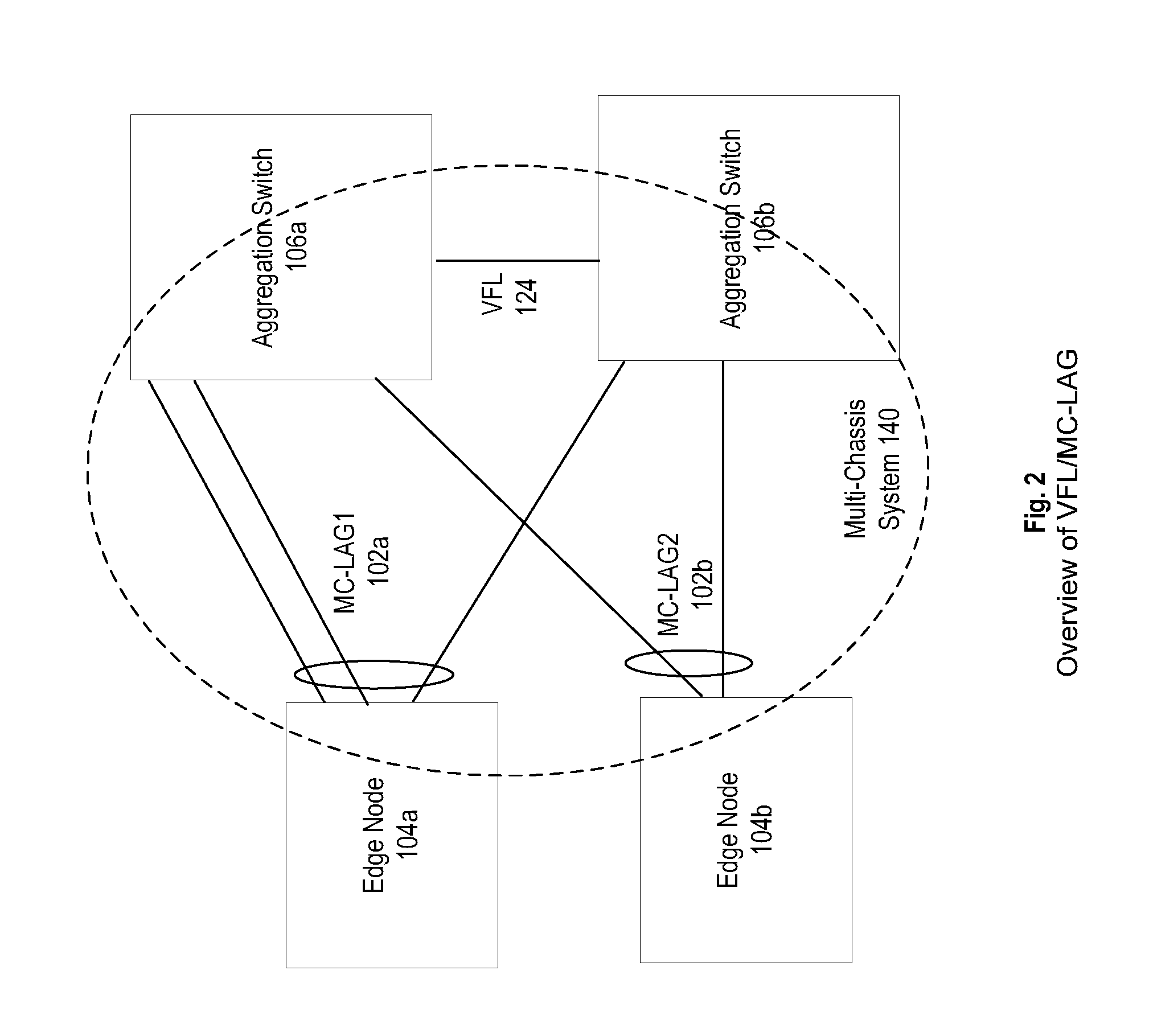
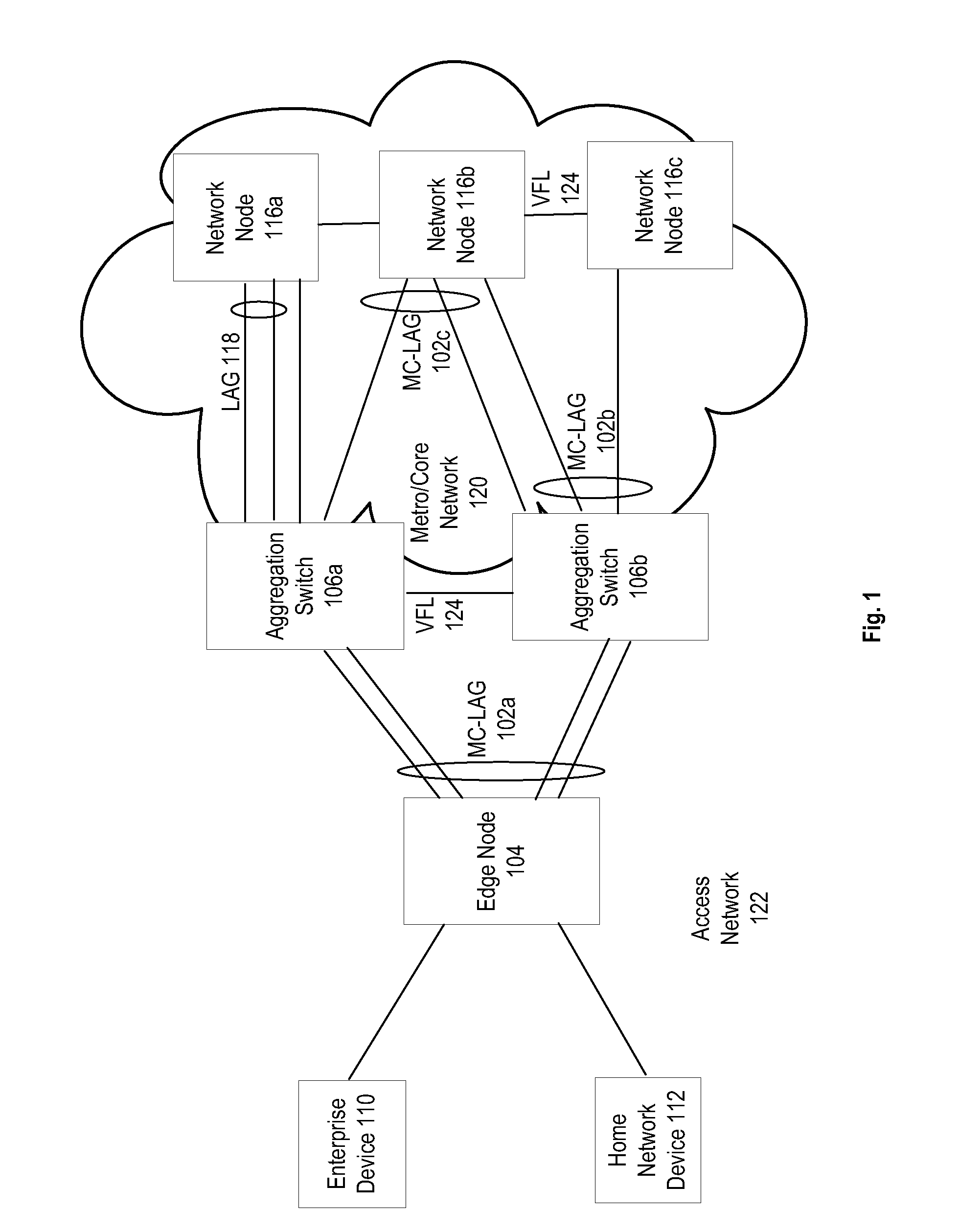
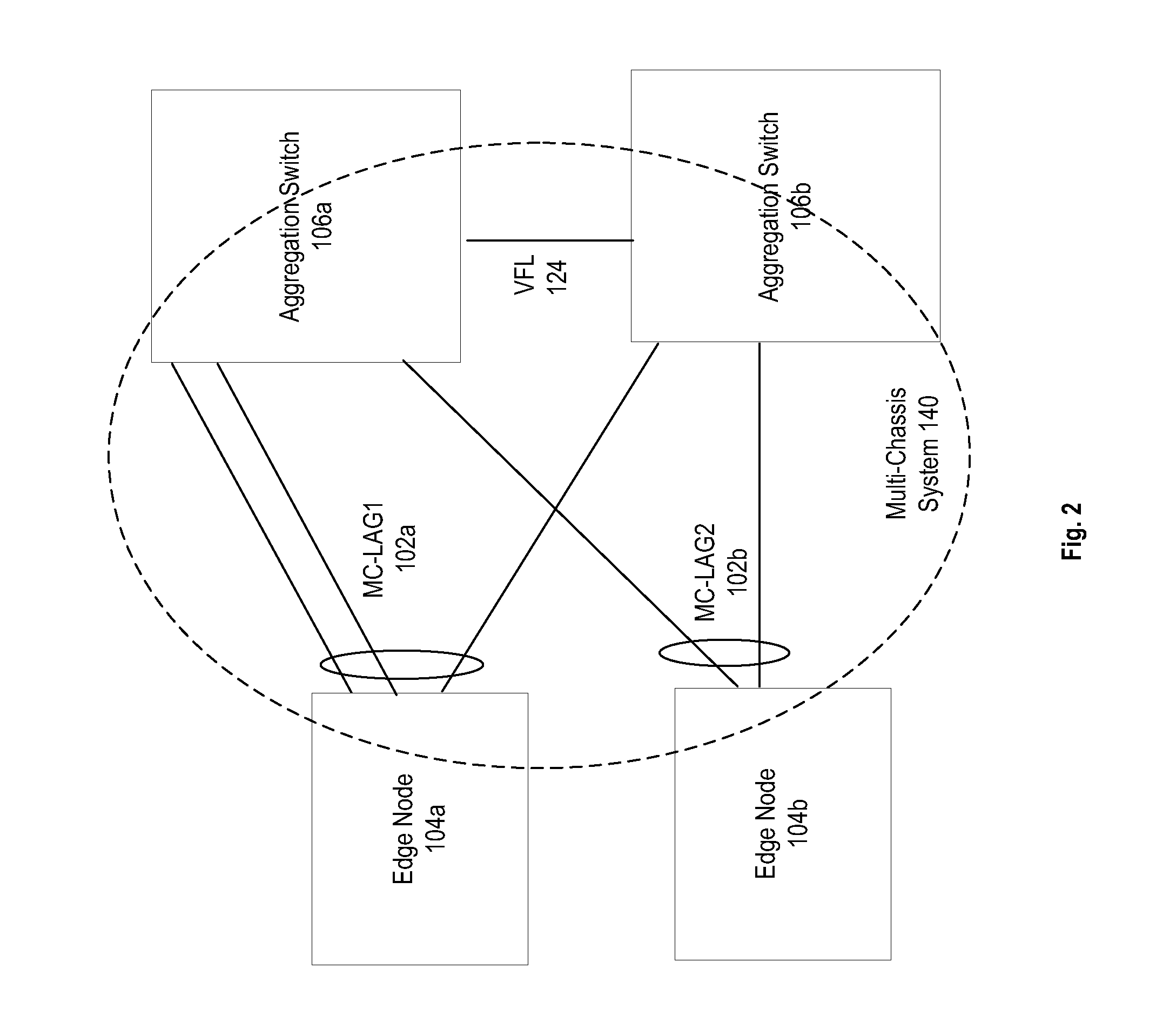
System and method for multi-chassis link aggregation
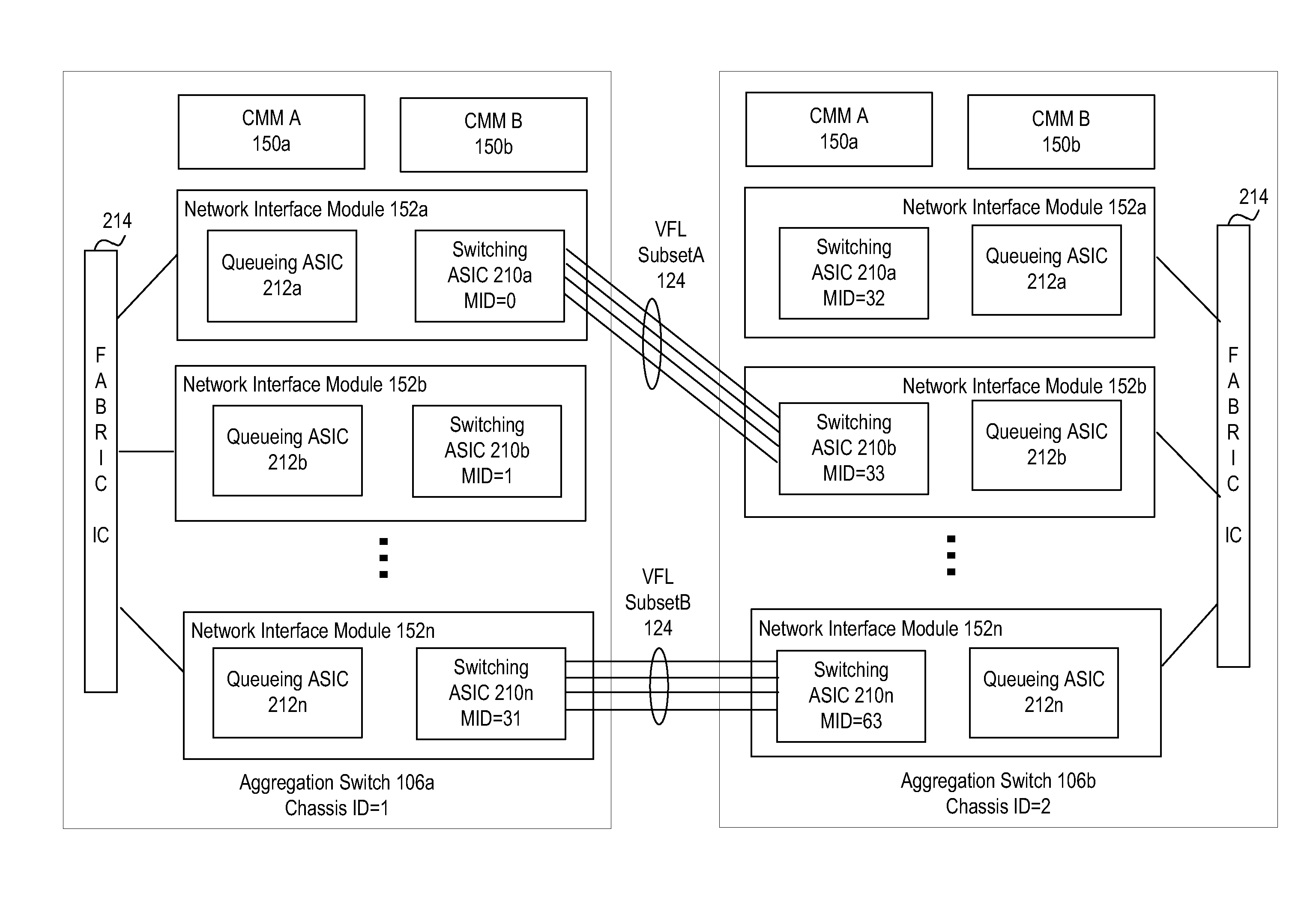
ActiveUS20120033665A1Energy efficient ICTData switching by path configurationExchange of informationLink aggregation
Aggregation Switches connected to an edge node by a multi-chassis link aggregation group, wherein the Aggregation Switches are connected by a virtual fabric link that provides a connection for exchange of information between the Aggregation Switches regarding MAC addressing to synchronize MAC address tables.
Owner:WSOU INVESTMENTS LLC
Method for initializing and allocating bandwidth in a permanent virtual connection for the transmission and control of audio, video, and computer data over a single network fabric
InactiveUS6539011B1Hybrid transportNetwork connectionsStructure of Management InformationNetwork structure
Owner:NETWORK 1 TECH
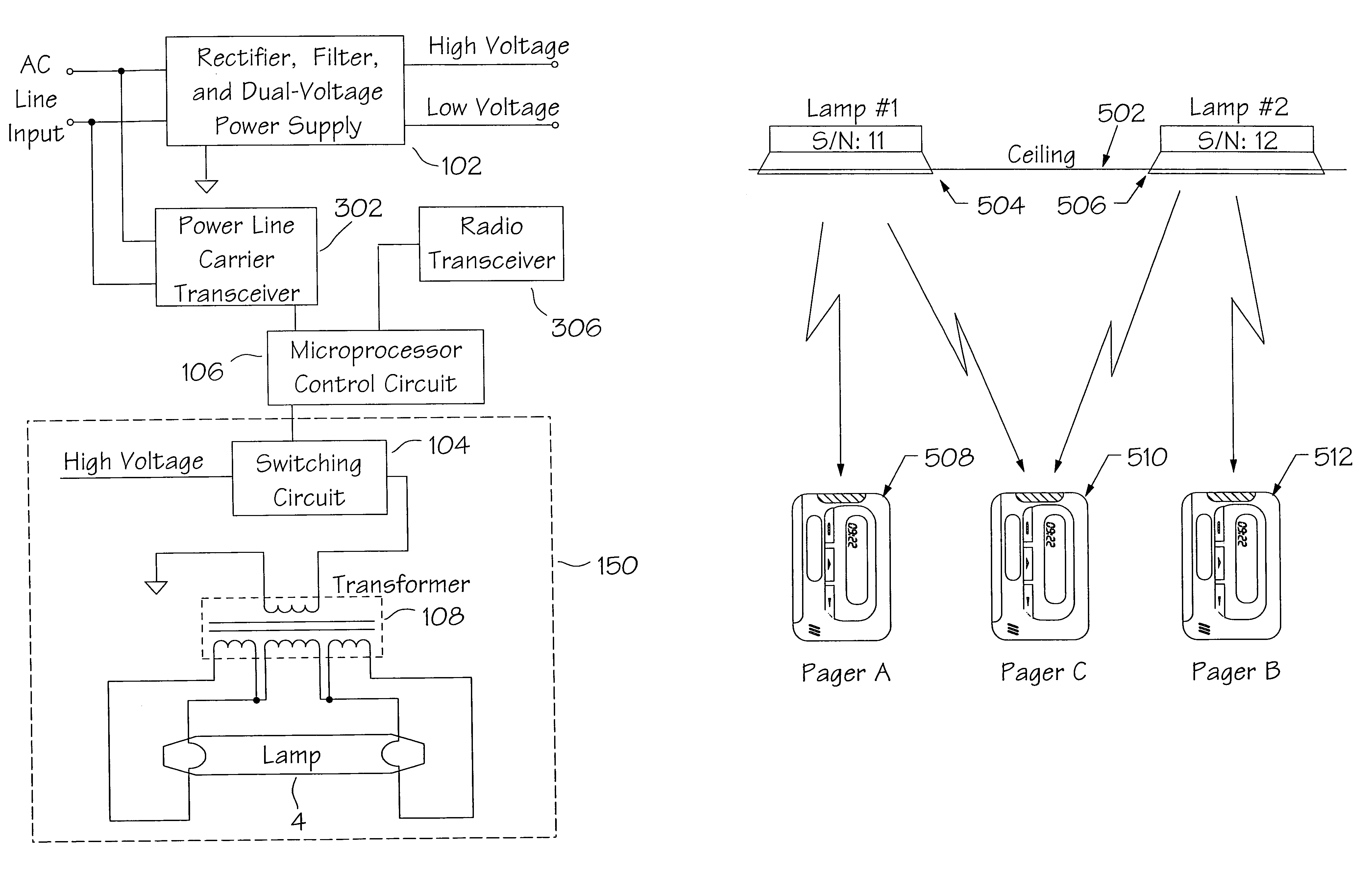
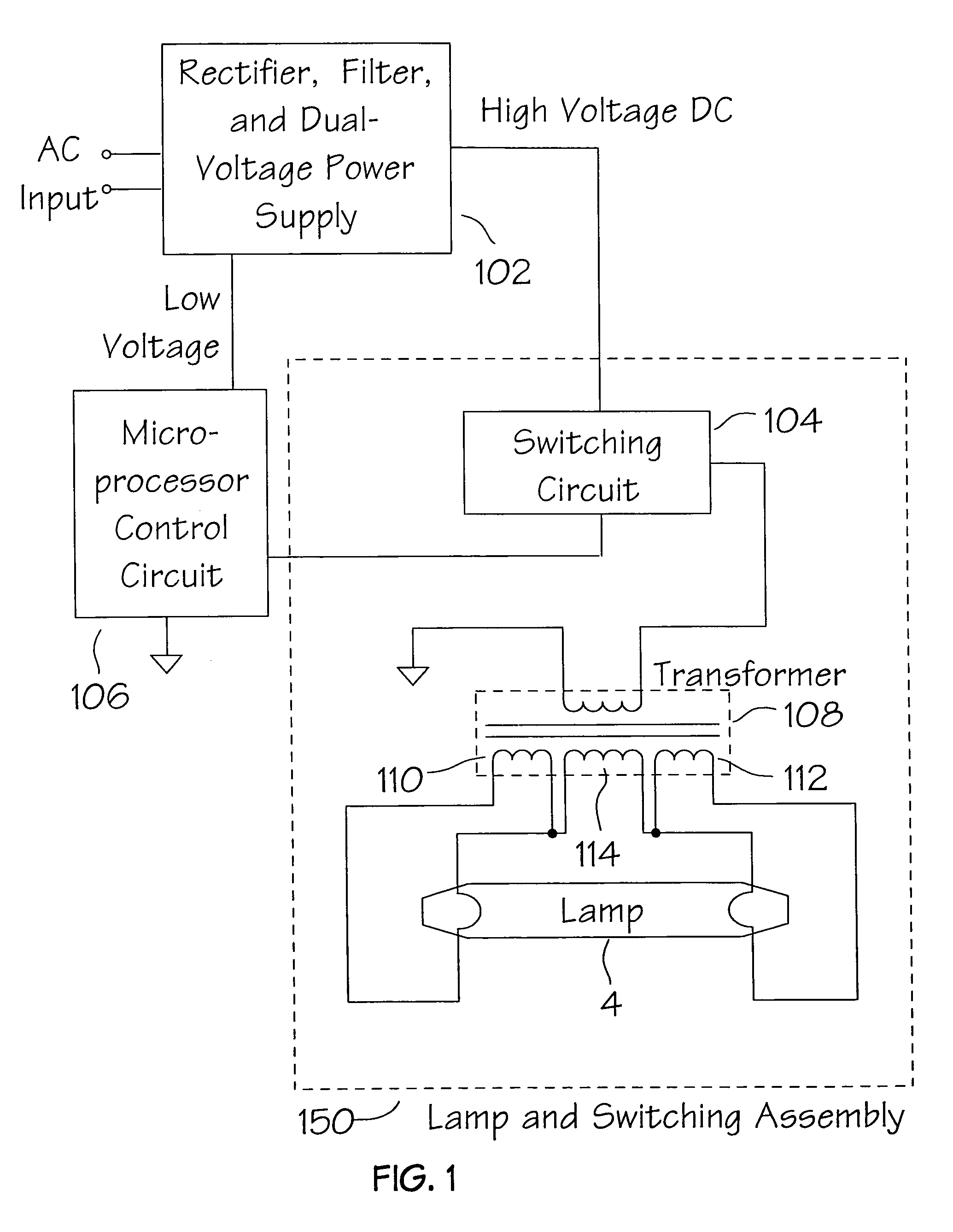
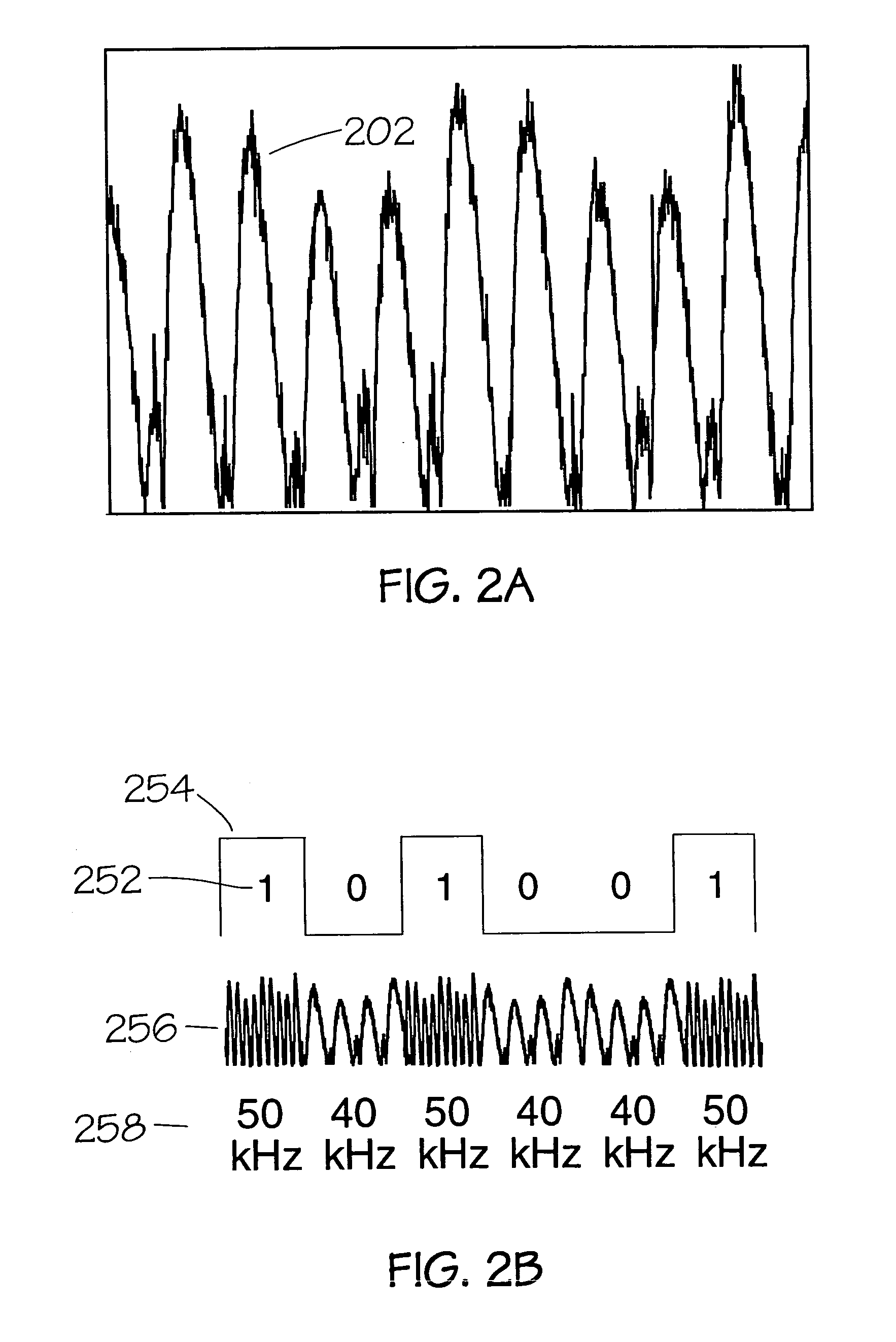
Method and apparatus for the zonal transmission of data using building lighting fixtures
This invention relates to the zonal transmission of data by the modulation of the light output of arc lamps or discharge lamps; including the visible or invisible light output of fluorescent lamps, mercury vapor lamps, high or low-pressure sodium lamps, metal-halide based lamps, or other arc or discharge lamps. The method results in an easily installed, easily maintained, and economical to purchase, optical-wave communications system which exploits the existing infrastructure of a building or facility to facilitate the transmission of data in individual zones; thereby facilitating the transmission of wide-area as well as zonal-specific data to compatible receivers, and further facilitating the determination of location of remote devices or users, and the delivery or exchange of information or data, utilizing limited range transmission techniques.
Owner:CONVERGENCE WIRELESS A CALIFORNIA CORP
System and method for traffic distribution in a multi-chassis link aggregation
ActiveUS20120033669A1Energy efficient ICTData switching by path configurationStructure of Management InformationEdge node
A pair of aggregation switches is connected to an edge node by a multi-chassis link aggregation group, wherein the aggregation switches are connected by a virtual fabric link (VFL) for exchange of information between the Aggregation Switches. The VFL includes a plurality of subsets of VFL physical links, wherein each subset is connected to a different pair of network interface modules on the Aggregation Switches. Traffic distribution across the plurality of subsets of VFL physical links is based on destination hardware device information in a pre-pended header of packets and / or based on a load balancing identifier in the pre-pended header.
Owner:WSOU INVESTMENTS LLC
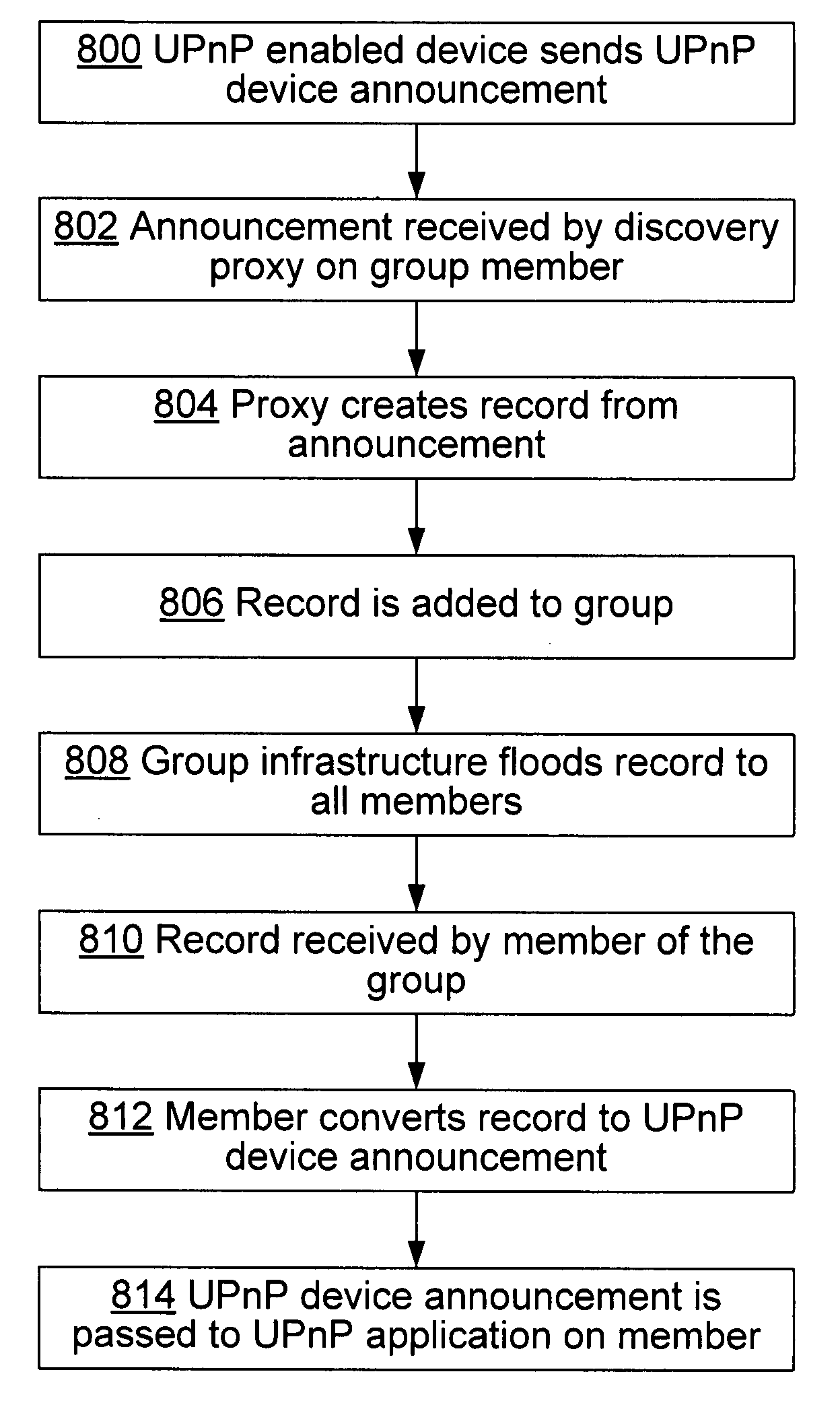
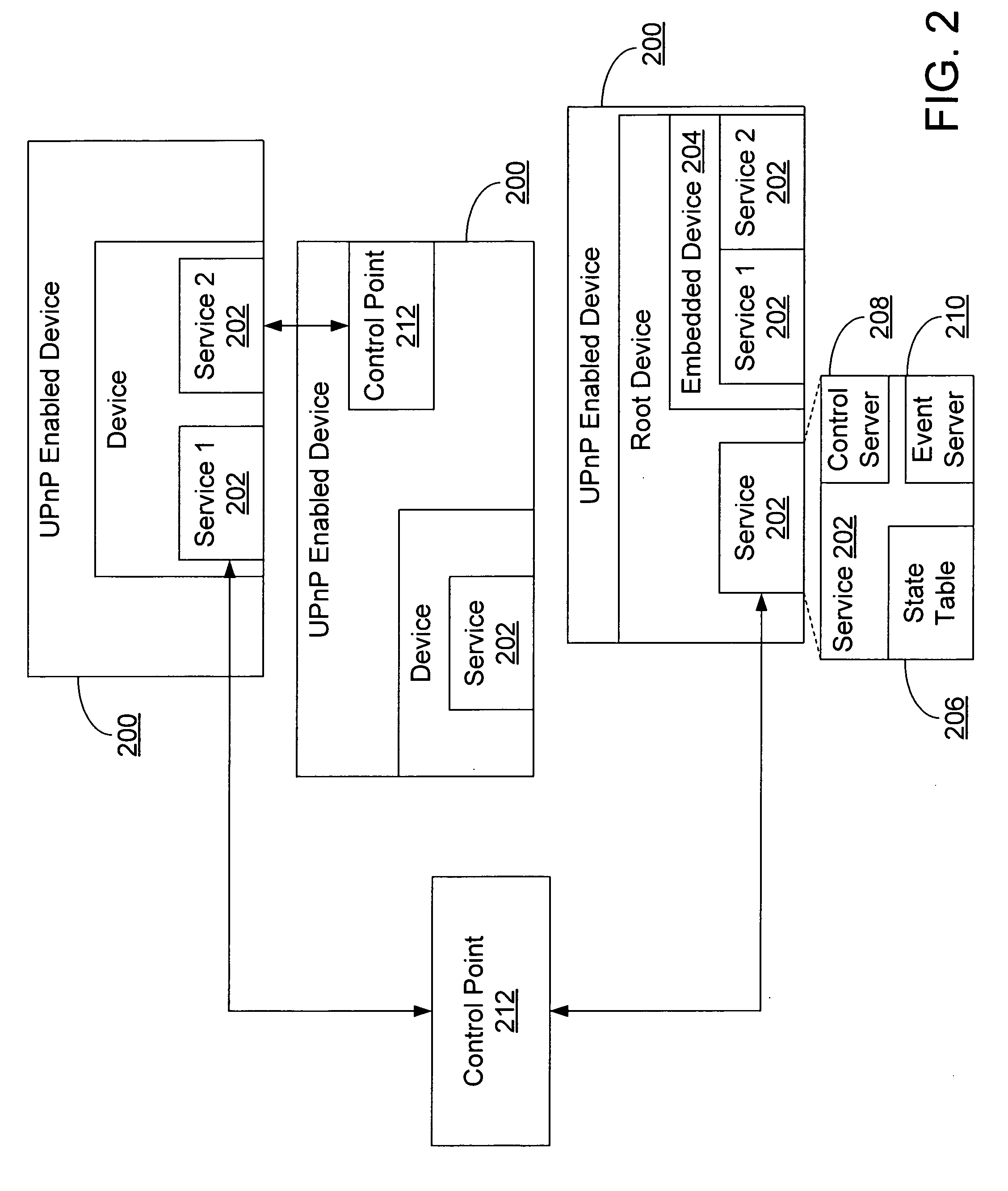
Scaling and extending UPnP v1.0 device discovery using peer groups
ActiveUS20060184693A1Effectively scaledFacilitate communicationMultiple digital computer combinationsData switching networksSemanticsComputer science
Disclosed is a method for scaling and extending the reach of UPnP device discovery and eventing by leveraging the use of a peer-to-peer network infrastructure. Peer-to-peer networking allows for the organization of a set of nodes into a group for efficient exchange of information and the group has an efficient and scalable mechanism for flooding data to all members in it. In one embodiment one PC in a peer group can receive device discovery announcements and subscribe for device event notifications. A discovery proxy and an eventing proxy running on the PC package the announcement and / or notification in a record and proceed to flood it to the group. The group flooding semantics route the notification to the subscribed controllers, which can subsequently take suitable action. Ultimately, this method produces a result whereby device discovery and eventing tasks can be fulfilled by locating the closest peer and obtaining the device announcements and notifications from that peer.
Owner:MICROSOFT TECH LICENSING LLC
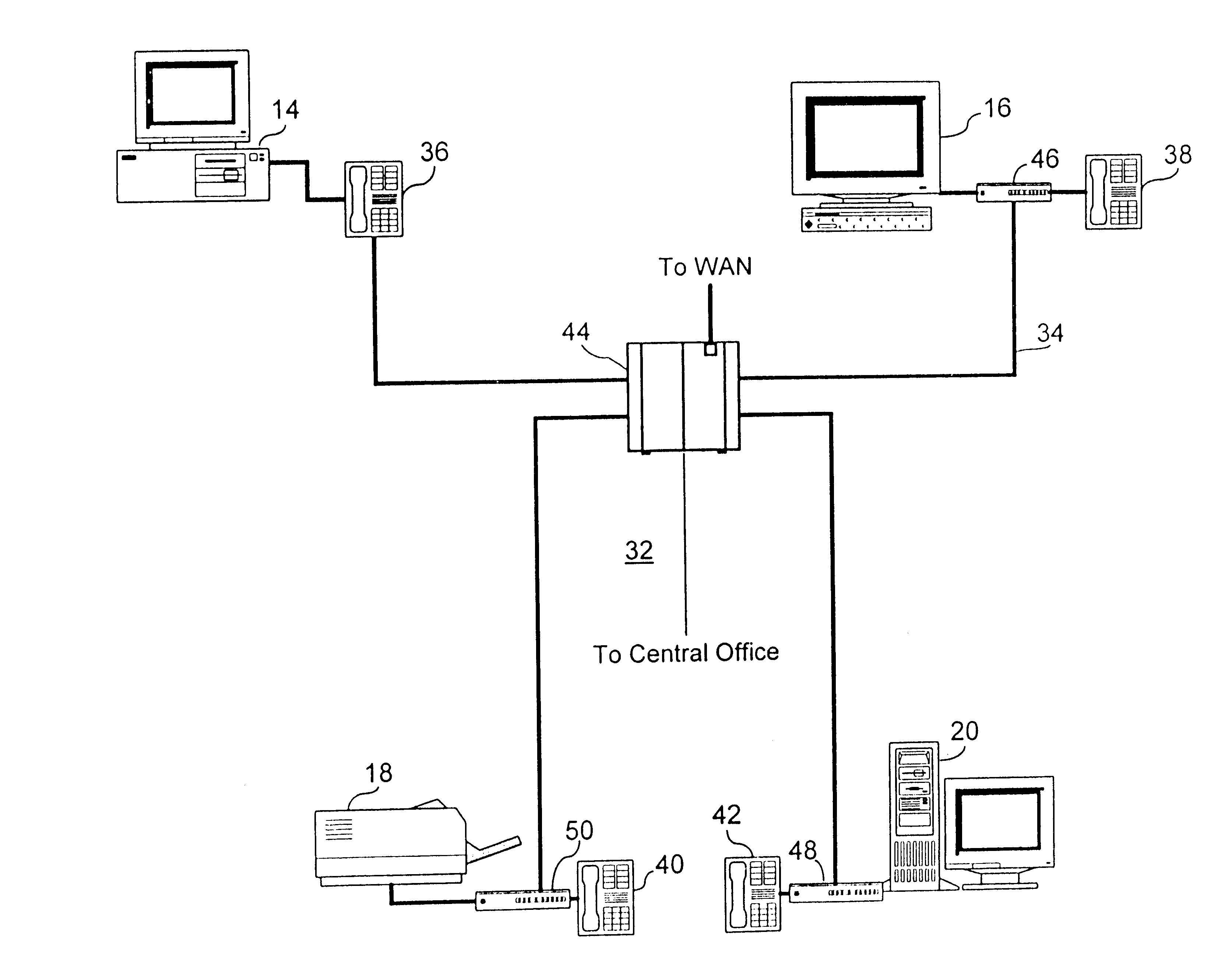
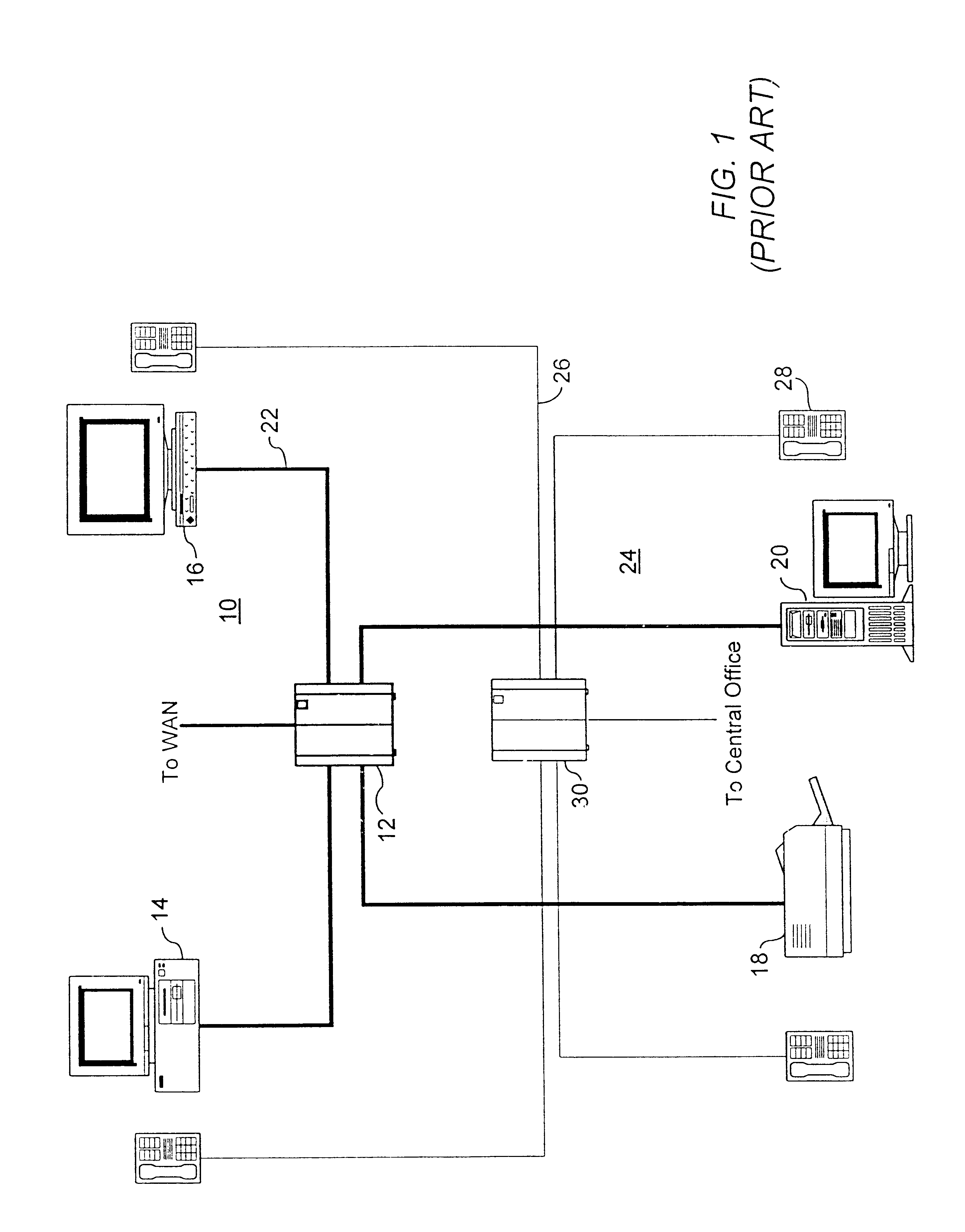
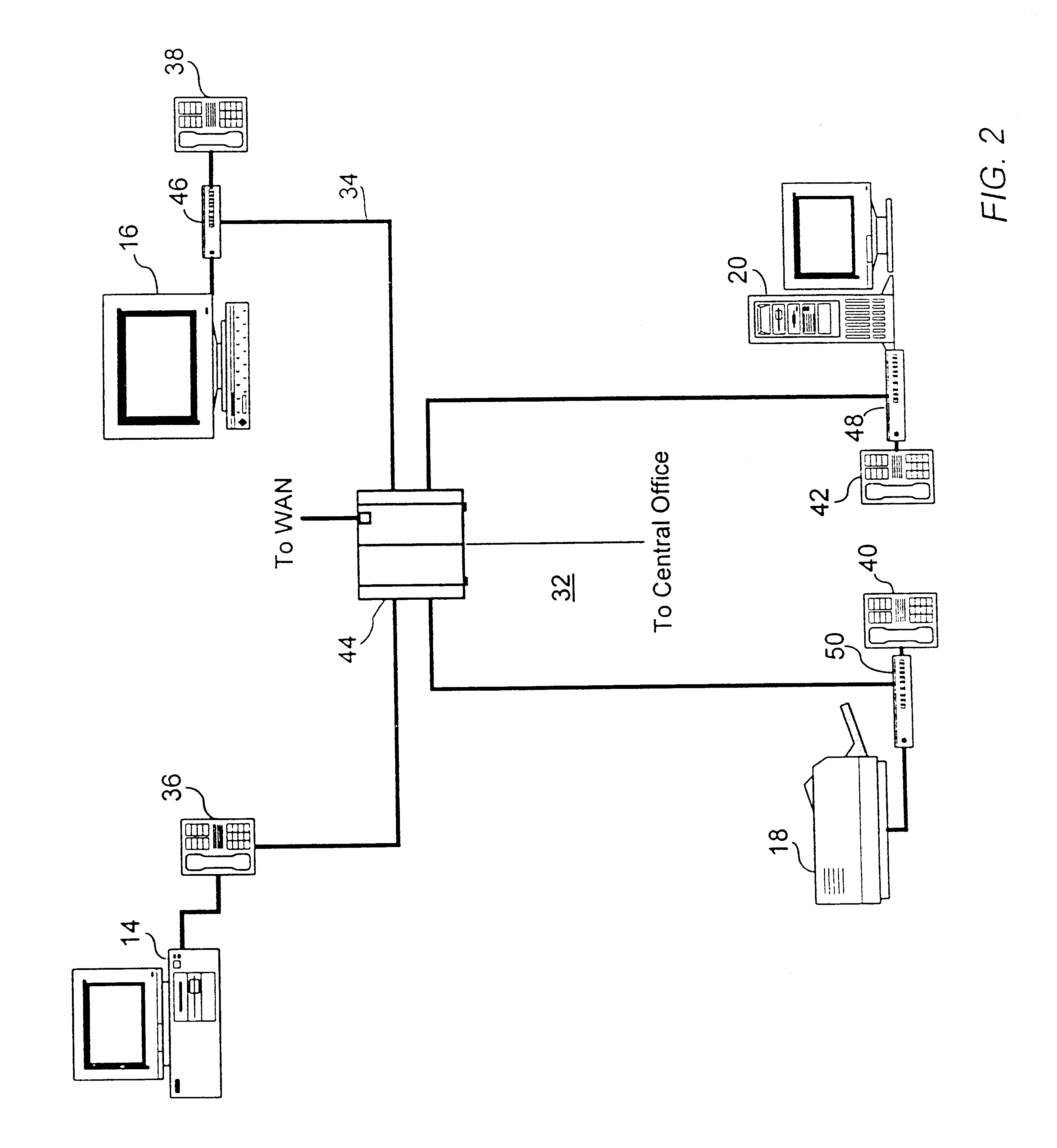
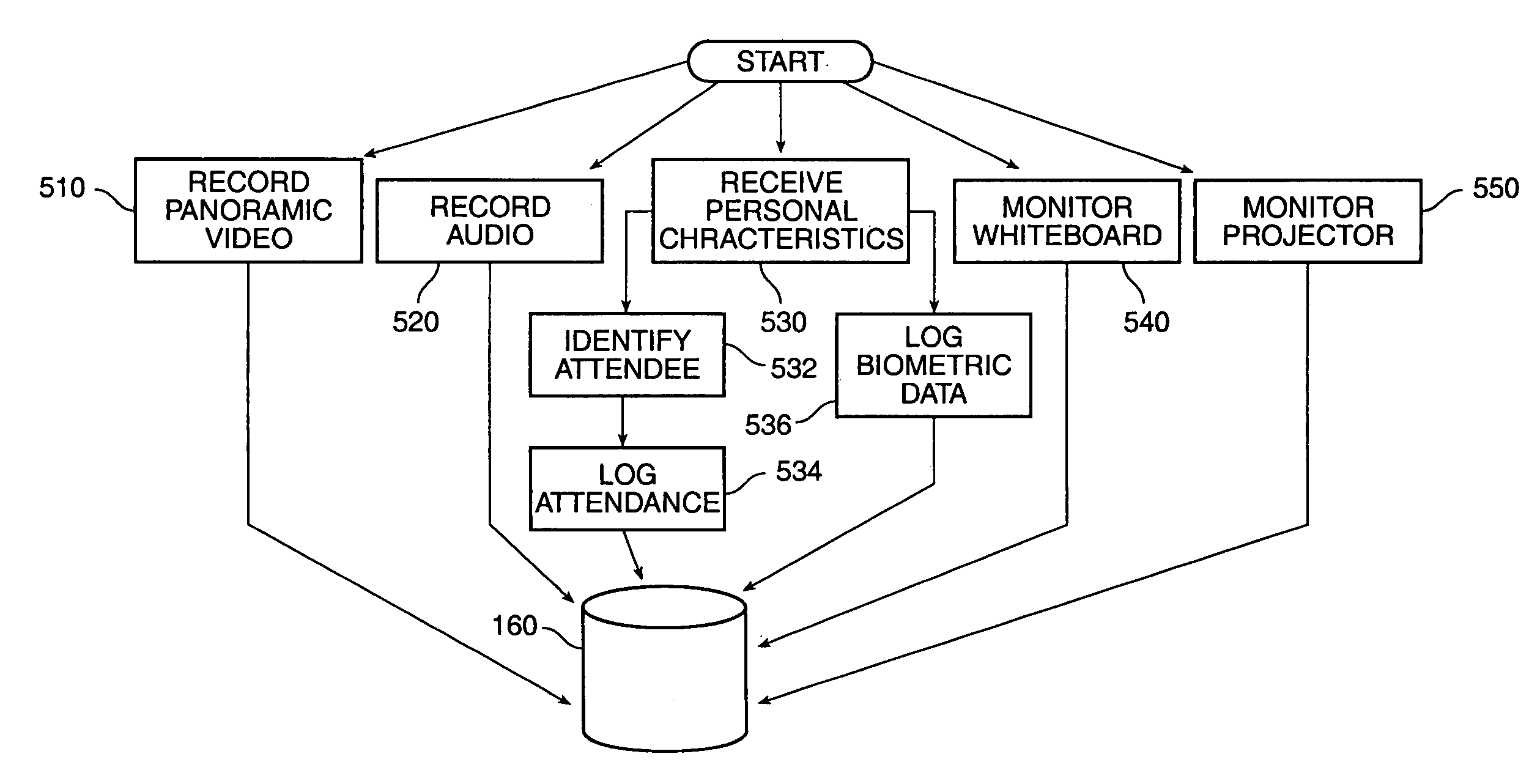
Method and system for information management to facilitate the exchange of ideas during a collaborative effort
InactiveUS7299405B1Easy to optimizeTelevision system detailsTelevision conference systemsDocumentationExchange of information
A unique combination of components is disclosed to facilitate information management during a collaborative effort. Interaction during a meeting is supported by the use of devices in a manner that allows attendees to quickly retrieve and display documents on-command or automatically. The information includes previously recorded meetings among other things. The disclosed method and system, thus, facilitates the exchange of information during meetings.
Owner:RICOH KK
Internet-based group website technology for content management and exchange (system and methods)
ActiveUS8353012B2Data processing applicationsDigital data processing detailsDomain nameContent management system
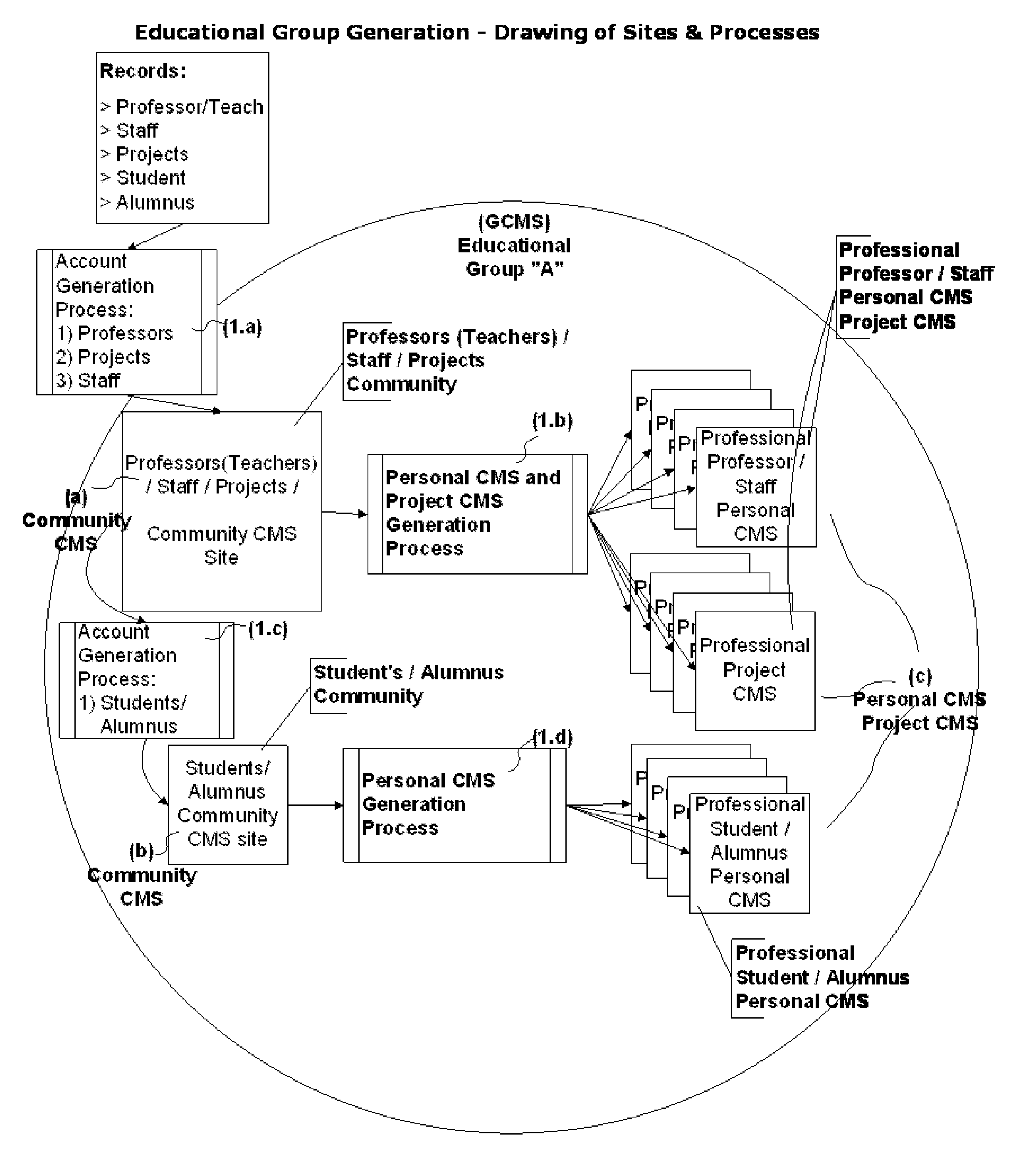
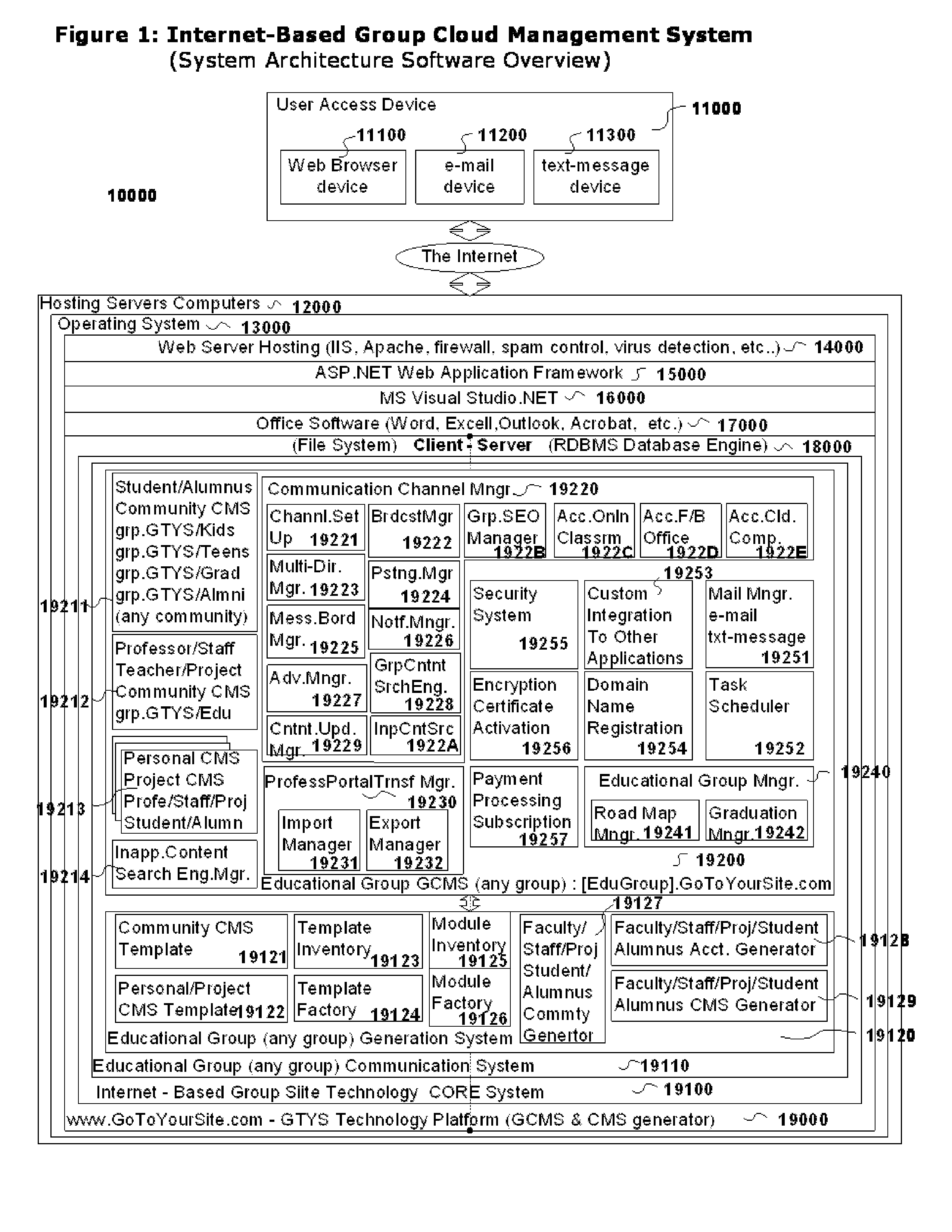
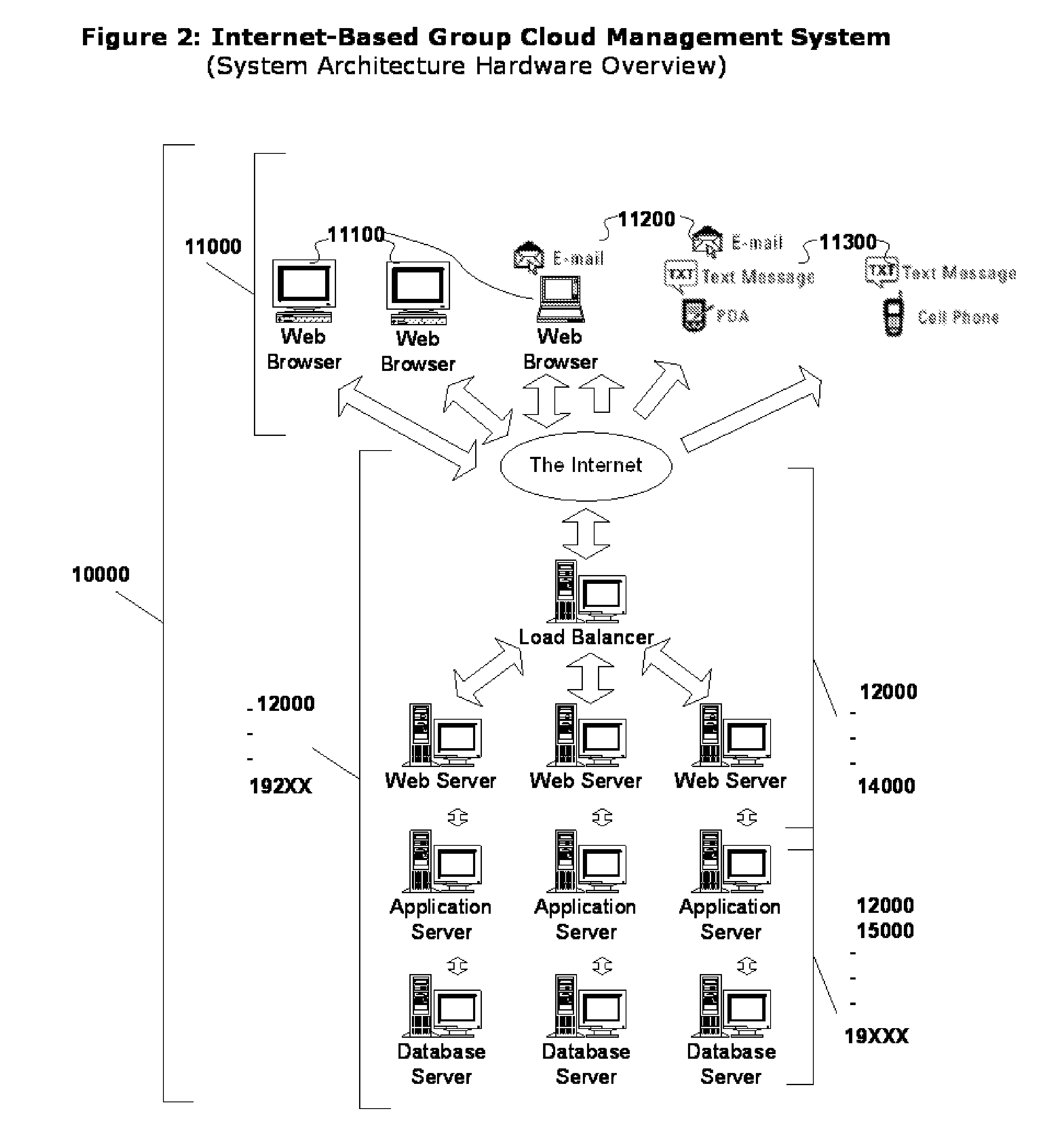
System and Methods for implementing a Internet-Based Group Cloud Management System (GCMS) comprised by several Cloud Management System sites (CMS sites), where providing institutions, means for: A) The Creation of the Educational Group comprised by: A1) Community CMS sites for Campuses and / or Groups of Users, A2) Personal CMS Sites for each Faculty, Staff, Student and Alumnus, A3) Project CMS sites for each Project Team. B) Communication within the Educational Group: B1) Among CMS Sites, B2) to e-mail and text-messaging devices. The CMS sites are reachable by their own domain names or sub-domain from the GCMS, and by any search engine. Each CMS site is multi-user and includes its own security system, user-defined and predefined pages for among others, Professional Profile, Web Apps, Virtual Desktop / Apps and Web / Cloud Services. Each CMS site is connected to the GCMS, allowing the Exchange of Information among CMS sites within the GCMS and among GCMS sites.
Owner:CITRIX SYST INC
Communication methods for networked gaming systems
ActiveUS20110230268A1Reduce overheadEasy to operateApparatus for meter-controlled dispensingVideo gamesThin clientExchange of information
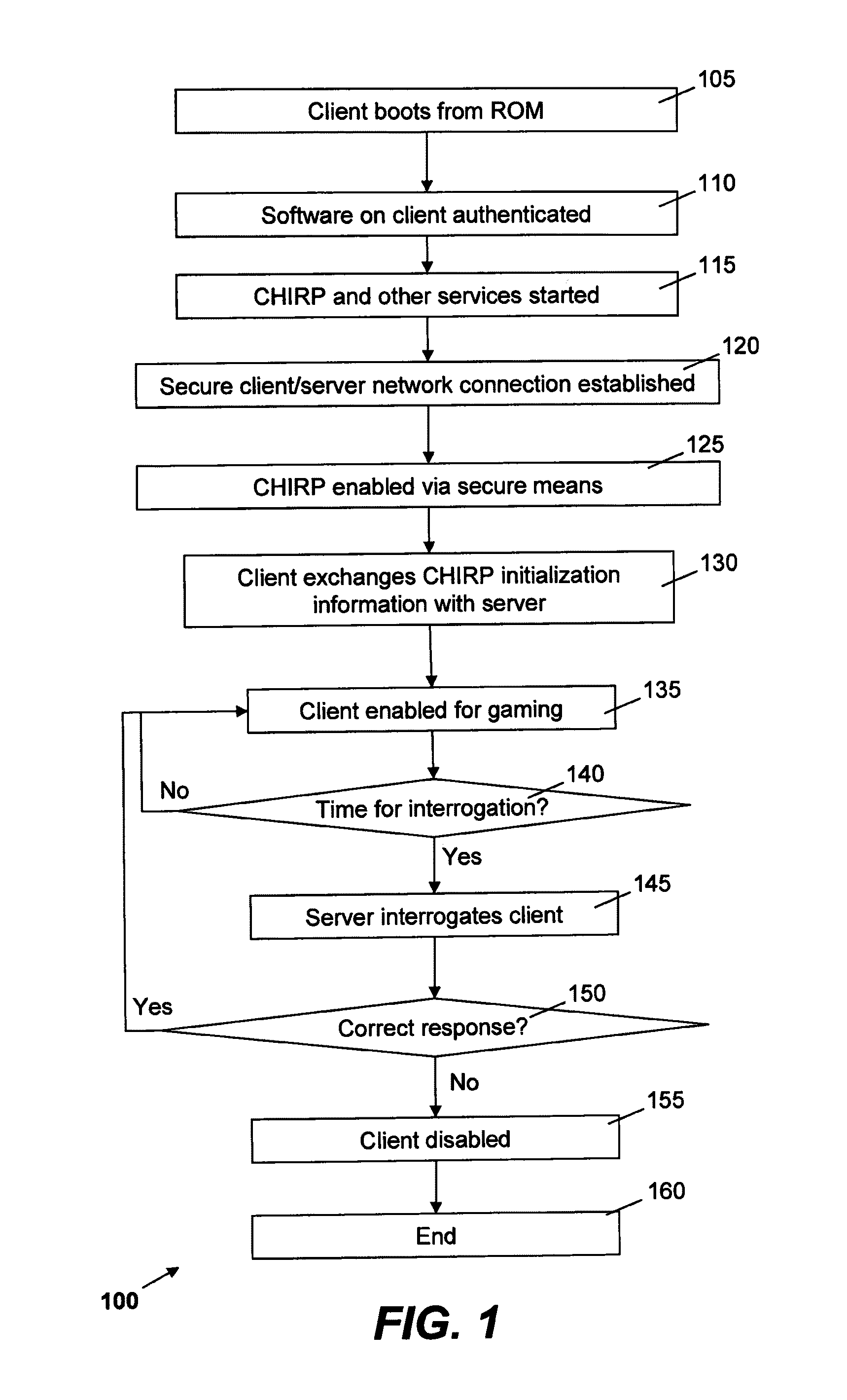
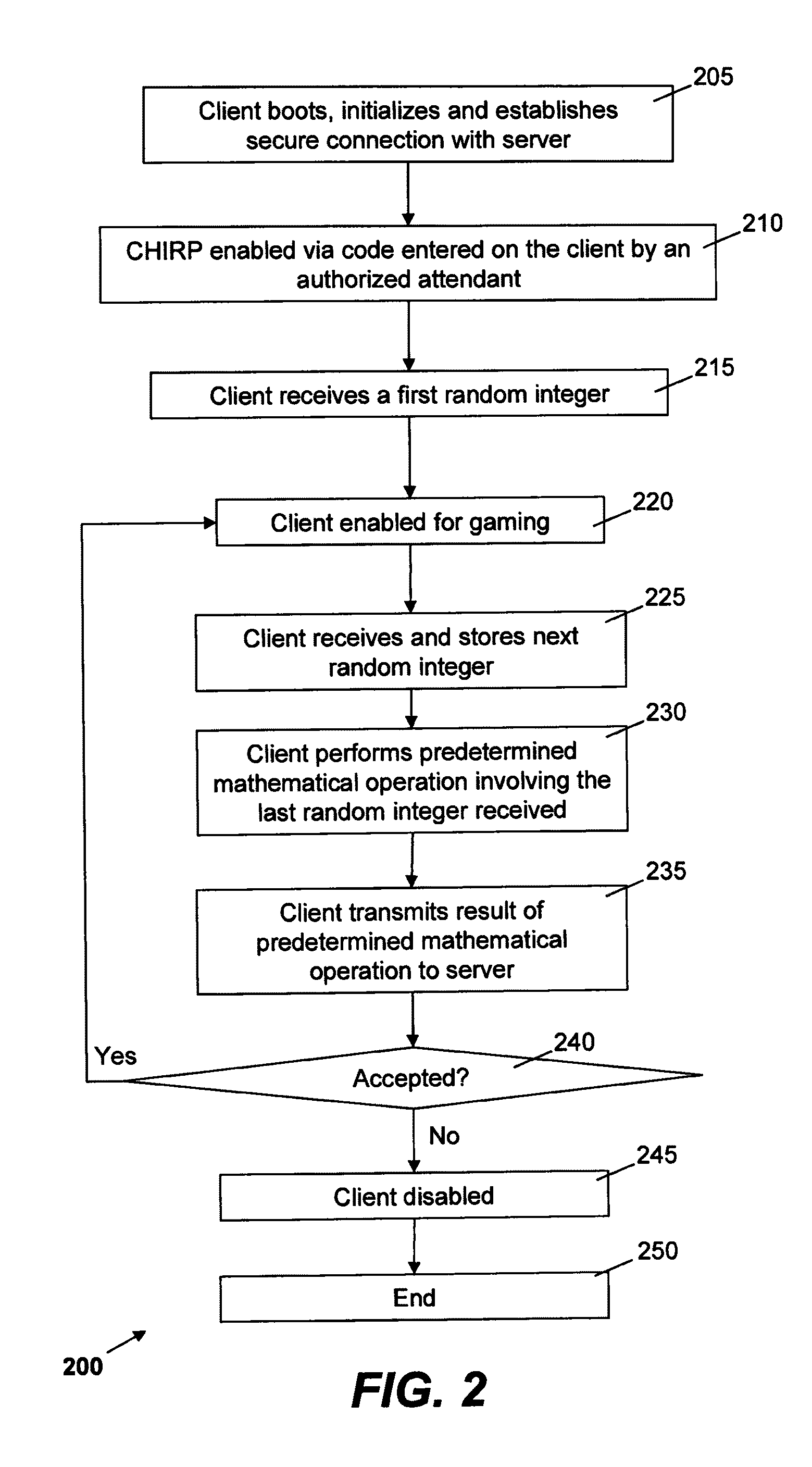
Methods and devices are provided for secure identification and authentication of computing hardware connected to wired or wireless networks, including but not limited to thin clients in server-based systems, mobile gaming devices, etc. Some implementations involve a frequent exchange of information between networked devices. In some implementations the exchange may be so frequent as to be effectively a constant exchange of information, though there may be small time intervals during which no such information is exchanged. Some preferred methods are effective against both external attacks and those benefiting from assistance or information provided by those with administrative access.
Owner:IGT
Communicative game system
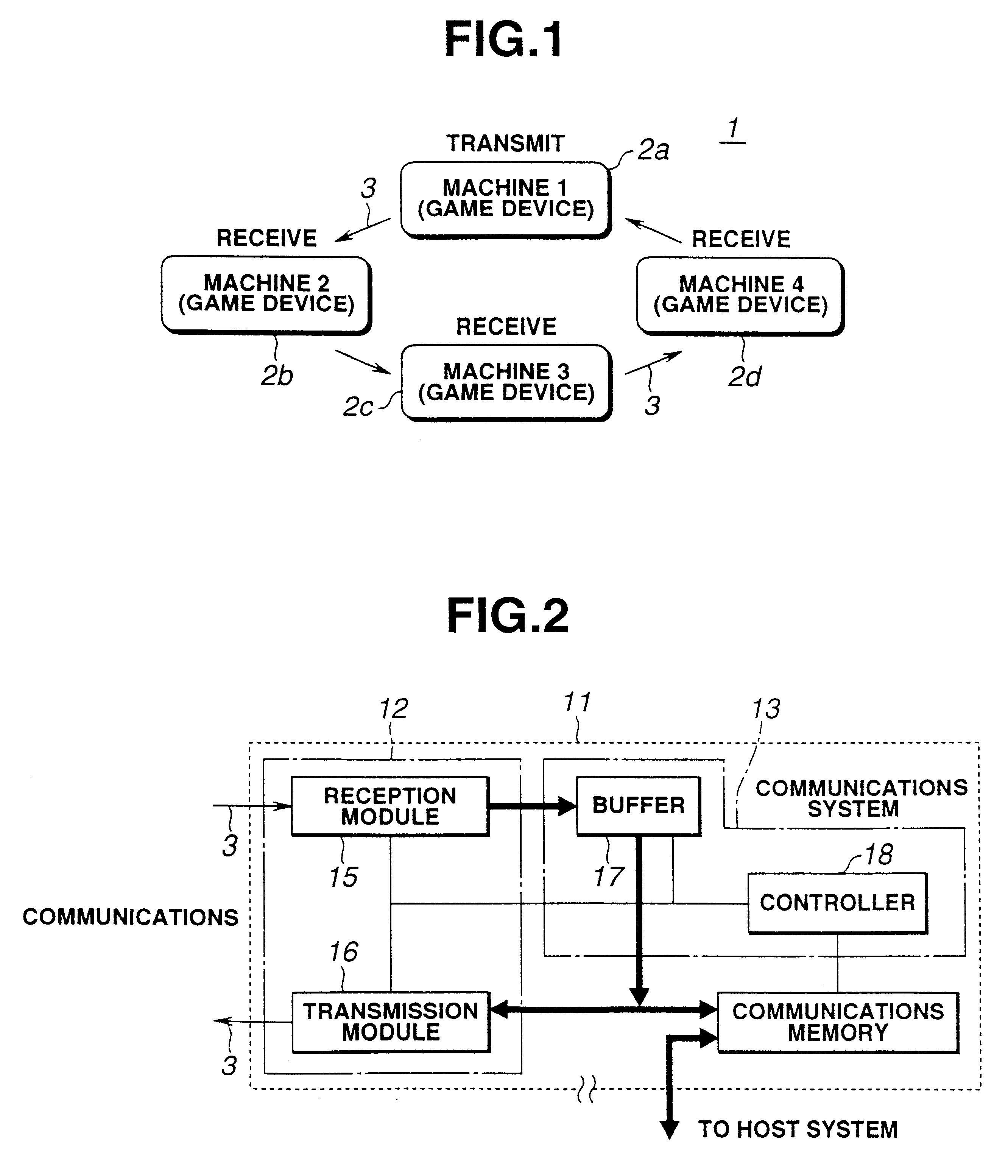
InactiveUS6306039B1Enhanced RealityCathode-ray tube indicatorsImage data processing detailsCommunications systemCommunications media
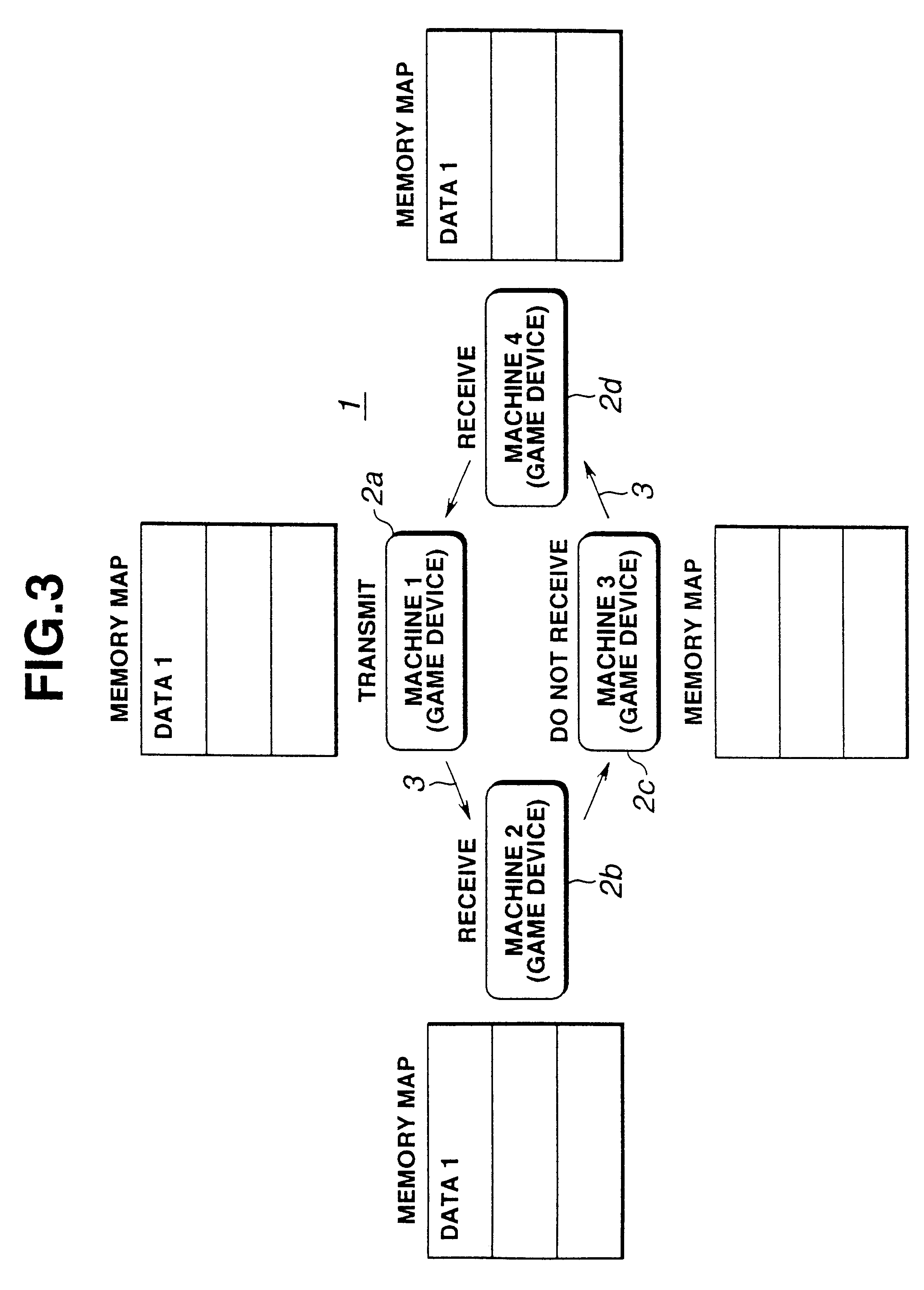
By enabling exchange of information relating to players, apart from game data, "communication" between the players is increased, and the sense of rivalry and level of interest generated by a game are raised. The communication game system 1 forms a network comprising a plurality of game devices 2a-2d connected mutually by communication media 3. The plurality of game devices 2a-2d respectively comprise a communications system 31 for receiving data transferred over the network and transferring the received data and data generated by the home game device onto the network, and a host system 32 for accessing the received data. By this means, data comprising a game packet, sound packet and video packet can be transmitted by conducting broadcast communications based on the communications system 31 and host system 32 between the plurality of game devices 2a-2d.
Owner:SEGA CORP
Method and system for performing perfectly secure key exchange and authenticated messaging
InactiveUS20060034456A1Public key for secure communicationSecret communicationBusiness processExchange of information
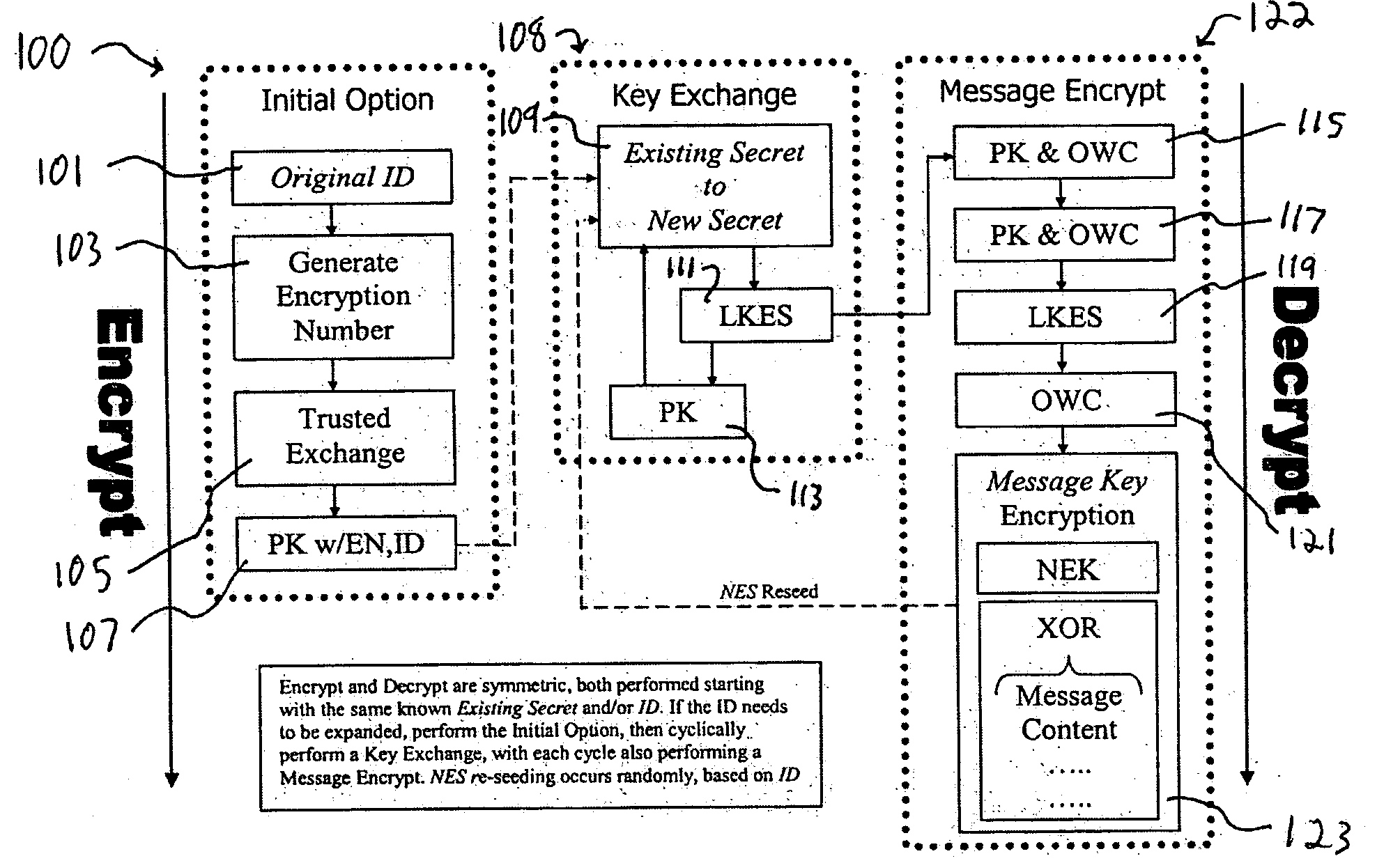
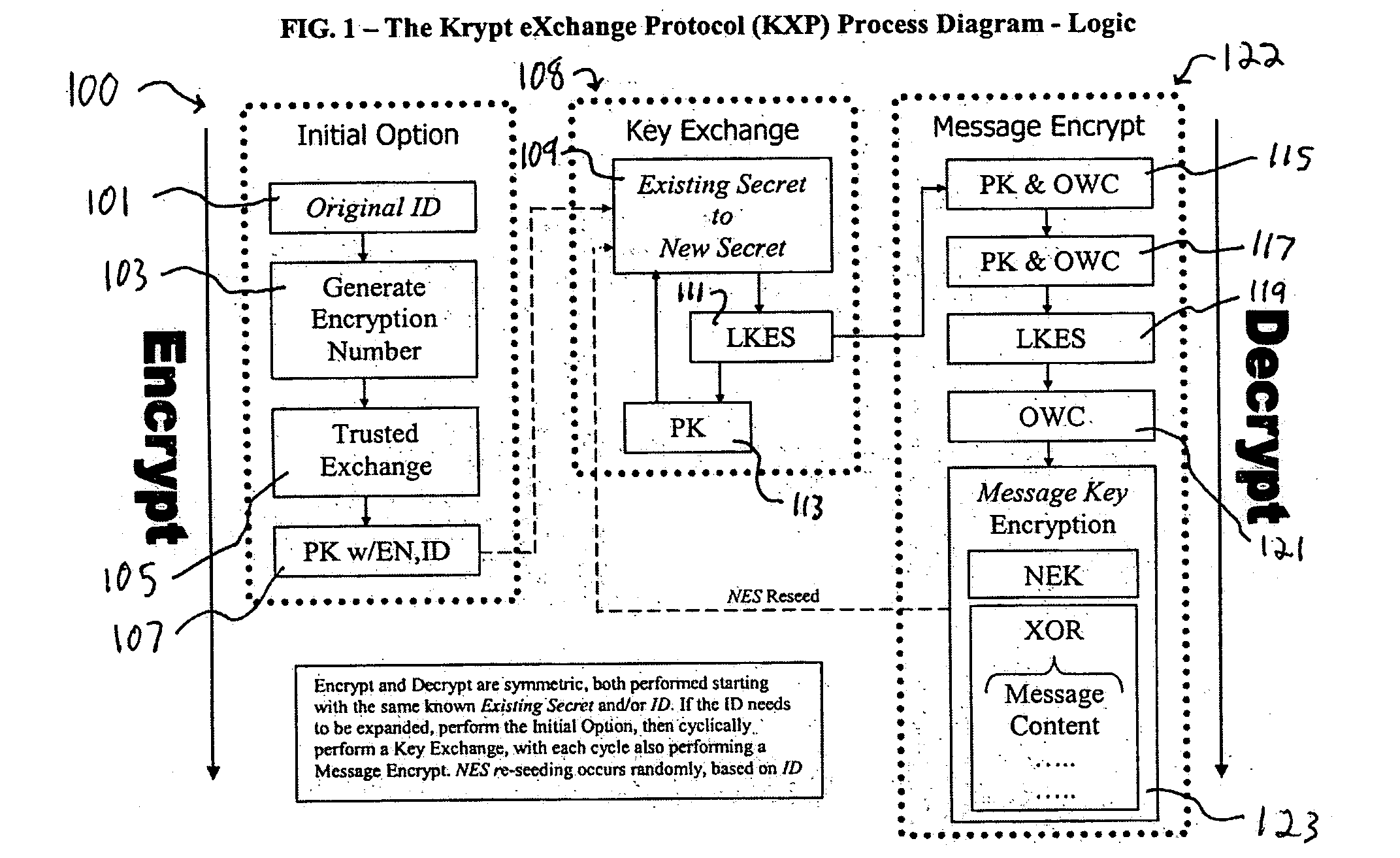
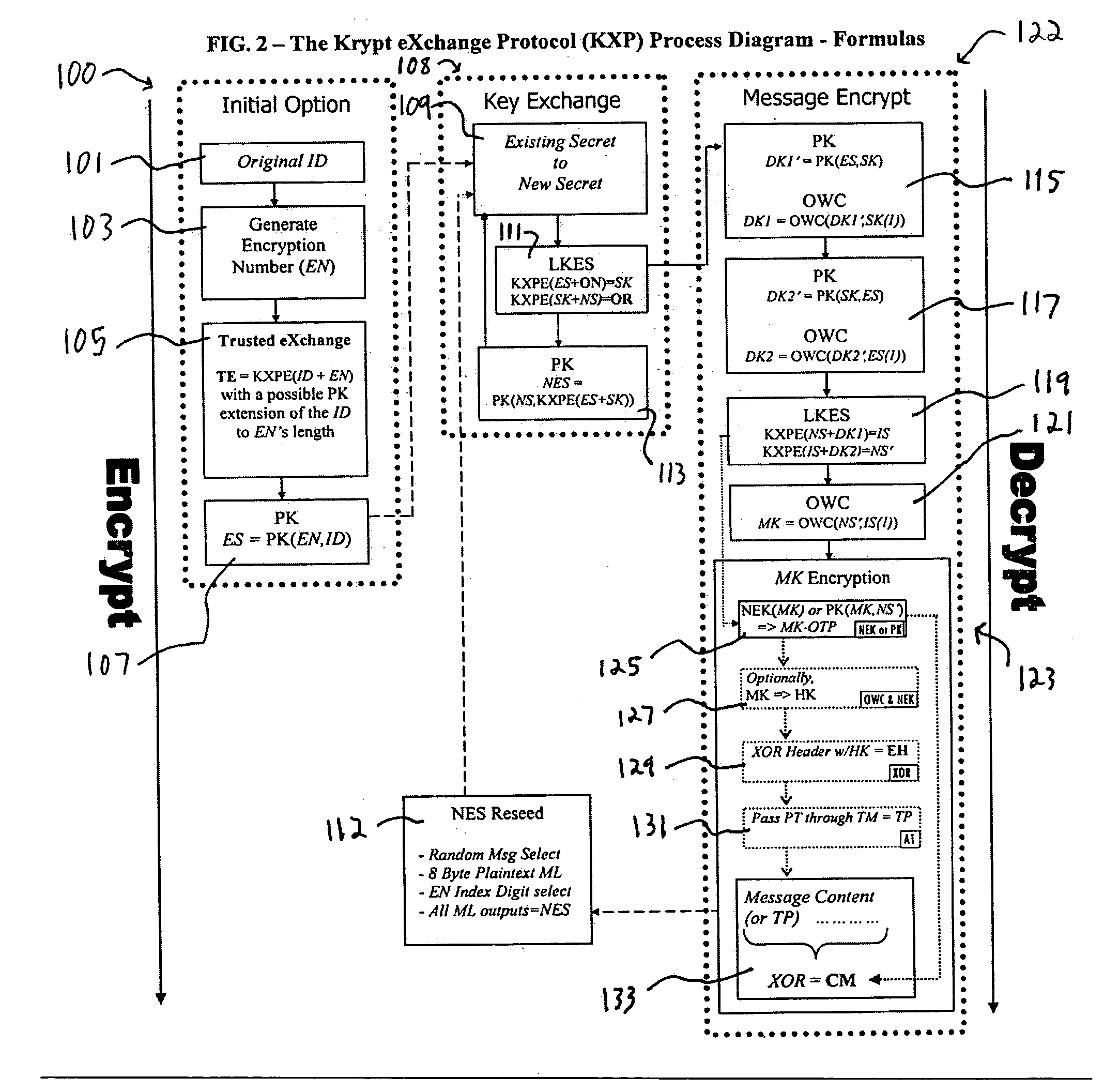
A system and method for the cryptographic exchange of information is provided which affords maximum security, process simplicity and participant convenience to any software application, business process or device used to communicate messages. The system provides the ability to openly exchange encryption keys for each communication between participants in a totally secure fashion. Along with the key exchange, the system and method can be used to secure all accompanying message content with a derived message key. The system and method derives the message key in such a manner that the original encryption key cannot positively be determined from a discovered message key. The system and method additionally provide a technique for authenticated exchange of new encryption keys such that the new key is completely dissimilar from any previous key, effectively eliminating any chained key knowledge.
Owner:RELEVANT SECURITY
Common user profile server and method
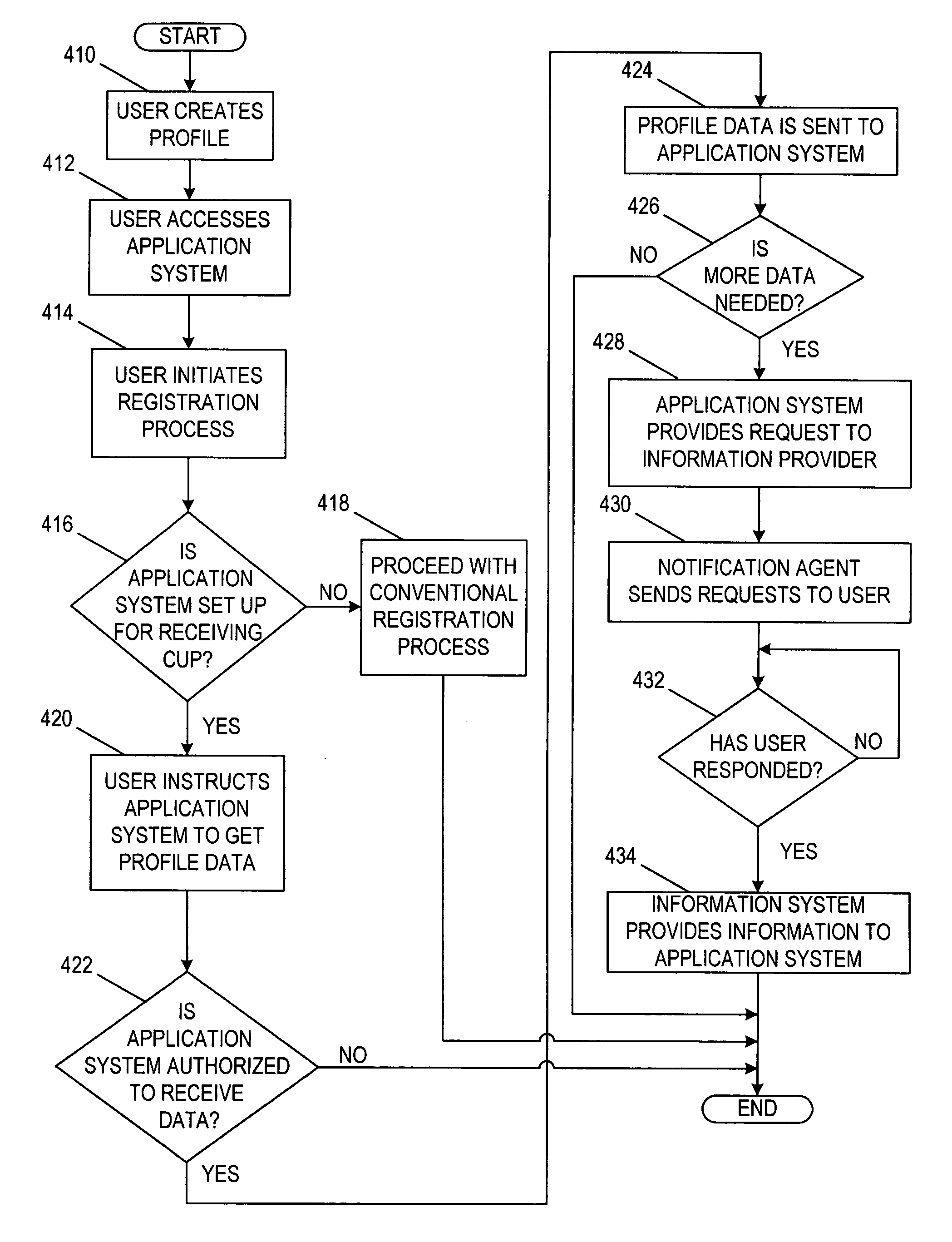
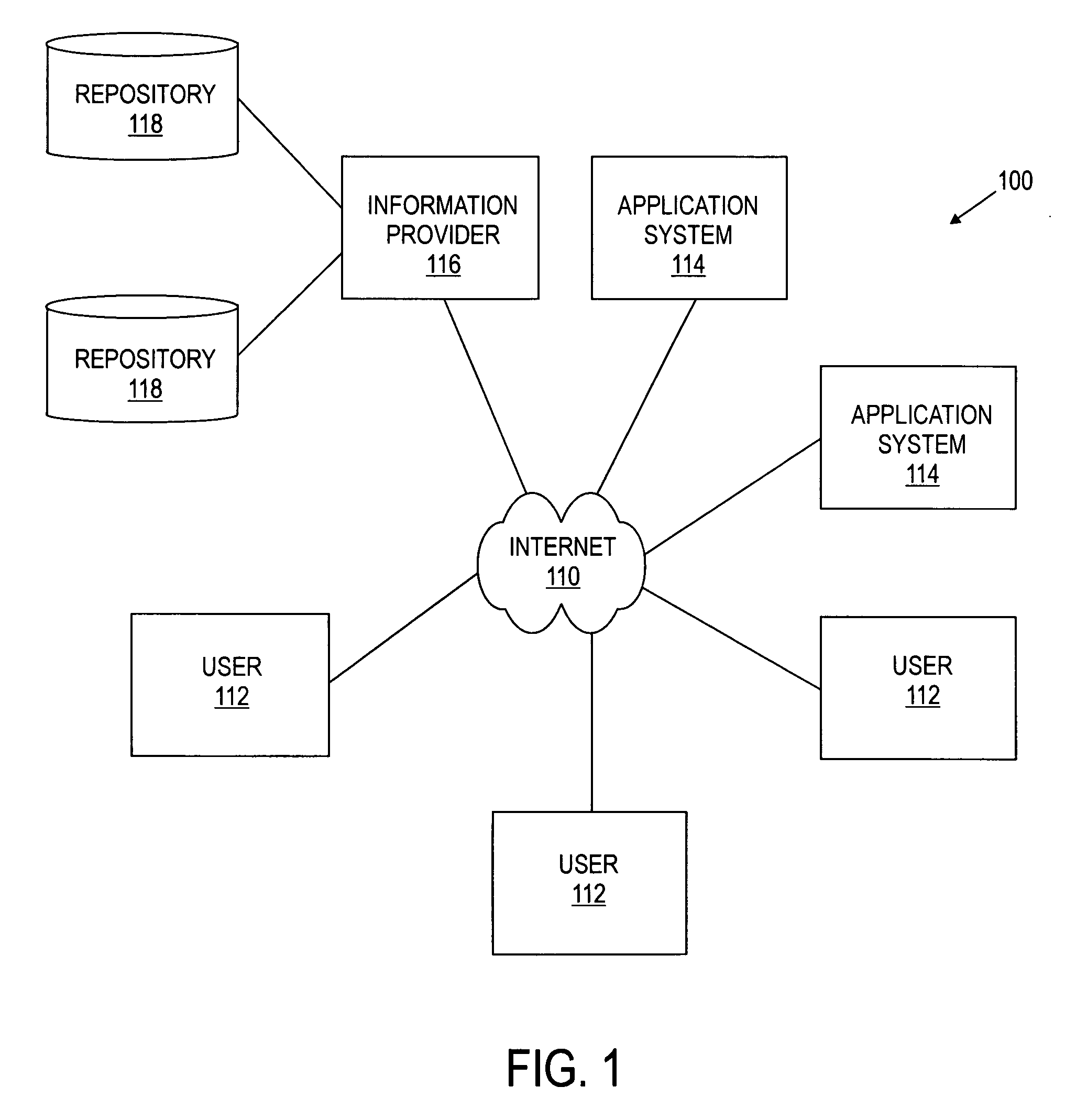
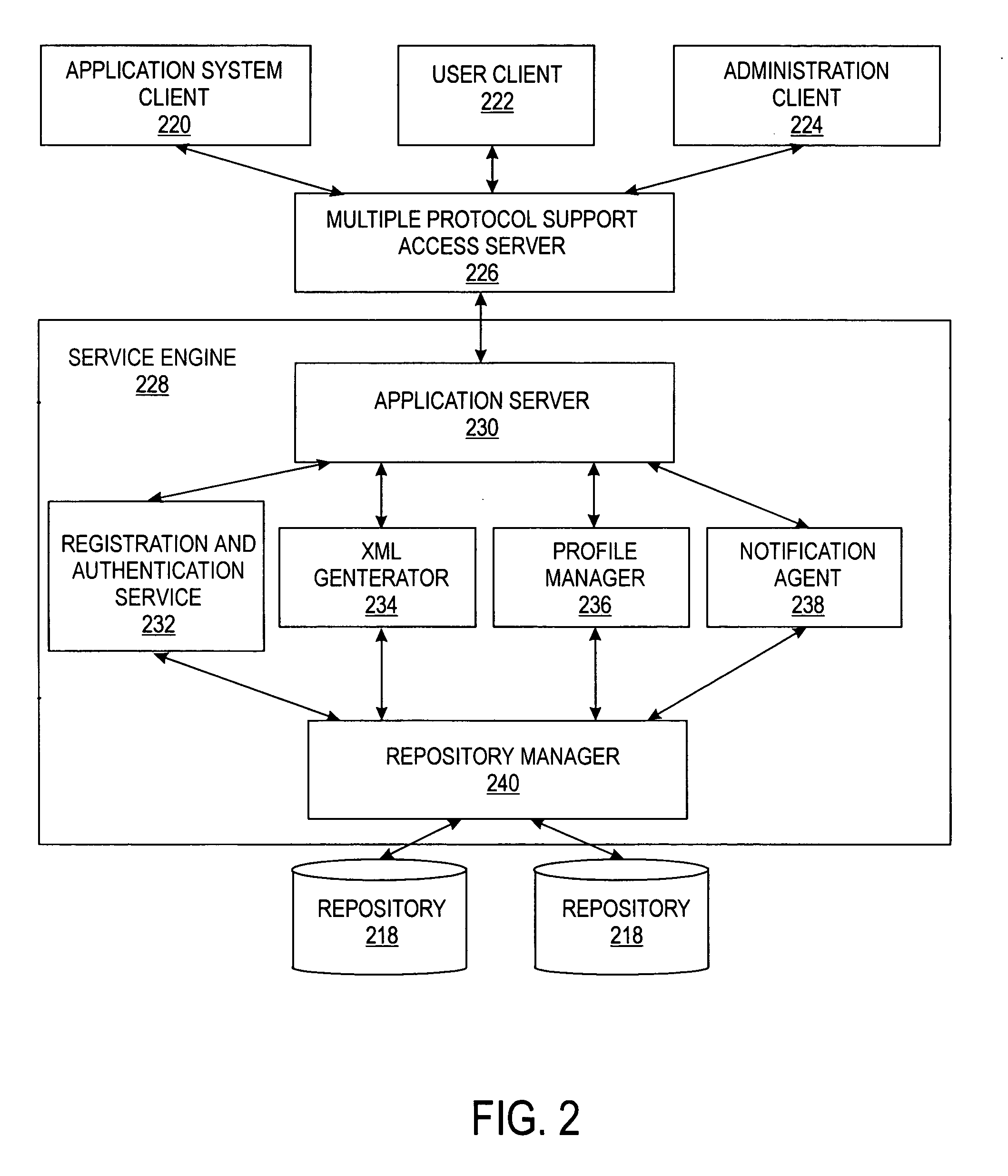
InactiveUS6944677B1Customer relationshipMultiple digital computer combinationsFile serverUser profile
A method and apparatus is provided for facilitating the exchange of user profile information between an information provider and an application system. The invention allows a user to create and edit user profile information stored by an information provider. The information provider stores the information and provides a mechanism for providing the user profile information, or portions thereof, to various application systems. When a user initiates a registration or similar process with an application system, the present invention facilitates the exchange of information between the application system and the information provider to streamline the registration process.
Owner:ASPECT COMM +1
System and method for virtual fabric link failure recovery
Aggregation switches are connected to an edge node by a multi-chassis link aggregation group and a virtual fiber link provides a connection for exchange of information between the aggregation switches regarding MAC addressing to synchronize MAC address tables across the aggregation switches. When failure of the virtual fiber link is detected, the multi-chassis link aggregation group is reconfigured into two or more link aggregates with each link aggregate connecting the edge node to one of the aggregation switches. A spanning tree protocol is initiated over the link aggregates to prevent loops in the network. MAC address tables are flushed and relearned with the two or more link aggregates.
Owner:WSOU INVESTMENTS LLC
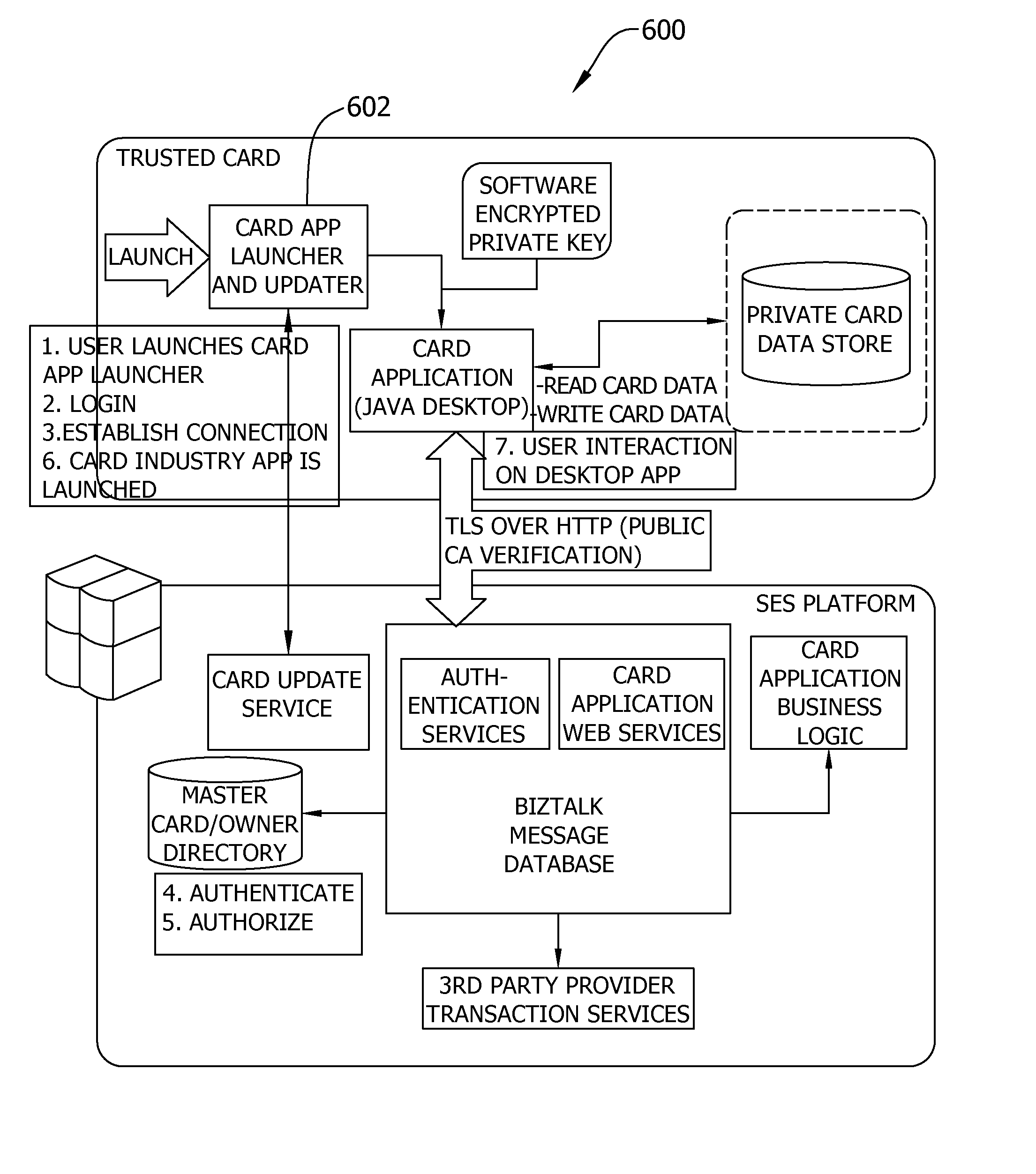
Trusted card system using secure exchange
InactiveUS20100042846A1Safe storageLimited accessDigital data processing detailsUser identity/authority verificationAccess methodCoupling
A system for secure, role-based exchange of information between a client and providers of services is described. The system includes a client device having a memory that includes a portion of the data relating to the client, a user access component, and an enforcement agent. The system also includes a central server running an authentication methodology and a roles server. The central server includes the data relating to the client. The system further includes an interface device capable of communications with the central server and capable of communicative coupling with the client device. The system is operable to, upon a communicative coupling between the interface device and the client device, activate the user access method, in conjunction with the authentication method, to ensure that the client is the proper holder of the client device. The enforcement agent is operable with the roles server and user interface input from the client to define access rights to the client data for the providers of services, who also have access to the central server.
Owner:SECURE EXCHANGE SOLUTIONS
Method and apparatus for the zonal transmission of data using building lighting fixtures
InactiveUS20050231128A1Electric light circuit arrangementClose-range type systemsEffect lightEngineering
This invention relates to the zonal transmission of data by the modulation of the light output of arc lamps or discharge lamps; including the visible or invisible light output of fluorescent lamps, mercury vapor lamps, high or low-pressure sodium lamps, metal-halide based lamps, or other arc or discharge lamps. The method results in an easily installed, easily maintained, and economical to purchase, optical-wave communications system which exploits the existing infrastructure of a building or facility to facilitate the transmission of data in individual zones; thereby facilitating the transmission of wide-area as well as zonal-specific data to compatible receivers, and further facilitating the determination of location of remote devices or users, and the delivery or exchange of information or data, utilizing limited range transmission techniques.
Owner:CONVERGENCE WIRELESS A CALIFORNIA CORP
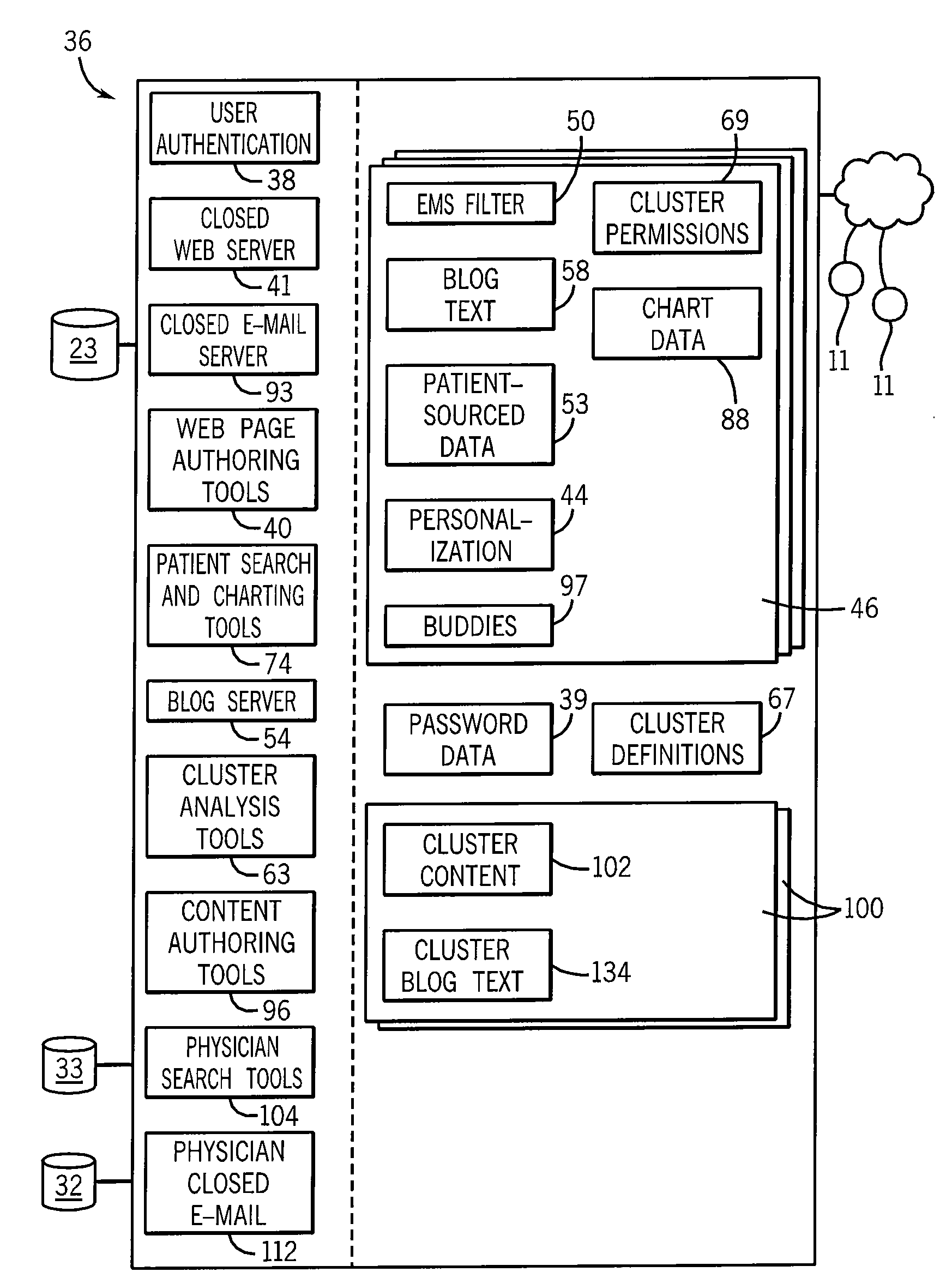
Patient Community System With Anonymized Electronic Medical Data
ActiveUS20100070306A1Quality improvementInterestingMedical communicationMedical data miningMedical recordCommunity system
A computerized system allows intercommunication of patients with respect to the treatment of their diseases. This system includes an electronic medical record database providing electronic medical records of a given set of patients as developed by healthcare professionals and linked to an anonymous identifier for each patient and a set of terminal devices accessible to the patients allowing for the electronic exchange of information through a display and data input device. A server system connects the anonymous medical record database and the terminal devices and executes a stored program to: (1) allow an authenticated connection by a given patient to the server system through a terminal device and associate the connection with an anonymous identifier; (2) permit authoring by the given patient of a patient site viewable on a terminal device incorporating medical records from the anonymous medical record database associated with the anonymous identifier; and (3) identify to the given patient other patient sites for other patients having shared medical conditions according to a predetermined clustering of data of the anonymous medical record database.
Owner:EPIC SYST CORP (US)
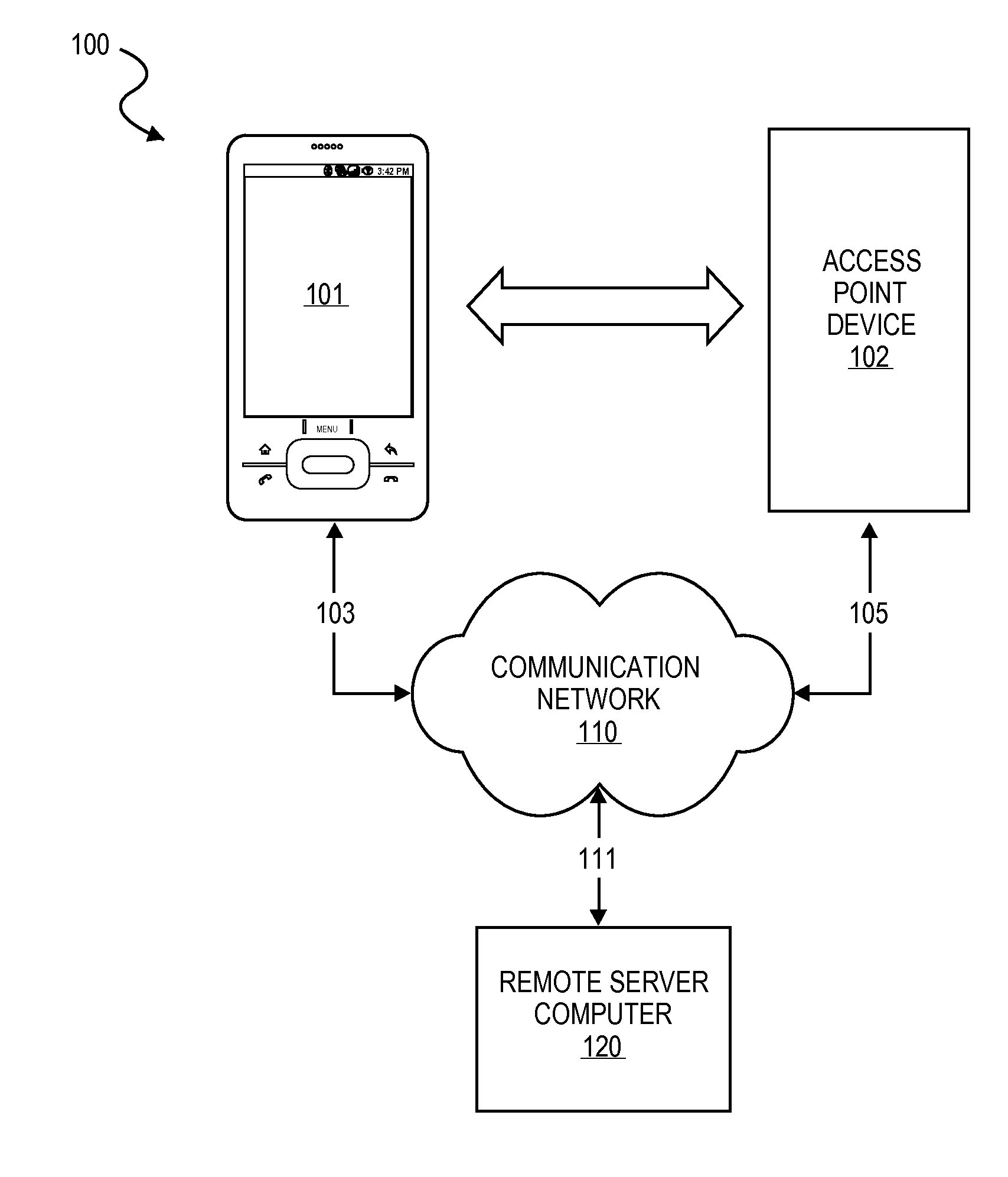
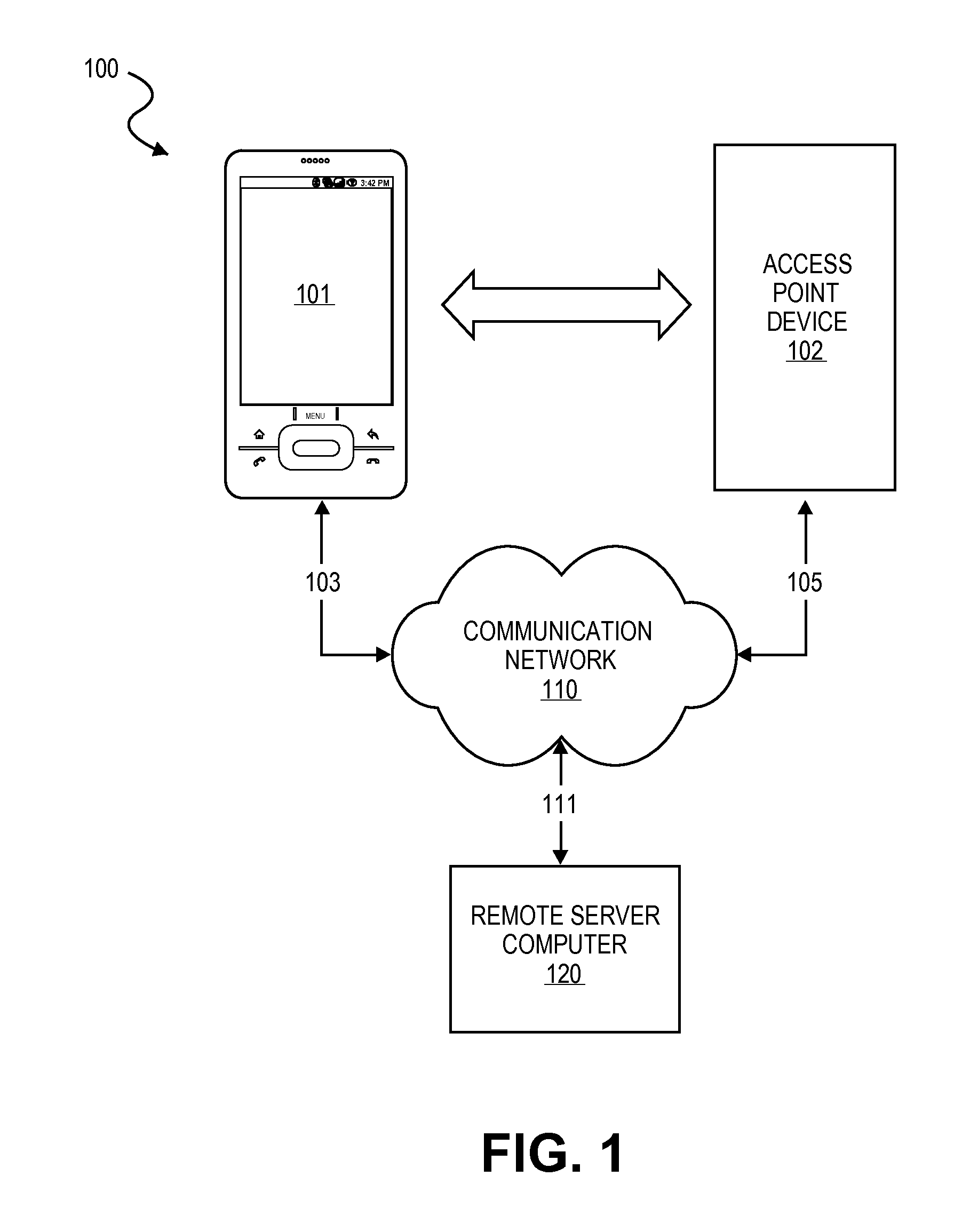
Access Using a Mobile Device with an Accelerometer
Embodiments of the present invention are directed to systems, apparatuses and methods for using a mobile device with an accelerometer to gain access into a secured or restricted area. A first device and a second device interact by making physical contact with each other thereby generating interaction data that is representative of the physical interaction between the first and second device. The first and second device may be mobile phones. The second device may be a point of sale terminal, access point device, or any other stationary (i.e., in a fixed position) device positioned at a line, door, gate, or entrance. A server computer determines, based on interaction data, that the first device and the second device made physical contact. After determining that the first device and the second device made contact, communications may be initiated between the devices. Communications may relate an access transaction comprising an exchange of information, such as credentials, between a prospective entrant (operating the first device) and a gatekeeper (operating the second device) to verify that the prospective entrant is permitted or is not permitted access to a particular area that is secured or restricted by the gatekeeper. Other embodiments are direct to confirmation transactions. Access transaction and confirmation transactions may be combined with a financial transaction using a payment processing network.
Owner:VISA INT SERVICE ASSOC
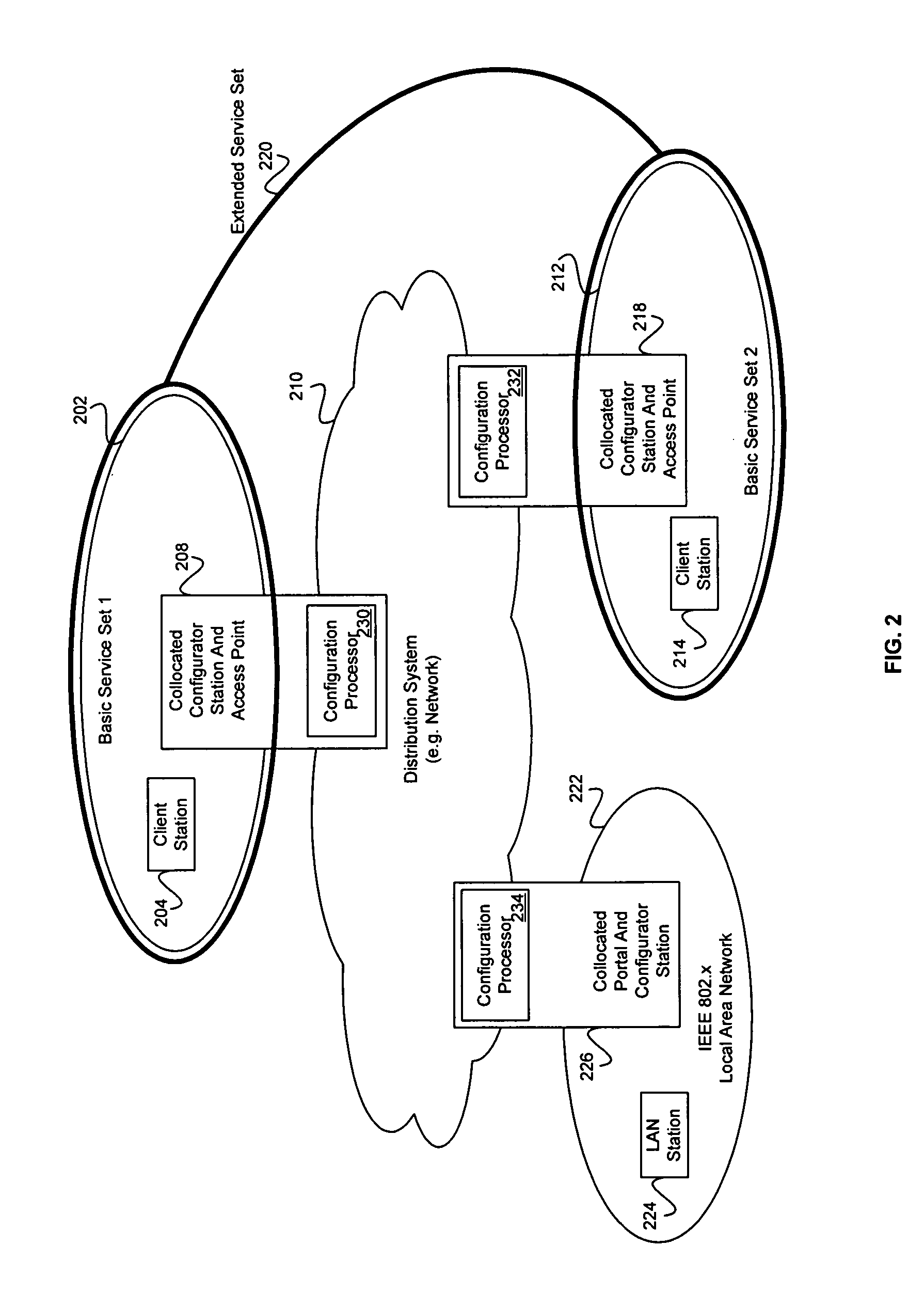
Method and system for exchanging setup configuration protocol information in beacon frames in a WLAN
InactiveUS20060039341A1Digital data processing detailsMultiple digital computer combinationsBeacon frameClient-side
Certain aspects of a method for enabling exchange of information in a secure communication system may comprise configuring at least one 802.11 client station via authentication enablement information comprising data that specifies a time period during which configuration is allowed. The data that specifies a time period during which configuration is allowed may comprise a configuration window open field, which indicates a period when a configuration setup window is open. At least one client station may be configured via the authentication enablement information comprising recently configured data, which indicates whether at least one configurator has configured at least one other client station within the time period during which the configuration is allowed.
Owner:AVAGO TECH INT SALES PTE LTD
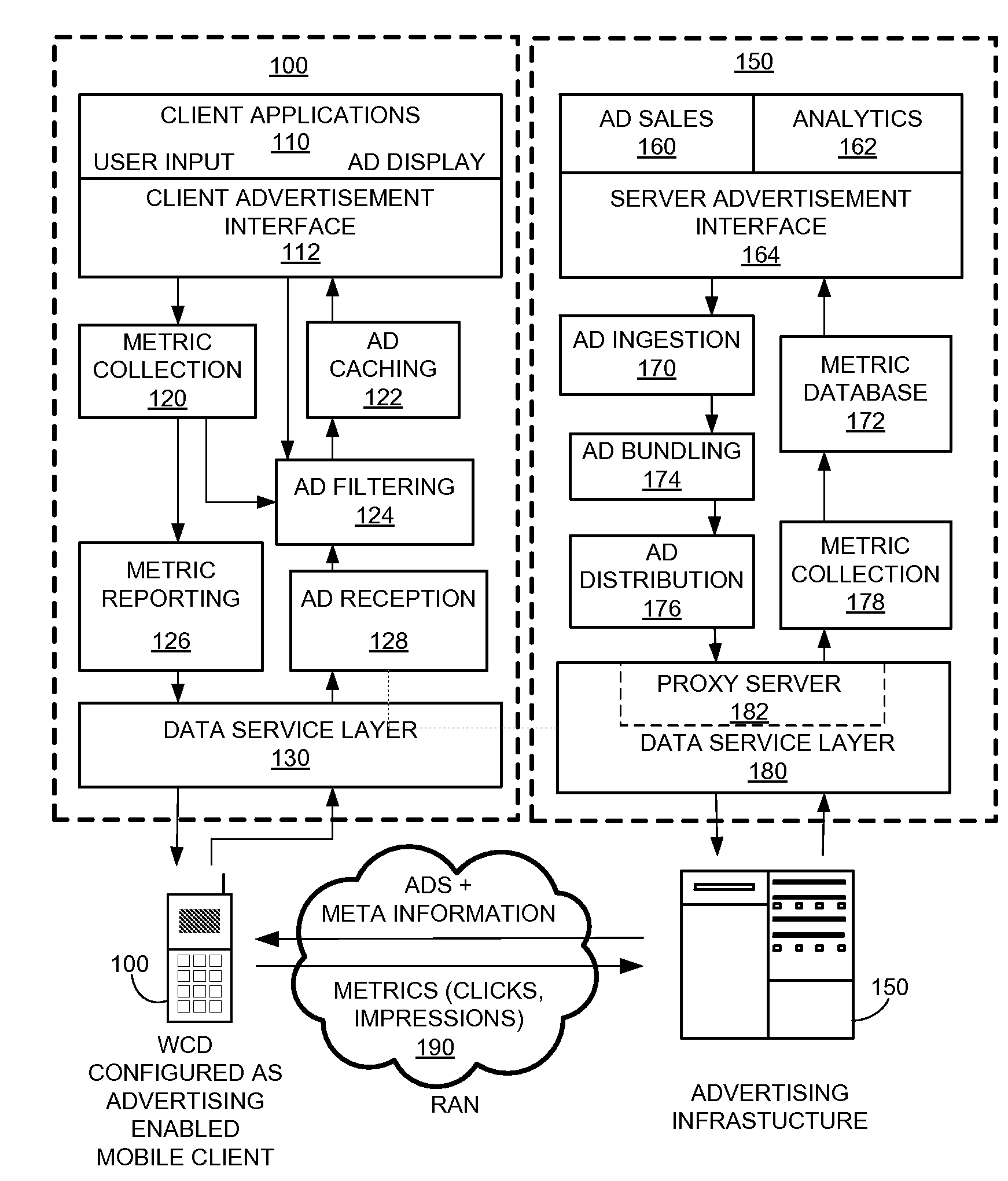
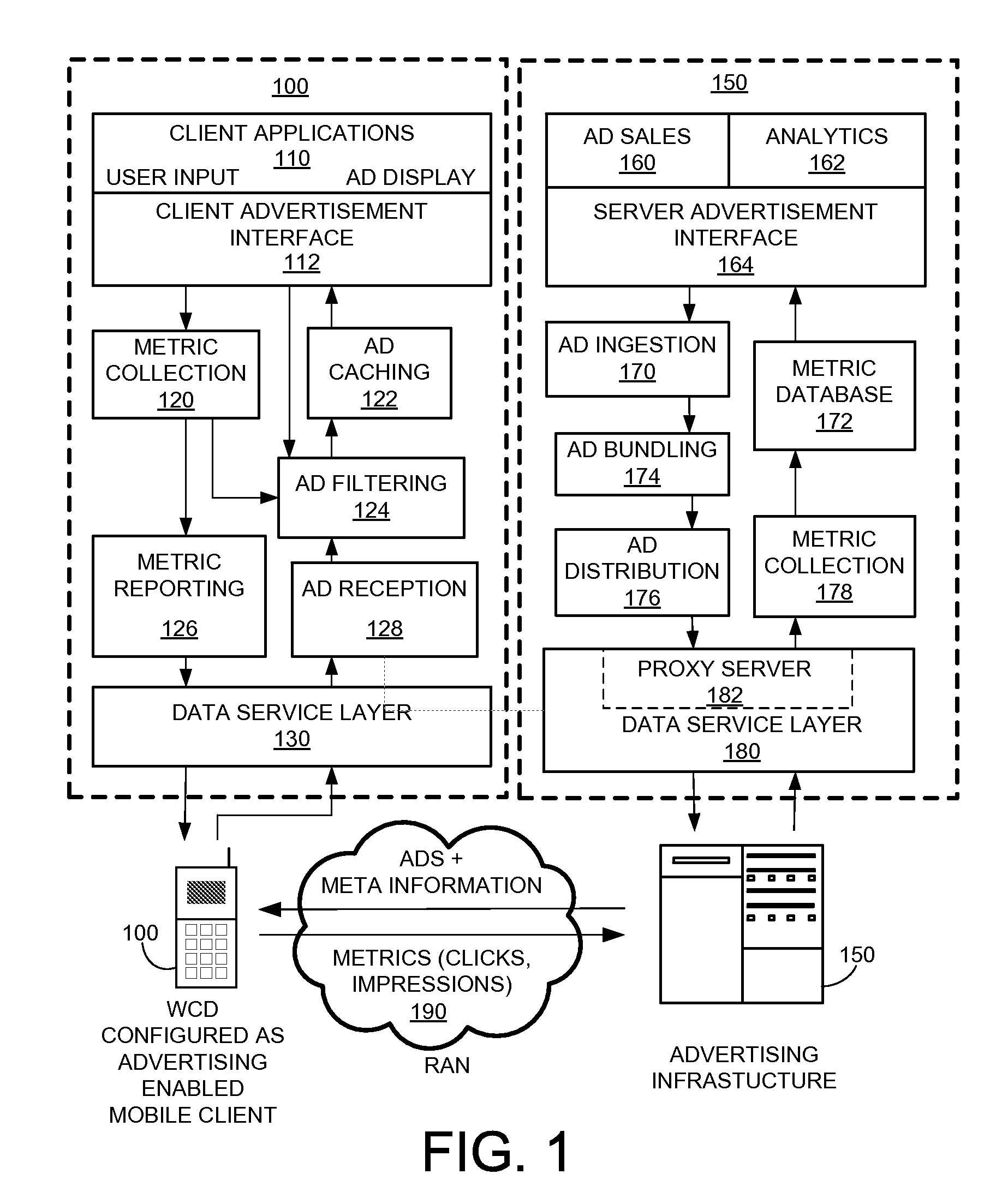
Method for transfer of information related to targeted content messages through a proxy server
InactiveUS20090013051A1Digital data information retrievalMultiple digital computer combinationsProxy serverInformation transfer
Information transfer methods for exchange of information with a wireless access terminal (W-AT) includes receiving a first message from the W-AT, the first message including first information provided by the W-AT and an address of the W-AT capable of identifying the W-AT, converting the first message to an anonymized message by replacing the W-AT address with a transaction identifier (ID), transmitting the anonymized message to a remote server, receiving a first response from the remote server, the first response having response information and the anonymized address information, converting the first response to a second response by replacing the transaction ID with the W-AT address, and transmitting the second response to the W-AT.
Owner:QUALCOMM INC
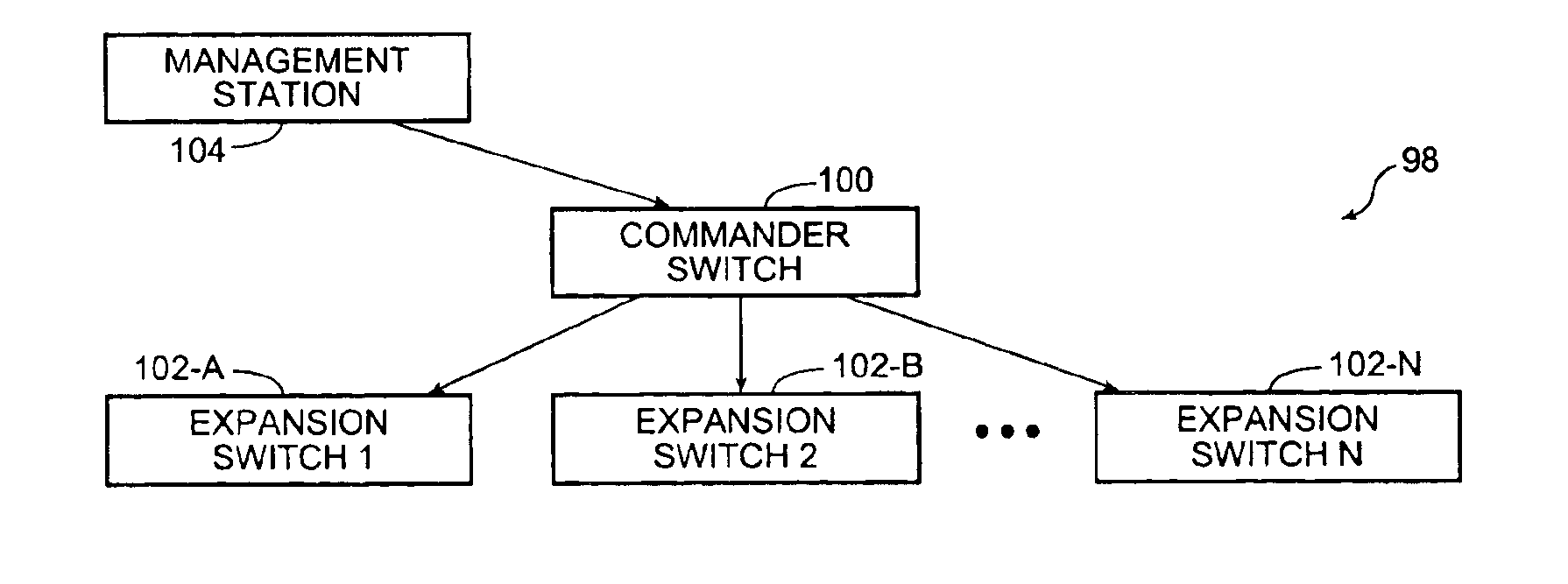
HTTP redirection of configuration data for network devices
InactiveUS6895433B1Easy to configureEasy to manageMultiple digital computer combinationsData switching networksWeb browserIp address
A group of network devices, such as Ethernet switches, are logically configured as a single cluster, with one commander device and one or more expansion devices. Each device in the cluster contains an embedded HTML server that facilitates configuration and management of the network device via a management station running a Web browser. Each device in the cluster is identified by a unique Universal Resource Locator (“URL”). However, only the cluster commander is required to have an IP address. The cluster commander redirects and translates configuration and management requests from the Web browser on the management station so that requests are processed by the appropriate device in the cluster. The exchange of information between the Web browser on the management station and the devices in a cluster is accomplished via redirection of HTTP GET and POST methods. This provides a consistent, device-independent interface between the device and the Web browser on the management station.
Owner:CISCO TECH INC
Online sales promotion method and device
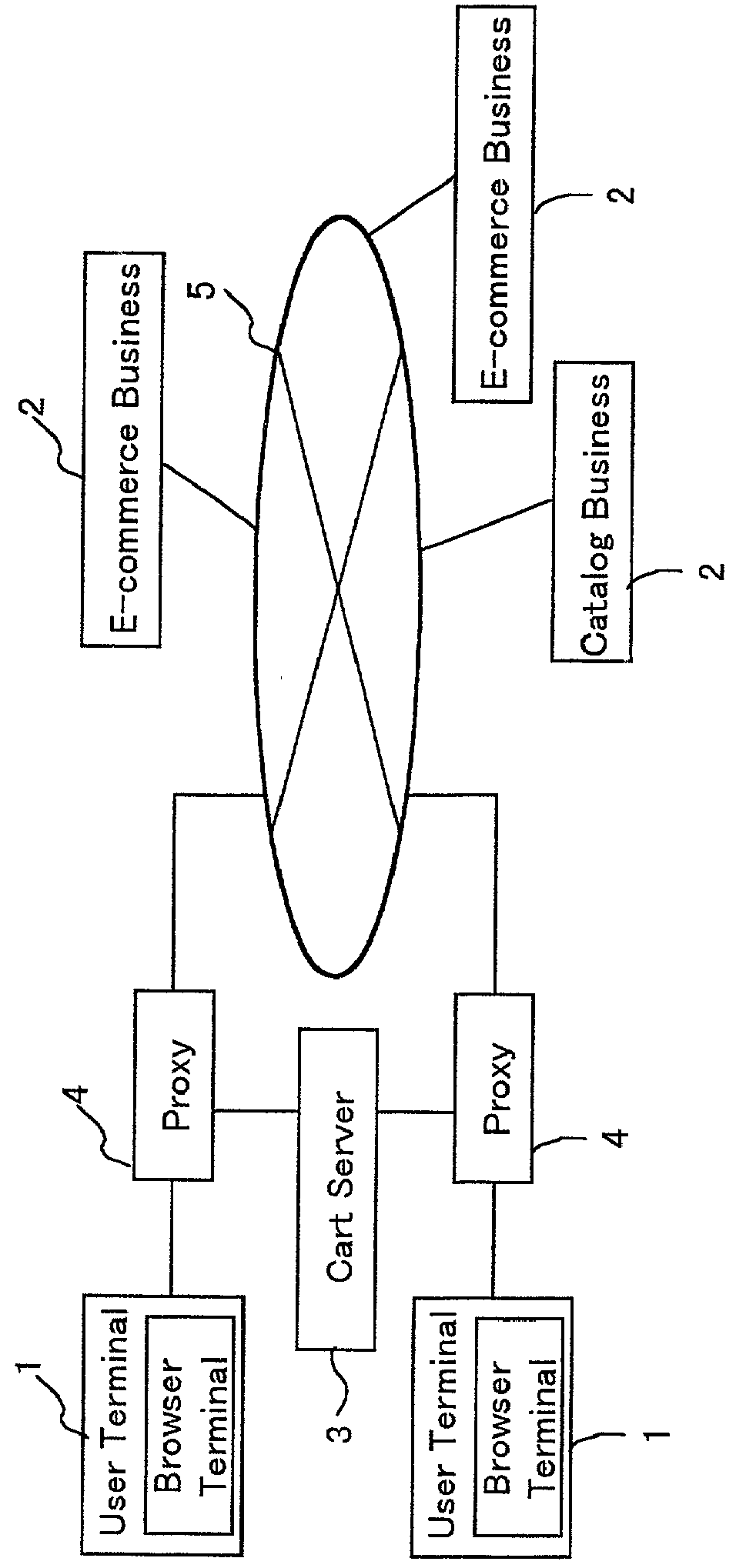
InactiveUS20010053998A1Increase salesEffective marketing strategyAdvertisementsBilling/invoicingSales promotionExchange of information
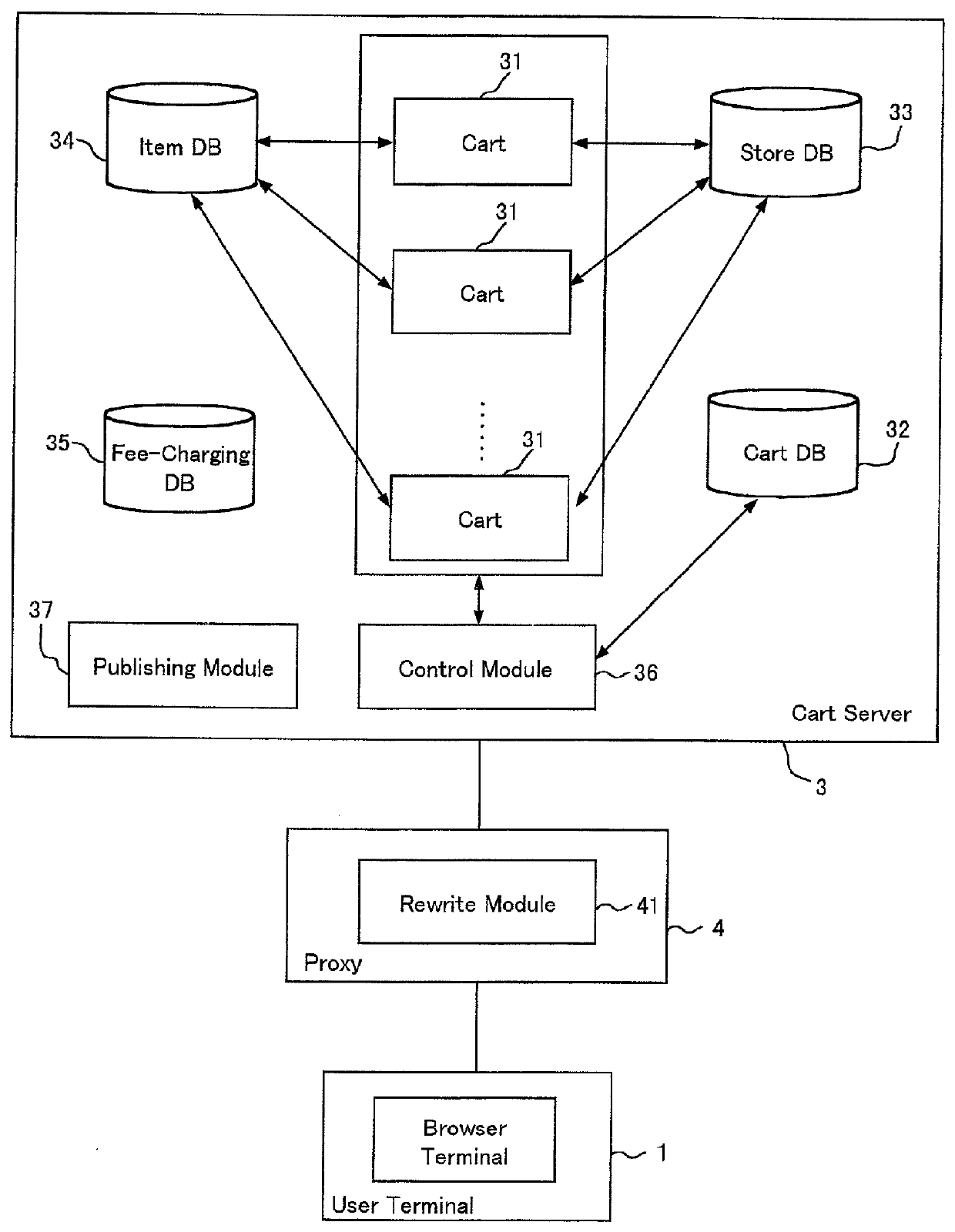
The object of the invention is to perform a constructive exchange of information between a user and a provider of products in virtual reality. A user places a product 154 that he is considering buying in a cart, designates product providers, and gives notification thereto of the cart contents. A designated product provider 153, by seeing the cart contents, can learn in what products the user is interested. The product provider 153 can provide to the cart from which the designation arose additional information 155, such as advertisements for its products. The user, by receiving various types of additional information from a product provider that he trusts, can find products that meet his desires, and can enjoy more satisfactory network-based shopping.
Owner:FUJITSU LTD
Secure network address provisioning
ActiveUS20100017597A1Reduce vulnerabilityAvoid problemsTransmissionConfidentialityNetwork addressing
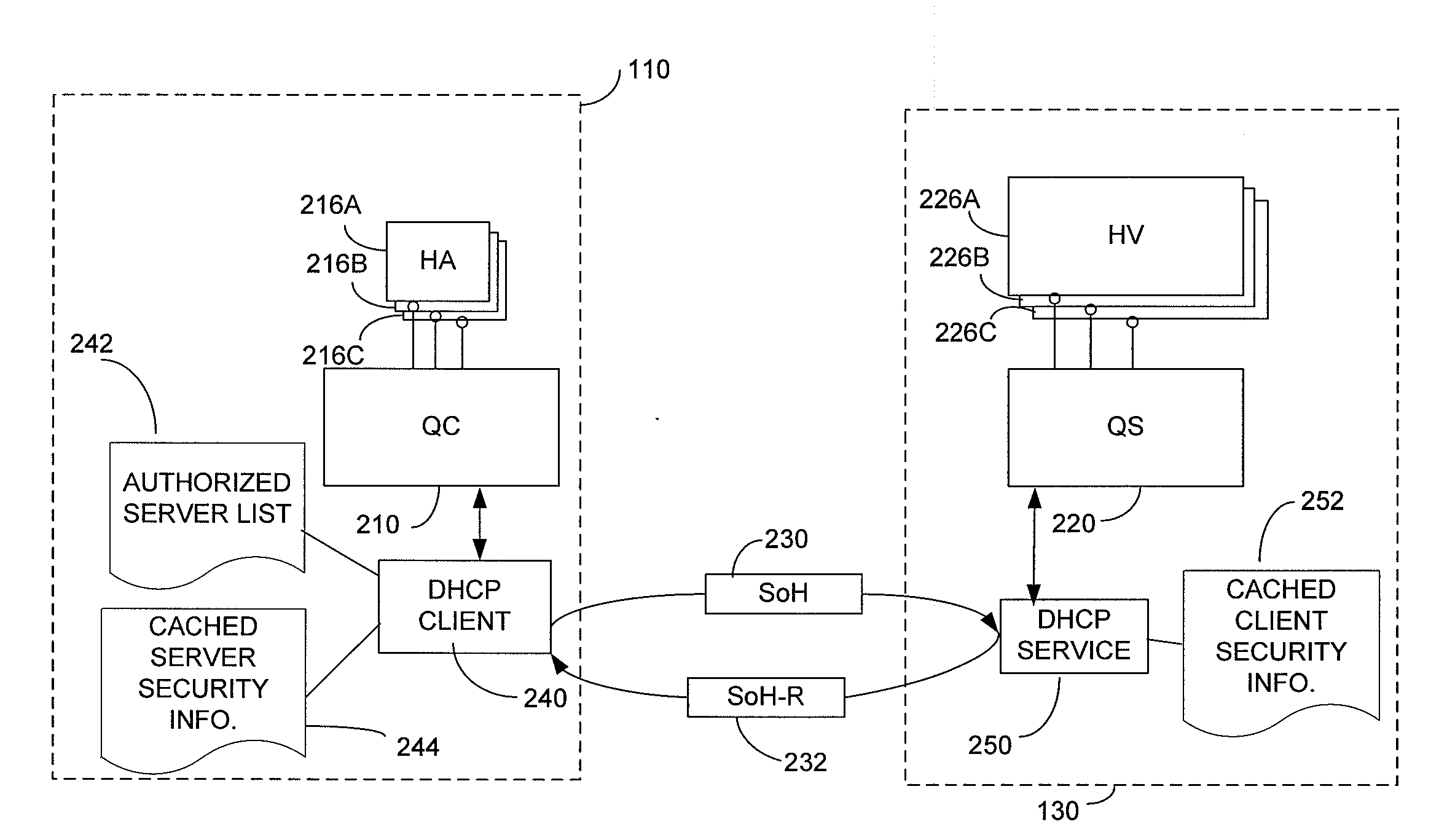
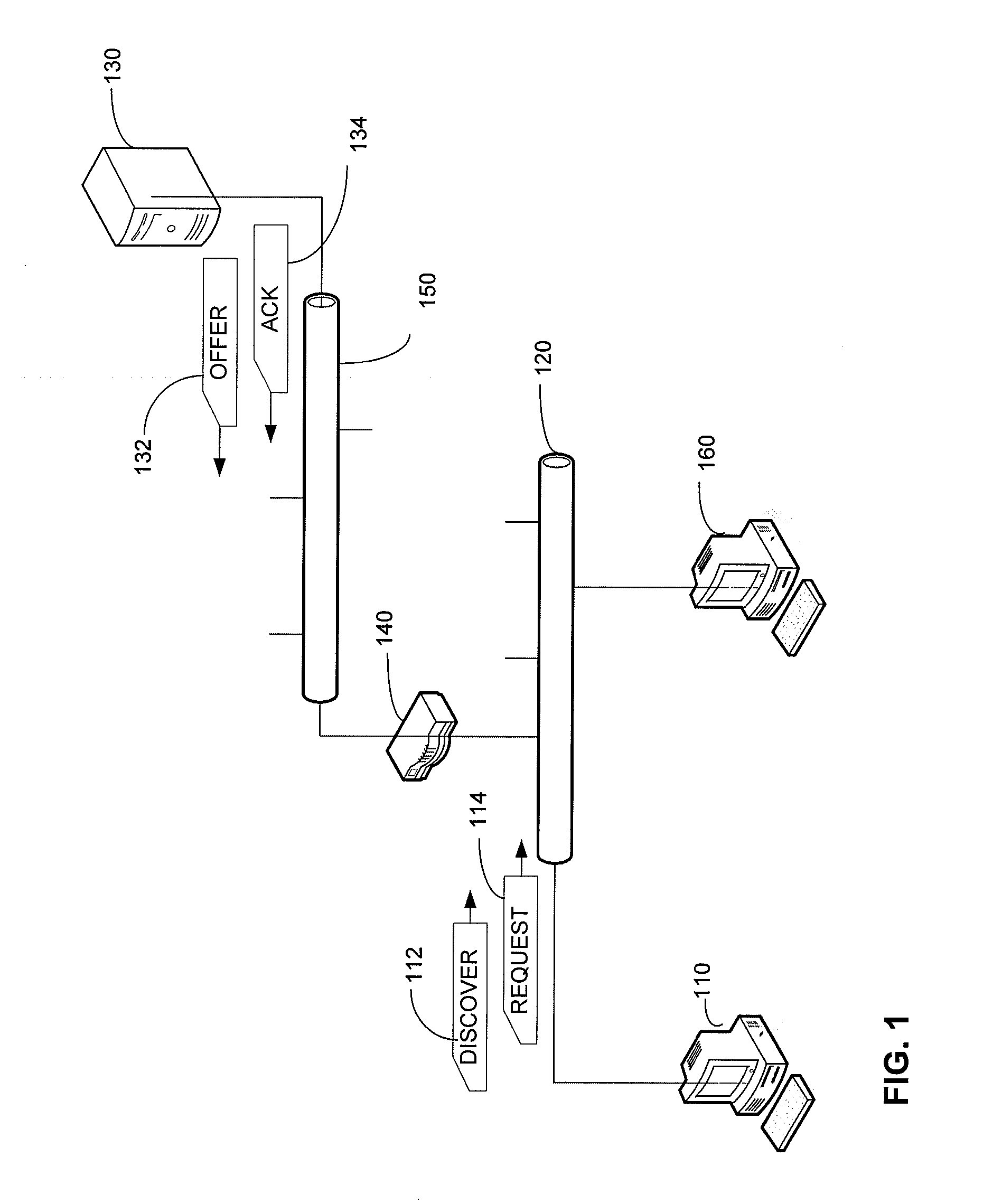
A network in which a client receives a network credential, such as a valid network address, following an exchange of messages with a credential server that includes security information. The security information may validate the credential, avoiding rogue devices inadvertently or maliciously distributing credential information that can interfere with clients attempting to connect to the network or with the network itself. If obtaining a network credential requires an exchange of information about the configuration of the client that could reveal security vulnerabilities, the security information may be used to ensure the confidentiality of that configuration information. The security information may be incorporated into messages according to a known protocol, such as by incorporating it into options fields of DHCP messages.
Owner:MICROSOFT TECH LICENSING LLC
Radio frequency identification well delivery communication system and method
A system for communicating with downhole components is provided comprising at least one RFID device configured with an identification code. The system further includes a device conduit extending next to the downhole components and a device propulsion system configured to translate the RFID devices next to the downhole components to facilitate an exchange of information between the downhole component and the RFID device. The device conduit may include a check valve or a turn-around sub depending upon the application. In some cases, the exchange of information may trigger actuation of one or more of the downhole components. A method is also provide comprising providing a device conduit near downhole components, propelling an RFID device near to the downhole components via the device conduit and a device propulsion system, and exchanging information between the RFID device and the downhole components.
Owner:SCHLUMBERGER TECH CORP
Systems and methods for managing shared resources in a computer system
InactiveUS8028298B2Improve performanceSimple designMultiprogramming arrangementsSoftware simulation/interpretation/emulationOperational systemShared resource
An operating system is provided wherein a plurality of objects are established and registered in response to requests from hardware or software associated with the computer system. The objects include at least one type, at least one attribute, and a handle. The plurality of objects are then manipulated to effect processing and exchange of information.
Owner:SYNAPTICS INC
Methods and systems for the secure exchange of information
InactiveUS20150271146A1Facilitate communicationUser identity/authority verificationComputer security arrangementsThird partyEncryption
Computer implemented system and methods for the secure transfer of files or data between persons and groups using a third party host, wherein the host of the system, while storing the encrypted information for ultimate delivery to a recipient, cannot decrypt the file or data being transferred because it is not in possession of the entire encryption means.
Owner:SENDSAFELY
Computer and mobile communication system
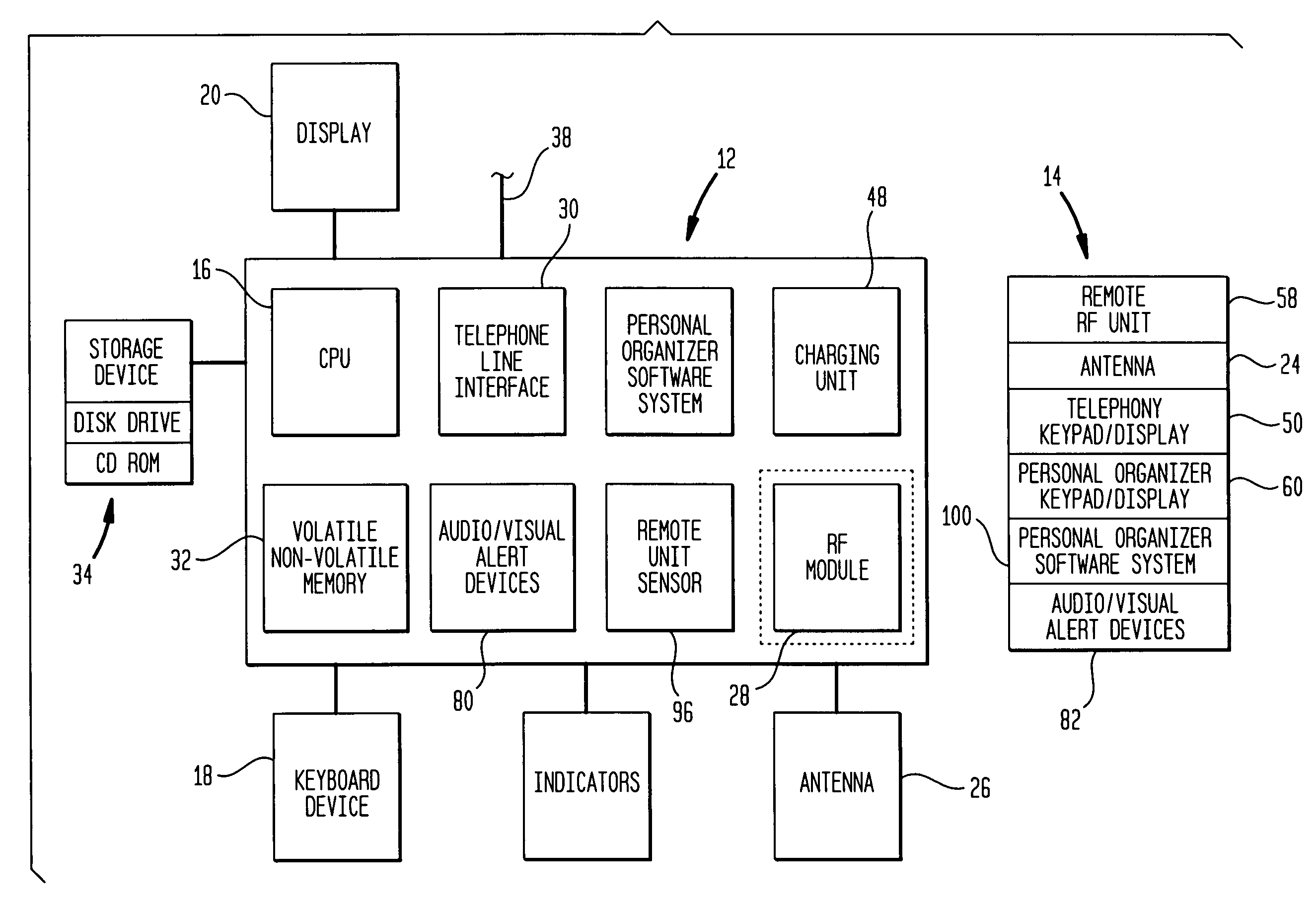
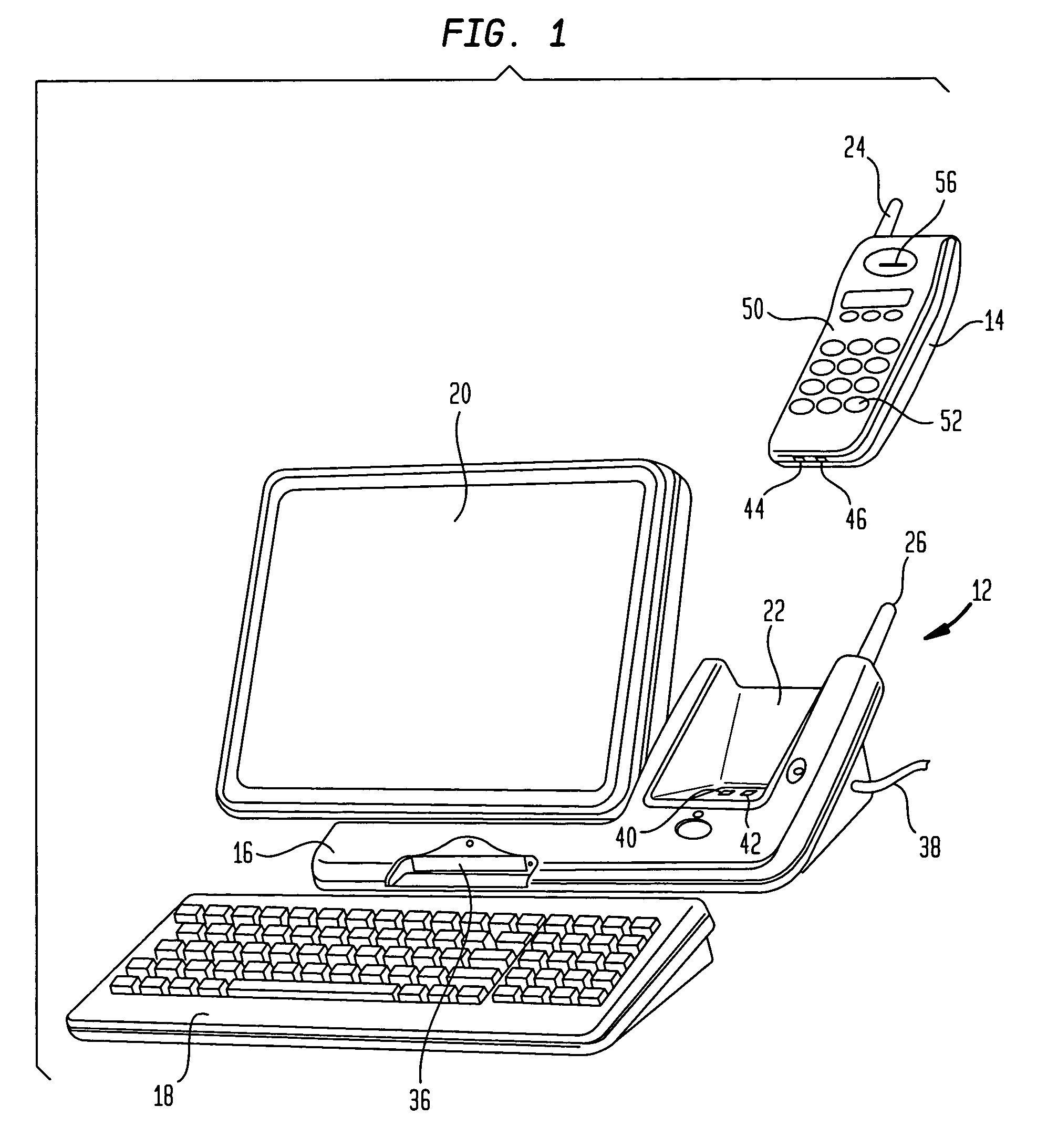
InactiveUS7047038B1Convenient and easy-to-useConvenient wireless communicationTransmissionTelephone set constructionsScheduling functionPersonal organizer
A computer and mobile communication system for performing wireless telephone, personal organizer and / or schedule alert functions is provided. The system may have a wireless handset for recording and playing messages, and for performing scheduling functions. The computer may be located in a base station with a common housing which contains a cradle to provide a conduit for exchange of information between the computer and the handset, as well as the circuitry to charge a battery in the handset. The handset may be switched between a telephone mode and a personal organizer mode by opening and closing a protective cover. A method of operating the system is also disclosed.
Owner:AVAYA INC
Method, system, and apparatus for social network based support platform using content packages and expert interaction
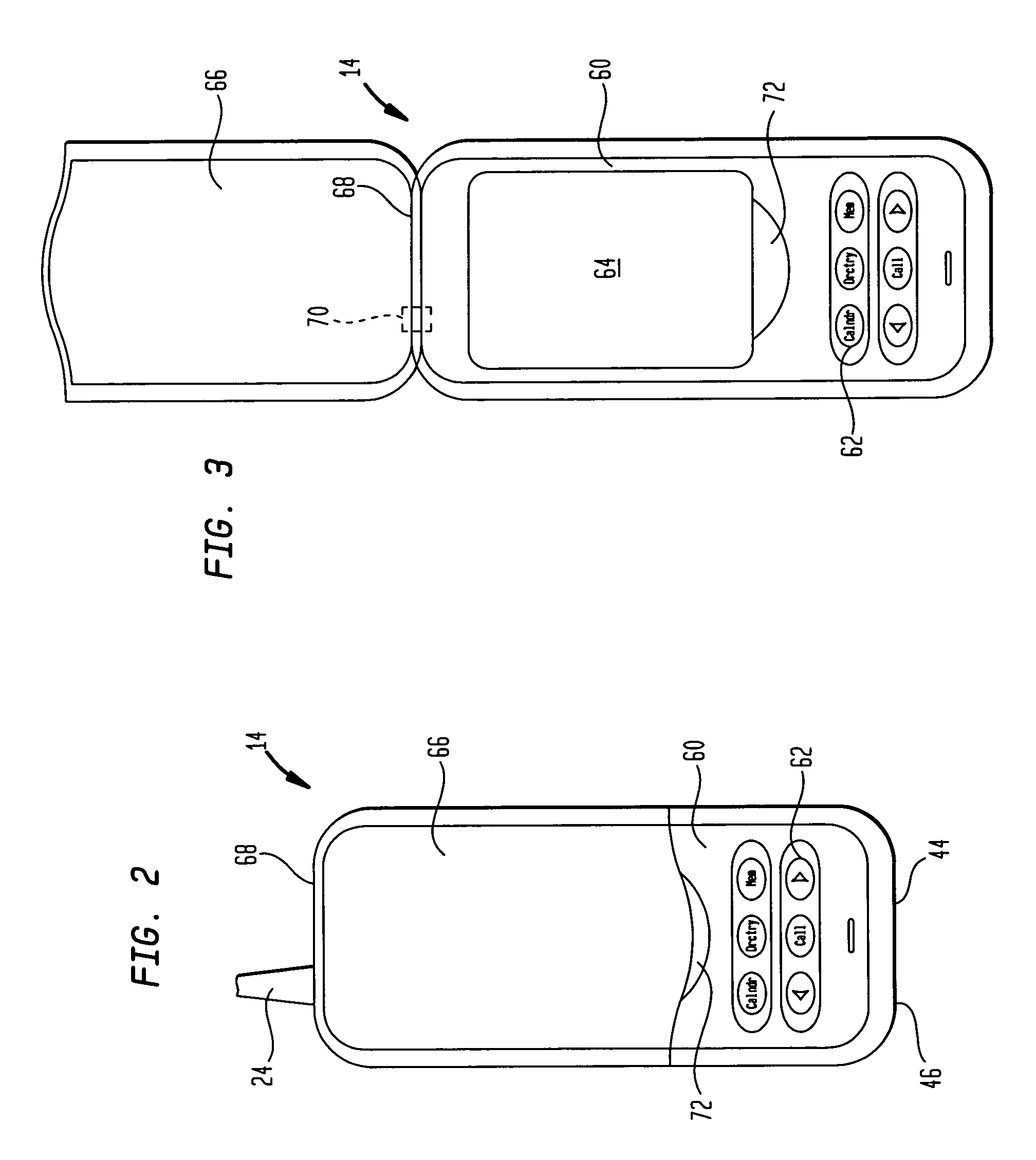
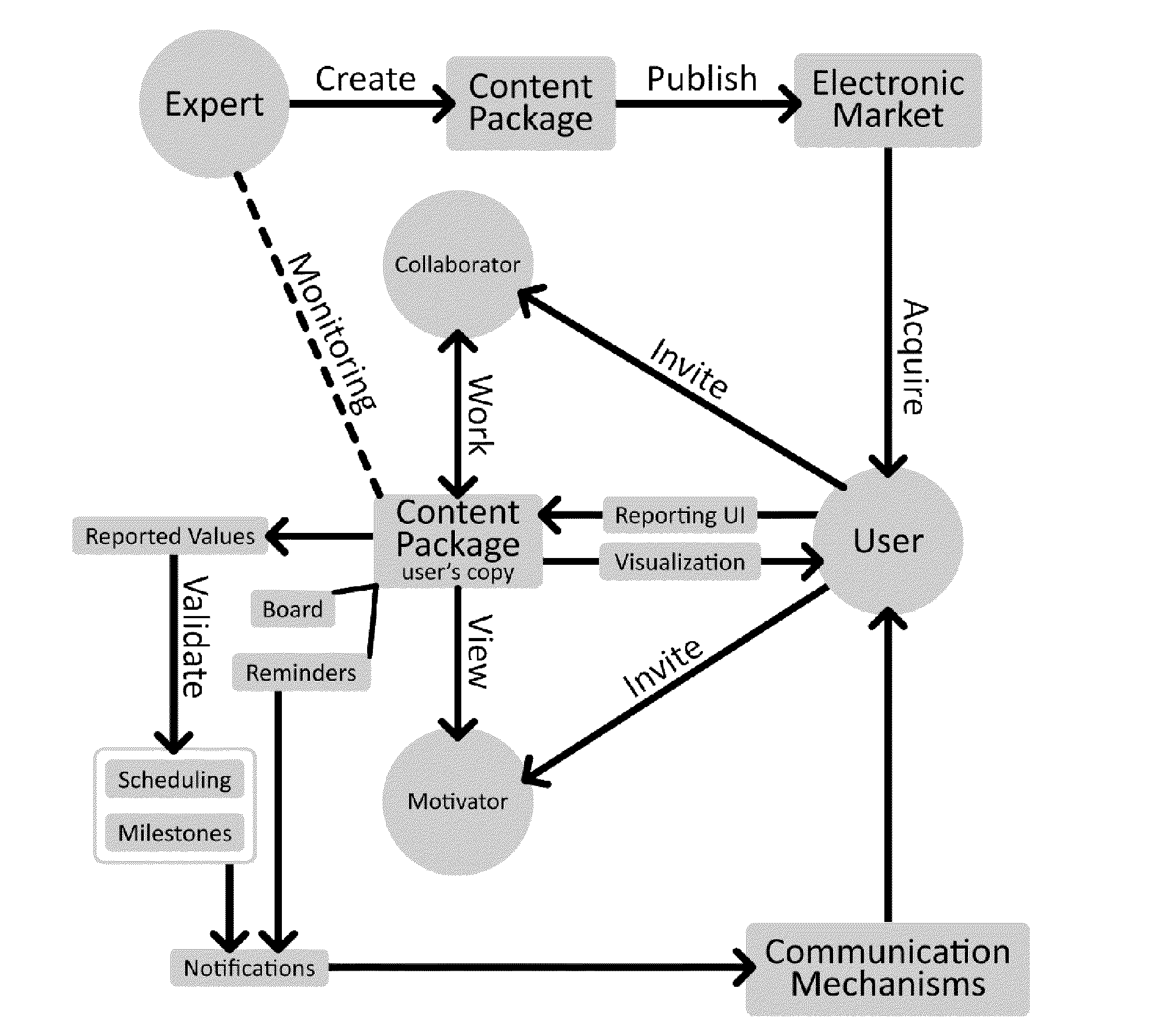
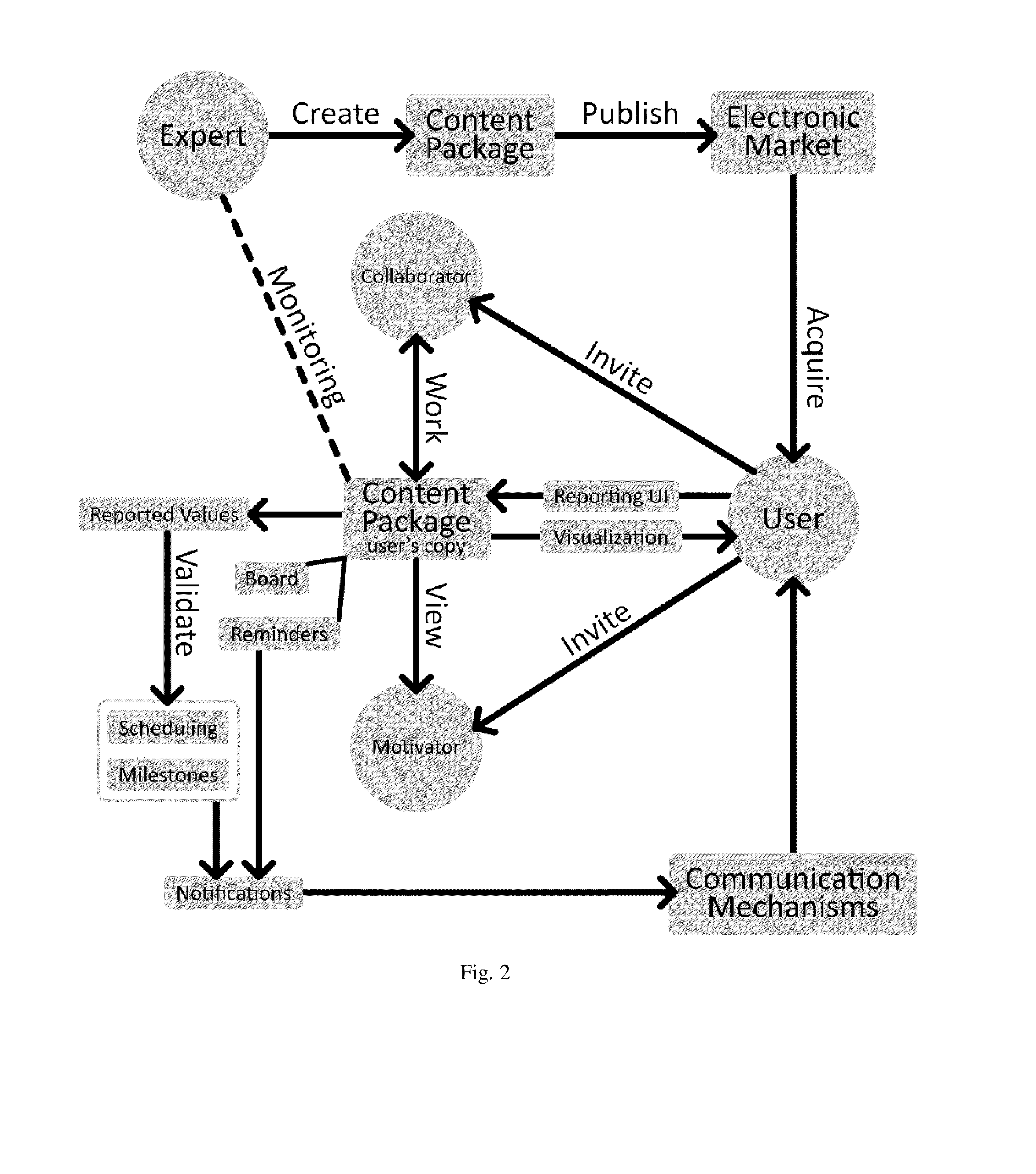
A computerized system and method for the exchange of information between and / or among instructors and users in a goal-oriented context. Embodiments of the present invention provide systems and methods in which an expert in a given field and / or instructor may interact with one or more users by providing packages and / or lectures, guides, literature, and other content, receiving user questions and input, scheduling and tracking user progress, as well as social interaction among end users. Embodiments of the present invention may also provide an infrastructure that allows for on-line registration and payment for packages and / or subscriptions.
Owner:FITANGO
Transmitting and receiving device
InactiveUS20050245995A1Low production costIncrease flexibilityElectrotherapyLocal control/monitoringData acquisitionWireless data
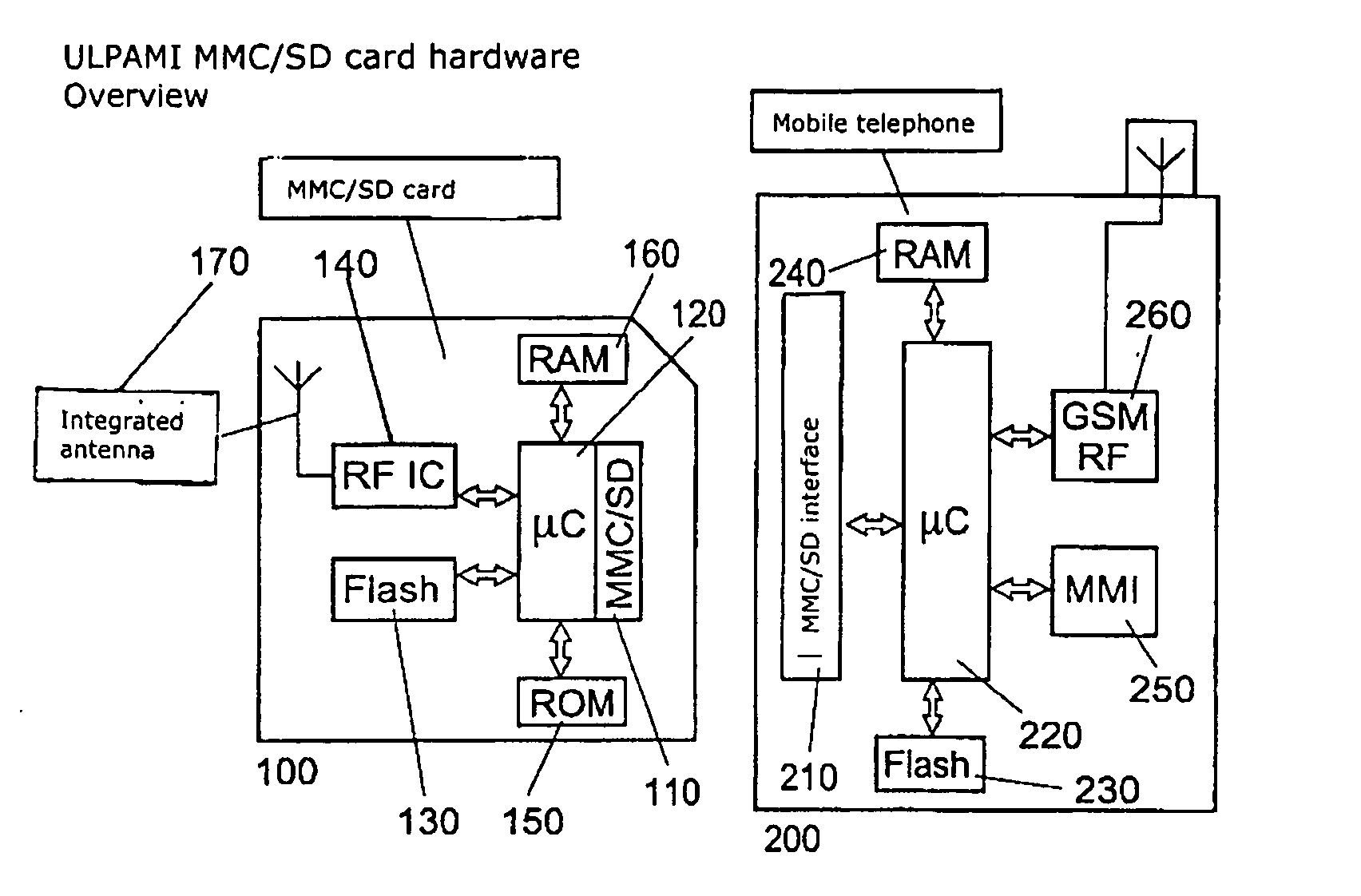
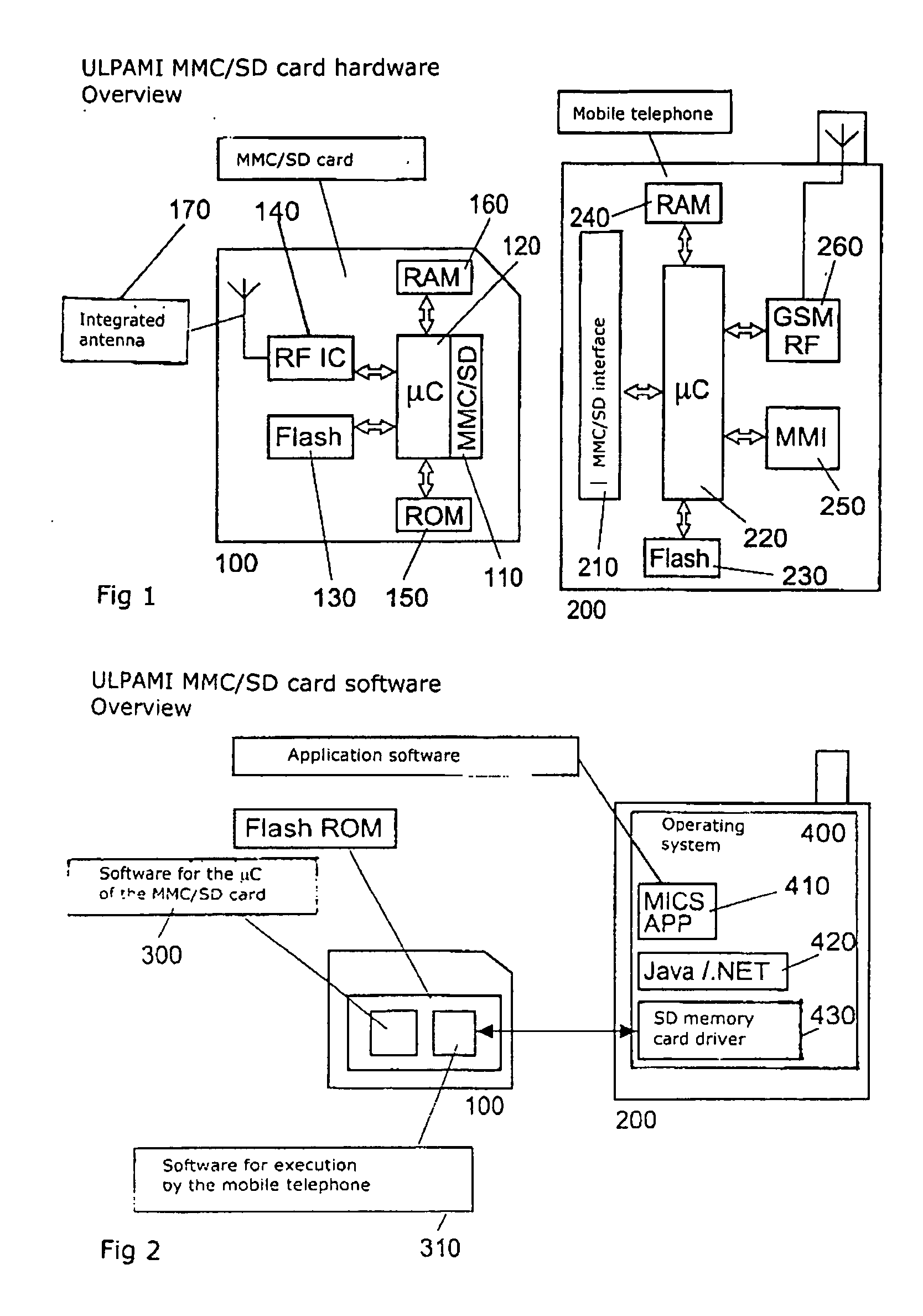
Certain embodiments of the present invention disclose a data transmission unit for wireless communication with an electromedical implant and a data acquisition and evaluation center (home monitoring service center) wherein the data transmission unit is an electronic plug-in card which can be inserted into a base device, in particular into a mobile telephone, and which has at least a wireless data interface for the exchange of information with an electromedical implant, a wired data interface with the base device for the exchange of information between the plug-in card and the base device, at least one control unit for controlling the exchange of data by way of at least the wireless data interface, and a write / read data memory which is readable by the base device by way of the wired data interface, wherein the control unit is adapted to write data received from an external device by way of the wireless data interface into the write / read data memory.
Owner:BIOTRONIX CRM PATENT AG
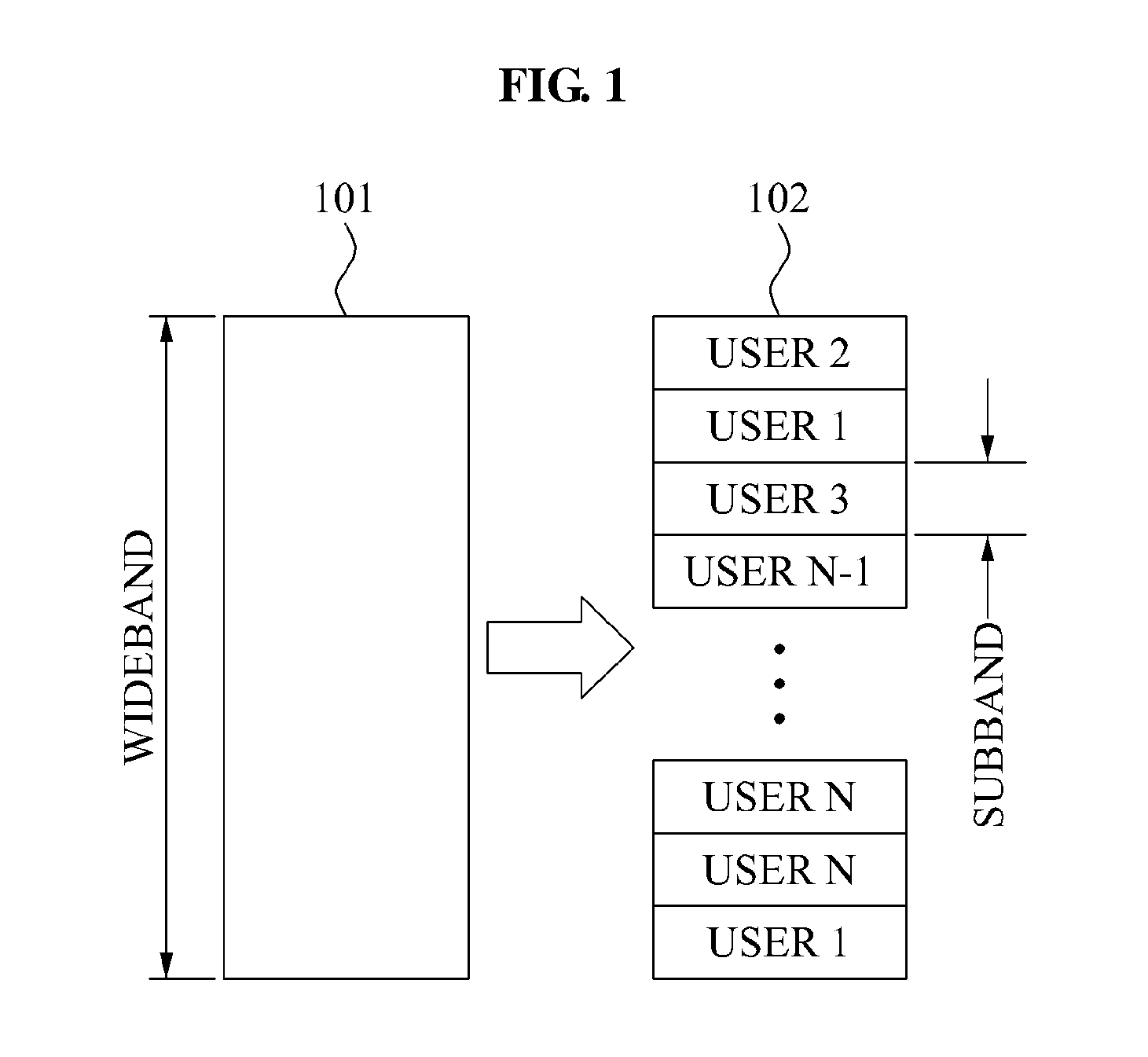
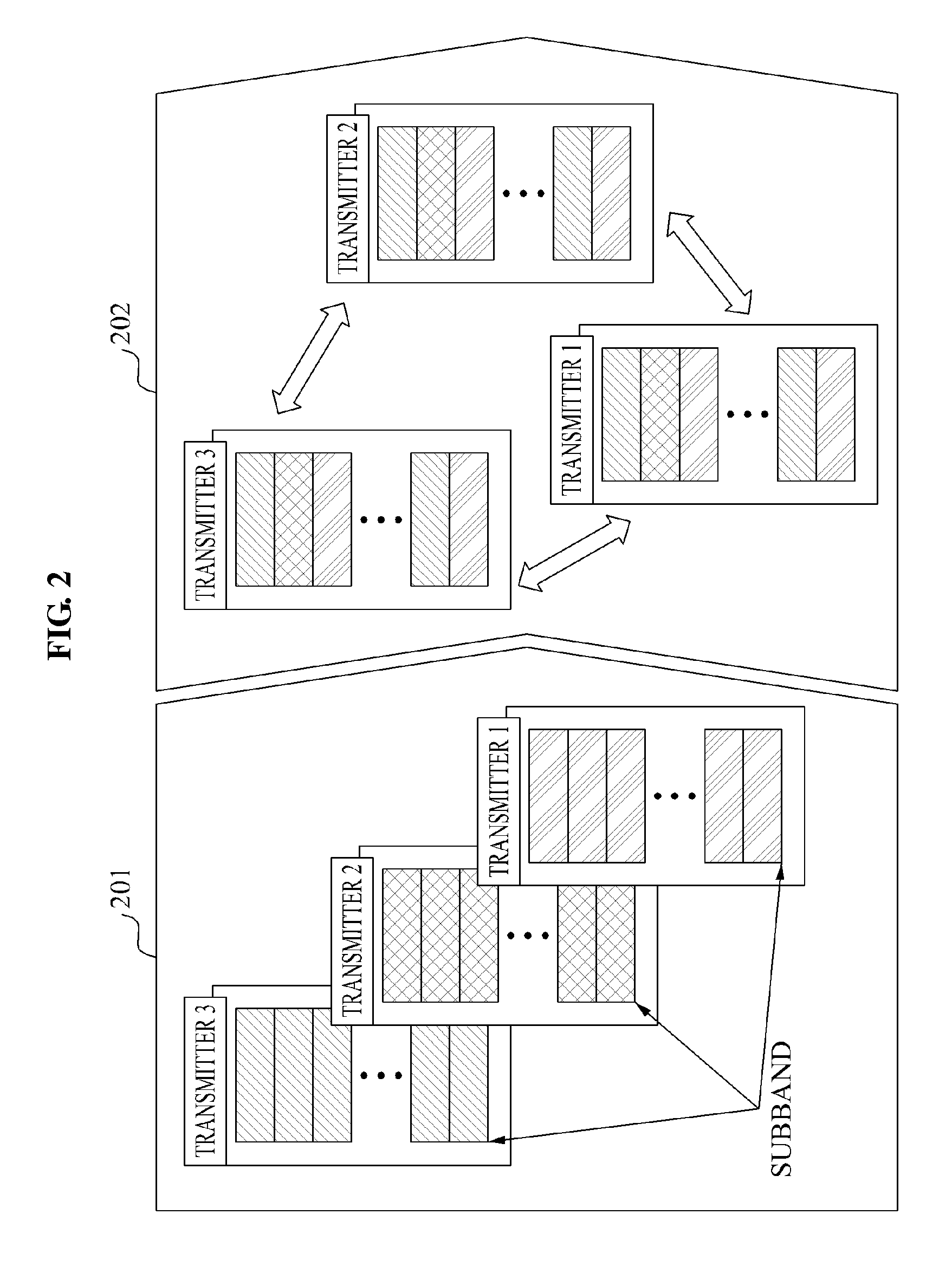
Method and apparatus for coordinated multi-point communication for each sub-band based on long-term channel state information
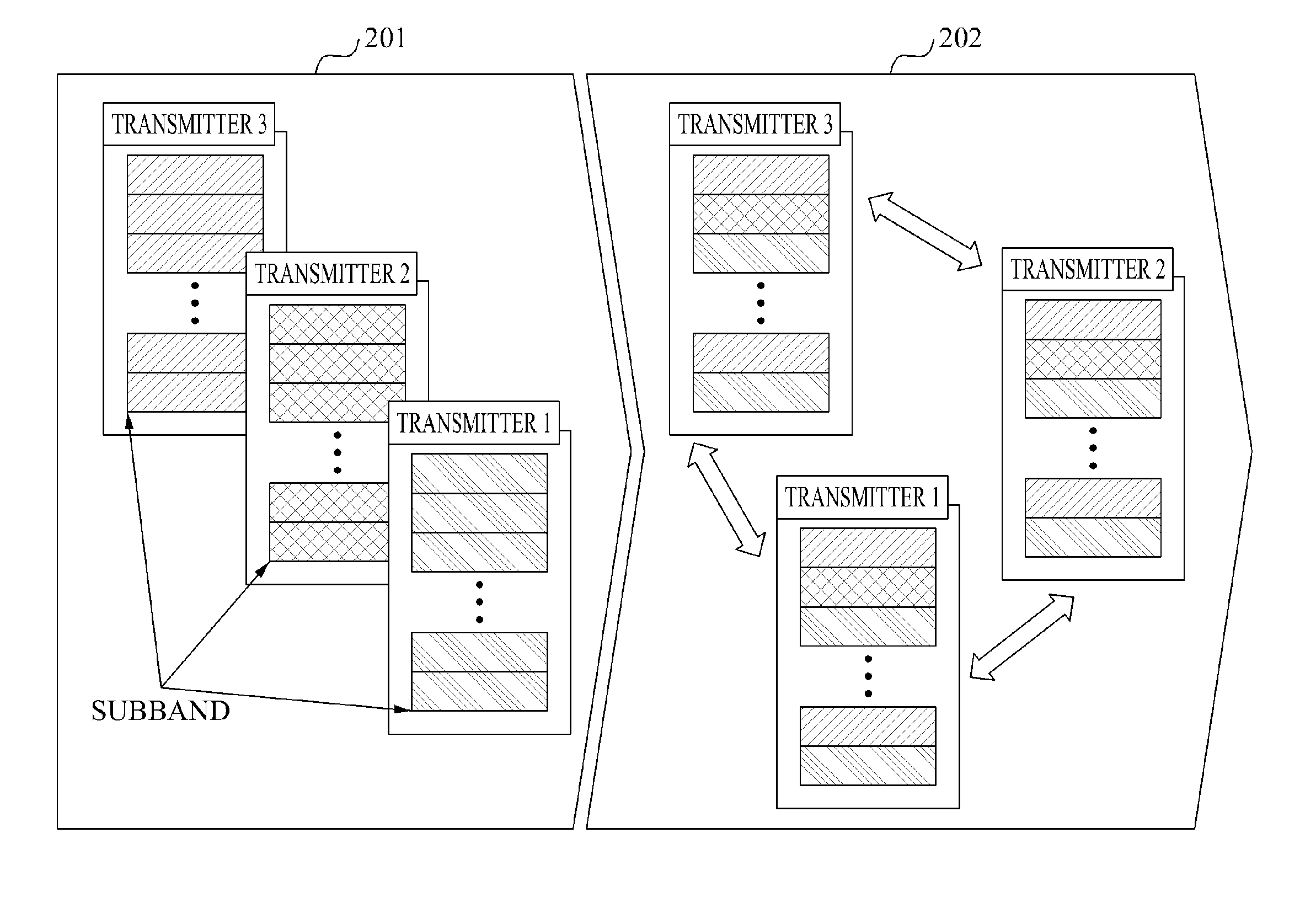
Provided is a coordinated communication method and apparatus that may perform coordinated communication based on long-term channel information, for each sub-band. Base stations may exchange scheduling information of each sub-band with each other to determine a priority among the base stations, and may perform rescheduling for each sub-band based on the determined priority. The base stations may obtain the long-term channel information, and thus may reduce overhead occurring with exchanging of information between a base station and a terminal or between base stations, and may decrease damage due to a delay of channel information associated with a terminal.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com