Patents
Literature
1327results about How to "Avoid repetition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
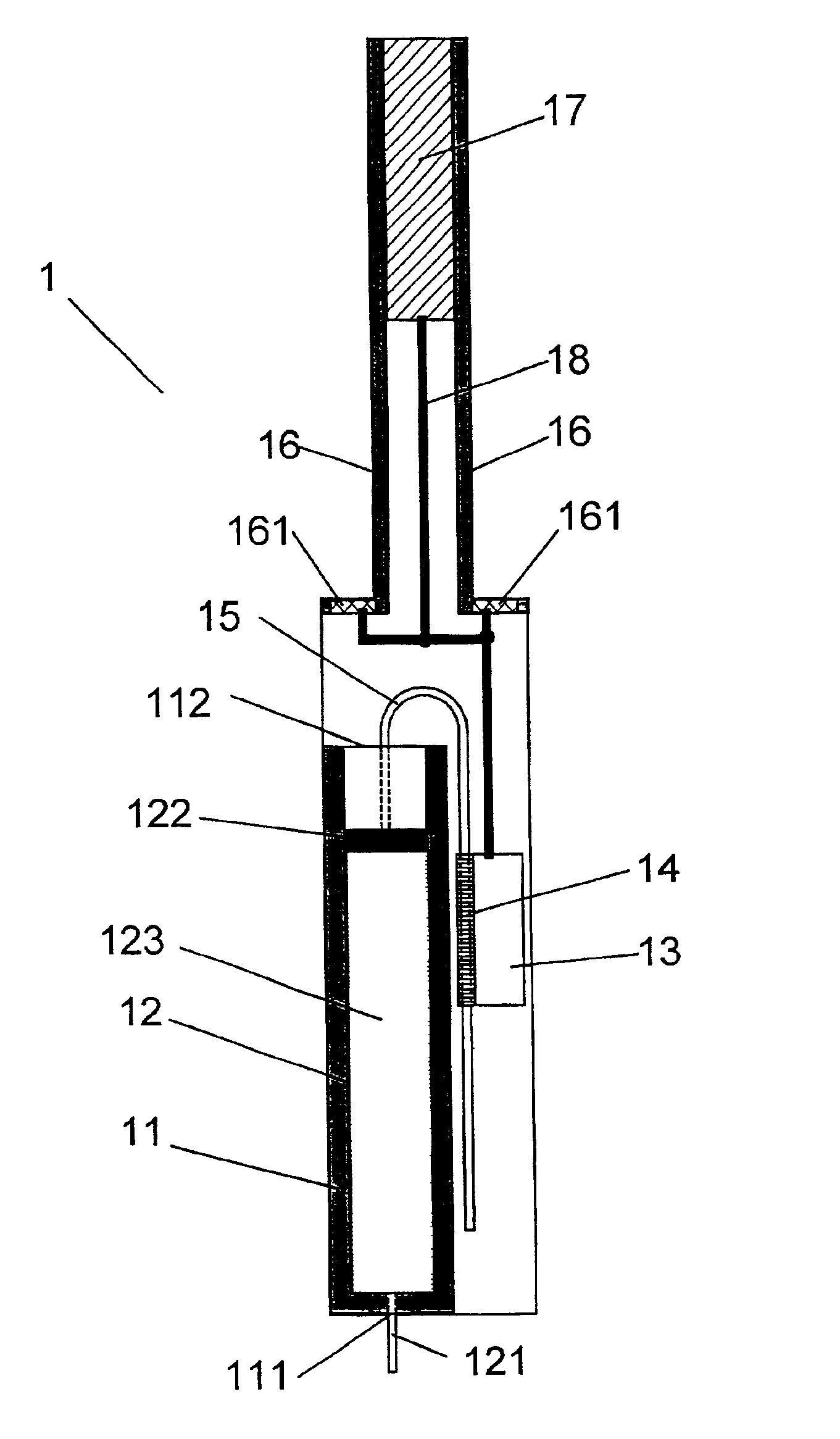
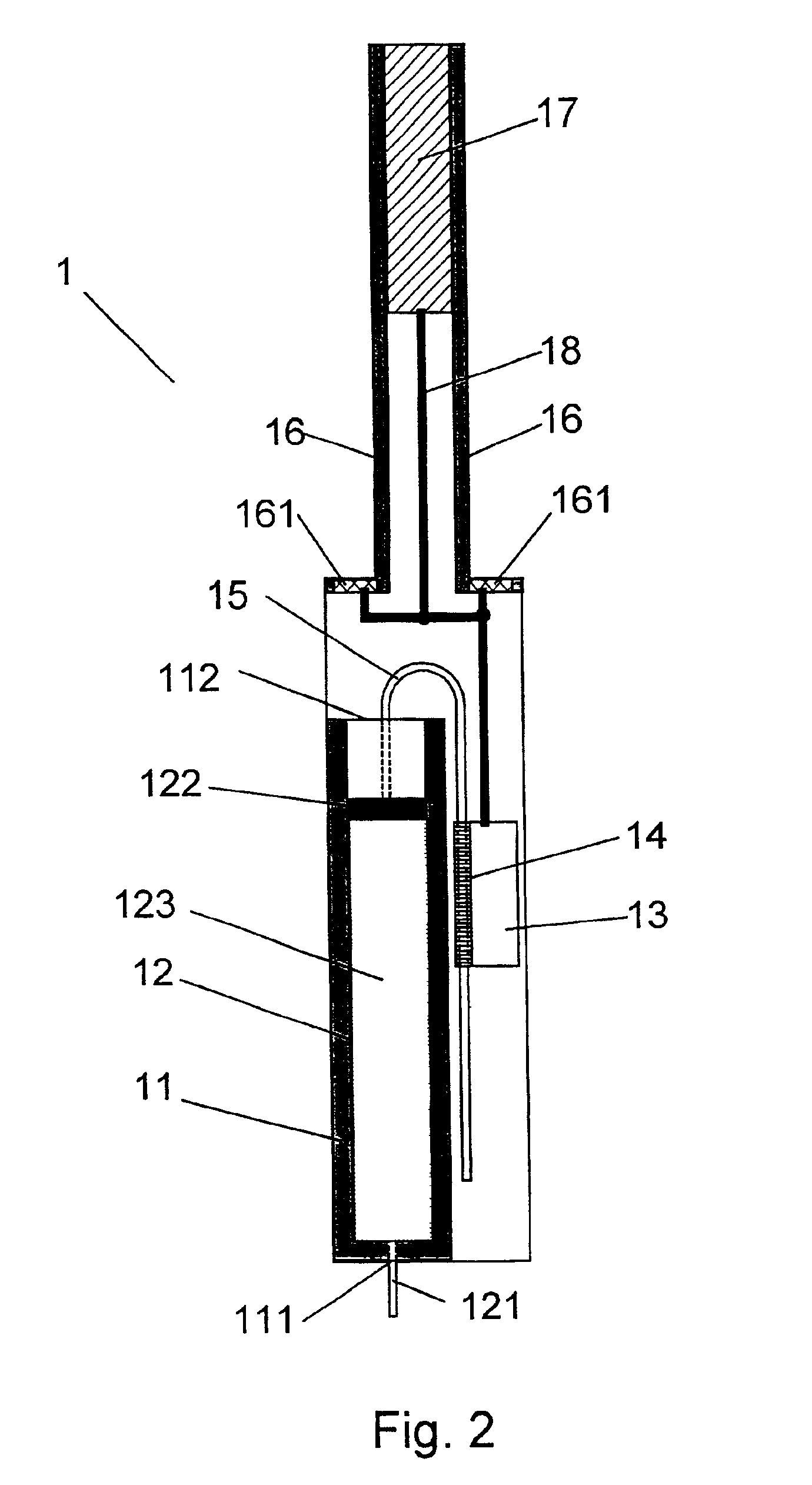
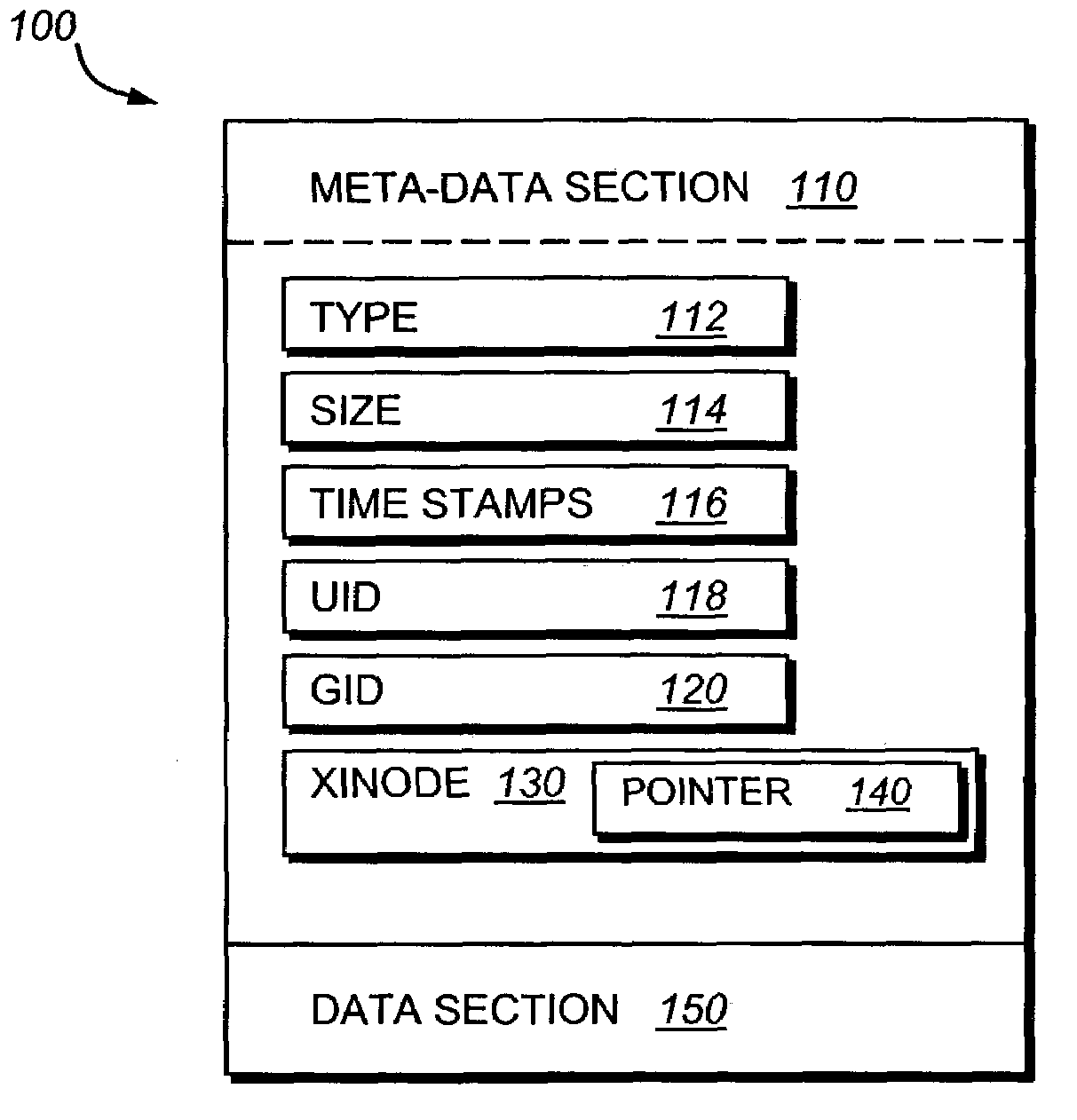
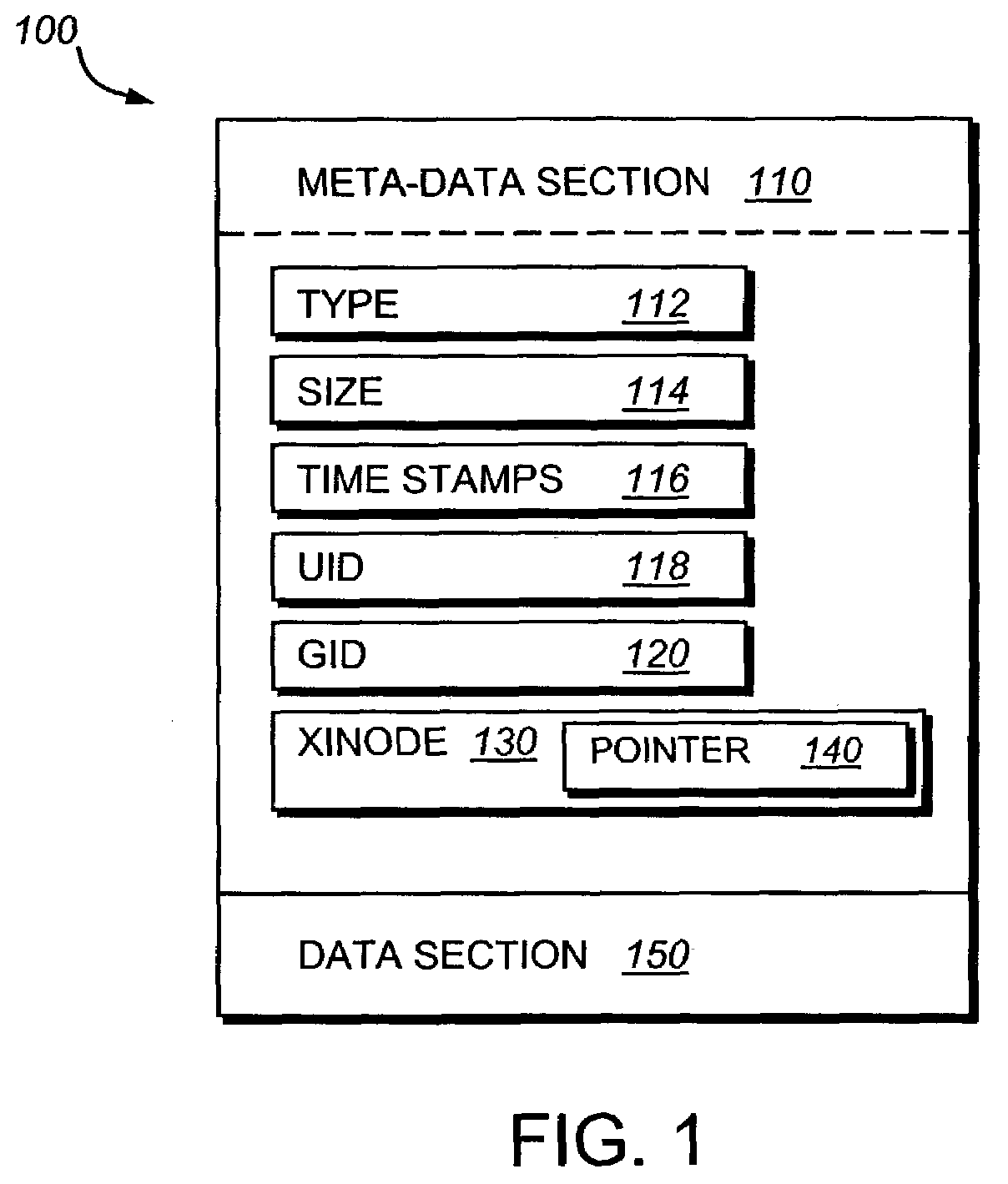
Medication delivery device with replaceable cooperating modules and a method of making same
InactiveUS6997911B2Easy to adjustAvoid repetitionJet injection syringesMedical devicesSpecific functionComputer module
The invention relates to: A medication delivery device and a method of making such a device. The object of the present invention is to provide a handy medication delivery device that may be easily adjusted to the different needs of a given user in different situations and to the different needs of different users, and which is economic from a production point of view. The problem is solved in that it comprises a basis module (1) and one or more replaceable modules (2, 3, 4, 5, 6), each of which is adapted to cooperate mechanically and / or electronically with the basis module to provide a specific function, and the basis module includes resources that are jointly used by the replaceable modules. This has the advantage of providing a rational concept for economically supplying high quality, mass-produced devices capable of being customized to individual users' needs for functionality by avoiding the duplication of key components. The invention may be used in injector type, medication pump type, inhaler or spray type devices for delivering a discrete dose or a continuous dose of a medication to a user.
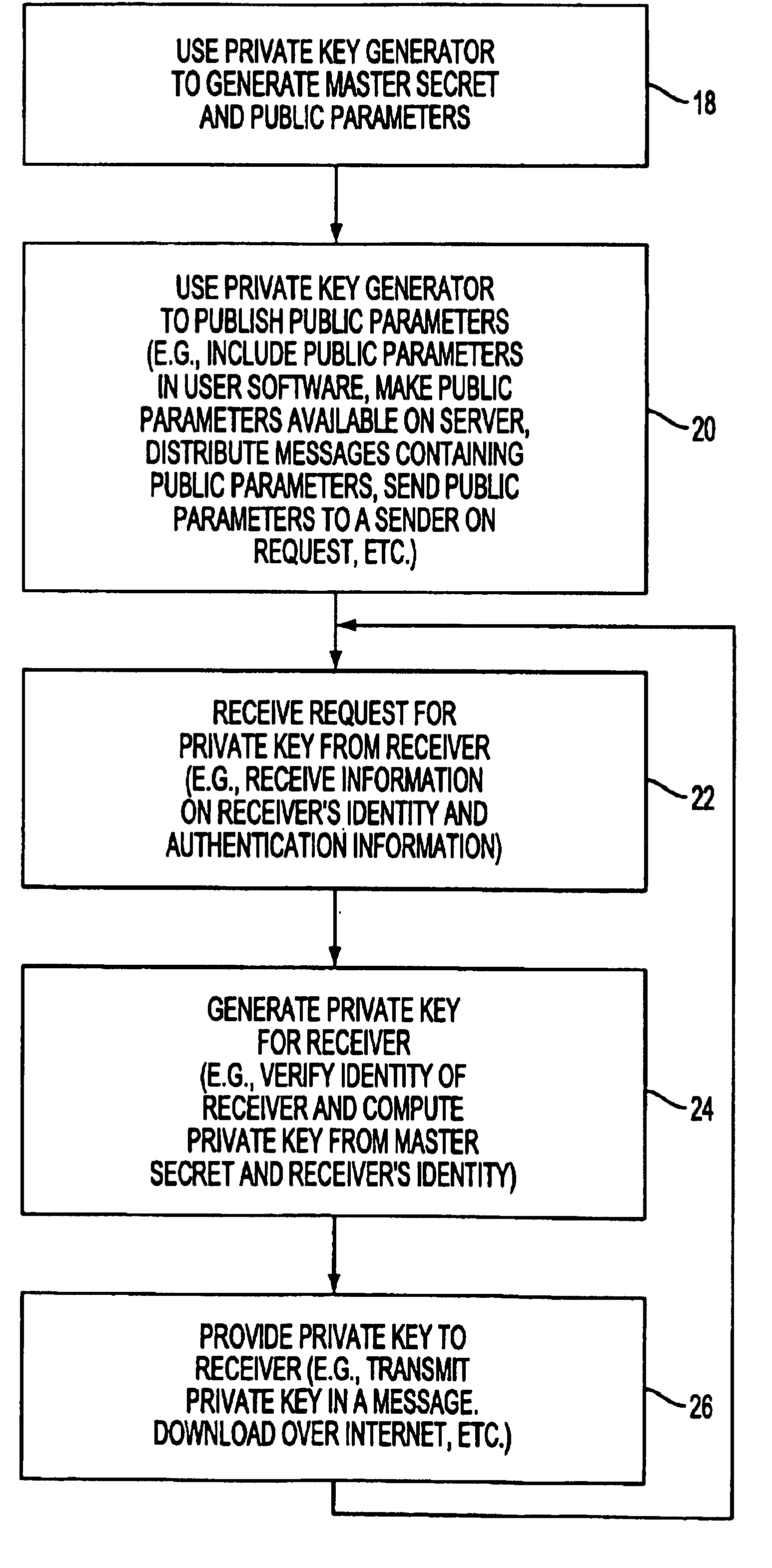
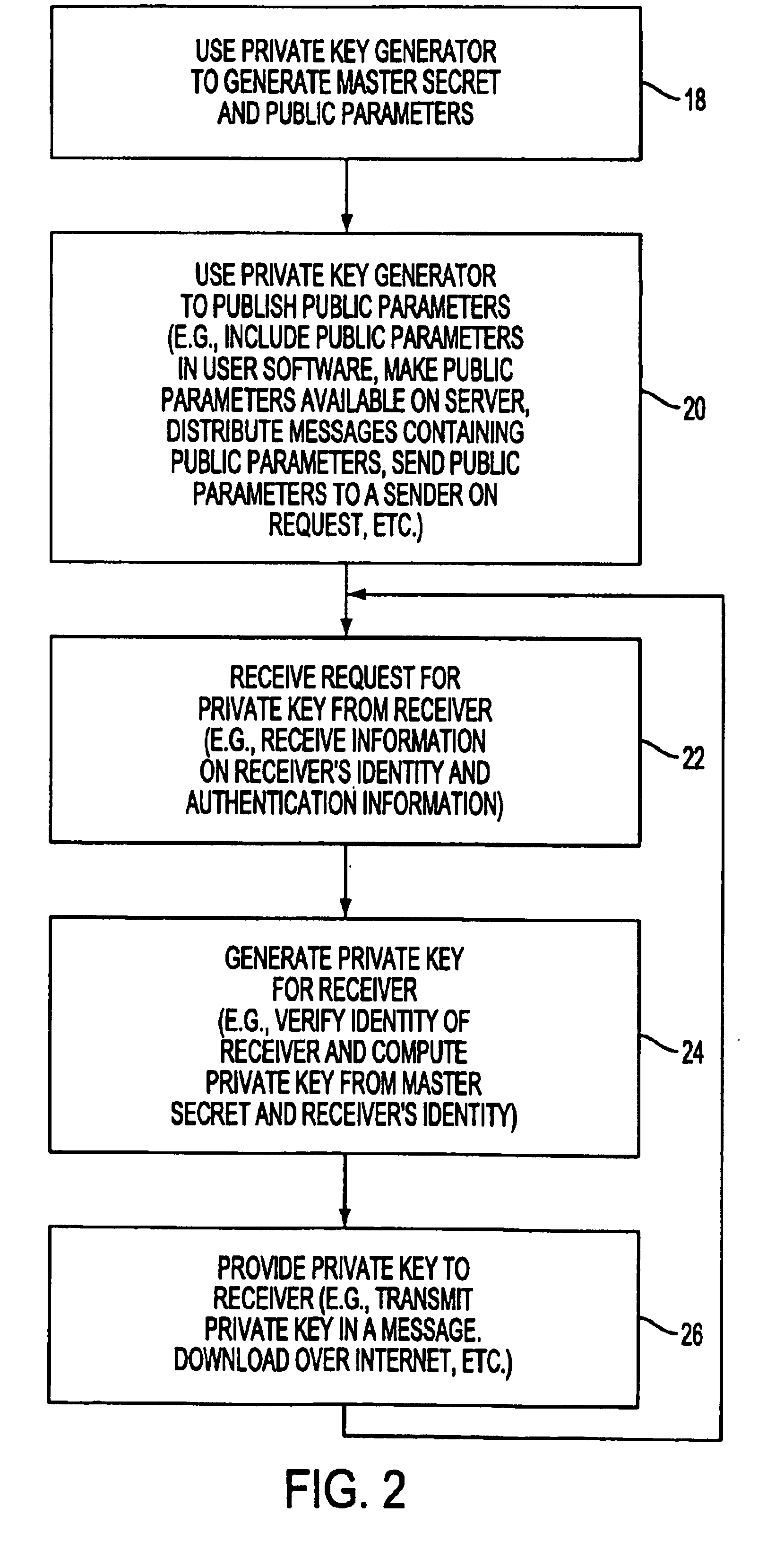
Owner:NOVO NORDISK AS
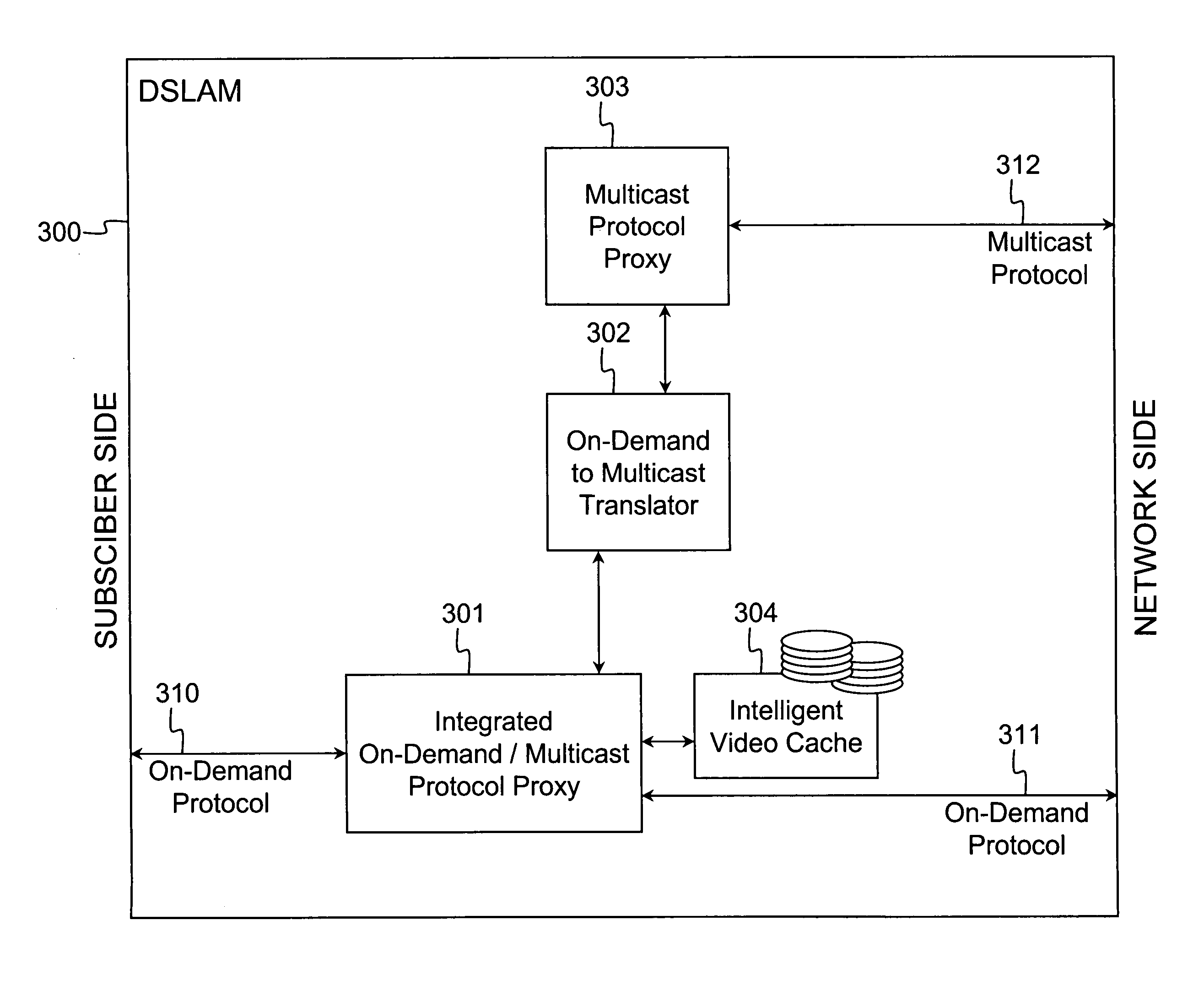
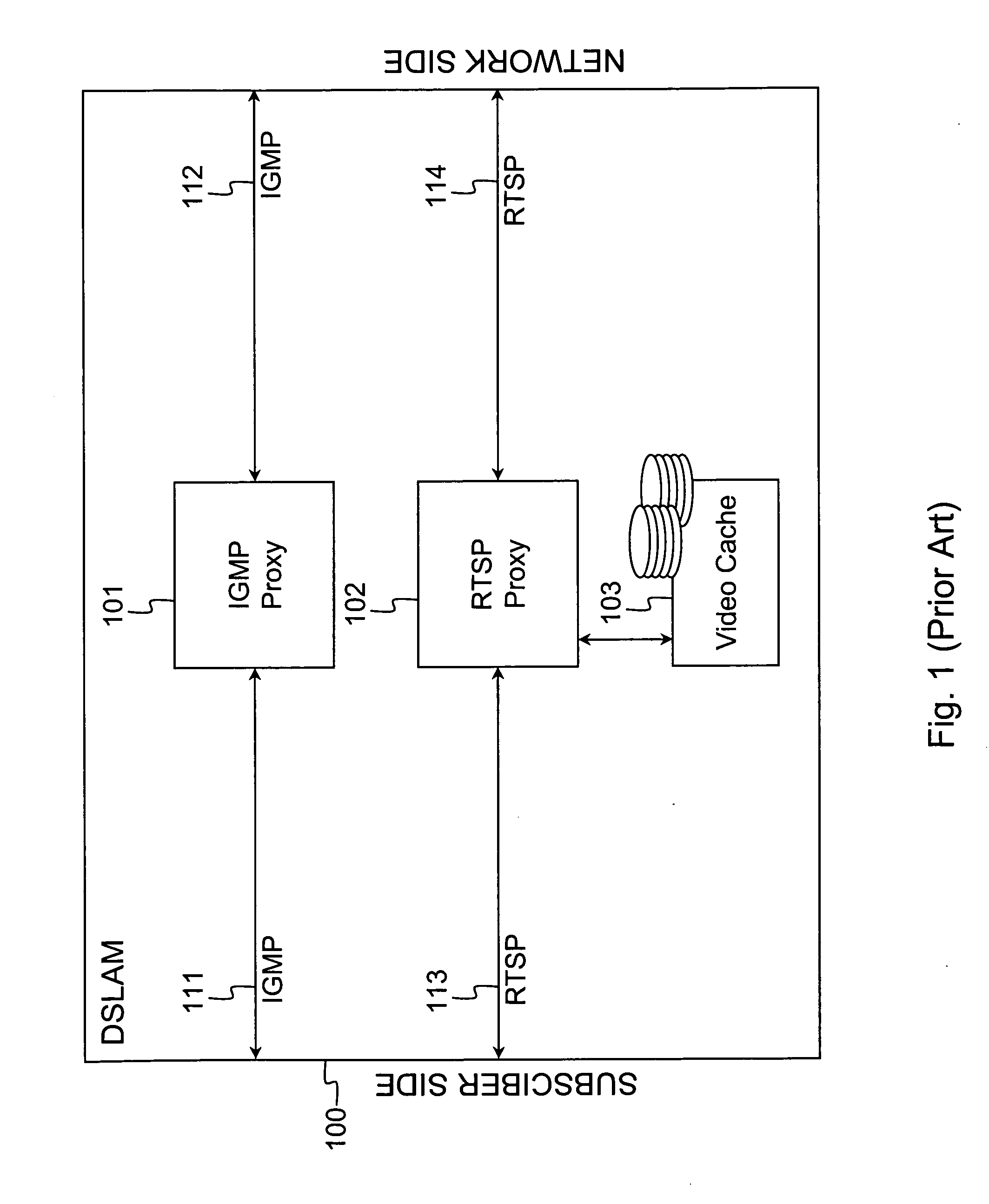
Access/edge node supporting multiple video streaming services using a single request protocol
ActiveUS20070101377A1Compact integrationReduce in quantityAnalogue secracy/subscription systemsClosed circuit television systemsEdge nodeService use
Owner:ALCATEL LUCENT SAS +2
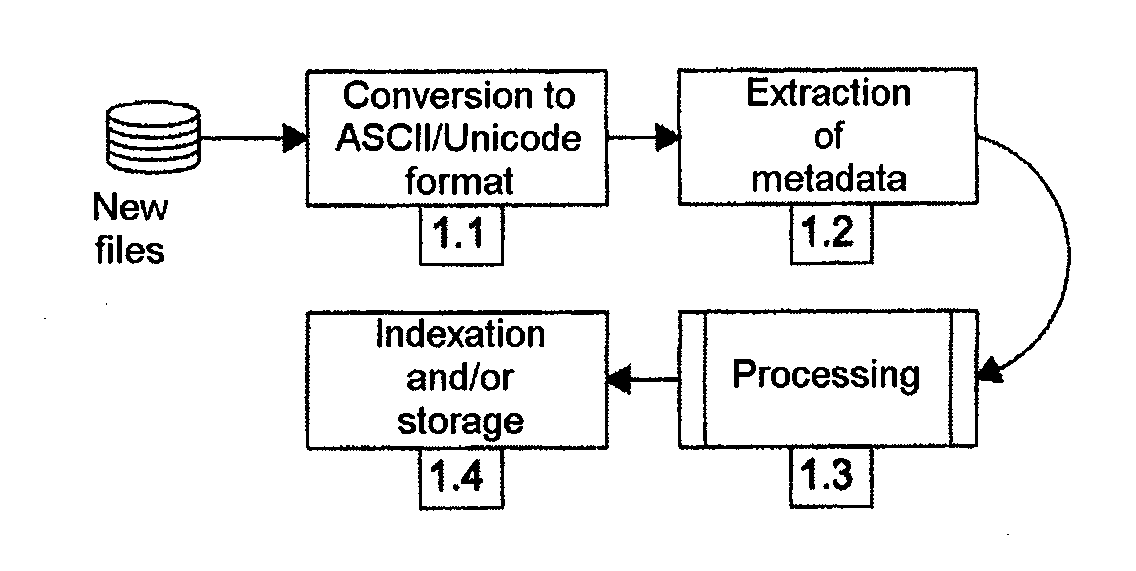
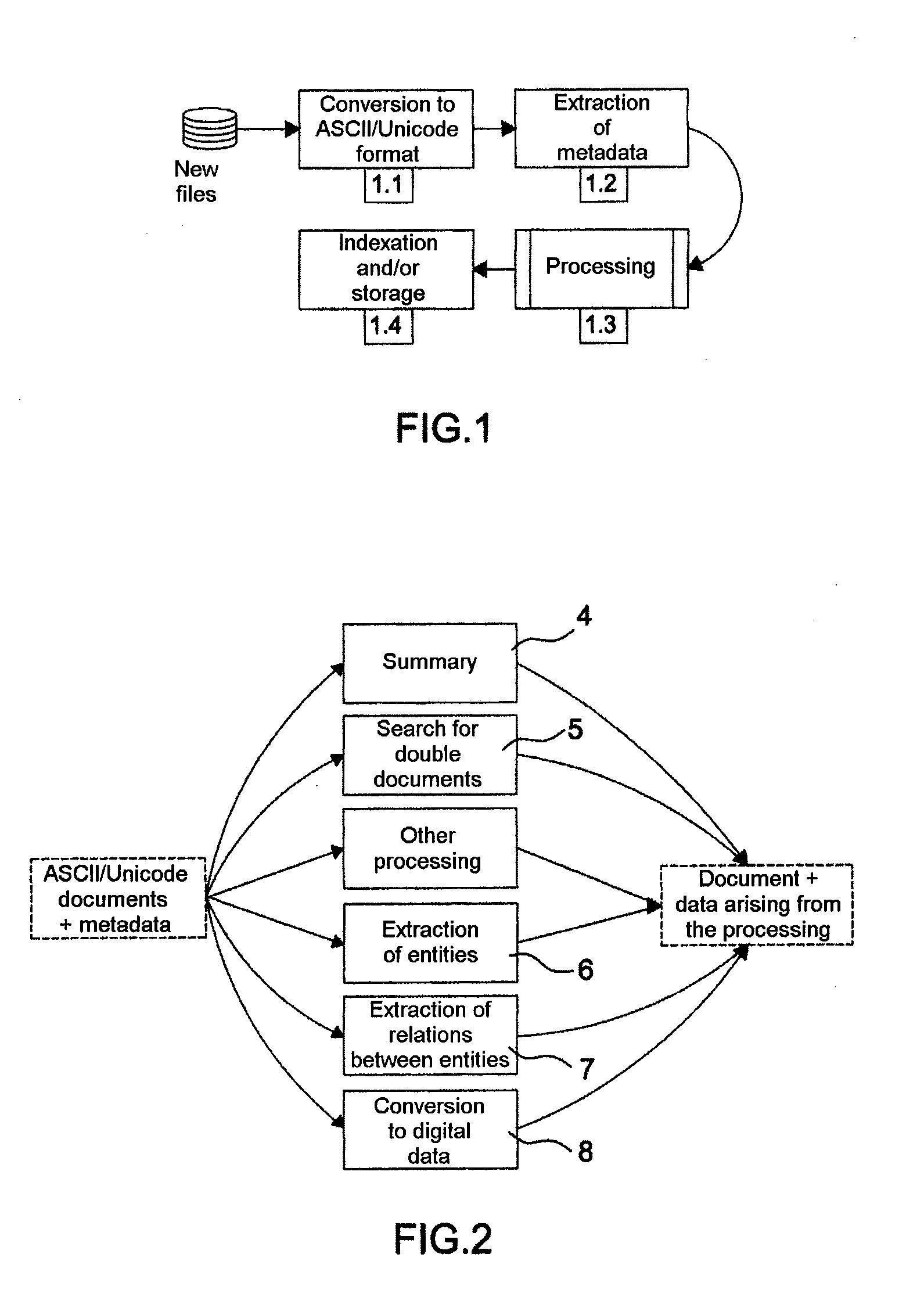
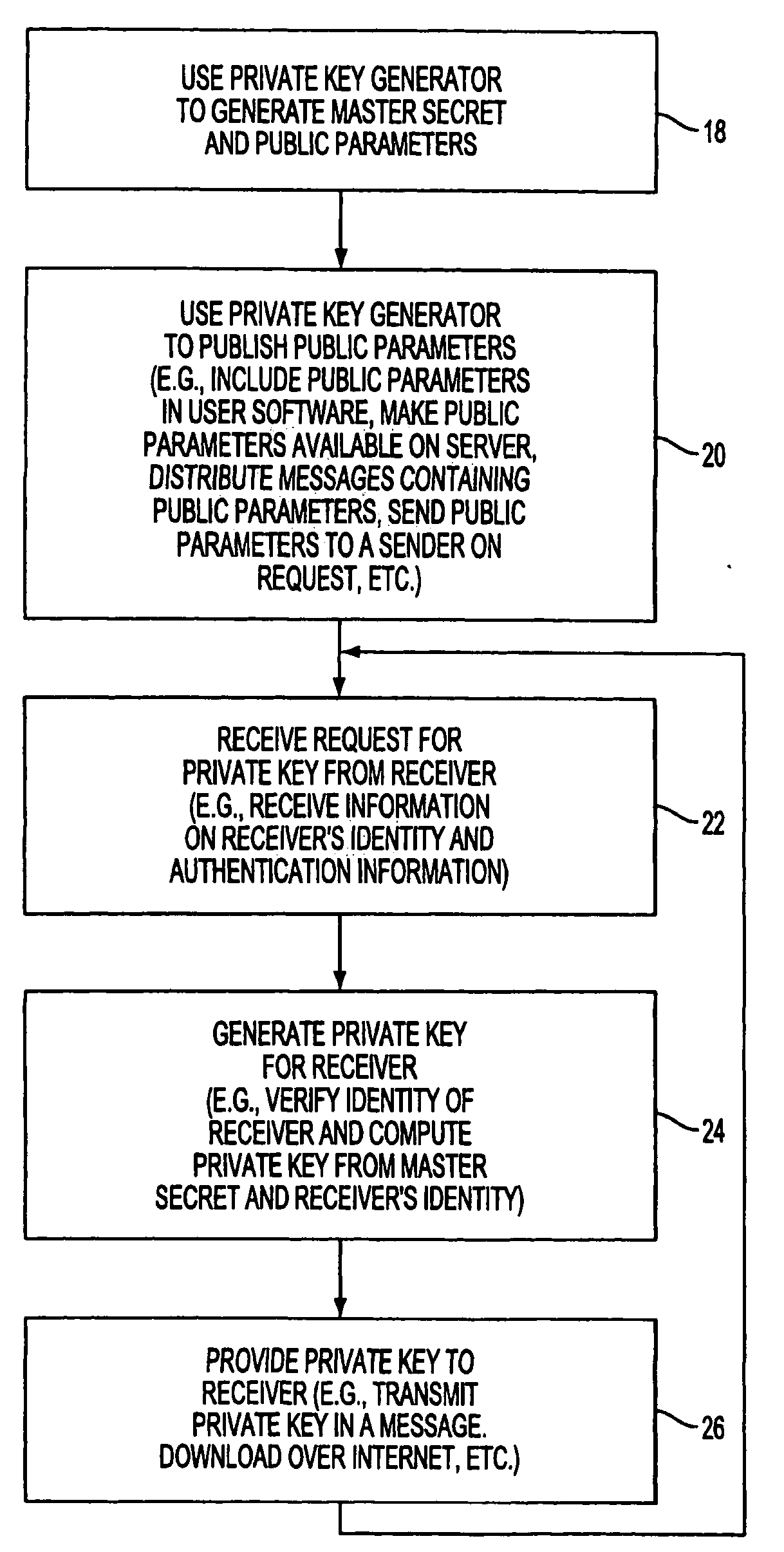
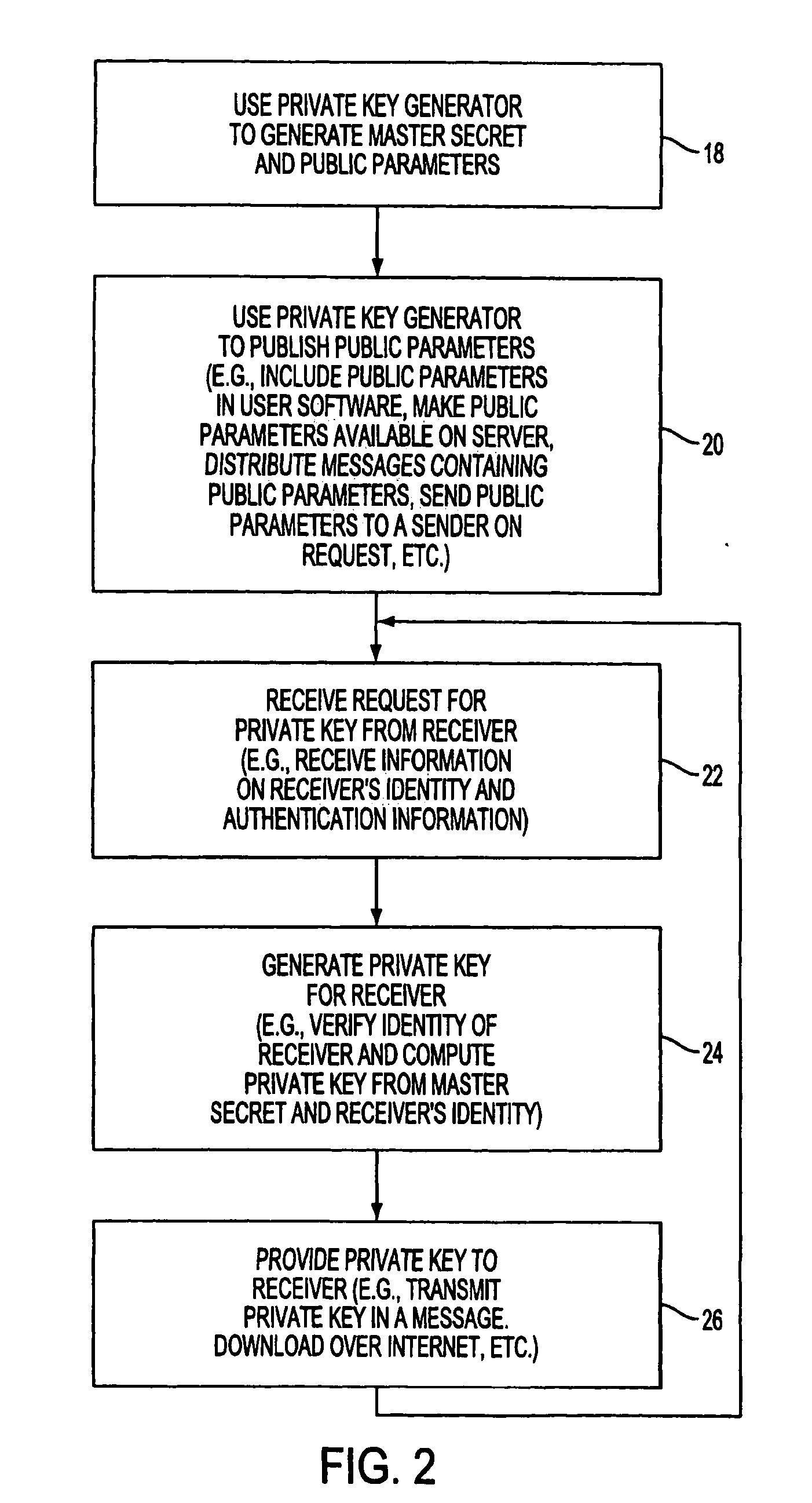
Method and device for retrieving data and transforming same into qualitative data of a text-based document
InactiveUS20100023318A1Avoid repetitionNatural language data processingSpecial data processing applicationsData conversionData file
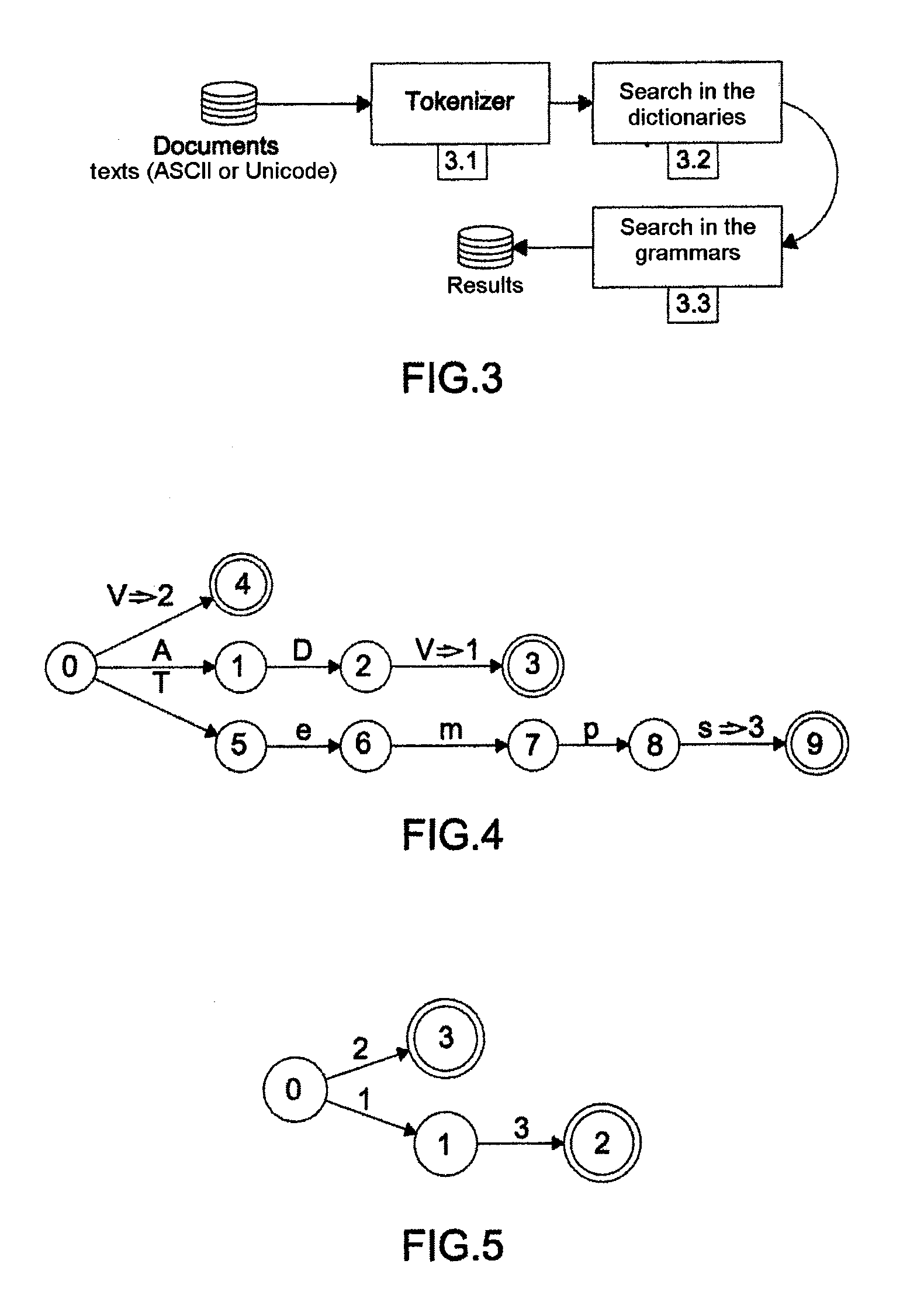
Method for extracting information from a data file comprising a first step wherein the data are transmitted to a device (3.1) or “tokenizer” adapted to convert them in the course of a first step into elementary units or “tokens”, the elementary units being transmitted to a second step of searching in the dictionaries (3.2) and a third step (3.3) of searching in grammars, characterized in that, for the conversion step, a sliding window of given size is used, the data are converted into “tokens” as and when they arrive in the tokenizer and the tokens are transmitted as and when they are formed to the step of searching in dictionaries (3.2), then to the step of searching in the grammars (3.3).
Owner:THALES SA
Identity-based encryption system
ActiveUS6886096B2Avoid duplicationAvoid repetitionPublic key for secure communicationUser identity/authority verificationSecure communicationKey generator
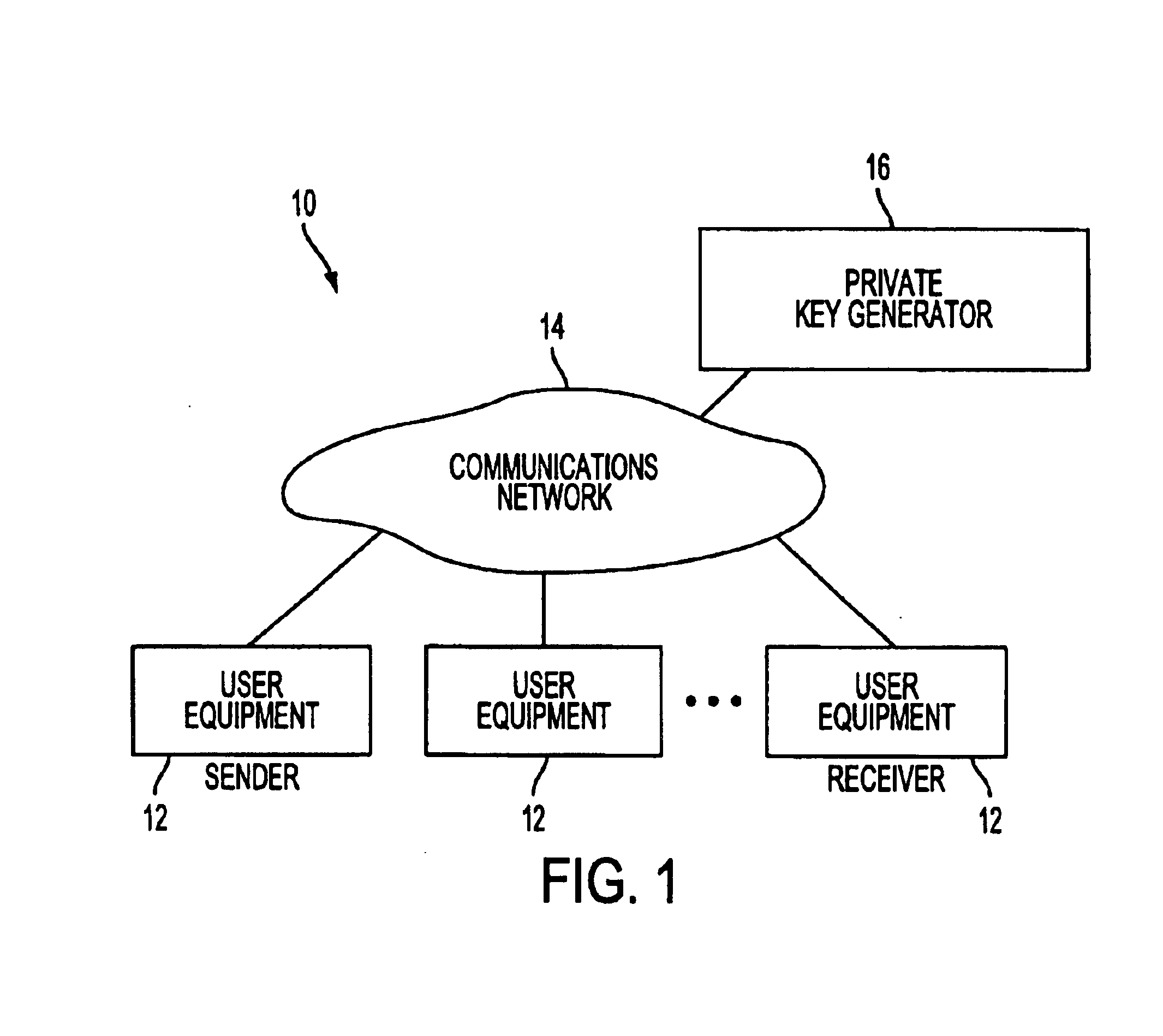
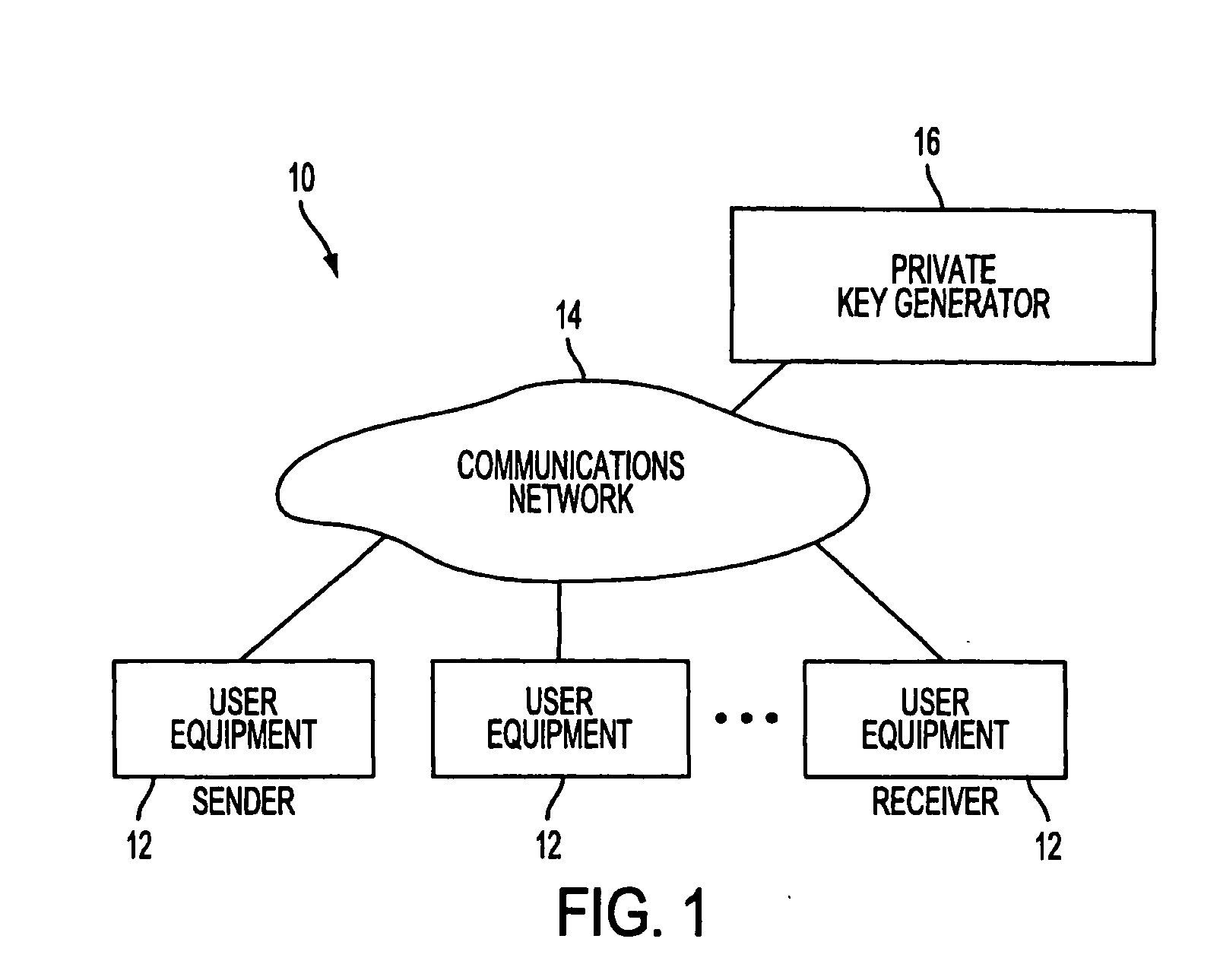
A system is provided that uses identity-based encryption to support secure communications. Messages from a sender to a receiver may be encrypted using the receiver's identity and public parameters that have been generated by a private key generator associated with the receiver. The private key generator associated with the receiver generates a private key for the receiver. The encrypted message may be decrypted by the receiver using the receiver's private key. The system may have multiple private key generators, each with a separate set of public parameters. Directory services may be used to provide a sender that is associated with one private key generator with appropriate public parameters to use when encrypting messages for a receiver that is associated with a different private key generator. A certification authority may be used to sign directory entries for the directory service. A clearinghouse may be used to avoid duplicative directory entries.
Owner:MICRO FOCUS LLC
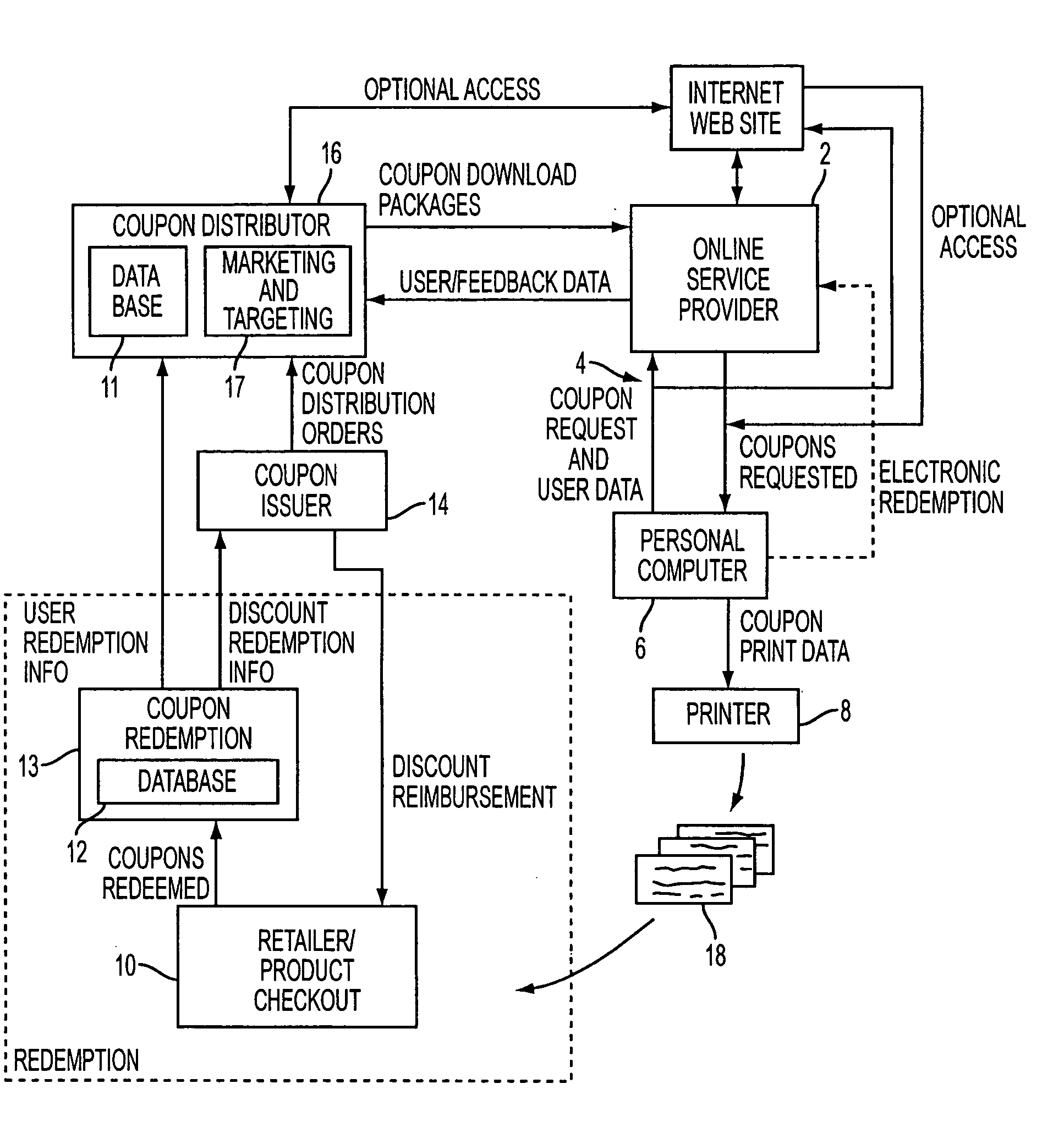
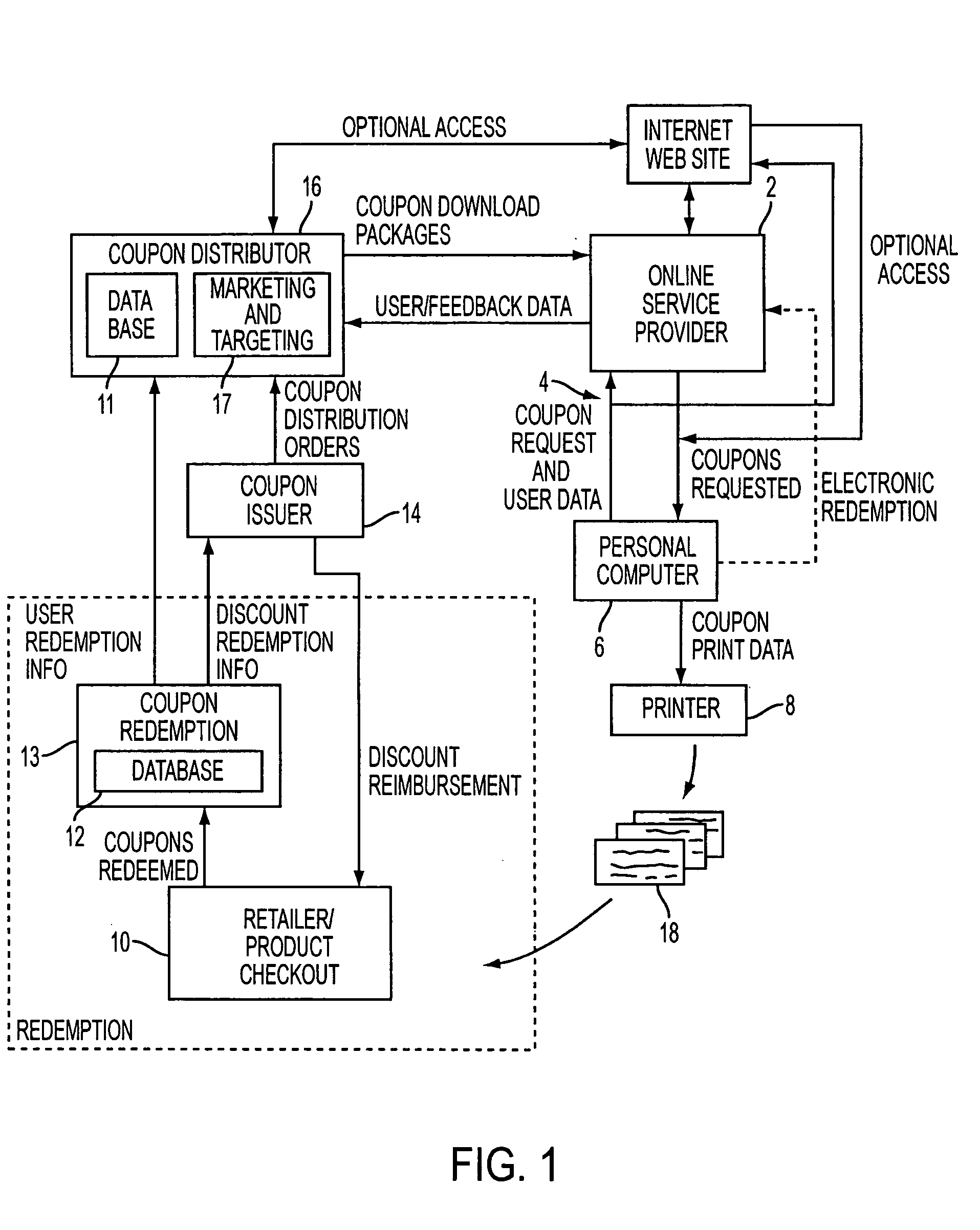
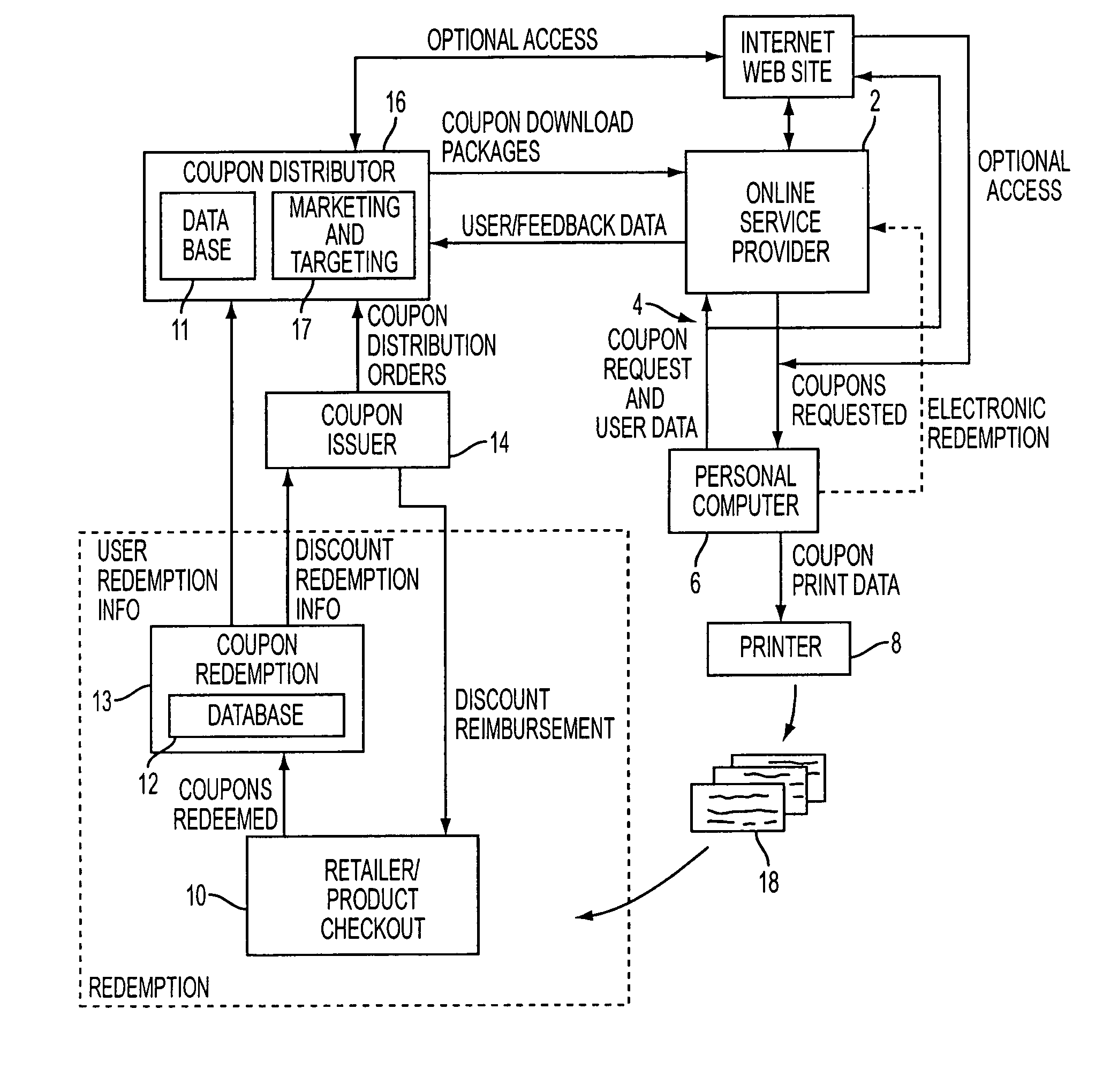
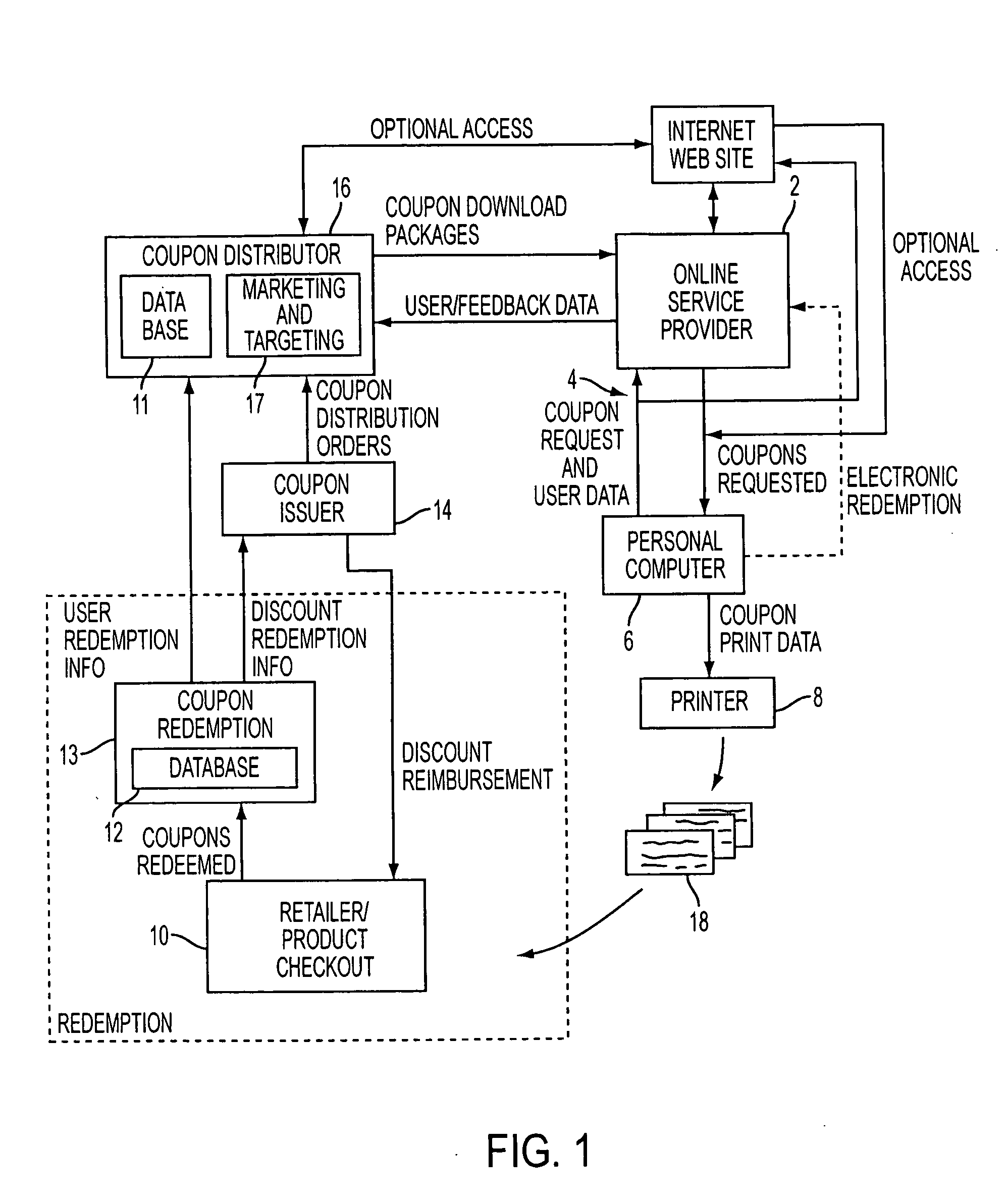
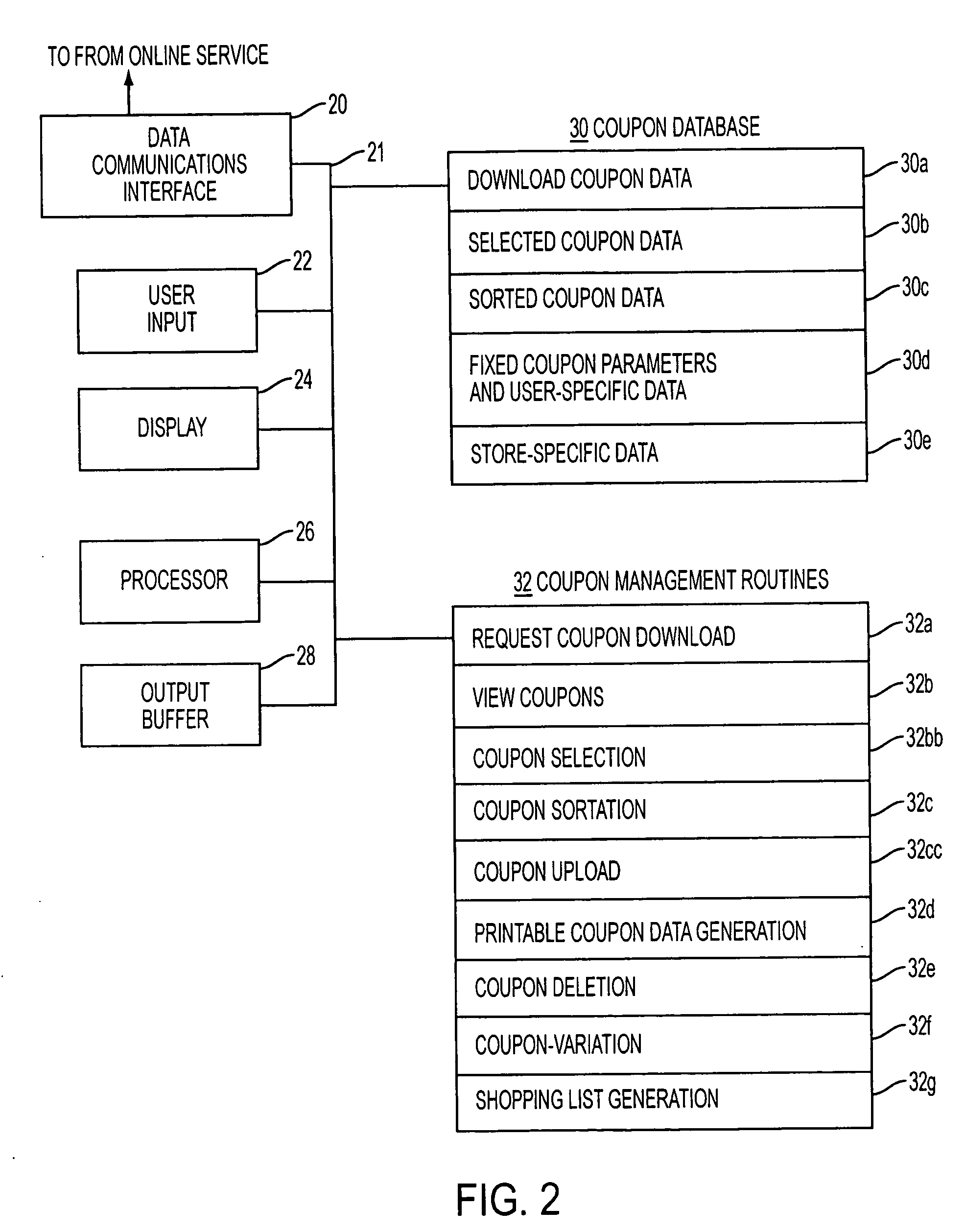
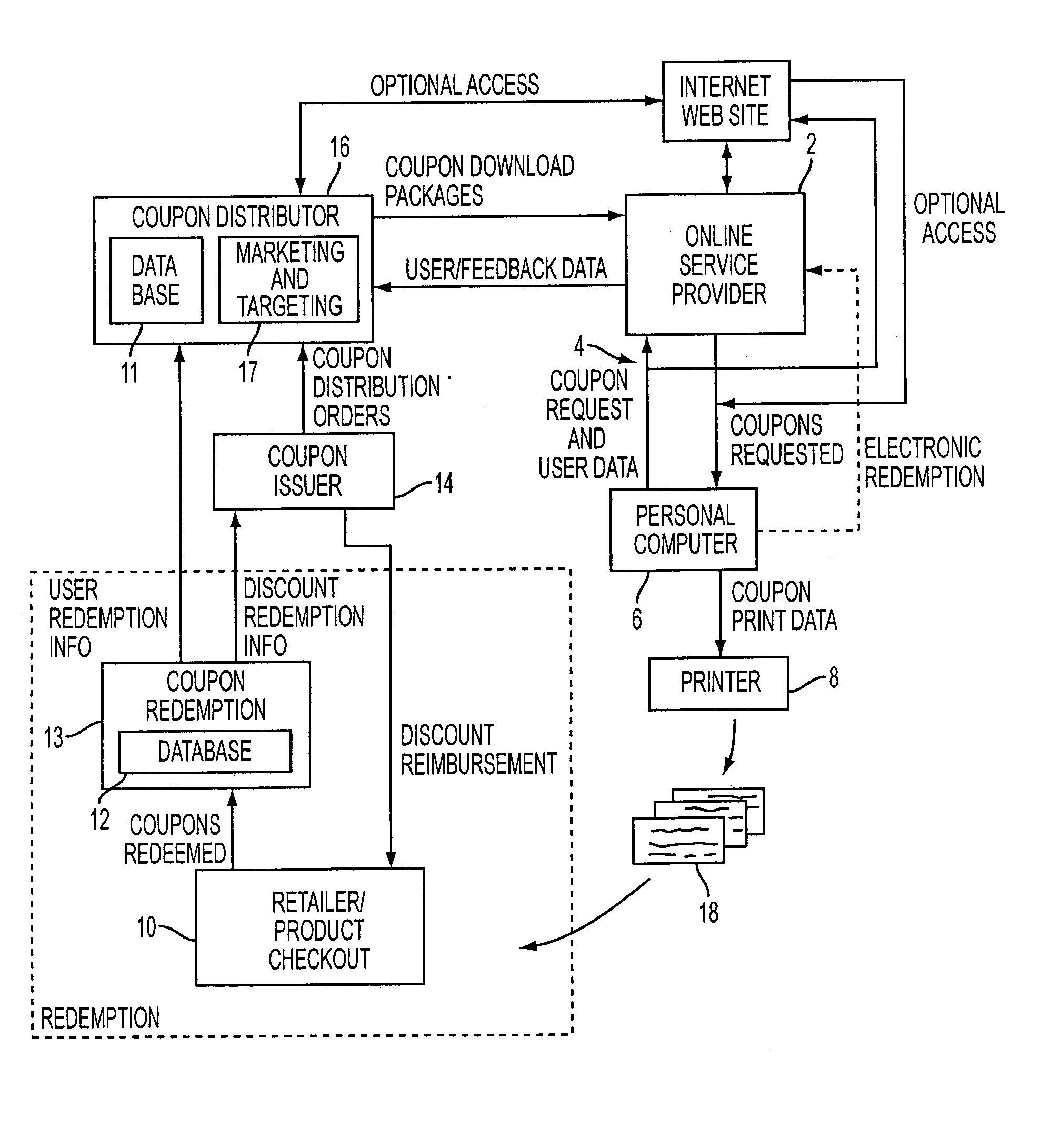
Proximity-based method and system for generating customized incentives
ActiveUS20050209921A1Cost effectiveAvoid repetitionDiscounts/incentivesSpecial data processing applications
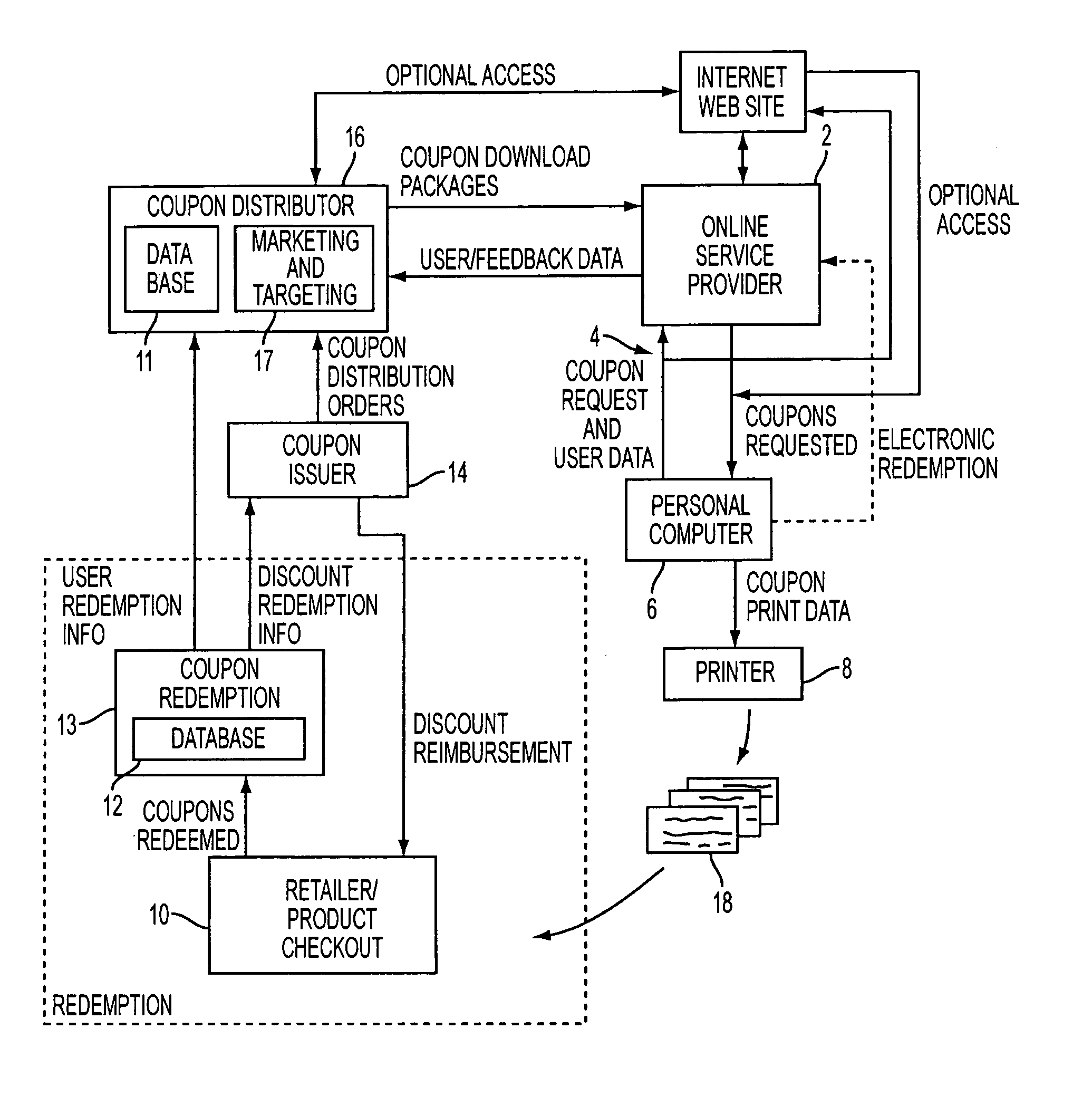
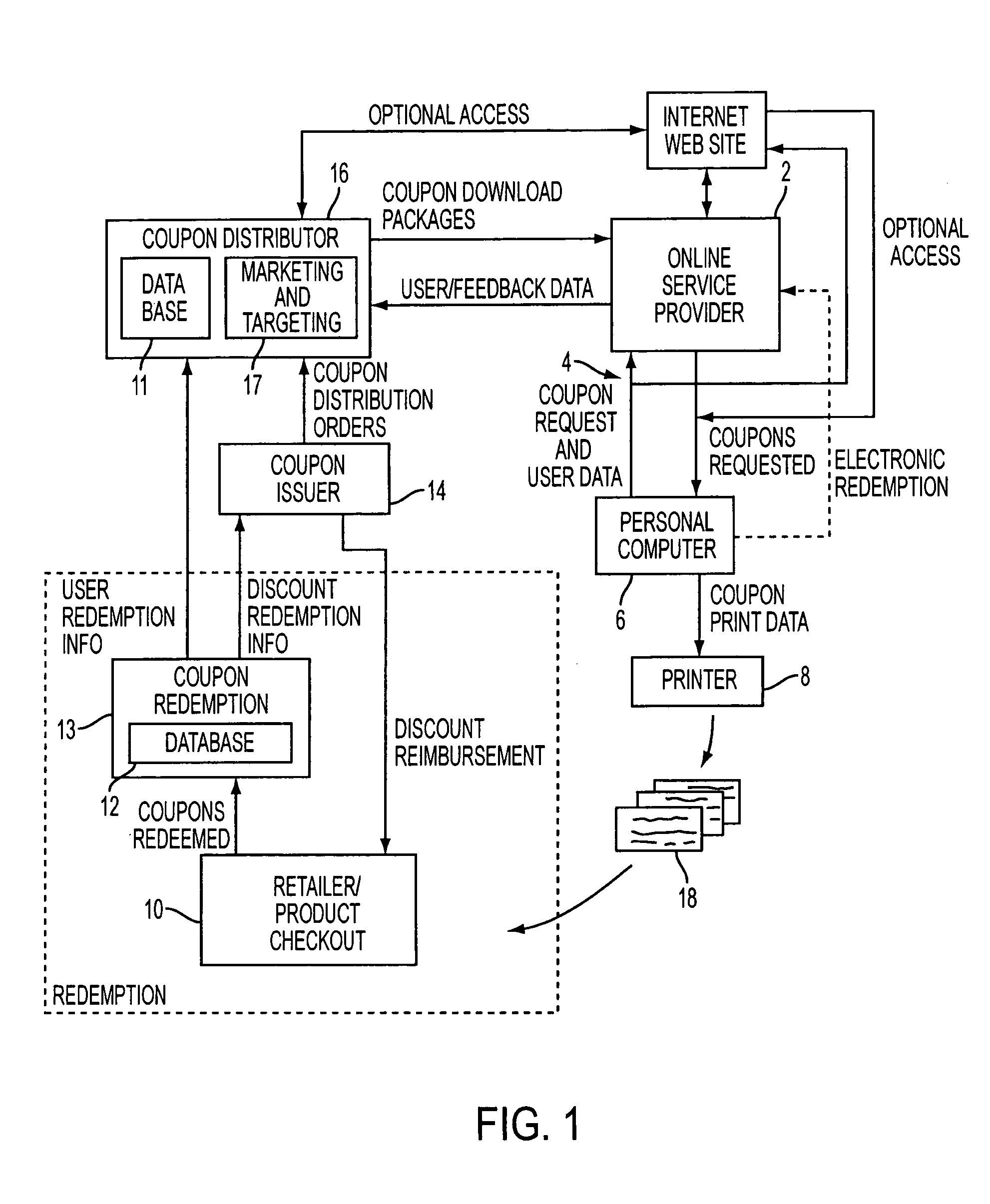
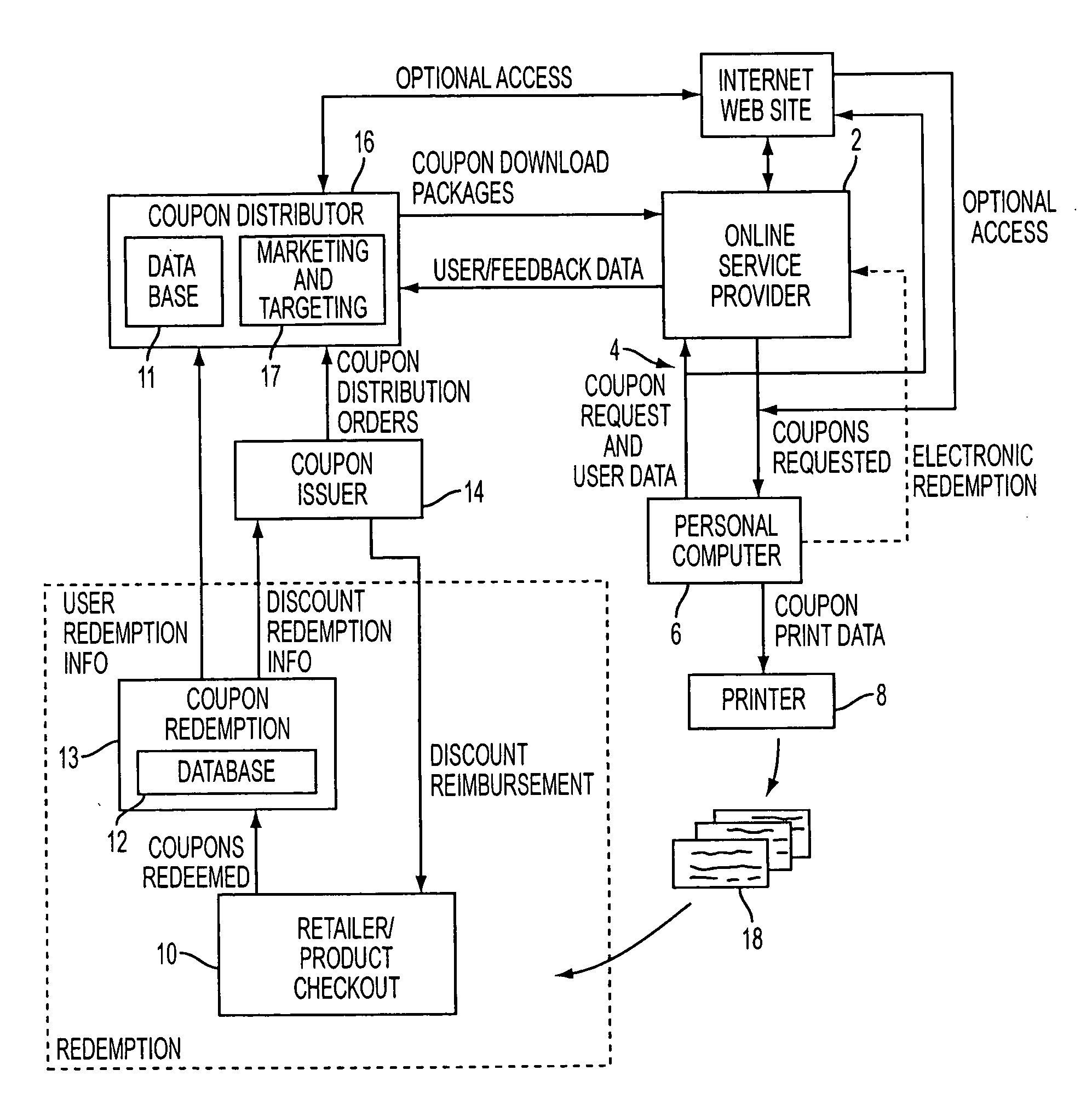
A method and system for generating customized incentives involving electronic distribution of coupons to remote personal computers based on proximity of the computer to a retail center are disclosed. A repository, such as an online service provider or a web site on the Internet, stores packages of incentive data for downloading automatically or on demand to a user's computer. A plurality of data fields is used to associate a user's location with a specific incentive.
Owner:CATALINA MARKETING CORP
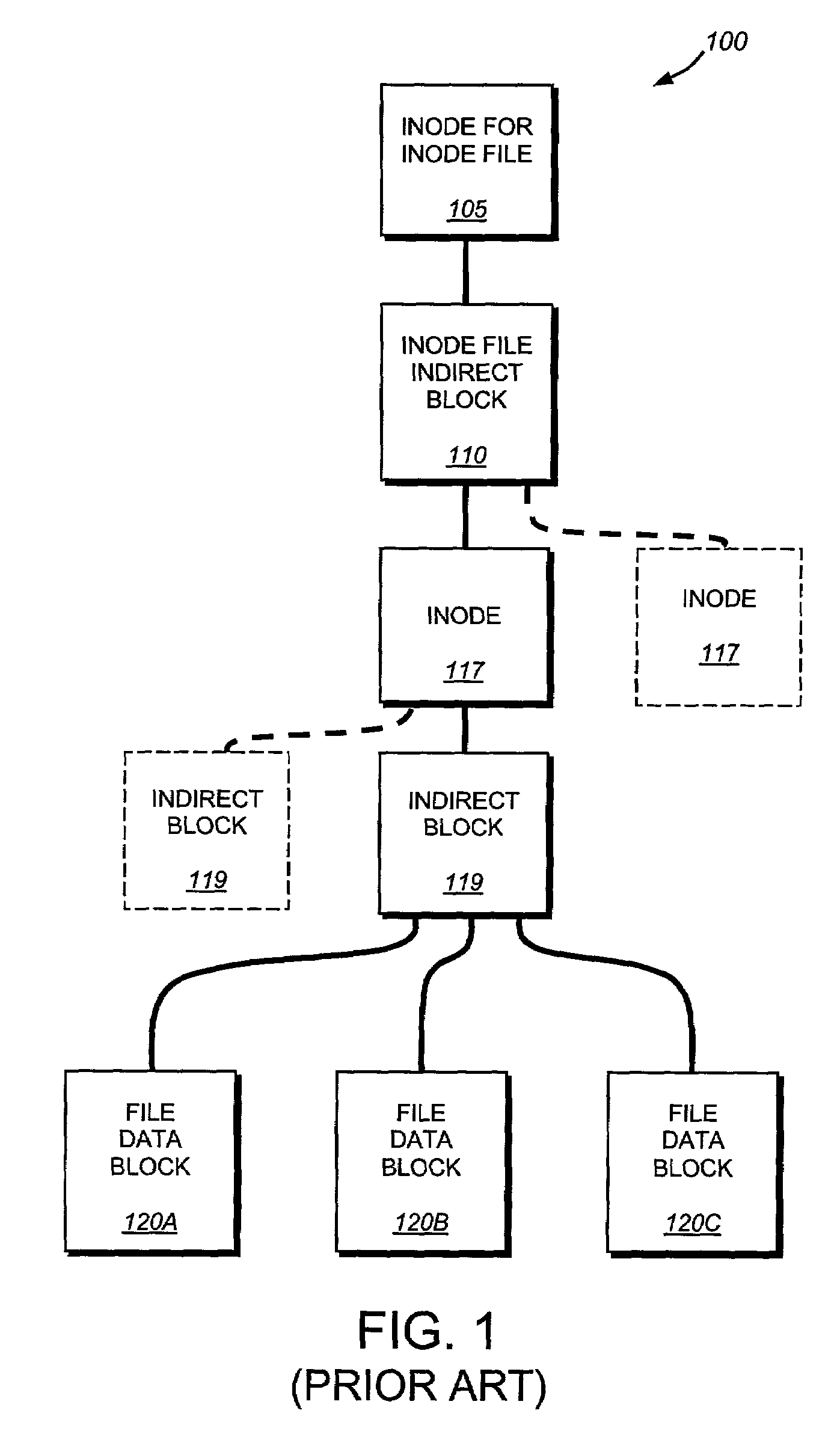
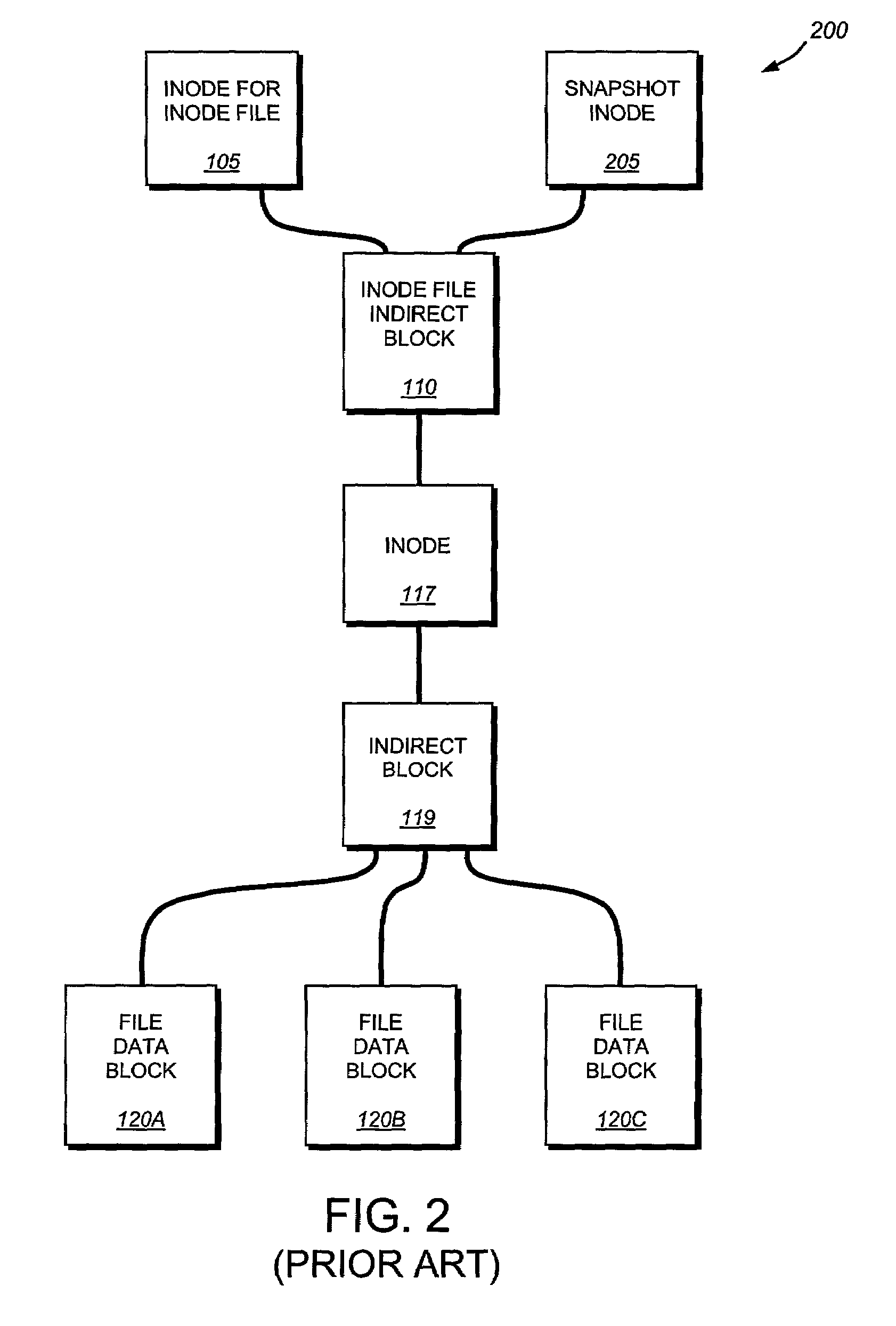
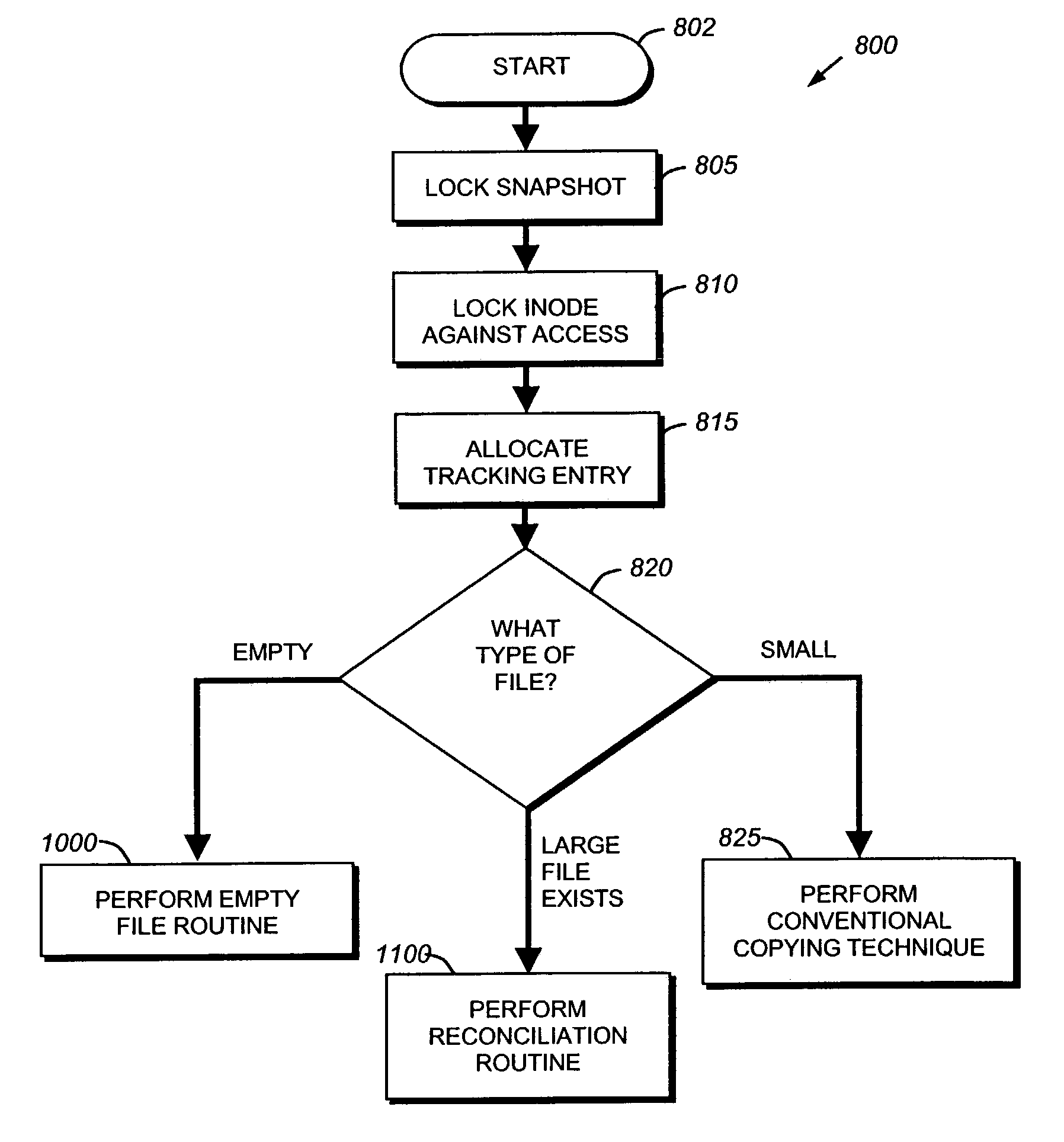
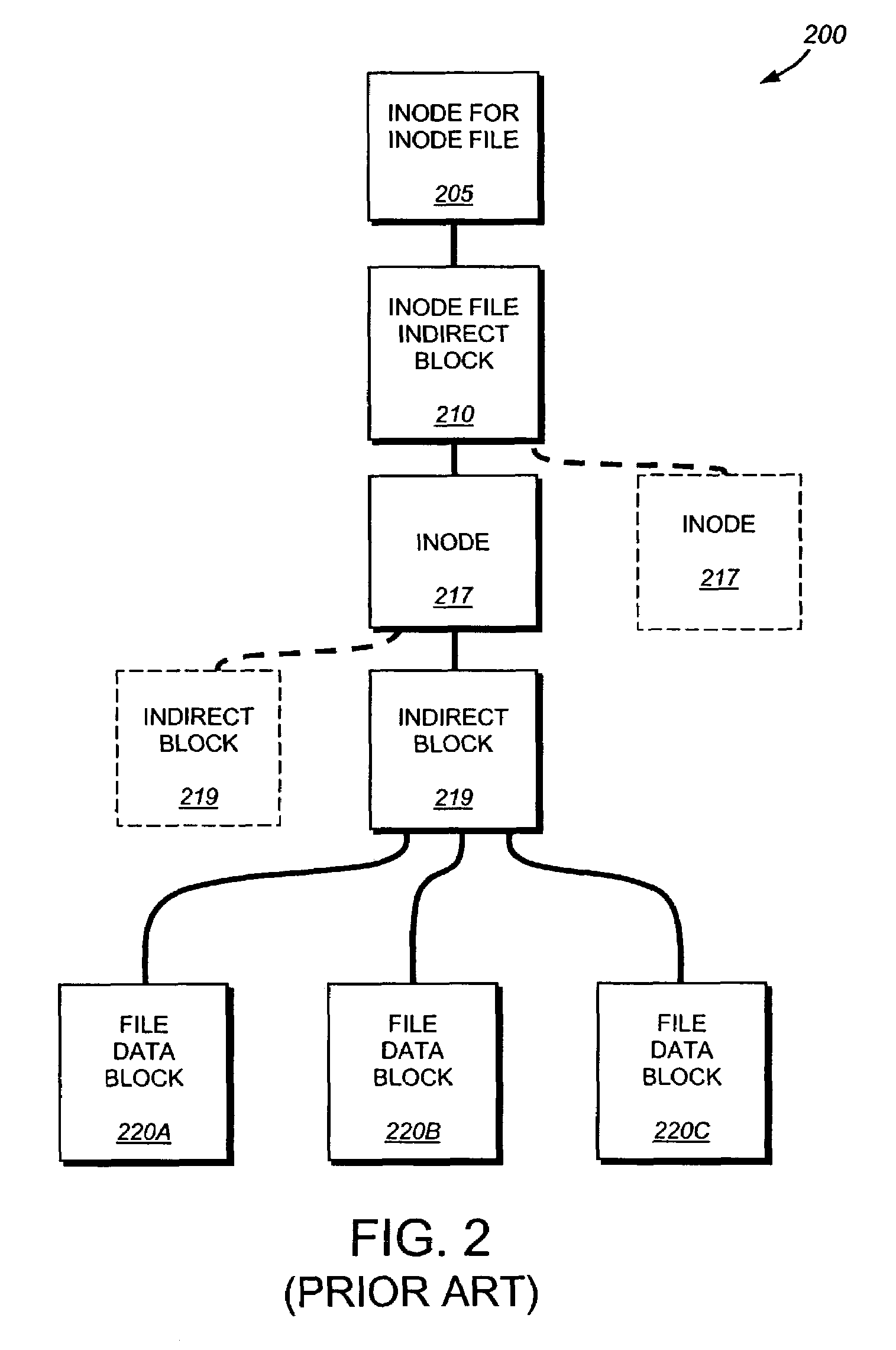
System and method for restoring a single file from a snapshot
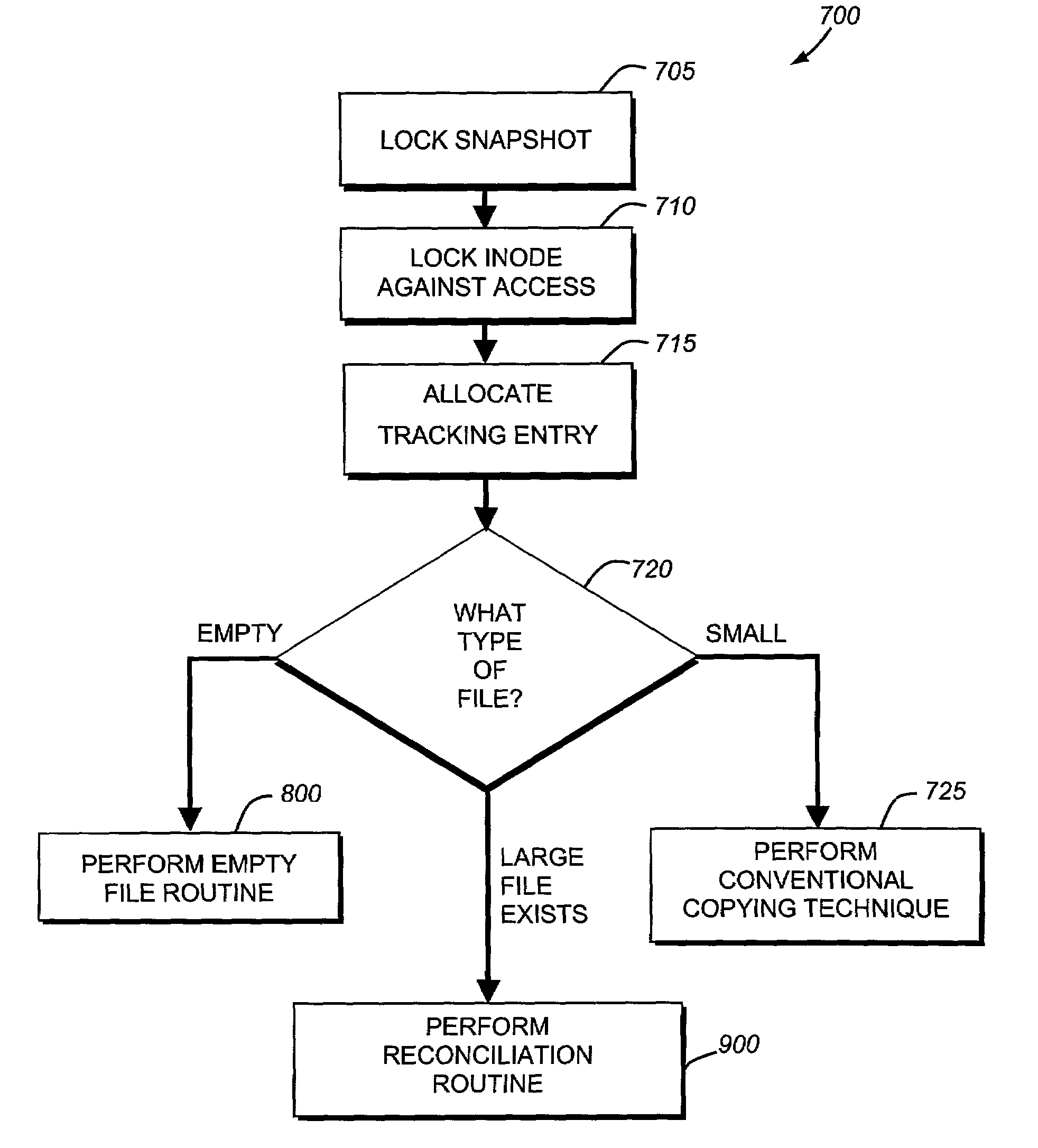
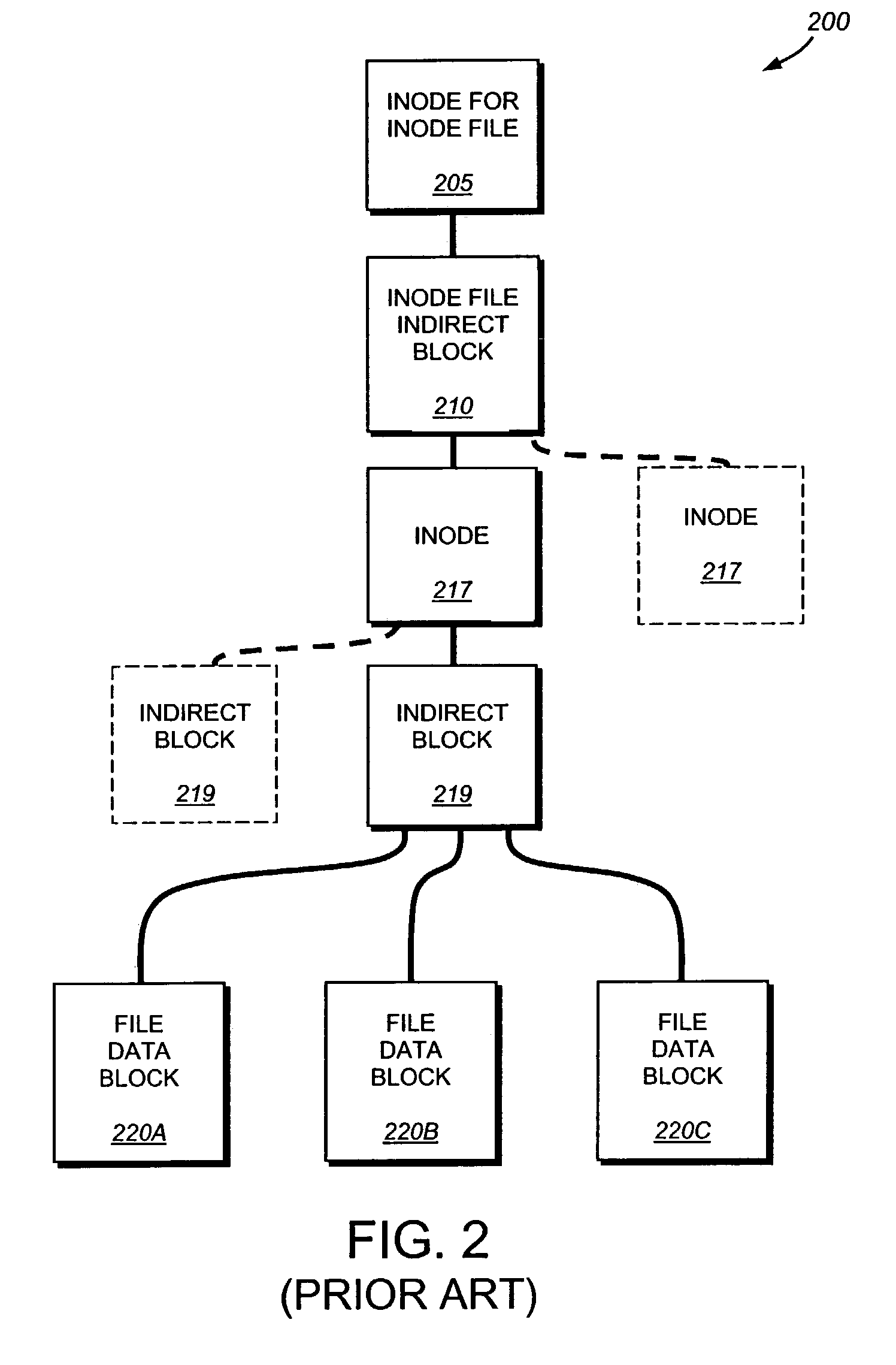
InactiveUS7051050B2Quickly restoring a fileSubstantial overheadDigital data processing detailsSpecial data processing applicationsInode
The present invention provides a system and method for restoring a single file from a snapshot without the need to copy every individual block or inode from the snapshot. A file restore process duplicates the inode of a file within the active file system and performs a reconciliation process between the blocks of the twin inode and the snapshot inode. If the file does not exist within the active file system, a new buffer tree is created that points to the data blocks stored in the snapshot.
Owner:NETWORK APPLIANCE INC
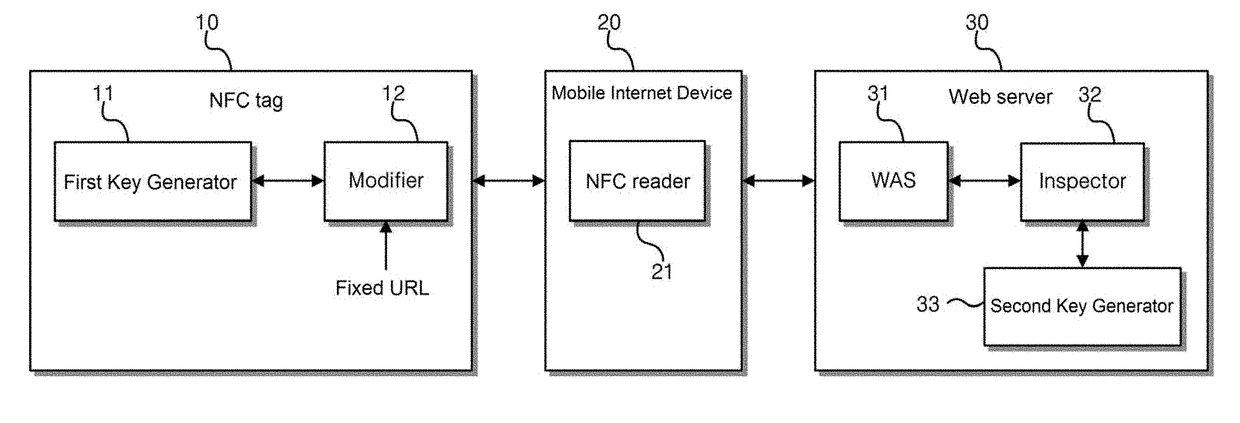
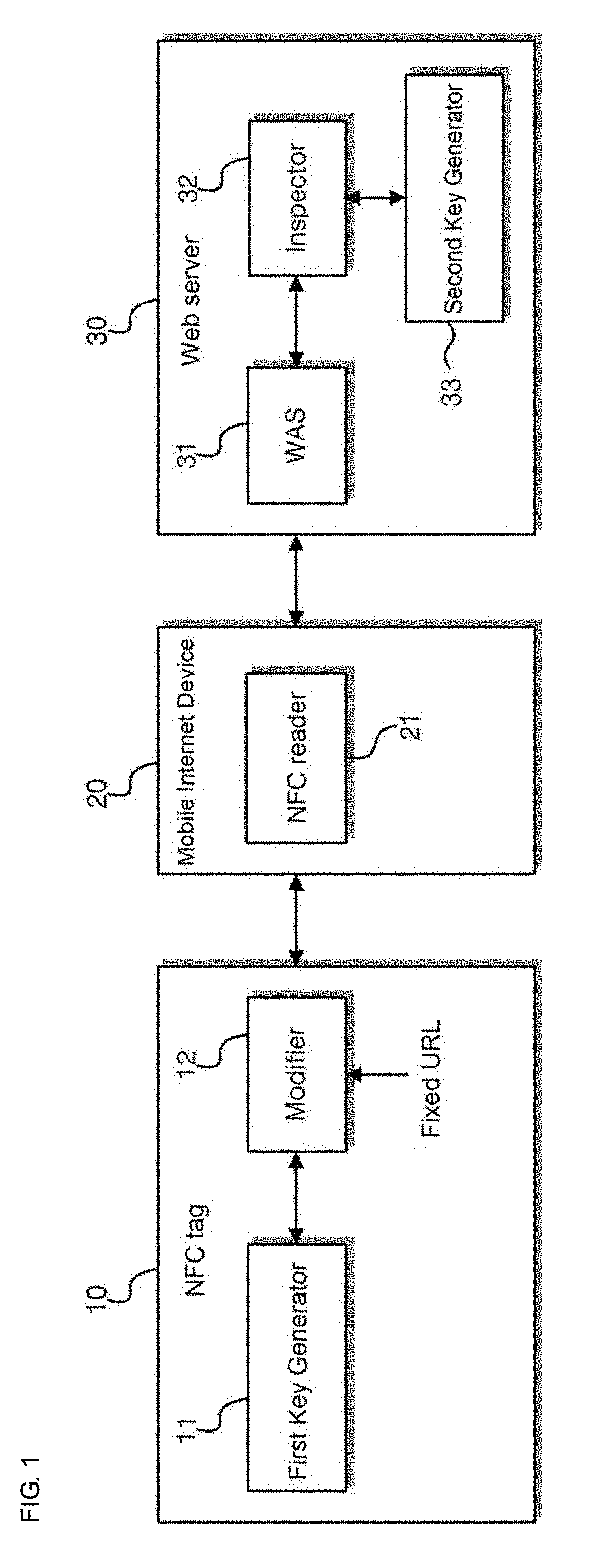
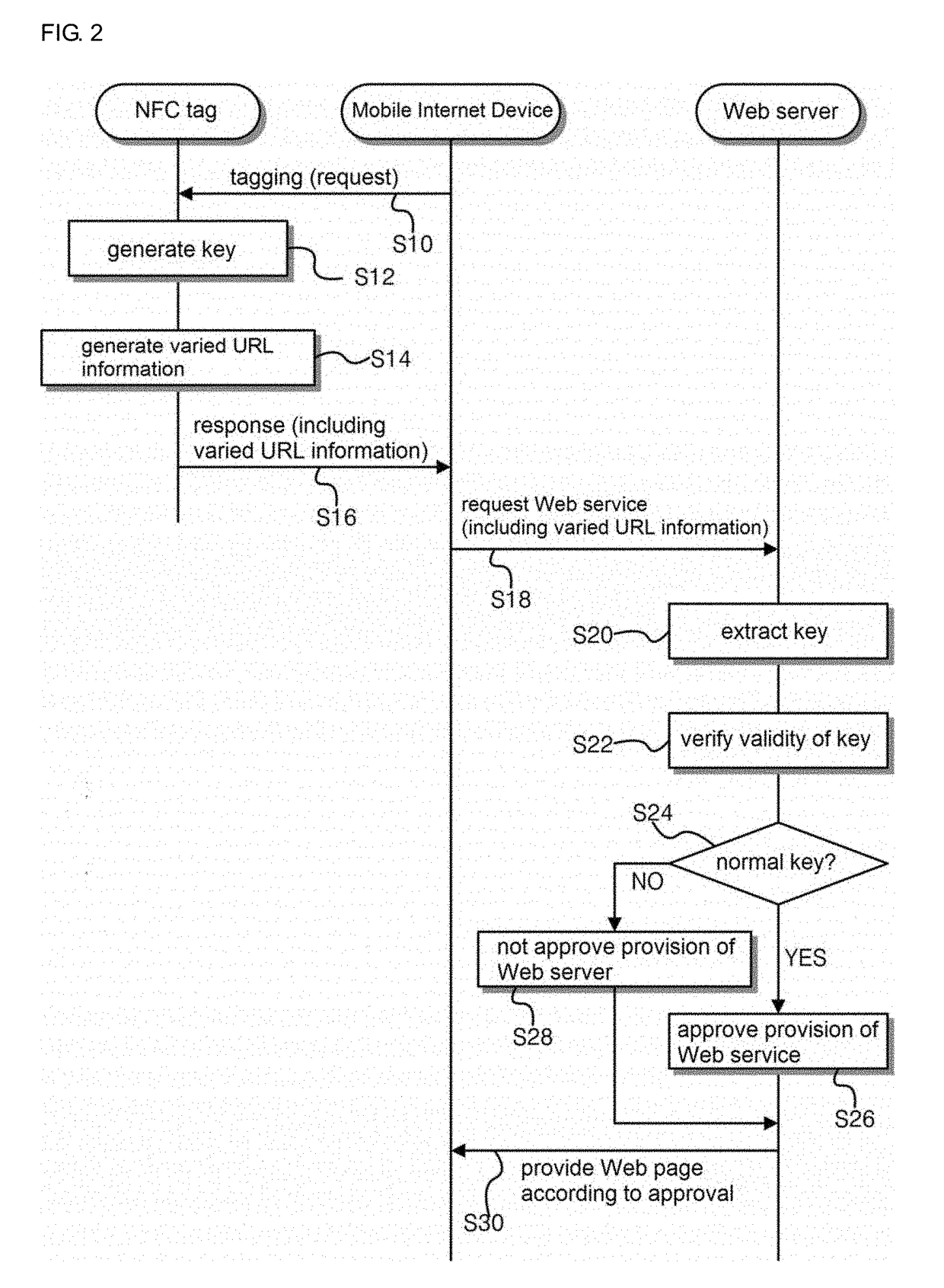
NFC tag-based web service system and method using Anti-simulation function
InactiveUS20180160255A1Avoid mockingReduce usageWireless commuication servicesTransmissionWeb serviceInternet appliance
An NFC tag-based Web service method based on an anti-simulation function includes a first operation of transmitting a response including URL information to the NFC reader when the NFC tag recognizes tagging of the NFC reader, and a second operation of receiving the URL information, by the Web server, the URL information from the mobile Internet device, and transmitting Web page information corresponding to the URL information to the mobile Internet device, wherein the URL information provided by the NFC tag to the NFC reader is varied URL information including a key changed and generated whenever tagging occurs, and the key is changed and generated according to a generation algorithm shared with the Web server.
Owner:PARK YOUNGSUCK
System and method for adaptive medical decision support
InactiveUS20160224760A1Reduce timeShorten the timeMedical simulationMedical data miningSelf adaptiveData sharing
A system, method and data sharing architecture are disclosed to be used by a group of people linked together in a network for treatment of human diseases, to assign preference rank to treatment option based on the similarity of the given patient's case to cases treated by the users of the same method previously.
Owner:ONCOMPASS GMBH
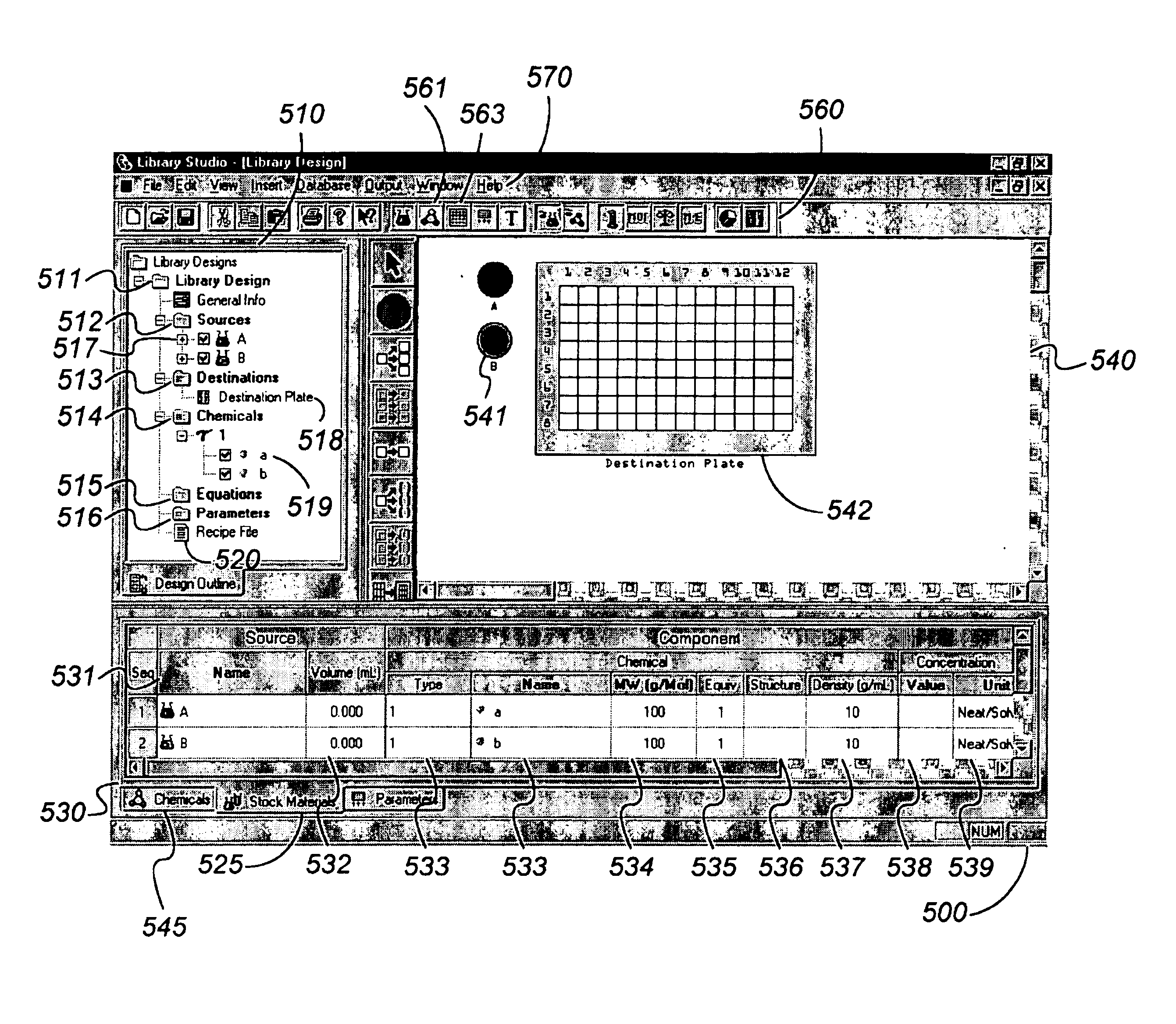
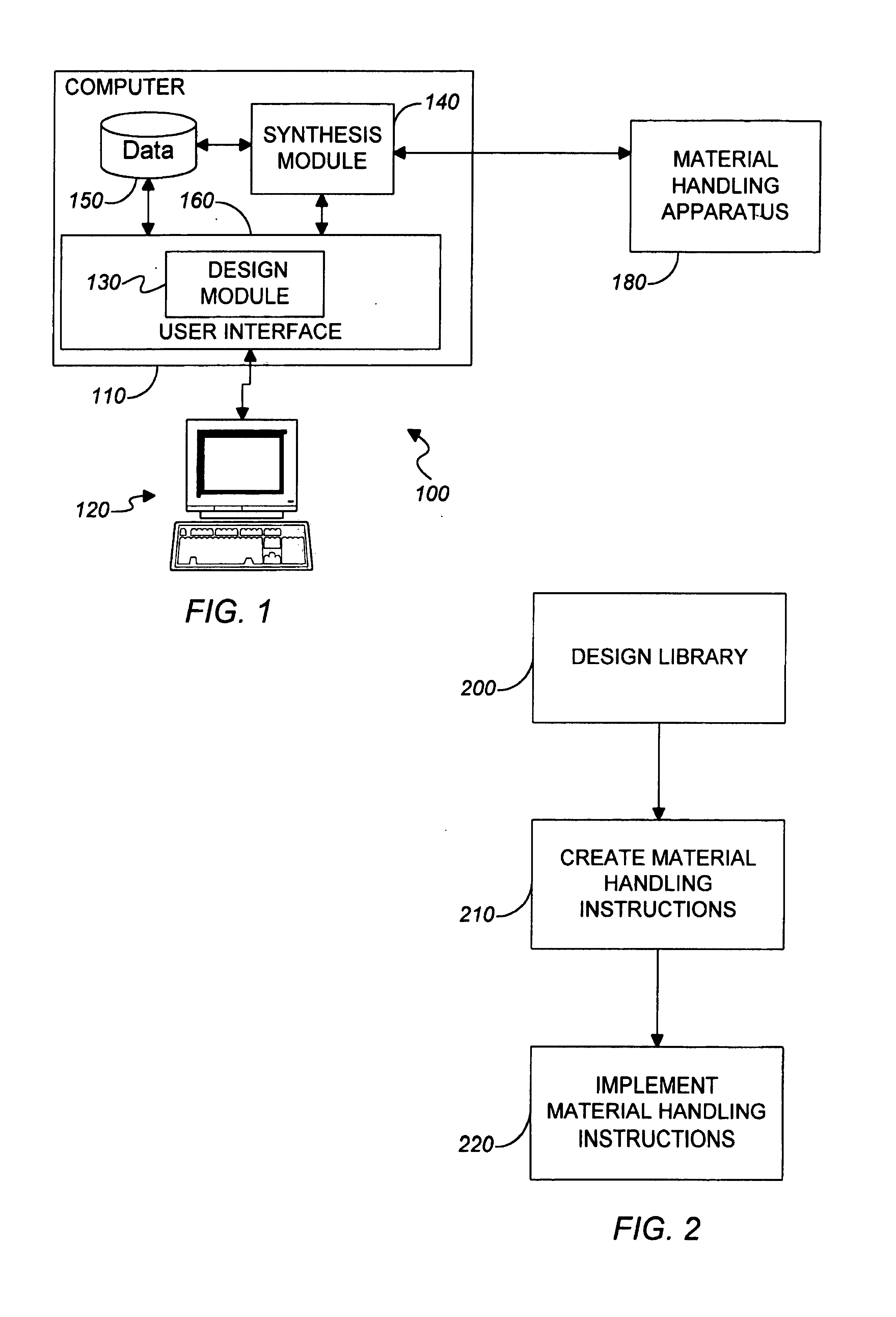
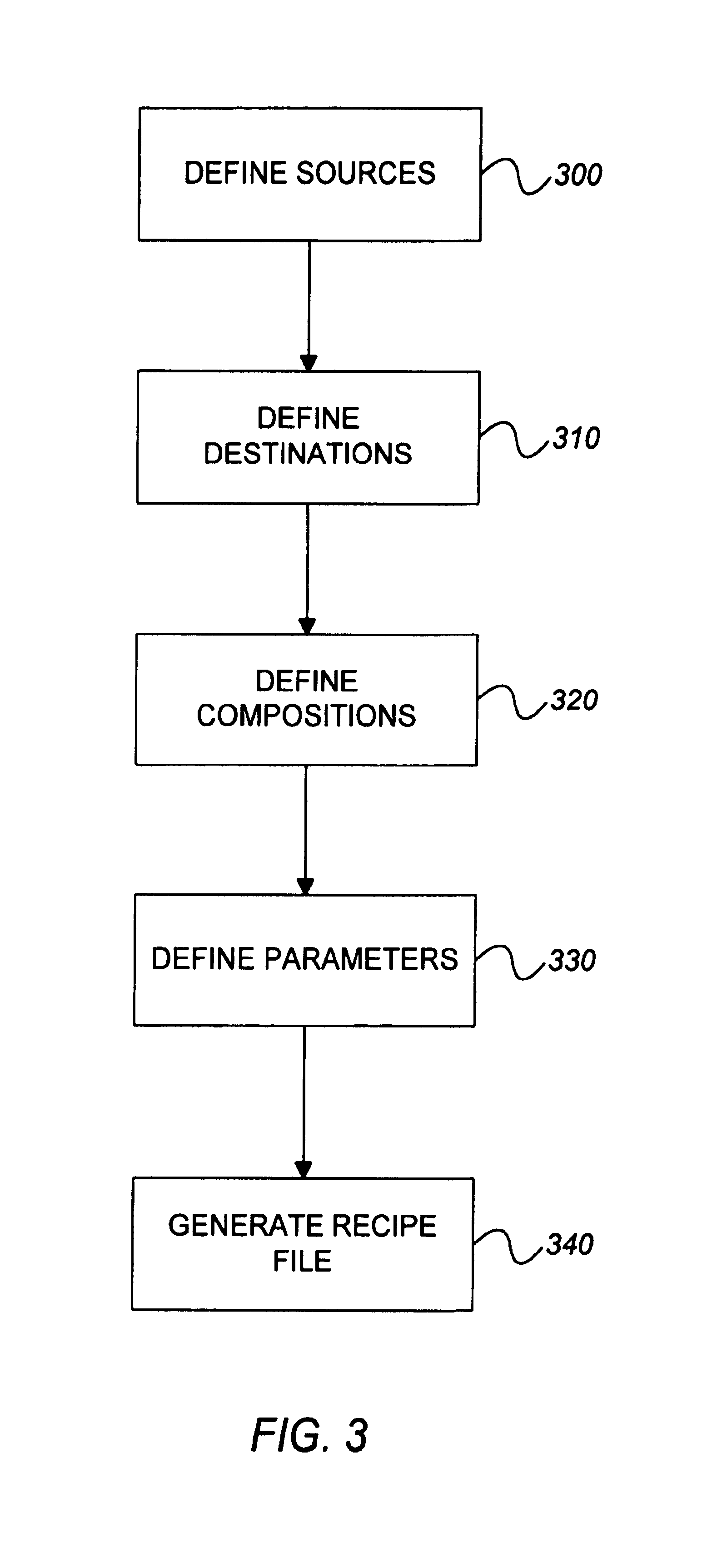
Graphic design of combinatorial material libraries
InactiveUS7199809B1Flexible definitionSpeed up library designOrganic chemistry methodsLibrary screeningGraphicsData file
Computer-implemented methods, programs and apparatus for generating a library design for a combinatorial library of materials. A library design includes a set of sources representing components to be used in preparing the combinatorial library, destinations replying arrangements of cells and mappings, defining one or more distribution patterns for assigning components to cells in the destination arrangement or arrangements. Mappings include gradients and sets of user-defined equations, and are used to calculate the amount of on components to be assigned to a cell or cells in an arrangement. A library design can also include one or more process parameters defined to vary over time or across a plurality of destination cells. The invention outputs a data file defining the library design, including electronic data representing the sources, the destinations and the mapping, in a format suitable for implementing manually or using automated material handling apparatus.
Owner:UNCHAINED LABS
Method and system for presenting banners having direct link to user profile information
A method and system for generating electronic advertisement, such as banner ads, based on user profile information and other information are disclosed. An online promotion service may receive profile information, location information and other information from a user. The user may also define a proximity preference which may include a range of distance the user is willing to travel to redeem one or more promotions. A service or product provider or other authorized entity may define a proximity preference which may include a target range of advertisement exposure. The online promotion service may present advertisements for incentives and other promotions based on user profile information as well as proximity preference information where the proximity preference is defined by the user, the provider, or both. The user may activate a user identifier displayed on the advertisement which provides a direct link to user profile information to enable the user to easily and quickly modify and update user profile information.
Owner:CATALINA MARKETING CORP
System and method for restoring a single data stream file from a snapshot
InactiveUS7165079B1Facilitate additionFast dataInput/output to record carriersData processing applicationsInodeData stream
The present invention provides a system and method for restoring a single data stream file from a snapshot without the need to copy every individual block or inode from the snapshot. A file restore process duplicates the inode of a file within the active file system and performs a reconciliation process between the blocks of the twin inode and the snapshot inode. If the file does not exist within the active file system, a new buffer tree is created that points to the data blocks stored in the snapshot.
Owner:NETWORK APPLIANCE INC
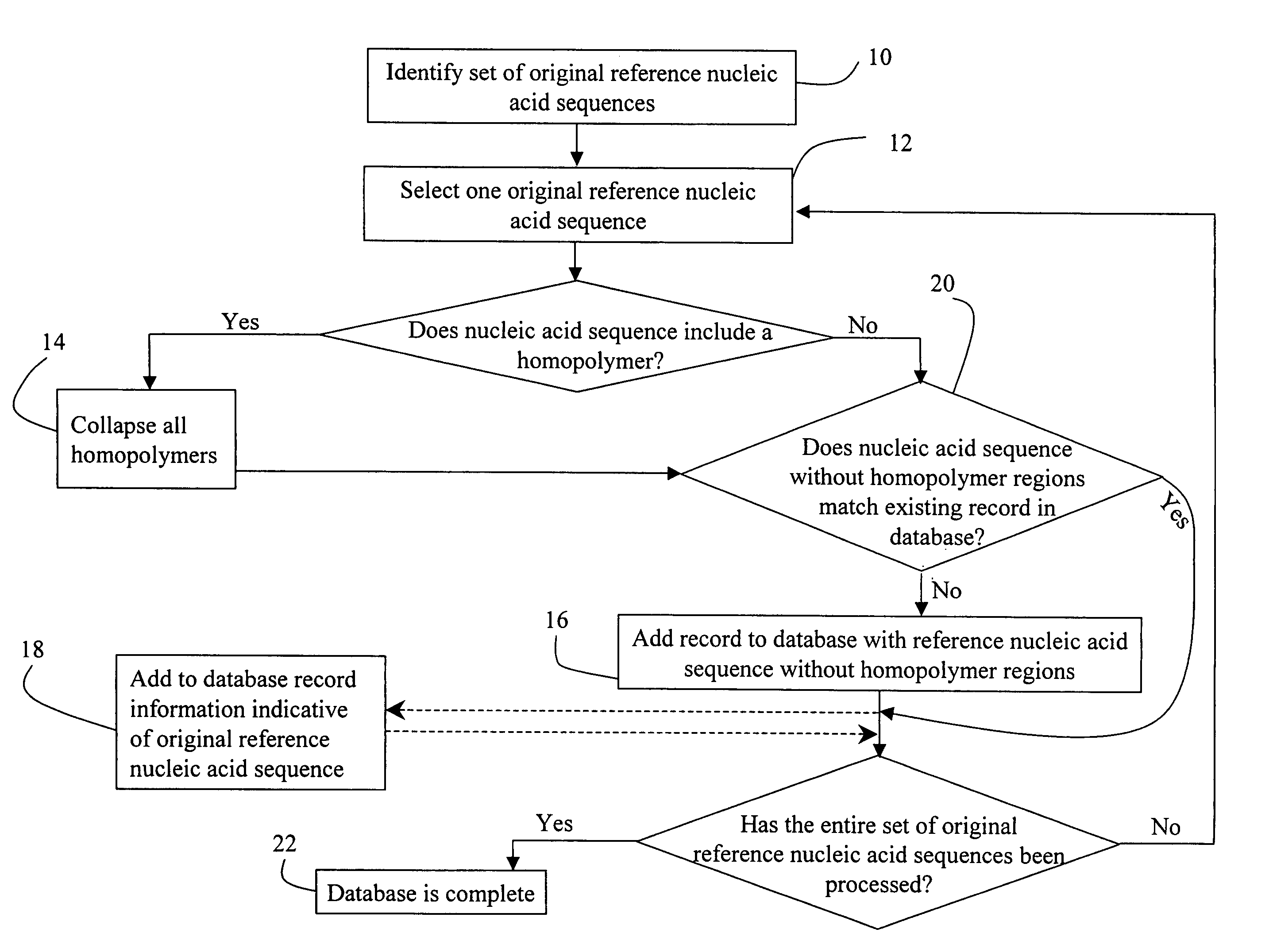
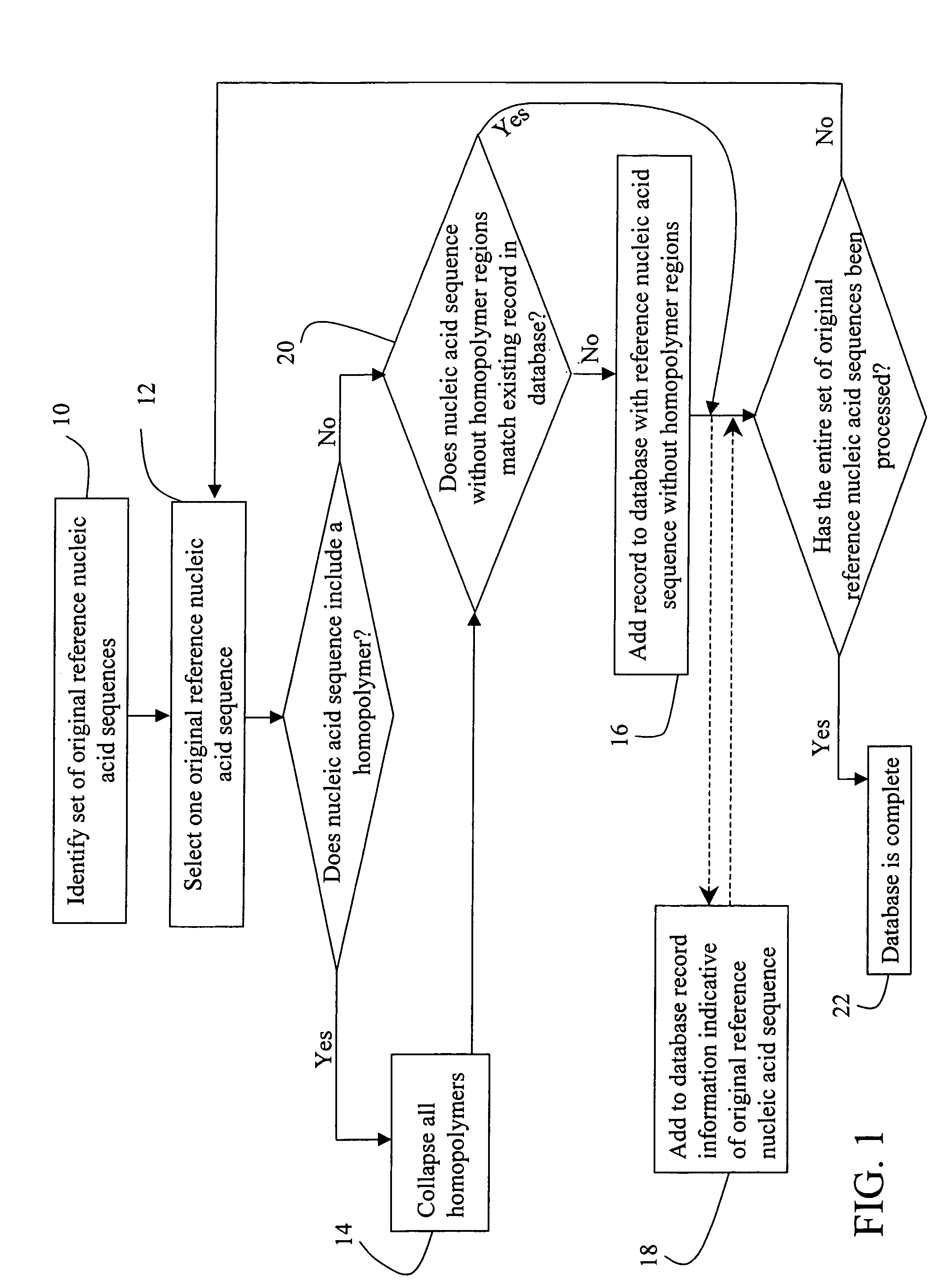
Nucleic acid analysis
InactiveUS7424371B2Data amountSmall sizeMicrobiological testing/measurementComputation using non-denominational number representationNucleic acid sequencingNucleic acid sequence
A sample nucleic acid sequence is compared against a database to find a matching sequence. In one embodiment, this comparison is accomplished with a table look-up approach that involves using sequences with collapsed homopolymer regions.
Owner:FLUIDIGM CORP
Method and system for electronic distribution of incentives having real-time consumer-based directions
ActiveUS20050216337A1Cost-effective mannerAvoid repetitionSpecial data processing applicationsMarketing
A method and system for electronic distribution of incentives having real-time consumer-based directions according to another embodiment of the present invention are disclosed. An online promotion service may receive user profile information, which may include demographic information, location information, user preferences, user requests, and other information. Online promotion service may provide targeted incentives and promotions to a particular user or class of users based on user profile information and other information. Incentives may include coupons, promotions, rebates, sales notifications, free samples, and other product or service related incentives. A map and street directions identifying the location of associated facilities, such as redemption and retail / point-of-sale facilities, from a user's location may also be provided. The user's location may be identified as the user's home address, work address, or other convenient locations.
Owner:CATALINA MARKETING CORP
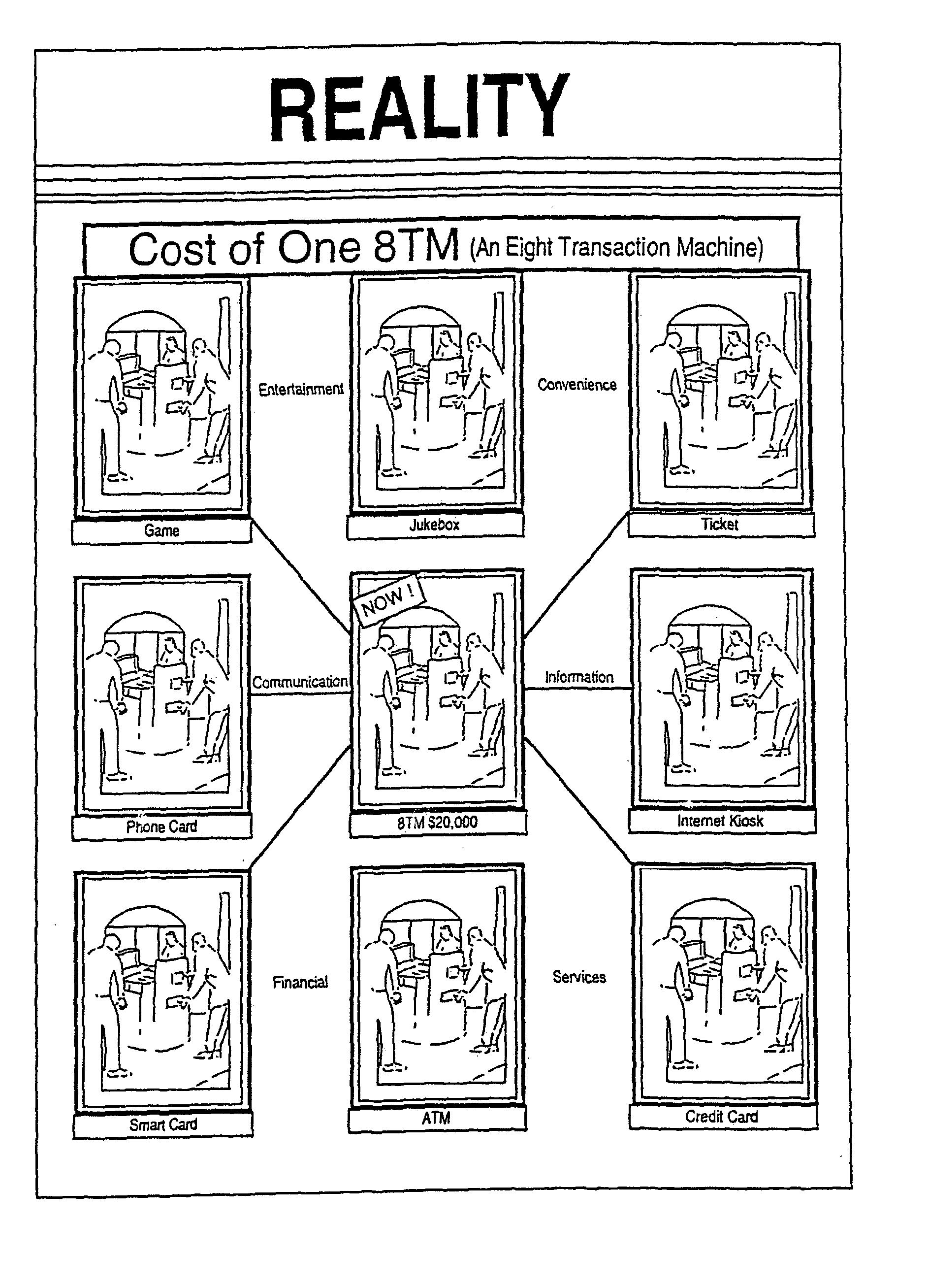
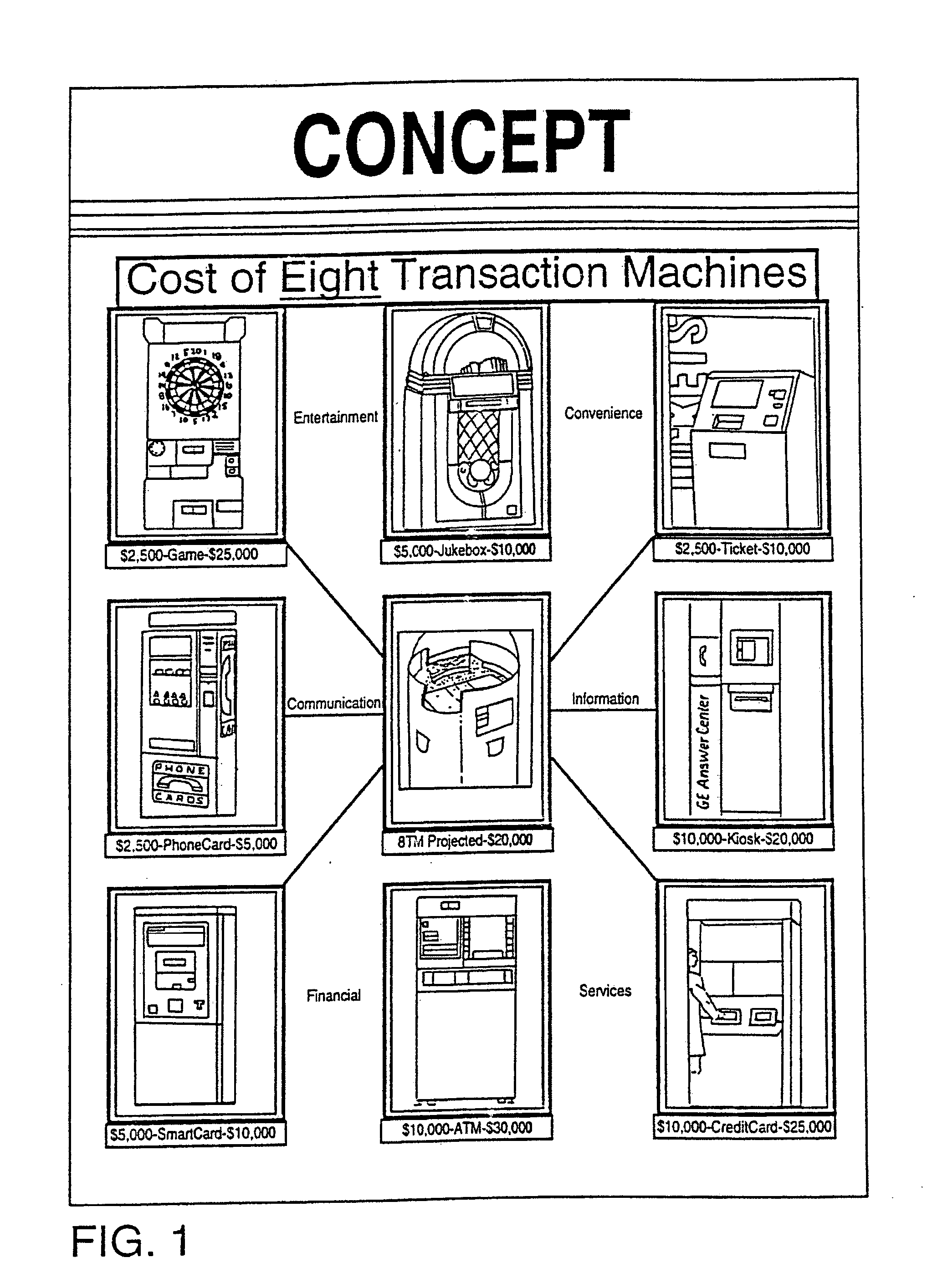
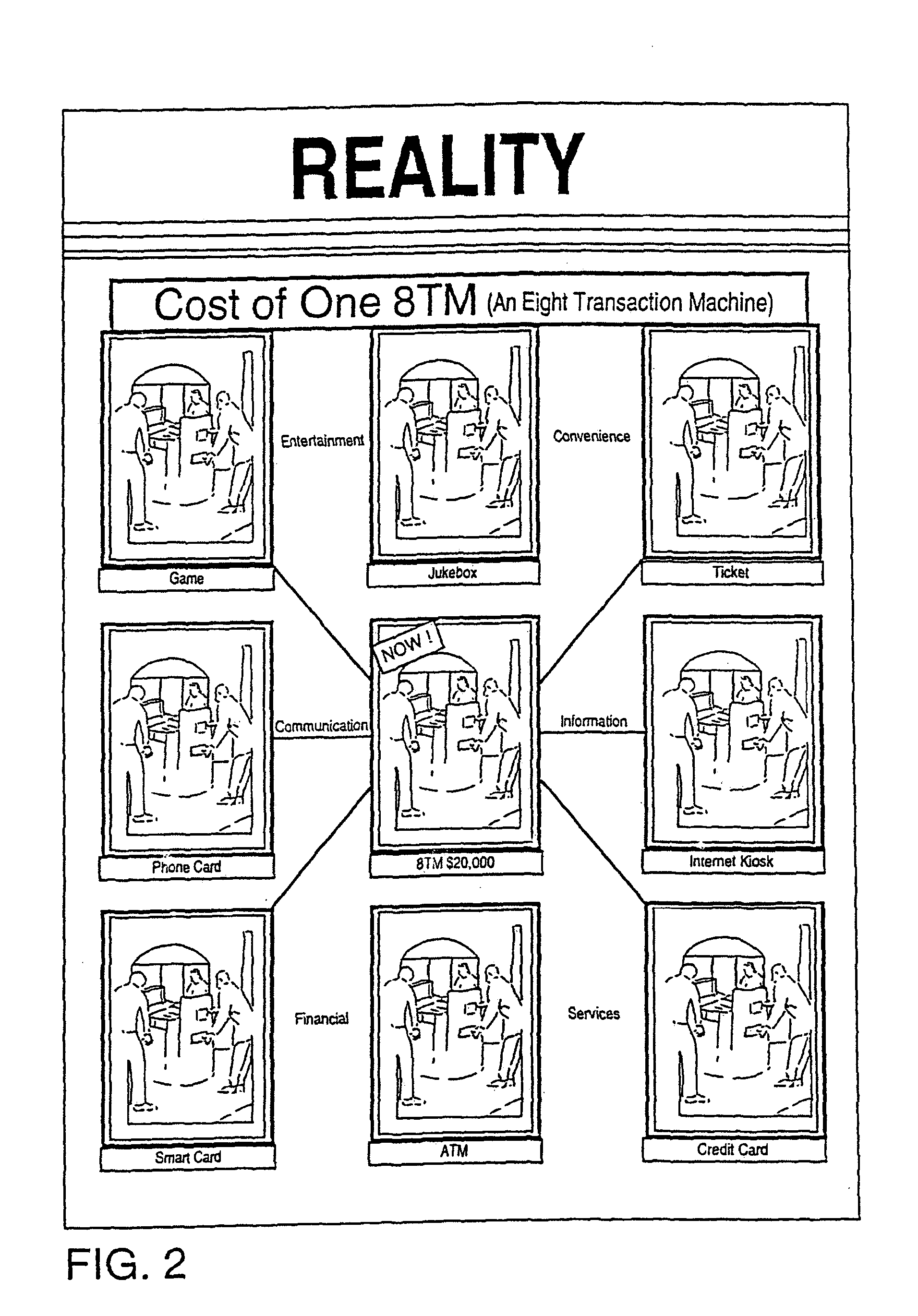
Automated transaction machine
An automated retail terminal in which a plurality of goods and / or services are provided in an integrated system. The integrated system generally avoids duplicating hardware or functions in the course of delivering the goods or services offered, so for example in a combination ATM and Internet kiosk the same credit card or smart card reader is used for both the ATM and the Internet kiosk functions, the same control screen activates the ATM functions and the Internet functions, and etc.
Owner:TRANSACTION HLDG L L C
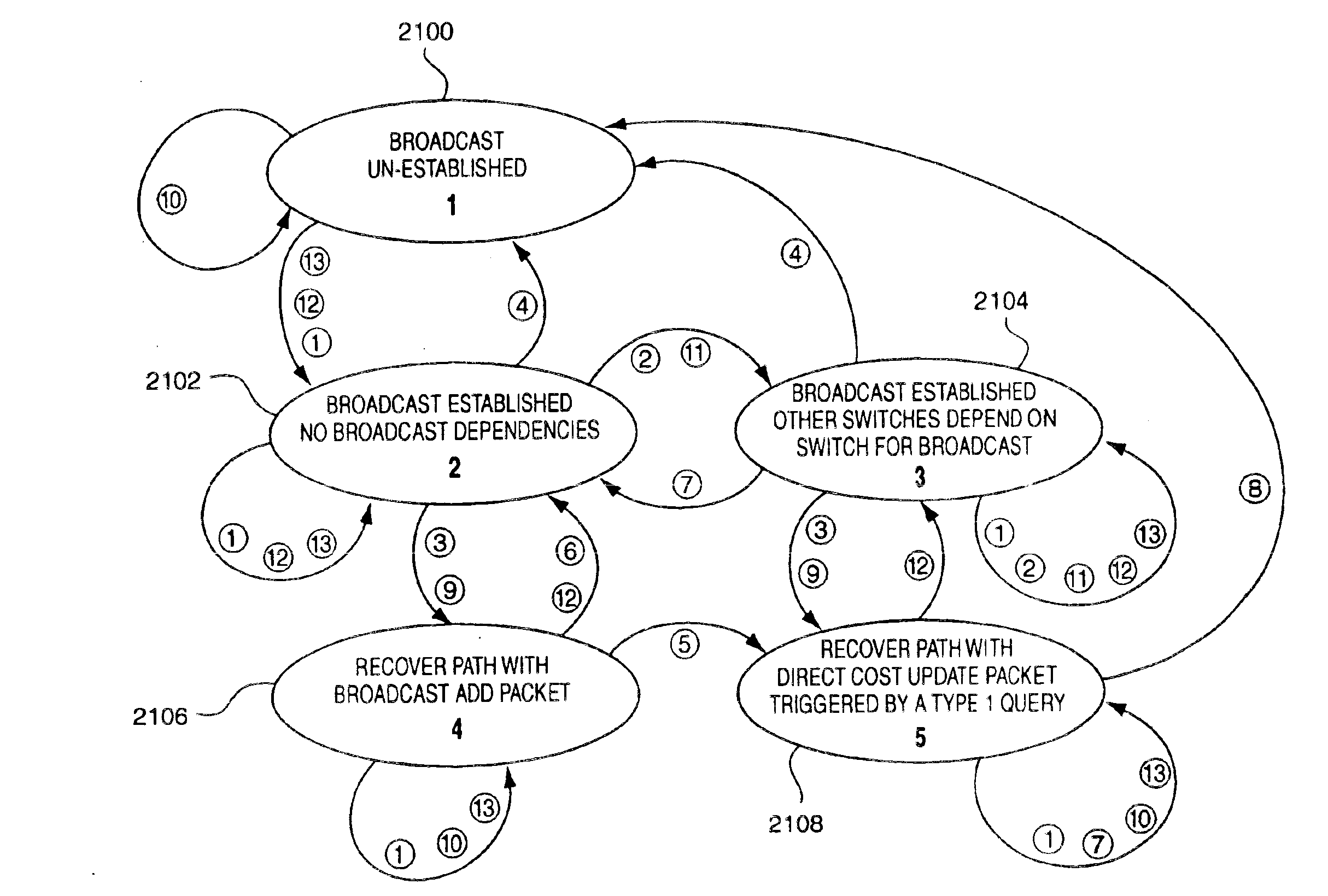
Broadcast tree determination in load balancing switch protocols
InactiveUS6865160B1Increase profitImprove scalabilitySpecial service provision for substationData switching by path configurationNetwork generationNetwork switch
A method for generating and maintaining a pruned broadcast tree for a network of switches operating multiple simultaneously active paths between devices with a load balancing family of protocols. The pruned broadcast tree is preferably generated as a by product of cost propagation aspects of the load balancing protocols exchanged among cooperating network switches. The load balance protocols operable within the network switches in association with the present invention permit multiple simultaneously active paths to be utilized among the network devices. The pruned broadcast tree is therefore used to reduce the latency of broadcast messages propagated within the network switches to reach all devices in the network. The broadcast tree defines a minimized set of devices to which a broadcast message need be forward to assure transmission to all network devices. The pruned broadcast tree, once established, is updated only in response to failure of a link and recovery of a failed link. A separate protocol of the present invention enables such pruned broadcast tree modifications and restoration.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Bar code reading device having image processing mode
InactiveUS20050167504A1Conveniently providedCorrect distortionCharacter and pattern recognitionSensing by electromagnetic radiationImaging processingComputer graphics (images)
The invention relates to a system for processing image data corresponding a scene comprising an imaging device and an image reading instruction indicia. In accordance with the invention, image data corresponding to a scene comprising an image reading instruction indicia is processed in a manner that depends on features of the image reading instruction indicia. If the image reading instruction indicia is of a type whose size, scaling, orientation, and distortion can be determined, scaling, orientation, and distortion characteristics determined from the image reading instruction indicia can be used to improve the image reading process.
Owner:HAND HELD PRODS
System and method for restoring a virtual disk from a snapshot
ActiveUS7076509B1Substantial overheadBig spaceInput/output to record carriersData processing applicationsInode
The present invention provides a system and method for restoring a vdisk from a snapshot without the need to copy every individual block or inode from the snapshot. A vdisk restore process duplicates the inode of a vdisk within the active file system and performs a reconciliation process between the blocks of the twin inode and the snapshot inode. If the vdisk does not exist within the active file system, a new buffer tree is created that points to the data blocks stored in the snapshot.
Owner:NETWORK APPLIANCE INC
Multiplayer handheld computer game system having tiled display and method of use
InactiveUS20090280905A1Prevent transferLarge effective screenVideo gamesSpecial data processing applicationsDisplay deviceComputer game
A multiplayer handheld game employs individual game units having individual displays. Players can prepare their moves in secret on their game unit using controls and the individual displays, but when the game units are joined together, the game plays out on the aggregated screen. The game units employ digital signatures to ensure that all play is fair and that the virtual game pieces and characters in play have not been doctored or are otherwise fraudulent. Game results can be uploaded to a remote, secure server, which also serves as a backup for user data. Customization, improvements, and additions to the virtual game pieces and characters can be performed in conjunction with the secure server.
Owner:WEISMAN JORDAN K +1
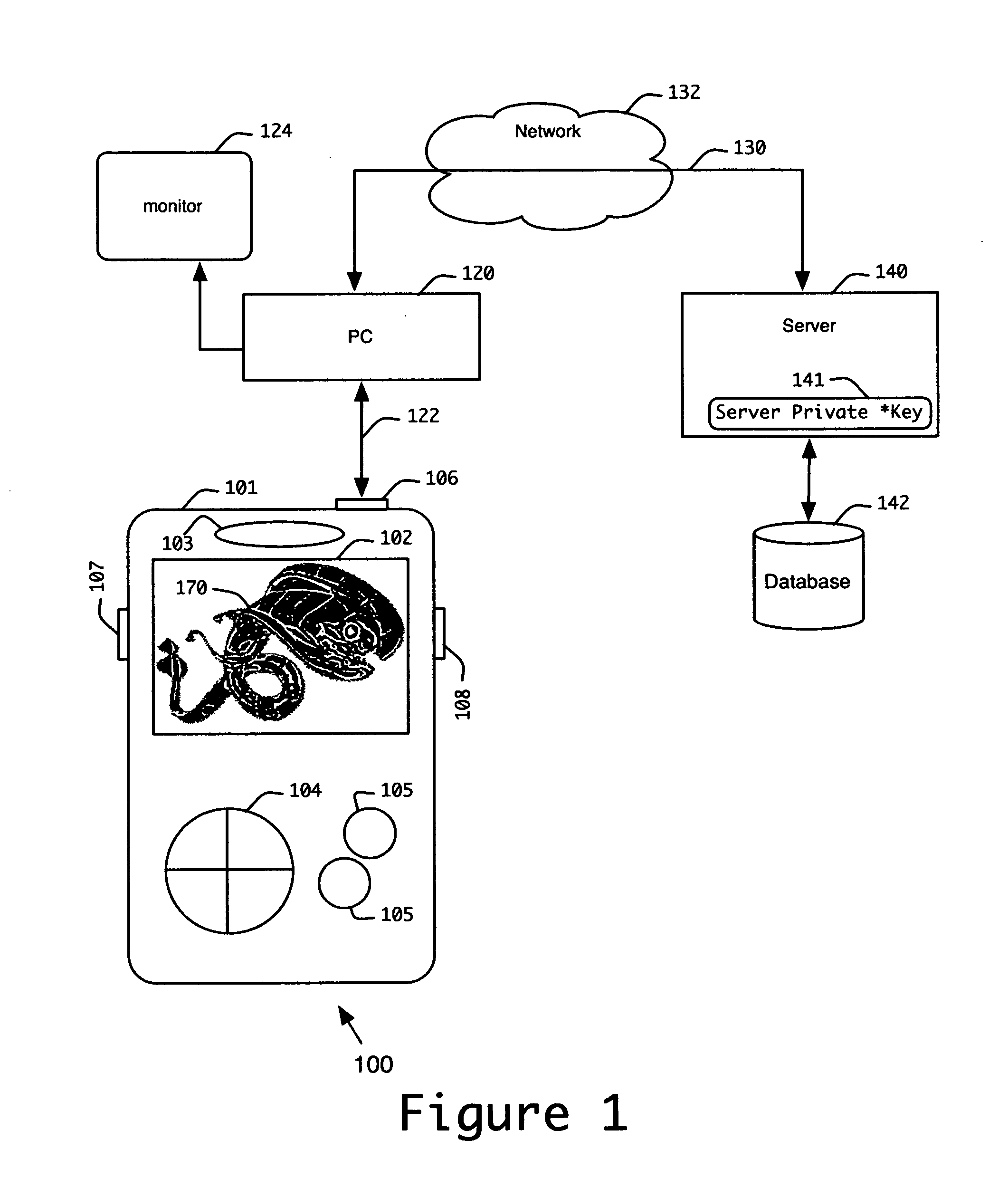
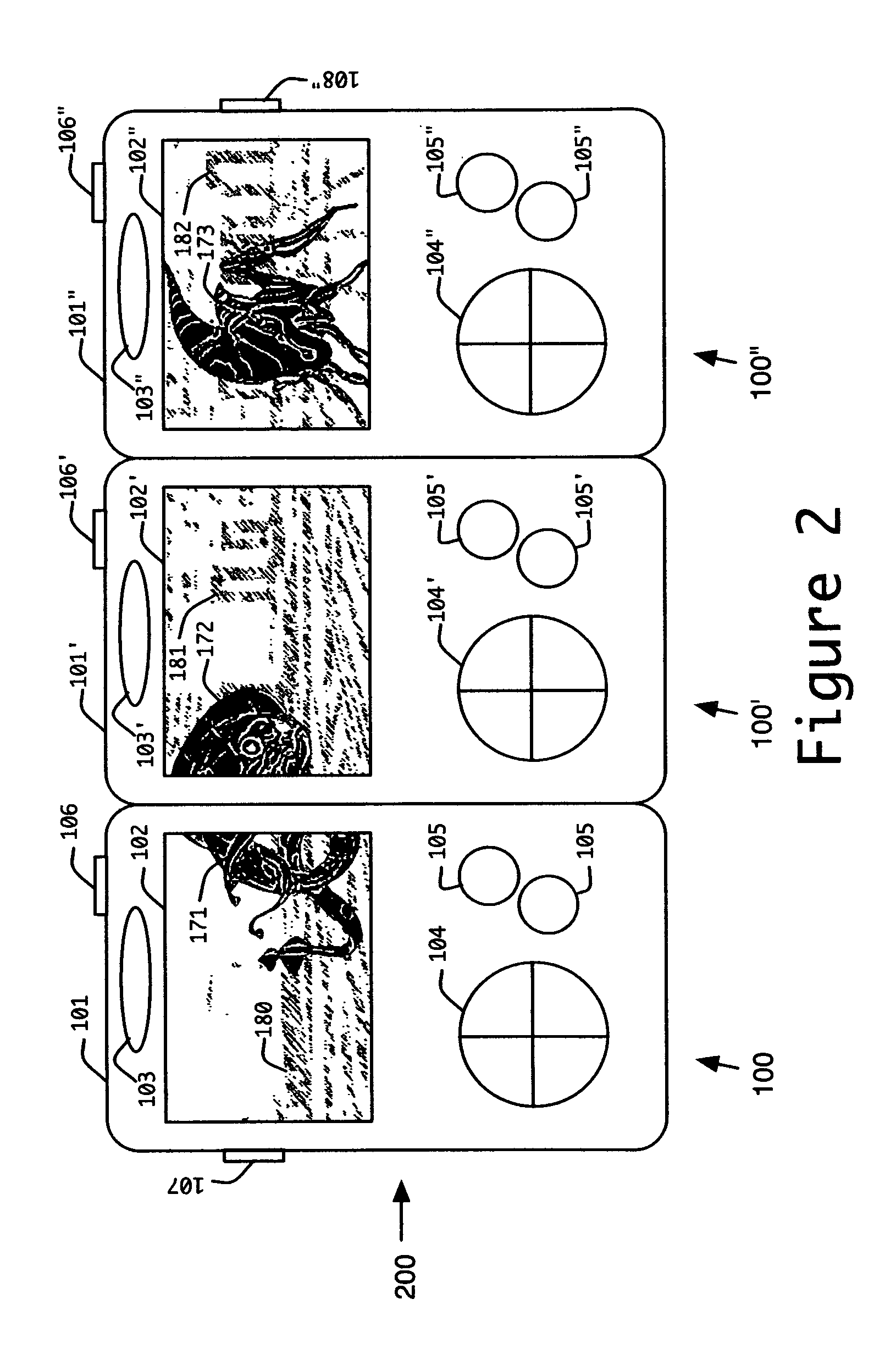
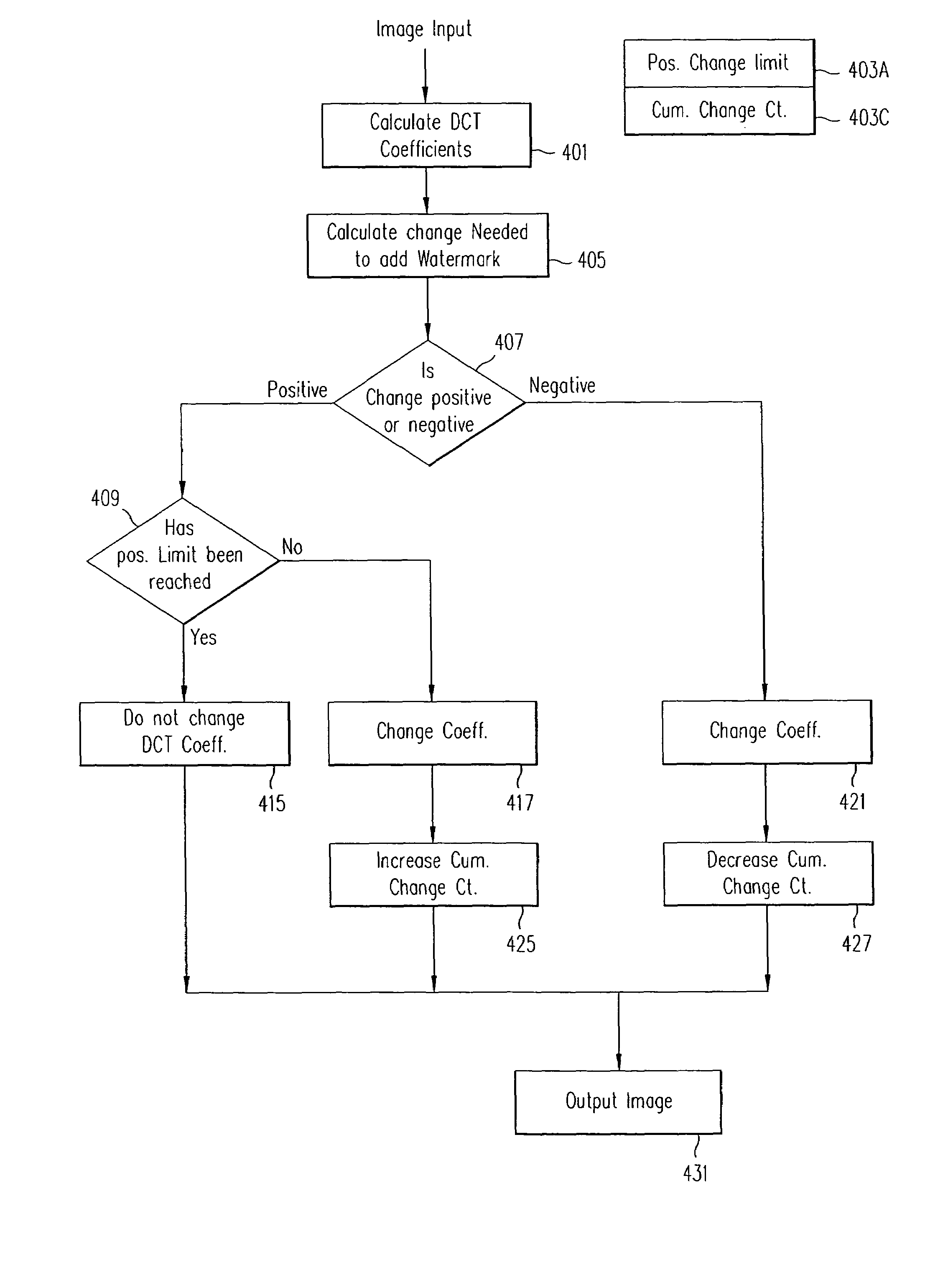
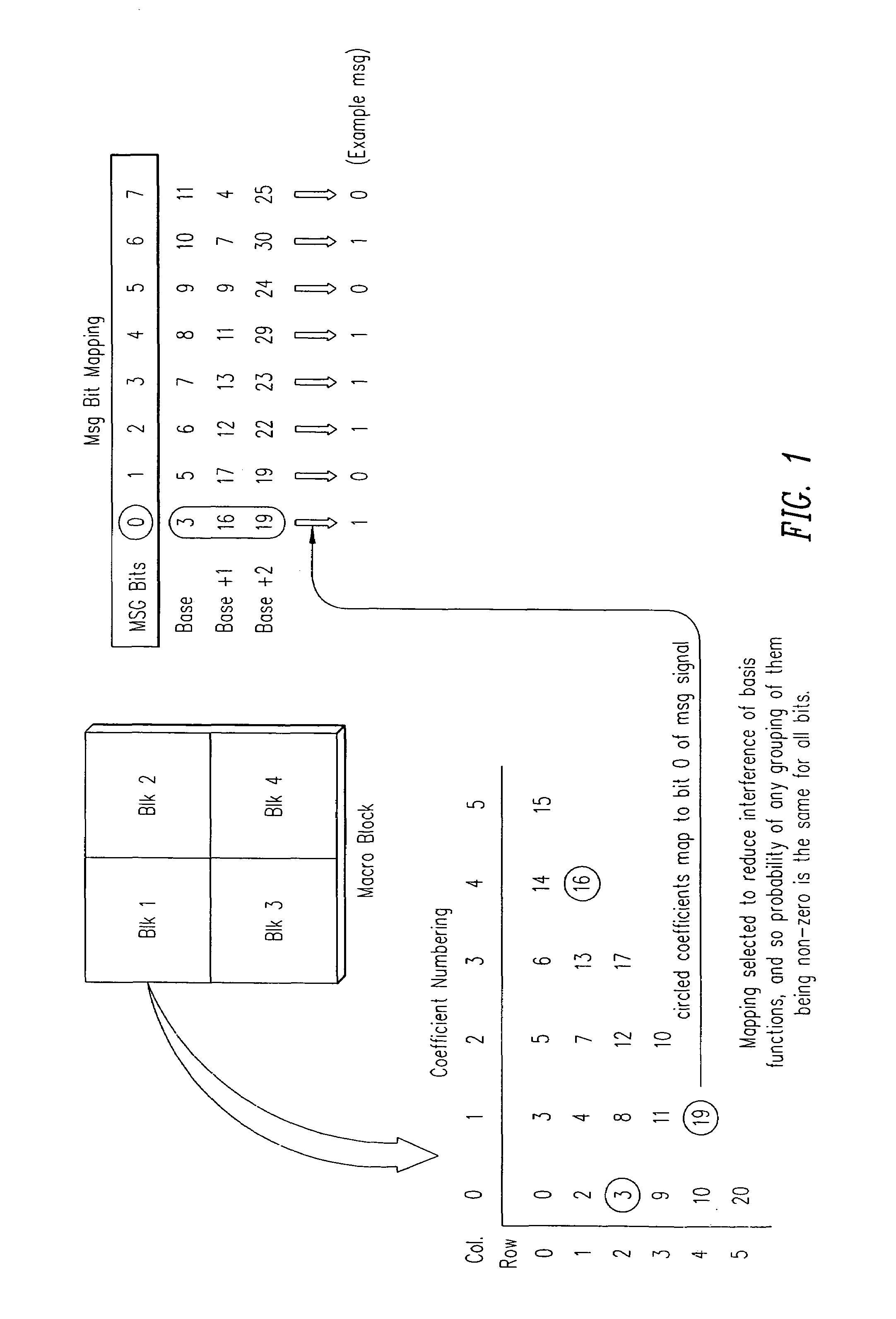
Transform domain watermarking of image signals
InactiveUS7139408B2Increased incentives for both casual and professional unauthorized copyingAvoid repetitionTelevision system detailsSpeech analysisJPEGImage signal
The invention provides methods and related systems for embedding and detecting watermarks in images, such as JPEG or MPEG formatted images as well as other types of image signals. One method receives transform coefficients of the image, and changes the value of selected coefficients to embed watermark data in the coefficients. The changing of the coefficients is controlled such that it both embeds the data and forms an orientation signal that facilitates determination of rotation or scale of the image. Another aspect of the invention is a variation of embedding a watermark in an image. This method receives message bits to be embedded in the image, receives transform coefficients of the image, and maps the message bits to selected transform coefficients. The method changes the value of selected coefficients to embed data in the coefficients. The characteristics of the image are used to control the change of transform coefficients to embed the watermark, and a bit rate control is used to modify the change of transform coefficients to embed the watermark according to a bit rate limit.
Owner:DIGIMARC CORP
Method for managing and accessing relational data in a relational cache
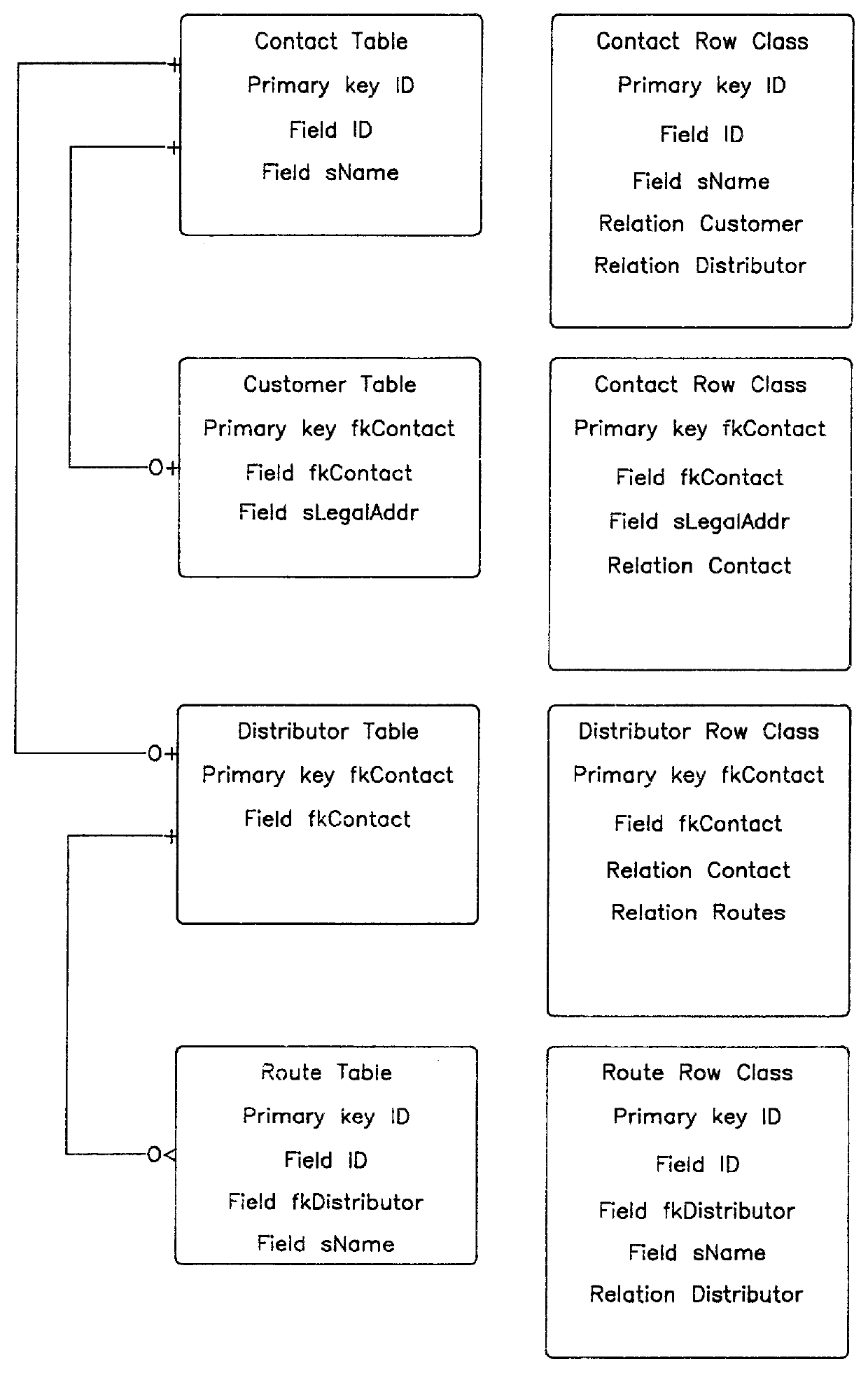
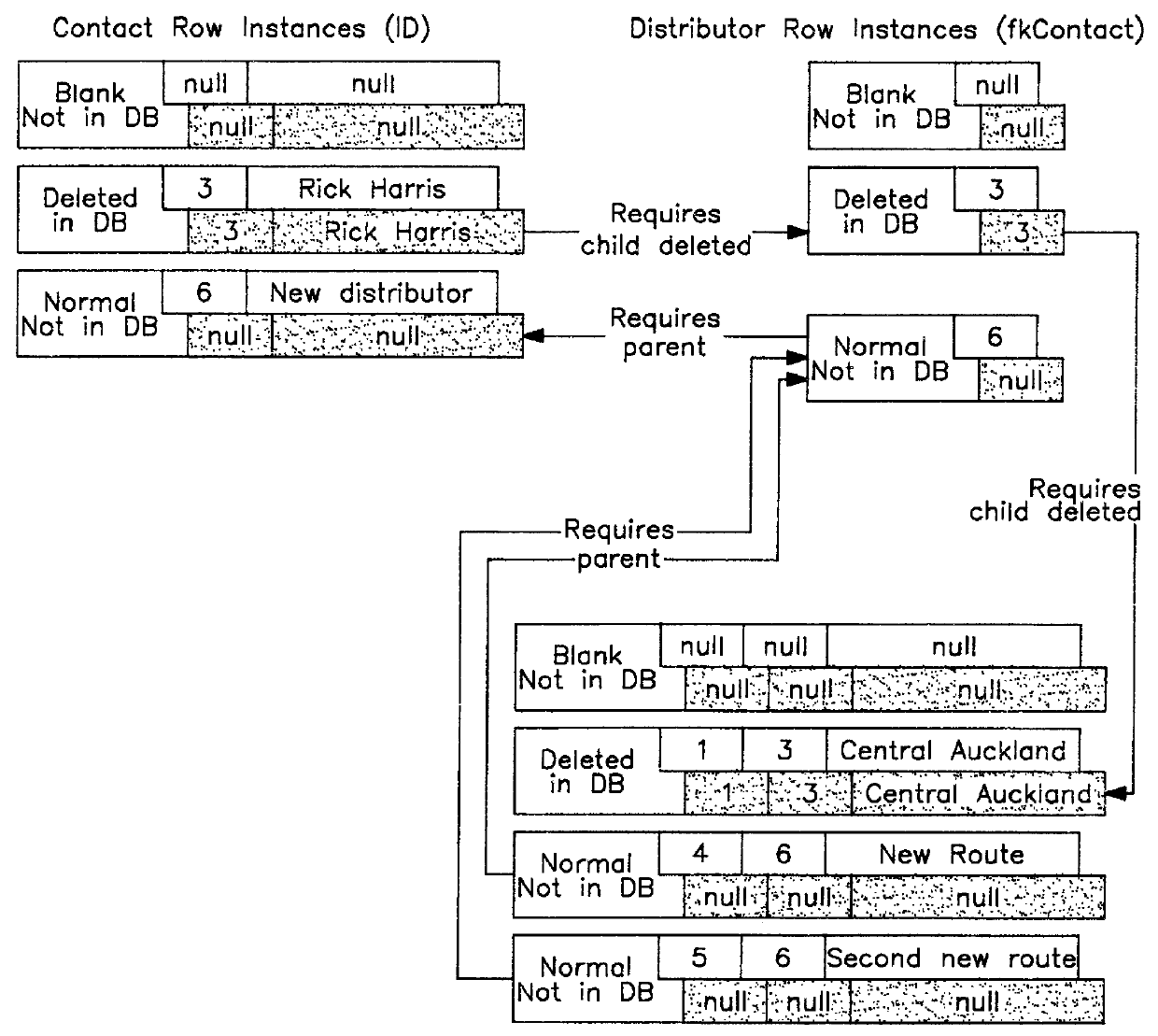
InactiveUS6070165AAvoid repetitionEasy accessData processing applicationsRelational databasesObject basedApplication software
For an object-based application being executed in a digital computing system a framework is provided for managing information retrieved from a structured database, such as a relational database. The processor is used to construct a single cohesive data structure, called a relational cache, that comprises all the row instances and that represents information retrieval from the structured database in a form suitable for use by one or more applications. An application may have several of these relational caches active at any one time, some of which may represent separate user editing sessions, where each session may be saved or discarded independently. The framework ensures that only one copy of a row instance is in a given cache at any given time, even if several different queries return the same information from the database. Row instances within the relational cache may be modified by the application, where the row instances are marked as modified but not saved to the database at that time. The framework ensures all modified row instances within the cache are saved at one time, which are presented to the database as a single transaction, with individual rows ordered so as not to violate database referential integrity rules. Other properties of the framework are disclosed.
Owner:WHITMORE THOMAS JOHN
Identity-based encryption system
ActiveUS20080148047A1Avoid repetitionPublic key for secure communicationUser identity/authority verificationSecure communicationKey generator
A system is provided that uses identity-based encryption to support secure communications. Messages from a sender to a receiver may be encrypted using the receiver's identity and public parameters that have been generated by a private key generator associated with the receiver. The private key generator associated with the receiver generates a private key for the receiver. The encrypted message may be decrypted by the receiver using the receiver's private key. The system may have multiple private key generators, each with a separate set of public parameters. Directory services may be used to provide a sender that is associated with one private key generator with appropriate public parameters to use when encrypting messages for a receiver that is associated with a different private key generator. A certification authority may be used to sign directory entries for the directory service. A clearinghouse may be used to avoid duplicative directory entries.
Owner:MICRO FOCUS LLC
Method and system for generating real-time directions associated with product promotions
ActiveUS20060089878A1Cost effectiveAvoid repetitionDiscounts/incentivesNavigation instrumentsWeb siteData pack
A method and system for generating customized incentives involving electronic distribution of coupons to remote personal computers based on proximity of the computer to a retail center are disclosed. A repository, such as an online service provider or a web site on the Internet, stores packages of incentive data for downloading automatically or on demand to a user's computer. A plurality of data fields is used to associate a user's location with a specific incentive. The incentive data corresponds to remote user computers in a predetermined geographic area. Means for identifying remote user computers in a predetermined geographic area and means for providing direction data, such as maps, etc. to the remote user computer are disclosed.
Owner:CATALINA MARKETING CORP
Error problem database system for student
InactiveCN101477755ASame review timeSame energyElectrical appliancesProgram planningStatistical analysis
The invention relates to a false answer bank system comprising a computer system connected to the internet. The computer system comprises an identity authentication module, a false answer database and a central processing module, wherein, the identity authentication module is used for authenticating the identity of a user who logs onto the system and assigning corresponding authorities to different users who log onto the system according to identity; the false answer database used for storing homework questions and answers to the questions, information about whether each question is answered right or not by each student and each class, and information about the amount of questions answered by each student and each class in each assignment or during a fixed learning cycle, accuracy rate and related analytical and statistical data; and the central processing module used for accepting and storing information input a user into the false answer database, and acquiring corresponding analytical and statistical data from the false answer database according to the operation by the user. The system can facilitate the statistical analysis of how a student or a whole class answers to a question and whether the answer is correct or not, so that the invention can provide a basis for setting up a teaching schedule and a learning schedule, and the purpose of improving the learning efficiency of students can be finally fulfilled.
Owner:陈诗周
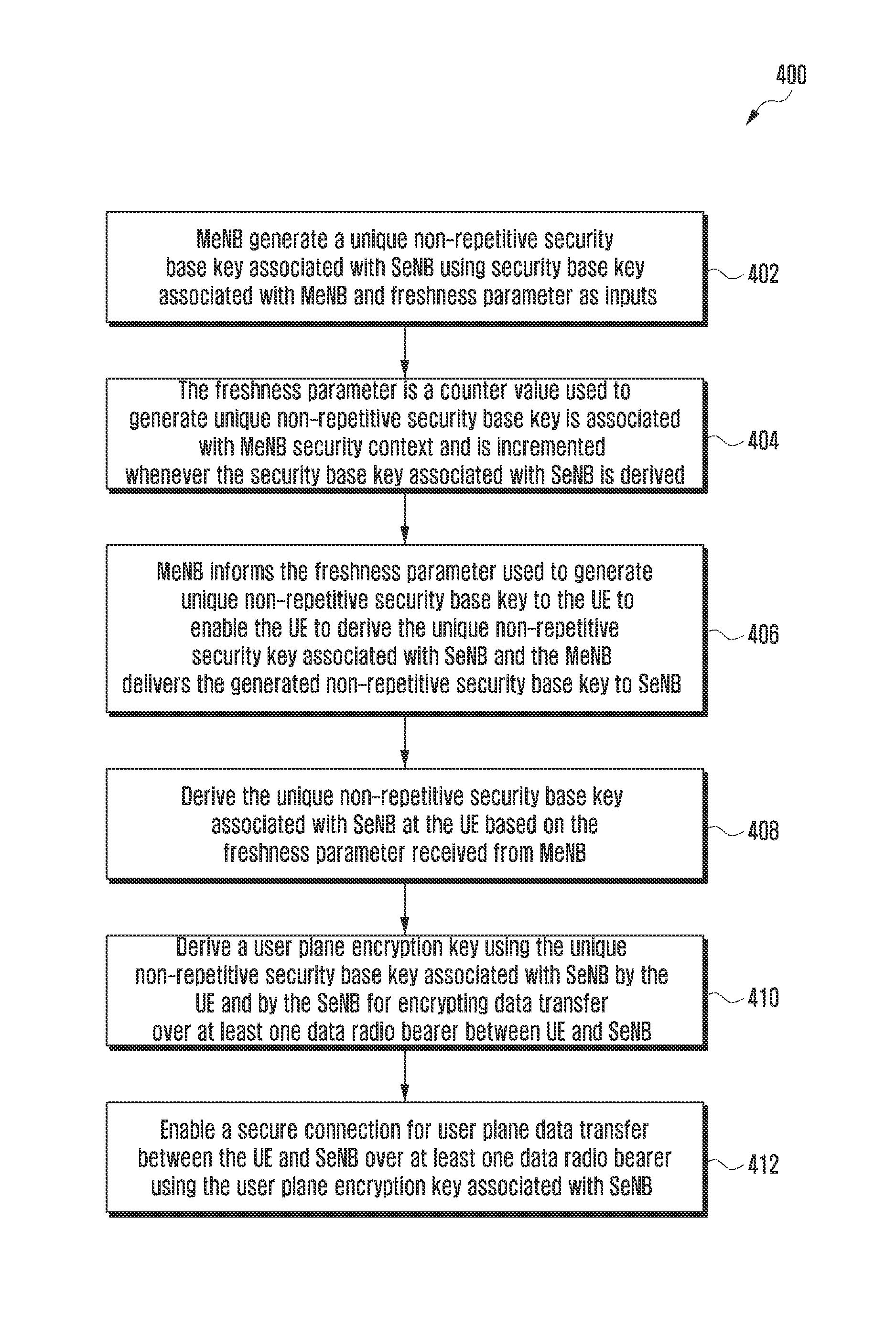
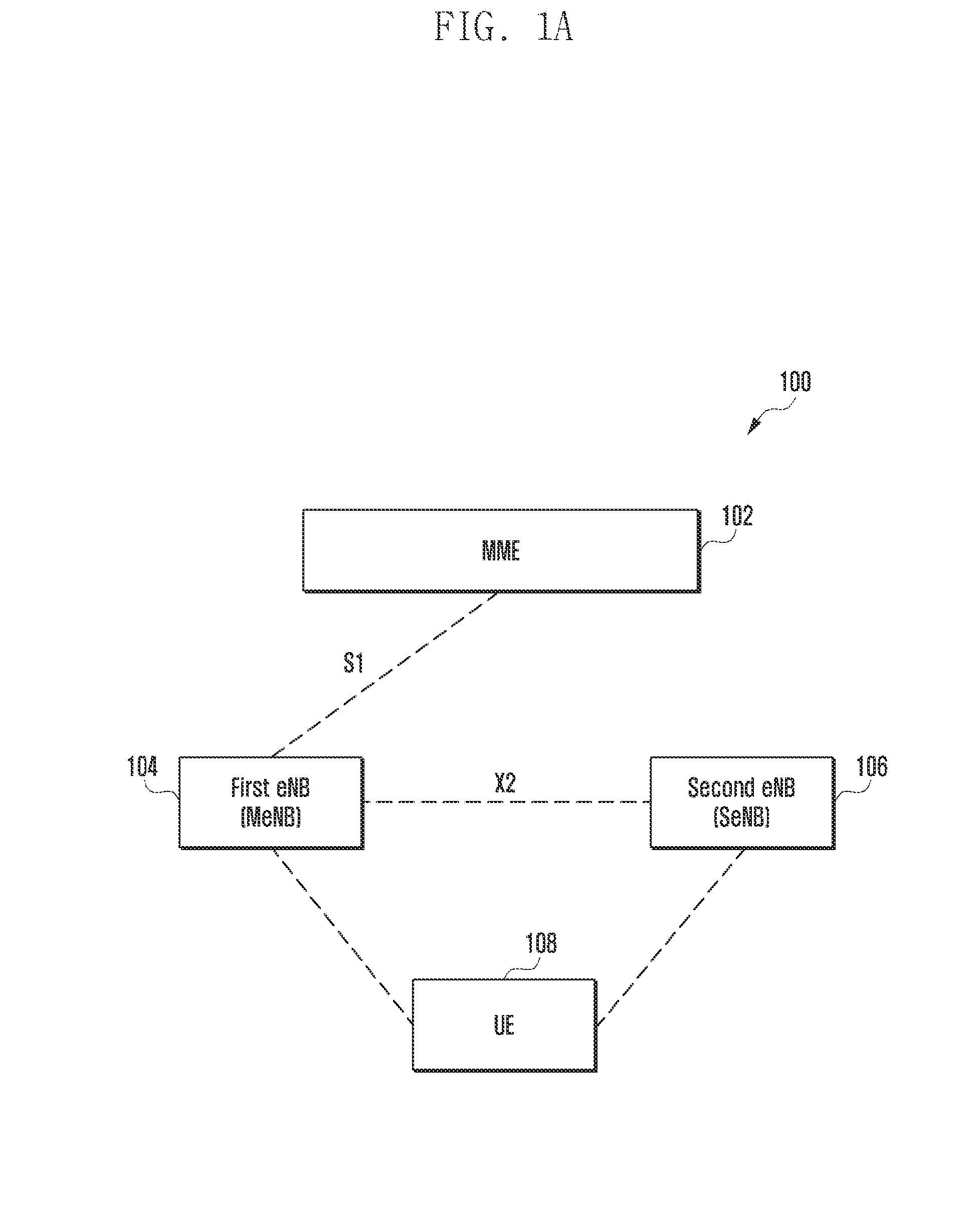
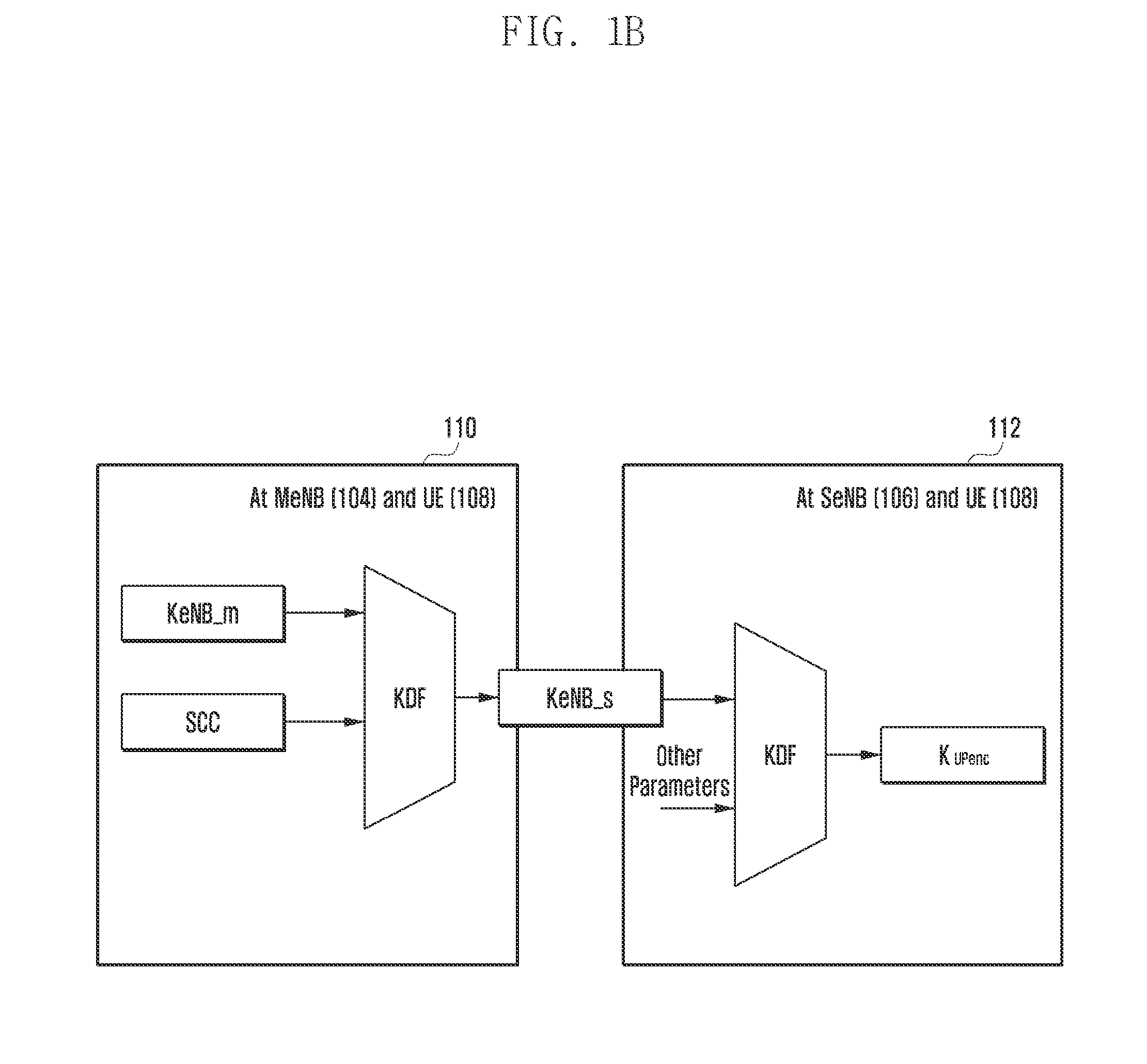
Method and system to enable secure communication for inter-enb transmission
ActiveUS20160029213A1Avoid key stream repetitionConnection securityKey distribution for secure communicationNetwork traffic/resource managementSecure communicationData radio bearer
The embodiments herein provide a method and system for creating a secure connection for a User Equipment (UE) in a wireless network including a UE, carrier aggregated with at least one first serving frequency served by a first eNB and at least one second serving frequency served by a second eNB. A unique non-repetitive security base key associated with the second eNB is generated using a freshness parameter and security key associated with the first eNB. The use of a different freshness parameter for each security base key derivation avoids key stream repetition. Further, a user plane encryption key is derived based on the generated unique non-repetitive security base key associated with the second eNB for encrypting data transfer over at least one data radio bearer.
Owner:SAMSUNG ELECTRONICS CO LTD
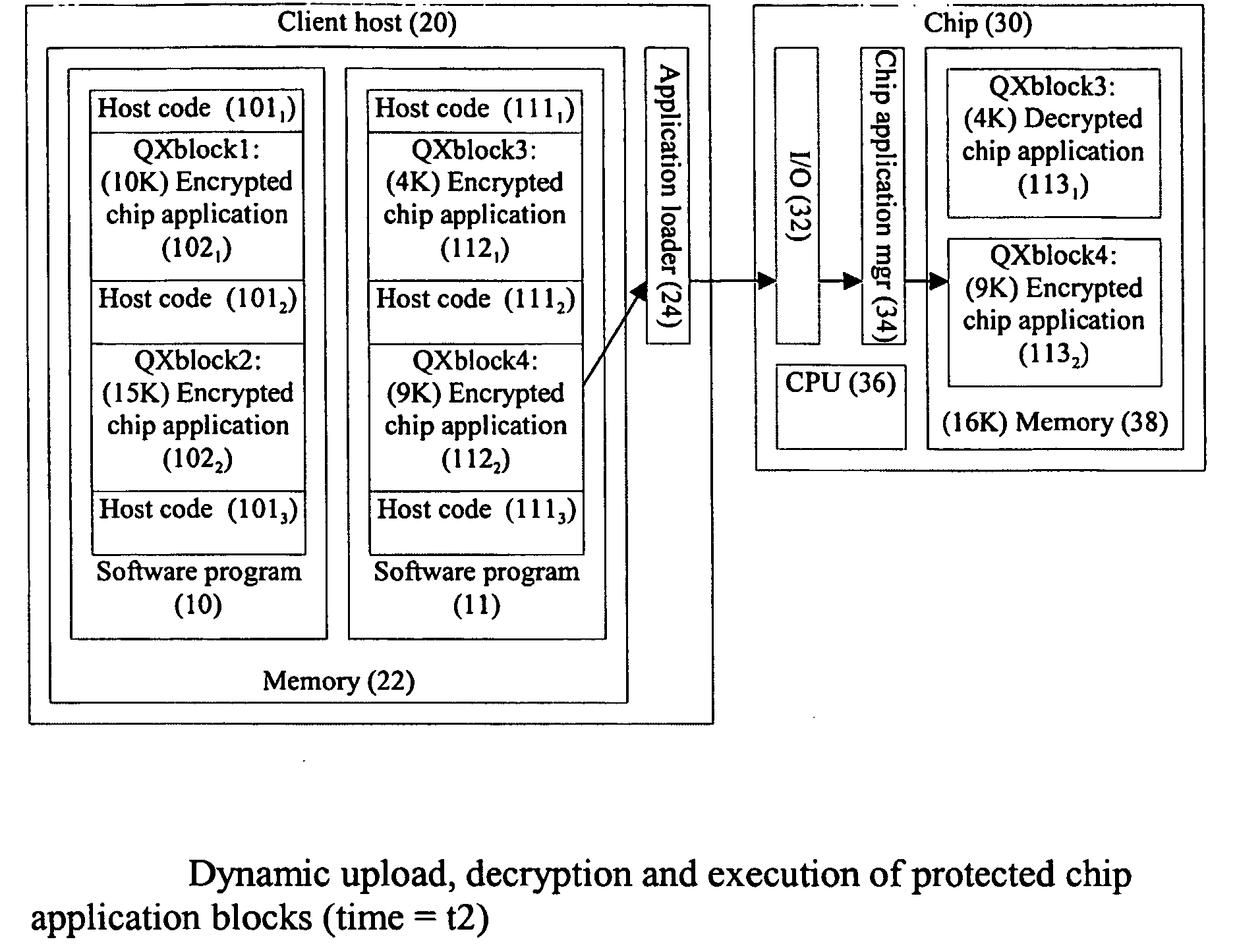
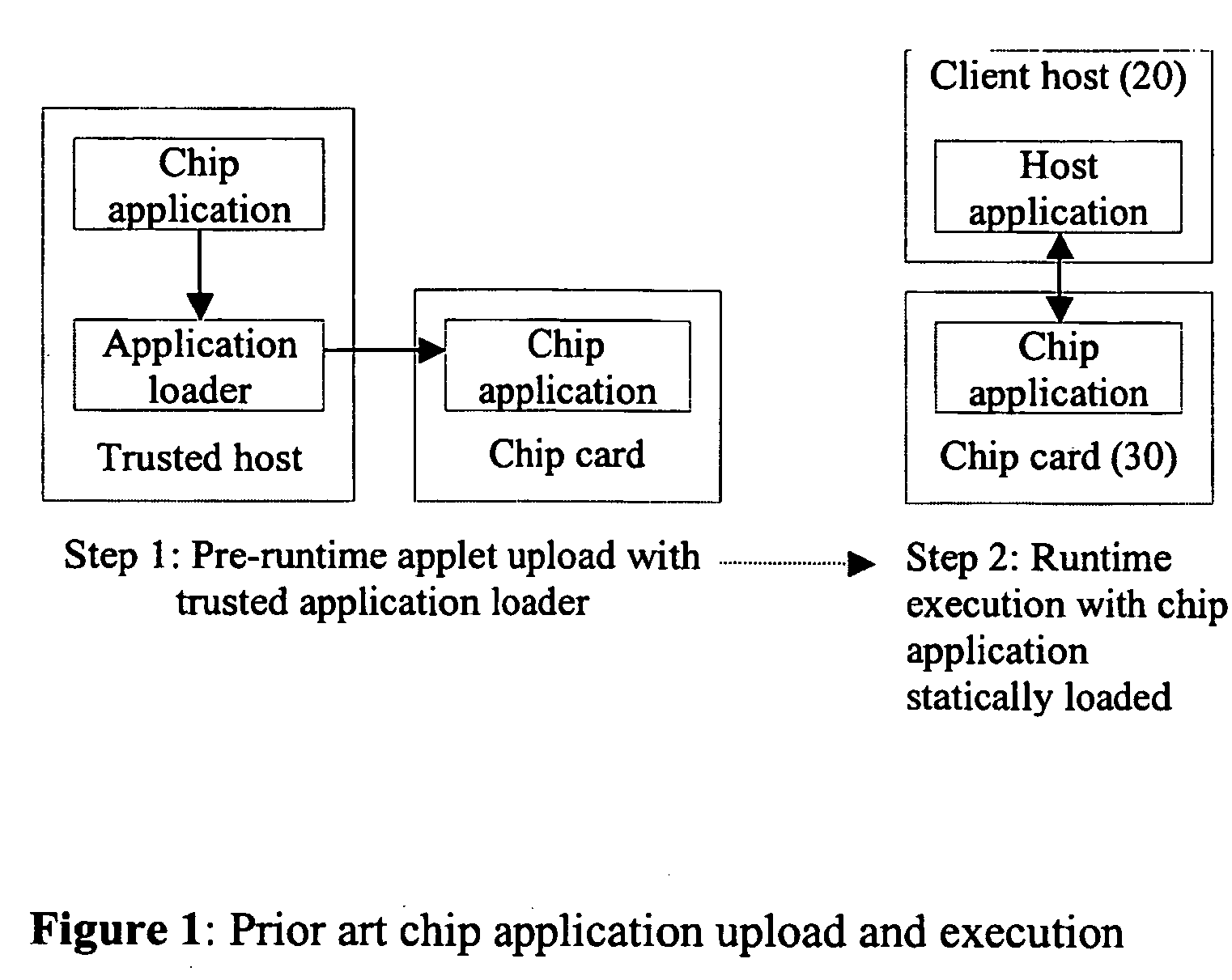
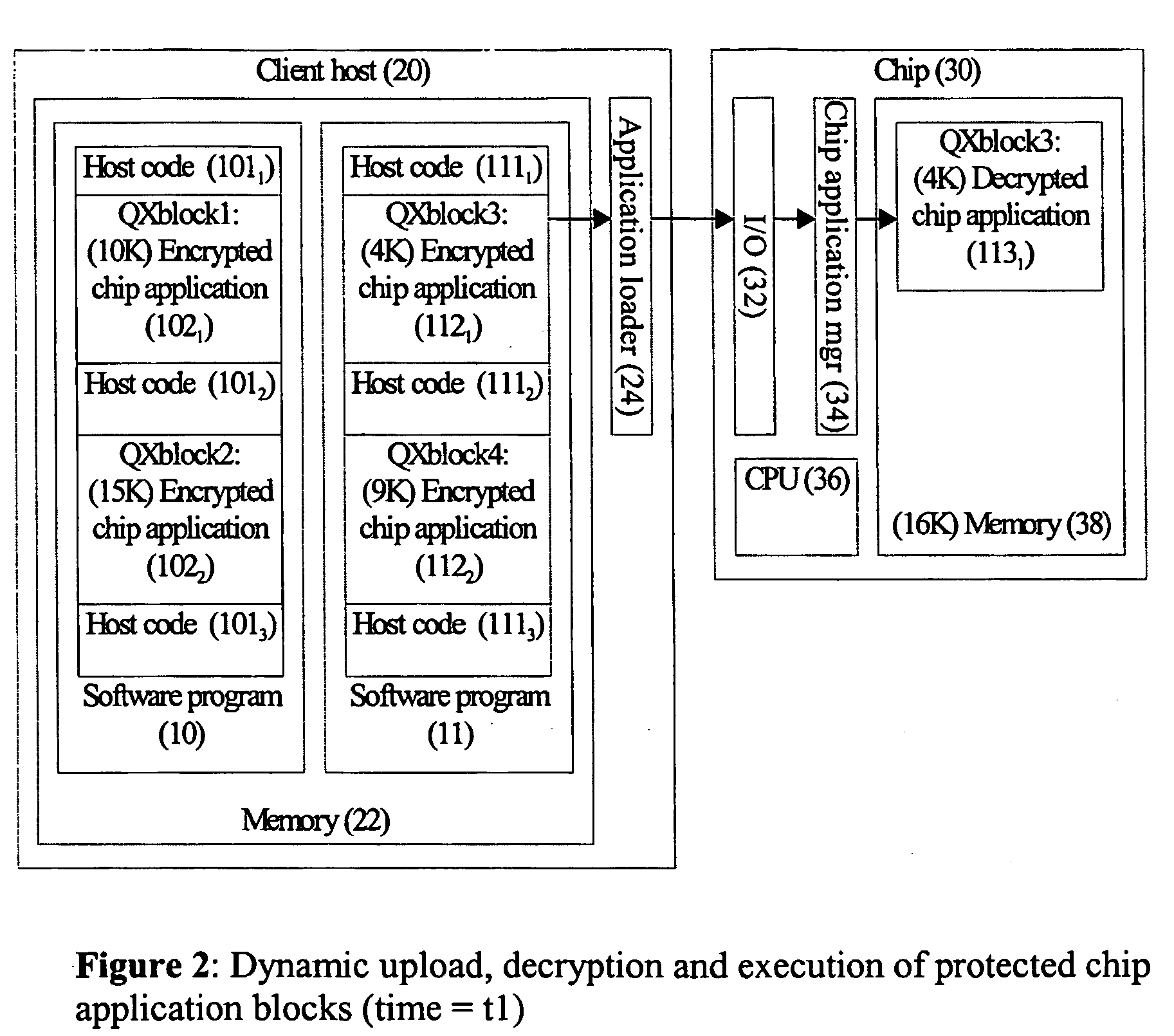
Process for compiling and executing software applications in a multi-processor environment
InactiveUS20060130128A1Avoid repetitionDigital data processing detailsSoftware engineeringMicrocontrollerComputer architecture
The present invention relates to multi-application, secure operating systems for small, secure devices, such as smart card microcontrollers. In particular, the present invention relates to mechanisms for secure runtime upload of applications onto small devices, authorisation mechanisms and the ability for authorised execution of multiple applications on the devices, where an application may be potentially larger than the microcontroller memory size. The mechanism simplifies life-cycle smart card management aspects related to post-issuance application (“applet”) upload and upgrade. Mechanisms to prepare applications (i.e. compiler techniques) using a common set of project files in one compiler toolset, for execution in a dual host & chip processor environment are described. These help automising the programming of the communication interfaces between the host and chip applications. An important motivation for the present invention is to provide a secure co-processor environment for general computer applications in order to counter software piracy, and to allow new models for secure electronic software distribution and software licensing.
Owner:SOSPITA
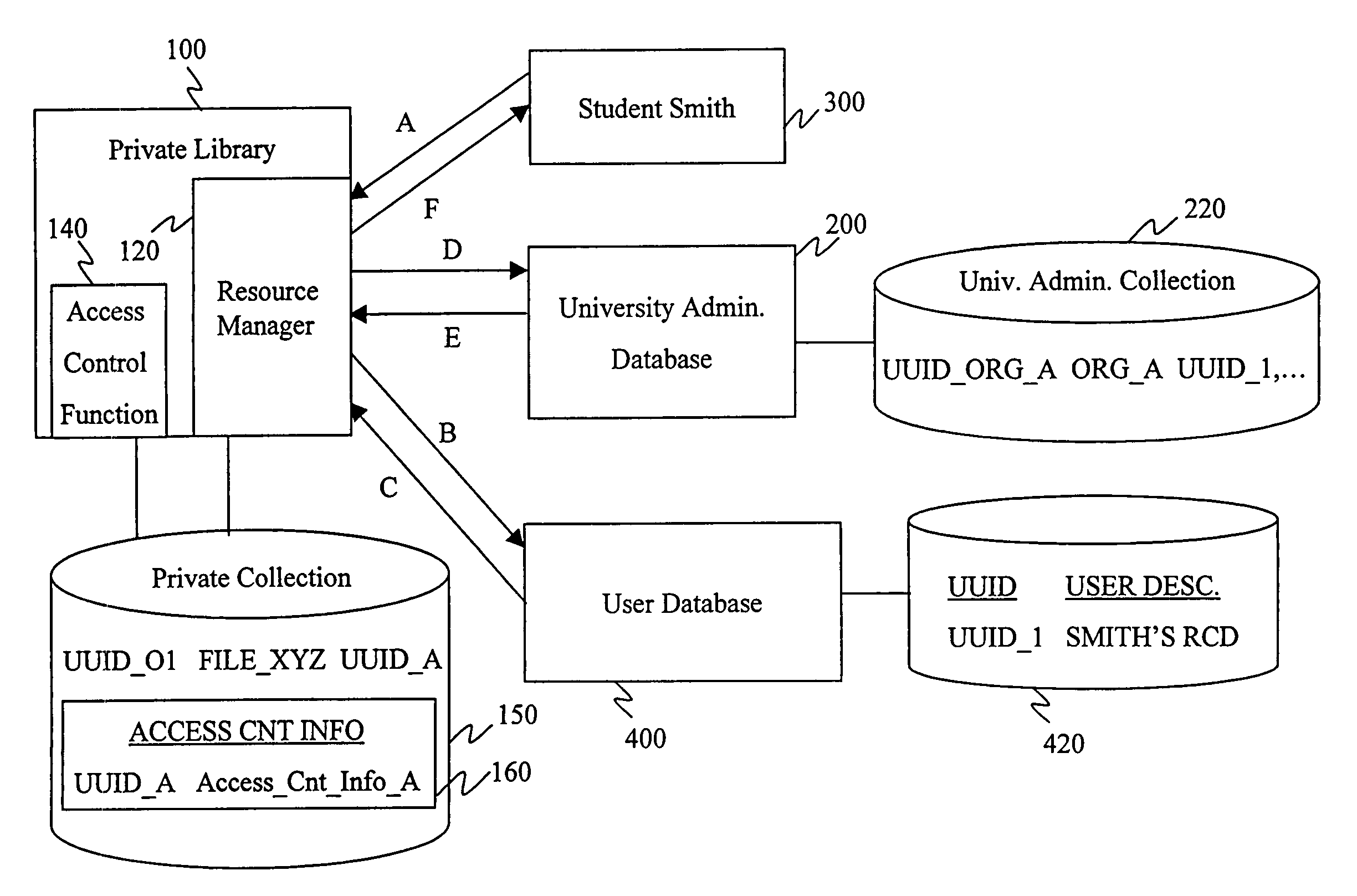
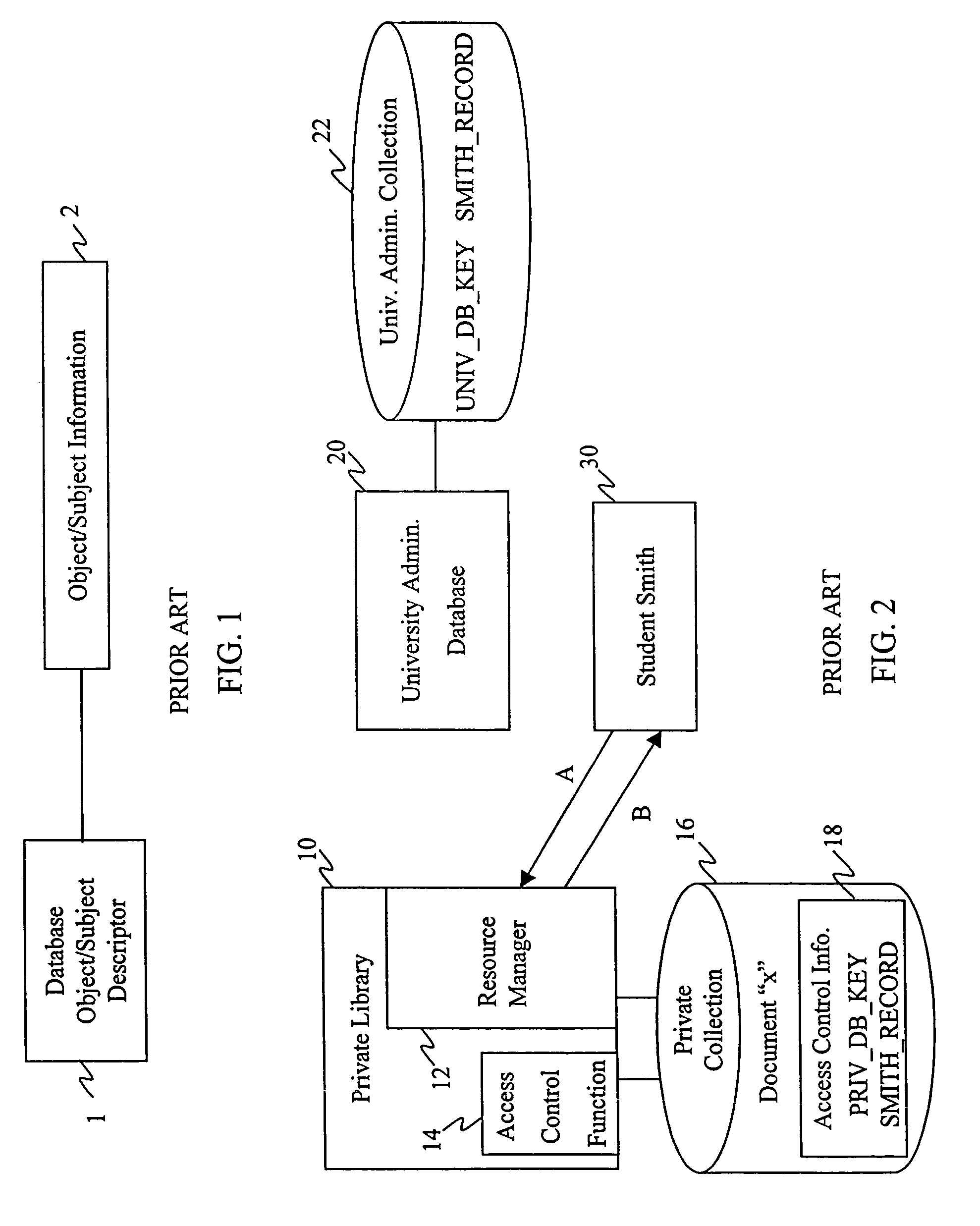
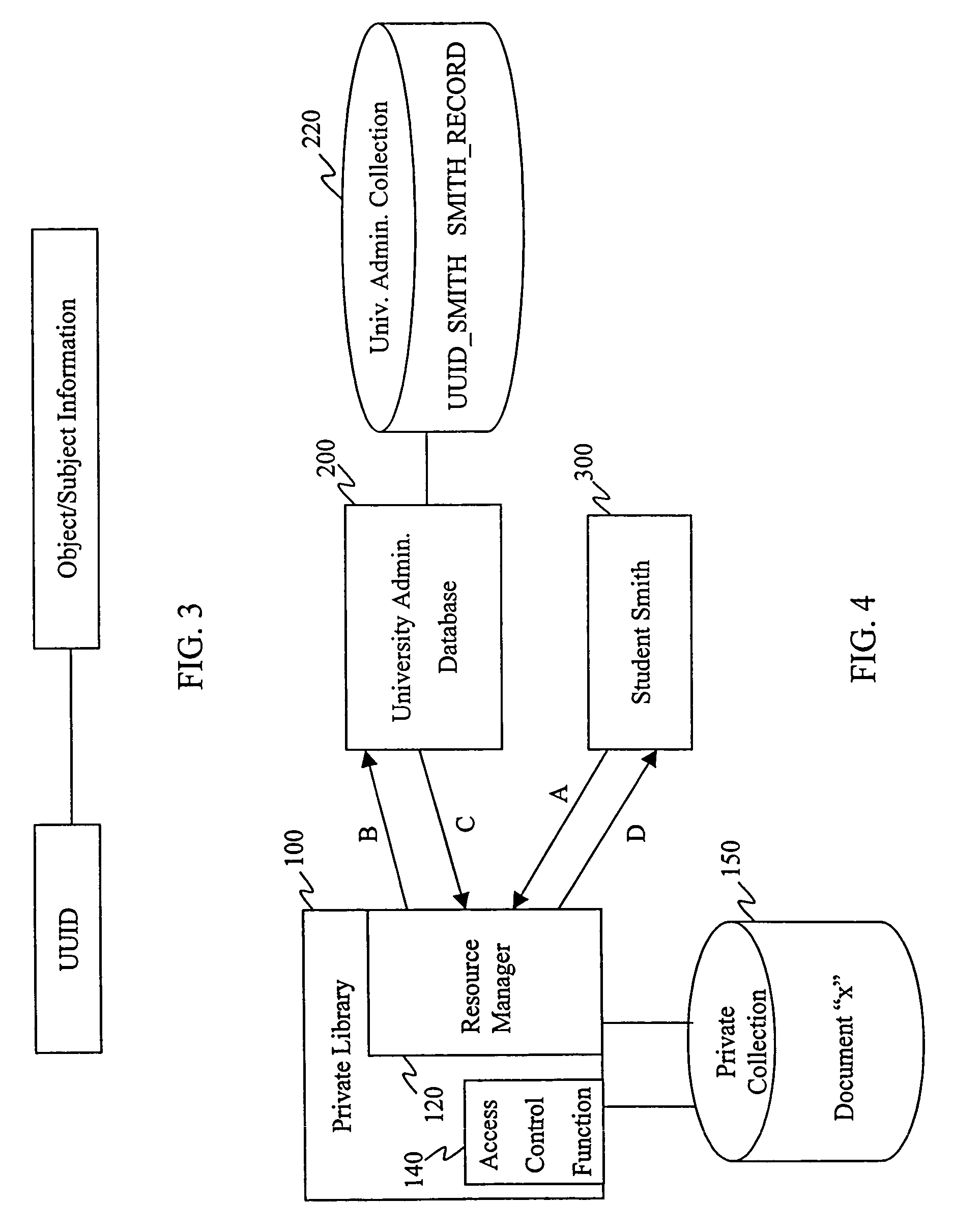
Distributed data structures for authorization and access control for computing resources
InactiveUS7331058B1Reduce significant administrative expenseSignificant expenseDigital data processing detailsUser identity/authority verificationArray data structureUniversally unique identifier
The invention relates to using a universally unique identifier in a database to uniquely identify, both within and outside of the database system, a user. A storage system, according to the invention, includes a first storage area having an object stored therein; and a second storage area having stored therein an object identifier that identifies the object. The object identifier is unique within and outside of the storage system, and can be a Universal Unique Identifier (UUID). The invention also relates methods for storing and retrieving objects identified based on the unique identifier.
Owner:IBM CORP
Method and system for managing inventory and promotions campaign based on redemption data
ActiveUS20050222910A1Cost-effective mannerAvoid repetitionHand manipulated computer devicesPayment architectureTransaction dataComputerized system
Provided is a method and system for the management of inventory and / or promotional campaigns associated with electronic distribution of secure money saving or discount incentives, including coupons and other marketing incentives and, in particular, to modifying a promotional campaign and / or modifying inventory levels and product ordering based on transaction data relating to coupons distributed as part of an online computer system for interactively distributing such incentives to remotely connected consumer computers.
Owner:CATALINA MARKETING CORP
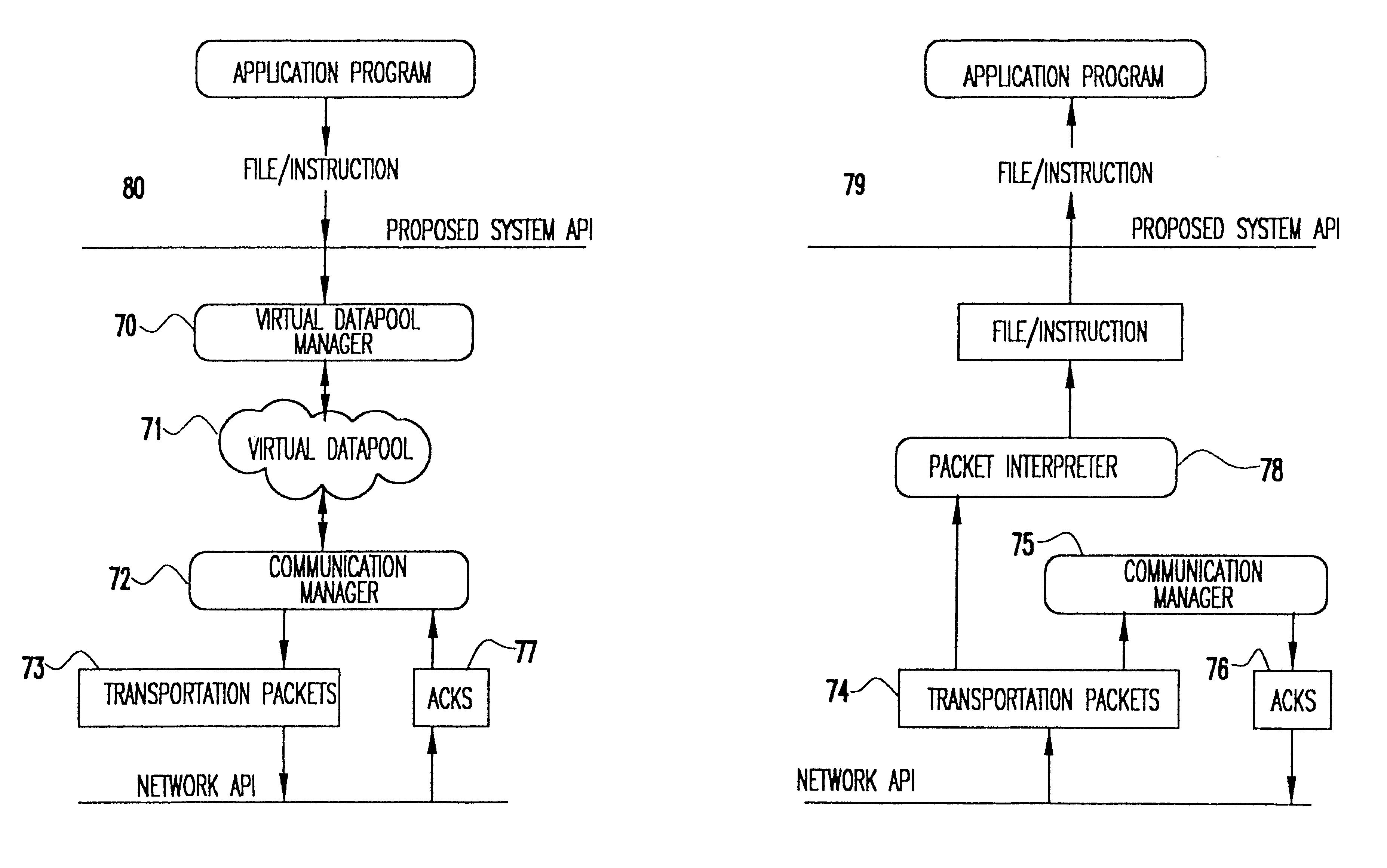
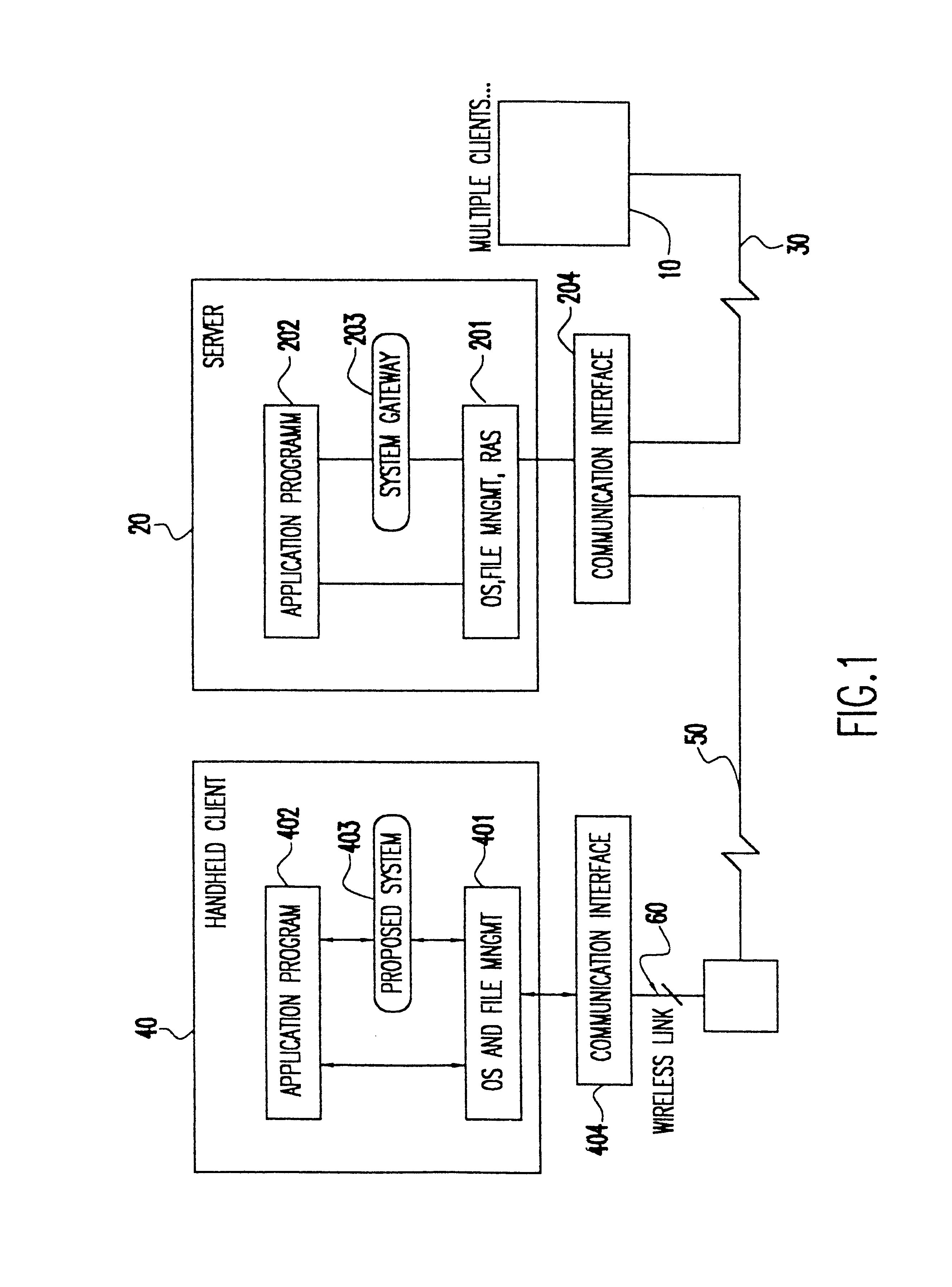
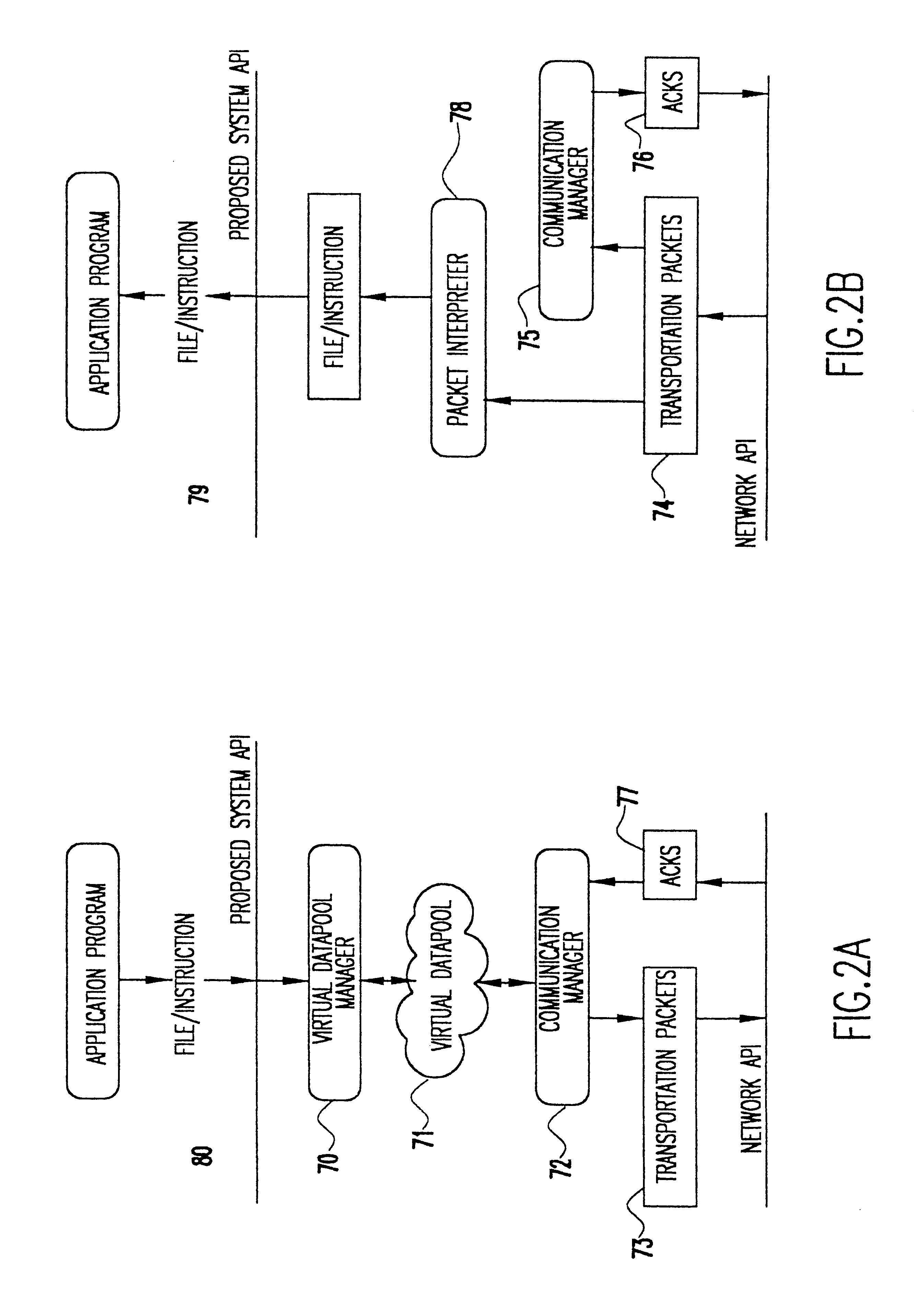
Data transfer mechanism for handheld devices over a wireless communication link
InactiveUS6775298B1Bandwidth is not as inexpensiveReduce battery power consumptionError preventionFrequency-division multiplex detailsTelecommunications linkNetwork packet
A method and apparatus for transferring data between a handheld device and a network over a wireless communications link. A datapool manager breaks files into virtual blocks and adds the virtual blocks to a datapool. A communications manager converts the virtual blocks into transportation packets and controls the transfer of the transportation packets between the handheld device and the network. After a transportation packet is transferred, an acknowledgment is returned indicating that the transfer was successful. If the transfer of a file is interrupted, then, upon reestablishing the wireless link, only those transportation packets for which an acknowledgment has not been returned are transferred. To properly reconstruct the file, a pointer indicates the location of each transportation packet in the file. Furthermore, to enable the use of a partially transferred file, a table of information is maintained indicating the validity of the partially transferred file. Transportation packets are identified as instruction packets or data packets. When determining the order of transfer, priority is placed on the transfer of instruction packets.
Owner:IBM CORP
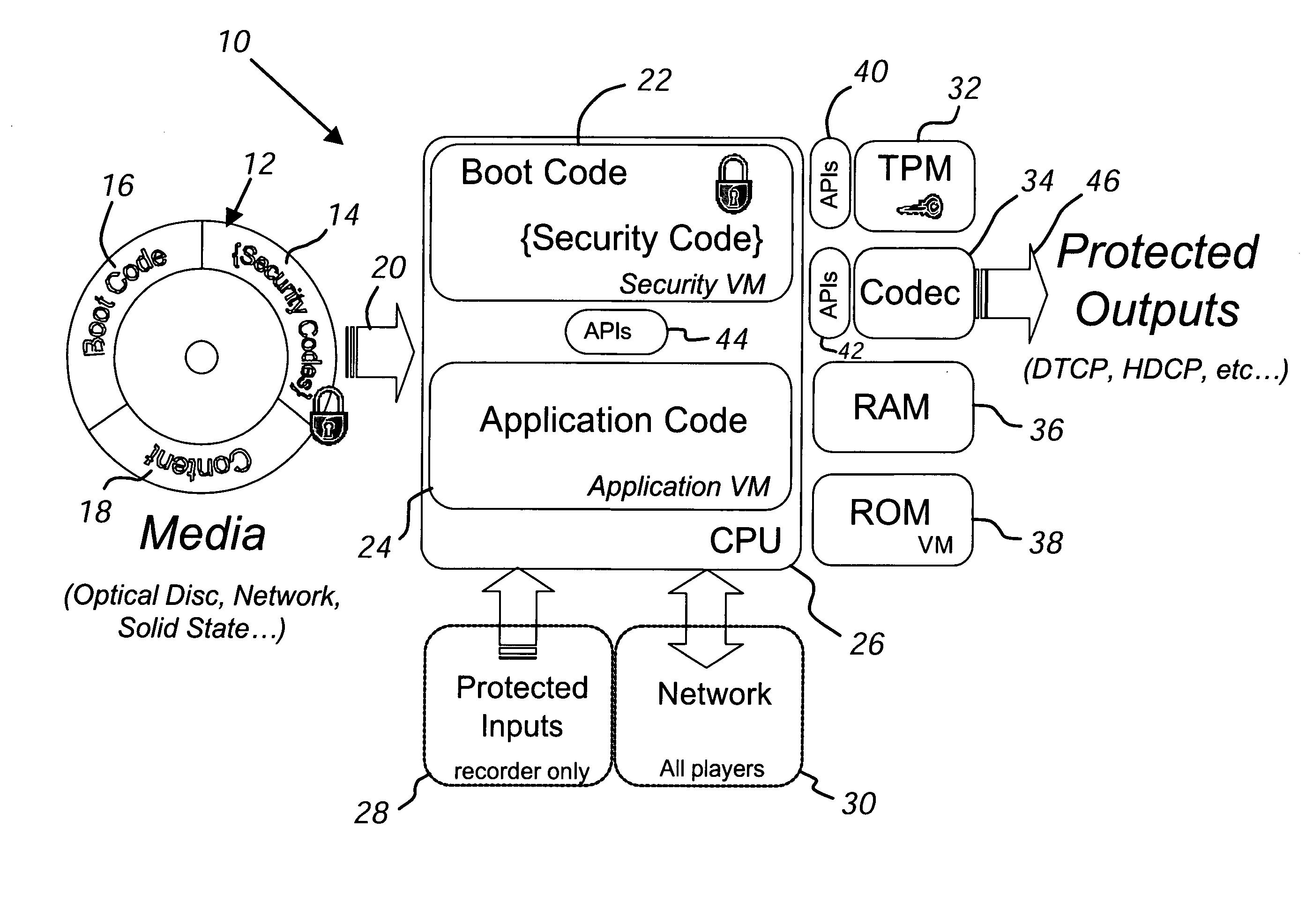
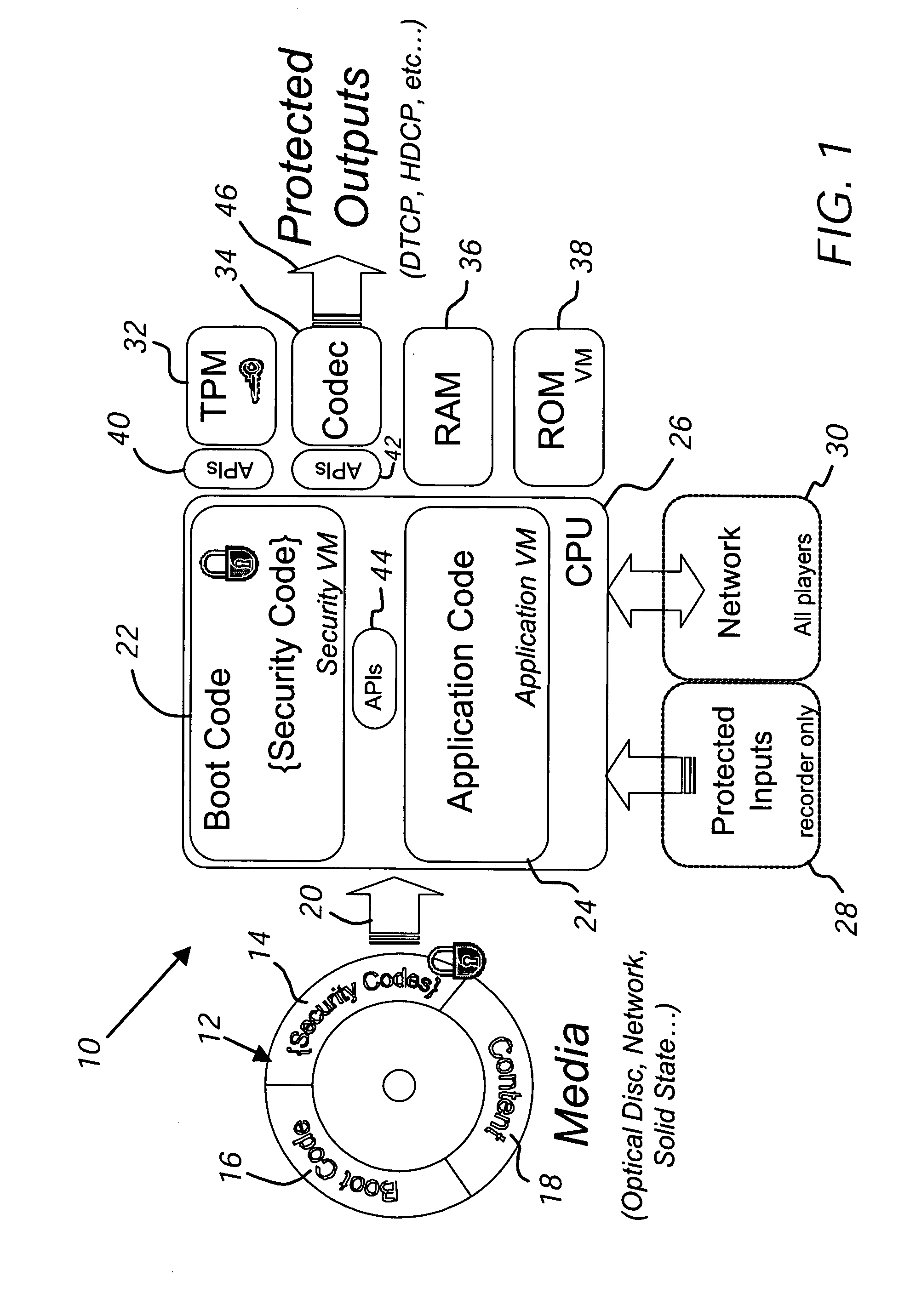
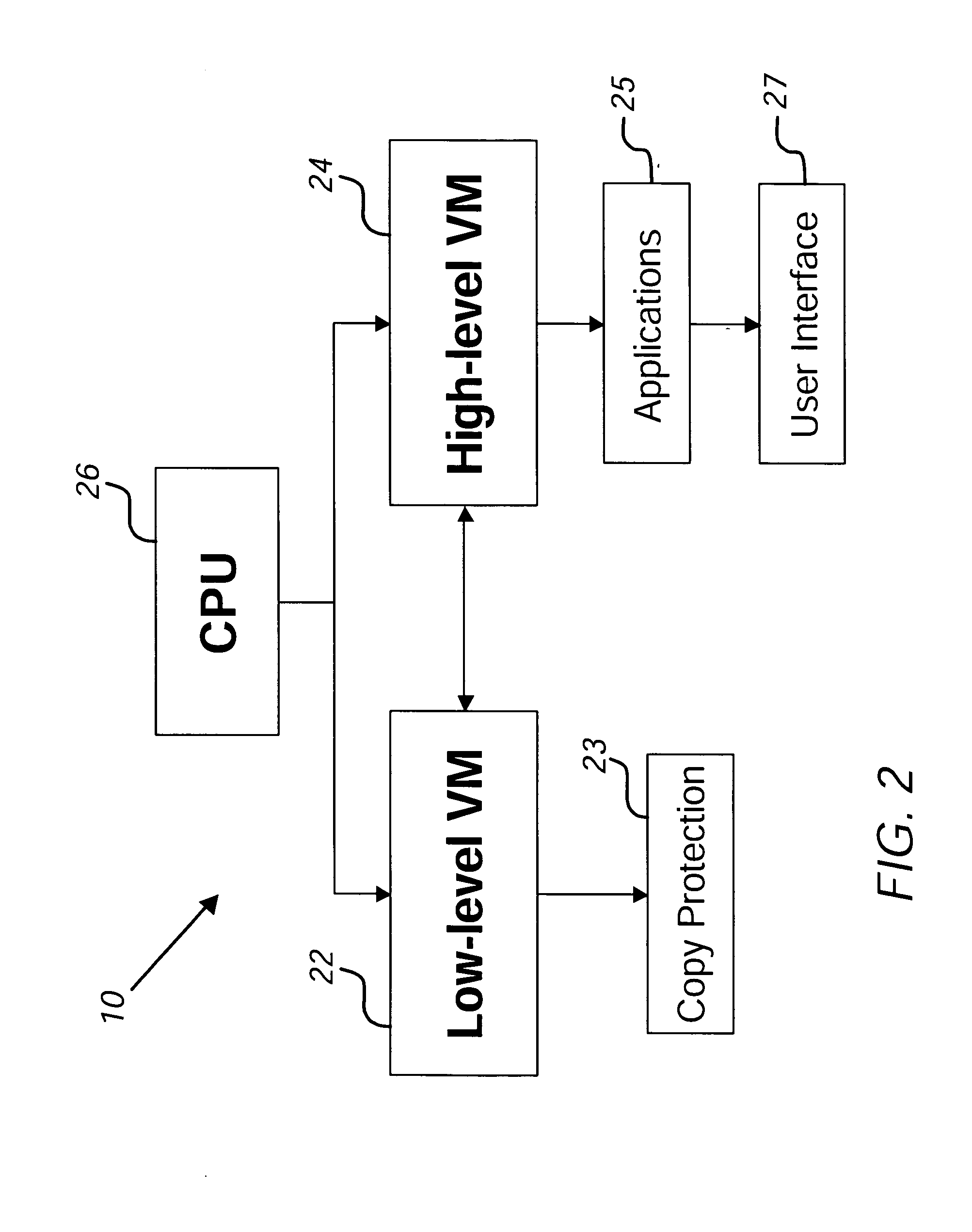
Dual virtual machine architecture for media devices
ActiveUS20050204126A1Precise managementPrevent unauthorized duplicationDigital data processing detailsUser identity/authority verificationSecure authenticationUser interface
A software computing based environment for providing secured authentication of media downloaded from a network or loaded from a media player includes two peer-mode operating virtual machines. The low-level virtual machine provides decoding and decryption functions whereas the high-level virtual machine provides application level functions such as user interface, input / output.
Owner:DISNEY ENTERPRISES INC
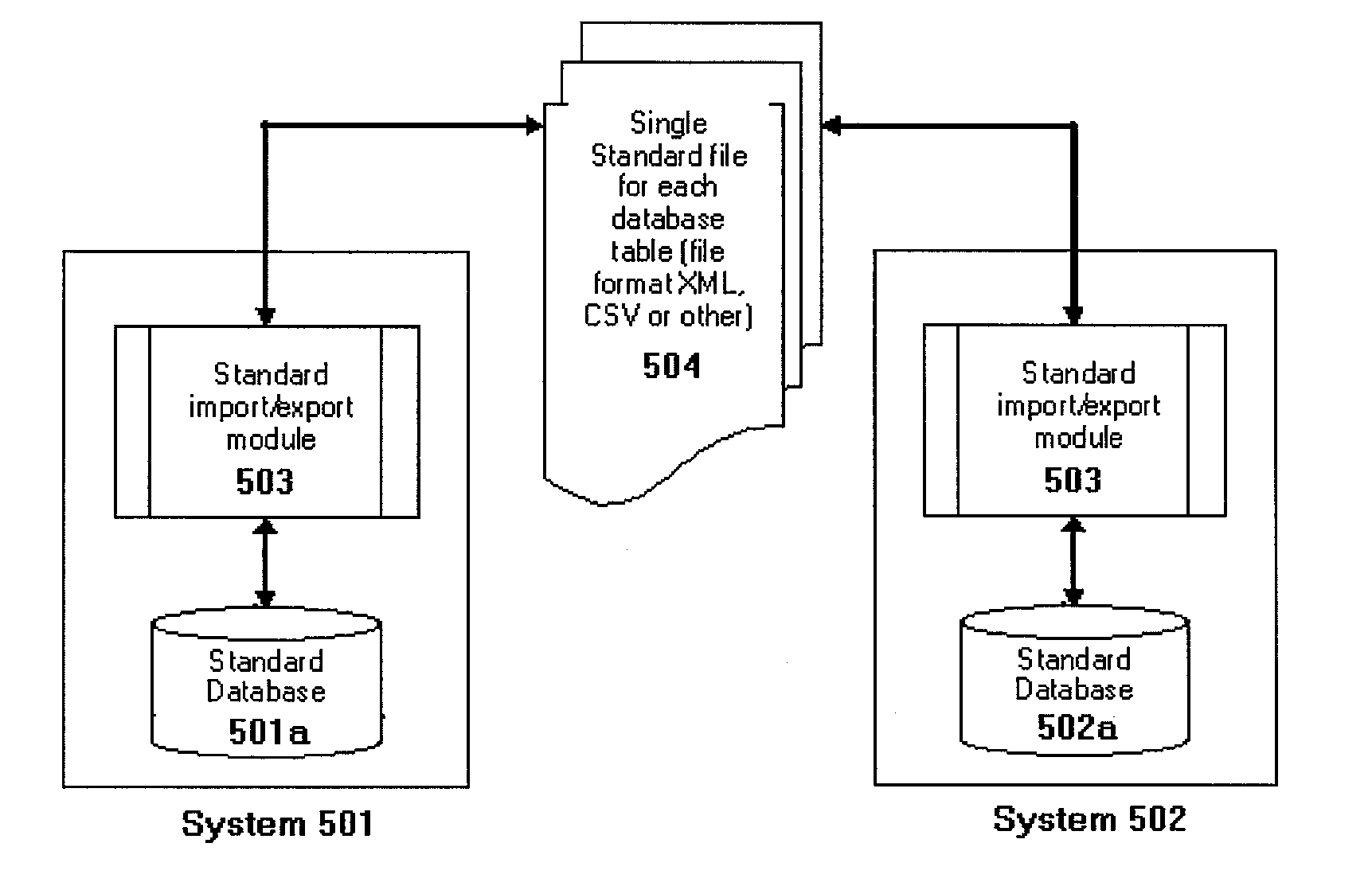
Global Information Management System and Method
ActiveUS20110320400A1Avoid repetitionDigital data processing detailsDatabase distribution/replicationRelational databaseGlobal information
A global information management system (GIMS) includes a collection of standards and methods that allow information management on a global scale. A GIMS computer network includes a central registration database (CRD) and one or more GIMS computer systems connected over a network. Each GIMS computer system includes a relational database having a set of standardized tables. The CRD may provide a GIMS network-unique system ID to each GIMS computer system. Each GIMS computer system uses the GIMS network-unique system ID as part of a primary key for each record generated by and stored in the set of standardized tables of the GIMS database. The GIMS enables global database normalization through the globally unique identification of database records.
Owner:NAMINI BORSU ASISI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com