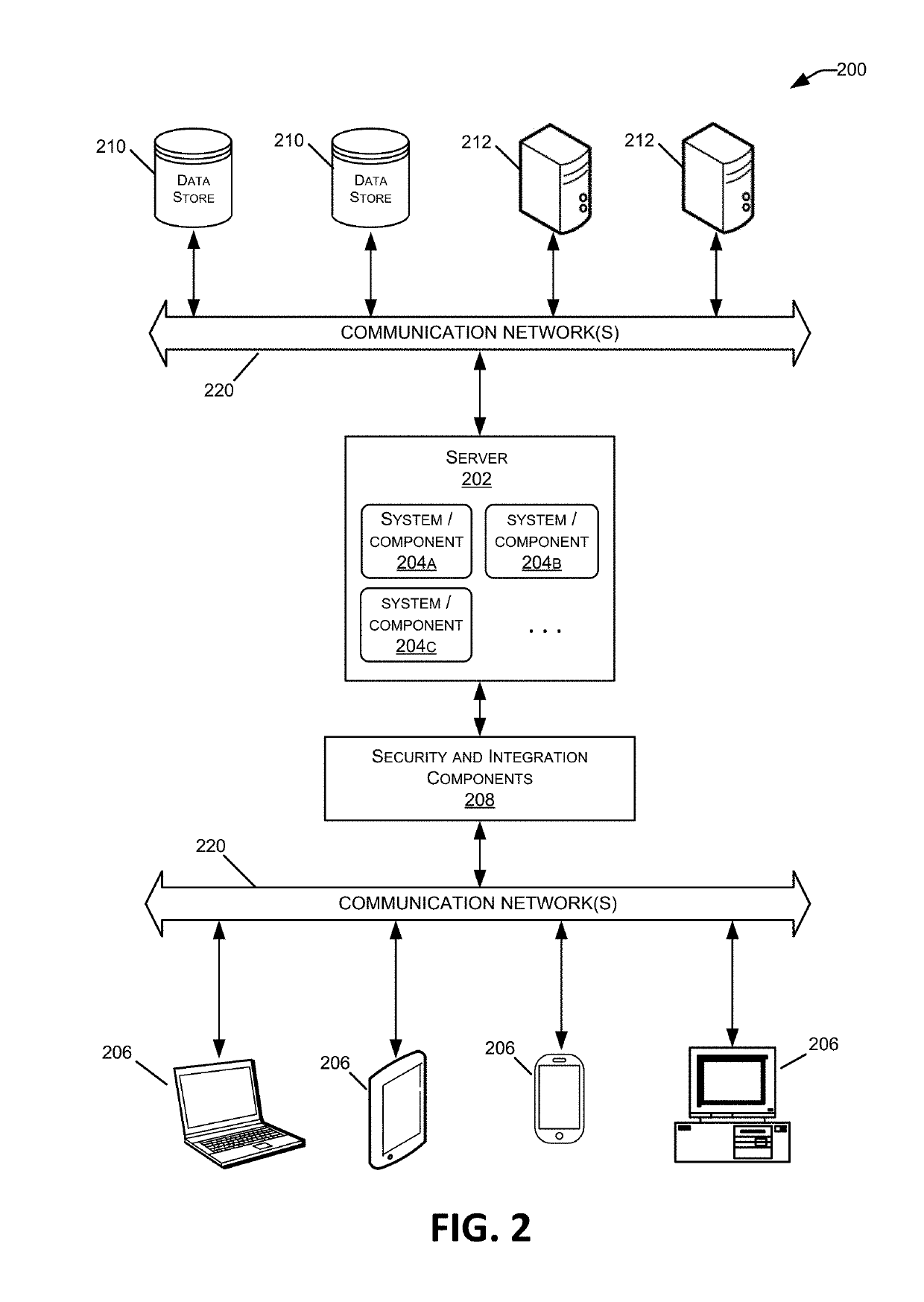
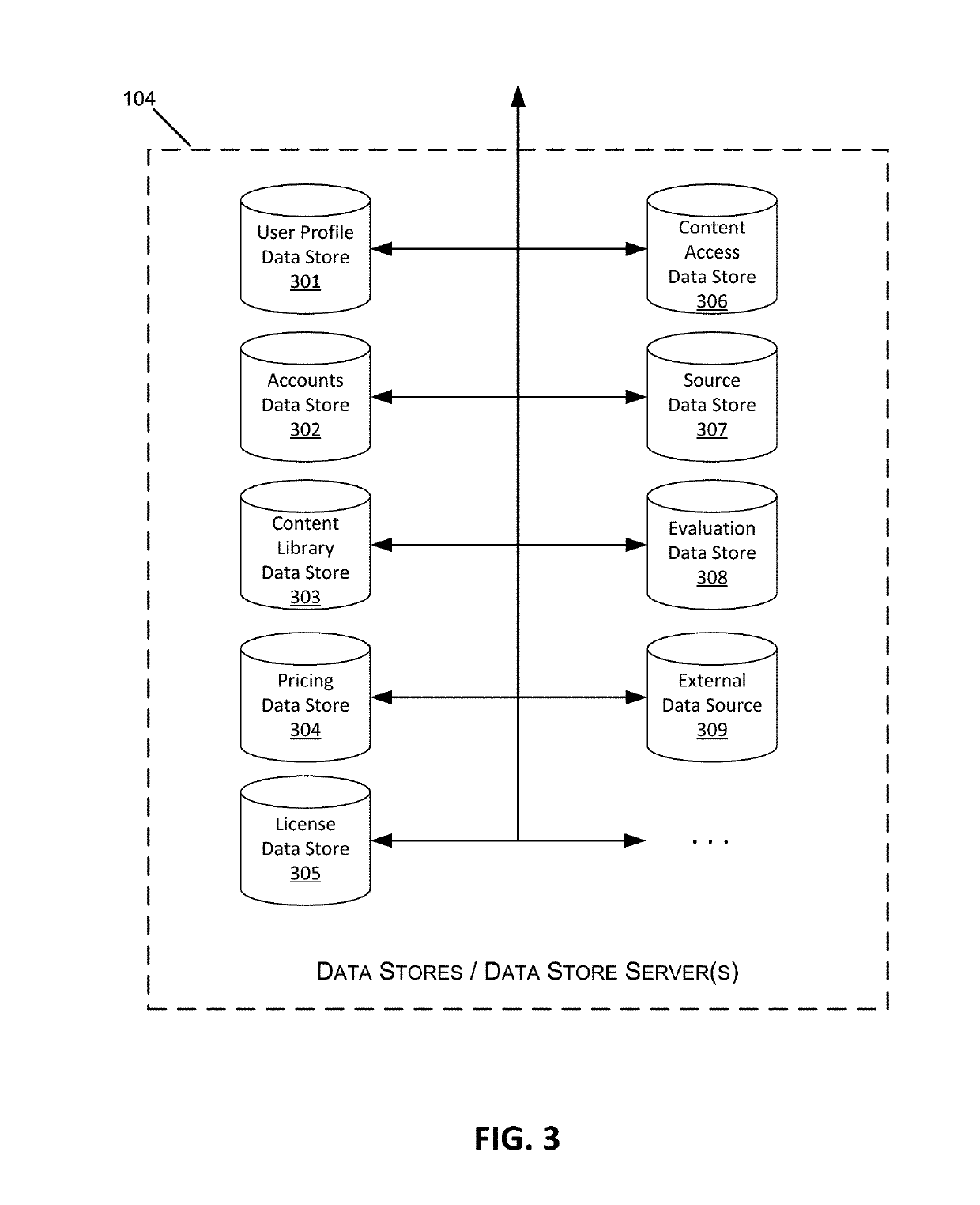
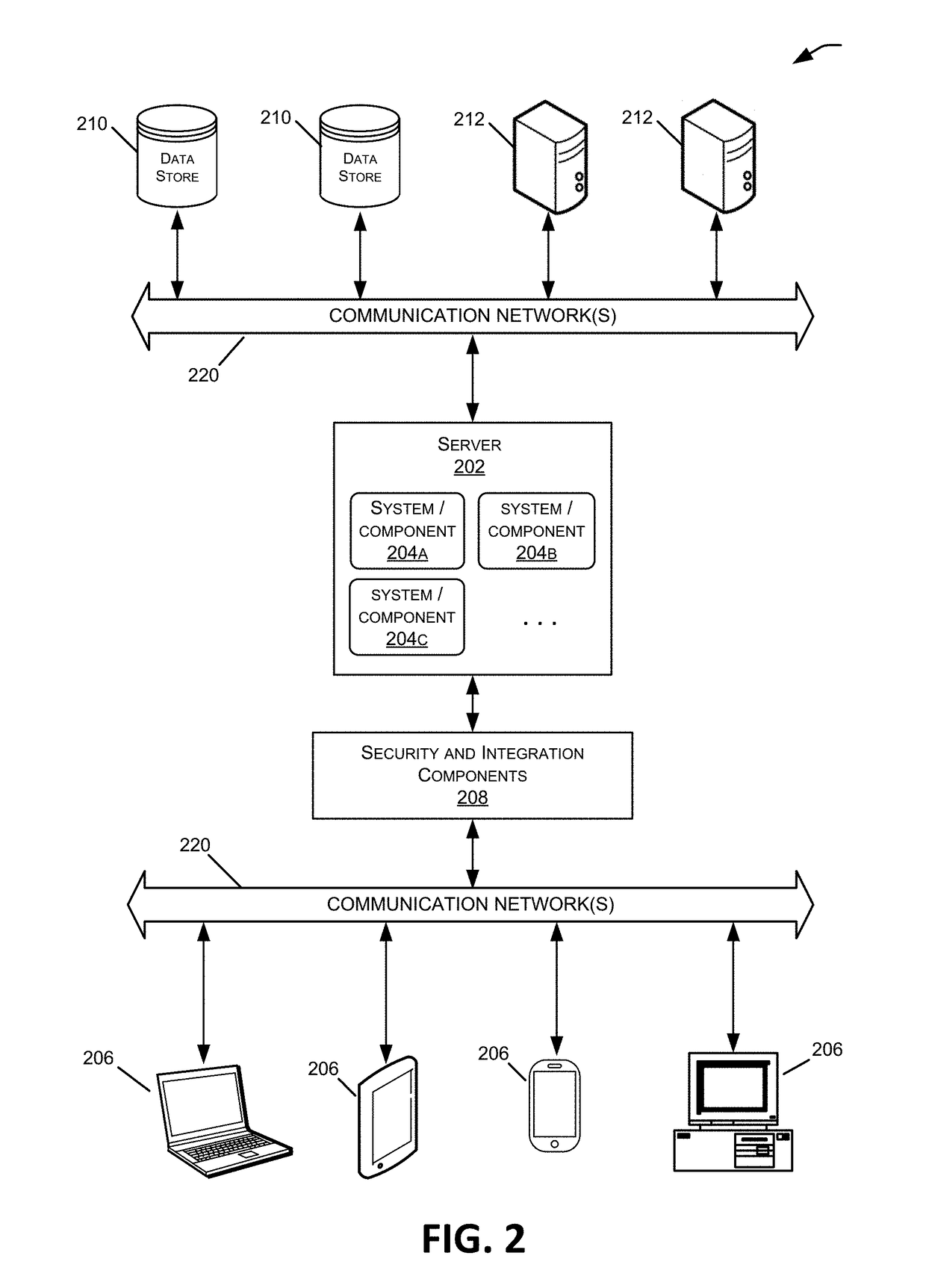
Patents
Literature
102 results about "Digital credential" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
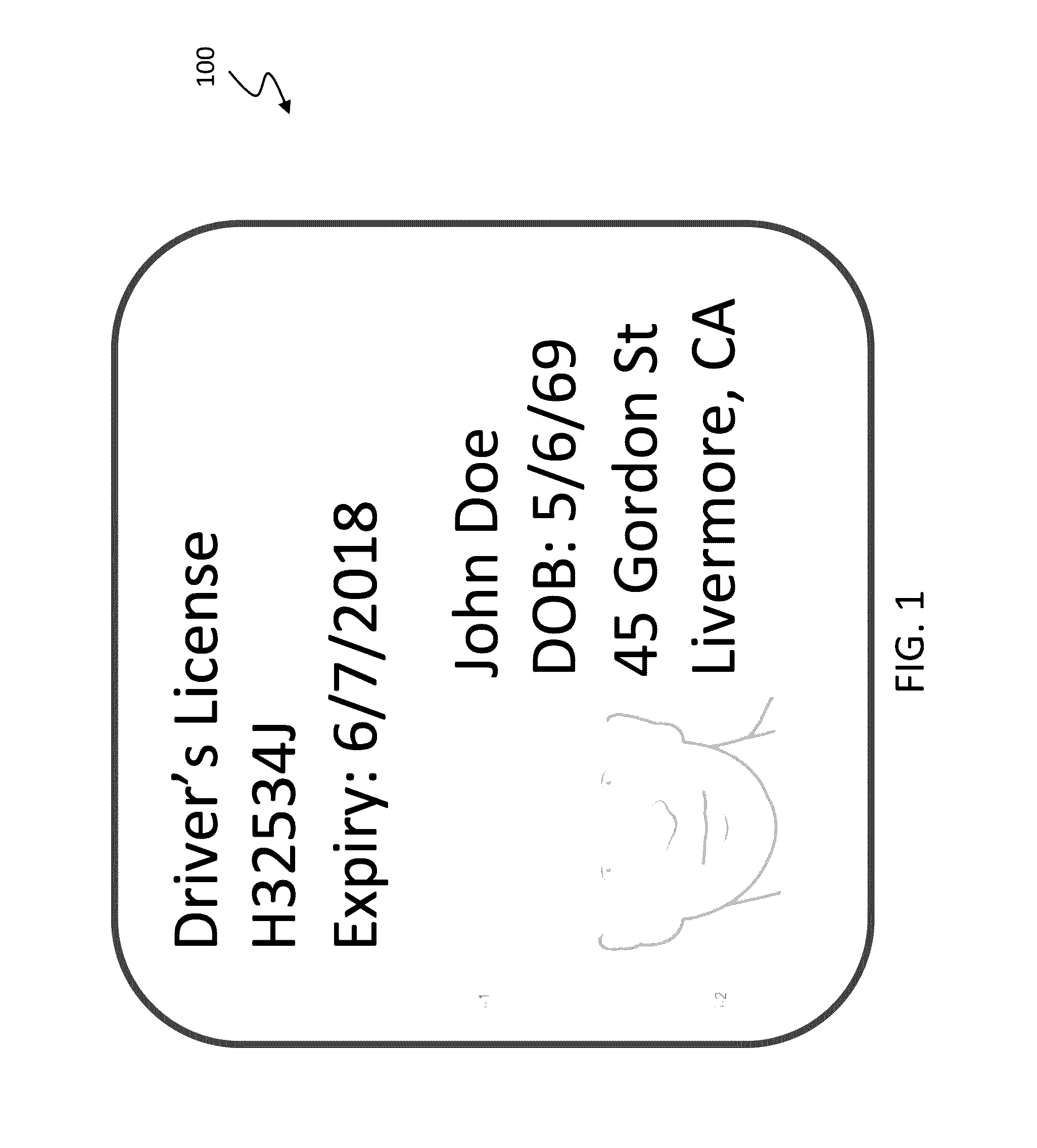
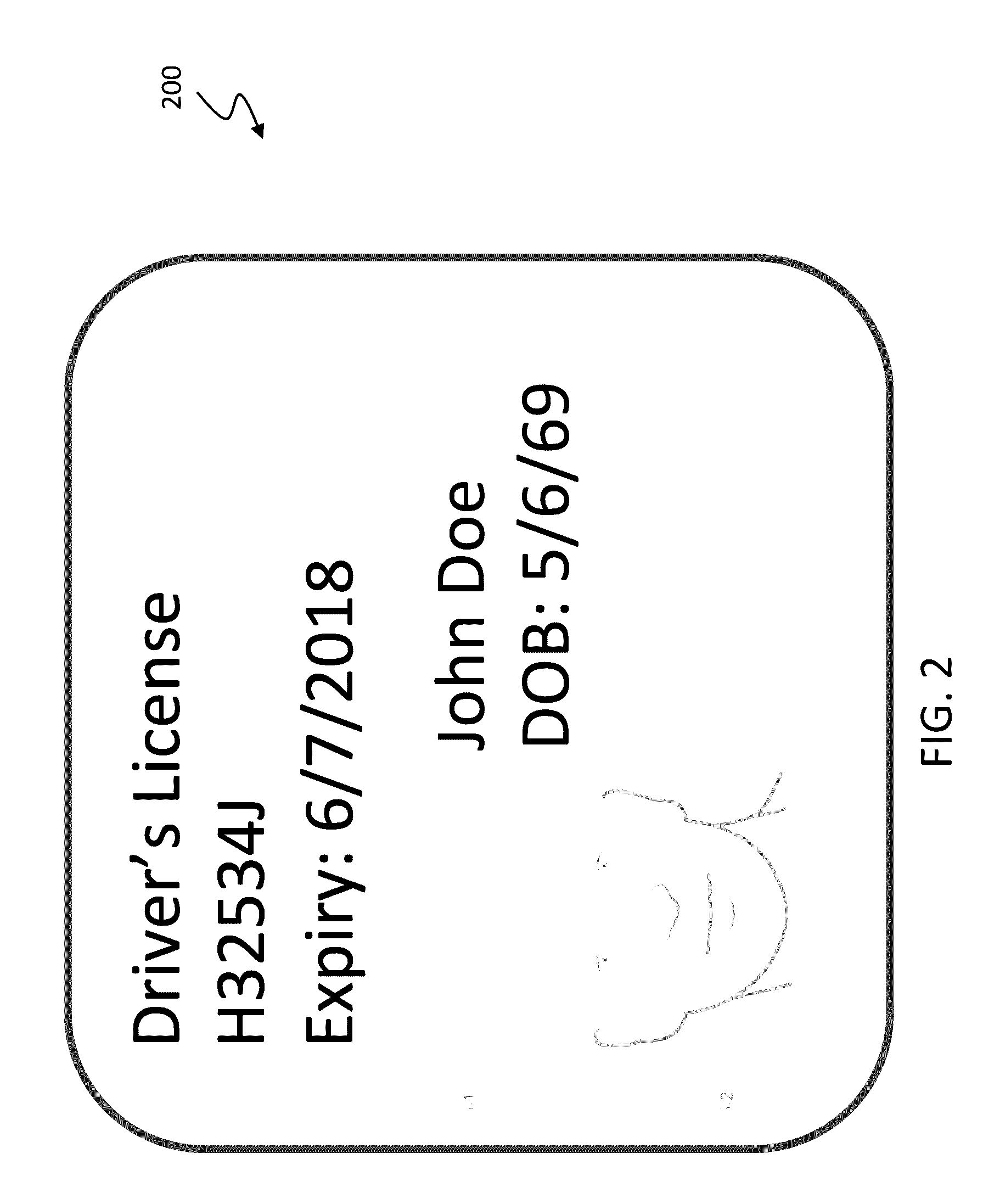
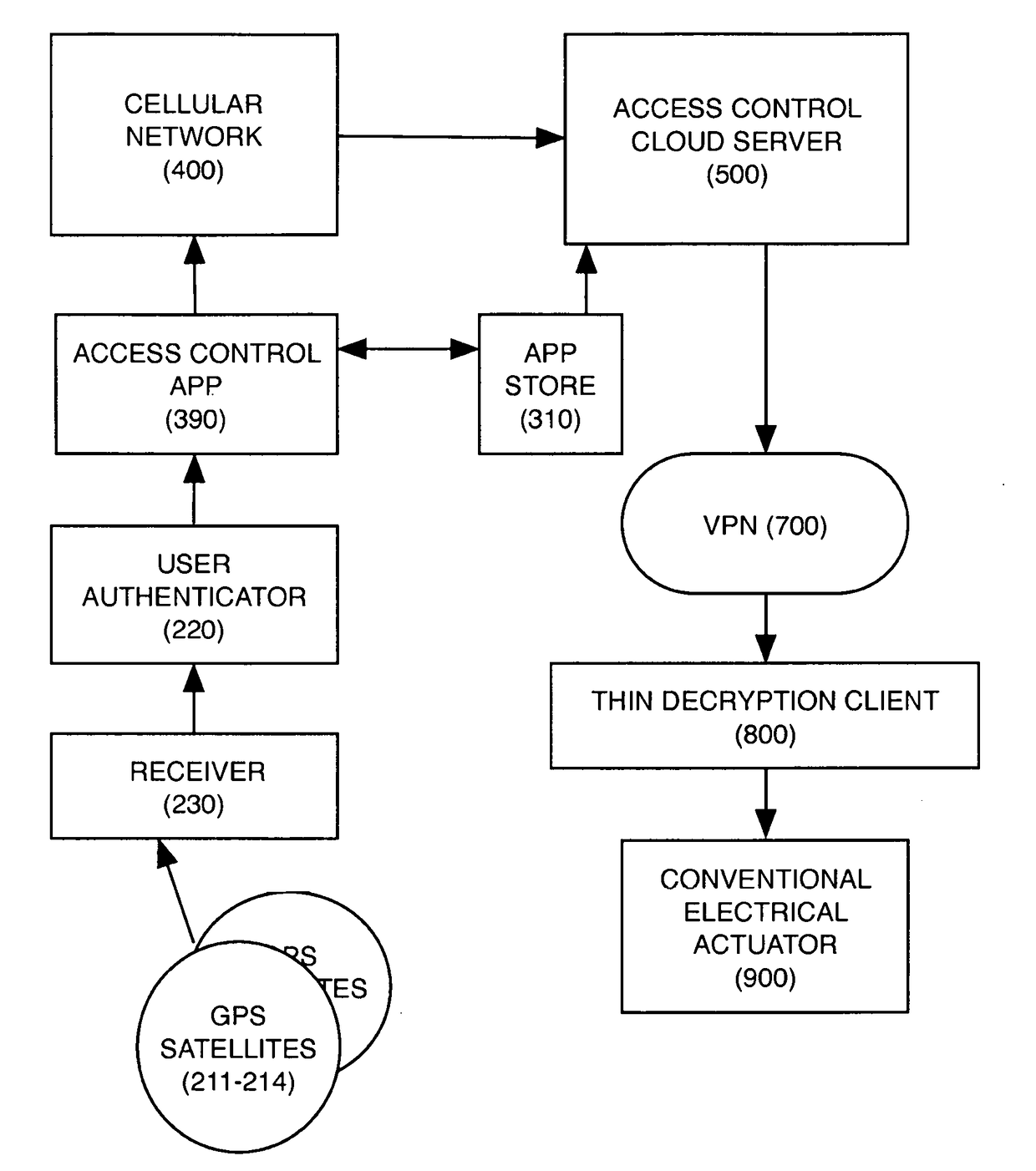
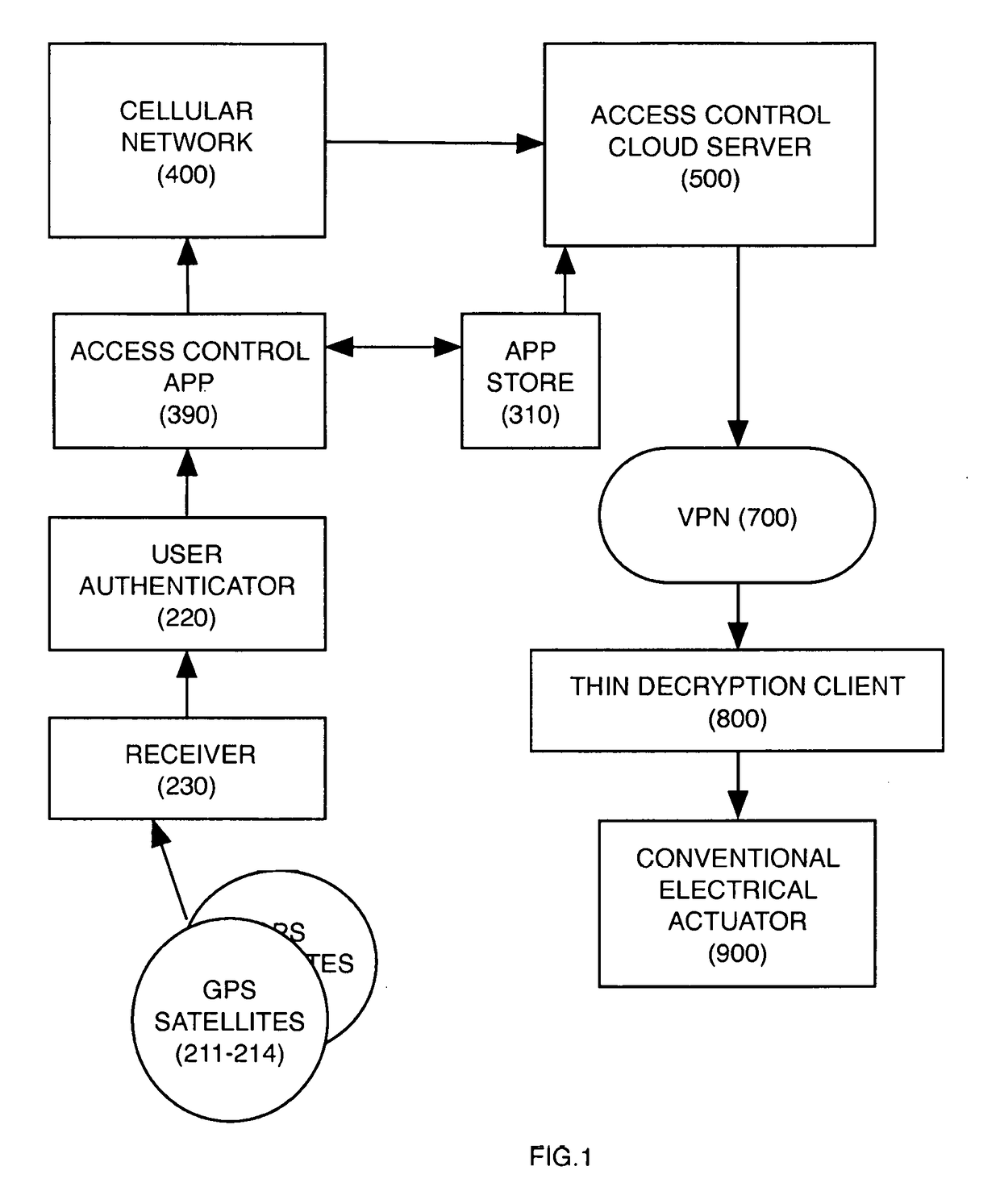
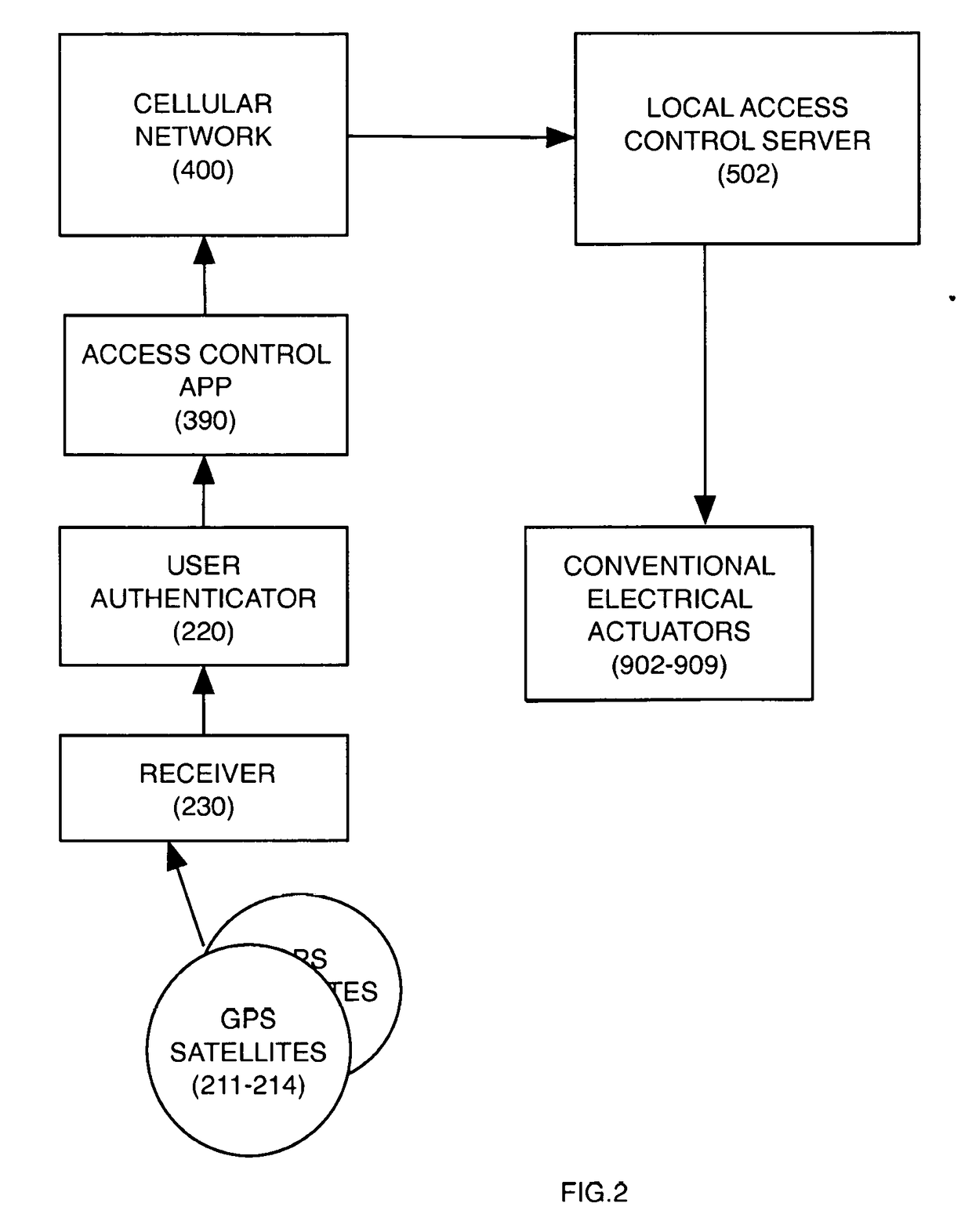
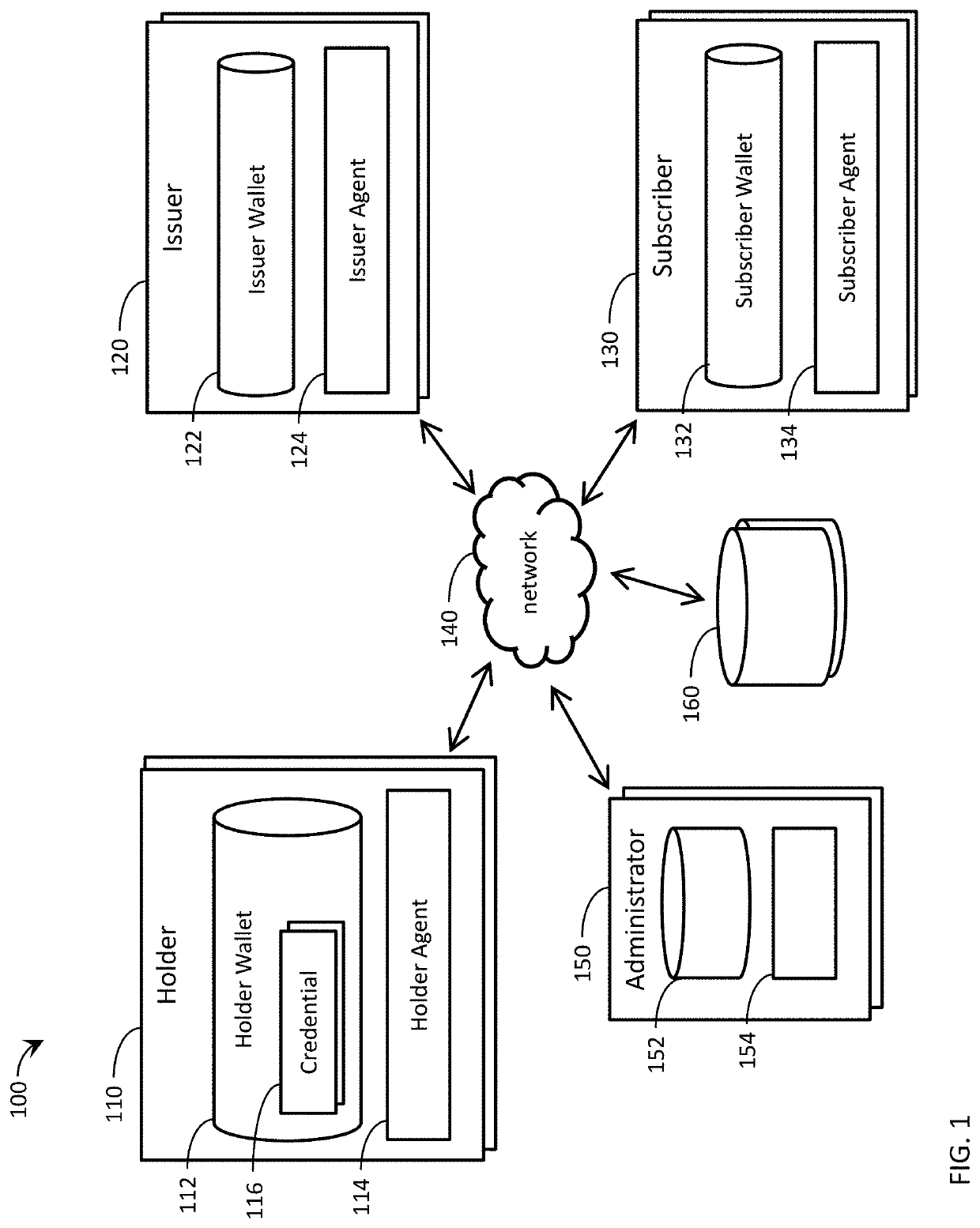
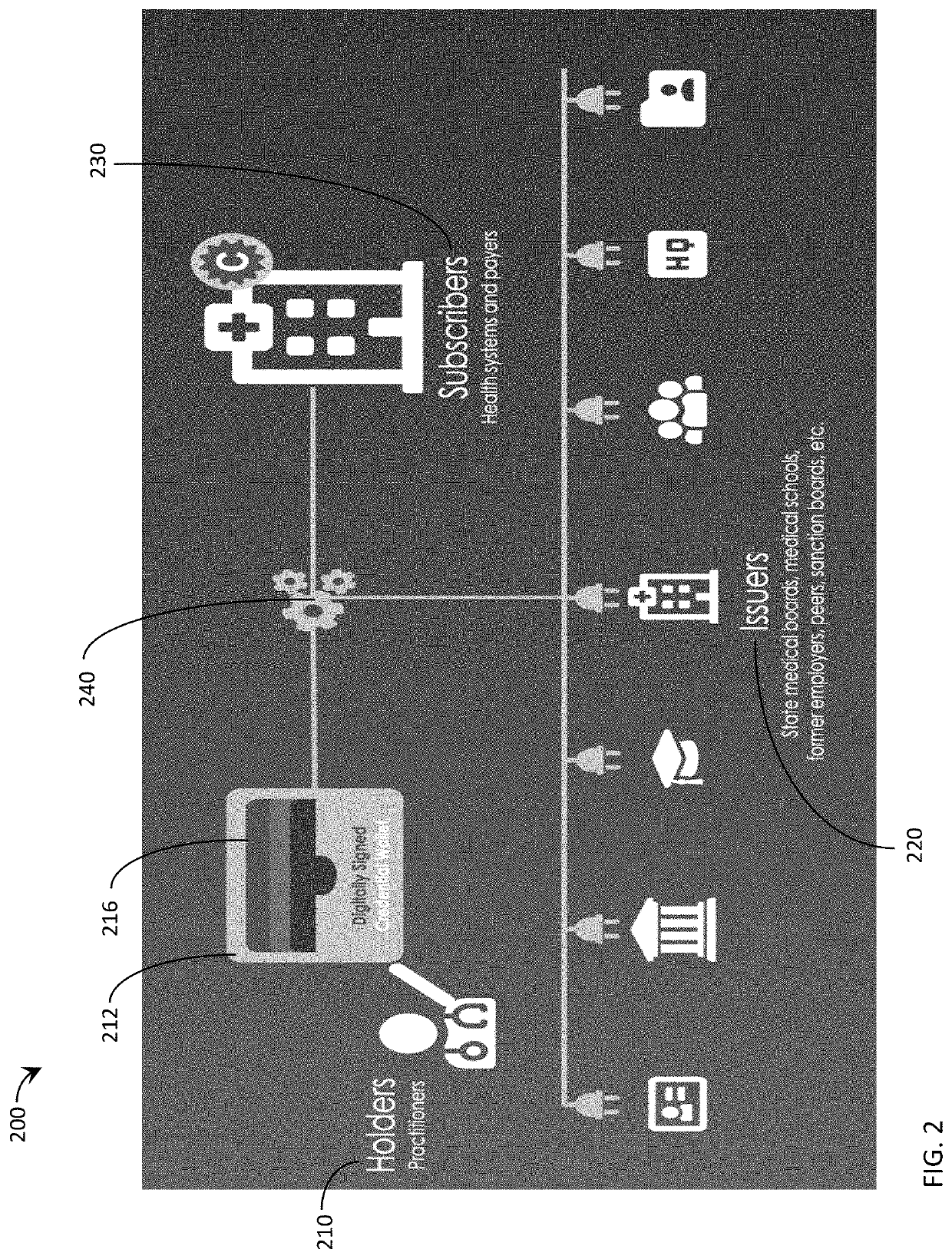
Digital credentials are the digital equivalent of paper-based credentials. Just as a paper-based credential could be a passport, a driver's license, a membership certificate or some kind of ticket to obtain some service, such as a cinema ticket or a public transport ticket, a digital credential is a proof of qualification, competence, or clearance that is attached to a person. Also, digital credentials prove something about their owner. Both types of credentials may contain personal information such as the person's name, birthplace, birthdate, and/or biometric information such as a picture or a finger print.
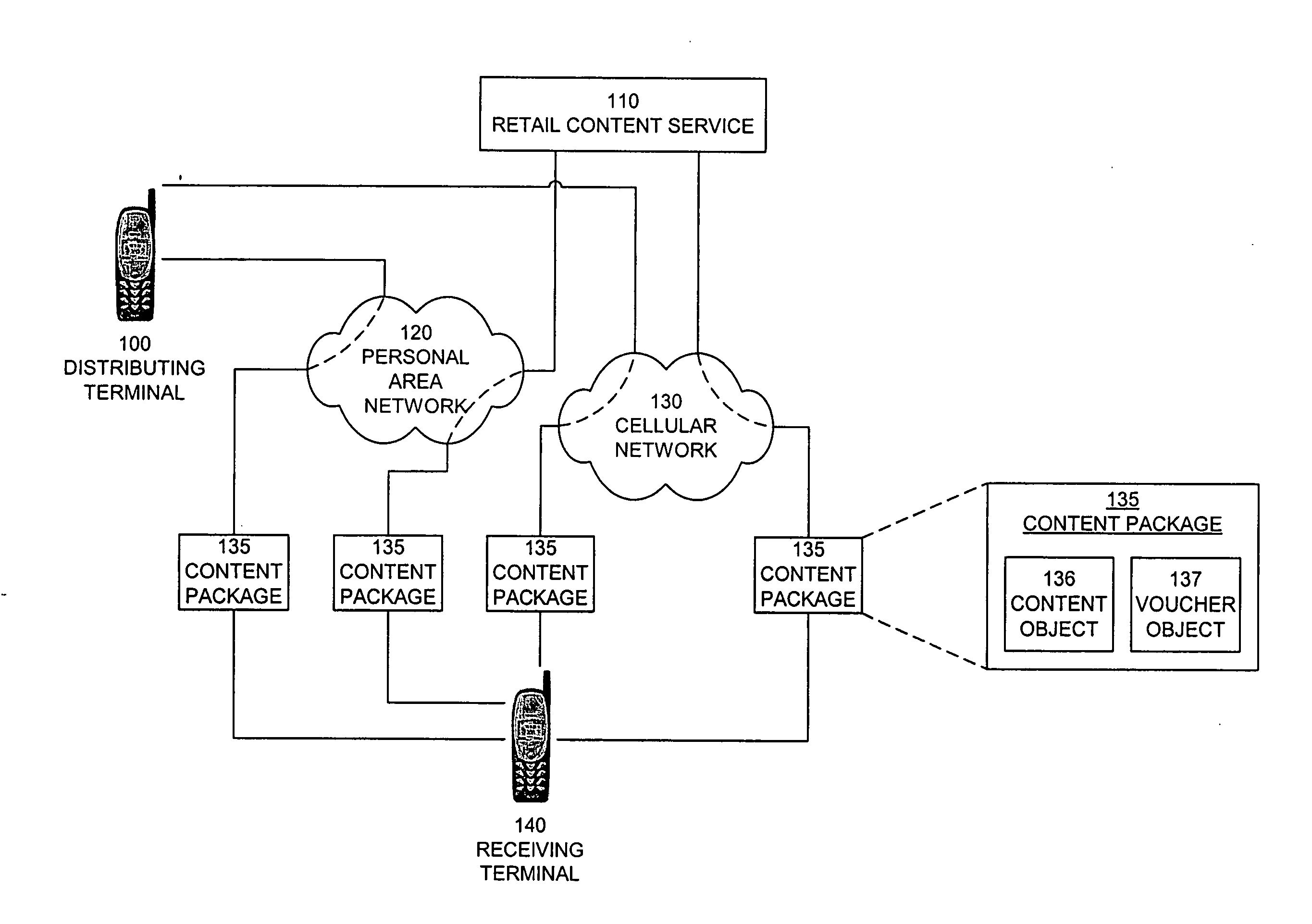
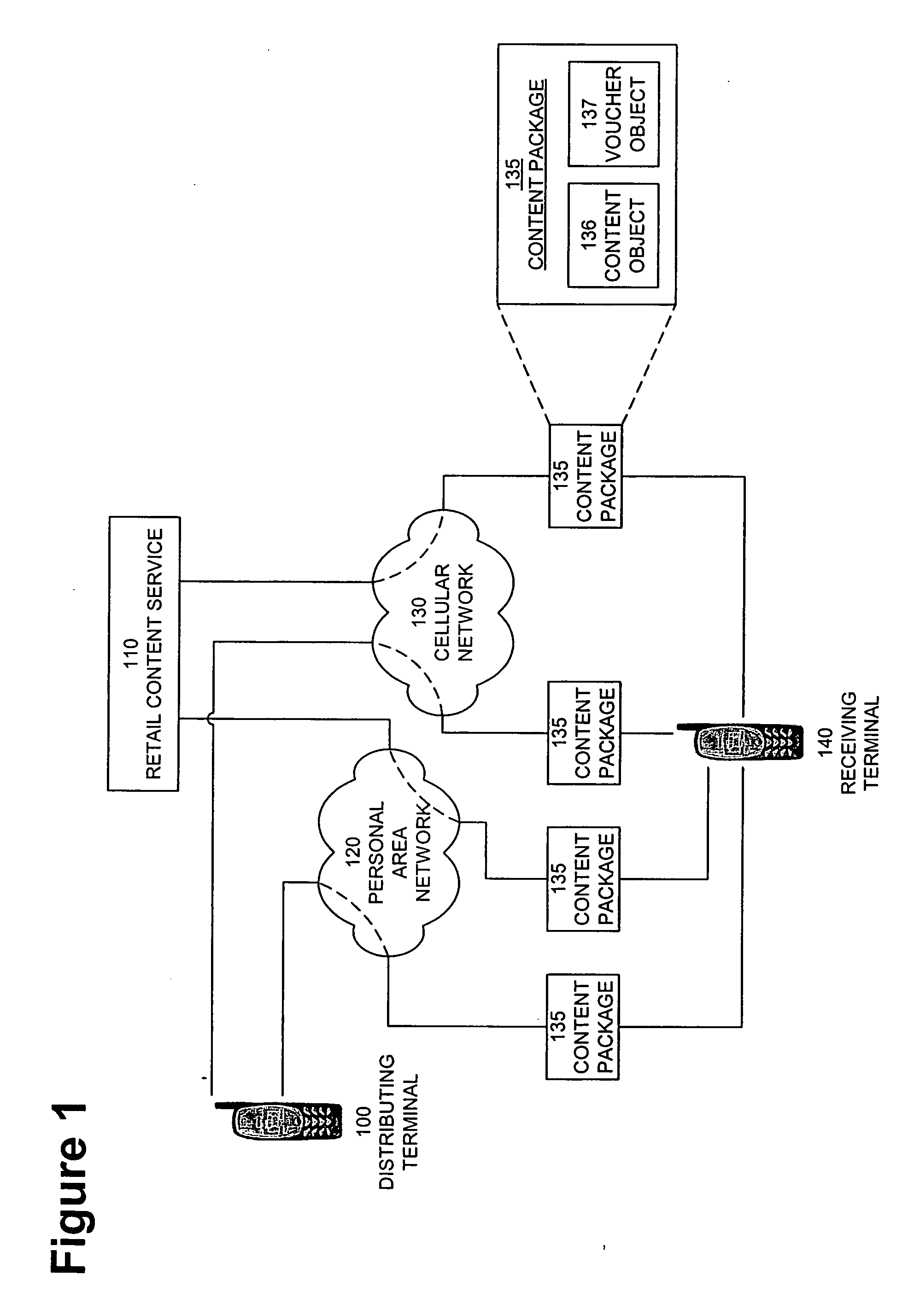
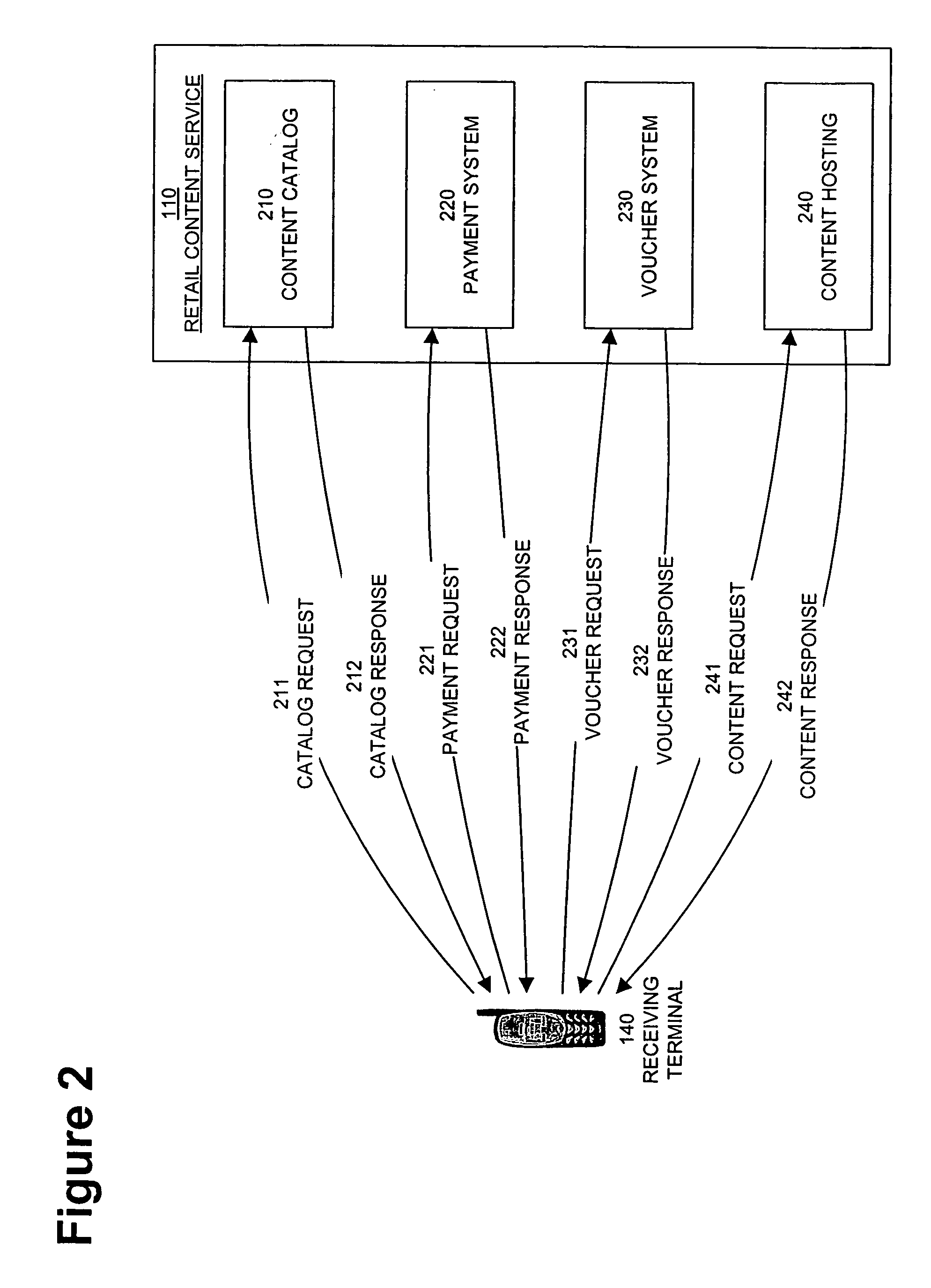
Digital rights management in a mobile communications environment
InactiveUS20070112676A1Payment architectureProgram/content distribution protectionDigital rights managementVoucher
The invention provides a method, system, and computer program product to control the access, copying, and / or transfer of a digital asset by mobile, wireless devices using a digital voucher. The digital voucher references a primary content that contains all of the expression for that particular asset and a secondary content that contains information that can be distilled out as a preview. The information in the primary content can be limited to a specified duration or a specific number of viewings. The author, owner, or possessor of the digital asset specifies the terms and conditions for distribution of the digital asset. The digital voucher authorizes the mobile, wireless device to access a specified primary or secondary content that may be located elsewhere in the network. The mobile, wireless device can download a copy of portions or all of the content depending on the terms specified in the voucher.
Owner:NOKIA CORP
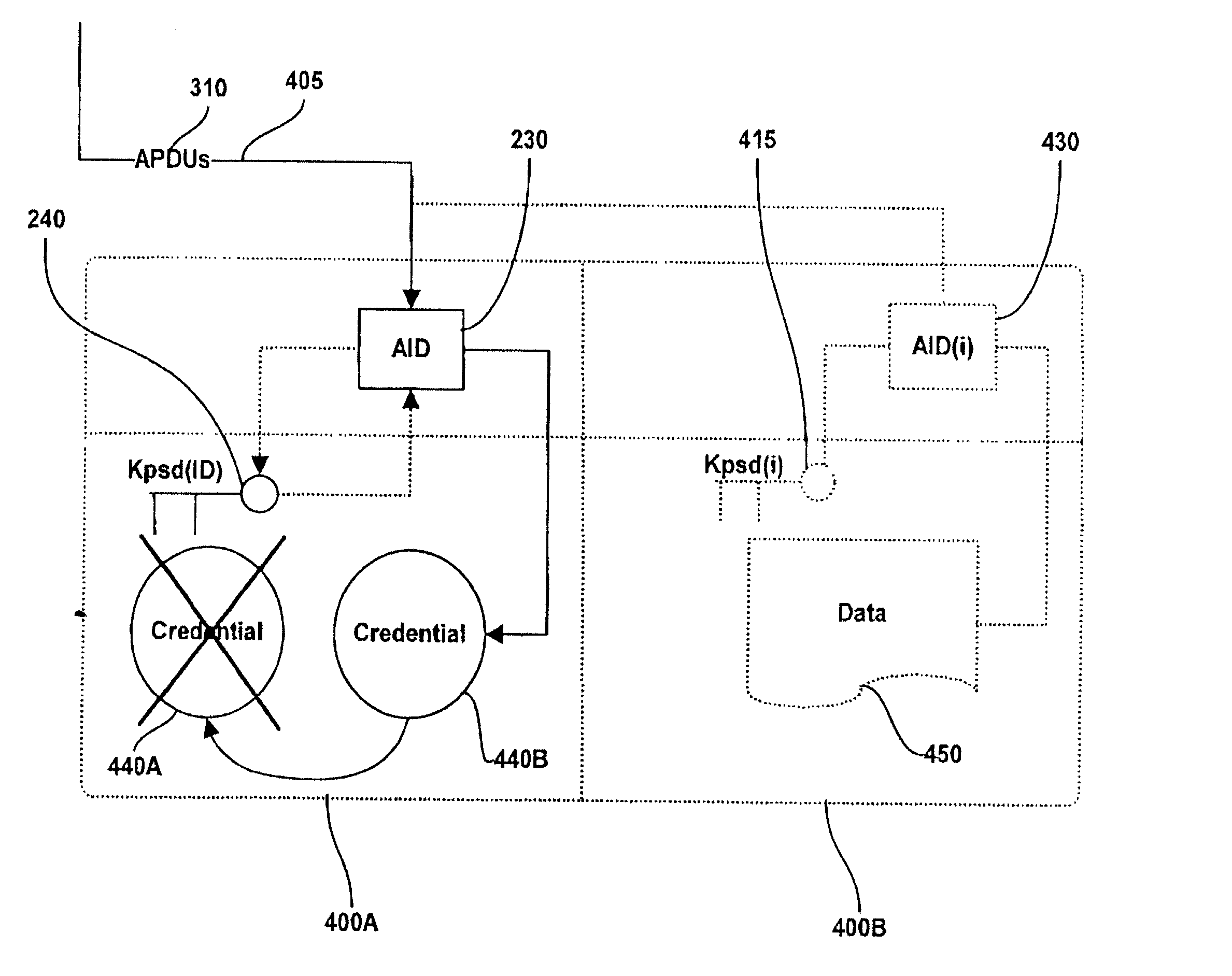
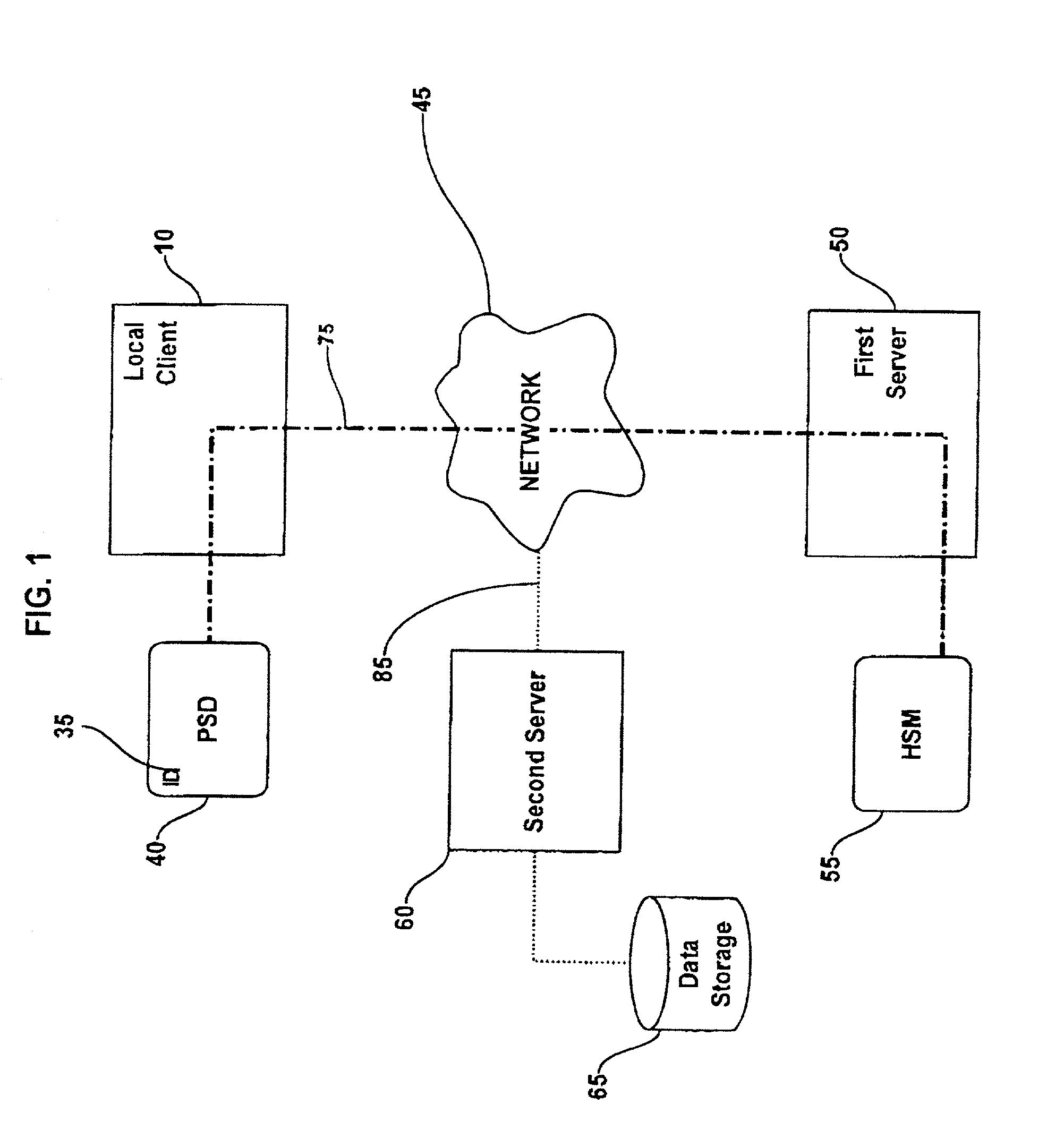
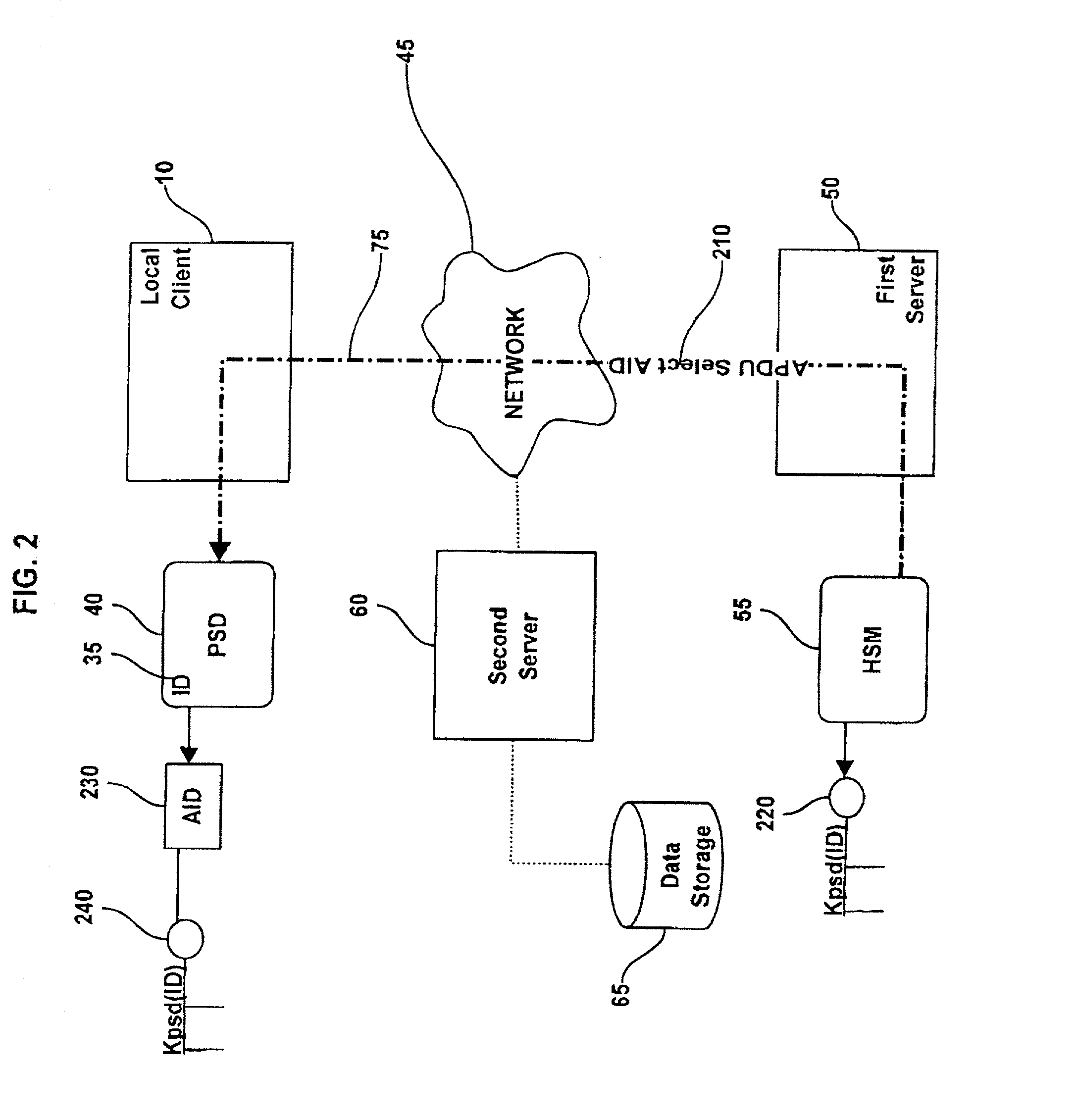
Method and system for performing post issuance configuration and data changes to a personal security device using a communications pipe
InactiveUS20030167399A1User identity/authority verificationUnauthorized memory use protectionHardware security moduleDigital credential
This invention provides a mechanism for performing secure configuration and data changes between a PSD and a hardware security module (HSM) using a communications pipe established between said PSD and said HSM. The data changes and configuration changes include but are not limited to installing, updating, replacing, deleting digital certificates, cryptographic keys, applets, other digital credentials, attributes of installed objects, or other stored proprietary information.
Owner:ACTIVCARD
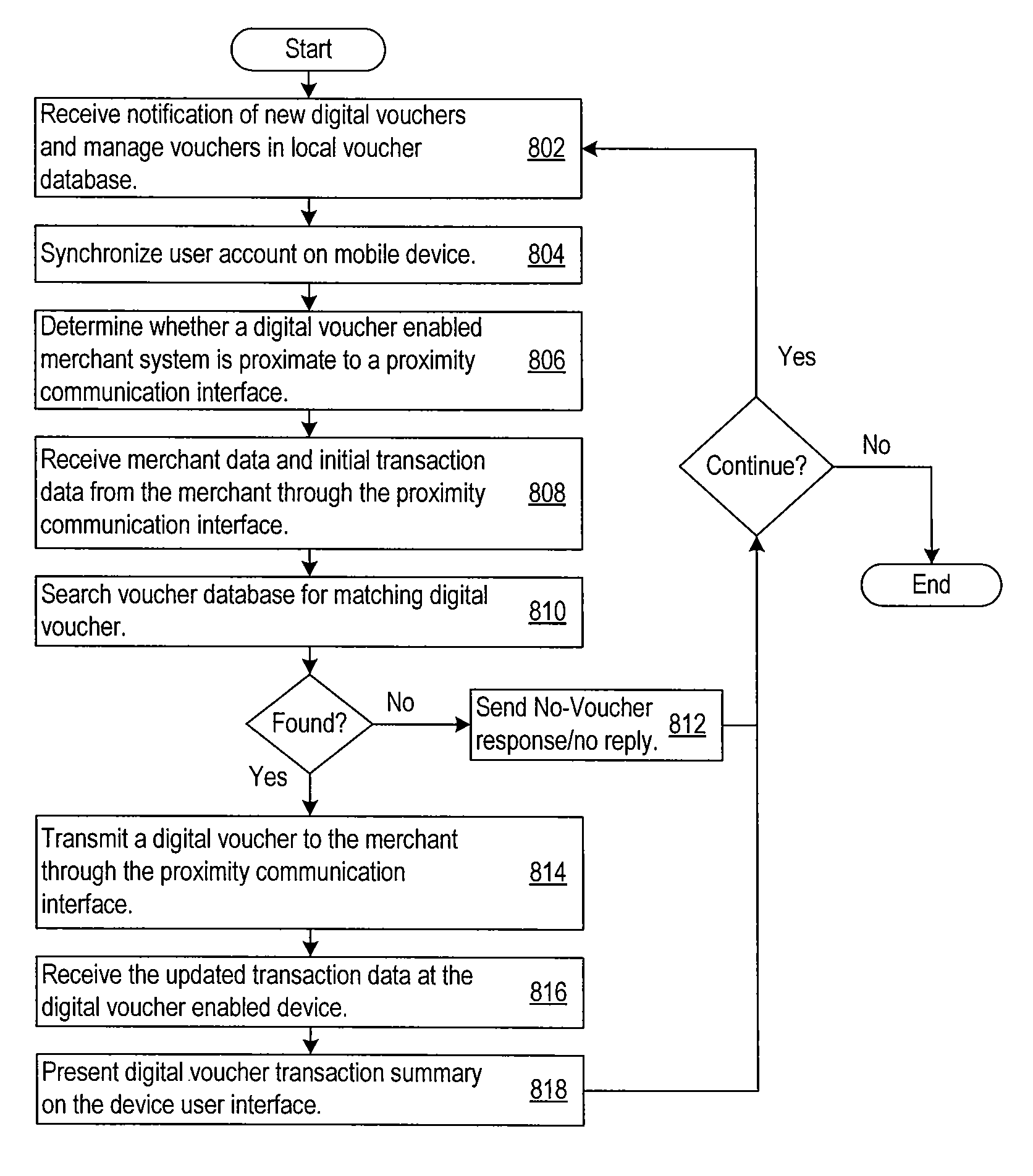
Digital voucher processing system
A digital voucher system facilitates the convenient application of vouchers against products and services purchased from a merchant by a consumer. A voucher enabled device carried by the consumer stores digital vouchers in memory. When the merchant detects a voucher enabled device nearby, the merchant queries and obtains applicable vouchers for the consumer from the voucher enabled device carried by the consumer, applies the vouchers to a transaction, and communicates the resulting transaction data back to the voucher enabled device.
Owner:ACCENTURE GLOBAL SERVICES LTD
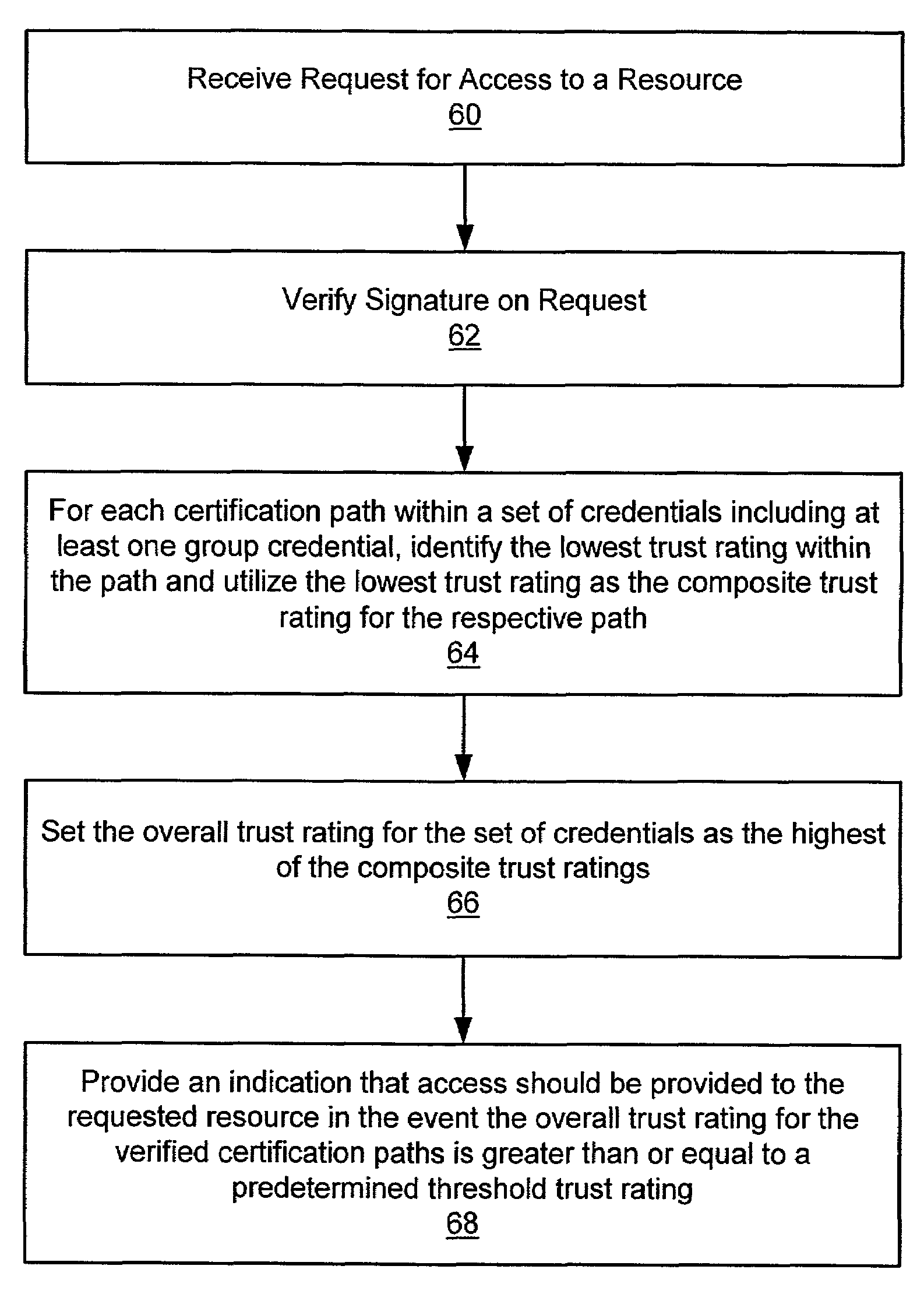
Trust ratings in group credentials
InactiveUS7085925B2Digital data processing detailsUser identity/authority verificationDigital credentialComputer science
A method and system for evaluating a set of credentials that includes at least one group credential and that may include one or more additional credentials. A trust rating is provided in association with the at least one group credential within the set of credentials and trust ratings may also be provided in other credentials within the set of credentials. Each trust rating provides an indication of the level of confidence in the information being certified in the respective credential. In response to a request for access to a resource or service, an evaluation of the group credentials is performed by an access control program to determine whether access to the requested resource or service should be provided. In one embodiment, within any given certification path a composite trust rating for the respective path is determined. An overall trust rating for the set of credentials is determined based upon the composite trust ratings. Upon a determination that a user requesting access to a resource has an acceptable set of credentials and a satisfactory trust rating, access to the requested resource or service is granted to the user.
Owner:ORACLE INT CORP
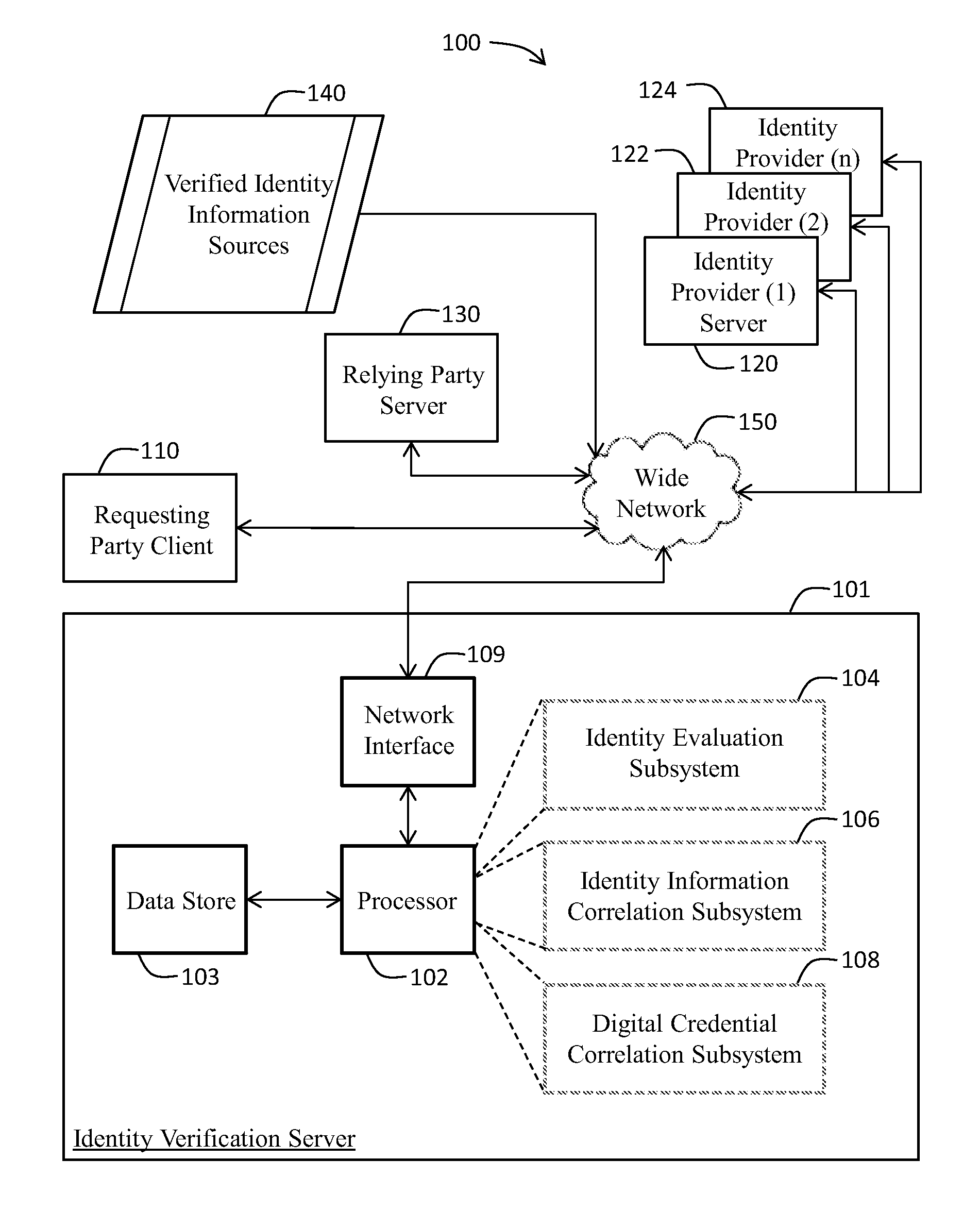
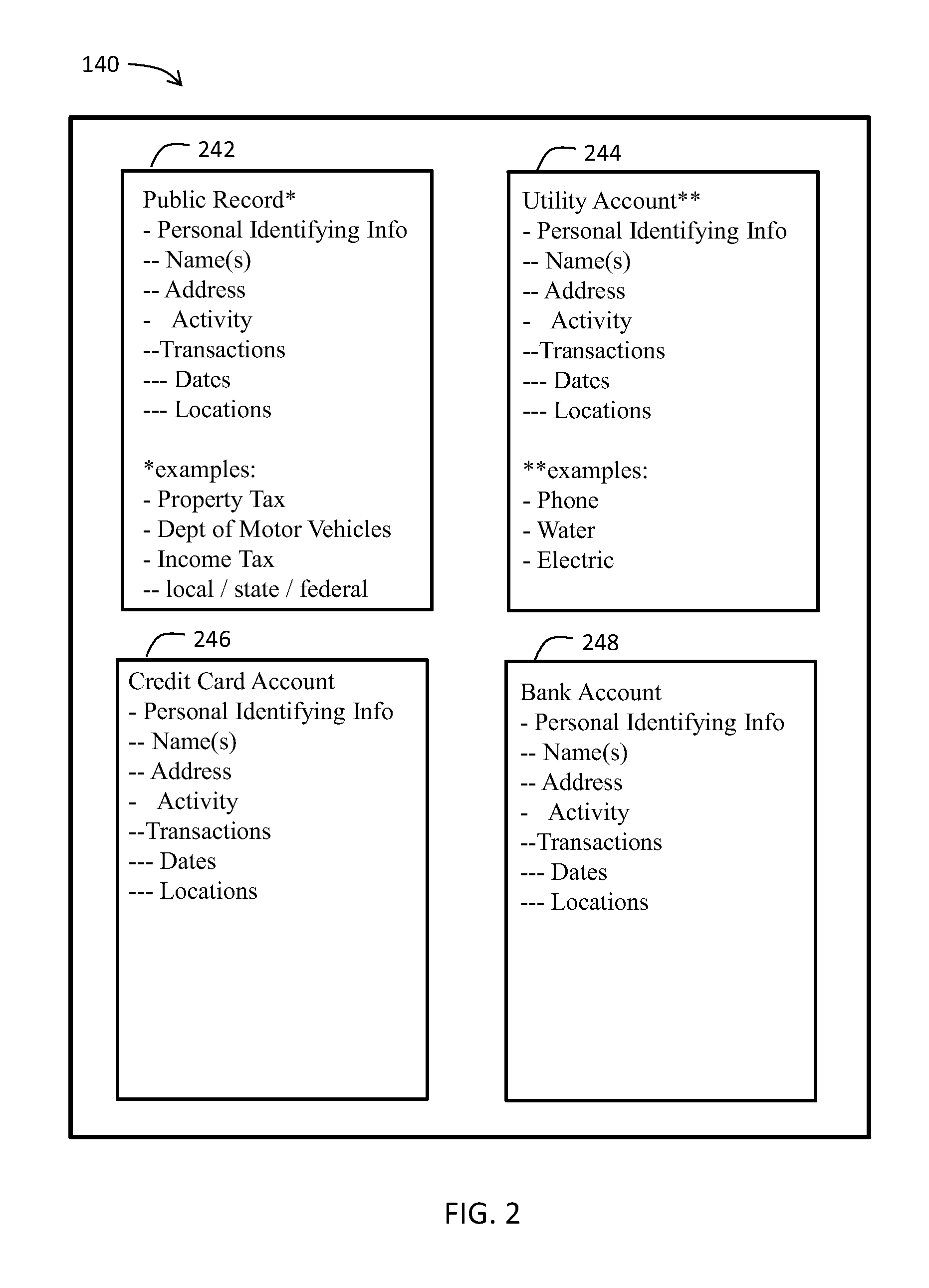
Identity validation system and associated methods
ActiveUS20150295906A1Better exploitedDigital data processing detailsUser identity/authority verificationThird partyInternet privacy
A computer system and associated methods for verifying user identities online. Identity claims made by a requestor of an online access and / or a trusted transaction may be verified by associating digital credentials to verified personal identification information (PII) retrieved from real world events. PII item(s) may be retrieved from third-party verified identity information sources. Verified personal attributes related to PII items may be identified and correlated with the requestor's digital credentials, and stored to a verified identity record. Additional digital credentials for the same requestor may be similarly identified, correlated, and stored to the verified identity record. A subsequent transaction request by a person claiming the requestor's identity may be compared with the verified identity record. An identity match indicator and / or a match confidence score may be created and used to determine the risk that the identity claim by the person requesting the transaction is false.
Owner:TRULIOO INFORMATION SERVICES
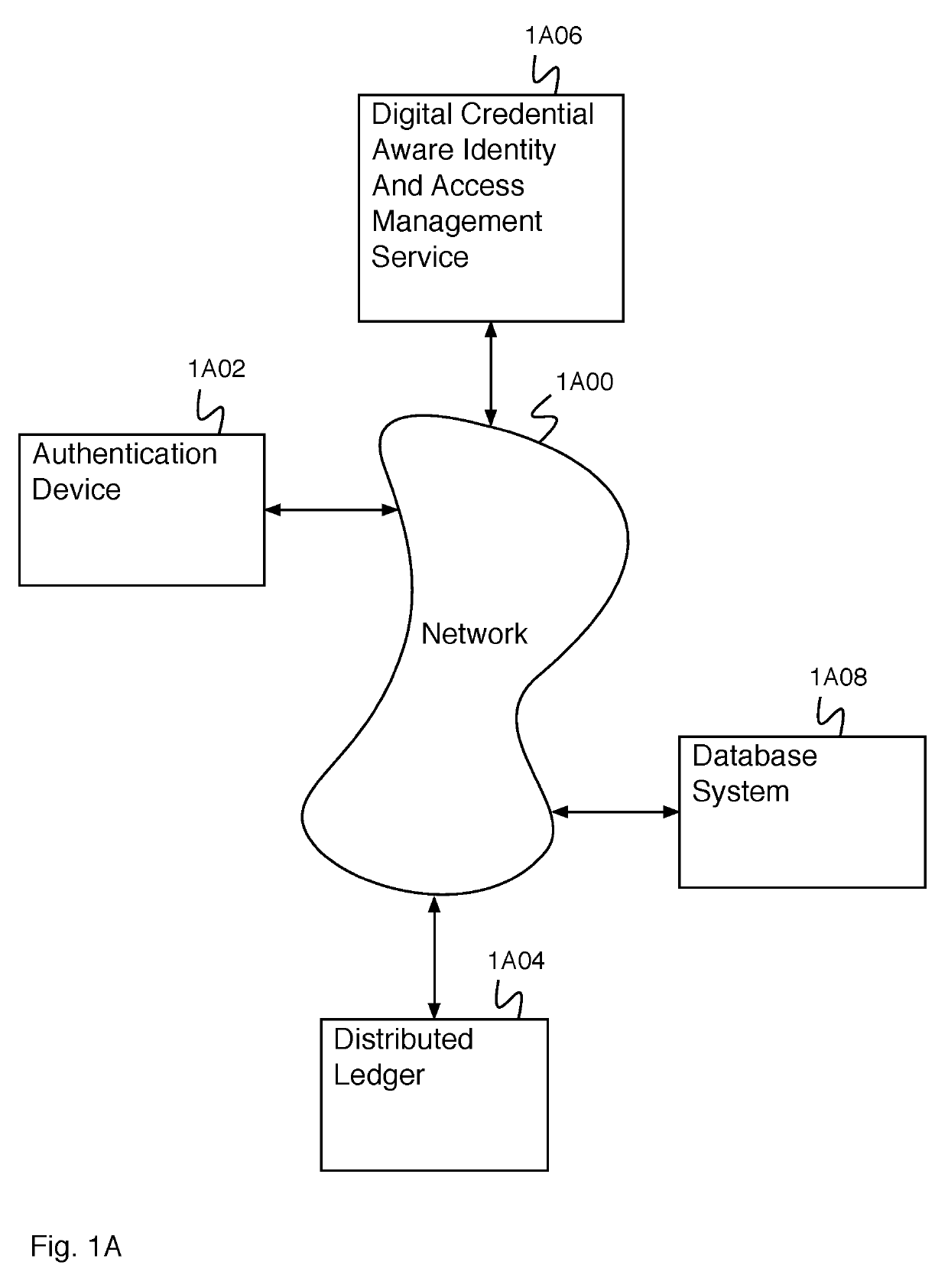
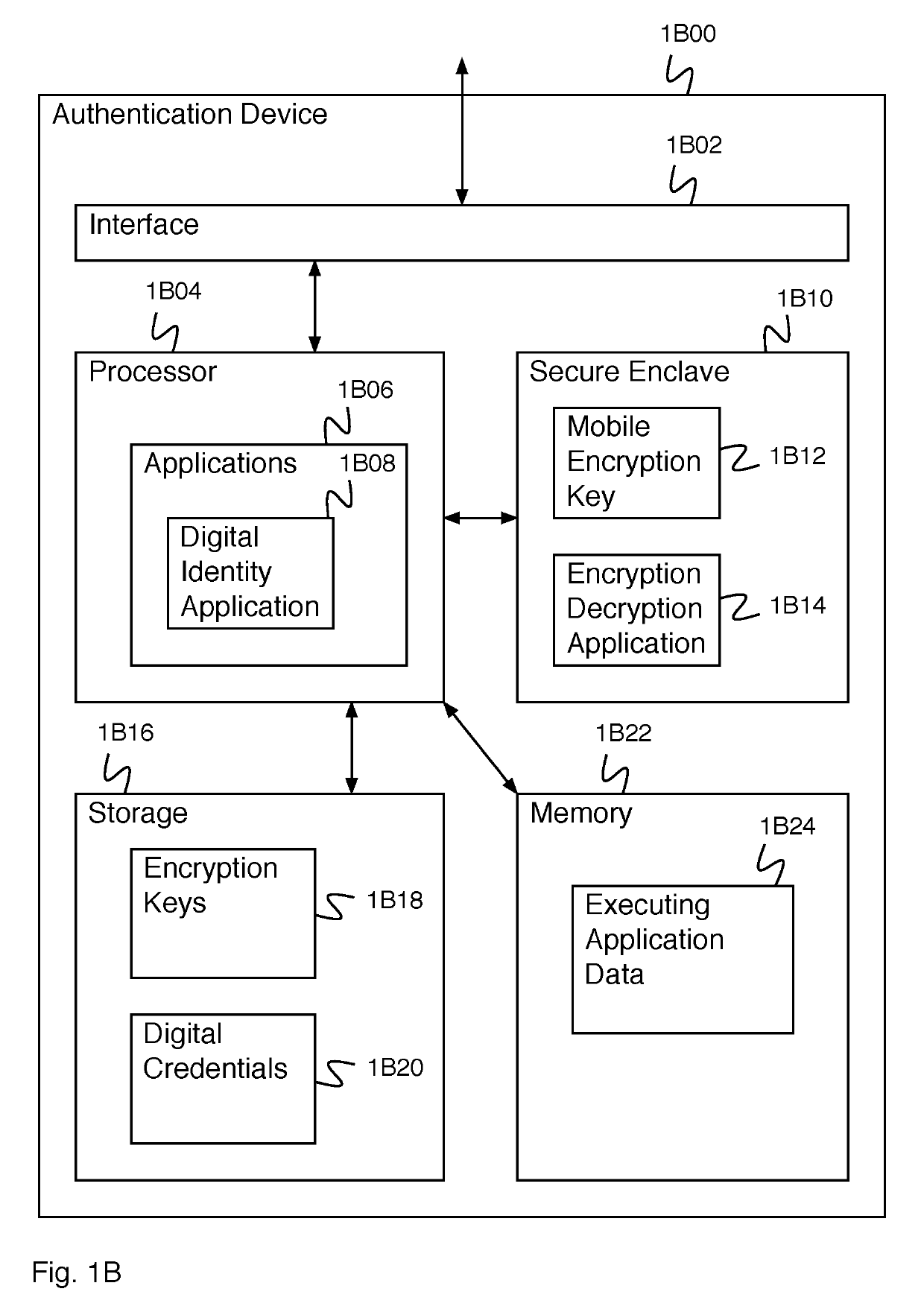
Digital credential authentication
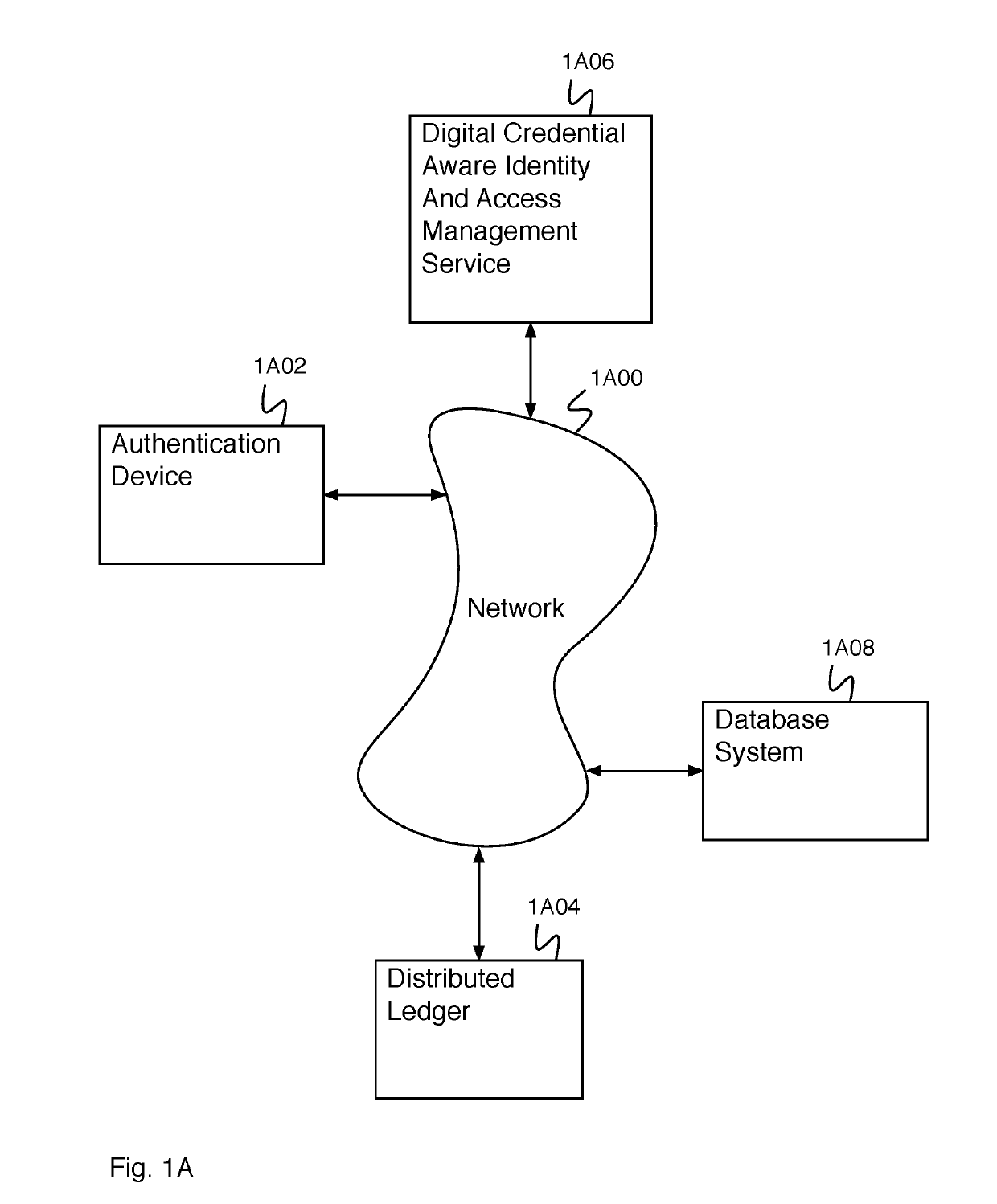
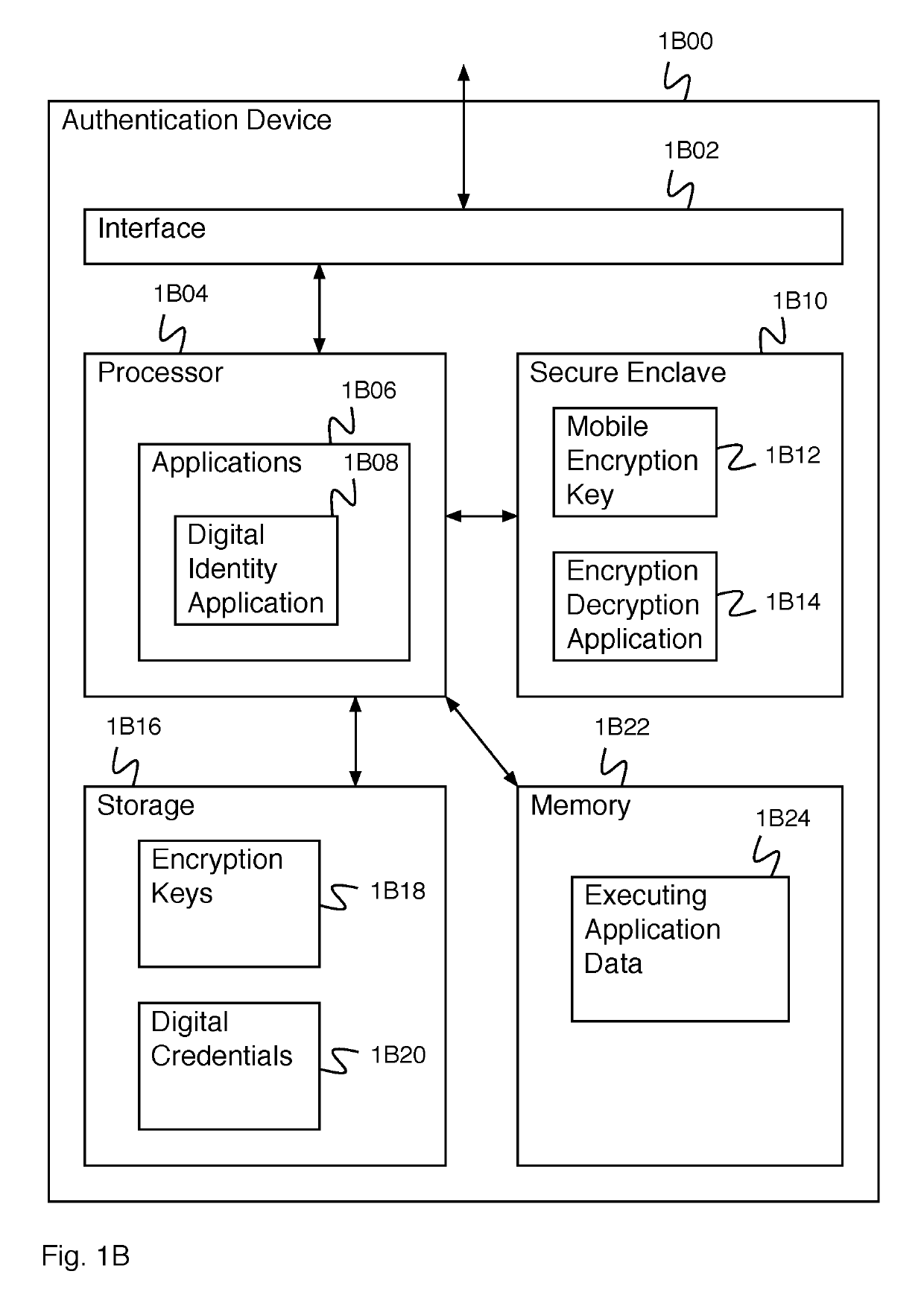
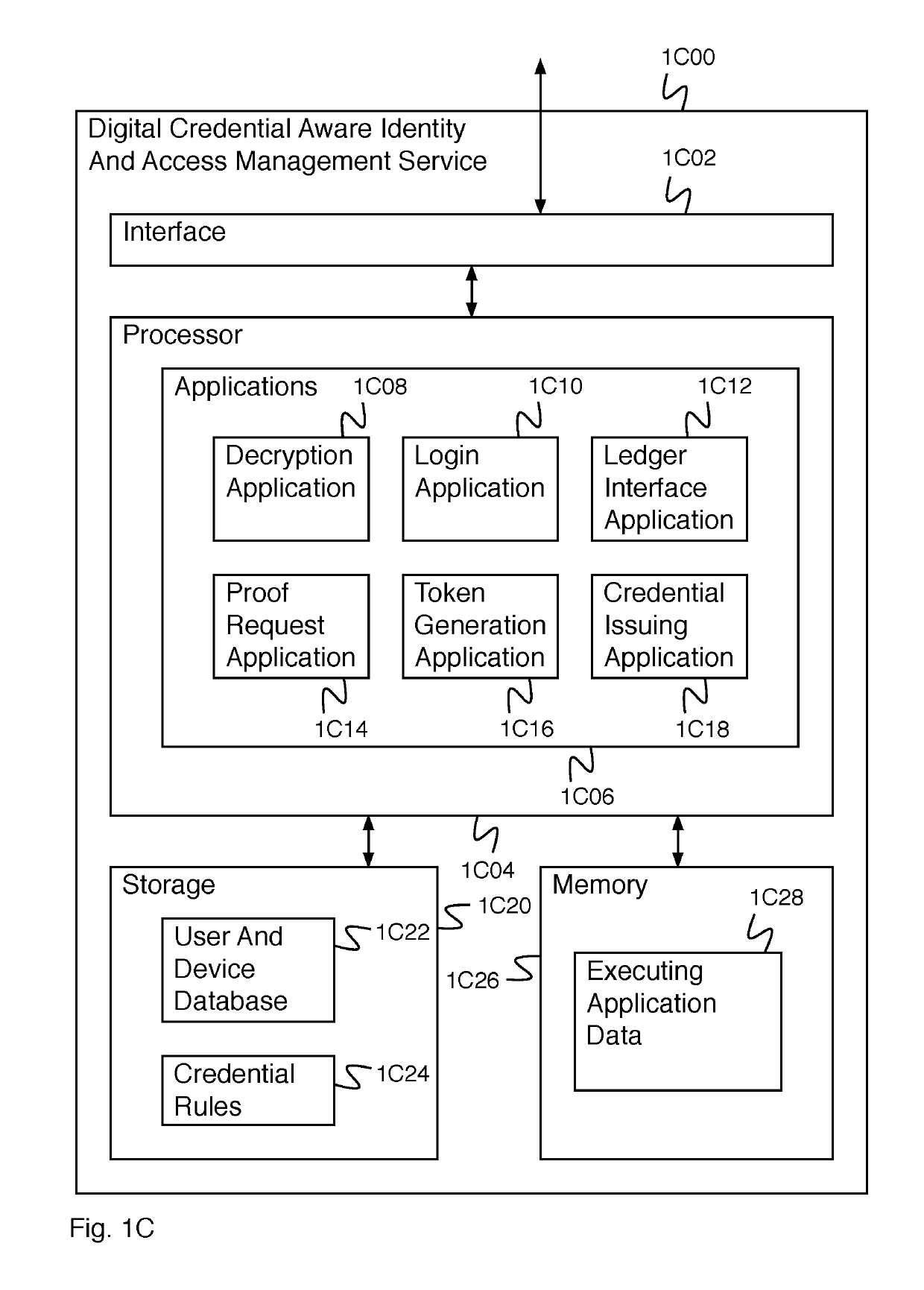
ActiveUS20190305952A1Key distribution for secure communicationMultiple keys/algorithms usageDocumentationDigital credential
A system for creating an identity mapping on a distributed ledger includes an interface and a processor. The interface is configured to receive a request to create an identity mapping on a distributed ledger. The processor is configured to generate an identity key pair; generate a mobile encryption key; encrypt a private identity key of the identity key pair using the mobile encryption key to create an encrypted private key; store the encrypted private key; create a mapping document; sign the mapping document with the private identity key of the identity key pair; and provide the signed mapping document to be stored in a distributed ledger.
Owner:WORKDAY INC
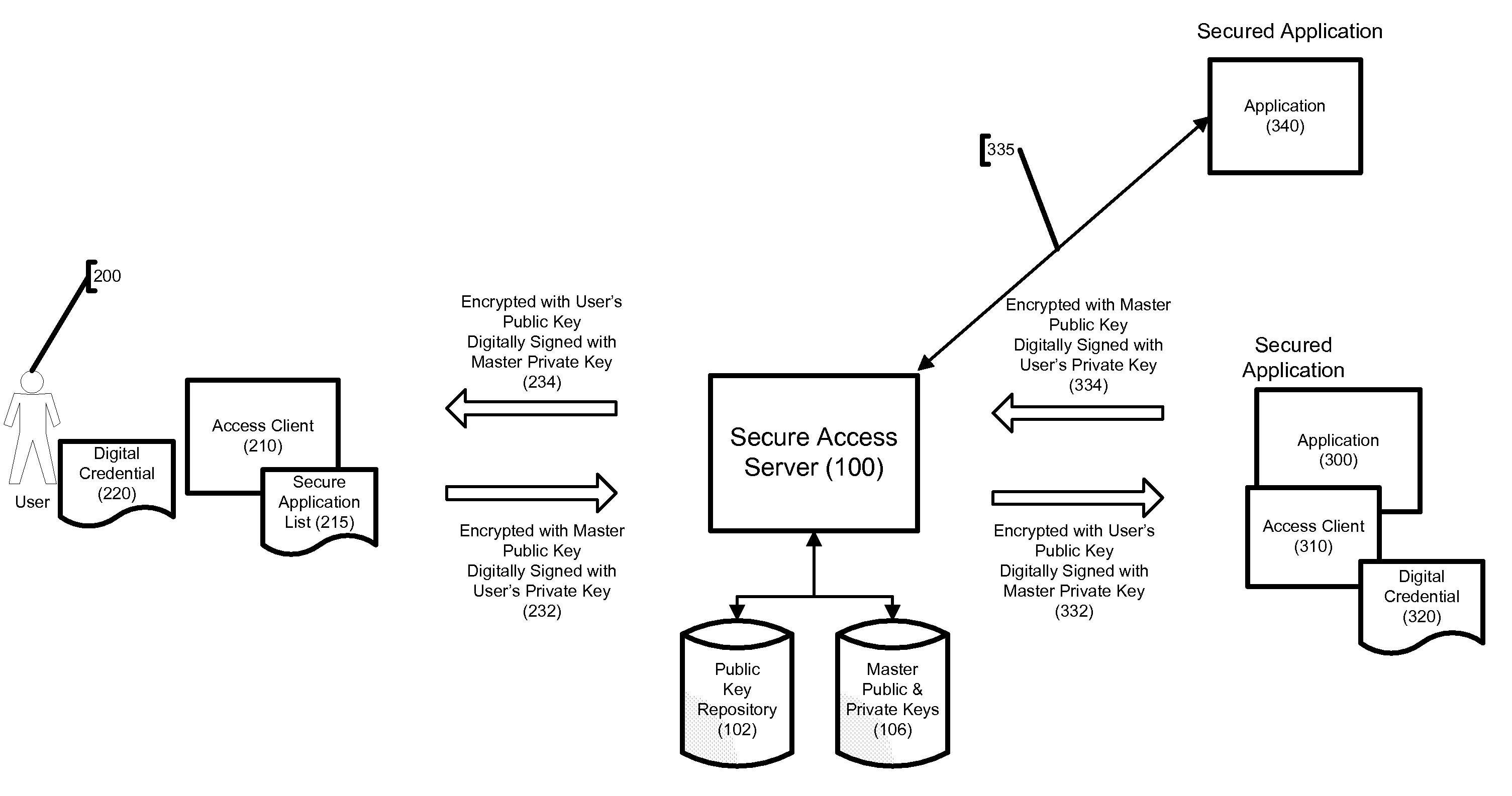
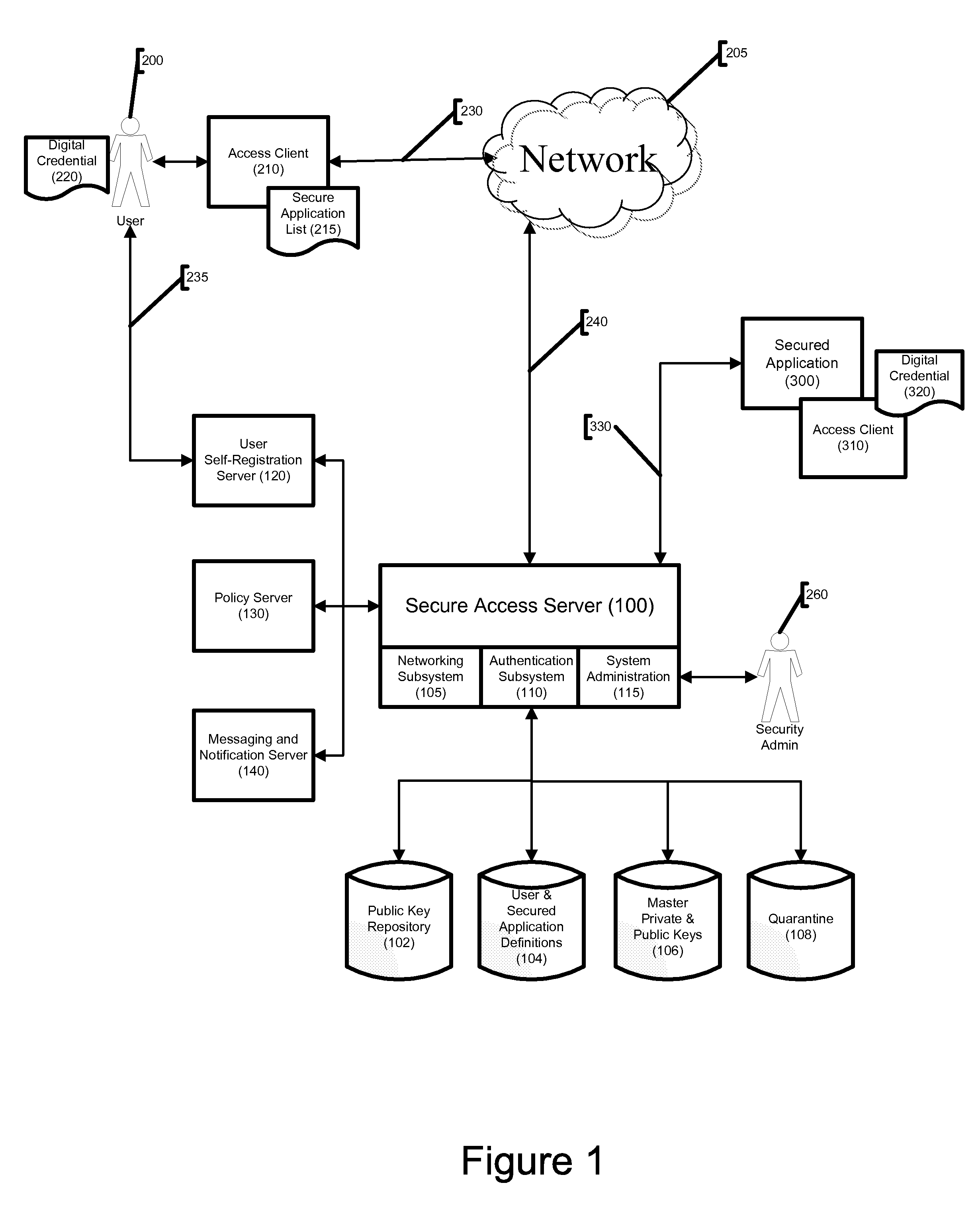
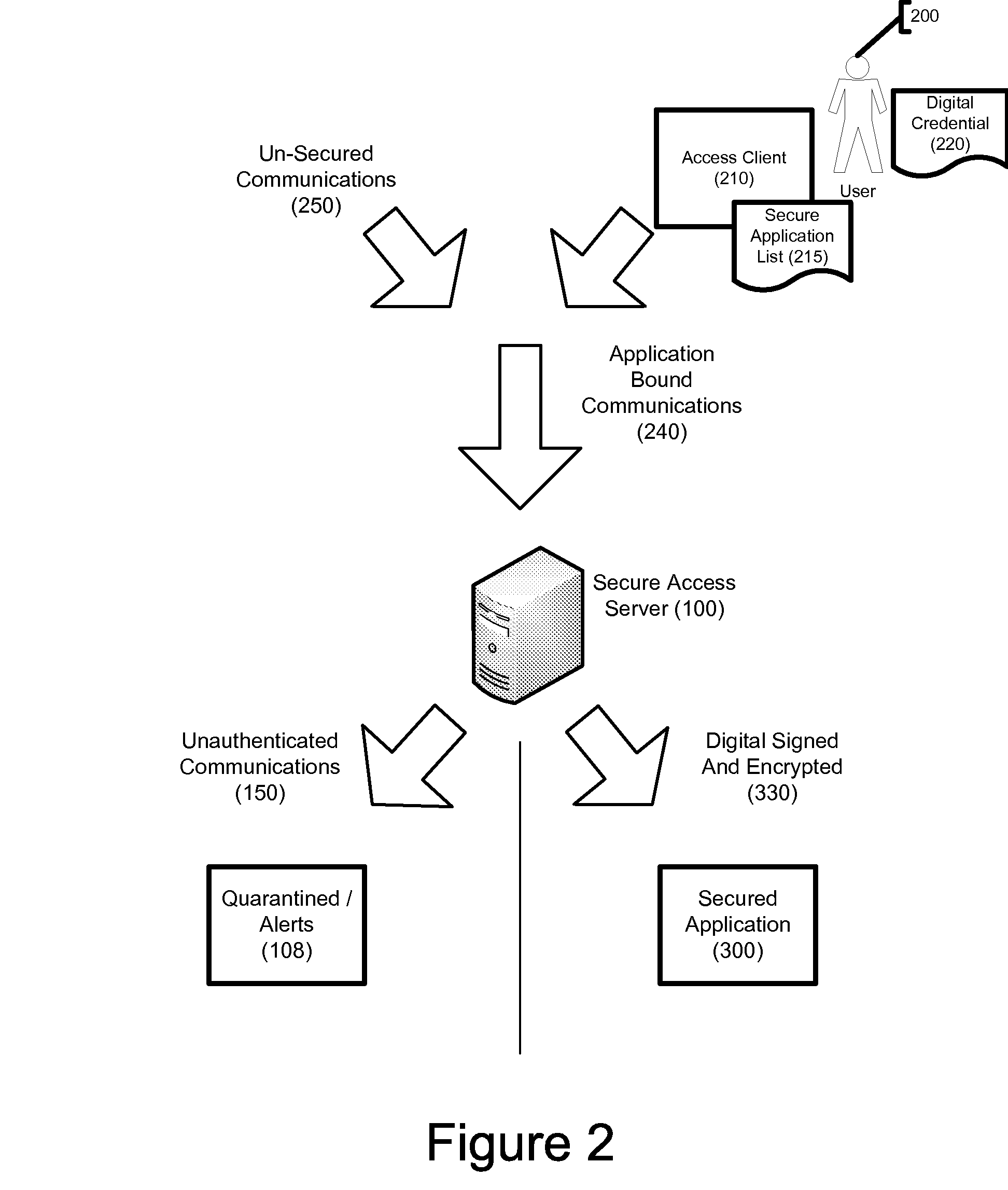
System and Method for Securing Software Applications
InactiveUS20080276309A1Public key for secure communicationDigital data processing detailsApplication serverDigital signature
A system and method for securing software applications installed on a computer network is disclosed. An authorized user is provided a digital credential and loads a secure access client onto a computerized device that can be connected to the network. The secure access client communicates with a secure access server within the network to authenticate the user and determine which applications the user is allowed to access. When the user sends a communication intended for a secured application, the secure access client intercepts the communication and uses cryptographic keys from the digital credential to encrypt and digitally sign the communication. The secure access server has access to cryptographic keys corresponding to those on the digital credential and is able to decrypt the communication and verify the digital credential. The decrypted message is then sent to an application server hosting the secured application.
Owner:IDENTITY VERIFICATION SYST
Decentralized Customer-Controlled Credit Verification
Systems and methods for decentralized distribution of verifiable information, such as financial information, without requiring resort to centralized information system at the time of a query or other request for information. A decentralized method includes the steps of creating a digital wallet, issuing / receiving an issued verifiable digital credential signed by a credential issuer acting as a trust anchor for a claim contained in the verifiable digital credential, storing the verifiable digital credential within the digital wallet, receiving a request for verified information, and providing the verifiable digital credential, including the claim, from the digital wallet. The verification of information may occur as a zero-knowledge proof such that a required standard is verified as satisfied without disclosing more information about a consumer or other user than is absolutely necessary.
Owner:FINICITY CORP
Virtual credentials and licenses
ActiveUS20160380774A1Prevent replay attacksData processing applicationsMultiple keys/algorithms usageGeographic siteVirtualization
Providing virtualized credentials of a holder includes authorizing a subset of credential data to be sent to a device of a relying party that is different from the holder, where the subset of credential data depends on a role of the relying party, selection by the holder, and / or contextual data of the relying party and includes displaying the subset of credential data on a screen of the device of the relying party. The contextual data may be a privacy level setting, distance between the relying party and the holder, and / or geolocation of the relying party. The role of the relying party may be provided by the relying party. Role information provided by the relying party may be provided in a verifiable format. The role information may be digitally signed or securely derived and determined by a mutual authentication algorithm between the relying party and the holder.
Owner:ASSA ABLOY AB
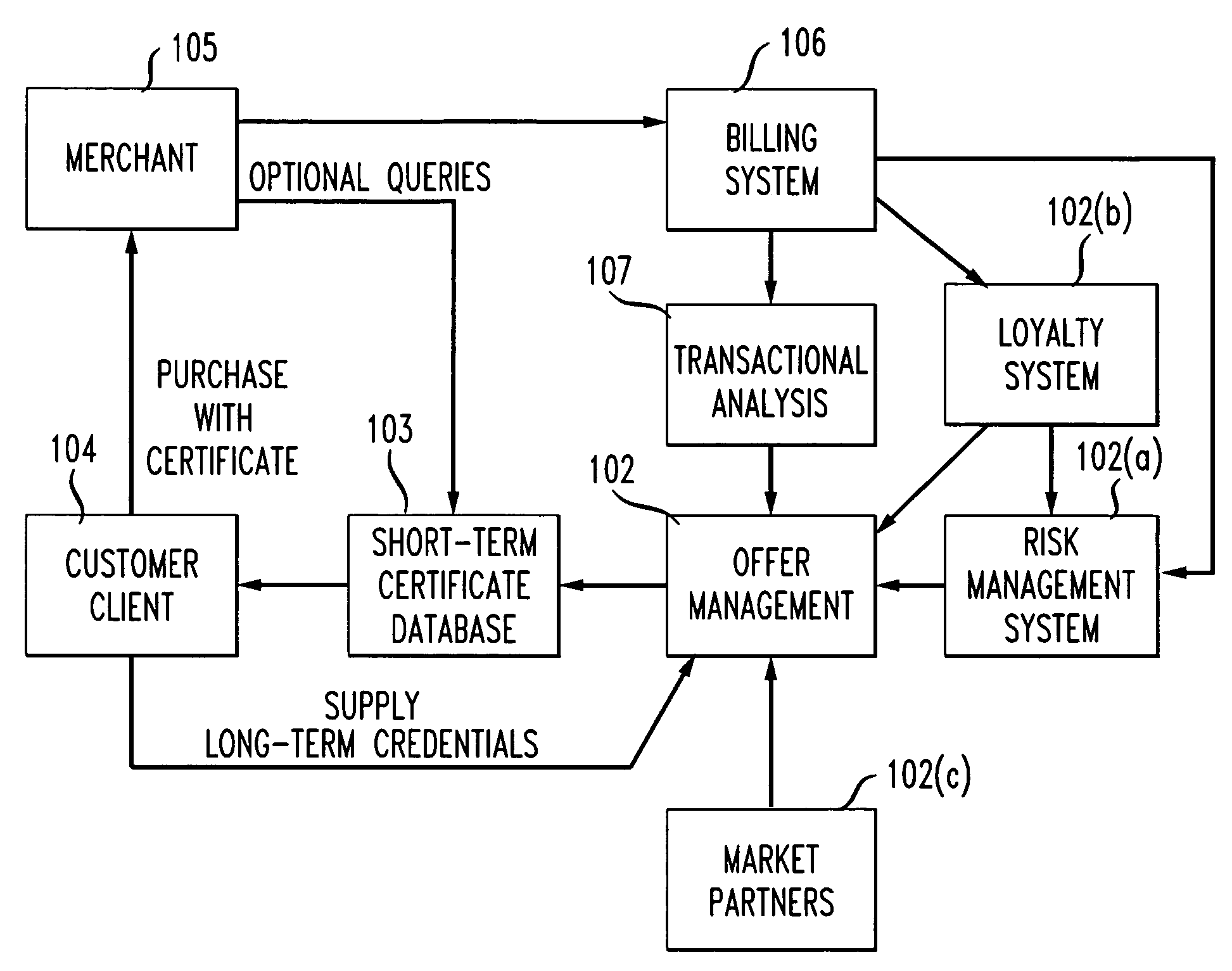
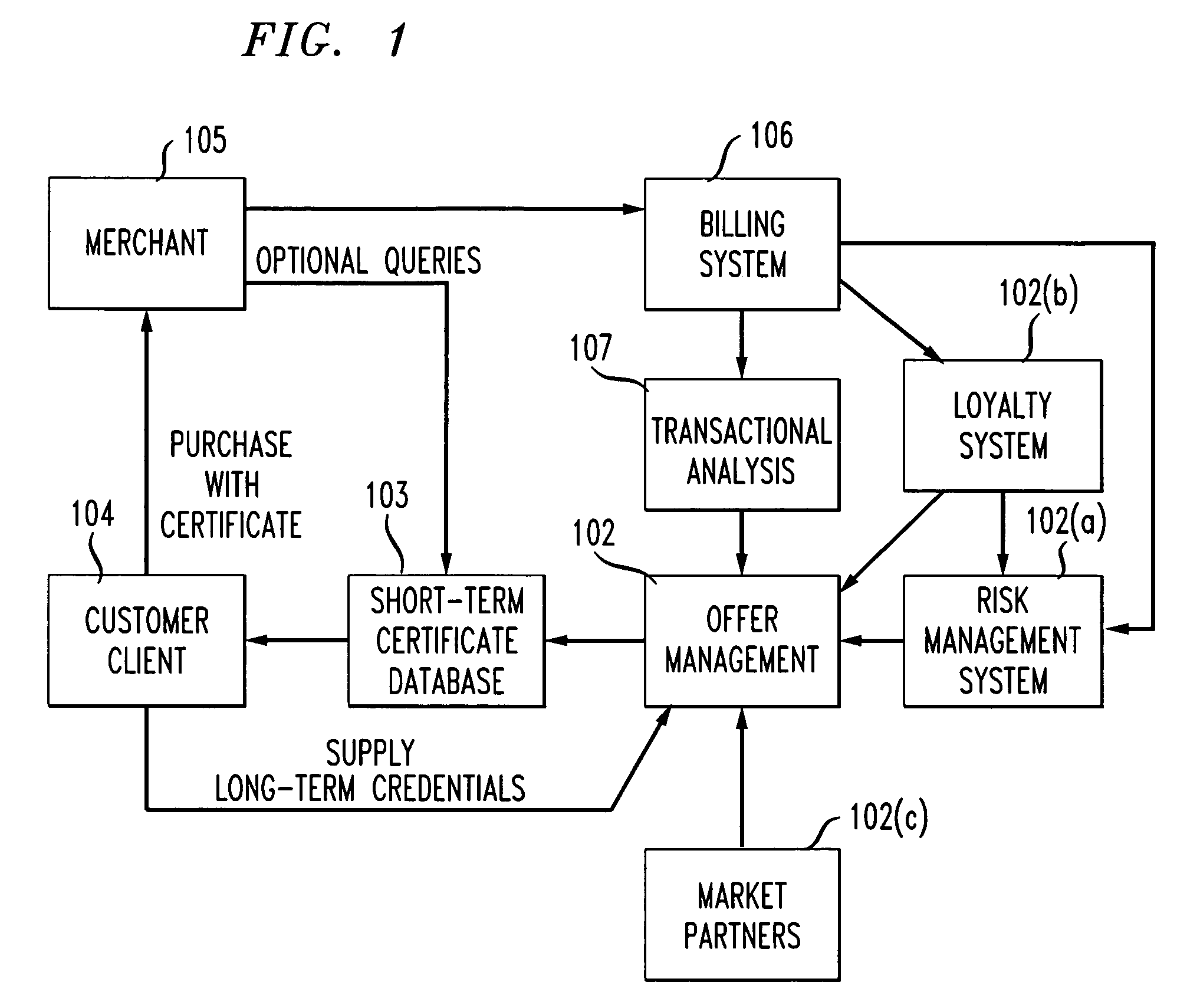
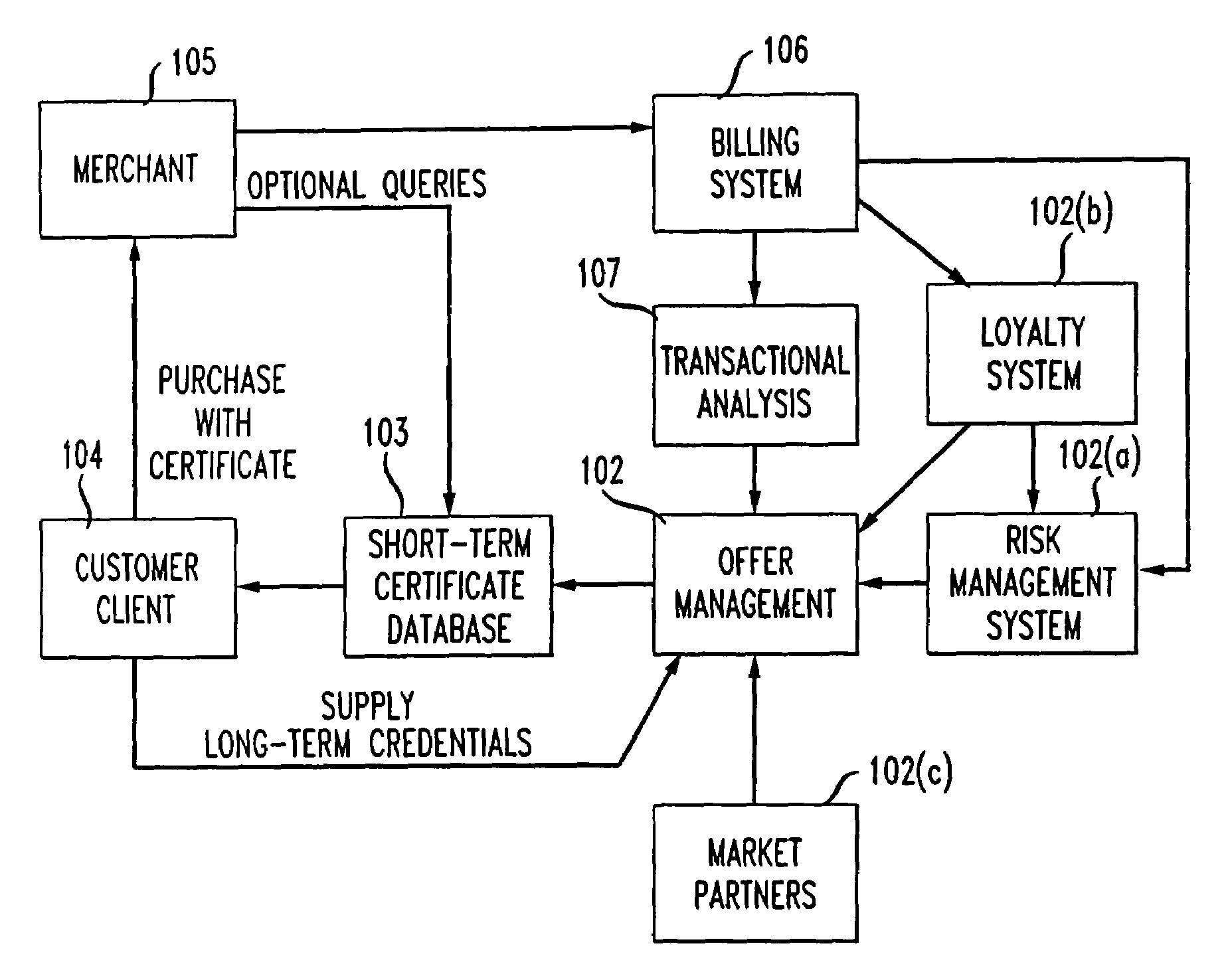
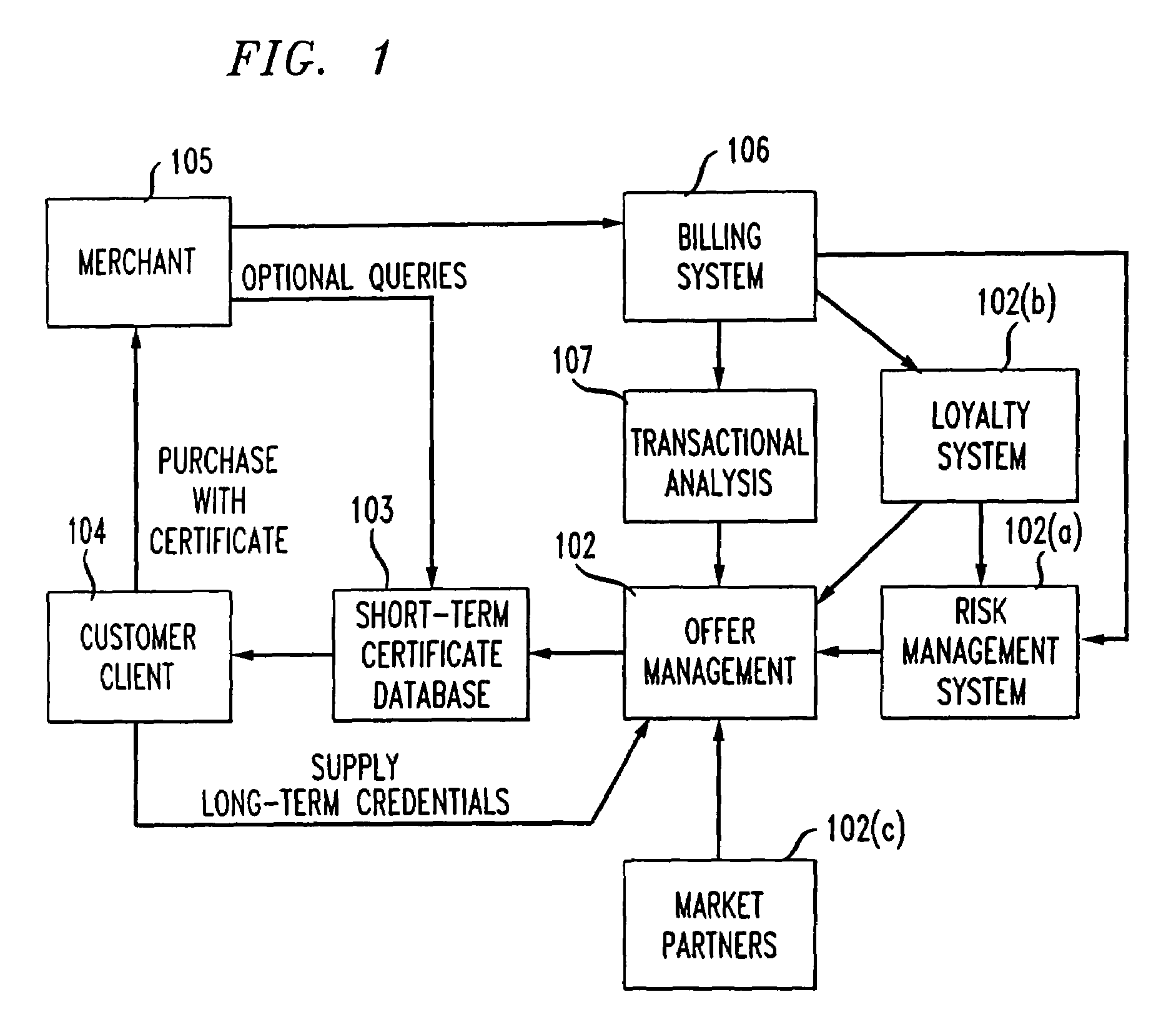
Method and apparatus using digital credentials and other electronic certificates for electronic transactions
InactiveUS7043441B1Facilitating commerceInformation can be presentedComplete banking machinesFinanceShort termsDigital credential
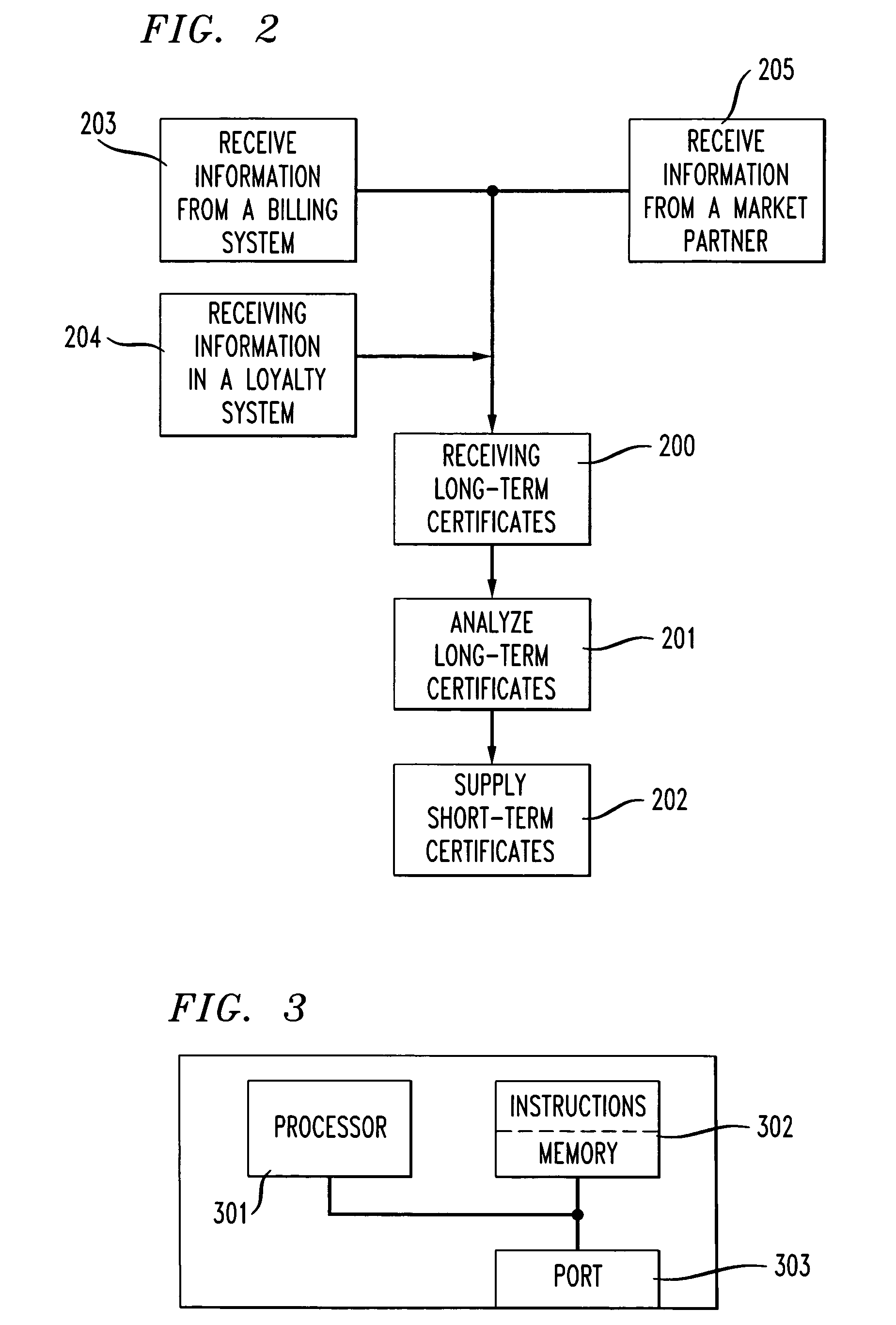
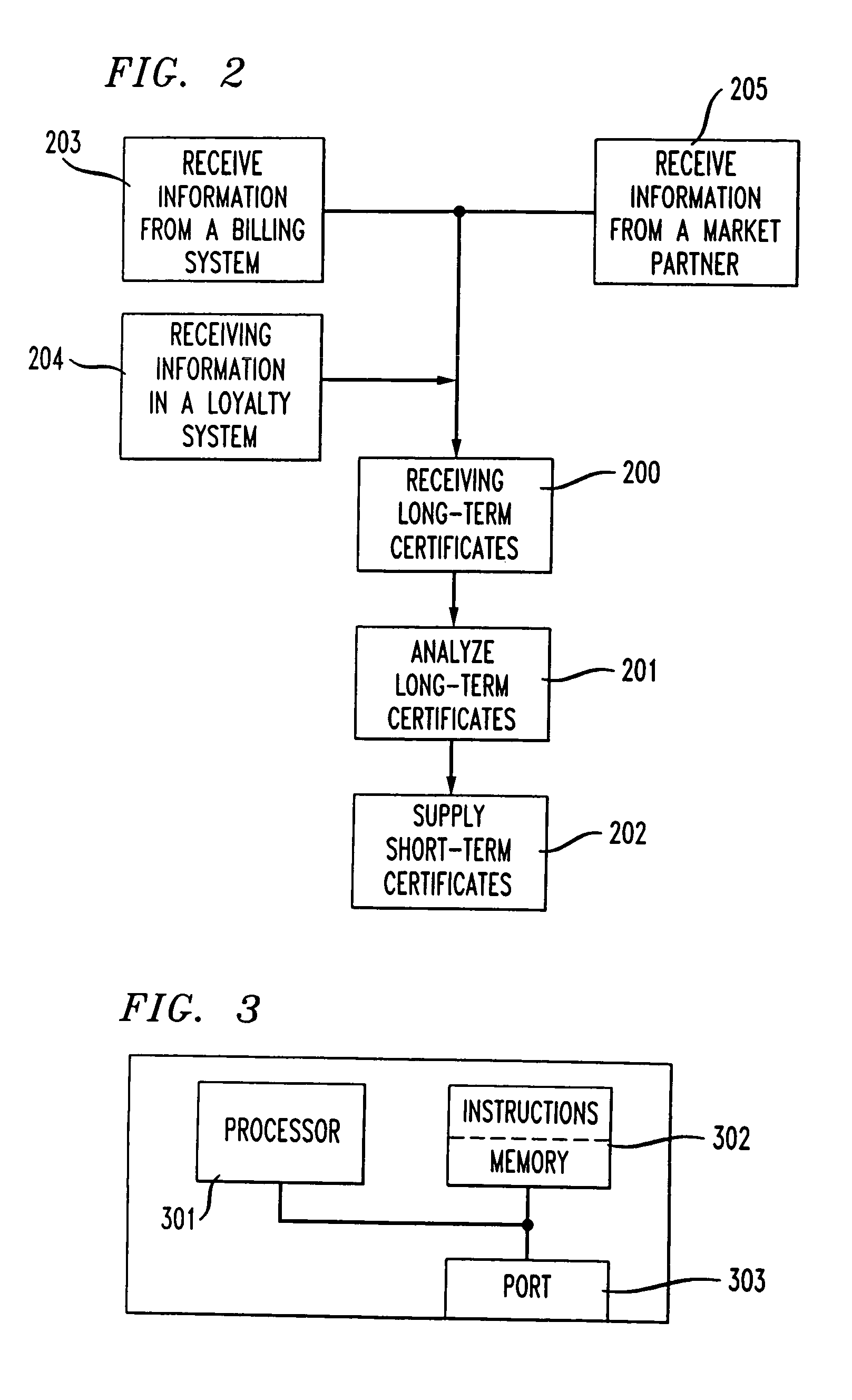
A method for performing electronic transactions, comprising receiving a long-term certificate, authenticating a user associated with the long-term certificate, and then sending a short-term certificate to the authenticated user. In addition, risk associated with the user can be evaluated, and this risk information, as well as other information, can be included in the short-term certificate.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
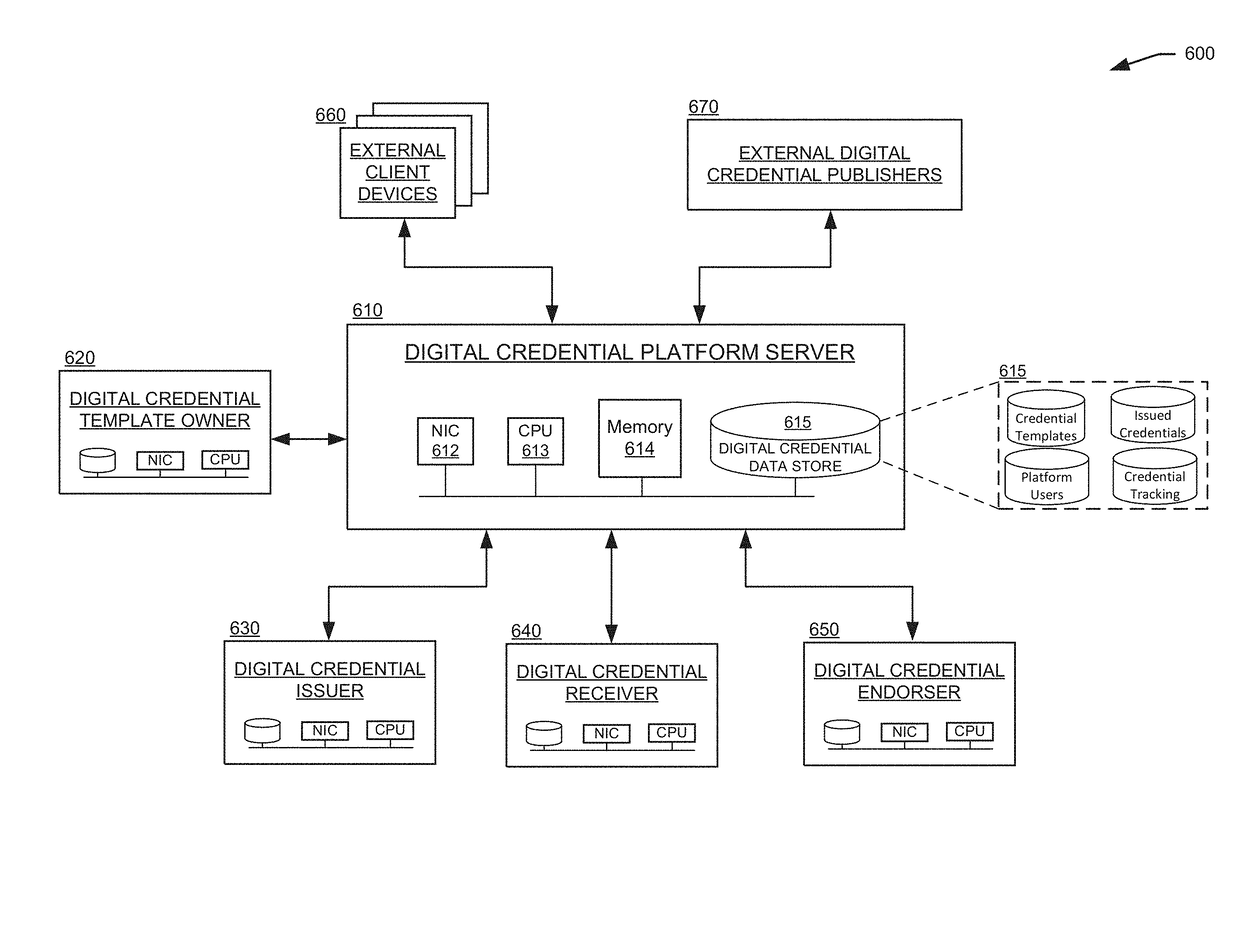
Generation, management, and tracking of digital credentials
ActiveUS20170279614A1User identity/authority verificationSecurity arrangementDigital credentialComputer security
Techniques described herein relate to generating and managing digital credentials using a digital credential platform in communication with various digital credential template owners and digital credential issuers. In some embodiments, a digital credential platform server may receive and coordinate requets and responses between the digital credential template owners and a set of digital credential issuers, to determine which digital credential issuers are authorized to issue digital credential based on which digital credential templates. The digital credential platform server may provide the authorized issuers with access to particular digital credential templates and the functionality to issue digital credentials to users based on any of the particular digital credential templates. Additional techniques described herein relate to tracking, analyzing, and reporting data metrics for issued digital credentials.
Owner:CREDLY INC
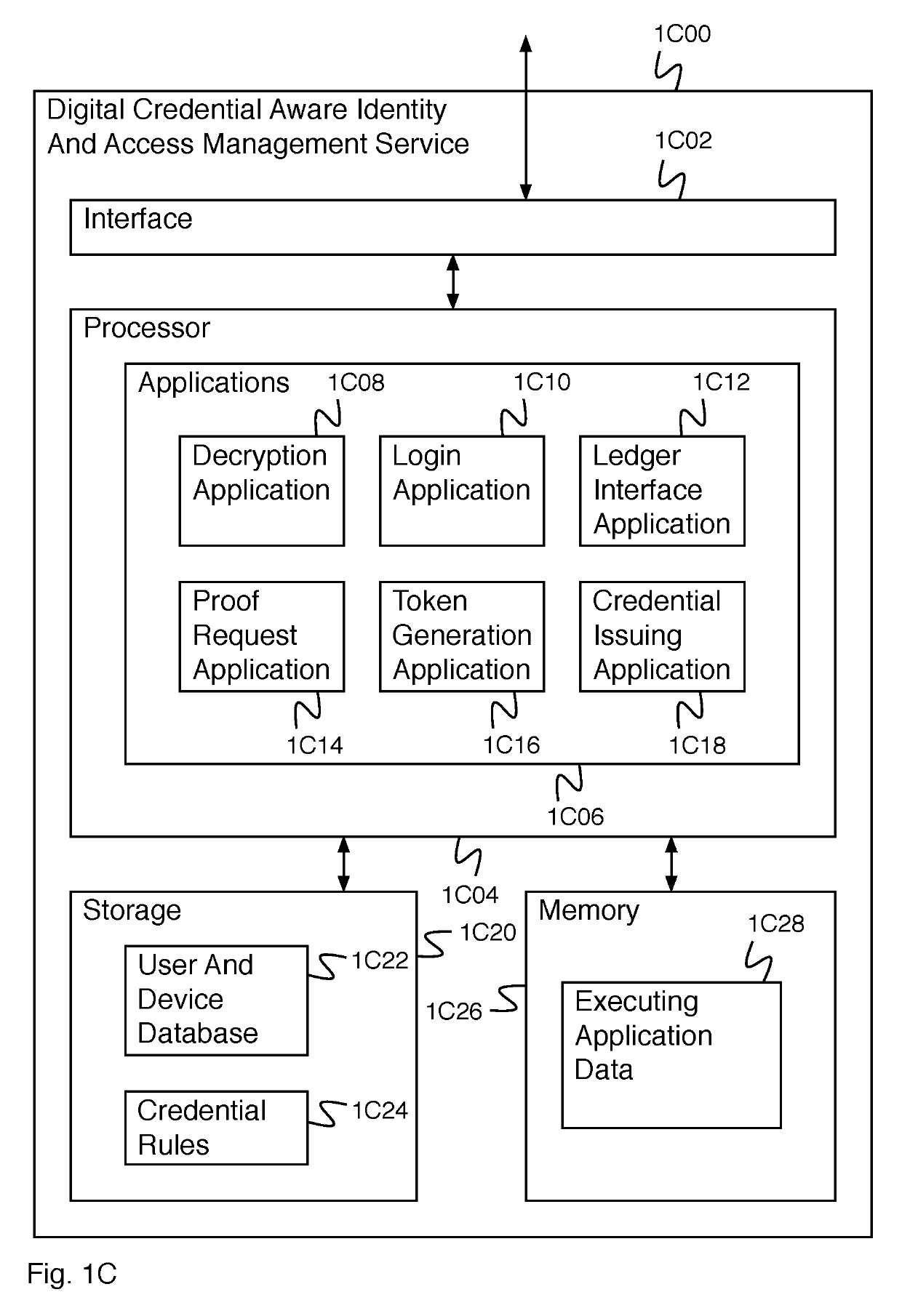
Digital credentials for user device authentication
PendingUS20190305964A1Key distribution for secure communicationPublic key for secure communicationUser deviceUser identifier
A system for credential authentication includes an interface and a processor. The interface is configured to receive a request from an application for authorization to access. Access to the application is requested by a user using a user device. The processor is configured to provide an authentication request to the user device, receive a device credential, wherein the device credential is backed by data stored in a distributed ledger, determine a user identifier and an authentication device associated with the user based at least in part on the device credential, provide a proof request to the authentication device, receive a proof response, determine that the proof response is valid, generate a token, and provide the token to the application authorizing access for the user.
Owner:WORKDAY INC
Secure device connection and operation
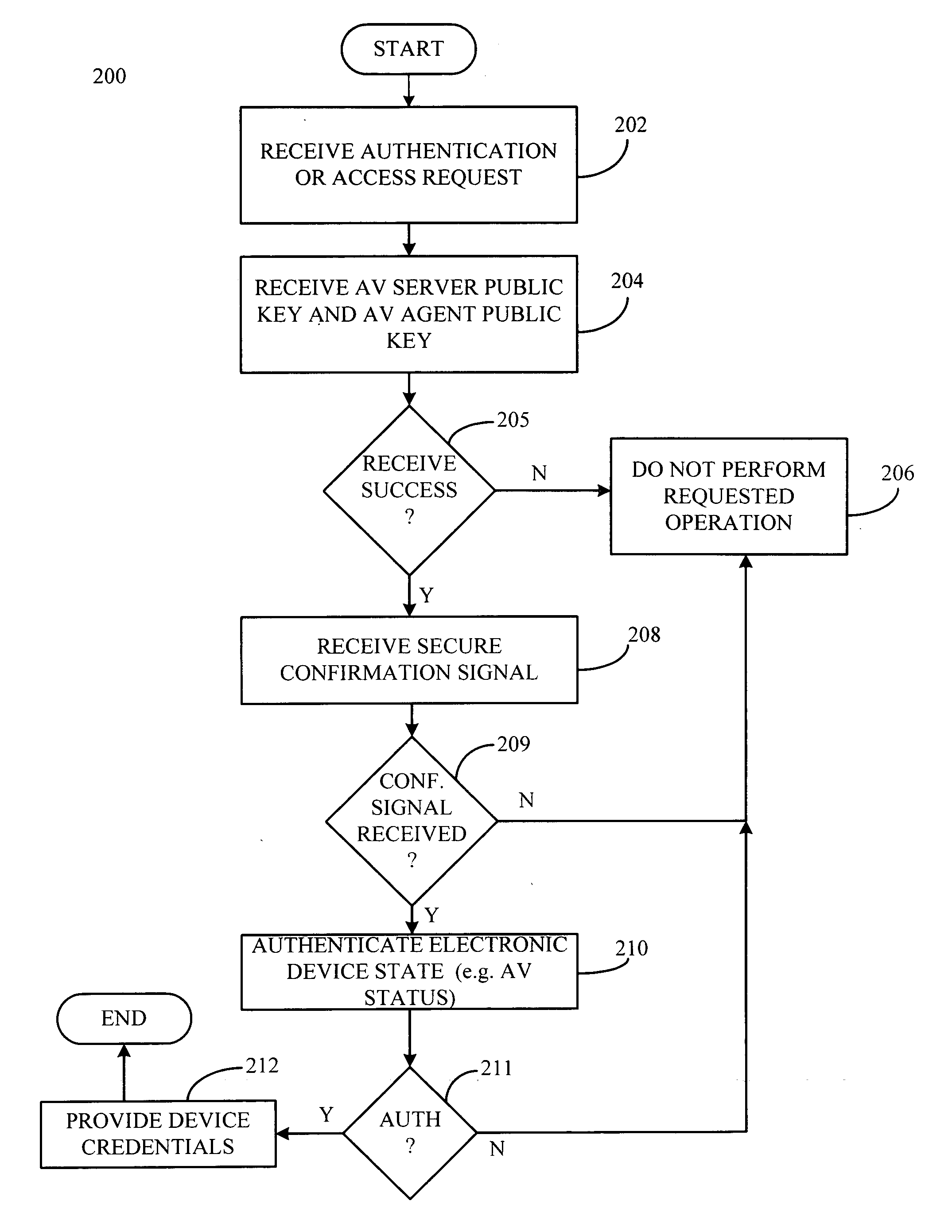
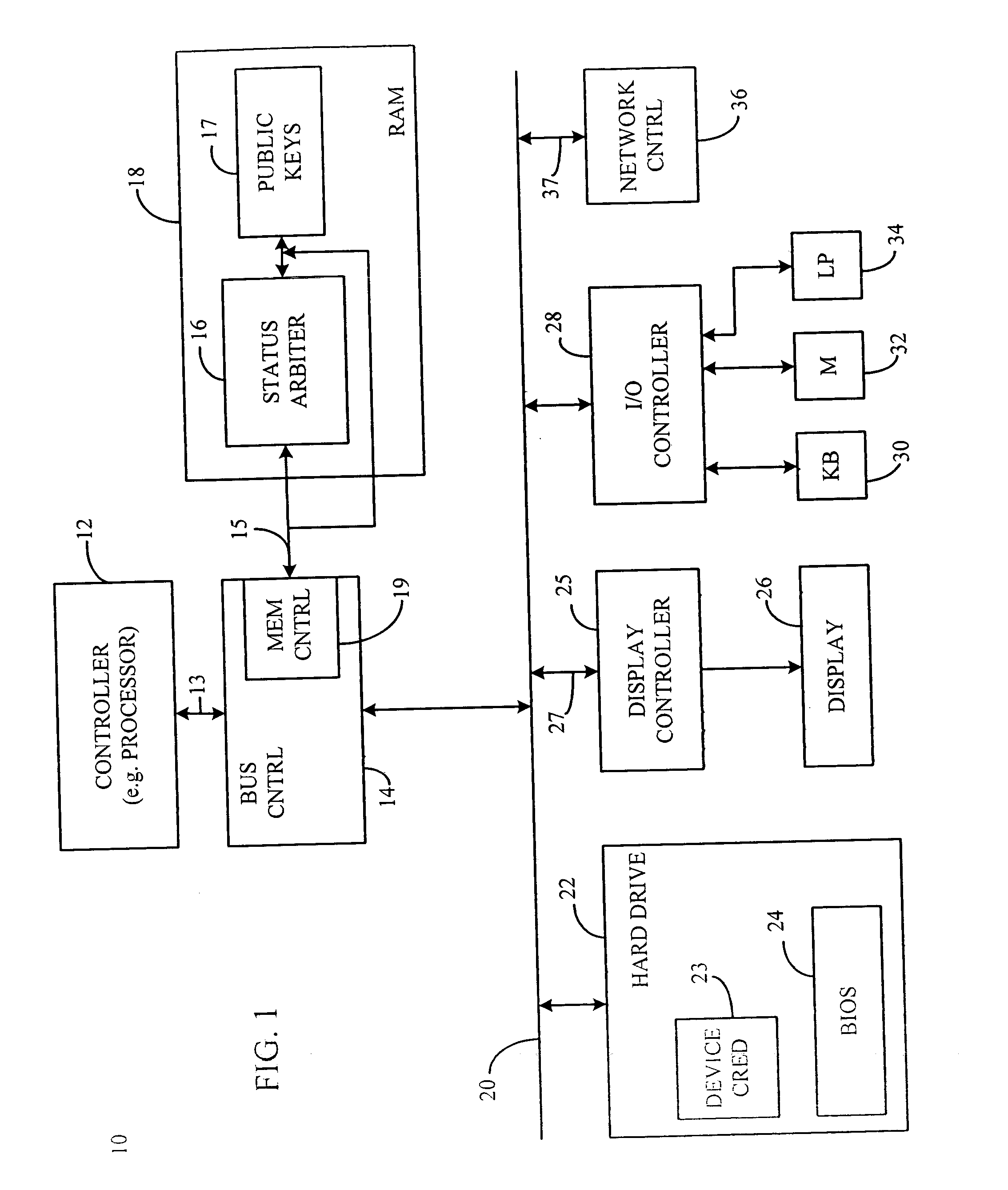
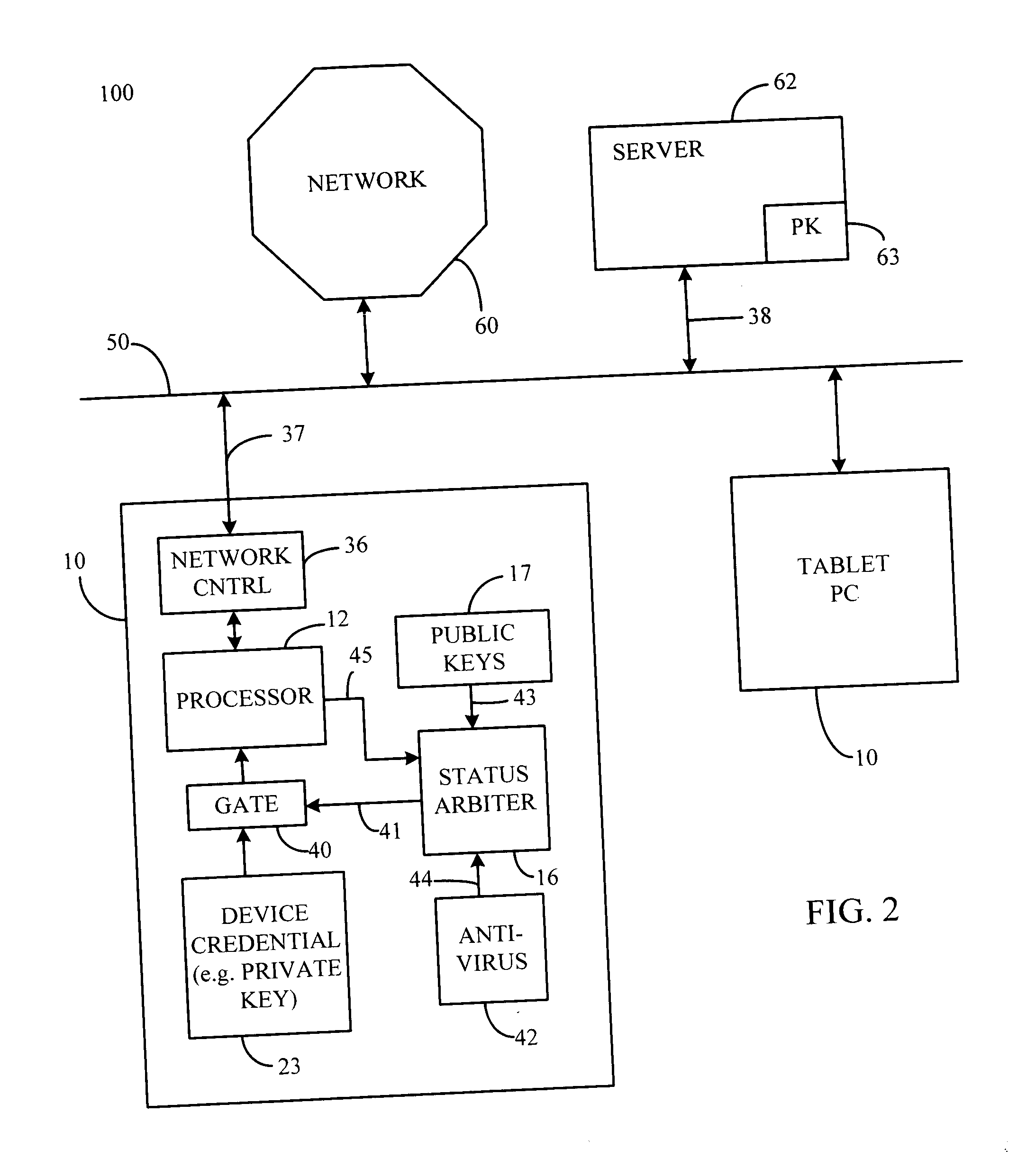
InactiveUS20050210266A1Avoid problemsAvoid attackDigital data processing detailsMultiple digital computer combinationsDevice statusDigital credential
A status arbiter includes a first input operative to receive at least one of a server public key and an agent public key. A second input is operative to receive a secure confirmation signal, where the secure confirmation signal may include an encrypted signal indicating of the state of an underlying device. An authenticating means for determining the state of the underlying device is coupled to the private key input, which provides for the release of digital credentials indicating that the underlying device is secure. A secure device operating method includes receiving an authentication request. Next, providing a device credential in response to the authentication request, where the device credential is provided in response to a secure confirmation signal indicating that the underlying device is authorized to perform the authentication request.
Owner:PHOENIX TECHNOLOGIES LTD
Revocation of anonymous certificates, credentials, and access rights
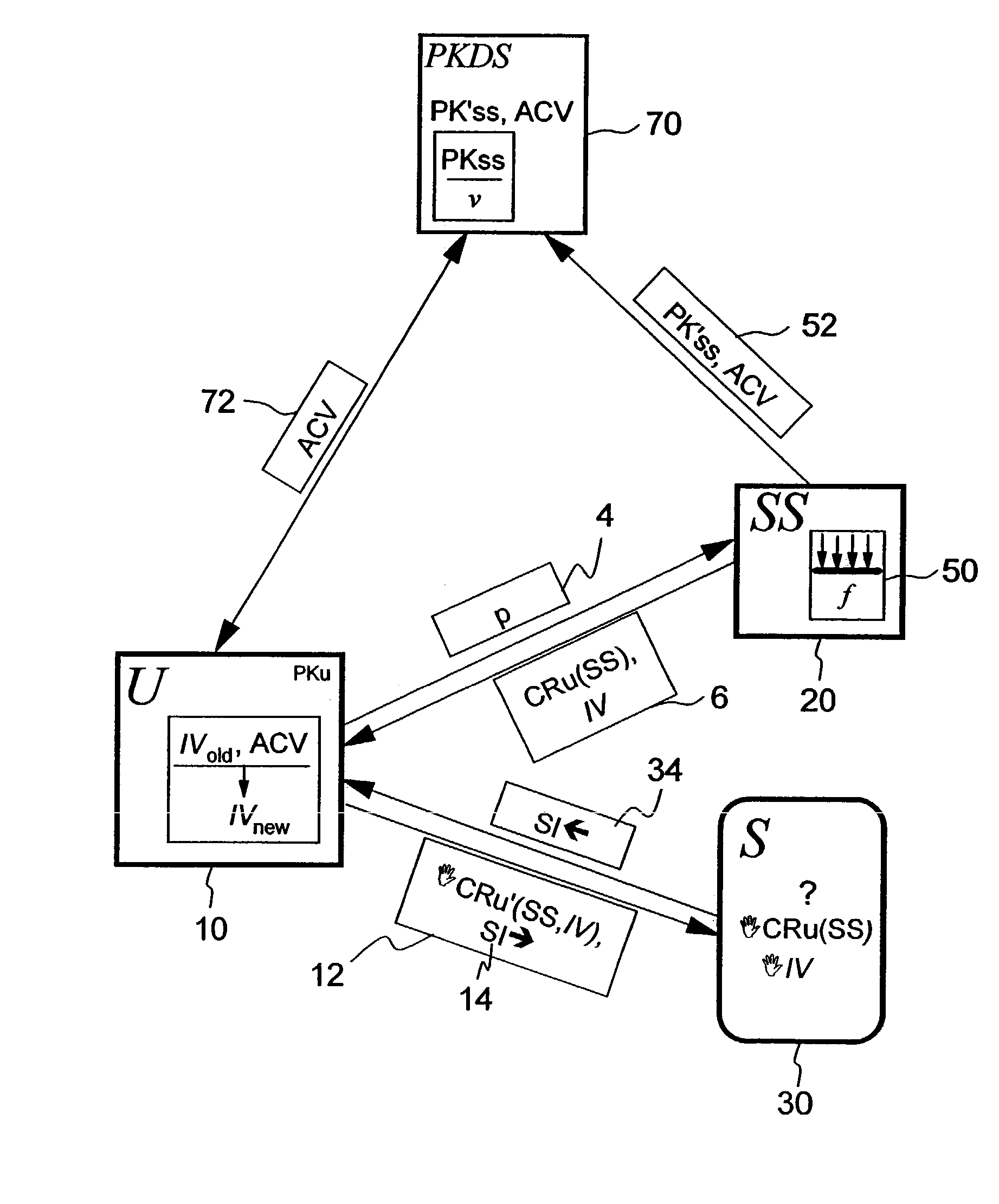
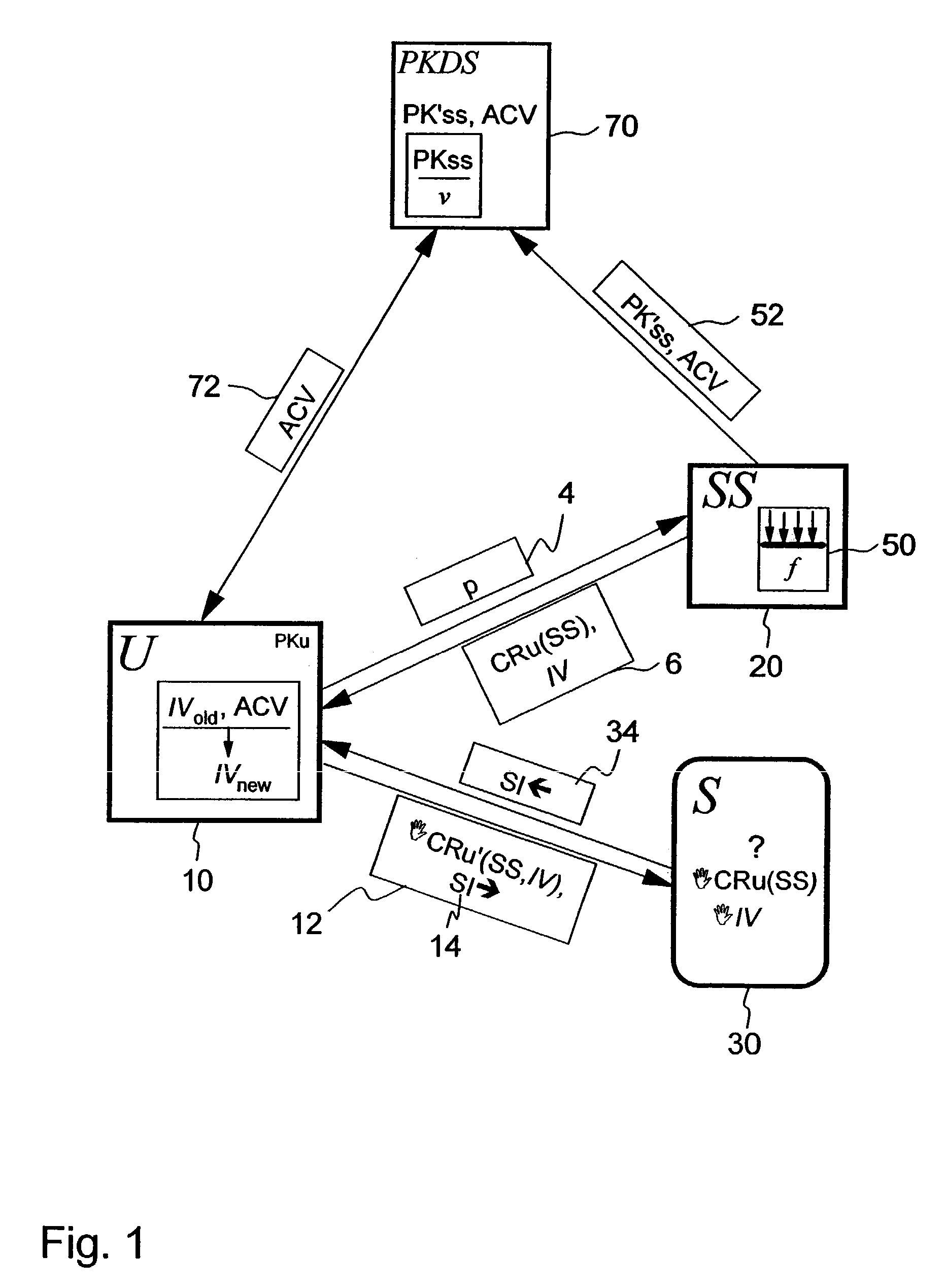
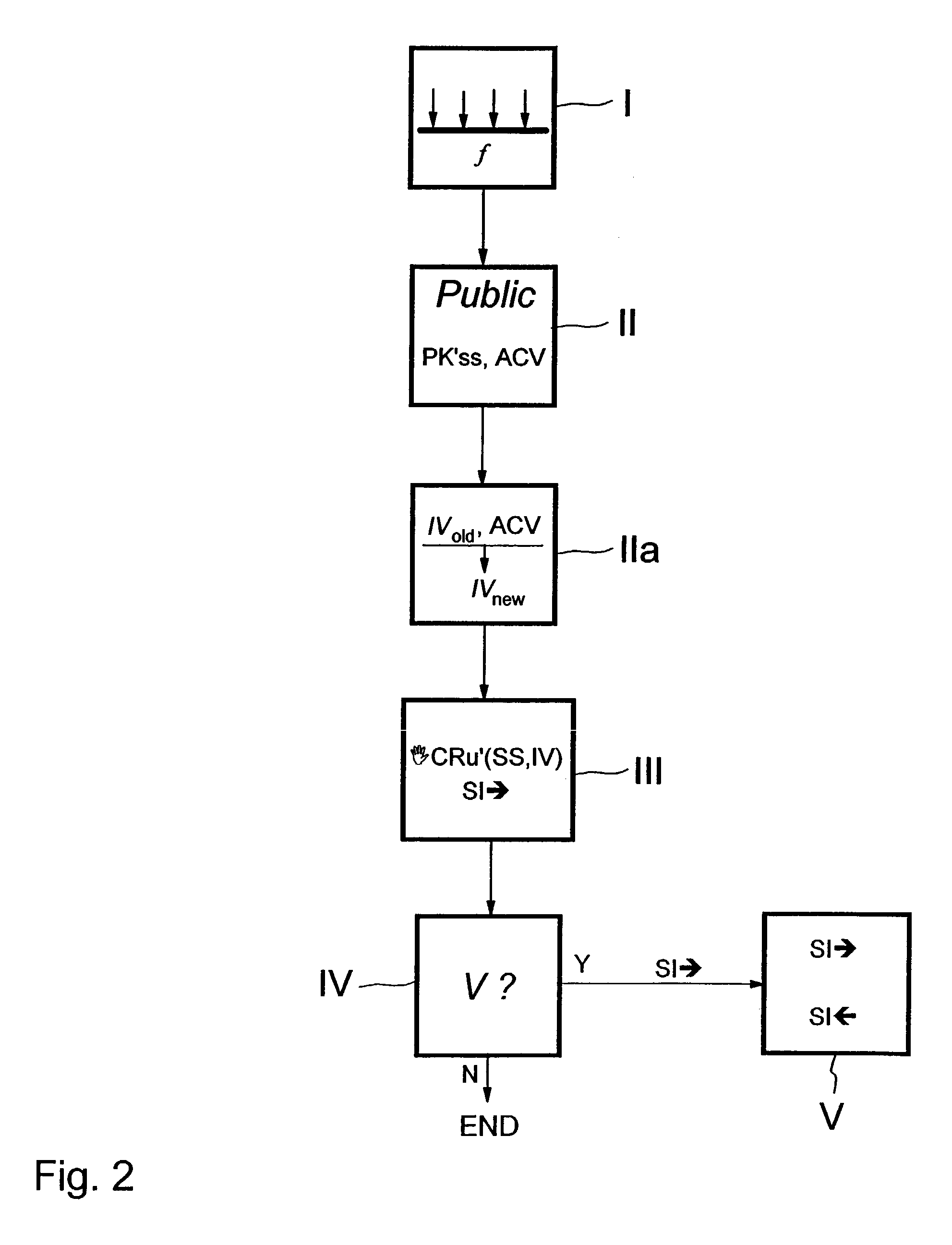
In accordance with the present invention, there is given methods, systems and apparatus for revoking a derived credential formed from an initial credential and an indication value within a network. An example method comprises the steps of: updating an accumulator value based on a plurality of user credential keys where each user credential key is associated with a user device entitled to the derived credential; providing public information that comprises a public key for verifying the initial credential and the accumulator value; an entity receiving from a user device derived-credential information comprising an initial-credential information and an indication-value information indicating that the user credential key is inherently included in the accumulator value, and request information; and, processing the request information in response to verifying by the entity that the initial-credential information and the indication-value information are valid.
Owner:AIRBNB
Generation, management, and tracking of digital credentials
Techniques described herein relate to generating and managing digital credentials using a digital credential platform in communication with various digital credential template owners and digital credential issuers. In some embodiments, a digital credential platform server may receive and coordinate requests and responses between the digital credential template owners and a set of digital credential issuers, to determine which digital credential issuers are authorized to issue digital credential based on which digital credential templates. The digital credential platform server may provide the authorized issuers with access to particular digital credential templates and the functionality to issue digital credentials to users based on any of the particular digital credential templates. Additional techniques described herein relate to tracking, analyzing, and reporting data metrics for issued digital credentials.
Owner:CREDLY INC
Analytic Identity Measures for Physical Access Control Methods
ActiveUS20180089916A1Protection attackPrevents recording and playbackParticular environment based servicesIndividual entry/exit registersFinancial transactionPhysical access
A personal electronic device enables access to and occupancy of a secure space by providing measures of behaviors, personal attributes, history of transactions and movements that are used to validate continuous authentication and authorization of the device's possessor. This addresses the vulnerability of a misplaced, lost, or stolen electronic credential. An anchor point is a physical measurement of personal physical identity such as voice recognition, fingerprint, iris scan, chemistry, or other biometric. Continuity from an anchor point is measured by GPS way points, financial transactions at familiar vendors, outgoing text messages or passphrases, gait analysis, heart rate, EKG rhythm, or transit time. A request for access is presented upon a challenge based on proximity to a portal location. A digital credential is used to encrypt two or more of the continuity milestones and an anchor point which can be matched against a previously stored or dynamically generated expected value.
Owner:BRIVO SYST LLC
Digital credential field mapping
ActiveUS20190129964A1Natural language data processingGeographical information databasesField mappingObject store
Techniques described herein relate to mapping of digital credential objects to various field data objects. For example, requests may be received by a digital credential platform server from digital credential template owner devices, issuer devices, and / or receiver devices. In response, the digital credential platform server may determine and transmit back mappings between the digital credentials and the selected field data objects. To generate mappings, digital credential objects may be tokenize and transformed into vectors within a multi-dimensional vector space. Individual field data objects stored within a high-performance text search engine also may be transformed into vectors within the same multi-dimensional vector space, and the distances between the vectors may be calculated to select a number of field data objects corresponding to the digital credential objects.
Owner:PEARSON EDUCATION
Method and apparatus using digital credentials and other electronic certificates for electronic transactions
A method for performing electronic transactions, comprising receiving a long-term certificate, authenticating a user associated with the long-term certificate, and then sending a short-term certificate to the authenticated user. In addition, risk associated with the user can be evaluated, and this risk information, as well as other information, can be included in the short-term certificate.
Owner:AT&T INTPROP II L P
Virtual credentials and licenses
PendingUS20180197263A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesVirtualizationGeographic site
Providing virtualized credentials of a holder includes setting conditions for determining which of a subset of credentials are to be sent to a device of a relying party that is different from the holder, where the conditions depend on a role of the relying party, selection by the holder, and / or contextual data of the holder or relying party, the relying party requesting specific ones of the credentials corresponding to the holder, the relying party receiving either none or at least some of the specific ones of the credentials according to the conditions, and displaying specific ones of the credentials received by the relying party on a screen of the device of the relying party. The contextual data may be a privacy level setting, distance between the relying party and the holder, and / or geolocation of the holder or relying party.
Owner:ASSA ABLOY AB
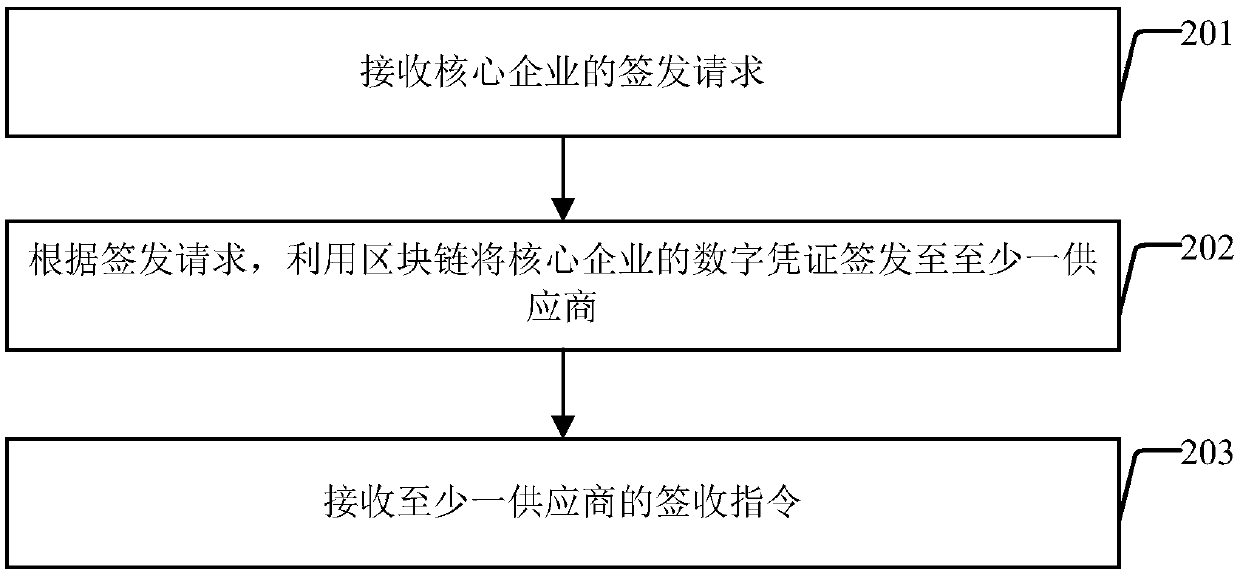
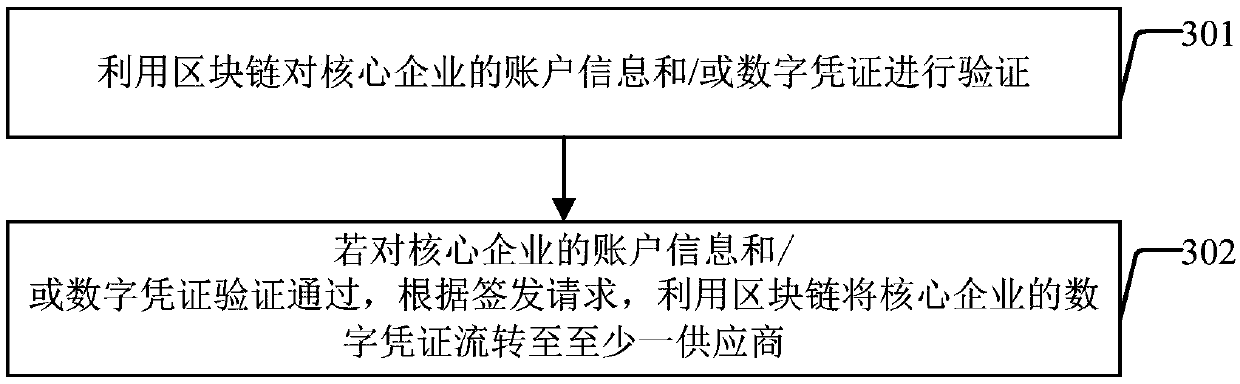
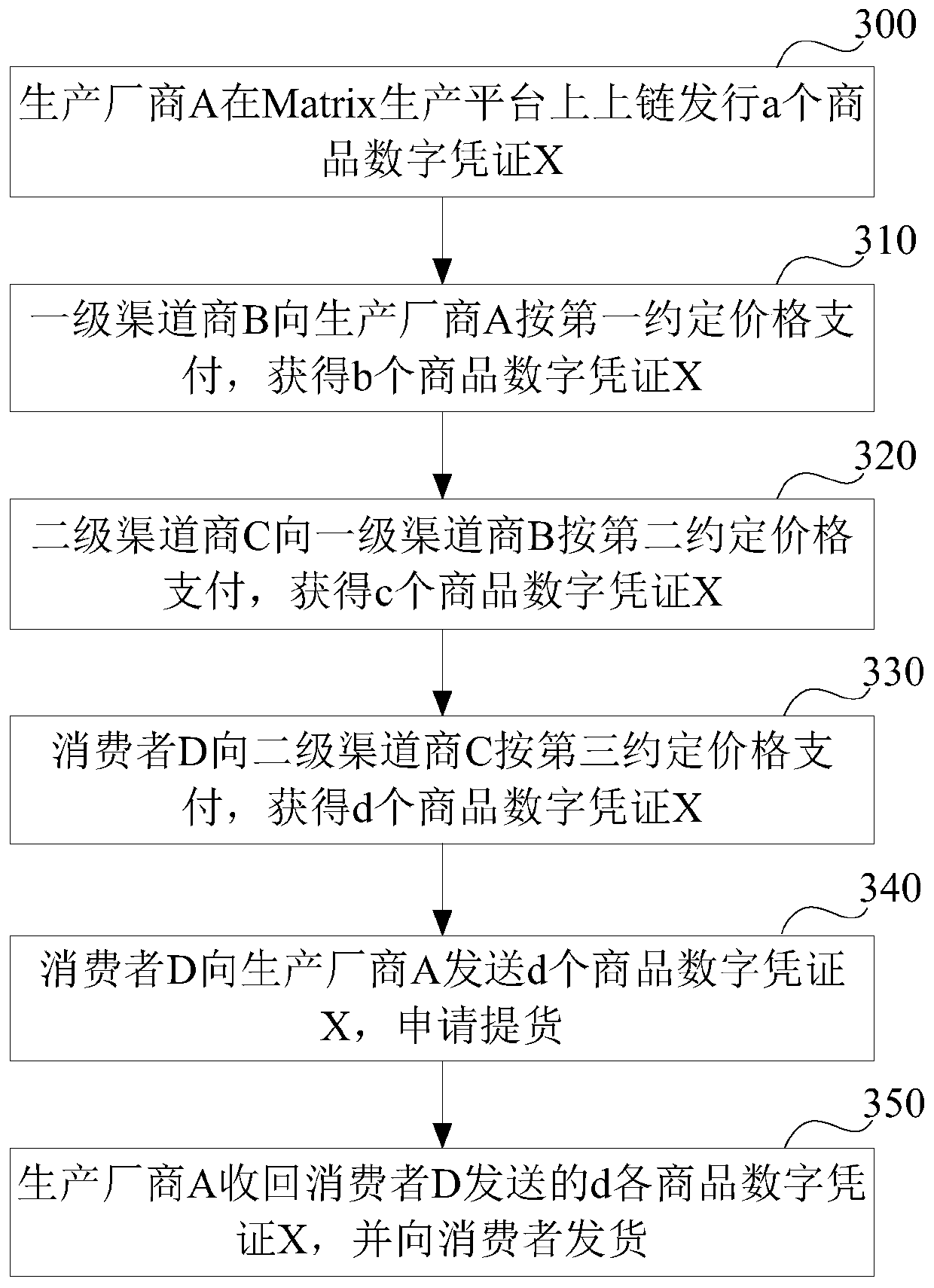
Digital certificate processing method and system and supply chain financial platform
InactiveCN109685648AEffective circulationFinanceDigital data protectionDigital credentialComputer science
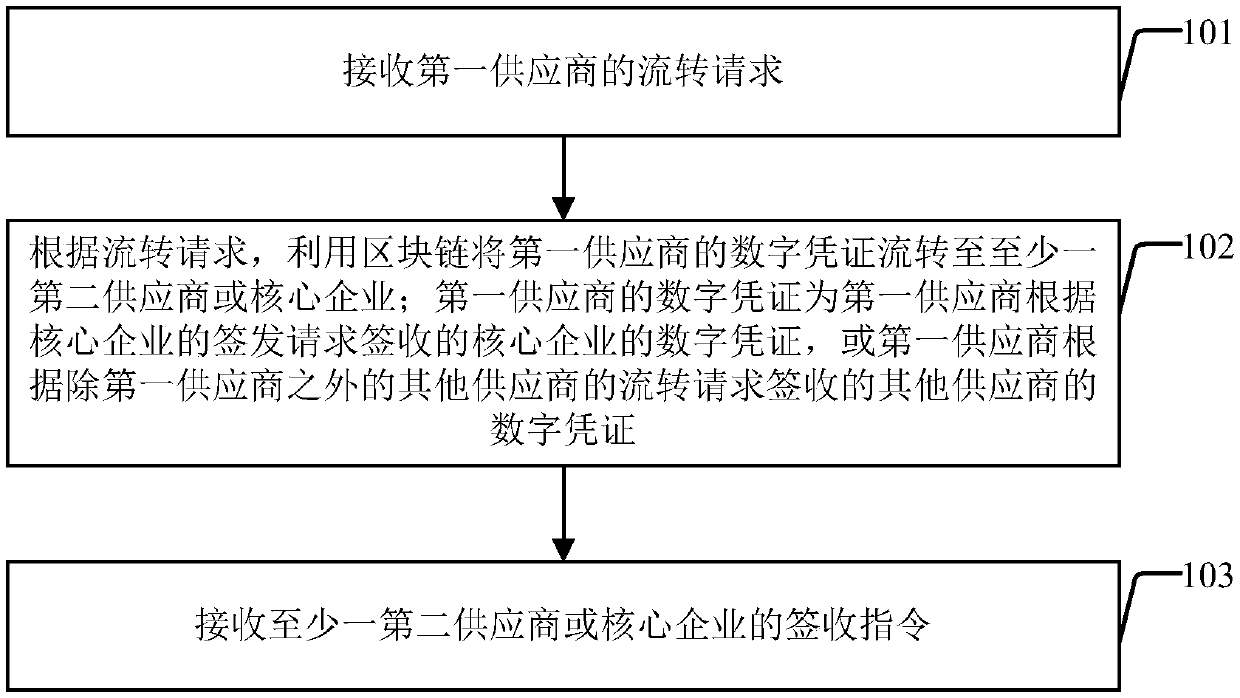
The invention discloses a digital certificate processing method, a digital certificate processing system and a supply chain financial platform. The digital certificate processing method comprises thefollowing steps: receiving a transfer request of a first supplier; According to the transfer request, transferring the digital certificate of the first supplier to at least one second supplier or coreenterprise by using a block chain; Wherein the digital certificate of the first supplier is the digital certificate of the core enterprise signed by the first supplier according to the issuing request of the core enterprise, or the digital certificate of other suppliers signed by the first supplier according to the circulation request of other suppliers except the first supplier; And receiving asigning instruction of at least one second supplier or core enterprise. According to the invention, the core enterprise signs and issues the digital certificate to the first supplier, and the first supplier transfers the digital certificate to at least one second supplier or the core enterprise by using the characteristics of decentralization and non-tampering of the block chain, so that the purpose of effectively transferring the digital certificate in the supply chain is achieved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
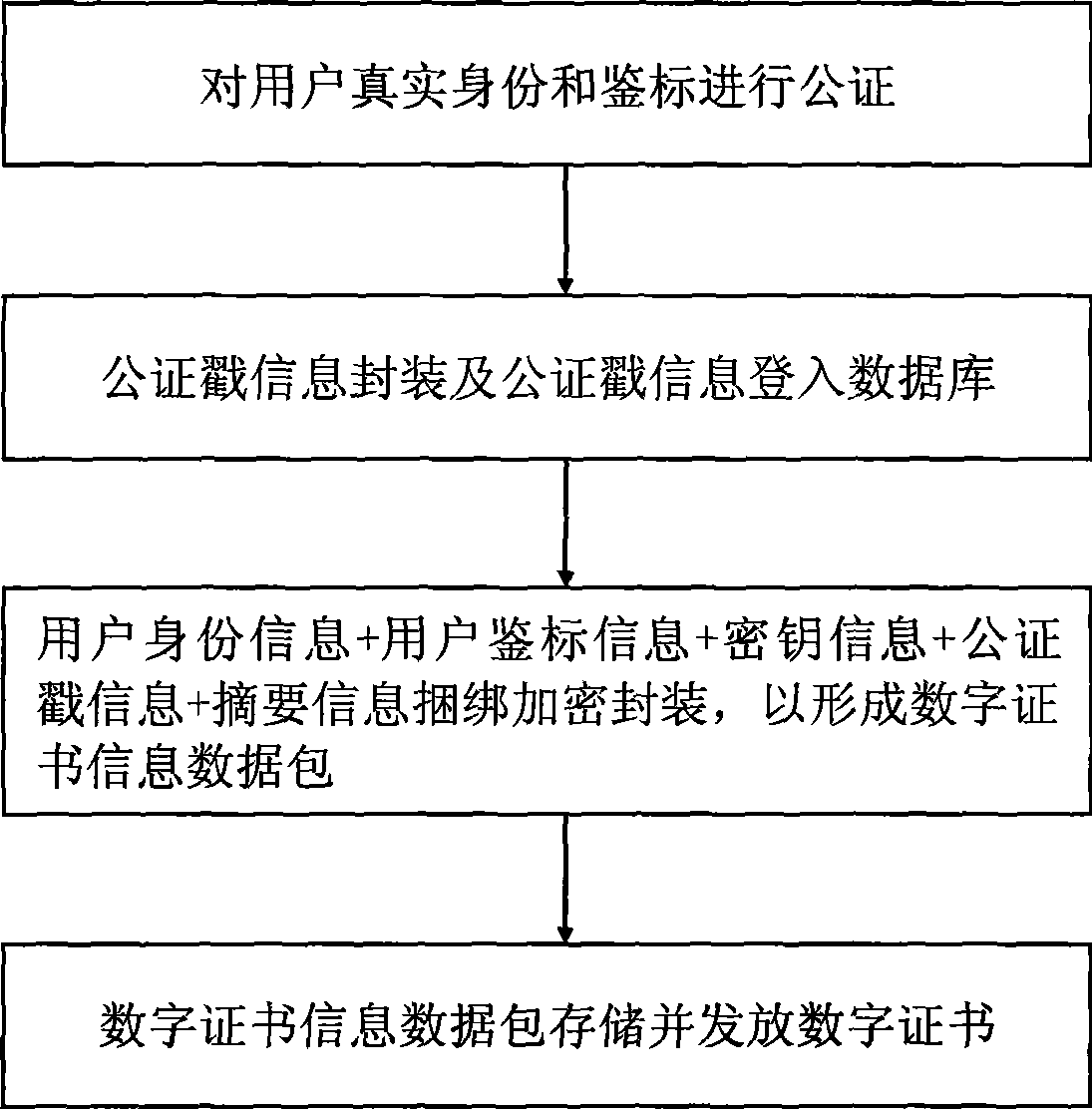
Digital credentials method based on notarization information
InactiveCN101447985AProof of solving real legal identitySolve the identification problemData processing applicationsTransmissionTechnical standardDigital credential
This invention discloses a digital credentials method based on notarization information. A notarization program of notarization organization is led to an electric identification certification so as to provide the public credibility certification of user true identification and credentials. The binding technical of using notarization mark technology and the credibility information of user related identification is used for forming the digital credentials used by the user identification certification and guaranteeing the integrity. Compared with the currently adopted CA certification organization mode under PKI system, this invention effectively conquers the drawbacks that the nonstandard technical standard, low authority of certification and fairness caused by the current PKI system, and the low commonality caused by remarkable region and professional, and has remarkable advantages of saving large amount of cost of creating the CA certification organization. And this invention can be immediately performed. This invention can be widely applied to the business windows, such as the electronic business, the electronic government affairs, the administration, the bank, the Telecommunications, the insurance, and can be applied to the user identification certification under the system of real name of fields of each special business system, hotel, traffic, customs and so on.
Owner:刘学明 +1
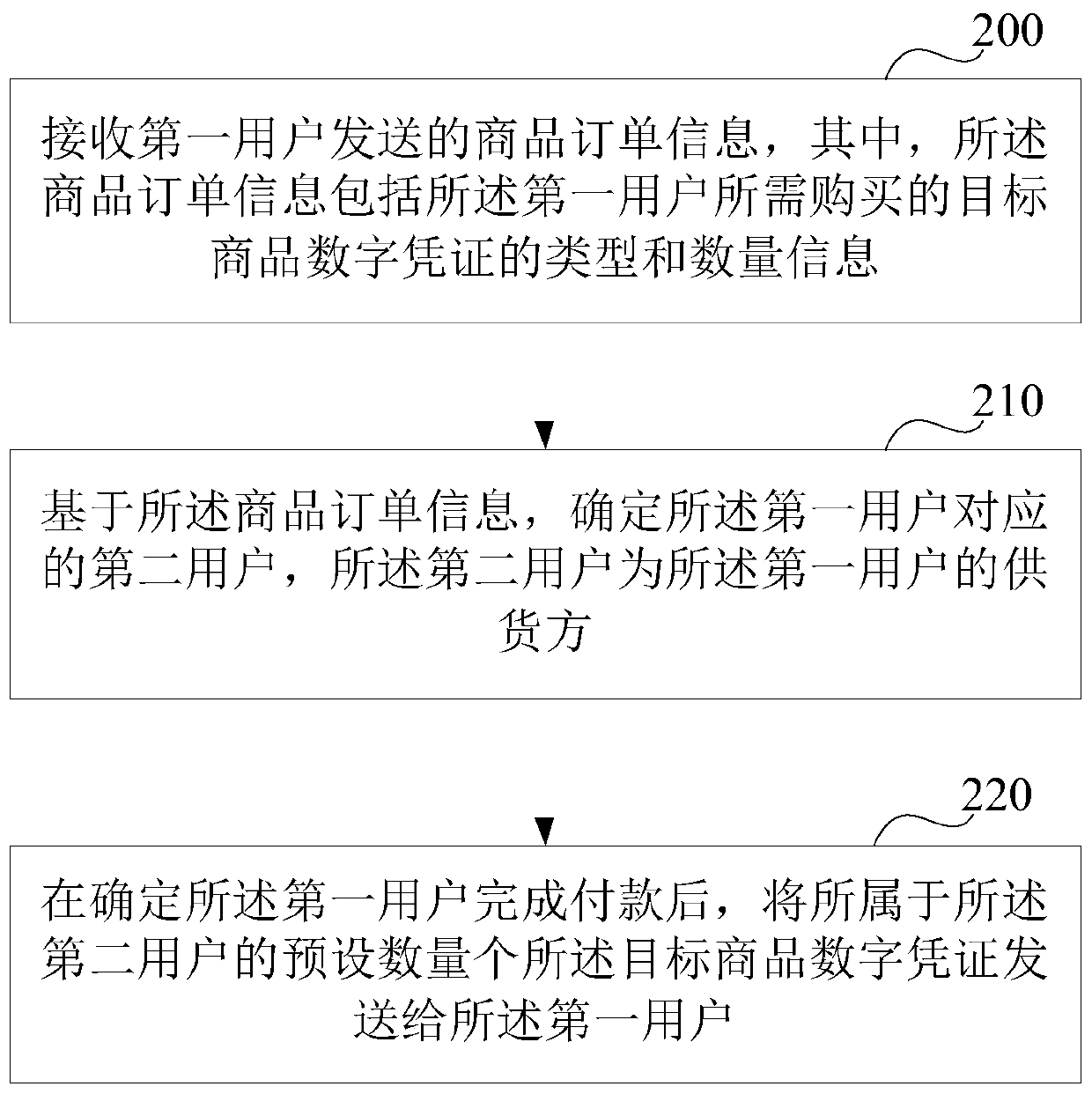
Commodity circulation method and device based on commodity digital certificate
InactiveCN110458671AImprove circulation efficiencyReduce logistics costsBuying/selling/leasing transactionsElectronic credentialsPaymentLogistics management
The invention relates to the technical field of block chains, in particular to a commodity circulation method and device based on commodity digital certificates, and the method comprises the steps: receiving commodity order information sent by a first user, wherein the commodity order information comprises the type and number information of target commodity digital certificates needing to be purchased by the first user; determining a second user corresponding to the first user based on the commodity order information, the second user being a supplier of the first user; after it is determined that the first user completes payment, the preset number of target commodity digital certificates belonging to the second user are sent to the first user, wherein the preset number of target commoditydigital certificates can be sold to a third user or used for picking up commodities from a manufacturer who issues the target commodity digital certificates. By adopting the scheme, the commodity circulation efficiency is improved, and the logistics cost is reduced.
Owner:弦子科技(北京)有限公司
Systems and methods for verifying and managing digital credentials
PendingUS20200220726A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationThird partyRating system
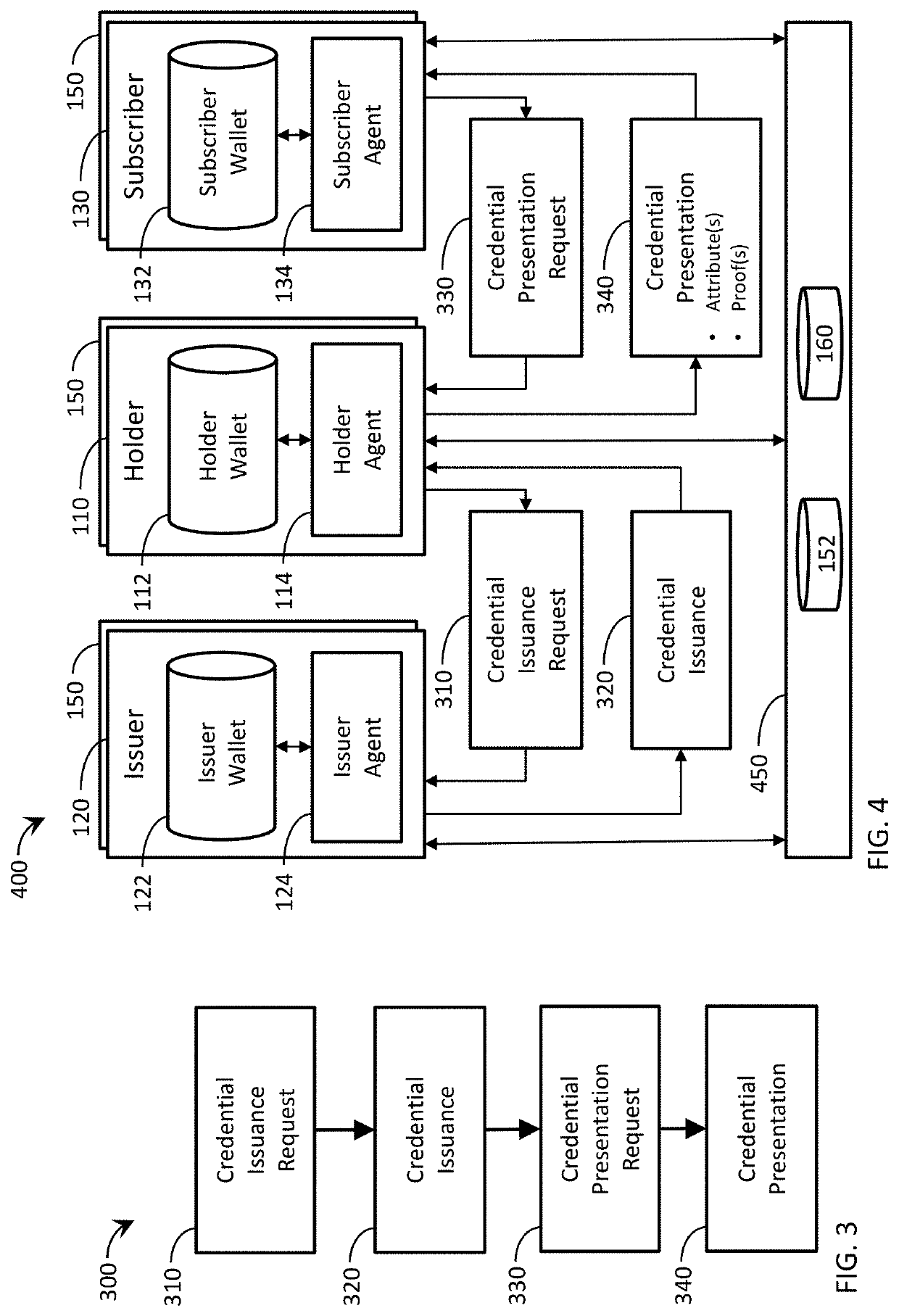
Systems and methods which provide the ability for users to track the lifecycle and conditional rules associated with credentials, which can include digitally verified third-party assertions of identity, education, licensing, work history, provenance, authenticity, outcomes, ingredients, etc. through a network of certified primary source or primary source equivalent issuers of credentials. Verifiable data registry technology can be used to provide access to information associated with the credentials, such as validity and schemas. Credential presentation and subscription processes are also utilized. Ecosystem communication and management functions can be executed through various agent instances associated with the actors, including administrators. Rating systems and fee transactions are also managed.
Owner:AXUALL INC
Regulation-violating behaviour evidence-obtaining system and method therefor
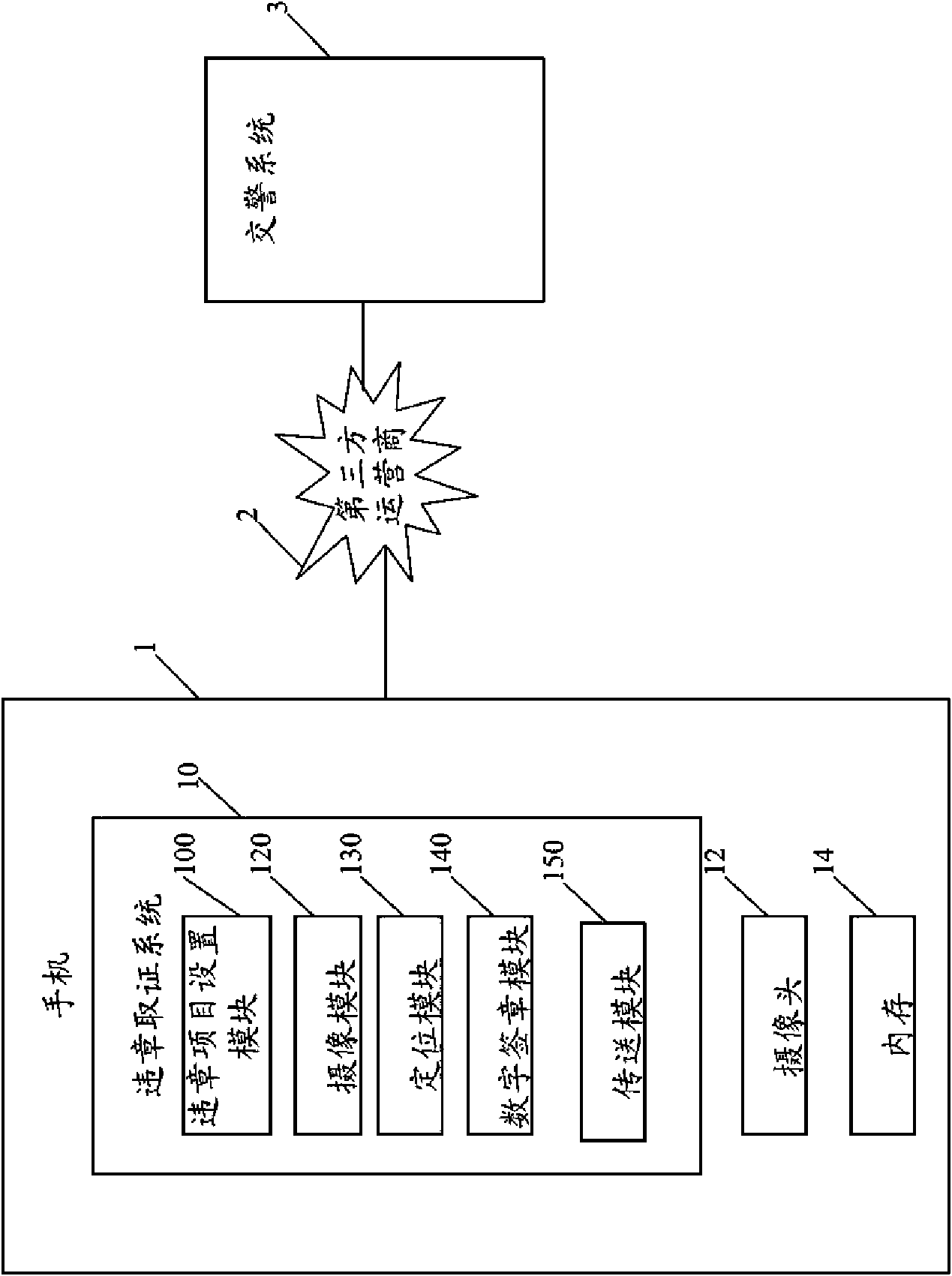
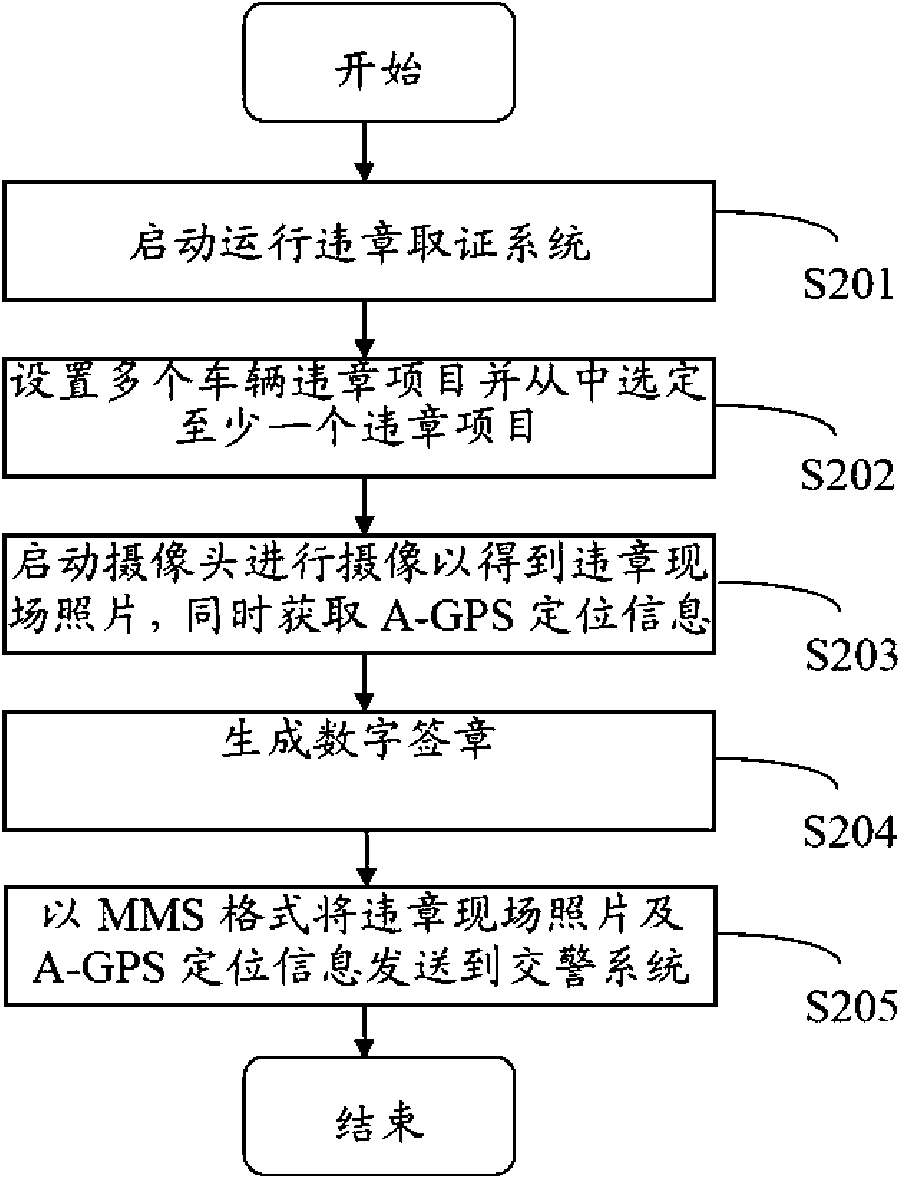
InactiveCN101620782AImprove work accuracyImprove work efficiencyRoad vehicles traffic controlDigital signatureDigital evidence
Owner:SHENZHEN FUTAIHONG PRECISION IND CO LTD +1
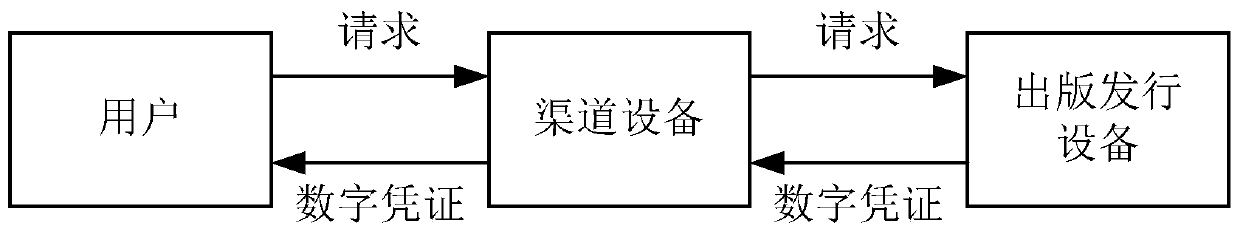
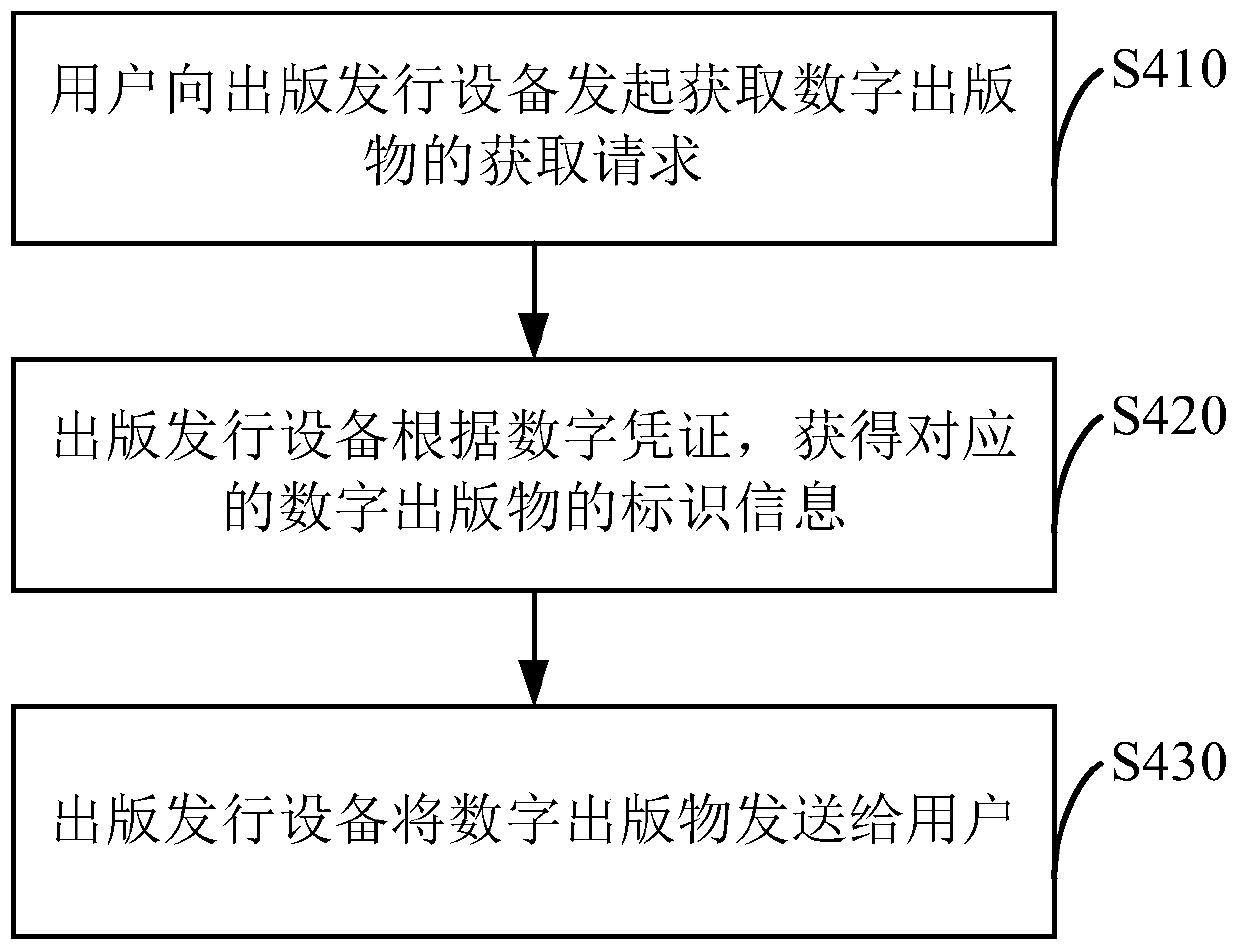
Method and device used for sending digital publication
ActiveCN105095691AGuaranteed right of reproductionHas property propertyProgram/content distribution protectionDigital workAuthorization
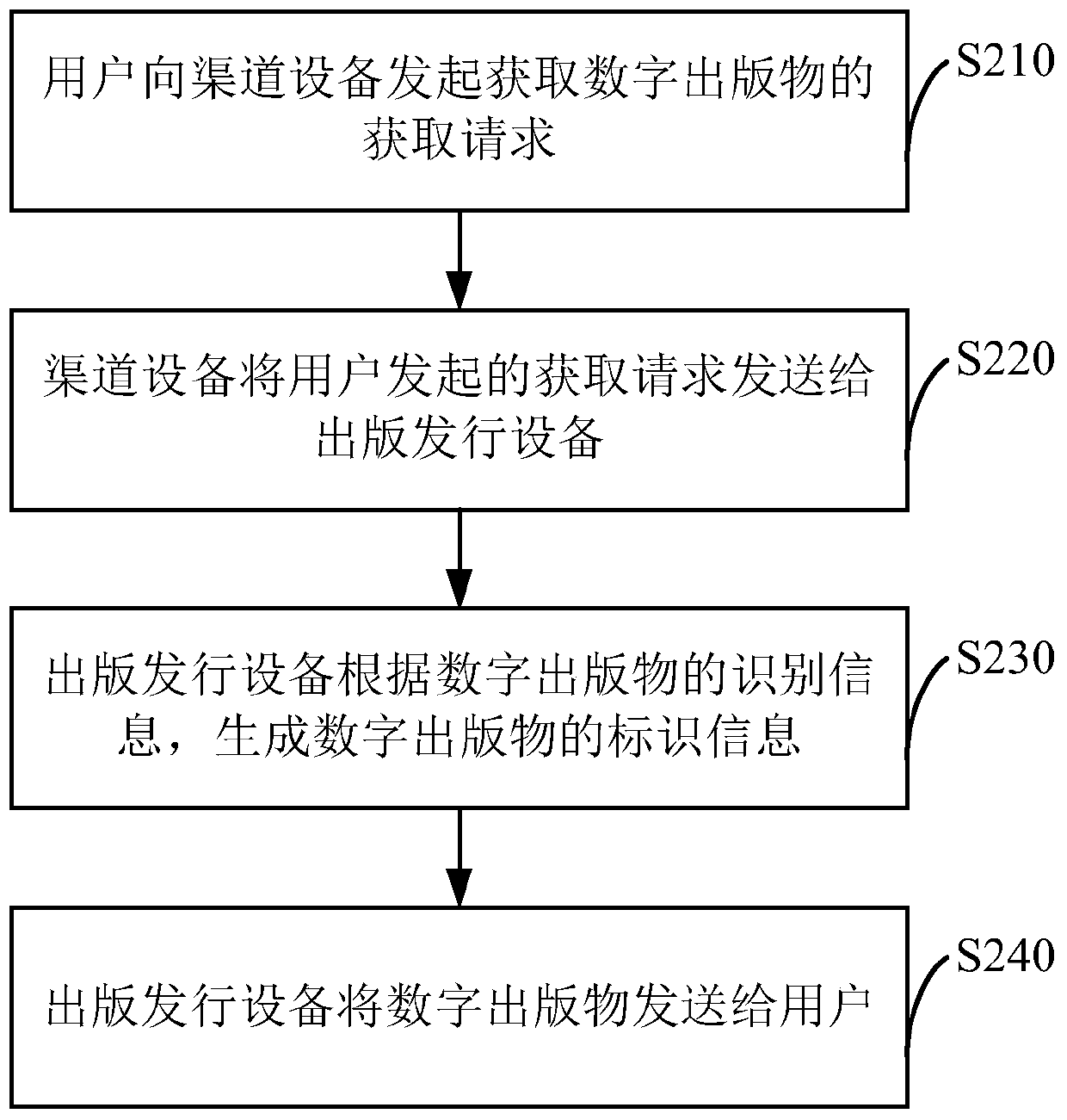
The invention discloses a method and device used for sending a digital publication, and overcomes the problem that at present, in the digital publication industry, the channel side goes beyond the authorization and distributes a digital publication, and the legitimate interest of the copyright owner is damaged. The method used for sending a digital publication comprises that an acquisition request for obtaining the digital publication of the user is received; the acquisition request at least comprises identification information of the user, and recognition information of the digital publication or a corresponding digital certification of the digital publication; the identification information of the digital publication is generated or obtained according to the recognition information of the digital publication or the digital certification; and the digital publication is sent according to the identification information of the user. According to the invention, the right of reproduction of digital works especially digital publications is guaranteed, usage of works in a copy mode can be permitted or forbidden, and rights of obtaining remuneration and the like can be firmly grasped by the copyright owner under the permission condition.
Owner:厦门润丰投资有限公司
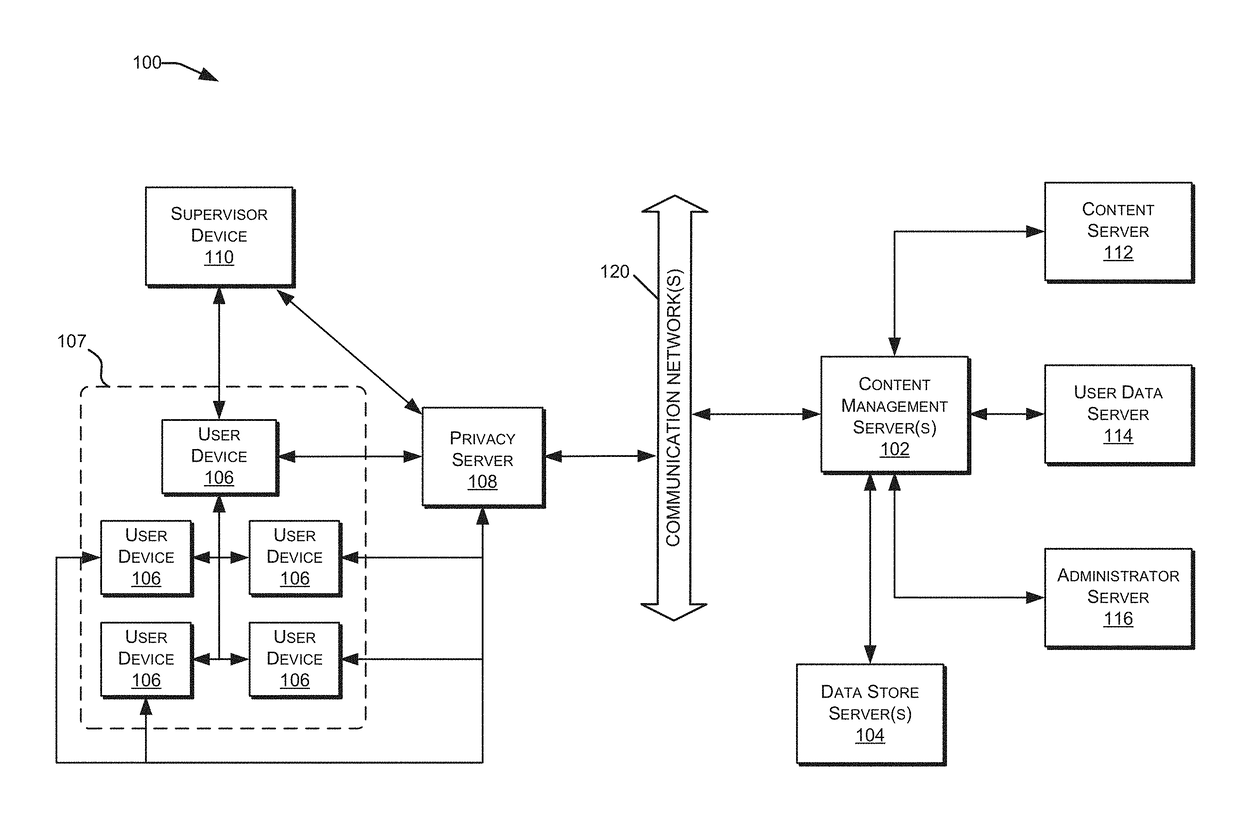
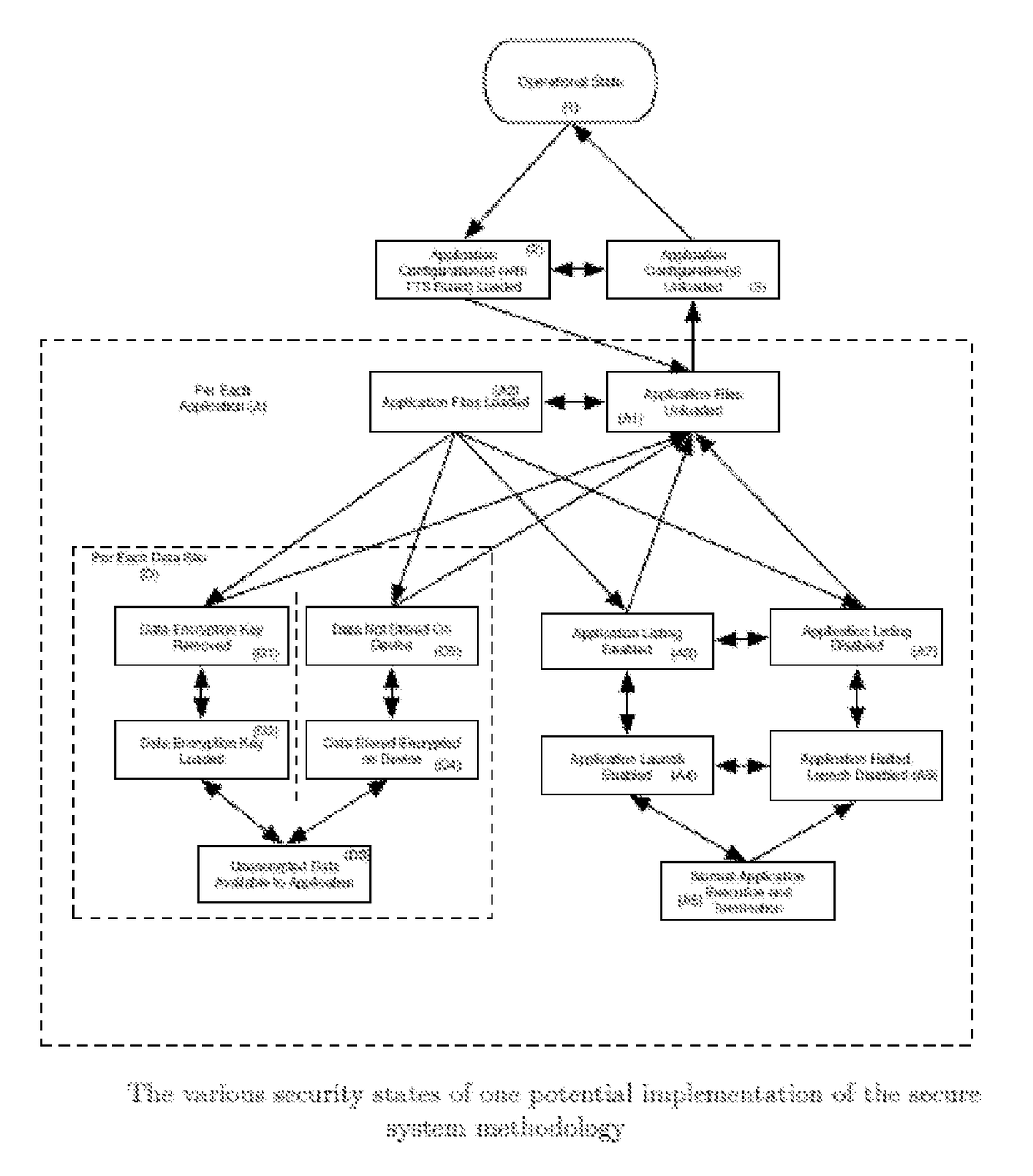
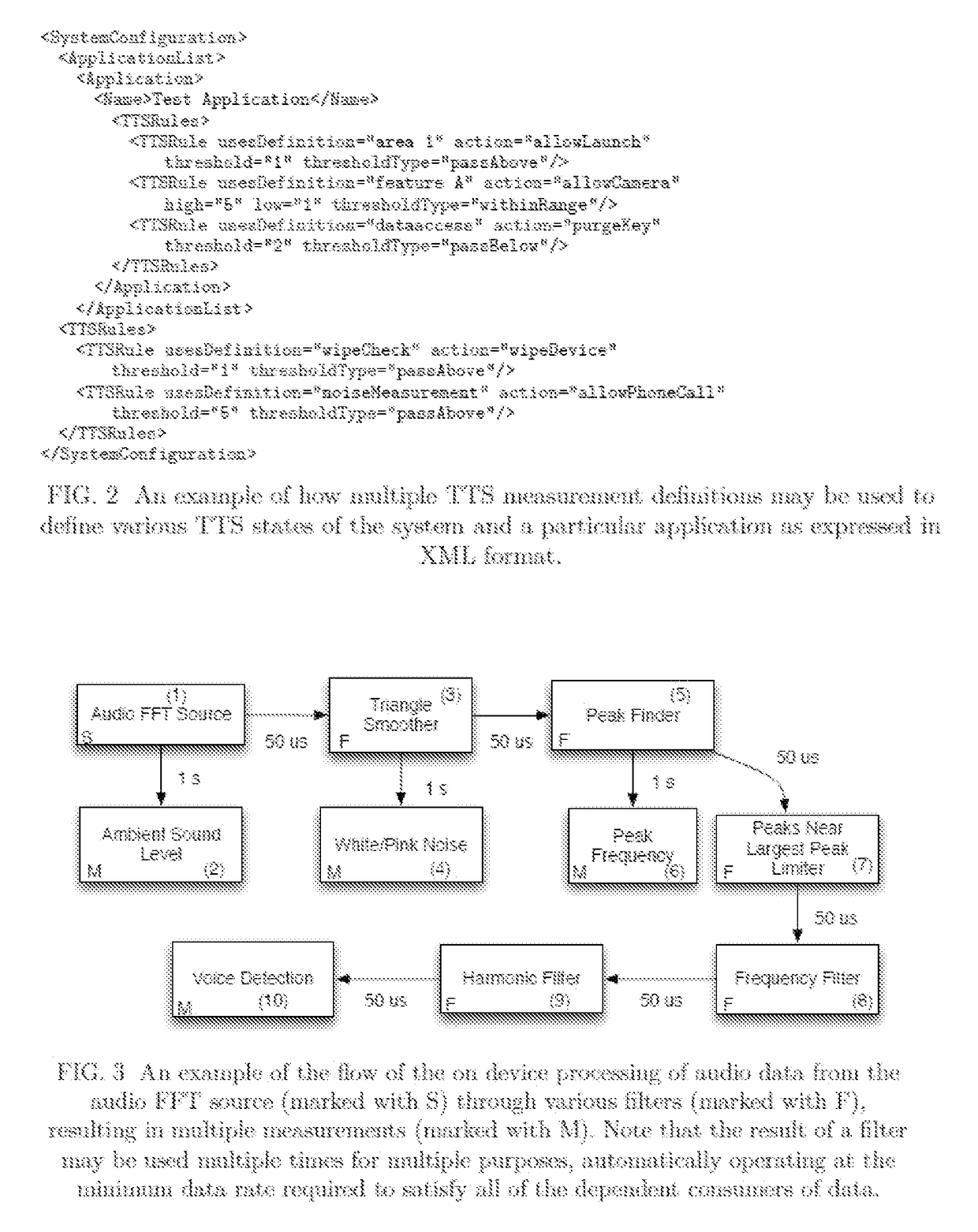
Methods of dynamically securing electronic devices and other communications through environmental and system measurements leveraging tailored trustworthy spaces
ActiveUS9721111B2Without the risk of the receiving device compromising the security of the sending systemExposure was also limitedDigital data protectionData sourceMobile security
This invention is for a system capable of securing one or more fixed or mobile computing device and connected system. Each device is configured to change its operating posture by allowing, limiting, or disallowing access to applications, application features, devices features, data, and other information based on the current Tailored Trustworthy Space (TTS) definitions and rules which provided for various situationally dependent scenarios. Multiple TTS may be defined for a given deployment, each of which specifies one or more sensors and algorithms for combining sensor data from the device, other connected devices, and / or other data sources from which the current TTS is identified. The device further achieves security by loading digital credentials through a unidirectional multidimensional physical representation process which allows for the device to obtain said credentials without the risk of compromising the credential issuing system through the data transfer process. This secure system methodology may be used to create a Mobile Secure Compartmentalized Information Facility (M-SCIF), among other applications.
Owner:INTERNET INFRASTRUCTURE SERVICES
Generation, management, and tracking of digital credentials
Techniques described herein relate to generating and managing digital credentials using a digital credential platform in communication with various digital credential template owners and digital credential issuers. In some embodiments, a digital credential platform server may receive and coordinate requests and responses between the digital credential template owners and a set of digital credential issuers, to determine which digital credential issuers are authorized to issue digital credential based on which digital credential templates. The digital credential platform server may provide the authorized issuers with access to particular digital credential templates and the functionality to issue digital credentials to users based on any of the particular digital credential templates. Additional techniques described herein relate to tracking, analyzing, and reporting data metrics for issued digital credentials.
Owner:CREDLY INC
Digital credential field data mapping
Techniques described herein relate to receiving multiple sources of verified data associated with a digital credential receiver, and mapping the digital credential receiver to one or more data field data objects based on analyses of the verified data. In some embodiments, a digital credential platform server may analyze the various data sources associated with the digital credential receiver, in order to determine and calculate correlation scores between the digital credential receiver and various field data objects. A combination of analyses and / or comparisons may be used between the credential receiver data and the corresponding retrieved from field data objects, such as the digital credential objects earned by the credential receiver, the credential receiver's verified evaluation records, and / or the career phase of the digital credential receiver.
Owner:PEARSON EDUCATION
Monitoring physical simulations within a digital credential platform
Techniques described herein relate to executing and monitoring physical simulations within a digital credential platform. Physical simulation evaluation systems may be implemented including sensor-based monitoring systems, simulation output systems, and / or simulation environment control systems. Particular types of digital credential simulations may be determined and executed within a physical environment, during which a plurality of sensors may be used to monitor the physical actions of a credential receiver during physical simulation. The physical action data may be analyzed and compared to digital credential requirements to determine one or more digital credentials to be generated and issued to the credential receiver.
Owner:PEARSON EDUCATION
System and method for achieving machine authentication without maintaining additional credentials
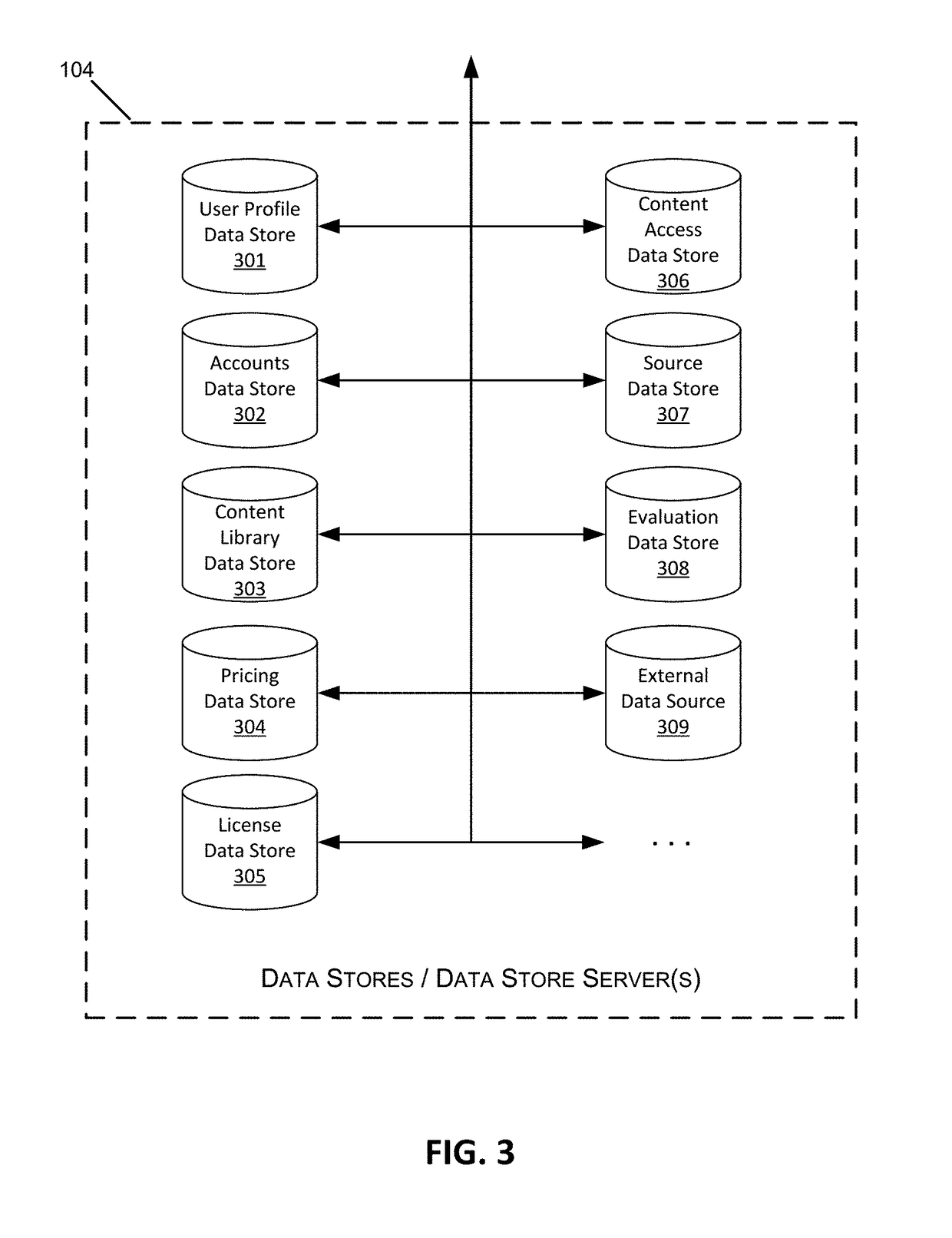
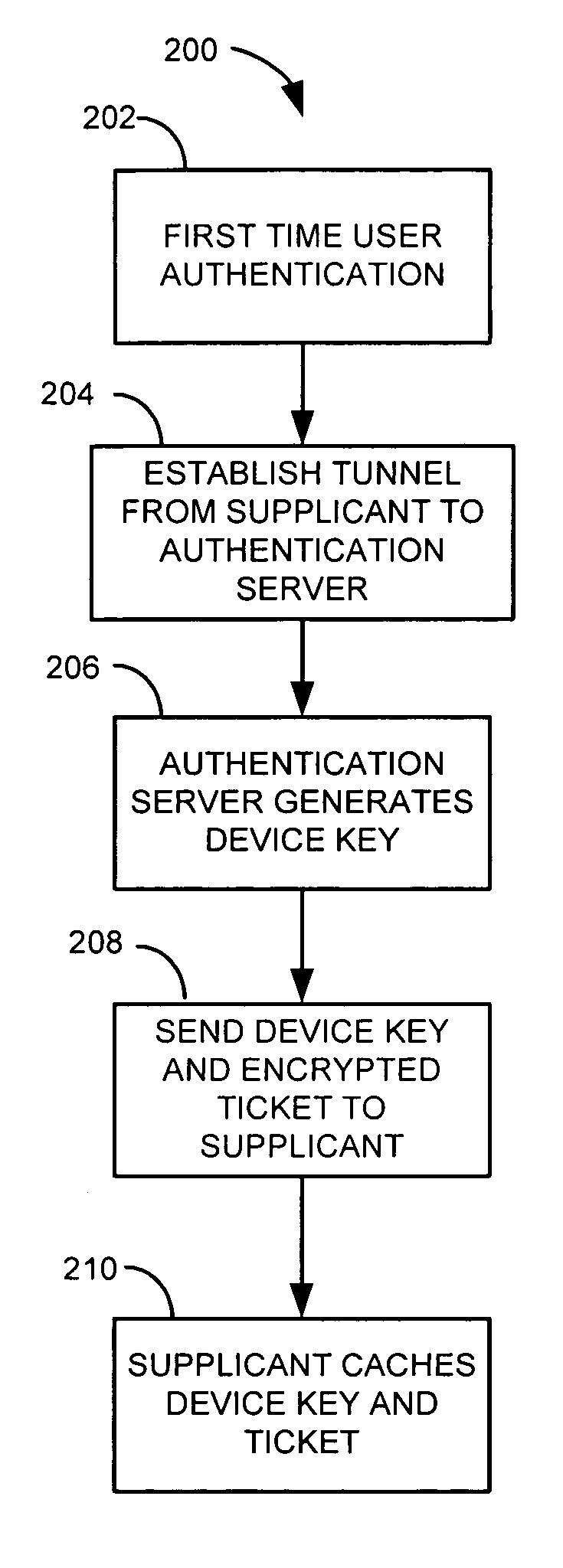
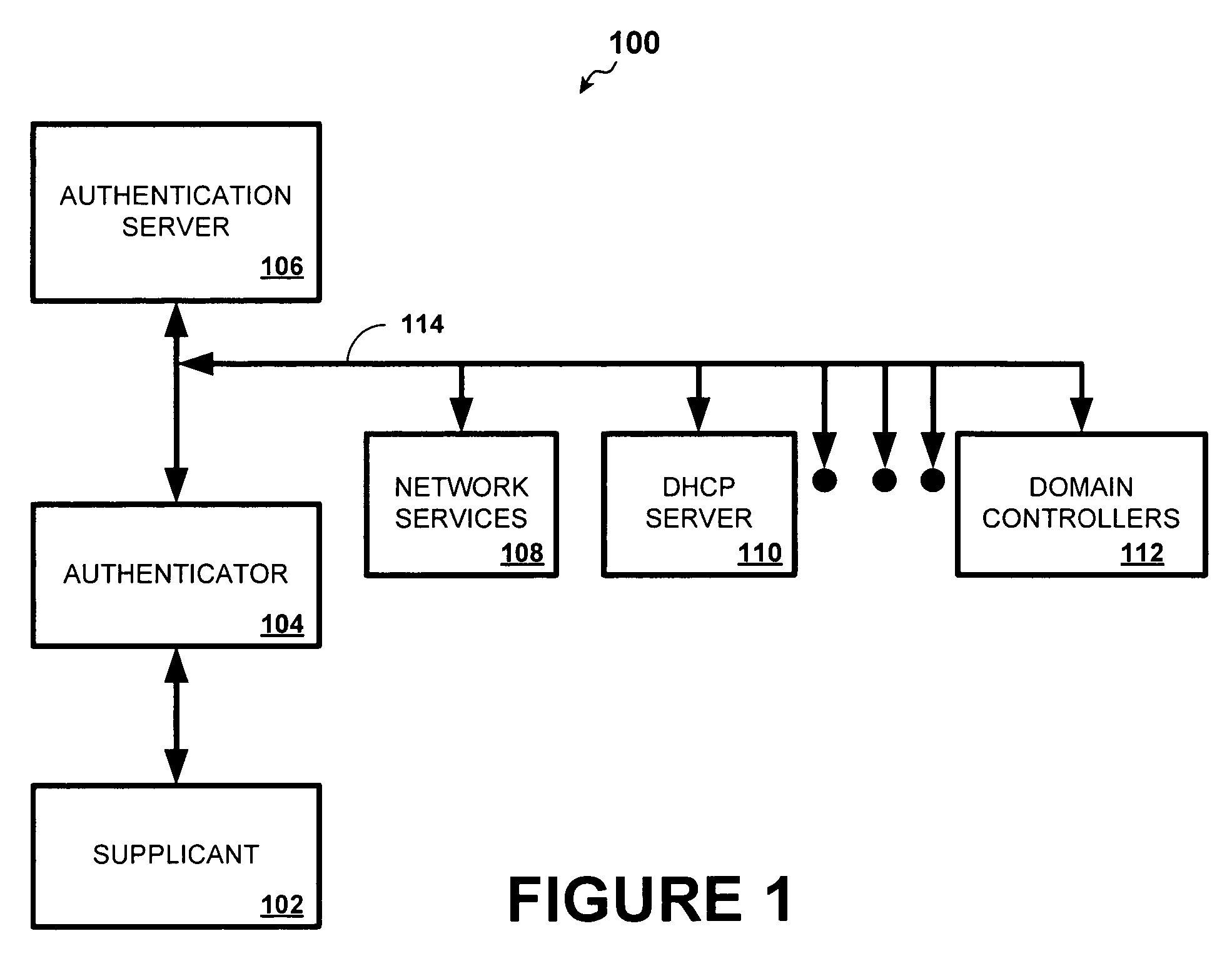
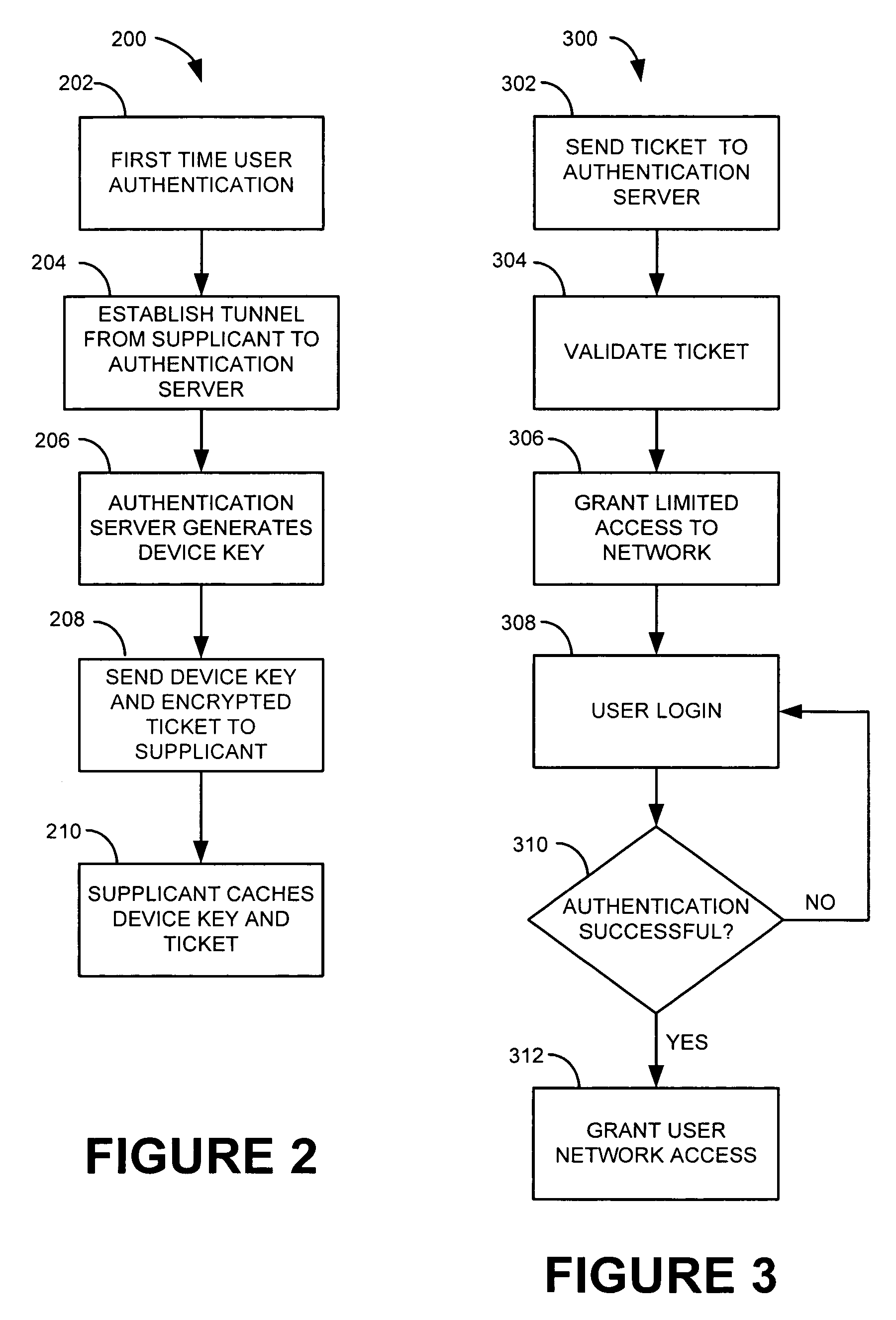
ActiveUS7640430B2Digital data processing detailsUser identity/authority verificationLimited accessUser input
A Machine Authentication PAC (Protected Access Credential) serves as machine credentials to obtain network access without requiring server storage and management of the additional set of credentials. The first time authentication is performed, user authentication is executed. After the supplicant and server have mutually authenticated each other and satisfied other validations, the supplicant requests a Machine Authentication PAC from the server. The Server randomly generates a cryptographic key (Device Key) and sends it to the supplicant along with an encrypted ticket, comprising the Device Key and other information and encrypted with a key only known to the Server. The supplicant caches the Machine Authentication PAC in its non-volatile memory for future use. When the machine needs to access certain network services before a user is available, the supplicant uses the Machine Authentication PAC to gain authorization for the machine to limited access on the network, without requiring user input.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com