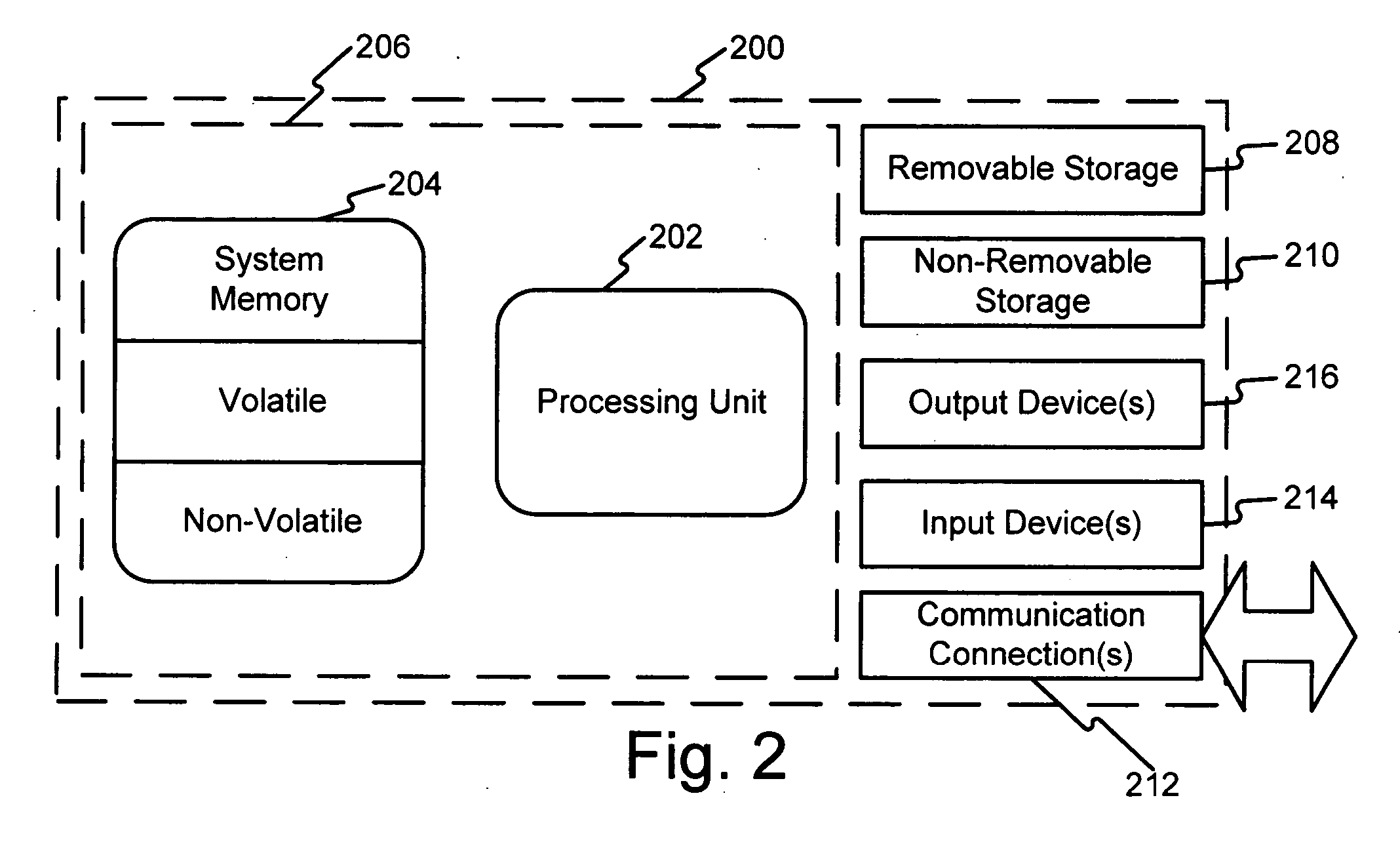
Patents
Literature
2876 results about "Data application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
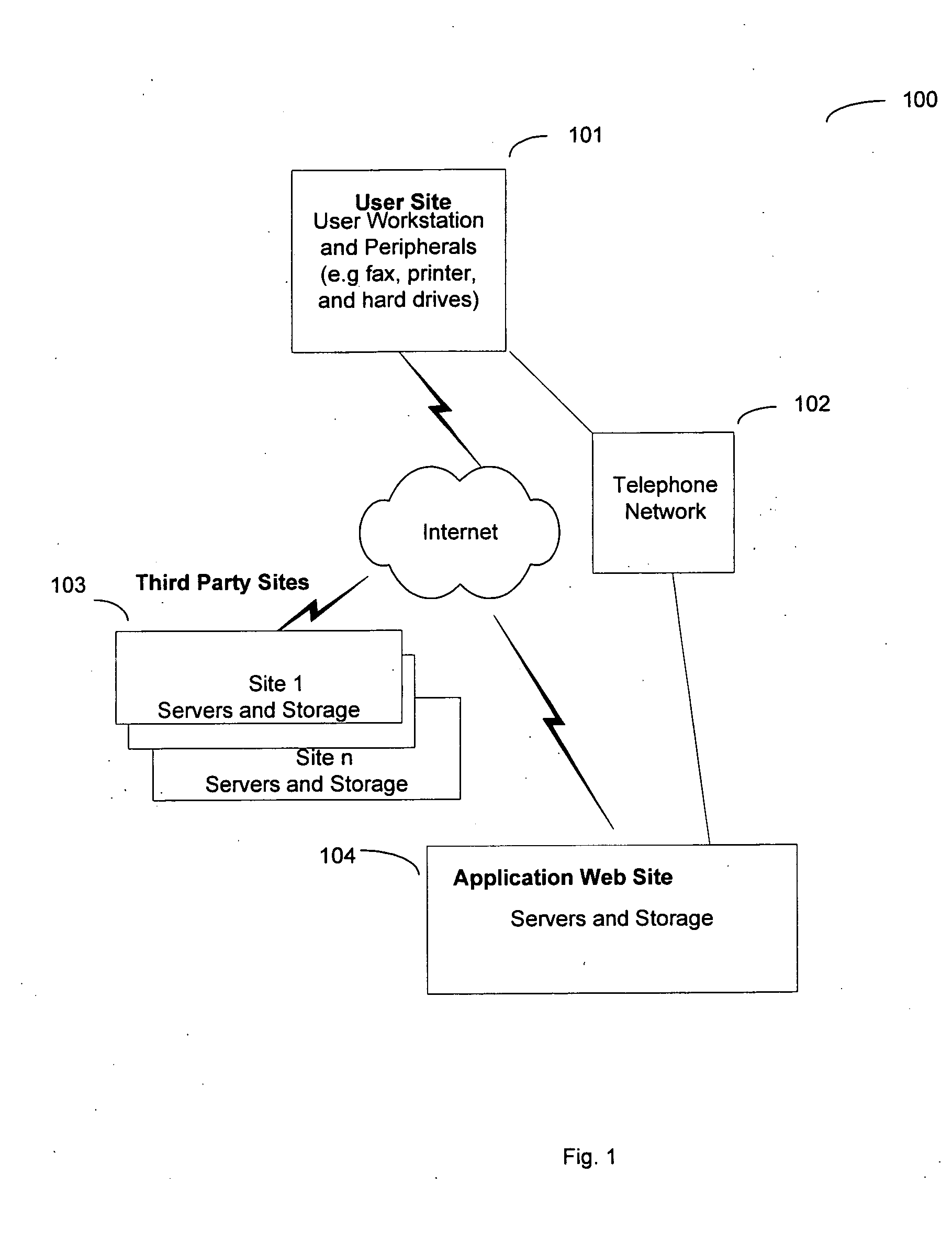
Application data is information that is specific to a user. The term applies to any data created and managed by an application. The following are common examples of application data. Information about the user such as a name, account number or user id.
Location-Based Real-time Casino Data
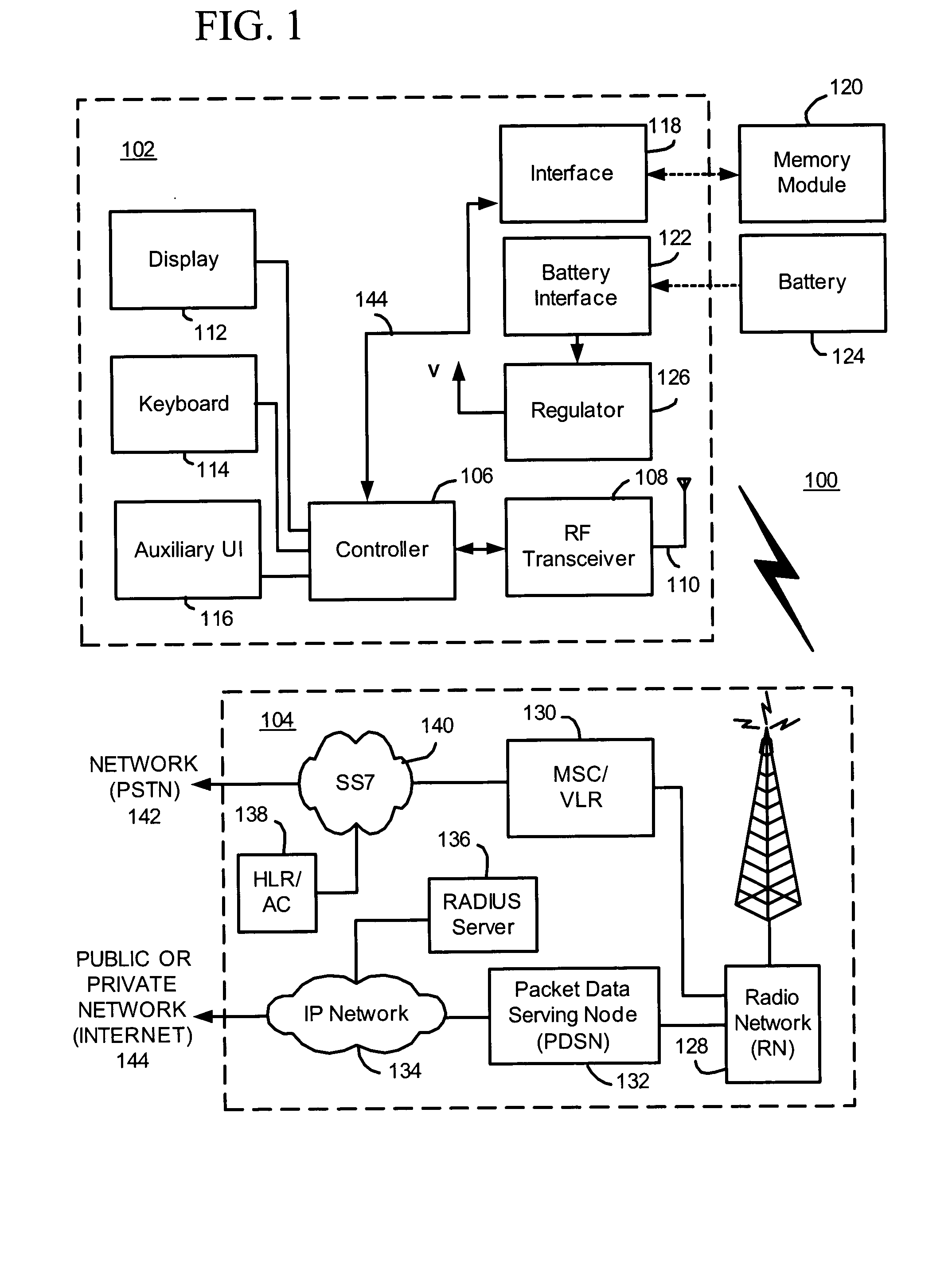
ActiveUS20110306400A1Apparatus for meter-controlled dispensingVideo gamesDisplay deviceElectric devices
An apparatus, method, and system to acquire and display casino data on a portable electronic device may include a portable electronic device having a processor operative with a real-time location based data application to transmit the location of the portable electronic device and acquire, prioritize, store and display real-time casino data. The real-time casino data may be periodically updated based on the location of the portable electronic device and visually presented to a user on a display of the portable electronic device.
Owner:ARISTOCRAT TECH INC ATI
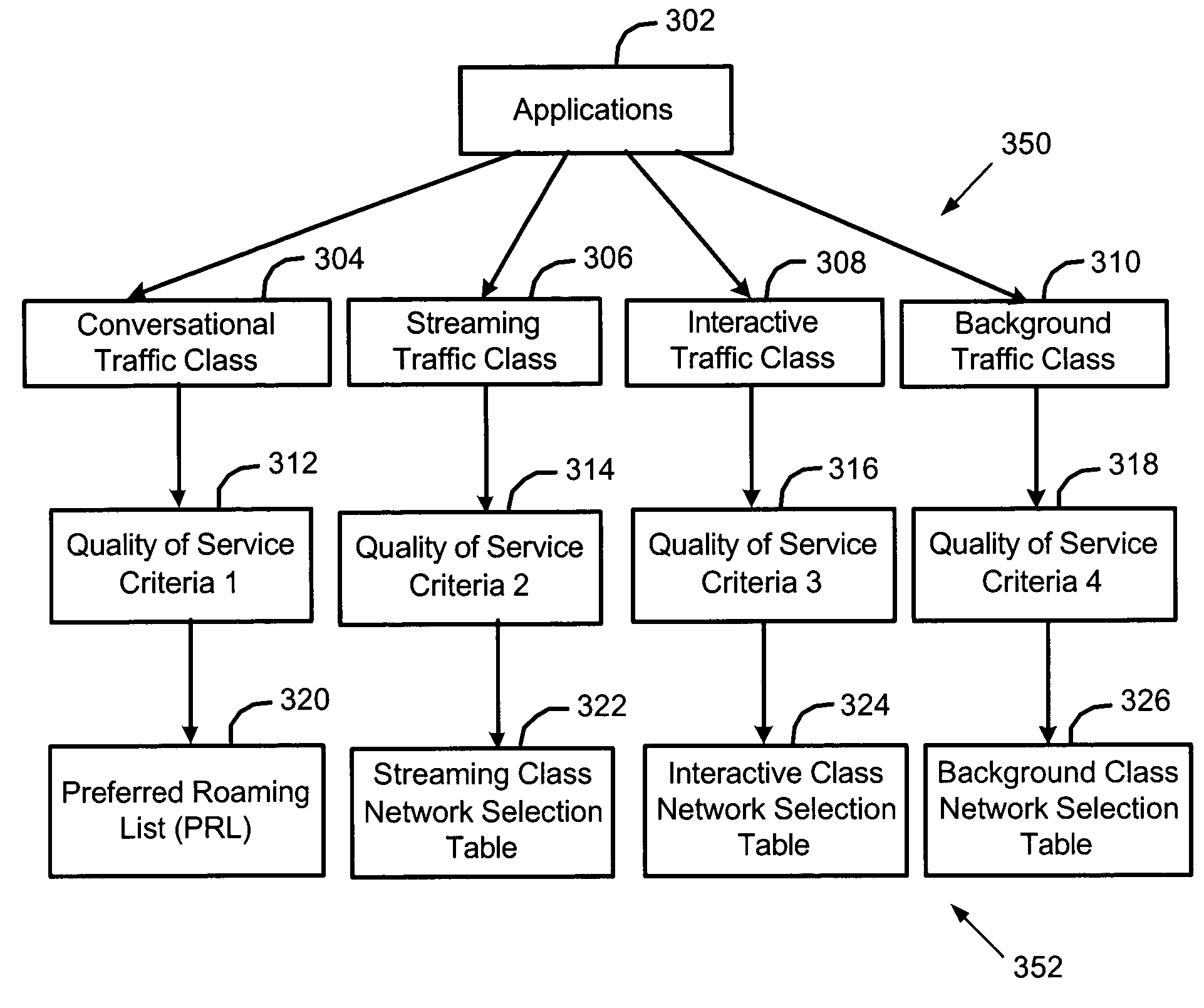
Methods and apparatus for selecting a wireless network based on quality of service (QoS) criteria associated with an application
ActiveUS20050059397A1Assess restrictionMultiple digital computer combinationsQuality of serviceVideo player
Methods and apparatus for selecting a wireless communication network based on quality of service criteria associated with an application are disclosed. In one illustrative example, one of several different software applications of a mobile communication device is executed. The software application may be, for example, an e-mail application, an Internet data application, a voice-over-IP application, a video player application, an audio player application, or a video game application. Each software application is associated with different quality of service (QoS) criteria for data communications through a wireless network. The quality of service criteria may include, for example, a bandwidth criterion, a delay criterion, a delay variation criterion, and a data loss criterion. A scanning operation is performed to identify a plurality of a wireless networks available in a coverage area of the mobile device. One of the identified wireless networks is selected for communication based on a match between its available quality of service and the quality of service criterion associated with the executed software application. Advantageously, the most suitable network may be chosen and utilized for each software application.
Owner:MALIKIE INNOVATIONS LTD
Context aware data presentation
InactiveUS20070027920A1Productive controlBridging of information communities and organizationsDigital data processing detailsTransmissionContact methodApplication software
A context aware data application presents information about a first user's contact means and methodologies. The application organizes, filters and present the information taking into account multiple inputs regarding the specific context and the relationship and preferred communication means between the first user and other users seeking to contact the first user. The information allows the users seeking to make contact to quickly take an action that is expected given the context of the first user as presenting the most relevant data allows the contacting users to take actions quickly and effectively.
Owner:SEVEN NETWORKS INC
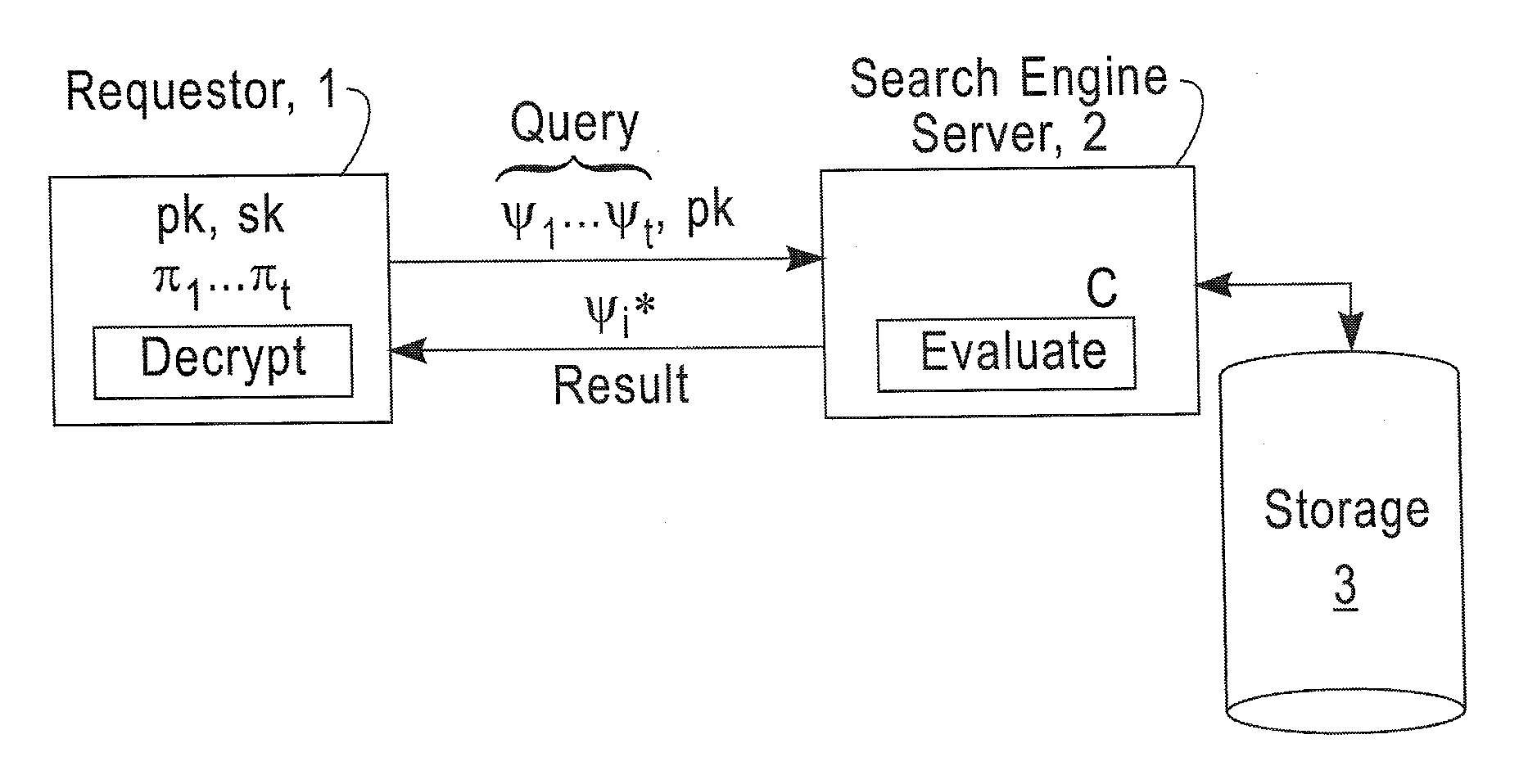
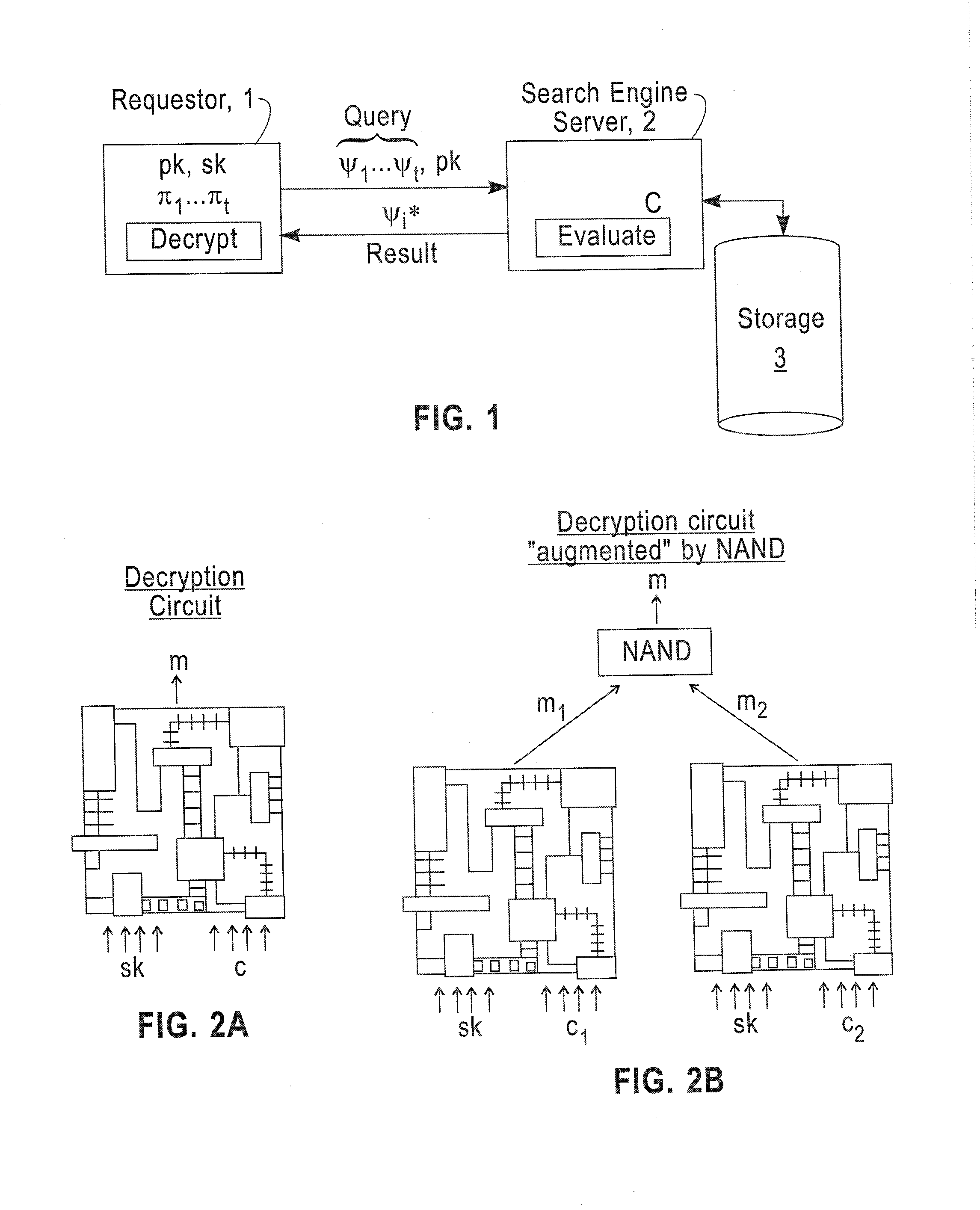
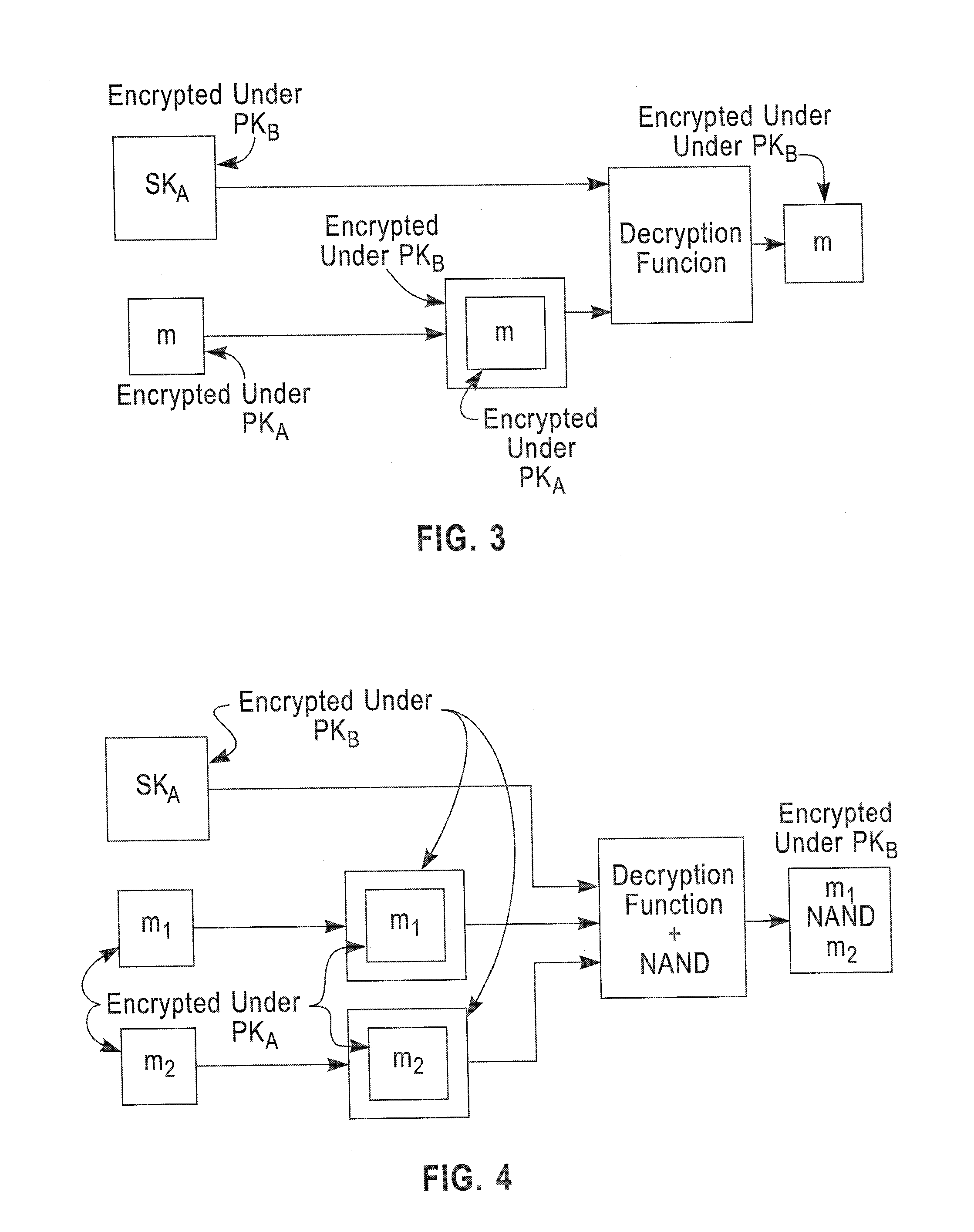
Fully homomorphic encryption method based on a bootstrappable encryption scheme, computer program and apparatus
ActiveUS20110110525A1Key distribution for secure communicationMultiple keys/algorithms usageAssessment dataData application
A method includes encrypting information in accordance with an encryption scheme that uses a public key; encrypting a plurality of instances of a secret key, each being encrypted using at least one additional instance of the public key; sending the encrypted information and the plurality of encrypted instances of the secret key to a destination; receiving an encrypted result from the destination; and decrypting the encrypted result. A further method includes receiving a plurality of encrypted secret keys and information descriptive of a function to be performed on data; converting the information to a circuit configured to perform the function on the data; and applying the data to inputs of the circuit and evaluating the data using, in turn, the plurality of encrypted secret keys.
Owner:IBM CORP
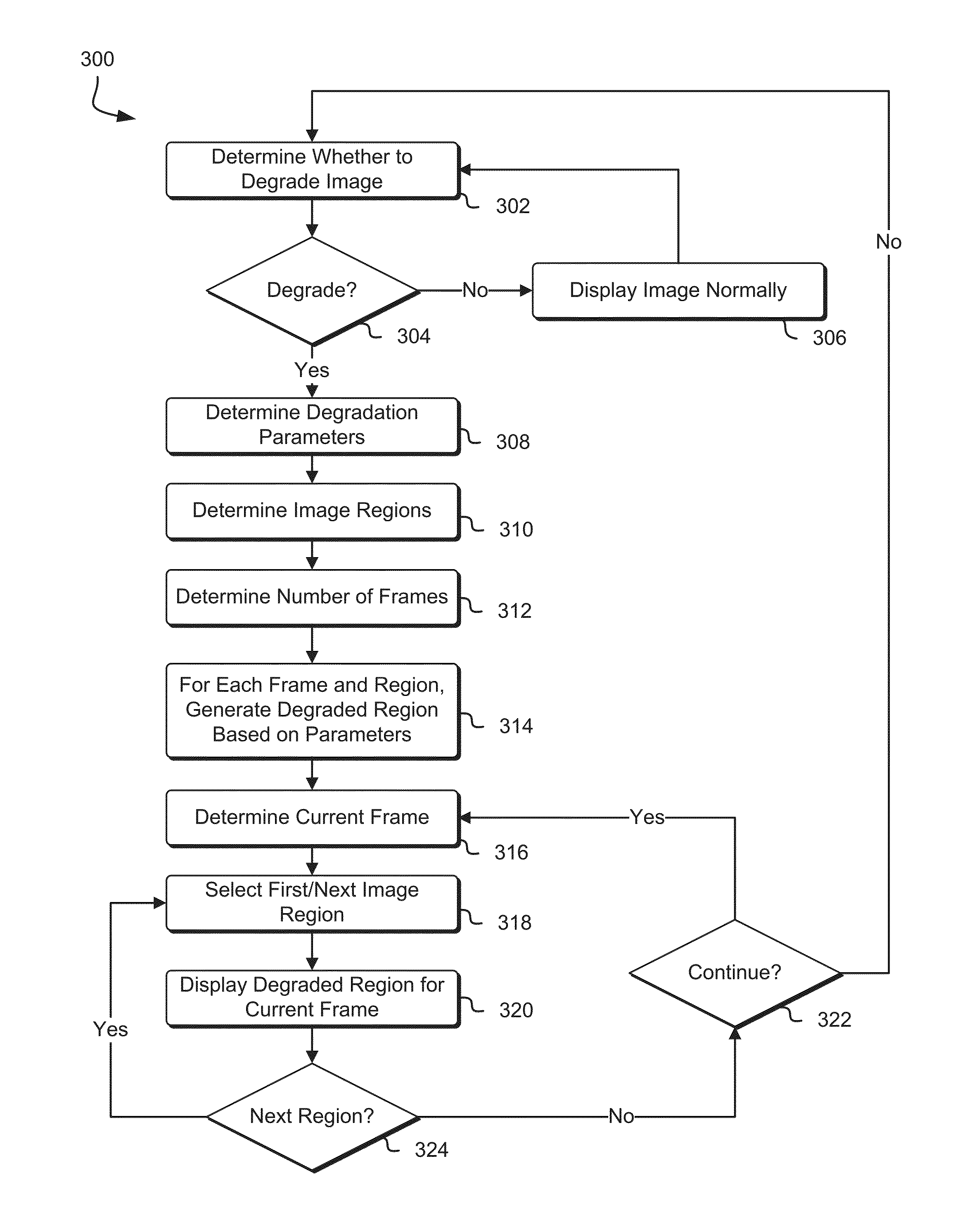
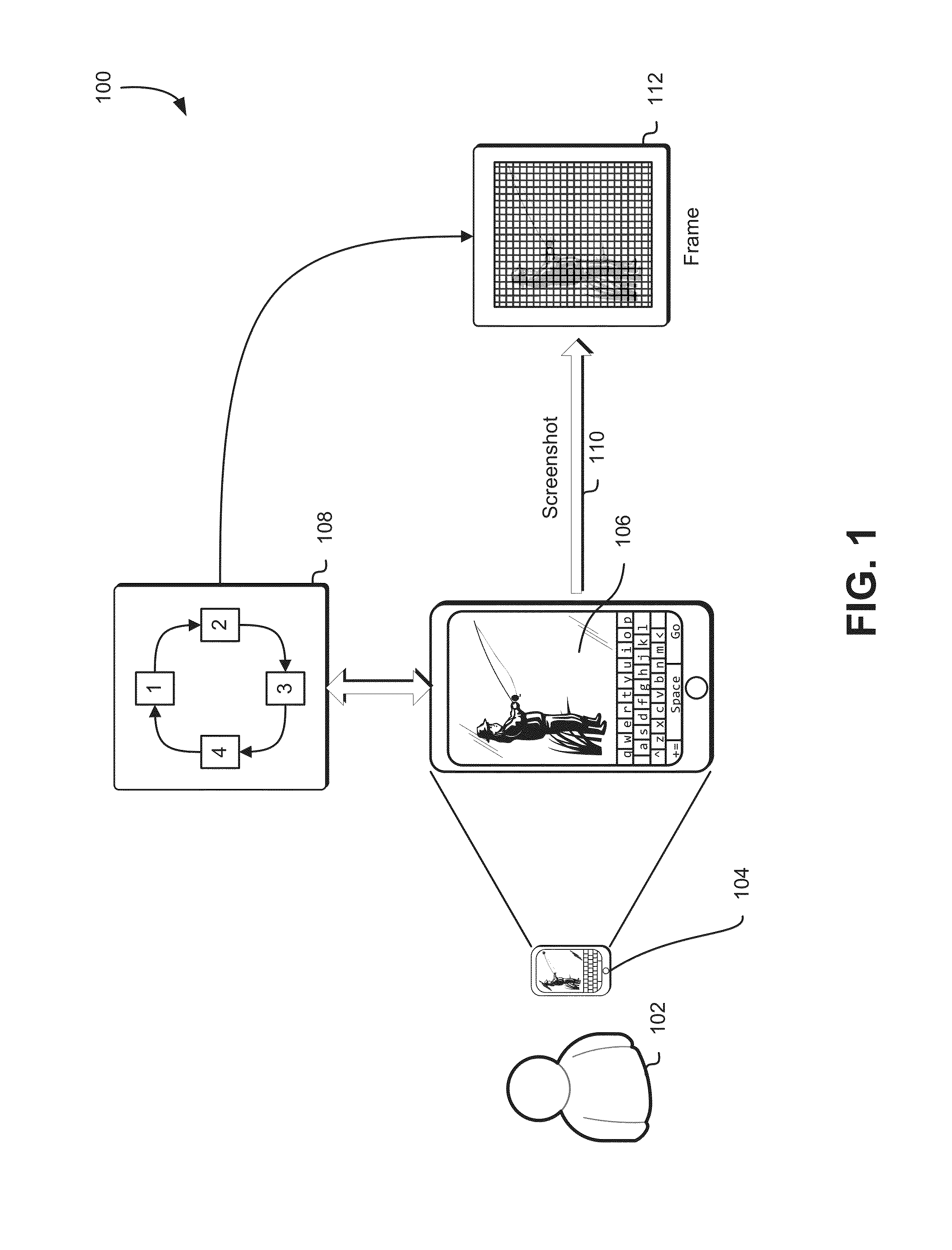
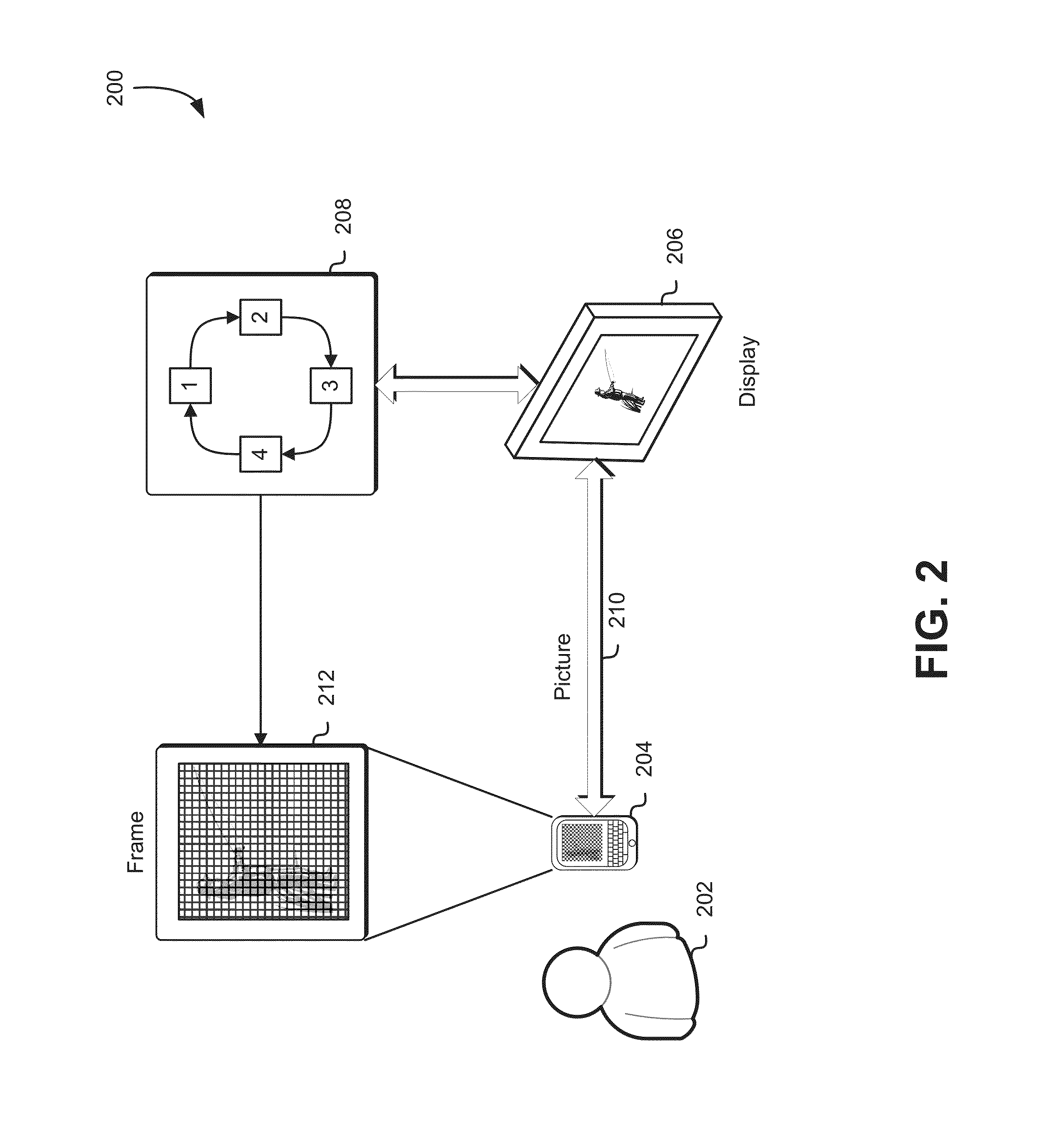
Techniques for displaying content on a display to reduce screenshot quality
Techniques for displaying content on a display to reduce screenshot quality are described herein comprising generating a set of degradation frames based on a source frame, with each degradation frame in the set of degradation frames based on applying one or more alterations to the data in the source frame based on a set of degradation parameters. A frame display order is determined and at least a subset of the degradation frames is displayed, corresponding to the frame display order.
Owner:HILL CHARLES +1
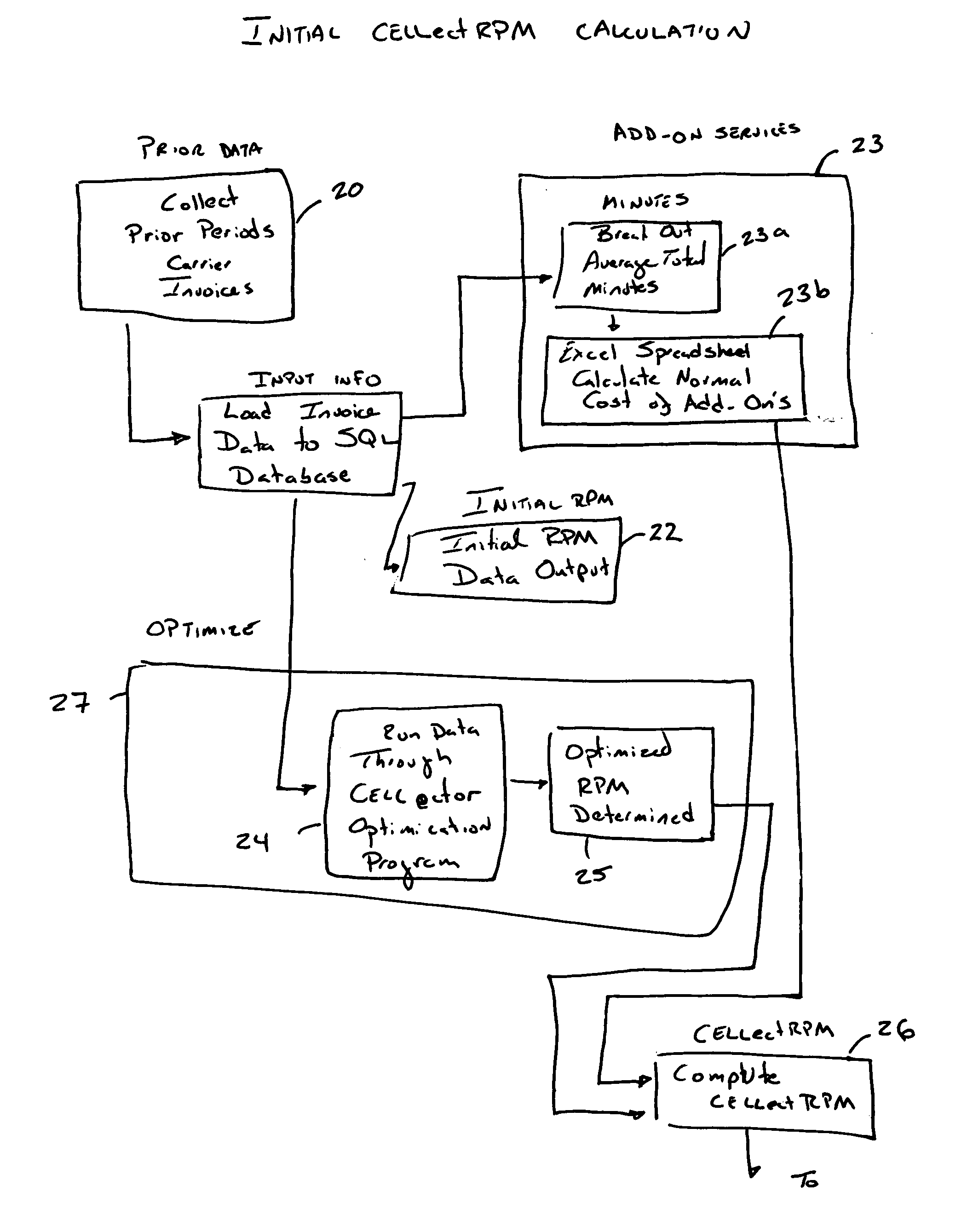
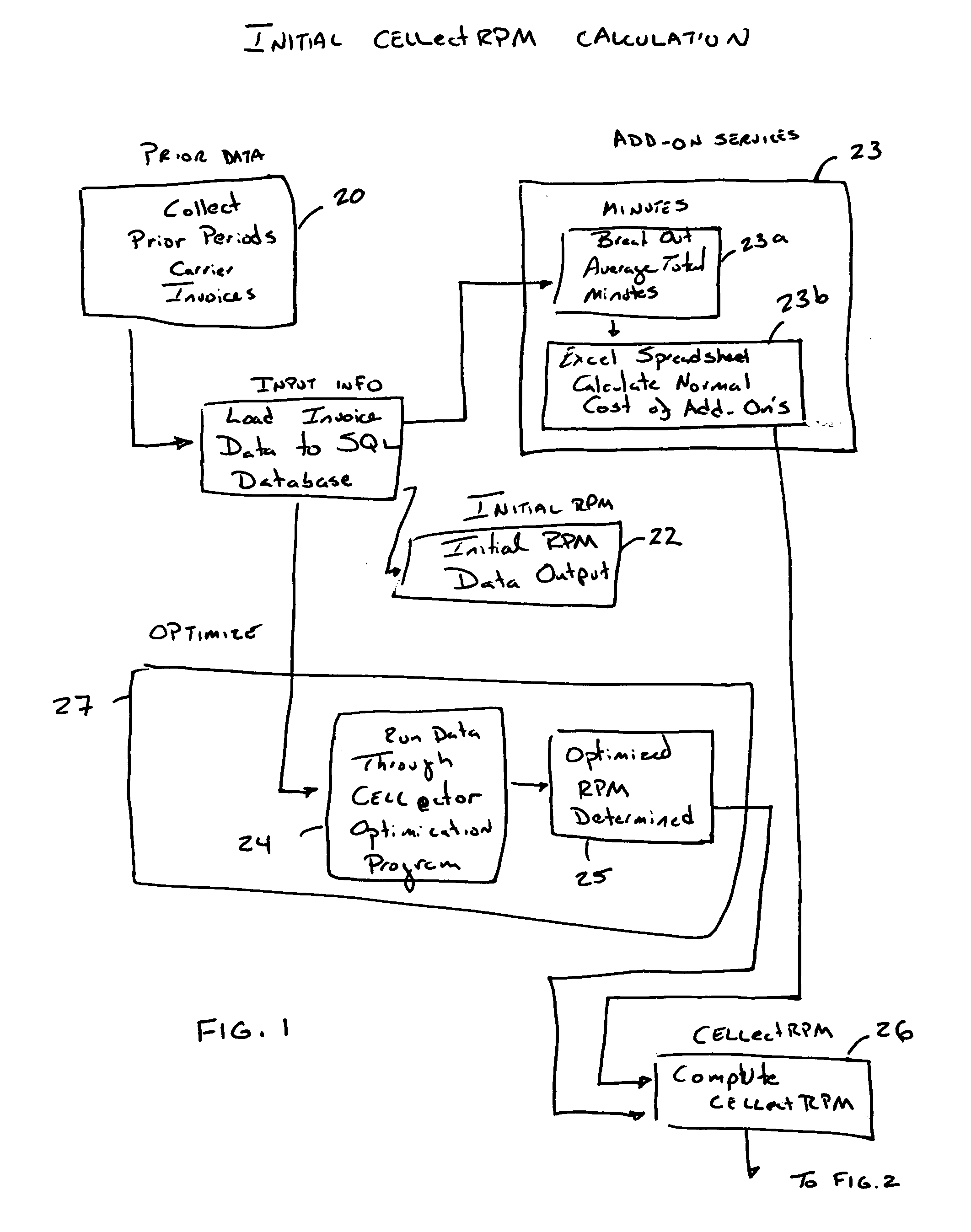
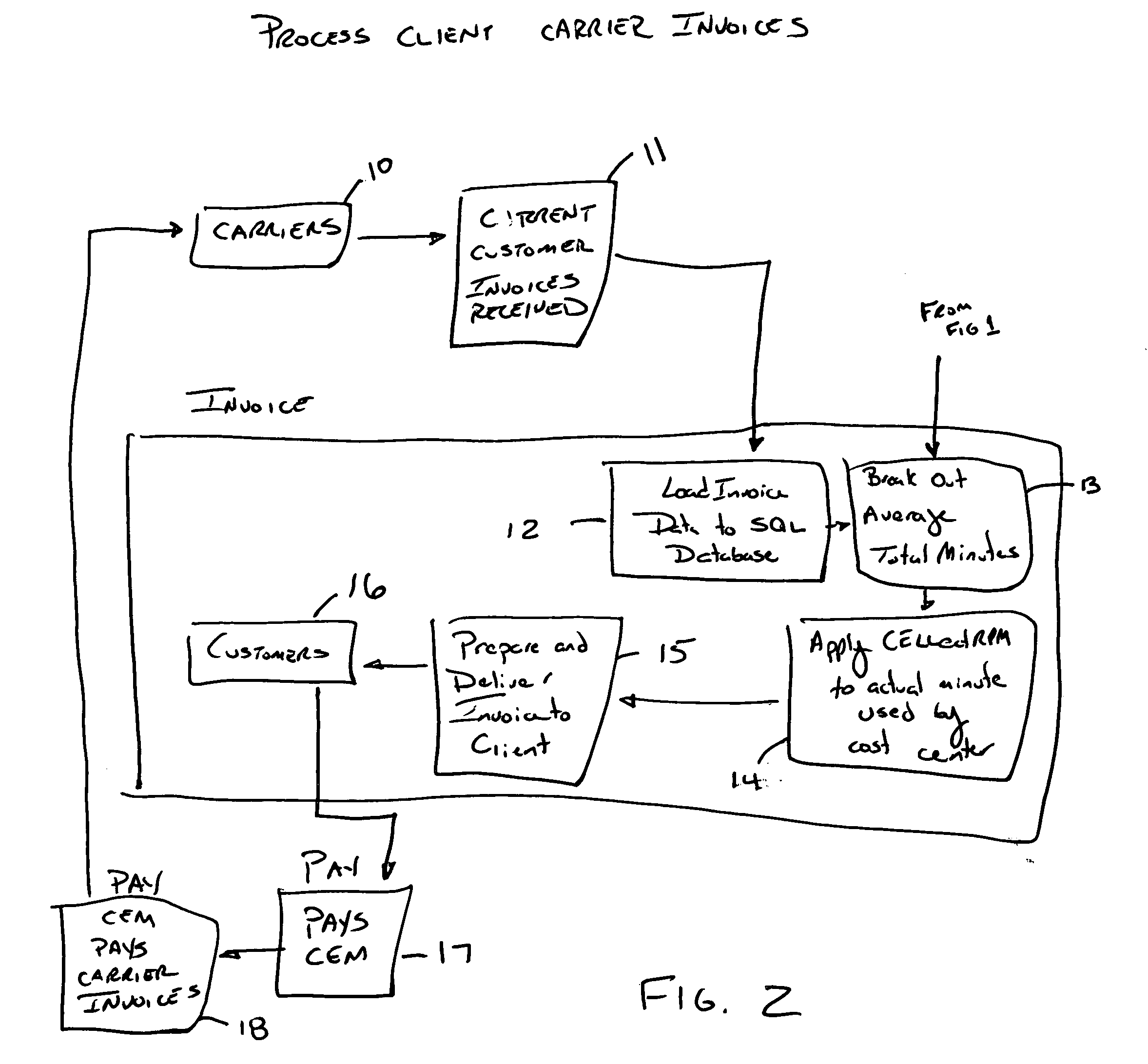
Optimized Communication Billing Management System
A business method is disclosed directed to attempting to saving clients money on their communications services. Specifically, billing information is obtained for a client and loaded into a database. An initial rate is determined based on this billing information, along with possibly an add on rate for add on services, which can provide a combined rate charge. At least one of the initial rate and combined rates are compared to a derived rate which is calculated by applying an algorithm to the database which applies the actual data to a plurality of rate plans provided by communications carriers to see which rate plan might provide savings for the client, if any. If savings are achieved, at least recommending if not switching to another rate plan, possibly of an other carrier.
Owner:IBM CORP
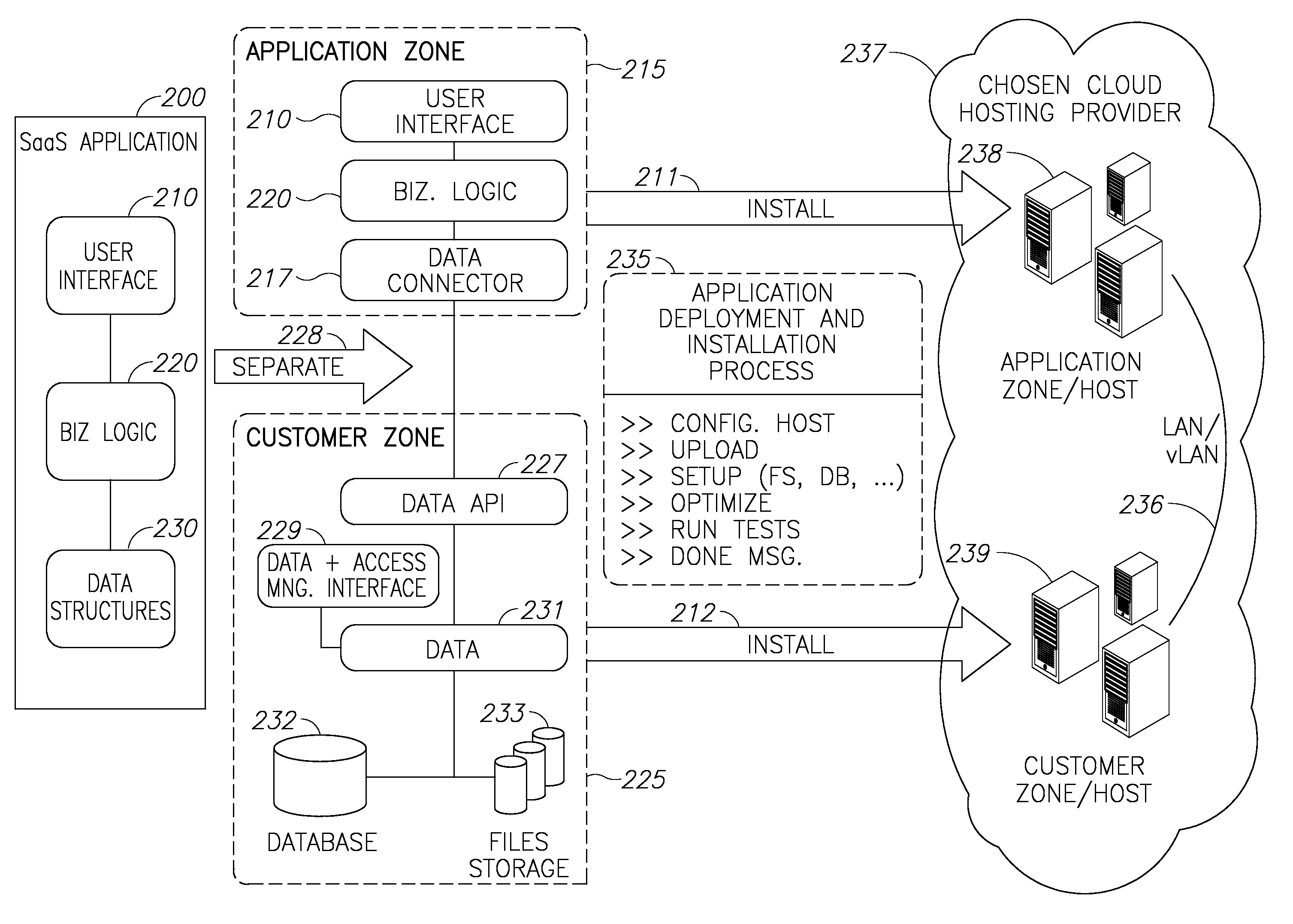
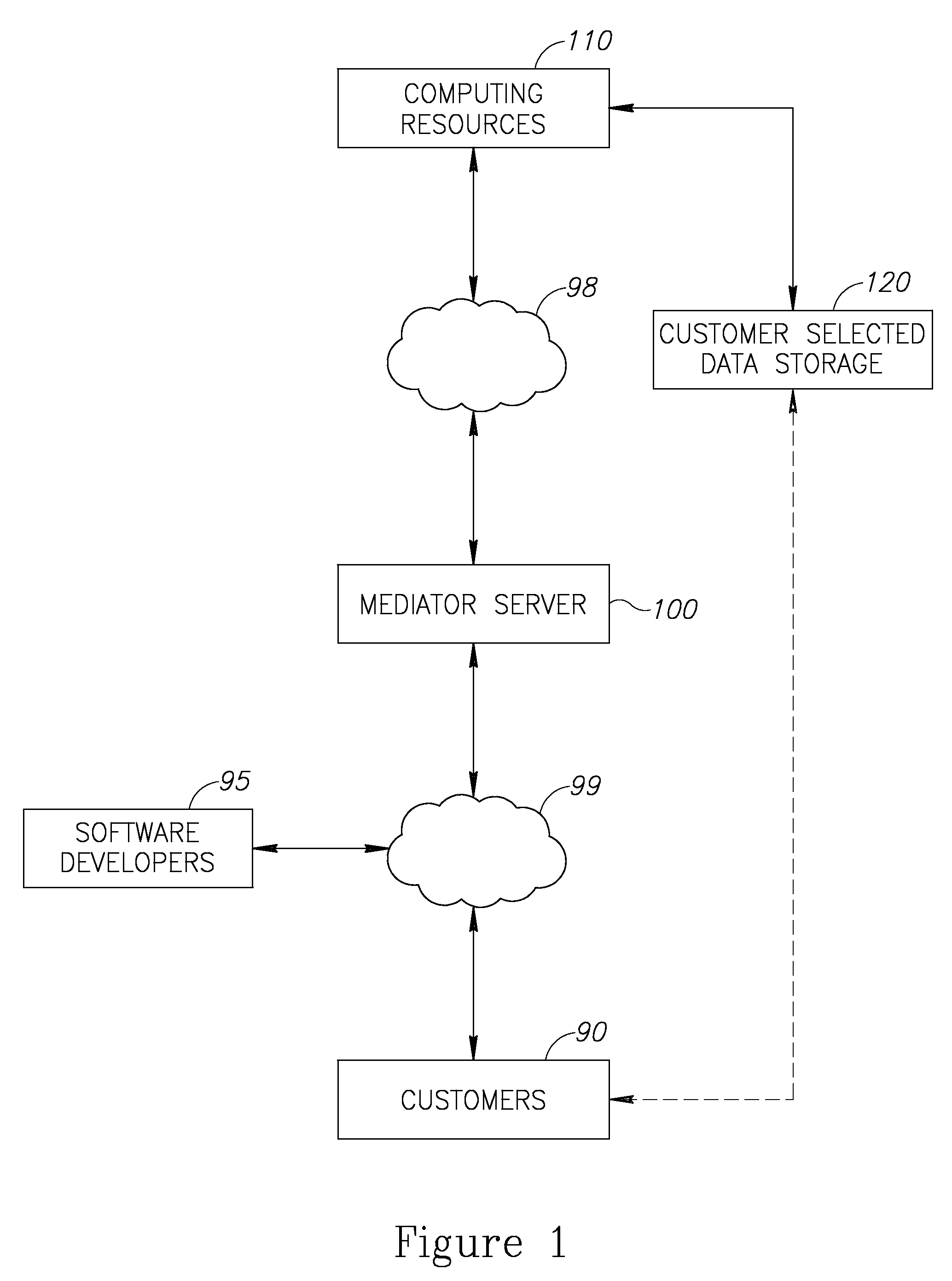
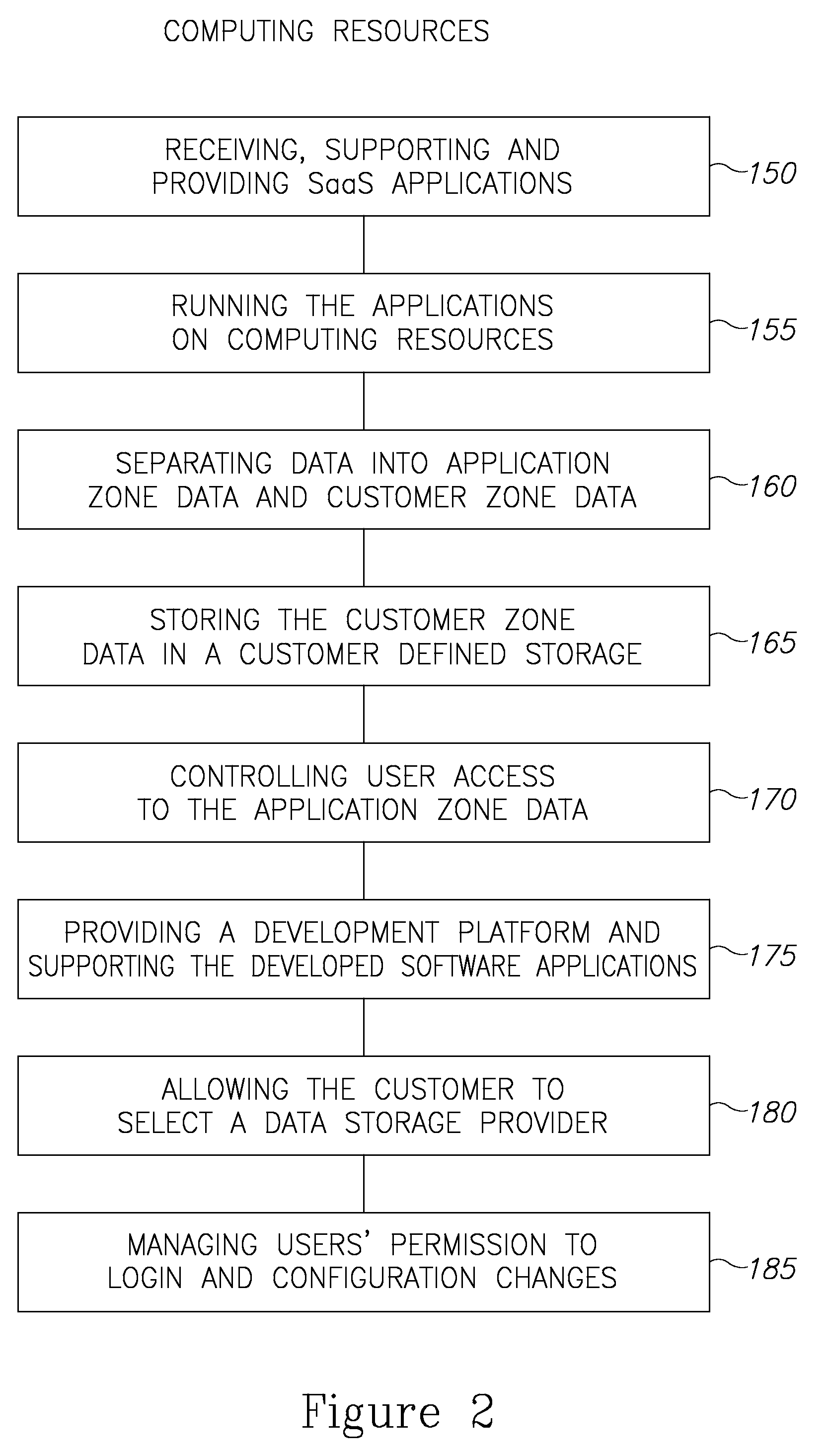
Cloud plarform for managing software as a service (SAAS) resources
InactiveUS20110126168A1Ensure availabilityEnsure data securityMultiple digital computer combinationsSpecific program execution arrangementsApplication softwareData availability
A cloud platform for managing Software as a Service (SaaS) resources is provided herein. The platform includes: a mediator server connected to computing resources, arranged to provide software developers a platform to develop SaaS applications, operable on the computing resources, wherein the SaaS applications and customer data are stored logically and physically independent of the computing resources, and data of SaaS application and the customer data are logically and physically separated. SaaS platform allows developers to provide software solutions via the mediator server directly to customers, and ensures data availability and data security. Access policy of users and developers to SaaS applications is centrally supervised and capable of integrating with other applications on the site of the customer. Upgrades to SaaS applications are performed in a predefined order of customers. Further, the SaaS platform facilitates selection and replacement of data storage provider.
Owner:CROWDSOURCE TECH
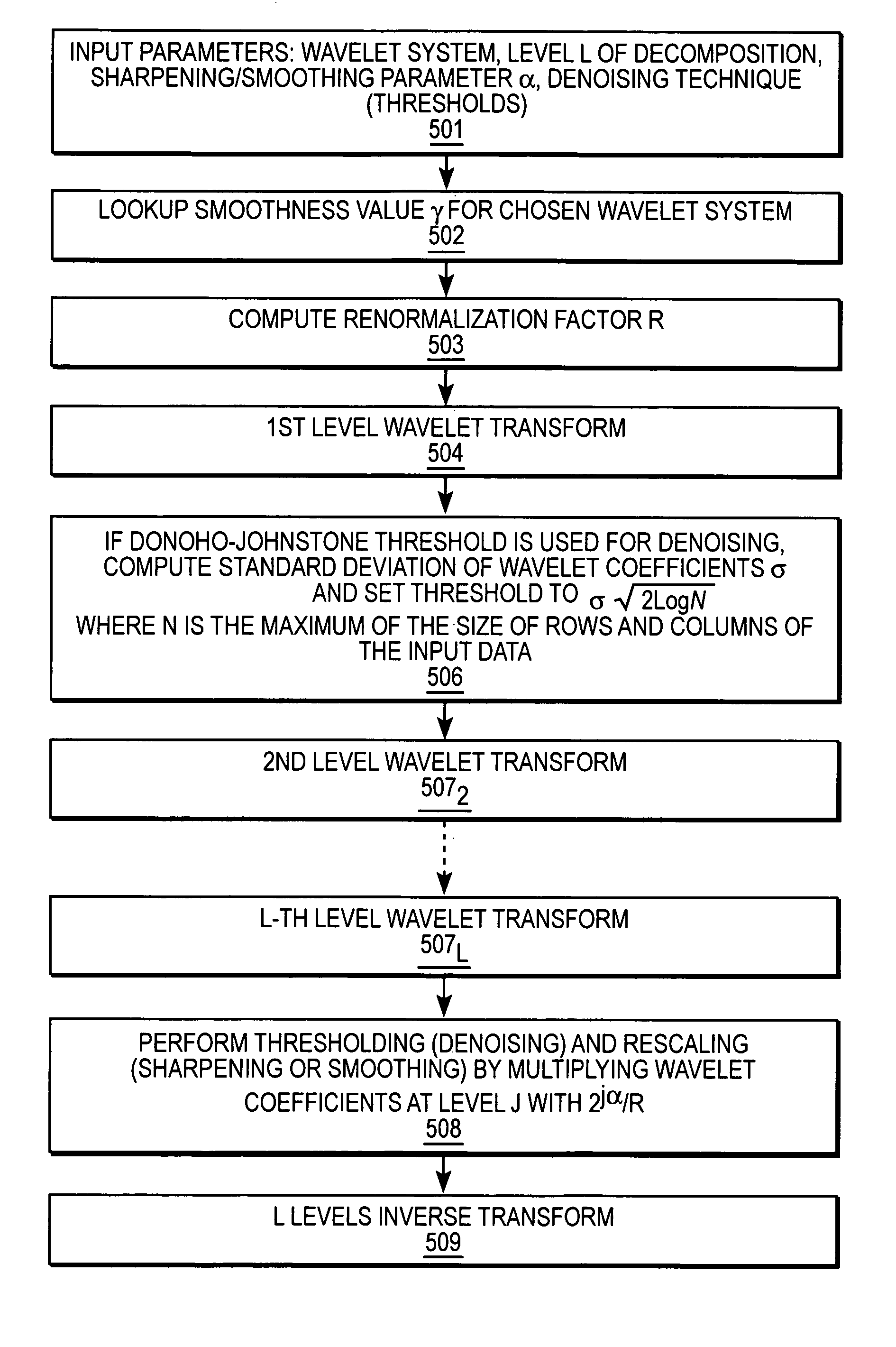
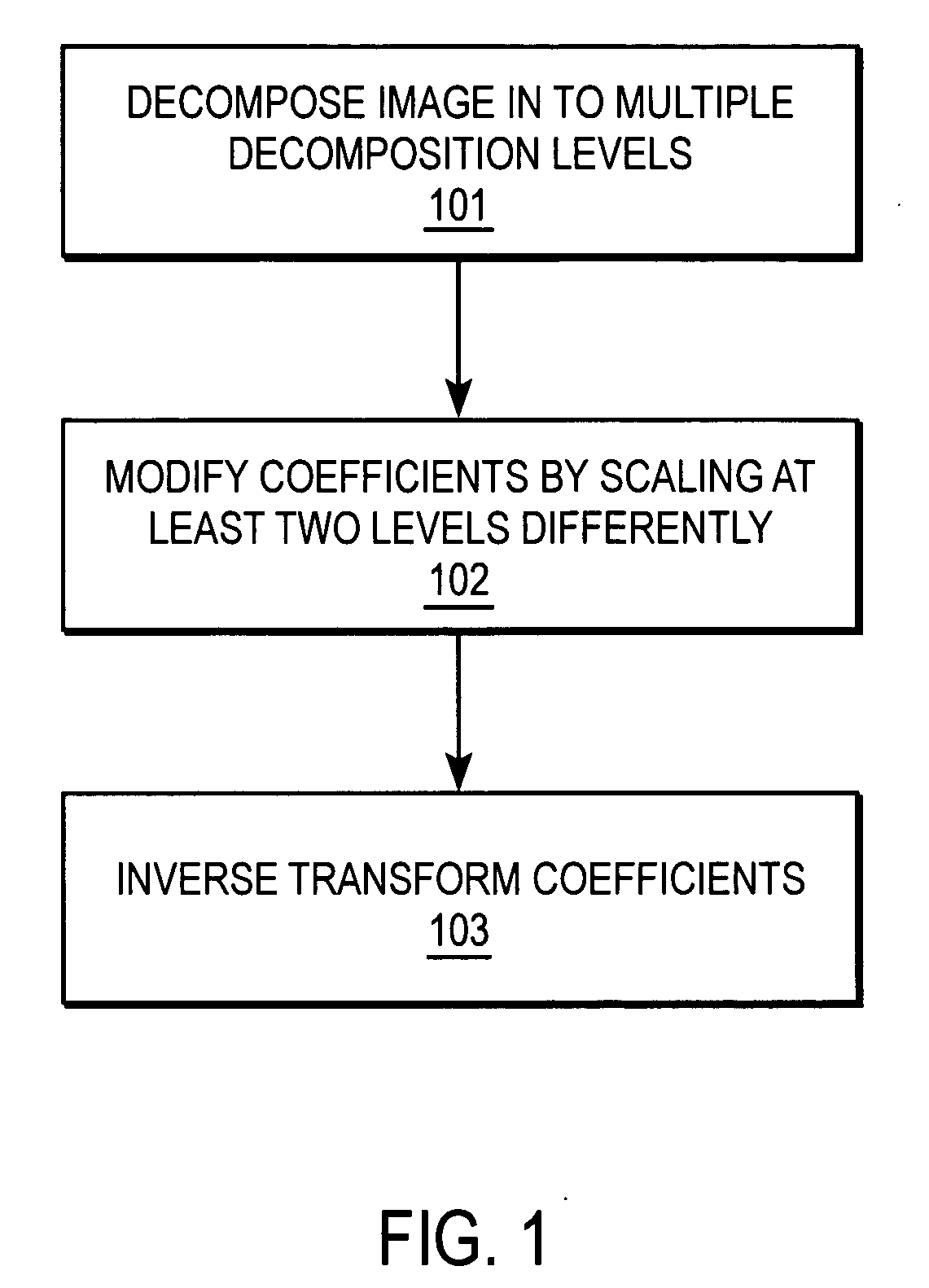
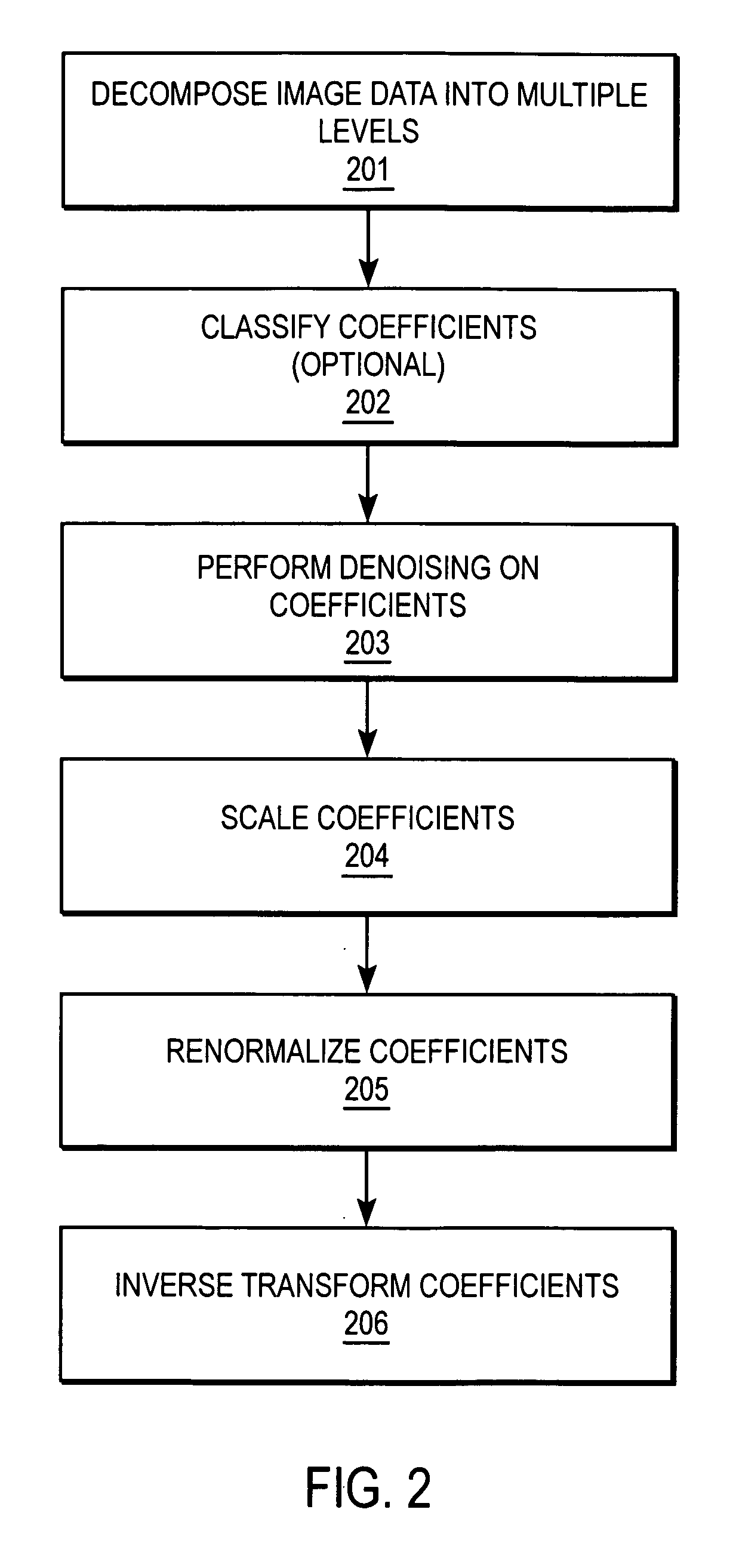
Multiscale sharpening and smoothing with wavelets
A method and apparatus for processing image data are described. In one embodiment, a method of processing image data comprises decomposing the image data into multiple decomposition levels by applying a wavelet transform to the image data, and modifying coefficients in at least two of the decomposition levels by scaling coefficients in theses decomposition levels using different scale dependent parameters for each of the decomposition levels.
Owner:RICOH KK
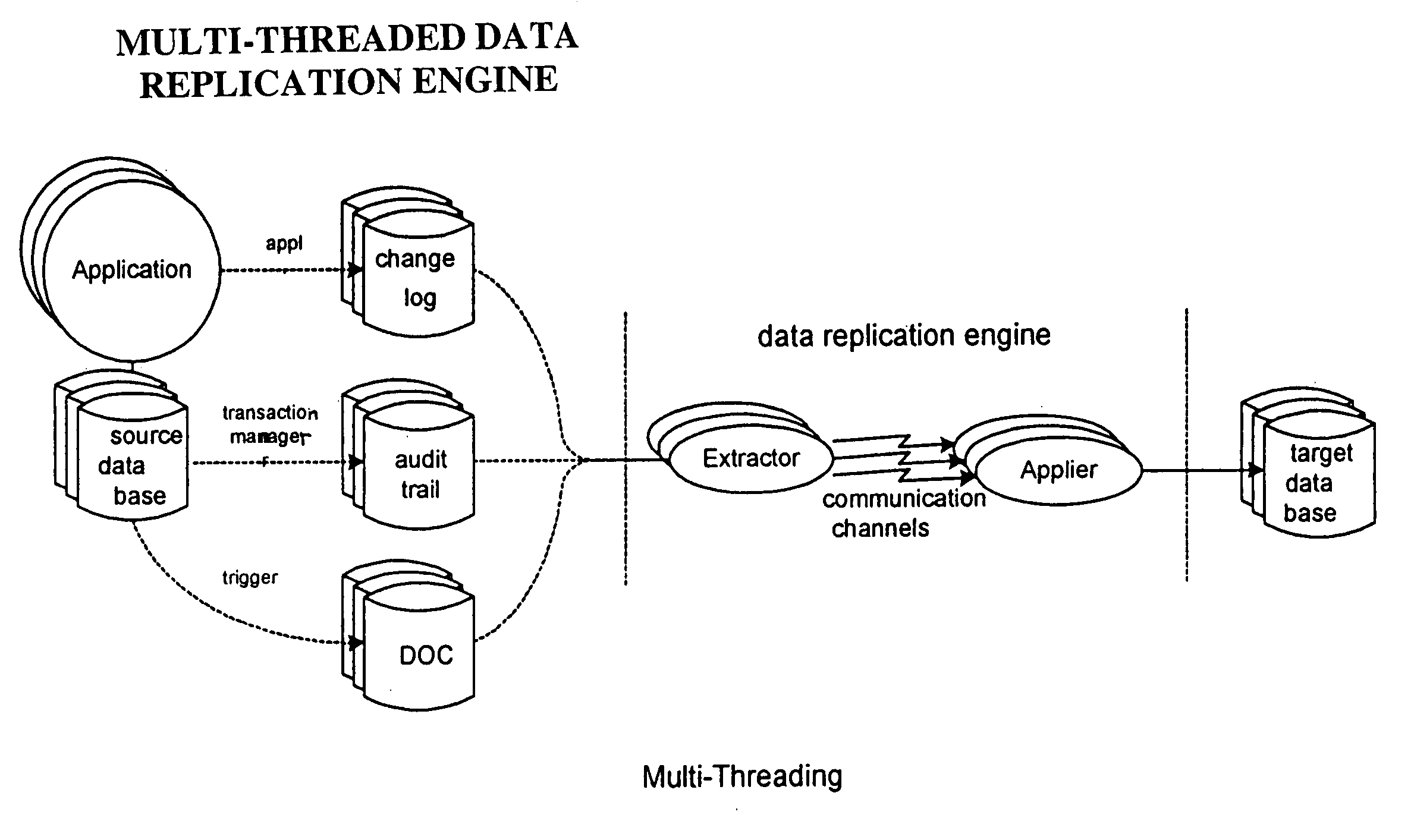
Method for ensuring referential integrity in multi-threaded replication engines
ActiveUS20050021567A1Digital data information retrievalDigital data processing detailsTransaction dataLoad capacity
During replication of transaction data from a source database to a target database via a change queue associated with the source database, one or more multiple paths are provided between the change queue and the target database. The one or more multiple paths cause at least some of the transaction data to become unserialized. At least some of the unserialized data is reserialized prior to or upon applying the originally unserialized transaction data to the target database. If the current transaction load is close or equal to the maximum transaction load capacity of a path between the change queue and the target database, another path is provided. If the maximum transaction threshold limit of an applier associated with the target database has been reached, open transactions may be prematurely committed.
Owner:INTEL CORP
Method and apparatus for data hierarchy maintenance in a system for mask description
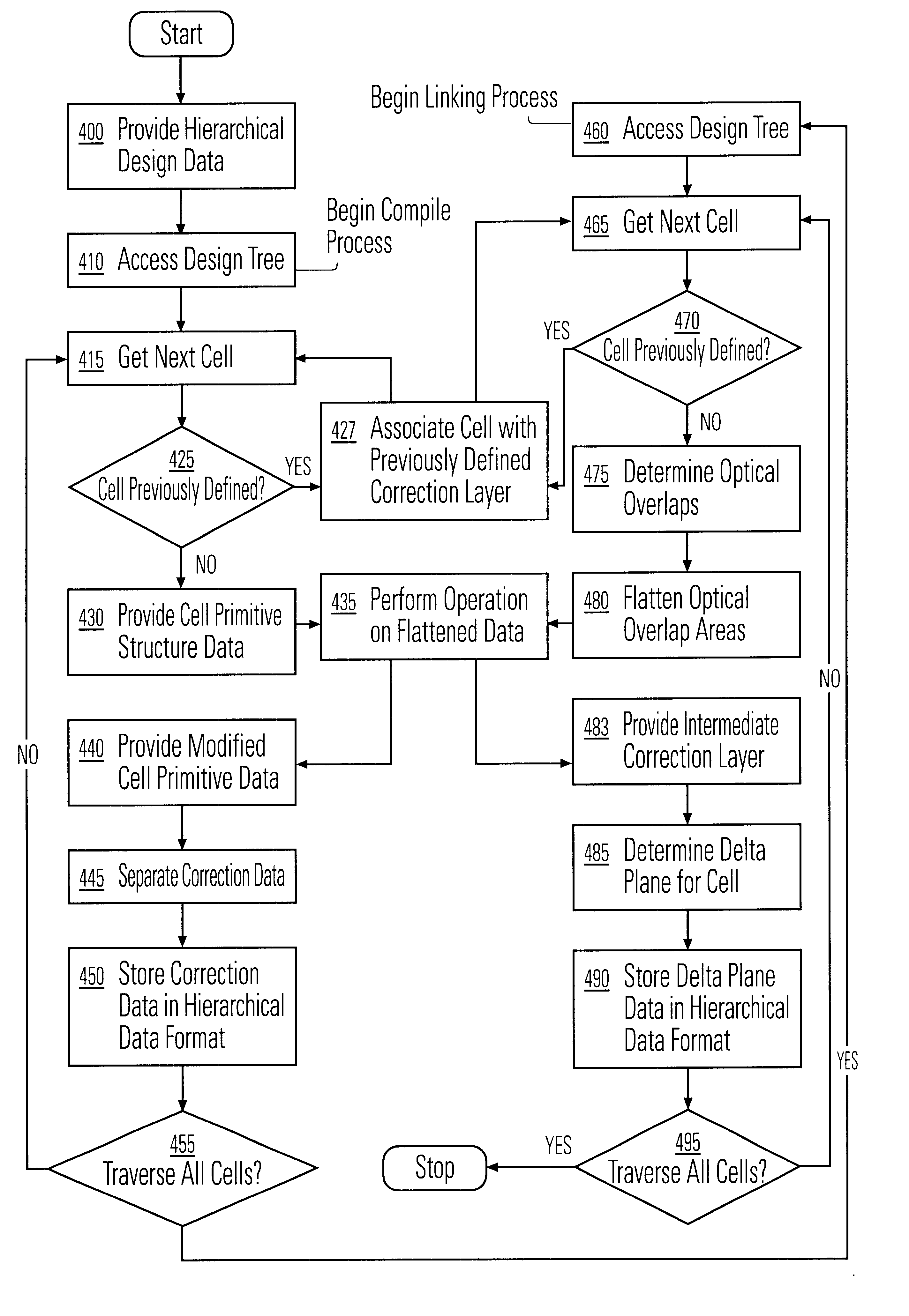
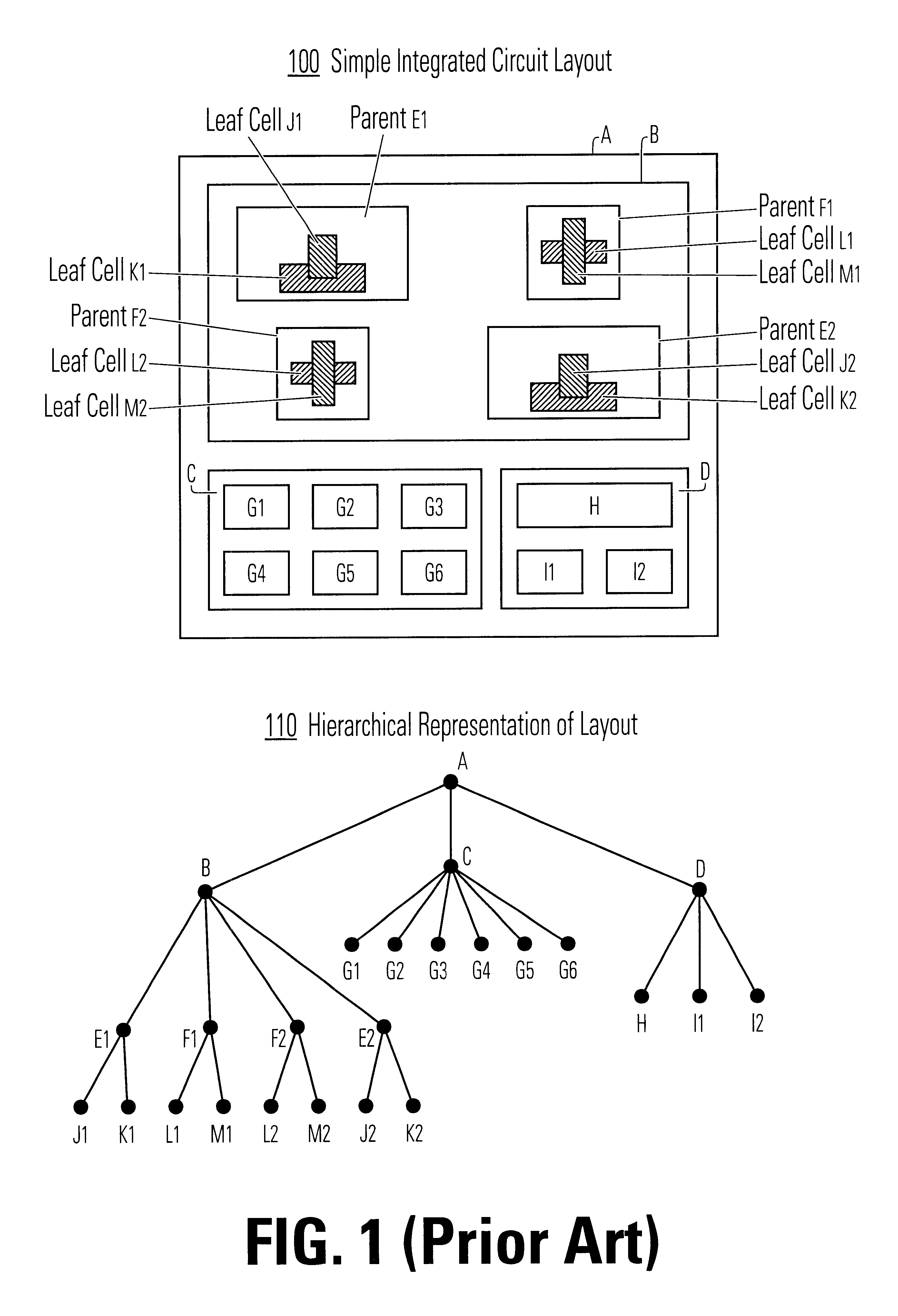
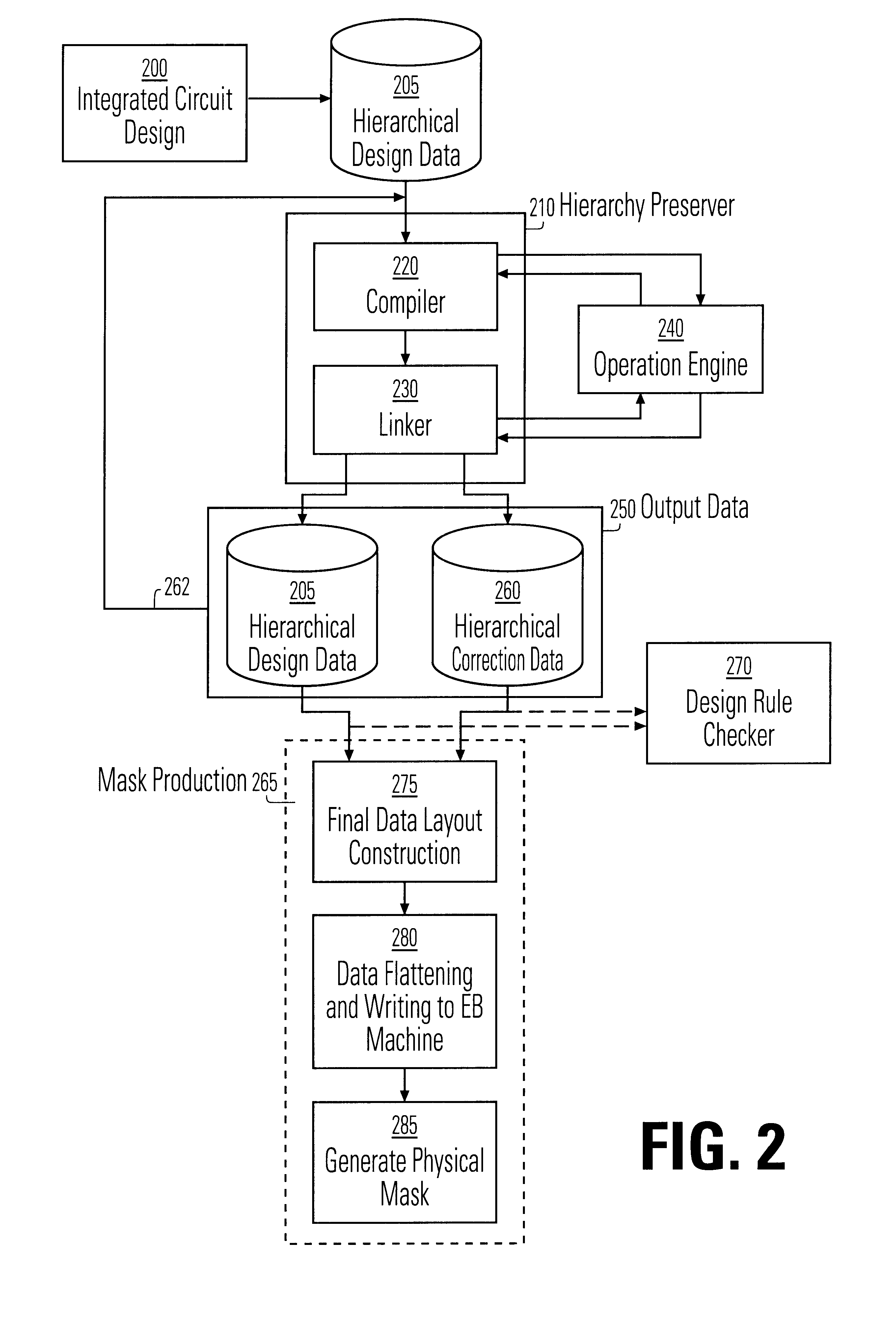
InactiveUS6453452B1Data augmentationReduce processing speedCAD circuit designProgram controlComputer architectureLogical operations
A method and apparatus for performing an operation on hierarchically described integrated circuit layouts such that the original hierarchy of the layout is maintained is provided. The method comprises providing a hierarchically described layout as a first input and providing a particular set of operating criteria corresponding to the operation to be performed as a second input. The mask operation, which may include operations such as OPC and logical operations such as NOT and OR, is then performed on the layout in accordance with the particular set of operating criteria. A first program data comprising hierarchically configured correction data corresponding to the hierarchically described layout is then generated in response to the layout operation such that if the first program data were applied to the flattened layout an output comprising data representative of the result of performing the operation on the layout would be generated. As the first program data is maintained in a true hierarchical format, layouts which are operated upon in accordance with this method are able to be processed through conventional design rule checkers. Further, this method is capable of being applied to all types of layouts including light and dark field designs and phase shifting layouts.
Owner:SYNOPSYS INC
Methods and apparatus for selecting a wireless network based on quality of service (QoS) criteria associated with an application
ActiveUS7318111B2Assess restrictionMultiple digital computer combinationsQuality of serviceVideo player
Methods and apparatus for selecting a wireless communication network based on quality of service criteria associated with an application are disclosed. In one illustrative example, one of several different software applications of a mobile communication device is executed. The software application may be, for example, an e-mail application, an Internet data application, a voice-over-IP application, a video player application, an audio player application, or a video game application. Each software application is associated with different quality of service (QoS) criteria for data communications through a wireless network. The quality of service criteria may include, for example, a bandwidth criterion, a delay criterion, a delay variation criterion, and a data loss criterion. A scanning operation is performed to identify a plurality of a wireless networks available in a coverage area of the mobile device. One of the identified wireless networks is selected for communication based on a match between its available quality of service and the quality of service criterion associated with the executed software application. Advantageously, the most suitable network may be chosen and utilized for each software application.
Owner:MALIKIE INNOVATIONS LTD
Systems and Methods for Graphical User Interface Interaction with Cloud-Based Applications
ActiveUS20130246932A1Small sizeExecution for user interfacesInput/output processes for data processingVirtualizationGraphics
Systems and methods may: execute a virtualized application instance in a virtual computing environment; receive from a remote client device first object data relating to a first set of user interactions received with respect to a client-side graphical use interface (GUI) object at the remote client device, the client-side GUI object representing a GUI object of the virtualized application instance; translating the first object data to second object data relating to the GUI object of the virtualized application instance, the second object data executing a command when applied to the GUI object of the virtualized application instance; and synchronizing the GUI object of the virtualized application instance with the client-side GUI object by applying the second object data to the GUI object of the virtualized application instance.
Owner:CLOUDON
Health information system and method
InactiveUS20060173715A1Reduce riskPrevent further degradationTelemedicineMedical automated diagnosisMedical recordDecision taking
The present invention relates to a distributed computer-based decision support technology for the healthcare industry. It also relates to a systematic knowledge diffusion technology for the healthcare industry. The tool and methodology packages and distributes computation and data processing software components in both centralized and federated fashions to process medical data in-situ and in real-time, applying the knowledge and best practices that can reflect the most recent advancement of medical sciences. This tool and methodology interacts with a healthcare organization's existing internal and external information sources, including those sources of its trading partners, such as practice management systems, health information systems, electronic medical records systems, lab systems, medical reference systems, and existing decision support systems. Due to this sharing of information and the ability to construct longitudinal medical records that was previously not possible, the quality of decision support can be rapidly improved, benchmarked, and standardized across the industry.
Owner:WANG HAO
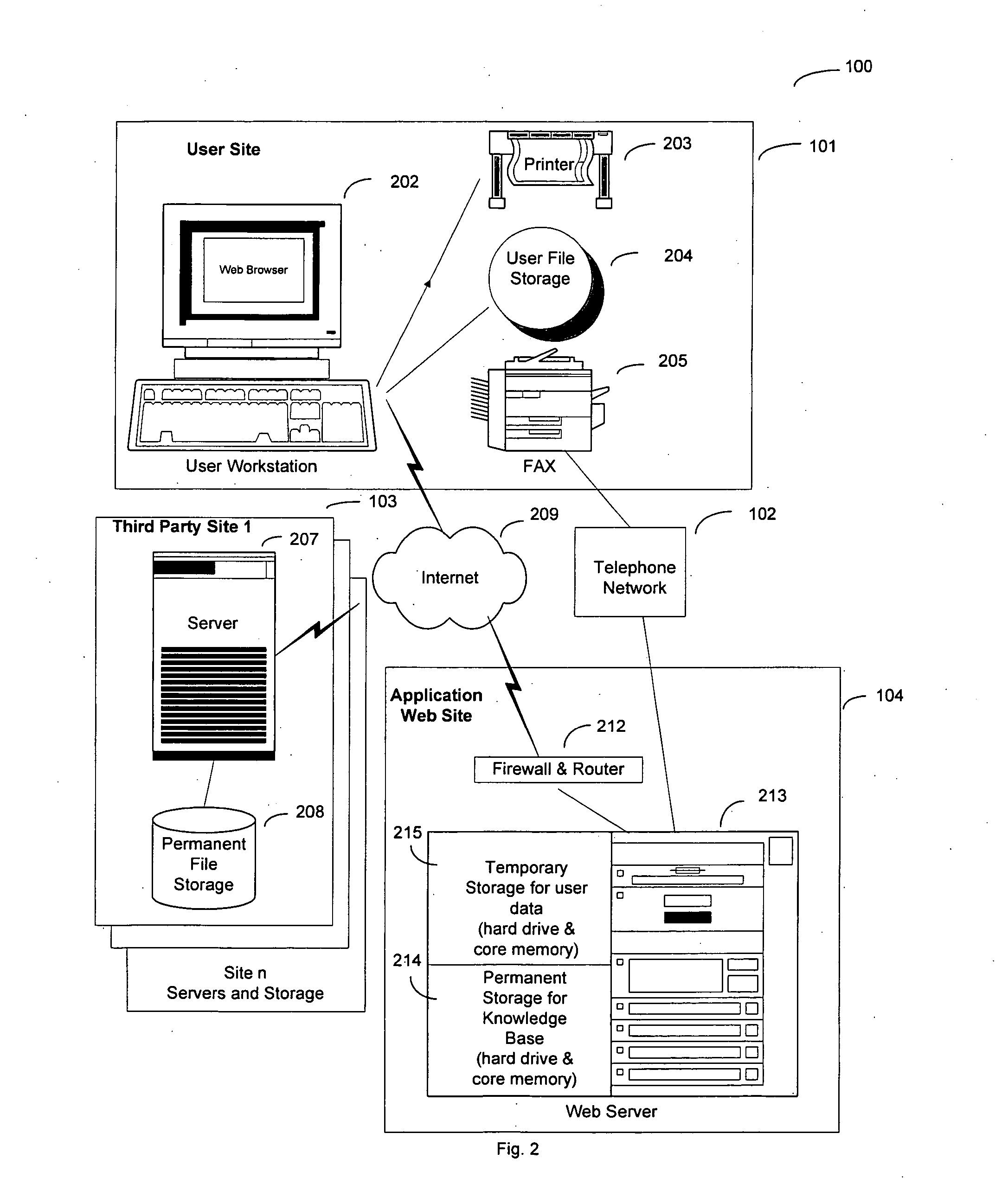
Method and system to edit and analyze longitudinal personal health data using a web-based application
In a global computer network, a system for processing personal health records is disclosed. The system includes a web-based application providing an application web server that does not store personal data. A user starts a new session using the application web site and begins entering medical data. During the session, with the user's data in transient storage, the application web site can perform health risk assessments and search other databases to provide information relevant to the user's health. At the end of the session, the user downloads a file that saves all of the data. Next, the application web site erases the user's data from the web site. The user continues data entry in the future by uploading the saved file. Since the user keeps the data, no identification of the user is necessary and privacy is preserved.
Owner:WU HARRY C
System, multi-tier interface and methods for management of operational structured data
ActiveUS20090125796A1Reduce the impactEasy to moveExecution for user interfacesInput/output processes for data processingSubject-matter expertObject based
Owner:AVRO COMPUTING
System used for constructing user figure
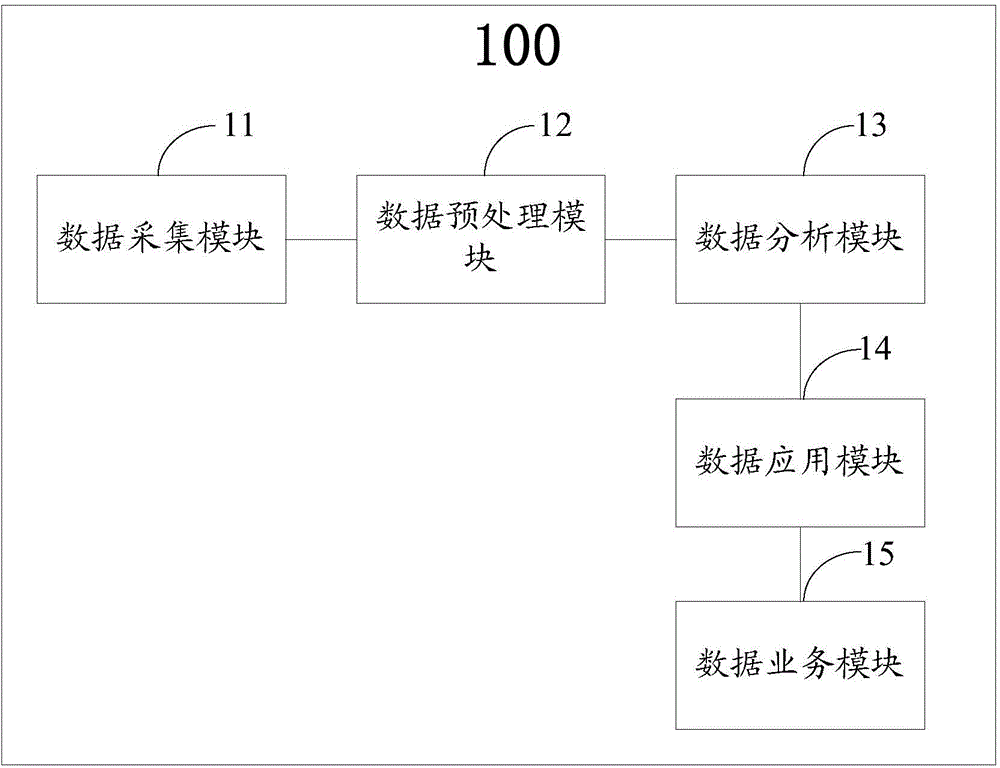
InactiveCN106504099AEasy to analyzeAccurate analysisData processing applicationsSpecial data processing applicationsFeature extractionData acquisition
The invention discloses a system used for constructing a user figure. The system comprises a data acquisition module used for acquiring the Internet surfing log data of a user, a data pre-processing module used for pre-processing the Internet surfing log data of the user, a data analysis module used for carrying out characteristic extraction for the Internet surfing log data after pre-processing to acquire attribute characteristics of the user, a data application module used for matching in a multi-dimensional database on the basis of label classification trained by an established multi-dimensional characteristic database according to the attribute characteristics of the user to acquire multi-dimensional attribute labels of the user, and a data business module used for constructing the user figure according to the multi-dimensional attribute labels. The system is advantaged in that the holographic multi-dimensional user figure can be constructed, and rapid precise advertisement delivery of service providers / enterprises / companies and consumption behavior recommendation of use groups can be satisfied.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
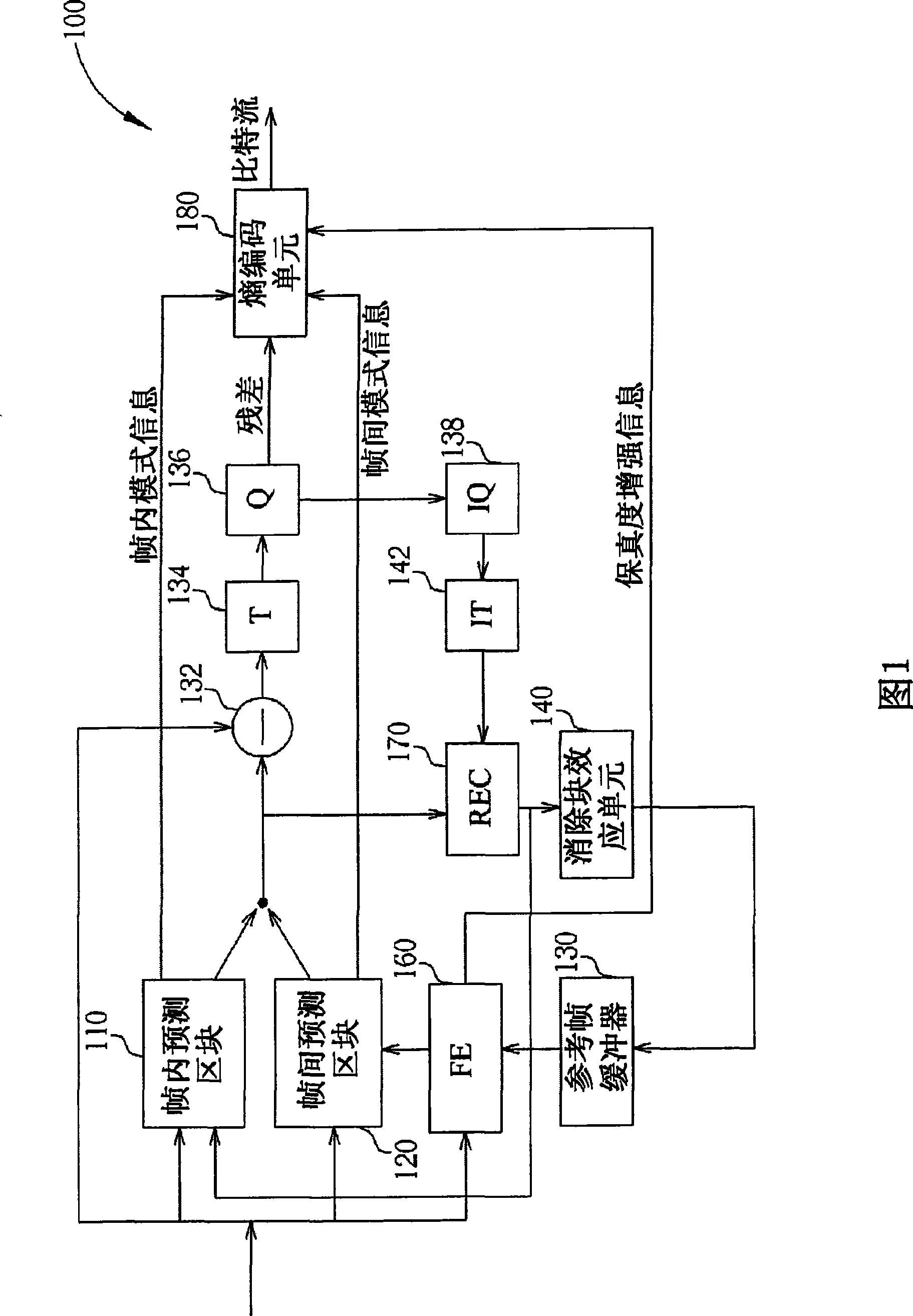
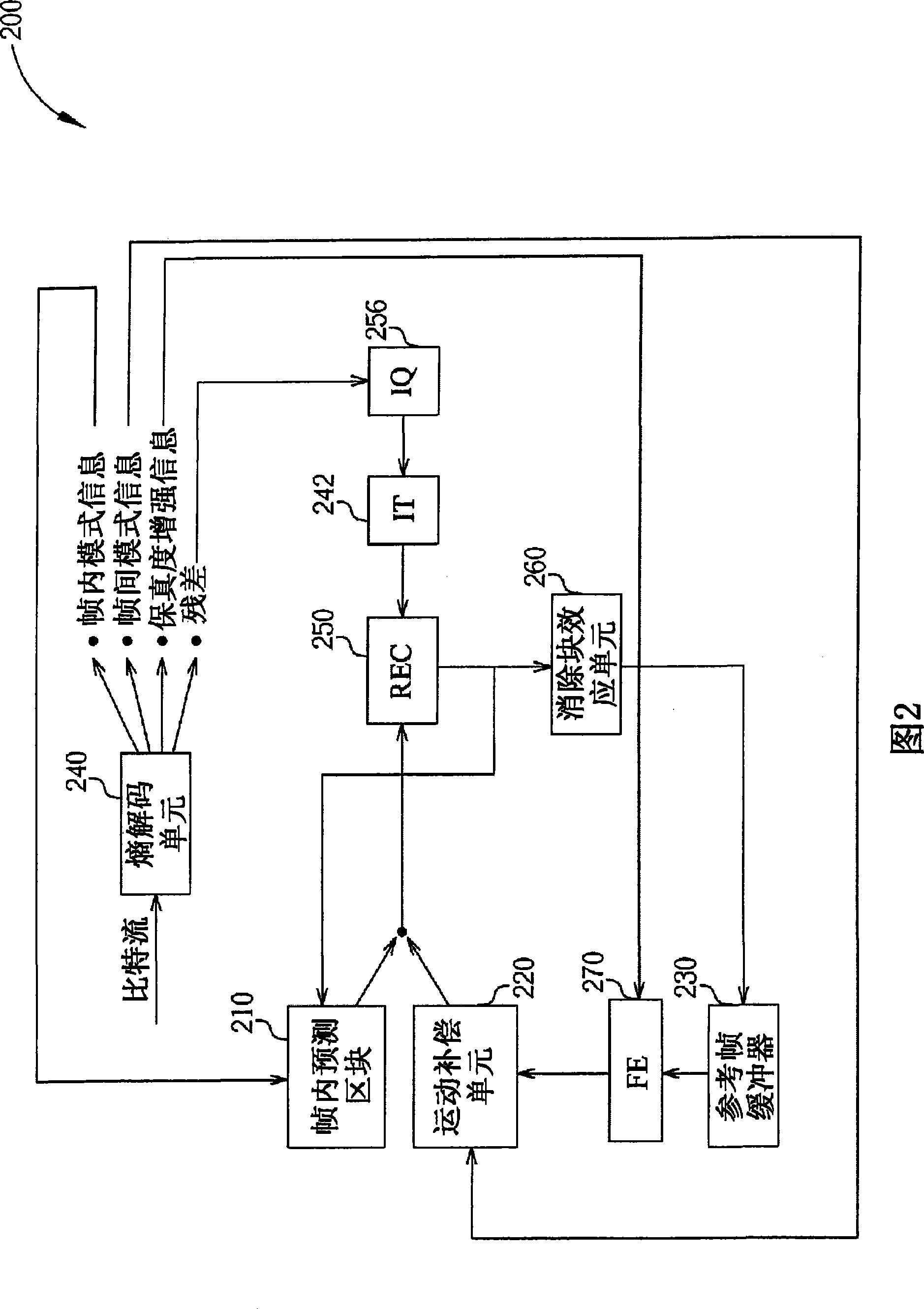
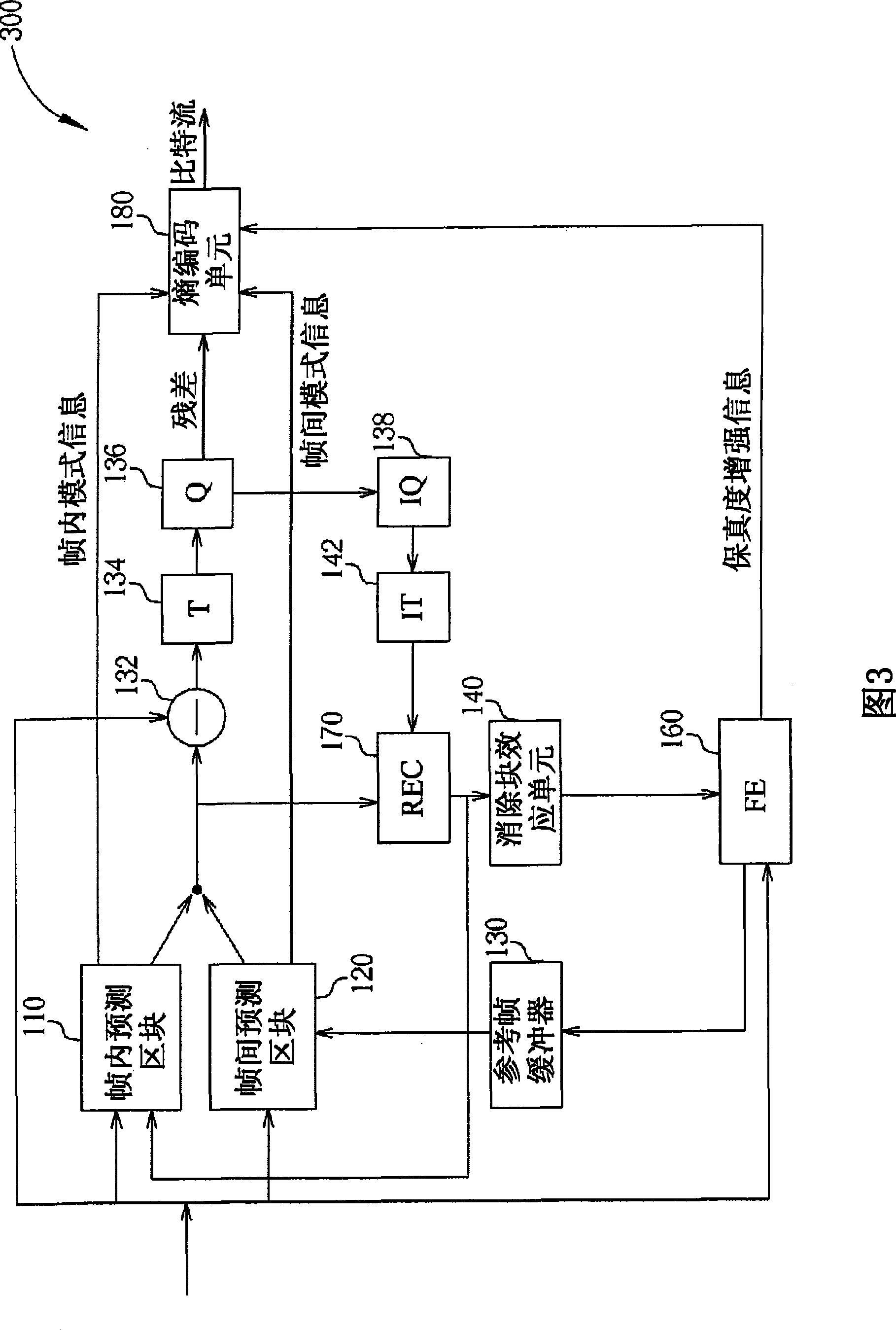
Encoder, decoder, video frame coding method and bit stream decoding method
ActiveCN101459847AImprove fidelityPulse modulation television signal transmissionDigital video signal modificationCoding blockComputer architecture
The invention provides an encoder, decoder, video frame encoding method and bit stream decoding method. The encoder for receiving a video frame and performing encoding processes to generate an encoded bit stream includes: a fidelity enhancement block, for performing a fidelity enhancement technique on the video frame utilizing a quad- tree partition, and generating fidelity enhancement information including a parameter associated with the quad-tree partition structure; and an entropy coding block, coupled to the fidelity enhancement block, for encoding the fidelity enhancement information, and embedding the encoded fidelity enhancement information into the encoded bit stream. The said method and device make the decoder immediately stores the fidelity enhancement information and execute the fidelity enhancement without waiting for decoding all the bit streams through indicating the position of the fidelity enhancement information by an indicating needle.
Owner:HFI INNOVATION INC
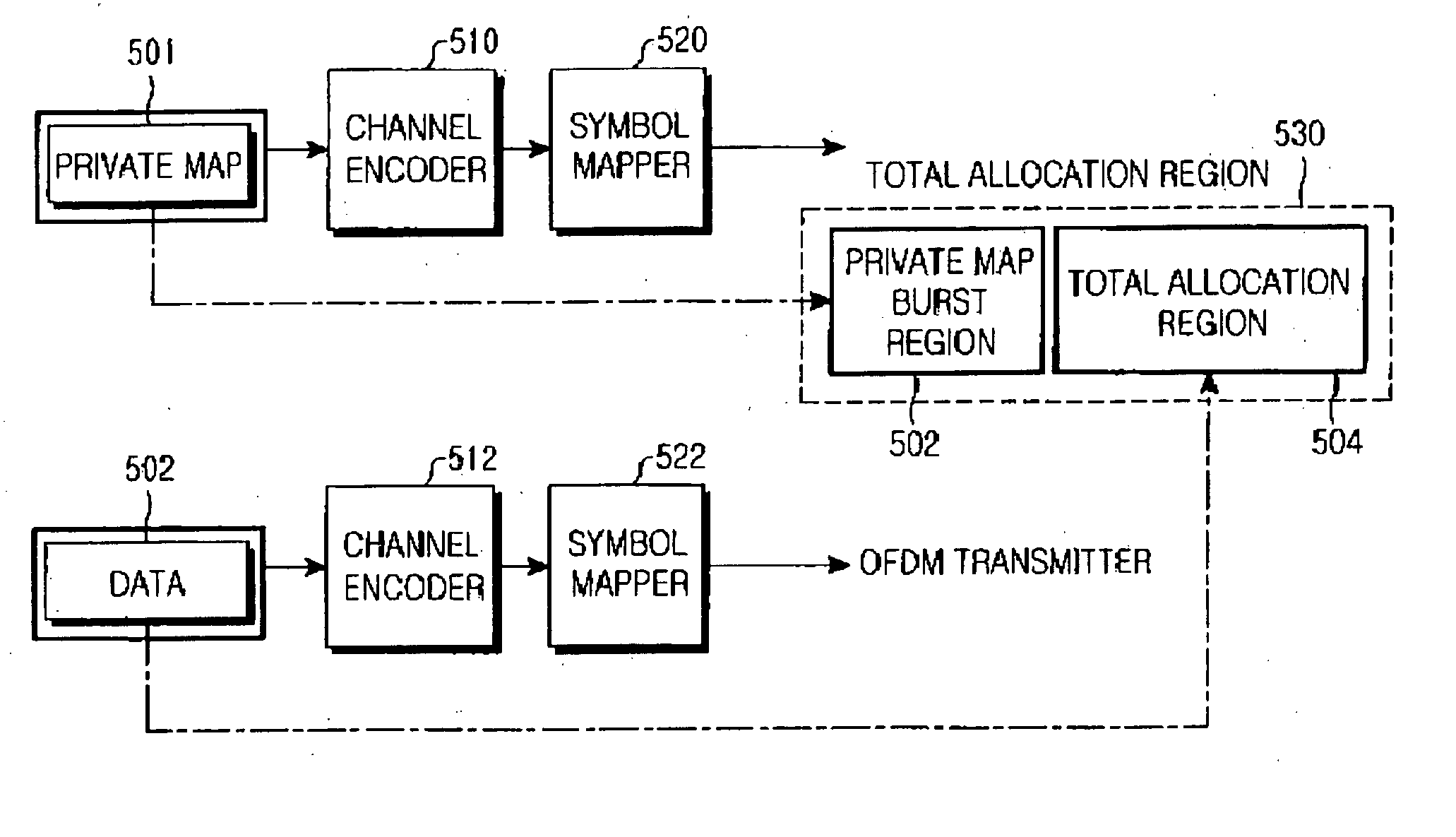
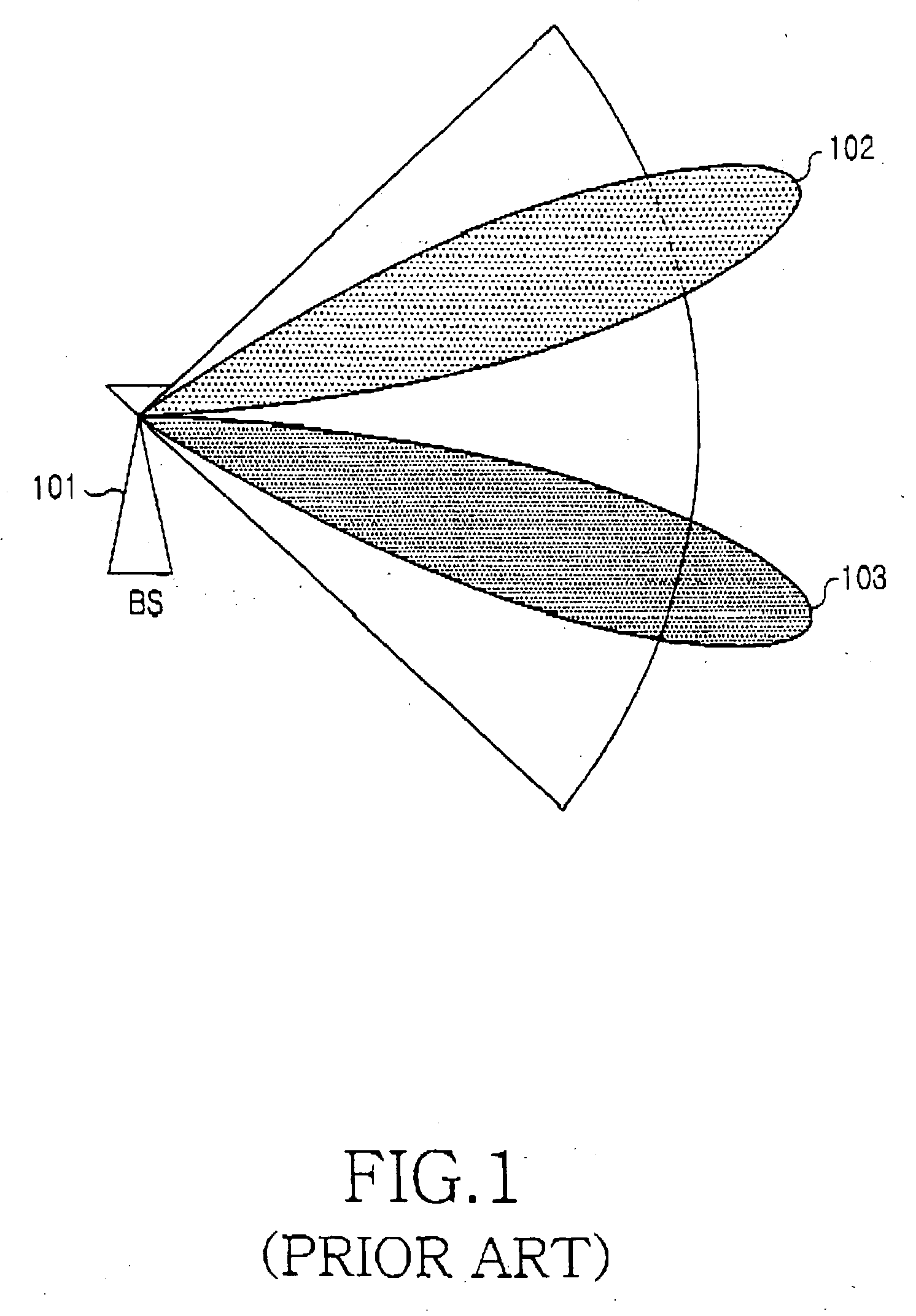
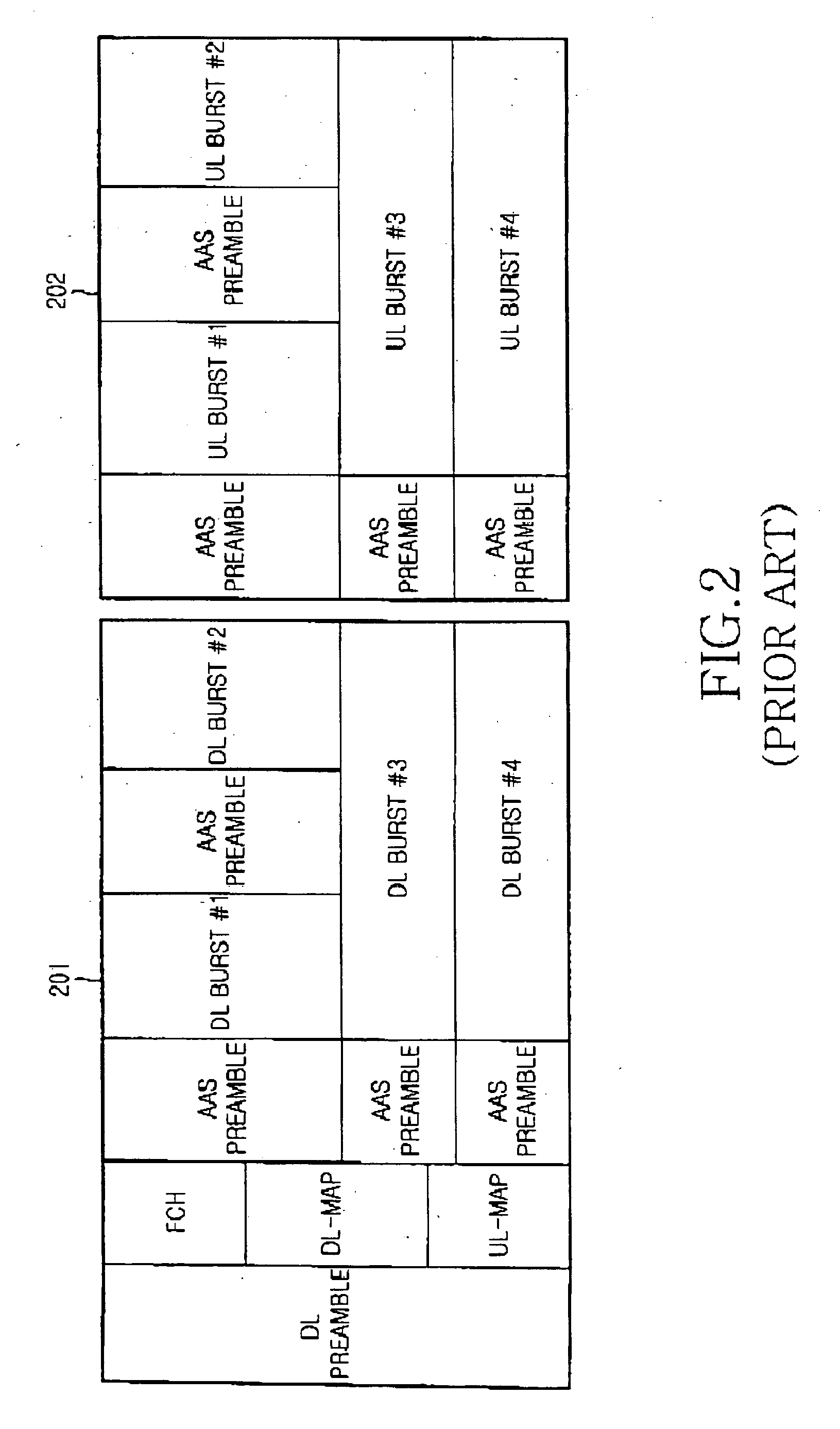
Apparatus and method for transmitting information data in a wireless communication system
InactiveUS20060153227A1Robust transmissionMultiple modulation transmitter/receiver arrangementsNetwork traffic/resource managementCommunications systemBroadband
A system and method for transmitting control information and data to a mobile station in a communication system using adaptive antenna technology defined in a broadband wireless communication system. In a method for transmitting and receiving information data in the wireless communication system, a base station separates information data to be transmitted into control information and user data, applies different modulation and coding schemes to the control information and the user data, and transmits the information data to an associated mobile station. The mobile station identifies the modulation and coding schemes of the information data received from the base station and demodulates a total of the information data according to the modulation and coding schemes, or independently demodulates the control information and the data according to the modulation and coding schemes.
Owner:SAMSUNG ELECTRONICS CO LTD
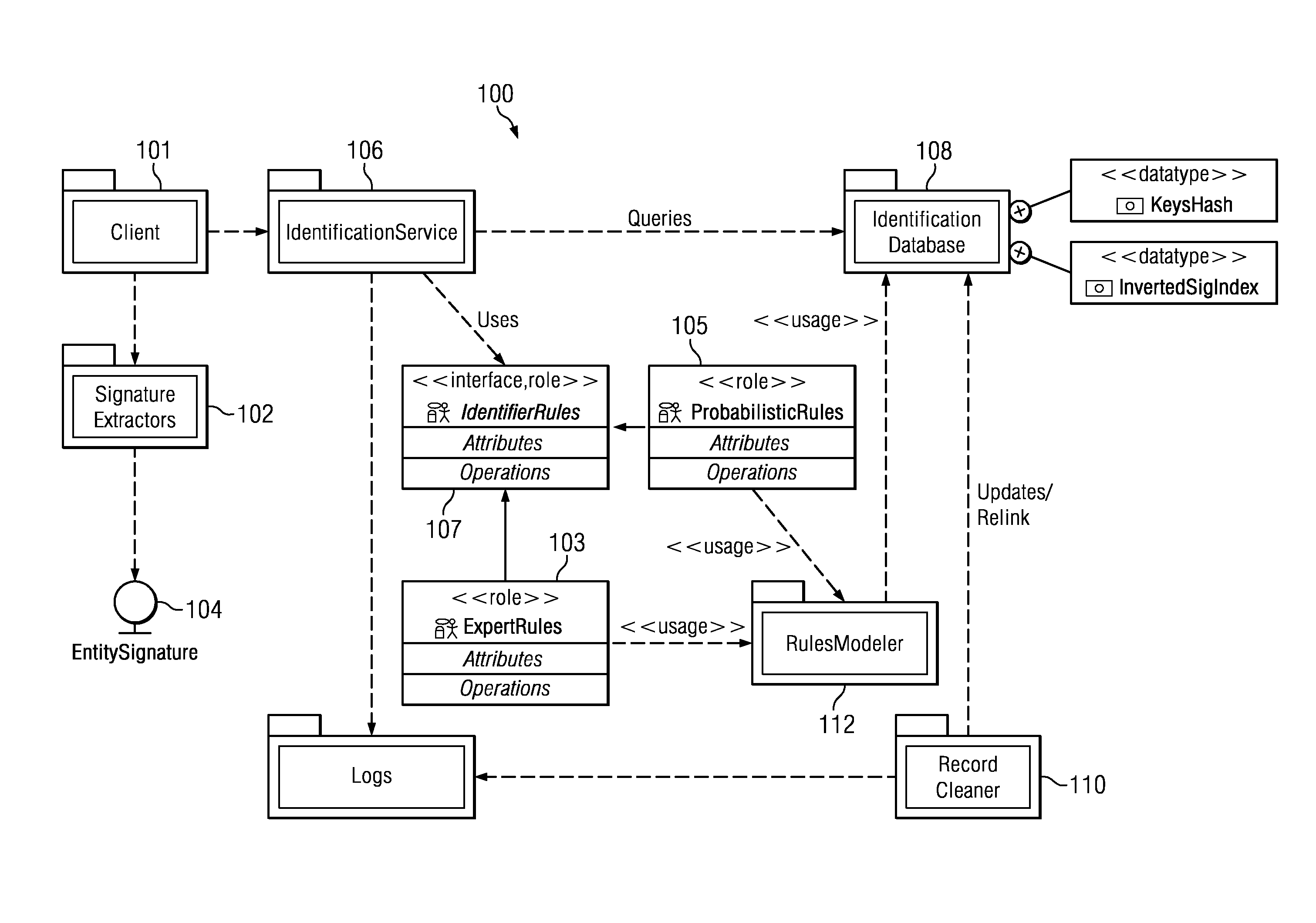
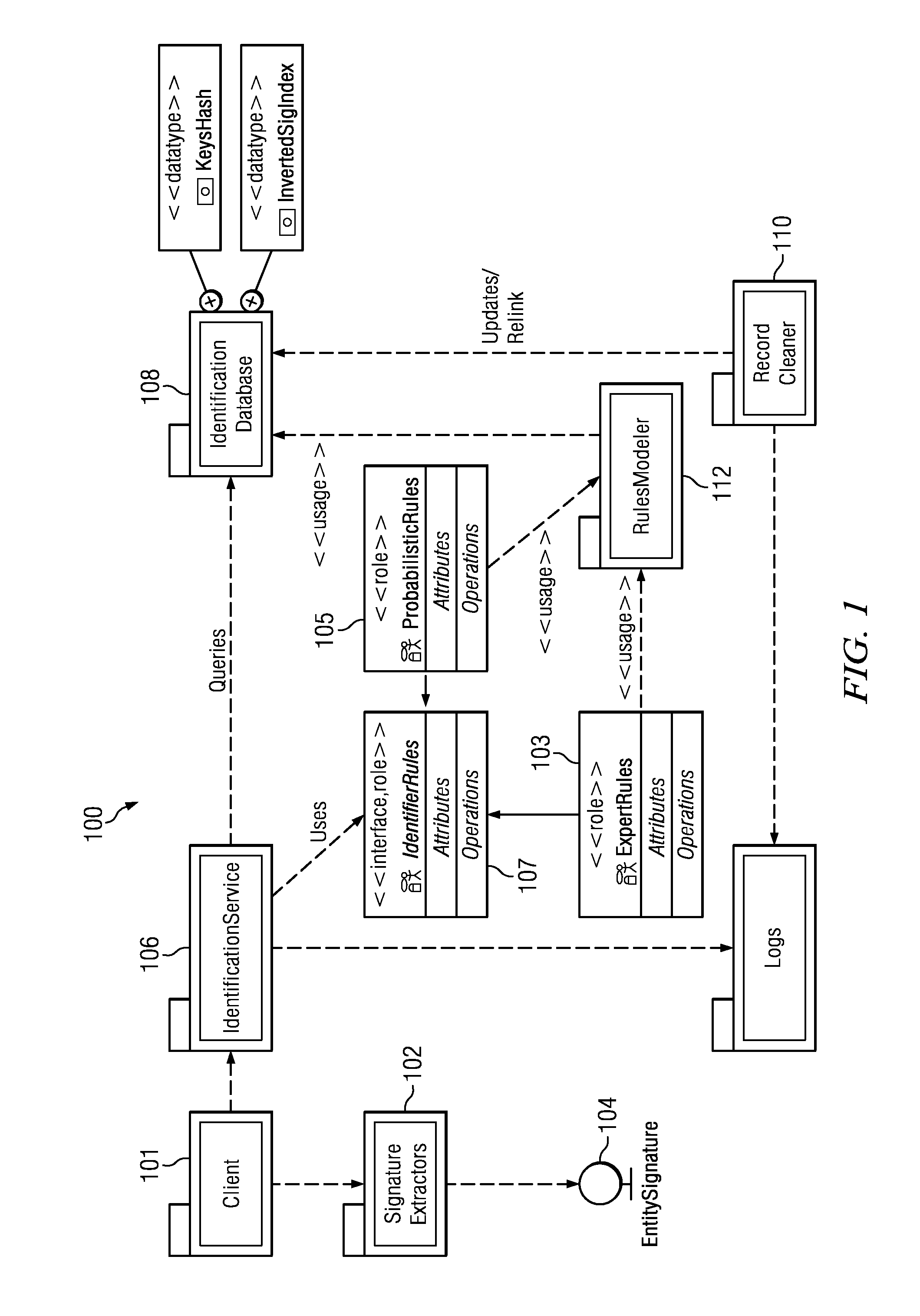
Uniquely identifying a network-connected entity
ActiveUS8438184B1Digital data processing detailsTransmissionNetwork connectionDeterministic algorithm
An entity (a device, a user of a device or set of devices, a user of one or more applications on a device, a group of users of the device or set of devices, or the like) is identified across multiple device, usage, and application domains. The entity is assigned a unique entity identity that is generated from a set of feature data that model the entity. The feature data typically includes deterministic data, device and system-specific feature data, and usage feature data. The identity is generated by applying to the feature data one or more rules that identify which of the feature data to use to generate the entity identity. The rules include at least one deterministic rule, and at least one probabilistic rule. Periodically, an identity is merged into one or more entity identities that are found, by applying a rule, to represent a same entity.
Owner:ADELPHIC LLC
Encoding method and system, decoding method and system
ActiveUS20100253555A1Correction errorAvoid modificationError detection/correctionCode conversionDecoding methodsComputer architecture
A decoder, an encoder, a decoding method and an encoding method are provided. The encoding method includes receiving data; generating a set of first codewords by applying a first encoding process on the received data; and performing a second encoding process on a folded version of each first codeword to provide a set of second codewords, wherein a folded version of a first codeword is representative of a storage of the first codeword in a two dimensional memory space, wherein the second codeword comprises redundancy bits.
Owner:AVAGO TECH INT SALES PTE LTD
Apparatus and method for optimized application of batched data to a database
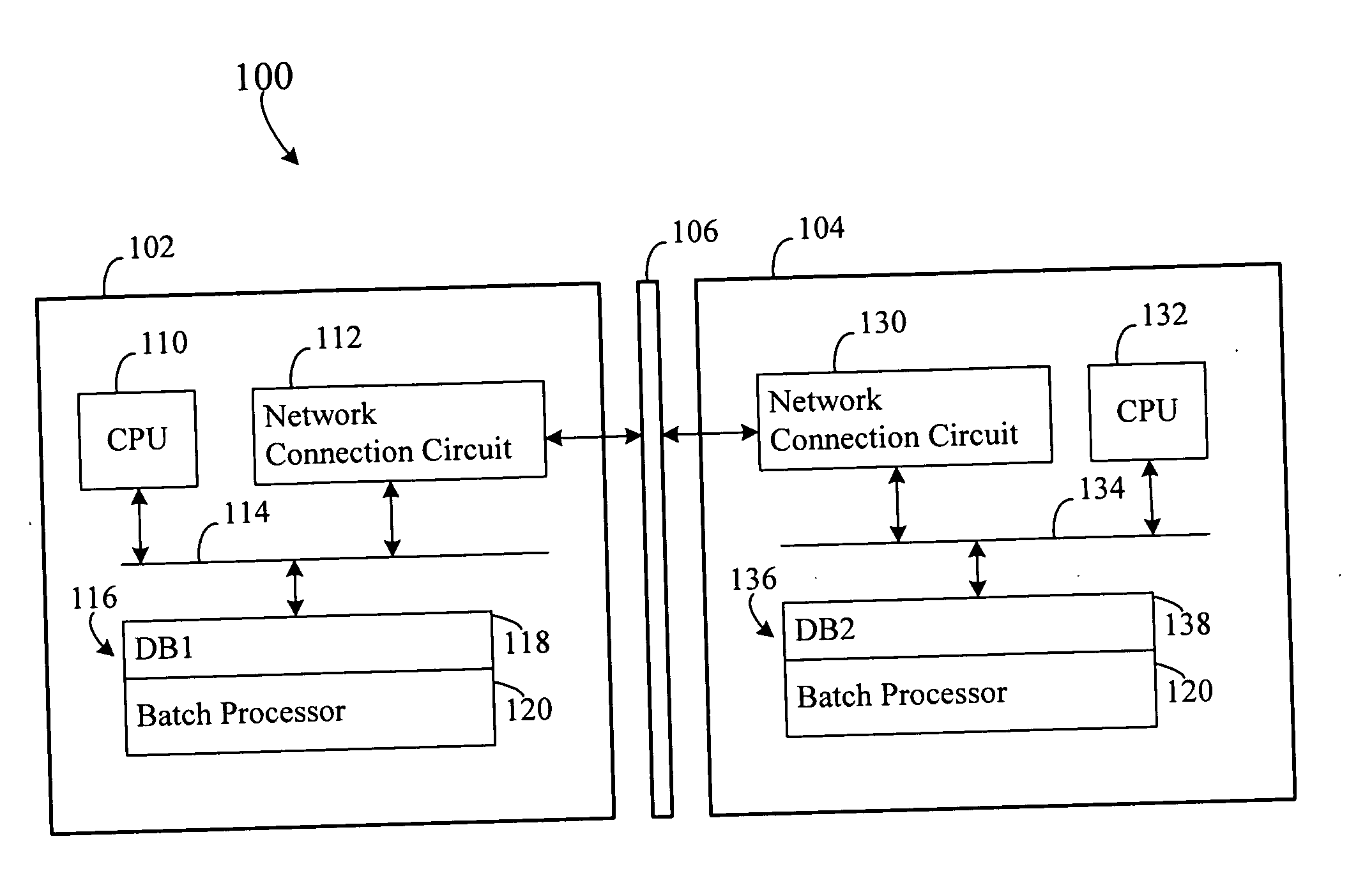
ActiveUS20110173619A1Flush cutImprove efficiencyDatabase distribution/replicationMultiprogramming arrangementsData applicationDependency relation
A computer readable medium storing executable instructions includes executable instructions to: receive a continuous stream of database transactions; form batches of database transactions from the continuous stream of database transactions; combine batches of database transactions with similar operations to form submission groups; identify dependencies between submission groups to designate priority submission groups; and apply priority submission groups to a database target substantially synchronously with the receipt of the continuous stream of database transactions.
Owner:ORACLE INT CORP
Filter and sort by color
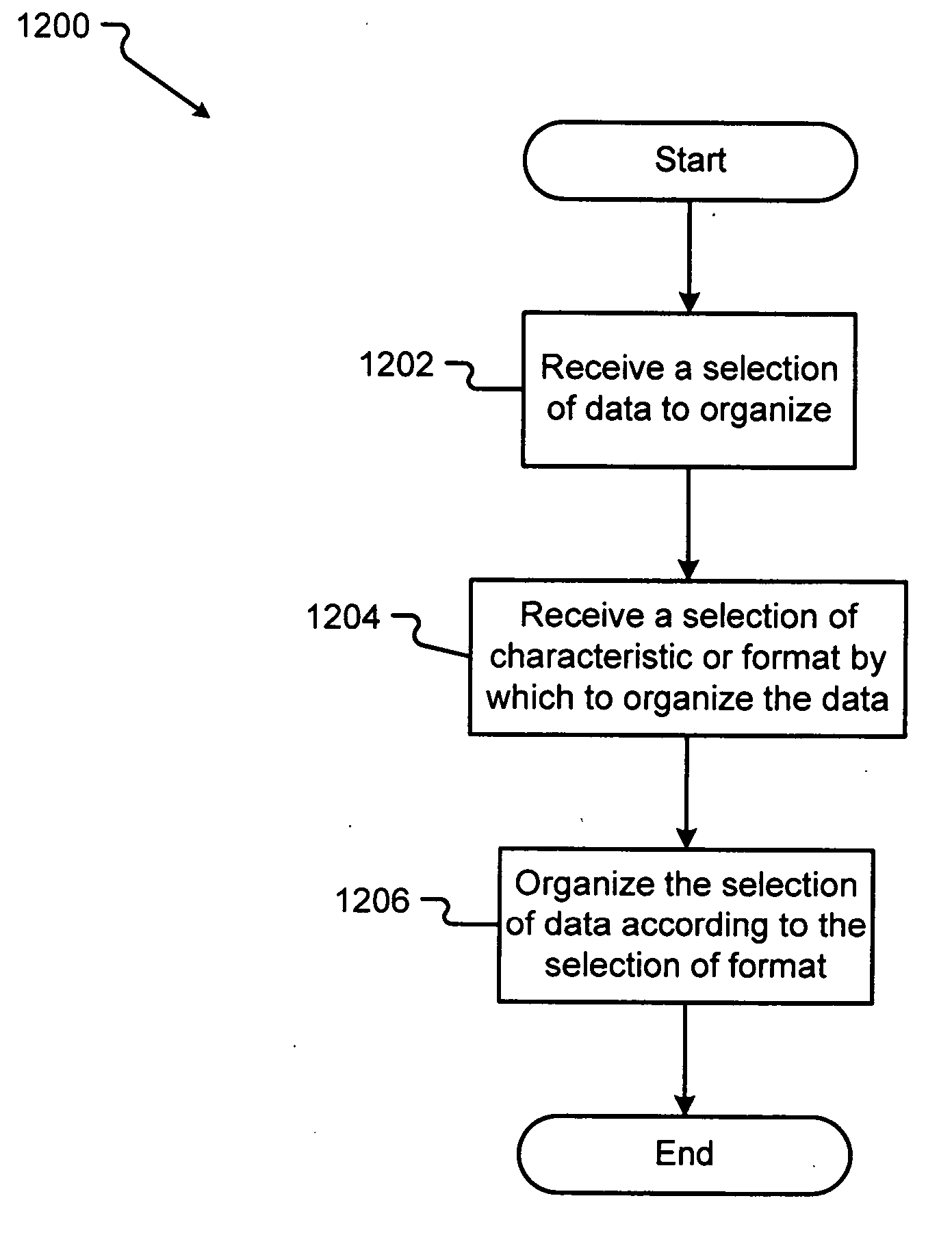
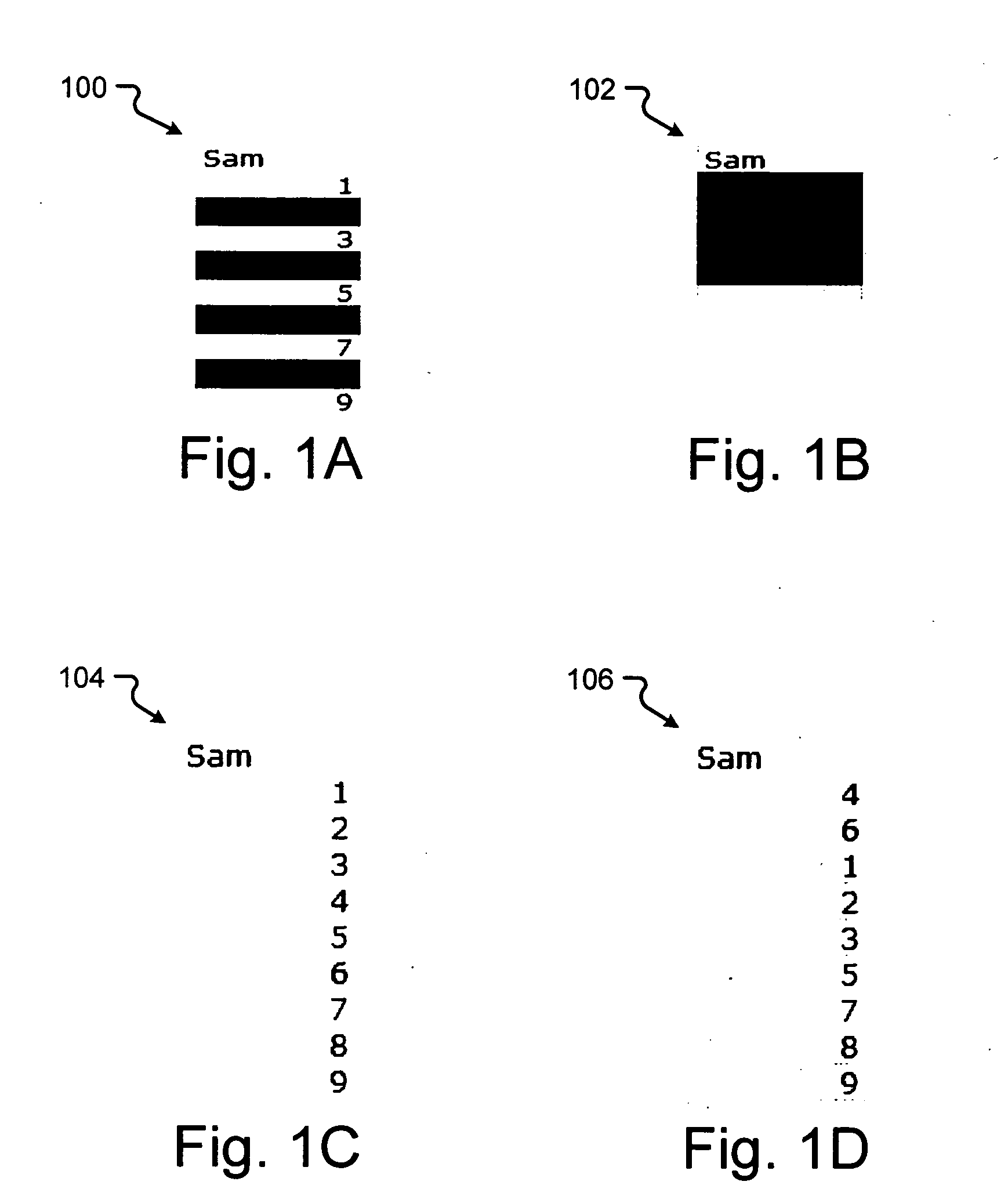
InactiveUS20060129914A1Text processingSpecial data processing applicationsData displayComputer science
The present invention comprises methods and user interfaces for organizing data displayed within a data application. Specifically, the present invention provides methods and systems for arranging the display of the data by a format applied to one or more portions of the data. The formats comprise different visual characteristics of the displayed data. In exemplary embodiments, the data application organizes the data by the fill color of the cell, the font color of the data within the cell, or the type of icon inserted into the cell. The organizations comprise any type of rearrangement of the data. In exemplary embodiments, the data application sorts or filters the displayed data according to the format.
Owner:MICROSOFT TECH LICENSING LLC
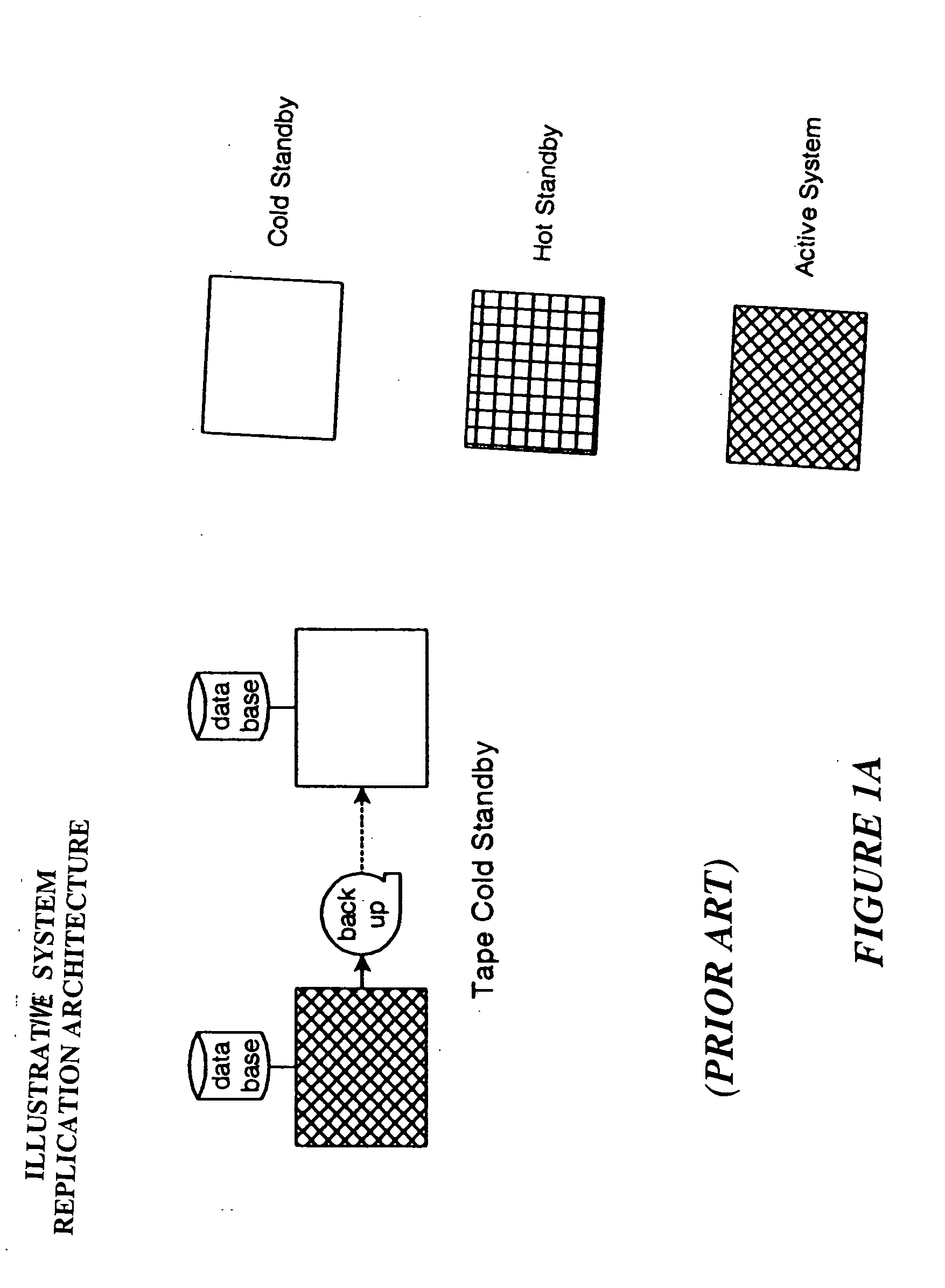
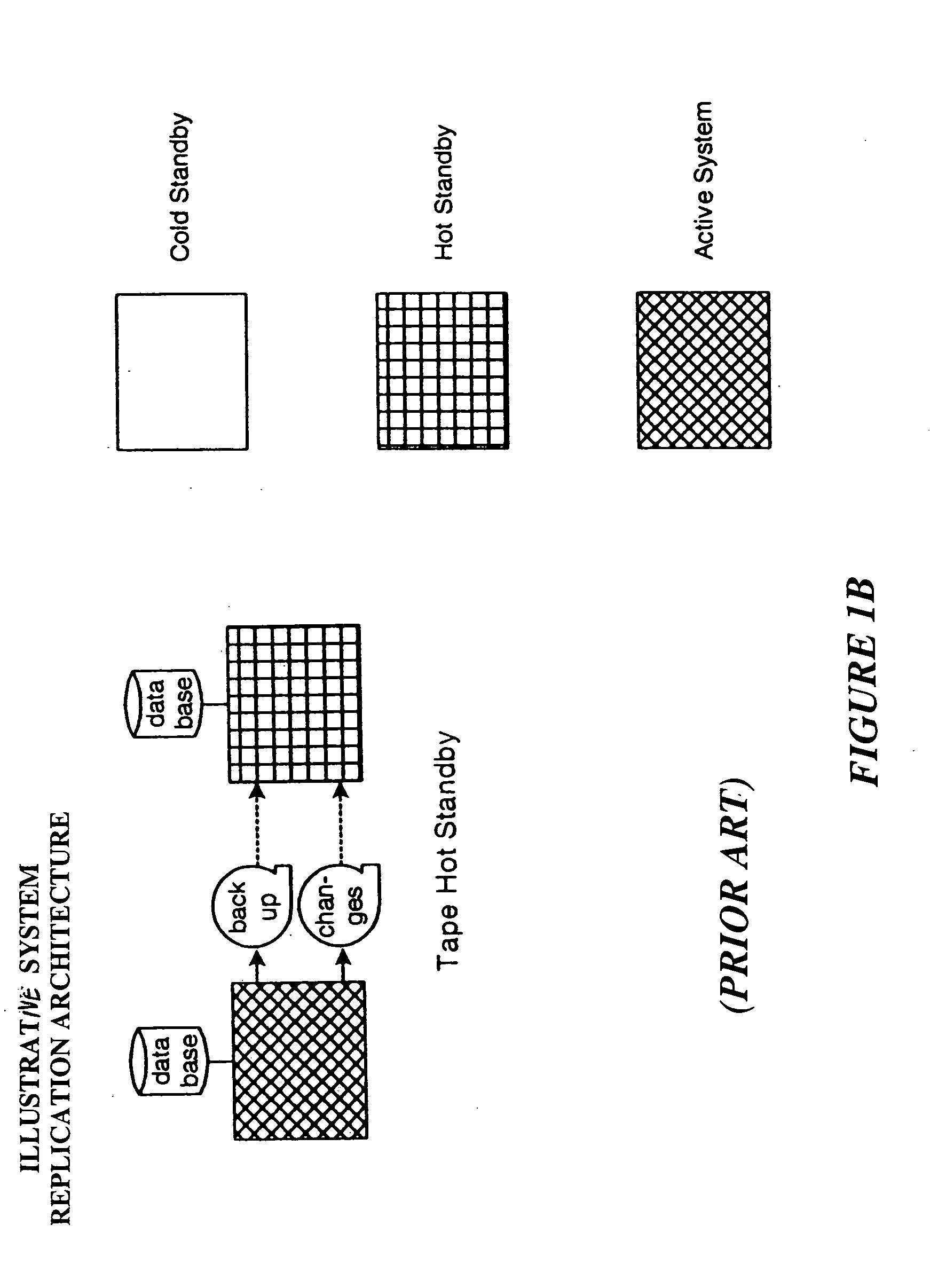
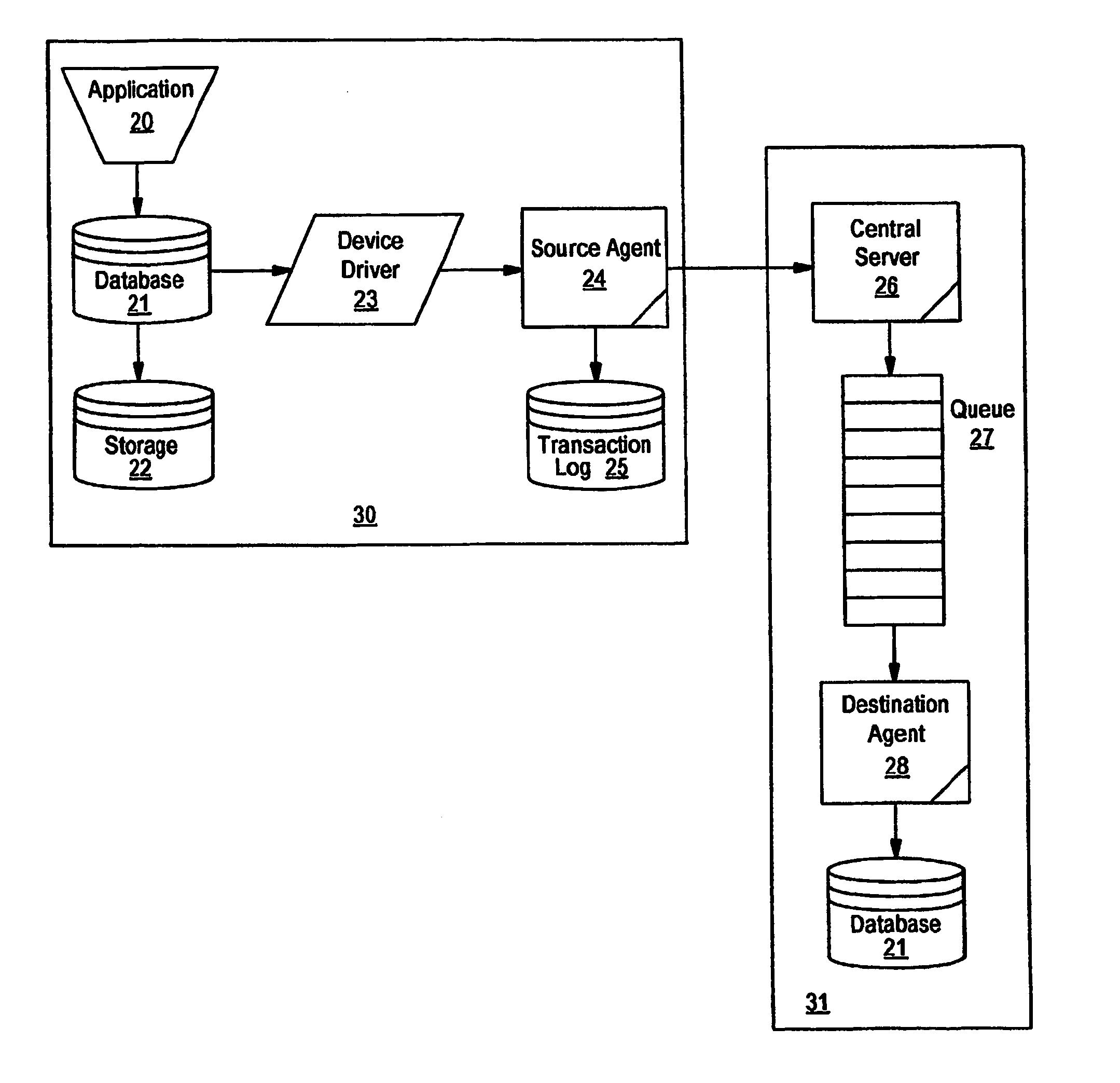
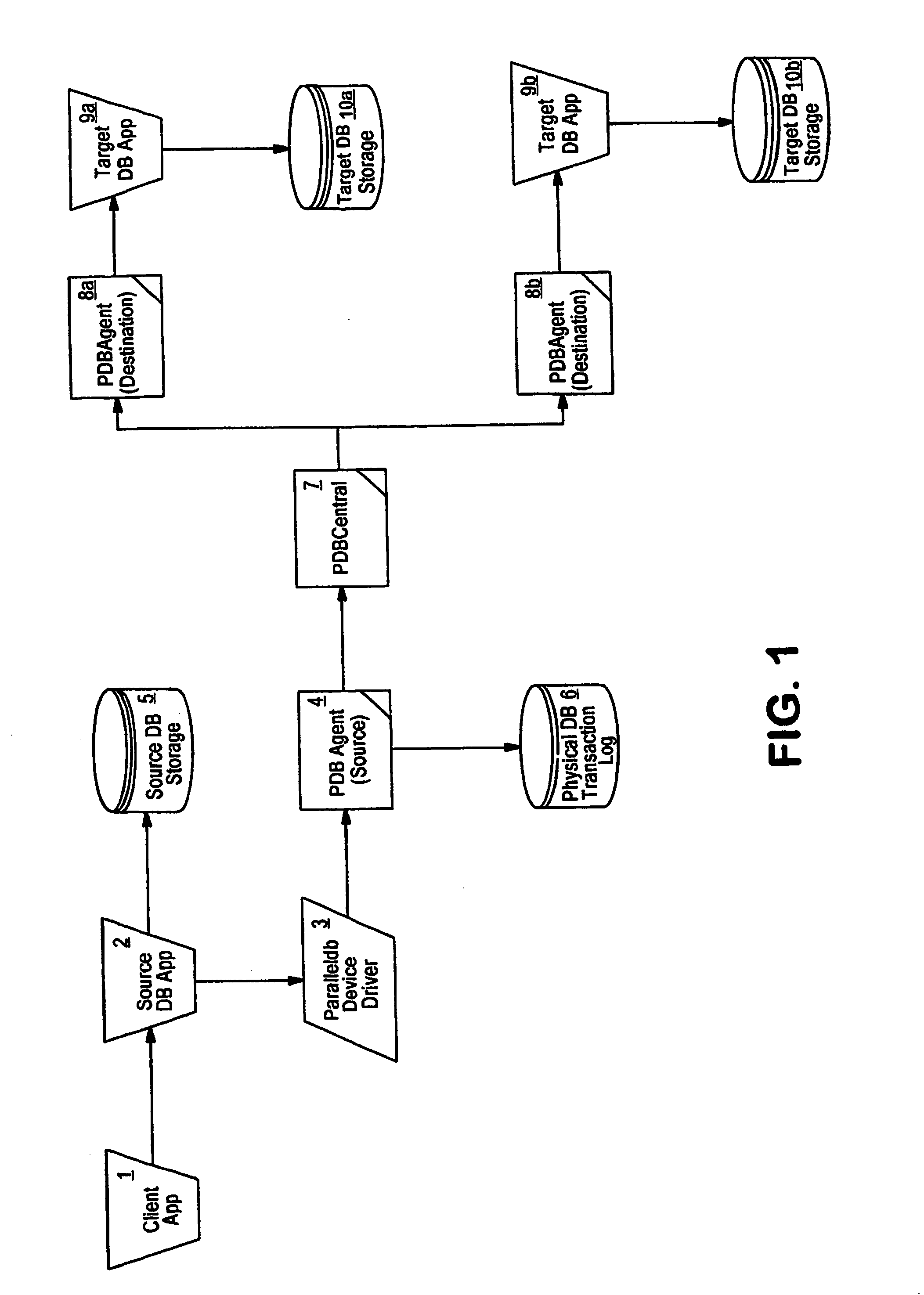
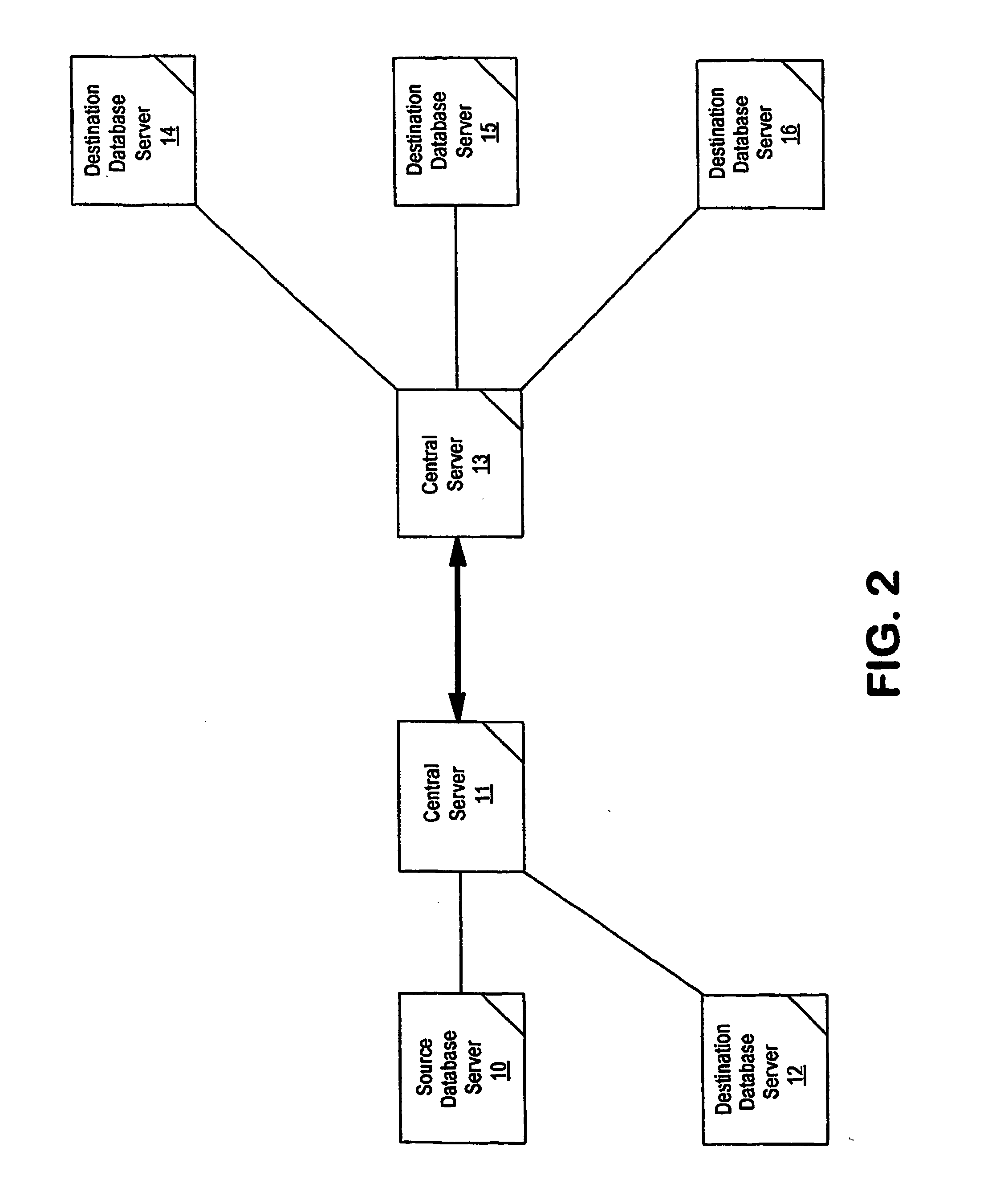
Data replication system and method
InactiveUS20050114285A1Error detection/correctionDigital data processing detailsSpecific functionDatabase server
System and method for sub-second data replication. The present invention provides the ability to replicate database transactions made on one computer to one or more local or remote computers instantly, utilizing the database management system's transaction log for the replication. The present invention intercepts transactions being sent to a database's transaction log and interprets and copies the transactions to one or more replica servers, as well as to the original existing database transaction log. This enables real-time reporting without taxing the transaction system, real-time backup and immediate disaster recovery, by offloading said activities from the transaction server to a replica server that synchronized with the transaction server in real-time. The system comprises a central server and a set of source and destination agents that can reside all in a local system, or can be remotely connected such as through a TCP / IP networks The central server controls a series of loadable modules to perform specific functions in the system, and an agent that runs on every machine in the system that has a relational database management system running. The agent is either a source agent, gathering data from a source database server, or a destination (or target) agent, applying the data to the destination database, or both a source and destination agent.
Owner:PARALLELDB
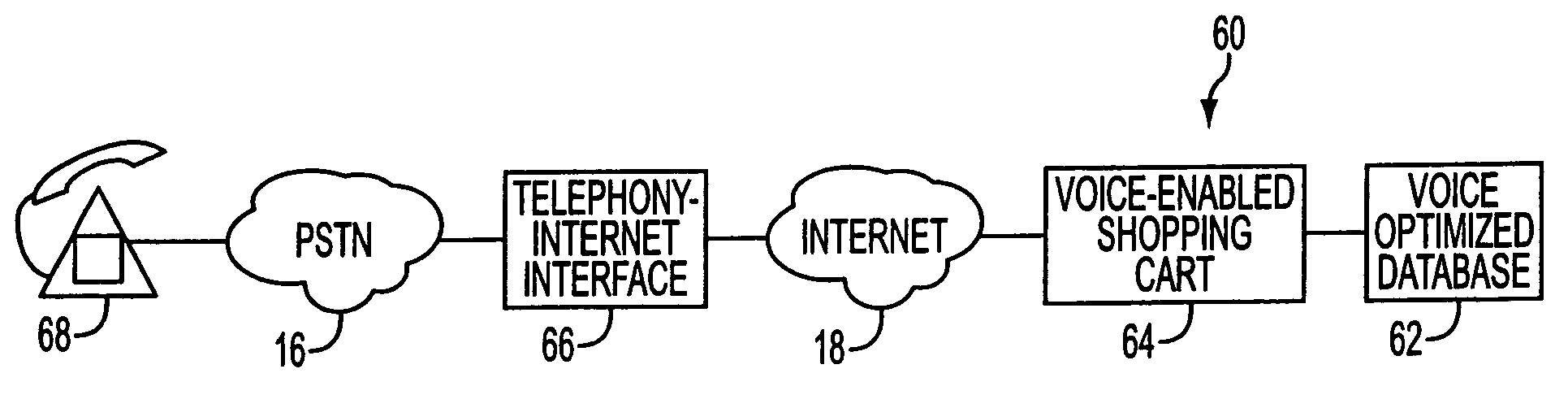
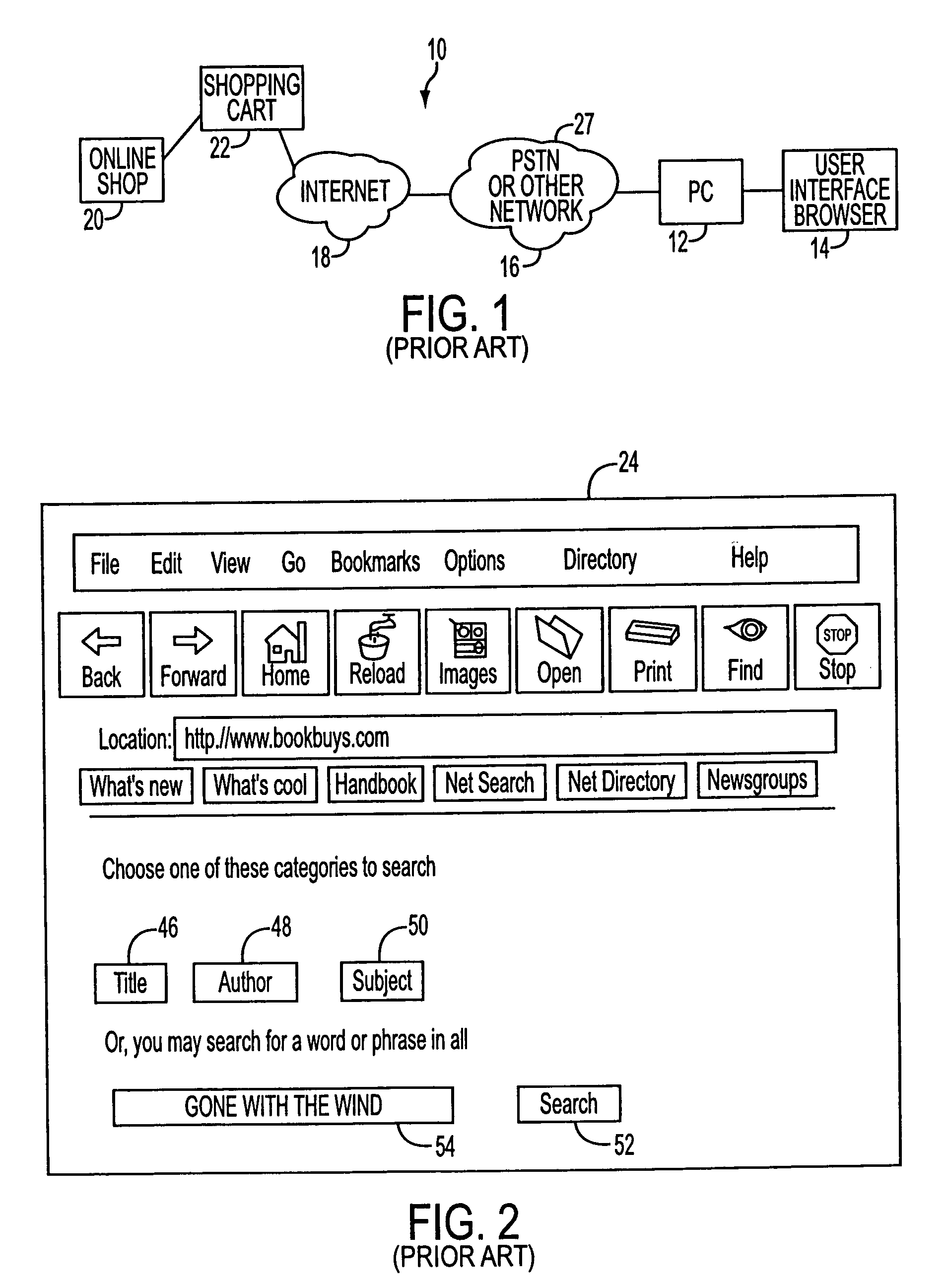
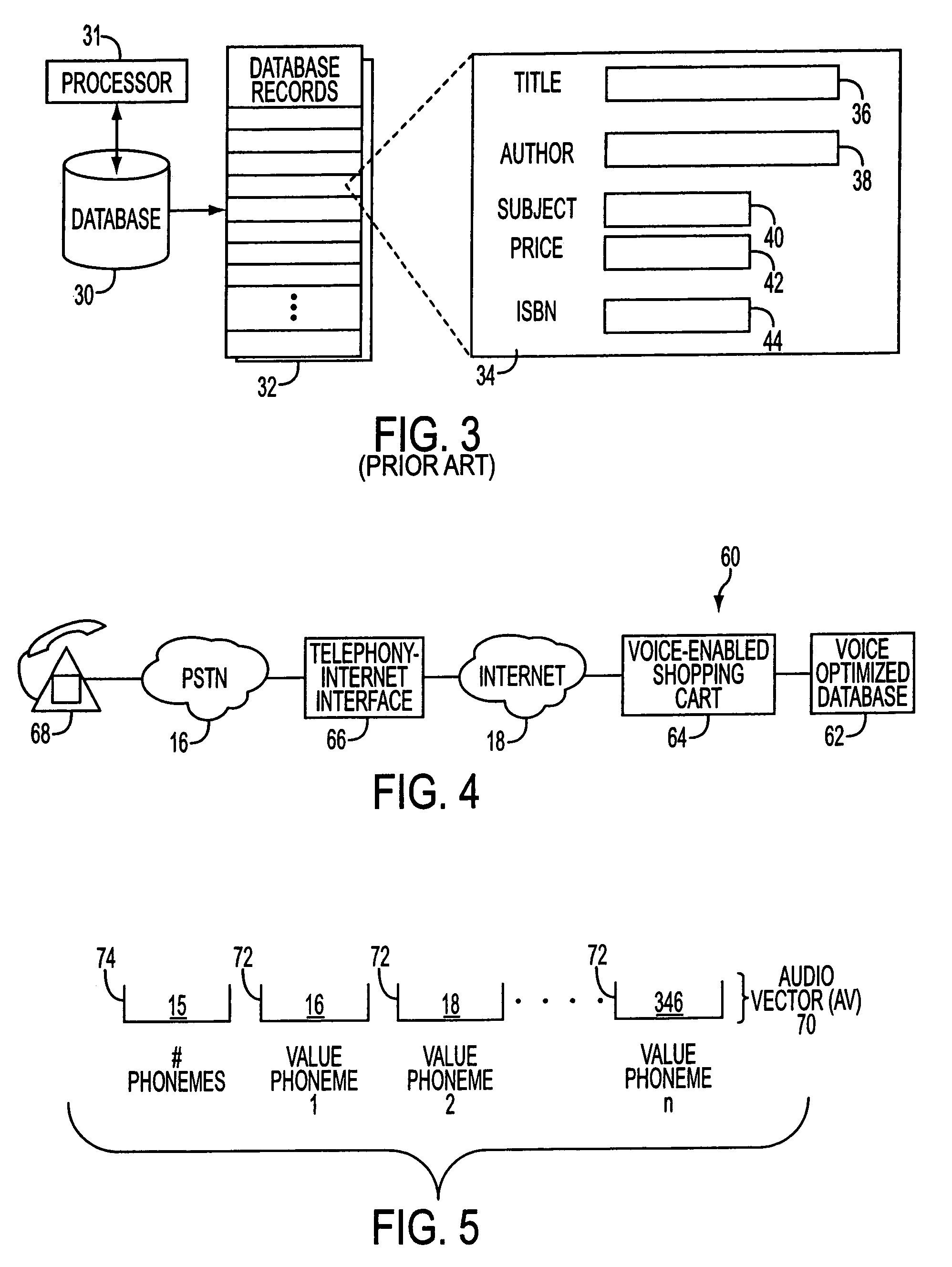
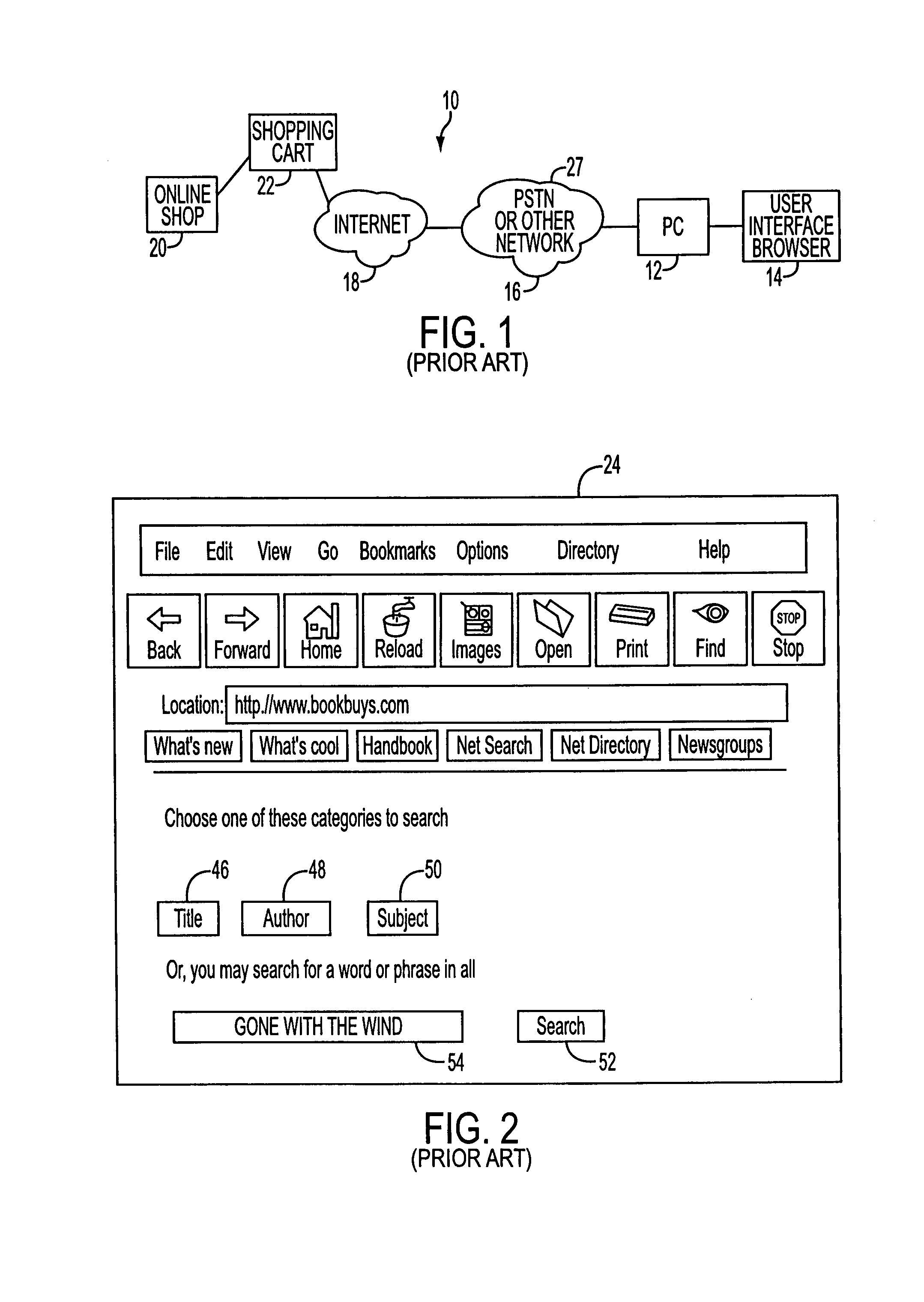
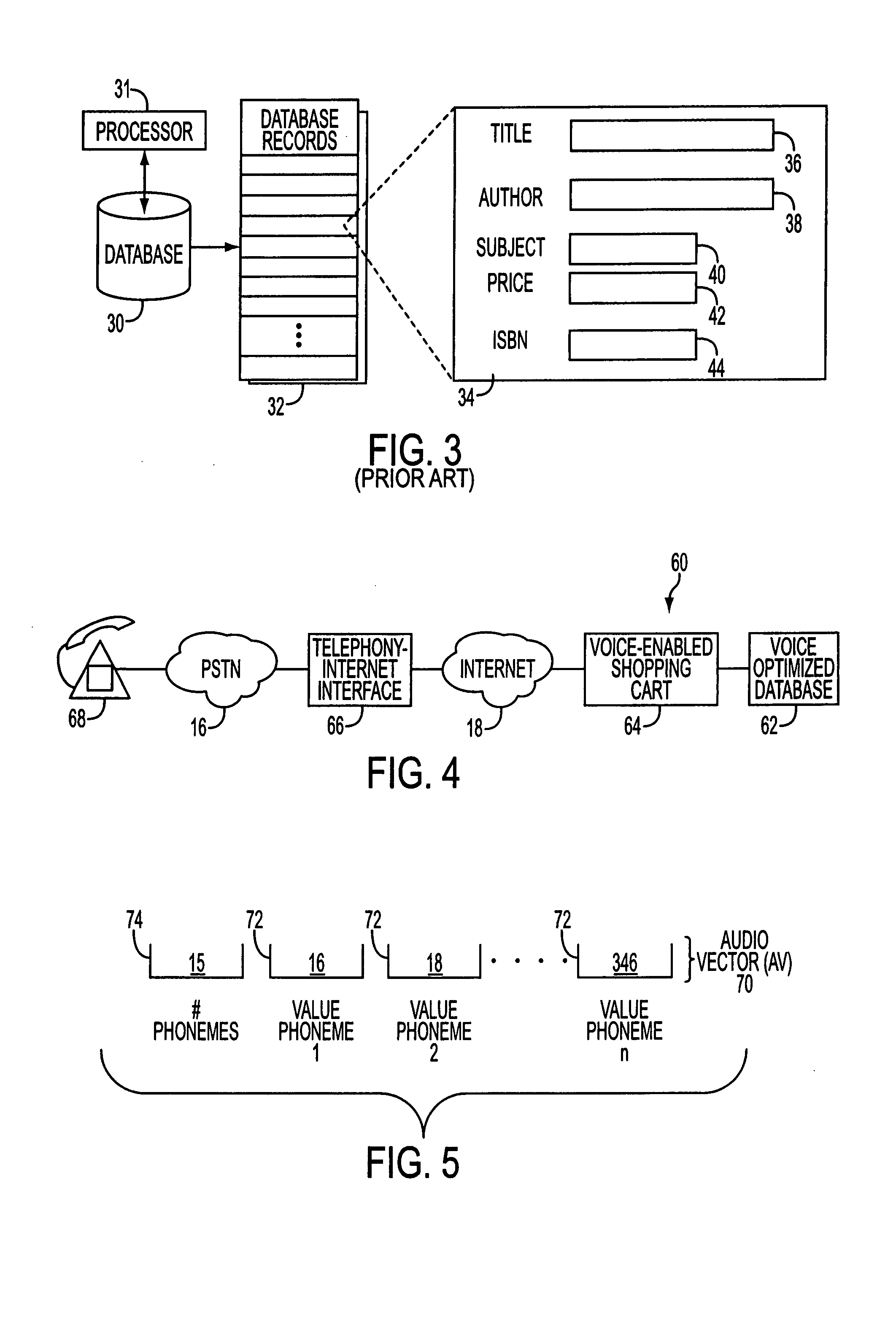
Telephony-data application interface apparatus and method for multi-modal access to data applications
InactiveUS6941273B1Overcome deficienciesTelephonic communicationBuying/selling/leasing transactionsCredit cardTTEthernet
A voice-enabled system for online shopping provides a voice and telephony interface, as well a text and graphic interface, for shopping over the Internet using a browser or a telephone. The system allows customers to access an online shop, search for desired database items, select items, and finally pay for selected items using a credit card, over a phone line or the Internet. A telephony-Internet interface converts spoken queries into electronic commands for transmission to an online shop or database. Markup language-type pages transmitted to callers from the online-shop or database are parsed to extract selected information. The selected information is then reported to the callers via audio messaging.
Owner:LOGIC TREE
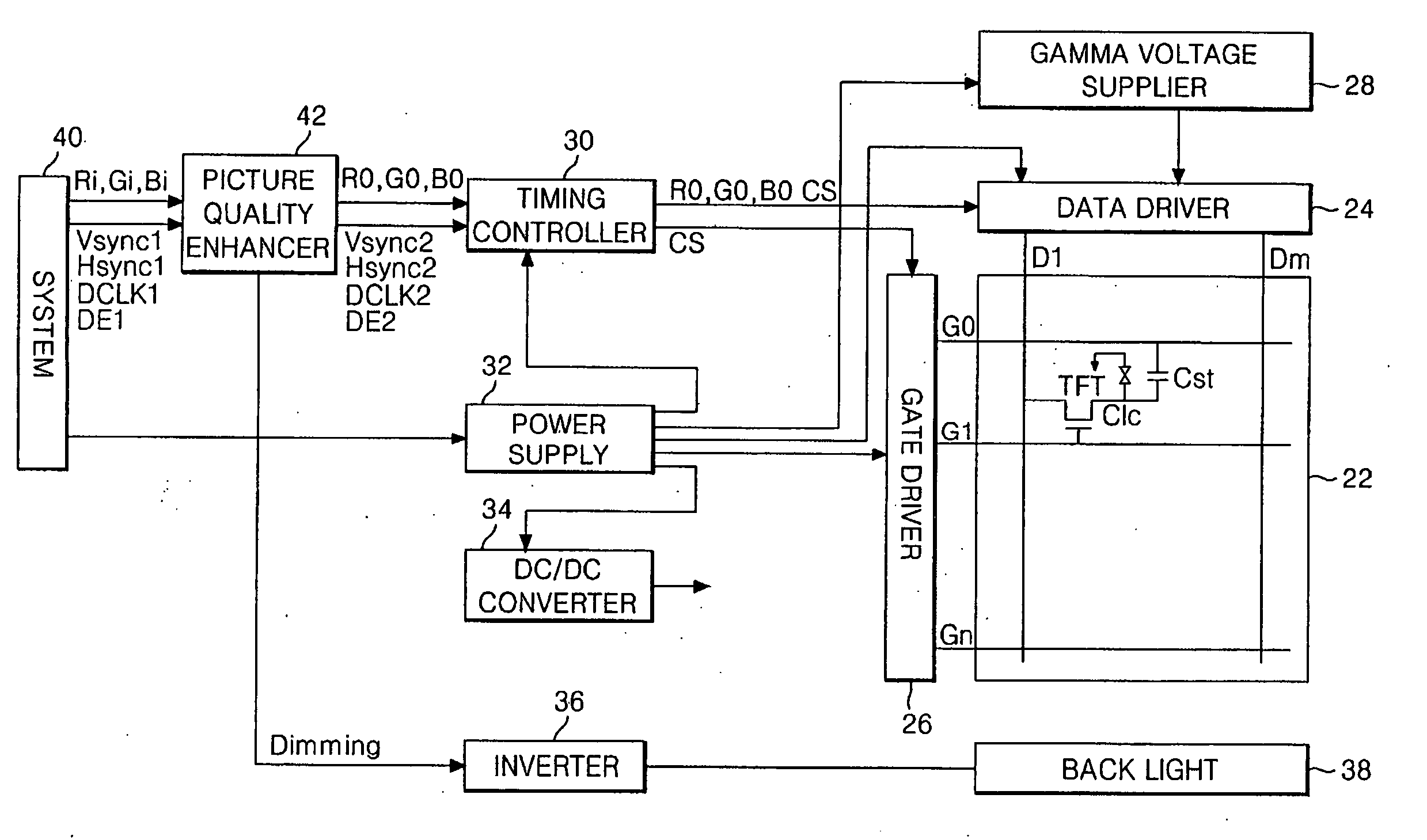
Method and apparatus for driving liquid crystal display
InactiveUS20050104837A1Increase contrastReduce manufacturing costStatic indicating devicesManufacturing cost reductionLiquid-crystal display
A driving method and apparatus for a liquid crystal display uses a comparison between the previous frame and the current frame to expand the contrast ratio and reduce the manufacturing cost. A limited amount of data from the current image may be used: either using a limited area of the image or merely the amount of green in the overall image or the limited area. In the apparatus, an image signal modulator expands the contrast of the input data when the previous image is analogous to the current image to thereby generate output data. A timing controller re-arranges the output data to apply the output data to a data driver.
Owner:LG DISPLAY CO LTD
Secure item identification and authentication system and method based on unclonable features
ActiveUS20110096955A1Improve efficiencyEasy to usePaper-money testing devicesCharacter and pattern recognitionKey exchangeDistributed source
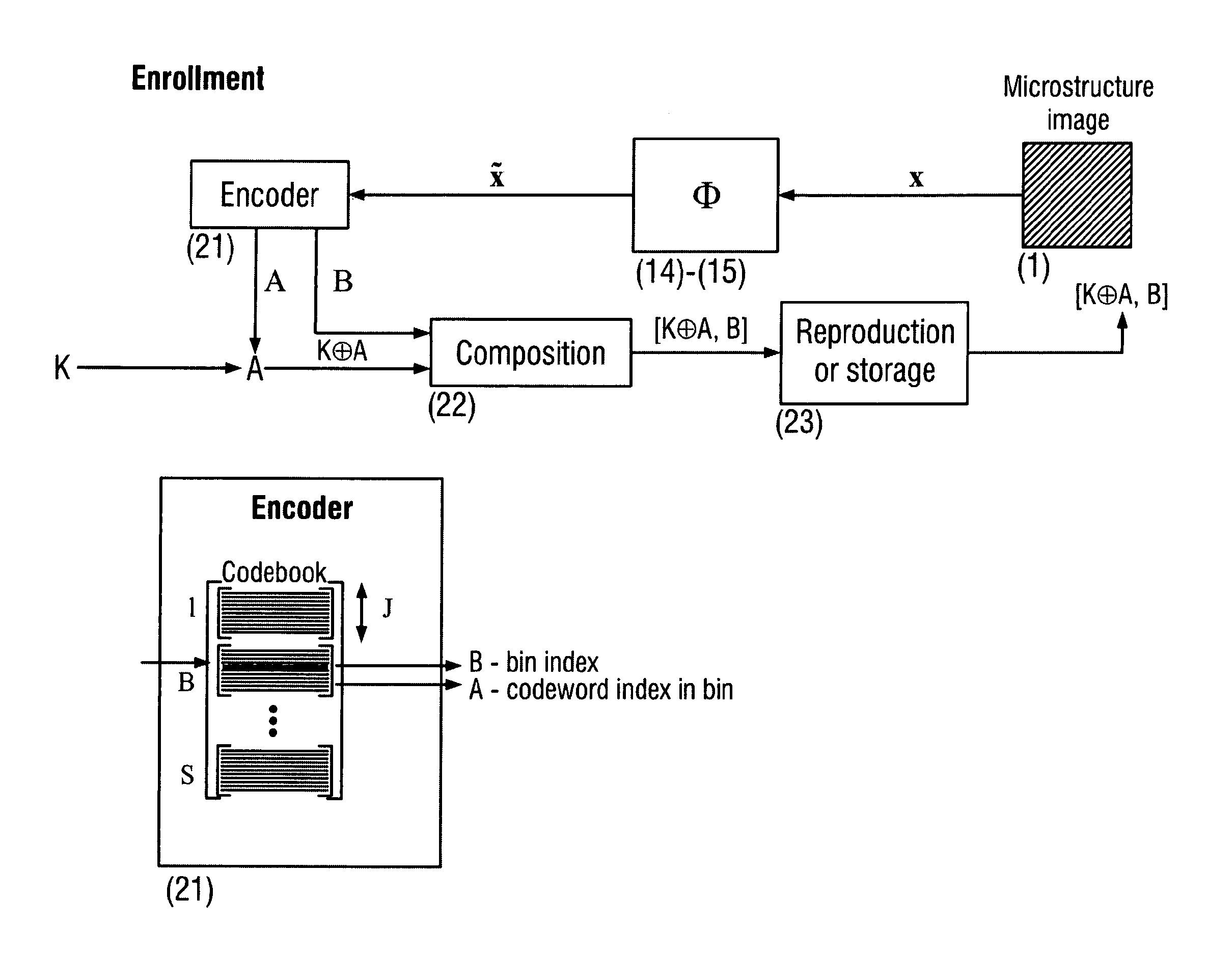
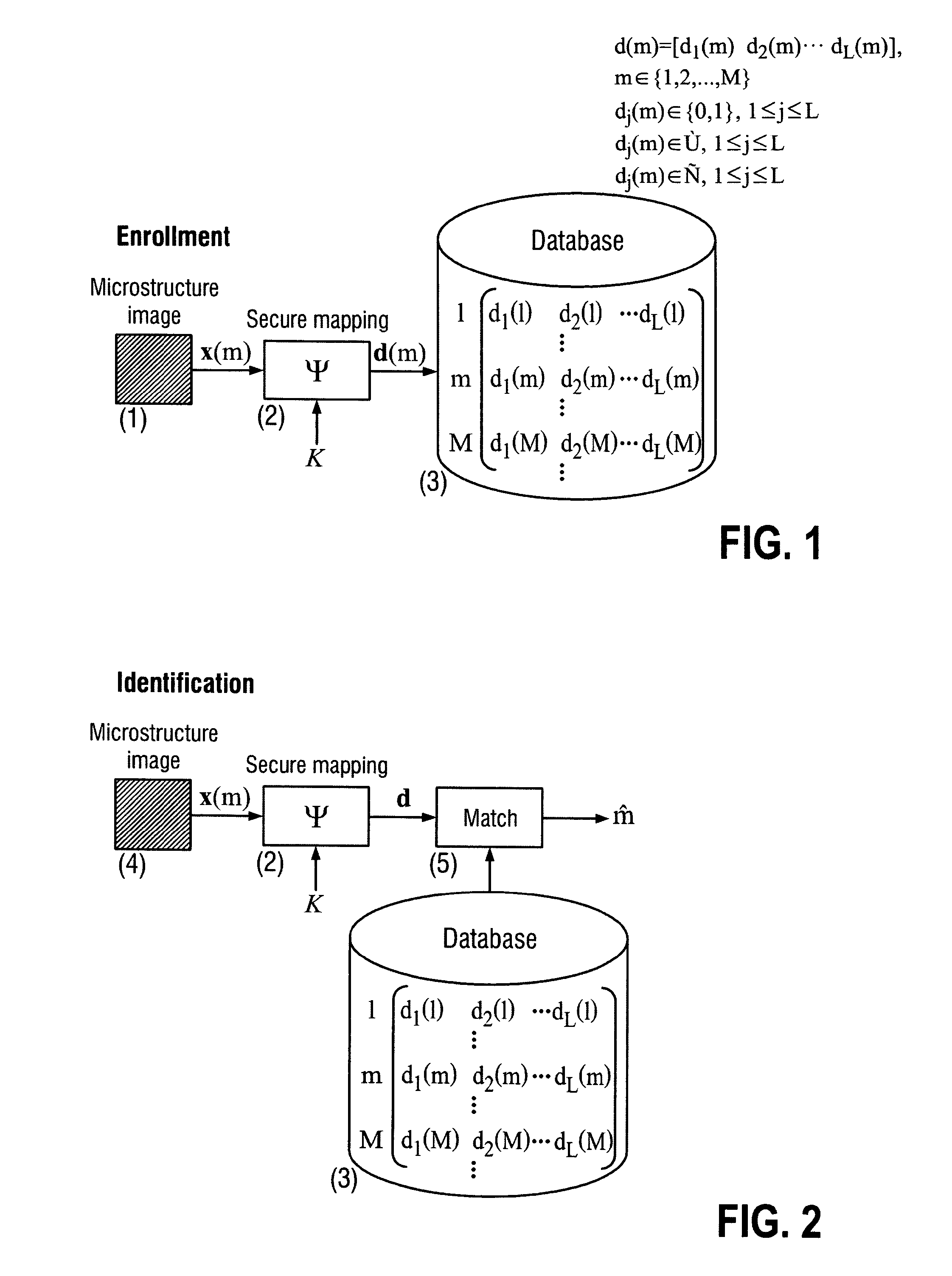
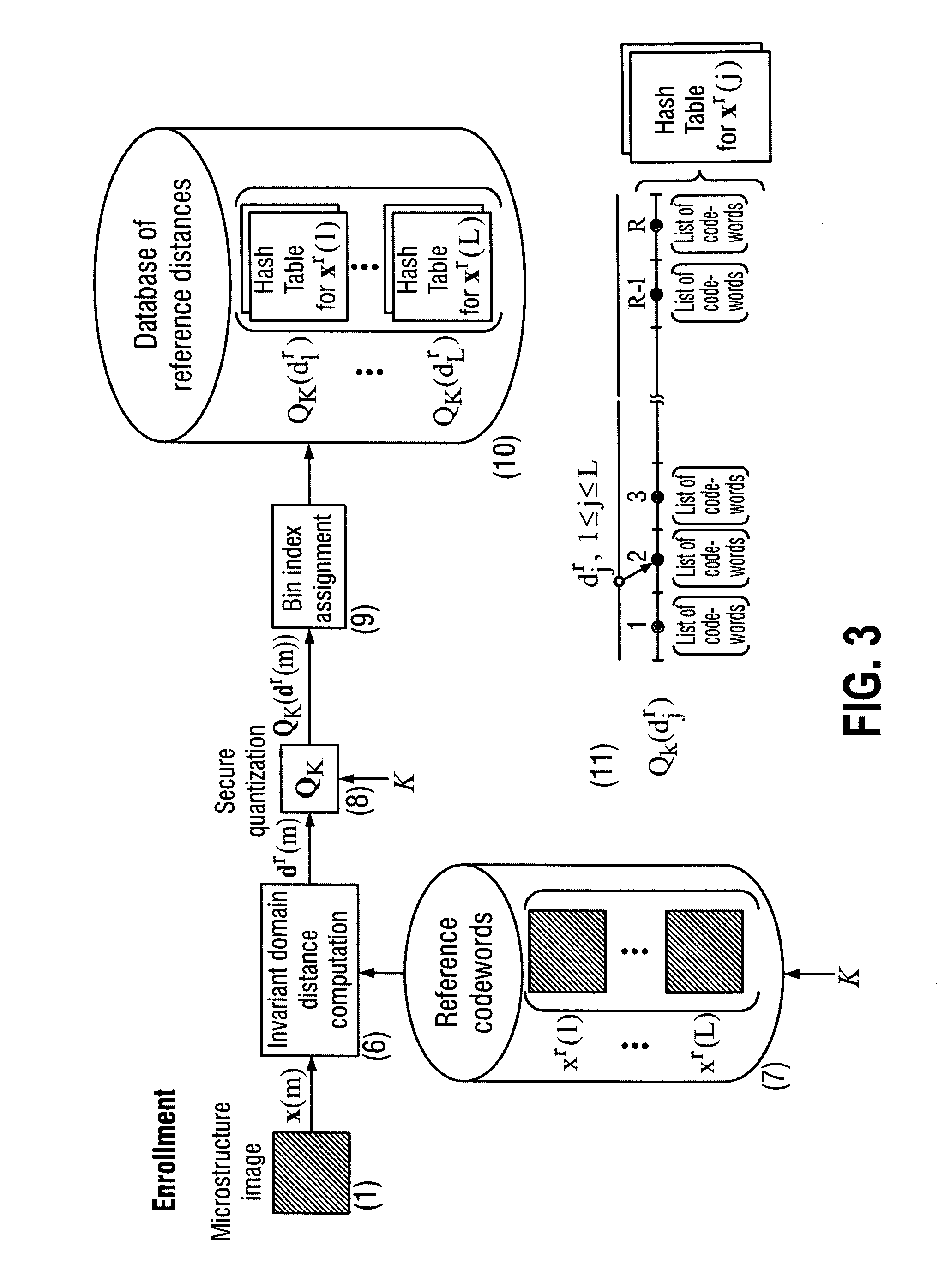
The present invention is a method and apparatus for protection of various items against counterfeiting using physical unclonable features of item microstructure images. The protection is based on the proposed identification and authentication protocols coupled with portable devices. In both cases a special transform is applied to data that provides a unique representation in the secure key-dependent domain of reduced dimensionality that also simultaneously resolves performance-security-complexity and memory storage requirement trade-offs. The enrolled database needed for the identification can be stored in the public domain without any risk to be used by the counterfeiters. Additionally, it can be easily transportable to various portable devices due to its small size. Notably, the proposed transformations are chosen in such a way to guarantee the best possible performance in terms of identification accuracy with respect to the identification in the raw data domain. The authentication protocol is based on the proposed transform jointly with the distributed source coding. Finally, the extensions of the described techniques to the protection of artworks and secure key exchange and extraction are disclosed in the invention.
Owner:UNIVERSITY OF GENEVA
Multi-modal voice-enabled content access and delivery system
InactiveUS7283973B1Overcome deficienciesAutomatic call-answering/message-recording/conversation-recordingMultiple digital computer combinationsCredit cardModal voice
A voice-enabled system for online content access and delivery provides a voice and telephony interface, as well a text and graphic interface, for browsing and accessing requested content or shopping over the Internet using a browser or a telephone. The system allows customers to access an online data application, search for desired content items, select content items, and finally pay for selected items using a credit card, over a phone line or the Internet. A telephony-Internet interface converts spoken queries into electronic commands for transmission to an online data application. Markup language-type pages transmitted to callers from the online data application are parsed to extract selected information. The selected information is then reported to the callers via audio messaging. A voice-enabled technology for mobile multi-modal interaction is also provided.
Owner:LOGIC TREE
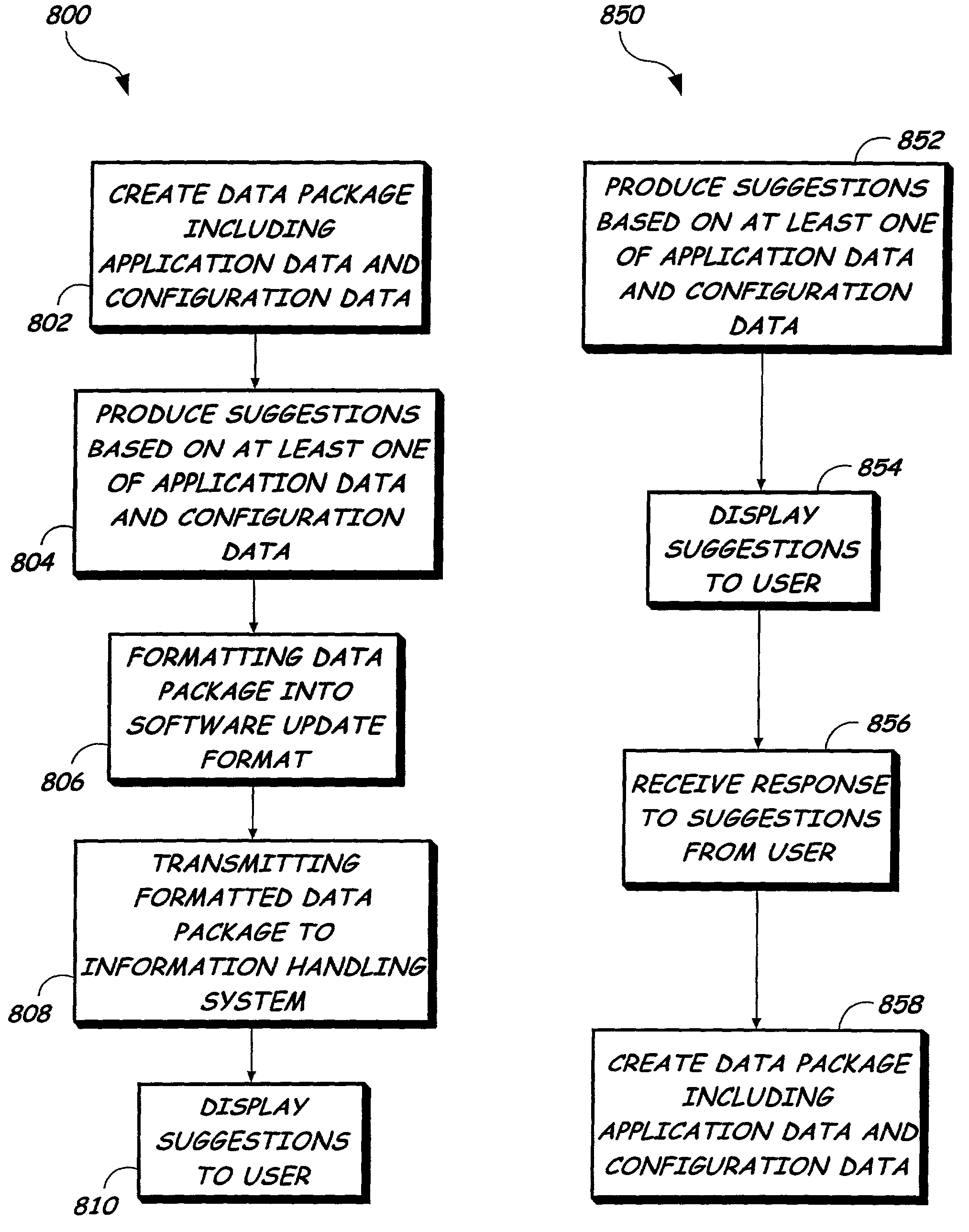
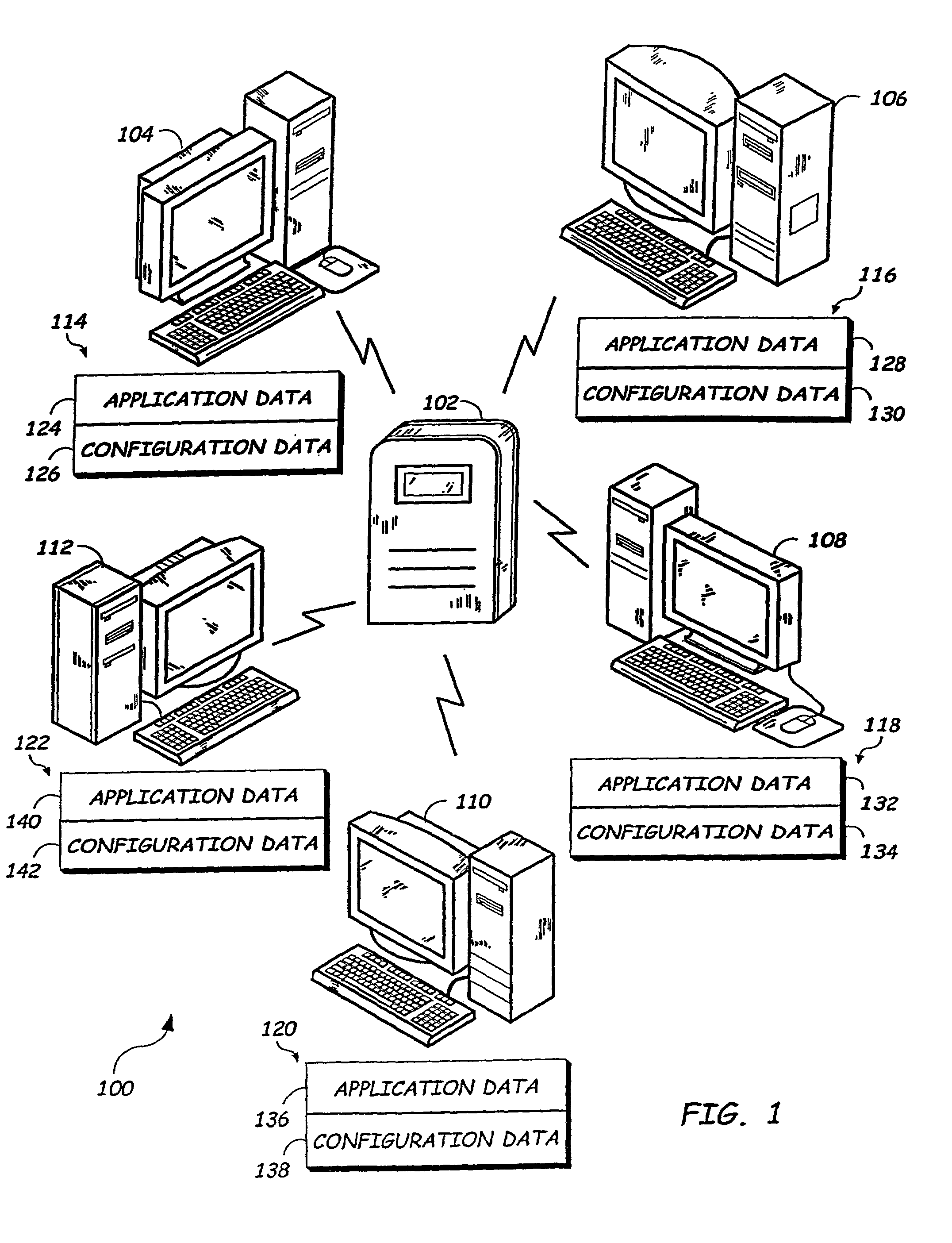
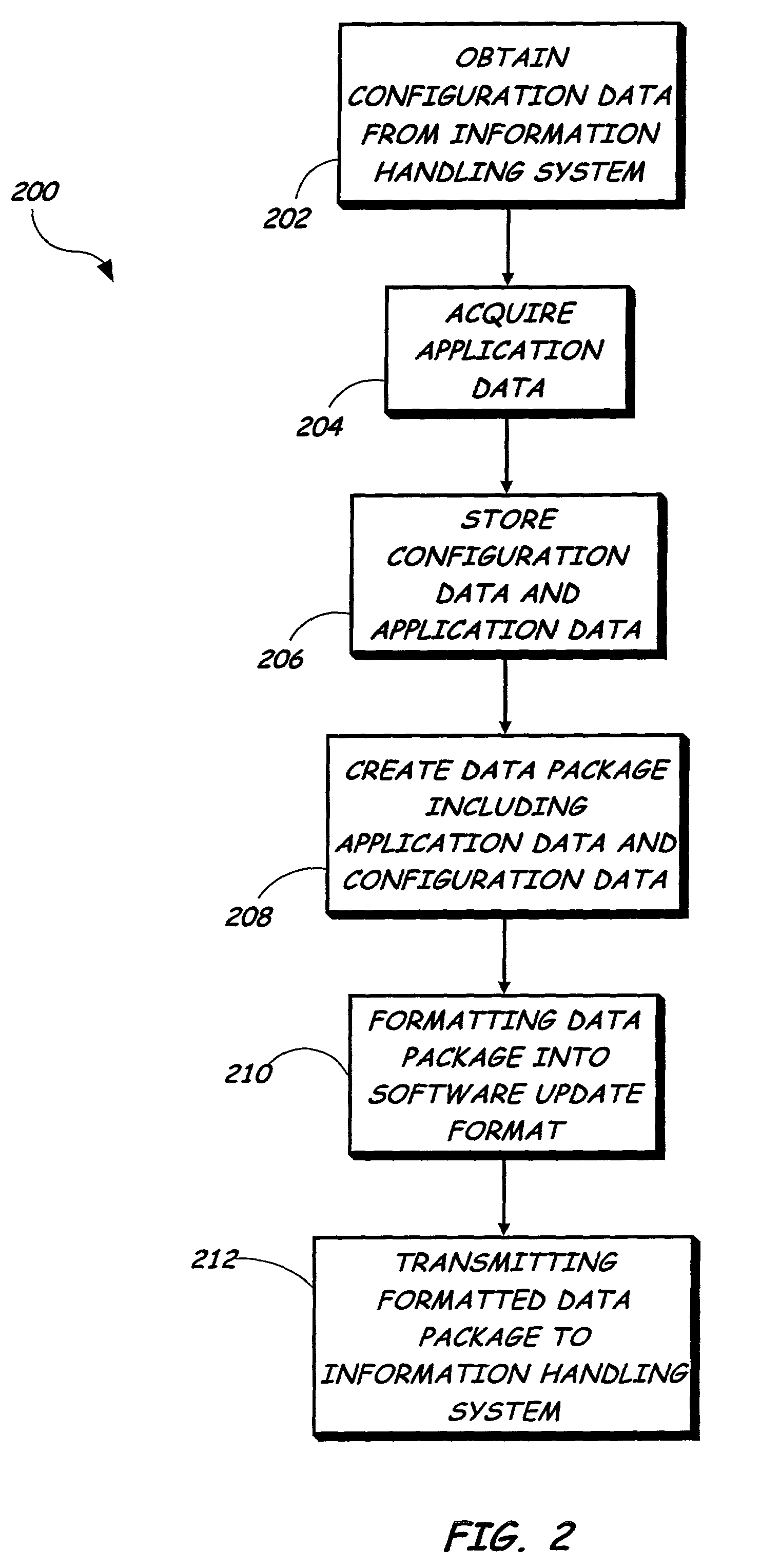
System for providing data backup and restore with updated version by creating data package based upon configuration data application data and user response to suggestion
InactiveUS7051327B1Improve functionalityGood serviceError detection/correctionProgram loading/initiatingNetwork connectionNetwork packet
The present invention is directed to a system and method for providing a data backup to an information handling system using software updates. The information handling system has one or more applications included thereon and is capable of being communicatively coupled to a remote server through a network connection. A data package is created based upon configuration data and application data stored on the server. The configuration data includes data previously obtained from the information handling system, such as settings and user data. The application data includes data corresponding to the applications included on the information handling system. The data package is formatted into a software update format and transmitted over the network connection to the information handling system. The data package is suitable for restoring the information handling system after failure, and may be utilized by the information handling system as a software update to restore itself.
Owner:GATEWAY
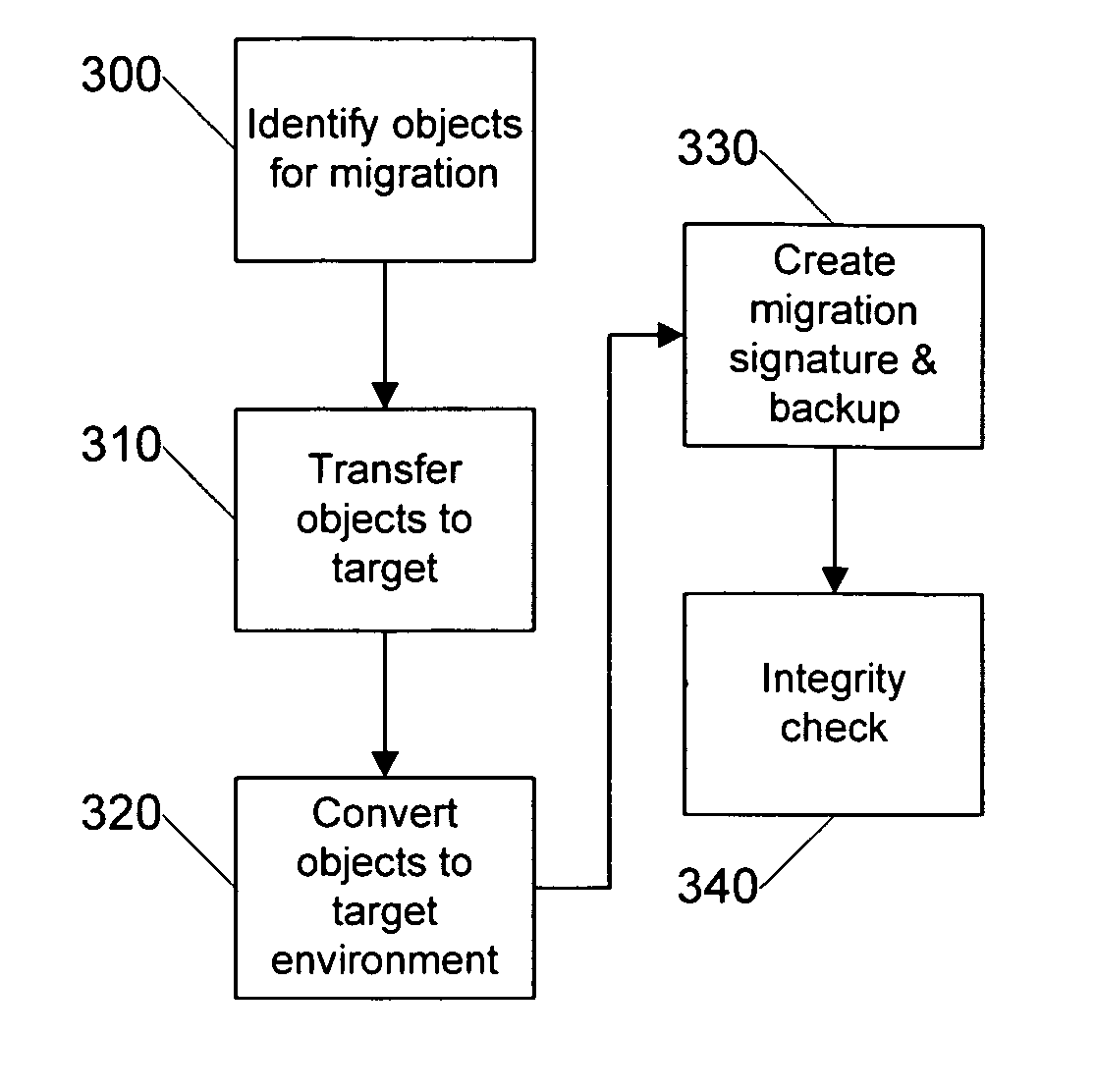
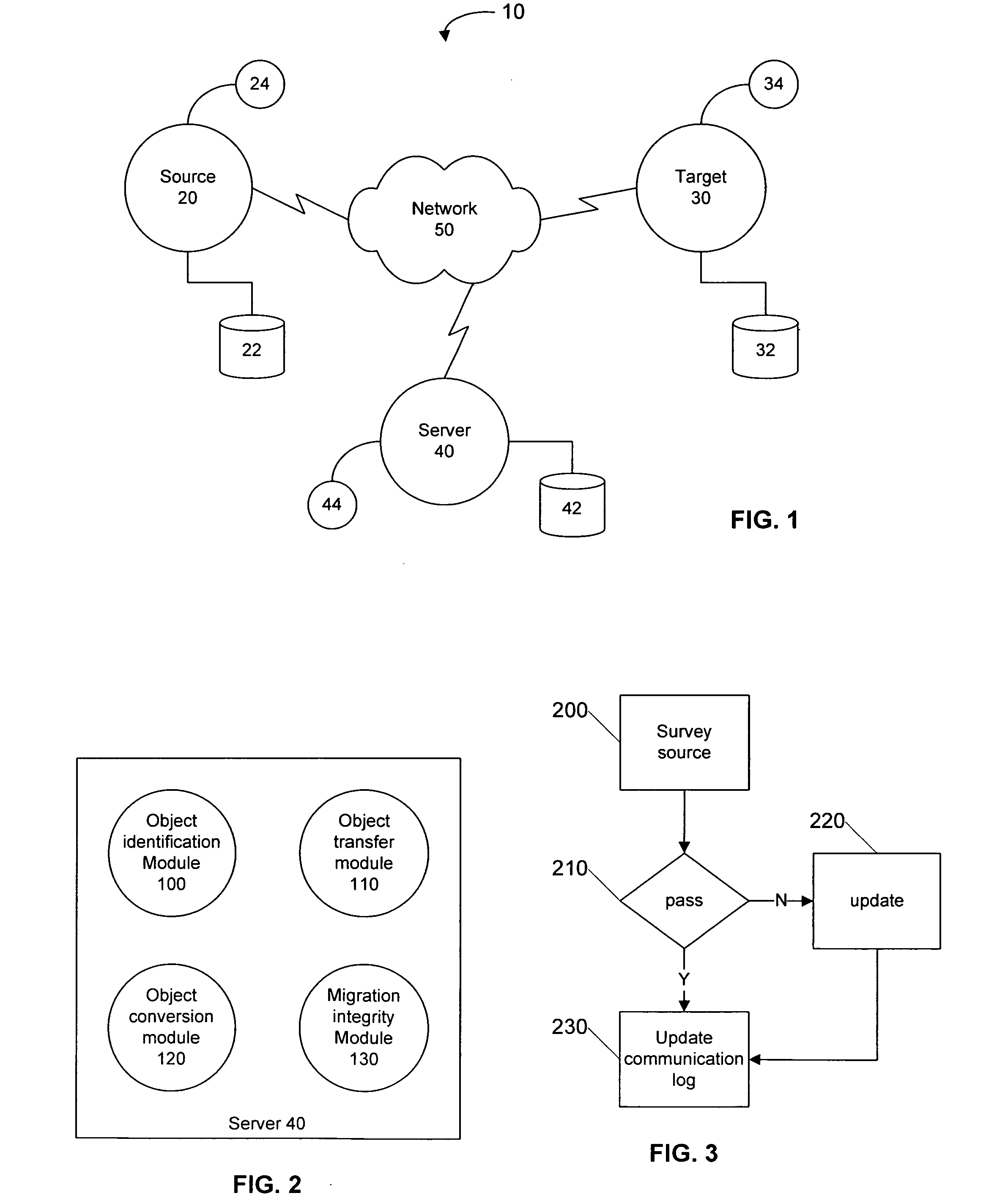
Systems and methods for operating system migration
InactiveUS20060026587A1Specific program execution arrangementsMemory systemsOperational systemGoal system
The present invention provides for systems and methods that recognize source and target devices and automatically identify, transfer, and convert user profiles, user settings, data, applications, and other information from the source device with its source operating system to the target device with its target operating system. The system surveys both the source device and the target device to ensure that each device has the appropriate resources and configuration to support the migration. Objects to be migrated are then identified, transferred to the target system and converted as necessary to create a similar environment on the target device as the previous environment on the source device. The post transfer integrity of the target device is then analyzed to ensure that the target system continues to work for its intended purpose and to further ensure that the migrated environment is also operational on the target device.
Owner:MONARCH LX LLC
Apparatus and method for watermarking a digital image
InactiveUS20020191810A1Minimizing introductionTelevision system detailsUser identity/authority verificationComputer hardwareDigital image
An apparatus for adding a watermark to a moving image as it is displayed comprises a watermark generator in which data representing a watermark is generated. The watermark contains at least one of location data and time data pertaining to the displaying of the moving image. The location and time data is protected by forward error encoding. The watermark also contains at least one of program data identifying the moving image and frame data unique in identifying each frame of the moving image. The program and time data is protected by scrambling. A watermark applicator applies the watermark data to image data representing substantially all of the moving image depending on a characteristic, such as amplitude, of the data.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com