Patents
Literature
509 results about "Key generator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
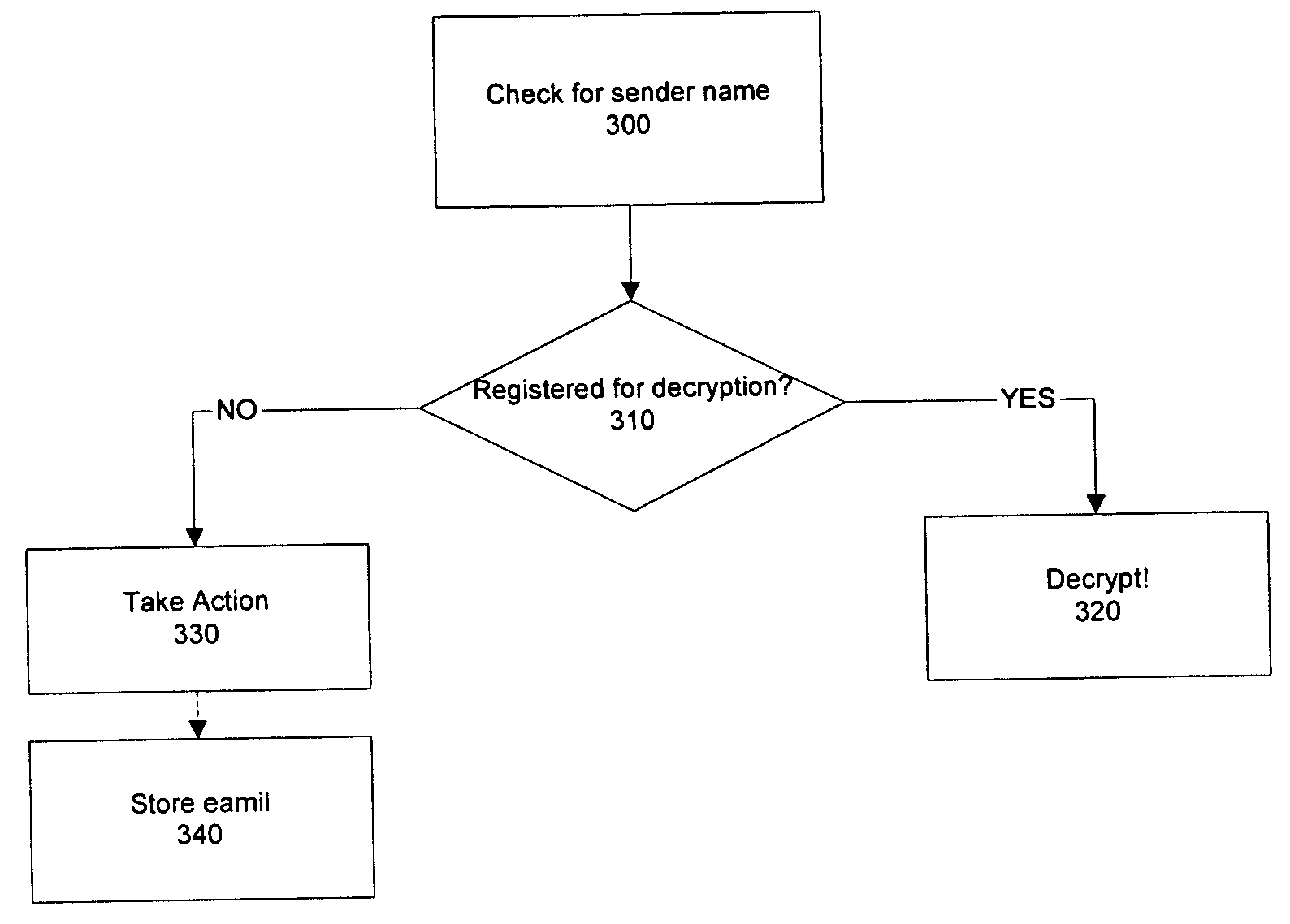
A key generator is used in many cryptographic protocols to generate a sequence with many pseudo-random characteristics. This sequence is used as an encryption key at one end of communication, and as a decryption key at the other.
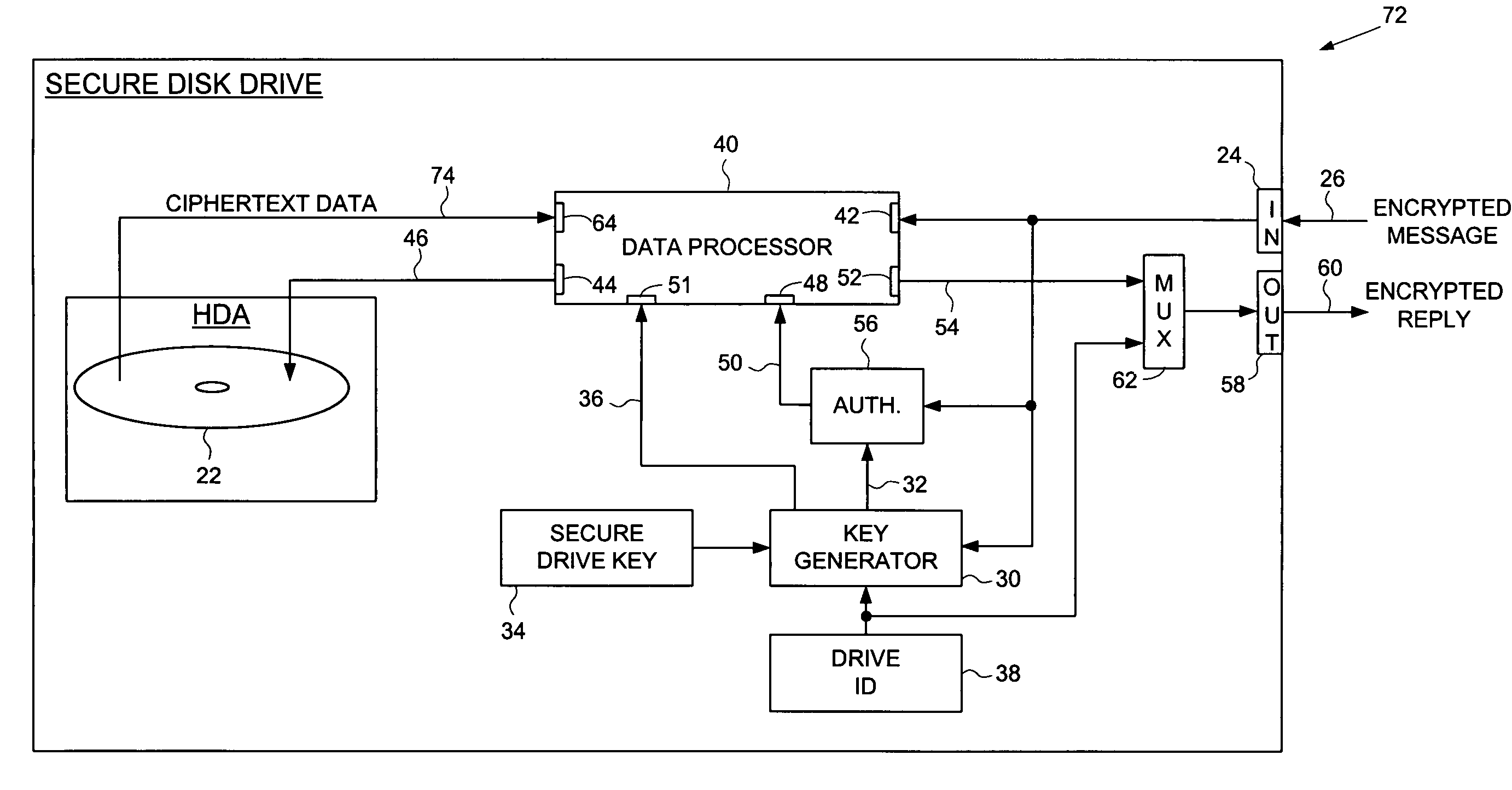
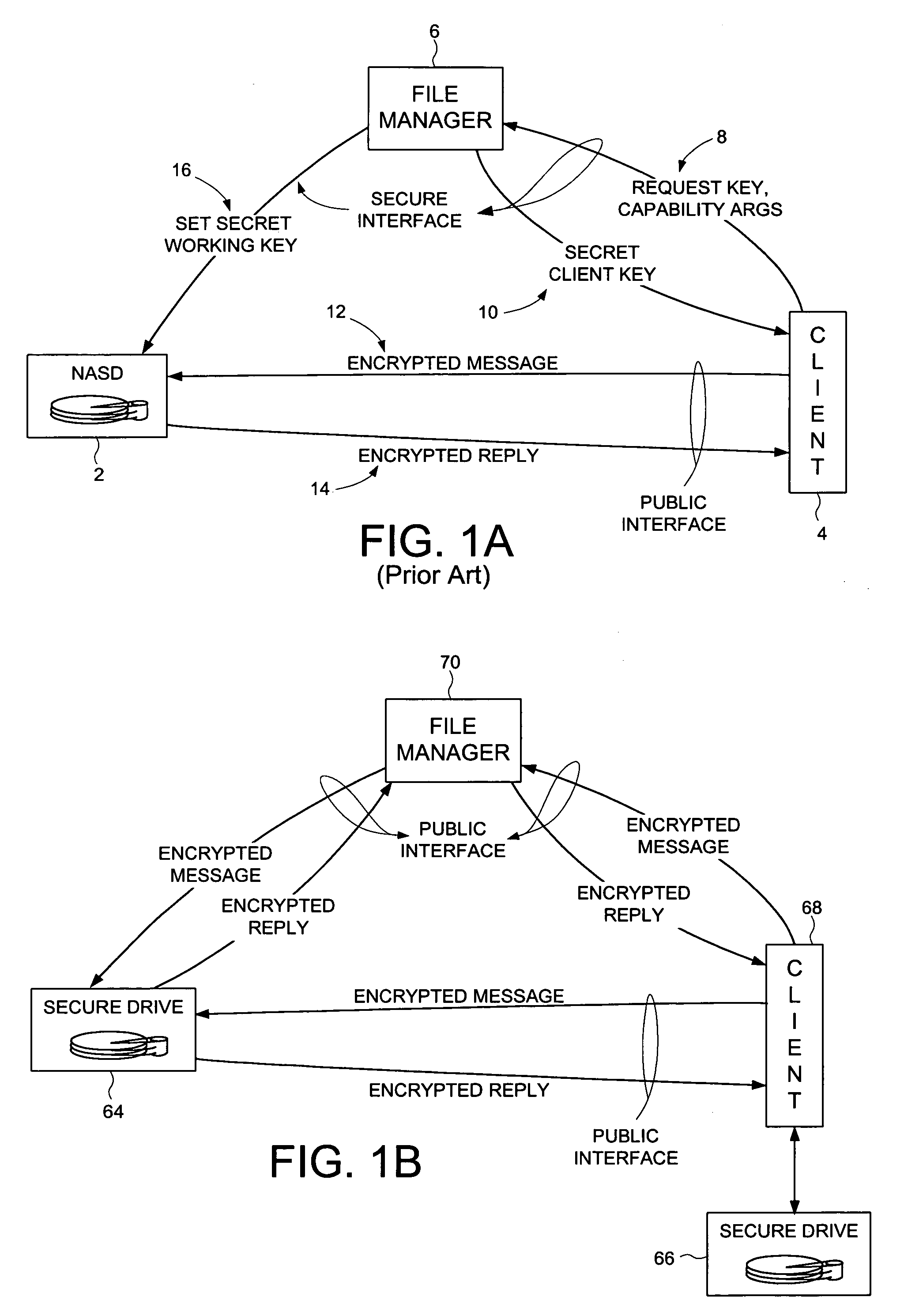
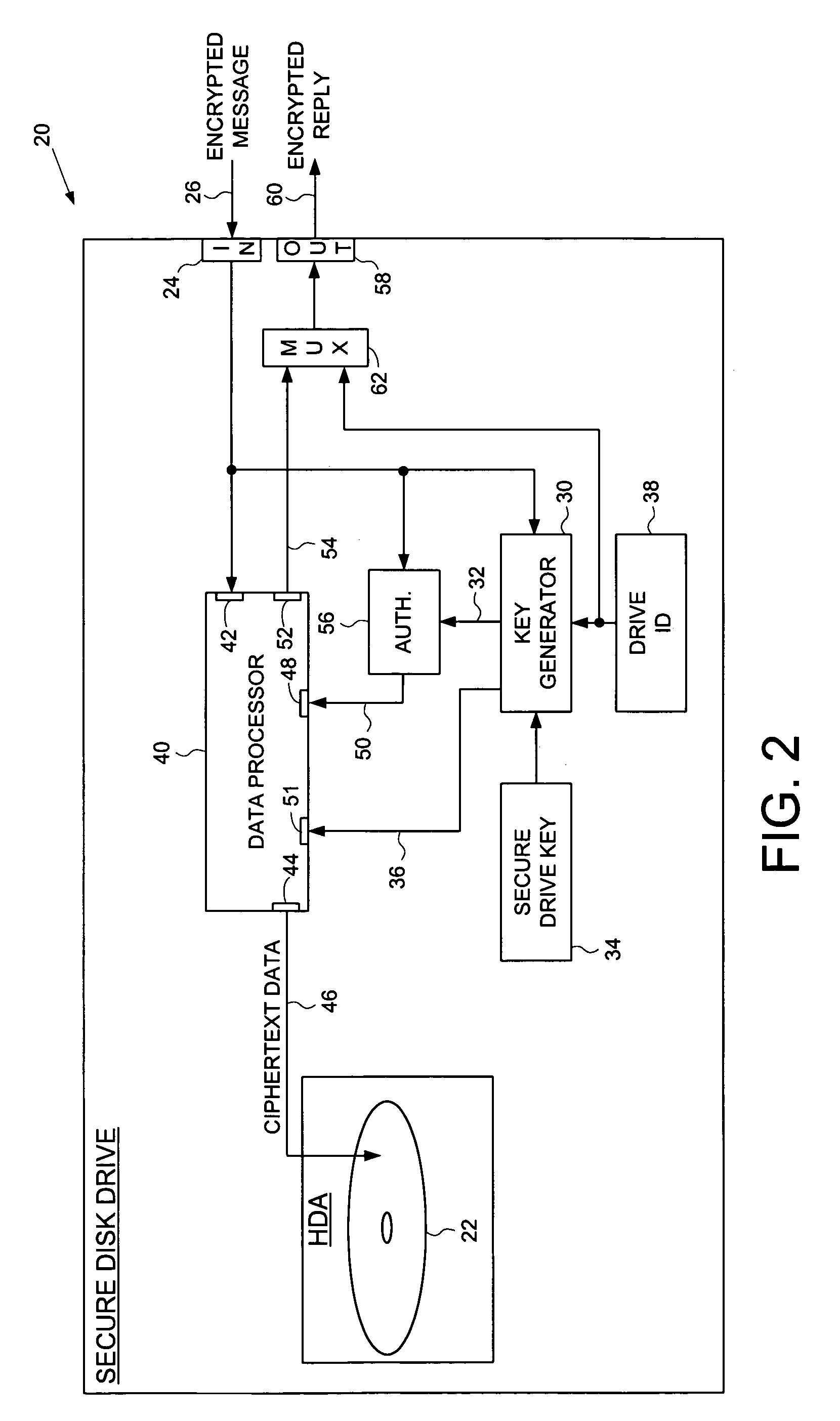
Secure disk drive comprising a secure drive key and a drive ID for implementing secure communication over a public network
InactiveUS7215771B1Volume/mass flow measurementUser identity/authority verificationSecure communicationCiphertext
A secure disk drive is disclosed comprising a disk for storing data, and an input for receiving an encrypted message from a client disk drive, the encrypted message comprising ciphertext data and a client drive ID identifying the client disk drive. The secure disk drive comprises a secure drive key and an internal drive ID. A key generator within the secure disk drive generates a client drive key based on the client drive ID and the secure drive key, and an internal drive key based on the internal drive ID and the secure drive key. The secure disk drive further comprises an authenticator for verifying the authenticity of the encrypted message and generating an enable signal, the authenticator is responsive to the encrypted message and the client drive key. The secure disk drive further comprises a data processor comprising a message input for receiving the encrypted message from the client disk drive, and a data output for outputting the ciphertext data to be written to the disk. The data processor further comprises an enable input for receiving the enable signal for enabling the data processor, and a key input for receiving the internal drive key, the internal drive key for use in generating a message authentication code. The data processor outputs reply data comprising the message authentication code. The secure disk drive outputs a reply to the client disk drive, the reply comprising the reply data and the internal drive ID.
Owner:WESTERN DIGITAL TECH INC
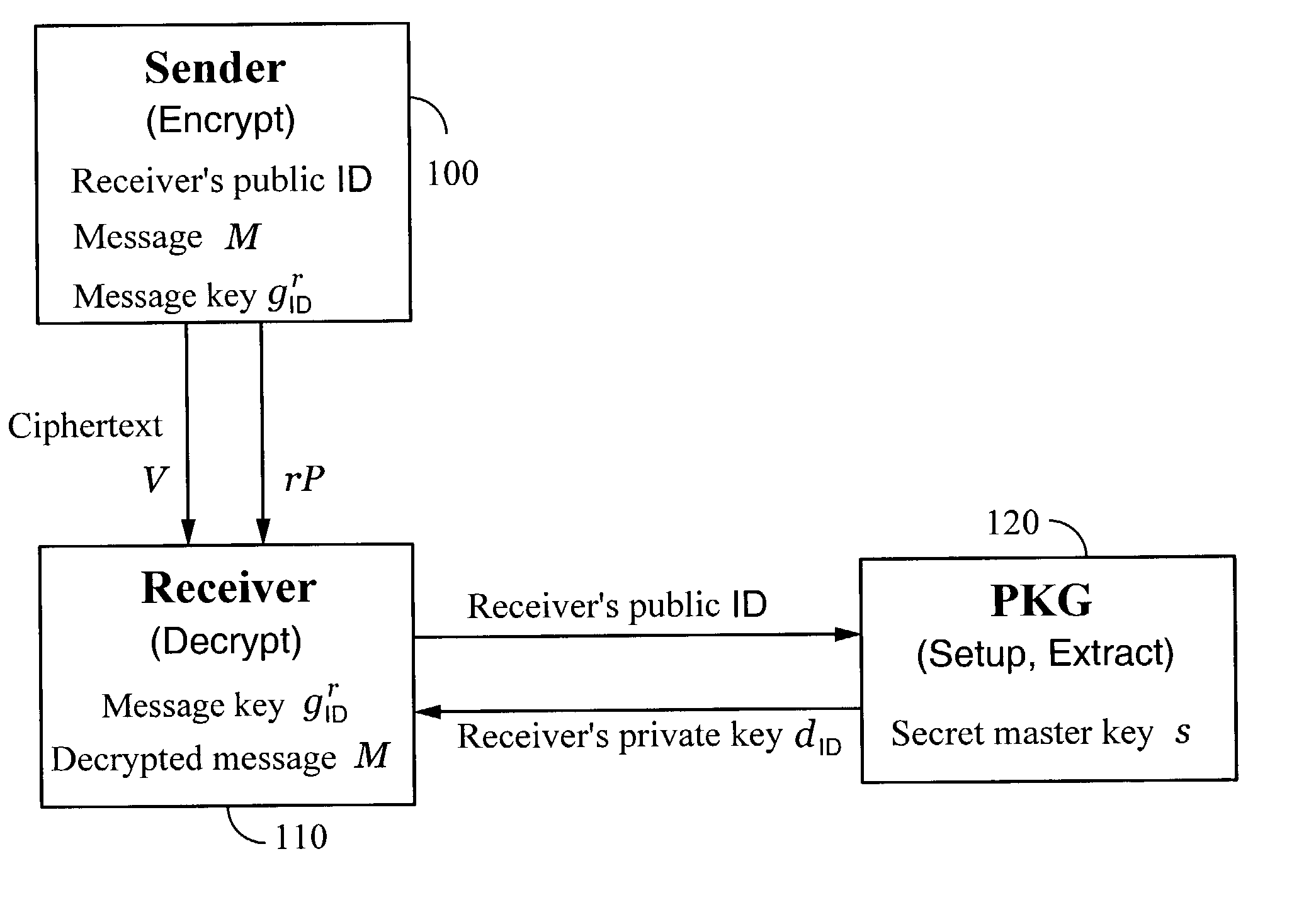
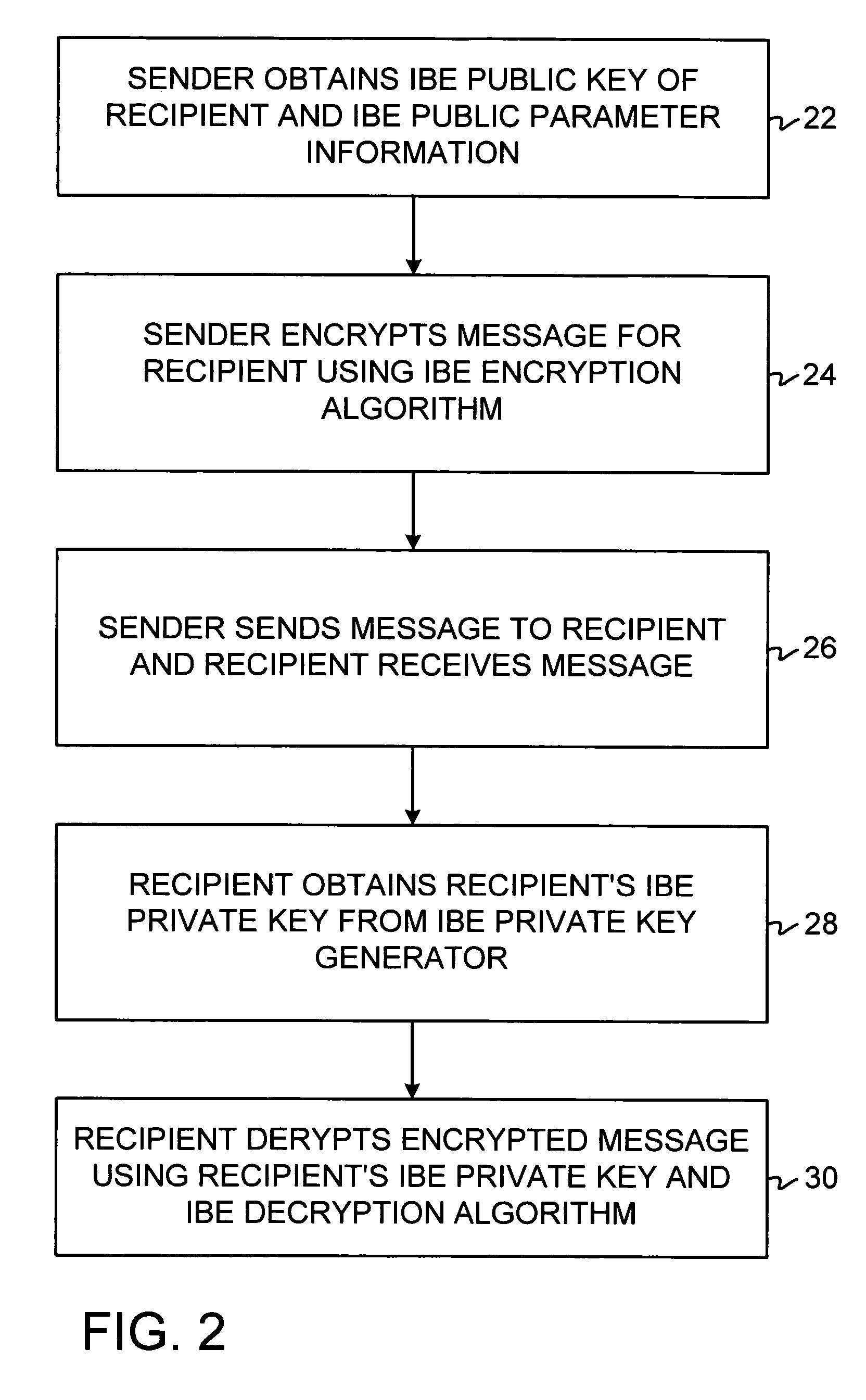
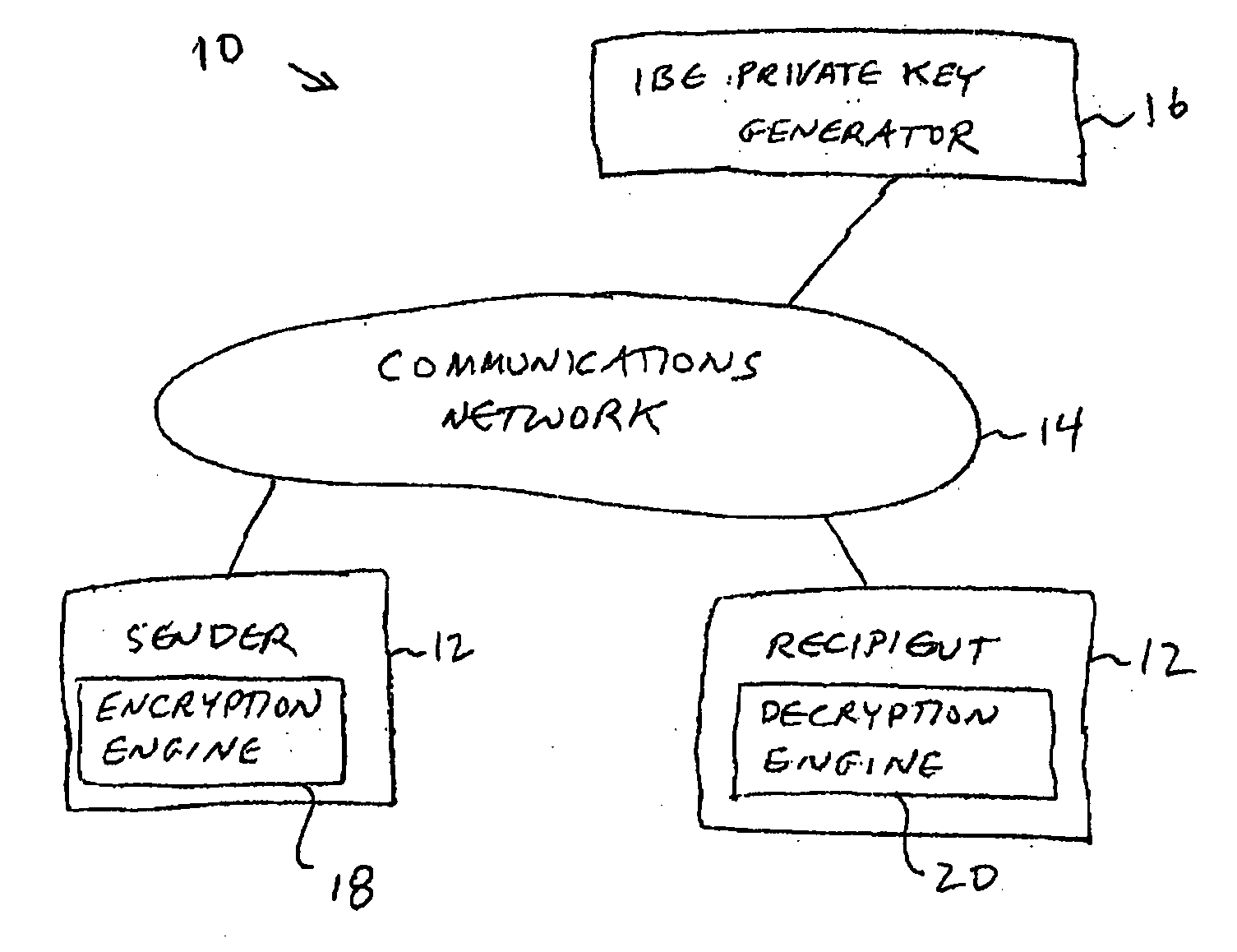
Systems and methods for identity-based encryption and related cryptographic techniques
ActiveUS7113594B2Key distribution for secure communicationPublic key for secure communicationEmail addressCiphertext
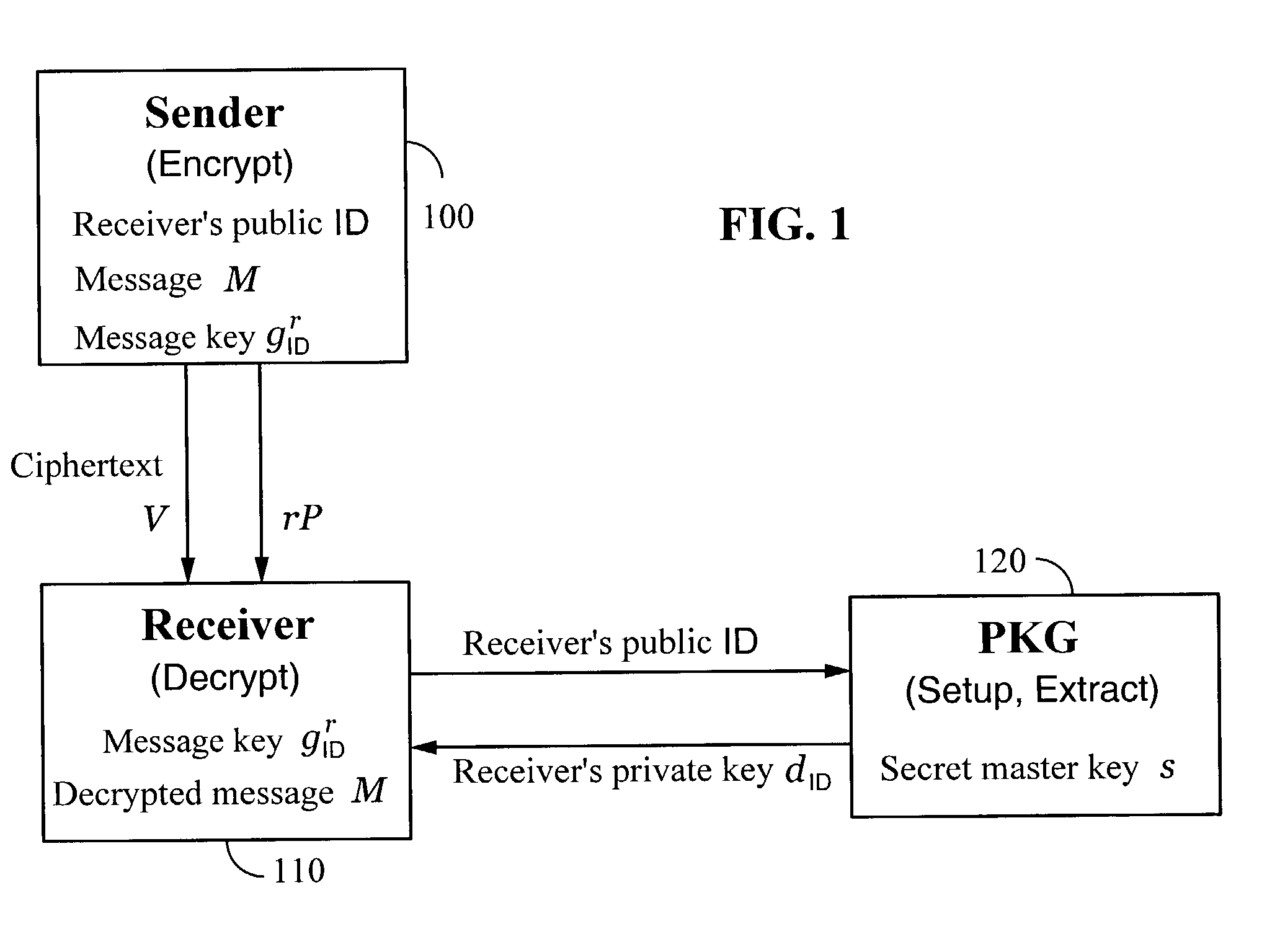
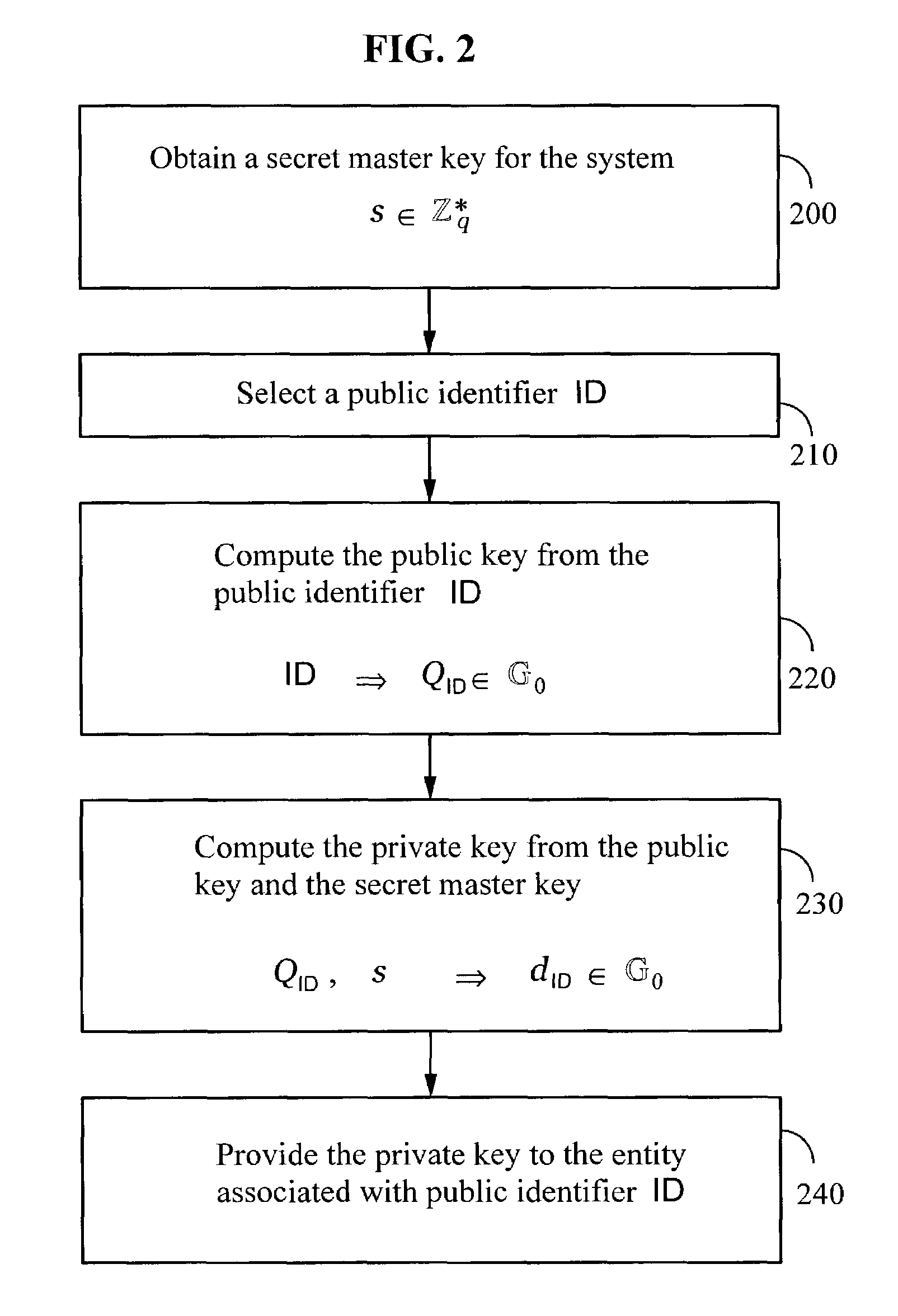
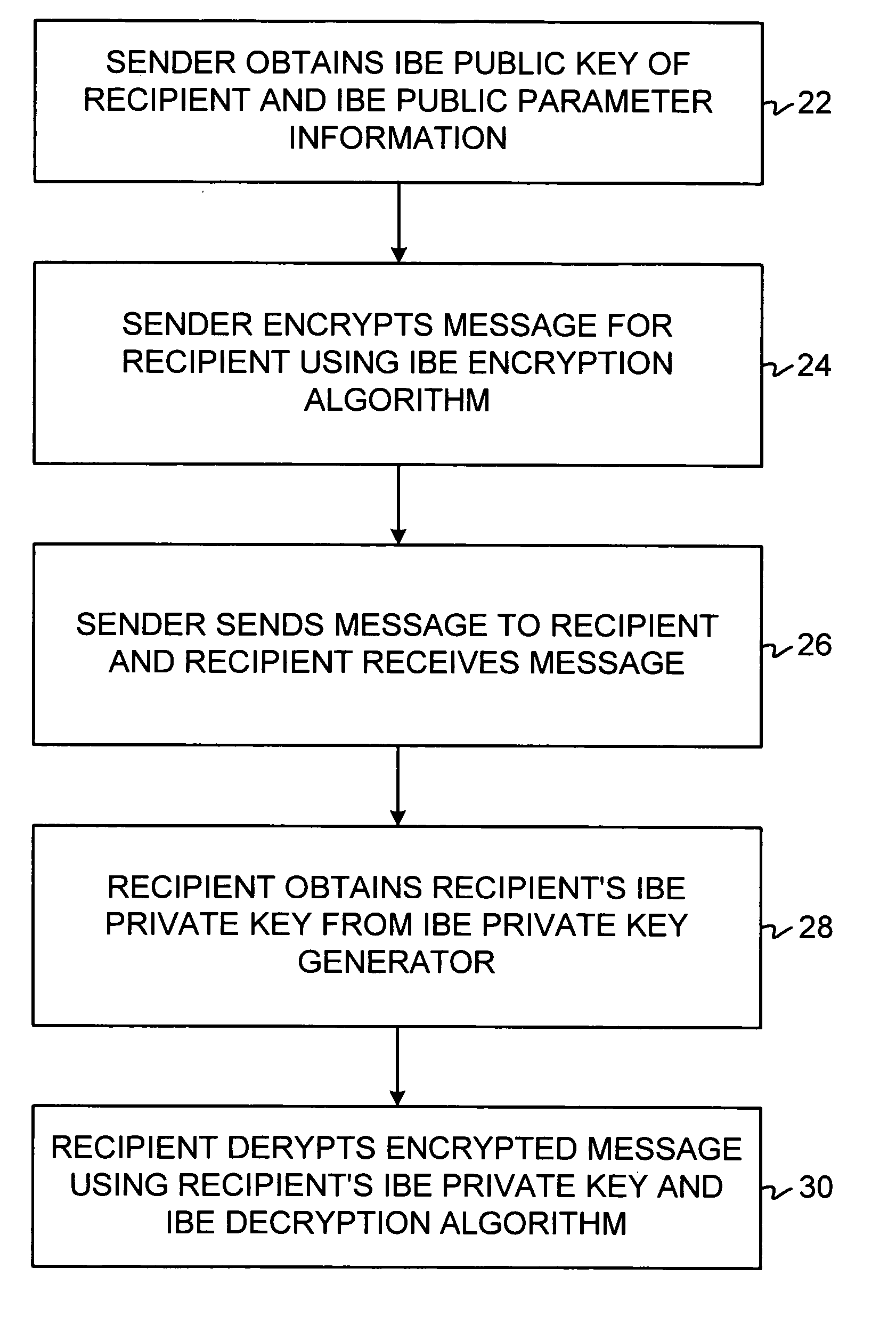
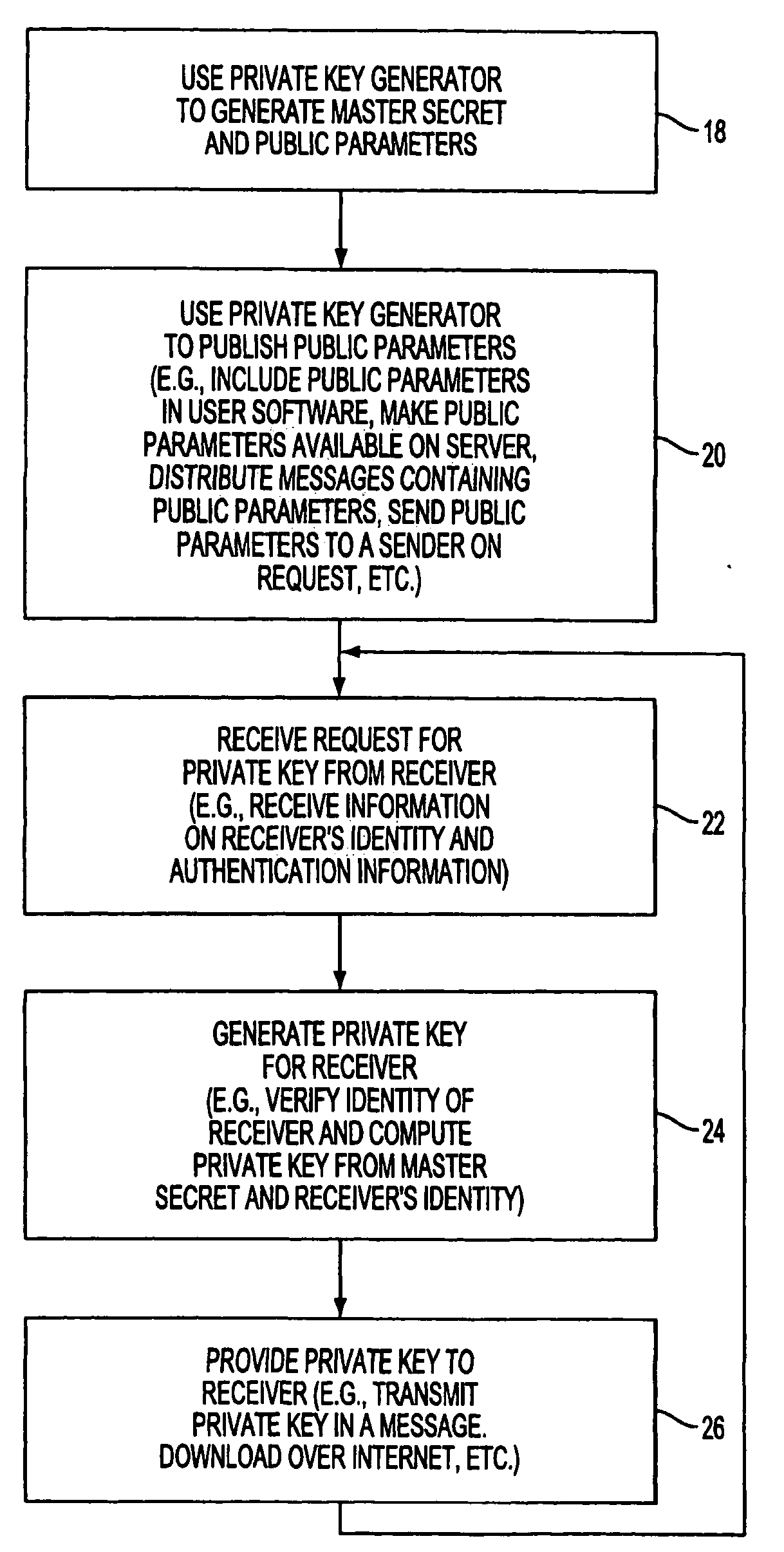
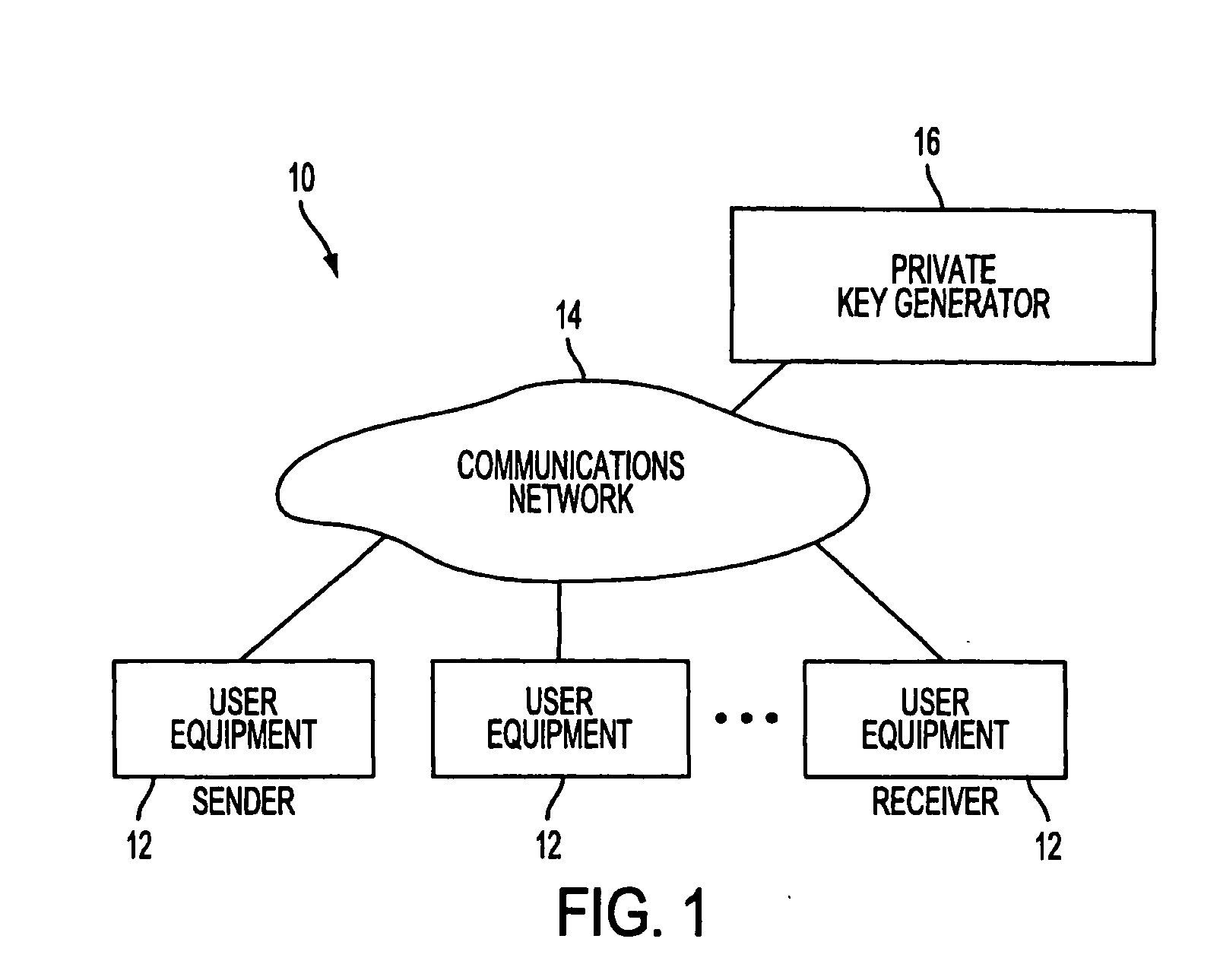
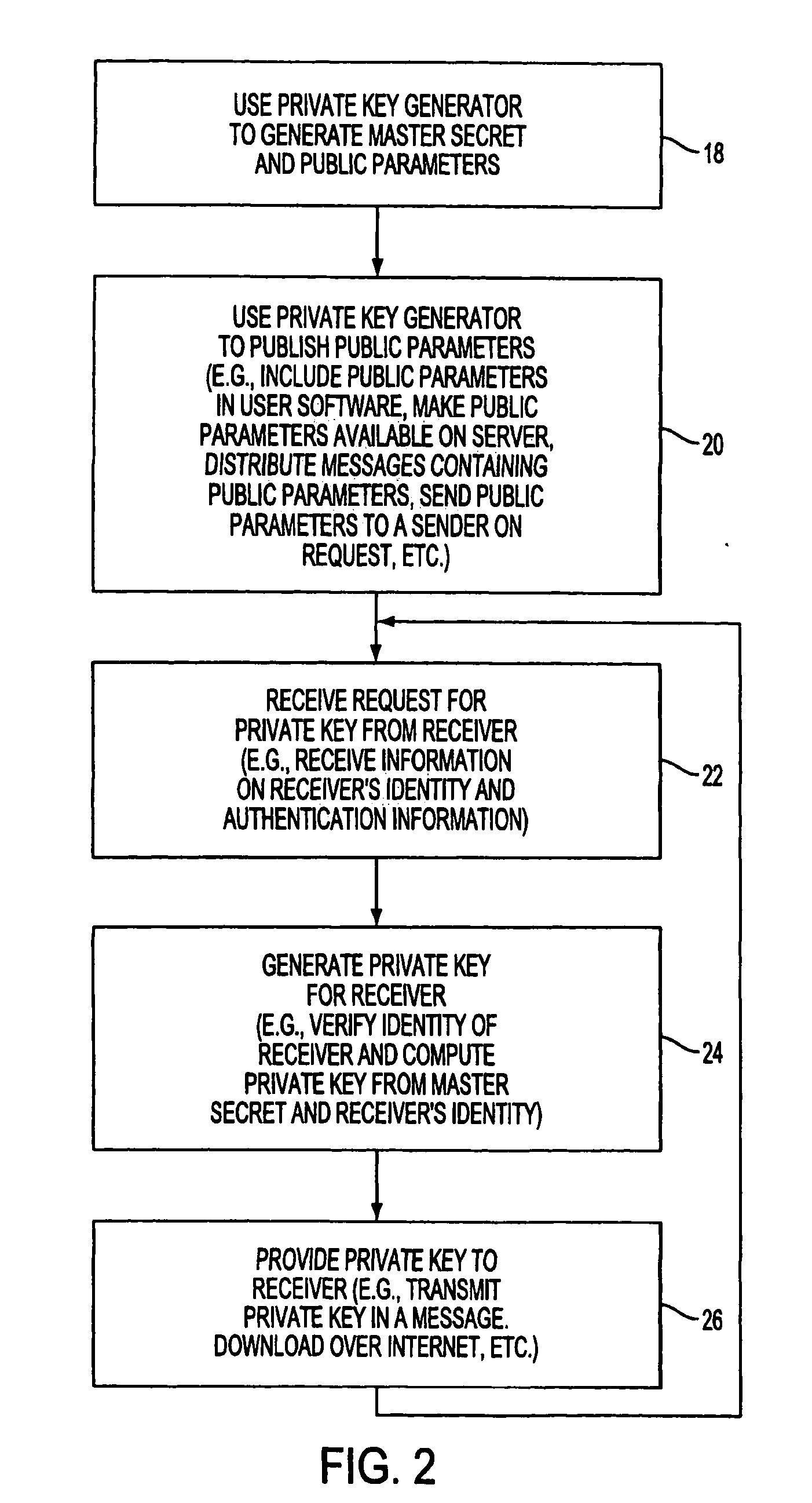
A method and system for encrypting a first piece of information M to be sent by a sender [100] to a receiver [110] allows both sender and receiver to compute a secret message key using identity-based information and a bilinear map. In a one embodiment, the sender [100] computes an identity-based encryption key from an identifier ID associated with the receiver [110]. The identifier ID may include various types of information such as the receiver's e-mail address, a receiver credential, a message identifier, or a date. The sender uses a bilinear map and the encryption key to compute a secret message key gIDr, which is then used to encrypt a message M, producing ciphertext V to be sent from the sender [100] to the receiver [110] together with an element rP. An identity-based decryption key dID is computed by a private key generator [120] based on the ID associated with the receiver and a secret master key s. After obtaining the private decryption key from the key generator [120], the receiver [110] uses it together with the element rP and the bilinear map to compute the secret message key gIDr, which is then used to decrypt V and recover the original message M. According to one embodiment, the bilinear map is based on a Weil pairing or a Tate pairing defined on a subgroup of an elliptic curve. Also described are several applications of the techniques, including key revocation, credential management, and return receipt notification.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
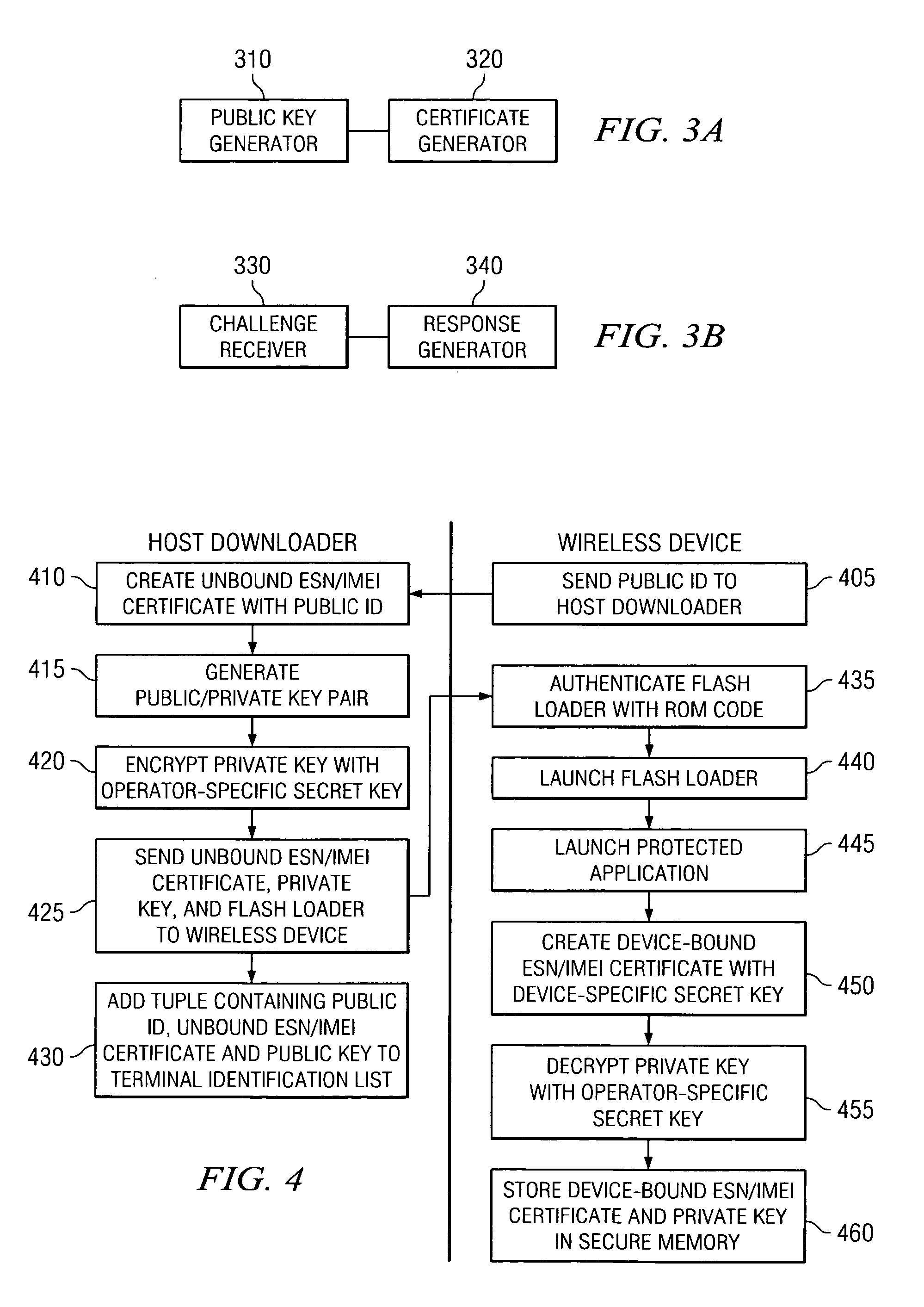
System and method for secure collaborative terminal identity authentication between a wireless communication device and a wireless operator
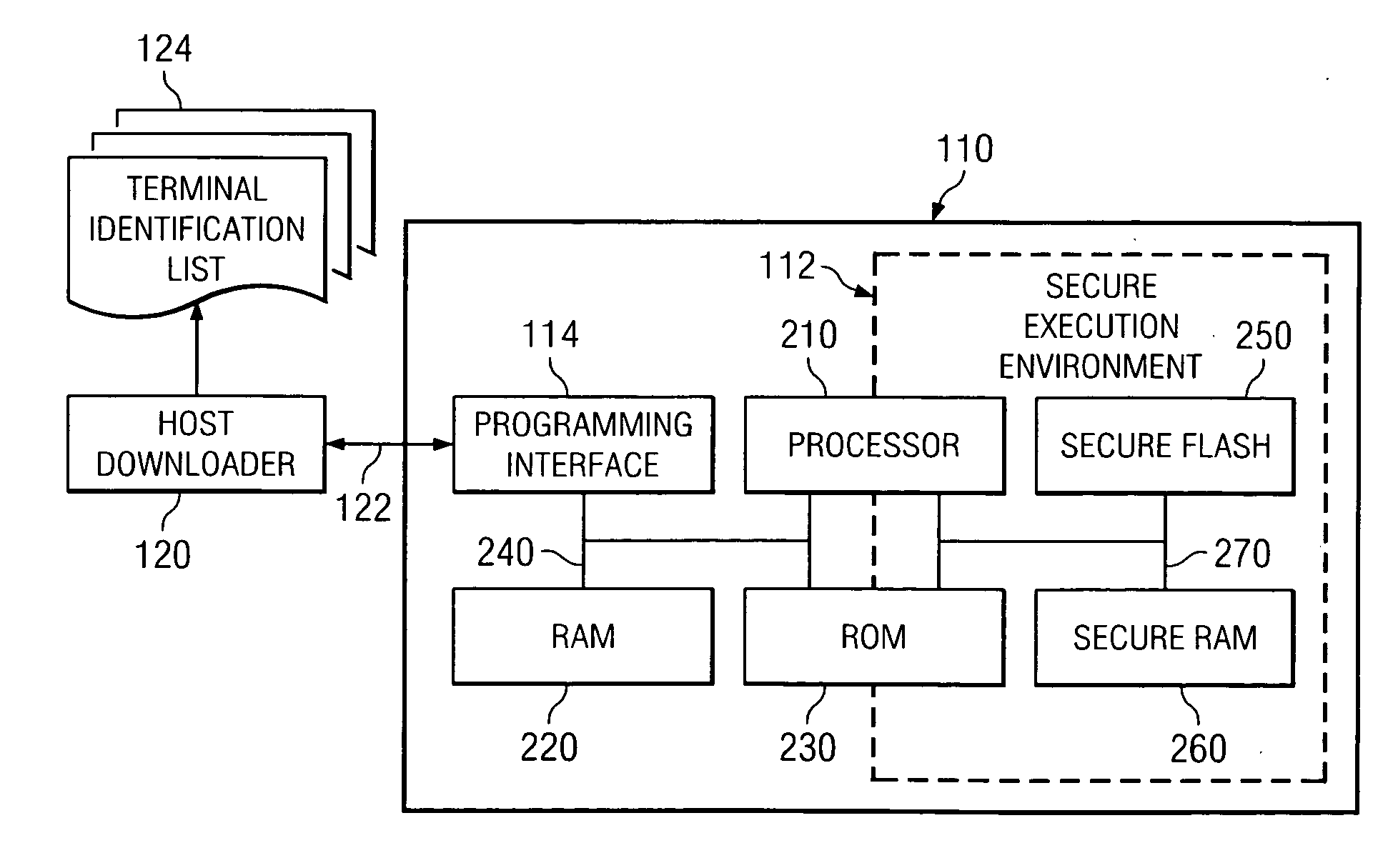
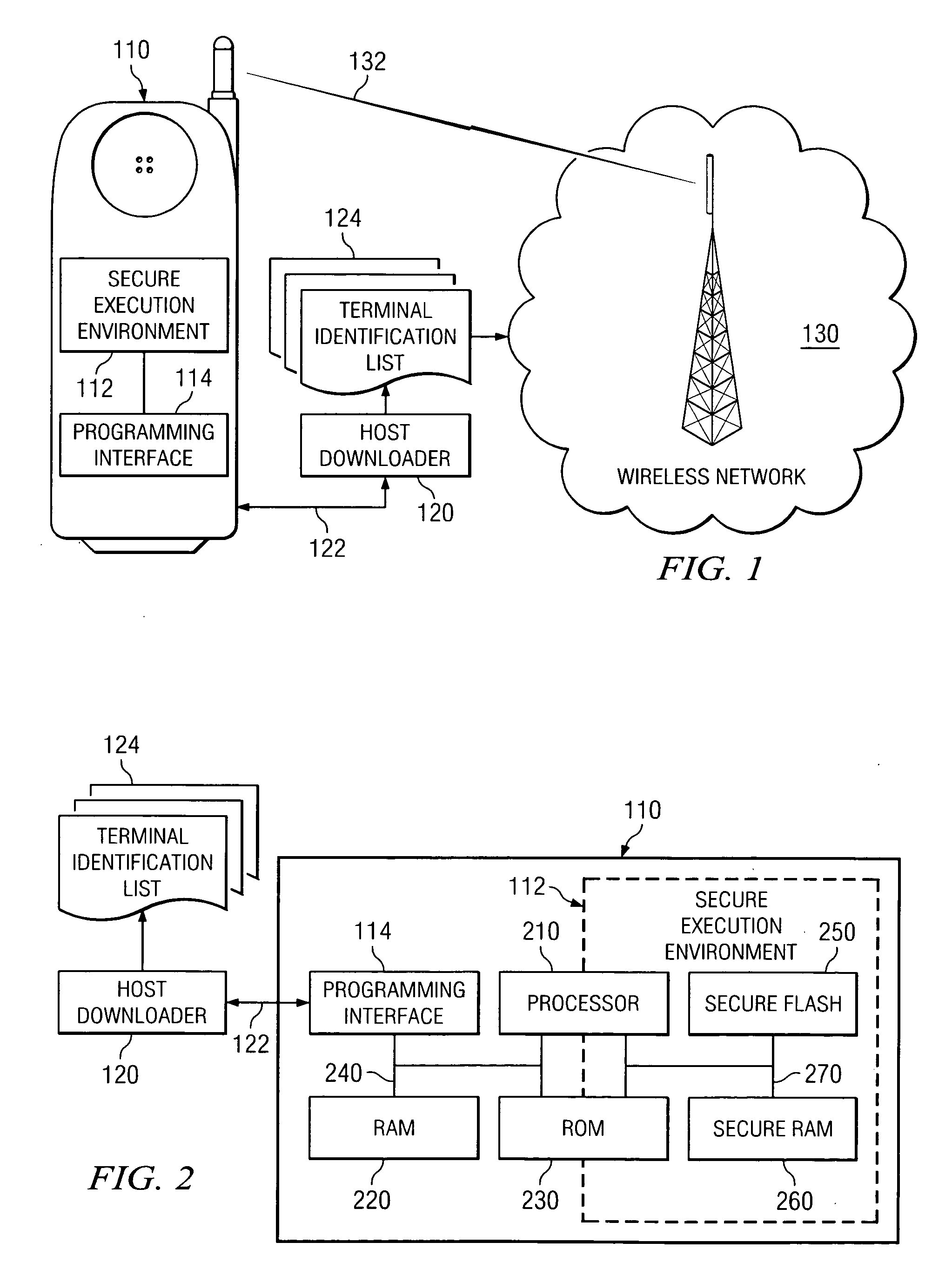
Systems and methods for providing a wireless communication device with secure terminal identity information and secure collaborative terminal identity authentication between the wireless communication device and a wireless operator. In one embodiment, the system for providing a wireless communication device with secure terminal identity information includes: (1) a public key generator configured to generate a unique public key and a unique private key based on an identity of the wireless communication device and cause the private key to be stored within a secure execution environment of the wireless communication device and (2) a certificate generator coupled to the public key generator and configured to create a device-bound certificate based on the identity and cause the device-bound certificate to be stored within the secure execution environment.
Owner:TEXAS INSTR INC
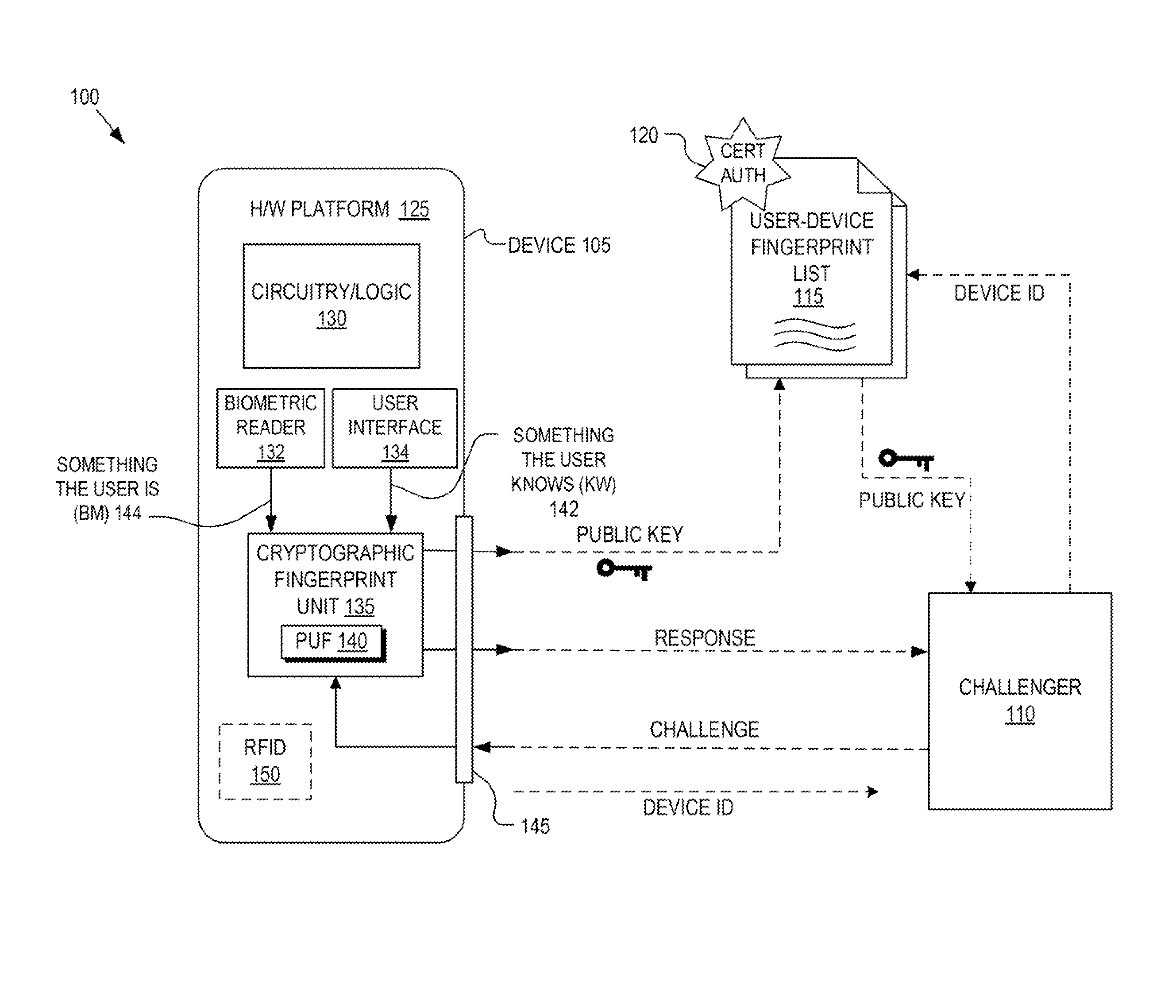
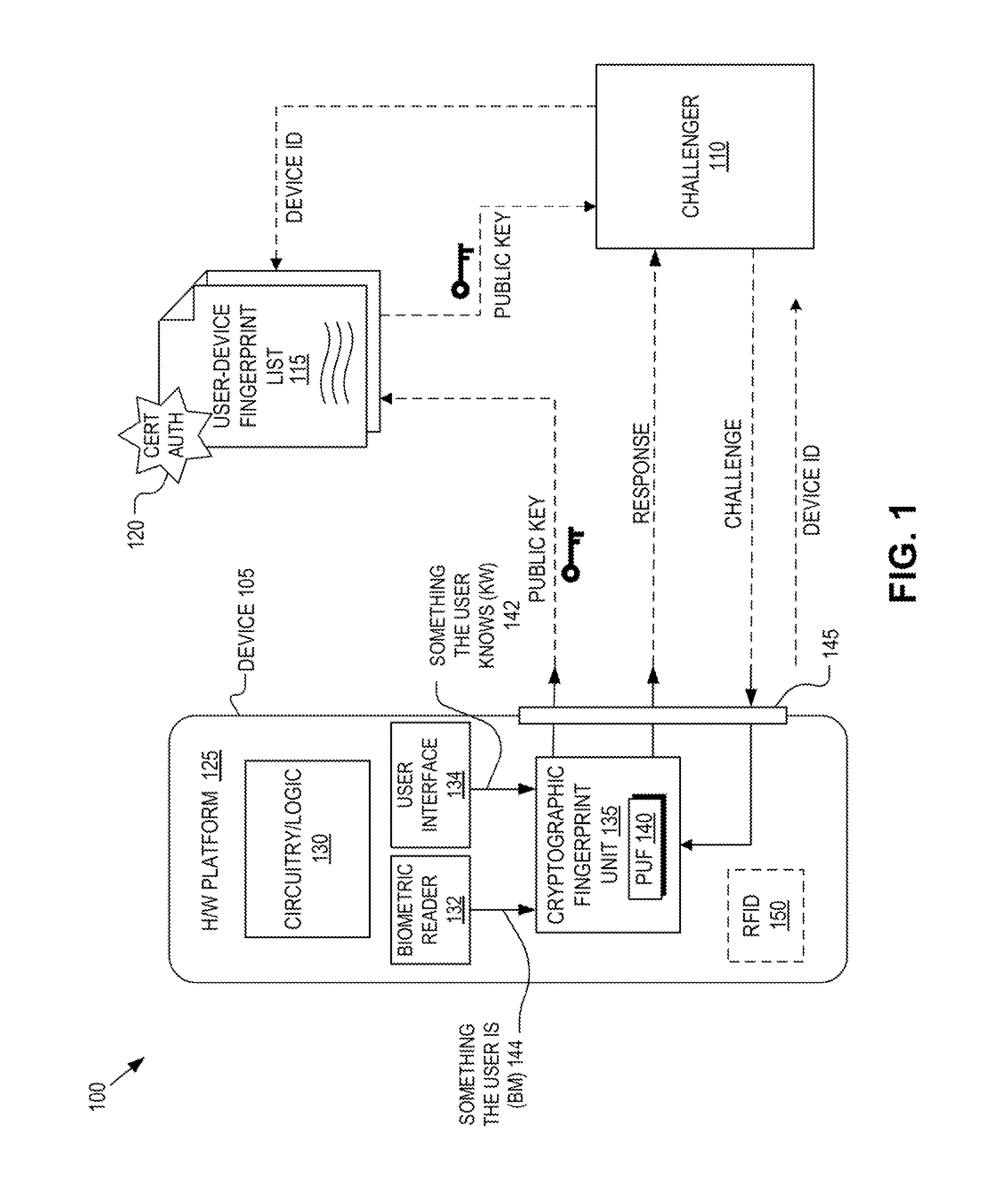
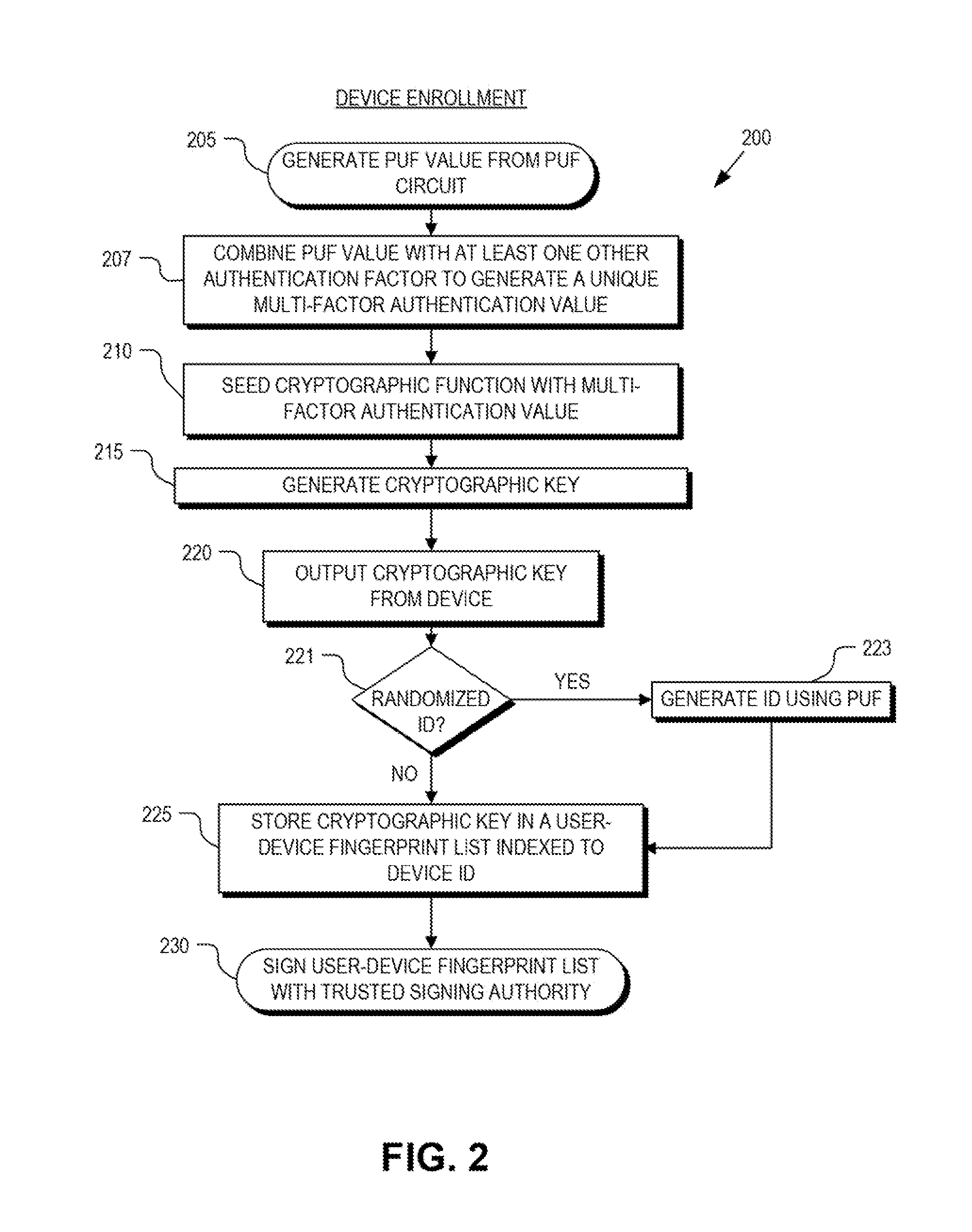
Multi-factor authentication
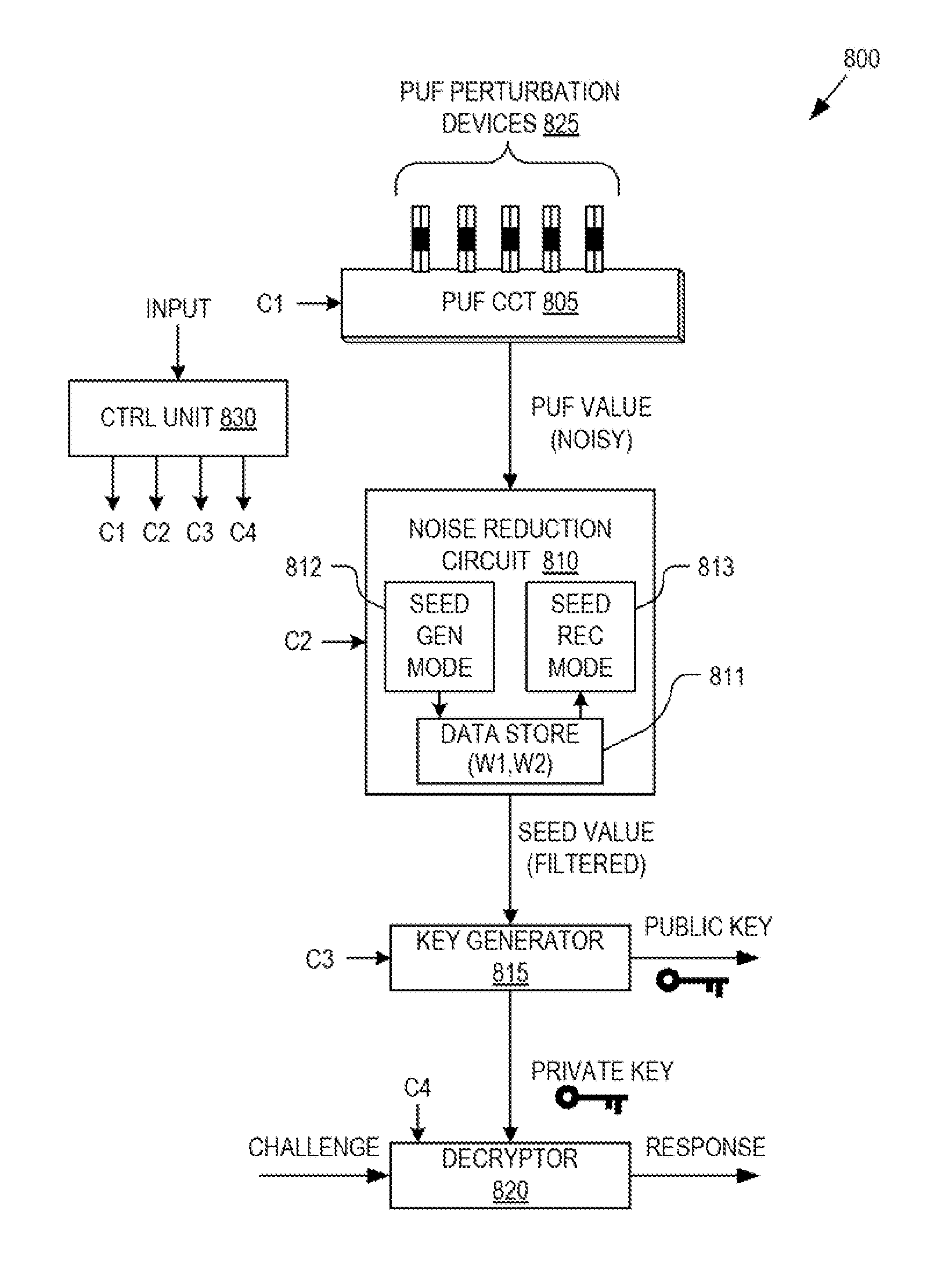
ActiveUS8868923B1Reliability increasing modificationsElectric signal transmission systemsPhysical unclonable functionUser authentication
Detection and deterrence of spoofing of user authentication may be achieved by including a cryptographic fingerprint unit within a hardware device for authenticating a user of the hardware device. The cryptographic fingerprint unit includes an internal physically unclonable function (“PUF”) circuit disposed in or on the hardware device, which generates a PUF value. Combining logic is coupled to receive the PUF value, combines the PUF value with one or more other authentication factors to generate a multi-factor authentication value. A key generator is coupled to generate a private key and a public key based on the multi-factor authentication value while a decryptor is coupled to receive an authentication challenge posed to the hardware device and encrypted with the public key and coupled to output a response to the authentication challenge decrypted with the private key.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
System and method for encrypting and decrypting files
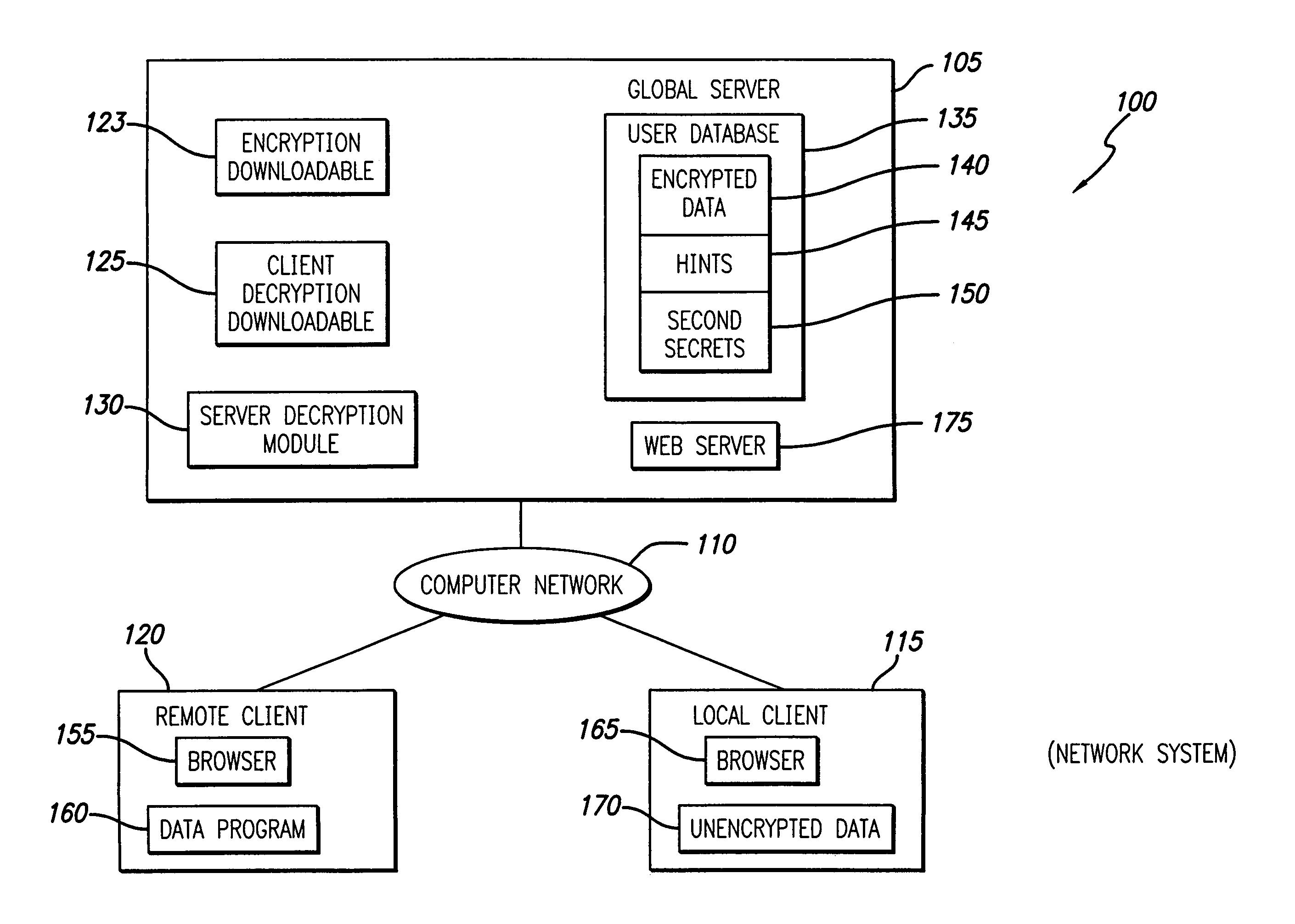
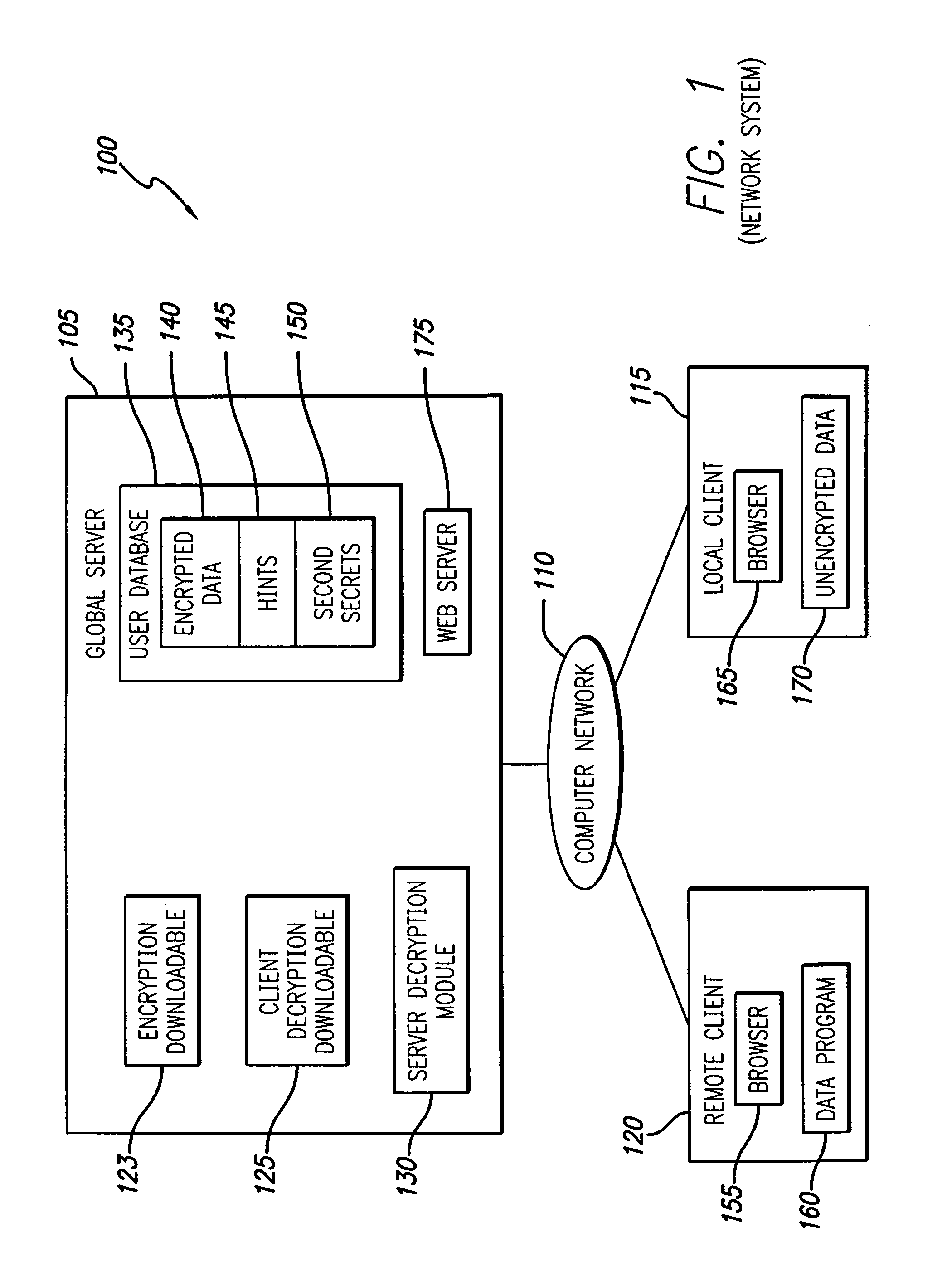
InactiveUS7373517B1Improve the level ofEasy accessKey distribution for secure communicationDigital data processing detailsPasswordClient-side
A system and method distribute the task of decryption between a server and a client. To encrypt data, the client generates an encryption / decryption key. Namely, a user interface obtains a password, generally from a user. A hint generator generates a hint. A key generator generates the key based on the password and the hint. In one embodiment, the key generator hashes the password to generate a first secret, hashes the first secret to generate a second secret, hashes the first secret with the hint to generate an intermediate index, and hashes the second secret and the intermediate index to generate the key. An encryption engine can then use the key to encrypt data. The client then sends the encrypted data and possibly the hint for storage on the server. To decrypt the data, the key must be determined. Accordingly, the server knows some information and the user knows some information for decrypting the data. To generate the key, the decrypting client must first obtain rights to retrieve the hint from the server and must obtain the password from the user. Increased level of security is achieved.
Owner:TACTICA INT +2
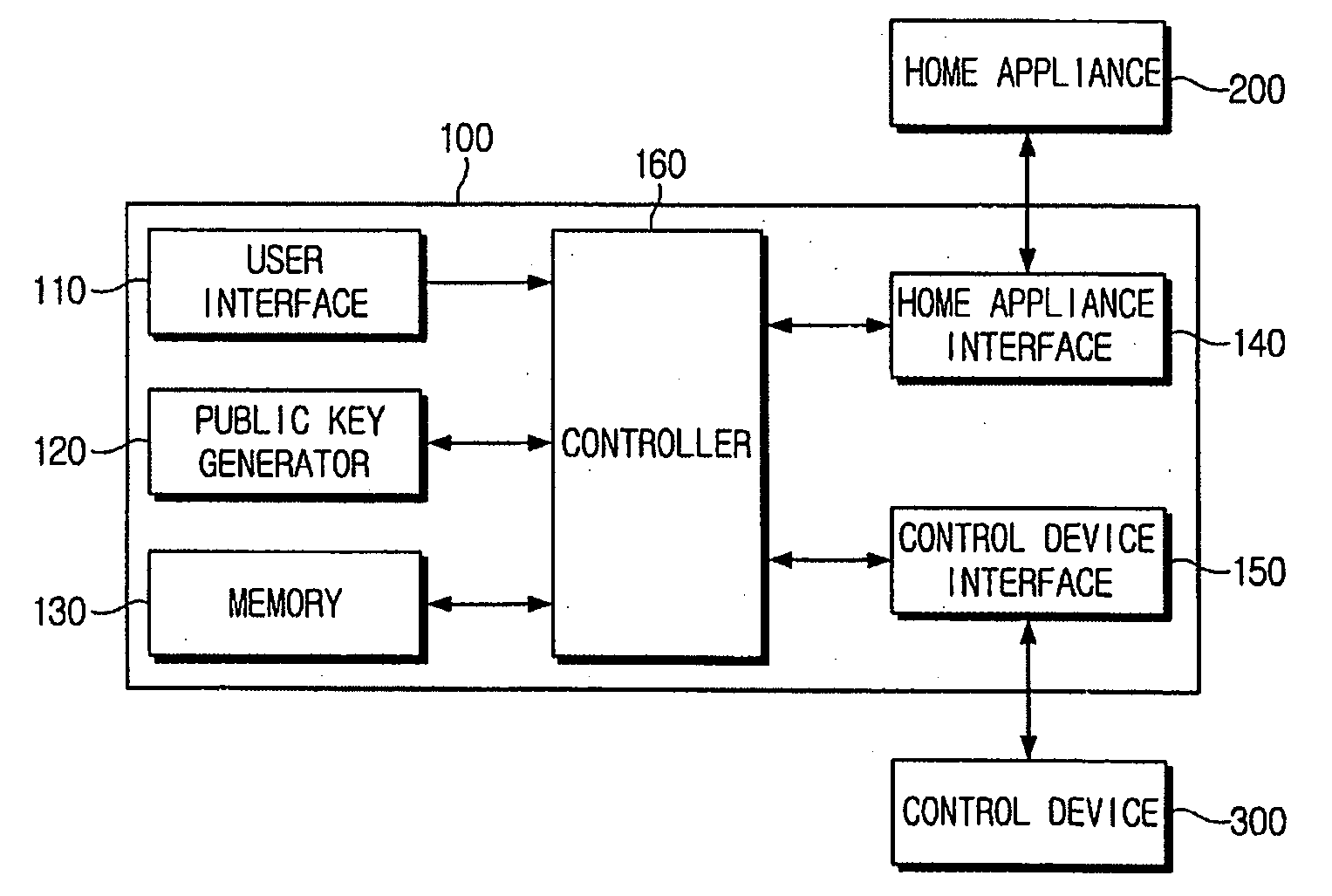
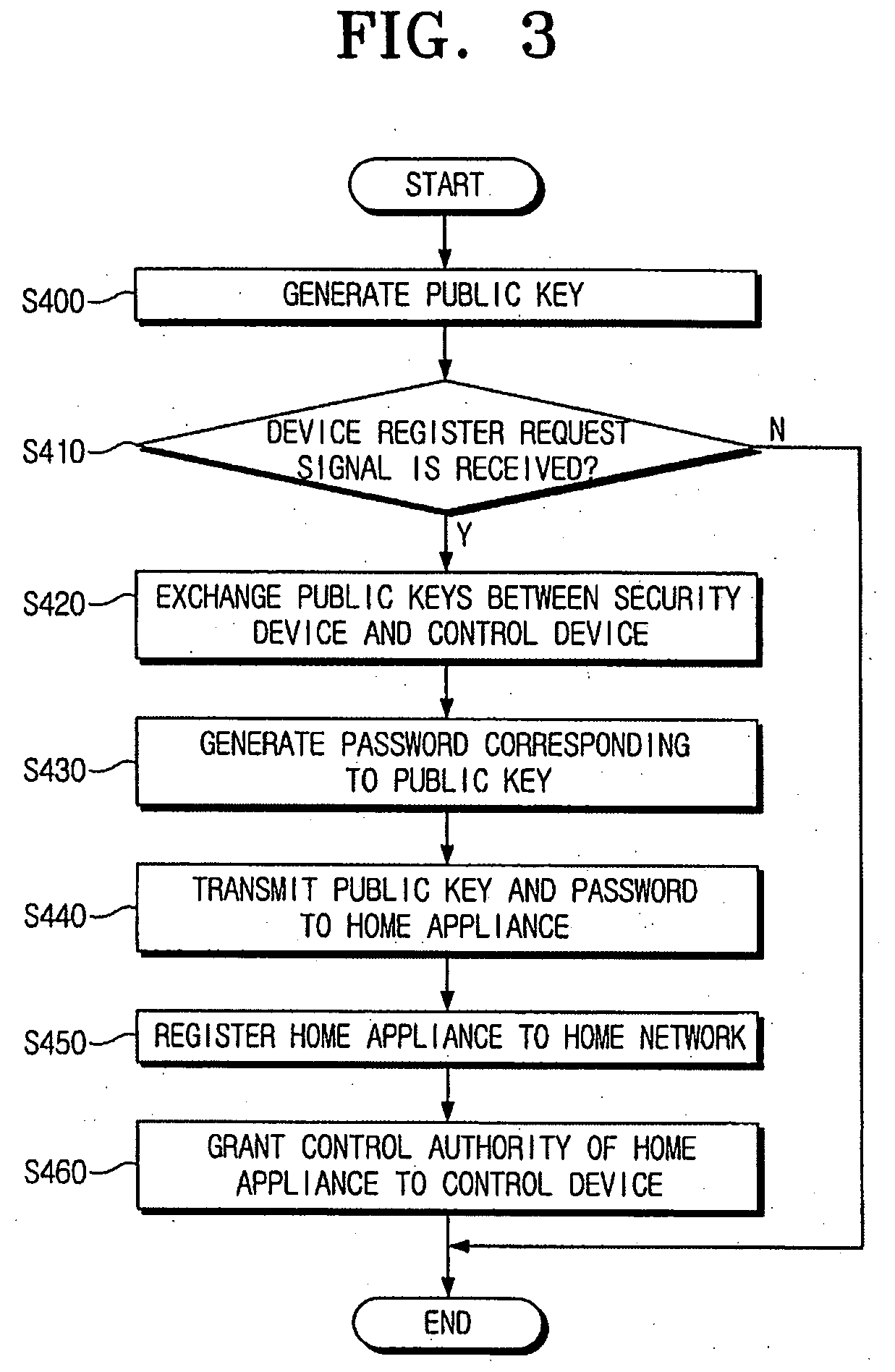
Security device for home network and security configuration method thereof
InactiveUS20060129837A1Public key for secure communicationSubstation remote connection/disconnectionDevice registerPassword
A security device for a home network and a security configuration method thereof. The security device for the home network includes a user interface to send at least one request signal that includes a device register request signal to register a home appliance to the home network; a public key generator to generate a public key and a password used for security configuration of the home network; a home appliance interface to interface with the home appliance; and a controller to control the home appliance interface to transmit the public key and the password to the home appliance, and the controller to control to register the home appliance to the home network according to a service discovery protocol when the device register request signal is received from the user interface. Accordingly, the security configuration of the home network can be facilitated.
Owner:SAMSUNG ELECTRONICS CO LTD
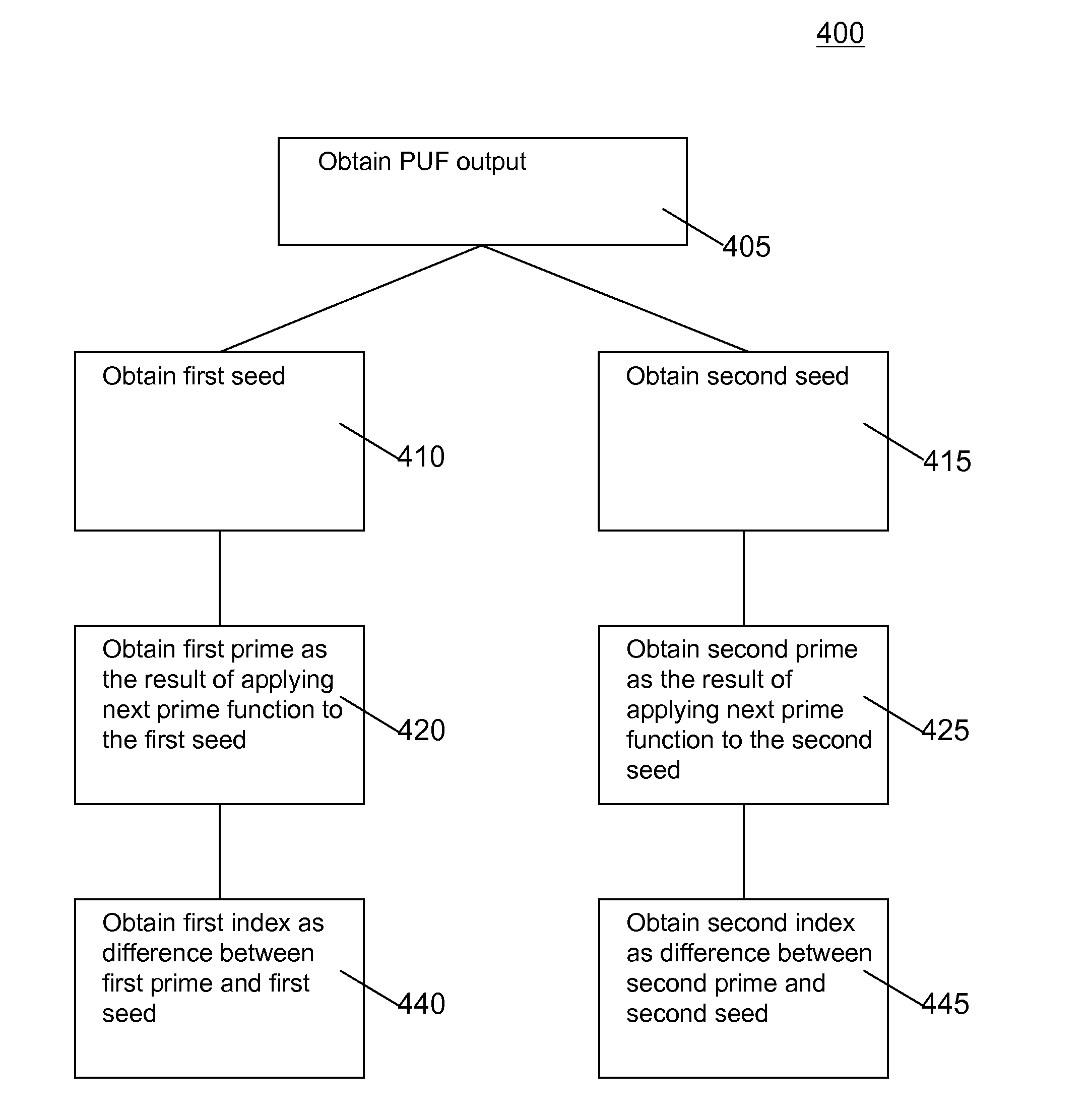
Device and method for obtaining a cryptographic key
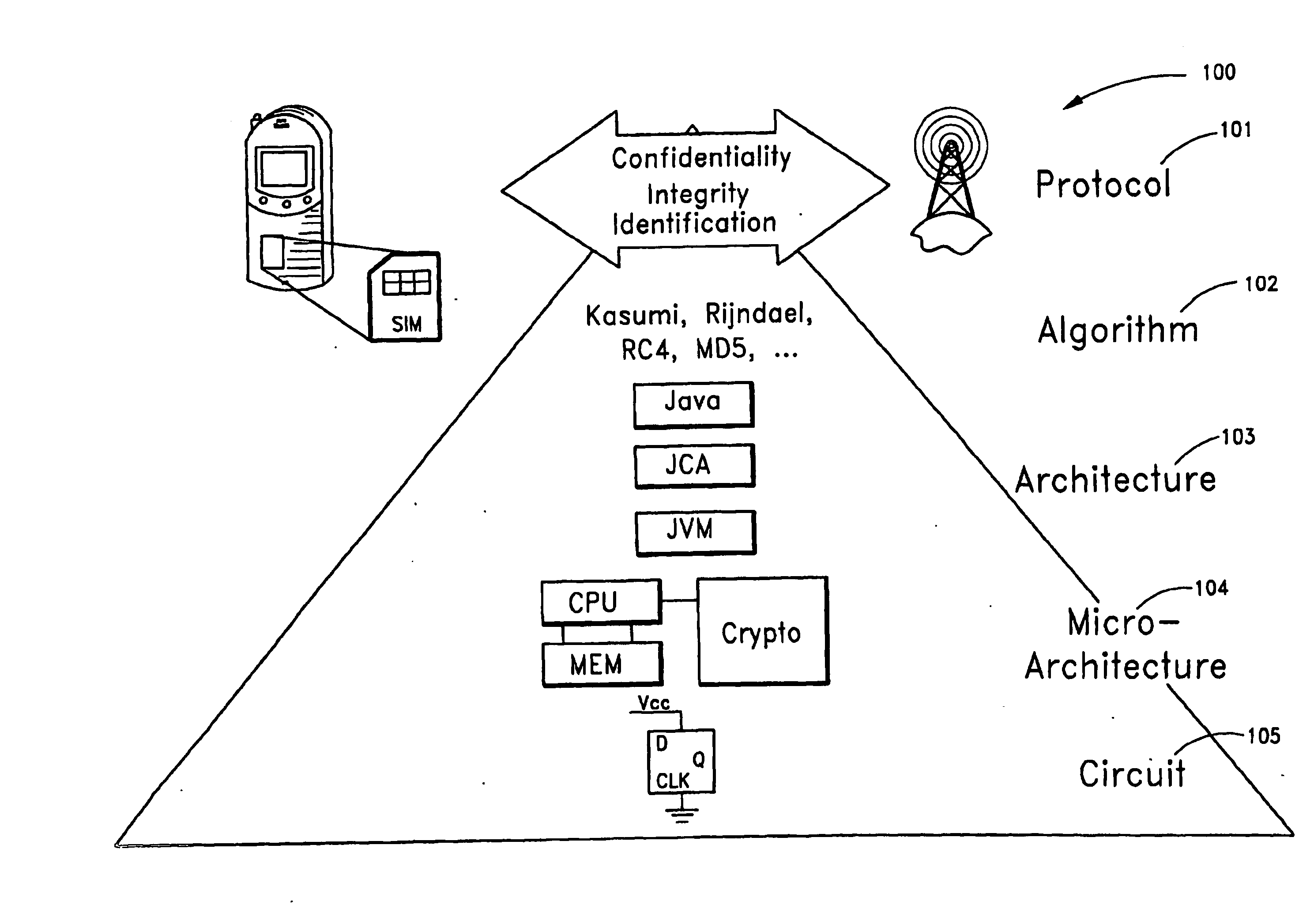
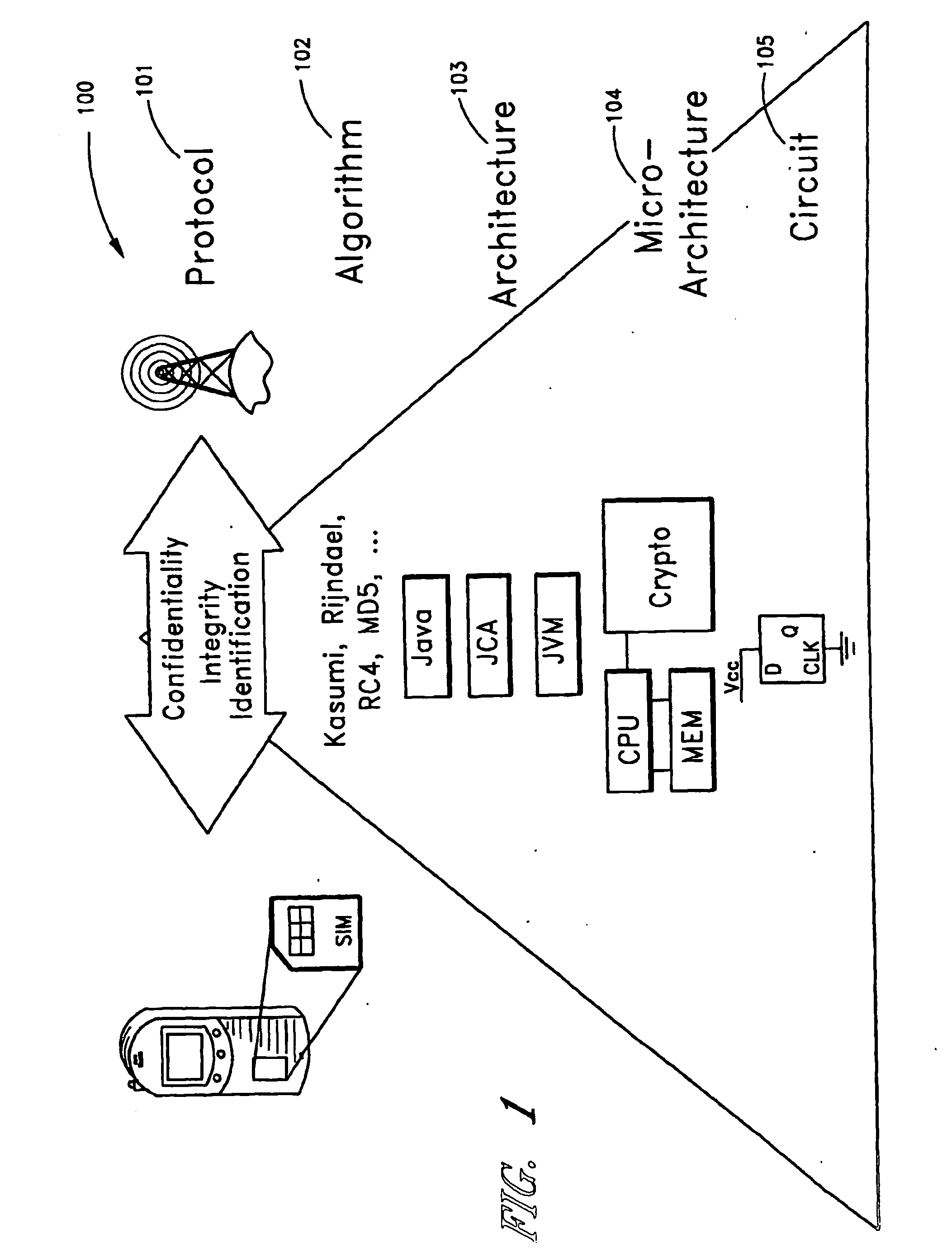
InactiveUS20130051552A1Small sizeShortened encrypted representationMultiple keys/algorithms usageDigital data protectionComputer hardwareKey generator
A computing device for obtaining a first cryptographic key during an enrollment phase, the computing device comprising a key generator for generating the first cryptographic key in dependence upon a seed, the computing device being configured for storing the first cryptographic key on a storage of the computing device for later cryptographic use of the first cryptographic key on the computing device during a usage phase coming after the enrollment phase wherein, the computing device further comprises a physically unclonable function, the key generator being configured for deriving the seed from an output of the physically unclonable function, and an encryption module for encrypting the first cryptographic key using a second cryptographic key derived from the output of the physically unclonable function, the computing device being configured for storing the first cryptographic key on the storage in encrypted form.
Owner:INTRINSIC ID
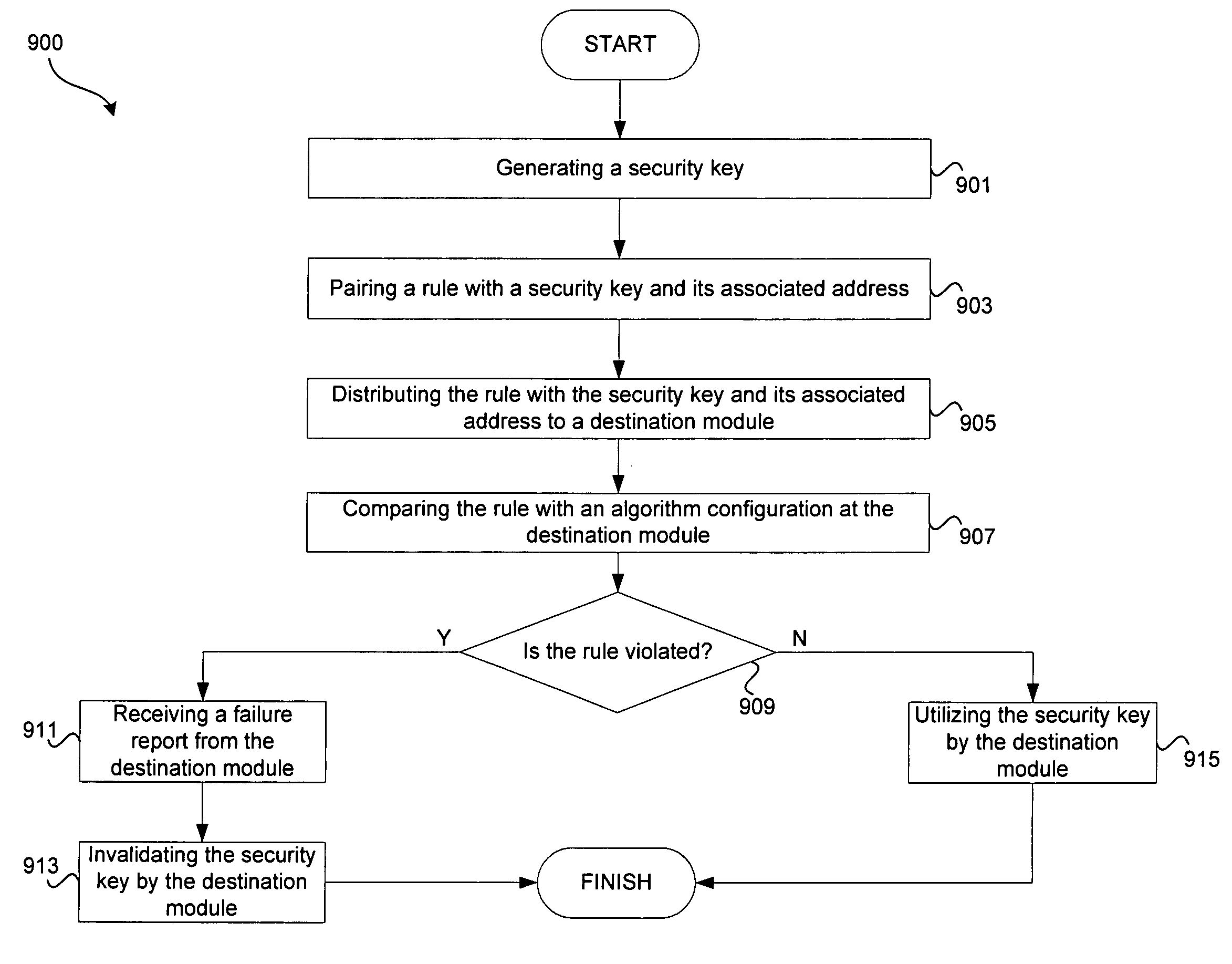
System and method for security key transmission with strong pairing to destination client
ActiveUS20050177741A1Key distribution for secure communicationUser identity/authority verificationKey sizeClient-side
Systems and methods for security key transmission with strong pairing to a destination client are disclosed. A security key may be generated by an on-chip key generator, an off-chip device, and / or software. A rule may then be paired with the security key and an address associated with the security key. The rule may define permissible usage by a destination module, which is defined by the associated address. The rule may comprise a command word, which may be implemented using a data structure associated with a permissible algorithm type, a security key size, and / or a security key source.
Owner:AVAGO TECH INT SALES PTE LTD
Indirect data protection using random key encryption
ActiveUS7299358B2Provide securityDigital data processing detailsUser identity/authority verificationData fileApplication software
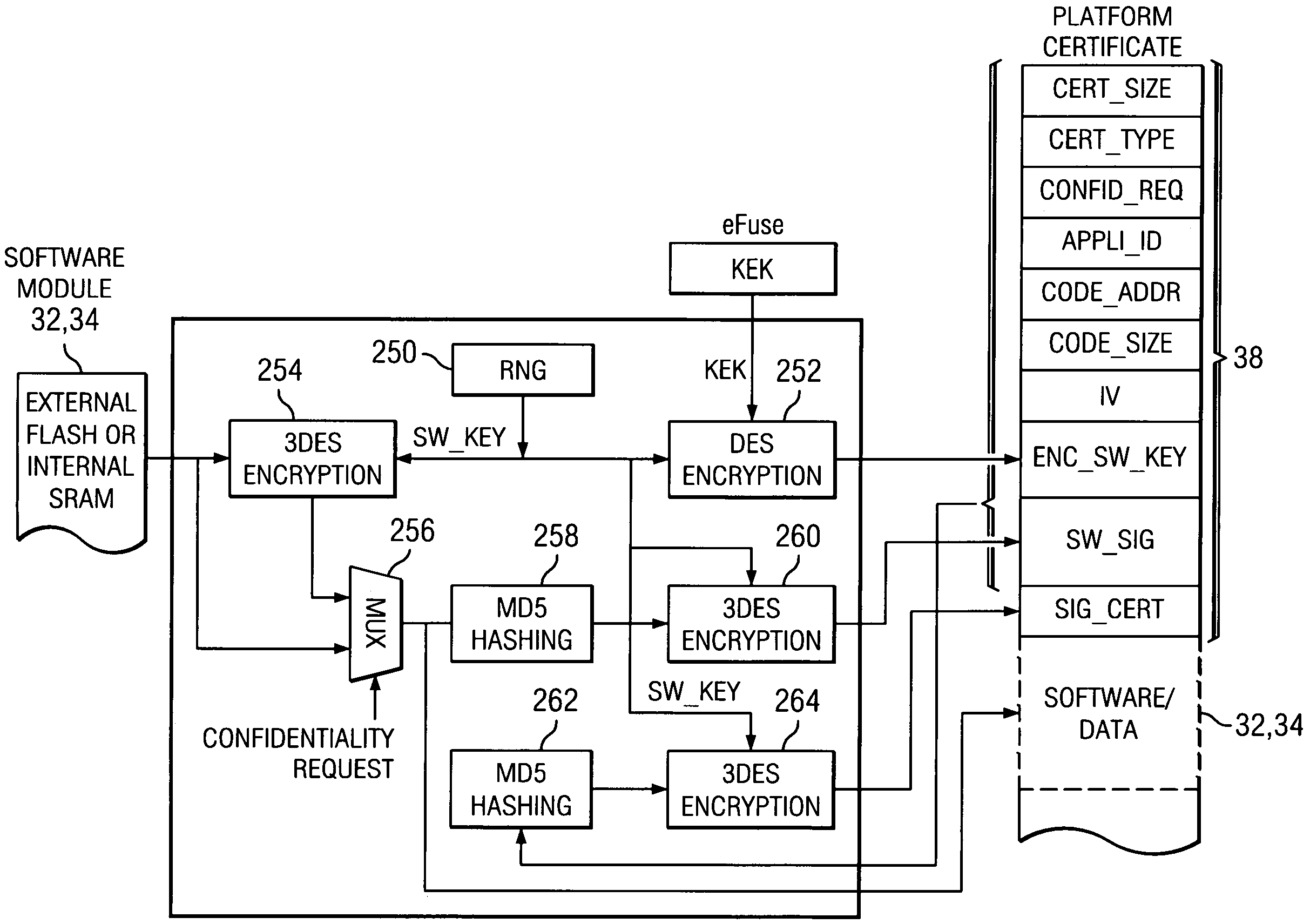
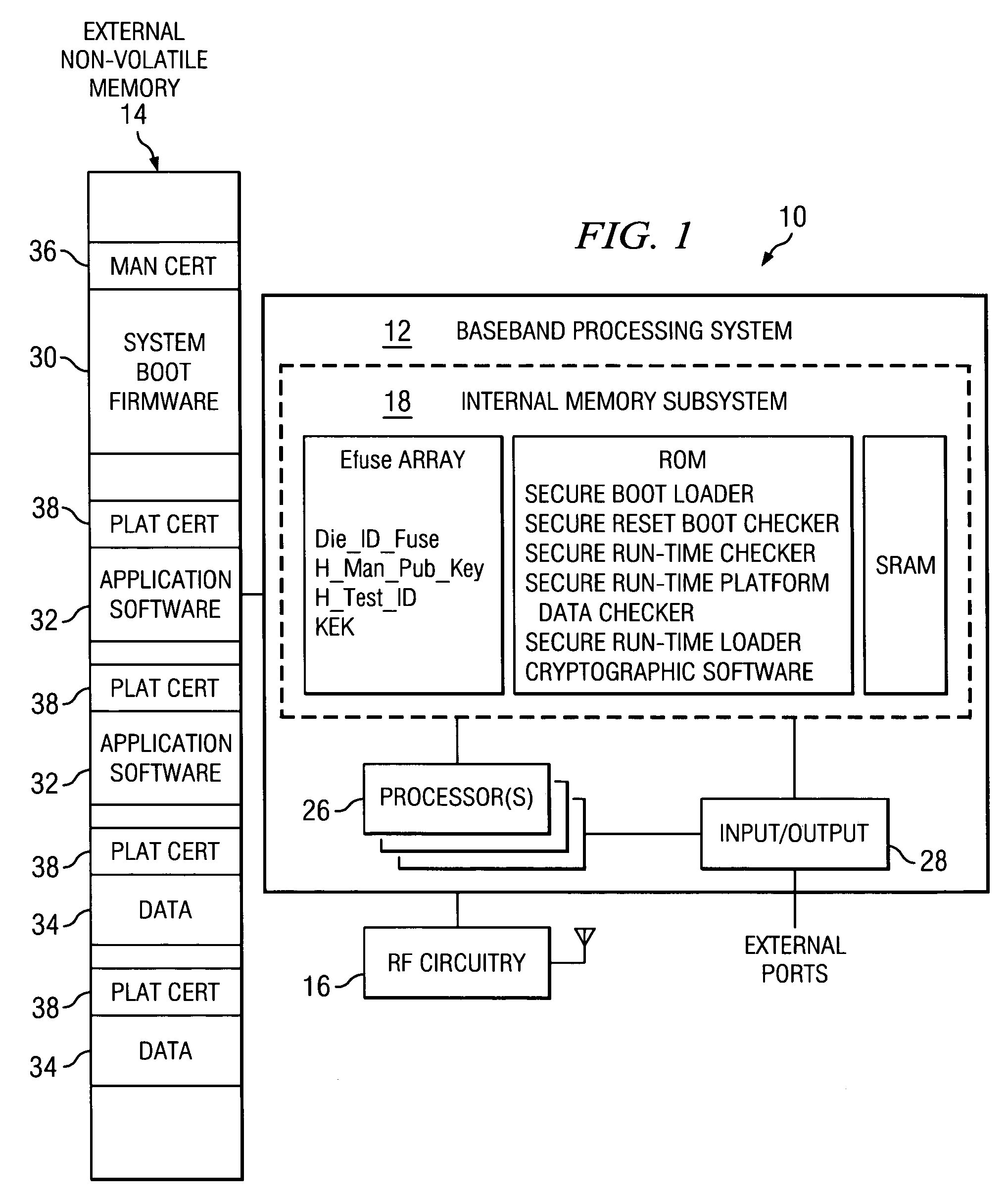
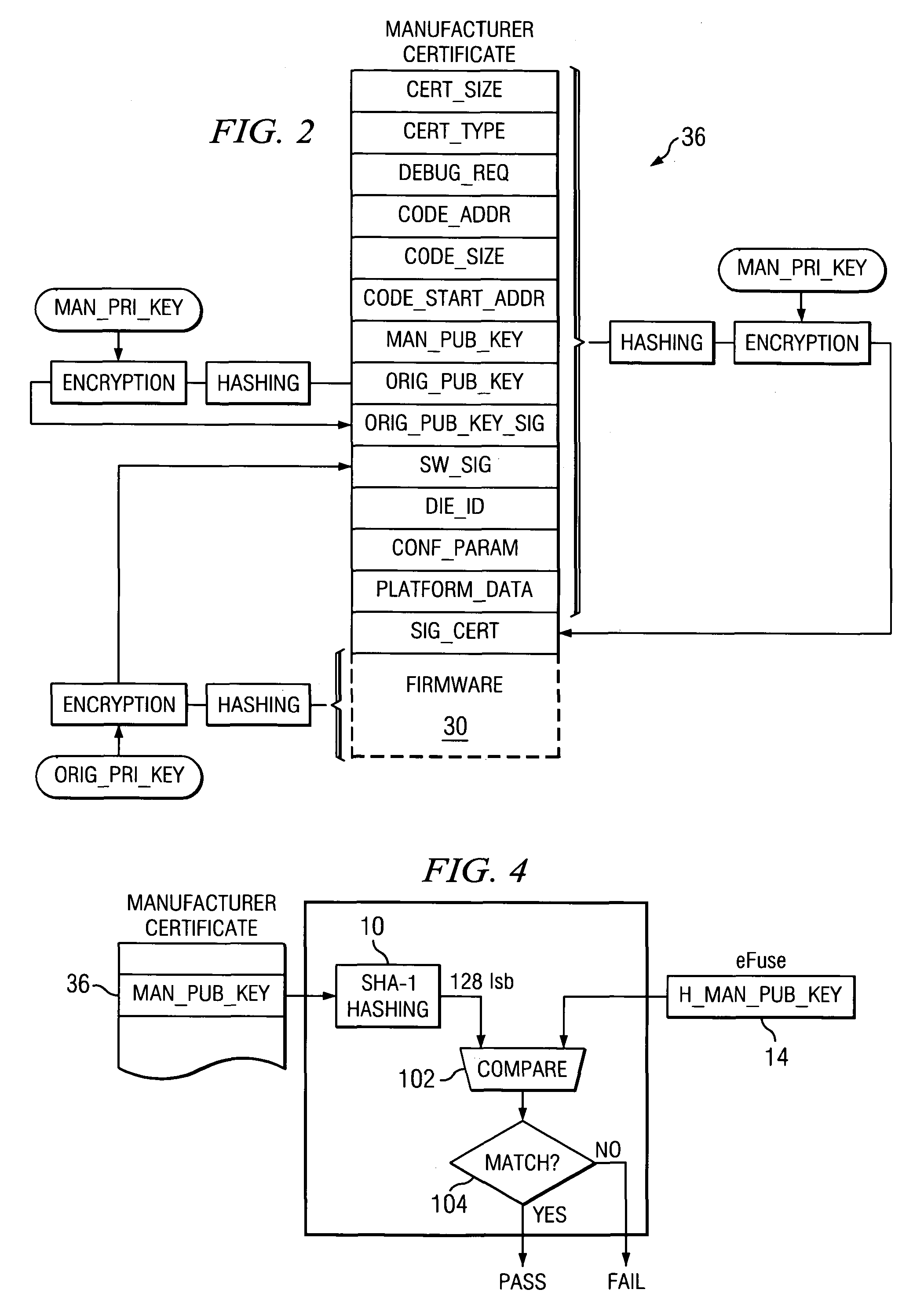
A computing platform (10) protects system firmware (30) using a manufacturer certificate (36). The manufacturer certificate binds the system firmware (30) to the particular computing platform (10). The manufacturer certificate may also store configuration parameters and device identification numbers. A secure run-time platform data checker (200) and a secure run-time checker (202) check the system firmware during operation of the computing platform (10) to ensure that the system firmware (30) or information in the manufacturer certificate (36) has not been altered. Application software files (32) and data files (34) are bound to the particular computing device (10) by a platform certificate (38). A key generator may be used to generate a random key and an encrypted key may be generated by encrypting the random key using a secret identification number associated with the particular computing platform (10). Only the encrypted key is stored in the platform certificate (36).
Owner:TEXAS INSTR INC
Identity-based-encryption system with district policy information
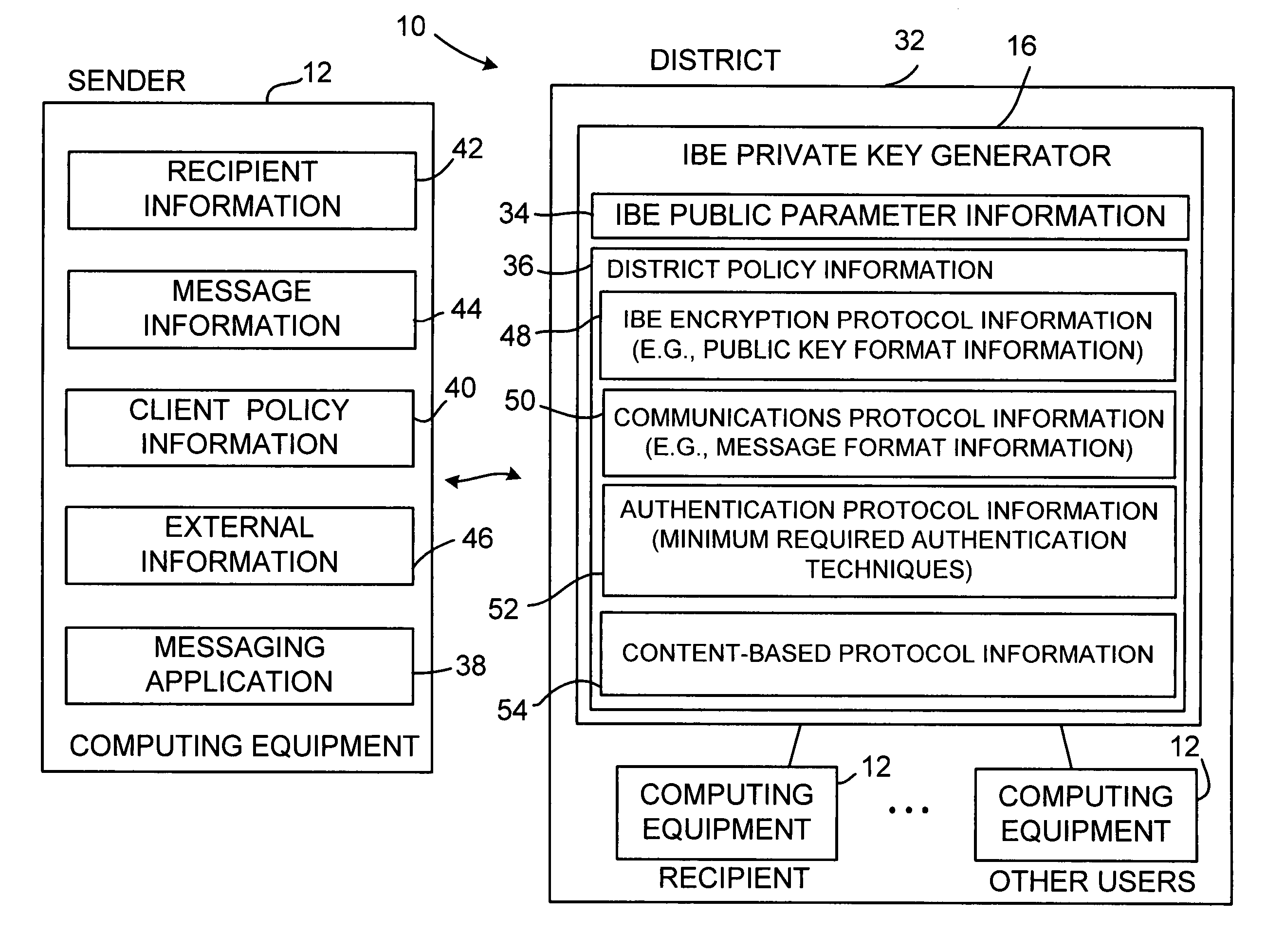
ActiveUS20050084100A1Public key for secure communicationSecret communicationNetwork Communication ProtocolsInformation security
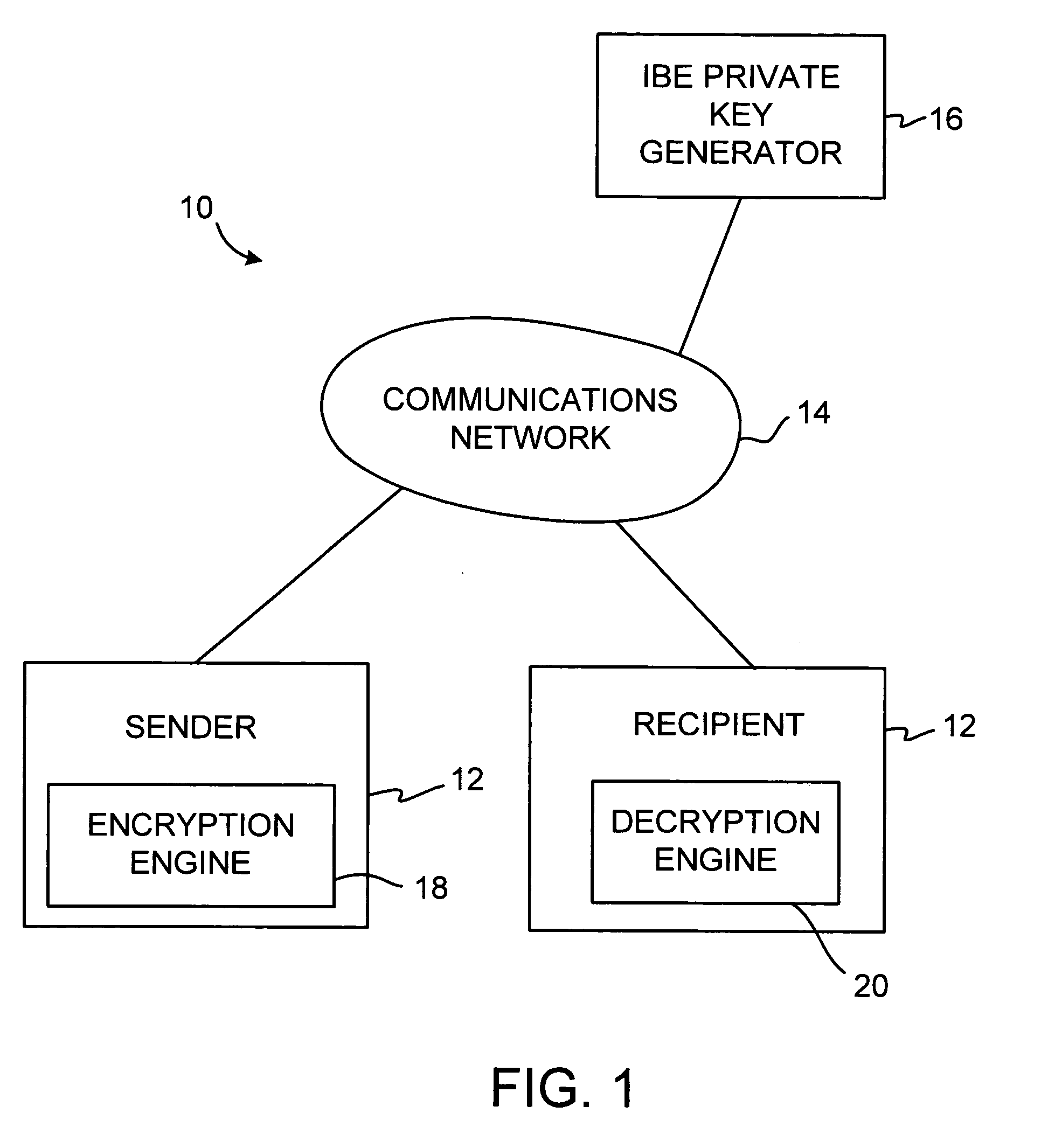
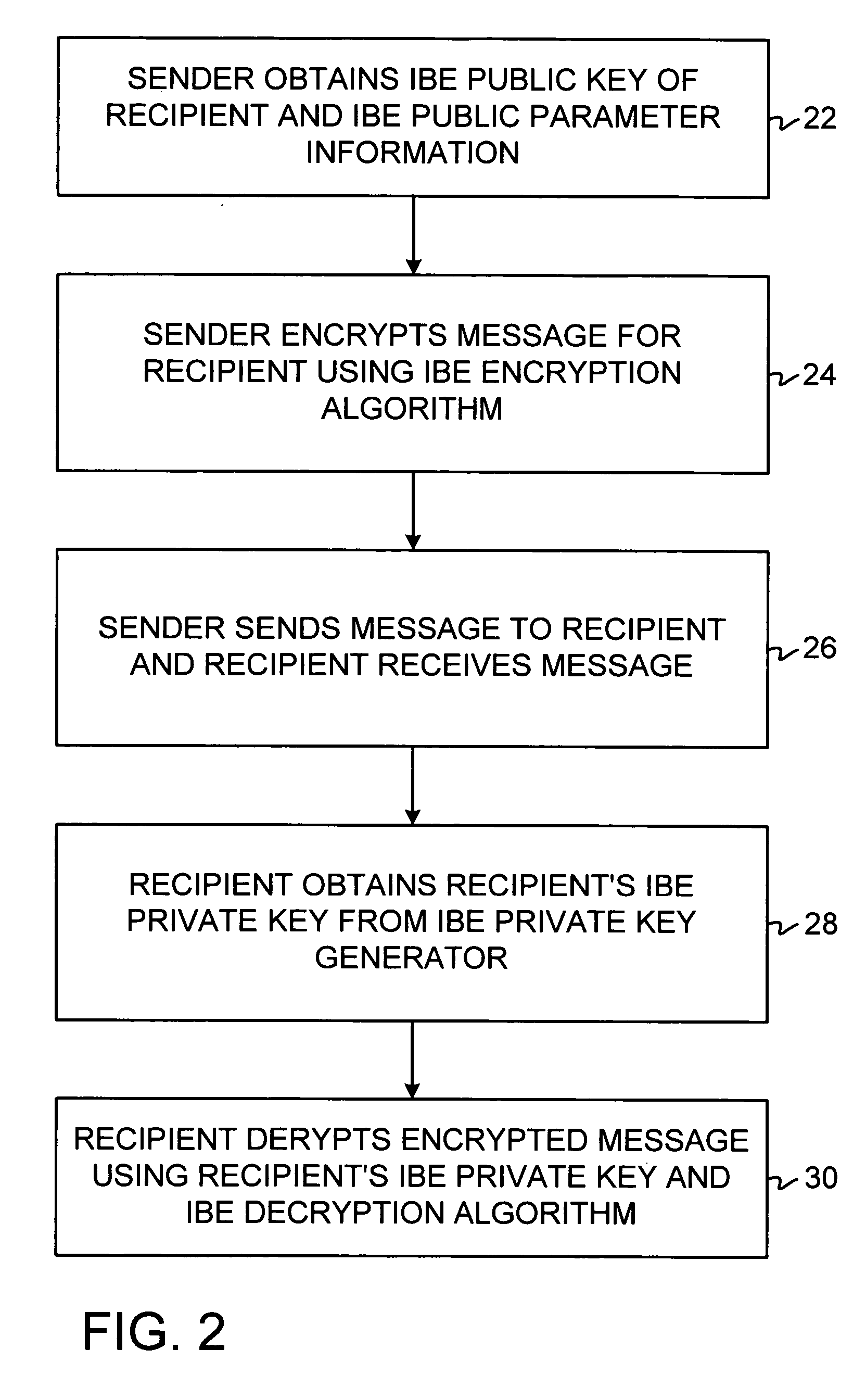
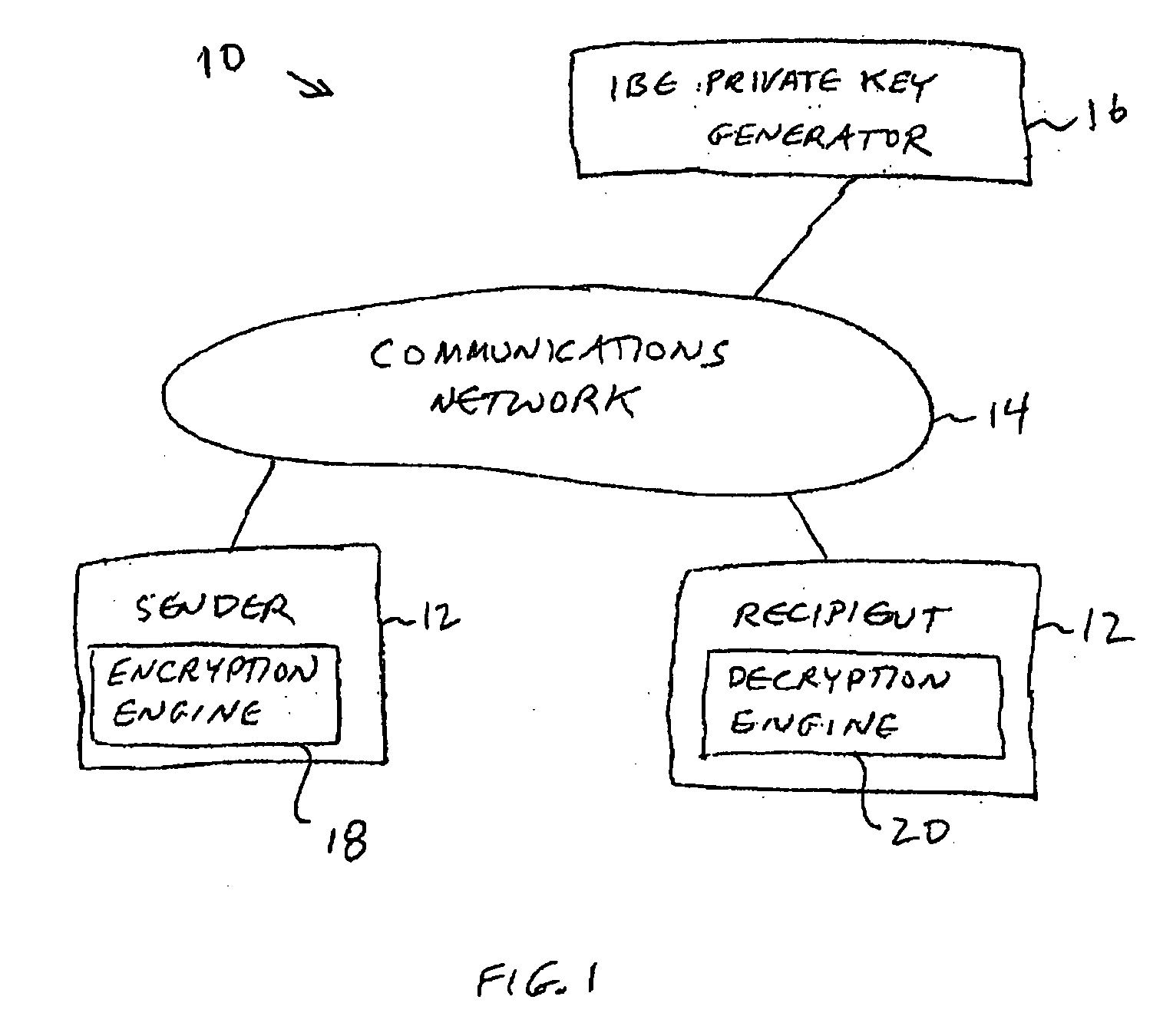
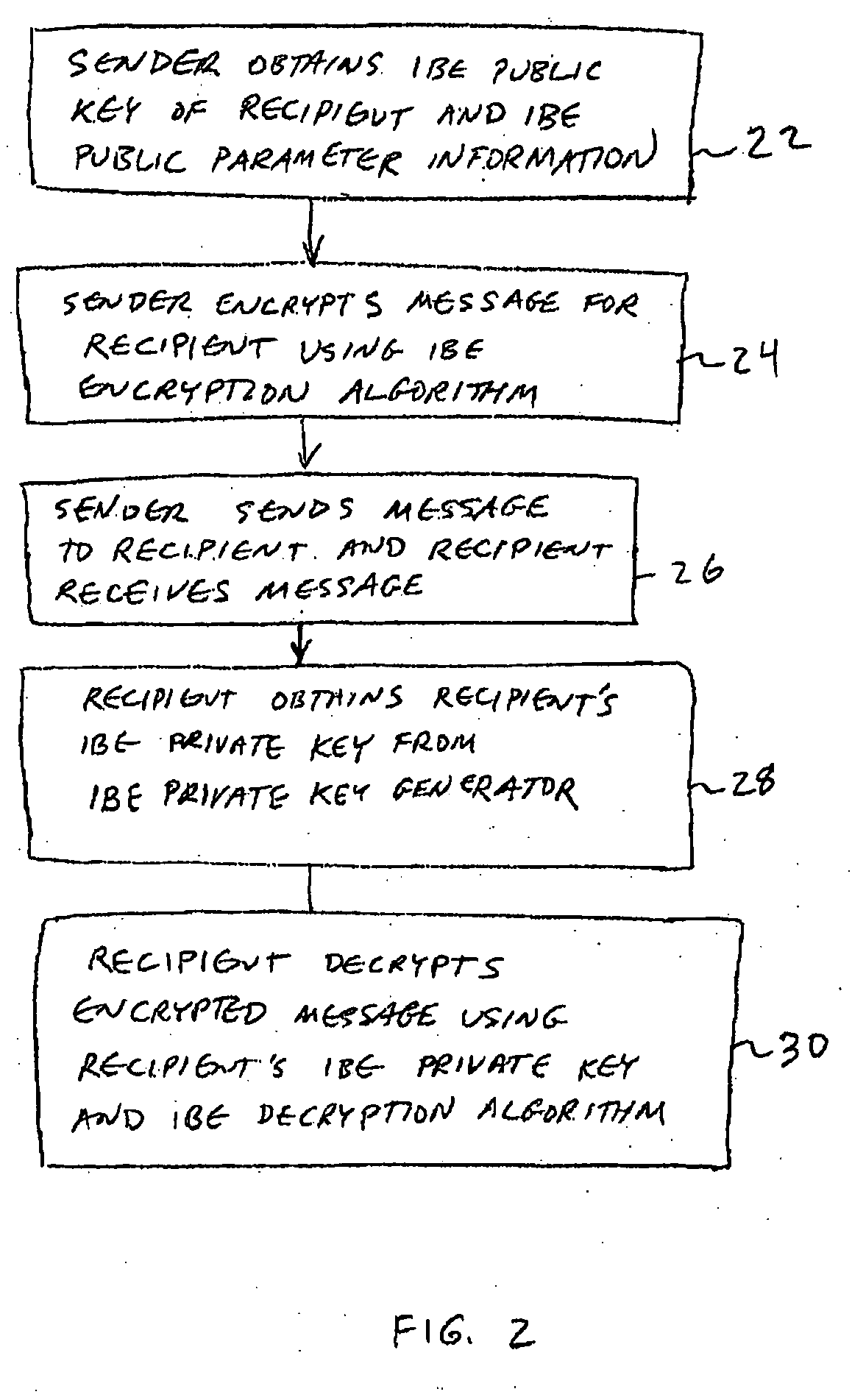
A system is provided that uses identity-based encryption (IBE) to allow a sender to securely convey information in a message to a recipient over a communications network. IBE public key information may be used to encrypt messages and corresponding IBE private key information may be used to decrypt messages. The IBE private keys may be provided to message recipients by an IBE private key generator. The IBE private key generator and the recipients who obtain their IBE private keys from that generator form a district. District policy information may be provided by the IBE private key generator that specifies which encryption and communications protocols are used by the district. The district policy information may also specify which authentication protocols are used by the district and may set forth how content-based protocols are implemented. This information may be used by senders in sending messages to recipients.
Owner:MICRO FOCUS LLC
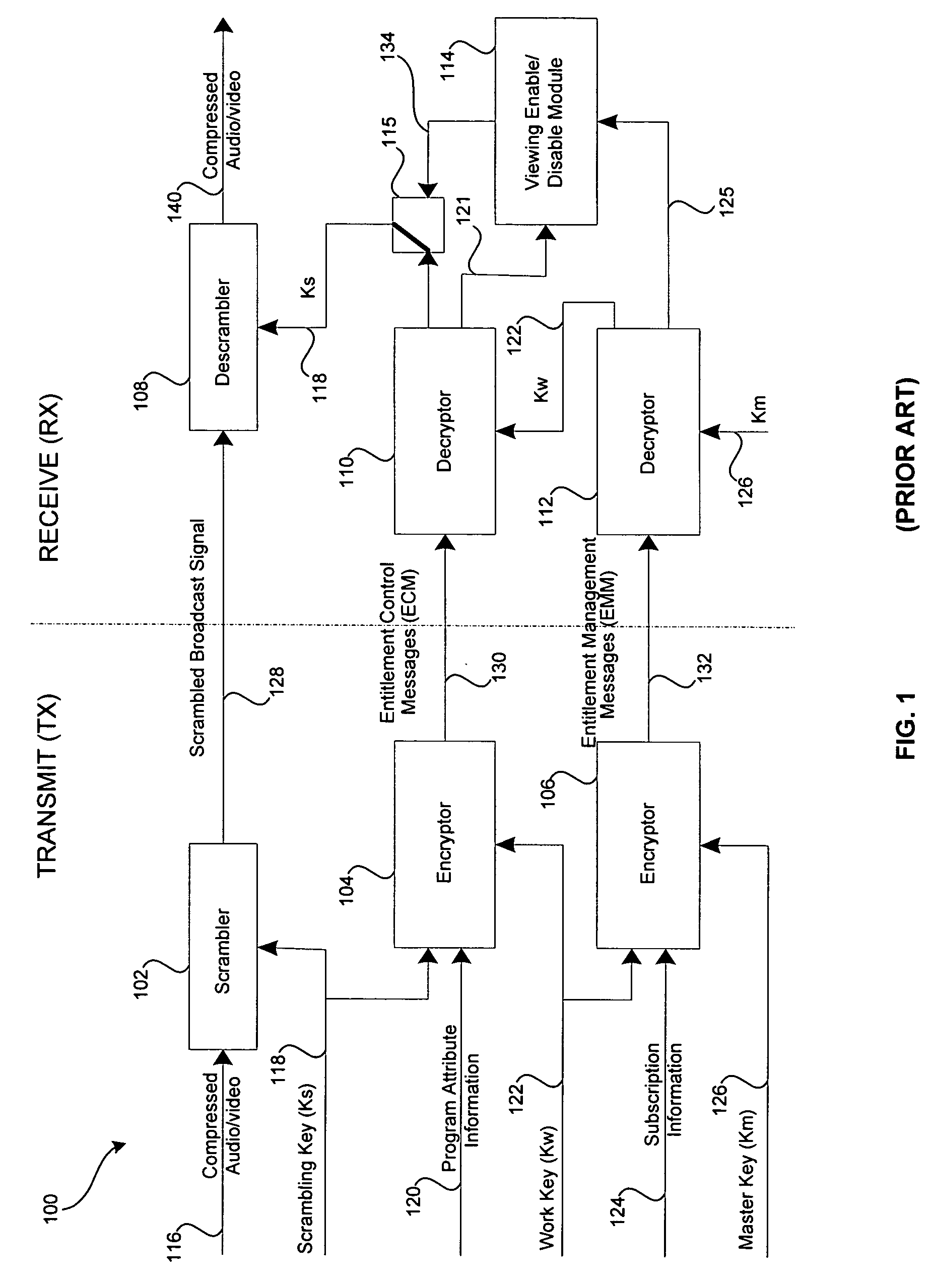
Cryptographic communications using pseudo-randomly generated cryptography keys
InactiveUS7120696B1High strengthImprove securitySynchronising transmission/receiving encryption devicesRandom number generatorsSecure communicationCommunications system
An apparatus and method for generating pseudo-random cryptographic keys in a cryptographic communications system, whereby, given a common set of initializing configuration data, the pseudo-random cryptographic keys can be duplicatively generated by various independent pseudo-random key generators of the cryptographic communications system. In accordance with the preferred embodiment of the present invention, users of the communications system can each possess an independent pseudo-random key generator to securely communicate with other users also holding independent pseudo-random key generator that share the same initialization configuration data, no matter where the other users are located or whether the users are connected via wire or wireless communication network. The present invention facilitates secure communication without the need to transport decryption keys in advanced, thereby reducing the risk of the secure communication becoming compromised via interception of decryption keys.
Owner:STEALTHKEY
System for biometric signal processing with hardware and software acceleration
InactiveUS20070038867A1Improve performanceKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareSystem design methodology
A secure embedded system that uses cryptographic and biometric signal processing acceleration is described. In one embodiment, the secure embedded system is configured as a wireless pay-point protocol for brick-and-mortar and e-commerce applications in which biometric information is localized and does not require transmission of biometric data for authentication. In one embodiment, a key-generation function uses a dynamic key generator and static biometric components. In one embodiment, an embedded system design methodology provides hardware and software acceleration transparency.
Owner:RGT UNIV OF CALIFORNIA
Identity-based-encryption system with district policy information
ActiveUS7103911B2Key distribution for secure communicationDigital data processing detailsNetwork Communication ProtocolsKey generator
A system is provided that uses identity-based encryption (IBE) to allow a sender to securely convey information in a message to a recipient over a communications network. IBE public key information may be used to encrypt messages and corresponding IBE private key information may be used to decrypt messages. The IBE private keys may be provided to message recipients by an IBE private key generator. The IBE private key generator and the recipients who obtain their IBE private keys from that generator form a district. District policy information may be provided by the IBE private key generator that specifies which encryption and communications protocols are used by the district. The district policy information may also specify which authentication protocols are used by the district and may set forth how content-based protocols are implemented. This information may be used by senders in sending messages to recipients.
Owner:MICRO FOCUS LLC
Methods, systems and computer program products for providing secure sharing of electronic data
InactiveUS6868160B1Easy retrievalImprove securityKey distribution for secure communicationPublic key for secure communicationSecure communicationElectronic information
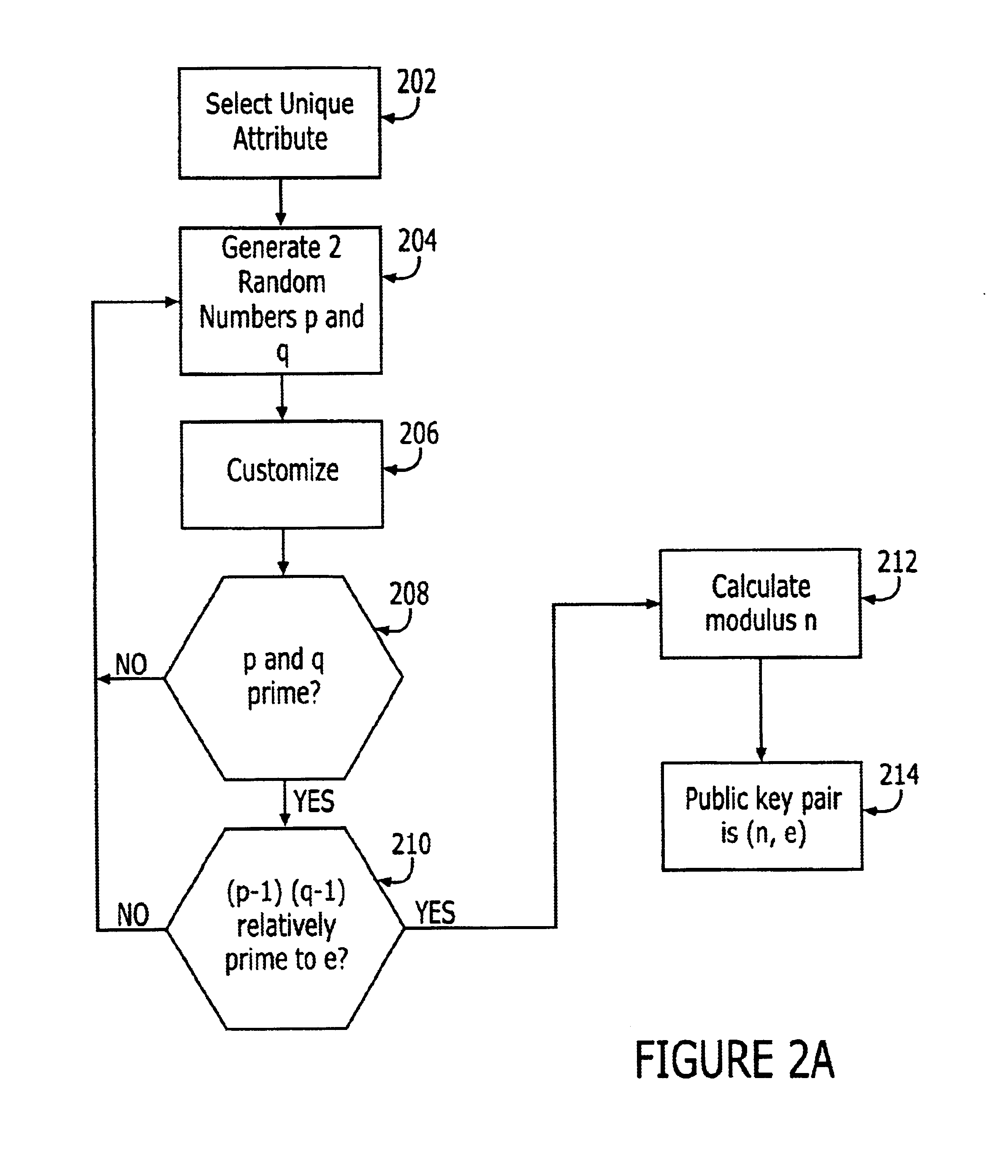
A system and method for secure sharing of electronic information uses public key encryption in which a key generator algorithmically generates public-private key pairs without requiring storage, maintenance, tracking and management of keys or certificates. The algorithm uses one or more unique attributes of an individual to generate the public private key pair for that individual. In a preferred embodiment, the one or more unique attributes are input to a random number generator which outputs random numbers used to generate the public-private key pairs that are used for secure communication.
Owner:BELLSOUTH INTPROP COR +1
System and method for secure handling of scanned documents
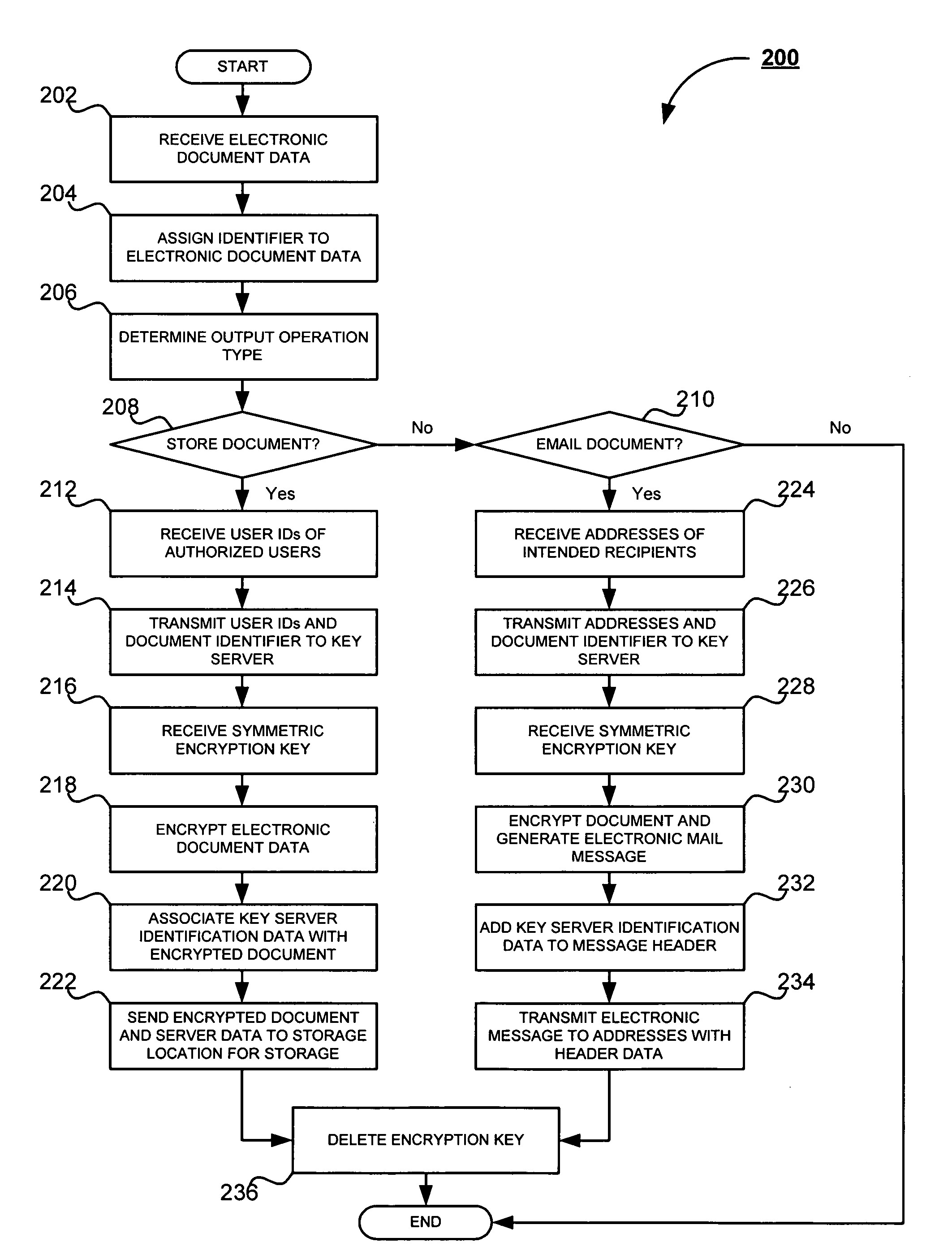
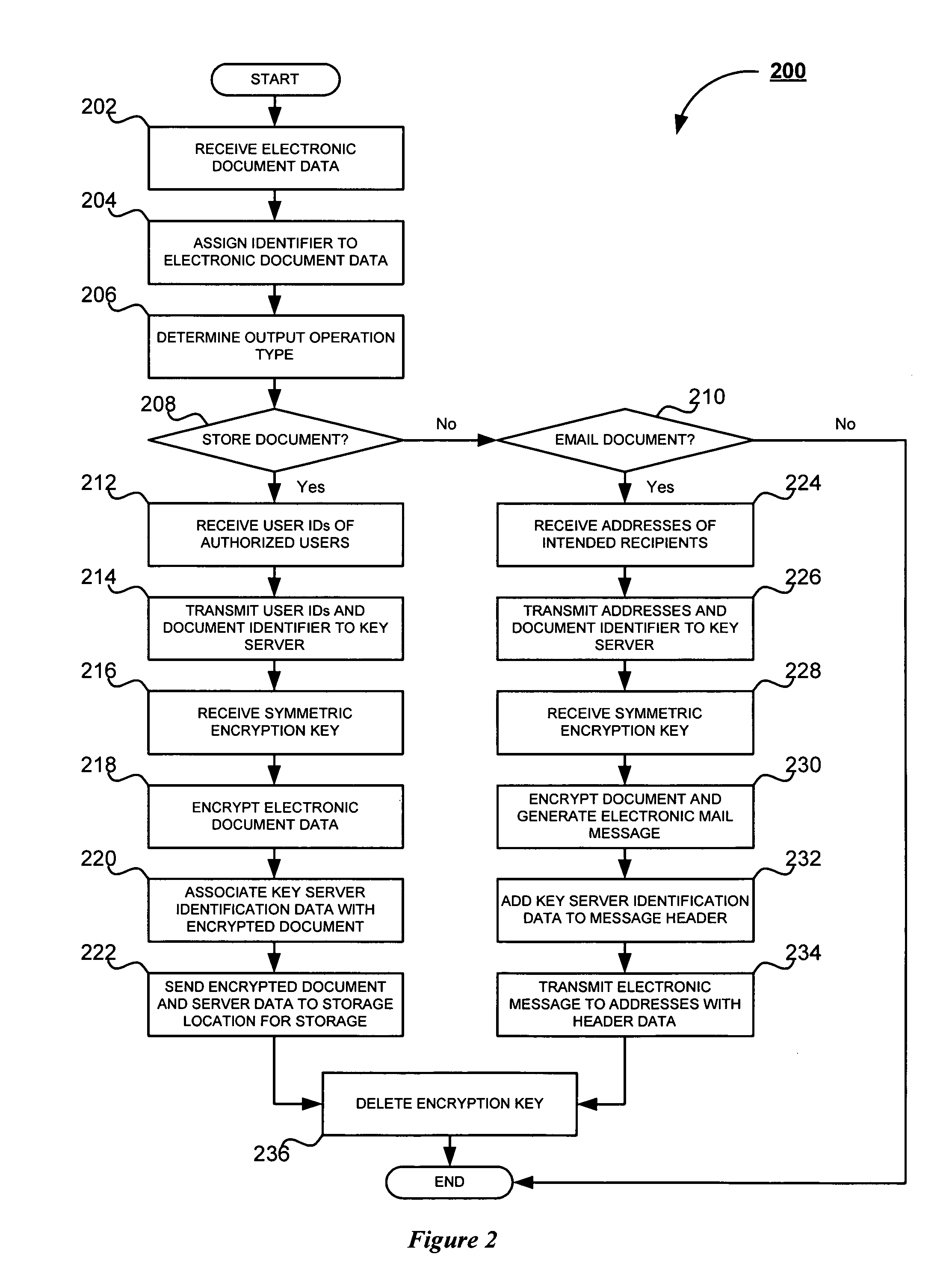
InactiveUS20070283446A1Safe handlingMultiple keys/algorithms usageDigital data processing detailsCryptographic key generationElectronic document
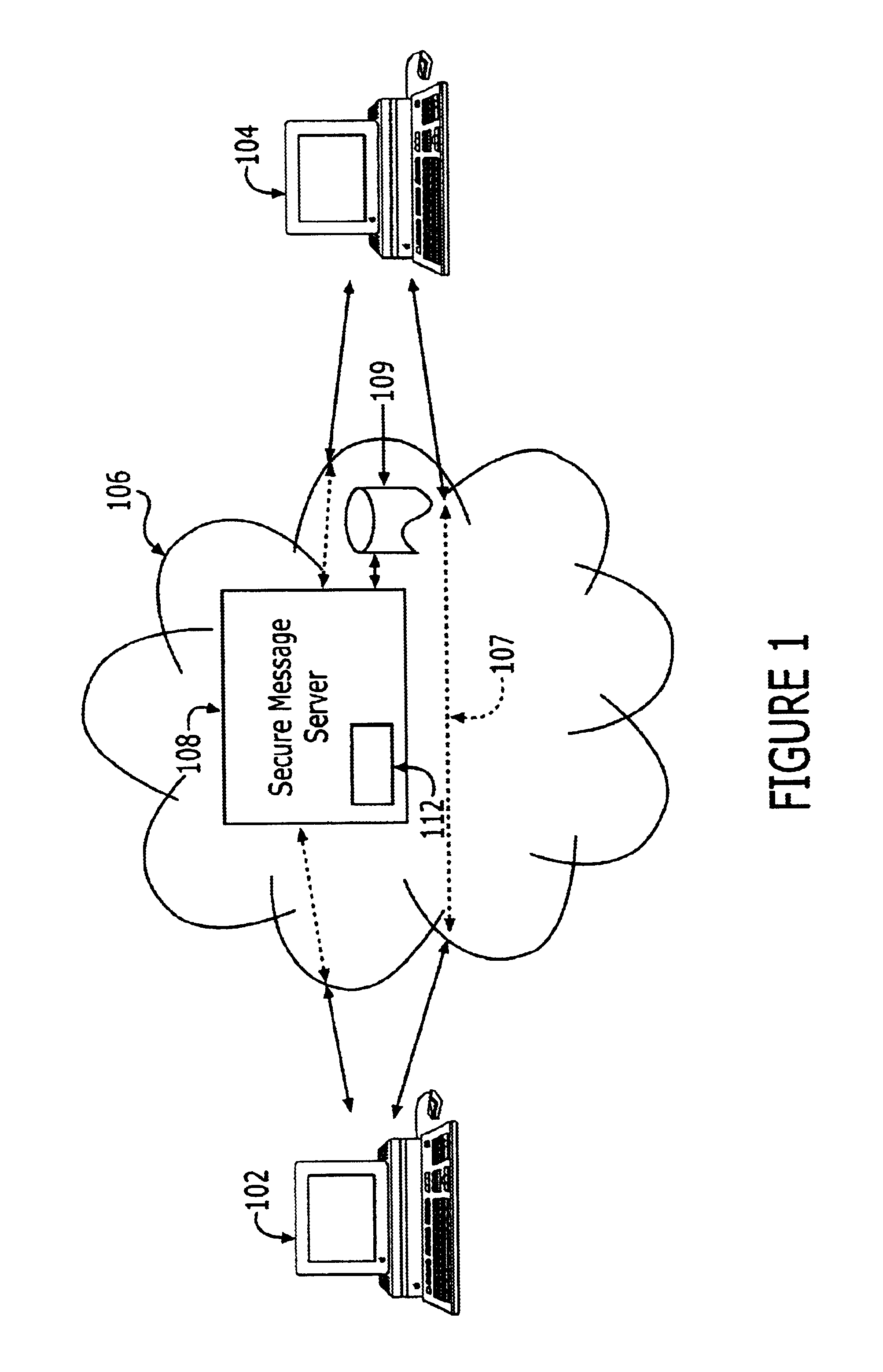
A system and method for secure handling of scanned documents is provided. Electronic document data is received by a document processing device and assigned an identifier unique to the document. A user ID or electronic mail address is then received corresponding to the selected output operation. The user ID or address is then transmitted, along with the identifier, to an encryption key generator, which then generates a symmetric encryption key. The encryption key is then returned to the document processing device, whereupon the electronic document data is encrypted and the key is deleted by the document processing device. The encrypted document is then stored or transmitted via electronic mail, in accordance with the selected output operation. Decryption is thereafter accomplished using the document identifier, user ID or email address, and key generator identification data.
Owner:KK TOSHIBA +1
Protecting software environment in isolated execution
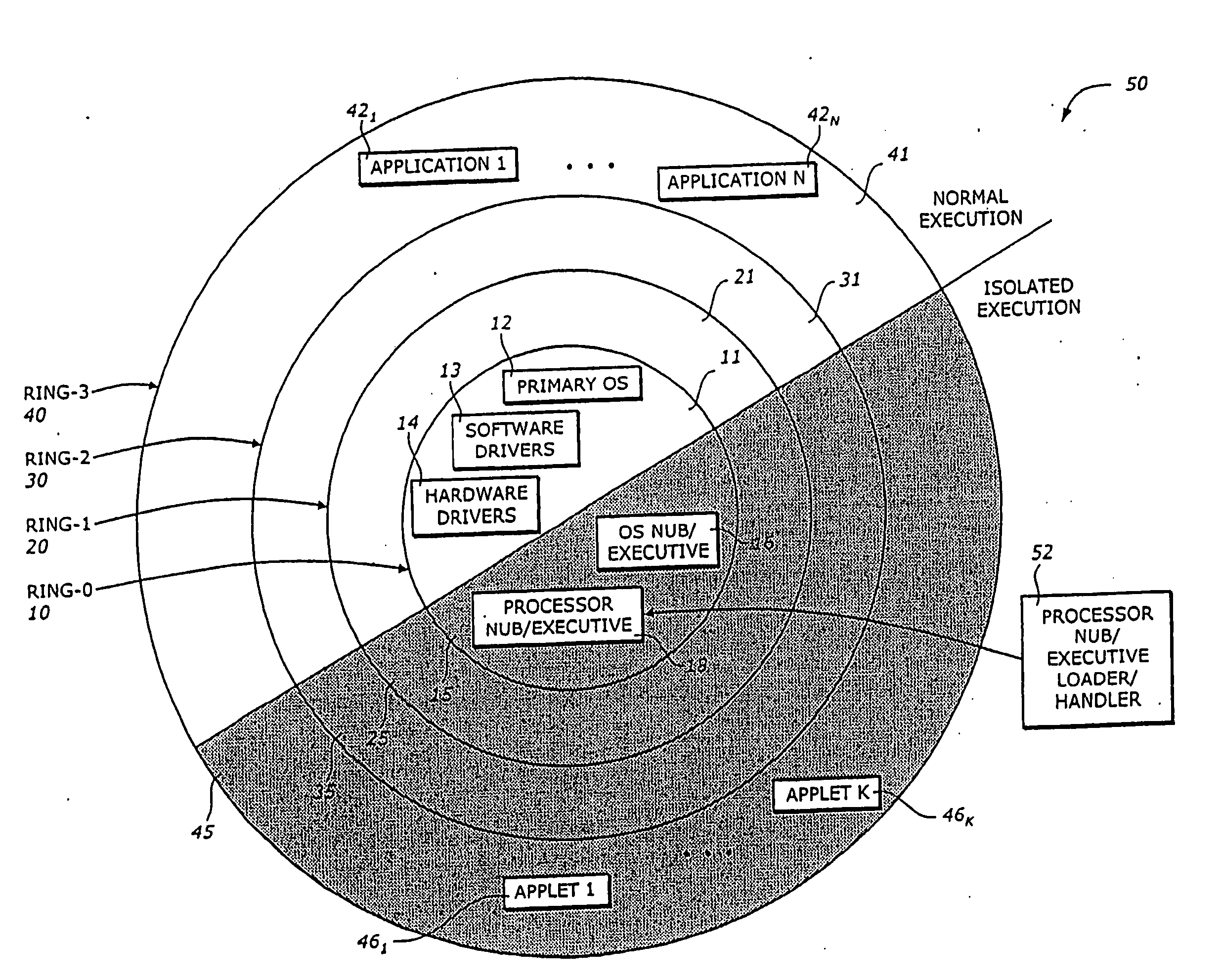
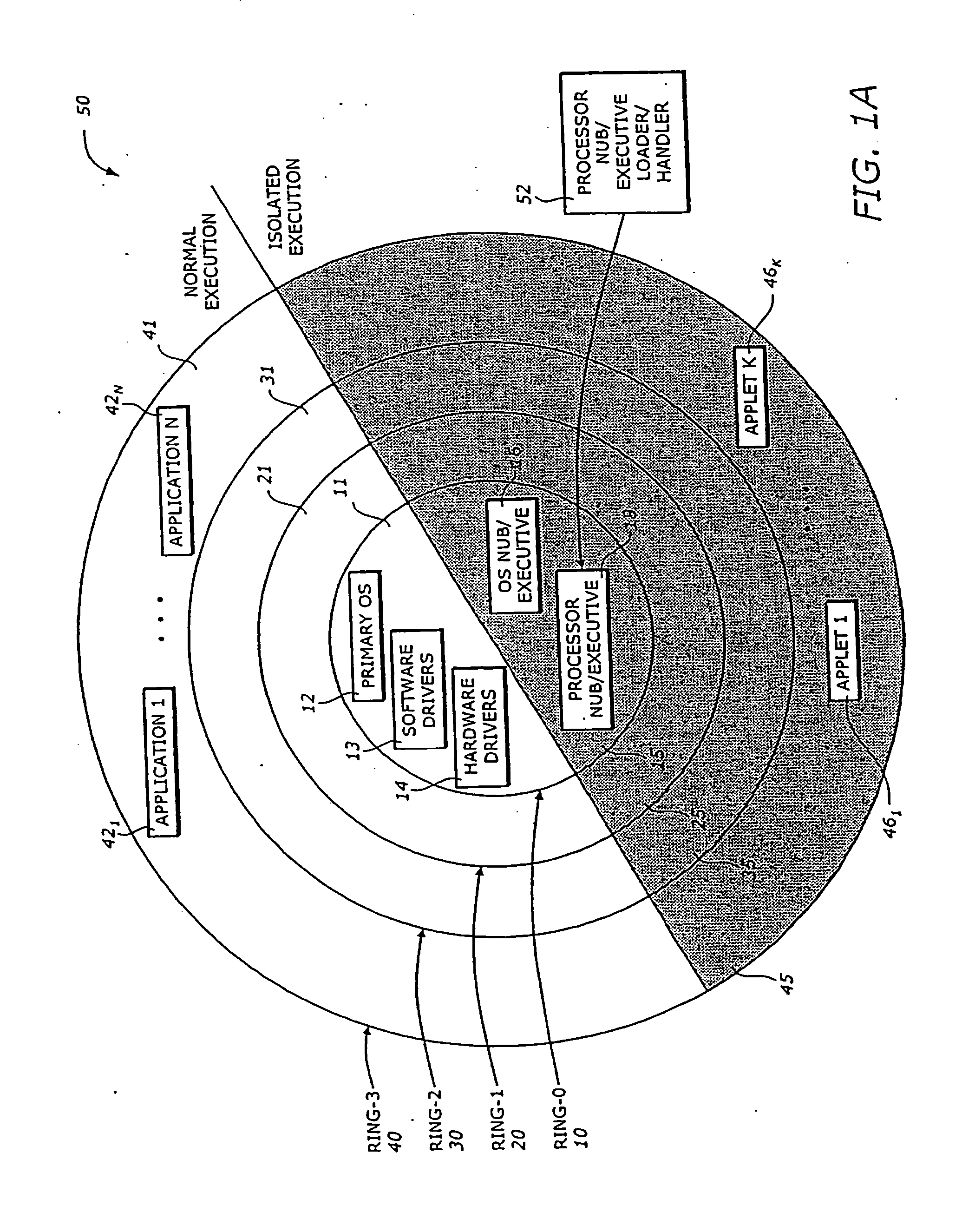
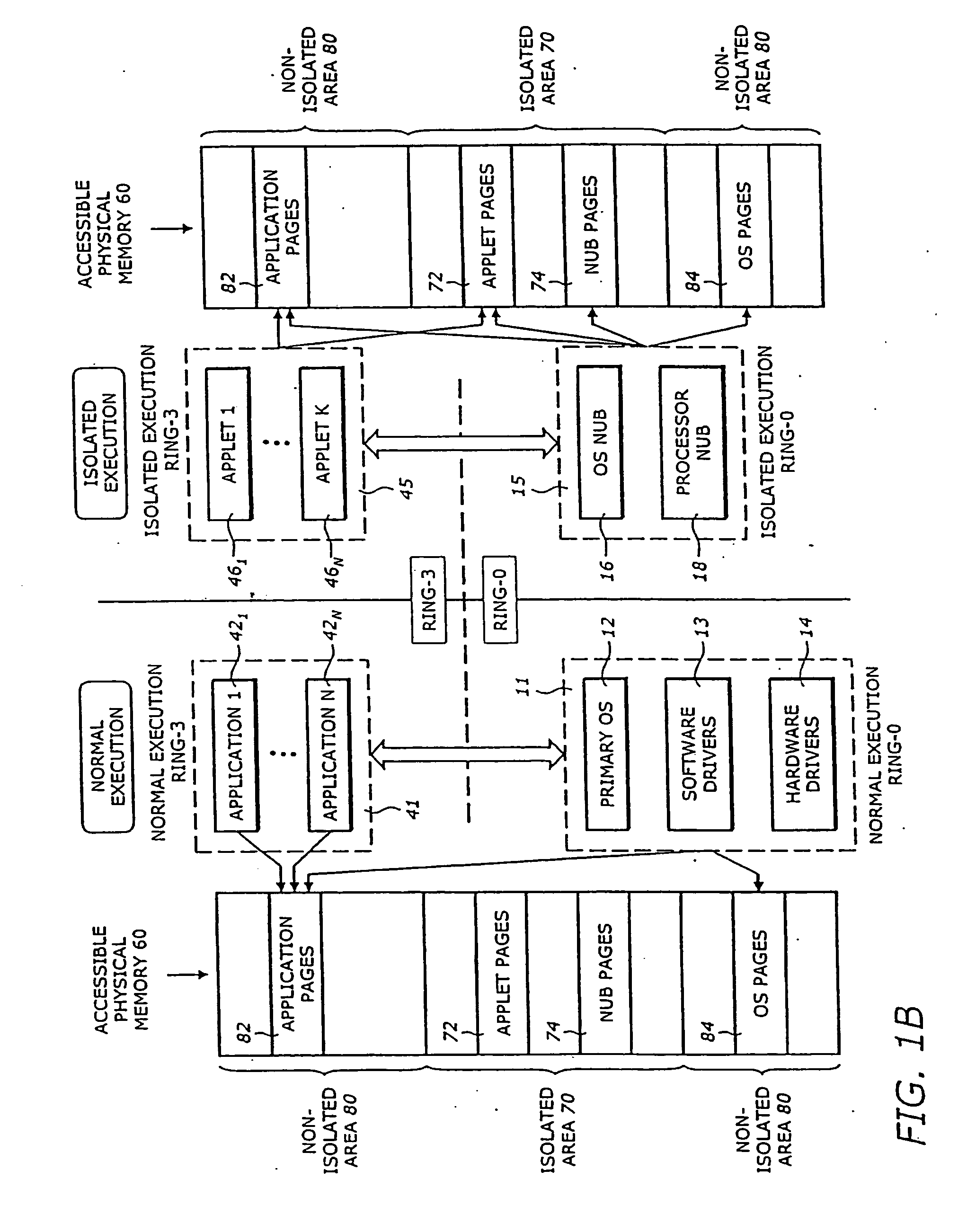
InactiveUS20060206943A1Specific access rightsDigital data processing detailsTerm memoryOperation mode
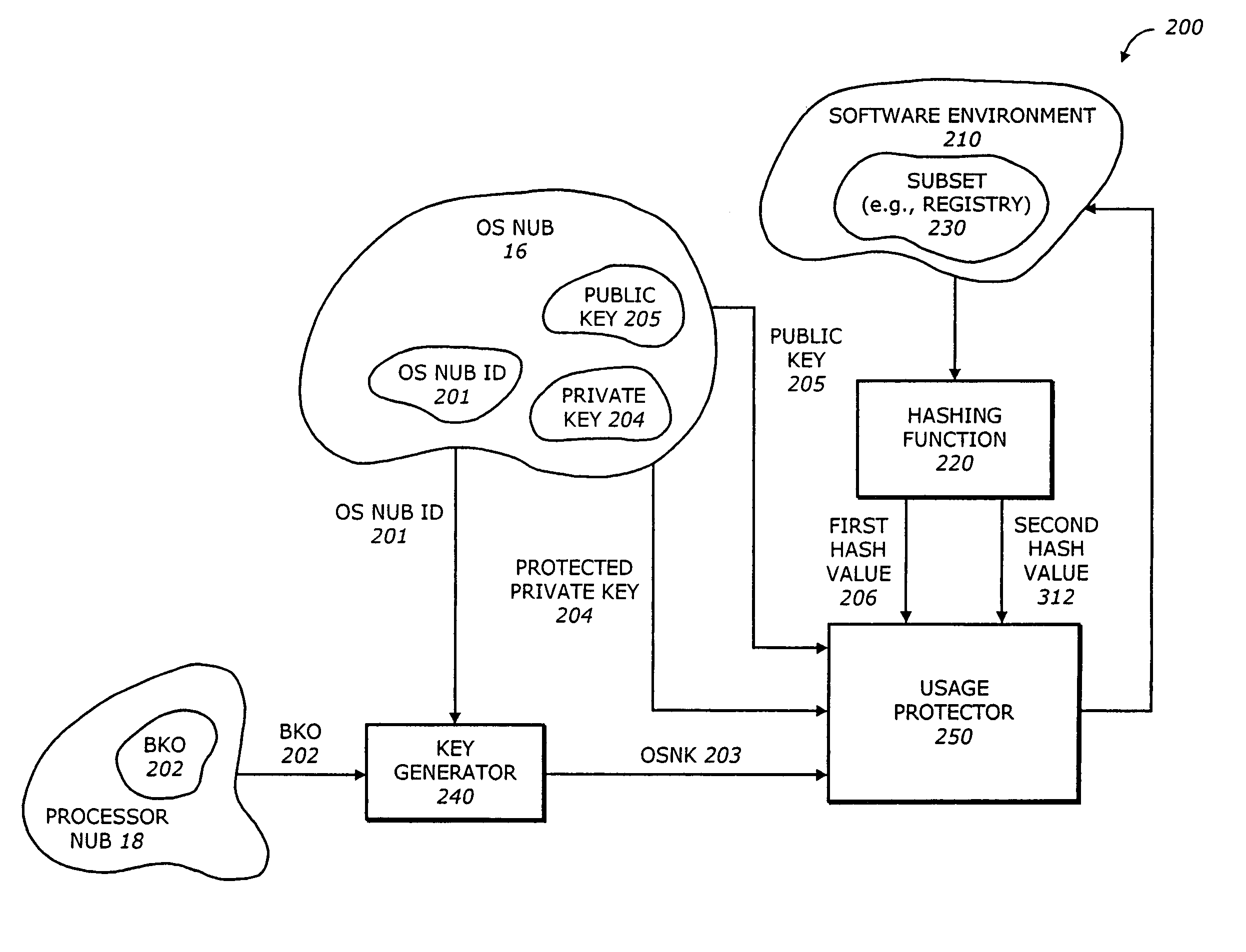
A processing system has a processor that can operate in a normal ring 0 operating mode and one or more higher ring operating modes above the normal ring 0 operating mode. In addition, the processor can operate in an isolated execution mode. A memory in the processing system may include an ordinary memory area that can be accessed from the normal ring 0 operating mode, as well as an isolated memory area that can be accessed from the isolated execution mode but not from the normal ring 0 operating mode. The processing system may also include an operating system (OS) nub, as well as a key generator. The key generator may generate an OS nub key (OSNK) based at least in part on an identification of the OS nub and a master binding key (BK0) of the platform. Other embodiments are described and claimed.
Owner:INTEL CORP
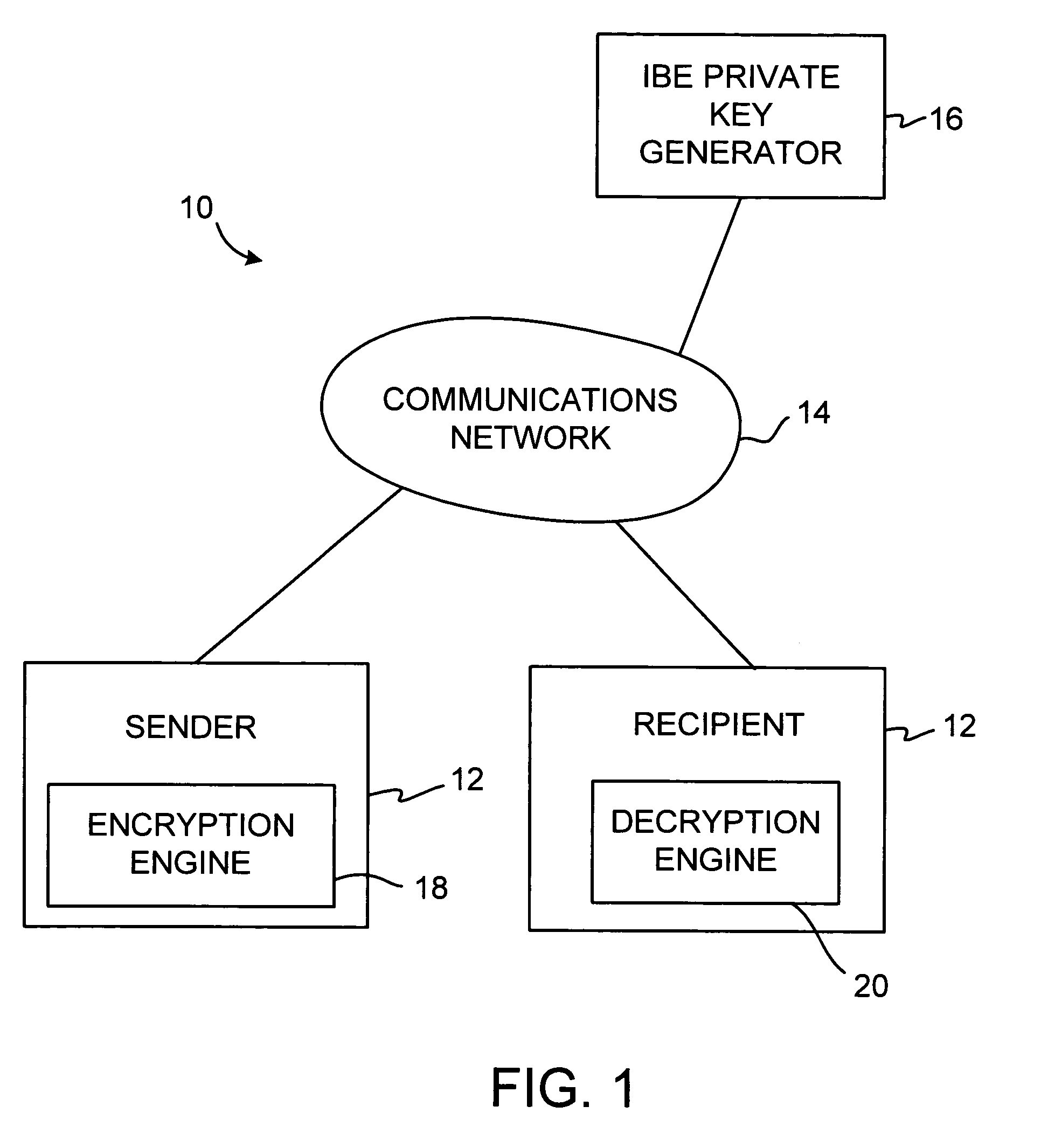
Identity-based encryption system
ActiveUS20080148047A1Avoid repetitionPublic key for secure communicationUser identity/authority verificationSecure communicationKey generator
A system is provided that uses identity-based encryption to support secure communications. Messages from a sender to a receiver may be encrypted using the receiver's identity and public parameters that have been generated by a private key generator associated with the receiver. The private key generator associated with the receiver generates a private key for the receiver. The encrypted message may be decrypted by the receiver using the receiver's private key. The system may have multiple private key generators, each with a separate set of public parameters. Directory services may be used to provide a sender that is associated with one private key generator with appropriate public parameters to use when encrypting messages for a receiver that is associated with a different private key generator. A certification authority may be used to sign directory entries for the directory service. A clearinghouse may be used to avoid duplicative directory entries.
Owner:MICRO FOCUS LLC
Continuous variable quantum key distribution system and synchronous realization method thereof
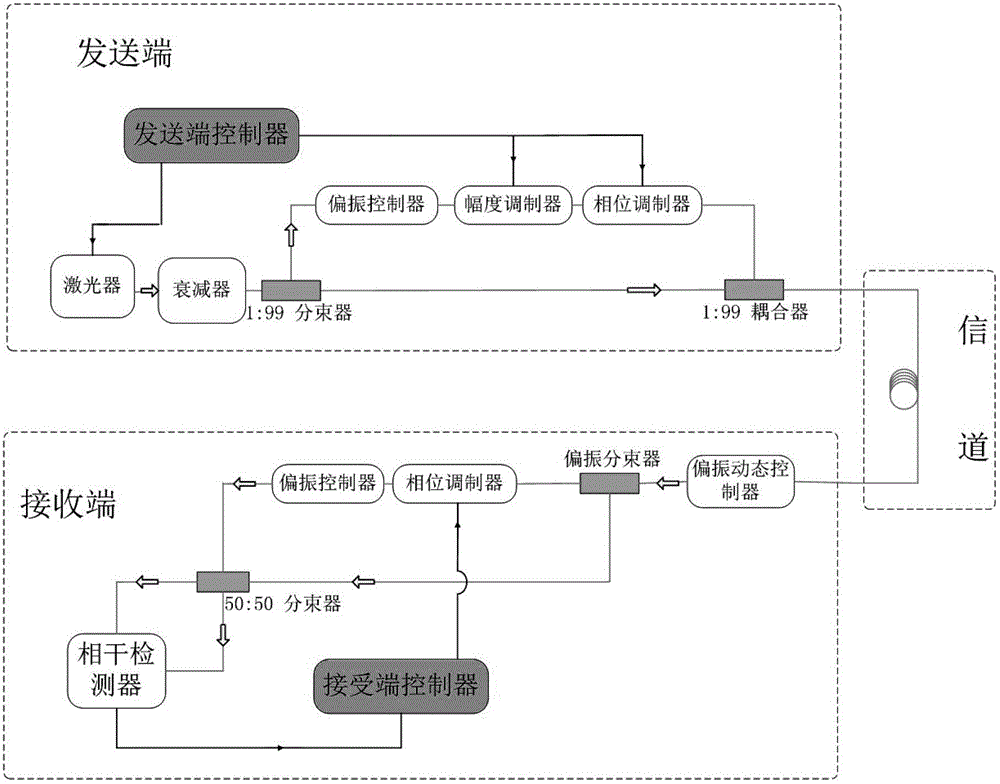
ActiveCN102724036AImprove bit error rateAvoid interferenceKey distribution for secure communicationMulti-frequency code systemsBeam splitterAmplitude control
The invention discloses a continuous variable quantum key distribution system and a synchronous realization method thereof. The continuous quantum key distribution system consists of a light path part and a circuit control part, wherein the light path part mainly consists of a laser, an attenuator, a beam splitter, a polarization controller, am amplitude controller, a phase controller and a coupler. A control part is a transmission end controller module and consists of a true random key generator, an analog voltage output and a trigger clock output. The synchronous method comprises a bit synchronizing step and a frame synchronizing step. The invention provides a completely novel synchronous realization scheme based on properties of continuous variable quantum in an optical fiber, the practical orientation of the continuous variable quantum key distribution system is promoted, and the interference that the continuous variable quantum on the synchronous realization in the optical communication process also can be effectively overcome.
Owner:SHANGHAI JIAODA INTELLECTUAL PORPERTY MANAGEMENT CO LTD +1
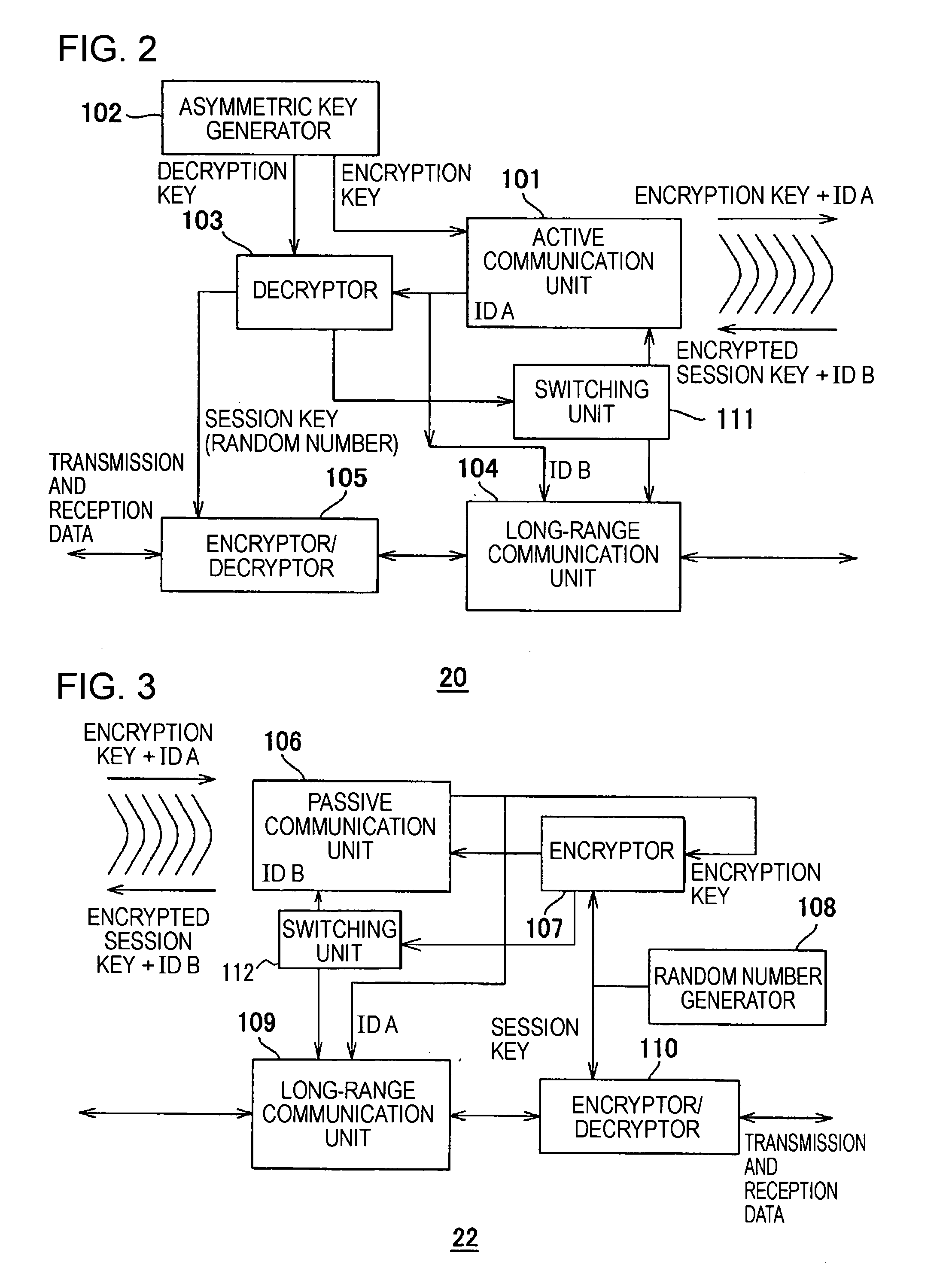
Communication System And Communication Device
InactiveUS20080020707A1Easy to identifyReduce riskKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareCommunications system
Owner:SONY CORP
Protecting software environment in isolated execution
InactiveUS7082615B1Specific access rightsDigital data processing detailsOperational systemKey generator
The present invention is a method and apparatus to protect a subset of a software environment. A key generator generates an operating system nub key (OSNK). The OSNK is unique to an operating system (OS) nub. The OS nub is part of an operating system in a secure platform. A usage protector uses the OSNK to protect usage of a subset of the software environment.
Owner:INTEL CORP
Method for transferring encrypted data and information processing system
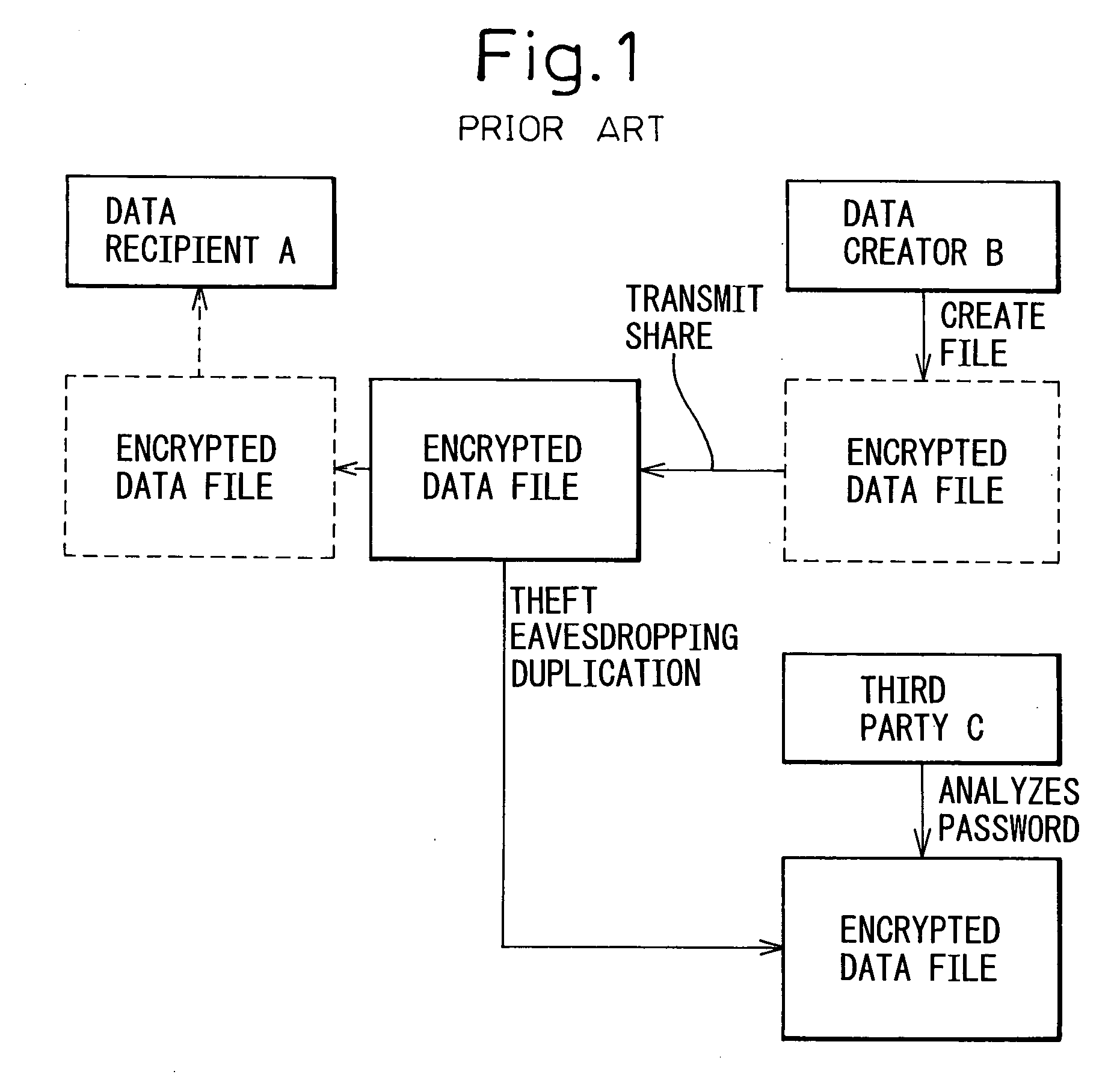
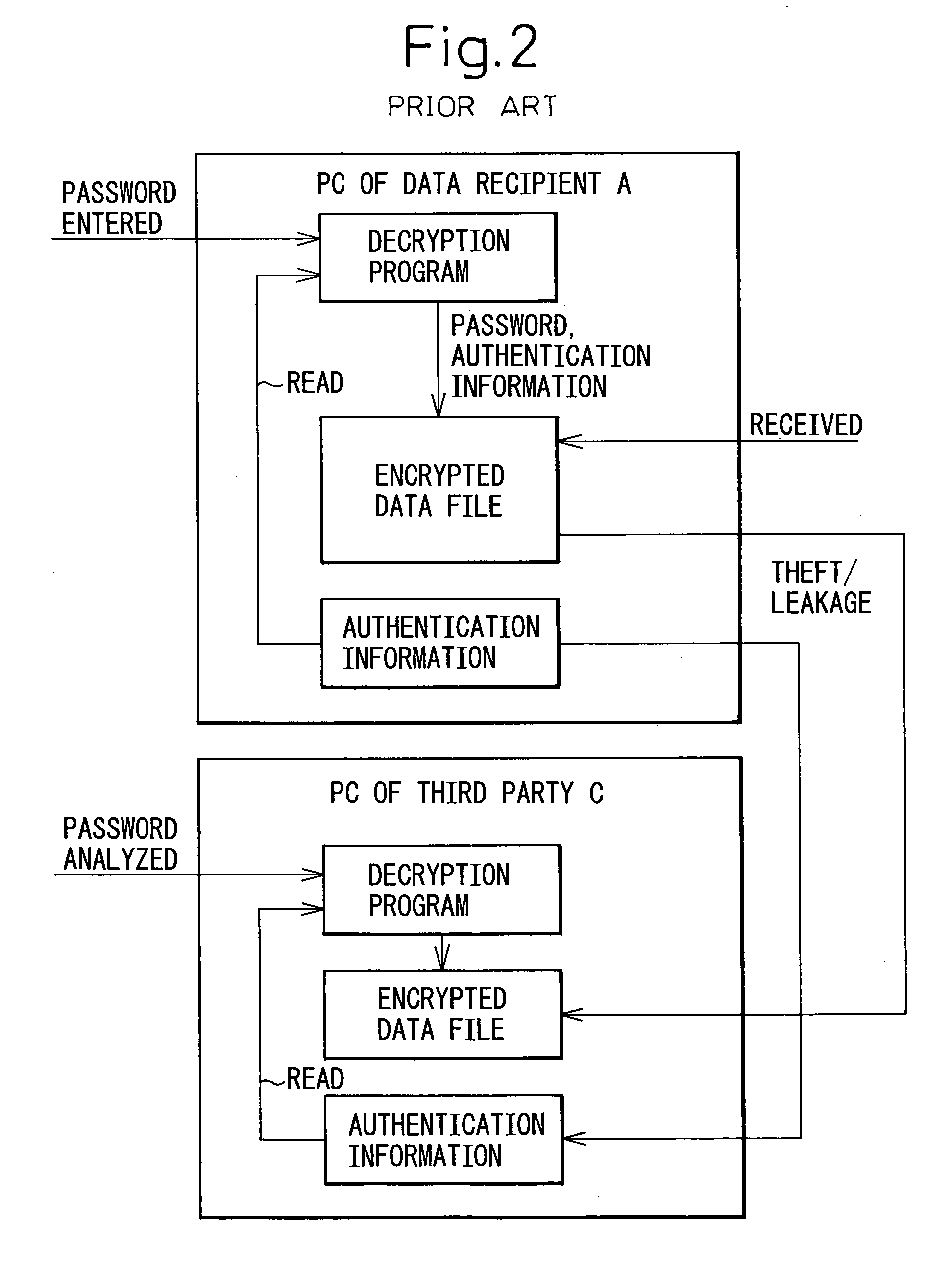
InactiveUS20070005974A1Improve securityUser identity/authority verificationUnauthorized memory use protectionInformation processingCryptographic key generation
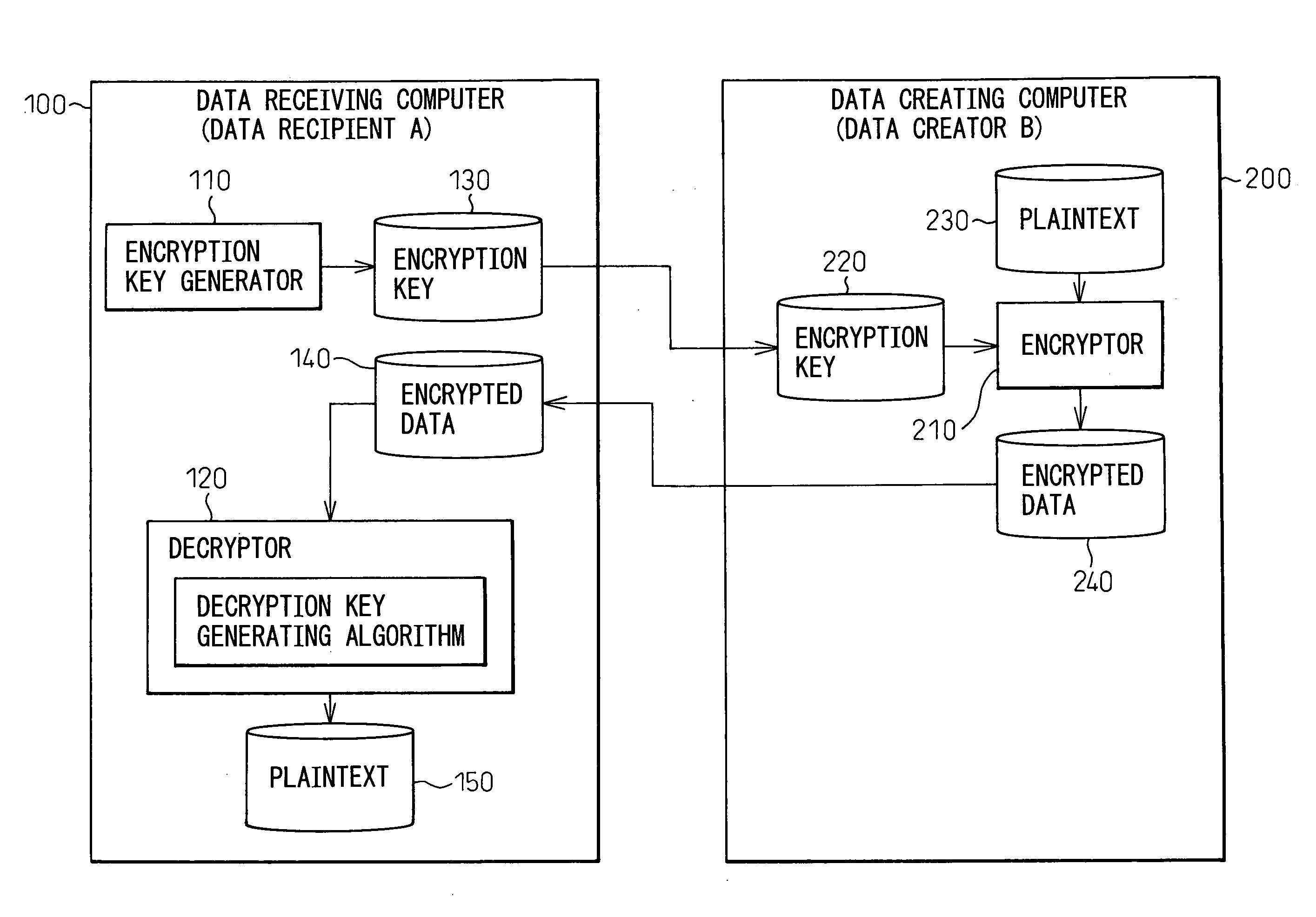
A method for transferring encrypted data and an information processing system for implementing the method, wherein provisions are made to enhance the security of the encrypted data by allowing only the intended data recipient to handle the decryption key when transferring the encrypted data. In a computer network over which encrypted data is transferred between a data creating computer and a data receiving computer, the data creating computer includes an encryptor which encrypts plaintext data into encrypted data by using en encryption key transferred from the data receiving computer, and which transmits the encrypted data to the data receiving computer, and the data receiving computer includes an encryption key generator which generates the encryption key and transmits it to the data creating computer, and a decryptor which holds therein decryption key information corresponding to the encryption key in a form that cannot be copied, and which generates the decryption key based on the decryption key information and, using the decryption key, decrypts the encrypted data transferred from the data creating computer.
Owner:FUJITSU LTD
Method and apparatus for securely moving and returning digital content
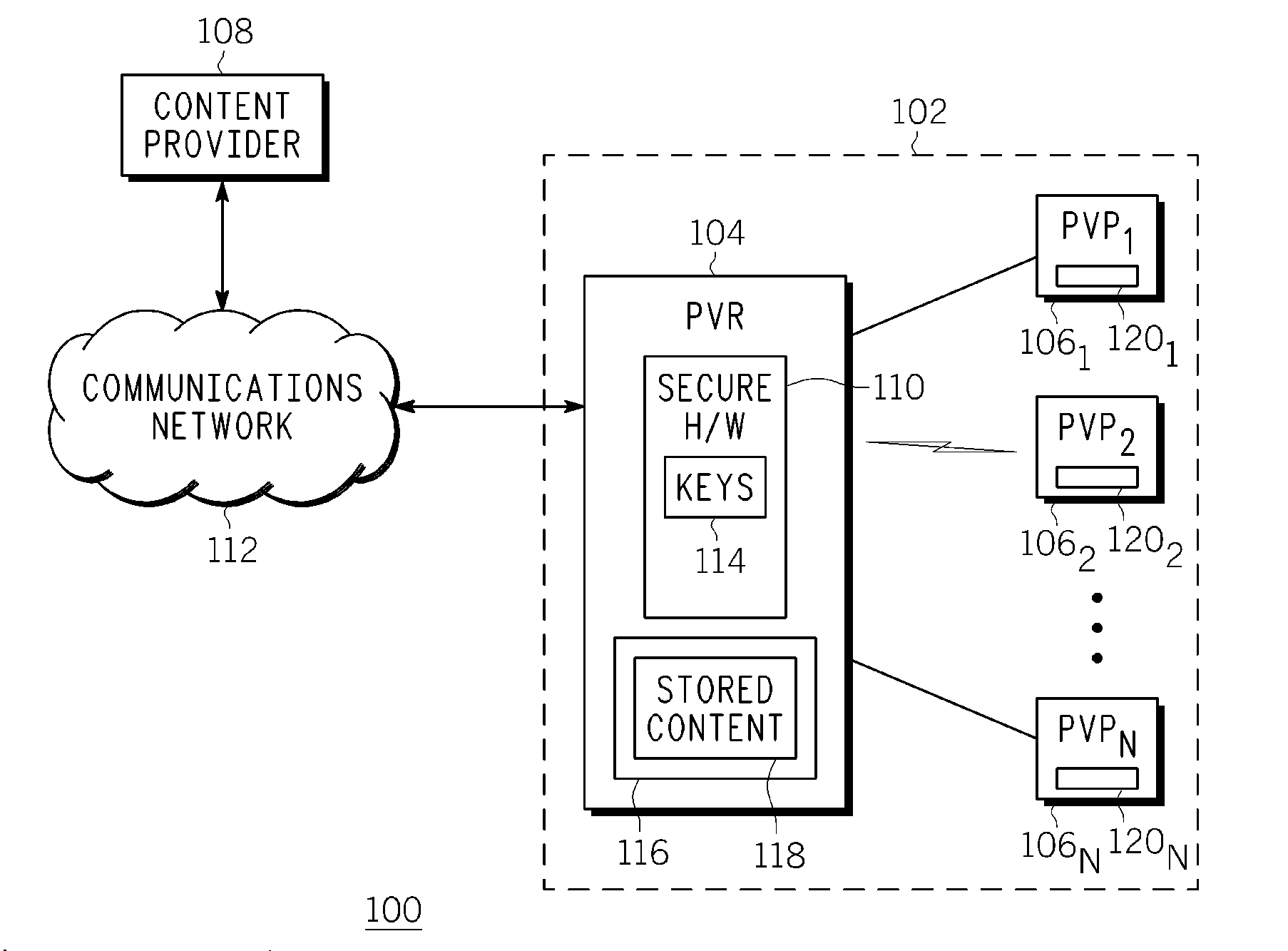
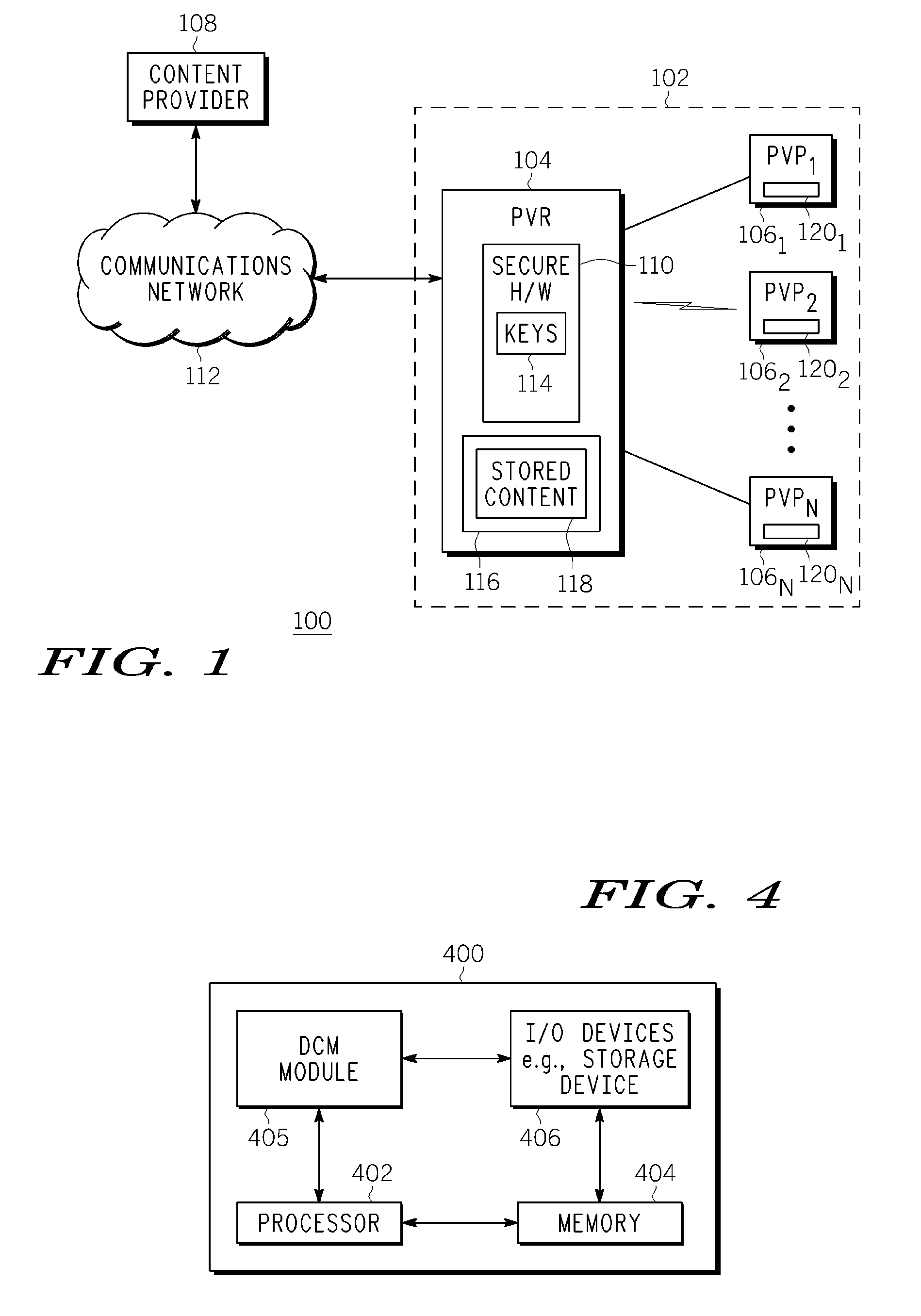
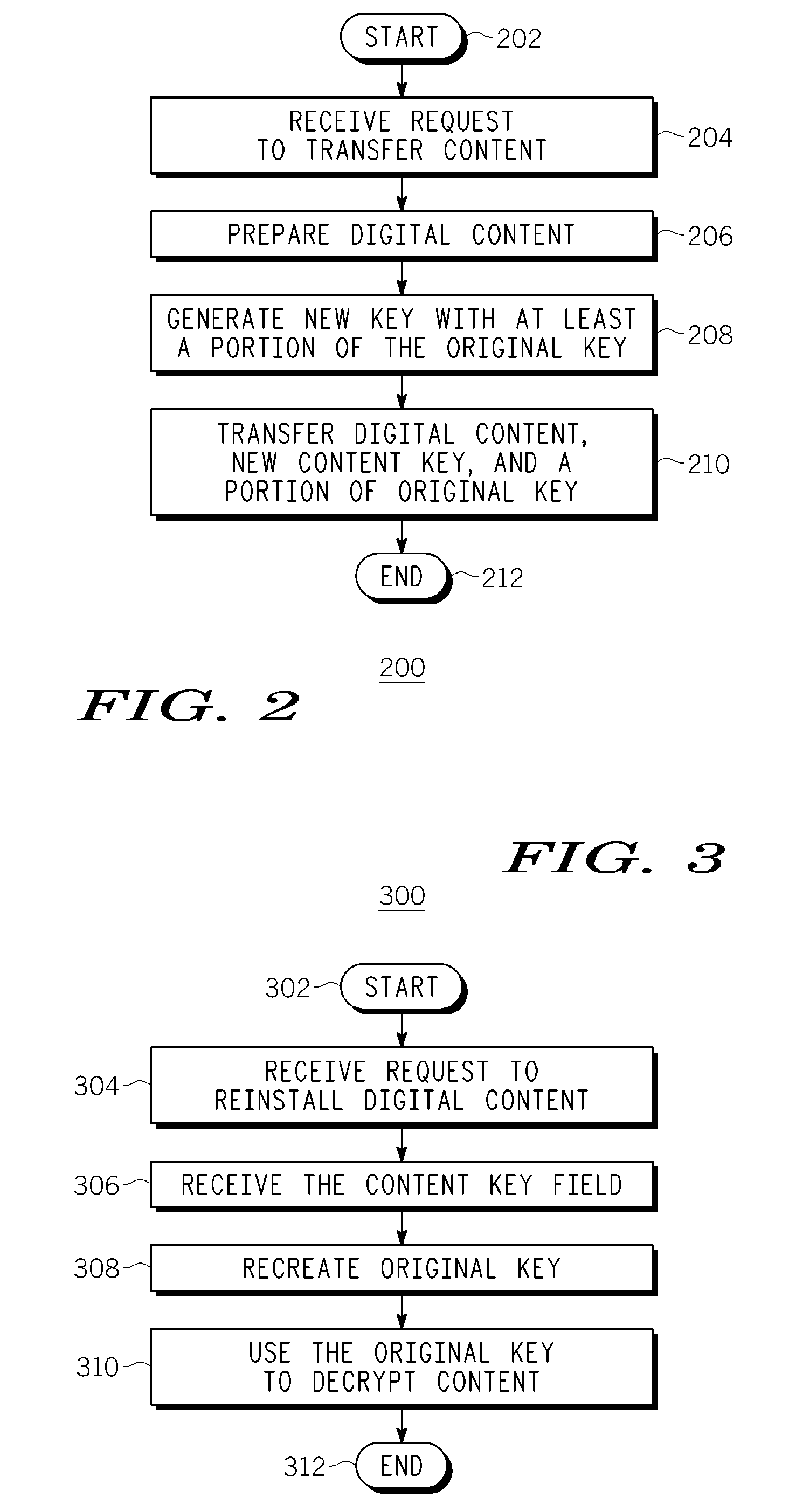
InactiveUS20080015997A1Data processing applicationsProgram/content distribution protectionDigital contentNumber content
The present invention discloses an apparatus and method for transferring digital content data. In one example, original digital content data stored on a first device content data. In one example, original digital content data stored on a first device in an encrypted state is transcoded (after being decrypted) to create a modified version of the original digital content data. The modified version of the original digital content data is then encrypted with a new content key. The modified version and at least one content key generator are transferred to a second device, where the at least one content key generator is used to recreate the new content key for enabling (and decrypting) the modified version of the original digital content data at the second device. Notably, the original digital content data stored in the first device is disabled contemporaneously with the transfer of the modified version and the at least one content key generator to the second device. Afterwards, the disabled original digital content data is re-enabled on the first device, and disabled on the second device.
Owner:GENERAL INSTR CORP
Deterrence of device counterfeiting, cloning, and subversion by substitution using hardware fingerprinting
ActiveUS8848905B1Digital data processing detailsUser identity/authority verificationPhysical unclonable functionKey generator
Deterrence of device subversion by substitution may be achieved by including a cryptographic fingerprint unit within a computing device for authenticating a hardware platform of the computing device. The cryptographic fingerprint unit includes a physically unclonable function (“PUF”) circuit disposed in or on the hardware platform. The PUF circuit is used to generate a PUF value. A key generator is coupled to generate a private key and a public key based on the PUF value while a decryptor is coupled to receive an authentication challenge posed to the computing device and encrypted with the public key and coupled to output a response to the authentication challenge decrypted with the private key.
Owner:UT BATTELLE LLC +1
Message security
InactiveUS20050114664A1Easy to buyKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer hardwareMessage handling
To provide a secure, effective but simple message handling, a method is provided for transmitting an electrical message, from a first user having a first terminal to a second user having a second terminal. The method comprises the steps of: transmitting said email in an encrypted form by said first terminal, said encrypted e-mail being encrypted by means of a key generated by a first key generator using a seed, providing once said second user with said seed for generating a key with a second key generator provided in said second terminal, providing to and storing said seed in said second terminal, using said seed by said second terminal for generating a key each time an encrypted email from said first user to said second user is received, synchronising a counting value in each terminal; and generating said key on the basis of said seed and a counting value in each terminal, independently of other terminal.
Owner:SECURED EMAIL GOTEBORG AB
Method and apparatus for protecting the transfer of data
ActiveUS7730300B2Digital variable displayKey distribution for secure communicationComputer hardwareKey generator
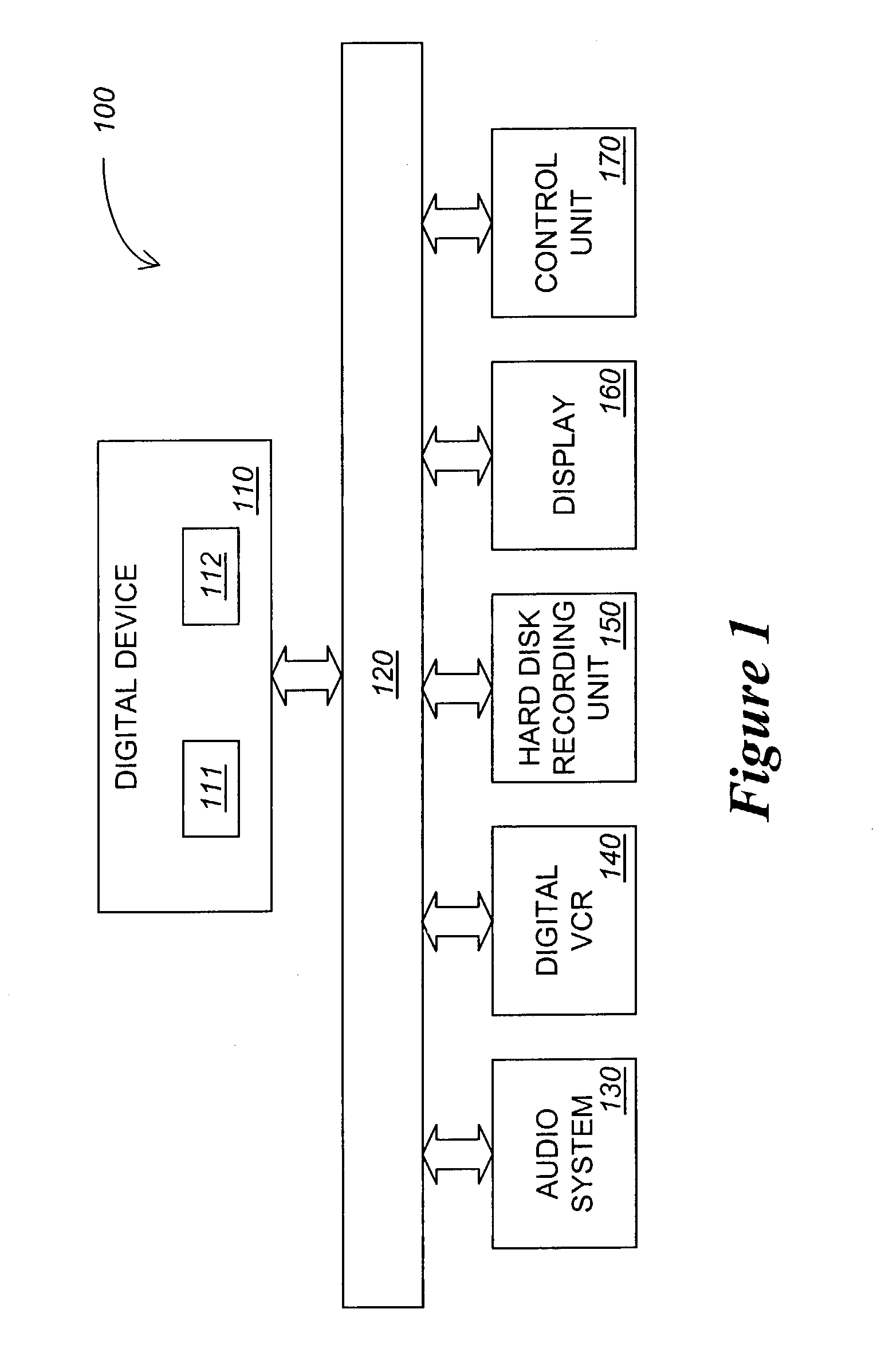
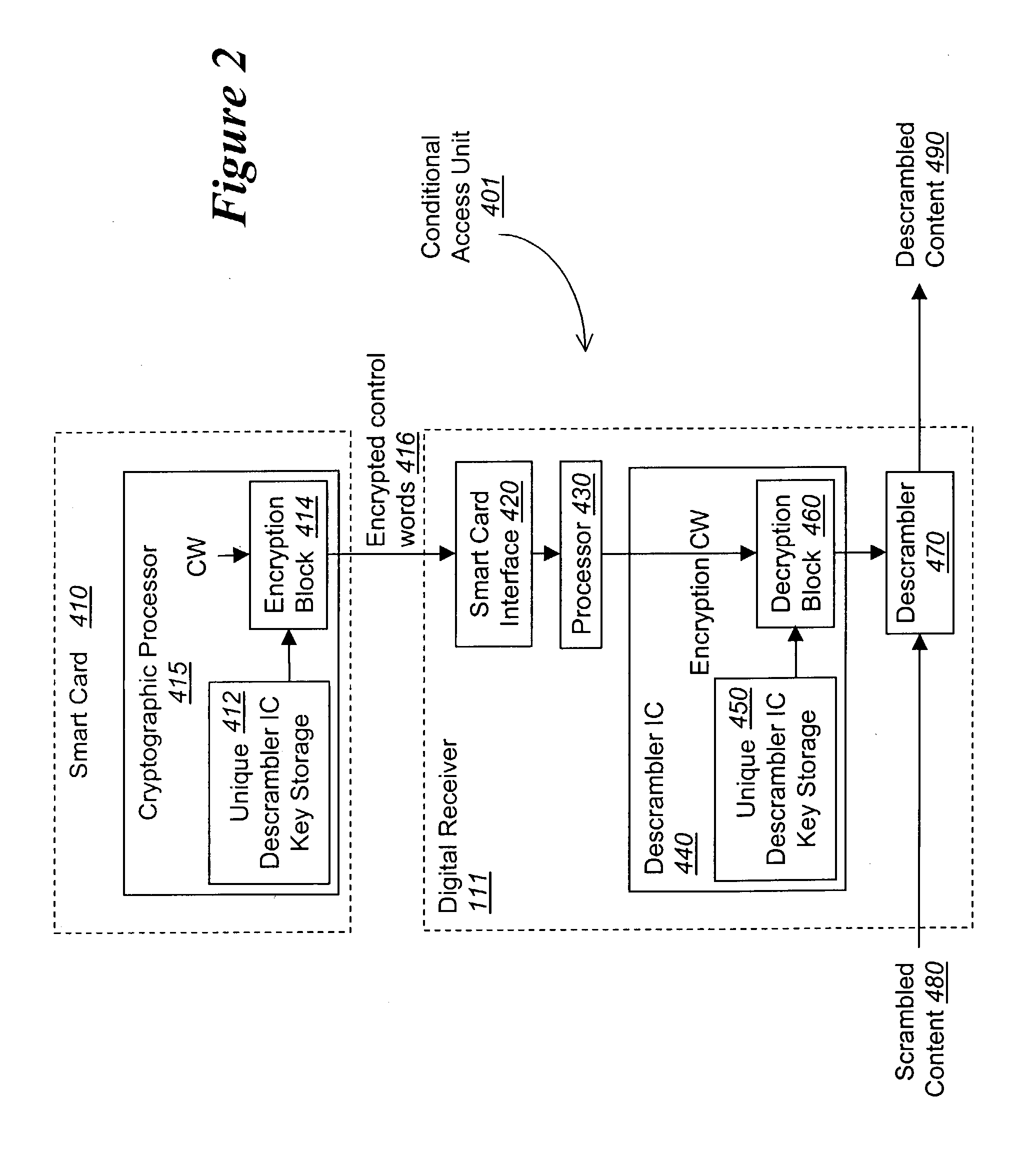
According to one embodiment, a method for scrambling and descrambling program data comprises the receipt of a mating key generator message including a manufacturer identifier. The mating key generator message is transmitted to a first remote source identified by the manufacturer identifier. In response, a mating key is received from the first remote source. Then, the mating key is supplied to a second remote source, the mating key being subsequently used to encrypt a service key used for scrambling program data.
Owner:SONY CORP +1
Cryptographic communications using in situ generated cryptographic keys for conditional access
InactiveUS7149308B1Improve securityFacilitate communicationKey distribution for secure communicationComputer security arrangementsCryptographic key generationCommunication interface
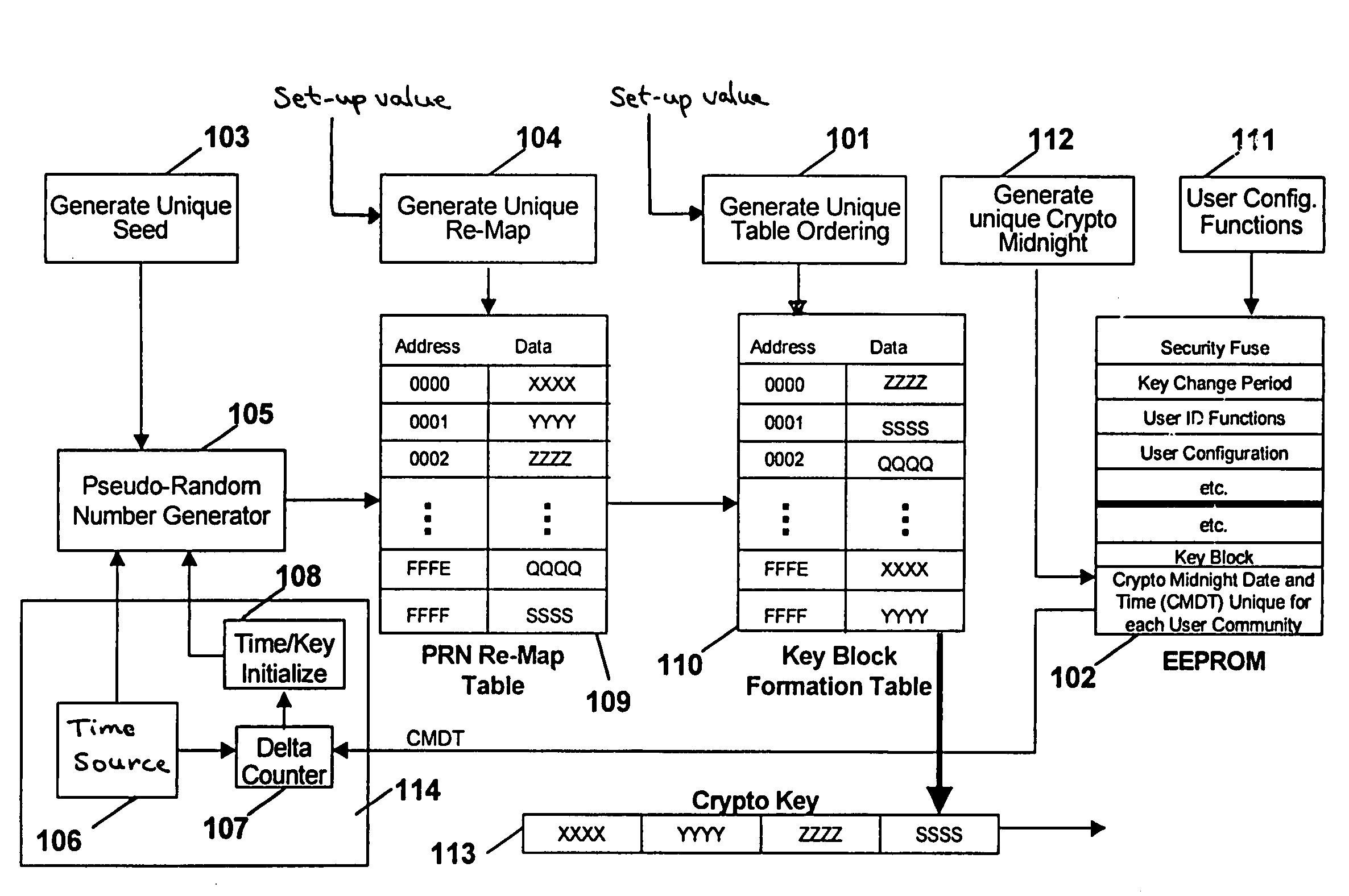
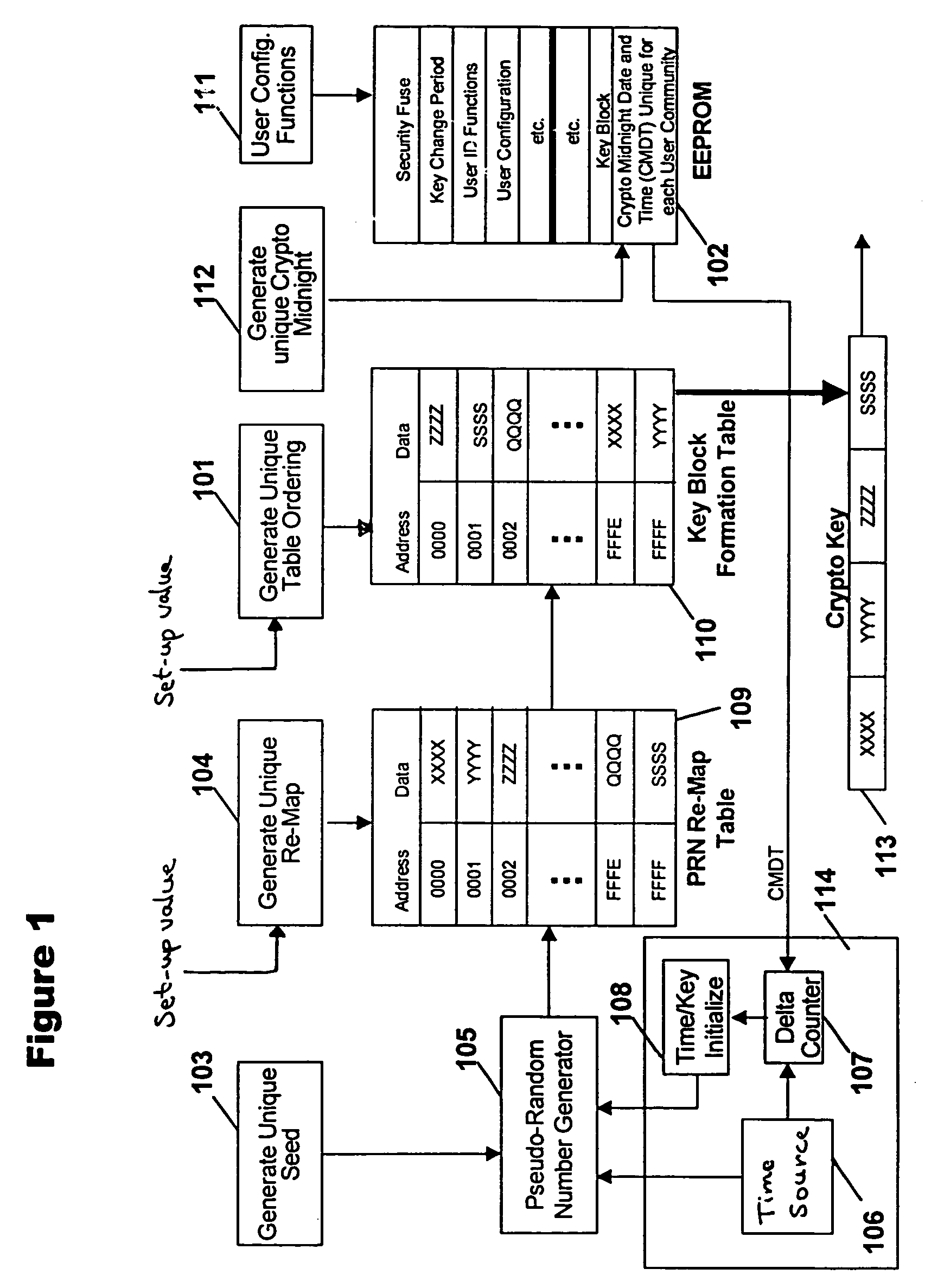
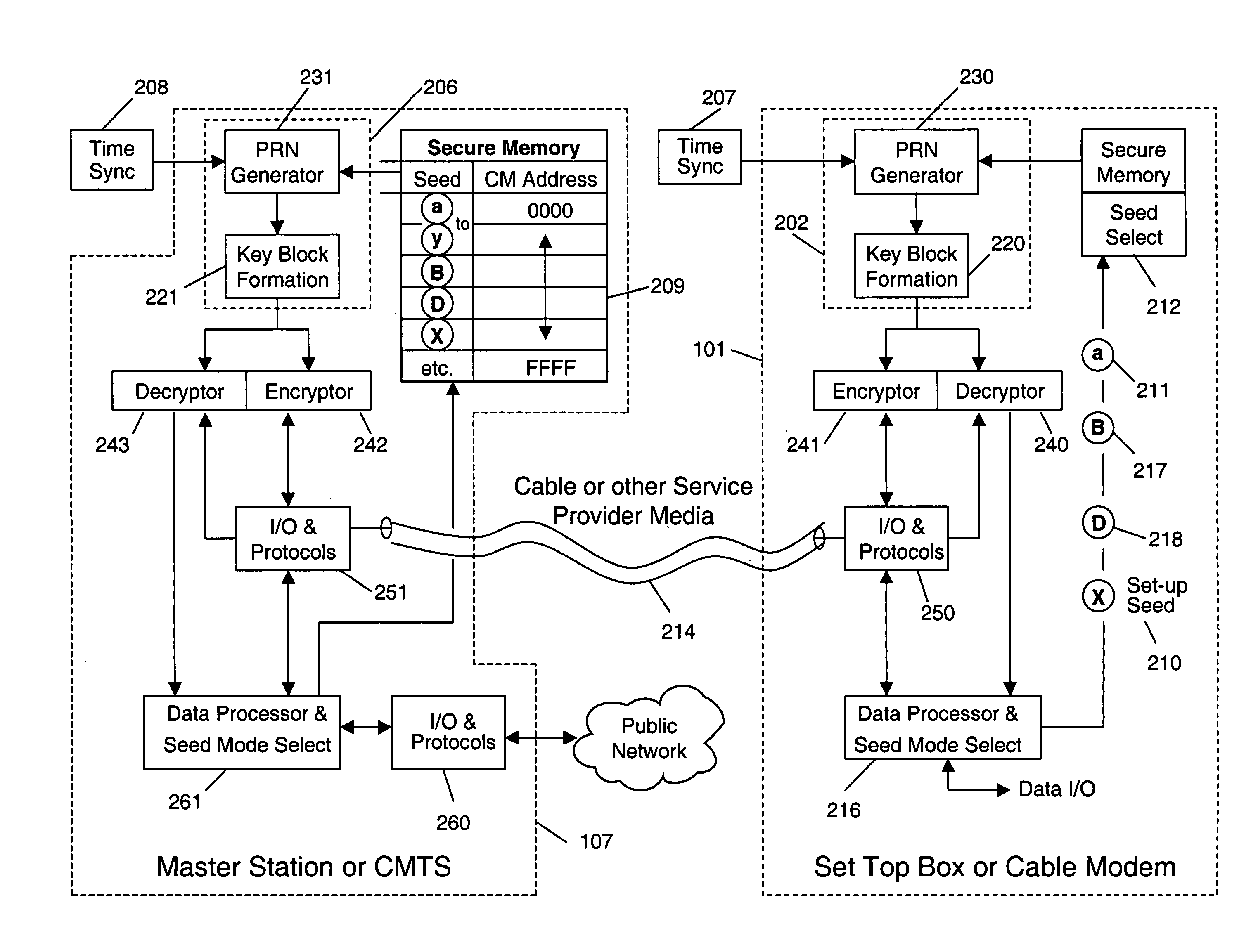
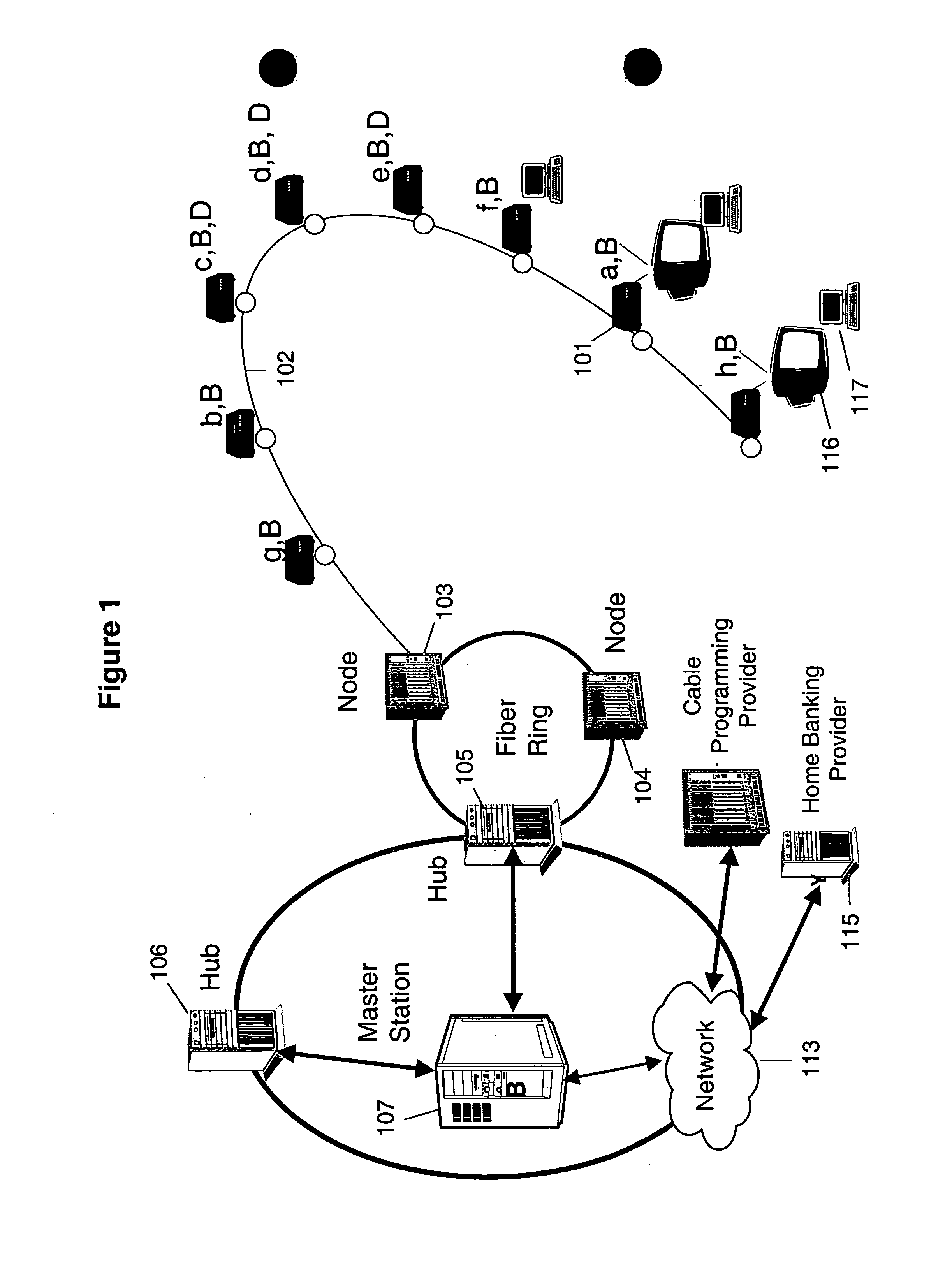
A system and method for cryptographic communication among multiple users and a central service provider using in situ generated cryptographic keys. Each user communicates with the central service provider preferably using a user communication interface that includes an in situ key generator, which, after initialization with the user's own individual seed value, generates a unique cryptographic key. By distributing different user individual seeds unique to each user, each user's in situ key generator generates a unique set of keys. The central service provider also possesses an in situ key generator, and also preferably possesses a copy of all the individual seeds assigned to authorized users. The central service provider preferably communicates in a secure encrypted fashion with each user using cryptographic keys generated from that user's individual seed. Distribution of additional seed values common to more than one user, via encrypted communication using said unique individual cryptographic key generations, then permit secure conditional access to said users via signal encryption using key generations resulting from a seed value common to the intended group of users.
Owner:STEALTHKEY
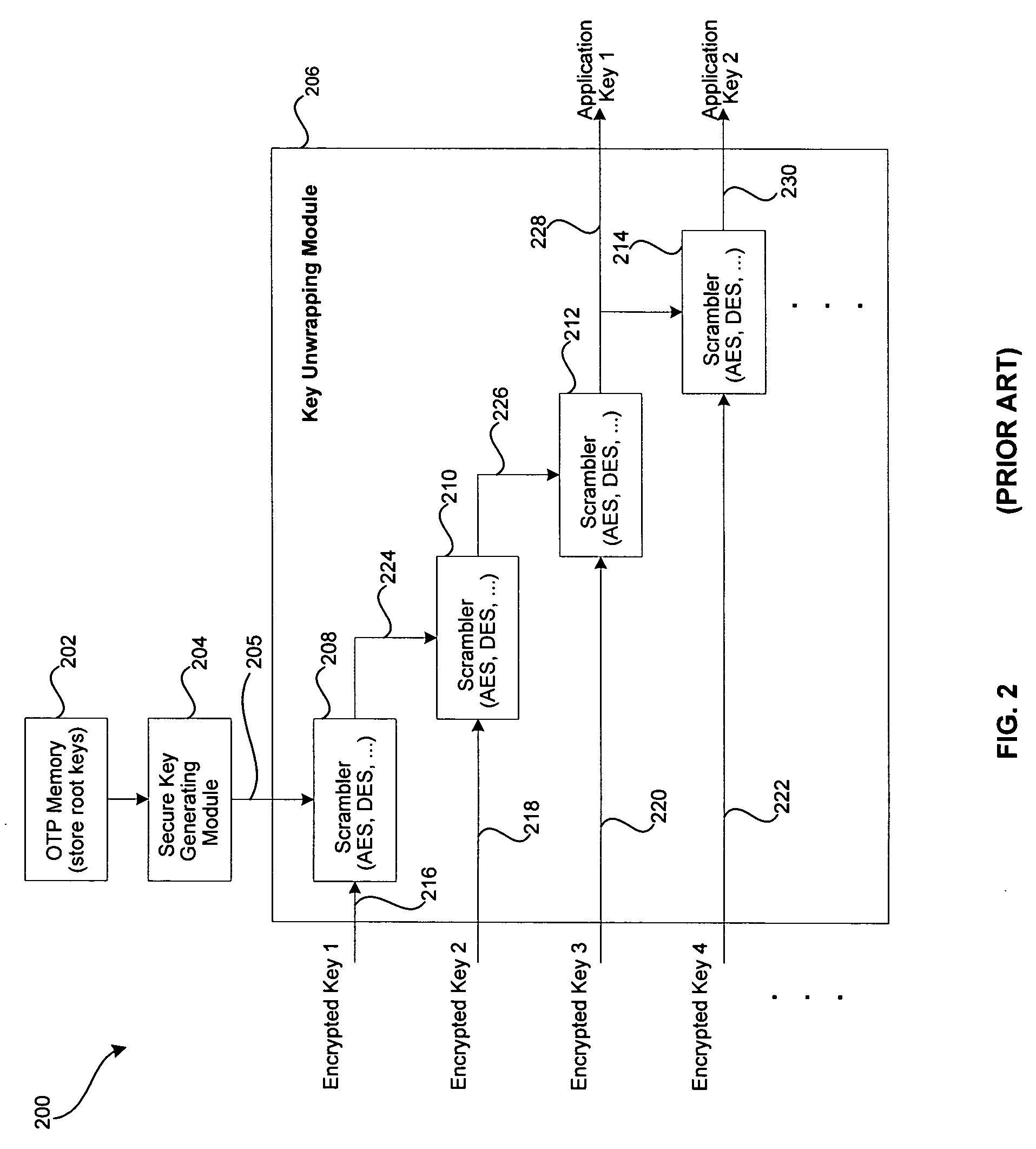
Multiple key security and method for electronic devices
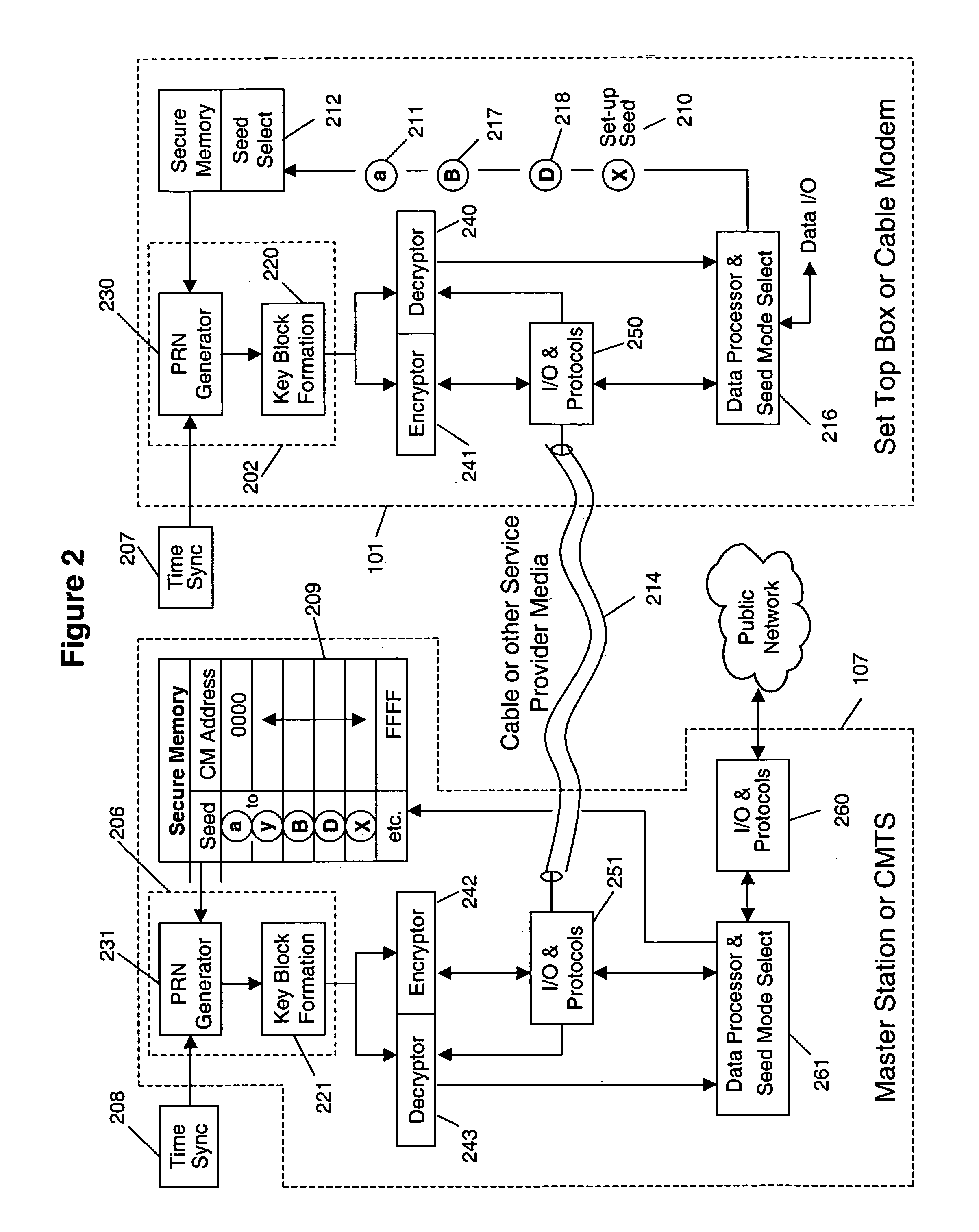
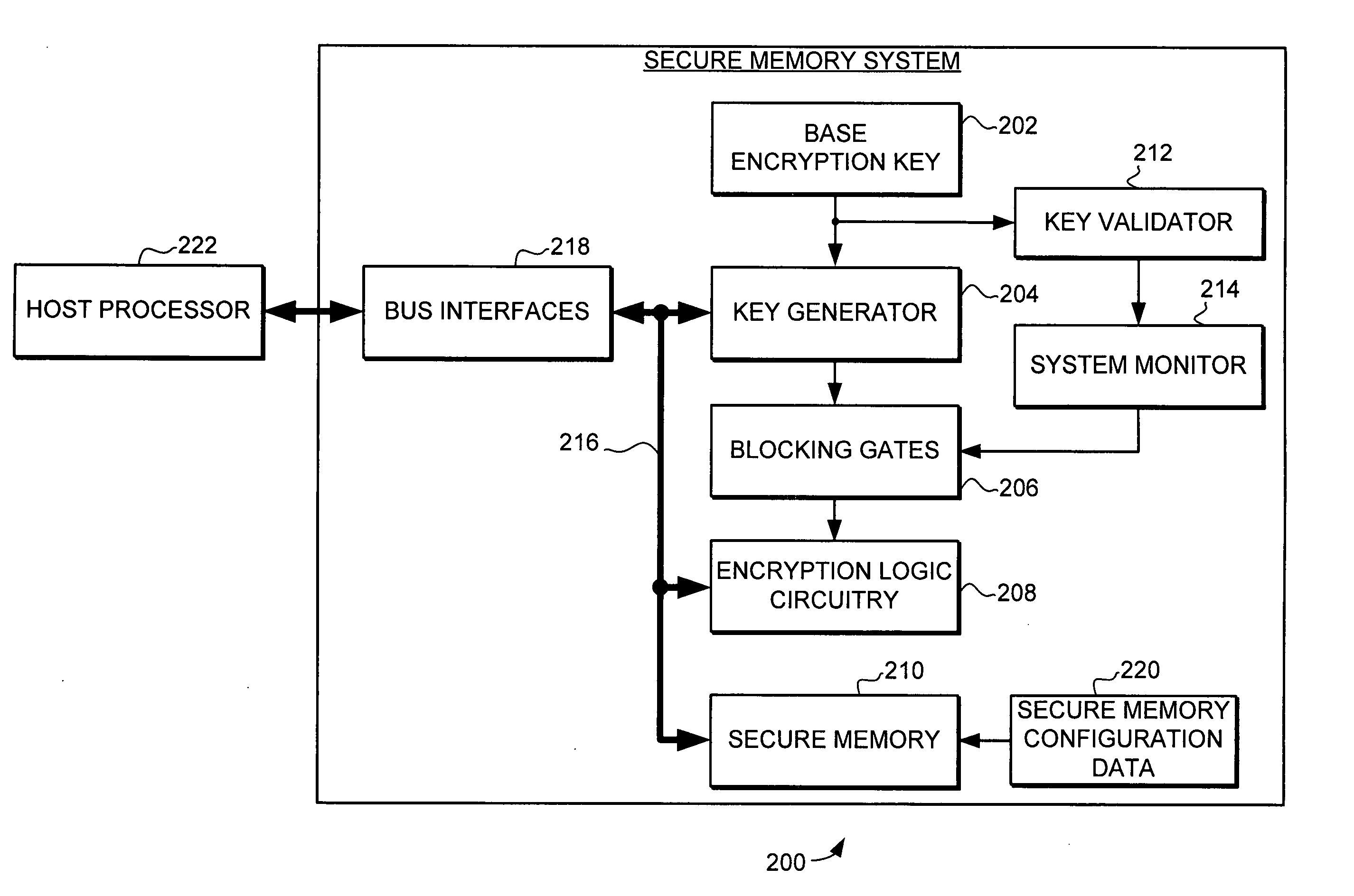
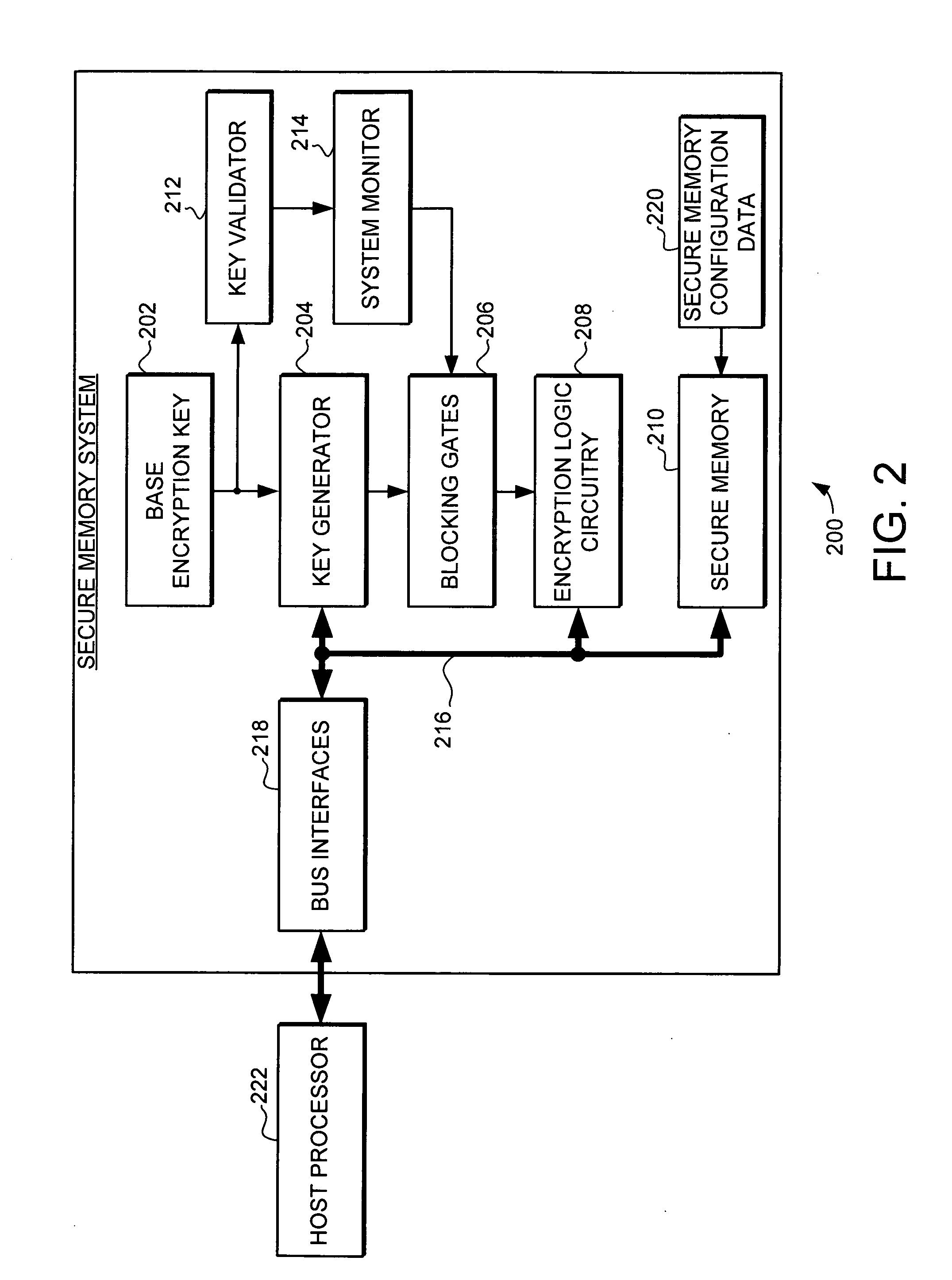
A secure processing system is provided with increased flexibility to secure different categories of data from different entities (e.g., different users or stakeholders) both from external access and from other entities that use the same system. In one embodiment, the secure processing system includes a host processor and a secure memory system which provides for the storage of sensitive data in encrypted form in a storage medium external to the secure processing system. In accordance with the embodiments of the invention, a key generator is provided that uses a base encryption key and a plurality of key modifiers to create a plurality of derivative keys. The derivative keys are used by encryption logic circuitry within the secure memory system for encrypting and decrypting sensitive information. The derivative keys created by the key generator are used to secure different categories of data from different entities.
Owner:FREESCALE SEMICON INC
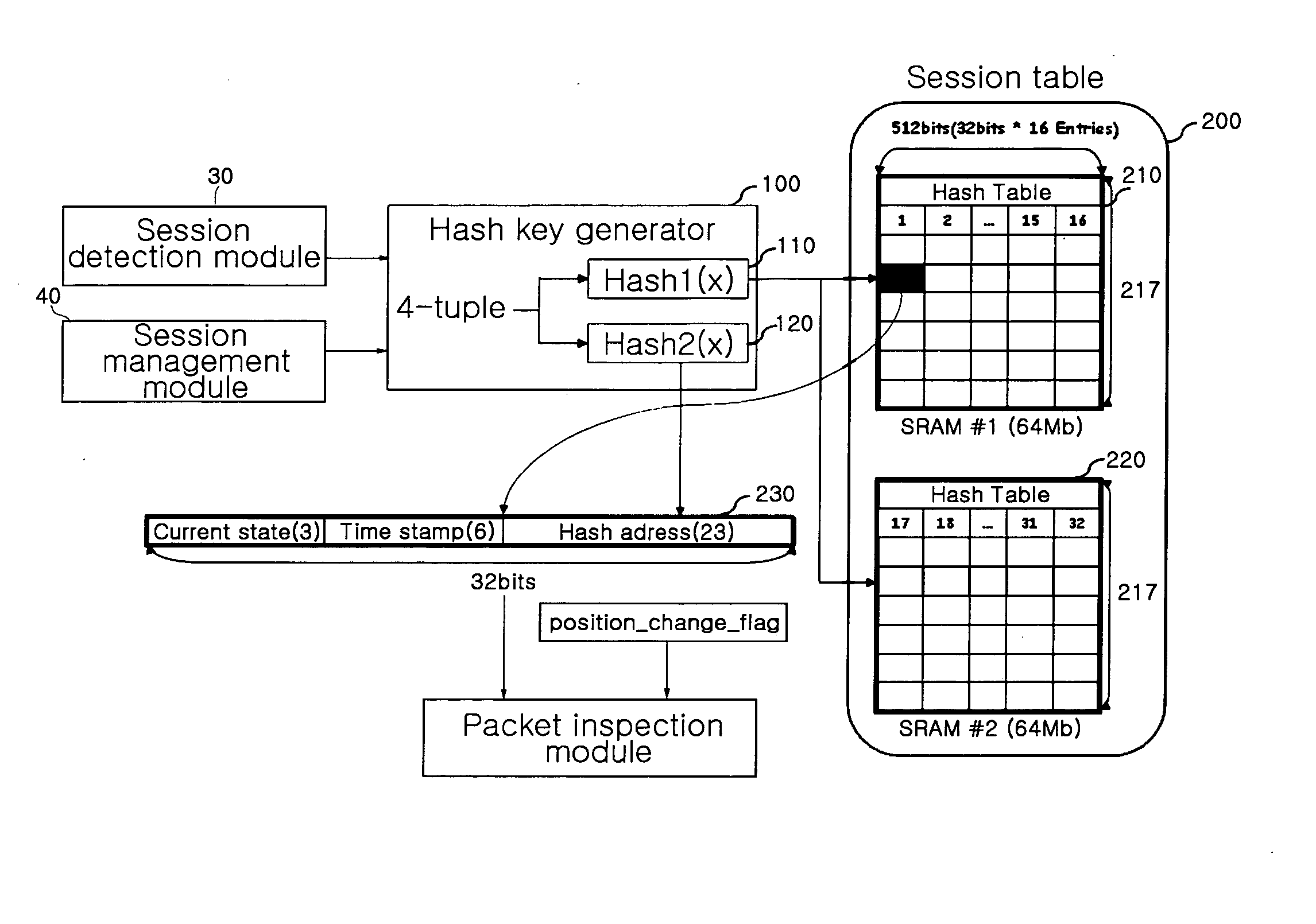
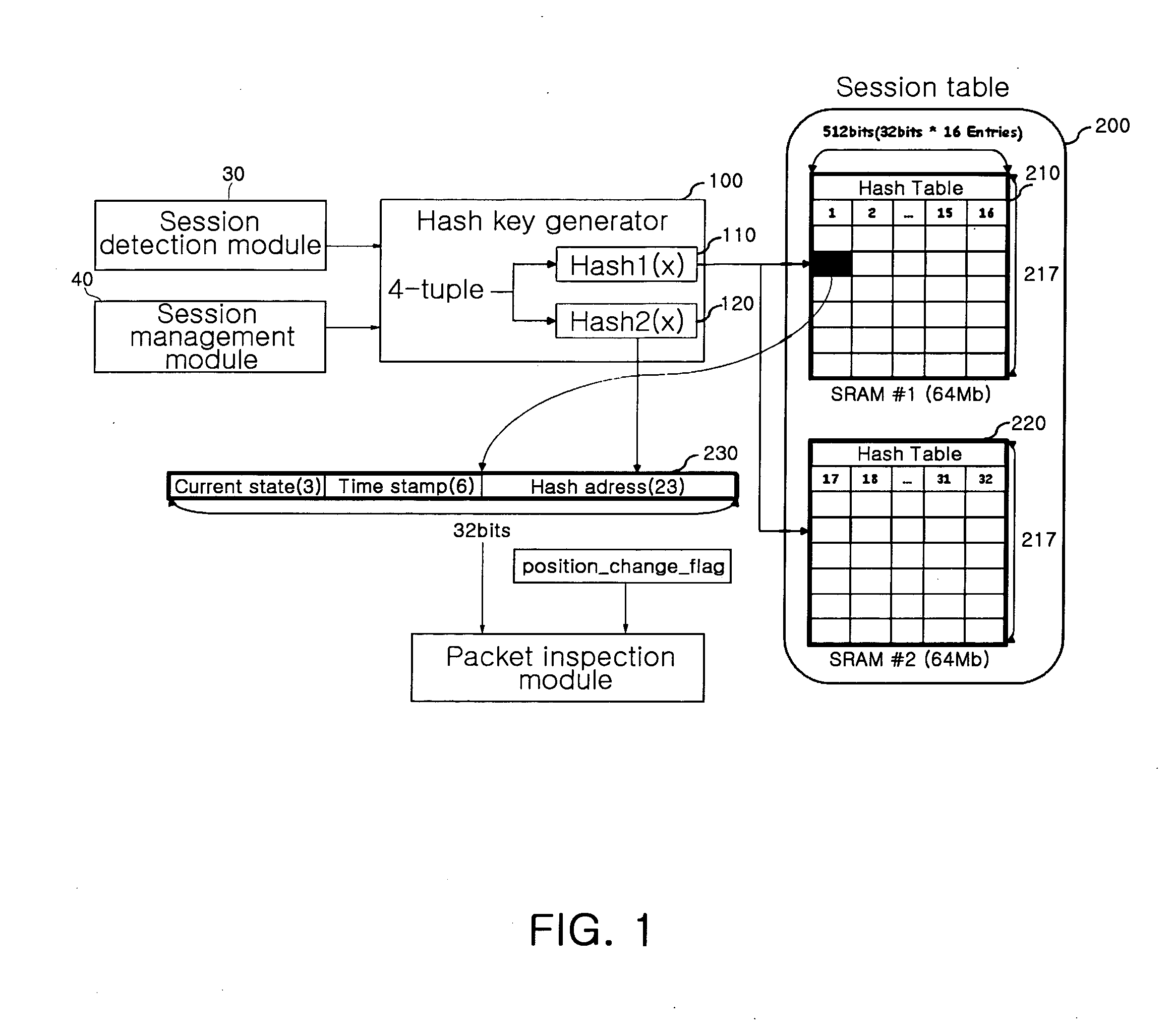
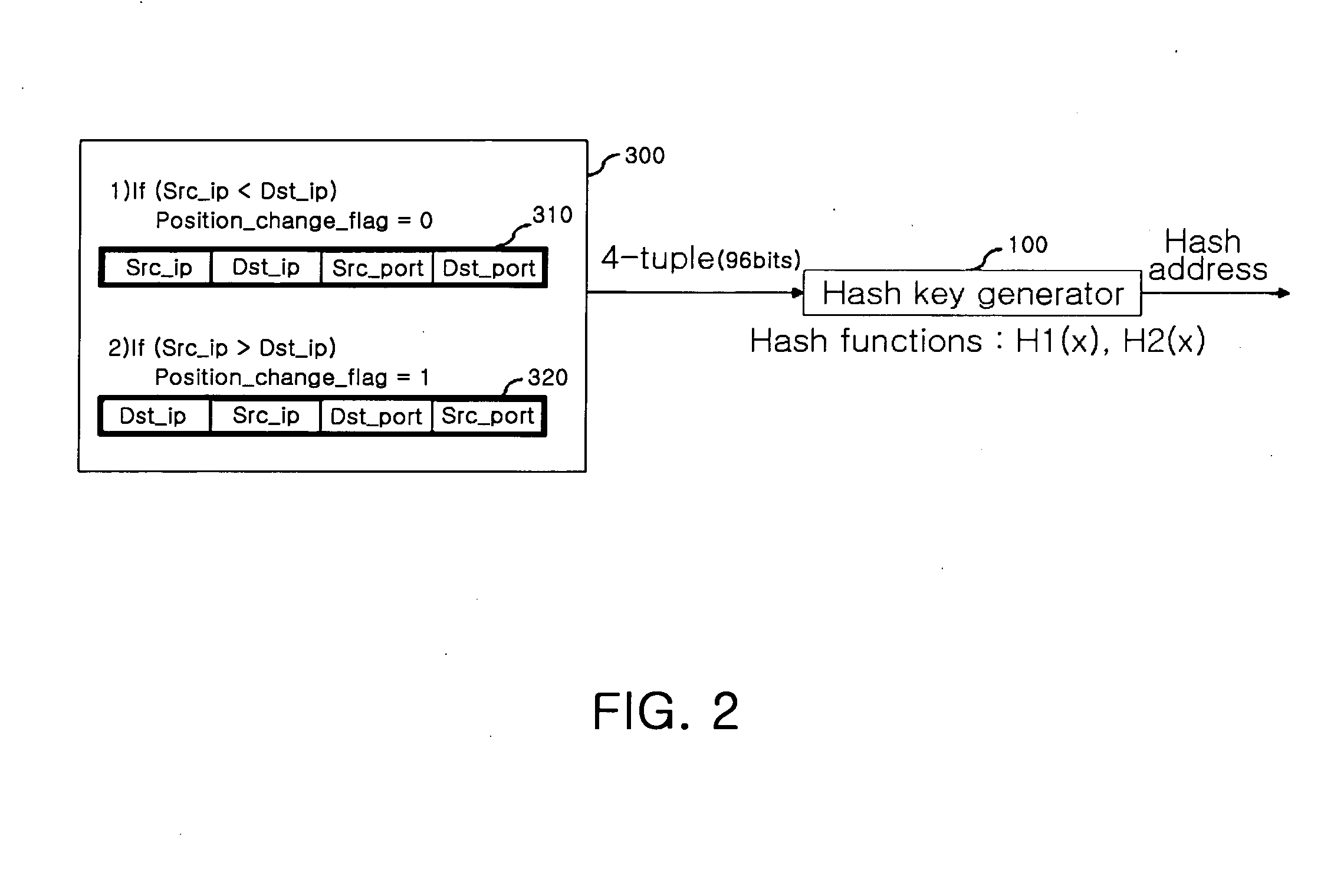
Real-time stateful packet inspection method and apparatus
InactiveUS20070297410A1Generate efficientlyDigital data processing detailsAnalogue secracy/subscription systemsComputer hardwareSession management
A real-time stateful packet inspection method and apparatus is provided, which uses a session table processing method that can efficiently generate state information. In the apparatus, a session table stores session data of a packet received from an external network. A hash key generator hashes a parameter extracted from the received packet and generates a hash pointer of the session table corresponding to the packet. A session detection module searches the session table for a session corresponding to the received packet. A session management module performs management of the session table such as addition, deletion, and change of sessions of the session table. A packet inspection module generates state information corresponding to the received packet from both directionality information of the packet and entry header information of the packet stored in the session table and then inspects the packet based on the generated state information.
Owner:ELECTRONICS & TELECOMM RES INST
Identity-based-encryption system
ActiveUS20100017593A1Encryption apparatus with shift registers/memoriesInformation securityKey generator
A system is provided that uses identity-based encryption (IBE) to allow a sender to securely convey information in a message to a recipient. A service name such as a universal resource locator based at least partly on the name of an organization may be associated with a local key server at the organization and a public key server external to the organization. Users at the organization may use the service name to access the local key server to obtain IBE public parameter information for performing message encryption and to obtain IBE private keys for message decryption. External to the organization, users may obtain IBE public parameter information and IBE private keys from the public key server using the same service name. The local key generator and the public key generator may maintain identical copies of the same IBE master secret.
Owner:MICRO FOCUS LLC
Method and apparatus for providing a bus-encrypted copy protection key to an unsecured bus
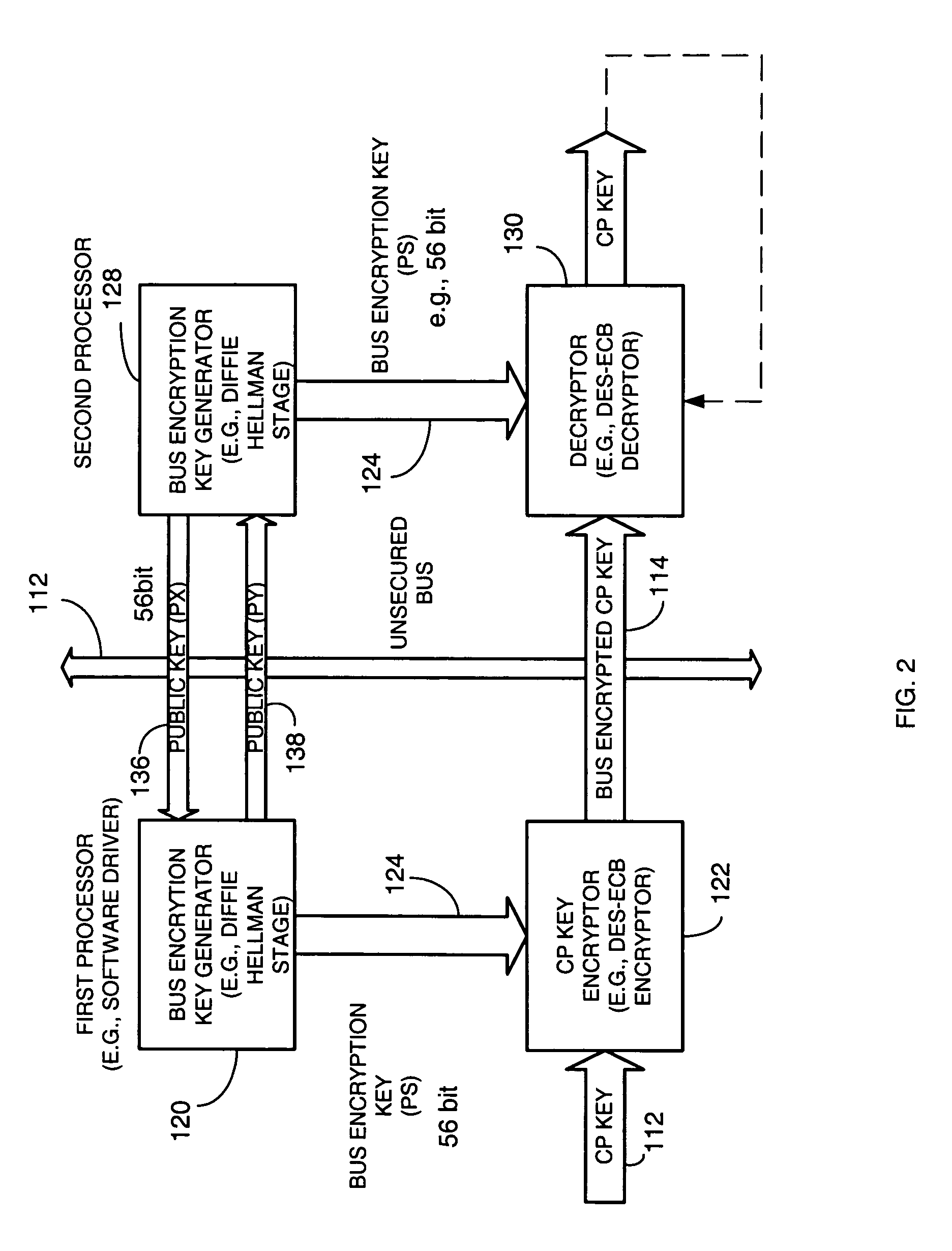
InactiveUS20050265547A1Key distribution for secure communicationPublic key for secure communicationComputer hardwareGraphics
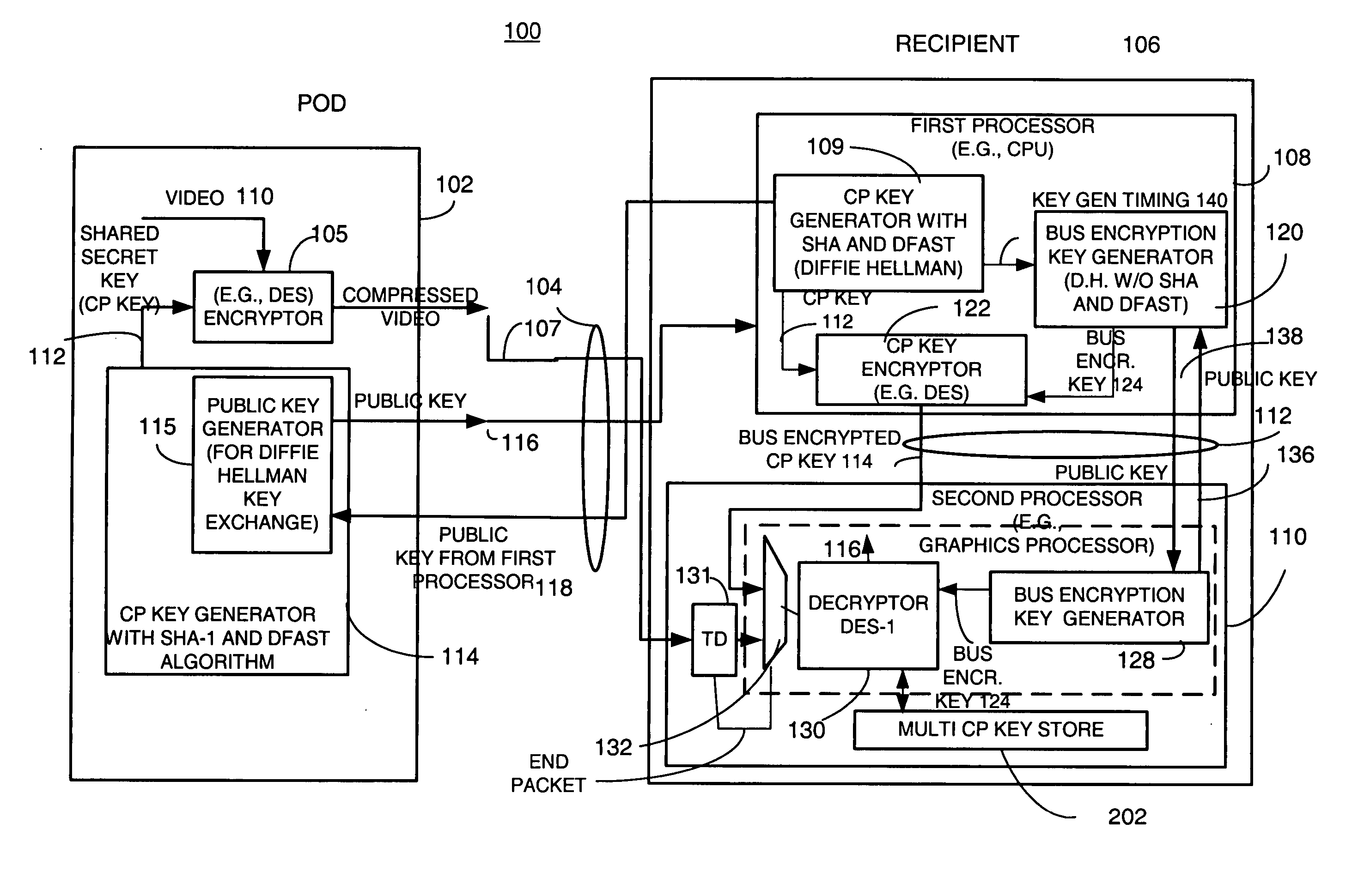
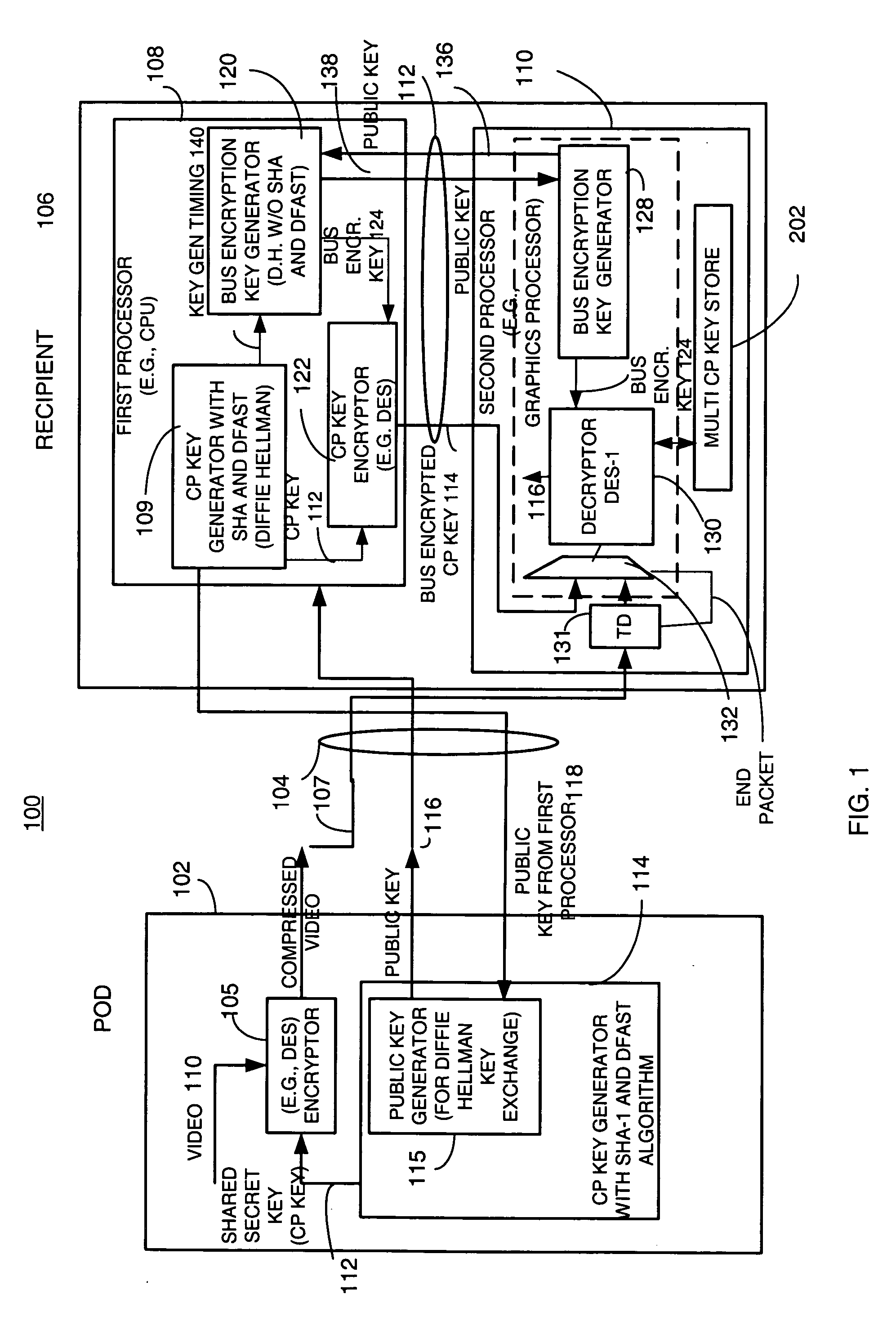
A copy protection (CP) key used by a sending source, such as a POD, to encrypt content such as audio and / or video information is derived by a first key generator associated with a first processor and is locally encrypted by the first processor using a locally generated bus encryption key to produce a bus encrypted CP key that is sent over a local unsecure bus to a second processor, such as a graphics processor. The second processor decrypts the bus encrypted copy key using a decryption engine to obtain the CP key. The second processor receives the encrypted content and in one embodiment, also uses the same decryption engine to decrypt the encrypted content. The first and second processors locally exchange public keys to each locally derive a bus encryption key used to encrypt the CP key before it is sent over the unsecure bus and decrypt the encrypted CP key after it is sent over the bus. The locally exchanged public keys are shorter in length than those used between the CPU and POD to produce the original CP key.
Owner:ATI TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com