Patents
Literature
100 results about "CODE protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
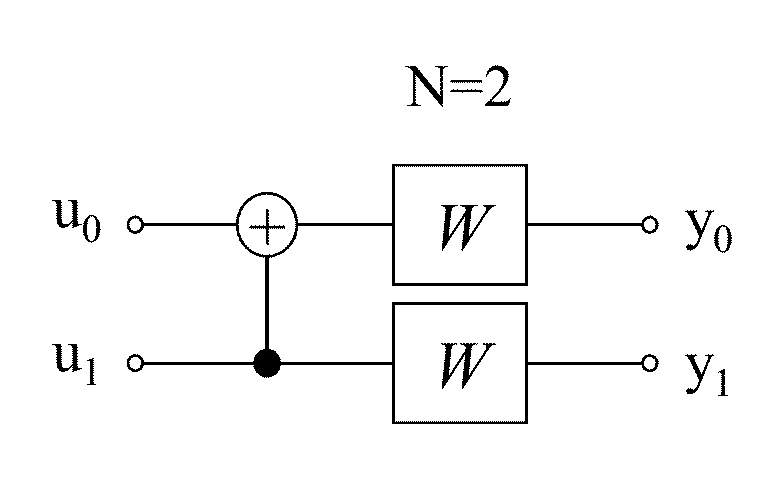
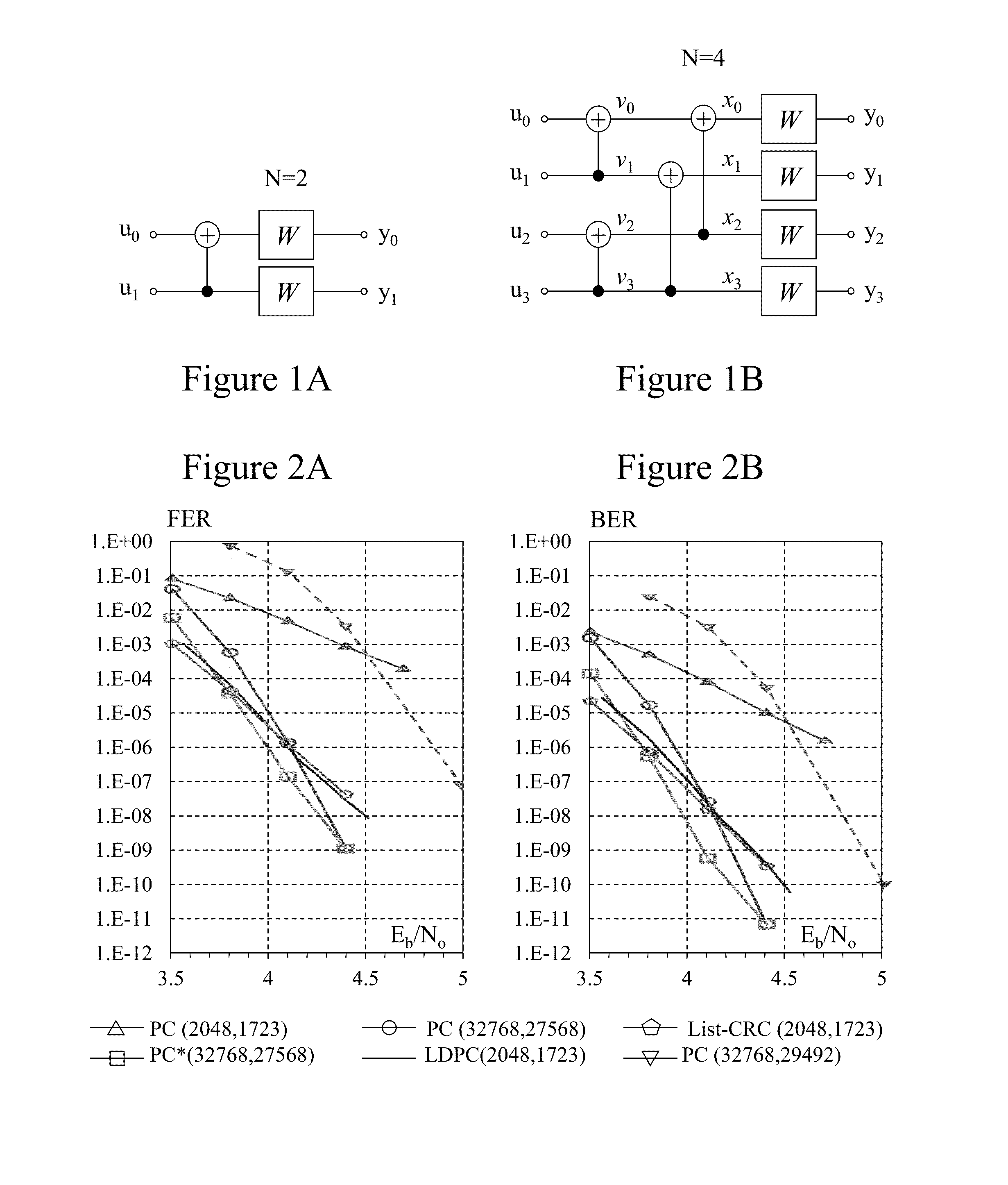
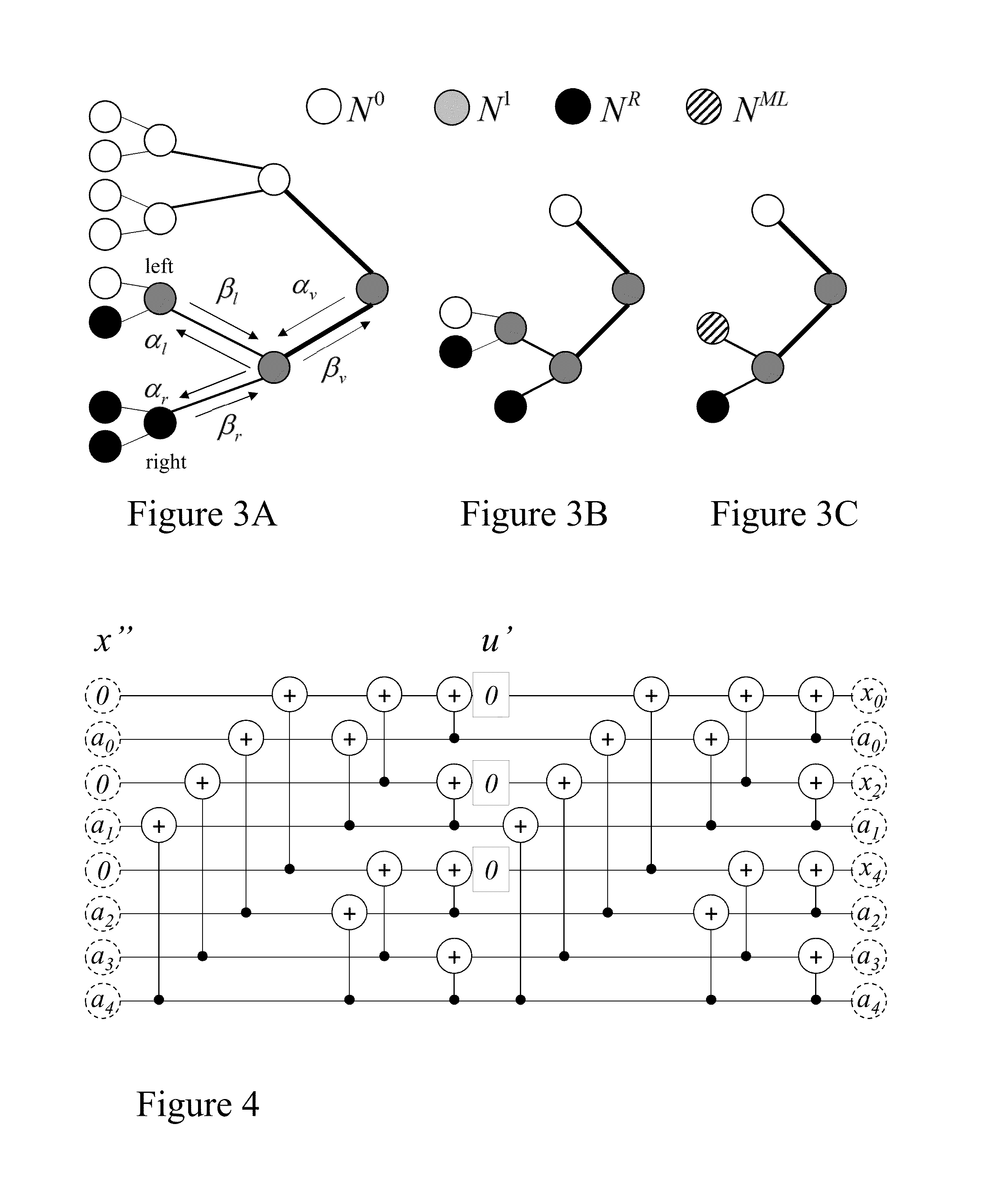
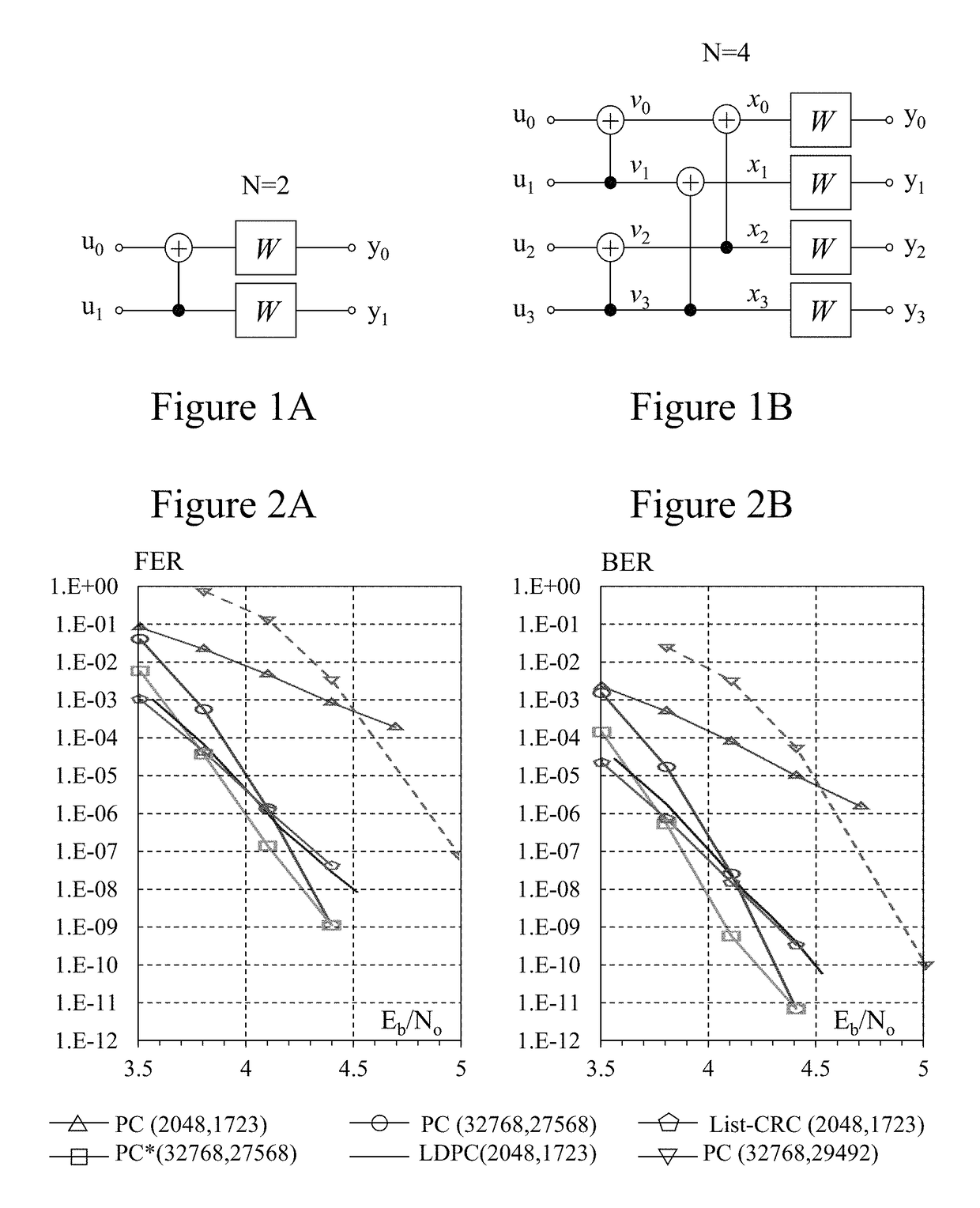
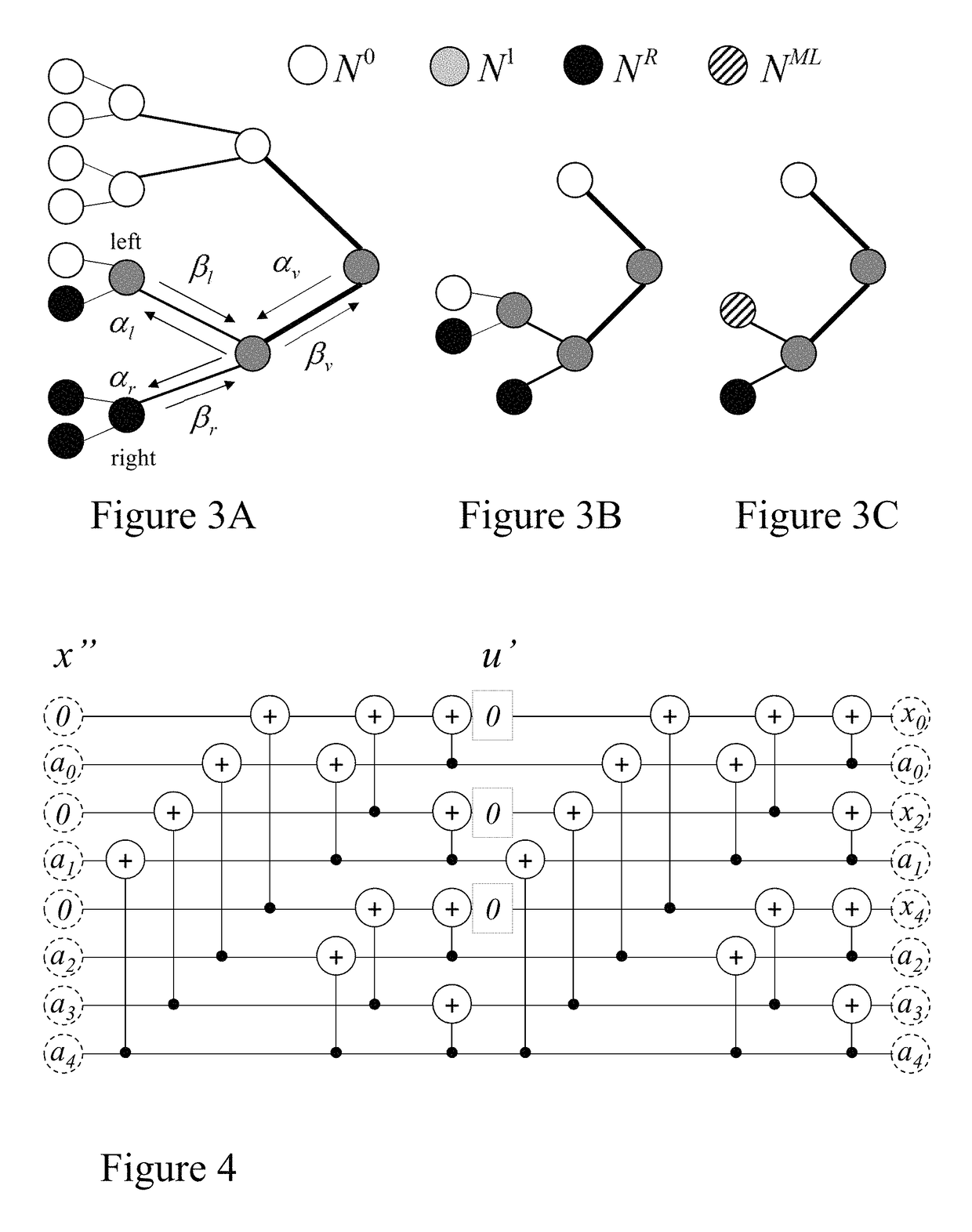
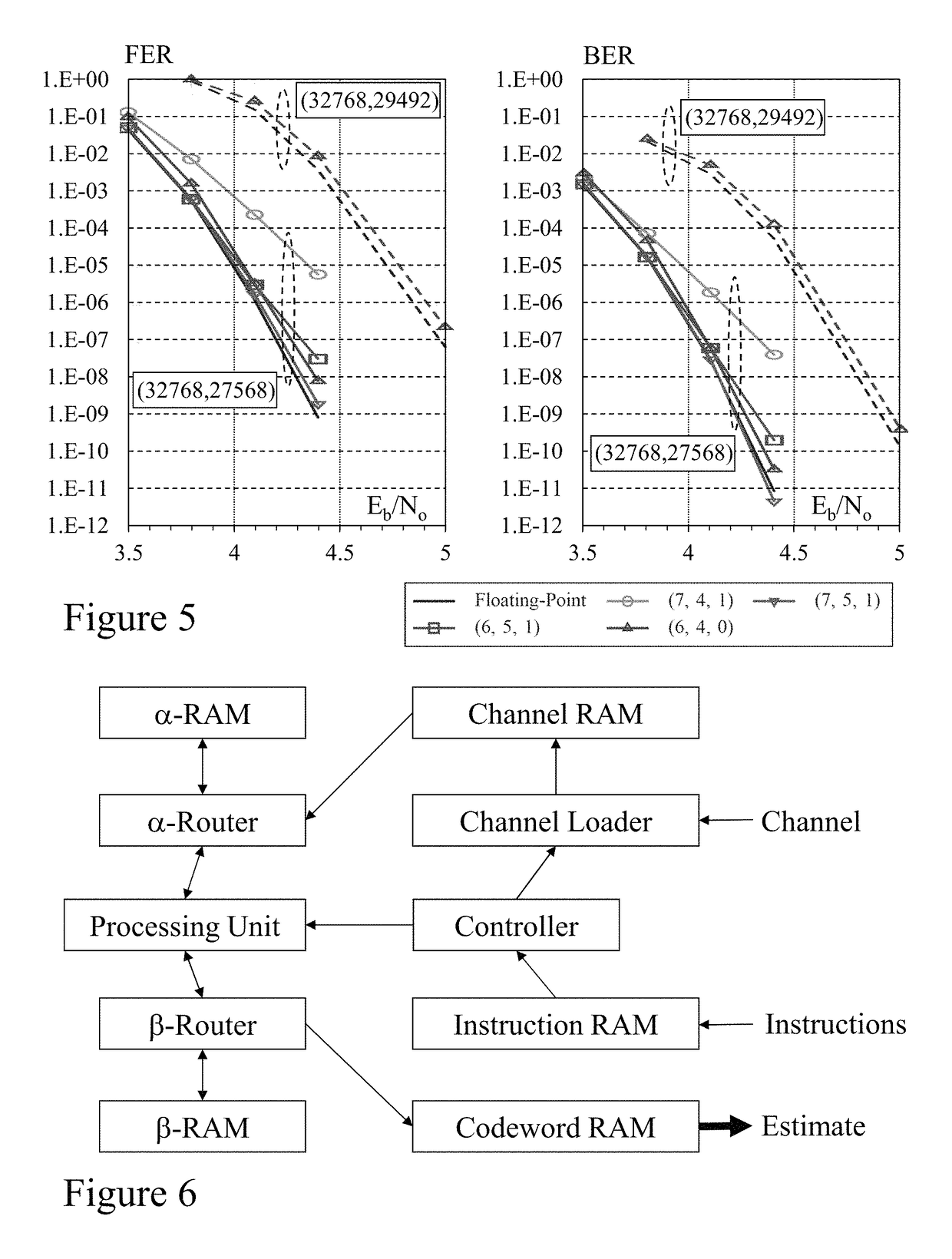
Flexible polar encoders and decoders
Modern communication systems must cope with varying channel conditions and differing throughput constraints. Polar codes despite being the first error-correcting codes with an explicit construction to achieve the symmetric capacity of memoryless channels are not currently employed against other older coding protocols such as low-density parity check (LDPC) codes as their performance at short / moderate lengths has been inferior and their decoding algorithm is serial leading to low decoding throughput. Accordingly techniques to address these issues are identified and disclosed including decoders that decode constituent codes without recursion and / or recognize classes of constituent directly decodable codes thereby increasing the decoder throughput. Flexible encoders and decoders supporting polar codes of any length up to a design maximum allow adaptive polar code systems responsive to communication link characteristics, performance, etc. whilst maximizing throughput. Further, designers are provided flexibility in implementing either hardware or software implementations.
Owner:POLAR TECH
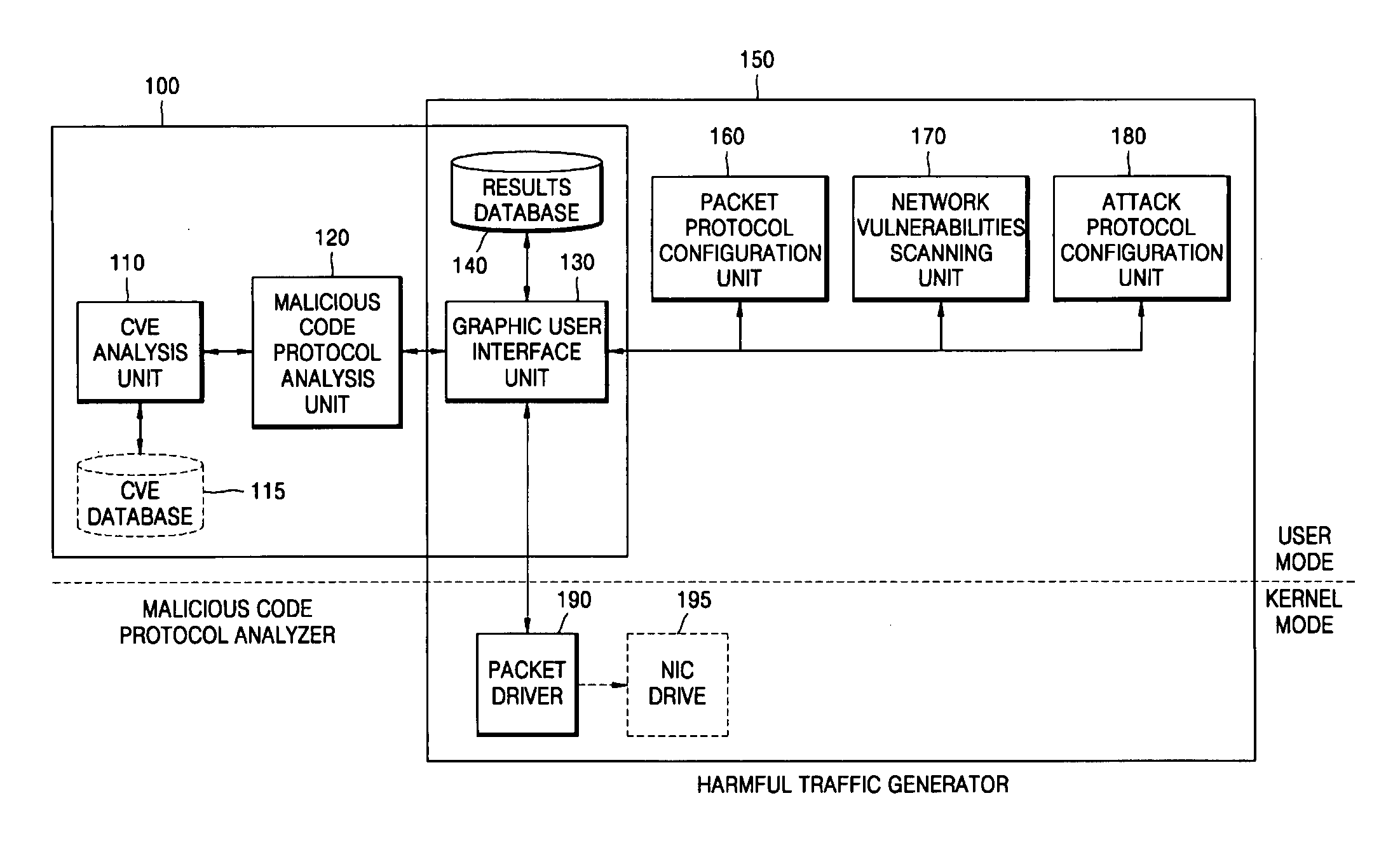
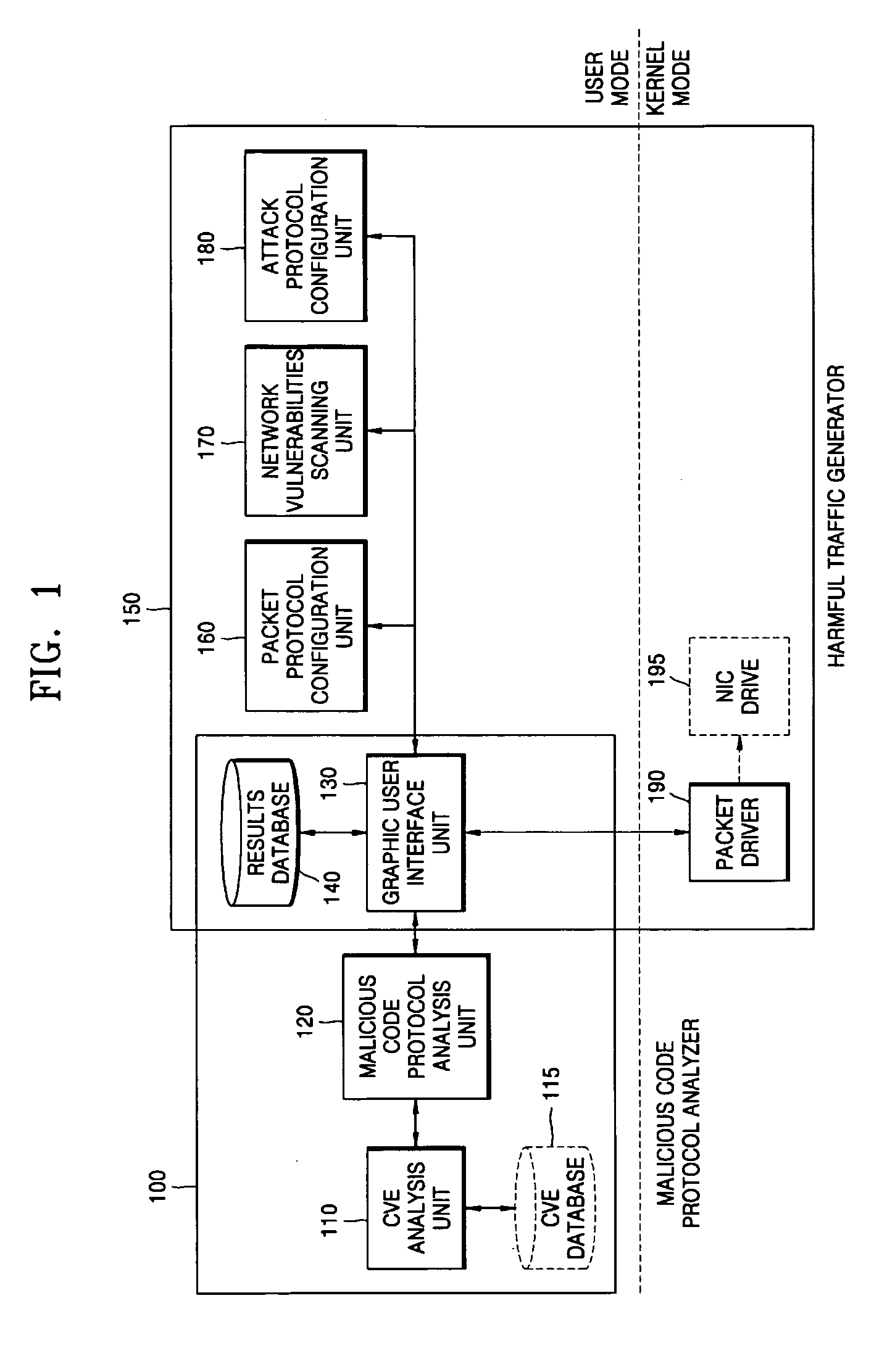
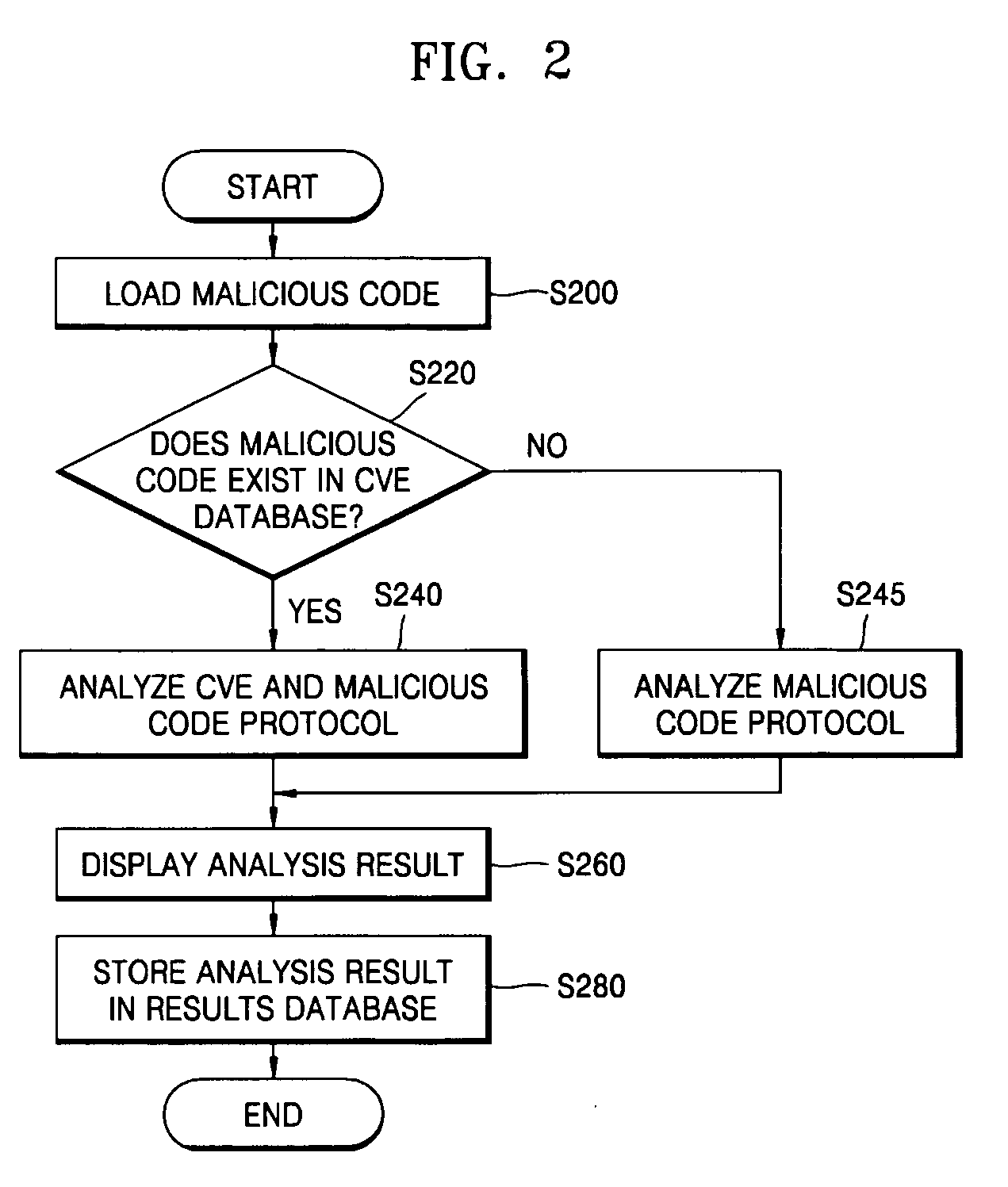
System and method for analyzing malicious code protocol and generating harmful traffic
The provided method and system is a method and system for analyzing the malicious code protocol and generating harmful traffic. The harmful traffic generating method constructs packet protocol information for generating a first attack packet corresponding to the TCP / IP protocol for generating network traffic, and then sets network vulnerability scanning for generating a second attack packet for carrying out network vulnerability scanning. Subsequently, the method constructs attack information for generating a third attack packet in the form of denial of service, and generates harmful traffic using the packet protocol information, network vulnerability scanning and attack information. Accordingly, performance testing of the network security system against malicious code attacks such as the Internet worm can be performed.
Owner:CHOI BYEONG CHEOL +1
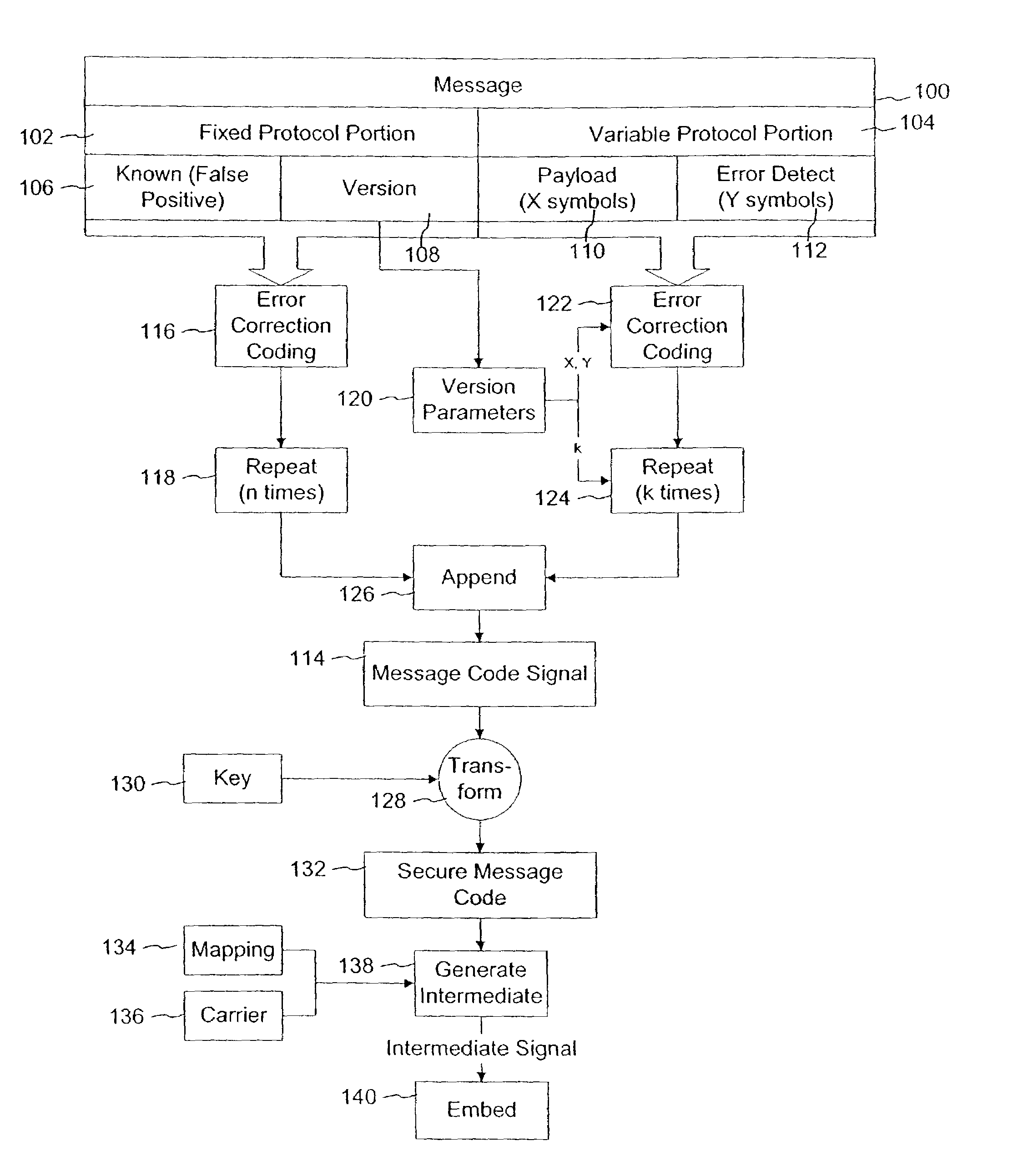
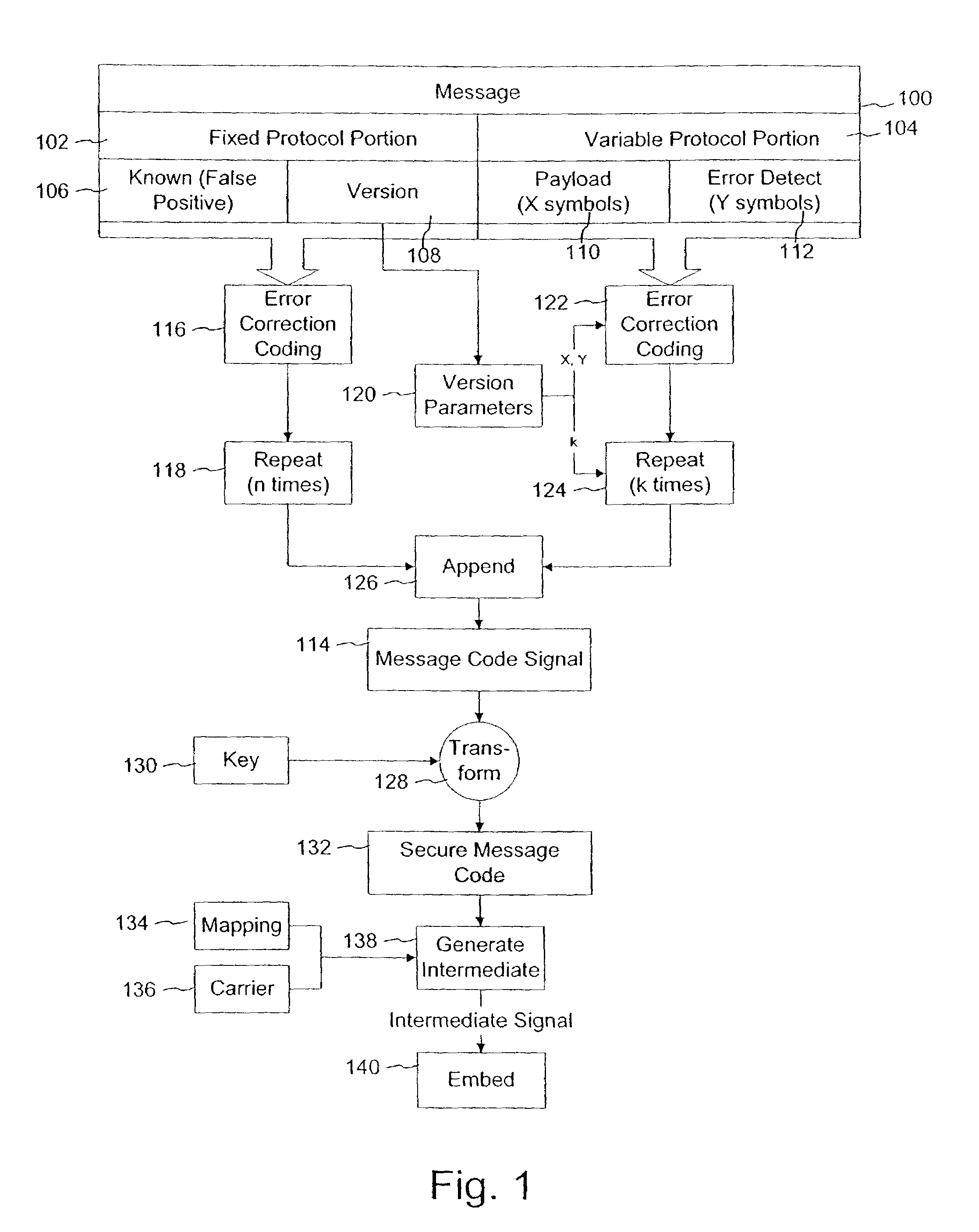
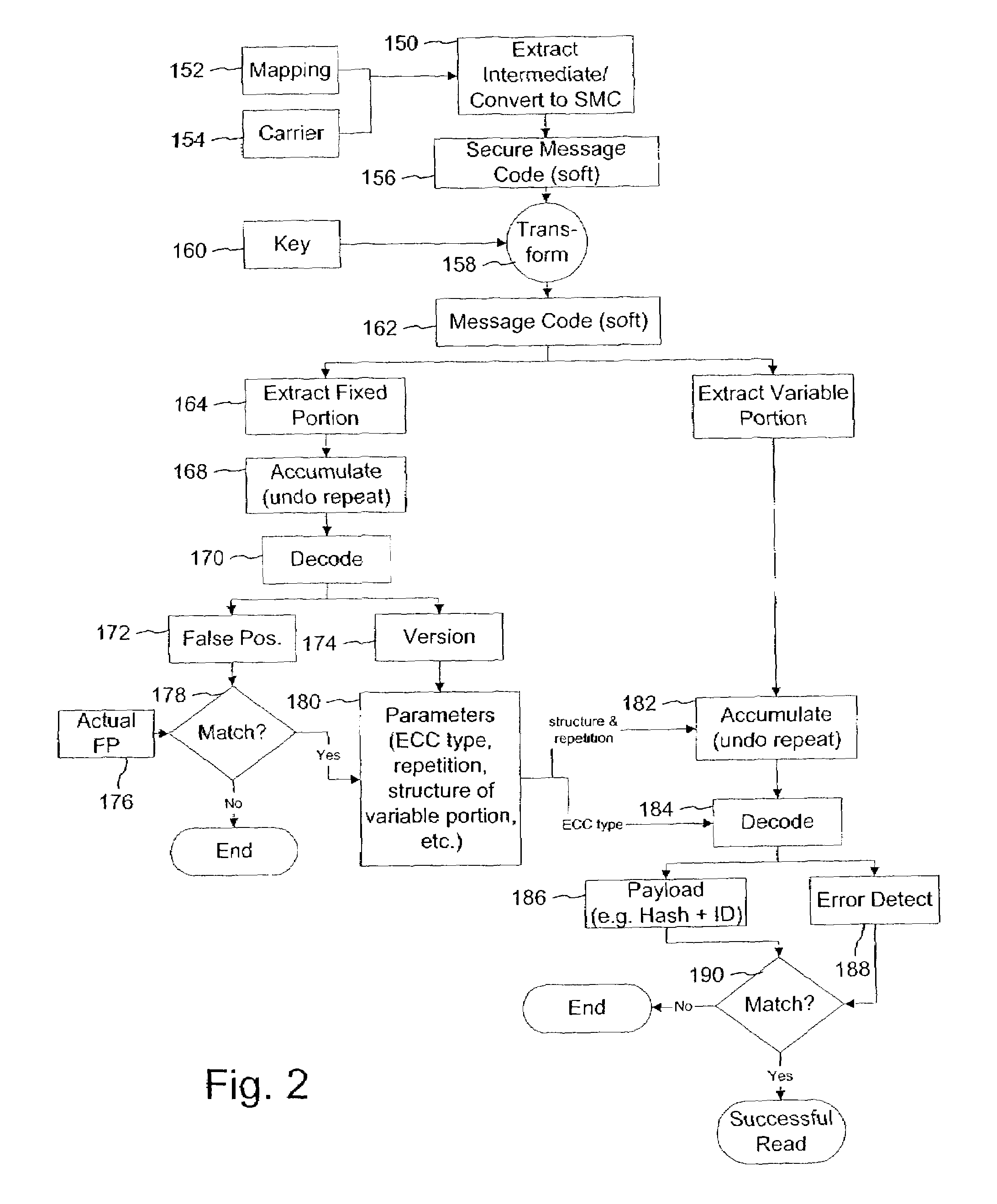
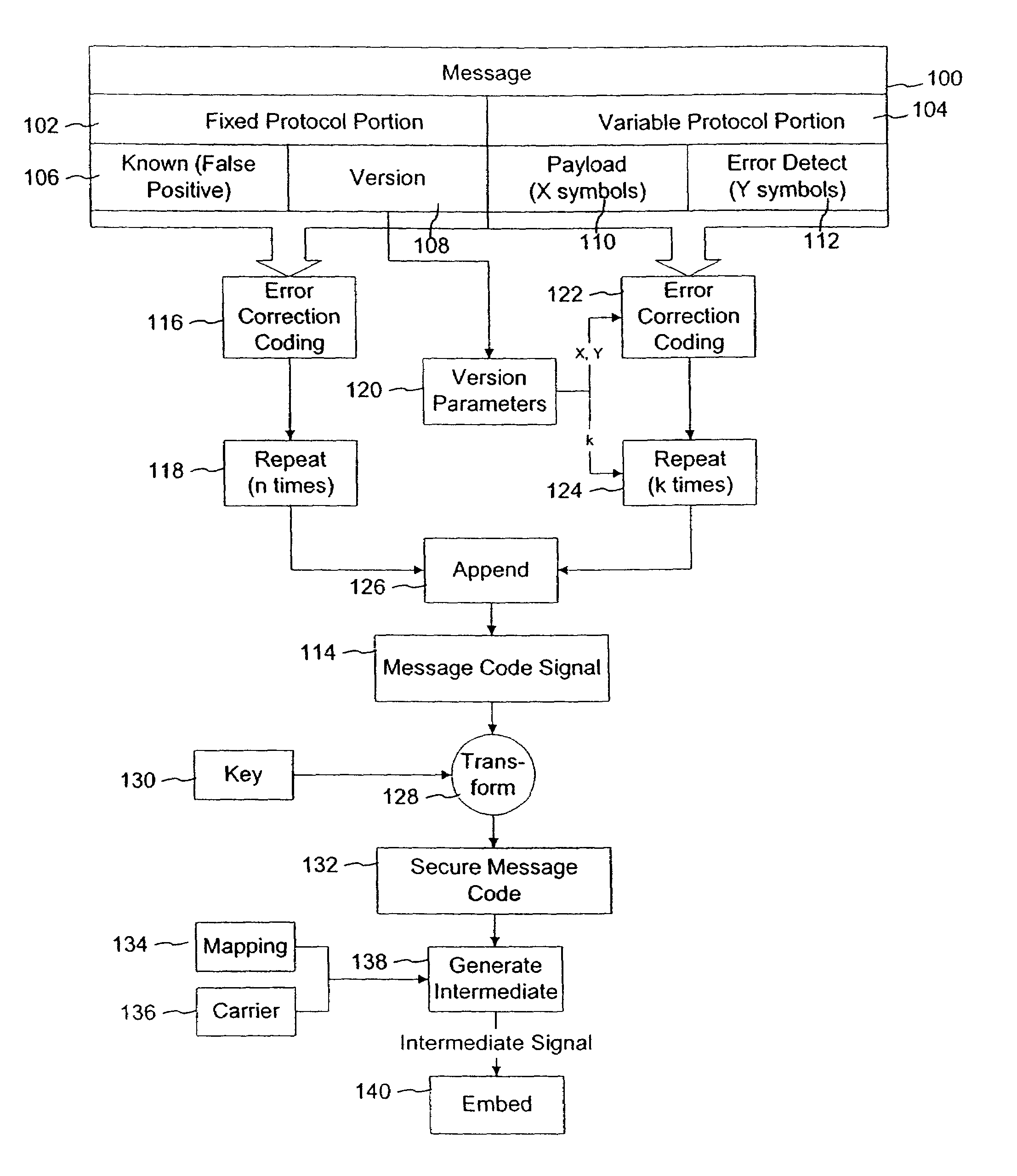
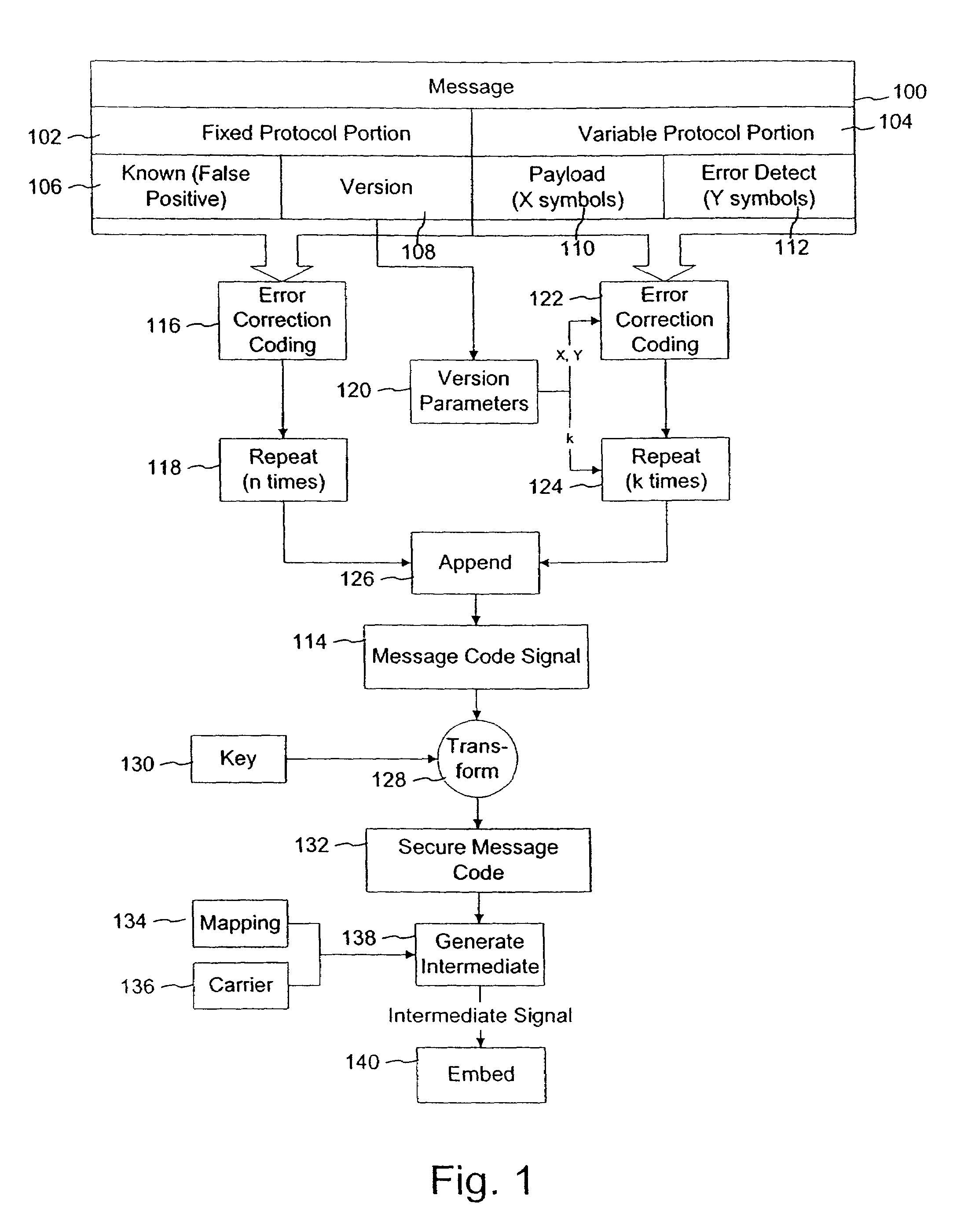
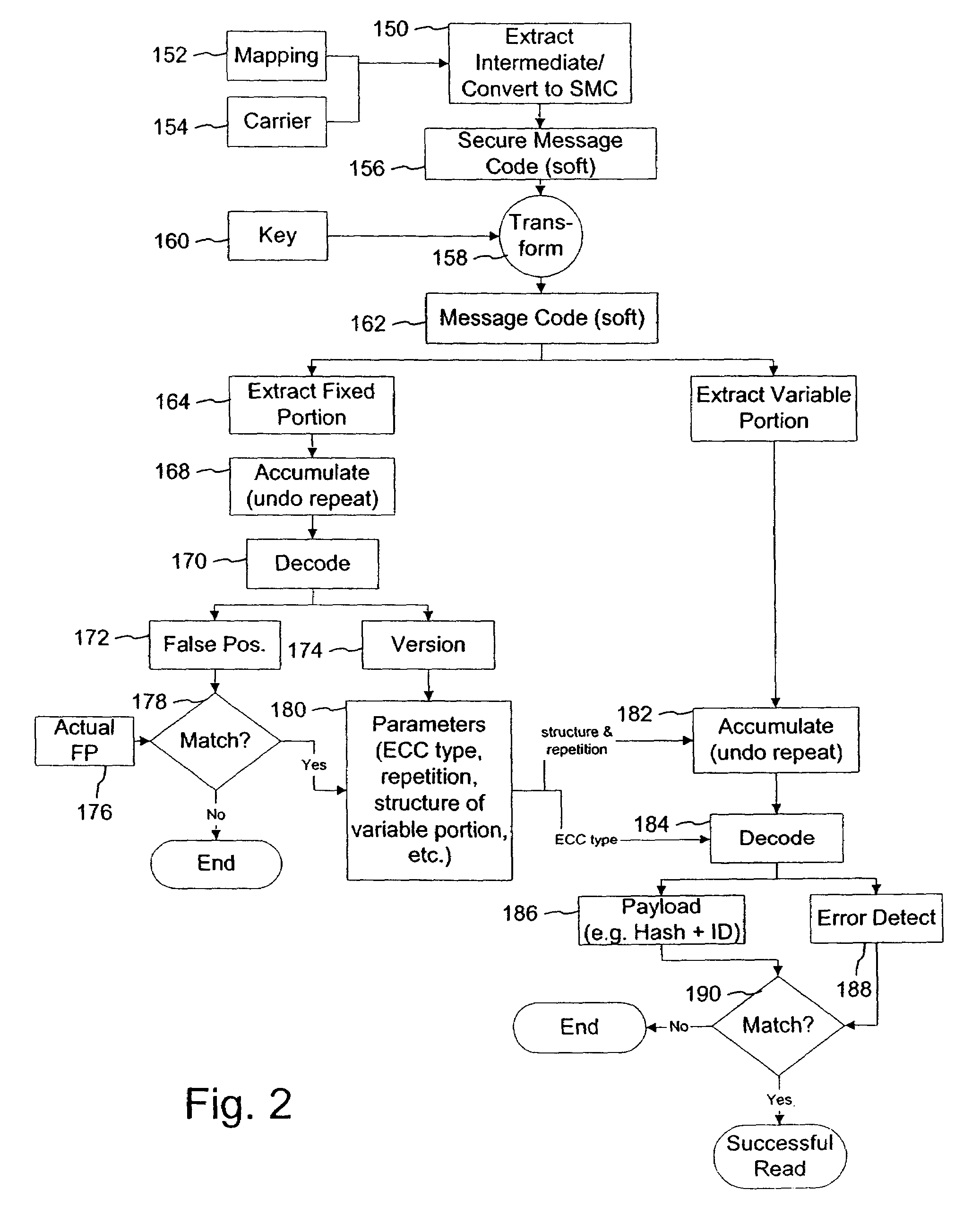
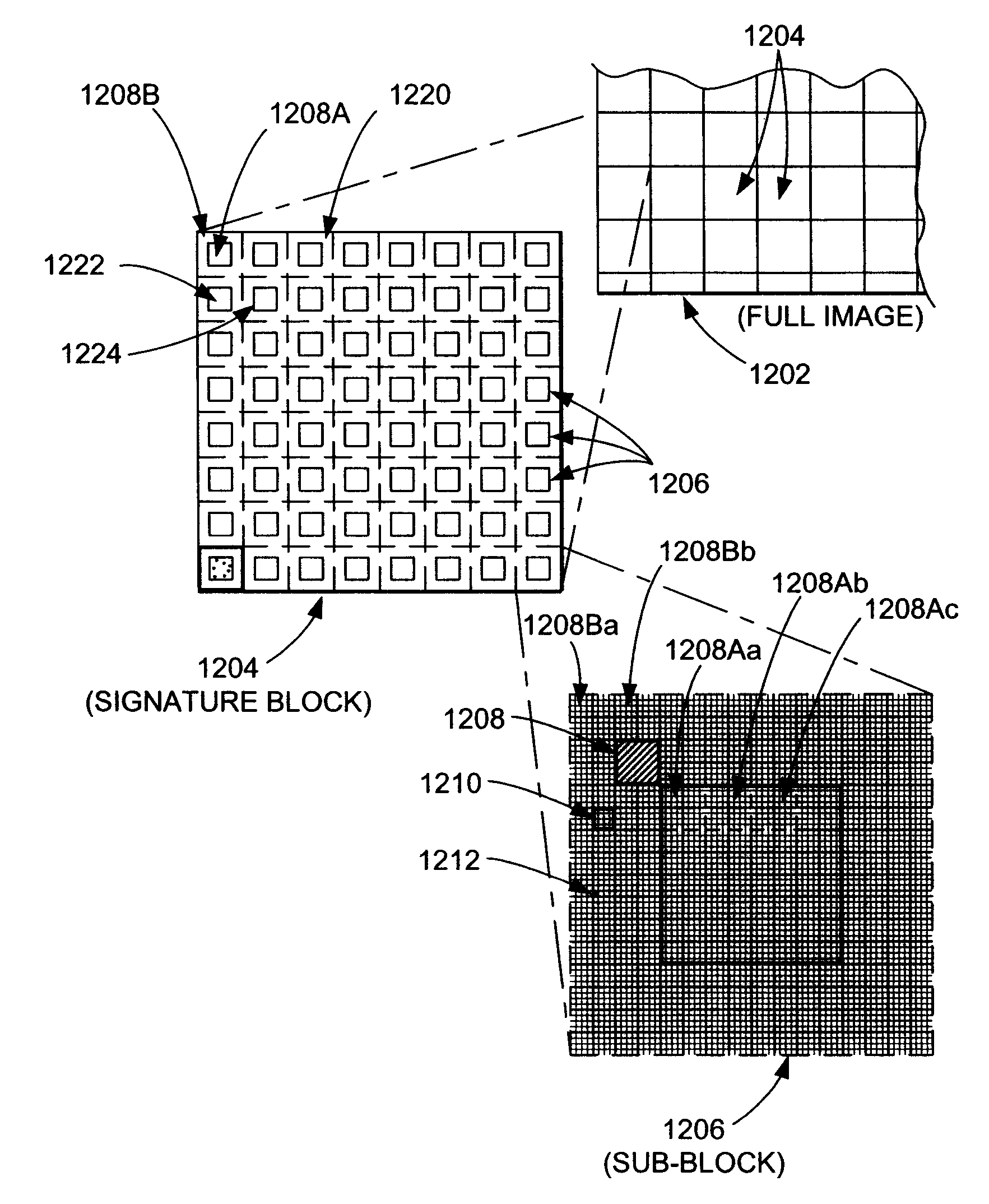
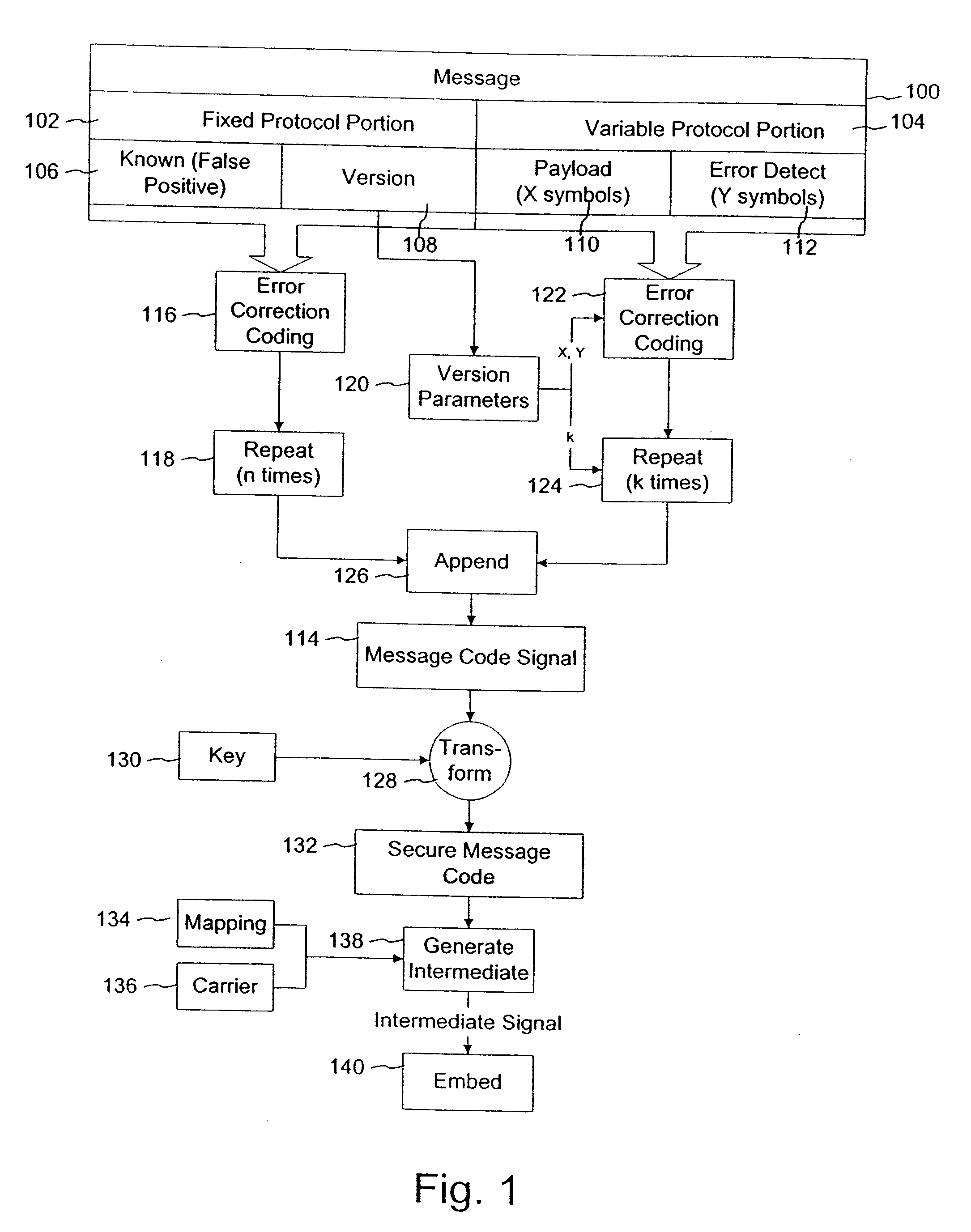
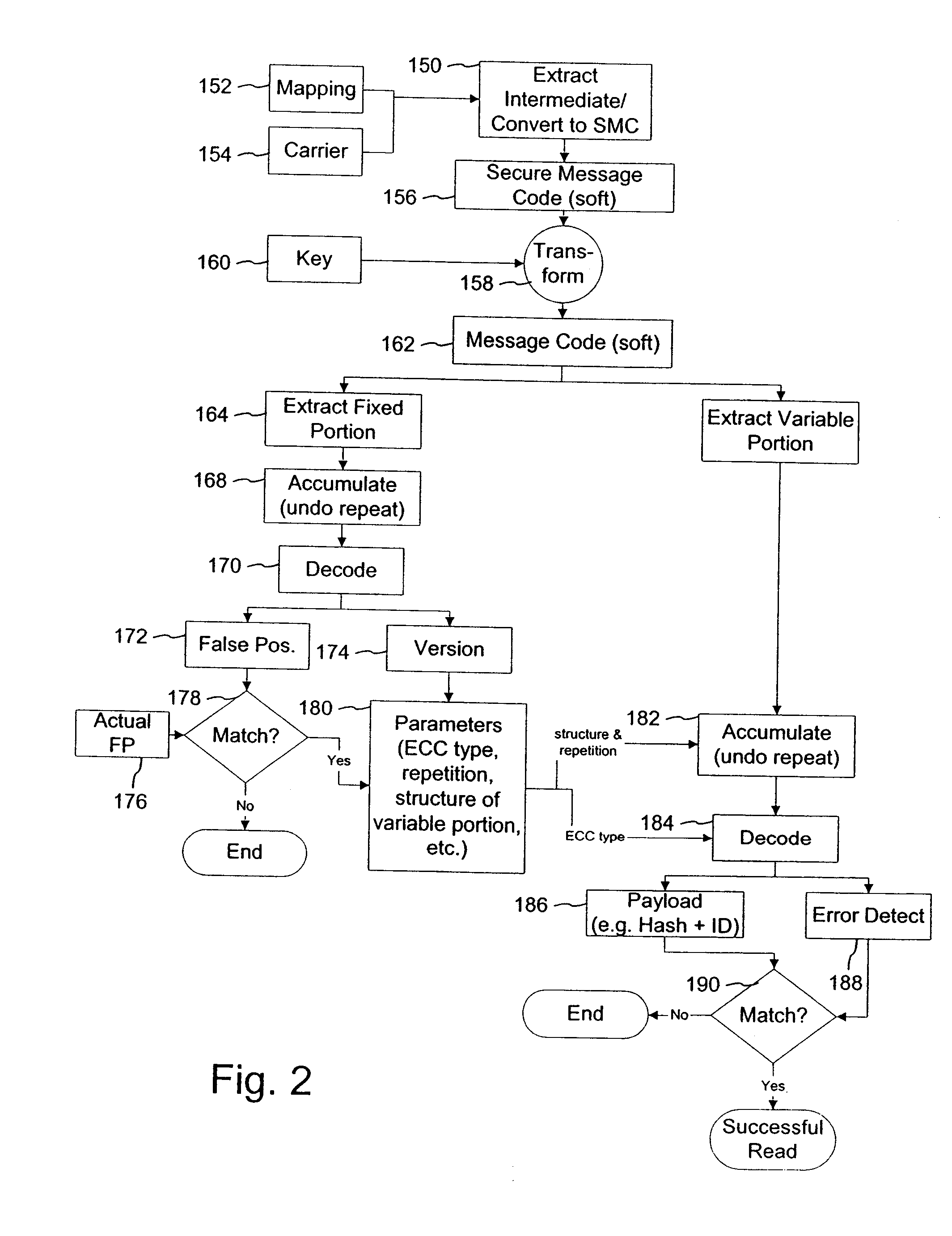
Variable message coding protocols for encoding auxiliary data in media signals
InactiveUS7412072B2Character and pattern recognitionImage watermarkingComputer hardwareCODE protocol
Variable message coding protocols enable greater flexibility in encoding auxiliary data in media signals. One such protocol employs a version identifier that indicates the type of coding used to process an auxiliary data message before it is embedded in a host media signal. This version identifier specifies the type of error robustness coding applied to a variable message. The error robustness coding may be varied to alter the message payload capacity for different versions of auxiliary data embedding and reading systems. Another protocol uses control symbols to specify the format and variable length of the variable message.
Owner:DIGIMARC CORP
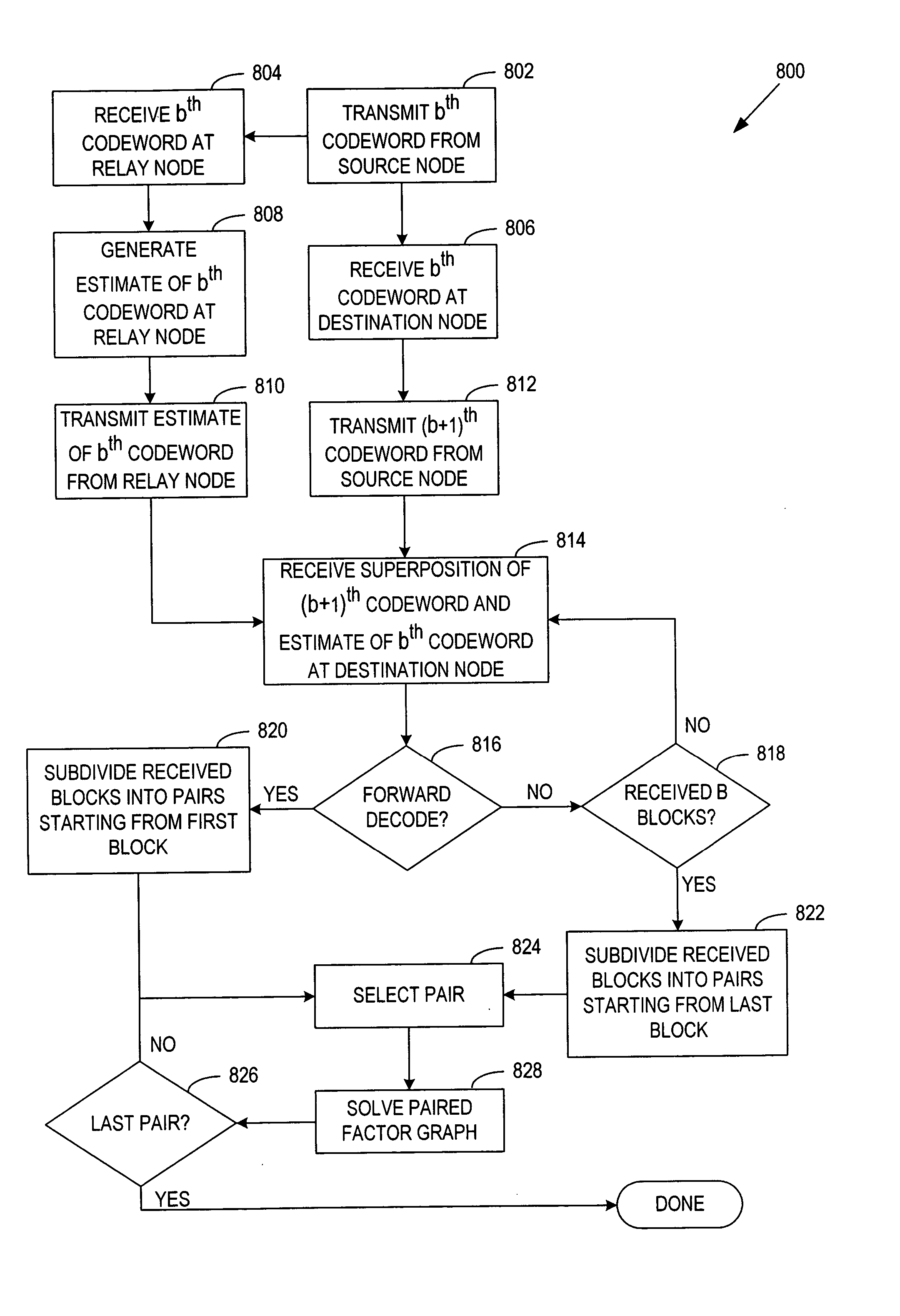
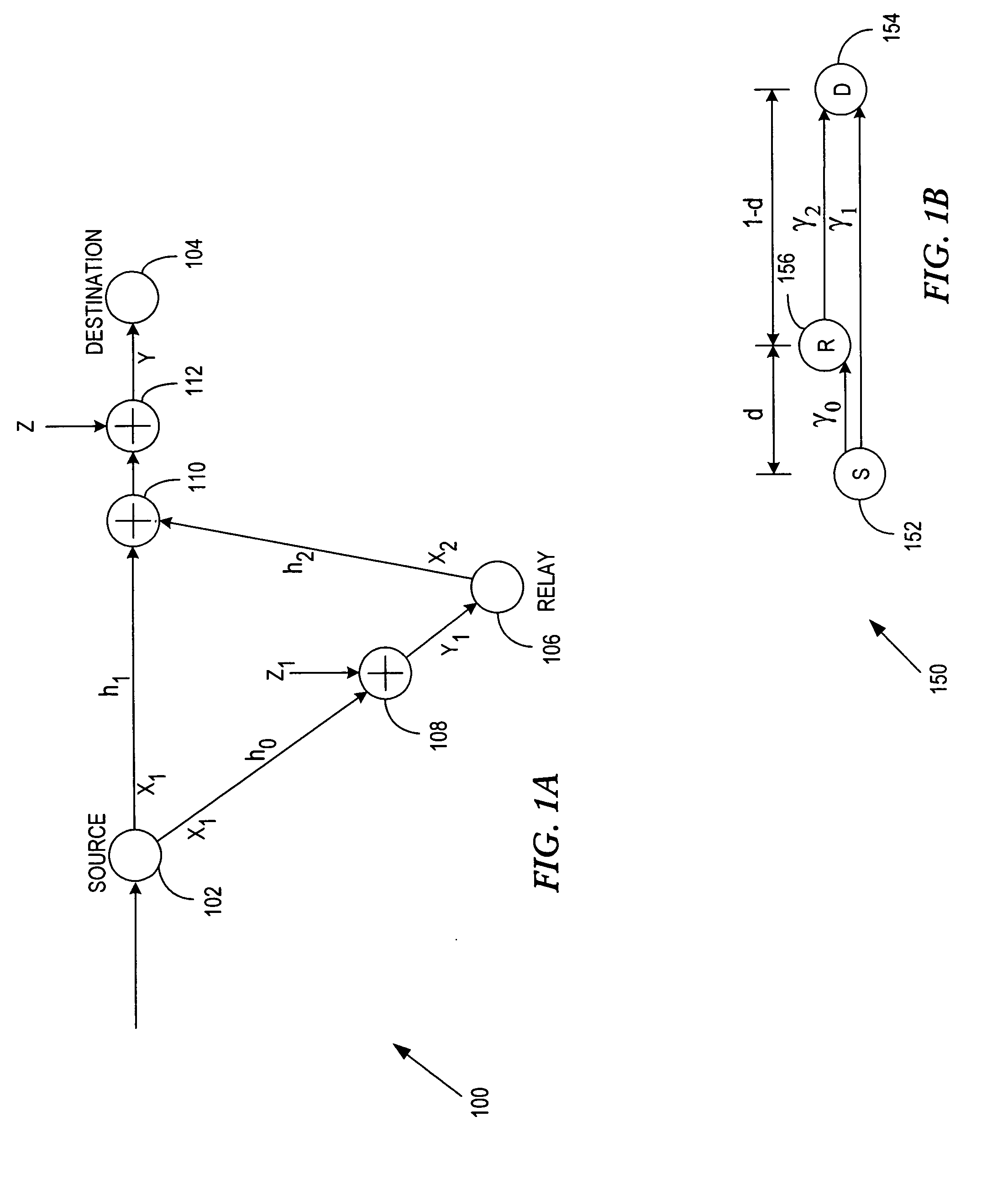
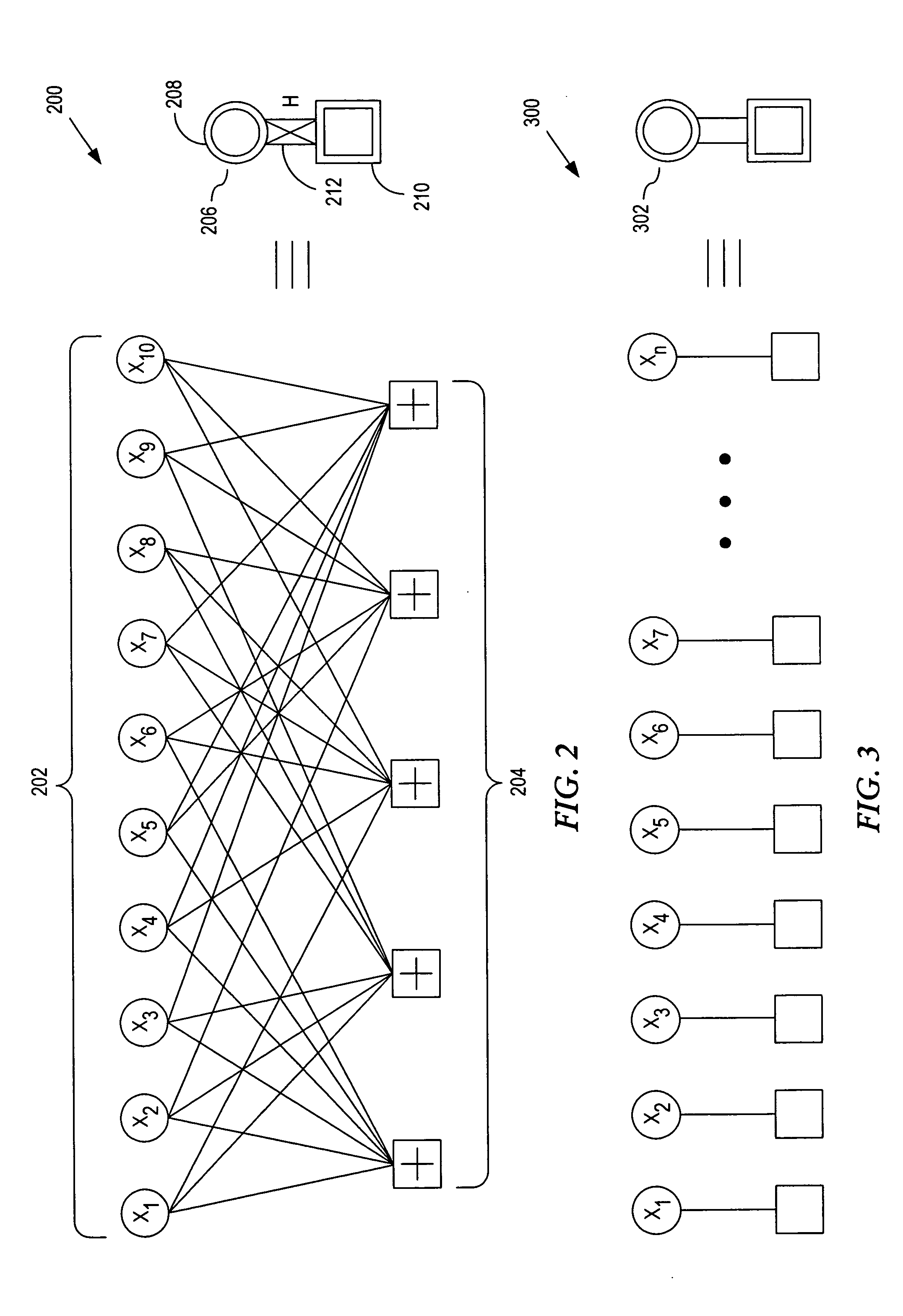
General code design for the relay channel and factor graph decoding
InactiveUS20050265387A1Improve accuracyImprove decoding accuracyError correction/detection using convolutional codesCode conversionParallel computingCODE protocol
A system and method of relay code design and factor graph decoding using a forward and a backward decoding scheme. The backward decoding scheme exploits the idea of the analytical decode-and-forward coding protocol and hence has good performance when the relay node is located relatively close to the source node. The forward decoding scheme exploits the idea of the analytical estimate-and-forward protocol and hence has good performance when the relay node is located relatively far from the source node. The optimal decoding factor graph is first broken into partial factor graphs and then solved iteratively using either the forward or backward decoding schemes.
Owner:NOKIA CORP
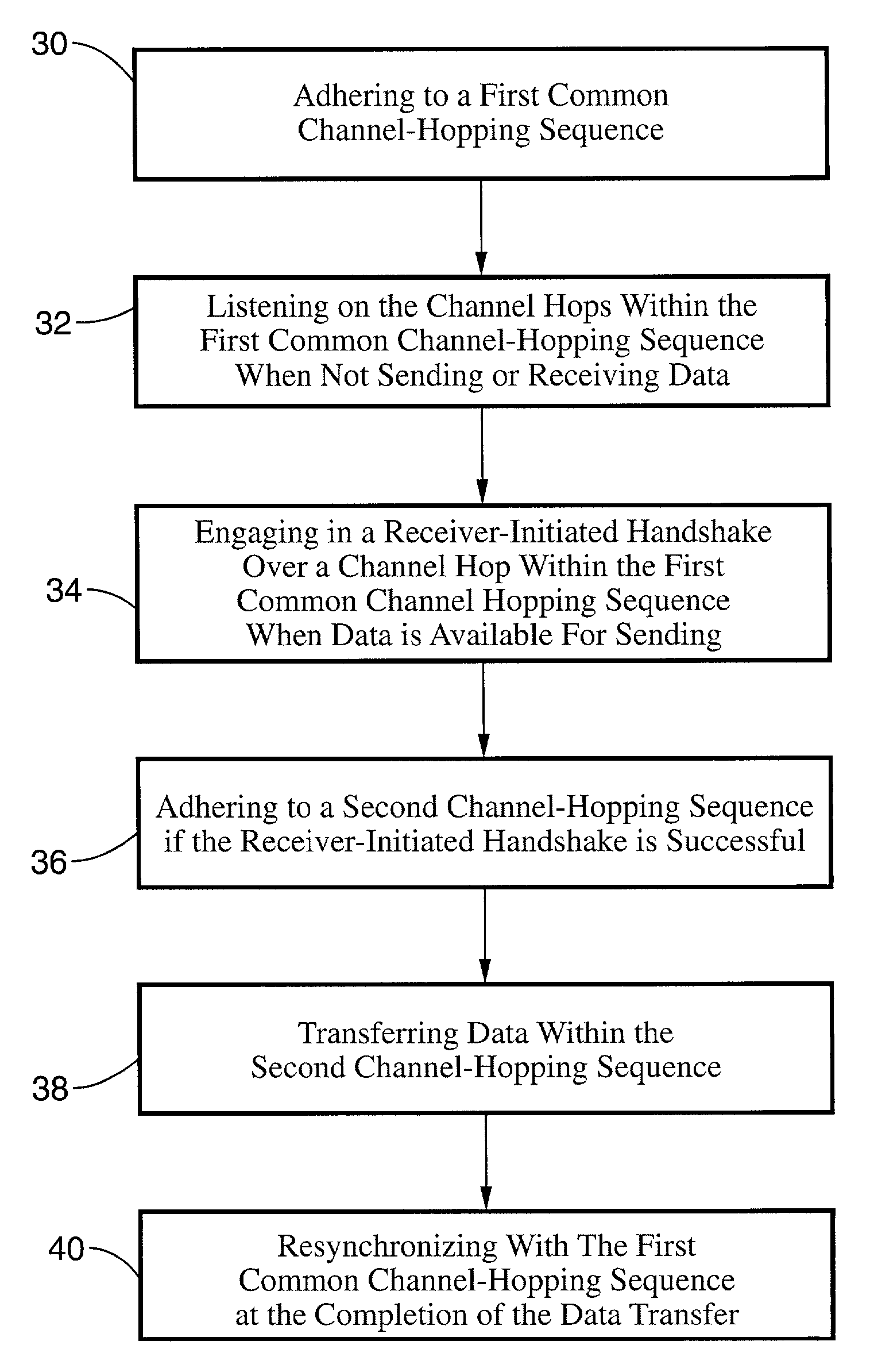
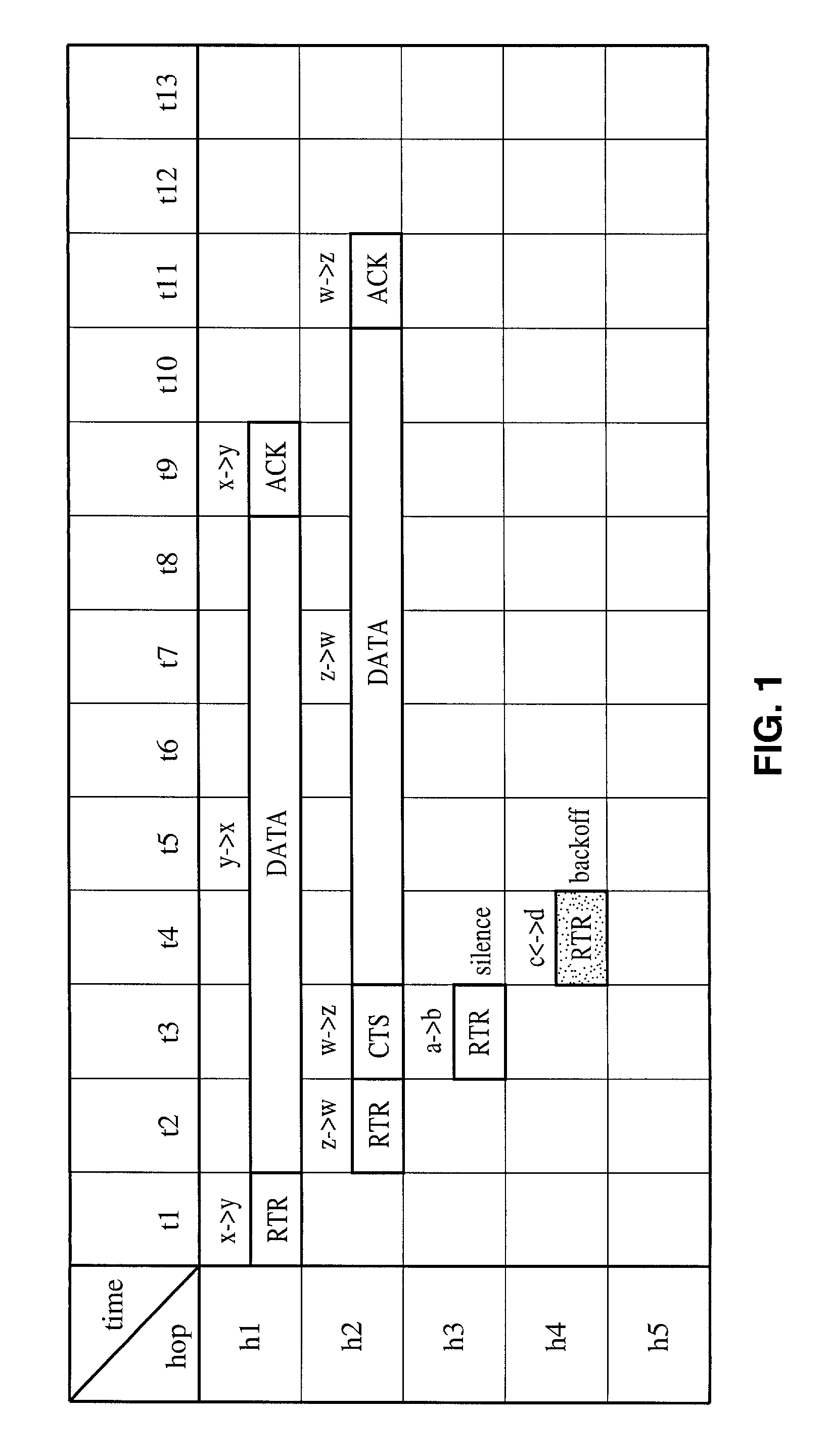
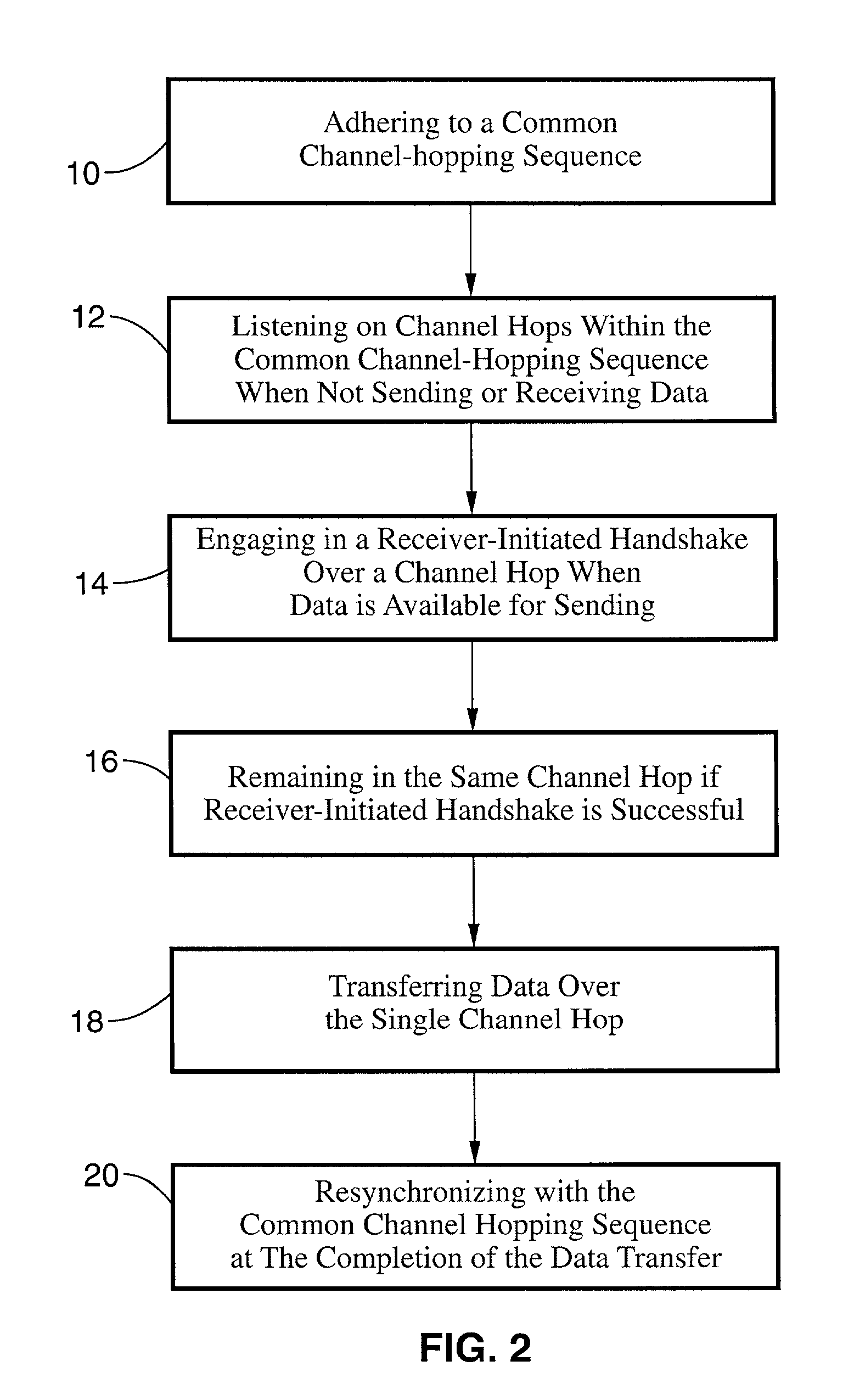
Receiver-initiated channel-hopping (RICH) method for wireless communication networks
ActiveUS7002910B2Improve communication throughputLow Latency FeaturesError preventionTransmission systemsData nodeData transmission
A family of medium-access (MAC) collision-avoidance receiver-initiated channel-hopping (RICH) protocols which do not rely on carrier-sensing, or unique codes to each node within the network. The RICH protocol requires that each network nodes adhere to a common channel-hopping sequence, and that nodes that are not in a state of sending or receiving data will listen on the common channel hop. To send data nodes enter into a receiver-initiated dialogue over the channel-hop at the time at which a data transmission is needed. Nodes which succeed in performing the collision-avoidance handshake remain in the same channel-hop for the remainder of the data transfer, while the remaining nodes continue with the common channel hopping sequence. The described RICH protocols are capable of providing collision-free operation even in the presence of hidden terminals.
Owner:RGT UNIV OF CALIFORNIA
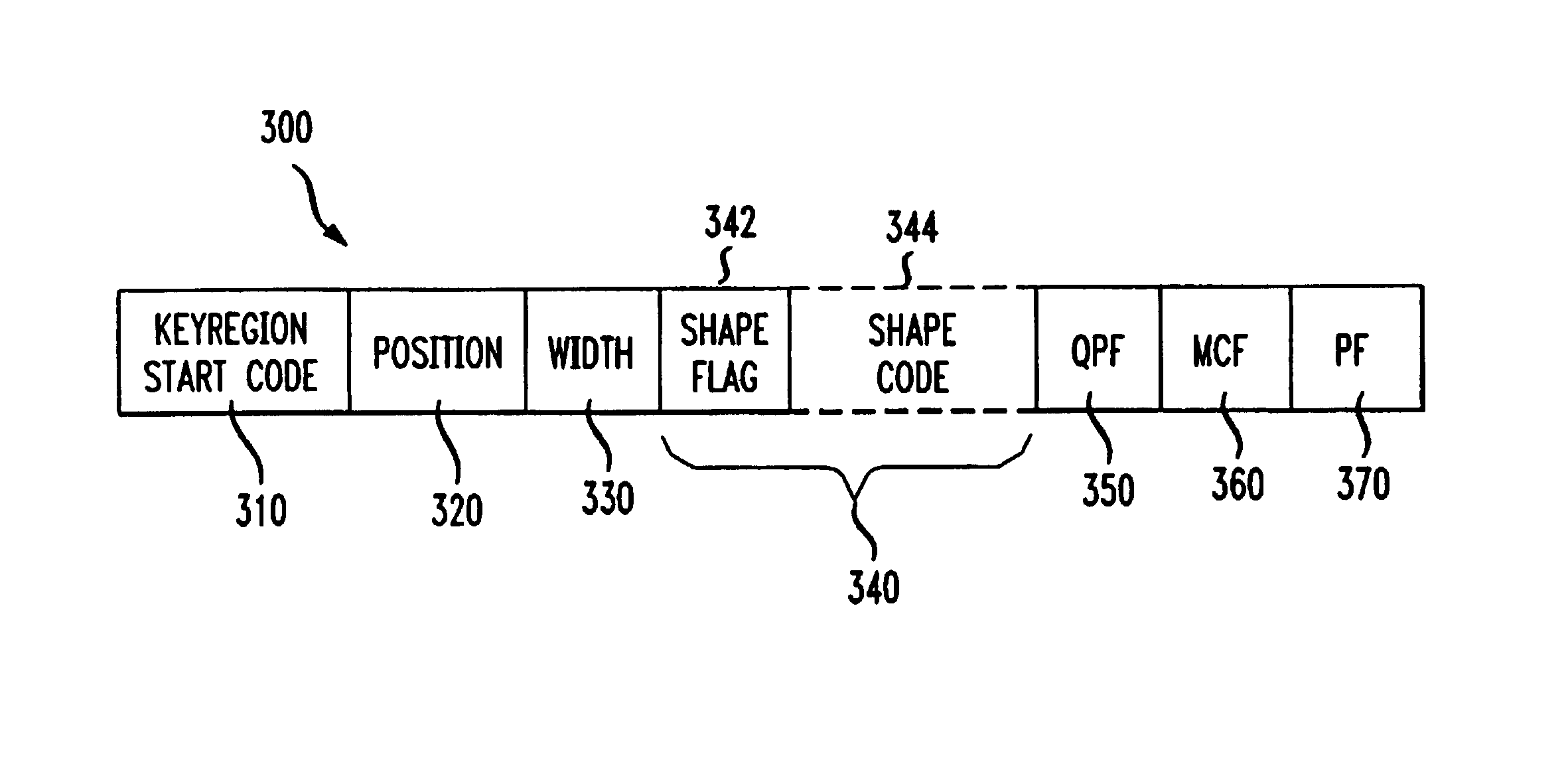
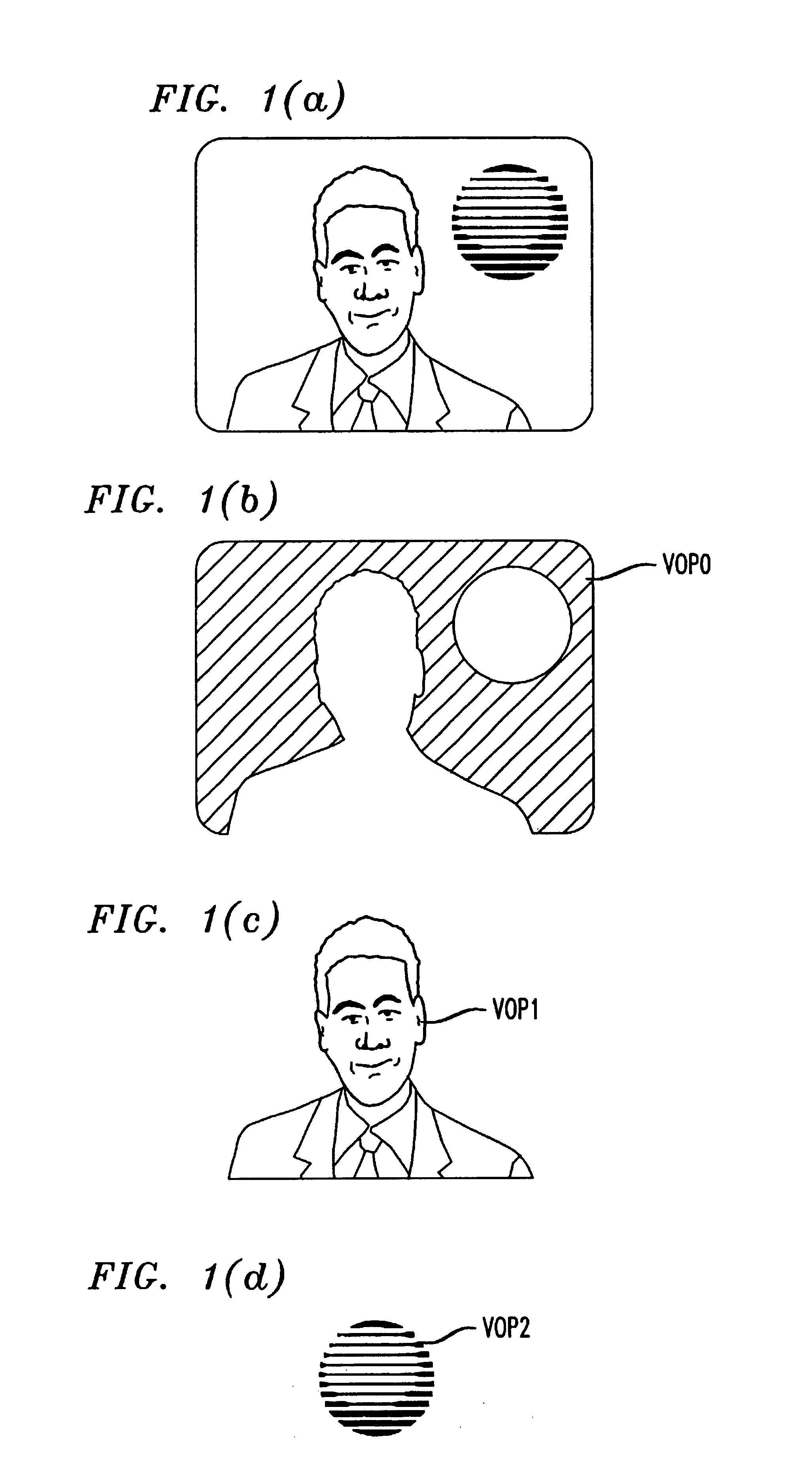
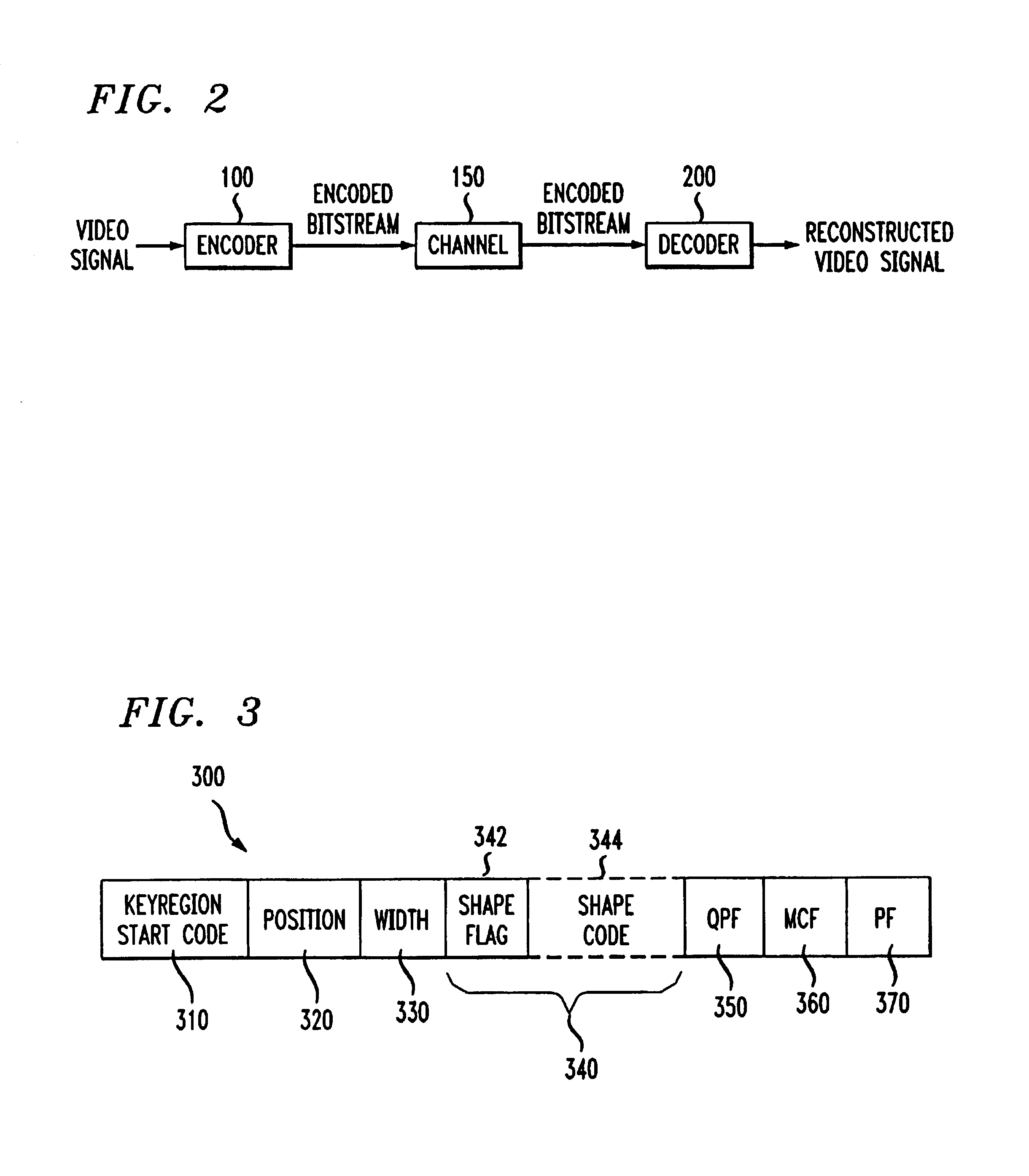
Video objects coded by keyregions
InactiveUS7076106B2Color television with pulse code modulationColor television with bandwidth reductionObject codeCODE protocol
A coding protocol provides for coding video data that has been organized as video objects. The protocol provides a keyregion to permit coding of a region of data within the video object having common attributes. According to the protocol a keyregion is identified by a keyregion header, which includes a resync marker that uniquely identifies the keyregion header, a keyregion position signal indicating an origin and a size of the keyregion; and data of the common attribute. Data following the keyregion is coded according to the common attribute.
Owner:HASKELL BARIN GEOFFRY +2
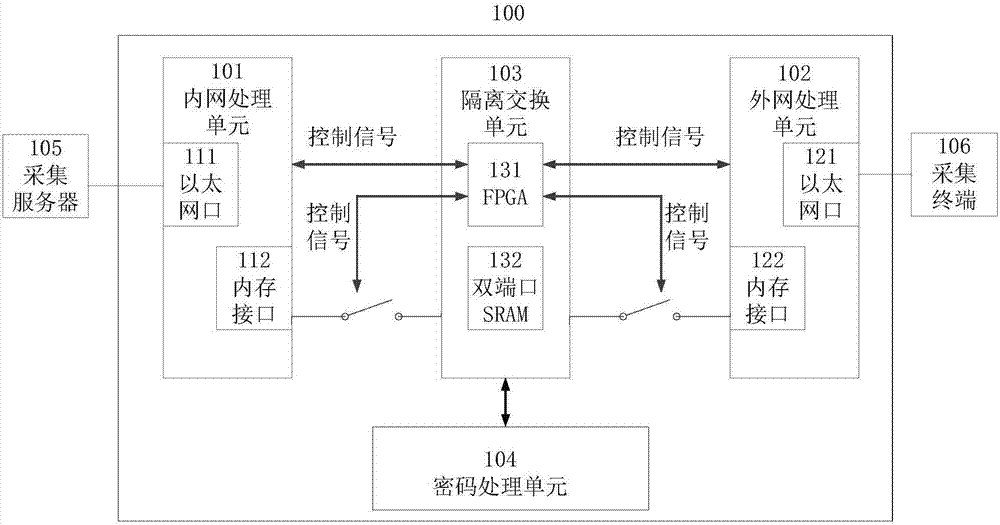
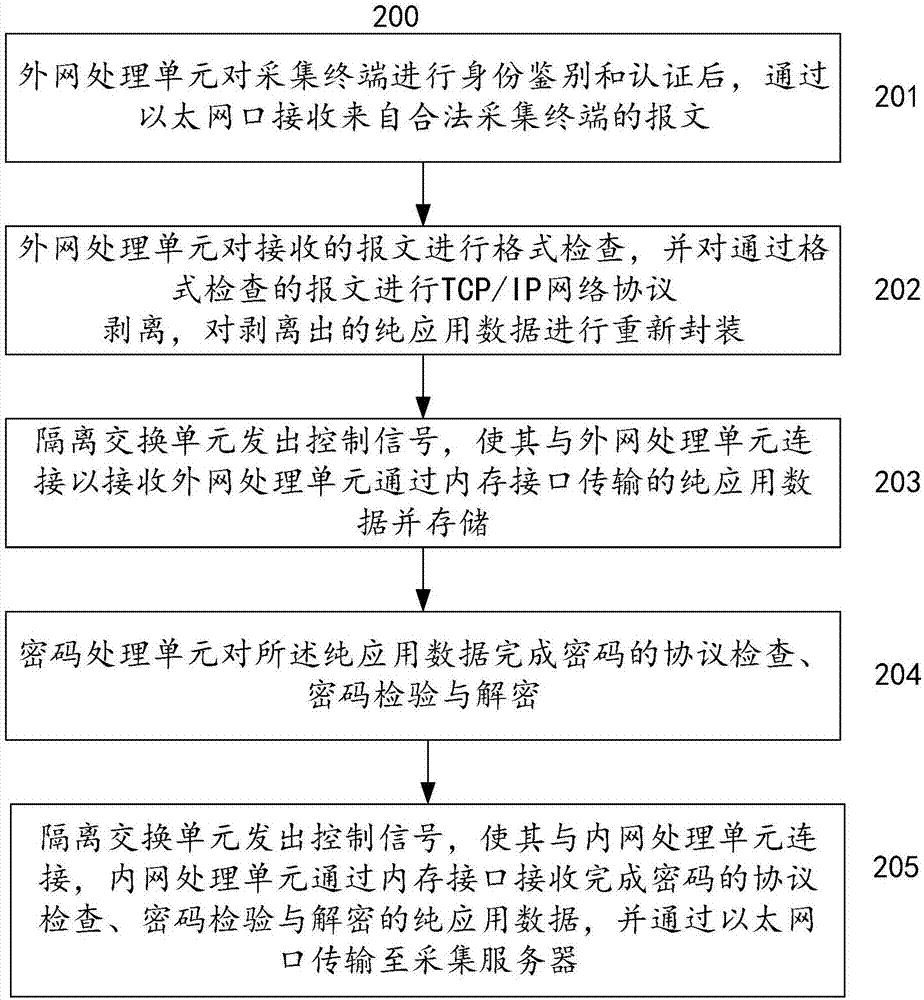
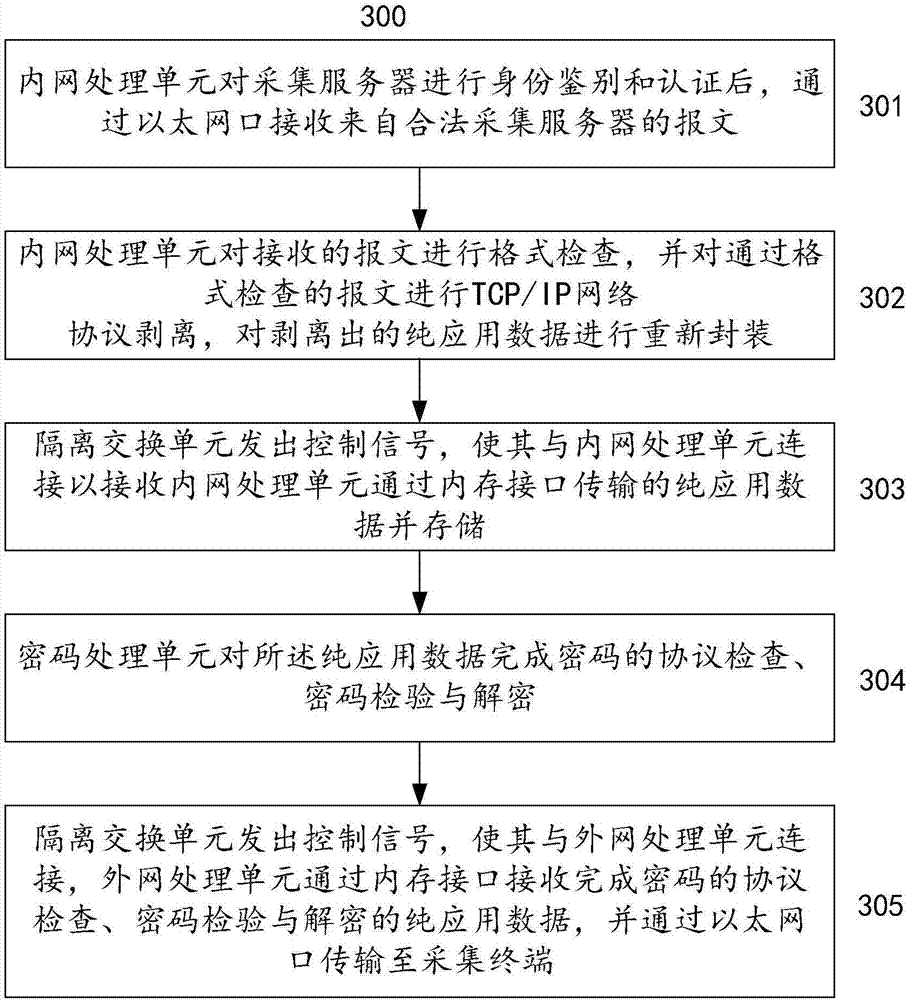
Power consumption information acquisition system safety isolation gateway and application method thereof
InactiveCN106941494AGuaranteed uptimePerfect and effective safety protection measuresTransmissionNetwork processing unitComputer terminal
The invention relates to a power consumption information acquisition system safety isolation gateway and an application method thereof; the safety isolation gateway comprises the following units: an internal network processing unit used for receiving a message sent by an acquisition server, sending packaged pure application data to an isolation exchange unit, and receiving the data transmitted by an external network processing unit from the isolation exchange unit; the external network processing unit used for receiving the message sent by the acquisition terminal, sending the packaged pour application data to the isolation exchange unit, and receiving the data transmitted by the internal network processing unit from the isolation exchange unit; the isolation exchange unit arranged between the internal and external network processing units and used for storing the pure application data transmitted by the internal and external network processing units, thus realizing controllable exchange of the pure application data between the internal and external network processing units; a code processing unit used for carrying out code protocol inspection for the data processed by the isolation exchange unit in a flow pass mode, and providing code examination and decryption services.
Owner:CHINA ELECTRIC POWER RES INST +1
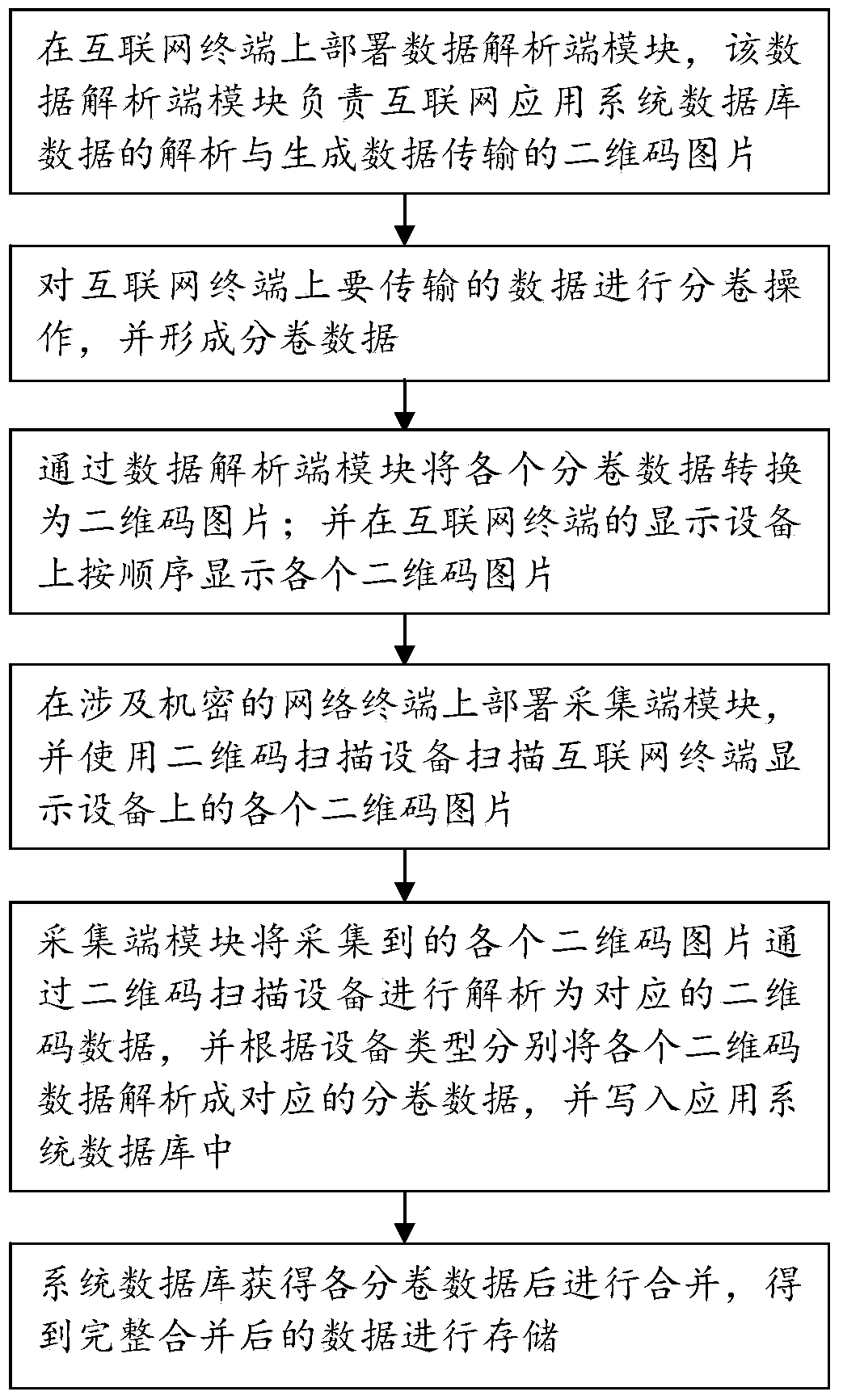
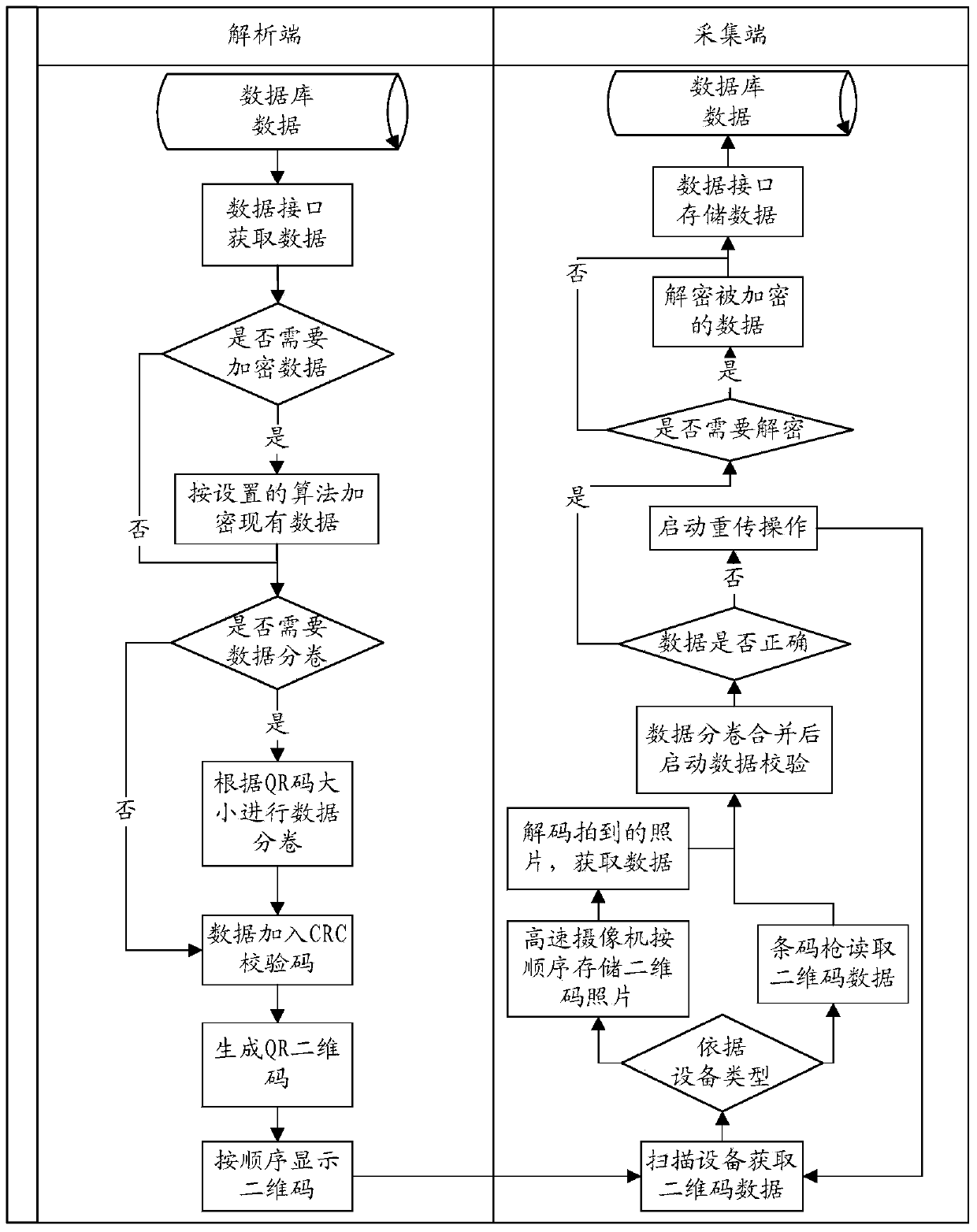
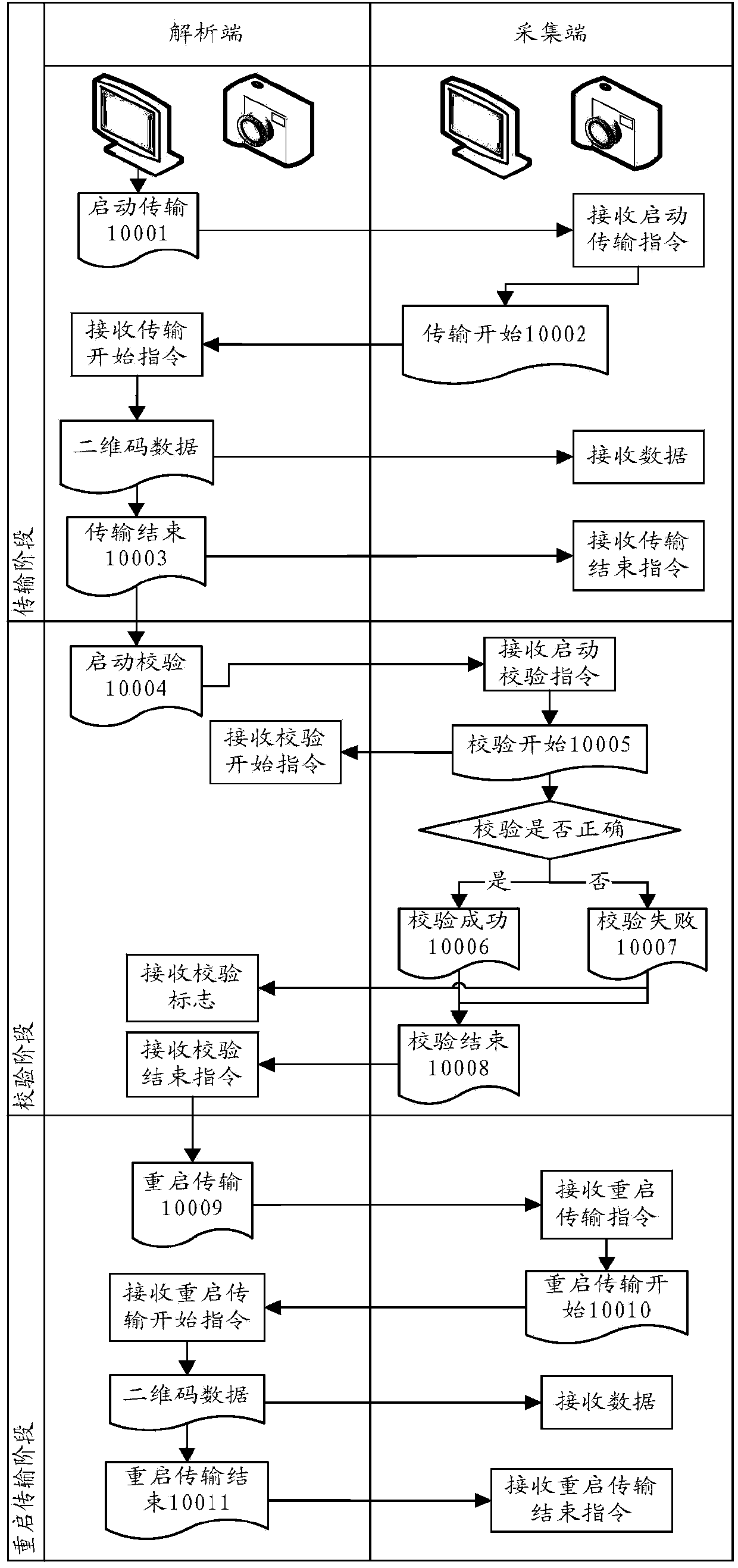
Method for transmitting large data flow through two-dimension code
ActiveCN103731589AAchieve synchronizationImprove work efficiencyRecord carriers used with machinesPictoral communicationParallel computingCODE protocol
The invention provides a method for transmitting a large data flow through a two-dimension code. The method achieves a bidirectional handshake process between a data analysis end and a collecting end through a two-dimension bar code protocol code. The protocol code is mainly used for a bidirectional handshake protocol of a transmission system and controls the operations such as transmission and retransmission. A starting end of the protocol code comprises the analysis end and the collecting end, and the two ends can respectively indicate the current operating state to the opposite side through the respective protocol code, and inform the opposite side of the next step of operation process. For transmission of a large data flow of two-dimension code data, dividing operation is carried out on the data, synchronization of inside and outside physical-isolation inter-network application system databases is achieved, the complex methods like disc recording are omitted, a large data flow of data can be transmitted, and work efficiency is largely improved.
Owner:LINEWELL SOFTWARE
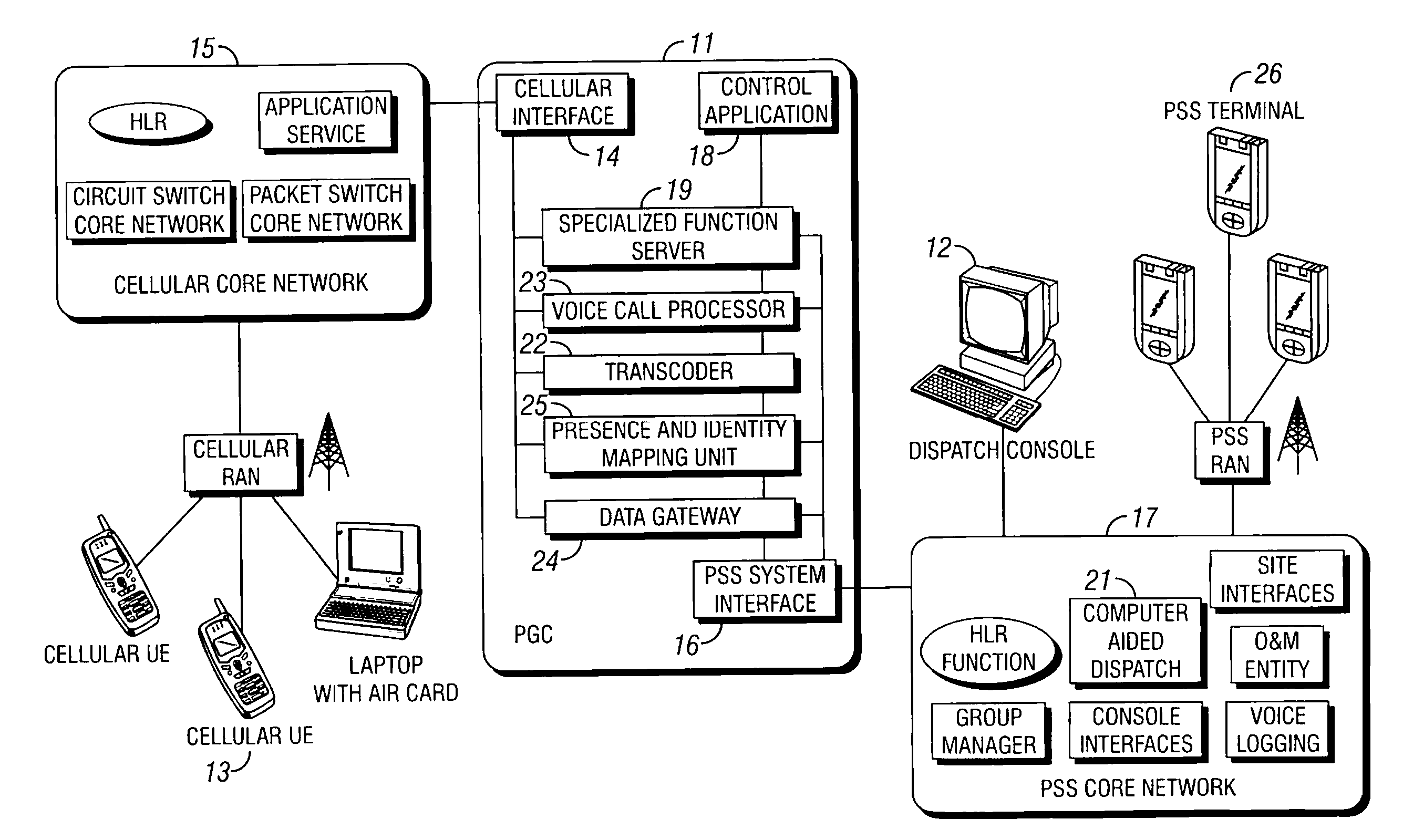
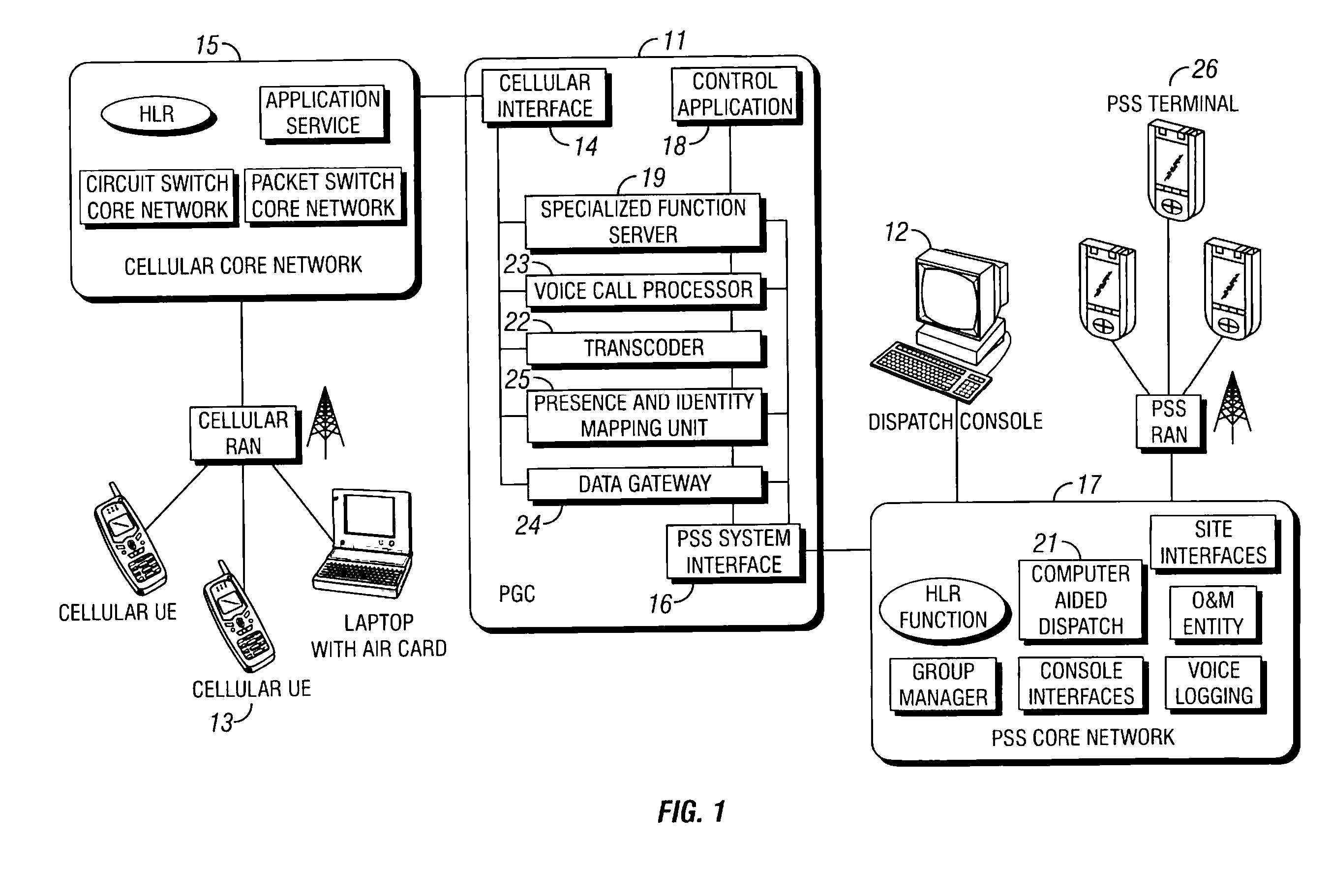
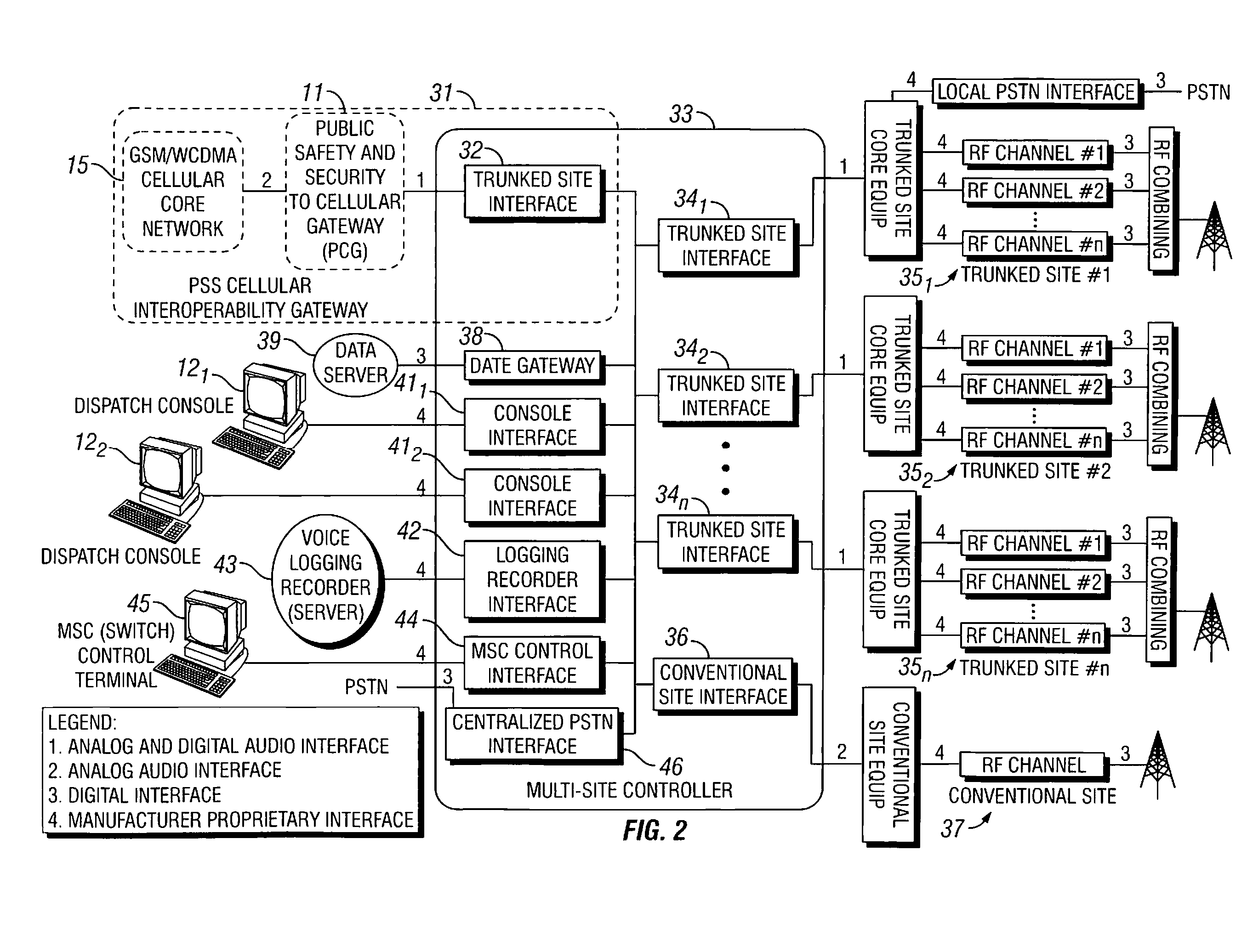
System, method, and gateway for interfacing public safety and security (PSS) systems and cellular communication systems
InactiveUS20080171533A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCall forwardingCODE protocol
A gateway, system, and method for providing seamless communications to Public Safety and Security (PSS) users operating between a PSS communication network and a cellular communication network irrespective of access technology or switching method. The gateway includes a presence and identity mapping unit for mapping a PSS user identity utilized in the PSS network to a cellular user identity utilized in the cellular network. The gateway provides an interface and establishes a session between the PSS network and a PSS user operating in the cellular network utilizing the mapped cellular user identity. A transcoder converts between PSS and cellular voice coding protocols. A data gateway converts between PSS and cellular data protocols. The gateway dynamically switches between voice and data, and provides group calling, call forwarding, and message replay services across the network interface.
Owner:TELEFON AB LM ERICSSON (PUBL)
Variable message coding protocols for encoding auxiliary data in media signals
InactiveUS7778442B2Character and pattern recognitionImage watermarkingComputer hardwareCODE protocol
Variable message coding protocols enable greater flexibility in encoding auxiliary data in media signals. One such protocol employs a version identifier that indicates the type of coding used to process an auxiliary data message before it is embedded in a host media signal. This version identifier specifies the type of error robustness coding applied to a variable message. The error robustness coding may be varied to alter the message payload capacity for different versions of auxiliary data embedding and reading systems. Another protocol uses control symbols to specify the format and variable length of the variable message.
Owner:DIGIMARC CORP
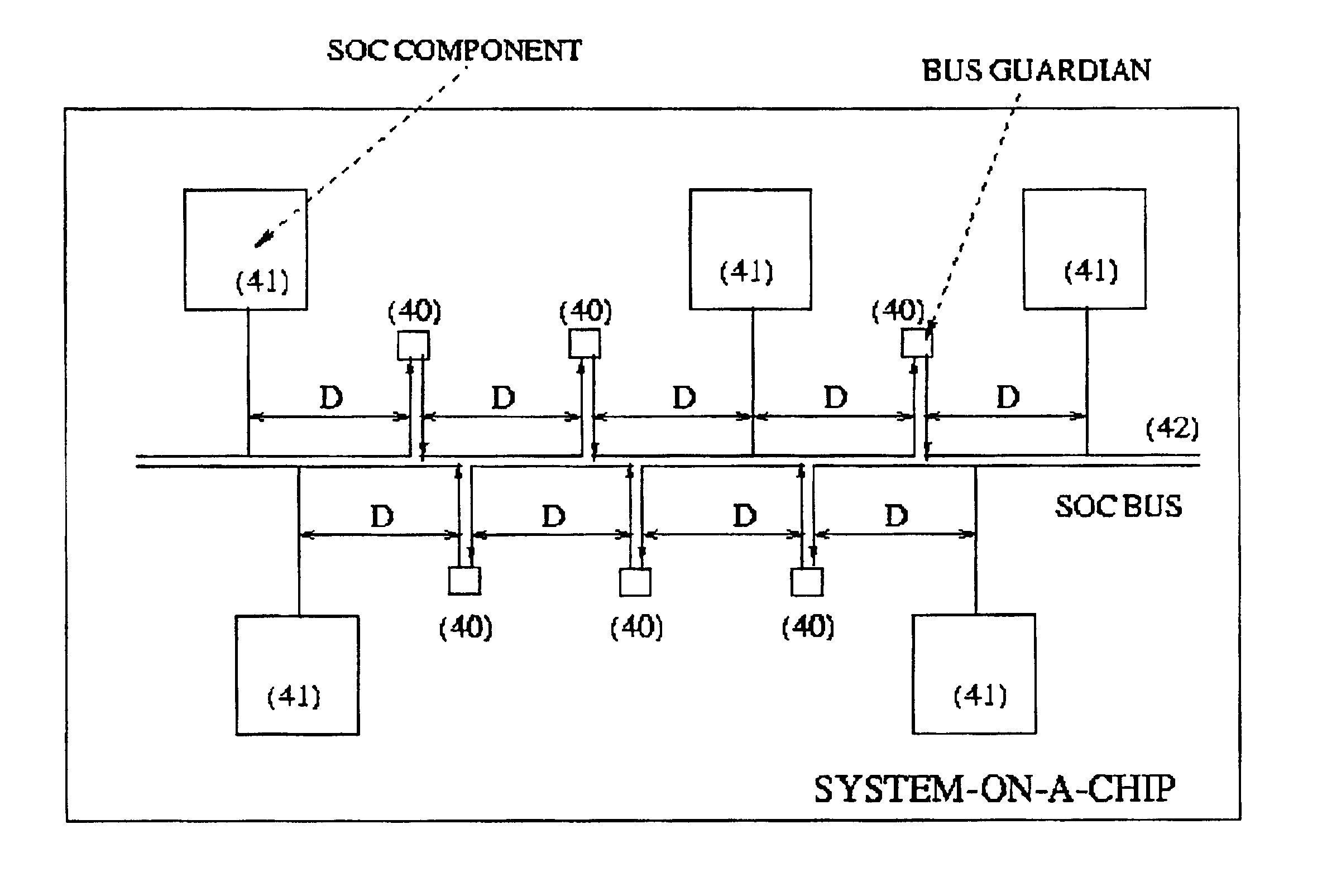
Method and apparatus for online detection and correction of faults affecting system-on-chip buses
InactiveUS6880112B2Error prevention/detection by using return channelCorrect operation testingHardware modulesCODE protocol
This paper presents a methodology for designing System-On-Chip interconnection architectures providing a high level of protection from crosstalk effects. An event driven simulator enriched with fault injection capabilities is exploited to evaluate the dependability level of the system being designed. The simulation environment supports several bus coding protocols and thus designers can easily evaluate different design alternatives. To enhance the dependability level of the interconnection architecture, we propose a distributed bus guardian scheme, where dedicated hardware modules monitor the integrity of the information transmitted over the bus and provide error correction mechanisms.
Owner:NEC CORP
Diagnositic and treatmetnt tool and method for electronic recording and indexing patient encounters for allowing instant search of patient history
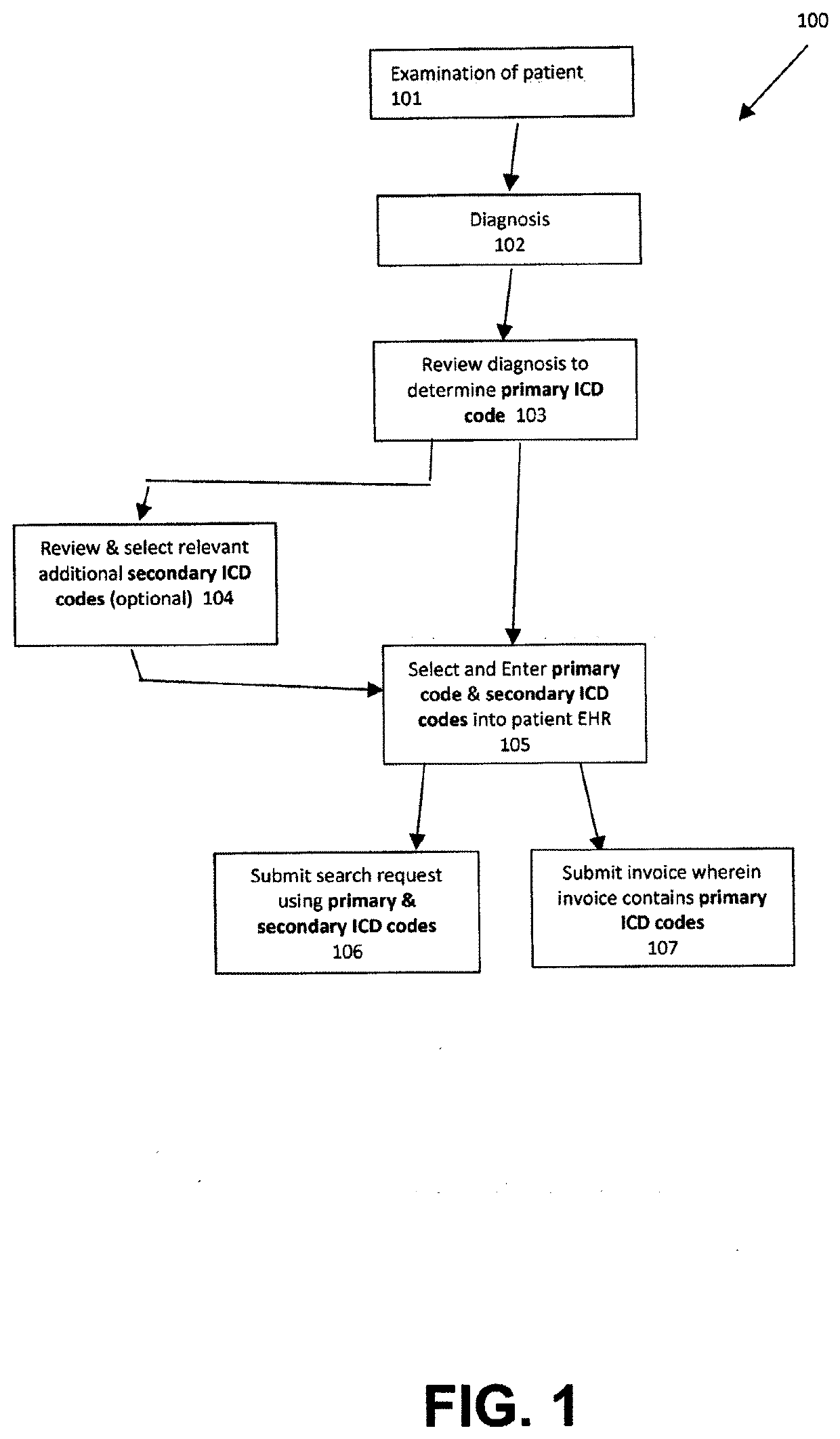
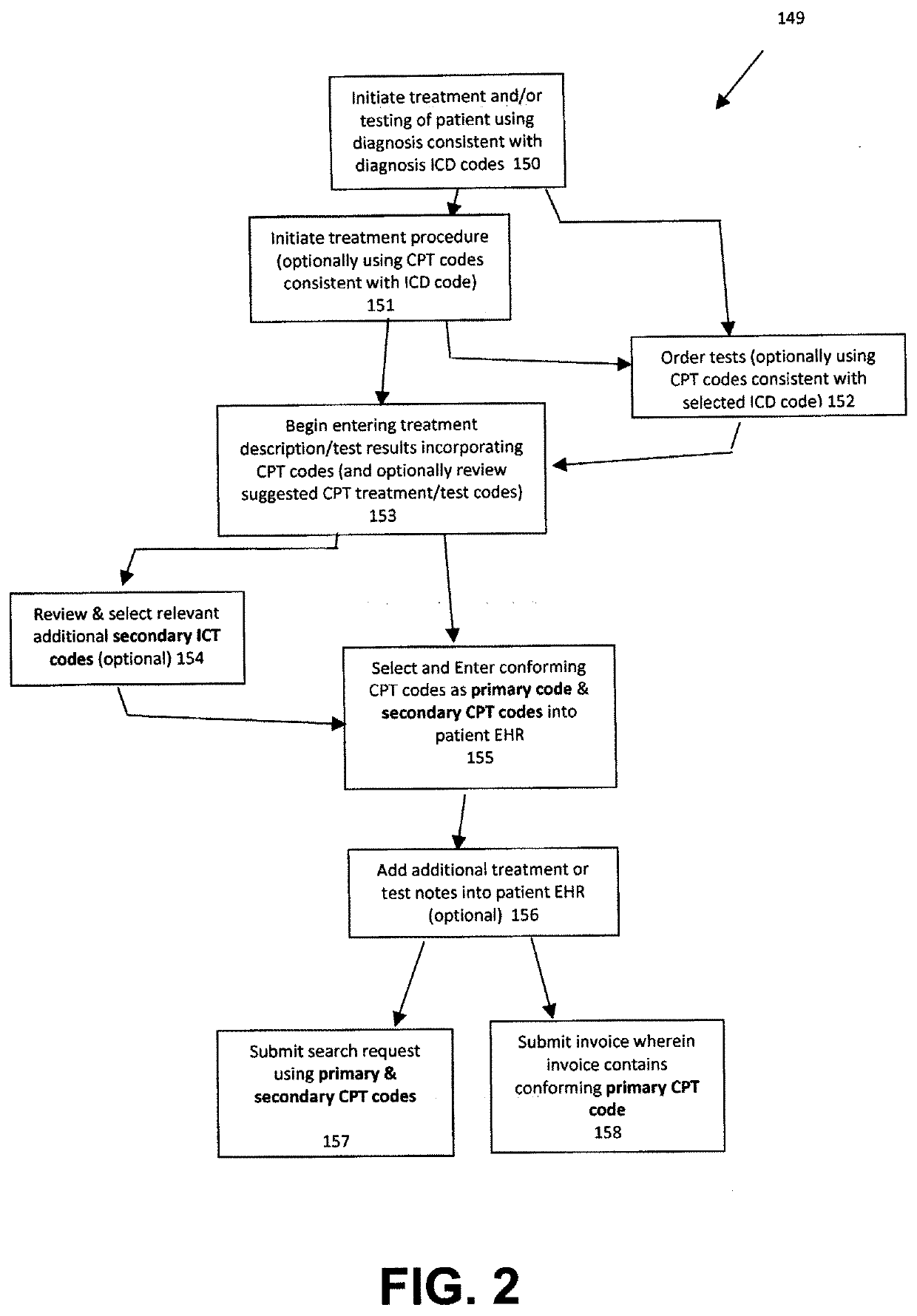
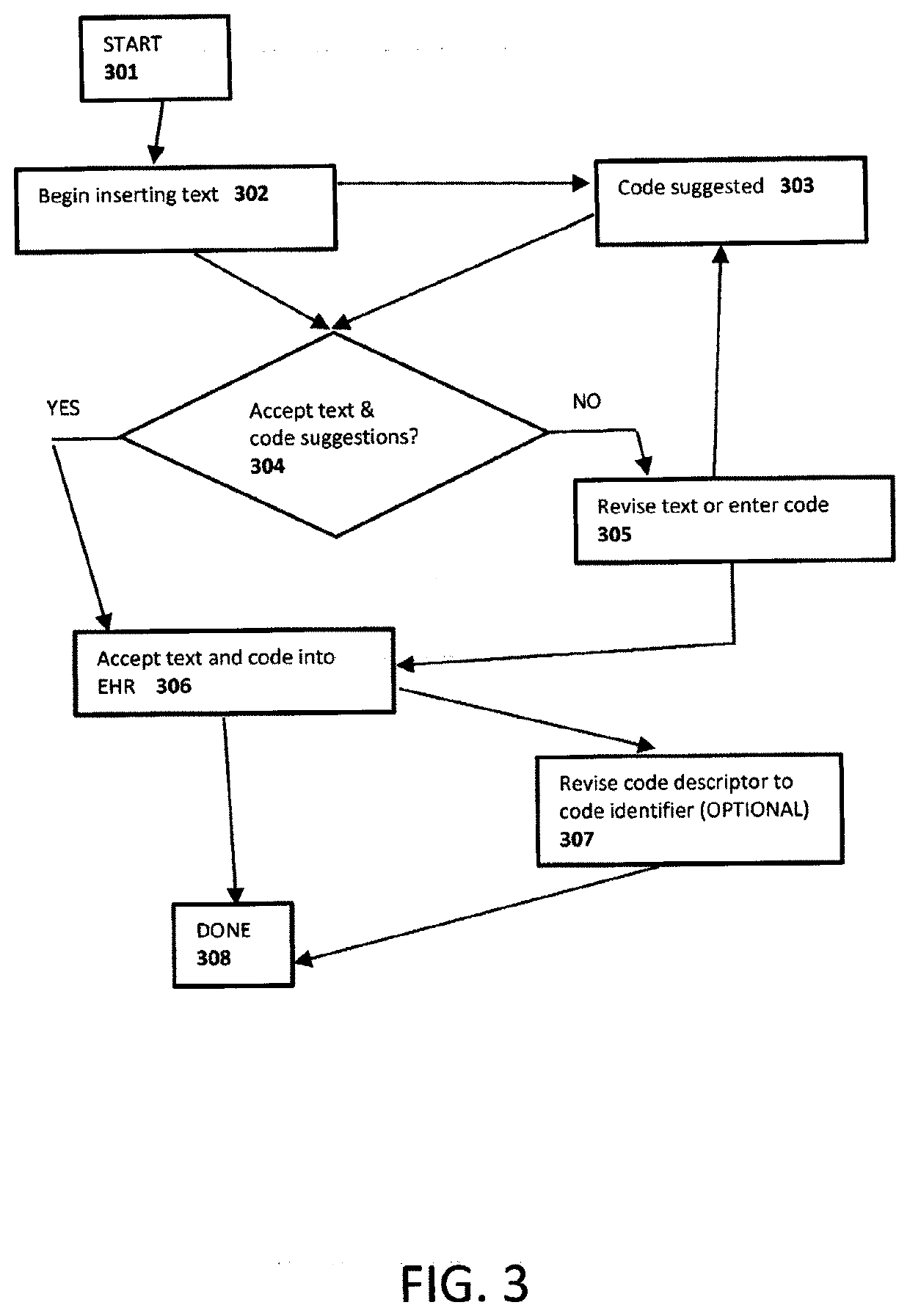
InactiveUS20200350072A1Effective treatmentAccurate currentRespiratory organ evaluationSpeech recognitionPatient diagnosisCODE protocol
Device and method for improved diagnosis and treatment of patients. Detailed coding protocols are instantly assigned to diagnoses and treatment plans created by clinicians based upon initial patient encounter. Past patient records (EHR) can be instantly searched using the assigned codes during the patient encounter, thereby allowing the clinician to make a more complete diagnosis and plan of treatment. The search of past patient records utilizes the assigned codes as a search index thereby filtering out unrelated-non relevant patient medical history. Clinician notations of symptoms and possible diagnosis can be utilized for an expanded correlation to codes of medical code protocols relevant to treatment or tests. This expanded listing of codes can be displayed to the clinician during the patient encounter for evaluation in determining a diagnosis. Correlated medical codes can be disclosed with calculated or past recorded reimbursement information.
Owner:MIRR LLC
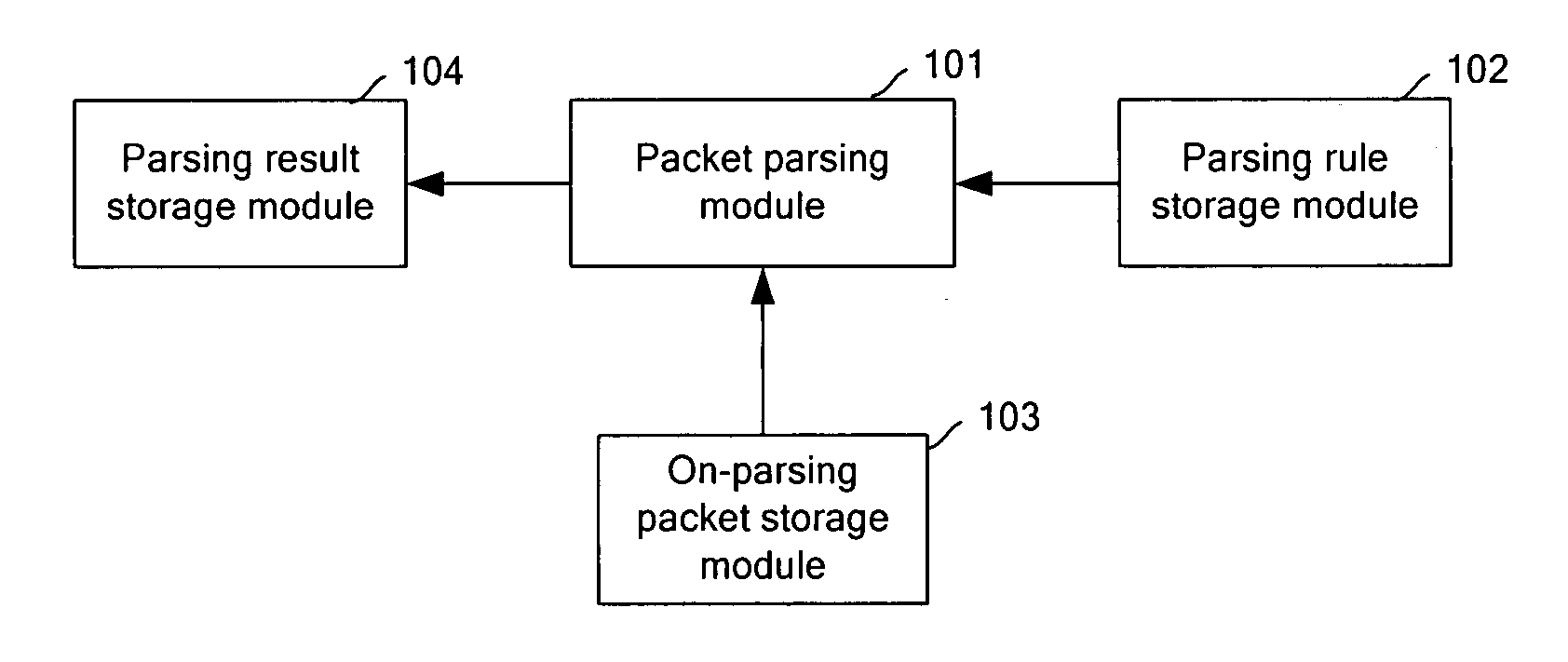
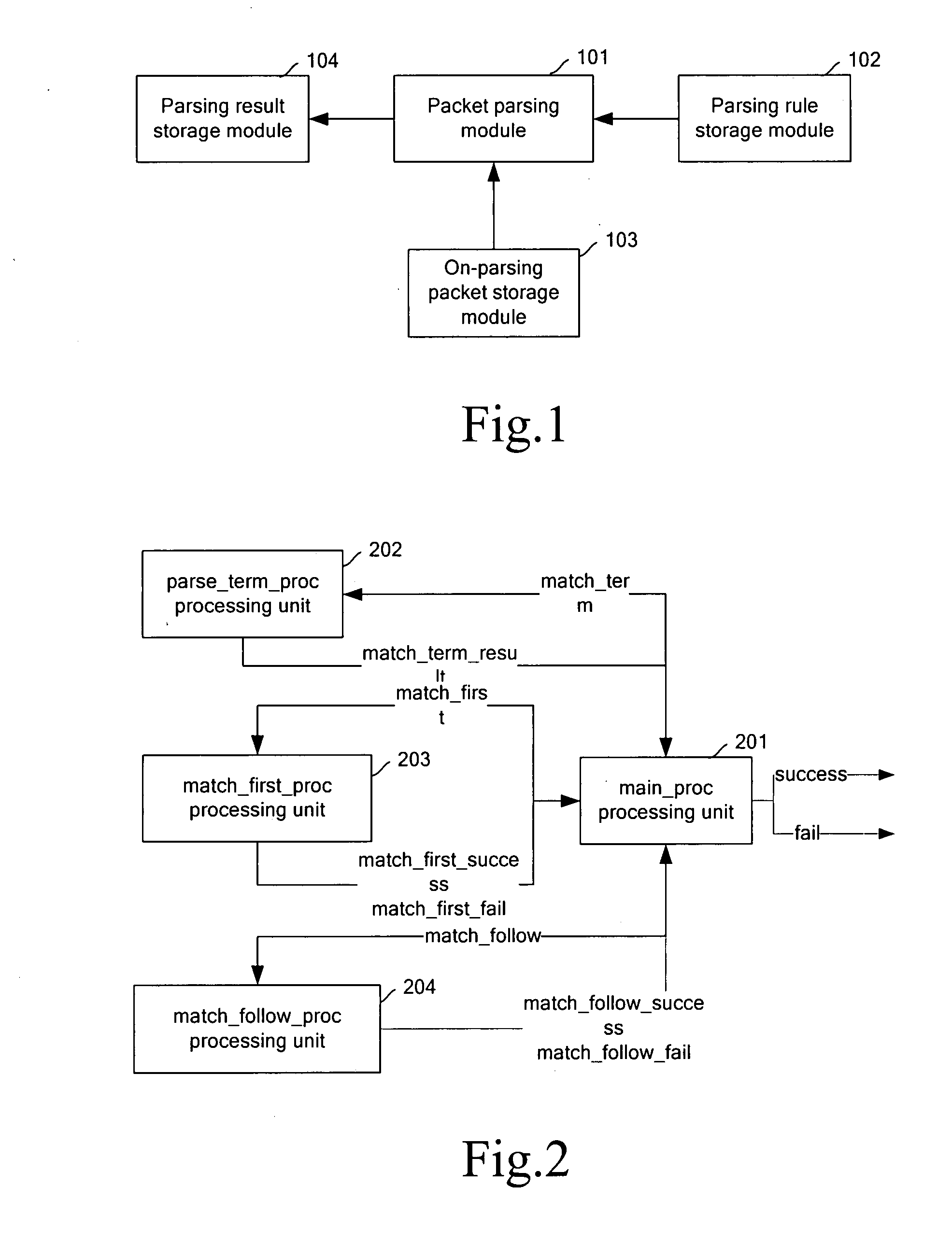
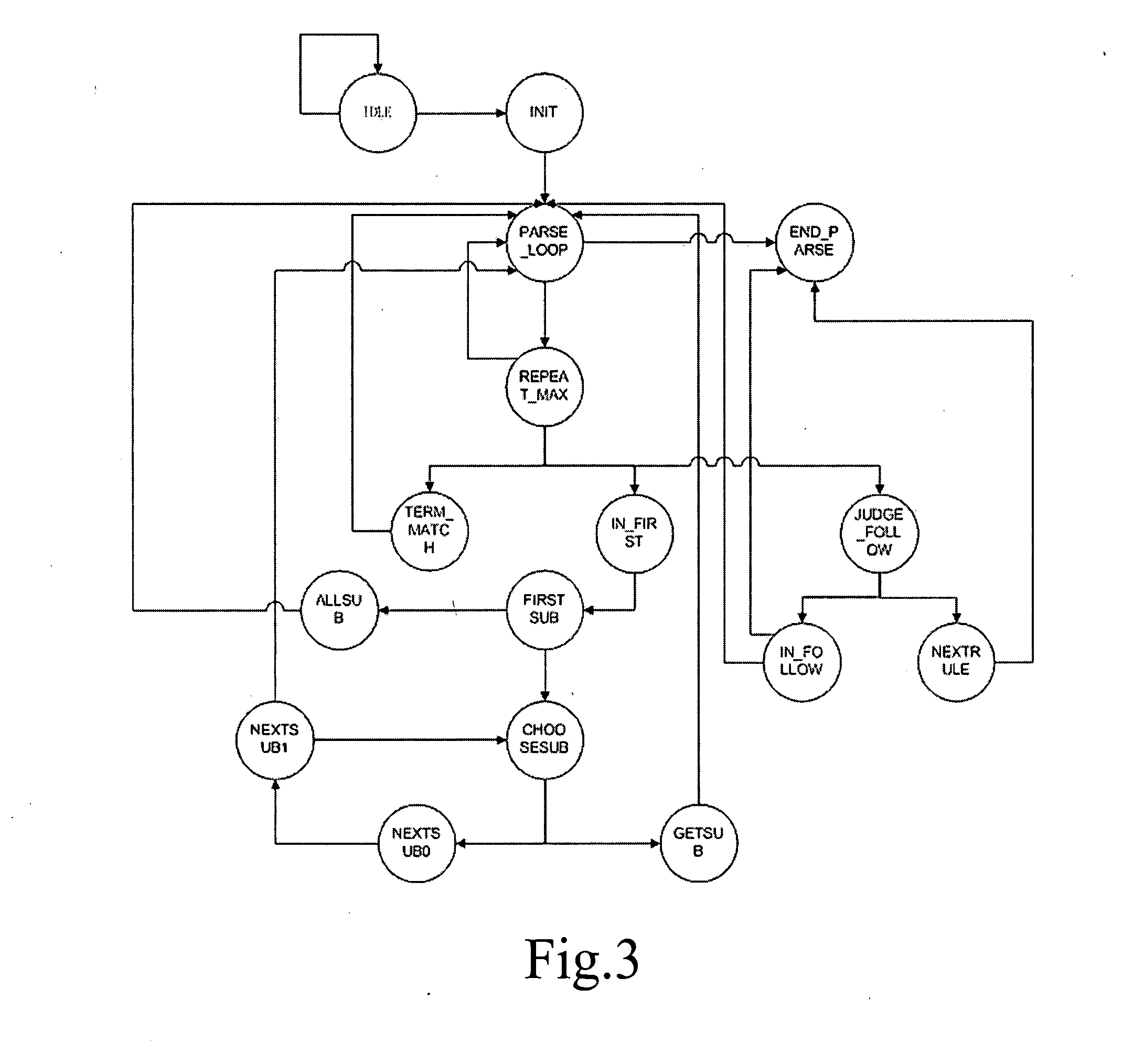
Parser for parsing text-coded protocol
ActiveUS20080040496A1Improve versatilityImprove efficiencyNatural language data processingMultiple digital computer combinationsCODE protocolParsing
A parser for parsing a text-coded protocol includes: a parsing rule storage module, configured to store a parsing rule for parsing a packet of the text-coded protocol; and a packet parsing module, implemented by a logic chip, configured to parse the packet according to the parsing rule stored in the parsing rule storage module, and output a parsing result. Compared with software-based parsers, the hardware-based parser provided by embodiments of the present invention improves parsing efficiency and reduces cost of the parser. In addition, the parser provided by embodiments of the present invention has a better generality.
Owner:HUAWEI TECH CO LTD +1
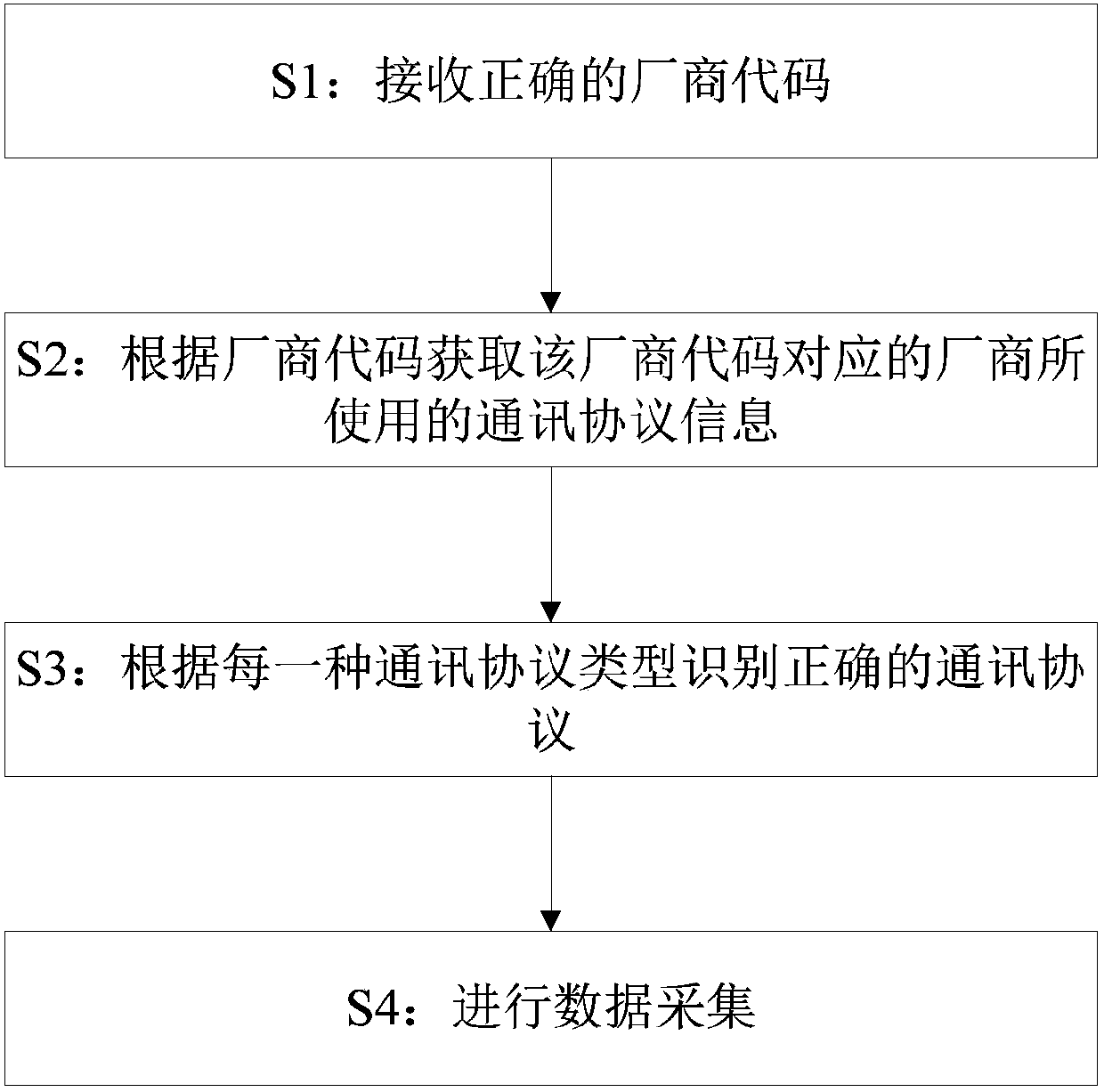
Data collection method based on RTU protocol, electronic equipment and storage medium
ActiveCN107770022AReduce procurement costsReduce management costsBus networksComputer hardwareProcessor register
The invention discloses a data collection method based on an RTU protocol. The data collection method comprises the following steps that a correct vendor code is received, wherein the vendor code comprises communication protocol type information; communication protocol information used by a vendor corresponding to the vendor code is acquired according to the vendor code, wherein the communicationprotocol information comprises various communication protocol types and register addresses where all the communication protocol types are located respectively; correct communication protocols are recognized according to all the communication protocol types; and communication is established according to the communication protocols, and a collection instruction is sent to a local collector to conduct data collection through the local collector. According to the data collection method, the vendor code protocols are accurately recognized through an automatic recognizing mechanism, multiple communication protocols can be integrated into a whole, therefore, the purchasing and management cost of the vendor is reduced, the installation cost of EPC users is reduced, and the defect that in the priorart, different data collectors need to be adopted is overcome.
Owner:深圳益邦阳光有限公司
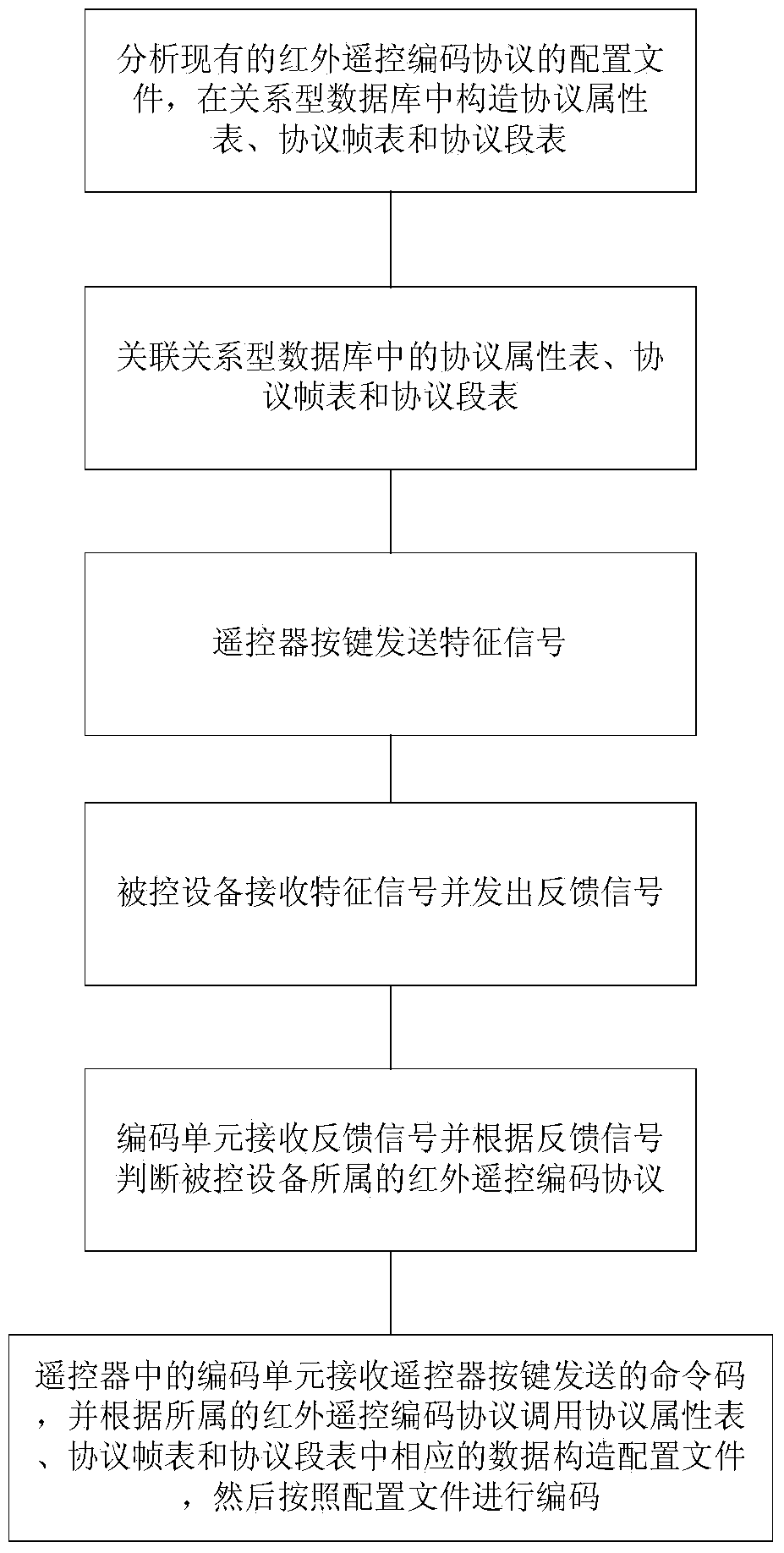
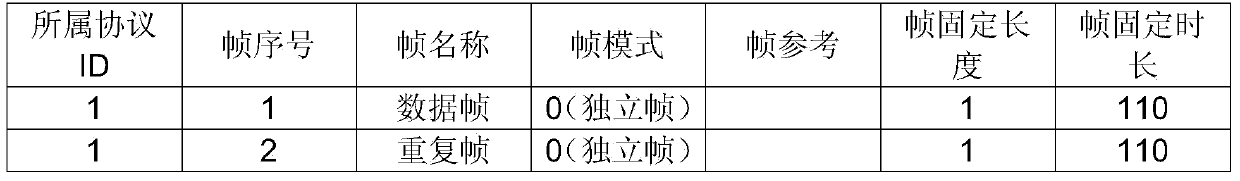
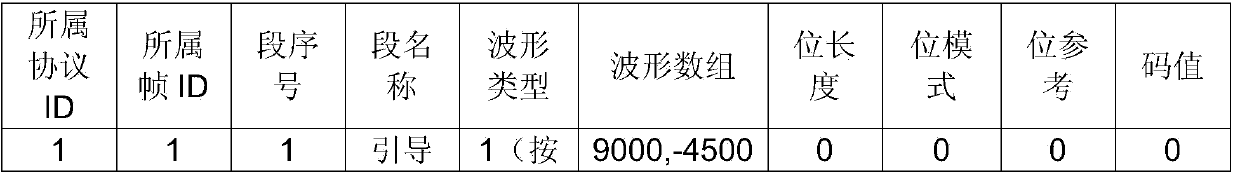
Infrared remote coding method
The invention discloses an infrared remote coding method. The method comprises the following steps: (1) analyzing a configuration file of a conventional infrared remote coding protocol, constructing a protocol attribute table in a relational database, constructing a protocol frame table, and constructing a protocol segment table; (2) associating the protocol attribute table, the protocol frame table and the protocol segment table in the relational database; (3) transmitting a characteristic signal by pressing a key of a remote controller; (4) receiving the characteristic signal and transmitting a feedback signal by controlled equipment; (5) receiving the feedback signal by a coding unit and judging the infrared remote coding protocol to which the controlled equipment belongs according to the feedback signal; (6) receiving a command code transmitted by the key of the remote controller by the coding unit in the remote controller, constructing the configuration file by calling corresponding data in the protocol attribute table, the protocol frame table and the protocol segment table according to the infrared remote coding protocol to which the controlled equipment belongs, and coding according to the configuration file. The infrared remote coding method can be compatible with conventional different infrared remote coding protocols.
Owner:WUXI THINGTEK TECH
Method for superposing voice in transmitting audio-video file
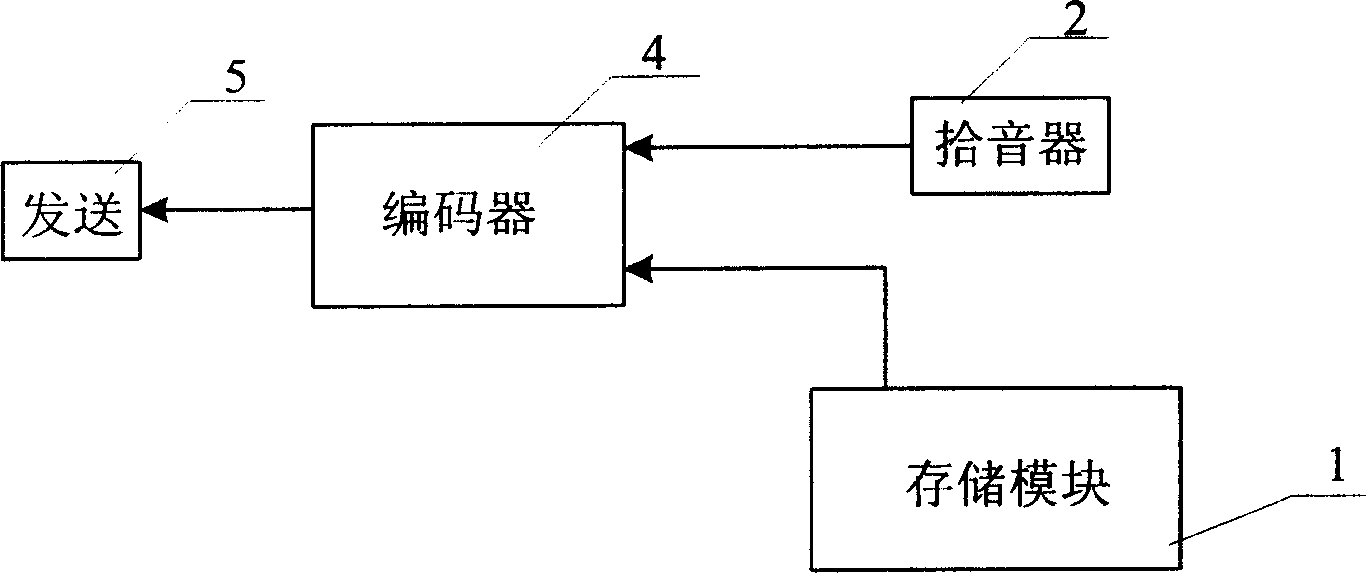
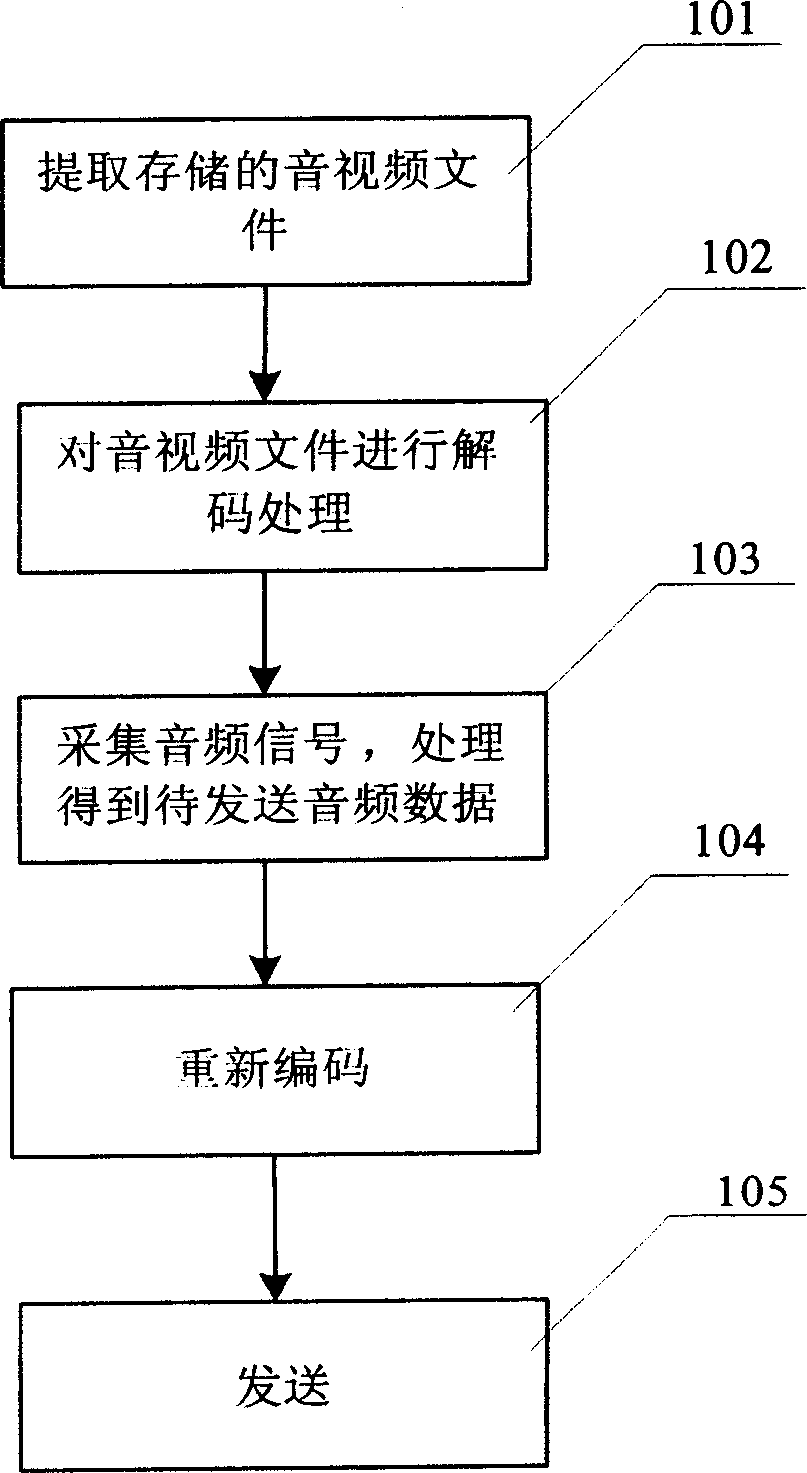
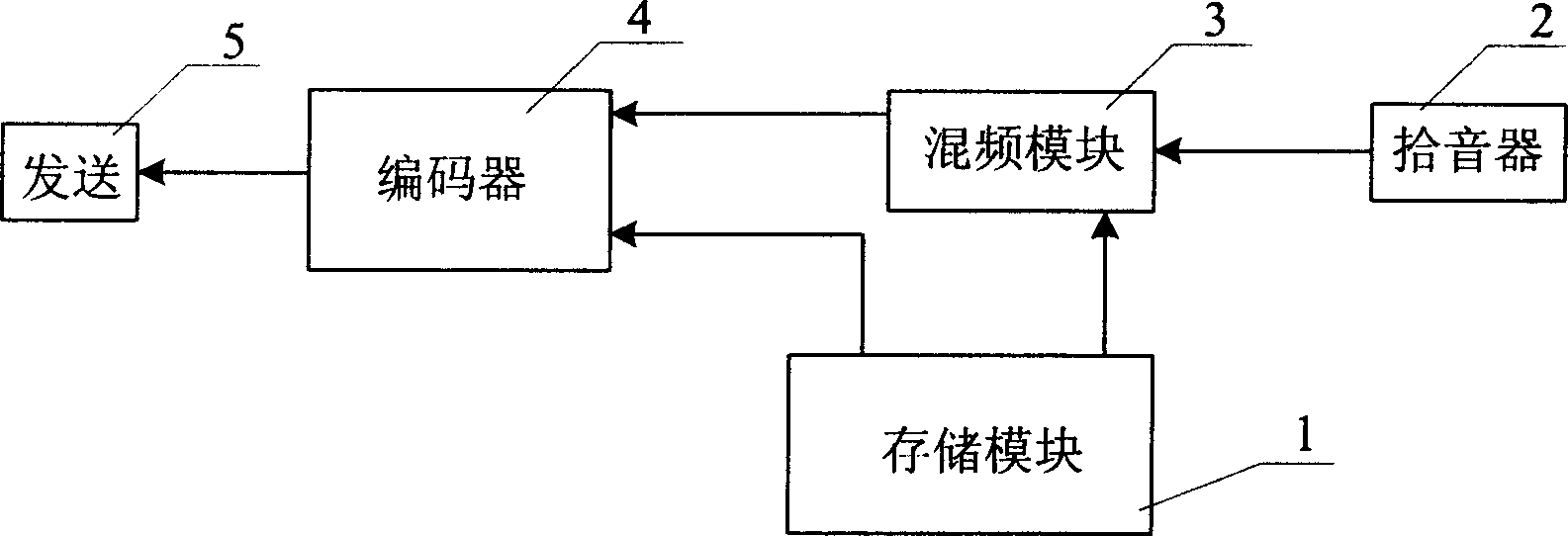
ActiveCN1878289AOvercoming the Insufficiency of Synchronous Voice TransmissionPulse modulation television signal transmissionTwo-way working systemsCODE protocolSpeech sound
The invention relates to a method for adding voice into voice video document, which comprises: the mobile terminal extracts the memorized voice video document to be decoded, to obtain the voice data and video data; using the voice picker of mobile terminal to collect the voice signal; processing the voice signal to obtain the sent voice data; using the coder to code the sent voice data and video data, based on the code protocol to form the sent document. The invention layers the real-time collected voice signal and video signal and mixes frequency when the mobile terminal sends out voice video document, to process coding and form new voice video data flow document, to make the receiver be able to play received voice video document, and listen the synchronously transmitted voice.
Owner:CHINA MOBILE COMM GRP CO LTD
Systems and methods for assigning a minimum value to a syntax structure in a parameter set
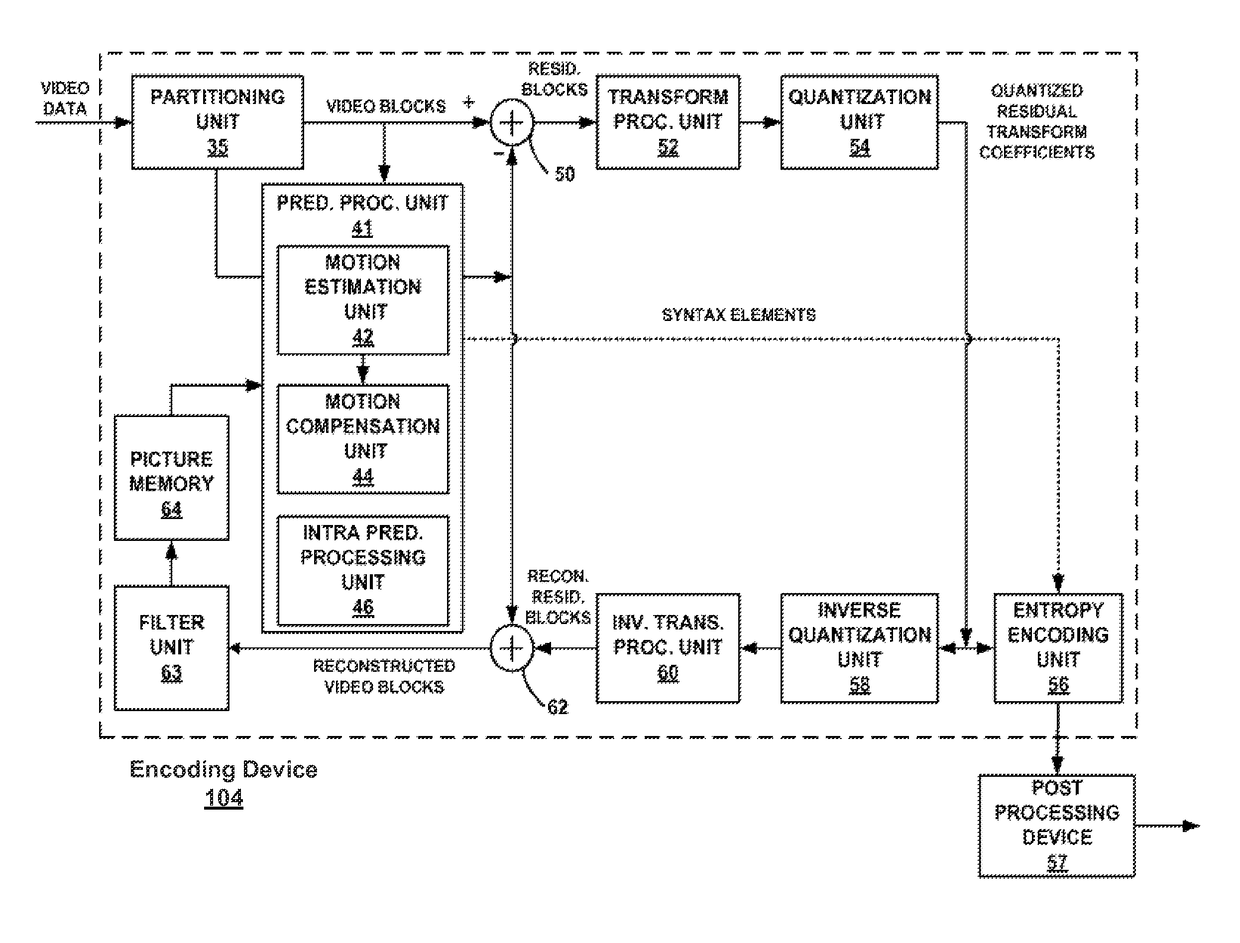
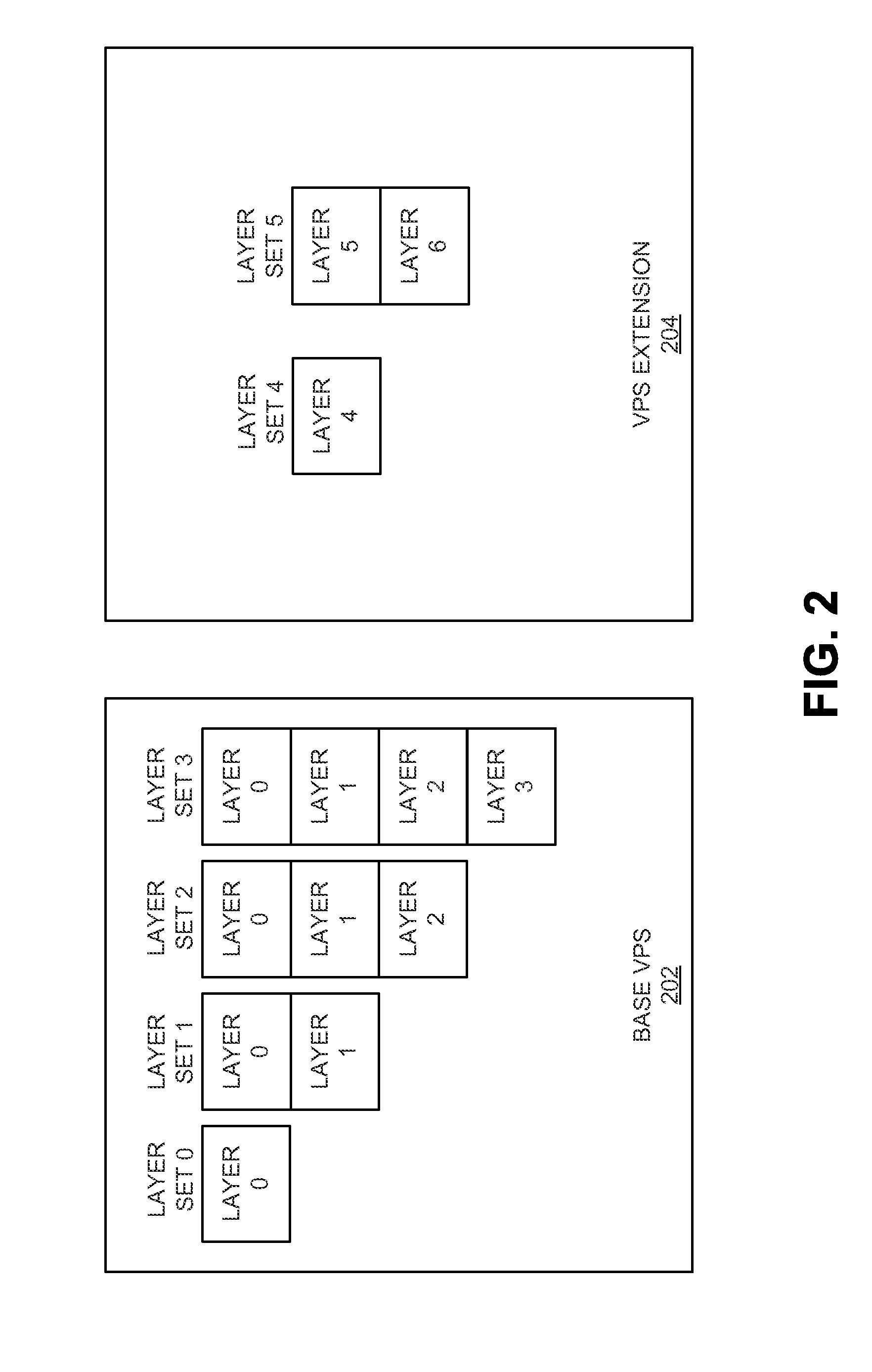
ActiveUS20150373333A1Color television with pulse code modulationColor television with bandwidth reductionVideo bitstreamCODE protocol
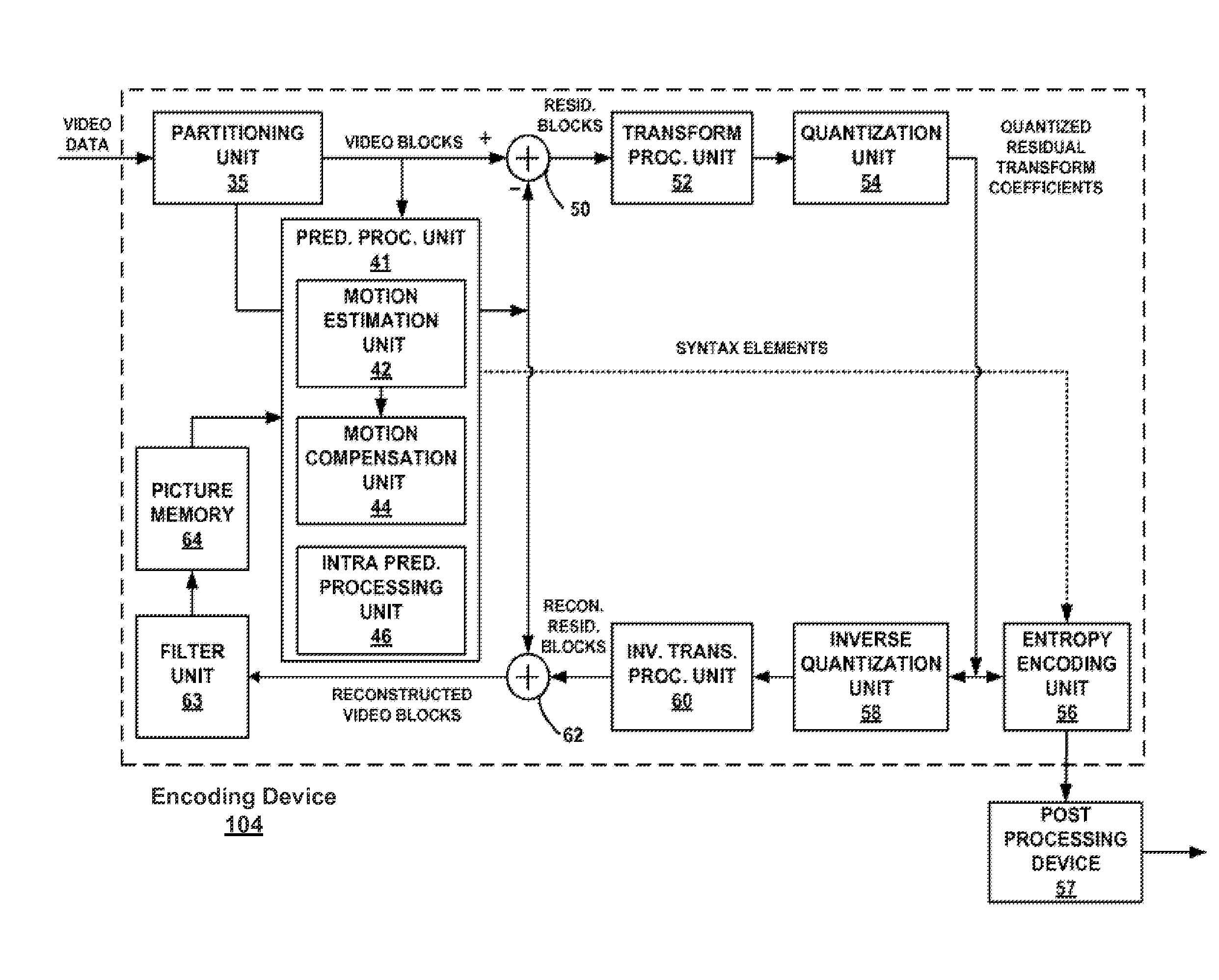
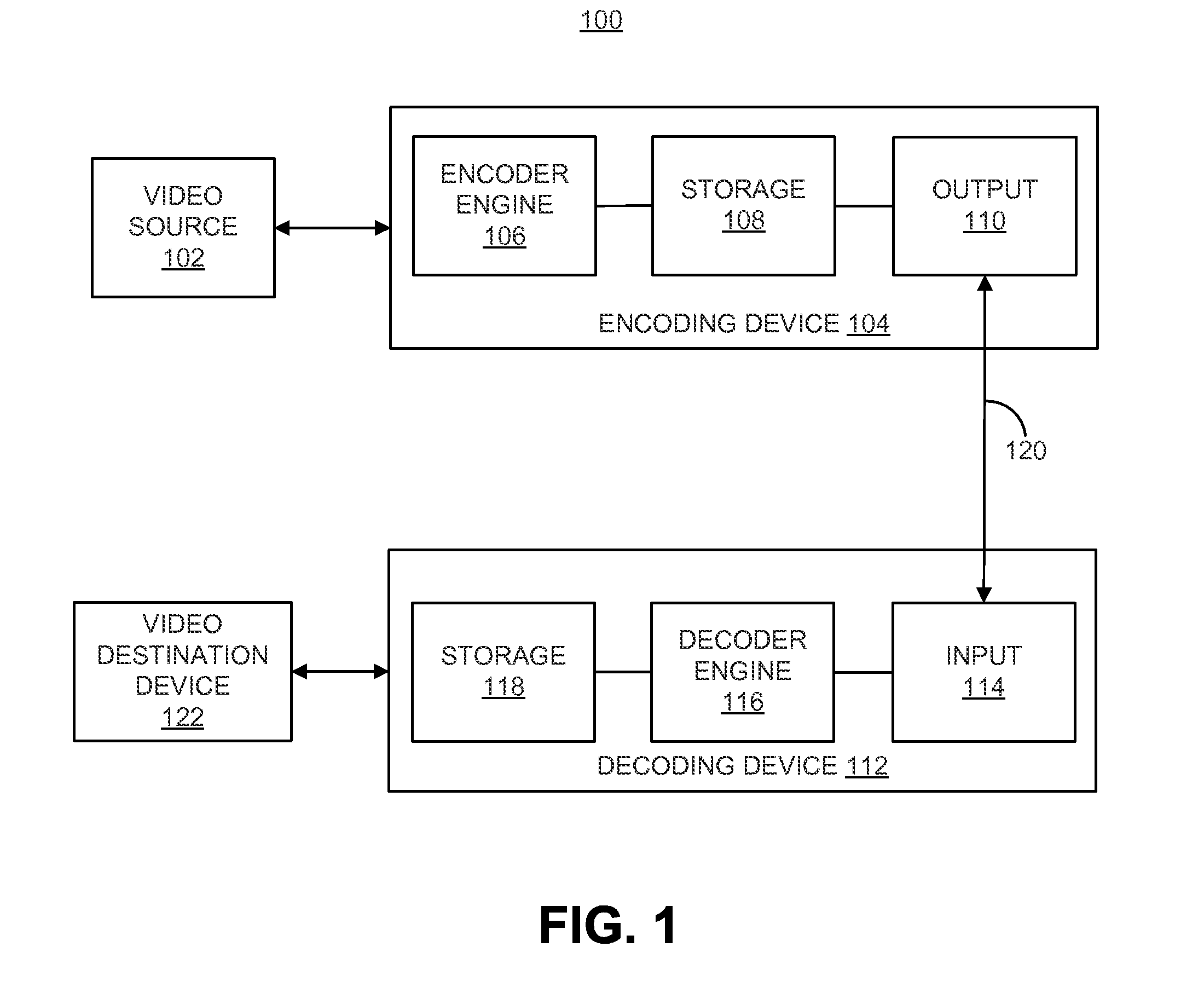
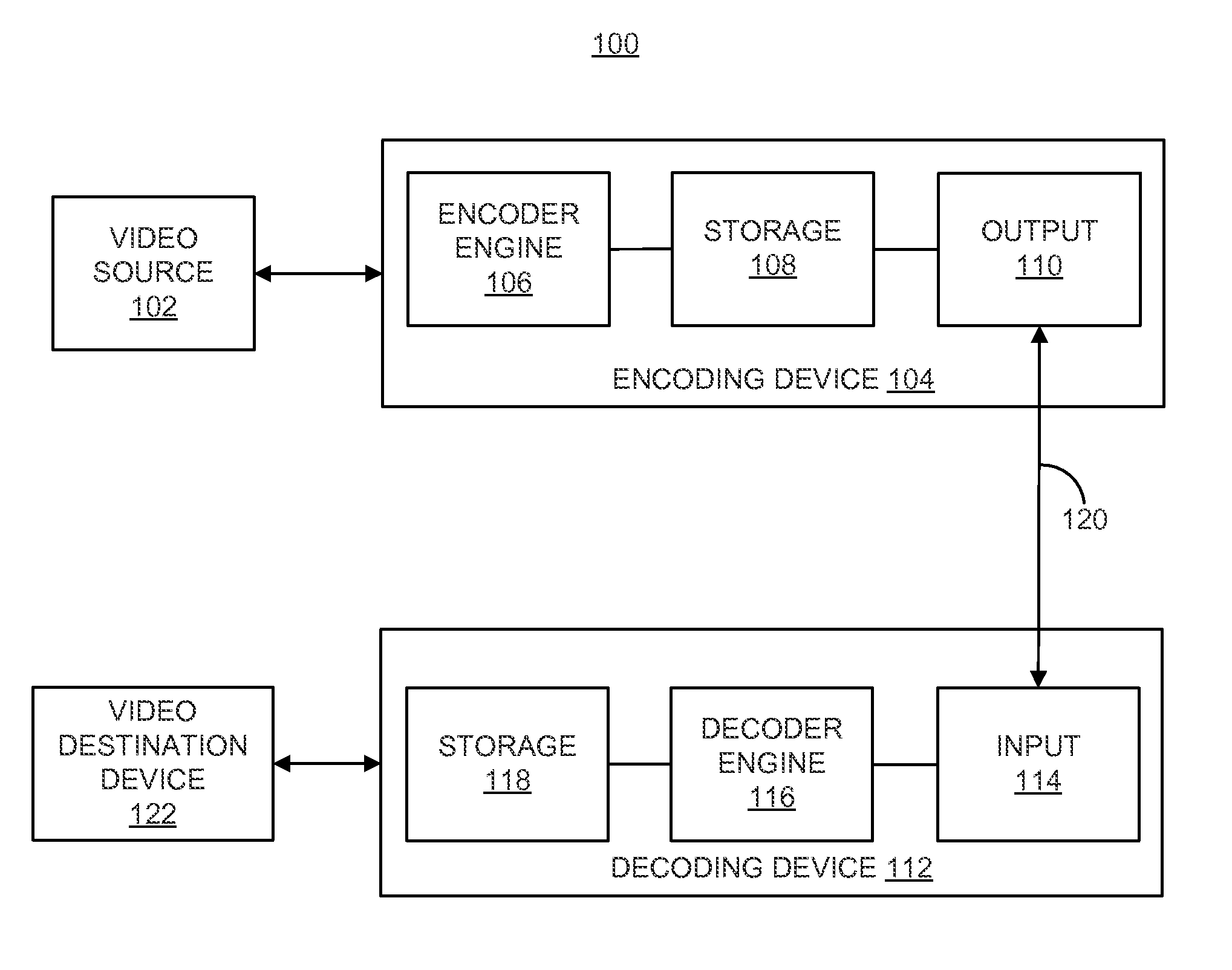
Techniques and systems are provided for encoding video data. For example, a method of encoding video data includes generating, by an encoder, an encoded video bitstream according to a first coding protocol. The encoded video bitstream includes one or more enhancement layers and a video parameter set defining parameters of the encoded video bitstream. The method further includes determining that a base layer is to be provided to a decoding device by an external source and is not to be provided as part of the encoded video bitstream. The method further includes assigning a minimum value to a syntax structure in the video parameter set when it is determined that the base layer is to be provided by the external source. The syntax structure defines profile, tier, and level parameters for the base layer.
Owner:QUALCOMM INC
Flexible polar encoders and decoders
Modern communication systems must cope with varying channel conditions and differing throughput constraints. Polar codes despite being the first error-correcting codes with an explicit construction to achieve the symmetric capacity of memoryless channels are not currently employed against other older coding protocols such as low-density parity check (LDPC) codes as their performance at short / moderate lengths has been inferior and their decoding algorithm is serial leading to low decoding throughput. Accordingly techniques to address these issues are identified and disclosed including decoders that decode constituent codes without recursion and / or recognize classes of constituent directly decodable codes thereby increasing the decoder throughput. Flexible encoders and decoders supporting polar codes of any length up to a design maximum allow adaptive polar code systems responsive to communication link characteristics, performance, etc. while maximizing throughput. Further, designers are provided flexibility in implementing either hardware or software implementations.
Owner:POLAR TECH
Systems and methods for assigning a minimum value to a syntax structure in a parameter set
ActiveUS9918091B2Television signal transmission by single/parallel channelsDigital video signal modificationVideo bitstreamCODE protocol
Techniques and systems are provided for encoding video data. For example, a method of encoding video data includes generating, by an encoder, an encoded video bitstream according to a first coding protocol. The encoded video bitstream includes one or more enhancement layers and a video parameter set defining parameters of the encoded video bitstream. The method further includes determining that a base layer is to be provided to a decoding device by an external source and is not to be provided as part of the encoded video bitstream. The method further includes assigning a minimum value to a syntax structure in the video parameter set when it is determined that the base layer is to be provided by the external source. The syntax structure defines profile, tier, and level parameters for the base layer.
Owner:QUALCOMM INC
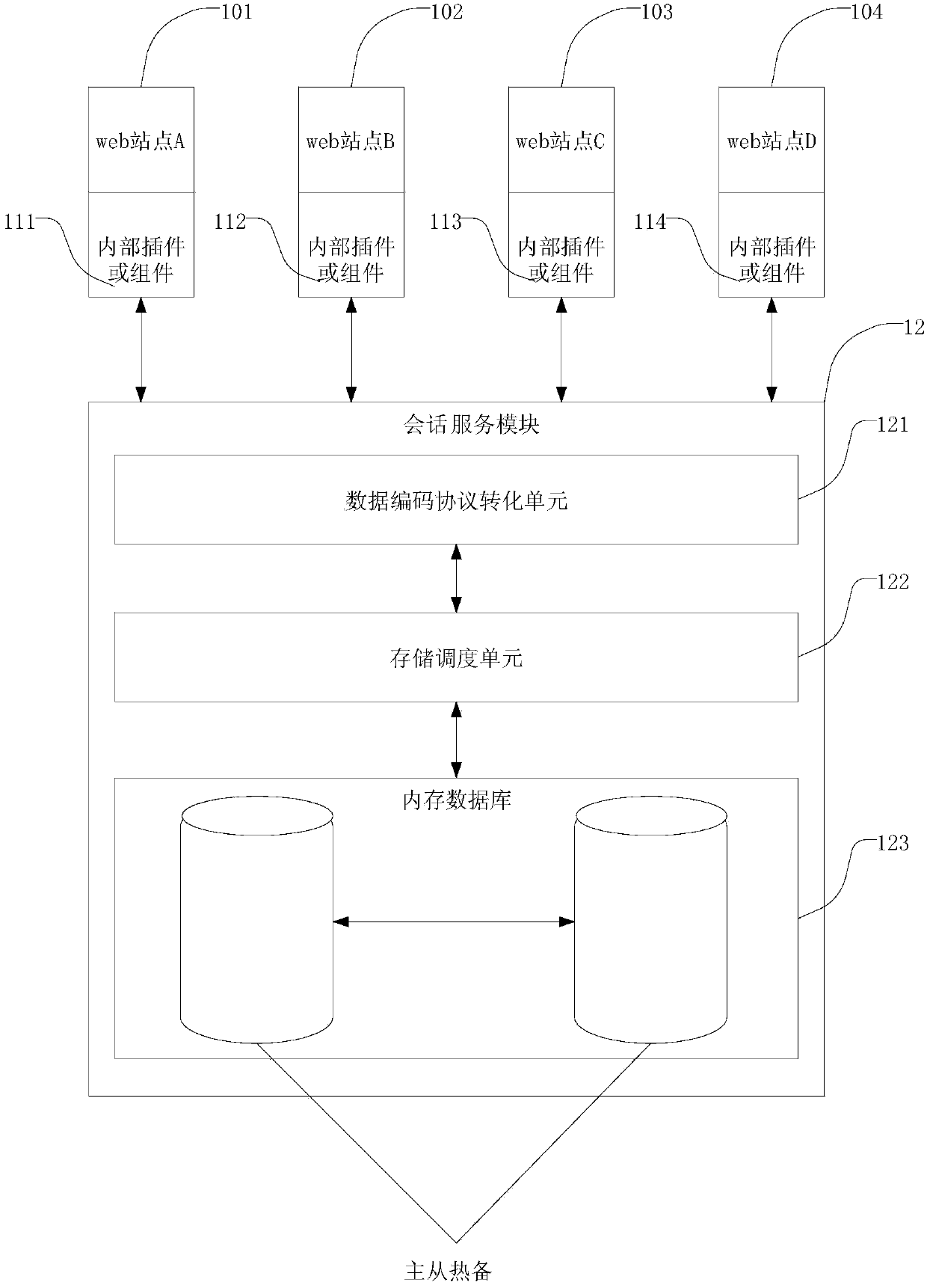
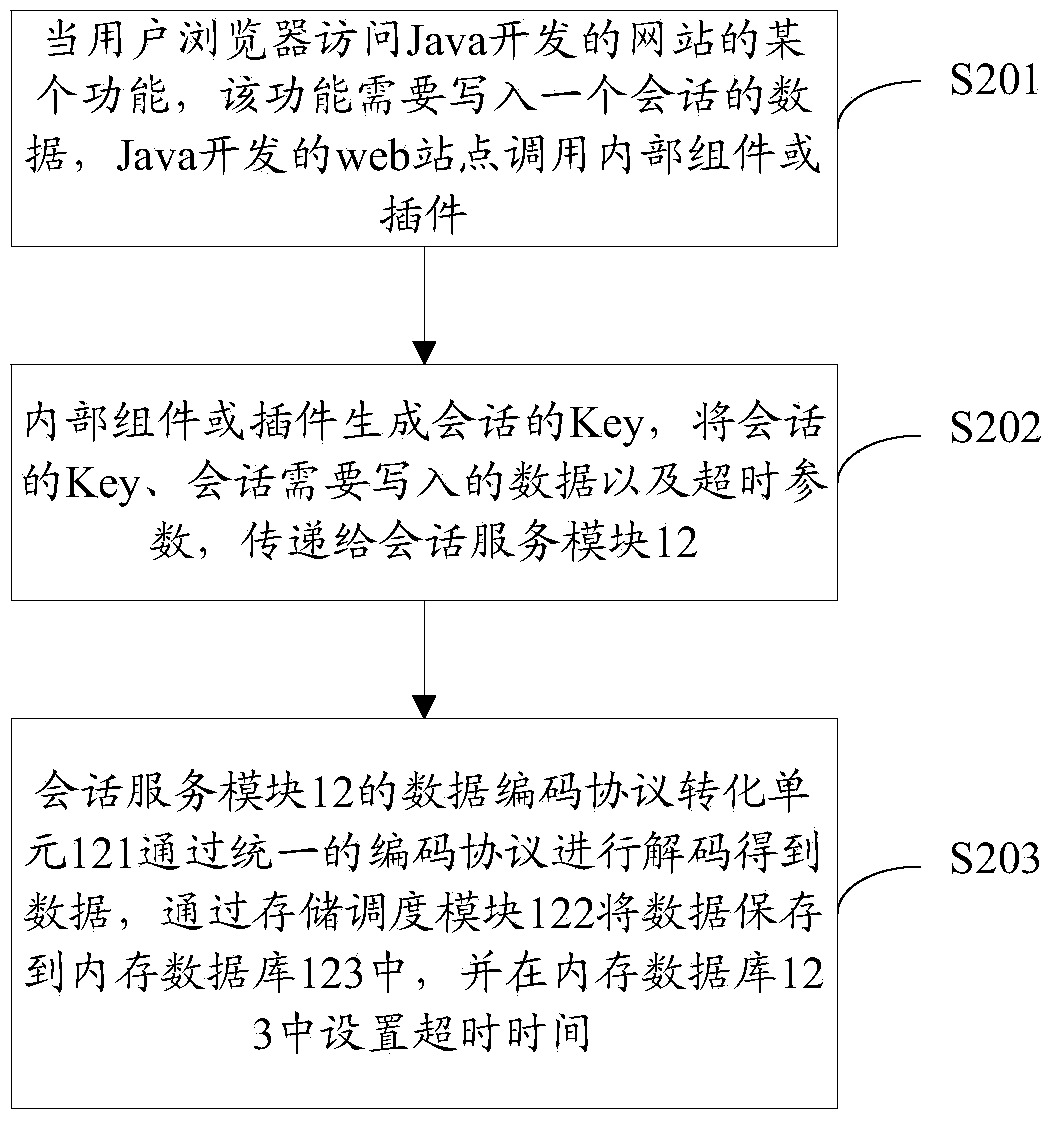
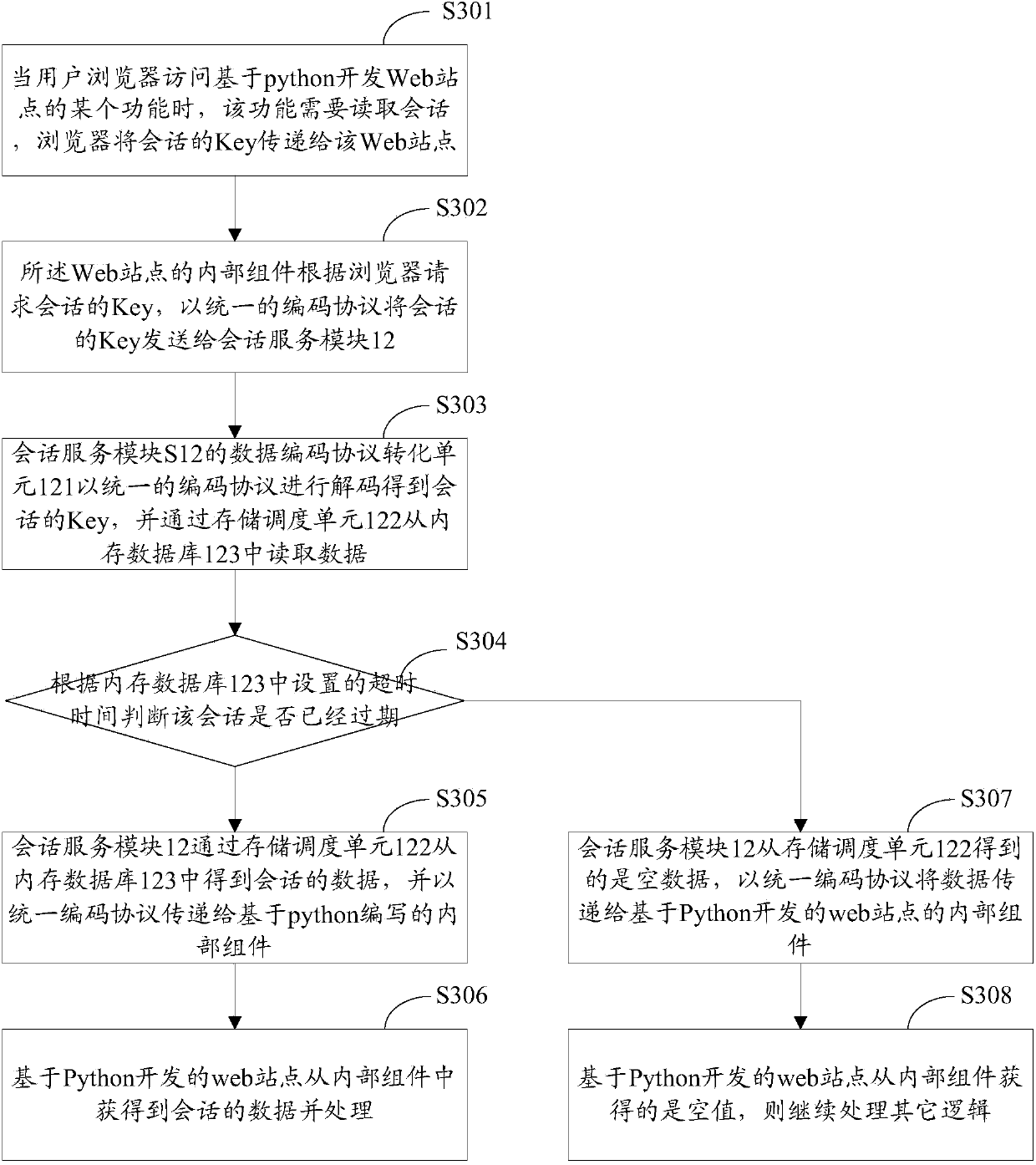
Method and system for realizing conversation sharing
The invention discloses a method for realizing conversation sharing. The method comprises the steps that an inner plug-in or assembly integrated in a web site generates a unique conversation key value according to the calling at the Web site and sends the conversation key value, conversation data needing to be written in and overtime to a conversation service module; the conversation service module decodes the received conversation key value, the conversation data needing to be written in and the overtime according to a unique coding protocol, stores the conversation key value and the corresponding conversation data and sets the corresponding overtime, wherein the number of the Web site is larger than 1, and at least two Web sites are based on different programming languages and different platforms. The invention also discloses a system for realizing conversation sharing. According to the technical scheme, the aim that web sites developed by different languages can share the conversation data information on different platforms is realized.
Owner:SHANGHAI HEHONG INFORMATION TECH
Systems and methods for selectively signaling different numbers of video signal information syntax structures in a parameter set
InactiveUS20150373376A1Color television with pulse code modulationColor television with bandwidth reductionPattern recognitionVideo bitstream
Techniques and systems are provided for encoding and decoding video data. For example, a method of decoding video data includes accessing an encoded video bitstream encoded according to a first coding protocol. The encoded video bitstream includes one or more enhancement layers and a video parameter set defining parameters of the encoded video bitstream. The method further includes determining that a syntax element indicative of a number of video signal information syntax structures provided in the encoded video bitstream is not present in the video parameter set. The method further includes determining whether a base layer is included in the encoded video bitstream or to be received from an external source. The method further includes determining the number of video signal information syntax structures included in the video parameter set to be a first value or a second value based on whether the base layer is included in the encoded video bitstream or to be received from the external source.
Owner:QUALCOMM INC
Bidirectional single-bit state preparation method based on Brown state and network coding
ActiveCN111510289AAchieve bidirectional preparationReduce resource consumptionKey distribution for secure communicationTelecommunicationsNetwork code
The invention discloses a bidirectional single-bit state preparation method based on a Brown state and network coding. According to the bidirectional single-bit state preparation method, state preparation based on the Brown state and network coding are combined for the first time, cross transmission is carried out between a sender and a receiver through a butterfly network and a five-bit Brown state, and an arbitrary single-bit quantum state scheme is prepared bidirectionally. The bidirectional single-bit state preparation method is mainly characterized in that a quantum network coding model is established through state preparation on the basis of a butterfly network coding protocol. A channel shared by a source node and a destination node is obtained by adding auxiliary particles in the five-bit Brown state and performing channel modulation through CNOT operation. The transmission of known information in the whole network model is realized, compared with a quantum stealth transmissionscheme, the resource consumption is lower, the transmission efficiency reaches a higher level, the bidirectional preparation is innovatively realized, and the communication capacity reaches four bitsper round. The bidirectional single-bit state preparation method has a wide application prospect in the technical field of quantum communication networks.
Owner:SUZHOU UNIV
Router with network encoding function and network organizing method based on network coding
InactiveCN101217489ASpecial service provision for substationError preventionIP multicastEncoding algorithm
The invention belongs to the field of routers and networking technology, which more particularly relates to a router with network coding function and a networking method based on the network coding. The router put forward by the invention is added with a coding algorithm module, a coding strategy module and the corresponding interface thereof based on the existing router and proposes the corresponding networking method and coding protocol to realize network encoding and decoding and routing function on the router. The network coding on the router is mainly characterized by coding an IP payload on a network layer. The network coding on the router can approach to the upper bound of the network throughput to improve an end-to-end performance. The advantages are that the invention is convenient for using concentration optimization encoding and decoding; the distribution topology is simplified, the hop count from end to end is reduced and the encoding times and the end-to-end delay are further reduced; the delay caused by the correlation when the end nodes are coded is reduced; if an IP multicast is adopted when the router is connected with each jurisdictional node, the invention can also save the time for accessing bandwidth.
Owner:FUDAN UNIV
General quantum network coding method based on non-entanglement clone
ActiveCN103414537AReduce resource costsEasy to implementError preventionNODALInformation transmission
Provided is a general quantum network coding method based on non-entanglement clone. The general quantum network coding method based on the non-entanglement clone comprises six steps: step (1), defining the nodes of fundamental types, wherein the nodes comprises 5 node types of source nodes, fork nodes, transmission nodes, cluster nodes and sink nodes; step (2), defining reduced conditions of a quantum network coding protocol; step (3), adopting a conversion scheme from a general graph to a D3 graph to obtain a new graph based on the D3 graph; step (4) further simplifying the protocol, and unifying the algorithm of coefficient parts as the algorithm of adding the transmission nodes; step (5), determining the overall sequence of v1, v2,..., vr according to node degrees in the graph, wherein the r is the number of all the nodes; step (6) carrying out specific operation on each node of the graph. According to the general quantum network coding method based on the non-entanglement clone, the non-entanglement approximate clone is adopted to achieve the copy link of quantum network coding, compared with pre-shared entanglement clone achieving the fact that transmission fidelity of quantum states is 1, the method is more suitable for information transmission of general graph models, low resource price is needed, and the method is easier to achieve.
Owner:BEIHANG UNIV
Method for reducing IP routing protocol band-width occupy
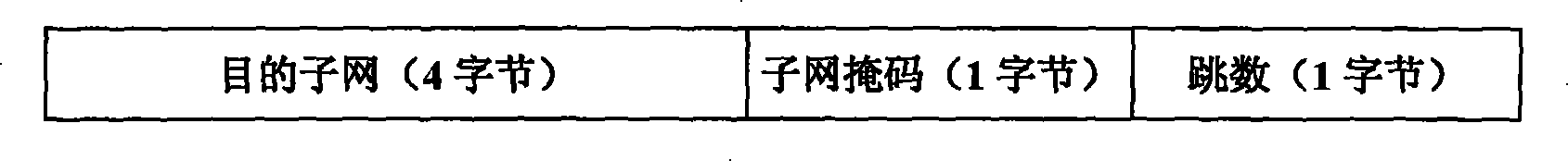
ActiveCN101252410AImprove transmission efficiencyReduce consumptionError preventionData switching networksInformation quantityCODE protocol
The invention discloses a method of reducing the bandwidth occupied by the IP route protocol. The method includes that the message head of the route protocol message adopts the high efficiency coding and decoding; the route list terms are coded and decoded; the increment update method is used for reducing the transmission information quantity of the route message; the high-efficiency coding and decoding of the message head of the route protocol message are realized through that the IP head of the common route message is replaced with a new coded protocol head by the sender; the receiver recovers the new coded protocol head to the normal IP head according to the coded protocol head; the coding and decoding of the route list items are realized through that each route list term with the length of 20 bytes of the route protocol in the wireless link is coded to a route list term with the length of 6 bytes and is transmitted by the sender; the receiver recovers the coded route list term to the normal route list term according to the coded route list term; the increment update includes the increment update content, the increment update storage format and the increment update processing process. The method of reducing the bandwidth occupied by the IP route protocol has the advantages that the transmission efficiency of the IP route protocol is improved in the wireless communication; the bandwidth consumption of the IP route protocol is reduced; the application range of the IP route protocol is extended.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Real-time acquisition and communication system and method of signal data
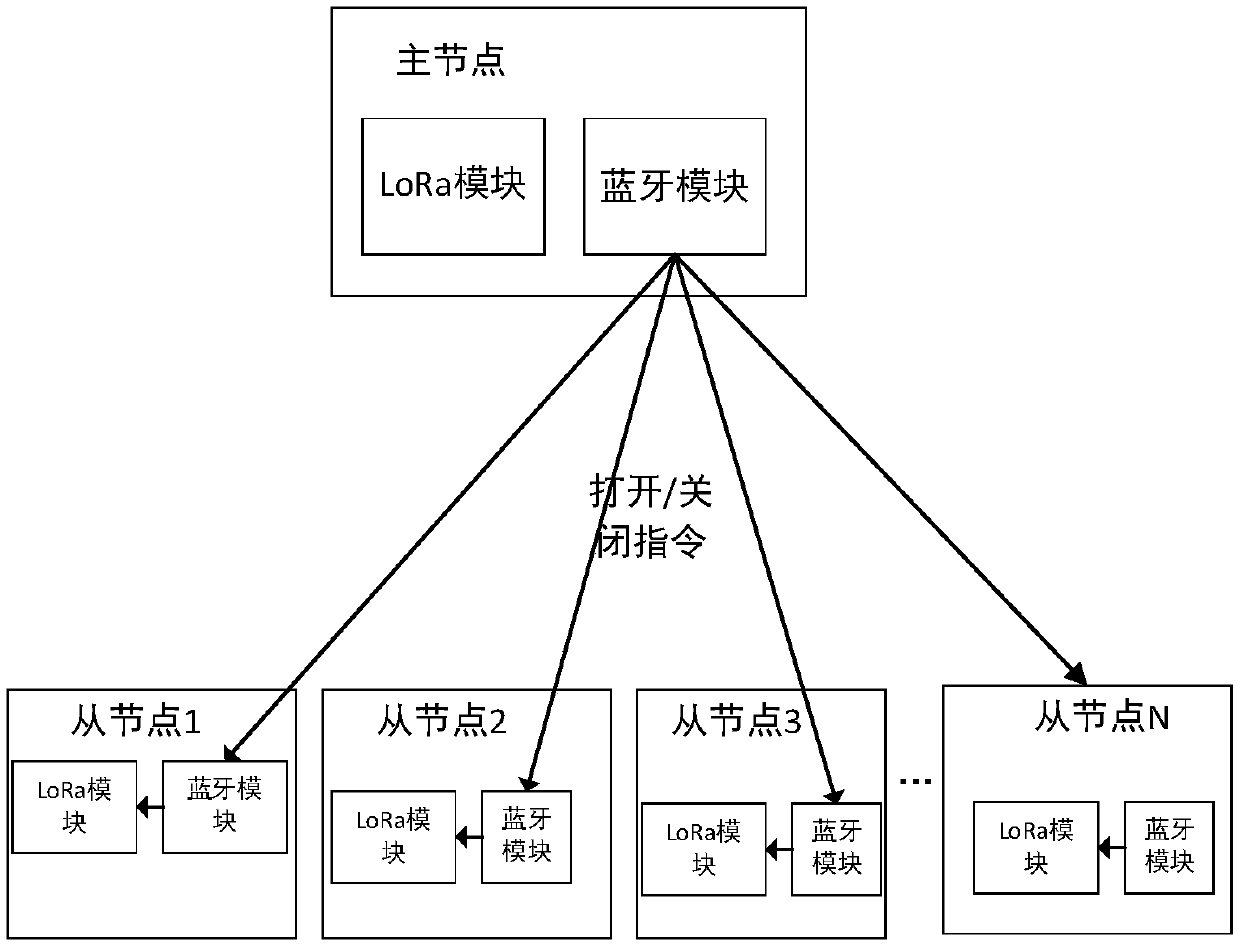
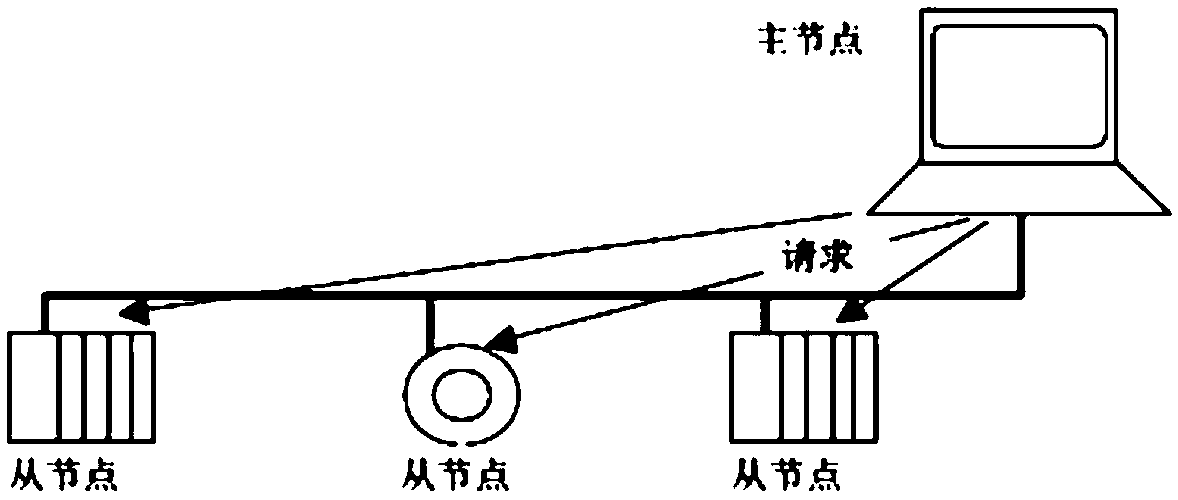
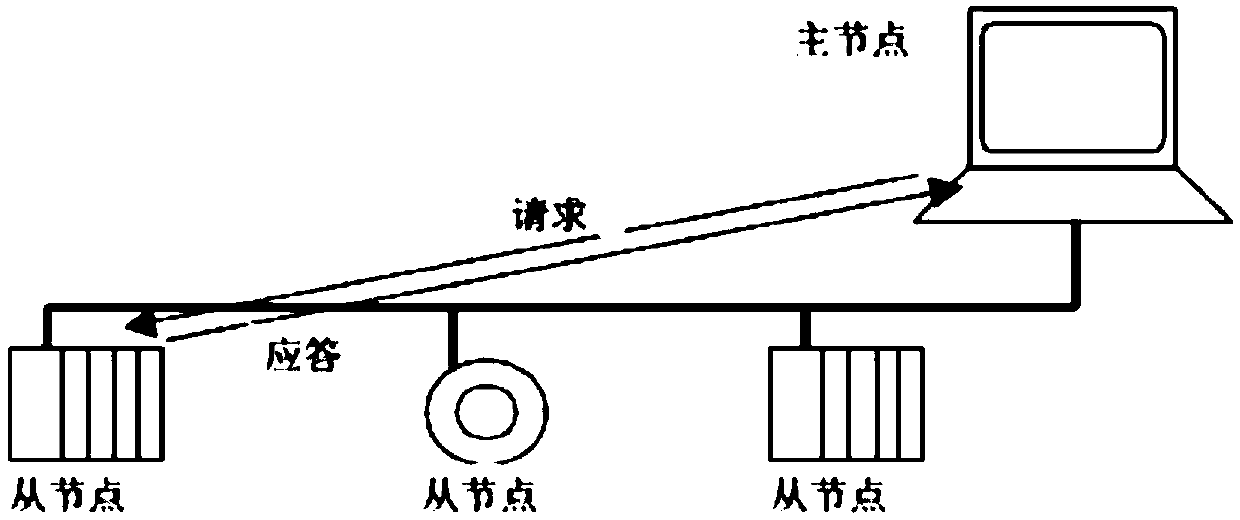
ActiveCN109688555AGuaranteed stabilityGuarantee controllabilityError preventionConnection managementCommunications systemData acquisition
The invention discloses a real-time acquisition and communication system of signal data. The system comprises a master node and a plurality of slave nodes in wireless communication with the master node, wherein the master node comprises a master node Bluetooth module and a master node LoRa module, each slave node comprises a slave node LoRa module and a slave node Bluetooth module, the master nodeBluetooth module issues an opening / closing instruction, and each slave node Bluetooth module receives the instruction, opens / closes the slave node LoRa module, and simultaneously writes to a LoRa channel; when the master node LoRa module and the slave node LoRa modules are in an opened state, the master node follows a master-slave node communication protocol and sends an instruction with an authentication code protocol format to the slave node LoRa modules, and the LoRa modules carry out corresponding processing. According to the scheme of the invention, the communication between acquisitiondevices does not need to be concerned, data can only be transferred according to the interface protocol standard during development, the convenience of use can be effectively improved, and the stability, controllability and flexibility of communication can be ensured.
Owner:CHENGDU GUORONG TECH
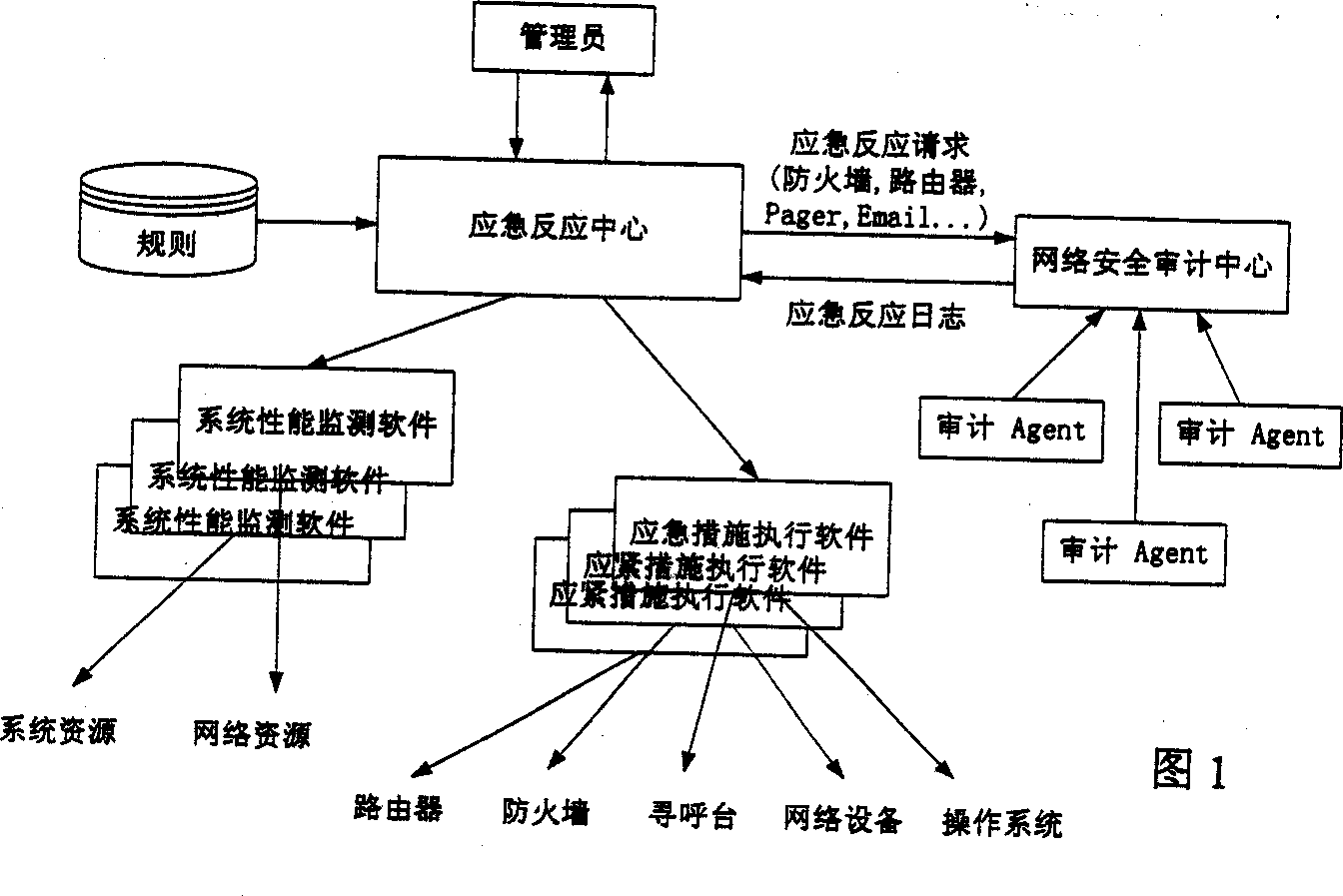
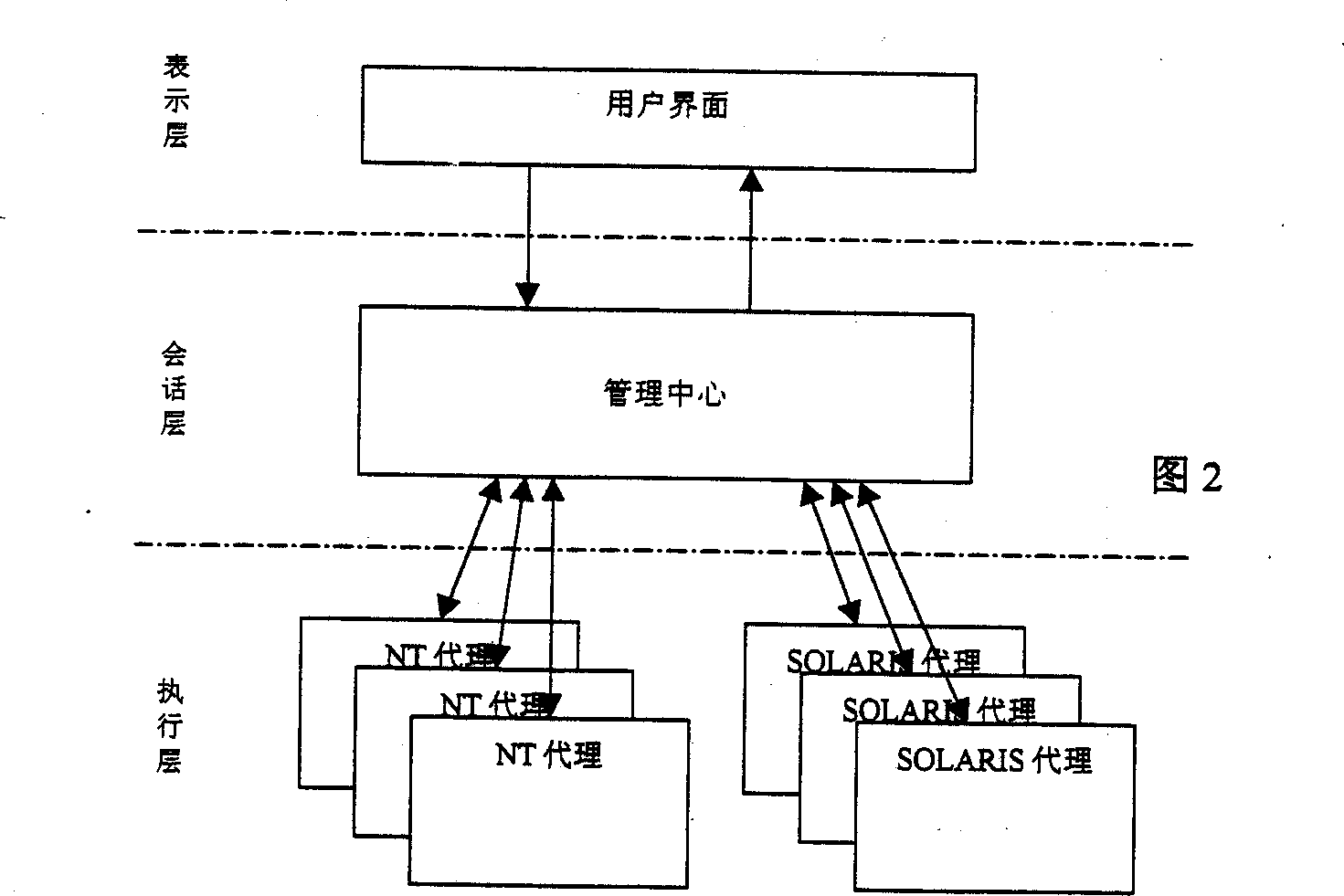
Distributed type emergency reaction control system
InactiveCN1349162AMultiple digital computer combinationsSpecific program execution arrangementsResponse controlUser interface
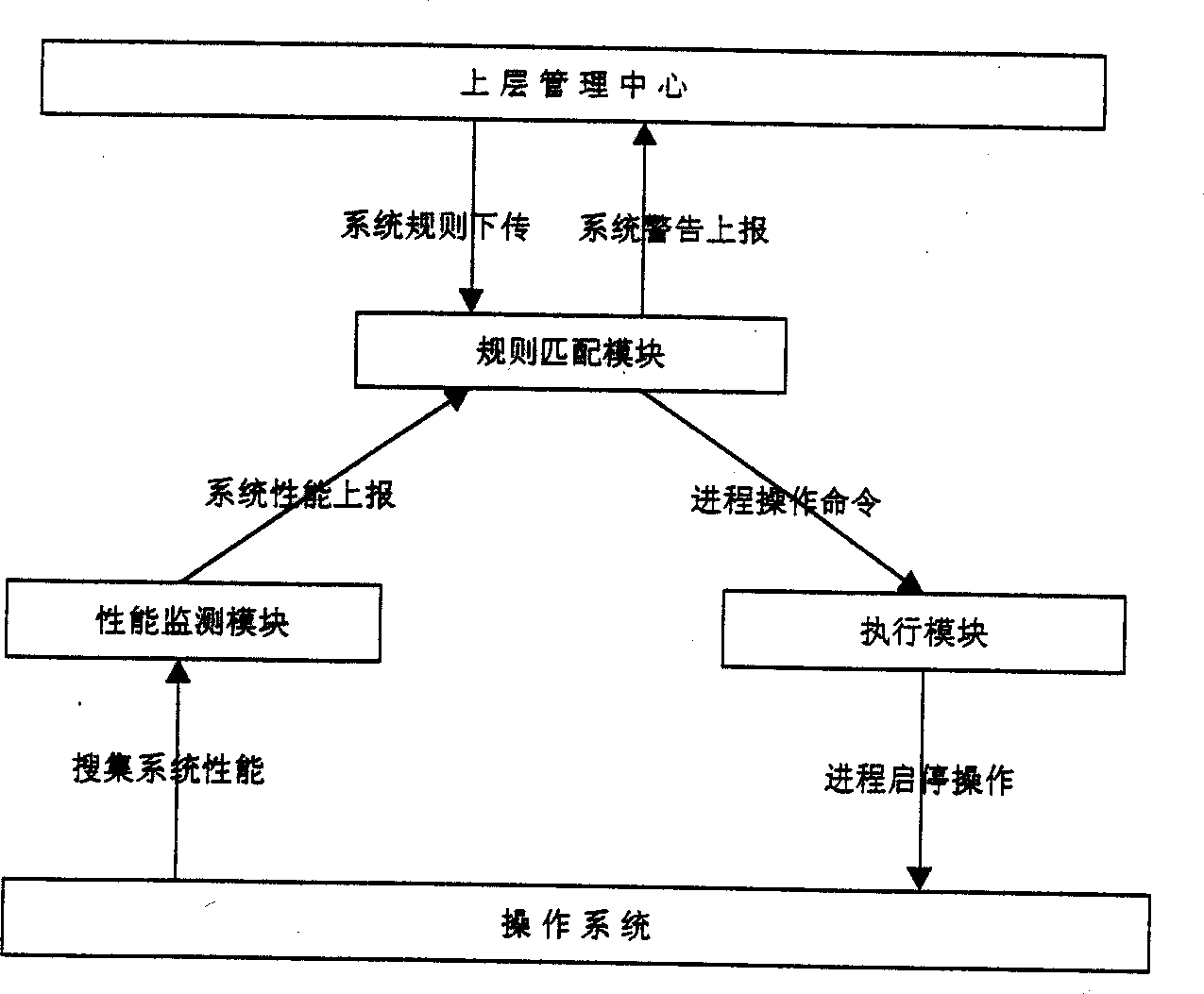
A distributed control system for emergency response is composed of three layers: user interface (presentation layer), management center (session layer) and agan (execute layer.). The information transferred between the center and agent follows coding protocol. The user interface receives the performance and alarm data transferred from the management center and sends the control information to agent process through the management center. The management center receives the performance data transferred from each agent, and then the data interpreted into the information of user readable is transferred to the user interface. According rules the management center writes alarm data to log and triggers a response. The invention can manage computers effectively, monitor working order of each computer and deals with violation with accuracy and automatically.
Owner:上海光华如新信息科技股份有限公司
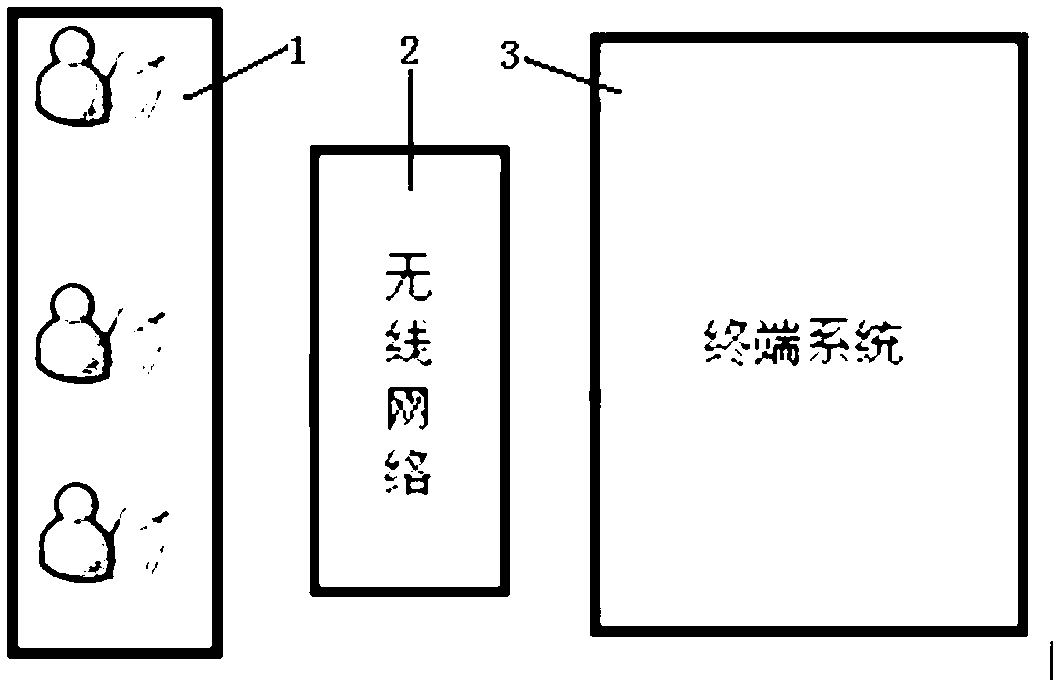
Automatic analysis processing and automatic scoring method for unmanned vehicle competition
ActiveCN102698424AEasy to operateRealize automatic transmissionSport apparatusCODE protocolComputer terminal
The invention discloses an automatic analysis processing and automatic scoring method for an unmanned vehicle competition. The method comprises the following steps of: 1, operating respective handheld operating boxes (1) through workers at different positions of a track, and inputting observed competition conditions to the handheld operating boxes (1) according to coding protocols; 2, transmitting the competition conditions to a terminal system (3) in a code form through a wireless network (2); and 3, when the terminal system (3) receives code data, determining that the data are valid data by adopting a message driving mechanism, performing data analysis processing, displaying related data on a software interface of a computer, and automatically storing the data.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Variable Message Coding Protocols for Encoding Auxiliary Data in Media Signals
InactiveUS20090060264A1Character and pattern recognitionImage watermarkingComputer hardwareCODE protocol
Variable message coding protocols enable greater flexibility in encoding auxiliary data in media signals. One such protocol employs a version identifier that indicates the type of coding used to process an auxiliary data message before it is embedded in a host media signal. This version identifier specifies the type of error robustness coding applied to a variable message. The error robustness coding may be varied to alter the message payload capacity for different versions of auxiliary data embedding and reading systems. Another protocol uses control symbols to specify the format and variable length of the variable message.
Owner:DIGIMARC CORP
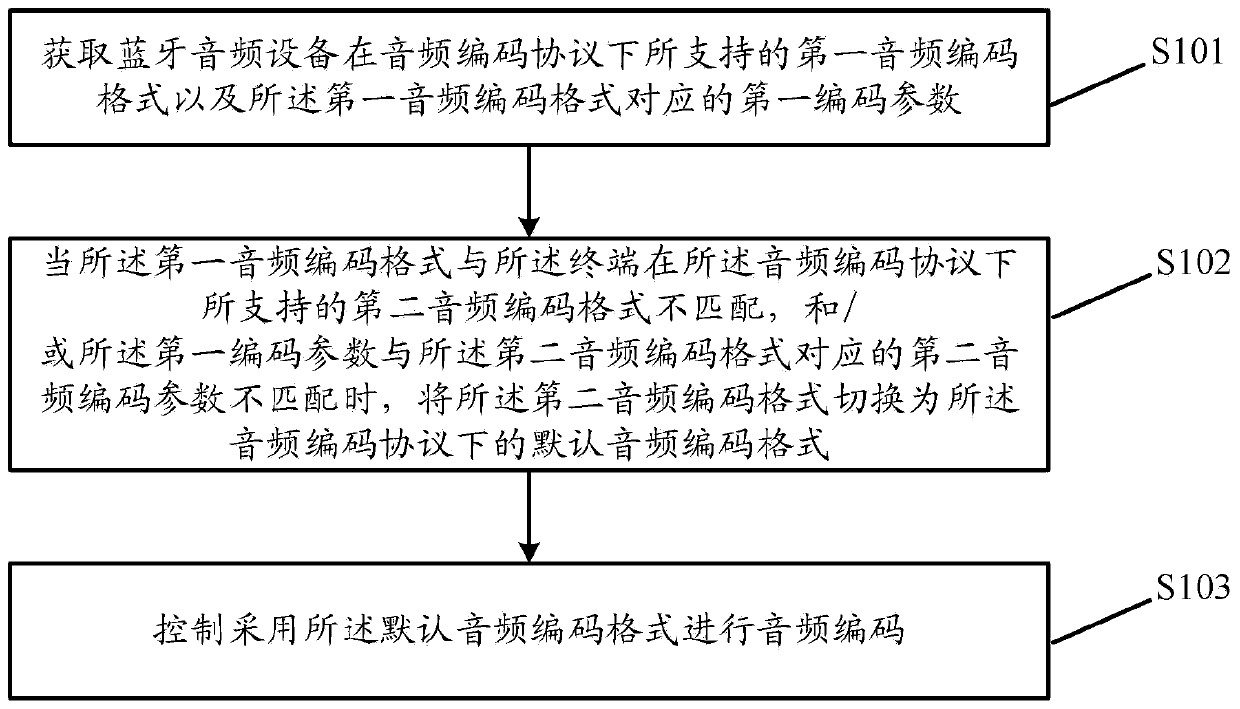
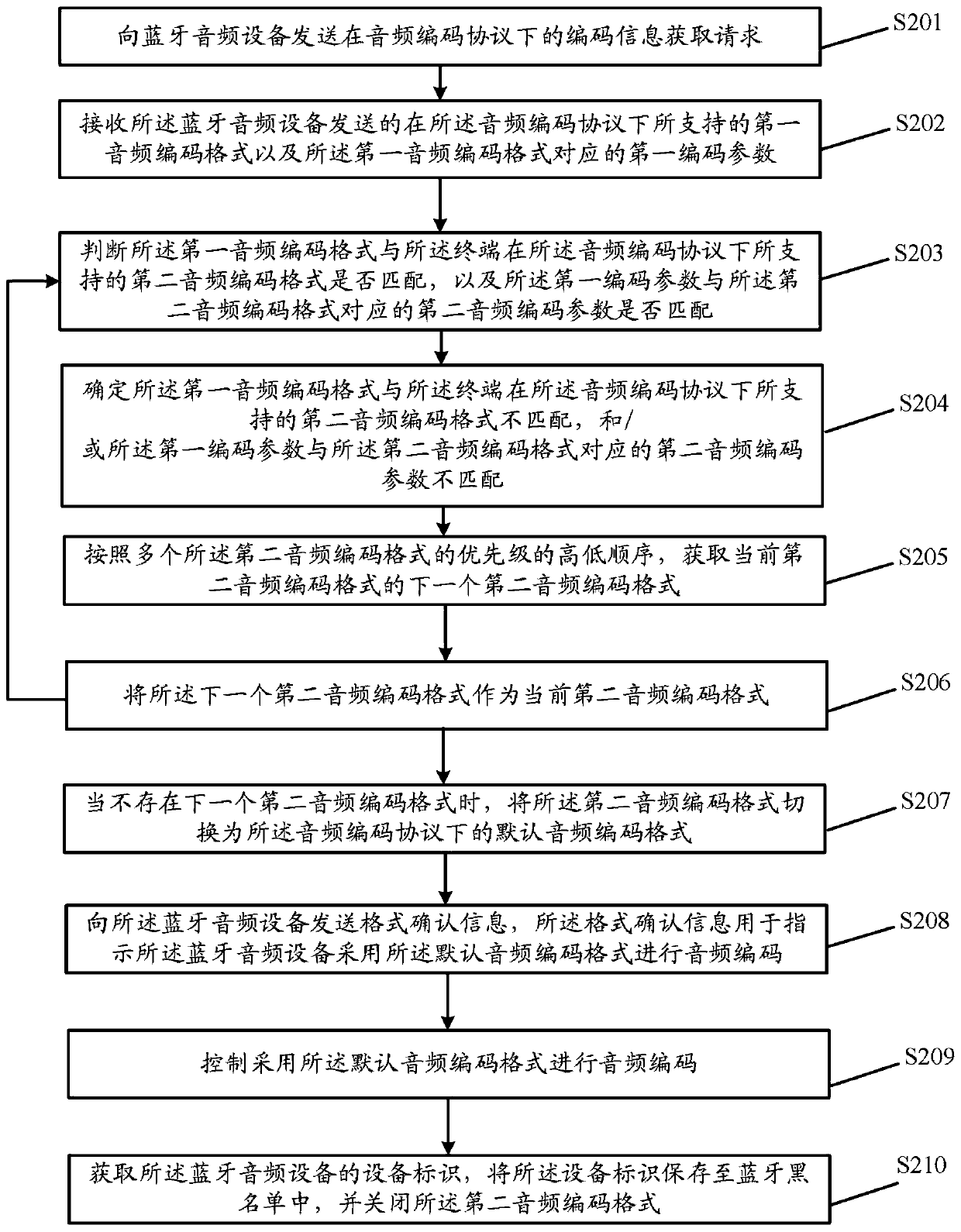
Audio coding format determination method and device, storage medium and electronic equipment
PendingCN111199743AImprove stabilityEasy to useSpeech analysisShort range communication serviceCODE protocolAudio equipment
The embodiment of the invention discloses an audio coding format determination method and device, a storage medium and electronic equipment. The method comprises the steps: obtaining a first audio coding format supported by Bluetooth audio equipment under an audio coding protocol and a first coding parameter corresponding to the first audio coding format, when the first audio coding format is notmatched with a second audio coding format supported by the terminal under the audio coding protocol, and / or when the first encoding parameter is not matched with a second audio encoding parameter corresponding to the second audio encoding format, switching the second audio encoding format to a default audio encoding format under the audio encoding protocol, and controlling to adopt the default audio encoding format to perform audio encoding. By adopting the embodiment of the invention, the stability of Bluetooth audio connection between the terminal and the Bluetooth audio equipment can be improved, and normal use of a Bluetooth audio function is ensured.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com