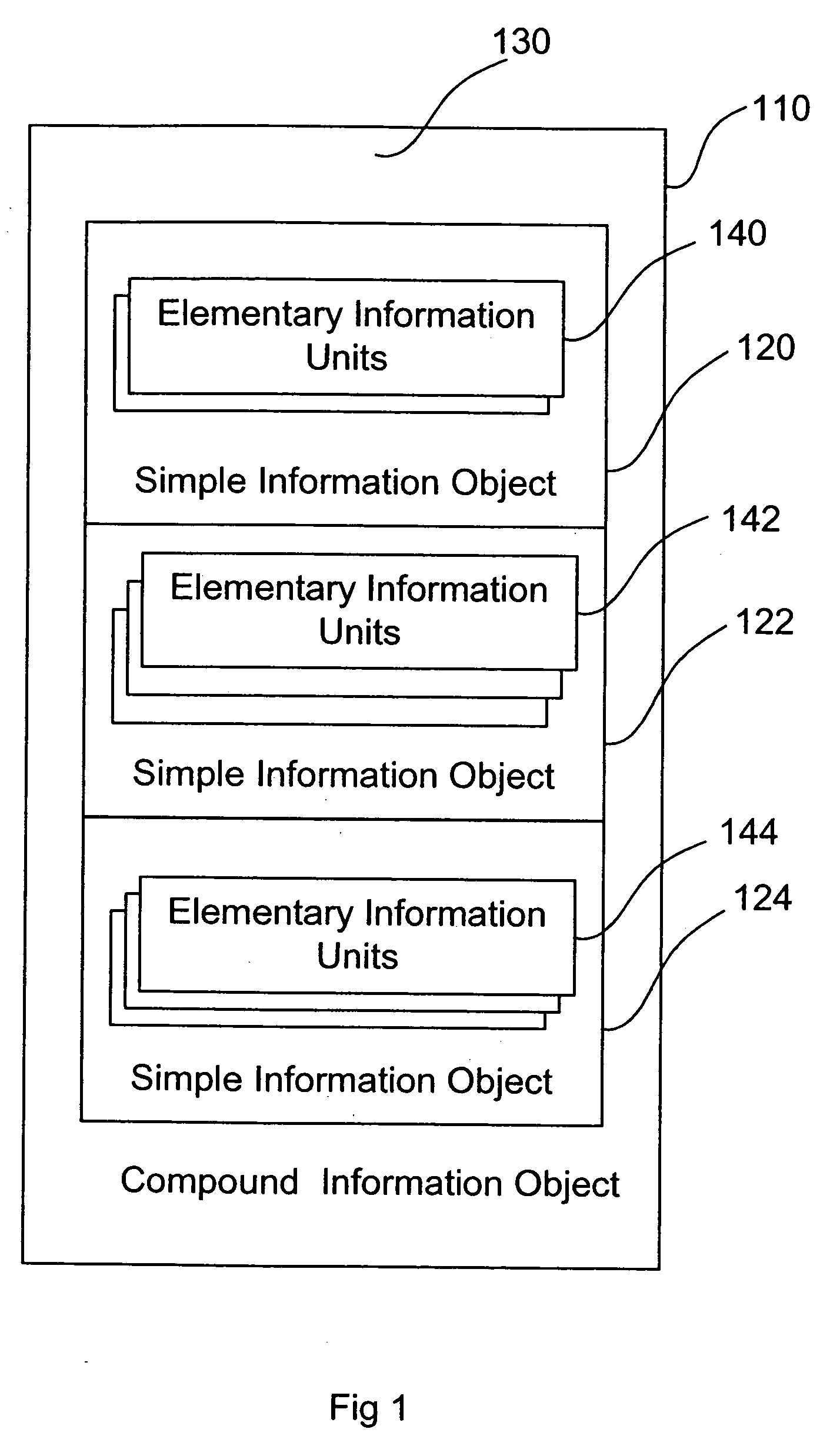
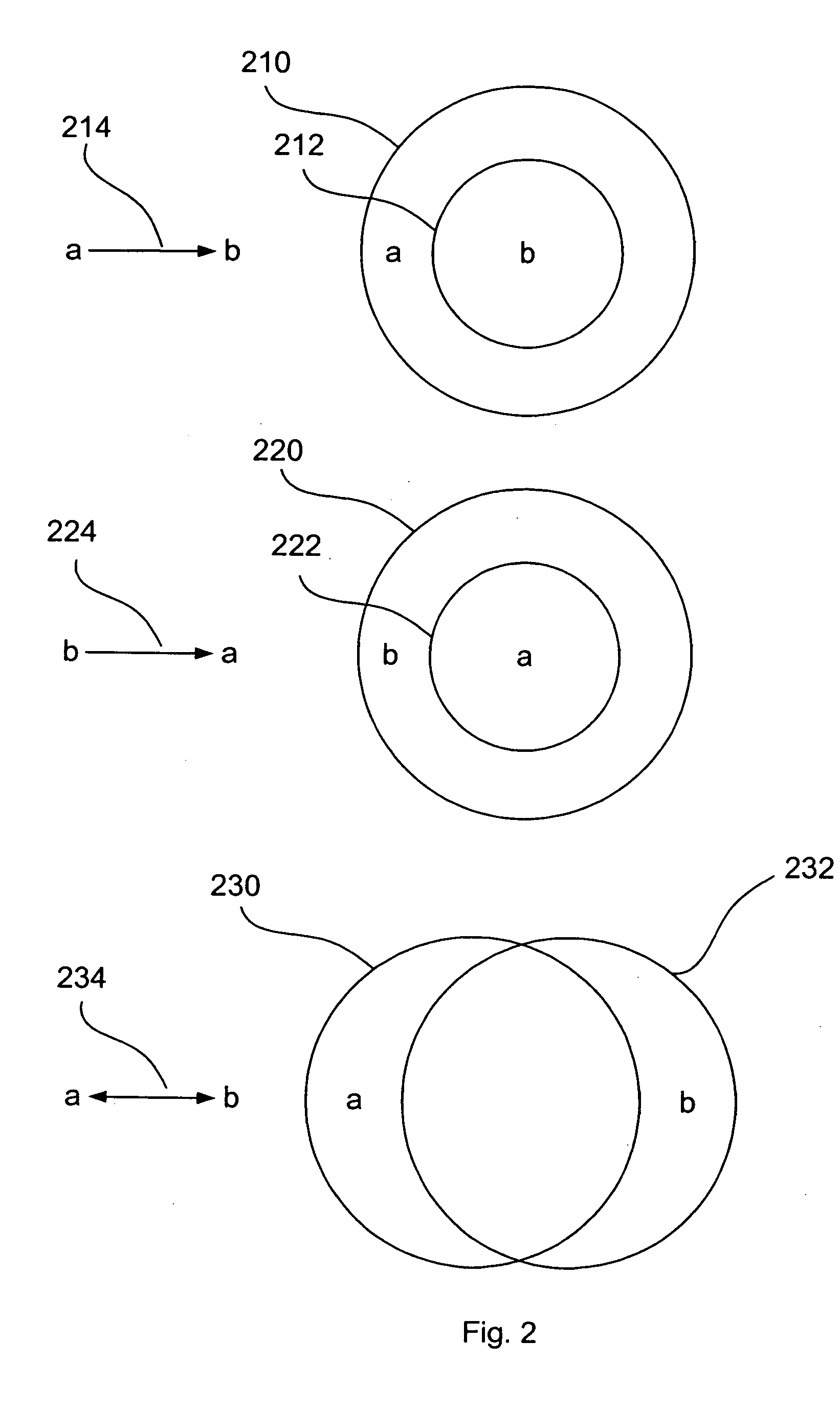
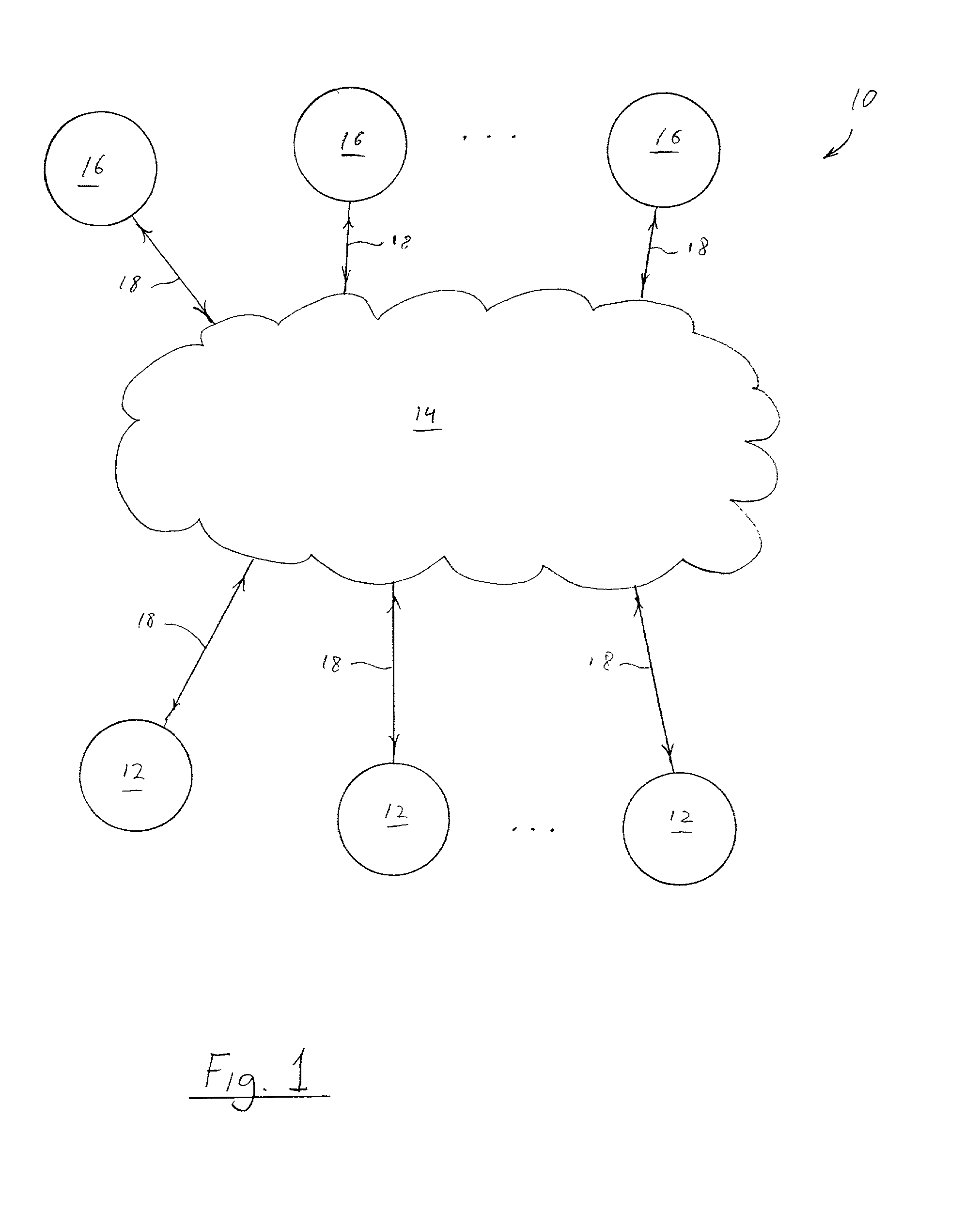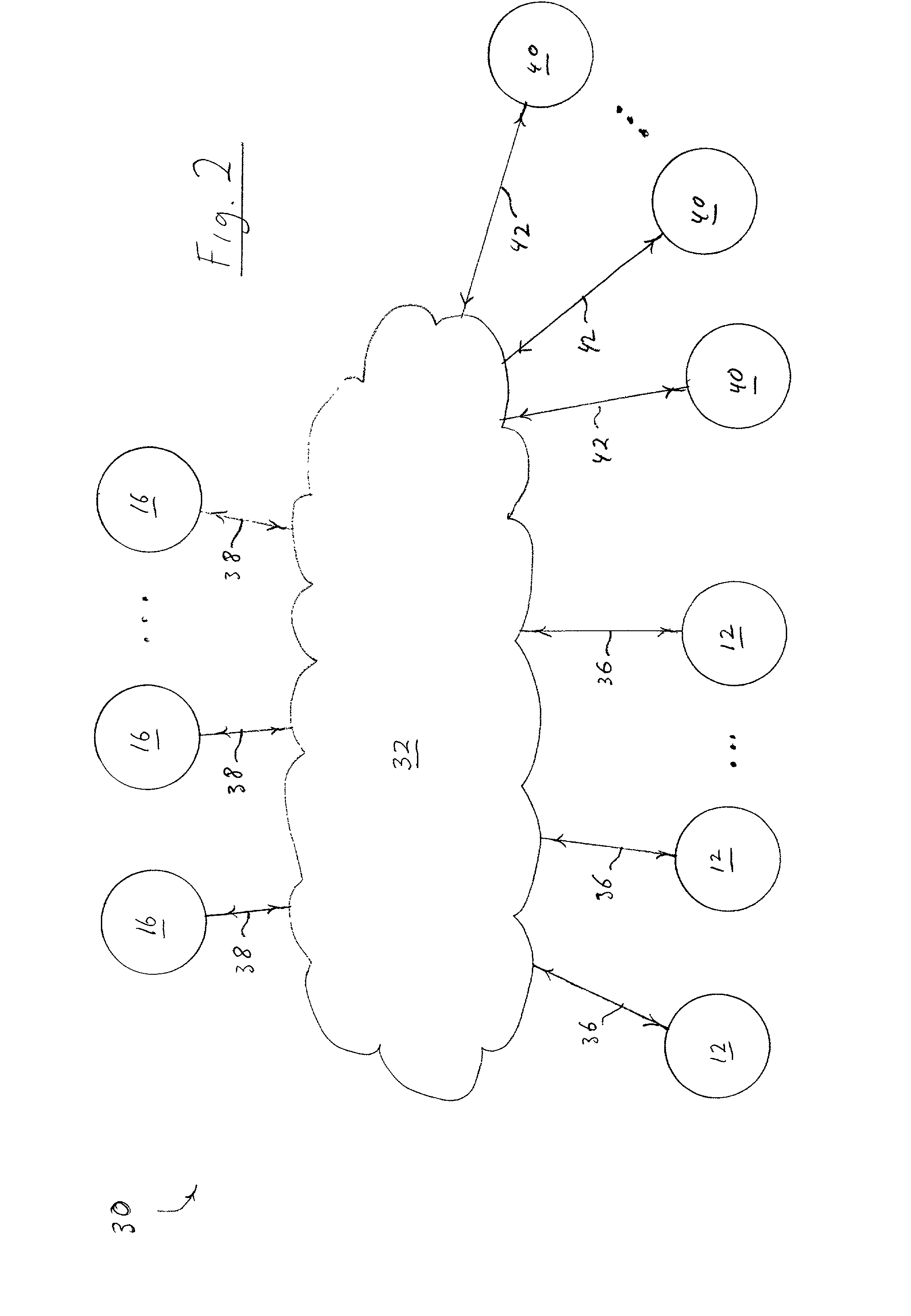Patents
Literature
15082 results about "Information management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
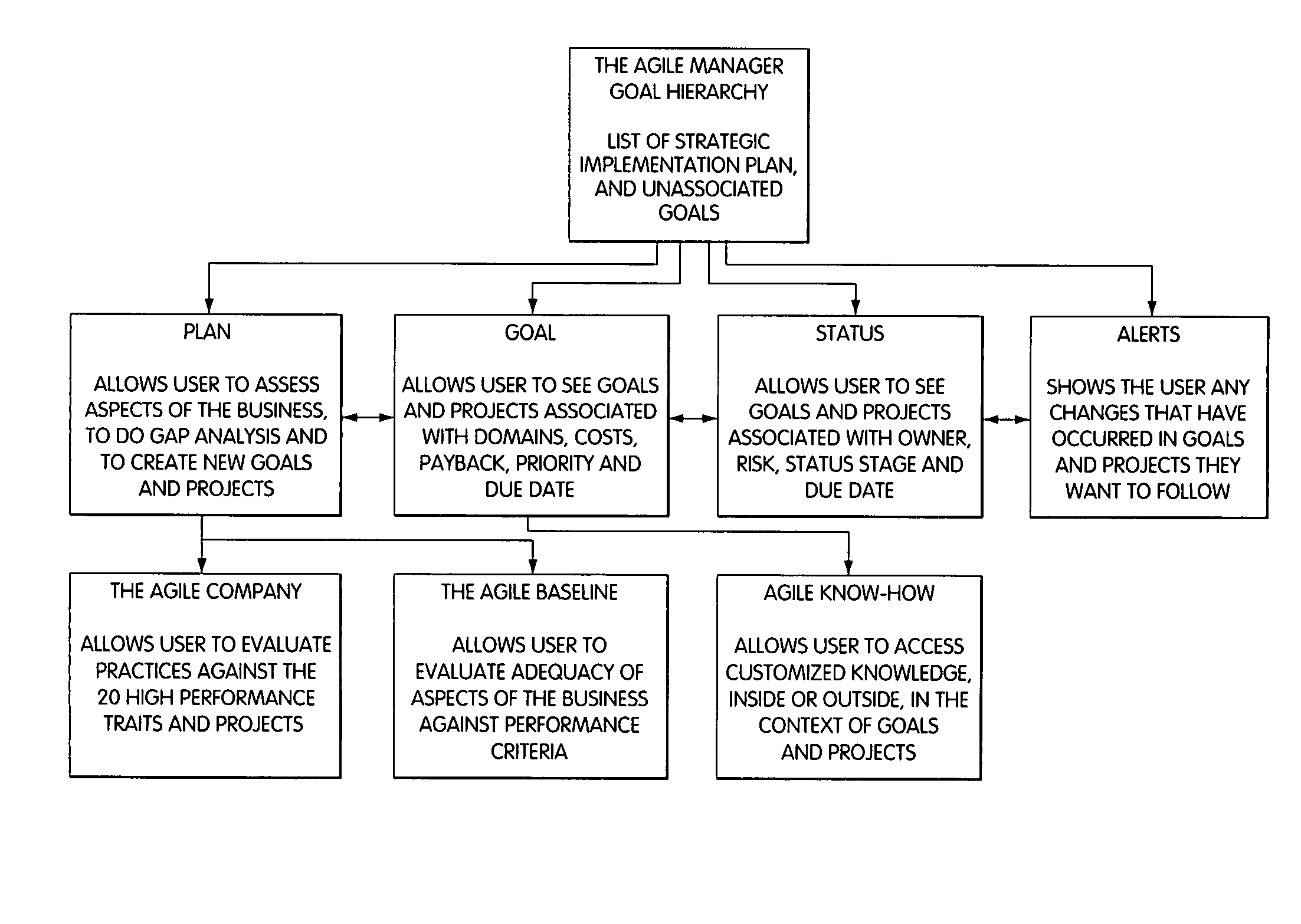
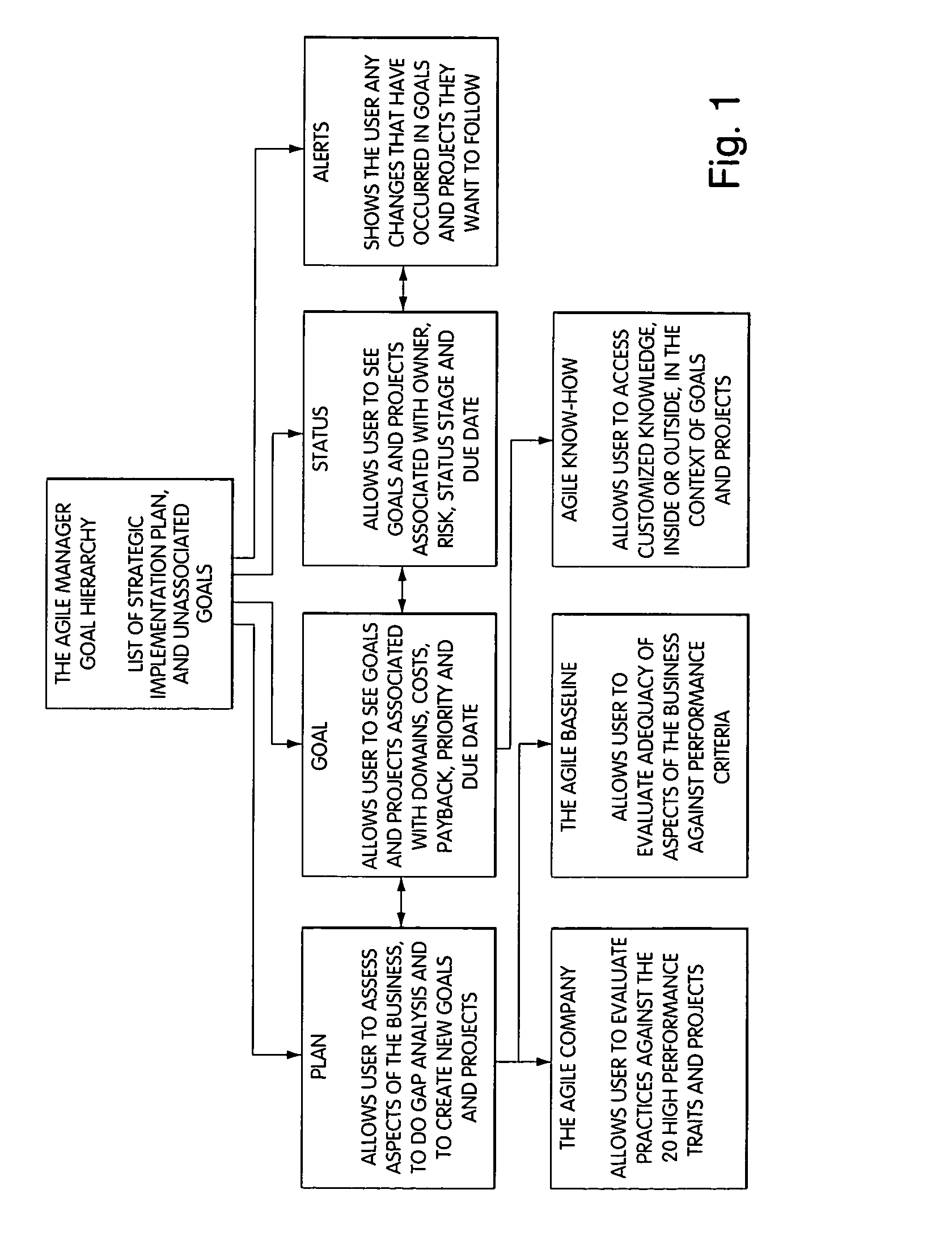
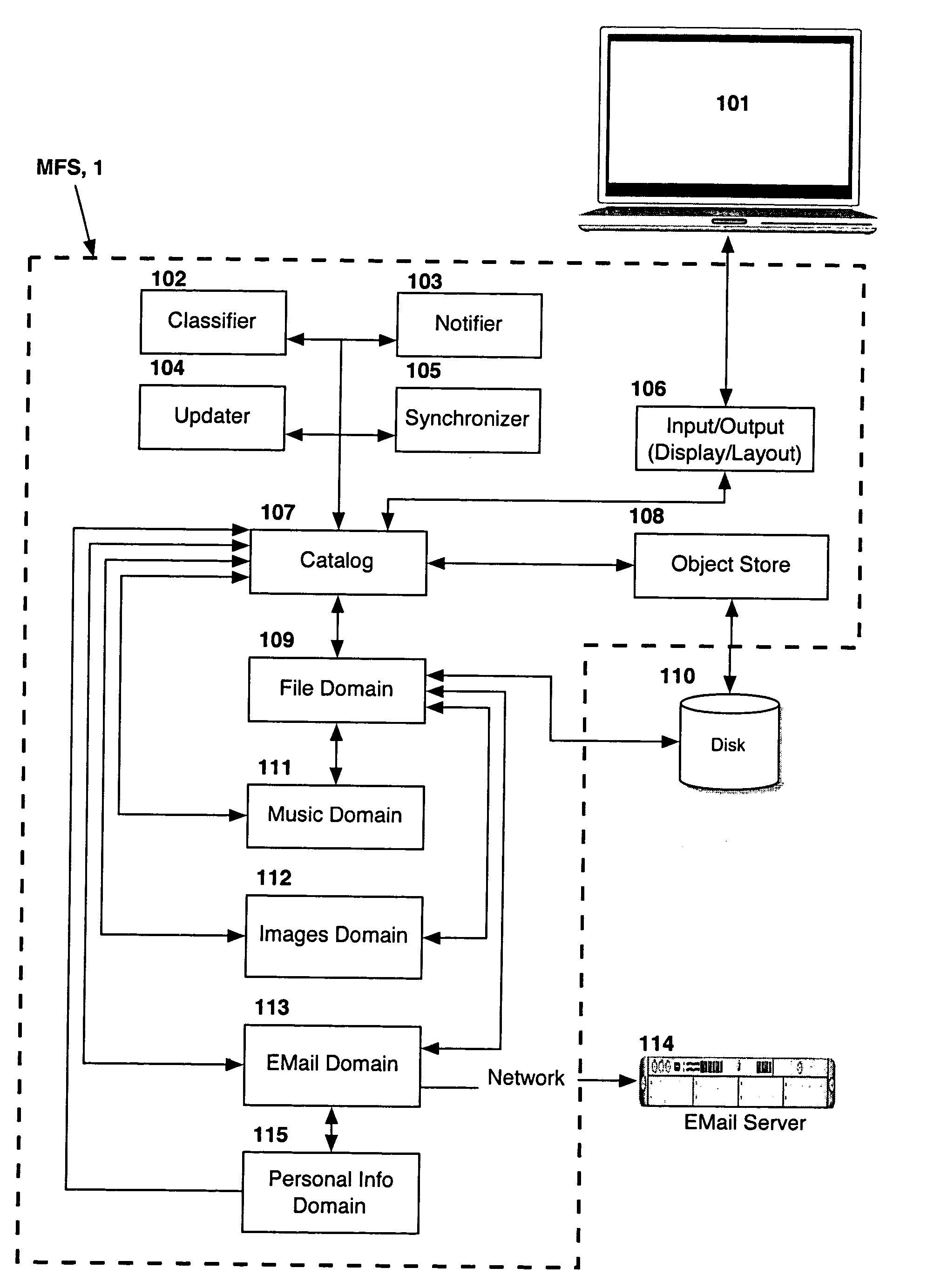
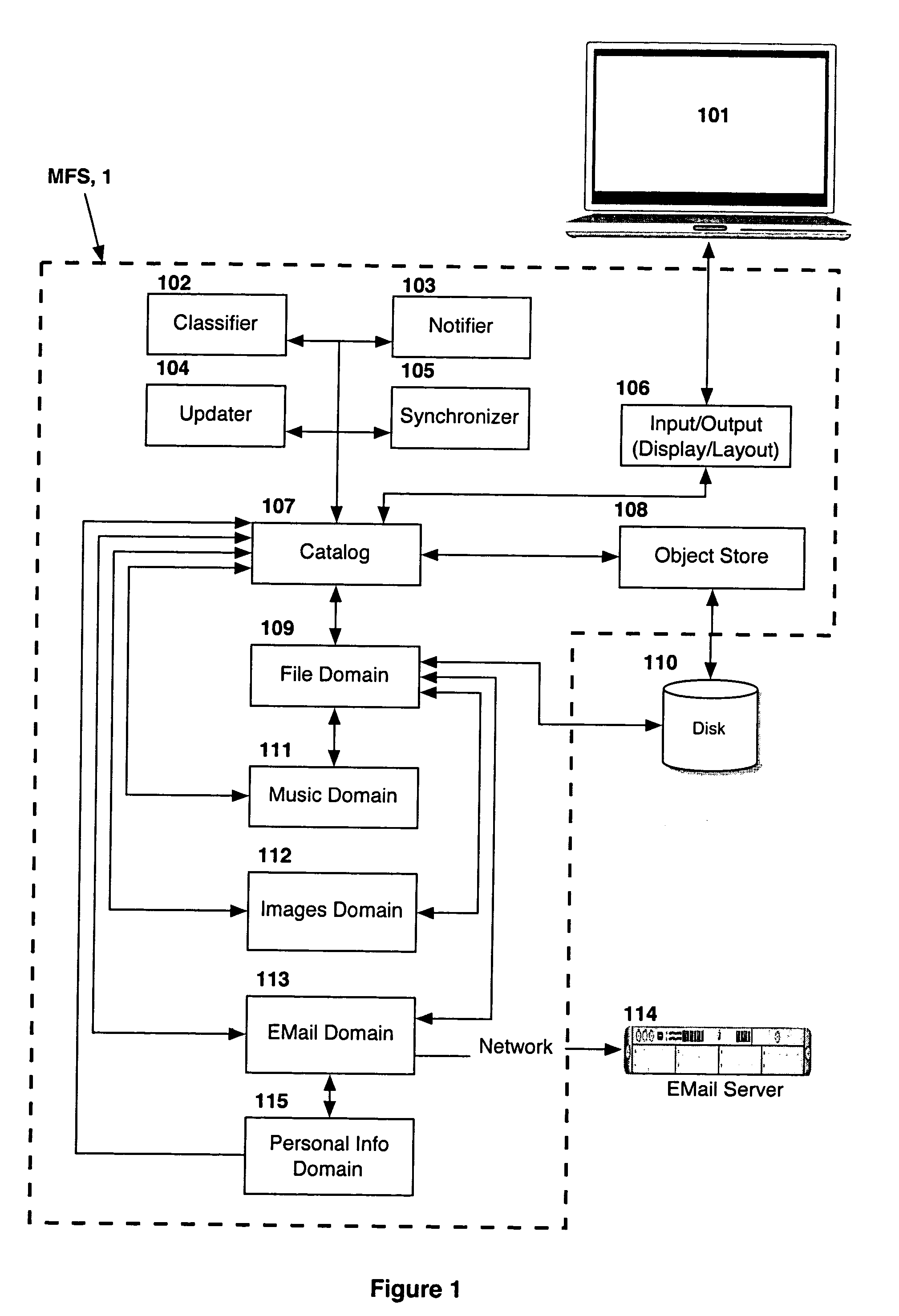
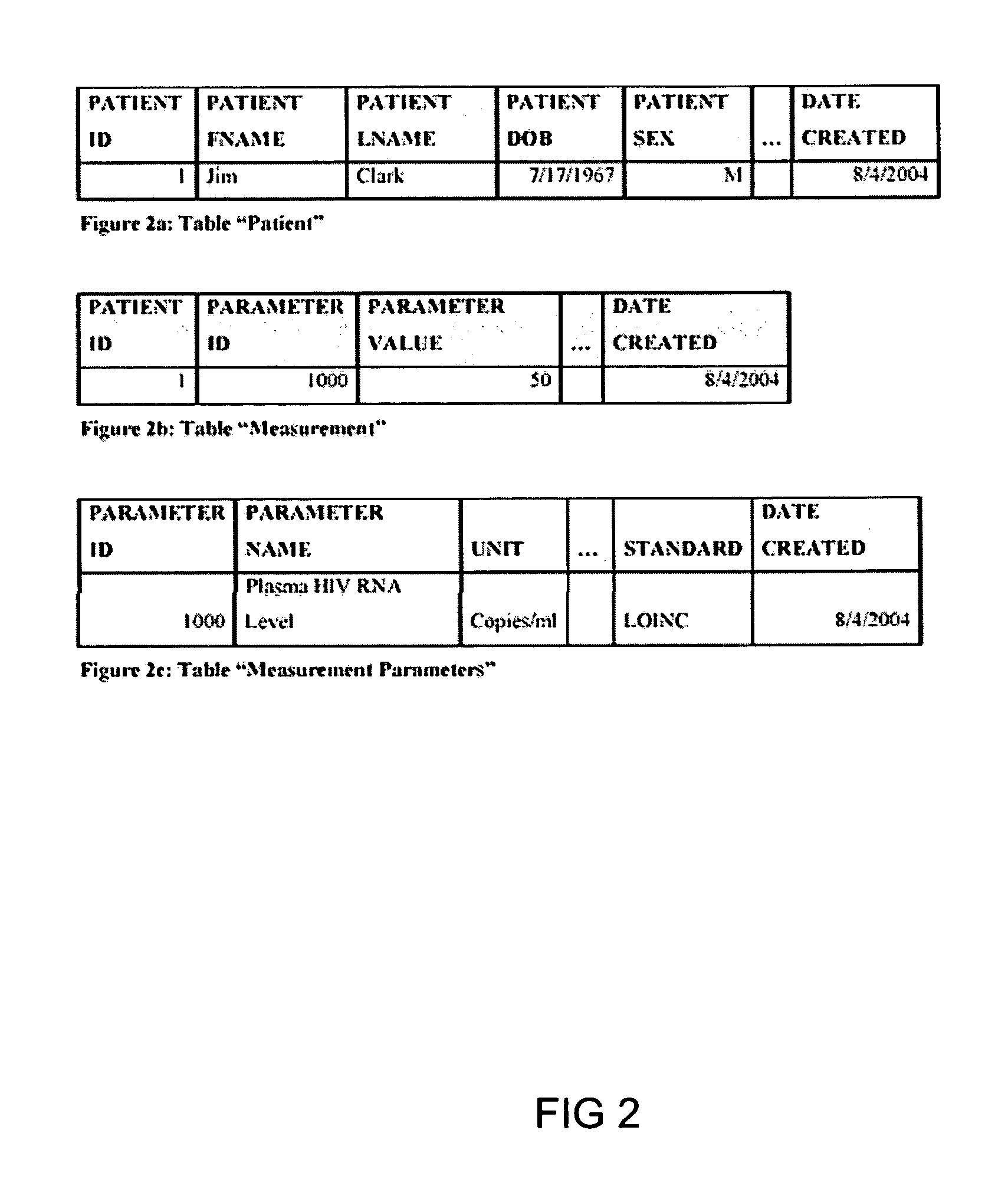
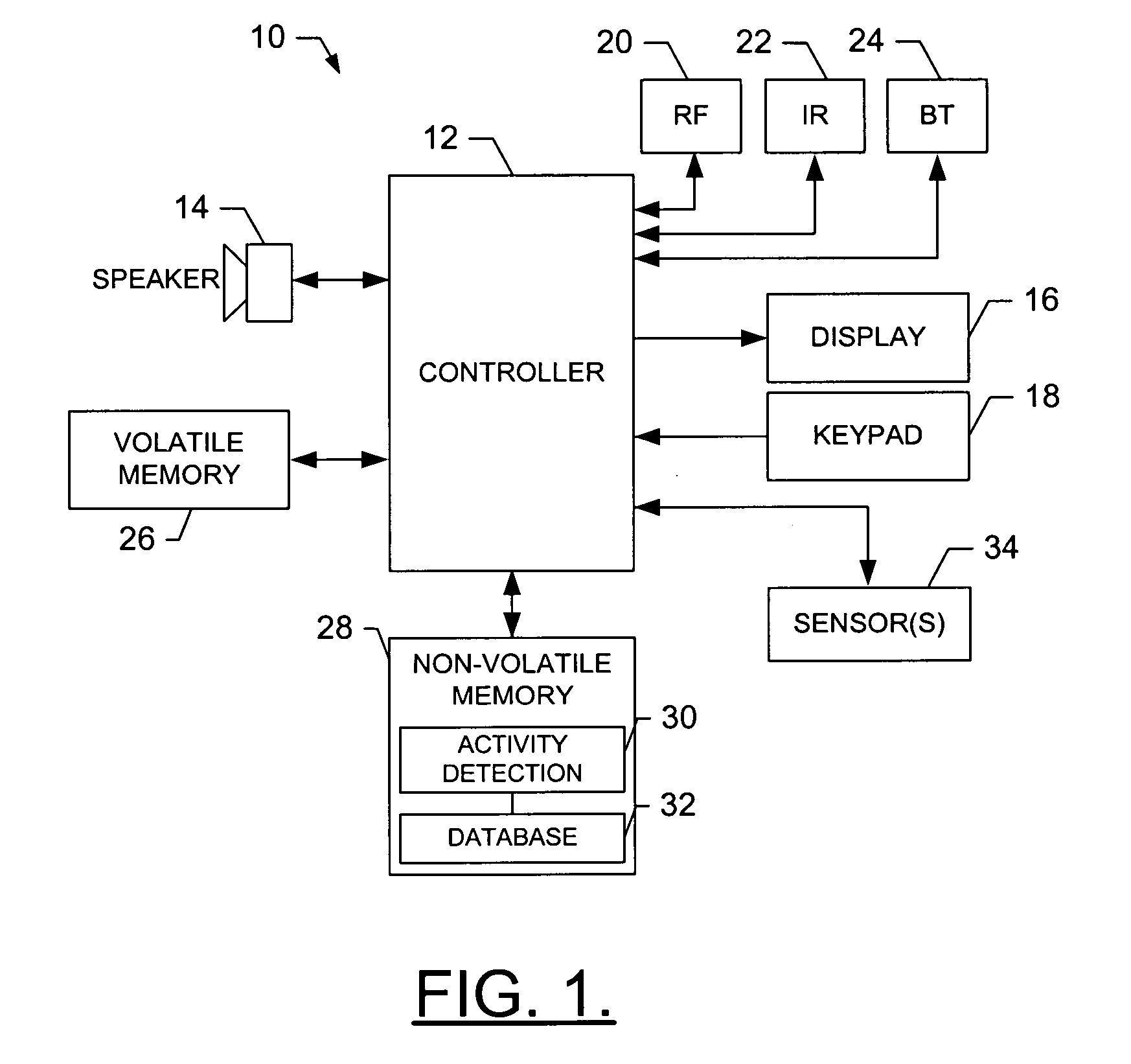
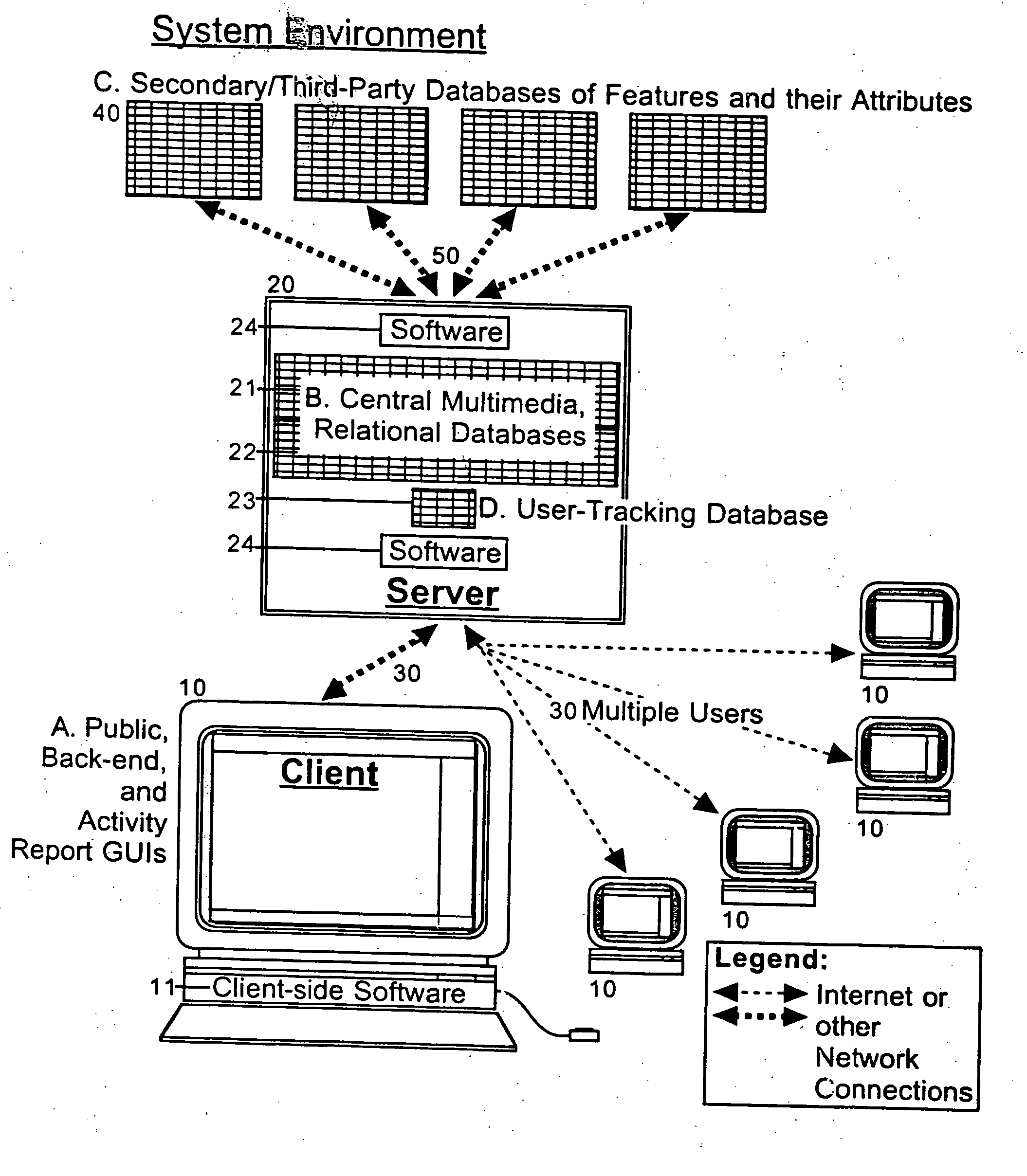
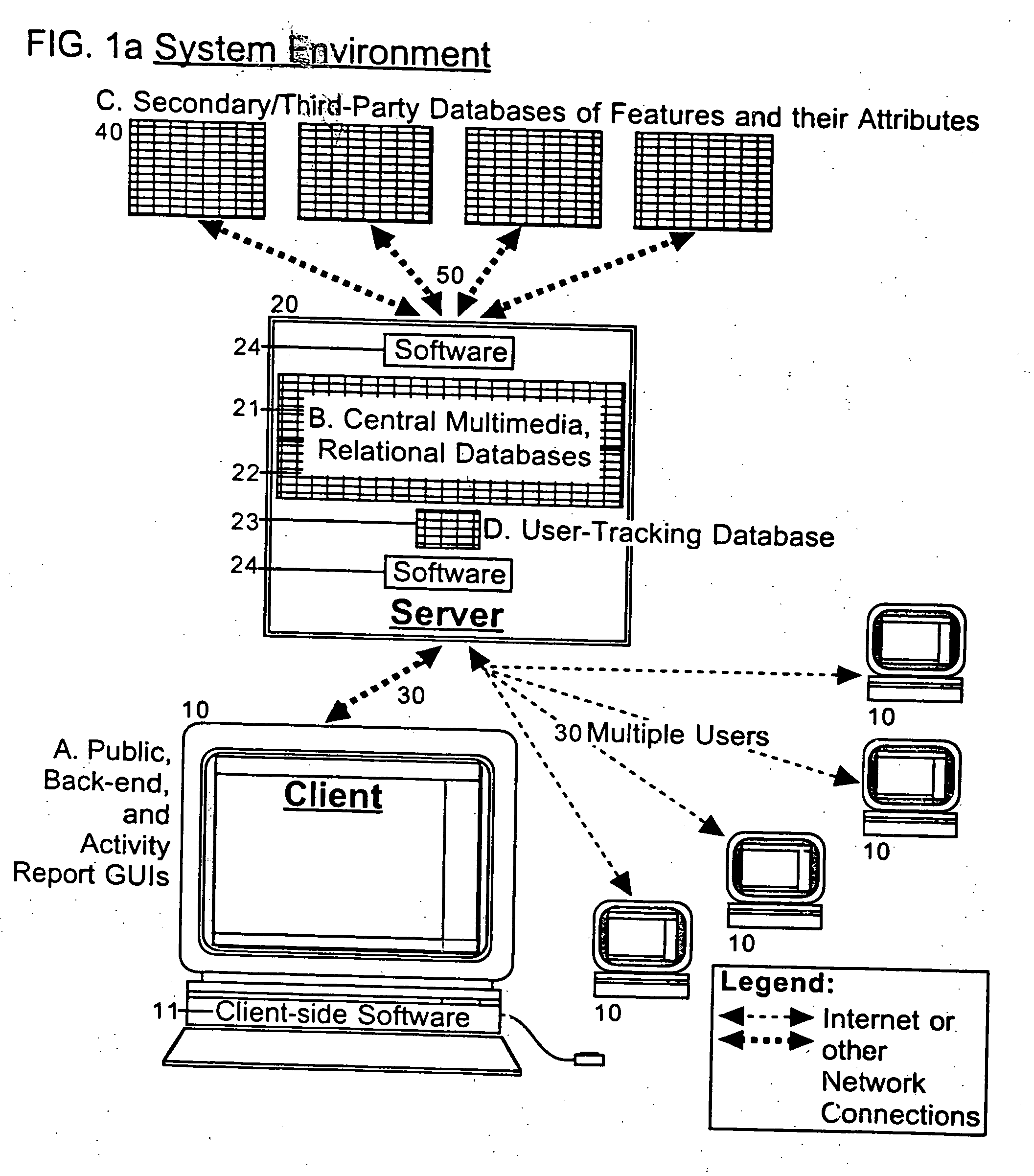
Information management (IM) concerns a cycle of organizational activity: the acquisition of information from one or more sources, the custodianship and the distribution of that information to those who need it, and its ultimate disposition through archiving or deletion.
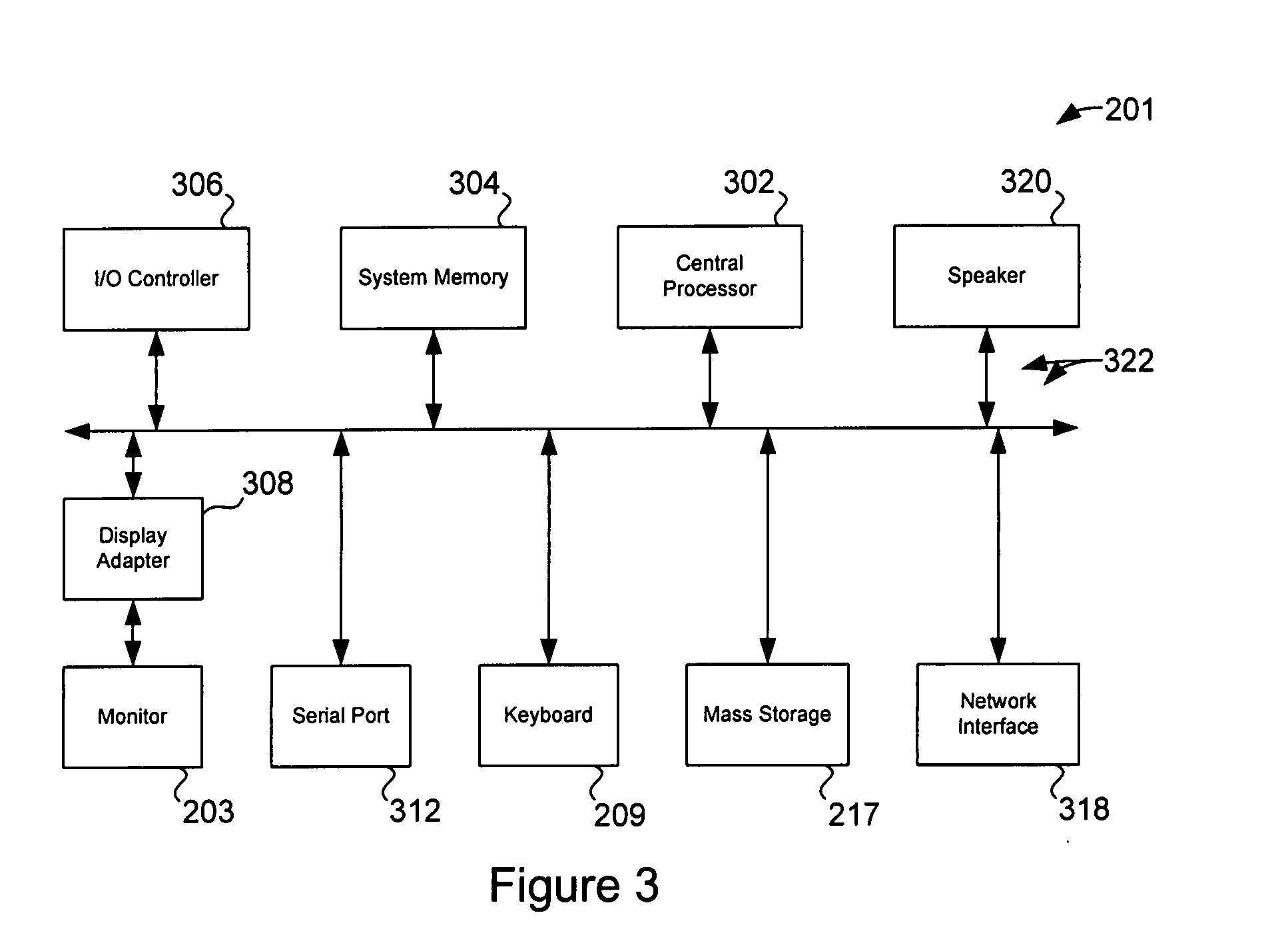
Processing management information
InactiveUS8095413B1Readily availableOffice automationTransmissionManagement information systemsData science
Owner:VIRTUALAGILITY
Dynamic information management system and method for content delivery and sharing in content-, metadata- & viewer-based, live social networking among users concurrently engaged in the same and/or similar content
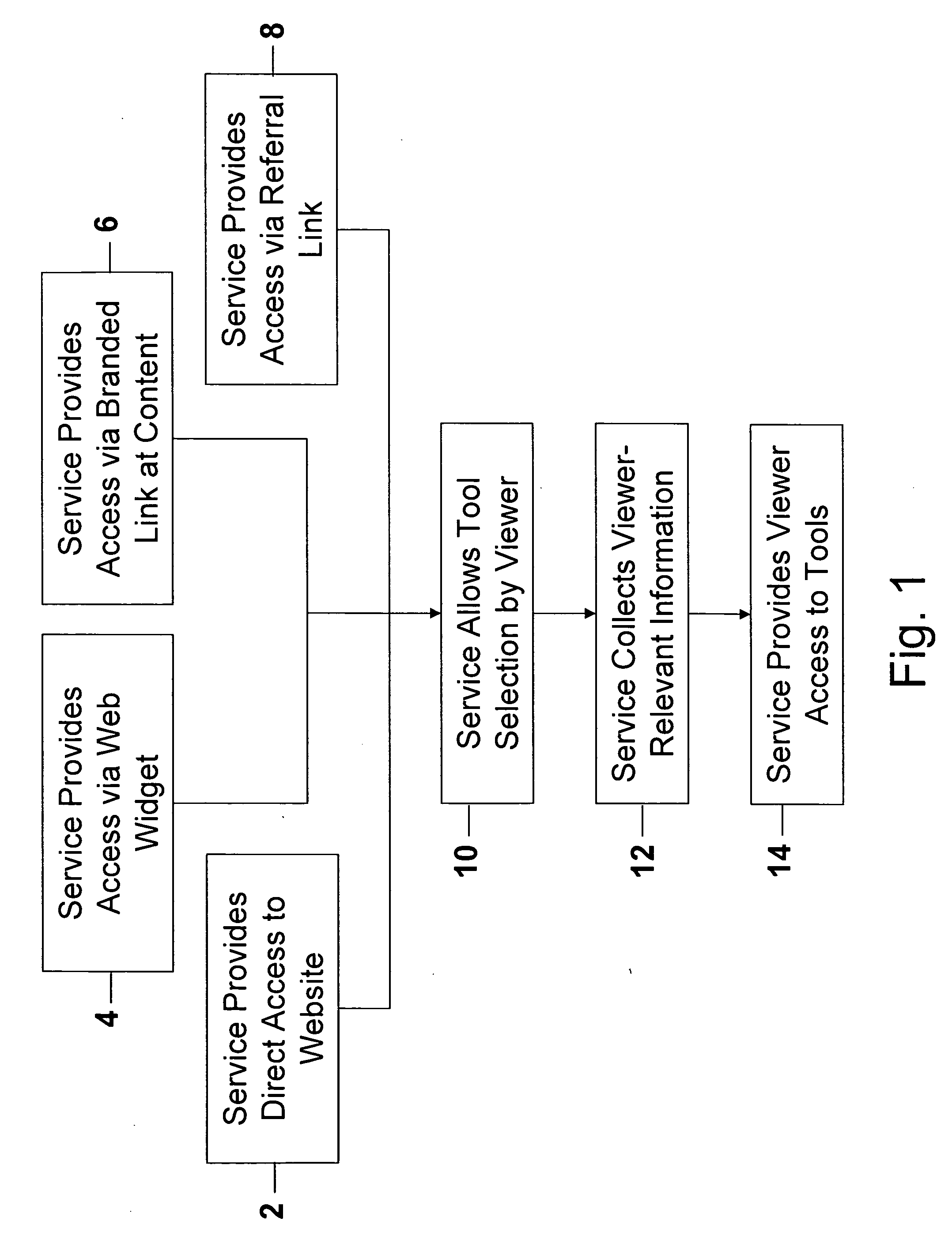
Disclosed are tools, methods, and systems for establishing generally live, Content-based social networks, and for concurrently sharing Content and Content-relevant information within a social network. A Service registers Viewers and / or n-Users, and provides tools that enable a Viewer to identify n-Users concurrently viewing the same or similar Content, or having an interest in the same or similar Content. A Viewer can initiate or join a Content-based social network, and can share their Content with others, or view others' Content, and interact with n-Users via any of several methods. Service tools also enable a Viewer to define and selectively block or alter objectionable material so that it is no longer perceivable in its objectionable form. The described tools, methods, and systems also enable numerous innovative approaches to generate revenue for a Service, for providers of product and / or services, for Content providers, and others.
Owner:NEONEKT LLC
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS7275063B2Facilitate communicationMultimedia data indexingFile access structuresPathPingSoftware system
Owner:EHIERARCHY LLC
Detecting Behavioral Patterns and Anomalies Using Activity Profiles
ActiveUS20080059474A1Potential security breachError detection/correctionDigital data processing detailsBehaviour patternActivity profile
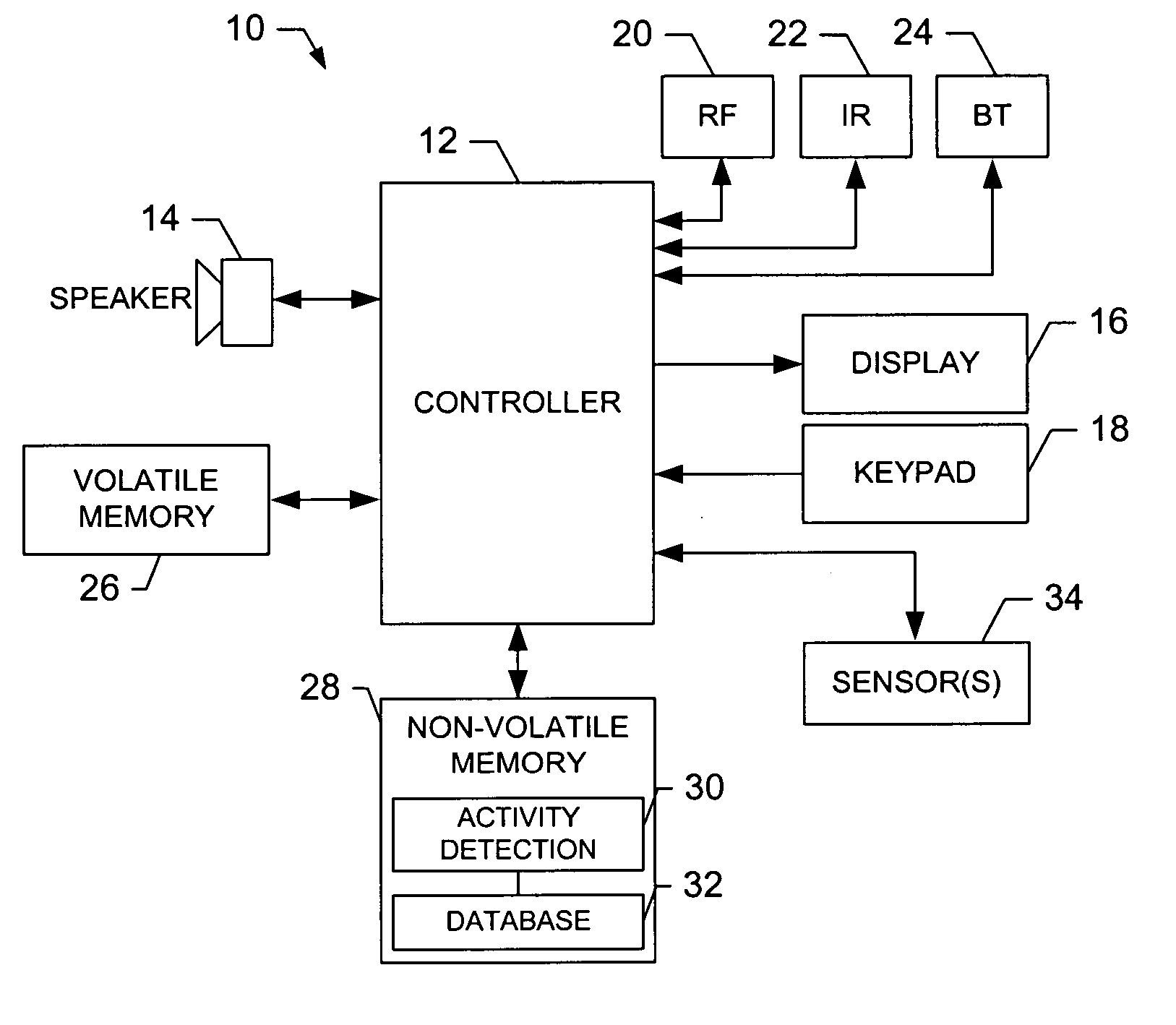
Activity data is analyzed or evaluated to detect behavioral patterns and anomalies. When a particular pattern or anomaly is detected, a system may send a notification or perform a particular task. This activity data may be collected in an information management system, which may be policy based. Notification may be by way e-mail, report, pop-up message, or system message. Some tasks to perform upon detection may include implementing a policy in the information management system, disallowing a user from connecting to the system, and restricting a user from being allowed to perform certain actions. To detect a pattern, activity data may be compared to a previously defined or generated activity profile.
Owner:NEXTLABS
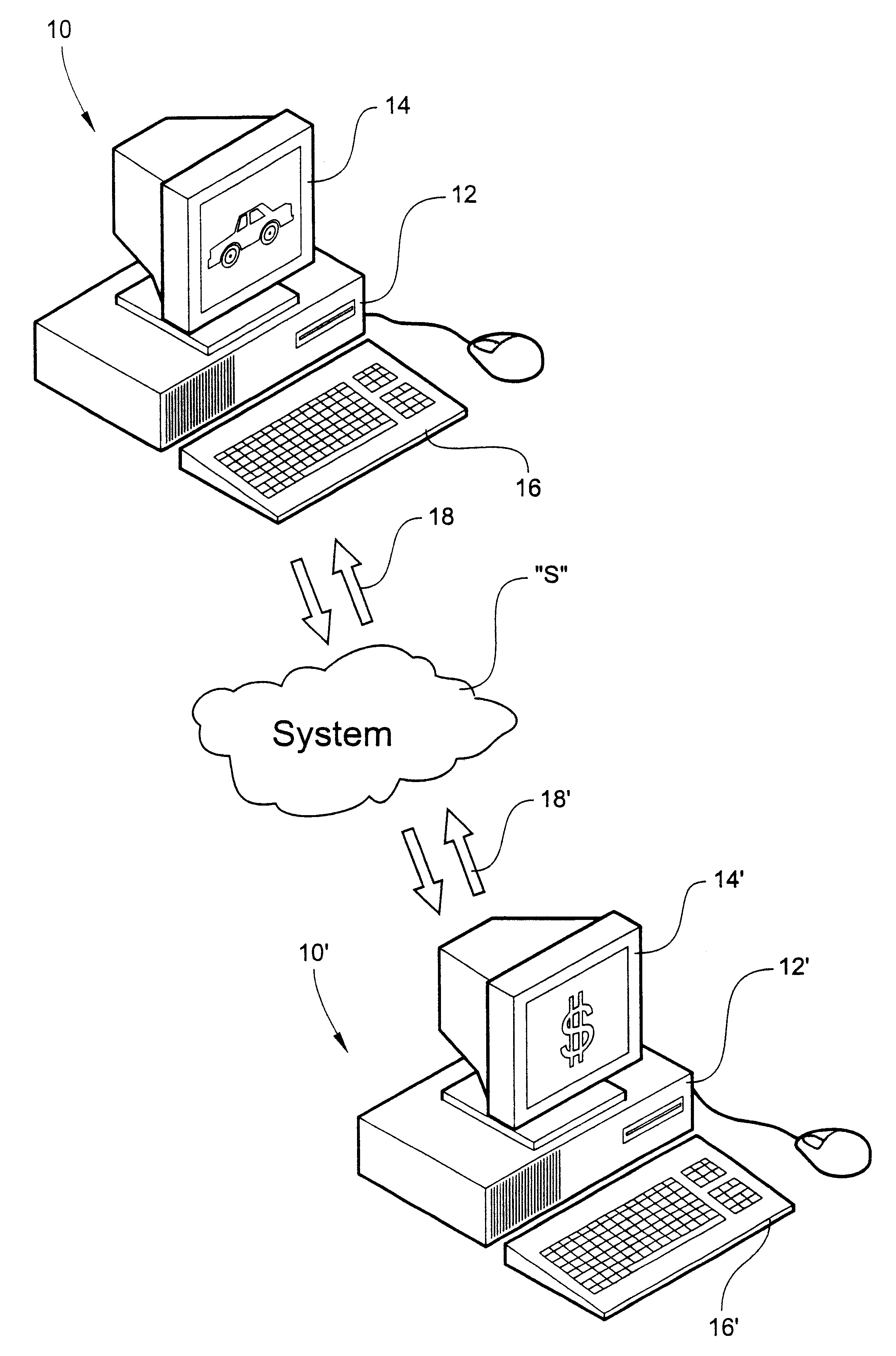
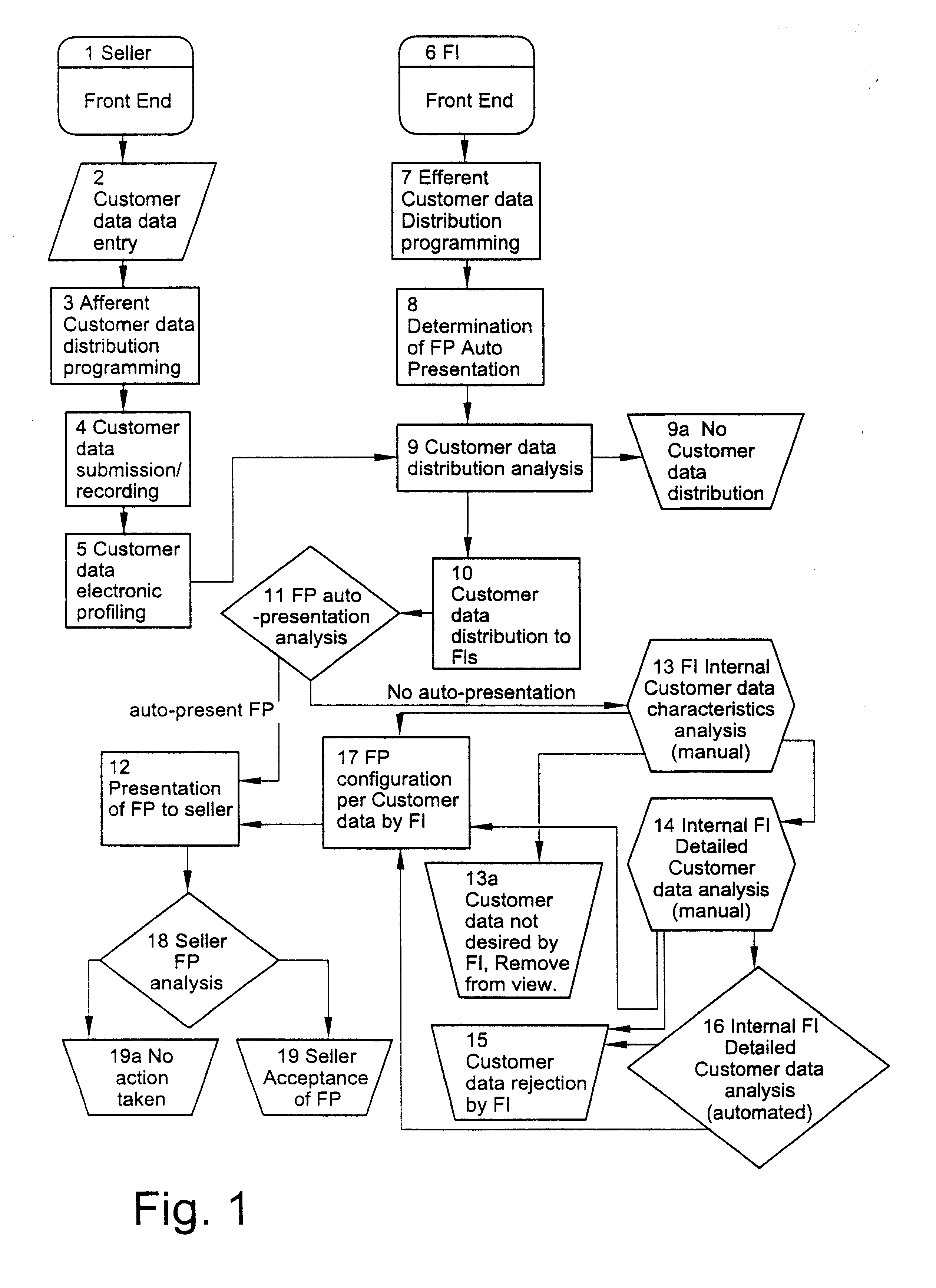
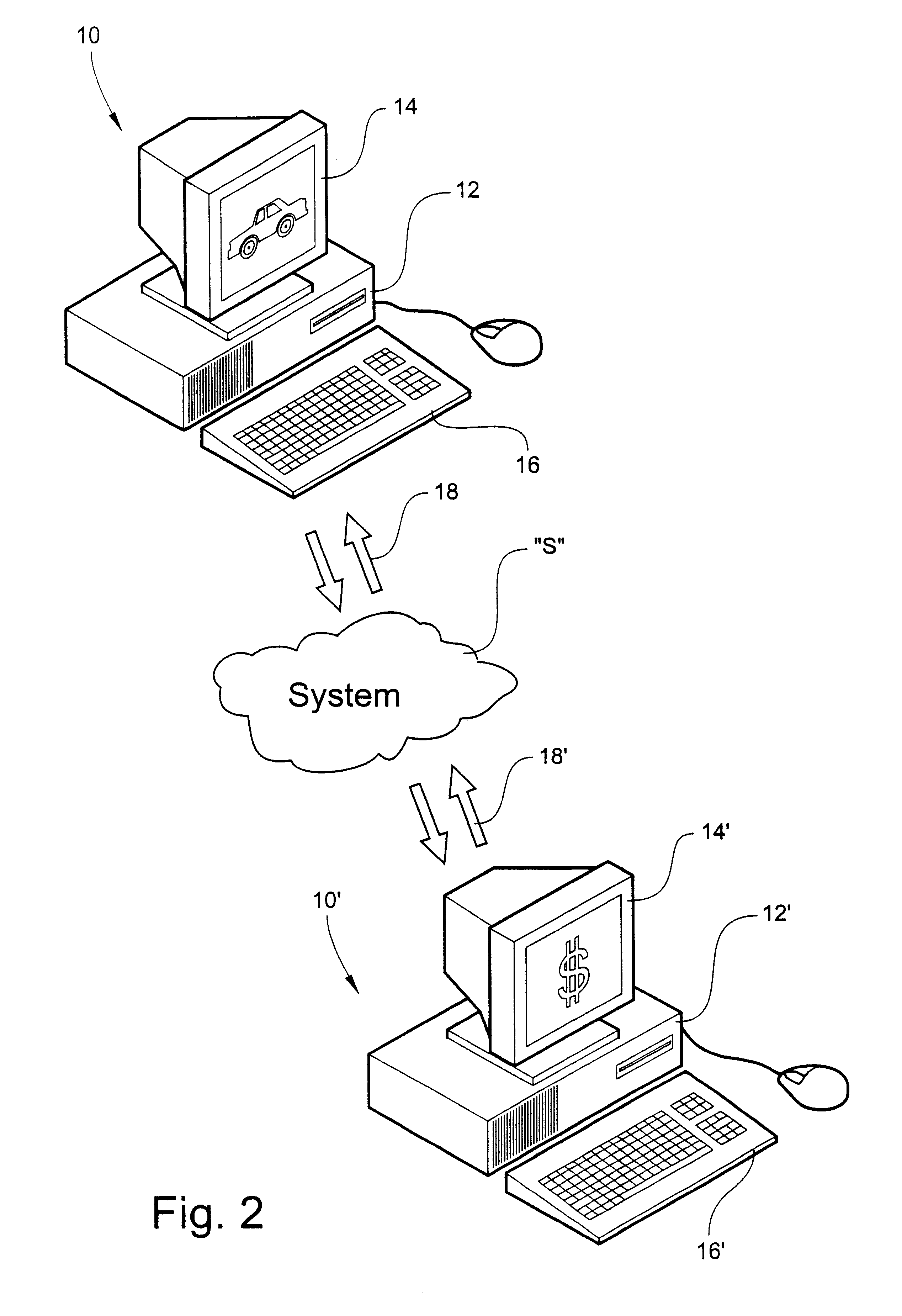
Computer-driven information management system for selectively matching credit applicants with money lenders through a global communications network
InactiveUS6208979B1Automate processingDetermine desirabilityFinanceBuying/selling/leasing transactionsComputer scienceComputer drive
A computer-driven information management system selectively matches credit applicants with money lenders through a global communications network. The system includes an applicant data entry device for entering applicant data into the system. The applicant data defines an electronic applicant profile of a credit applicant seeking financing. A model data entry device is provided for entering model data into the system. The model data is established by the lender and defines an electronic model profile representing characteristics of a desired applicant. A filter electronically compares the applicant profile with the model profile, such that for those credit applicants matching the model profile, the applicant data is made available through the system to lender. For those credit applicants not matching the model profile, no applicant data is made available through the system to the lender.
Owner:DEALERTRACK
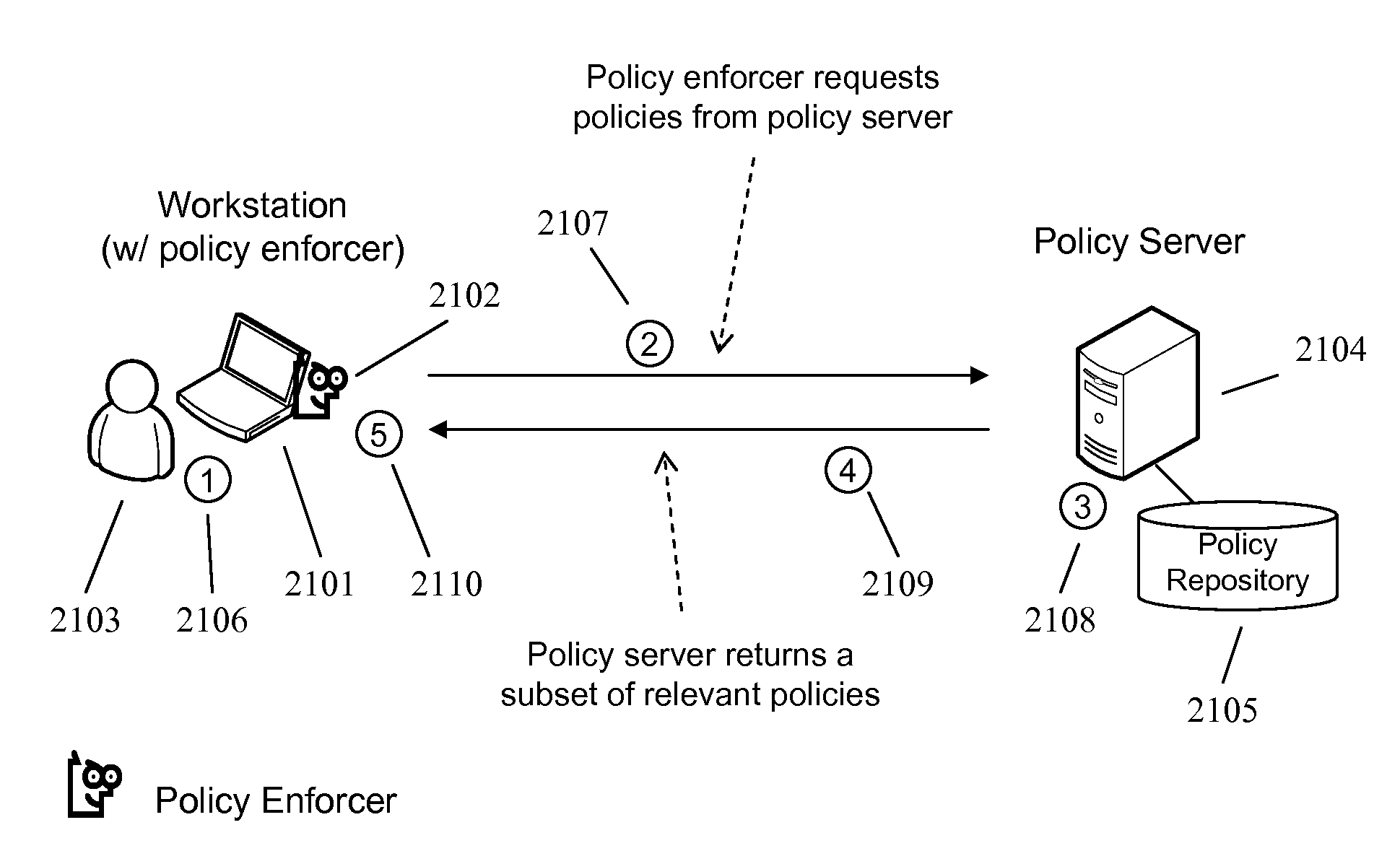
Techniques and System to Deploy Policies Intelligently
ActiveUS20070156659A1Reduce the amount requiredImprove execution speedDigital data processing detailsComputer security arrangementsSpace requirementsOperating system
In an information management system, relevant policies are deployed to targets while policies which are not relevant are not. By deploying relevant policies, this reduces the amount of space requirements at the target to store the policies and the amount of data that needs to be sent to the target. Also, execution speed at the target may increase since the target does not need to evaluate policies that are not relevant.
Owner:NEXTLABS
Techniques of Transforming Policies to Enforce Control in an Information Management System
ActiveUS20080066150A1Digital data processing detailsUser identity/authority verificationReal-time computingInformation management
In an information management system, policies are deployed to targets and targets can evaluate the policies whether they are connected or disconnected to the system. The policies may be transferred to the target, which may be a device or user. Relevant policies may be transferred while not relevant policies are not. The policies may have policy abstractions.
Owner:NEXTLABS
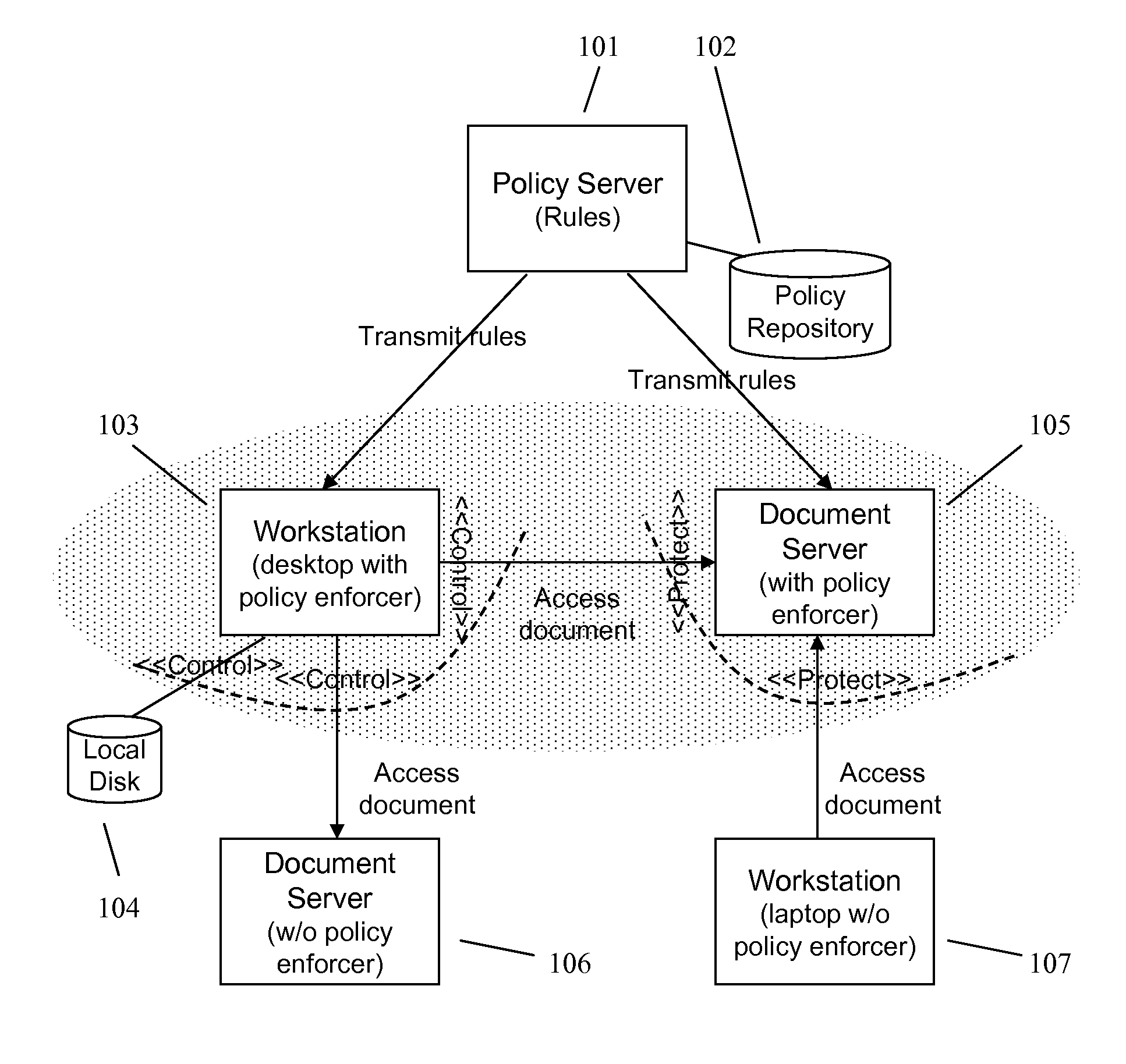
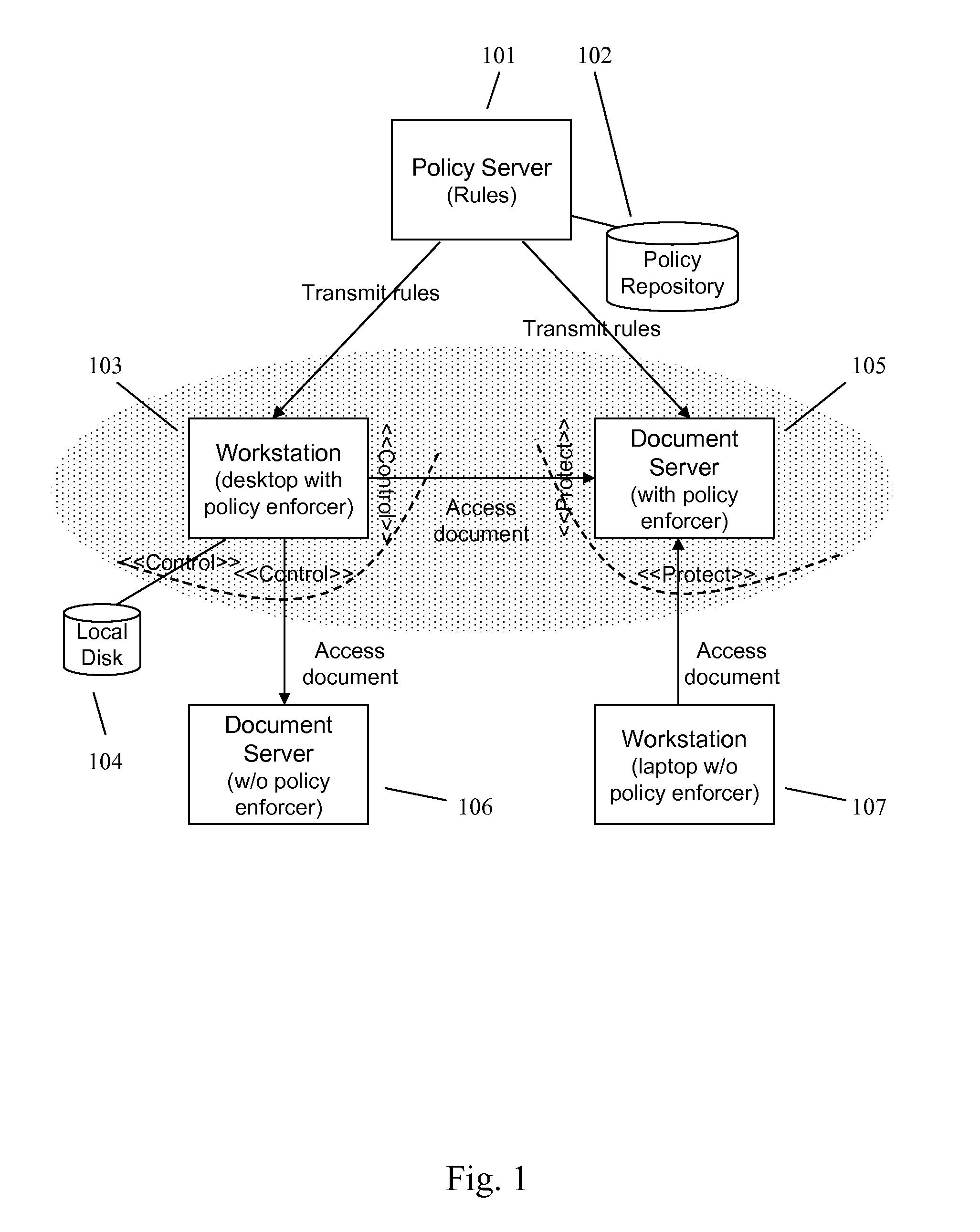
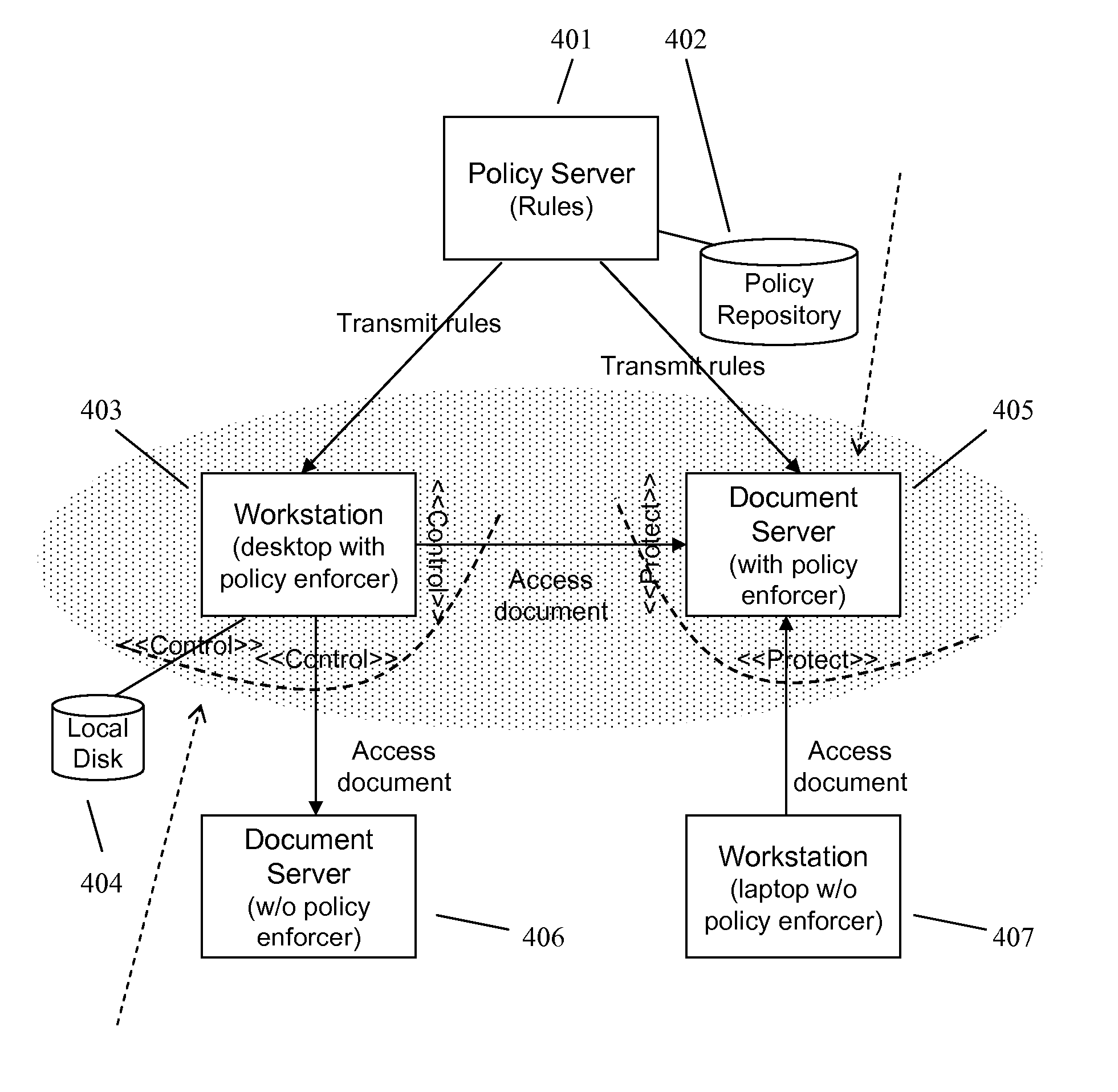
Enforcing Control Policies in an Information Management System
ActiveUS20070156897A1Digital data processing detailsDigital computer detailsClient-sideCentralized management
A method and apparatus for controlling document access and application usage using centrally managed rules. The rules are stored and manipulated in a central rule database via a rule server. Policy enforcers are installed on client systems and / or on servers and perform document access and application usage control for both direct user document accesses and application usage, and application program document accesses by evaluating the rules sent to the policy enforcer. The rule server decides which rules are required by each policy enforcer. A policy enforcer can also perform obligation and remediation operations as a part of rule evaluation. Policy enforcers on client systems and servers can operate autonomously, evaluating policies that have been received, when communications have been discontinued with the rule server.
Owner:BLUE JUNGLE
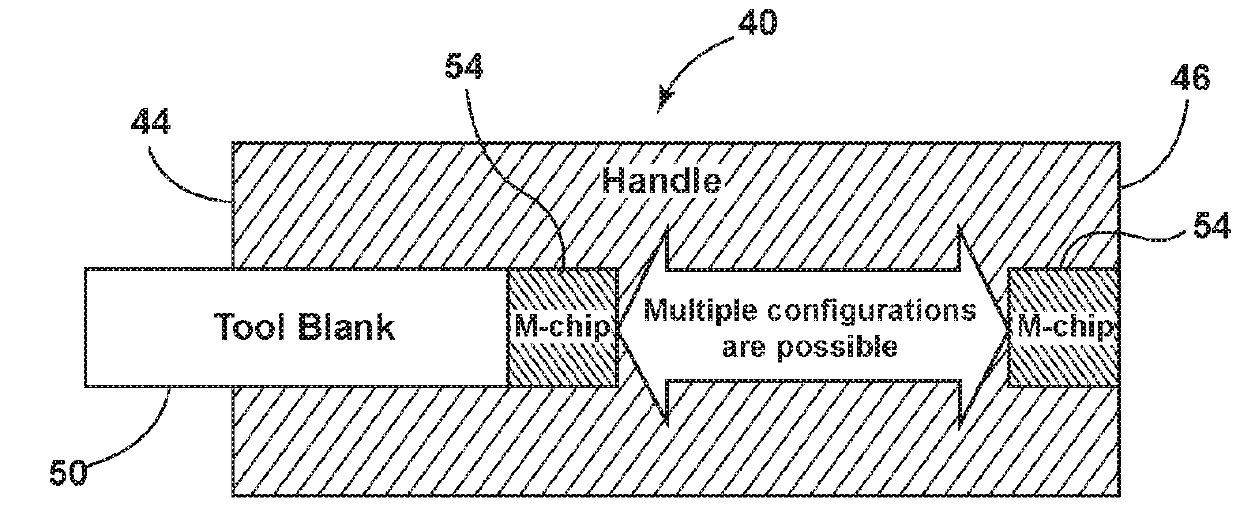
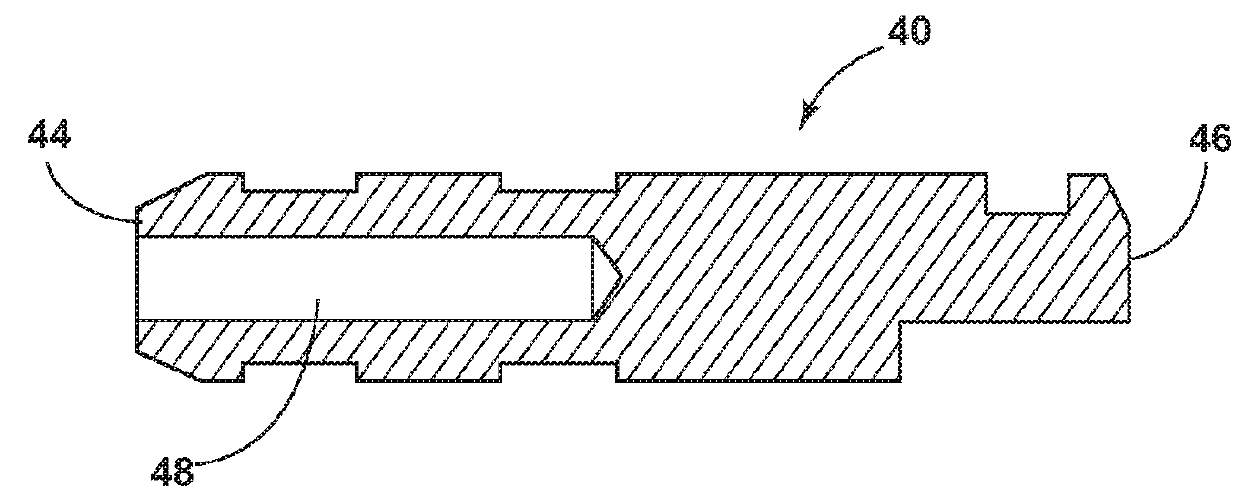
Electronic tool recognition system for dental devices
A tool for use with an electronic tool recognition system includes a tool blank with a distal tip configured for performing a procedure and a proximal handle encasing, fixedly, a proximal end of the tool blank. A tool-identifying apparatus including a mechanical resonator is embedded in a proximal end of the tool blank to provide a tool identifier. A conductive wire in electrical contact with the resonator provides the identifier to a processor. In another arrangement, conductive brushes in contact with slip rings provide the identifier to a processor. In another arrangement, a dental tool handle includes an insulating portion defining a recess in a proximal end of the handle configured to receive either a sensor or an information-managing chip.
Owner:THE KERR
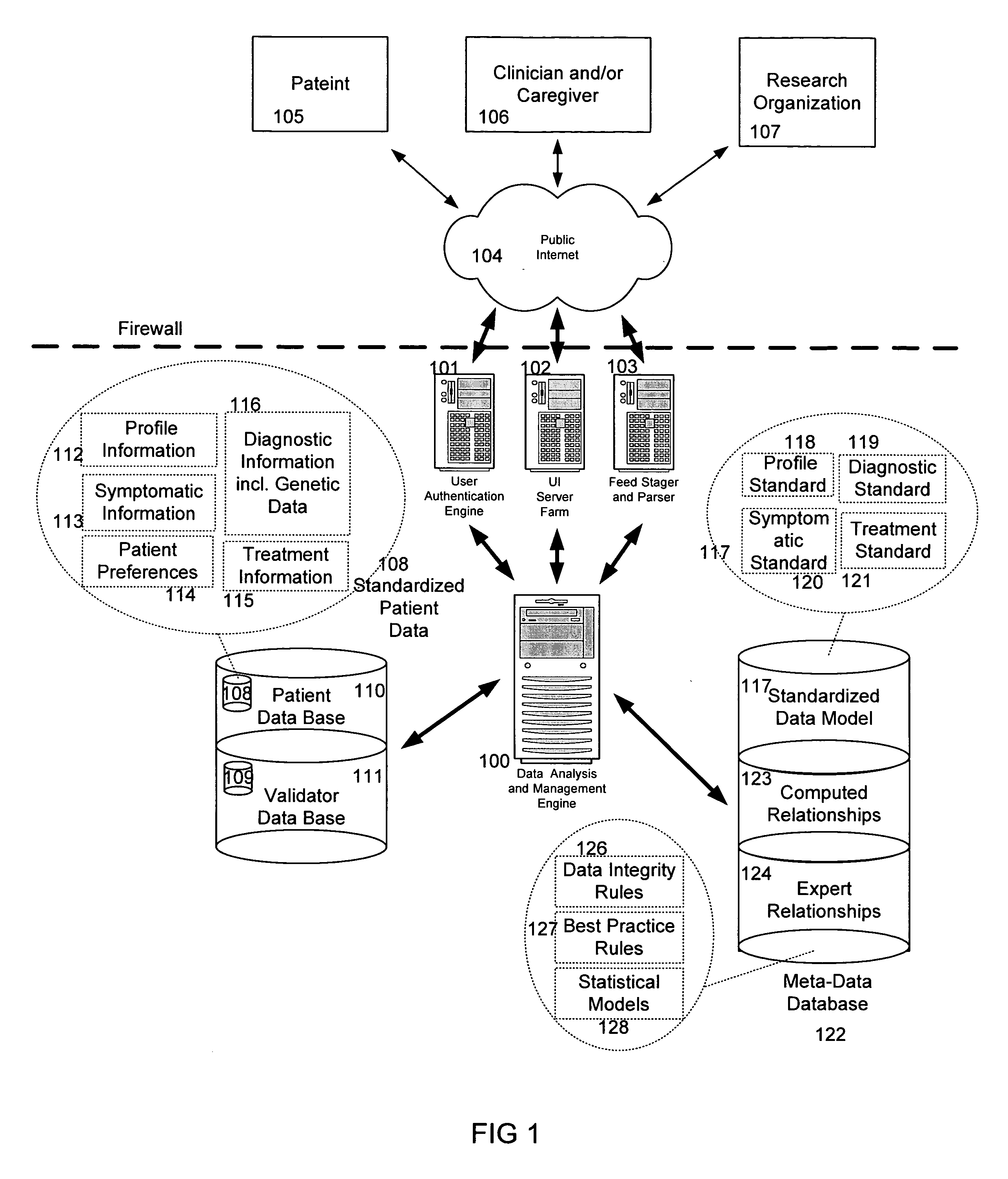
System and method for improving clinical decisions by aggregating, validating and analysing genetic and phenotypic data
The information management system disclosed enables caregivers to make better decisions, faster, using aggregated genetic and phenotypic data. The system enables the integration, validation and analysis of genetic, phenotypic and clinical data from multiple subjects who may be at distributed facilities. A standardized data model stores a range of patient data in standardized data classes that encompass patient profile information, patient symptomatic information, patient treatment information, and patient diagnostic information including genetic information. Data from other systems is converted into the format of the standardized data classes using a data parser, or cartridge, specifically tailored to the source system. Relationships exist between standardized data classes that are based on expert rules and statistical models. The relationships are used both to validate new data, and to predict phenotypic outcomes based on available data. The prediction may relate to a clinical outcome in response to a proposed intervention by a caregiver. The statistical models may be inhaled into the system from electronic publications that define statistical models and methods for training those models, according to a standardized template. Methods are described for selecting, creating and training the statistical models to operate on genetic, phenotypic and clinical data, in particular for underdetermined data sets that are typical of genetic information. The disclosure also describes how security of the data is maintained by means of a robust security architecture, and robust user authentication such as biometric authentication, combined with application-level and data-level access privileges.
Owner:NATERA
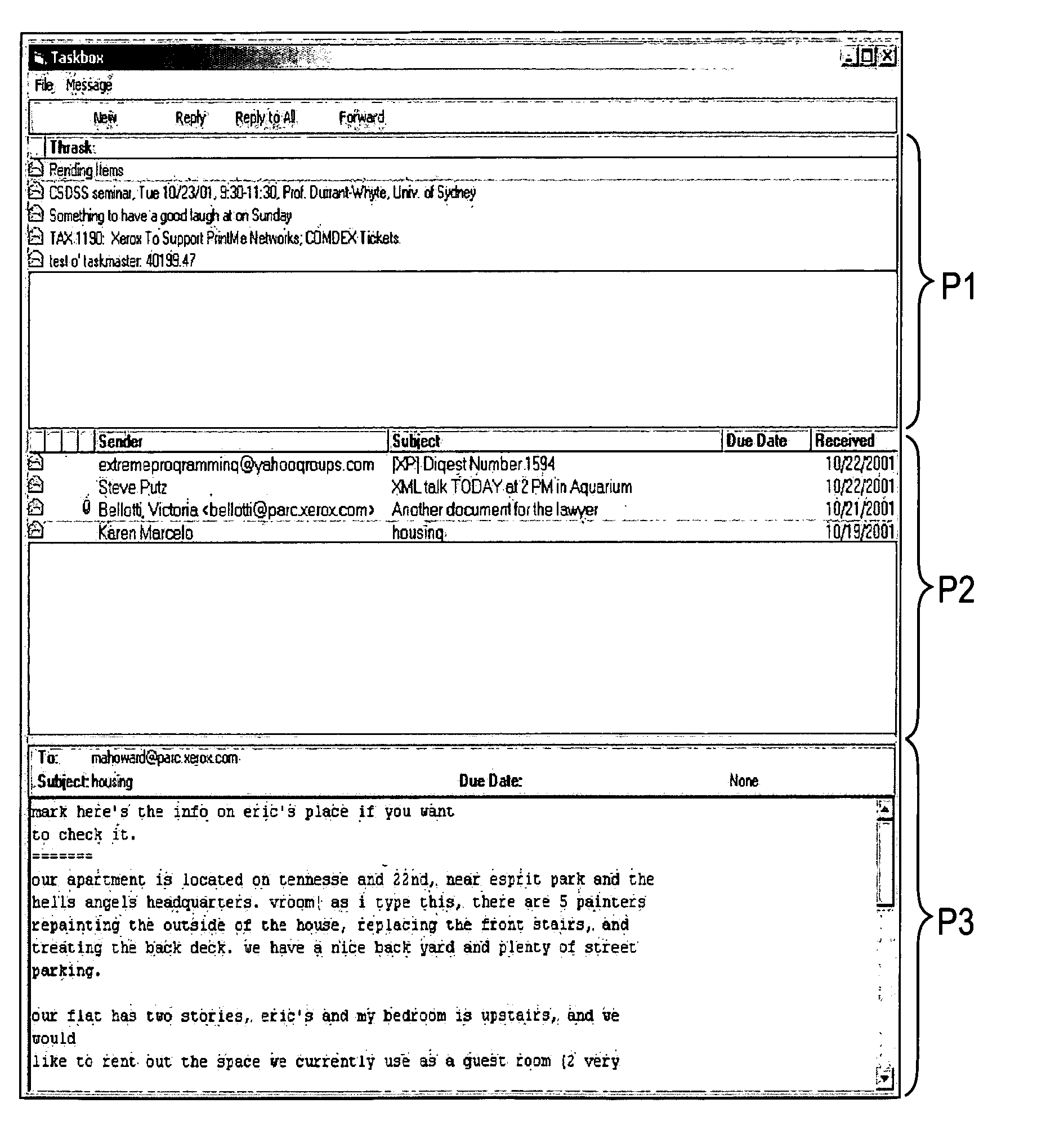
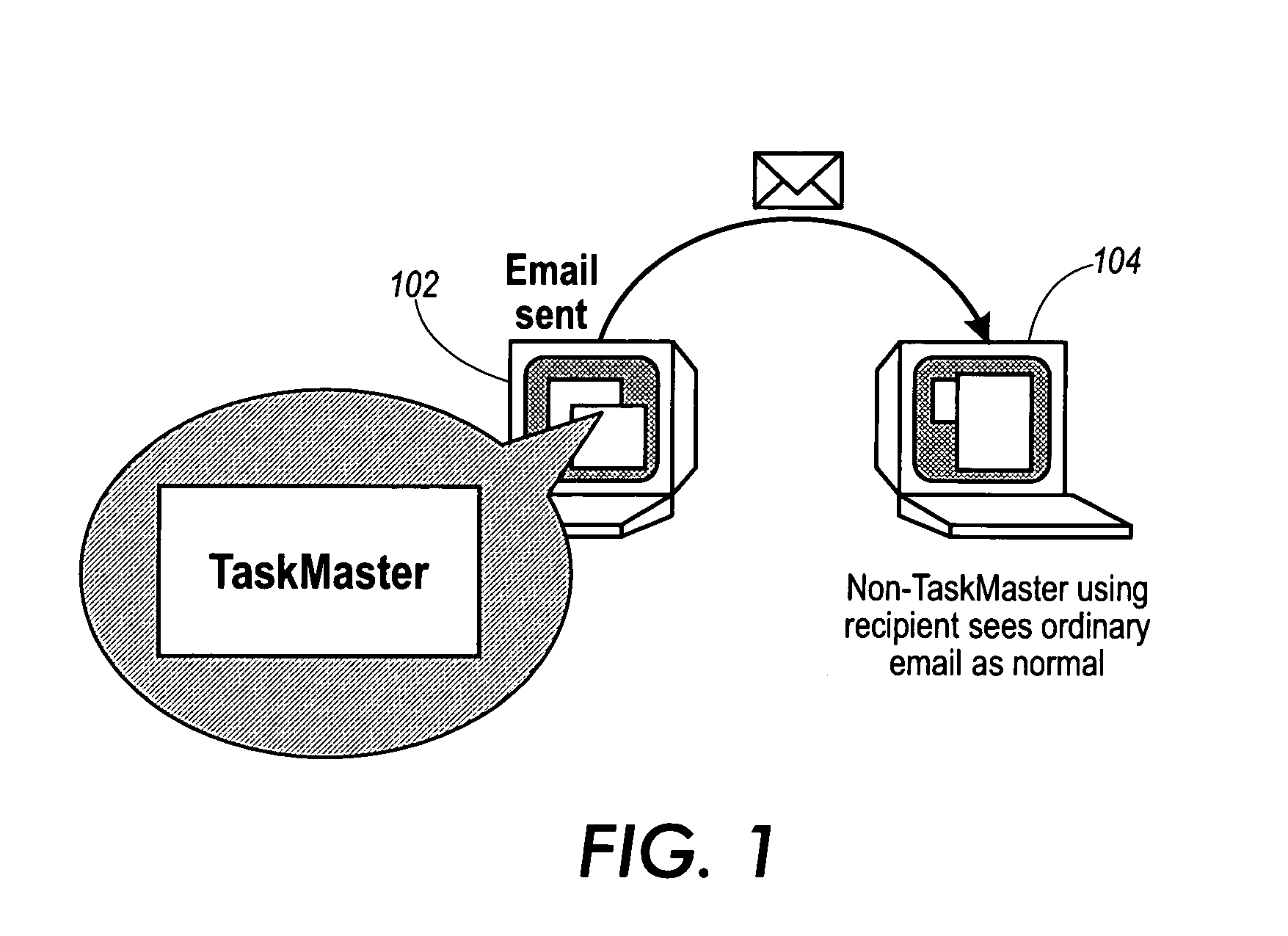
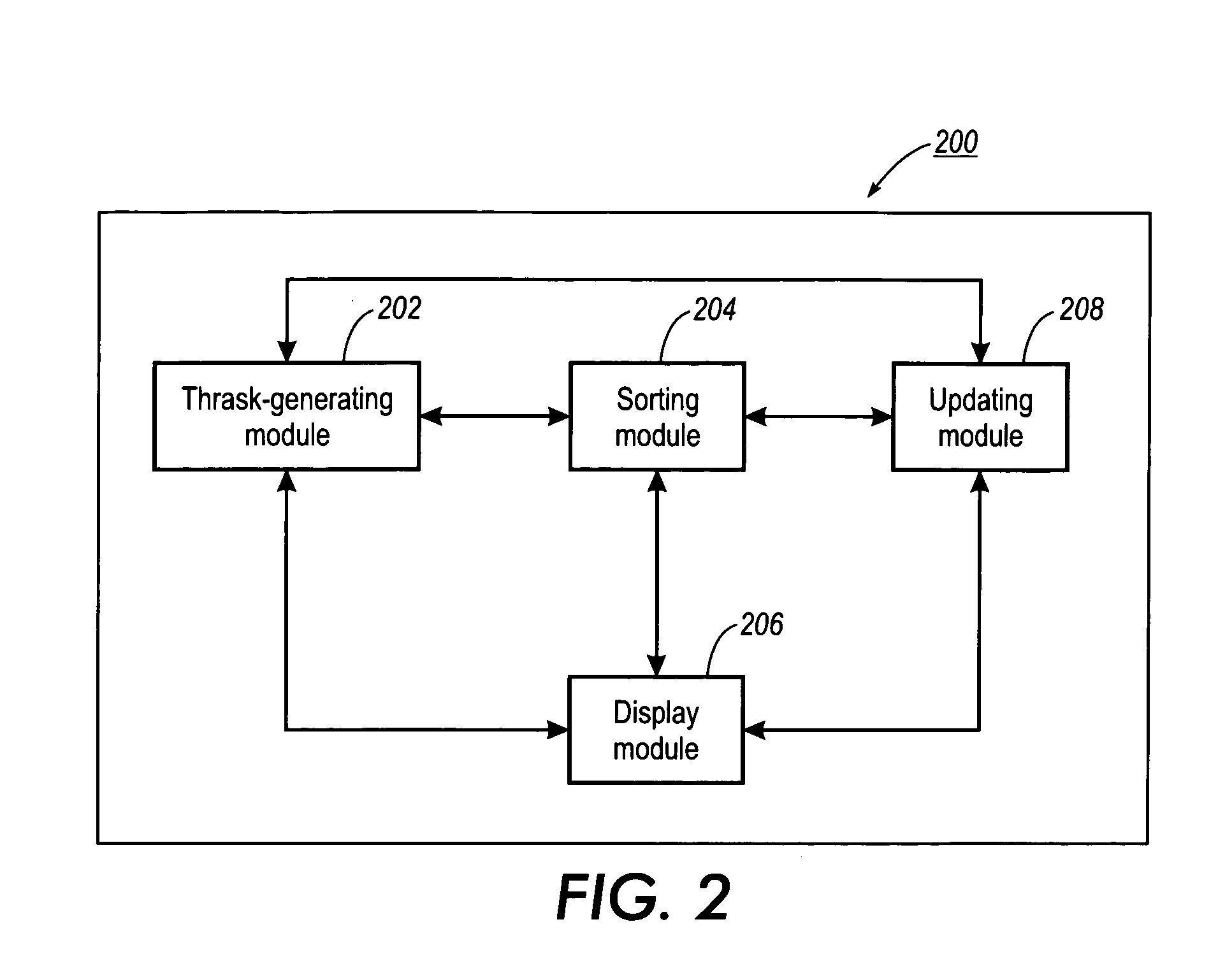
User interface for a message-based system having embedded information management capabilities
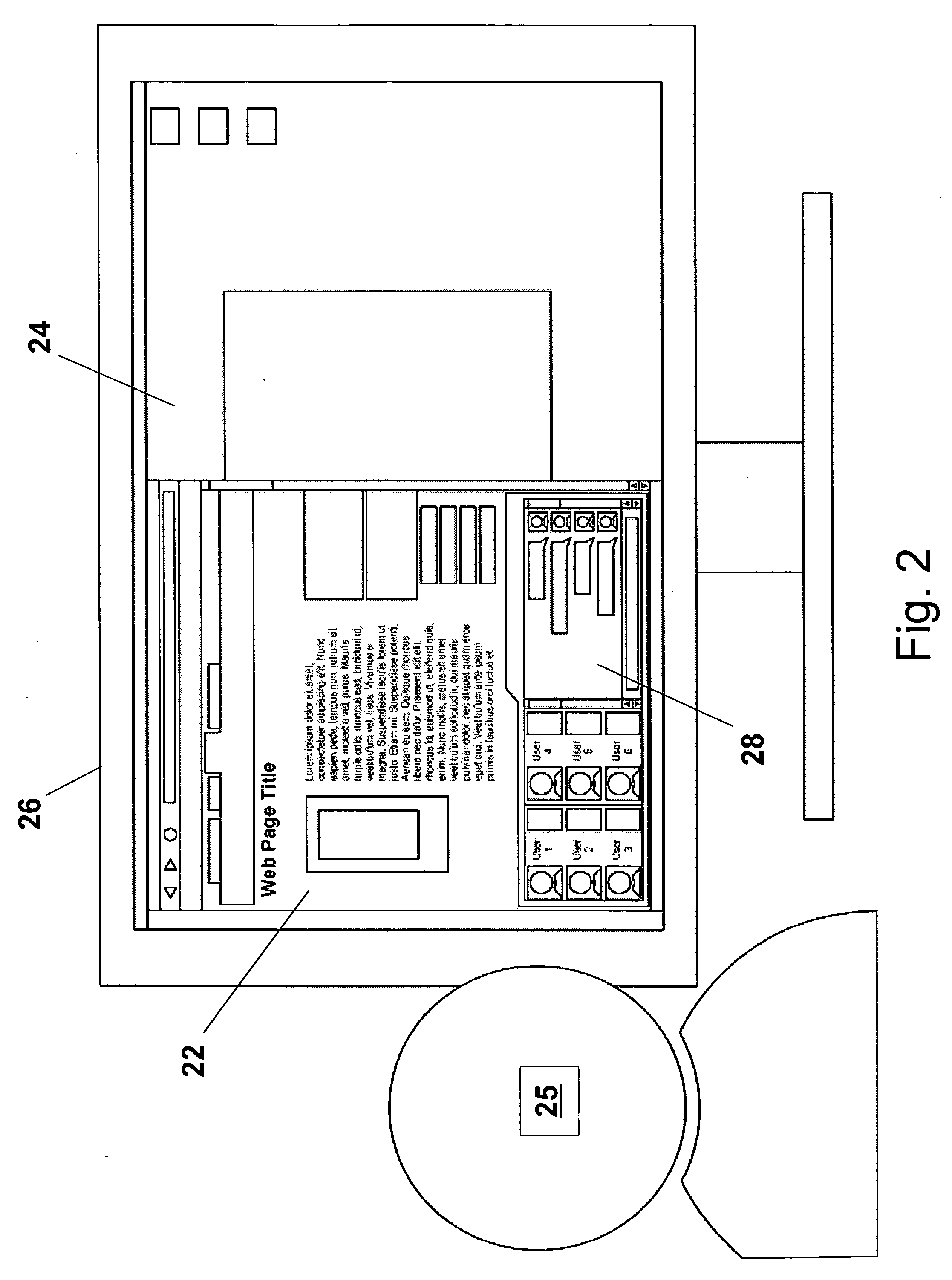
A method for managing and tracking information items within a message-based system. The message-based system has a viewer which include a first, a second and a third viewing panes. A plurality of thrasks is generated. Each of the thrasks includes at least one information item having a set of metadata. A new information item is sorted into one of the thrasks in accordance with at least one criterion. Some of the thrasks are displayed in the first viewing pane. A list of the information items of a thrask selected from the displayed thrasks is displayed in the second viewing pane. For each of the displayed information items at least one of the respective metadata is displayed. Some of the content of an information item selected from the list of the displayed information items is displayed in the third viewing pane.
Owner:III HLDG 6
Systems and methods for using reputation scores in network services and transactions to calculate security risks to computer systems and platforms
ActiveUS20130298192A1Memory loss protectionError detection/correctionMathematical CalculusInternet privacy
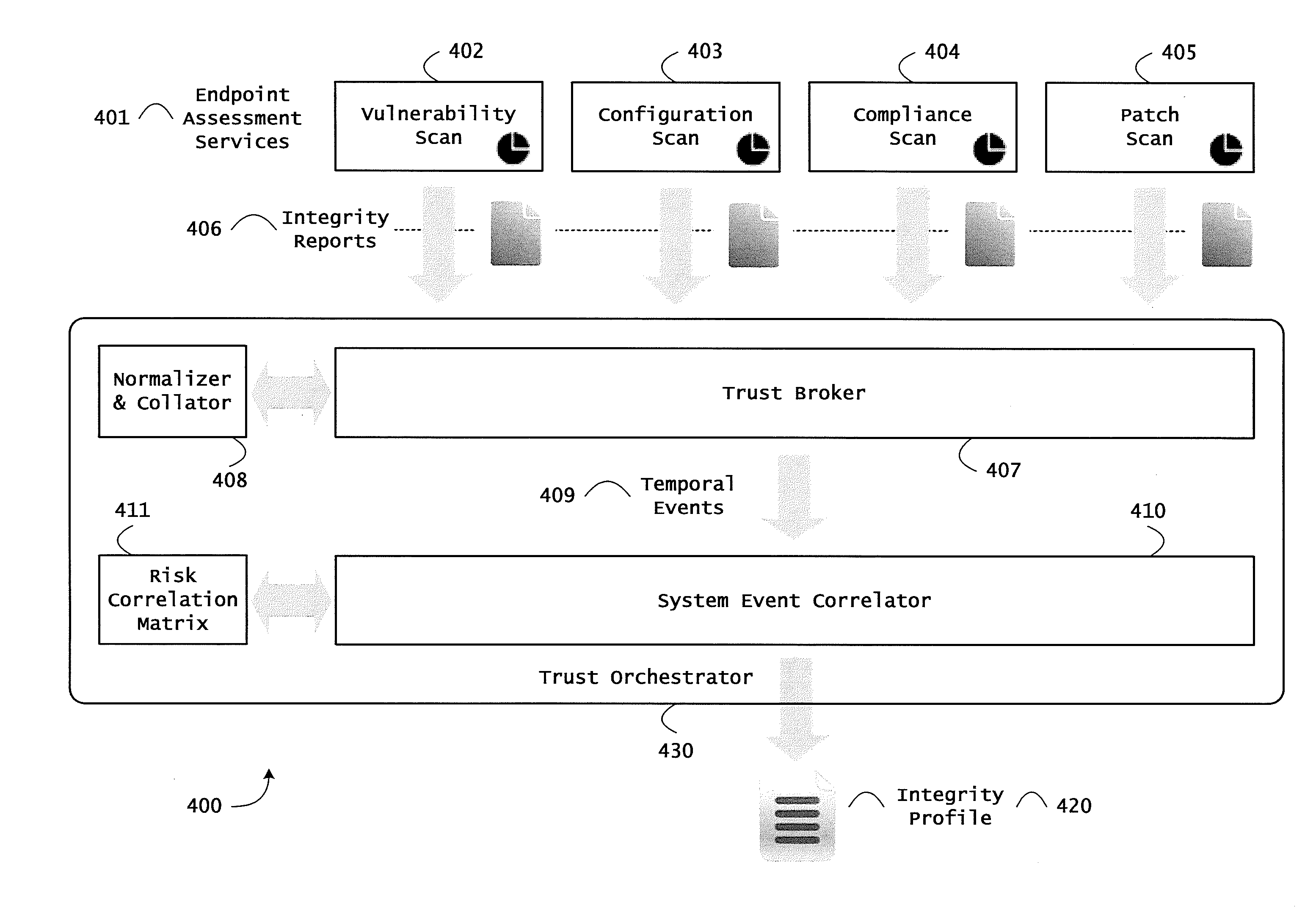
Instrumented networks, computer systems and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for calculating security risks by determining subject reputation scores. In an embodiment, a system receives a query for a reputation score of a subject, initiates directed queries to external information management systems to interrogate attributes associated with the subject, and analyzes responses. The system receives a hierarchical subject reputation score based on a calculus of risk and returns a reputation token. In another embodiment, a method provides real time attestation of a subject's reputation to a service provider using an endpoint trust agent, and a trust orchestrator comprising a reputation broker and a trust broker.
Owner:TAASERA LICENSING LLC
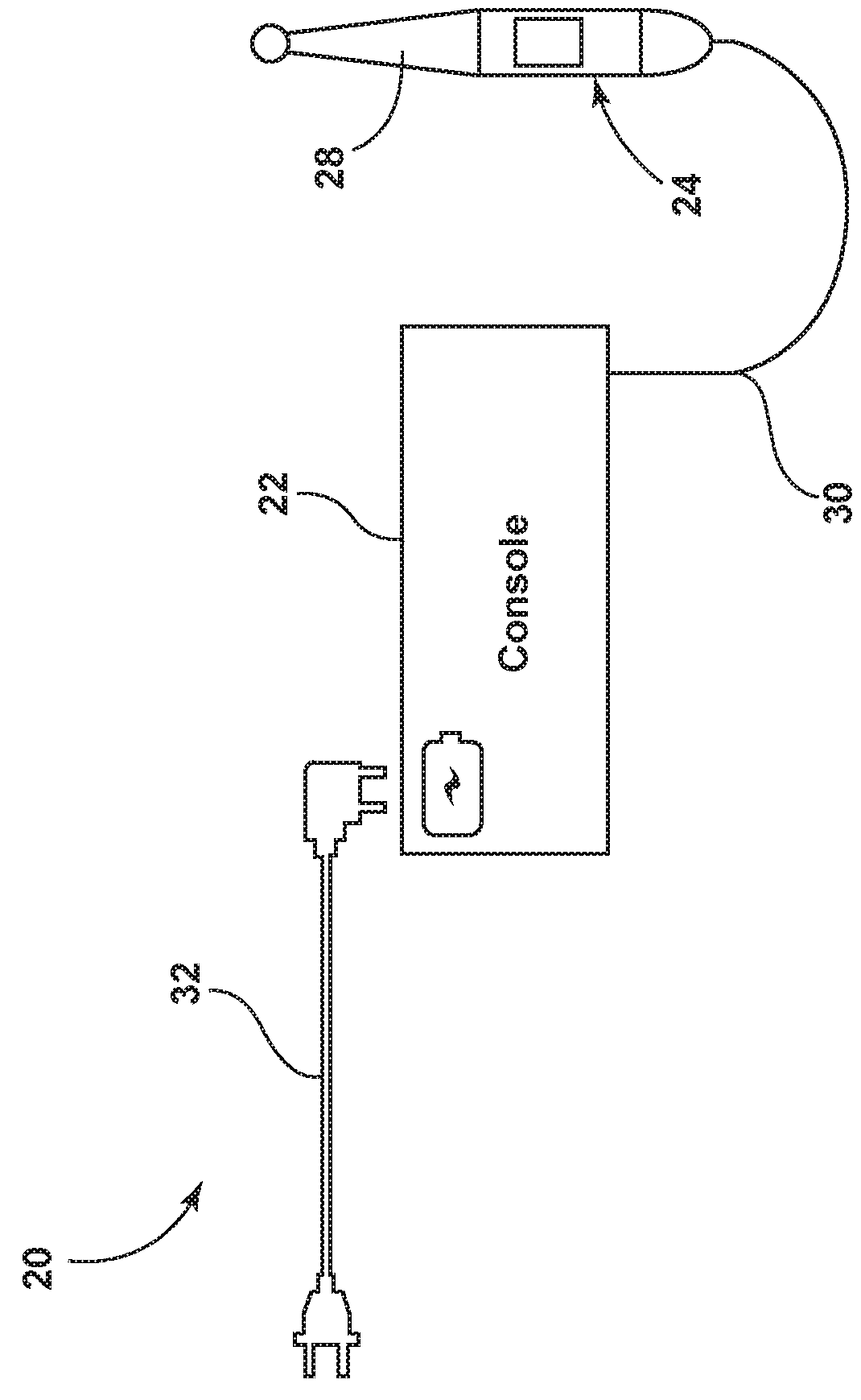
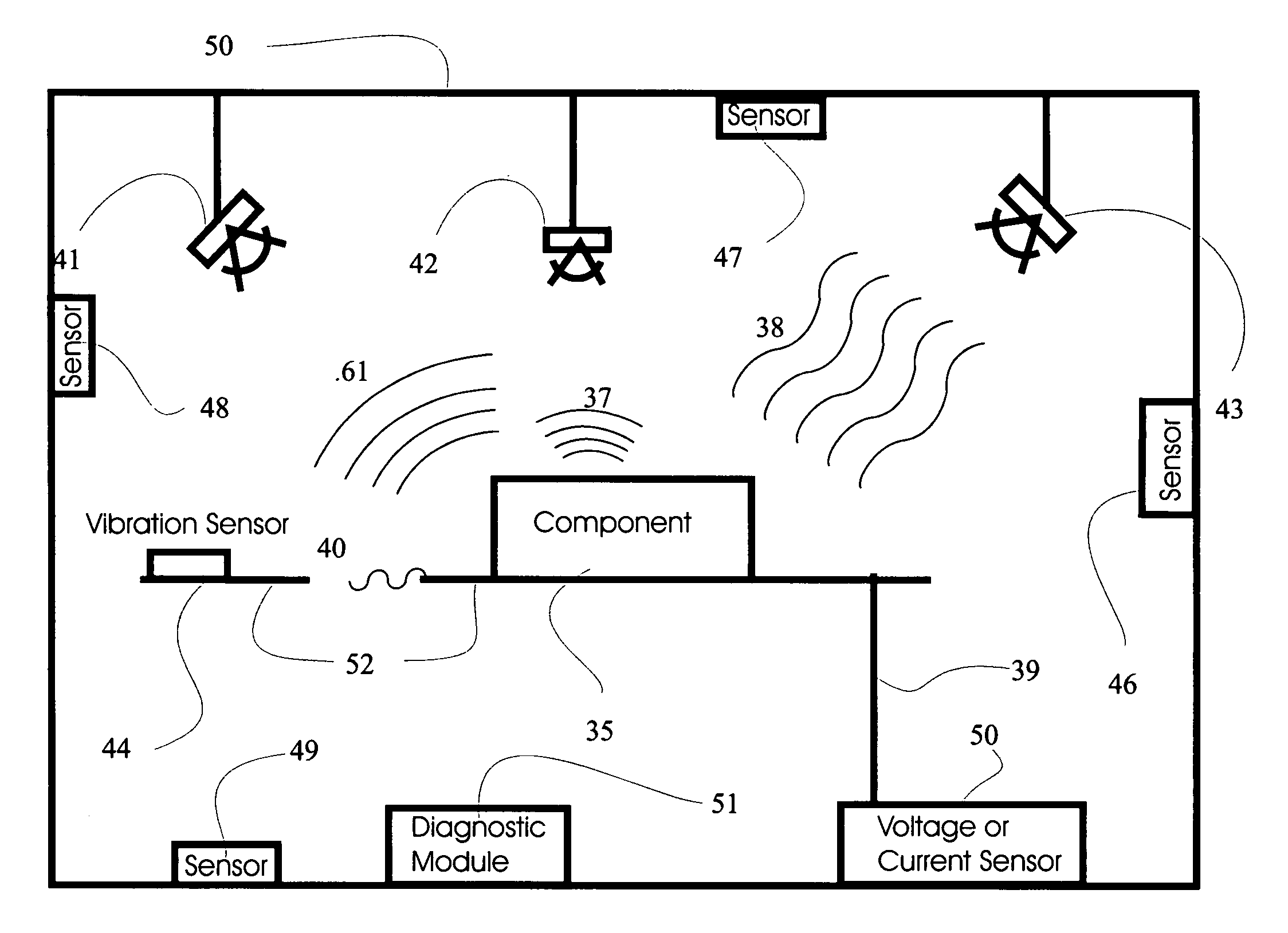
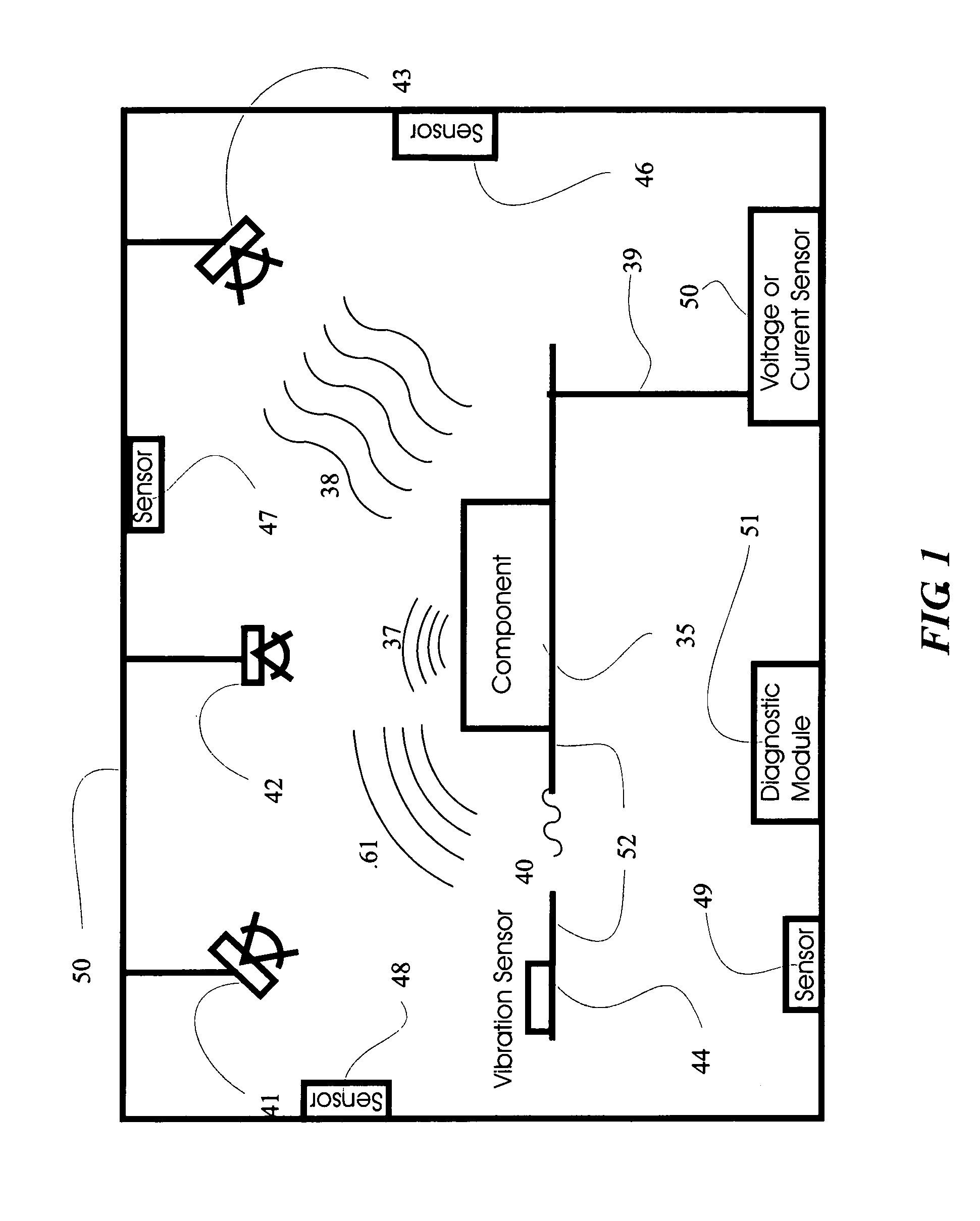
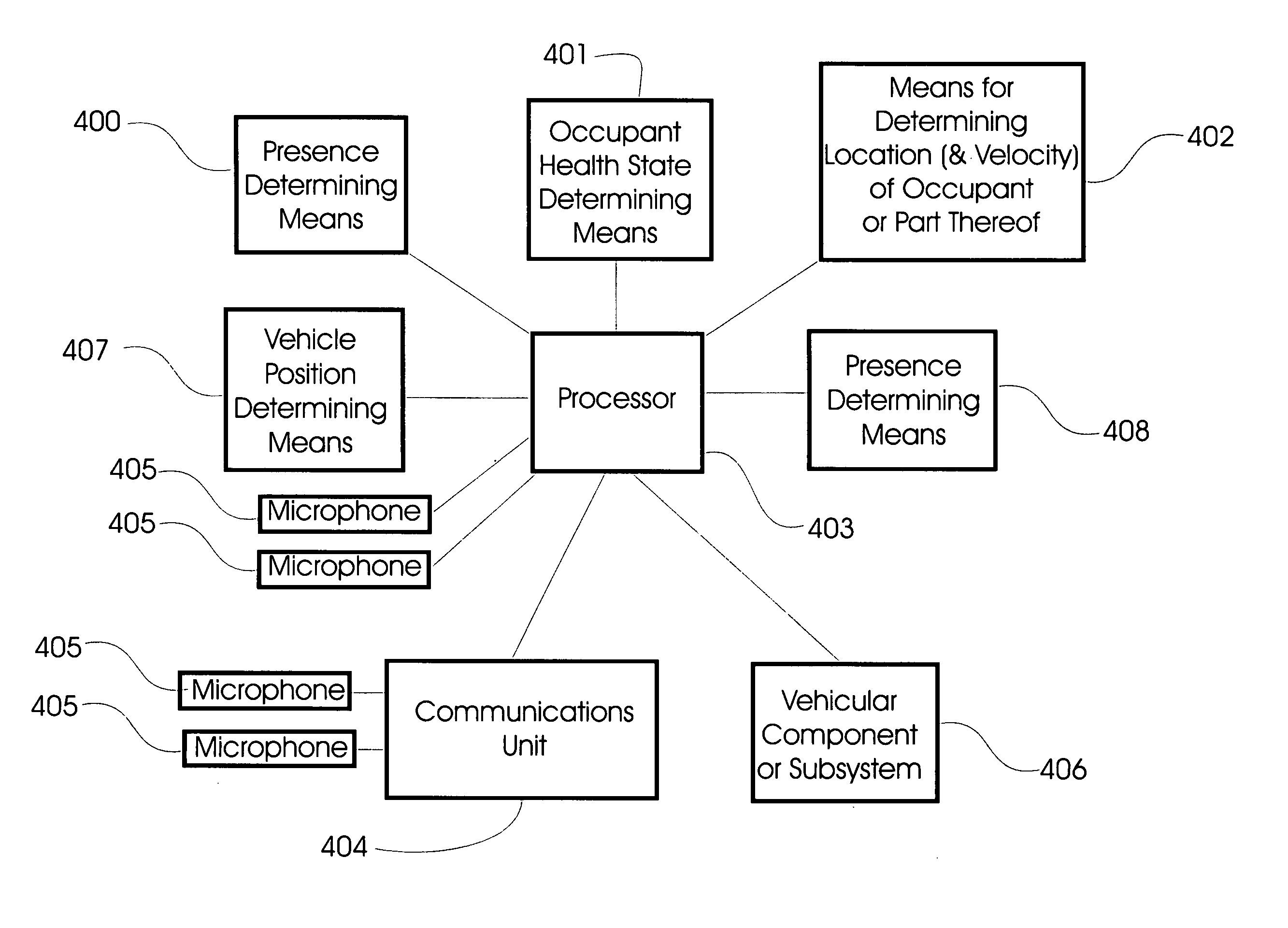
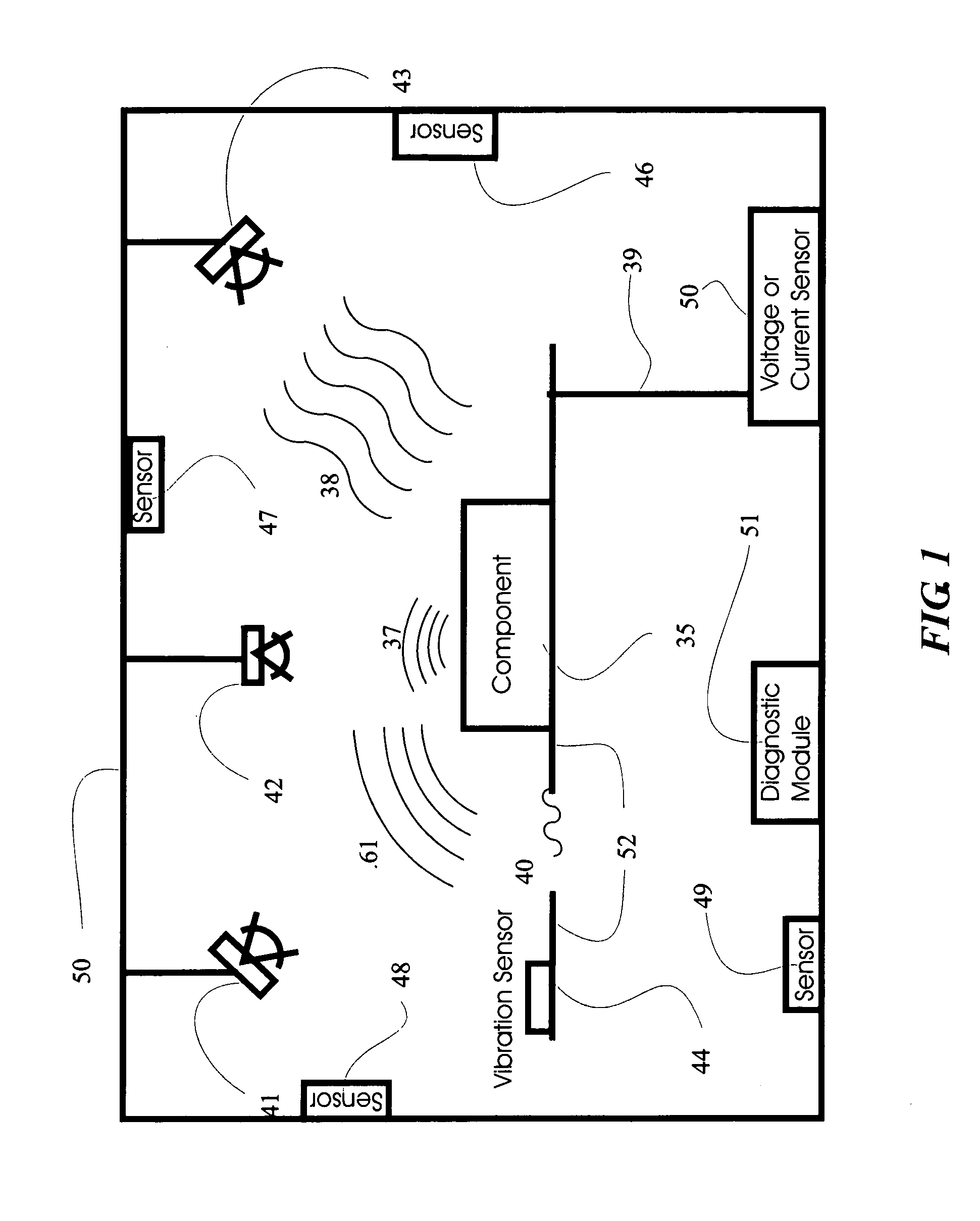
Vehicular information and monitoring system and methods
InactiveUS7082359B2Low costIncrease valueVehicle testingVehicle seatsCommunications systemDriver/operator
Information management and monitoring system for a vehicle including a vehicle monitoring system including a plurality of sensors for monitoring vehicular components, a diagnostic module arranged on the vehicle and coupled to the vehicle monitoring system to receive and process data about the components therefrom, and a remote service center capable of servicing the components. A communication system, e.g., a cellular telephone capable of voice communications, is arranged on the vehicle and coupled to the diagnostic module to enable communications of data from the diagnostic module to the remote service center such that the remote service center receives data about the vehicular components. The remote service center can be situated at a dealer which can have its personnel contact the driver, e.g., via the telephone, to schedule service of the vehicle, the service being determined based on the communicated data from the diagnostic module on the vehicle.
Owner:AMERICAN VEHICULAR SCI
Medical information management system and patient interface appliance
A medical information management system and method that stores and manages patient information and that enables a patient and an authorized third party, such as a friend or family member, to access the patient's medical information. The presentation format, substance of the patient's medical information provided, or both are customized depending on whether the patient, a healthcare professional or the third party is accessing the patient's medical information. The present invention also pertains to a method of subsidizing such a medical information system by selling advertising space in the presentation shown to the third party, patient, or the healthcare professional. The present invention further pertains to a patient interface appliance that includes a display containing multiple viewing fields, one of which is a general information field and one of which is an advertising field, to present information and advertisements to a user during a patient interactive session. Patient participation in conducting the survey is fostered by offering a survey completion reward to the patient upon completing the survey.
Owner:SUN JIANGUO +6
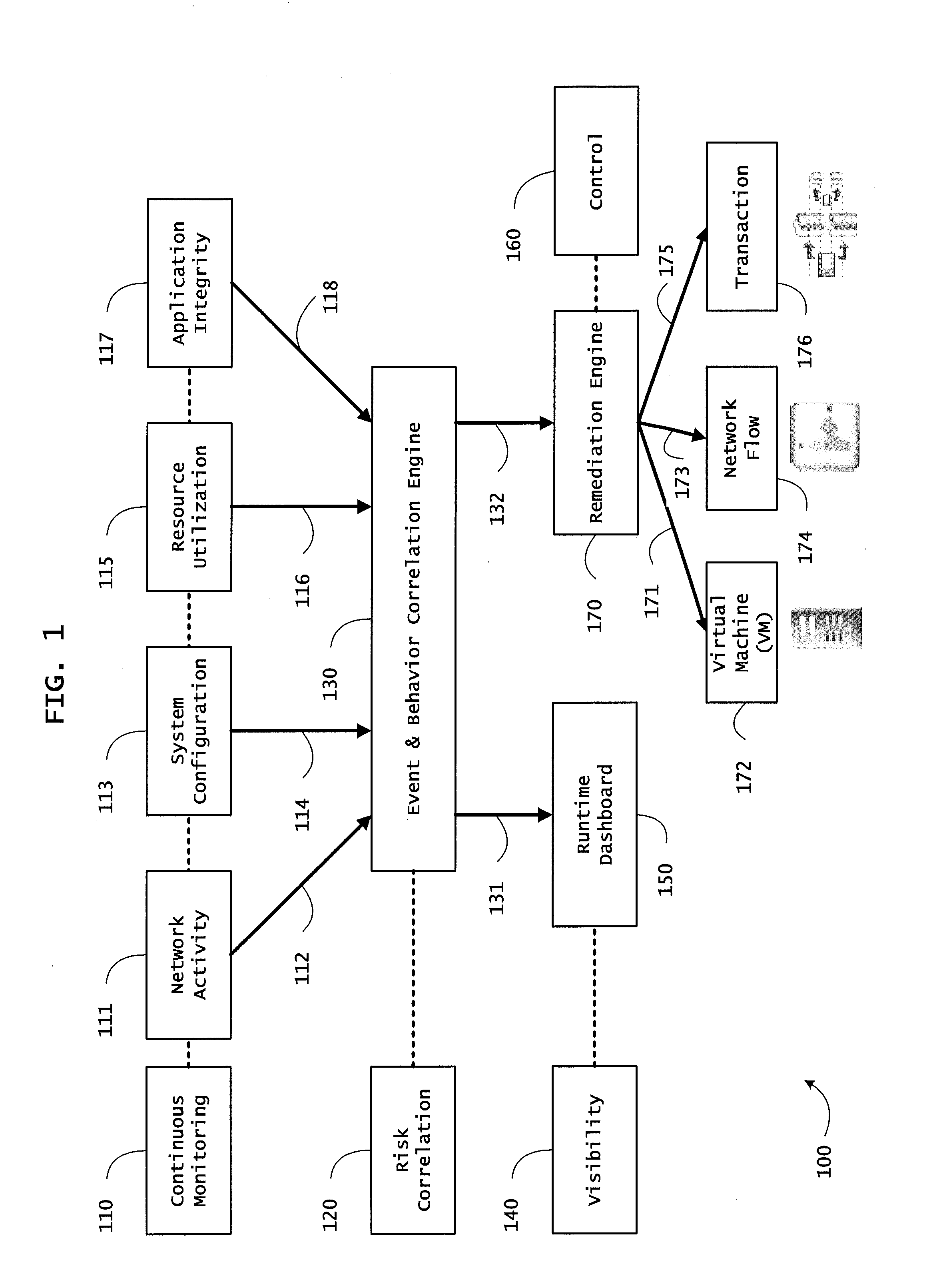
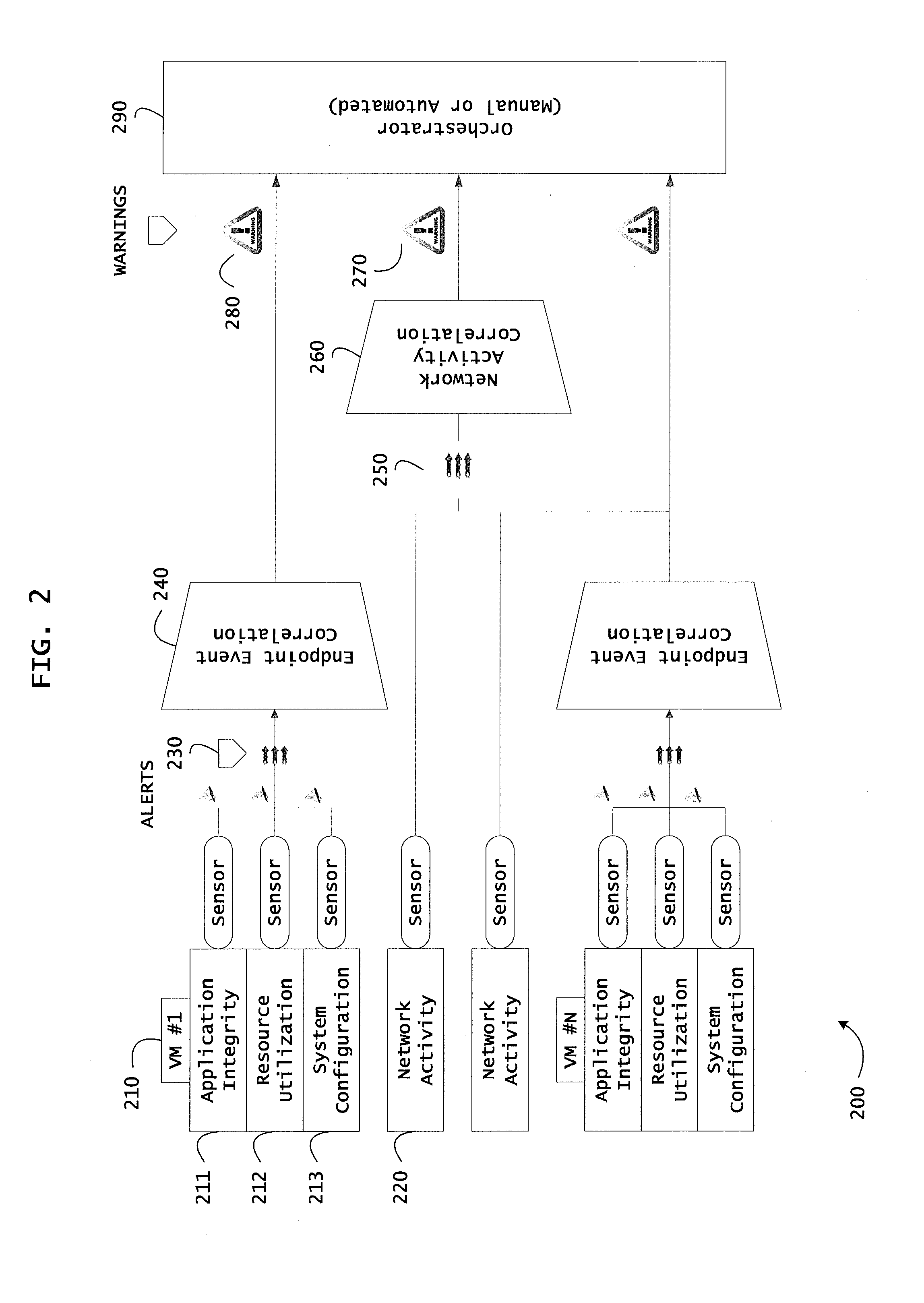
Analyzing Activity Data of an Information Management System
ActiveUS20080066149A1Error detection/correctionComputer security arrangementsDocumentationManagement system
In an information management system, activity data is collected and analyzed for patterns. The information management system may be policy based. Activity data may be organized as entries including information on user, application, machine, action, object or document, time, and location. When checking for patterns in the activity or historical data, techniques may include inferencing, frequency checking, location and distance checking, and relationship checking, and any combination of these. Analyzing the activity data may include comparing like types or categories of information for two or more entries.
Owner:NEXTLABS
Vehicular information and monitoring system and methods
InactiveUS20050125117A1Reduce harmLow costVehicle testingVehicle seatsCommunications systemVoice communication
Information management and monitoring system for a vehicle including a vehicle monitoring system including a plurality of sensors for monitoring vehicular components, a diagnostic module arranged on the vehicle and coupled to the vehicle monitoring system to receive and process data about the components therefrom, and a remote service center capable of servicing the components. A communication system, e.g., a cellular telephone capable of voice communications, is arranged on the vehicle and coupled to the diagnostic module to enable communications of data from the diagnostic module to the remote service center such that the remote service center receives data about the vehicular components. The remote service center can be situated at a dealer which can have its personnel contact the driver, e.g., via the telephone, to schedule service of the vehicle, the service being determined based on the communicated data from the diagnostic module on the vehicle.
Owner:AMERICAN VEHICULAR SCI
Vehicle managing method
InactiveUS20060136291A1Vehicle testingRegistering/indicating working of vehiclesComputer scienceSecurity information
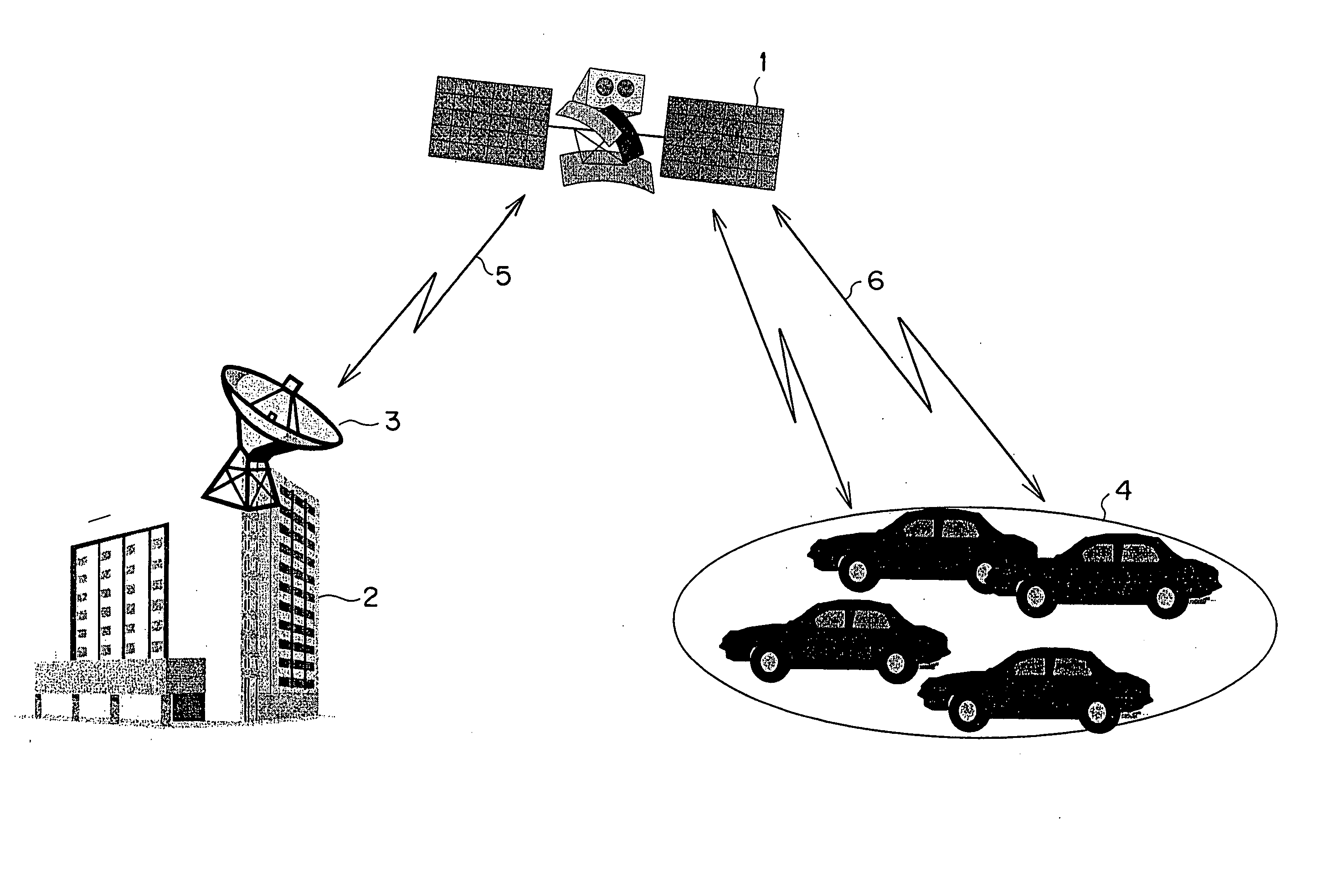
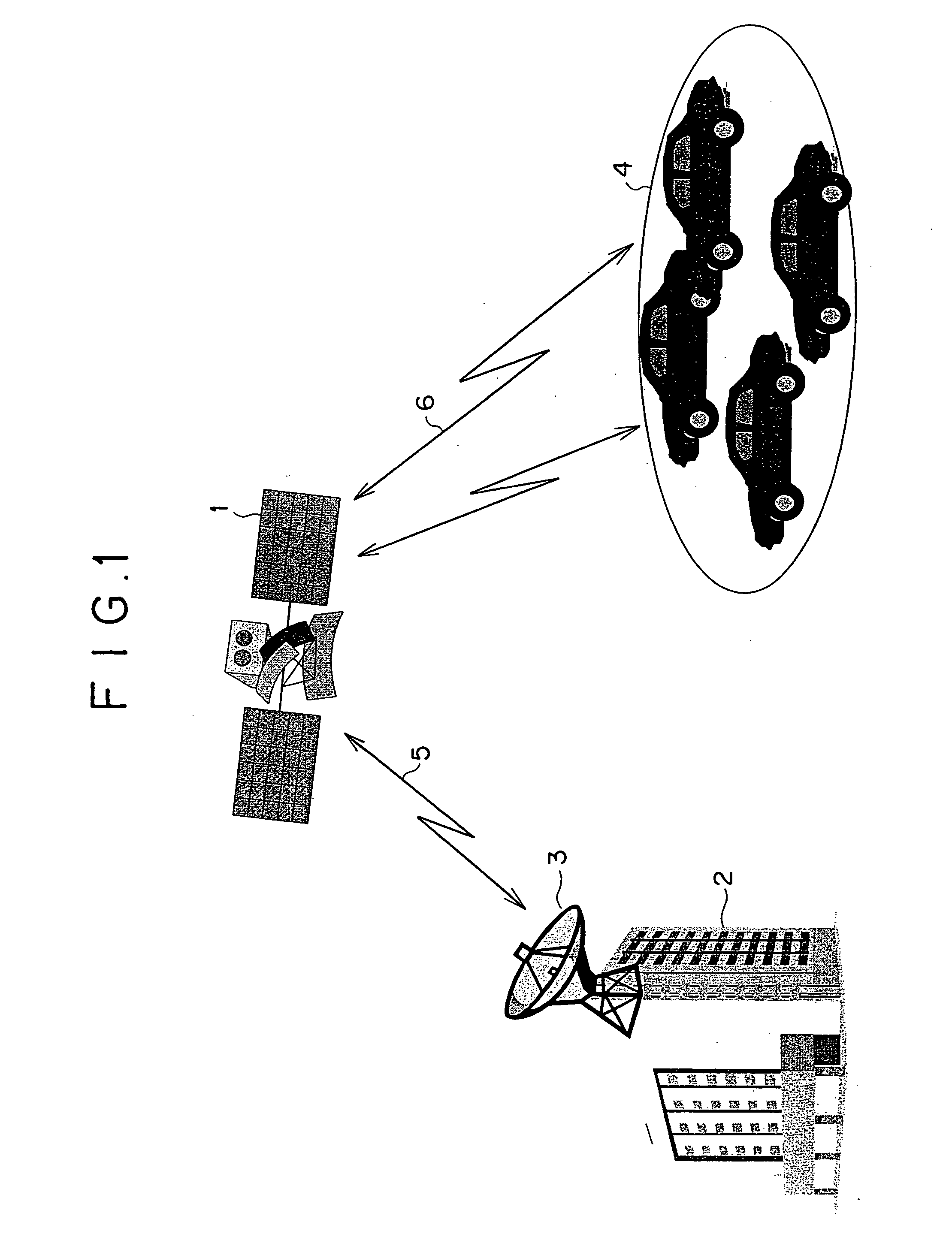
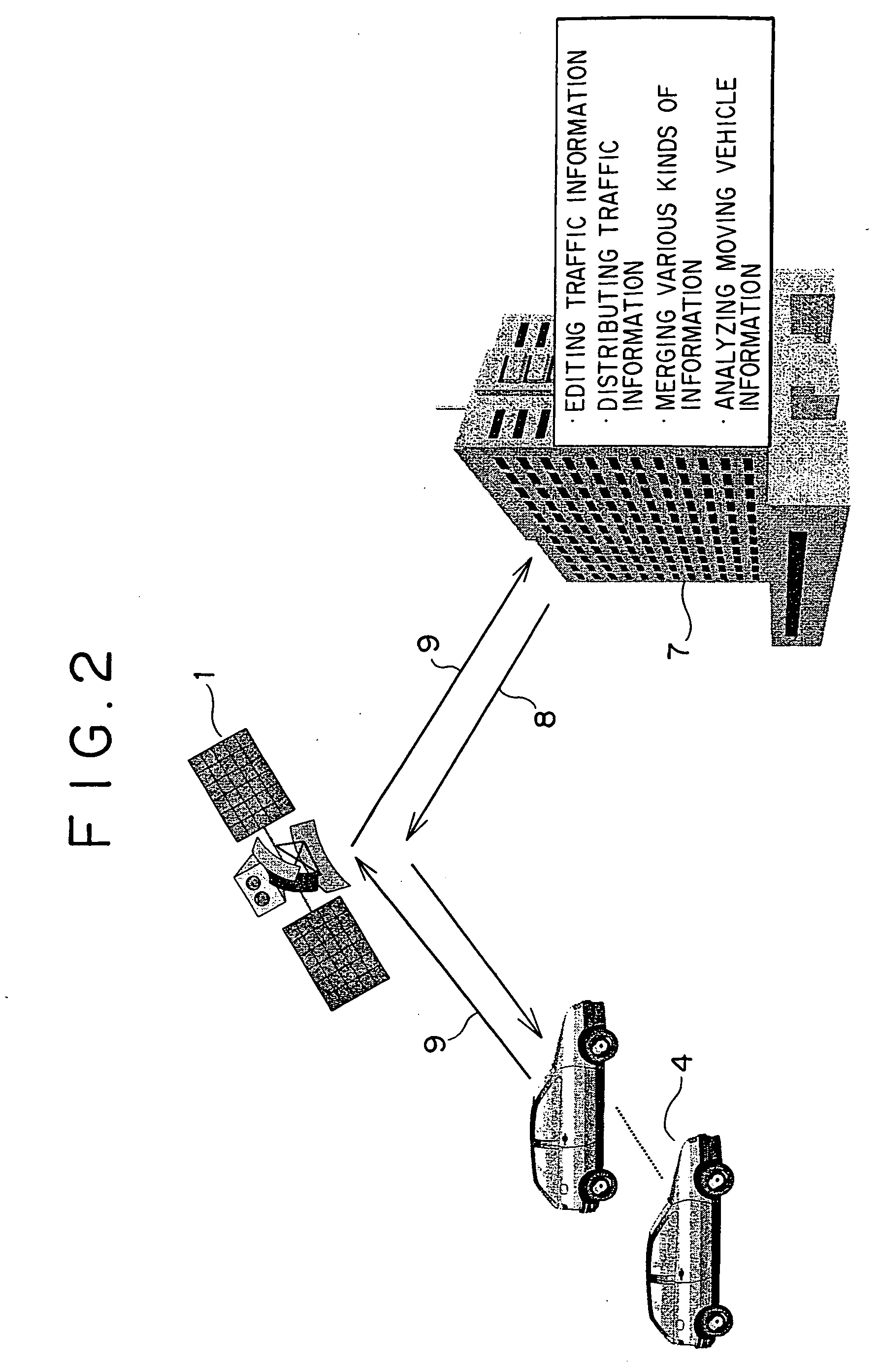
A vehicle overall interactive managing method is disclosed. Uplink information transmitted by way of an artificial satellite to a center includes emergency information and periodic information. Downlink information transmitted from the center via the artificial satellite to each vehicle includes audio and image. There is provided at a ground station a movable body overall information management system that is provided with databases storing various types of data and an analysis system. Mandatory automobile inspection information, user information, traffic and road information, safety information, and other types of information are distributed to each of information requiring organizations through this system.
Owner:HITACHI LTD
System, method and computer program product for managing physiological information relating to a terminal user
ActiveUS20050171410A1Improve user experienceImprove experiencePhysical therapies and activitiesElectrotherapyMobile stationSystems approaches
A system for managing physiological information includes a mobile terminal and at least one destination. The terminal is capable of transferring physiological information relating to a terminal user. The destination(s), in turn, are capable of receiving the physiological information and performing at least one operation based upon the physiological information. The destinations can return content to the terminal, where the content is selected based upon the operation(s) performed by the destination(s). Upon receiving the content, then, the terminal is also capable of performing at least one operation based upon the content. The system can also include a mobile station for facilitating the transfer of physiological information and content between the terminal and the destination(s).
Owner:NOKIA TECHNOLOGLES OY
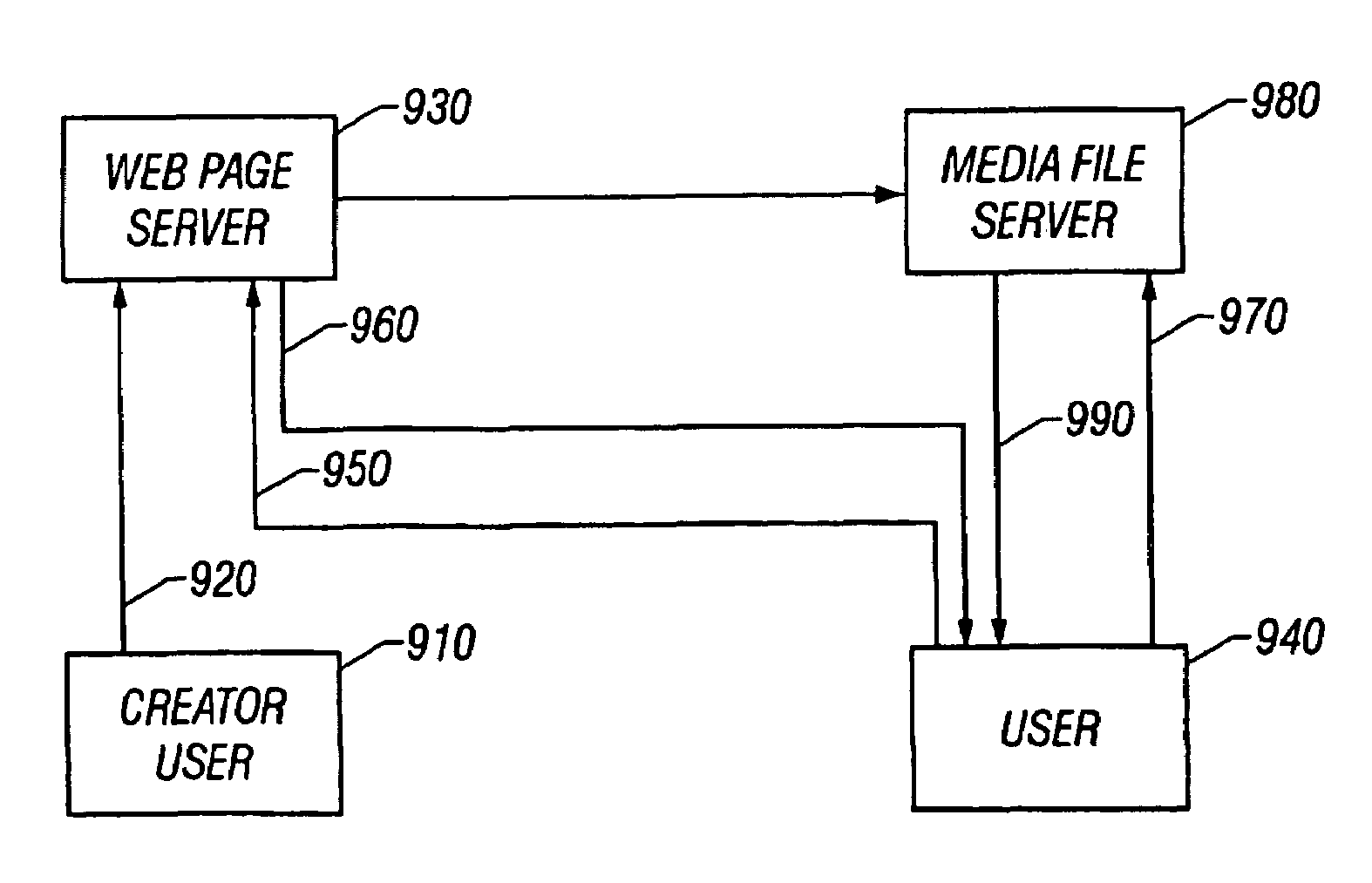
System and method for creating and posting media lists for purposes of subsequent playback
InactiveUS7069310B1Create quicklyEasy to processDigital data information retrievalError detection/correctionDigital signal processingENCODE
A method and apparatus for creating and posting media is provided. For example, the invention allows a user to quickly create, signal process, encode, and transfer media files to a server for storage, posting, distribution, and retrieval. Thus, media such as audio, video, display, photo, spreadsheet, Web Clips, and HTML pages can be combined into a media file for uploading to a server and accessed from listings posted at web sites. In accordance with embodiments, a user downloads and installs a plug-in at the user's client computer. The user then registers and logs onto the server to perform various tasks. For example, the user can create a combined audio and photo media file at the client computer, in accordance with server based control parameters received from the system server. The plug-in then allows the user to perform digital signal processing and encoding of the media file at the client computer. After the file is encoded, it may be uploaded to a server for storage, posting, distribution, and retrieval. A file management system provides copies and listings of the file to other servers and web sites as permitted. Thus, other user having access to the database or web site lists via other client computers may select the file for retrieval. In accordance with another aspect of the invention, an information management system provides file and file list rankings based upon selection or click through of files and file listings.
Owner:POST MEDIA SYST LLC
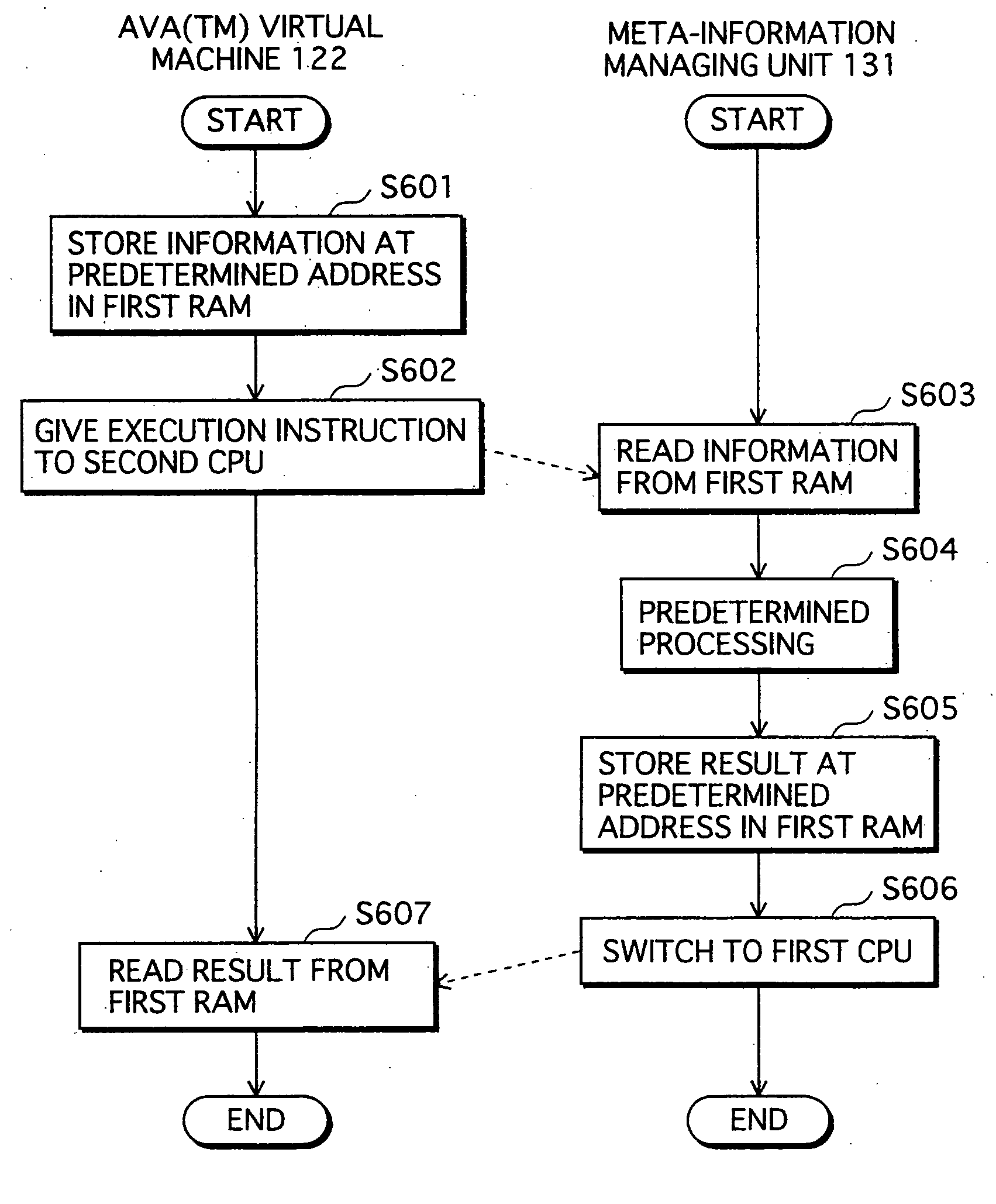
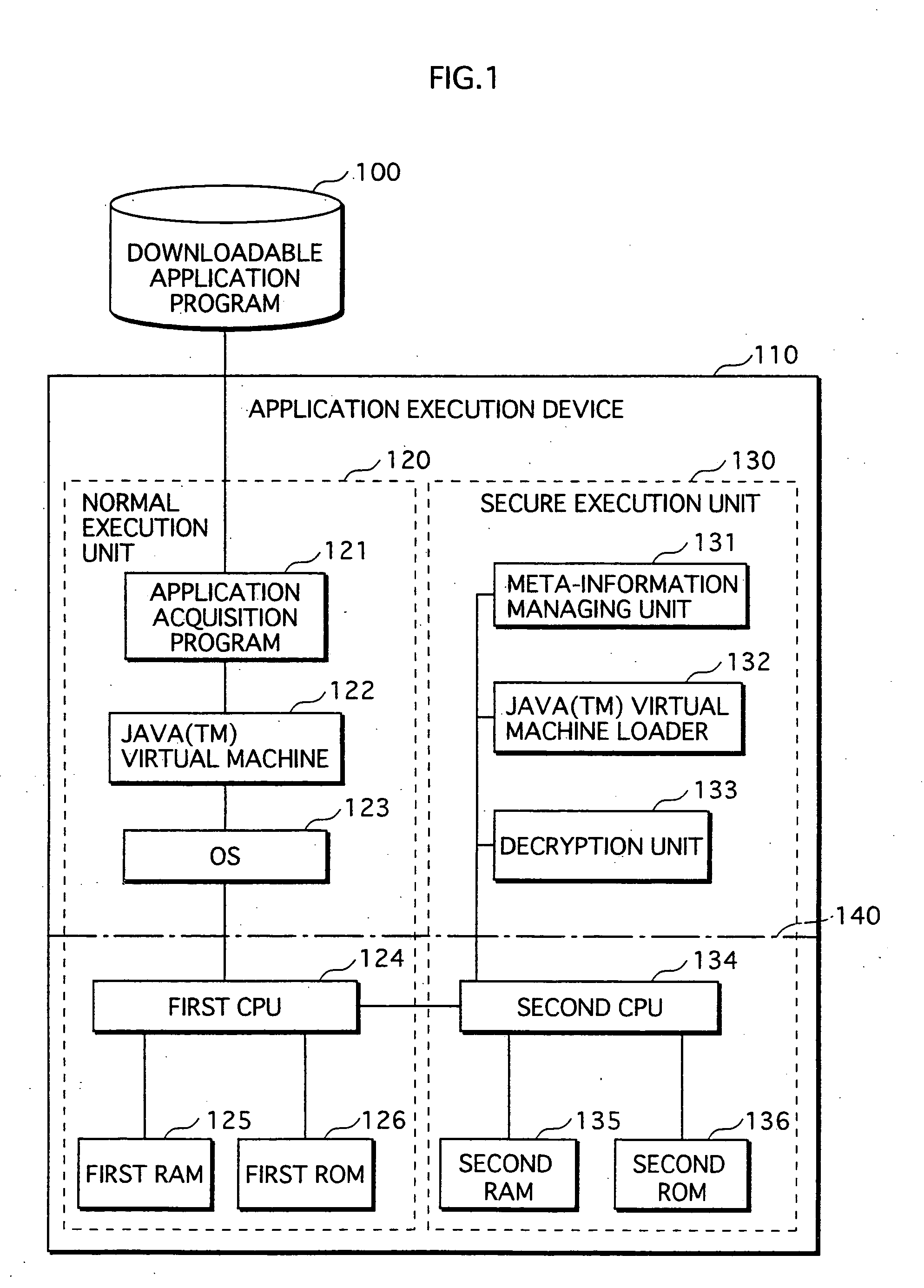
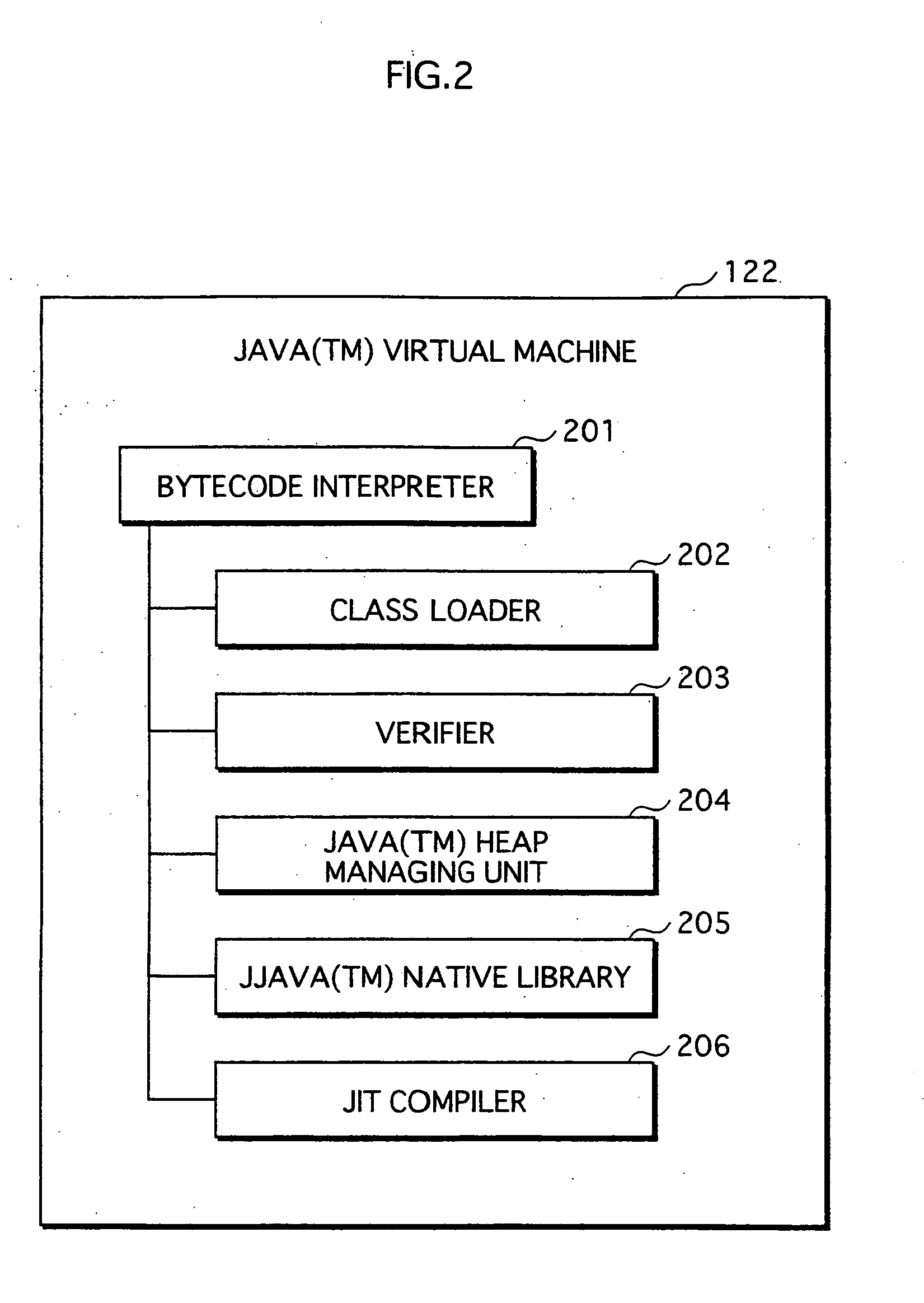
Application Execution Device and Application Execution Device Application Execution Method
InactiveUS20070271446A1High protection levelDigital computer detailsPlatform integrity maintainanceExecution unitOperating system
The conventional application protection technique complicates an application to make it difficult to analyze the application. However, with such a complication method, the complicate program can be analyzed sooner or later by taking a lot of time no matter how the degree of the complication is high. Also, it is impossible to protect the application from unauthorized copying. The meta-information managing unit that is to be executed in the secure execution unit stores the meta-information of the application in an area that can not be accessed by a debugger. When the meta-information is required by the normal execution unit to execute the application, a result of predetermined calculation using the meta-information is notified to the normal execution unit. In this way, the meta-information of the application can be kept secret.
Owner:PANASONIC CORP
Graphic-information flow method and system for visually analyzing patterns and relationships
InactiveUS20060174209A1Simplified and intuitive processEasy to operateInstruments for road network navigationRoad vehicles traffic controlGraphicsData stream
A novel display control and information management system seamlessly integrates layered and slotted formatted data from local and remote sources to provide a highly versatile information display. The system permits selective control of display and display features so that complex data and data flows can be seamlessly accessed with enhanced cognition of salient information by a user.
Owner:CEDAR LANE TECH INC
Secure, networked and wireless access, storage and retrival system and method utilizing tags and modular nodes
InactiveUS20050062603A1Quick and seamless handlingHigh levelIndividual entry/exit registersElectric signalling detailsComputer hardwareMedical equipment
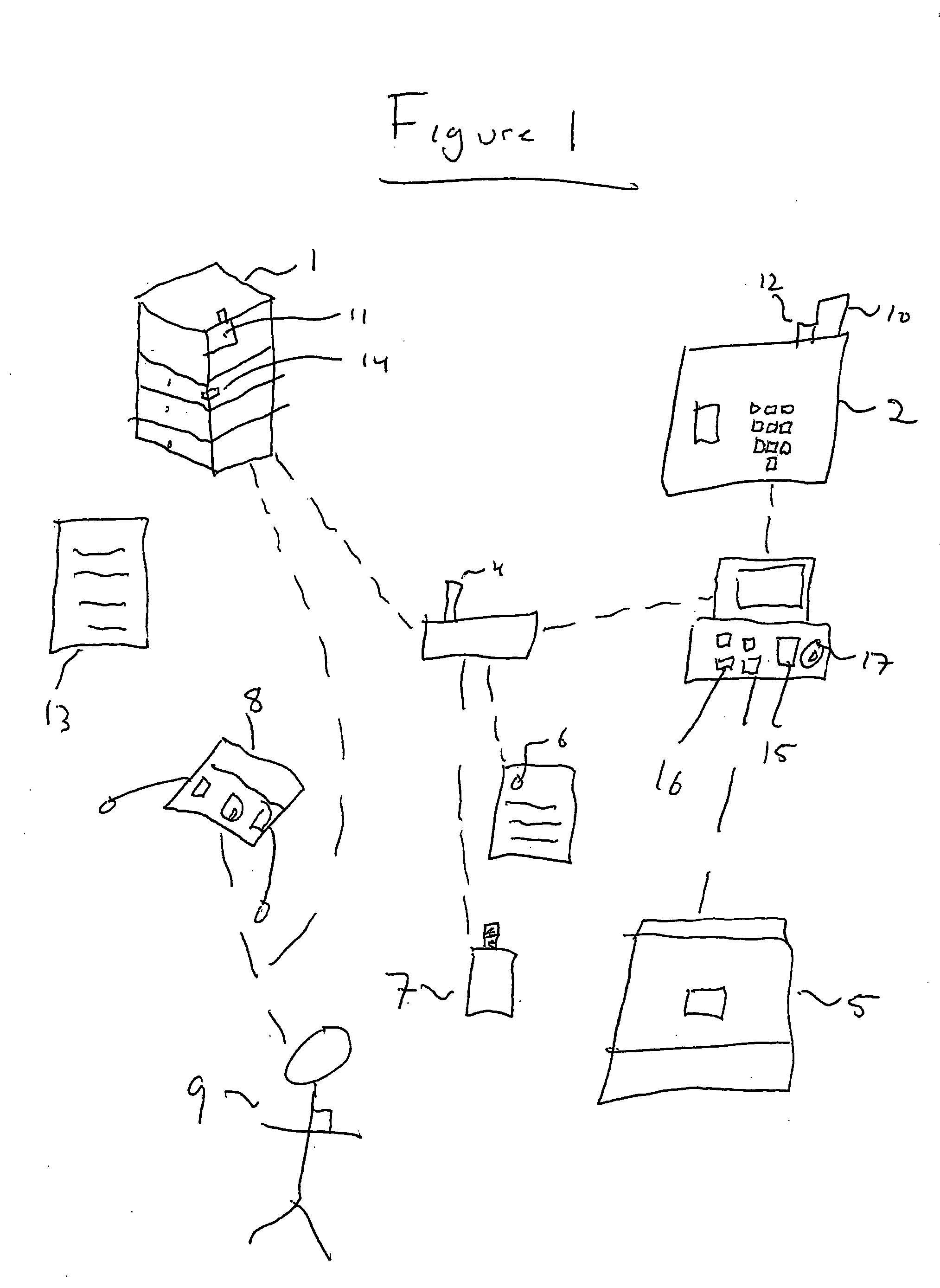
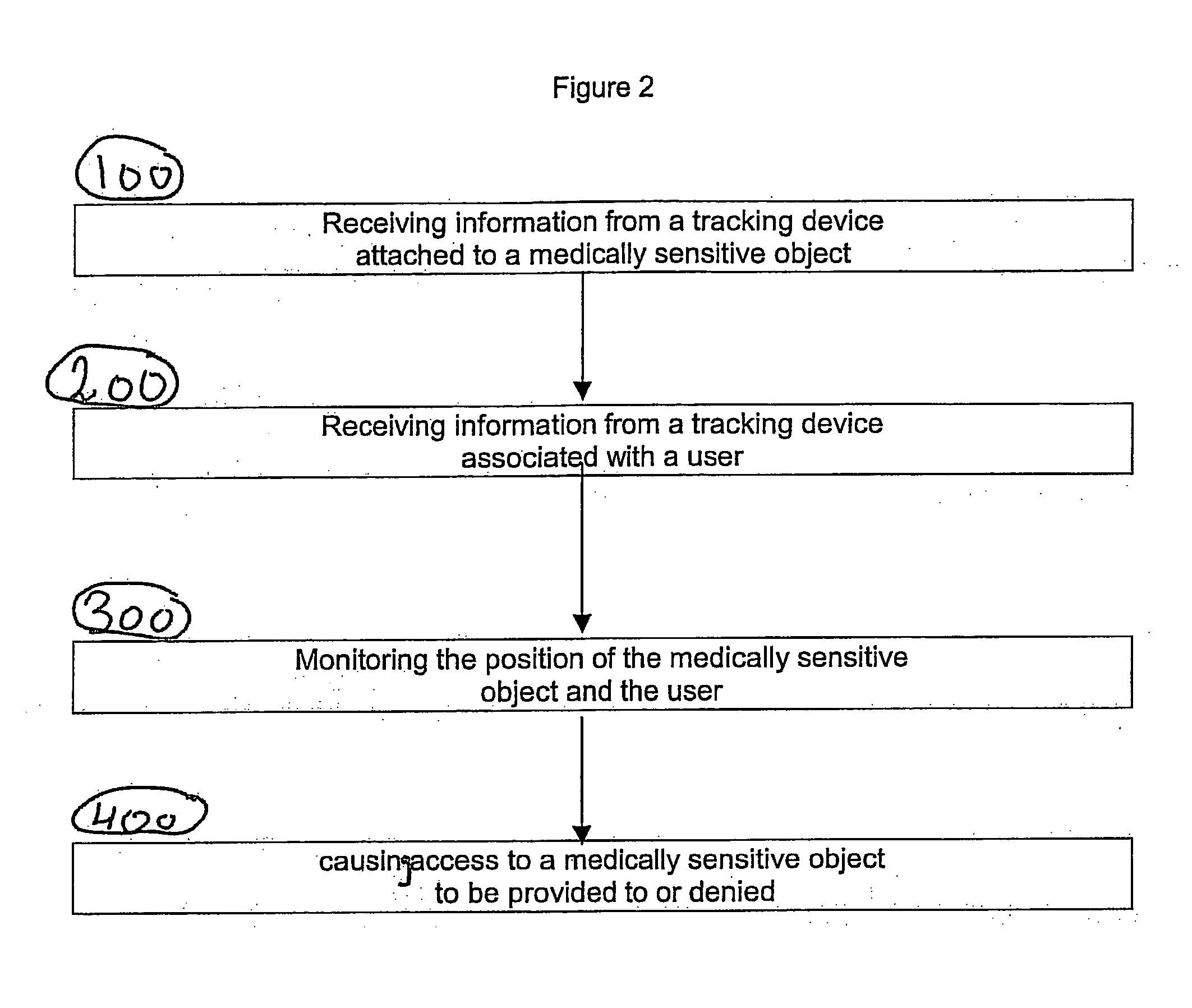
A system apparatus and method of monitoring in a secured fashion the access, storage and retrieval of information, using a networked modular wireless device. The system may include a network of wireless, Wi-Fi devices (or any other wireless communication mechanism such as GPRS, GSM, iDen), or Nodes, each one of them possibly controlling the access to a medically sensitive object, such as a drawer (or cabinet) or to a medical device, or to another information source, item of equipment, drug, etc as well as tracking via RFid readers the access to the records or information contained in it. In the case of a physical file, each file has an RFid tag on it that is being read when removed or returned to the cabinet. Access to the cabinet and physical records, or to the medical device is monitored by reading the RFiD identity card of personnel accessing the cabinet or medical devices. In addition to controlling the access to the cabinet or medical device by controlling the cabinet lock (or in the case of a small medical device, the lock of an IV, injection device, specimen collection unit, or of a large medical device such as a defibrillator), the node can alert electronically by sending a message to the controlling unit, or by sending a physical alert (such as an alarm signal), when unauthorized personnel is attempting to access the cabinet, the files or devices. The system is useful in the context of monitoring the information contained in physical files, such as medical information, and can be used for access to medical devices, in order to better monitor the authorization rights of personnel participating in processes such as drug delivery or specimen collection. A control unit monitors activity at a plurality of nodes, and assists in storing the list of authorized personnel and files, and can store electronically captured information regarding the physical files (for example, the reason for accessing the file and reasons for changes in it) or medical device. The system can communicate with other information management systems.
Owner:G D H
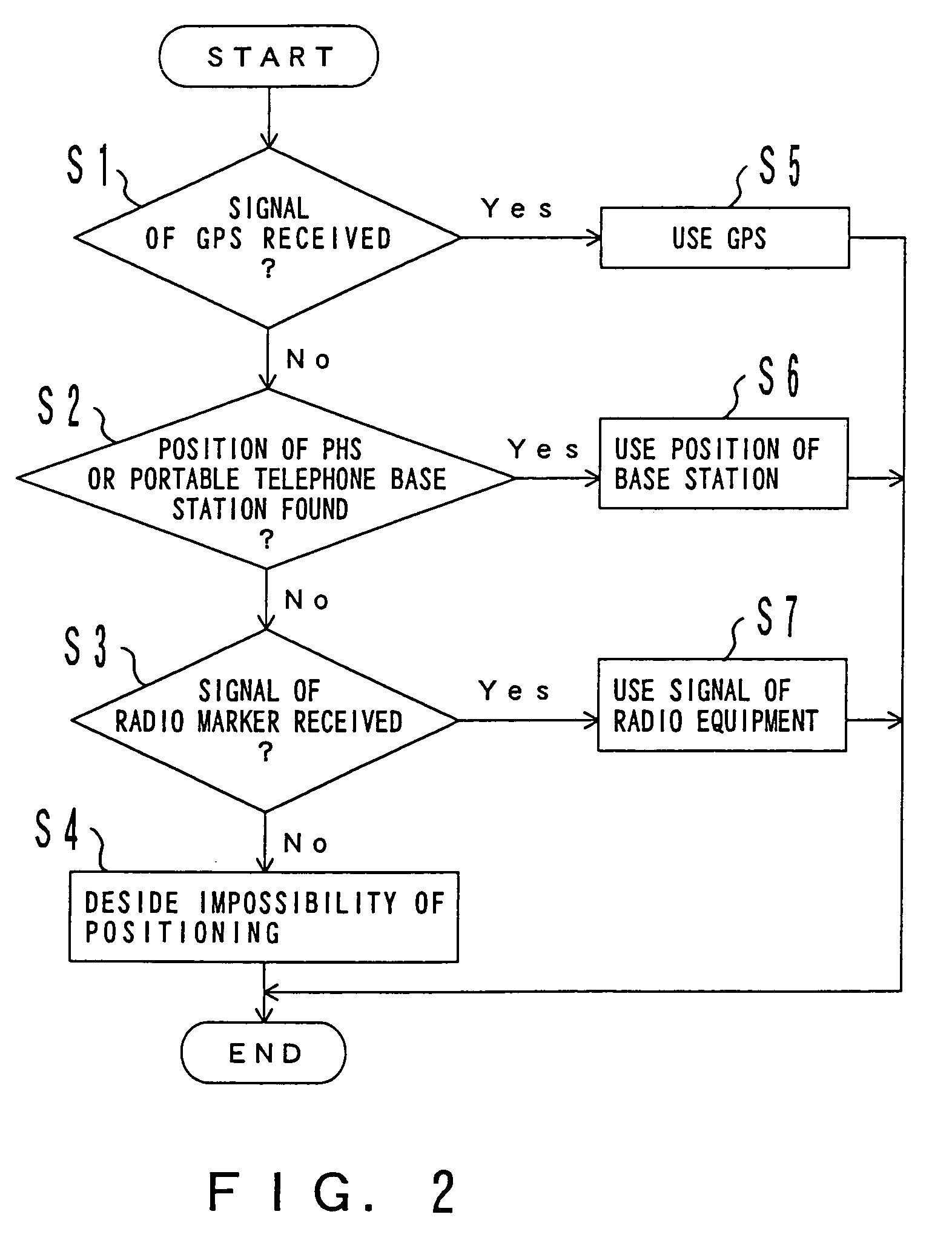
Position information management system
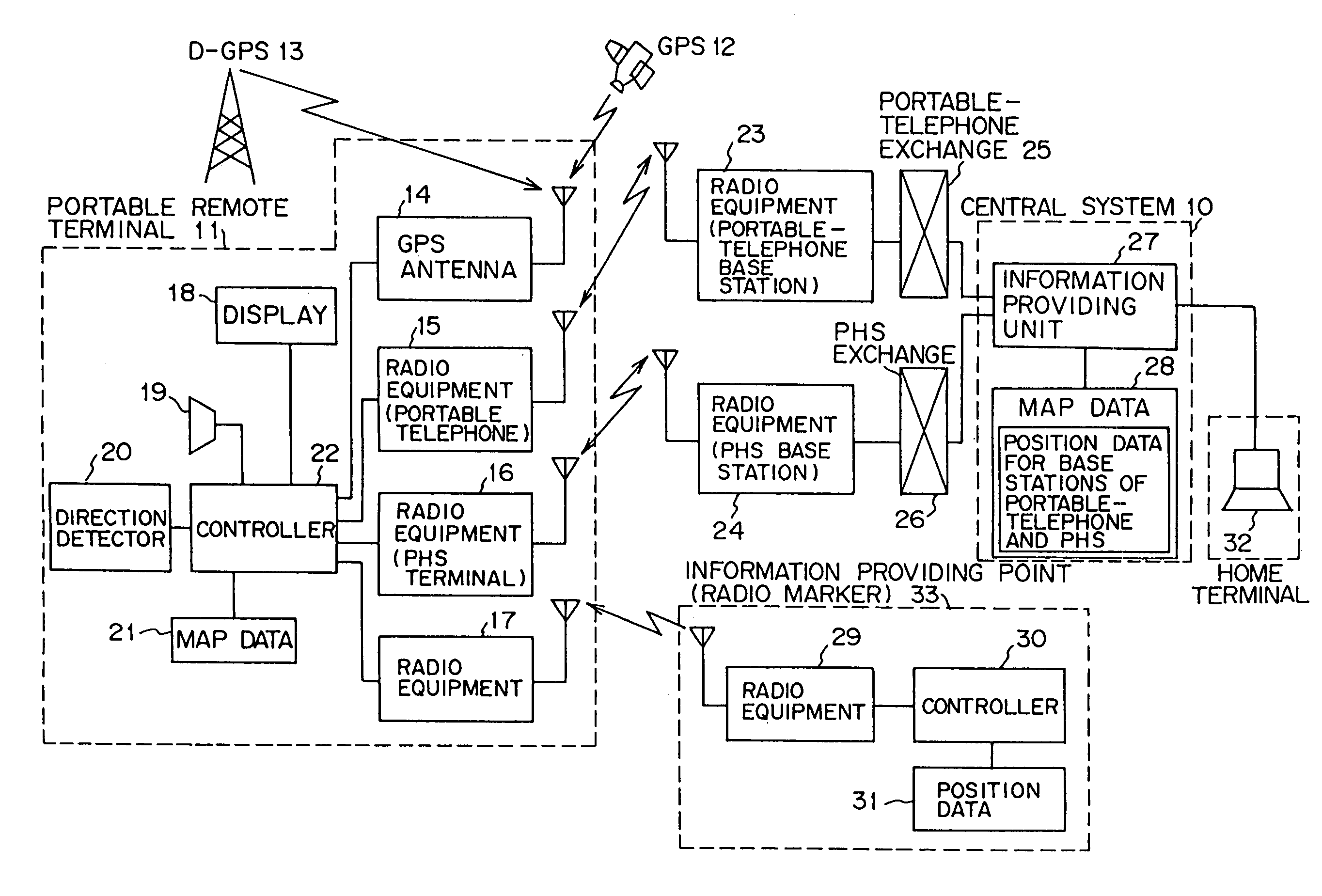
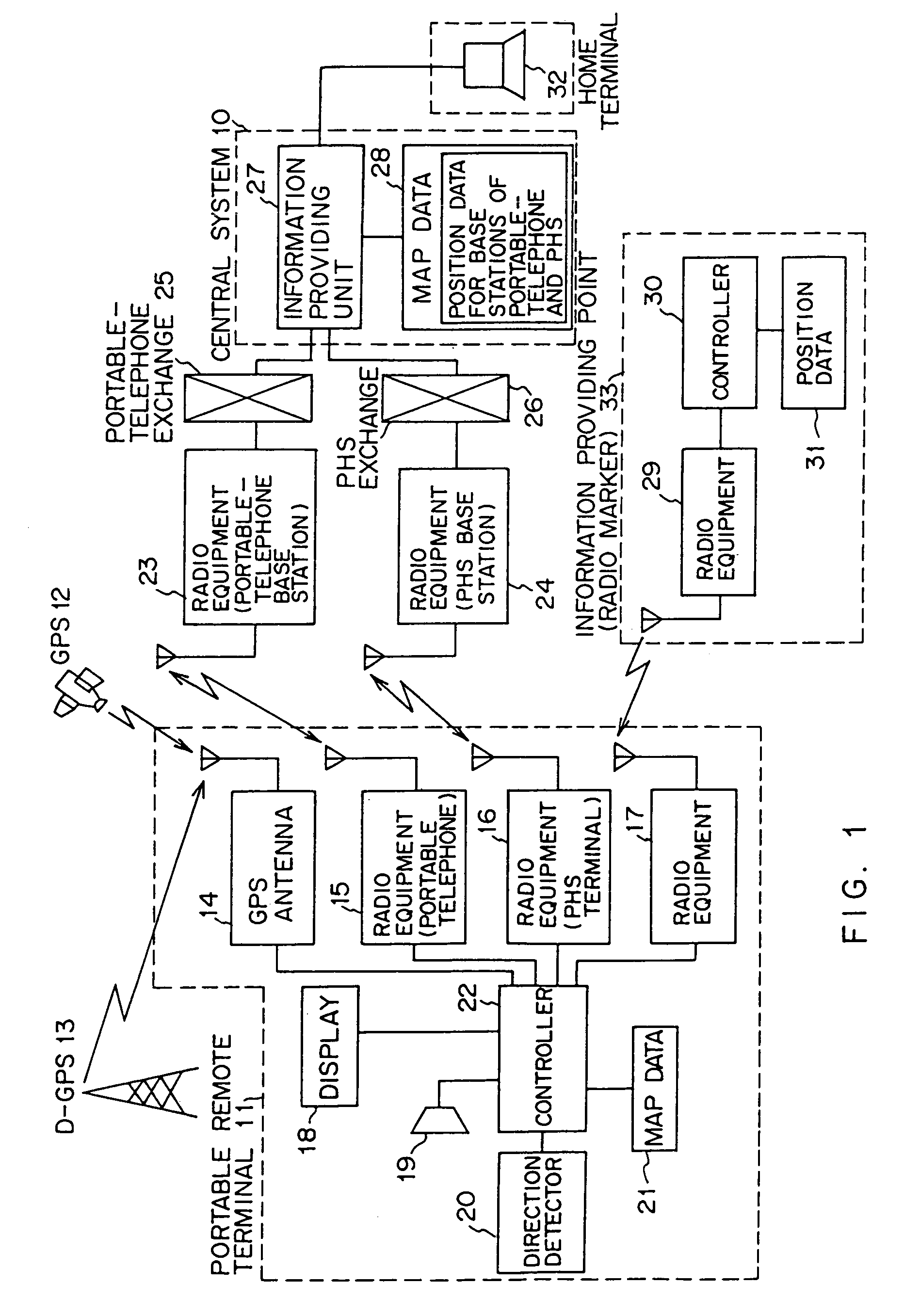
InactiveUS6999779B1Improve applicabilitySmall sizeTelephonic communicationPosition fixationThird partyComputer terminal
A position information management system in which a portable remote terminal includes a plurality of kinds of positioning means for positioning based on a GPS, positioning based on a portable-telephone or PHS base station, positioning based on a radio marker, and independent positioning based on a direction detector, so that the holder of the portable remote terminal can be navigated anywhere. The holder of the portable remote terminal can know the position of a third party similarly holding such a portable remote terminal, by inquiring of a central system, and he / she can supervise, for example, the action of an old person, a child, or a skier in a skiing area. Further, only the map data of a district which is often used by the holder is stored in the portable remote terminal. In this regard, when the holder is in a district not contained within the retained map data, he / she downloads corresponding map data from the central system and uses the downloaded map data.
Owner:FUJITSU LTD
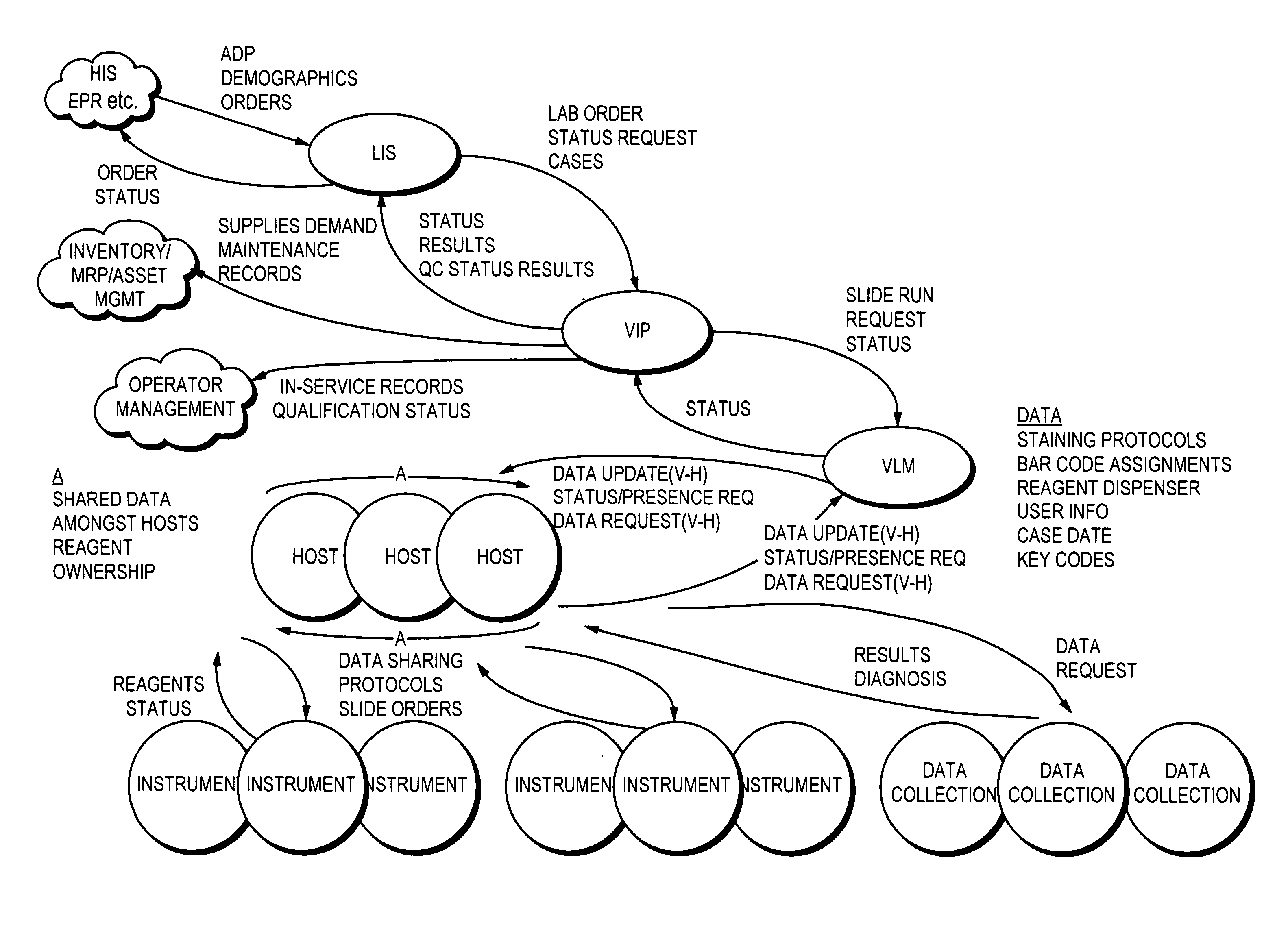
Laboratory instrumentation information management and control network
ActiveUS20050159982A1Maximize throughputComputer-assisted medical data acquisitionOffice automationCommunication interfaceInterface point
An interface point network (IPN) and a method for communication with a laboratory information system using an IPN, wherein the IPN includes at least one host computer in communication with at least one laboratory instrument, the laboratory information system and an interface point server in communication with the host computer and the laboratory information system, the interface point server being configured to function as a communication interface between the host computer and the laboratory information system in a manner responsive to a predetermined communication protocol. Use of bar code and RFID labels for tracking samples and in maintaining sample data is described.
Owner:VENTANA MEDICAL SYST INC
Method and system for controlled distribution of contact information over a network
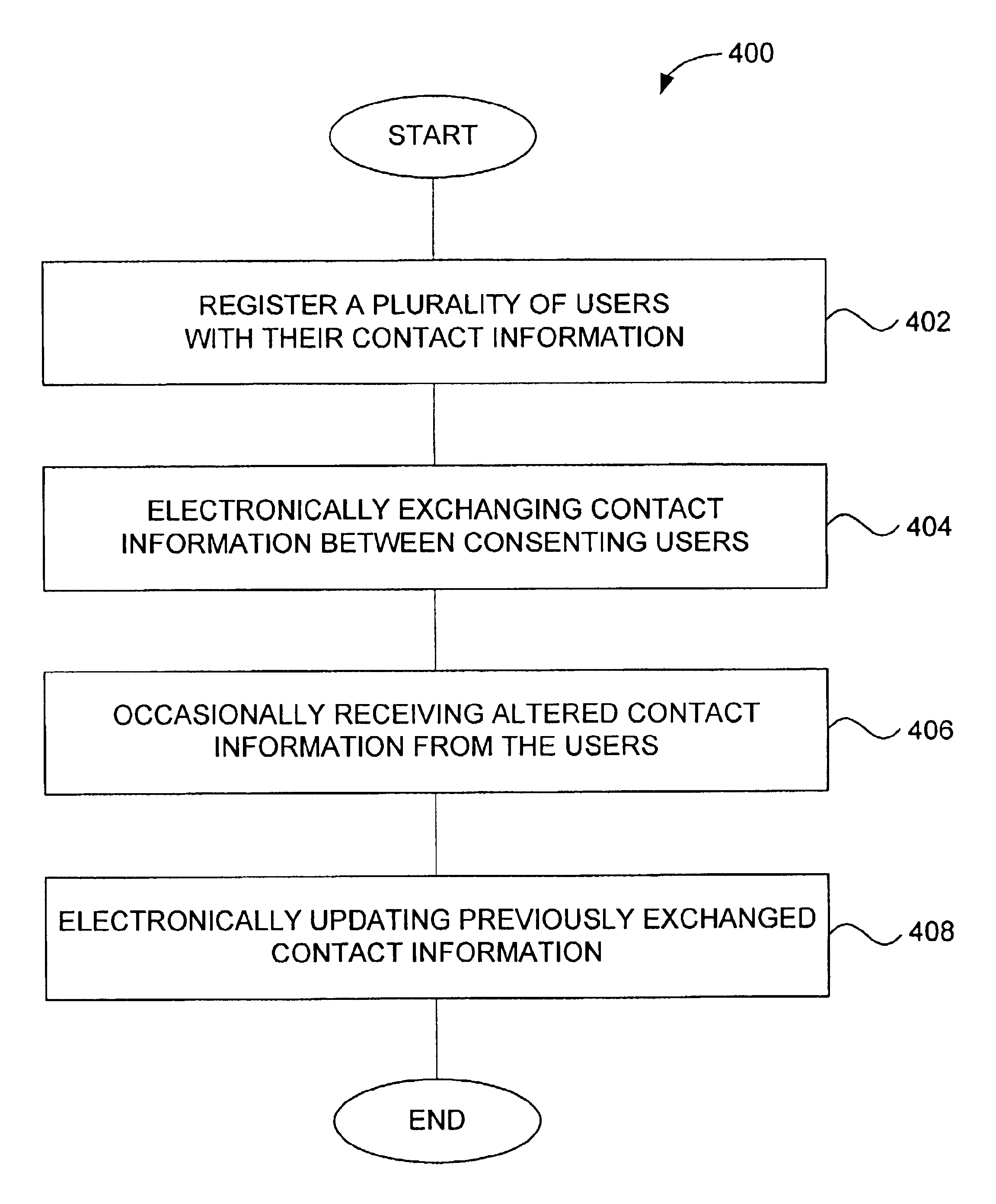
InactiveUS7003546B1Effective contactAutomate updatesMultiple digital computer combinationsOffice automationNetwork controlDistribution system
An information management and distribution system is disclosed. The information management and distribution system includes a client-side application and a server application that interact to facilitate the controlled exchange of contact information over a network. The client-side application can provide creation and design, rolodex, exchange, and update features. The information management and distribution system can also include a corporate administrator application. Still another aspect of the invention is that contact information can be distributed to registered users in a common format.
Owner:META PLATFORMS INC
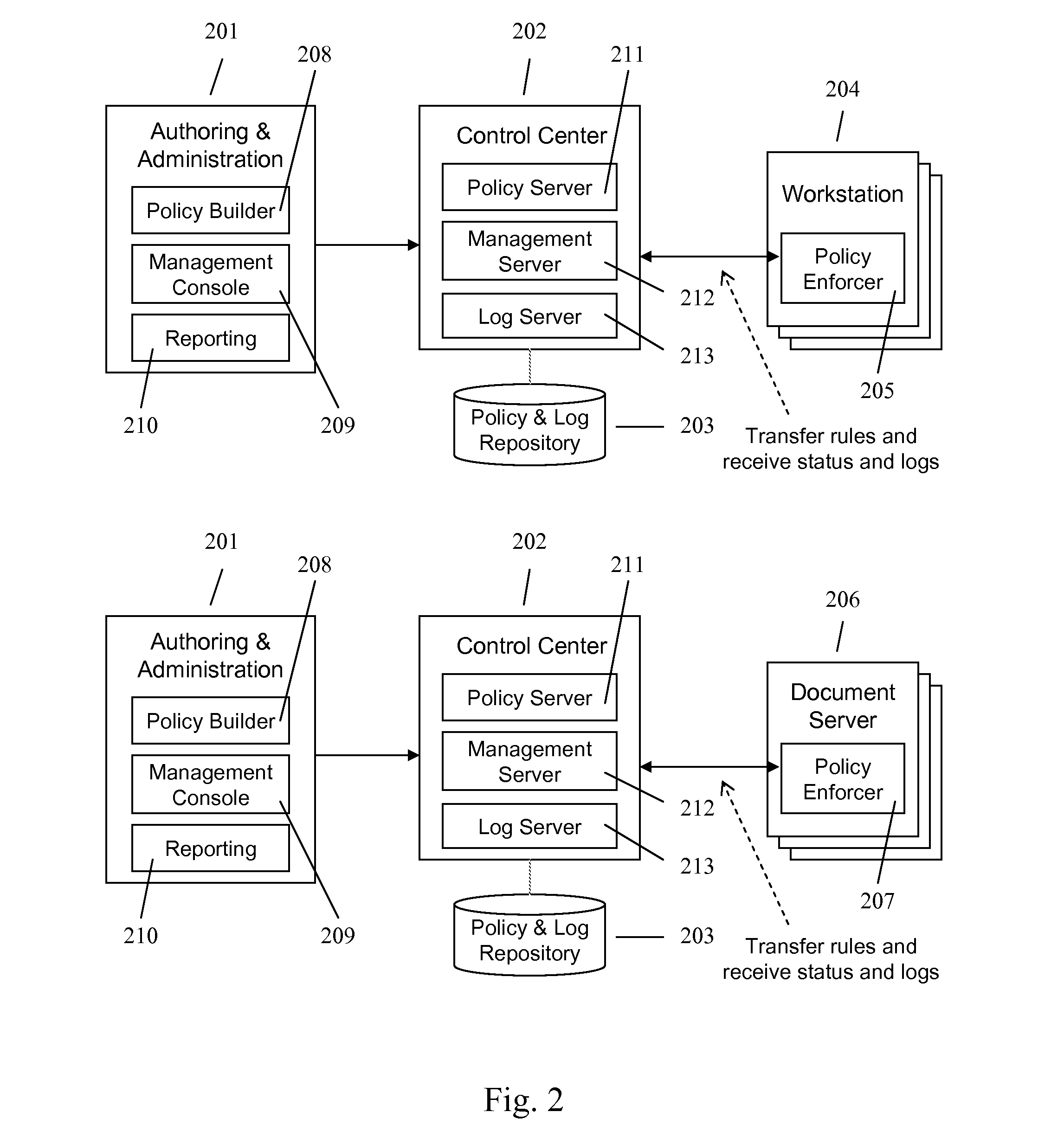
Techniques of optimizing policies in an information management system
In an information management system, policies are optimized before they are associated to a device in order to increase evaluation speed or reduce space requirements, or both. Optimization techniques may include common subexpression elimination, constant folding, constant propagation, comparison optimization, dead code or subexpression removal, map or lookup table generation, policy rewriting, redundant policy elimination, heuristic-based policy ordering, or policy-format transformation, and combinations of these.
Owner:NEXTLABS
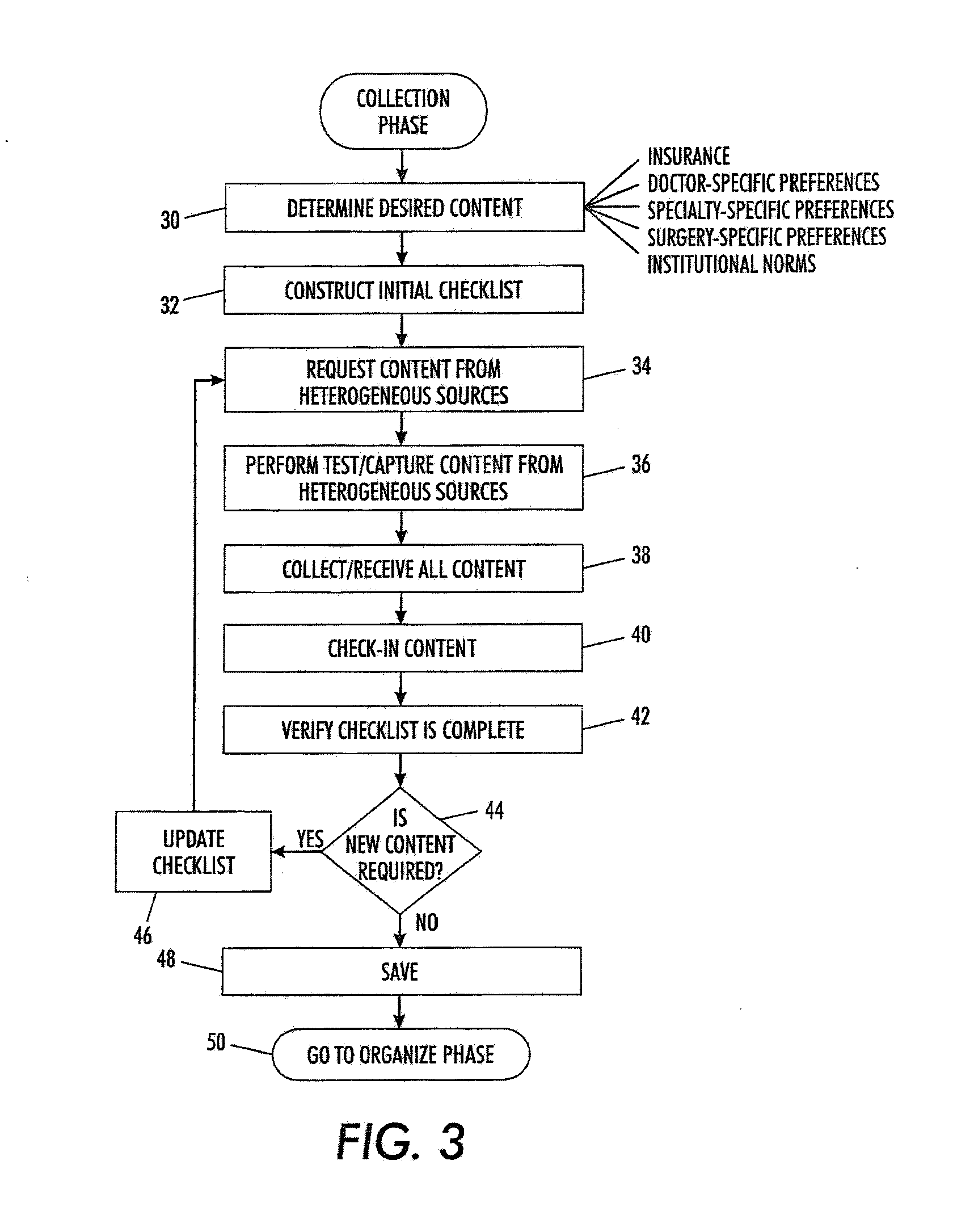
Automated information management process
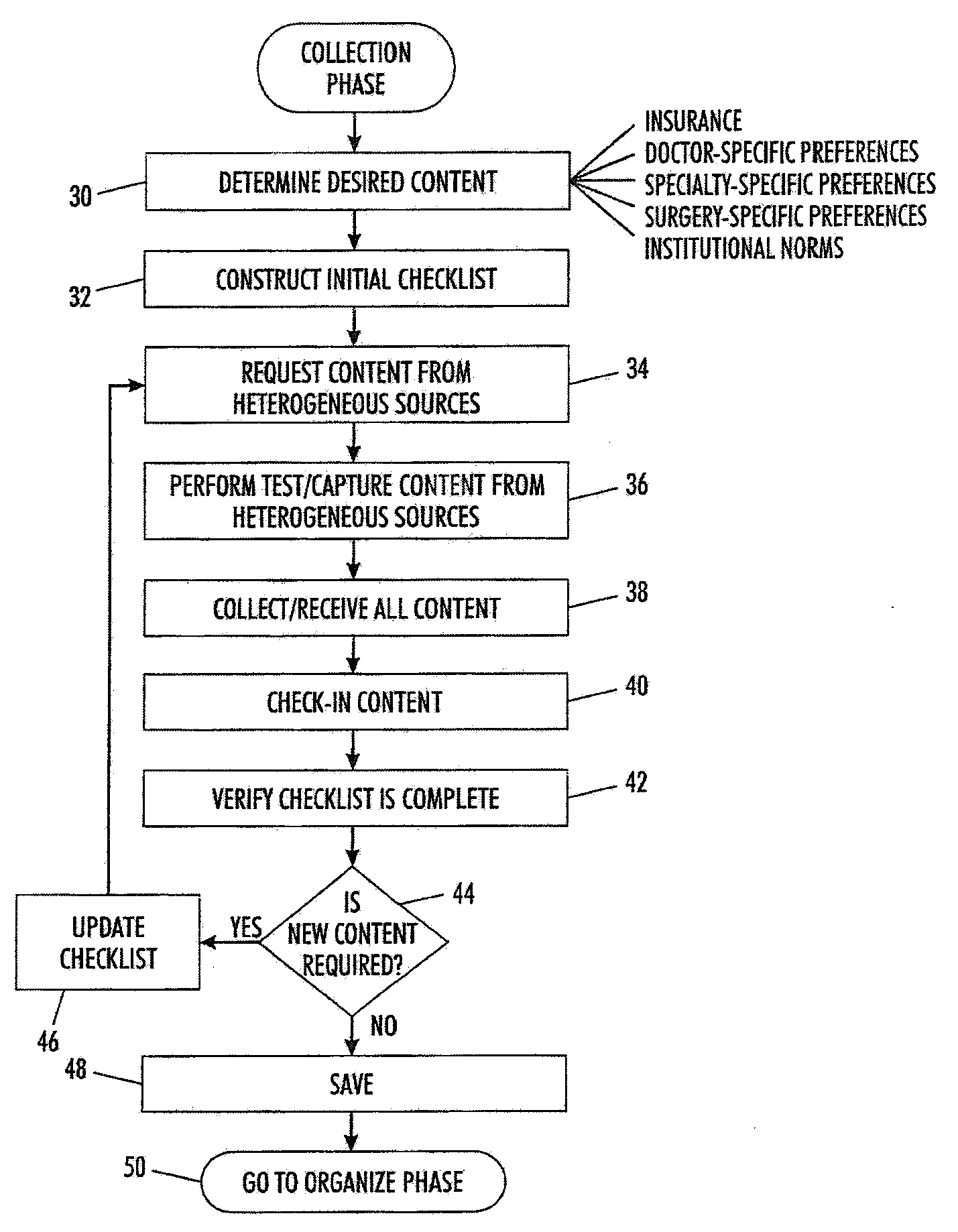
InactiveUS20090182577A1Medical automated diagnosisResourcesManagement processStructure of Management Information
A method of automating a healthcare facility workflow process includes creating a rule set governing at least one of a collection phase, an organize phase, and a display phase of the healthcare facility workflow process. The rule set is based on at least one of a plurality of decision factors. The method also includes automatically processing a plurality of content based on the rule set. Automatically processing the plurality of content includes one of collecting the plurality of content from a plurality of heterogeneous content sources, organizing the plurality of content based on a desired content hierarchy, and displaying at least one content of the plurality of content based on the desired content hierarchy.
Owner:CARESTREAM HEALTH INC
Method and apparatus for a centralized facility for administering and performing connectivity and information management tasks for a mobile user
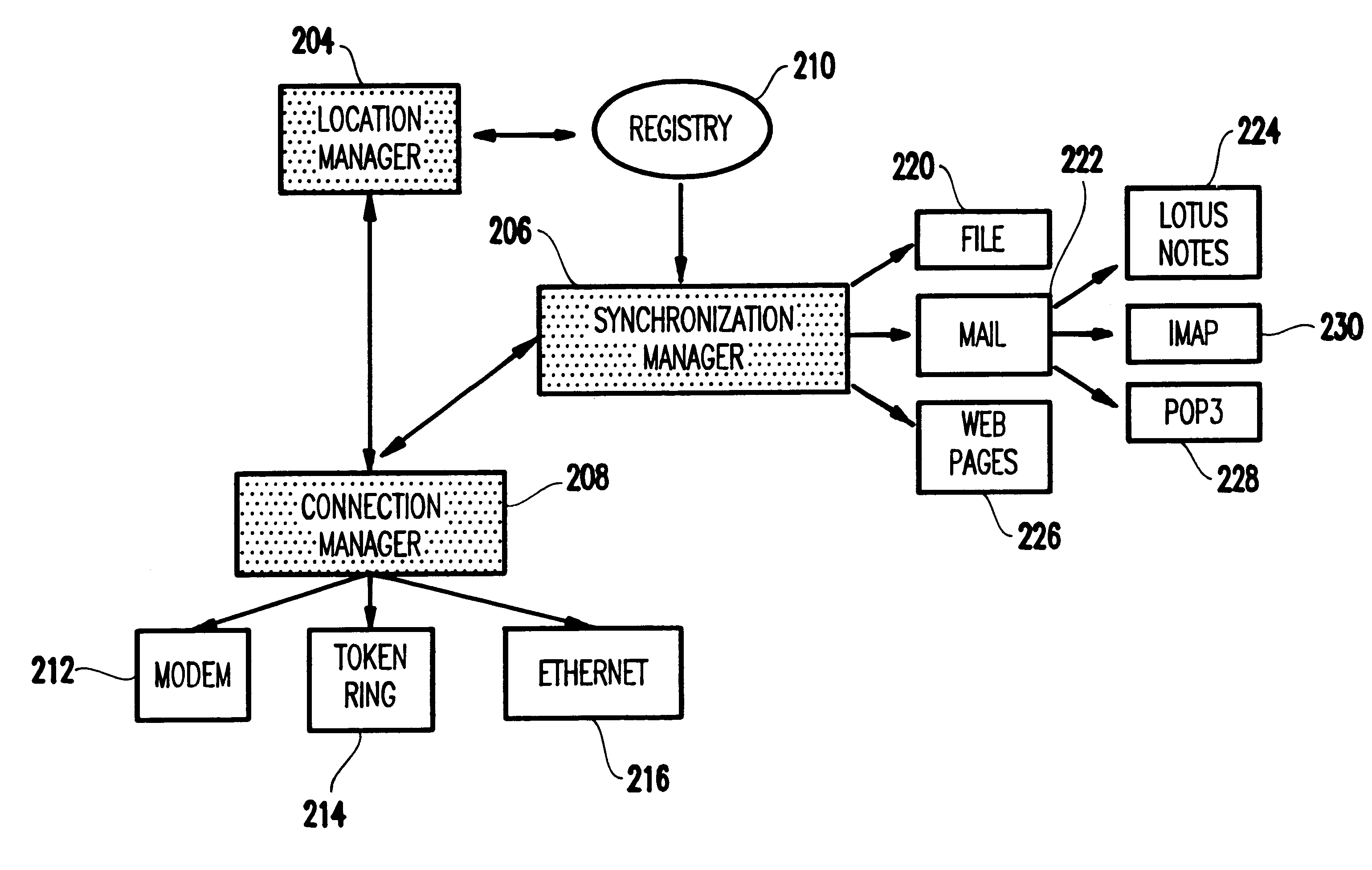
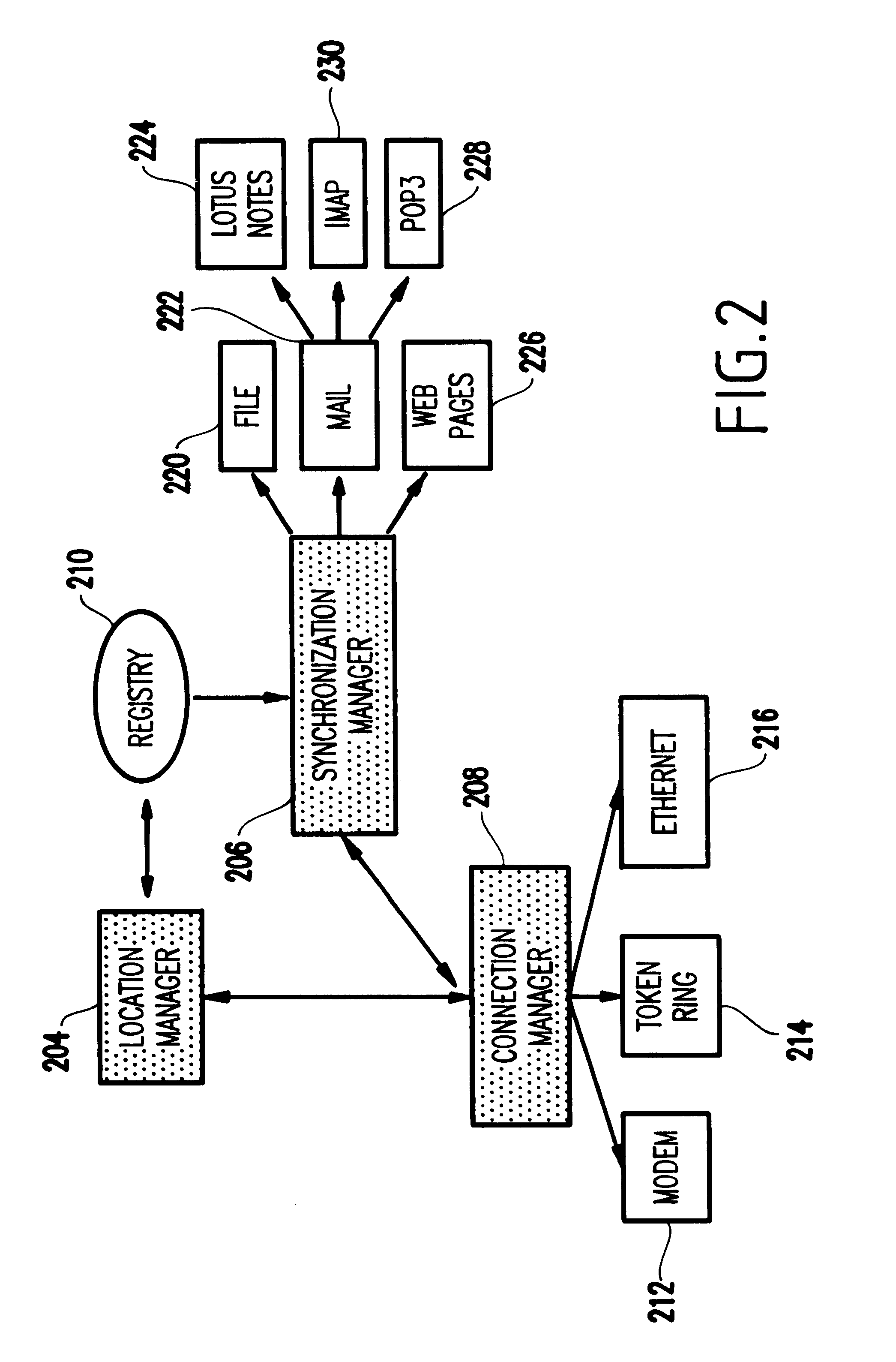
InactiveUS6615276B1Digital data information retrievalNetwork traffic/resource managementInformation objectSoftware
A software facility for administering and executing connectivity and information management tasks for a portable device, includes a module for selectively adding, deleting, and editing a location object, and a module for selectively initiating a request for a connection, disconnection, and information synchronization, based on the location object. The location object represents all location-specific information for the portable device and includes an information object including information management tasks that must be performed for a specific location for the portable device to connect to a remote network.
Owner:IBM CORP
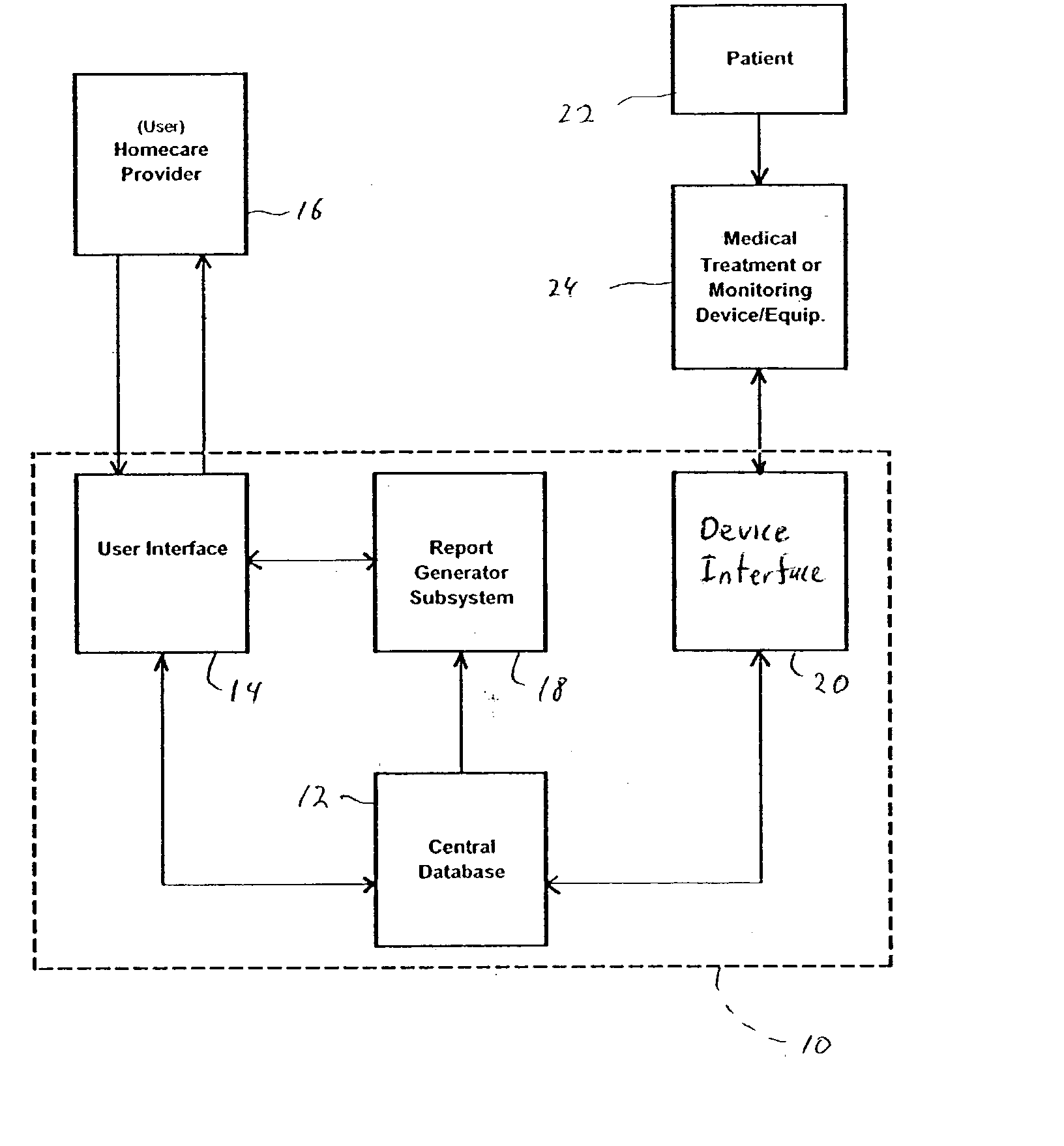
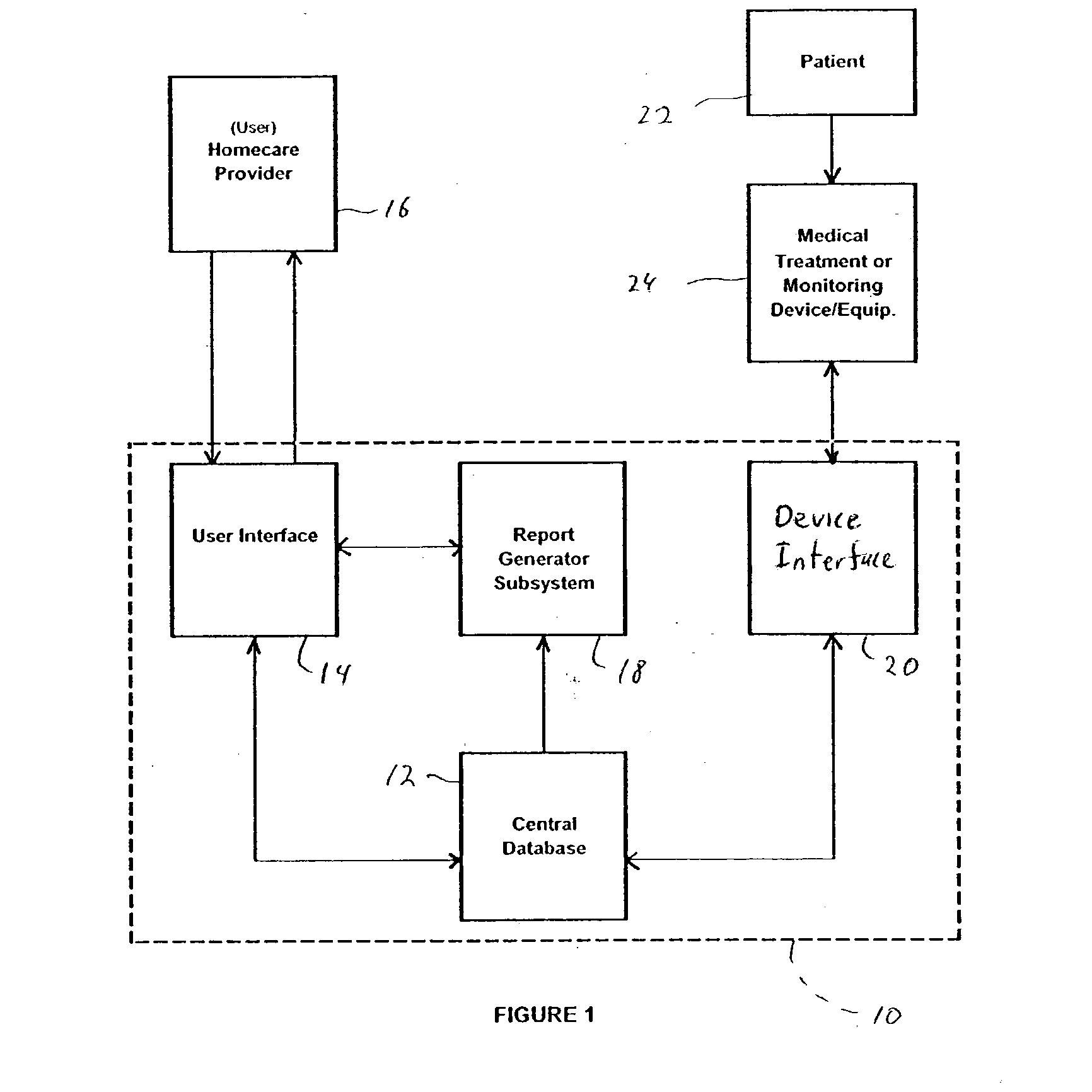
Method for managing medical information and medical information management system
InactiveUS20030208465A1None of data is presentedEffective trackingMechanical/radiation/invasive therapiesDigital data processing detailsUser inputData field
A computer-implemented method for managing medical information that includes the steps of: providing a central database of information having disparate data fields containing data, and performing an action based upon the data in the disparate data fields. The method includes of sorting, providing warnings or reminders, searching, organizing, transmitting, and presenting data from the database. The medical information management system includes a central database resident on a computing system. The central database has multiple disparate data fields containing data pertaining to patient-related information. A user interface communicates with the central database for accepting user input and transmitting system output. A visual display also communicates with the user interface to display the disparate data fields in selected or selectable formats. The system can include a report generating module, a device interface, and a compliance calculation module, all of which are in communication with the central database.
Owner:RIC INVESTMENTS LLC
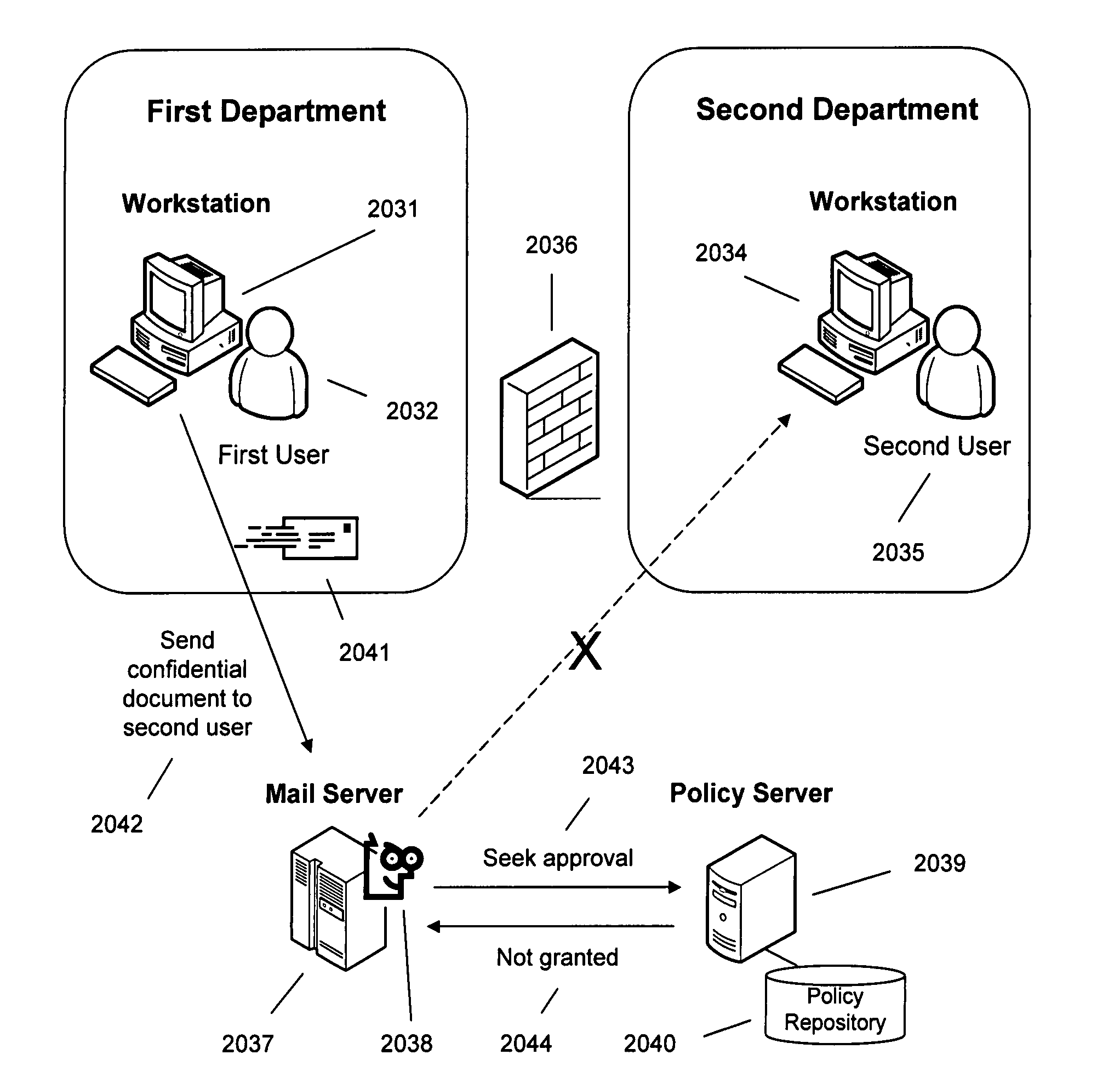
Method and system for managing confidential information
ActiveUS20050288939A1Flexible and efficient policy managementFlexible and efficient and enforcementDigital data protectionMultiple digital computer combinationsDigital dataElectronic form
A method and a system for information management and control is presented, based on modular and abstract description of the information. Identifiers are used to identify features of interest in the information and information use policies are assigned directly or indirectly on the basis of the identifiers, allowing for flexible and efficient policy management and enforcement, in that a policy can be defined with a direct relationship to the actual information content of digital data items. The information content can be of various kinds: e.g., textual documents, numerical spreadsheets, audio and video files, pictures and images, drawings etc. The system can provide protection against information policy breaches such as information misuse, unauthorized distribution and leakage, and for information tracking.
Owner:FORCEPOINT LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com