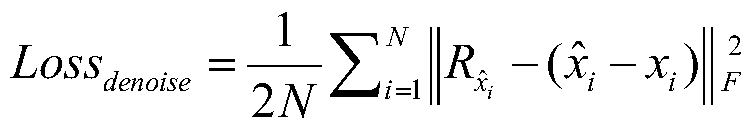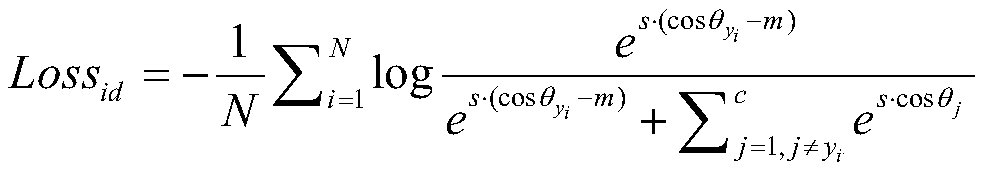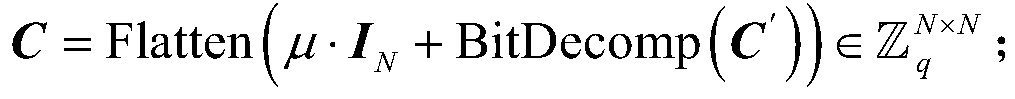Patents
Literature
81 results about "Identity mapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
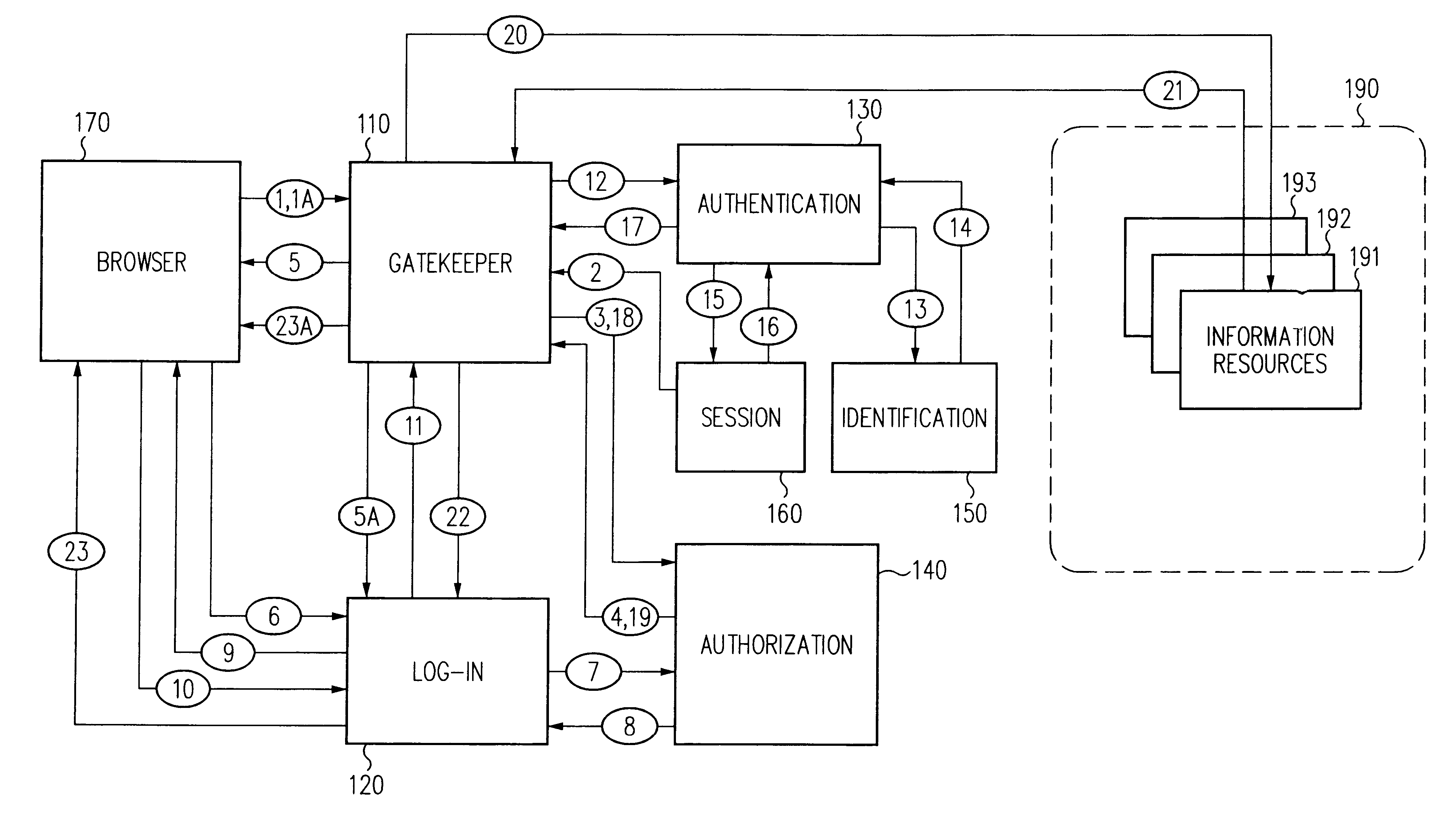
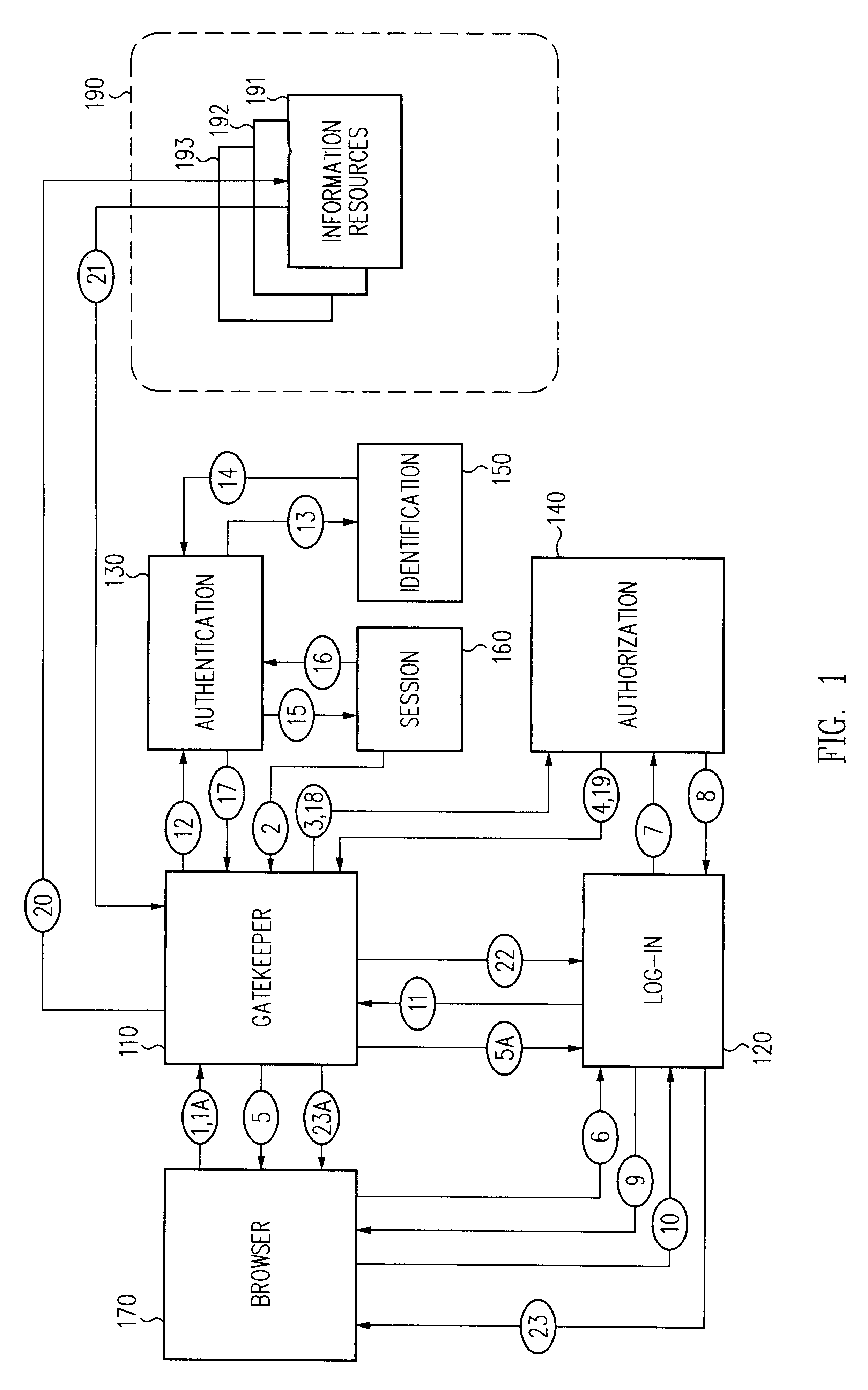
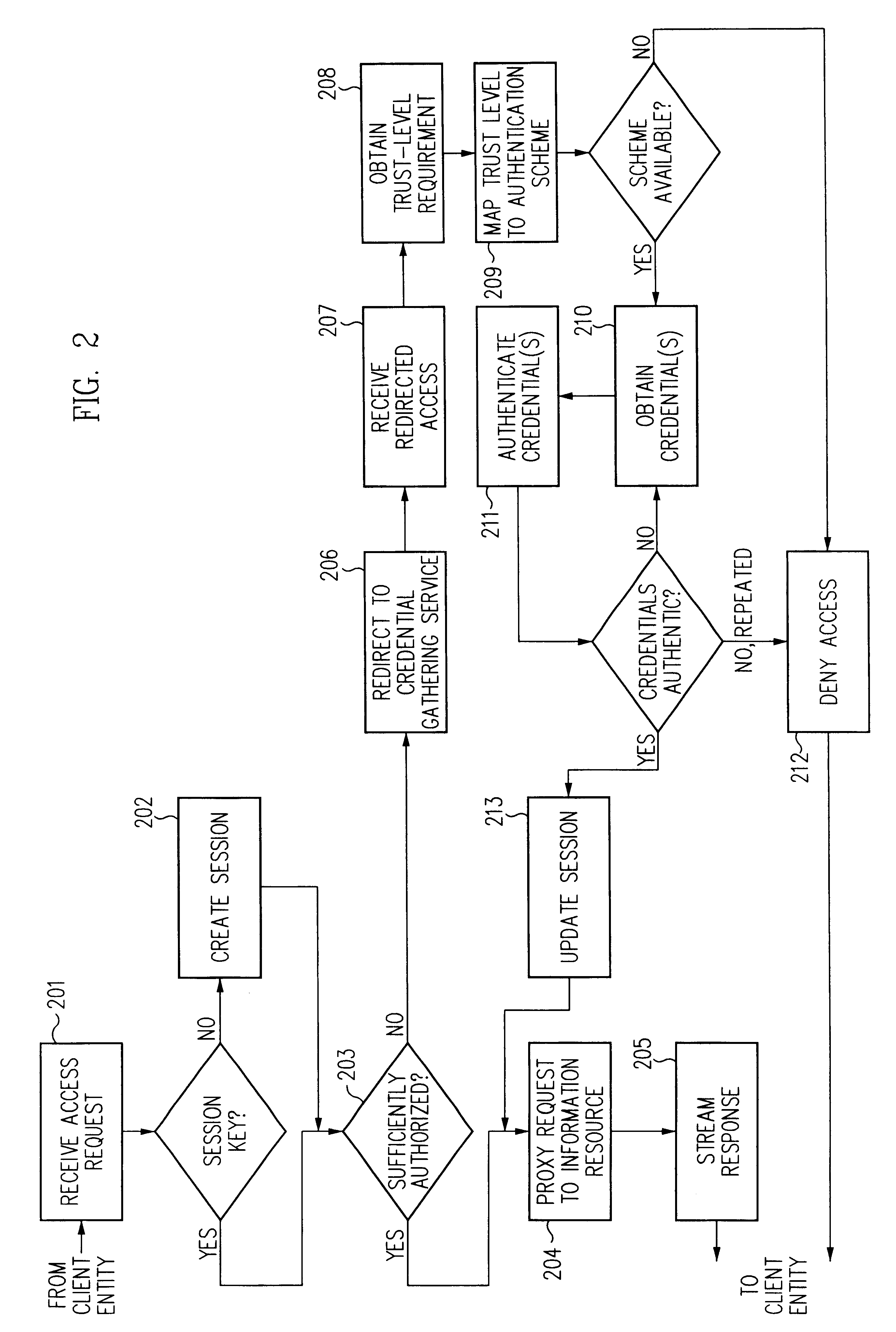
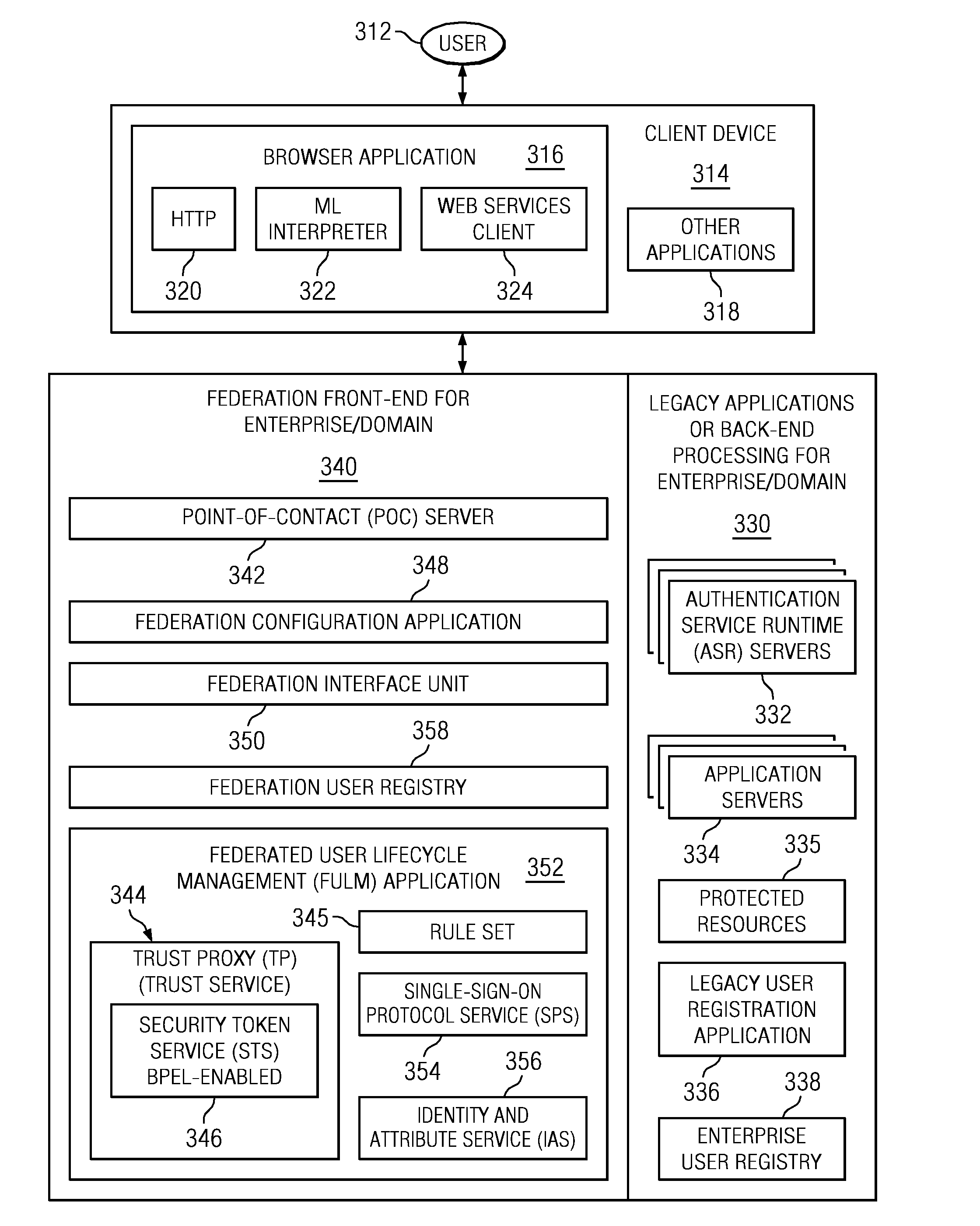
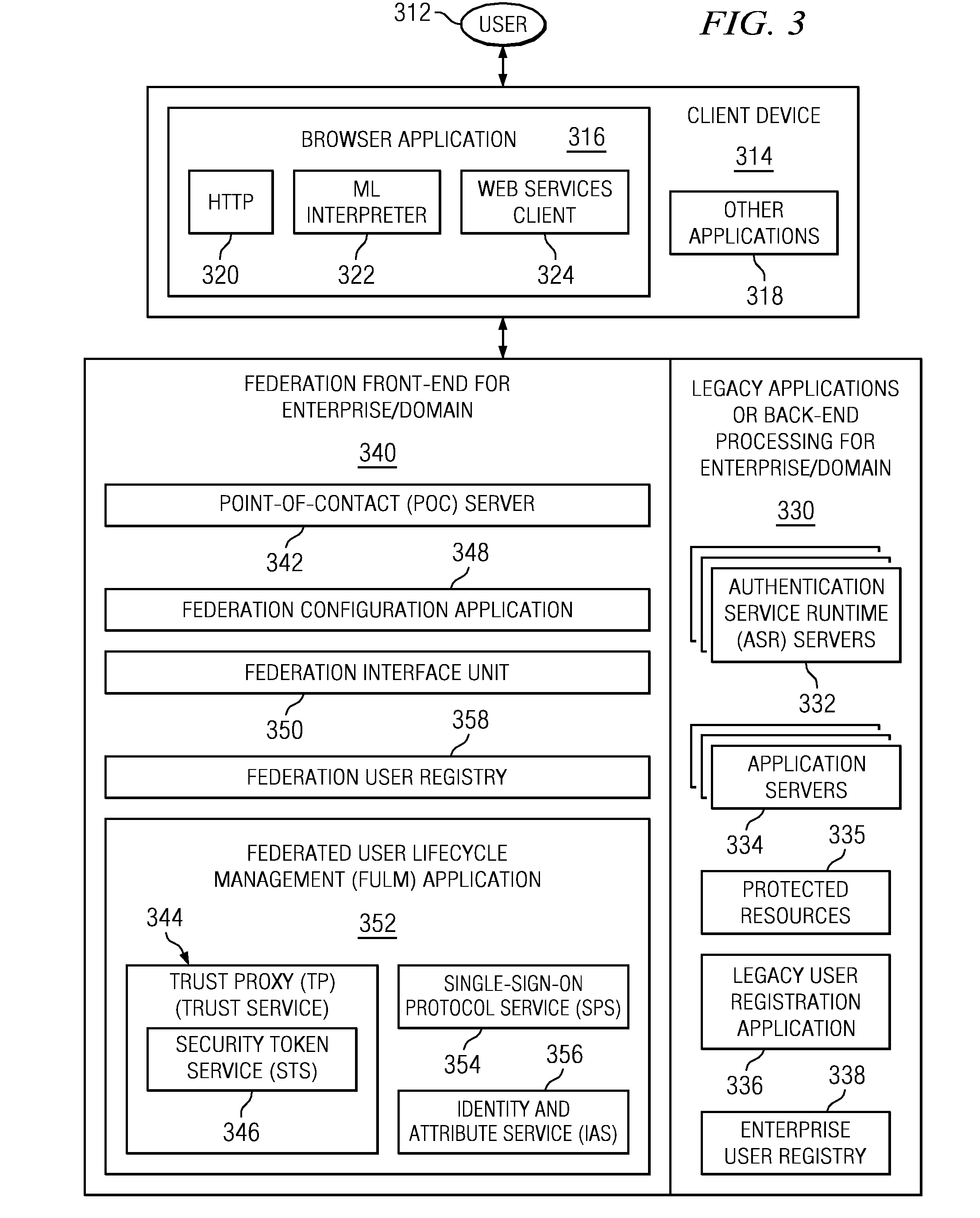
Log-on service providing credential level change without loss of session continuity
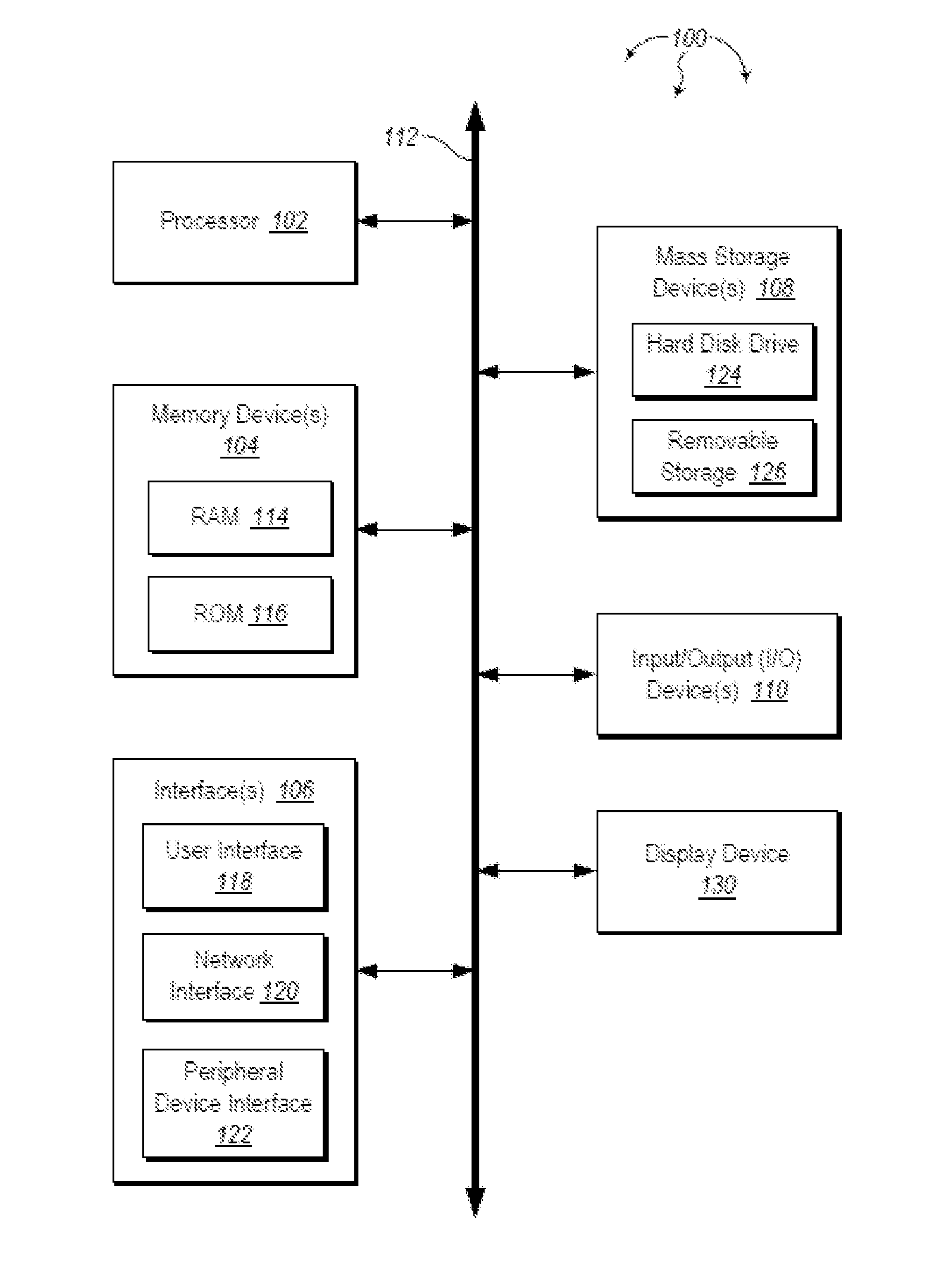
InactiveUS6609198B1Volume/mass flow measurementMultiple digital computer combinationsInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient. The security architecture allows upgrade of credentials for a given session. This capability is particularly advantageous in the context of a single, enterprise-wide log-on. An entity (e.g., a user or an application) may initially log-on with a credential suitable for one or more resources in an initial resource set, but then require access to resource requiring authentication at higher trust level. In such case, the log-on service allows additional credentials to be provided to authenticate at the higher trust level. The log-on service allows upgrading and / or downgrading without loss of session continuity (i.e., without loss of identity mappings, authorizations, permissions, and environmental variables, etc.).
Owner:ORACLE INT CORP
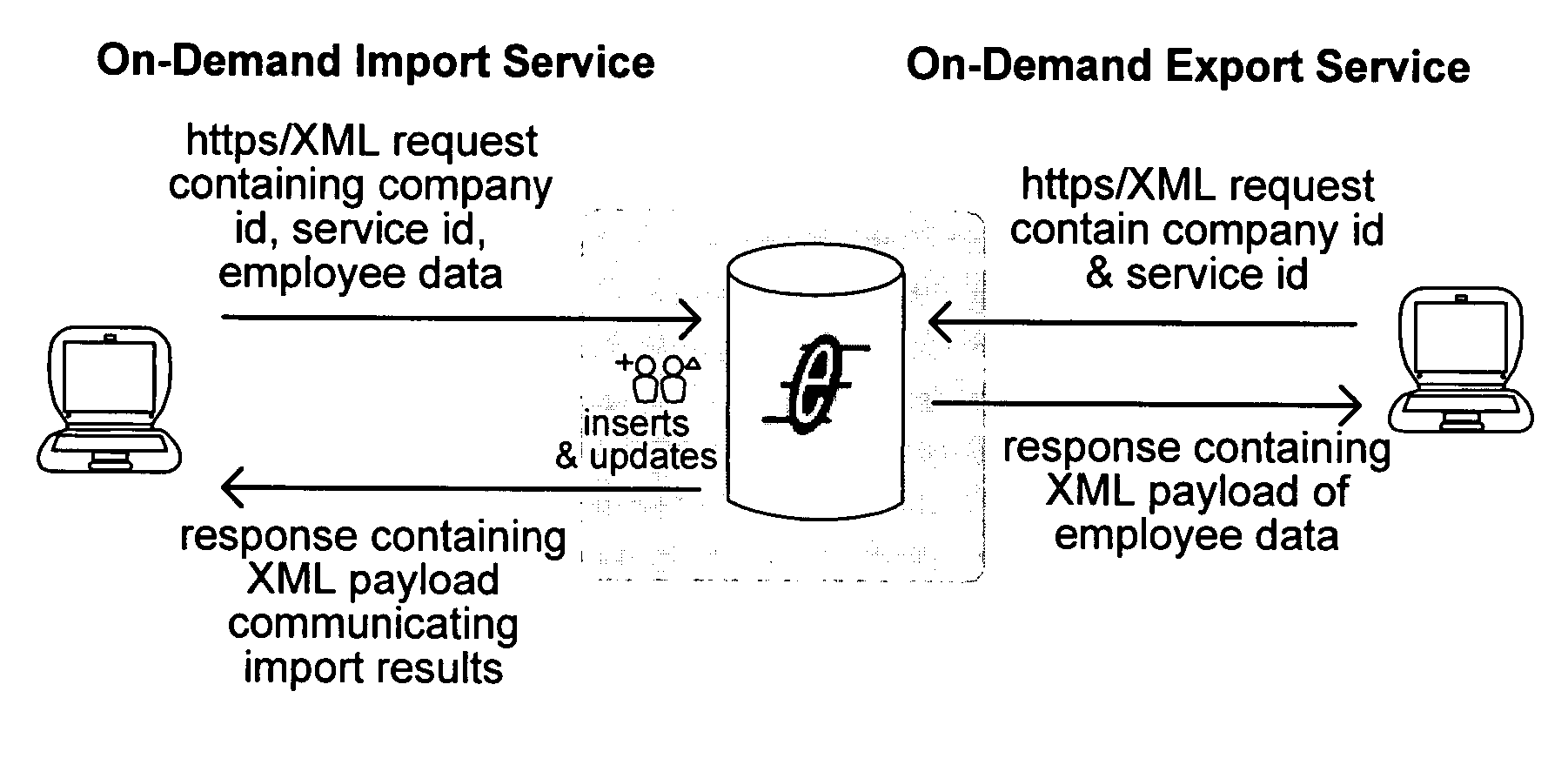
Providing on-demand access to services in a wide area network
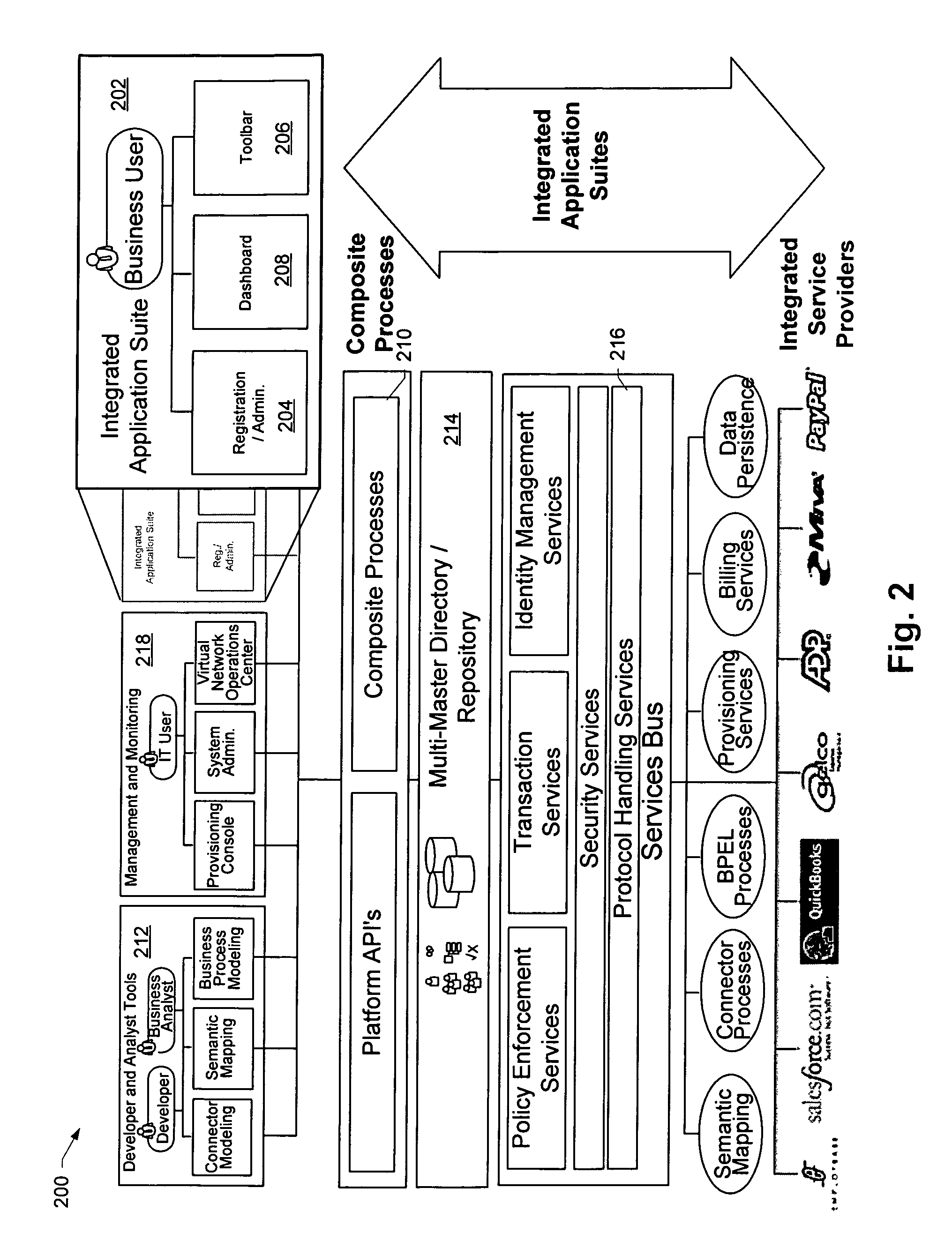
ActiveUS20060031225A1Easy accessEnhanced interactionDigital data information retrievalDigital data processing detailsComposite servicesService provision
An integration services network is described which is operable to facilitate access to a composite service by a plurality of users having associated client machines. Each of the users is associated with one of a plurality of independent enterprises. At least one data store has a directory stored therein which maps an identity for each of the users to a policy framework which defines access information relating to a plurality of services. At least one computing device is operable to set up the composite service by integrating operation of the plurality of services. The plurality of services are associated with and controlled by a plurality of independent service providers. The at least one computing device is further operable to connect with the client machines and each of the services, and to selectively facilitate interaction among the client machines and the services with reference to the directory and the policy framework, thereby enabling each of the users to access the plurality of services as an integrated solution.
Owner:SALESFORCE COM INC
Providing on-demand access to services in a wide area network
ActiveUS7725605B2Easy accessEnhanced interactionDigital data information retrievalDigital data processing detailsData memoryFile area network
An integration services network is described which is operable to facilitate access to a composite service by a plurality of users having associated client machines. Each of the users is associated with one of a plurality of independent enterprises. At least one data store has a directory stored therein which maps an identity for each of the users to a policy framework which defines access information relating to a plurality of services. At least one computing device is operable to set up the composite service by integrating operation of the plurality of services. The plurality of services are associated with and controlled by a plurality of independent service providers. The at least one computing device is further operable to connect with the client machines and each of the services, and to selectively facilitate interaction among the client machines and the services with reference to the directory and the policy framework, thereby enabling each of the users to access the plurality of services as an integrated solution.
Owner:SALESFORCE COM INC
ResLCNN model-based short text classification method
InactiveCN107562784AImprove classification effectNeural architecturesSpecial data processing applicationsText miningText categorization
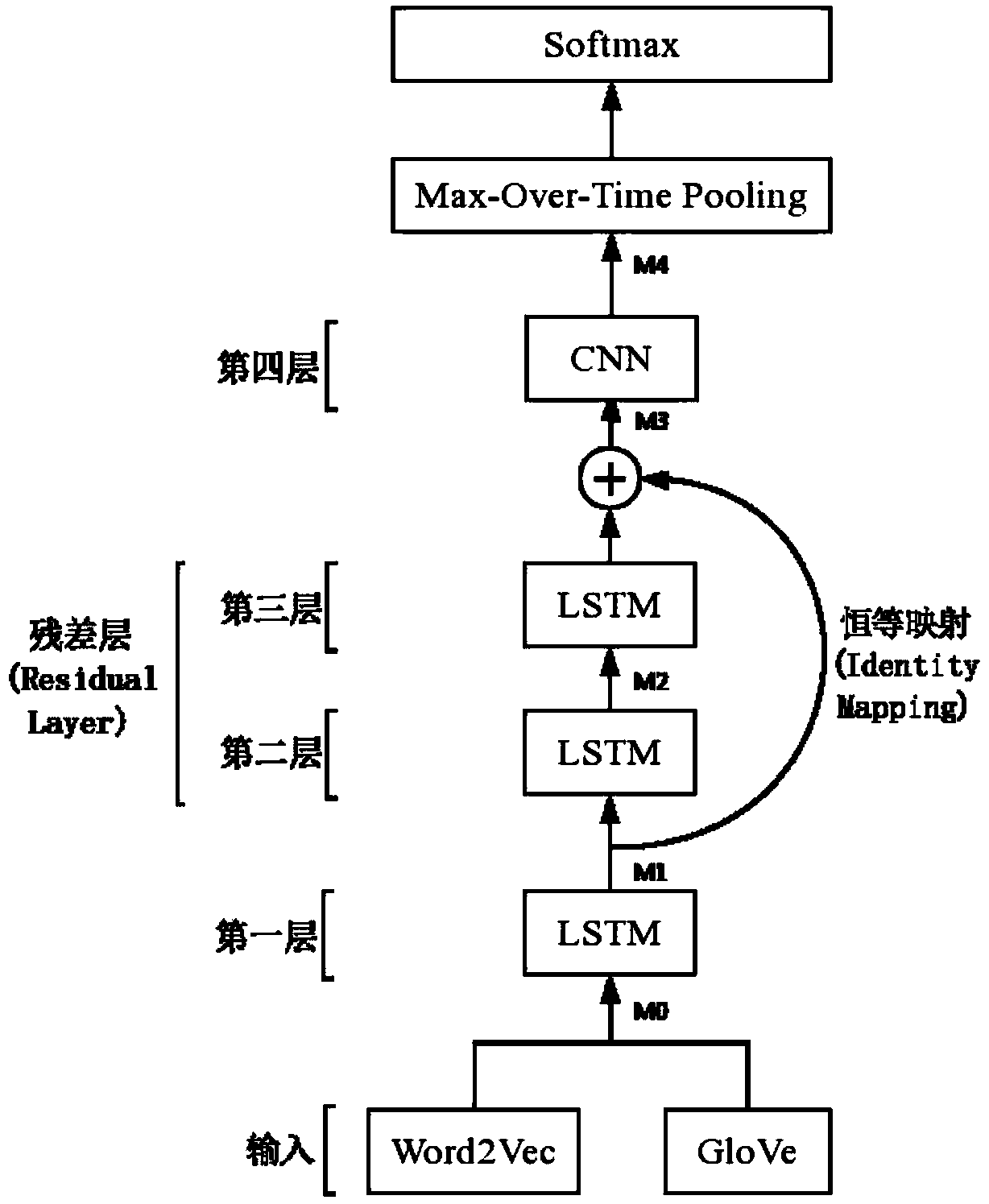
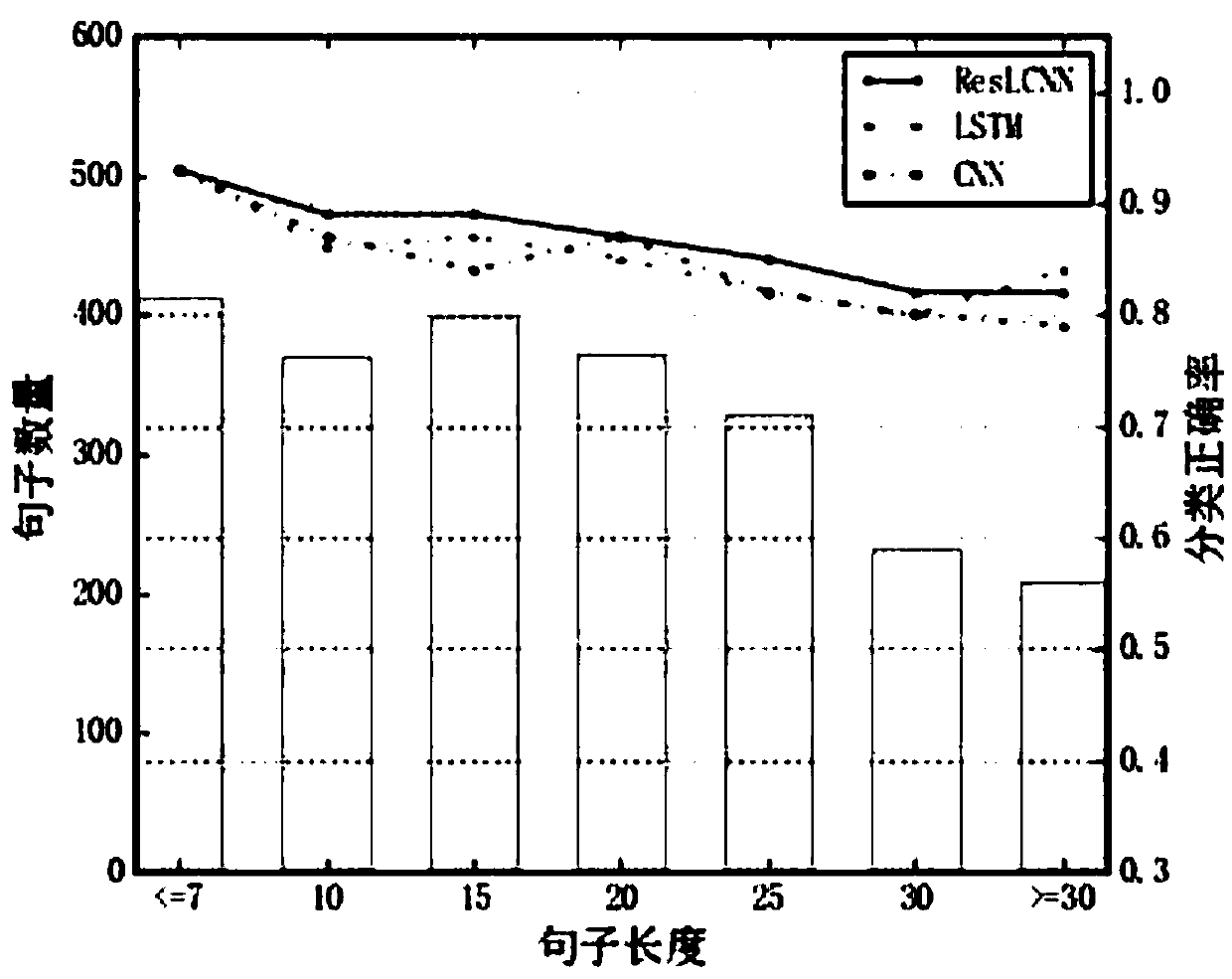
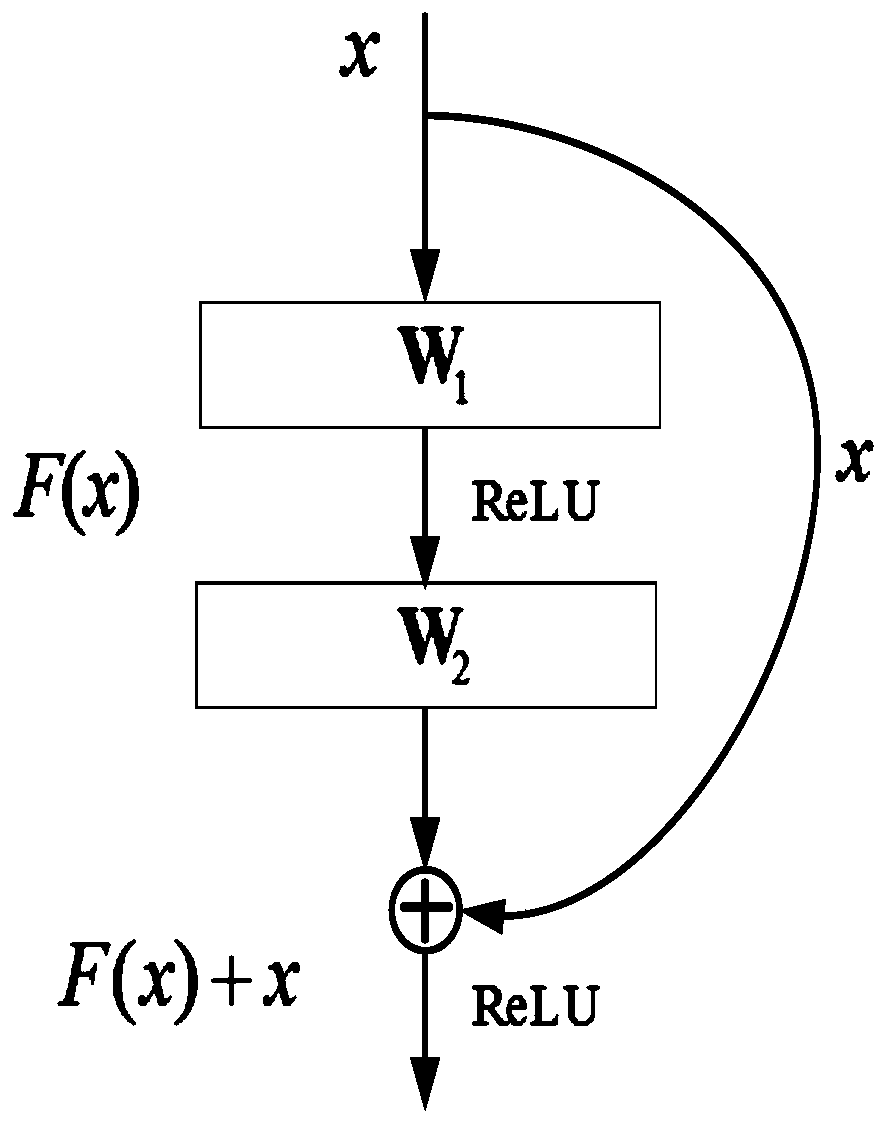
The invention discloses a ResLCNN model-based short text classification method, relates to the technical field of text mining and deep learning, and in particular to a deep learning model for short text classification. According to the method, characteristics of a long-short term memory network and a convolutional neural network are combined to build a ResLCNN deep text classification model for short text classification. The model comprises three long-short term memory network layer and one convolutional neural network layer; and through using a residual model theory for reference, identity mapping is added between the first long-short term memory network layer and the convolutional neural network layer to construct a residual layer, so that the problem of deep model gradient missing is relieved. According to the model, the advantage, of obtaining long-distance dependency characteristics of text sequence data, of the long-short term memory network and the advantage, of obtaining localfeatures of sentences through convolution, of the convolutional neural network are effectively combined, so that the short text classification effect is improved.
Owner:TONGJI UNIV
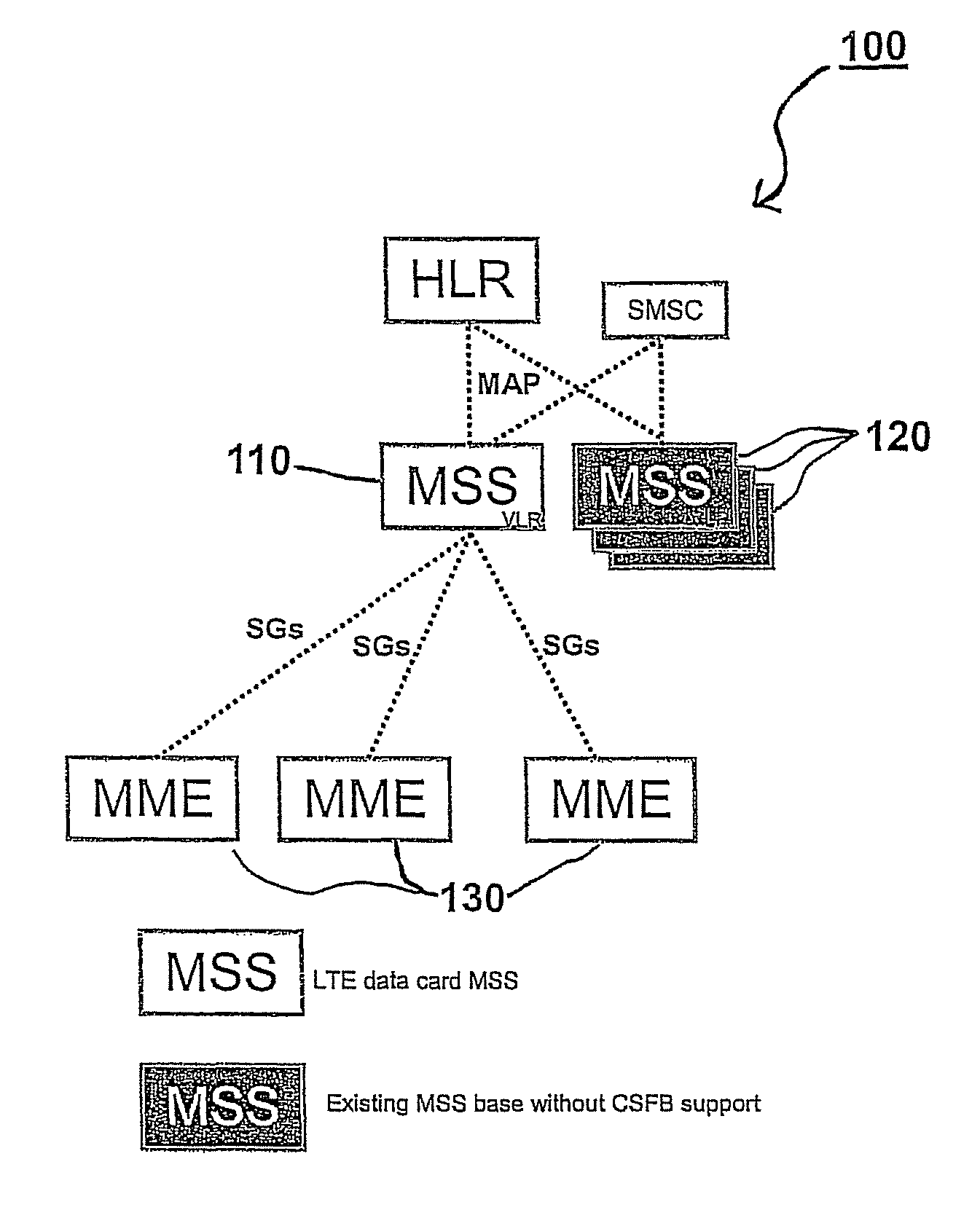
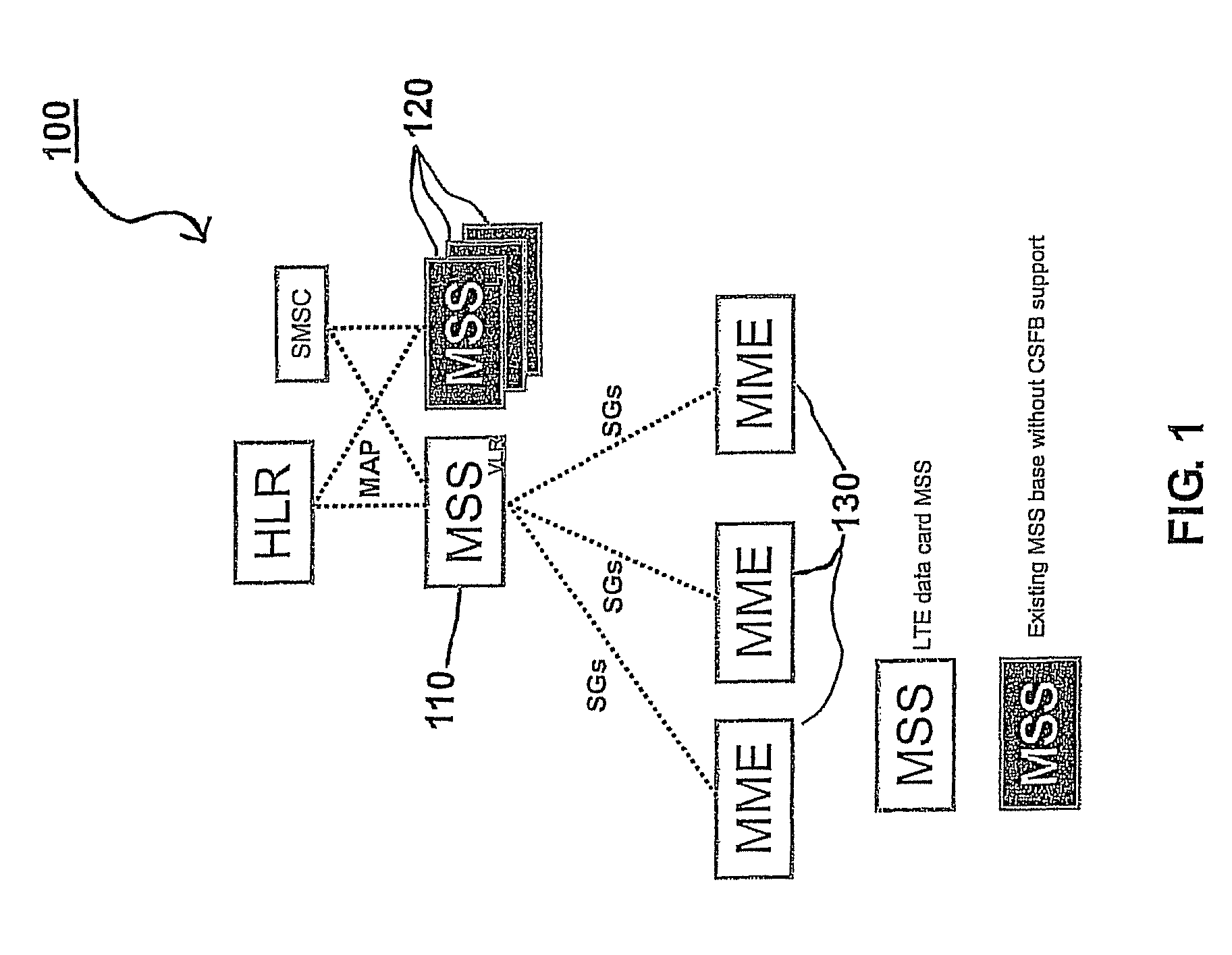
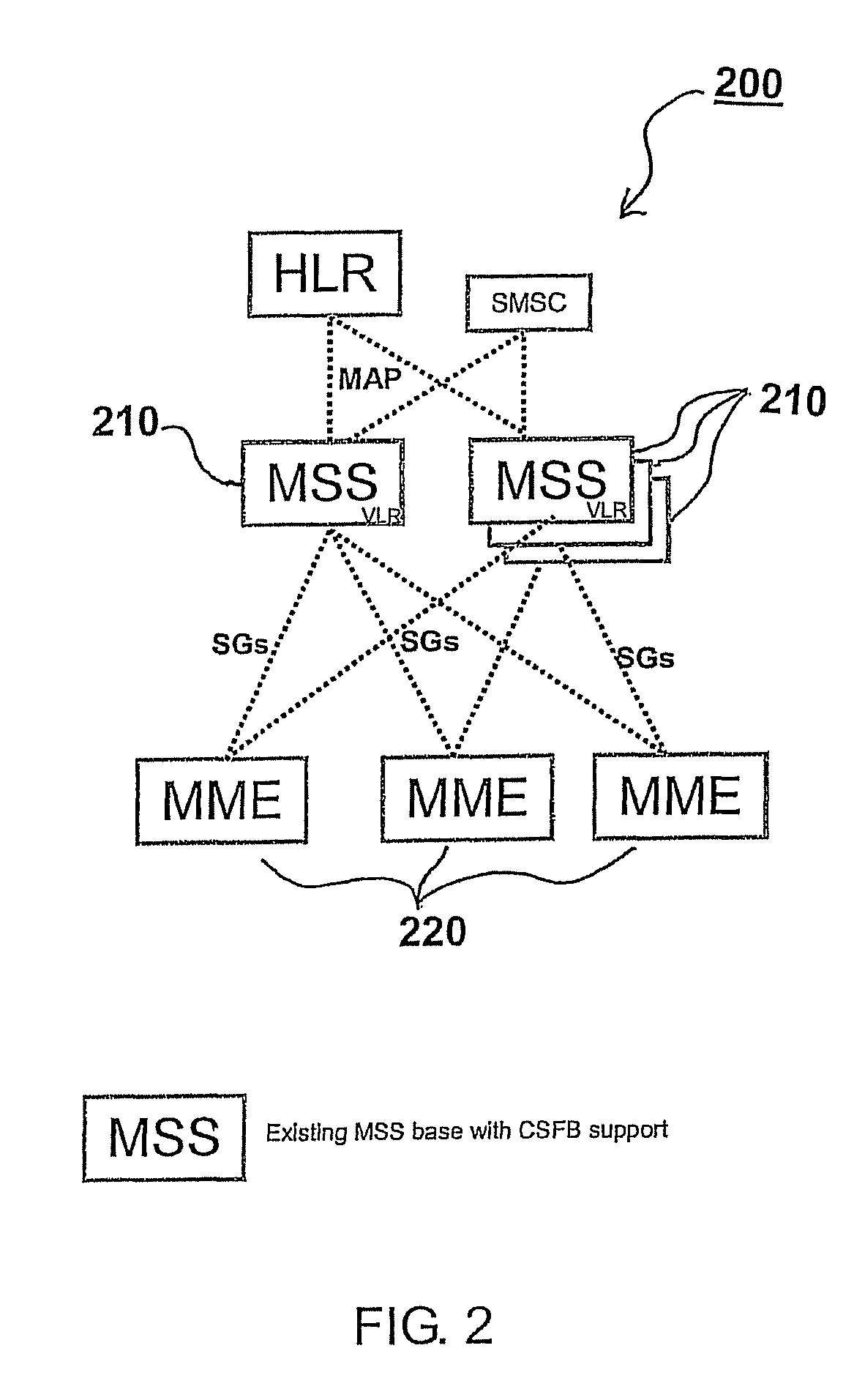
Mobile management entity operating in communications network and selection method therefor
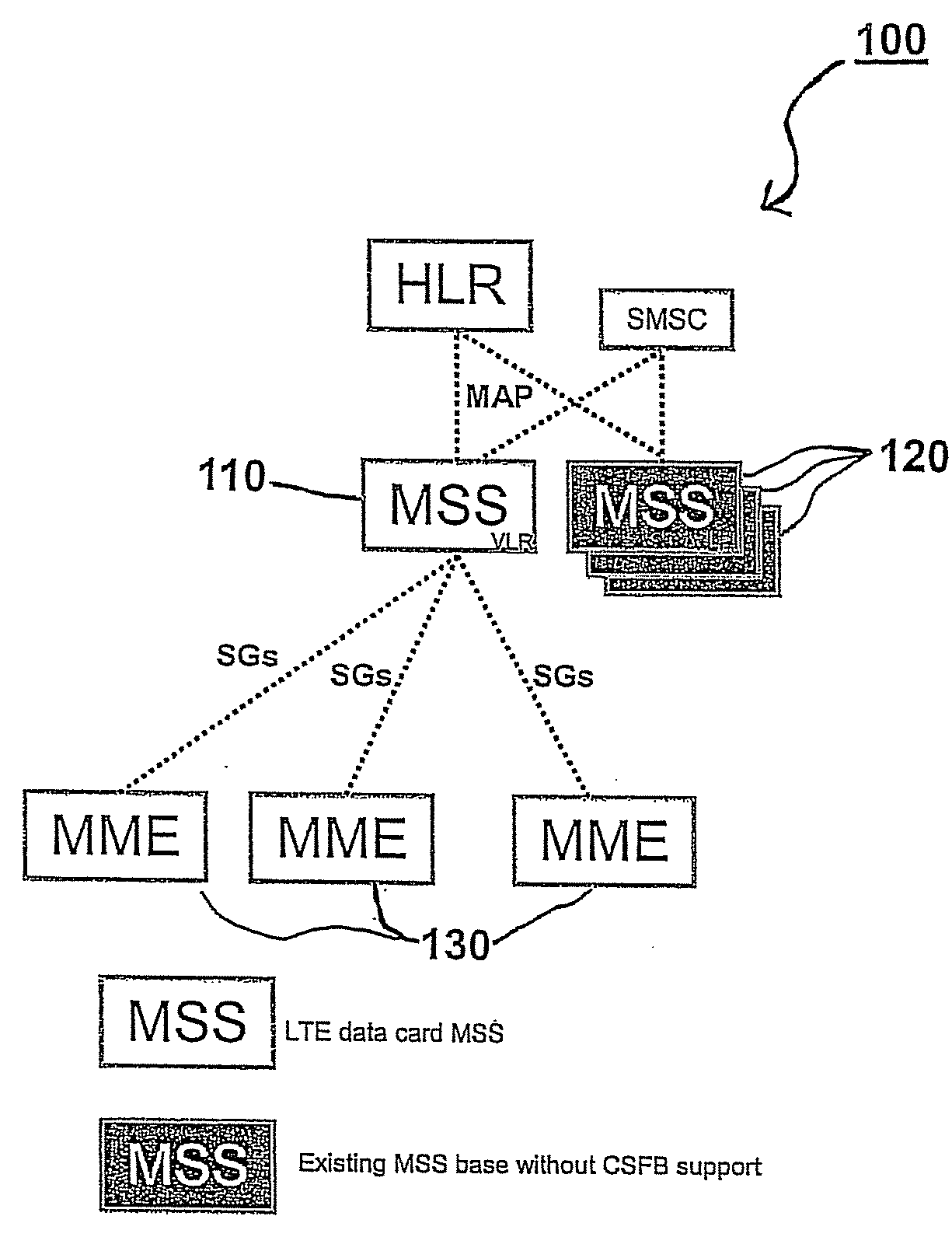
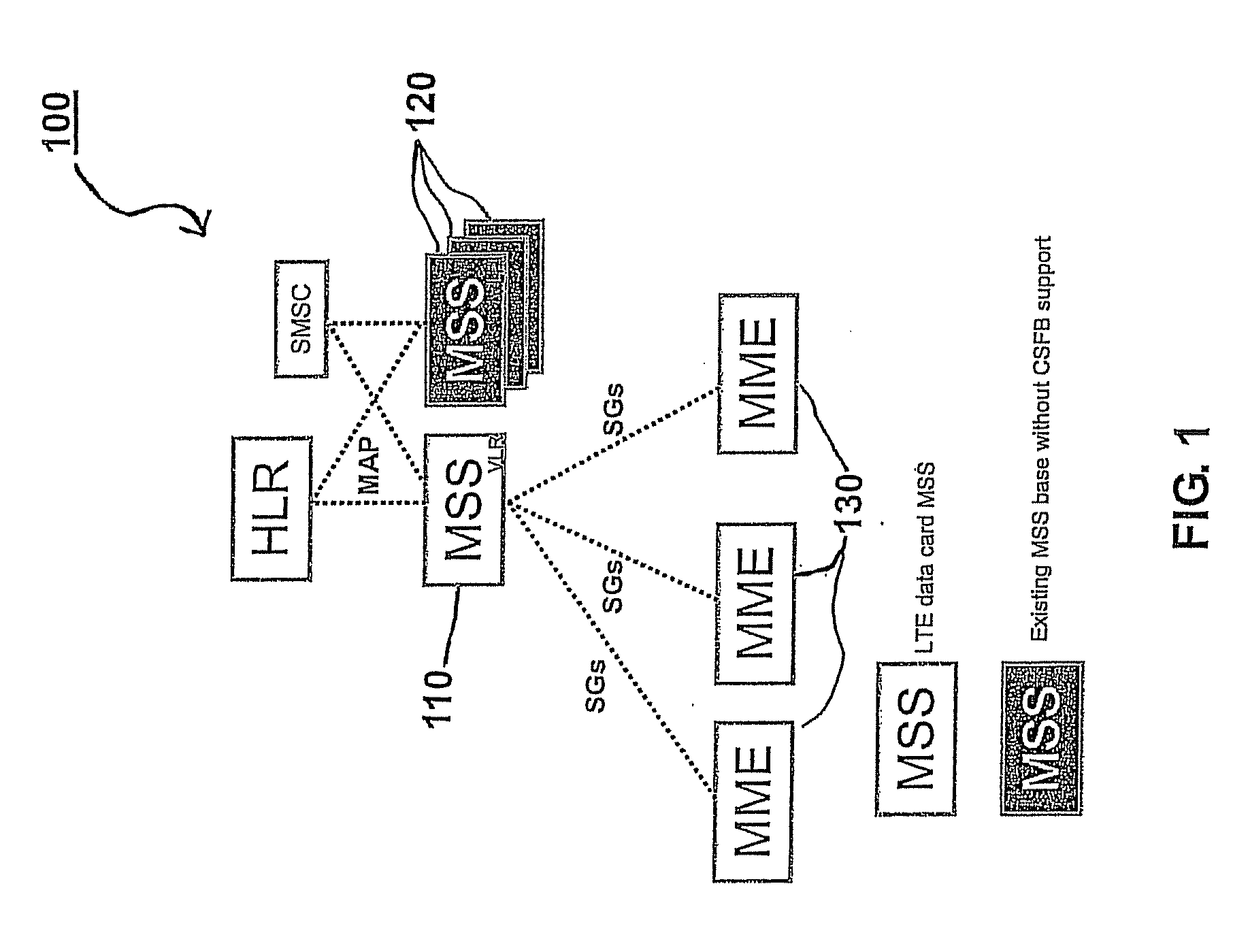
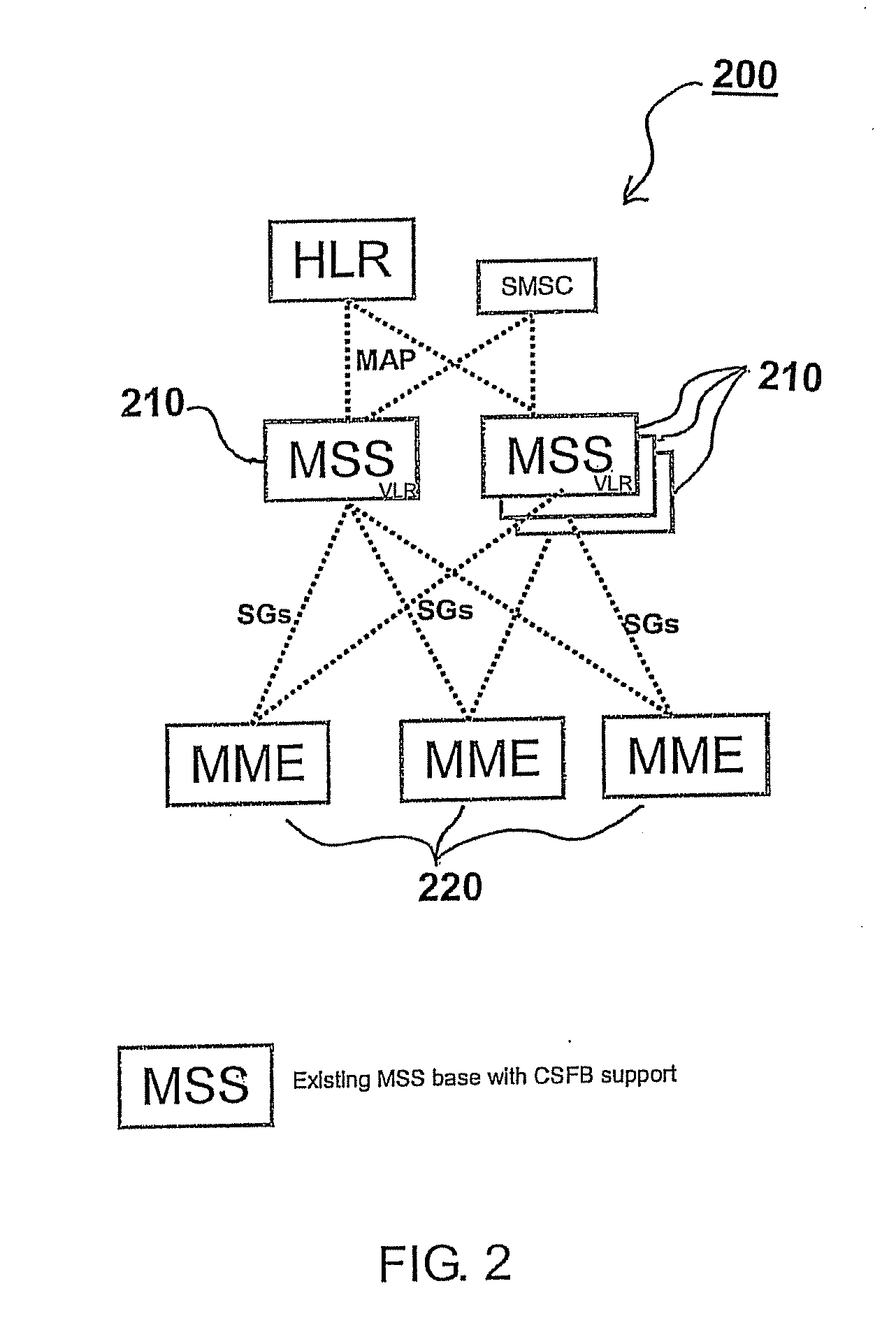
A selection method implemented as an algorithm in a mobile management entity (MME) operating in a communications network. The method includes receiving a unique identifier of a subscriber operating within the network and determining, based on the unique identifier, whether the subscriber has full circuit switching fallback (CSFB) capability or has only packet switching (PS) capability. When it is determined that the subscriber has full CSFB capability, a mobile switching center server (MSS) is selected based on original tracking area matrices and / or tracking area identity-location area identity mapping defined in the 3rd Generation Partnership Project (3GPP). When it is determined that the subscriber has only PS capability, an MSS is selected from a group of MSSs having CSFB support only for short message service (SMS) delivery.
Owner:NOKIA SOLUTIONS & NETWORKS OY
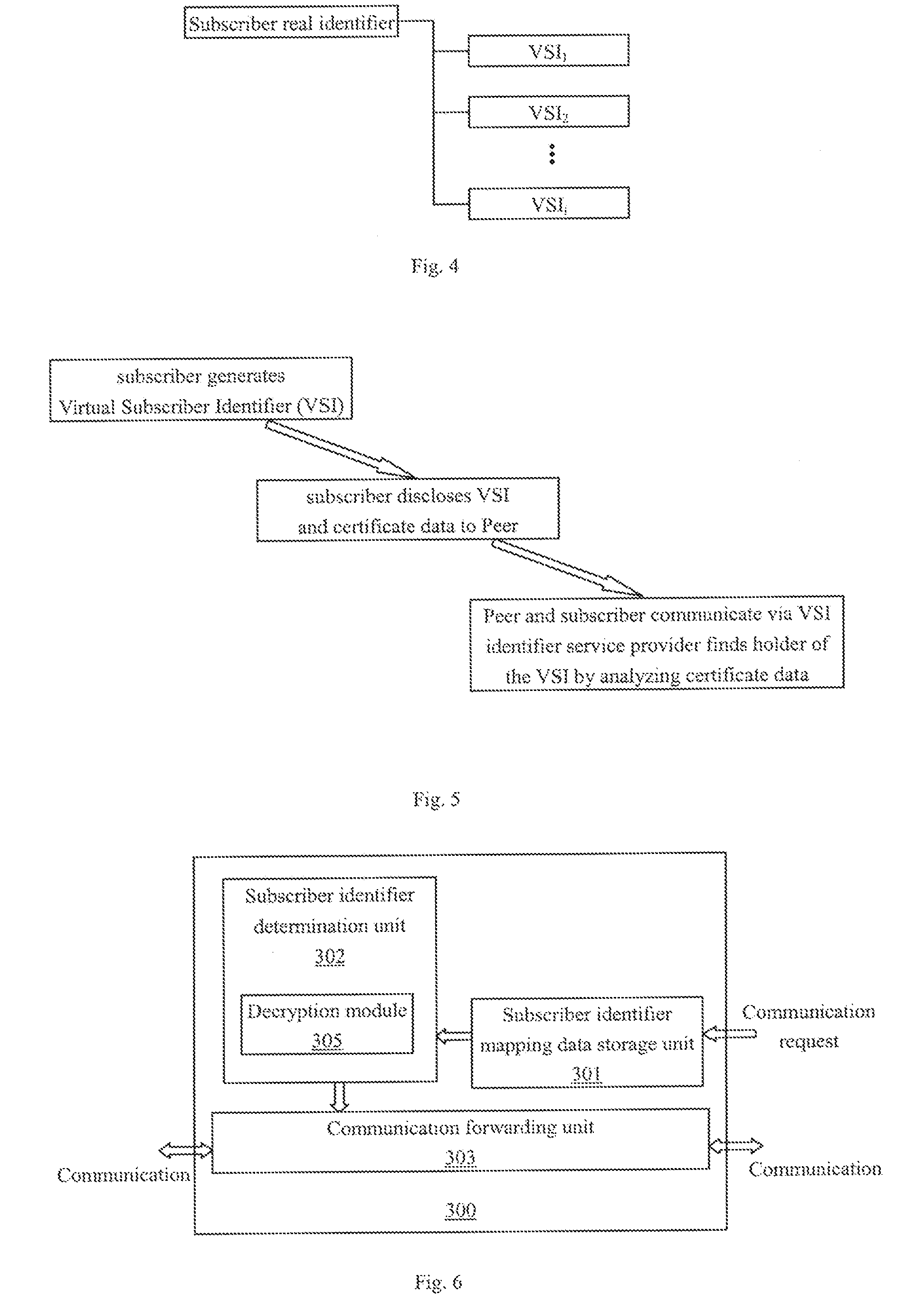
Virtual subscriber identifier system and method
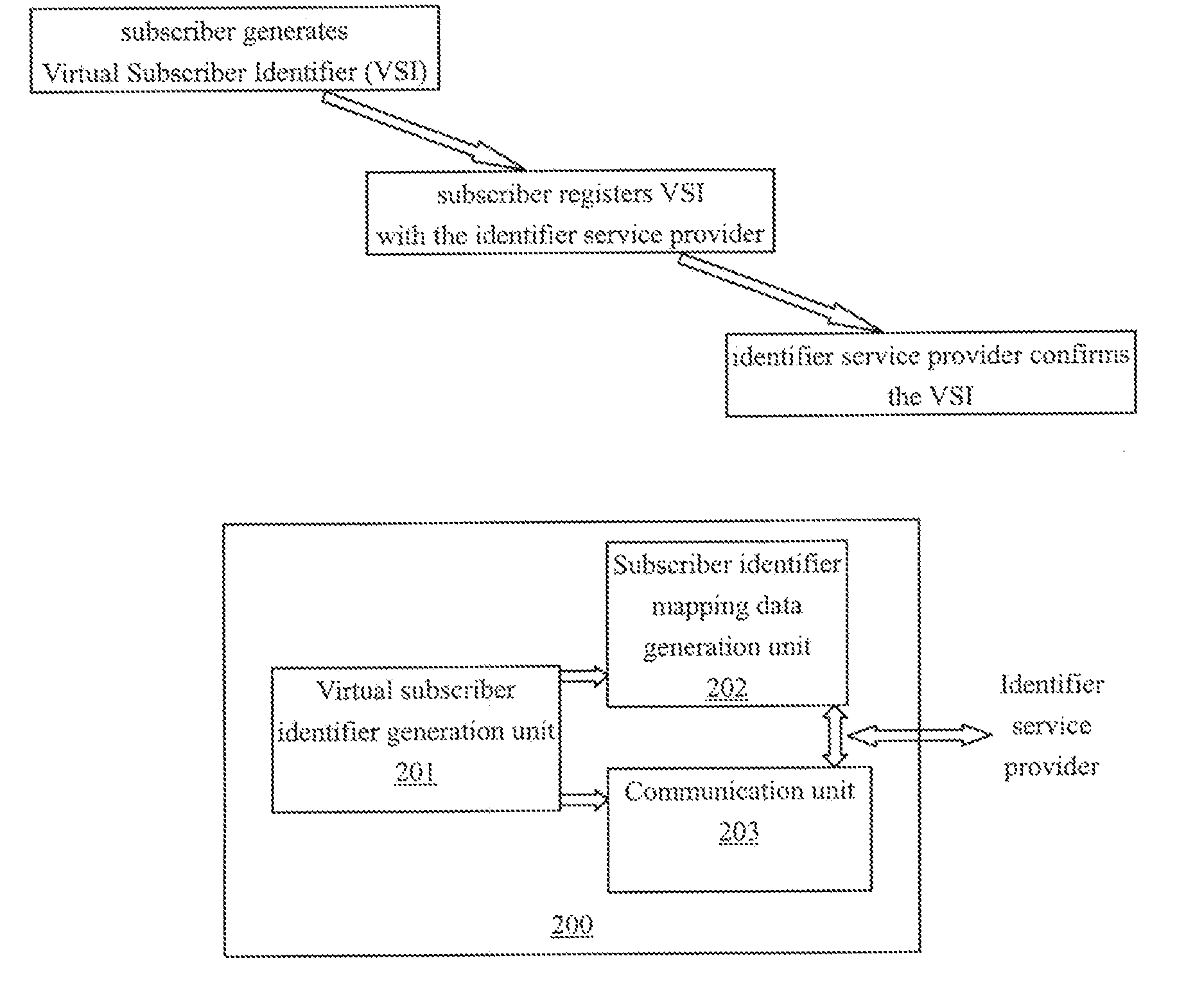
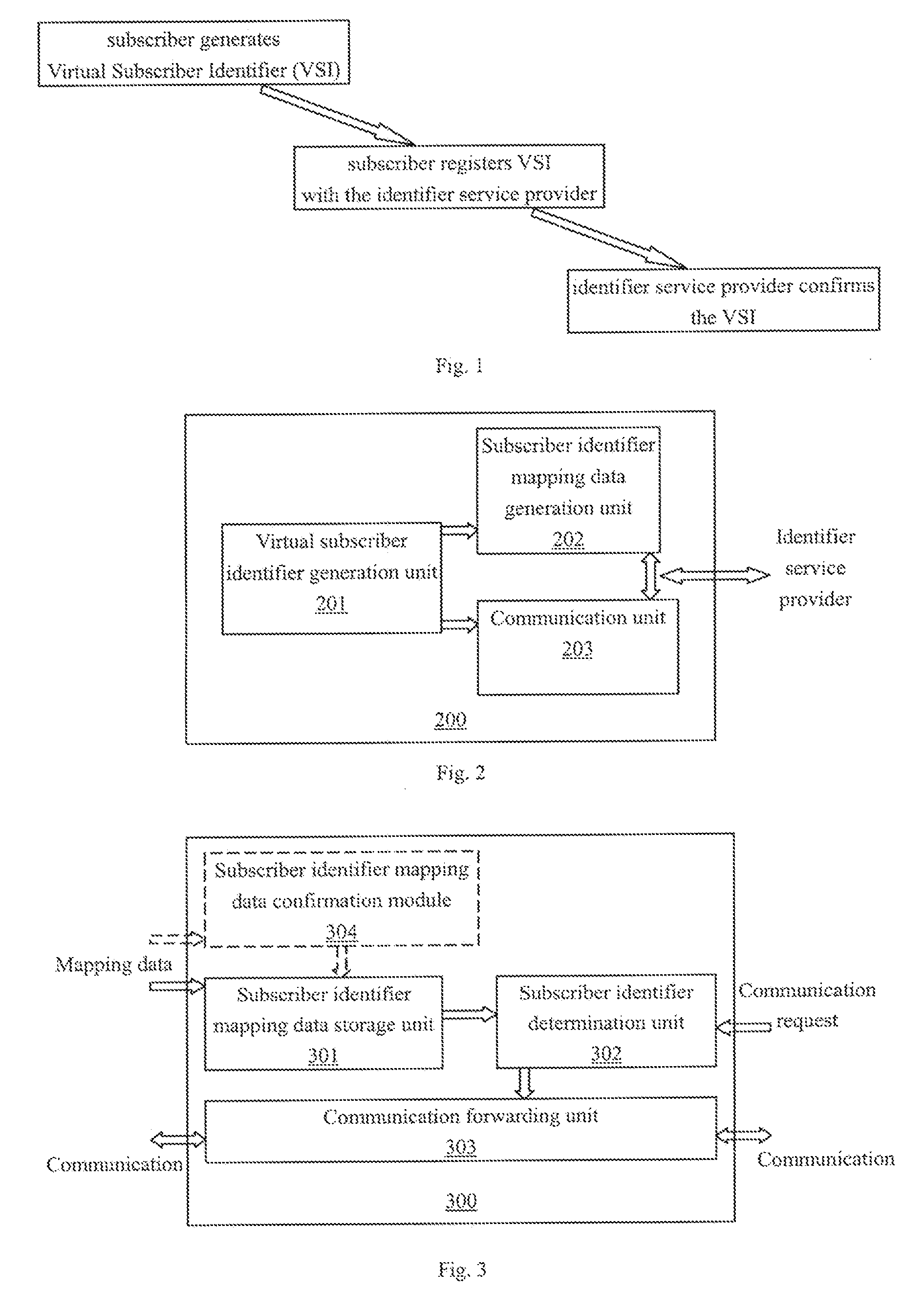
InactiveUS20070130465A1User identity/authority verificationDigital data authenticationVirtual userService provision
The invention provides a virtual subscriber identifier system and method of a communication network. According to one embodiment of the invention, a subscriber generates virtual subscriber identifiers by him / her self, generates a subscriber identity mapping data by which a identifier service provider can figure out the real identifier of the owner of the virtual subscriber identifier, and informs peers of the virtual subscriber identifiers. The subscriber identify mapping data may be a data in which a virtual subscriber identifier is associated to the real identifier of the subscriber, and be registered by the subscriber with the identifier service provider. A peer generates a communicating request including a virtual subscriber identifier as target, and sends the request to the identifier service provider, the identifier service provider determines the real identifier of the subscriber from the subscriber identity mapping data, and forwards the communication between the peer and the subscriber's terminal. In another embodiment, the subscriber identity mapping data may be a secret data of the subscriber, by which the virtual subscriber identifier can figure out the real identifier of the subscriber. When receiving the communication request, the identifier service provider decrypts the real identifier of the owner of the virtual subscriber identifier from the secret data received from the peer. In one embodiment, the virtual subscriber identifier is generated from the public key of the subscriber. The virtual subscriber identifier may be equipped with a certificate, or be associated with a magic word. With the invention, the use of the virtual subscriber identifiers is more flexible to the system and versatile to the subscriber.
Owner:NEC (CHINA) CO LTD
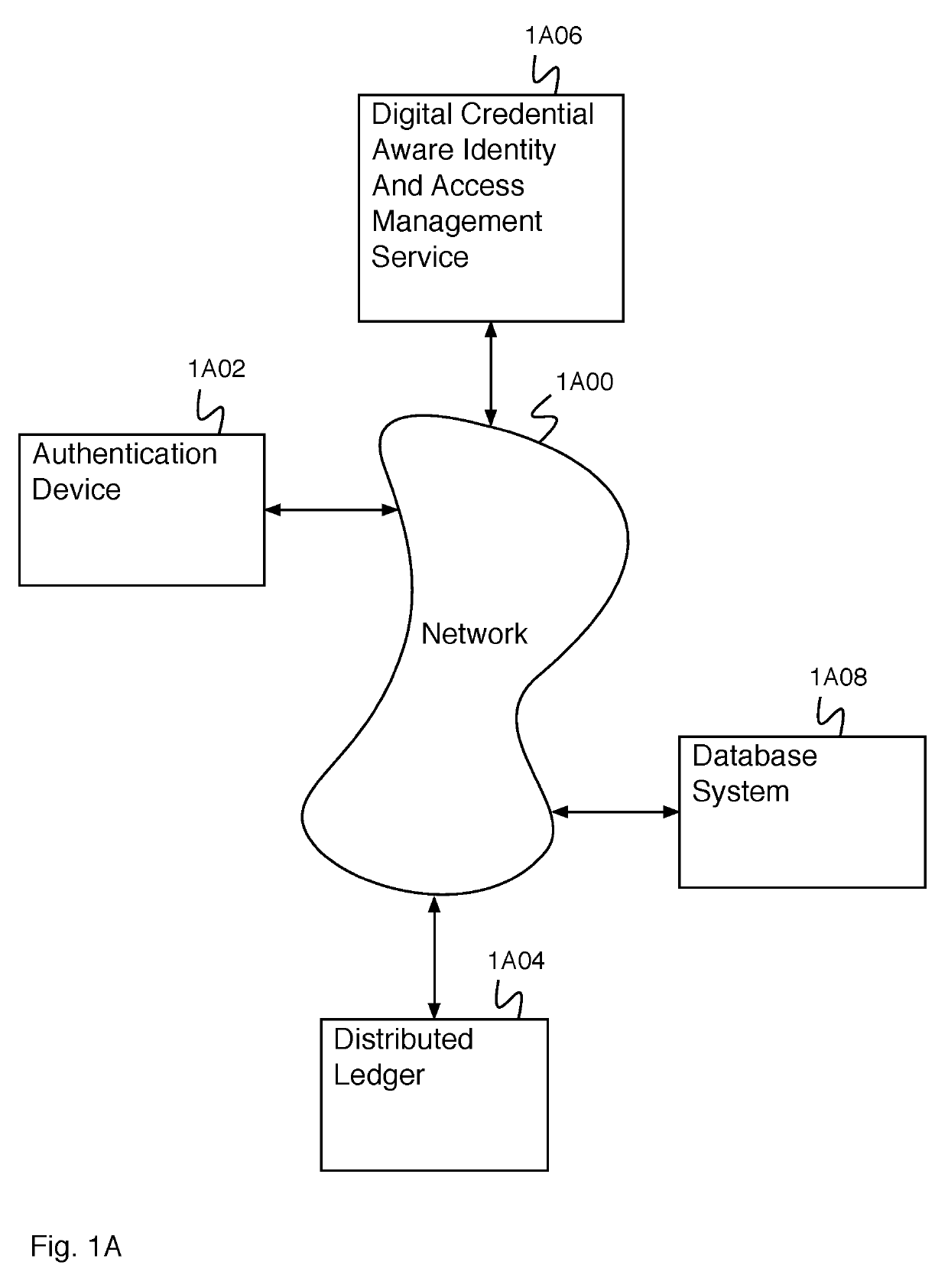
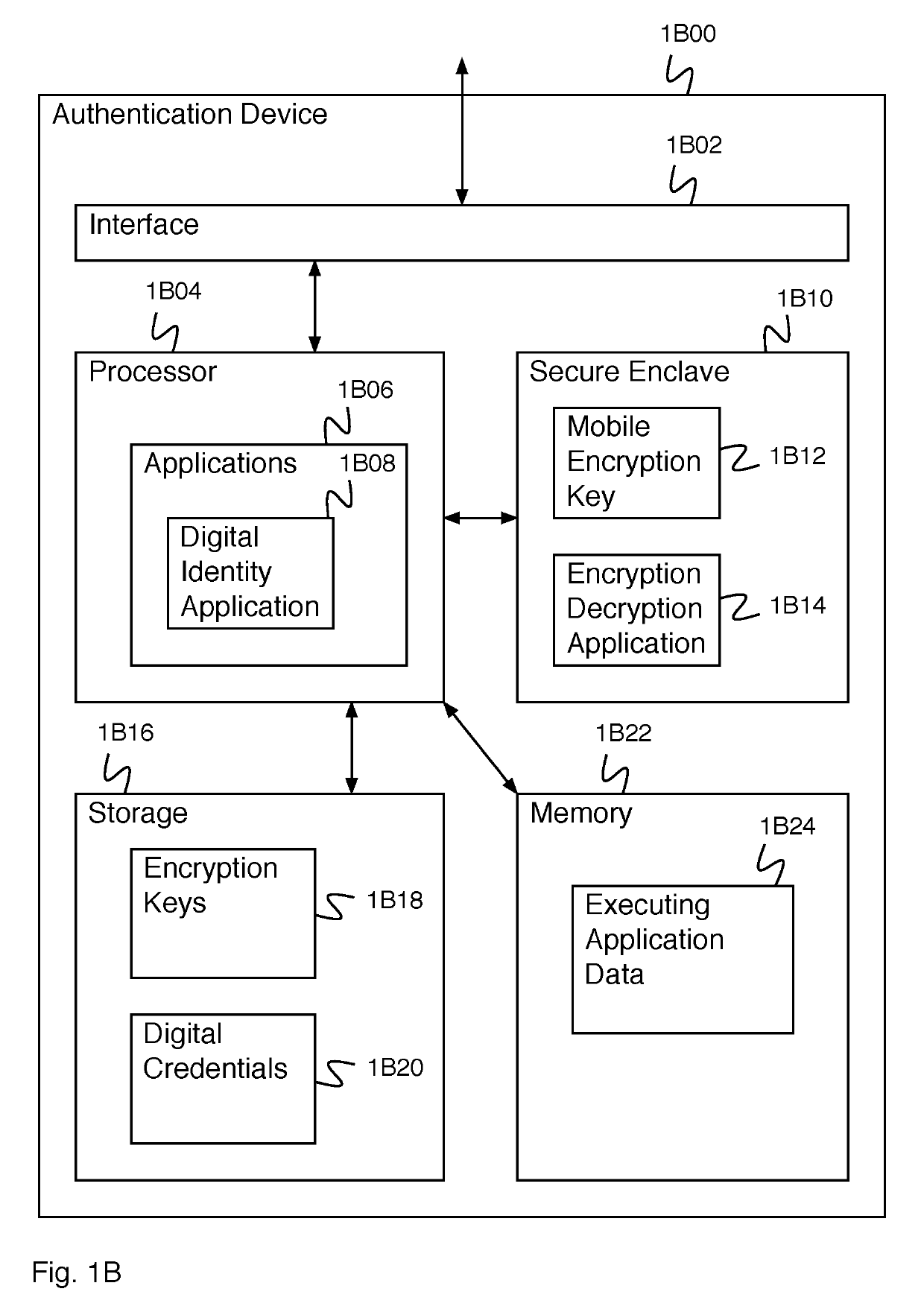
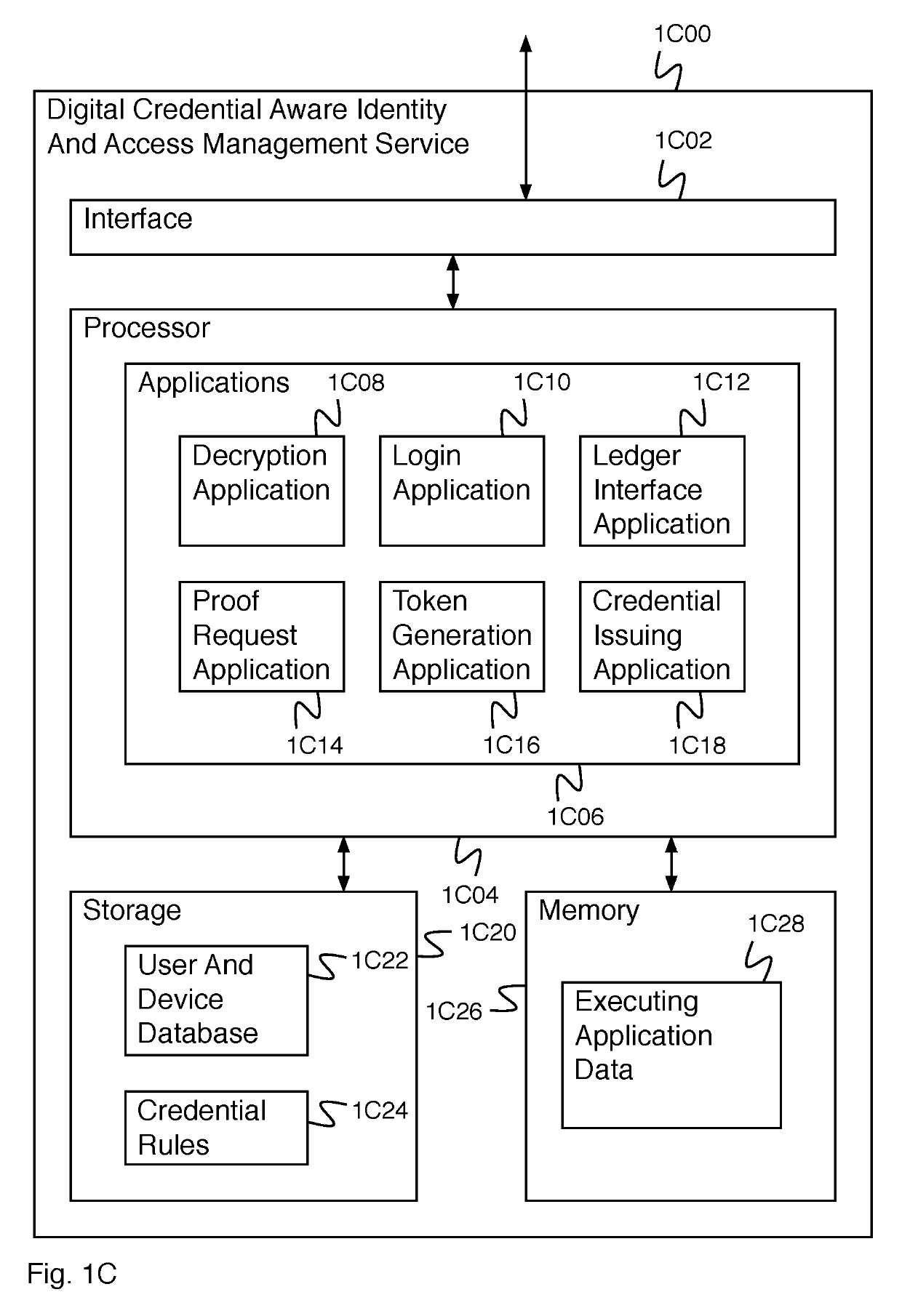
Digital credential authentication
ActiveUS20190305952A1Key distribution for secure communicationMultiple keys/algorithms usageDocumentationDigital credential
A system for creating an identity mapping on a distributed ledger includes an interface and a processor. The interface is configured to receive a request to create an identity mapping on a distributed ledger. The processor is configured to generate an identity key pair; generate a mobile encryption key; encrypt a private identity key of the identity key pair using the mobile encryption key to create an encrypted private key; store the encrypted private key; create a mapping document; sign the mapping document with the private identity key of the identity key pair; and provide the signed mapping document to be stored in a distributed ledger.
Owner:WORKDAY INC
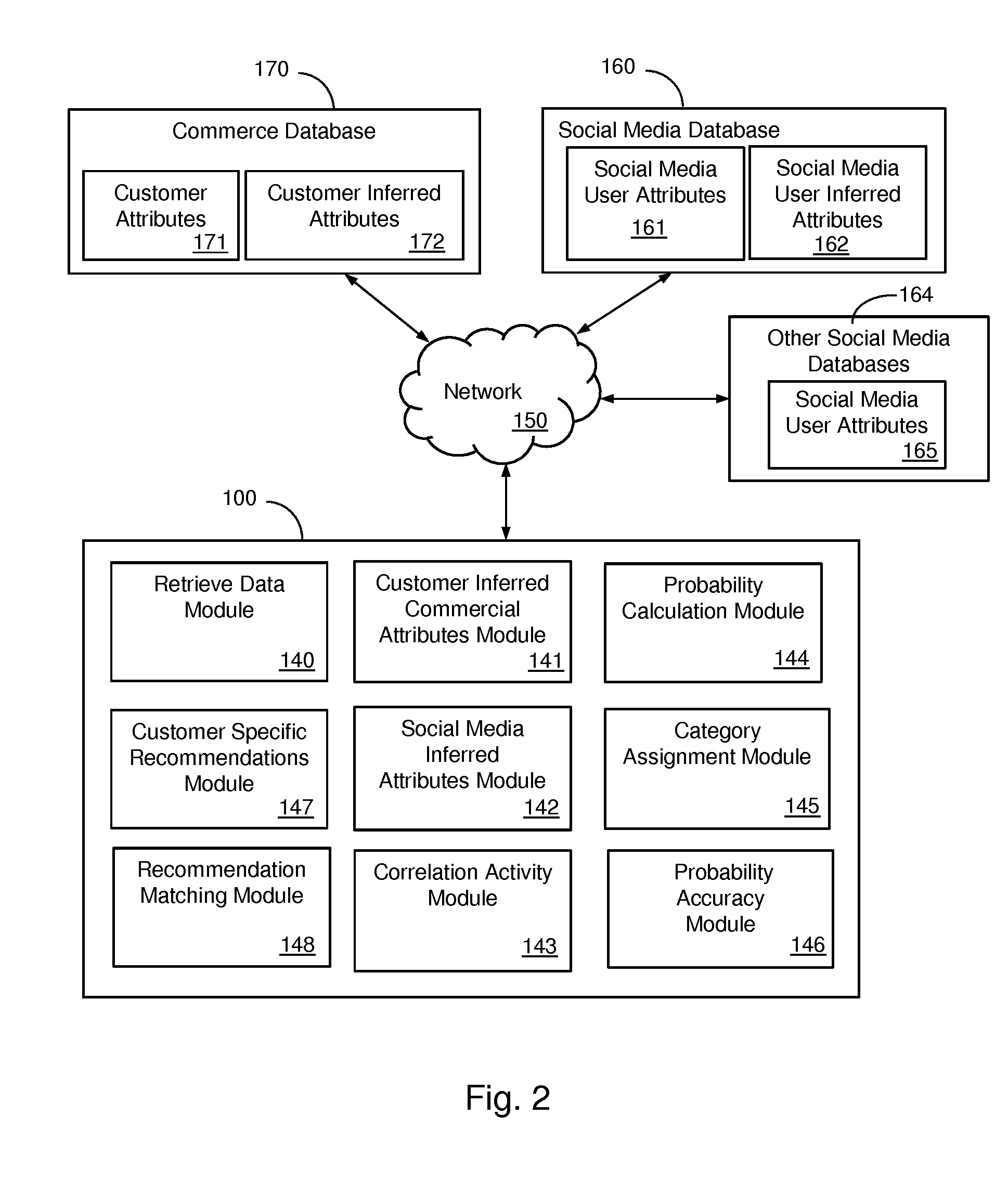
Identity Mapping Between Commerce Customers And Social Media Users
The present disclosure extends to methods, systems, and computer program products for identity mapping between commerce customers and social media users. Aspects of the invention use inferred attributes and activity correlations from both commerce data and social media data to map identities. In one aspect, activity correlations are calculated between a commerce customer account and each of the one or more candidate social media user accounts. For each of the one or more candidate social media user accounts, a probability that the commerce customer account and the social media user account map to the same identity is calculated. In another aspect, the accuracy of a mapping between a commerce customer account and a social media user is evaluated using additional social media data.
Owner:WALMART APOLLO LLC
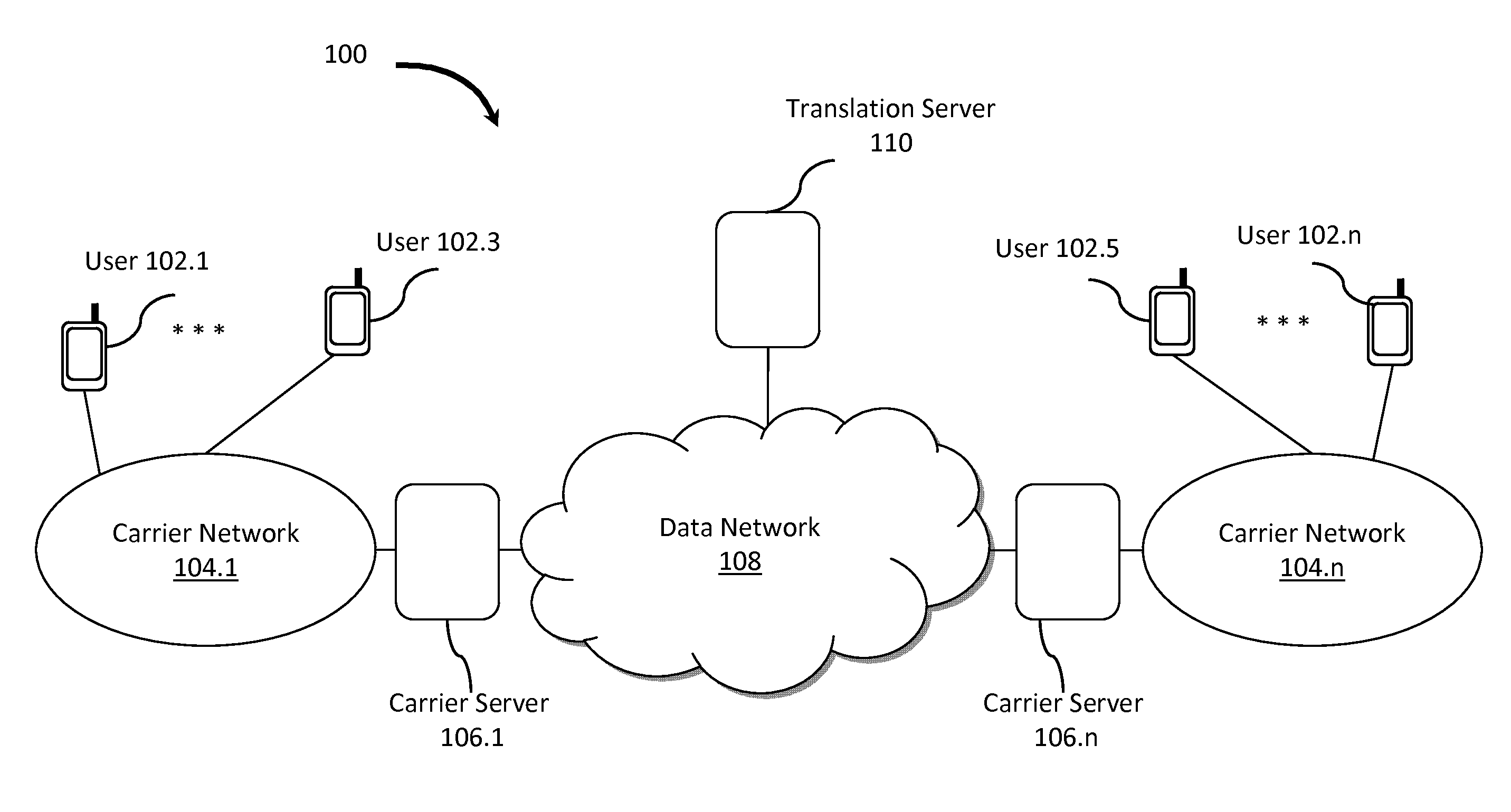
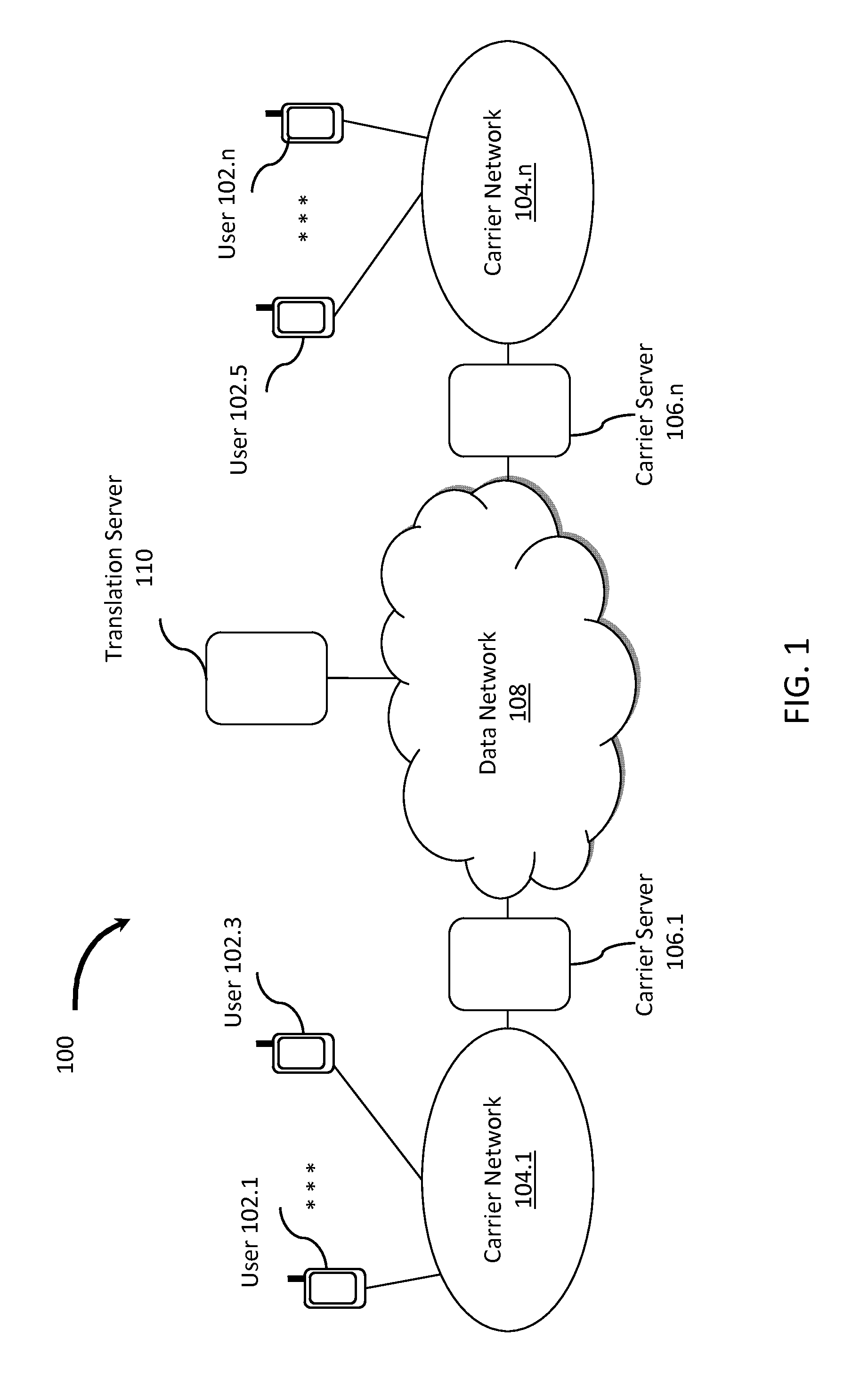
User-Defined Identity Mapping for Directed Communications
InactiveUS20120051529A1Robust parental controlImprove communication serviceInterconnection arrangementsCalled number recording/indicationInterconnectionSpeech sound
Methods and systems for mapping user-defined identities in data communication networks. By mapping and translating identities based on a calling party identifier, a called party identifier, and the carrier instance, enhanced communication services are enabled. Enhanced communication services offer virtual private phone numbers, shared group numbers, and interconnection between different voice and messaging services and applications.
Owner:CLOUDTREE
Customizing dvr functionality
ActiveUS20110067048A1Television system detailsRecording carrier detailsSoftware engineeringOperating system
Owner:TIVO SOLUTIONS INC
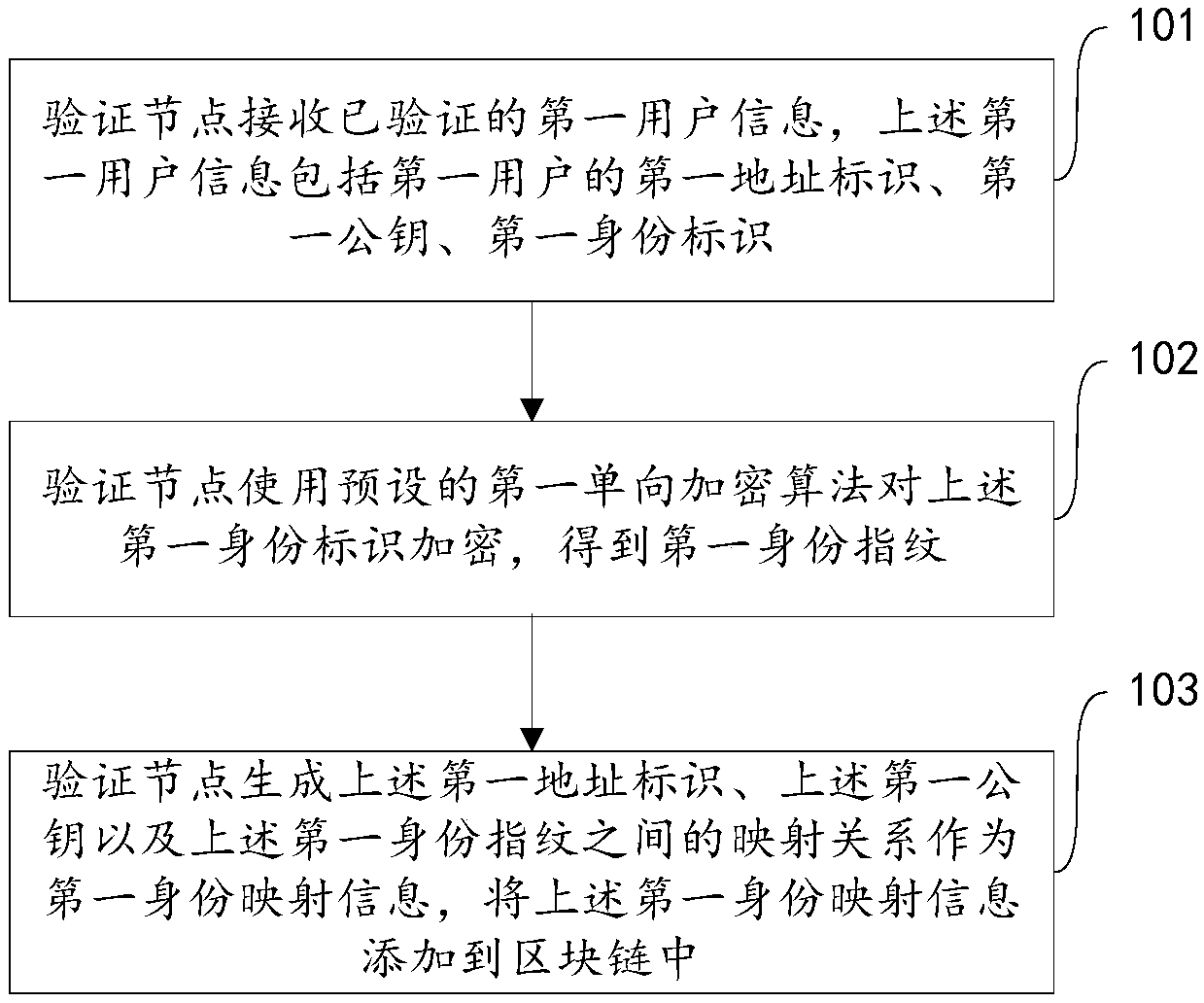
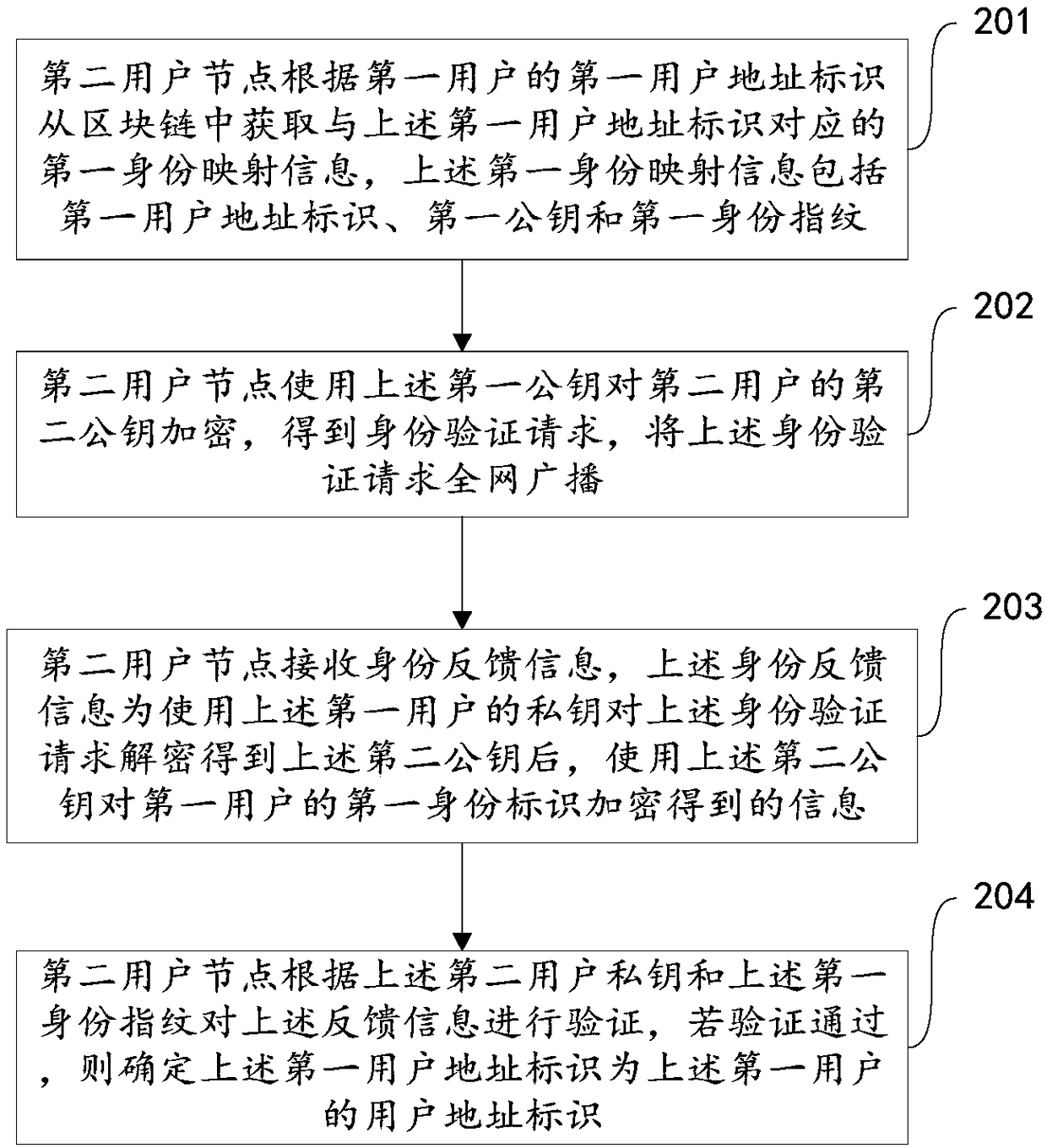
Identity authentication method, identity authentication device, and computer-readable medium
The embodiment of the present application discloses an identity authentication method,an identity authentication device and a computer-readable medium. The method comprises the following steps: the second user node obtains the first identity mapping information corresponding to the first user address identification from the block chain according to the first user address identification of the first user, the first identity mapping information including the first user address identification, the first public key and the first identity fingerprint; the second user node obtains the first identitymapping information corresponding to the first user address identification from the block chain according to the first user address identification. Encrypting the second public key of the second userby using the first public key, obtaining an authentication request, and broadcasting the authentication request to the whole network; receiving identity feedback information; the feedback informationis verified according to the second user private key and the first identity fingerprint, and if the verification is passed, it is determined that the first user address identification is the user address identification of the first user. As shown in the embodiment of the present application, the user's public key can be distributed securely, efficiently and inexpensively, and the user's identitycan be effectively verified.
Owner:PING AN TECH (SHENZHEN) CO LTD
Rolling bearing fault diagnosis method based on multi-branch multi-scale convolutional neural network
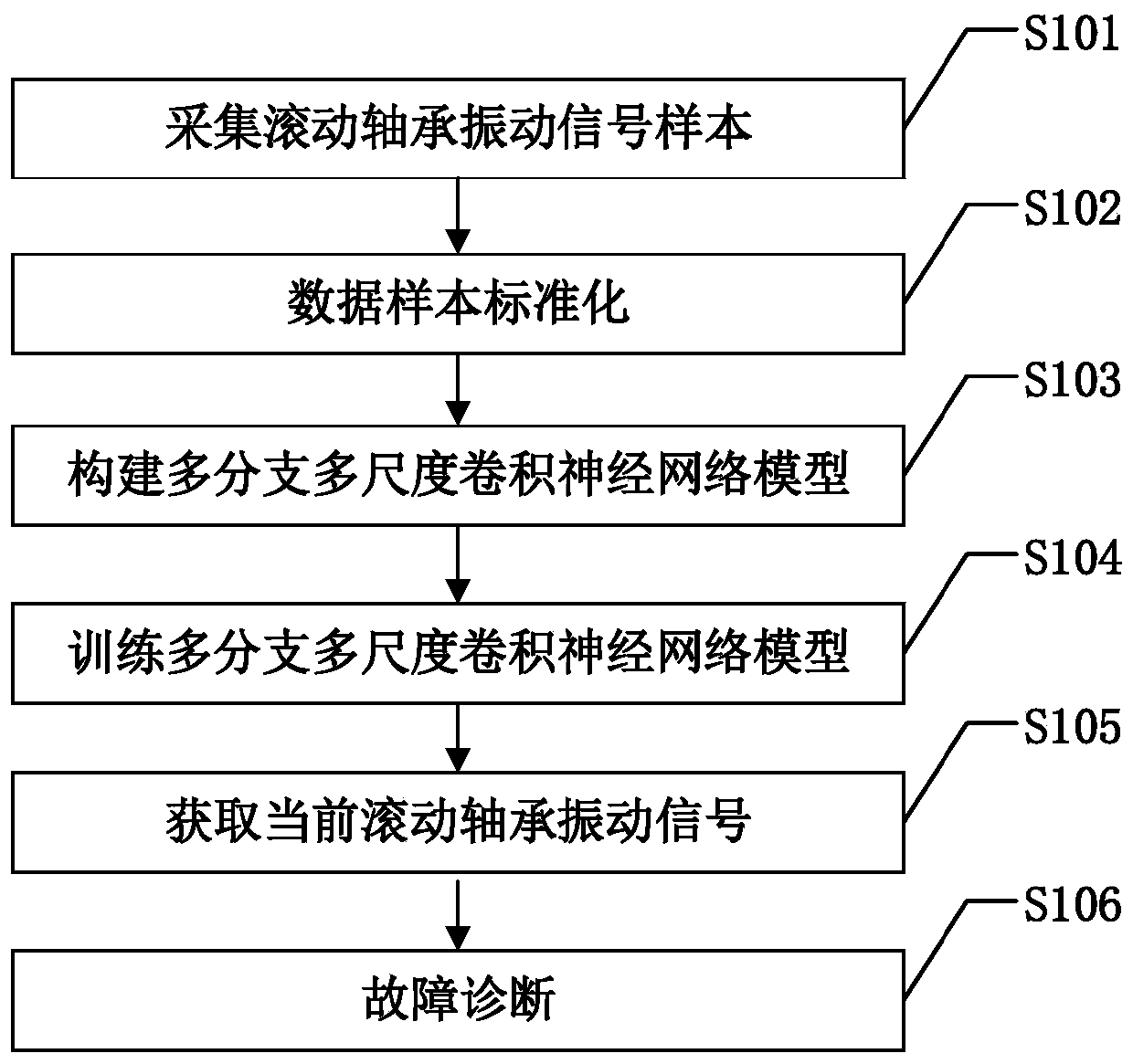
ActiveCN110595775AEasy to judgeImprove learning effectMachine bearings testingCharacter and pattern recognitionEngineeringVariable load
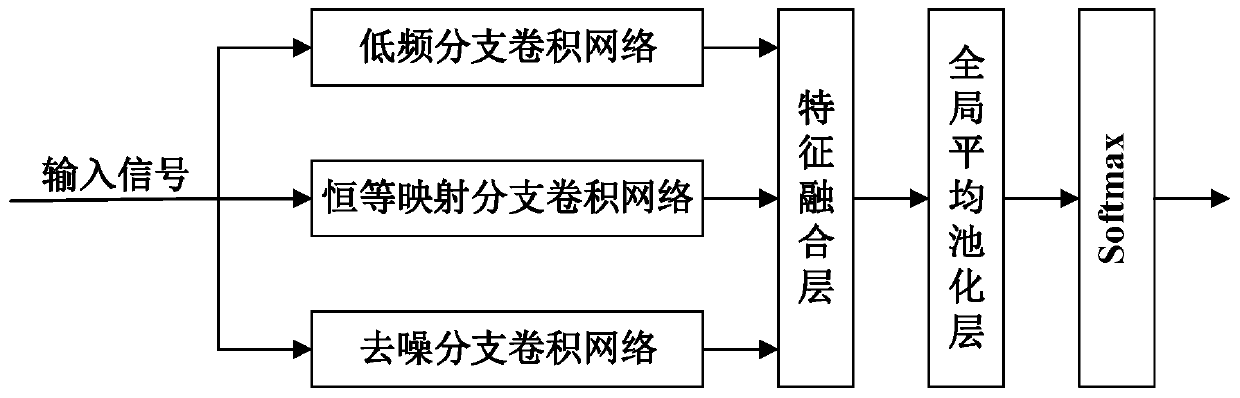
The invention discloses a rolling bearing fault diagnosis method based on a multi-branch multi-scale convolutional neural network. The rolling bearing fault diagnosis method comprises the steps of: acquiring acceleration vibration signals of rolling bearings without faults and with different faults in different operating states at first; setting a fault state label according to the fault state corresponding to each acceleration vibration signal; standardizing each acceleration vibration signal; training a multi-branch multi-scale convolutional neural network model by taking the standardized acceleration vibration signals as a training sample, wherein the multi-branch multi-scale convolutional neural network model comprises a low-frequency branch convolutional network, an identity mapping branch convolutional network, a denoising branch convolutional network, a feature fusion layer, a global average pooling layer and a Softmax layer; and then acquiring current acceleration vibration signals of the rolling bearings, and sending the current acceleration vibration signals into the multi-branch multi-scale convolutional neural network model for fault diagnosis. By adopting the multi-branch multi-scale convolutional neural network model, the rolling bearing fault diagnosis method can effectively improve the fault diagnosis performance of the rolling bearing in a strong noise environment and under a variable load working condition.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
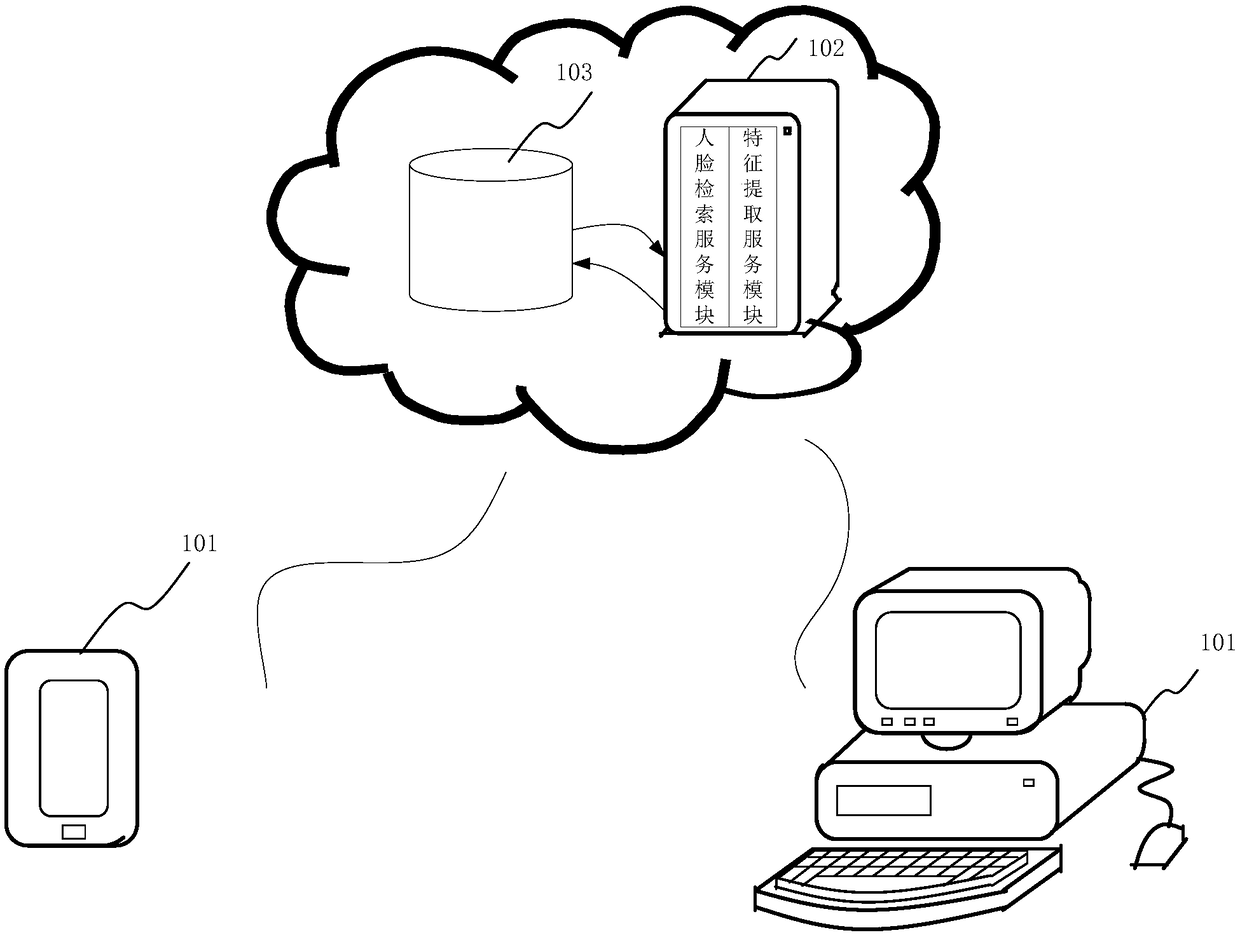
Face retrieval method and apparatus as well as storage medium and device
ActiveCN108108499AGuaranteed accuracyImprove stabilityCharacter and pattern recognitionEnergy efficient computingFeature extractionRetrieval result
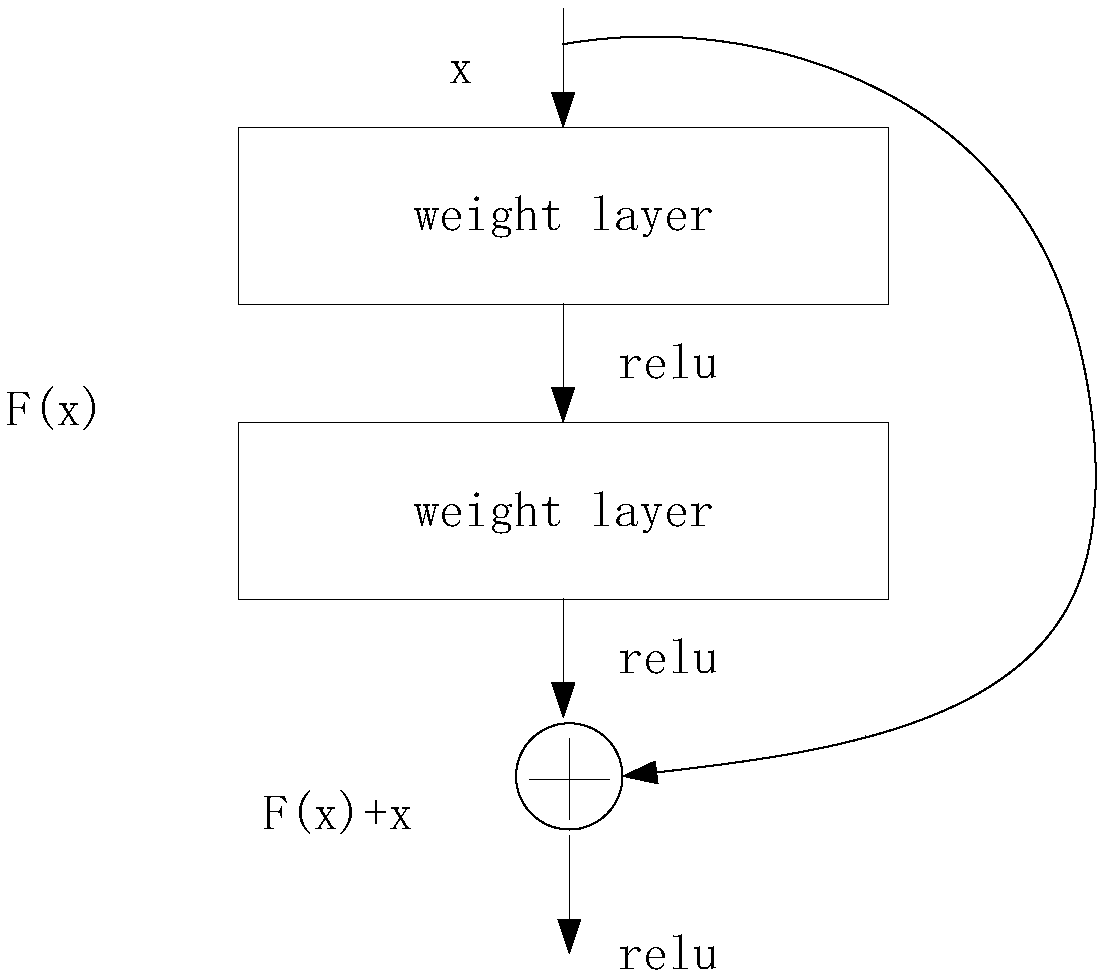
The invention discloses a face retrieval method and apparatus as well as a storage medium and device, which belongs to the technical field of deep learning. The method comprises the following steps: acquiring a target face image to be retrieved; extracting features of the target face image according to each residual block connected successively in a deep residual network to obtain target face feature information, wherein any one residual block comprises an identity mapping and at least two convolution layers, and the identity mapping of any one residual block points, from an input end of anyone residual block, to an output end of any one residual block; and performing the face retrieval in a face database according to the target face feature information to obtain a face retrieval result, wherein the face retrieval result at least comprises an identity marker matched with the target face feature information. By adopting the face retrieval method and apparatus, the face retrieval is realized on the basis of the deep residual network, the retrieval accuracy of the deep residual network is not prone to influence by external factors, the face retrieval method is excellent in stability, and the face retrieval accuracy is also ensured.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
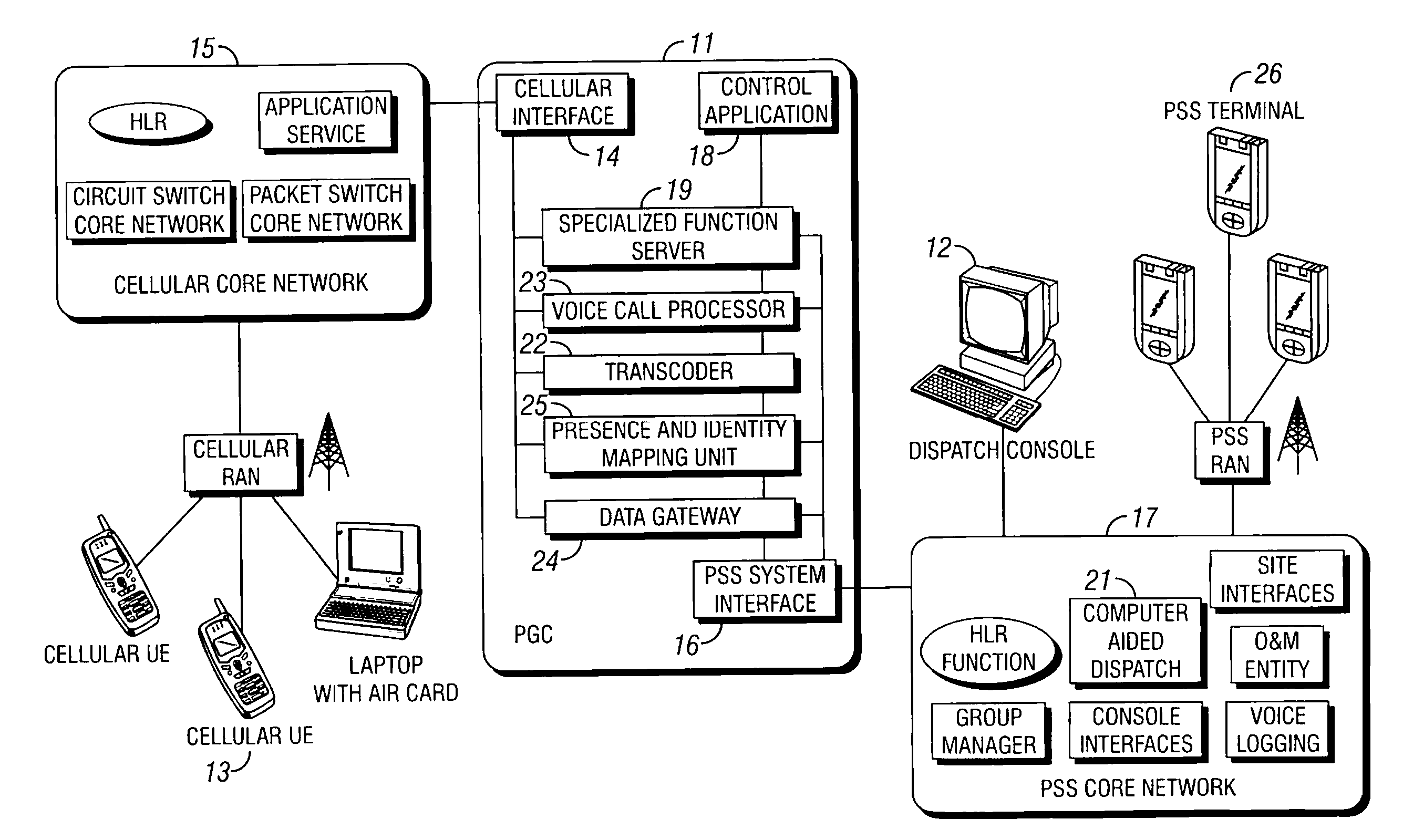
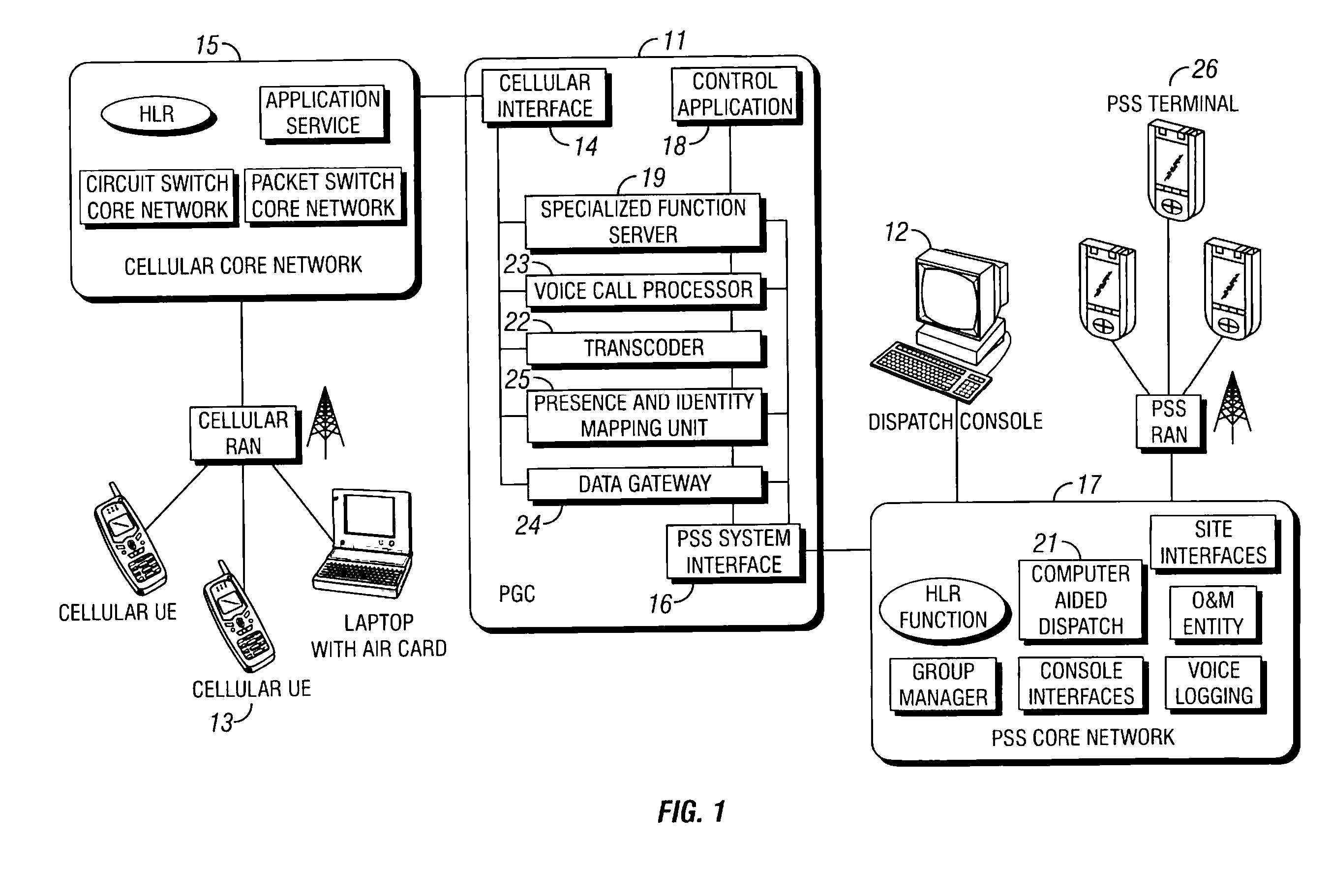
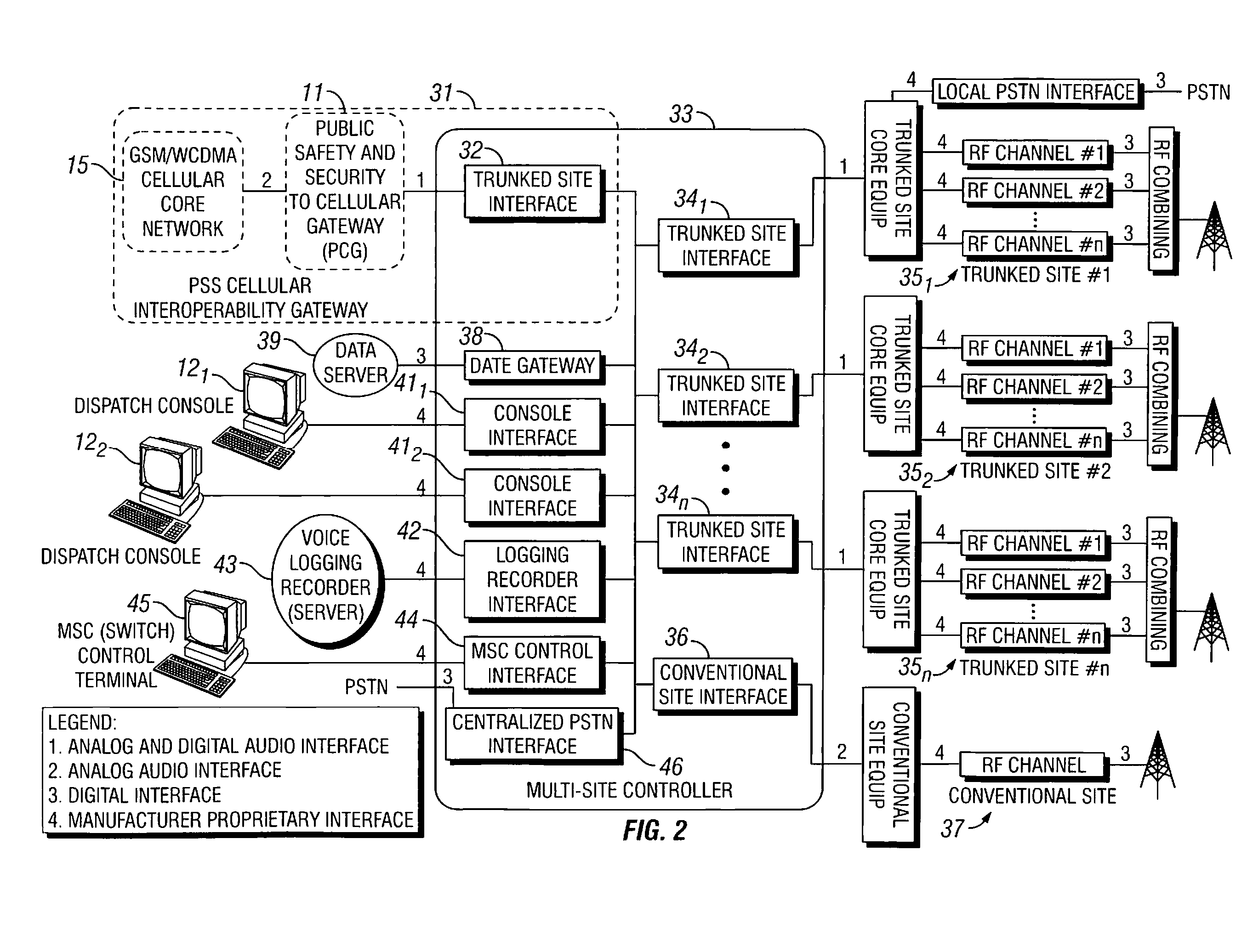
System, method, and gateway for interfacing public safety and security (PSS) systems and cellular communication systems
InactiveUS20080171533A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCall forwardingCODE protocol
A gateway, system, and method for providing seamless communications to Public Safety and Security (PSS) users operating between a PSS communication network and a cellular communication network irrespective of access technology or switching method. The gateway includes a presence and identity mapping unit for mapping a PSS user identity utilized in the PSS network to a cellular user identity utilized in the cellular network. The gateway provides an interface and establishes a session between the PSS network and a PSS user operating in the cellular network utilizing the mapped cellular user identity. A transcoder converts between PSS and cellular voice coding protocols. A data gateway converts between PSS and cellular data protocols. The gateway dynamically switches between voice and data, and provides group calling, call forwarding, and message replay services across the network interface.
Owner:TELEFON AB LM ERICSSON (PUBL)
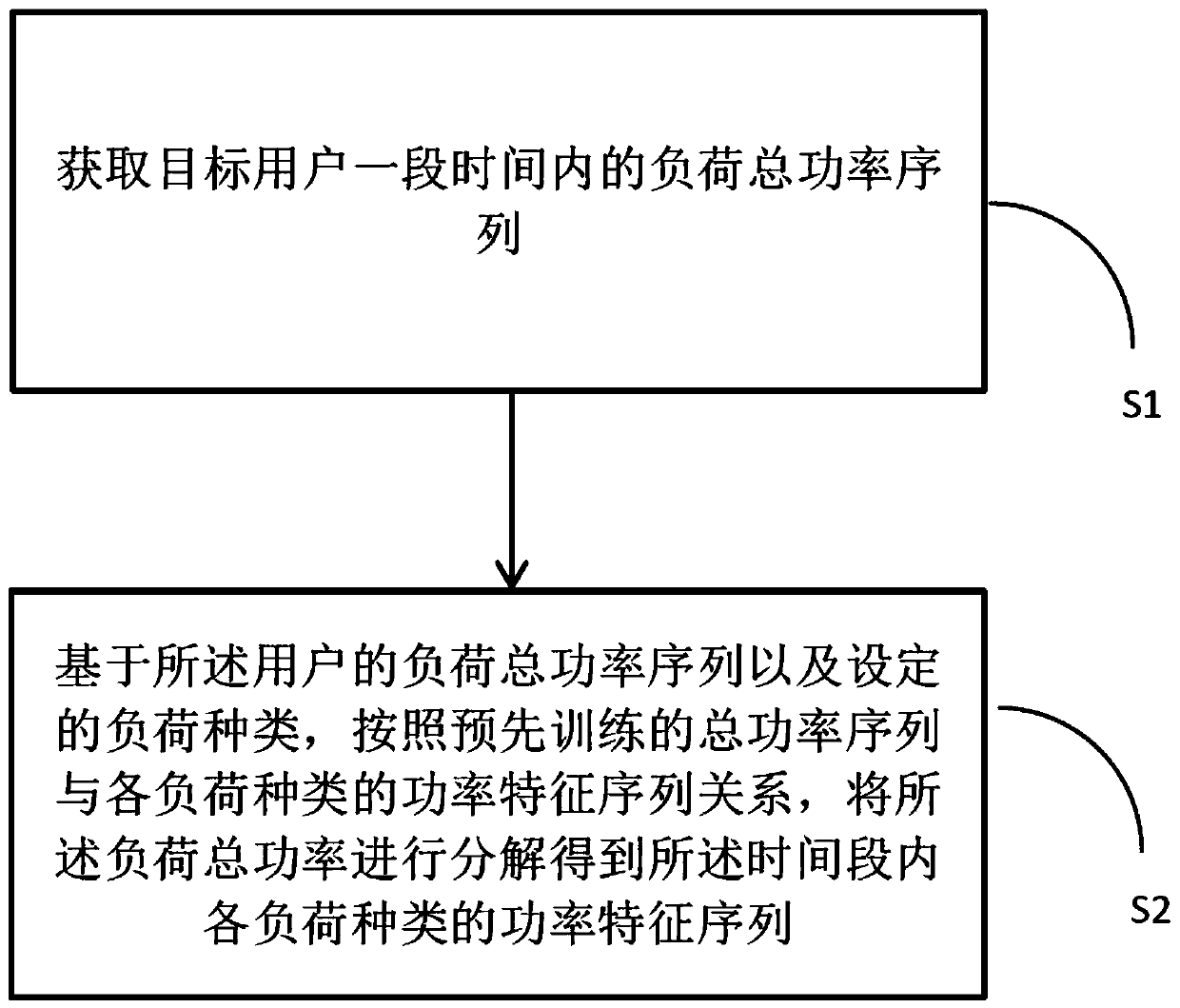
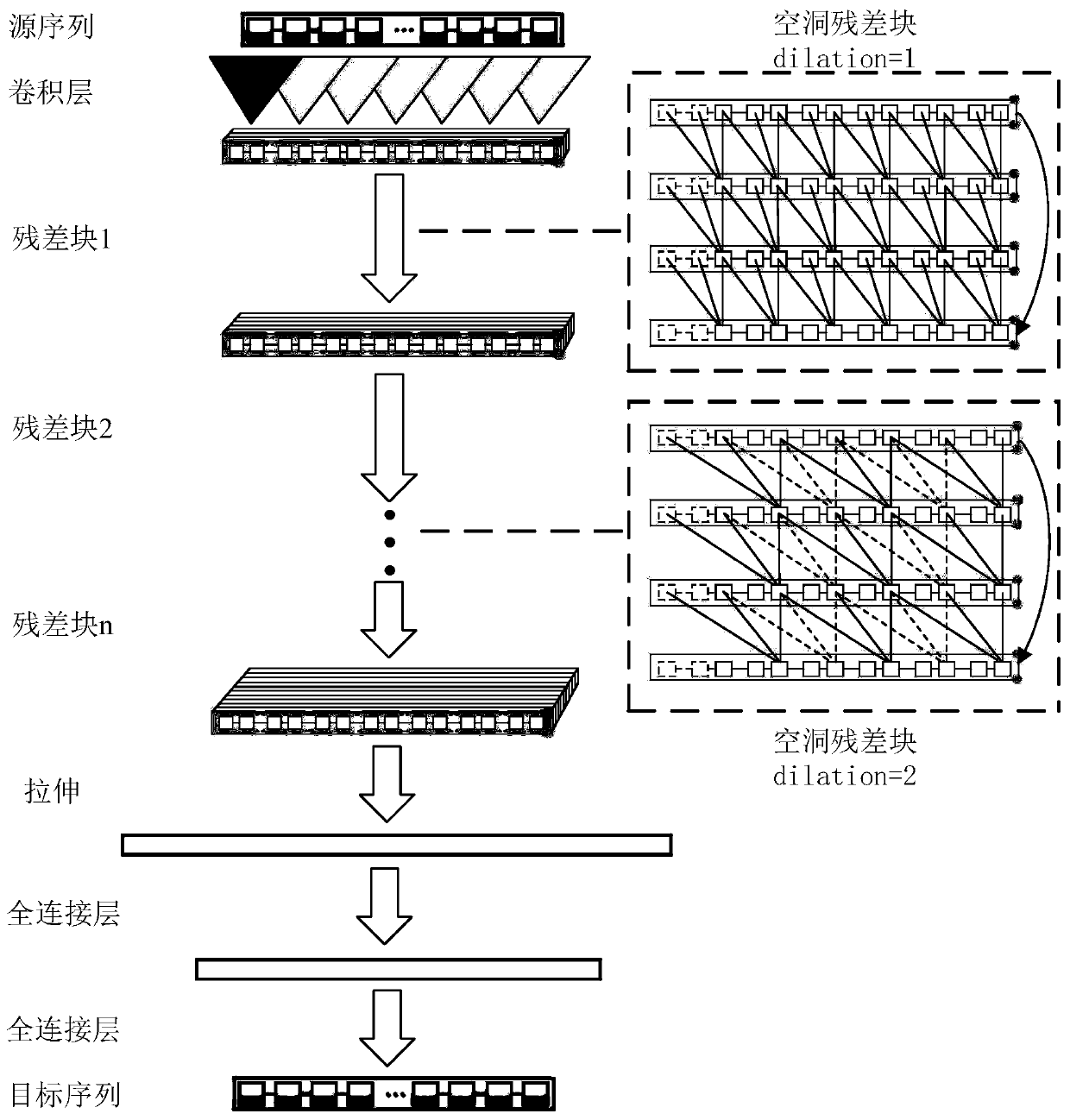
Non-invasive load decomposition method and system
PendingCN110445126AImprove accuracyGuarantee authenticityAc network circuit arrangementsDecompositionNon invasive
The invention discloses a non-invasive load decomposition method and system. According to the scheme, the method comprises the steps of acquiring a load total power sequence of a target user within aperiod of time; and based on the load total power sequence of the user and set load types, decomposing load total power to obtain power characteristic sequences of the load types in the time period according to pre-trained relations between the total power sequence and the power characteristic sequences of the load types, wherein the load types are determined by using conditions of household appliances by the user. The training process comprises the steps of performing receptive field amplification based on identity mapping and a time sequence. The non-invasive load is decomposed through the pre-trained relations between the total power sequence and the power characteristic sequences of the load types, so that the correctness and accuracy of a load decomposition result are improved; and inthe training process, the load total power is subjected to a receptive field method according to the time sequence through the identity mapping, so that the problem of gradient disappearance in the load decomposition process is solved, the receptive field is expanded, and the load decomposition result is more authentic.
Owner:CHINA ELECTRIC POWER RES INST +3
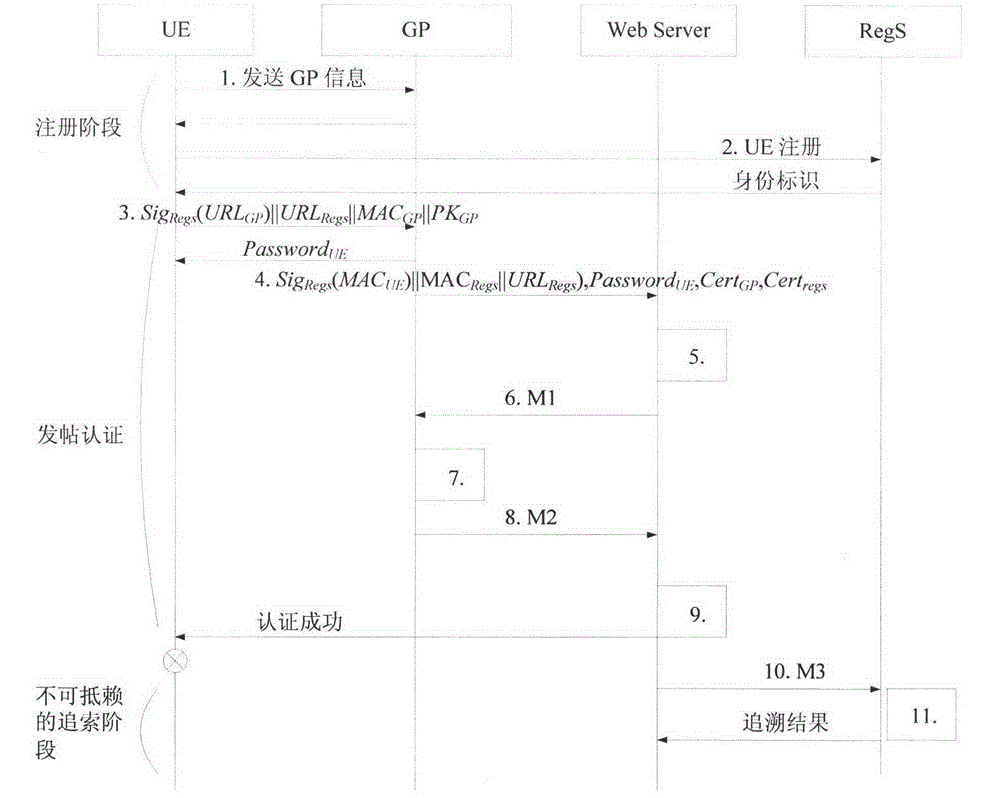
Safe and controllable internet real-name certification mechanism
InactiveCN104683306AAvoid duplicate registrationAchieve front-end anonymityUser identity/authority verificationInformation processingInternet users
The invention belongs to the technical field of network safety, relates to the technologies of network identity authentication, identity mapping, network identity management and information protection, and aims to design a set of controllable real-name certification mechanism which is used for an internet and has high safety on the premise that the safety of user real identity is ensured. The mechanism is characterized in that a web server and a real-name register server which is used for judging whether the user identity is true or false are connected through a network, the real-name register server is used for recording user real-name information, the web server does not save true original personal identity information, and encrypted information processing is carried out in both a real-name register process and an identity tracing process. The mechanism disclosed by the invention has the advantages that abuse on the personal identity information is effectively and completely eradicated, controllability and searchability on an anonymous network behavior of an internet user can be realized, and valuable reference is provided for internet supervision.
Owner:CHINESE PEOPLE'S PUBLIC SECURITY UNIVERSITY +1
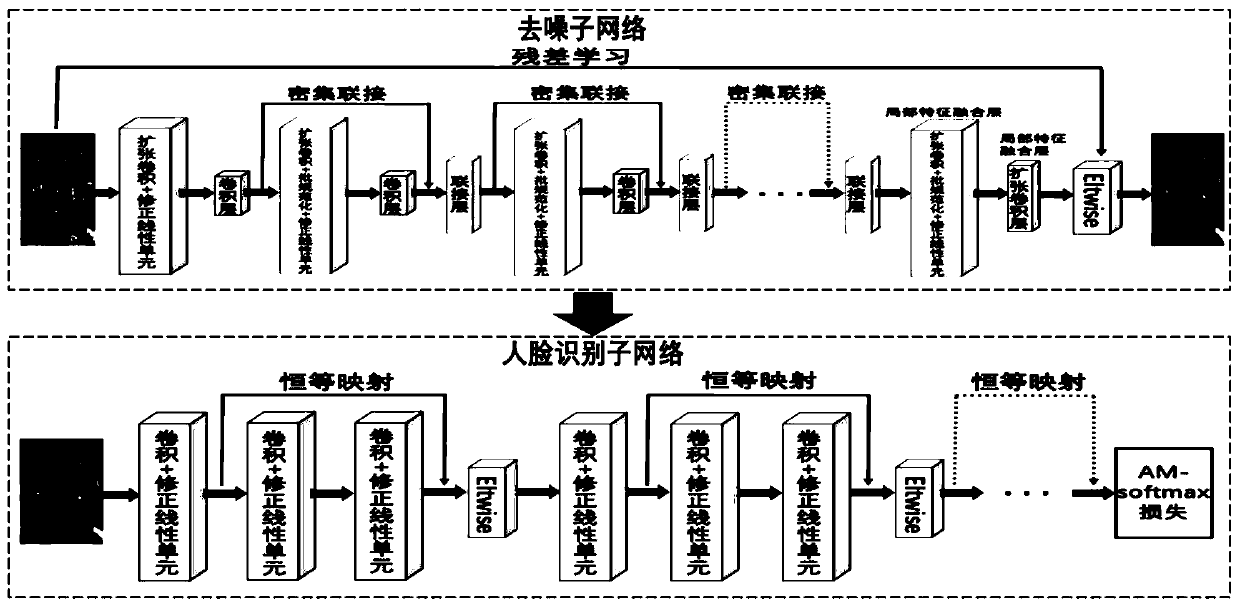
A noise robust face recognition method based on a cascade deep convolutional neural network
ActiveCN109948573ARich in detailsMultiple background informationCharacter and pattern recognitionNetwork structureNetwork model
The invention discloses a noise robust face recognition method based on a cascade deep convolutional neural network, and relates to a computer vision technology. The method comprises the following steps: firstly, designing a denoising sub-network and a face recognition sub-network, and in the denoising sub-network, connecting feature maps generated by all layers in front six layers of the networklayer by layer from front to back by using a dense connection method so as to fully utilize face features generated by a shallow-layer network. A residual network structure is adopted in the face recognition sub-network, and an identity mapping method is used for performing shortcut connection between different layers of the network, so that a gradient vanishing phenomenon in a deep network structure can be effectively reduced; and then, joint training is carried out on the de-noising sub-network and the face recognition sub-network by adopting a cascade method to obtain noise robust face representation, and a joint loss function is designed for weight updating of the two sub-networks. And finally, a final noise face recognition result is obtained according to the trained network model.
Owner:XIAMEN UNIV
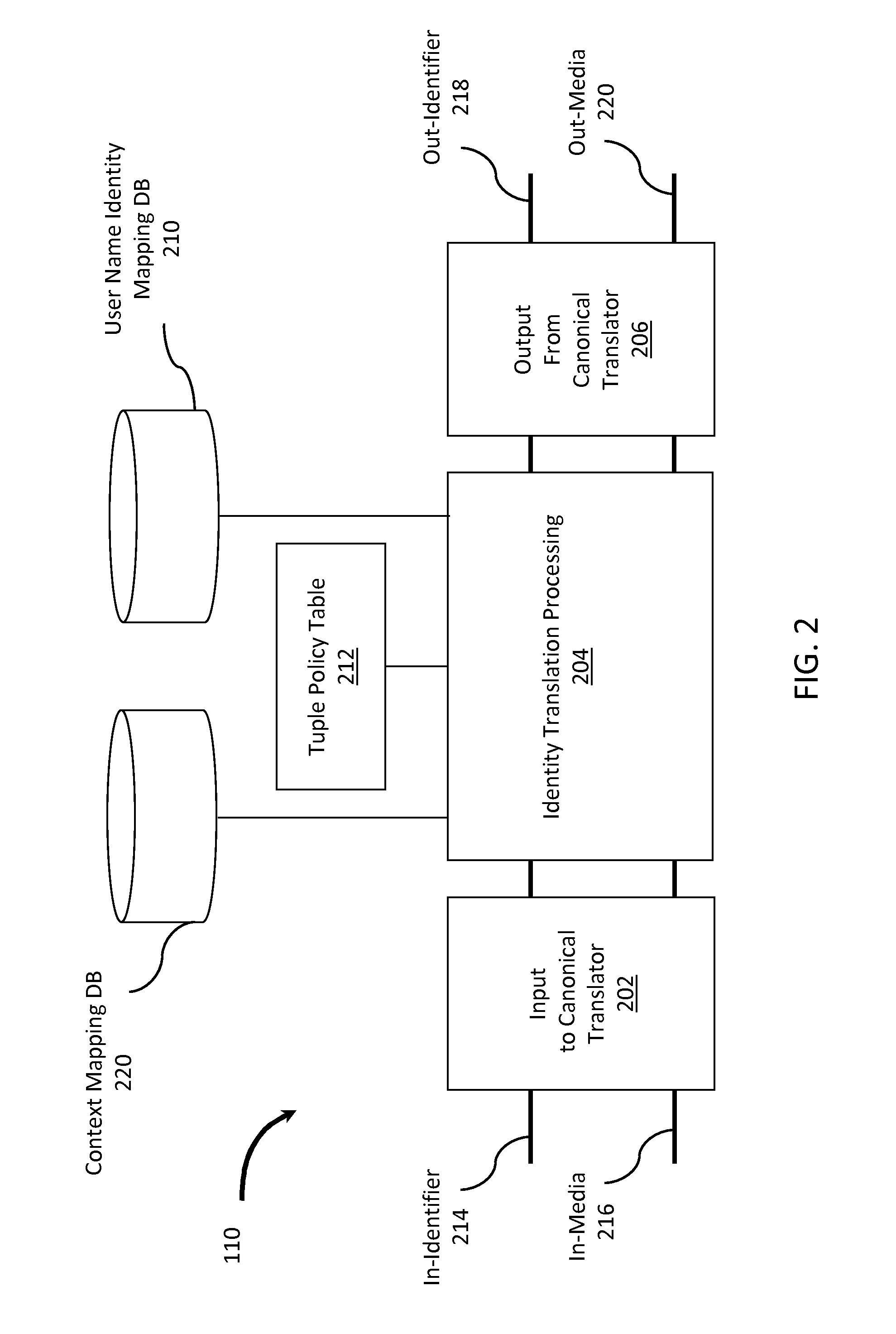
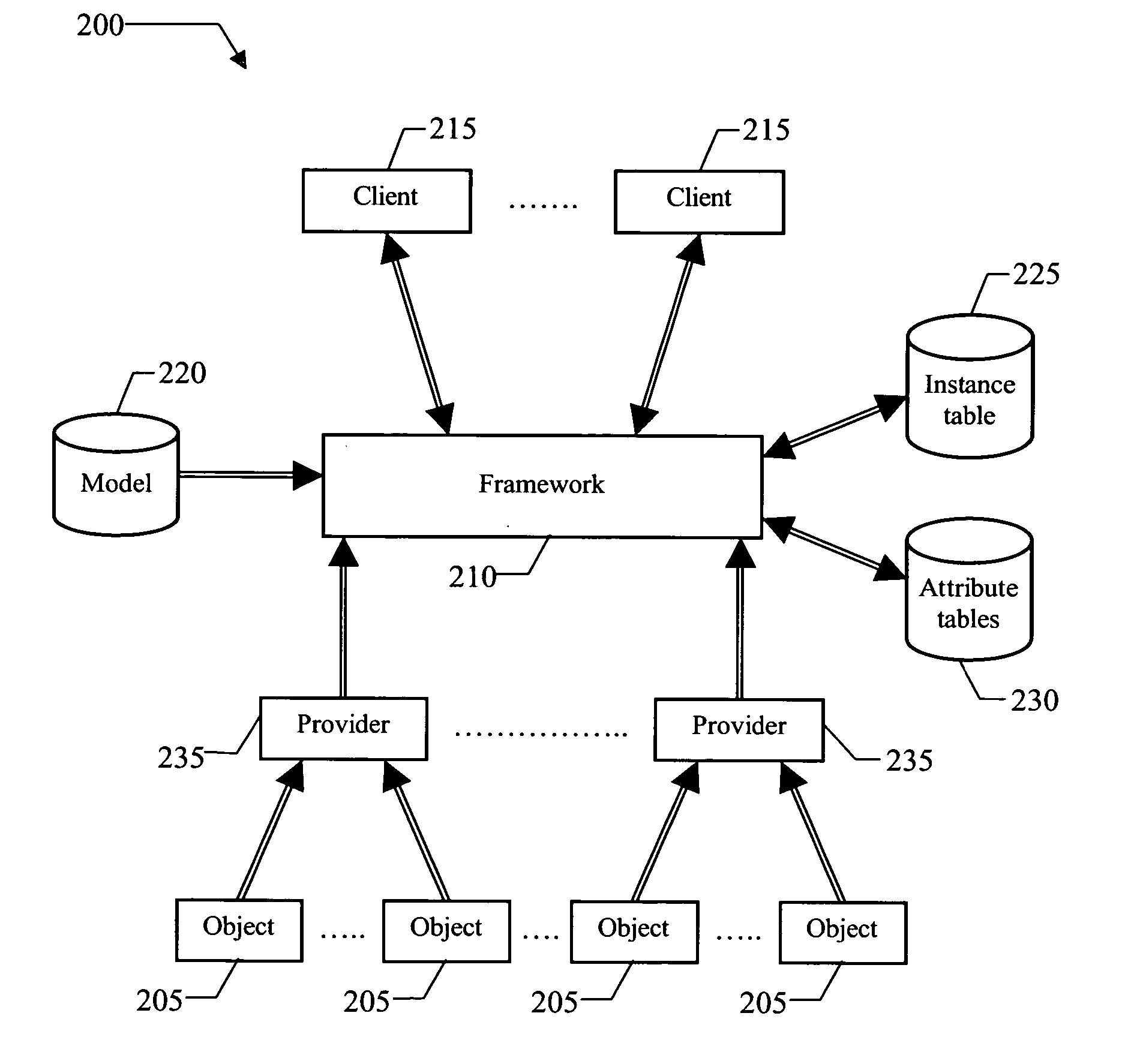
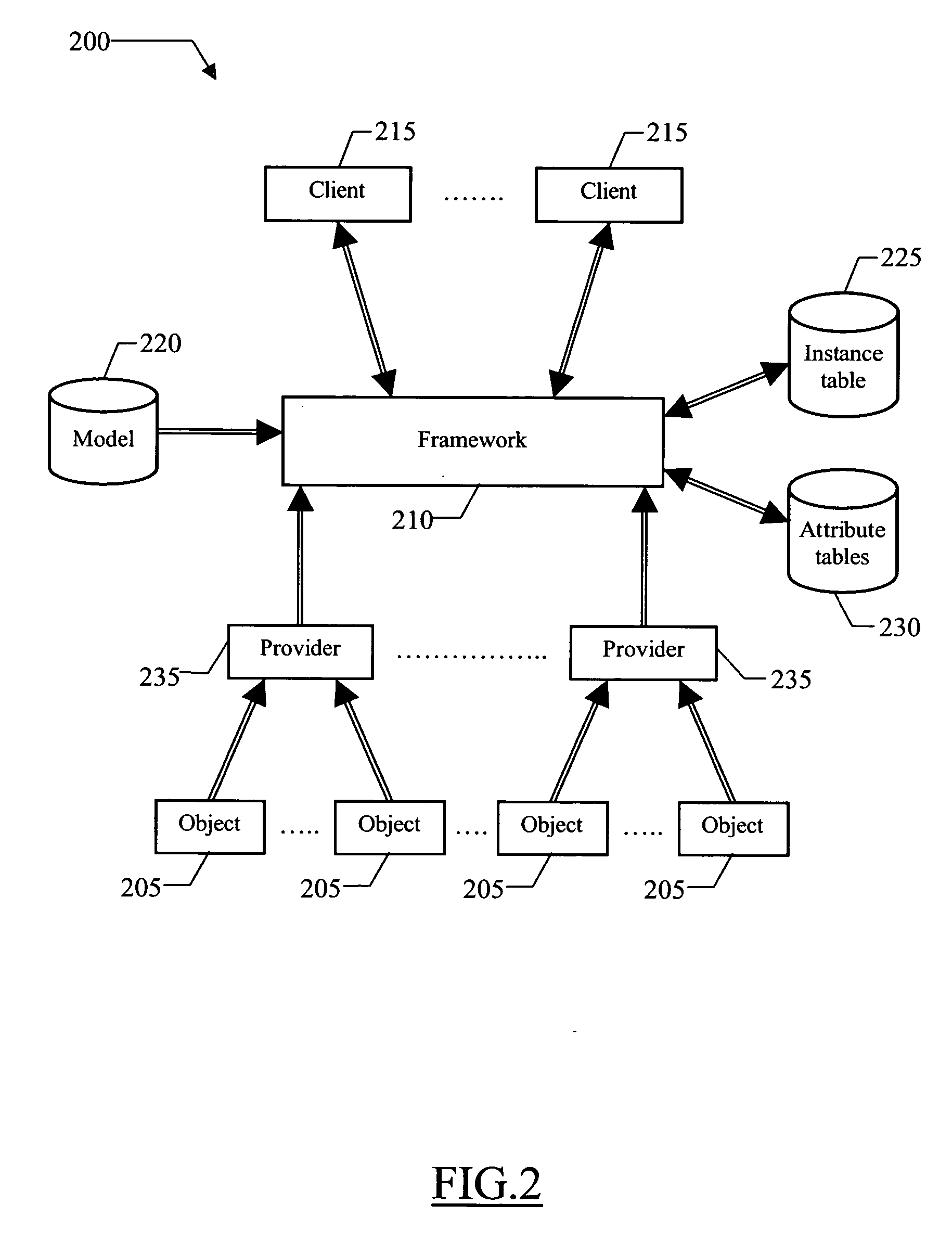
Resource management method and system enabling identity mapping between resources and objects
InactiveUS20060212473A1Digital data processing detailsResourcesRelational databaseResource management
A resource management infrastructure (200) is proposed, wherein every resource may be represented by multiple (specialized) objects (B1,C1,D1;C2), which instantiate corresponding (specialized) classes (315) modeling different aspects of the resources. In the proposed solution, an edge class (310) is associated with the specialized classes; each resource is associated with a corresponding edge object (A1; A2) instantiating the edge class (which object is identified by a corresponding edge name). More specifically, the classes are organized into a specialization tree (300); the edge classes directly depend on abstract classes, while the specialized classes in turn depend on the edge classes. Each specialized object is then associated with the edge name of the corresponding edge object. In this way, the specialized objects associated with each edge name represent the same corresponding resource. An optimized structure of a relational database (225,230) implementing the proposed solution is also proposed.
Owner:IBM CORP
Asynchronous cross-domain identify mark mapping method for internet security
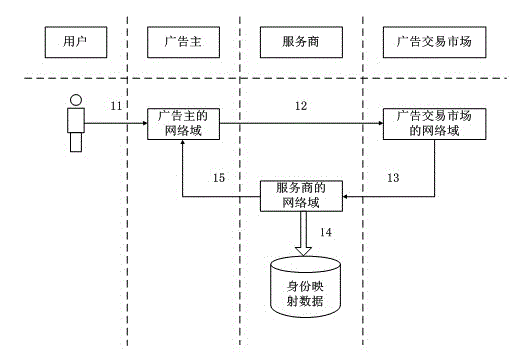
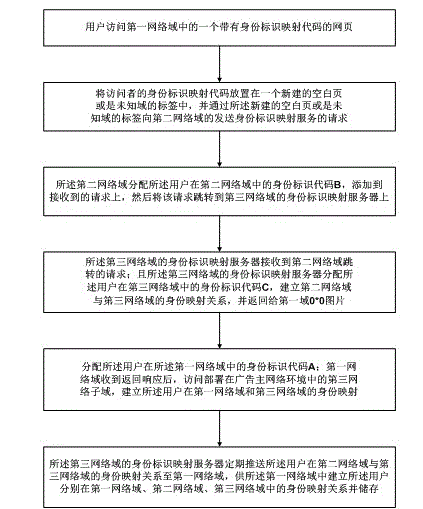
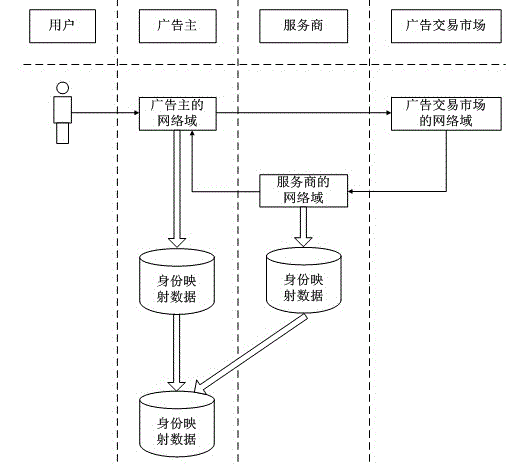
ActiveCN103152445AImprove securityLow experience impactTransmissionMarketingInternet privacyThe Internet
The invention discloses an asynchronous cross-domain identity mark mapping method for internet security, which has high safety. An identity mapping request code is placed in a mark comprising a blank page or an unknown domain, any contact party in the whole process cannot speculate a request initiating webpage source and core data of an advertiser is safe; and the asynchronous cross-domain identity mark mapping method completely has the data autonomous right, a browser identity mapping relation in each domain is held by the advertiser, and data is completely used by the advertiser.
Owner:JINGZAN ADVERTISING SHANGHAI CO LTD
Mobile management entity operating in communications network and selection method therefor
A selection method implemented as an algorithm in a mobile management entity (MME) operating in a communications network. The method includes receiving a unique identifier of a subscriber operating within the network and determining, based on the unique identifier, whether the subscriber has full circuit switching fallback (CSFB) capability or has only packet switching (PS) capability. When it is determined that the subscriber has full CSFB capability, a mobile switching center server (MSS) is selected based on original tracking area matrices and / or tracking area identity-location area identity mapping defined in the 3rd Generation Partnership Project (3GPP). When it is determined that the subscriber has only PS capability, an MSS is selected from a group of MSSs having CSFB support only for short message service (SMS) delivery.
Owner:NOKIA SOLUTIONS & NETWORKS OY
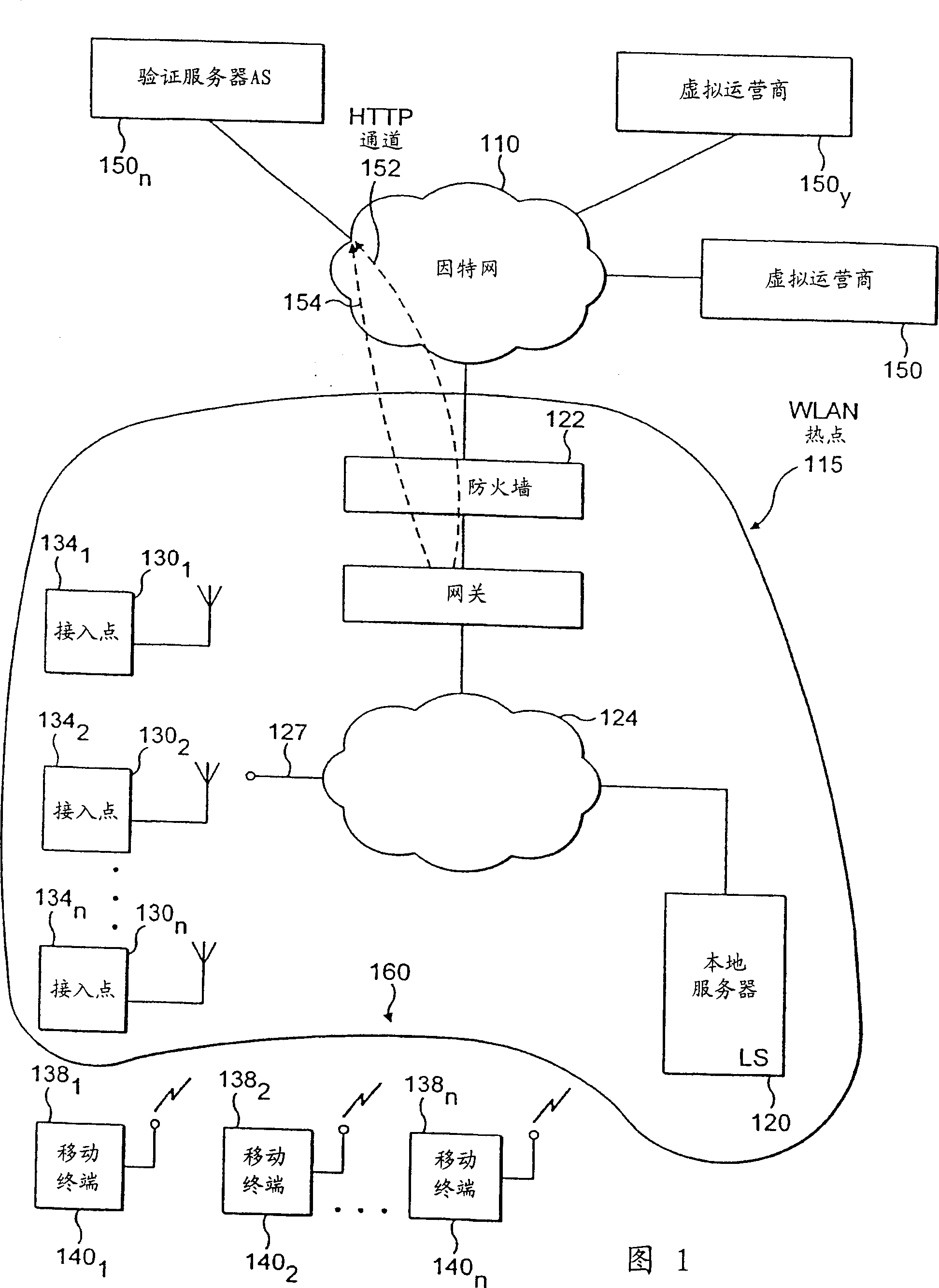
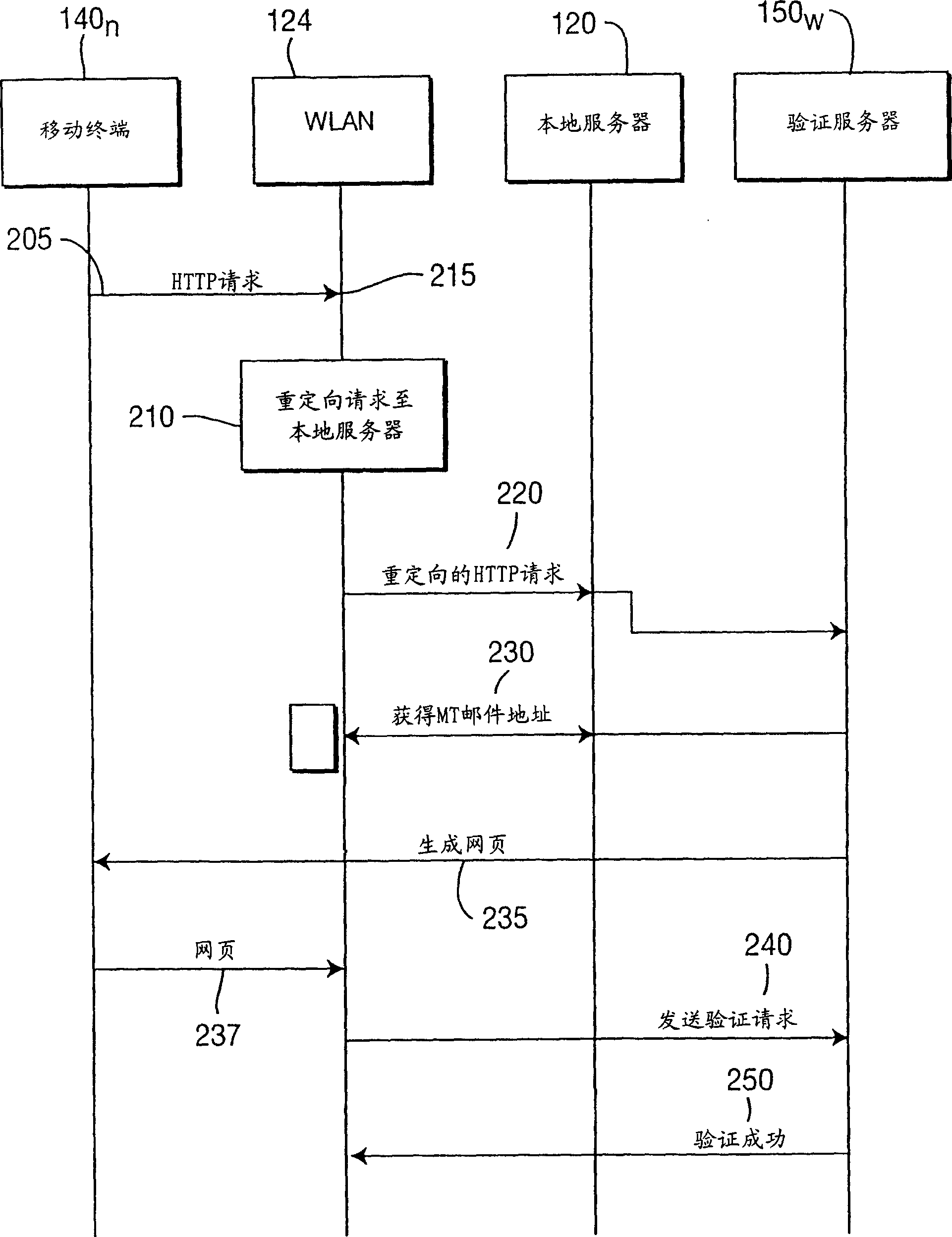
An identity mapping mechanism in wlan access control with public authentication servers
InactiveCN1759558AUser identity/authority verificationNetwork topologiesIp addressAuthentication server
A method for improving the security of a mobile terminal in a WLAN (124) environment by redirecting the browser request, embedding a session identification (session ID) inside an HTTP request and matching two HTTP sessions using such a session ID in the authentication server (150). The access point (130) processes the web request from the mobile terminal such that a session ID becomes embedded in the universal resource locator (URL). Additionally a mapping between this session ID and the MAC address or the IP address of the mobile terminal is maintained in the WLAN. When the authentication server notifies the access point about the authentication result, the session ID is used to uniquely identify the mobile terminal. All these operations are transparent to the mobile terminal (140).
Owner:THOMSON LICENSING SA
Federated identity mapping using delegated authorization
ActiveUS20150128242A1Data processing applicationsDigital data processing detailsWeb serviceFederated identity
A method for identity mapping across web services uses a delegated authorization protocol, such as OAuth. In response to a request from a first user at a first web service, a connection to a second web service is established using the protocol. The second web service responds by sending information associated with a second user of the first web service who previously logged into the second web service from the first web service using the protocol. The second user may be a “contact” of the first user. The information received from the second web service is a access token that was obtained by the second user during that prior login. The access token is provided in lieu of data associated with the second user's account at the second web service. Thereafter, the first web service uses the access token it received to map to an identity of the second user.
Owner:IBM CORP
Authentication interworking in communications networks
ActiveUS9401908B1Security arrangementSecuring communicationWeb authenticationReal-time communication
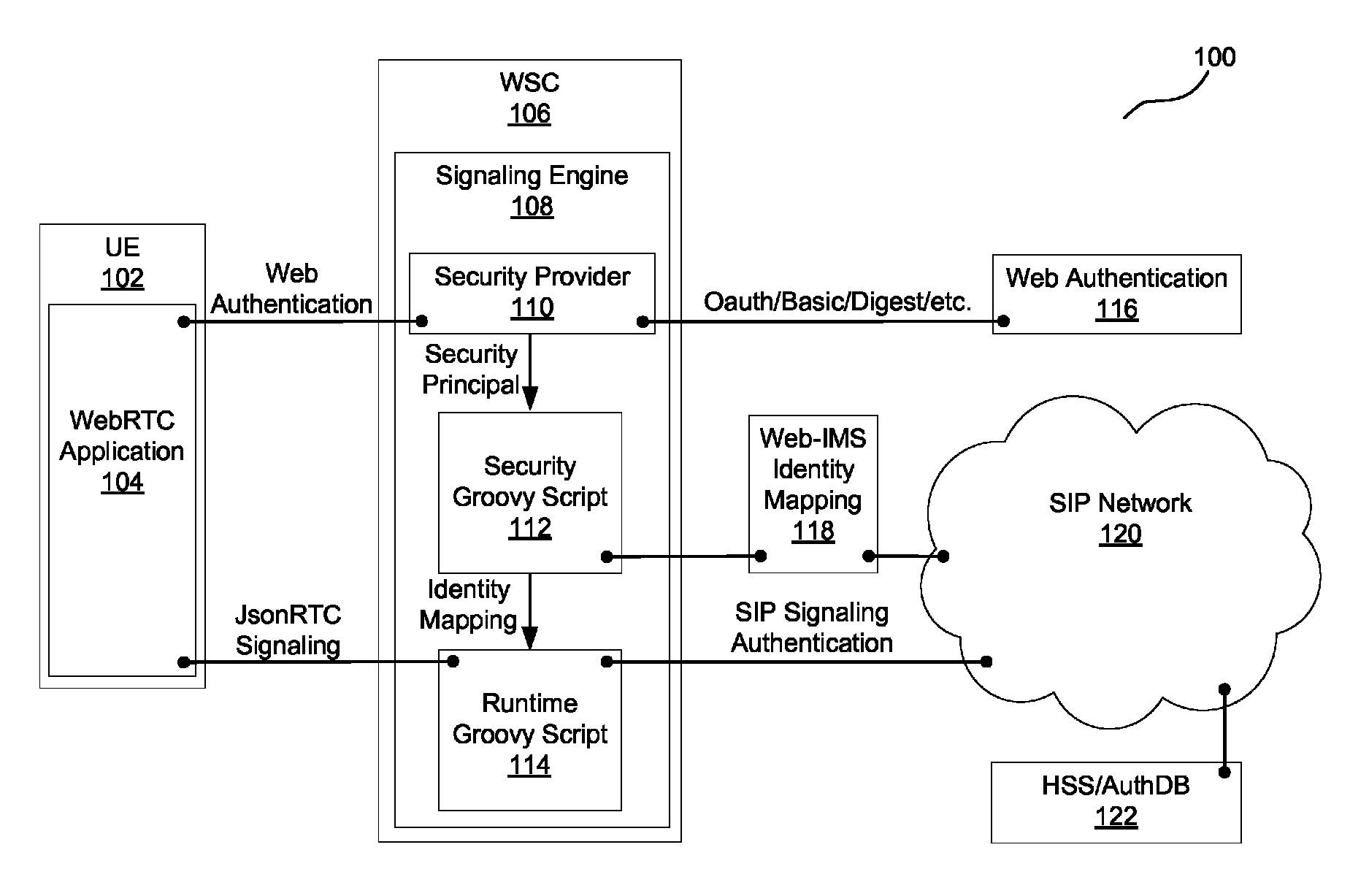
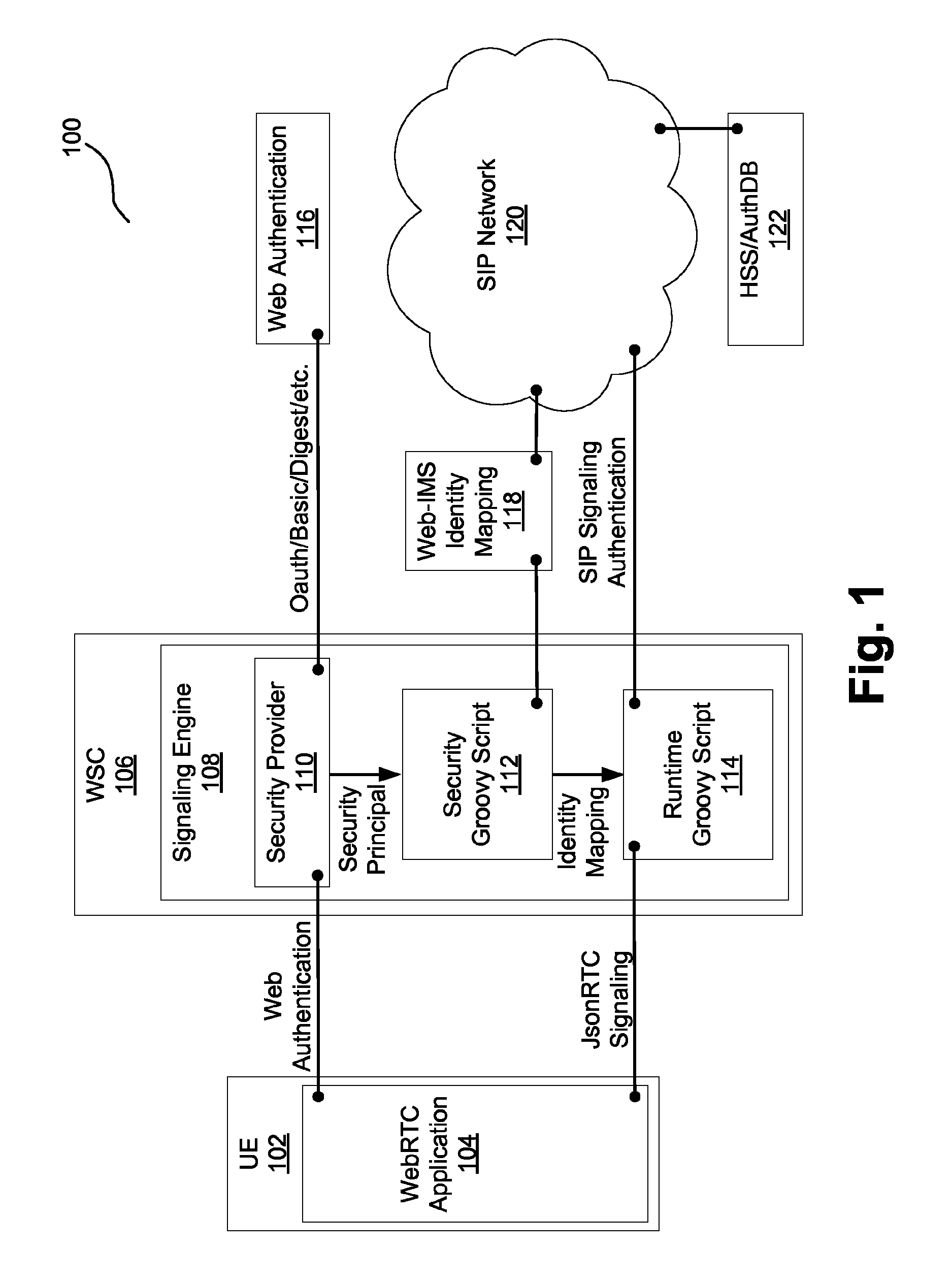
A system performs authentication for real-time communications (RTC). The system receives a request from a browser application for web authentication of a user. The system then performs the web authentication by a security provider by reaching a first resource, where the security provider determines a security principal for the user. Subsequently, the system executes a security Groovy script to obtain an identity mapping from a second resource different than the first resource, where the identity mapping maps the security principal to an Internet Protocol (IP) Multimedia Subsystem (IMS) identity. The system then provides the identity mapping to a runtime Groovy script.
Owner:ORACLE INT CORP
Method for realizing intelligent home based on RFID (radio frequency identification devices) labels and identity mapping of hash functions
ActiveCN104407600AAchieve normalizationImprove communication efficiencyComputer controlCo-operative working arrangementsHash functionData mining
The invention discloses a method for realizing an intelligent home based on RFID (radio frequency identification devices) labels and identity mapping of hash functions. The method specifically comprises the following steps: deploying an active RFID label for each home sensor, and putting active RFID label readers in corresponding intelligent home gateways; collecting real-time state index data by the sensors; encapsulating the collected real-time state index data and sensor parameters into the corresponding active RFID labels in the form of an electronic data table of a transmitter with the standard of IEEE1451.7; accessing the RFID labels by the active RFID label readers, performing normalized mapping transformation on the accessed RFID labels and the numbers of the intelligent home gateways through different hash functions, and generating identity symbols with unified lengths and formats; analyzing the numbers of the intelligent home gateways, the real-time state index data of various home detecting targets and the sensor parameters by an intelligent home monitoring and managing platform according to the corresponding hash functions. According to the invention, the wiring limitation of a wired network is solved, standard signal collecting interfaces and unified data formats of the sensors are realized, the safety is high, and the management is efficient and unified.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Method, system and access gateway for intercommunication between local equipment and IMS (IP Multimedia Subsystem) network
ActiveCN103338213AConversation processing is simple and convenientEasy to deployNetwork connectionsSession Initiation ProtocolDomain name
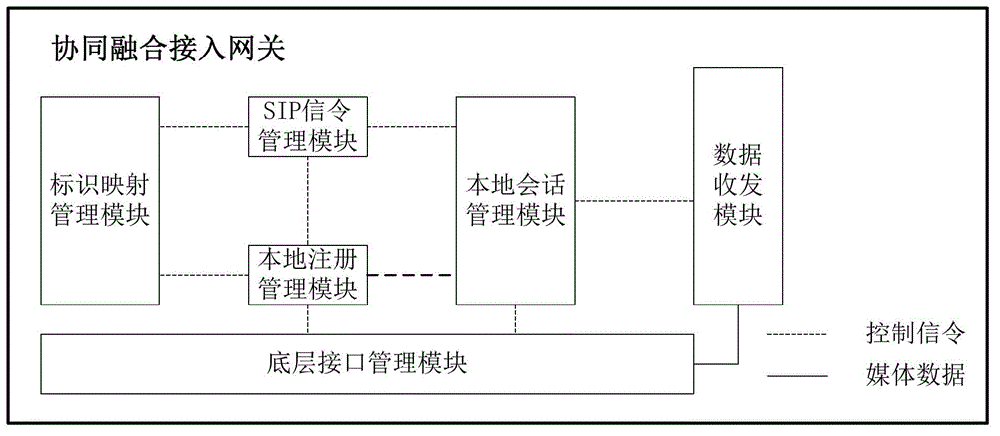
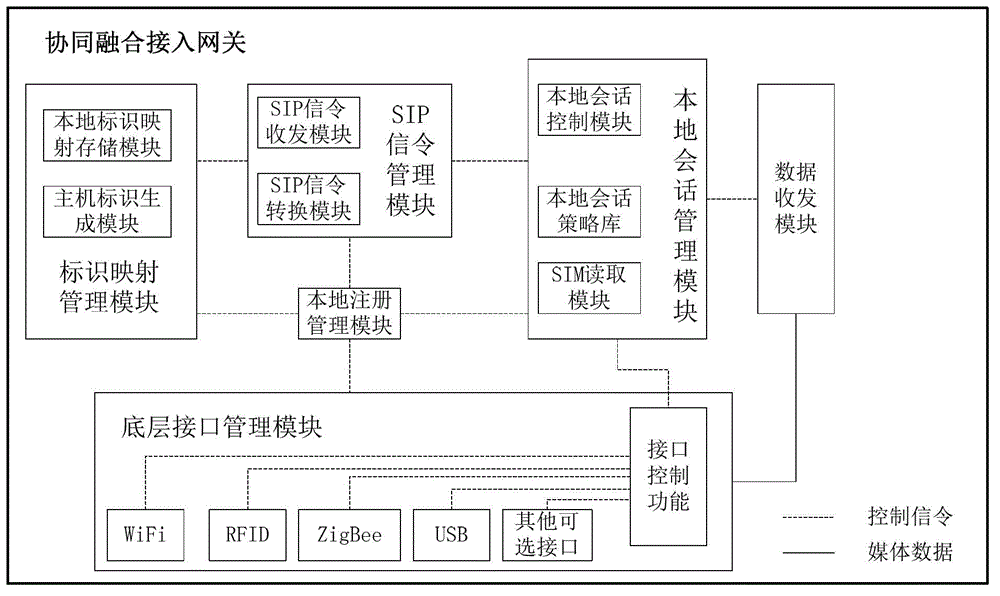
The invention discloses a method, a system and an access gateway for intercommunication between local equipment and an IMS (IP Multimedia Subsystem) network. The method comprises the steps that an IMS network host identity field is added in the SIP (Session Initiation Protocol); the collaborative fusion access gateway generates IMS network host identities and host names for the local equipment, then a mapping relationship between the IMS network host identities and the host names is registered in a DNS (Domain Name Server) in the IMS network; IMS users inquire to obtain the host identifies of the local equipment and write the host names and the host identities of the local equipment in the host identity field in SIP session requests; and the collaborative fusion access gateway performs addressing for the local equipment according to the host identity field to realize the adaptation and the forwarding of signaling protocols and data protocols between the local equipment and the IMS users. The collaborative fusion access gateway comprises a bottom layer interface management module, a local registration management module, a local session management module, a data transceiver module, an SIP signaling management module and an identity mapping management module. The method, the system and the access gateway for intercommunication between the local equipment and the IMS network have the advantages that the communication between the IMS users and the designated local equipment is realized and the application prospect is wide.
Owner:PLA UNIV OF SCI & TECH
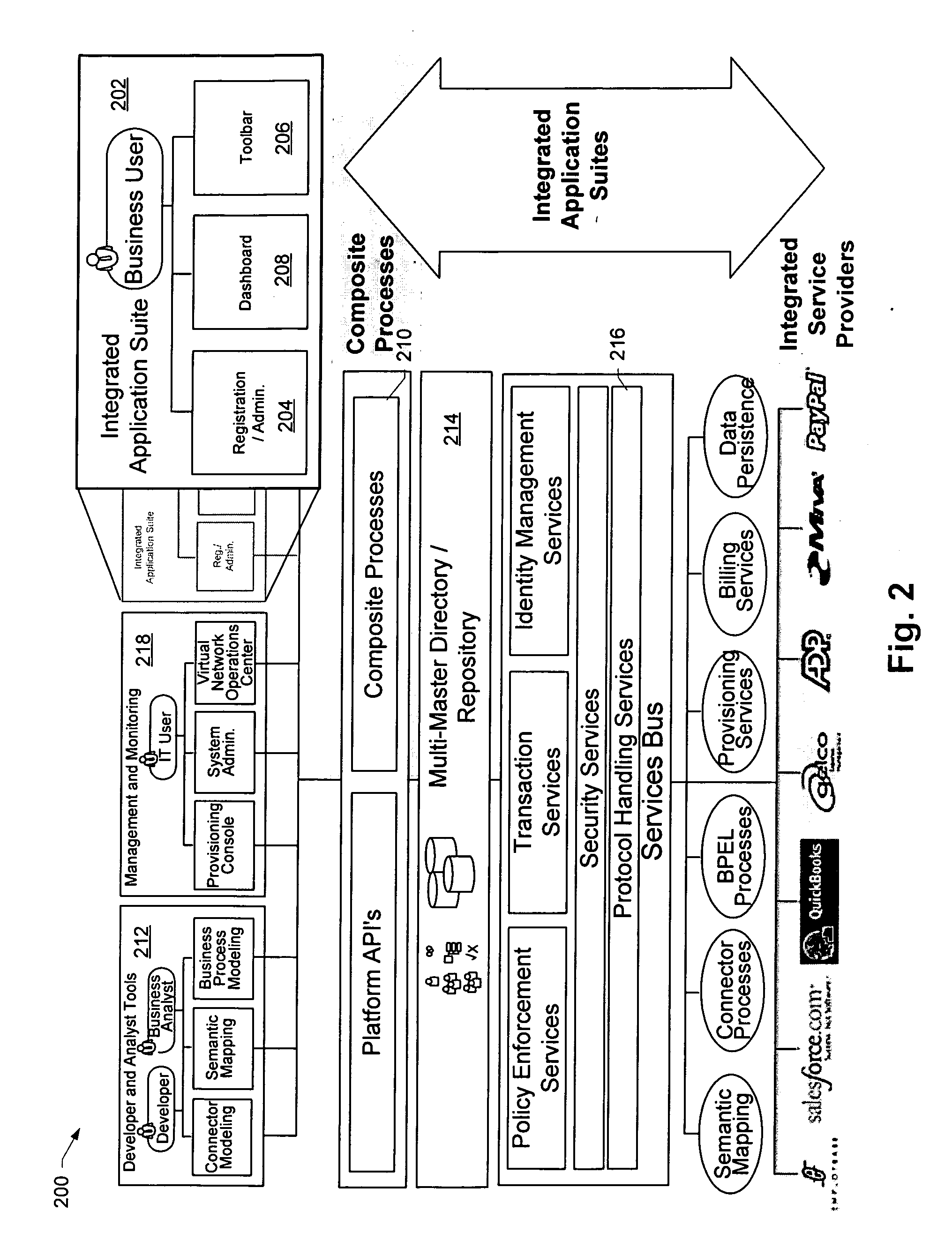
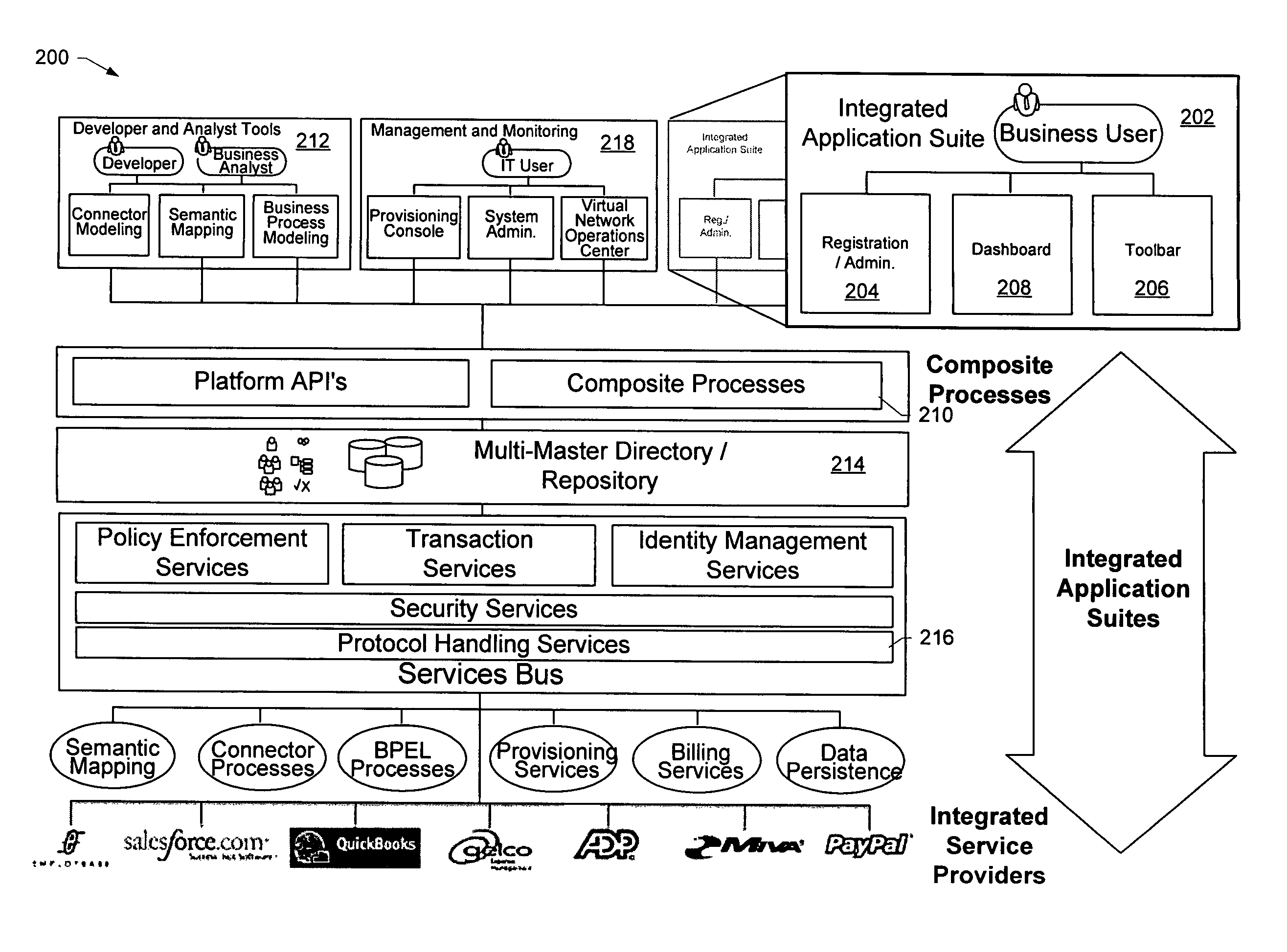
Business Process Enablement For Identity Management
ActiveUS20110162055A1Improve identityEasily exposedSpecific access rightsDigital data processing detailsVoucherIdentity management
A method, system and computer program for business process automation facilitates transforming a user's identity / credentials as part of the enablement of transaction fulfillment, e.g., within a SOA environment. In one embodiment, identity and attribute information is added to one or more business process models that each represents a sub-transaction within an overall transaction fulfillment business process flow. As the business model is mapped to an execution environment, the identity and attribute information in the model is used to configure appropriate tooling to define the identity / attribute transformation required to complete the particular portion of the transaction represented by the model. In a representative implementation, the business process models conform to BPEL4WS, and one or more of these models are extended with identity mapping information such that, during transaction fulfillment, local identity mapping transformations provide the identity / credential propagation required to support the business process.
Owner:IBM CORP
Machine type communication interworking function proxy
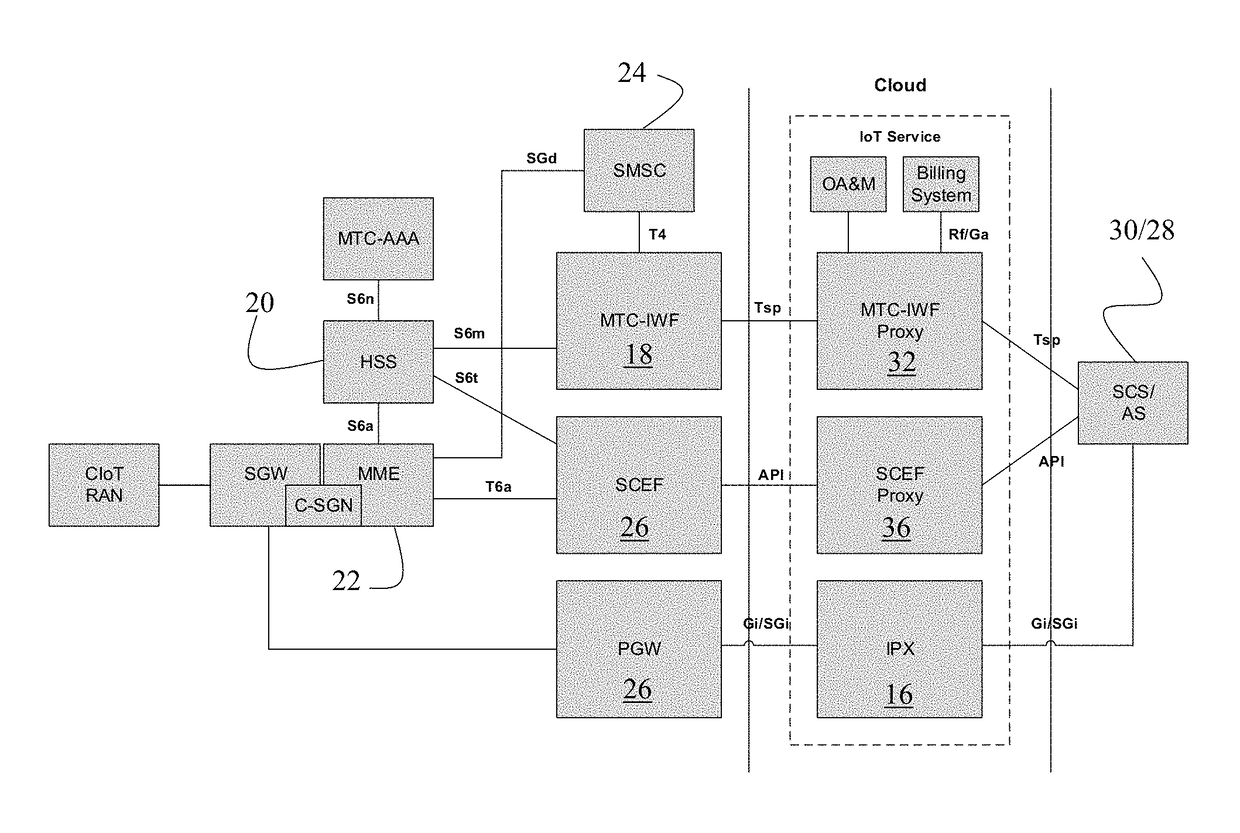
ActiveUS9948646B1Service provisioningWireless commuication servicesSignaling protocolNetwork service
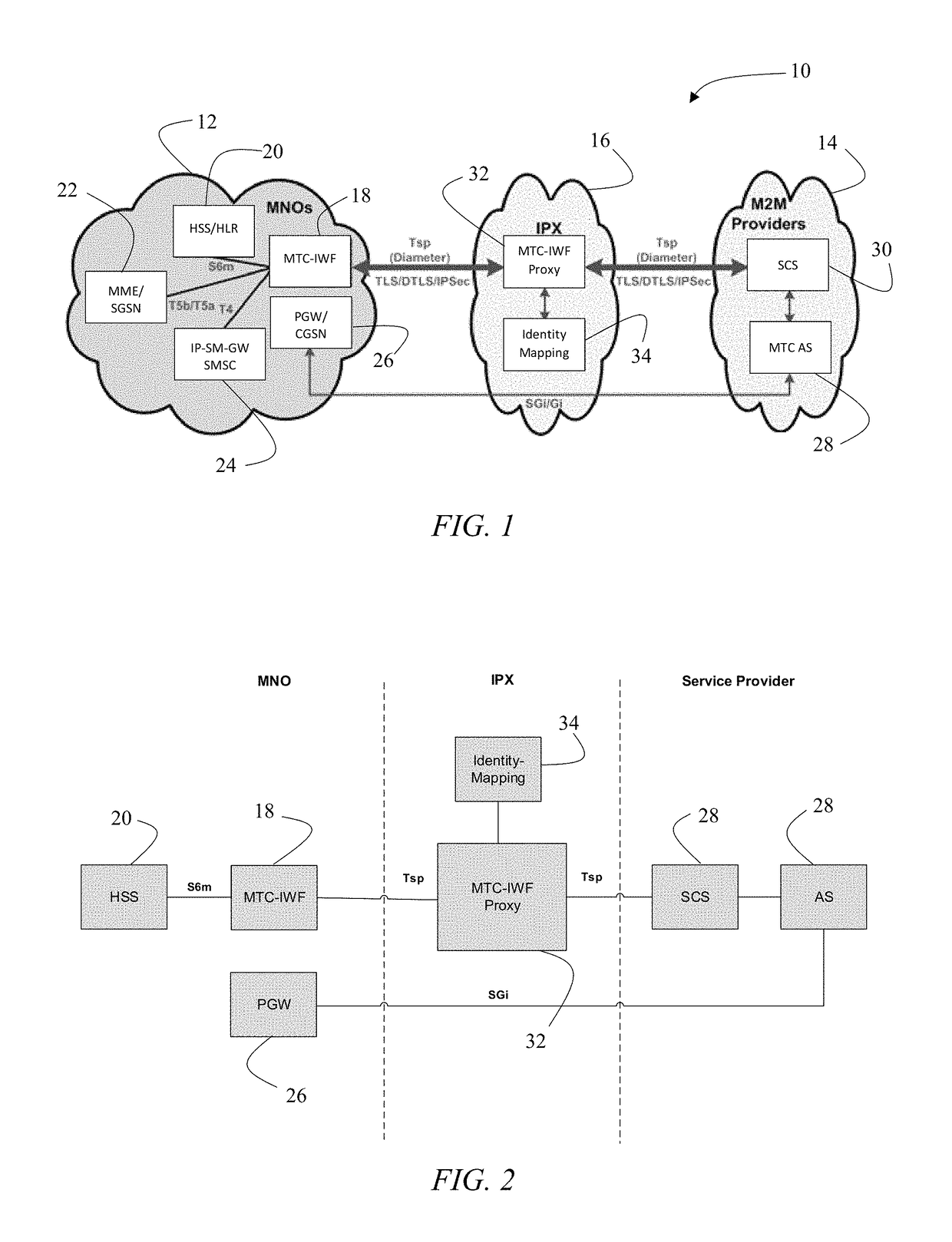
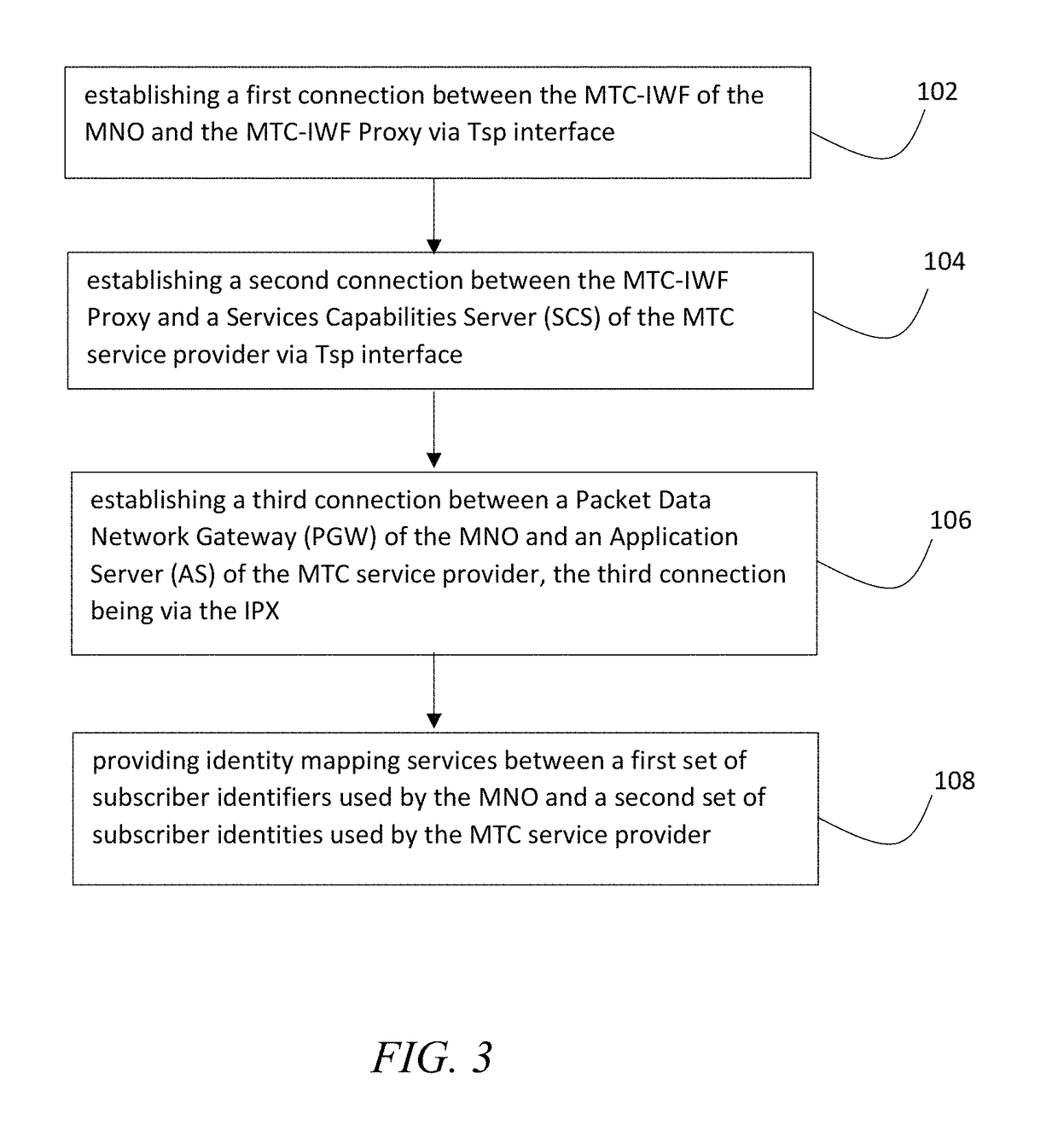
A method of establishing connectivity between a mobile network operator (MNO) and a machine type communications (MTC) service provider. A machine type communications interworking function (MTC-IWF) Proxy is hosted on an IPX network service. MTC-IWF Proxy is connected to a MTC-IWF of the MNO and is also connected to a Service Capacities Center (SCS) of the MTC service provider. MTC-IWF Proxy connects to the MNO and the MTC service providers via trigger-service provider (Tsp) interface. Identity mapping services are provided between a first set of subscriber identifiers used by the MNO and a second set of subscriber identities used by the MTC service provider. The MTC-IWF Proxy hides the internal topology and relays signaling protocols used over a Tsp interface, thus enabling the MTC service providers and MNOs communicate without modifying their internal signaling protocols.
Owner:SYNIVERSE TECH
Lattice-based multi-identity fully homomorphic encryption method
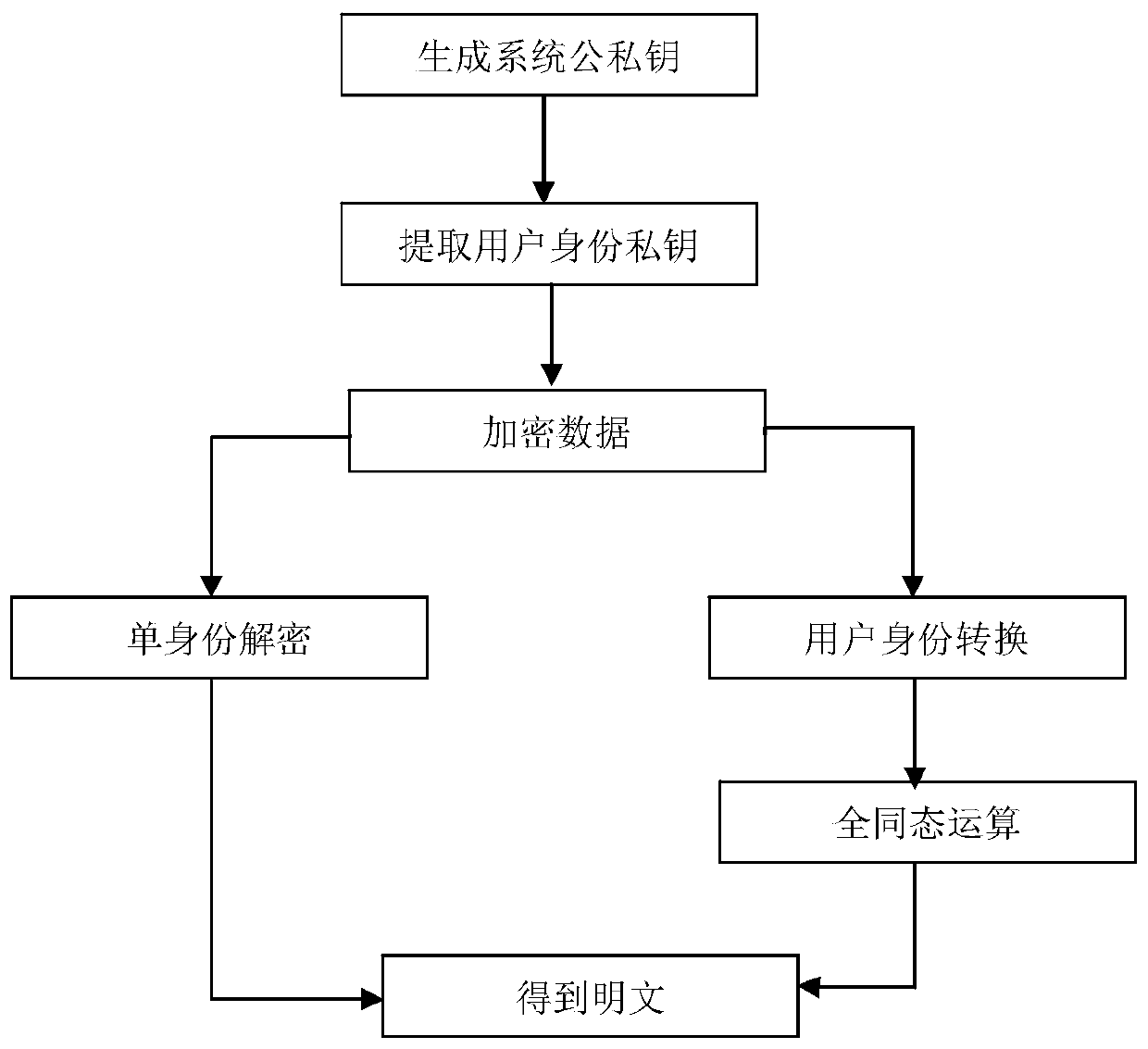
PendingCN111526002AImprove throughputCorrect fully homomorphic operationKey distribution for secure communicationPublic key for secure communicationIdentity transformAlgorithm
The invention discloses a lattice-based multi-identity fully homomorphic encryption method. The method comprises the following steps: initializing a system; extracting a user key: mapping the first user identity and the second user identity into a reversible matrix by using a full-rank function, and generating a first private key corresponding to the first user identity and a second private key corresponding to the second user identity through vector operation; performing ciphertext generation: obtaining encryption selection of a first user identity, selecting a plaintext message to be encrypted, and performing encrypting to obtain a first ciphertext; decrypting the single identity: decrypting the first user identity through a first private key to obtain a plaintext message; identity conversion: converting the first ciphertext of the first user identity into a second ciphertext corresponding to a second user identity through an identity conversion algorithm; and performing fully homomorphic evaluation: carrying out fully homomorphic operation on the ciphertext after identity conversion and then decrypting the ciphertext. Encryption and decryption of a ciphertext with a single identity are converted into encryption and decryption of a ciphertext with multiple identities, and correct fully homomorphic operation can be realized.
Owner:JINAN UNIVERSITY
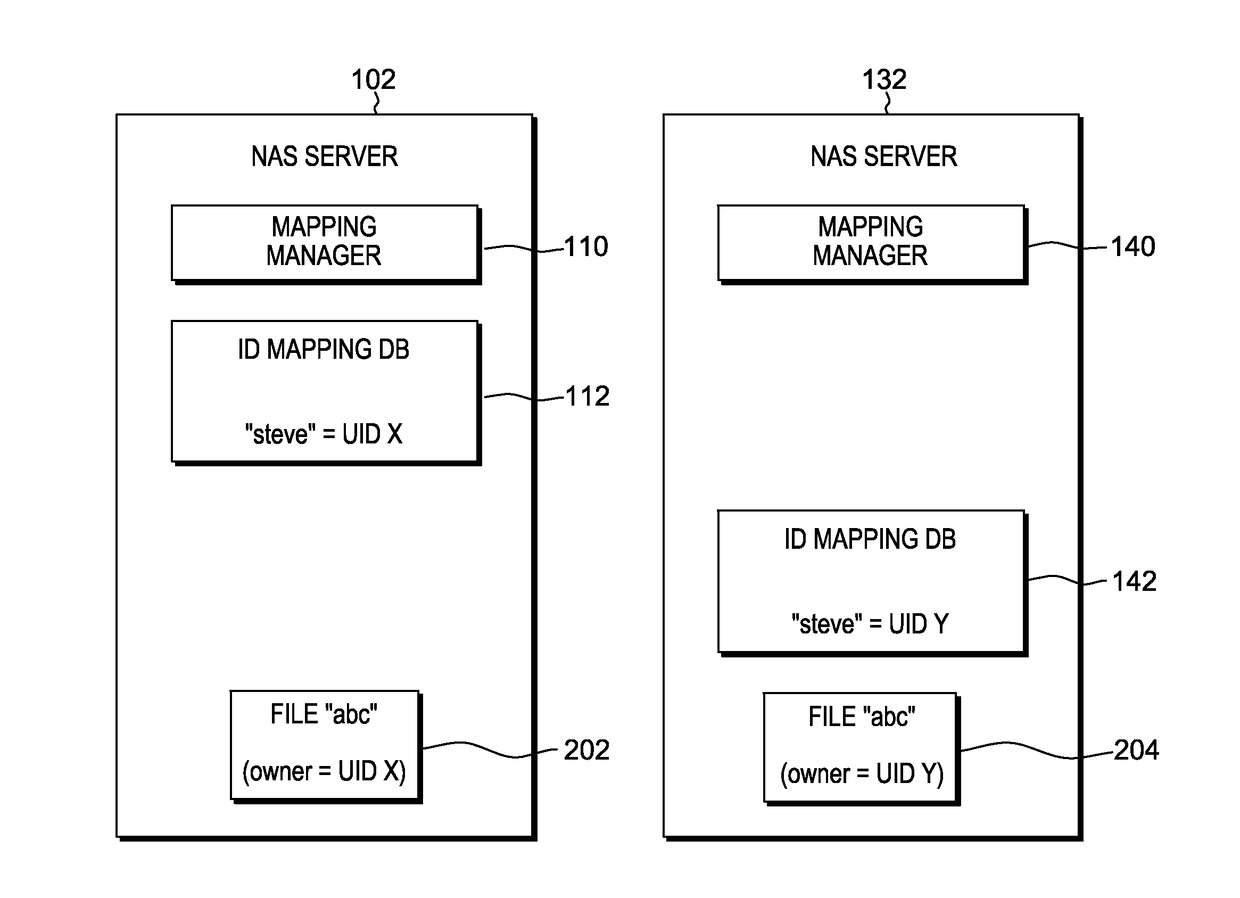
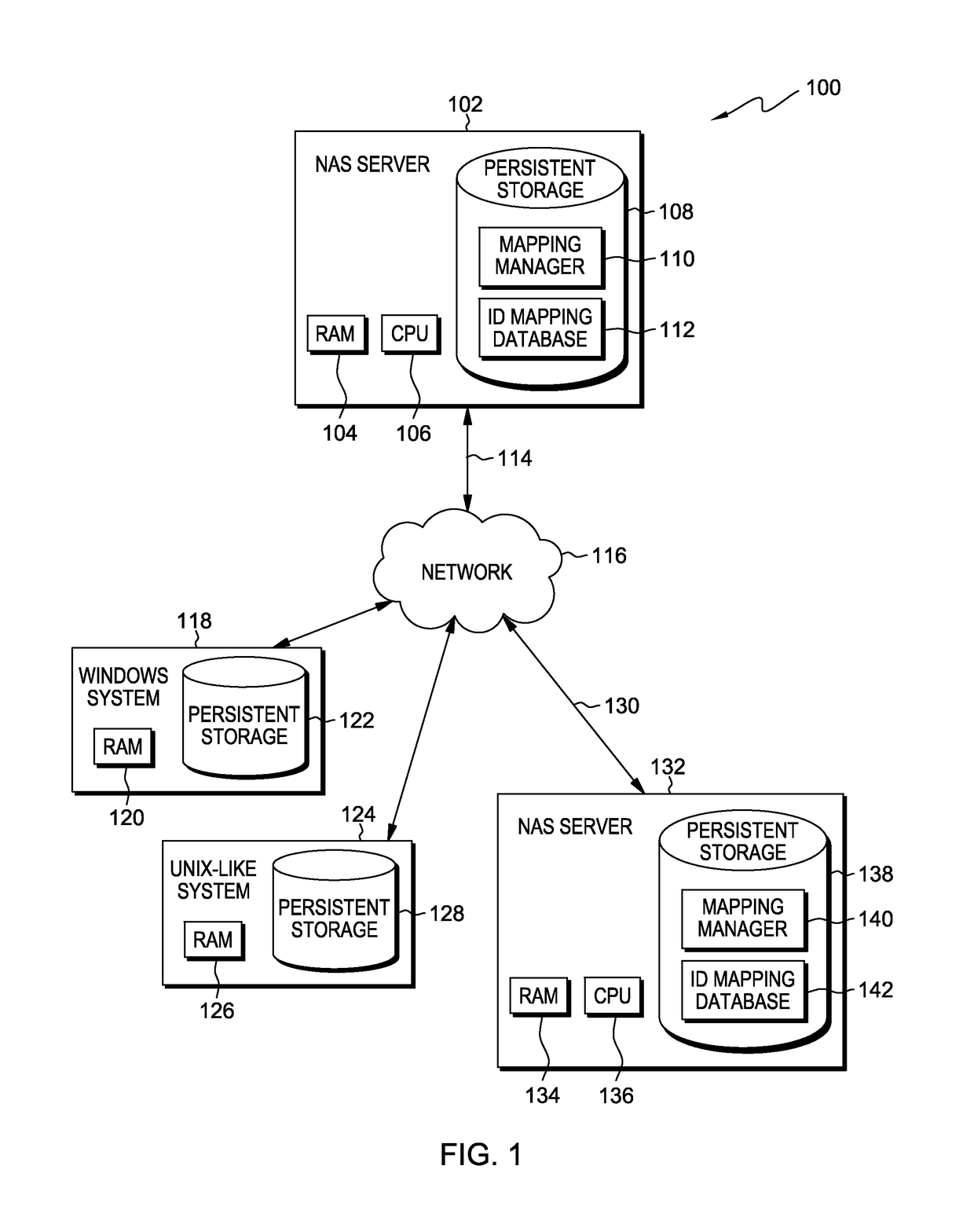
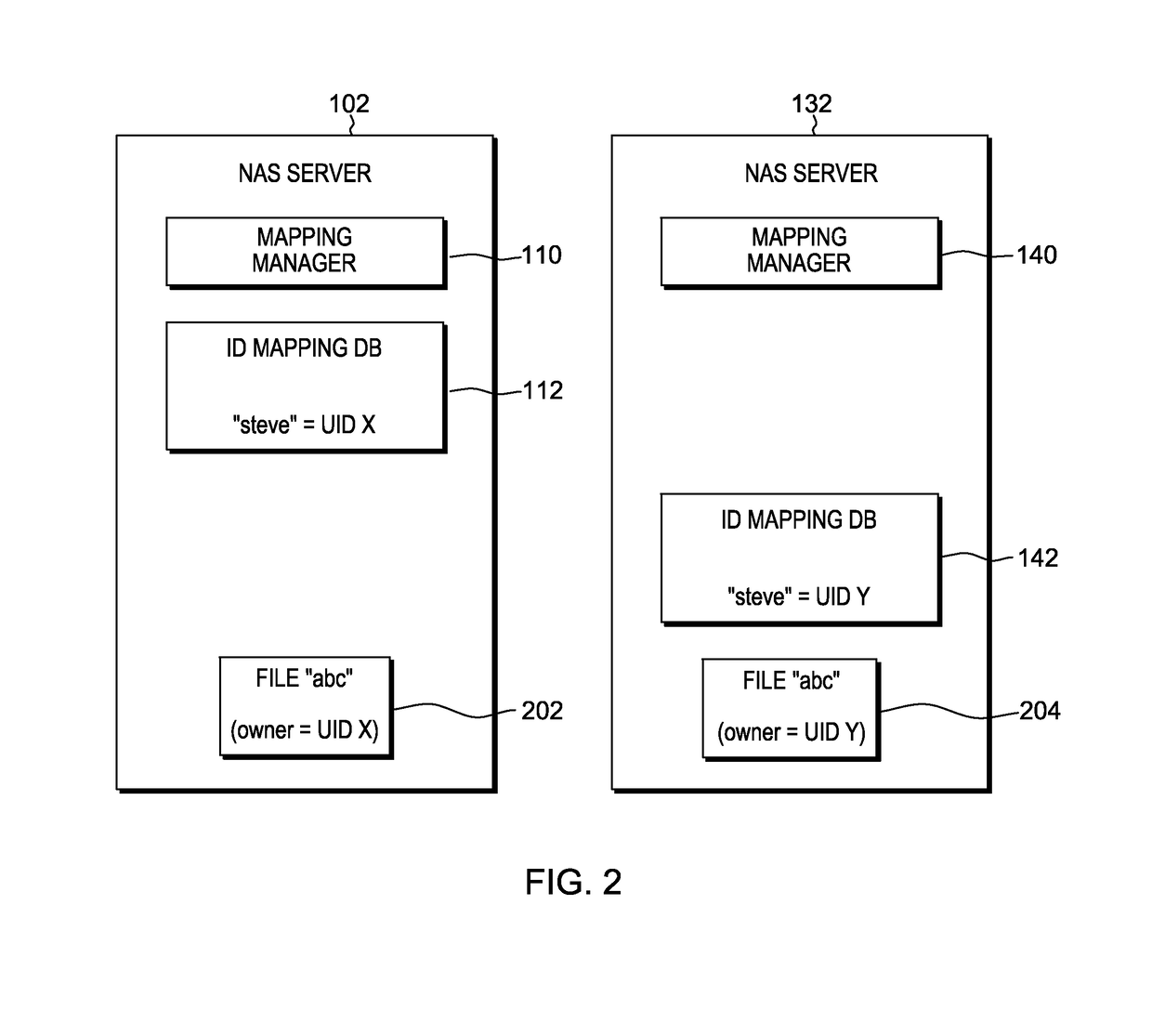
Data mirroring for network attached storage
InactiveUS9678679B2Input/output to record carriersError detection/correctionNetwork connectionData file
A computer-implemented method for data mirroring for network attached storage includes duplicating an identity mapping database on a second NAS server and creating a queue of updated data files containing updated elements since a prior synchronization. Data files containing the updated elements are transmitted from the first NAS server to the second NAS server. An updated copy of the identity mapping database from the first NAS server is stored at the second NAS server. The updated data files and metadata information from the first NAS server are written to the second NAS server. The permission entries of the transmitted data files from the first NAS server are translated using the identity mapping databases of the first and second NAS servers, such that the permission entries reflect the local ID mapping database on the second NAS server.
Owner:INT BUSINESS MASCH CORP
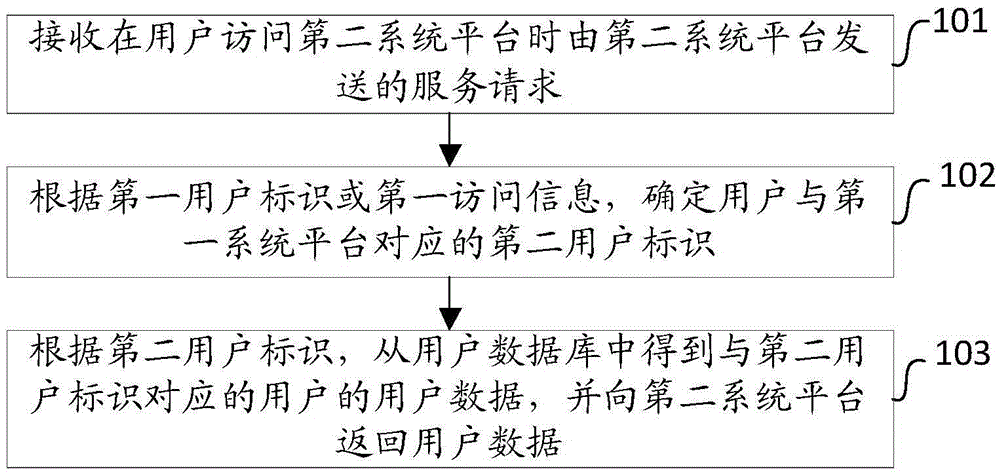
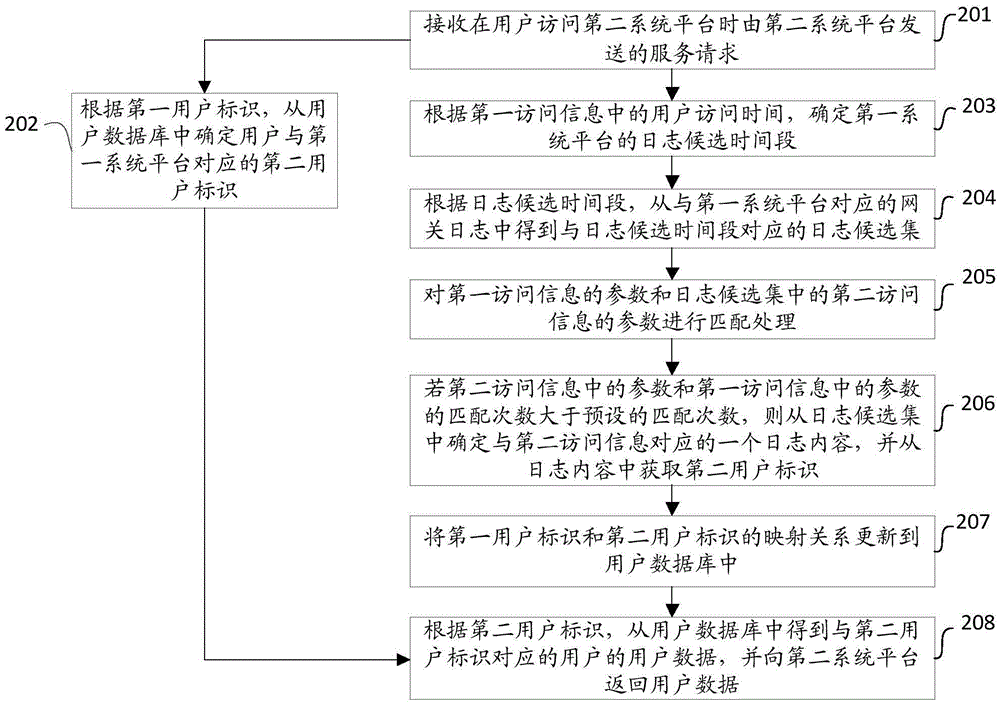
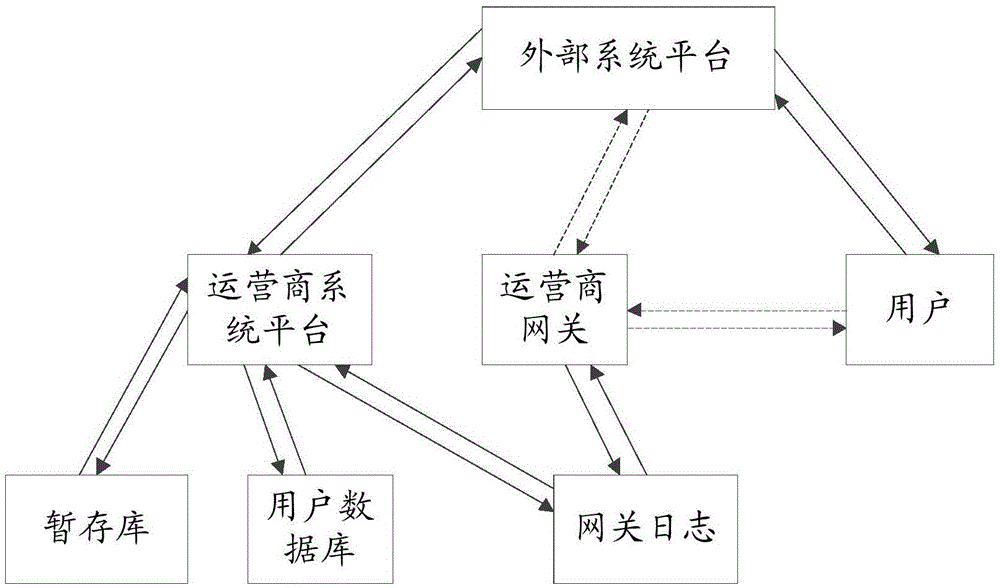
User identity mapping method and user identity mapping device based on operator gateway log
ActiveCN106656934ASolve the problem of being easily leakedSolve problems that are difficult to provide services externallyTransmissionSpecial data processing applicationsInternet privacyUser privacy
The invention provides a user identity mapping method and a user identity mapping device based on an operator gateway log. The method comprises the following steps: receiving a service request sent by a second system platform when a user accesses the second system platform, wherein the service request at least includes a first user identity of the user corresponding to the second system platform and first access information of the user's access to the second system platform; determining a second user identity corresponding to a first system platform according to the first user identity or the first access information; and getting user data of the user corresponding to the second user identity according to the second user identity, and returning the user data to the second system platform. The problem that the data of an operator system platform has a limited range of use and can be hardly used for external service as the operator system platform and an external system platform provide inconsistent user identity is solved, and the problem that user privacy is easy to leak is solved effectively.
Owner:CHINA MOBILE COMM GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com