Patents
Literature
1054 results about "Data publishing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data publishing (also data publication) is the act of releasing research data in published form for (re)use by others. It is a practice consisting in preparing certain data or data set(s) for public use thus to make them available to everyone to use as they wish. This practice is an integral part of the open science movement. There is a large and multidisciplinary consensus on the benefits resulting from this practice.
Processing management information
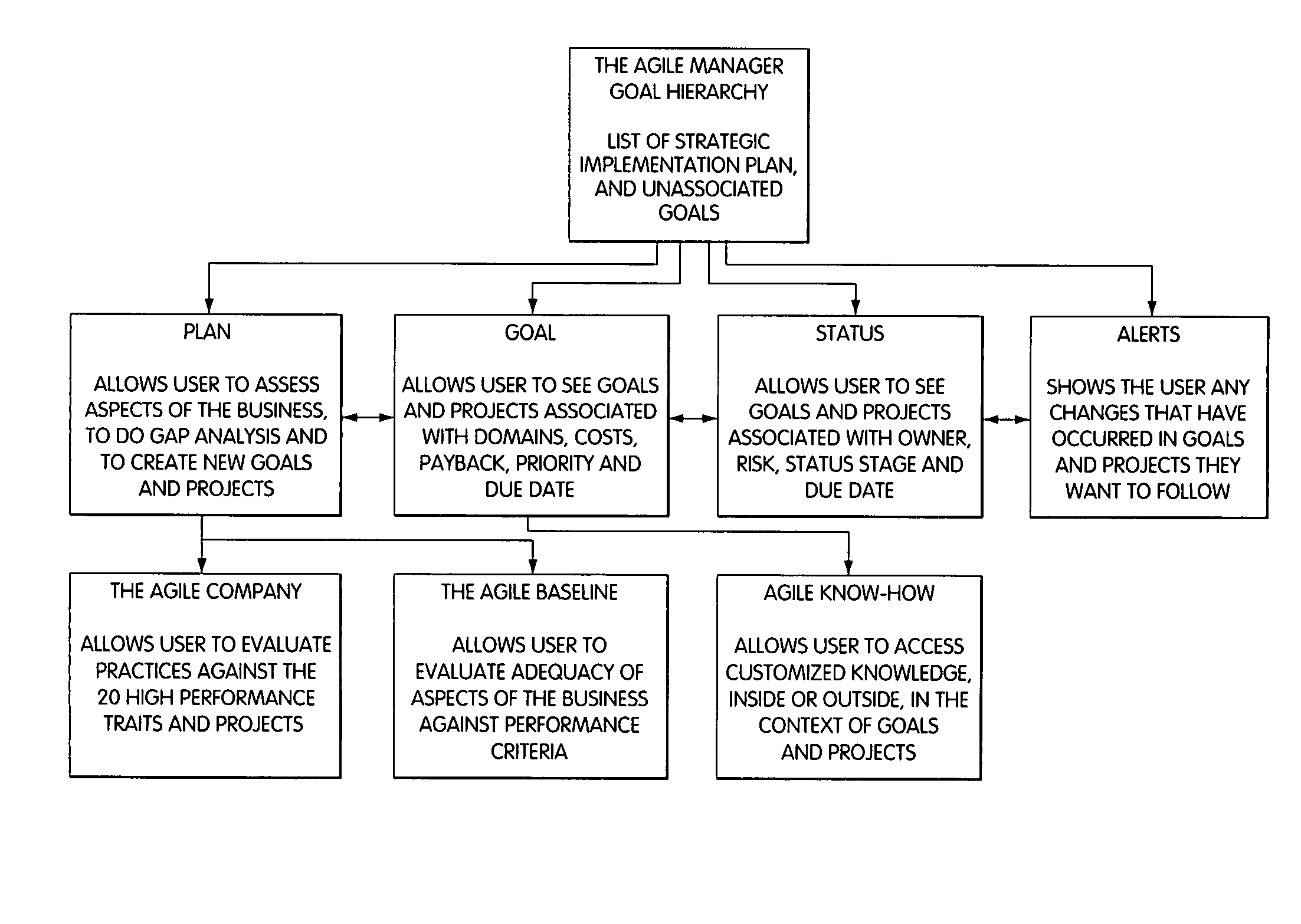
InactiveUS8095413B1Readily availableOffice automationTransmissionManagement information systemsData science
Owner:VIRTUALAGILITY
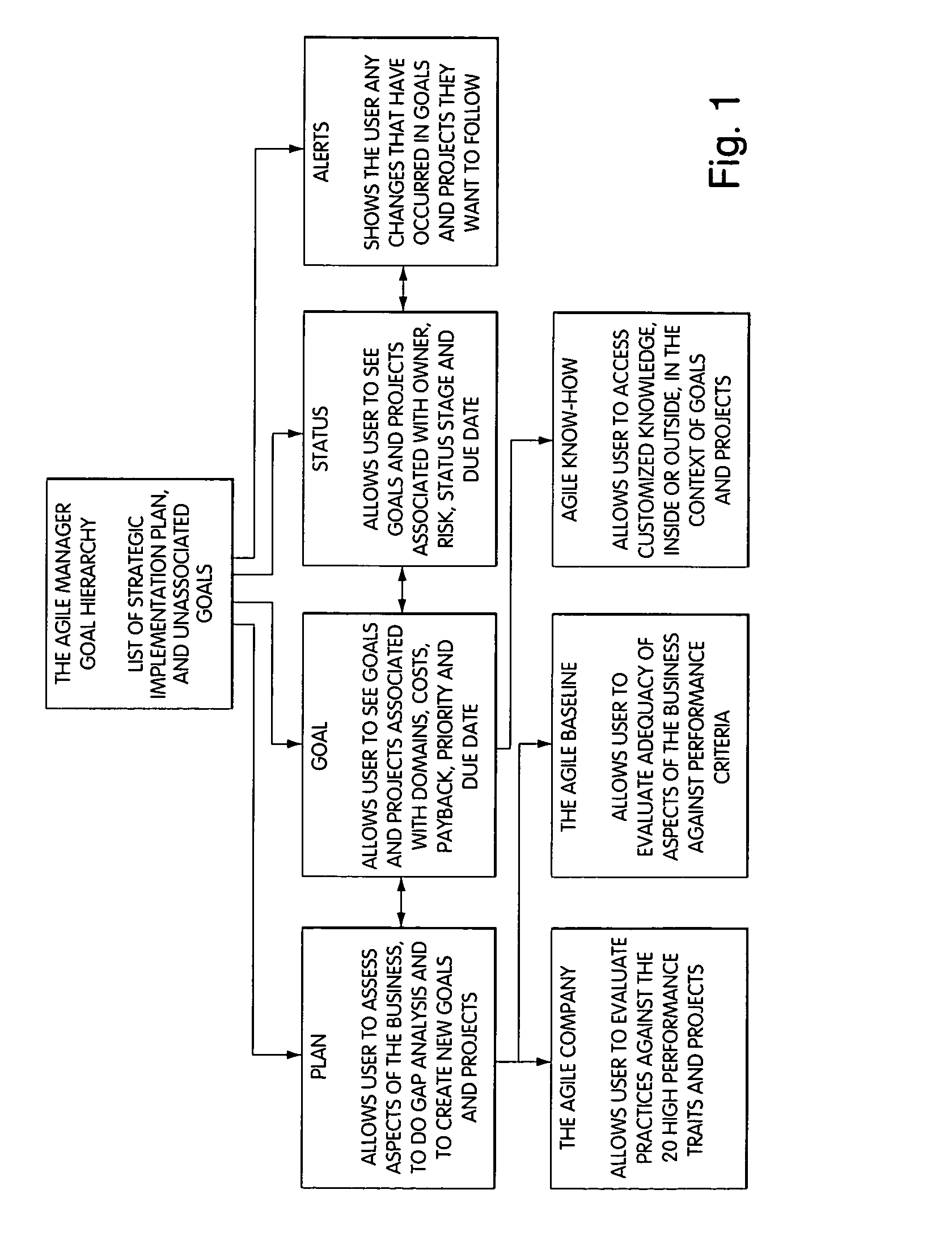
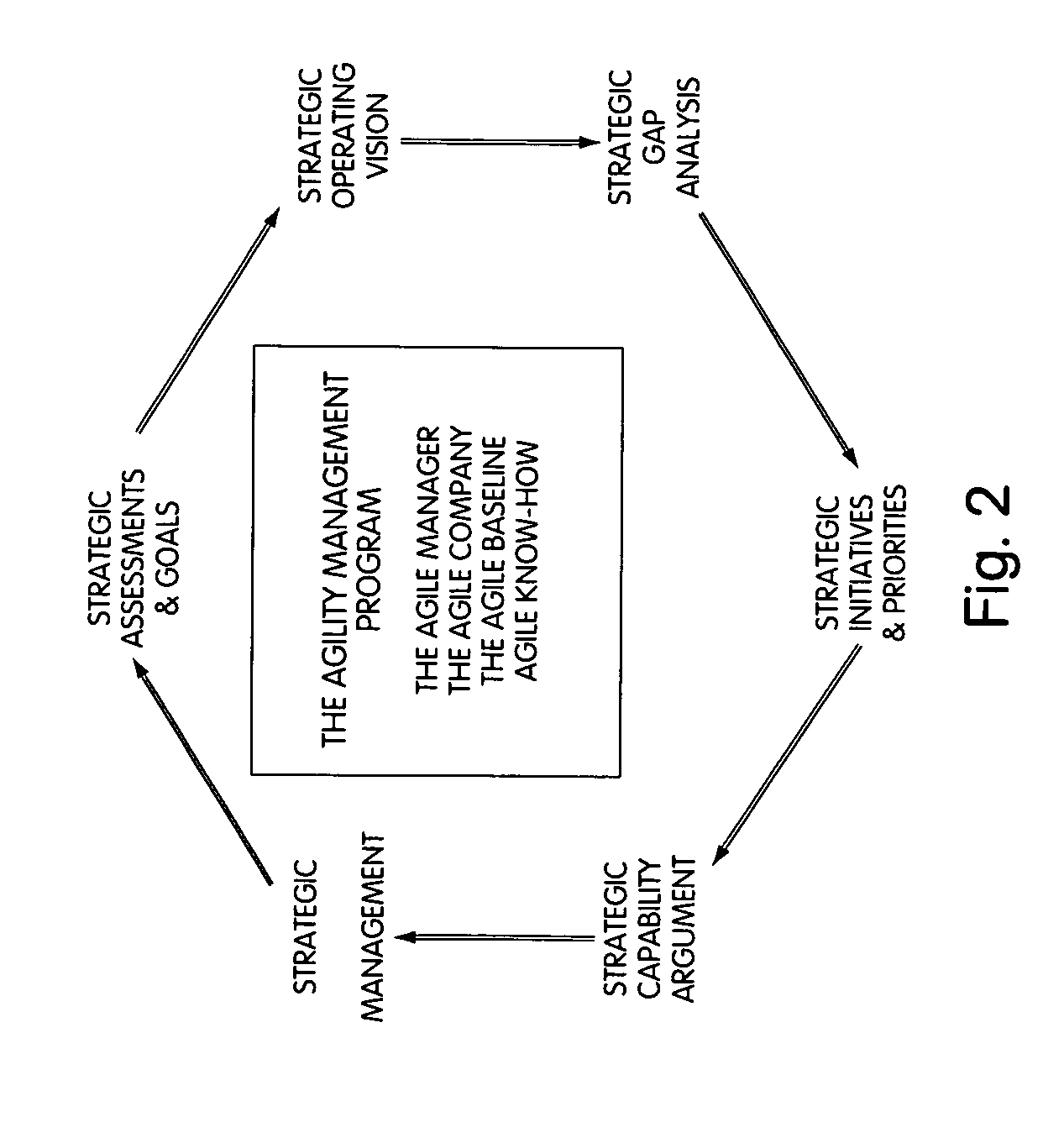
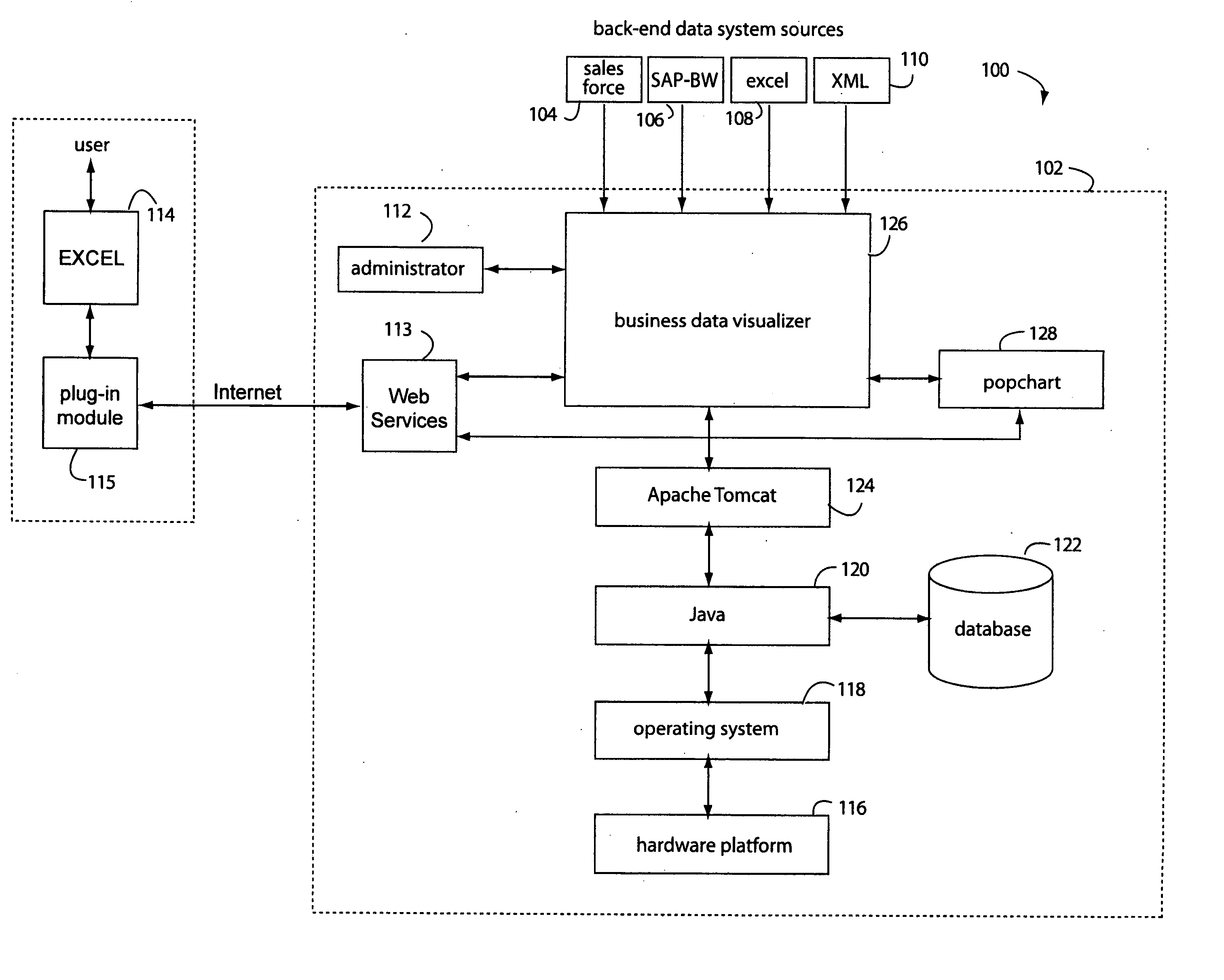
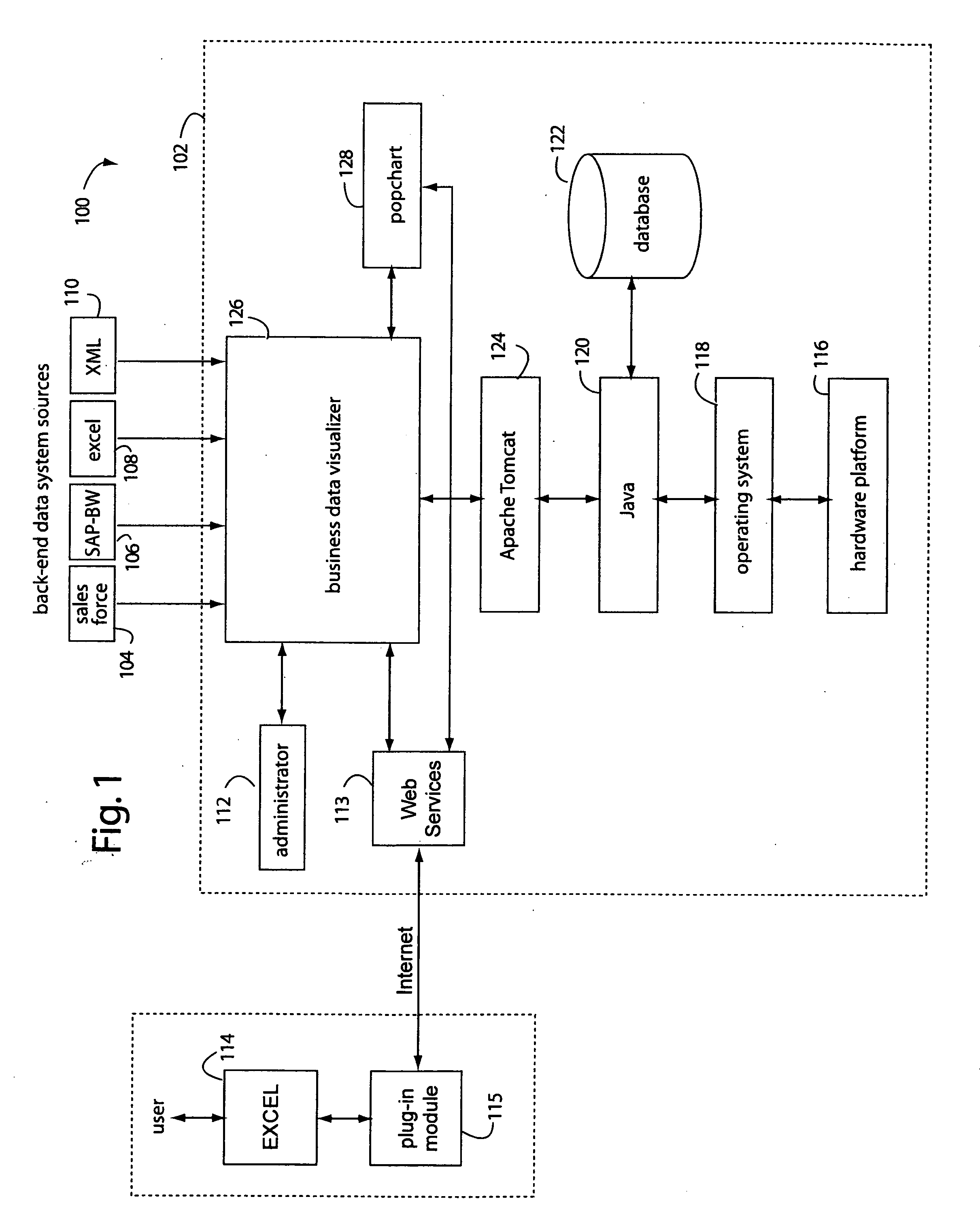
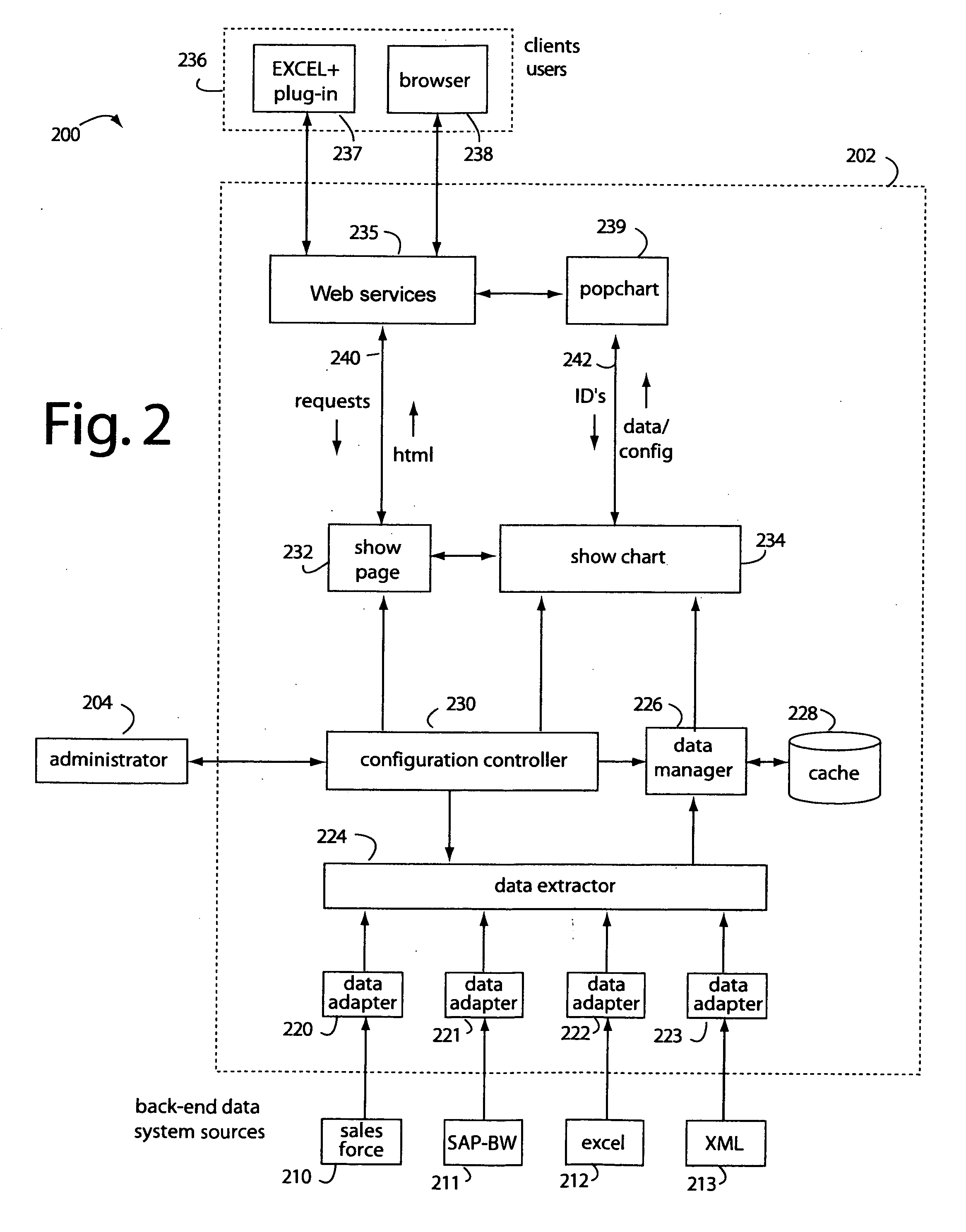
Spreadsheet user-interfaced business data visualization and publishing system
InactiveUS20060112123A1Improve strategic decisionFacilitate communicationDigital data processing detailsText processingDashboardData set
A spreadsheet user-interfaced web-based business data publishing system allows users to input and visualize field data and analytical results with interactive charts through a familiar MS-EXCEL user interface. A plug-in module associated with the user's browser and EXCEL application enables a background, web-services connection over the Internet to a management sub-system which extracts, transforms, and publishes data. Charts are customized using a WYSIWYG interface, and business dashboards are constructed through a simple drag-n-drop process. An account management system is included with access control to protect information security. The system is used for visualizing data managing reports, providing special tools to use SAP data, access Query Cubes in SAP BW, and standard and custom R / 3 reports. Once data has been extracted from SAP, it is transformed, merged with other data sources, and published as a dashboard or in a business portal. Its management and configuration functions are suited for enterprise reporting and sharing business data.
Owner:MACNICA
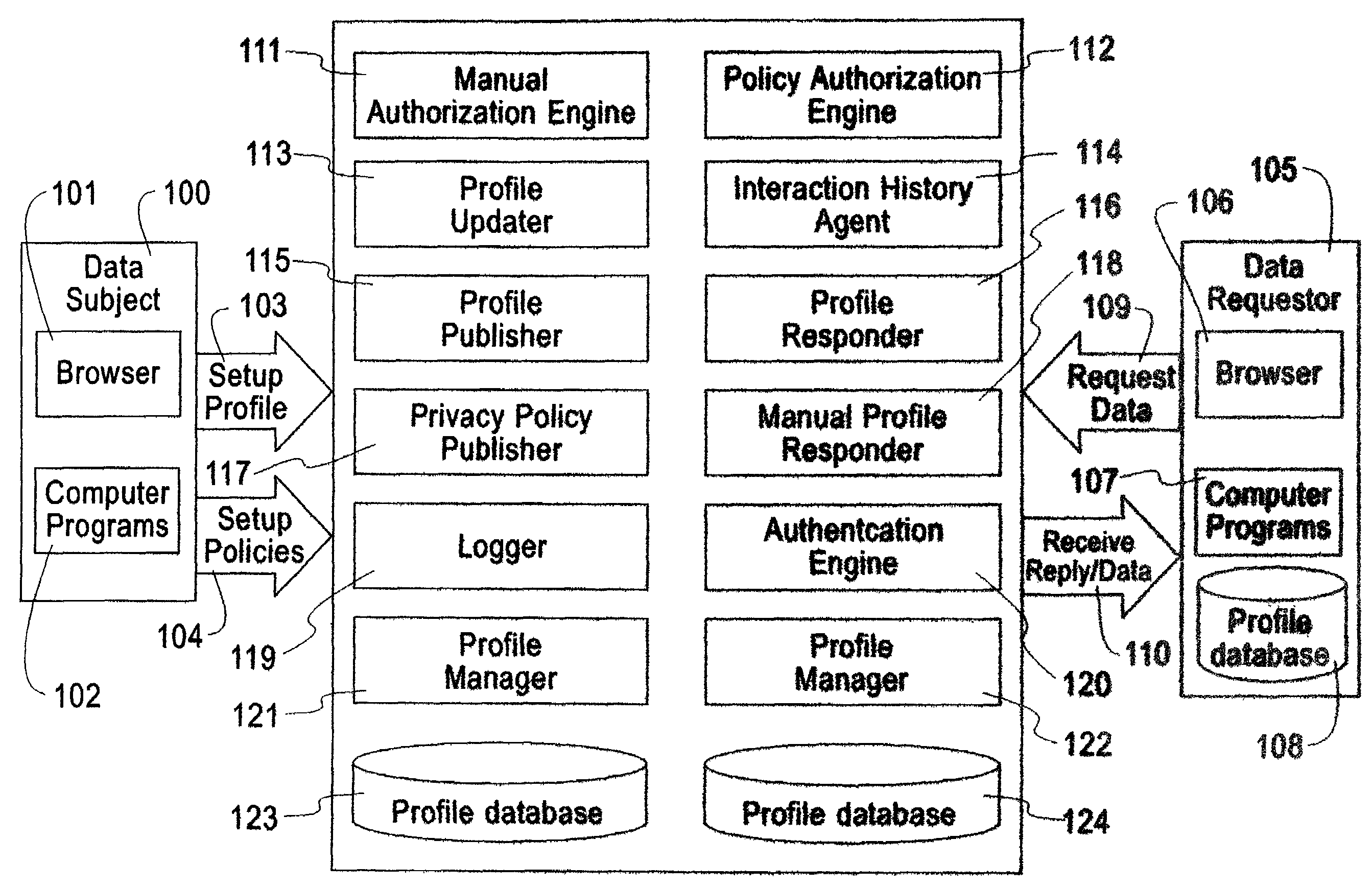
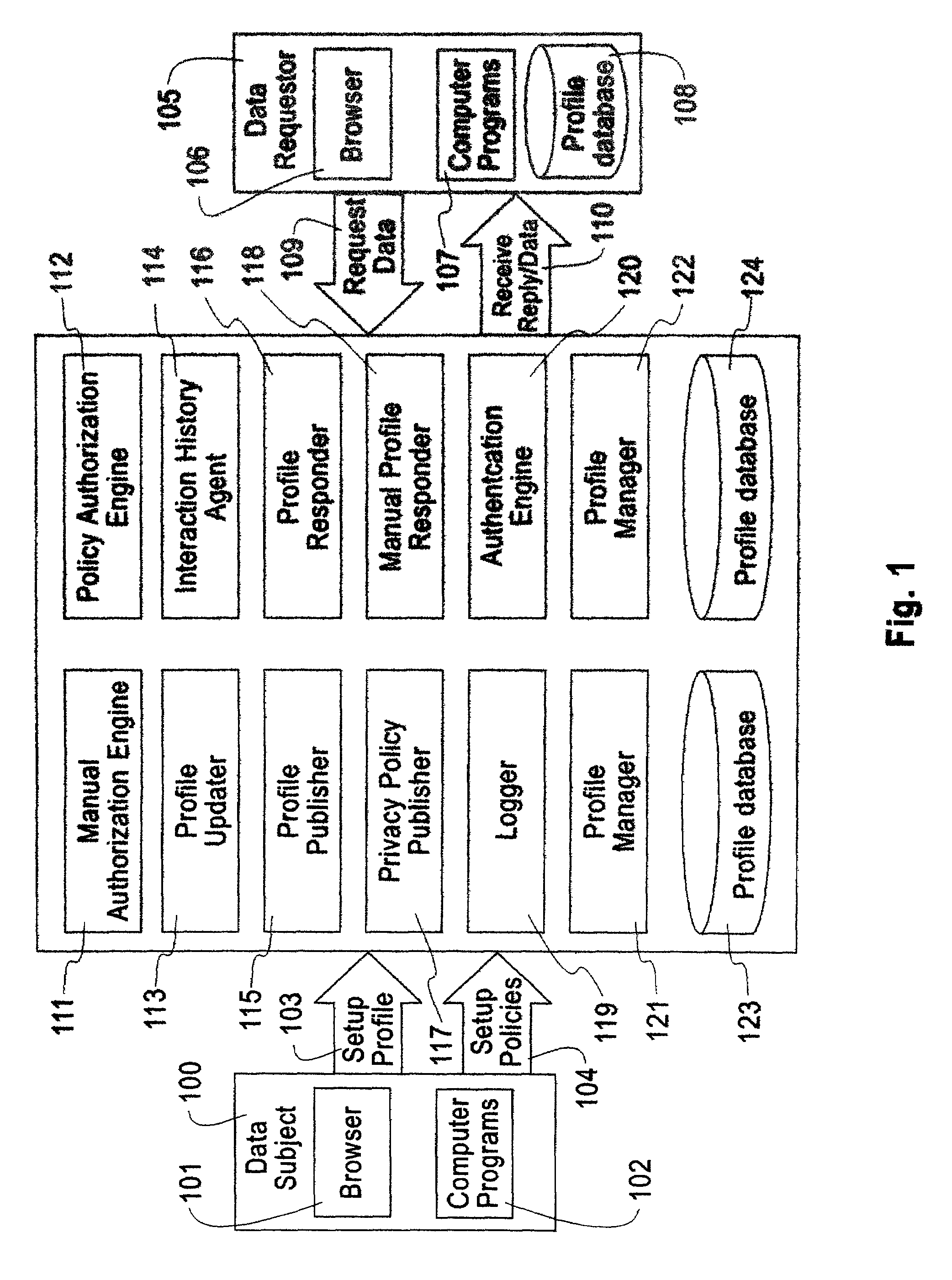
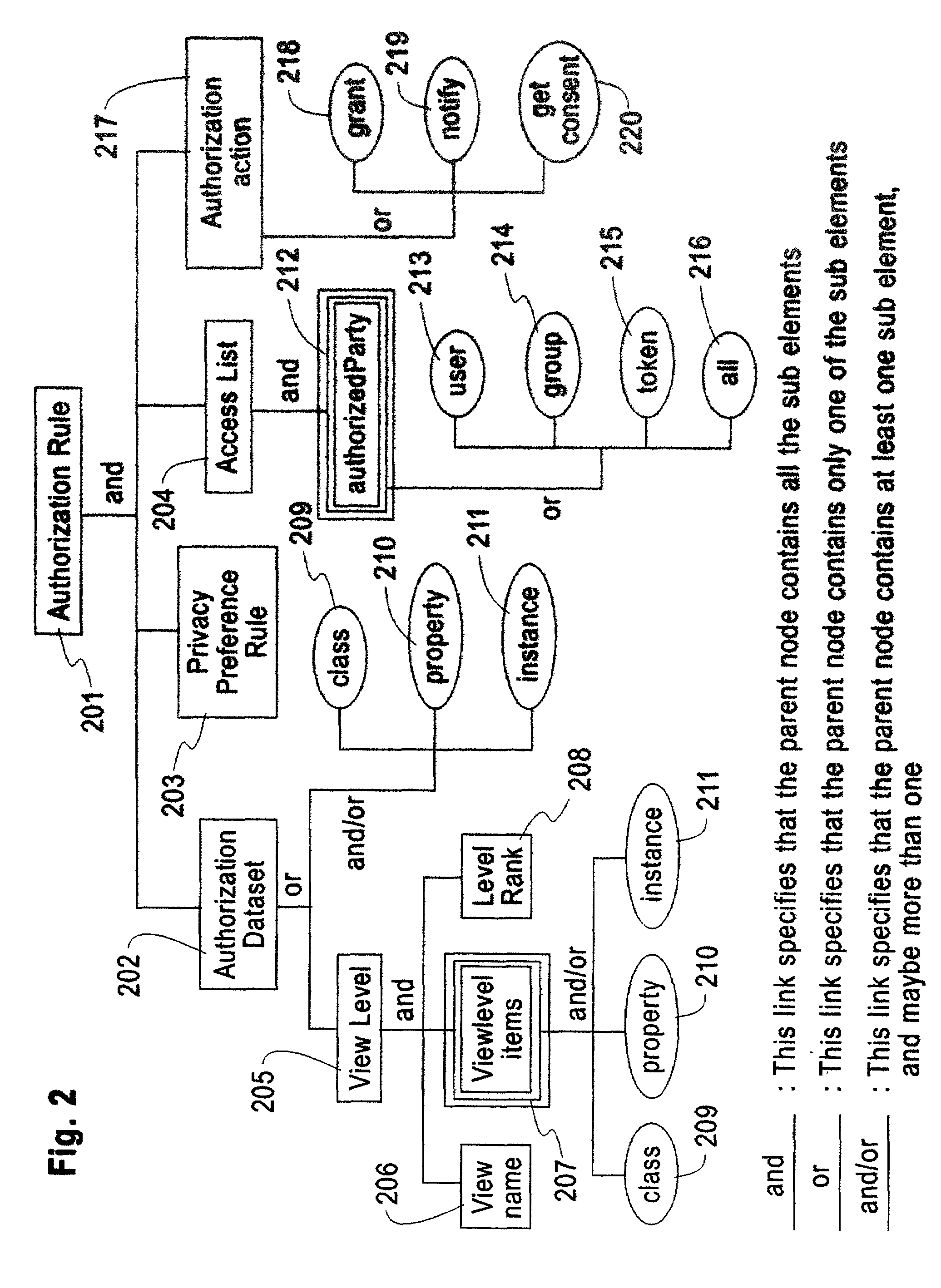
System, method, and business methods for enforcing privacy preferences on personal-data exchanges across a network
ActiveUS7478157B2Digital data processing detailsDigital computer detailsInternet privacyData exchange
An exemplary embodiment of the present invention includes a method to enforce privacy preferences on exchanges of personal data of a data-subject. The method comprises the steps of: specifying data-subject authorization rule sets having subject constraints, receiving a request message from a requester and a requester privacy statement, comparing the requester privacy statement to the subject constraints, and releasing the data-subject data in a response message to the requester only if the subject constraints are satisfied. The requester privacy statement includes purpose, retention, recipient, and access information, wherein the purpose information specifies the purpose for which the requested data is acquired, the retention information specifies a retention policy for the requested data, the recipient information specifies the recipients of the requested data, and the access information specifies whether the requested data should be accessing to the data-subject after the data has been released.
Owner:IBM CORP
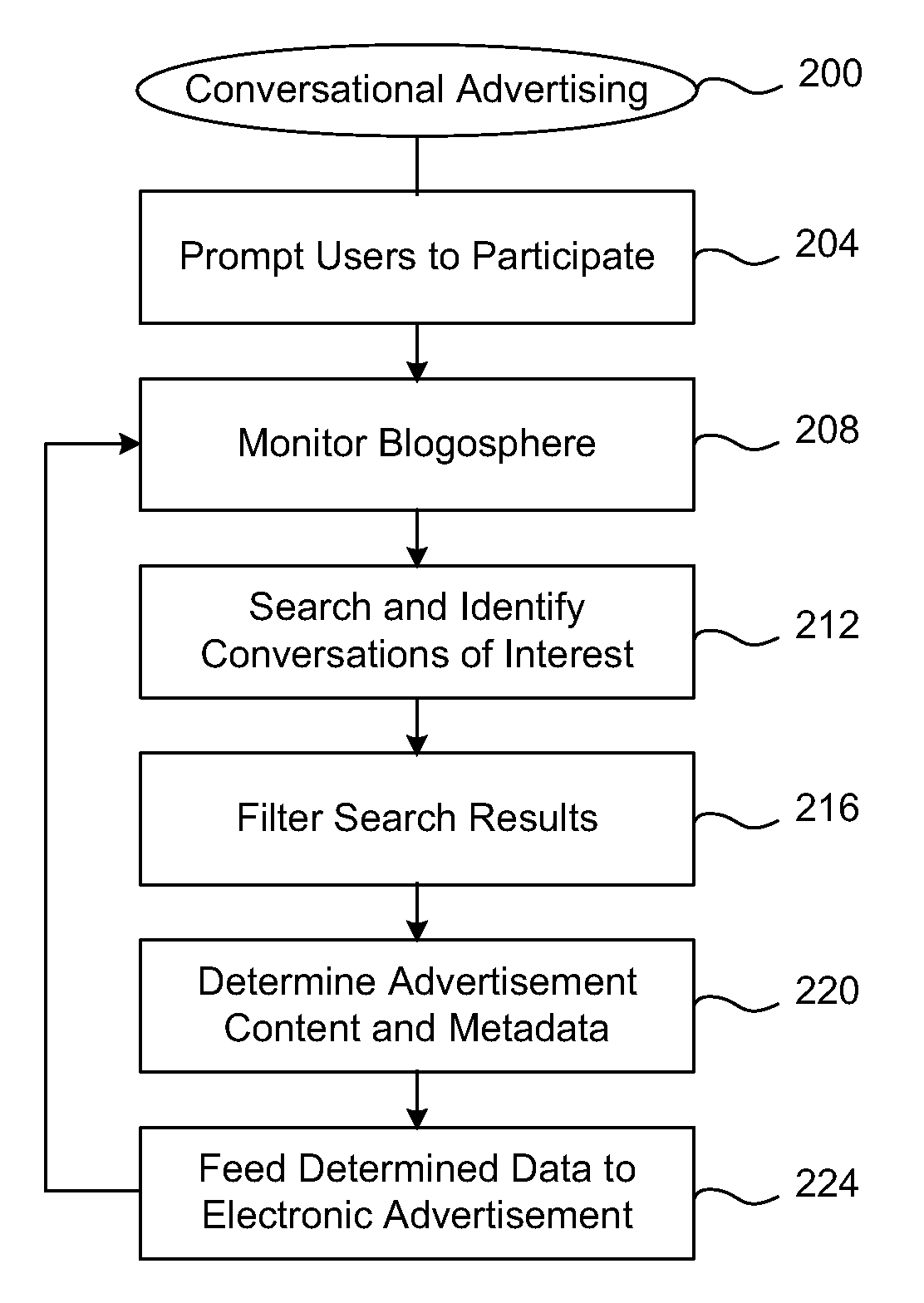
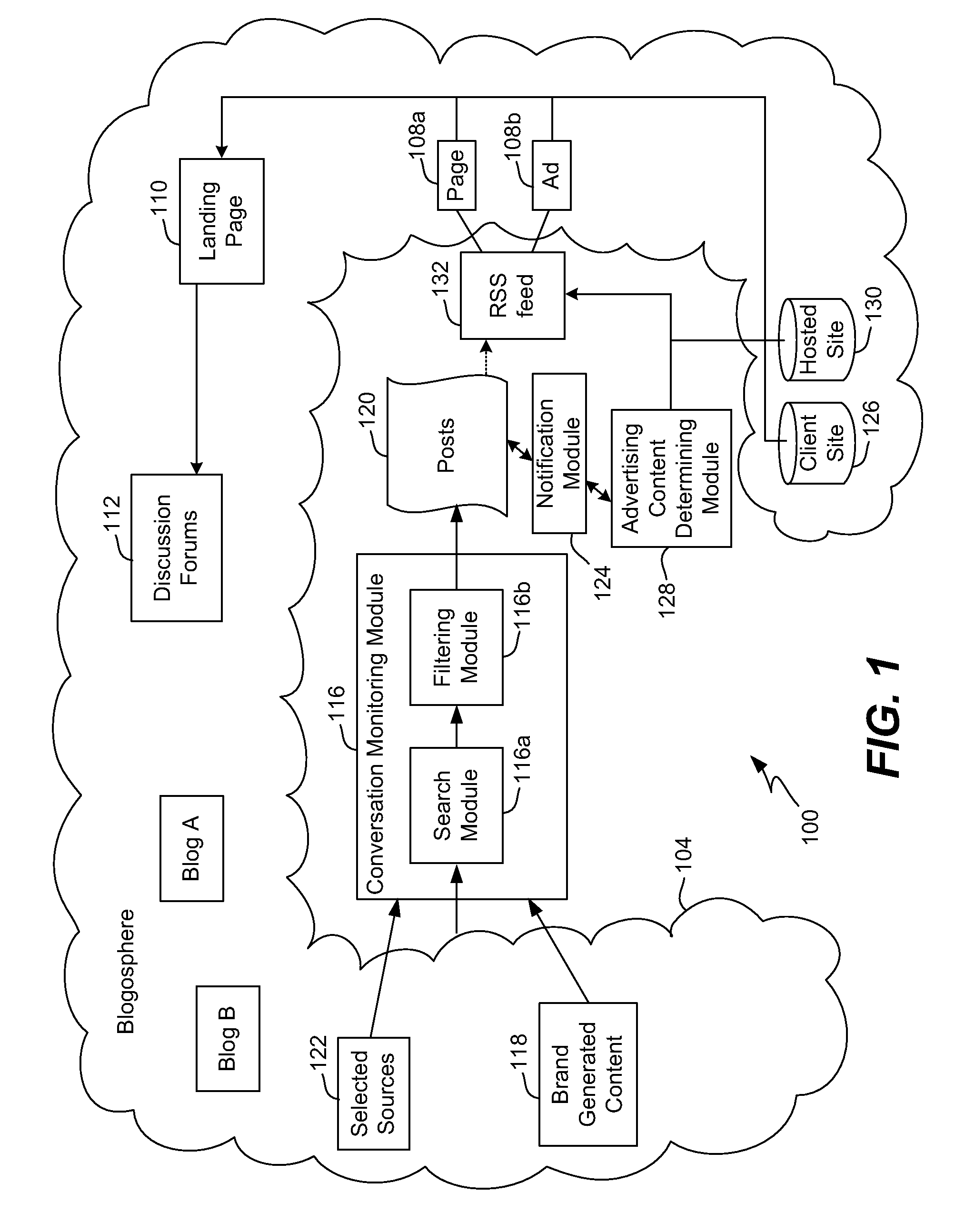
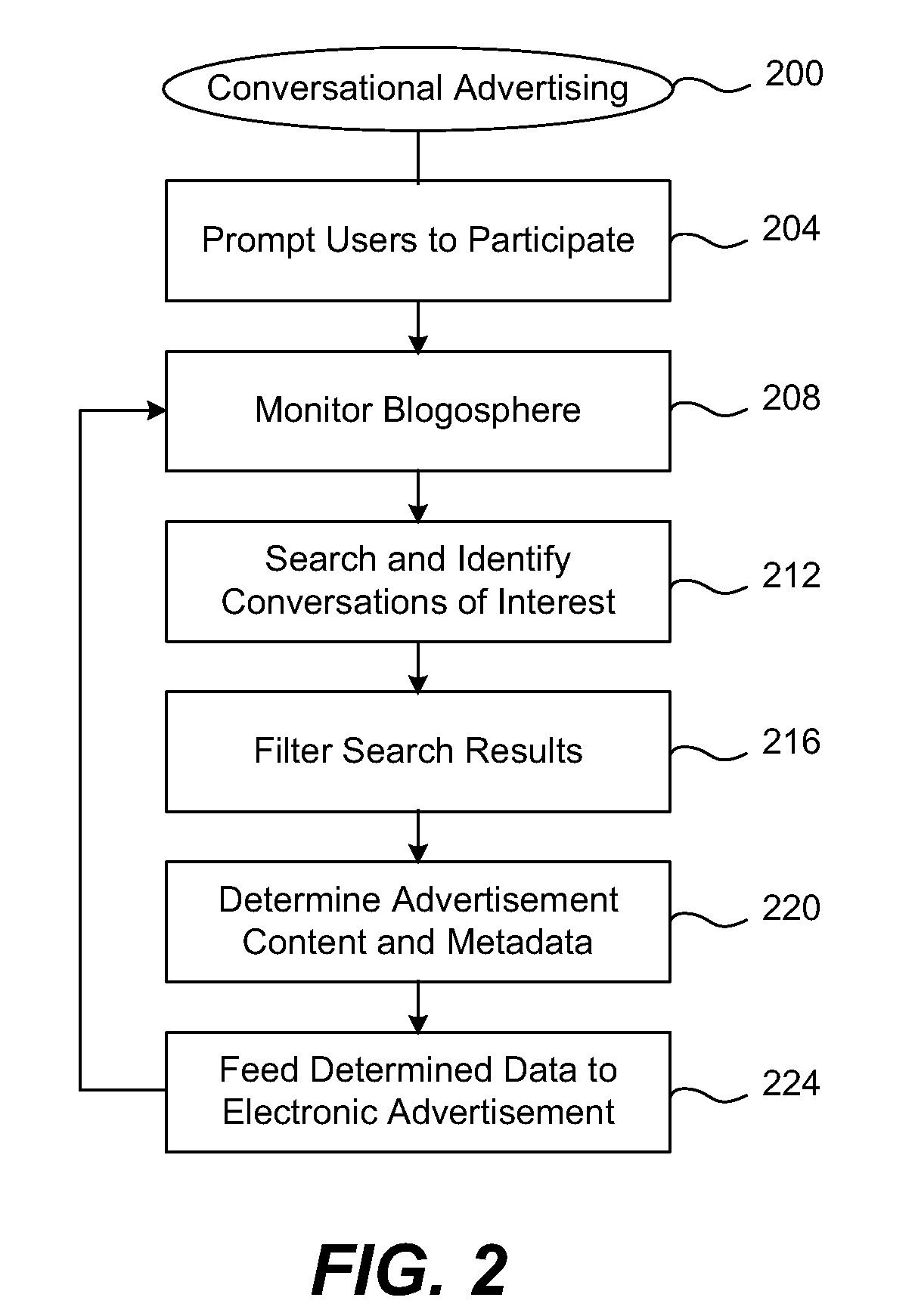
Methods and apparatus for conversational advertising
Disclosed are methods and apparatus, including computer program products, implementing and using techniques for conversational advertising. Online commentary data representing comments and / or conversation is published on a data network. Relevant commentary data associated with an electronic advertisement can be identified on one or more electronic forums accessible over the data network. The identified commentary data can be filtered according to one or more parameters. The parameters can include, for example: commentary content, conversation volume, a designated timeframe, a topic, a tag, a keyword, an index, a link, a classification scheme, an authority, a relevance measure, a meme, a word, a phrase, and / or a ranking. Advertisement content, such as selected comments and / or metadata, is determined based on the commentary data. The determined advertisement content can be provided over the data network, for instance, as an RSS feed, to the electronic advertisement for incorporation into the electronic advertisement. Further commentary data on one or more electronic forums can similarly be processed to dynamically update and refine the advertisement.
Owner:TECHNORATI
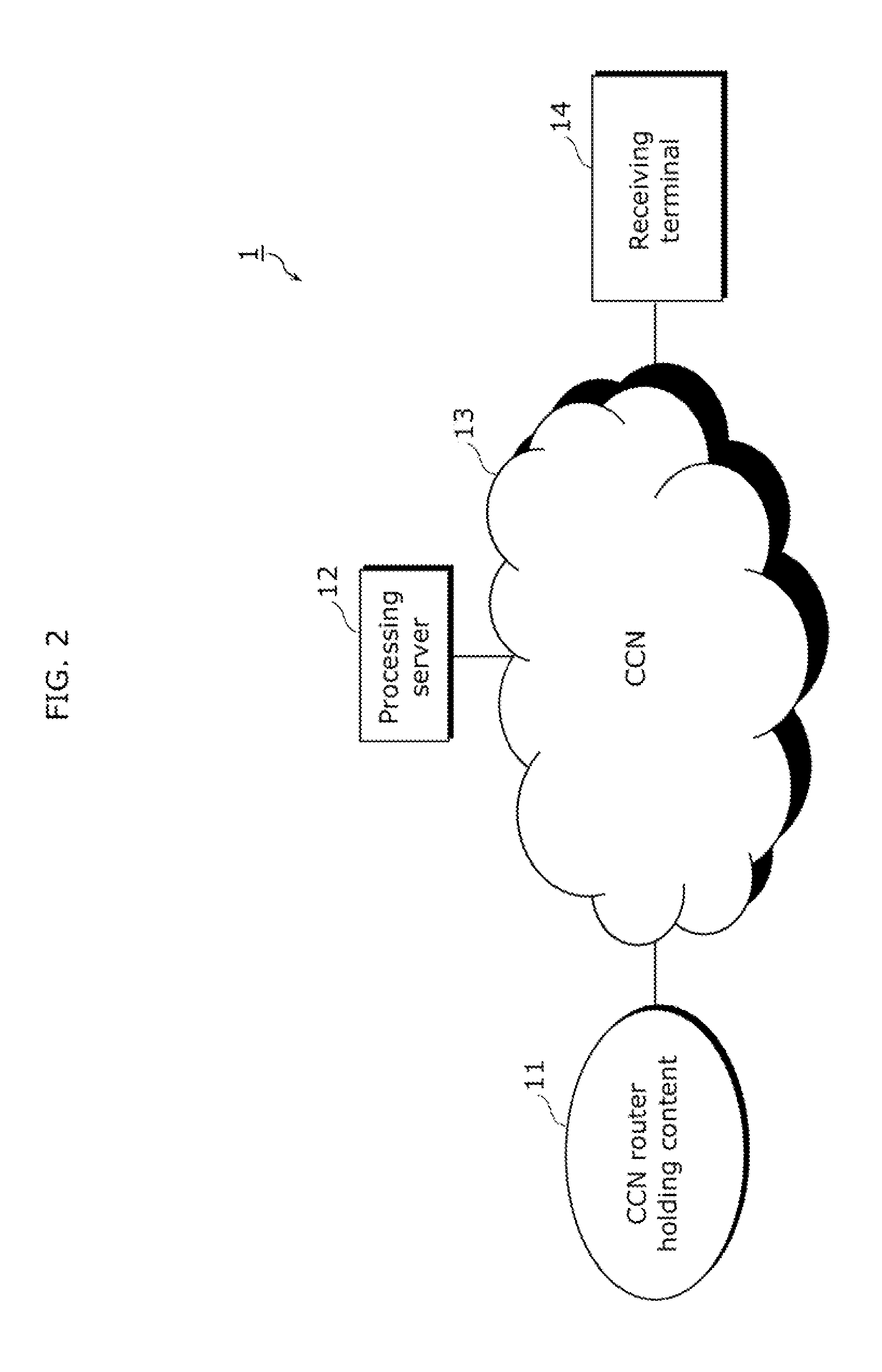
Server, router, receiving terminal, and processing method
ActiveUS20150095481A1Digital computer detailsForward error control useRouting tableComputer terminal
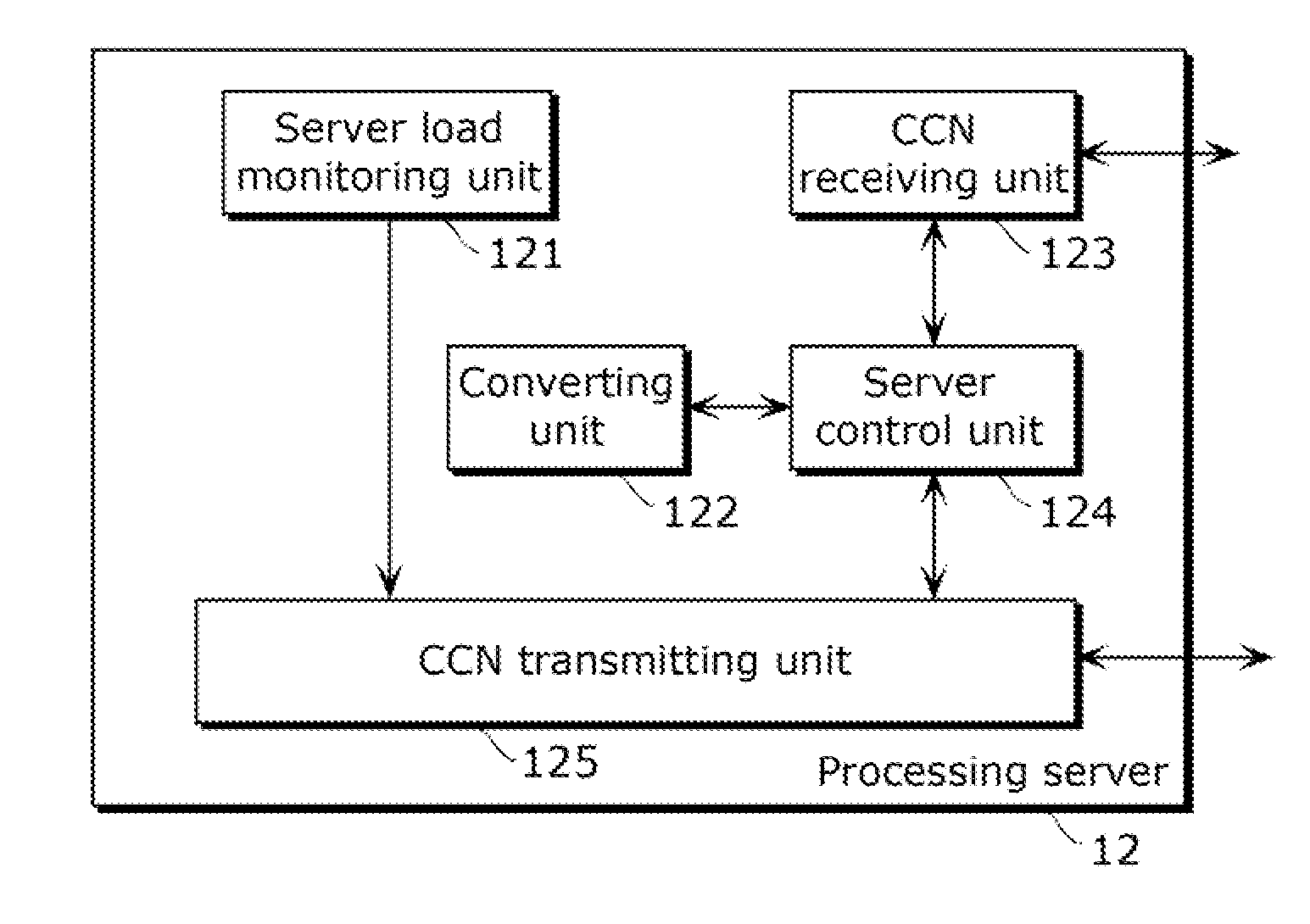
A server according to the present disclosure includes: a converting unit that converts content data to enhance a real-time property, and creates a packet of the converted content data; and a server control unit that updates a routing table that describes processing for an interest packet, wherein when an interest packet for content including converted content data is received, the server control unit performs control of issuing an interest packet for original content data of the content which is to be converted, and when original content data to be processed is received from a CCN, the server control unit performs control of causing the original content data to be converted, a packet of the converted original content data to be created, and the packet of the converted original content data to be transmitted as a response packet for the interest packet for the content including the converted content data.
Owner:PANASONIC CORP
System for low power operation of wireless LAN interfaces
InactiveUS7752330B2Easy to save energyPower managementEnergy efficient ICTWireless lanApplication software
A computer program product includes instructions for causing a processor to: alert a client of the configuration of said computer program product; use a memory space for buffering the network application data destined for the client; release the network application data to the client, based on at least one occurrence of a specified condition that promotes energy savings; and purposely delay at least some of said data with an amount of time greater than zero to promote energy savings.
Owner:INT BUSINESS MASCH CORP
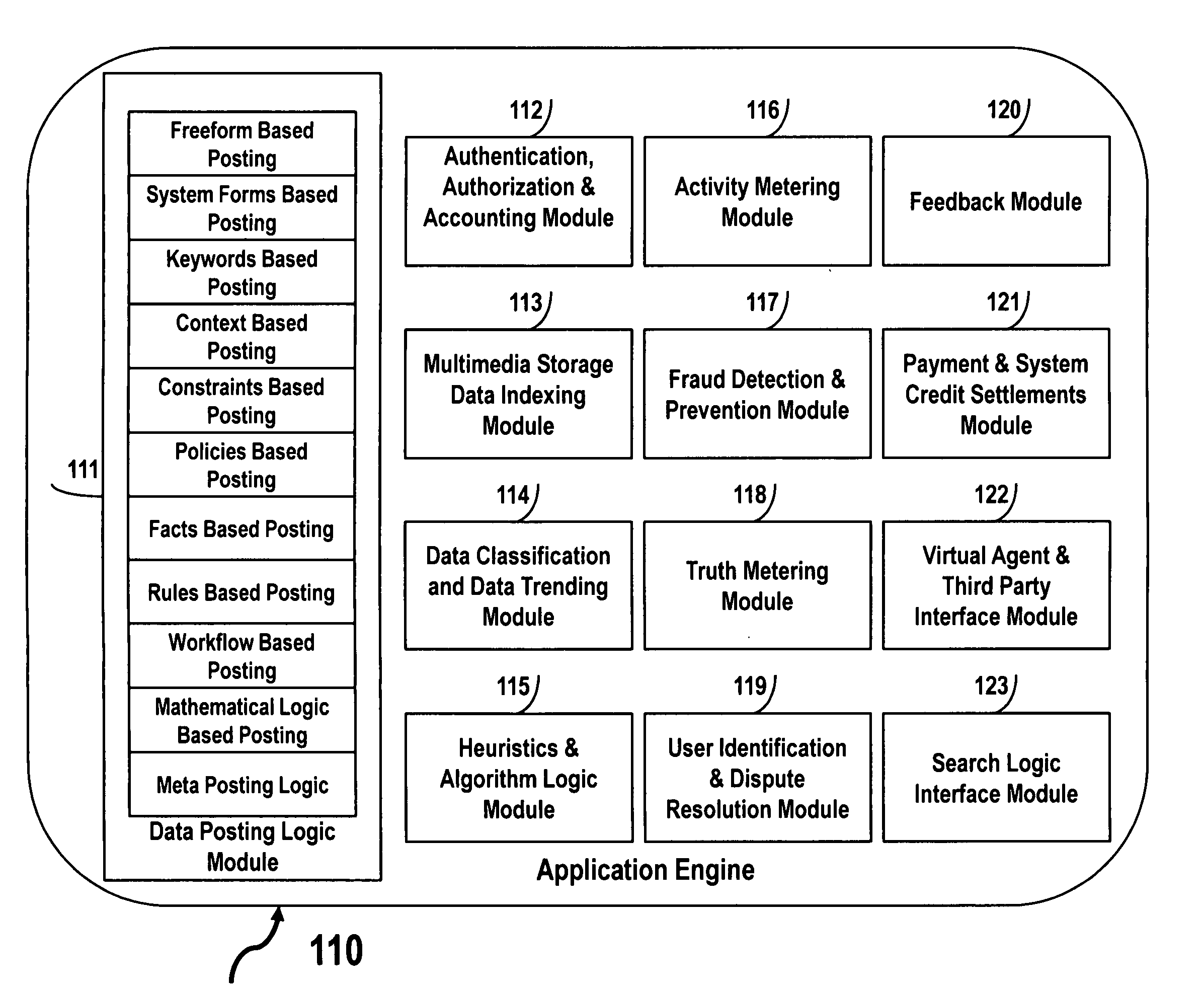
Internet eco system for transacting information and transactional data for compensation
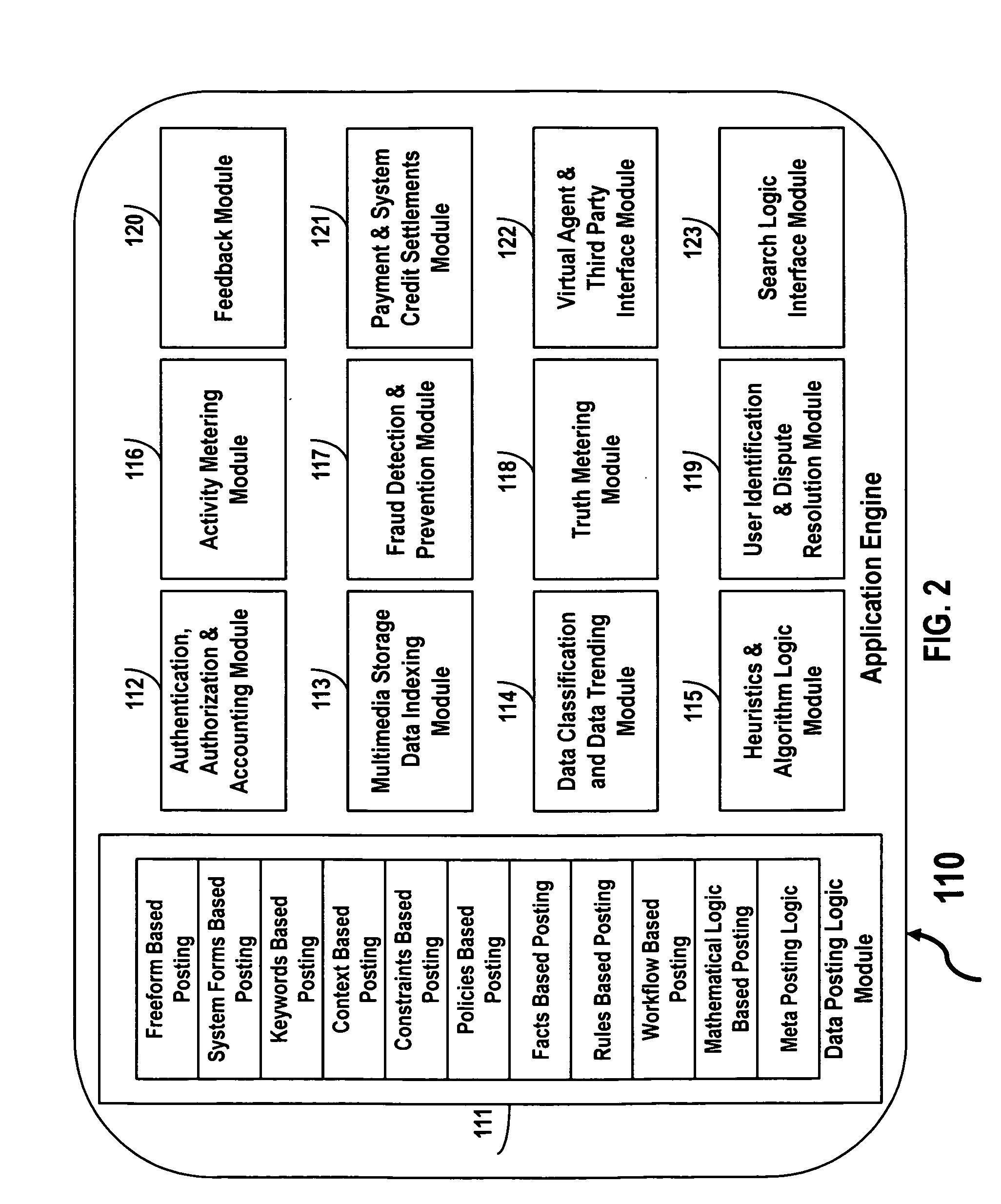
In one embodiment, an Internet eco system includes a data posting platform securely accessible over the Internet to post personal, confidential and business data for conducting informational and transactional transactions for compensation. In another embodiment, the Internet eco system enables data providers to earn monetary compensation, system credits compensation or barter based compensation. In another embodiment, the Internet eco system enables data posting based upon freeform, system forms, keywords, mathematical logic, constraints, policies, facts, rules, workflow, or context logic; such data can be searched and retrieved based upon keywords, mathematical logic, constraints, policies, facts, rules, workflow, or context based search criteria. In yet another embodiment, the Internet eco system provides methods for authentication, authorization, accounting, data indexing, data classification, heuristics, activity metering, fraud detection and prevention, user identification, verification and dispute resolution, providing feedback, payments and systems credit settlement, providing virtual agent capabilities and third party interfacing capabilities and for providing interfaces to search logic. In yet another embodiment of the Internet eco system provides methods for data providers and data consumers to engage in and to consummate social networking based transactions.
Owner:HADI ALTAF
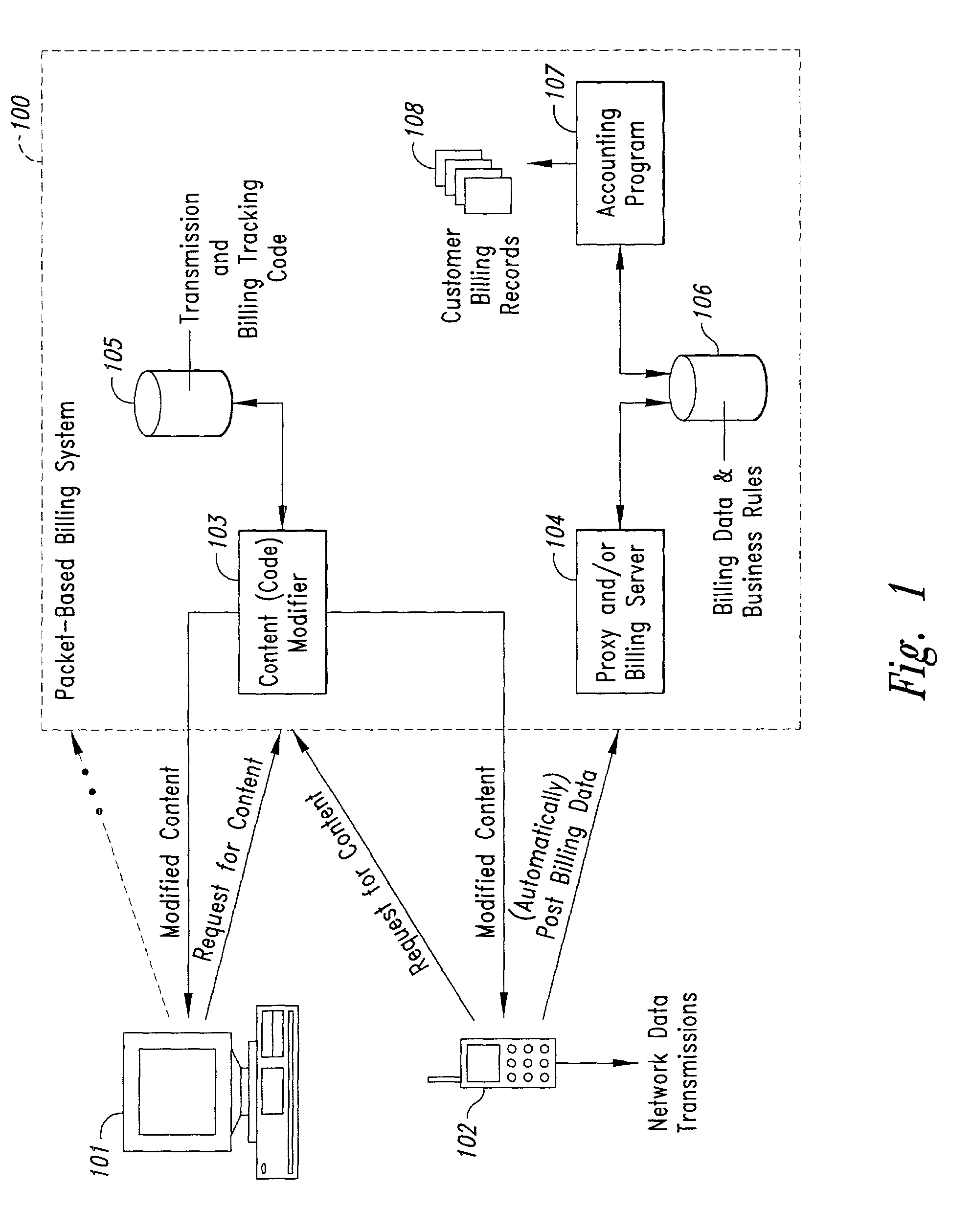
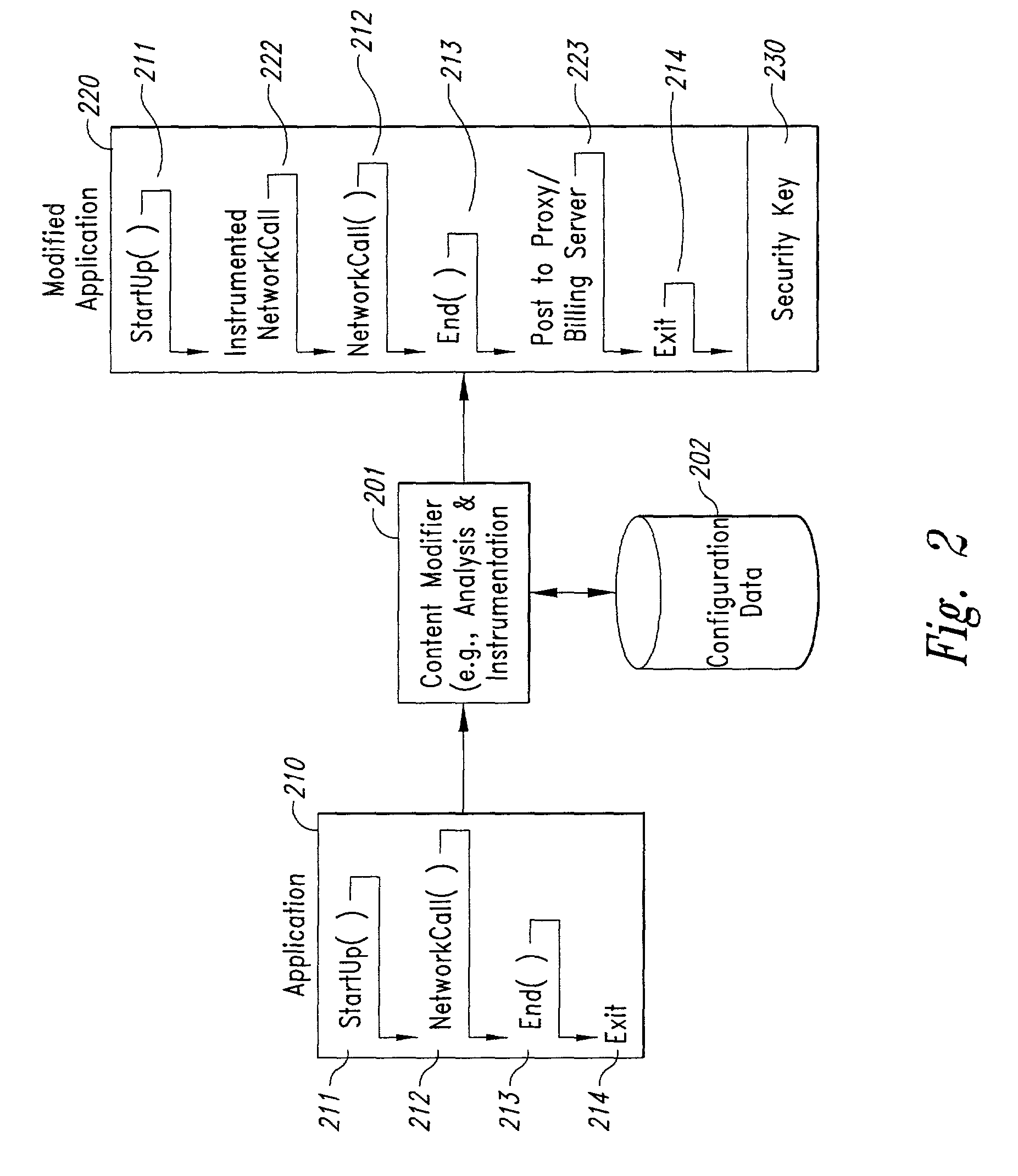
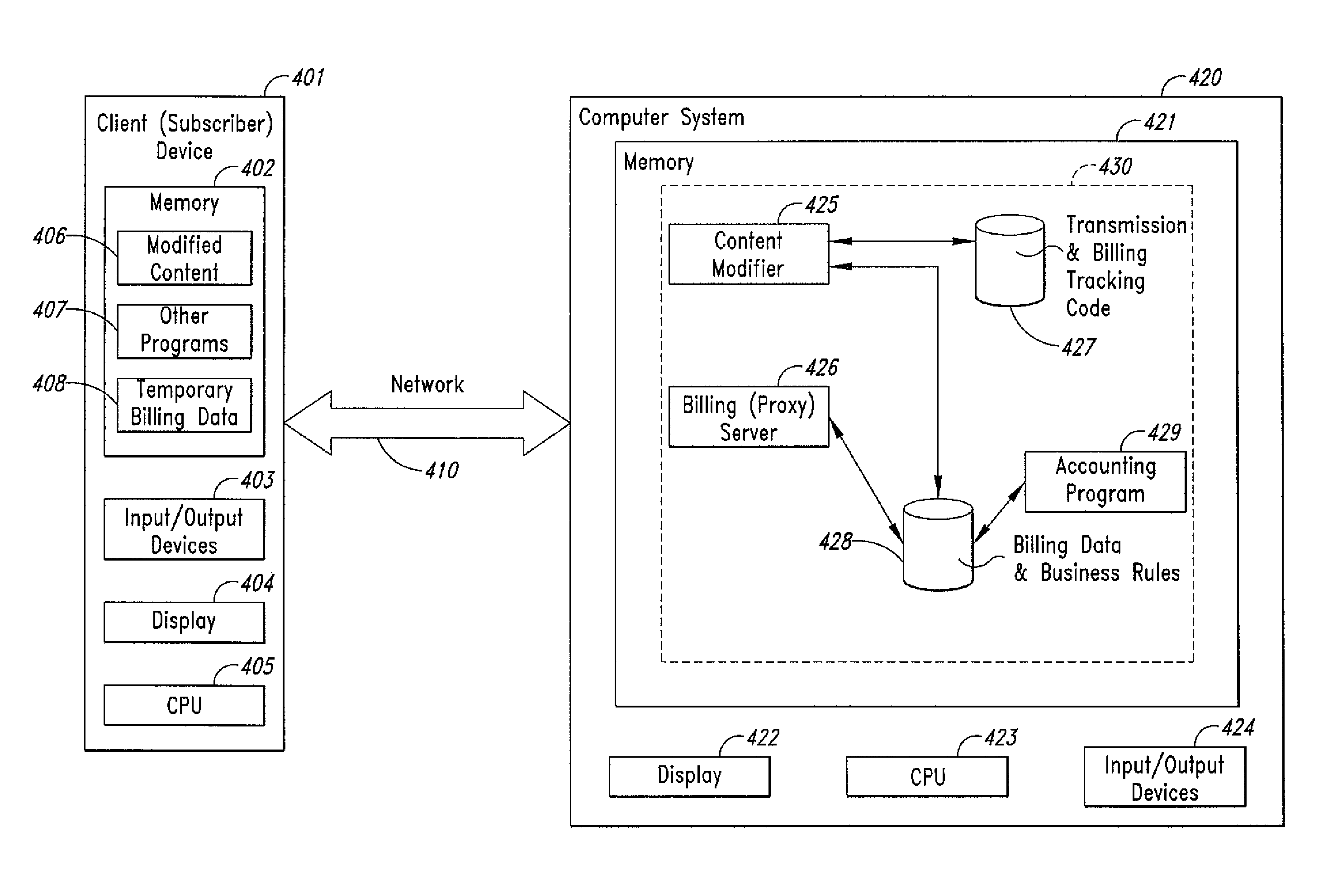
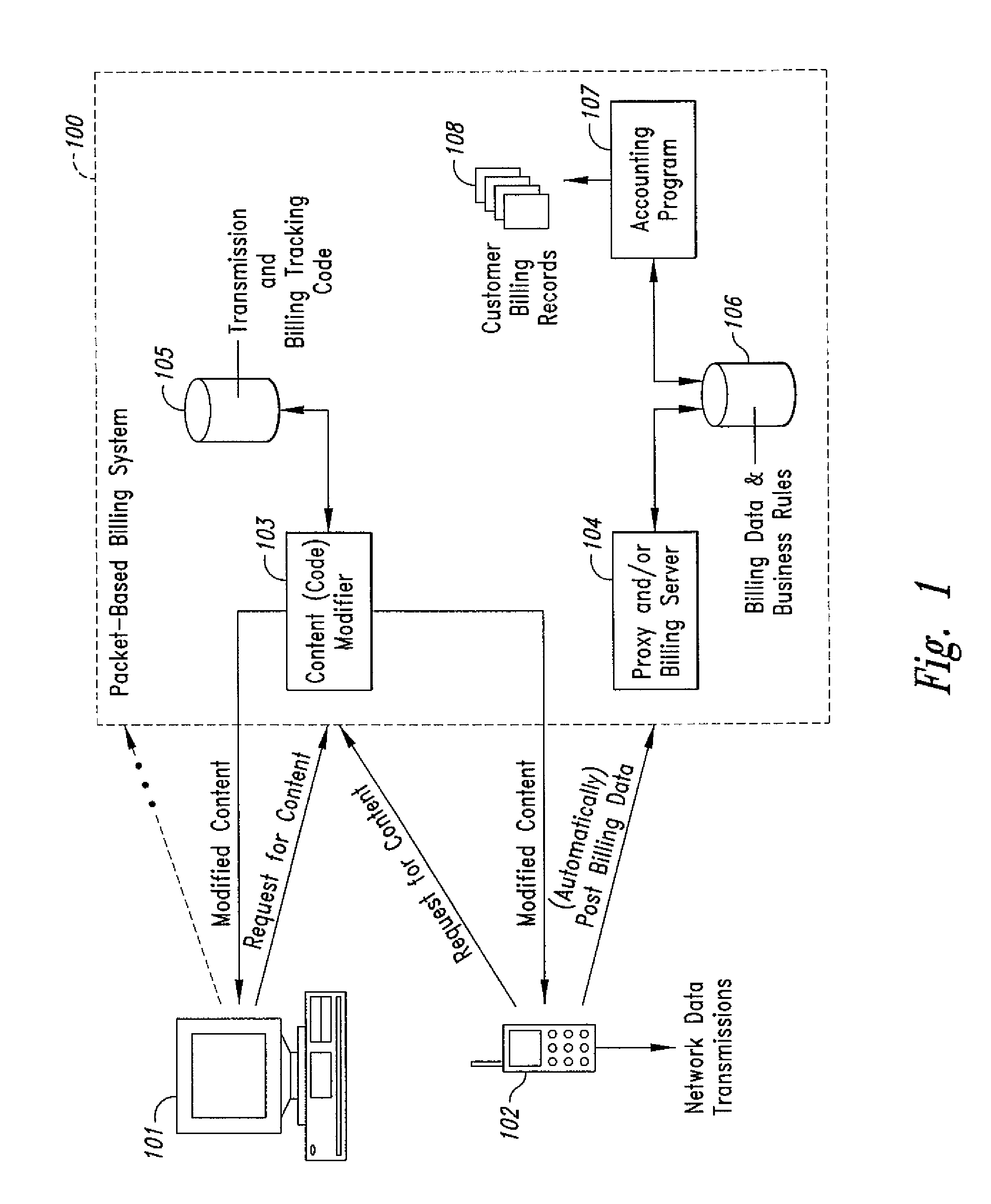
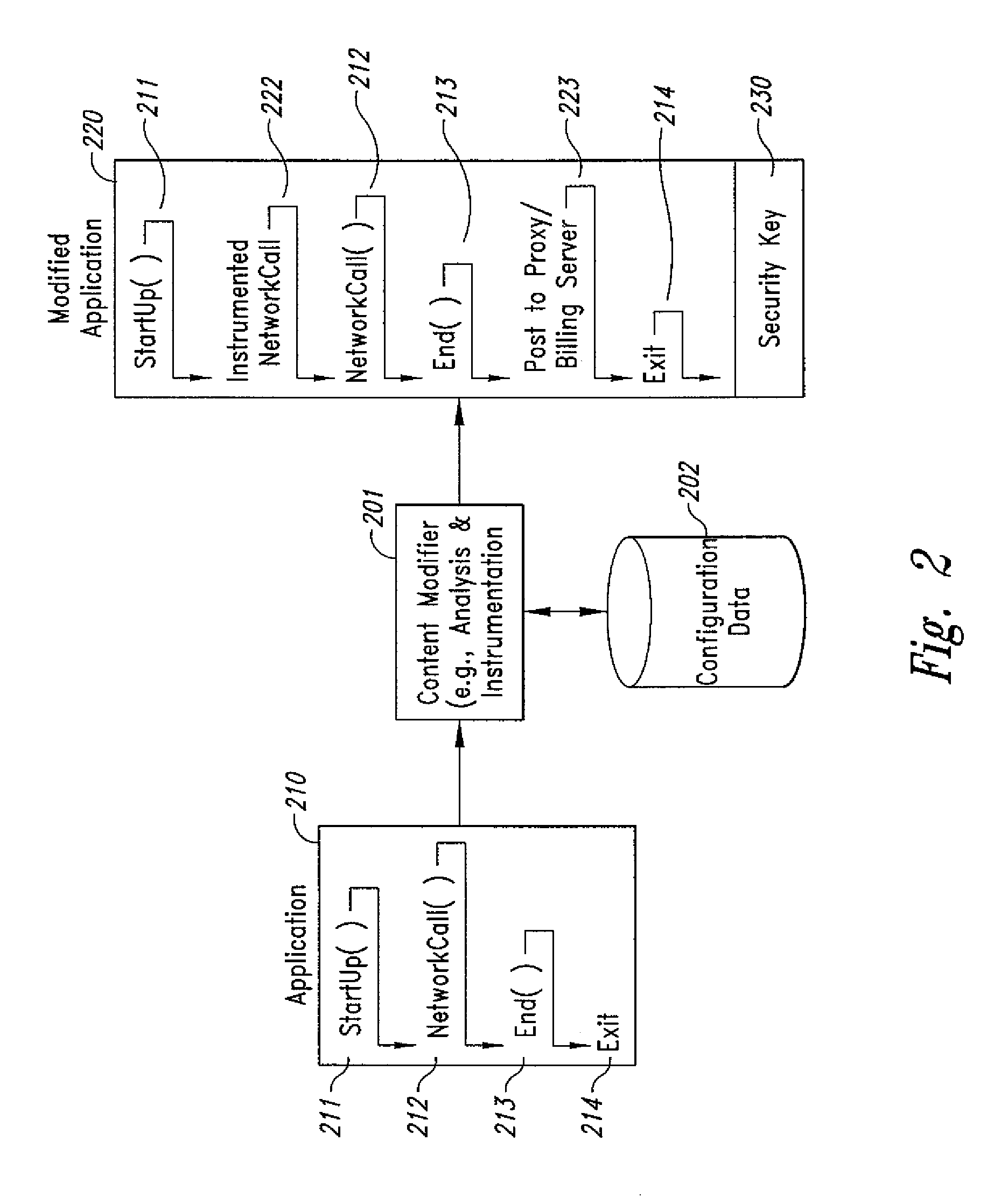
Method and system for transmission-based billing of applications
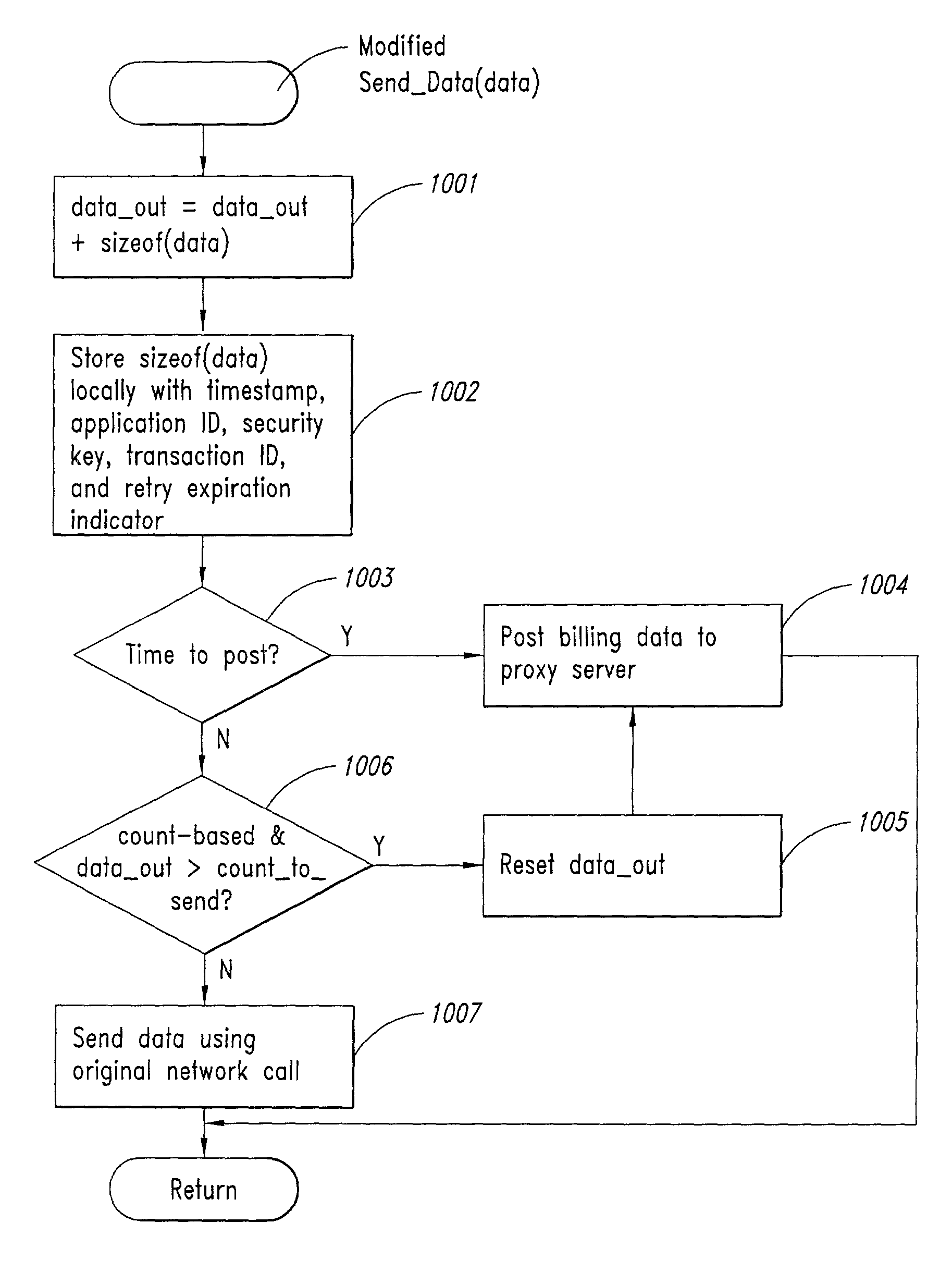
InactiveUS20020128984A1Short response timeImprove efficiencyMetering/charging/biilling arrangementsAccounting/billing servicesApplication computersApplication software
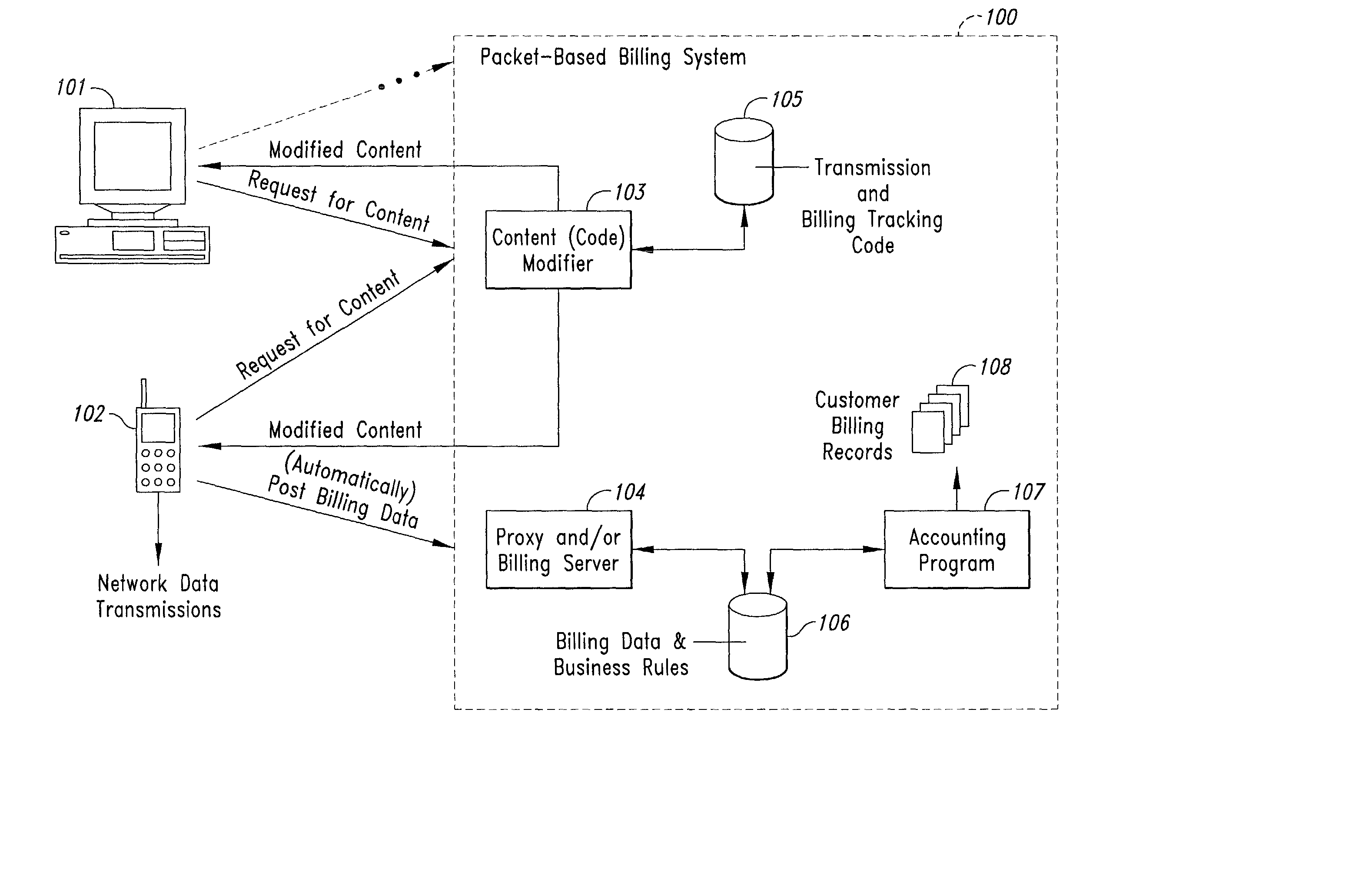
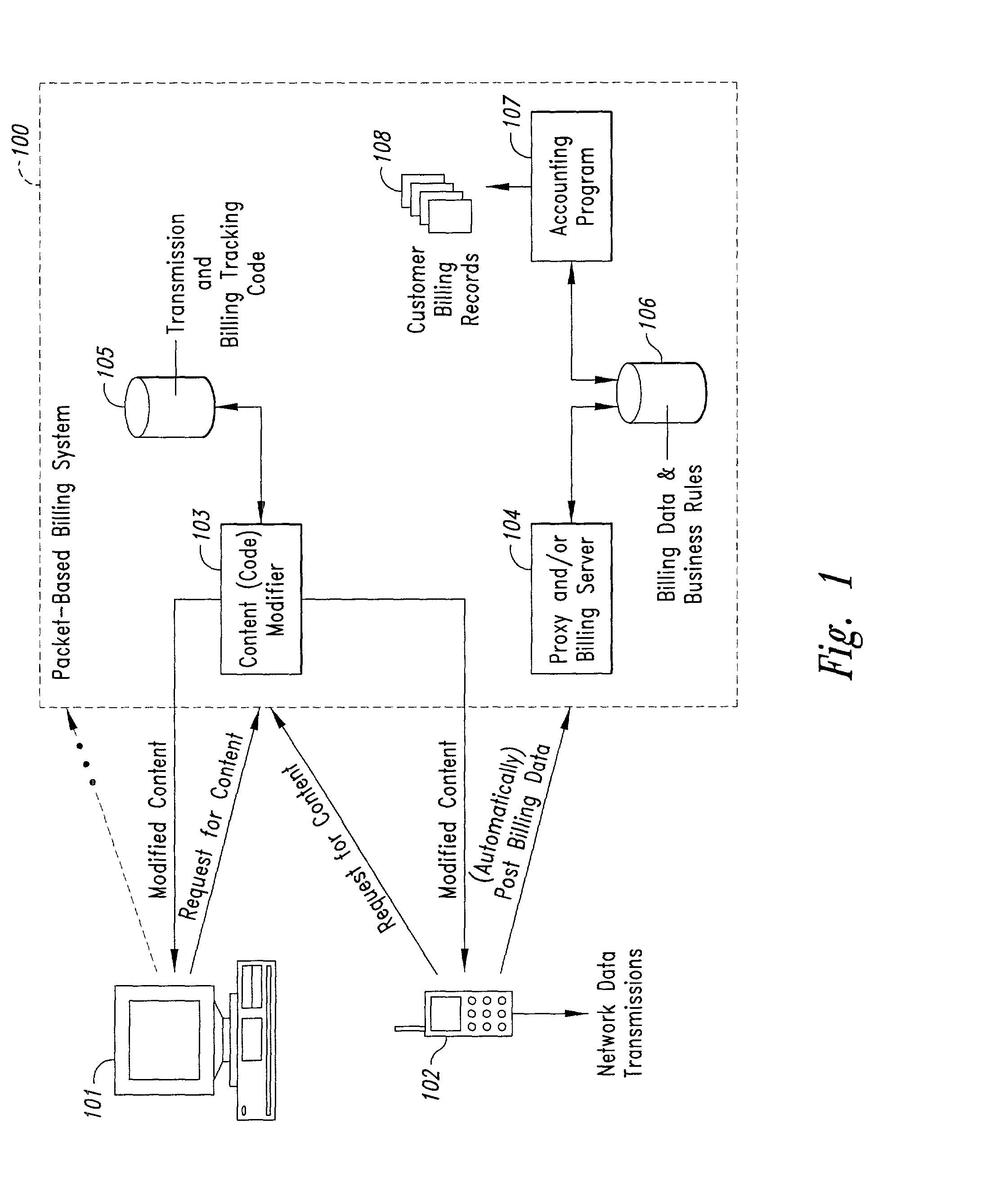
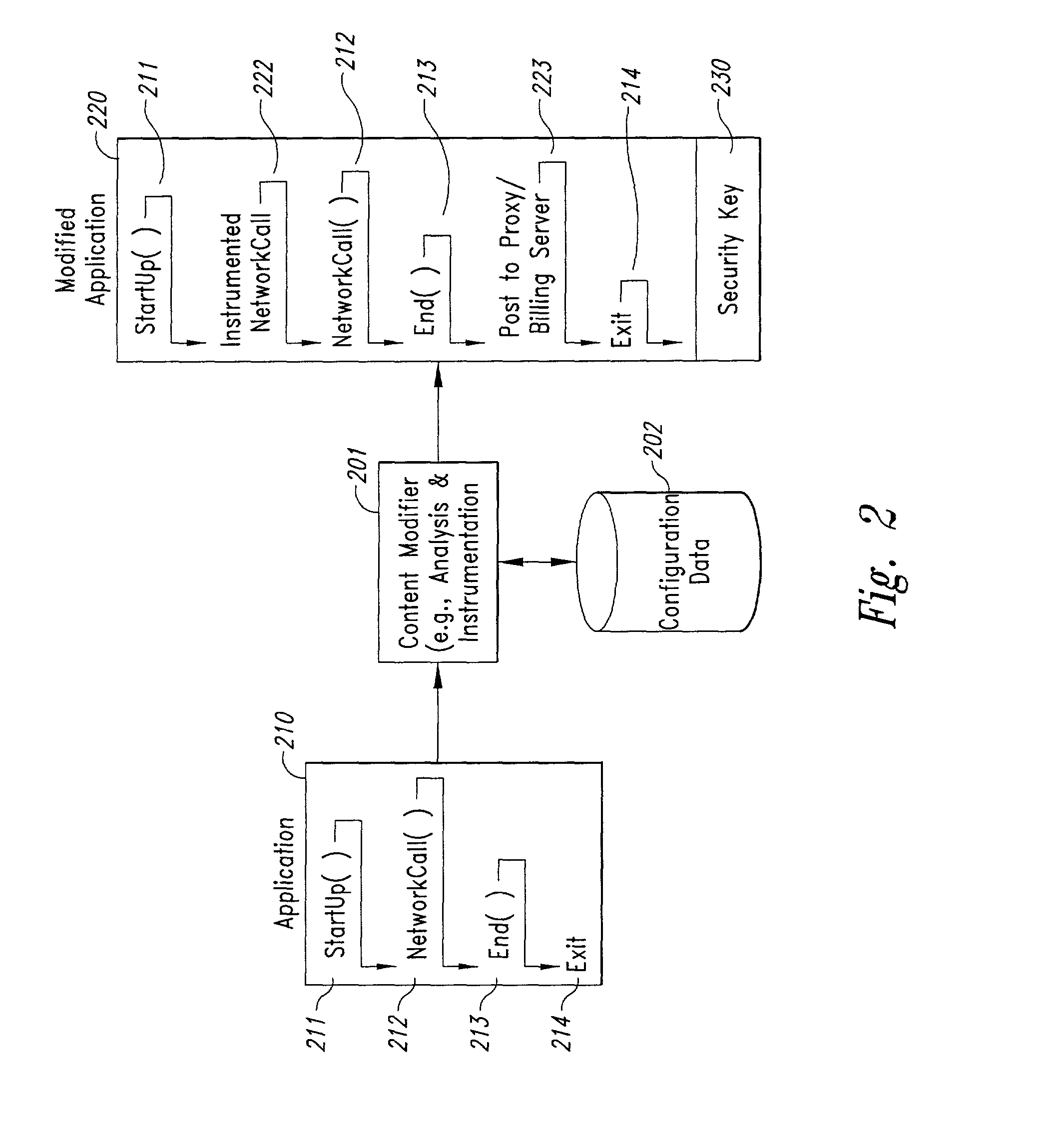
Computer-and network-based methods and systems for transmission-based billing are provided. Example embodiments provide a Packet-Based Billing System ("PBBS"), which enables application providers, such as carriers and content providers, to bill subscribers for the use of content on mobile subscriber devices, such as wireless devices, on a per-application, per-user basis based upon the extent of the usage. Embodiments of the present invention can also be used to bill subscribers for the use of content on a per-application, per-user basis for wired subscriber devices as well, using the same techniques. In operation, the PBBS provides modified content by inserting billing and tracking code into content returned to a requesting device. The modified content, when executed, tracks the amount of data sent and received between the content and a network and posts the accumulated data to a proxy / billing server according to business rules for an interval / frequency to post such data. The proxy / billing server stores the raw billing data and an accounting program retrieves the billing data to generate customer (call) data records. Business rules that specific different charges for different content or users can be incorporated into the system.
Owner:GOOGLE TECH HLDG LLC +1
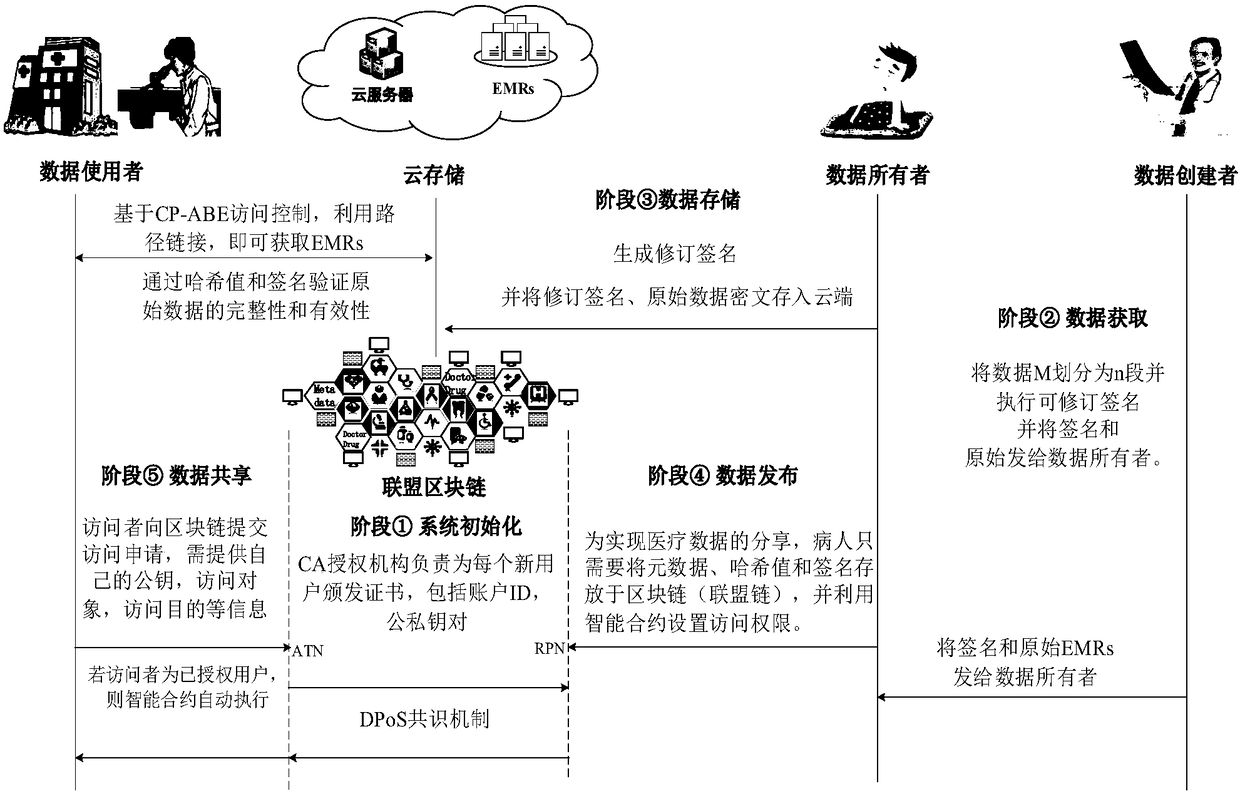
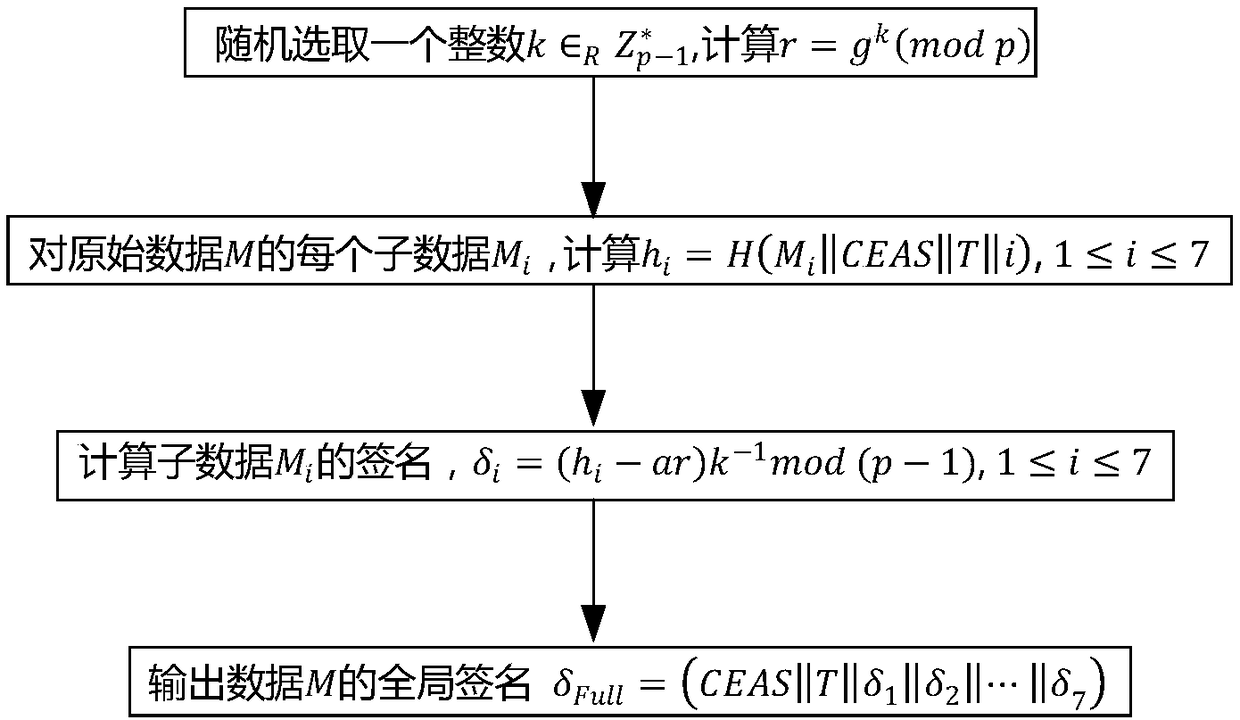
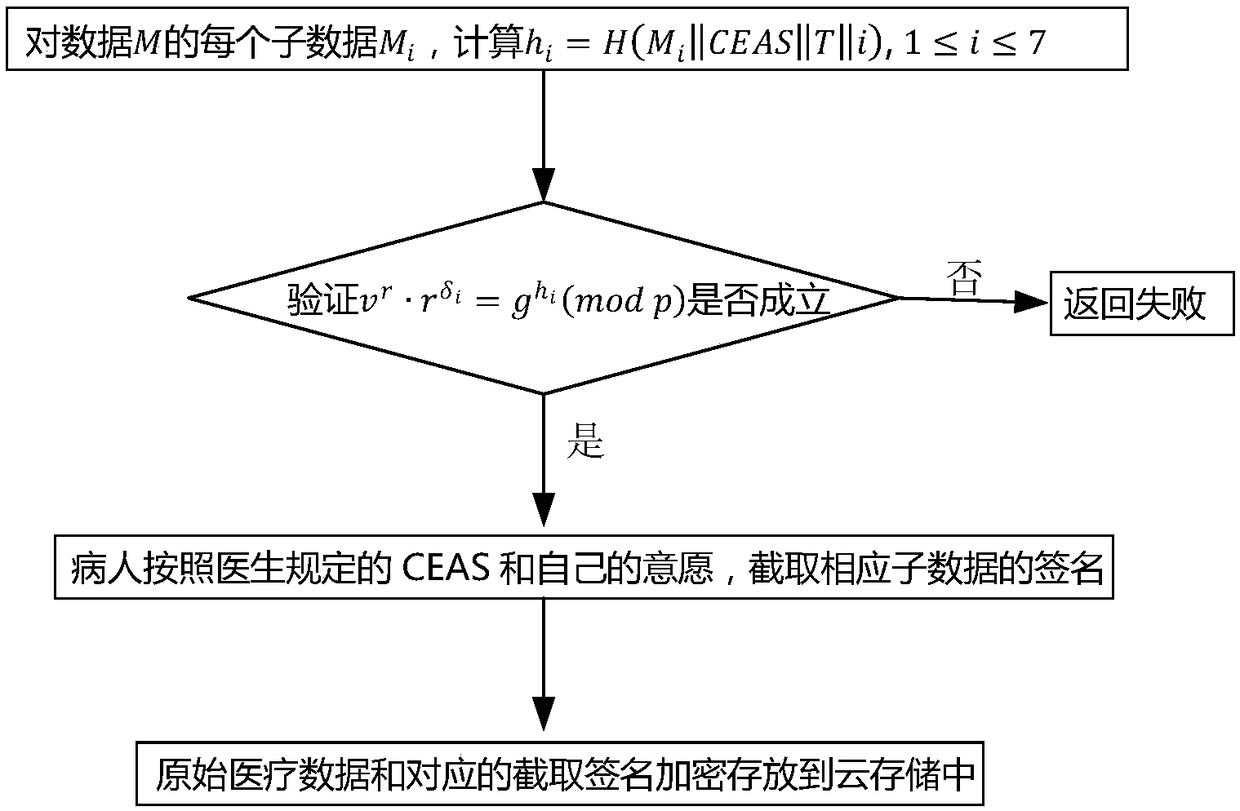
Electronic medical record storage and sharing model and method based on blockchains
ActiveCN109326337AEasy to controlImplement storage securityDigital data protectionPatient-specific dataPrivacy protectionData access
The invention discloses an electronic medical record storage and sharing model and method based on the blockchains and solves problems of patient's rights of access to personal medical data and insecure storage and sharing of sensitive medical data in the prior art. The model is characterized by comprising data creators, data owners, cloud storage, federated blockchains and data consumers, whereinthe blockchain is a control center. The method comprises steps that system initialization is performed; medical data are acquired, and data storage with intercepted signatures is employed; data publishing with the improved DPOS consensus mechanism is employed; data sharing based on smart contracts is performed. The method is advantaged in that security, reliability, privacy protection and securestorage are achieved, in combination with the cloud storage technology and the interceptable signature technology, in the federated blockchains, users can set sharing conditions through the smart contracts, safe and effective data sharing and access can be realized, and strong practicality is achieved.
Owner:XIDIAN UNIV
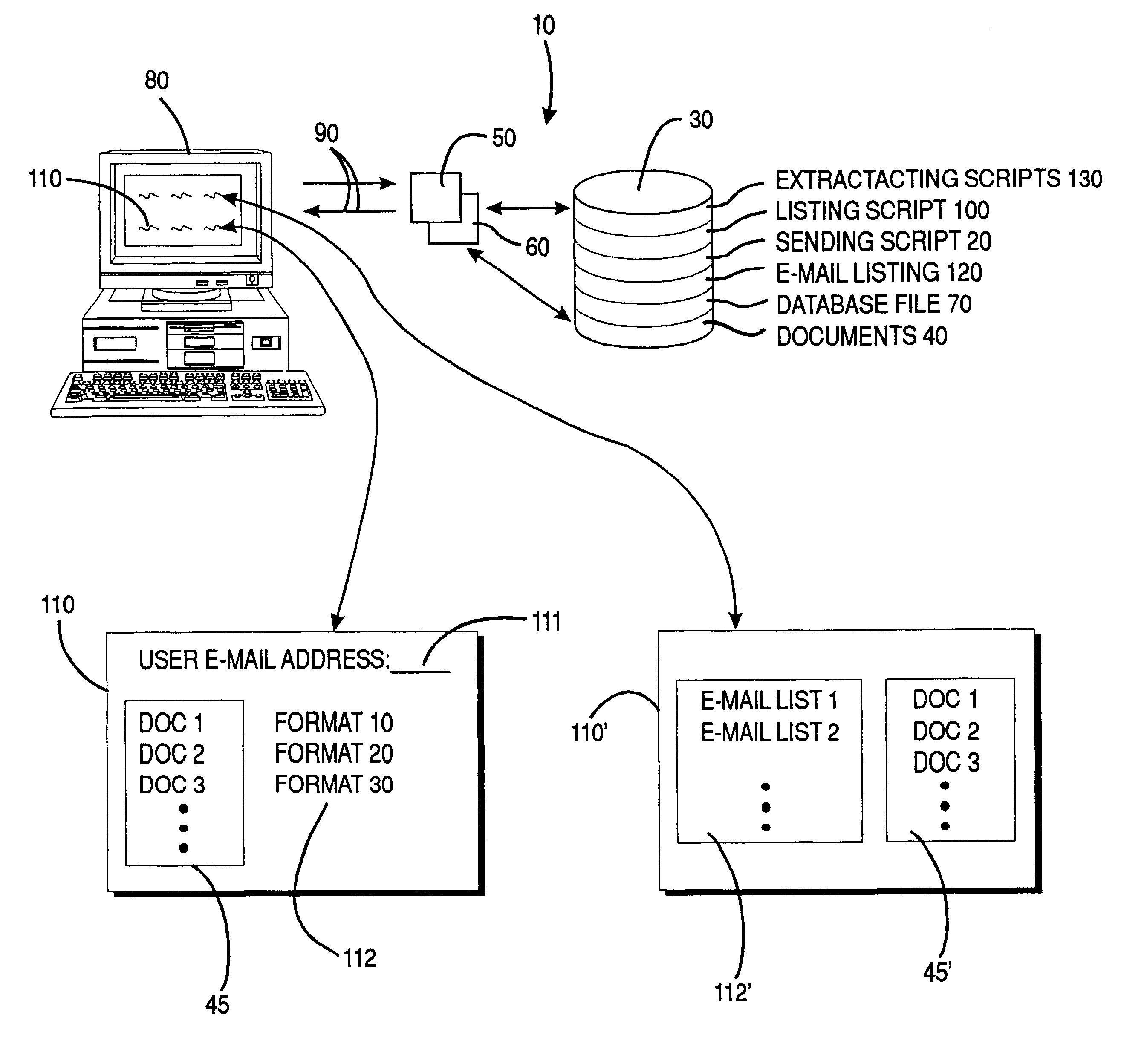
Transferring selected formatted documents over a computer network using interface script
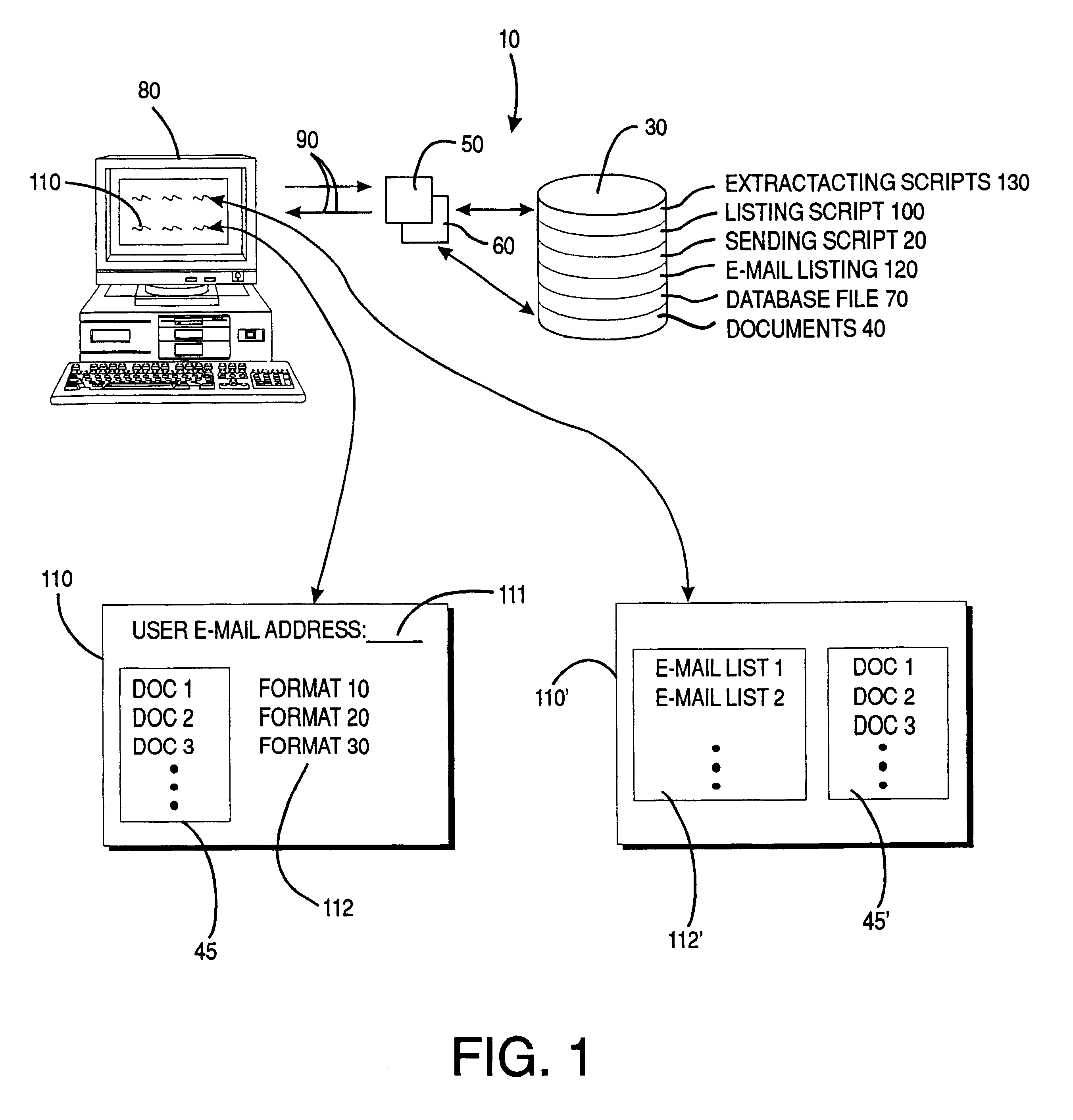
InactiveUS6272485B1Low costReduce usageData processing applicationsMultiple digital computer combinationsSpread sheetEmail address
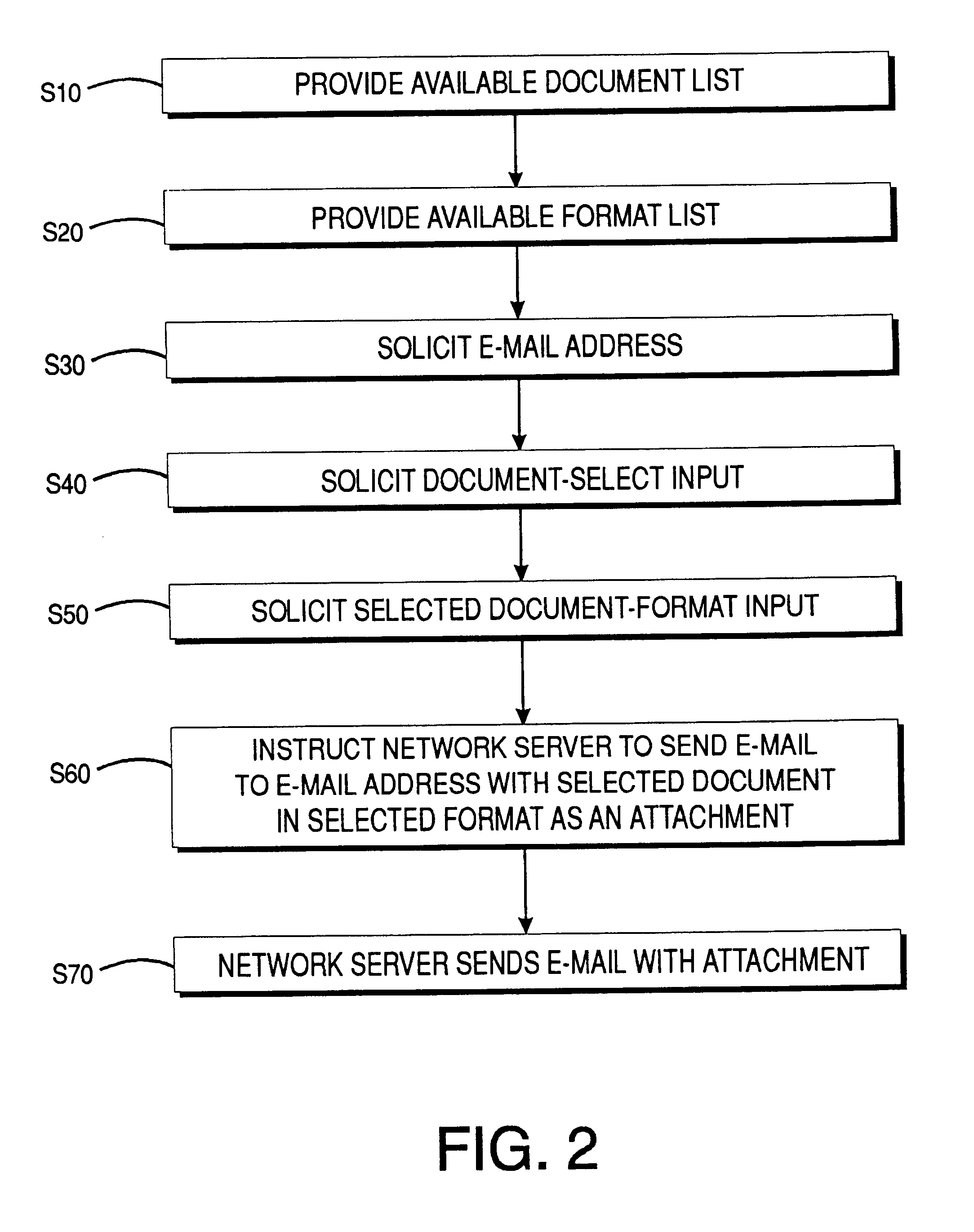
A system and method for transmission of documents including word processing, spread sheets, and other formatted documents, over a computer network with no need for additional formatting software by using a CGI sending script to send e-mail with the selected document, in its native format, as an attachment to e-mail submissions or obtained directly from websites using standard word processing programs, with end user prerequisites for using the method and system being standard word processing software and e-mail capability; the form may returned to the server in electronic form, and the accompanying data posted to one or more databases, or automatically stored on disk, printed, or routed to other e-mail addresses.
Owner:CREATIVE INTERNET APPL
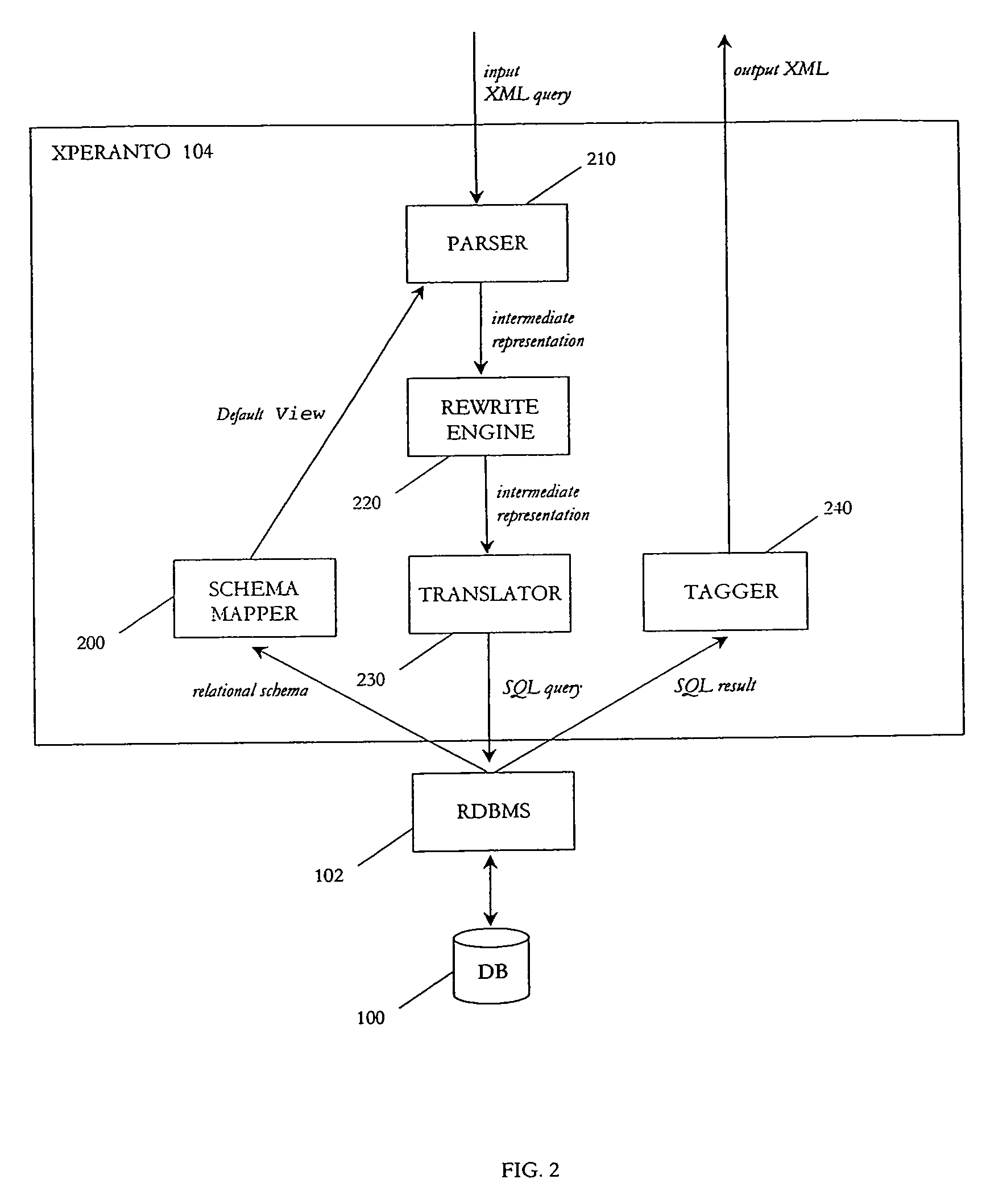
Using an XML query language to publish relational data as XML
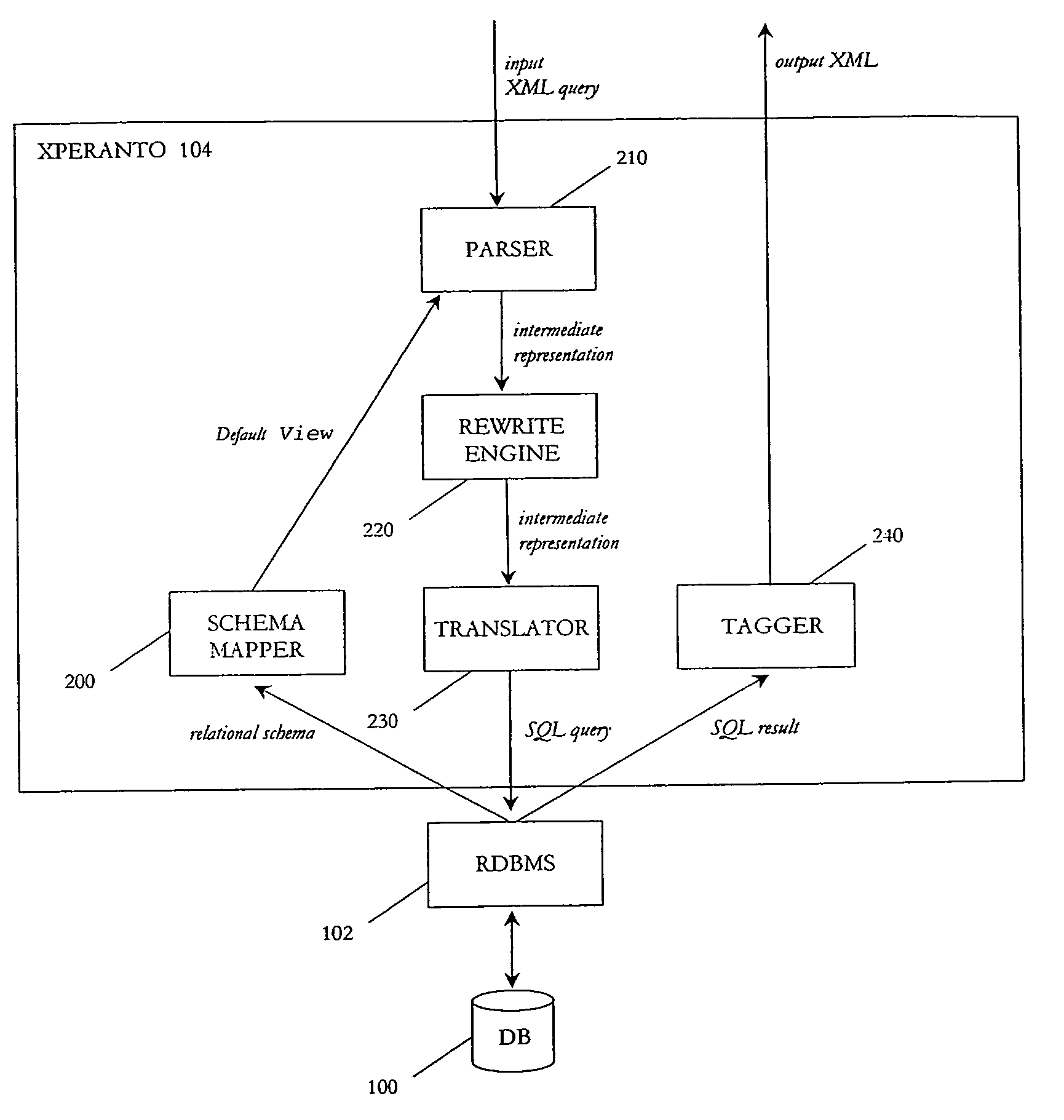
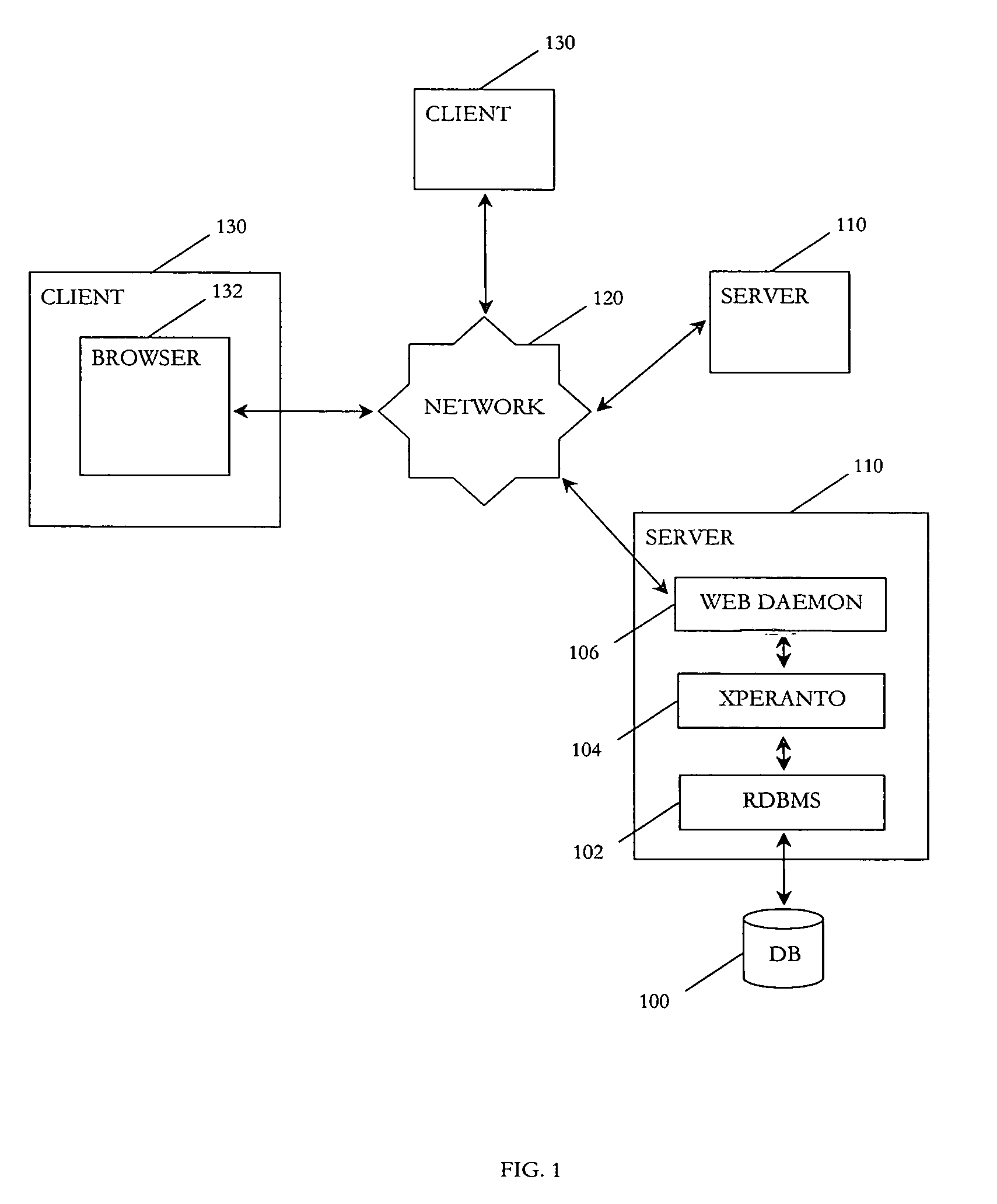
InactiveUS6947945B1Data processing applicationsDigital data information retrievalRDF query languageXML database
A method for publishing relational data as XML by translating XML queries into queries against an relational database. Conversion of the relational database into an XML database is not required. Each relational table is mapped to a virtual XML document, and XML queries are issued over these virtual documents. An XML query is parsed and transformed into a language-neutral intermediate representation, which is a sequence of operations describing how the output document is derived from the underlying relational tables. The intermediate representation is then translated into an SQL query over the underlying relational tables and into instructions for a tagger. The SQL query is executed, and the SQL query results are then fed into the tagger, which follows tagger instructions to generate the marked up output.
Owner:IBM CORP
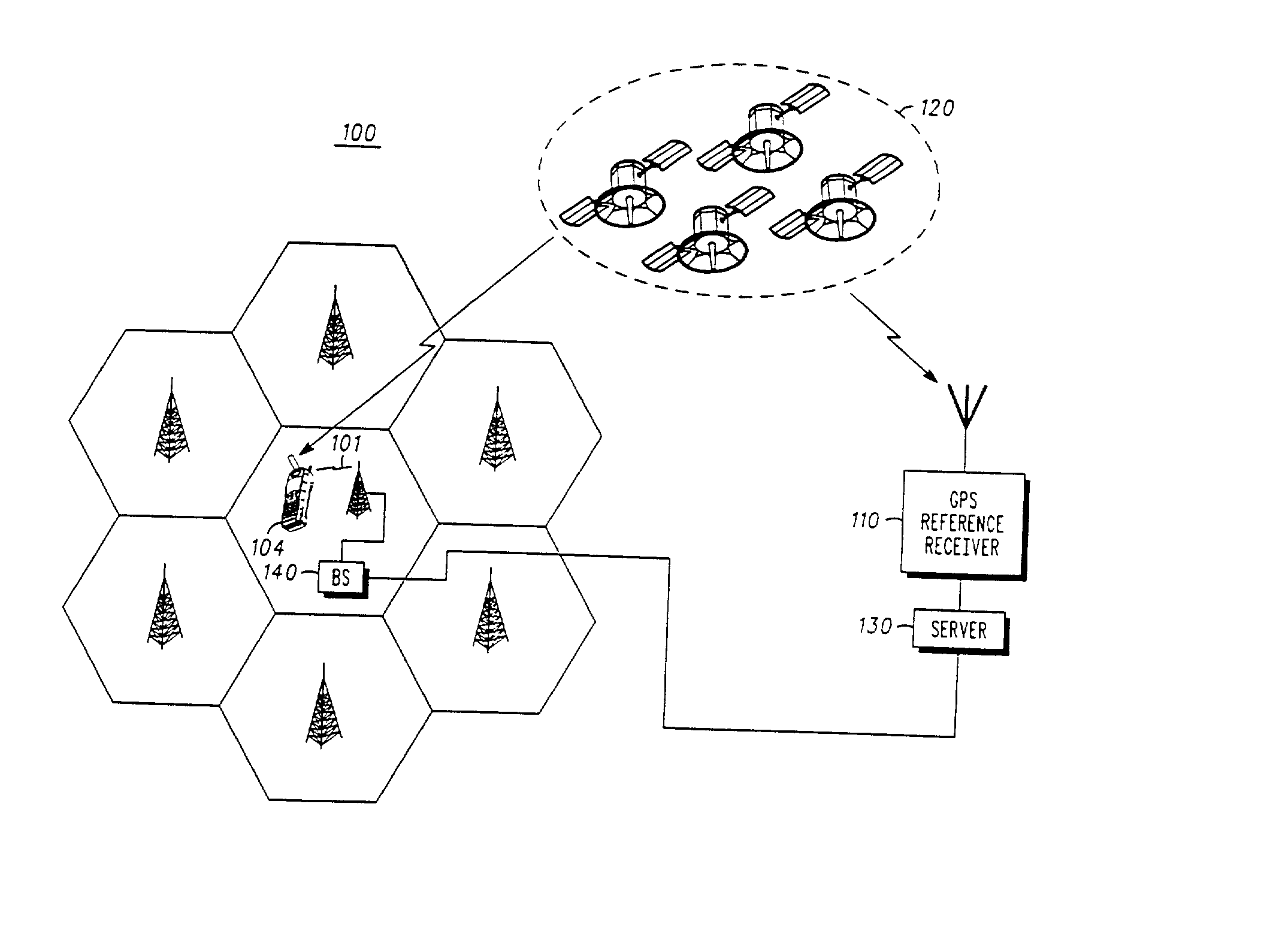
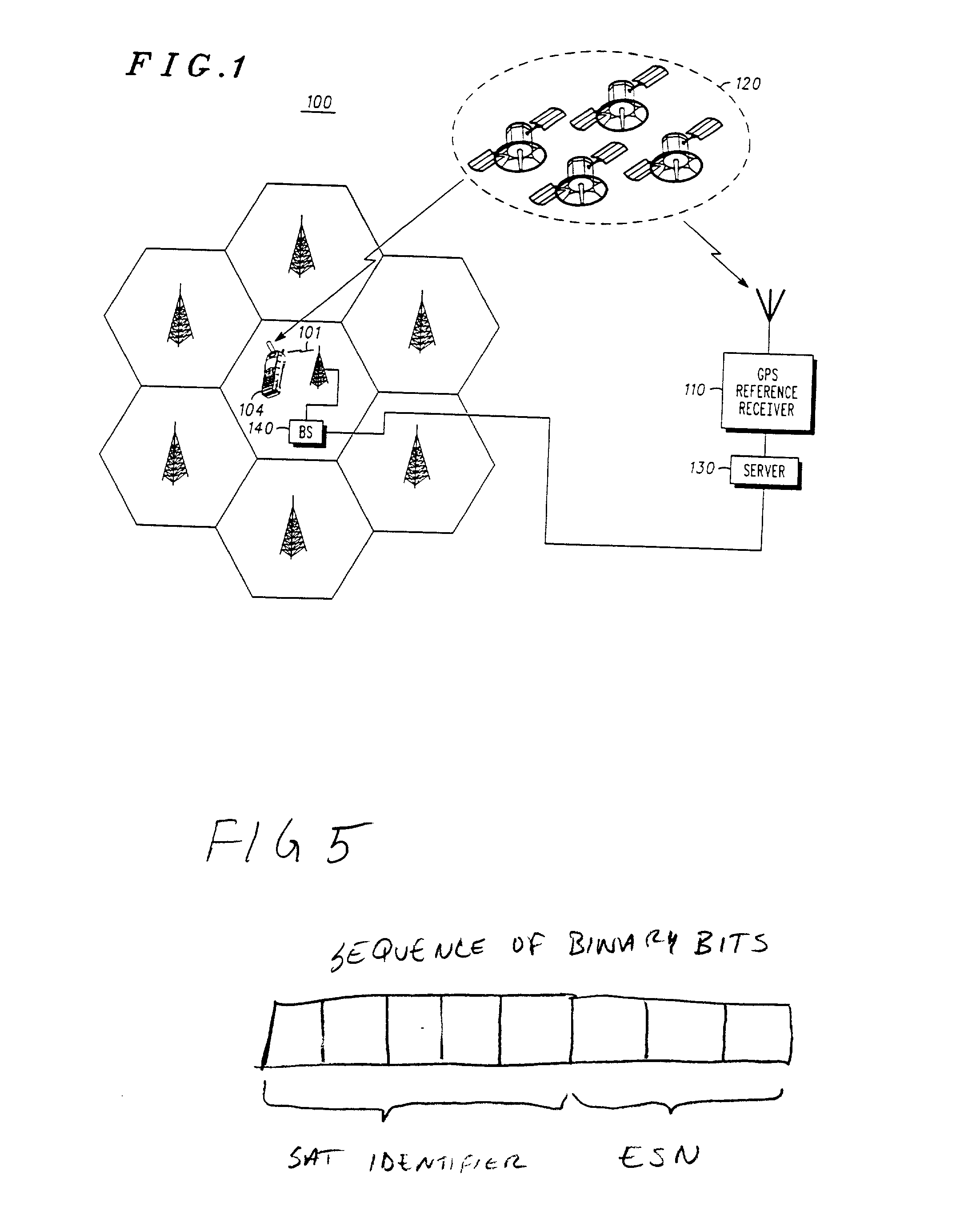
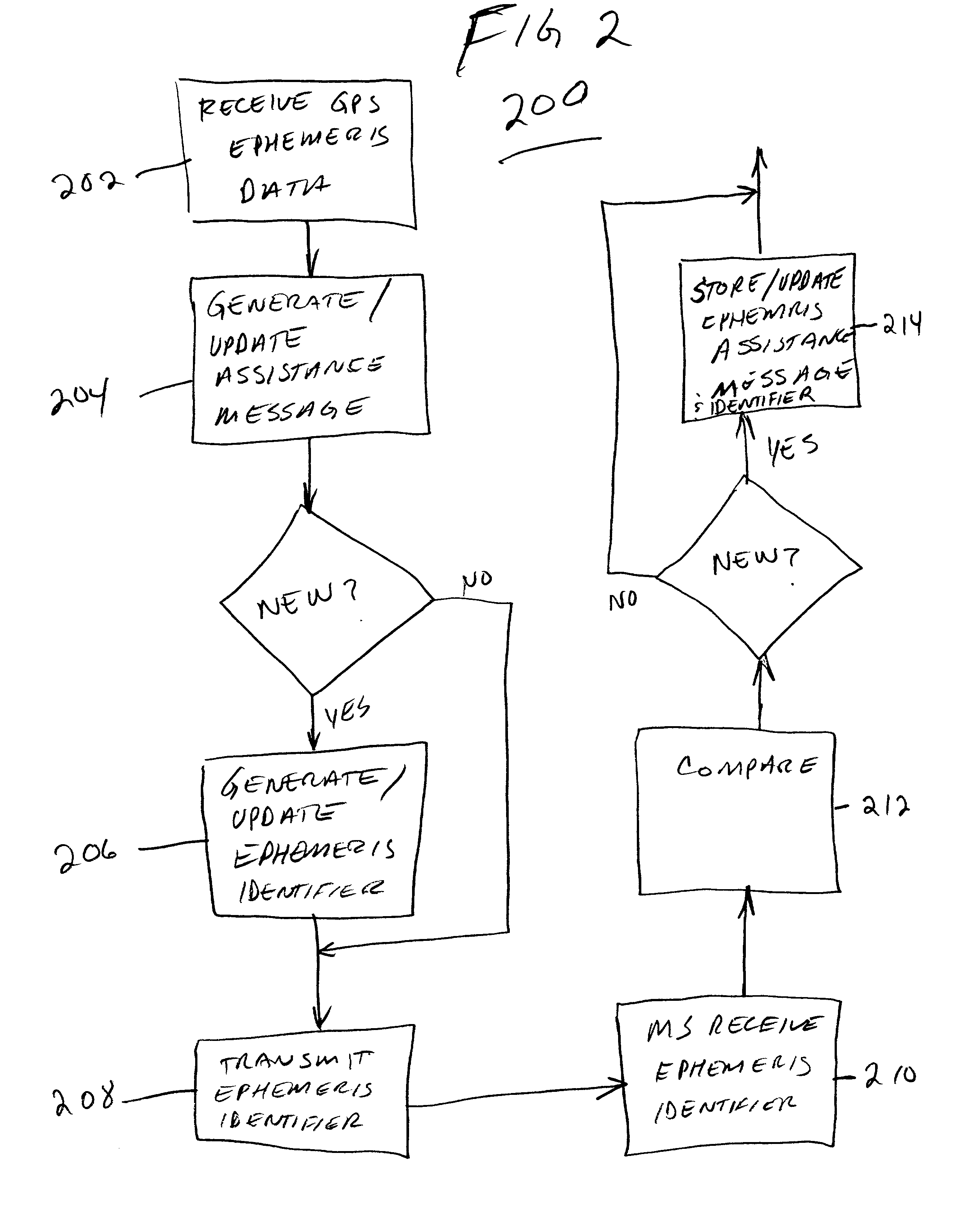
GPS assistance messages in cellular communications networks and methods therefor
InactiveUS20020168985A1Energy efficient ICTRadio/inductive link selection arrangementsEphemerisMobile station
GPS assistance message and data issue identifiers for transmission to GPS enabled mobile stations in cellular communications networks and methods therefor. The GPS data issue identifiers indicate whether GPS data, for example corresponding ephemeris and almanac data, stored at the mobile station requires updating. In the exemplary 3rd generation (W-CDMA / UMTS) architecture, the GPS assistance message is a System Information Block (SIB), and the GPS ephemeris data identifier and corresponding satellite identifier is encoded in a value tag included in a Master Information Block (MIB).
Owner:GOOGLE TECH HLDG LLC
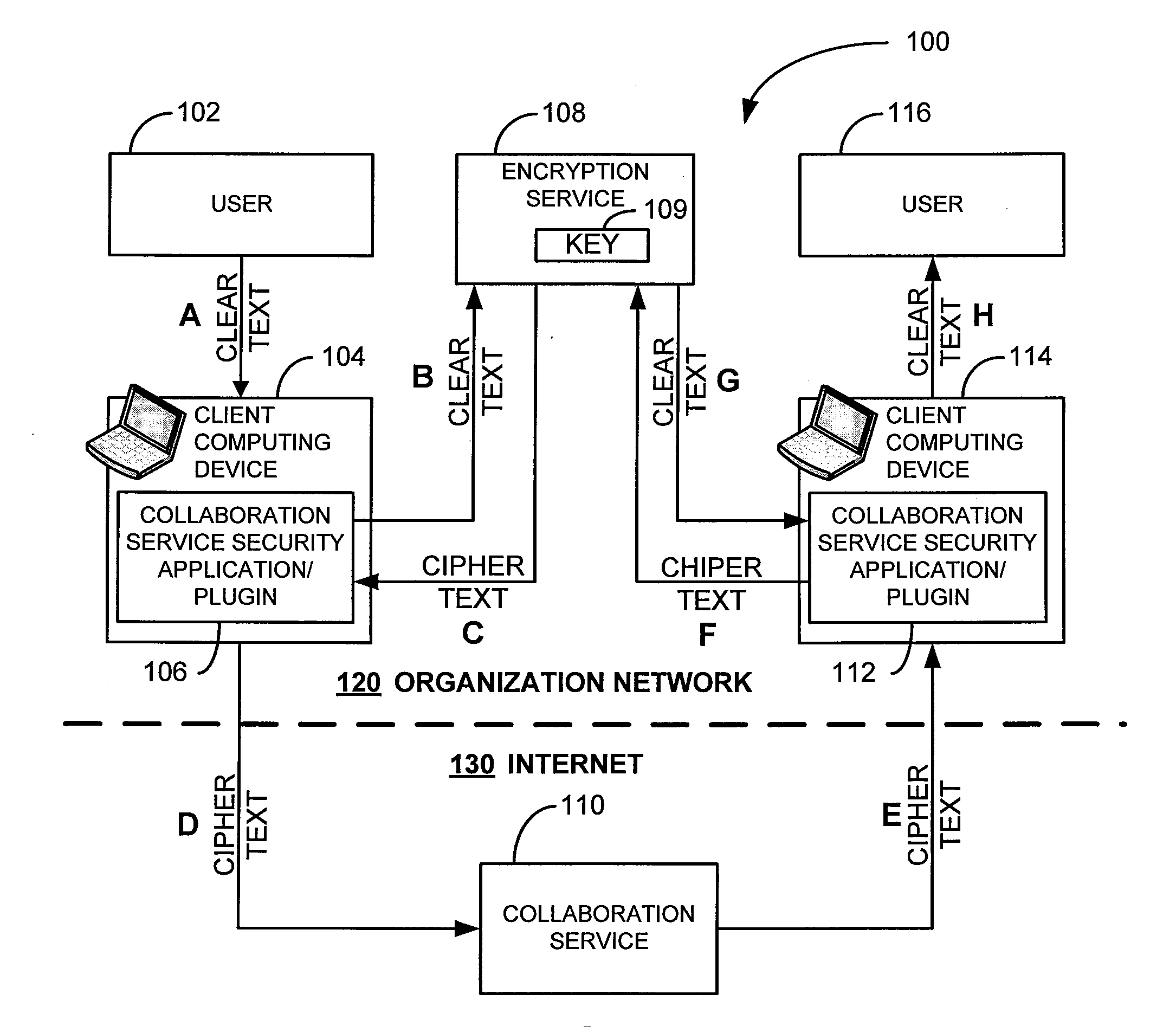
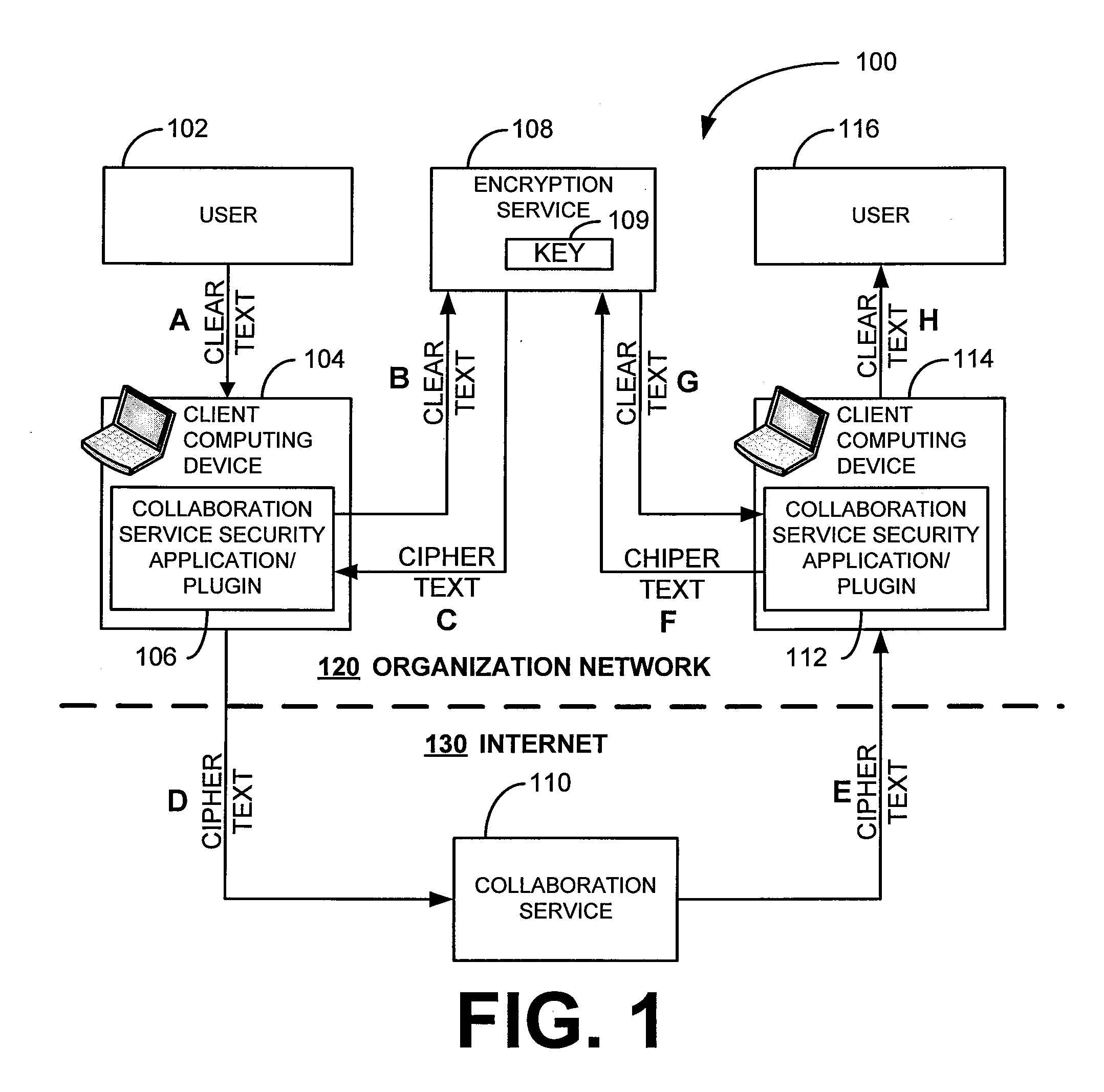
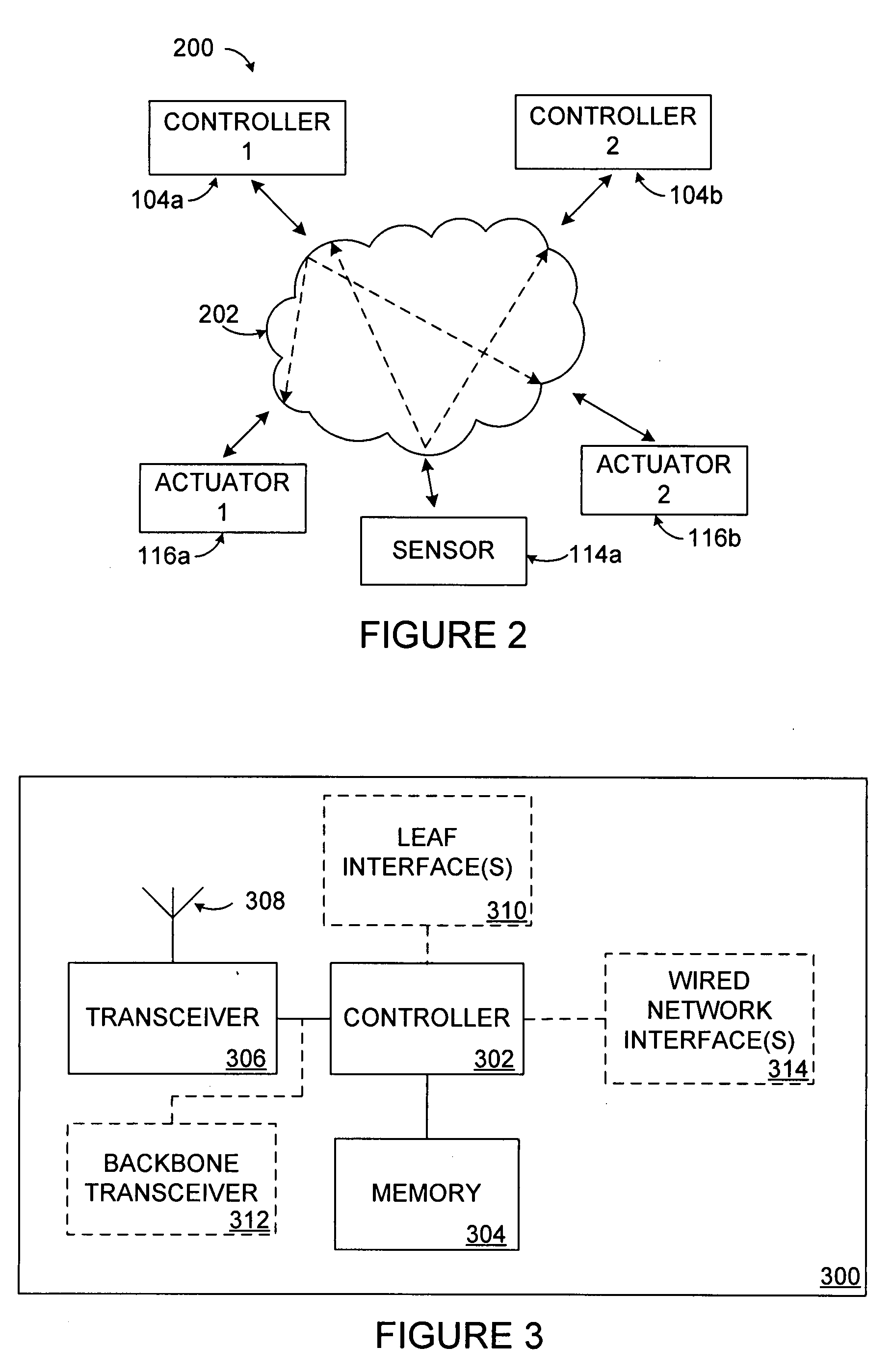
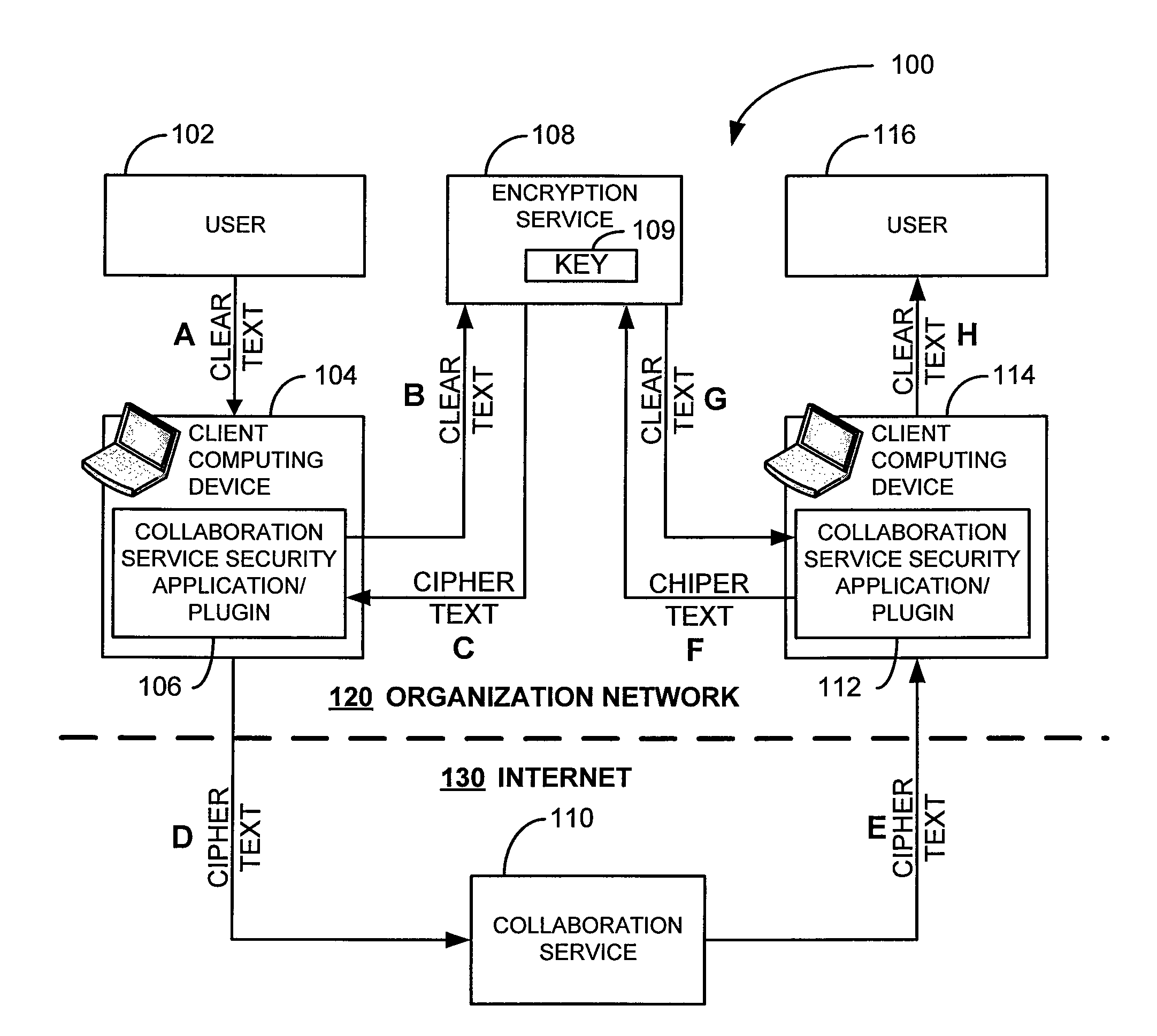
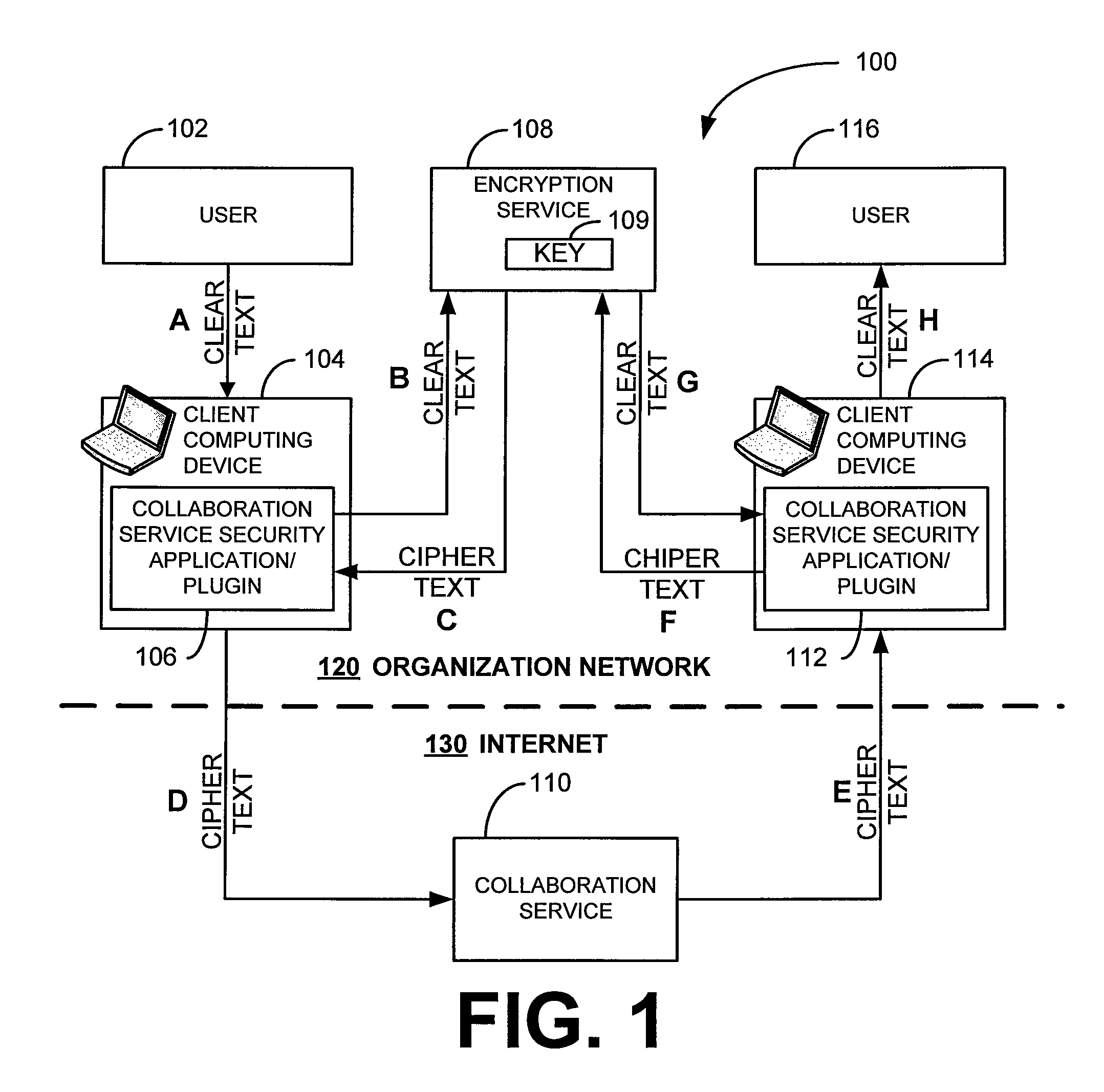
Security for collaboration services
ActiveUS20110145571A1Key distribution for secure communicationUser identity/authority verificationSecurity solutionApplication software
Owner:SAP AG
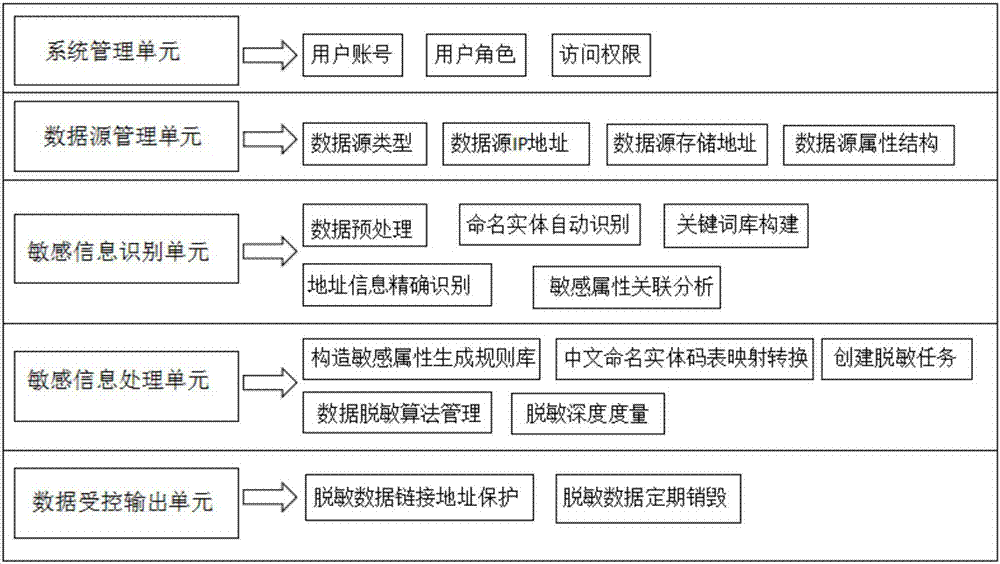
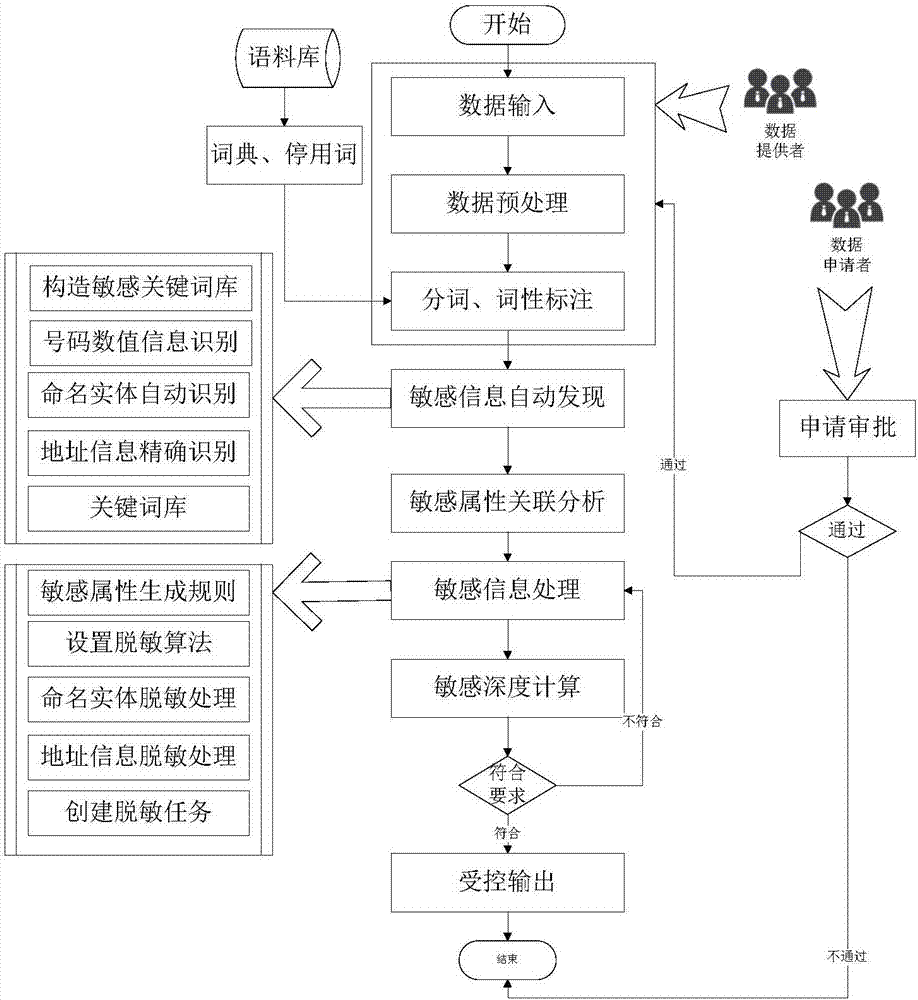
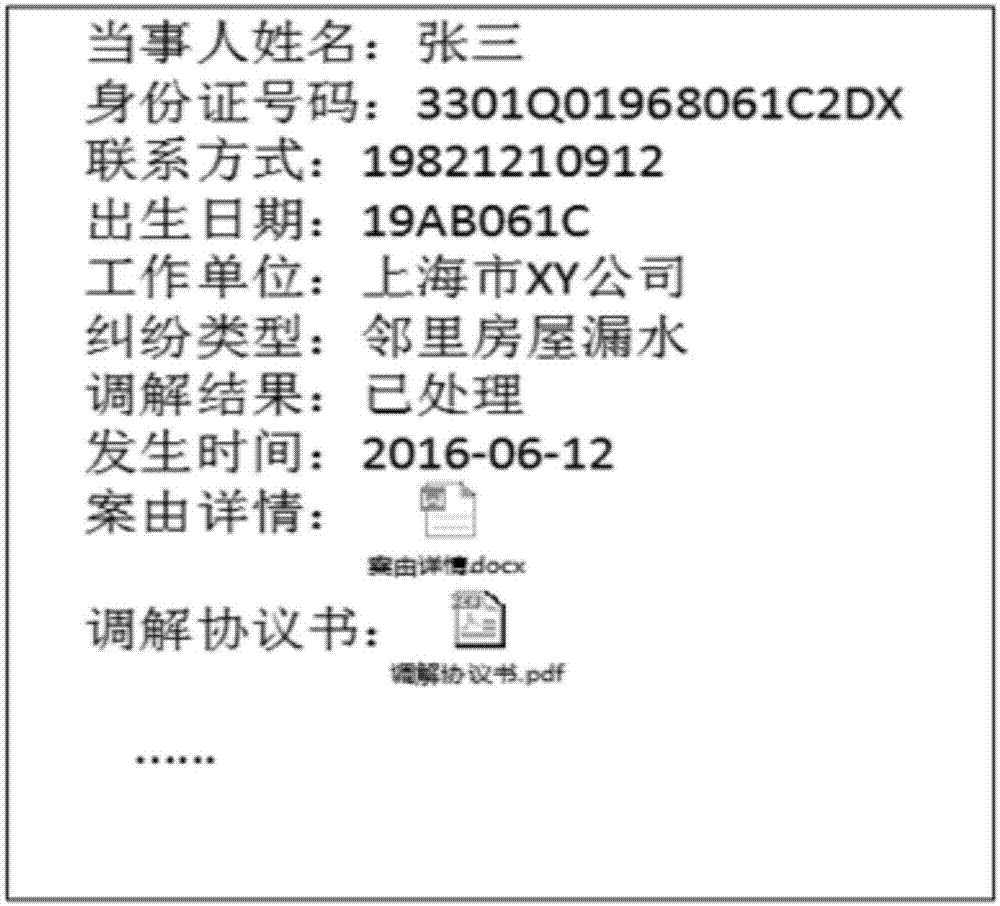
Sensitive information desensitization method and system for data sharing
ActiveCN107480549AAvoid duplicationAvoid rebuildingDigital data protectionSpecial data processing applicationsInformation processingData set
The invention relates to a sensitive information desensitization method and system for data sharing. According to the method, by adopting statistics, a natural language processing technology and a machine learning technology, the protection of sensitive data in the whole process from data publishing to data application and usage, and automatic identification of sensitive information of such as named entities and addresses is put forward on the basis of the establishment of a sensitive information keyword library, named entities, addresses and the like is put forward; a Sigmoid function is used for calculating the correlation degree of sensitive attributes; a desensitization strategy is carried out in a combined mode of establishing a sensitive attribute generation rule library and adopting a named entity desensitization rule and a core desensitization algorithm; deep desensitization calculation is conducted in combination with numerical sensitive attributes and classified sensitive attributes separately, the desensitization degree of a whole data set is obtained, and the controlled output of data and the like are achieved by downloading a link address hash; thus, the safety of data sensitive information and a sensitive information processing strategy which meets analysis and mining requirements to the maximize degree can be ensured, and the method and system have the advantages of being good in desensitization effect, high in reliability and the like.
Owner:ENJOYOR COMPANY LIMITED
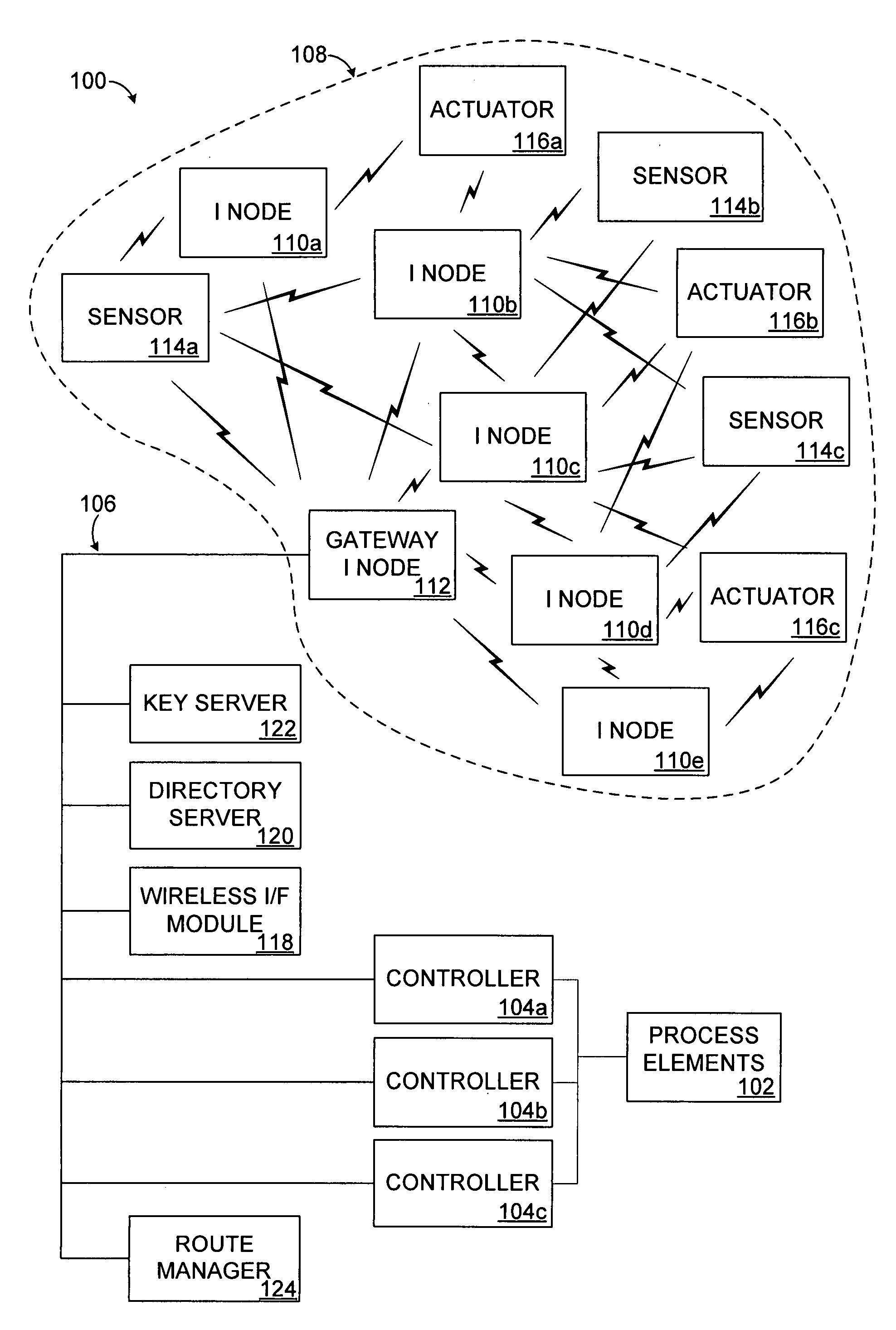
System and method for providing simultaneous connectivity between devices in an industrial control and automation or other system
ActiveUS20090109889A1Readily apparentBroadcast transmission systemsData switching networksNetwork addressingNetwork address
A system, apparatuses, and methods support simultaneous connectivity between devices in an industrial control and automation or other system. For example, a data publisher can publish or provide data to multiple data subscribers. This can be done using a multicast group associated with the multiple data subscribers. The data publisher transmits a data message using a network address associated with the multicast group. Each data subscriber associated with the multicast group receives a copy of the data message. As a particular example, the data publisher could represent a wireless sensor or wireless actuator in the industrial control and automation or other system. Also, the data subscribers could represent multiple controllers or actuators in the industrial control and automation or other system. In this way, the multicasting functionality allows for simpler connectivity or interaction between devices in the industrial control and automation or other system.
Owner:HONEYWELL INT INC
Security for collaboration services
ActiveUS8572369B2Key distribution for secure communicationUser identity/authority verificationSecurity solutionApplication software
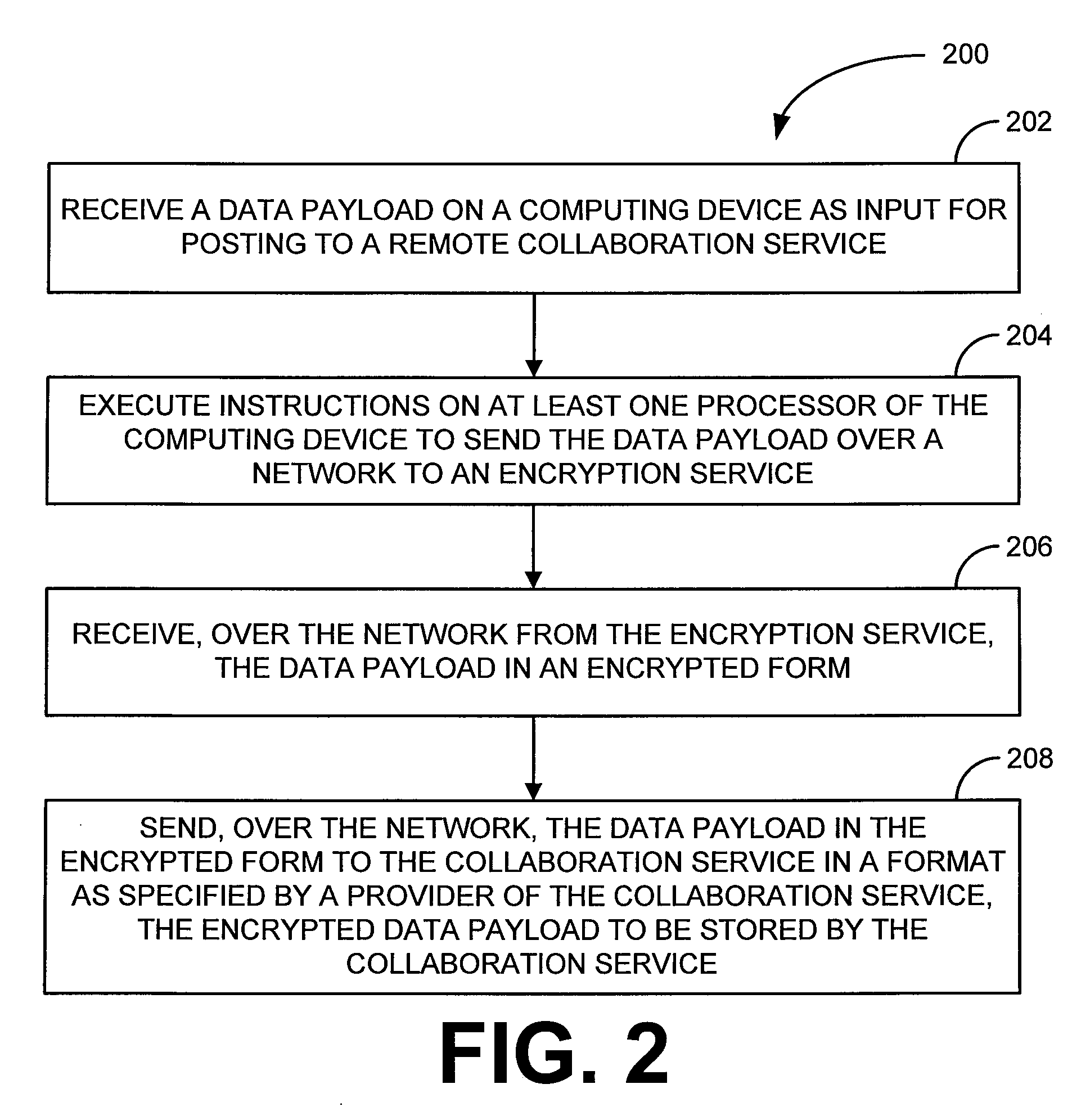
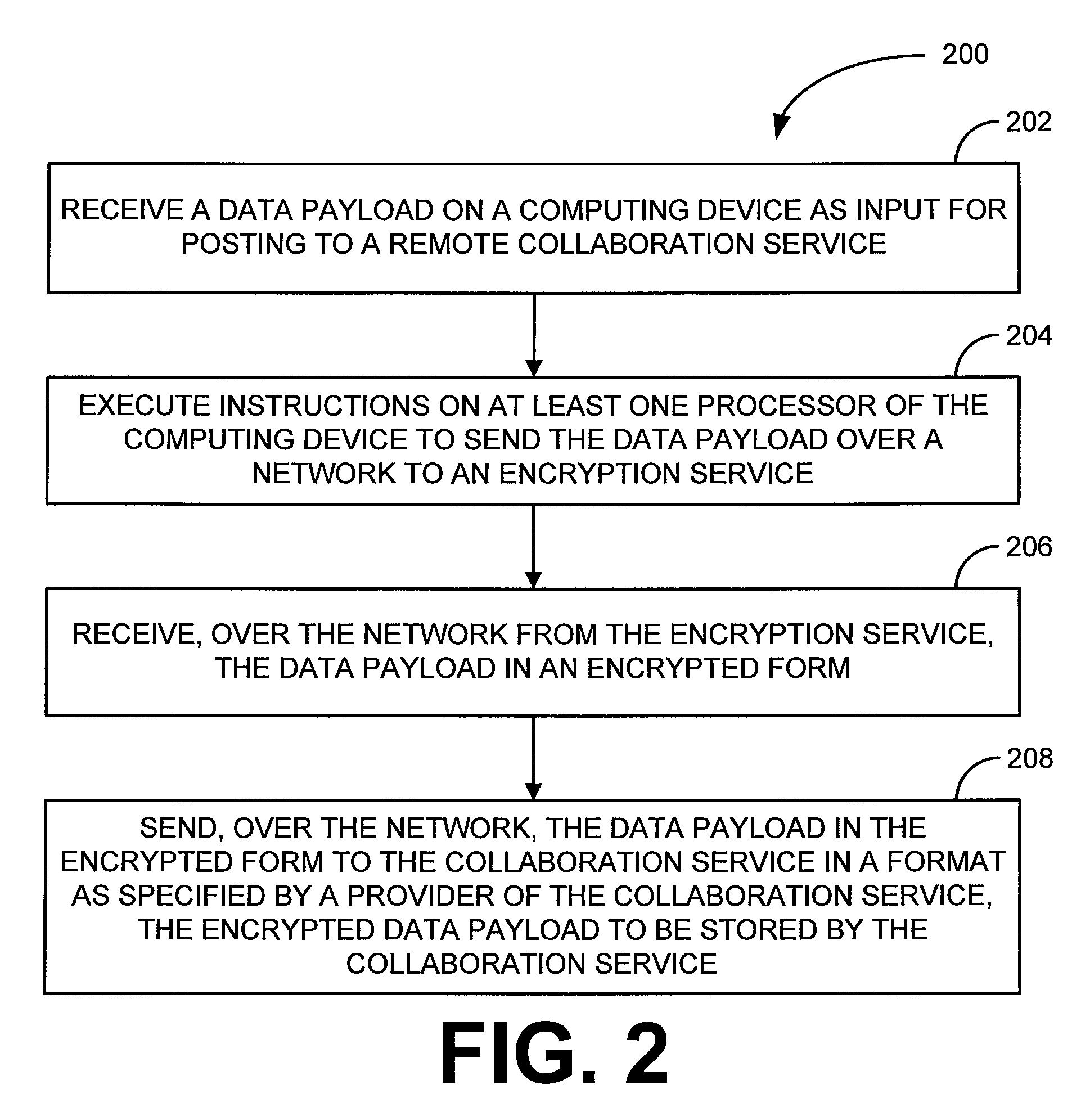
Various embodiments, in the form of at least one of systems, methods, and software, are provided that include security solutions for use of collaboration services. Some embodiments include encrypting data to be sent to and stored by a collaboration service. These and other embodiments include capturing, within a computer application used to post data to a collaboration service, data to be sent to the collaboration service, encrypting the captured data, and returning the data in an encrypted form to the computer application for posting to the collaboration service.
Owner:SAP AG
Spread-spectrum data publishing system
InactiveUS6118824ASpecial service provision for substationSpatial transmit diversityBroadcast channelsSpread spectrum
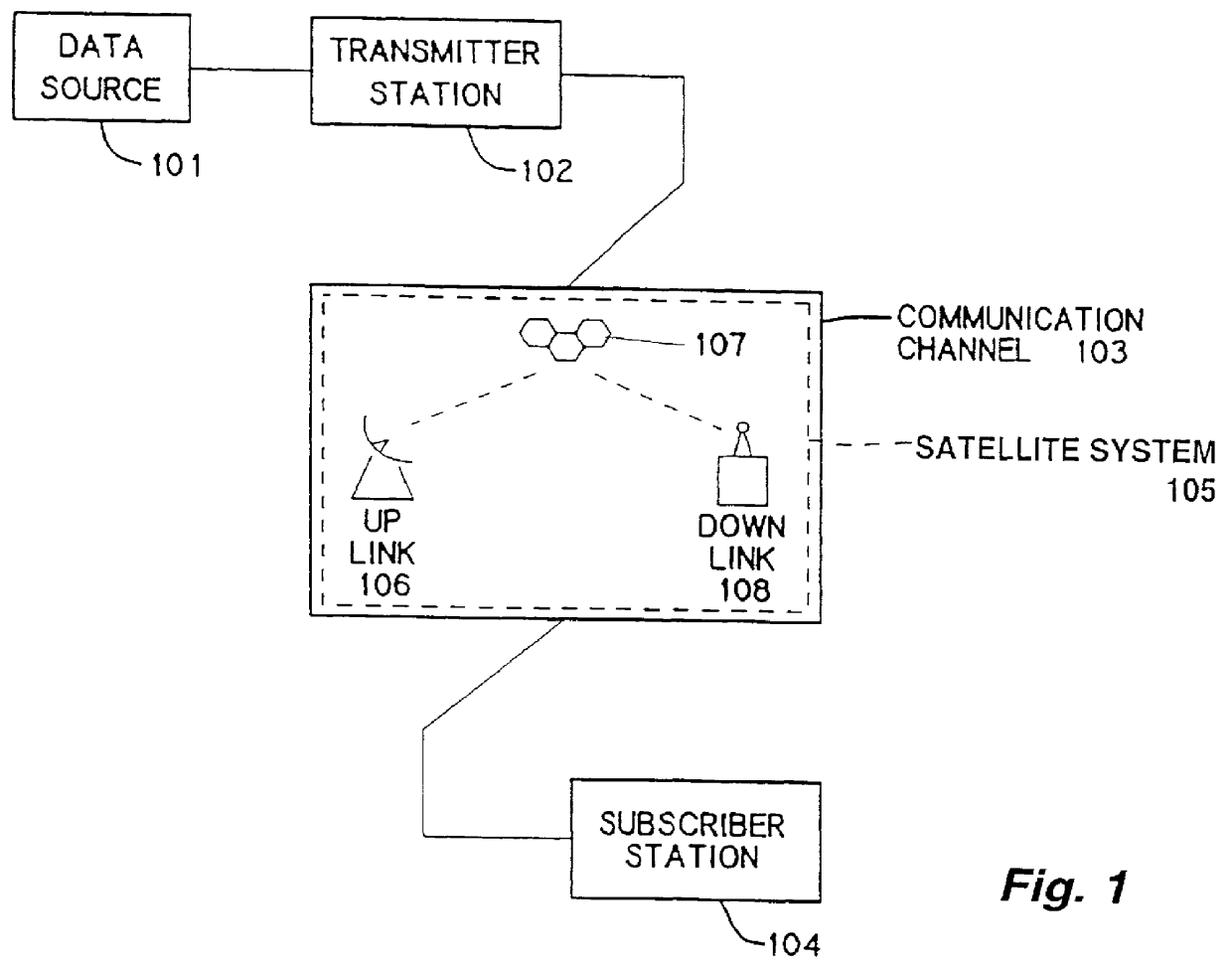
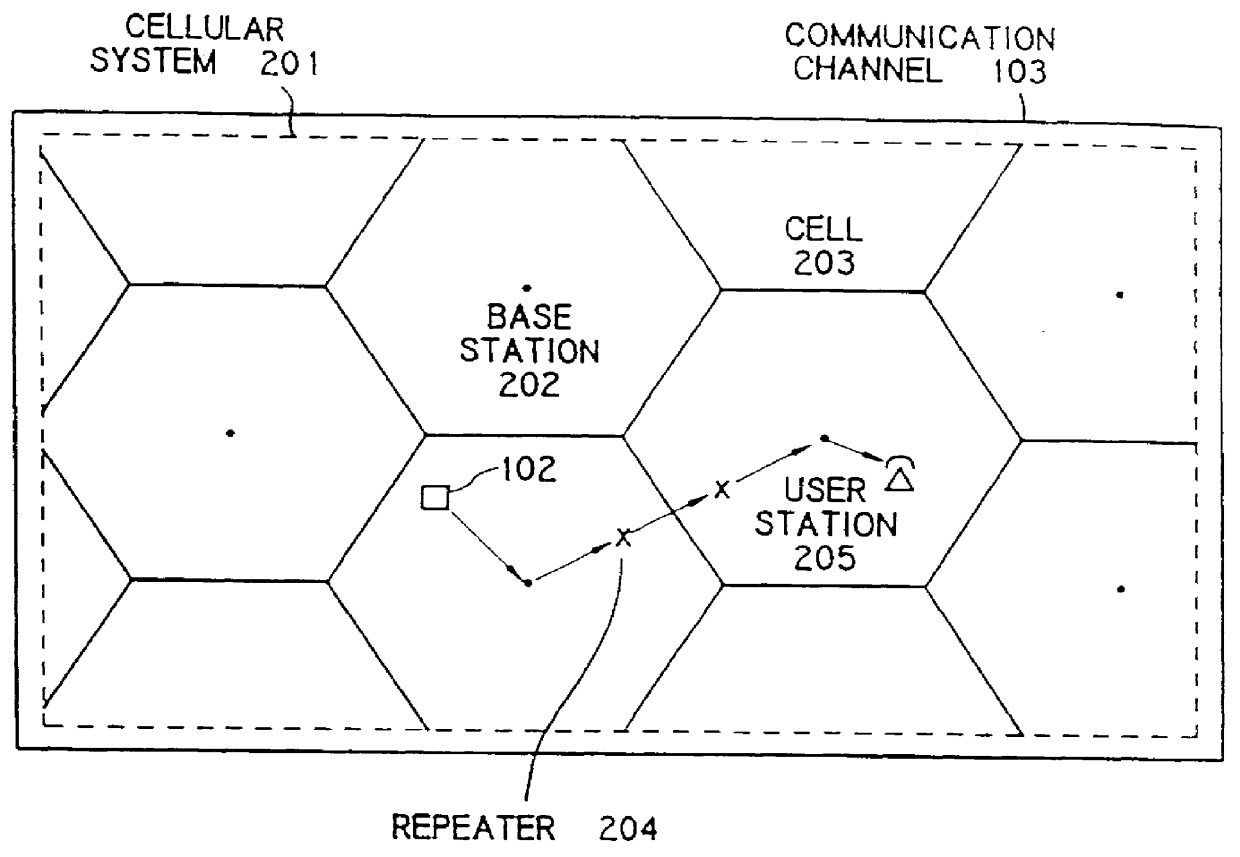
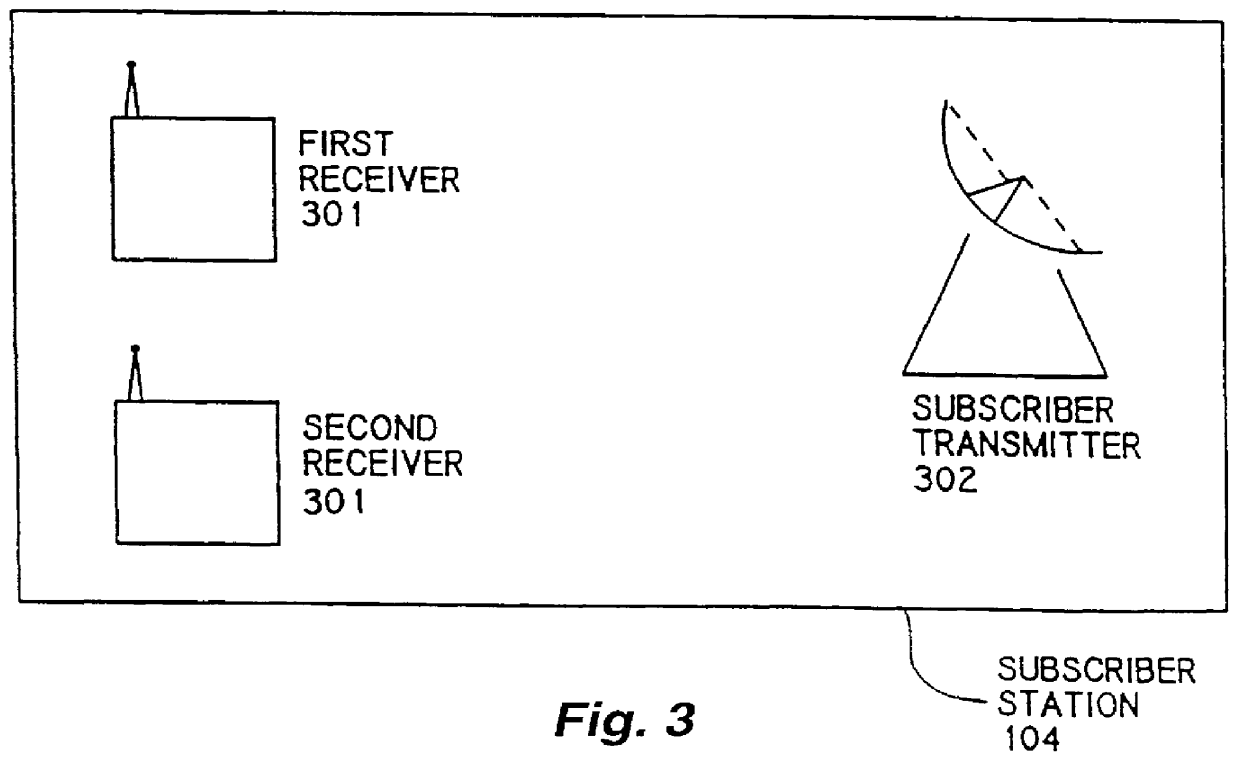
A system for publishing data on shared broadcast channels using spread-spectrum techniques, which may comprise a spread-spectrum encoder capable of receiving data and placing it in a spread-spectrum signal format and a transmitter operating on a shared communication channel or frequency band, such as might be allocated to terrestrial point-to-point or broadcast communications. The shared communication channel may comprise a cellular system, in which data may be transmitted using spread-spectrum techniques using the transmitters and repeaters of the cellular system simultaneously with voice and other transmissions associated with the cellular system. A subscriber station may be capable of receiving using a plurality of different communication channels or frequency bands, such as a first receiver capable of cellular reception and a second receiver capable of satellite reception, at least one of which uses spread-spectrum techniques. The subscriber station may also comprise a transmitter using at least one communication channel or frequency band, so that the subscriber station may receive data or other transmissions using one channel and may request further data or other transmissions using a second channel.
Owner:INTEL CORP
System operation monitoring and controlling visual platform
InactiveCN103491354AMonitor operating conditionsReduce the potential risk of operation and maintenanceClosed circuit television systemsTransmissionTime dataReliability engineering
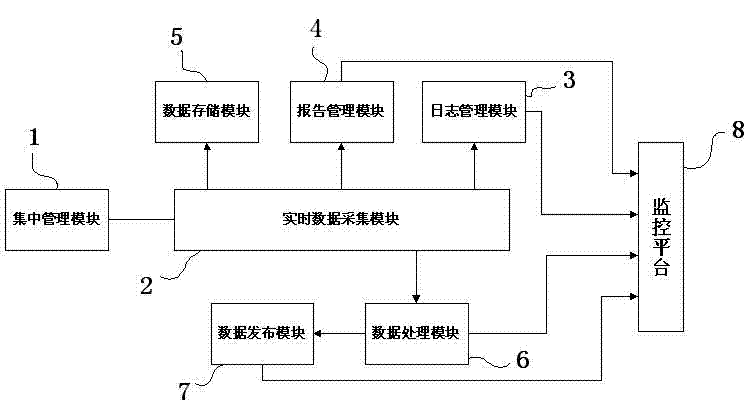
The invention provides a system operation monitoring and controlling visual platform which comprises a monitoring and controlling platform body (8). The system operation monitoring and controlling visual platform is characterized by comprising a centralized management module (1), a real-time data collecting module (2), a log management module (3), a report management module (4), a data storage module (5), a data processing module (6) and a data releasing module (7). According to the system operation monitoring and controlling visual platform, the operation situations of a power grid dispatching system can be collected, disposed, processed and summarized, information of operation and other aspects of service systems can be reflected in a centralized mode, and the system operation monitoring and controlling visual platform has the functions such as centralized displaying, managing and customizing. On the basis, the statistic analysis can be carried out on operation data of the power grid dispatching system, the variation trend of key data can be predicted, events having a significant effect on the system can be recognized, and a necessary basis is provided for daily maintaining management and an operation decision analysis. The emphasis is laid on founding various alarms and performance abnormalities in time and improving the speed that an operator responds to various events.
Owner:STATE GRID CORP OF CHINA +2
Method for changing mno in embedded sim on basis of special privilege, and embedded sim and recording medium therefor
ActiveUS20140134981A1Unauthorised/fraudulent call preventionAssess restrictionComputer hardwareSecure communication
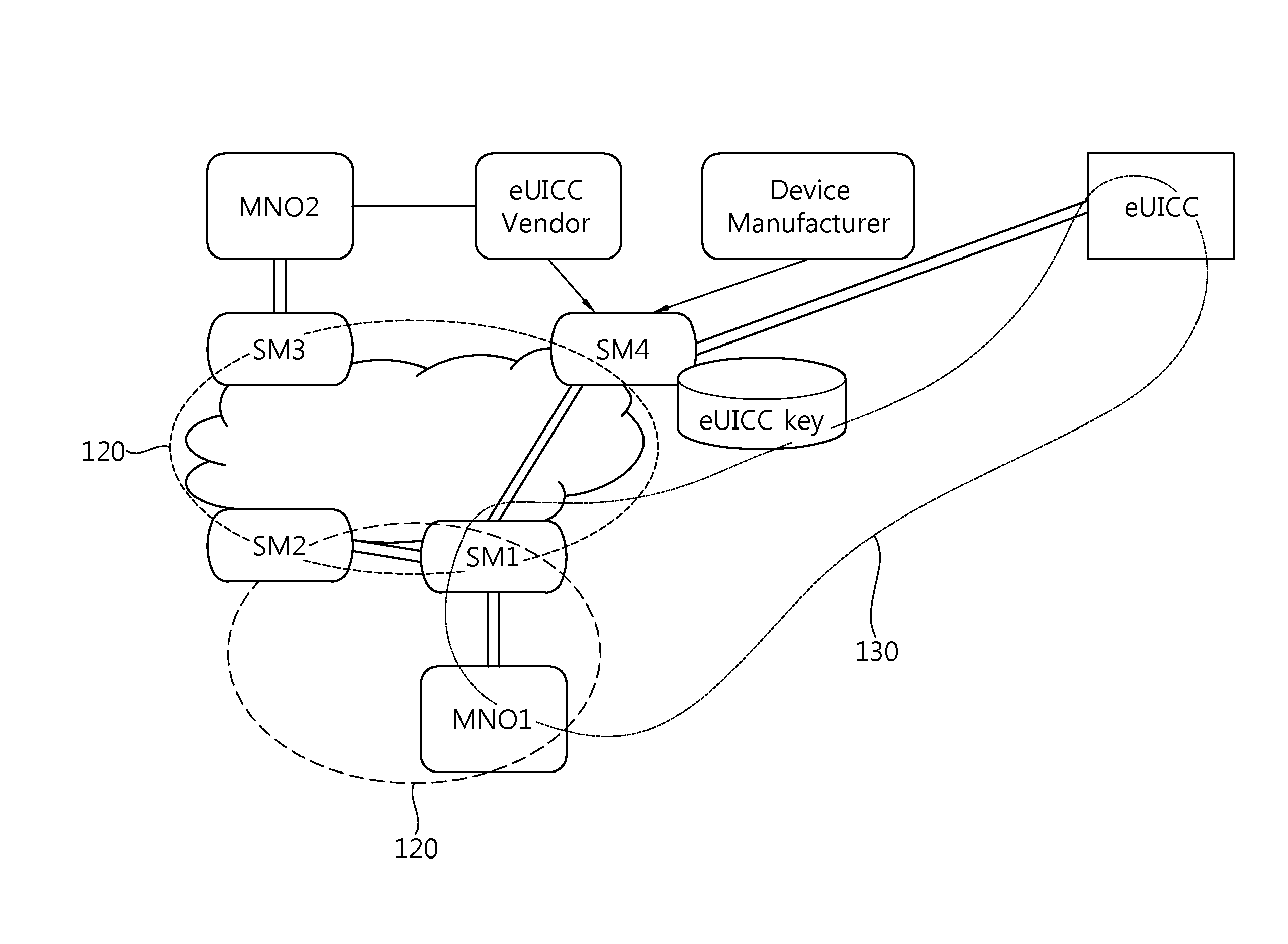
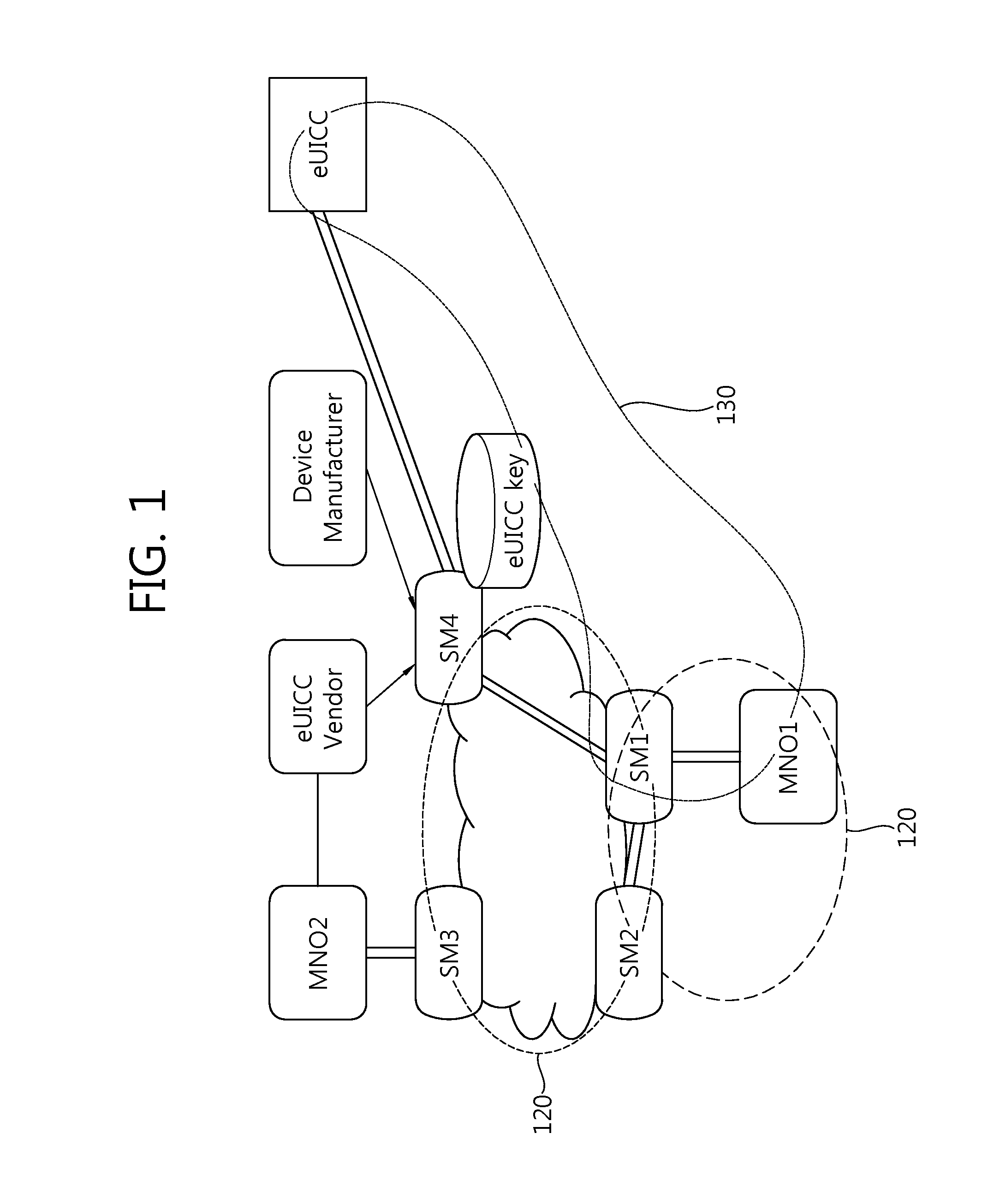
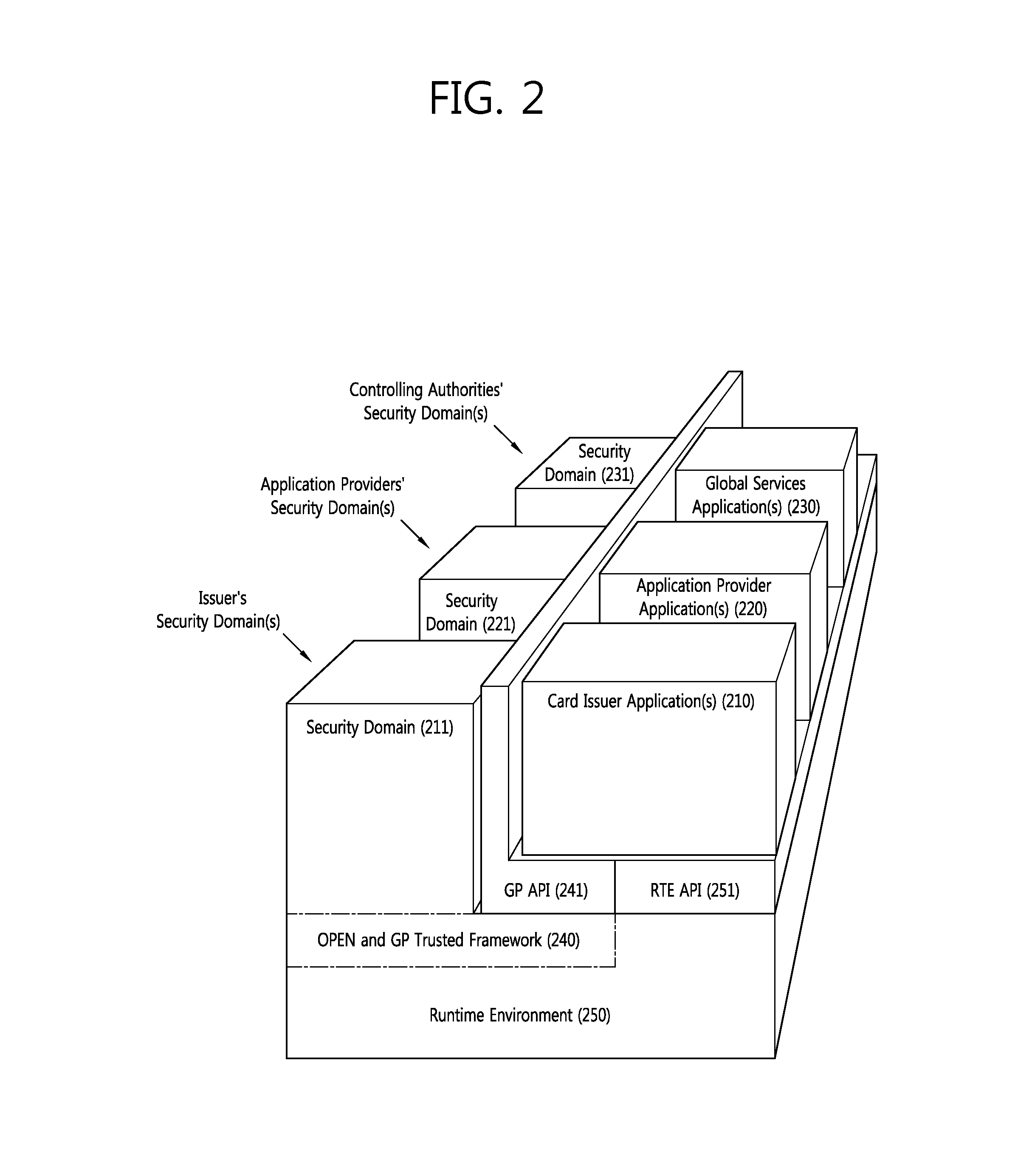
The present invention provides a method and an apparatus for managing (mutual authorization with a SIM, secure communication, channel formation, application and data issuance, etc.) an embedded SIM (eSIM or eUICC) by generating and extraditing a security domain using GlobalPlatform technology in which authorized management privilege and delegated management privilege functions are implemented.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for transmission-based billing of applications
InactiveUS7436816B2Avoid dataAvoid misappropriationSpecial service provision for substationMetering/charging/biilling arrangementsApplication computersApplication software
Computer- and network-based methods and systems for transmission-based billing are provided. Example embodiments provide a Packet-Based Billing System (“PBBS”), which enables application providers, such as carriers and content providers, to bill subscribers for the use of content on mobile subscriber devices, such as wireless devices, on a per-application, per-user basis based upon the extent of the usage. Embodiments of the present invention can also be used to bill subscribers for the use of content on a per-application, per-user basis for wired subscriber devices as well, using the same techniques. In operation, the PBBS provides modified content by inserting billing and tracking code into content returned to a requesting device. The modified content, when executed, tracks the amount of data sent and received between the content and a network and posts the accumulated data to a proxy / billing server according to business rules for an interval / frequency to post such data. The proxy / billing server stores the raw billing data and an accounting program retrieves the billing data to generate customer (call) data records. Business rules that specific different charges for different content or users can be incorporated into the system.
Owner:GOOGLE TECH HLDG LLC +1
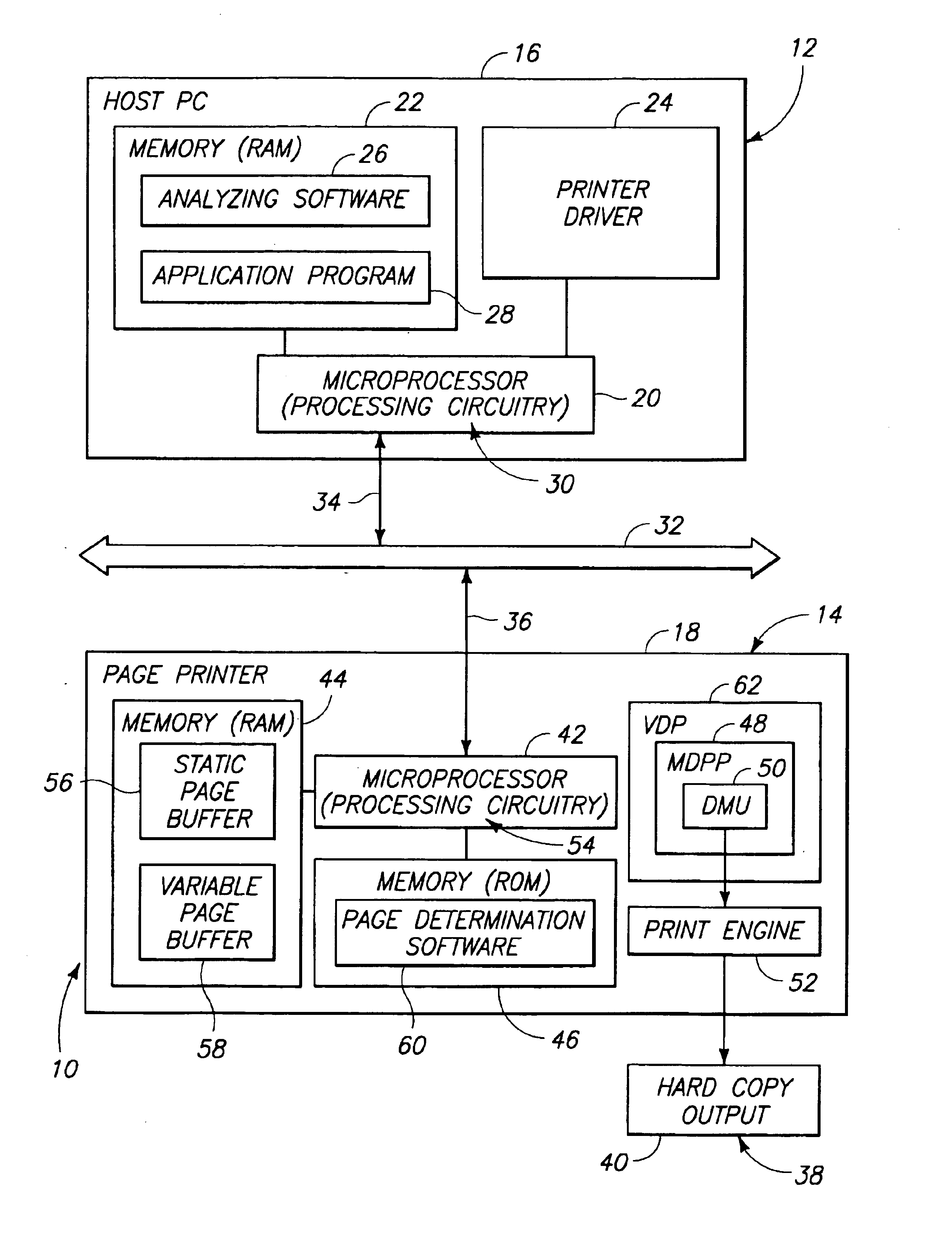
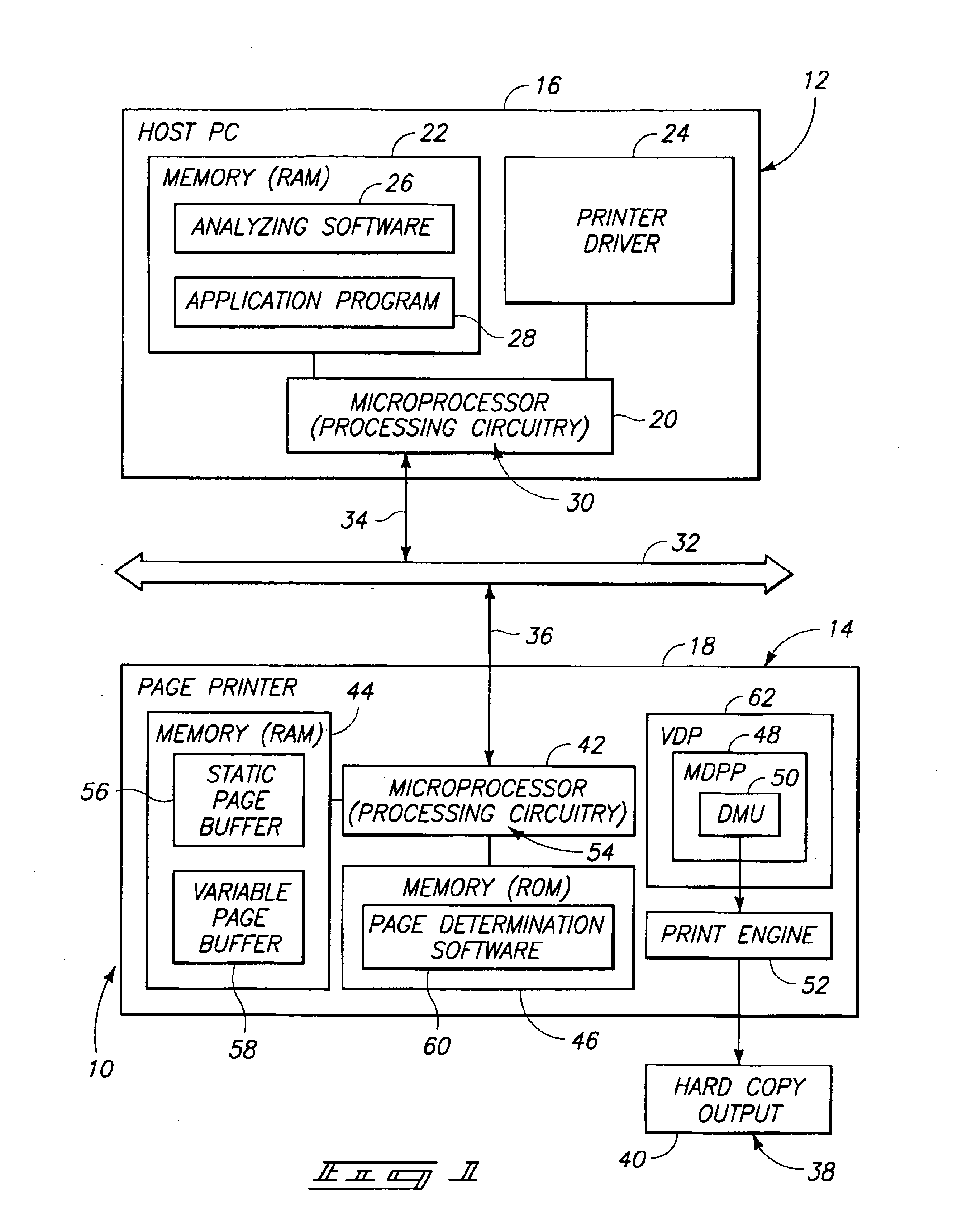
Printing performance enhancements for variable data publishing
InactiveUS6919967B1Improve printing effectGeometric image transformationVisual presentation using printersProgramming languagePerformance enhancement
An apparatus for printing pages of a print job includes a page analyzer, a converting apparatus, an identifying apparatus, an optimizer apparatus, a storage apparatus, and a merging apparatus. The page analyzer is operative to identify static page aspects and variable page aspects from page data within a print job. The converting apparatus communicates with the page analyzer and is operative to convert the static page aspects into static page layout objects and the variable page aspects into variable print data. The identifying apparatus communicates with the converting apparatus and is operative to identify the static page layout objects in the manner allowing for an optimized form to be created, and to allow for appropriate merging with the variable print data. The optimizer apparatus communicates with the identifying apparatus and is operative to convert the static page layout objects to an optimized form. The storage apparatus communicates with the optimizer apparatus and is operative to store at least one instantiation of the static page layout objects in the optimized form. A merging apparatus communicates with the storing apparatus and is operative to merge the static page layout objects with the variable print data to create merged print data. A method is also provided.
Owner:HEWLETT PACKARD DEV CO LP
Method for mitigating web-based "one-click" attacks
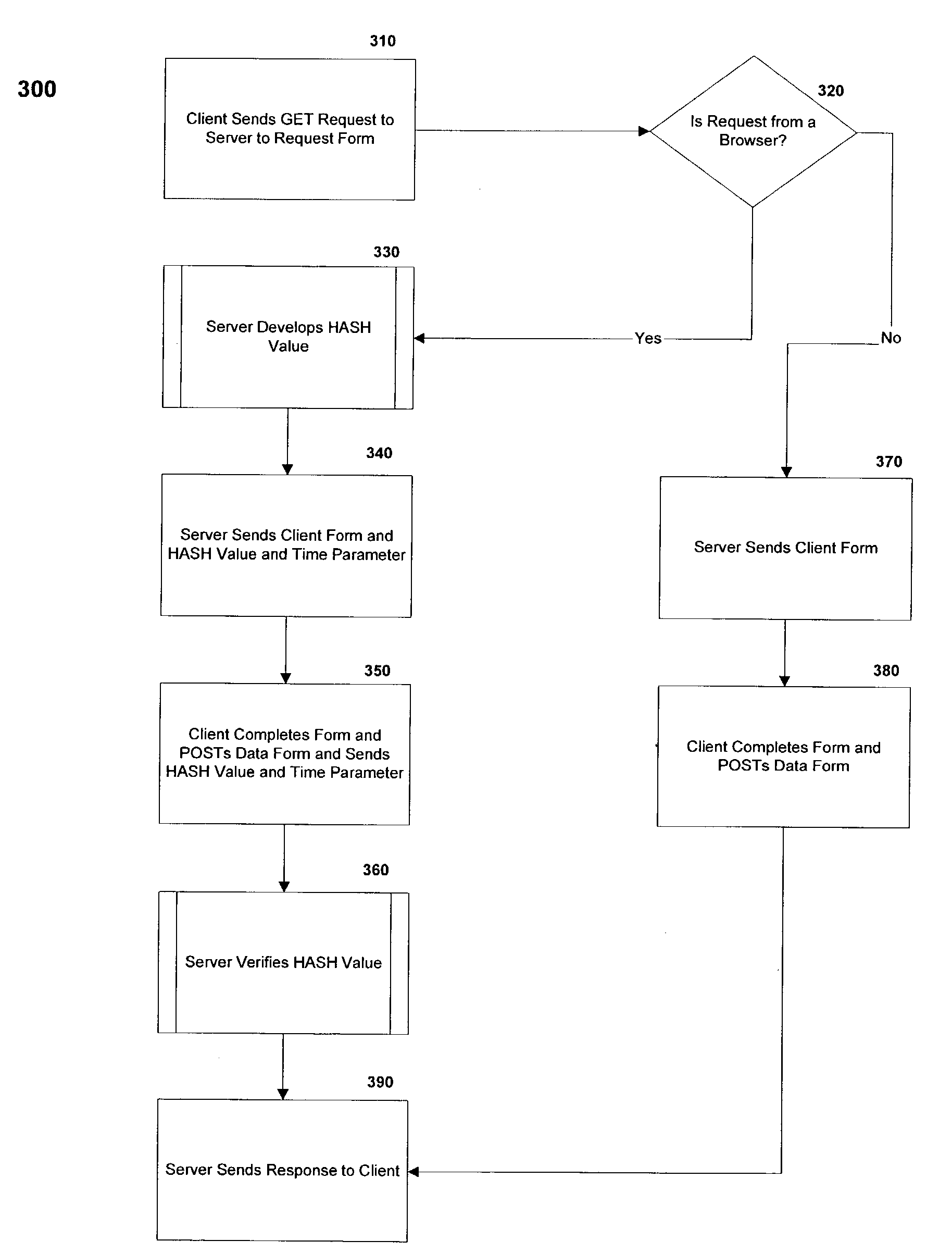
Preventing unauthorized data posts to a server hosting an information site, such as a site on the Web. A HASH value can be generated at a server computer hosting the information site using a message digest algorithm and appended, along with an additional data item present in the message used to generate the HASH value, to a data form in response to a request for the data form. In response to receiving a post containing data corresponding to data required by the data form, the server computer can determine if a HASH value and data item has been attached to the data post and if the HASH value is the same value as the HASH value sent with the form file. If data are posted without a correct HASH value, the data can be rejected by the server computer, preventing unauthorized posts of data to the information site.
Owner:MICROSOFT TECH LICENSING LLC
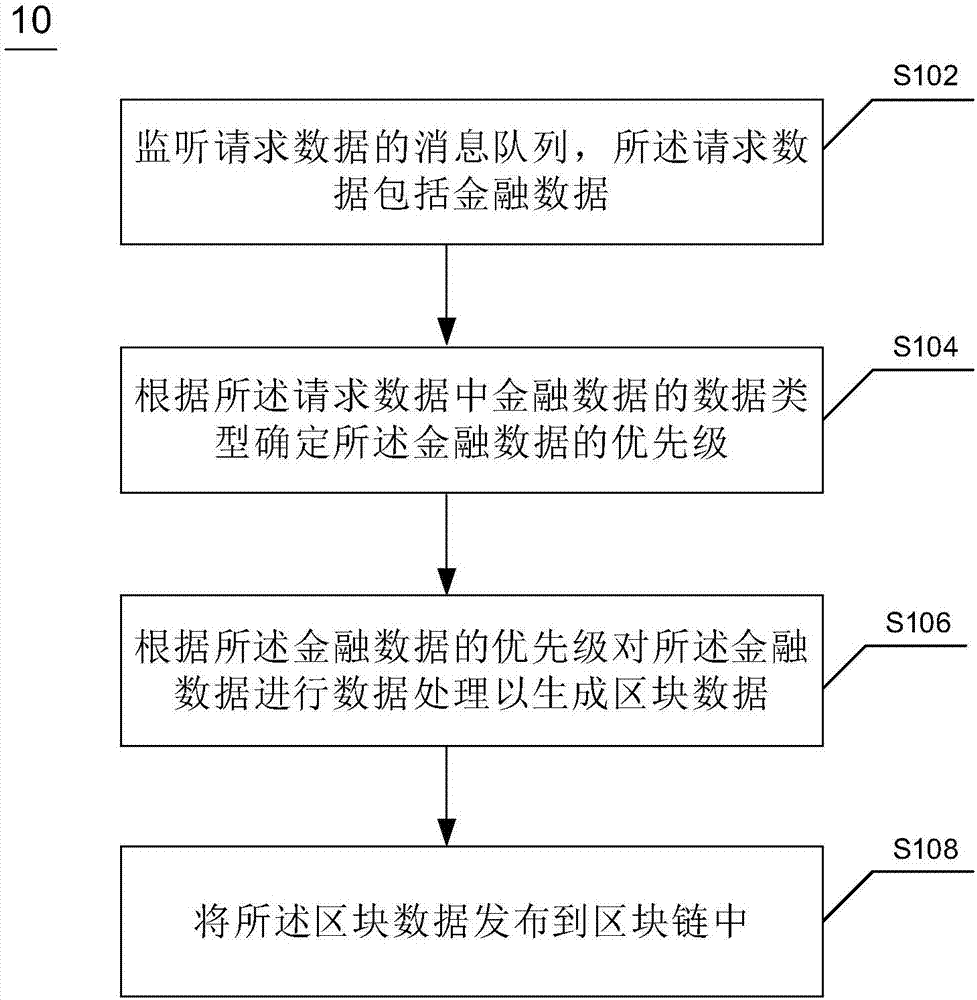
Financial data processing method and device based on blockchain and electronic equipment
InactiveCN106991164ASolve high concurrency issuesDatabase distribution/replicationSpecial data processing applicationsMessage queueFinancial data processing
The invention discloses a financial data processing method and device based on the blockchain and electronic equipment. The method includes the steps that a message queue of request data is monitored, wherein the request data includes financial data; the priority of the financial data is determined according to the data type of the financial data in the request data; the financial data is processed according to the priority of the financial data to generate block data; the block data is issued into the blockchain. The financial data processing method and device based on the blockchain and the electronic equipment can solve the problem of high concurrency of the upper chains of transactions in the process of issuing the financial data into the blockchain.
Owner:JINGDONG TECH HLDG CO LTD
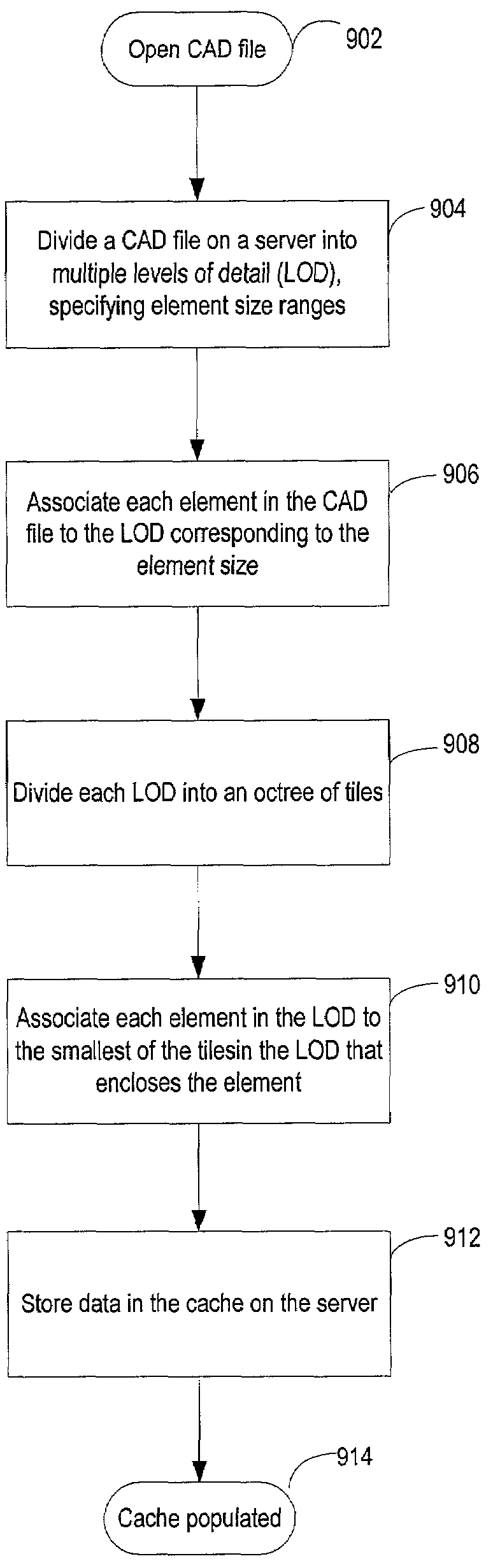
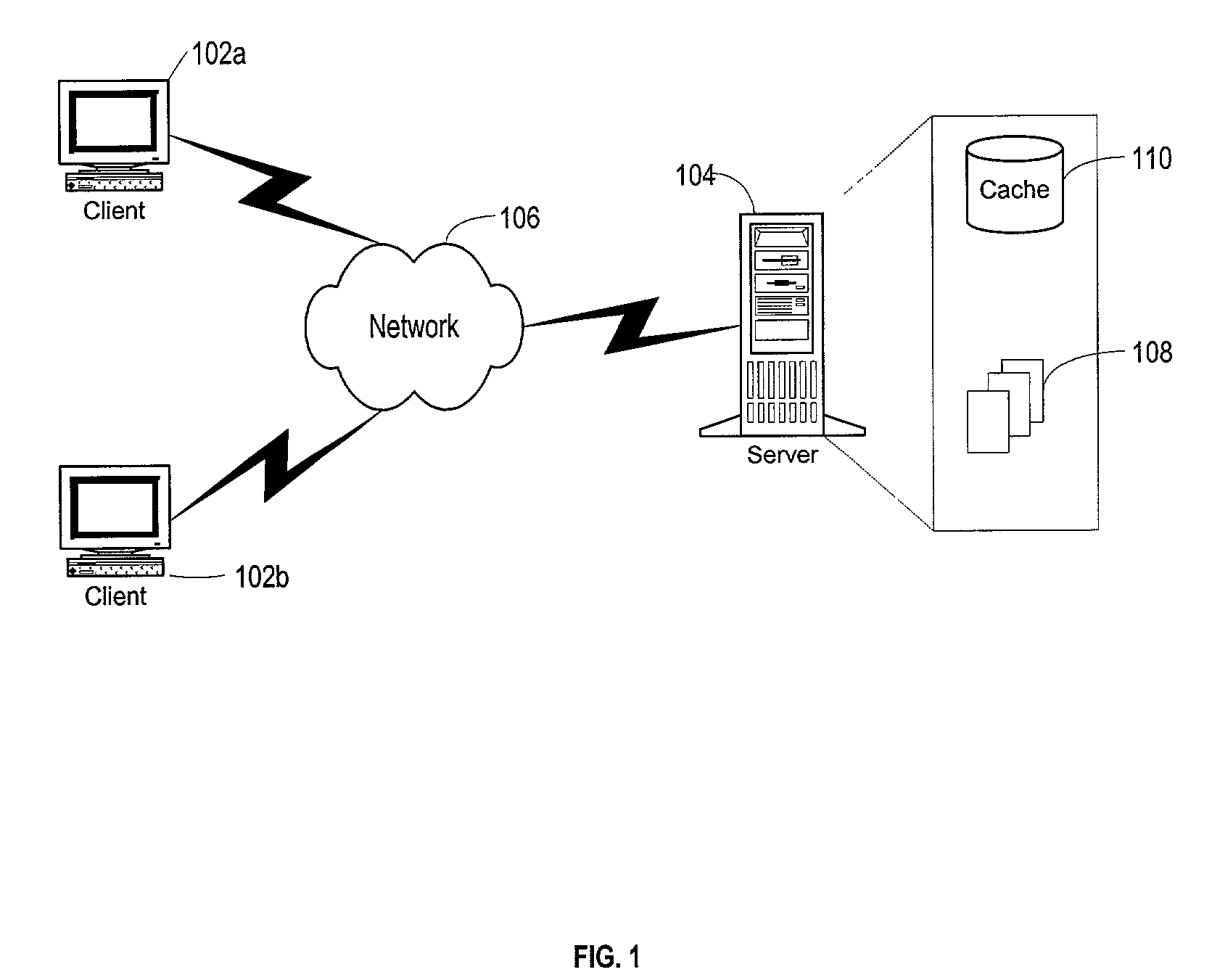
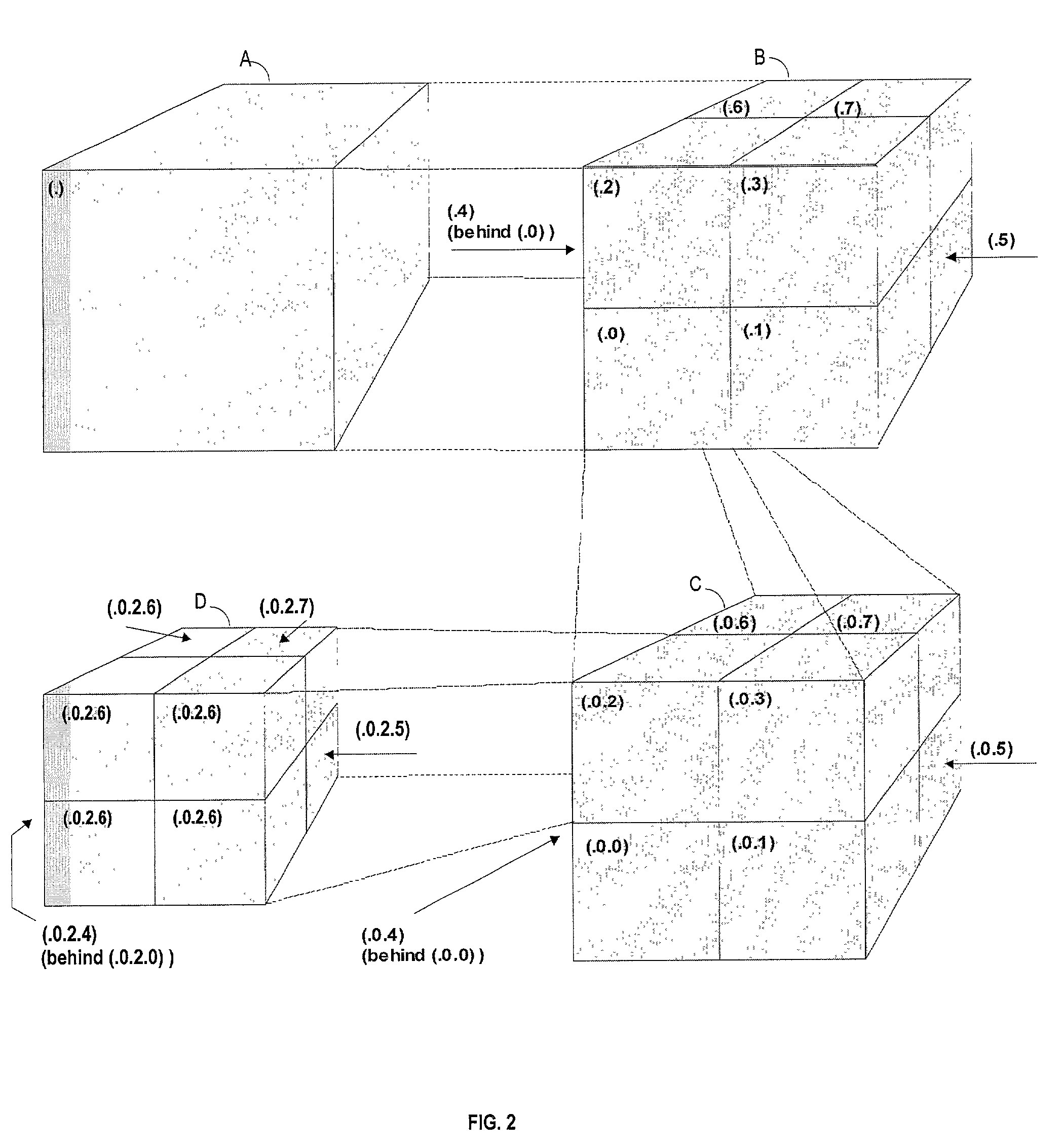
Hierarchical tile-based data structure for efficient client-server publishing of data over network connections
In a system of a client and a server, the server stores three dimensional CAD data in a cache. The CAD data is stored in the cache in levels of detail further divided into tiles. When a client receives a request from a user to view part of a CAD file, the client determines which portion of the CAD file is being viewed, and at what resolution. The client then checks a client cache for tiles already stored for the desired view. The client requests the view data from the server by providing to the server the client's resolution, the boundary of the viewing area and a list of tiles that the client already has. The server uses the request information to return to the client only the data that is needed for the client's resolution and that is not already stored on the client.
Owner:BENTLEY SYST INC
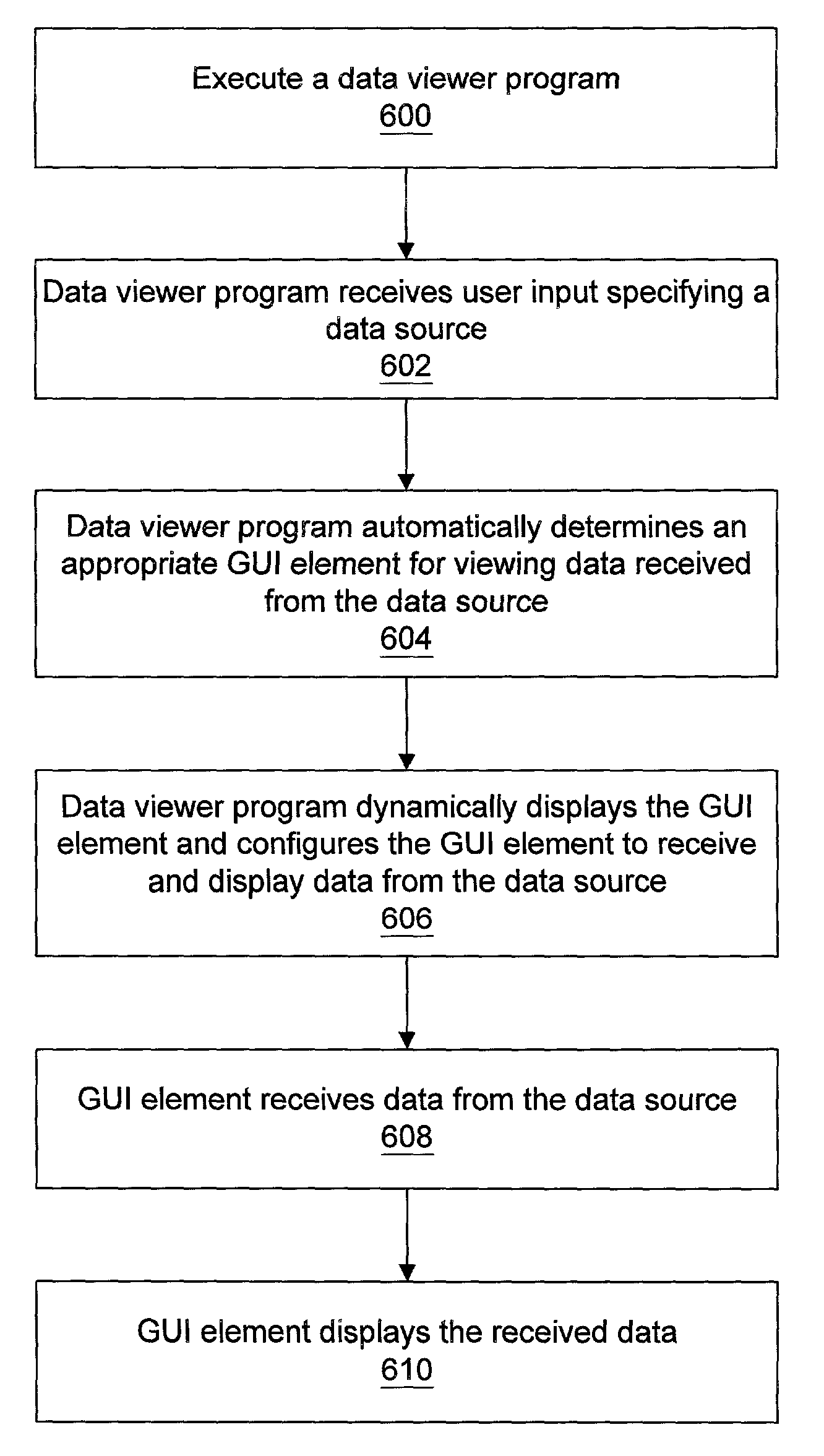
Configuring a GUI element to subscribe to data
InactiveUS7287230B2OptimizationImprove user friendlinessMultiple digital computer combinationsSpecific program execution arrangementsGraphicsData connection
System and method for configuring a graphical user interface (GUI) element to publish data to a data target and / or subscribe to data from a data source. During program development, a developer associates a GUI element with a program, e.g., for receiving user input data and / or indicating data to the user. The developer configures the GUI element to publish data associated with the GUI element to a data target and / or to subscribe to data from a data source, and specifies a data source or target for the data connection. The program is executed, during which the program automatically determines and uses an appropriate protocol for interfacing with the data source / target to connect to or open the data source and / or target, and receive data from the data source, which is provided to and displayed by the GUI element, and / or send or write data associated with the GUI element to the data target.
Owner:NATIONAL INSTRUMENTS
Method and system for transmission-based billing applications
InactiveUS8310943B2Avoid dataAvoid misappropriationSpecial service provision for substationMetering/charging/biilling arrangementsApplication computersDatabase
Computer- and network-based methods and systems for transmission-based billing are provided. Example embodiments provide a Packet-Based Billing System (“PBBS”), which enables application providers, such as carriers and content providers, to bill subscribers for the use of content on mobile subscriber devices, such as wireless devices, on a per-application, per-user basis based upon the extent of the usage. Embodiments of the present invention can also be used to bill subscribers for the use of content on a per-application, per-user basis for wired subscriber devices as well, using the same techniques. In operation, the PBBS provides modified content by inserting billing and tracking code into content returned to a requesting device. The modified content, when executed, tracks the amount of data sent and received between the content and a network and posts the accumulated data to a proxy / billing server according to business rules for an interval / frequency to post such data. The proxy / billing server stores the raw billing data and an accounting program retrieves the billing data to generate customer (call) data records. Business rules that specific different charges for different content or users can be incorporated into the system.
Owner:MOTOROLA MOBILITY LLC
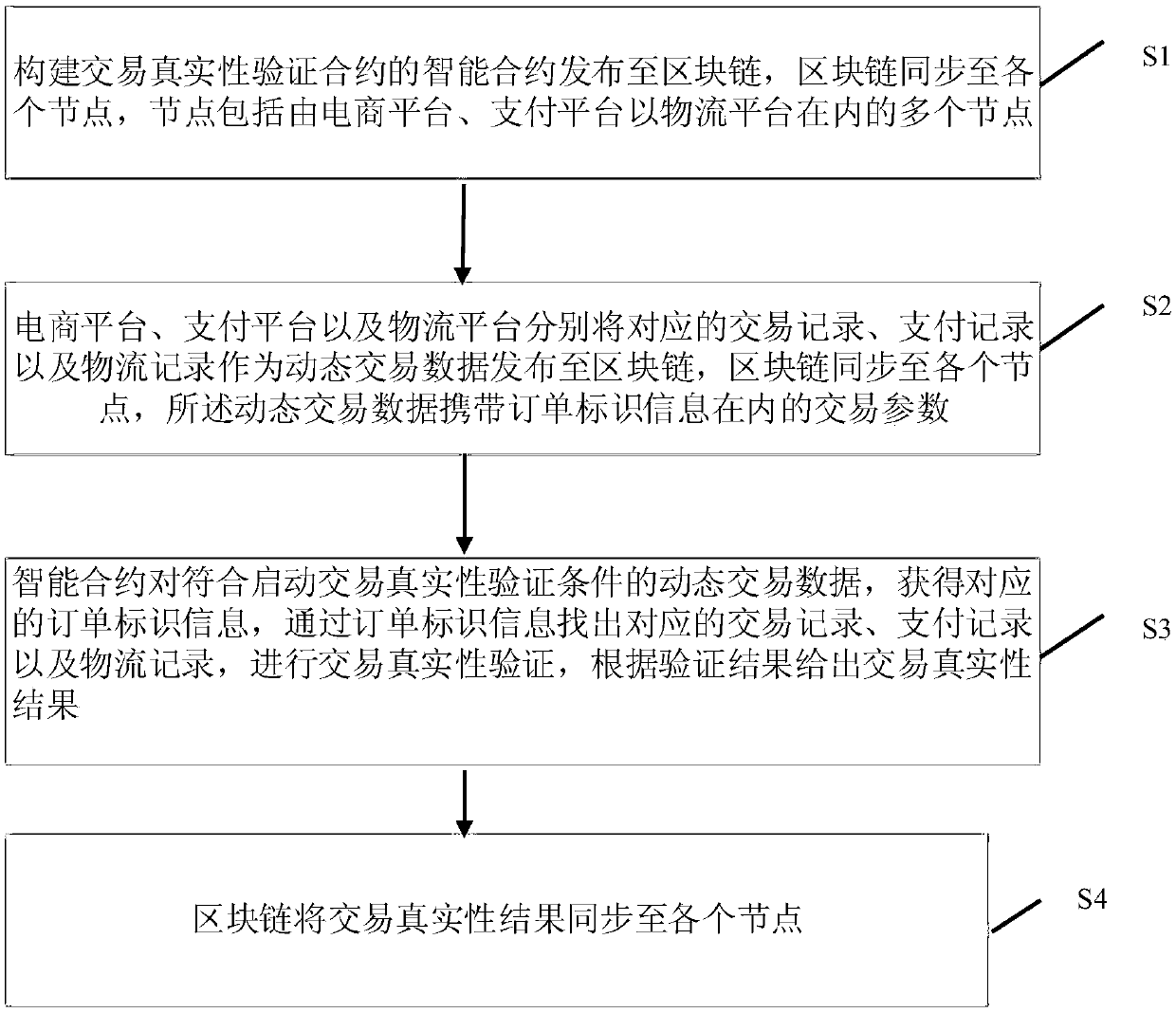
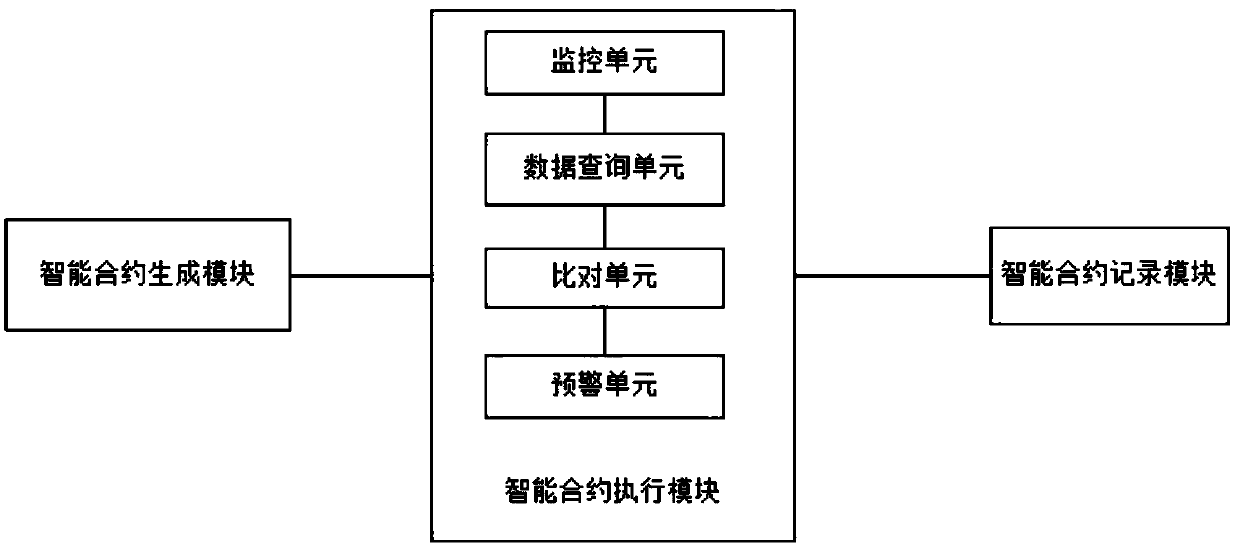
A transaction authenticity verification method and system based on block chain and intelligent contract
A transaction authenticity verification method and system based on block chain and intelligent contract iare disclosed. The method includes: S1. The intelligent contract verified by transaction authenticity is constructed and published to block chain. The node comprises a plurality of nodes including an e-commerce platform and a payment platform as a logistics platform. S2, the e-commerce platform, the payment platform and the logistics platform respectively publish the corresponding transaction records, the payment records and the logistics records as the dynamic transaction data to the blockchain, wherein the dynamic transaction data carries the transaction parameters including the order identification information; S3: the intelligent contract of the node obtains the corresponding orderidentification information according to the dynamic transaction data which meets the verification condition of the authenticity of the starting transaction, finds out the corresponding transaction records, payment records and logistics records through the order identification information, verifies the authenticity of the transaction, and gives the authenticity result of the transaction accordingto the verification result; S4: The block chain synchronizes the transaction authenticity result to each node.
Owner:HANGZHOU PINGPONG INTELLIGENT TECH CO LTD
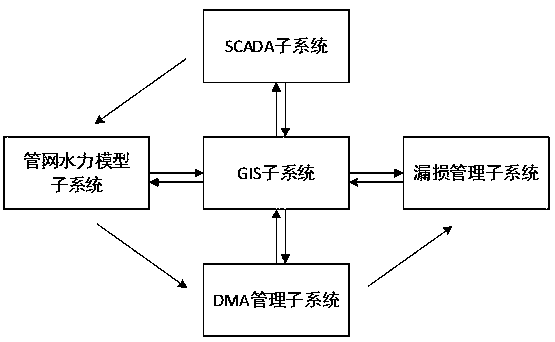
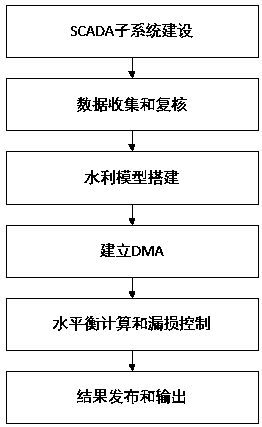
Water supply pipe network leakage management system and establishment method and system application thereof
InactiveCN107767012ALeak management rationalizationImprove distributionResourcesSpecial data processing applicationsData acquisitionNetworking hardware
The invention belongs to the field of water supply pipe network leakage management systems, in particular to a water supply pipe network leakage management system and an establishment method and system application thereof. In the prior art, through DMA (District Metering Area) zone metering, the independent metering and management of a complex pipe network is realized, and common DMA zone meteringhas the problems of high hardware investment, insufficient hardware laying reasonability, extensive leakage management, shortage of leakage economic evaluation system, imperfect data releasing and sharing mechanism. The water supply pipe network leakage management system comprises a pipe network hydraulic model subsystem, an SCADA (Supervisory Control And Data Acquisition) subsystem, a DMA management subsystem, a leakage management subsystem and a water affairs GIS (Geographic Information System) management subsystem. Through the guidance of basic data, an optimal hydraulic model is established, independent metering zone division is guided through the hydraulic model, pipe network hardware laying is guided, the economic benefit of a laying scheme is accurately evaluated, leakage management is reasonably carried out, and multiple pieces of system data can be shared.
Owner:浙江钛合工程技术有限公司
Data protection transmission method of P2P network
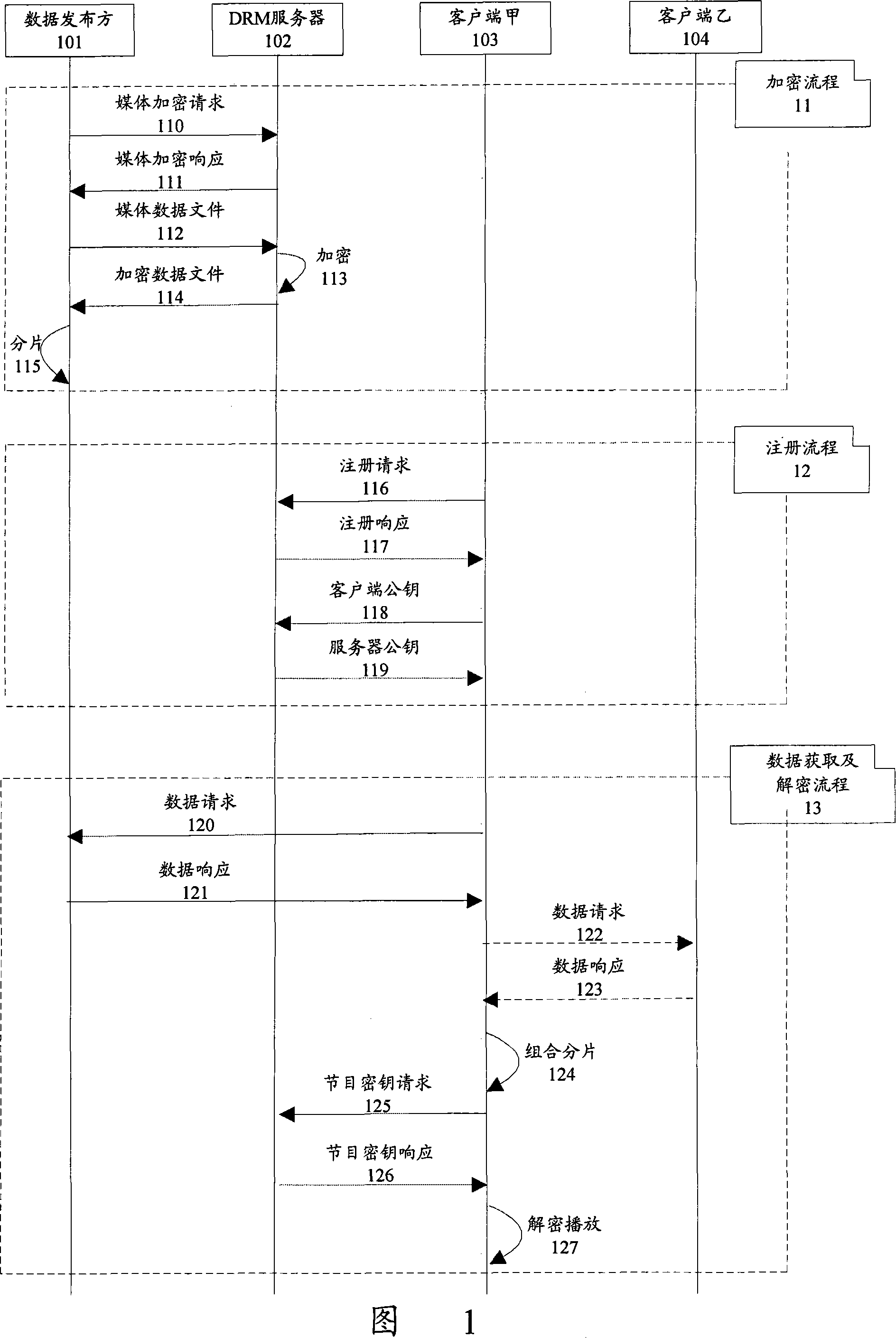
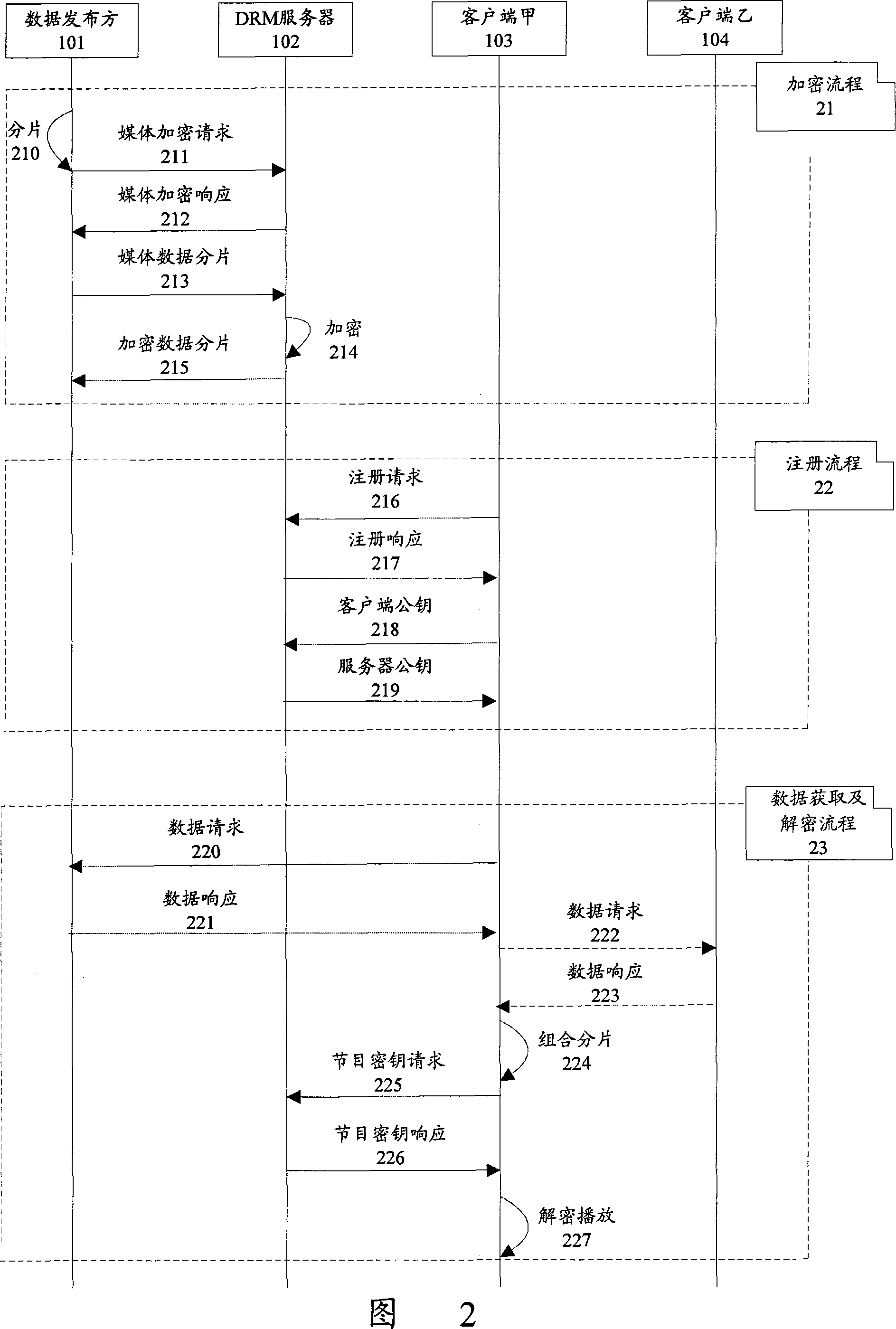
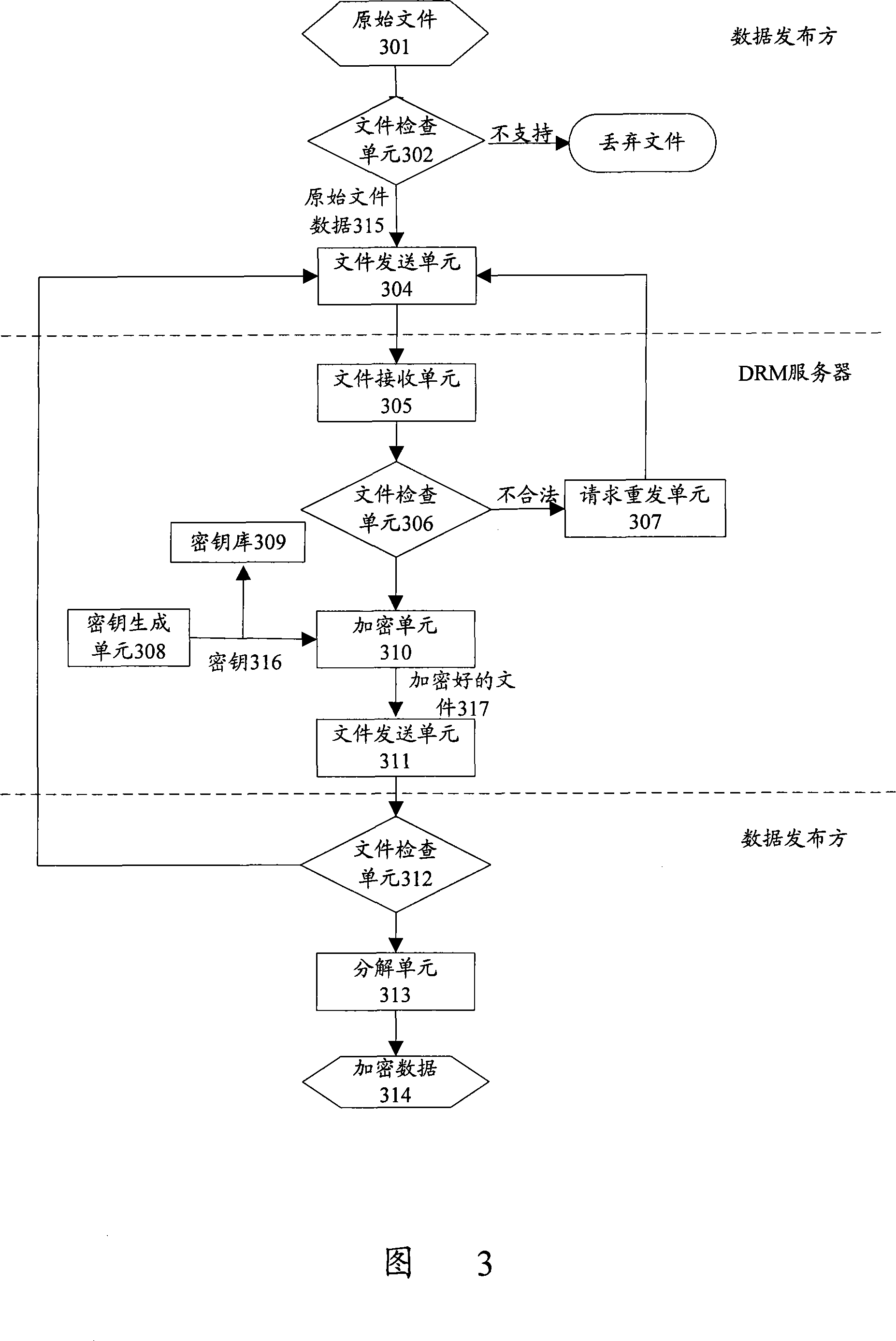
The present invention discloses a data protection transmission method for peer-to-peer network. The method has an encryption server arranged in a peer-to-peer network, and comprises following the steps that: A. a data publication party sends data needing to be published to the encryption server; B. the encryption server encrypts the data needing to be published, saves a corresponding key and returns the encrypted data to the data publication party; C. the data publication party publishes the encrypted data in different pieces; D. a data request client collects the published encrypted data pieces through the peer-to-peer network; the data request client acquires the corresponding key from the encryption server and decrypts the collected encrypted data pieces according to the key. The present invention can be applicable to the characteristics of the peer-to-peer network, improve the data transmission security of the peer-to-peer network, prevent hackers from attacking the peer-to-peer network data and guarantee the rights and benefits of data owners and users.
Owner:新疆新颖电子科技有限公司
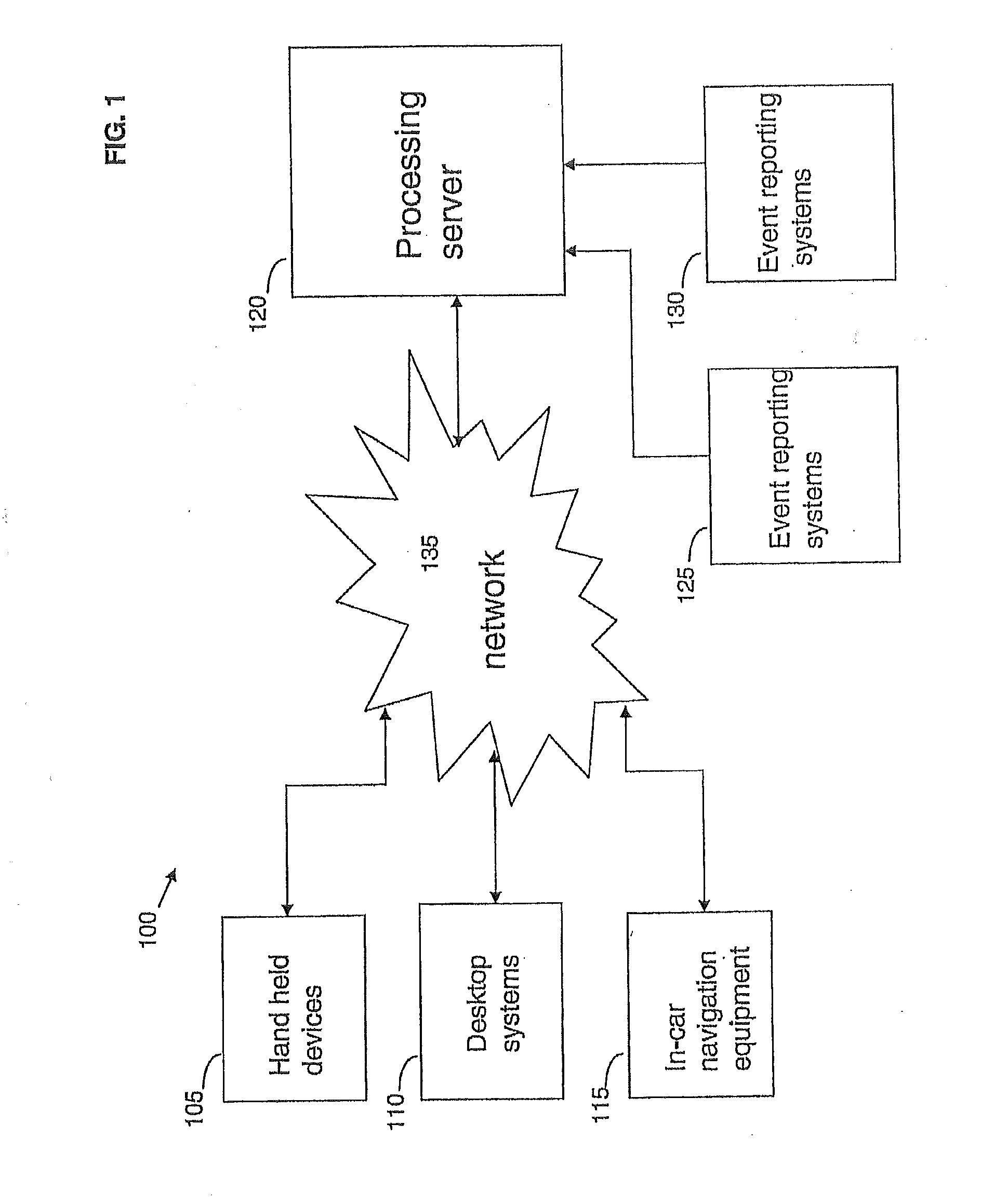
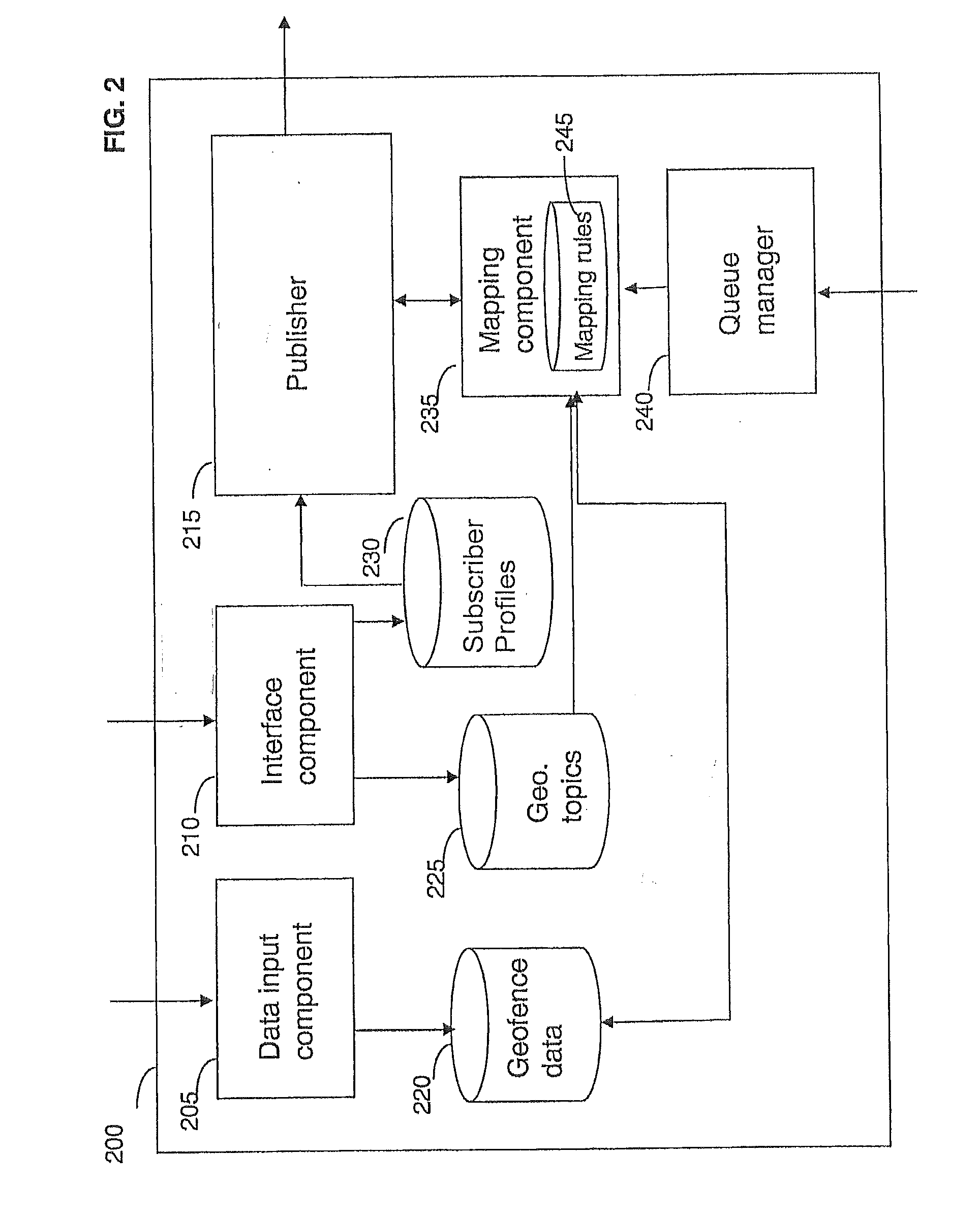
Method and apparatus for providing location specific information
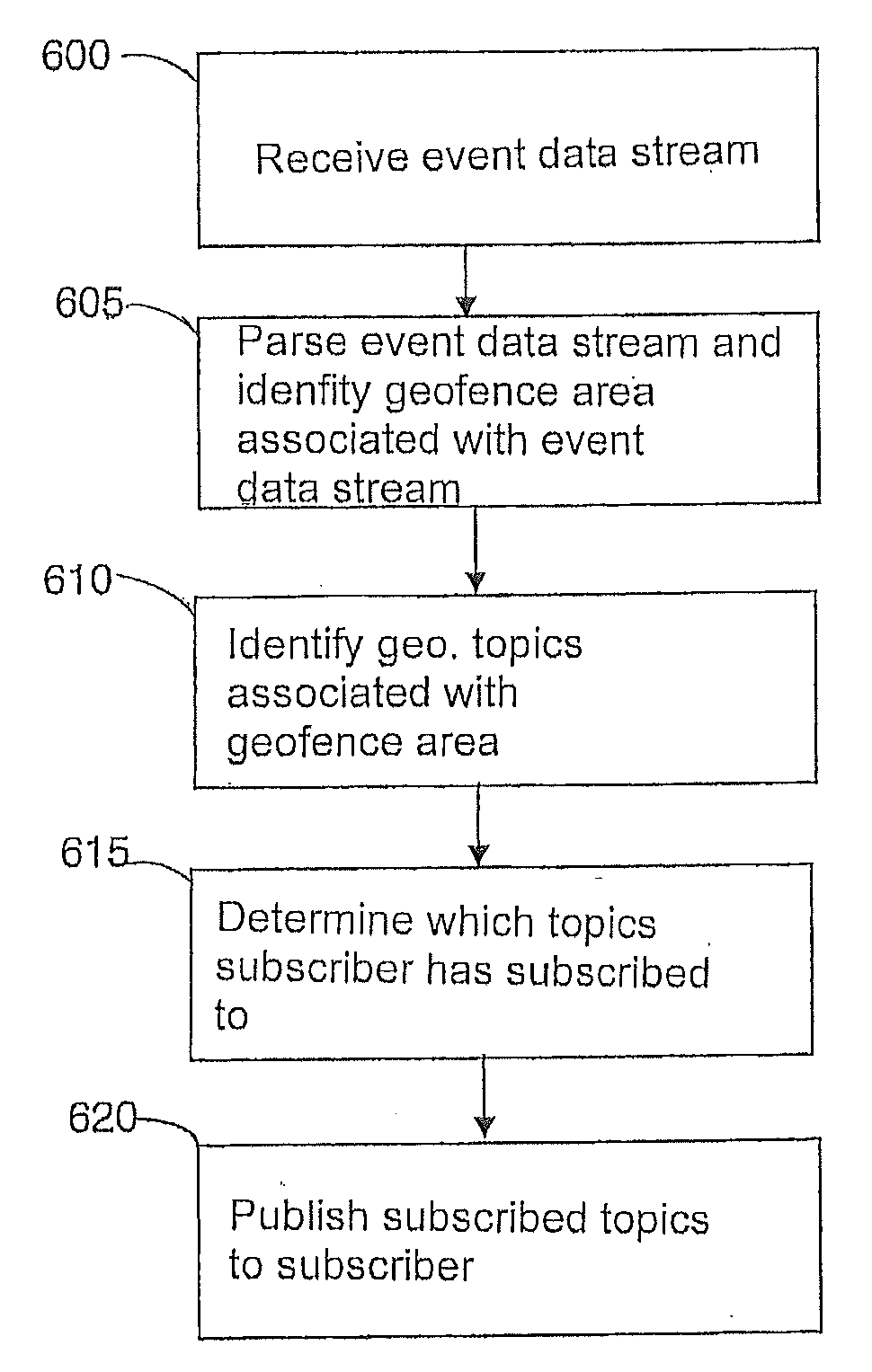
ActiveUS20080183485A1Location information based serviceSpecial data processing applicationsEvent typeEvent data
A method and apparatus for providing location specific information. Event data pertaining to an event is received from an event reporting system that has gathered the event data from a data gathering means. The event data includes location identification data, event type data, and event description data. At least one geofence associated with the location identification data is identified from the location identification data in the received event data. Each geofence of the at least one geofence has a geometric shape located within a geographic area. A topic associated with the event type data and associated with the identified at least one geofence is identified. Subscribers having a subscription to the topic in association with the geographic area are identified. The subscription entitles the subscribers to be notified about events pertaining to the topic in association with the selected geographic area. The event description data is published to each subscriber.
Owner:KYNDRYL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com