Patents
Literature
534 results about "Bipartite graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
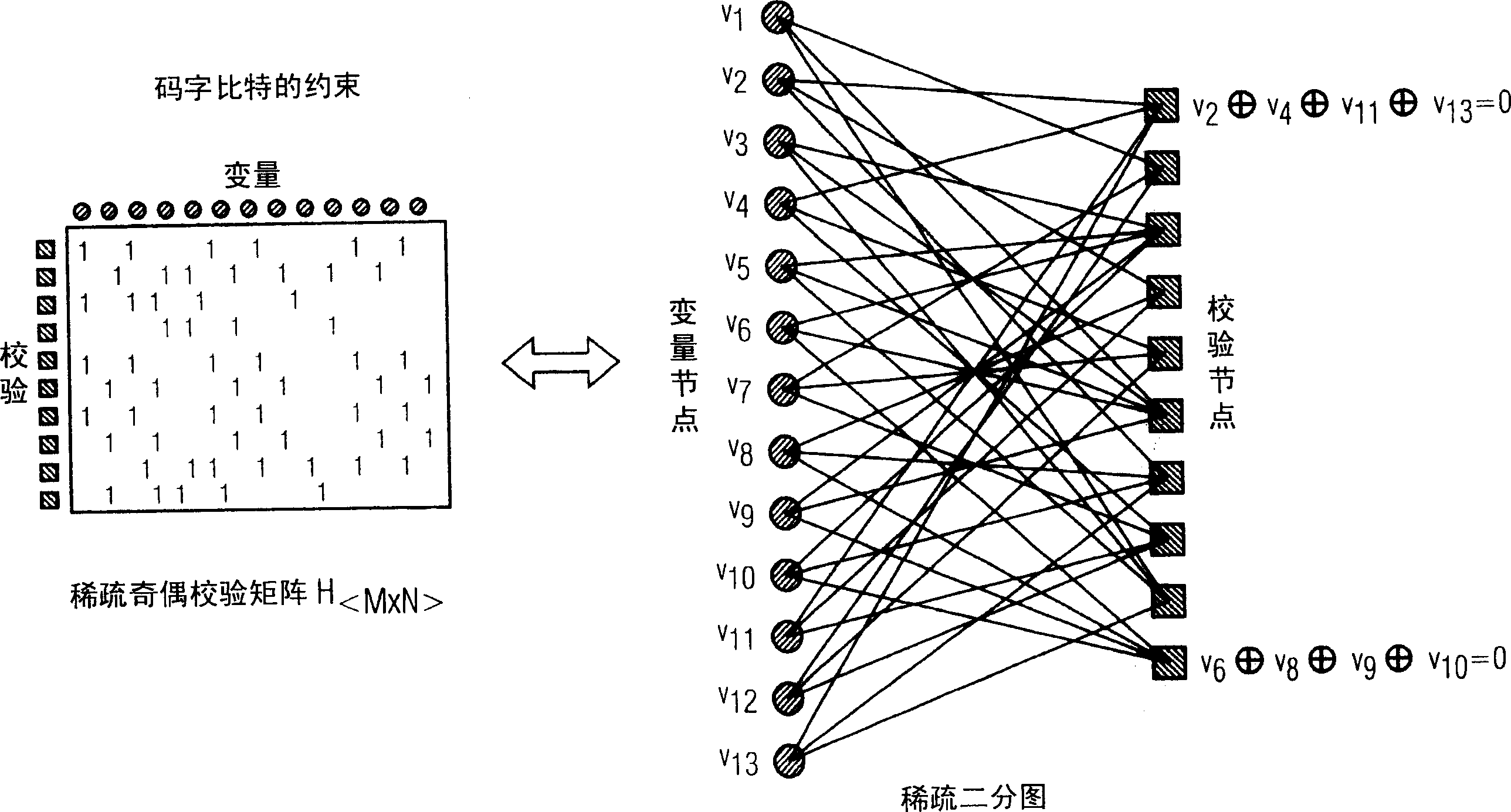
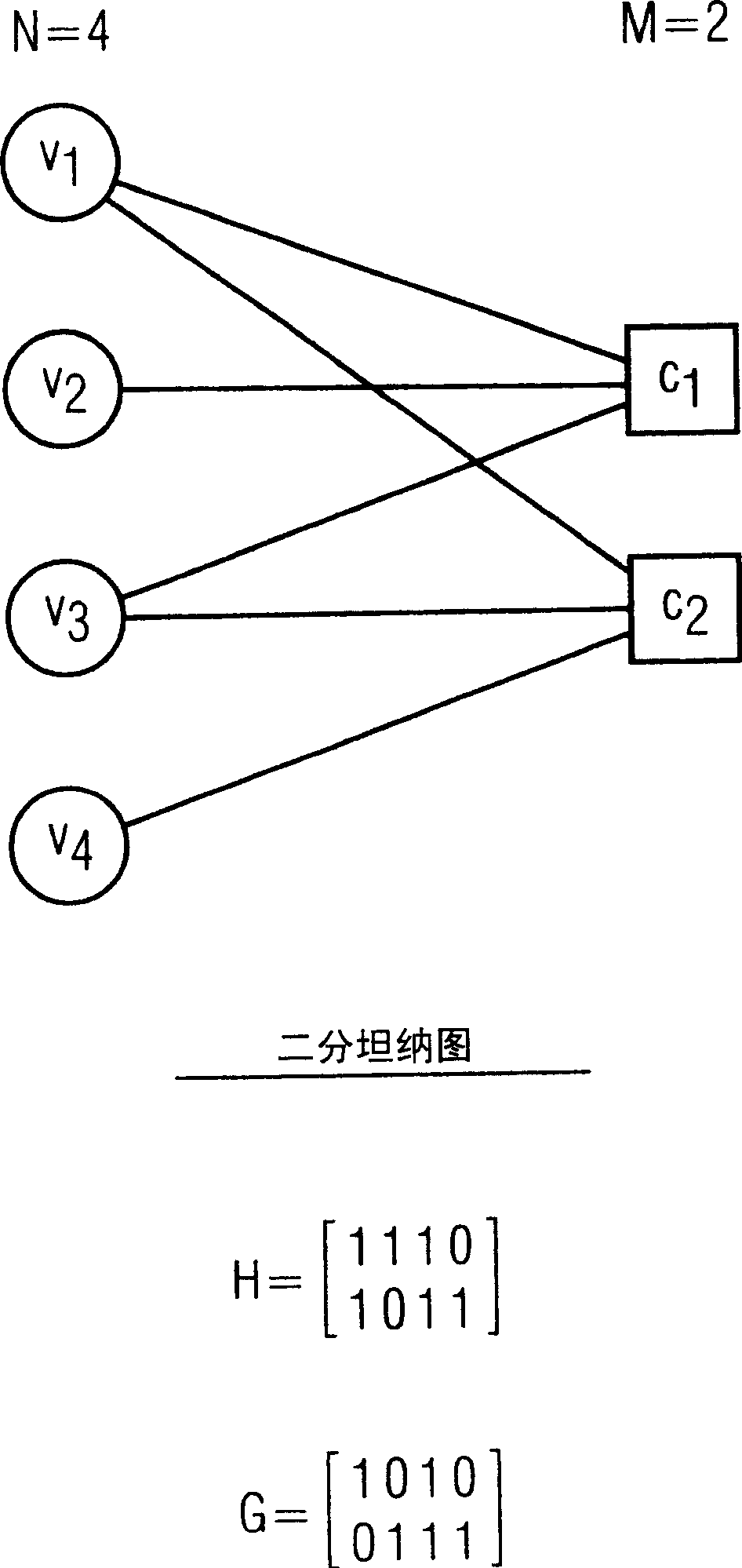
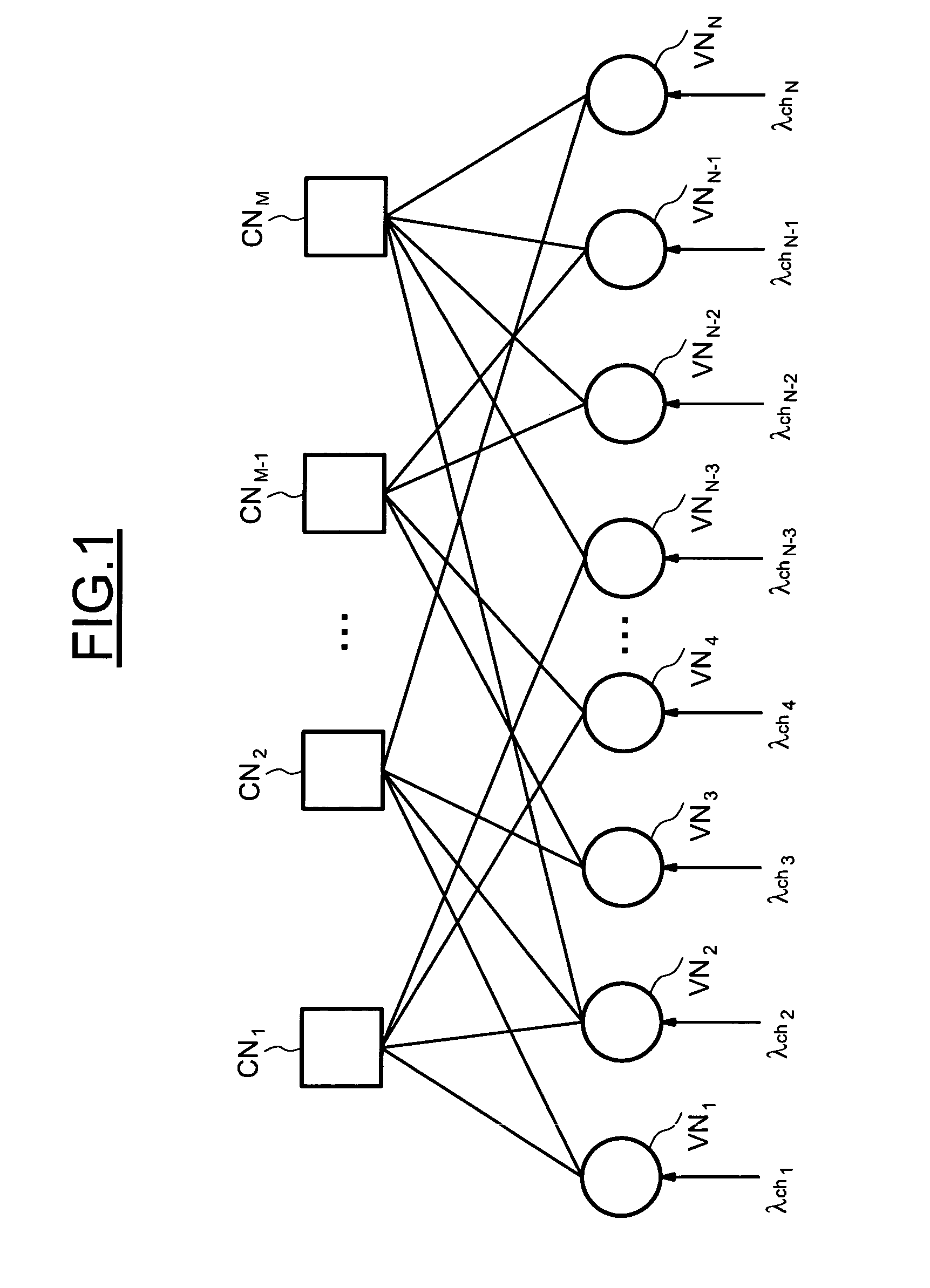
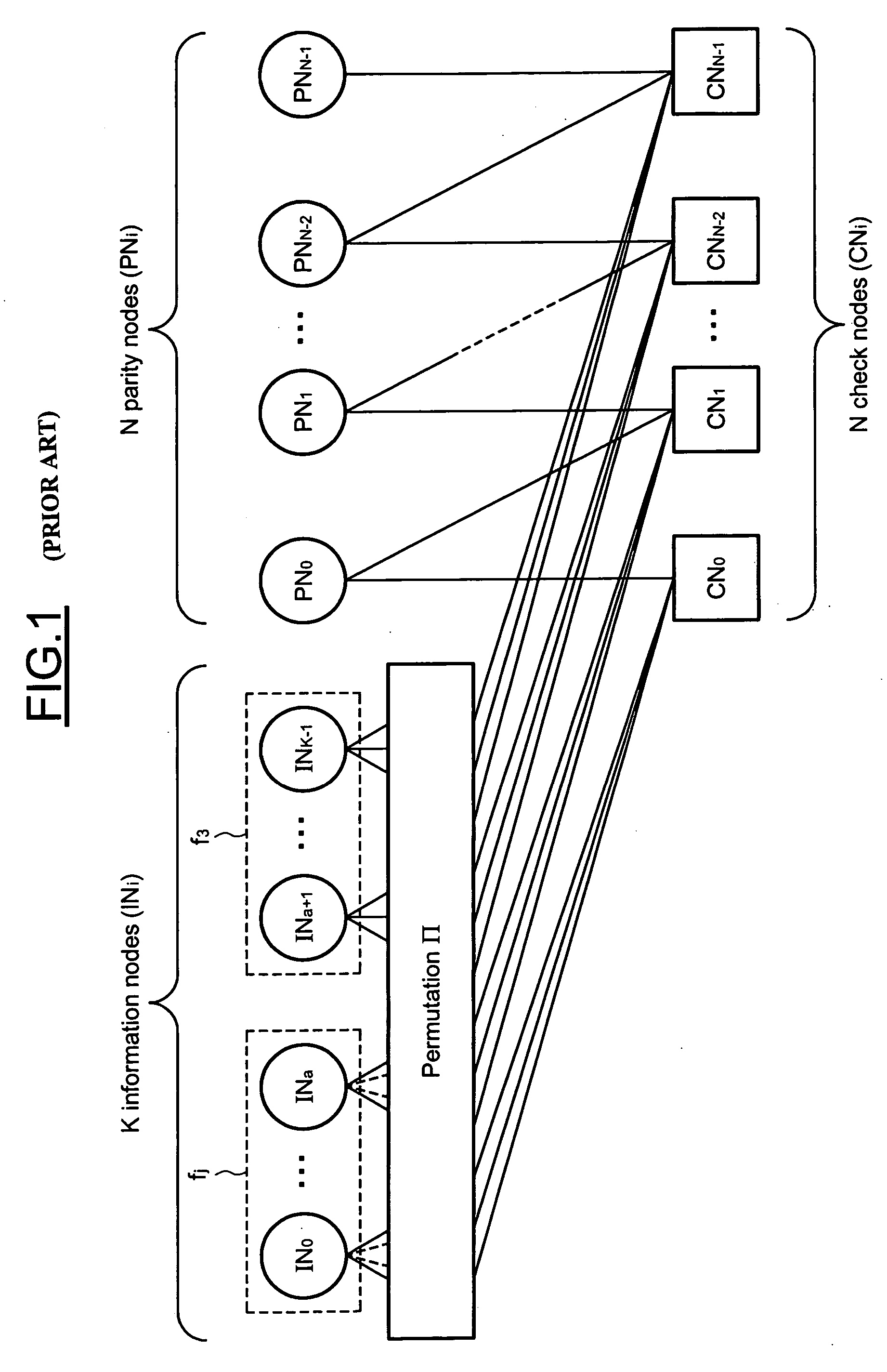
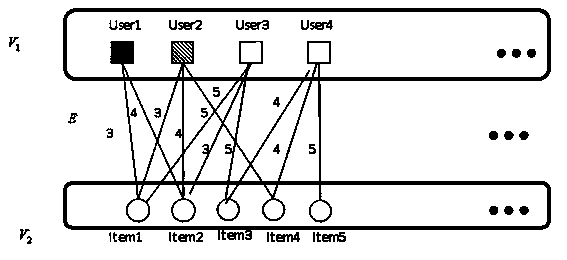
In the mathematical field of graph theory, a bipartite graph (or bigraph) is a graph whose vertices can be divided into two disjoint and independent sets U and V such that every edge connects a vertex in U to one in V. Vertex sets U and V are usually called the parts of the graph. Equivalently, a bipartite graph is a graph that does not contain any odd-length cycles. The two sets U and V may be thought of as a coloring of the graph with two colors: if one colors all nodes in U blue, and all nodes in V green, each edge has endpoints of differing colors, as is required in the graph coloring problem.
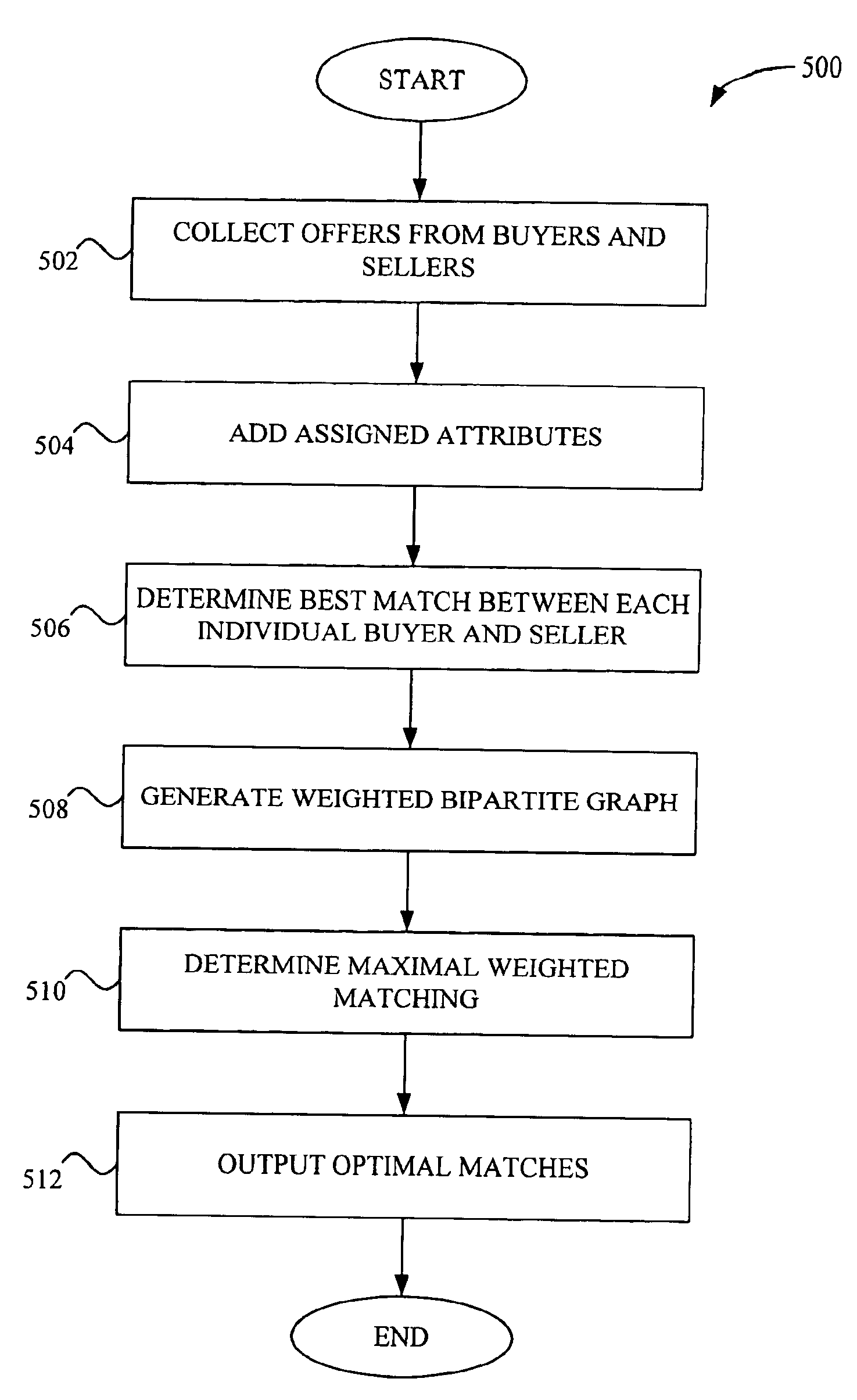
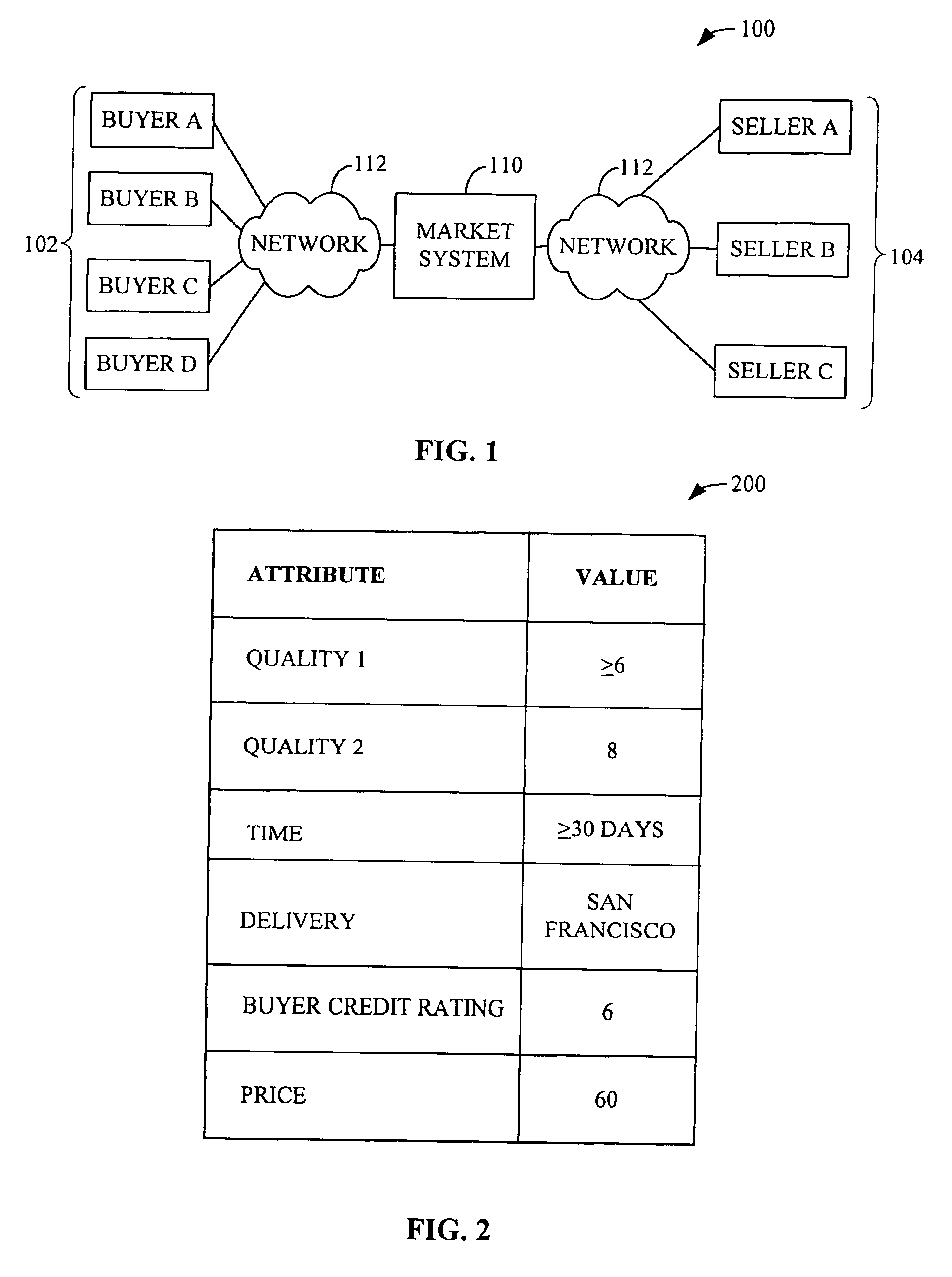
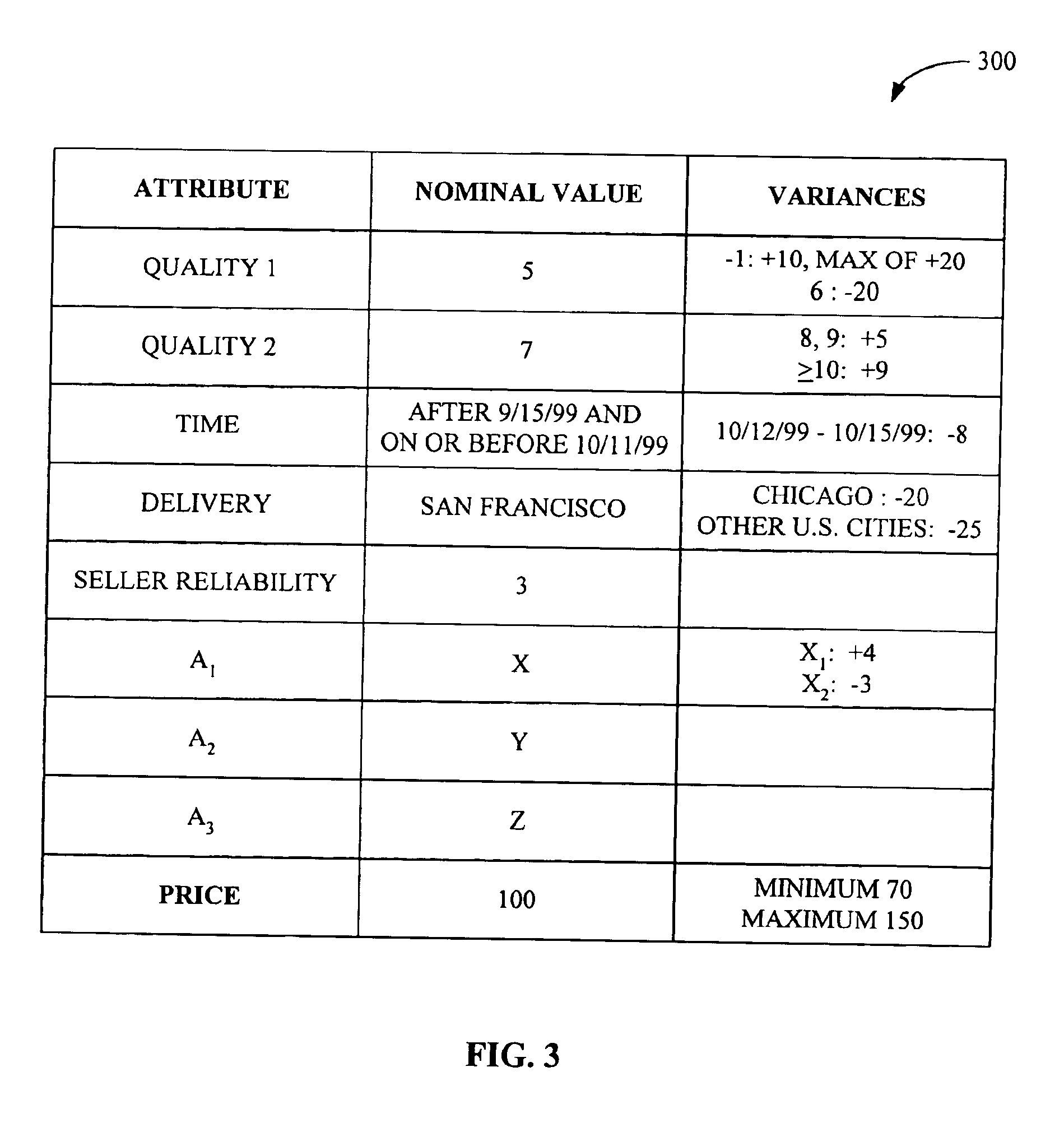
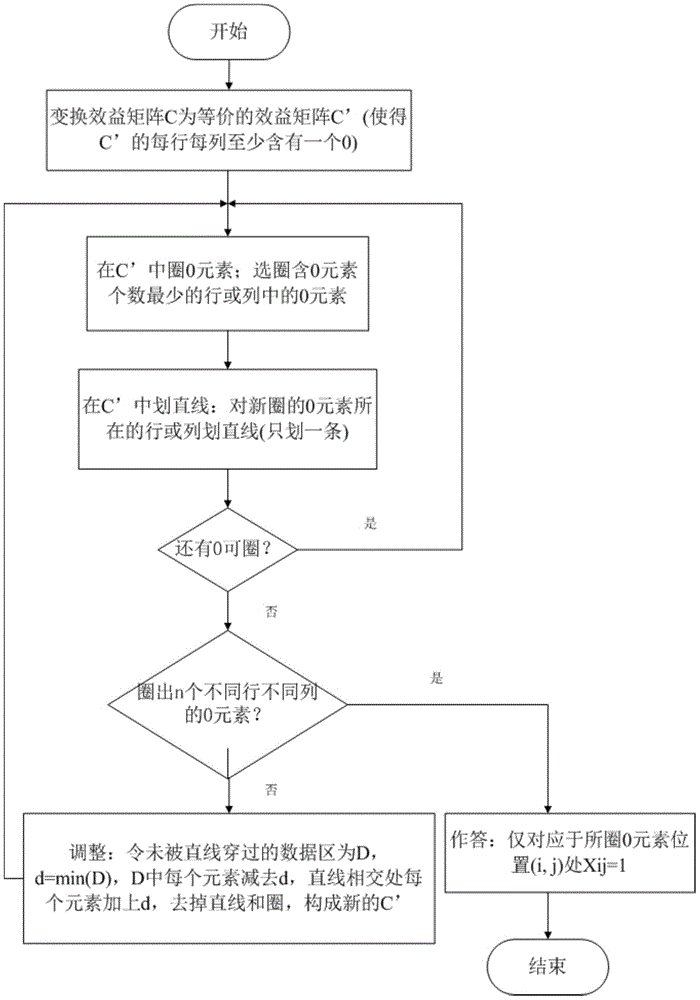
System and method for matching multi-attribute auction bids
A system and a method for matching multi-attribute auction bids are disclosed. A set of multi-attribute bids or bid values are collected from one or more buyers and one or more sellers. The set of bid values may include variances from nominal bid values. Buyer and seller bids are generated from the set of buyer and seller multi-attribute bid values after predetermined attribute values, if any, are added. A pair of bids between each buyer and each seller having a highest surplus is selected. The method generates a weighted bipartite graph having buyer nodes and seller nodes and an edge between each buyer node and each seller node, each edge having the highest surplus of the pair of bids between the buyer and seller as a weight. The maximal weighted matching bids from the highest surplus pairs of bids are determined using the weighted bipartite graph.
Owner:ARIBA INC
Method and apparatus for semantic search of schema repositories
InactiveUS20070185868A1Leveling precisionSemi-structured data indexingSpecial data processing applicationsWeb serviceThe Internet
Mechanisms for searching XML repositories for semantically related schemas from a variety of structured metadata sources, including web services, XSD documents and relational tables, in databases and Internet applications. A search is formulated as a problem of computing a maximum matching in pairwise bipartite graphs formed from query and repository schemas. The edges of such a bipartite graph capture the semantic similarity between corresponding attributes of the schema based on their name and type semantics. Tight upper and lower bounds are also derived on the maximum matching that can be used for fast ranking of matchings whilst still maintaining specified levels of precision and recall. Schema indexing is performed by ‘attribute hashing’, in which matching schemas of a database are found by indexing using query attributes, performing lower bound computations for maximum matching and recording peaks in the resulting histogram of hits.
Owner:IBM CORP
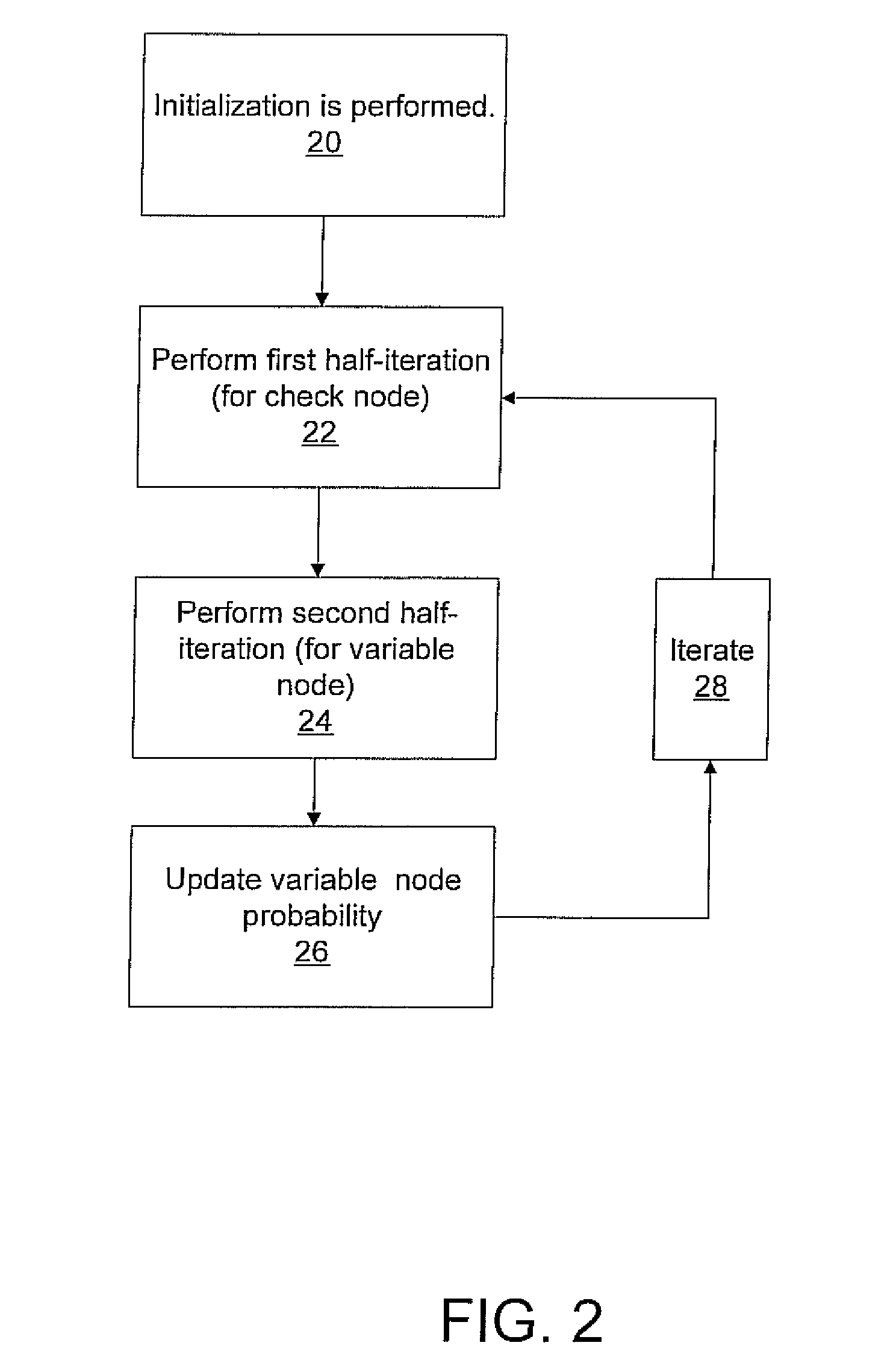
Method of error floor mitigation in low-density parity-check codes
ActiveUS20120266040A1Improve performanceError correction/detection using LDPC codesCode conversionComputer hardwareMaximum magnitude
A digital communication decoding method for low-density parity-check coded messages. The decoding method decodes the low-density parity-check coded messages within a bipartite graph having check nodes and variable nodes. Messages from check nodes are partially hard limited, so that every message which would otherwise have a magnitude at or above a certain level is re-assigned to a maximum magnitude.
Owner:CALIFORNIA INST OF TECH
Automatic composition of services through semantic attribute matching
ActiveUS20060136428A1Maximizing numberDatabase management systemsDigital data processing detailsSemantic propertyComposite pattern
A method of automatically matching schemas begins by extracting schemas from sources and targets. Then, source and target attributes are extracted from the schemas. Each source schema will have multiple source attributes and each target schema will also have multiple target attributes. The source attributes and the target attributes are presented as nodes in a bipartite graph. This bipartite graph has edges between nodes that are related to each other. A plurality of similarity scores are defined between each set of related nodes. Each of the similarity scores is based on a different context-specific cue of the attributes that the nodes represent. These context-specific cues can comprise lexical name, semantic name, type, structure, functional mappings, etc. An overall weight is computed for each edge in the bipartite graph by combining the similarity scores of each set of nodes that form an edge. In addition, an optimal matching of the schemas is assembled, so as to indicate the level of similarity between each of the source and target schemas. The optimal matching selects pairs of nodes between source and target schemas that maximizes the number of nodes matched as well as the overall score of match for the nodes selected.
Owner:SERVICENOW INC
Phishing webpage detection method based on Hungary matching algorithm
InactiveCN101826105AImprove scalabilityThe detection process is fastSpecial data processing applicationsPattern recognitionRegression analysis
A phishing webpage detection method based on Hungary matching algorithm is characterized by firstly extracting the text feature signatures, image feature signatures and general webpage feature signatures of the rendered webpages and more comprehensively depicting the features after access to webpages; and then computing the optimal matching of bipartite graphs by Hungary algorithm to search for the matched feature pairs among different webpage signatures and more objectively measuring the similarity among the webpages on the basis, thereby improving the phishing webpage detection efficiency. The method is also characterized by determining the inside weights of the text features, image features and global image features by utilizing the area under curve and determining the relative weightsamong the text similarity, image similarity and global image similarity during webpage similarity computation by utilizing logarithmic regression analysis. The precision and the recall rate are greatly improved in the method provided by the invention.
Owner:NANJING UNIV OF POSTS & TELECOMM
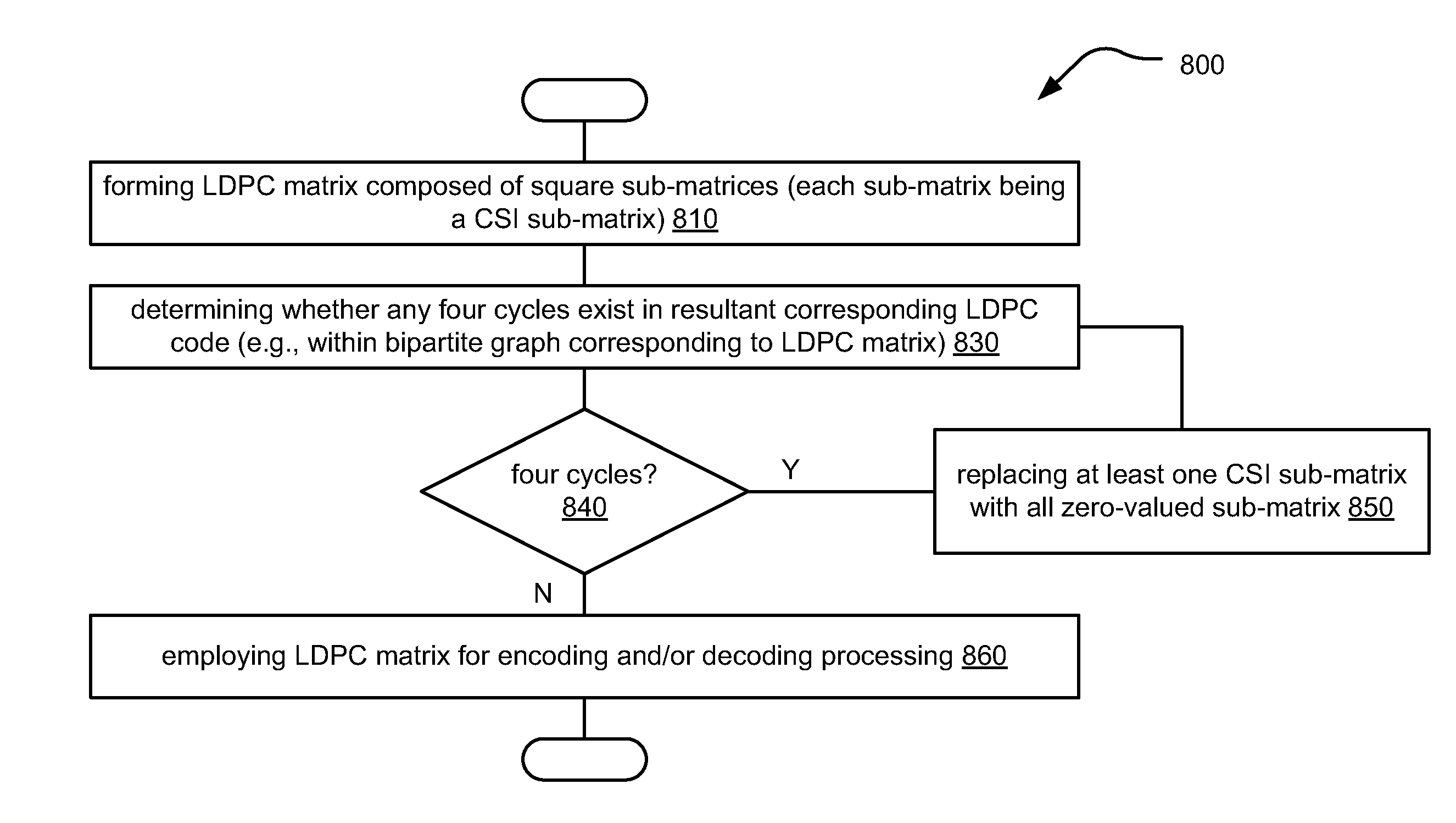
Quasi-cyclic LDPC (low density parity check) code construction
ActiveUS8341492B2Error preventionCode conversionLow-density parity-check codeTheoretical computer science
Quasi-cyclic LDPC (Low Density Parity Check) code construction is presented that ensures no four cycles therein (e.g., in the bipartite graphs corresponding to the LDPC codes). Each LDPC code has a corresponding LDPC matrix that is composed of square sub-matrices, and based on the size of the sub-matrices of a particular LDPC matrix, then sub-matrix-based cyclic shifting is performed as not only a function of sub-matrix size, but also the row and column indices, to generate CSI (Cyclic Shifted Identity) sub-matrices. When the sub-matrix size is prime (e.g., each sub-matrix being size q×q, where q is a prime number), then it is guaranteed that no four cycles will exist in the resulting bipartite graph corresponding to the LDPC code of that LDPC matrix. When q is a non-prime number, an avoidance set can be used and / or one or more sub-matrices can be made to be an all zero-valued sub-matrix.
Owner:AVAGO TECH INT SALES PTE LTD
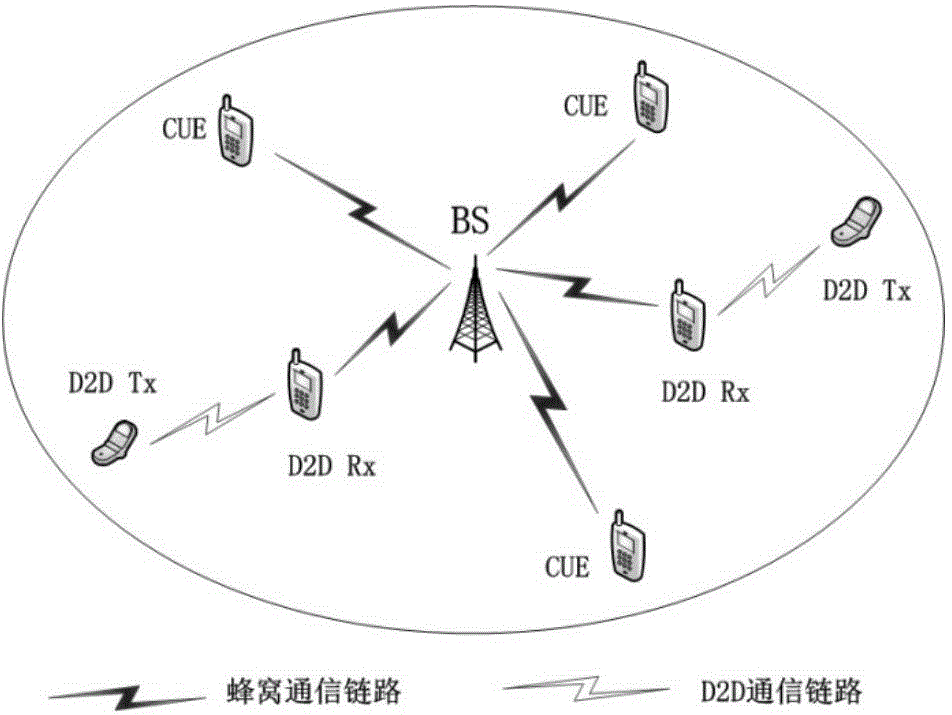
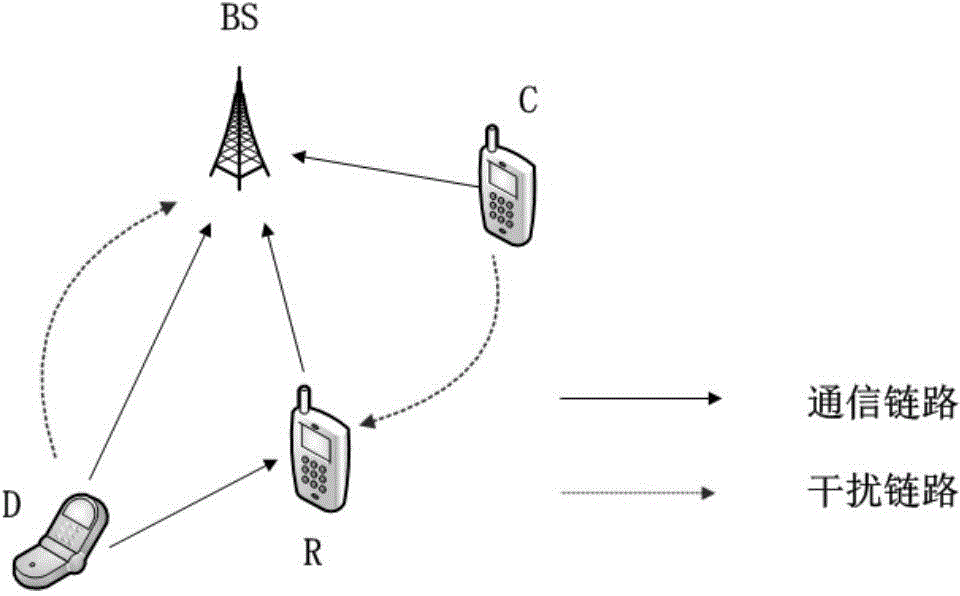
Relay selection method based on D2D relay communication
InactiveCN104105158AImprove energy efficiencyReduced energy efficiencyHigh level techniquesWireless communicationUser needsTransmitted power
The invention discloses a relay selection method based on D2D relay communication. A base station selects honeycomb communication users who do not meet energy efficiency conditions according to current honeycomb communication resource use conditions and idle user distribution conditions and the selected honeycomb communication users serve as communication users needing relay assistance, idle users meeting standards are added to a standby relay set according to the energy efficiency conditions and capacity limitation conditions so as to carry out D2D communication with the communication users needing relay assistance and assist the communication users needing relay assistance in communication with the base station, and meanwhile, transmitting power ranges of the communication users are determined according to interference limiting conditions. Accordingly, the largest signal to interference and noise ratio of communication achieved through relay assistance is obtained, best relays are correspondingly selected for the users by means of best match of a bipartite graph, D2D communication pairs are formed, and two-hop communication of the communication users and the base station is achieved. According to the relay selection method, energy efficiency of a system is effectively improved and transmission power of the communication users is reduced.
Owner:XI AN JIAOTONG UNIV
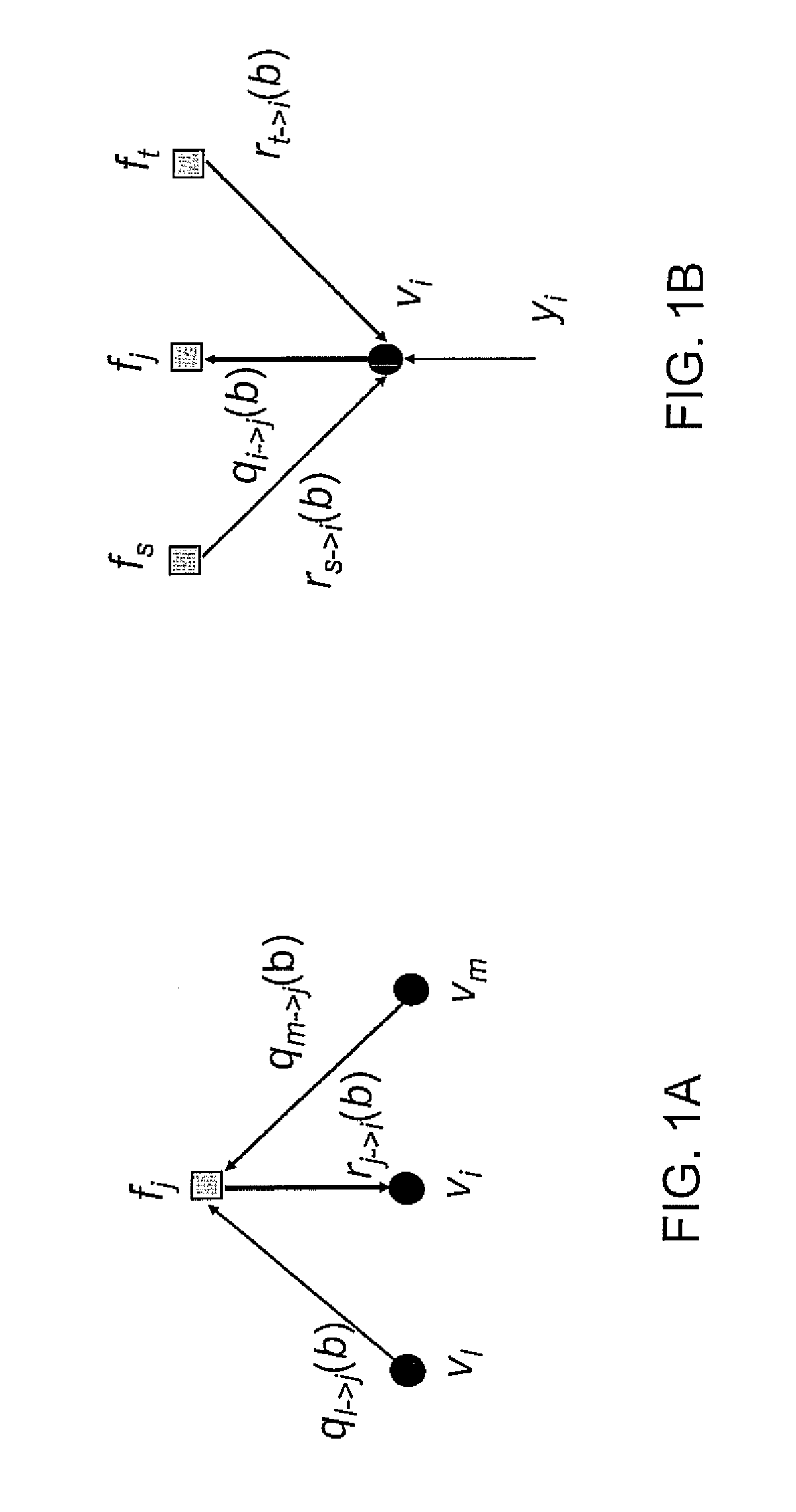
Decoding low density parity check codes
InactiveUS7000167B2Error correction/detection using LDPC codesError correction/detection using multiple parity bitsTheoretical computer scienceLow density
A method for decoding Low Density Parity Check (LDPC) codes comprises executing a sum product algorithm to recover a set of information bits from an LDPC code represented as a bipartite graph of symbol nodes and check nodes, the sum product algorithm being responsive to input log likelihood ratios associated with the symbol nodes. The check nodes are updated by generating a set of forward difference metrics and a set of backward difference metrics in dependence on the ratios of logarithmic probabilities each associated with a corresponding symbol node of the LDPC code, updating each metric in the set of forward difference metrics in dependence on the absolute value of the log likelihood ratio associated with the symbol node and the absolute value of the previous metric in the set, updating each metric in the set of backward difference metrics in dependence on the absolute value of the log likelihood ratio associated with the symbol node and the absolute value of the previous metric in the set, and generating log likelihood ratios to be propagated back to each symbol node in dependence on the updated sets of forward and backward difference metrics.
Owner:IBM CORP
Cross-camera tracking method for multiple moving targets
ActiveCN102156863AComplete descriptionImage analysisCharacter and pattern recognitionHuman bodyFilter model
The invention relates to image process, motion analysis and the like. In order to implement cross-camera tracking of moving targets, the invention uses the technical scheme that the cross-camera tracking method for the multiple moving targets comprises the following steps of: 1, motion filtering for a single camera, specifically, decomposing complex motions of human body into a finite number of combinations of relatively simple motion filtering models, wherein each single motion filtering model is represented by a combination of a linear motion state transition model and a gaussian noise, and the motion filtering method comprises the two following core parts: a motion model: an observation model; zk = Hsk + wk2, cross-camera oriented motion association: (1) creation of a panorama; (2) target similarity measurement; (3) motion trail association; and transforming the problem of cross-camera association of multiple motion trails into the problem of matching of bipartite graphs, and solving the problem through the integer programming under the following constraint conditions. The cross-camera tracking method for the multiple moving targets is mainly used in the image processing, the motion analysis and the like.
Owner:ZHEJIANG E VISION ELECTRONICS TECH
Apparatus and method to transmit/receive signal in a communication system
InactiveUS20080059862A1Other error detection/correction/protectionError correction/detection using multiple parity bitsCommunications systemParity-check matrix
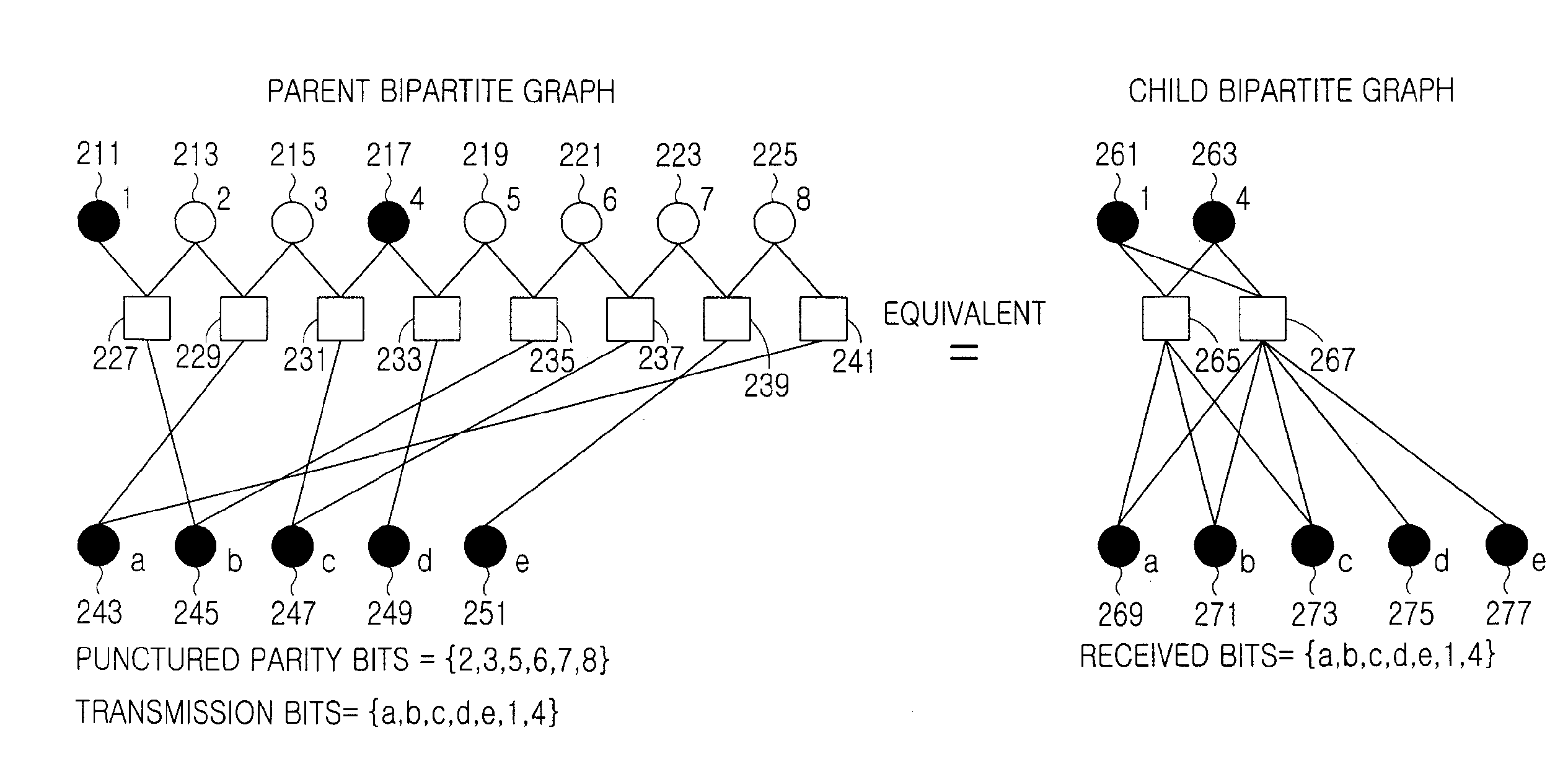
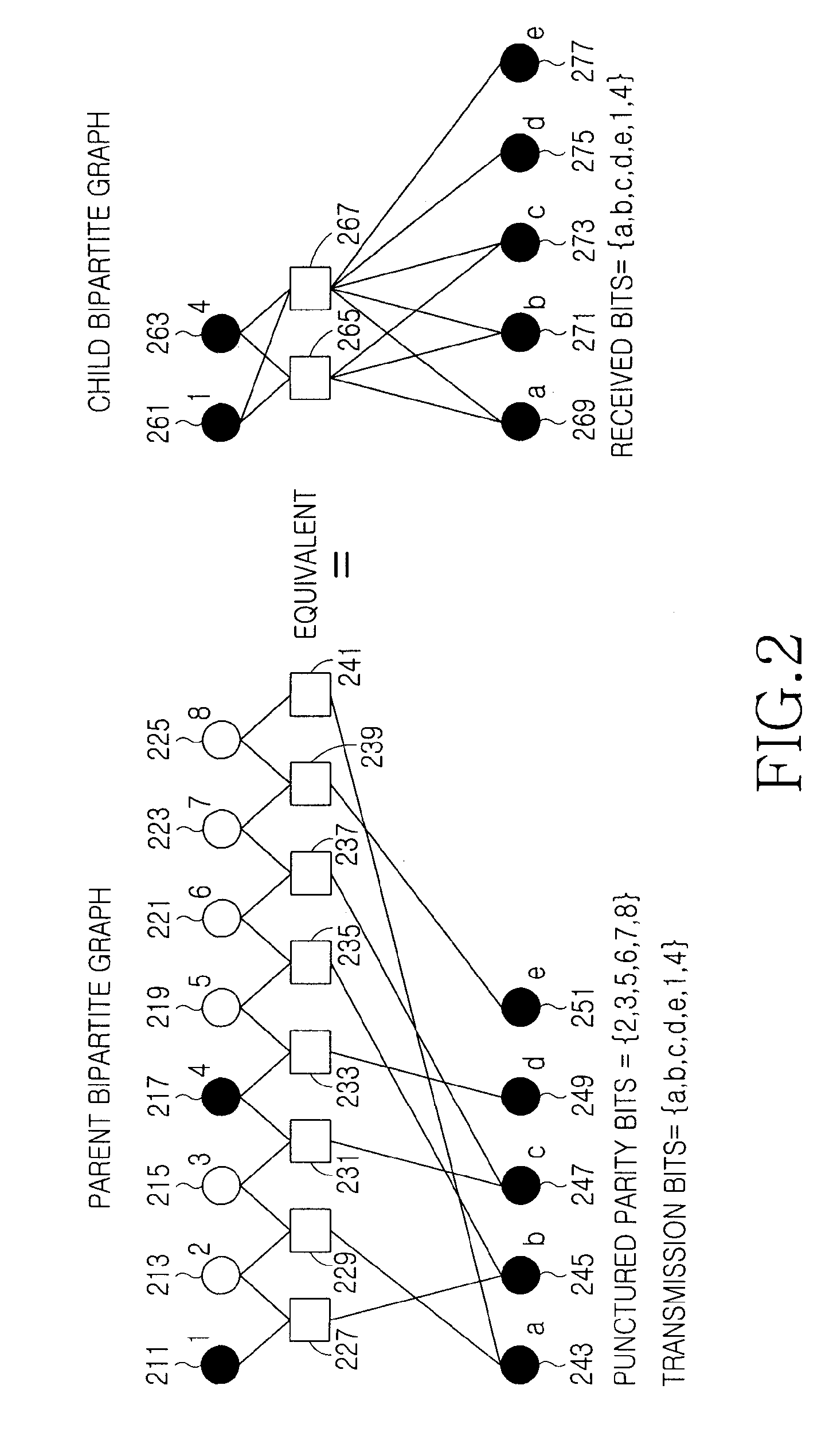
An apparatus and method for transmitting / receiving a signal in a communication system are provided. A signal reception apparatus of a communication system receives a signal and generates a child Low Density Parity Check (LDPC) codeword vector by decoding the received signal according to a child parity check matrix supporting a first coding rate. The child LDPC codeword vector includes an information vector including A (A≧1) information bits, and when the first coding rate is equal to a coding rate for a case where D (D≧1) parity bits are punctured among B (B≧1)+C (C≧1) parity bits included in a parent LDPC codeword vector generated by encoding the information vector according to a parent parity check matrix supporting a second coding rate, a child bipartite graph corresponding to the child parity check matrix is generated such that a parent bipartite graph corresponding to the parent parity check matrix corresponds to an edge merge scheme.
Owner:SAMSUNG ELECTRONICS CO LTD
Evaluating and optimizing error-correcting codes using a renormalization group transformation
InactiveUS6857097B2Improve performanceCorrect operation testingOther decoding techniquesRenormalizationParity-check matrix
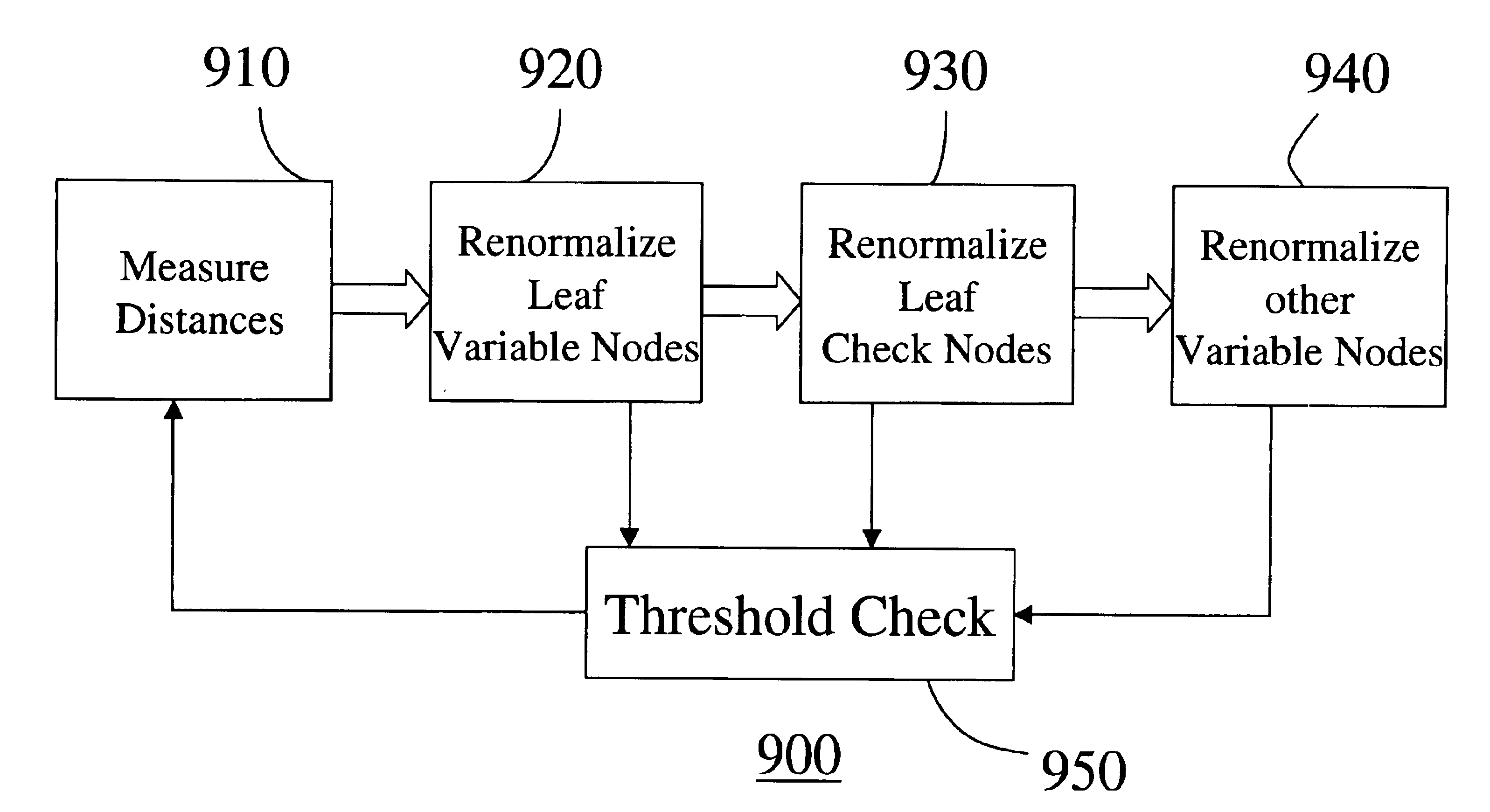
A method evaluates an error-correcting code for a data block of a finite size. An error-correcting code is defined by a parity check matrix, wherein columns represent variable bits and rows represent parity bits. The parity check matrix is represented as a bipartite graph. A single node in the bipartite graph is iteratively renormalized until the number of nodes in the bipartite graph is less than a predetermine threshold. During the iterative renormalization, a particular variable node is selected as a target node, and a distance between the target node and every other node in the bipartite graph is measured. Then, if there is at least one leaf variable node, renormalize the leaf variable node farthest from the target node, otherwise, renormalize a leaf check node farthest from the target node, and otherwise renormalize a variable node farthest from the target node and having fewest directly connected check nodes. By evaluating many error-correcting codes according to the method, an optimal code according to selected criteria can be obtained.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Method of decoding by message passing with scheduling depending on neighbourhood reliability
InactiveUS20090313525A1Error correction/detection using multiple parity bitsCode conversionDecoding methodsDependability
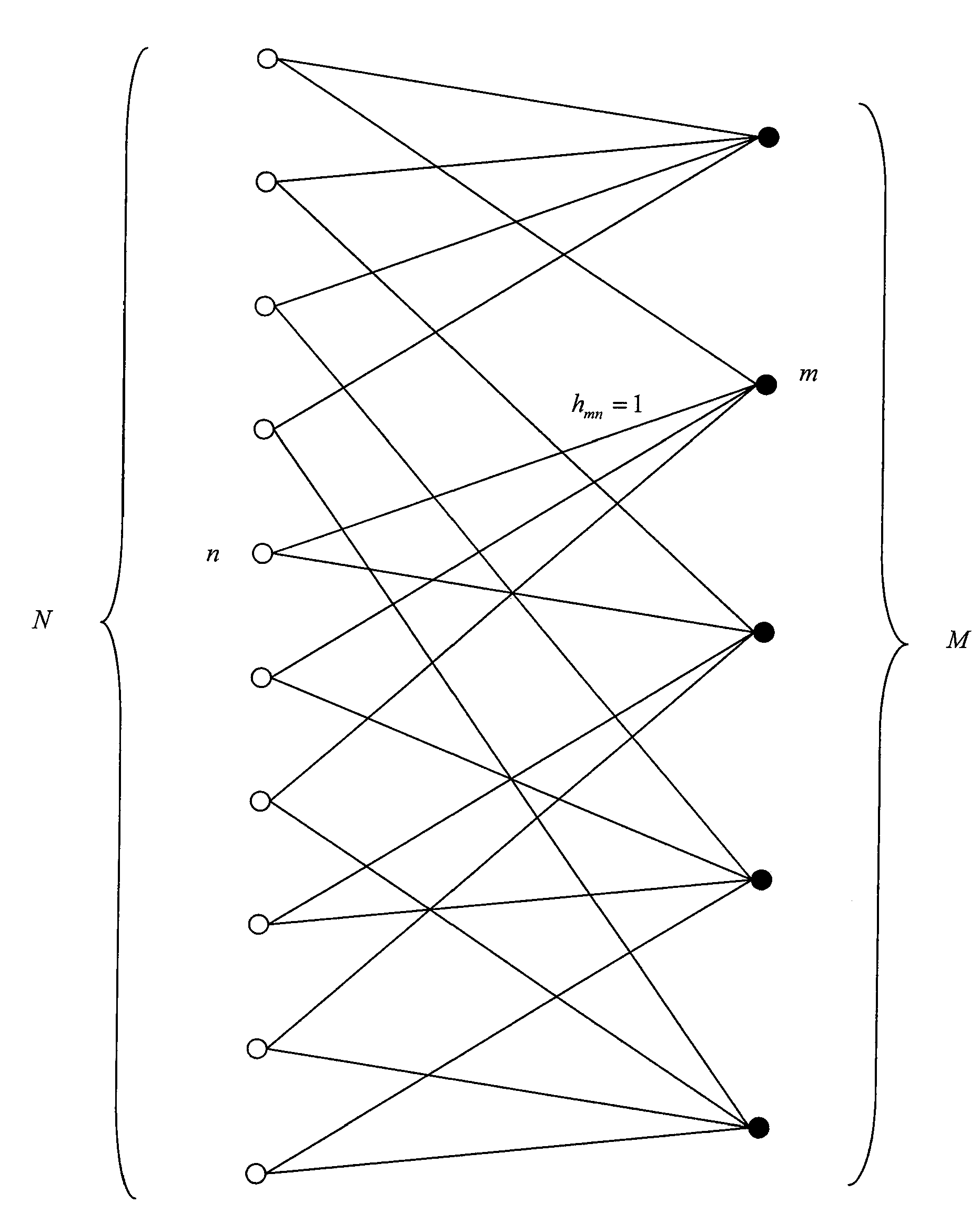
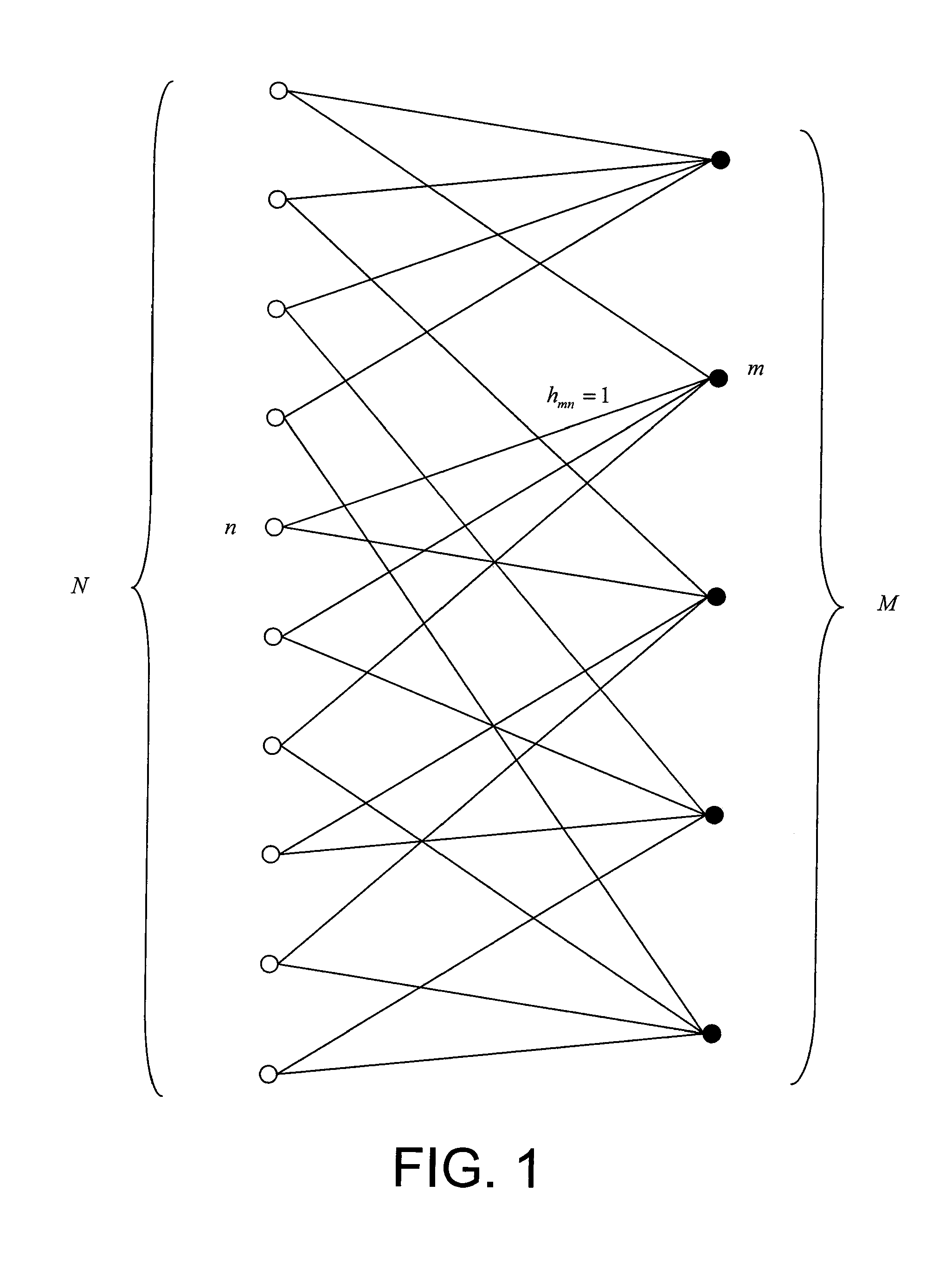
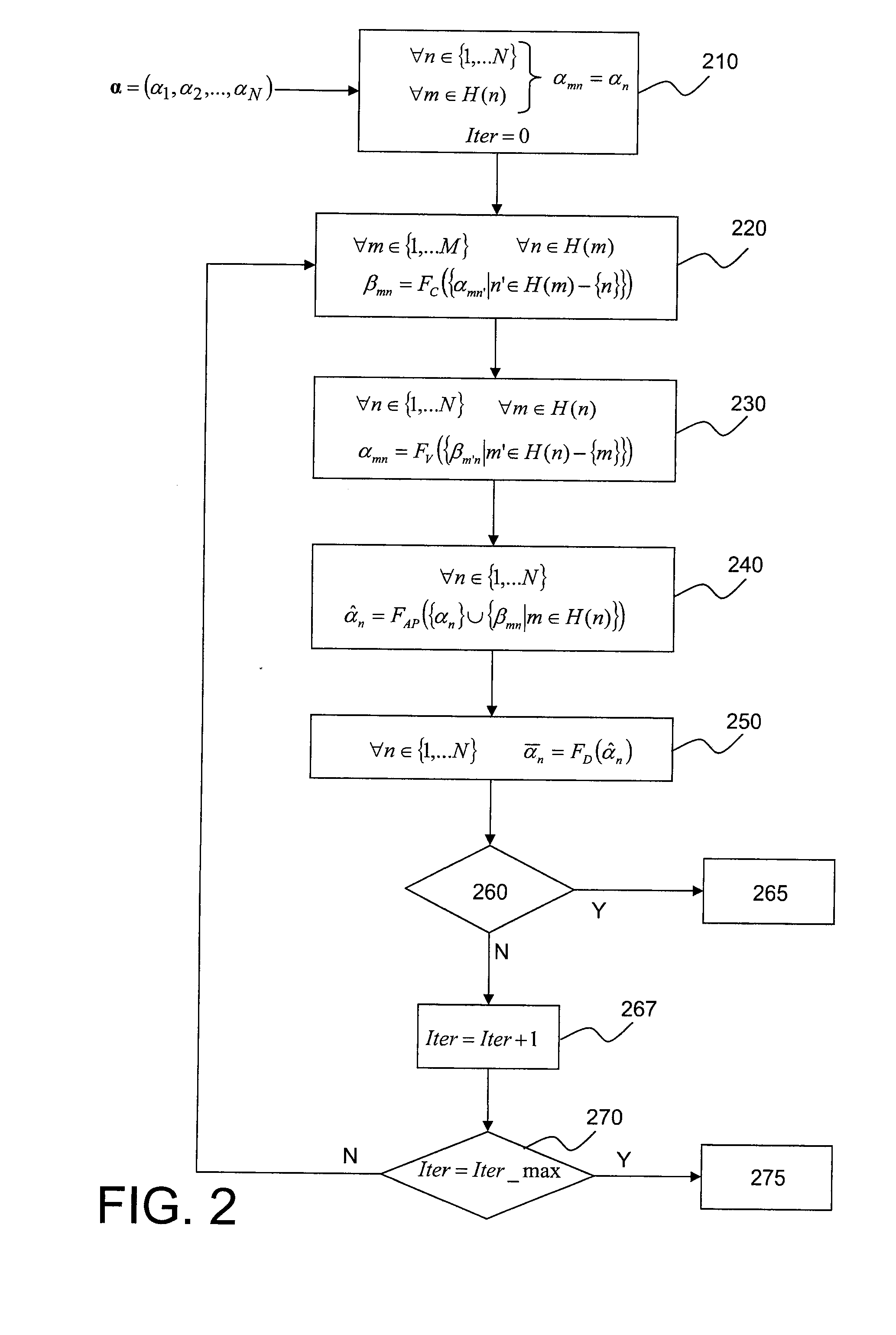
The invention relates to an iterative method by message passing for decoding of an error correction code that can be displayed in a bipartite graph comprising a plurality of variable nodes and a plurality of check nodes. For each iteration in a plurality of decoding iterations of said method:variable nodes or check nodes are classified (720) as a function of the corresponding degrees of reliability of decoding information available in the neighbourhoods (Vn(d),Vm(d)) of these nodes, a node with a high degree of reliability being classified before a node with a low degree of reliability;each node thus classified (725) passes at least one message (αmn,βmn) to an adjacent node, in the order defined by said classification.The invention also relates to a computer program designed to implement said decoding method.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
LDPC decoder for decoding a low-density parity check (LDPC) codewords
InactiveCN1713530AImprove performanceError correction/detection using multiple parity bitsChannel parameterTheoretical computer science
As a result of transmitting a low-density parity-check (LDPC) codeword (b) having a number (N) of codeword bits consisting of K information bits and N parity bits, for the received An LDPC decoder for decoding a codeword (Y), comprising: a memory for receiving codeword bits of a noisy codeword (Y), storing the codeword bits from the received noisy codeword (Y) and from The a priori estimate (Qv) of the predetermined value of the predetermined parameter of the communication channel; the generalized check node processing unit, iteratively calculates the messages on the edge of the bipartite graph according to the serial scheduling, and in each iteration, the check for the bipartite graph Node (C), all adjacent variable nodes (V) connected to the check node (C), calculate the input message (Qvc) from the adjacent variable node (V) to the check node (C) and from Output message (RCV) from a check node (C) to a neighboring variable node (V).
Owner:INFINEON TECH AG
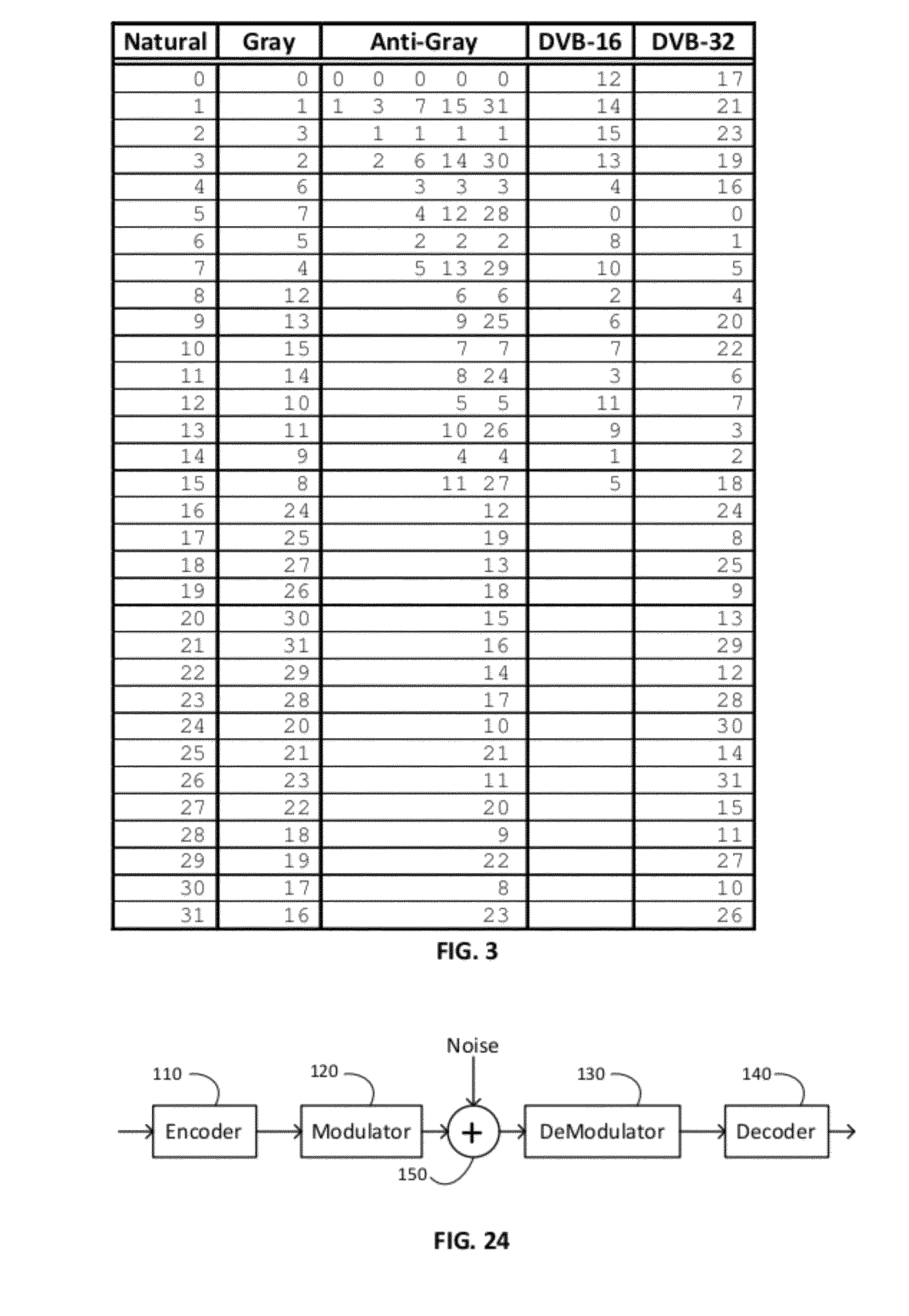
Method and device for controlling the decoding of a LDPC encoded codeword, in particular for DVB-S2 LDPC encoded codewords
ActiveUS8010869B2Sufficient energyEnough timeCode conversionCoding detailsDigital dataComputer science
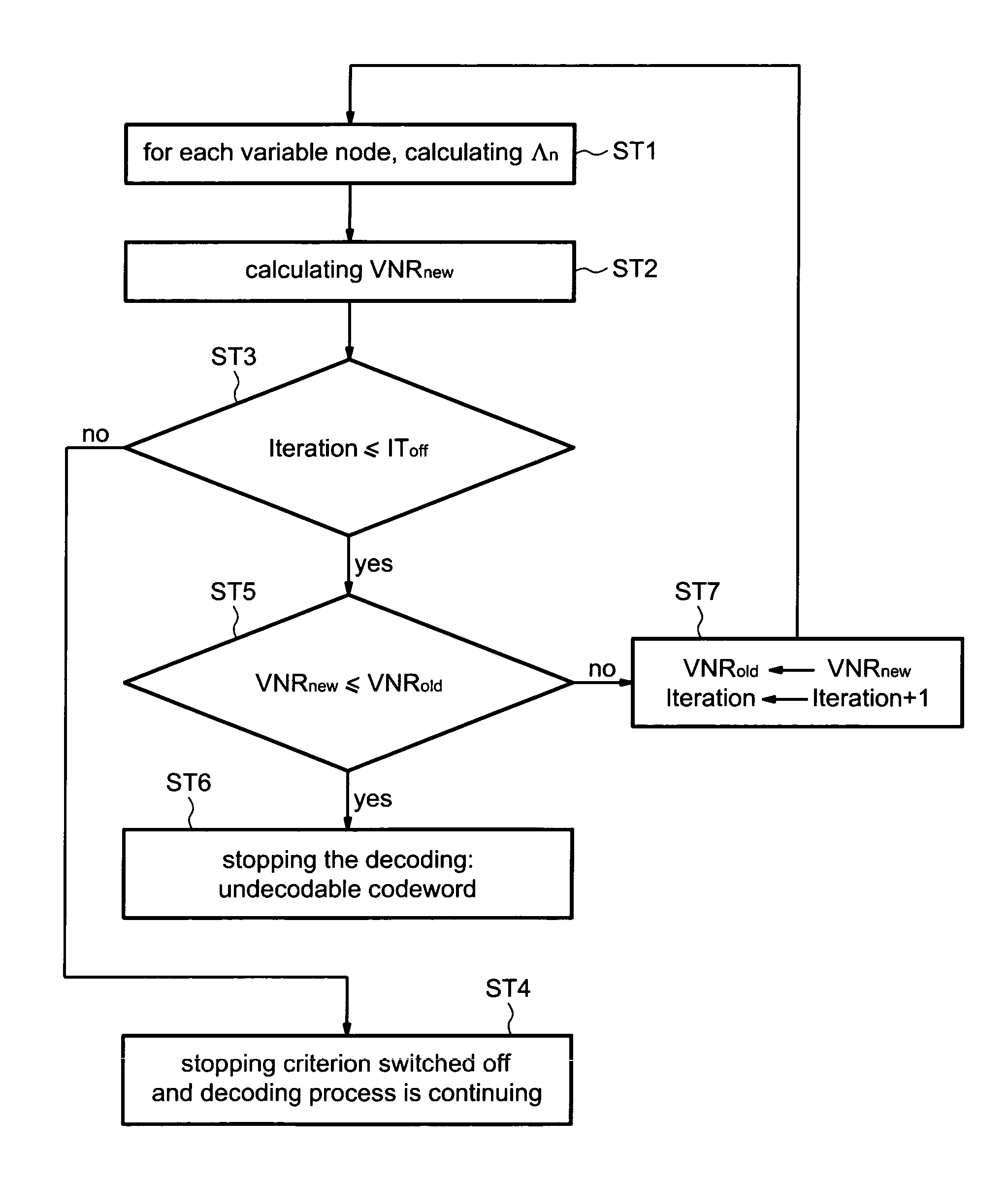
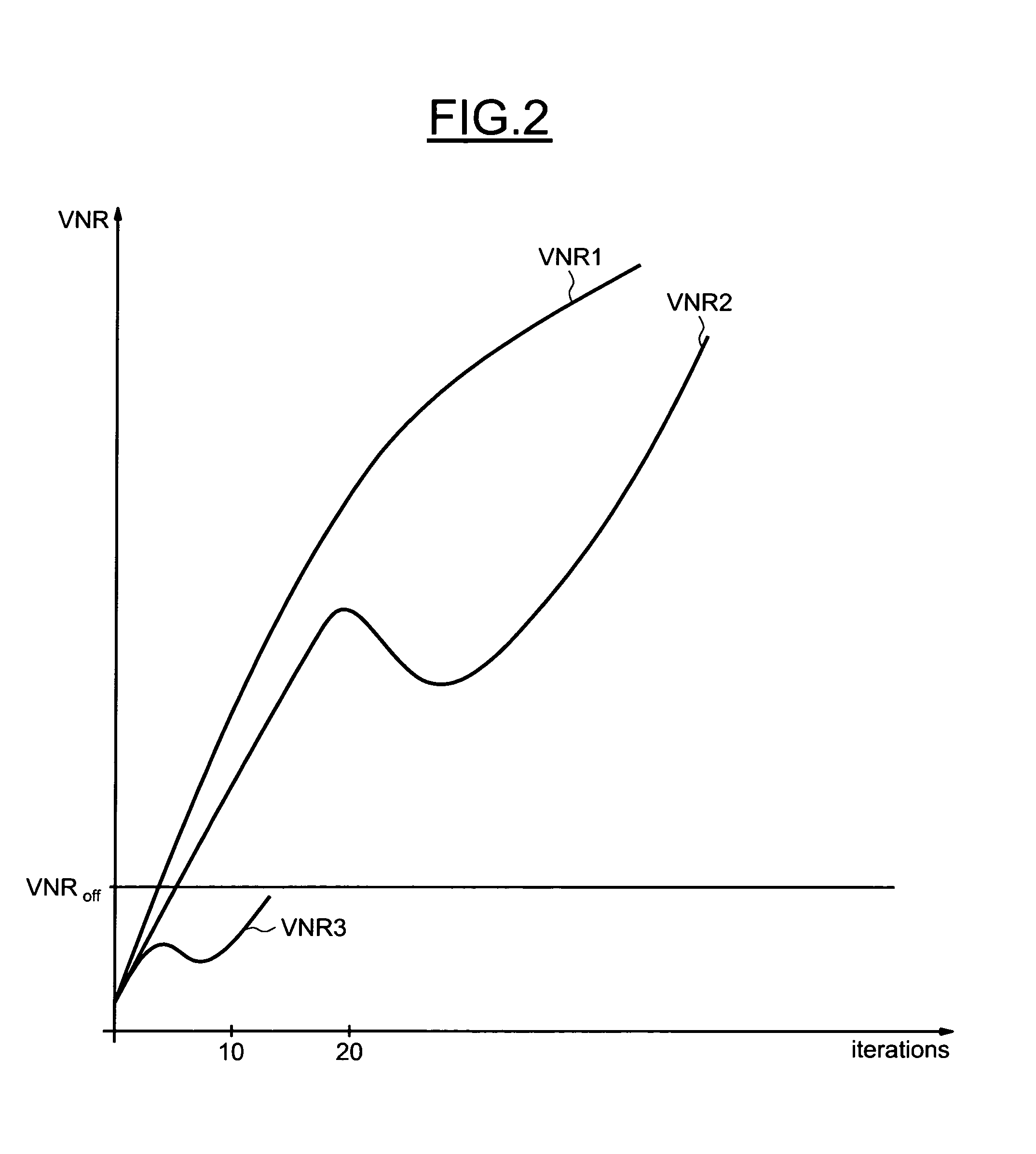
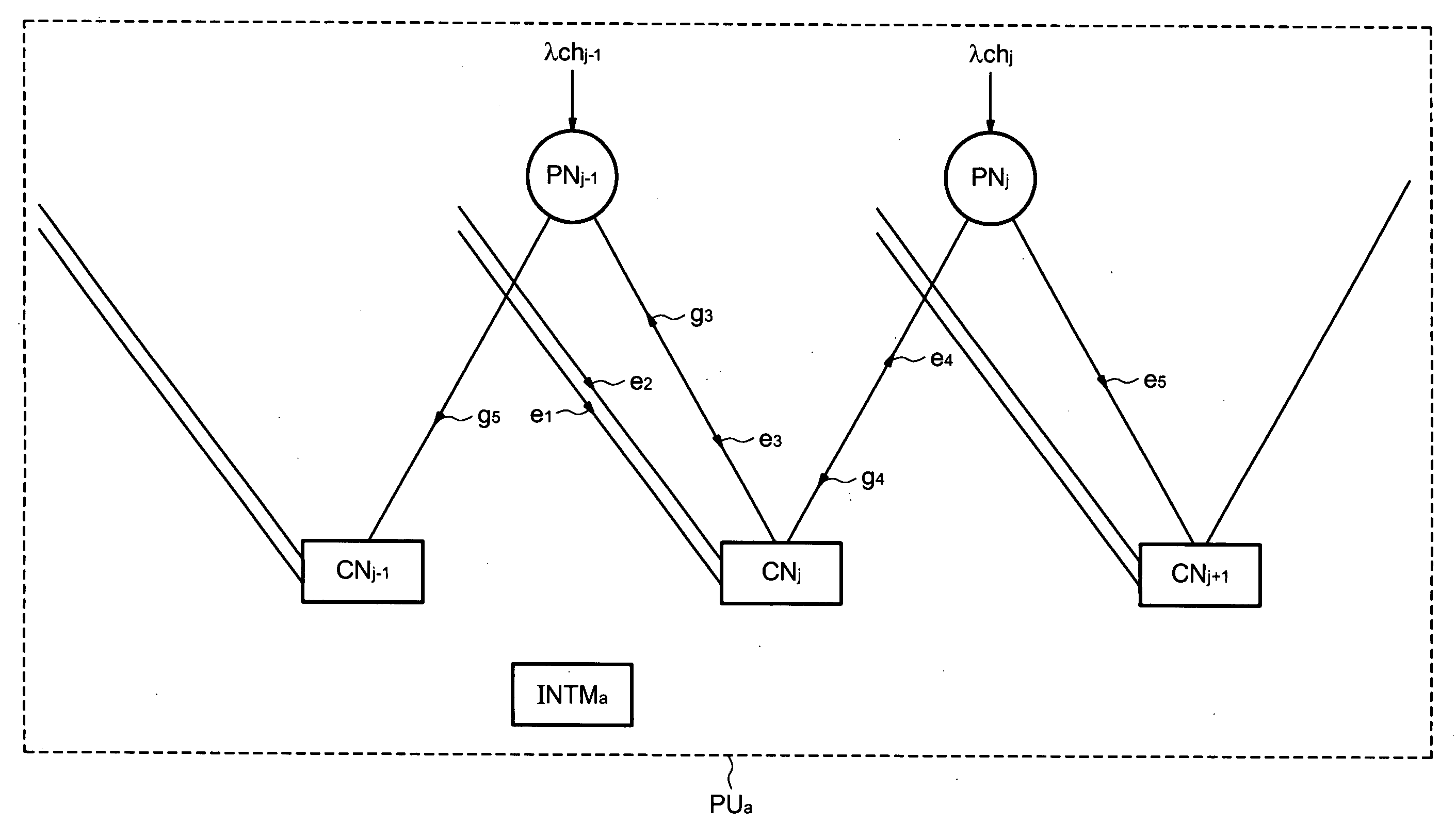
This is a method for controlling the decoding of a LDPC encoded codeword composed of several digital data, said LDPC code being represented by a bipartite graph between check nodes (CN1) and variable nodes (VNi). Said method comprises updating messages exchanged iteratively between variable nodes (VN1) and check nodes (CN1). Said method comprises, at each iteration, calculating for each variable node a first sum (Λn) of all the incident messages (λi) received by said variable node and the corresponding digital data (λch) and calculating a second sum (VNRnew) of all the absolute values of the first sums (Λn), and stopping the decoding process if the second sum (VNRnew) is unchanged or decreases within two successive iterations and if a predetermined threshold condition is satisfied.
Owner:STMICROELECTRONICS INT NV
Personalized recommendation method based on bilateral diffusion of bipartite network
The invention discloses a personalized recommendation method based on bilateral diffusion of a bipartite network, which mainly solves the conflicts among several main arithmetic performance indexes including accuracy, diversity and novelty of a recommendation list with respect to personalized recommendation of Top-N. The method comprises the following steps: (1) constructing a user-article associated bipartite graph network, wherein it is supposed that each target user node has certain allocable resource, which can be allocated to other node objects according to a preset allocation mechanism; (2) establishing an article-article and user-user second-order correlation matrix; (3) implementing a bilateral diffusion process to obtain a user-article interest matrix; and (4) giving a recommendation list of each user with the length N to complete the recommendation of Top-N. Based on the thought of network communication, the effect of the method is obviously better than that of a classical collaborative filtering method, the long tail mining concerned by a personalized recommendation system is better realized, and the method can be used for solving the Top-N problem of personalized recommendation.
Owner:XIDIAN UNIV
Method and apparatus for providing anonymization of data
ActiveUS20110041184A1Digital data processing detailsAnalogue secracy/subscription systemsData miningData anonymization
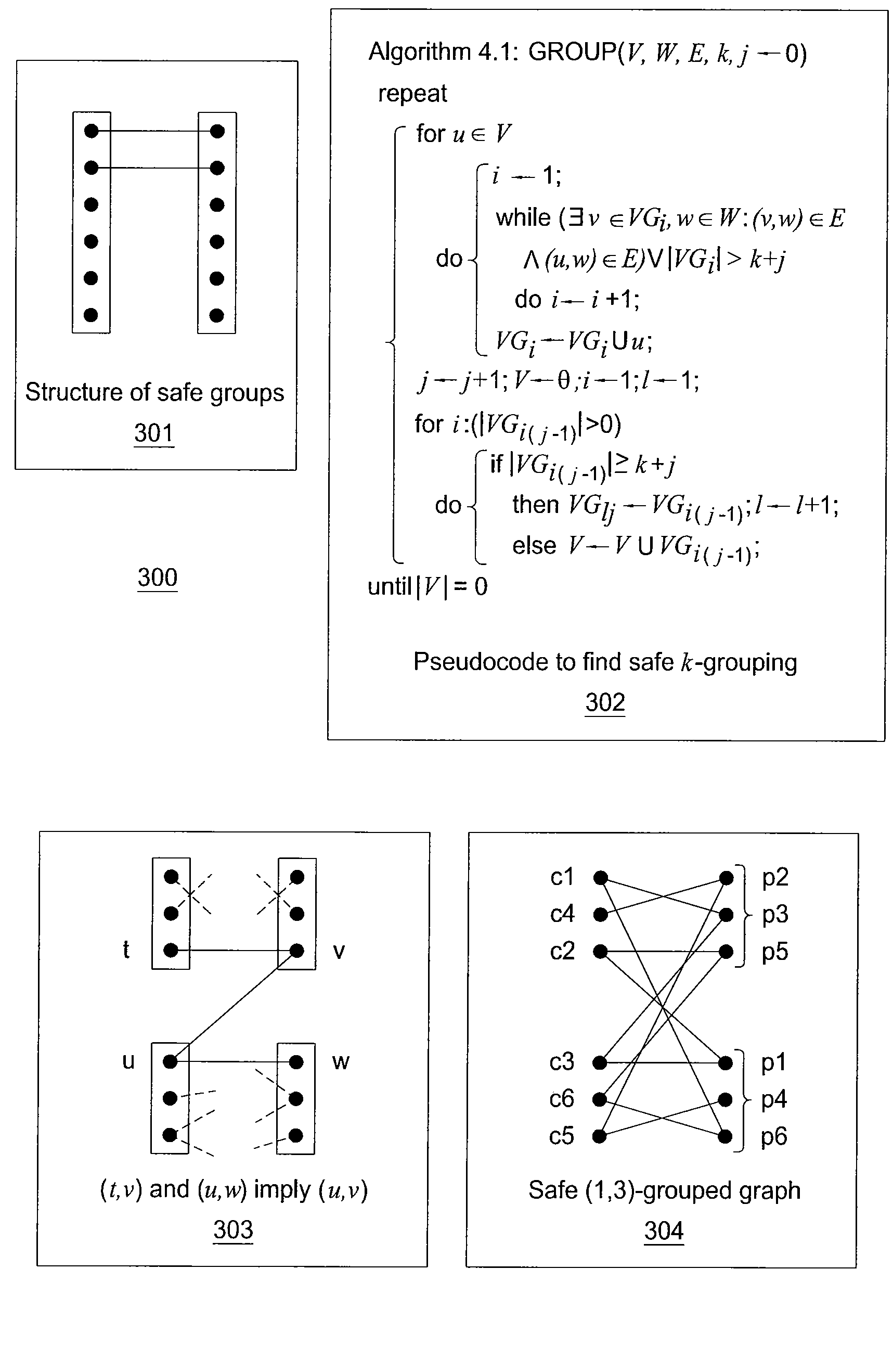
A method and apparatus for providing an anonymization of data are disclosed. For example, the method receives a request for anonymizing, wherein the request comprises a bipartite graph for a plurality of associations or a table that encodes the plurality of associations for the bipartite graph. The method places each node in the bipartite graph in a safe group and provides an anonymized graph that encodes the plurality of associations of the bipartite graph, if a safe group for all nodes of the bipartite graph is found.
Owner:AT&T INTPROP I L P
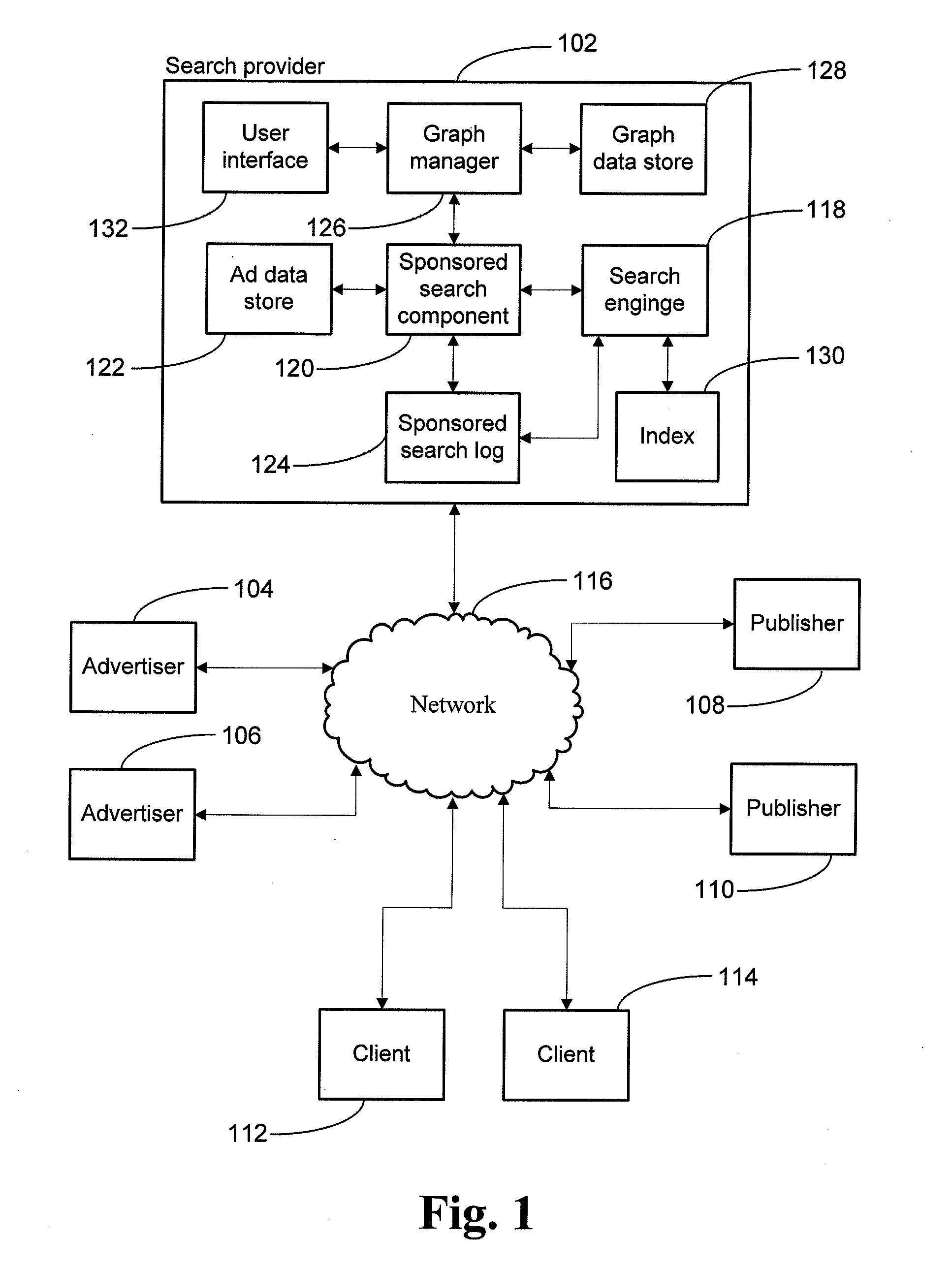
System and method for understanding relationships between keywords and advertisements
InactiveUS20080256034A1Increase competitionMarketingSpecial data processing applicationsTheoretical computer scienceBipartite graph
An impression graph is generated comprising keywords as nodes on a first side of the impression graph and advertisement listing as nodes on a second side of the impression graph, an impression relationship between a given keyword and a given advertisement listing represented by an impression edge connection. A click graph is also generated comprising keywords as nodes on a first side of the click graph and advertisement listing as nodes on a second side of the click graph, a relationship between a given keyword and a given advertisement listing represented by a click edge connection. A mapping function is applied to calculate one or more weights for a given edge in the impression graph and the click graph and the one or more edge weights, the impression graph and the click graph are transformed into a unified bipartite graph.
Owner:OATH INC
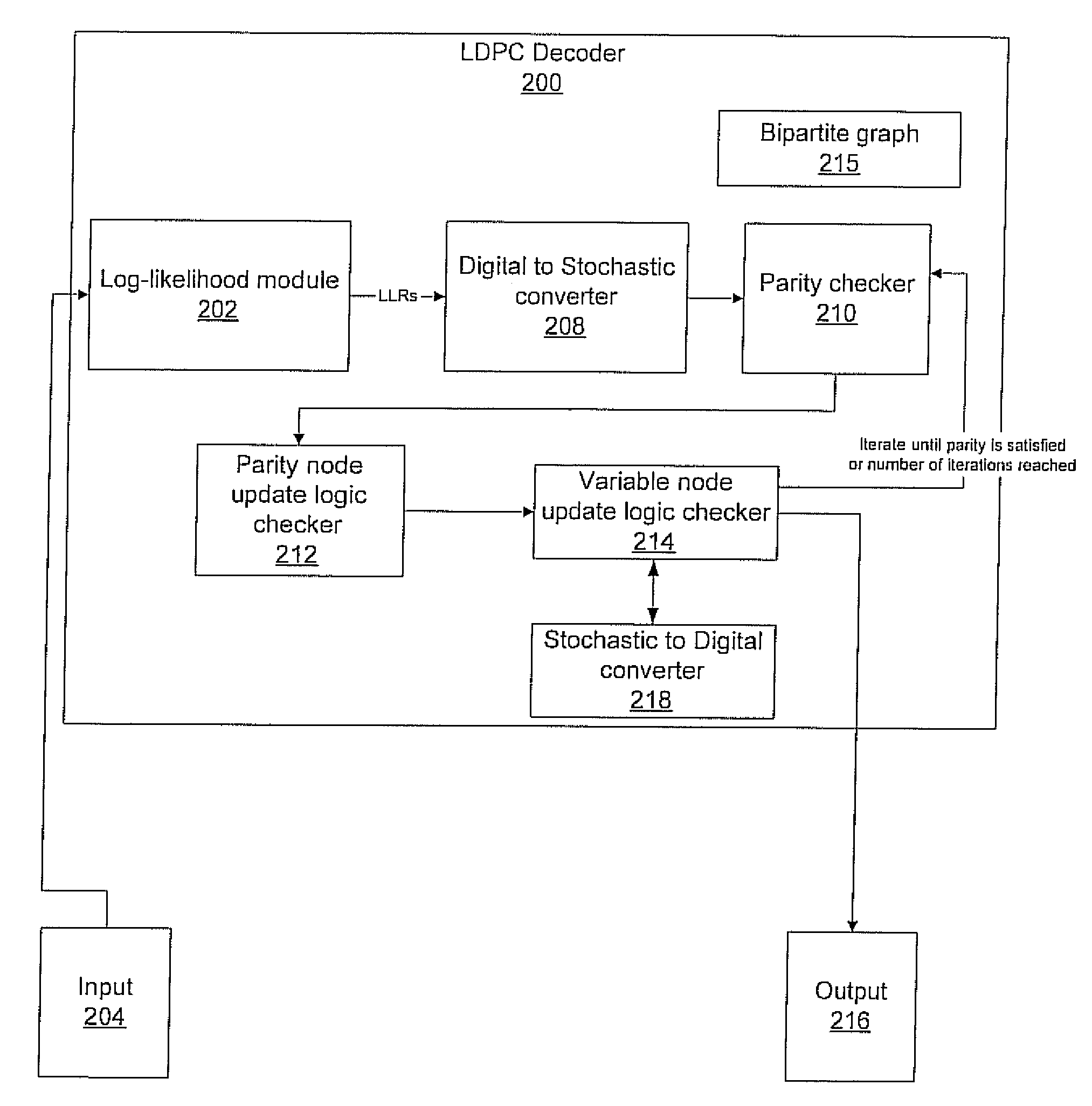
LDPC codes and stochastic decoding for optical transmission
ActiveUS20090259912A1Lack of operationError correction/detection using multiple parity bitsCode conversionParity-check matrixTheoretical computer science
A method for error correction and a decoder using low density parity check (LDPC) codes includes initializing extrinsic probability information between variable nodes and check nodes in a bipartite graph including generating a Bernoulli sequence according to a probability of a bit having a value one. Parity checking is performed in accordance with a parity check equation. If the parity check equation is not satisfied, then extrinsic information is updated in check nodes from variable nodes using a parity node update logic circuit in a first half iteration, extrinsic information is updated in variable nodes from check nodes using a variable node update logic circuit in a second half iteration, and the variable nodes are updated with a probability based upon the extrinsic information passed between check nodes and variable nodes wherein the probability represents a likelihood that an ith bit is a one. Information bits are passed when the parity check equation is satisfied or a predetermined number of iterations has been reached.
Owner:NEC CORP
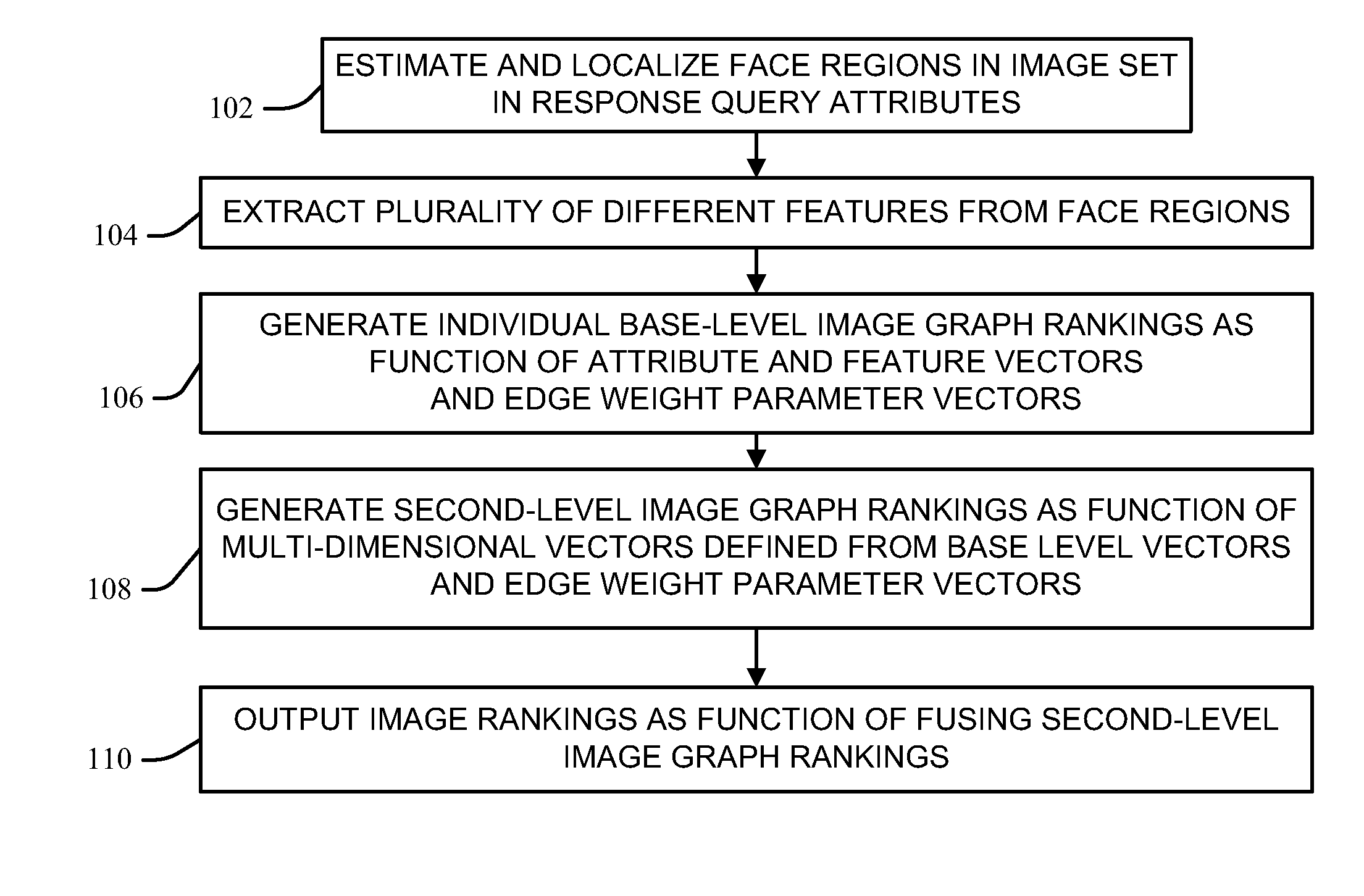
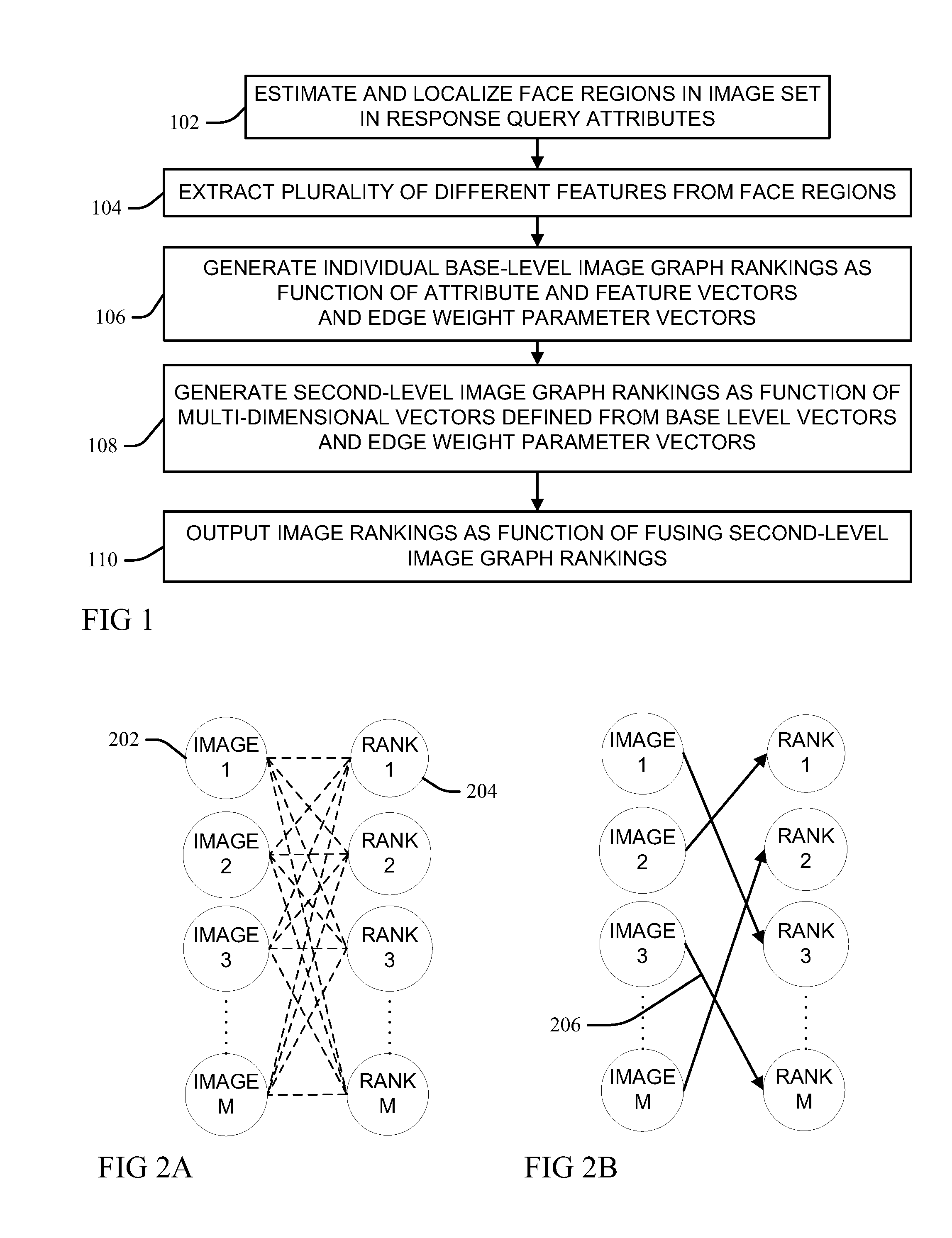
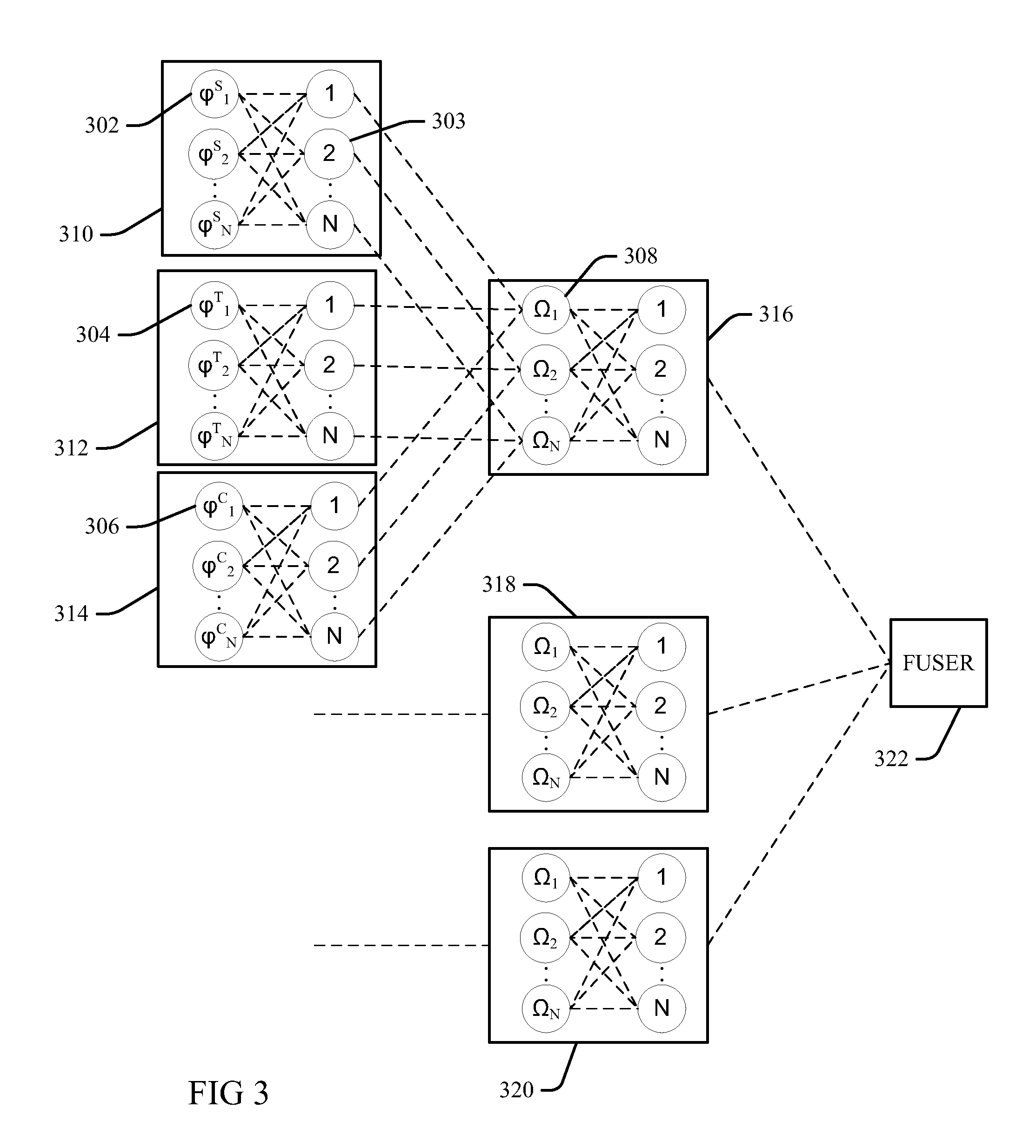
Hierarchical ranking of facial attributes
InactiveUS20120233159A1Data processing applicationsDigital data processing detailsFeature vectorFacial region
In response to a query of discernible facial attributes, the locations of distinct and different facial regions are estimated from face image data, each relevant to different attributes. Different features are extracted from the estimated facial regions from database facial images, which are ranked in base layer rankings by matching feature vectors in a bipartite graph to a base layer ranking sequence as a function of edge weights parameterized by an associated base layer parameter vector. Second-layer rankings define second-layer attribute vectors as bilinear combinations of the base-layer feature vectors and associated base layer parameter vectors for common attributes, which are matched in a bipartite graph to a second-layer ranking sequence as a function of edge weights parameterized by associated second-layer parameter vectors. The images are thus ranked for relevance to the query as a function of fusing the second-layer rankings.
Owner:IBM CORP
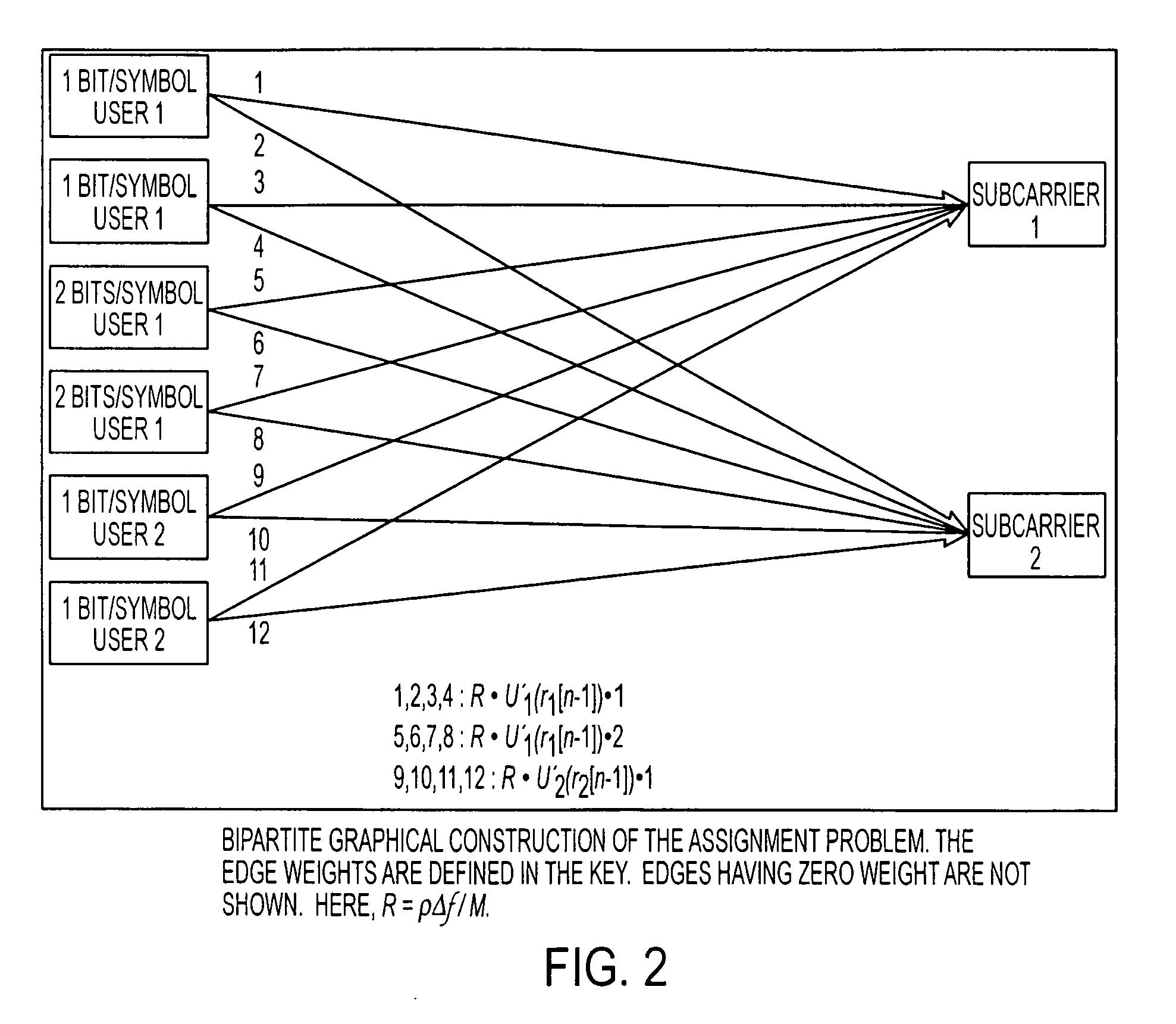
Cross layer network optimization for OFDMA systems using message passing algorithm
InactiveUS20090110089A1Maximize fairnessMaximize throughputTransmission path divisionCriteria allocationChannel state informationResource management
A method determines channel state information of a channel of a wireless network. Each of the wireless devices is configured to operate over the wireless network. An allocation of available transmission resources is performed according to a utility-based cross-layer resource management framework that transforms a utility function into an equivalent bipartite graph to concurrently maximize throughput and fairness in the resource allocation.
Owner:RPX CORP
Historical behavior baseline modeling and anomaly detection in machine generated end to end event log
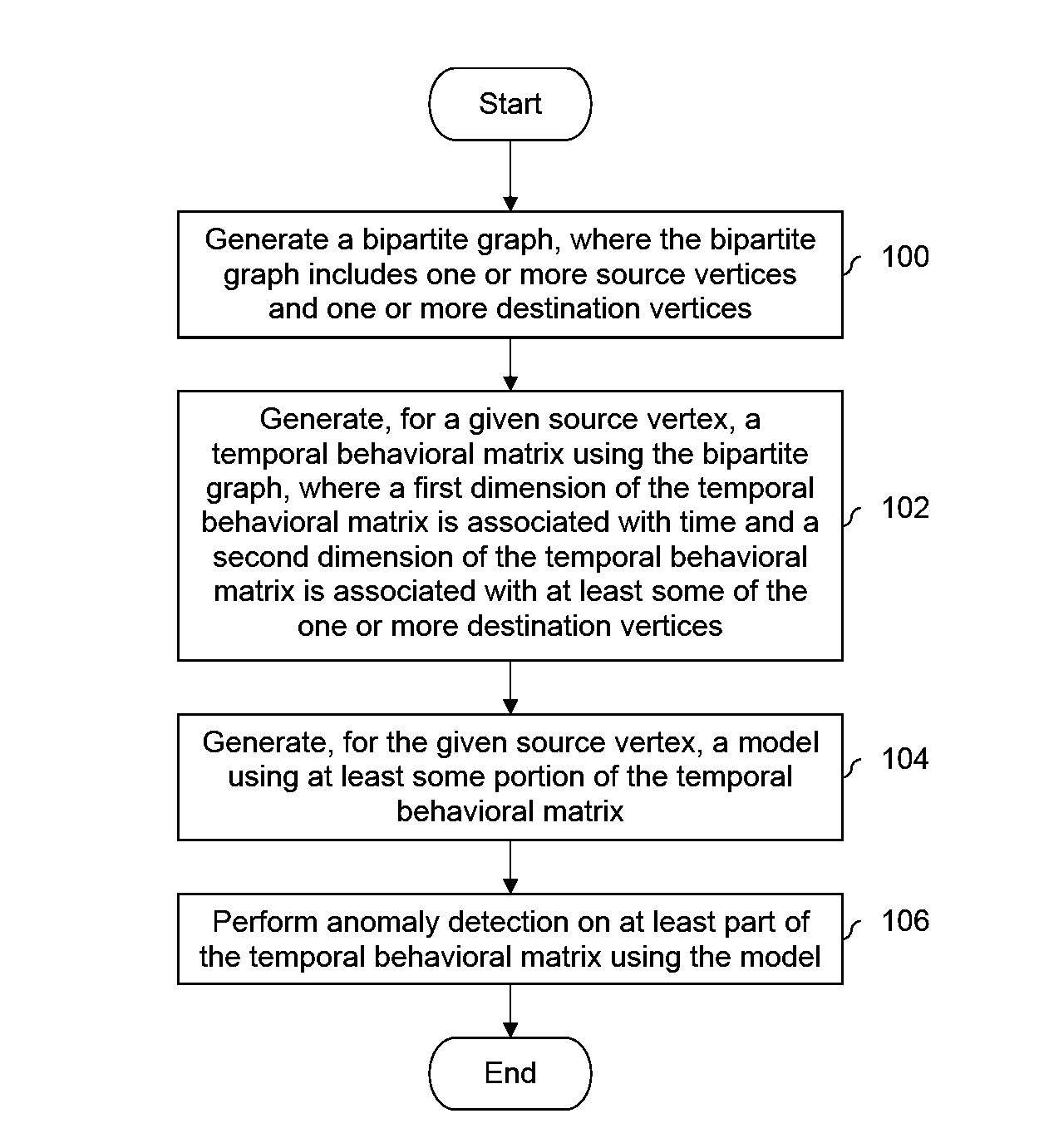
ActiveUS9189623B1Platform integrity maintainanceTransmissionAnomaly detectionTheoretical computer science
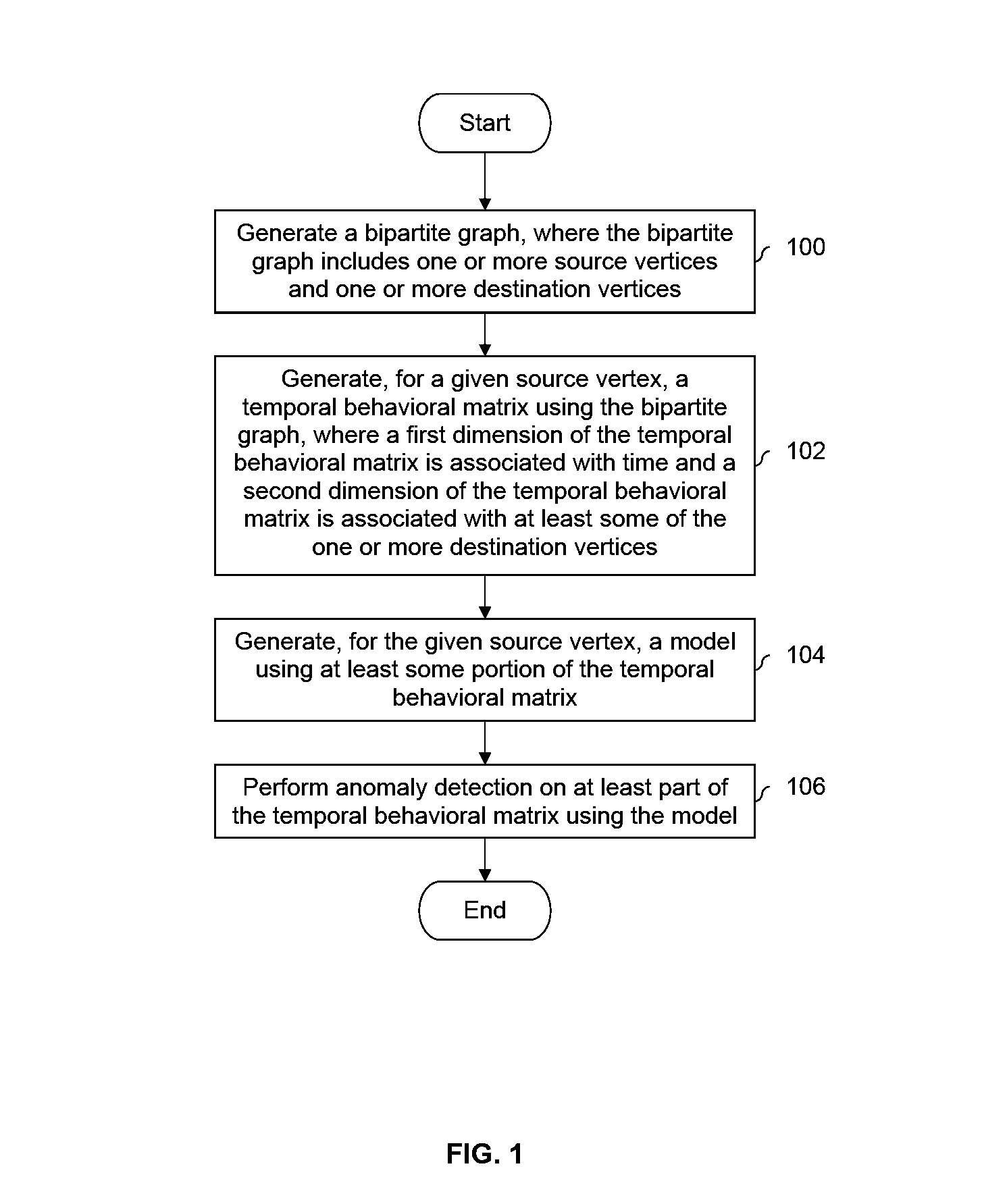
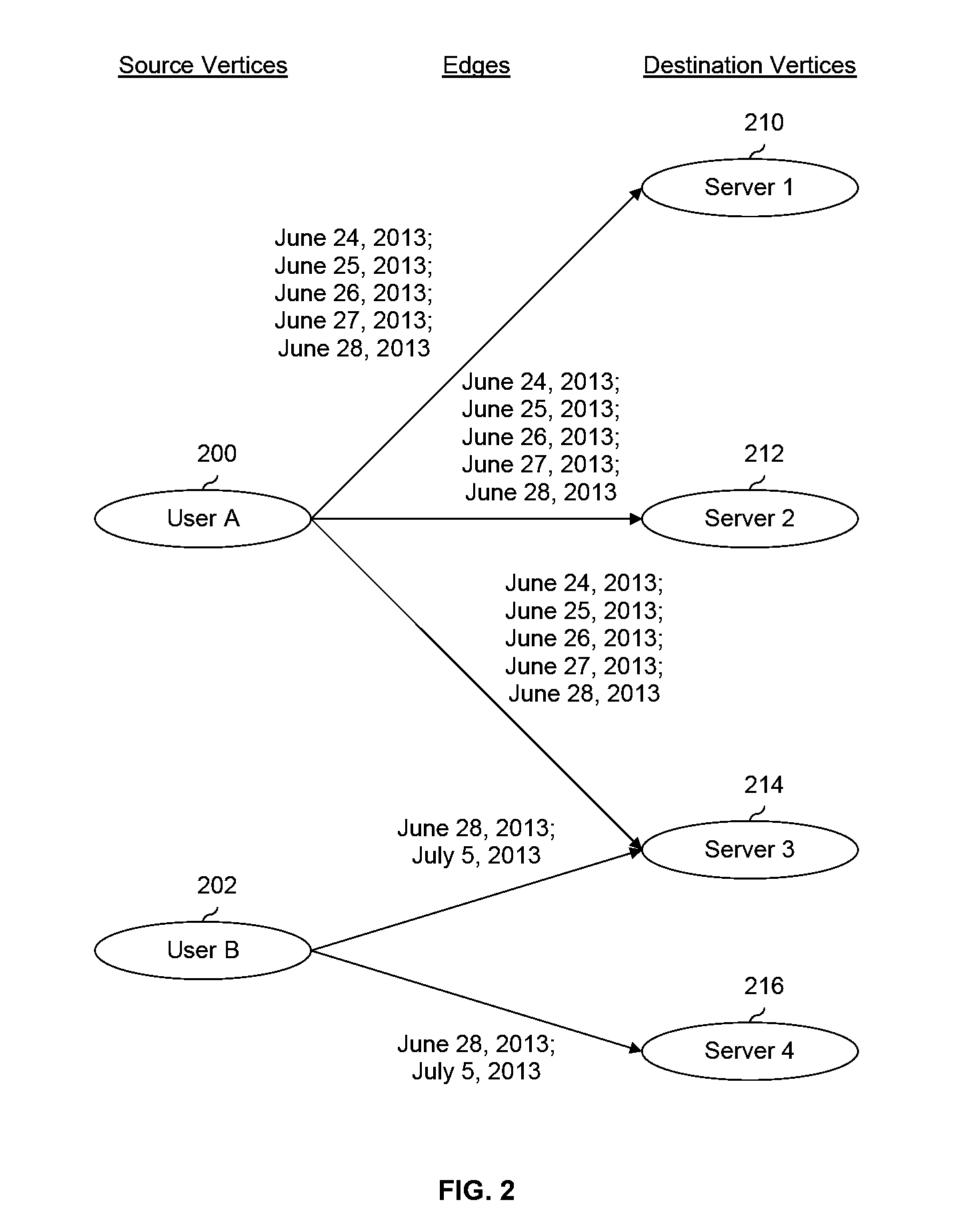
A bipartite graph is generated which includes one or more source vertices and one or more destination vertices. For a given source vertex, a temporal behavioral matrix is generated using the bipartite graph where a first dimension of the temporal behavioral matrix is associated with time and a second dimension of the temporal behavioral matrix is associated with at least some of the one or more destination vertices. For the given source vertex, a model is generated using at least some portion of the temporal behavioral matrix. Anomaly detection is performed on at least part of the temporal behavioral matrix using the model.
Owner:EMC IP HLDG CO LLC
Systems and methods for organizing and analyzing audio content derived from media files
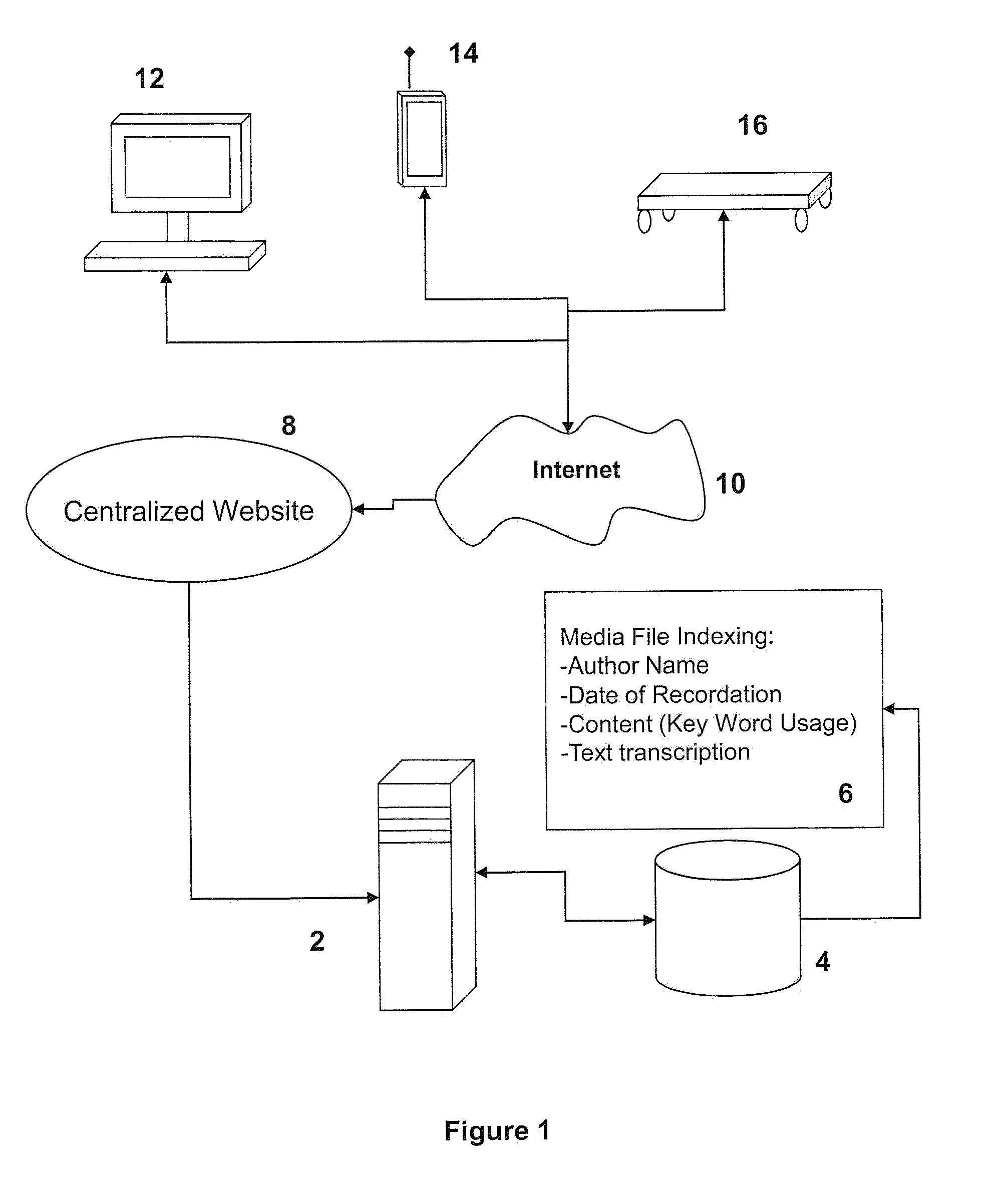
ActiveUS20160004773A1Efficiently convey relevancyWeb data indexingDigital data processing detailsFile systemWorld Wide Web
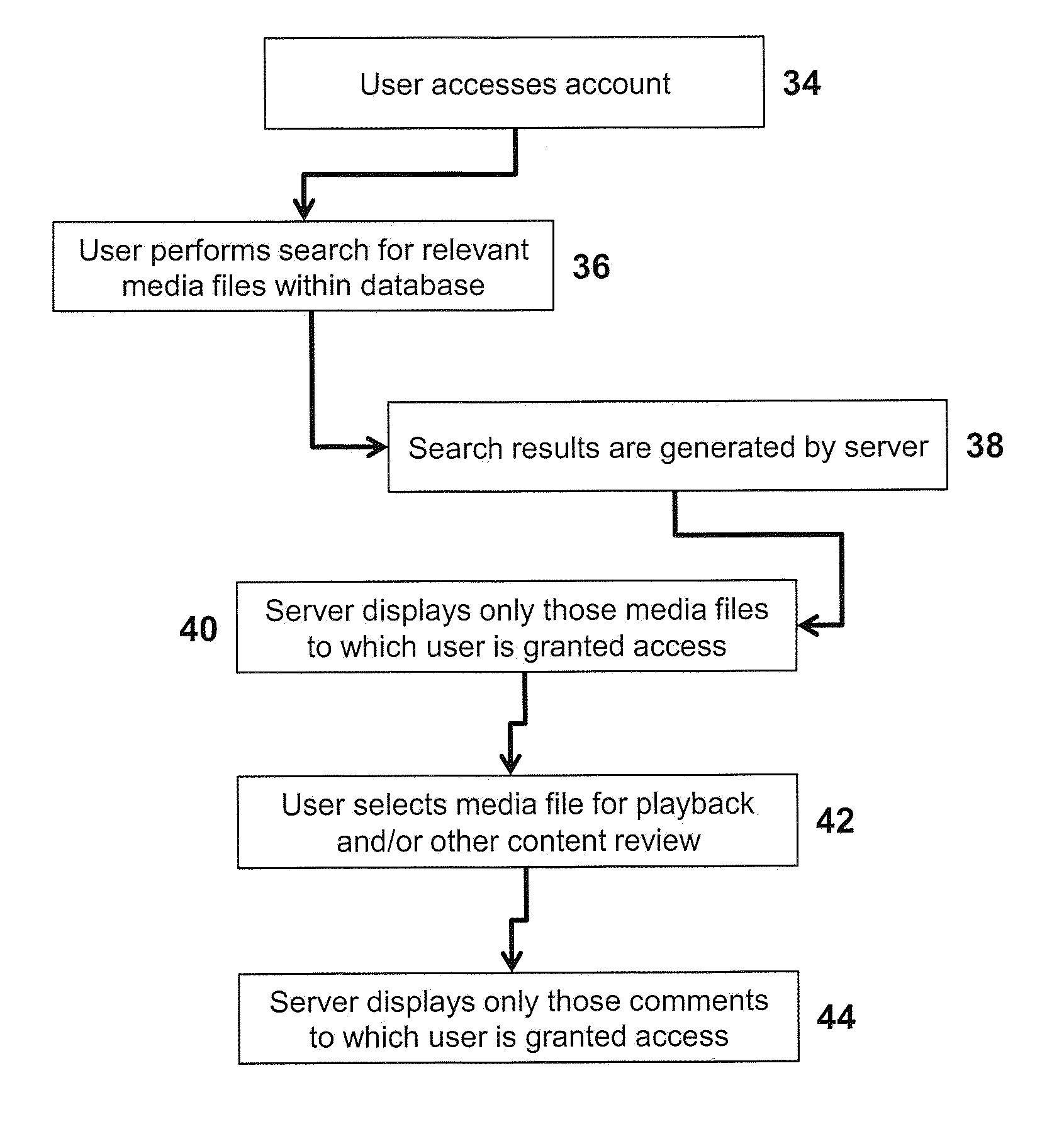
Systems for receiving, analyzing, and organizing audio content contained within a plurality of media files are disclosed. The systems generally include a server that is configured to receive, index, and store a plurality of media files, which are received by the server from a plurality of sources, within at least one database in communication with the server. In addition, the server is configured to make one or more of the media files accessible to and searchable by, one or more persons other than the original sources of such media files. Still further, the server may be configured to organize audio content included within each of the plurality of media files into bipartite graphs; segment media files into parts that exhibit similar attributes; extract and present meta data to a user that pertain to each media file; and employ multi-variable ranking methods to prioritize media file search results.
Owner:VOICEBASE
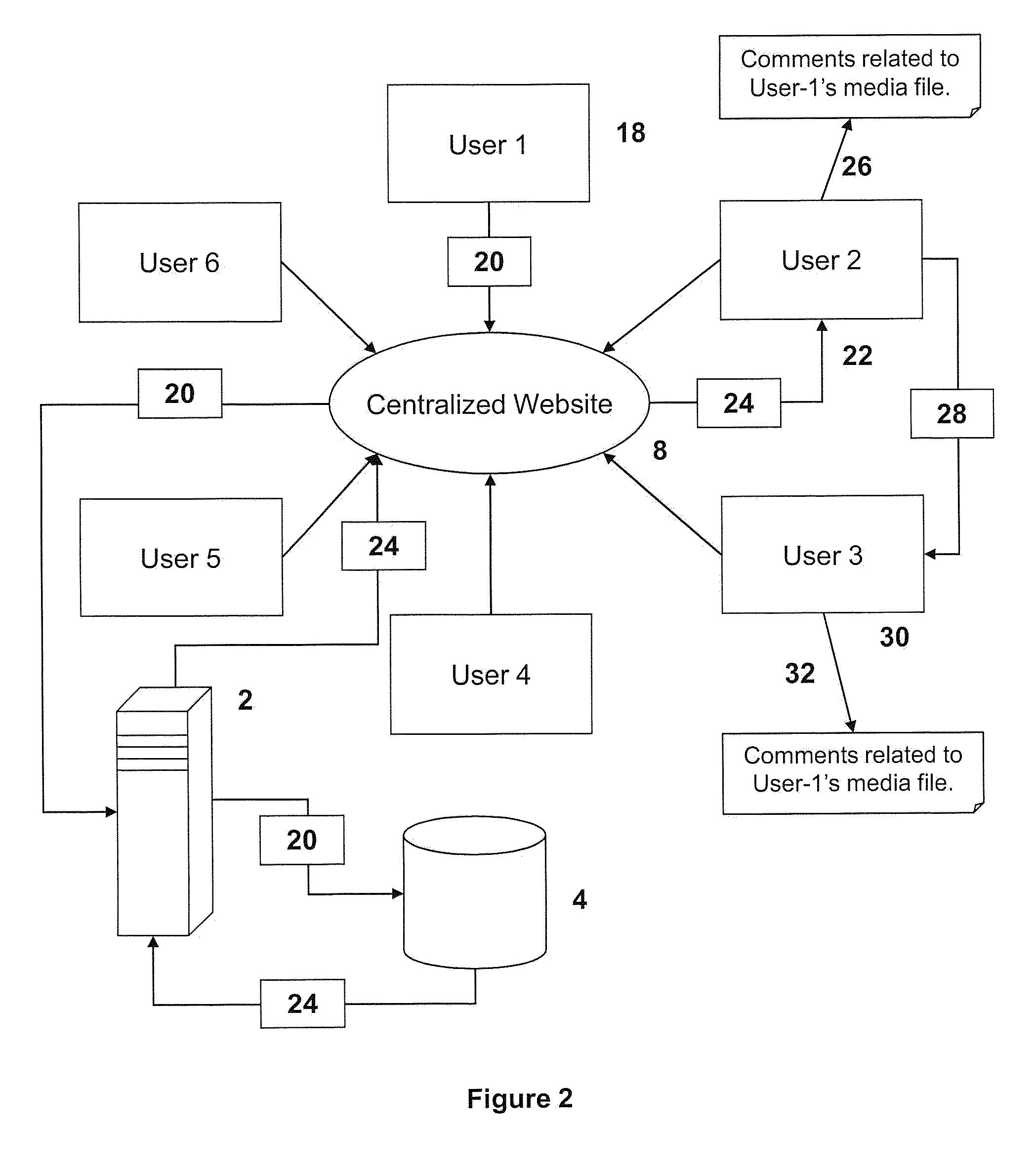
Identifying malicious web infrastructures
Identifying malicious servers is provided. Malicious edges between server vertices corresponding to visible servers and invisible servers involved in network traffic redirection chains are determined based on determined graph-based features within a bipartite graph corresponding to invisible server vertices involved in the network traffic redirection chains and determined distance-based features corresponding to the invisible server vertices involved in the network traffic redirection chains. Malicious server vertices are identified in the bipartite graph based on the determined malicious edges between the server vertices corresponding to the visible servers and invisible servers involved in the network traffic redirection chains. Access by client devices is blocked to malicious servers corresponding to the identified malicious server vertices in the bipartite graph.
Owner:IBM CORP
Method and device for decoding DVB-S2 LDPC encoded codewords
ActiveUS20060206779A1Reduce in quantityImprove communication performanceCode conversionCoding detailsDVB-S2Distributed computing
The method is for decoding an LDPC encoded codeword, the LDPC code being represented by a bipartite graph between check nodes and variable nodes including first variable nodes and second variable nodes connected to the check nodes by a zigzag connectivity. The method includes updating messages exchanged iteratively between variable nodes and check nodes including a first variable processing phase during which all the messages from the first variable nodes to the check nodes are updated and a check nodes processing phase during which all the messages from the check nodes to the first variable nodes are updated. The check nodes processing phase further includes updating all the messages from the second variable nodes to the check nodes, and directly passing an updated message processed by a check node to the next check node through the zigzag connectivity.
Owner:STMICROELECTRONICS INT NV
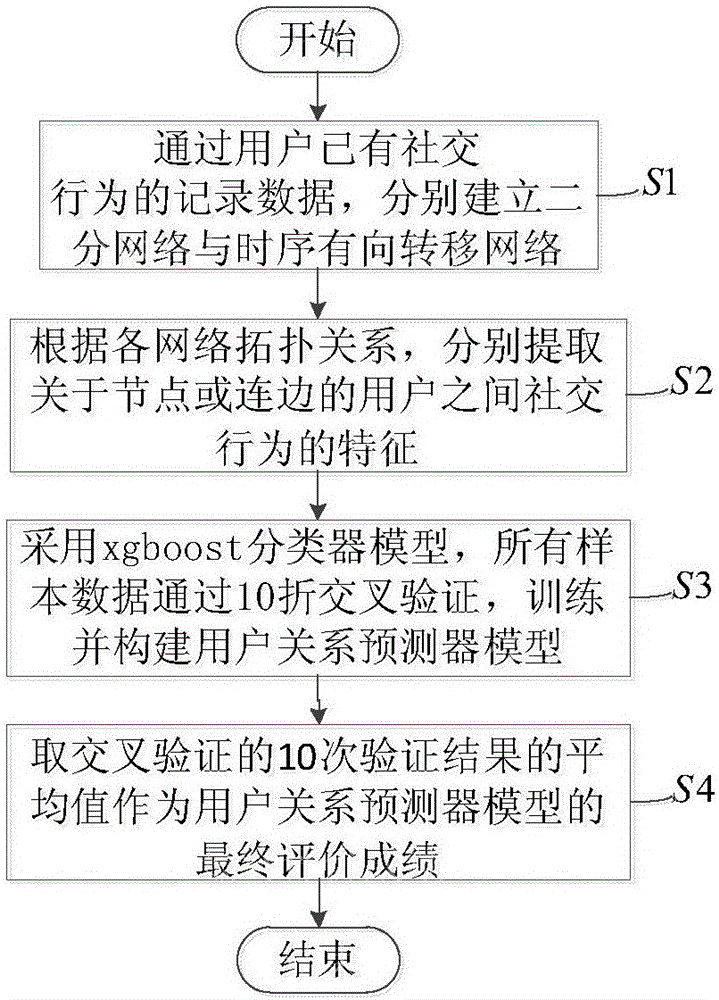
Friend relation mining method based on user behaviors in social network
ActiveCN106326345AGood forecastData processing applicationsCharacter and pattern recognitionEvaluation resultNODAL
The invention discloses a friend relation mining method based on user behaviors in a social network. The friend relation mining method comprises the following steps: (1) respectively establishing a bipartite graph and a directed transition network, namely user-restaurant and user-taste based on record data of existing social behaviors of users; (2) respectively extracting characteristic variables for characterizing social behaviors between two users about a node or a connection side according to a network topology relation; (3) carrying out 10-fold cross-validation on all sample data by using a machine learning classifier model xgboost, training and establishing a user relation predictor model; and (4) taking the average value of 10-fold verification results as a final evaluation result of the model. The friend relation mining method is capable of mapping social behaviors of people to the network, reflecting common variables of the social behaviors by using network topology characteristics and enabling the result of the predicted friend relation between the users to be high in accuracy, and is favorable for guiding the users to find appropriate new friends and helpful for businesses to recommend more valuable information.
Owner:ZHEJIANG UNIV OF TECH
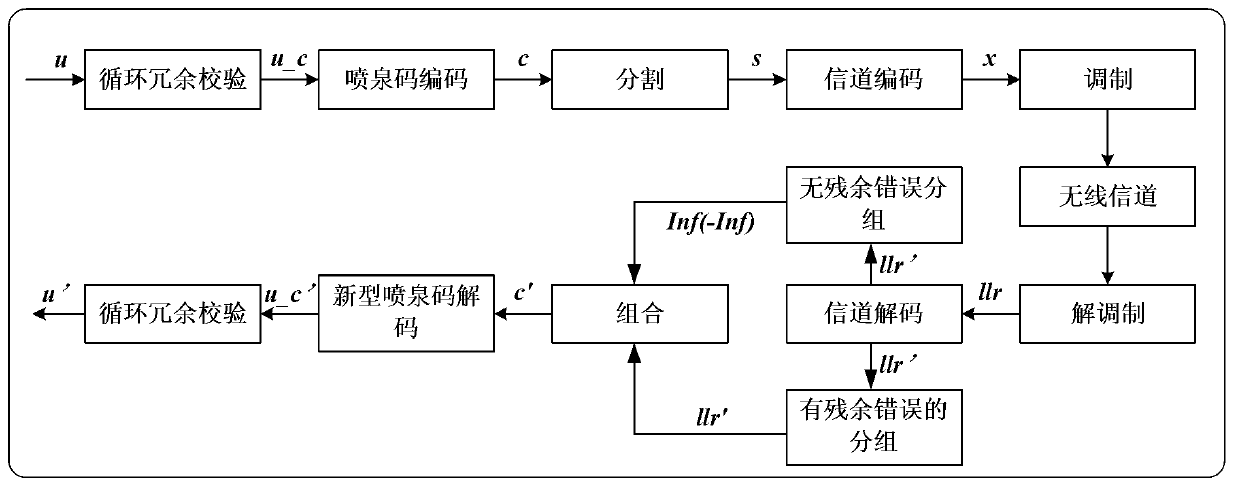
Fountain code decoding method suitable for radio broadcasting system
ActiveCN103001739AImprove spectral efficiencyReduce complexityError preventionFountain codeFrequency spectrum
The invention provides a fountain code decoding method suitable for a radio broadcasting system. The decoding method includes: step one, calcifying signals after passing a channel decoder into a group with residual errors and a group without residual errors at the receiving end; step two, for the group without the residual errors, setting a log likelihood ratio (LLR) value with a corresponding bit of zero as a large positive number (such as the positive infinity) and an LLR value with a corresponding bit of one as a small negative number (such as the negative infinity), and collecting LLR values of the group with the residual errors to participate in the decoding process of the function code; and step three, trying to decode all source symbol sets through hard iteration of a coded symbol with certain messages and updating a bipartite graph of the fountain code in a bit domain and an LLR domain during the iteration. The method has the advantages of high spectrum efficiency due to retention of the group with the residual errors and low decoding complexity.
Owner:SHANGHAI JIAO TONG UNIV
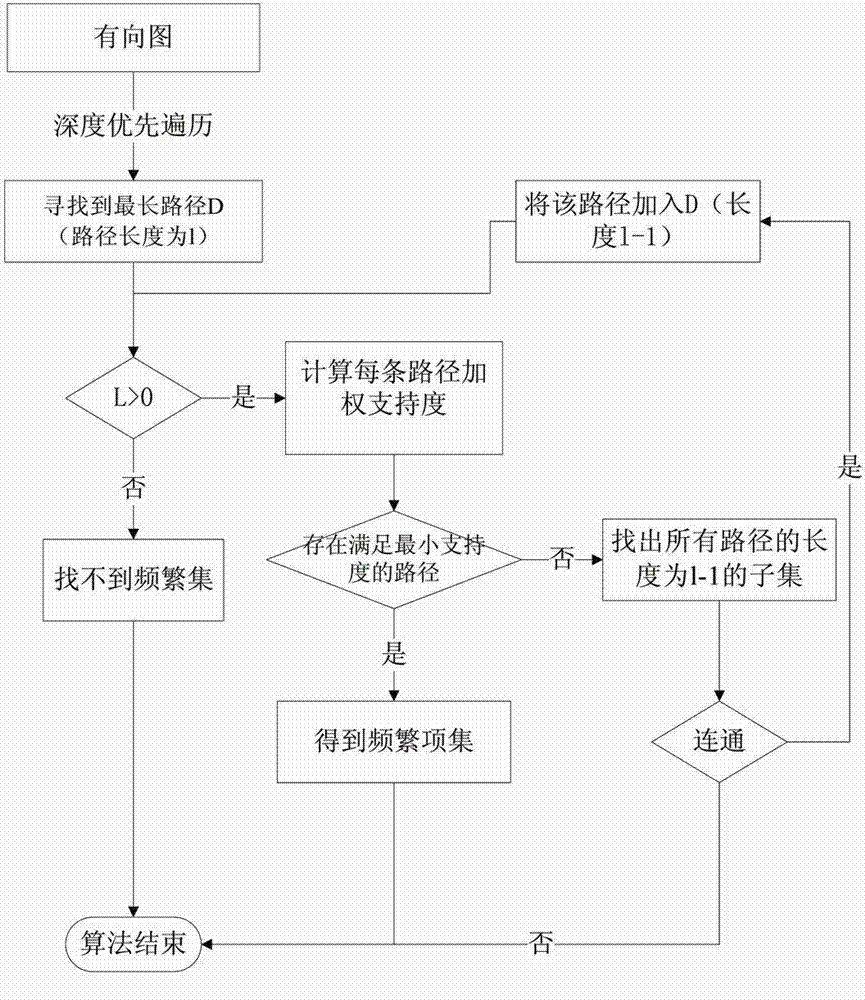
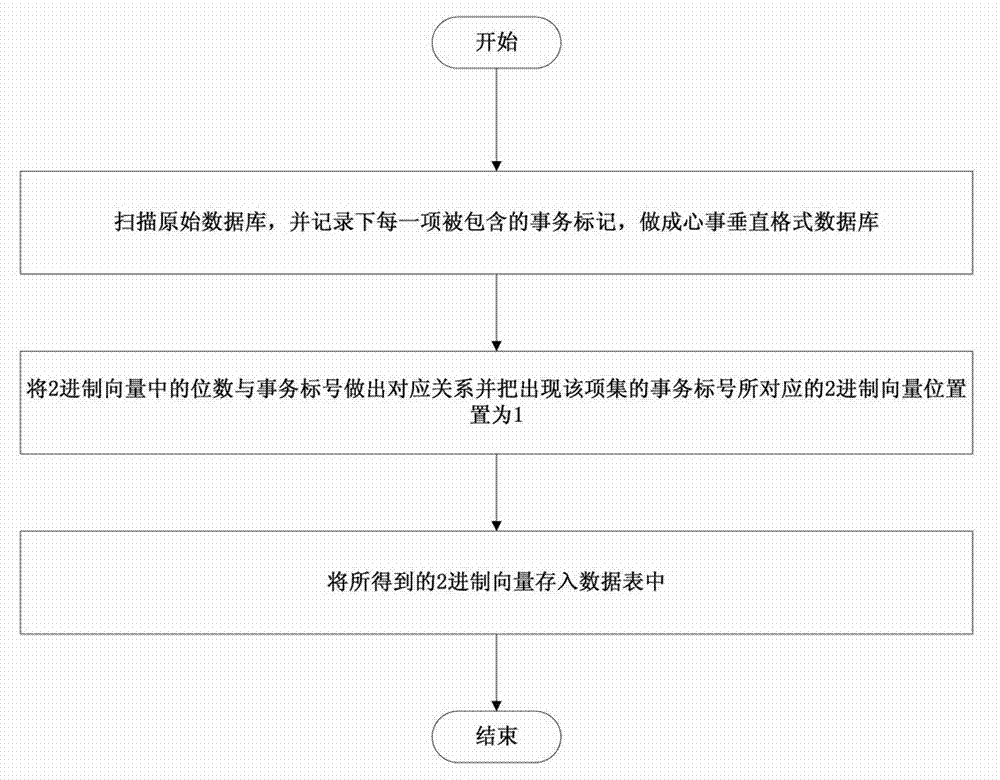
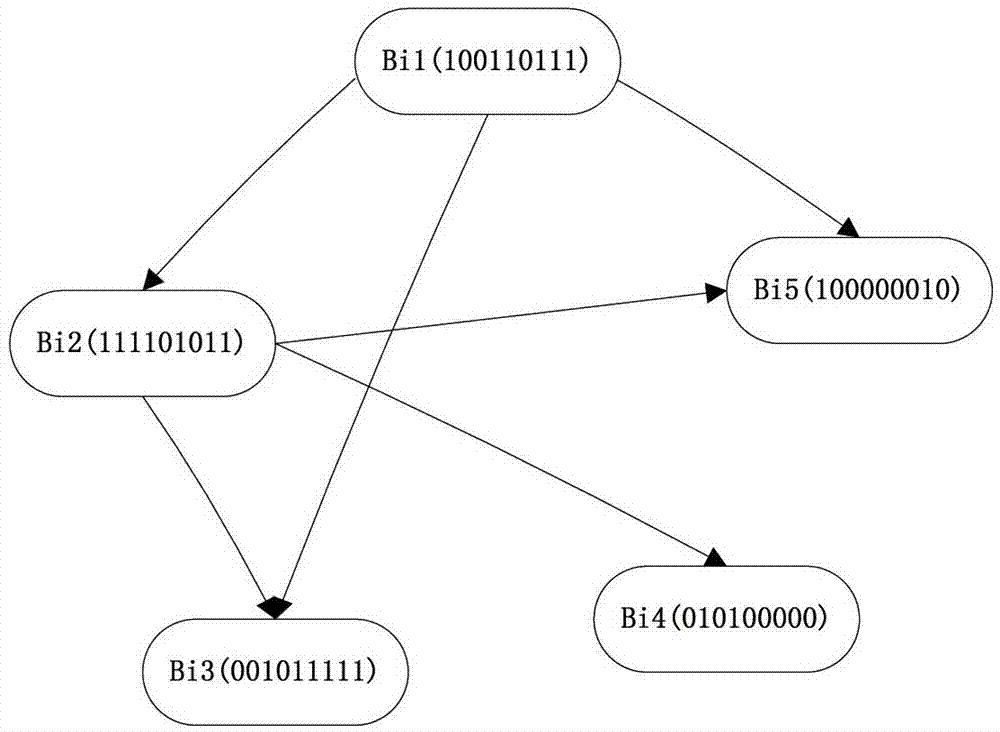
Lightning activity data statistics method based on modified Apriori algorithm
InactiveCN103593400AOvercoming Handling DeficienciesMeet needsMulti-dimensional databasesSpecial data processing applicationsGraph generationConfidence metric
The invention provides a lightning activity data statistics method based on a modified Apriori algorithm. The method includes: 1, calculating weighted support and weighted confidence; 2, performing vertical bit vector format conversion; 3, generating frequent bipartite graphs; 4, mining candidate sets. Items are imparted with proper weights according to actual needs, and the original support and the original confidence are modified into weighted support and weighted confidence which are more practical. In addition, according to the algorithm, item information is stored in the bit vector vertical data format, storage space is saved, and I / O efficiency is improved; according to the modified algorithm, based on the top-down concept, longest frequent item sets meeting the support and confidence requirements are located through frequent bipartite digraphs, and all frequent items meeting the requirements are generated according to properties of the frequent time sets. Through the application of the algorithm, the efficiency of the Apriori algorithm is improved in terms of both space and time, and the algorithm better meets the actual needs.
Owner:陕西省气象局
User behavior analysis method and apparatus
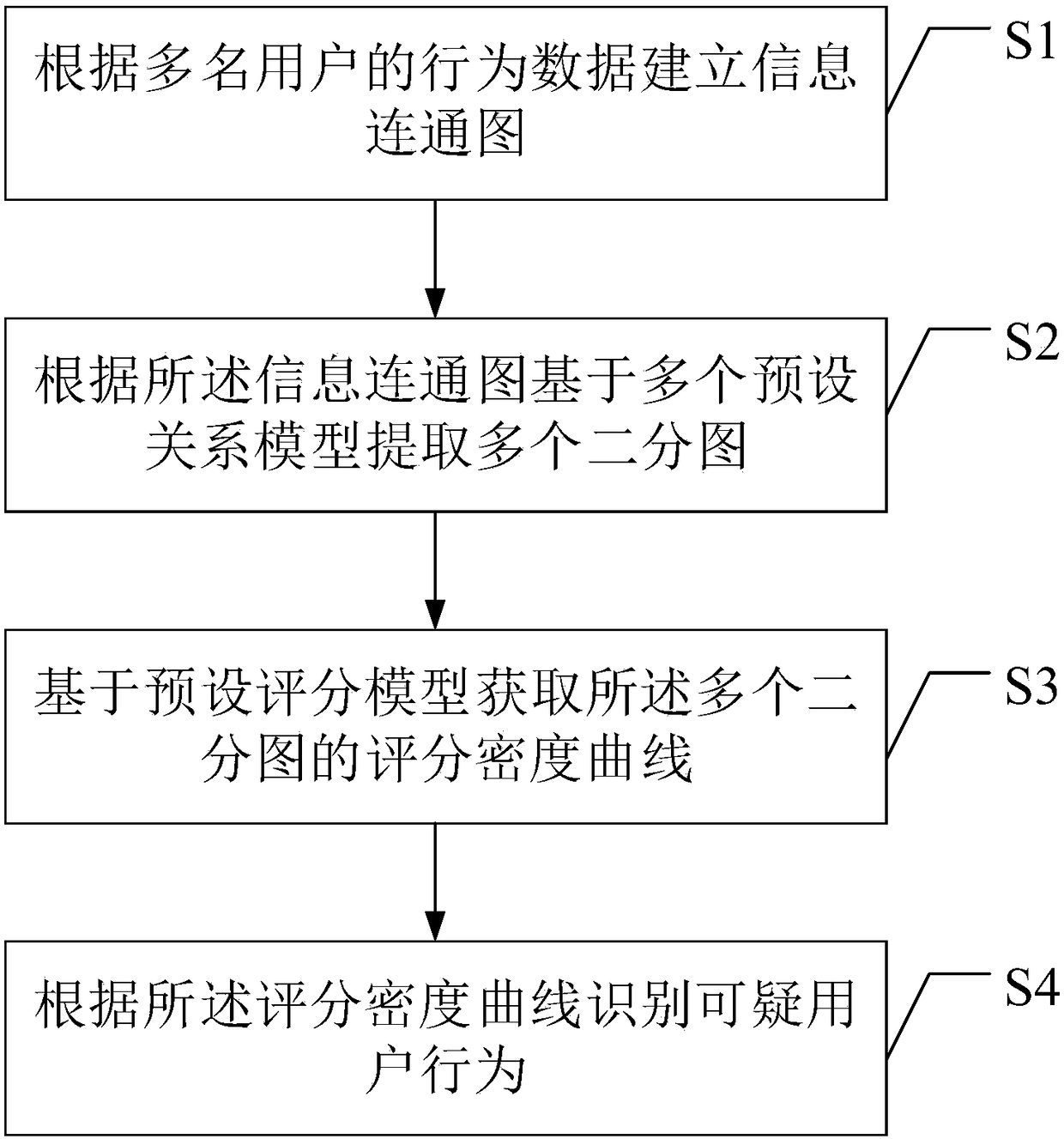
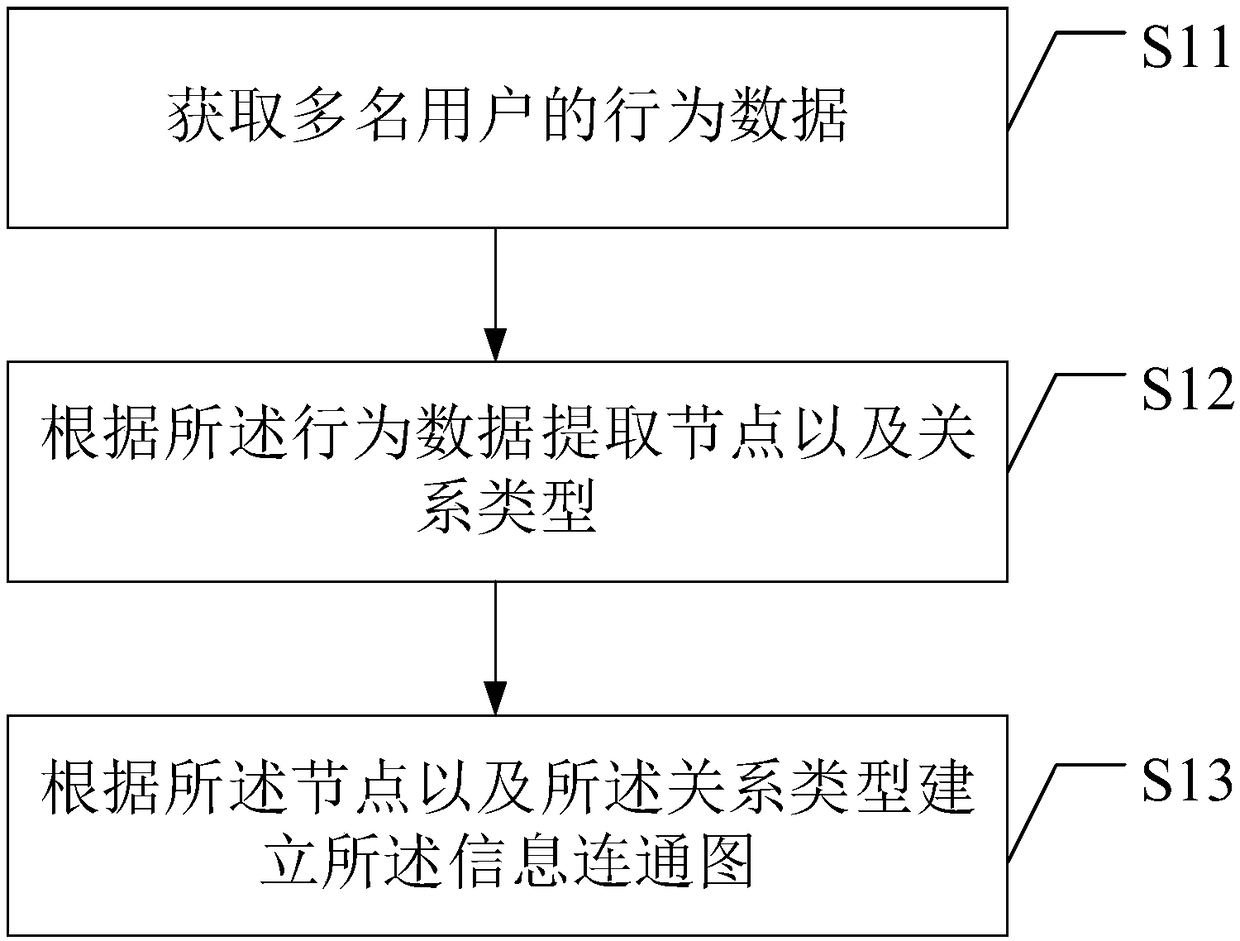
ActiveCN108322473AIncrease success rateCharacter and pattern recognitionData switching networksDensity curveTheoretical computer science
The invention provides a user behavior analysis method and apparatus. The user behavior analysis method comprises the following steps: establishing an information connectivity graph according to the behavior data of a plurality of users; extracting a plurality of bipartite graphs based on a plurality of preset relationship models according to the information connectivity graph; obtaining a score density curve of the plurality of bipartite graphs based on a preset scoring model; and identifying suspicious user behaviors based on the score density curve. By adoption of the user behavior analysismethod provided by the invention, the abnormal user behaviors can be effectively identified, which is helpful for discovering a new network fraud mode and preventing the network fraud.
Owner:JINGDONG TECH HLDG CO LTD
Information recommendation method and system
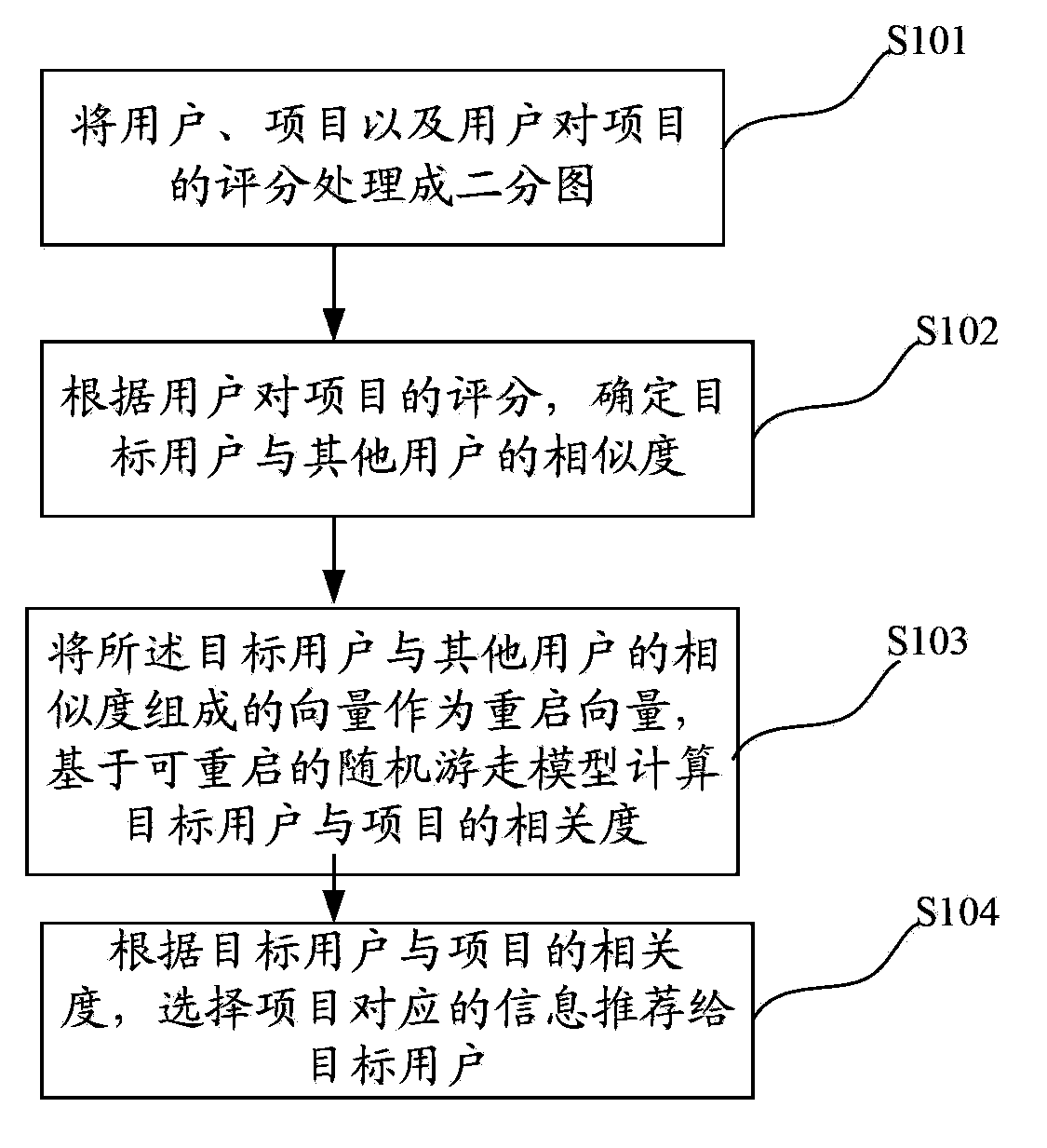
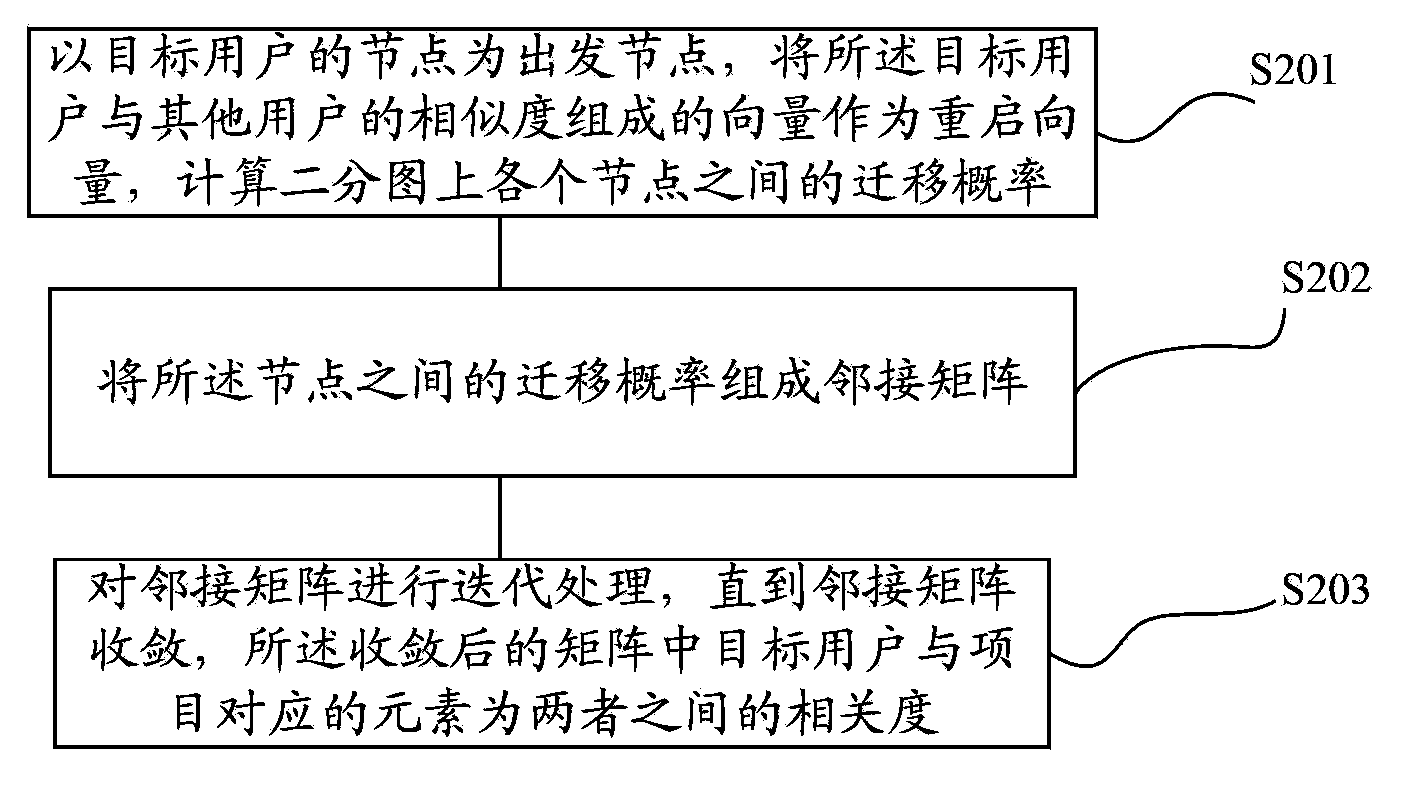
InactiveCN103778145AFully tap the correlationReduce the impactSpecial data processing applicationsRecommendation qualityComputer science
The invention provides an information recommendation method and system. The method includes processing users, items and grades of the items and from the users into a bipartite graph; determining the similarity between a target user and other users according to the grades of the items and from the users; utilizing vector composed of the similarity of the target user and other users as a restarting vector and calculating relevancy between the target user and the items based on a restartable random walk model; selecting information that the items correspond to and recommending the information to the target user according to the relevancy. According to the information recommendation method, the relevancy between the target user and other users is determined according to the grades of the items and from the users, the relevancy between user nodes and item nodes is completely excavated, the data sparse problem effect is greatly reduced, the grade items that the users are interested in can be accurately recommended, and the recommendation quality is improved.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
Relational query method implemented on large-scale data set
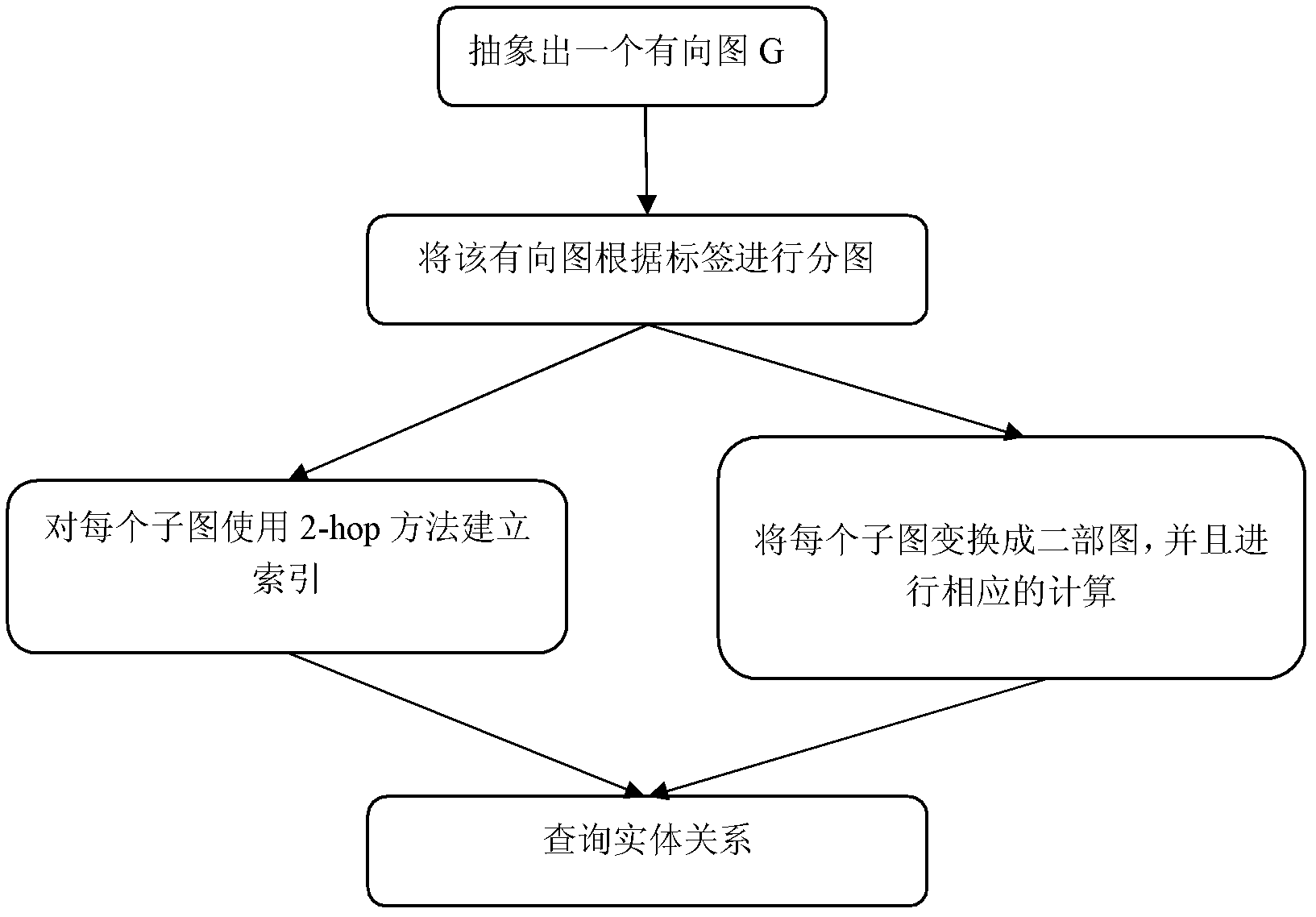
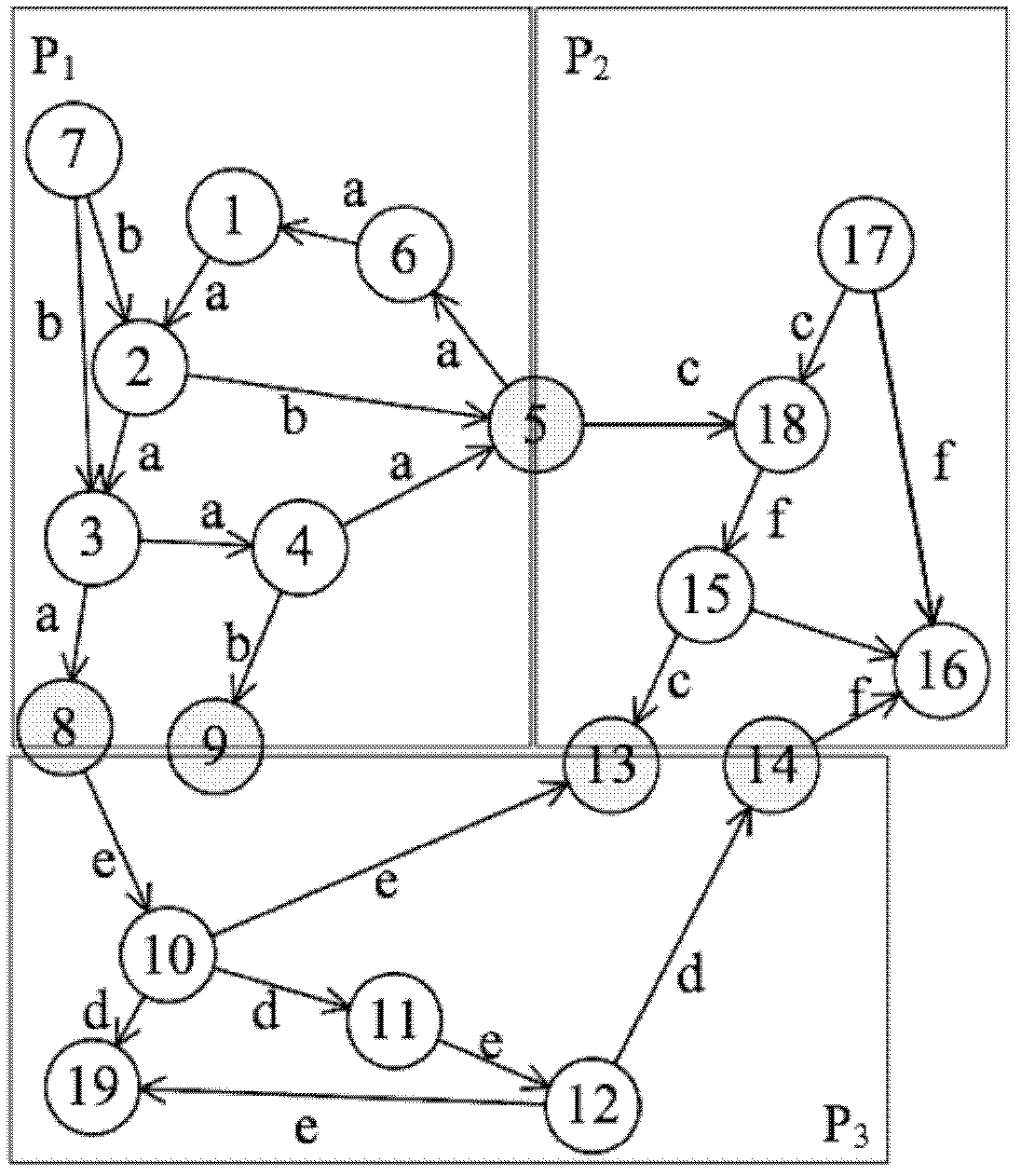
ActiveCN102332009AProve superiorityRelational query supportSpecial data processing applicationsComputational semanticsData set
The invention discloses a relational query method implemented on a large-scale data set and belongs to the field of semantic webs. The method comprises the following steps: 1) calculating connective subgraphs (only containing a same type of tags) in a semantic data directed graph G; 2) merging the connective subgraphs, and dividing the directed graph G into a plurality of subgraphs; 3) calculating a strongest connective subgraph C in each subgraph subjected to merging, and calculating a bipartite graph of the strongest connective subgraph C; 4) storing the shortest path of all the subgraphs Cinto a path set RS; 5) recording the tags (containing two points of a non-redundant tag path) in each divided subgraph so as to obtain a tag set of each subgraph; and 6) judging whether paths conforming to the query conditions exist in the directed graph G by using the tag set, if so, returning path query results, otherwise, carrying out traversal among the subgraphs, determining subgraphs which can reach a target node according to the path set RS, and then, returning the path query results by using the tag set of the subgraph. The method disclosed by the invention is used for supporting the relational query of mass data, and is strong in expandability.
Owner:PEKING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com