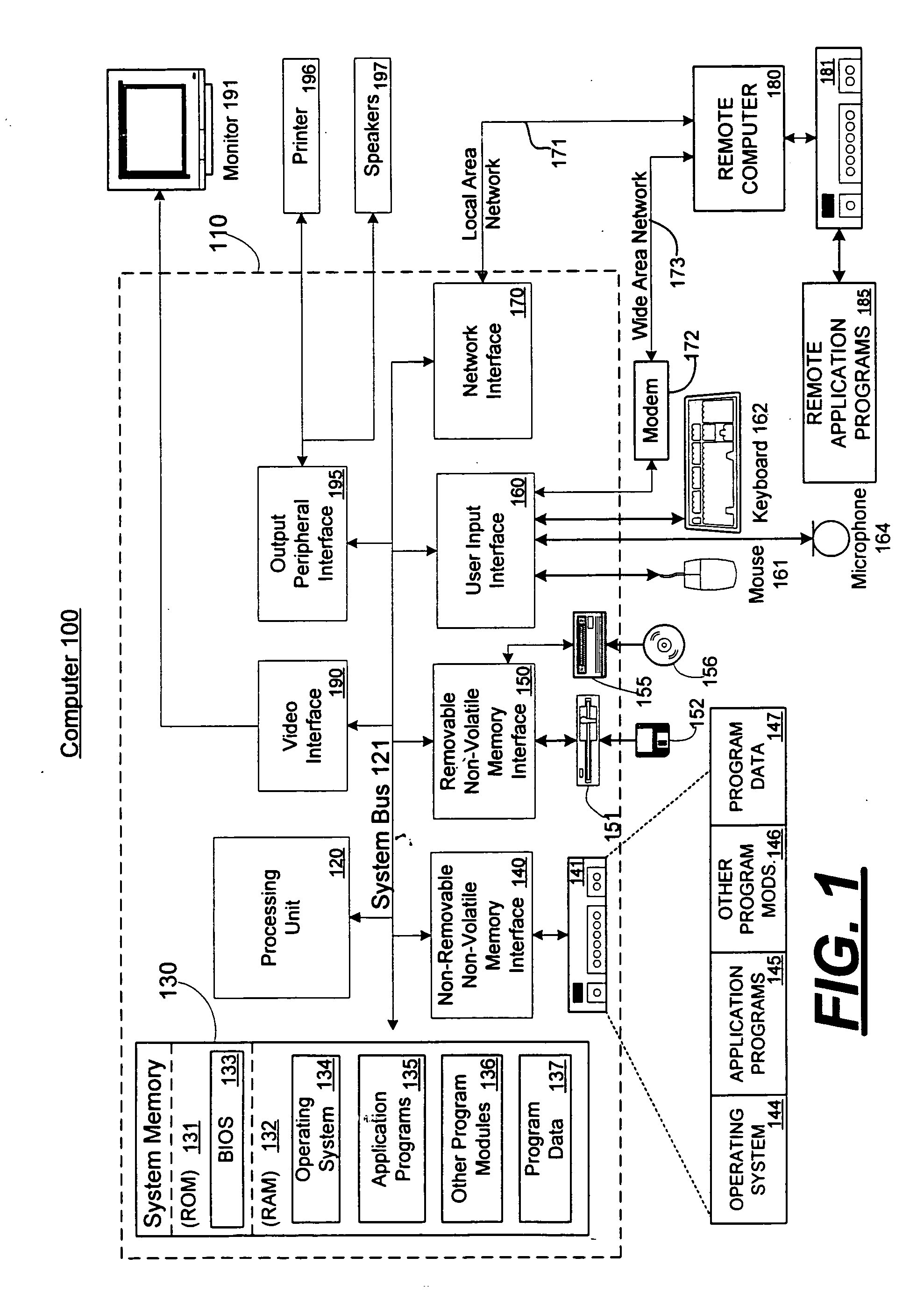
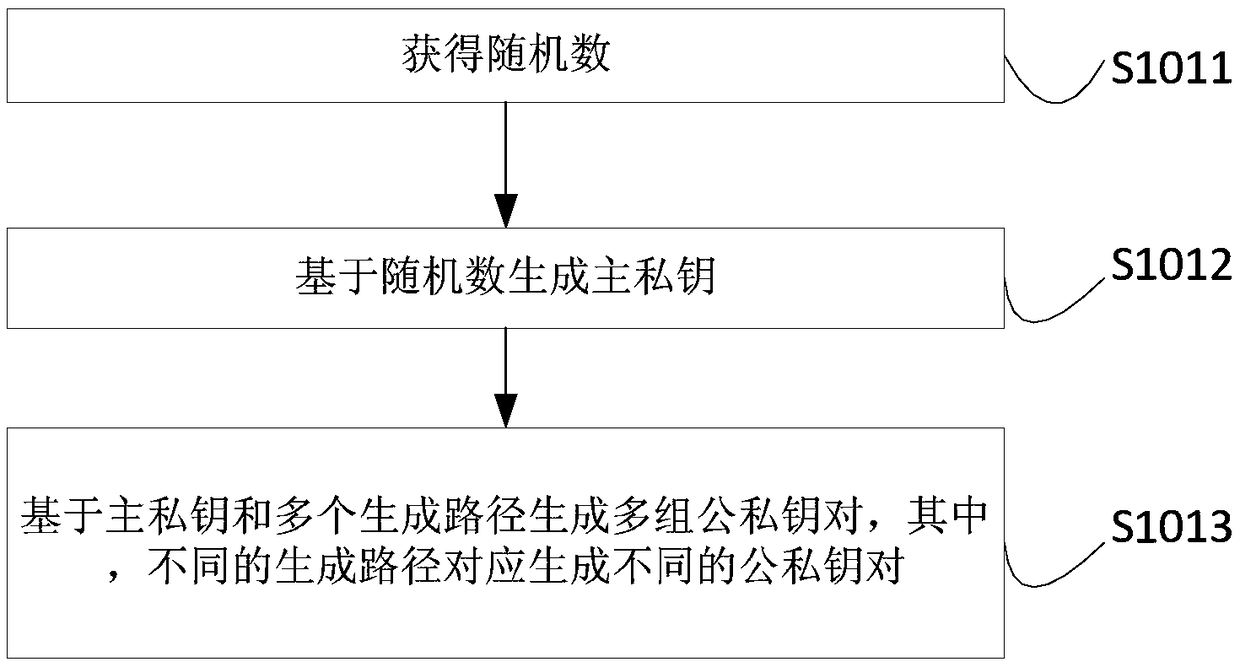
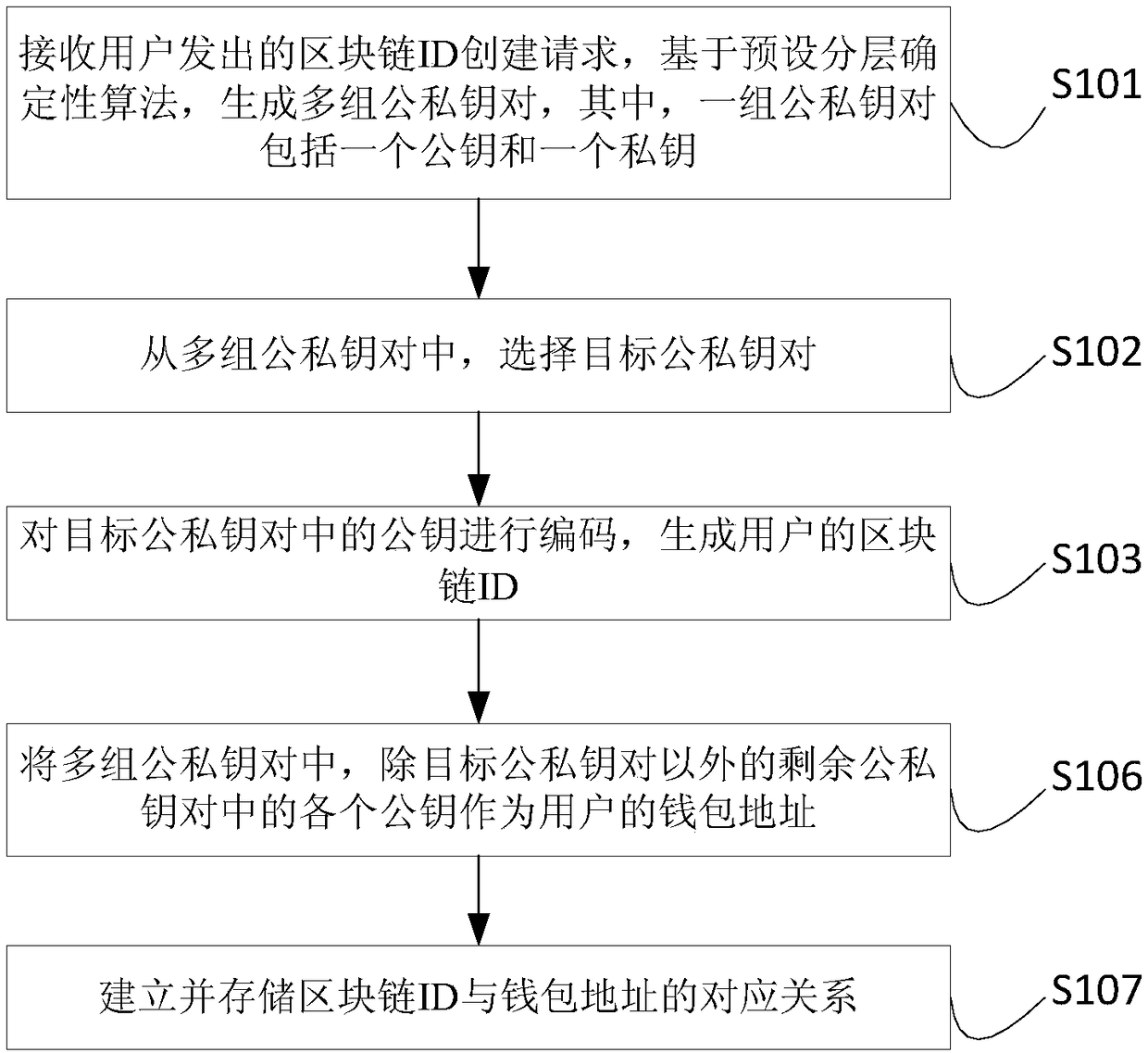
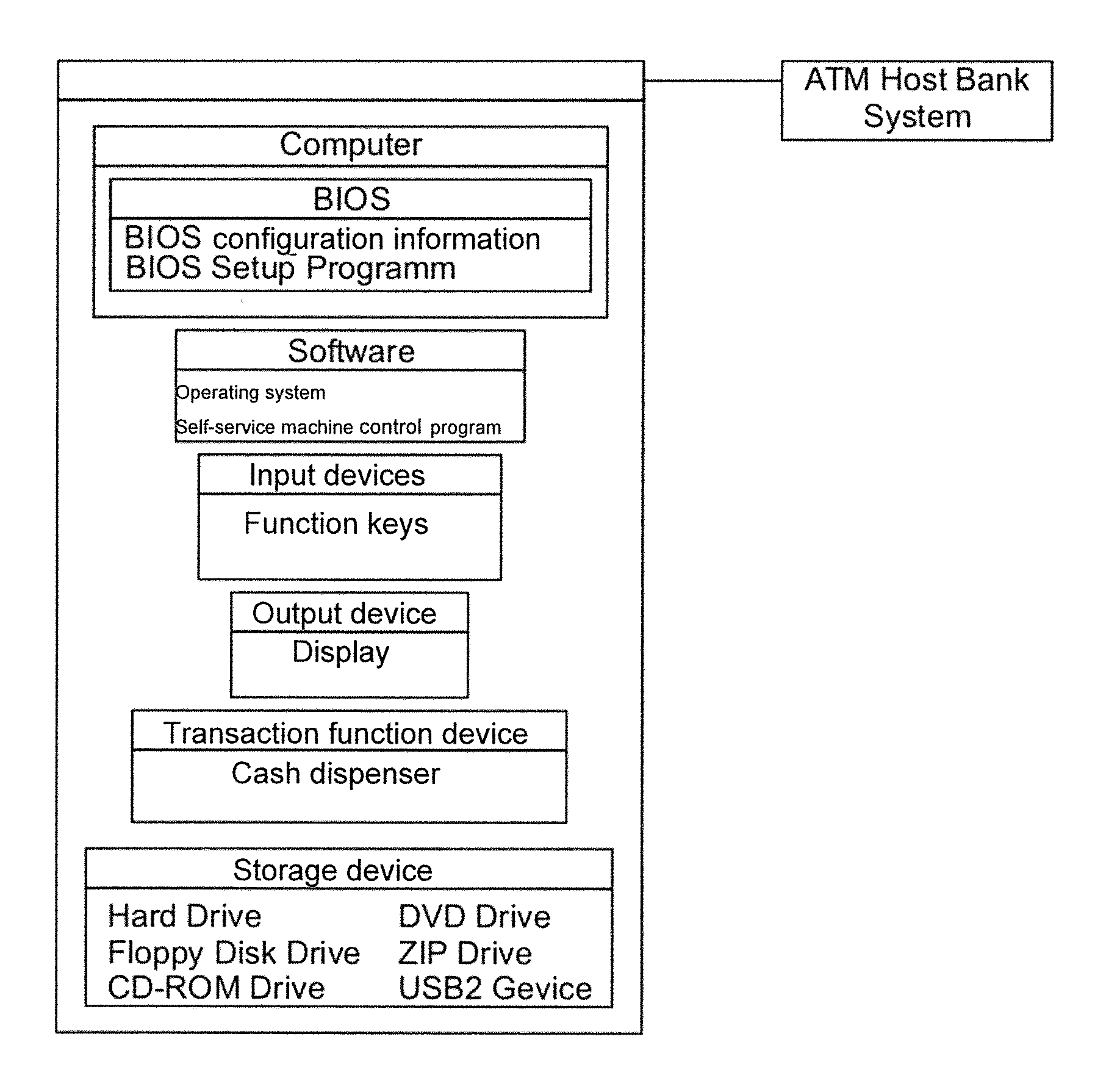
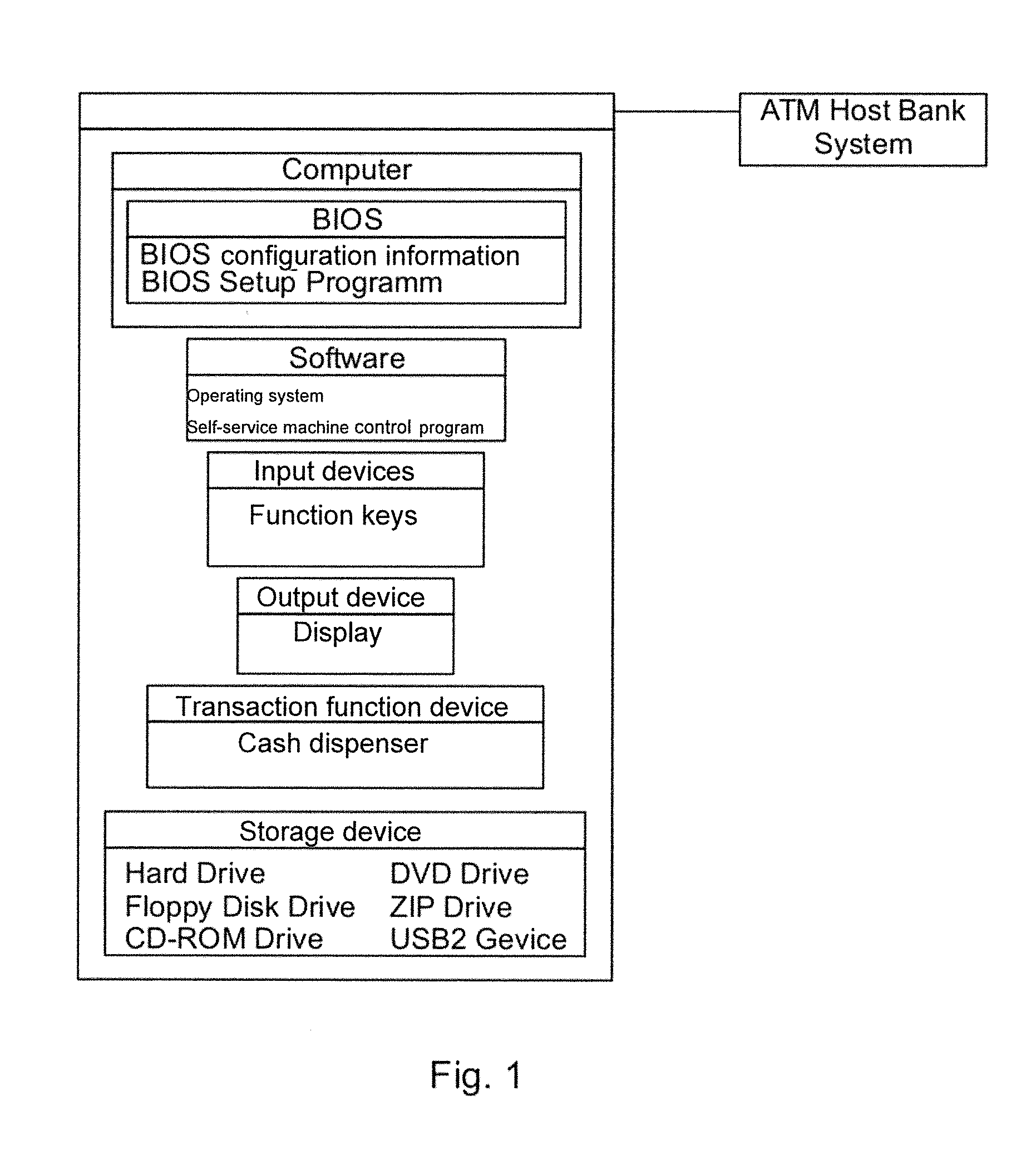
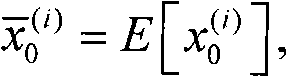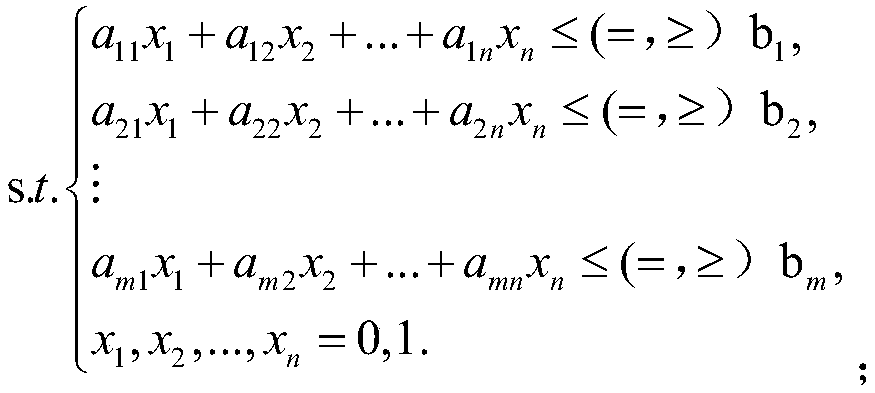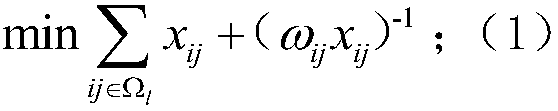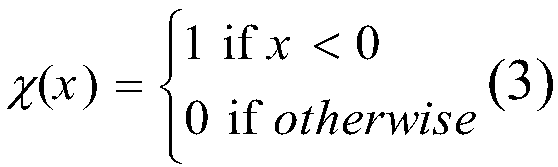Patents
Literature
61 results about "Deterministic algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a deterministic algorithm is an algorithm which, given a particular input, will always produce the same output, with the underlying machine always passing through the same sequence of states. Deterministic algorithms are by far the most studied and familiar kind of algorithm, as well as one of the most practical, since they can be run on real machines efficiently.
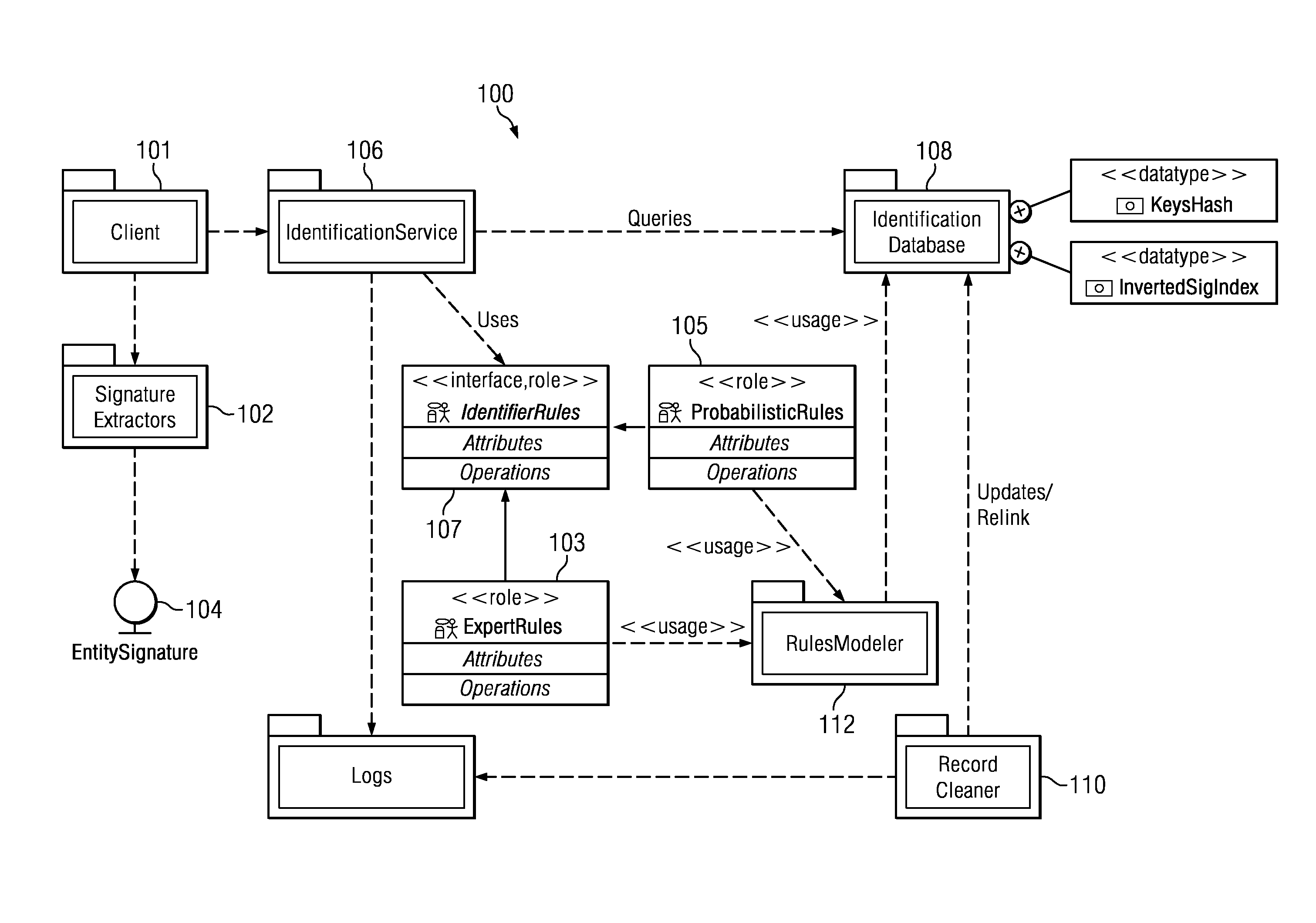
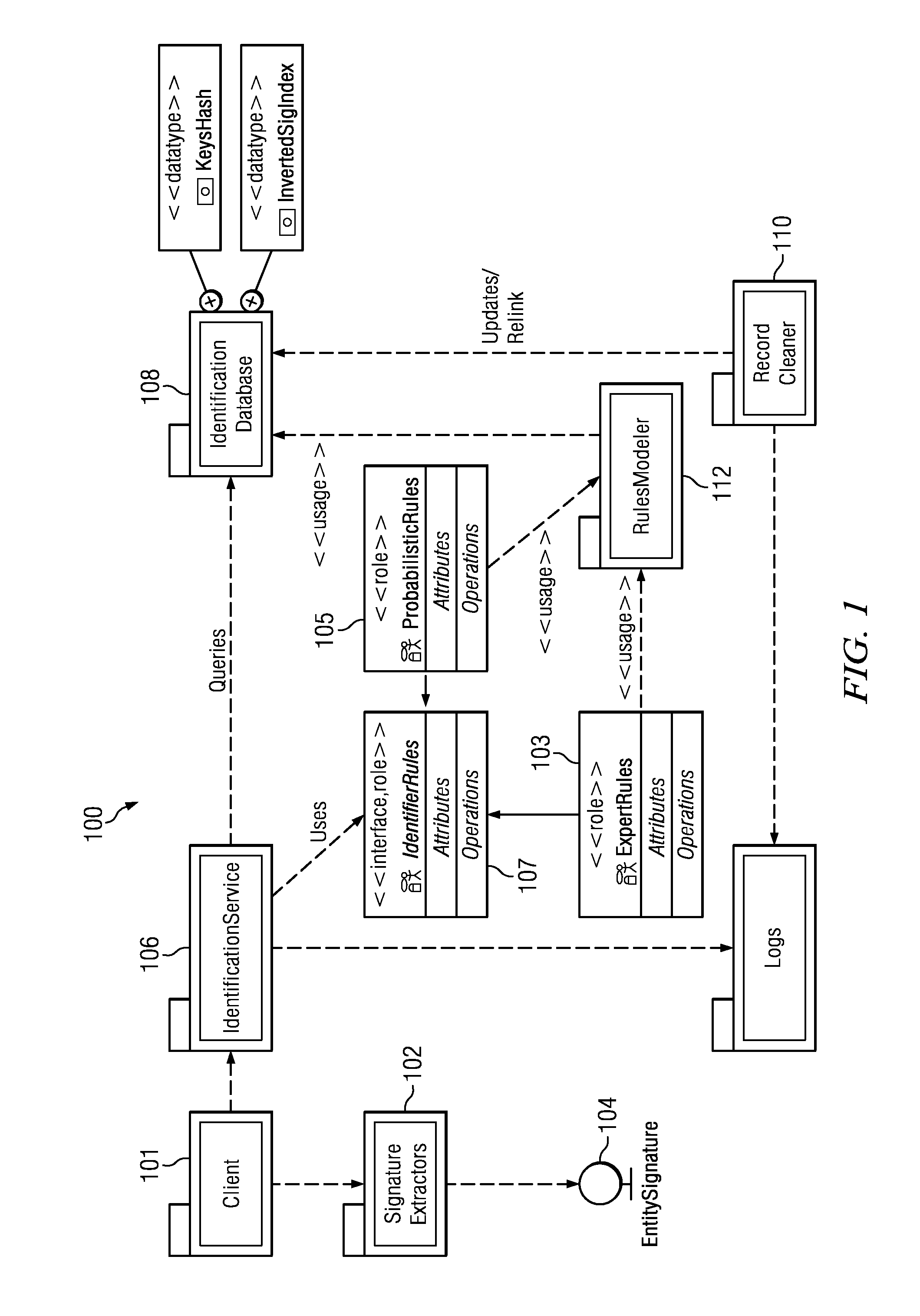
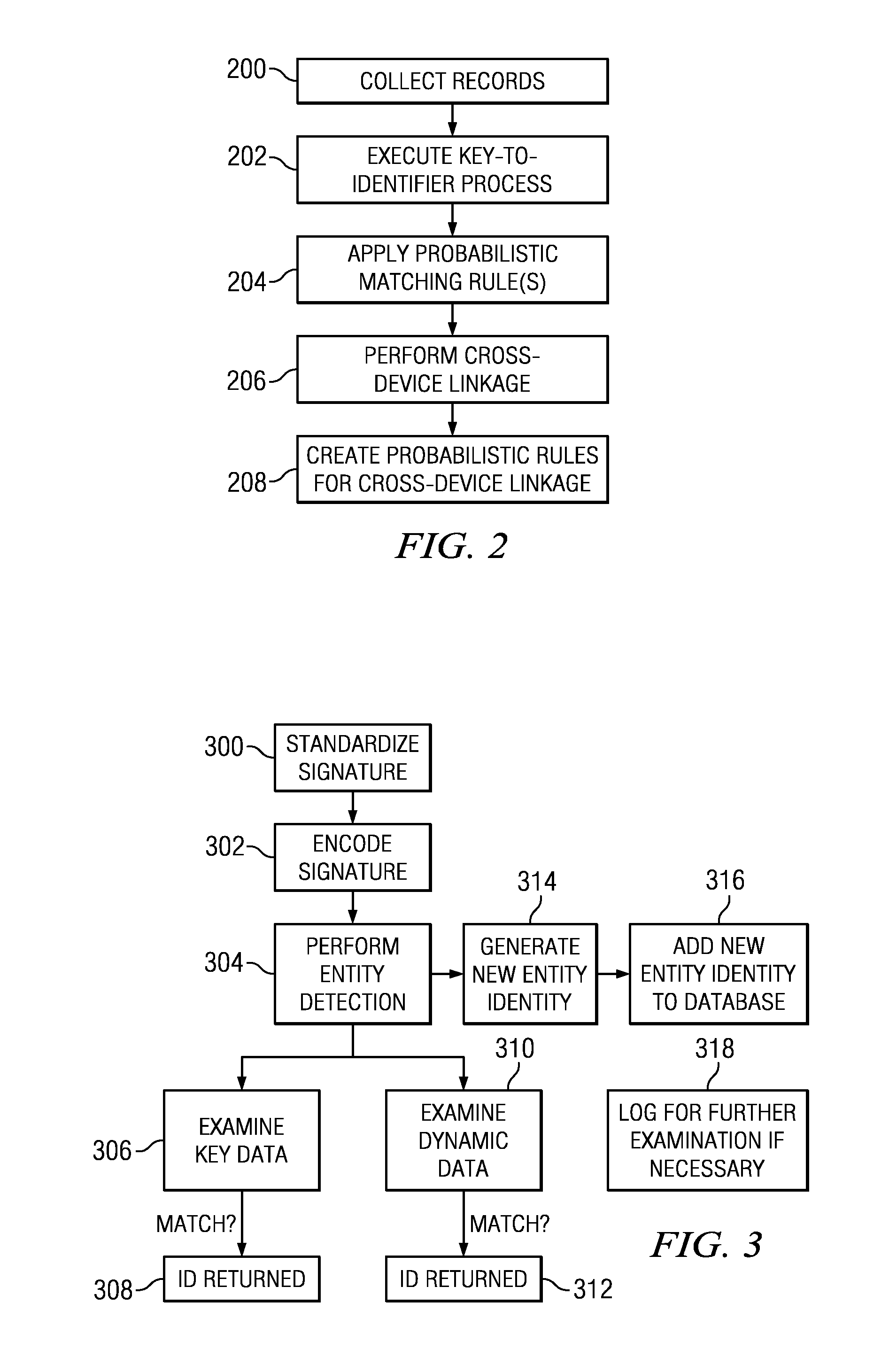
Uniquely identifying a network-connected entity
ActiveUS8438184B1Digital data processing detailsTransmissionNetwork connectionDeterministic algorithm
An entity (a device, a user of a device or set of devices, a user of one or more applications on a device, a group of users of the device or set of devices, or the like) is identified across multiple device, usage, and application domains. The entity is assigned a unique entity identity that is generated from a set of feature data that model the entity. The feature data typically includes deterministic data, device and system-specific feature data, and usage feature data. The identity is generated by applying to the feature data one or more rules that identify which of the feature data to use to generate the entity identity. The rules include at least one deterministic rule, and at least one probabilistic rule. Periodically, an identity is merged into one or more entity identities that are found, by applying a rule, to represent a same entity.
Owner:ADELPHIC LLC
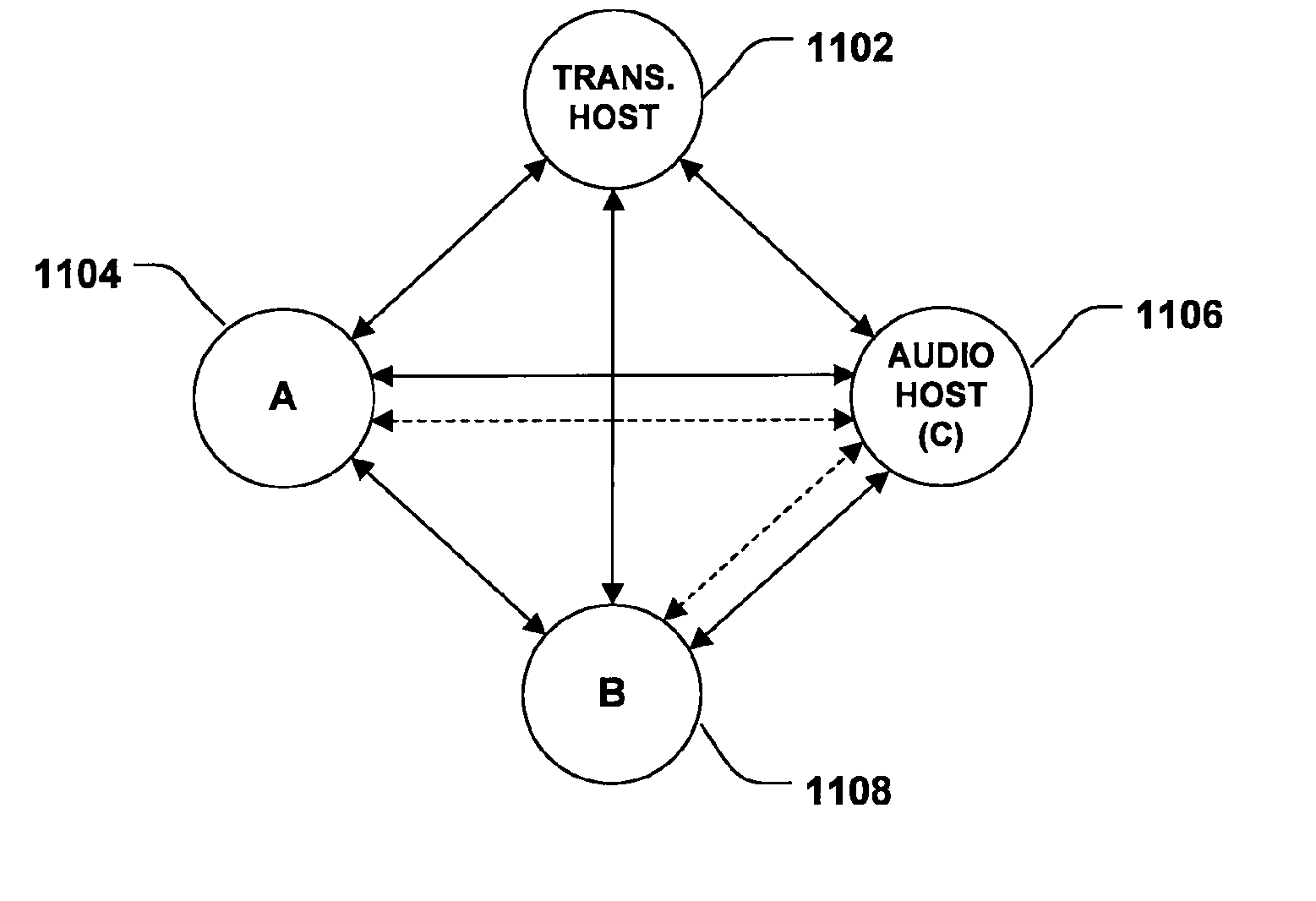
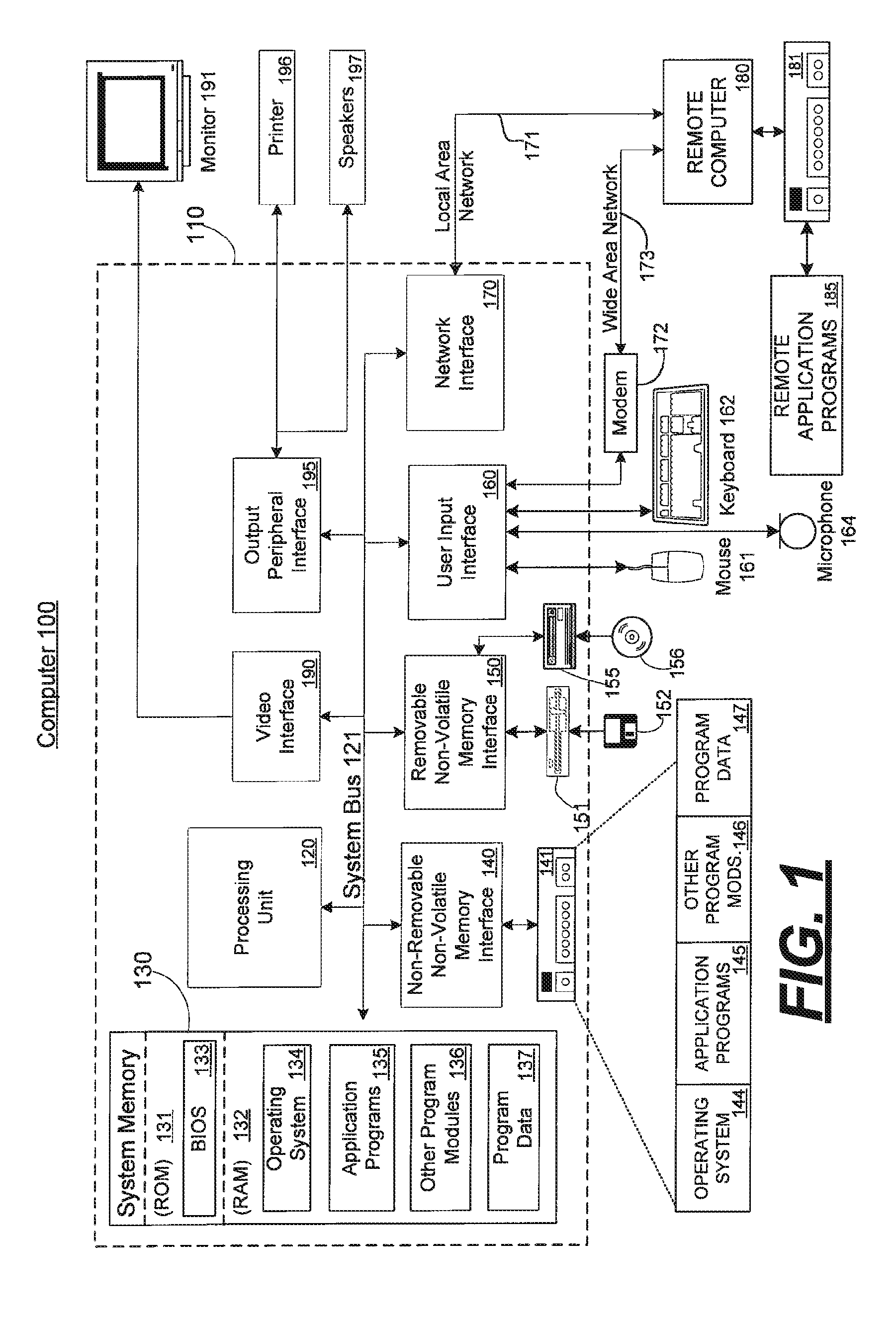
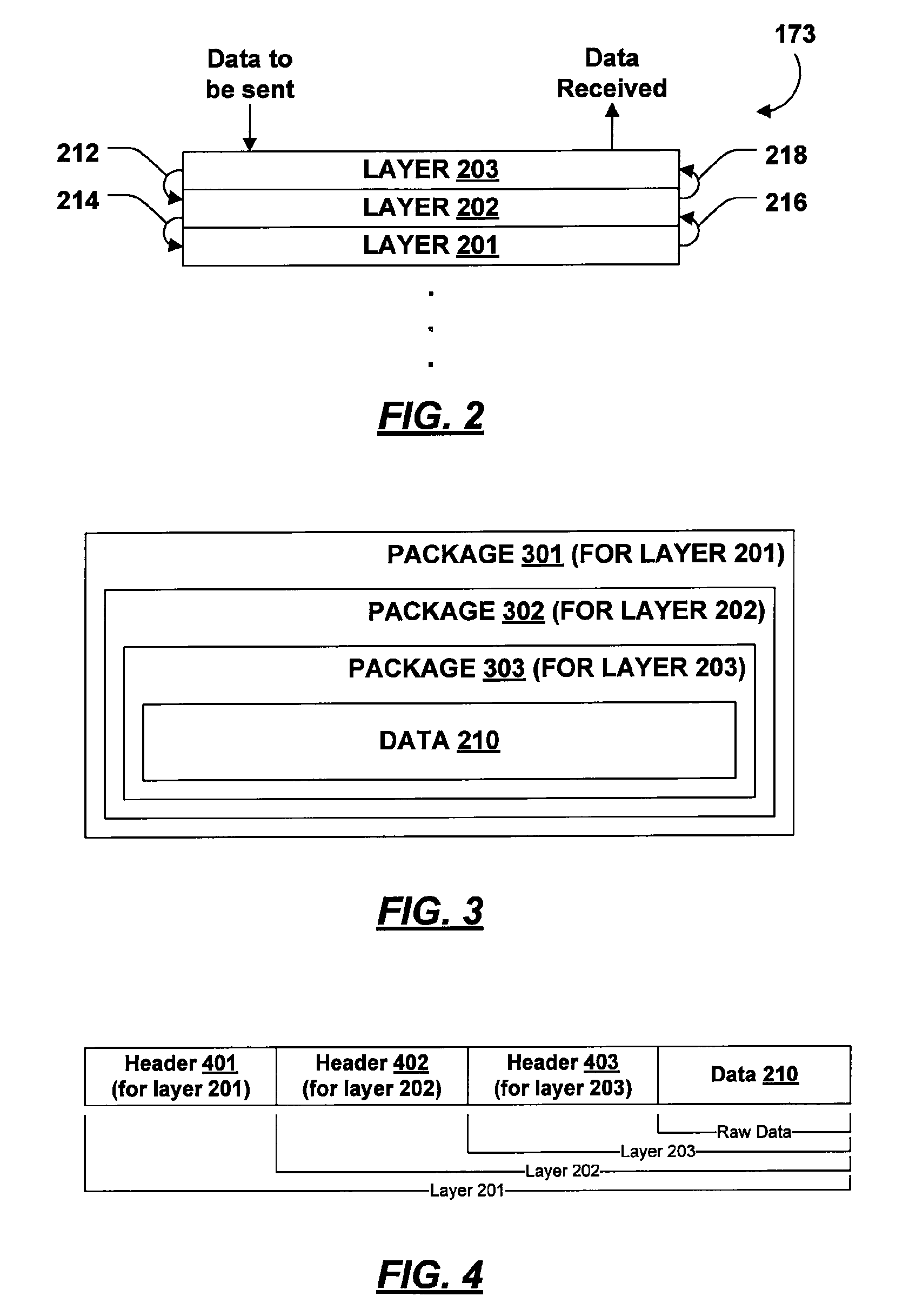
System and method for multi-layered network communications
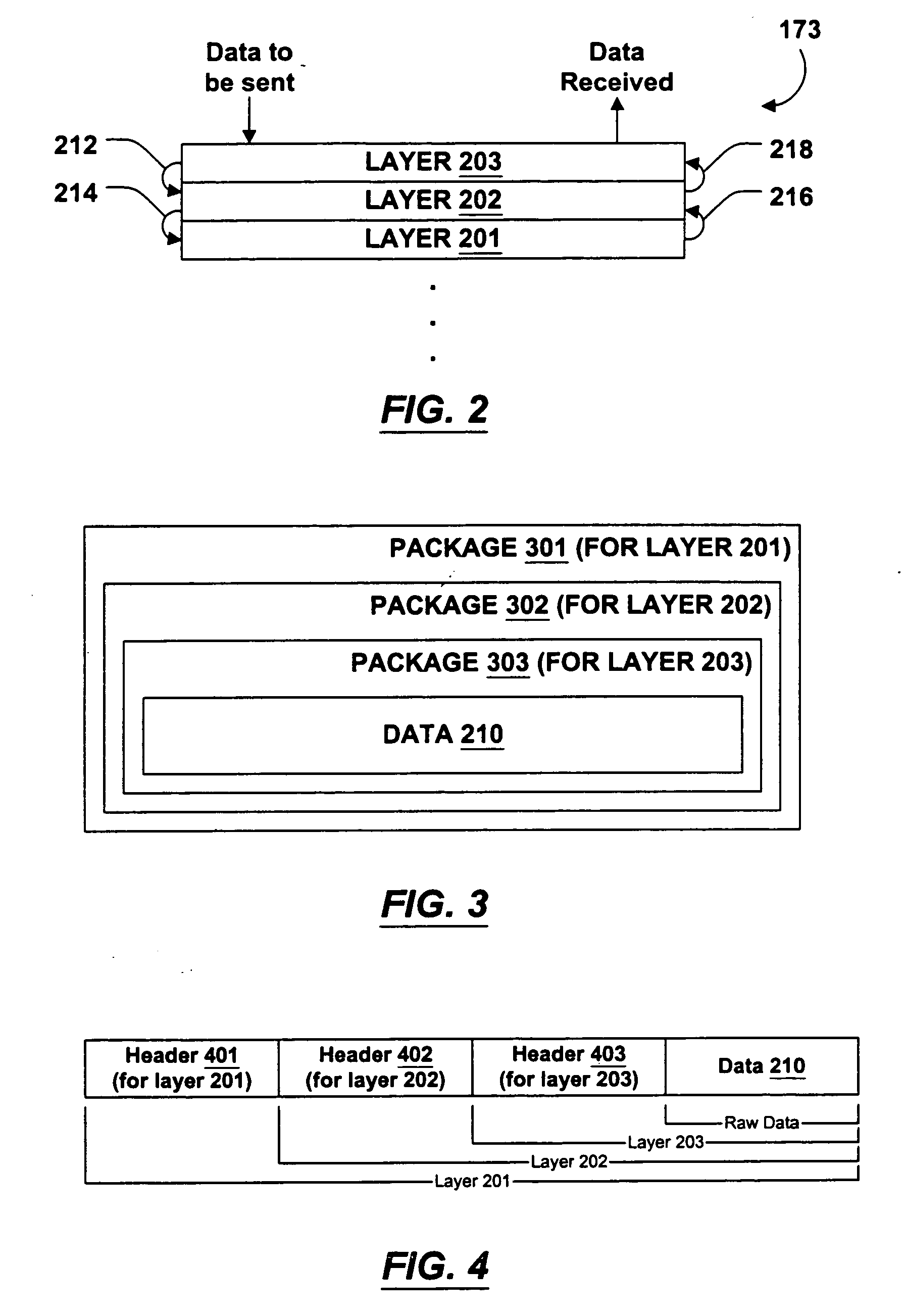
InactiveUS20070130253A1Multiple digital computer combinationsSecuring communicationDeterministic algorithmNetwork communication
A multi-layered network for transporting data comprises a first network layer that provides a first session topology, and a second network layer that provides a second session topology. The second network layer uses the first network layer to transport data. In one embodiment of the invention, the data sent by the second layer is real-time audio data, such as voice. Each session topology may be either peer-to-peer or client / server. The first and second layers may have different topologies and / or different session hosts. A deterministic algorithm is provided whereby a new session host is selected when the current host leaves the session.
Owner:MICROSOFT TECH LICENSING LLC
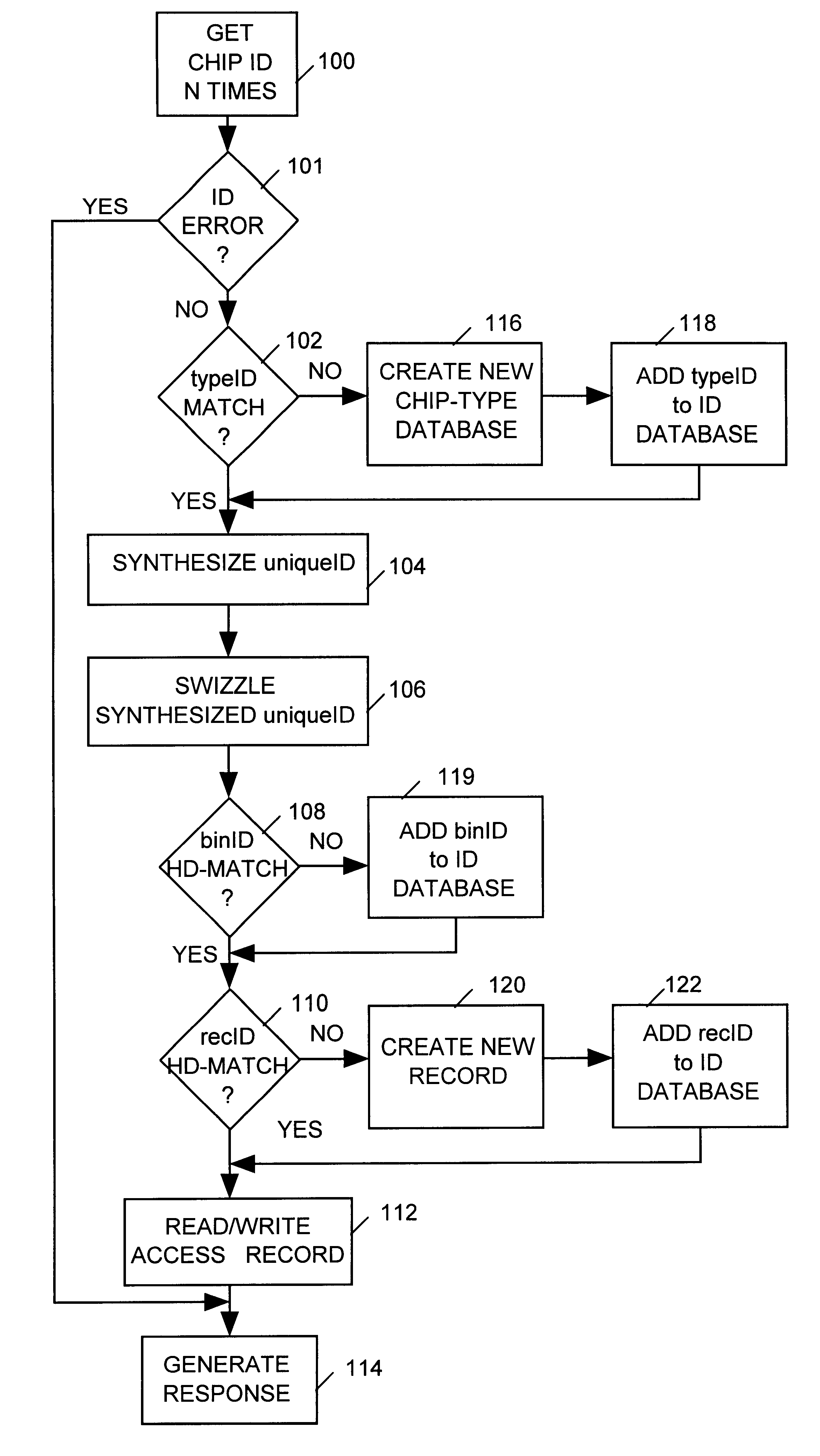
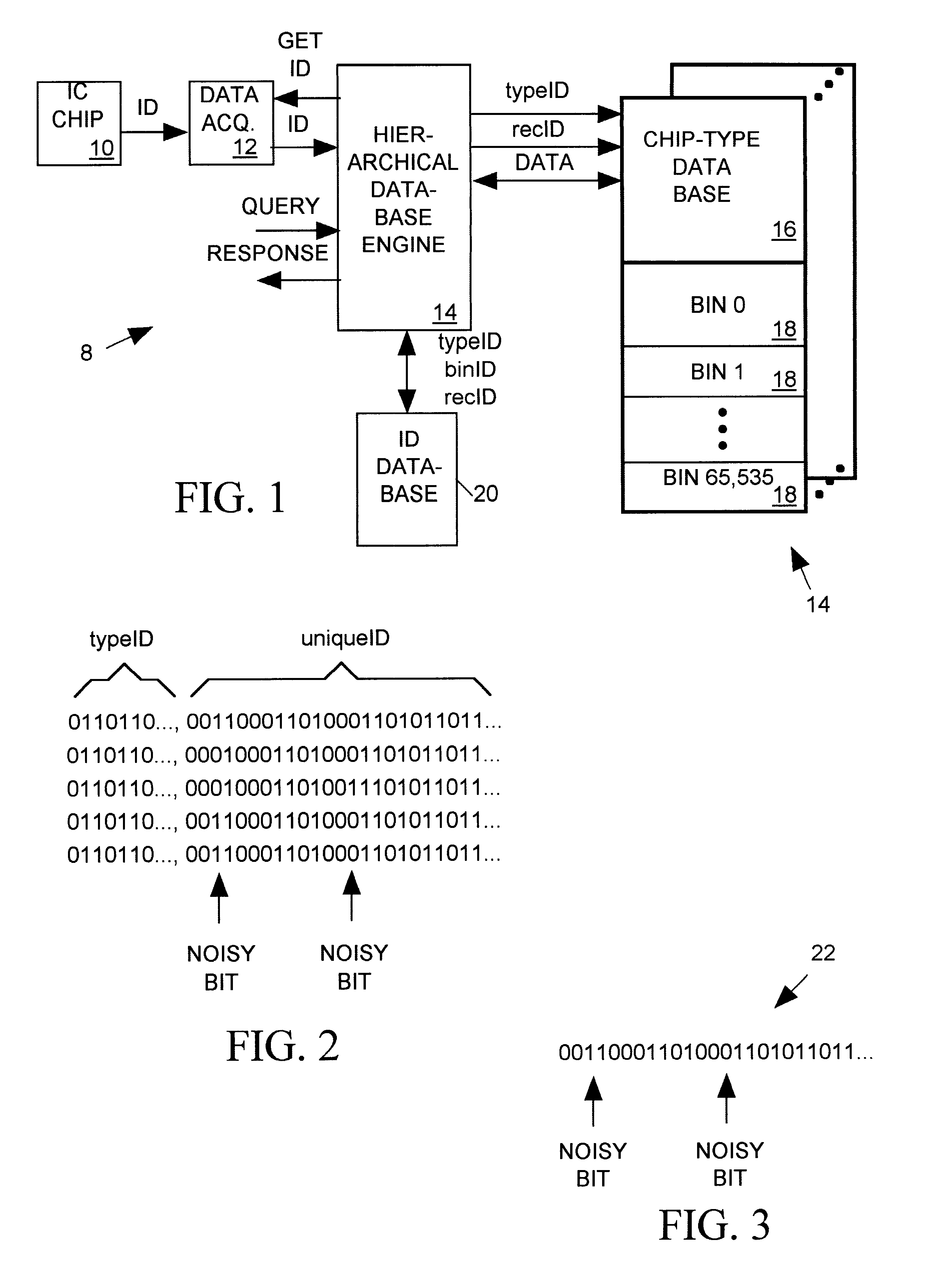
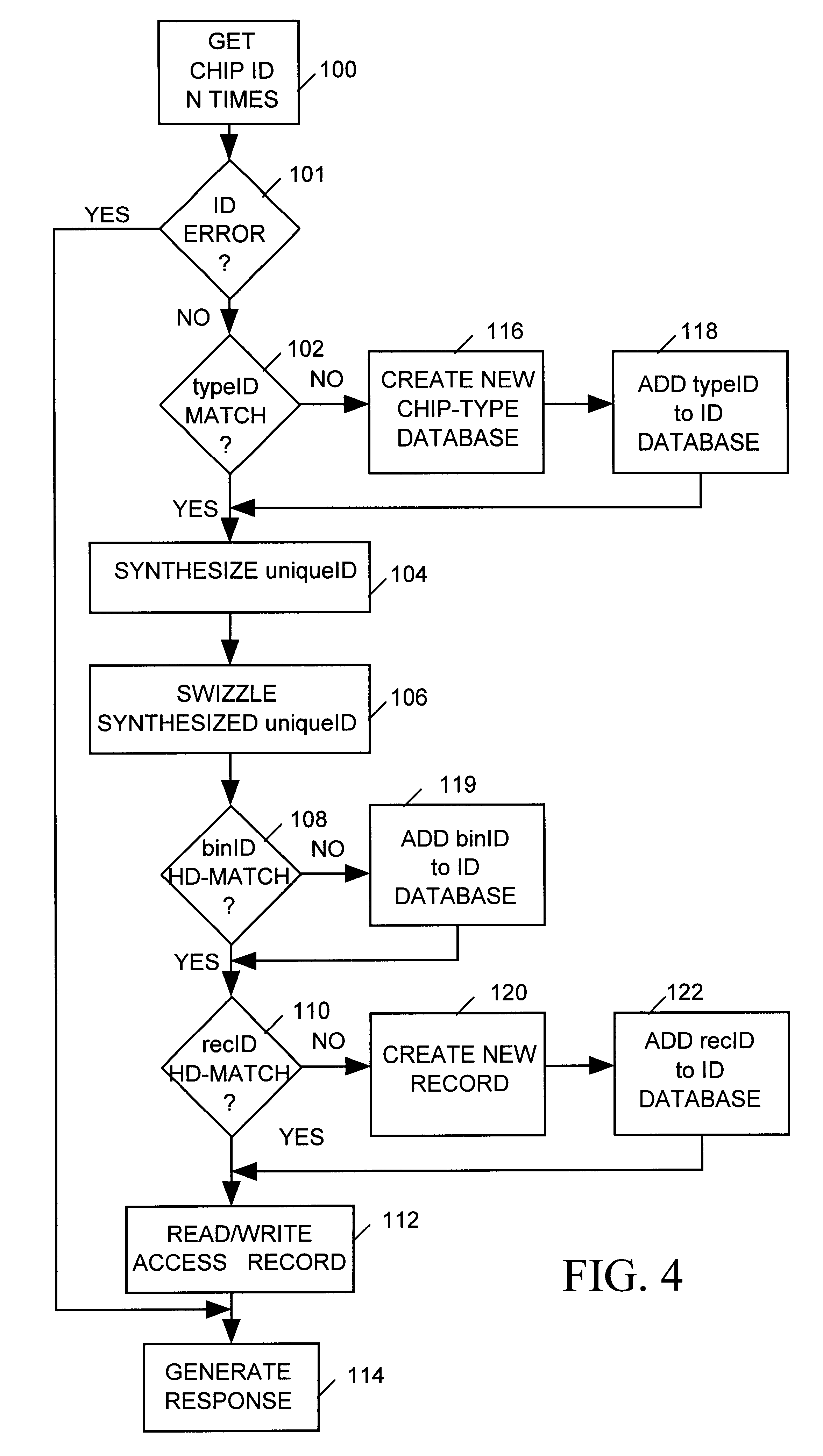
Database system using a record key having some randomly positioned, non-deterministic bits
InactiveUS6738788B1Data processing applicationsDigital data processing detailsDeterministic algorithmData mining
A database system accesses database records referenced by a binary number key having two fields, a typeID field containing only deterministic bits, and a uniqueID field permissibly containing one or more non-deterministic bits at any bit positions therein. The database system maintains a set of databases, each being identified by a separate value of the typeID field of the binary number key. The records of each database are allocated among a plurality of bins, with each bin being identified (keyed) by separate value of a binID field, and with each record being identified (keyed) by a separate value of a recID field. The database system locates a record of interest referenced by the binary number key by first selecting a particular one of the databases that is identified by the typeID field of the binary number key. It then compares a portion of selected bits of the binary number key's uniqueID field to binID values identifying bins of the selected database to determine a subset of the bins that may include the record of interest. The database system then compares the full uniqueID field of the binary number key to the recIDs values for records of the subset of bins to determine which particular recID field identifies the record of interest.
Owner:ICID
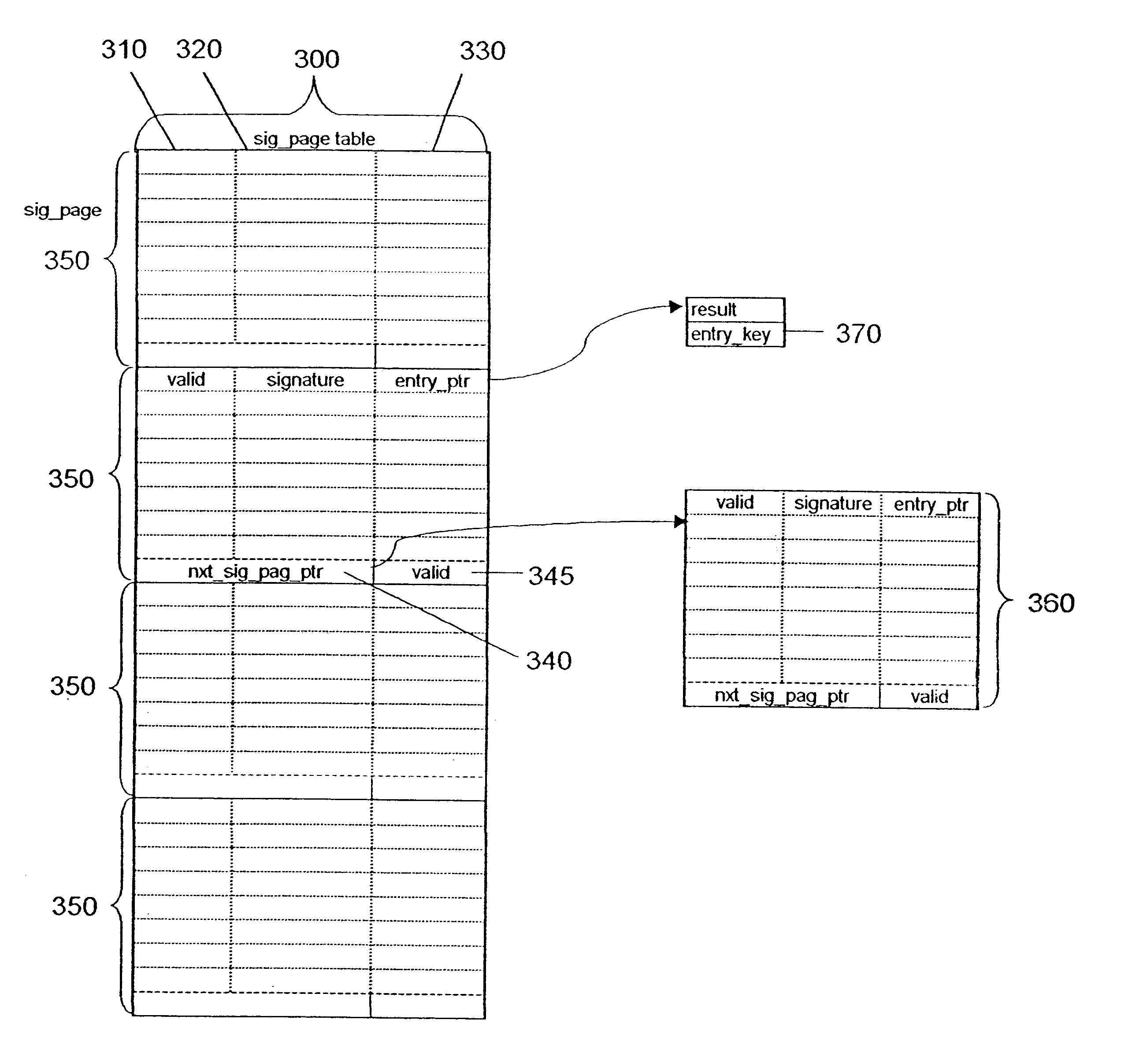
Deterministic search algorithm
InactiveUS6625612B1Digital data information retrievalData processing applicationsDeterministic algorithmTheoretical computer science
A method for storing and retrieving a key using a hash table, the method comprising the steps of: (a) hashing the key using a first hash function, thereby transforming the key into a table address in the hash table; (b) hashing the key using a second hash function, distinct from the first hash function, thereby transforming the key into a key signature; and (c) entering the key signature in a signature page located at the table address.
Owner:PLENUS TECH LTD +1
Method and system for searching for patterns in data
InactiveUS20100138376A1Efficient executionFacilitate and accelerate and applicationsDigital data information retrievalBiostatisticsNondeterministic algorithmGraphics
Methods and systems for searching by computer for patterns in data are disclosed. These have particular, but not exclusive application to searching for target nucleotide sequences within a gene database. In the method can be performed by a computer that computer includes a central processing unit (CPU) that has one or more processing core, main memory accessible for read and write operations by the CPU, one or more graphics processing unit (GPU), and graphics memory accessible for read and write operations by the GPU. The method includes a step in which data to be processed as part of the pattern matching algorithm are transferred to the graphics memory, the GPU is operated to perform one or more processing step on the data. Following completion of the processing step, processed data are transferred from the graphics memory to the main memory. Algorithms that can be implemented using the invention include deterministic algorithms (e.g., Smith-Waterman) and non-deterministic algorithms (e.g., BLAST).
Owner:INVENTANET
System and method for multi-layered network communications
InactiveUS20060092942A1Data switching by path configurationStore-and-forward switching systemsDeterministic algorithmNetwork communication
A multi-layered network for transporting data comprises a first network layer that provides a first session topology, and a second network layer that provides a second session topology. The second network layer uses the first network layer to transport data. In one embodiment of the invention, the data sent by the second layer is real-time audio data, such as voice. Each session topology may be either peer-to-peer or client / server. The first and second layers may have different topologies and / or different session hosts. A deterministic algorithm is provided whereby a new session host is selected when the current host leaves the session.
Owner:MICROSOFT TECH LICENSING LLC
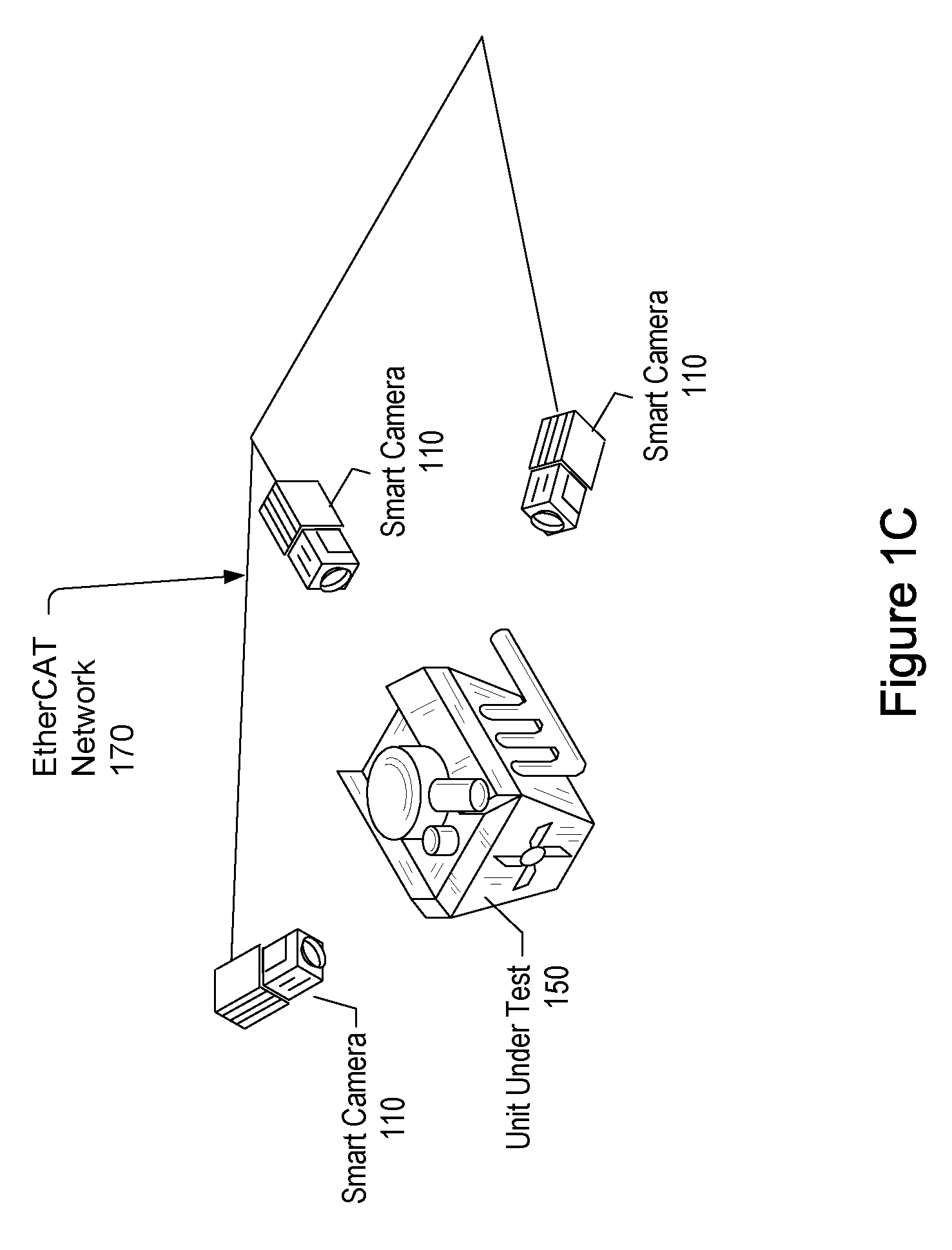
Vision System With Deterministic Low-Latency Communication
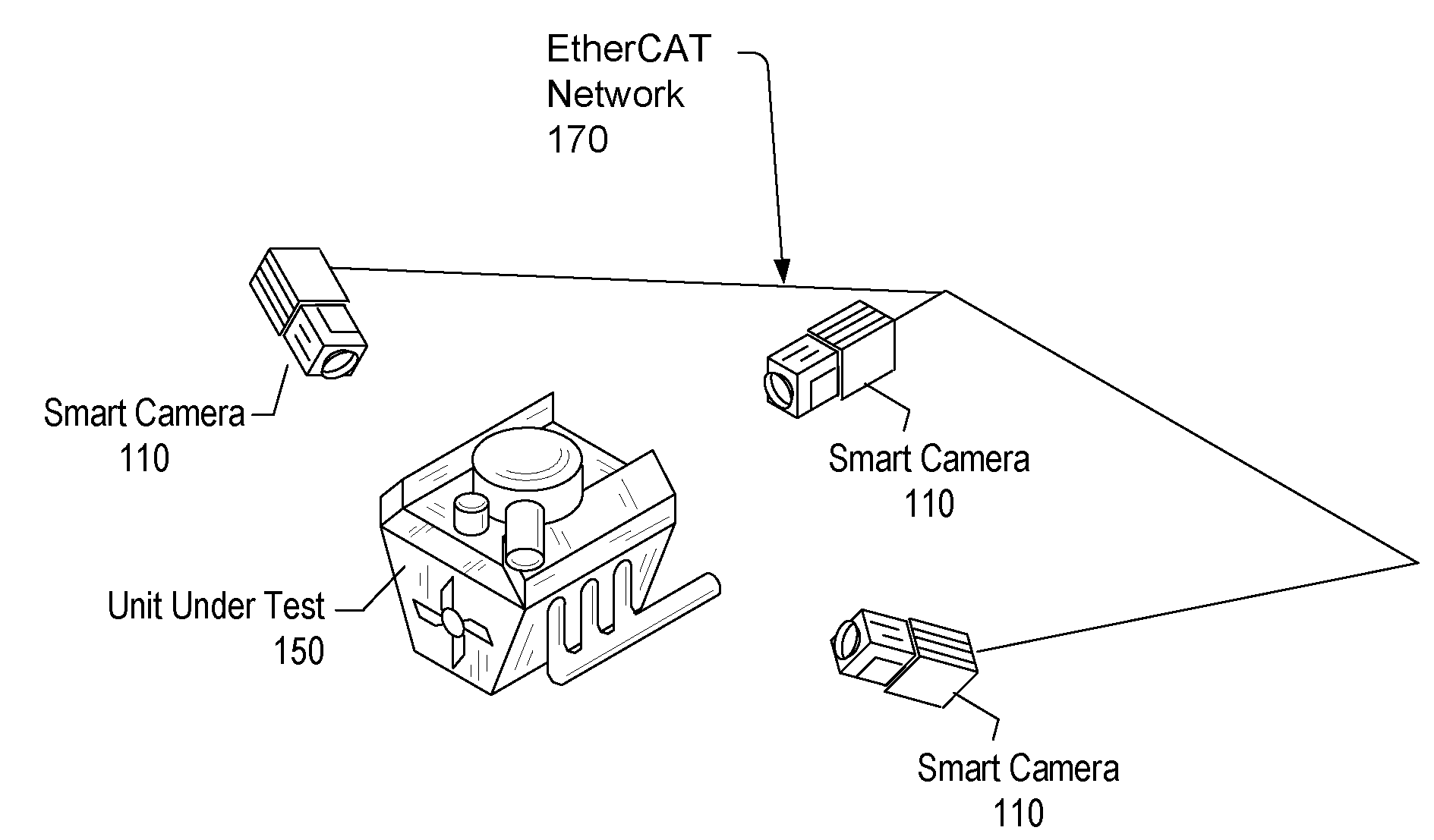
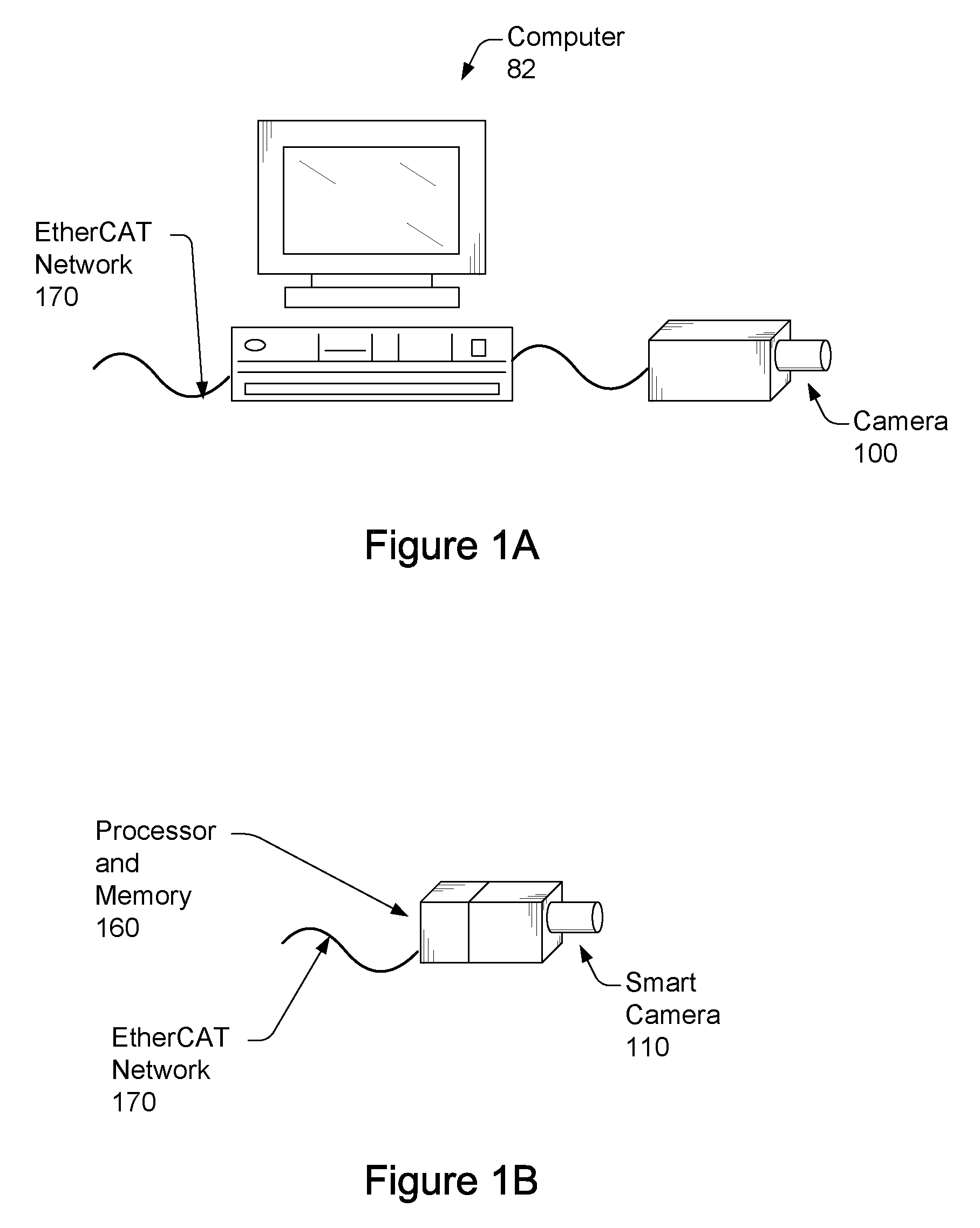
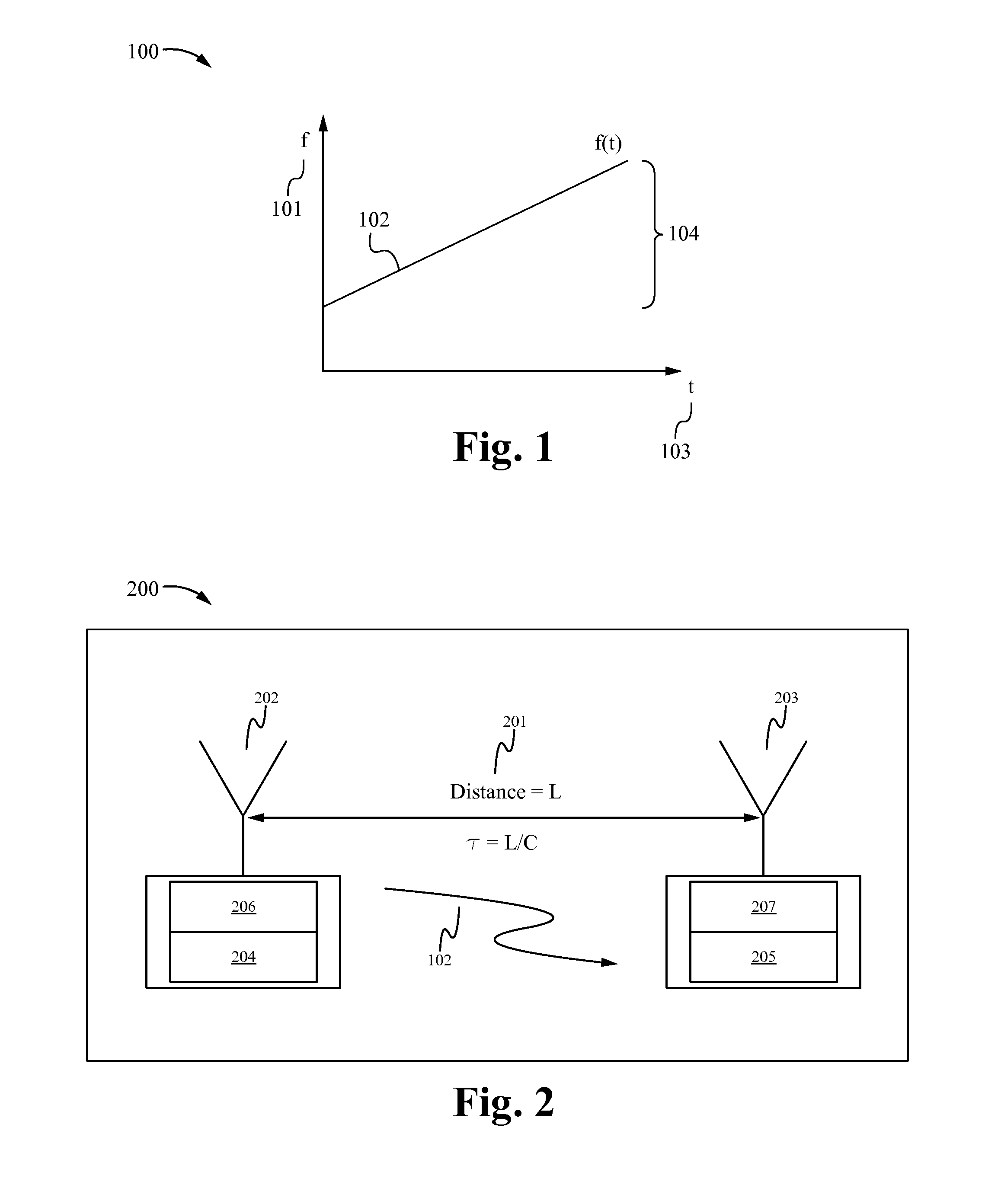
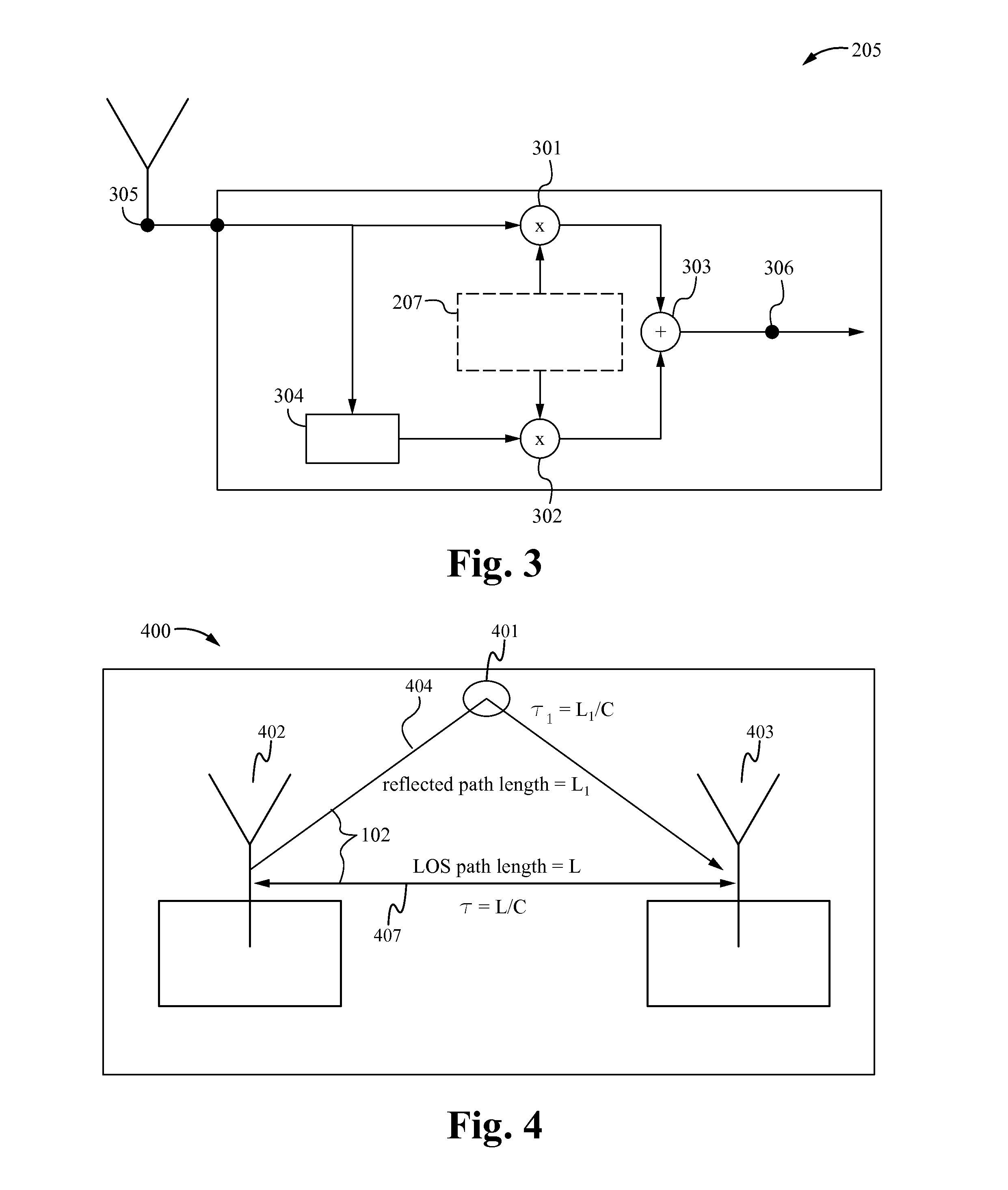
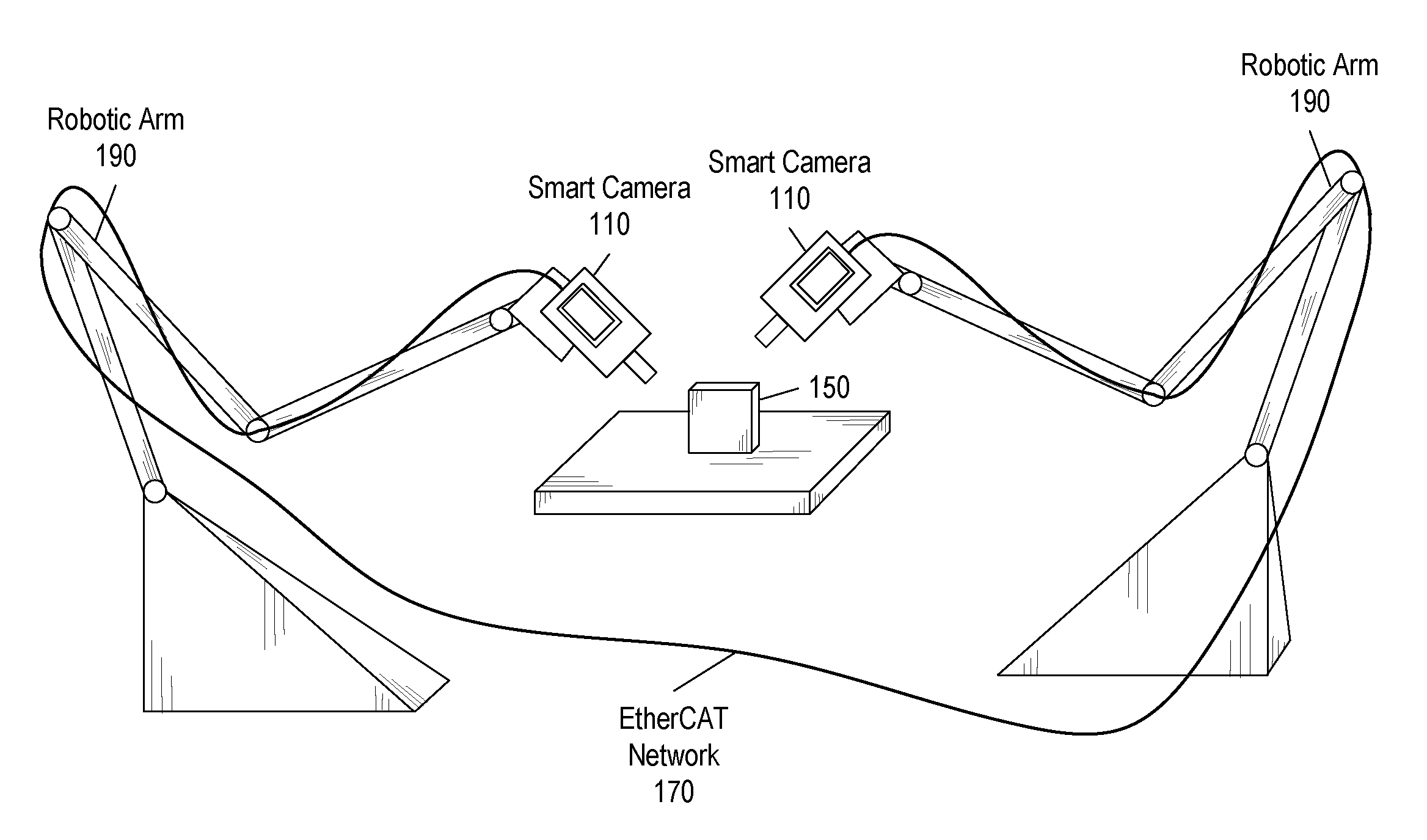
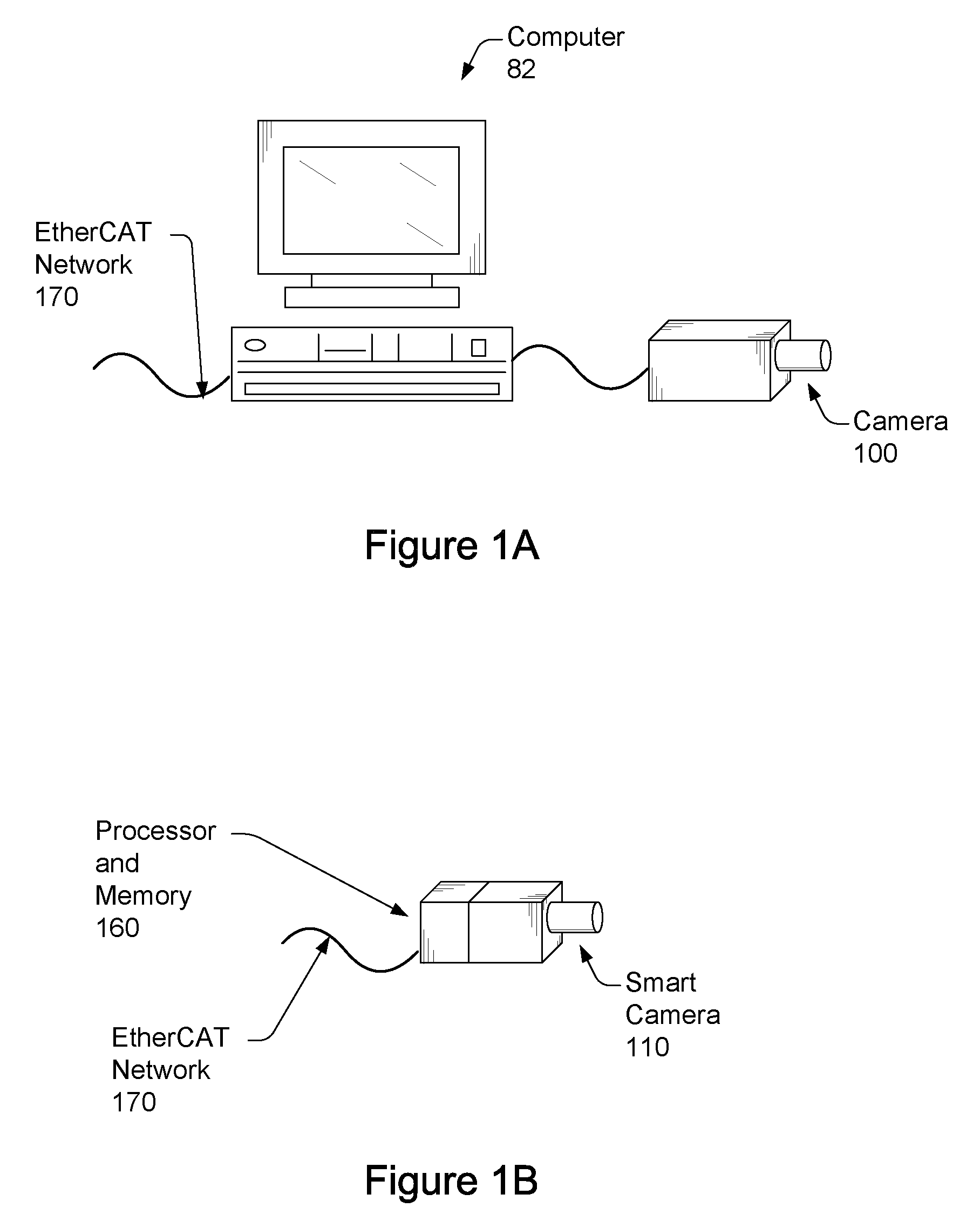
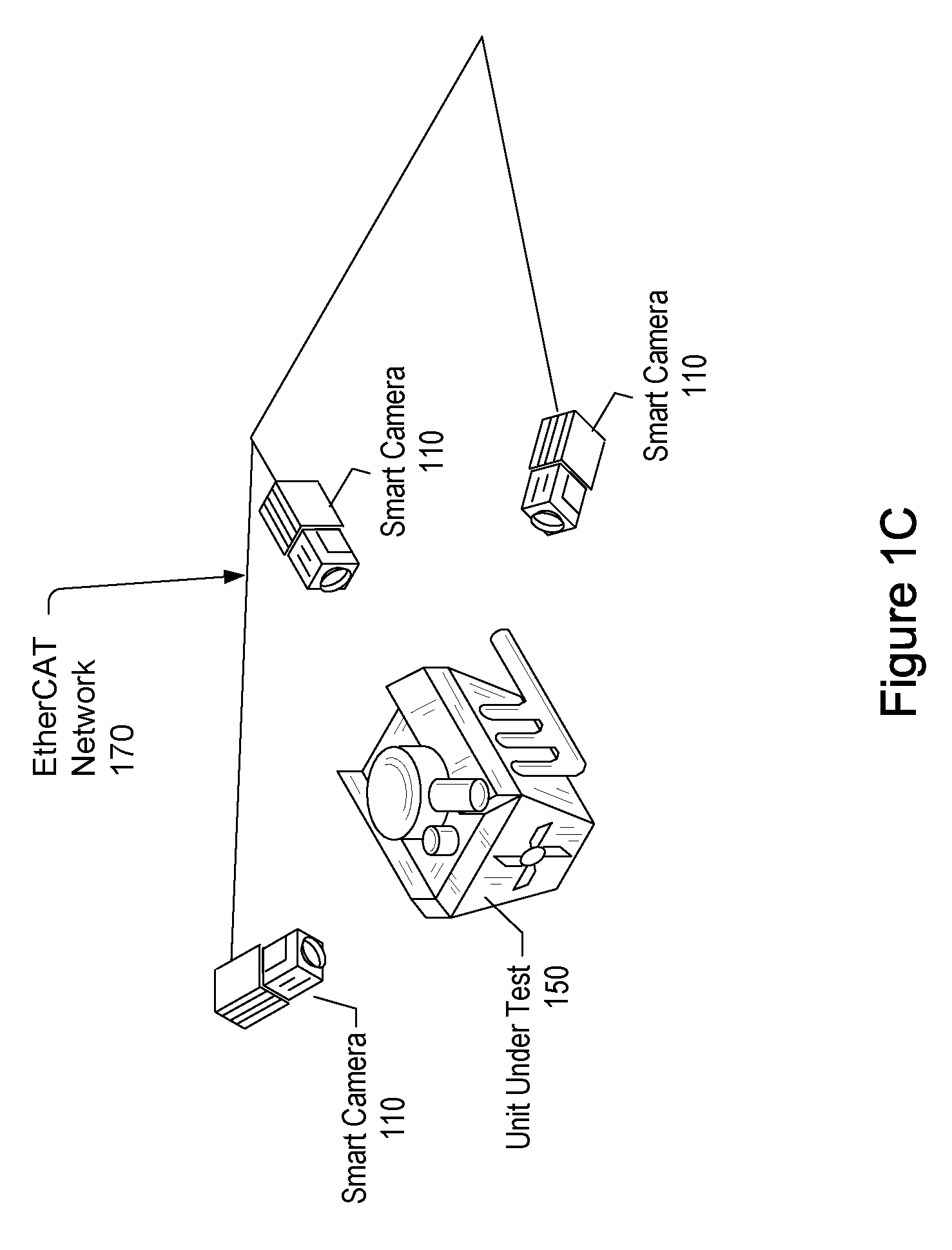
ActiveUS20090027509A1Lower latencyTelevision system detailsComputer controlClosed loop feedbackEvent trigger
Vision system and method. The system includes a vision system, including: a camera, a processor and memory, coupled to the camera, and an EtherCAT interface, coupled to the processor and memory, possibly contained in a chassis, and operable to couple to an EtherCAT network that provides for deterministic low-latency communication between the vision system and devices coupled to the EtherCAT network. The vision system may be configurable to operate as any of: an EtherCAT master device, an EtherCAT slave device, or a TCP / IP Ethernet device. One or more additional vision systems may couple to the EtherCAT network. The vision systems may be synchronized using an EtherCAT distributed clock technique, time-based triggered, and / or event triggered, via the EtherCAT network, e.g., in a multi-view vision, collaborative processing, control, I / O, or video servoing application, e.g., using an EtherCAT deterministic low latency closed loop feedback system, including processing, control, or I / O devices.
Owner:NATIONAL INSTRUMENTS
Method for generating trusted random numbers by applying block chains
The invention discloses a method for generating trusted random numbers by applying block chains. According to the method, a number, with certain randomness, generated by another block chain system canbe taken as input, or a random number generated in the last round can be taken as the input; a set of random number generators is selected from all the nodes of a block chain through a transparent and open certainty algorithm; the generators respectively generate respective random number seeds; all the random number seeds are used, or the random number input is used with the random number seeds to serve as parameters; and a new trusted random number is generated by applying the transparent and open certainty algorithm.
Owner:胡晓东 +1
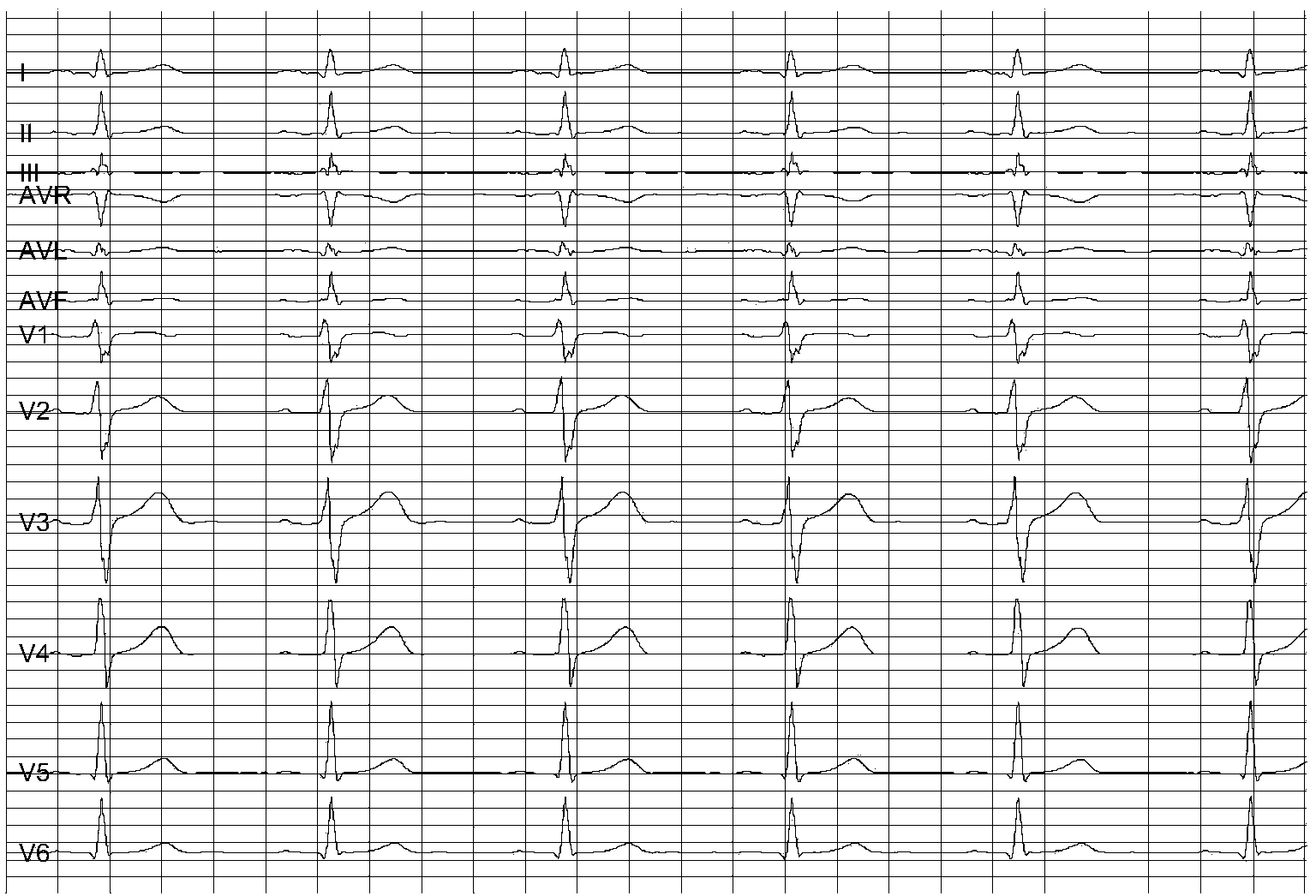
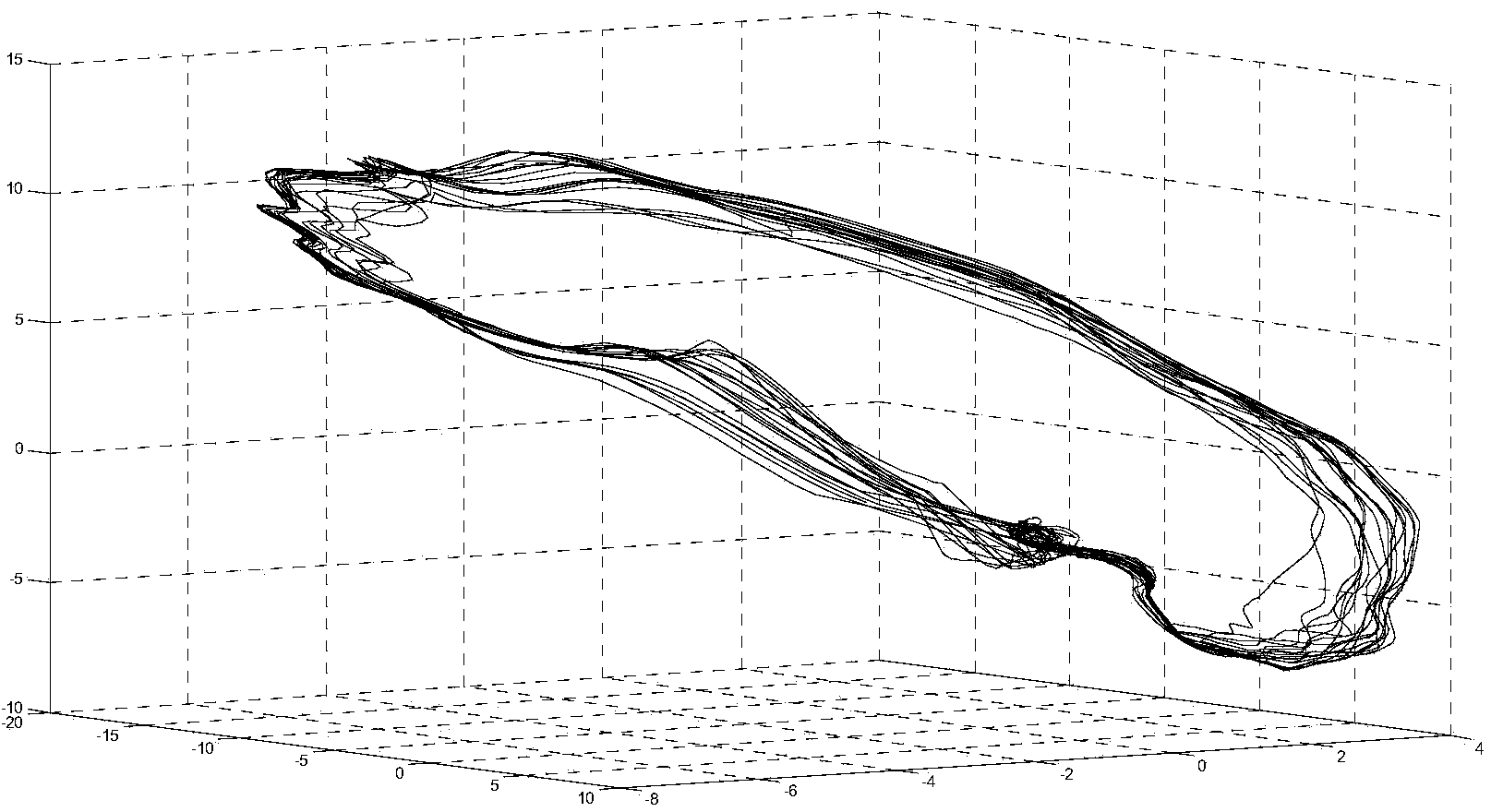
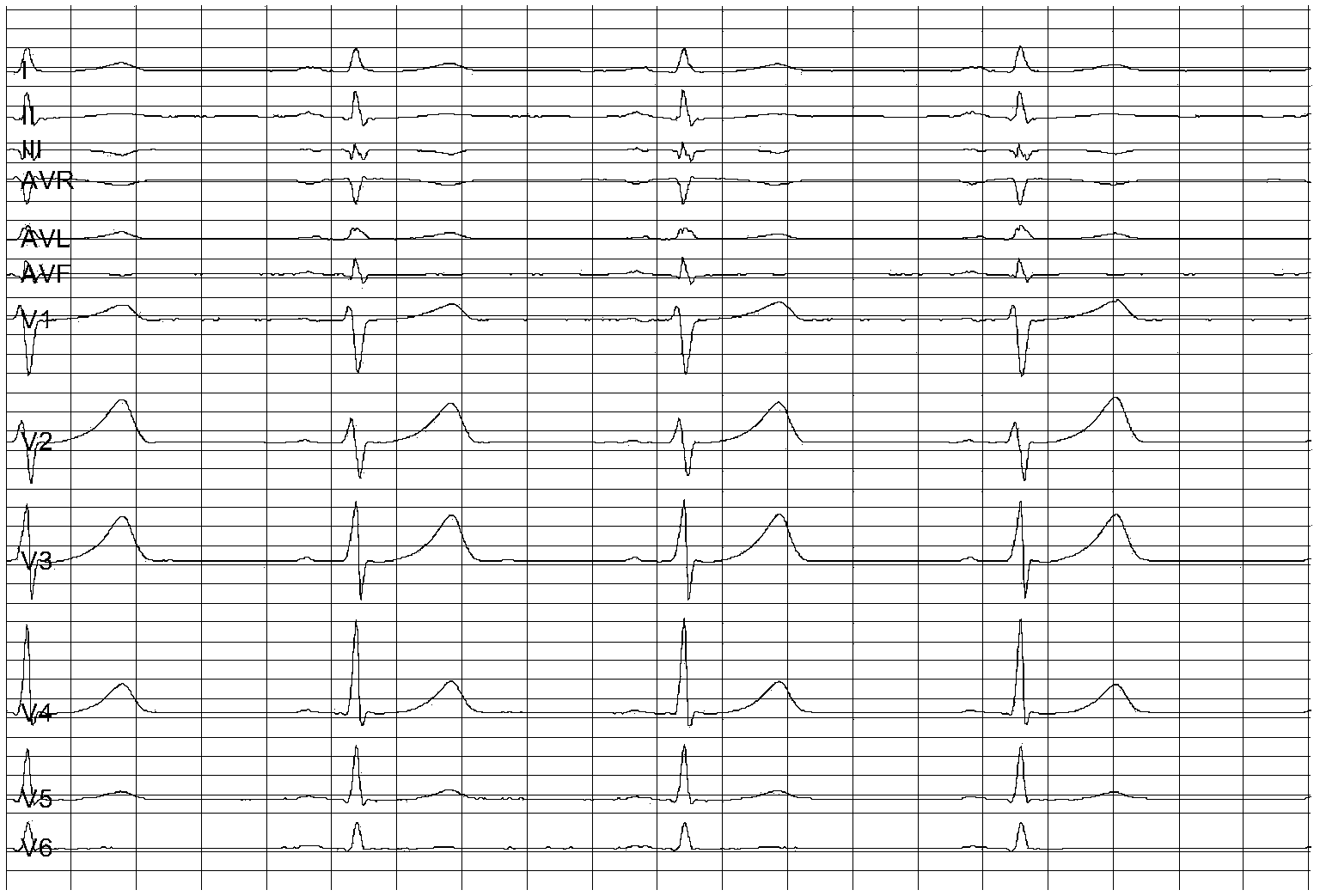
Myocardial ischemia auxiliary detecting method based on deterministic learning theory
ActiveCN103549949ASensitive detection effectIntuitive test resultsDiagnostic recording/measuringSensorsHigh risk factorsCardiac muscle
The invention discloses a myocardial ischemia auxiliary detecting method based on a deterministic learning theory. The method includes the following steps that data is pre-processed to obtain electrocardiogram ST-T loop data; a deterministic learning algorithm is adopted to conduct local correct modeling on inner system dynamics of an ST-T loop, modeled system dynamics are displayed in a three-dimensional visualization mode to obtain CDVG; according to a CDVG form, and by combining high risk factors and clinic information, auxiliary detecting results are obtained. The method is characterized in that the CDVG is obtained and analyzed based on the deterministic learning algorithm. The method is applicable to myocardial ischemia detecting when an electrocardiogram is not obviously changed, can prompt cardiovascular diseases effectively, can be used for conducting evaluation of a cardiovascular disease treatment effect and has the advantages of being simple in detecting process, economical and noninvasive and reducing burdens of patients and the like.
Owner:SOUTH CHINA UNIV OF TECH
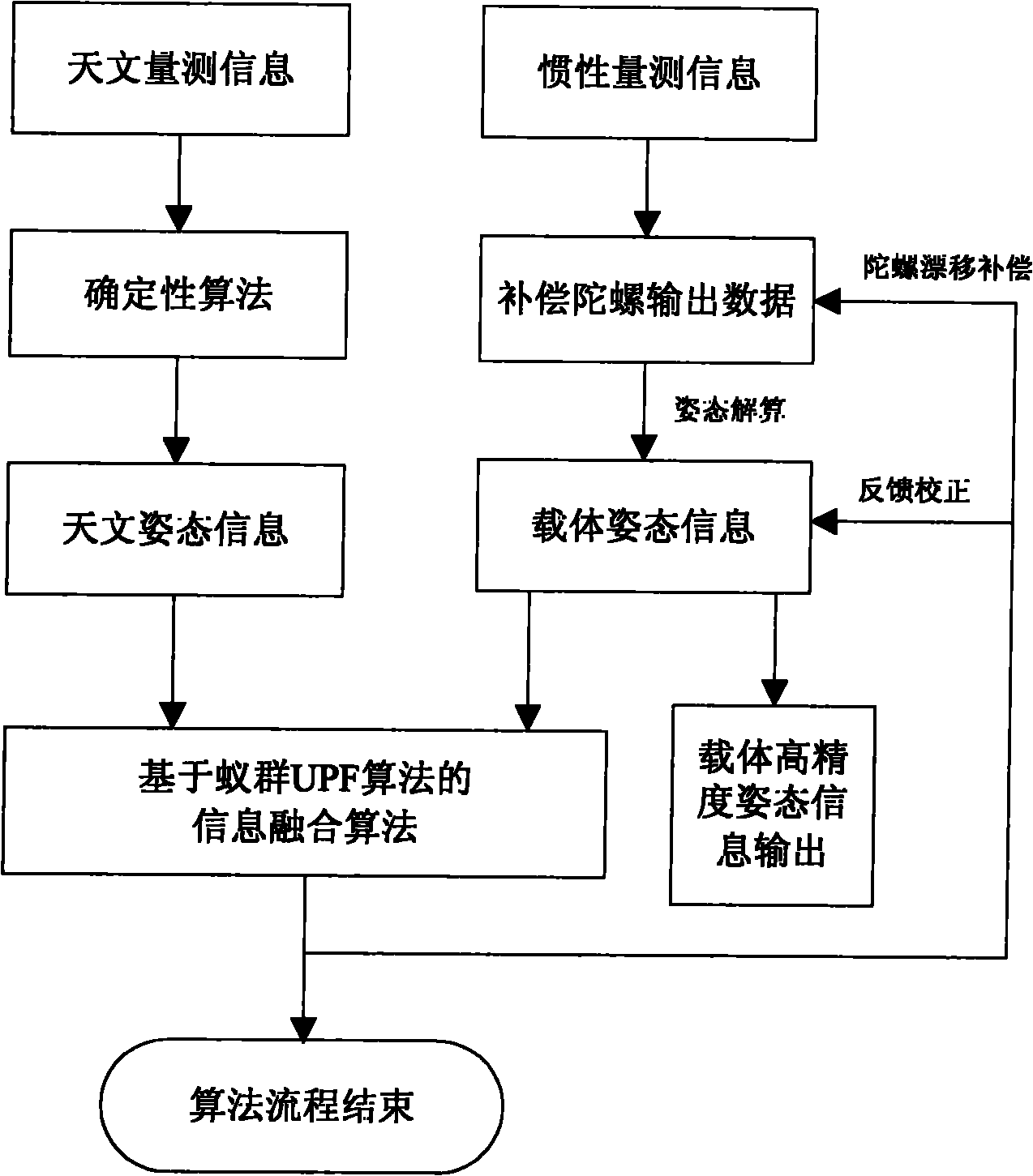
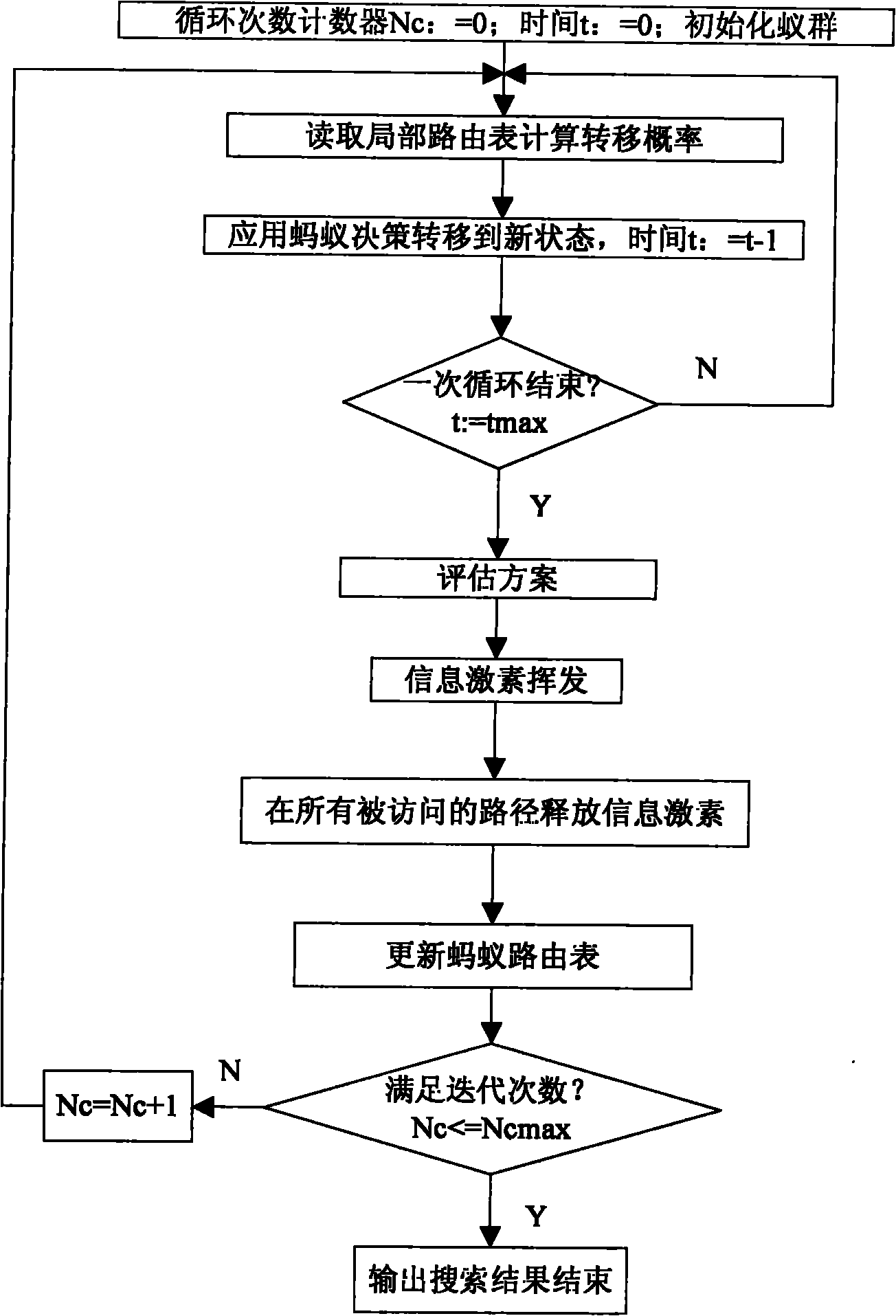
Integrated attitude determination method based on ant colony unscented particle filter algorithm
ActiveCN102156478ASolve the degradation problemAvoid missingAttitude controlParticle filtering algorithmDeterministic algorithm
The invention discloses an integrated attitude determination method based on an ant colony unscented particle filter algorithm, which relates to an inertial / astronomical integrated attitude determination method. The method comprises the following steps of: compensating gyro output data by using inertial measurement information and acquiring carrier attitude information through attitude calculation; acquiring required astronomical attitude information by using astronomical measurement information through a deterministic algorithm; fusing the astronomical attitude information with the carrier attitude information by using an ant colony unscented particle filter algorithm, solving nonlinear and noise non-Gaussian problems of a system, solving high-accuracy carrier attitude information, estimating gyro drift, and feeding back and correcting carrier attitude and compensating the gyro drift; and finally realizing on-line correction of eliminating random errors of a gyro of an inertial / astronomical integrated navigation system in real time based on the astronomical measurement information, and finishing long-term and high-accuracy combined attitude determination of a spacecraft.
Owner:BEIHANG UNIV
System and method for enhanced point-to-point direction finding
A system, device and method that enables units to communicate with each other and point to each other's location without requiring line-of-sight to satellites or any other infrastructure. Further, the system, device and method are able to operate outdoors as well as indoors and overcome multipath interference in a deterministic algorithm, while providing bearings at three dimensions, not only location but actual direction.
Owner:ISEELOC INC
Vision system with deterministic low-latency communication
Vision system and method. The system includes a vision system, including: a camera, a processor and memory, coupled to the camera, and an EtherCAT interface, coupled to the processor and memory, possibly contained in a chassis, and operable to couple to an EtherCAT network that provides for deterministic low-latency communication between the vision system and devices coupled to the EtherCAT network. The vision system may be configurable to operate as any of: an EtherCAT master device, an EtherCAT slave device, or a TCP / IP Ethernet device. One or more additional vision systems may couple to the EtherCAT network. The vision systems may be synchronized using an EtherCAT distributed clock technique, time-based triggered, and / or event triggered, via the EtherCAT network, e.g., in a multi-view vision, collaborative processing, control, I / O, or video servoing application, e.g., using an EtherCAT deterministic low latency closed loop feedback system, including processing, control, or I / O devices.
Owner:NATIONAL INSTRUMENTS
New method and system for determining characteristic curve of water pump in pump station
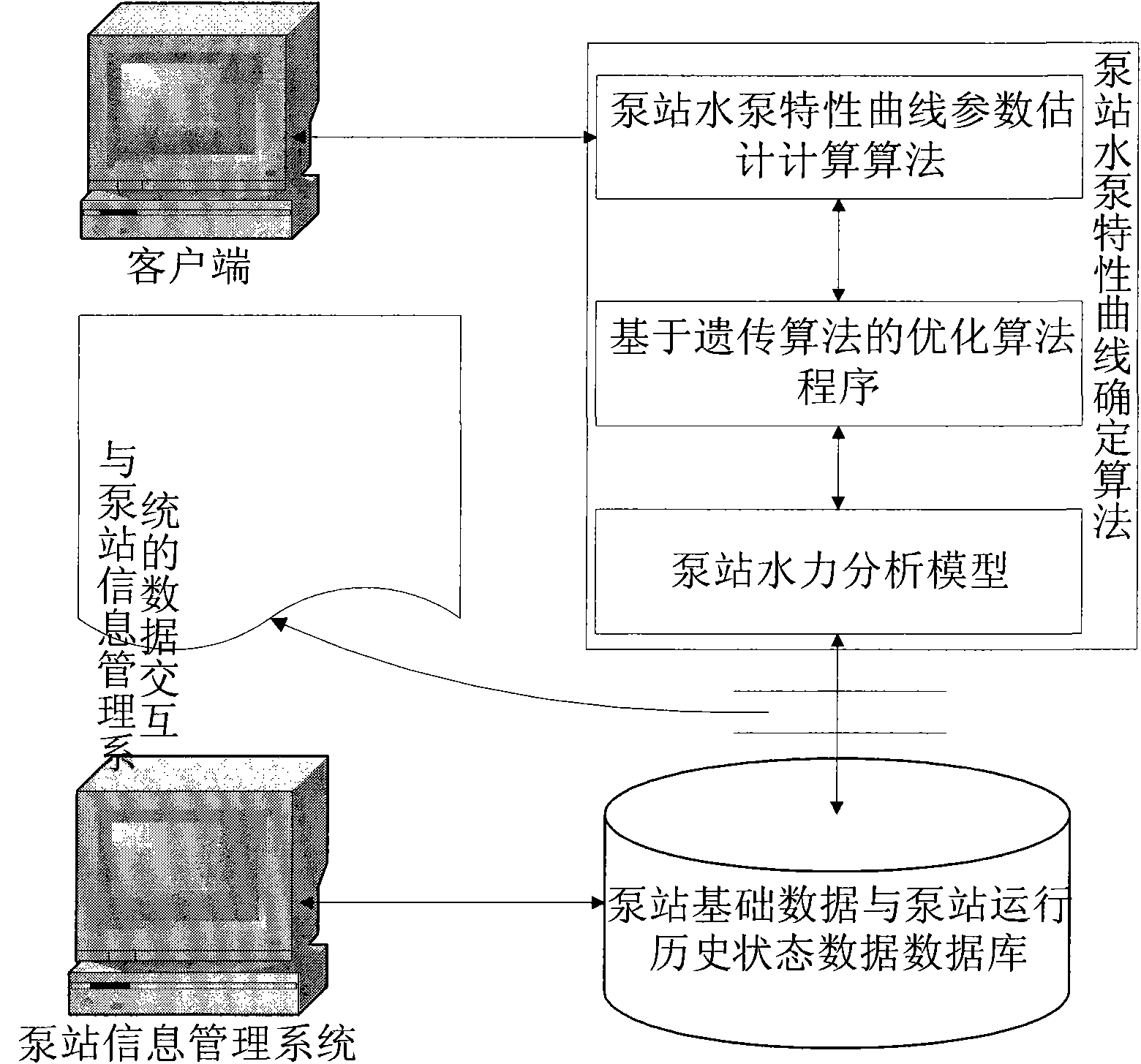
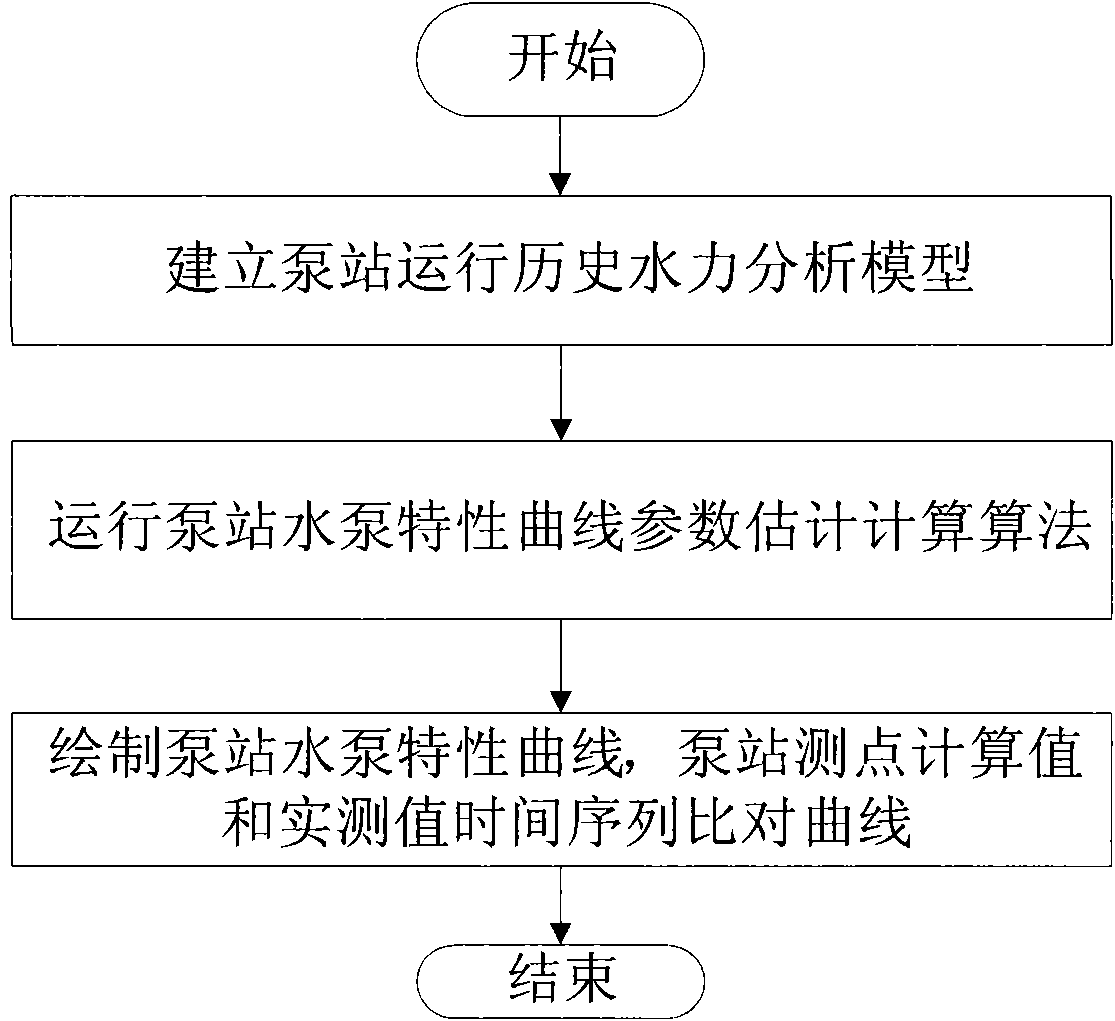
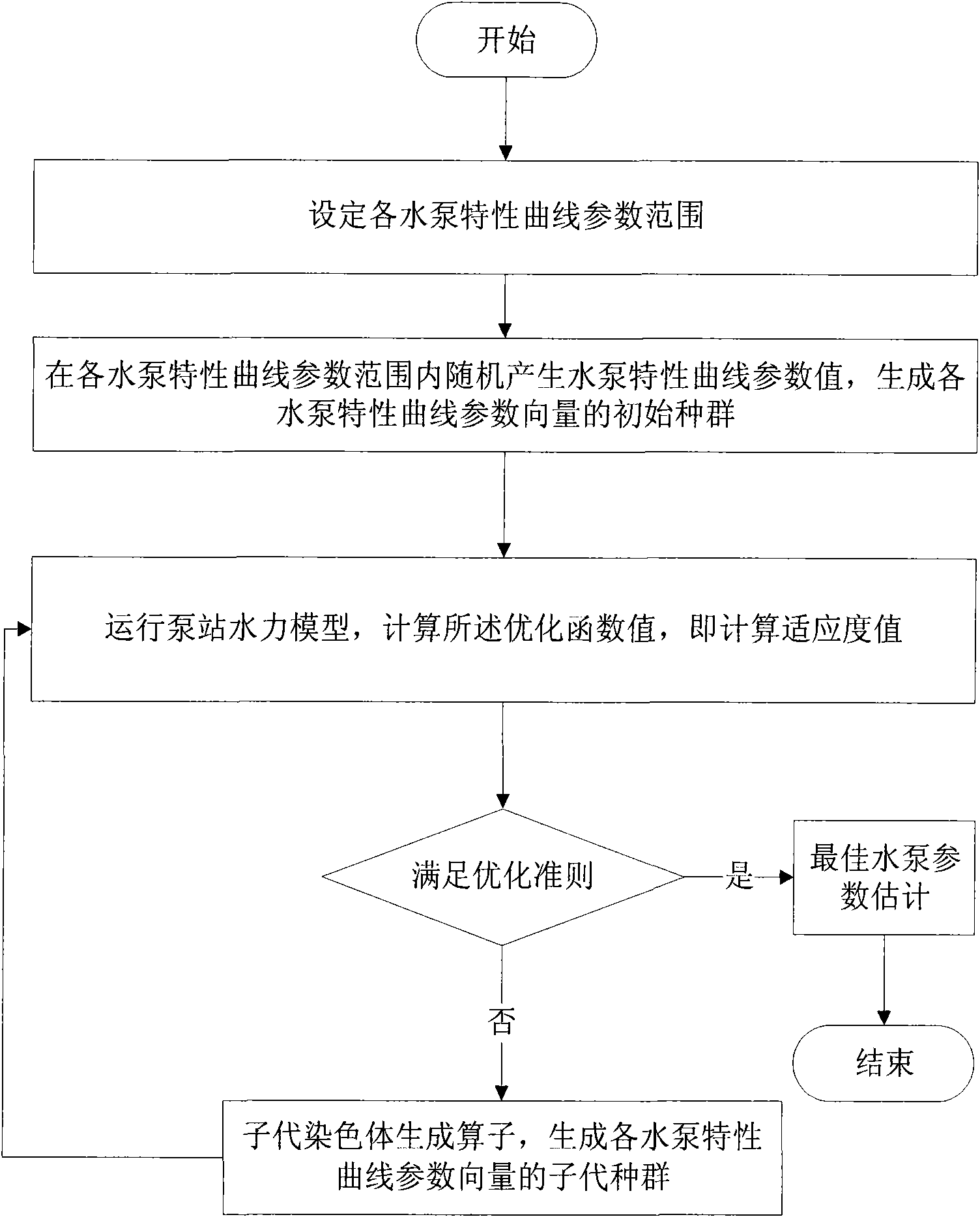
InactiveCN101871448AAvoid shock loadsReduce test costsPump testingPositive-displacement liquid enginesDaily operationGenetic algorithm
The invention discloses a method and a system for determining a characteristic curve of a water pump in a pump station, and belongs to the field of estimation and measurement of parameters of equipment of a water supply pipe network. The system comprises each pump station basic data database, a pump station historical operating state data database, a pump station water pump characteristic curve deterministic algorithm and a GUI interface, wherein each pump station basic data database and the pump station historical operating state data database are collocated in a pump station management information system and based on GIS or CAD; the pump station water pump characteristic curve deterministic algorithm comprises at least a GIS-based or CAD-based pump station hydraulic analysis model, a genetic algorithm-based optimal algorithm routine and a pump station water pump characteristic curve estimation algorithm; and the GUI interface is allocated at a client. In the method, the characteristic curve of each water pump in the pump station is determined according to the historical operating data of the pump station by using the pump station water pump characteristic curve deterministicalgorithm. Due to the adoption of the method and the system, the characteristic curve of the water pump can be determined by only collecting and using the historical daily operation data of the pump station and each pump in the pump station does not need to be specially tested, so the testing cost of the water pump is saved and the damage to the equipment of the pump station and the influence on the water consumers are reduced.
Owner:TONGJI UNIV
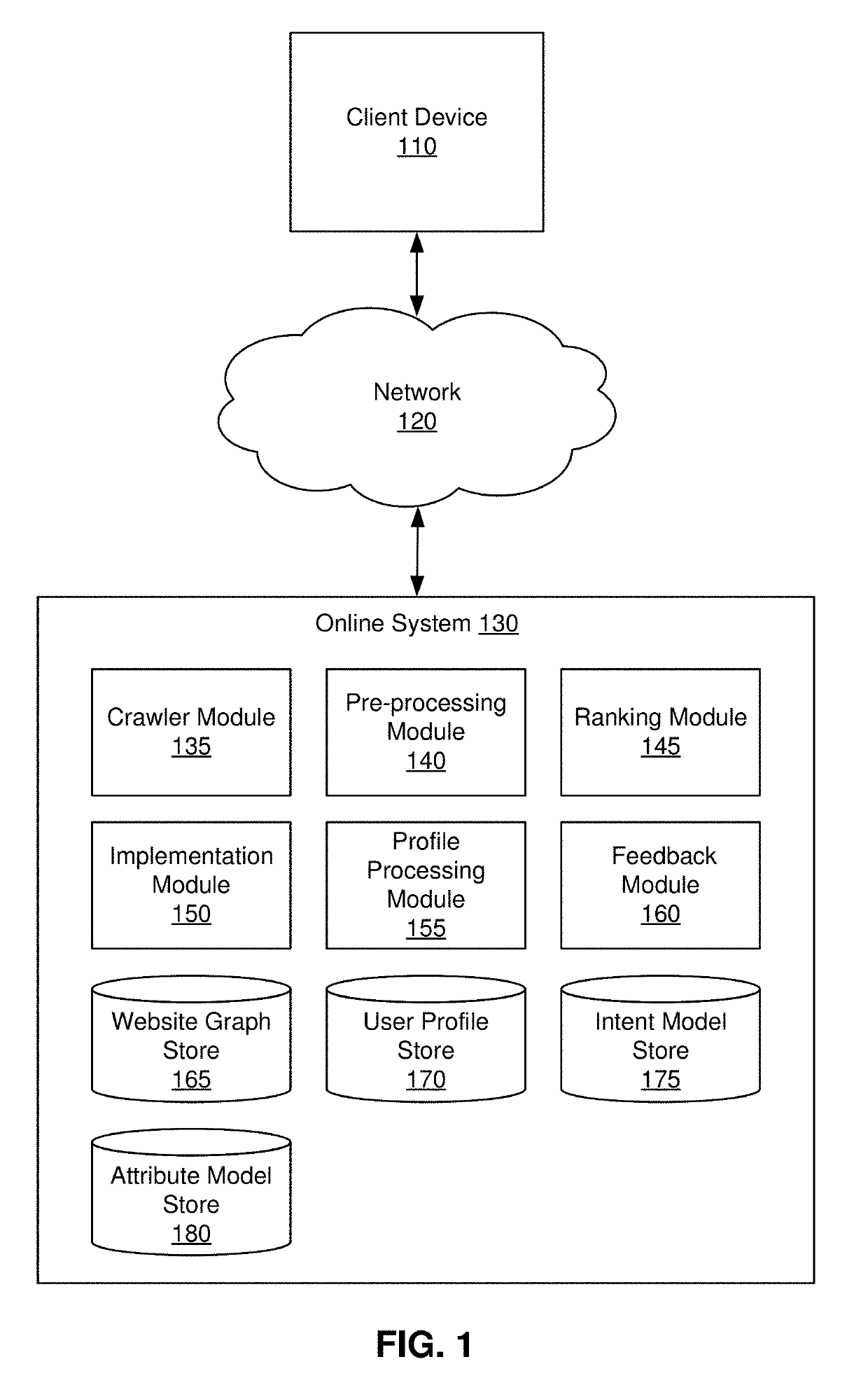
Dynamic website content optimization
PendingUS20190228105A1Improve efficiencyImprove usabilityWeb data indexingNatural language data processingRelational graphHide markov model
A system presents content to a website user based on a predicted future intent of the user. Hidden Markov models (HMMs) are developed based on a hierarchical and relational graph of a website. Given a sequence of observed actions performed by a user on the website, a HMM can be used to predict a likely intent the user has most recently acted on. Using a deterministic algorithm or a Monte Carlo Tree Search algorithm, the system can then predict likelihoods that each possible user intent associated with the website is a future intent of the particular user. Website content and formatting can be adjusted based on predictions about a user's future intents.
Owner:ZETA GLOBAL CORP
Method for extracting induced polarization model parameters prospected by electrical method
InactiveCN101706587AFast extractionEasy extractionElectric/magnetic detectionComplex mathematical operationsElectromagnetic couplingRelative phase
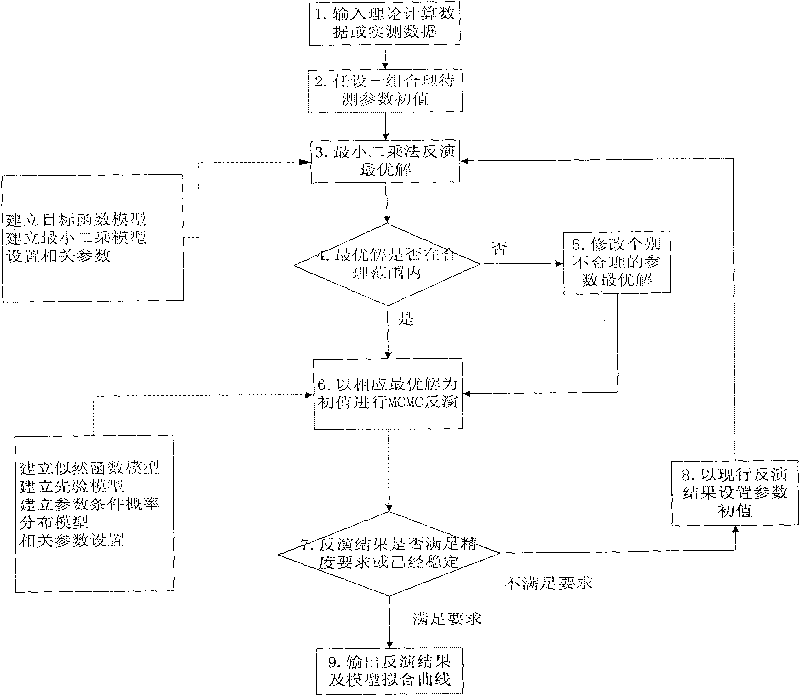
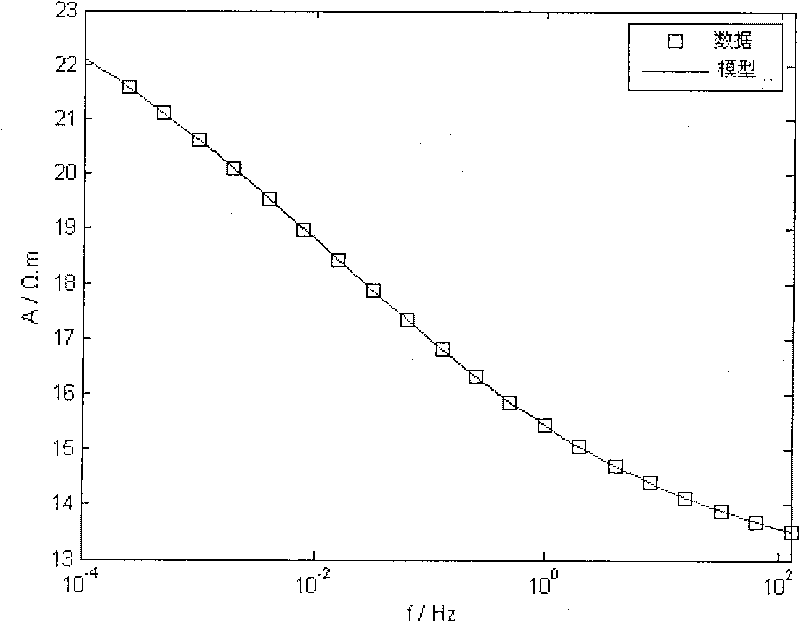
The invention relates to a method for extracting induced polarization model parameters prospected by electrical methods. The method adopts relative phase spectrum and amplitude spectrum to extract four parameters of a Cole-Cole model. With the effective restriction of the relative phase spectrum to electromagnetic coupling effect, only four parameters of a single Cole-Cole model are needed to be extracted; the extraction method is a combined extraction method which combines the MCMC method in random statistical algorithm with the least square method in deterministic algorithm, and the method has high extraction speed and high extraction accuracy, thus effectively enhancing the work efficiency of induced polarization model parameters, reducing extraction time and effectively restricting interference of electromagnetic effects.
Owner:CENT SOUTH UNIV
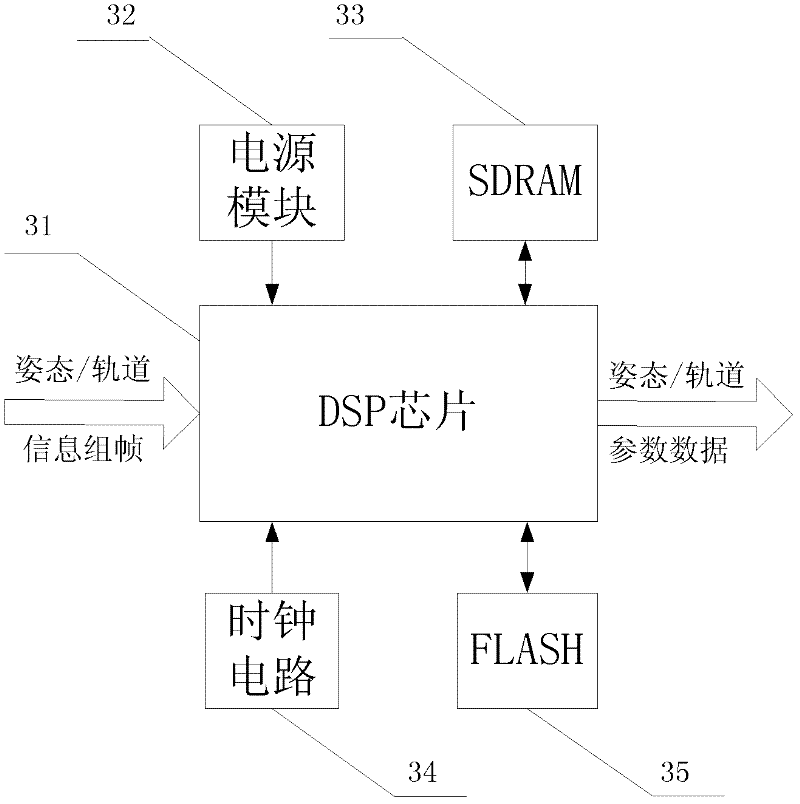
High-precision posture/track integrated measurement device
ActiveCN102494687AMeet information needsSmall footprintInstruments for comonautical navigationGyroscopeMeasurement device
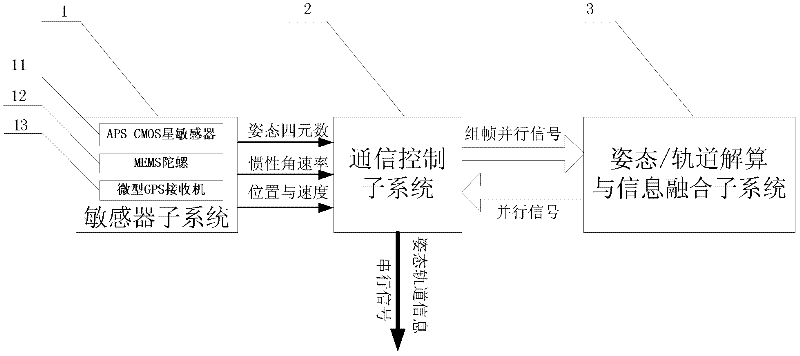
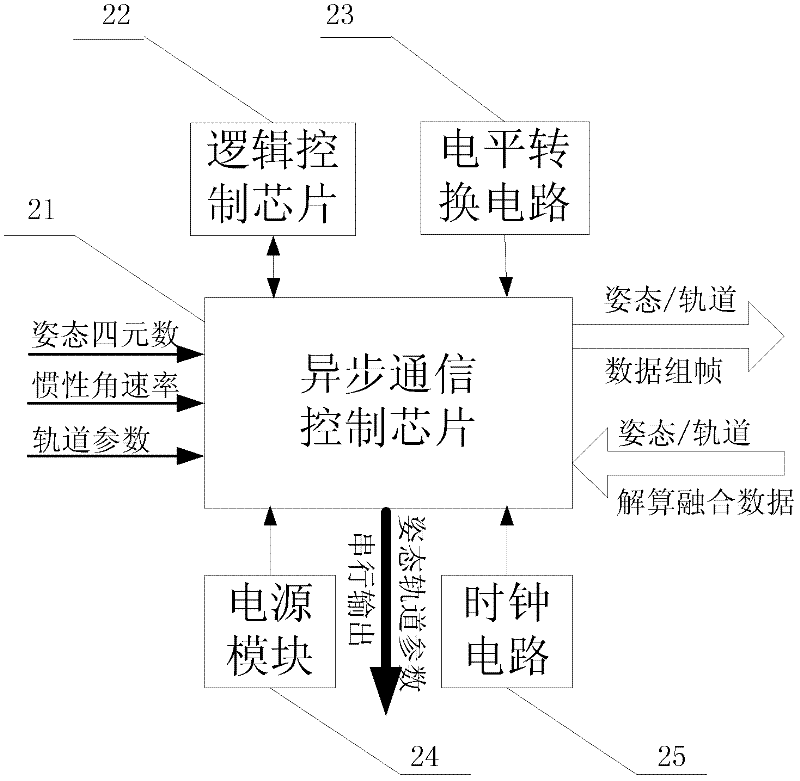
The invention relates to a high-precision posture / track integrated measurement device, which is composed of a sensor sub-system, a communication control sub-system and a posture / track resolving and information fusion sub-system; the sensor sub-system is composed of APSCMOS star sensors, an MEMS (Micro Electro Mechanical System) gyroscope and a miniature GPS (Global Position System) receiver; the three sensors are used for respectively providing measured digital signals of posture quaternion, inertia angular rate, position and speed, and then inputting the digital signals to the communication control sub-system in a serial manner; the communication control sub-system is used for framing the received serial digital signals into parallel signals, and outputting the parallel signals to the posture / track resolving and information fusion sub-system to be subjected to a UDEKF-based track deterministic algorithm and an SRSSUKF-based posture deterministic algorithm; and complete posture / track measurement information can be obtained by comprehensively calculating through a posture / track information optimization and fusion method and used by a spacecraft. The high-precision posture / track integrated measurement device disclosed by the invention is small in volume, light in weight, low in power consumption and low in cost and is applied to high-precision posture / track measurement of a tinyspacecraft.
Owner:TSINGHUA UNIV
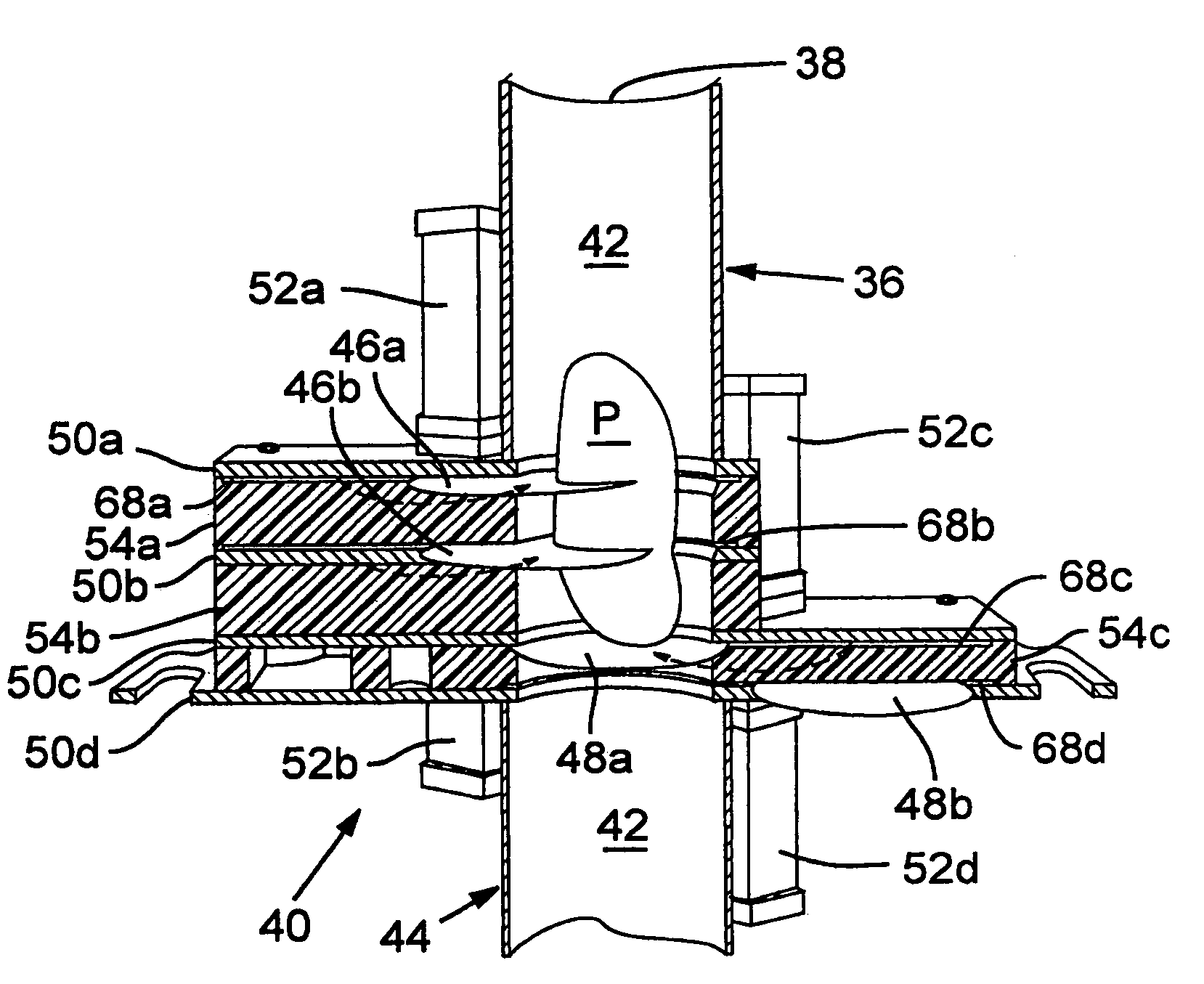
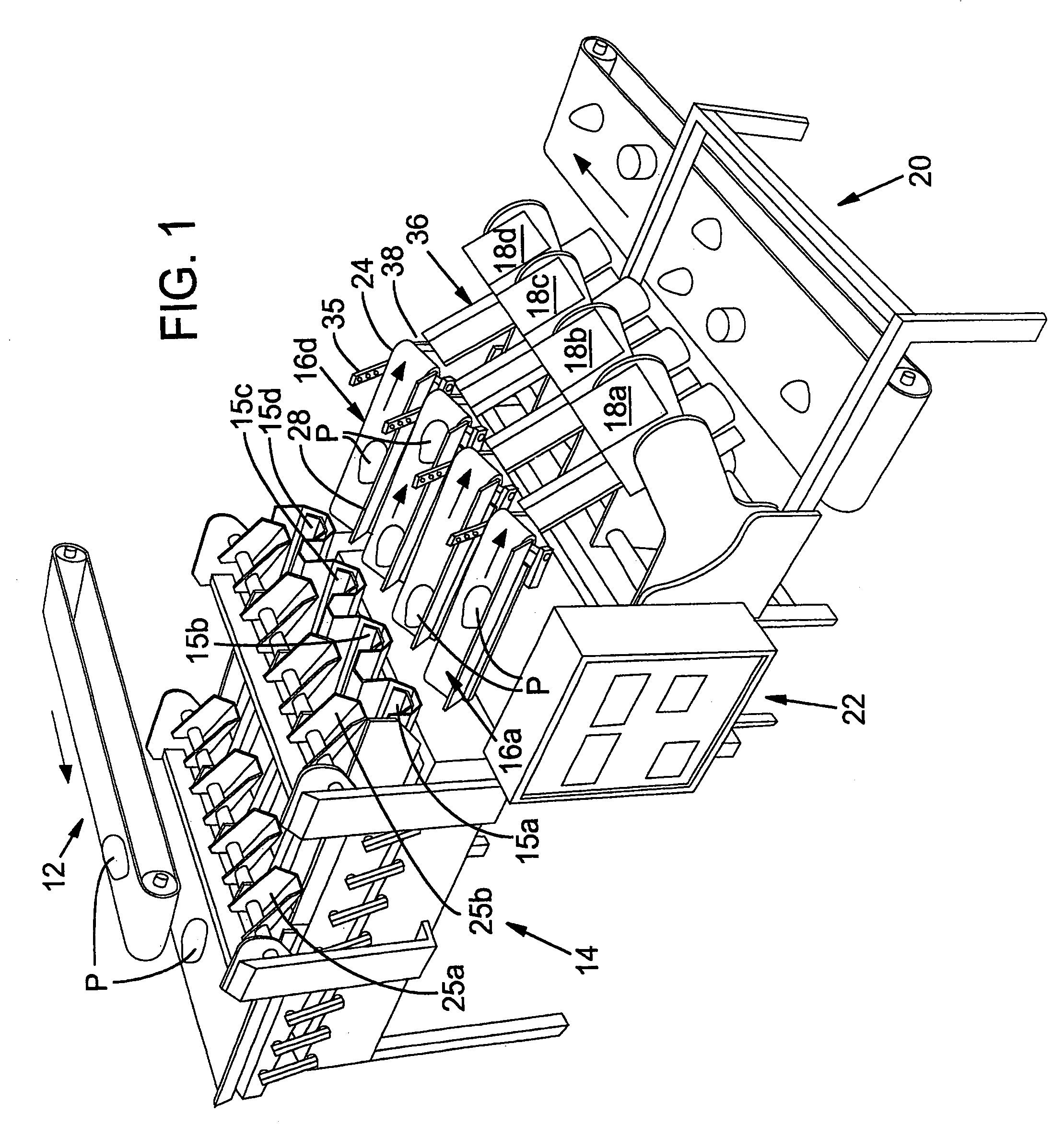
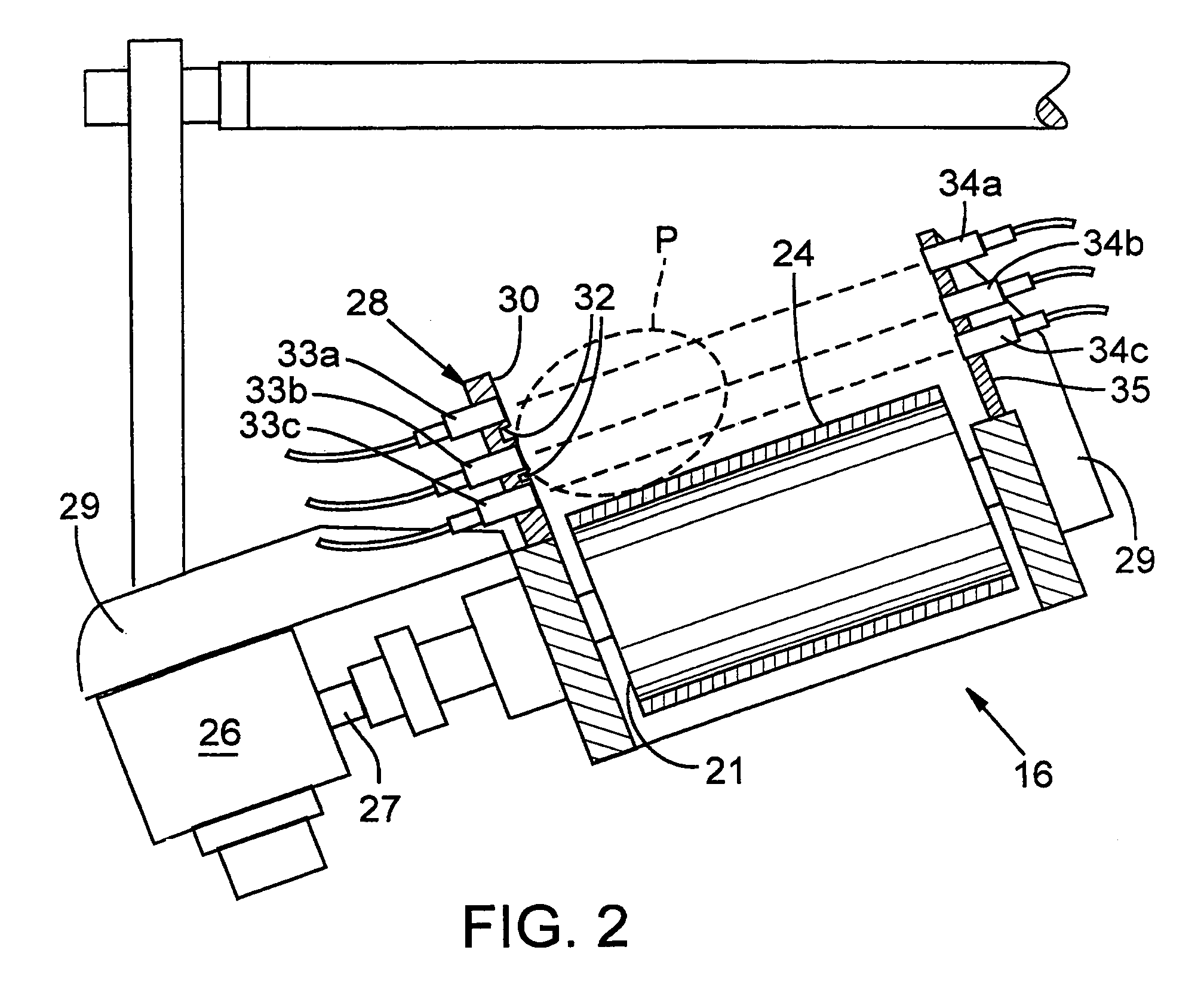
Proportional length food slicing system
ActiveUS7430947B2Juice extractionSteering linkagesProgrammable logic controllerDeterministic algorithm
This invention includes a system for cutting food products, such as potatoes, into proportional length pieces. In a one embodiment, the system includes a cutting assembly, sensors upstream of the cutting assembly and a programmable logic controller. The cutting assembly preferably includes a housing defining a passageway, at least two separately actuatable stops extendable into the passageway to provide an abutment to hold the food product in place, and at least two separately actuatable blades for slicing the food product into pieces. The controller cooperates with the sensors to determine the length of each food product and, based on a length determinative algorithm, selectively actuate one of the stops and at least one of the blades to determine how many times the food product will be sliced and location of the cut(s) relative to the leading end of the food product.
Owner:LAMB WESTON INC
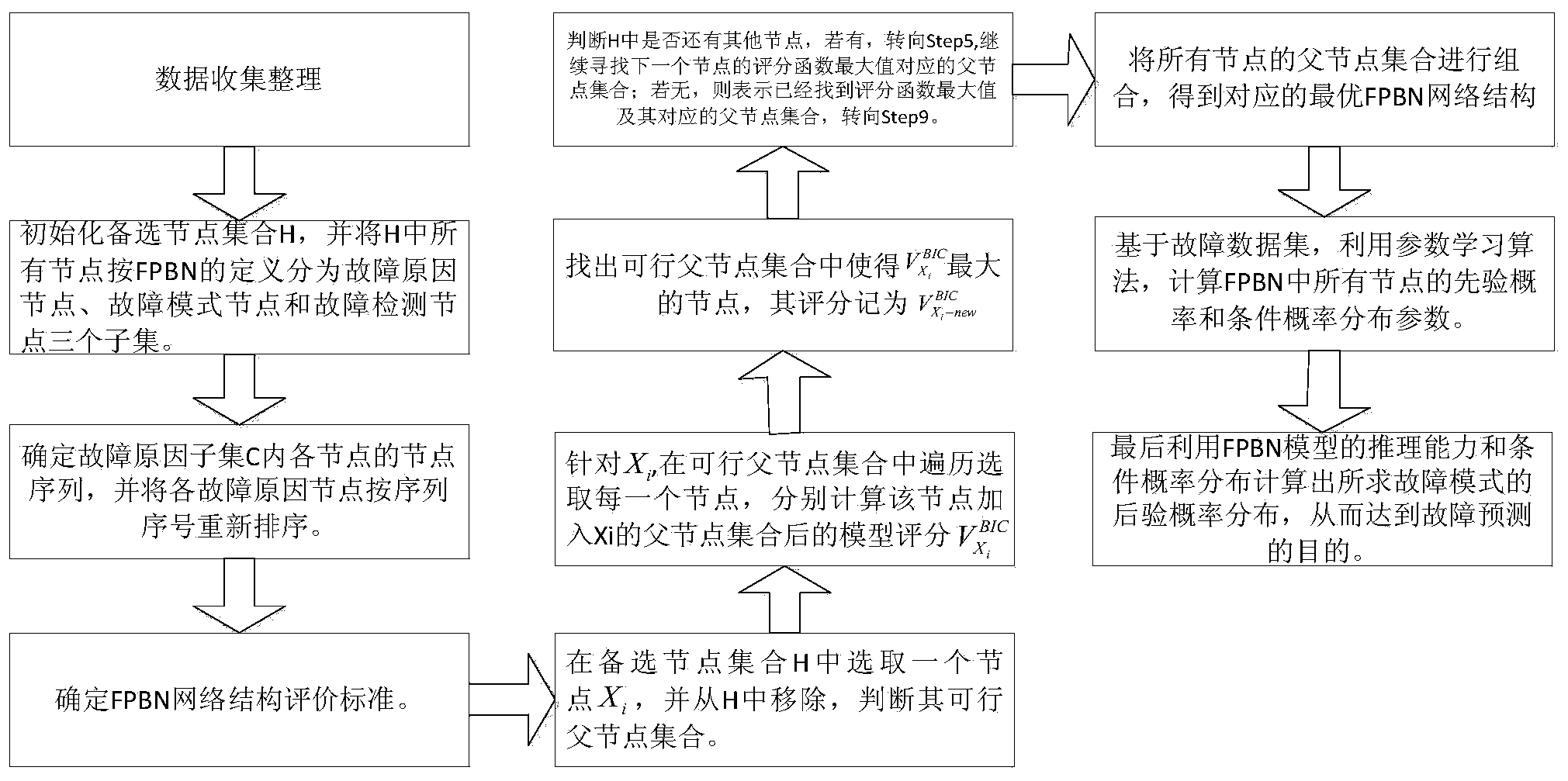
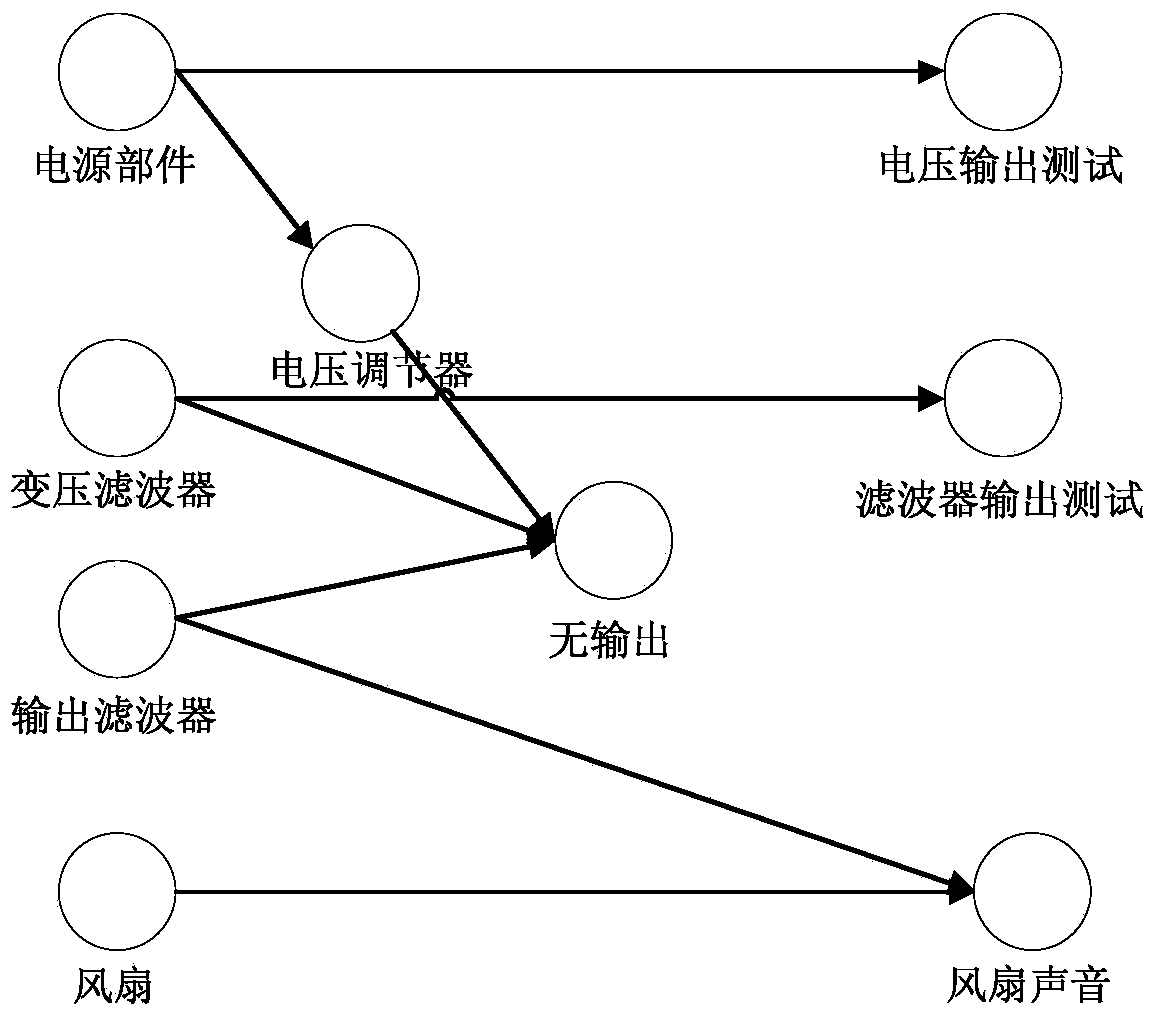
Equipment failure Bayesian network prediction method based on K2 algorithm
ActiveCN104217251AImprove search efficiencyReduce the number of calculationsForecastingData setDeterministic algorithm
The invention discloses an equipment failure Bayesian network prediction method based on a K2 algorithm, and is used for solving the technical problem of low searching efficiency of a conventional equipment failure Bayesian network prediction method. The equipment failure Bayesian network prediction method has the technical scheme that an FPBN (Failure Prediction Bayesian Network) structure learning algorithm based on a K2 searching algorithm is adopted for building an FPBN structure capable of really reflecting each variable incidence relation in a failure data set, so that an FPBN model is built. Finally, the actual operation state of equipment is predicted by uitlizing a parameter learning algorithm on the basis of a built failure prediction model. The method uses the K2 searching algorithm as the basis; the failure knowledge, the expertise and the failure data are effectively fused; and the problem of modeling difficulty in system to FPBN conversion in the equipment prediction process is solved. In addition, the FPBN-K2 algorithm calculation process totally adopts deterministic searching algorithms, and repeated searching for many times is not needed; the searching space is reduced; the number of scoring function calculation times is reduced; and the searching efficiency of the FPBN structure learning algorithm is improved.
Owner:DONGGUAN PANRUI ELECTROMECHANICAL TECH CO LTD
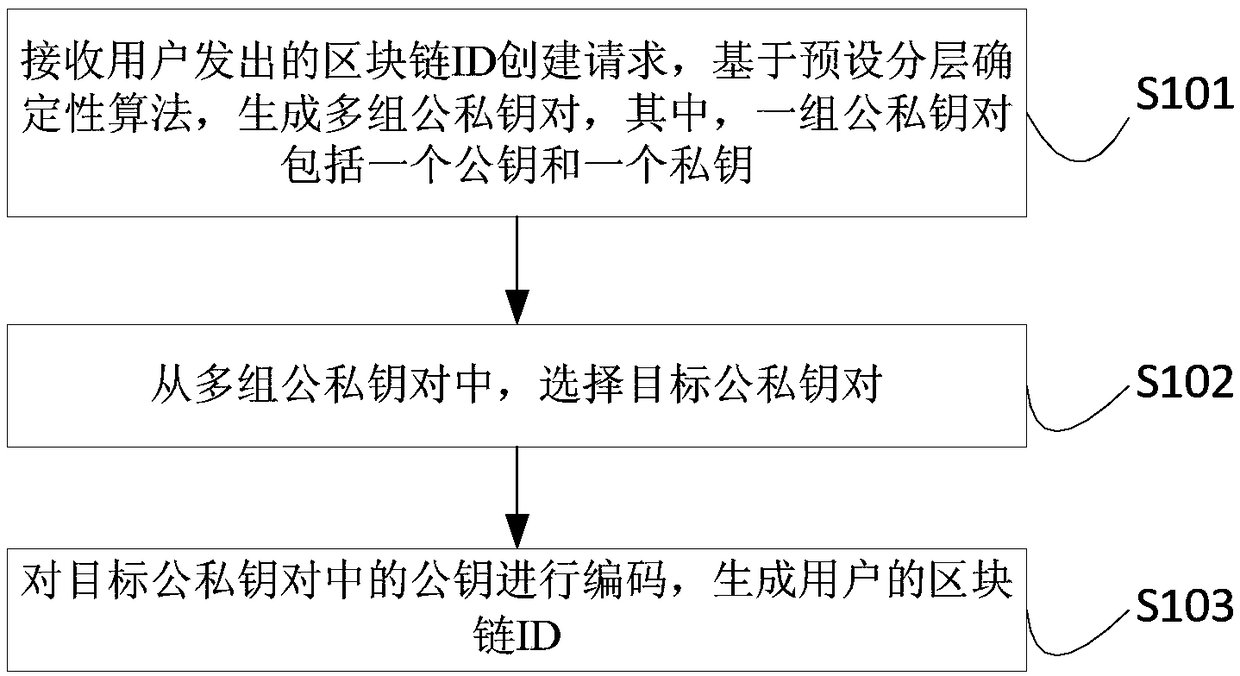
Blockchain ID generation method, blockchain ID generation apparatus, blockchain ID usage method, blockchain ID usage apparatus, electronic device and storage medium
ActiveCN109347632AKey distribution for secure communicationPublic key for secure communicationDeterministic algorithmBlockchain
The embodiment of the invention provides a blockchain ID generation method, a blockchain ID generation apparatus, a blockchain ID usage method, a blockchain ID usage apparatus, an electronic device and a storage medium. The blockchain ID generation method comprises the following steps: receiving a blockchain ID creation request sent by a user, generating multiple groups of public and private key pairs based on a preset hierarchical deterministic algorithm, wherein one group of public and private key pairs comprises one public key and one private key; selecting a target public and private key pair from the multiple groups of public and private key pairs; and encoding the public key in the target public and private key pair, and generating a blockchain ID of the user. In the blockchain ID generation method, firstly, the multiple groups of public and private key pairs are generated based on the preset hierarchical deterministic algorithm, then, the target public and private key pair is selected out from the multiple groups of public and private key pairs, and finally, the blockchain ID of the user is generated by means of encoding the public key in the target public and private key pair, thereby, the blockchain ID is taken as an identifier of the user in the blockchain so as to represent the user.
Owner:KINGSOFT
PC protection by means of BIOS/(u)EFI expansions
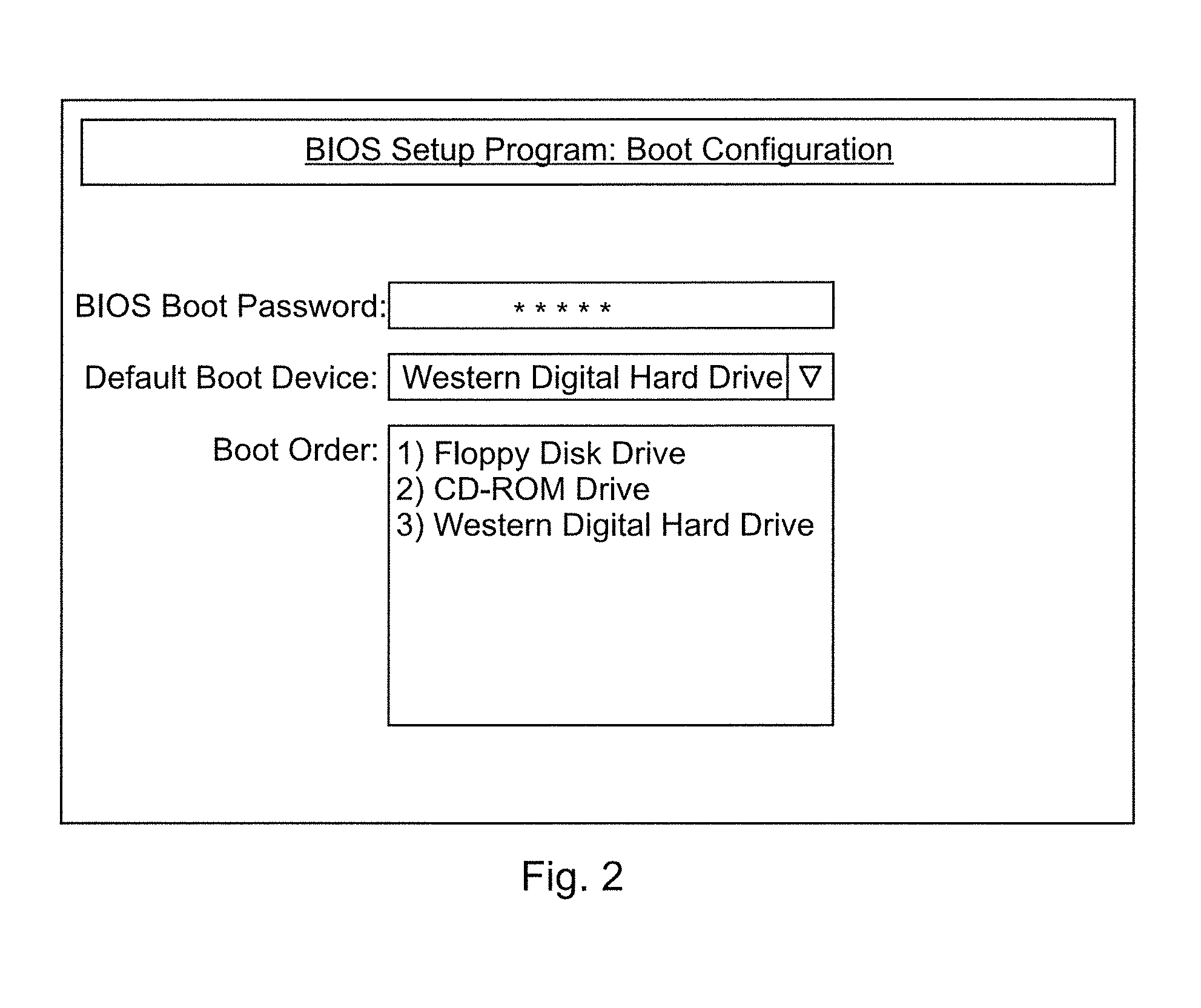
ActiveUS20150047022A1Difficult to separateEasy to readDigital data processing detailsUnauthorized memory use protectionPasswordDeterministic algorithm
A method is provided for controlling access to the BIOS / (U)EFI or for controlling sub-functions of the BIOS of a self-service machine. The password of the BIOS is calculated via a deterministic algorithm incorporating code-generating information that changes over time. The method includes displaying code-generating information that changes over time on a screen of the self-service machine during access to the BIOS of the self-service machine. The method proceeds by inputting the code-generating information in a program on a second computer that also has the deterministic algorithm for calculating the password for the BIOS, and calculating and displaying the password on the second computer. The method then includes inputting the password on the self-service machine and checking the password by the deterministic algorithm to allow access to the BIOS if the password is correct.
Owner:DIEBOLD NIXDORF SYST GMBH
An elastic guaranteed bottom network rack search modeling method based on 0-1 programming model
InactiveCN109638821AImprove search efficiencyImprove practicalityForecastingAc network circuit arrangementsRobustificationPower flow
The invention relates to the technical field of core backbone network search of a power system, and particularly relates to an elastic guaranteed bottom network rack search modeling method based on a0-1 programming model, and the specific steps include: S1: establishing an objective function of a sum of a line number and a subnet search weight as reference factors; S2: establishing an equality constraint of the optimization model, establishing a branch power constraint and a branch current constraint based on the power flow constraint; S3: establishing an inequality constraint of the optimization model, including a voltage constraint, a generator power limiting constraint and a line power limiting constraint; S4: solving the model, so that the length of the final scheme grid line is smalland the electrical interface index is large. The method can solve the problem of the uncertainty of the traditional intelligent algorithm result and the poor robustness of the algorithm, can obtain the guaranteed bottom network rack with the fewest lines, and can obtain the situation that the generator is put into operation. The method has high flexibility and strong scalability and effectively improves the efficiency and practicability of the guaranteed bottom net rack.
Owner:ELECTRIC POWER RES INST OF GUANGXI POWER GRID CO LTD
Identifying RFID categories
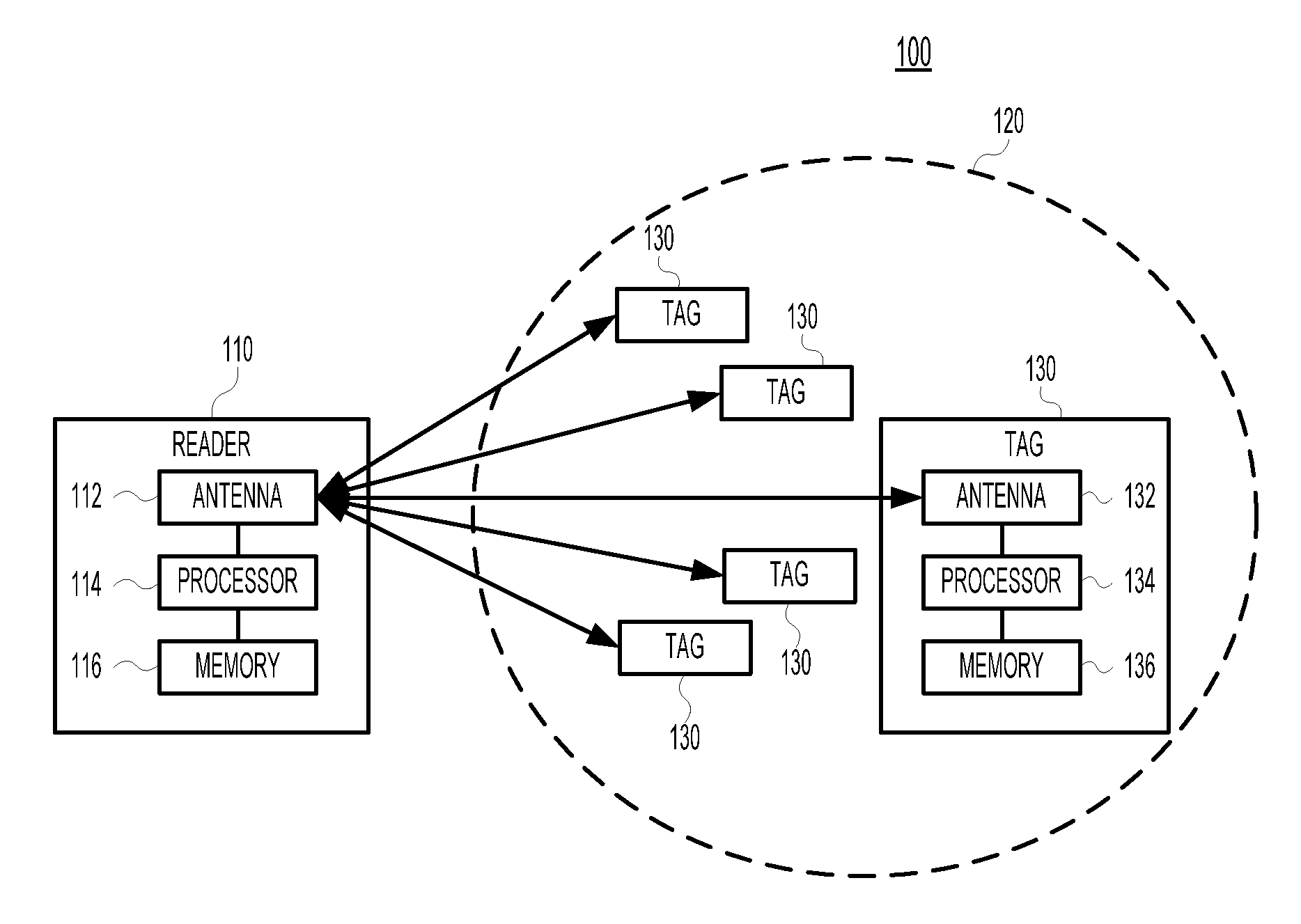
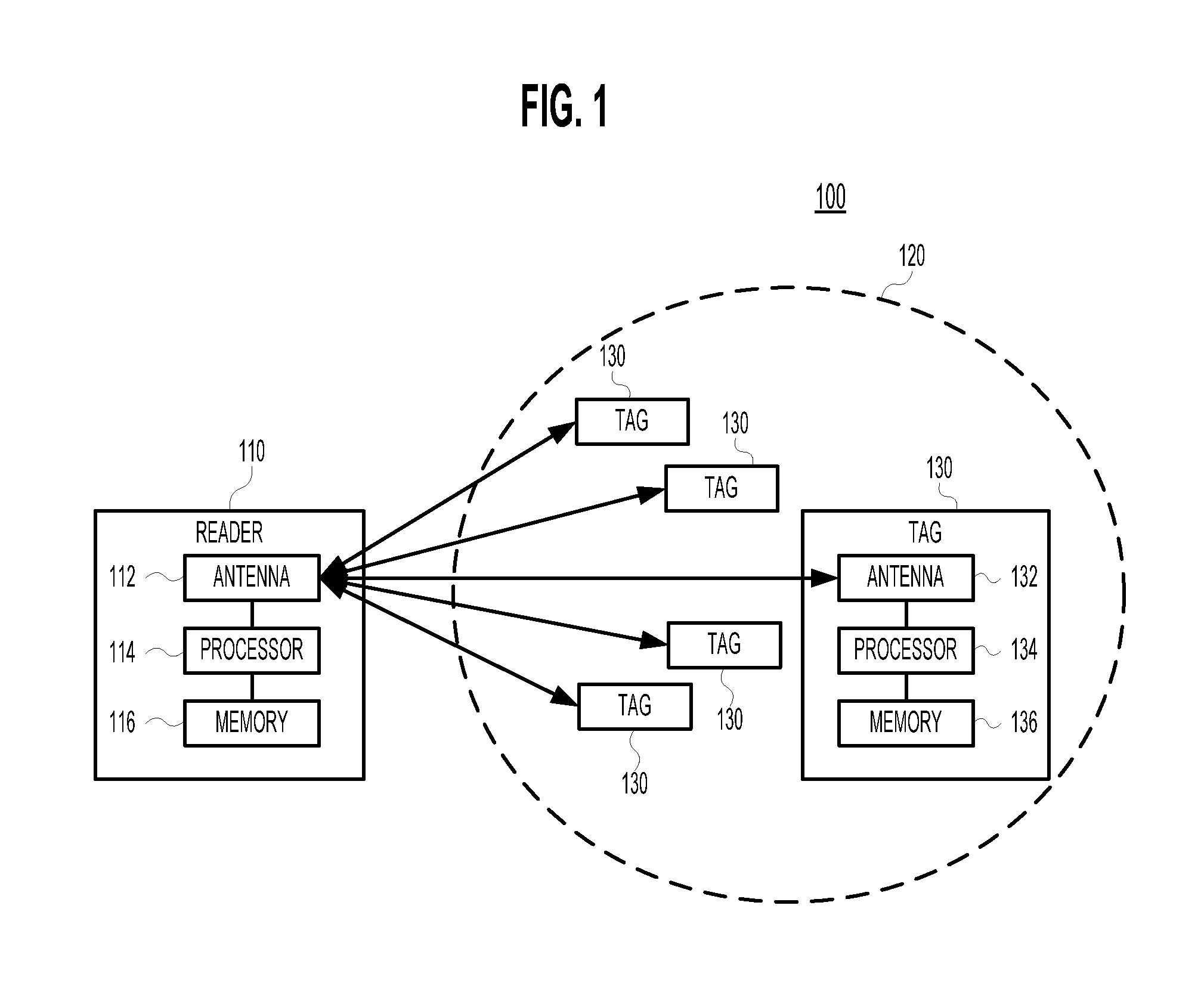
ActiveUS20100295659A1Memory record carrier reading problemsSubscribers indirect connectionTheoretical computer scienceDeterministic algorithm
The set T of all categories in a population of RFID tags is estimated within a specified error bound. For each of one or more frames, a reader broadcasts a probability p, a multiplicity d, a frame size M, and a seed value R to the present tags. A deterministic algorithm on each tag, and known to the reader, calculates (i) whether the tag will transmit in this frame, and, if so, (ii) in which slots the tag will transmit a single “1.” When the tags have responded, the reader calculates set T by initially assuming that all possible categories are in set T and then eliminating those categories that would have transmitted in those slots in which no tag transmitted. Alternatively, the reader initially assumes that set T is empty, and adds those categories that would have transmitted in those slots in which one or more tags did transmit.
Owner:ALCATEL LUCENT SAS
Internet Domain Name Super Variants
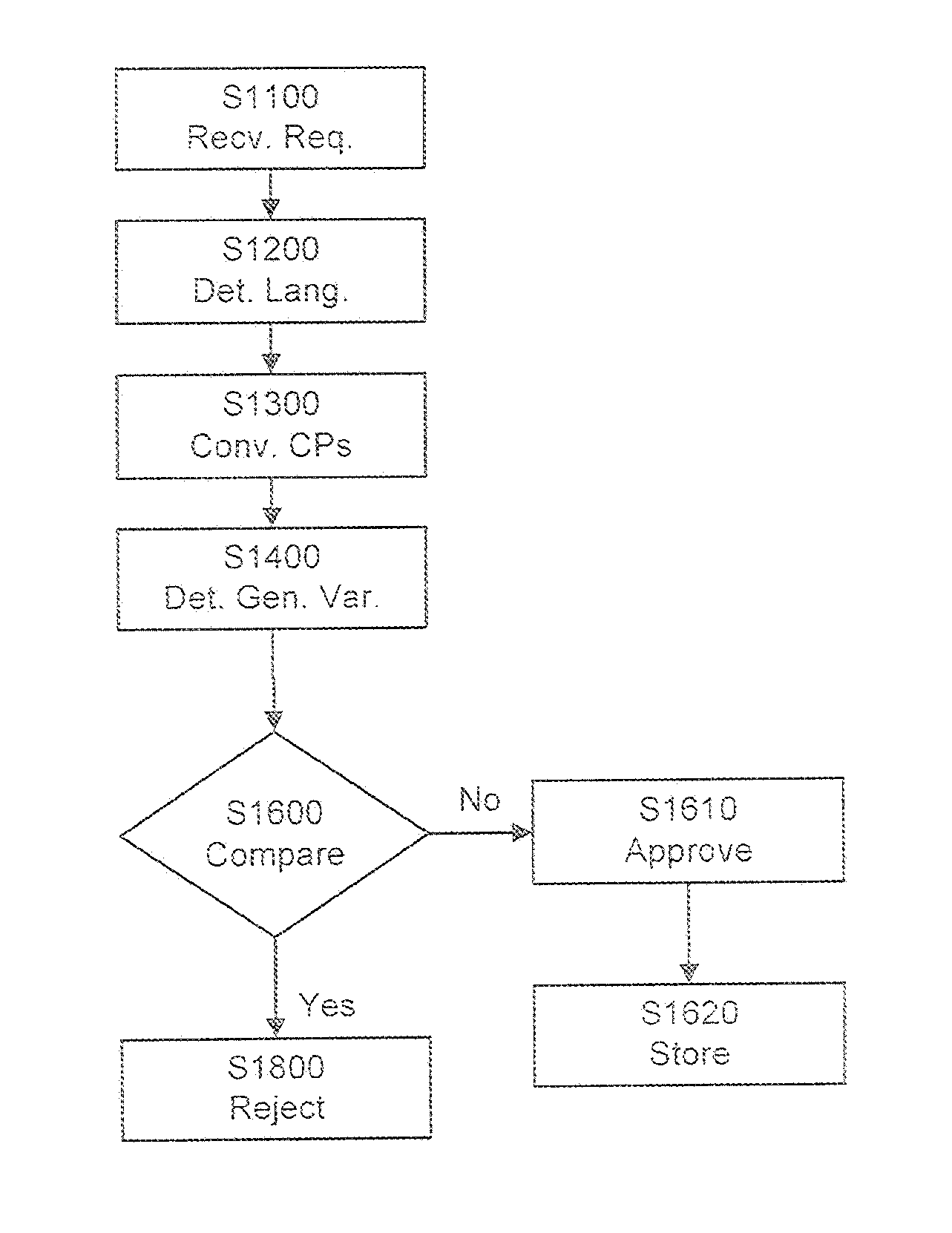
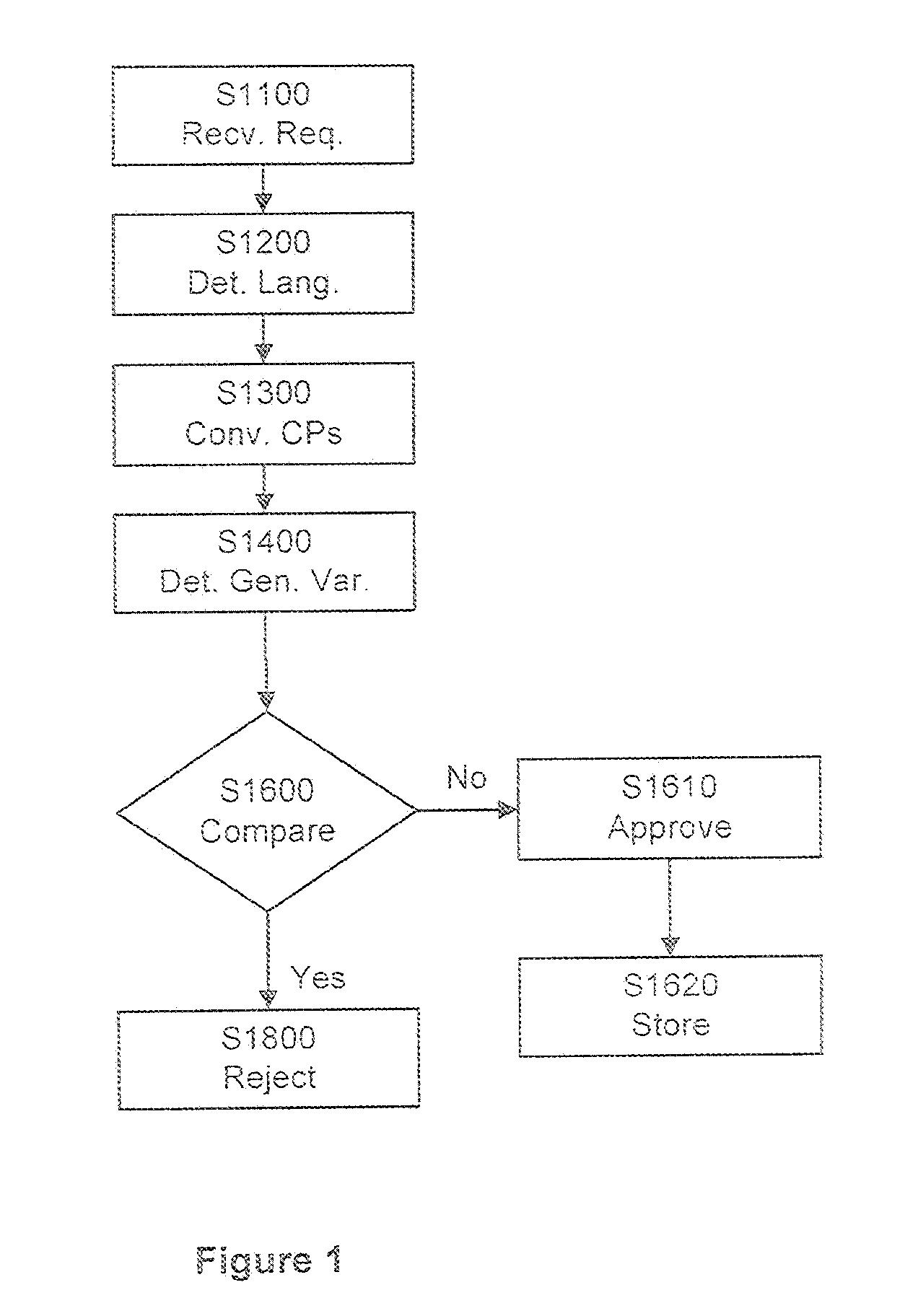
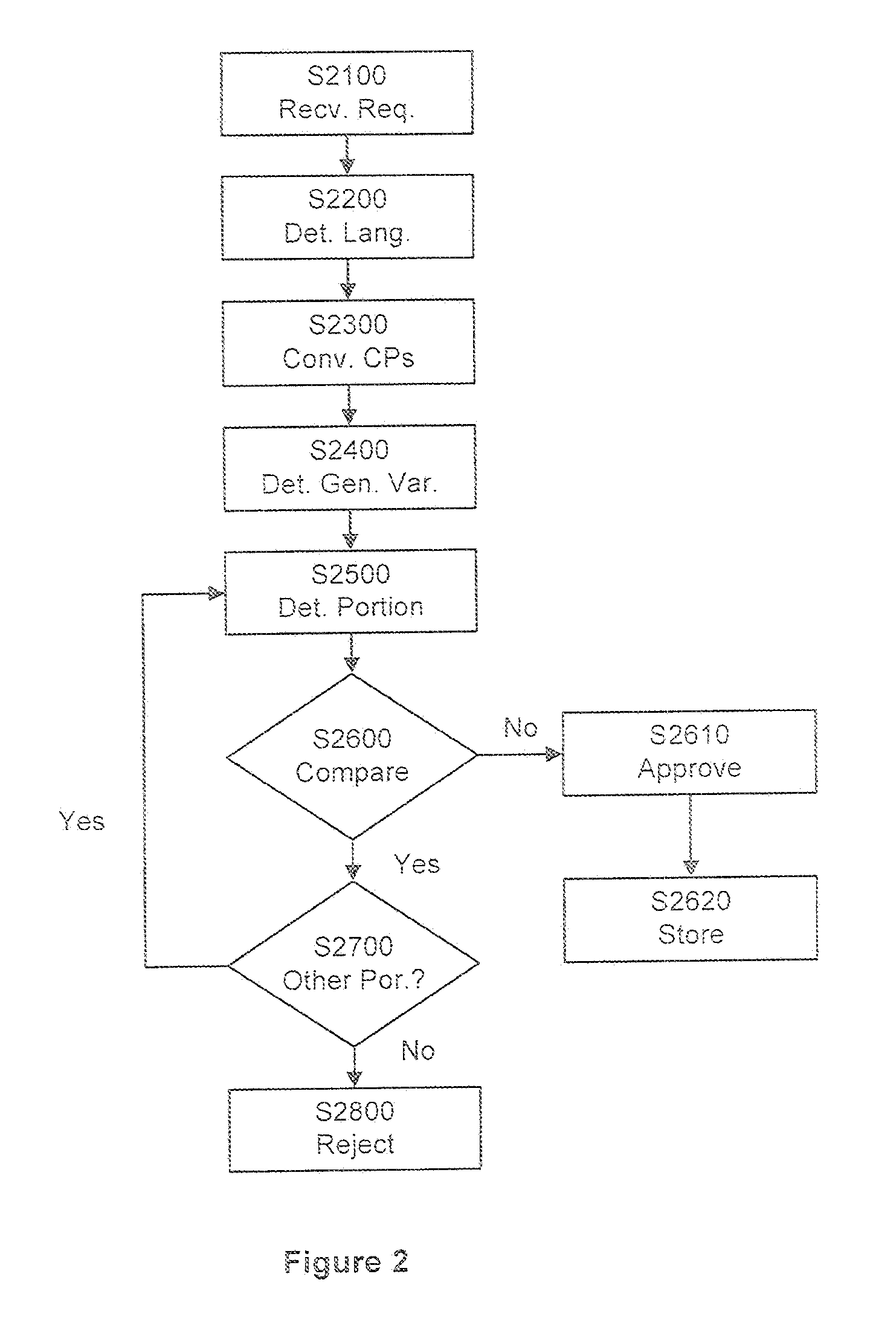
ActiveUS20110106924A1Convenient registrationSimple processNatural language data processingMultiple digital computer combinationsProgramming languageDomain name
Systems and methods for registering a domain, including Internationalized Domain Names (IDNs), including receiving a request to register an IDN and determining a language category of the request. Code points of the request are converted to yield a generalized variant of the IDN. The generalized variant is compared to a stored database of registered IDNs that may include similar generalized variants of the registered IDNs. Based on the comparison, it is determined whether or not to resister the IDN. In the case the that ION registration is allowed the generalized variant of the IDN may be stored in the database to protect against later registration by similar IDNs. Converting the code points of the request may include identifying corresponding code points of variants within the language category, and converting each of the code points of the requested IDN based on a deterministic algorithm applied to the corresponding code points. The deterministic algorithm may be applied to a value of each of the corresponding code points to yield a representative code point from among the corresponding code points, and the generalized variant may include a representative code point for each of the code points of the request.
Owner:VERISIGN
A traffic flow pattern recognition method based on density peak clustering algorithm
InactiveCN109255384AMeet real-time requirementsImprove service capabilitiesCharacter and pattern recognitionPattern recognitionCluster algorithm
The invention provides an elevator traffic pattern recognition method based on a density peak clustering algorithm. Firstly, the local density of each data point and the minimum distance from the datapoint with higher density are calculated. Then, a decision chart is drawn by the two methods, and the cluster center is selected manually. Finally, the remaining data points are categorized accordingto the category of higher density data points nearest to them. The algorithm has the following advantages: First, it inherits the advantages of density clustering algorithm, does not need to specifythe number of clusters and can cluster arbitrary shape data. Second, it can be adapted to different data sets with different densities in different clusters. Third, accommodate arbitrary metrics as distances. Fourth, the algorithm is deterministic algorithm, not iterative algorithm, and the computational load is small. Fifth, outliers and noise points can be excluded.
Owner:HUZHOU CITY SPECIAL EQUIP INSPECTION INST
Technique for solving np-hard problems using polynomial sequential time and polylogarithmic parallel time
InactiveUS20080235315A1Complex mathematical operationsKnowledge based modelsDeterministic algorithmEfficient algorithm
A system and technique, called Solution Enumeration technique, for finding efficient algorithms for NP-hard combinatorial problems is presented. The solution space of these problems grows exponentially with the problem size. Some examples in this class are: Hamiltonian Circuit, SAT, Graph Isomorphism, and Perfect Matching problems. The core of this technique is a graph theoretical model of an NP-hard problem, viz., counting the perfect matchings in a bipartite graph. This technique is then applied to develop deterministic algorithms using polynomial sequential time or polylogarithmic parallel time (for massively parallel computers) for the search and counting associated with all NP-complete problems. In the past no polynomial time algorithms for these problems were found, and thus are believed to be intractable. This invention thus makes a theoretical as well as practical contribution to the field of computing, and has practical applications in many diverse areas.
Owner:ASLAM JAVAID
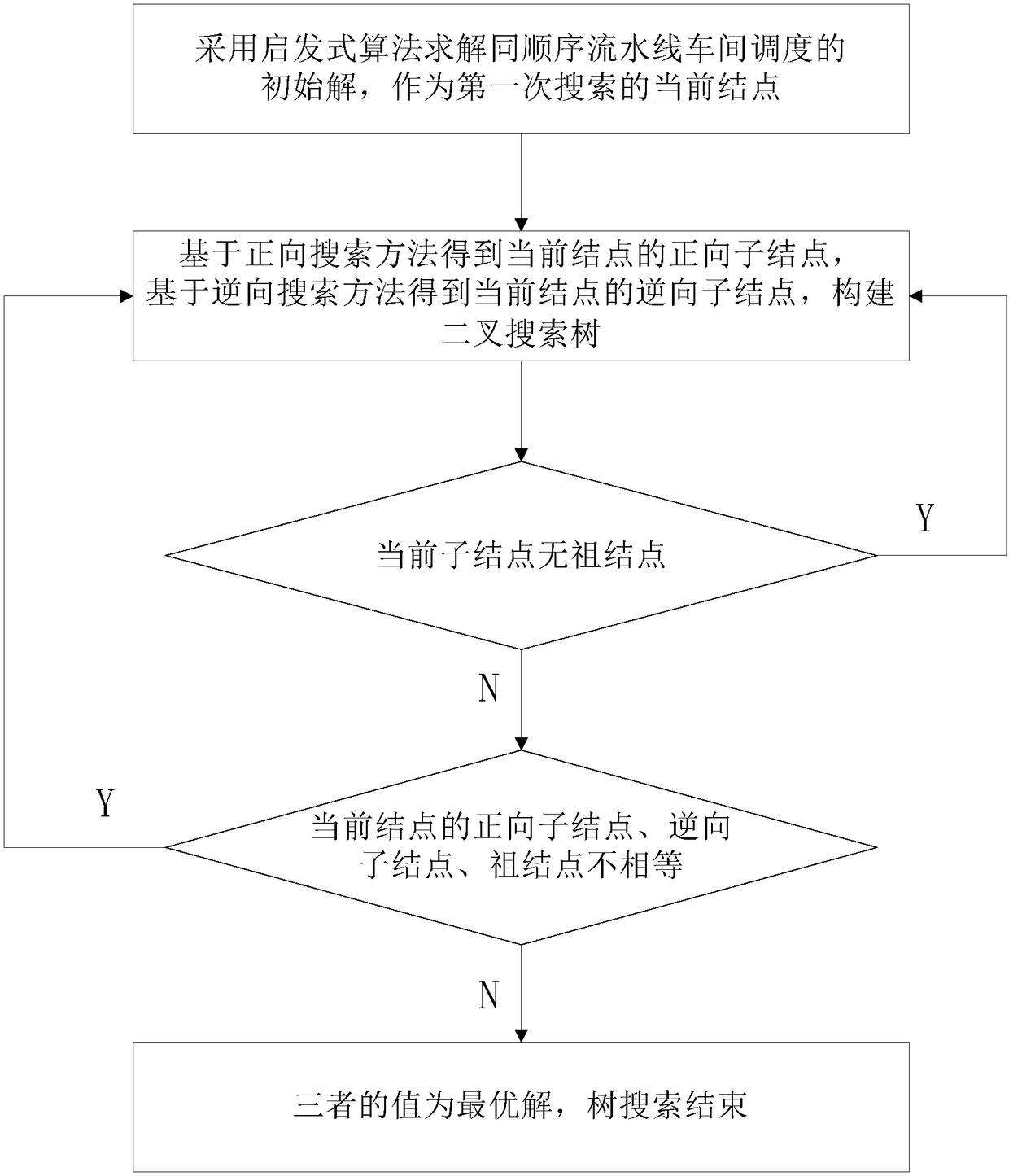
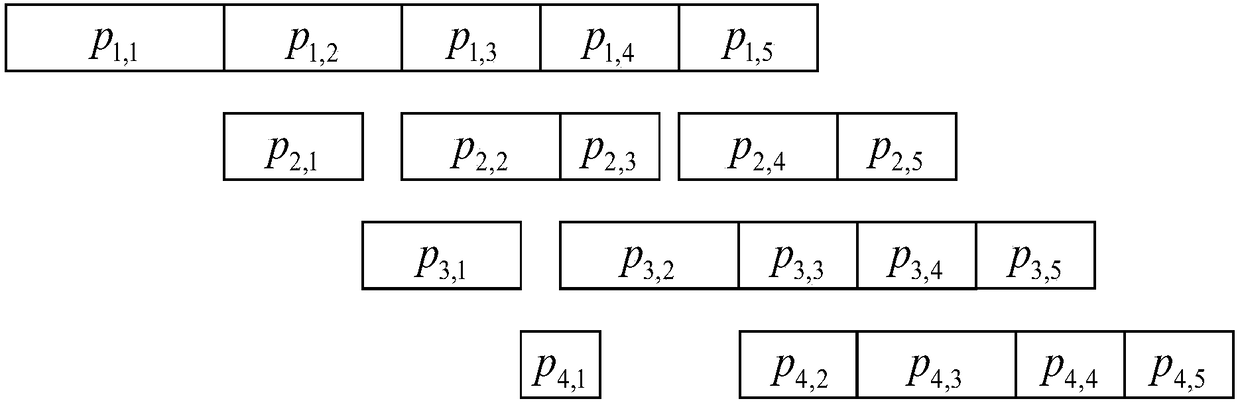
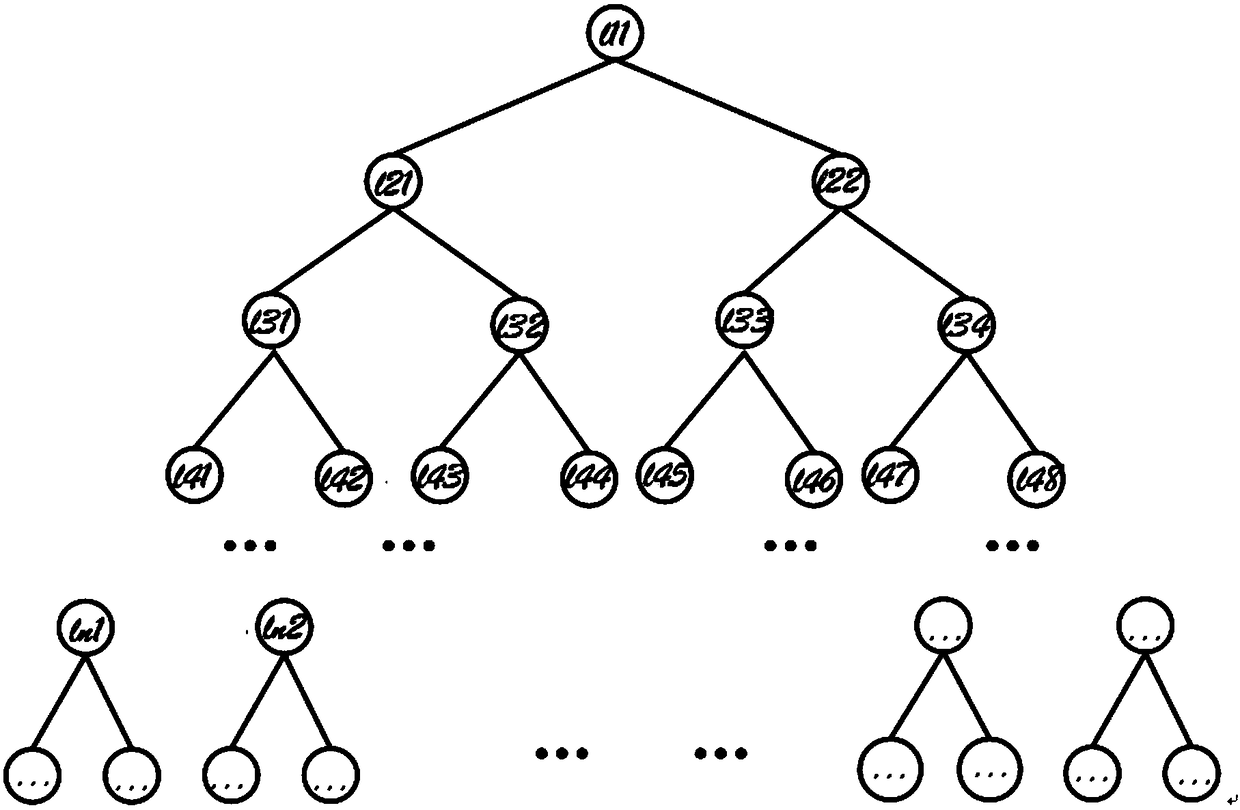
Tree search method and device for homosequential assembly line workshop scheduling problem
ActiveCN108446814AShorten the maximum completion timeIncrease productivityMachine learningResourcesCompletion timeDeterministic algorithm
The invention belongs to the field of assembly line workshop scheduling, and specifically relates to a tree search method and device for a homosequential assembly line workshop scheduling problem. Theinvention aims at solving an optimized scheduling problem of the homosequential assembly line workshop. The method comprises the steps: employing an NEH algorithm for solving an initial solution; taking forwarding search and reverse search as two branches of a father node through combining with a tree search method, respectively carrying out the optimization, carrying out the comparison with thefather node, obtaining a forwarding optimal solution and a reverse optimal solution, i.e., two generated two subnodes. A tree structure is constructed in the above mode, thereby achieving the optimized scheduling of the homosequential assembly line workshop. Compared with the prior art, the method shortens the maximum completion time. Moreover, the algorithm is a deterministic algorithm, and a solving result is a deterministic stable solution.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
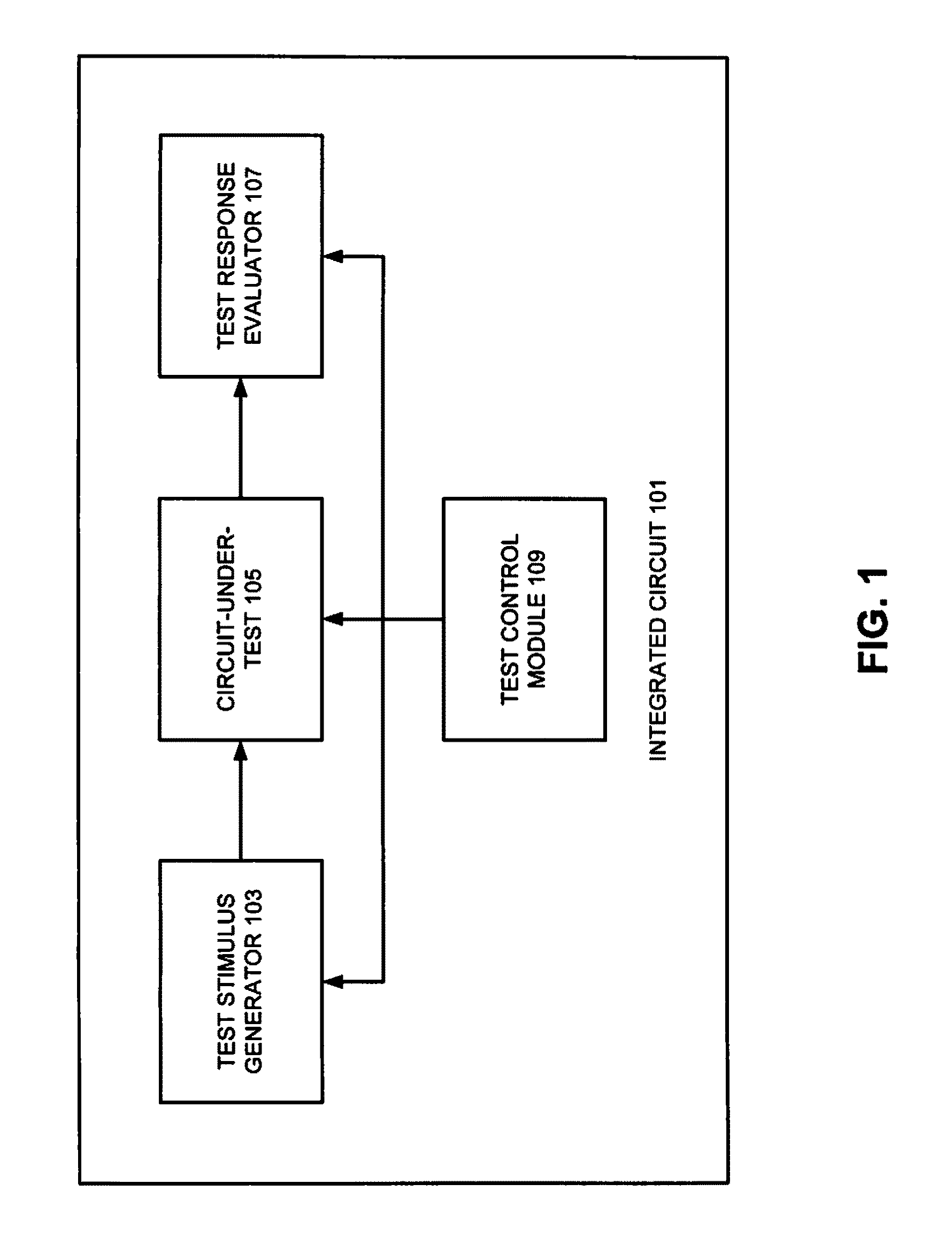
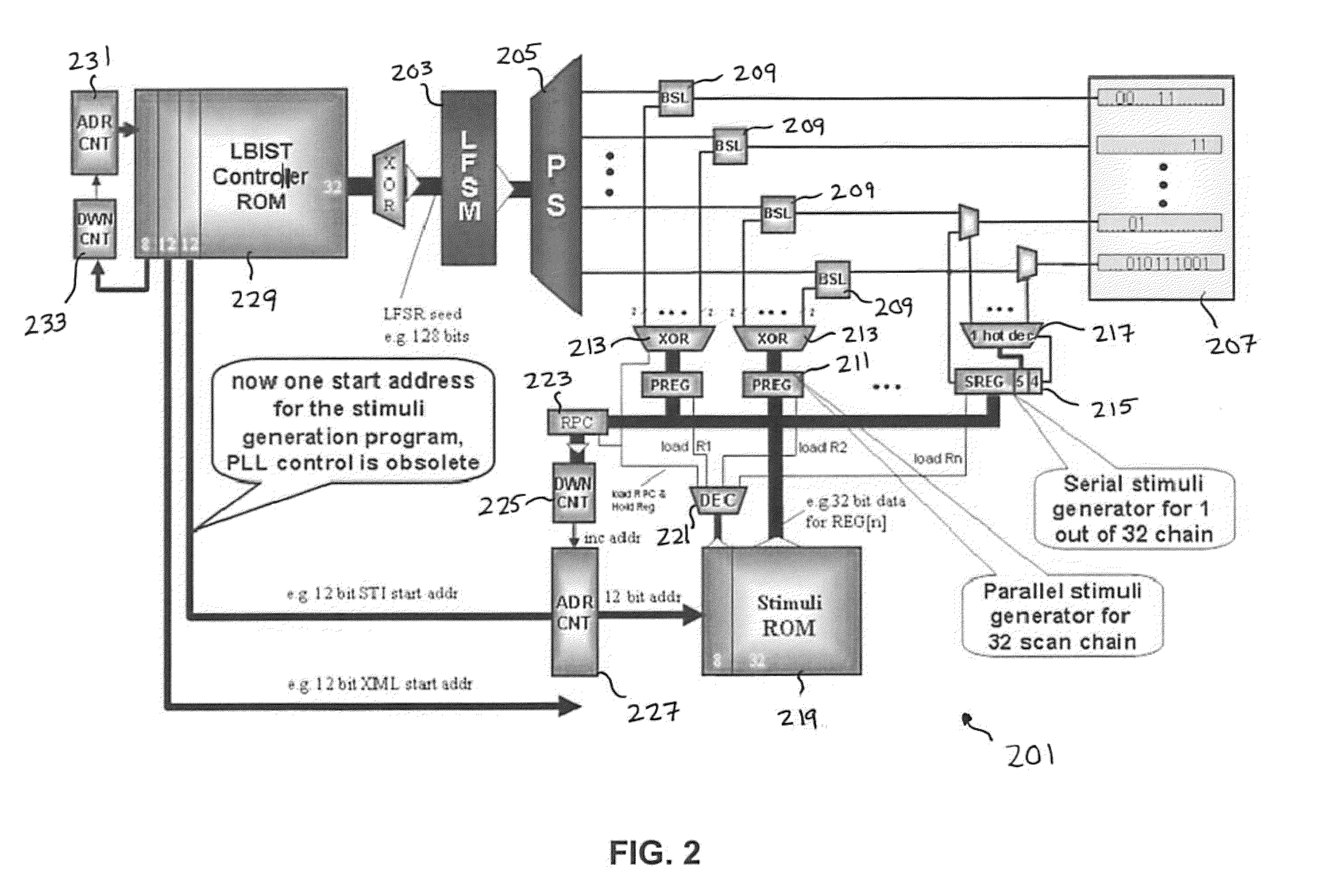
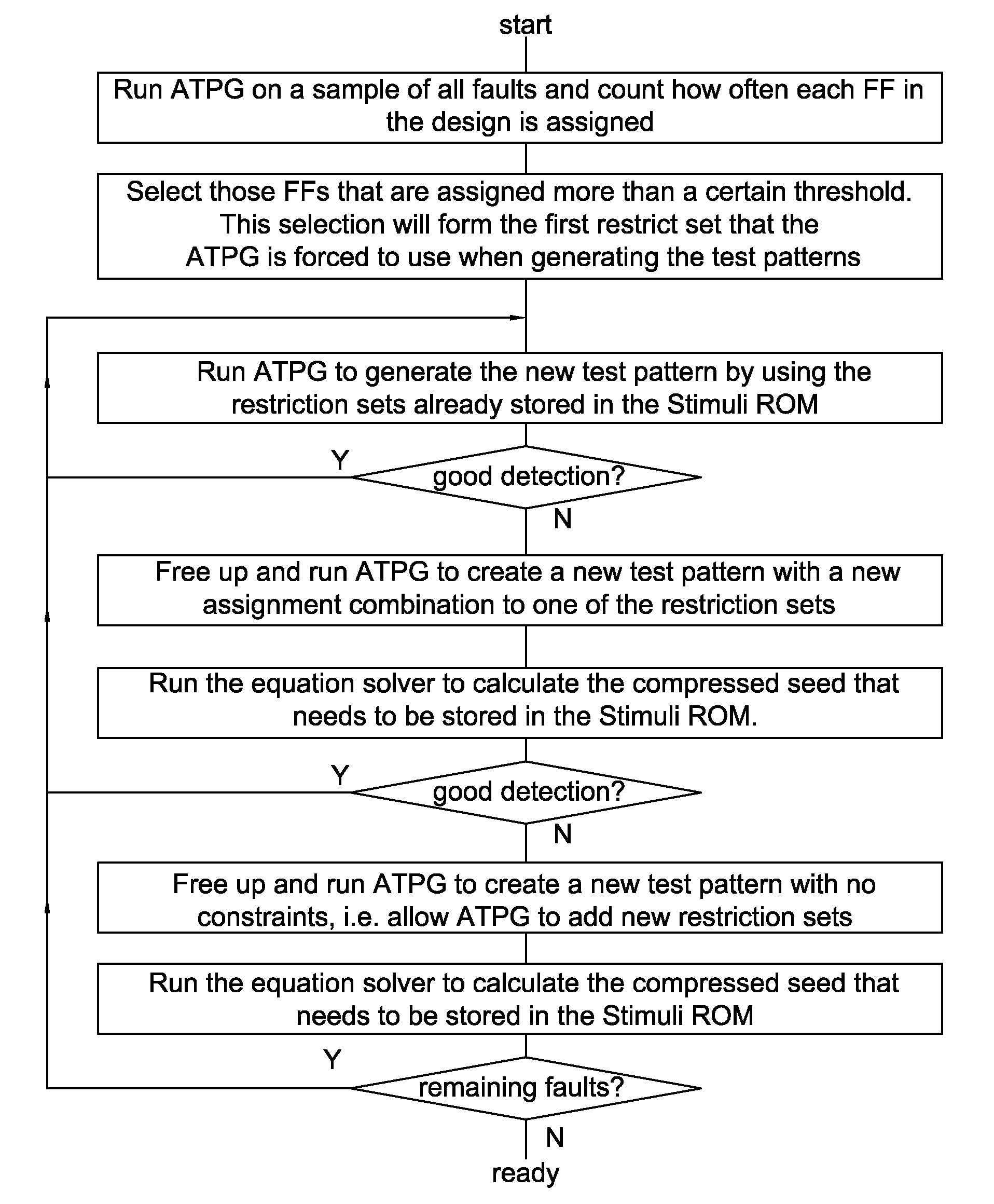
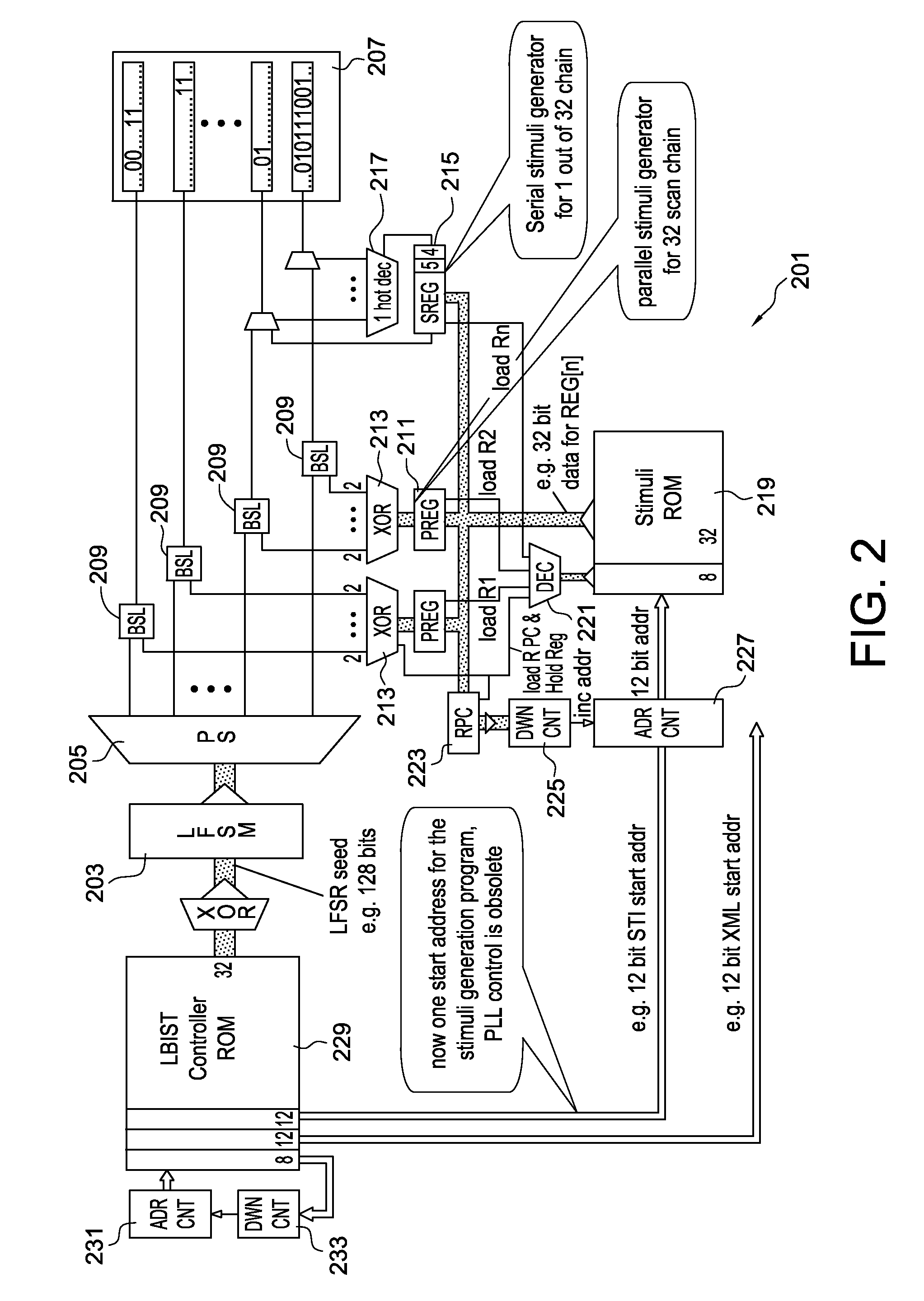
Deterministic Logic Built-In Self-Test Stimuli Generation
InactiveUS20100275075A1Efficiently provideEfficient storageElectronic circuit testingLogical operation testingDeterministic algorithmLogic built-in self-test
Techniques for storing and using compressed restrict values for selected scan chains and flip-flops, such that the states that need to be applied to those flip flops need not be solved by a linear equation system solver, such as a linear equation system solver provided by an automatic test pattern generation (ATPG) tool. Selected restrict values can then be injected into test patterns for those flip-flop combinations that need to be set in a certain shift cycle or those flip-flops that need to be initialized one after another (e.g., for serial settings in one scan chain).
Owner:MENTOR GRAPHICS CORP
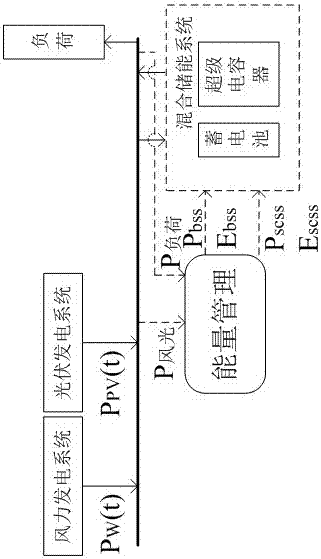
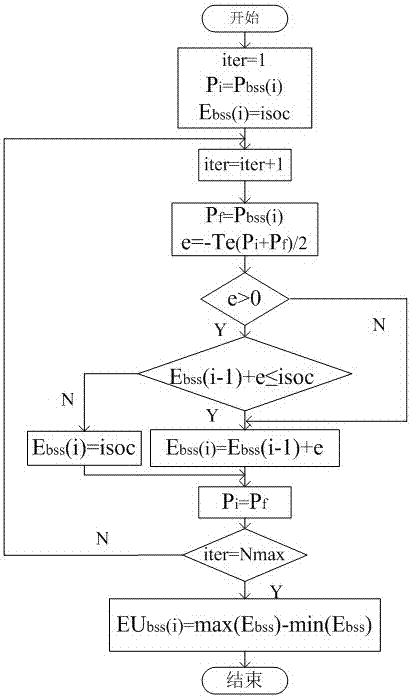
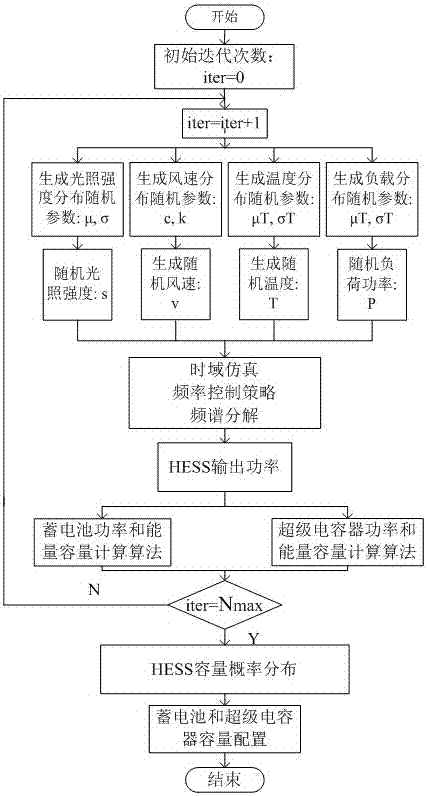
Hybrid energy storage system capacity optimization configuration method based on statistical model
InactiveCN107492903AImprove economyImprove reliabilityBatteries circuit arrangementsAc network load balancingSystem capacityEnergy control
The invention provides a hybrid energy storage system capacity optimization configuration method based on a statistical model and belongs to the technical field of energy storage. The invention provides the configuration method based on the statistical model so as to solve the problem of energy storage capacity configuration of a wind / photovoltaic / energy storage combined power generation system. The method comprises the following steps: to begin with, carrying out probabilistic statistical analysis on historical data of wind speed and illumination intensity and the like to determine accurate distribution of power output of a wind and photovoltaic system; then, exploring a capacity configuration sub-algorithm based on a super capacitor and a storage battery; besides, providing an energy control strategy to improve storage battery operation environment so as to prolong the service life of the storage battery; and carrying out Monte-Carlo simulation on the statistical analysis to obtain capacity probability distribution of the hybrid energy storage system. The statistical analysis method determines the capacity of the hybrid energy storage system under different cumulative probability levels, and helps planning personnel to carry out reasonable configuration on the capacity of the hybrid energy storage system according to running conditions and requirements of the power generation system; and compared with a conventional capacity configuration method, the statistical analysis method takes a lot of uncertainty factors in the configuration process into consideration, thereby improving conservation of a conventional deterministic algorithm and improving economy and reliability of the configuration method.
Owner:NORTHEAST DIANLI UNIVERSITY +2
Deterministic logic built-in self-test stimuli generation
InactiveUS8112686B2Reduce memory sizeIncrease probabilityElectronic circuit testingError detection/correctionDeterministic algorithmLogic built-in self-test
Techniques for storing and using compressed restrict values for selected scan chains and flip-flops, such that the states that need to be applied to those flip flops need not be solved by a linear equation system solver, such as a linear equation system solver provided by an automatic test pattern generation (ATPG) tool. Selected restrict values can then be injected into test patterns for those flip-flop combinations that need to be set in a certain shift cycle or those flip-flops that need to be initialized one after another (e.g., for serial settings in one scan chain).
Owner:MENTOR GRAPHICS CORP
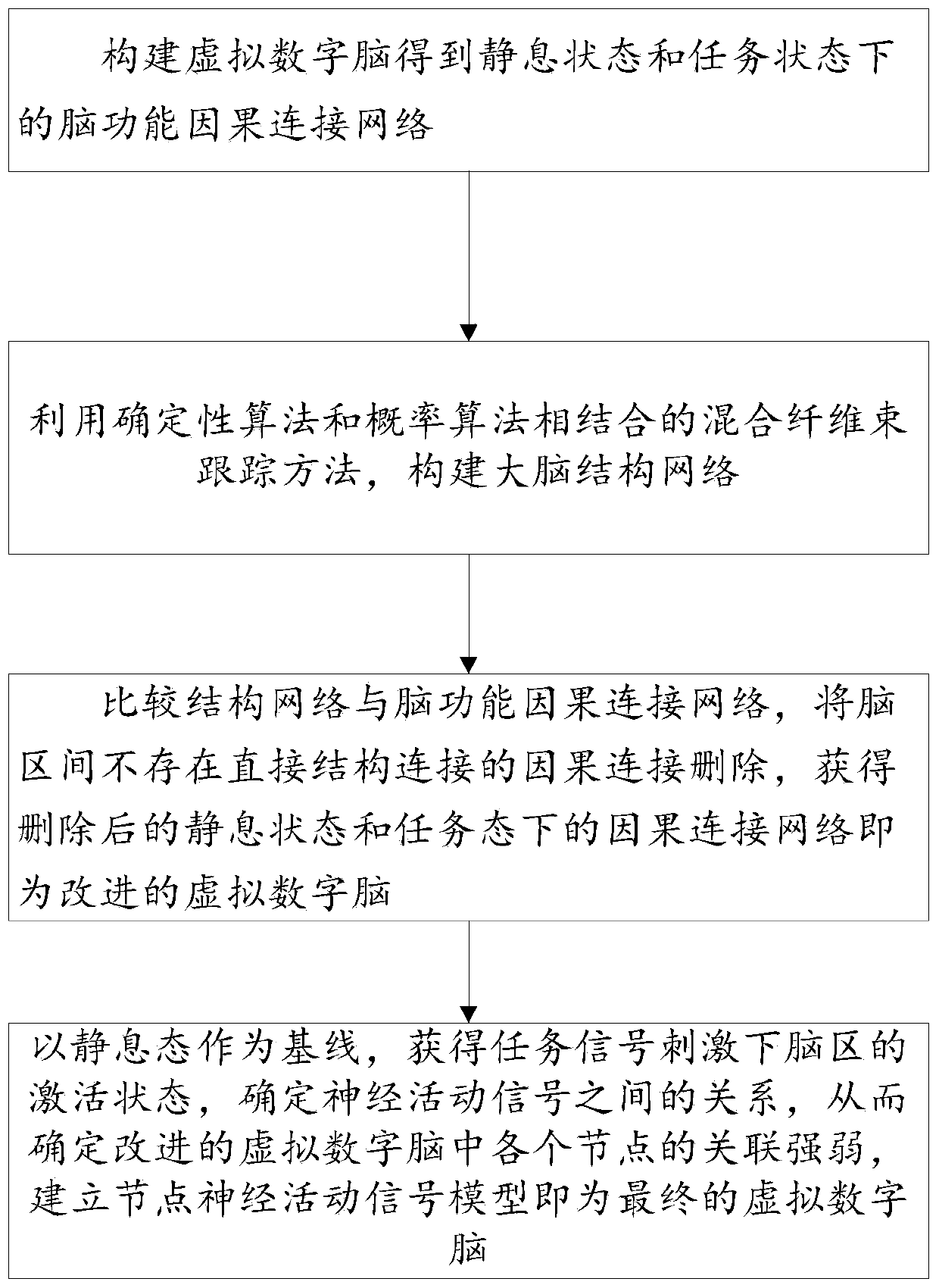
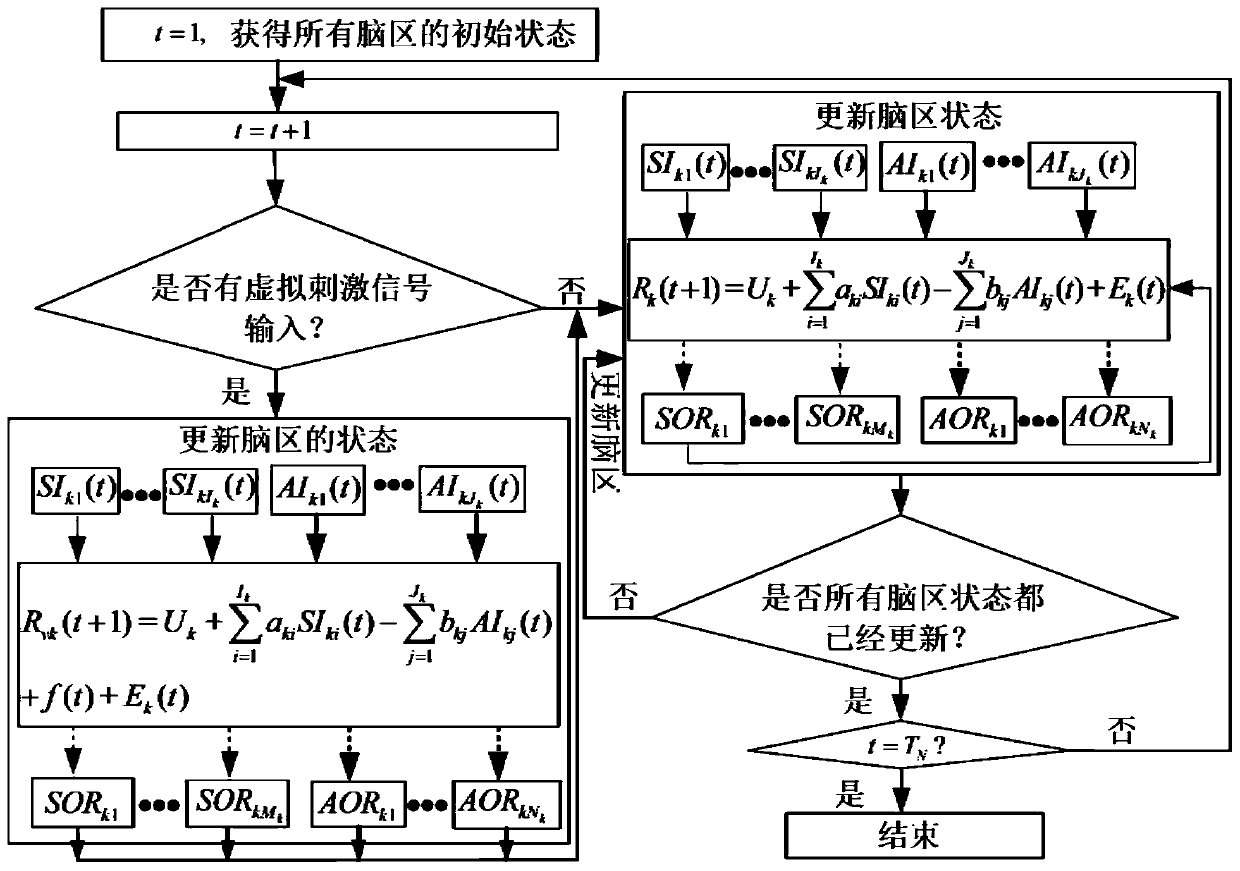
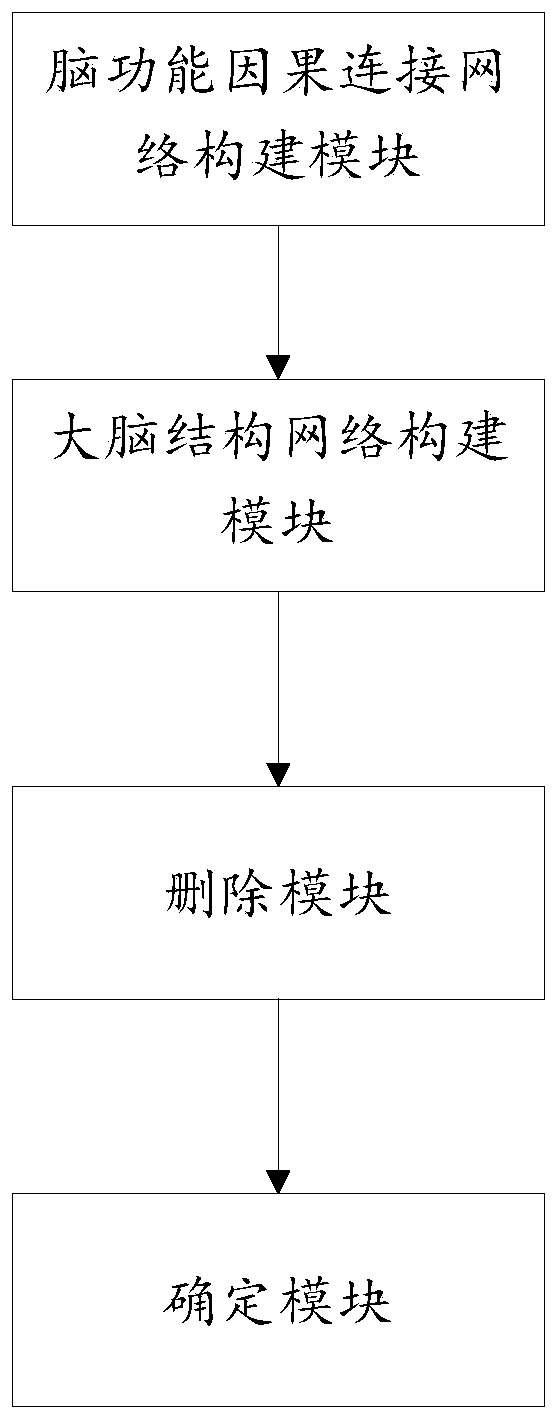
Virtual digital brain construction method and system and intelligent robot control system
ActiveCN111539509AIntelligent controlAccurate operationMathematical modelsArtificial lifeFiber bundleDeterministic algorithm
The invention provides a virtual digital brain construction method and system and an intelligent robot control system. The virtual digital brain construction method comprises the following steps of: constructing a virtual digital brain to obtain a brain function causal connection network in a resting state and a task state; constructing a brain structure network by using a hybrid fiber bundle tracking method combining a deterministic algorithm and a probabilistic algorithm; comparing the structure network with the brain function causal connection network, and deleting causal connection withoutdirect structure connection in the brain interval to obtain an improved virtual digital brain; and taking the resting state as a base line, acquiring an activation state of a brain region under tasksignal stimulation, and establishing a node neural activity signal prediction model, namely a final virtual digital brain. According to the invention, the brain function causal connection network is improved through the structure network, and the causal connection without direct structure connection in the brain interval is deleted and the influence of indirect connection is removed by jointly using the function and structure information, so that the establishment of a more effective node neural activity signal prediction model in subsequent processing is facilitated.
Owner:SHANDONG FIRST MEDICAL UNIV & SHANDONG ACADEMY OF MEDICAL SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com