Method for safety verifying financial business information in electronic business
A technology for business information and security authentication, which is applied in the field of financial business information security authentication in e-commerce, and can solve problems such as the impact of e-commerce
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
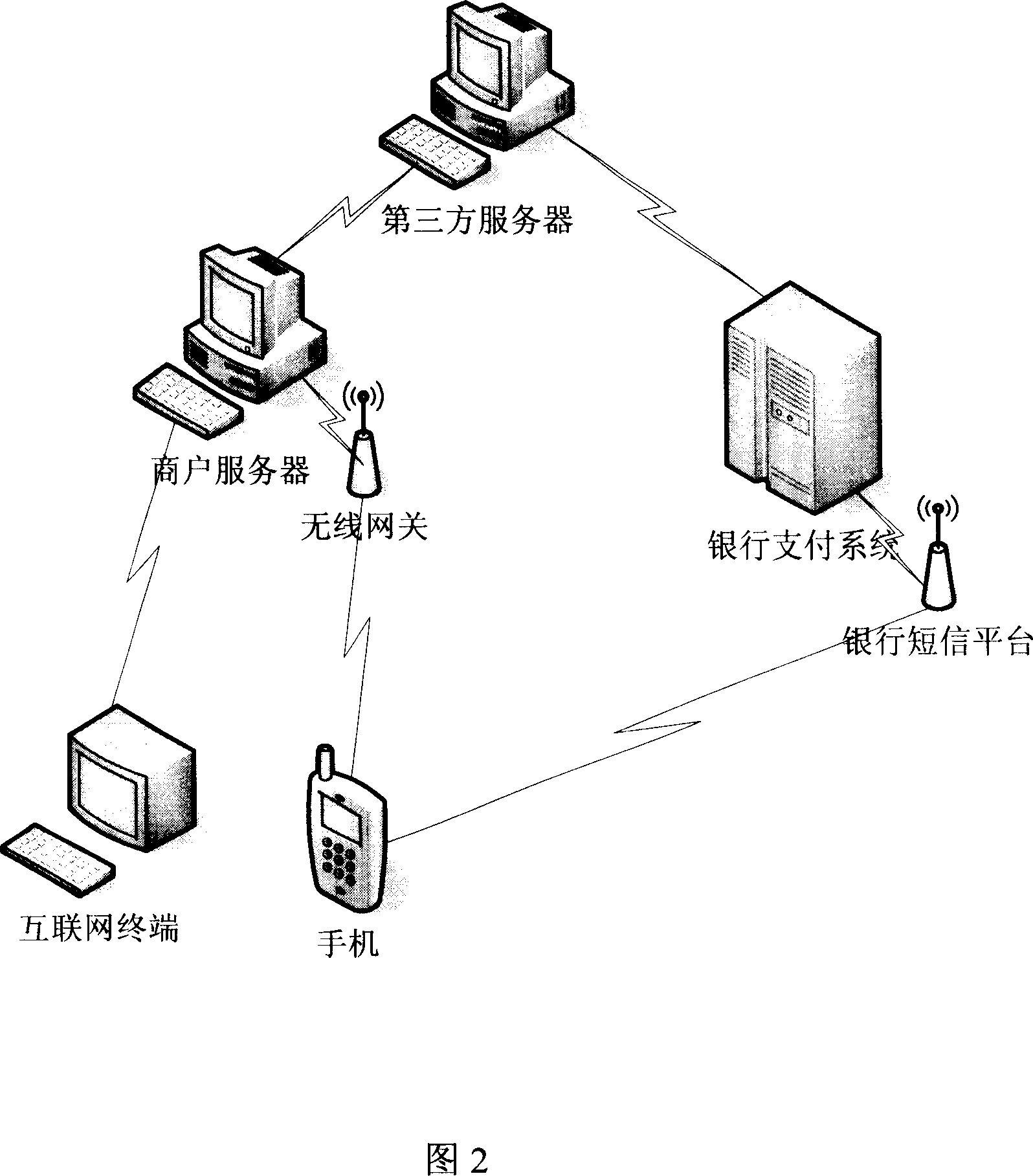
Image
Examples
no. 1 example
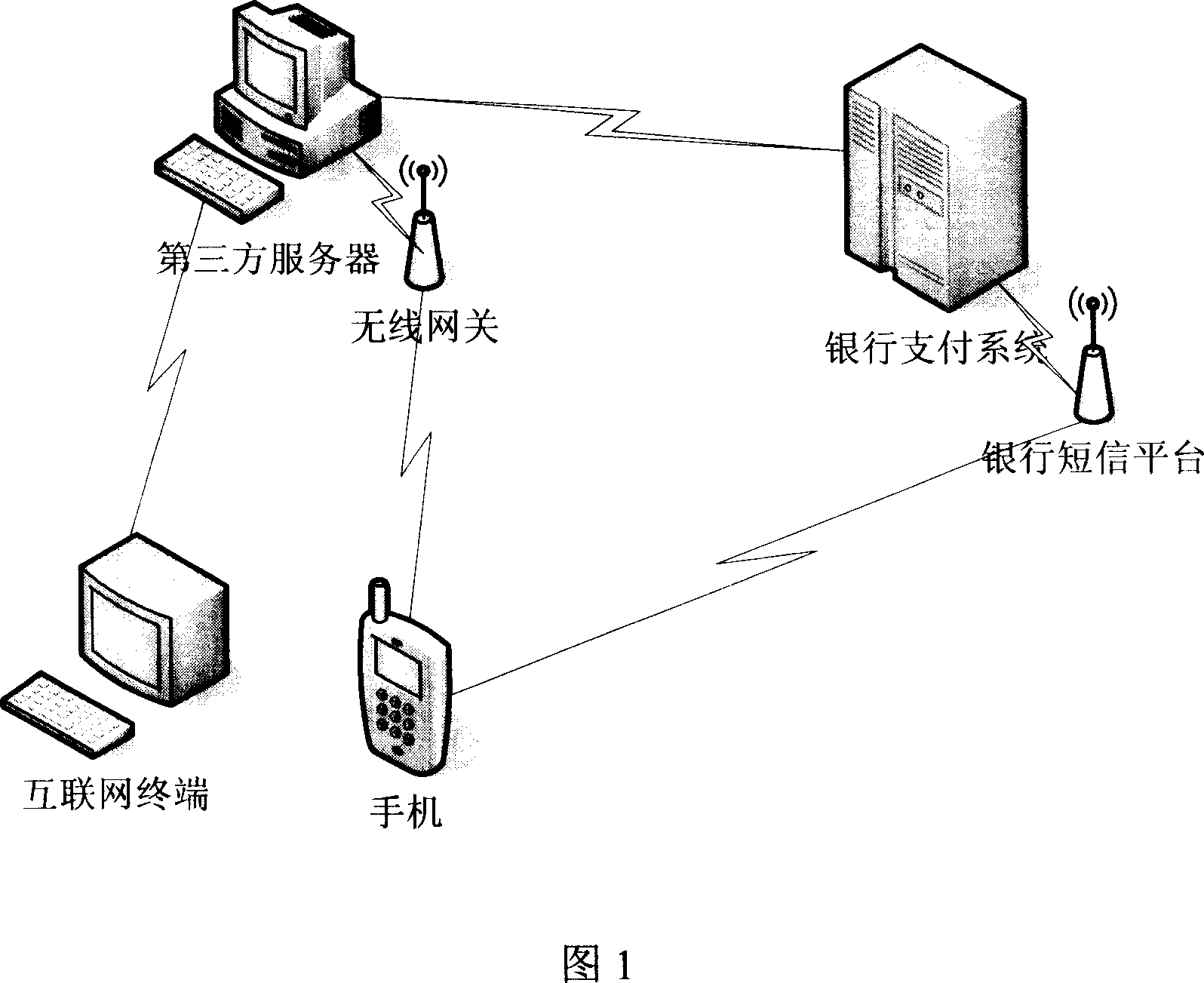
[0116] The first financial business information security authentication method of the present invention is illustrated below in conjunction with Fig. 1, and this first embodiment is as follows:
[0117] Step 1: The user applies to the bank to bind his mobile phone number 13911111111, ID number 110100123456789 with his bank account 6666666666, and establishes an authentication database containing the user's mobile phone number, ID number, bank account and payment password 654321 in the bank payment system , agreeing with the bank that the payment password 654321 is used as the confirmation password for the bank payment system to confirm with the user through the SMS platform;
[0118] Step 2: The user applies for member registration on the third-party server, and records the user identity information and mobile phone number 13911111111 in the third-party server. The user identity information can include the ID number 110100123456789; "Encyclopedia Publishing House" provides thro...
no. 2 example
[0128] Below in conjunction with Fig. 1, illustrate the second financial business information security authentication method of the present invention, this second embodiment is as follows:
[0129] Step 1: The user applies to the bank to bind his mobile phone number 13911111111, ID number 110100123456789 with his bank account 6666666666, and establishes an authentication database containing the user's mobile phone number, ID number, bank account and payment password 654321 in the bank payment system , agreeing with the bank that the payment password 654321 is used as the confirmation password for the bank payment system to confirm with the user through the SMS platform;
[0130] Step 2: The user applies for member registration on the third-party server, and records the user identity information and mobile phone number 13911111111 in the third-party server. The user identity information can include the ID number 110100123456789; "Encyclopedia Publishing House" provides through t...
no. 3 example
[0140] Below in conjunction with Fig. 1, illustrate the third financial business information security authentication method of the present invention, this third embodiment is as follows:
[0141] Step 1: The user applies to the bank to bind his mobile phone number 13911111111, ID number 110100123456789 with his bank account 6666666666, and establishes an authentication database containing the user's mobile phone number, ID number, bank account and payment password 654321 in the bank payment system , agreeing with the bank that the payment password 654321 is used as the confirmation password for the bank payment system to confirm with the user through the SMS platform;
[0142]Step 2: The user applies for member registration on the third-party server, and records the user identity information and mobile phone number 13911111111 in the third-party server. The user identity information can include the ID number 110100123456789; "Encyclopedia Publishing House" provides through the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com