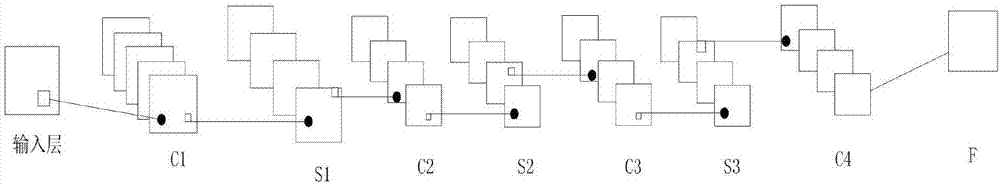
Patents
Literature
906 results about "Confidence metric" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Confidence level is a metric for individual predictions that tells you how confident the algorithm is for each prediction. For instance, let’s say you are extracting information from a document, such as invoices, and want different pieces of information like ‘dates’, ‘quantity’, item description, etc.
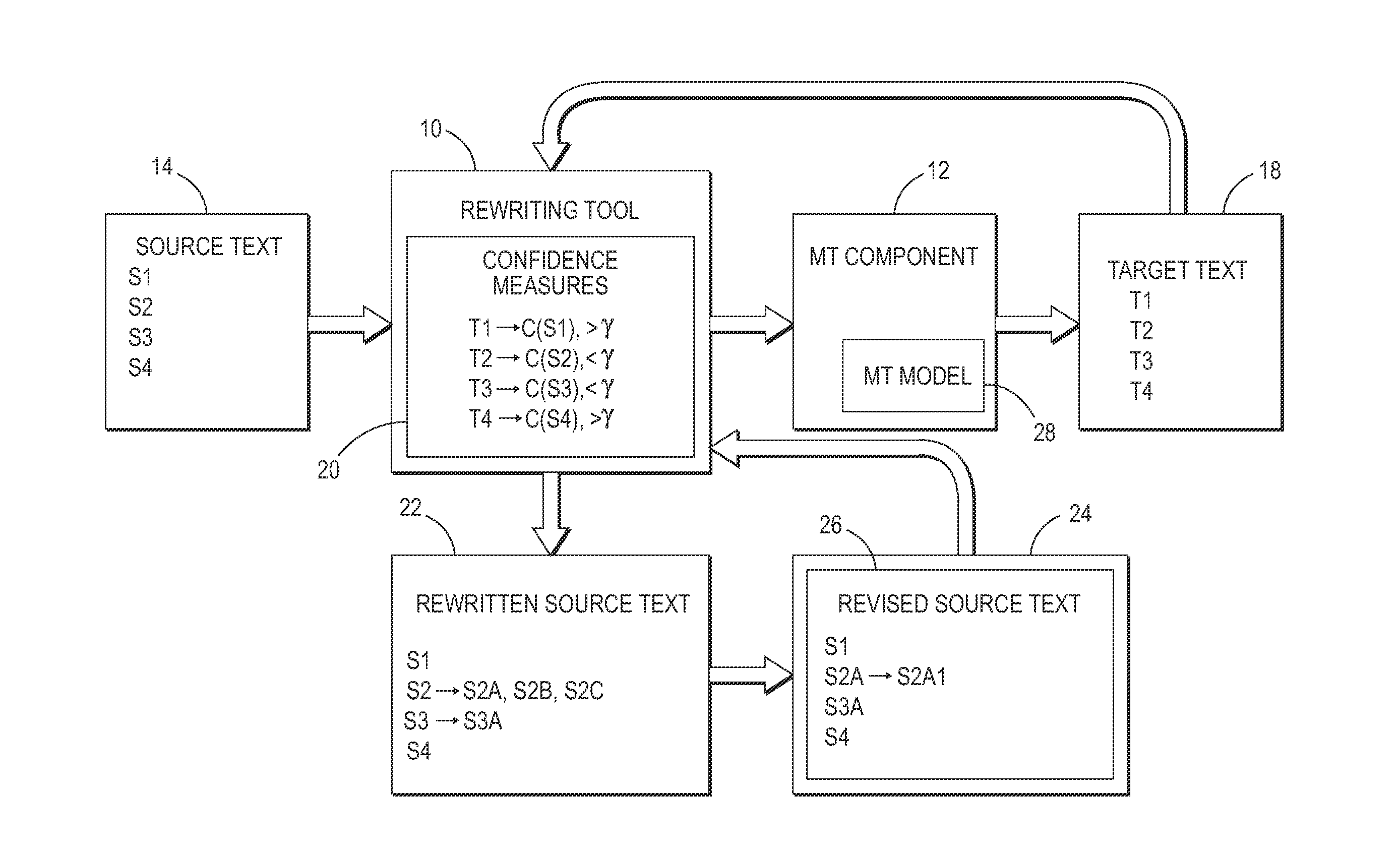
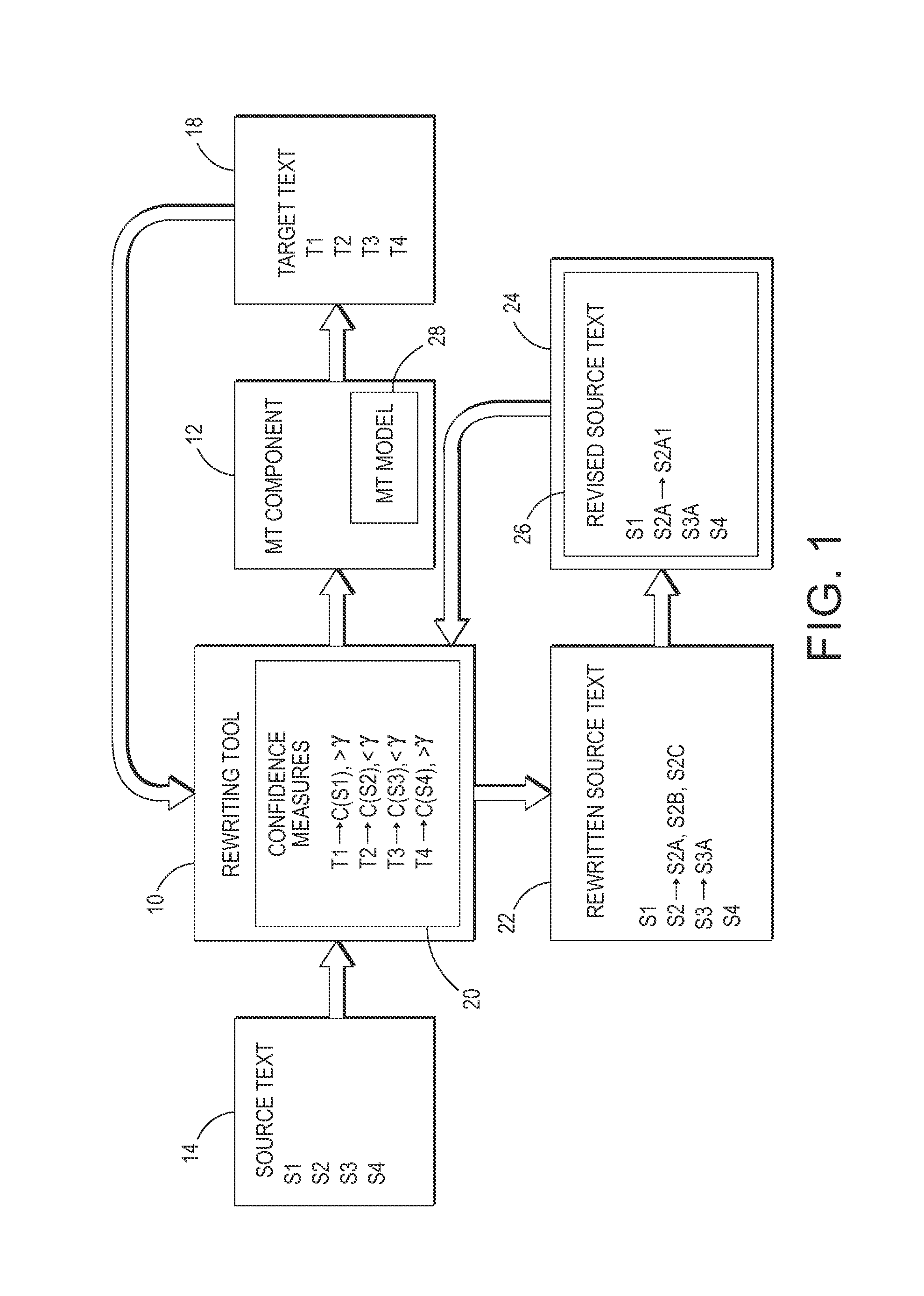
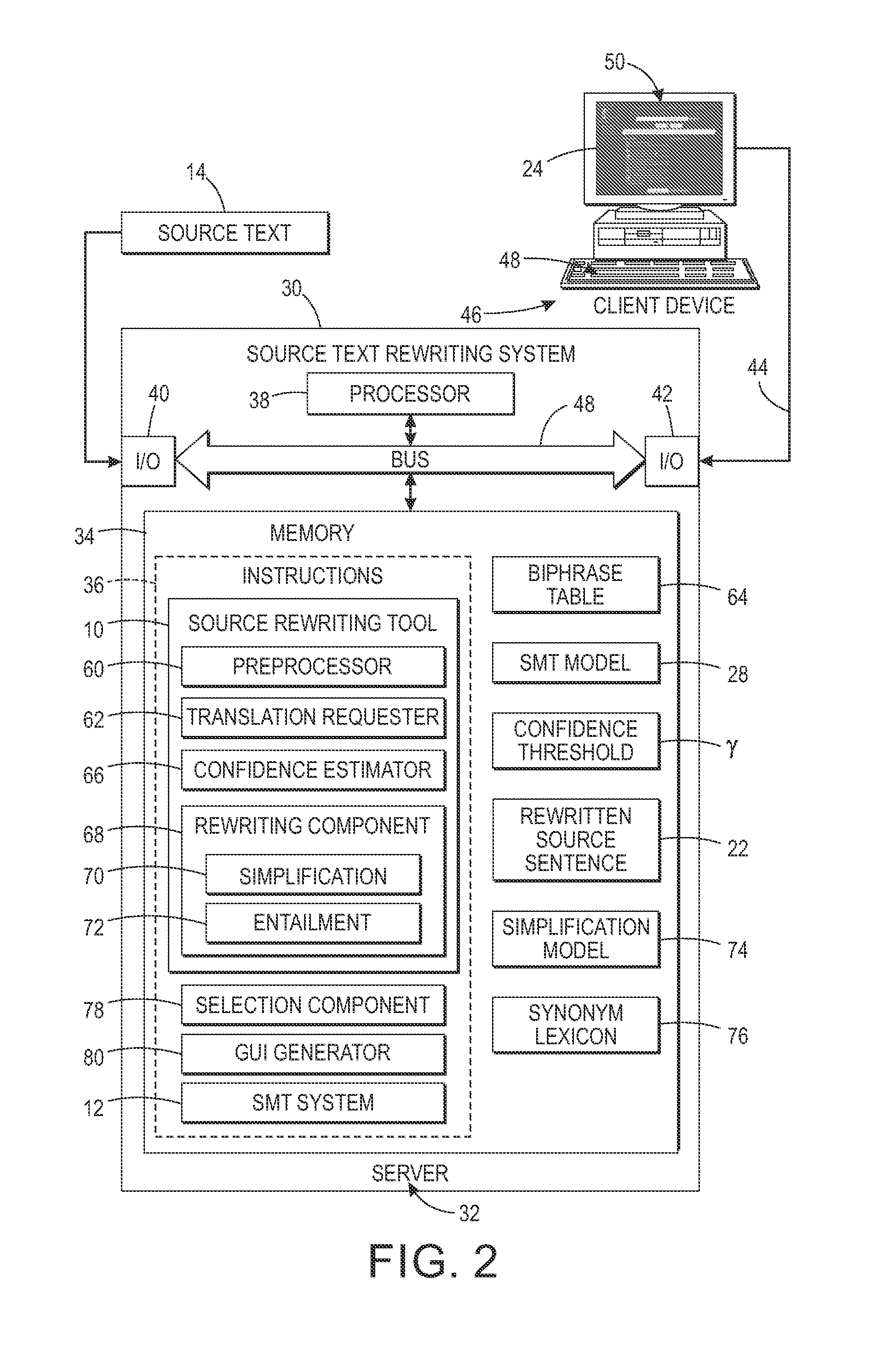
Confidence-driven rewriting of source texts for improved translation
InactiveUS20140358519A1Natural language translationSpecial data processing applicationsGraphicsGraphical user interface
A method for rewriting source text includes receiving source text including a source text string in a first natural language. The source text string is translated with a machine translation system to generate a first target text string in a second natural language. A translation confidence for the source text string is computed, based on the first target text string. At least one alternative text string is generated, where possible, in the first natural language by automatically rewriting the source string. Each alternative string is translated to generate a second target text string in the second natural language. A translation confidence is computed for the alternative text string based on the second target string. Based on the computed translation confidences, one of the alternative text strings may be selected as a candidate replacement for the source text string and may be proposed to a user on a graphical user interface.
Owner:XEROX CORP
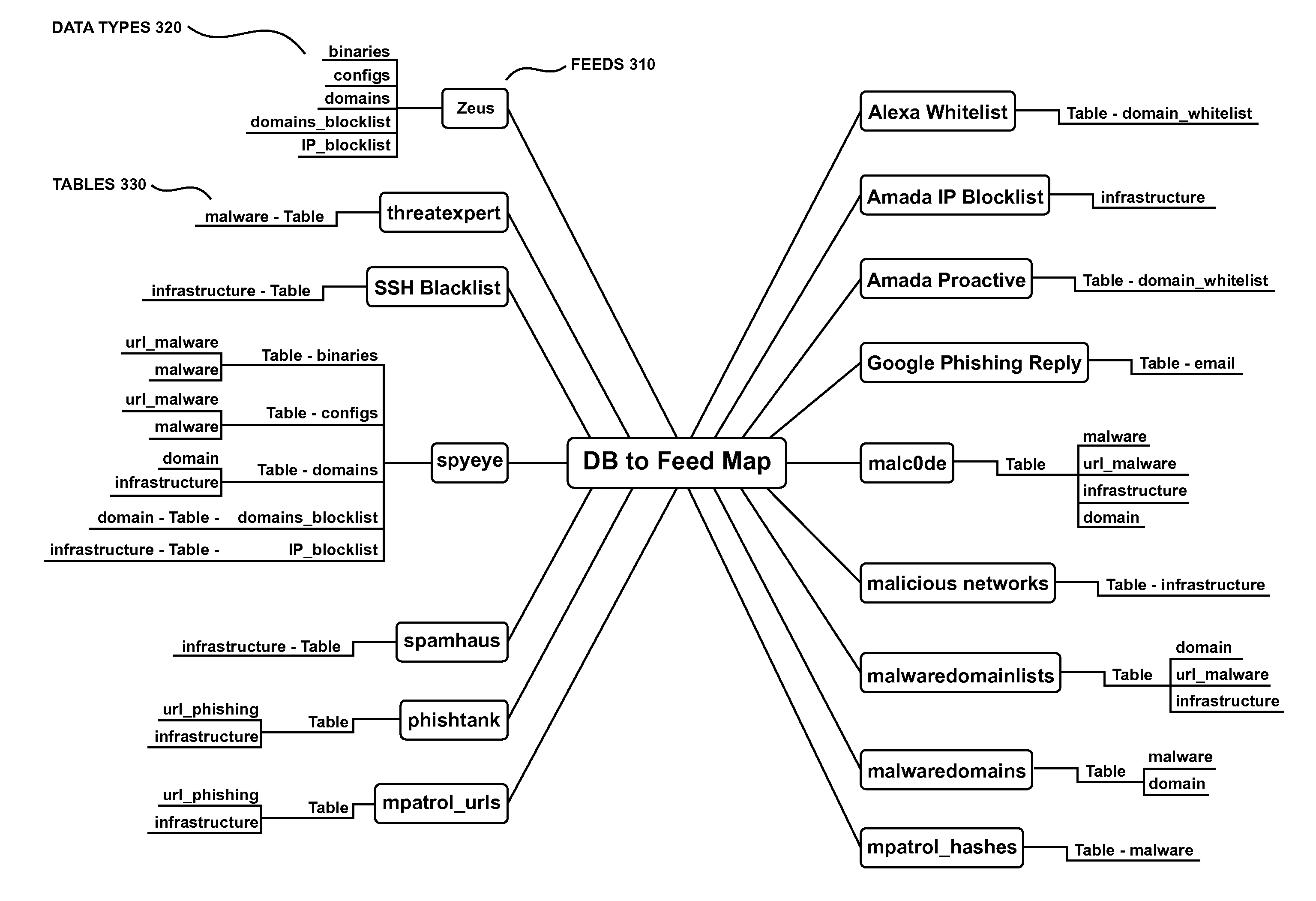
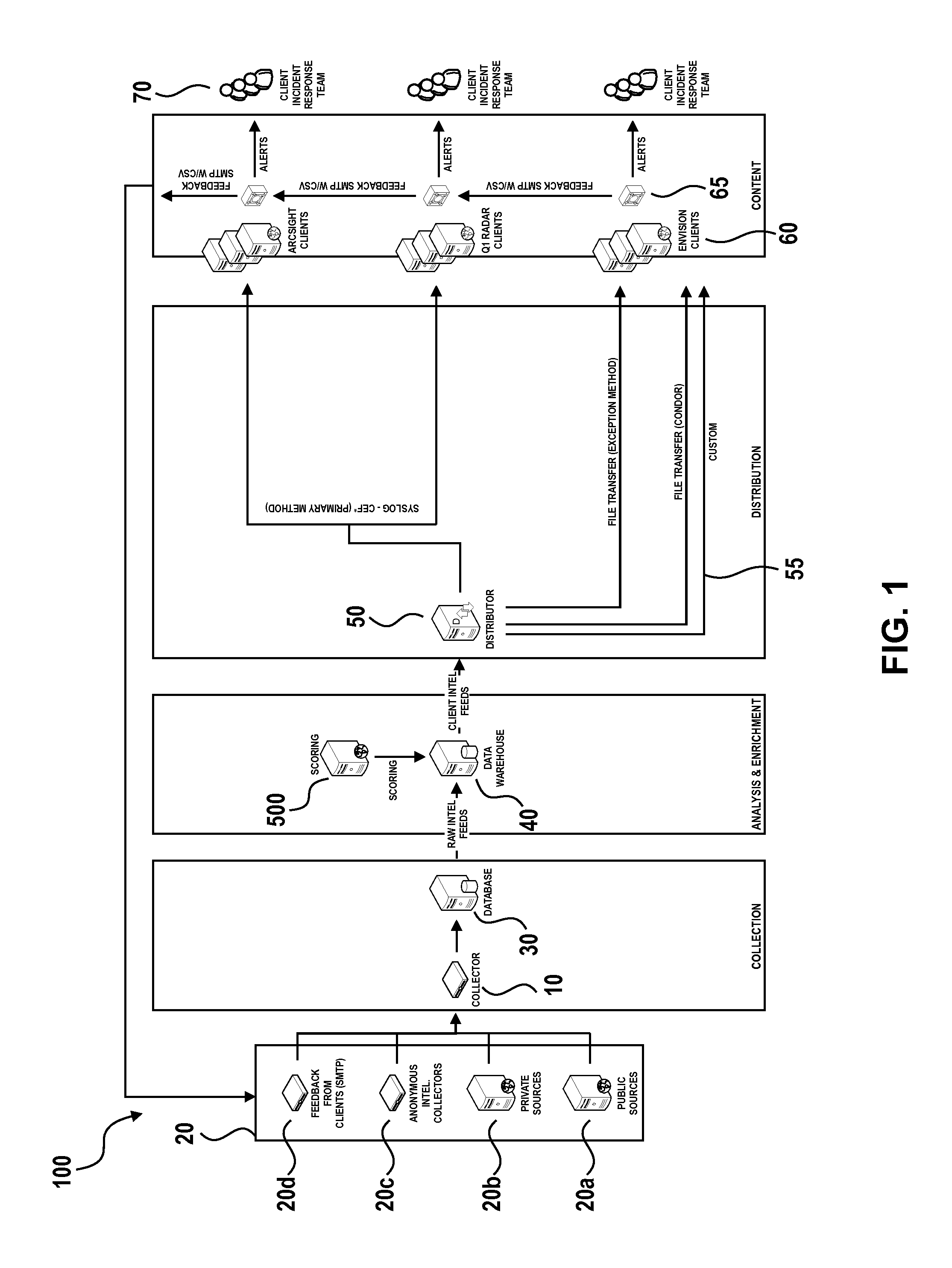
Collective Threat Intelligence Gathering System
ActiveUS20140007238A1Quality improvementImprove information qualityMemory loss protectionError detection/correctionIp addressInformation networks
Threat intelligence is collected from a variety of different sources. The threat intelligence information is aggregated, normalized, filtered and scored to identify threats to an information network. Threats are categorized by type, maliciousness and confidence level. Threats are reported to network administrators in a plurality of threat feeds, including for example malicious domains, malicious IP addresses, malicious e-mail addresses, malicious URLs and malicious software files.
Owner:DELOITTE DEV
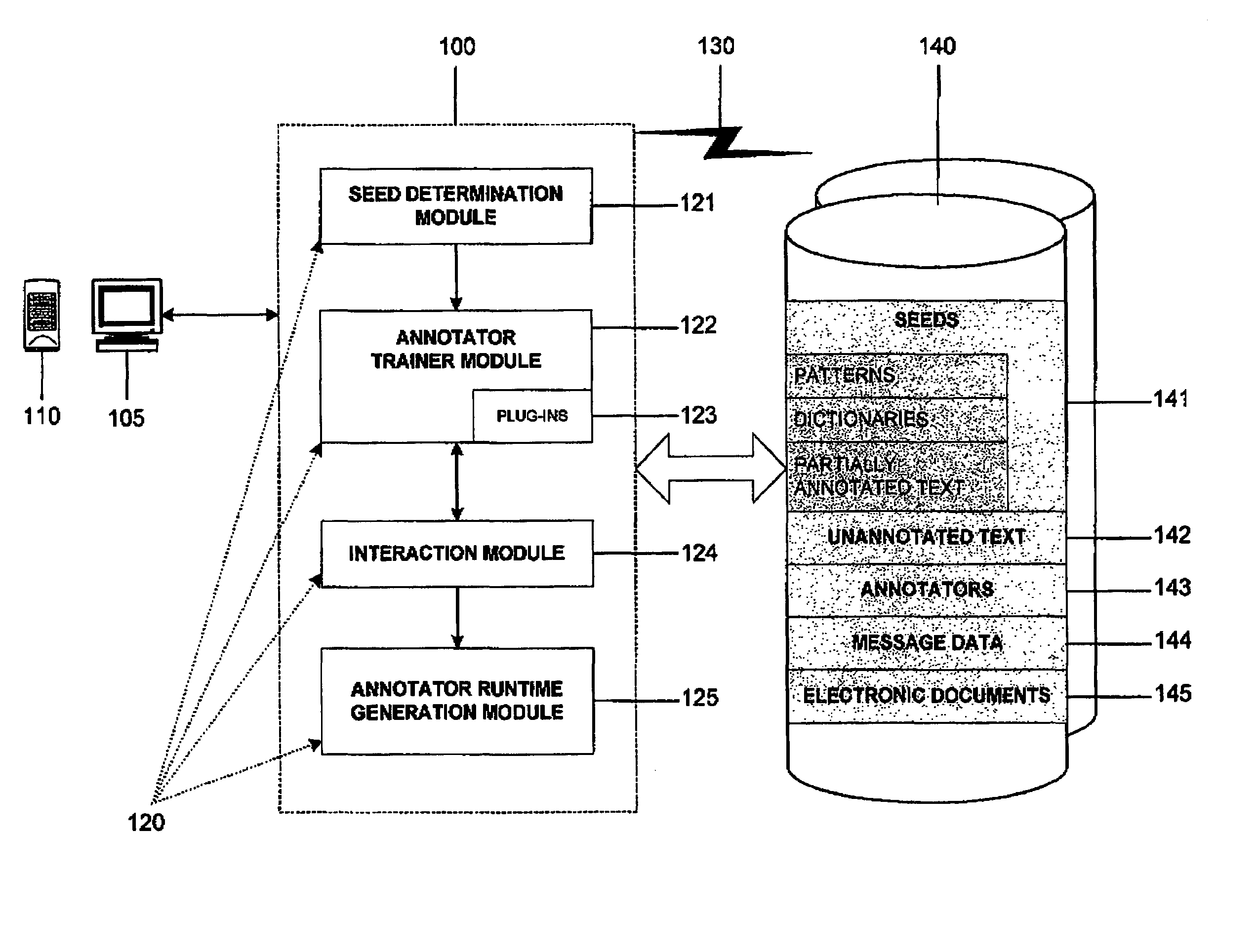
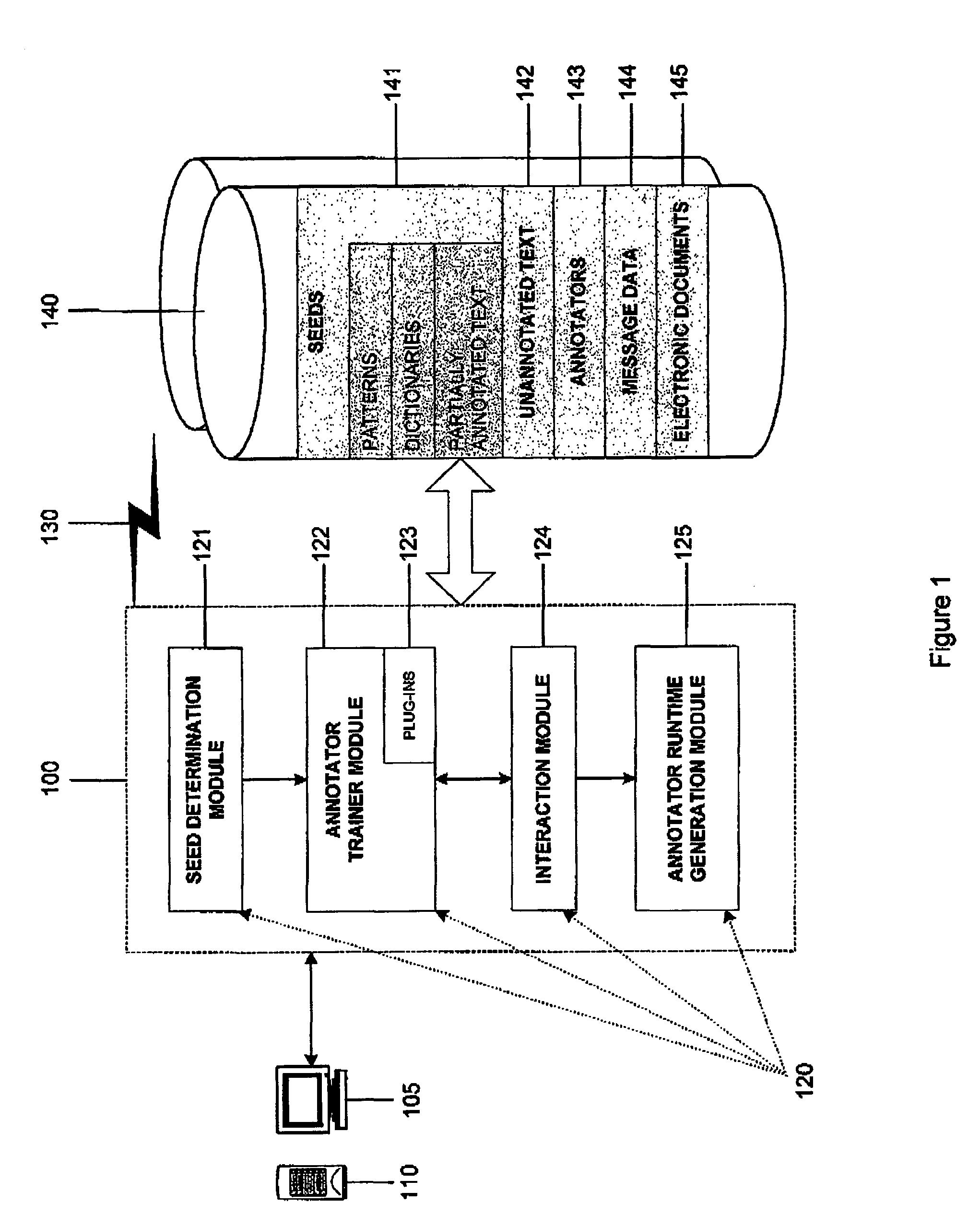
Interactive machine learning system for automated annotation of information in text
InactiveUS20050027664A1Natural language translationDigital computer detailsLearning basedConfidence metric
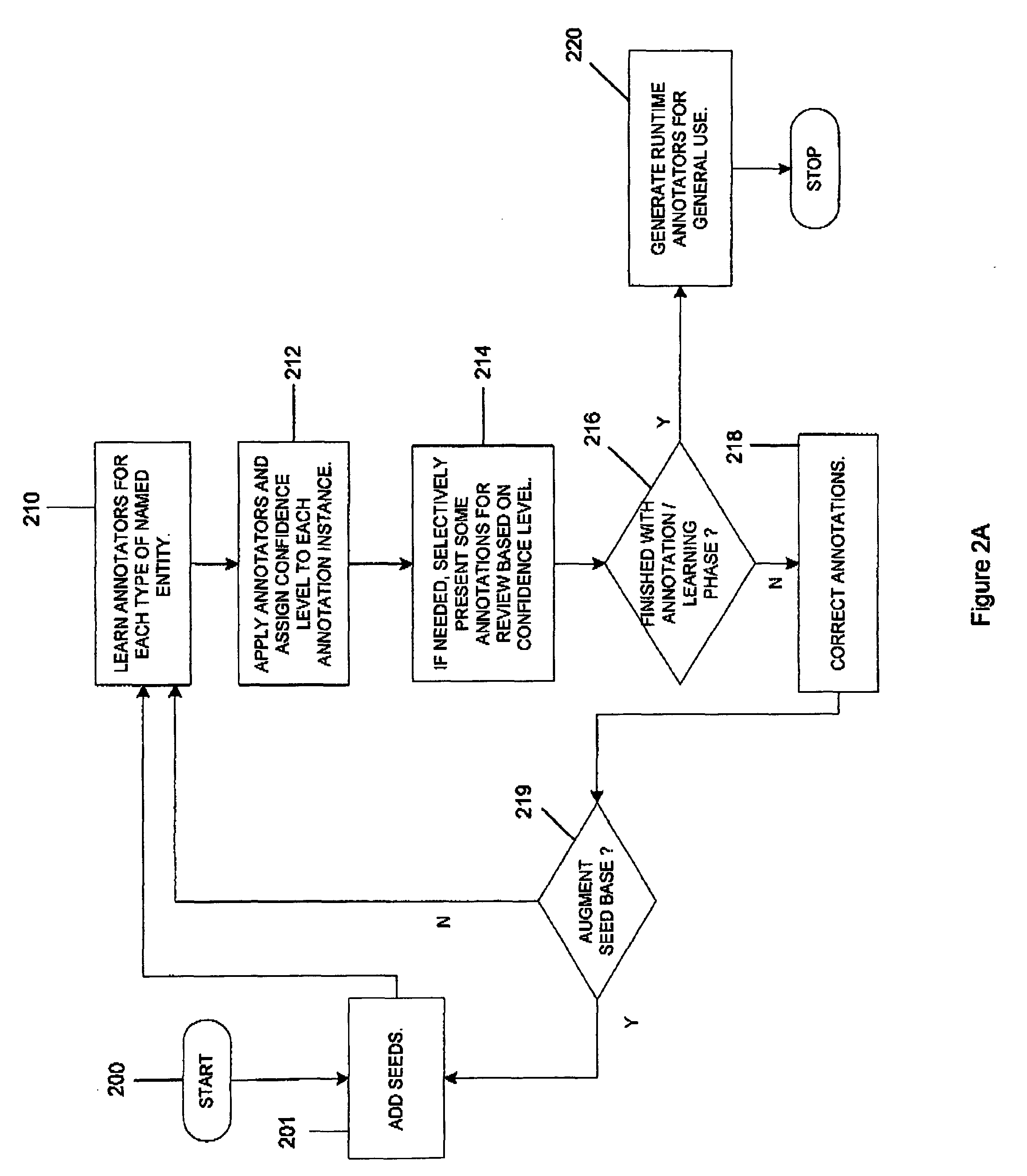
An interactive machine learning based system that incrementally learns, on the basis of text data, how to annotate new text data. The system and method starts with partially annotated training data or alternatively unannotated training data and a set of examples of what is to be learned. Through iterative interactive training sessions with a user the system trains annotators, and these are in turn used to discover more annotations in the text data. Once all of the text data or a sufficient amount of the text data is annotated, at the user's discretion, the system learns a final annotator or annotators, which are exported and available to annotate new textual data. As the iterative training process occurs the user is selectively presented for review and appropriate action, system-determined representations of the annotation instances and provided a convenient and efficient interface so that context of use can be verified if necessary in order to evaluate the annotations and correct them, where required. At the user's discretion, annotations that receive a high confidence level can be automatically accepted and those with low confidence levels can be automatically rejected.
Owner:IBM CORP
Systems and methods for assessing the risk of a financial transaction using biometric information
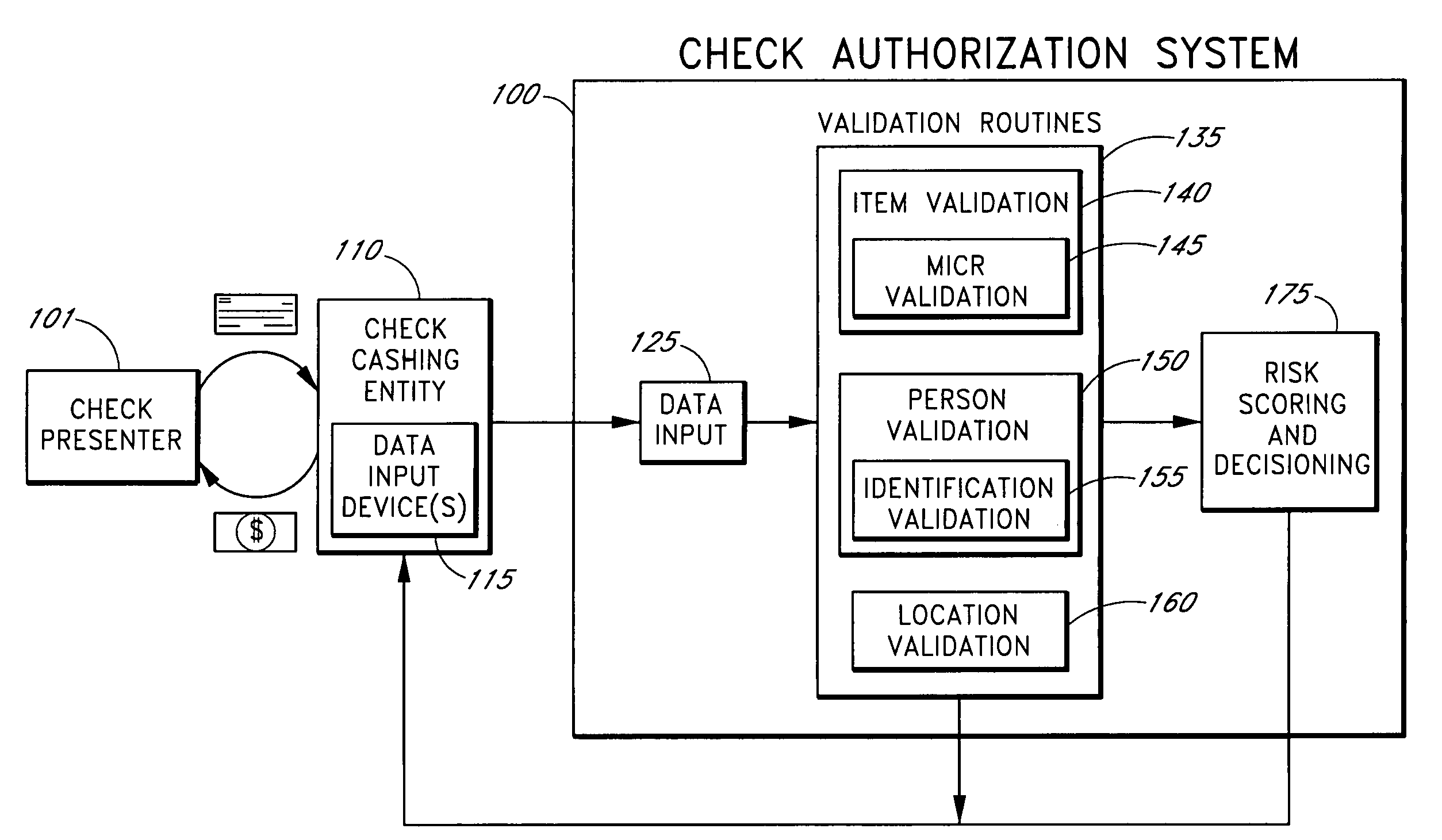
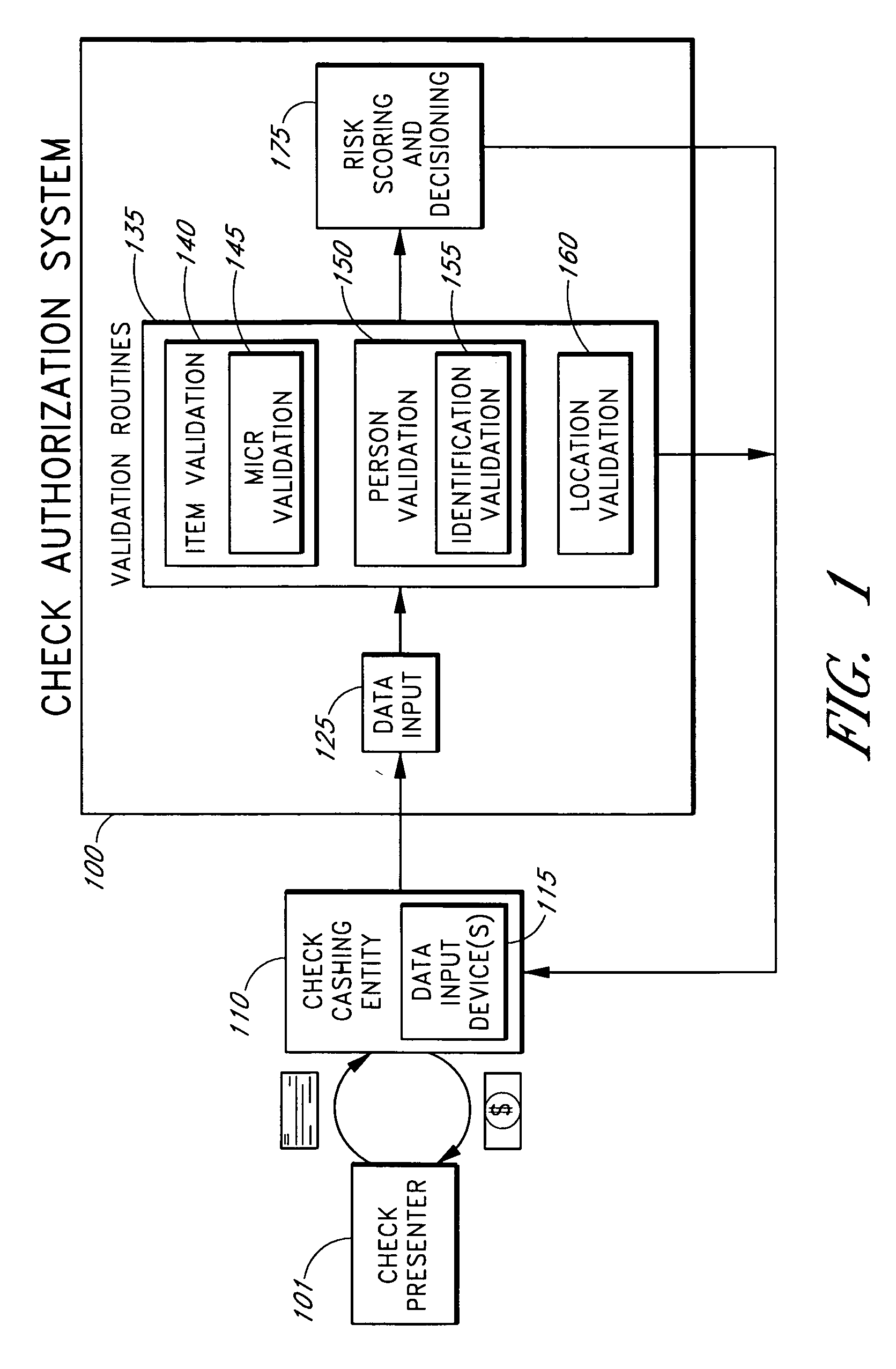
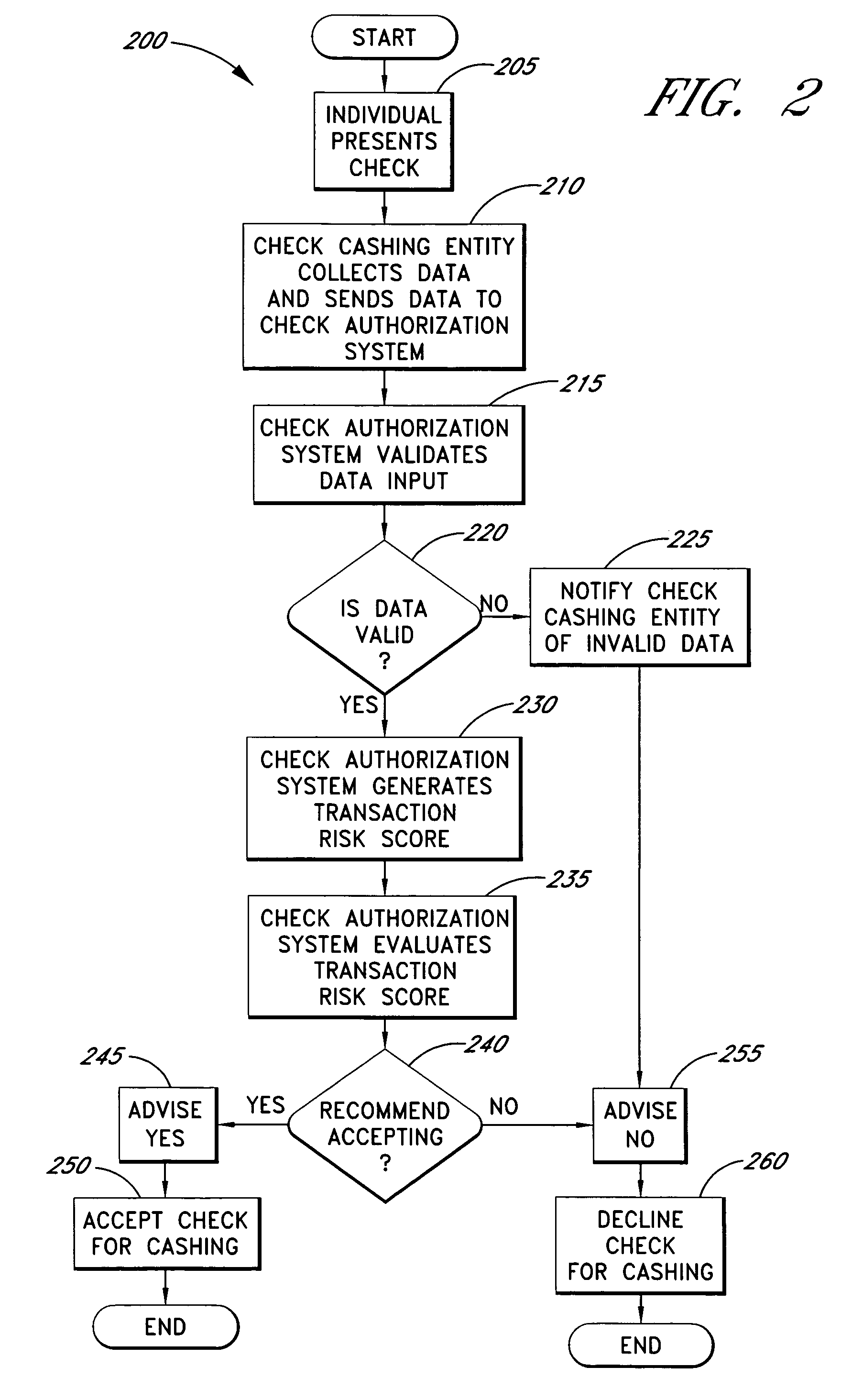
ActiveUS20050125339A1Accurate descriptionAccurate transactionFinancePayment architectureConfidence metricFinancial transaction
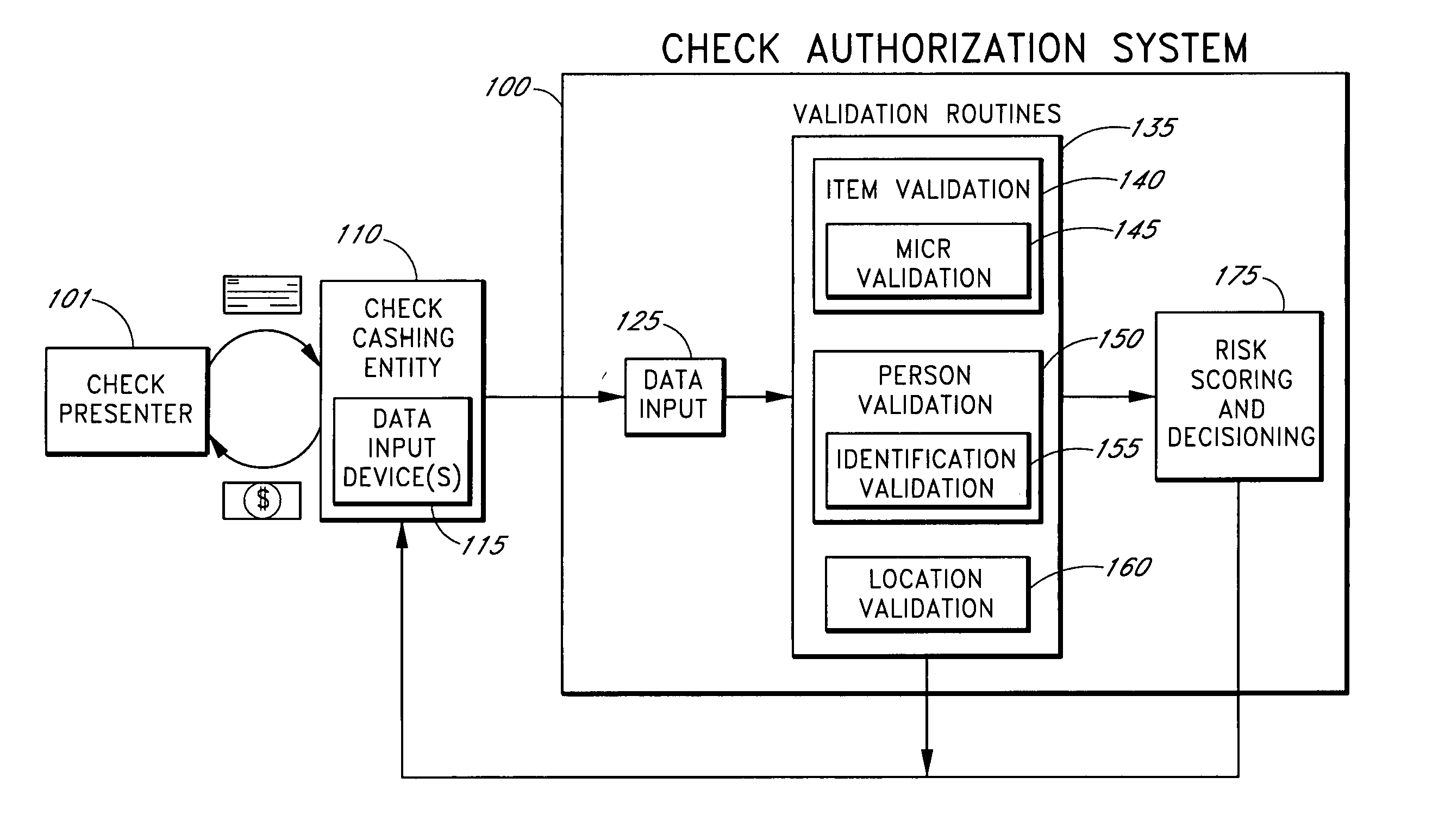
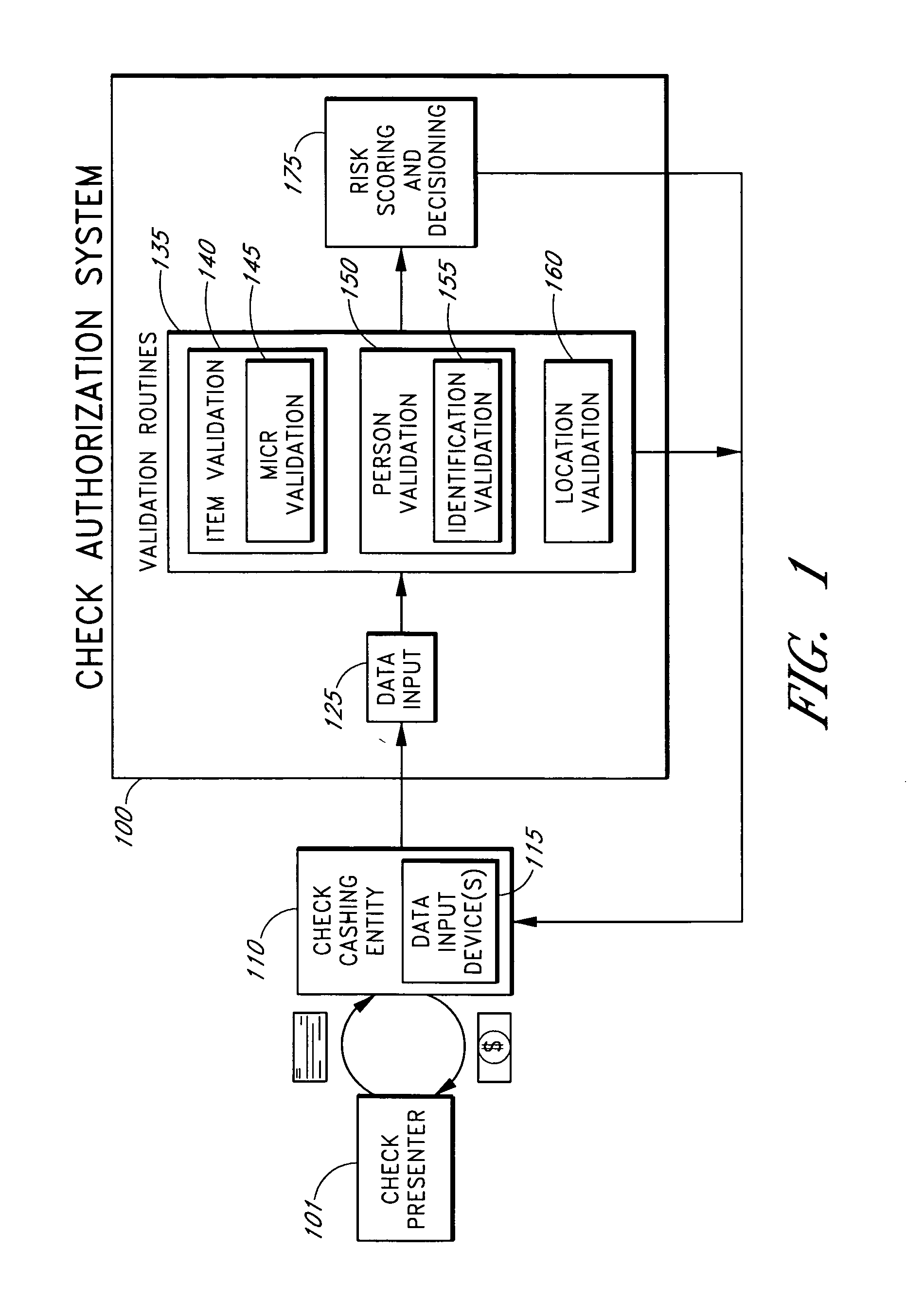
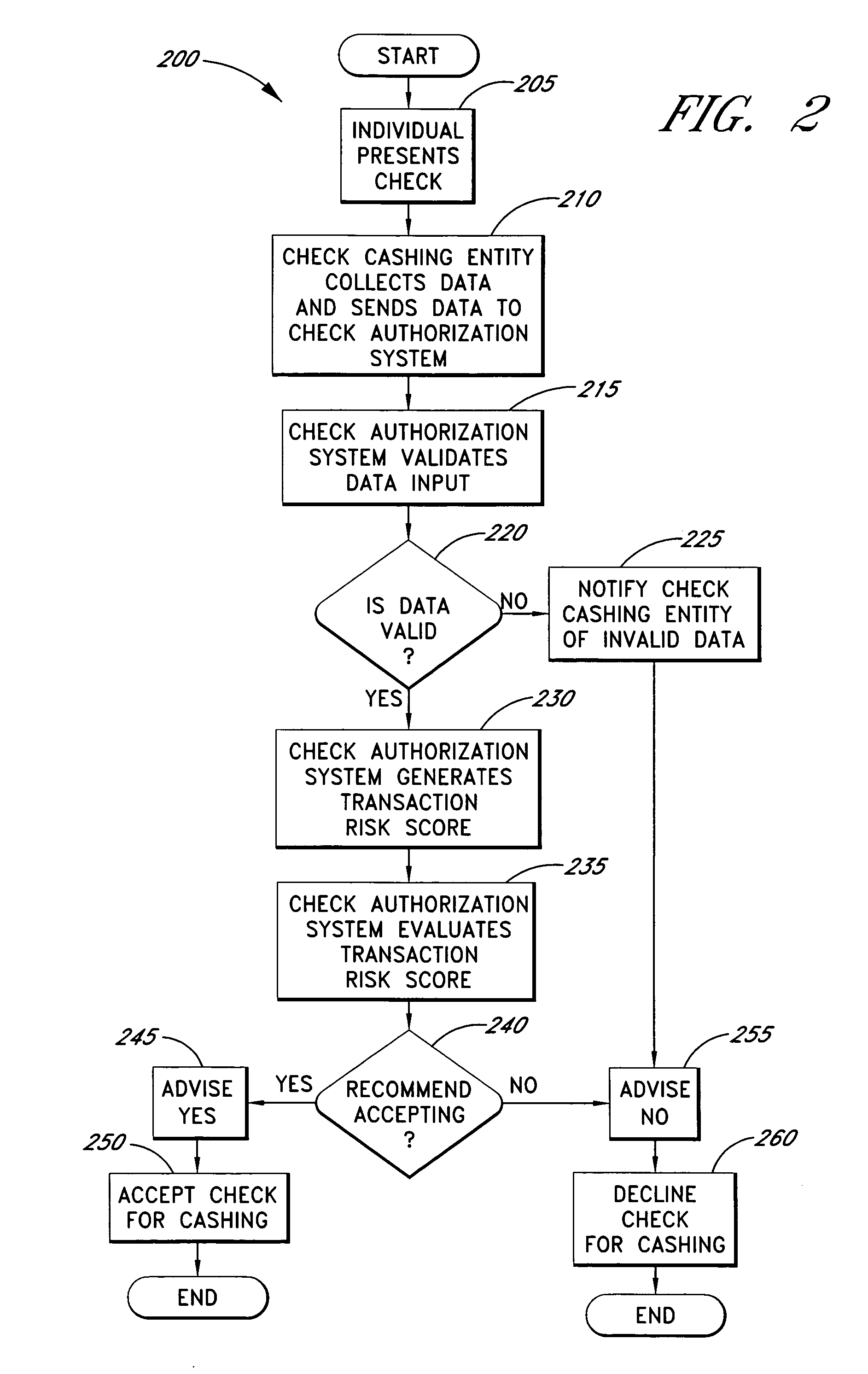
Systems and methods are described for better assessing risk associated with cashing second-party checks and other negotiable instruments by using biometric information obtained from an individual who presents a check or other negotiable instrument in a check-cashing transaction. In various embodiments, the obtained biometric information may be compared with stored biometric information in order to enhance confidence in the accurate identification of the check presenter. In various embodiments, a gradated biometric risk score, based at least in part on the comparison, may be generated for the check-cashing transaction. In various embodiments, the biometric risk score may be combined with risk scores that are descriptive of other aspects of the check-cashing transaction to calculate a risk score for the transaction as a whole. In some embodiments, the risk scores may be used to generate an accept / decline recommendation for the transaction as a whole.
Owner:FIRST DATA
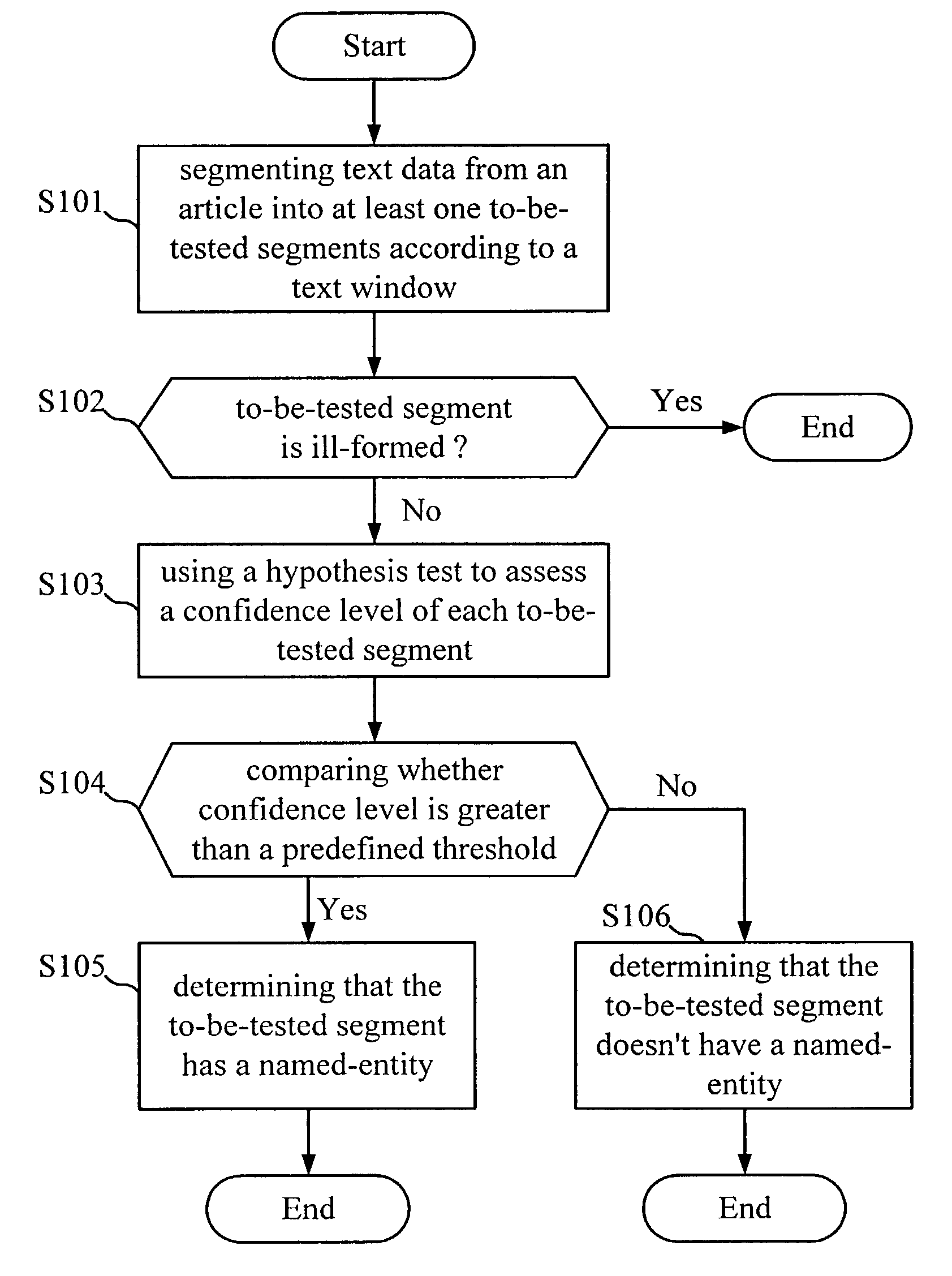
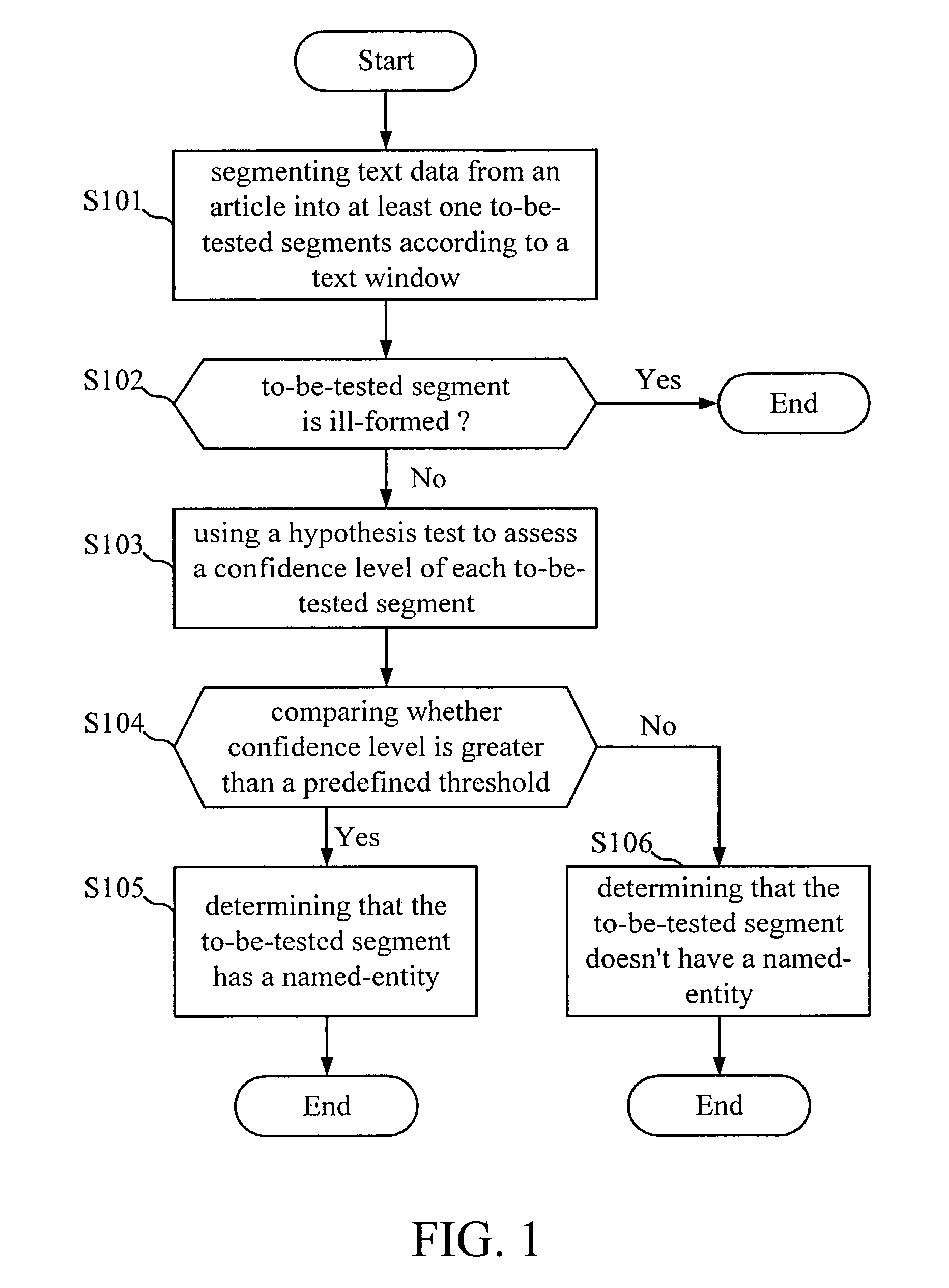
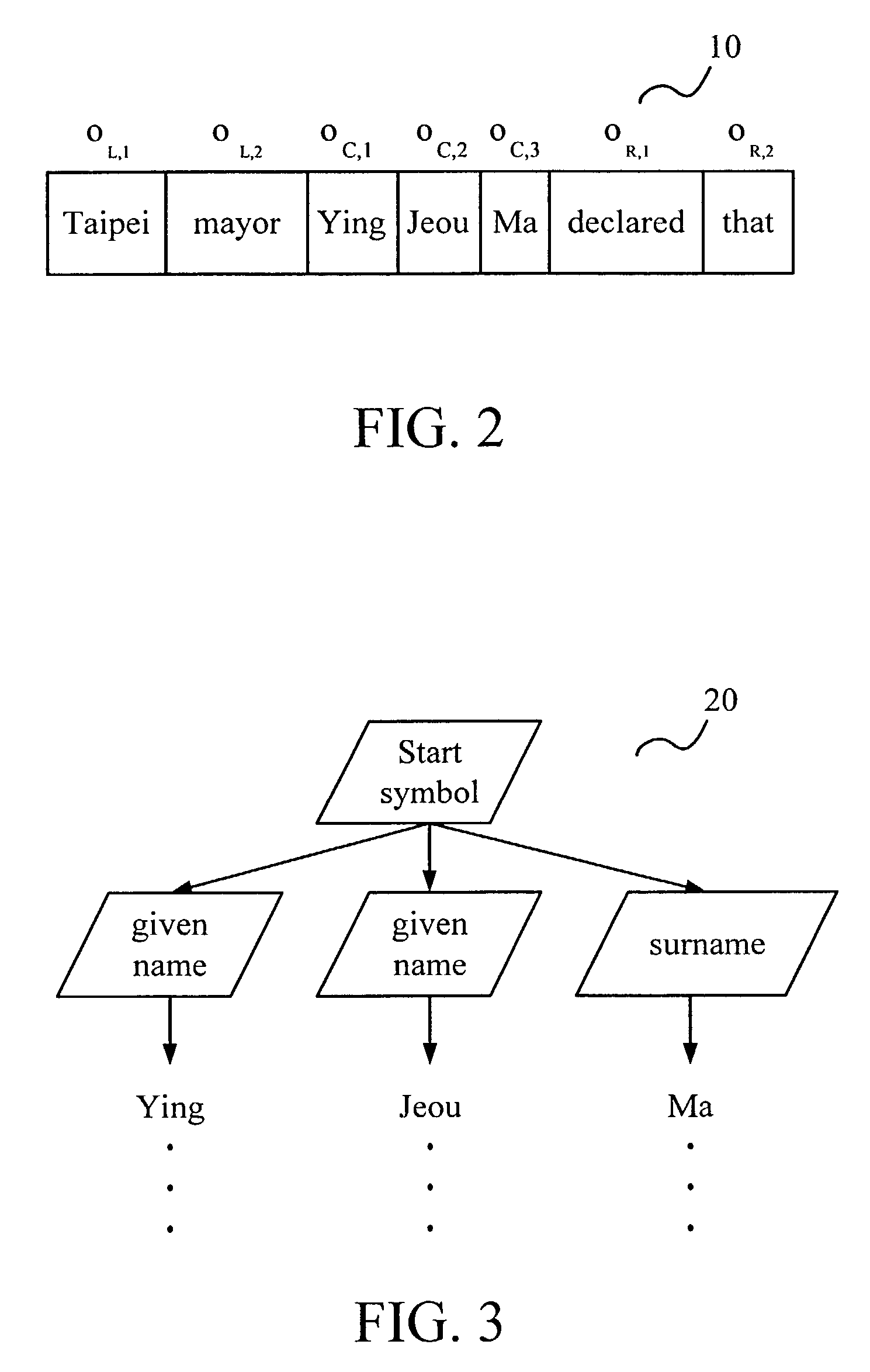
Method for named-entity recognition and verification
InactiveUS7171350B2Easy programmingImprove portabilityNatural language data processingSpecial data processing applicationsPattern recognitionNamed-entity recognition
A method for named-entity (NE) recognition and verification is provided. The method can extract at least one to-be-tested segments from an article according to a text window, and use a predefined grammar to parse the at least one to-be-tested segments to remove ill-formed ones. Then, a statistical verification model is used to calculate the confidence measurement of each to-be-tested segment to determine where the to-be-tested segment has a named-entity or not. If the confidence measurement is less than a predefined threshold, the to-be-tested segment will be rejected. Otherwise, it will be accepted.
Owner:IND TECH RES INST
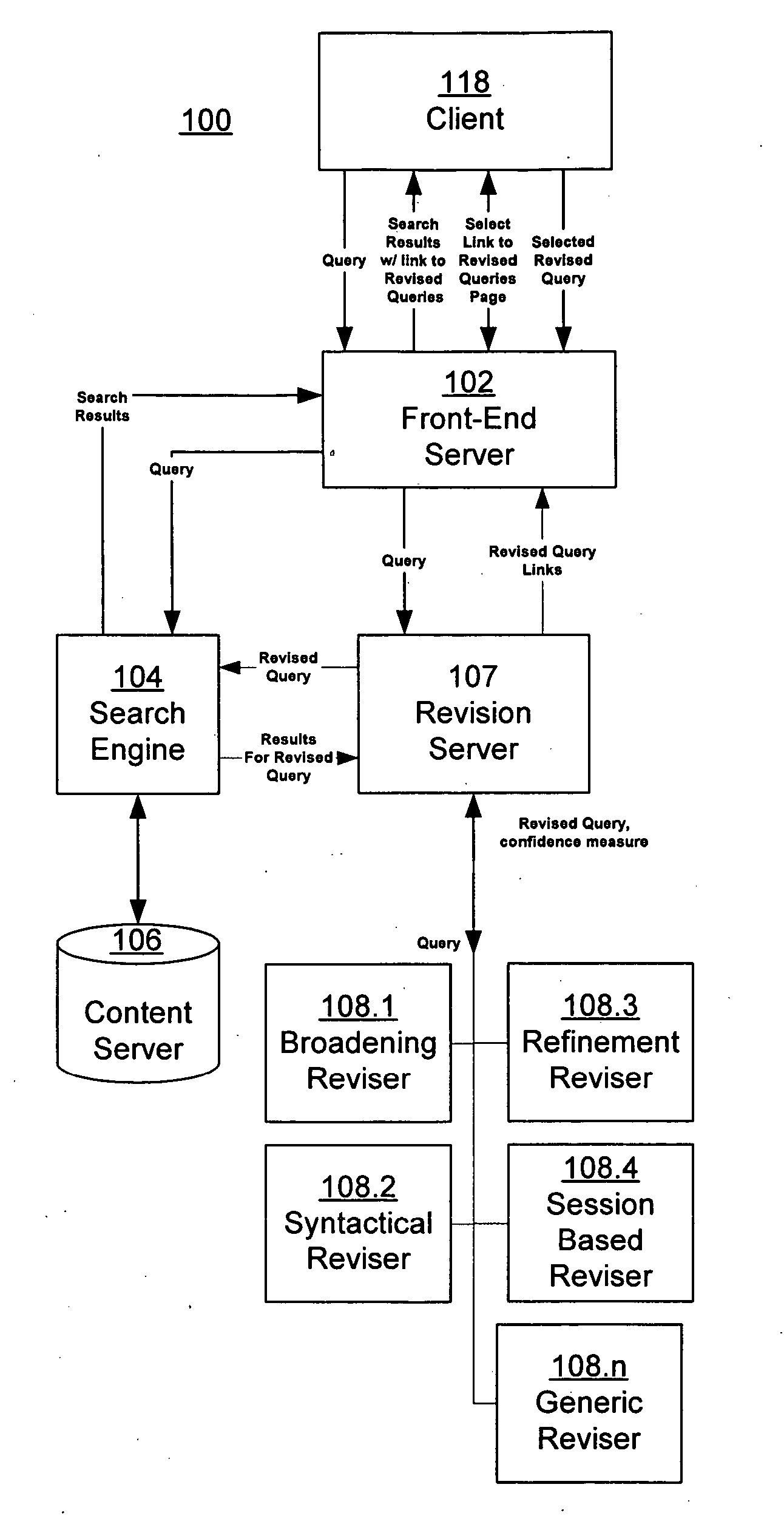
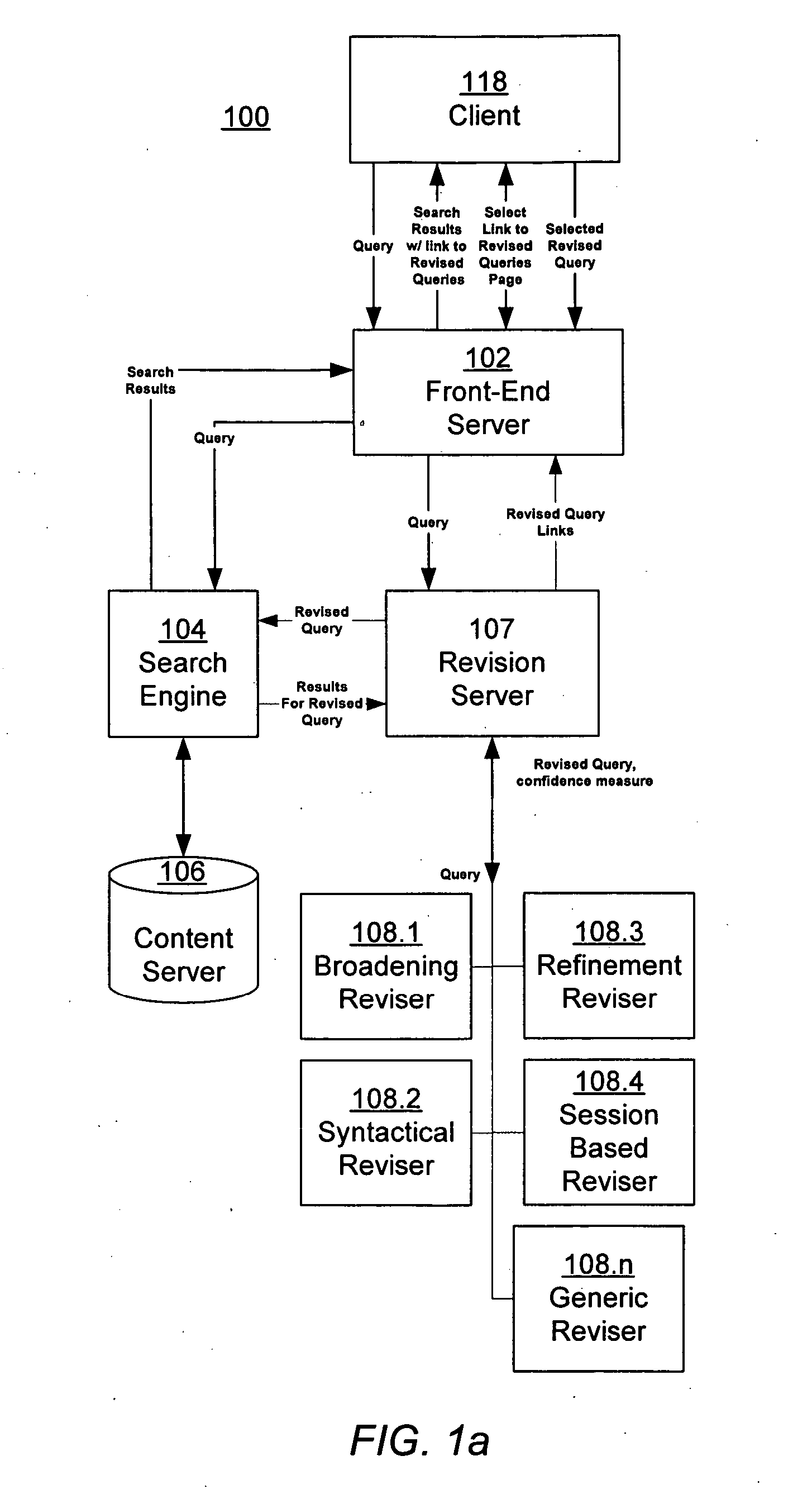
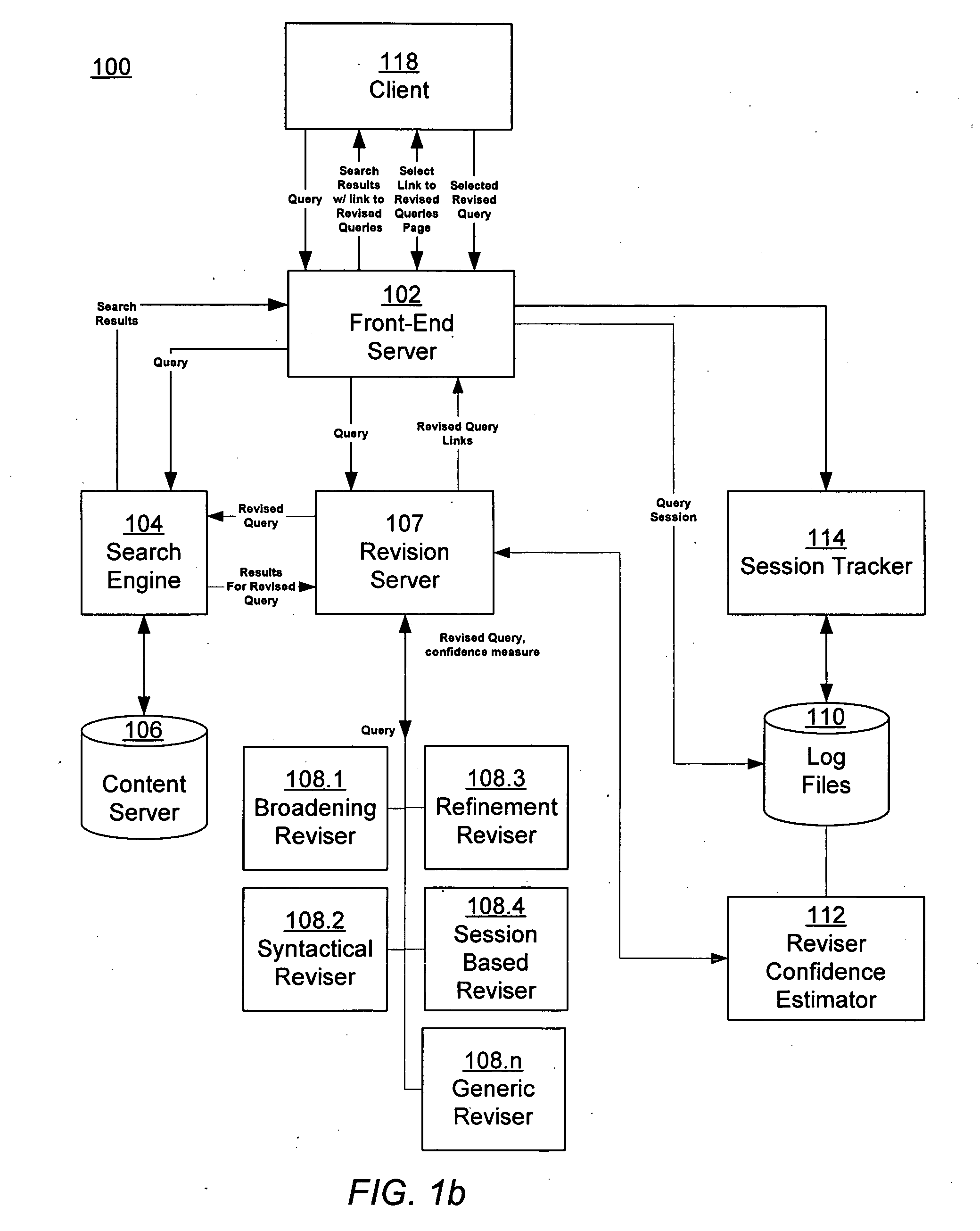
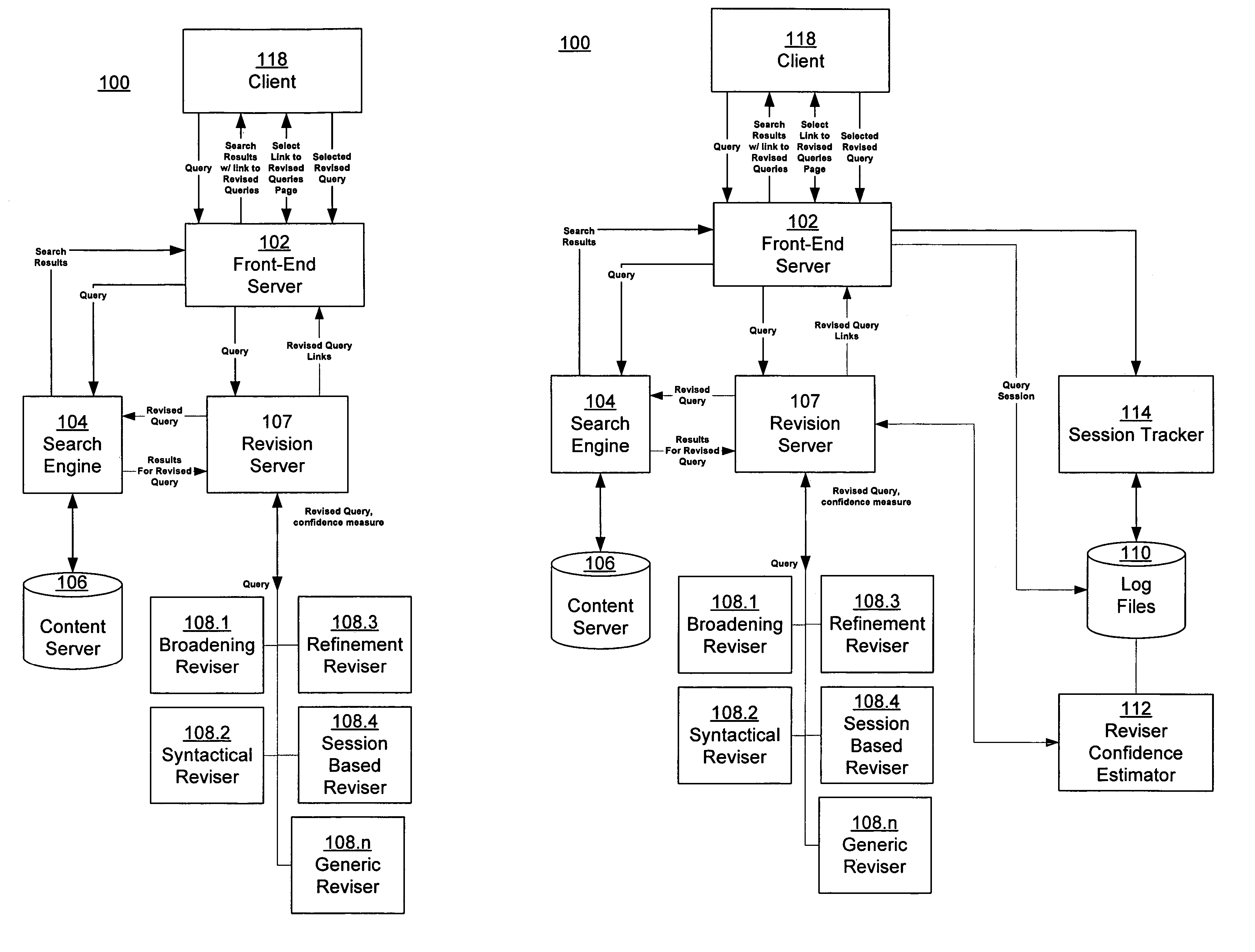
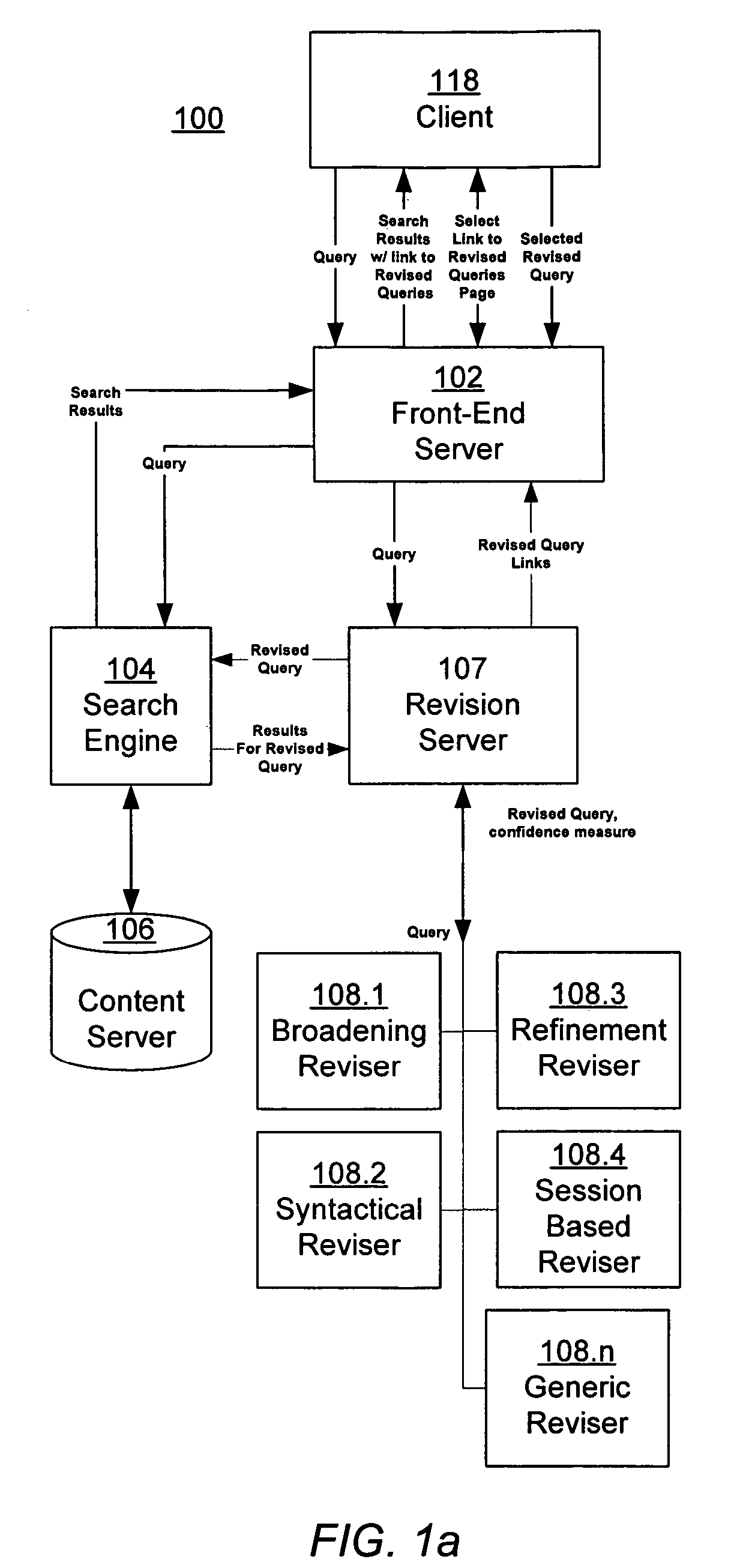
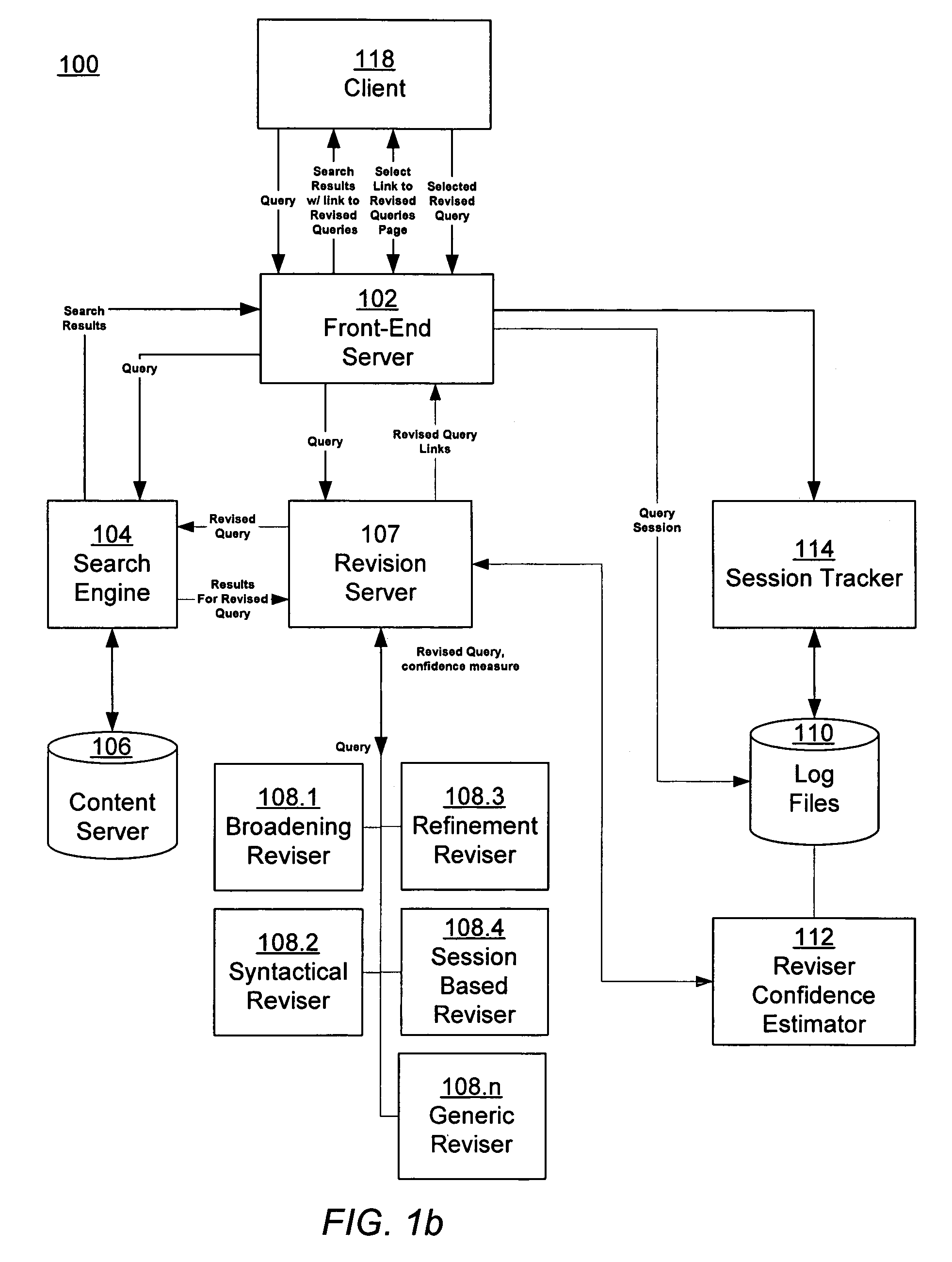
Estimating confidence for query revision models
ActiveUS20060230035A1Data processing applicationsWeb data indexingConfidence metricFrequency of occurrence
An information retrieval system includes a query revision architecture that integrates multiple different query revisers, each implementing one or more query revision strategies. A revision server receives a user's query, and interfaces with the various query revisers, each of which generates one or more potential revised queries. The revision server evaluates the potential revised queries, and selects one or more of them to provide to the user. A session-based reviser suggests one or more revised queries, given a first query, by calculating an expected utility for the revised query. The expected utility is calculated as the product of a frequency of occurrence of the query pair and an increase in quality of the revised query over the first query.
Owner:GOOGLE LLC
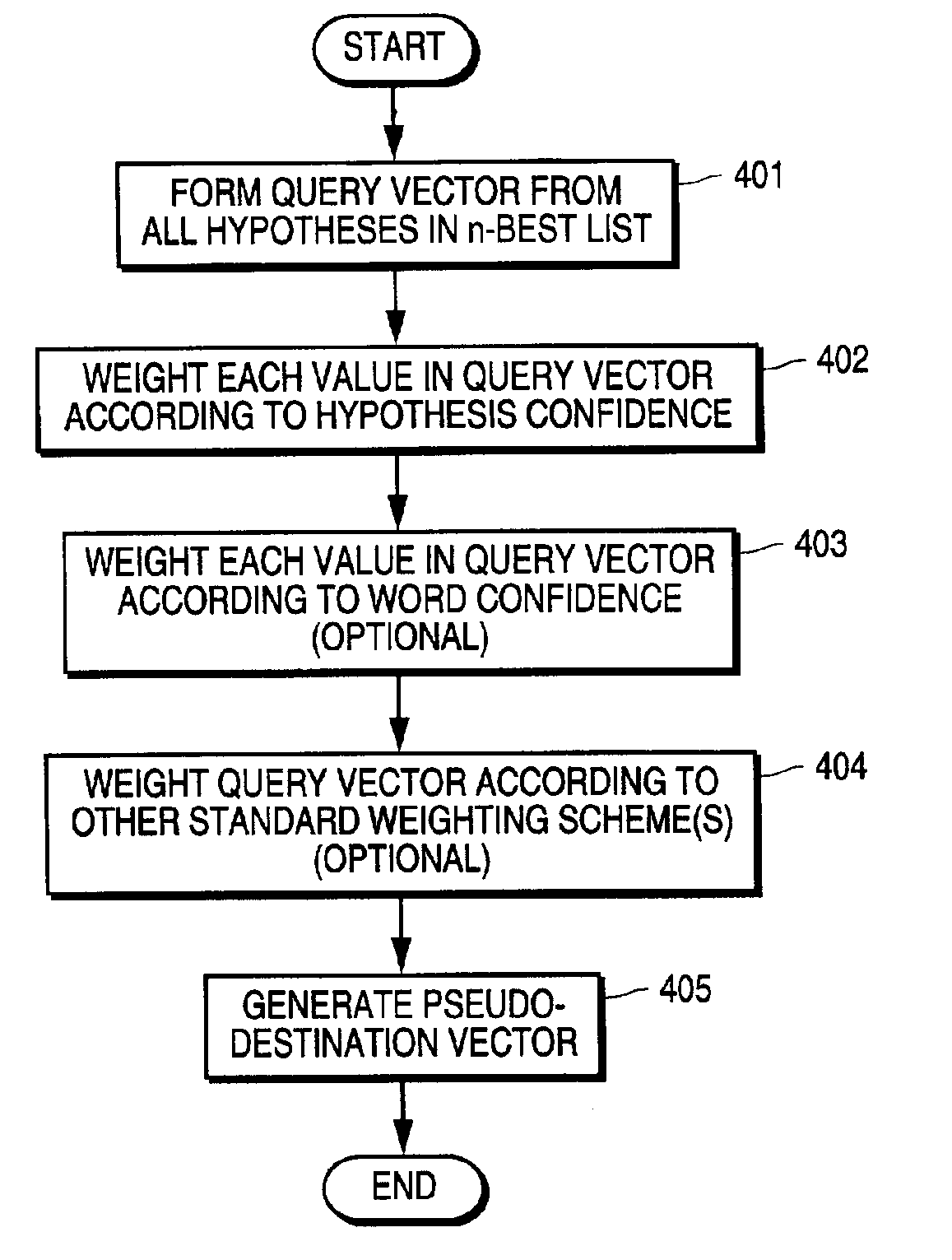
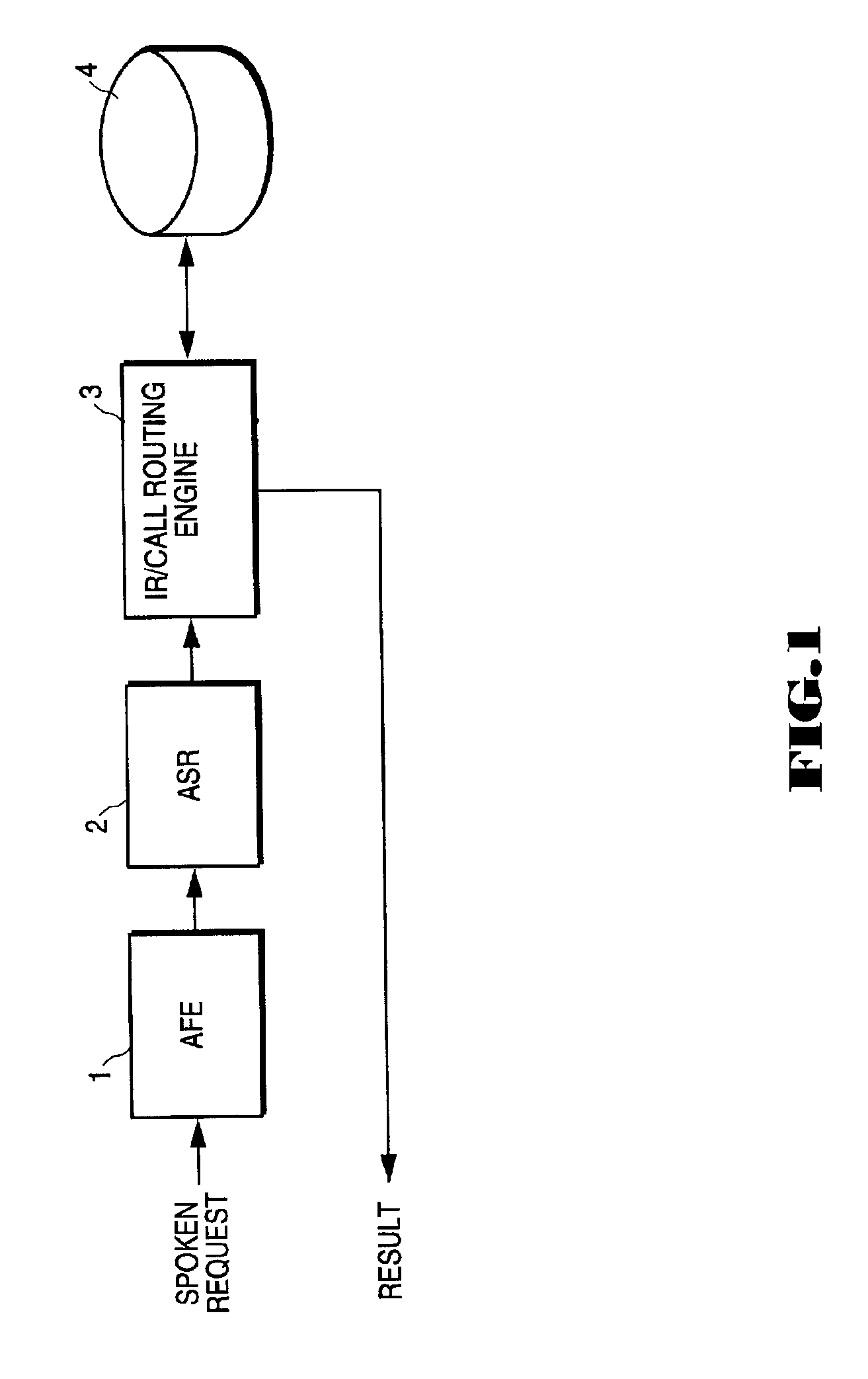
Query expansion and weighting based on results of automatic speech recognition
InactiveUS6856957B1Automatic call-answering/message-recording/conversation-recordingSpeech recognitionHypothesisConfidence metric
A technique for identifying one or more items from amongst a plurality of items in response to a spoken utterance is used to improve call routing and information retrieval systems which employ automatic speech recognition (ASR). An automatic speech recognizer is used to recognize the utterance, including generating a plurality of hypotheses for the utterance. A query element is then generated for use in identifying one or more items from amongst the plurality of items. The query element includes a set of values representing two or more of the hypotheses, each value corresponding to one of the words in the hypotheses. Each value in the query element is then weighted based on hypothesis confidence, word confidence, or both, as determined by the ASR process. The query element is then applied to the plurality of items to identify one or more items which satisfy the query.
Owner:NUANCE COMM INC
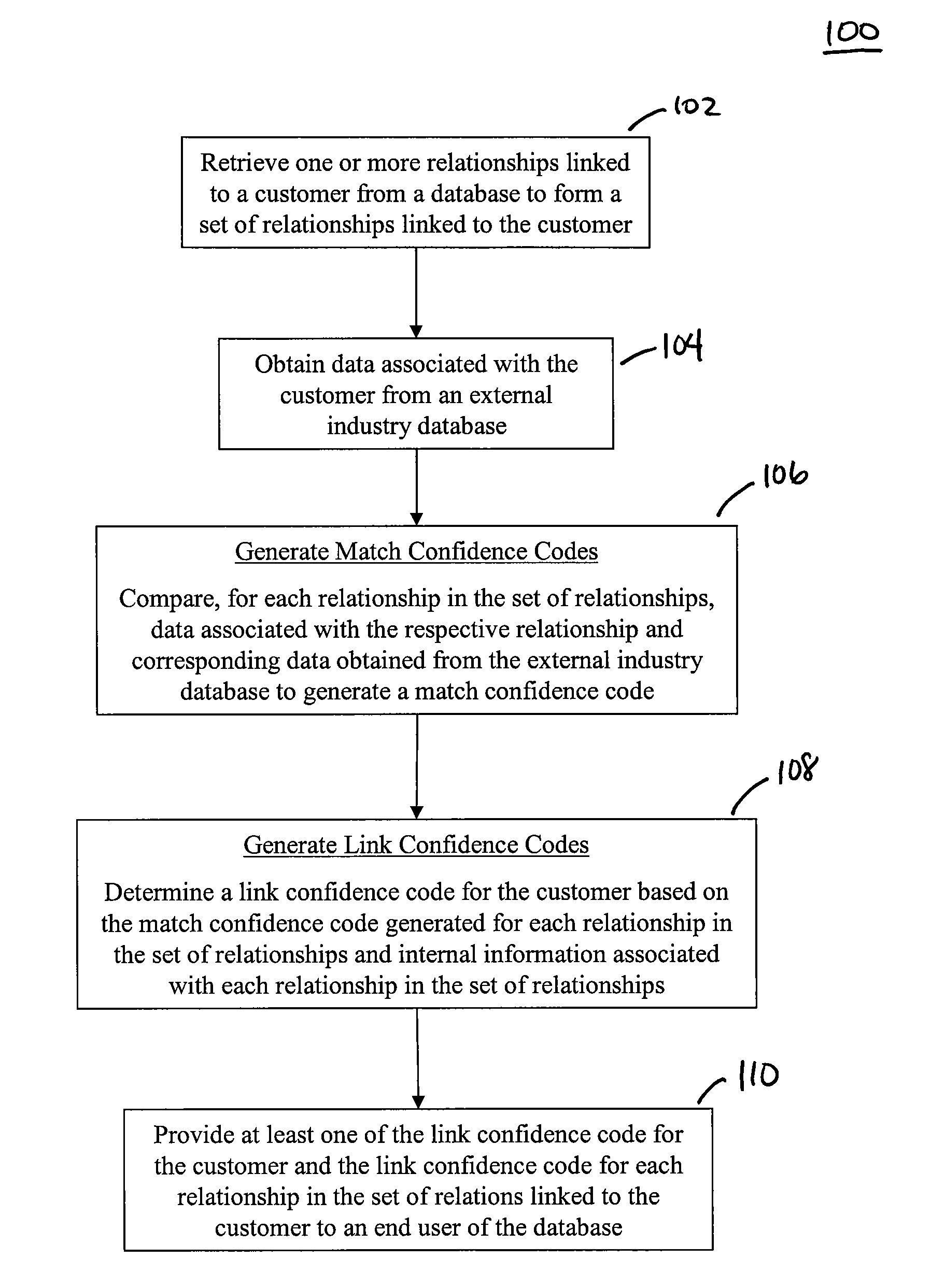
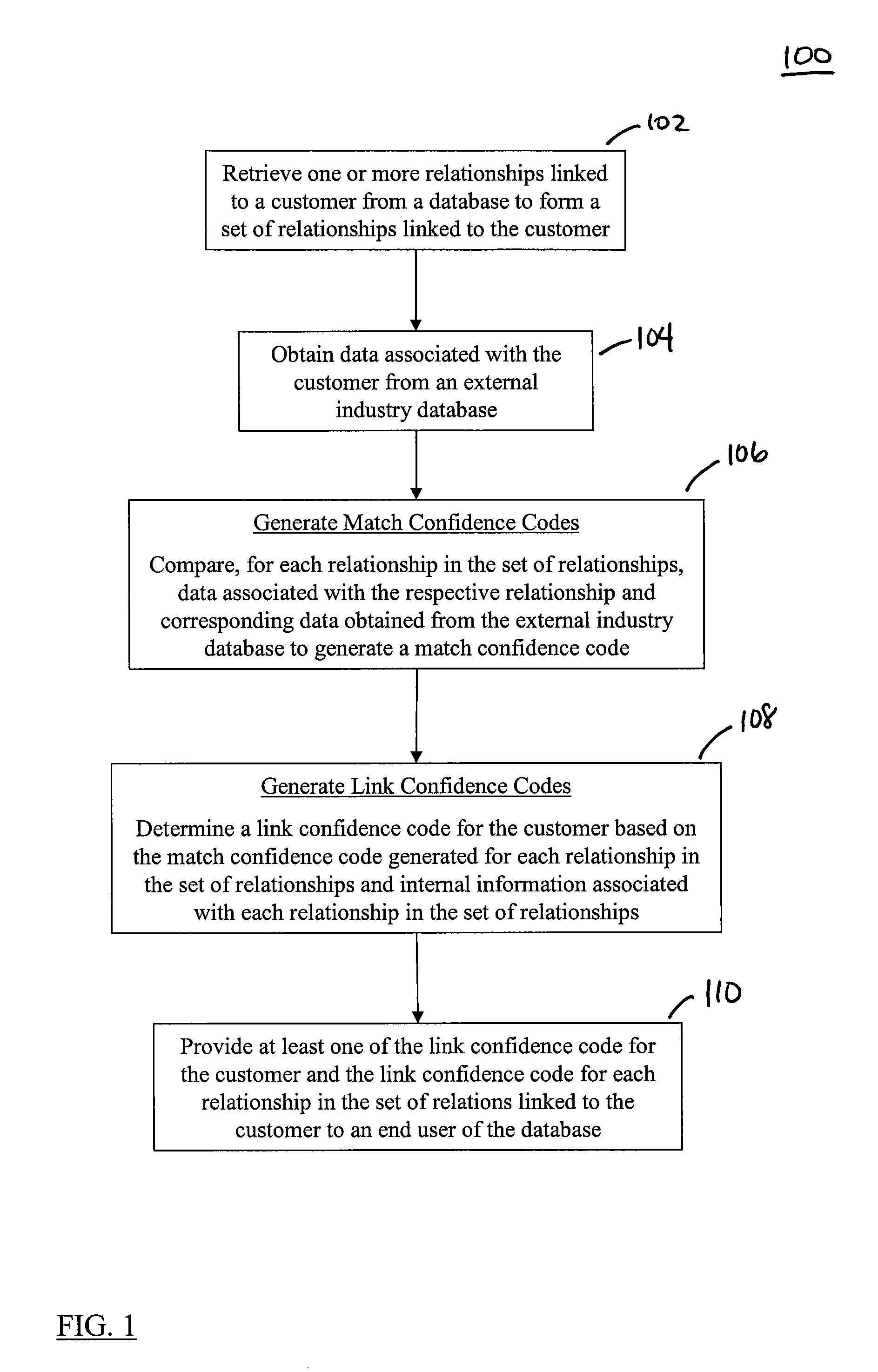
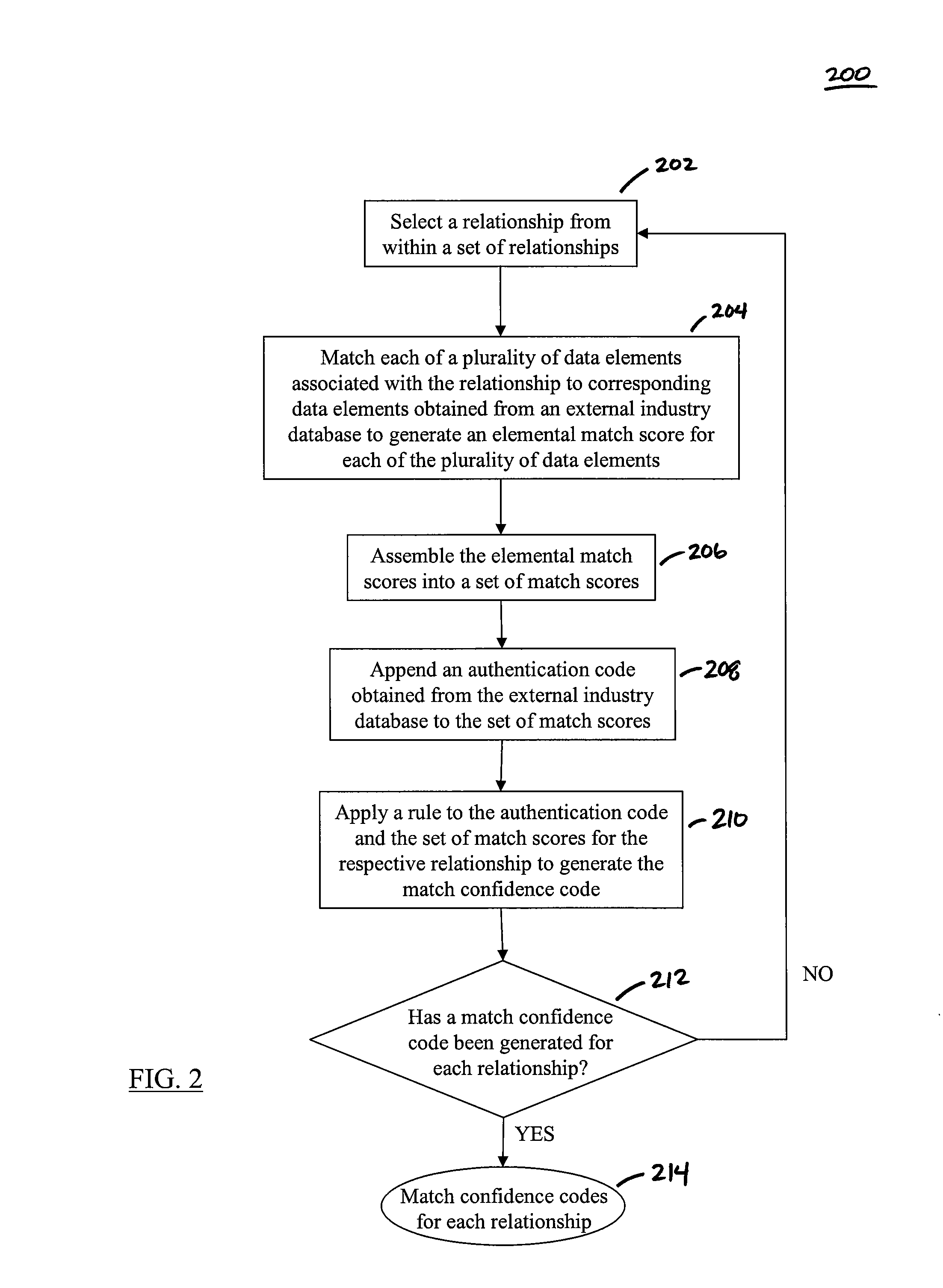
Methods, Systems, and Computer Program Products for Generating Data Quality Indicators for Relationships in a Database
The disclosed methods, systems, and computer-program products allow a business to generate data quality indicators for relationships in a database. In an embodiment, one or more relationships linked to a customer are retrieved from a database to form a set of relationships. A match confidence code is generated for each relationship based on a score generated by the comparison of customer data associated with the respective relationship and corresponding customer data obtained from an external industry database. A link confidence code is subsequently determined for the customer based on a score generated by the scores used to define the match confidence code for each relationship in the set of relationships and on internal data associated with each relationship in the set of relationships. The link confidence code for the customer and the match confidence codes and the respective scores for the set of relationships may be provided to an end user of the database in order to improve decisions made by the end user at the customer level.
Owner:LIBERTY PEAK VENTURES LLC
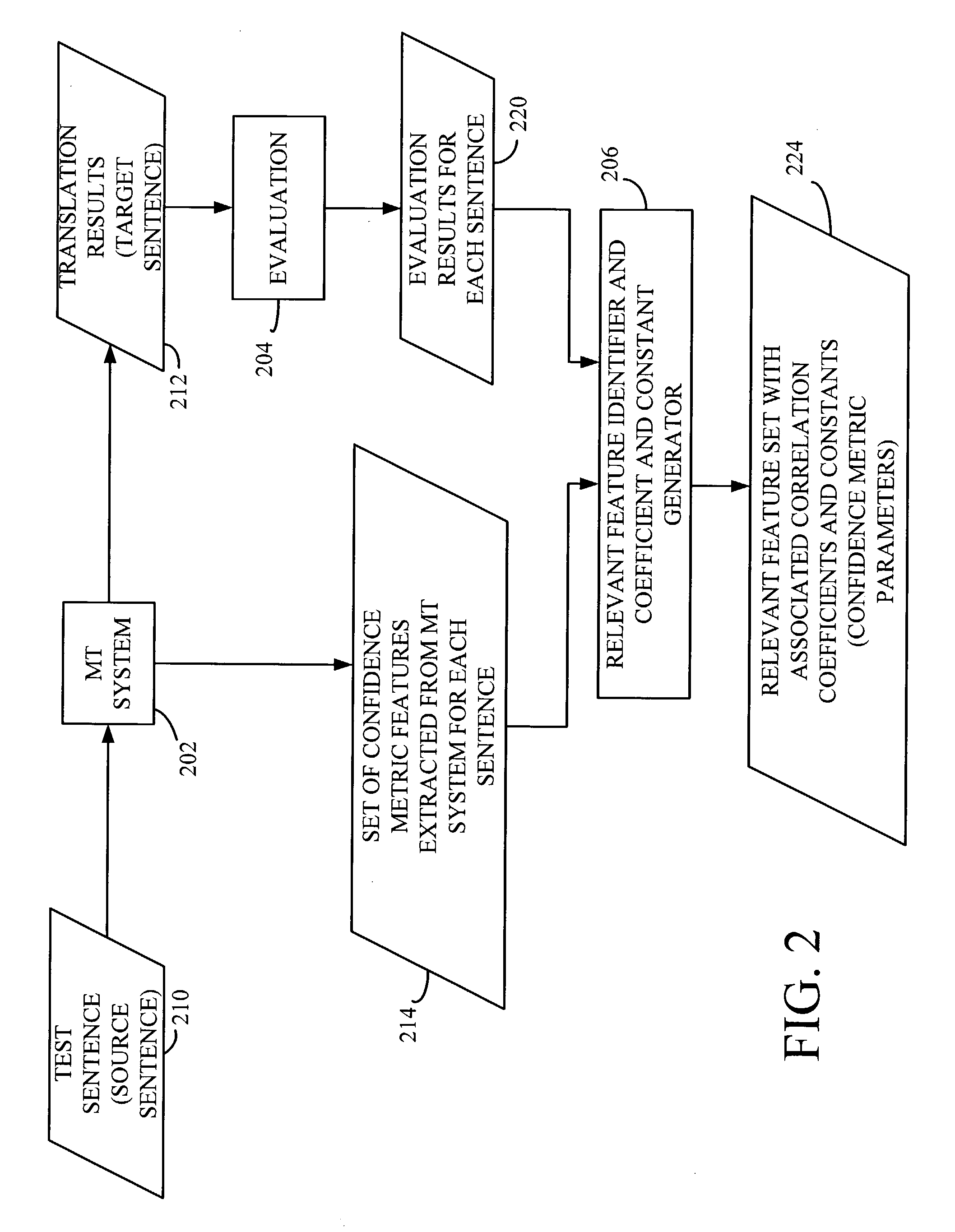
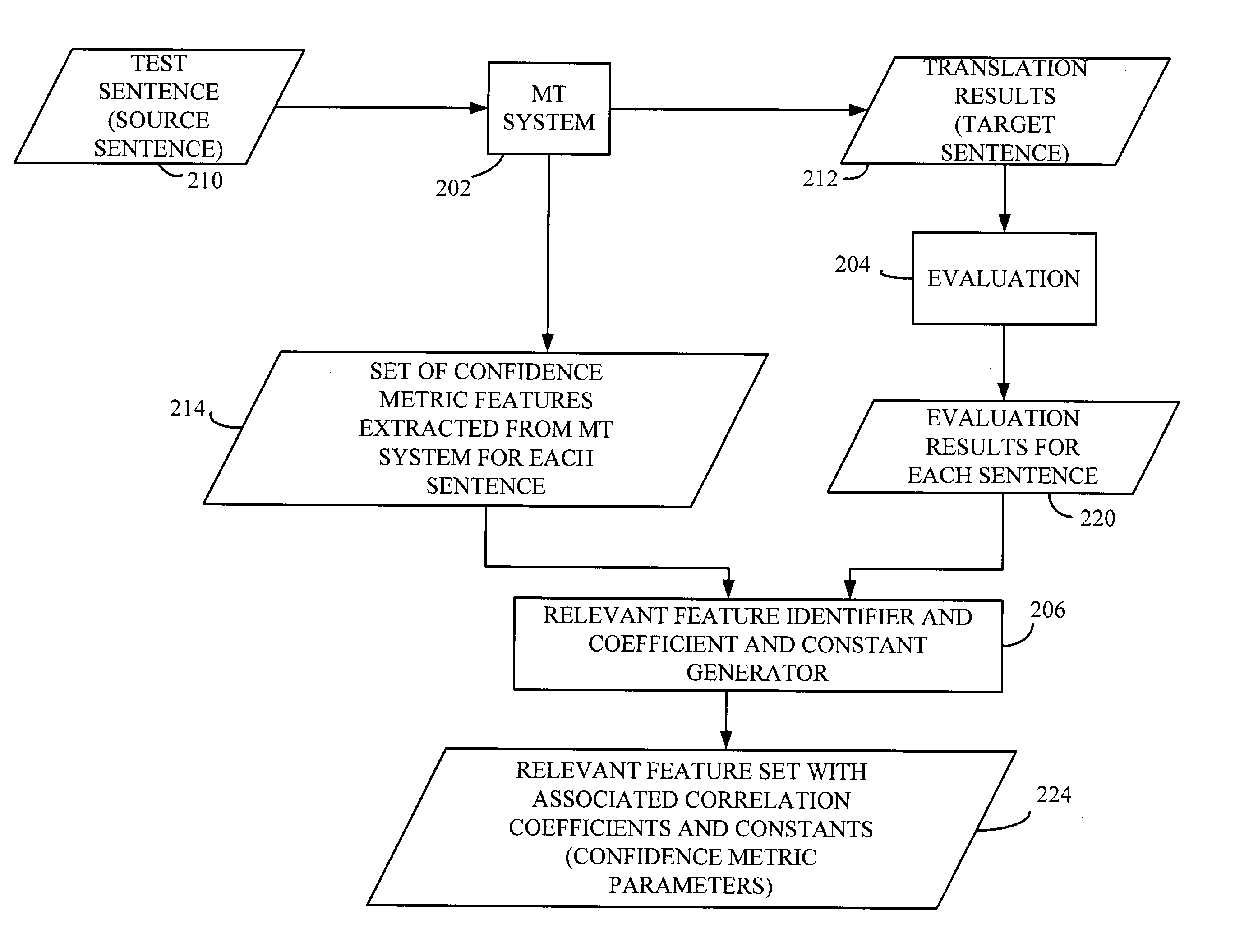
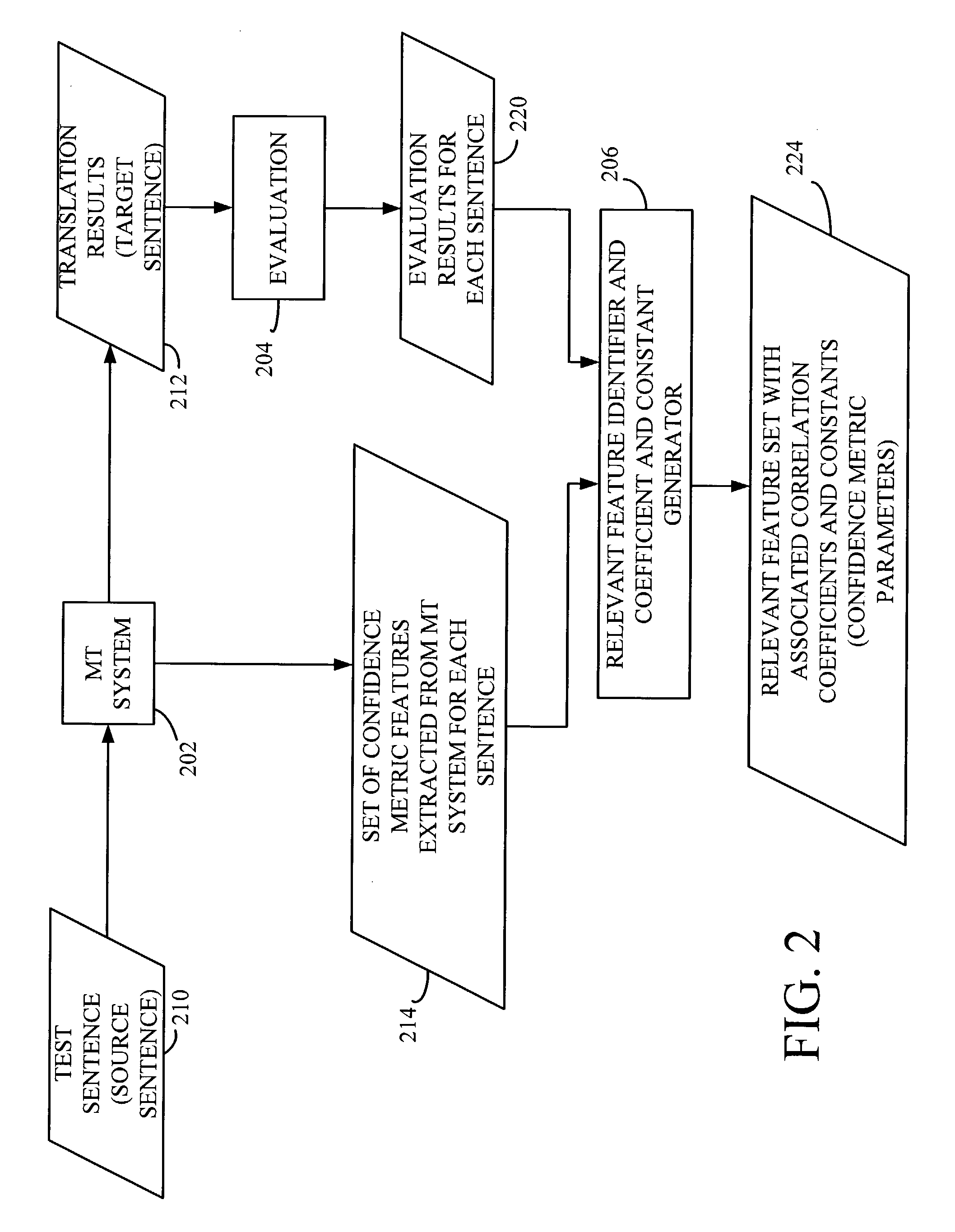
System and method for machine learning a confidence metric for machine translation
ActiveUS20050102130A1Natural language translationSpeech analysisConfidence metricMachine translation system
A machine translation system is trained to generate confidence scores indicative of a quality of a translation result. A source string is translated with a machine translator to generate a target string. Features indicative of translation operations performed are extracted from the machine translator. A trusted entity-assigned translation score is obtained and is indicative of a trusted entity-assigned translation quality of the translated string. A relationship between a subset of the extracted features and the trusted entity-assigned translation score is identified.
Owner:MICROSOFT TECH LICENSING LLC
System and method for machine learning a confidence metric for machine translation
ActiveUS7209875B2Natural language translationSpeech analysisMachine translation systemConfidence metric
A machine translation system is trained to generate confidence scores indicative of a quality of a translation result. A source string is translated with a machine translator to generate a target string. Features indicative of translation operations performed are extracted from the machine translator. A trusted entity-assigned translation score is obtained and is indicative of a trusted entity-assigned translation quality of the translated string. A relationship between a subset of the extracted features and the trusted entity-assigned translation score is identified.
Owner:MICROSOFT TECH LICENSING LLC
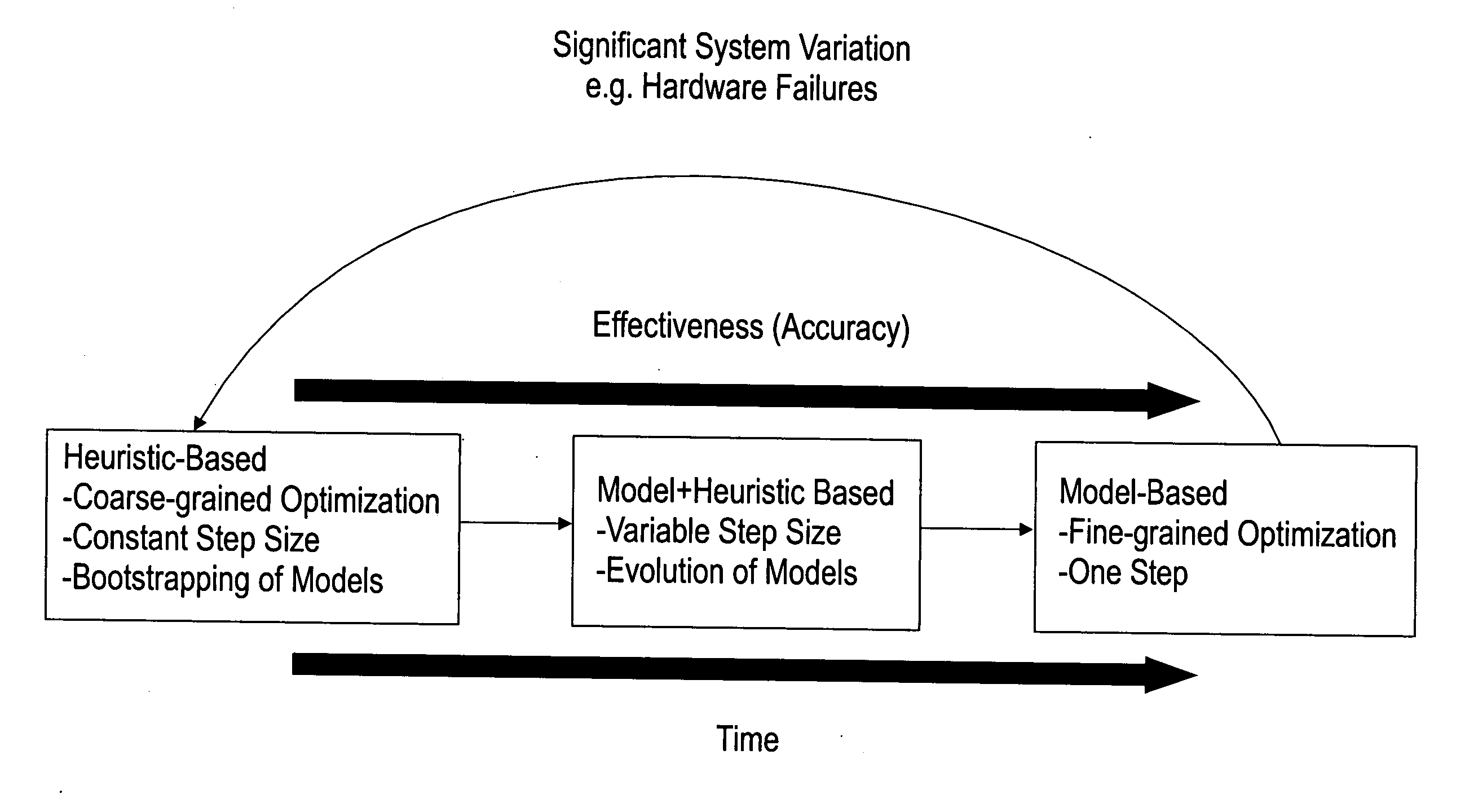
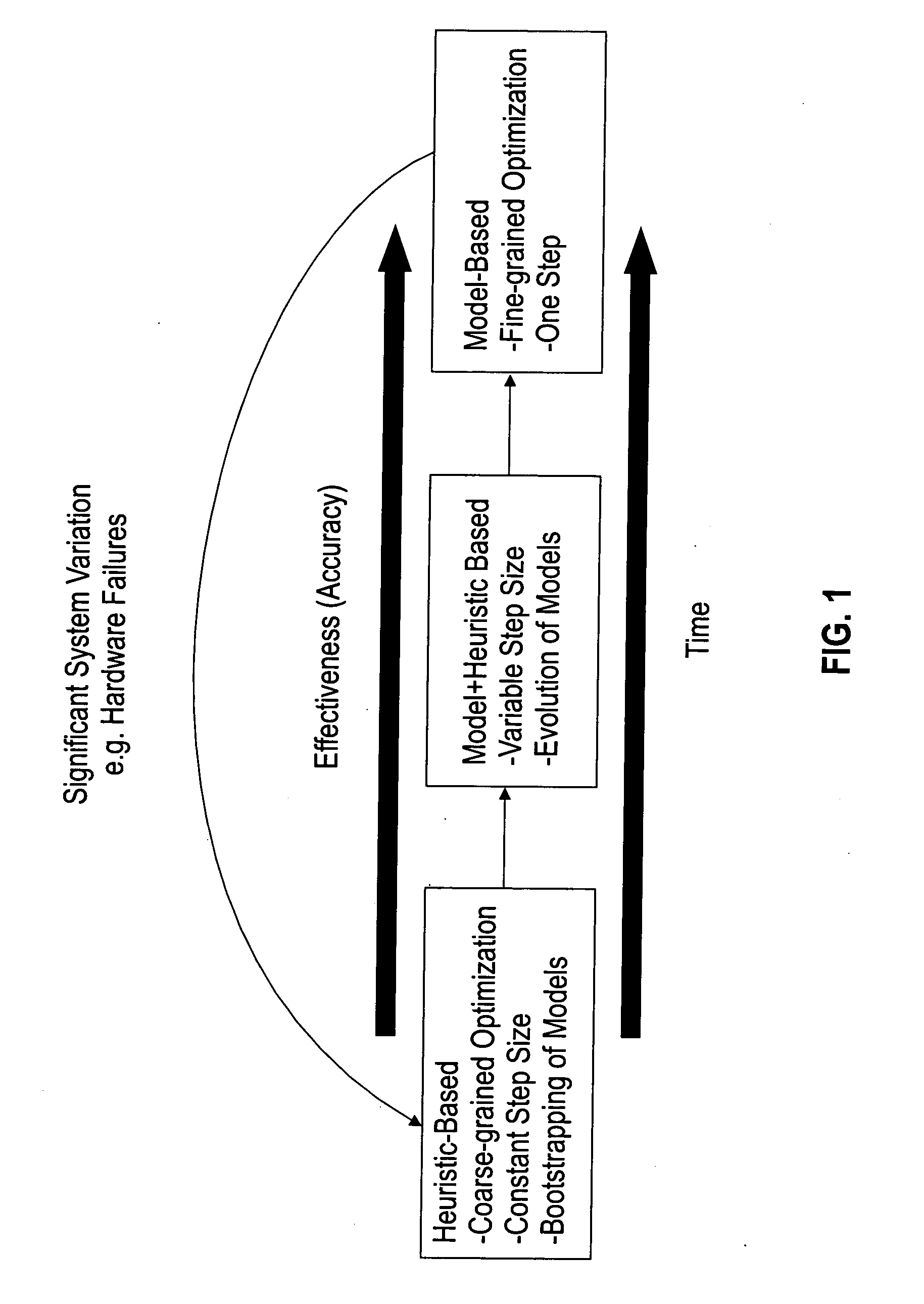
Approach based on self-evolving models for performance guarantees in a shared storage system
InactiveUS20070112723A1Improve accuracyResource allocationSpecial data processing applicationsResource allocationOperating system
A technique of allocating shared resources in a computer network-based storage system comprises taking periodic performance samples on a running storage system; evaluating an objective function that takes as input the performance samples to quantify how aligned a current state of the storage system is with organizational objectives; building and maintaining models of behavior and capabilities of the storage system by using the performance samples as input; determining how resources of the storage system should be allocated among client computers in the storage system by selecting one among many possible allocations based on predictions generated by the models in order to maximize a value of the objective function; calculating a confidence statistic value for a chosen resource allocation based on an accuracy of the models; and enforcing the chosen resource allocation on the running storage system when the confidence statistic value is at or above a predetermined threshold value.
Owner:IBM CORP
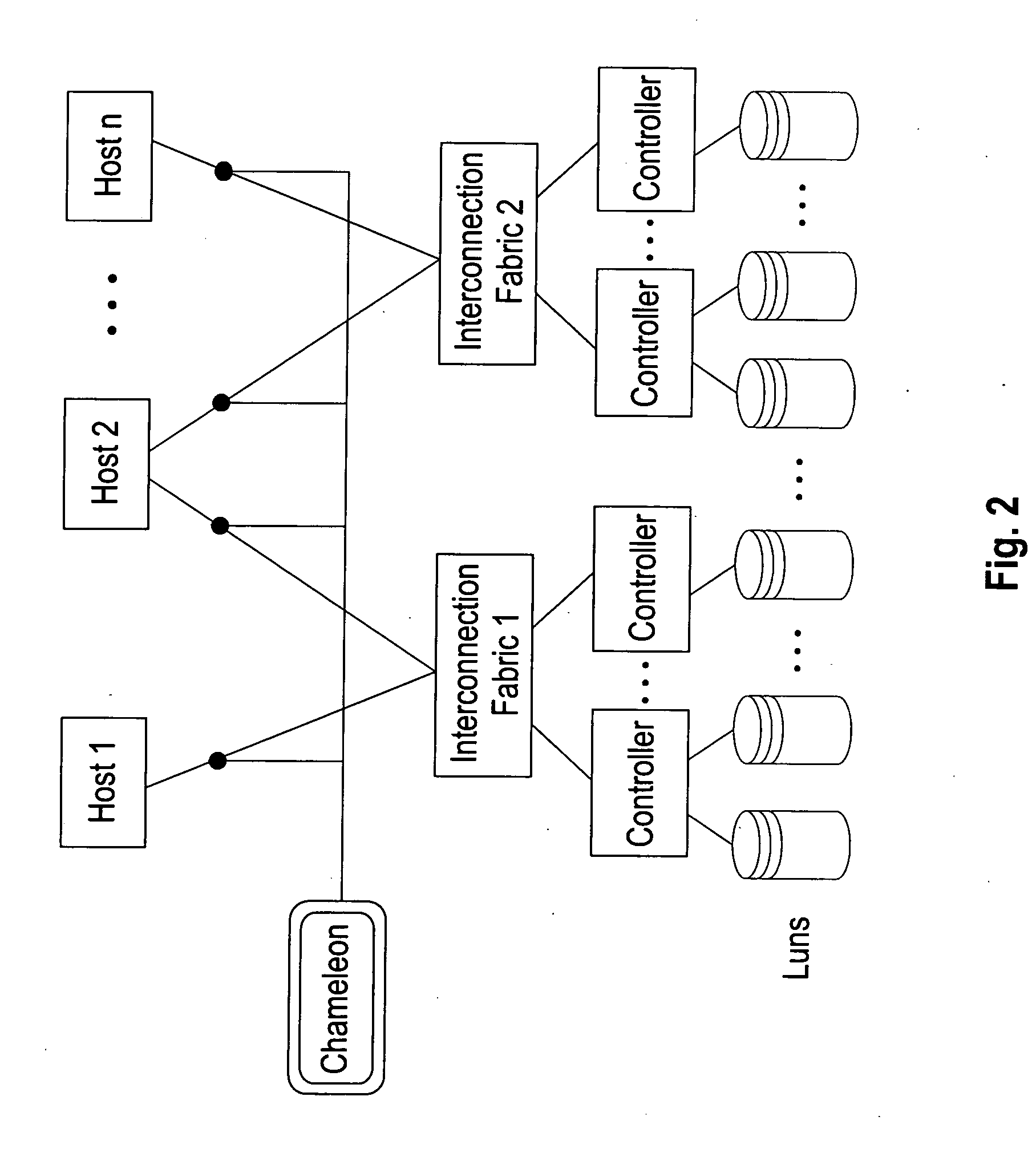
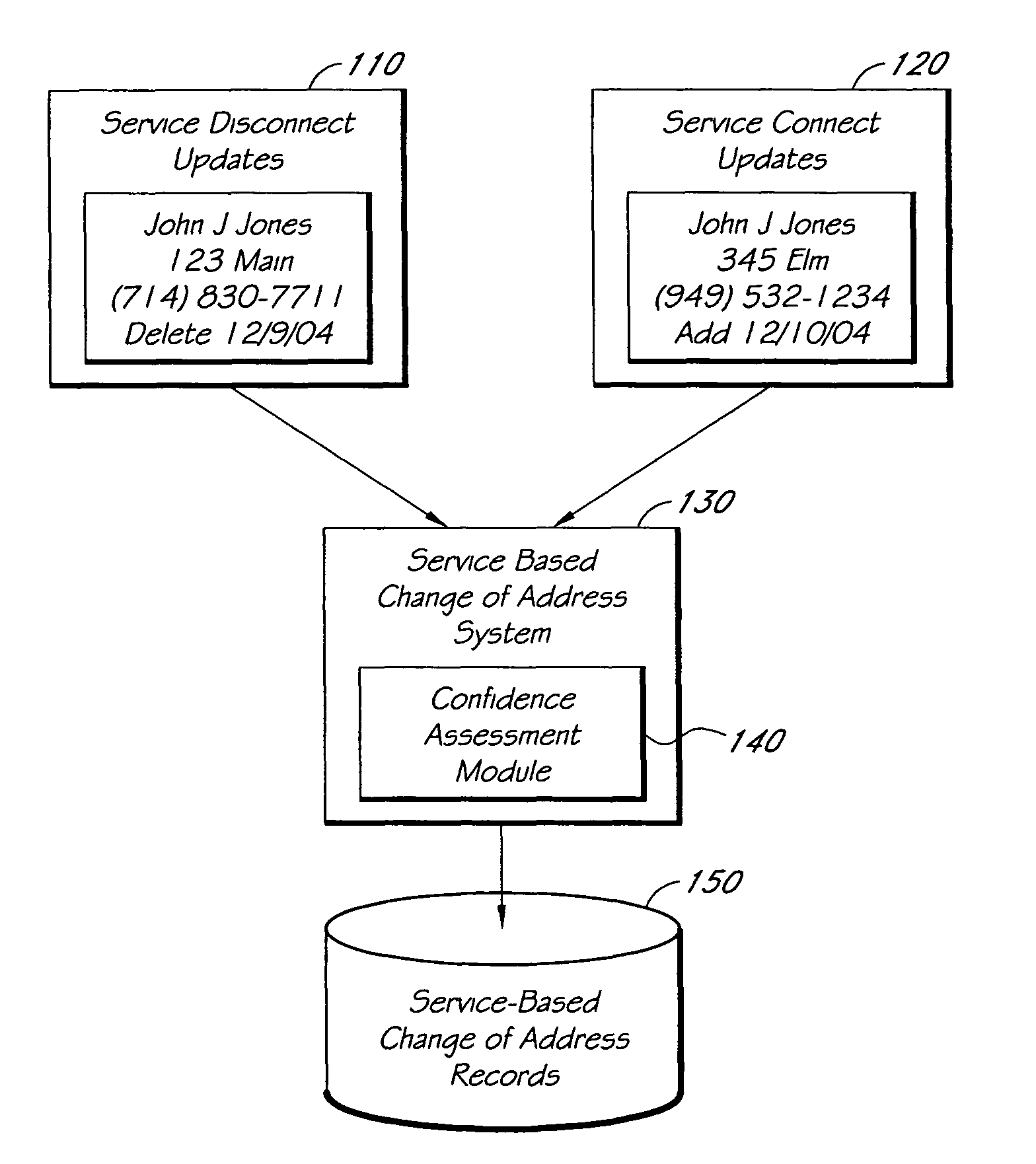
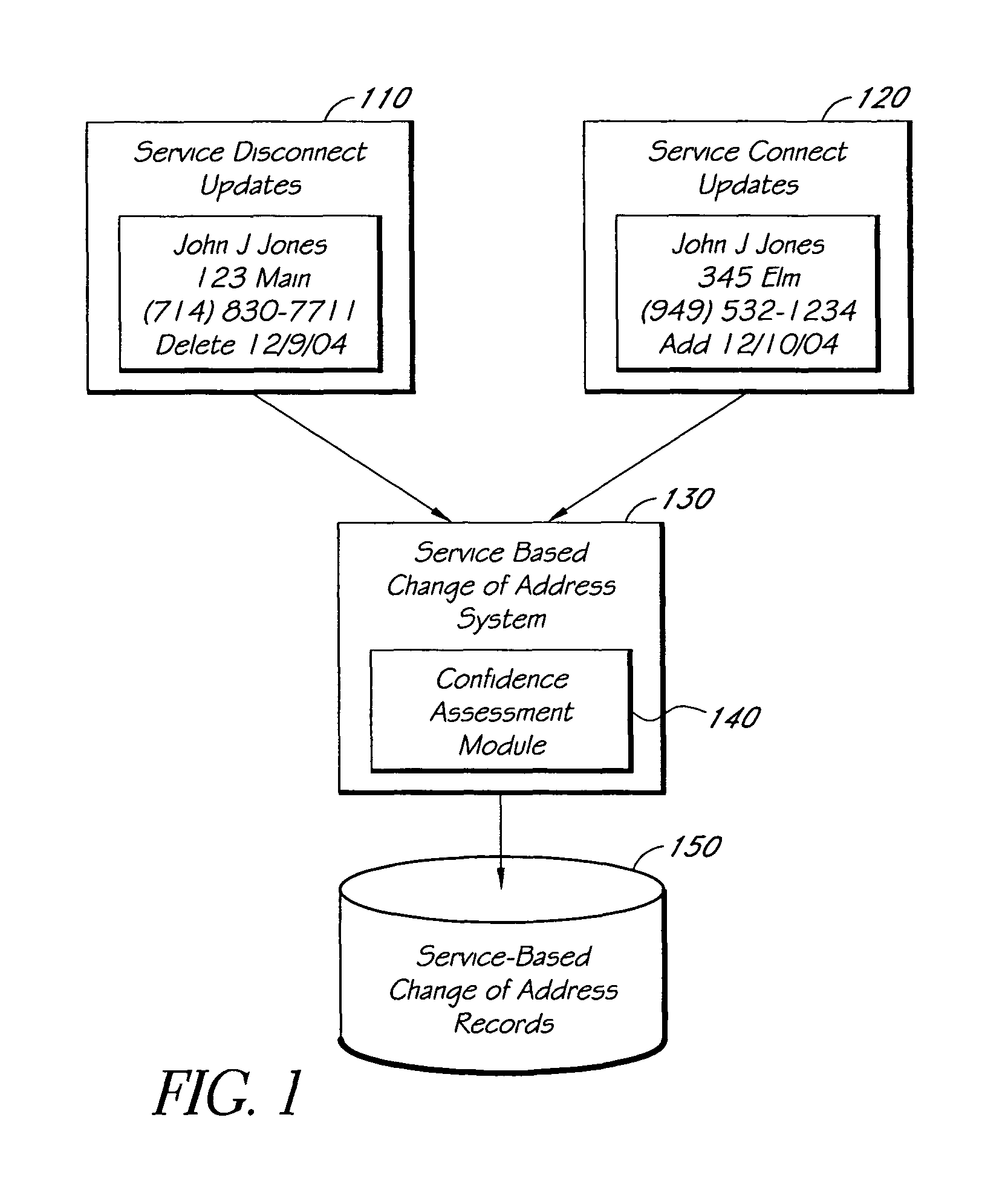
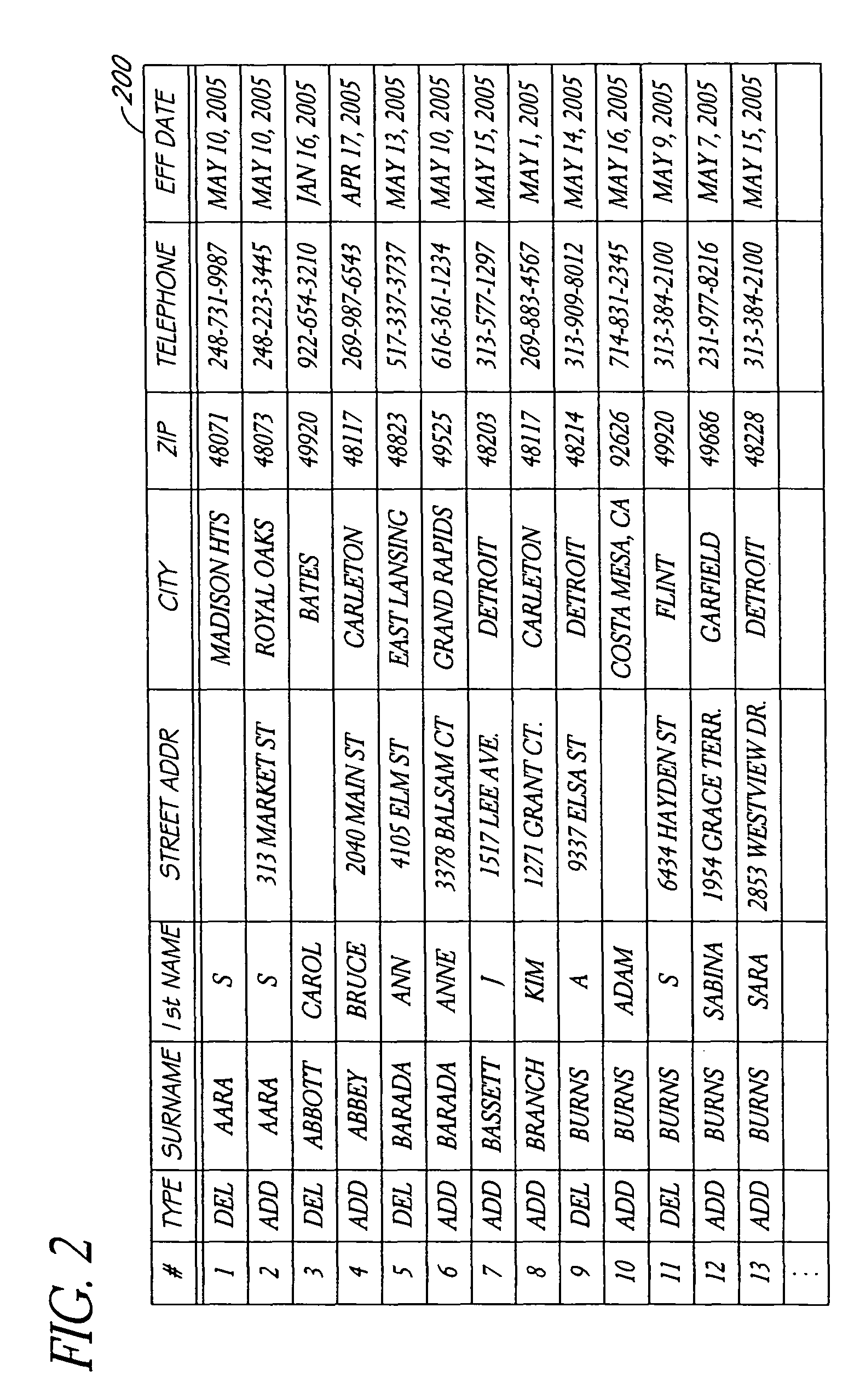
Systems and methods for tracking changes of address based on service disconnect/connect data
ActiveUS8175889B1Quick updateCustomer relationshipDigital data processing detailsEffective dateConfidence metric
A computer-implemented system for updating mailing address or other contact information using service disconnect and connect information, such as for telephone, utility, or other service, is described. Electronic information about service disconnect requests and service connection requests is received and compared to identify requests that are linked to the same individual, household, or other entity. A confidence assessment module may produce an indicator, such as a score, of a confidence level in a correct matching of a disconnect and a connect request, based at least in part on similarity of names or other account information, proximity of addresses, and proximity of effective dates associated with potentially matching service connect and disconnect requests. In some embodiments, service disconnect and connect records from a plurality of services are used.
Owner:EXPERIAN INFORMATION SOLUTIONS
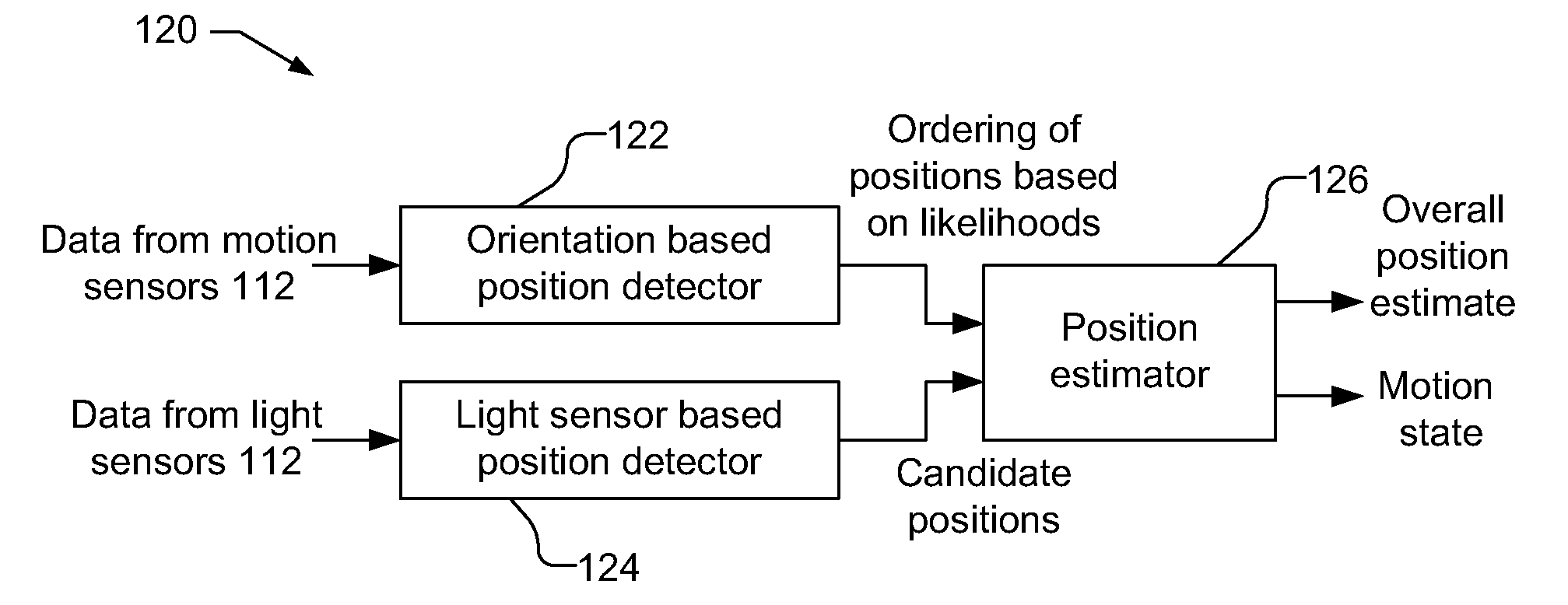
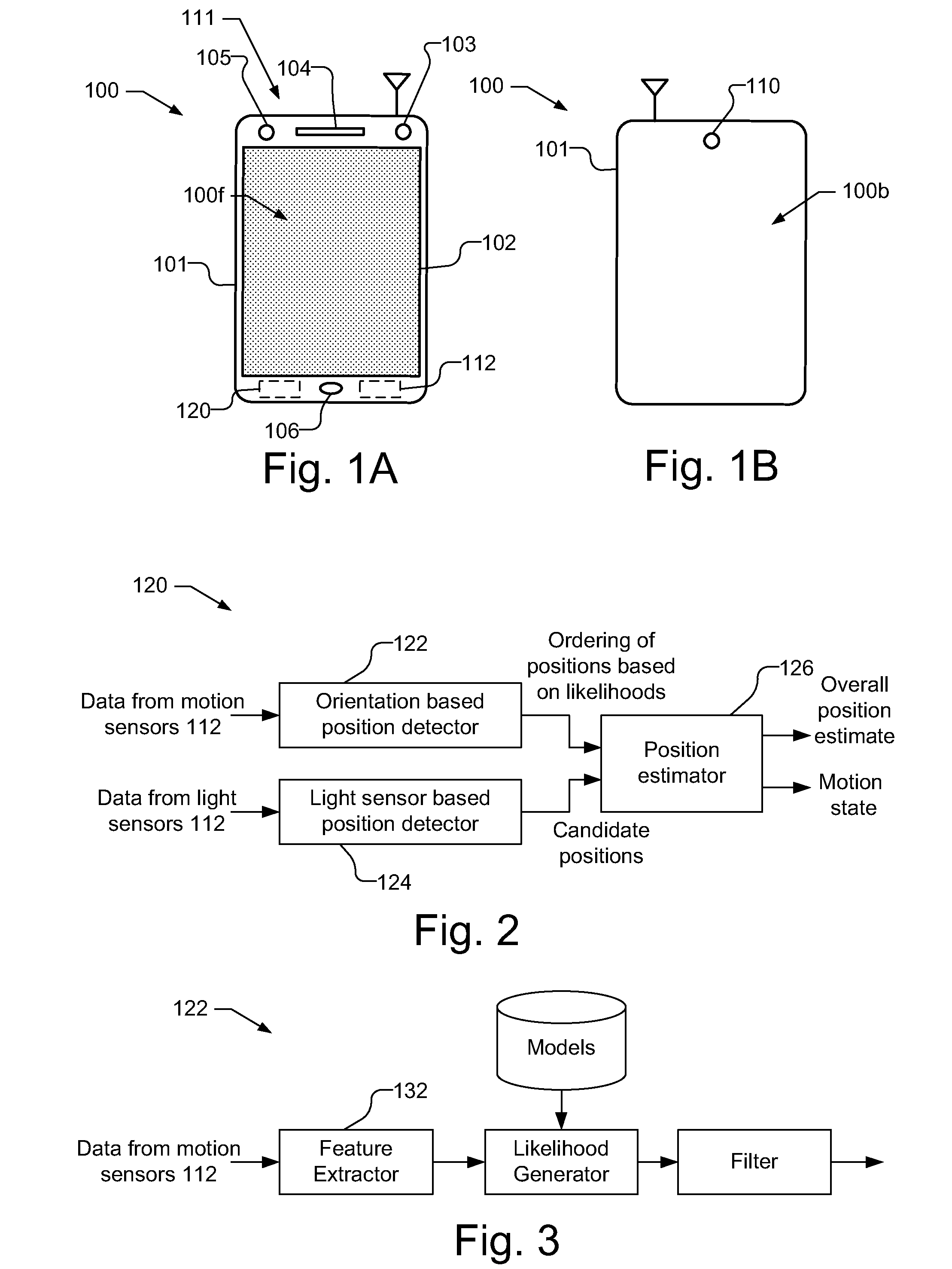
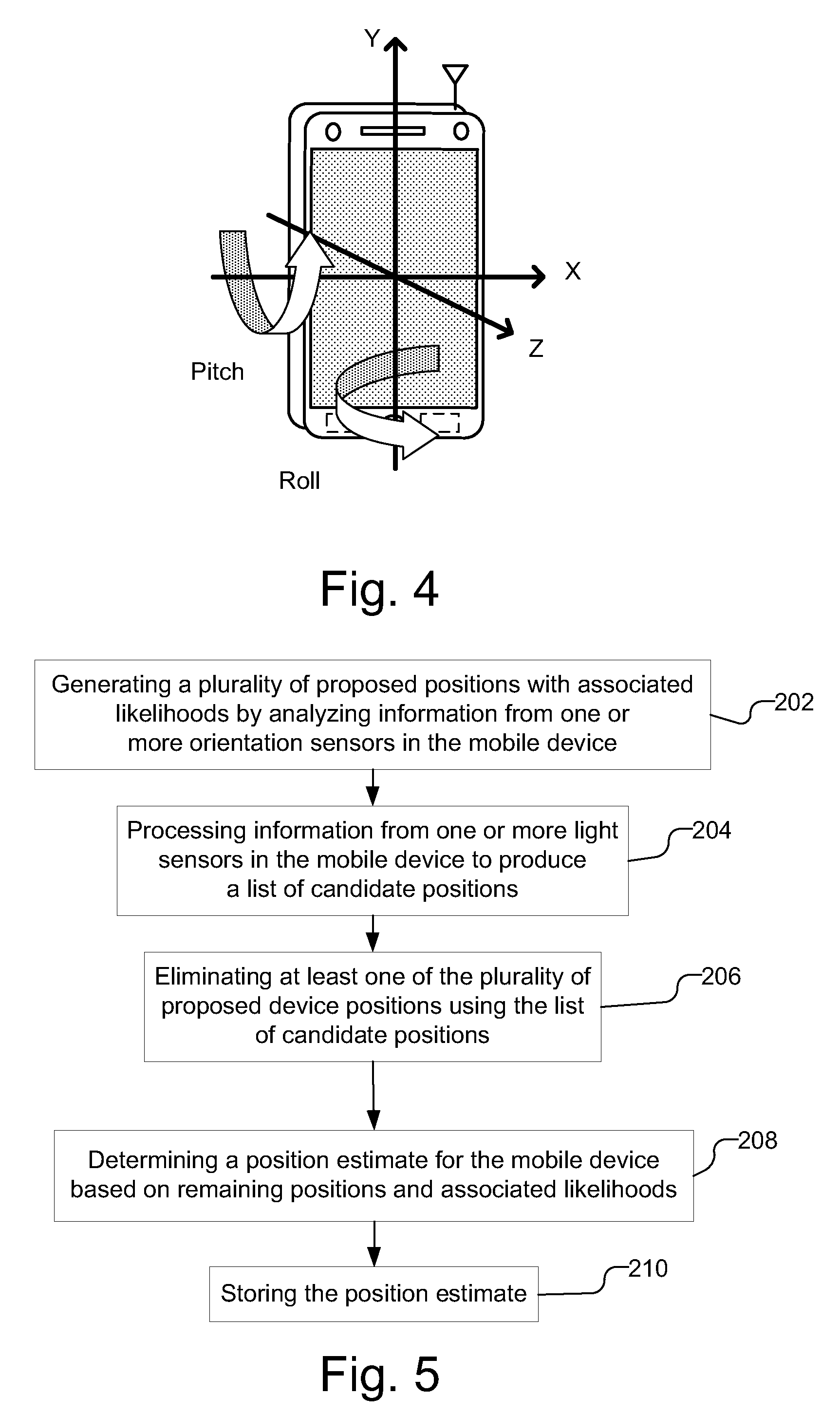
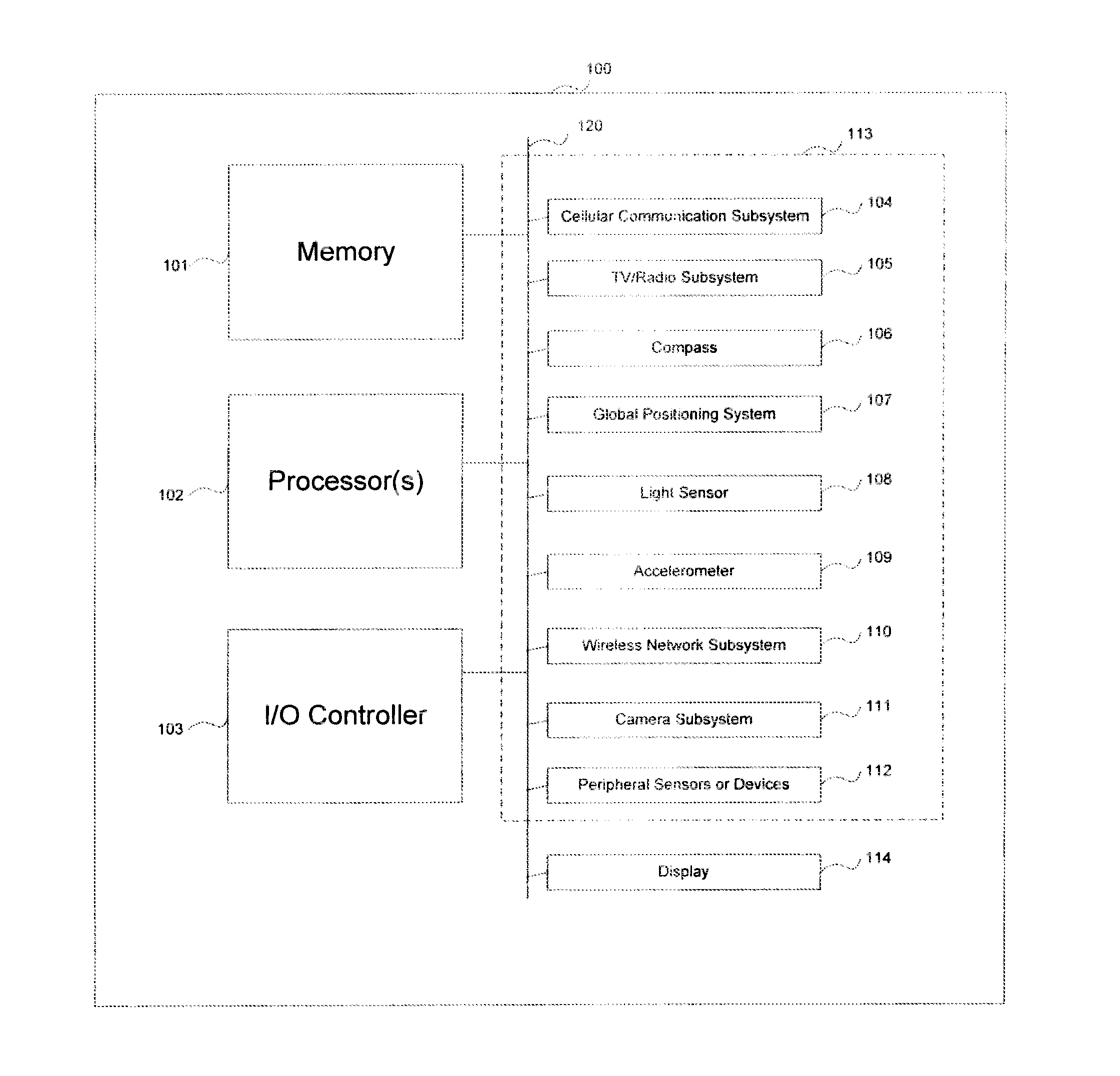
Device position estimates from motion and ambient light classifiers
ActiveUS20120265482A1Digital data processing detailsDigital computer detailsProximity sensorAccelerometer
A position estimate for a mobile device is generated using data from motion sensors, such as accelerometers, magnetometers, and / or gyroscopes, and data from light sensors, such as an ambient light sensor, proximity sensor and / or camera intensity sensor. A plurality of proposed positions with associated likelihoods is generated by analyzing information from the motion sensors and a list of candidate positions is produced based on information from the light sensors. At least one of the plurality of proposed positions is eliminated using the list of candidate positions and a position estimate for the mobile device is determined based on the remaining proposed positions and associated likelihoods. The proposed positions may be generated by extracting features from the information from the motion sensors and using models to generate likelihoods for the proposed positions. The likelihoods may be filtered over time. Additionally, a confidence metric may be generated for the estimated position.
Owner:QUALCOMM INC
System and method for constraint-based rule mining in large, dense data-sets
InactiveUS6278997B1Data processing applicationsDigital data information retrievalData setConfidence metric
A dense data-set mining system and method is provided that directly exploits all user-specified constraints including minimum support, minimum confidence, and a new constraint, known as minimum gap, which prunes any rule having conditions that do not contribute to its predictive accuracy. The method maintains efficiency even at low supports on data that is dense in the sense that many items appear with high frequency (e.g. relational data).
Owner:IBM CORP
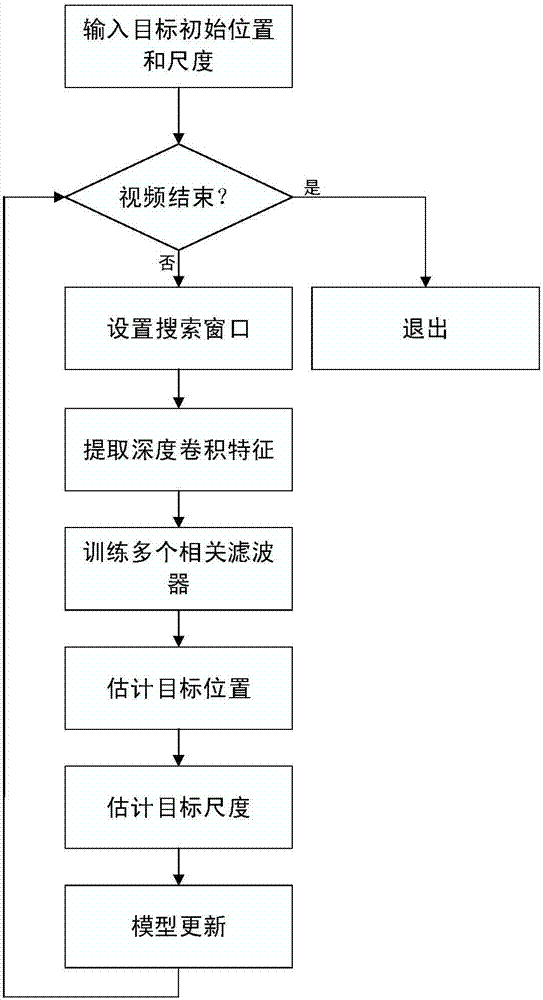
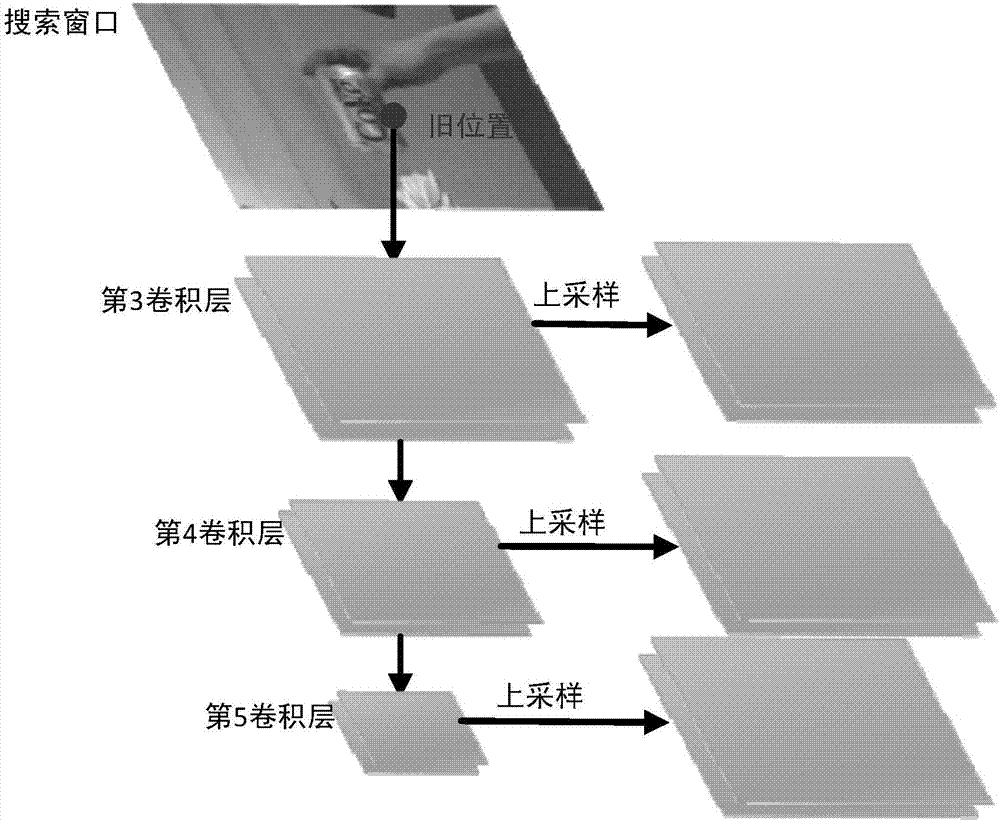
Scale adaptive target-tracking method based on depth characteristic kernel correlation filter
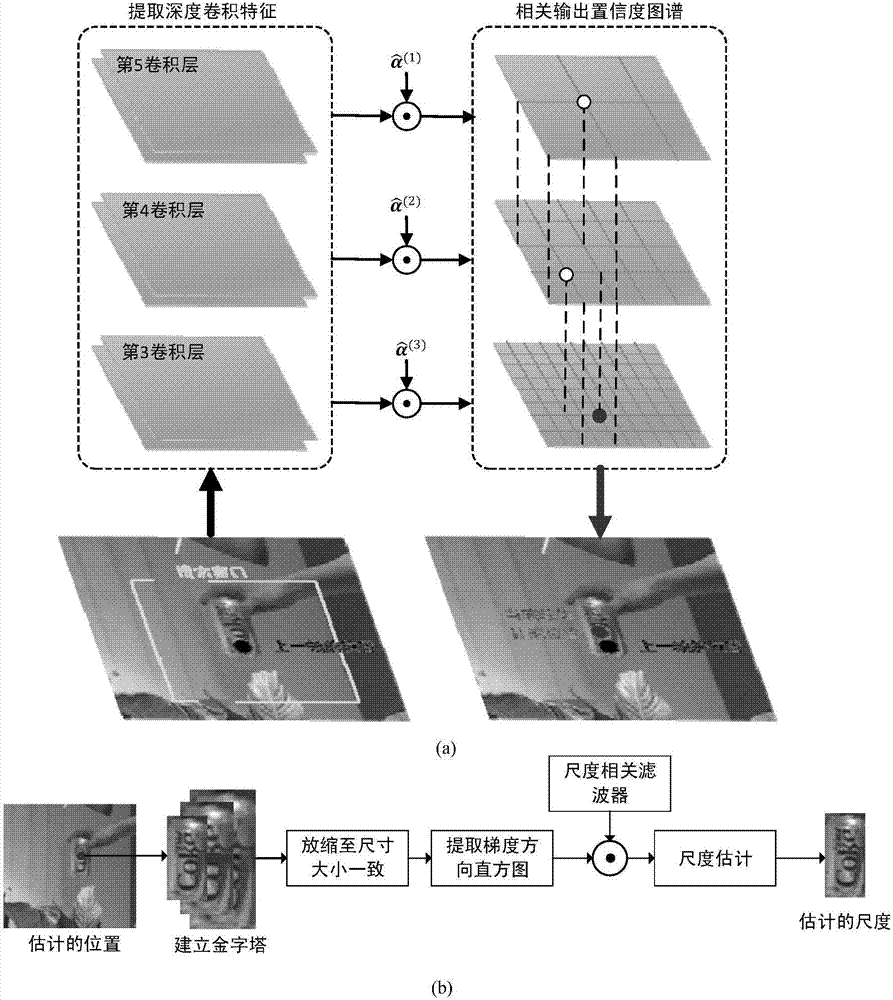
InactiveCN107154024AImprove robustnessReduce the risk of driftingImage enhancementImage analysisScale estimationCorrelation filter
The invention discloses a scale adaptive target-tracking method based on a depth characteristic kernel correlation filter. The method comprises the following steps: inputting an image into a pre-trained convolution neural network, and extracting depth convolution features; tracking a target, and estimating the position and scale of the target through the trained model; training the kernel correlation filter according to the currently detected target position and scale; and updating the kernel correlation filter through employing an adaptive high-confidence model updating method. According to the invention, the depth convolution features are extracted, and the adaptive scale estimation method and the adaptive high-confidence model updating strategy are improved, thereby improving the target tracking robustness under the conditions of complex scenes and appearance changes. The method can achieve the high-efficiency and accurate processing of the scale change of the target. In addition, the adaptive high-confidence model updating strategy is employed, so the model tracking drift is reduced as much as possible.
Owner:NANJING UNIV OF SCI & TECH
Identification and automatic propagation of geo-location associations to un-located documents
InactiveUS20070112777A1High location confidenceLocation confidenceDigital data information retrievalData processing applicationsConfidence metricDocument preparation
Systems and methods are provided for identifying pages that can be authoritatively, to some confidence level or another, associated with a geographic location, and systems and methods for grouping documents such that authoritative location associations can be propagated from pages with higher location confidence to pages with lower location confidence. Pages might be identified with authoritative indicators, groups of pages identified including at least one addressed page and at least one unaddressed page, wherein an addressed page is a page having a higher confidence level than an unaddressed page, and at least one processing step performed that is location specific. The confidence level assigned to a page as part of the process represents the confidence that the page is associated with an identifiable geographic location, with documents having a high confidence level being determined to be strongly associated with a particular geographic location while documents having a low confidence level being determined to be weakly associated with a particular geographic location or not associated at all with a geographic location.
Owner:R2 SOLUTIONS
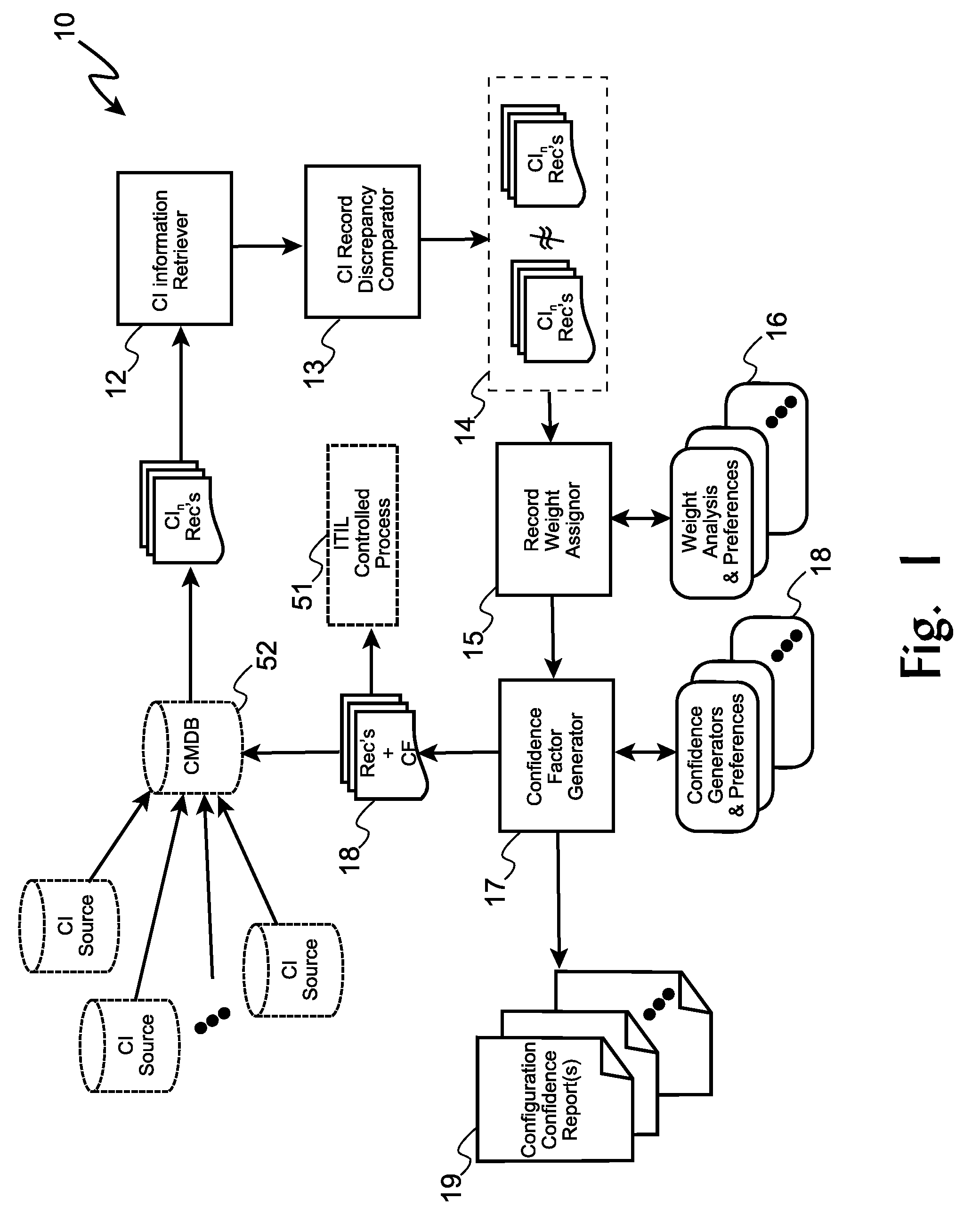
Weighted Determination in Configuration Management Systems
A system, method, and medium for providing configurable item configuration data by receiving a plurality of configuration data sets from a plurality of sources, all which pertain to the same configurable item (CI), then using weighting rules and preferences to assign weight values for each option, feature, and component in each report according to discrepancies and commonalities between the data sets, creating a new data set for the configurable item by selecting options, features, and components having the greatest weight values among all of the data sets, assigning confidence factors to each option, feature, and component by weight comparisons between the plurality of data sets; updating a configuration management database entry for the configurable item accordingly. The confidence factors are useful for inhibiting regulated processes, such as software release processes and change control processes, and for generating human-readable configuration reports indicating confidence levels of the reports and their contents.
Owner:IBM CORP
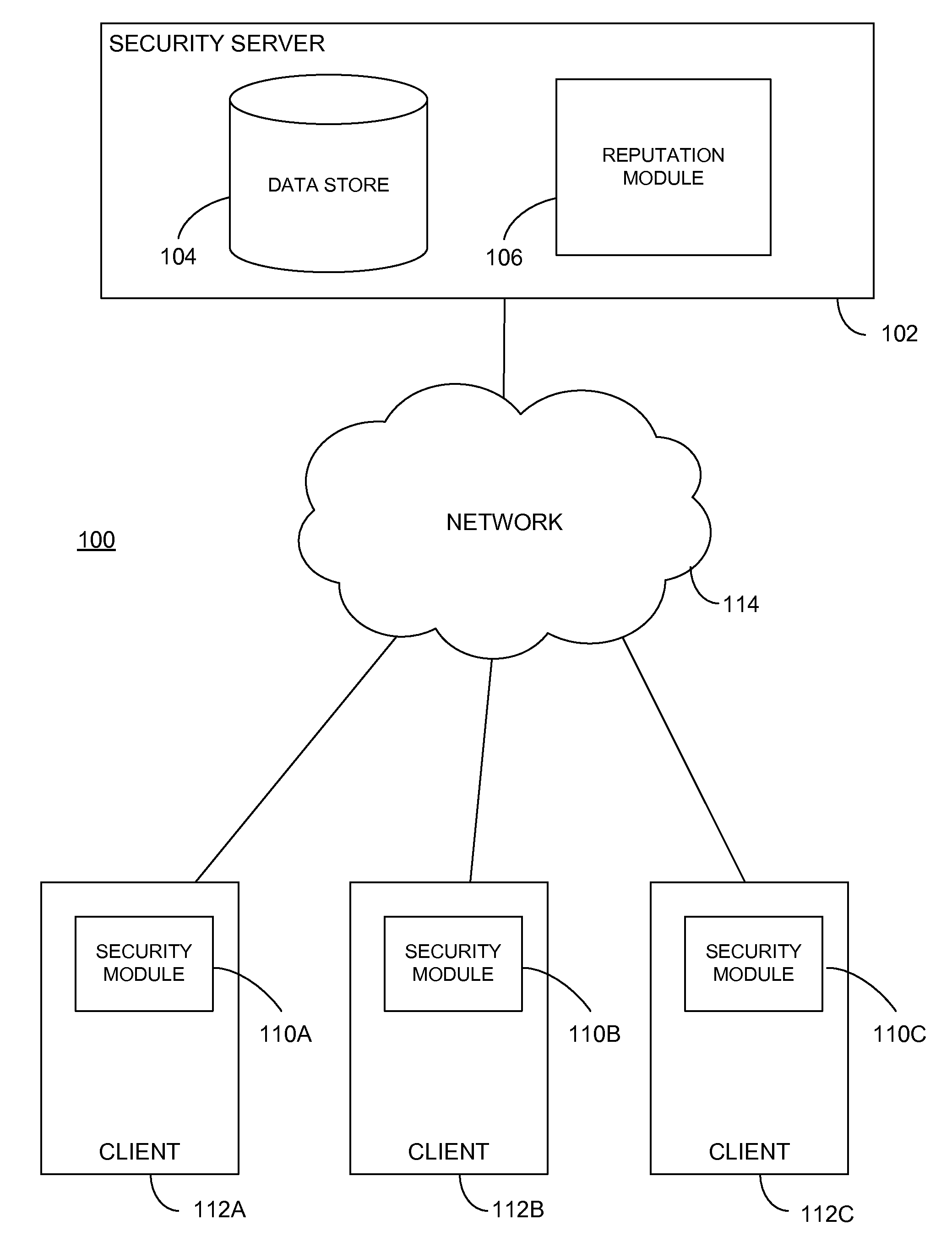
Using Confidence About User Intent In A Reputation System
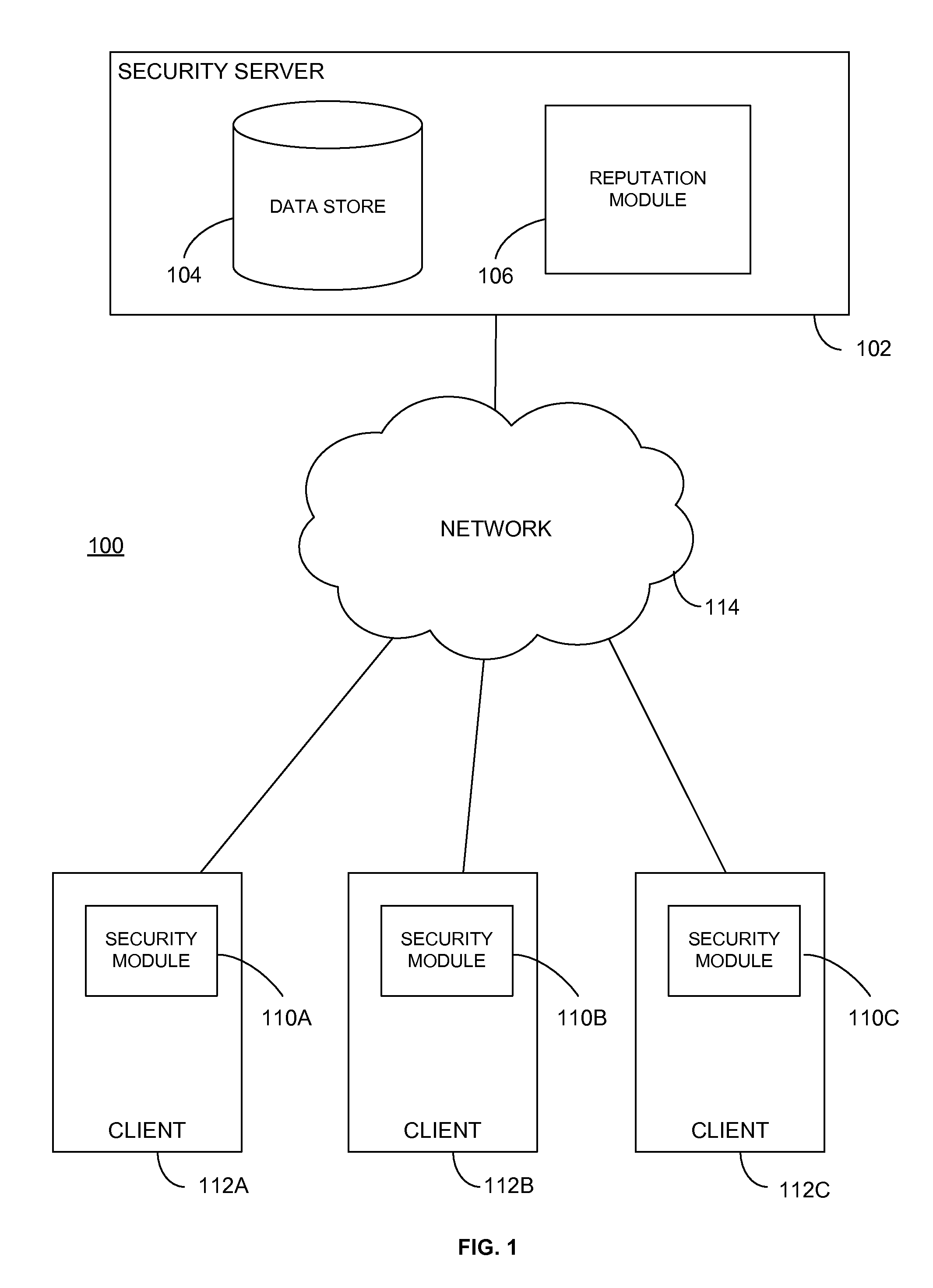
ActiveUS20110040825A1Multiple digital computer combinationsPlatform integrity maintainanceConfidence metricUser confidence
Reputations of objects are determined by a reputation system using reports from clients identifying the objects. Confidence metrics for the clients are generated using information determined from the reports. Confidence metrics indicate the amounts of confidence in the veracity of the reports. Reputation scores of objects are calculated using the reports from the clients and the confidence metrics for the clients. Confidence metrics and reputation scores are stored in correlation with identifiers for the objects. An object's reputation score is provided to a client in response to a request.
Owner:CA TECH INC
System or method for classifying images
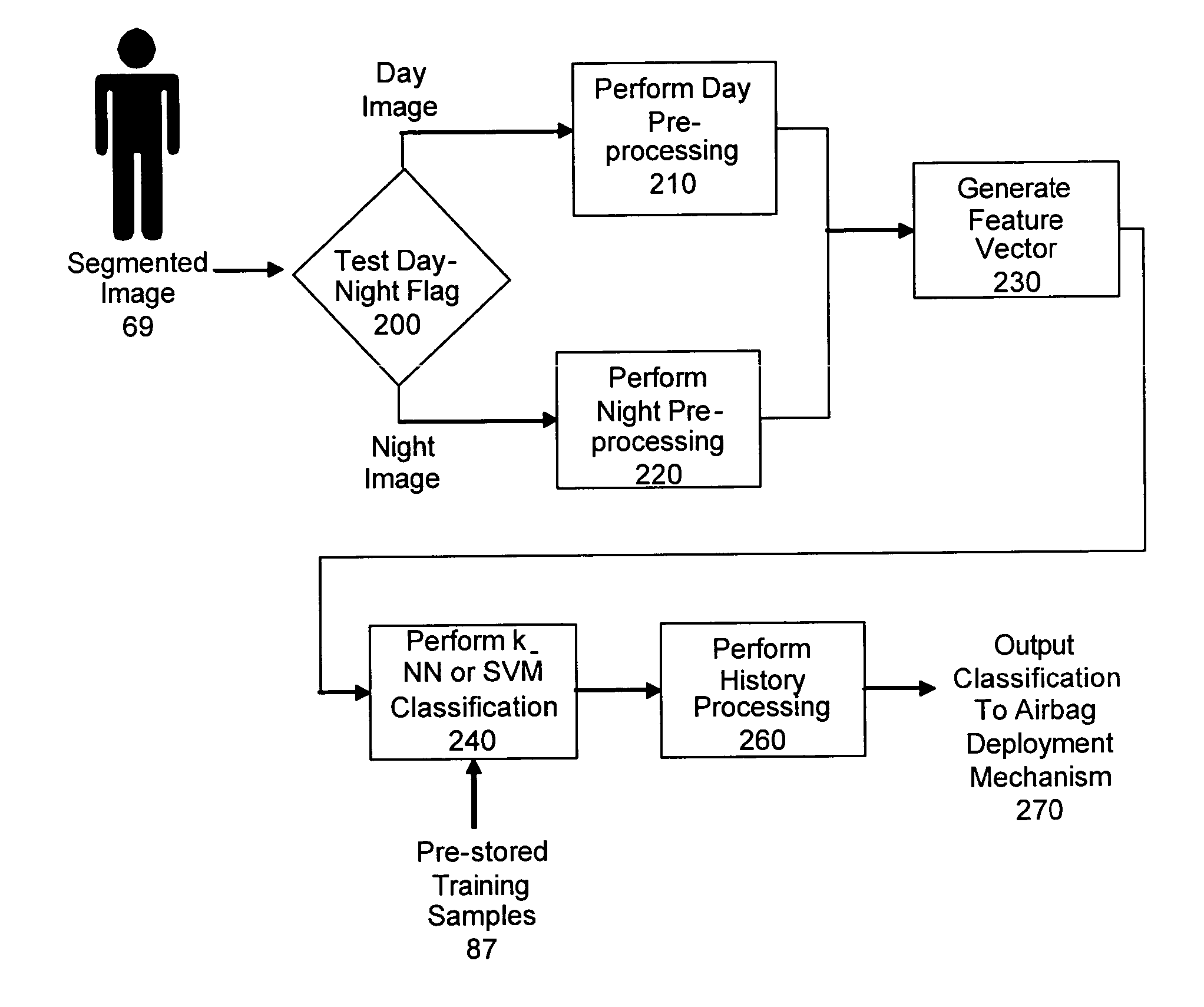
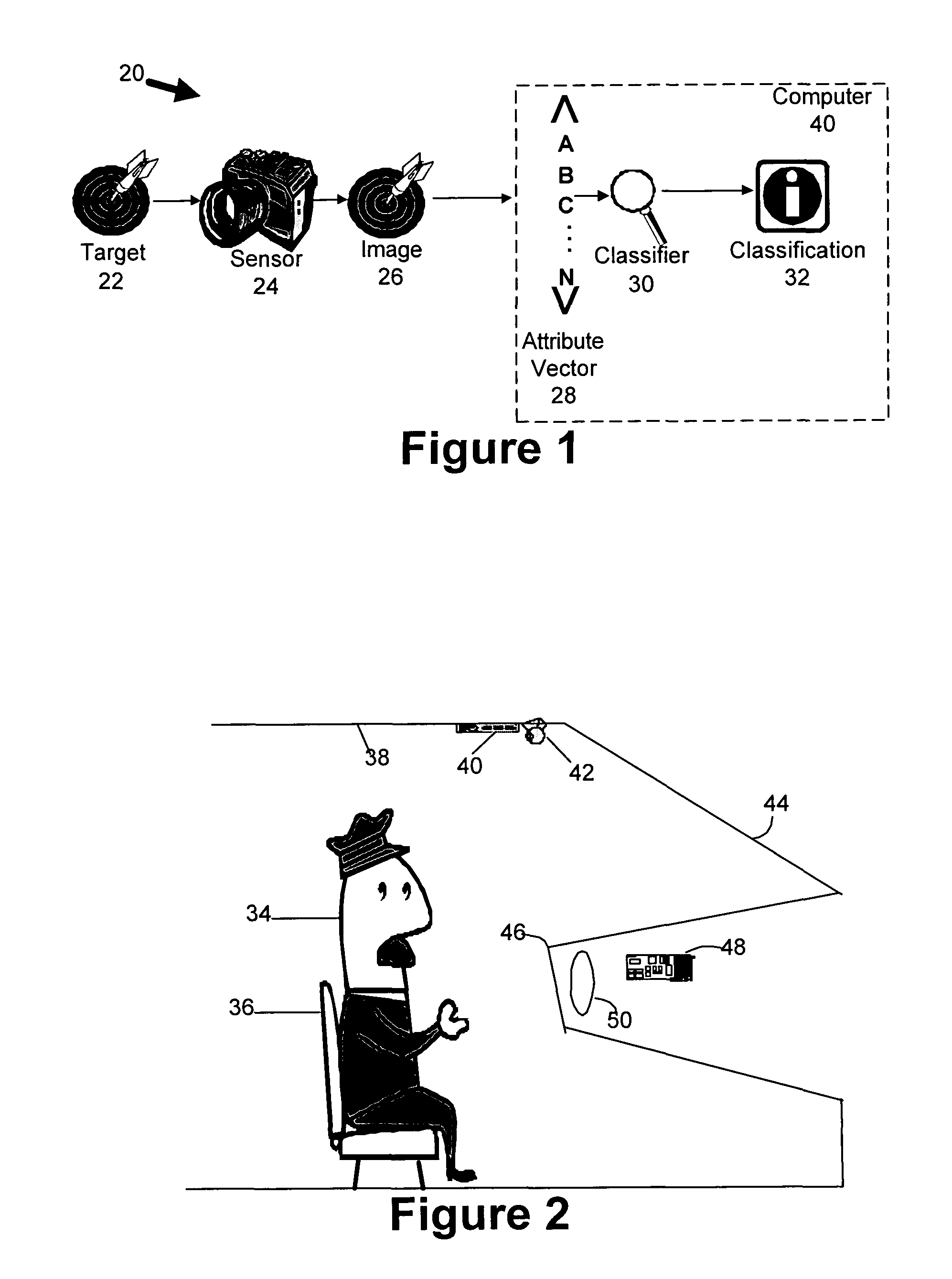
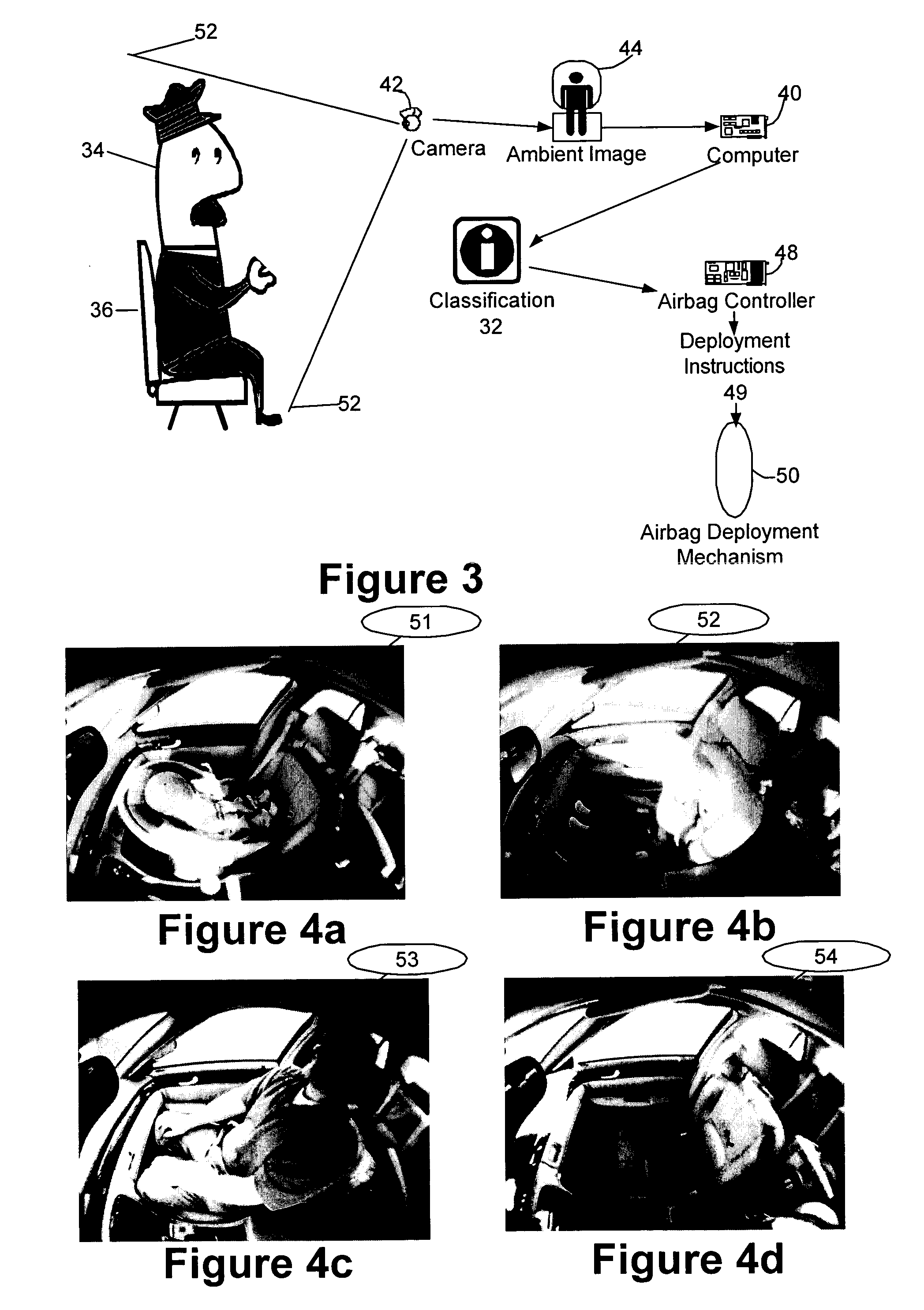
InactiveUS20050271280A1Pedestrian/occupant safety arrangementBiometric pattern recognitionTwo-vectorHeuristic
A system or method (collectively “classification system”) is disclosed for classifying sensor images into one of several pre-defined classifications. Mathematical moments relating to various features or attributes in the sensor image are used to populated a vector of attributes, which are then compared to a corresponding template vector of attribute values. The template vector contains values for known classifications which are preferably predefined. By comparing the two vectors, various votes and confidence metrics are used to ultimately select the appropriate classification. In some embodiments, preparation processing is performed before loading the attribute vector with values. Image segmentation is often desirable. The performance of heuristics to adjust for environmental factors such as lighting can also be desirable. One embodiment of the system is to prevent the deployment of an airbag when the occupant in the seat is a child, a rear-facing infant seat, or when the seat is empty.
Owner:EATON CORP
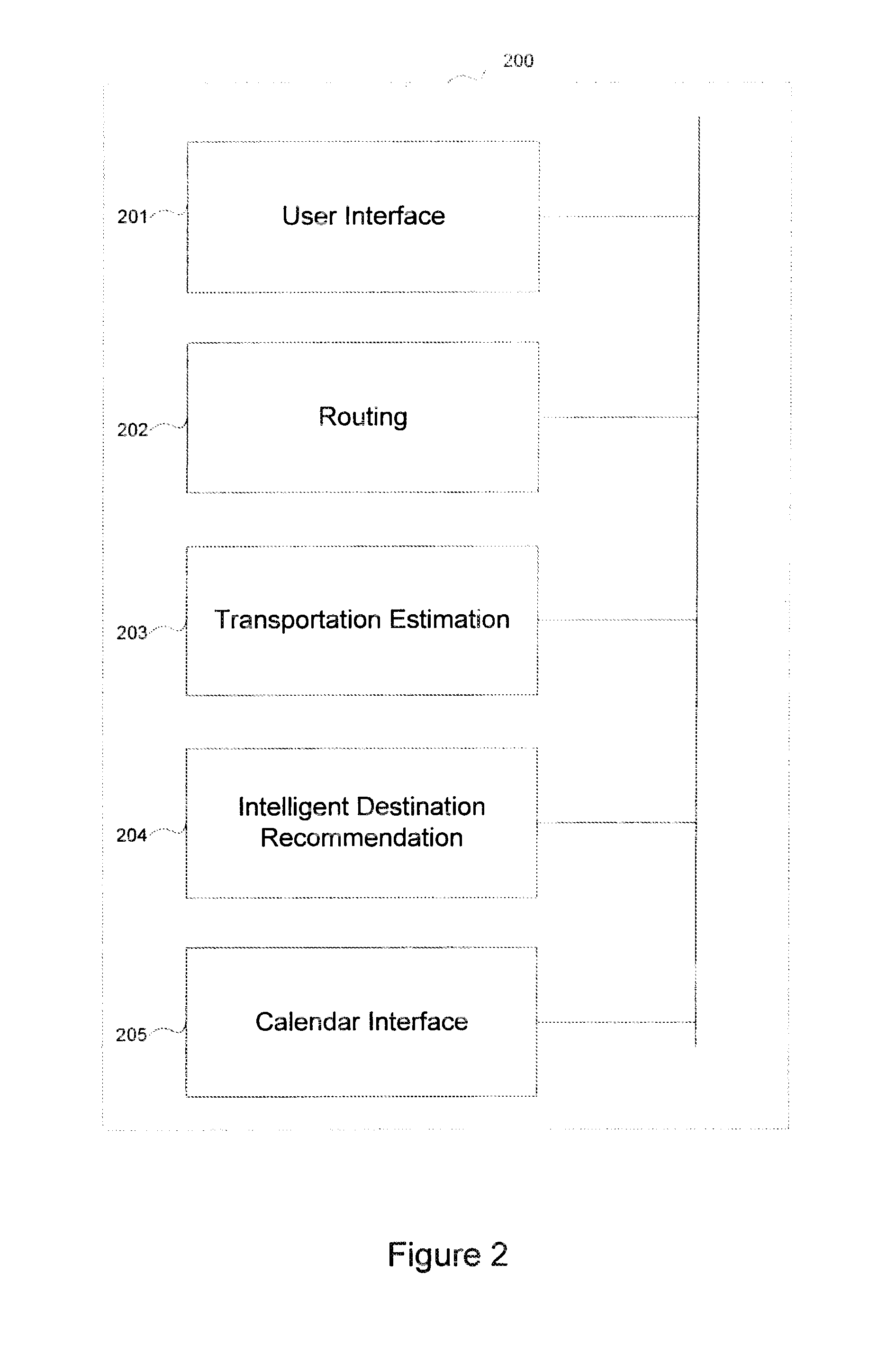
Intelligent destination recommendations based on historical data
ActiveUS20130238241A1Raise the possibilityInstruments for road network navigationRoad vehicles traffic controlConfidence metricTime data
Apparatuses and methods relating to navigation and calendar integration are described. In one implementation, confidence ratings are calculated for one or more destinations. Each destination has an associated confidence rating and confidence ratings are based on a match between the current time and time data for each destination. A destination is selected based on confidence rating and displayed. A calendar event is created based upon the selected destination.
Owner:APPLE INC
System and method of analyzing risk in risk-based software testing
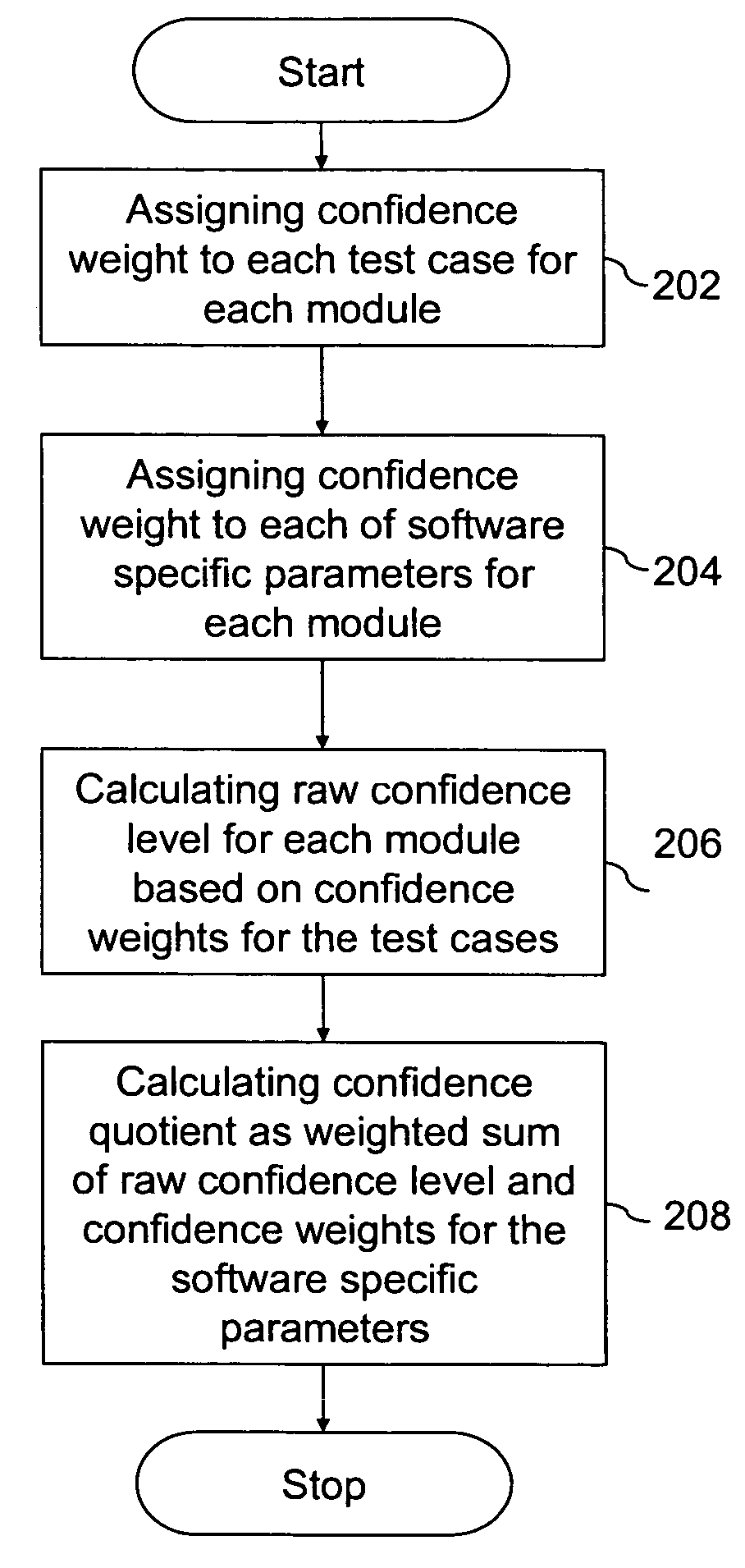
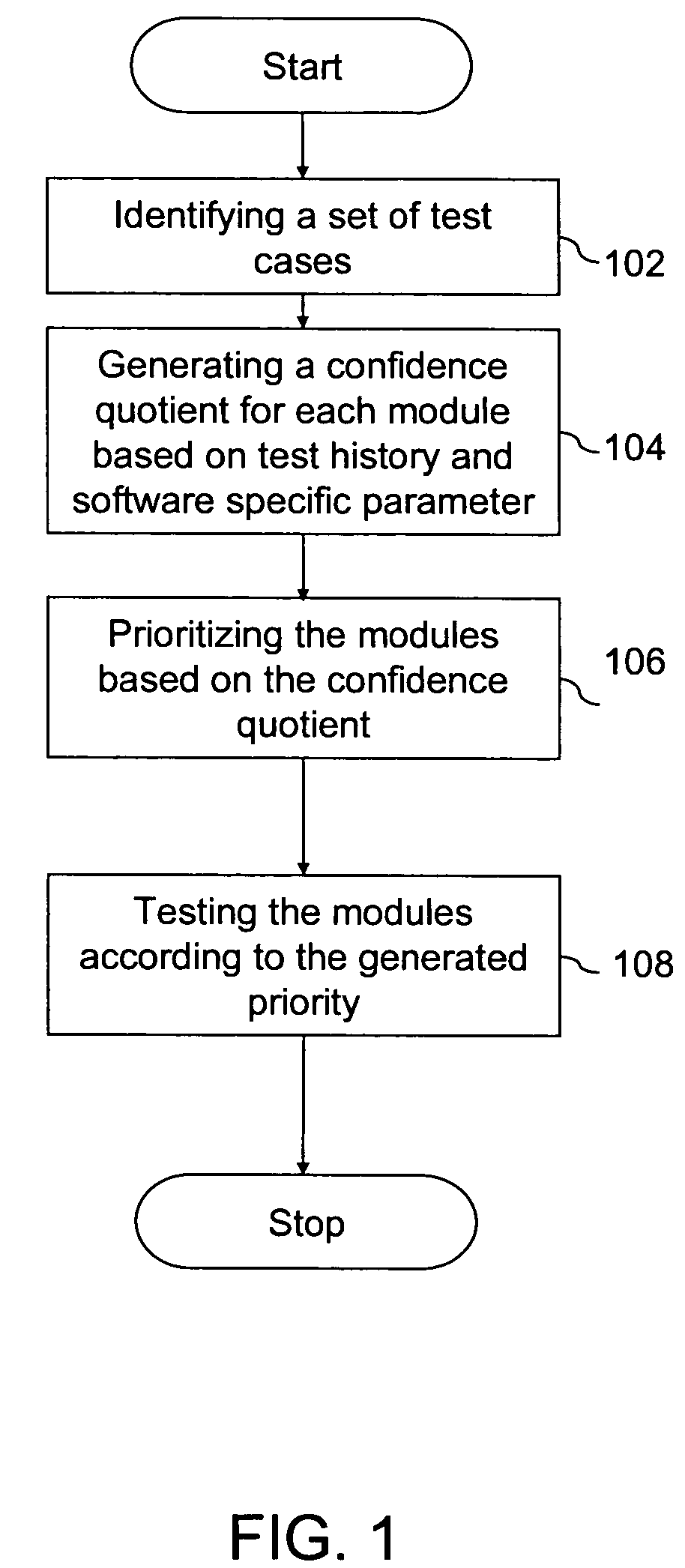
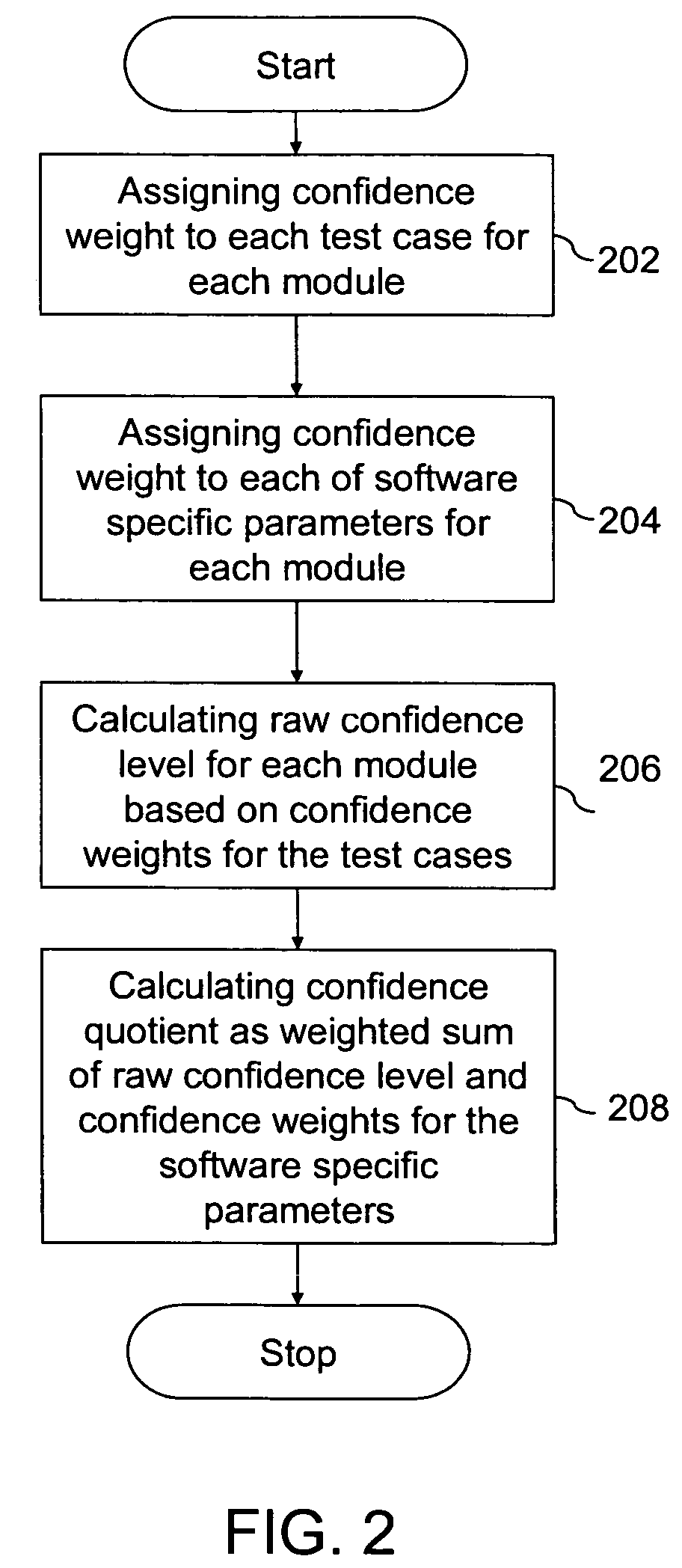
InactiveUS7747987B1Error detection/correctionDigital computer detailsConfidence metricConfidence factor
A system and a method are provided to quantitatively analyze the risk for a risk-based testing of software having at least one module. The risk-based testing comprises obtaining behavior of each module to a set of test cases. The method to quantitatively analyze the risk comprises assigning a confidence weight to each test case for each module based on its test history, assigning a confidence weight to each of a plurality of software specific parameters for each module, calculating a raw confidence level for each module based on the assigned confidence weights to the test cases, and calculating a confidence quotient for each module as a weighted sum of the raw confidence level for each module and the confidence weight for each software specific parameter. The confidence quotient indicates the risk of defects in each module. The module with the smallest confidence quotient is assigned the highest priority during the testing of the software.
Owner:CISCO TECH INC
Systems and methods for assessing the risk of a financial transaction using biometric information
ActiveUS7398925B2Accurate descriptionAccurate transactionFinancePayment architectureConfidence metricCheque
Owner:FIRST DATA
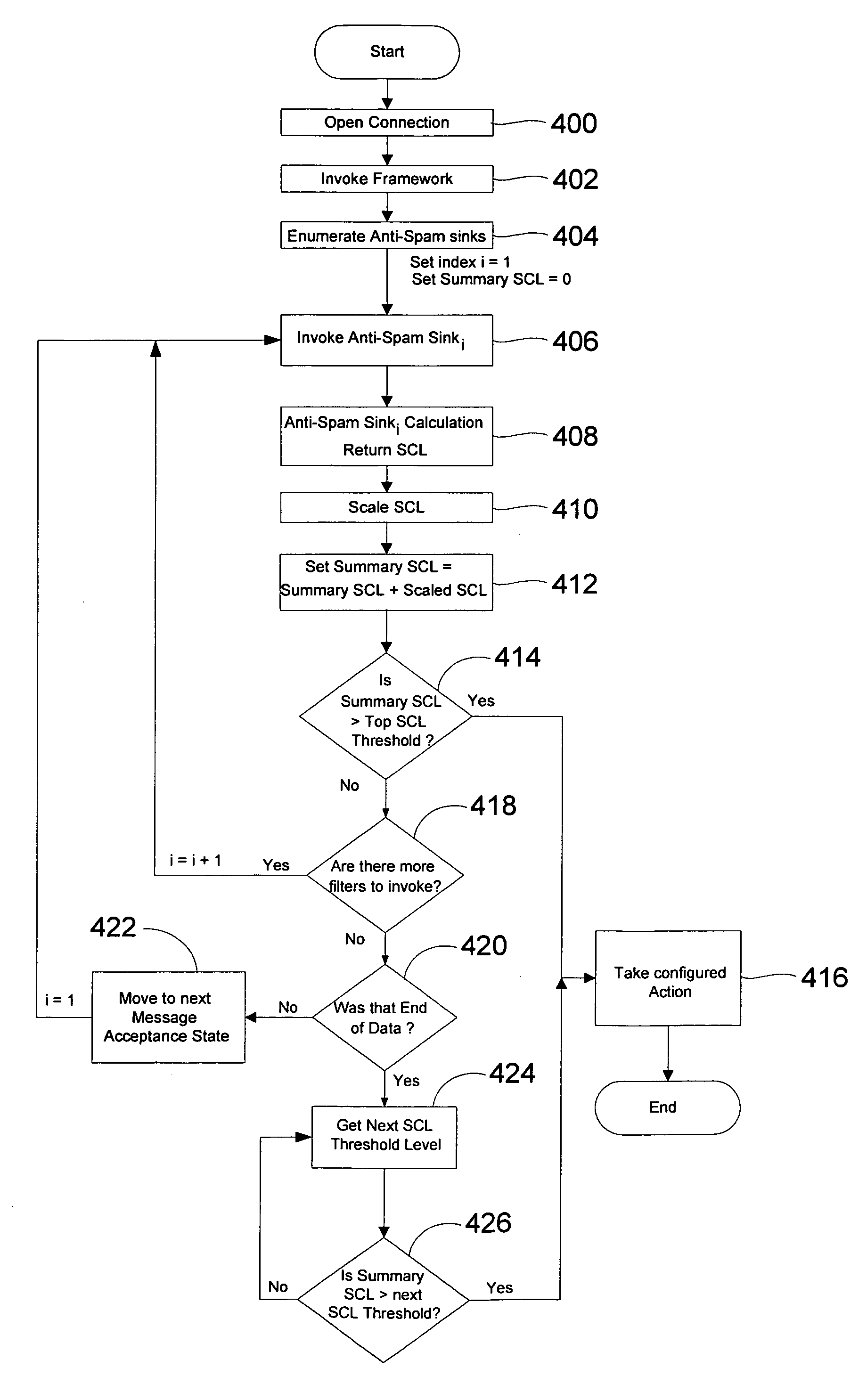
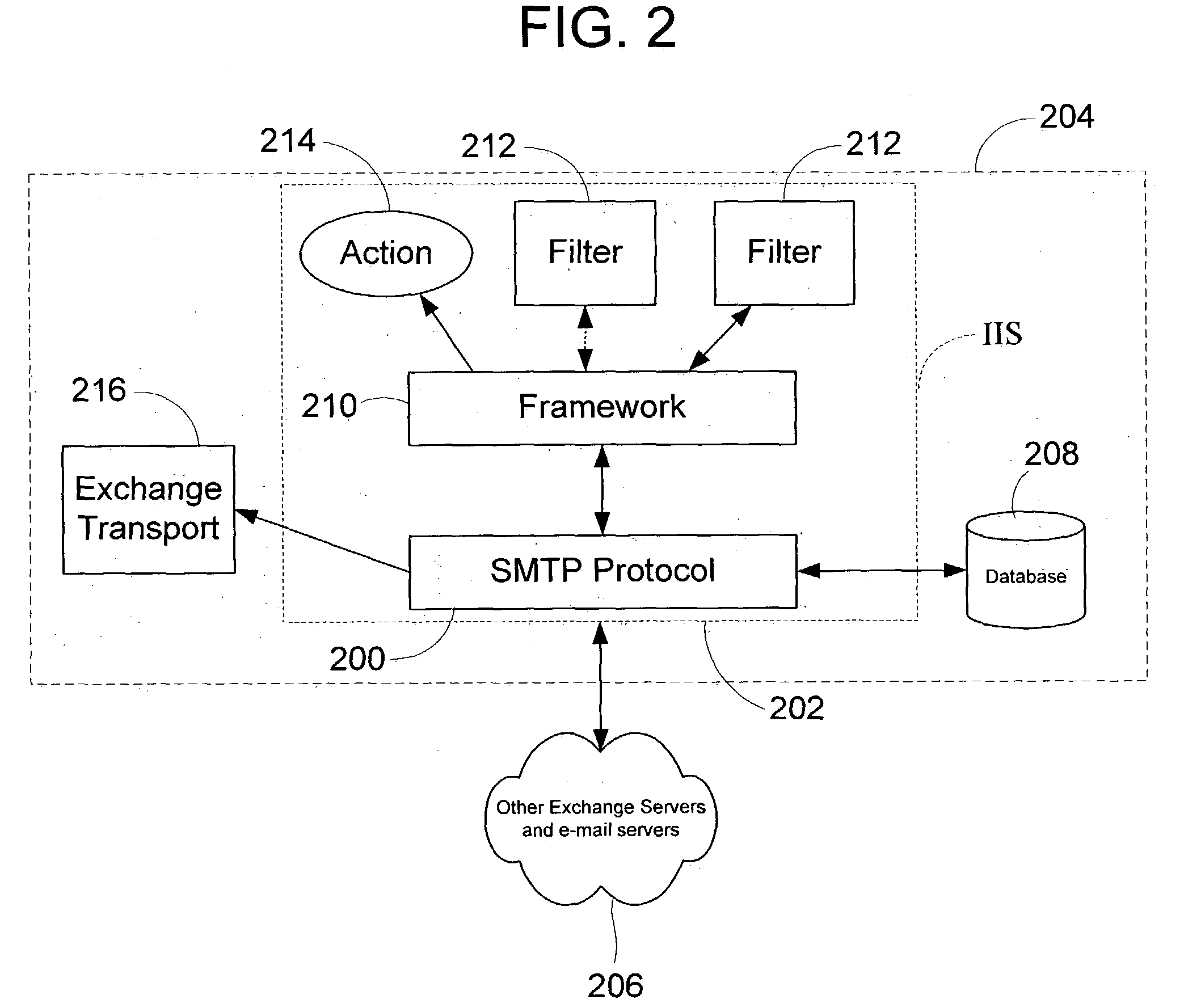
Framework to enable integration of anti-spam technologies
ActiveUS7171450B2Rapid deploymentEngine sealsJoints with sealing surfacesAnti-spam techniquesConfidence metric
Owner:MICROSOFT TECH LICENSING LLC
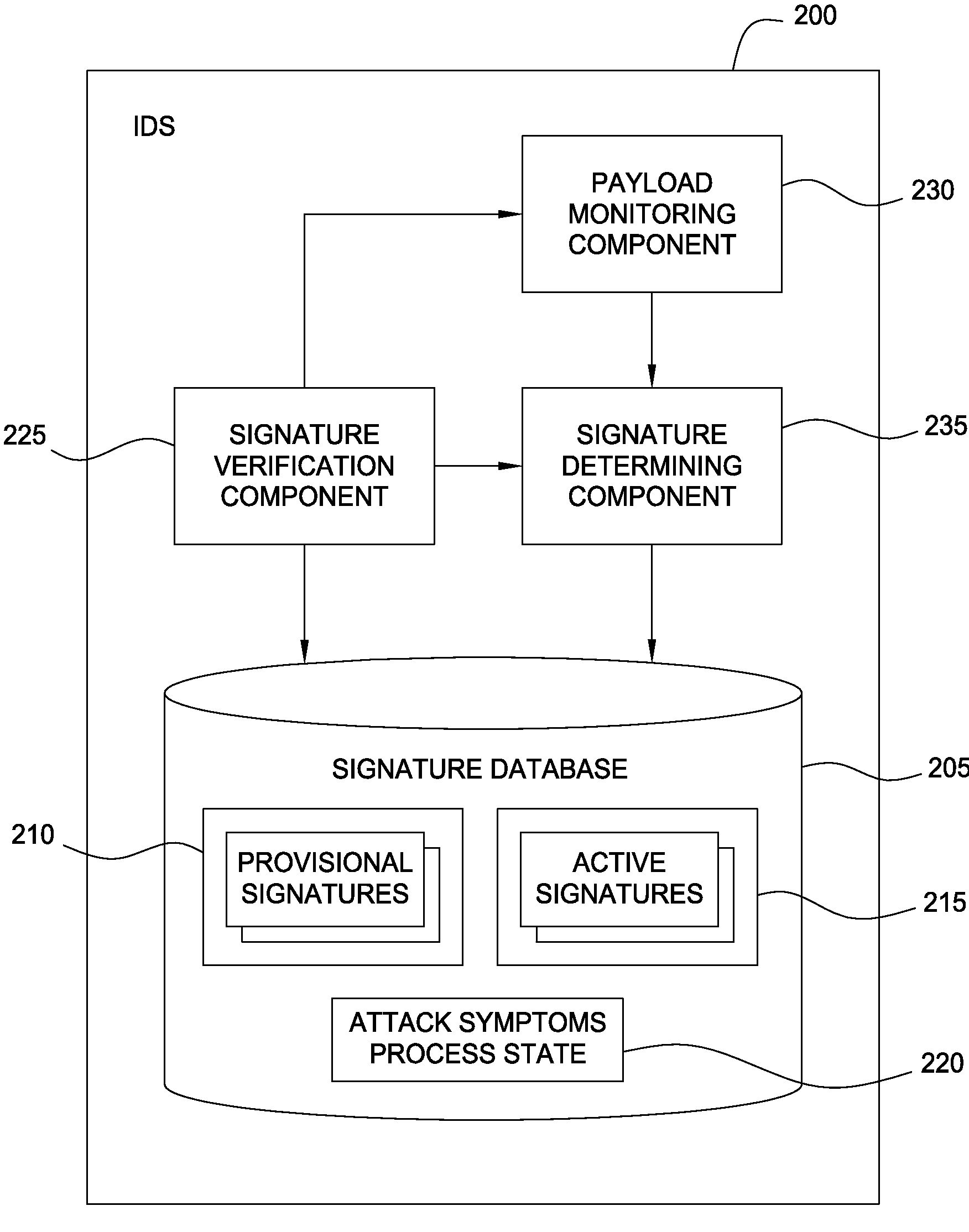
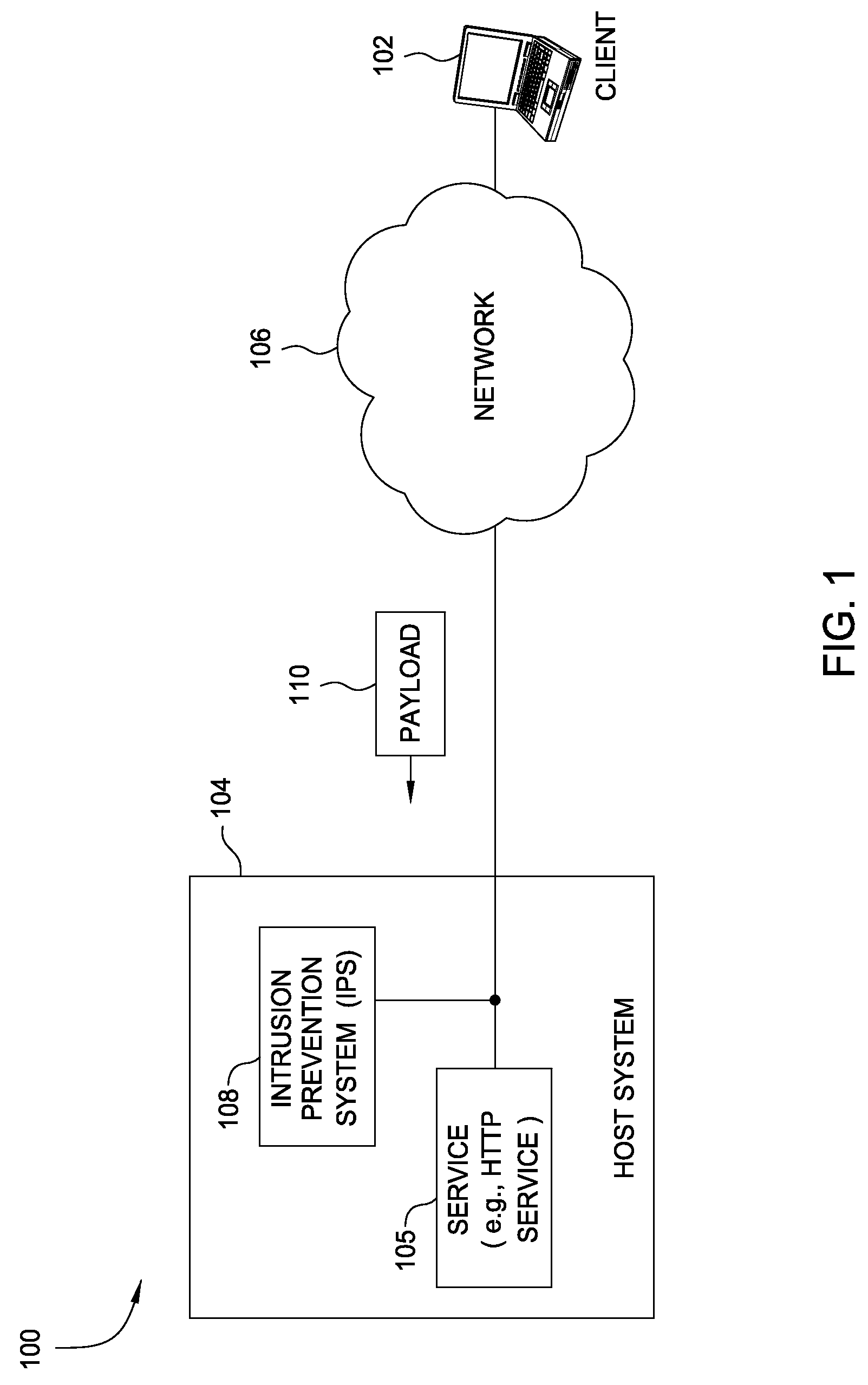
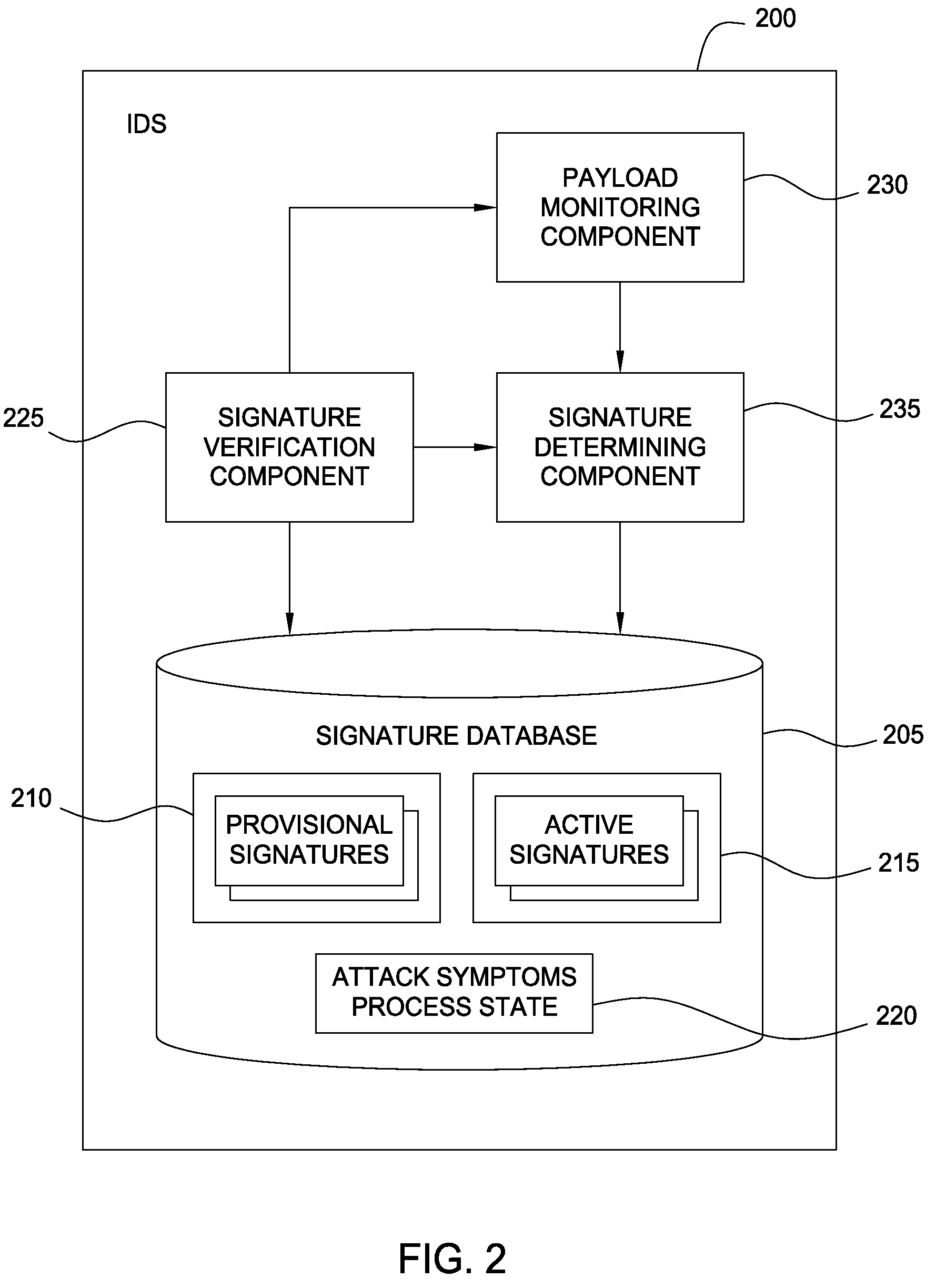
Attack-resistant verification of auto-generated Anti-malware signatures
Techniques are disclosed for verifying whether payload signatures correspond to a vulnerability or exploit. Generally a security system may be configured to detect an attack on a server while the server is processing a payload. The security system generates (or obtains) a provisional signature corresponding to the vulnerability. For example, a provisional signature may be generated for a vulnerability from a group of payloads determined to correspond to that vulnerability. The effects of subsequent payloads which match the provisional signature may be monitored. If the effects of a payload duplicate the attack symptoms, a confidence metric for provisional signature may be increased. Once the confidence metric exceeds a predetermined threshold, then the provisional signature may be made active and used to block traffic from reaching an intended destination.
Owner:CISCO TECH INC
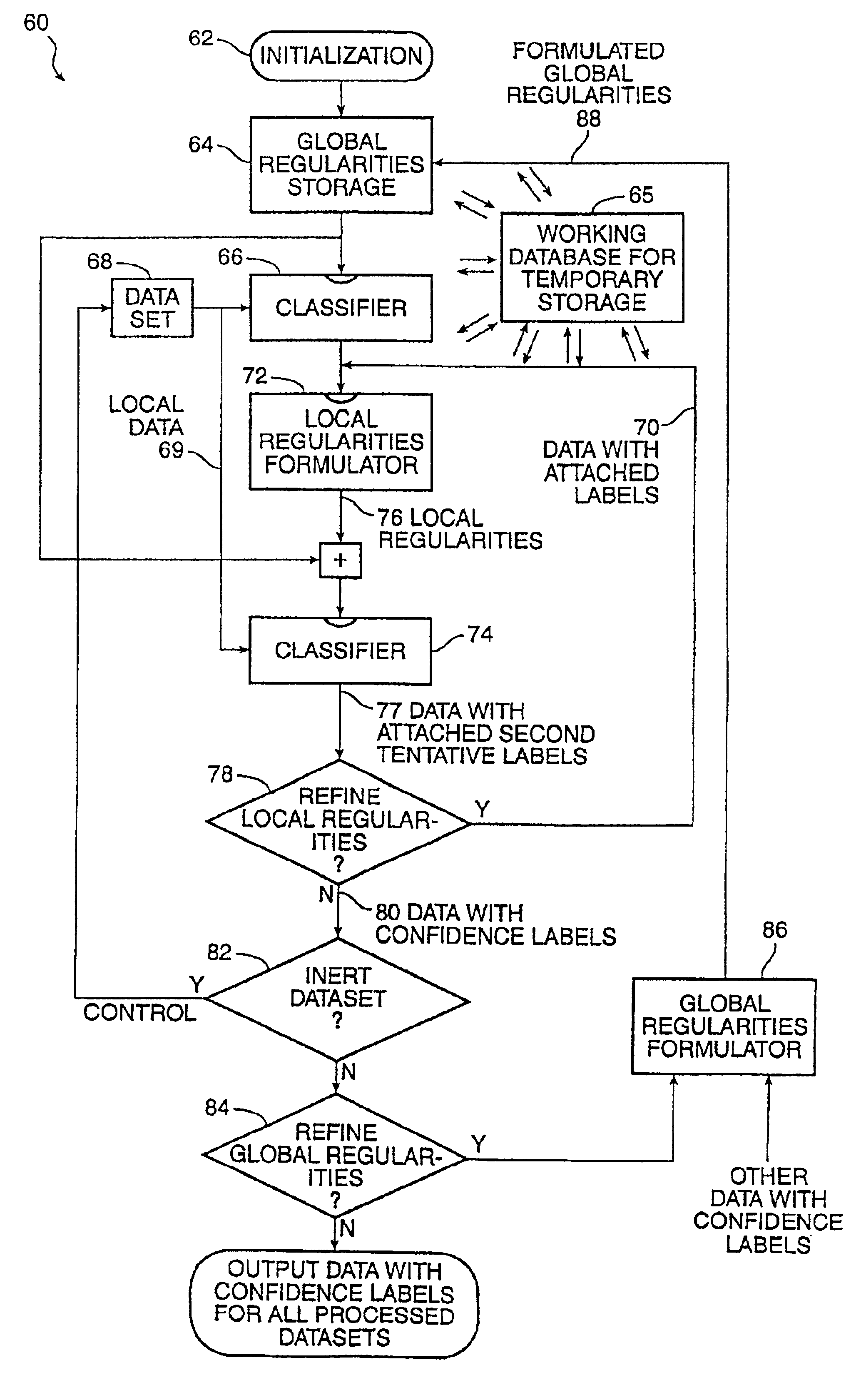
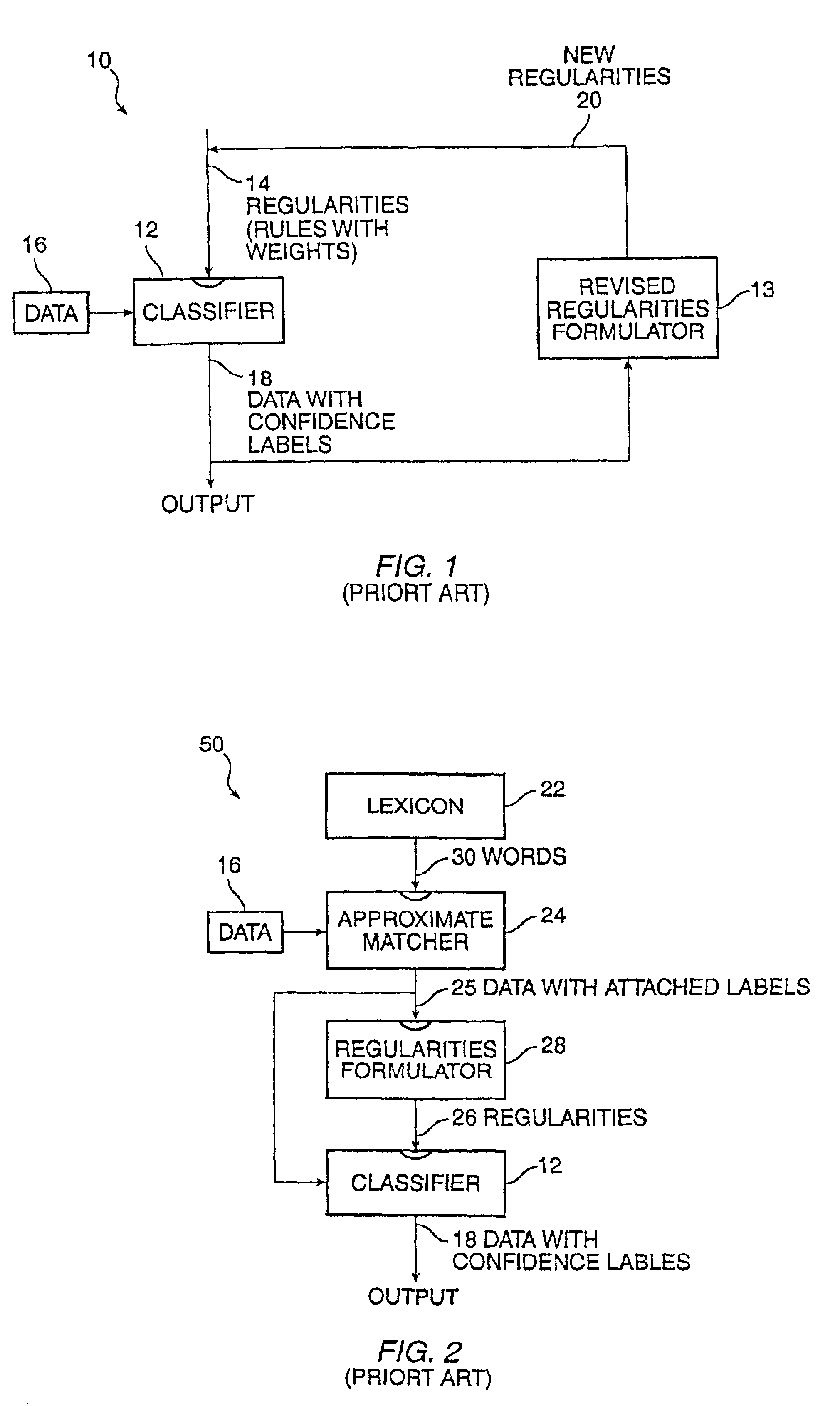
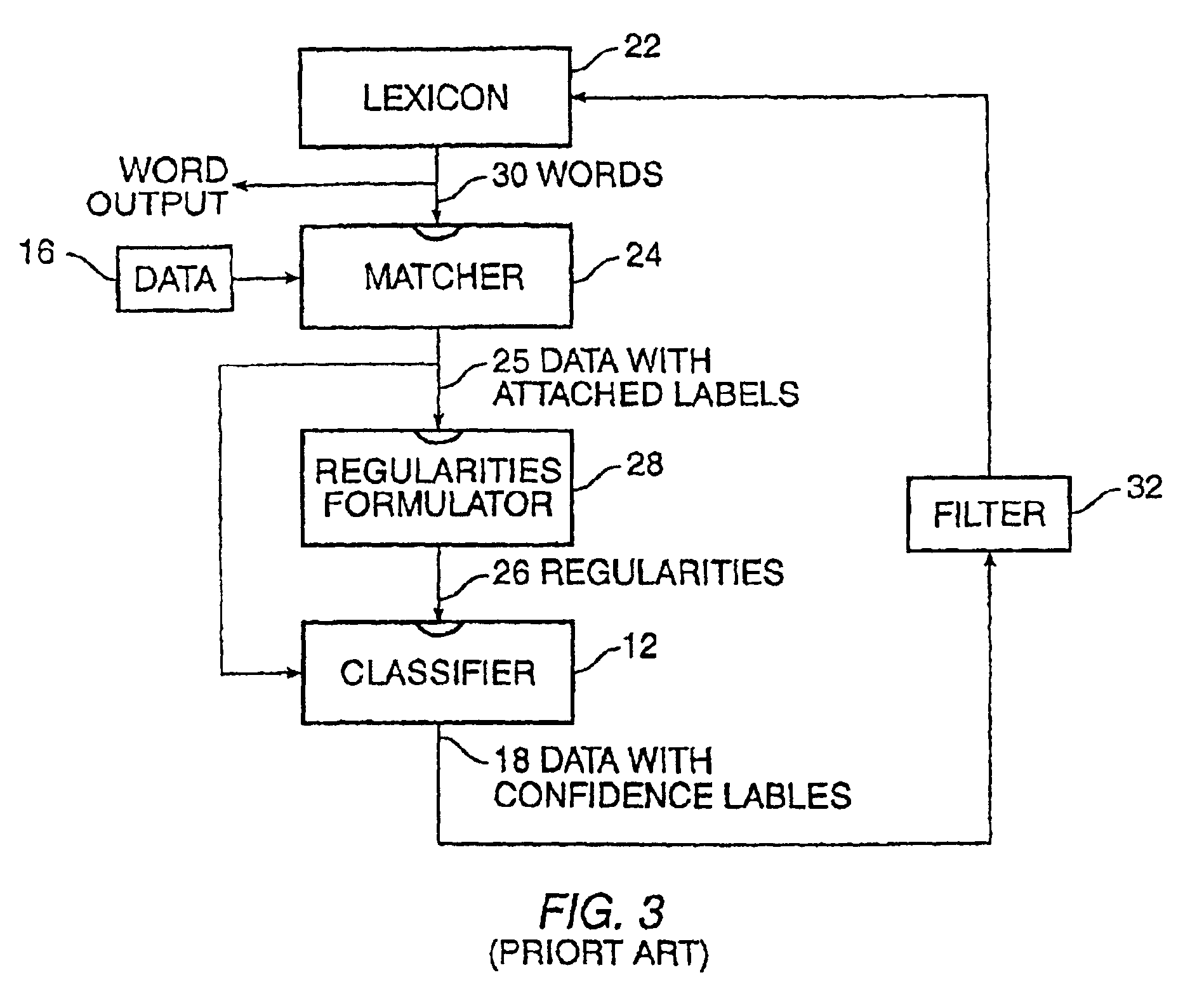
Method for learning and combining global and local regularities for information extraction and classification
InactiveUS6892189B2Digital data processing detailsDigital computer detailsPattern recognitionData set
A method is provided for information extraction and classification which combines aspects of local regularities formulation with global regularities formulation. A candidate subset is identified. Then tentative labels are created so they can be associated with elements in the subset that have the global regularities, and the initial tentative labels are attached onto the identified elements of the candidate subset. The attached tentative labels are employed to formulate or “learn” initial local regularities. Further tentative labels are created so they can be associated with elements in the subset that have a combination of global and local regularities, and the further tentative labels are attached onto the identified elements of the candidate subset. Each new dataset is processed with reference to an increasingly-refined set of global regularities, and the output data with their associated confidence labels can be readily evaluated as to import and relevance.
Owner:WHIZBANG LABS
Estimating confidence for query revision models
ActiveUS7617205B2Data processing applicationsWeb data indexingConfidence metricFrequency of occurrence
An information retrieval system includes a query revision architecture that integrates multiple different query revisers, each implementing one or more query revision strategies. A revision server receives a user's query, and interfaces with the various query revisers, each of which generates one or more potential revised queries. The revision server evaluates the potential revised queries, and selects one or more of them to provide to the user. A session-based reviser suggests one or more revised queries, given a first query, by calculating an expected utility for the revised query. The expected utility is calculated as the product of a frequency of occurrence of the query pair and an increase in quality of the revised query over the first query.
Owner:GOOGLE LLC
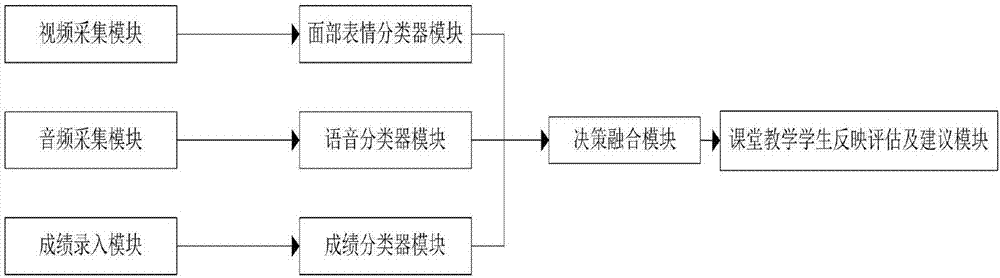
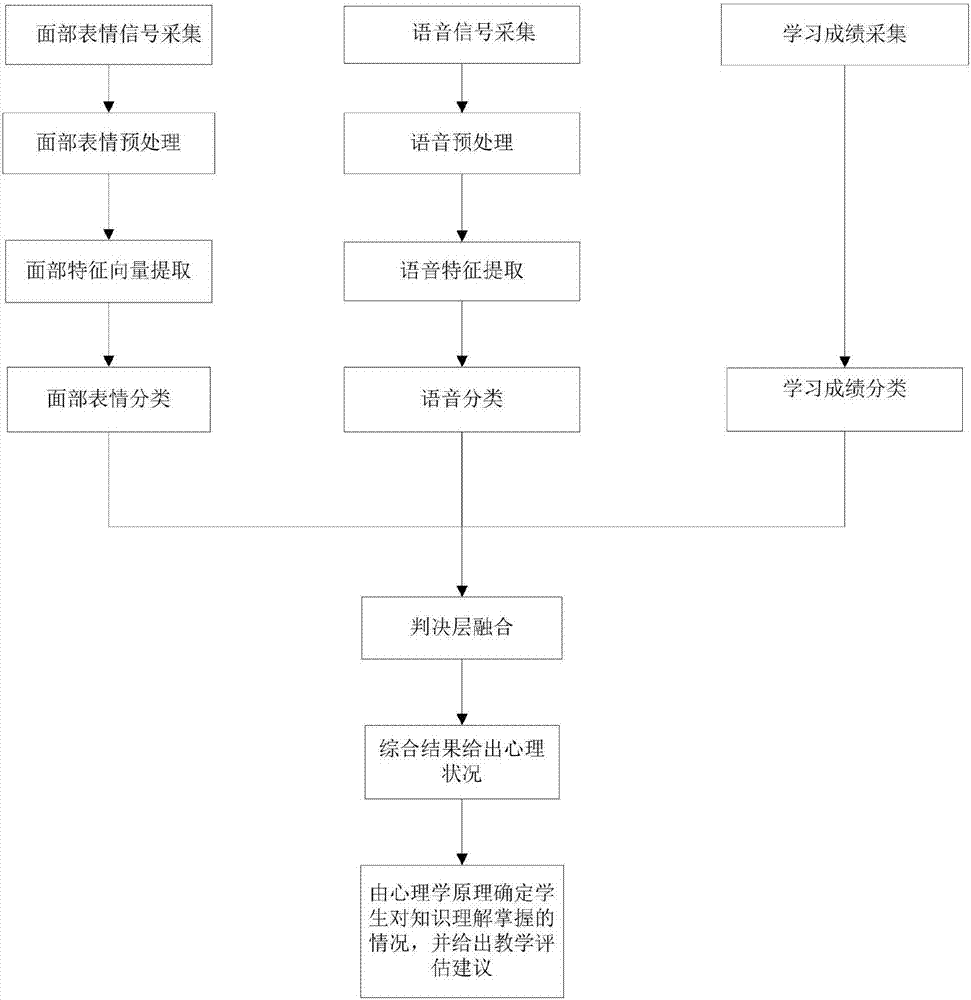
System and method for evaluating students' mastery degree in class based on multiple sensors
ActiveCN106878677AReduce performanceAssess MasteryClosed circuit television systemsSpeech recognitionFacial expressionConfidence metric
The invention discloses a system and a method for evaluating students' mastery degree in class based on multiple sensors. The method comprises the following steps: collecting student data; preprocessing a student face image sequence and a speech sequence; extracting facial expressions and speech features; classifying facial expressions, speeches and examination results; using a Gaussian mixture model to integrate the classification results; and analyzing the integration result and giving class evaluation and suggestions. The convolution neural network in deep learning is adopted in speech emotion processing, and complicated artificial feature extraction is avoided. Through use of the Gaussian mixture model, the degree of classification confidence of classifiers is determined according to sample distribution and fused adaptively. A novel student in-class mastery degree evaluation scheme based on multiple sensors is designed by combining the facial expressions, speeches and examination results of students. The mastery degree of students in class can be evaluated more objectively and accurately, the mastery degree of students can be judged, and a teaching evaluation result and corresponding suggestions can be given.
Owner:XIDIAN UNIV
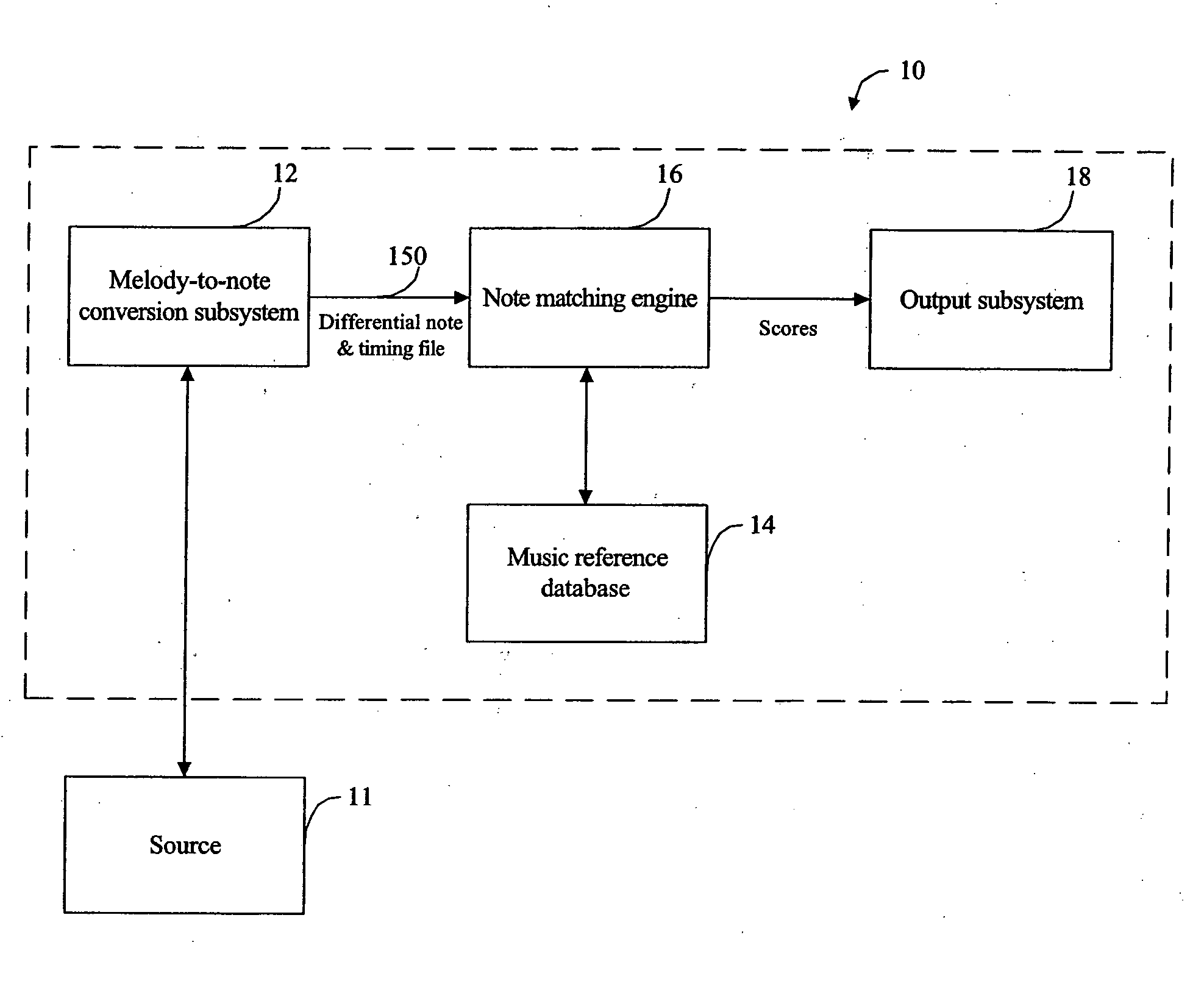
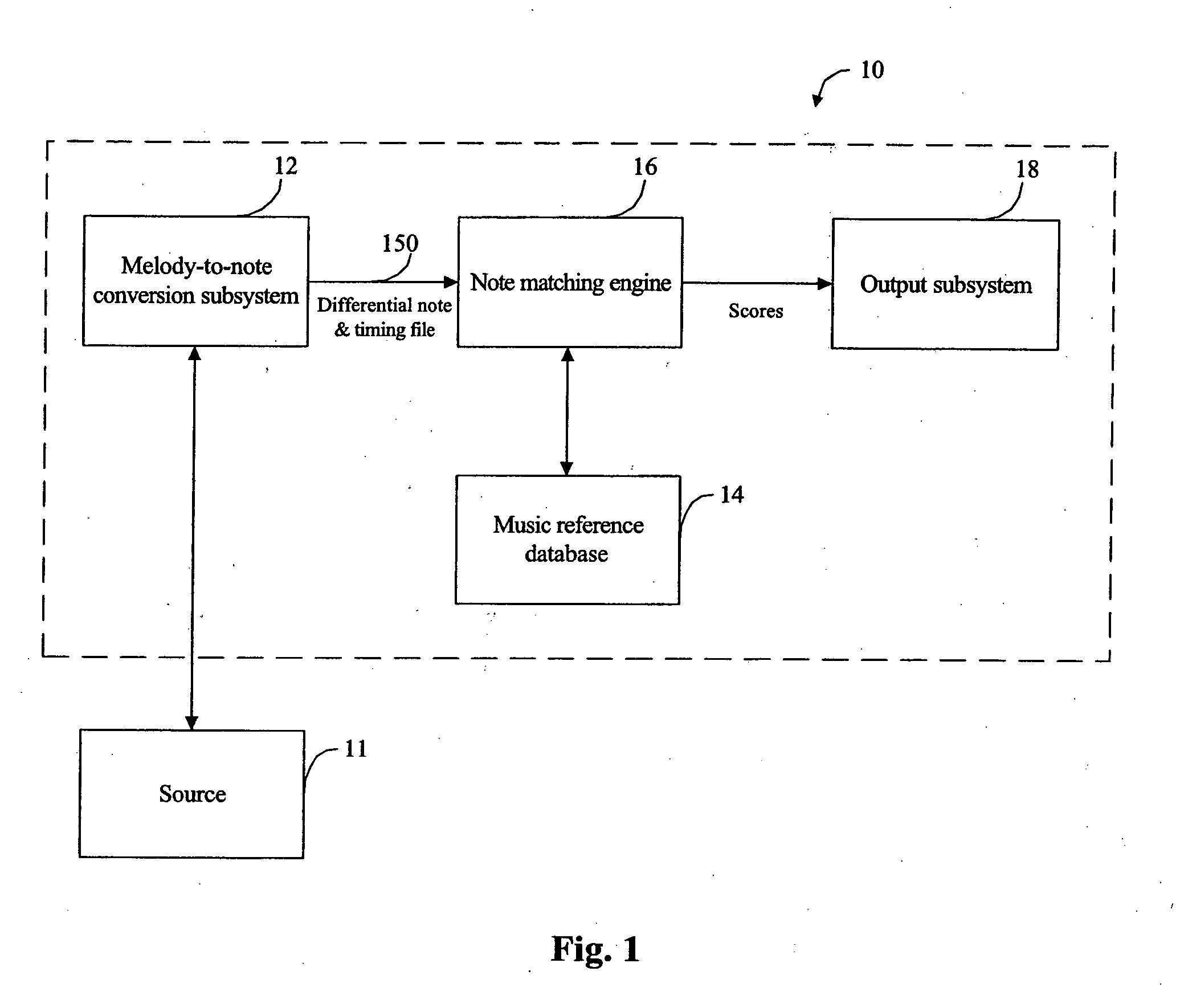
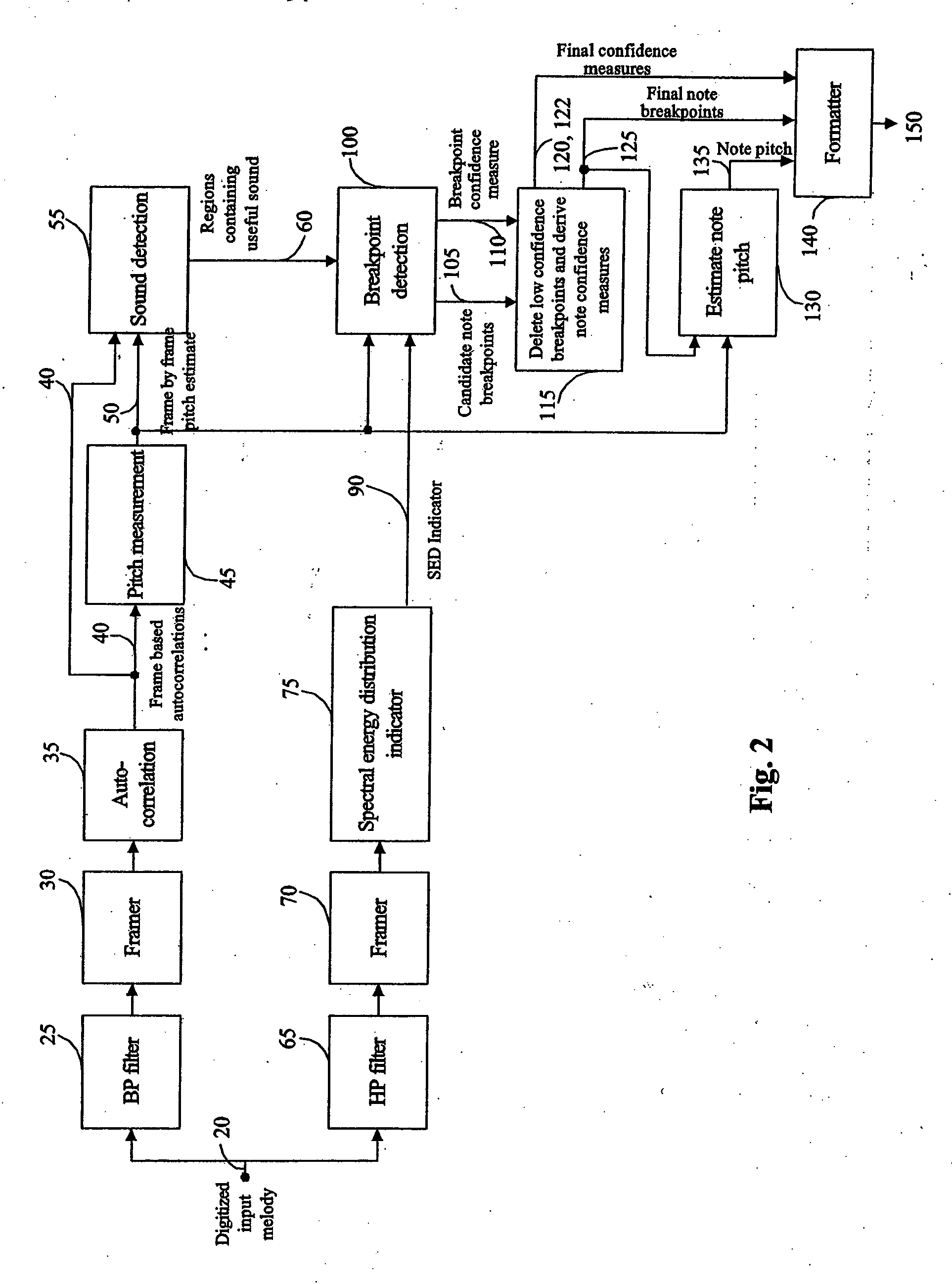
Melody retrieval system
InactiveUS20070163425A1Lower matching costsPenalize costGearworksMusical toysNatural language processingFrequency spectrum
A music retrieval system which take an input melody as the query. In one embodiment, changes or differences in the distribution of energy across the frequency spectrum over time are used to find breakpoints in the input melody in order to separate it into distinct notes. In another embodiment the breakpoints are identified based on changes in pitch over time. A confidence level is preferably associated with each breakpoint and / or note extracted from the input melody. The confidence level is based on one or more of: changes in pitch, absolute values of a spectral energy distribution indicator, relative values of the spectral energy distribution indicator, and the energy level of the input melody. The process of matching the input melody with songs in the music database is based on minimizing a cost computation that takes into account errors in the insertion and deletion of notes, and penalizes these errors in accordance with the confidence levels of the breakpoints and / or notes.
Owner:PERCEPTION DIGITAL TECH BVI
Biocharacteristics fusioned identity distinguishing and identification method
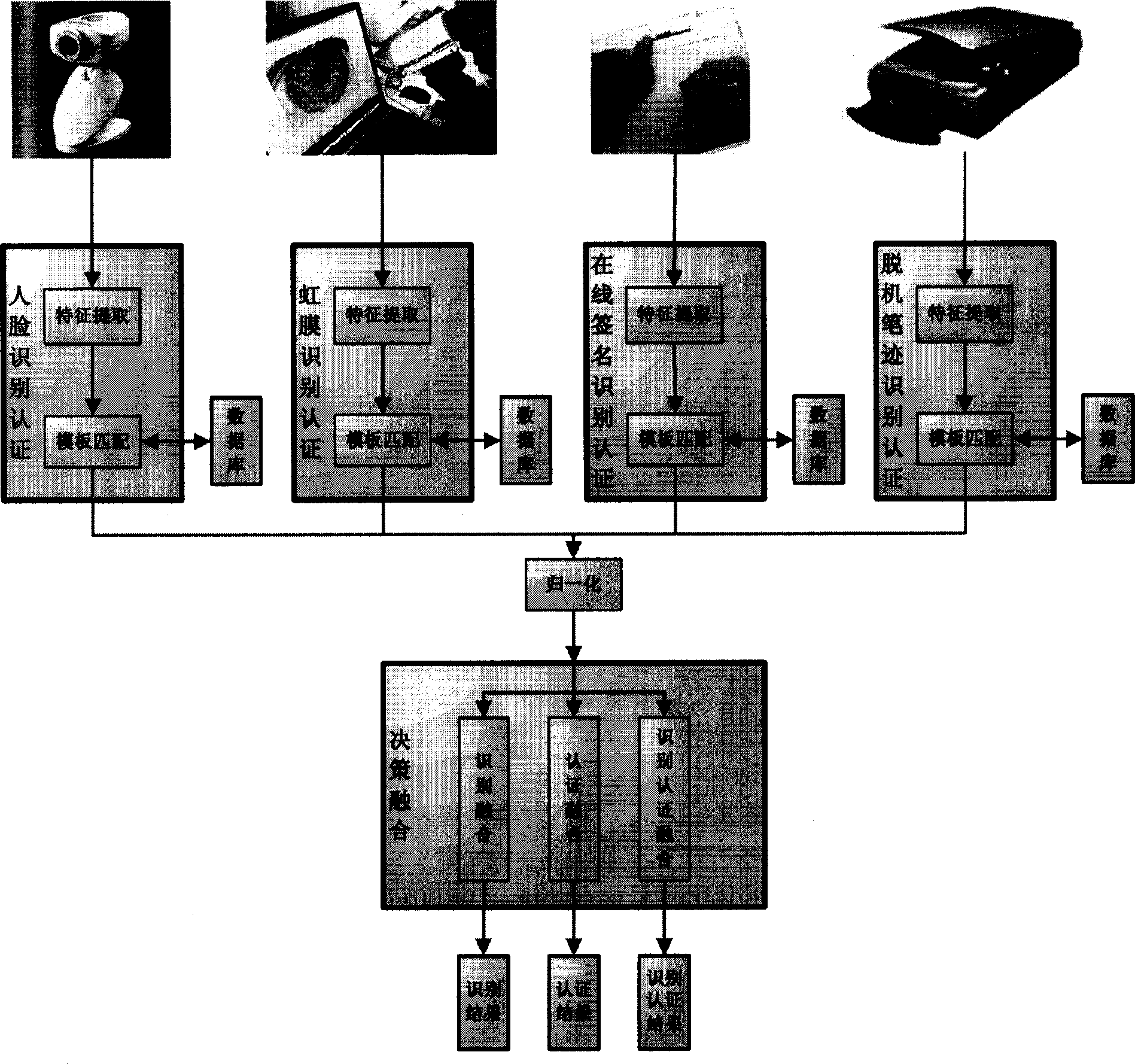
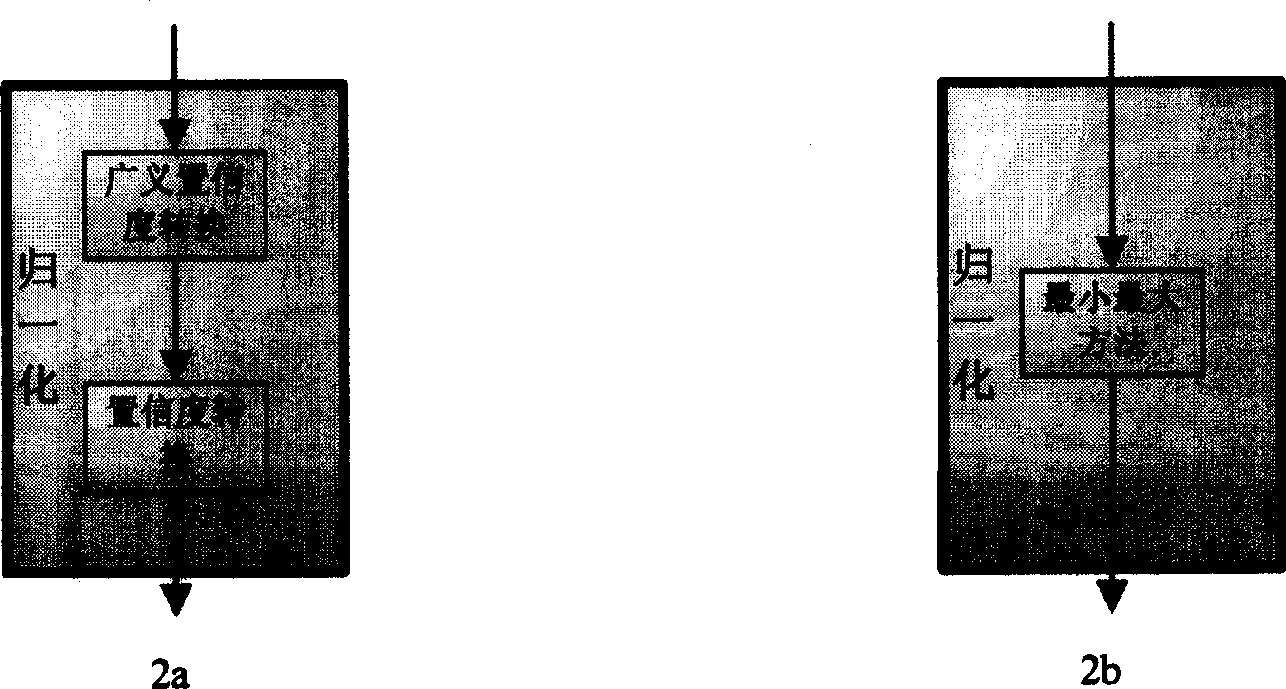
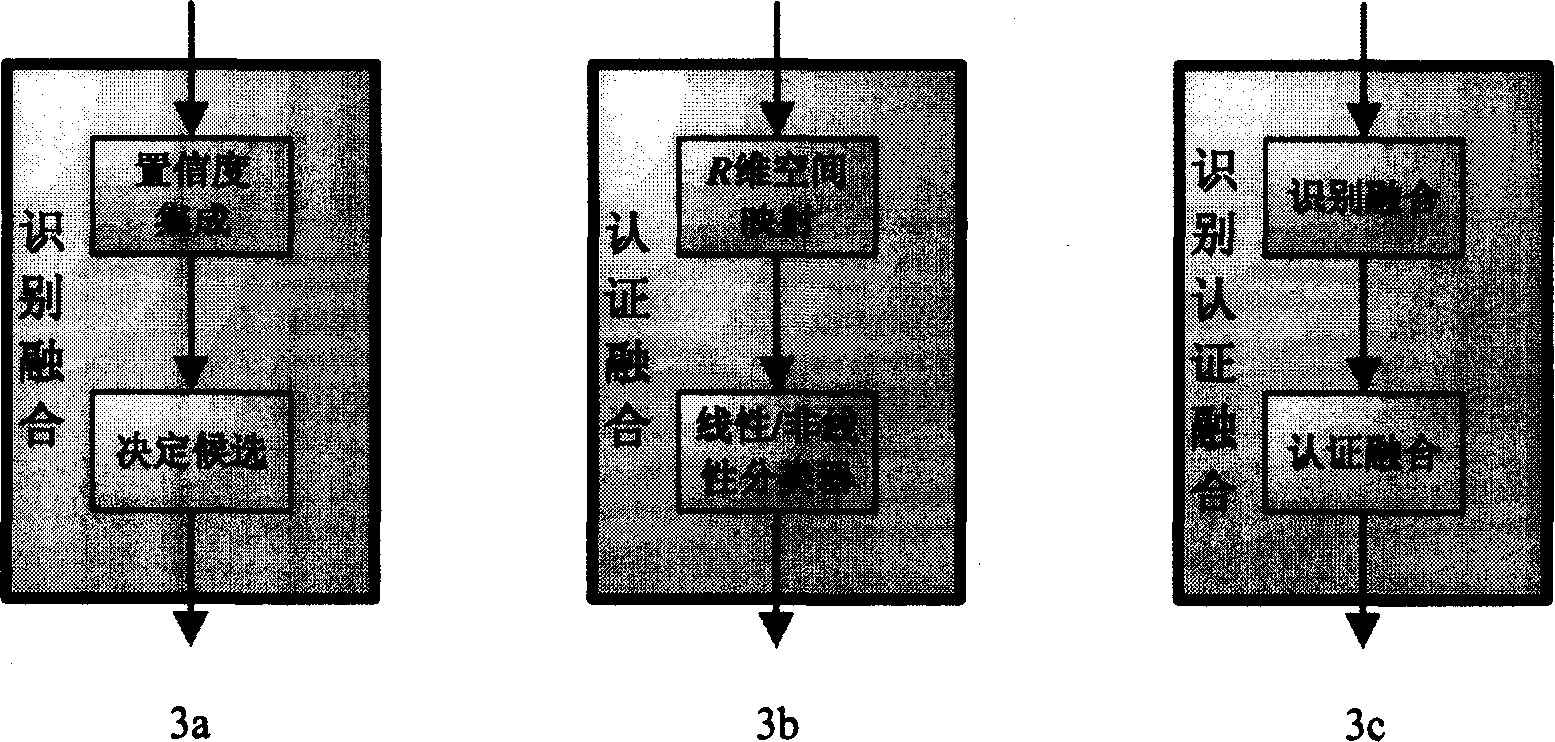
This invention relates to a sorter integration and mode identification field characterizing in obtaining characters of man-face, iris, on-line signature and off-line handwriting of a user by various collecting devices then sending them to corresponding certification sub-modules to pick up the characters and match with the molding boards and outputting the matched marks to be normalized and sent to an identification combined module to get the final identification result by confidence integration or sent to a certification module to be imaged to a multi-dimension space to be sorted by a sorter to get a final result or to be certified and combined to get the final identification result.
Owner:TSINGHUA UNIV
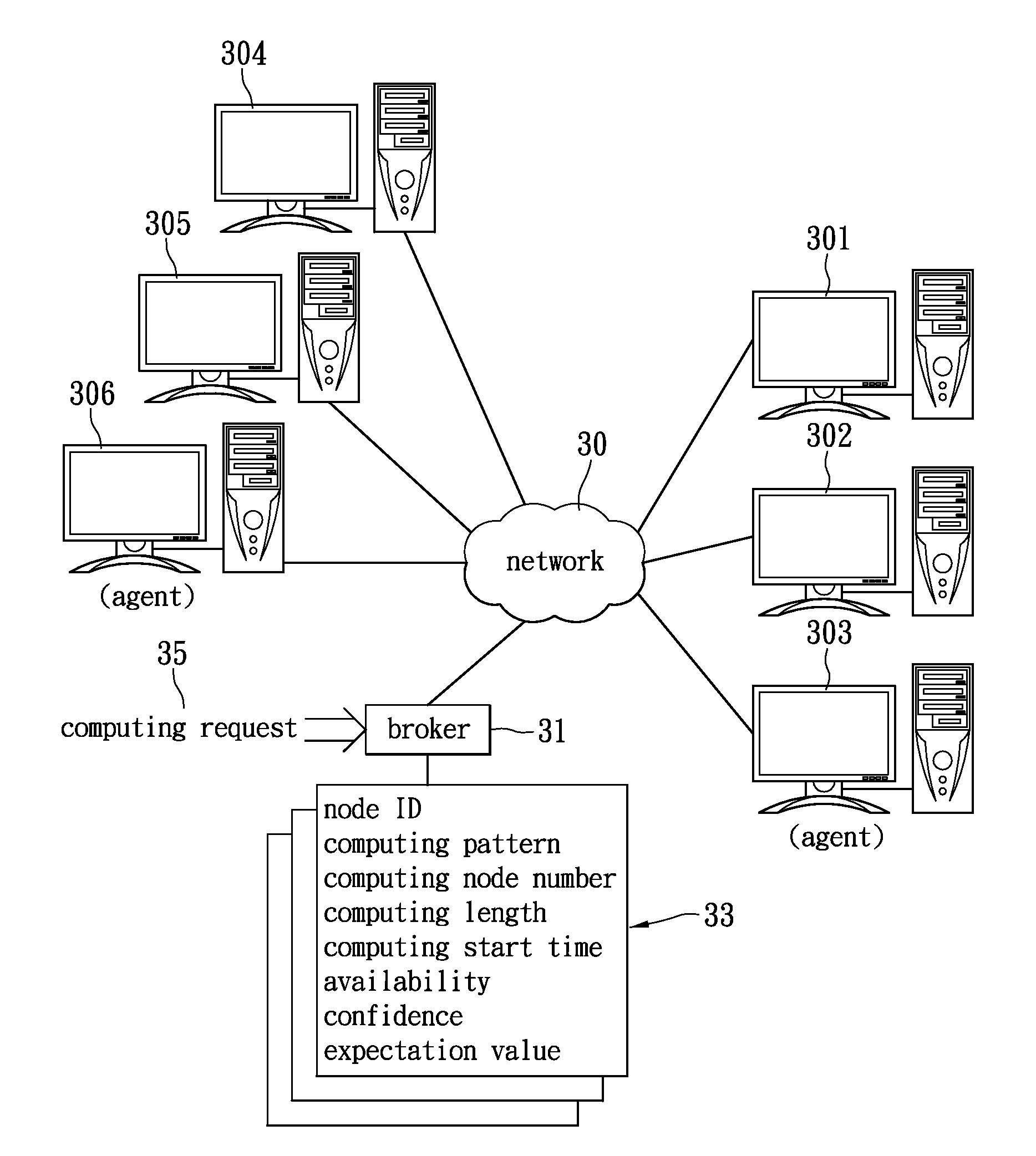
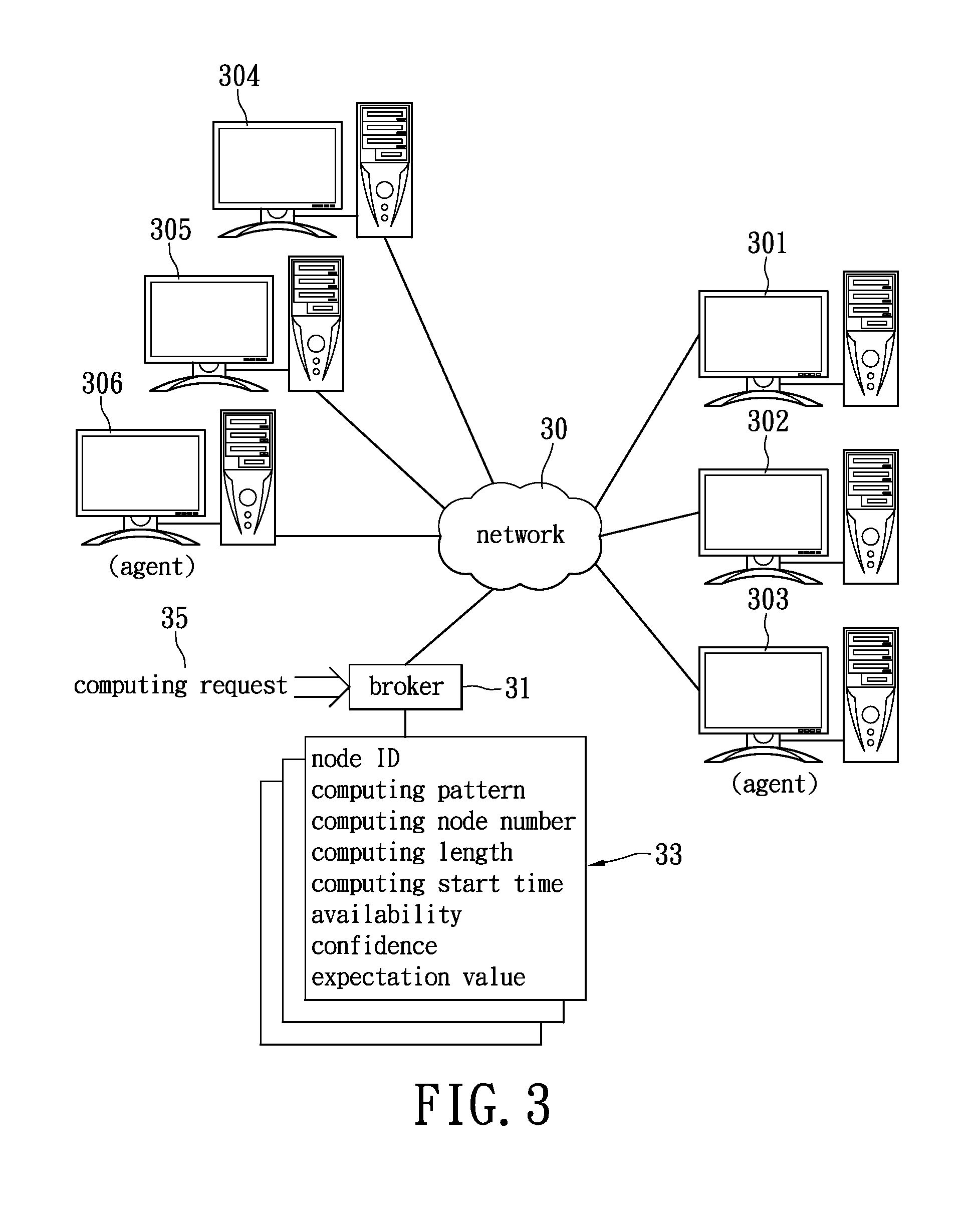
Method for scheduling cloud-computing resource and system applying the same
ActiveUS20110202657A1Enhance cloud-computing capabilityImprove abilitiesDigital computer detailsProgram controlStart timeConfidence metric
Provided is a method for scheduling cloud-computing resource, and a system applying the method is herein disclosed. It is featured that the load history record becomes a basis to obtain a computing pattern for each computing node based on a request. The load history is the basis to predict the future computing capability, and accordingly to distribute the computing task. The cloud-computing capability can therefore be advanced. The method firstly receives a computing request. The request includes a number of computing nodes, a start time of computing, and a length of computing time. A computing resource table is established based on the load history for each node, and used to calculate availability and confidence. After that, a resource expectation value is obtained from the availability and confidence. After sorting the expectation values, one or more computing nodes are selected for further task distribution.
Owner:ELITEGROUP COMPUTER SYSTEMS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com