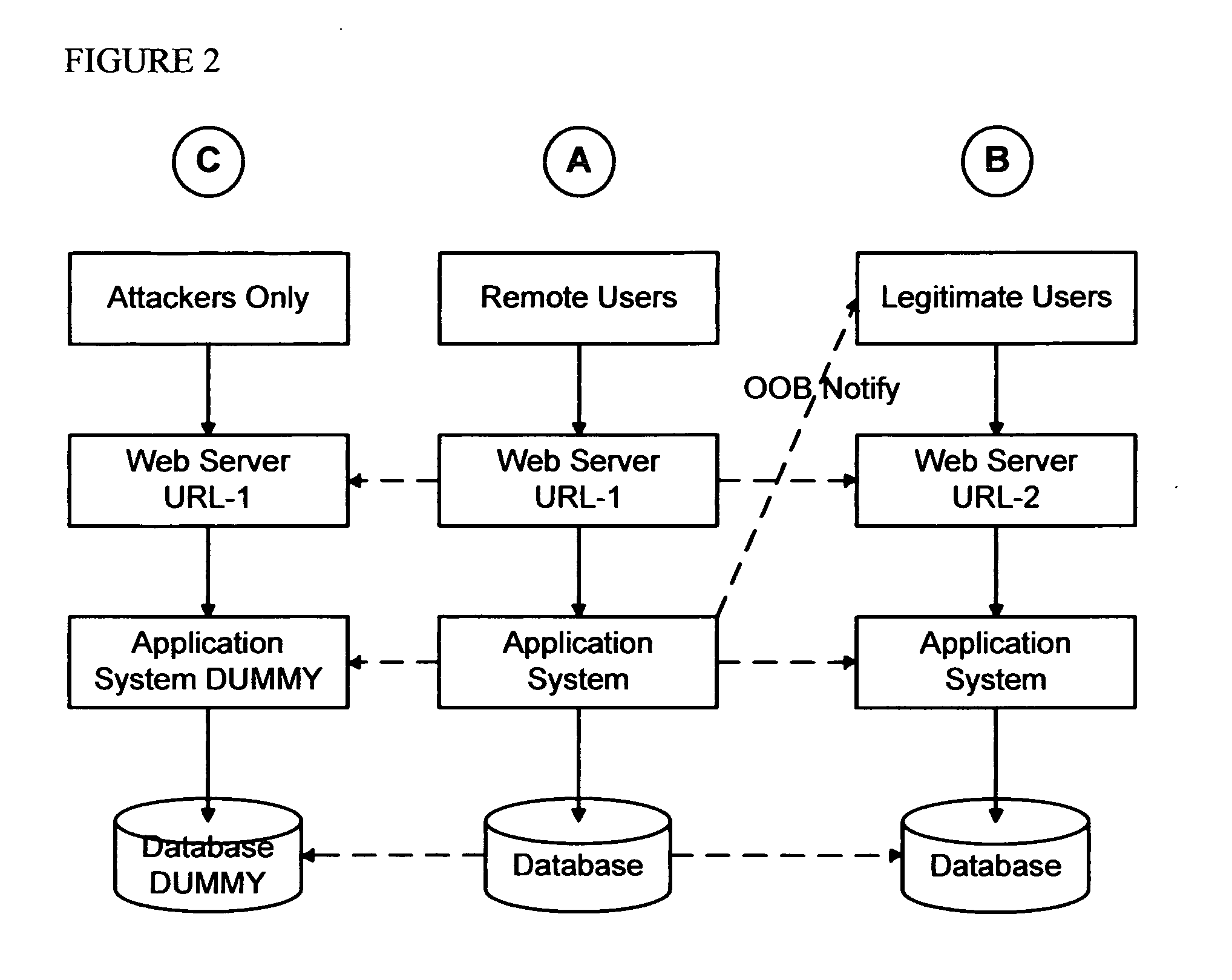
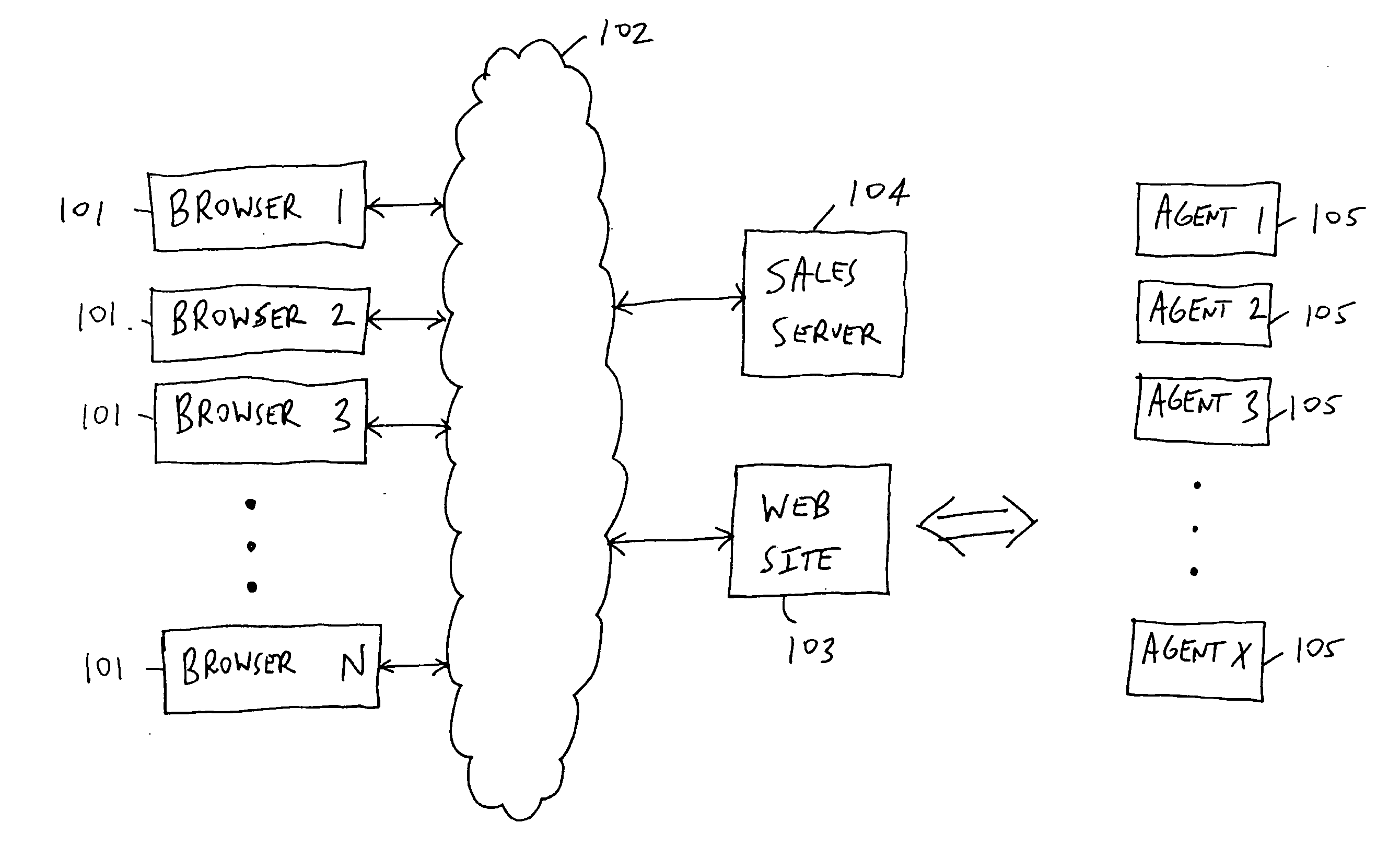
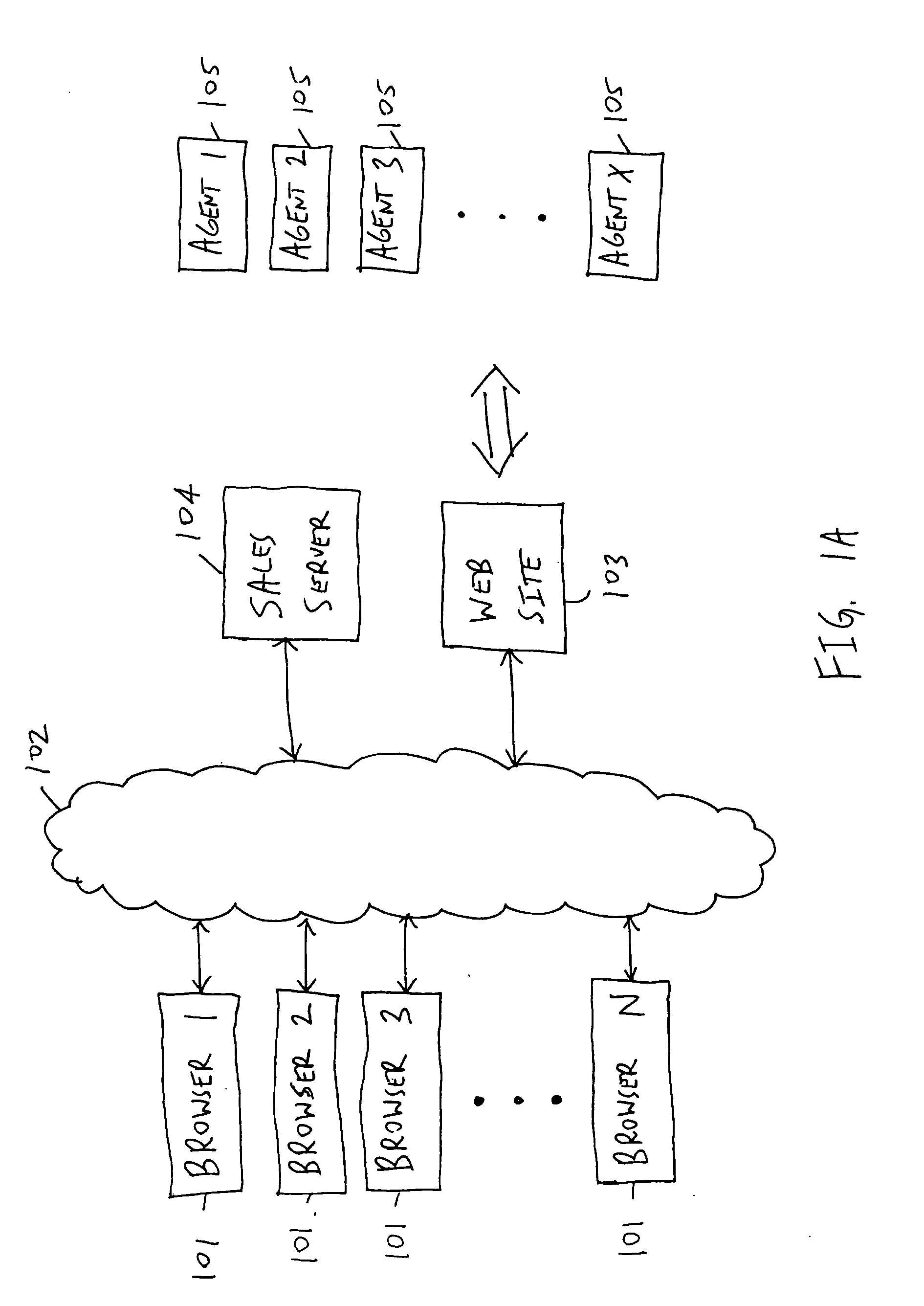
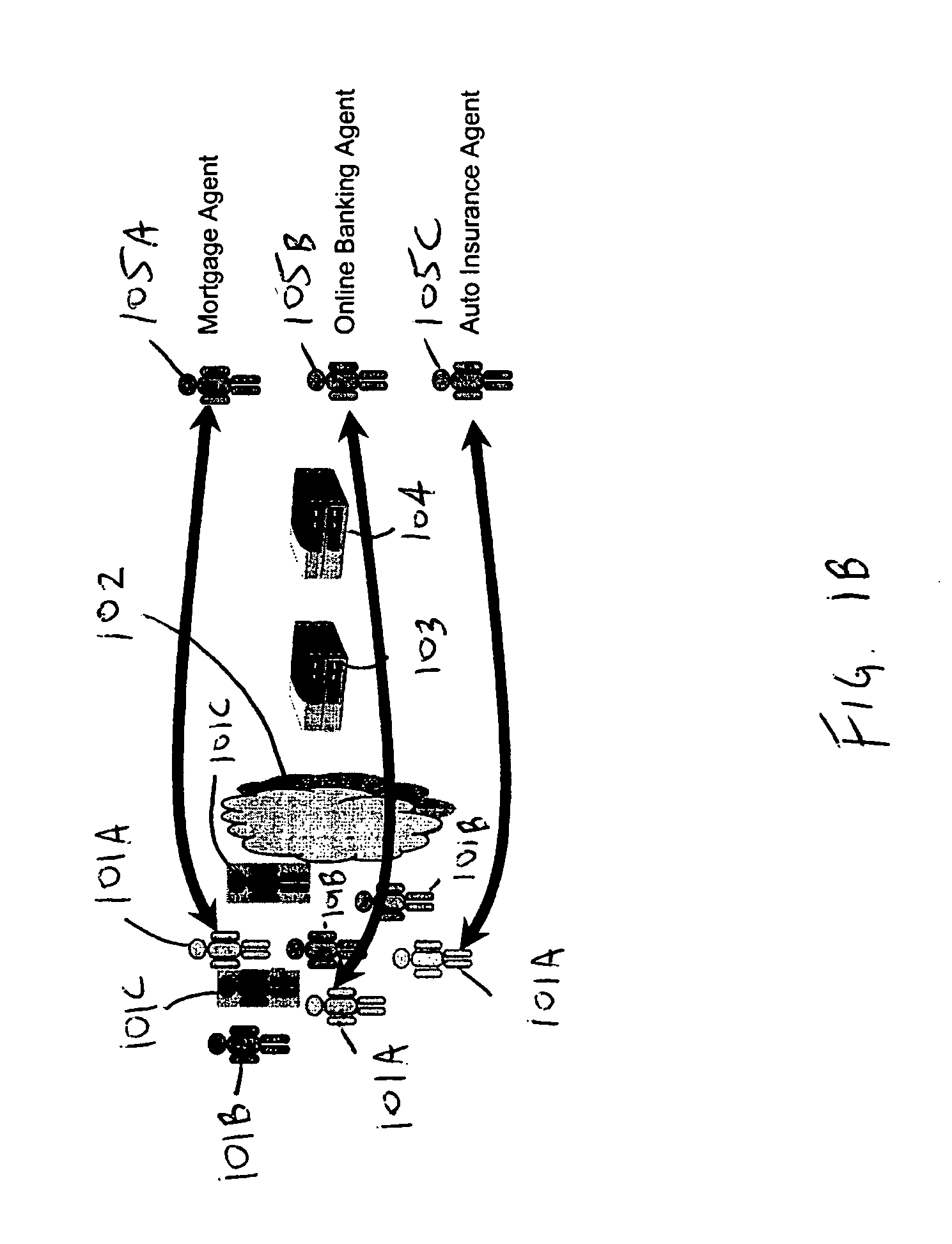
Patents
Literature
863 results about "Electronic business" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Online Business or e-business is any kind of business or commercial transaction that includes sharing information across the internet. Commerce constitutes the exchange of products and services between businesses, groups and individuals and can be seen as one of the essential activities of any business. Electronic commerce focuses on the use of ICT to enable the external activities and relationships of the business with individuals, groups and other businesses, while e-business refers to business with help of the internet. The term "e-business" was coined by IBM's marketing and Internet team in 1996.
System and method for establishing eletronic business systems for supporting communications servuces commerce
ActiveUS20060059107A1Easy to addEasy to liftPayment protocolsBilling/invoicingEnterprise application integrationSupporting system
Owner:NETCRACKER TECH SOLUTIONS
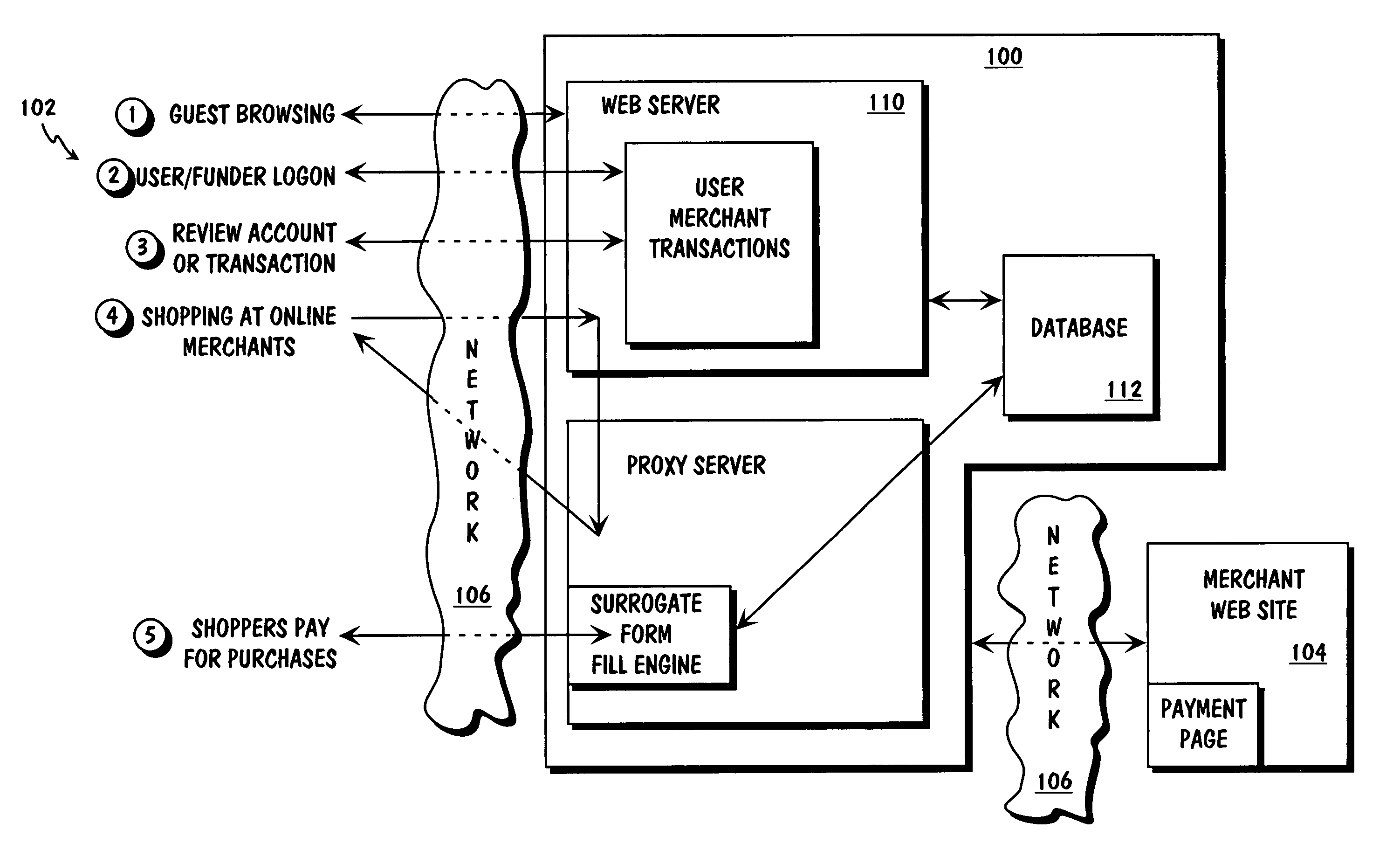
Method and apparatus for surrogate control of network-based electronic transactions
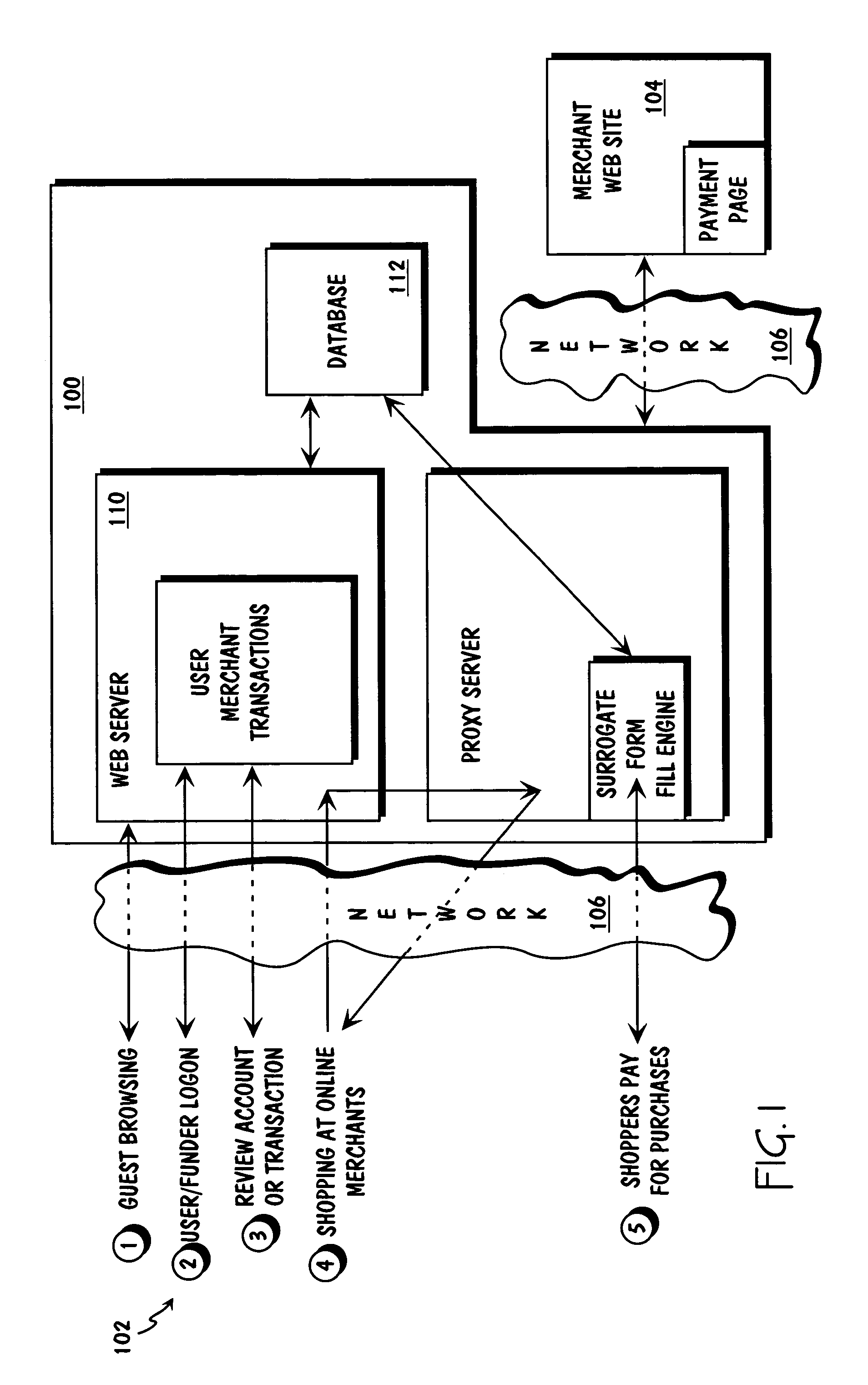
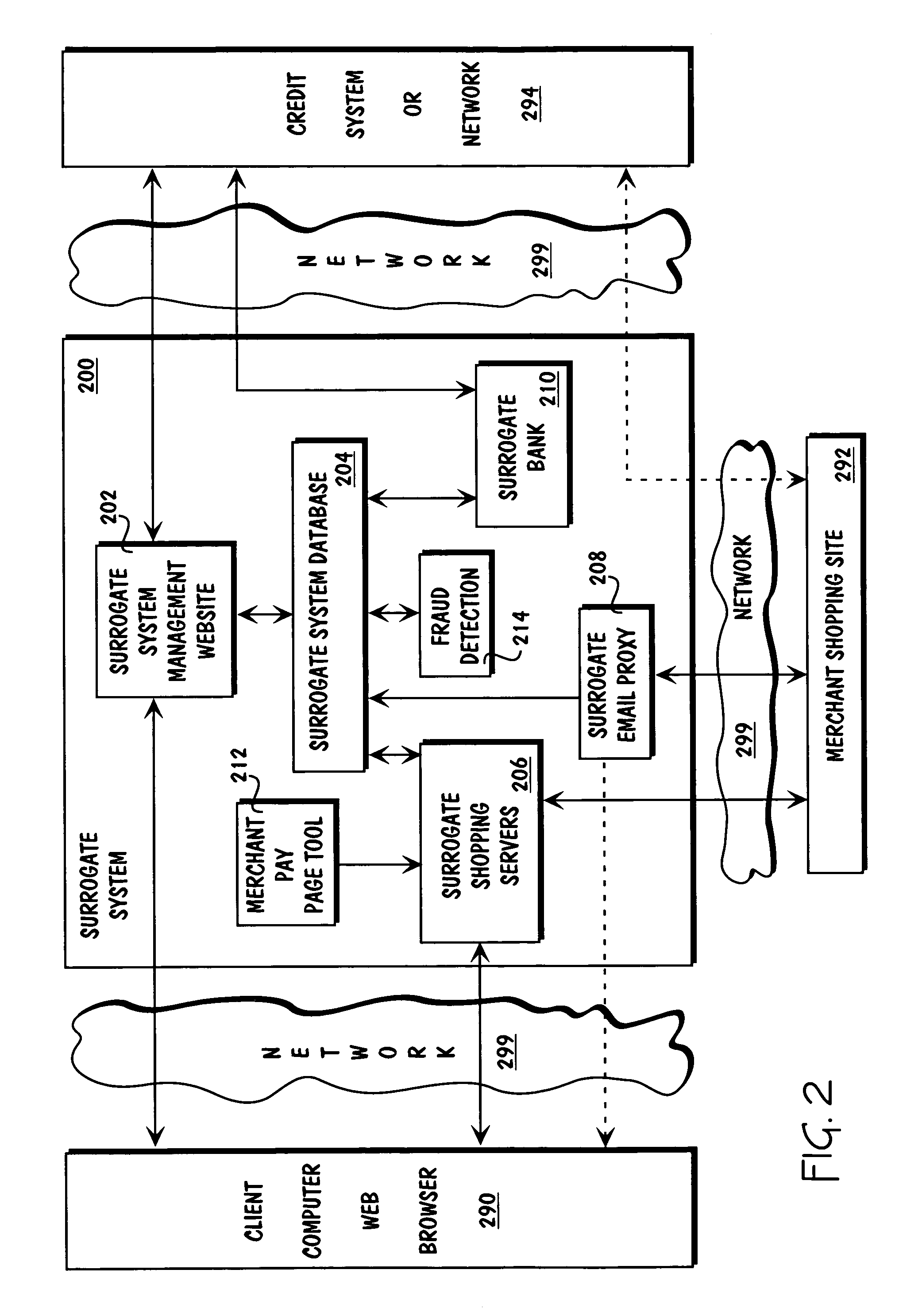
A surrogate system for the transparent control of electronic commerce transactions is provided through which an individual without a credit card is enabled to shop at online merchant sites. Upon opening an account within the surrogate system, the account can be funded using numerous fund sources, for example credit cards, checking accounts, money orders, gift certificates, incentive codes, online currency, coupons, and stored value cards. A user with a funded account can shop at numerous merchant web sites through the surrogate system. When merchandise is selected for purchase, a purchase transaction is executed in which a credit card belonging to the surrogate system is temporarily or permanently assigned to the user. The credit card, once loaded with funds from the user's corresponding funded account, is used to complete the purchase transaction. The surrogate system provides controls that include monitoring the data streams and, in response, controlling the information flow between the user and the merchant sites.
Owner:THE COCA-COLA CO
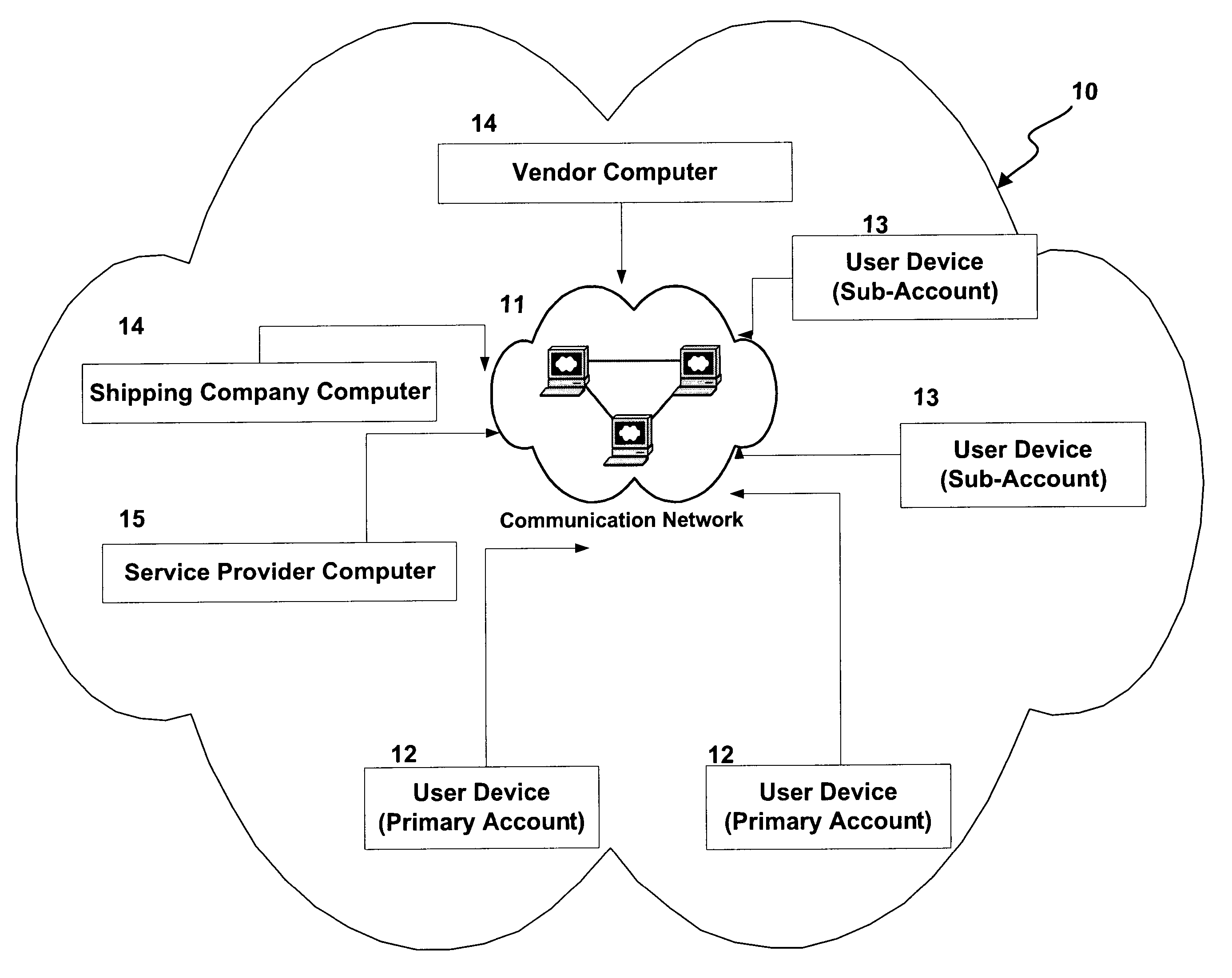
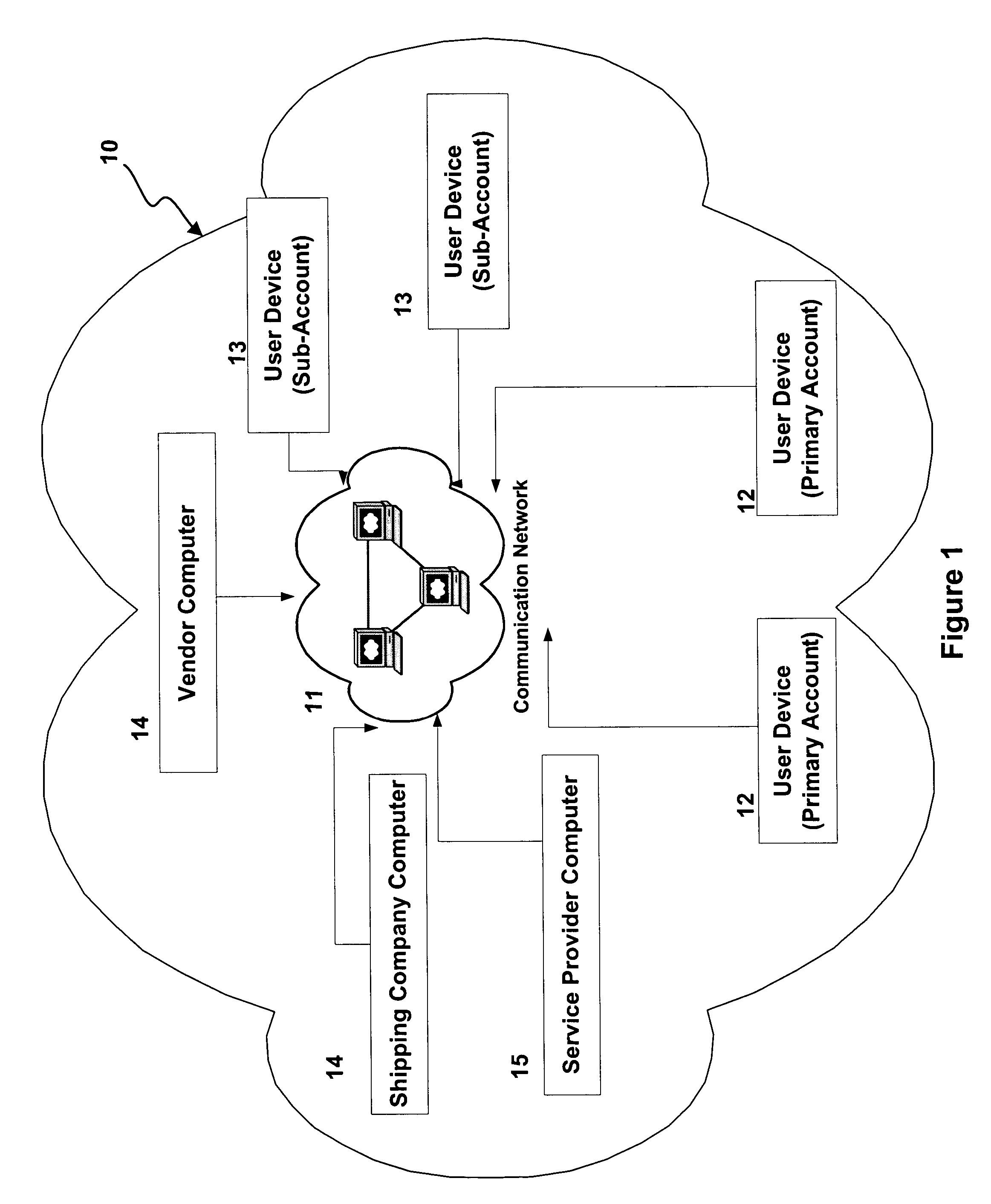
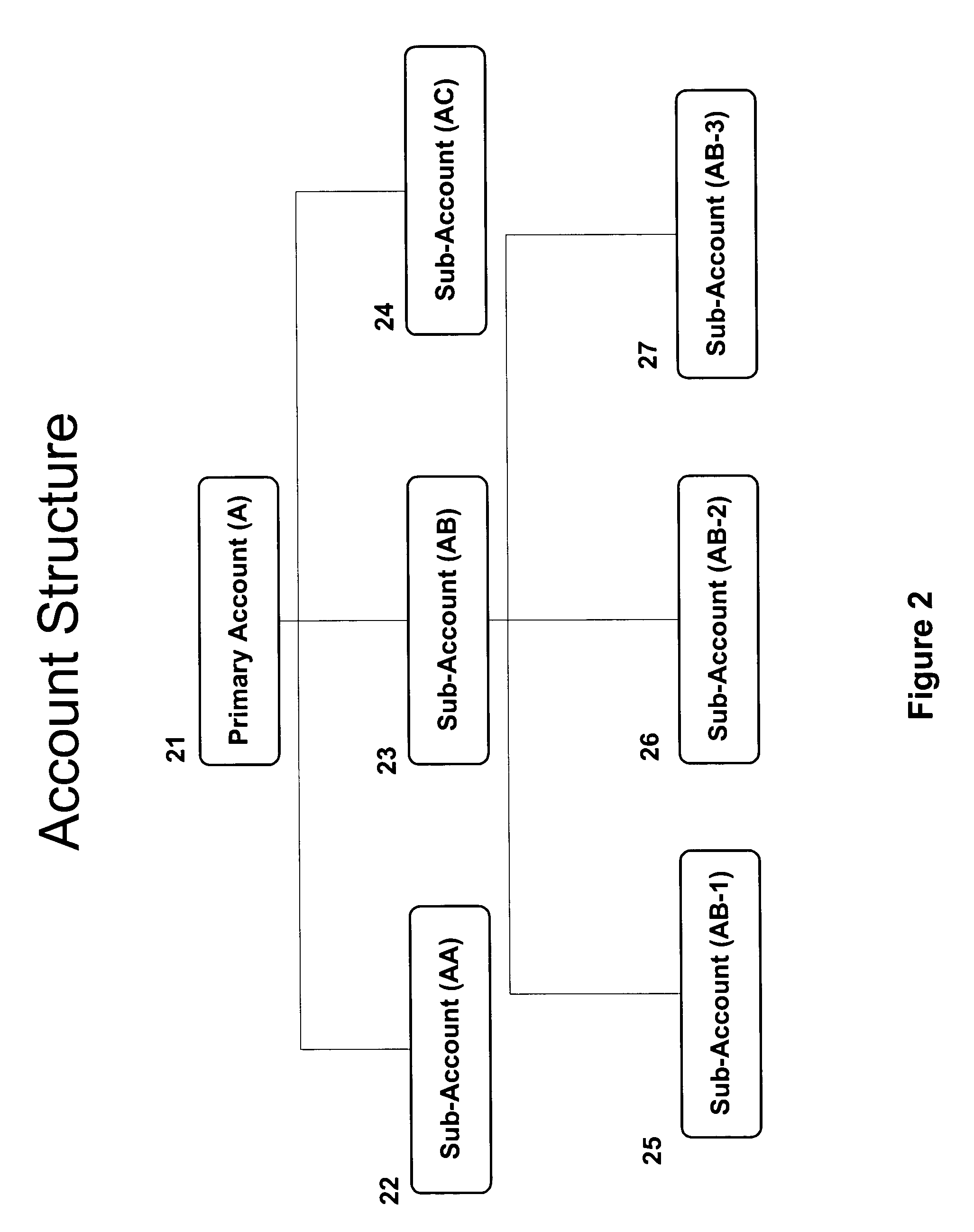
Methods and apparatus for transacting electronic commerce using account hierarchy and locking of accounts
Apparatus and methods are provided for facilitating electronic commerce in an environment in which a service provider handles business transactions between registered users and participating vendors and shipping companies, wherein users may establish and manage primary accounts and sub-accounts to purchase goods and services from participating vendors' web sites.
Owner:AML IP LLC
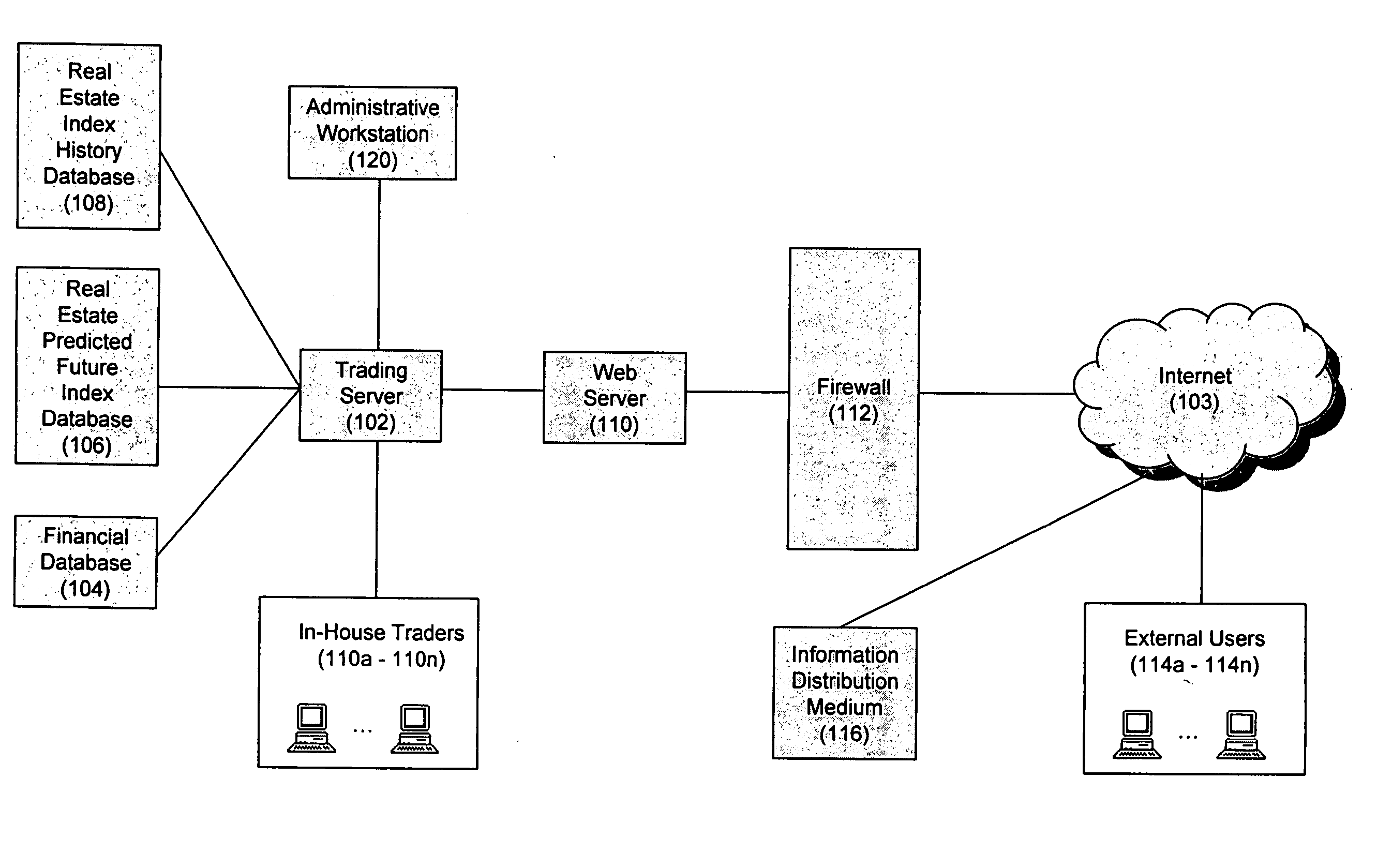
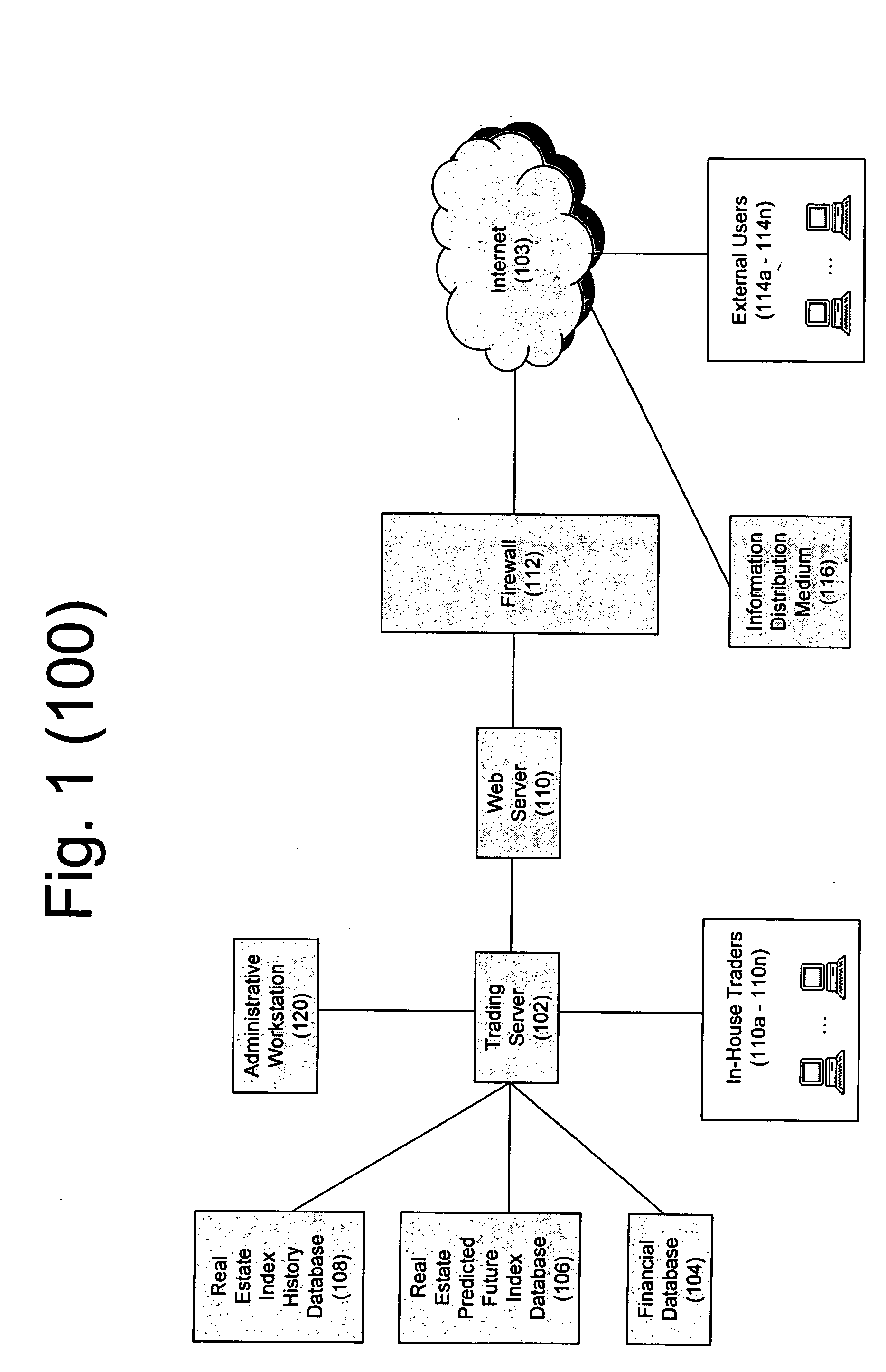
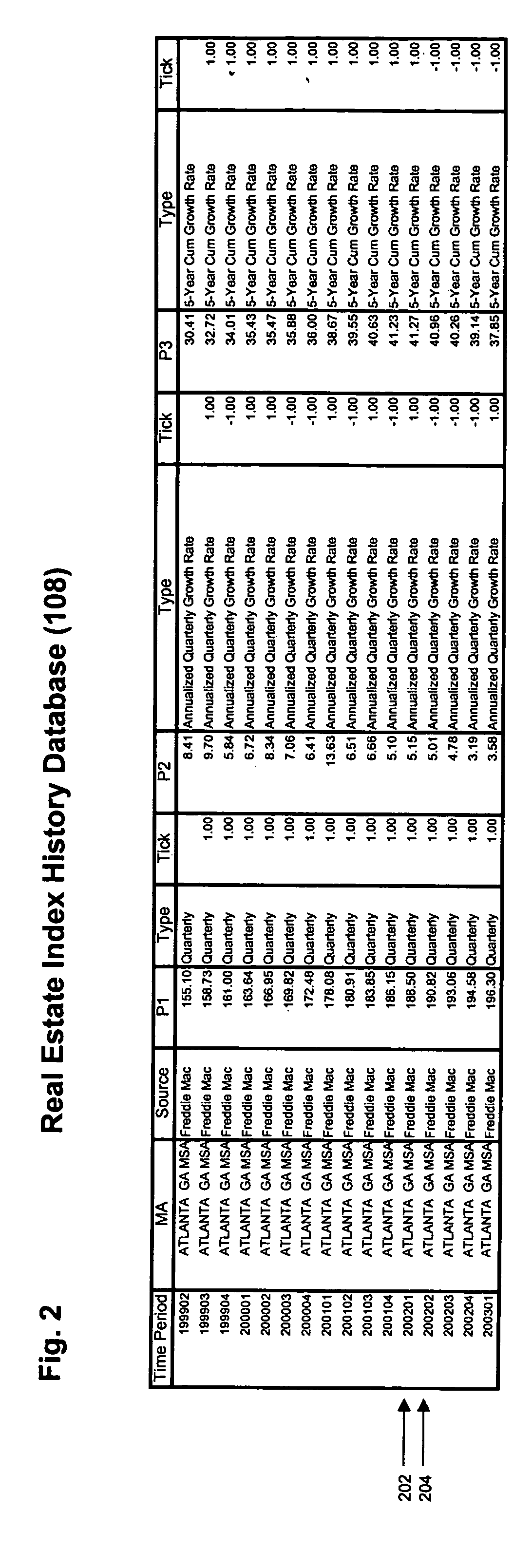
System, method, and computer program for creating and valuing financial instruments linked to real estate indices
InactiveUS20050216384A1Easy to implementFinanceSpecial data processing applicationsData miningCounterparty
A system, method and computer program for creating and valuing financial instruments (including but not limited to futures, forwards, call options, put options, swaps, “swaptions”, and “op-swaps”) linked to published real estate indices. The present invention will be referred to in this application as a real estate index linked financial instrument, and is defined as a financial instrument whose value changes based on movements in underlying indices based on real estate prices. These indices are published by sovereign governments, government-chartered agencies and departments (such as Fannie Mae, Freddie Mac, Office of Management and Budget, and the Treasury Department in the U.S.), non-governmental organizations, commercial banks, investment banks, realty agencies and many other organizations. The instruments can be written, with a published index number from any real estate index or indices as the initial value upon which the financial instrument's terms are based. The predicted future value of the real estate index or indices will change in response to market buy / sell demand based on investor expectations of the predicted future value of the real estate index or indices related to one or more real estate index linked financial instrument(s). Thus, the predicted future value of the index or indices will change in response to the market demand as investors offer to buy and / or sell real estate index linked financial instruments which will be listed on securities exchanges and electronic commerce networks (ECNs) as well as over the counter (OTC) and in private transactions. Each predicted future index value will change based on the investor expectation of how strong demand will be for the underlying real estate market upon which each index or indices are based. Thus, the present invention gives investors a means of taking or adjusting positions upon price movements in local, city, regional, state, national, or multinational / international real estate markets. It is important to note that real estate index linked financial instruments can be created either in standardized contract sizes that can be traded on futures, options or other securities exchanges, ECNs and / or OTC, or can be customized to meet the specifications of a transactional counterparty which wishes to speculate on movements in local, city, regional, state, national, or multinational / international real estate prices. Such instruments may also be created from a plurality of indices, thus allowing an investor to package movements from several different real estate indices into a single financial instrument. Such instruments may also involve a combination of real estate index linked financial instruments, either with each other or with other financial instruments in a combination containing at least one real estate index linked financial instrument.
Owner:WORLD RISK GRP
Method and system for providing interactive business directory services
InactiveUS20050044061A1Easy to acceptLow costDigital data processing detailsMarketingThe InternetDisplay device
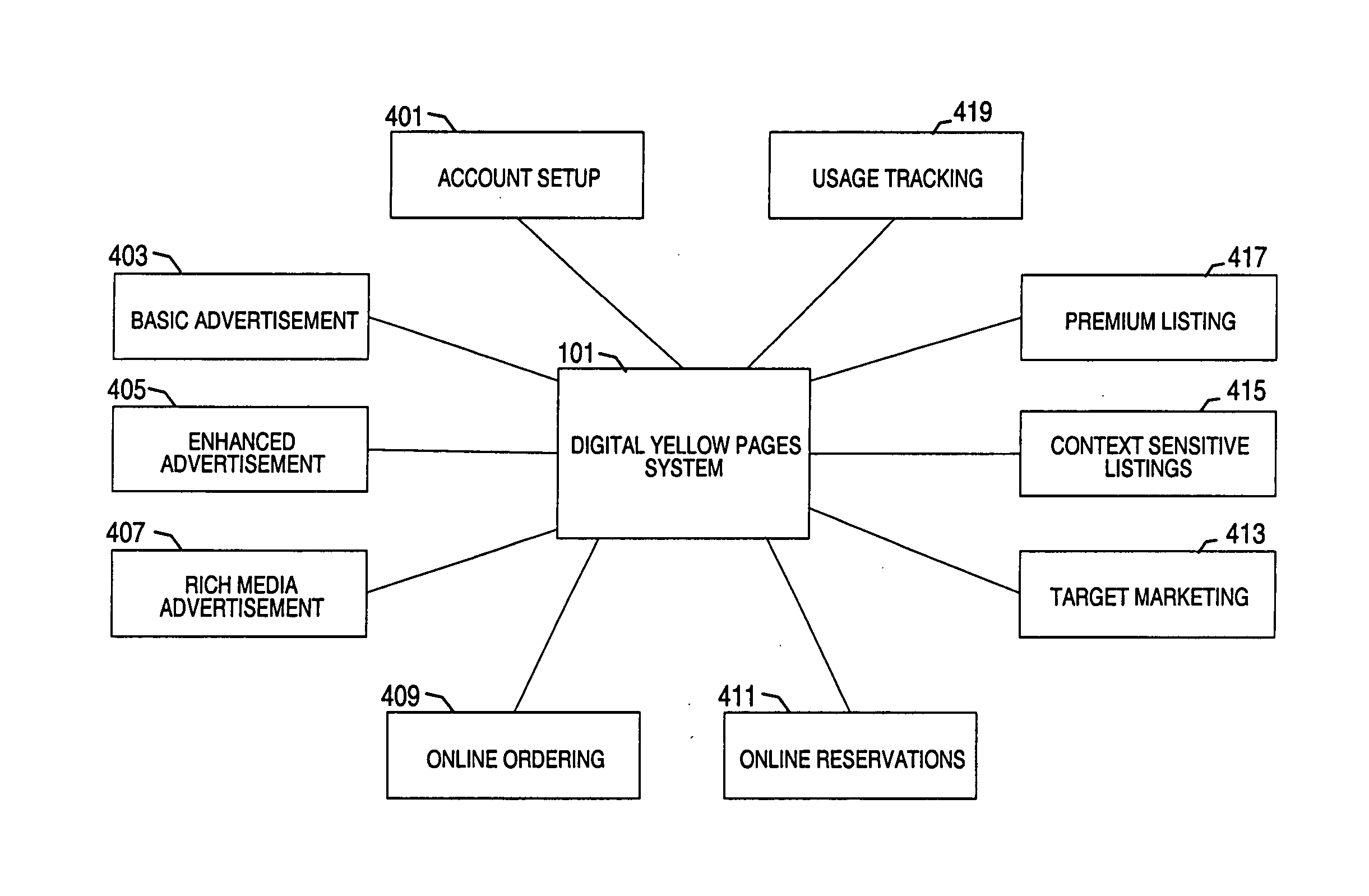
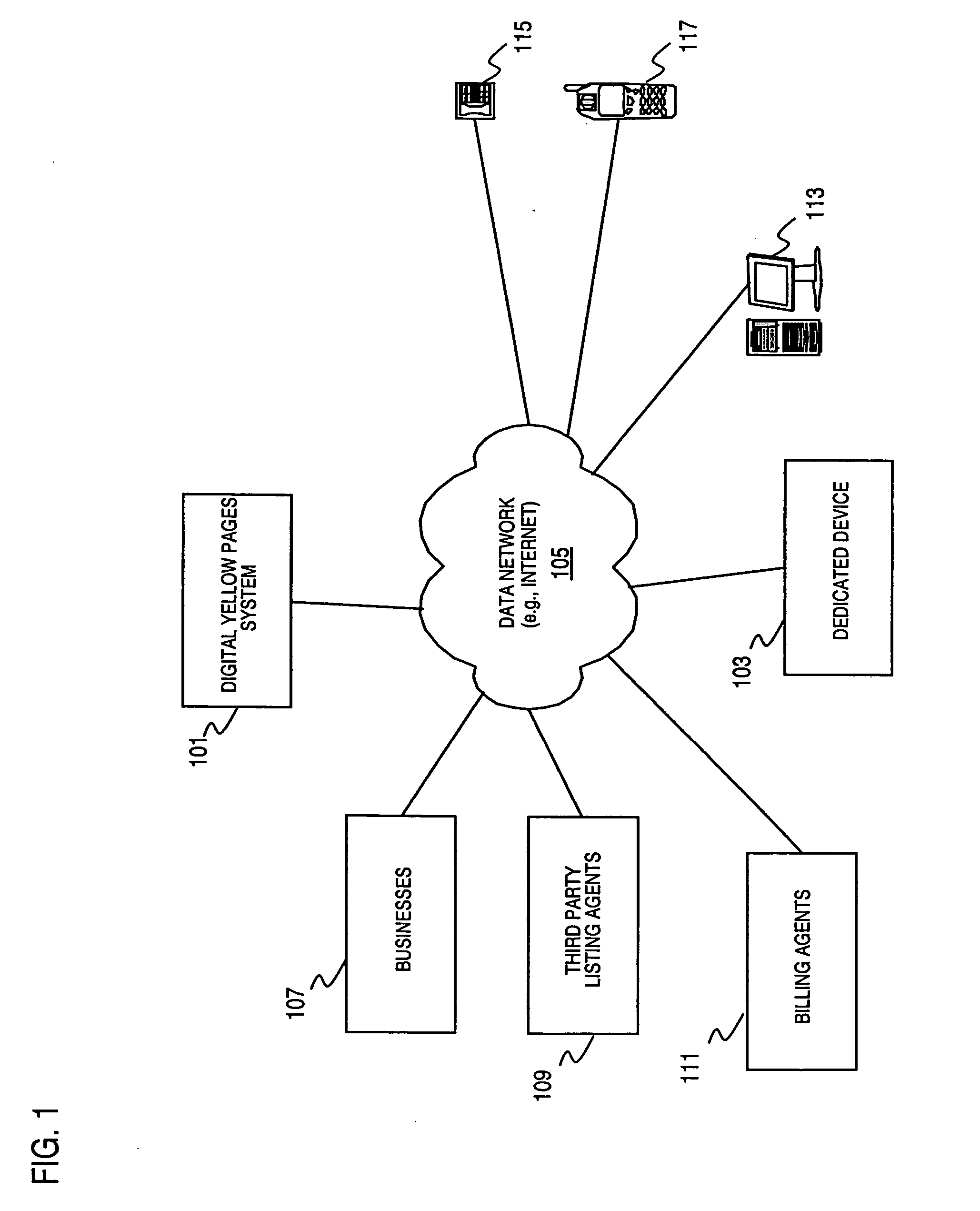
An approach for providing an electronic business directory (e.g., Digital Yellow Pages) with interactive services over an electronic consumer device. The device includes means for retrieving information from a remote database storing business directory listings and advertisements, wherein the remote database is accessed over a data network (e.g., the global Internet) and is capable of being modified directly by a business listed in the directory or by an agent of the business. According to one embodiment of the present invention, the device also includes a touch screen display for displaying the information and for receiving input relating to the retrieved information associated with the interactive services.
Owner:JK GRP THE
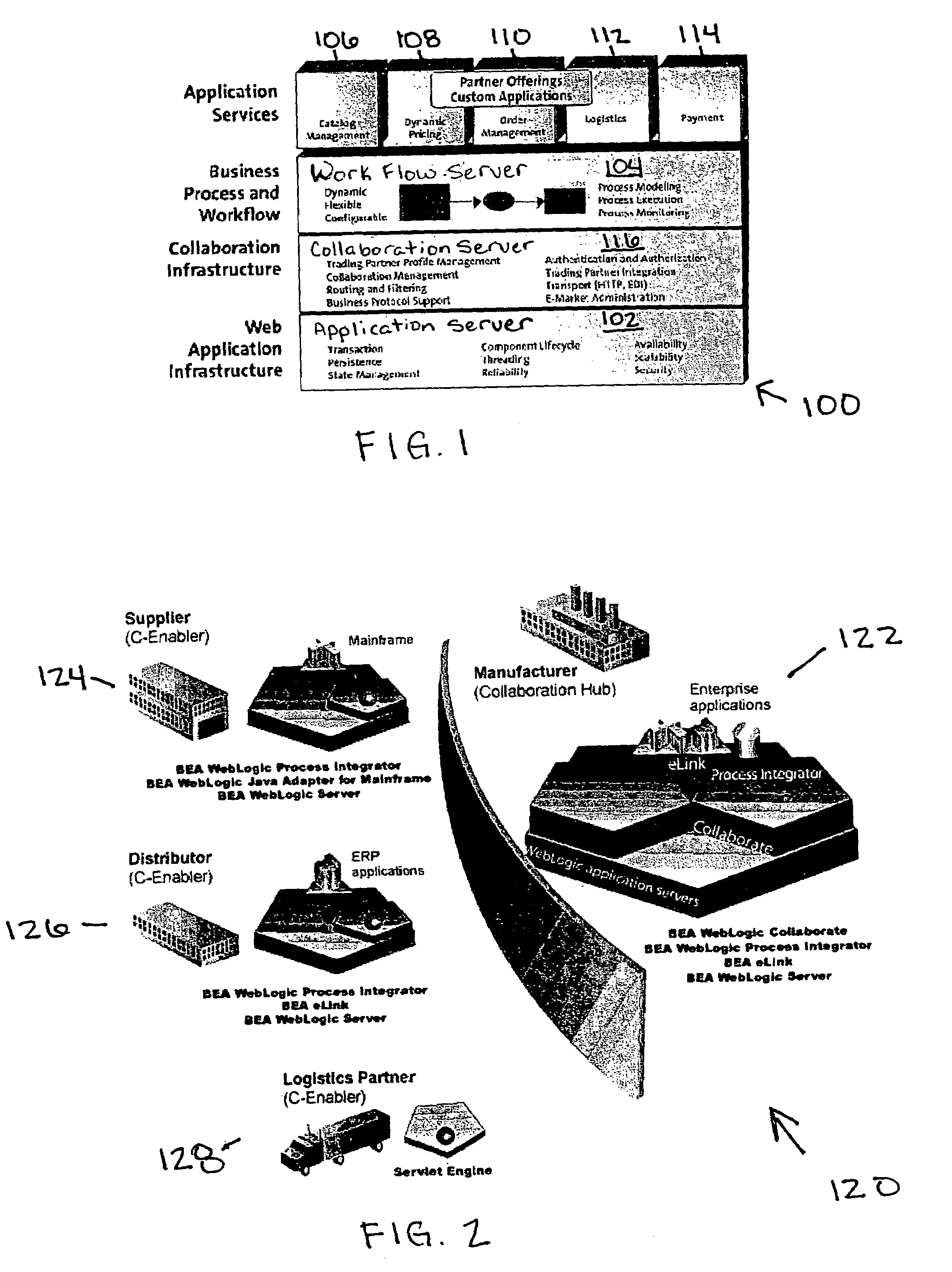
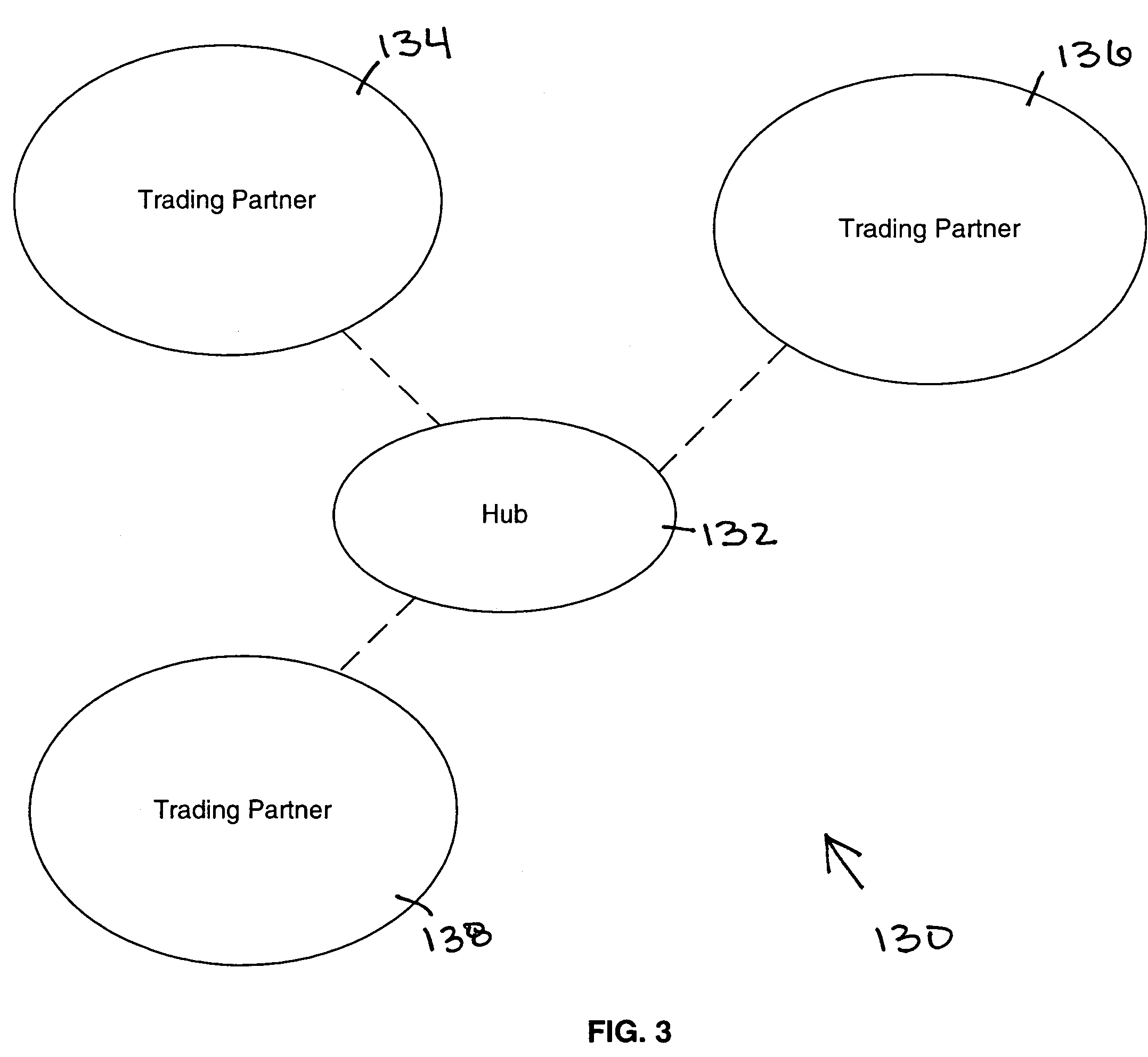
Workflow integration system for enterprise wide electronic collaboration
InactiveUS7051071B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsEnterprise levelElectronic business
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides a workflow integration system for enterprise wide electronic collaboration. An embodiment of the invention includes a workflow integration system for a collaboration system that allows for sharing of workflow information between collaboration participants, comprising a collaboration server having stored thereon an enterprise workflow, a workflow server having stored thereon a participant workflow and an integration mechanism for allowing said enterprise workflow and said participant workflow to interact with one another.
Owner:ORACLE INT CORP
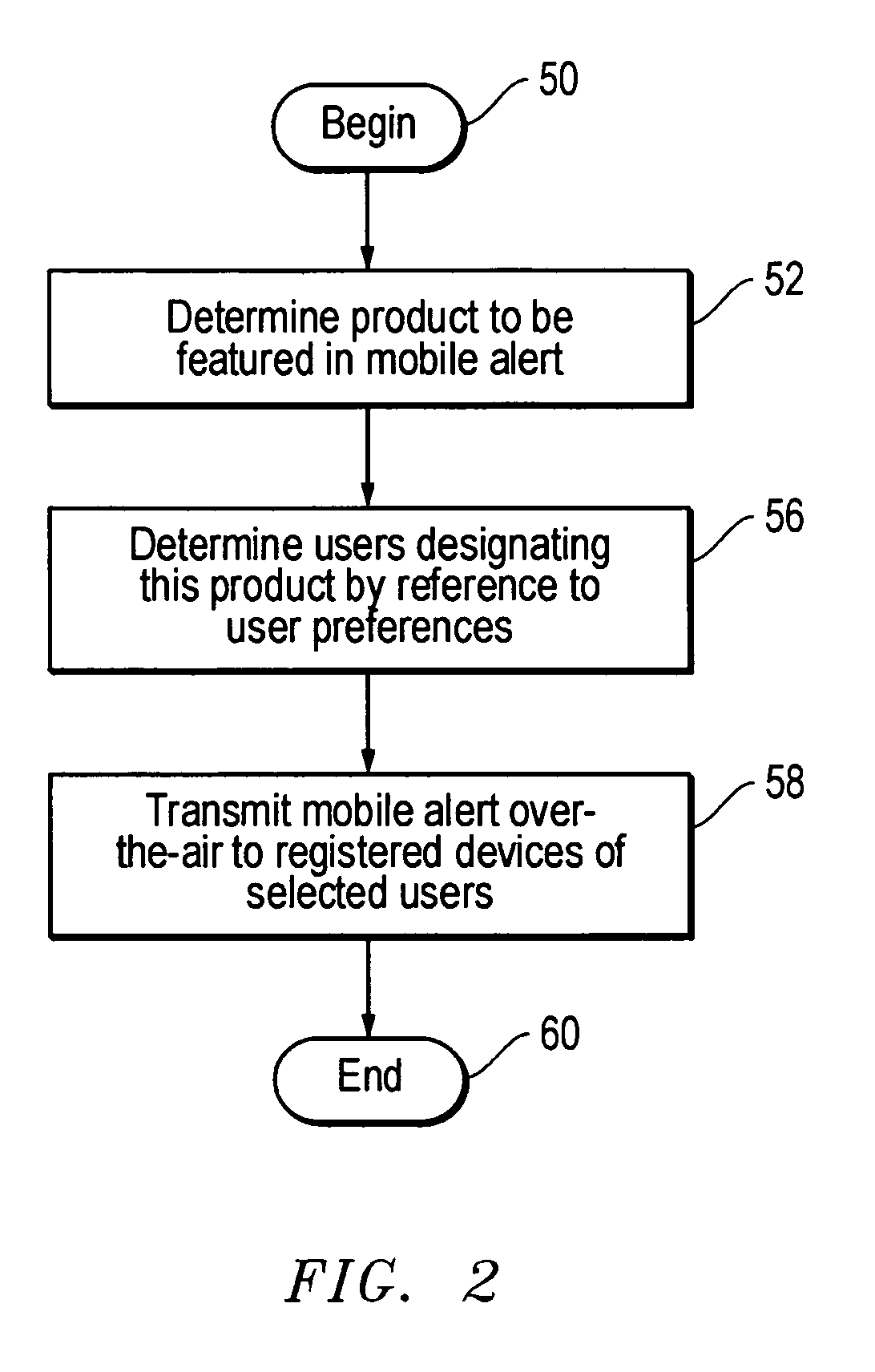
Method, system and program product for communicating e-commerce content over-the-air to mobile devices
InactiveUS20050131837A1Easy to optimizeFacilitating wireless mobile e-commerceConnection managementData switching by path configurationGraphicsService information
Product or service information in the form of selected wireless e-commerce content is transmitted from a server to a mobile device, such as mobile telephone or personal digital assistant. The e-commerce content is transmitted either in response to an explicit user request for communication of the e-commerce content, or, in the alternative, is “pushed” to the mobile device as permitted by a user but in the absence of a specific request. The e-commerce content received at the mobile device is presented to a user by the mobile device in textual or graphical format in conjunction with an indication of a communication needed to consummate an e-commerce transaction. If the user desires to purchase the good or service represented by the e-commerce content, the user initiates the communication indicated by the e-commerce content.
Owner:OVERSTOCK COM
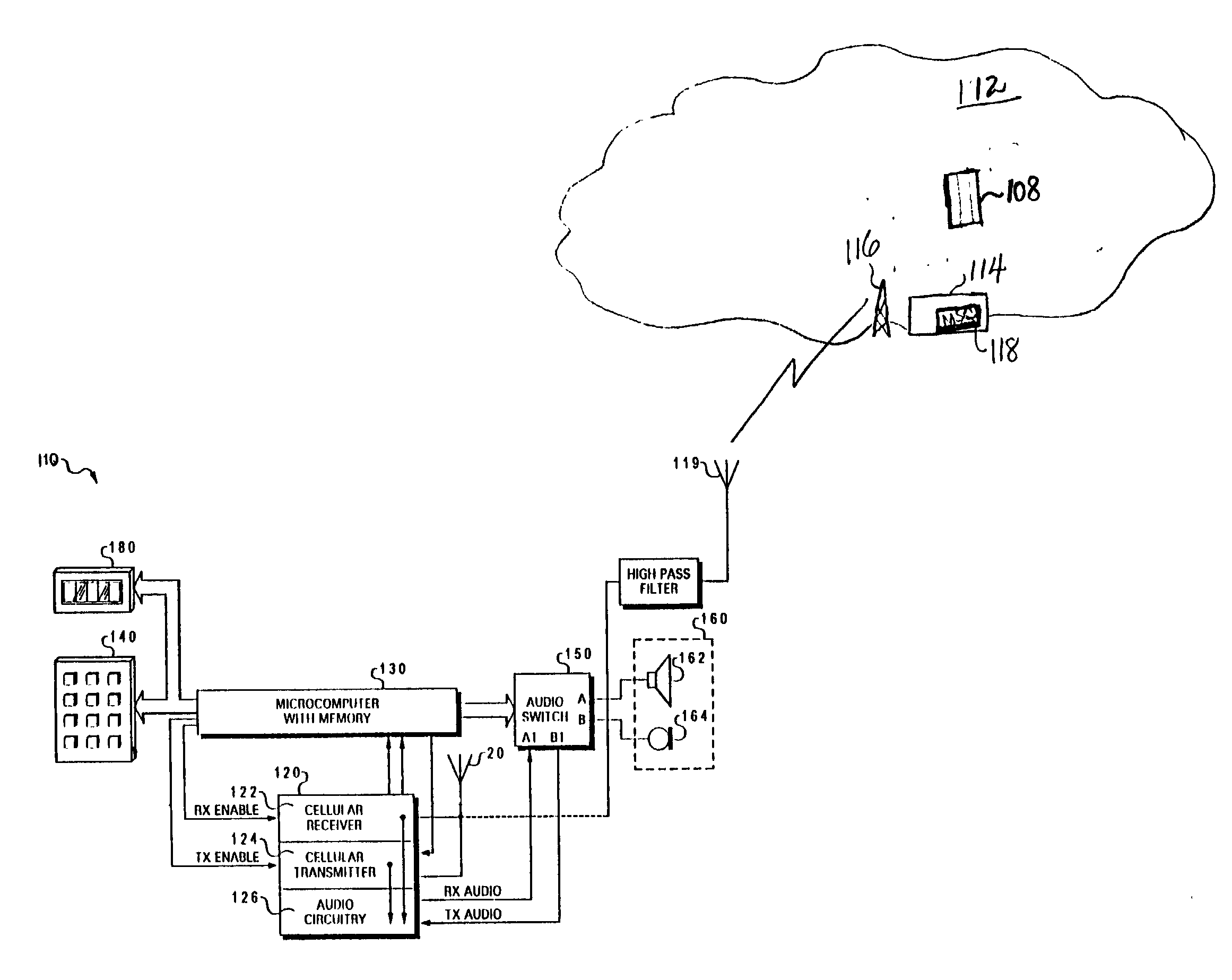
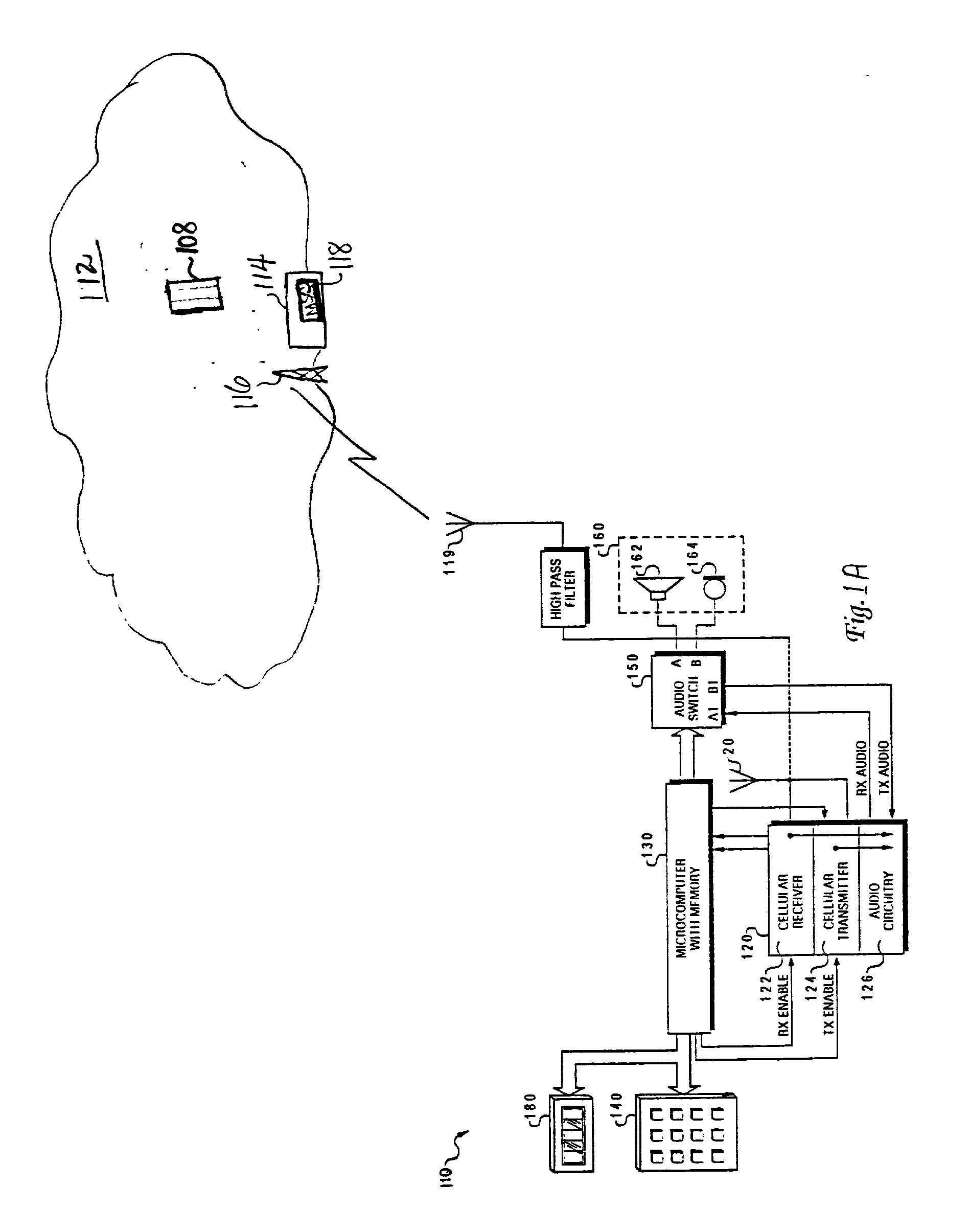
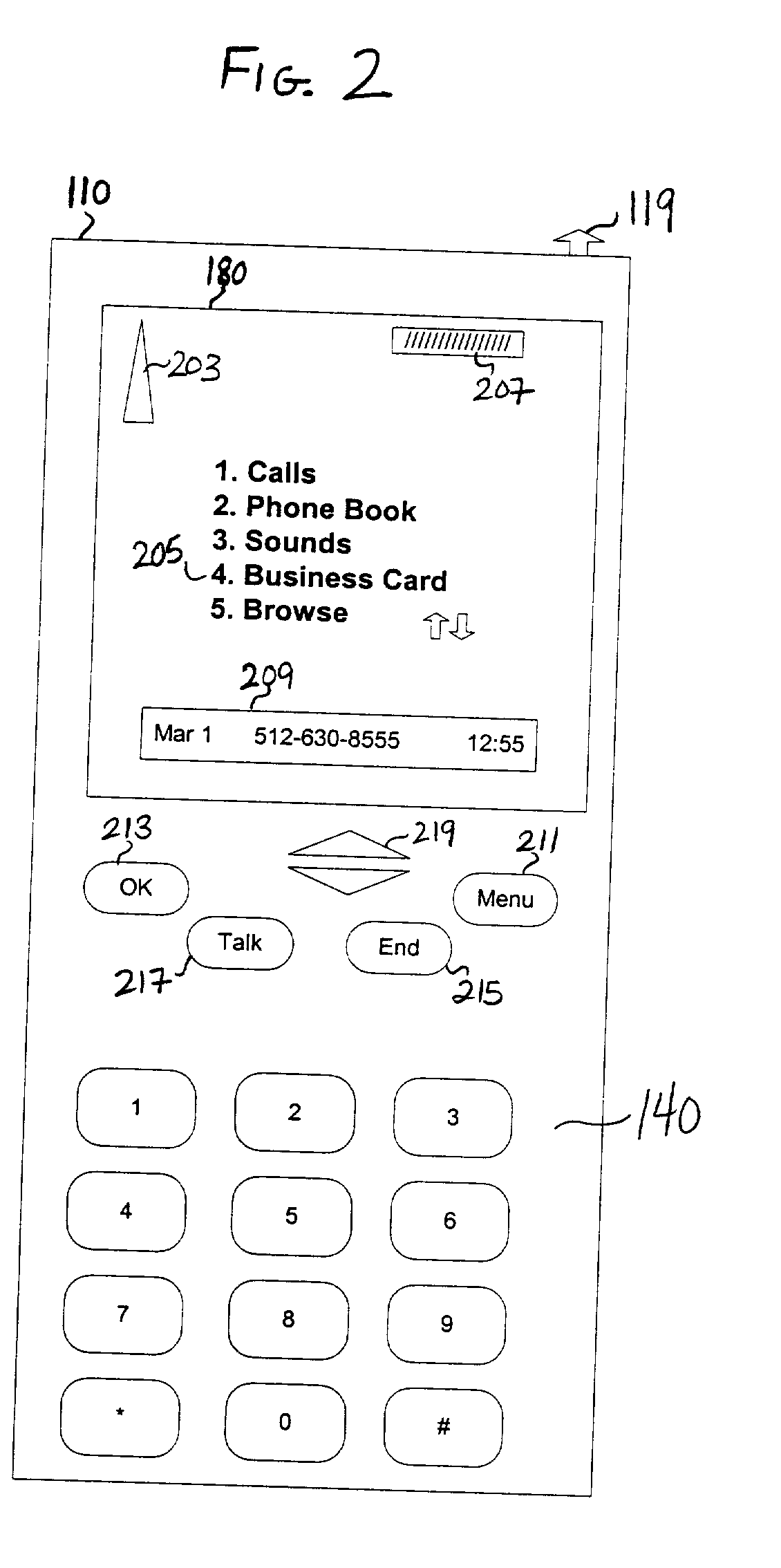
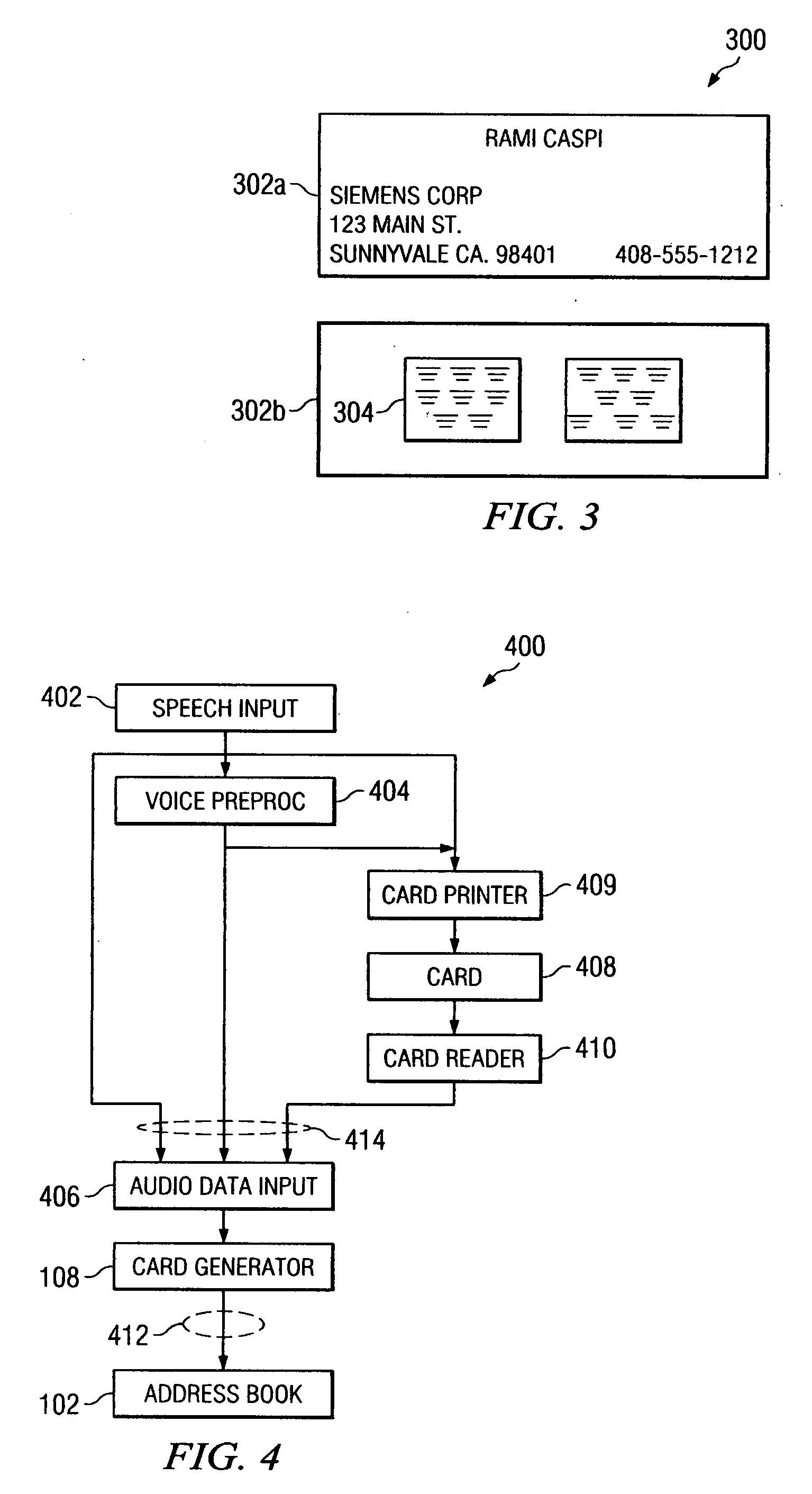
Business card presentation via mobile phone
A method for providing an electronic business card to a contact via a cellular phone is disclosed. Several business card menu options are provided to a user of a cellular telephone. The cellular phone user enters business card information / data into the cellular phone utilizing the business card menu options. The business card data is stored locally on the cellular phone or in a service provider database. When the user is in communication via cellular phone with someone he wishes to provide his business card to, the user selects a menu item that activates the transmission of the electronic business card to the desired recipient's cellular phone.
Owner:IBM CORP
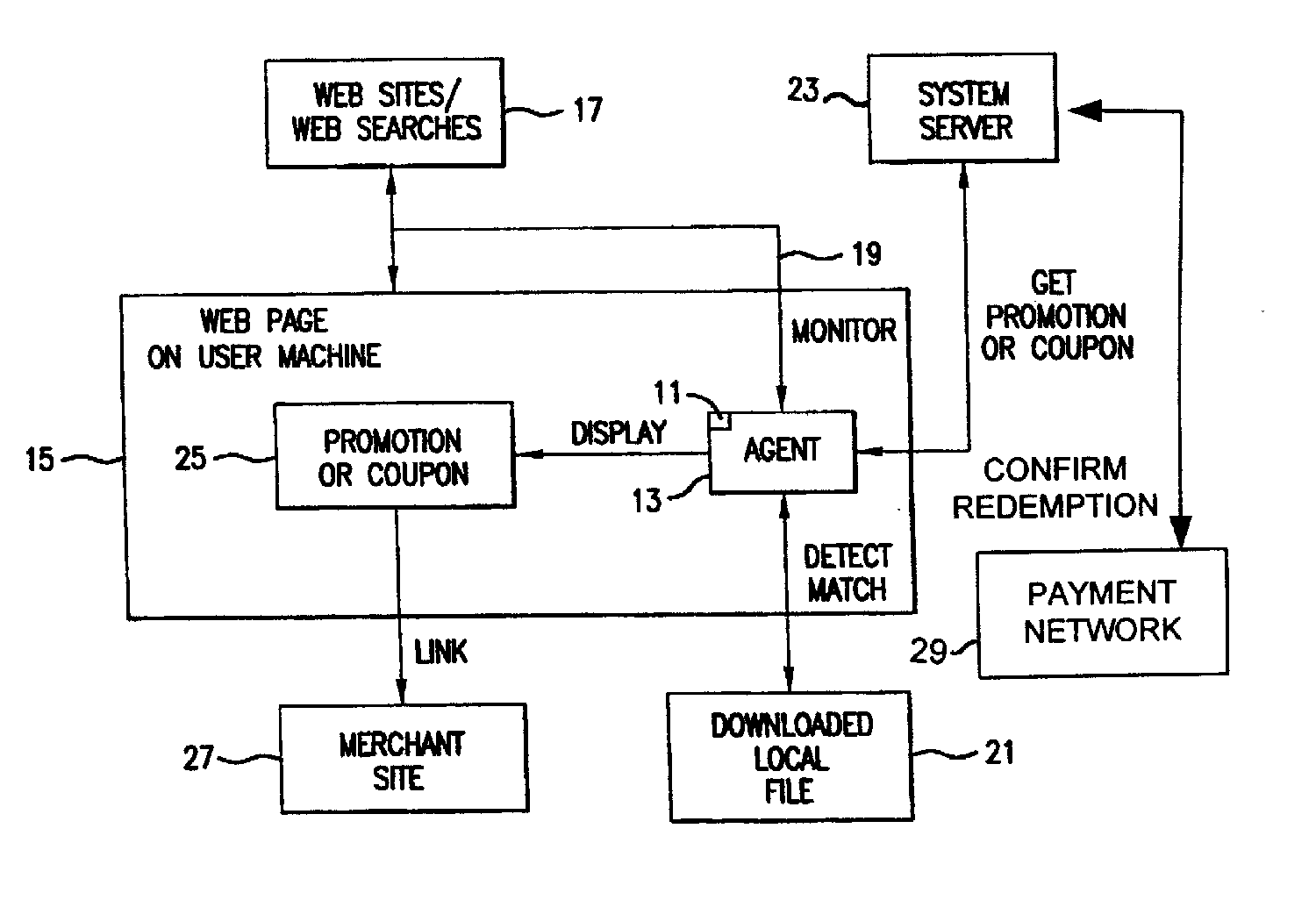
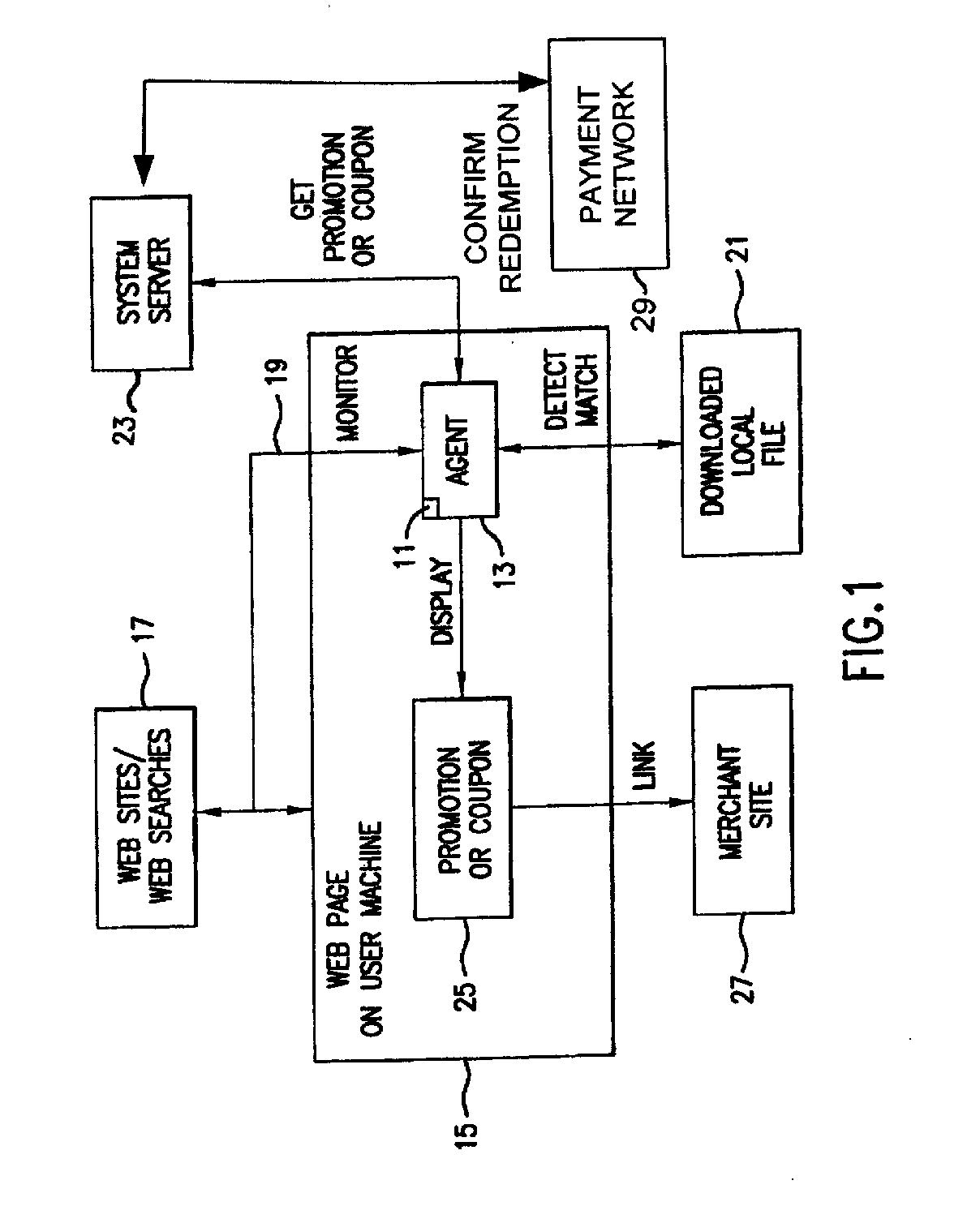
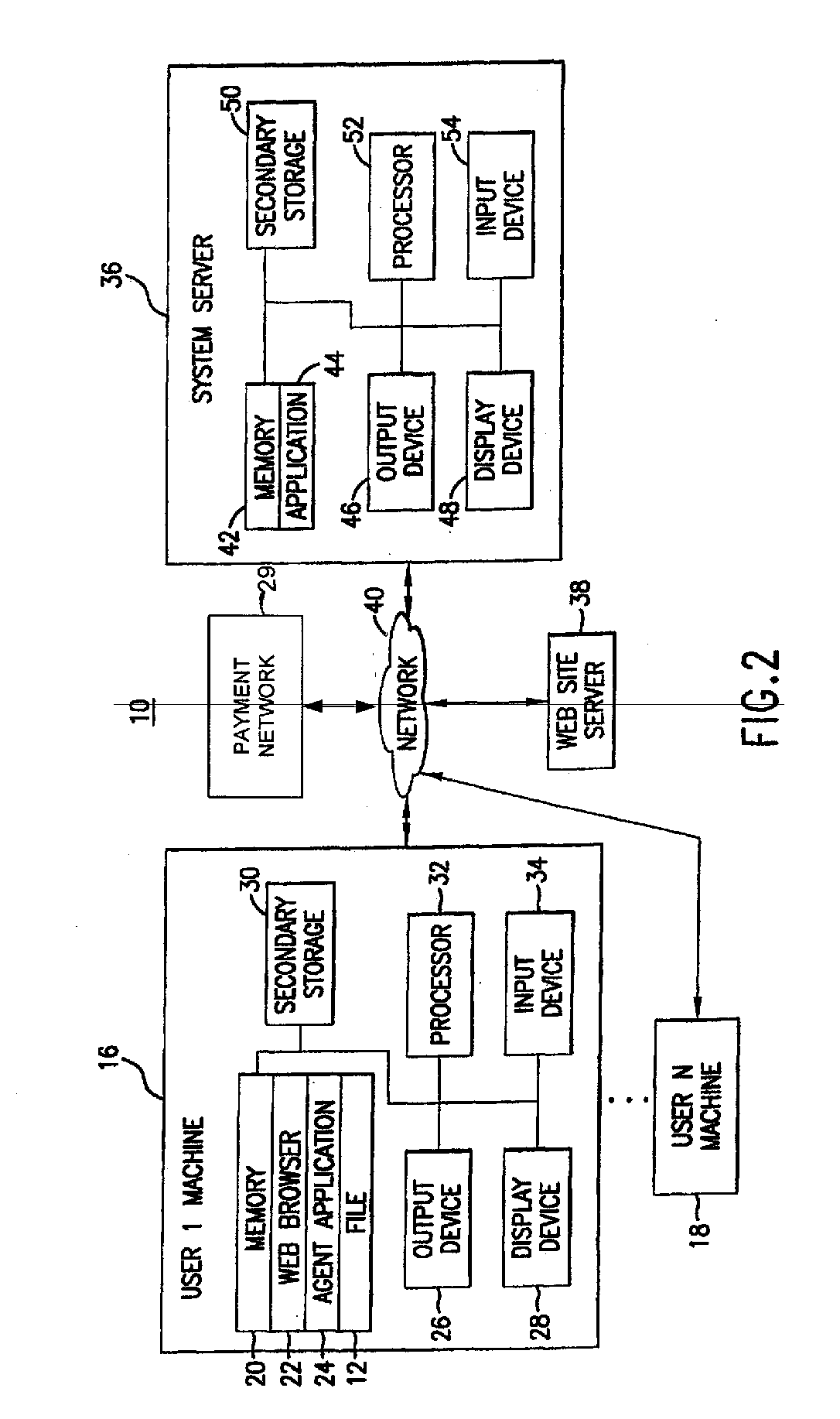
Software agent for facilitating electronic commerce transactions through display of targeted promotions or coupons
InactiveUS20060015405A1Easy to confirmAdvertisementsBroadcast information monitoringNetwork addressSoftware
A software agent for locally tracking a user's network interaction, such as web browsing, and providing targeted promotions with optional coupons to the user. The monitoring involves use of a downloaded file of network addresses and words potentially tailored to each individual user. The software agent locally compares network addresses and content of web sites accessed and search terms entered against the stored addresses and key words in the file. Upon detecting a match, the software agent contacts a system server to obtain a promotion with an optional coupon for the match, and displays an indication of the promotion or coupon to the user, providing the user with the option to view, decline, save, or defer the promotion. The user is provided with redeemable credits for viewing promotions, visiting the site of a merchant offering the promotion, completing a transaction, and spending at least a threshold dollar amount. The coupons can include coupons targeted to users geographically close to particular merchants so that the coupons can be printed and redeemed at the merchant's establishment. Transactions related to the promotions, whether completed online or in-store, are confirmed to demonstrate the efficacy of the promotions, award additional loyalty rewards to a user's account, or to compensate an advertiser or affiliate. Confirmation of in-store transactions may be accomplished by accessing transaction data routed through third-party payment networks used for credit and debit card transactions and cellular phone transactions and the like.
Owner:KNOWLEDGEFLOW
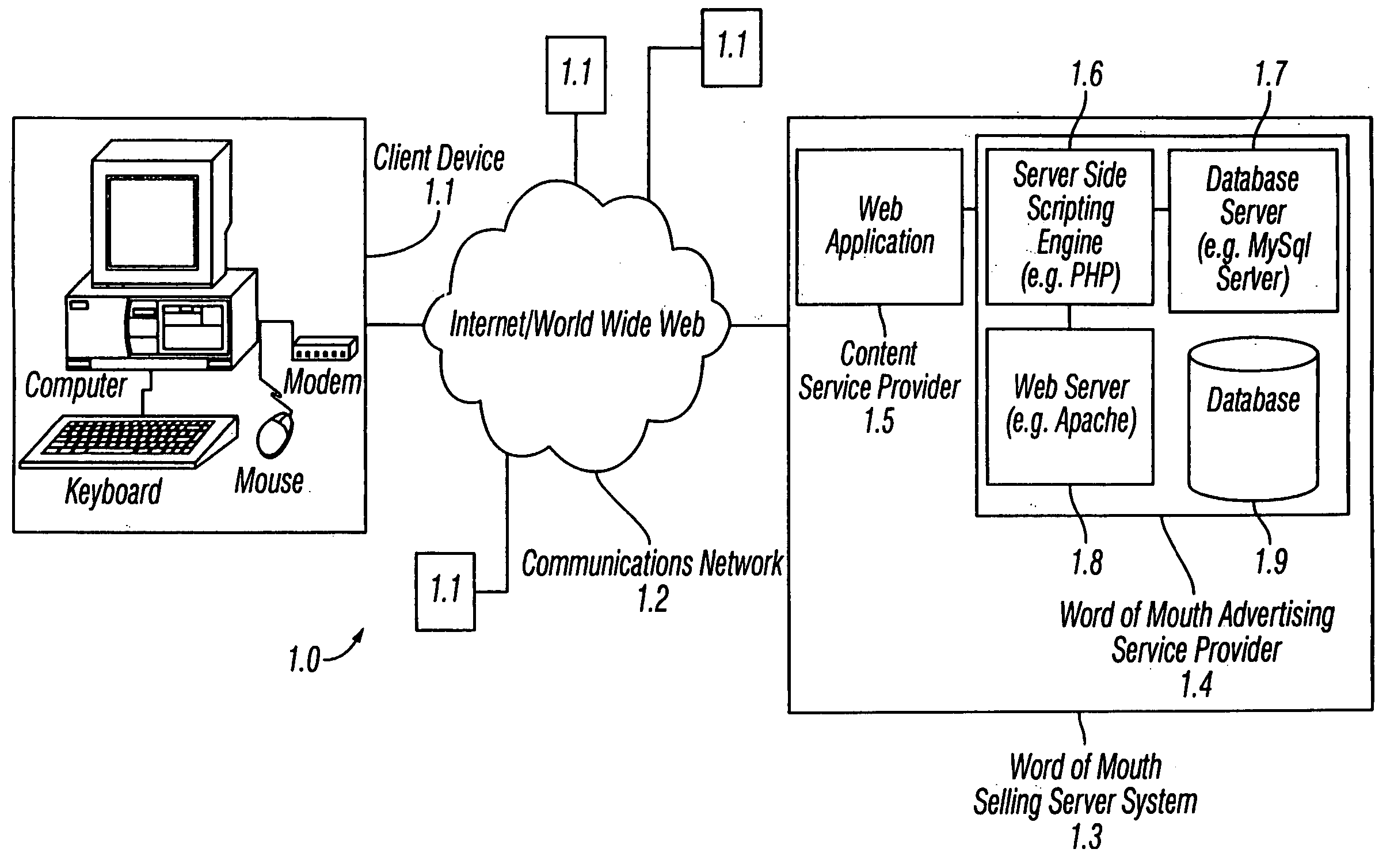
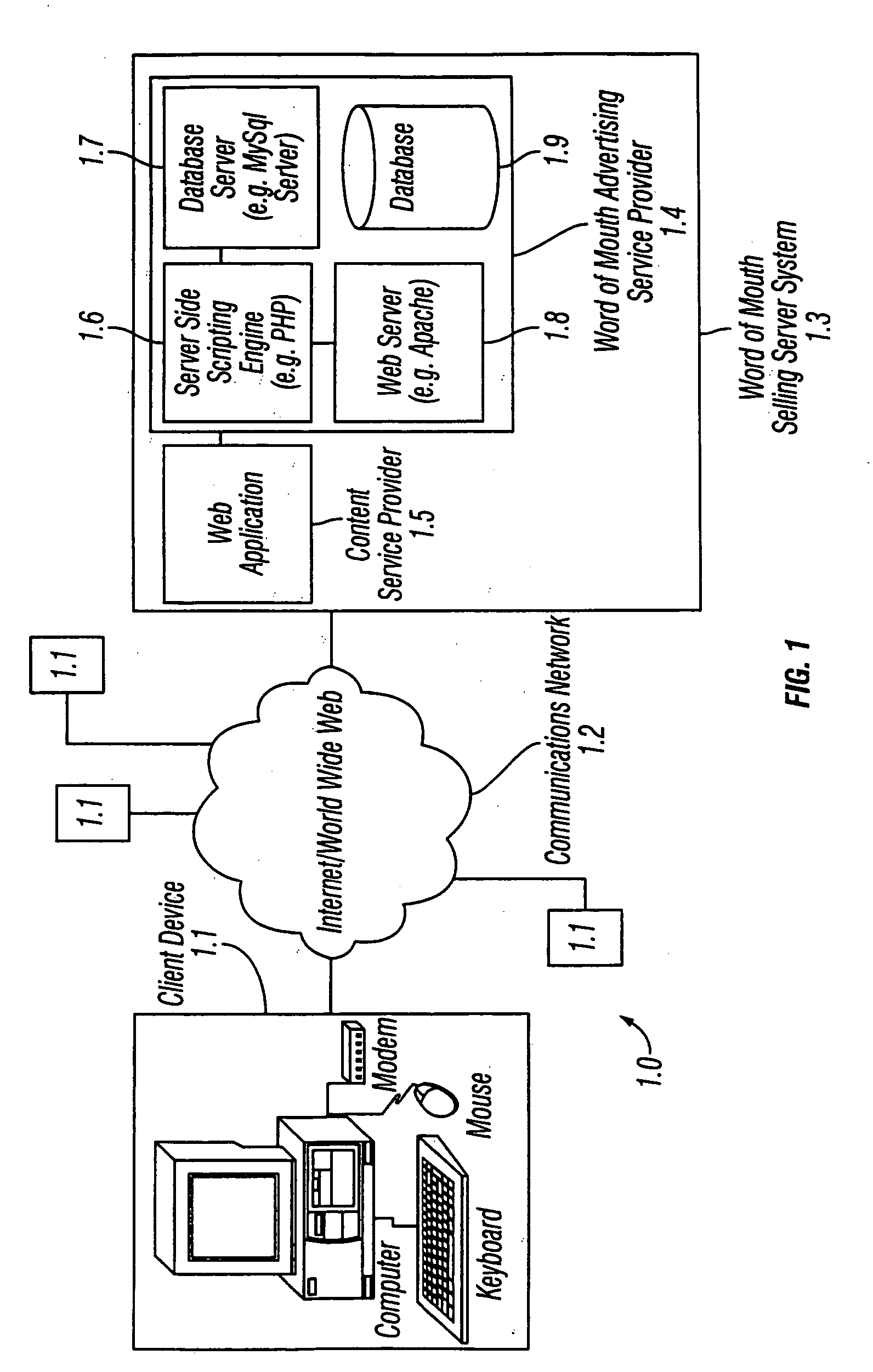
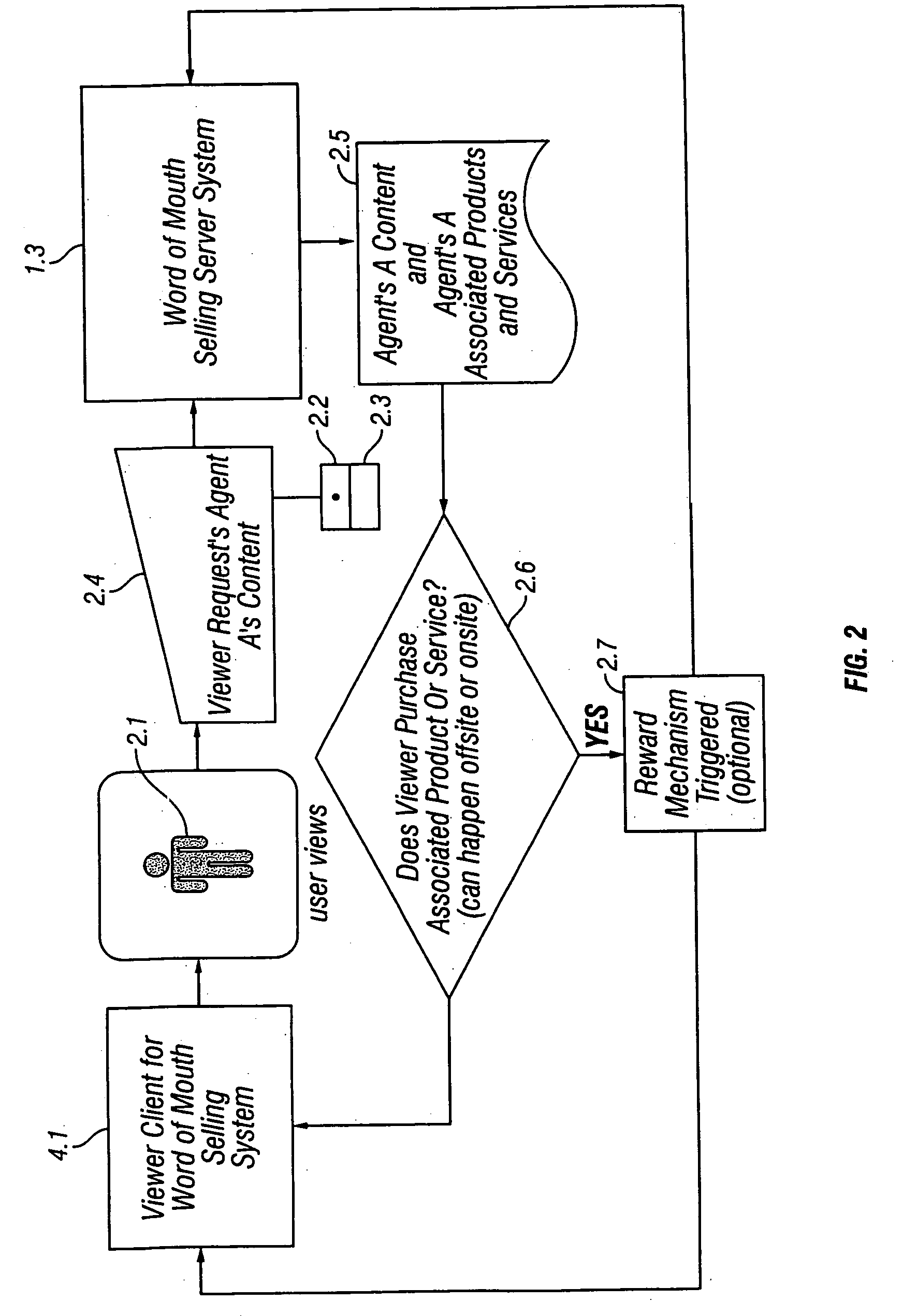
Method and apparatus for word of mouth selling via a communications network
ActiveUS20050234781A1Reduce disadvantagesSpecial data processing applicationsMarketingPurchasingElectronic business
A selling method and system that allows individuals or groups to interactively select associate products and services with their online presence in exchange for the online service, as part of an online service, or for some reward, monetary or otherwise. Individuals or groups select products and services from a pool of partner e-commerce retailers or import them from their purchasing histories based on personal preference and may use them as a means of expression for their online audience as part of an online service. This provides e-commerce retailers with self-selected targeted marketing and referral selling to affinity groups, the online version of word of mouth selling. E-commerce retailers share revenue and pay for referrals that occur via this word of mouth selling framework. Online services that have any form of user identity within the context of a larger audience may utilize this form of user based referral selling as a revenue generating tool.
Owner:RAKUTEN COMMERCE
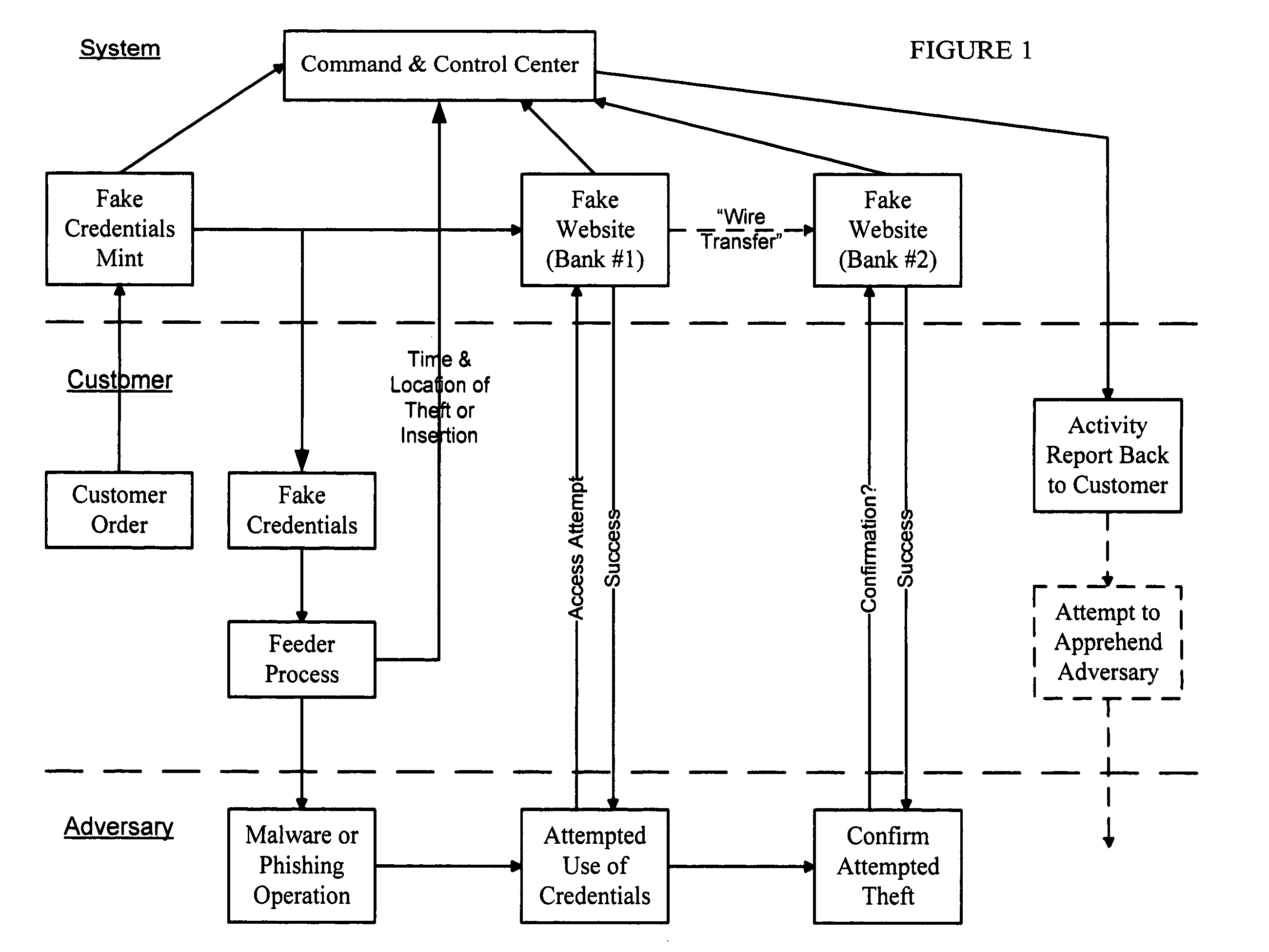
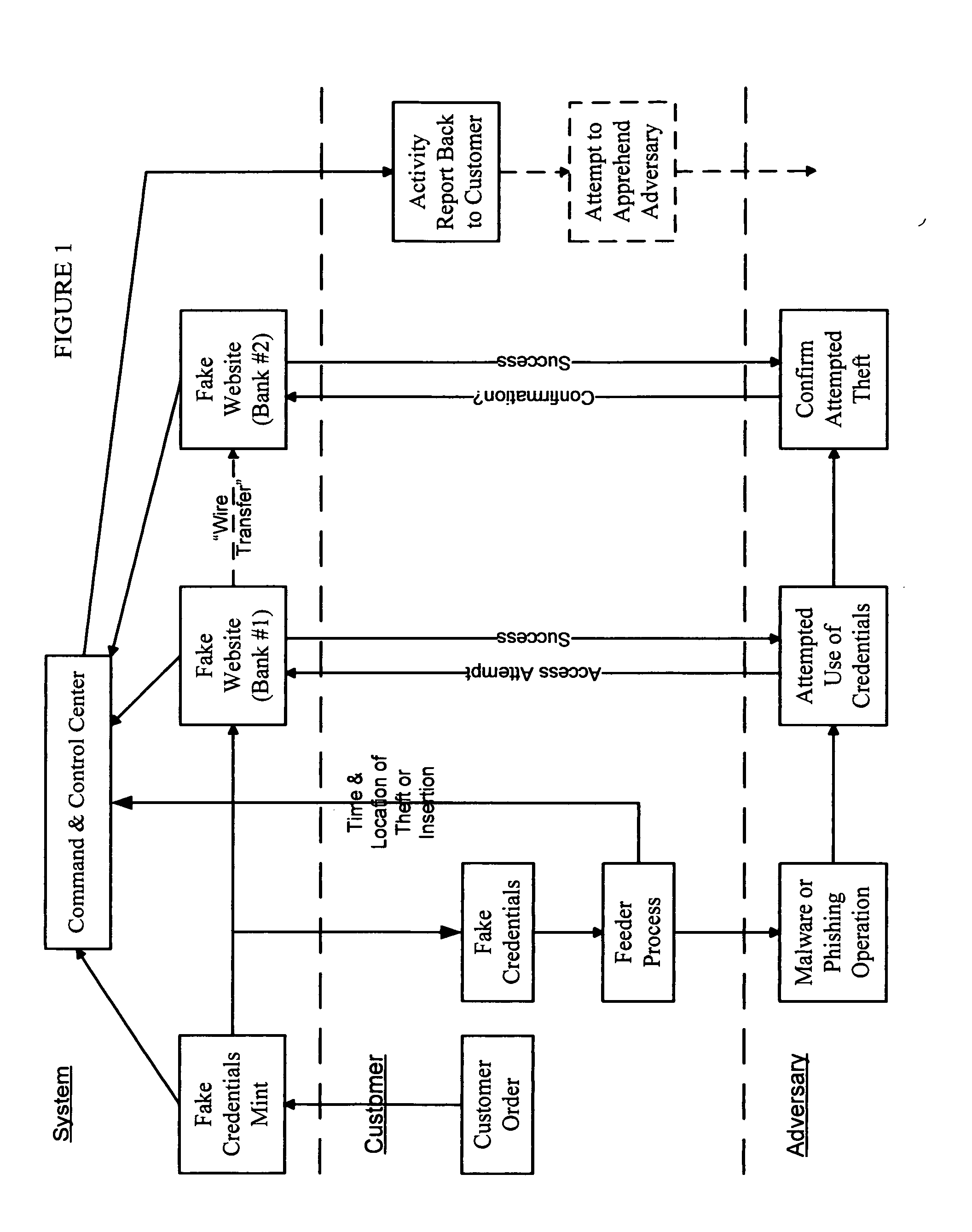
False Banking, Credit Card, and Ecommerce System
InactiveUS20130263226A1Divert attentionDelays attackDigital data processing detailsAnalogue secracy/subscription systemsCredit cardE-commerce
A false banking, credit card, and ecommerce system provides a family of inter-related computer software programs and processes that can a) generate and distribute seemingly valid false credentials that are made available to be “stolen” by criminals, b) provide an assortment of seemingly valid websites, business servers, or ecommerce sites that will apparently accept the false credentials, and c) track each use and provide trace information for use by law enforcement to apprehend and prosecute cyber offenders.
Owner:SUDIA FR W
System and method for identifying and approaching browsers most likely to transact business based upon real-time data mining
The present invention is directed to a system and functionality that removes the guess work out of trying to determine which browsers on a web site are more likely to end up with a good disposition. One approach introduced by the present invention is to first make sure the sales server captures as much information about browsers as is possible with respect to their activity on the website / ecommerce server. Then the server enables the enterprise to use business rules to define the population of browsers that are eligible for chat invitations. Out of this population, the server, on behalf of individual agents, approaches browsers as randomly as possible. As agents are entering into engagements and recording their disposition codes, the server periodically determines if it can identify any patterns in behavior of those engagements that end up with a good disposition code. For example, the server may note that browsers who were invited to chat in the 8th minute of their session and those who had seen 2 product pages end up in good engagements four times more often than the average browser. Once a sufficient sample set of engagements is conducted to allow the server to develop a statistically valid profile / model of browsers who end up with good engagements, the server compares all new browsers against this model and provides a numeric number representing how close the new browser is to the model. This number, called a score, is then used by the system to sort the browsers in real time and used as the criteria as to who should be approached and in which order.
Owner:LIVEPERSON
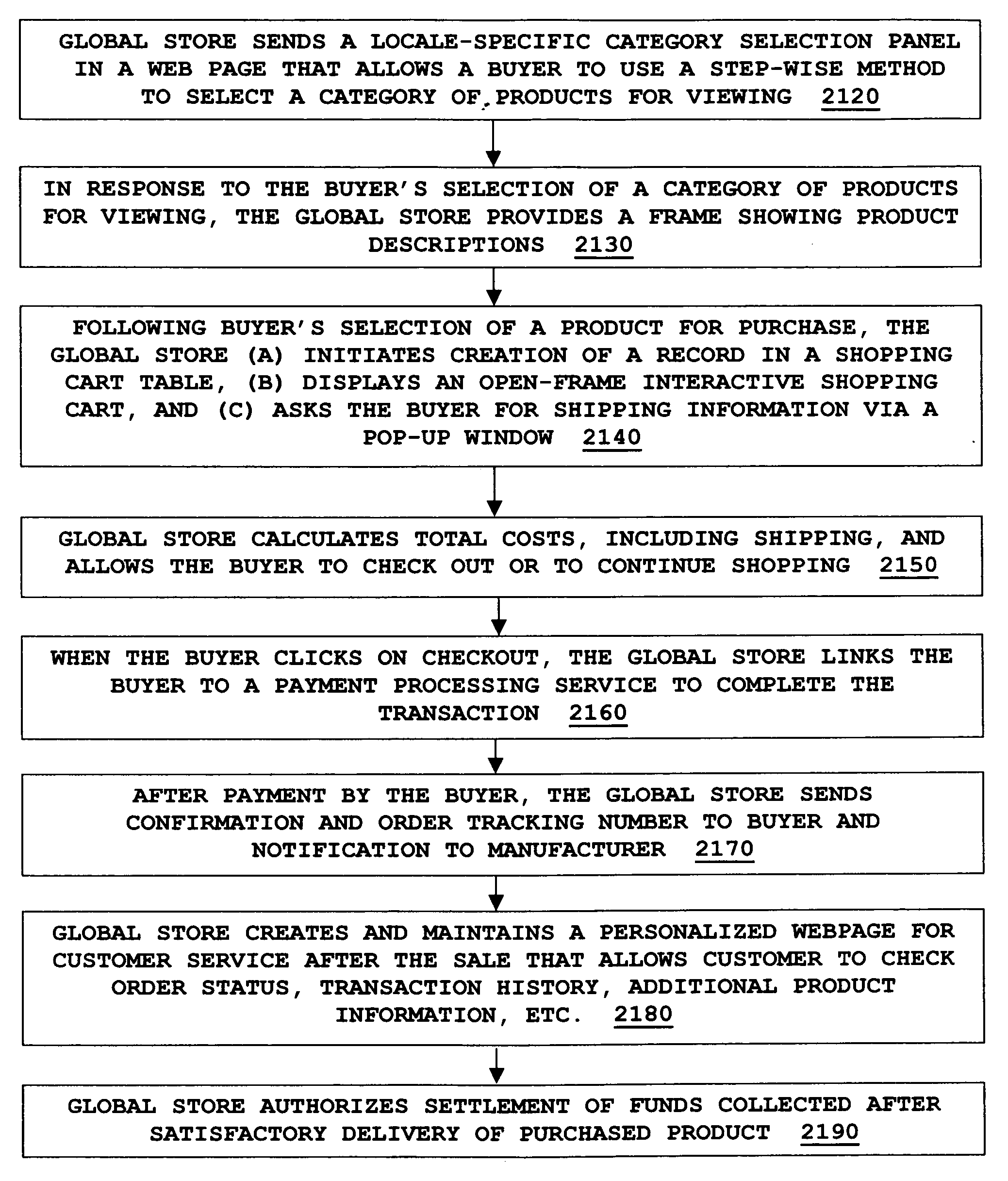
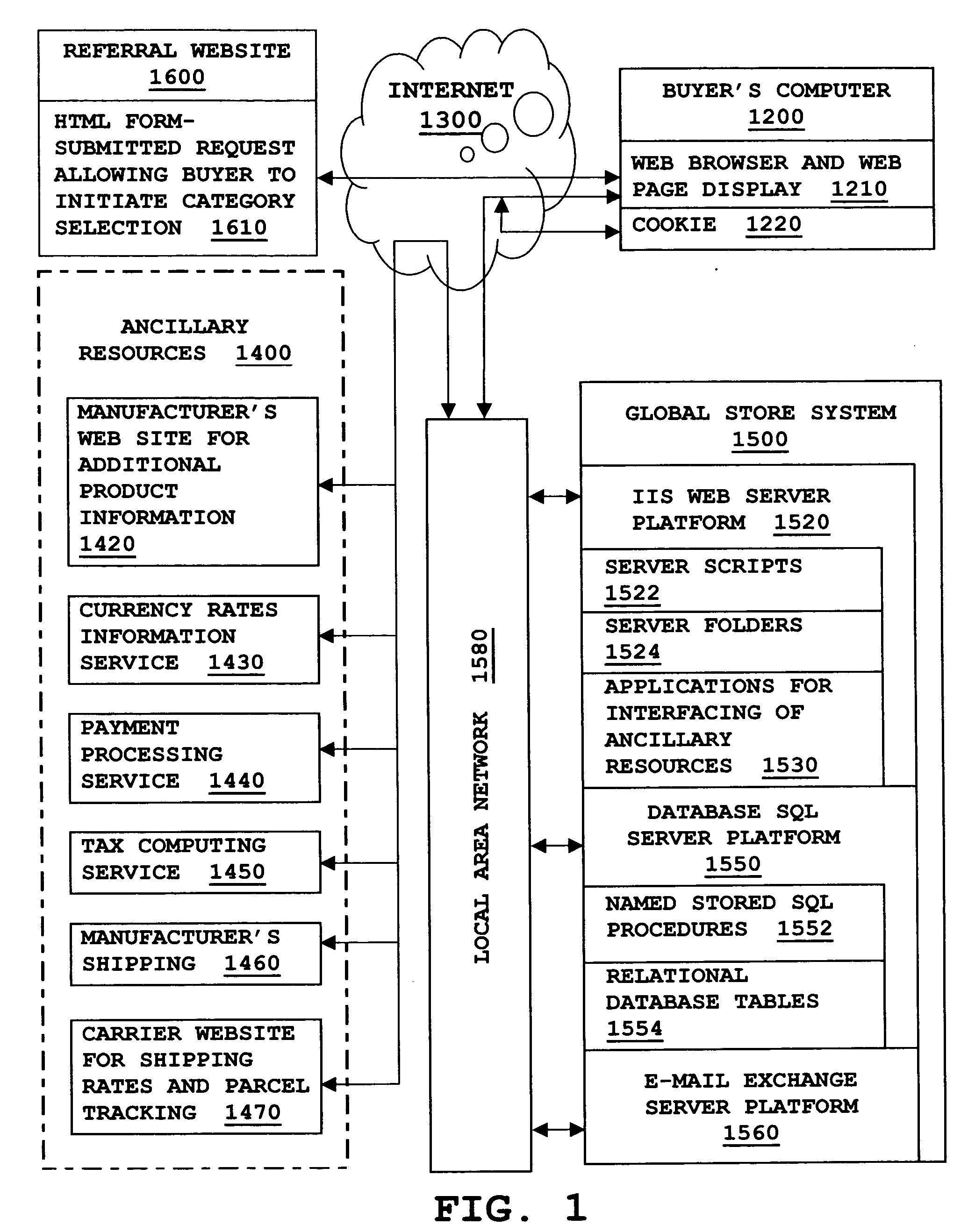
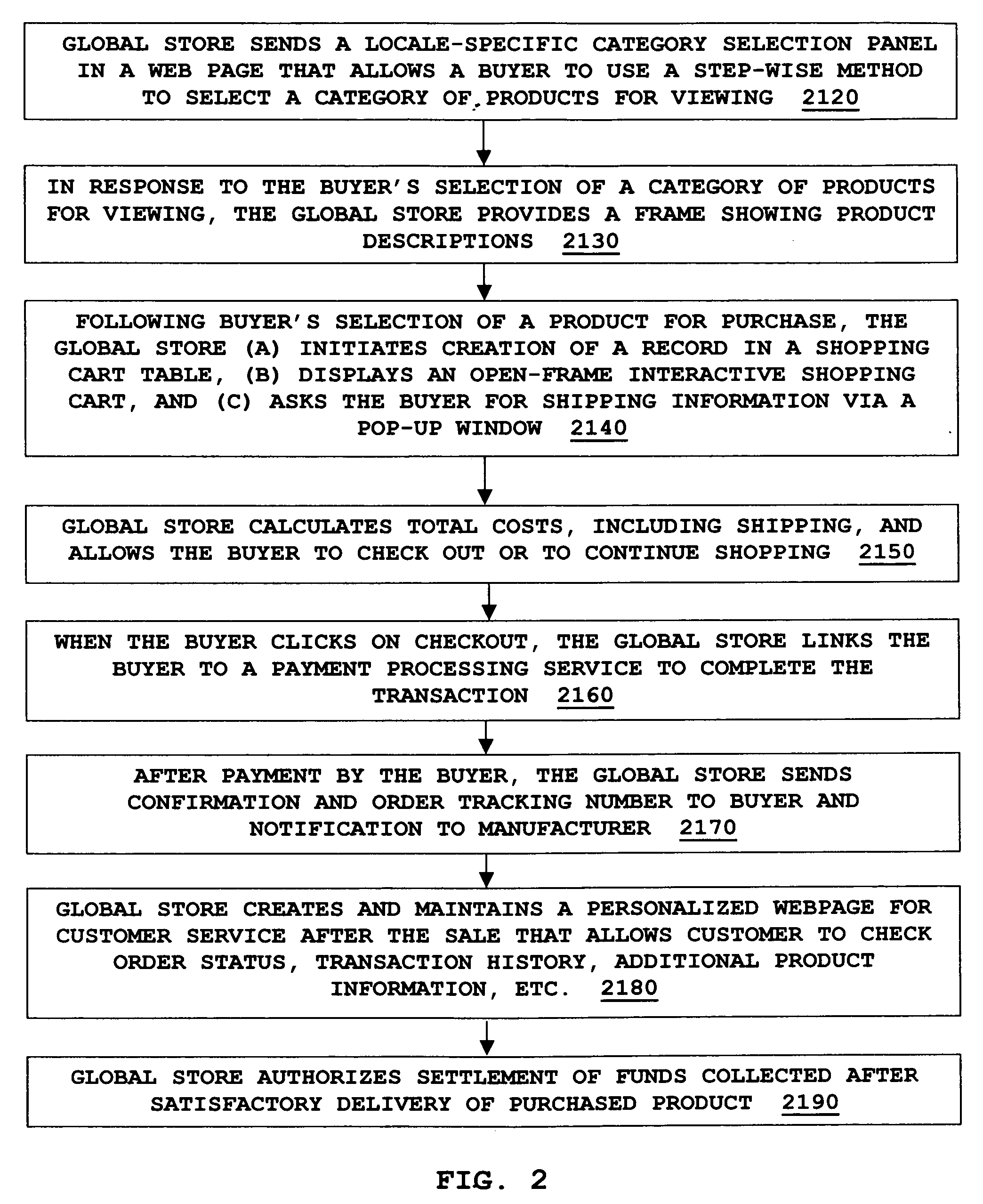
Global electronic commerce system
InactiveUS20060136309A1Multiple digital computer combinationsBuying/selling/leasing transactionsPersonalizationRelational database
A comprehensive system effectuates global electronic commerce on the Internet across frontiers of nations, cultures, and languages. Referral Websites serving various locales offer Buyers the opportunity to view products for purchase. A Buyer selects categories of products for viewing by using drop-down menus that organize products into a clear taxonomy that can be expressed across all languages. Having selected a category of products for viewing, a Buyer receives, from a multi-version relational database, a version of marketing information about each product. The version is one automatically sent from the database to match the Buyer's language, culture, and nationality, as deduced from the use of a particular Referral Website. A shopping cart allows Buyers to select a product for purchase in an interactive way that encourages completion of the purchase. Products can be offered with custom options and in wholesale quantities. Personalized Web pages allow comprehensive customer service after a sale.
Owner:ADVANCED TRANSACTIONS LLC
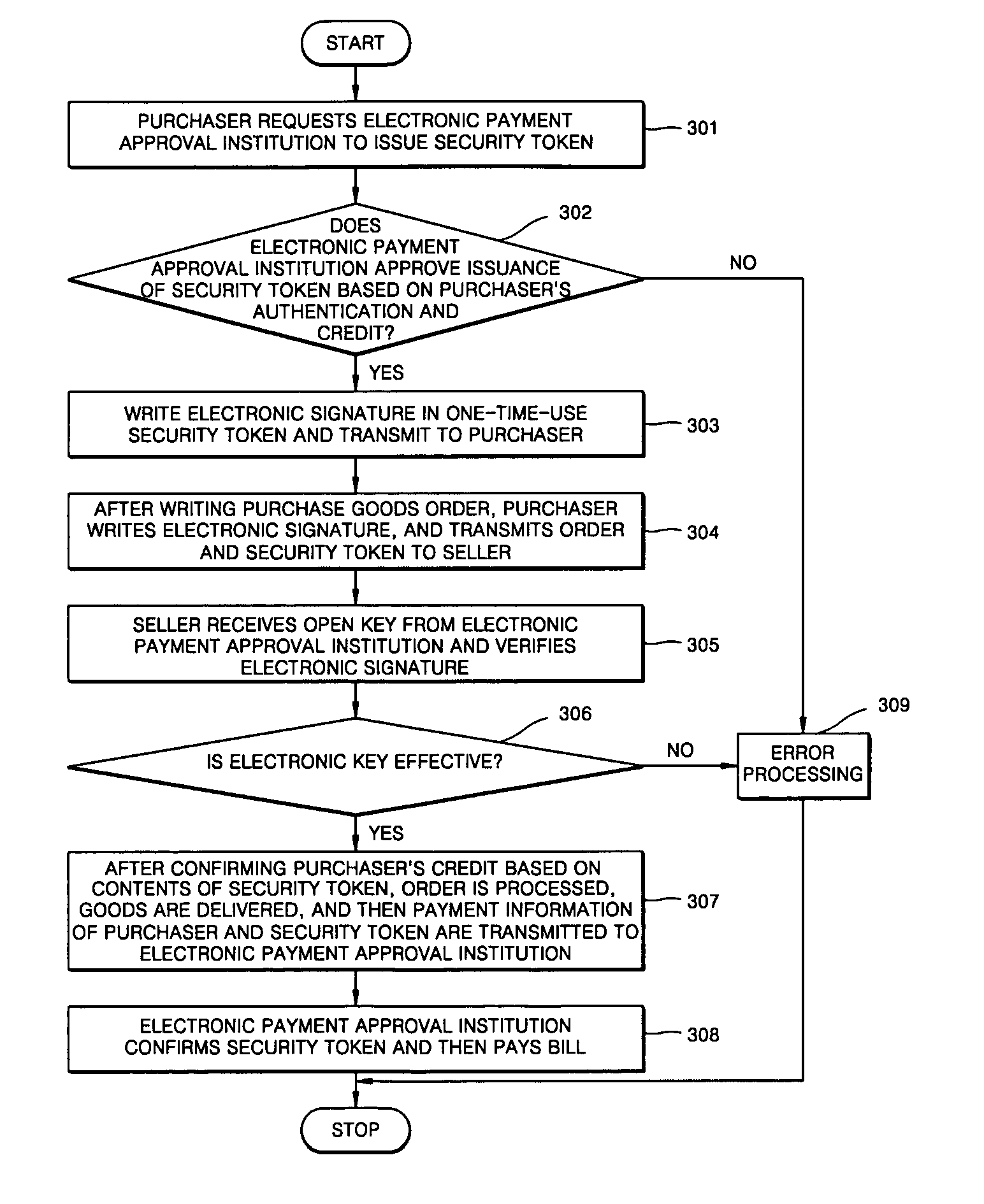
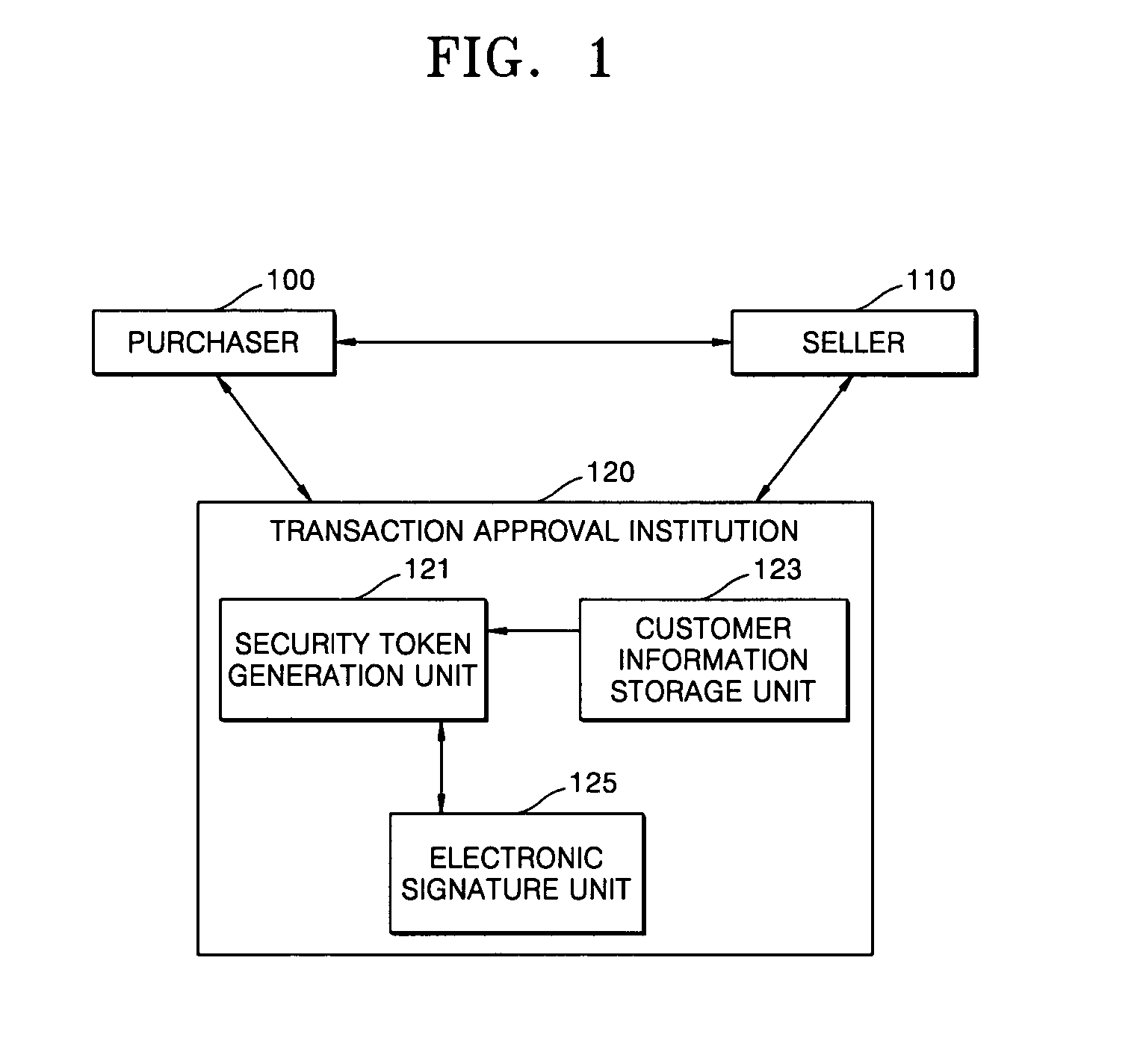
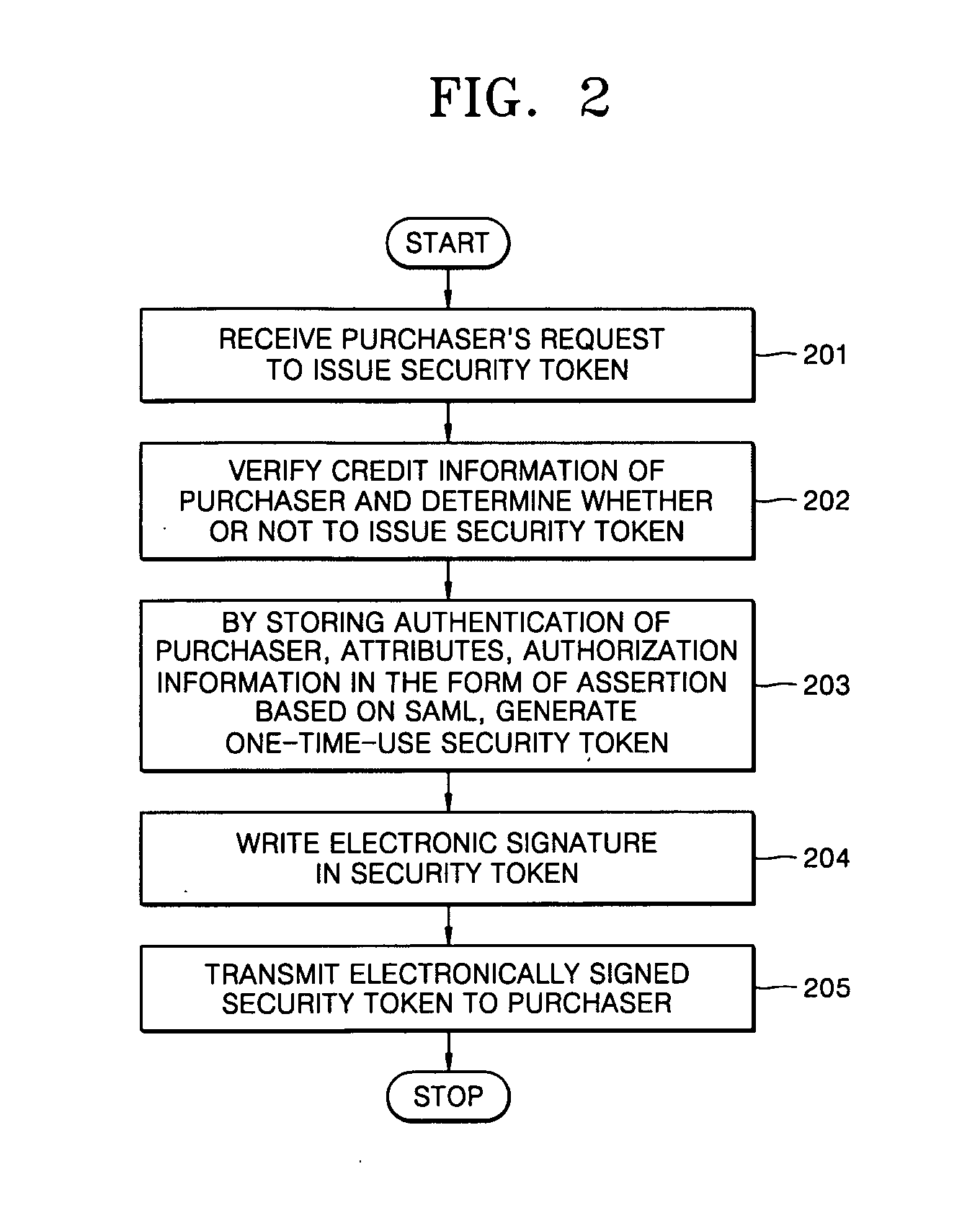
Method for electronic commerce using security token and apparatus thereof
InactiveUS20050097060A1Securing communicationPayments involving neutral partyConfidentialityExtensible markup
A method for electronic commerce using a security token and an apparatus thereof are provided. The electronic commerce method using a security token comprises a transaction approval institution generating a security token based on a security assertion markup language (SAML), using credit information of a purchaser who requests to issue a security token, and transmitting the security token to the purchaser; the purchaser writing an electronic signature on an order and transmitting the order together with the security token to a seller; the seller verifying the received order and security token, and then delivering goods according to the order to the purchaser; and the transaction approval institution performing payment for the seller and the purchaser. The method can solve the problems of personal information leakage and privacy infringement that may happen when a purchaser sends his personal information to a seller for electronic commerce. Since the token is one-time-use data, even if a security token sent is counterfeited or stolen, the loss can be minimized. In addition, by writing an extensible markup language (XML) electronic signature in the security token, authentication, integrity, and non-repudiation for a transmitted message can be guaranteed and through simple object access protocol (SOAP) security technology, confidentiality is maintained.
Owner:ELECTRONICS & TELECOMM RES INST
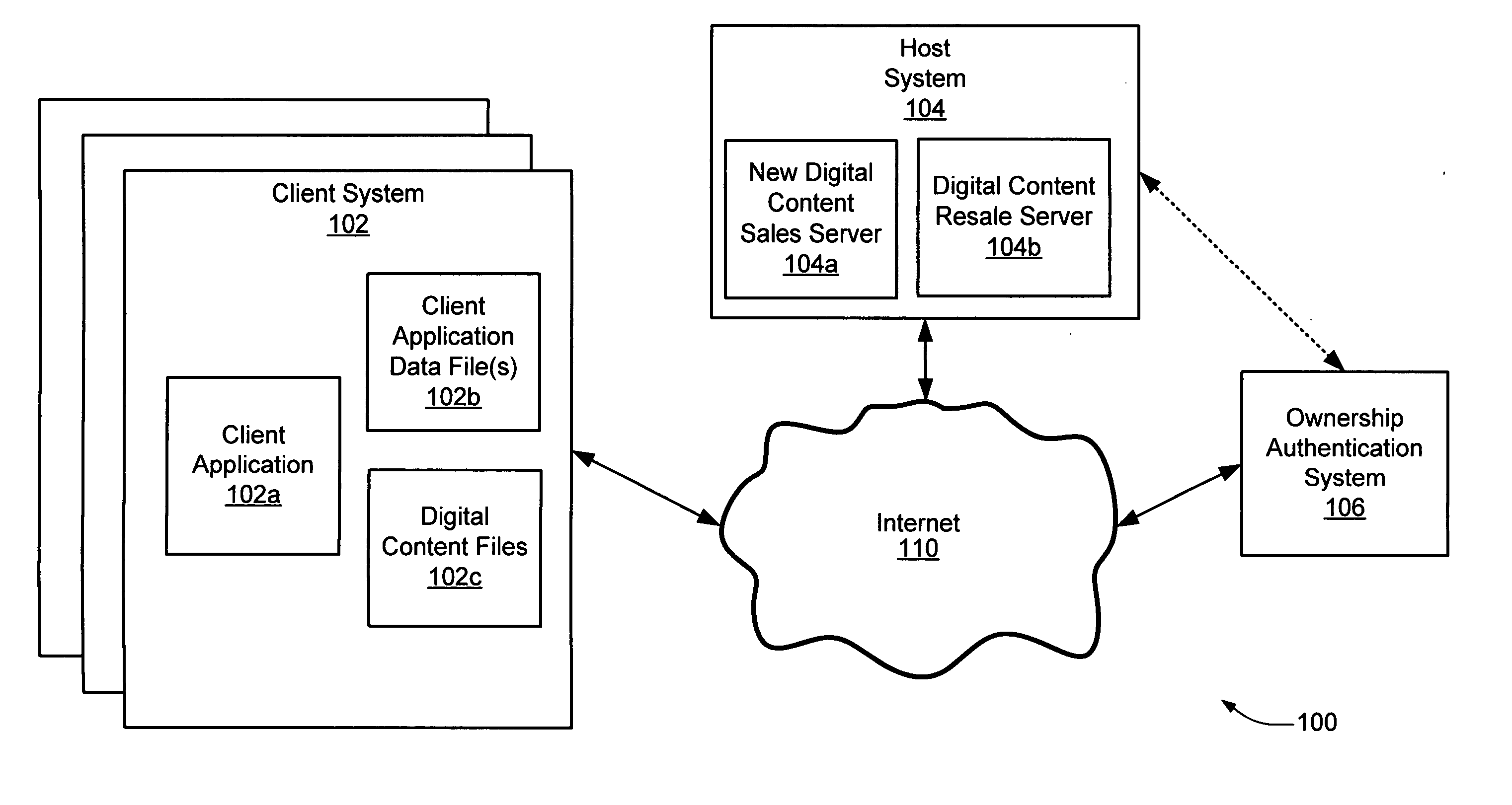
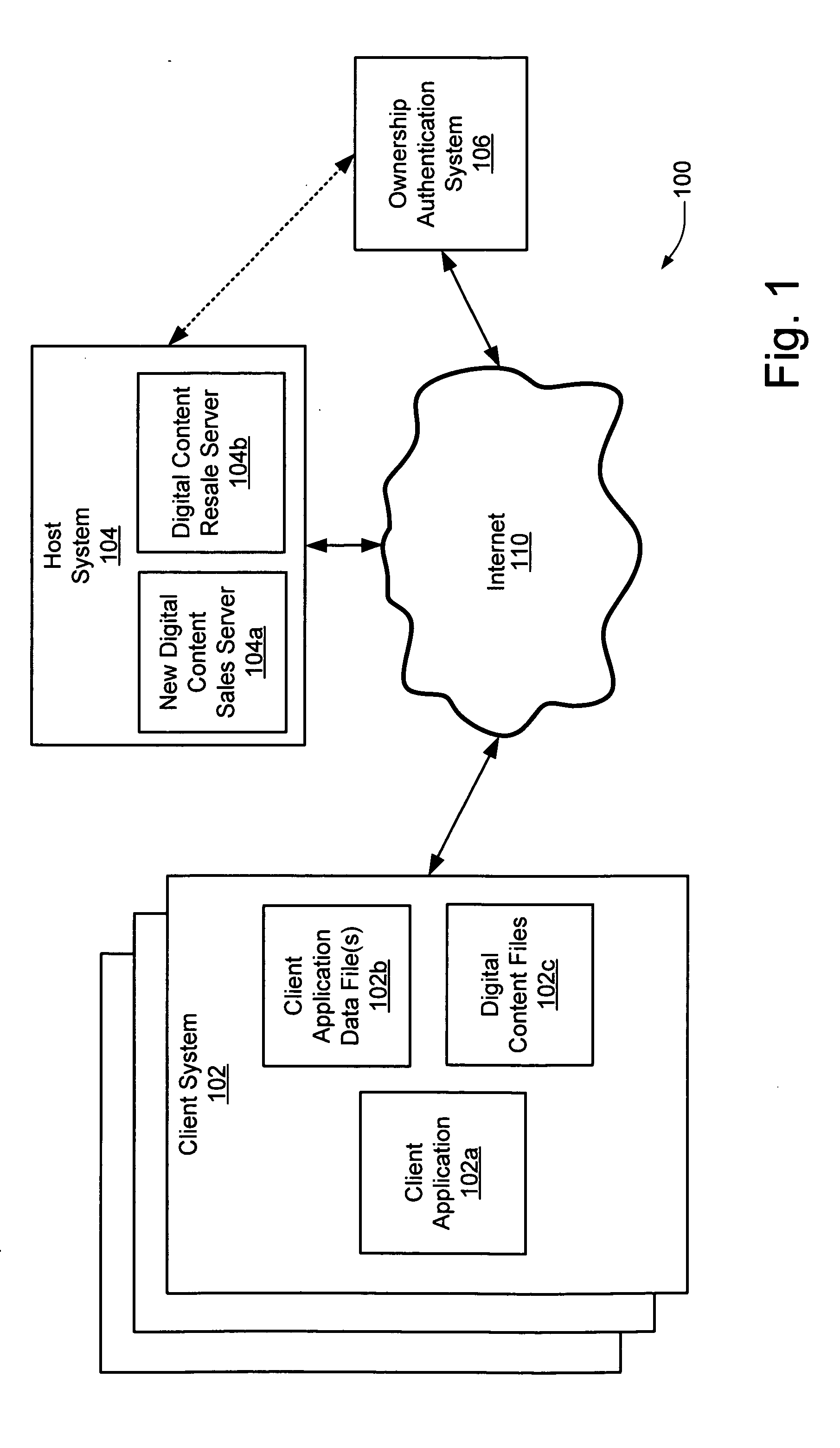
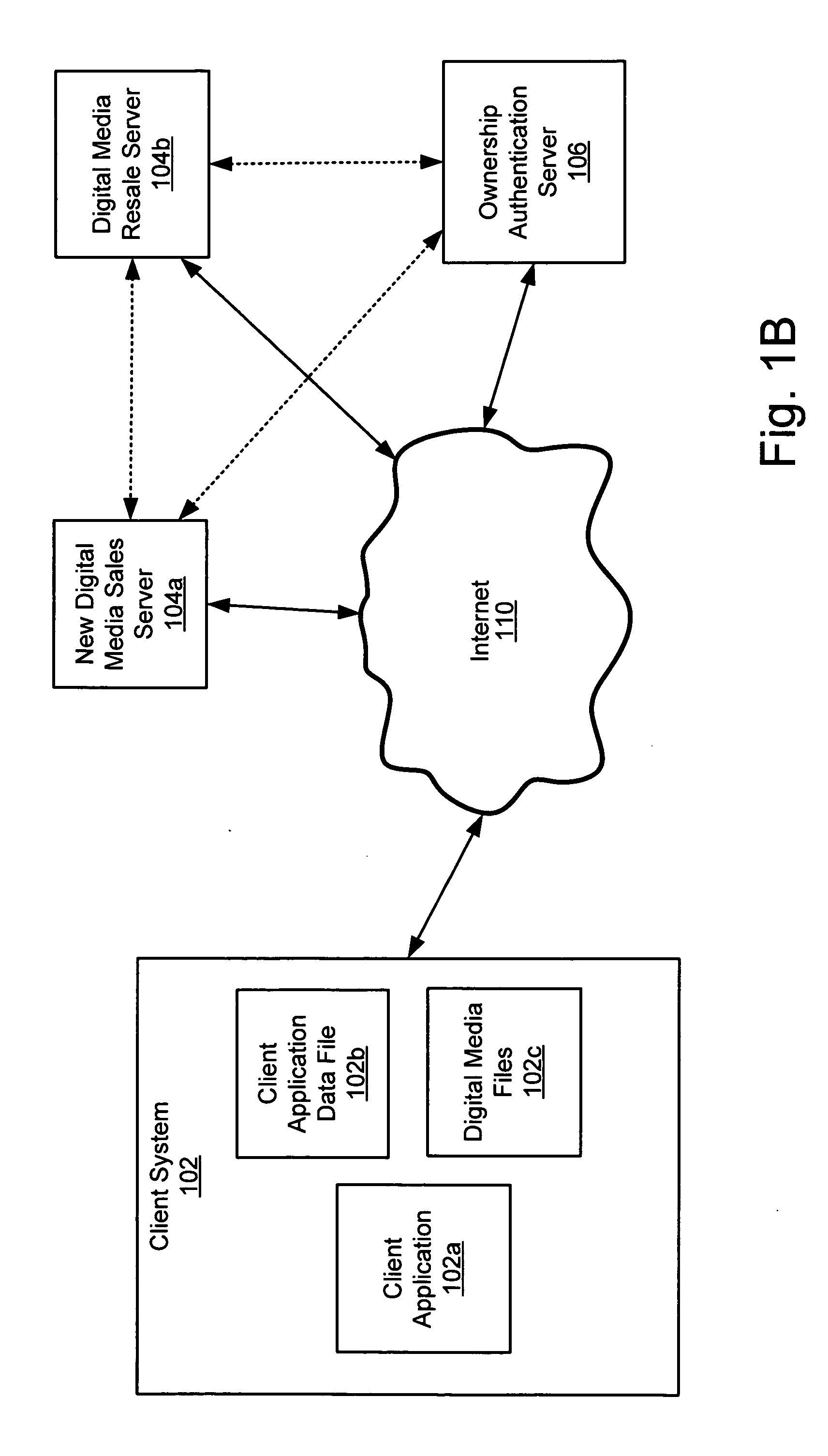
Technique for facilitating resale of digital content over a computer network
InactiveUS20060010075A1Facilitating resale of digital contentComputer security arrangementsBuying/selling/leasing transactionsDigital contentElectronic business
A technique is described for facilitating resale of digital content purchased via an electronic commerce transaction.
Owner:WOLF DEAN
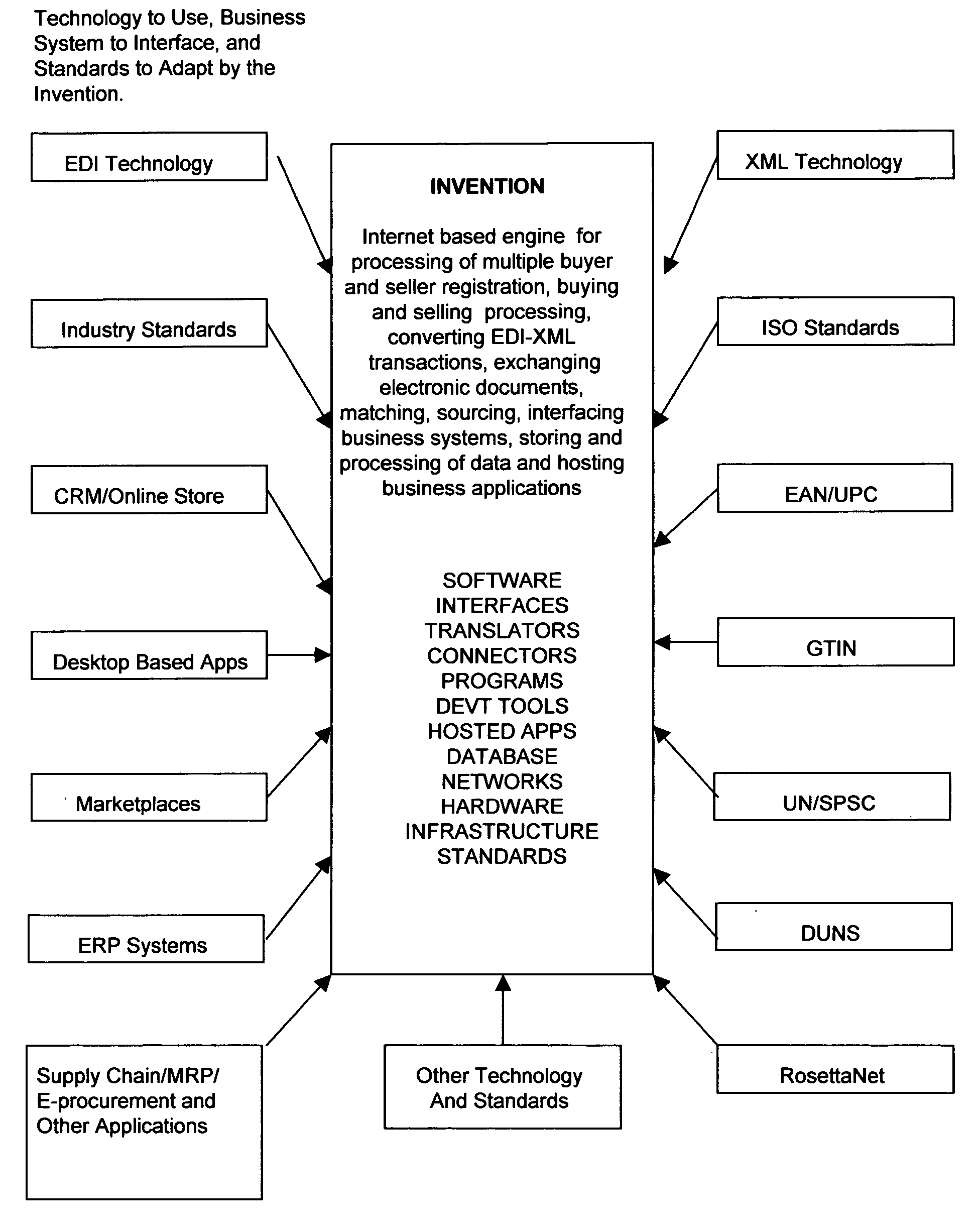
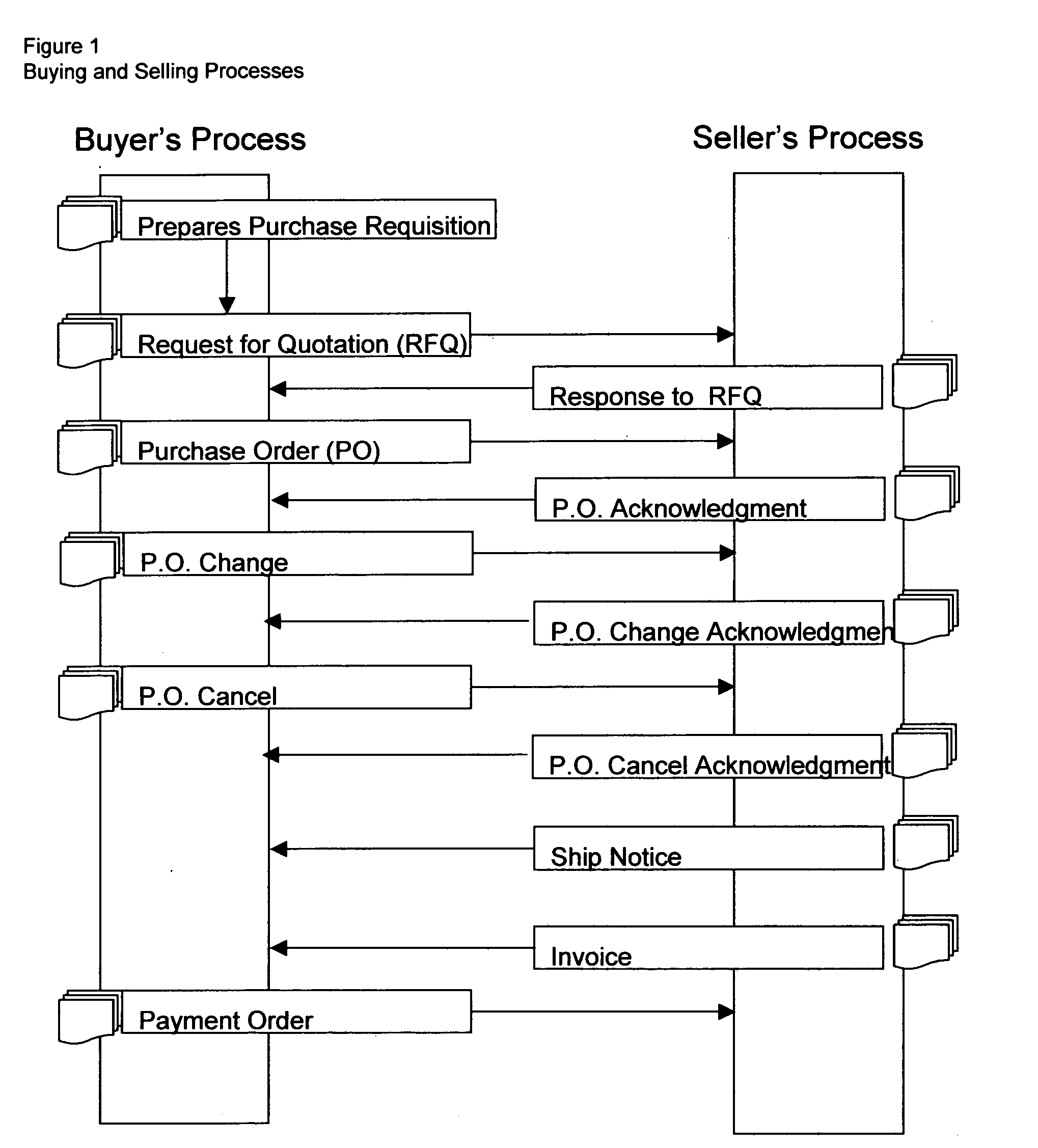
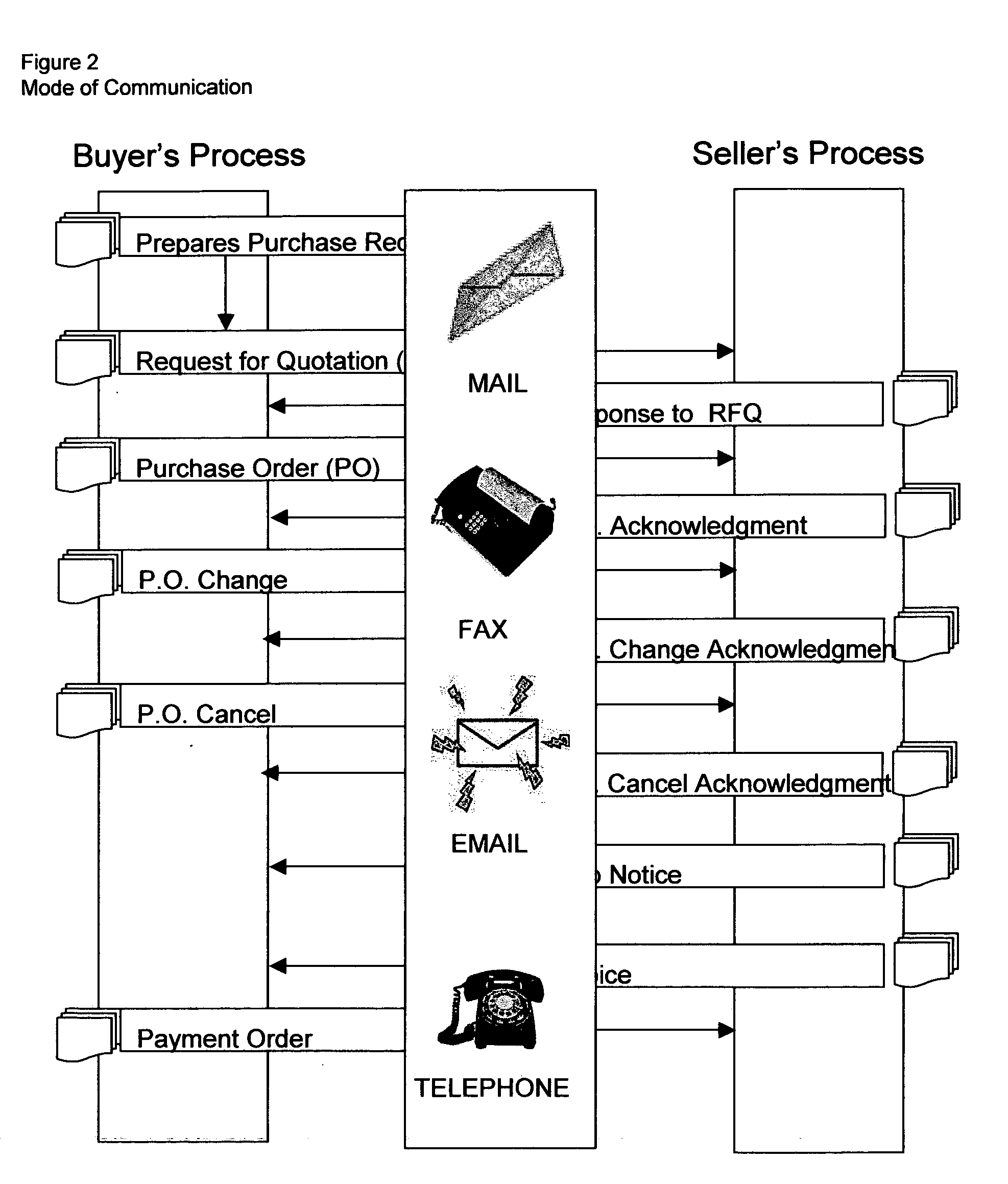
System and method for business-to-business buying, selling, sourcing and matching of proudcts and services across multiple business partners over the internet
This invention relates in general to a system and method for business-to-business buying, selling, sourcing and matching of products and services across multiple business partners over the Internet. The invention covers an internet based solution comprise of: 1) business partner registration, 2) buying and selling processing, 3) matching of codes, 4) conversion of EDI transactions, 5) sourcing / offering of products / services and 6) electronic documents processing. The invention provides: 1) support on EDI technology conversion into Rosettanet technology, 2) enhancements to Rosettanet technology so that code matching is possible for companies with or without support on GTIN, DUNS, ISO, UN / SPSC and other globally set codes, 3) an intermediary infrastructure for consolidation and standardization of business data across multiple electronic business applications (EBAs) and platforms with or without manufacturer part number (MPN) and customer part number (CPN) support, 4) a conversion mechanism where internet published auctions and reverse auctions are converted into sales quotations (SQs) and request for quotations (RFQ) respectively, 5) a solution to extract data from various EBAs, interface, update, match and store codes such as company codes, product / service codes, currency code, unit of measure code, country code and class code from globally defined codes and business partner defined codes and 7) a sourcing / offering mechanism where it detects potential suppliers and buyers based on the calculation logic described on FIGS. 21 and 22.
Owner:PADILLA RAYMUND MARCOS
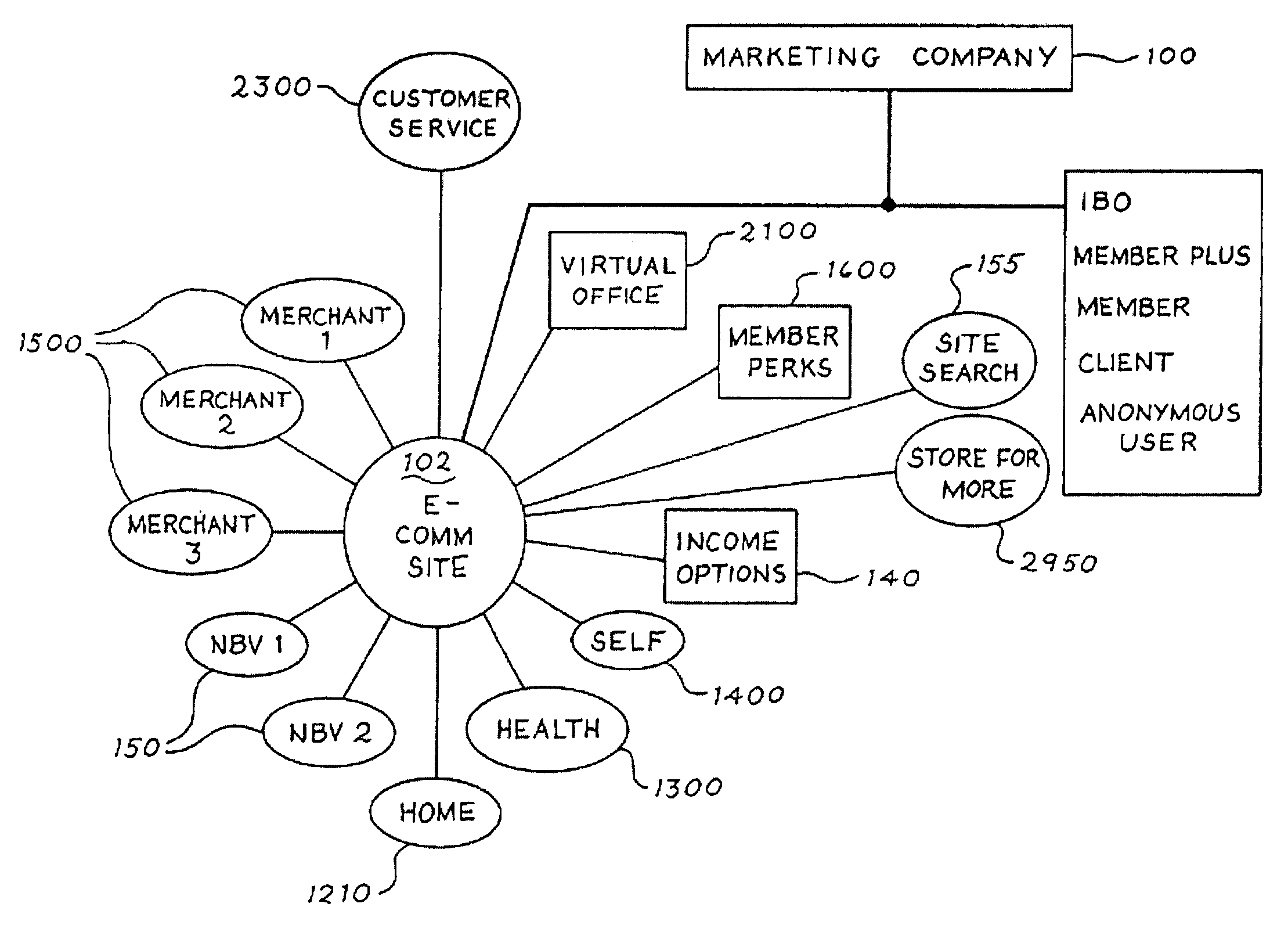
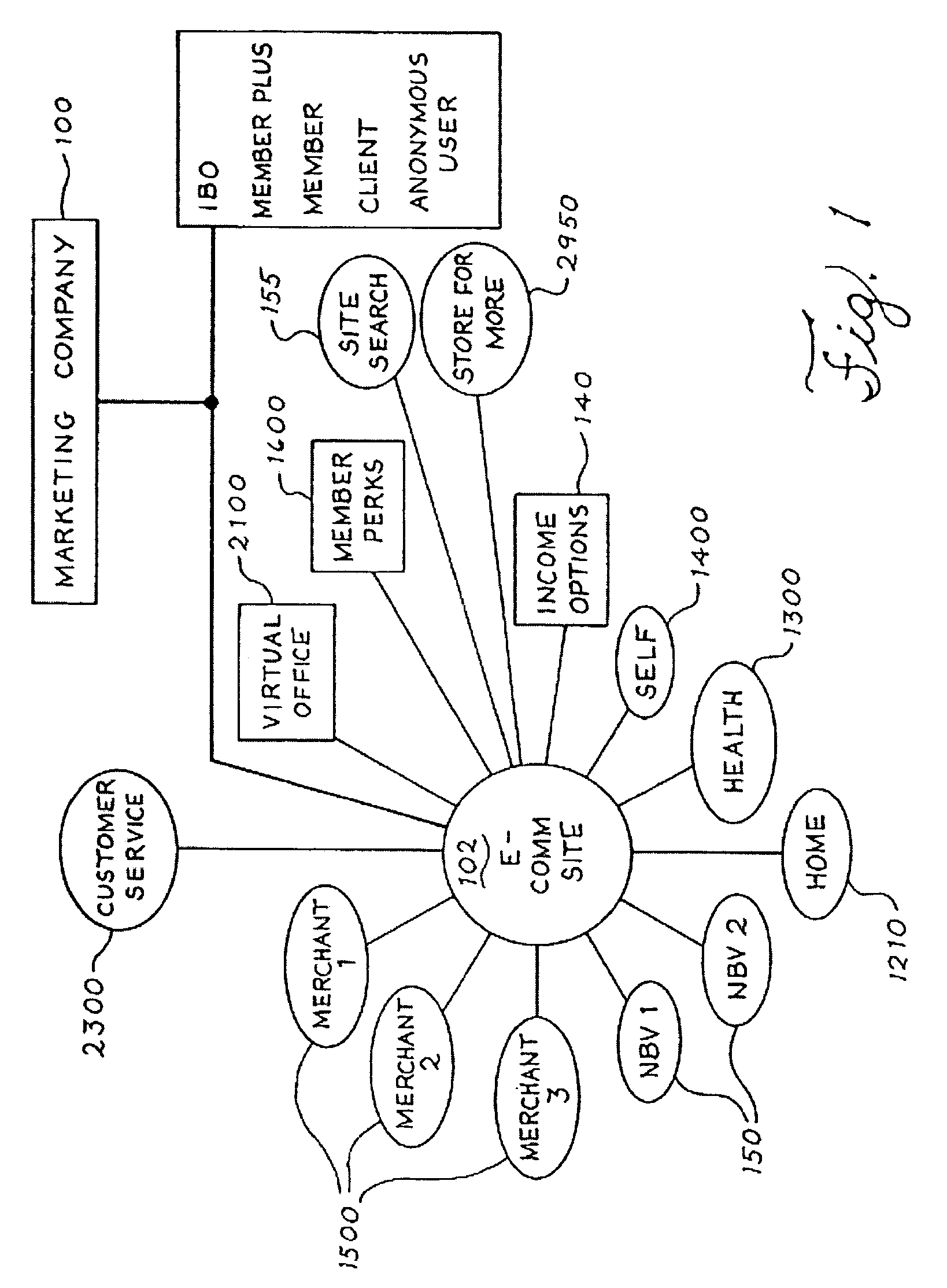
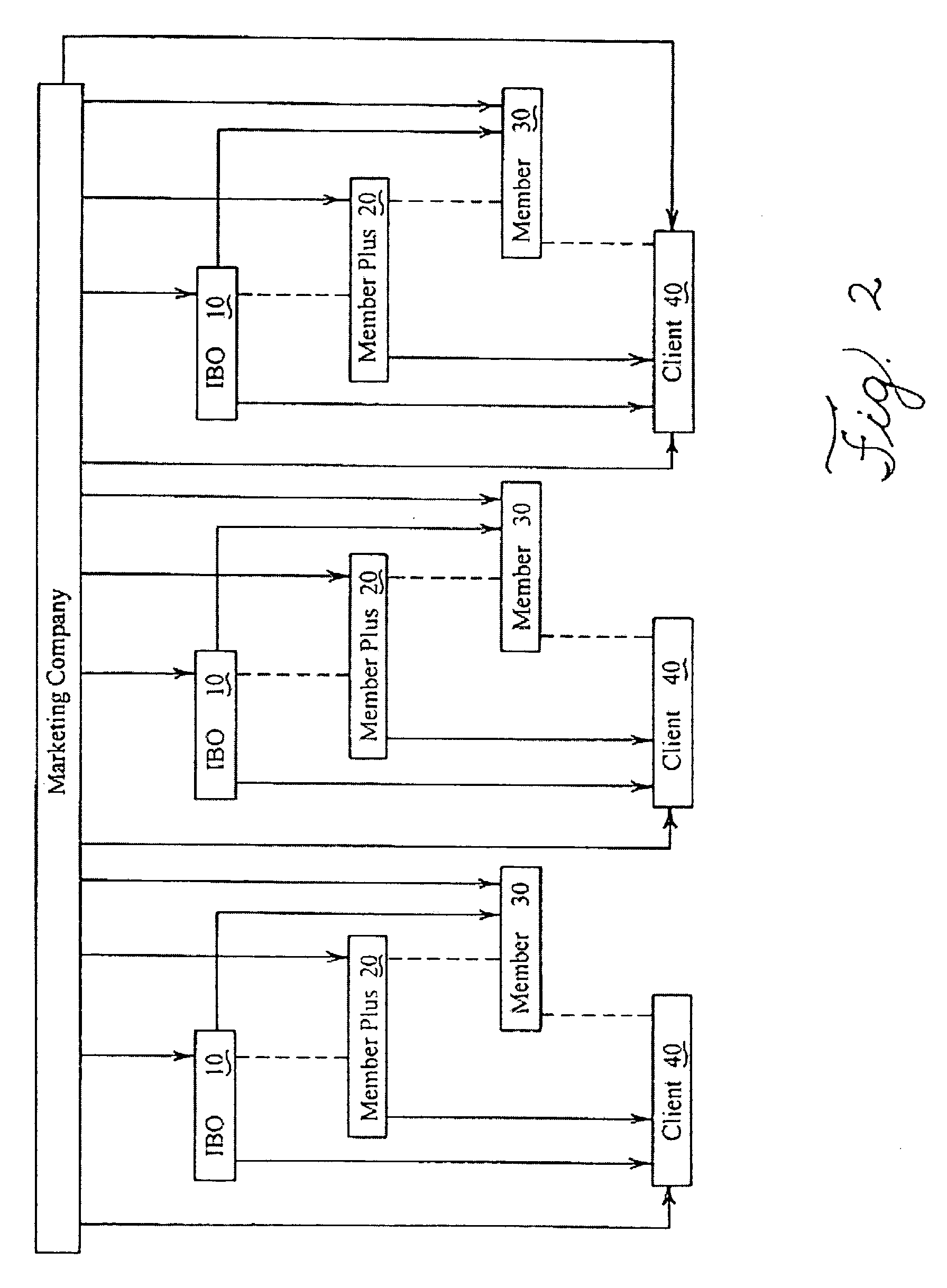
Electronic commerce transactions within a marketing system that may contain a membership buying opportunity
InactiveUS20060235764A1Great market shareIncrease salesFinanceAdvertisementsKnowledge managementEngagement marketing
The present invention is directed to a system and method for providing complete electronic commerce (“E-Commerce”) transactions and solutions for a marketing company's products via the World Wide Web, including facilities for signing up new customers and recruiting, training and supporting new Independent Business Owners through an interactive online process. In another aspect, the present invention relates to the combination of a marketing business with a membership buying opportunity using both electronic commerce and face-to-face transactions. The present invention is also directed to a system and method for combining a marketing business with a membership buying opportunity, so that Independent Business Owners participating in the marketing plan can introduce customers to a membership buying opportunity and earn bonuses or commissions based on the purchases by those members, while Members in the buying opportunity can consume products or, at their option, qualify to become Independent Business Owners.
Owner:AMUEI CORP
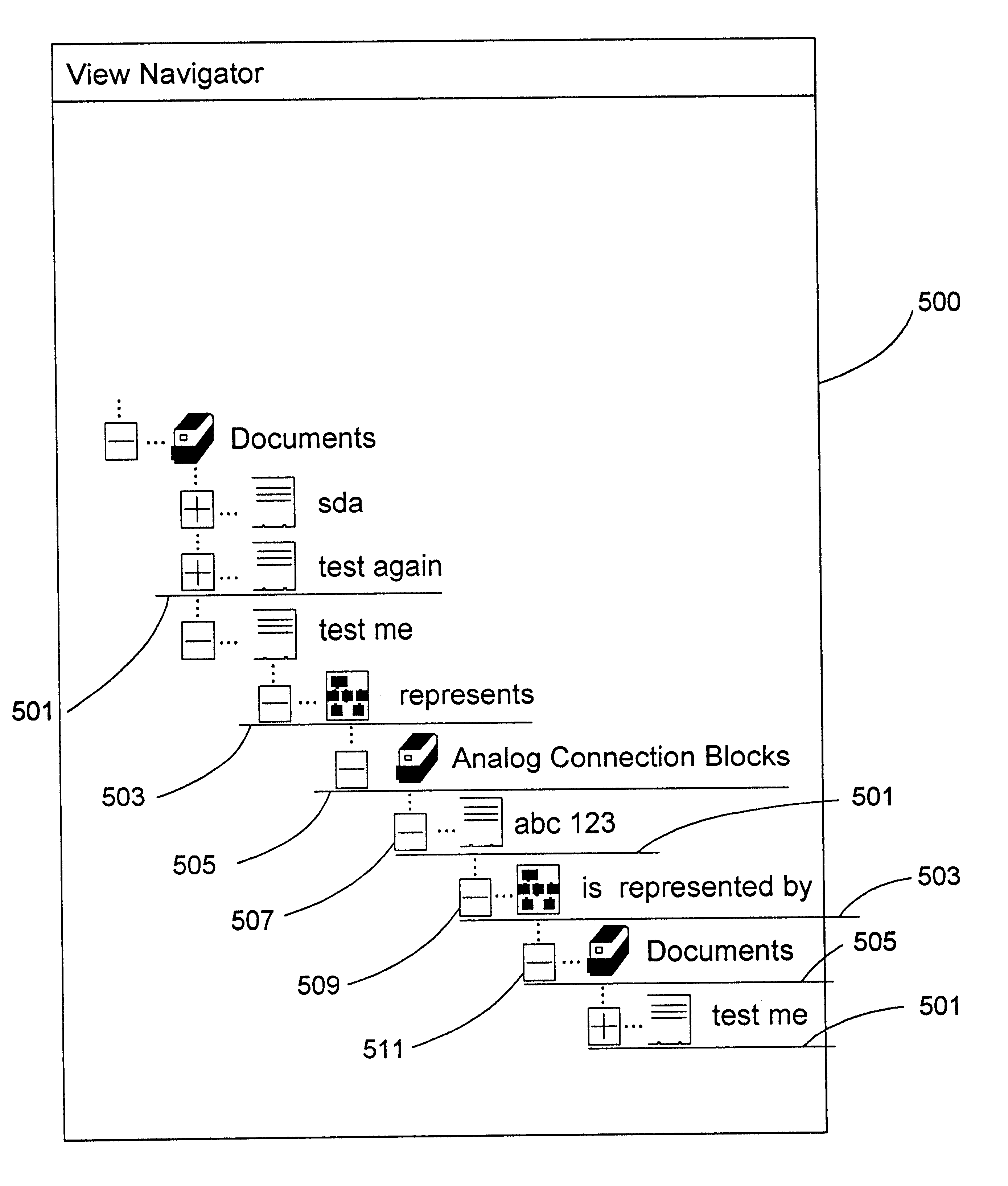
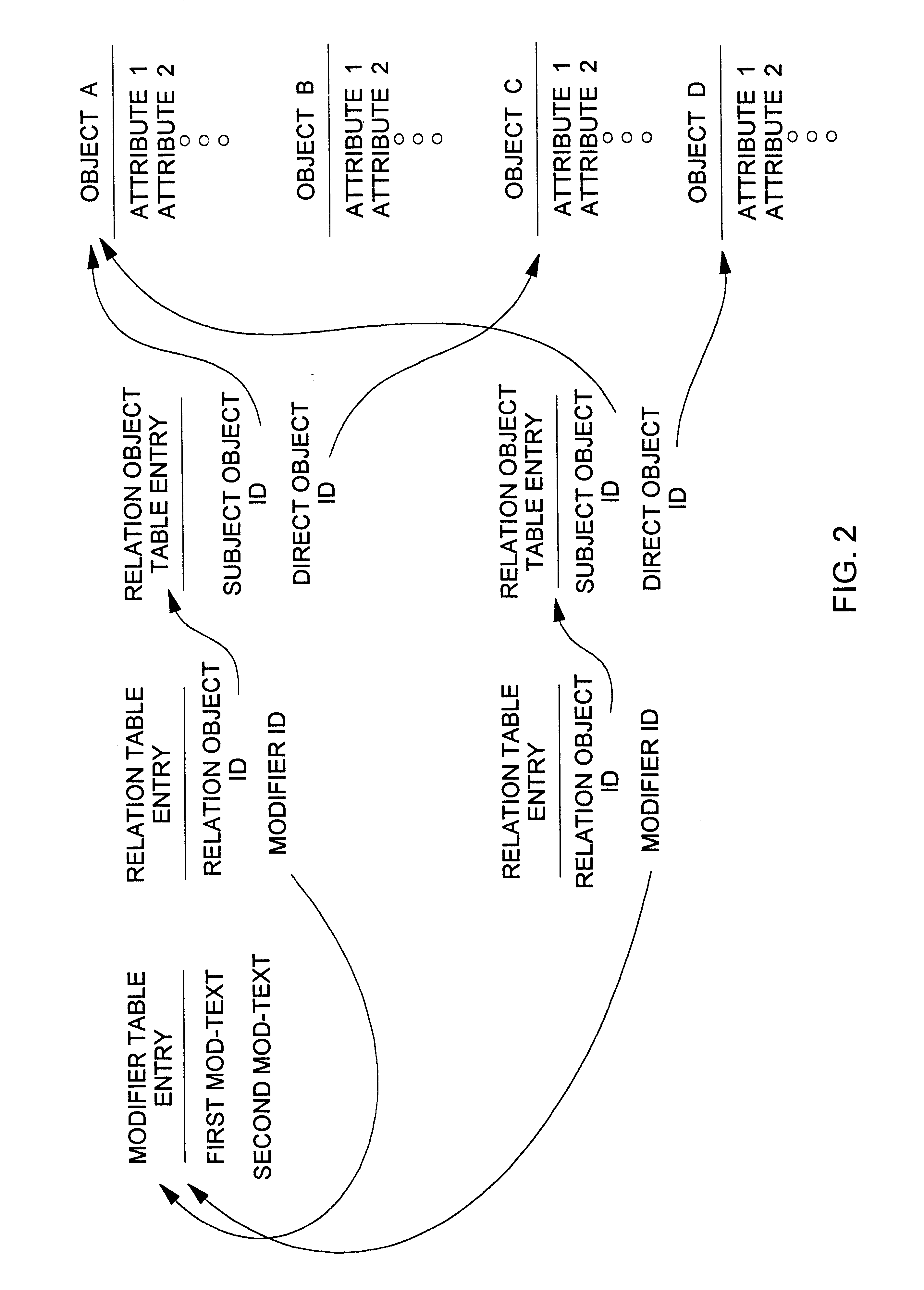
View navigation for creation, update and querying of data objects and textual annotations of relations between data objects
InactiveUS6618733B1EffectivelySave storage spaceData processing applicationsDigital data processing detailsCustomer relationship managementOperational system
A method (and corresponding database system) for displaying in a view window information characterizing semantics of relations between objects. For each given relation between at least one subject object and at least one direct object, bi-directional modifier data is stored that represents first text characterizing semantics of a relationship of the at least one first object to the at least one second object, and represents second text characterizing semantics of a relationship of the at least one second object to the at least one first object. In response to predetermined user input associated with an object node displayed in the view window, a set of relations whose at least one subject object or at least one direct object is associated with the object node is identified. For at least one relation in the set of relations, the view window is updated to include a second node comprising a graphical representation of: the first text of the given relation in the event that the given object is a subject object in the given relation, or the second text of the given relation in the event that the given object is a direct object in the given relation. The second node may be a relation node associated with a given relation, or a mixed node associated with a relation-type pair. In response to predetermined input with a second node, the second node may be expanded to identify and display one or more object nodes (identifying direct object(s) of relations derived from expansion of a subject object associated therewith or identifying subject object(s) of relations derived from expansion of a direct object associated therewith). Preferably, this expansion routine is recursive in nature.The method (and database system) of the present invention may be used in a wide assortment of software applications, including enterprise applications (such as e-business applications, supply chain management applications, customer relationship management applications, decision support applications), the file system in operating systems, web browsers, e-mail applications and personal information management applications. Importantly, the method (and database system) provides an easy, user friendly and efficient mechanism to define, view and query the organization of the data elements (and the relationships therebetween) stored and accessed in such software applications, in a manner that conveys the real-world meaning of such relationships.
Owner:REVELINK
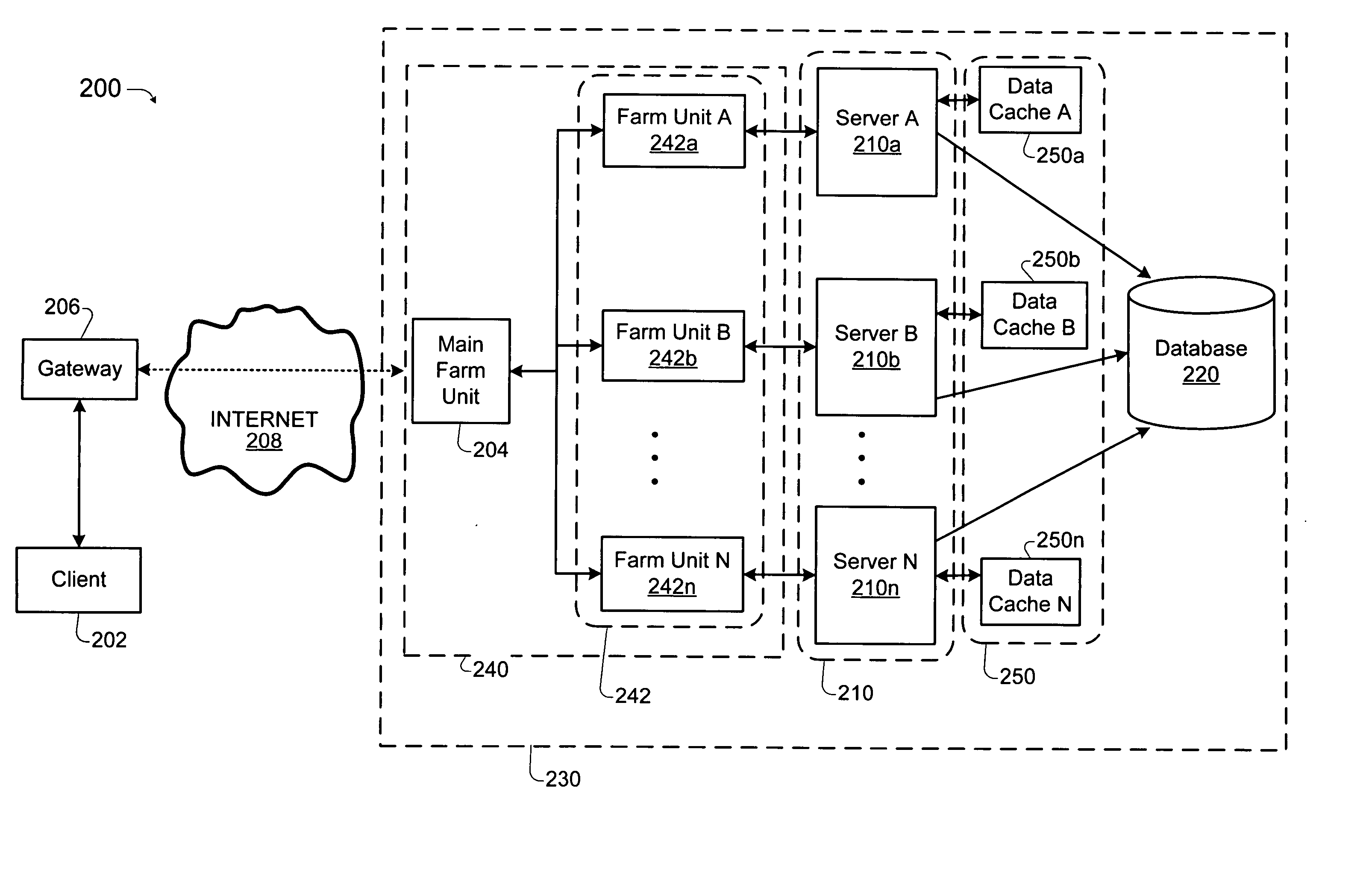
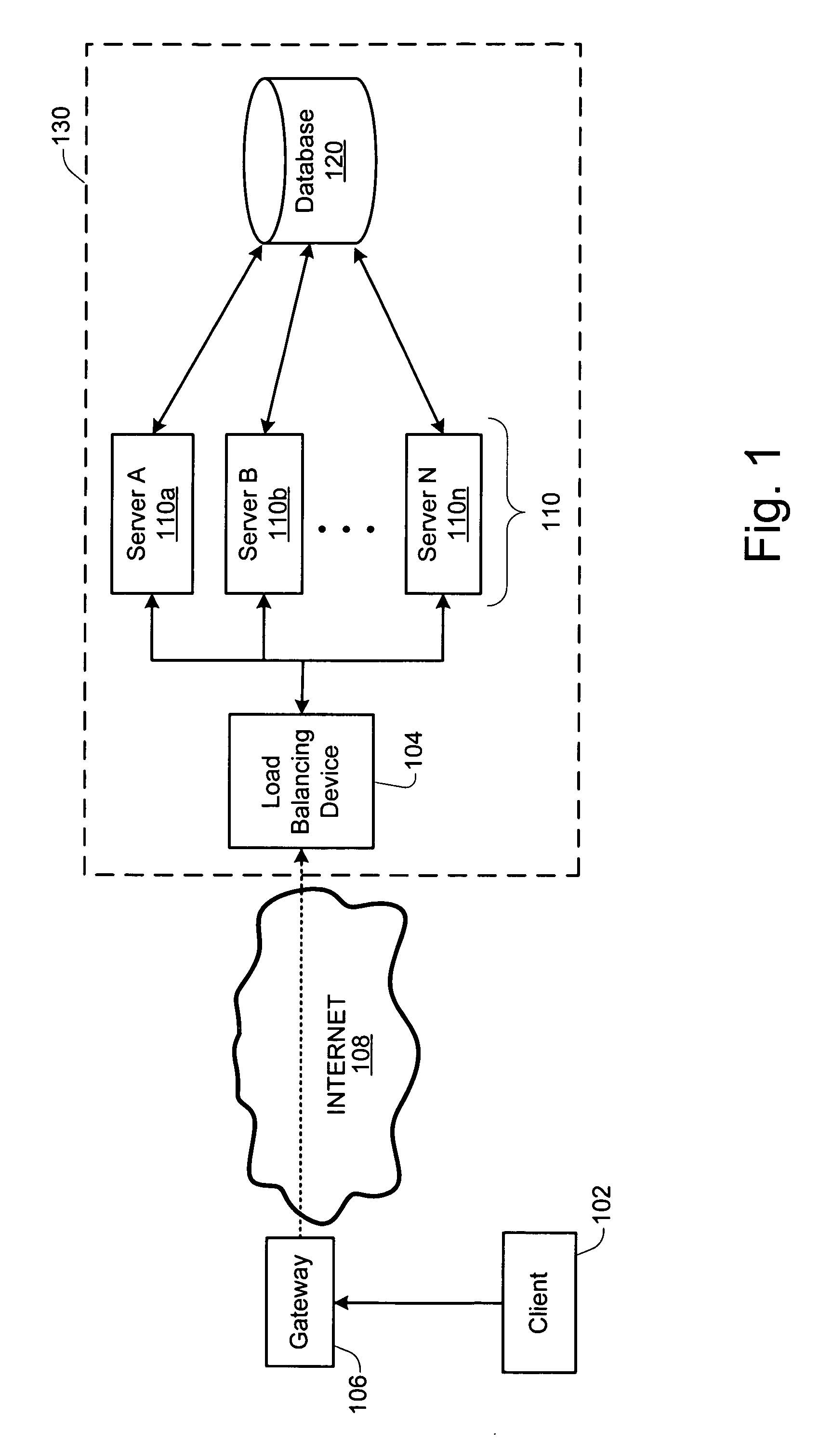
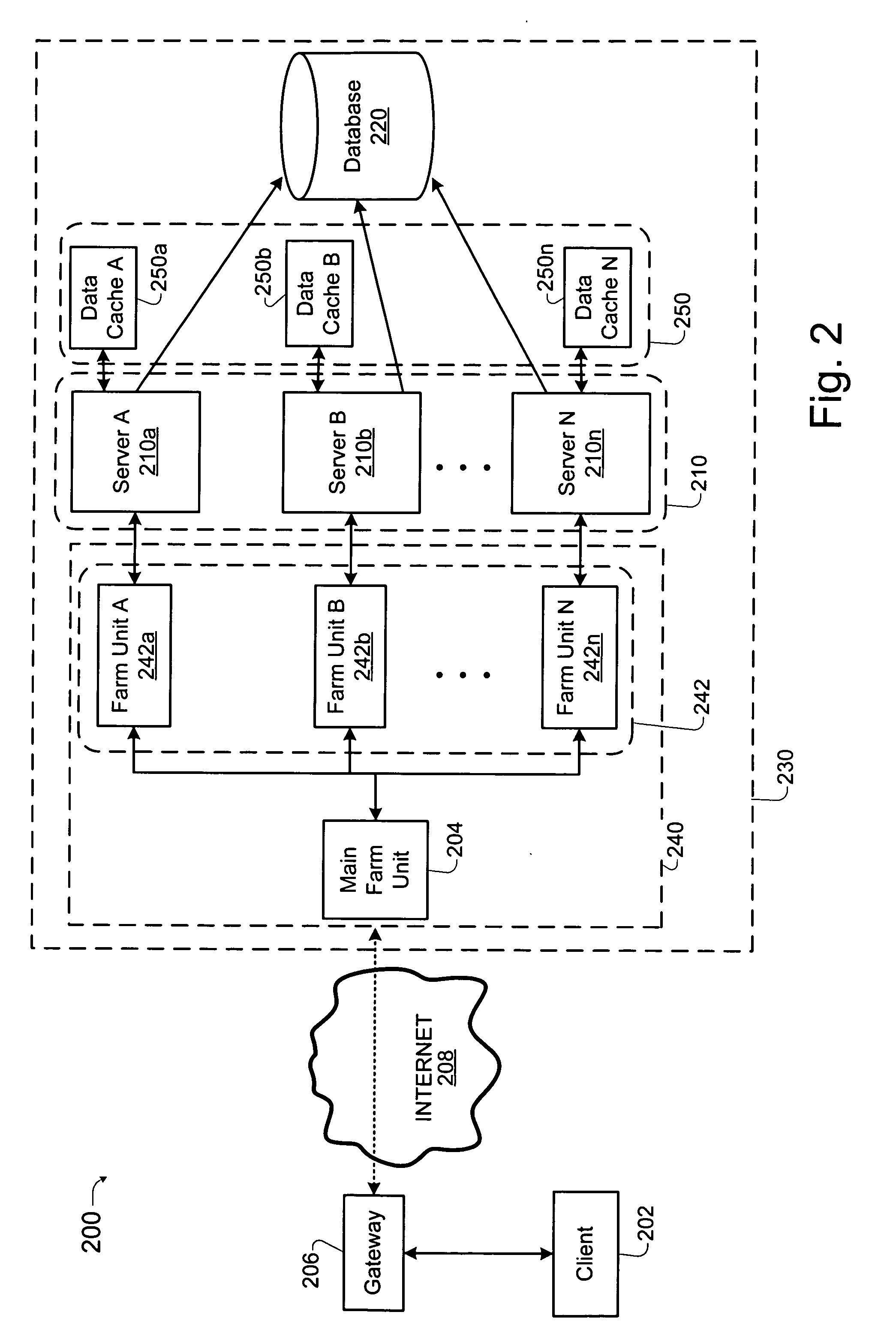
Load balancing technique implemented in a data network device utilizing a data cache
InactiveUS20050261985A1Easy to useDigital data information retrievalMultiprogramming arrangementsLoad SheddingData pack
Techniques for implementing a load balanced server system are described which may be used for effecting electronic commerce over a data network. The system comprises a load balancing system and a plurality of servers in communication with the load balancing system. Each of the plurality of servers may include a respective data cache for storing state information relating to client session transactions conducted between the server and a particular client. The load balancing system can be configured to select, using a load balancing protocol, an available first server from the plurality of servers to process an initial packet received from a source device such as, for example, a client machine of a customer. The load balancing system can also configured to route subsequent packets received from the source device to the first server. Before generating its response, the first server may verify that the state information relating to a specific client session stored in the data cache is up-to-date. If the first server determines that the state information stored in the data cache is not up-to-date, then the first server may be configured to retrieve the desired up-to-date state information from a database which is configured to store all state information relating to client sessions which have been initiated with the server system.
Owner:JUNE RAY
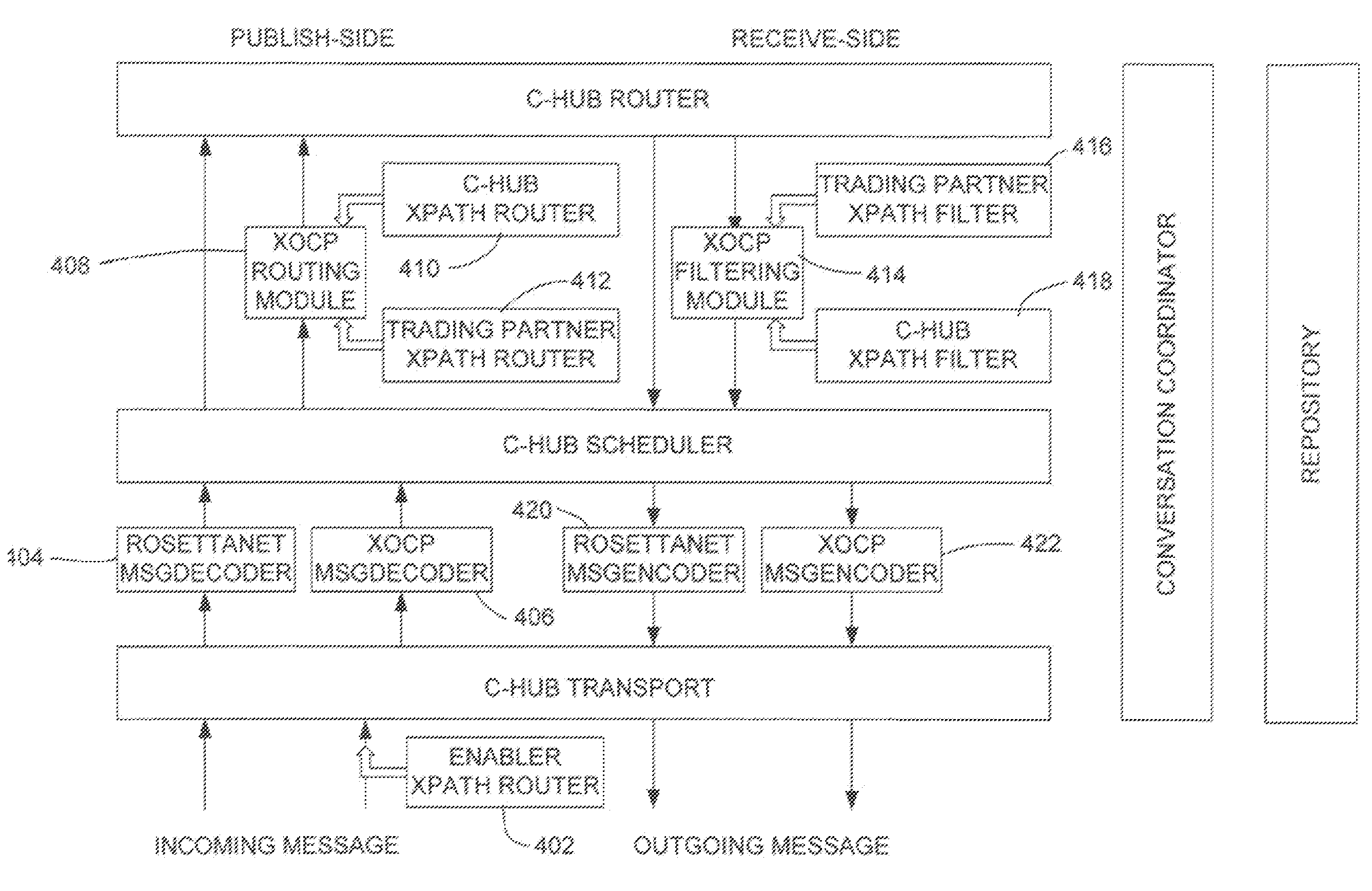
Pluggable hub system for enterprise wide electronic collaboration
InactiveUS7143186B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsSession managementMessage flow
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides a pluggable hub system for enterprise wide electronic collaboration. An embodiment of the invention includes a collaboration hub for use with a collaboration system, comprising a hub transport for receiving messages from participants and sending messages to participants, a hub router for routing messages from a first participant to a second participant, a hub scheduler for scheduling the flow of messages between the hub router and the hub transport, a conversation manager for managing the flow of messages between participants, and a repository for storing conversation management data.
Owner:ORACLE INT CORP
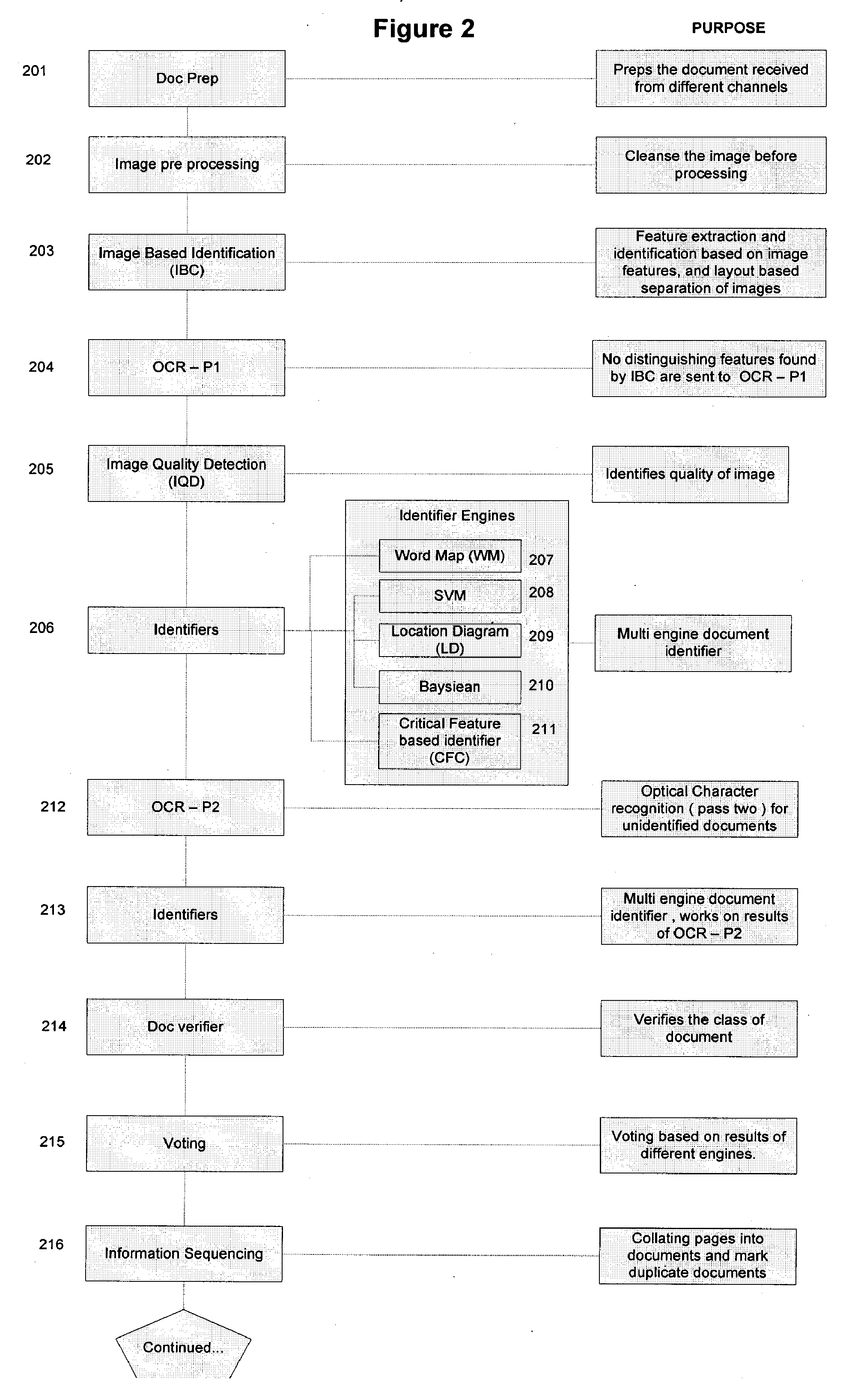
Business Method Using The Automated Processing of Paper and Unstructured Electronic Documents
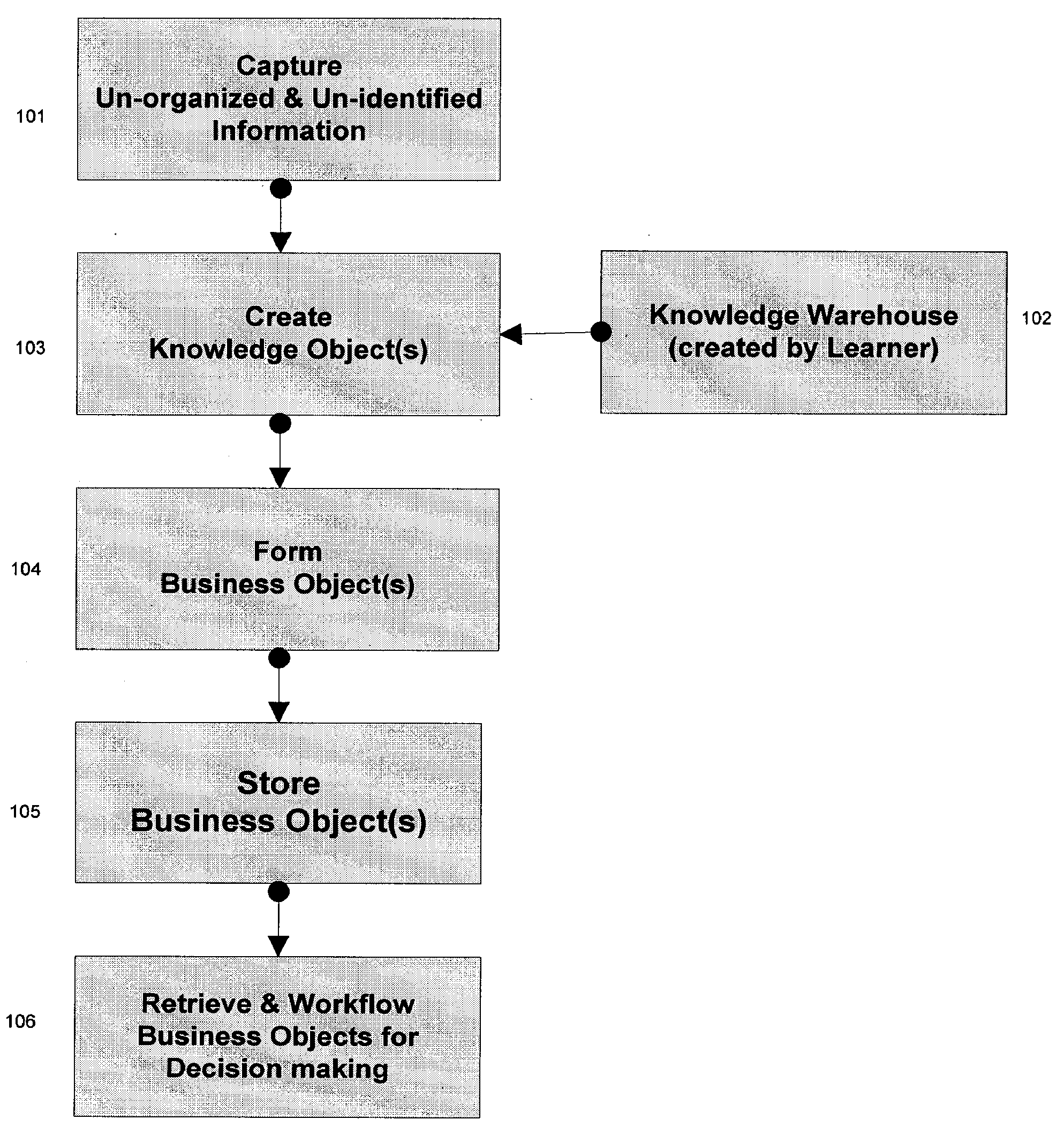
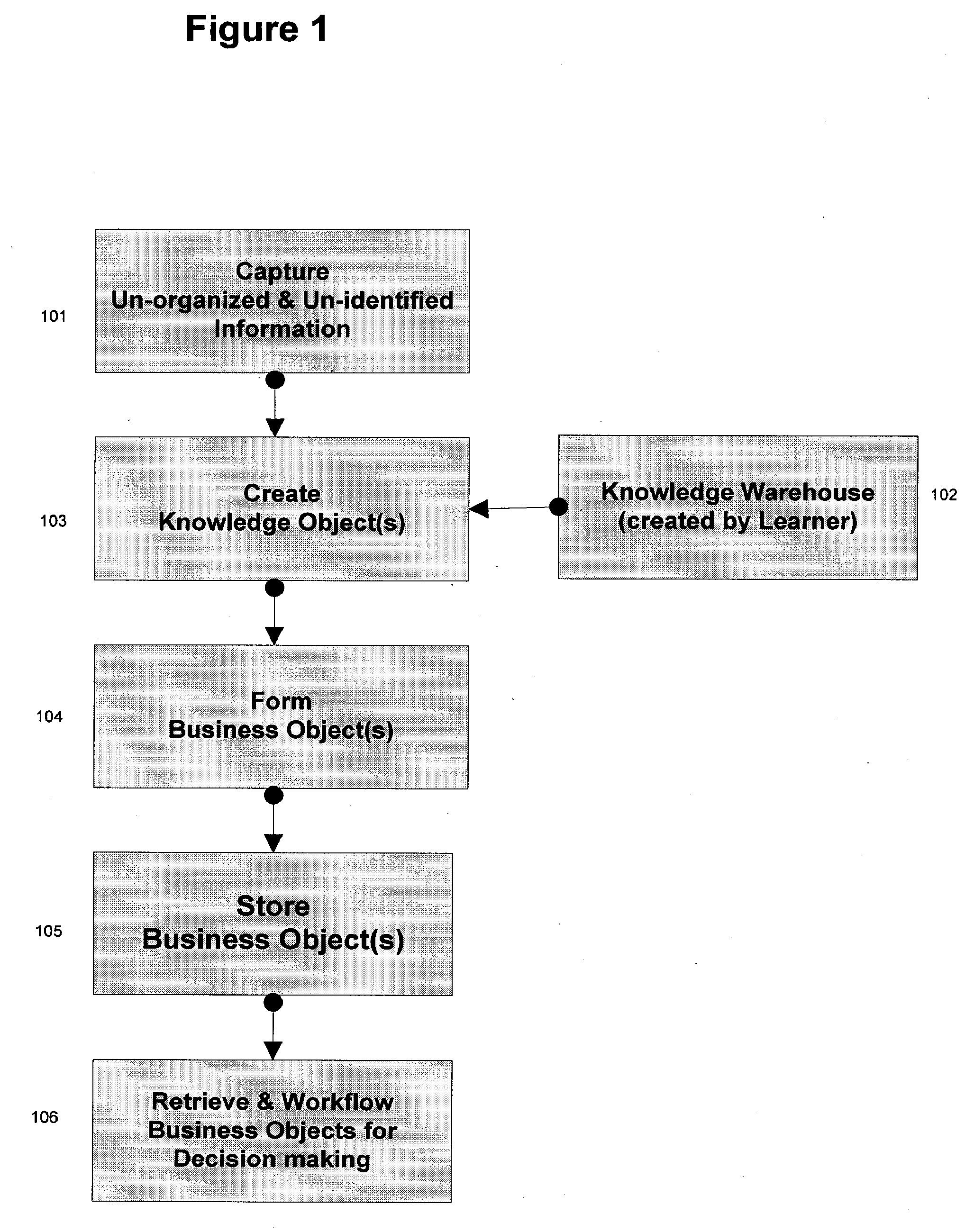
The invention features a business method that takes advantage of the ability to convert unorganized information in the form of paper documents, document images, and electronic documents arid converts the information to an organized electronic form referred to as Knowledge Objects. The invention further encompasses forming electronic Business Objects, such as documents and data sets, useful for business decision making and information exchange. The methods of the invention may utilize computerized storage and computerized decision-making systems to enable making more rapid critical business decisions.
Owner:ICE MORTGAGE TECH INC
Automatic Learning Multi-Modal Fraud Prevention (LMFP) System
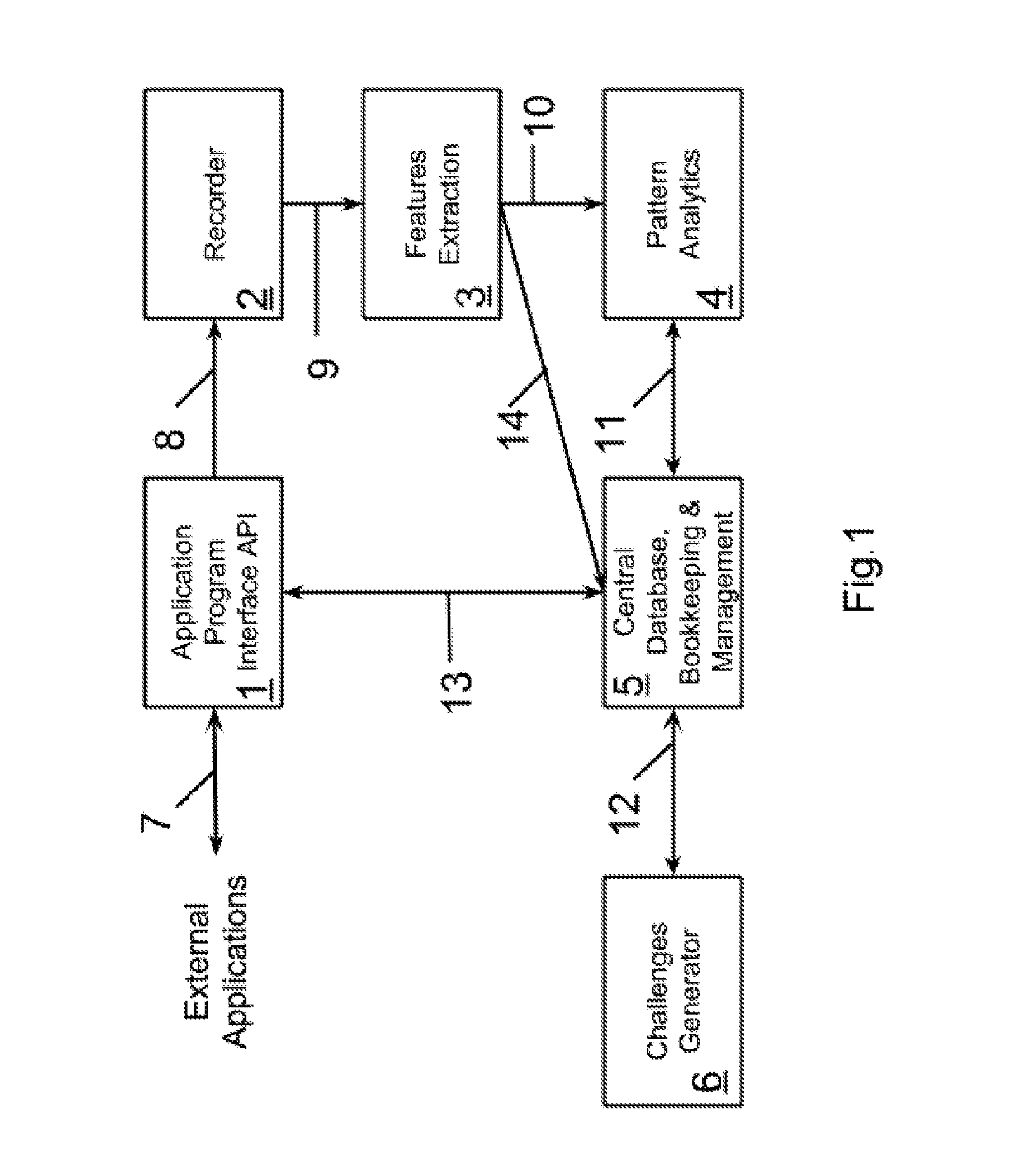
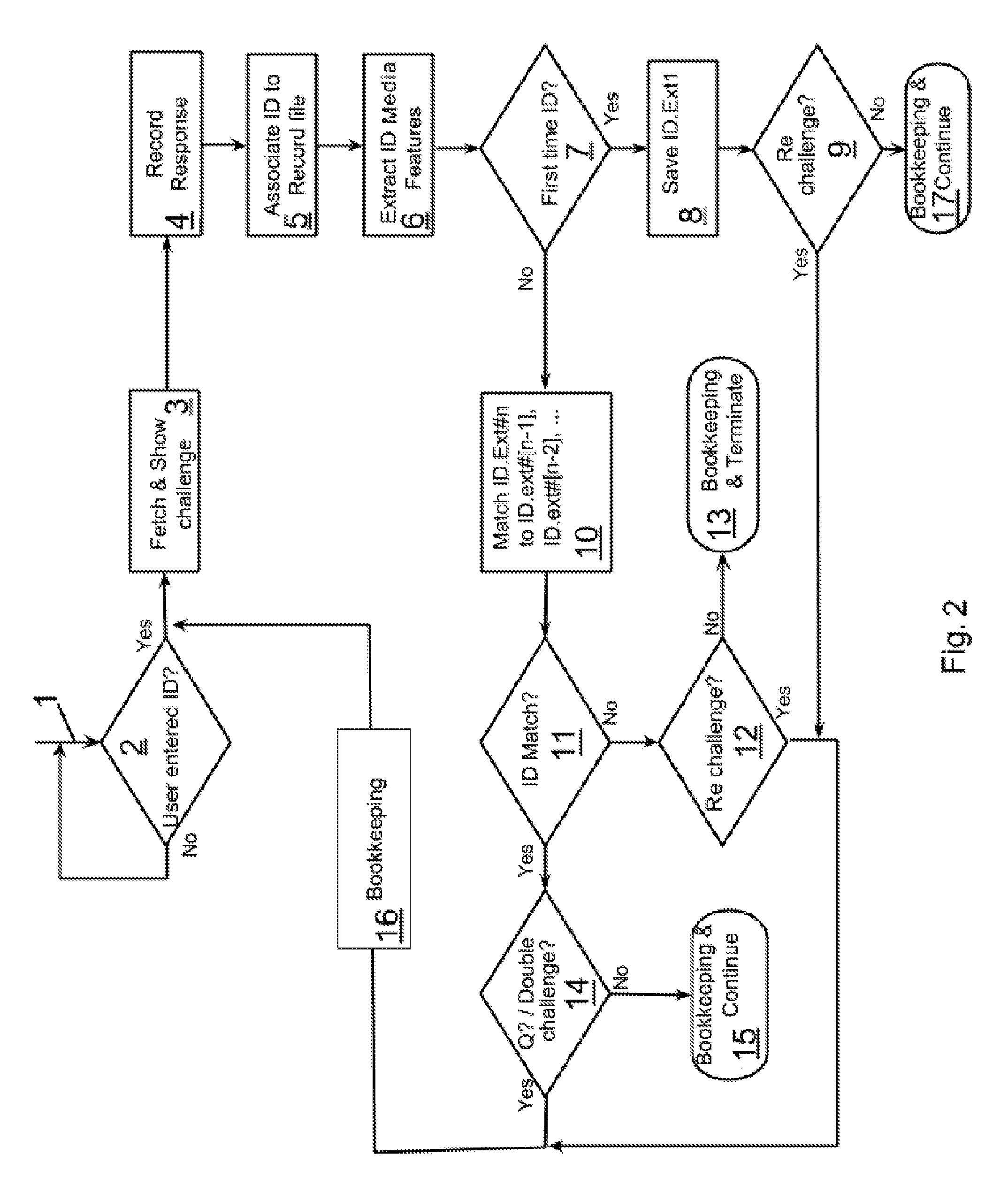
ActiveUS20140289867A1Increase probabilityHigh quality factorDigital data processing detailsAnalogue secracy/subscription systemsRe challengeChallenge response
A computerized learning multi-modal fraud prevention system and method for generating a data signature of a user, such as one engaged in electronic commerce, to prevent fraudulent activities by machines and persons imitating the user. Steps comprise: fetching a signal of a user's signature stored in memory; generating at least one challenge sequence based on the signal to create a second signature; presenting the generated challenge sequence to the user; collecting the user's challenge response to the generated challenge sequence; computing a quality factor between the user's challenge response and the generated challenge sequence; computing a transaction quality factor and content quality factor and reporting an impostor or re-challenging if the quality factor is below a threshold. Lastly, generating a new signature based on any portion of a user's challenge response and / or any portion of the previously generated signature and / or any portion of collectable information from the user's device memory.
Owner:BUKAI DROR
Delivery of advertisments over broadcasts to receivers with upstream connection and the associated compensation models
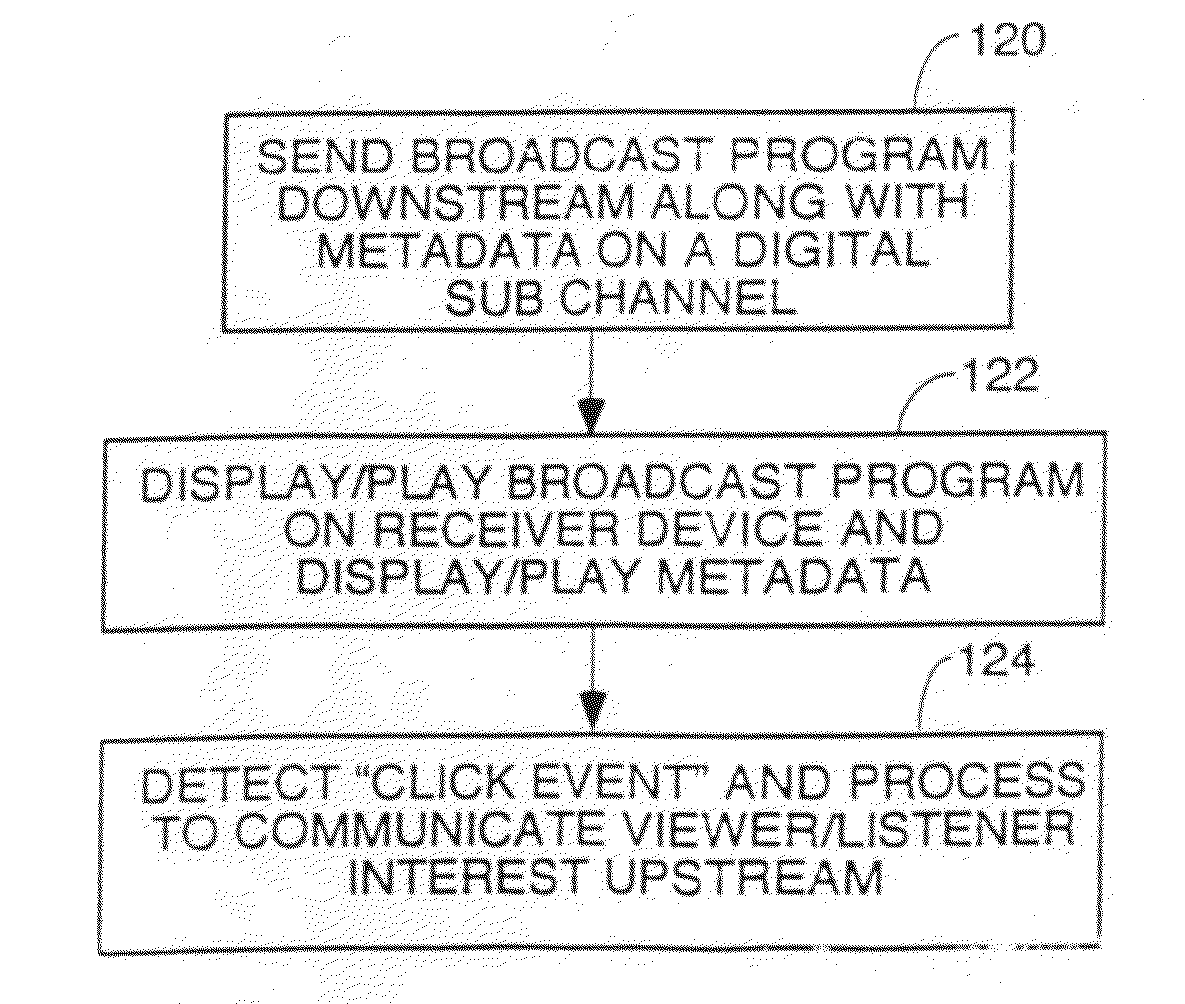
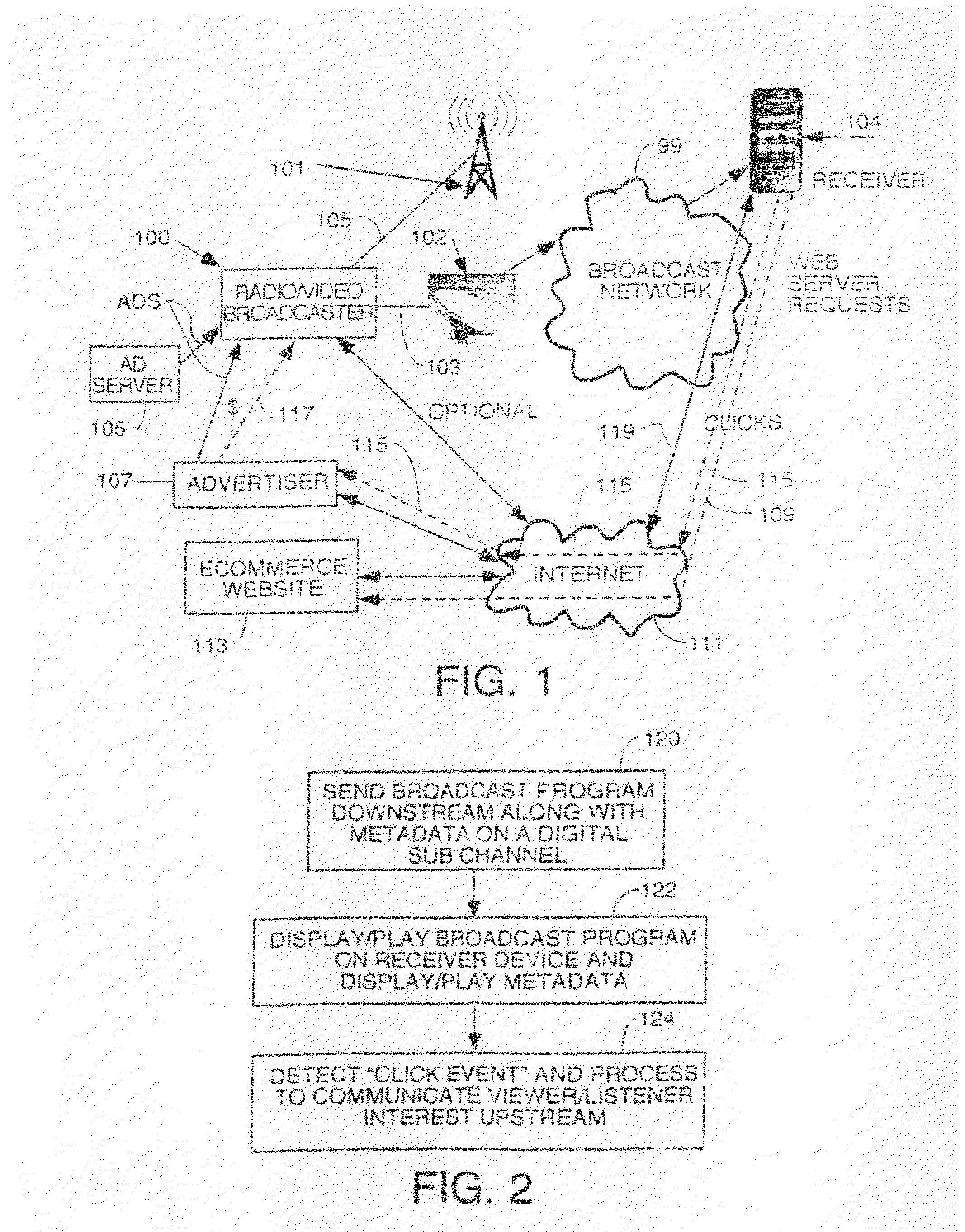
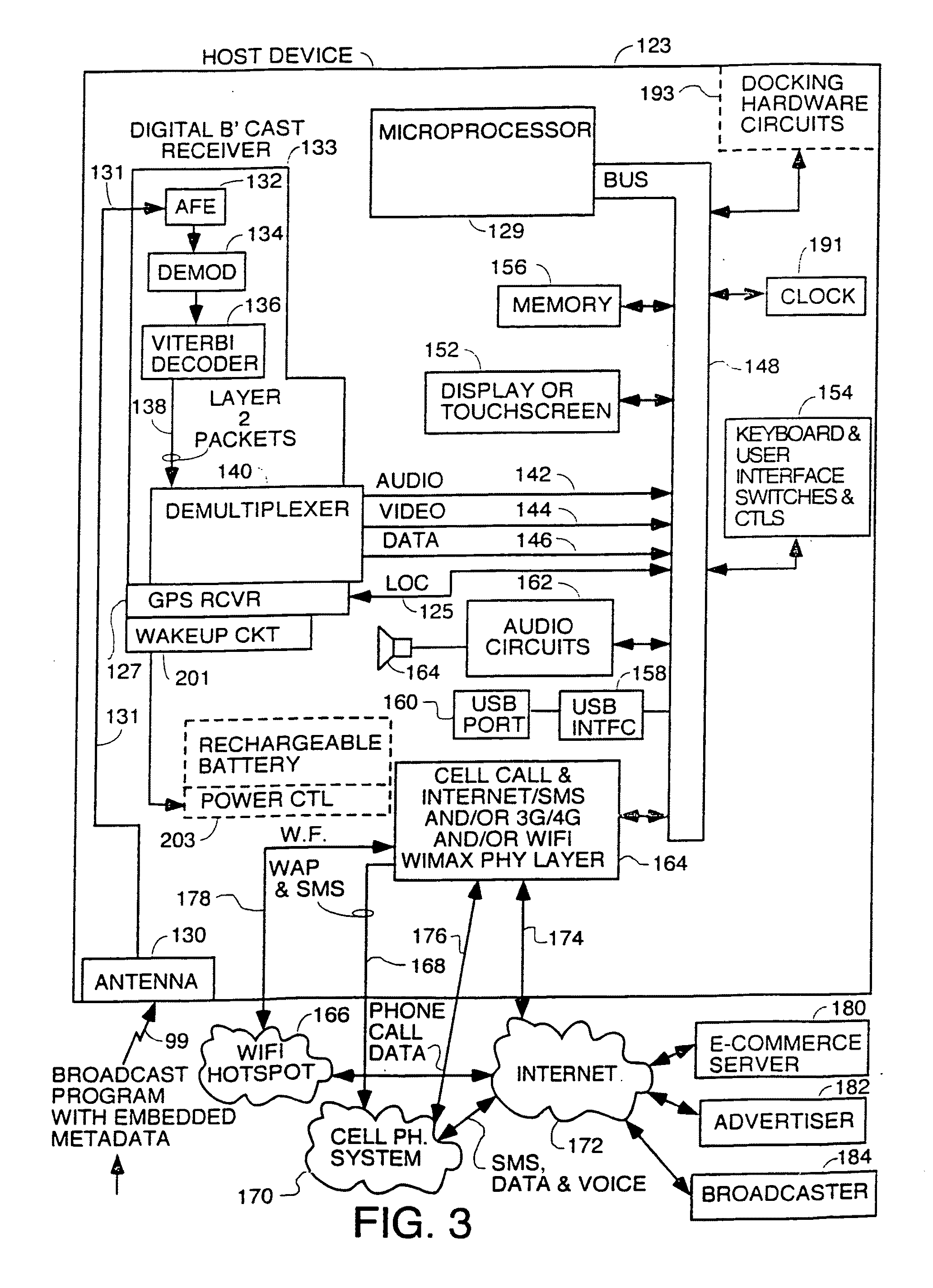
InactiveUS20110202270A1Instruments for road network navigationAdvertisementsDigital dataTablet computer
A system to add metadata to downstream broadcasts to devices such as smart phones, MP3 music players, tablet computers, etc. equipped with receivers to receive said downstream broadcasts and a full time or part time upstream digital data communication path. The devices are controlled to display or playback advertisements, images etc. in the metadata, detect click events indicating interest by a user in something in the metadata and communicate that click event upstream over a full time or part time internet or an SMS data path connection. Upstream communications to implement user interest such as visit web pages, make a phone call, start an e-commerce transaction are implemented by the client devices. The Transmitters have structure to insert metadata in band or out of band with the broadcast program content and can be coupled to ad servers.
Owner:INTEL CORP
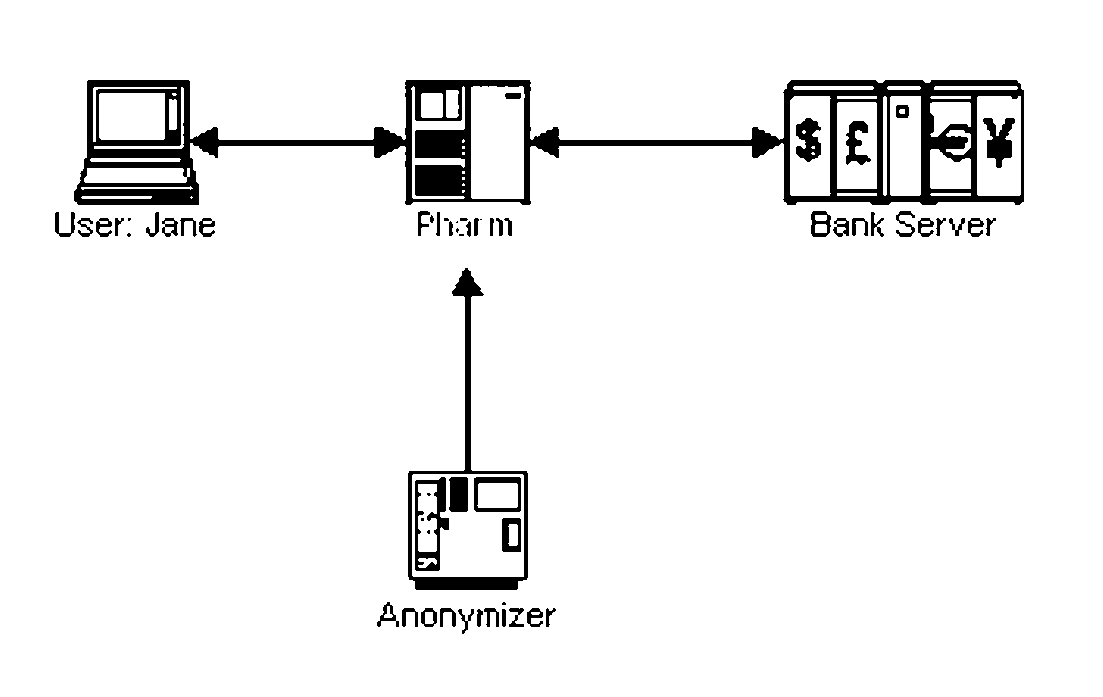
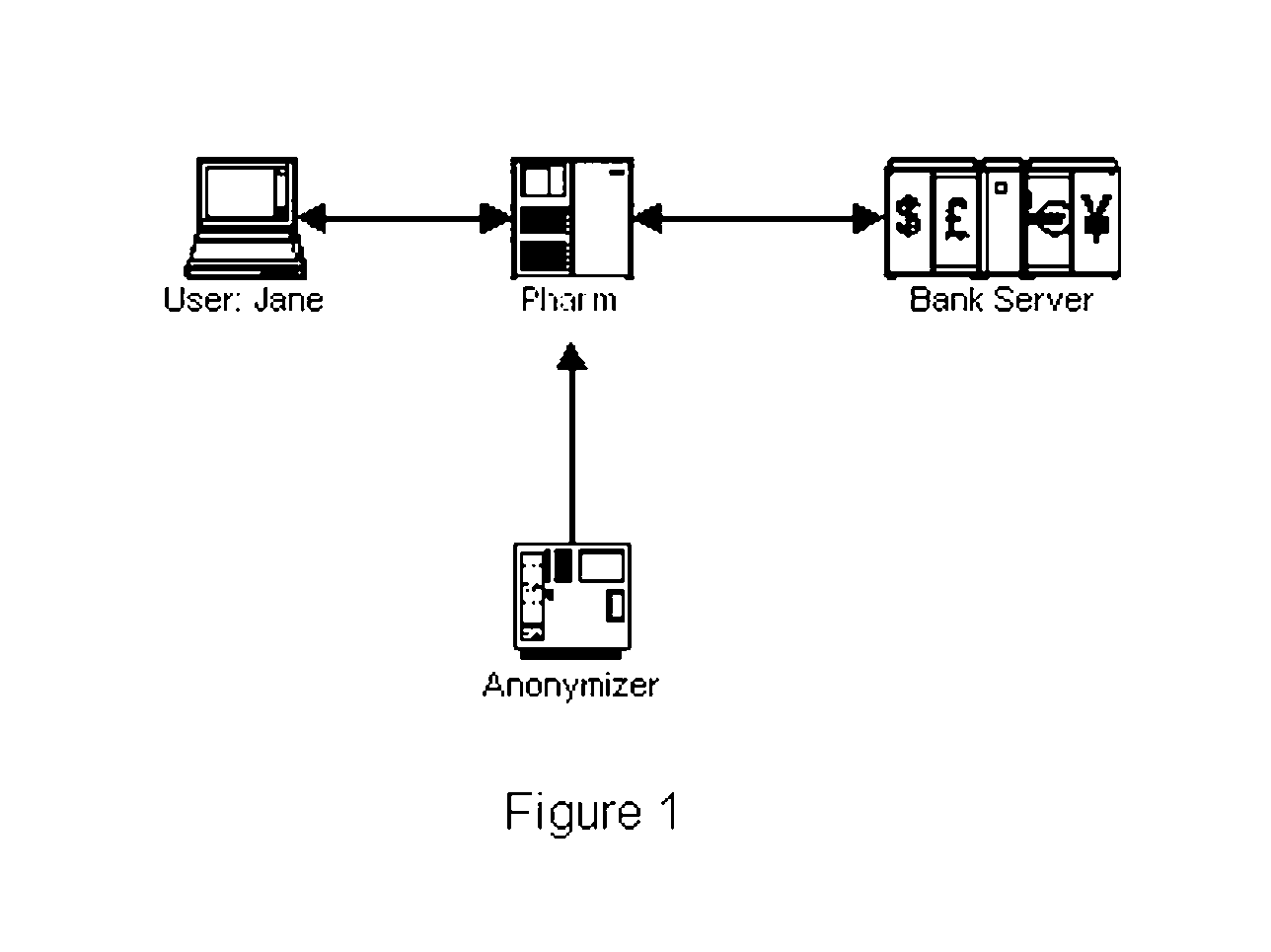
System and Method of Mobile Anti-Pharming and Improving Two Factor Usage
InactiveUS20070174630A1Improve securityLow costRandom number generatorsUser identity/authority verificationPrivate networkSoftware
A variant of phishing involves subverting an Internet access point, often used for mobile computing. Malware can route user requests for bank websites into a phisher's private network, with fake bank websites (pharming). The user can have a “mobile password” at the bank. When she connects from an access point, she sends a hash, found from the password, starting at some position in it. The bank returns a hash, found from the same password, starting at another position in it. Each can verify the other. We protect both from a man in the middle attack. By hashing a web page and the mobile password, and inserting the hash into the page that is sent, the recipient can verify that the page is untampered. We use an anonymizer, external to the access point. A user pre-establishes a password with the anonymizer. At the access point, she and the anonymizer use a zero knowledge protocol to verify each other, based on the password. Then, the password encrypts communication between them. From the anonymizer, she logins elsewhere. The anonymizer is our man in the middle, to defeat a man in the middle attack. W extend earlier antiphishing methods, to attack pharms for non-existent banks, or that are unauthorized websites for actual companies. We show how to use a plug-in to let websites share several two factor implementations. This reduces the cost and inconvenience to consumers, who might otherwise have to carry and use a different two factor gadget, for each of their bank accounts or other corporate websites that mandates the usage of two factor authentication. By expanding the scope of two factor usage, we improve the security of e-commerce, without having to use a public key infrastructure.
Owner:METASWARM INC
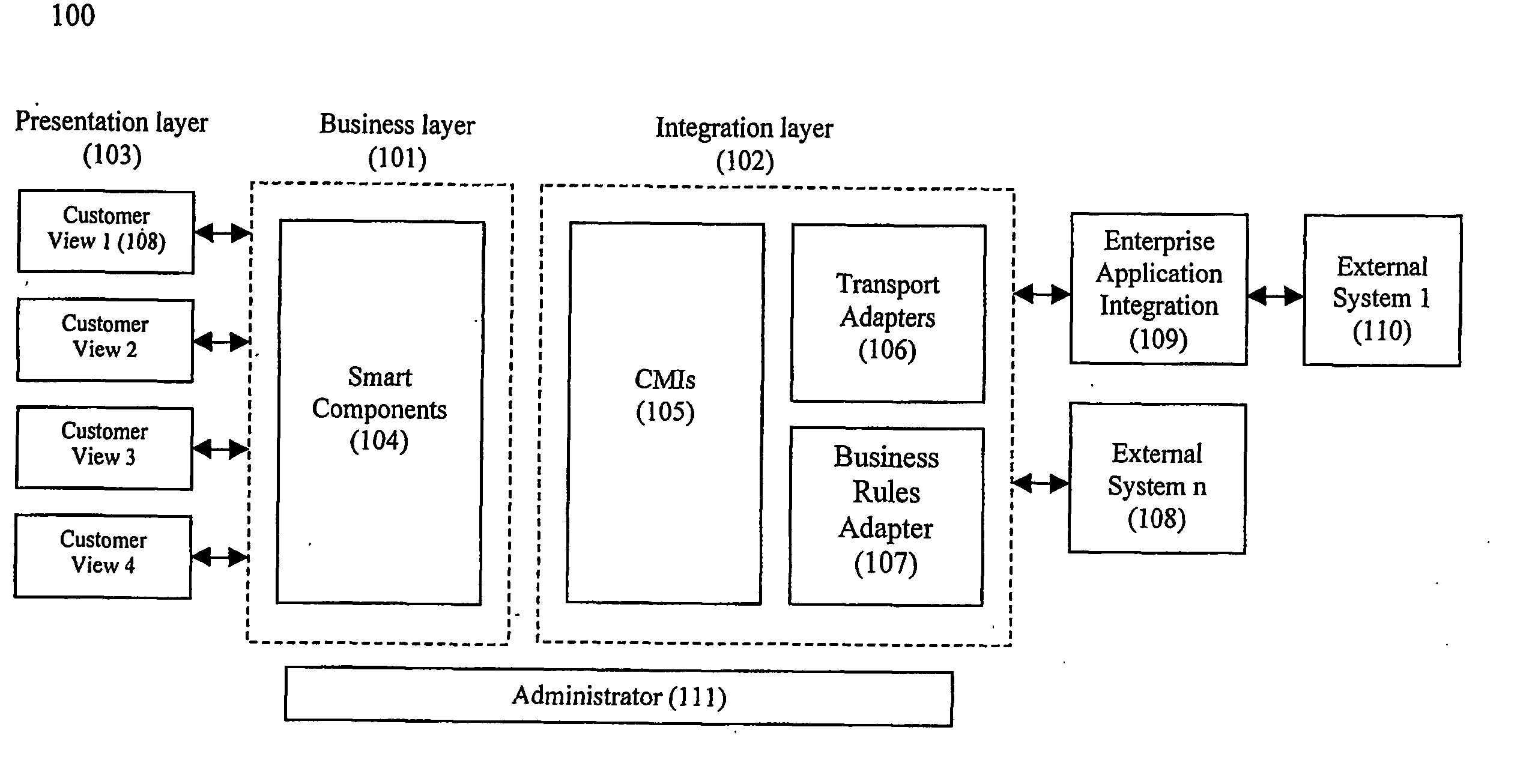
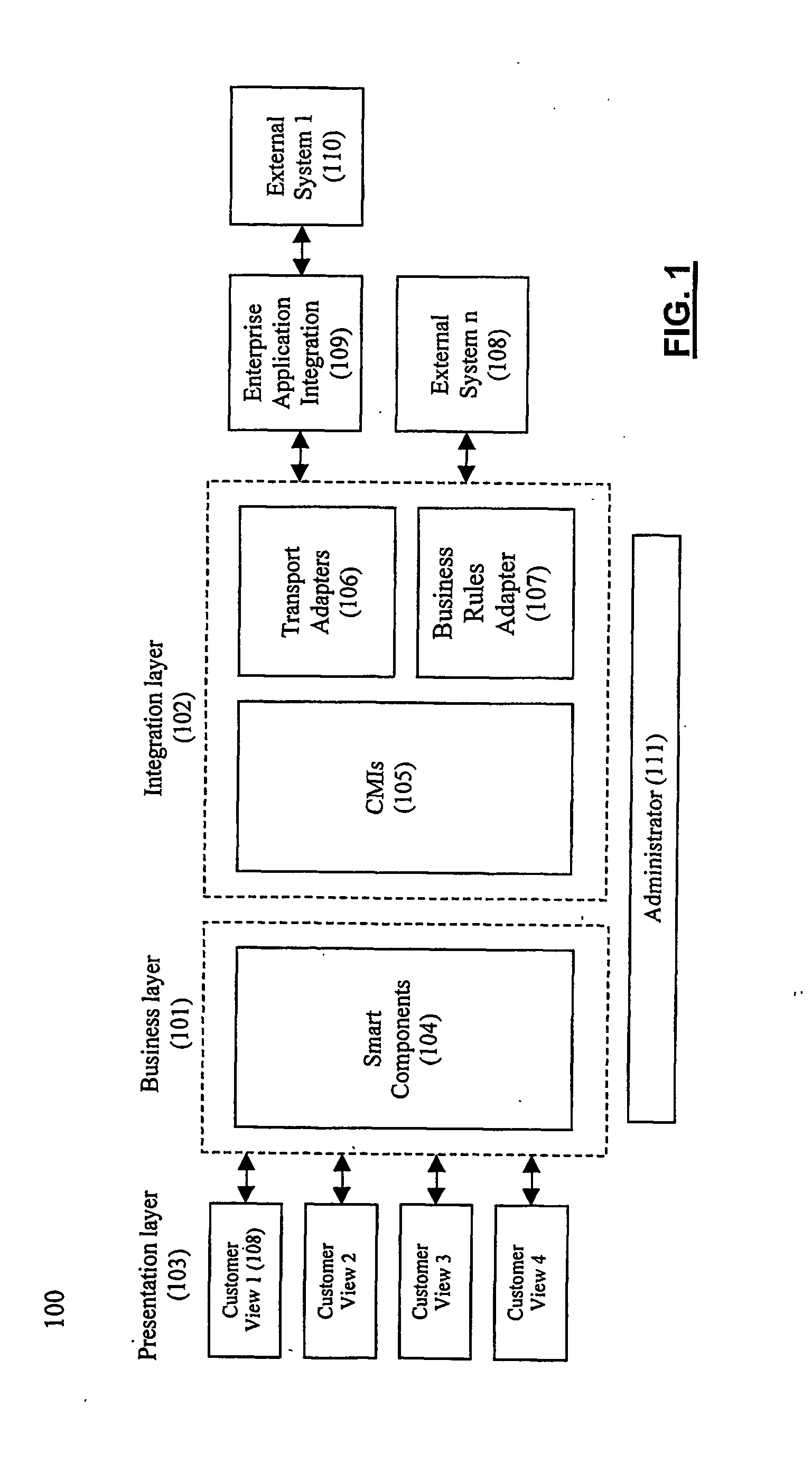
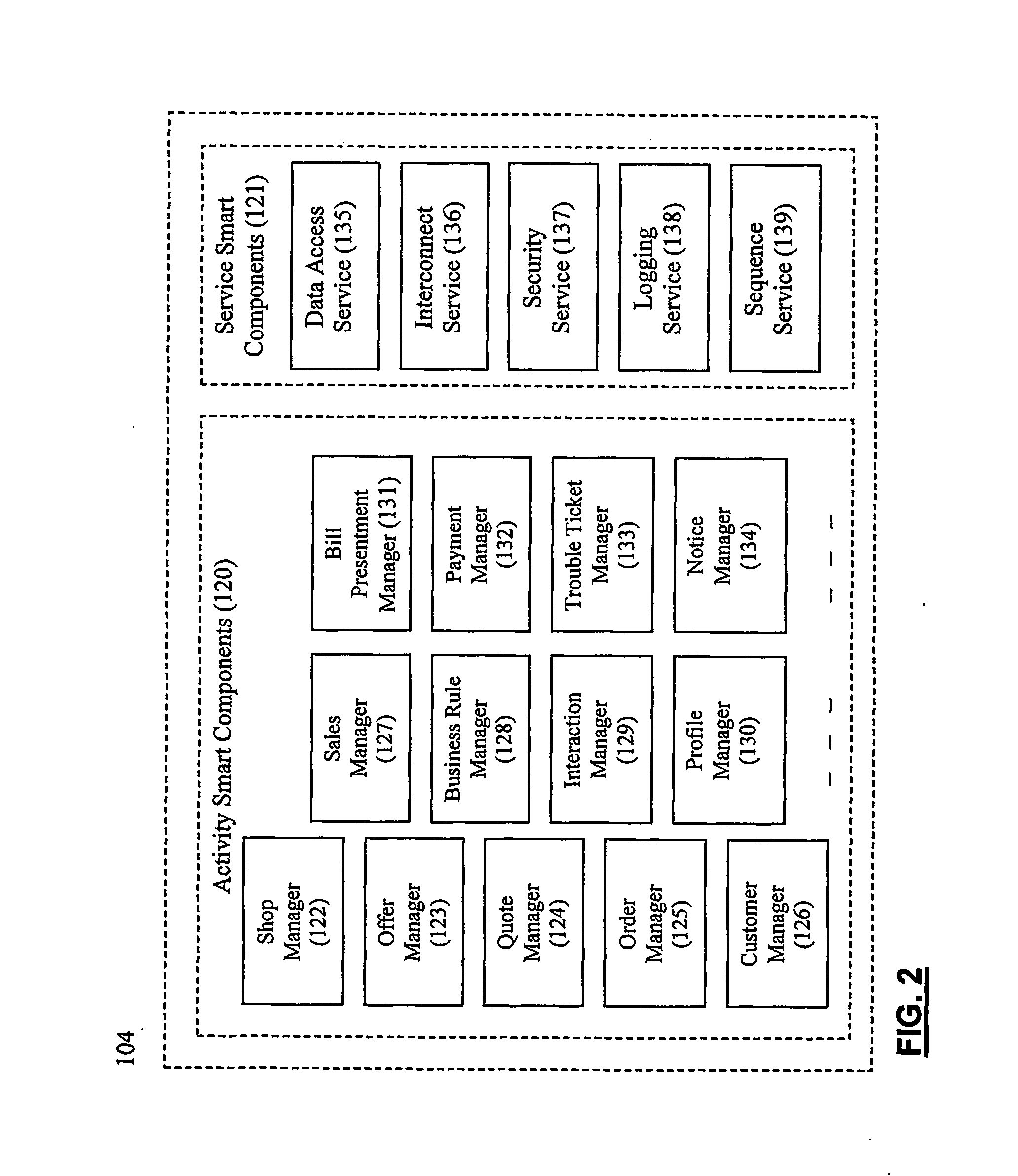
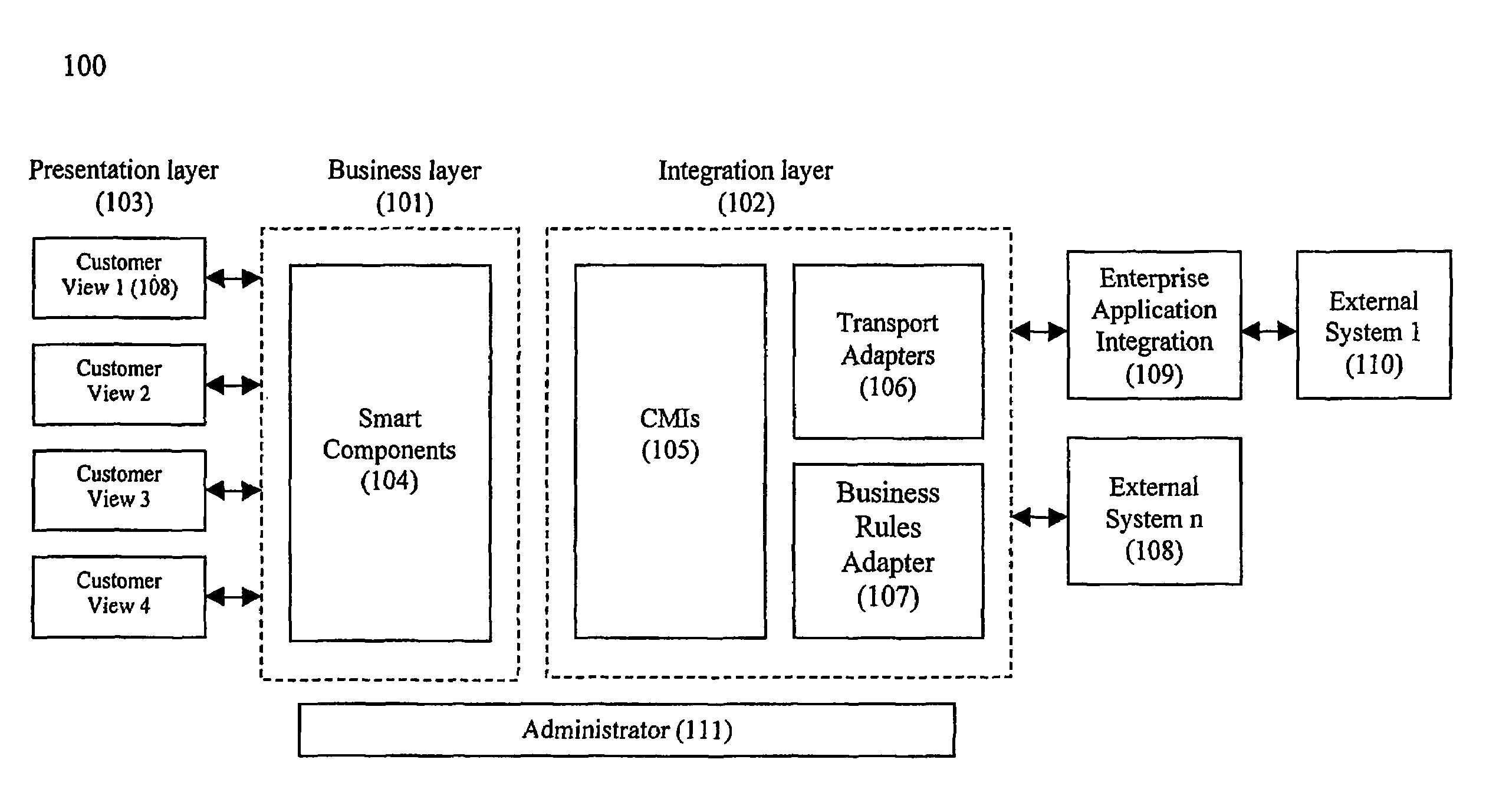
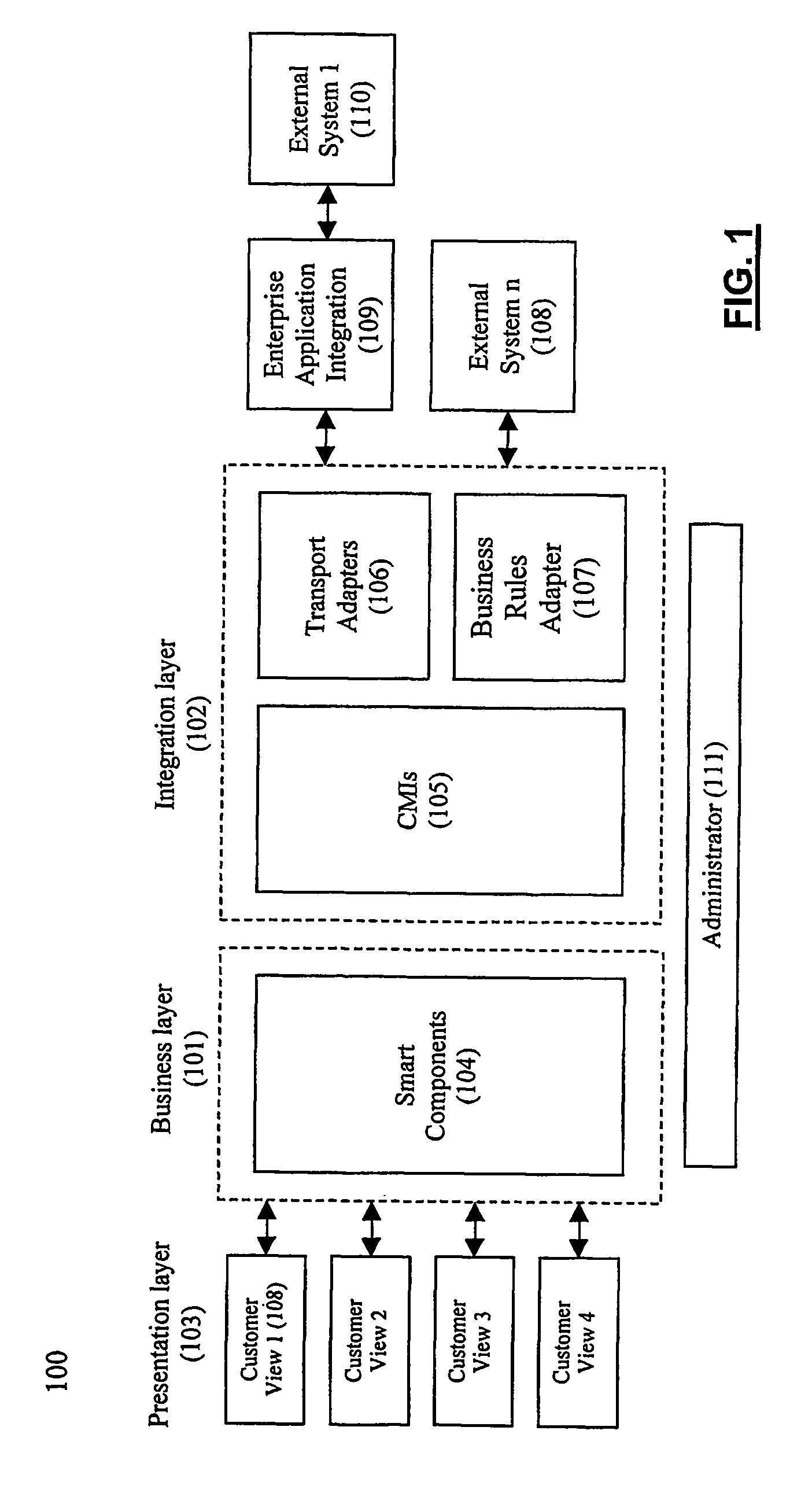
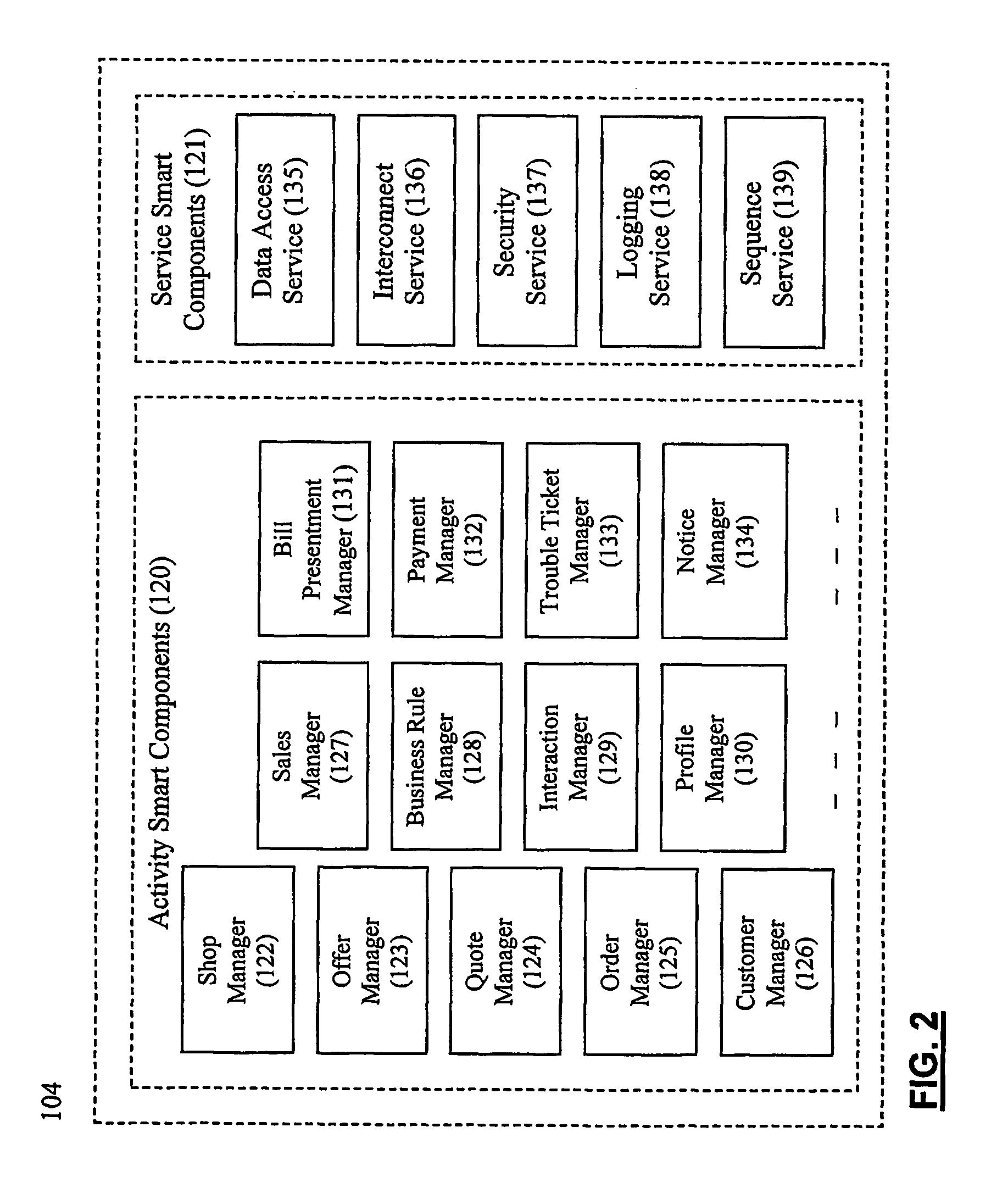
System and method for establishing electronic business systems for supporting communications services commerce
ActiveUS7657436B2Quick implementationReduce maintenance costsComplete banking machinesTelephonic communicationEnterprise application integrationSupporting system
A comprehensive electronic business support system comprises three layers: (1) the business layer, including various smart components which unify data and business processes across all customer interactions; (2) the integration layer, including various communications messaging interfaces and enterprise application integration adapters, which provide a flexible, automated, and process driven solution for integrating across business applications and operations support systems; and (3) the presentation layer, including various customer views, which are presented via particular business portals. A smart component server provides the core services and comprehensive business process logic required to successfully conduct business online. The communications messaging interfaces integrate with back-office systems for functions such as billing, provisioning, and interconnection.
Owner:NETCRACKER TECH SOLUTIONS
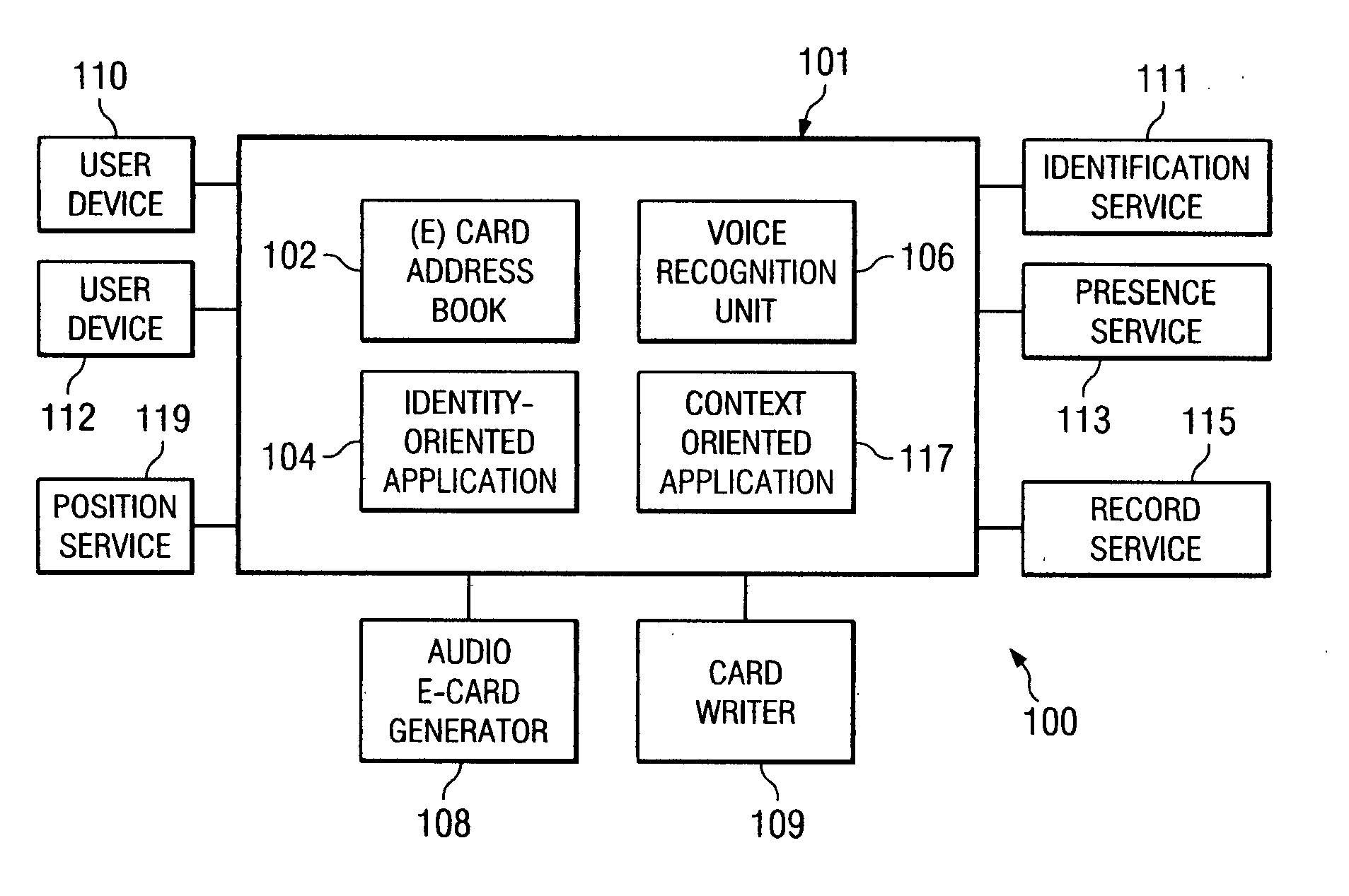
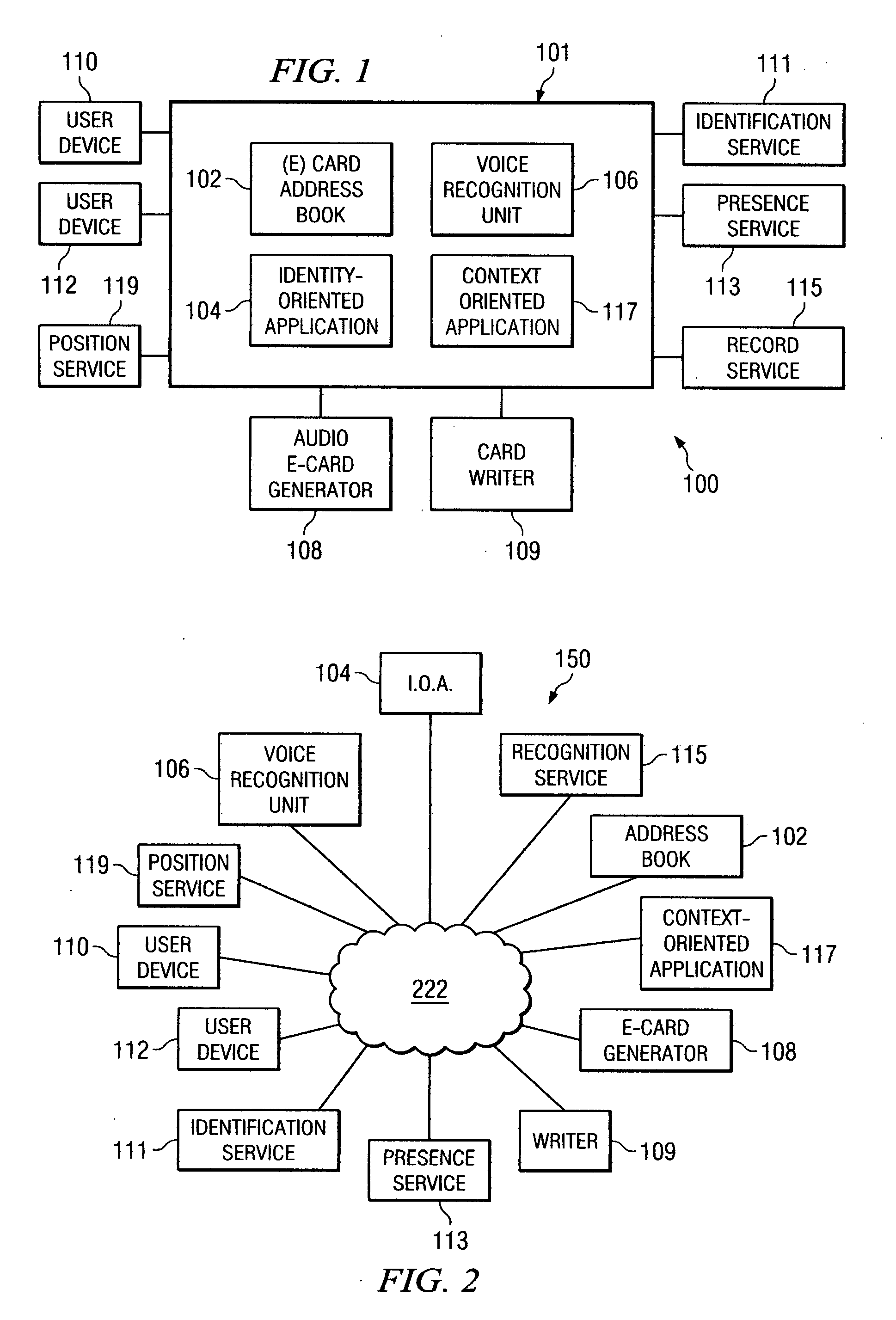
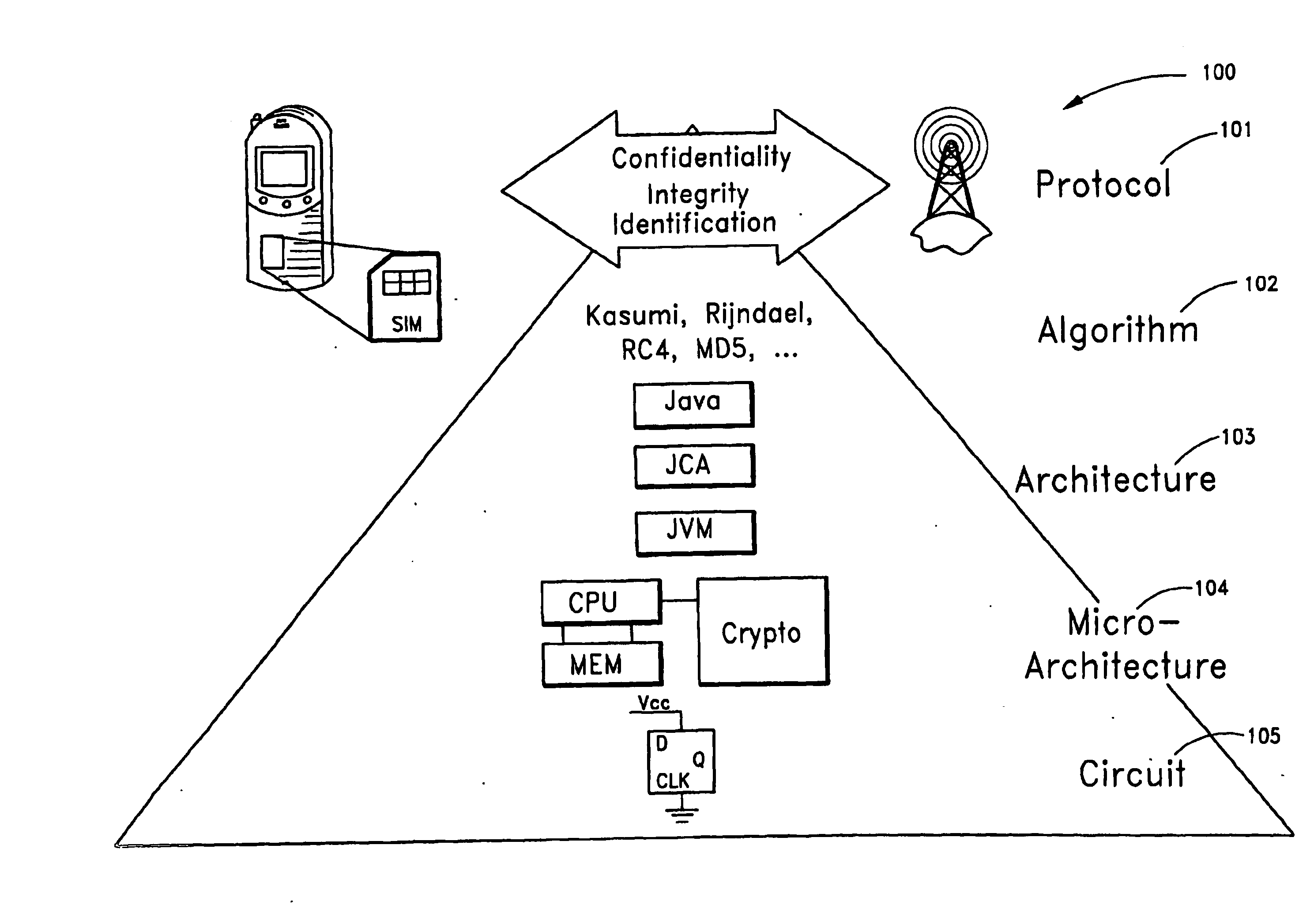
Method and apparatus for identification of conference call participants
ActiveUS20090089055A1Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingUser deviceSpeech identification
A system including a conferencing telephone coupled to or in communication with an identification service. The identification service is configured to poll user devices of conference participants to determine or confirm identities. In response, the user devices transmit audio electronic business cards, which can include user voice samples and / or preprocessed voice recognition data. The identification service stores the resulting audio electronic business card data. When the corresponding participant speaks during the conference, the identification service identifies the speaker.
Owner:RINGCENTRAL INC
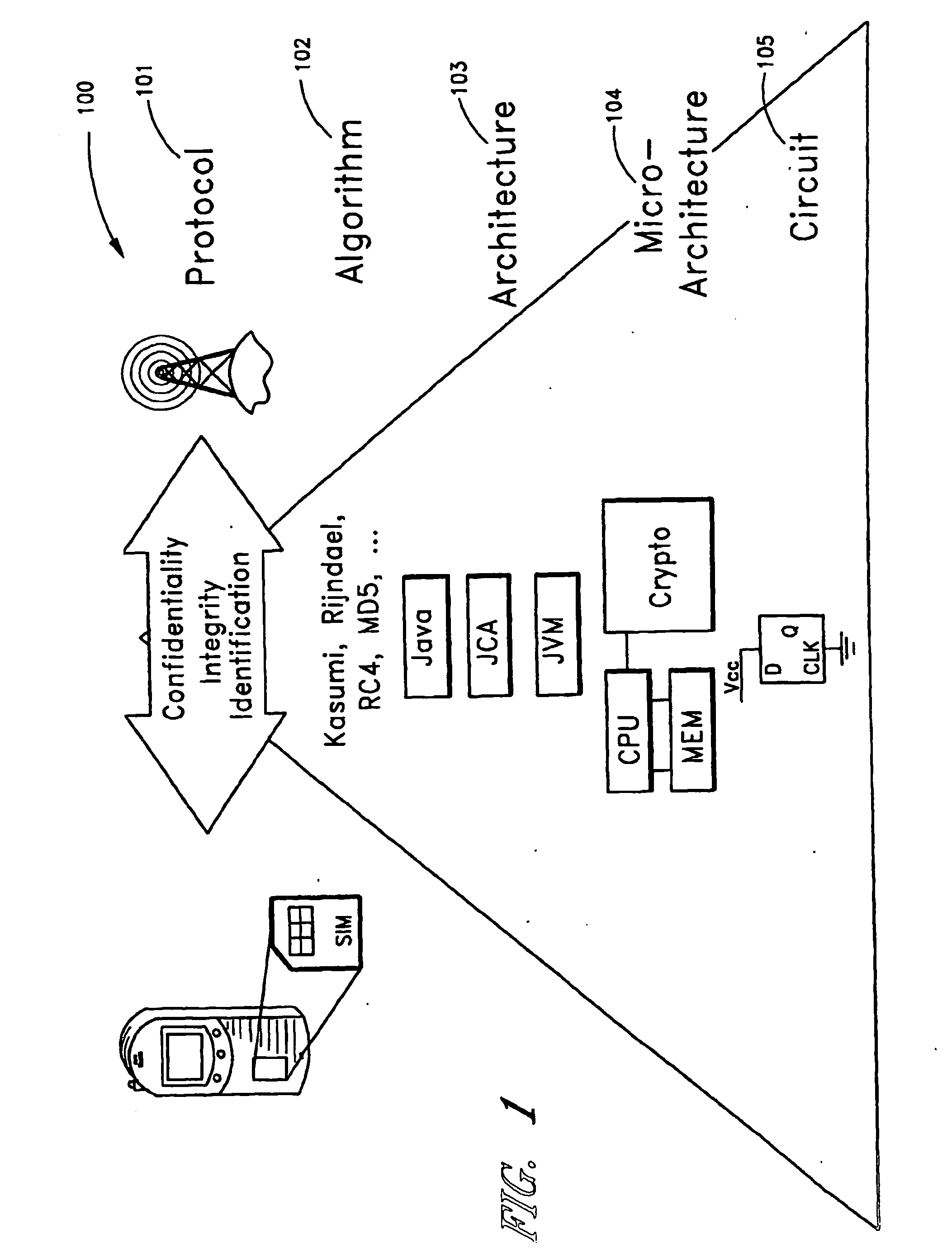
System for biometric signal processing with hardware and software acceleration
InactiveUS20070038867A1Improve performanceKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareSystem design methodology
A secure embedded system that uses cryptographic and biometric signal processing acceleration is described. In one embodiment, the secure embedded system is configured as a wireless pay-point protocol for brick-and-mortar and e-commerce applications in which biometric information is localized and does not require transmission of biometric data for authentication. In one embodiment, a key-generation function uses a dynamic key generator and static biometric components. In one embodiment, an embedded system design methodology provides hardware and software acceleration transparency.
Owner:RGT UNIV OF CALIFORNIA
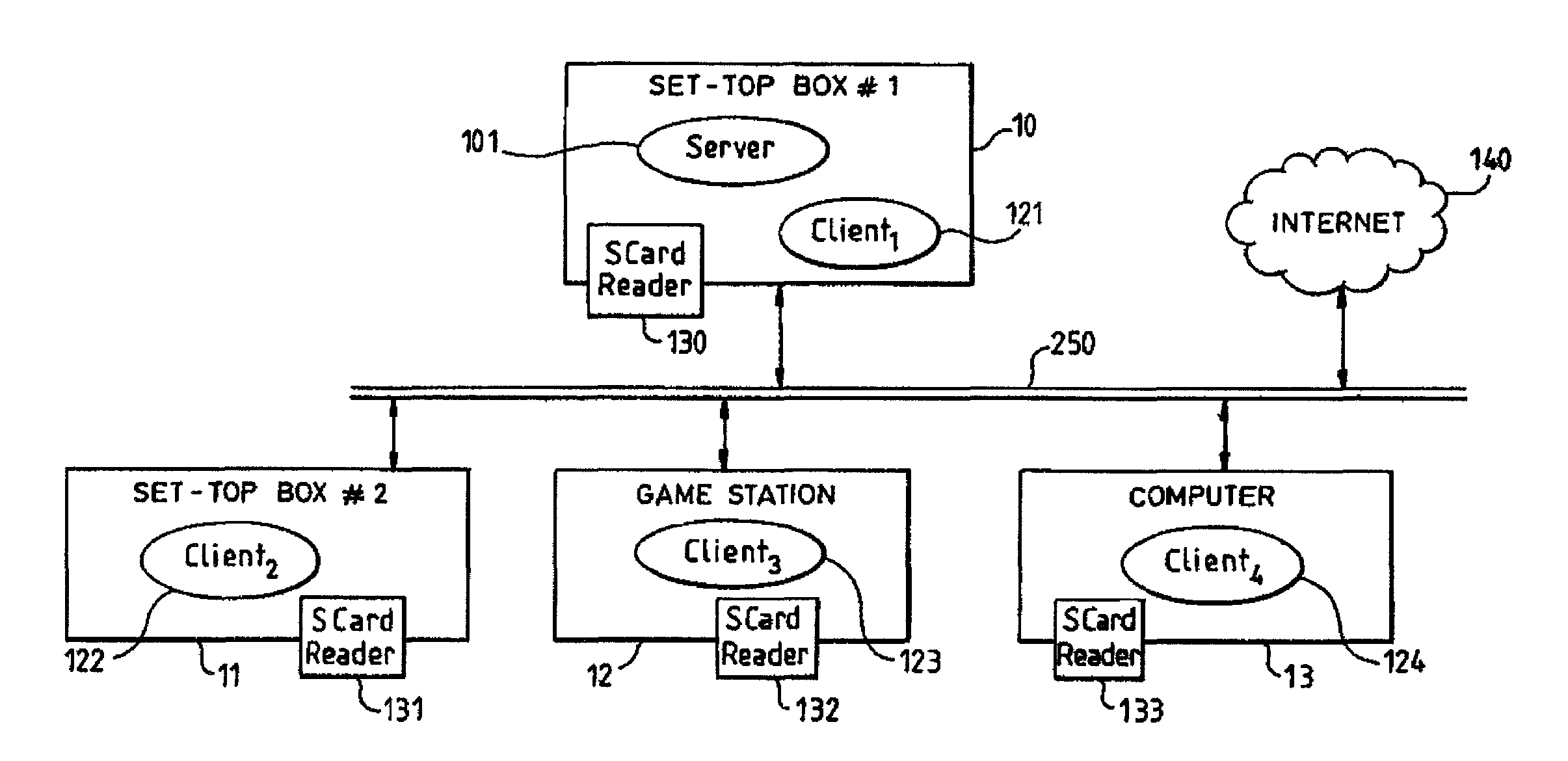
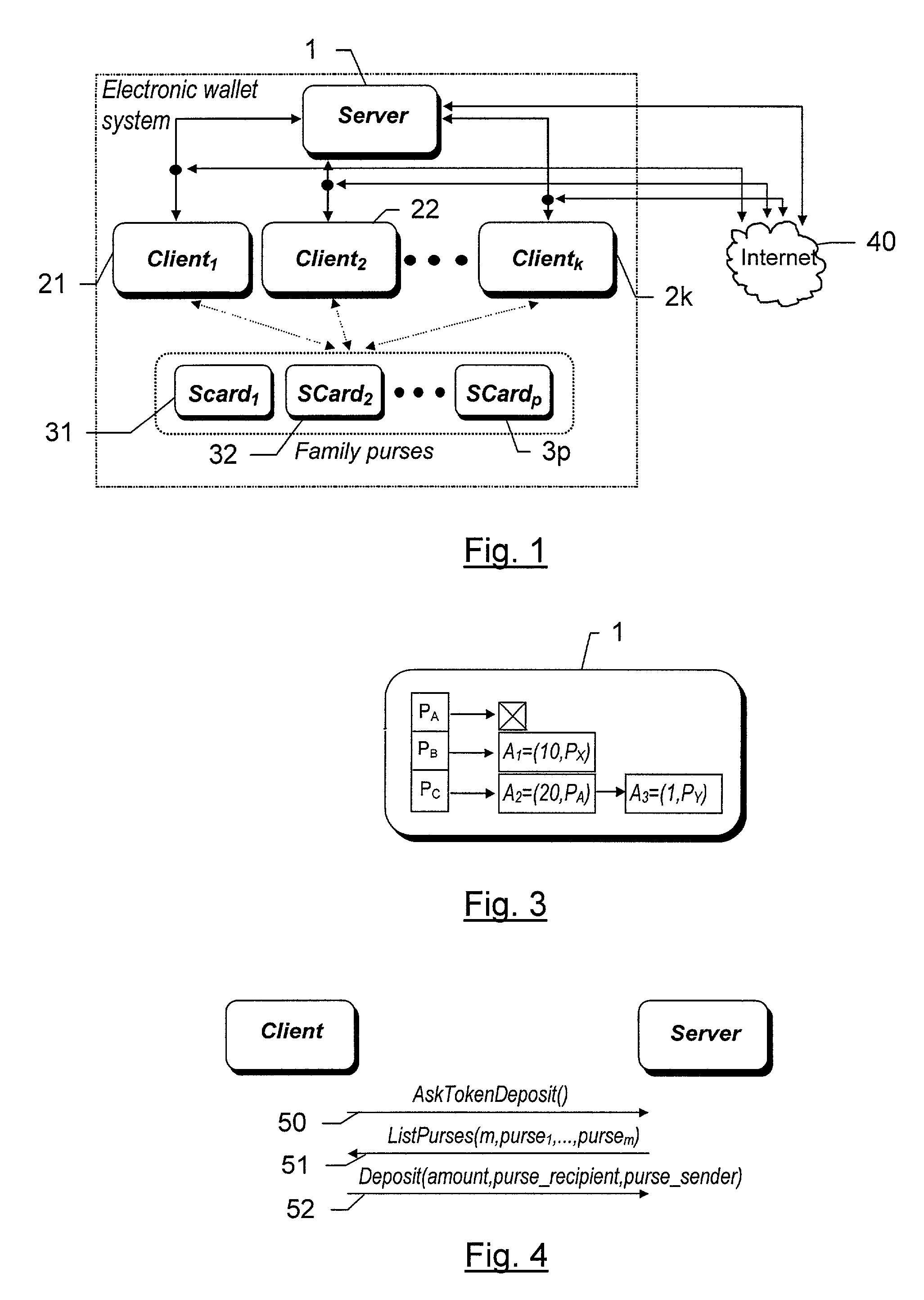
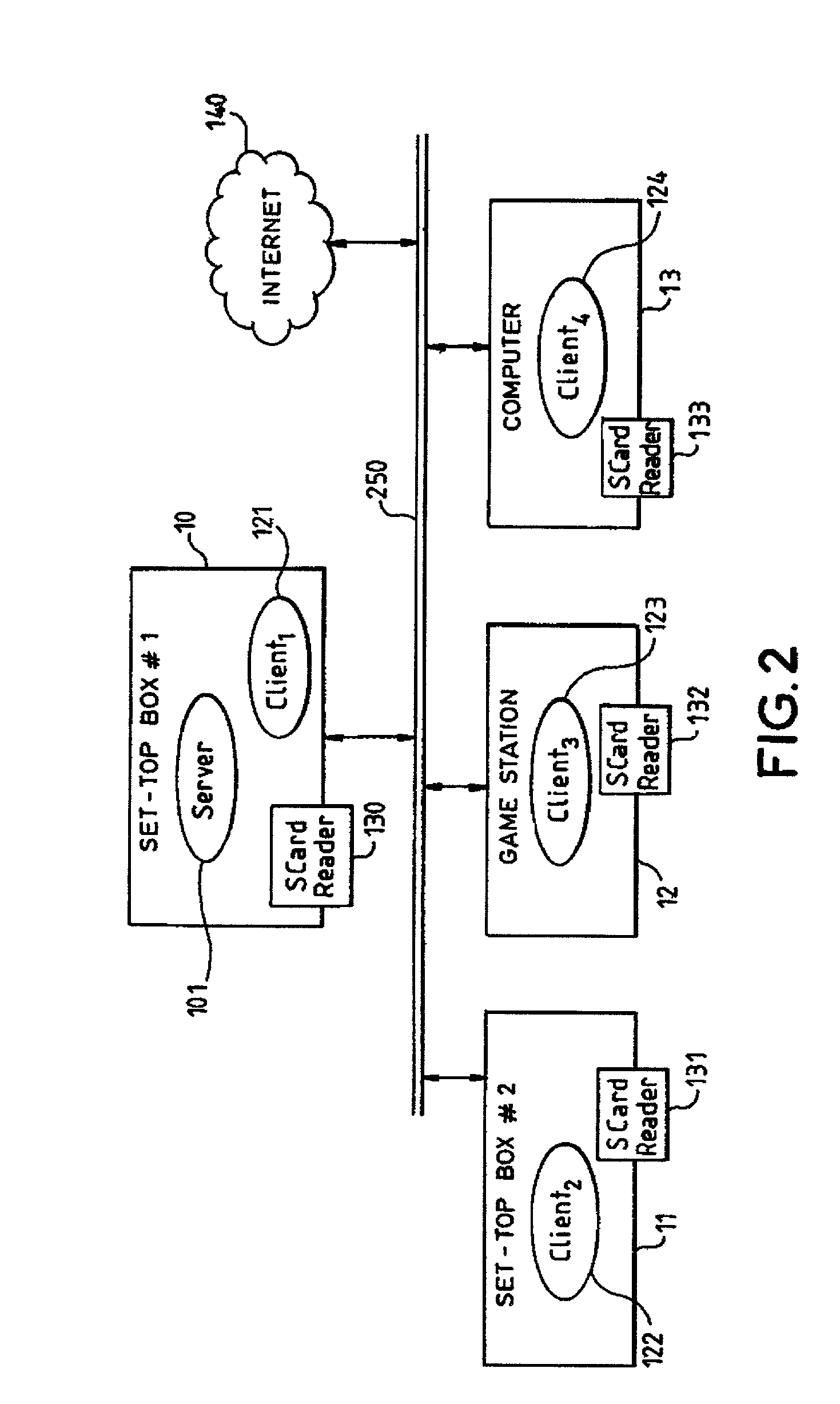
Electronic wallet system
ActiveUS7206769B2Possible transferPayment circuitsCoded identity card or credit card actuationFinancial transactionCard reader
The electronic wallet system comprises a plurality of devices interconnected through a local network and capable of conducting electronic business transaction on an open network (40). Each device contains a smart card reader. A plurality of smart cards (31–3p) represent the electronic purses of the system. One of the devices comprises an entity called the server which contains a list of purses liable to receive tokens from others purses of the system. The tokens transferred between purses are stored temporally by said server.Application to a family wallet system allowing children to participate to electronic commerce.The system makes it possible to transfer tokens from one first purse to a second purse without having in hands the smart card corresponding to the second purse.
Owner:THOMSON LICENSING SA +1
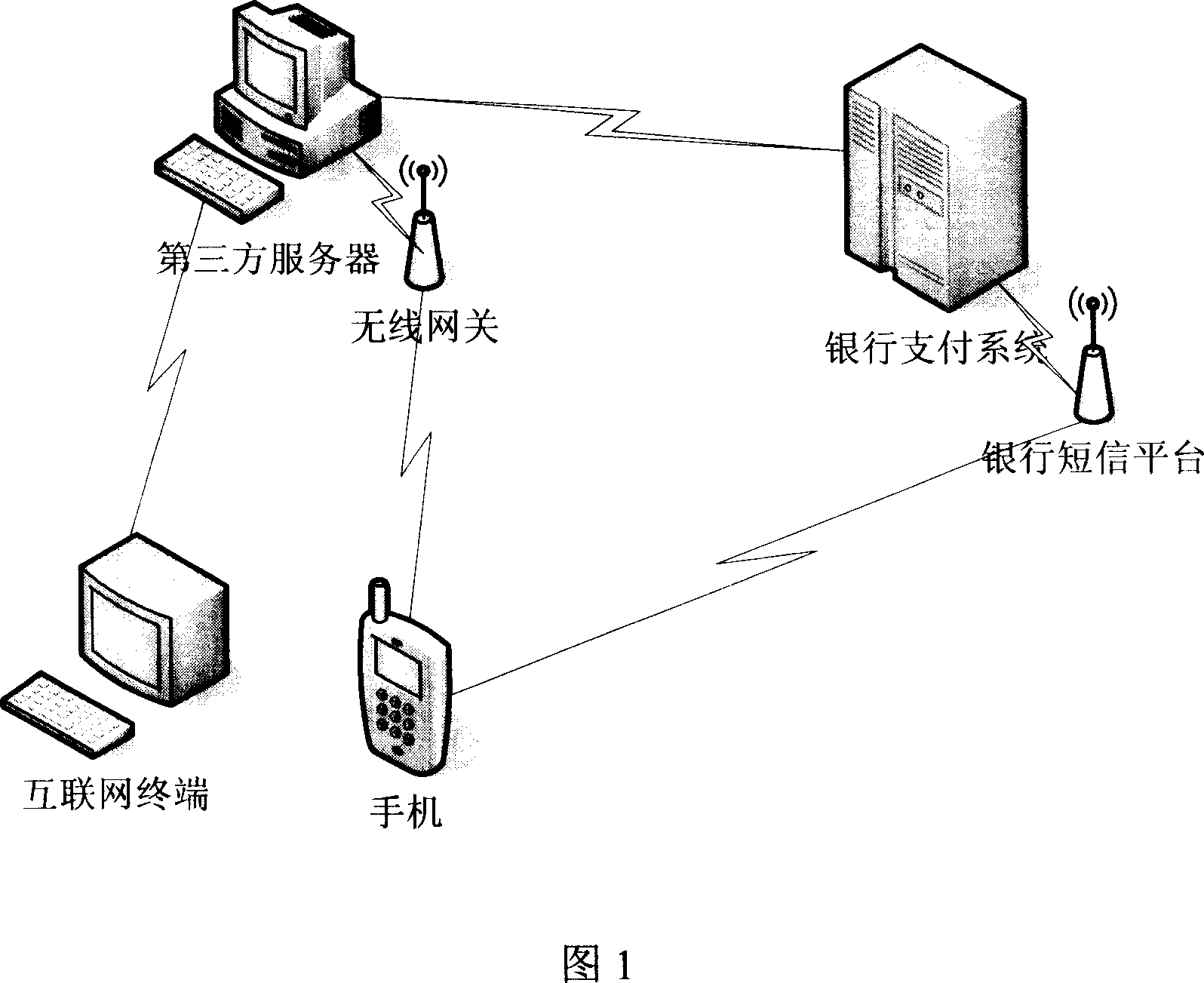
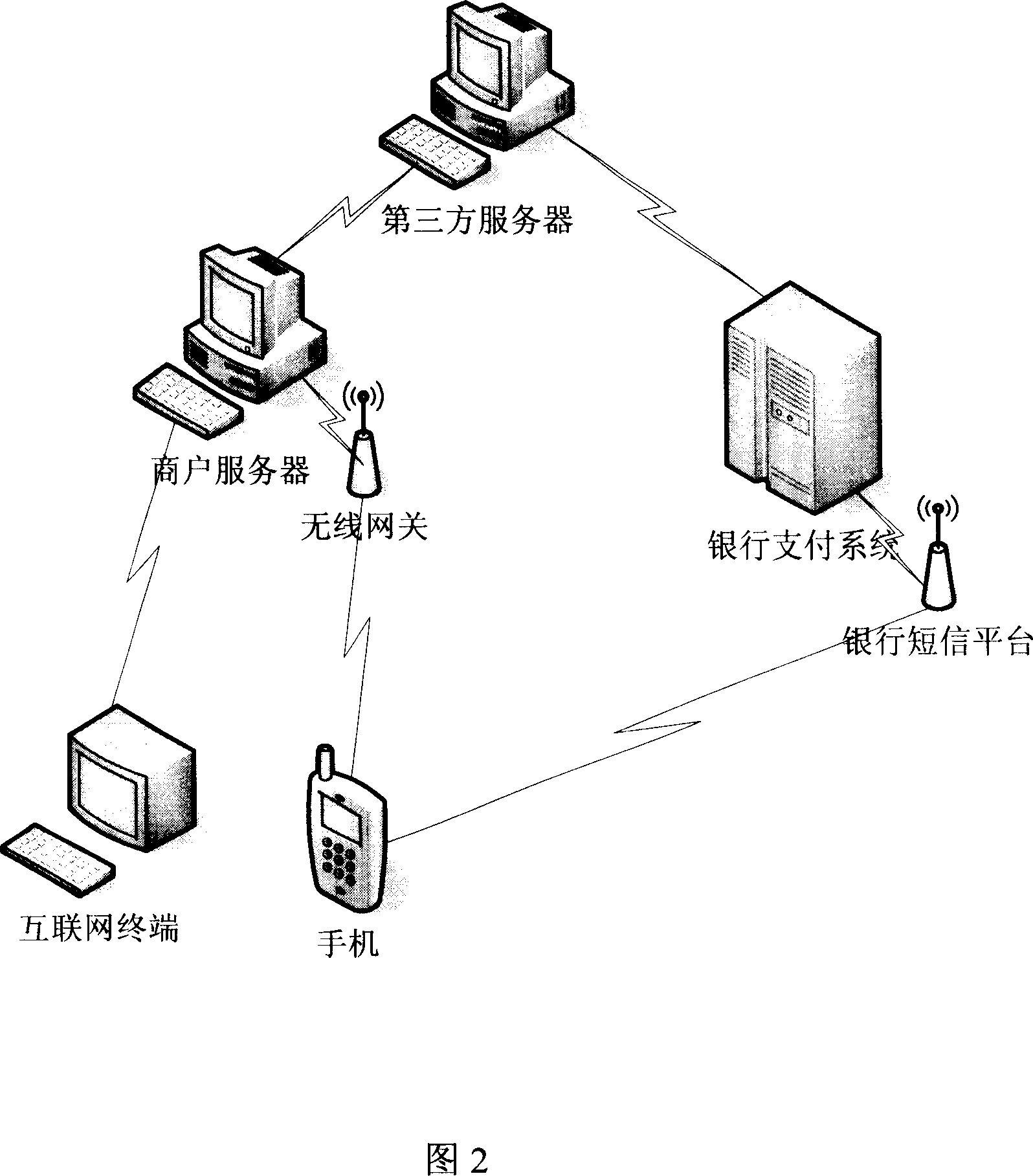
Method for safety verifying financial business information in electronic business
InactiveCN101051372AEliminate financial security concernsBroaden the fieldPayment protocolsCommerceThird partyBank account
The present invention relates to a method capable of making financial service information undergo the process of safety authentication in the electronic business. It is characterized by that it utilizes personal identity information stored and transferred to bank payment system by third party server and combines said personal identity information with user handset short-mail authorization and acknowledgement to implement safety authentication of bank payment service. Besides, said invention also provides the concrete steps of said method.
Owner:BEIJING YIFUJINCHUAN TECH
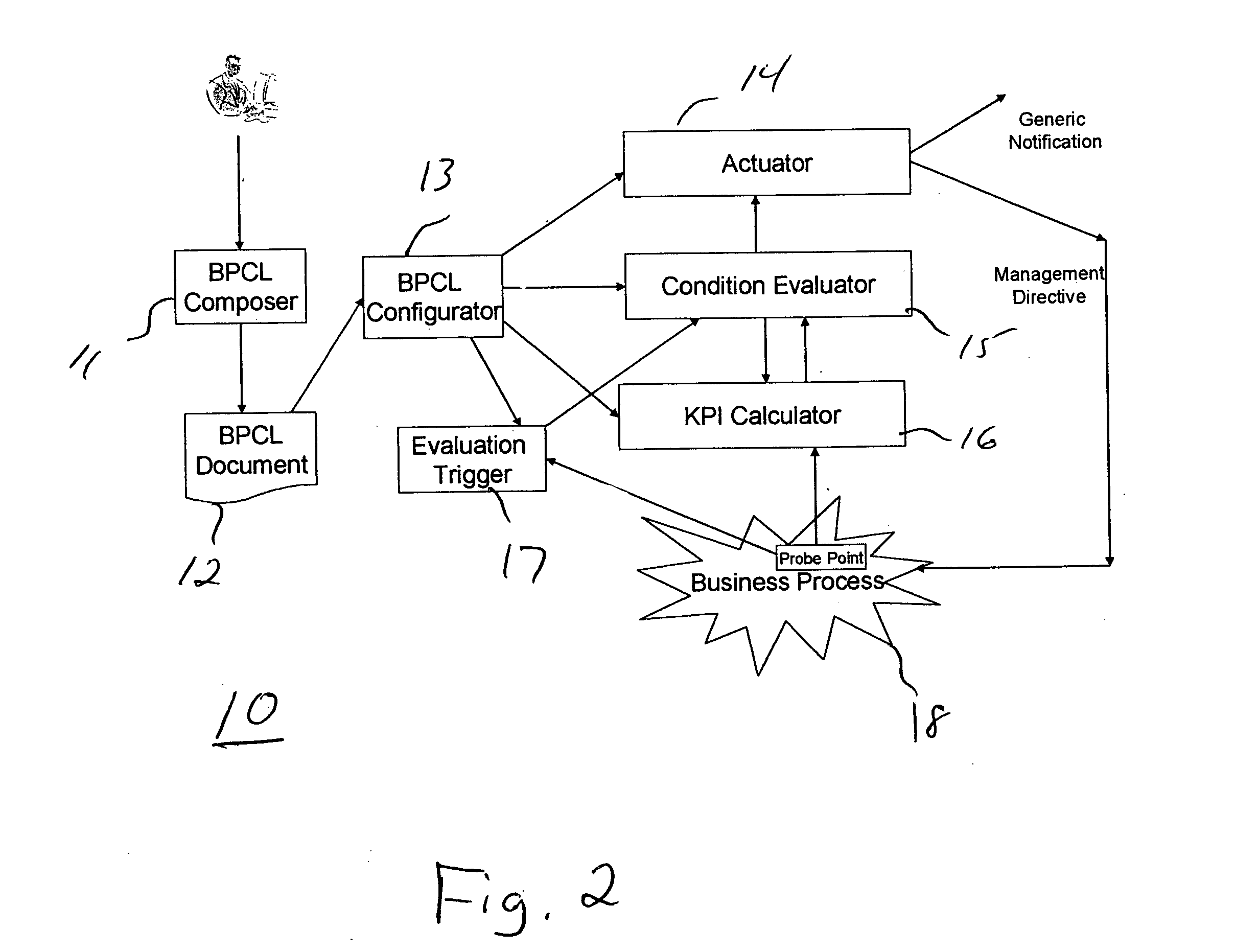
Systems and methods for monitoring and controlling business level service level agreements
Systems and methods for monitoring and controlling business level SLAs (Service level Agreements), and more particularly, systems and method for monitoring and controlling business level SLAs using probe points, KPIs (Key Performance Indicators) and business commitments. An XML (extensible Markup Language)-based specification referred to as BPCL (Business Process Commitment Language) is used to describe business commitments. BPCL specifications are used by a business process management (BPM) system to configure, monitor, and control business processes based on business commitments. Business Commitments and BPCL provide a path toward model-based management for dynamic e-business solutions.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com