Patents
Literature
2483 results about "Information networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information networks. What is information network/ computer network? Explain its uses. An information network is a set of two or more computers connected together to share information and resources like printer and hard disk etc. it is also called computer network. The information network uses two important technologies.
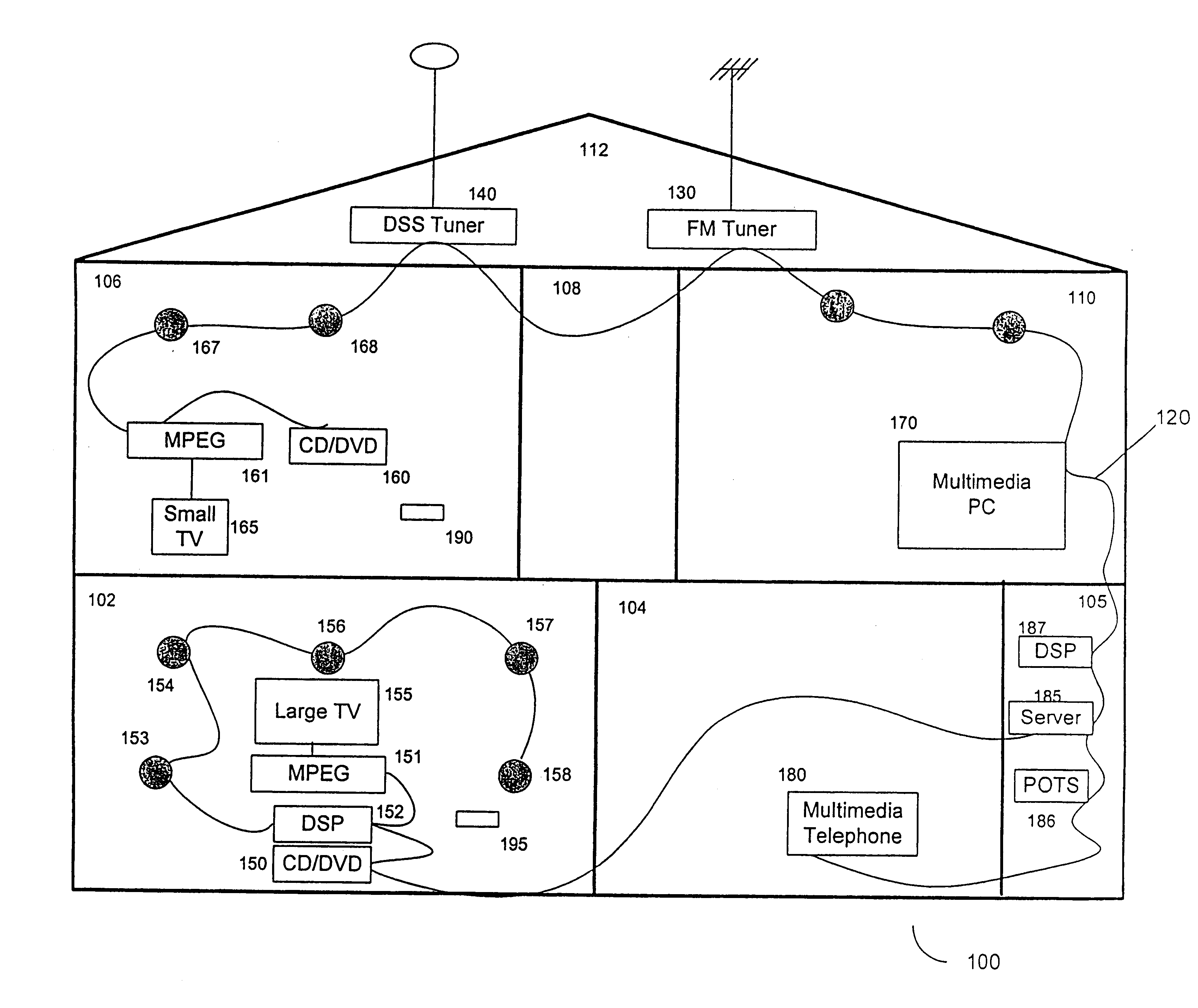
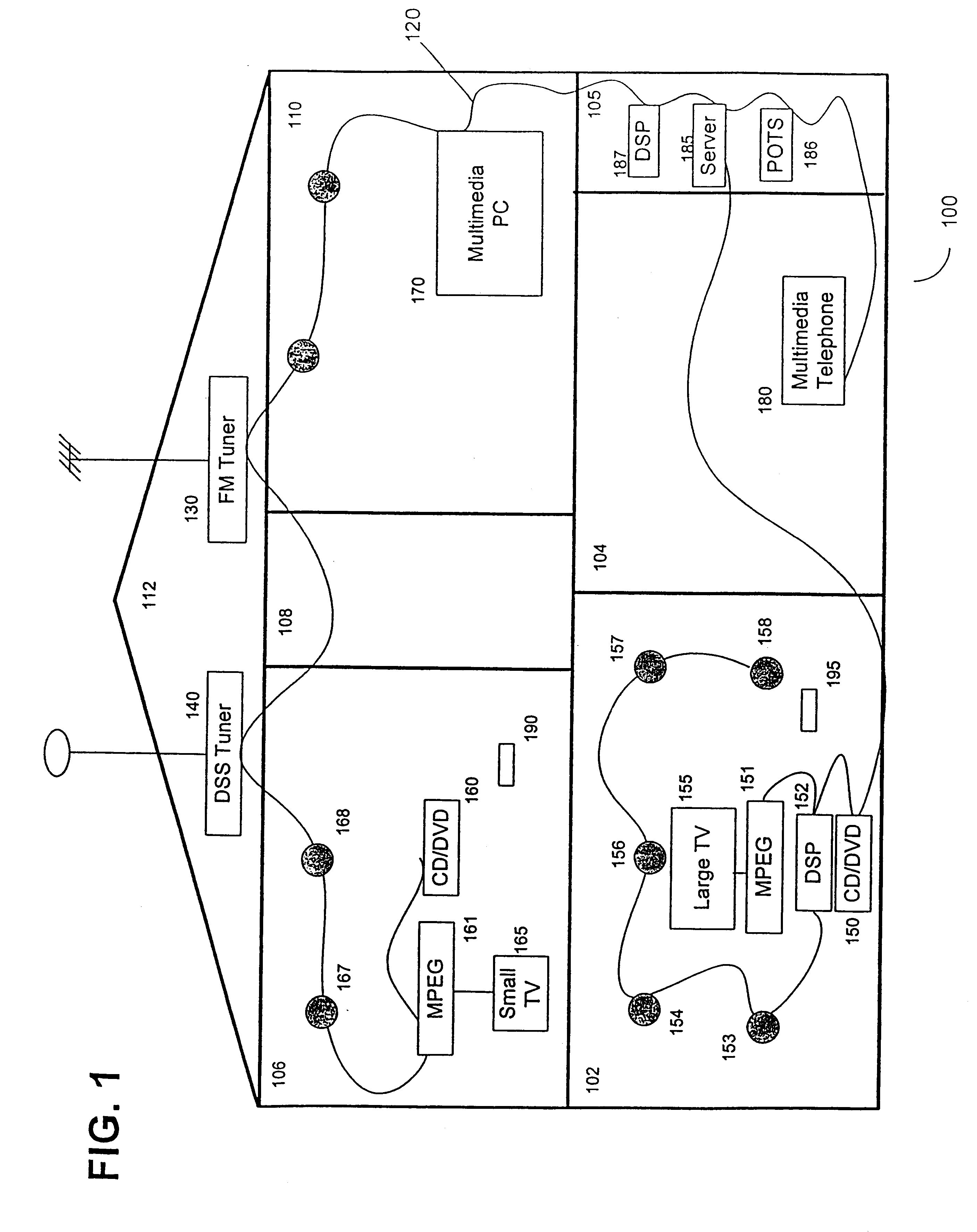
Synchronous network for digital media streams
InactiveUS6611537B1Avoid collisionPulse modulation television signal transmissionTime-division multiplexData streamNetwork clock
A network adapter for a synchronous logical ring network operates on existing physical twisted-pair telephone topologies. Information propagates around the logical ring, reaching every device on each revolution around the network. Network devices are full-duplex, transmitting and receiving information on every clock cycle. Network devices arbitrate to be elected the network clock device. By synchronizing all network devices to a single reference clock, and providing fixed frames of information propagating around the network at consistent time intervals, the logical ring network ensures that information propagates from one device to another at consistent time intervals. The fixed-length frames are divided into two independent streams: a data stream for the distribution of real-time continuous digital media streams; and a system command stream for the distribution of system commands.
Owner:CENTILLIUM COMM
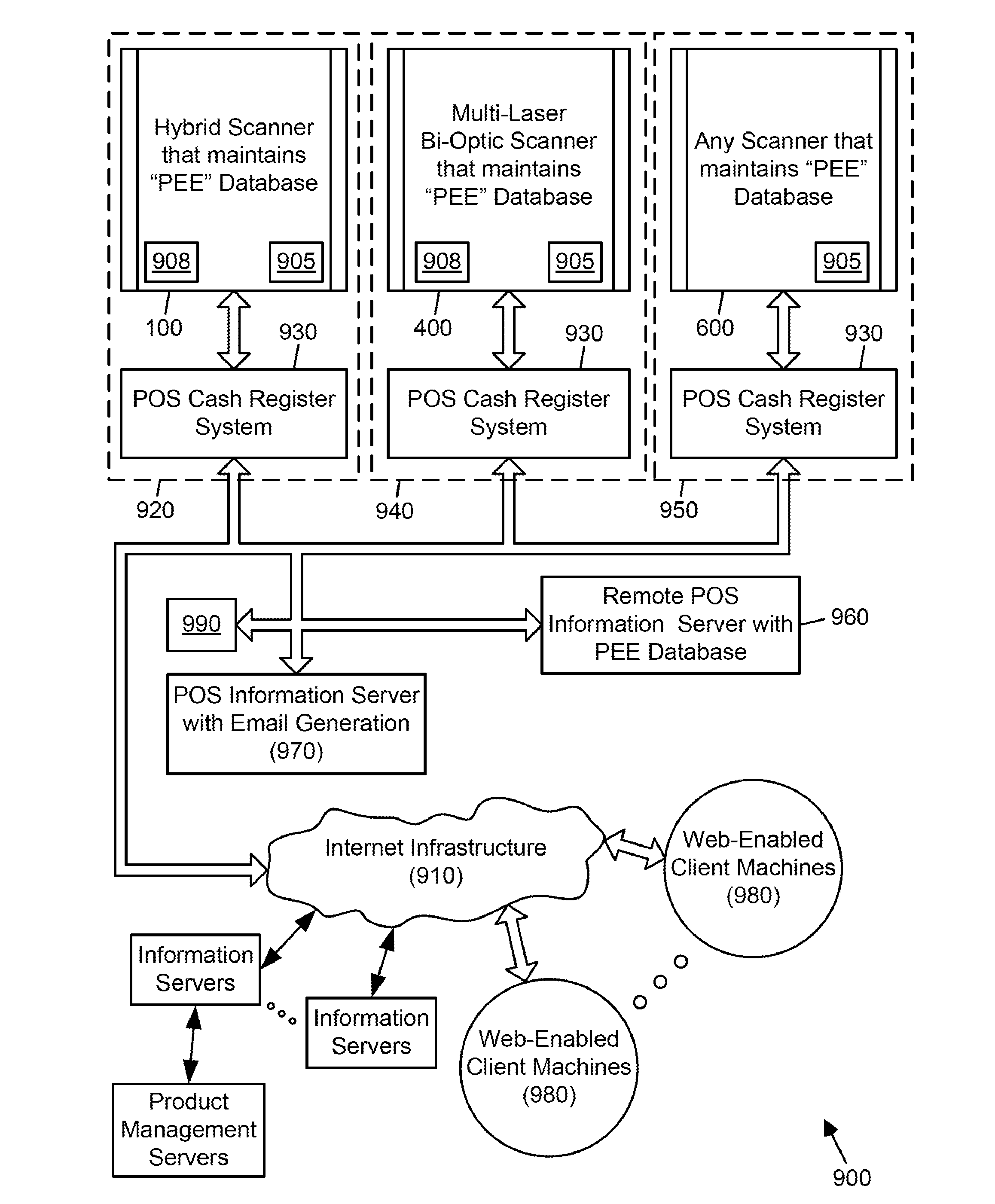
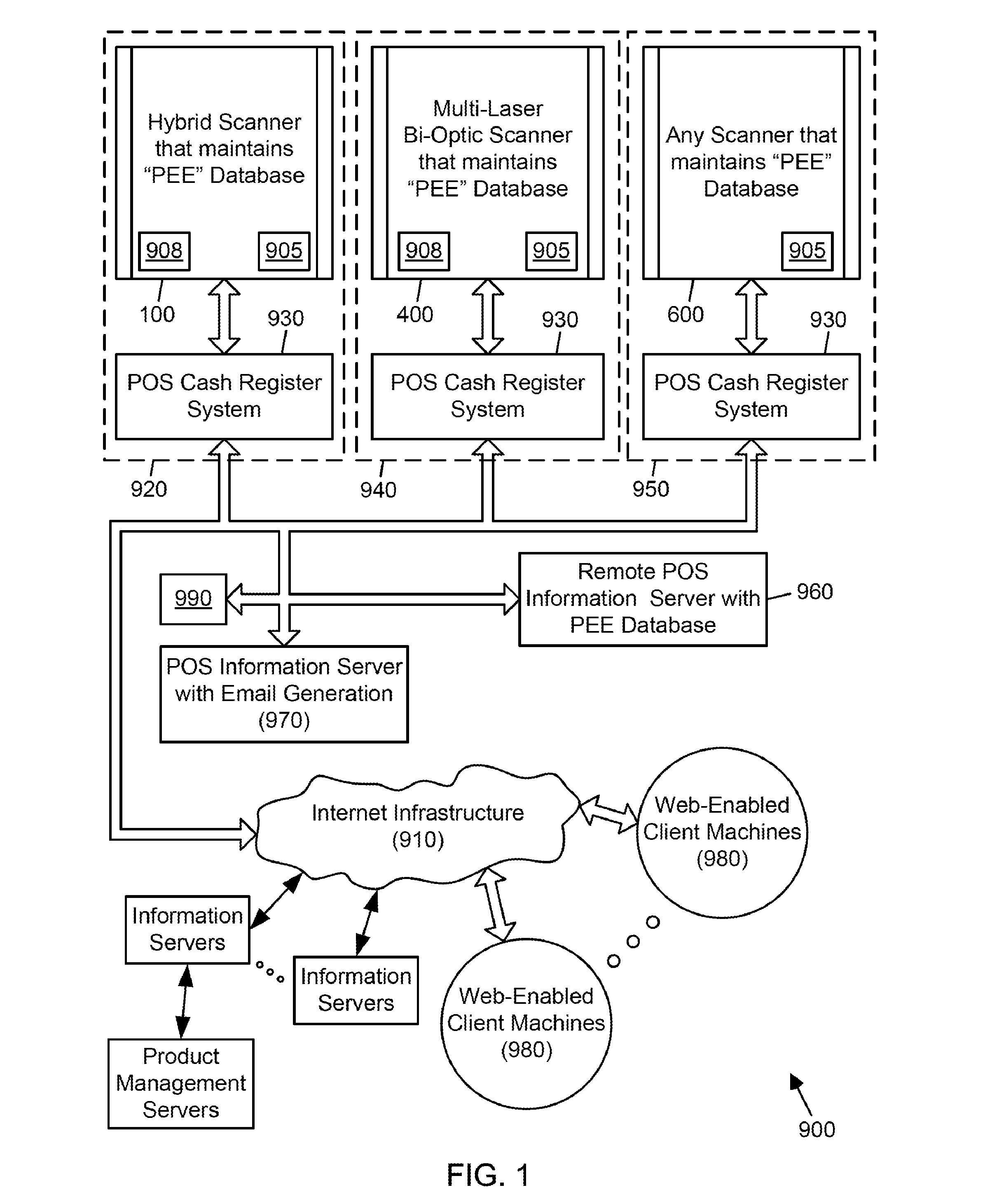
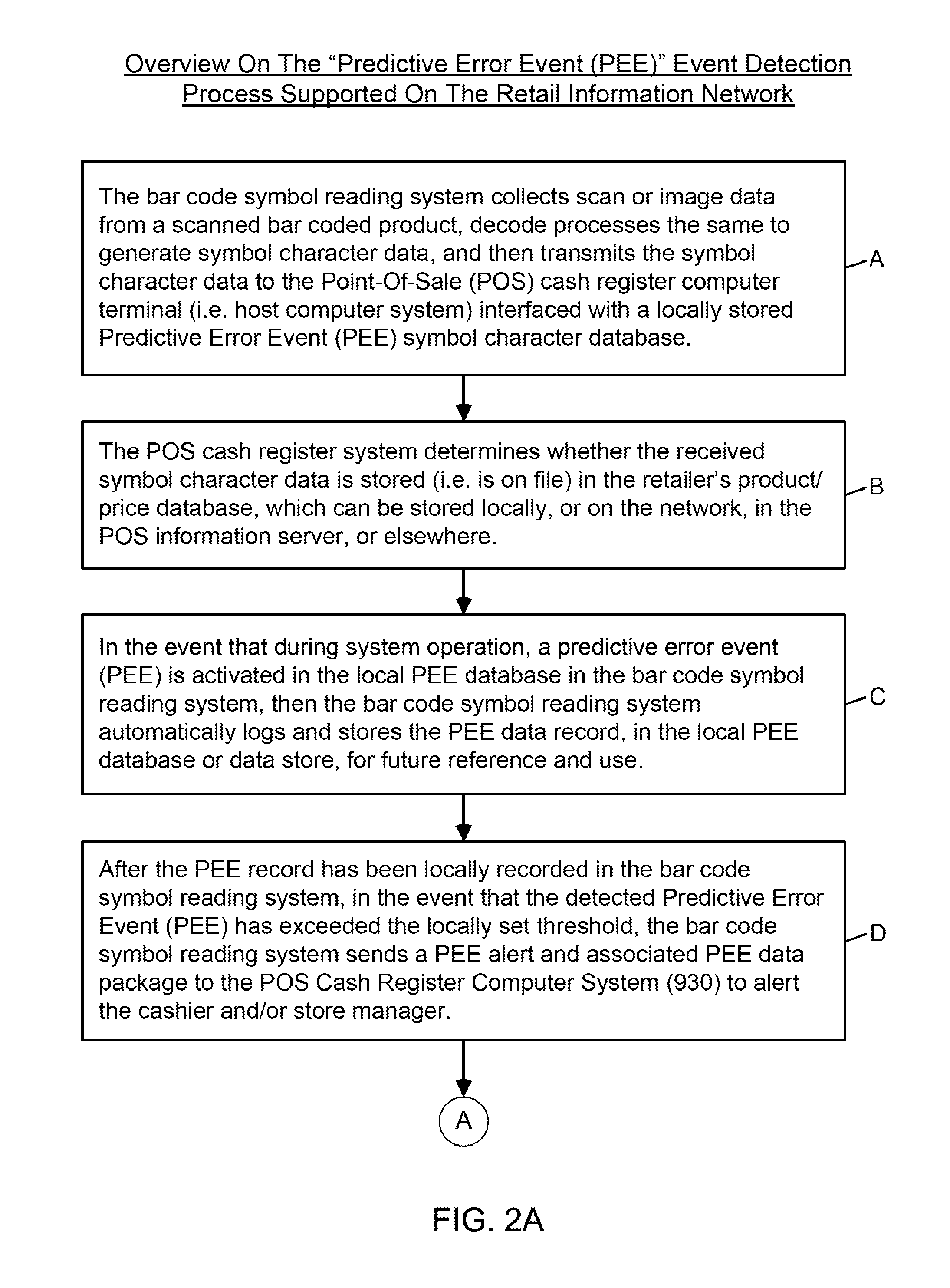
Symbol reading system having predictive diagnostics
ActiveUS9022288B2Improve the level ofEasy maintenanceTesting sensing arrangementsSensing by electromagnetic radiationInformation networksBarcode
A retail information network includes one or more POS scanning and checkout systems, each including (i) a bar code symbol reading subsystem, and (ii) a cash register computer subsystem interfaced with the bar code symbol reading subsystem and a network infrastructure, and each having access to product and price data maintained in a product / price database. The bar code symbol reading subsystem includes a local predictive error event (PEE) data store for logging and storing predictive error events (PEEs) detected within the bar code symbol reading system, wherein said PEEs are subsequently sent to POS information servers used to create predictive error alerts (PEAs) and corresponding instructions to maintain and / or repair certain aspects of the bar code symbol reading system.
Owner:METROLOGIC INSTR
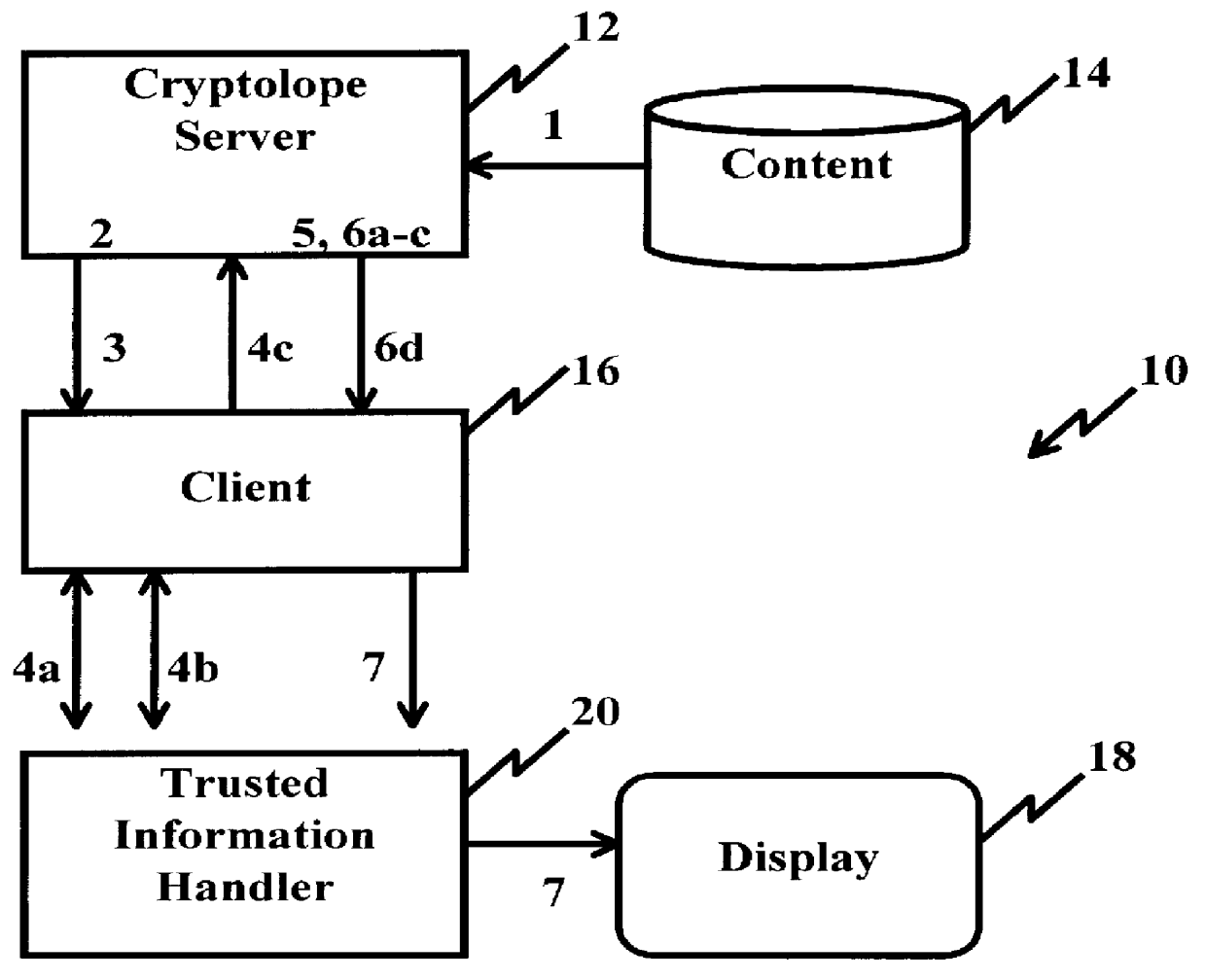
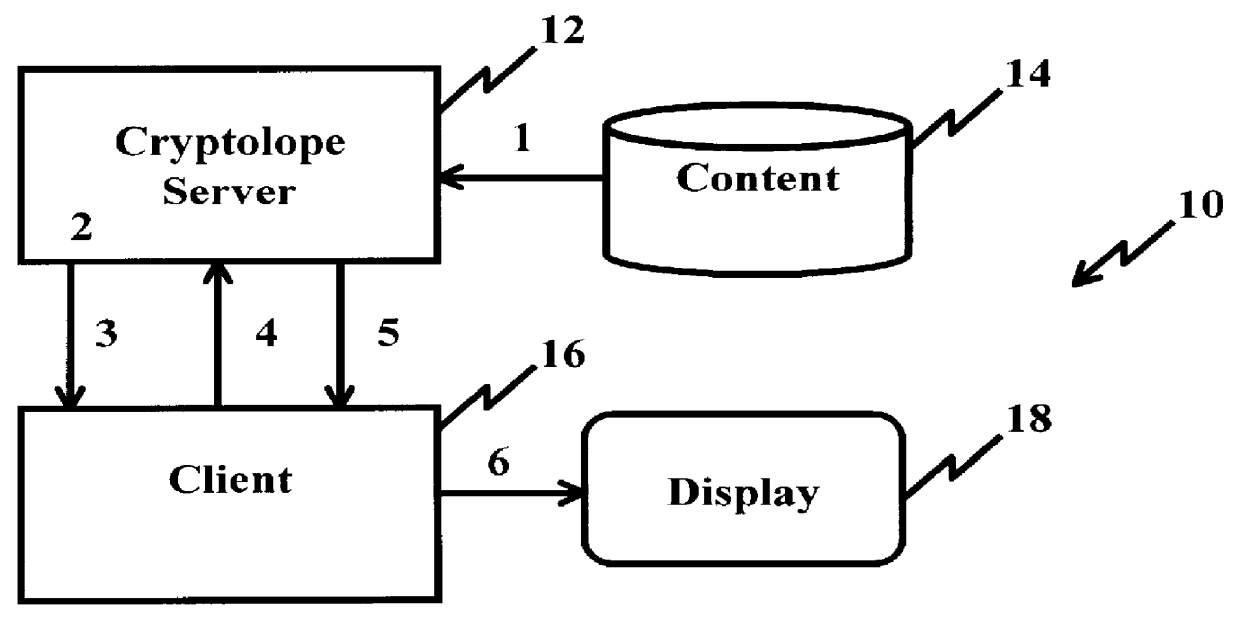
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
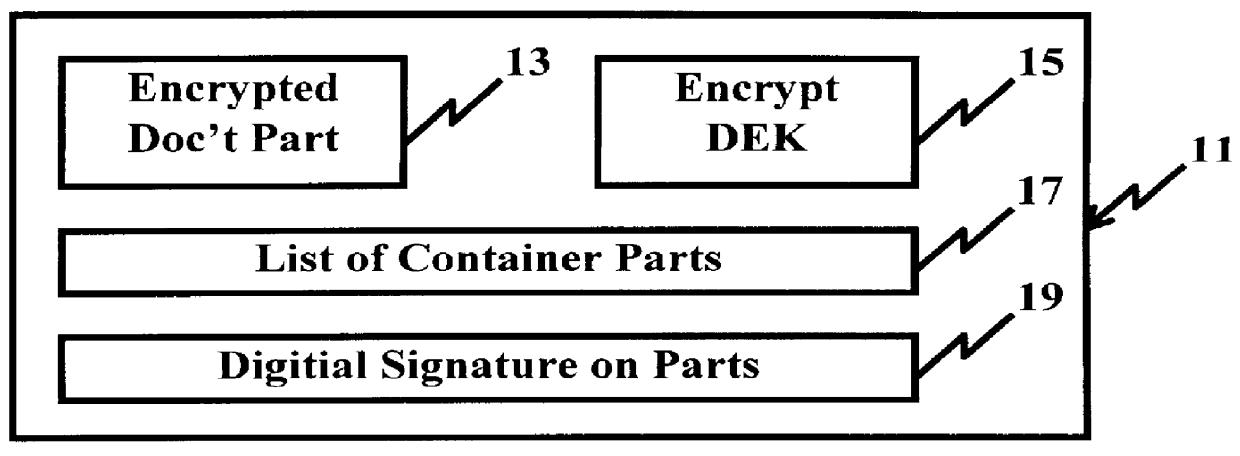
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
Displaying and tagging places of interest on location-aware mobile communication devices in a local area network
InactiveUS20070281690A1Facilitate information sharingInformation formatContent conversionInformation networksDisplay device
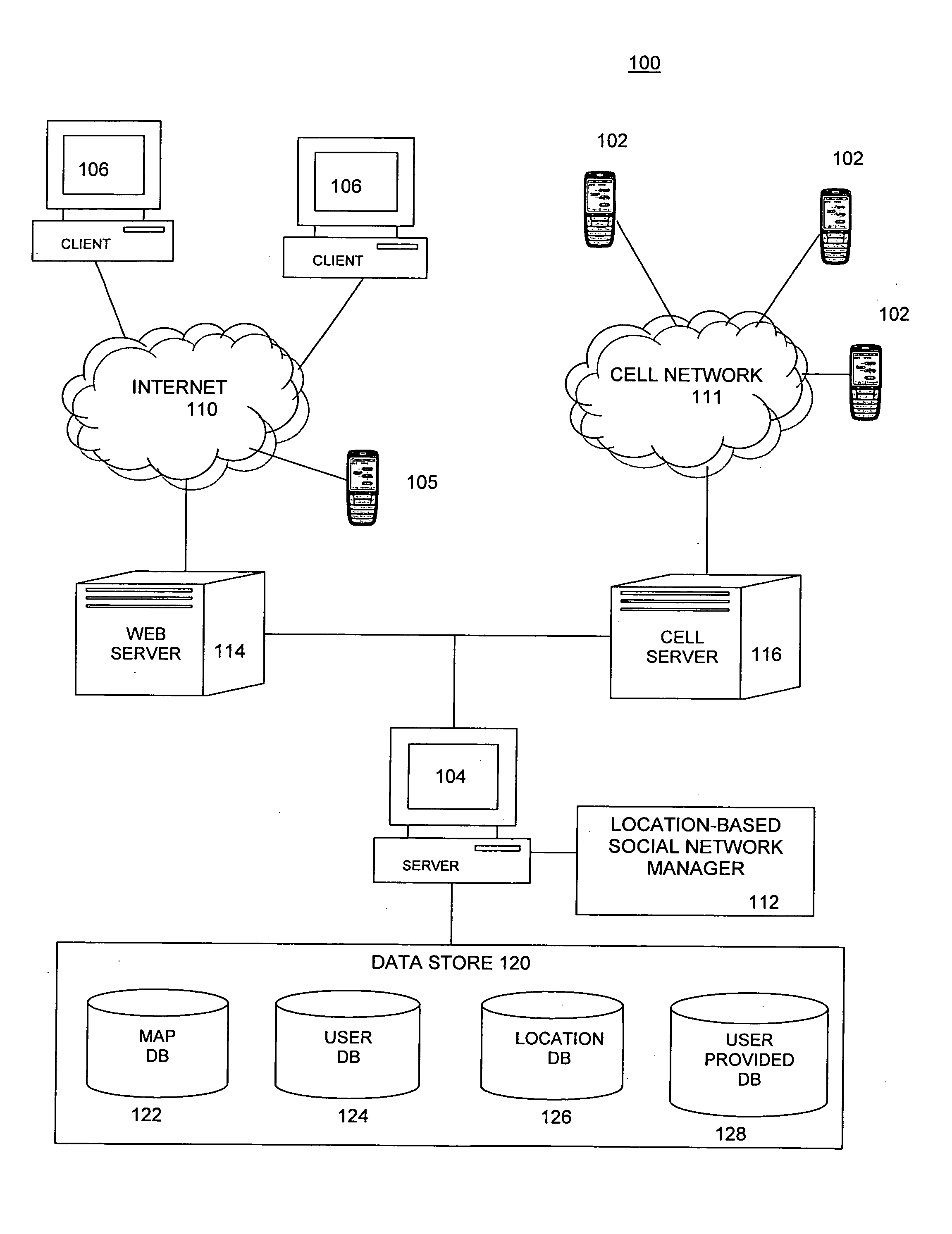
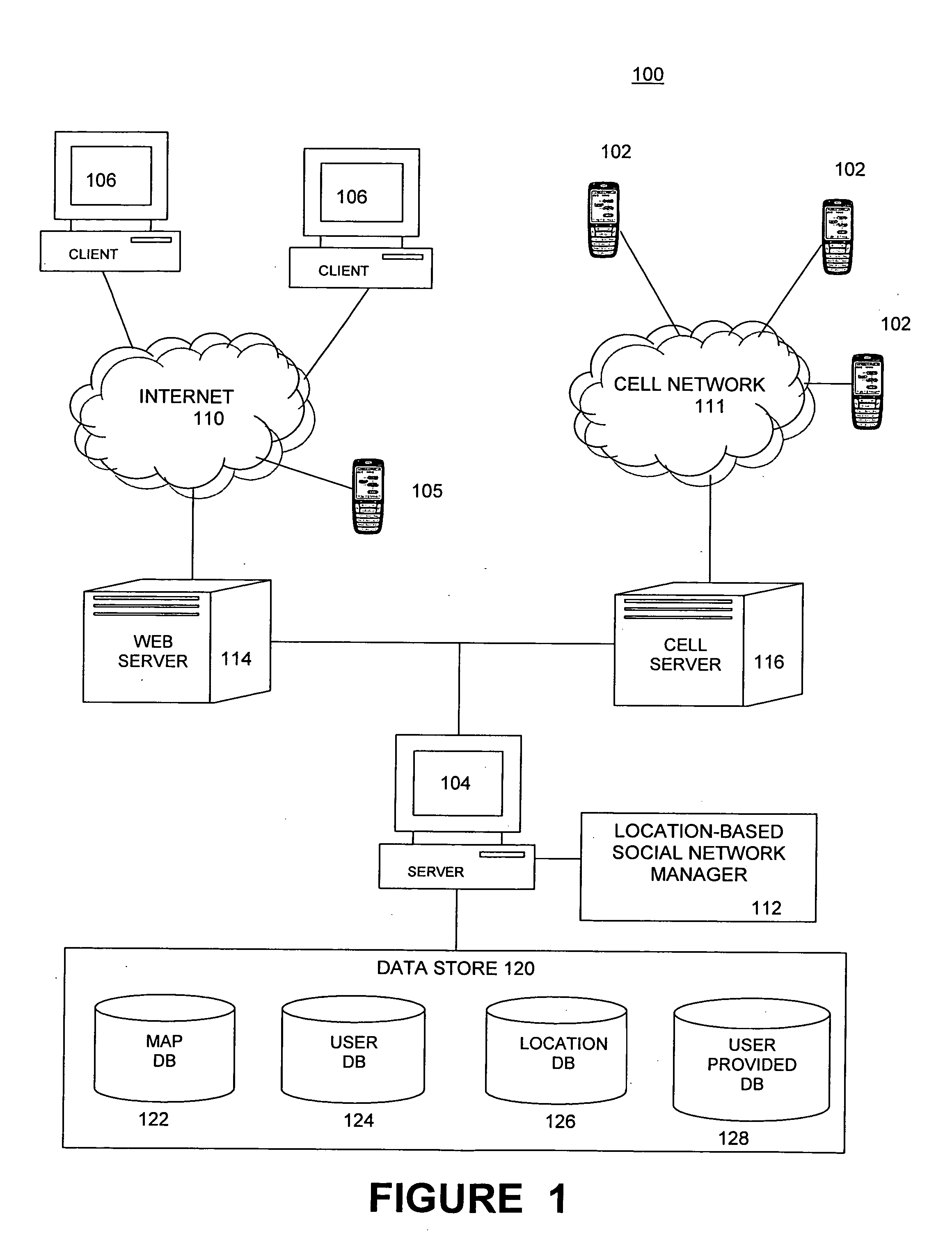
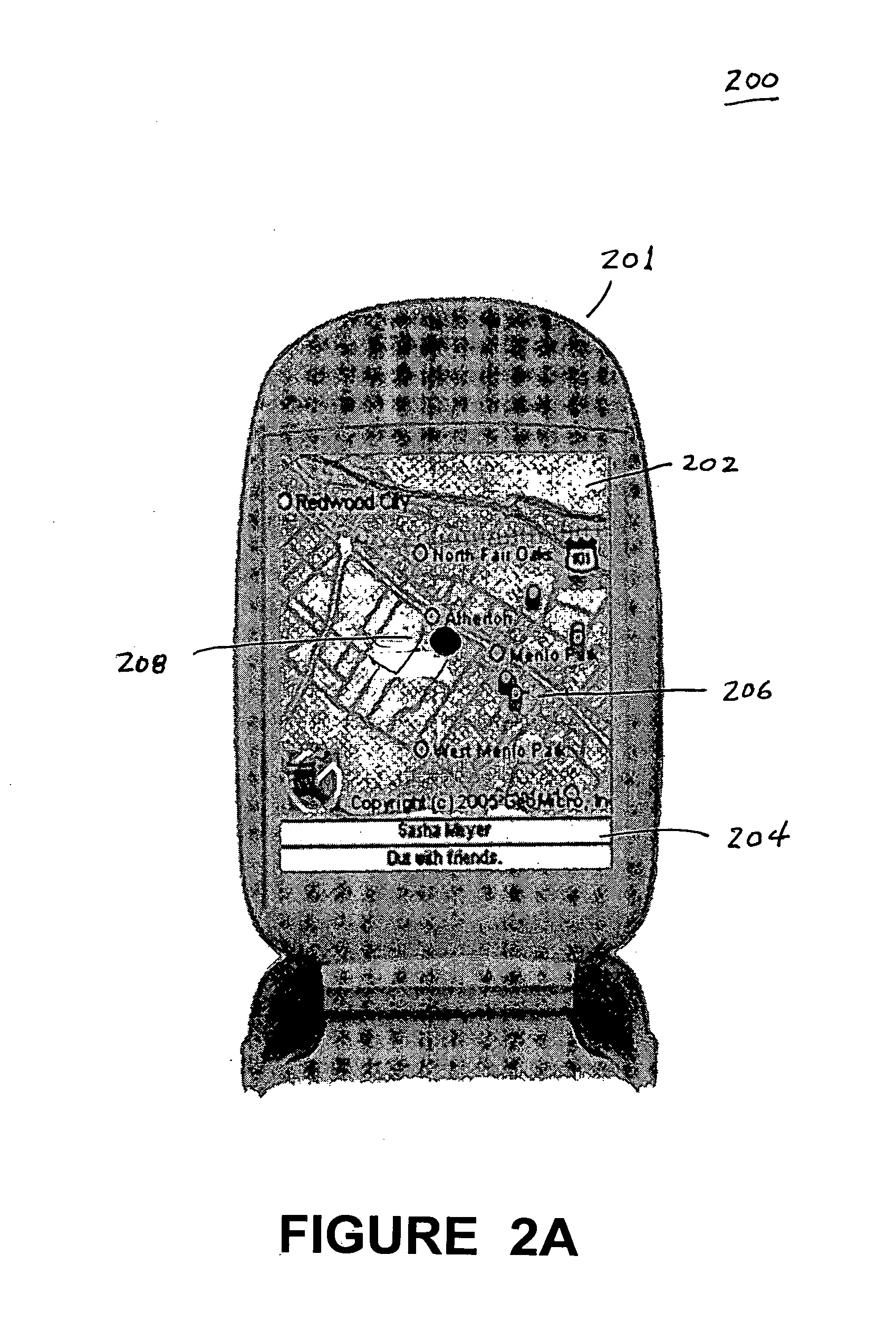
Embodiments of a location-based social network manager process are described. The process is executed on a server computer coupled to a plurality of location-aware mobile communication devices over a wireless network. The process determines the geographic location of a mobile communication device operated by a user within an area, displays a map representation of the area around the mobile communication device on a graphical user interface of the mobile communication device, and superimposes on the map the respective locations of one or more other users of mobile communication devices coupled to the mobile communication device over the network. The process establishes communication links between the user and the plurality of acquaintances through respective location aware mobile communication devices through a network protocol. The process facilitates the sharing information about places of interest among a plurality of users. The system stores location information for a place of interest in a region in a database along with information related to the place of interest. The location of the place of interest is displayed on each user's mobile communication device as an icon superimposed on the map shown on the display. The location of the users can be established with respect to their distance relative to a place of interest. Users can define their own places of interest as well as provide a quantitative or qualitative ranking for places of interest within a region. This information can then be shared with other users in the network.
Owner:LOOPT
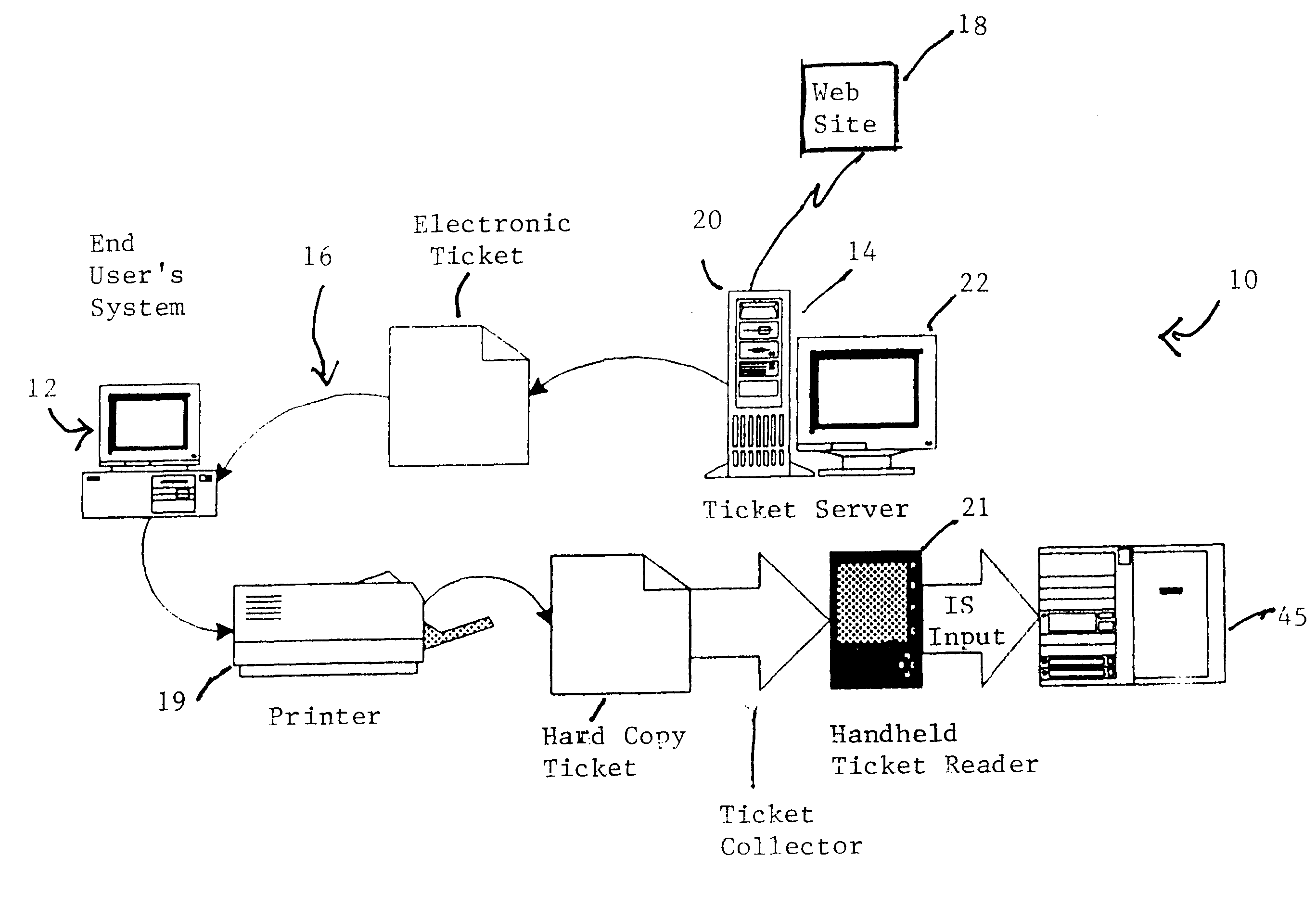
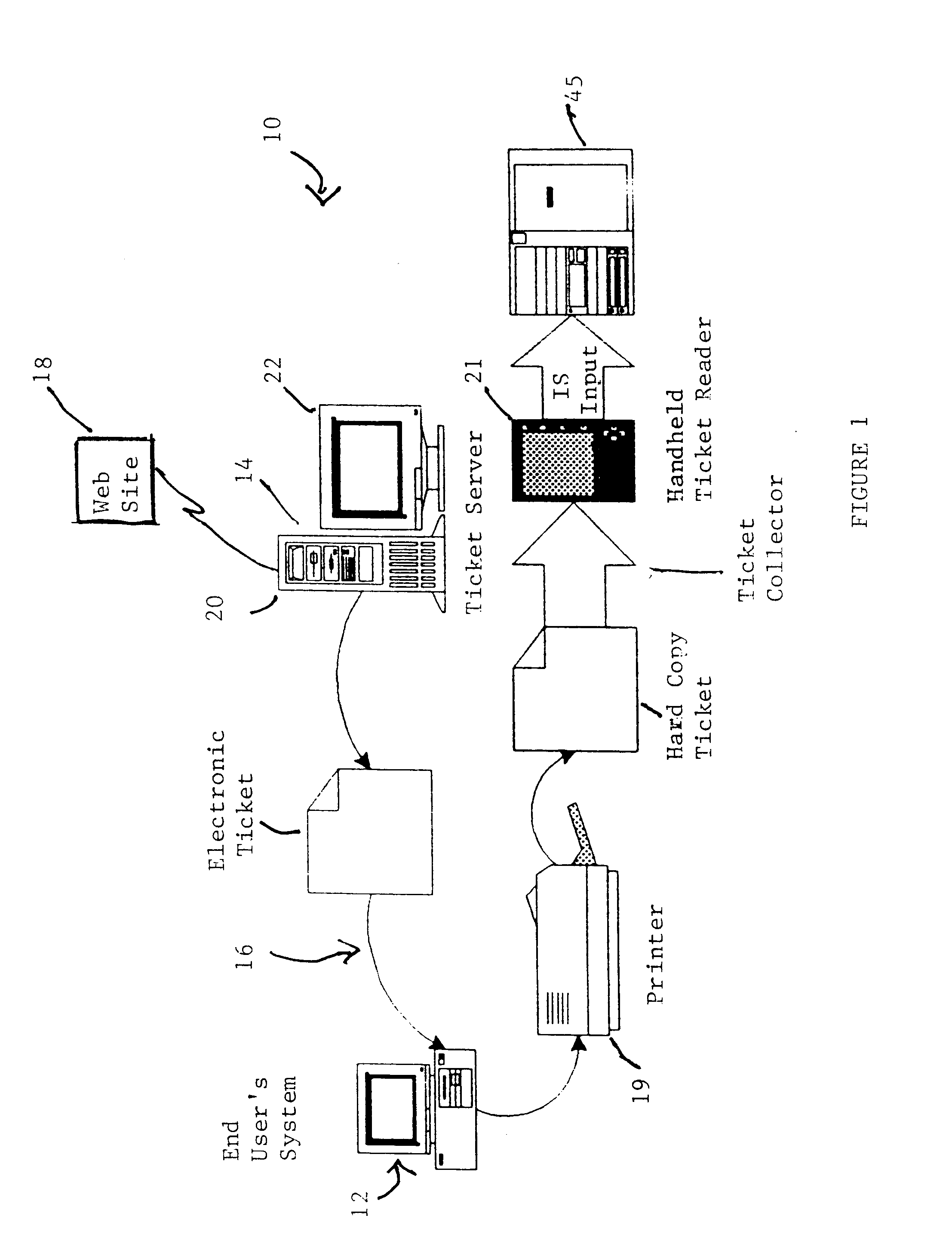
Cryptographic encoded ticket issuing and collection system for remote purchasers
InactiveUS6223166B1Prevent ticket fraudTicket-issuing apparatusElectrical apparatusCollection systemInformation networks
A cryptographic encoded, ticket issuing and collection system for real-time purchase of tickets by purchasers at remote user stations in an information network that includes a plurality of remote user stations coupled to a server in an information network, e.g., the Internet, for purchase of services, products, or tickets to an event. An operator of the remote user station selects a ticket for purchase to an event using standard protocols of information network. An electronic ticket is transmitted to the operator and includes a cypher code created using a public key cryptography system. The operator displays the electronic ticket for verification purposes and proceeds to print out the ticket at the station. The ticket is presented to a ticket collector whereupon the ticket is scanned by a portable terminal for decoding the cypher code using a public key reloaded into the terminal by the producers of the event. The decoded cypher code is compared against the event description stored in the portable terminal and if equal, the ticket is accepted for admission to the event. The ticket information is stored in the portable terminal and subsequently uploaded to the information system to check for duplicate tickets.
Owner:IBM CORP
System for storing, accessing and displaying html encoded
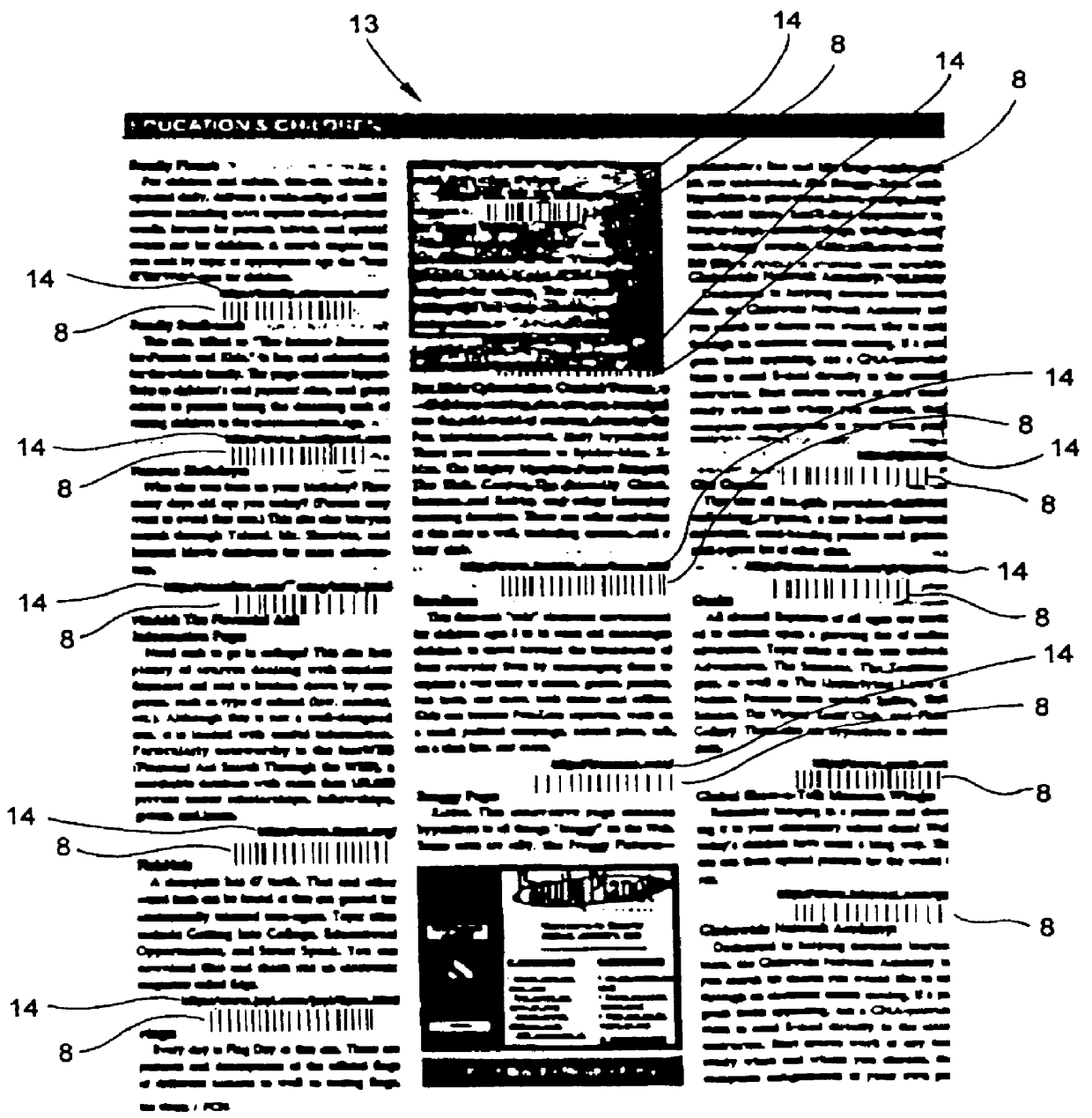
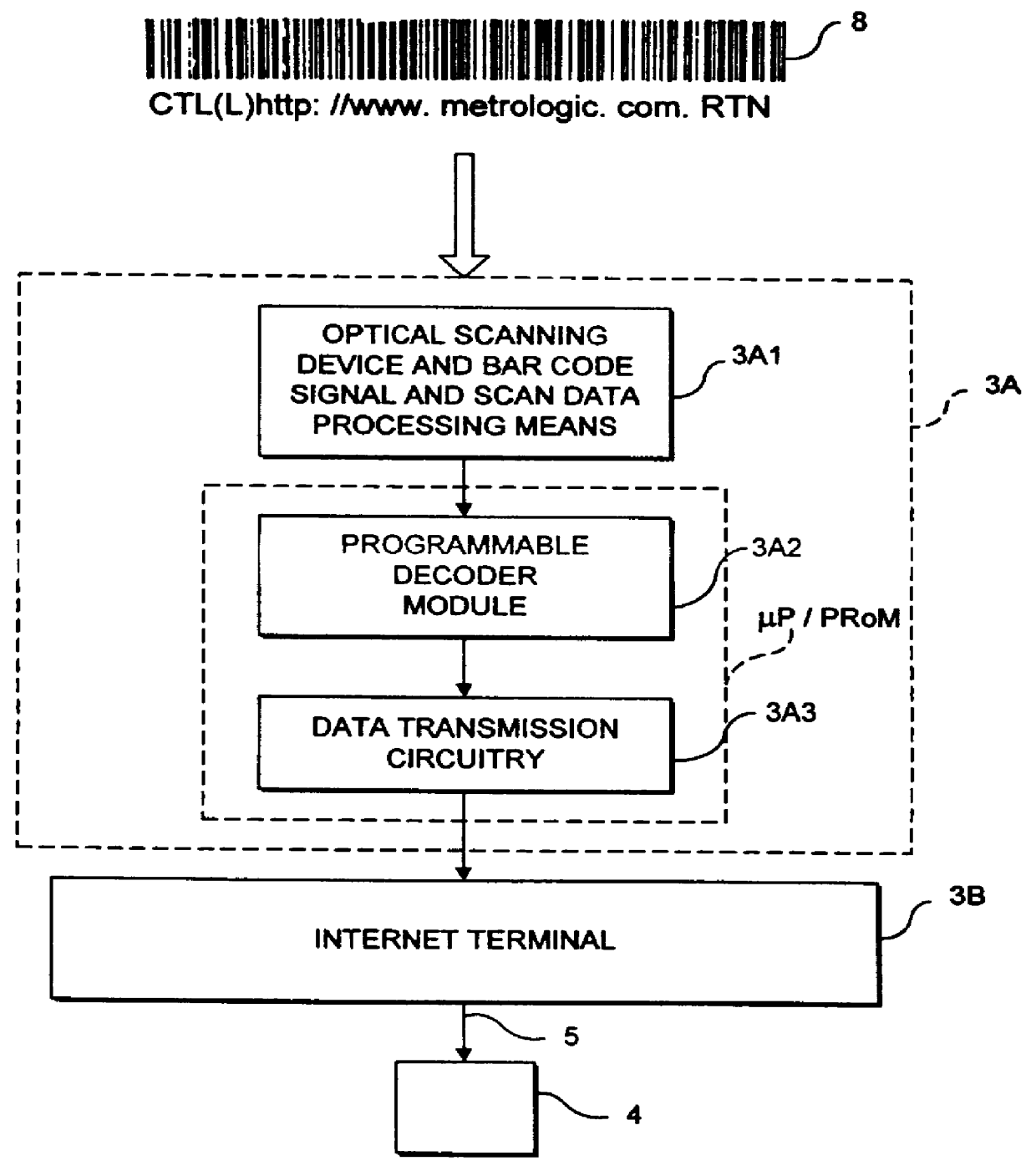
InactiveUS6152369AEasy accessDigital data information retrievalCharacter and pattern recognitionObject pointDisplay device
A system for storing, accessing and displaying HTML-encoded documents relating to an object being worked upon in a work environment by a human operator. The human operator wears a body-wearable http-enabled client system equipped with a code symbol reader programmed to read a URL-encoded symbol on the object pointing to a HTML-encoded document stored on one or more http-enabled information servers. The http-enabled client system is connected to the information network by a two-way wireless telecommunication link. The code symbol reader is programmed for reading the URL-encoded symbol affixed to the object and automatically produces symbol character data representative of the read code symbol and the URL encoded therewithin. The http-enabled client system also includes a network accessing mechanism and a display device. The network accessing mechanism is programmed for automatically accessing one or more of the HTML-encoded documents from one or more of the http-enabled information servers in response to symbol character data being produced by the code symbol reader. The display device is operably connected to the network accessing mechanism, for visually displaying HTML-encoded documents accessed from the http-enabled information servers in response to symbol character data being produced by the code symbol reader. As a result of the present invention, the human operator is enabled to freely review the HTML-encoded documents displayed on the display device while working with the object in diverse work environments involving, for example, inventory management, assembly-line and / or plant inspection, and craft or vehicle inspection and / or repair.
Owner:METROLOGIC INSTR
Portable browser device with voice recognition and feedback capability
InactiveUS7203721B1Special service for subscribersDigital computer detailsCommunication interfaceMobile vehicle
A mobile information network browser device with audio feedback capability that is capable of transmitting a request for information via a wireless communication interface from one or more servers in an information network. The browser device further includes an audio interface capable of receiving data from the wireless communication interface that is responsive to the request for information. The browser device interfaces with a wireless communication network so that it may be used in a mobile vehicle, such as an automobile. Receiving the requested information in audio format relieves the user from having to view an output display screen to receive the information while trying to operate the mobile vehicle.
Owner:TRIMBLE NAVIGATION LTD
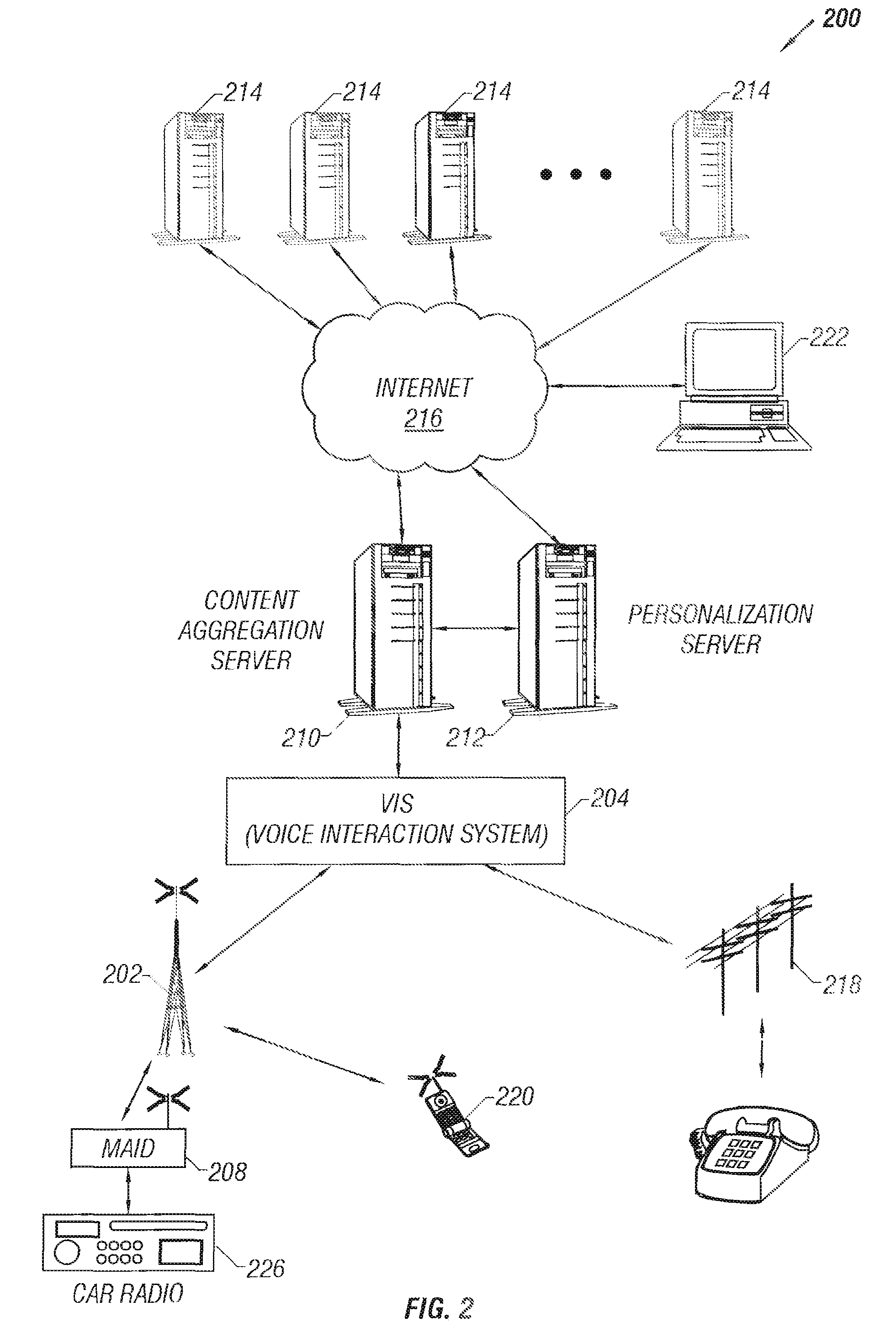
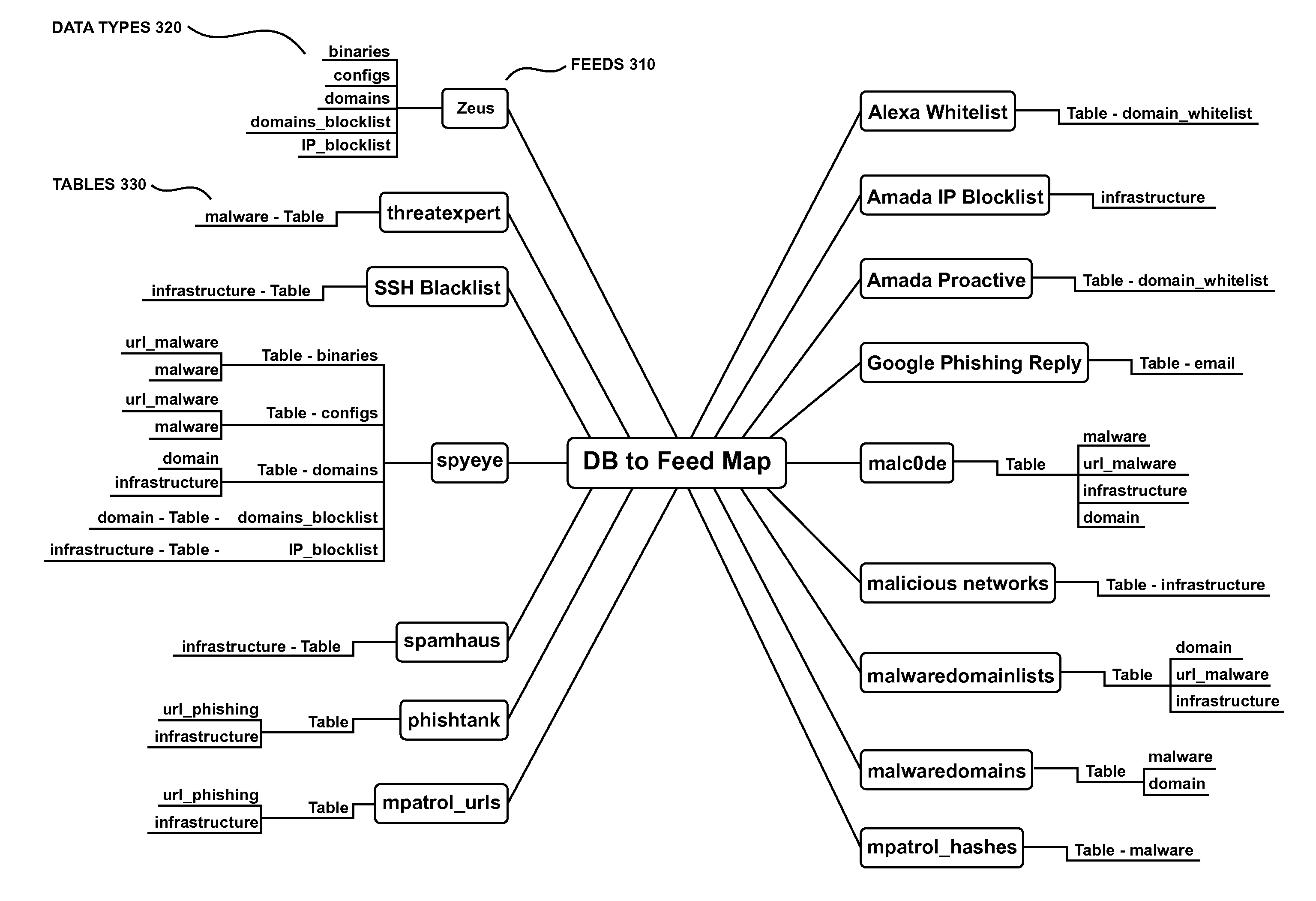
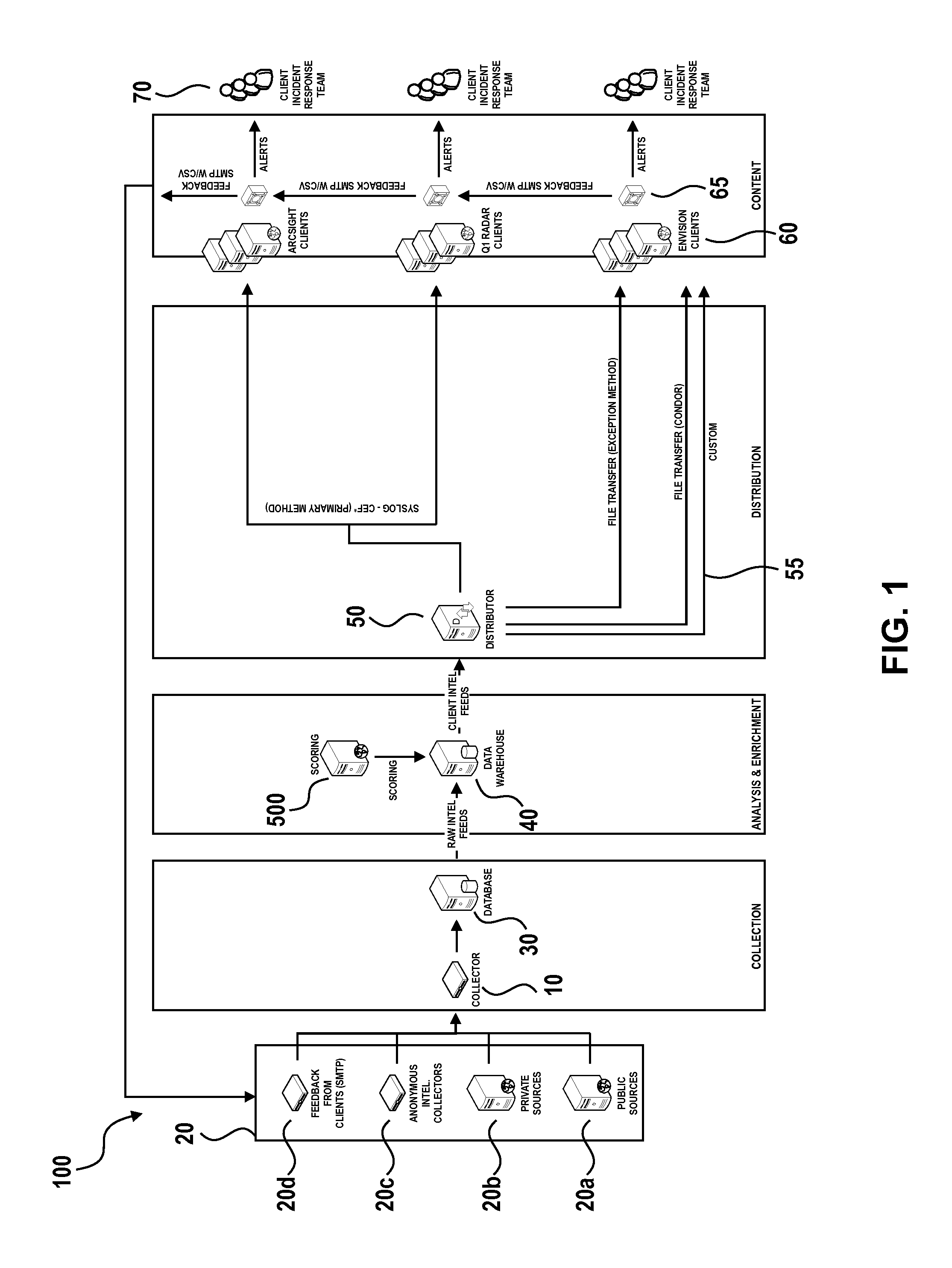
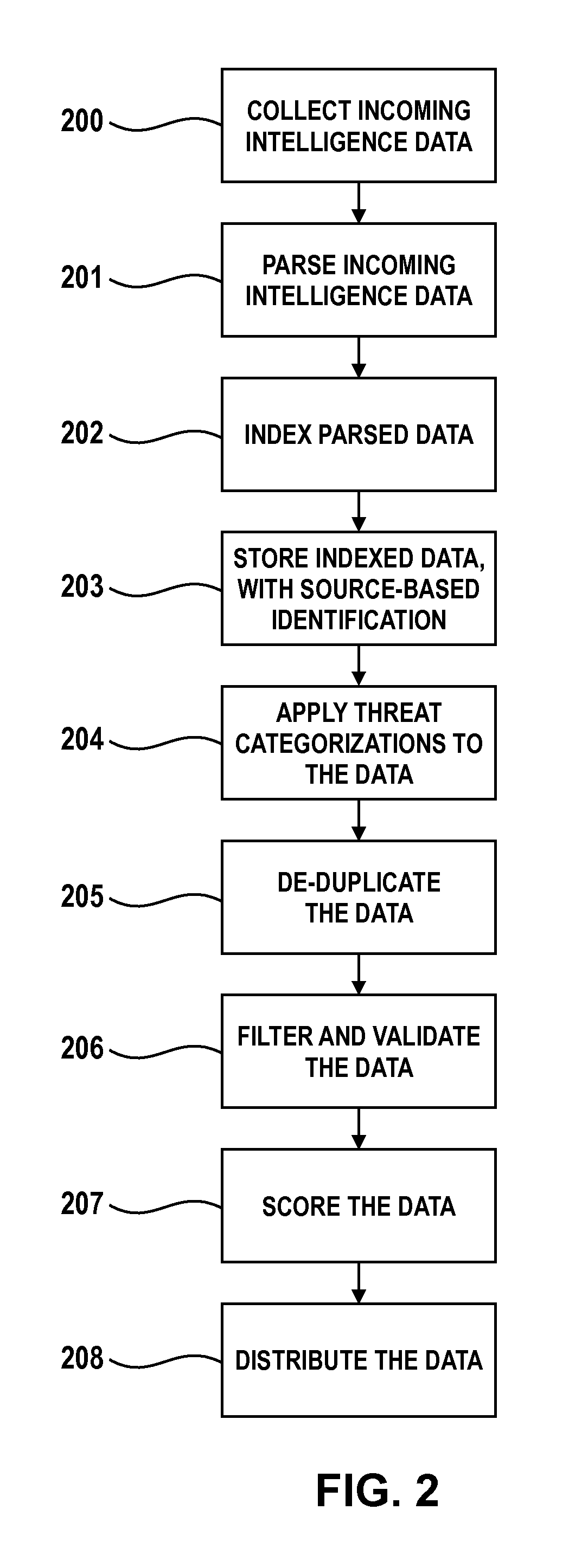
Collective Threat Intelligence Gathering System
ActiveUS20140007238A1Quality improvementImprove information qualityMemory loss protectionError detection/correctionIp addressInformation networks
Threat intelligence is collected from a variety of different sources. The threat intelligence information is aggregated, normalized, filtered and scored to identify threats to an information network. Threats are categorized by type, maliciousness and confidence level. Threats are reported to network administrators in a plurality of threat feeds, including for example malicious domains, malicious IP addresses, malicious e-mail addresses, malicious URLs and malicious software files.
Owner:DELOITTE DEV
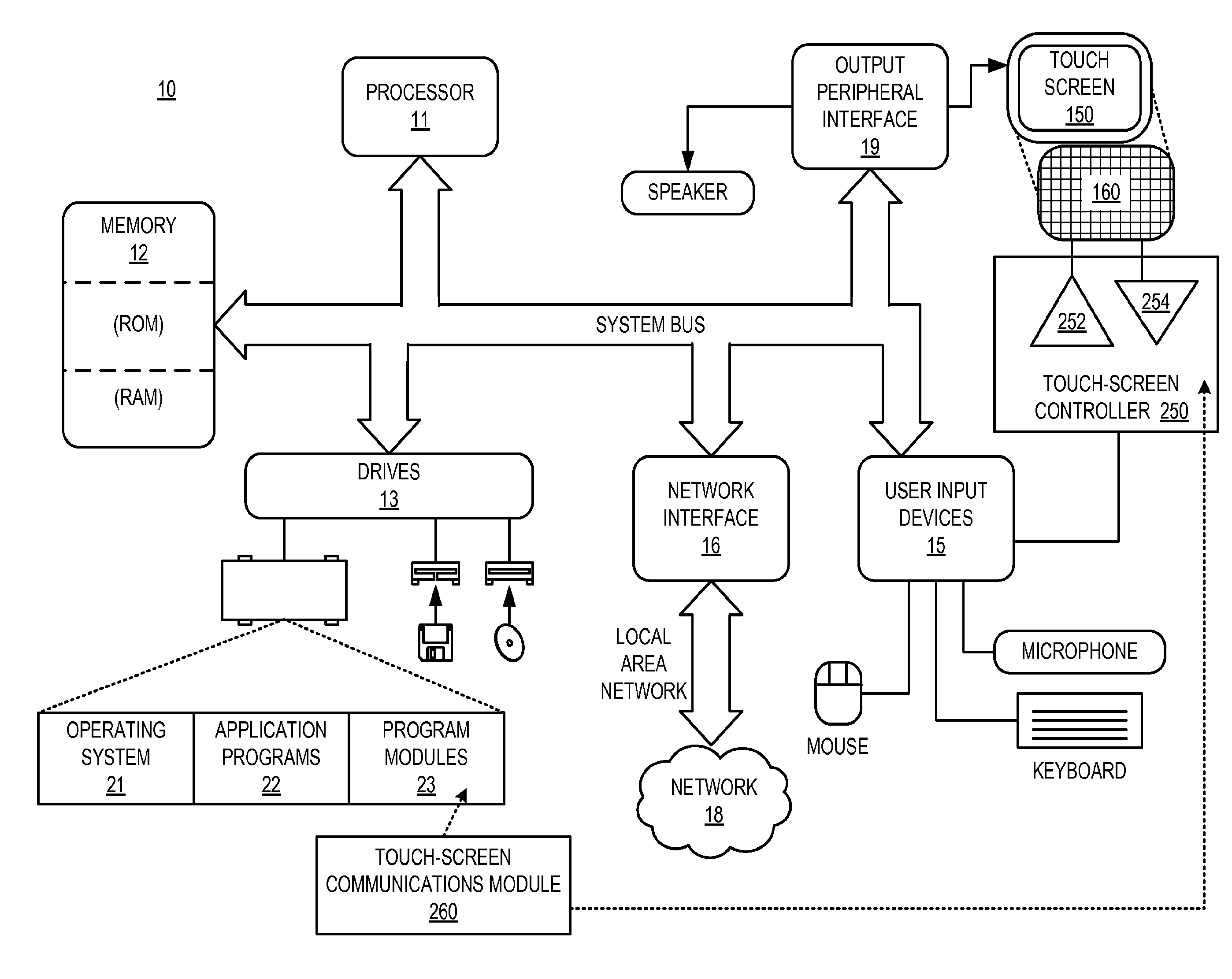
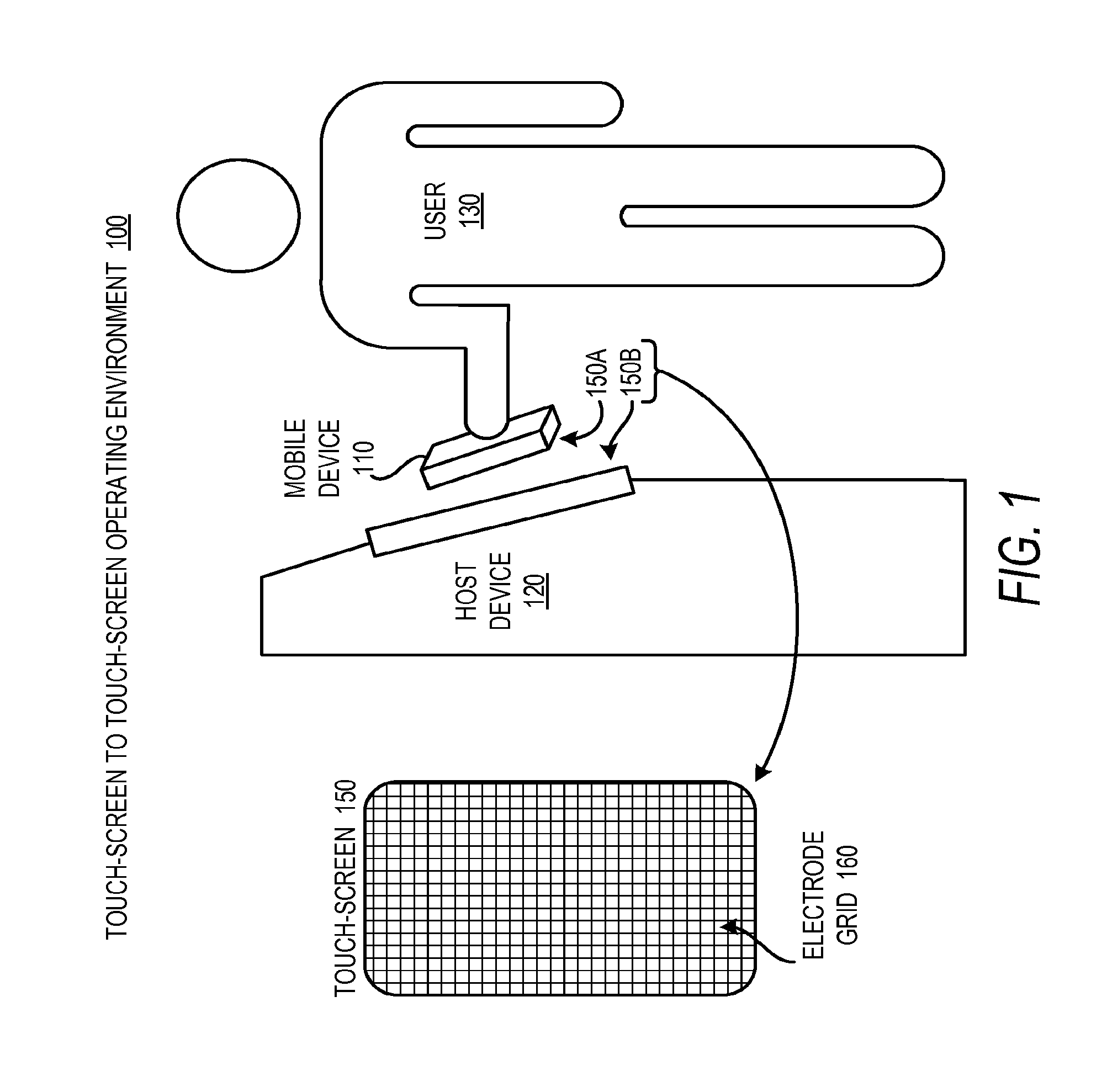
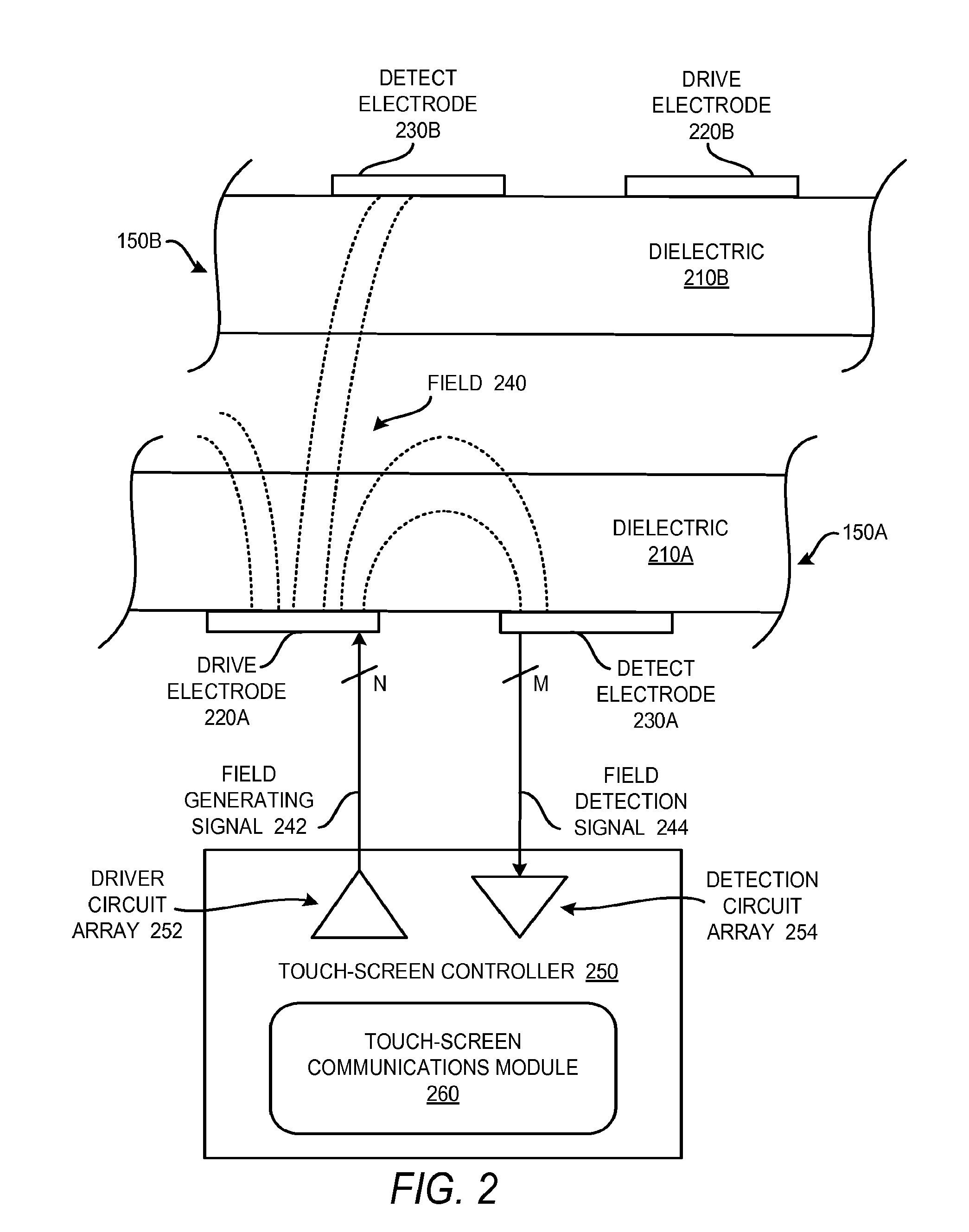
Communication Between Touch-Panel Devices
InactiveUS20110304583A1Digital data processing detailsInternal/peripheral component protectionNetwork addressTouch panel
Technologies described herein generally relate to communications between electronic systems. Each electronic system includes a touch-panel device that may be positioned in proximity to one another such that the near field emissions of the touch-panel devices interact with one another. The touch-panel devices can be adapted to sense one another based on these near field emissions. Once detected, the touch-panel devices can be configured to establish a communication channel to communicate information between one another via modulated near field emissions. Such exchanged information may include identification information, network addresses, security keys, and so forth. The exchanged information may be used for discovery or pairing between the touch-panel devices. The technology presented herein can support an intuitive user experience and improved security over traditional wireless pairing approaches.
Owner:VIBRANT LICENSING LLC
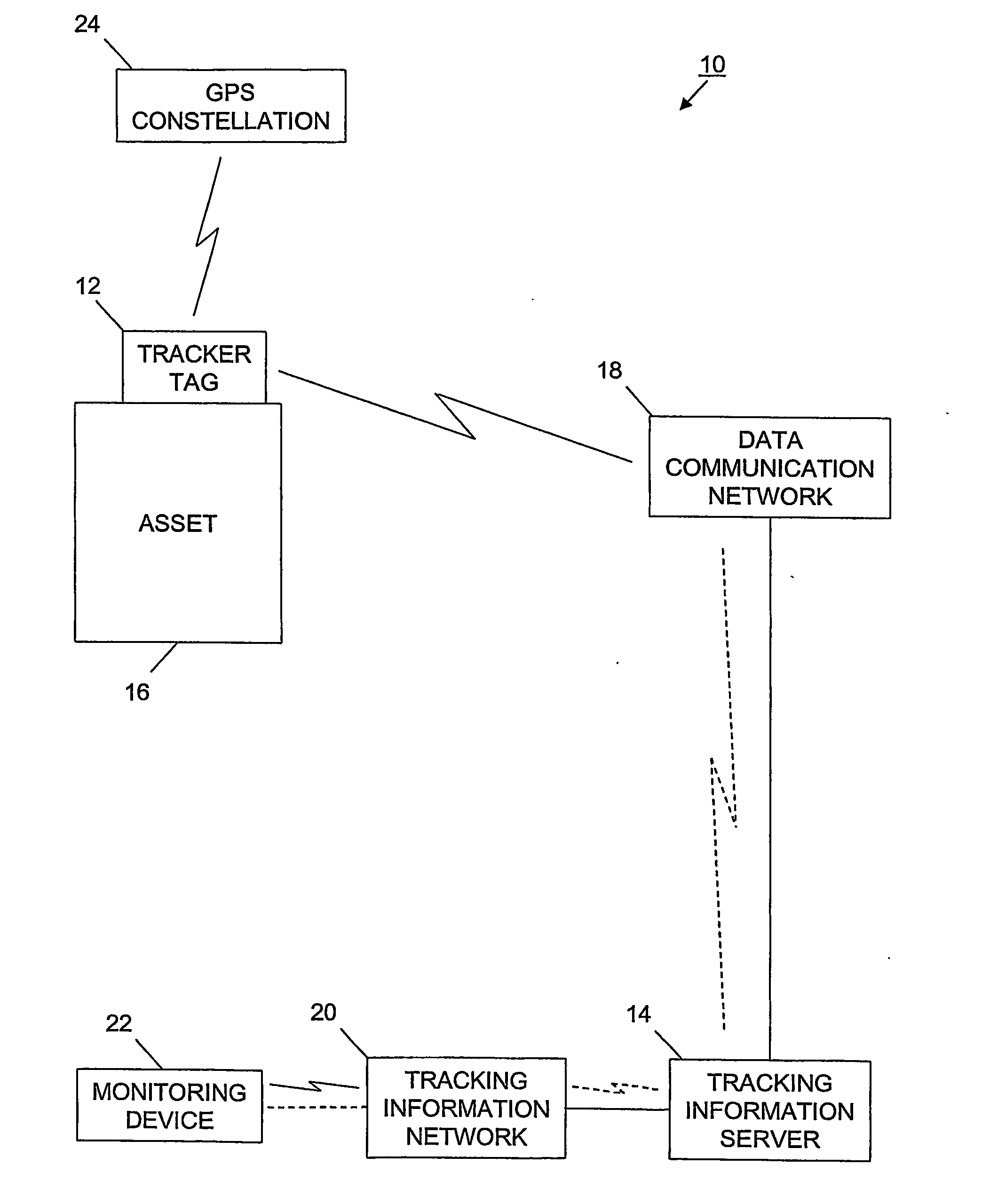
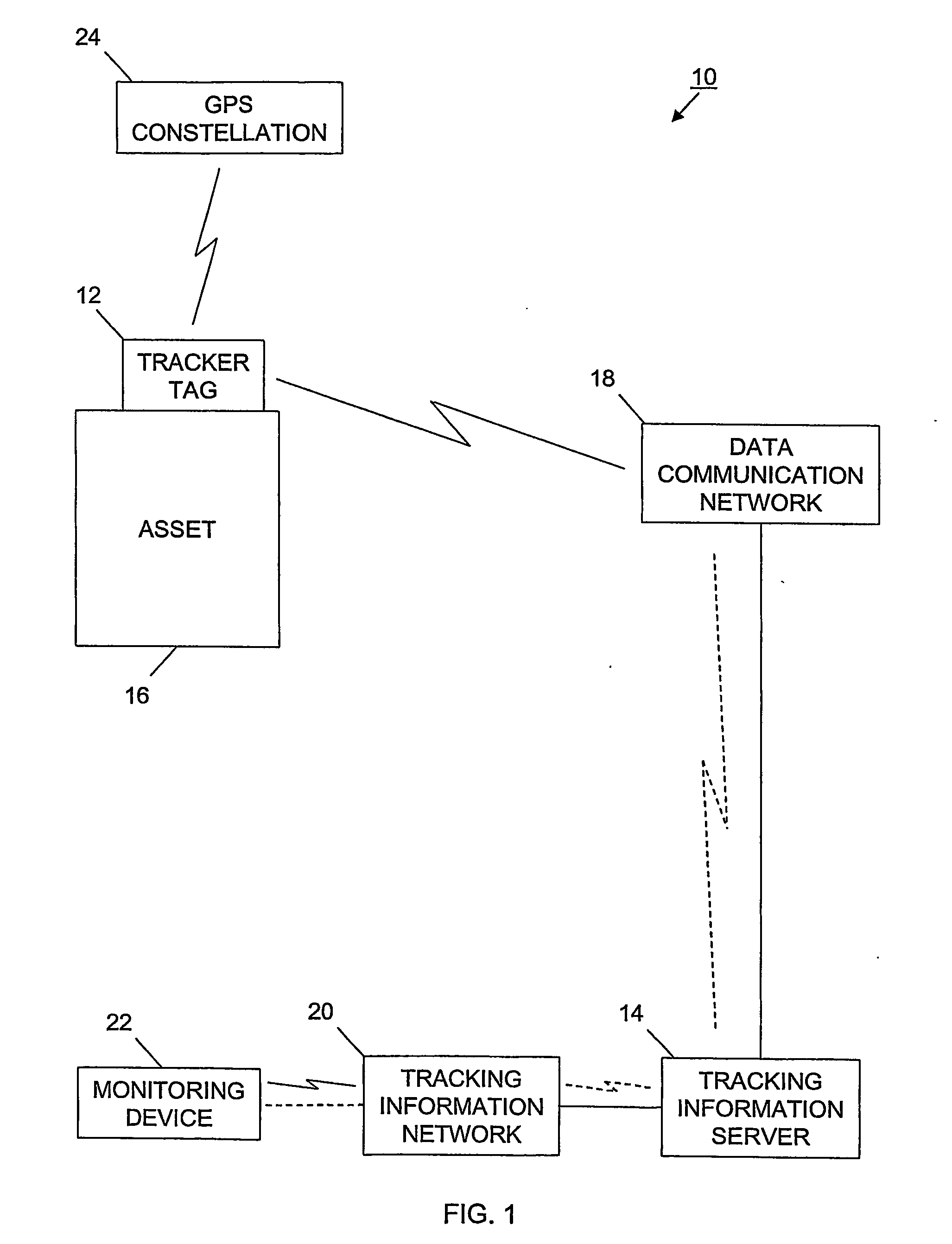
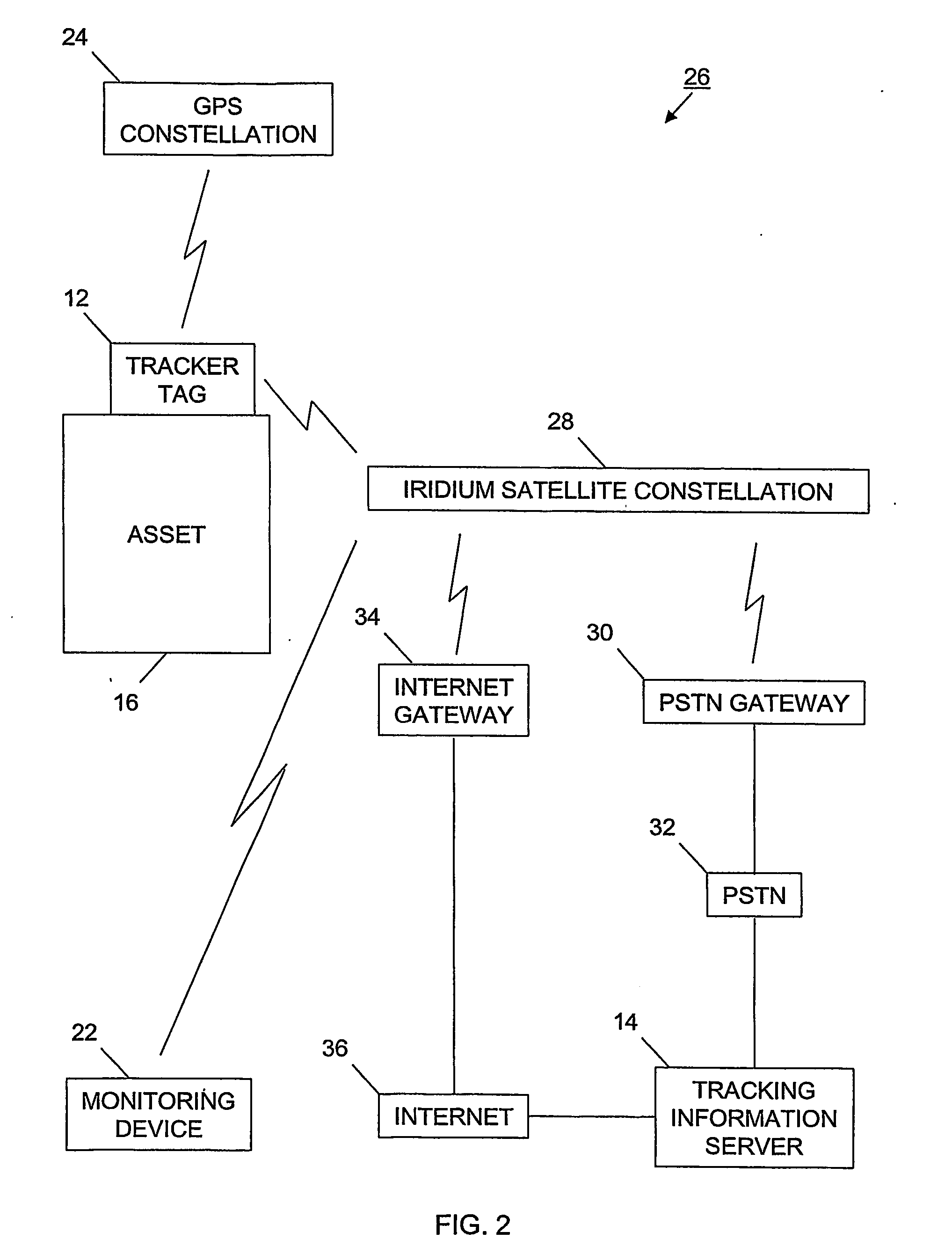
Tracking system and associated method
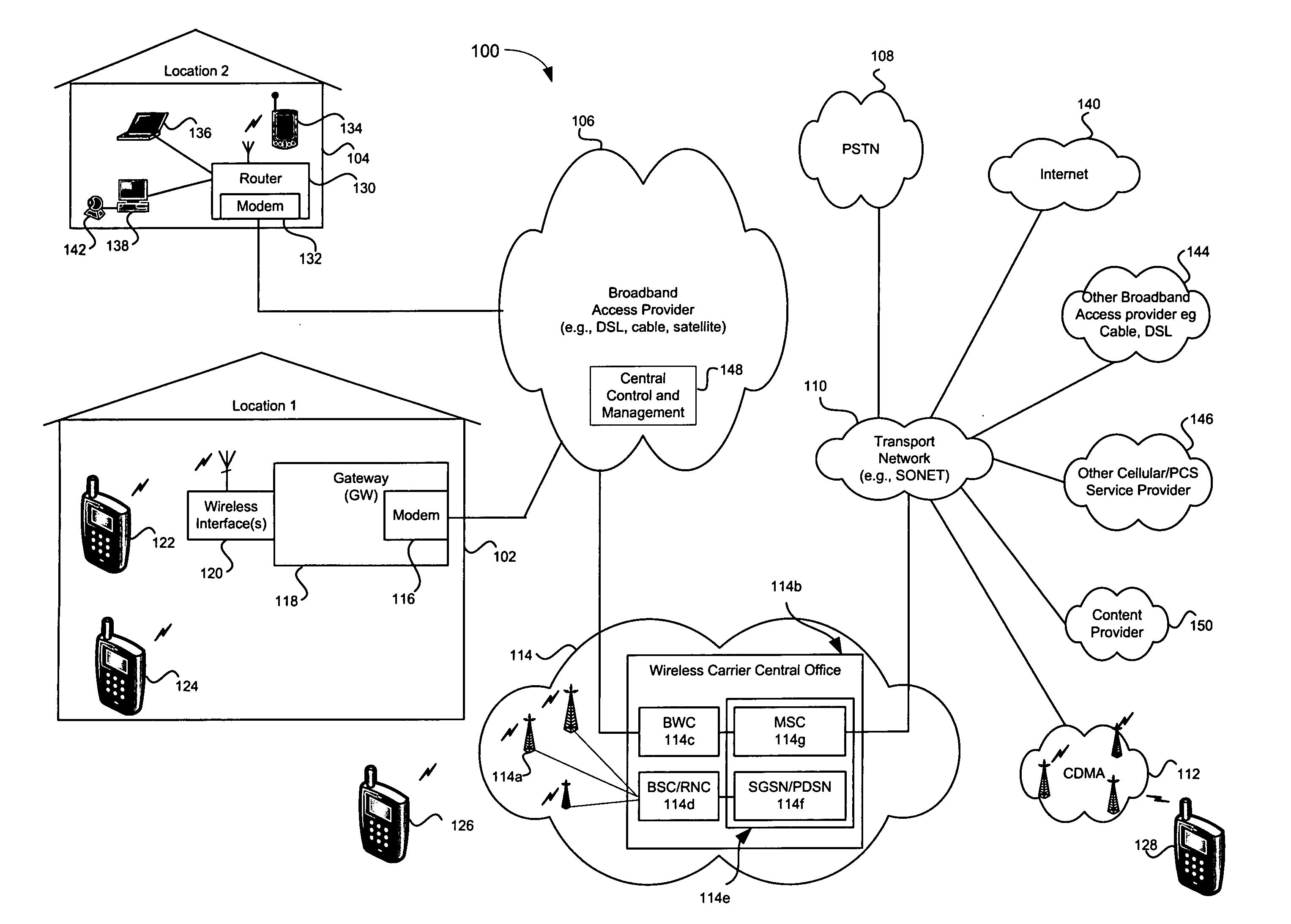
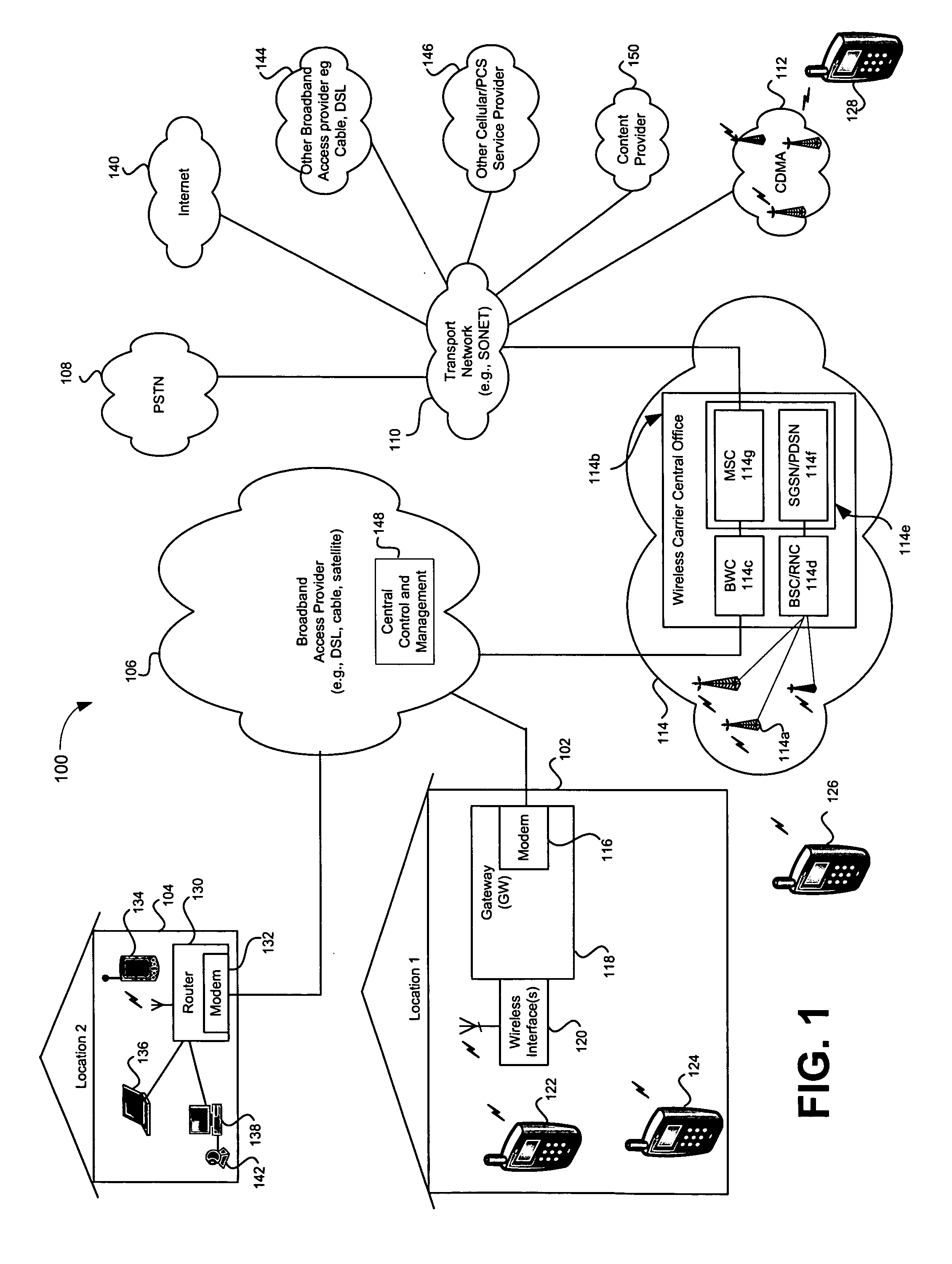
InactiveUS20060187026A1Easy to receiveVehicle testingRegistering/indicating working of vehiclesProgram instructionIridium satellite constellation
A tracking system (10) for tracking movable assets (16) and several methods for using the system are provided. The tracking system includes a monitoring device (22), a tracking information network (20), a data communication network (18), a tracker tag (12), and a tracking information server (14). The tracker tag uses GPS technology. The tracking information server provides programmed instructions to the tracker tag in messages via a messaging system. The tracker tag selectively retrieves the messages from the messaging system. The tracking information server provides tracking information and related information to a subscriber. In one embodiment, the tracker tag is in communication with an Iridium satellite constellation (28) and tracking information is displayed to the subscriber when the asset is substantially anywhere in the world. In another embodiment, the monitoring device is in communication with the Iridium satellite constellation and tracking information is displayed to the subscriber when the subscriber is substantially anywhere in the world, preferably via the Internet (36).
Owner:ARGO TECH CORP
Distributed globally accessible information network
InactiveUS7430587B2Facilitate a trend of “de-centralizationCooperate effectivelyData processing applicationsWeb data indexingTelecommunications linkInformation networks
Owner:KOLOGIK LLC
Wireless mine tracking, monitoring, and rescue communications system
InactiveUS20080137589A1Emergency connection handlingParticular environment based servicesRelevant informationCommunications system
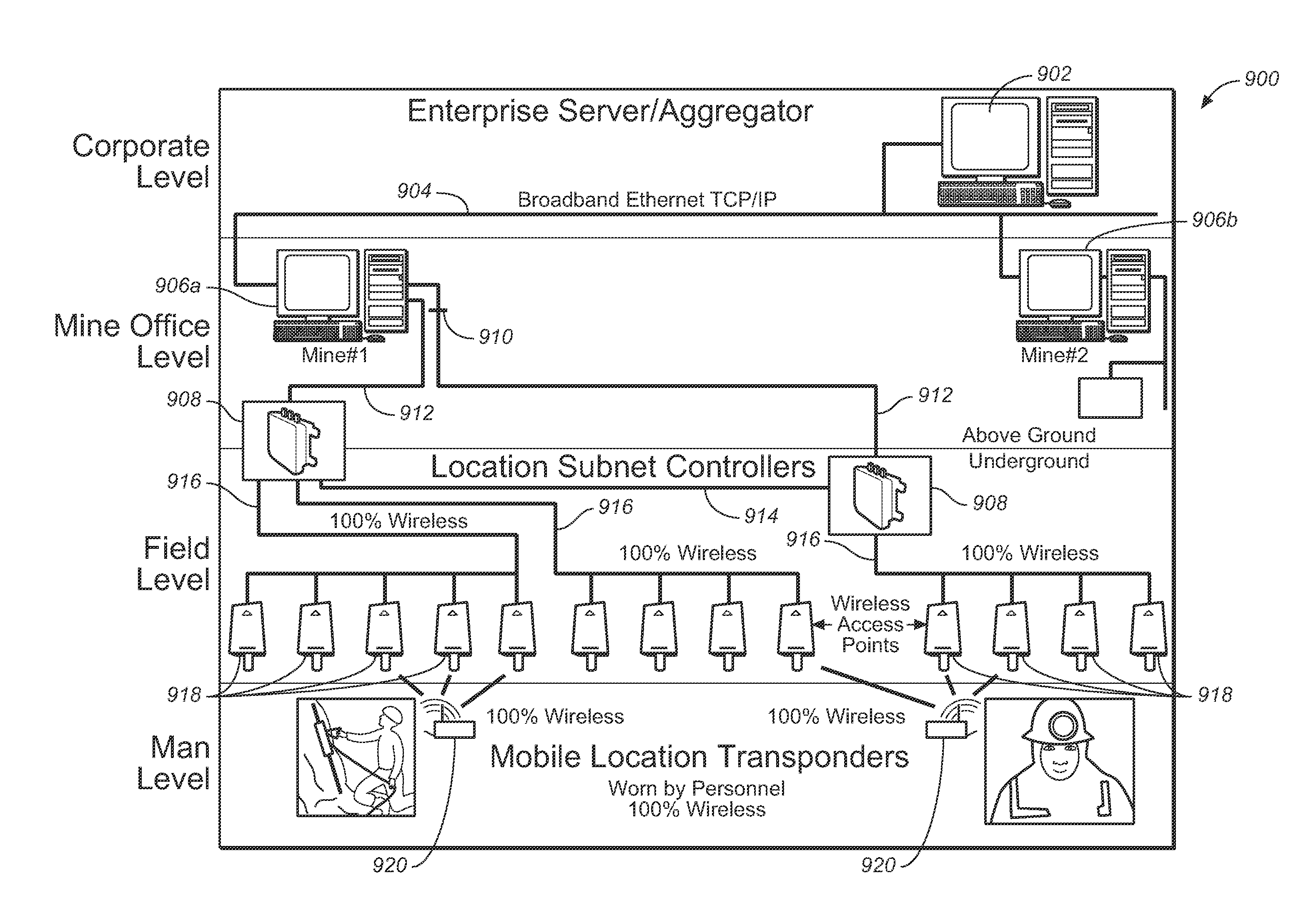
An intrinsically safe accurate location information network for personnel and assets in underground mines, including wireless access points and subnetwork controllers, active wireless locator / messenger tags, network controller(s), and enterprise servers running application control software. The wireless access points are installed in mine entries and crosscuts and track the active wireless locator / messenger tags. The active tags may be worn by mine personnel or installed in mining equipment. The network subsystems form relay networks that wirelessly carry telemetry and control data without the need to penetrate the earth. The subsystems determine the location of persons and assets underground and monitor safety-related information, which can be used for disaster avoidance, early warning of impending disaster, and improved rescue effectiveness. .
Owner:VENTURE CORP LTD
Electric vehicle lease management system on basis of charging piles and lease management method implemented by electric vehicle lease management system
InactiveCN104282088AGuarantee the safety of usePrevent and resolve theftApparatus for meter-controlled dispensingElectric vehicle charging technologyInformation networksComputer module
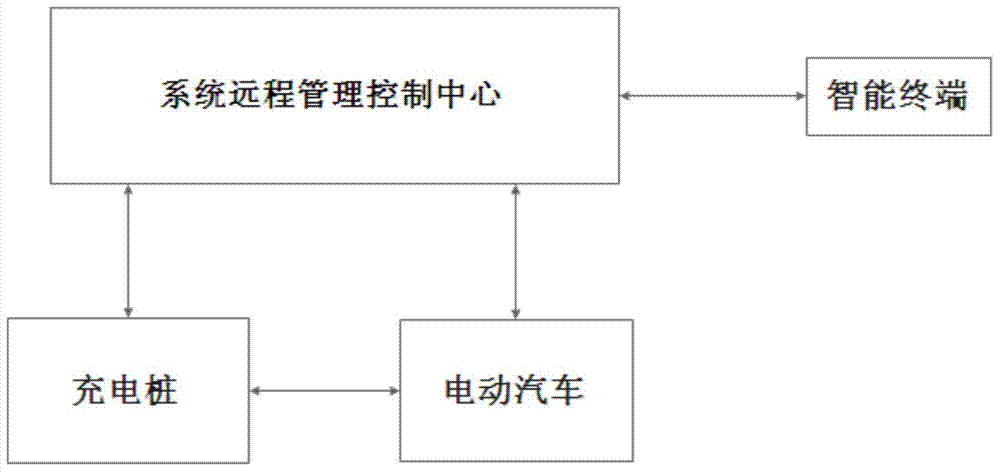
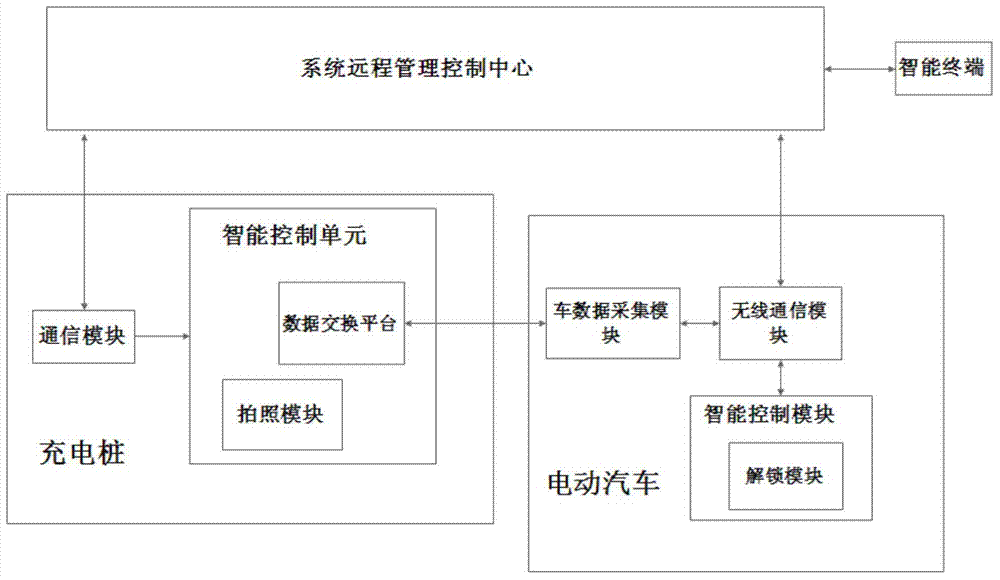
The invention discloses an electric vehicle lease management system on the basis of charging piles. The electric vehicle lease management system comprises a system remote management control center, electric vehicles, the charging piles and intelligent terminals. A vehicle battery data acquisition module, a wireless communication module and an intelligent control module are mounted on each electric vehicle; an intelligent control unit and a communication module are mounted on each charging pile, each intelligent terminal is wirelessly communicated with the system remote management control center, and the wireless communication module of each electric vehicle is wirelessly communicated with the system remote management control center. The electric vehicle lease management system has the advantages that lease systems which are used by vehicle lease users and management staffs can be conveniently and quickly implemented by the aid of modern information network technologies, the users can order lease application and check relevant lease information via the intelligent terminals or directly via computers at any time in any places, and the management staffs can monitor various indexes such as electric vehicle location data and battery data in real time, and prompting effects can be timely realized.
Owner:WUHU HENGTIAN YIKAI SOFTWARE TECH CO LTD
Connector and receptacle containing a physical security feature
InactiveUS7325976B2Imparts physical securityFacilitates discriminationIncorrect coupling preventionCoupling light guidesPhysical securityInformation networks
A network comprising: (a) a plurality of different receptacles for facilitating an optical connection to different information networks requiring different access authorization, each different receptacle coupled to one and only one different information network, each receptacle having an inner surface with a first geometry, the first geometry comprising at least a slot, a certain number of receptacles having different first geometries in which the slots are in different positions; and (b) a plurality of different plugs for coupling with the different receptacles, each plug having a second geometry, the second geometry comprising at least a key in a certain position, the certain number of plugs having different second geometries in which the keys are in different positions, each different first geometry corresponding to one and only one second geometry such that the plugs and receptacles of corresponding first and second geometries are mating pairs.
Owner:COMMSCOPE TECH LLC
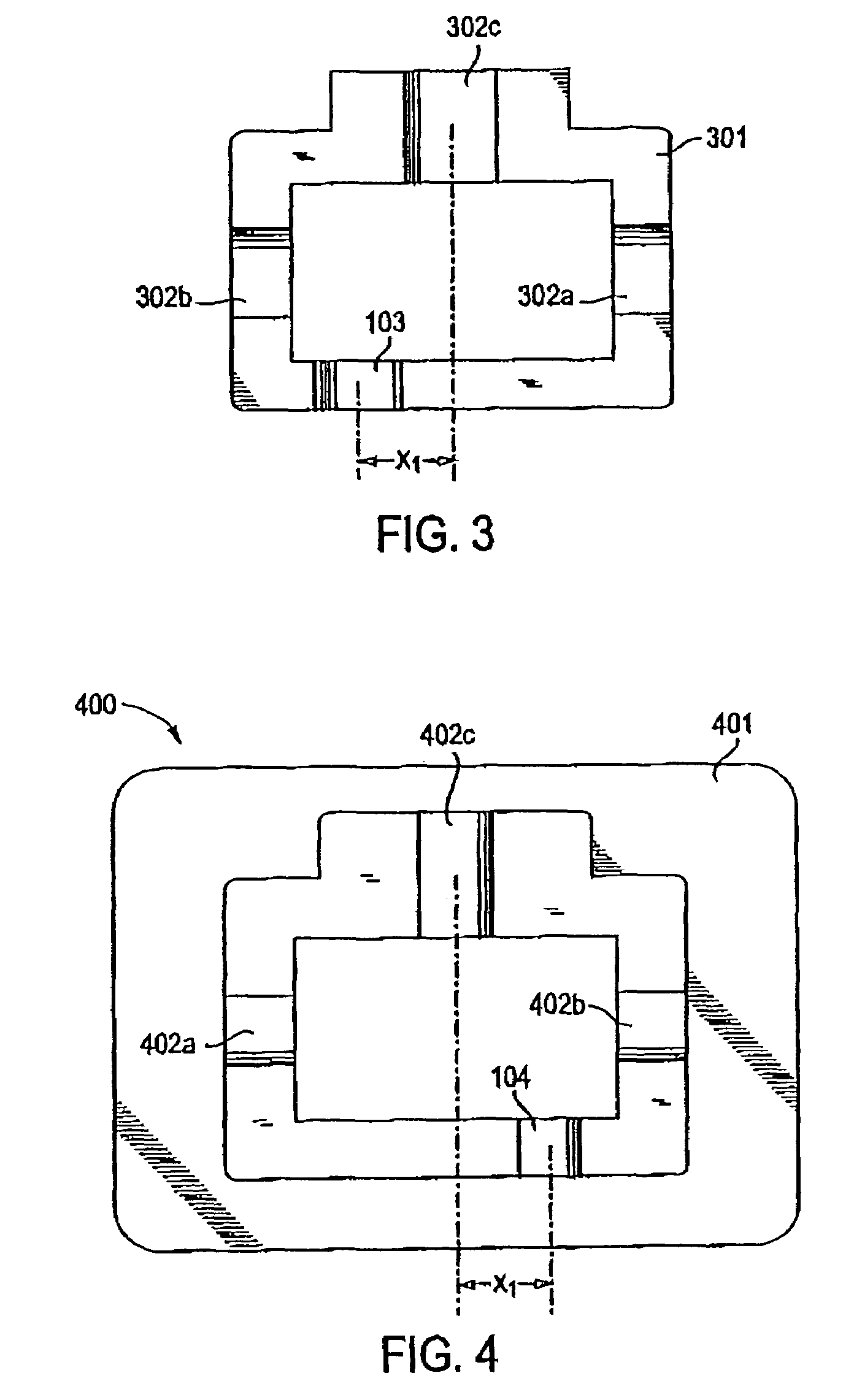
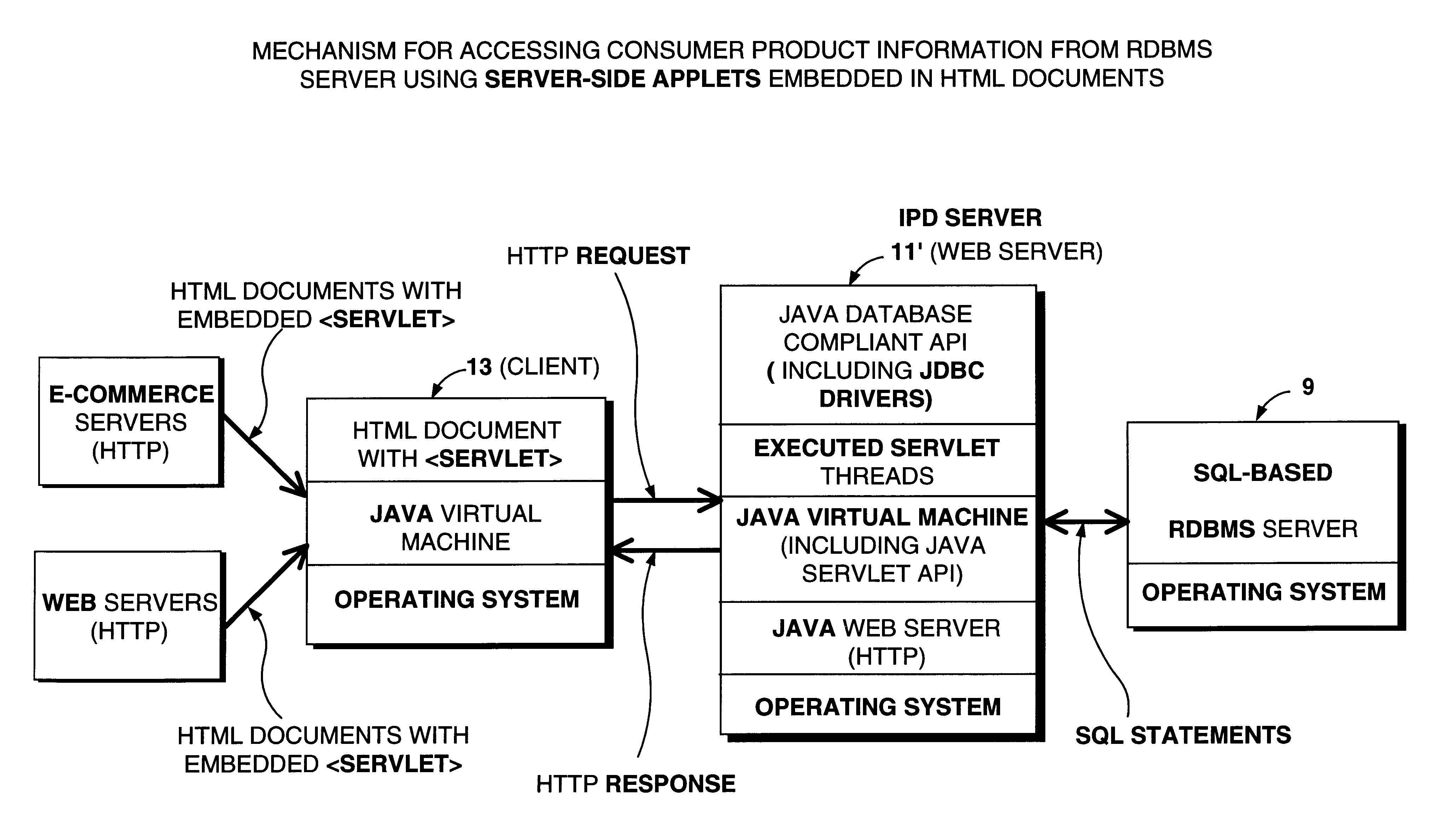
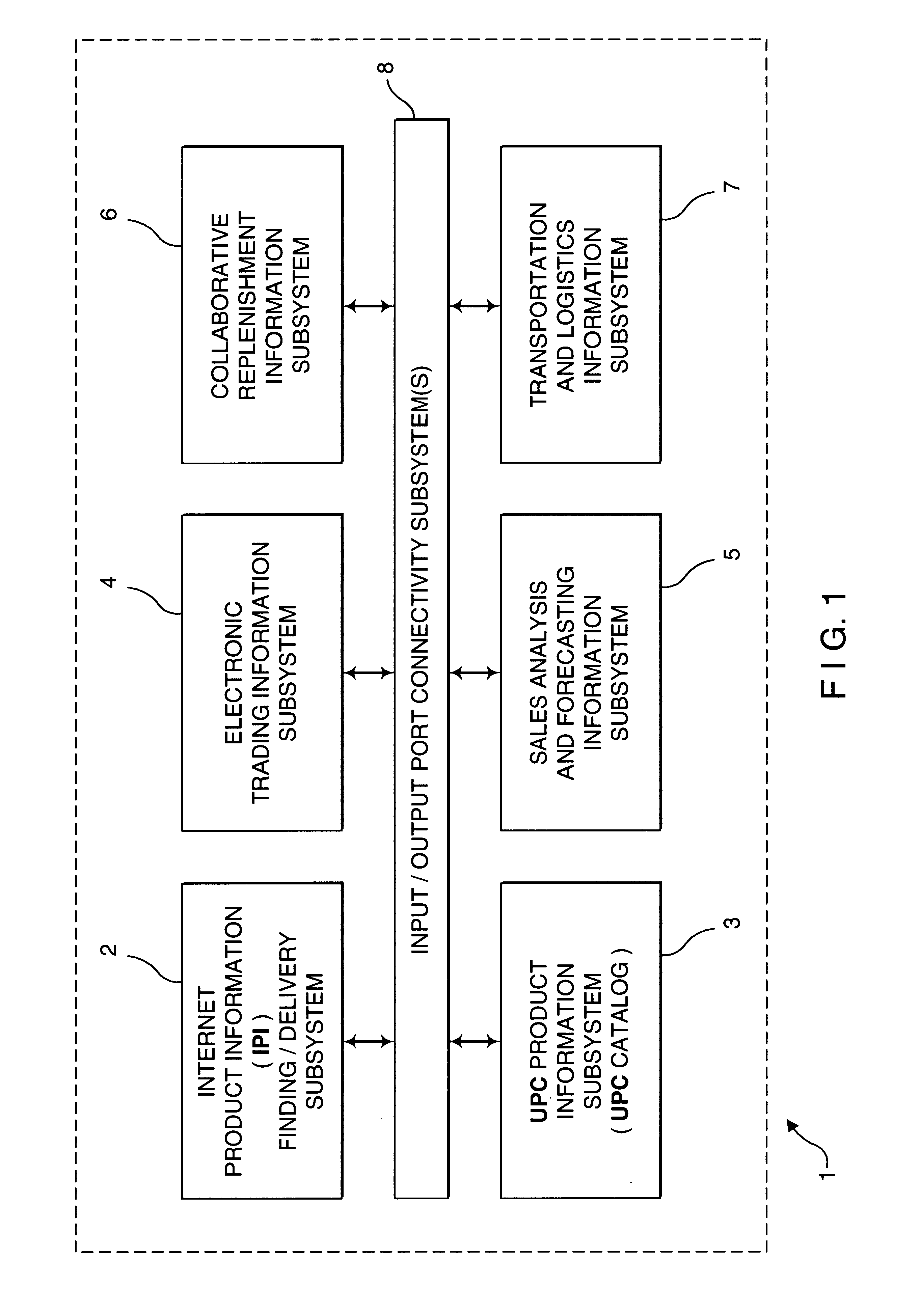
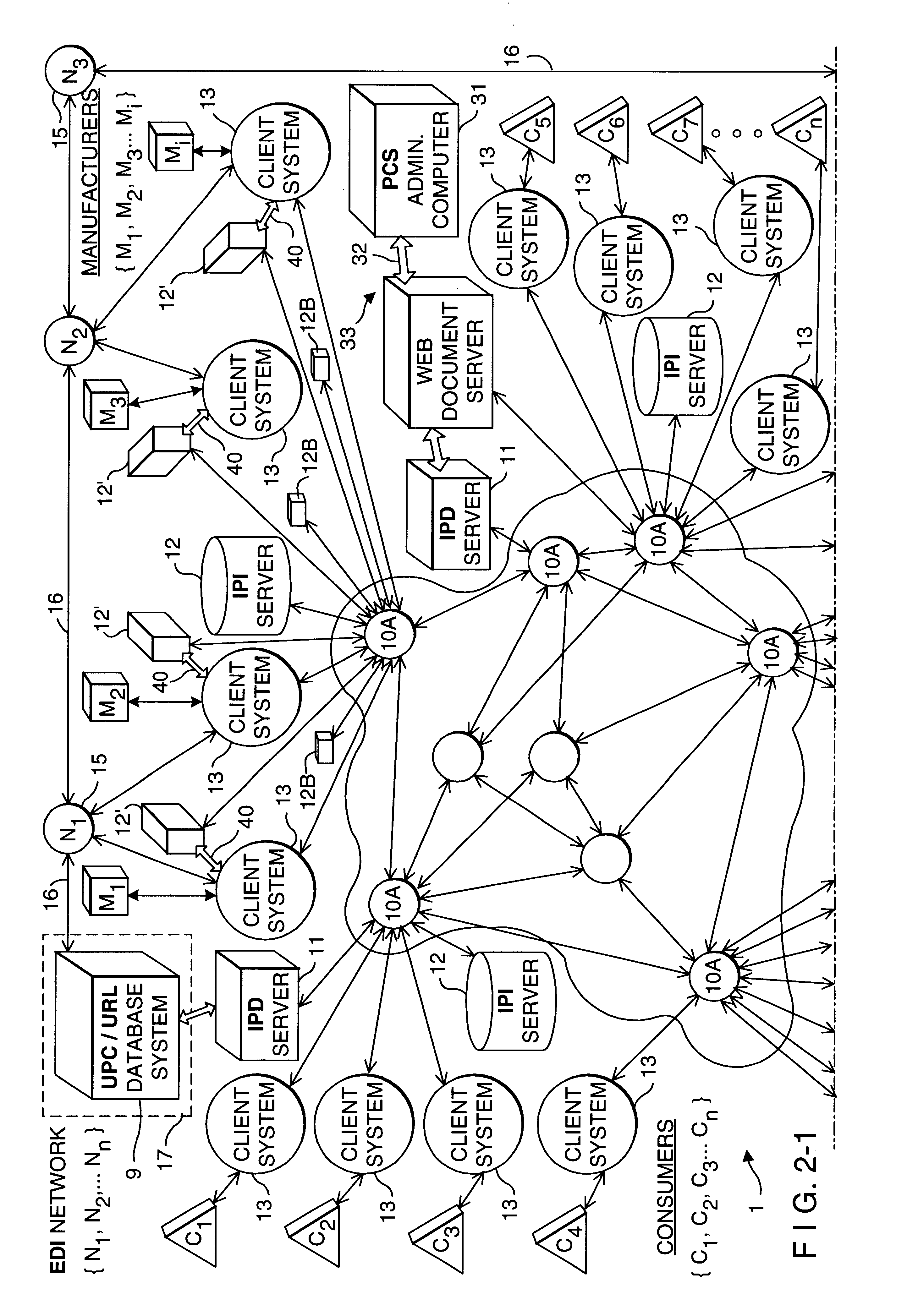
Consumer product information request (CPIR) enabling servlets and web-based consumer product information catalogs employing the same
InactiveUS6961712B1High acceptanceEasy to disassembleDigital data information retrievalAdvertisementsInformation resourceInformation networks
A consumer product information requesting (CPIR) enabling Servlet for execution on the server-side of an information network such as the Internet. The CPIR-enabling Servlet comprises a Universal Product Number (UPN) a uniquely associated with a particular consumer product on which an information search is to be carried out within a database management subsystem. One or more classes are loaded on a an Internet-enabled information server. When the consumer selects a CPIR-enabling Servlet tag embedded within the WWW and corresponding CPIR-enabling Servlet, a UPN-directed-search is automatically carried out within the database management subsystem, the a graphical user interface (GUI) is displayed within the Internet-enabled browser program used by the consumer, and the results from the UPN-directed search are displayed within the GUI in the form of a menu of categorized URLs pointing to consumer product related information resources published on the WWW, without disturbing the consumer's point of presence thereon. The CPIR-enabling Servlets can be used to build various types of consumer product information systems for operation on the WWW.
Owner:PERKOWSKI THOMAS J
Integrated web-based workspace with curated tree-structure database schema
InactiveUS20120096389A1Streamlining actionStreamlining flowWebsite content managementSpecial data processing applicationsDocumentation procedureDocument preparation
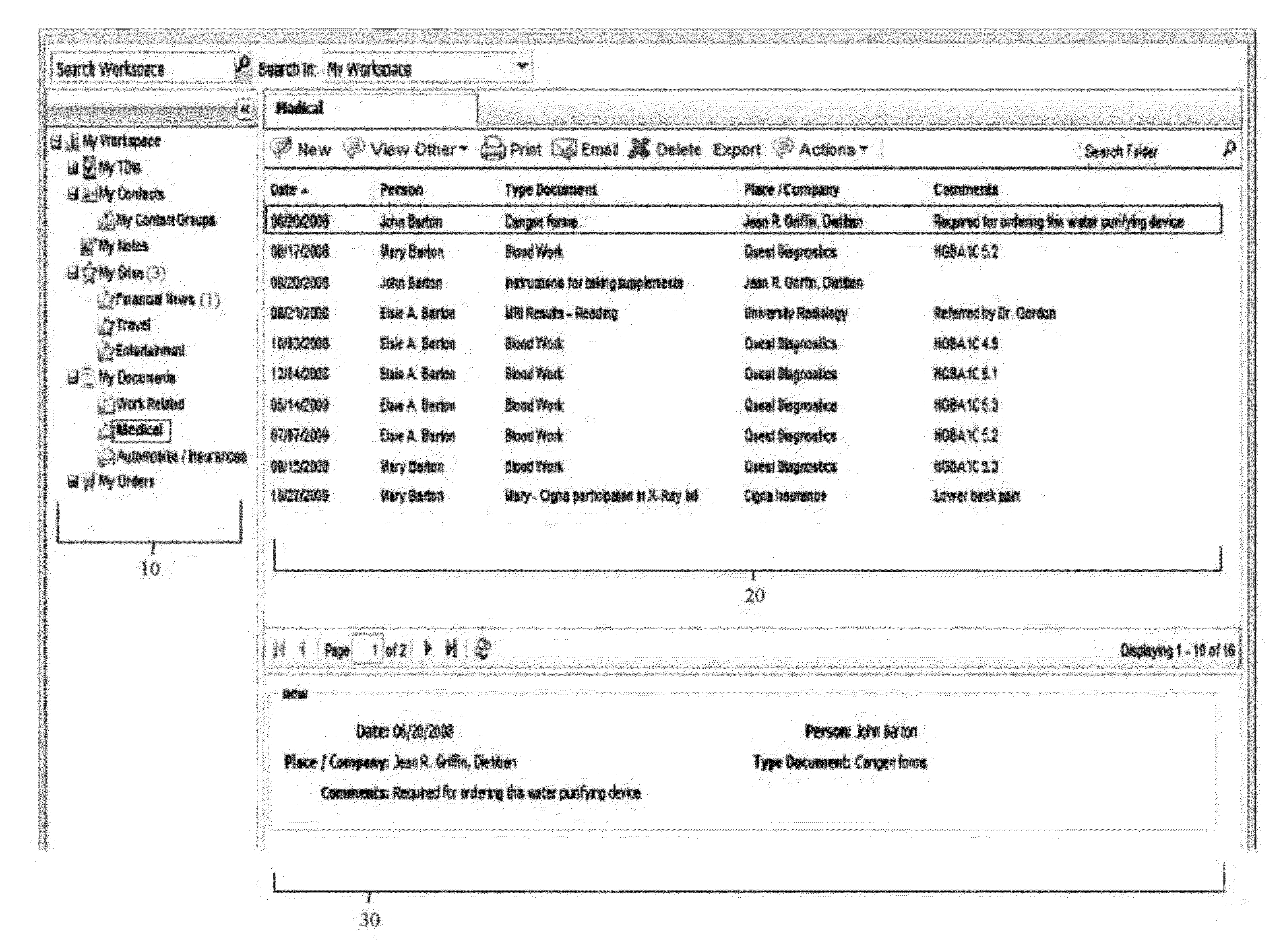
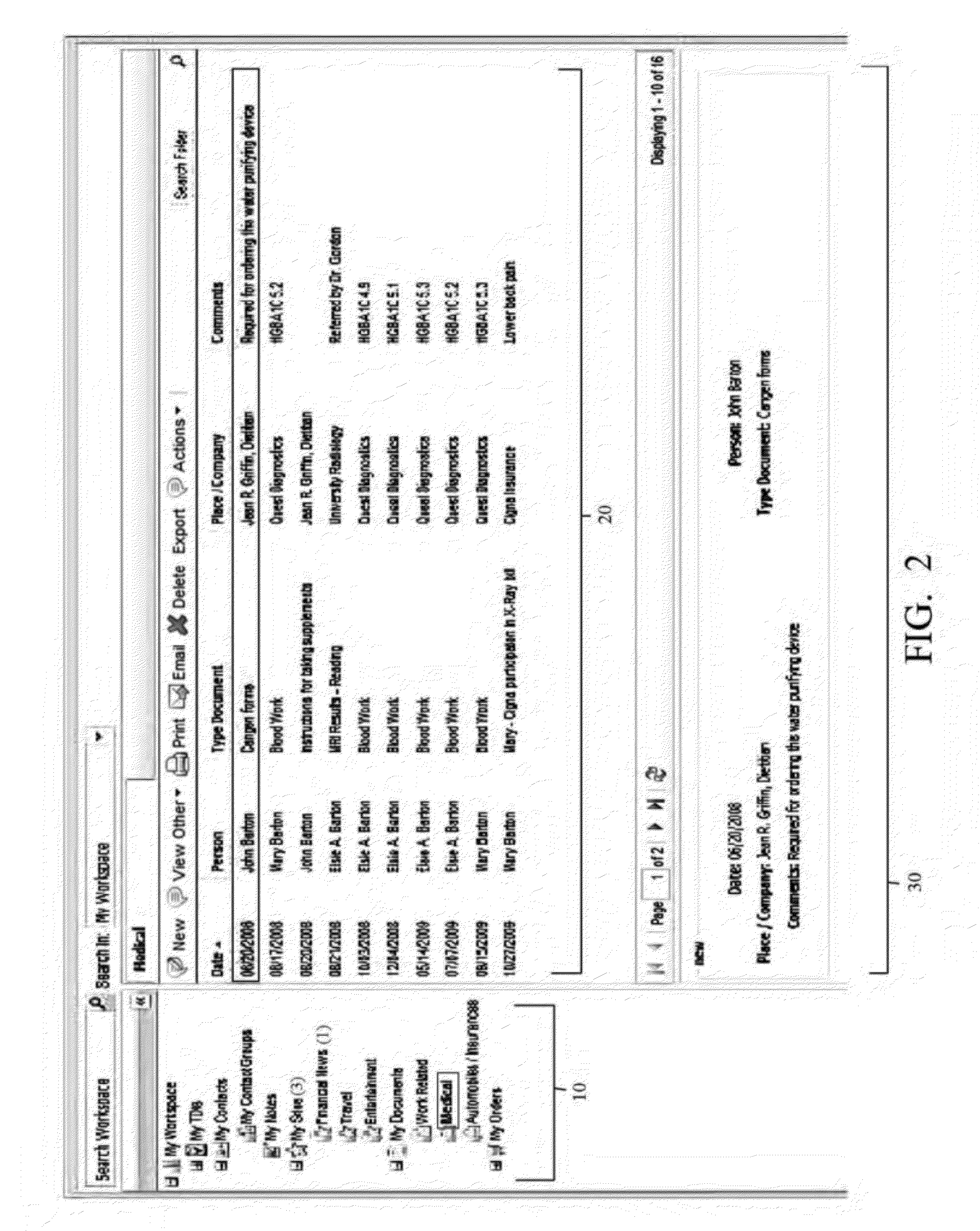
A virtual web-based computing platform combining a particular network database hierarchy, graphical user interface, and integrated suite of computational tools accessible on demand, by which users gain access to an integrated Virtual Workspace for organizing emails, contacts, bookmarks, tasks, documents, notes, and all other relevant information. The network database hierarchy employs unique data structure and methods, allowing the user to centrally store and manage all data, regardless of type, as well as activities (actions taken and documented by the user). Nevertheless, the interface to said database offers a familiar folder / sub-folder “look and feel” using a tree data hierarchy, which gives a common, centralized and unified approach for storing, managing, displaying, and various types of data, regardless of object- and data-types.
Owner:IQTELL COM
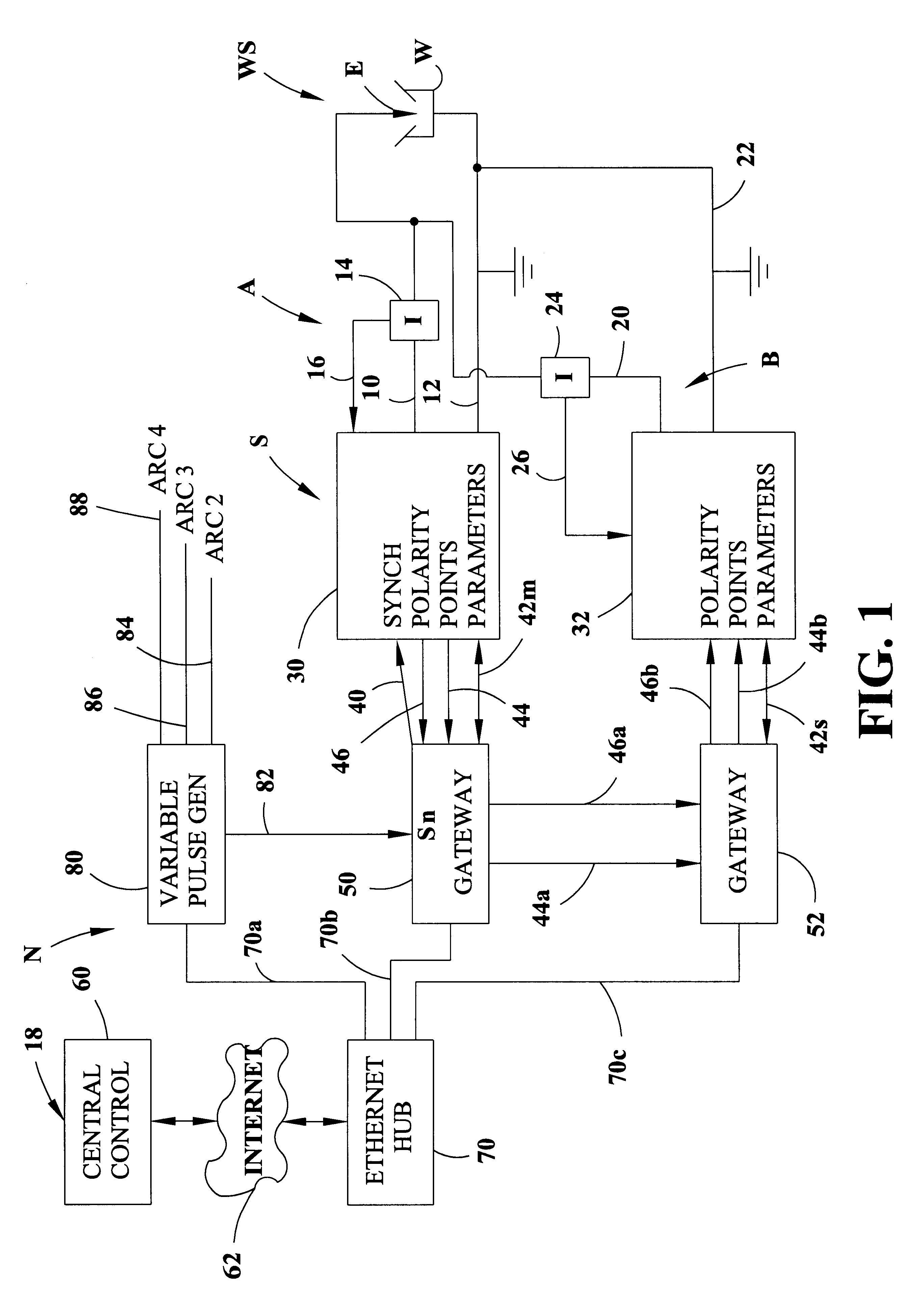
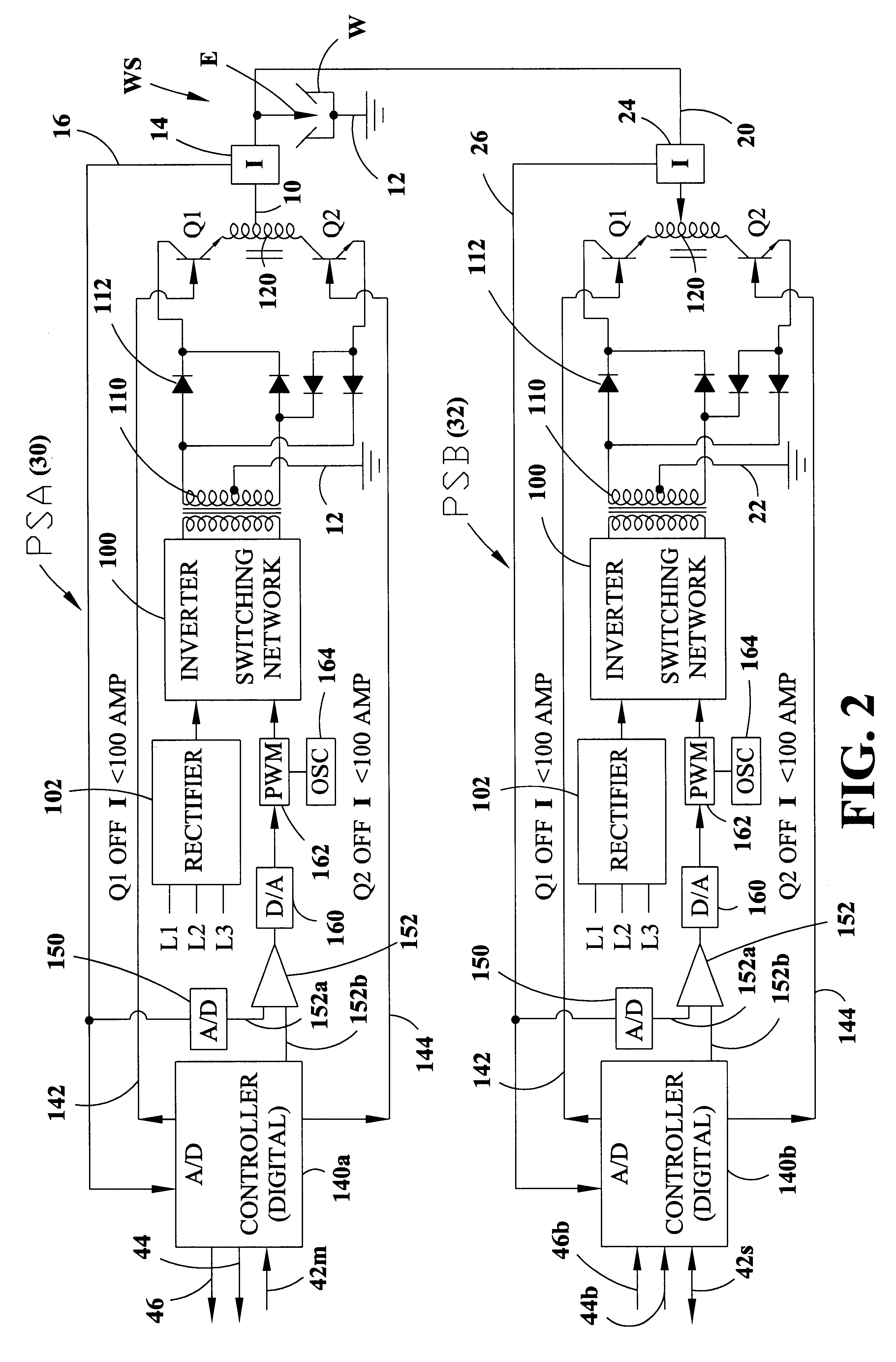
Electric arc welding system
InactiveUS6472634B1Prevent and reduce electrode interferenceLarge capacityElectric discharge heatingArc welding apparatusPower flowDigital interface
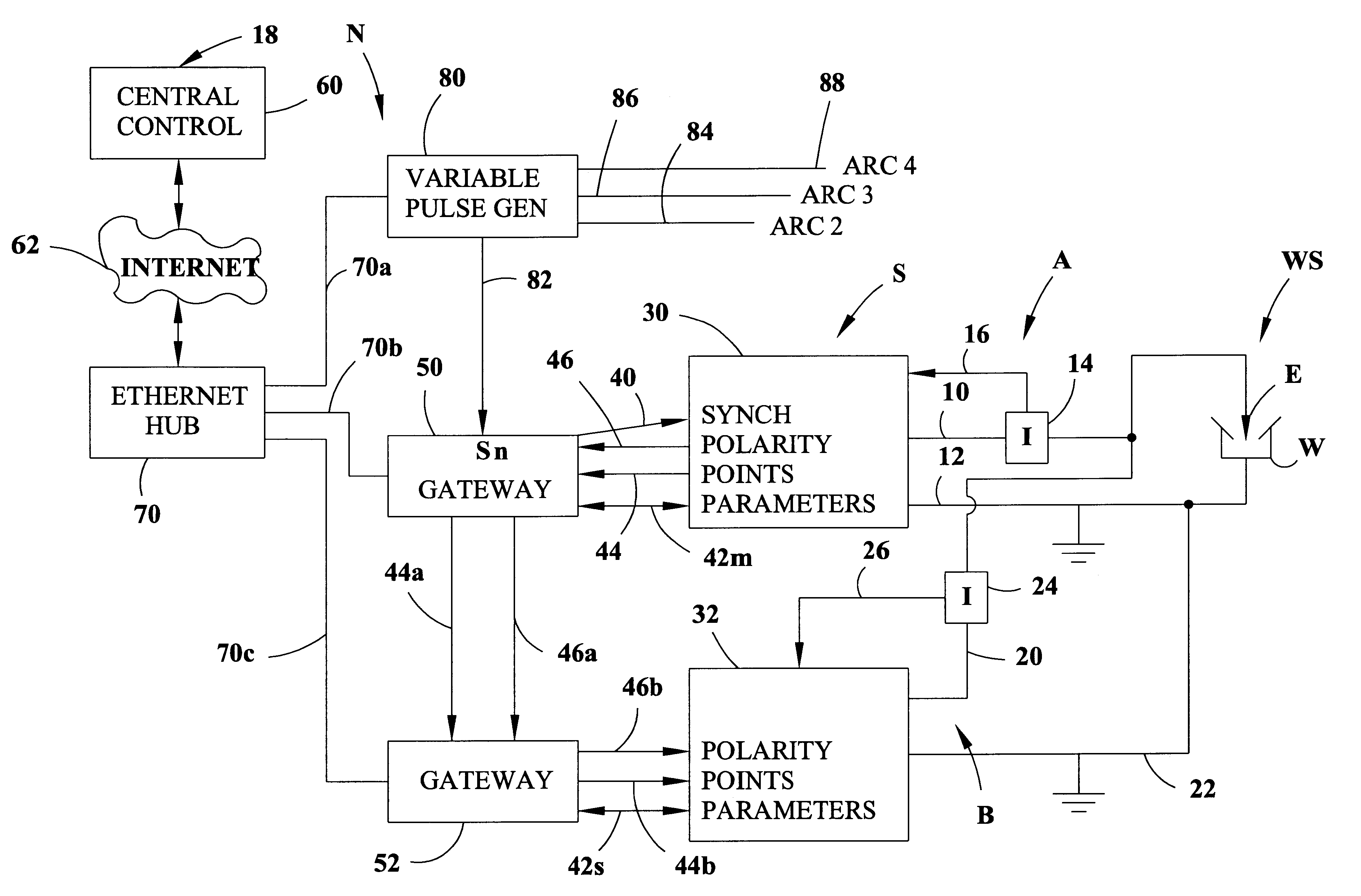
An electric arc welding system for creating an AC welding arc between an electrode and a workpiece wherein the system comprises a first controller for a first power supply to cause the first power supply to create an AC current between the electrode and workpiece by generating a switch signal or command with polarity reversing switching points in the first controller, with the first controller operated at first welding parameters in response to first power supply specific parameter signals to the first controller. The system has at least one slave controller for operating a slave power supply to create an AC current between the electrode and workpiece by reversing polarity of the AC current at switching points where the slave controller is operated at second welding parameters in response to second power supply specific parameter signals to the slave controller. An information network connected to the first controller and the slave controller and containing digital first and second power supply specific parameter signals for the first controller and the slave controller and a digital interface connects the first controller with the slave controller to control the switching points of said second power supply by the switch signal or command from the first controller.
Owner:LINCOLN GLOBAL INC
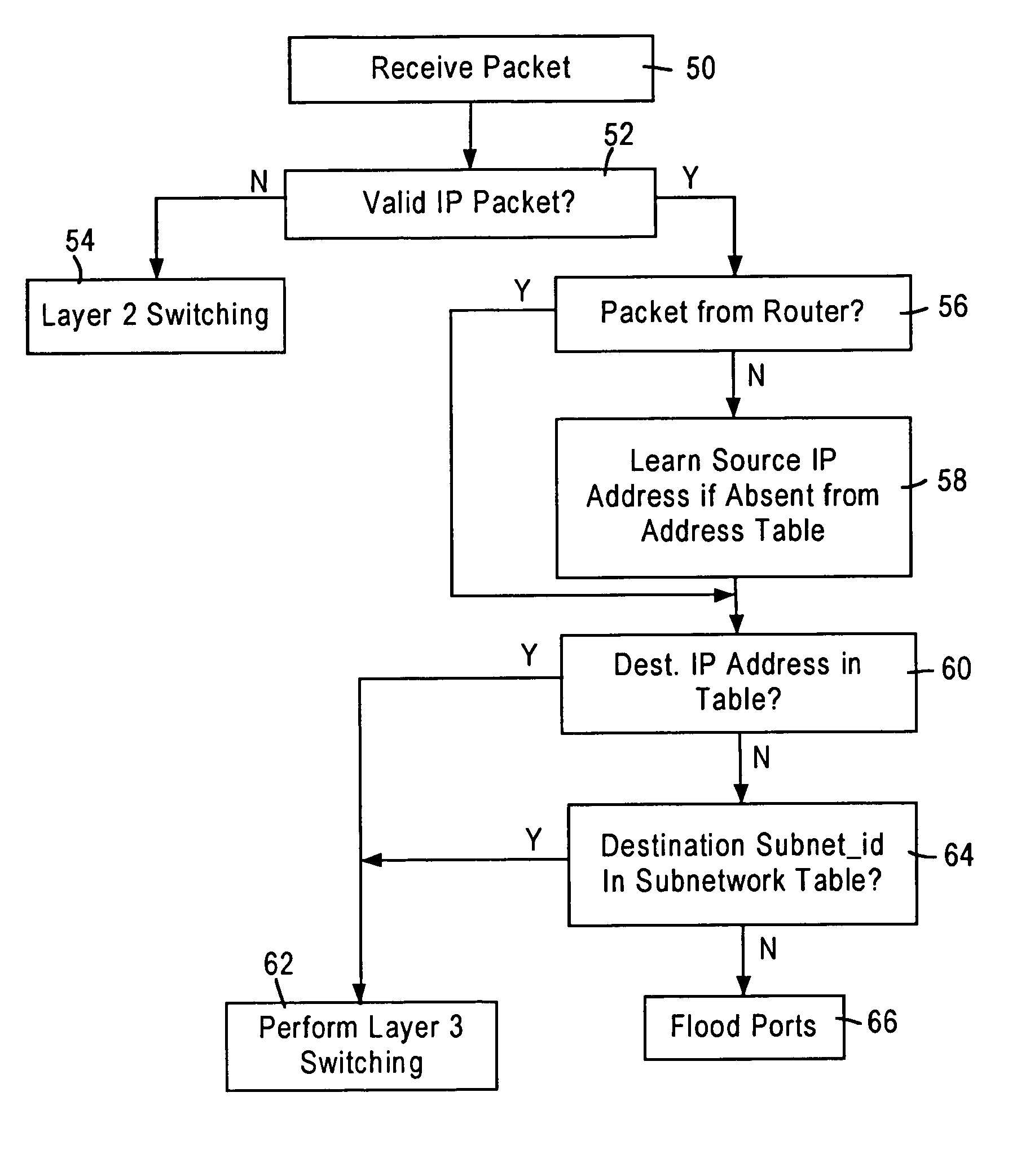
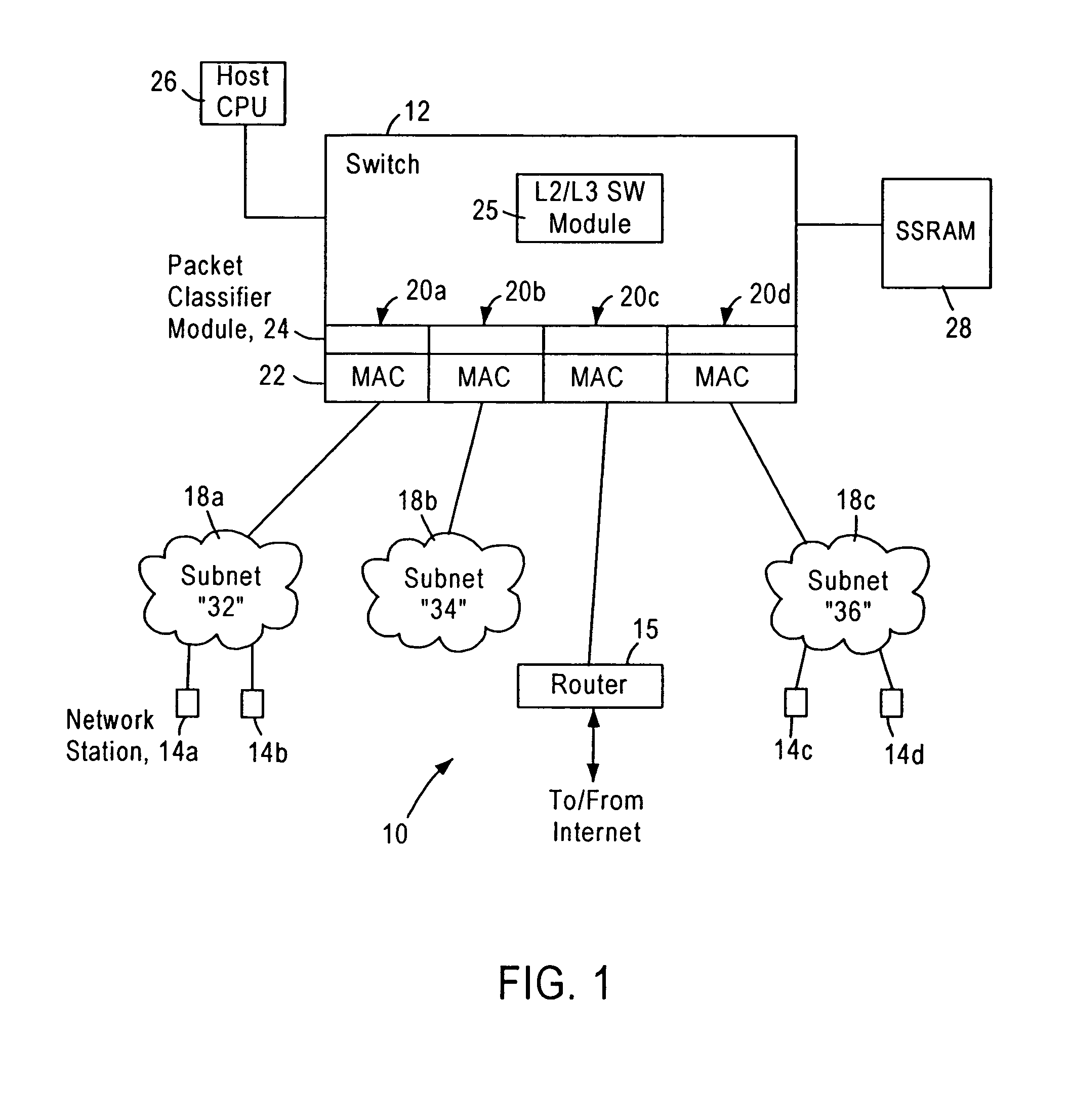
Layer 3 switching logic architecture in an integrated network switch
InactiveUS7079537B1Improve performanceTime-division multiplexData switching by path configurationNetwork switchEthernet
A network switch, configured for performing layer 2 and layer 3 switching in an Ethernet (IEEE 802.3) network without blocking of incoming data packets, includes a switching module for performing layer 2 and layer 3 (specifically Internet Protocol) switching operations, and a plurality of network switch ports, each configured for connecting the network switch to a corresponding subnetwork. The switching module includes address tables for storing address information (e.g., layer 2 and layer 3 address and switching information). The network switching module is configured for performing prescribed layer 3 switching that enables transfer of data packets between subnetworks, bypassing a router that normally would need to manage Internet protocol switching between subnetworks of the network. Hence, the network switch performs Internet Protocol switching for intranetwork (i.e., inter-subnetwork) traffic, improving efficiency of the router by enabling the router resources to support more subnetworks.
Owner:ADVANCED MICRO DEVICES INC
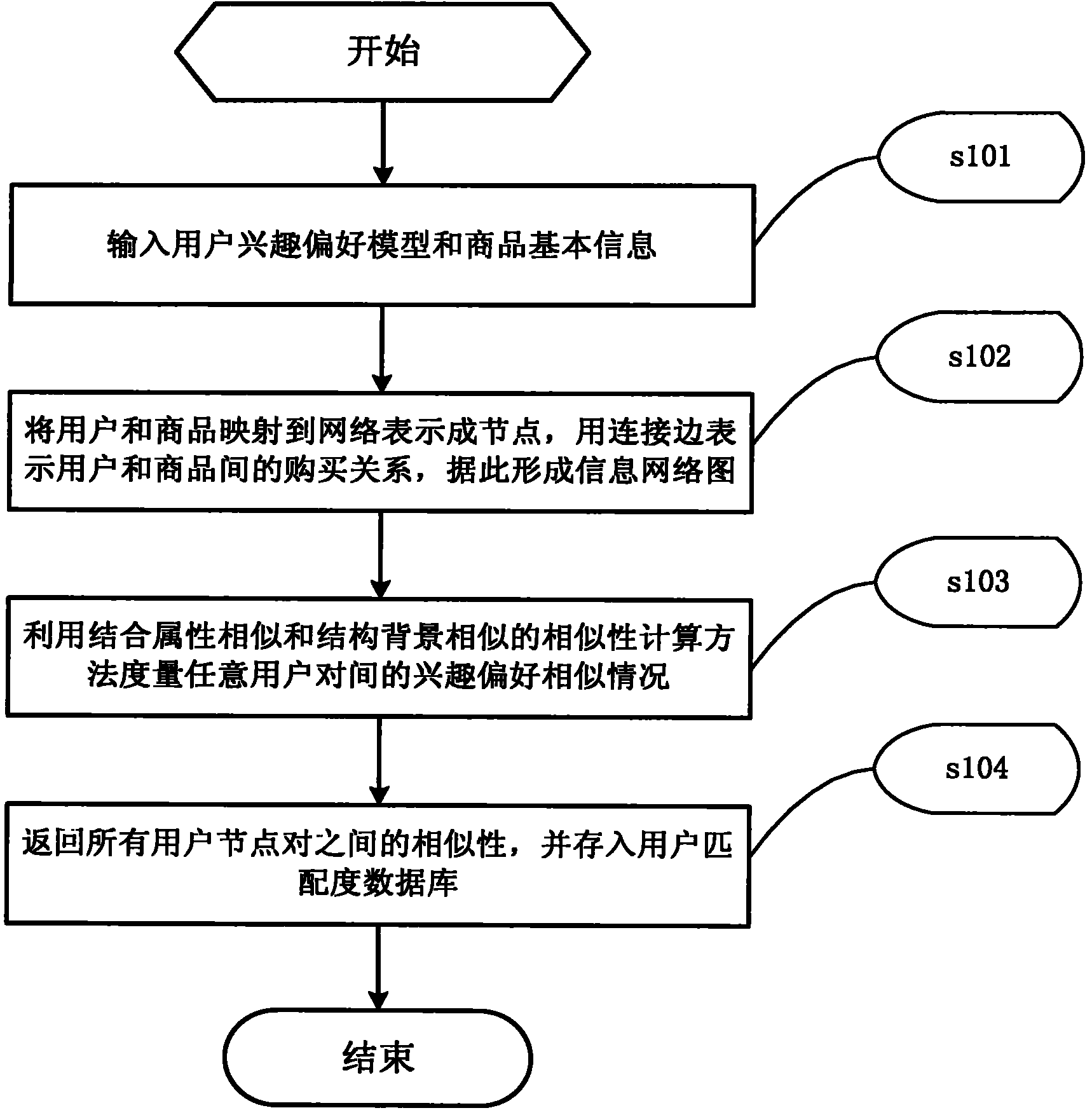
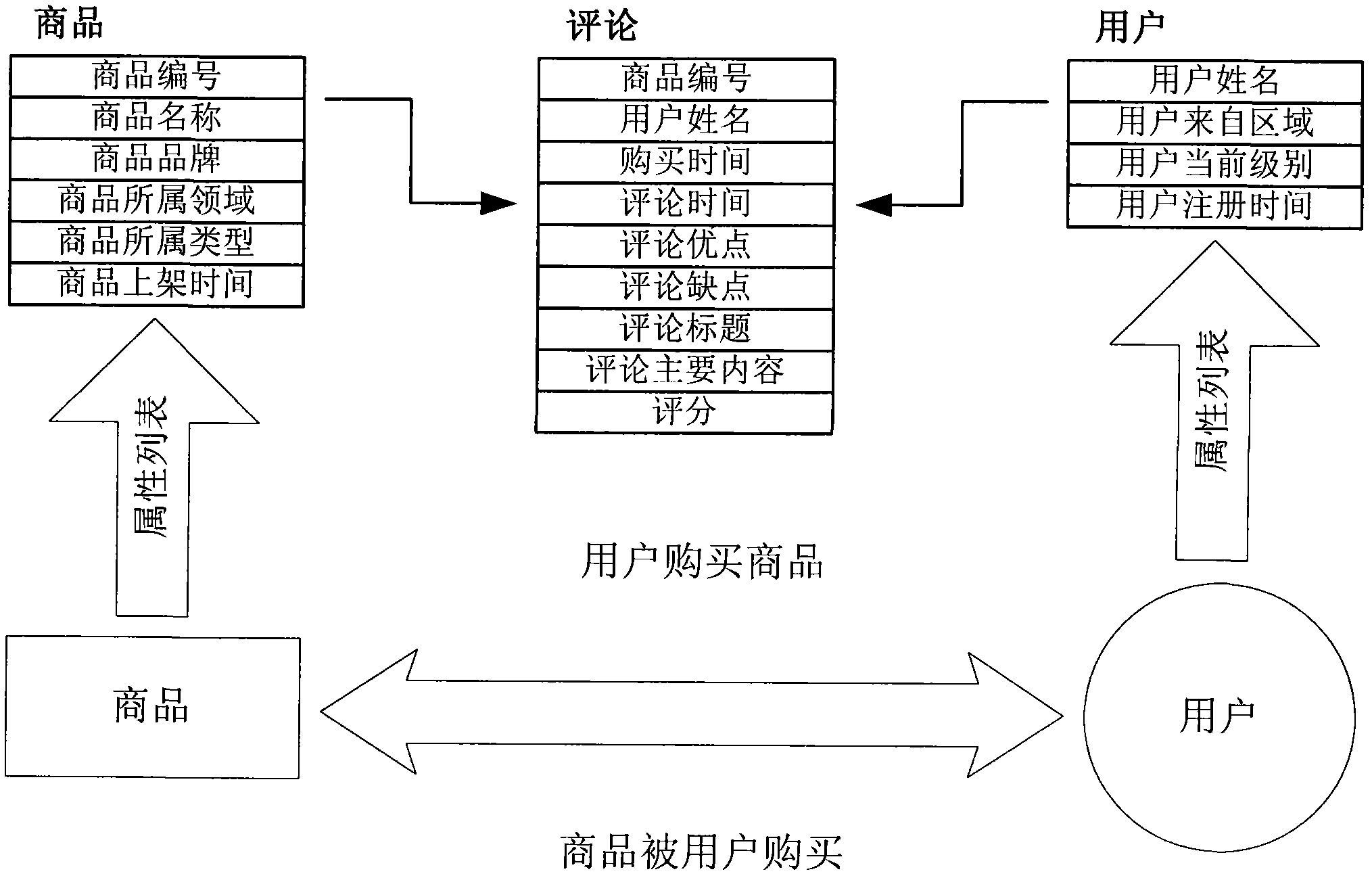
Personalized commodity recommending method and system which integrate attributes and structural similarity
InactiveCN102254028AQuick referral requests in real timeRespond to referral requestsCommerceSpecial data processing applicationsPersonalizationNear neighbor
The invention discloses a personalized commodity recommending method which integrates attributes and structural similarity. In the method, users and commodities are used as nodes with characteristic information to be mapped to a network by integrating the attribute information and structural similarity information, and an information network chart is established according to the purchasing relation between customers and the commodities; and interests and preference among user node pairs are measured by the integrated attributes and structural similarity in the information network chart, and the nearest neighbor is selected by the interests and the preference to improve the accuracy of recommending. On the basis of the recommending method, the invention also discloses a personalized commodity recommending method which integrates the measurement of the attributes and the structural similarity. In the system, the interests and the preference of the users are measured accurately by a computing method of integrating the similarity of the attributes and the similarity of node structure backgrounds in the information network chart, and the generation efficiency of the nearest neighbor is improved by utilizing clustering technology. The method and the system can be applied to electronic commerce, and provide personalized commodity recommending for the users.
Owner:QINGDAO TECHNOLOGICAL UNIVERSITY
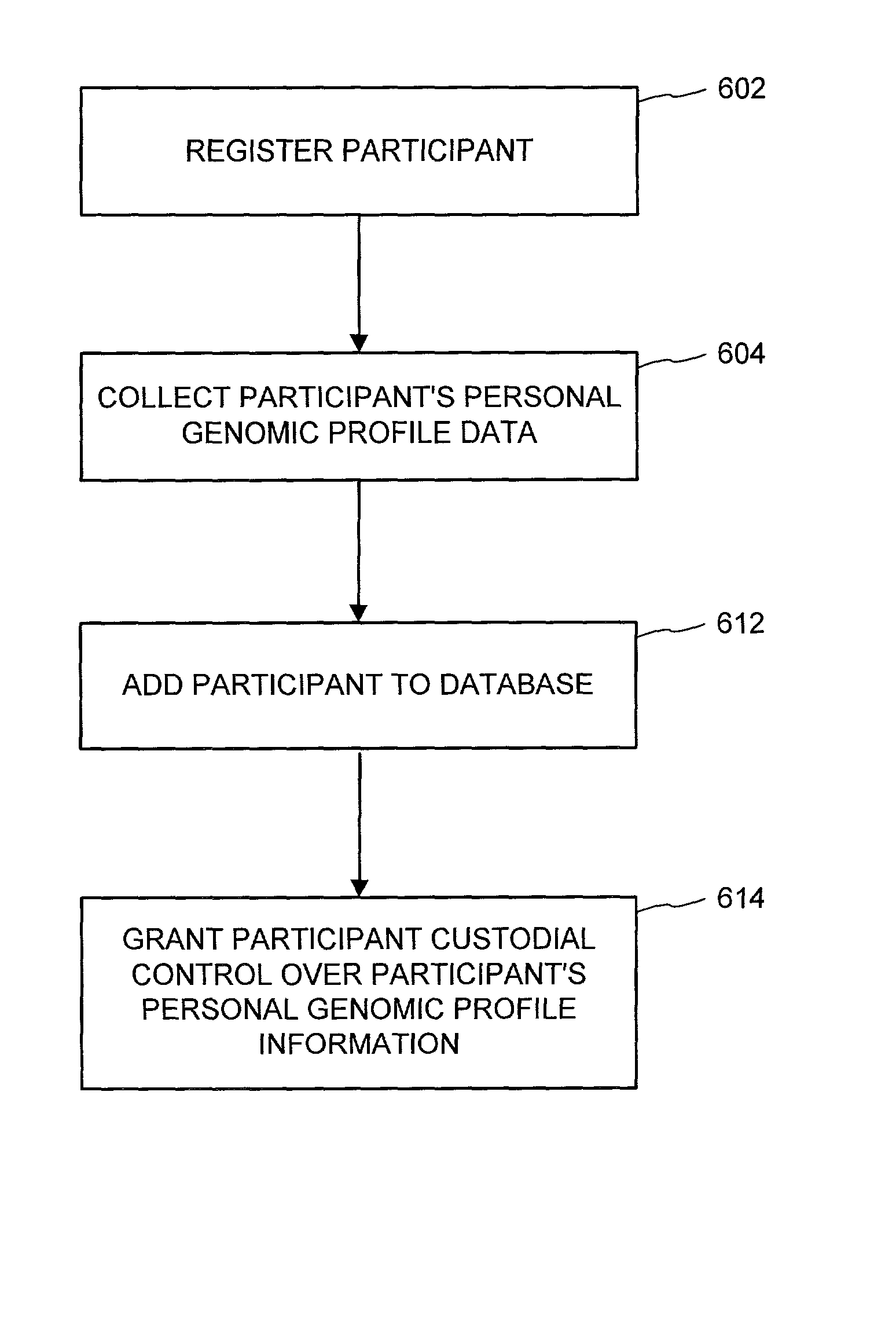
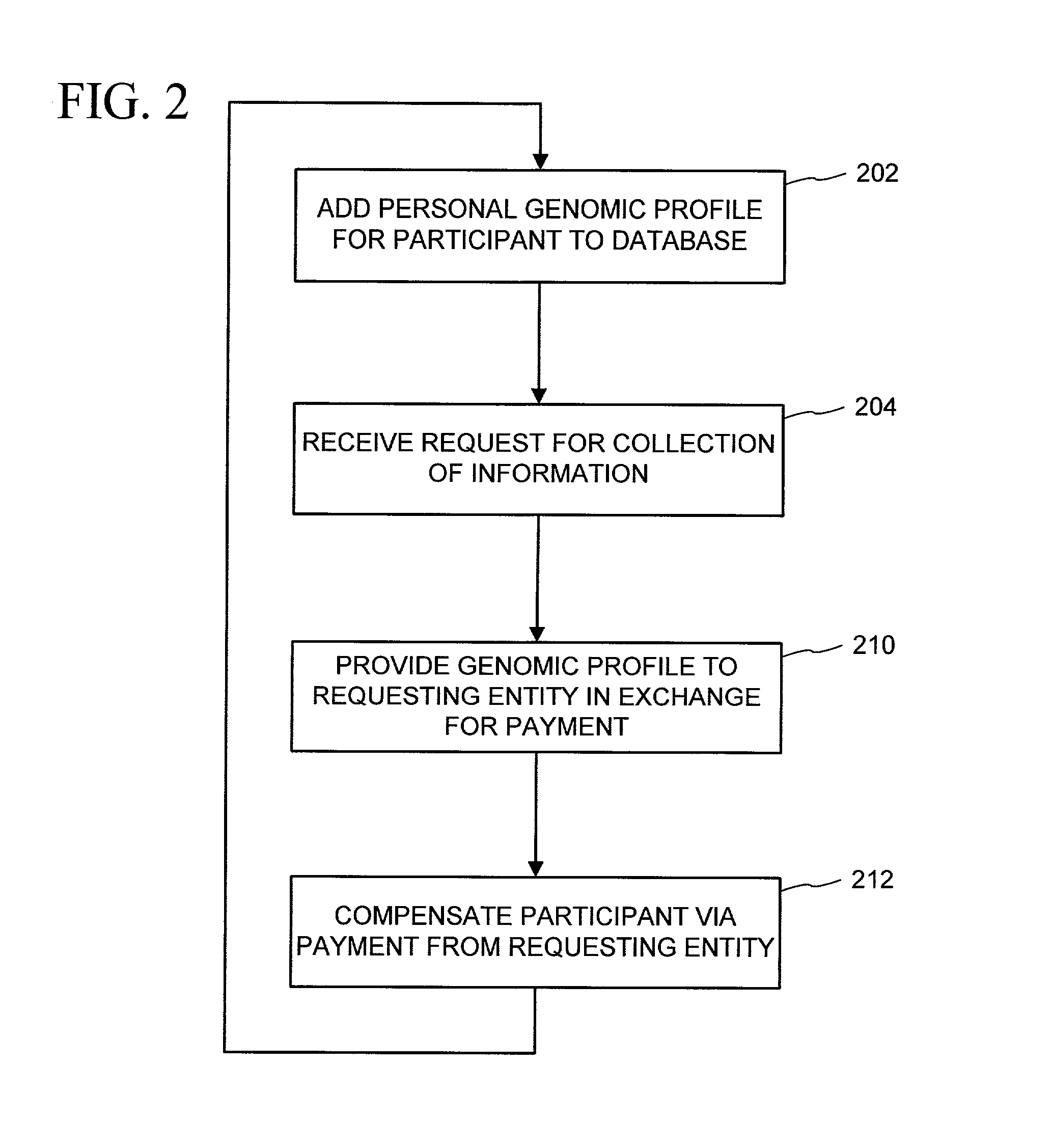
Genomic profile information systems and methods
InactiveUS20020095585A1Increase valueSignificant compensationComputer security arrangementsProteomicsInformation networksAnonymity
A variety of methods and systems related to genomic profile information and related participants are described. Participants can be encouraged to allow access to their genomic profile information in a variety of ways. A peer-to-peer genomic profile information network can be implemented. A collection of genomic profile information for a large number of participants can be built, and anonymity of the participants can be maintained. Participants can maintain custodial control over their genomic profile information. Comparative tools and groups can help participants identify and communicate with other participants having similar information.
Owner:GENOMIC HEALTH INC
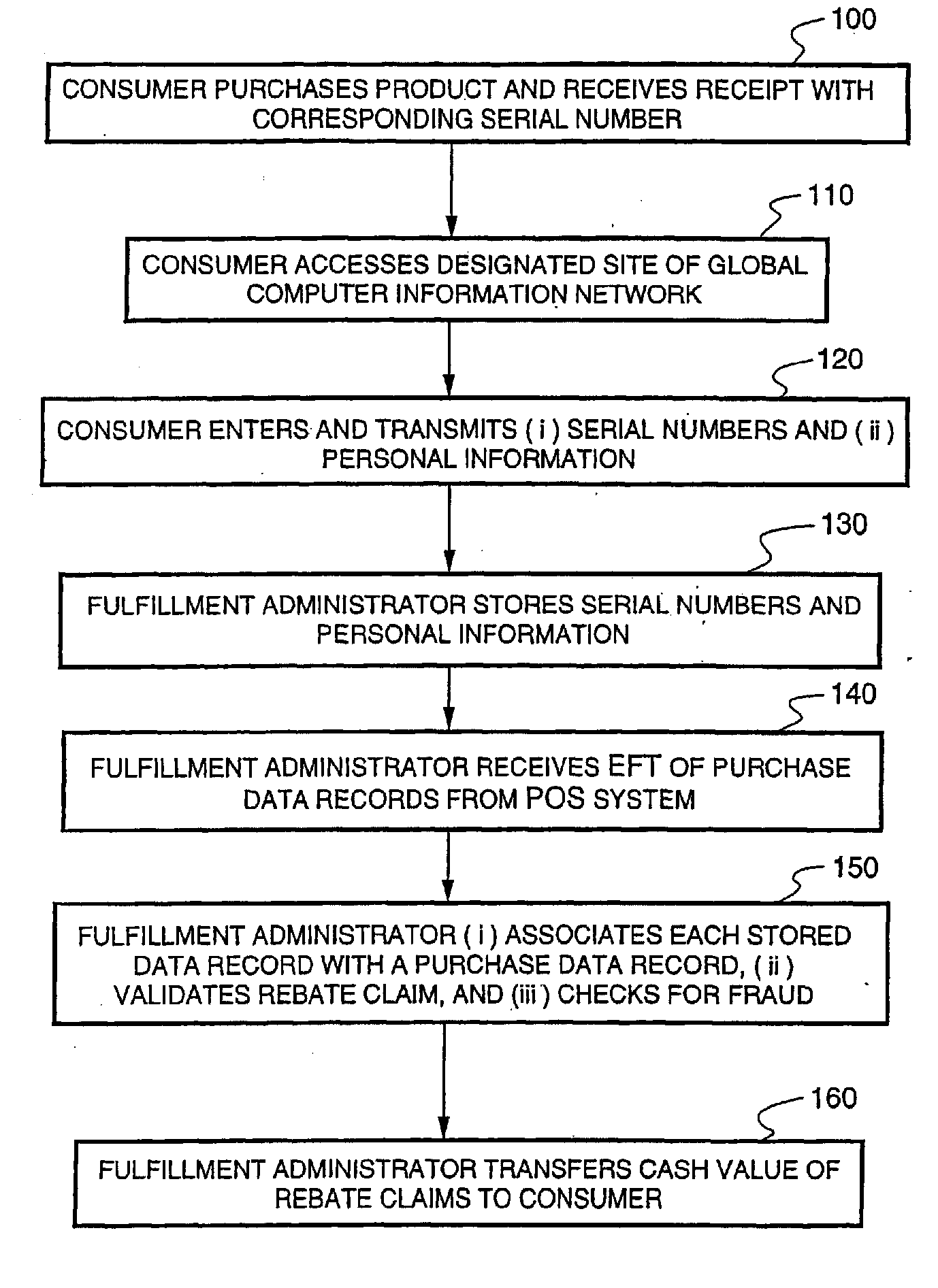
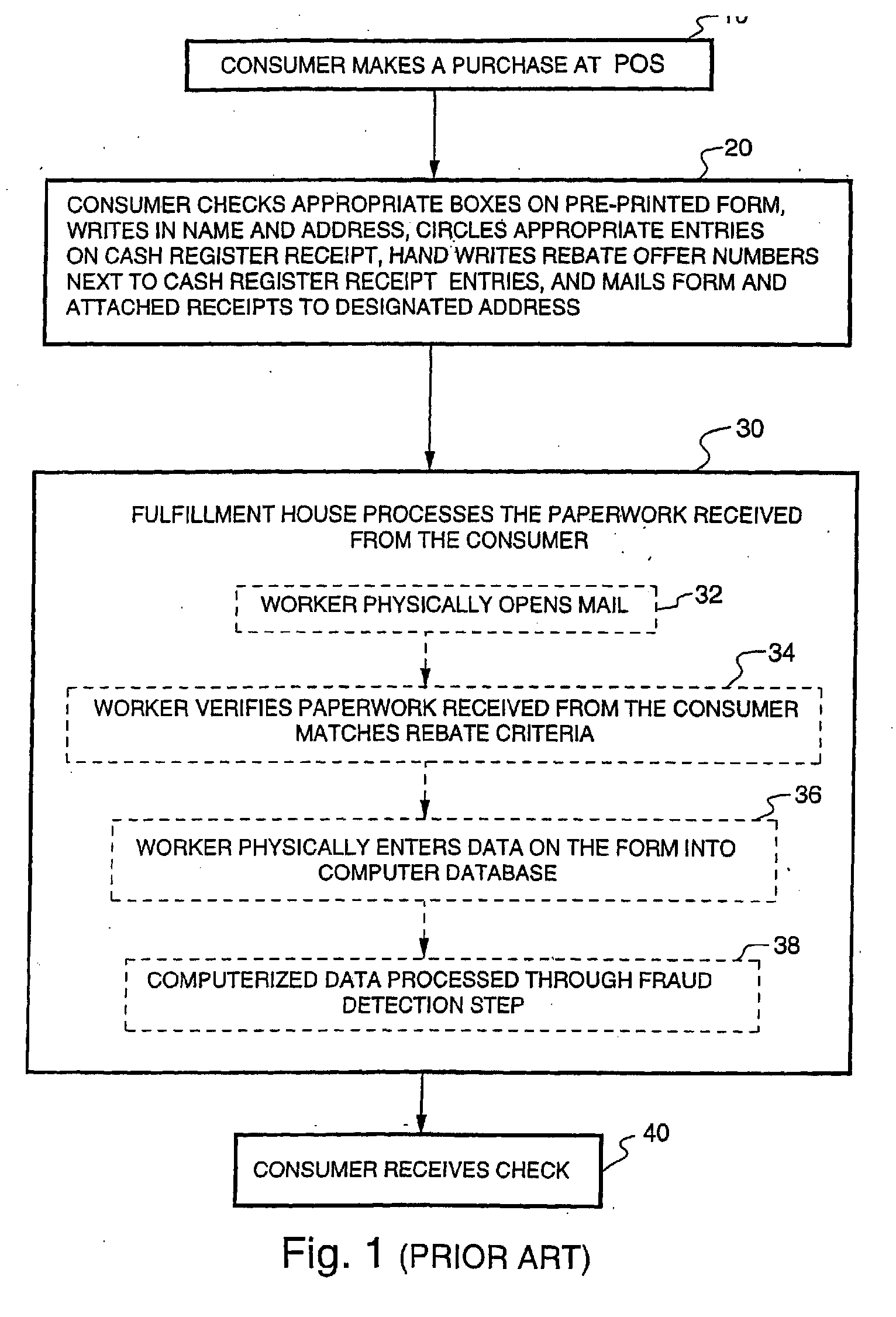
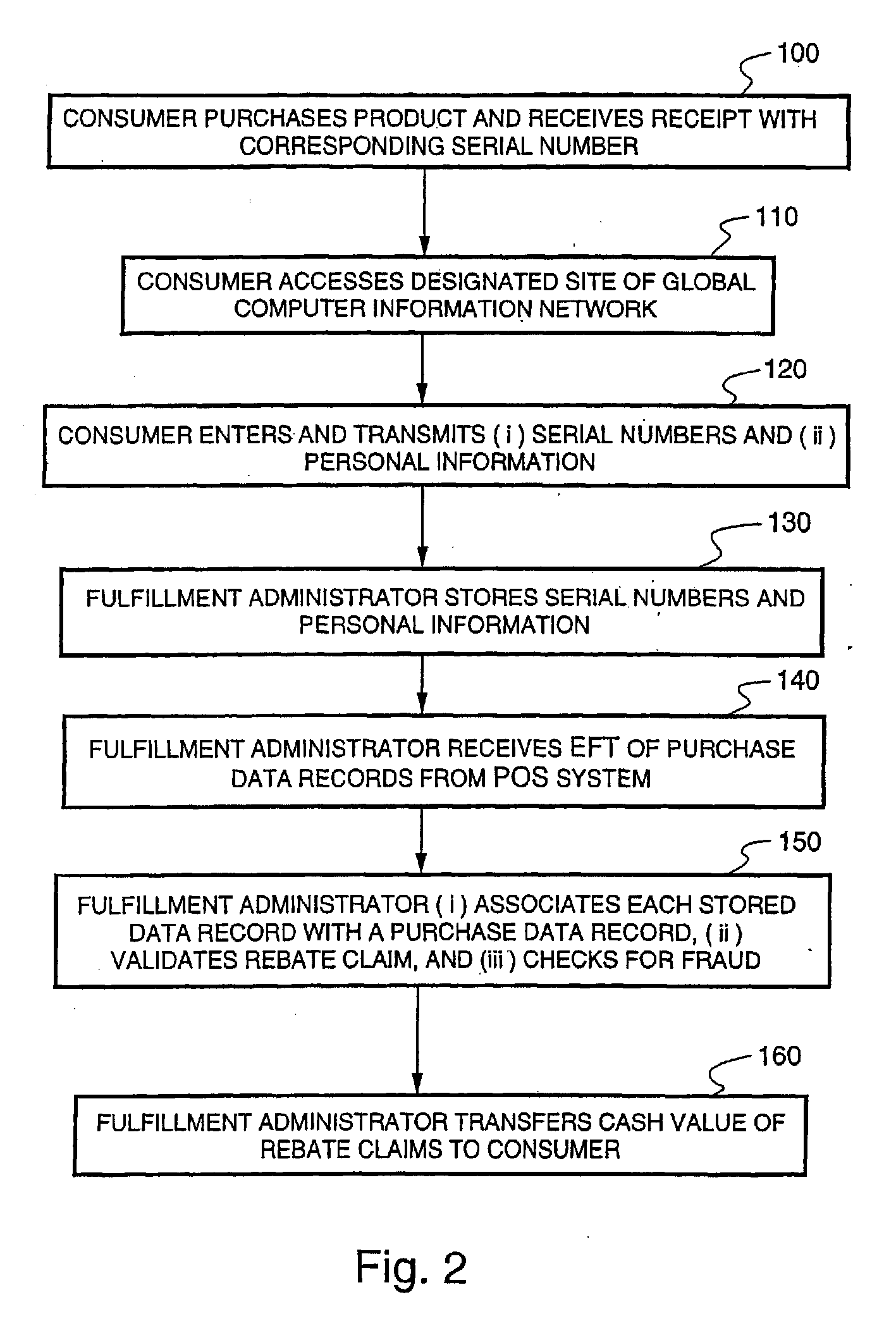
Method and system for redeeming product marketing rebates
Owner:THE OHANA COMPANY
Collection of enhanced caller ID information
ActiveUS20050232247A1Enhanced identification informationTelevision system detailsError preventionComputer networkEmail address
Network entities such as an access device and a gateway analyze messages exchanged during a communication session to identify information items of interest such as, for example, email addresses, universal resource locators, file paths, and attachments. References to and / or the contents of the identified information items may be stored in a database that associates the identified information items with the participants of the communication session. The participants in the communication session may be identified by conventional caller ID information, or by an Internet protocol address, an electronic serial number, or a variety of other identifiers. Information received at the beginning of a later communication session that identifies participant(s) in that communication session may then be used to select from the database, information items from previous communication session, that are associated with the identified participant in the current communication session. Information about the selected information items may be delivered as enhanced caller ID information to parties of the communication session, allowing them to have easy access to the previously exchanged information.
Owner:AVAGO TECH INT SALES PTE LTD
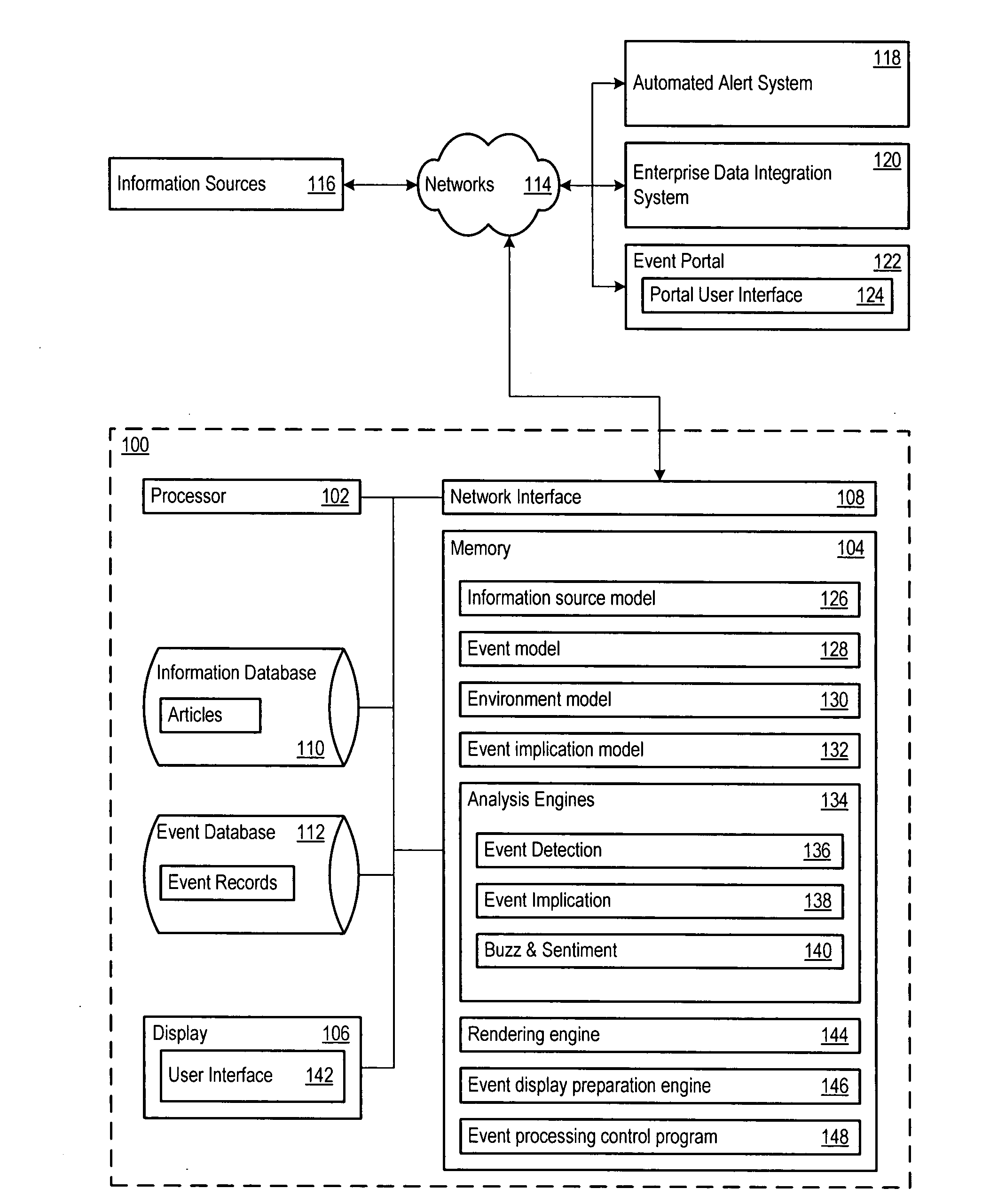
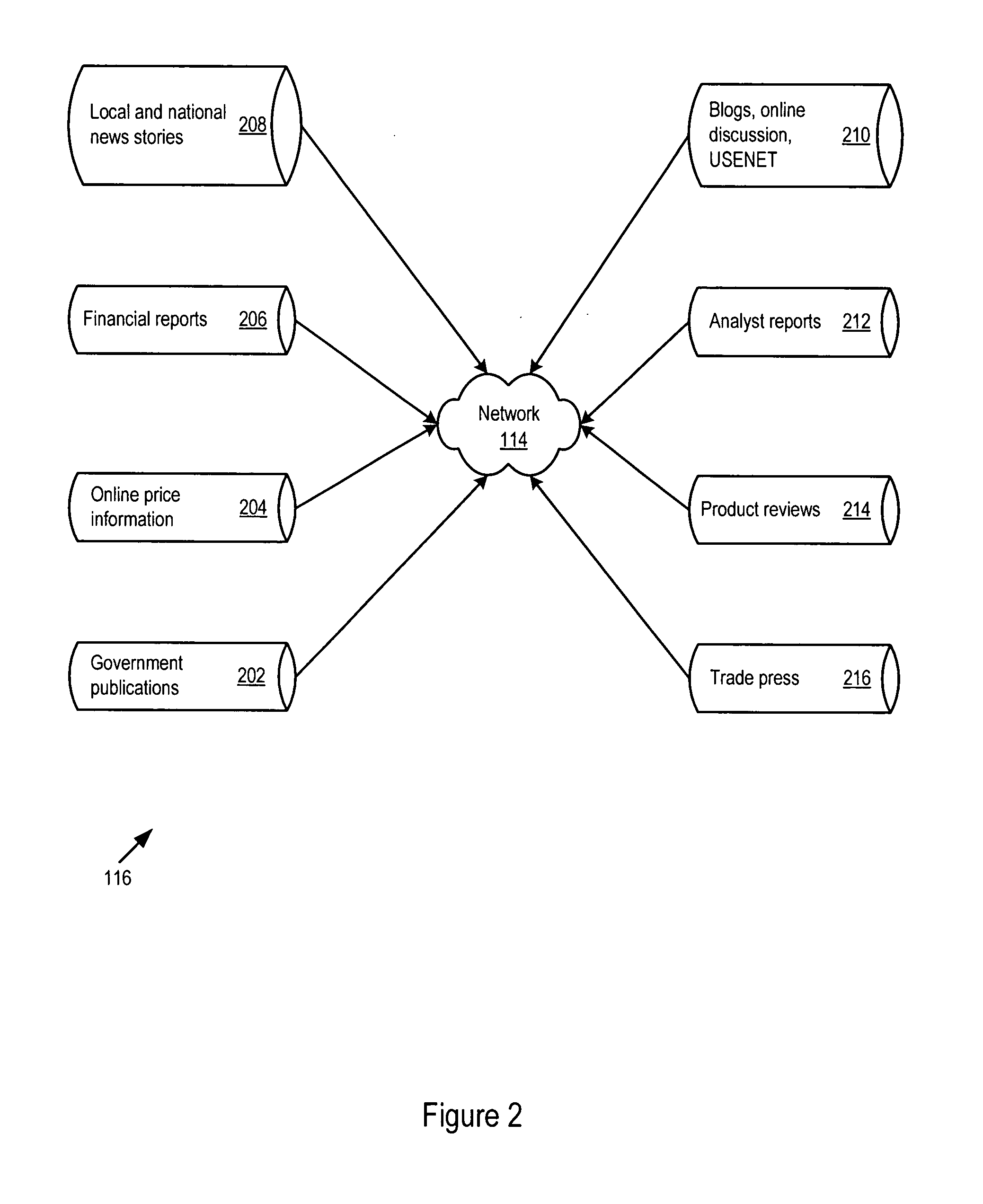
Technology event detection, analysis, and reporting system
ActiveUS20080086363A1Enhanced future performance of systemForecastingComputation using non-denominational number representationHypothesisRadar
A technology analysis system automatically monitors information available from both publicly and privately distributed networks of information for details that are relevant to a technology hypothesis. The technology analysis system provides a technology radar that assists with determining how the technology hypothesis stands up against ongoing developments in technology. The technology analysis system also visualizes the technology hypothesis and its underlying precursor predictions using a web portal, dynamic document, or other visualization technique.
Owner:ACCENTURE GLOBAL SERVICES LTD
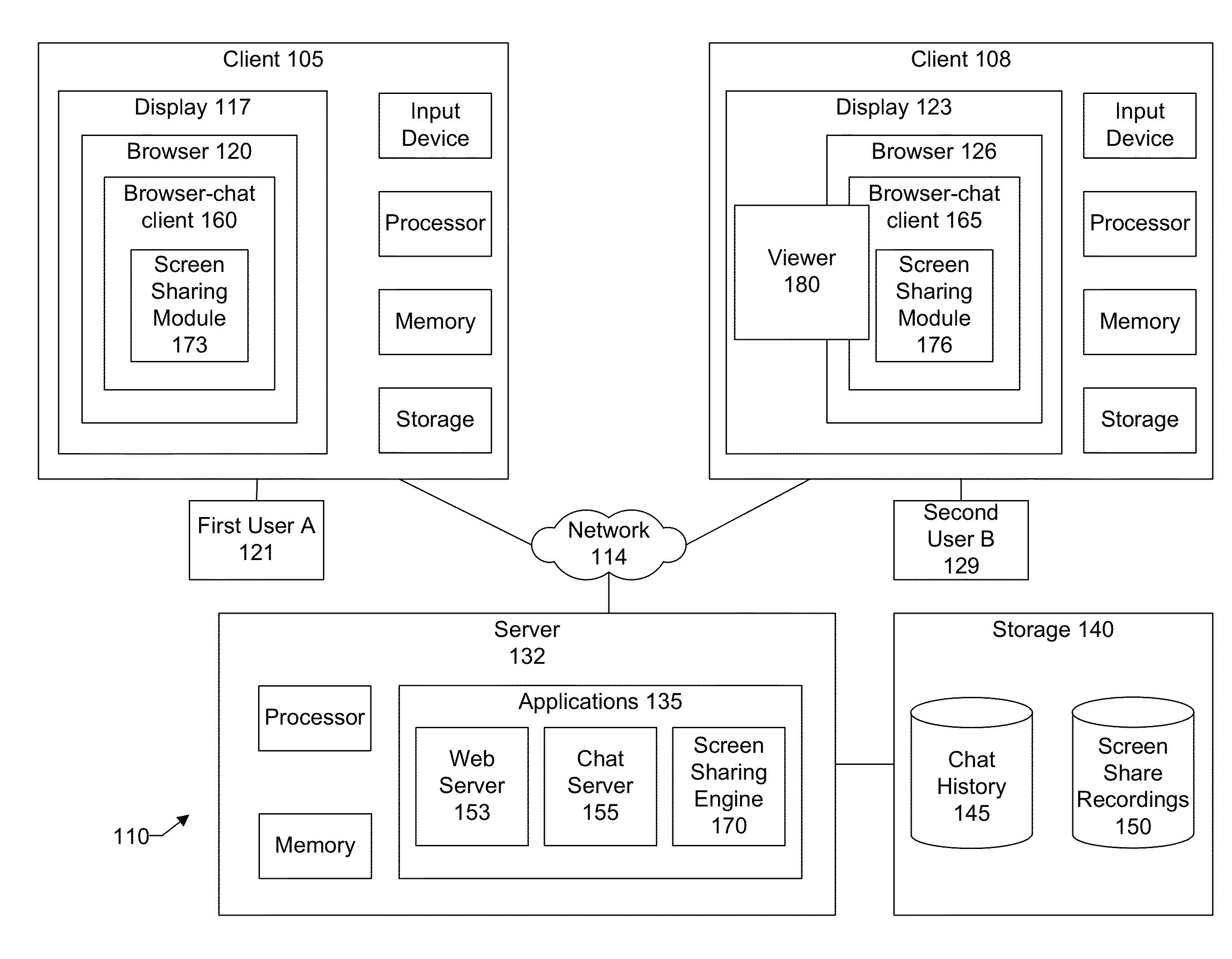
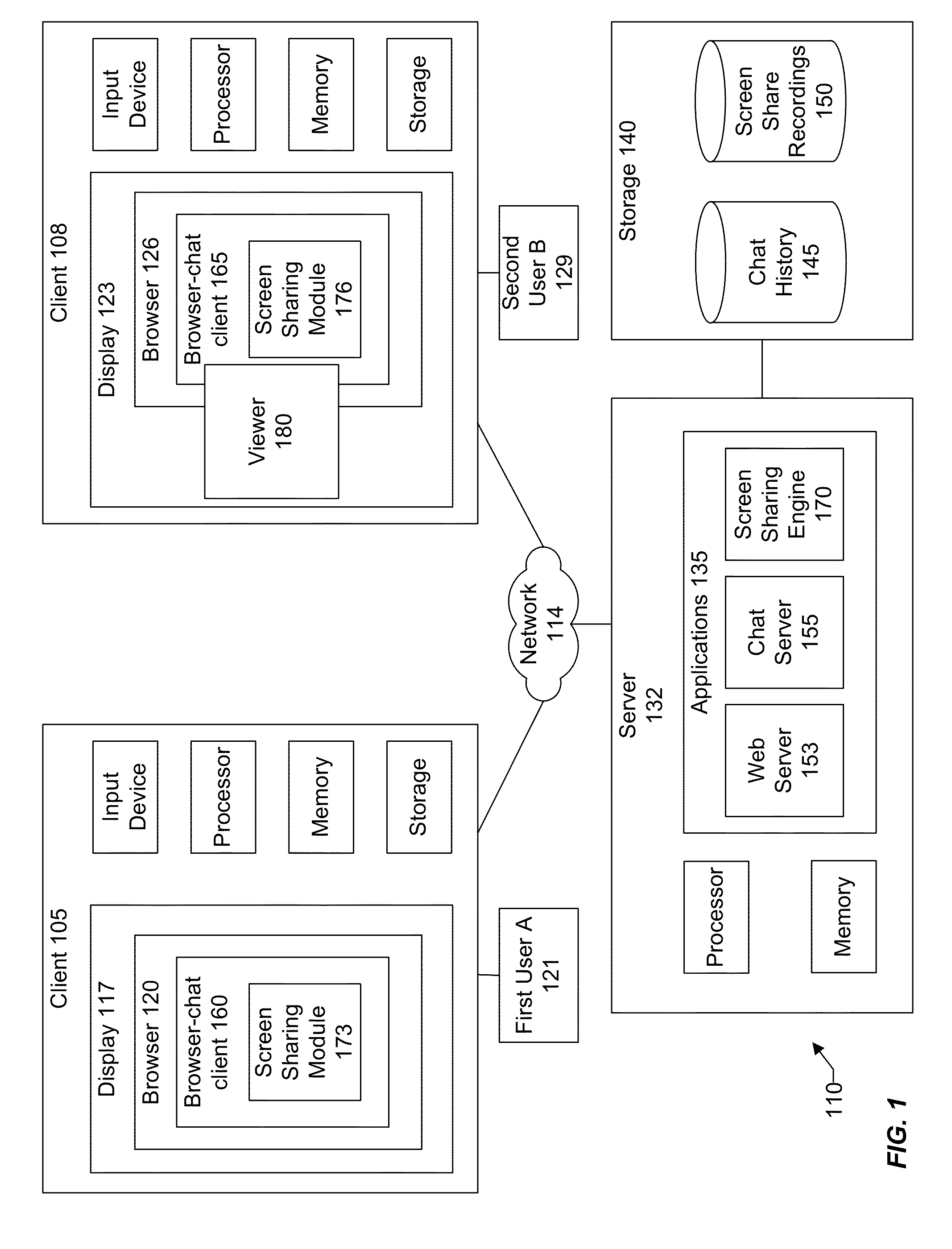
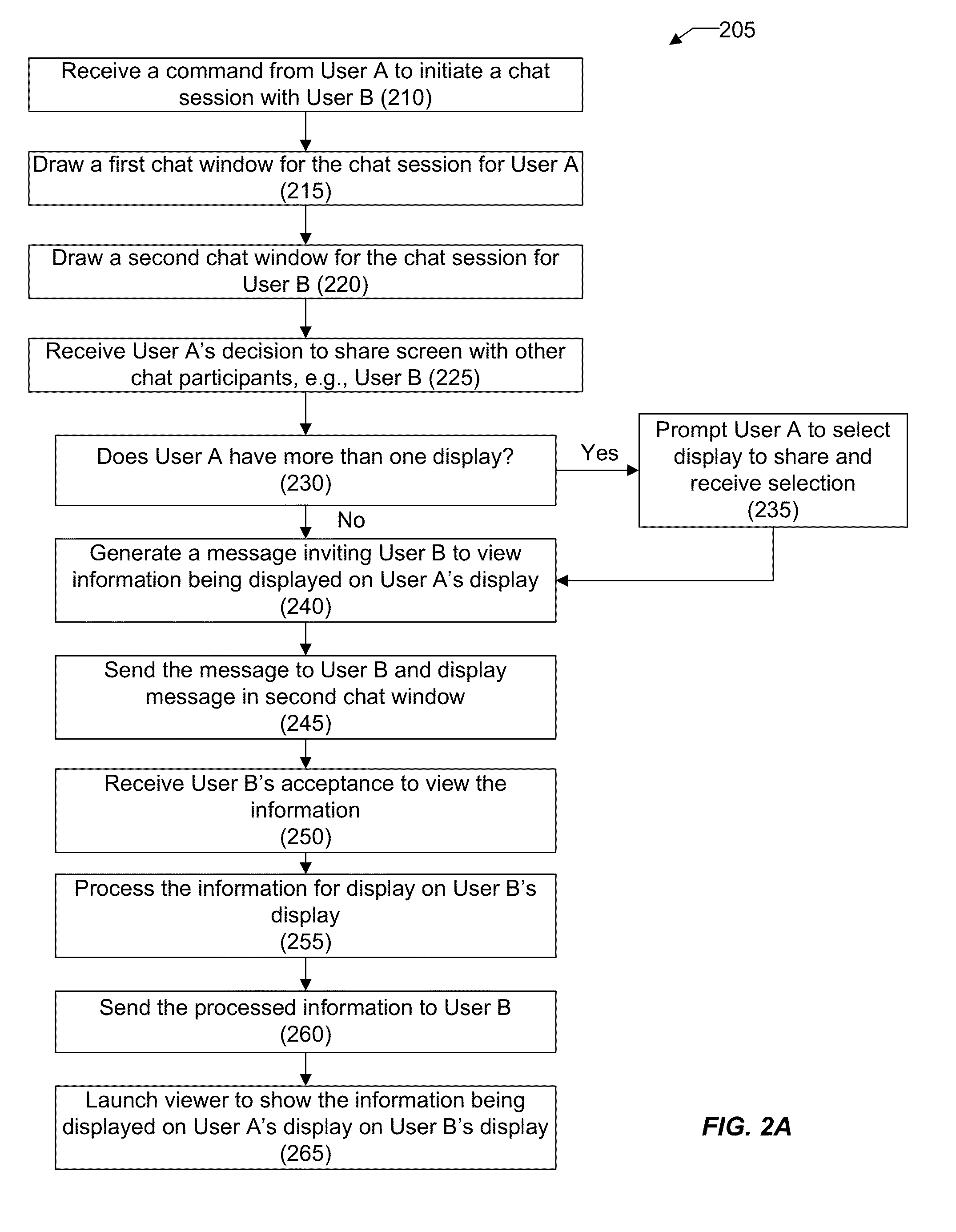
Application sharing functionality in an information networking environment
InactiveUS20150032686A1Not addressStatic indicating devicesDigital data processing detailsScreen sharingInformation networks
A user engaged in an online chat session with one or more other users can start a screen sharing session with the other users without having to leave the context of the online chat session. In an implementation, a chat window for the chat session includes a screen sharing button. The screen sharing button can be clicked to start a screen sharing session with the other chat participants. A system generated message is displayed within the chat windows of the other chat participants inviting them to view the remote screen. Upon accepting the invite, a viewer is launched to show the information being displayed on the remote screen. A variety of enhanced features and functions are also presented in the context of screen sharing in an information networking environment.
Owner:SALESFORCE COM INC
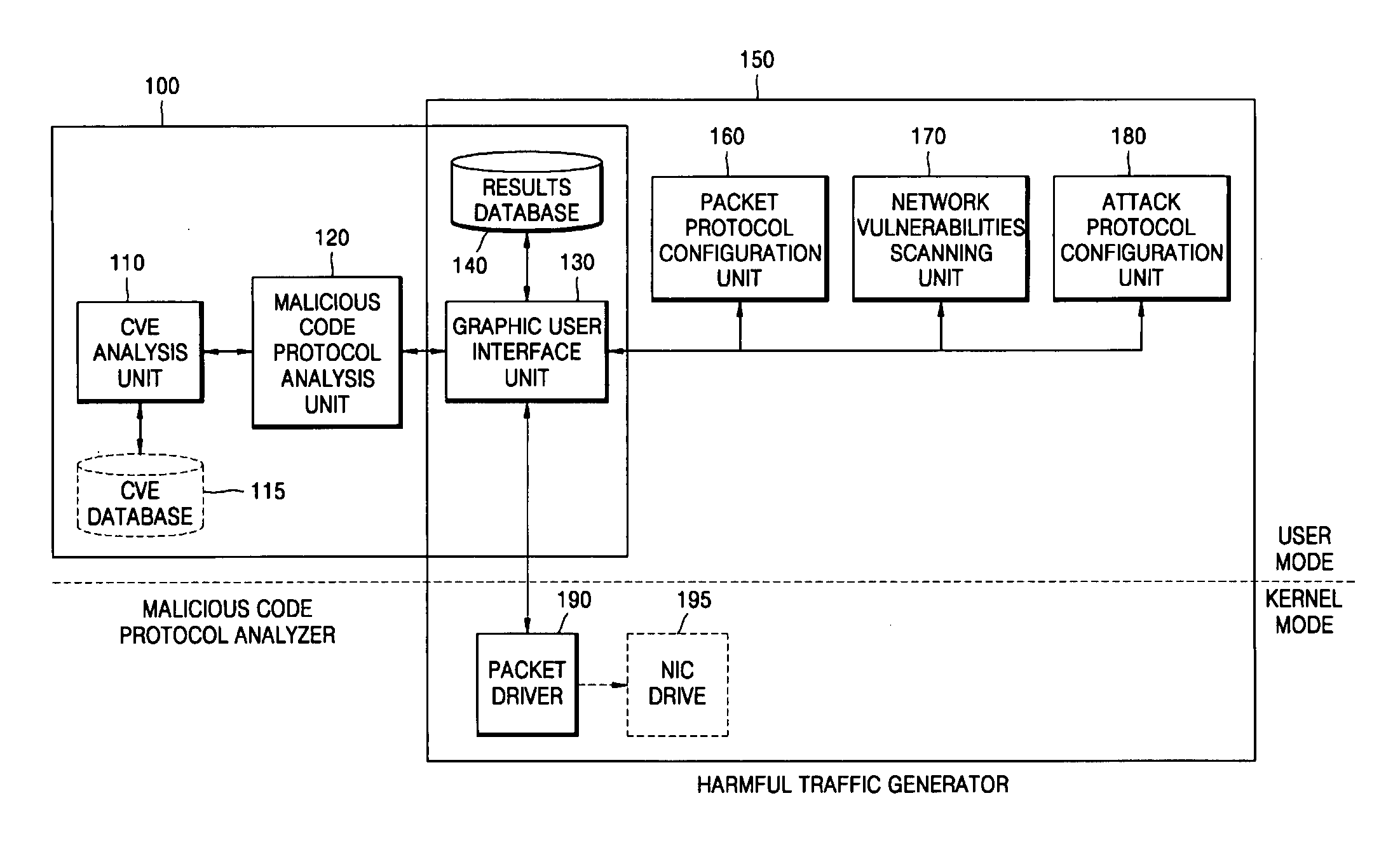
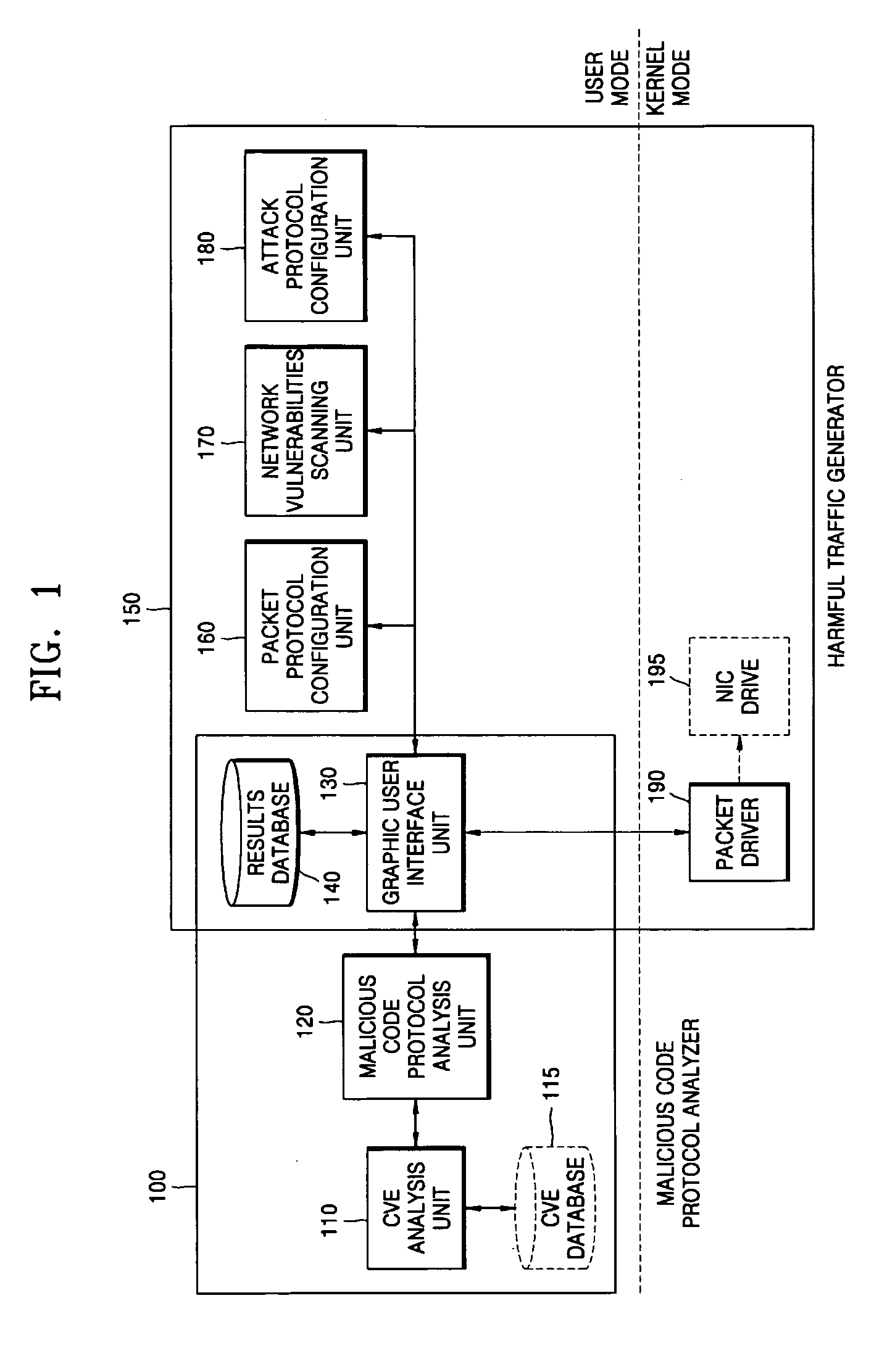
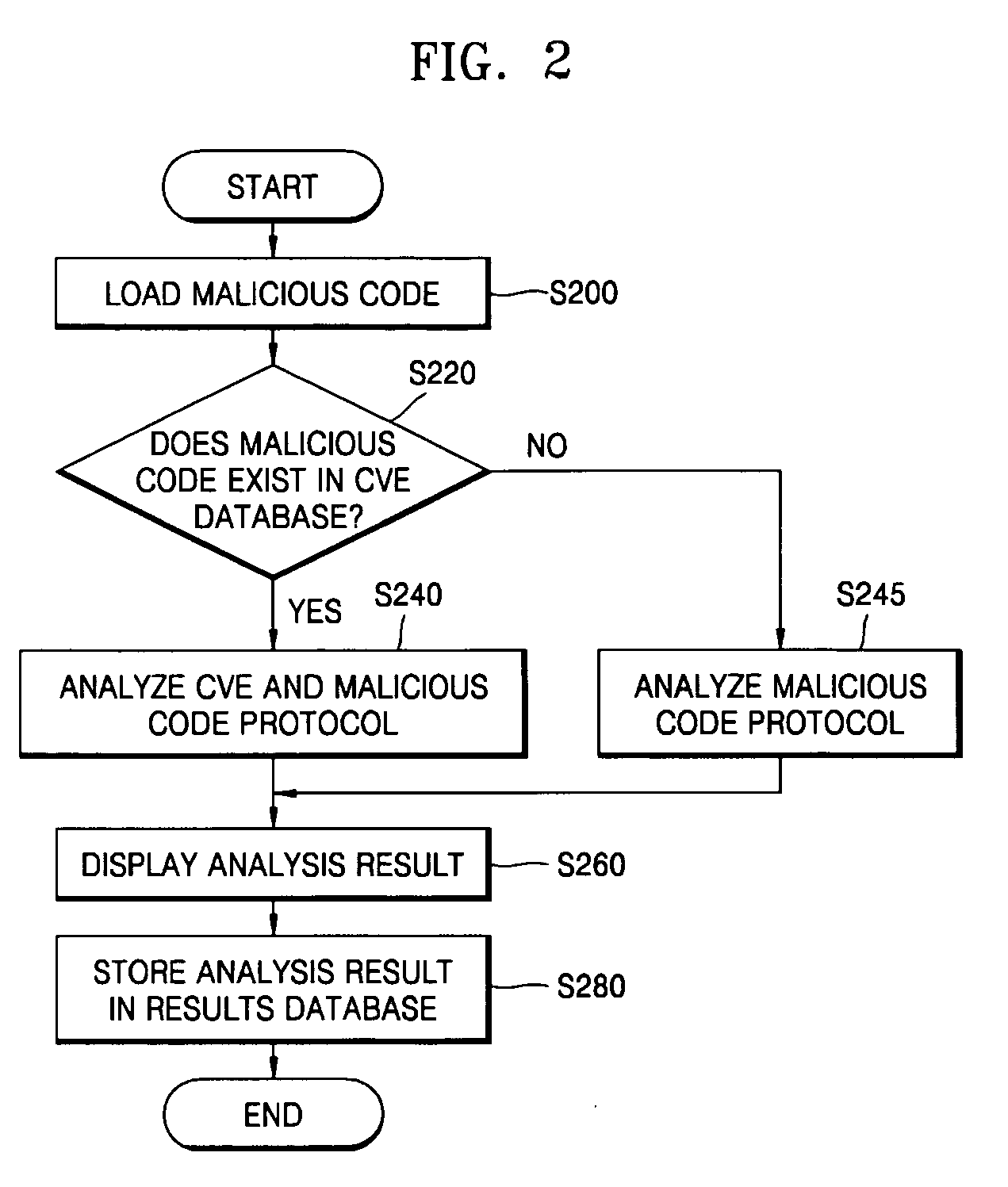
System and method for analyzing malicious code protocol and generating harmful traffic
The provided method and system is a method and system for analyzing the malicious code protocol and generating harmful traffic. The harmful traffic generating method constructs packet protocol information for generating a first attack packet corresponding to the TCP / IP protocol for generating network traffic, and then sets network vulnerability scanning for generating a second attack packet for carrying out network vulnerability scanning. Subsequently, the method constructs attack information for generating a third attack packet in the form of denial of service, and generates harmful traffic using the packet protocol information, network vulnerability scanning and attack information. Accordingly, performance testing of the network security system against malicious code attacks such as the Internet worm can be performed.
Owner:CHOI BYEONG CHEOL +1
Managing congestion and potential traffic growth in an information network
Owner:SOUND VIEW INNOVATIONS
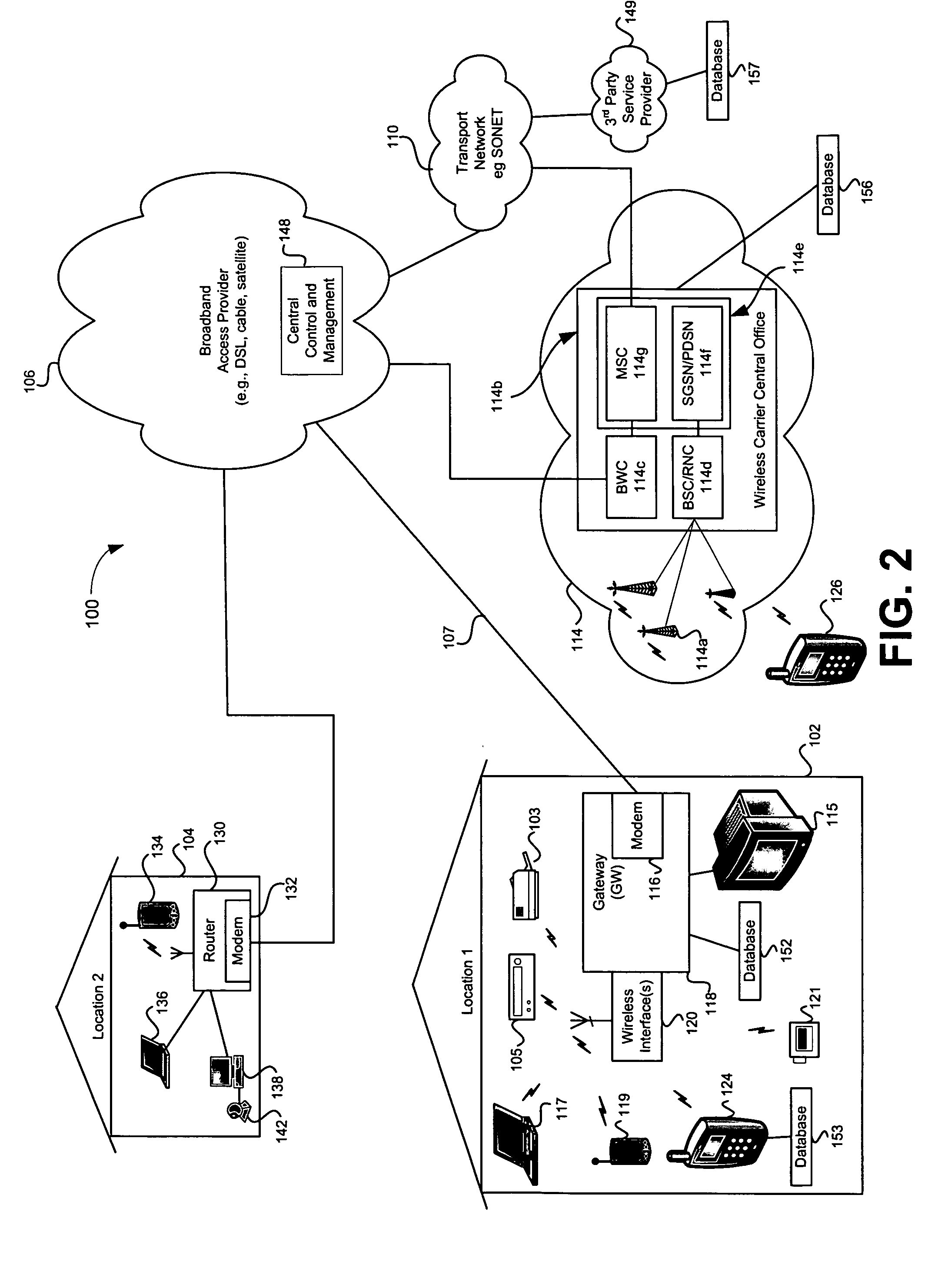
System and method for providing an information network on the internet
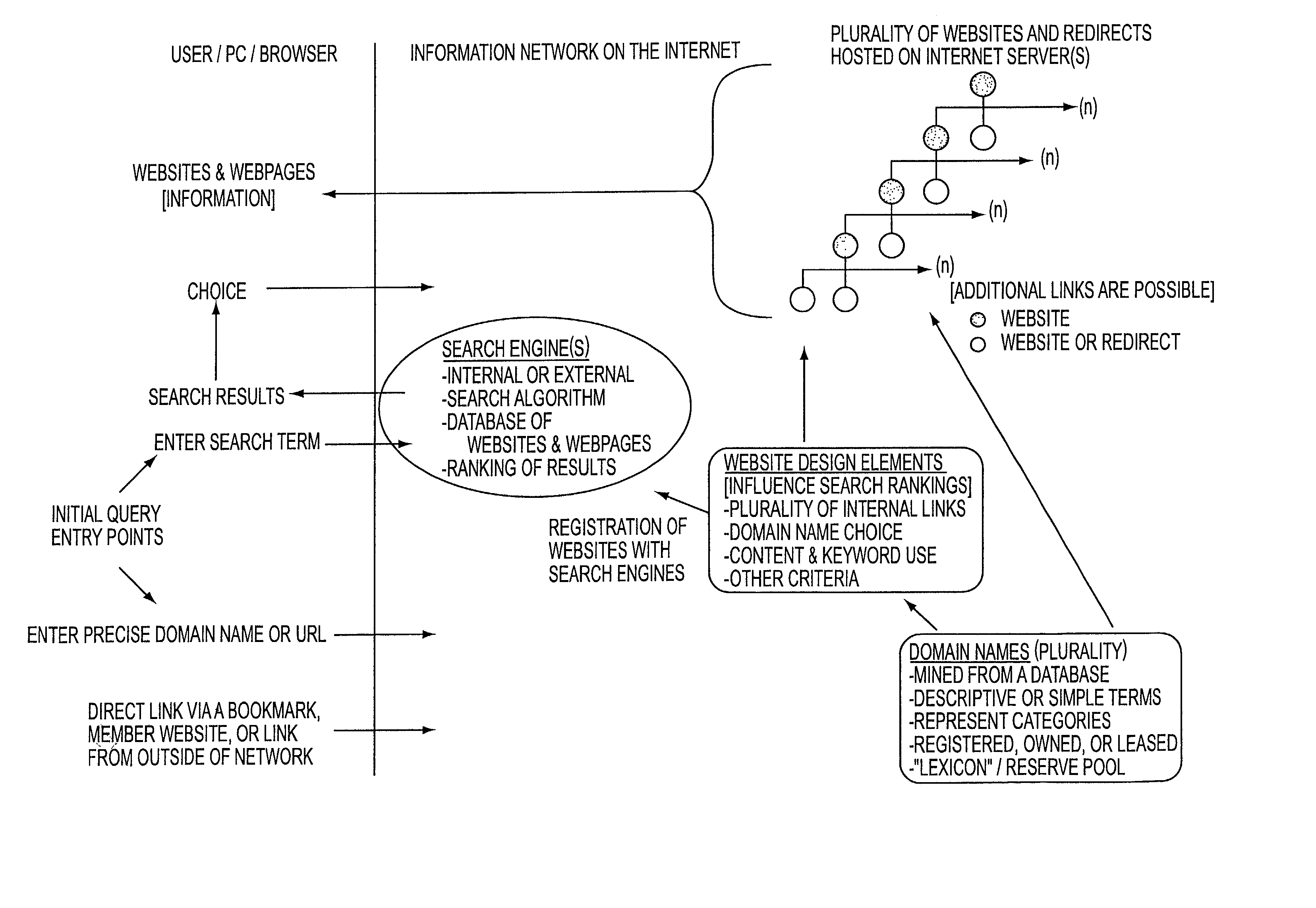
InactiveUS20020035611A1Web data indexingMultiple digital computer combinationsDomain nameInformation networks
A system and method for providing an information network on the Internet is provided. The system includes a plurality of websites and at least one redirect assigned to each website. The websites each include a category, information about the category and a domain name that corresponds to the category. The redirect includes a URL redirect that directs a browser or a server to the assigned website. The method includes the steps of: (1) providing a plurality of websites; (2) providing each website with a category, information about the category, and a domain name that corresponds to the category; (3) providing at least one redirect assigned to each website; and (4) providing each redirect with a URL redirect that directs at least one of a browser and a server to the assigned website.
Owner:ALTRUIS
Information processing apparatus, information processing method and identification code
InactiveUS20010043594A1Telephone data network interconnectionsSpecial service for subscribersInformation processingThe Internet
There is provided an information processing apparatus which may be applied to an information processing apparatus being connected, for example, to an information network such as Internet for transmitting and receiving various pieces of information in order to make access to such network through a terminal of simplified structure such as a telephone terminal. A code for uniquely identifying, for example, a telephone terminal and a computer terminal may be formed with the codes corresponding to operators of a telephone terminal.
Owner:SONY CORP
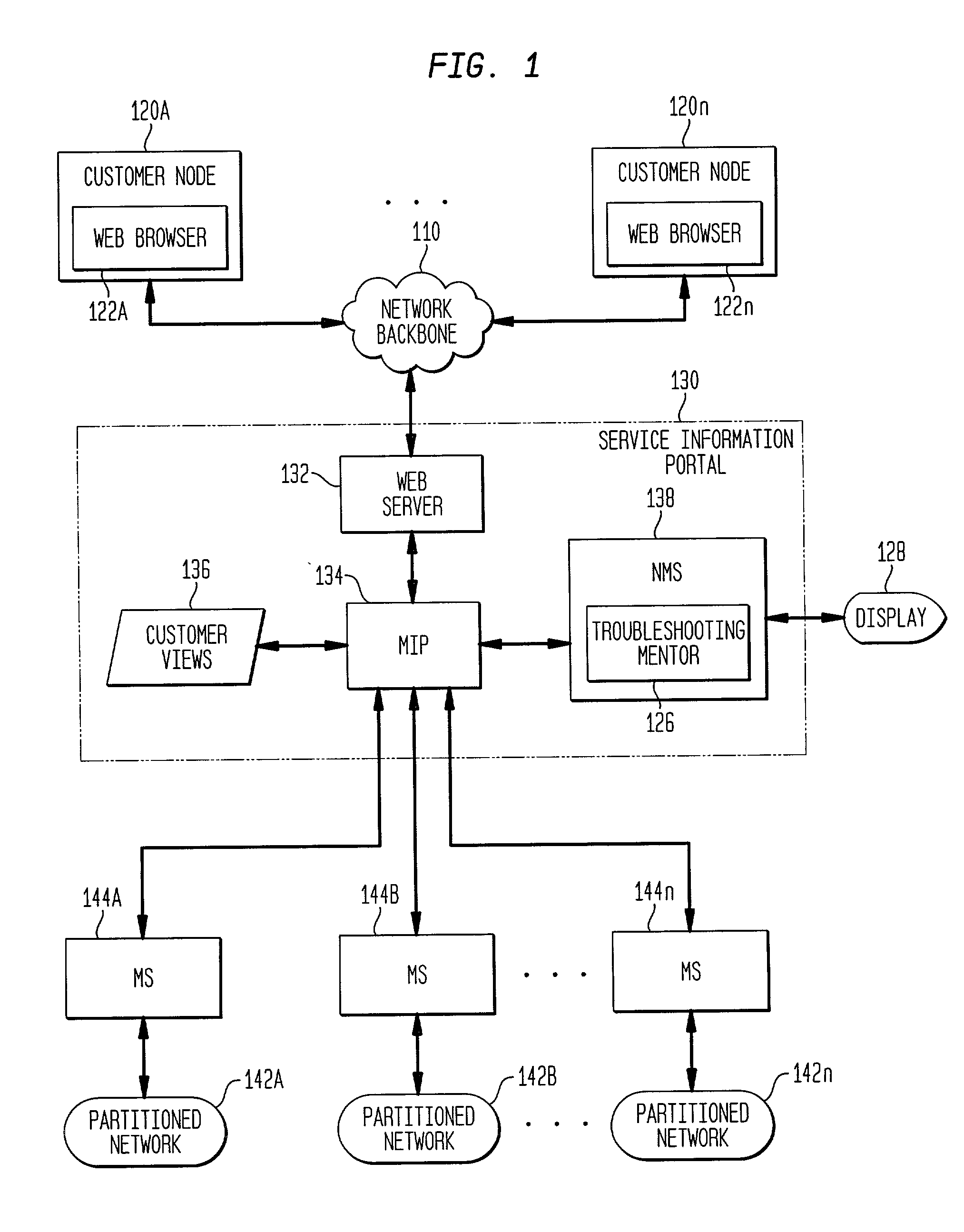
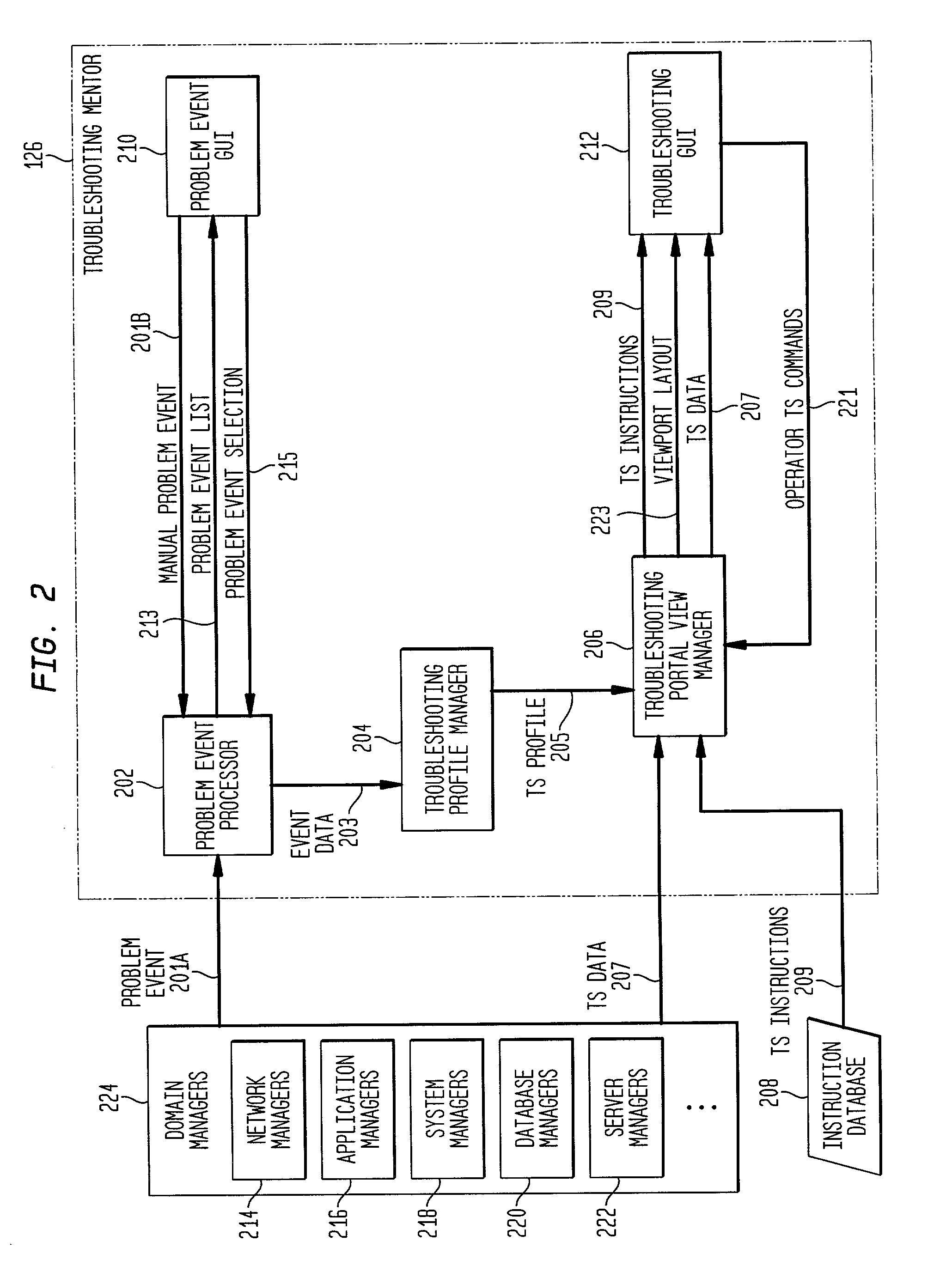
Dynamic generation of context-sensitive data and instructions for troubleshooting problem events in information network systems
InactiveUS20020161875A1Easy diagnosisEliminate needError detection/correctionDigital computer detailsDiagnostic dataRelevant information
A system and method for dynamically providing information to an administrator of a computing environment such as an administrator of a network system that is relevant to a particular problem event. This information includes contextual instructions and diagnostic data that will assist the network administrator in the analysis of the problem event. Generally, the invention automatically obtains from relevant computing environment entities pertinent information likely to be necessary to troubleshoot the particular problem event. The context-sensitive information is presented dynamically on a display for consideration and interaction by the network administrator. Specifically, the invention includes a database of executable troubleshooting (TS) profiles each specifically designed for a particular type of problem event. Each such TS profile references one or more troubleshooting data miner modules included in a library of such modules that accesses particular hardware or software entities in the network system for particular information. When a TS profile is invoked to assist a network administrator troubleshoot a particular type of problem event, the referenced data miner modules are executed and generate or cause the generator of troubleshooting instructions and diagnostic data which is then displayed to the network administrator.
Owner:VALTRUS INNOVATIONS LTD
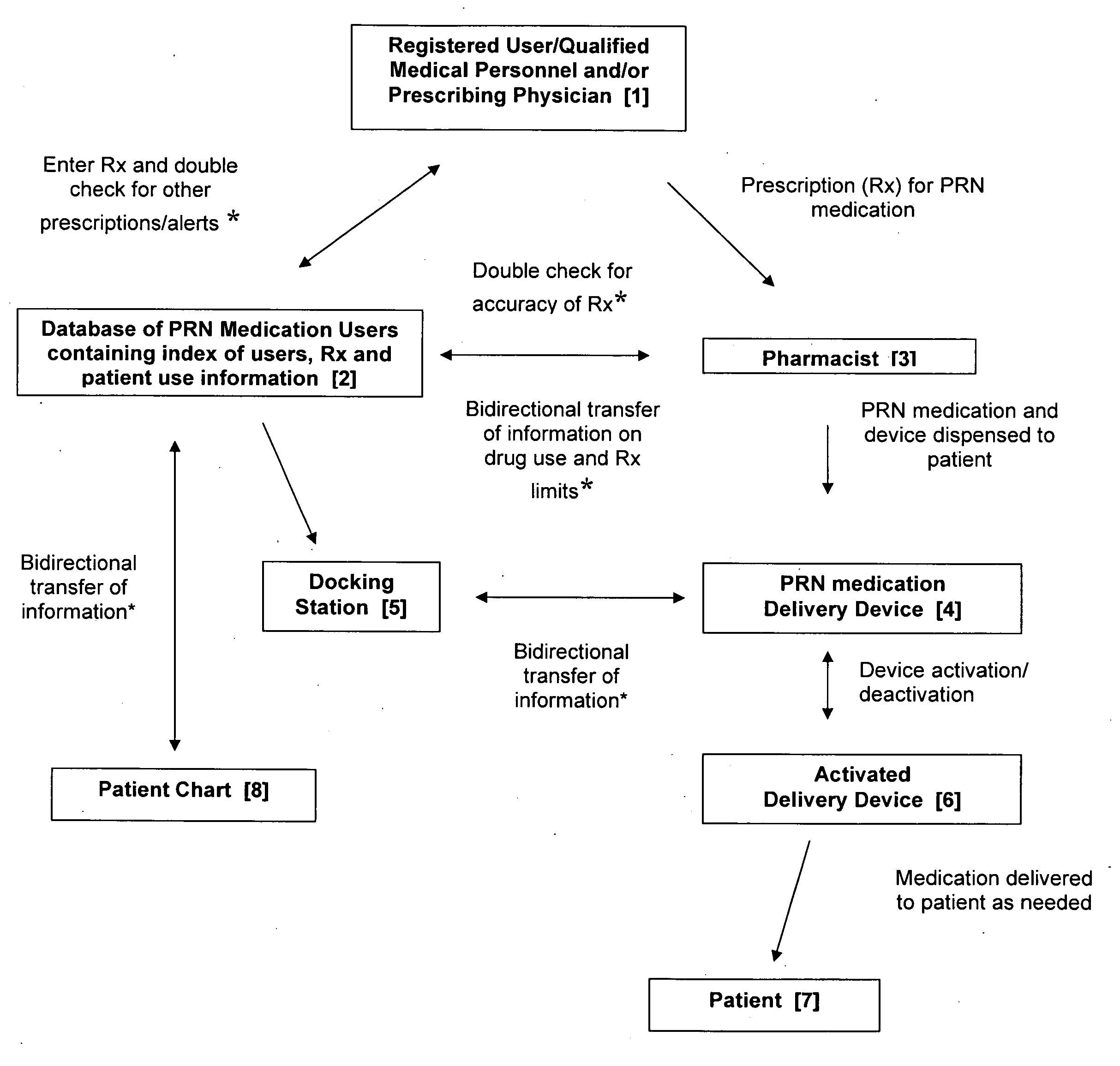
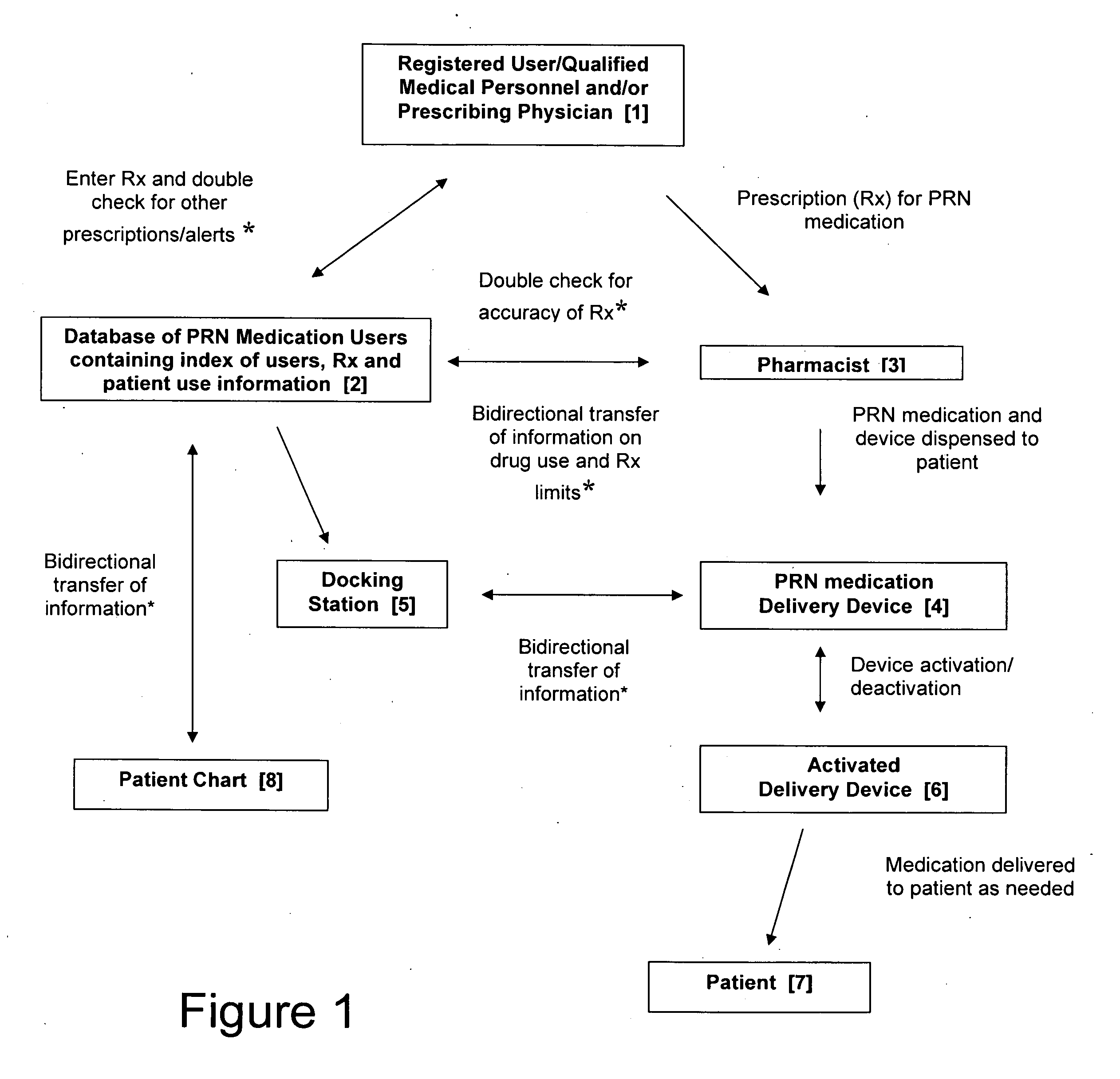
Inpatient system for patient-controlled delivery of oral transmucosal medications dosed as needed
InactiveUS20070299687A1Data processing applicationsDigital data processing detailsMedication doseInformation networks
A system is provided for controlled delivery of oral transmucosal medications as needed (PRN), which includes a drug delivery device having a detection mechanism for patient identification, safety features such as timed lock-out, the ability to be linked to an information network and one or more databases for storing prescription and patient usage information.
Owner:ACEIRX PHARM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com