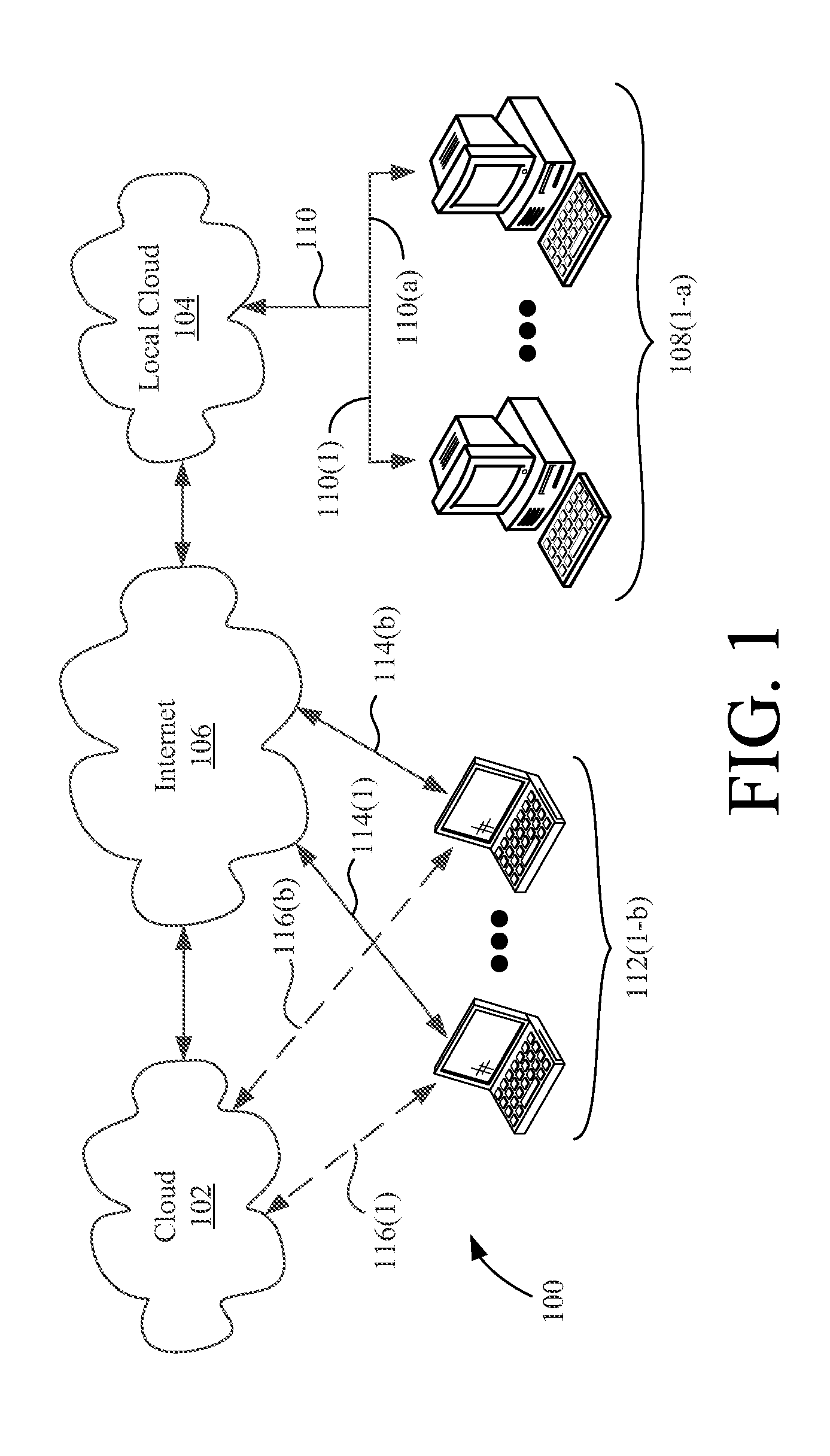
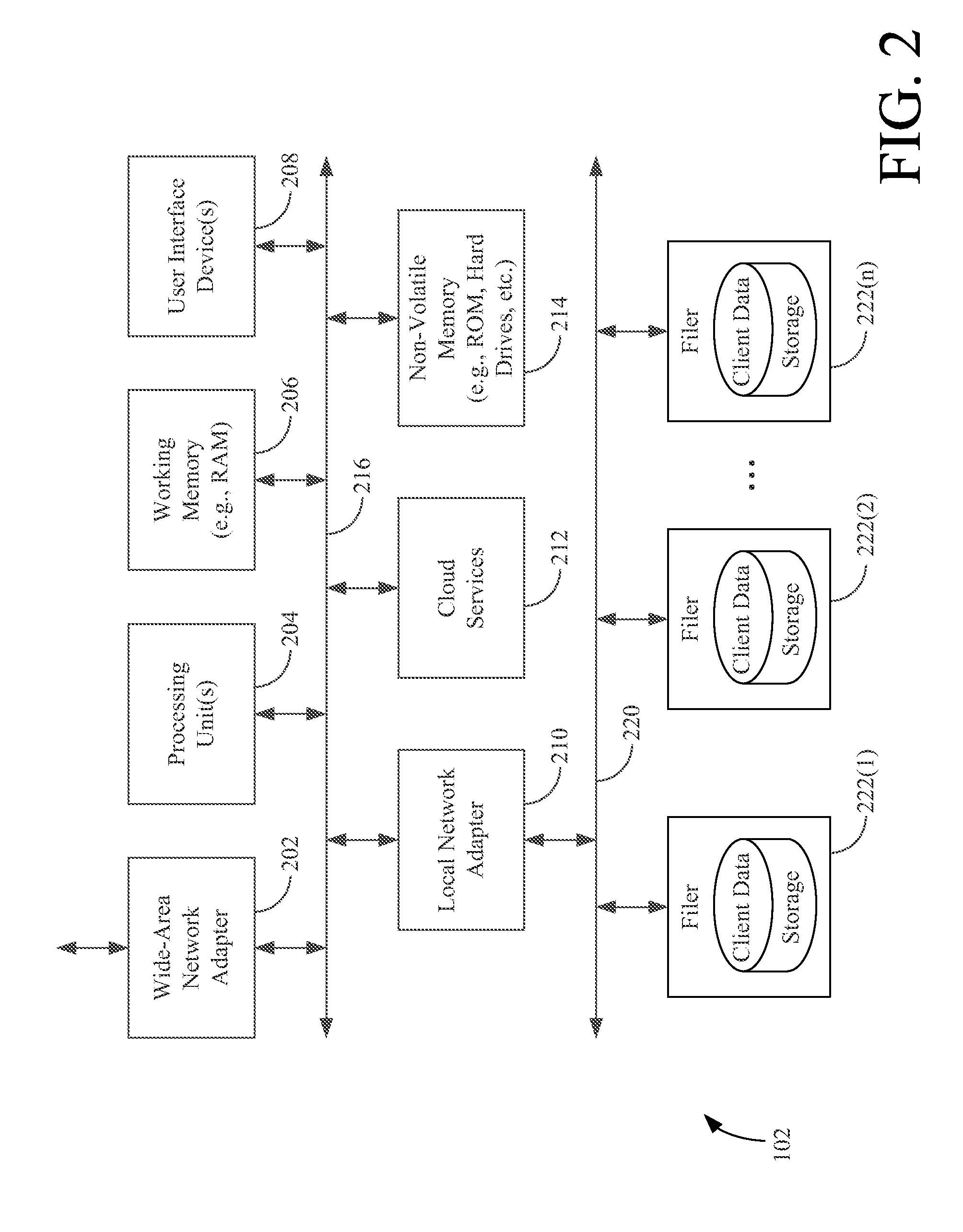
Patents
Literature
224 results about "Universally unique identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A universally unique identifier (UUID) is a 128-bit number used to identify information in computer systems. The term globally unique identifier (GUID) is also used, typically in software created by Microsoft.
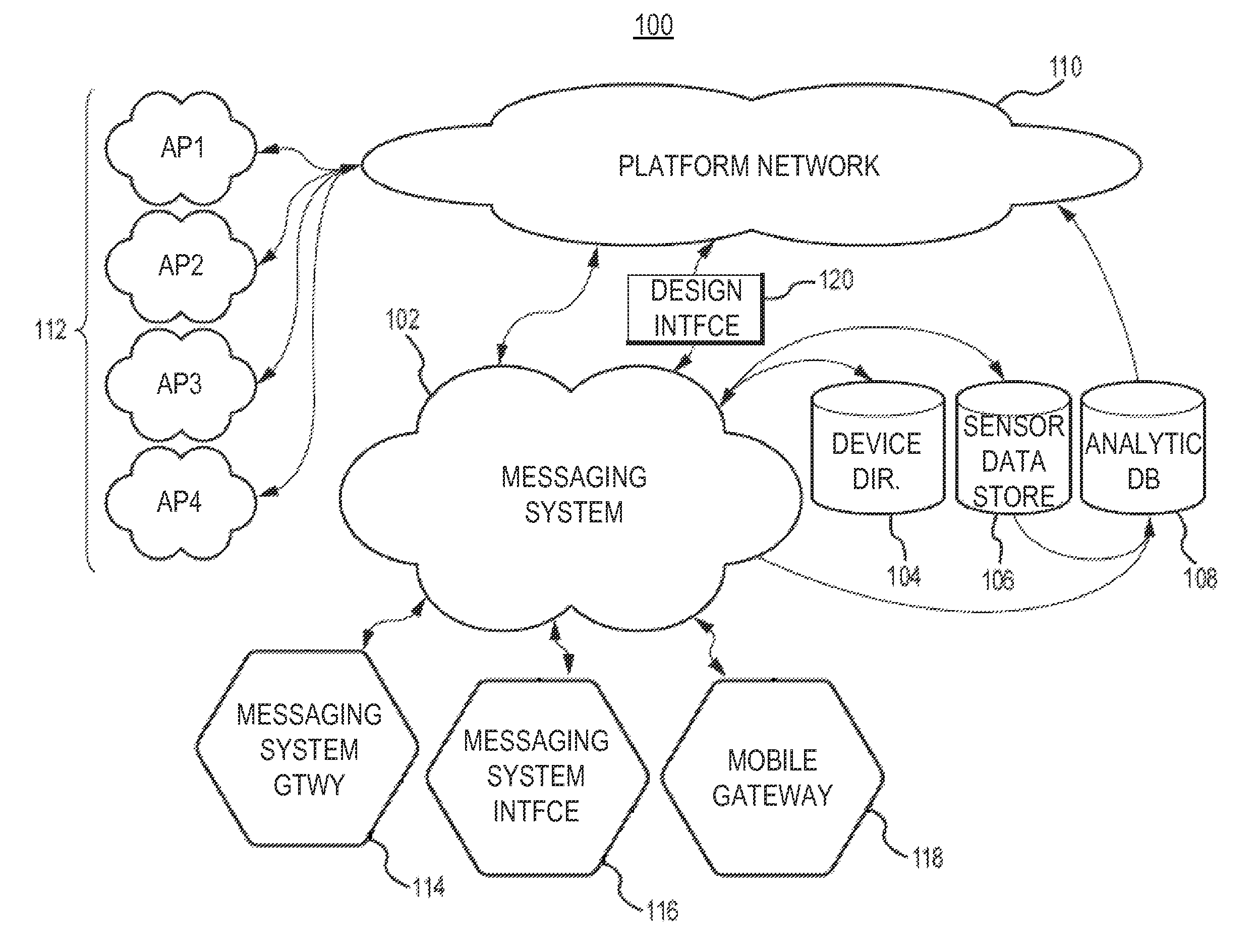
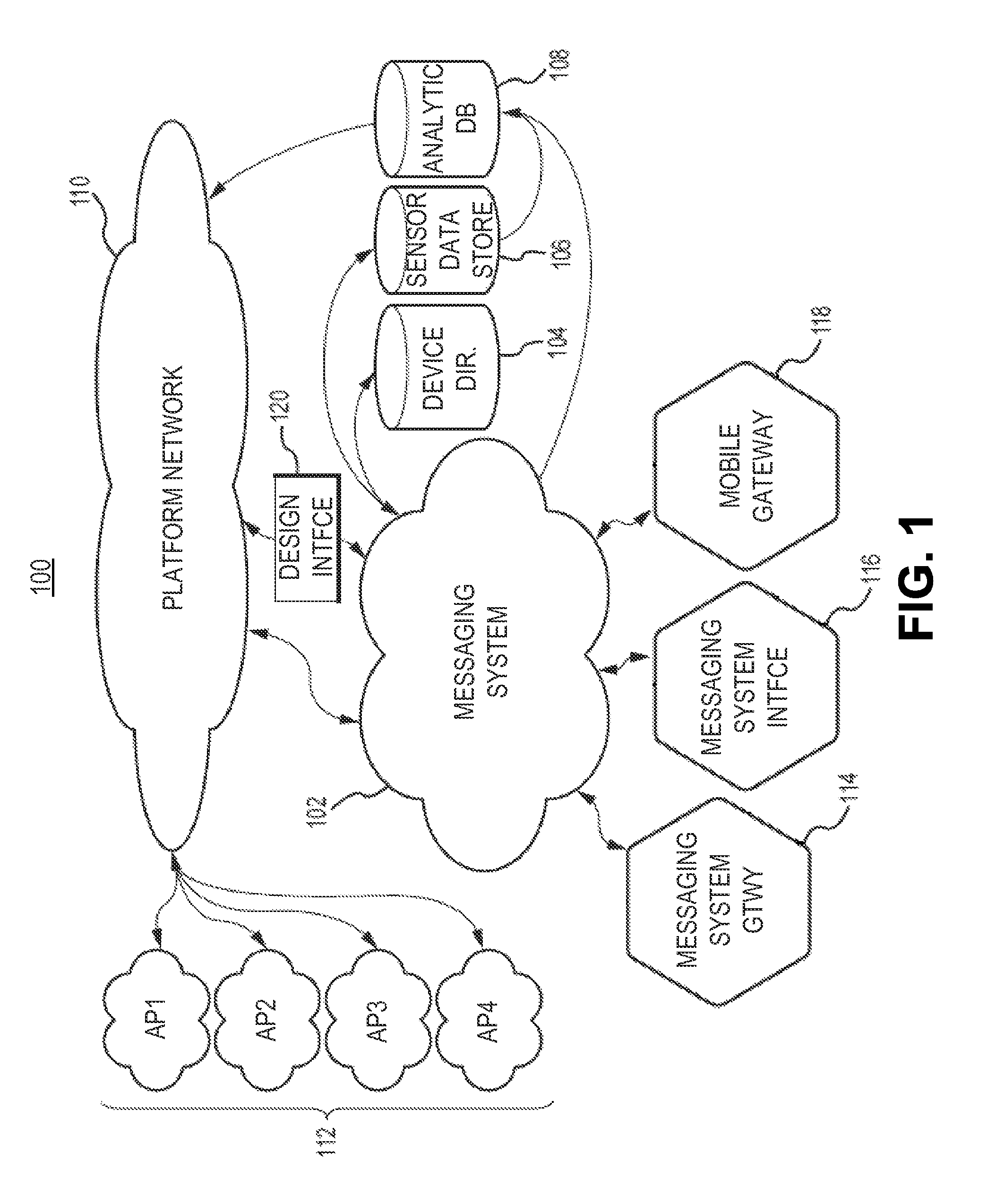
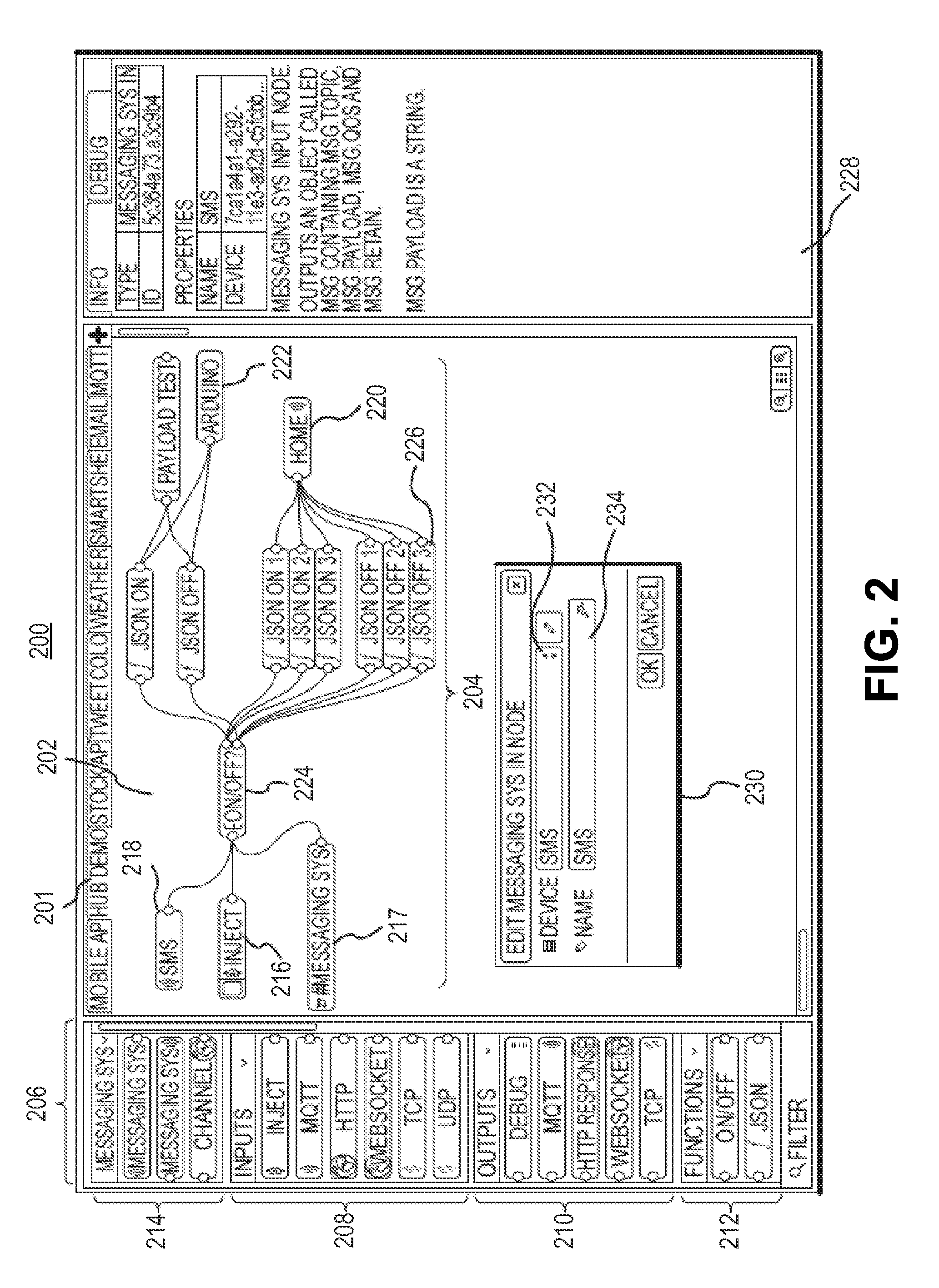
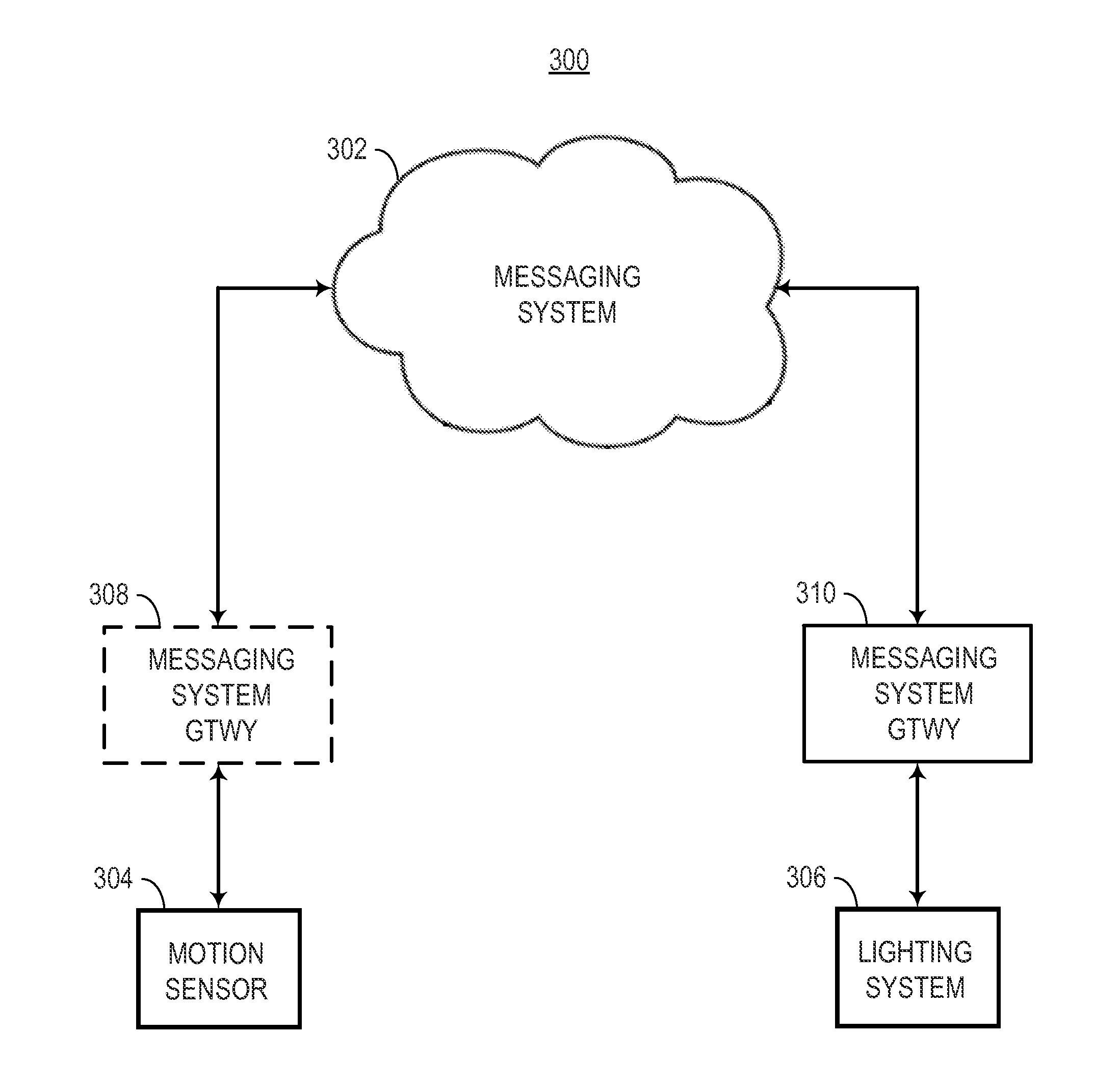
Security and rights management in a machine-to-machine messaging system
Techniques for providing security and rights management in a machine-to-machine messaging system are provided, such as a computing device, a method, and a computer-program product for detecting unauthorized message attempts. For example, the method may receive a communication sent from a first Internet of Things (IoT) device and destined for a second IoT device. The first IoT device is assigned a first universally unique identifier, and the communication includes a second universally unique identifier assigned to the second IoT device. The method may further include obtaining the second universally unique identifier, determining that the second universally unique identifier is assigned to the second IoT device, and determining, using the second universally unique identifier, that the communication received from the first IoT device is an unauthorized message attempt by the first IoT device to exchange a message with the second IoT device.
Owner:CITRIX SYST INC
System and method of implementing an object storage infrastructure for cloud-based services
ActiveUS20140149794A1Easy retrievalWeb data indexingDigital data processing detailsUniversally unique identifierNetwork connection
A method for storing objects in an object storage system includes the steps of establishing a network connection with a client over an inter-network, receiving an upload request indicating an object to be uploaded by the client, selecting at least two storage nodes on which the object will be stored, receiving the object from the client via the network connection, and streaming the object to each of the selected storage nodes such that the object is stored on each of the selected storage nodes. The method can also include writing an object record associating the object and the selected storage nodes to a shard of an object database and generating a Universally Unique Identifier (UUID). The UUID indicates the shard and the object ID of the object record, such that the object record can be quickly retrieved. Object storage infrastructures are also disclosed.
Owner:EGNYTE
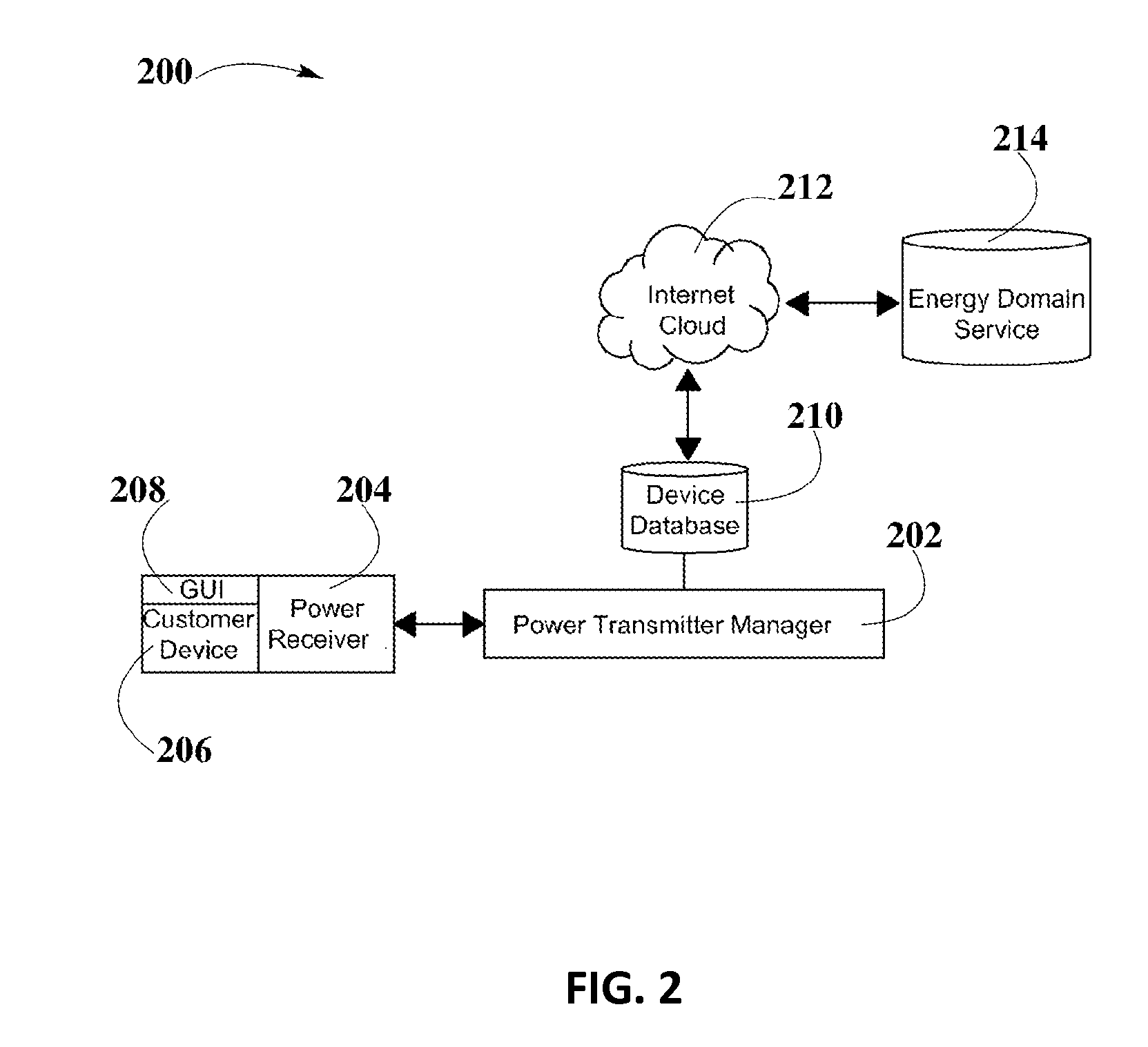
System and Method for Smart Registration of Wireless Power Receivers in a Wireless Power Network
ActiveUS20160020649A1Avoid abuseNear-field transmissionElectromagnetic wave systemElectric power transmissionUniversally unique identifier
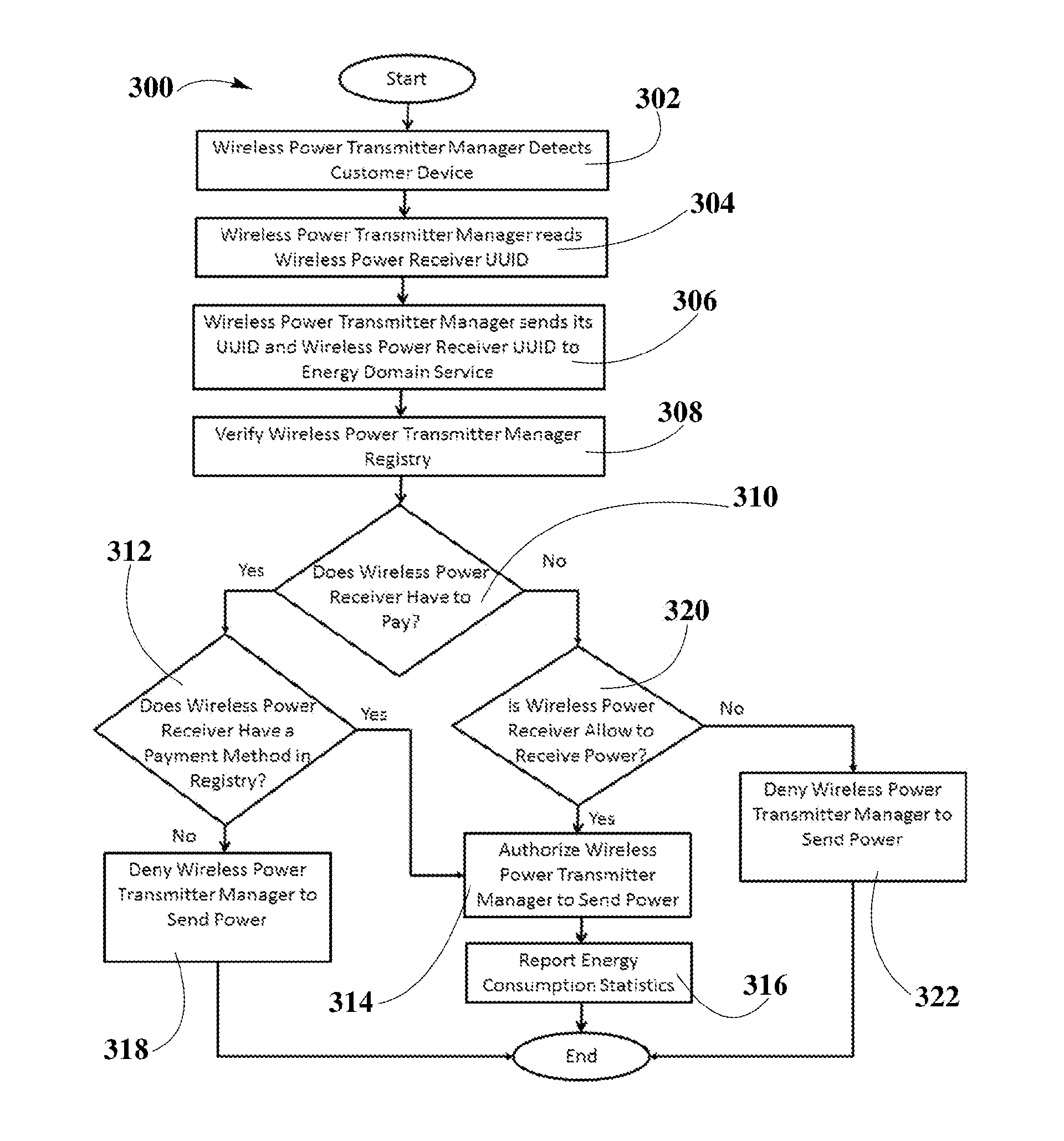
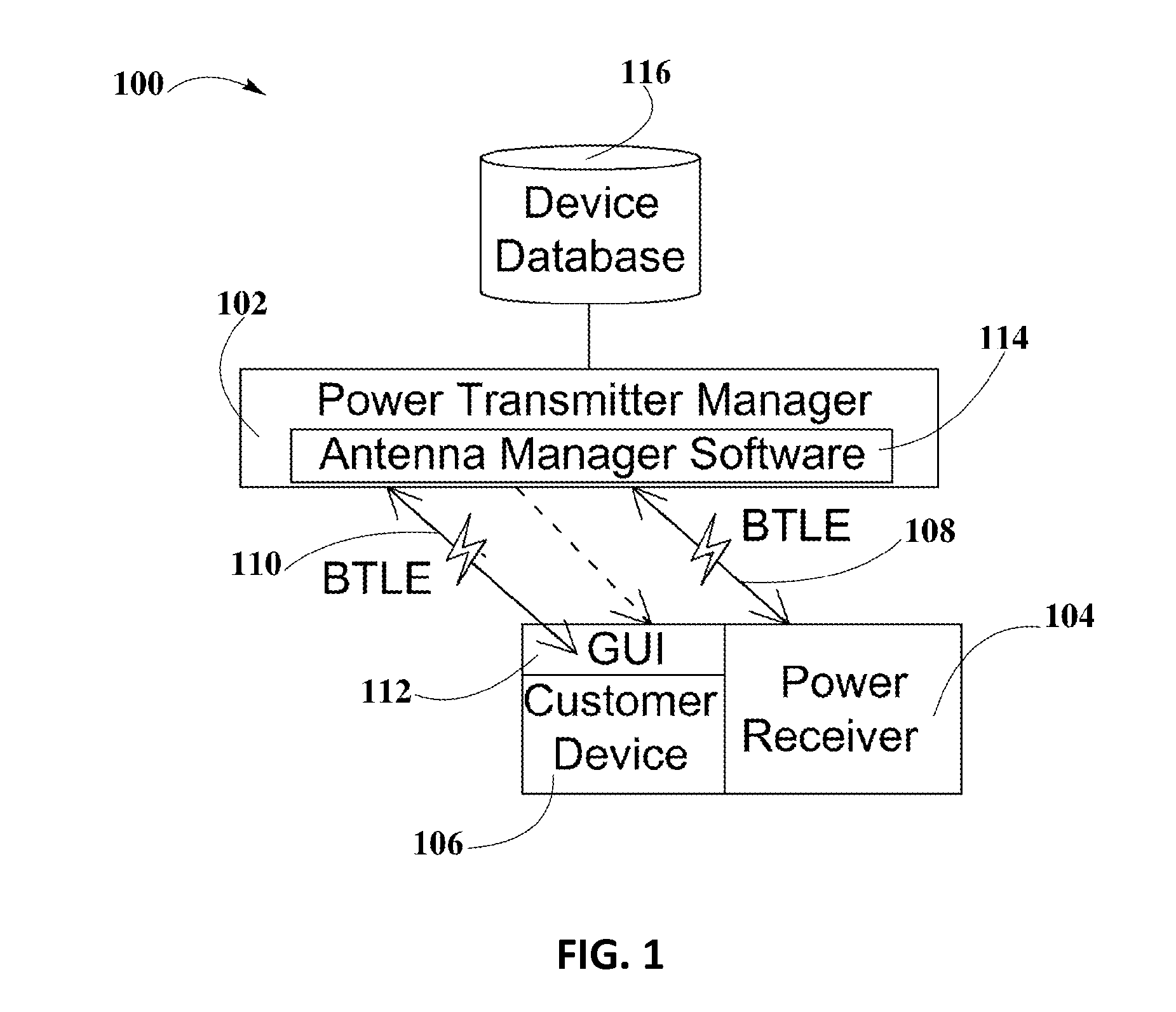
A system and method for smart registration of wireless power receivers within a wireless power network is disclosed. Each wireless power device may include a universally unique identifier (UUID). Each wireless power device bought by a customer may be registered, at the time of purchase or later. The registry may be stored in an energy domain service, where energy domain service may be one or more cloud-based servers. The method for smart registration may include the steps of detecting a customer device; establishing a connection with a wireless power receiver to read its UUID; sending wireless power transmitter manager's UUID and wireless power receiver's UUID to energy domain service; inspecting wireless power transmitter manager registry; verifying wireless power receiver registry; authorizing power transfer to wireless power receiver; and reporting energy consumption for subsequent billing of customer depending on billing policy of wireless power transmitter manager specified within registry.
Owner:ENERGOUS CORPORATION
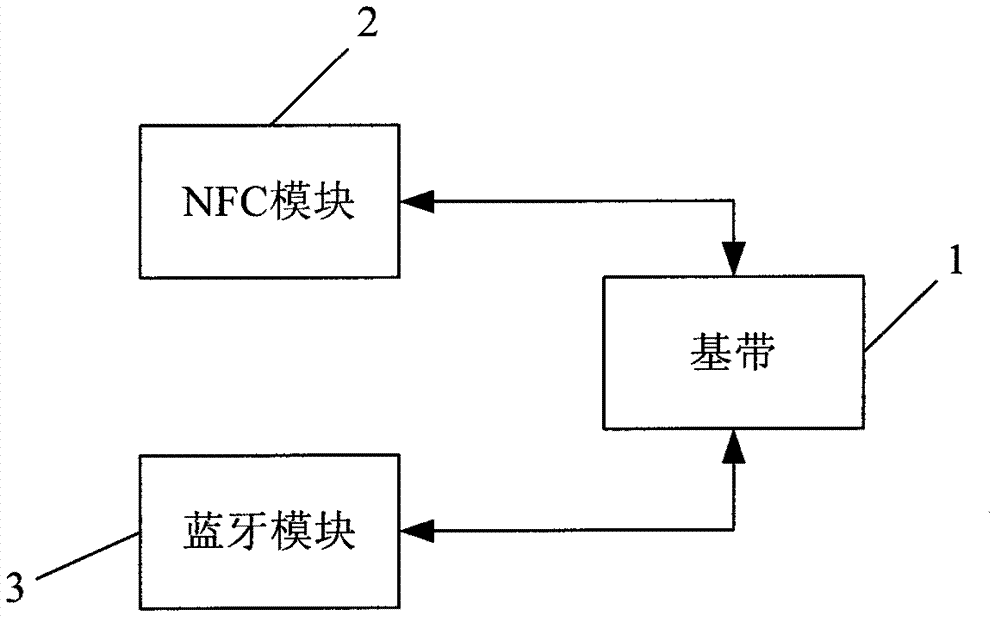
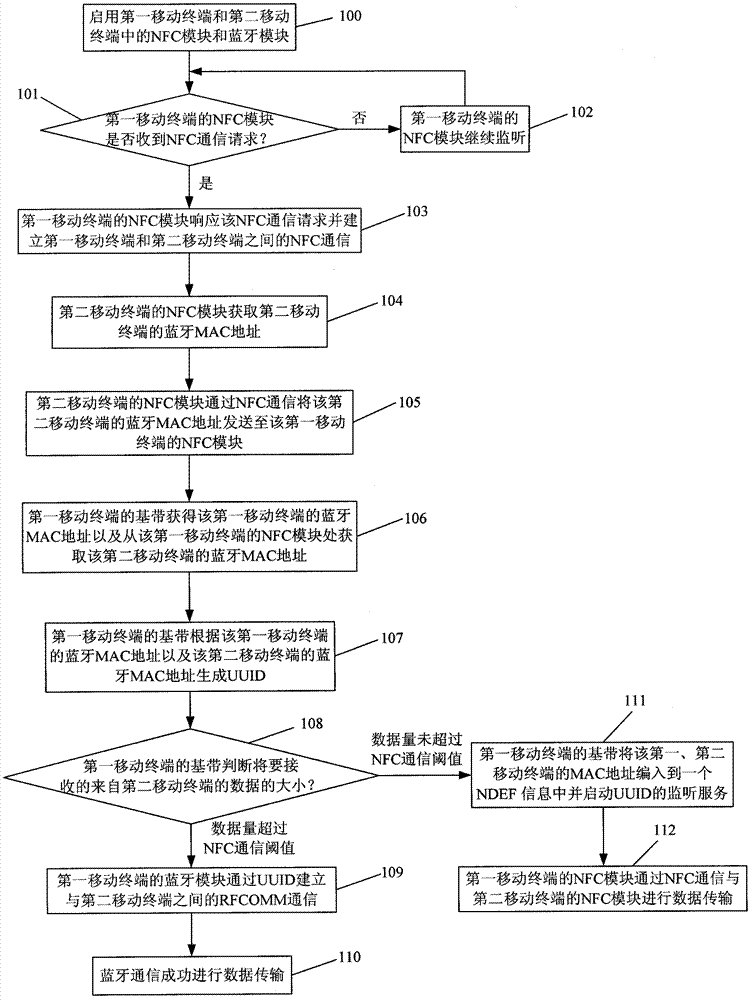
Mobile terminal and method for realizing Bluetooth communication between mobile terminals
InactiveCN102780513AExtension of timeShorten the timeNear-field systems using receiversSecurity arrangementUniversally unique identifierMedia access control
The invention discloses a mobile terminal, which comprises a base band, an NFC (near field communication) module and a Bluetooth module, wherein the NFC module and the Bluetooth module are respectively connected with the base band; the NFC module is used for carrying out NFC with other mobile terminals, obtaining a Bluetooth MAC (media access control) address of the mobile terminal from the base band, receiving Bluetooth MAC addresses of other mobile terminals and sending the Bluetooth MAC addresses of other mobile terminals into the base band; the Bluetooth module is used for carrying out Bluetooth communication with other mobile terminals; the base band obtains the Bluetooth MAC address of the mobile terminal, and receives the Bluetooth MAC addresses of other mobile terminals, which are from the NFC module; according to the Bluetooth MAC address of the mobile terminal and the Bluetooth MAC addresses of other mobile terminals, UUID (universally unique identifier) is generated; and according to the UUID, the Bluetooth communication between the mobile terminal and other mobile terminals is established. The invention also discloses a method for realizing Bluetooth communication between mobile terminals. According to the mobile terminal disclosed by the invention, the opposite-side Bluetooth MAC address is obtained by the NFC to realize the direct pairing of the Bluetooth.
Owner:SHANGHAI SIMCOM LTD
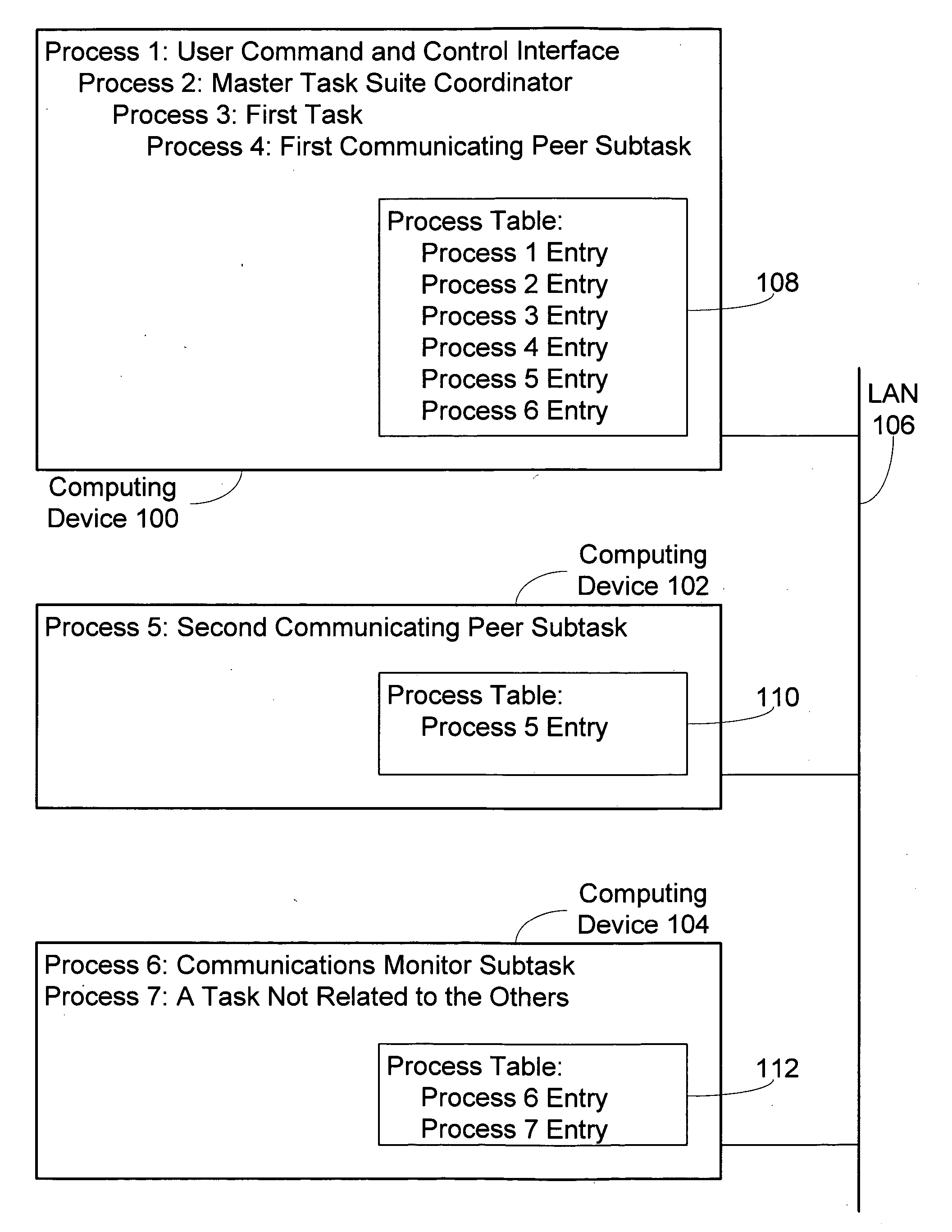
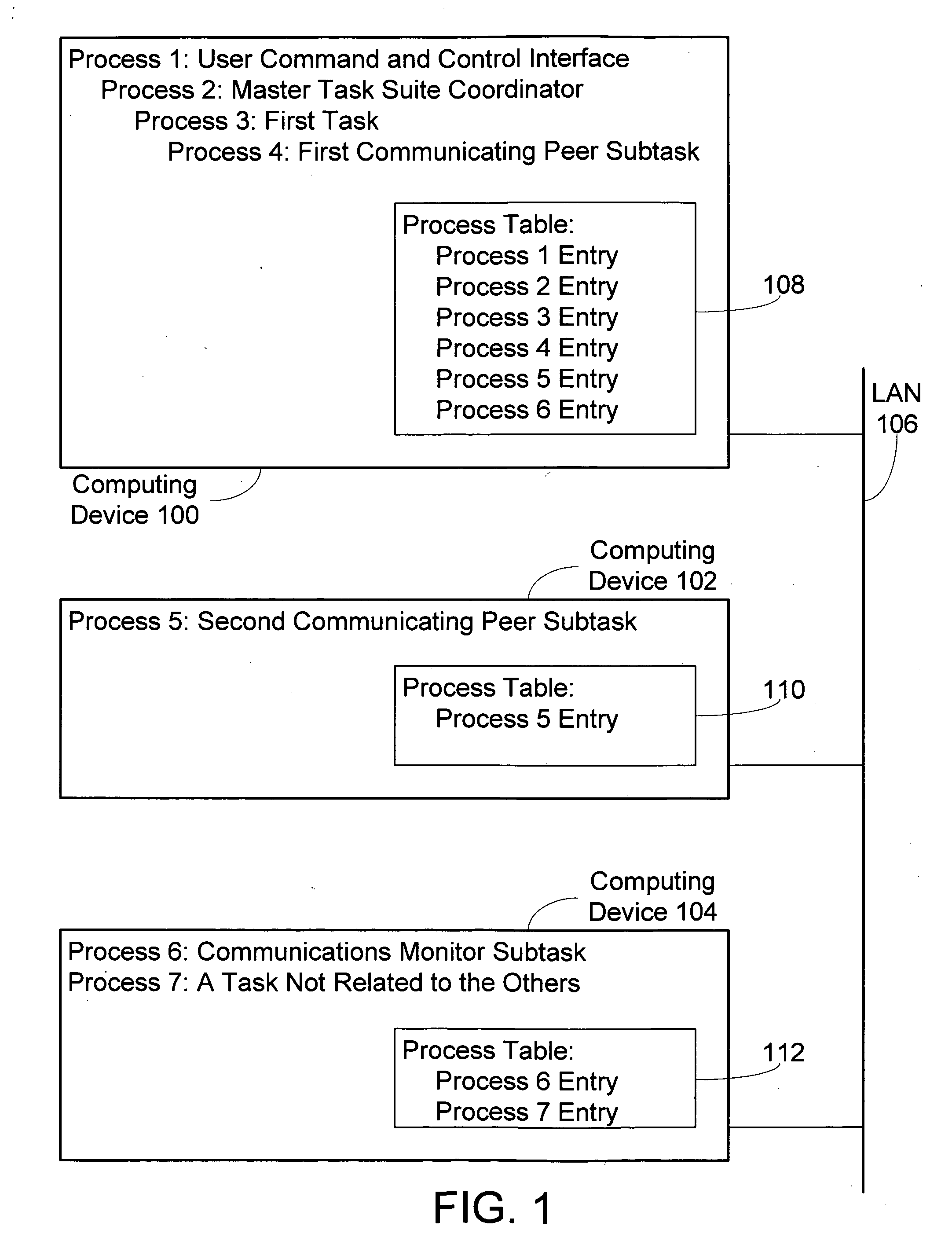
Methods and systems for creating and communicating with computer processes
InactiveUS20050138624A1Interprogram communicationMemory systemsUniversally unique identifierApplication programming interface
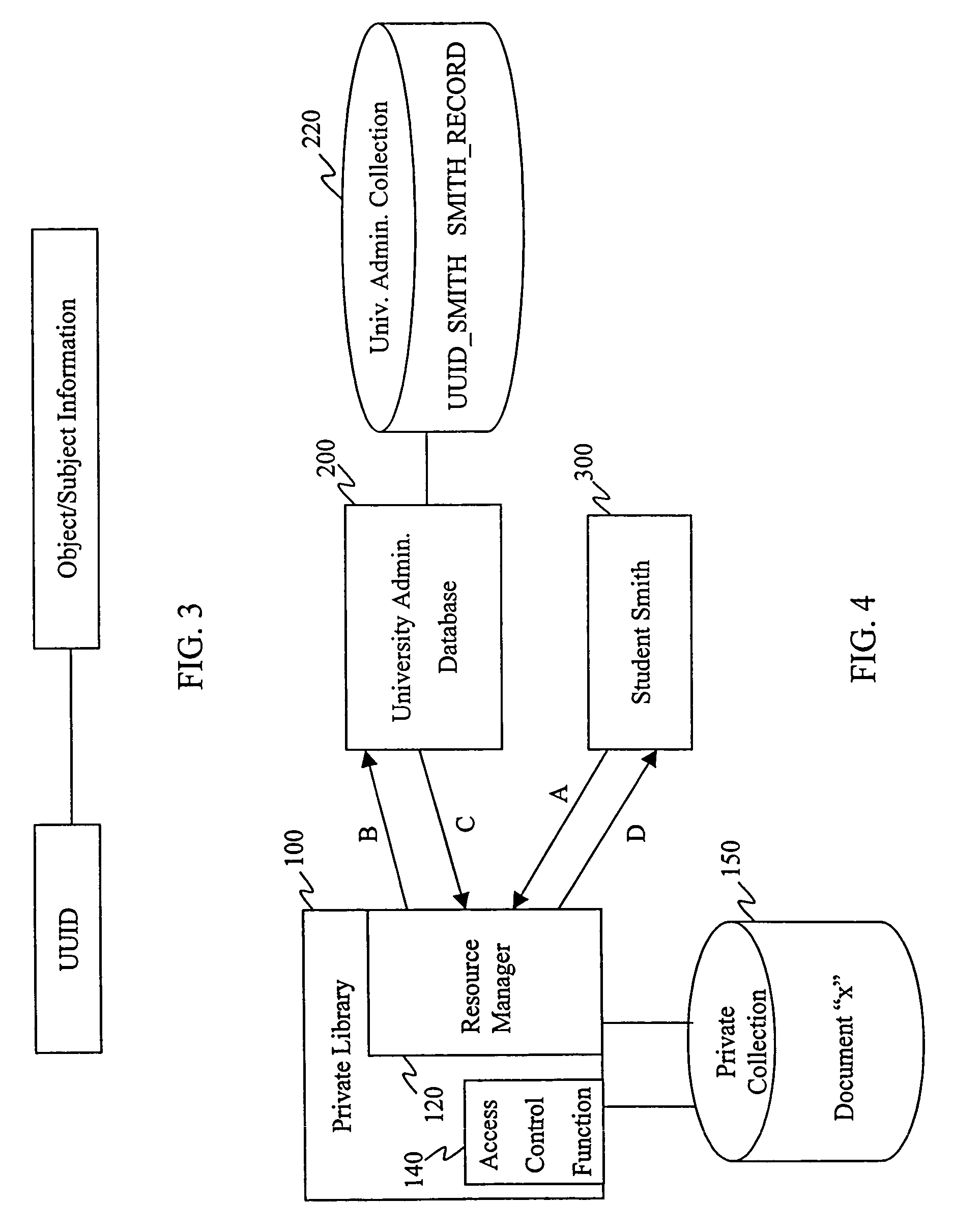
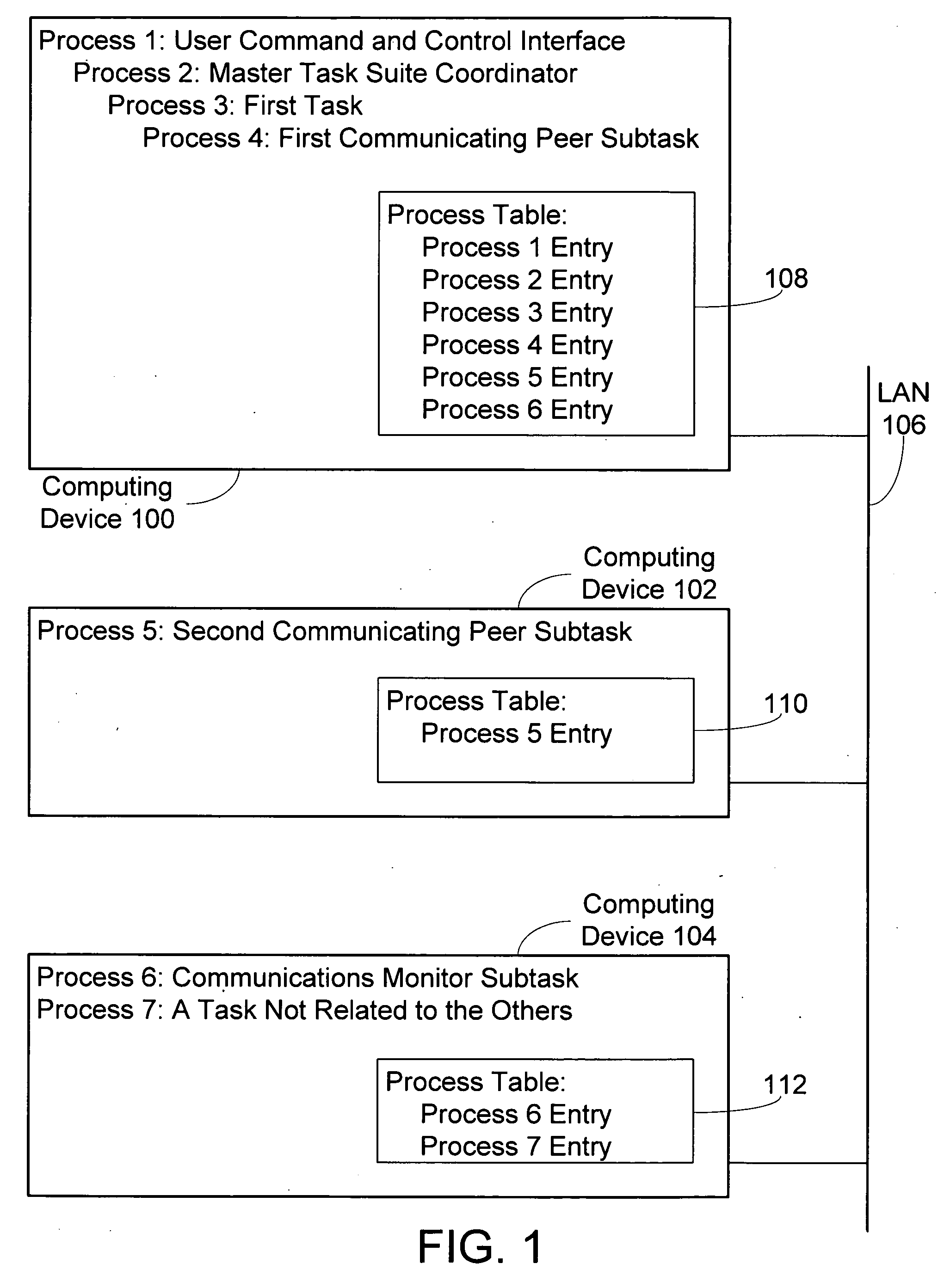
Disclosed are mechanisms for creating and communicating with computer processes. An application programming interface (API) presents services of the system to applications. The API is usable with all processes, local and remote, and is transparent with respect to the location of processes. A process table stores information about processes created using the system. The process table supports centralized process control and peer-to-peer process communication and synchronization. Each process is assigned a Universally Unique Identifier (UUID) that uniquely identifies the process no matter the computing device on which it runs. A parent UUID and a group UUID may be attached to the process and used for enforcing dependencies (e.g., for halting the process and all of its child processes) and for managing arbitrary, user-defined groups, respectively. A global event is associated with each process. When a process receives this event, it performs a controlled shutdown, cleans up, and reports status.
Owner:MICROSOFT TECH LICENSING LLC
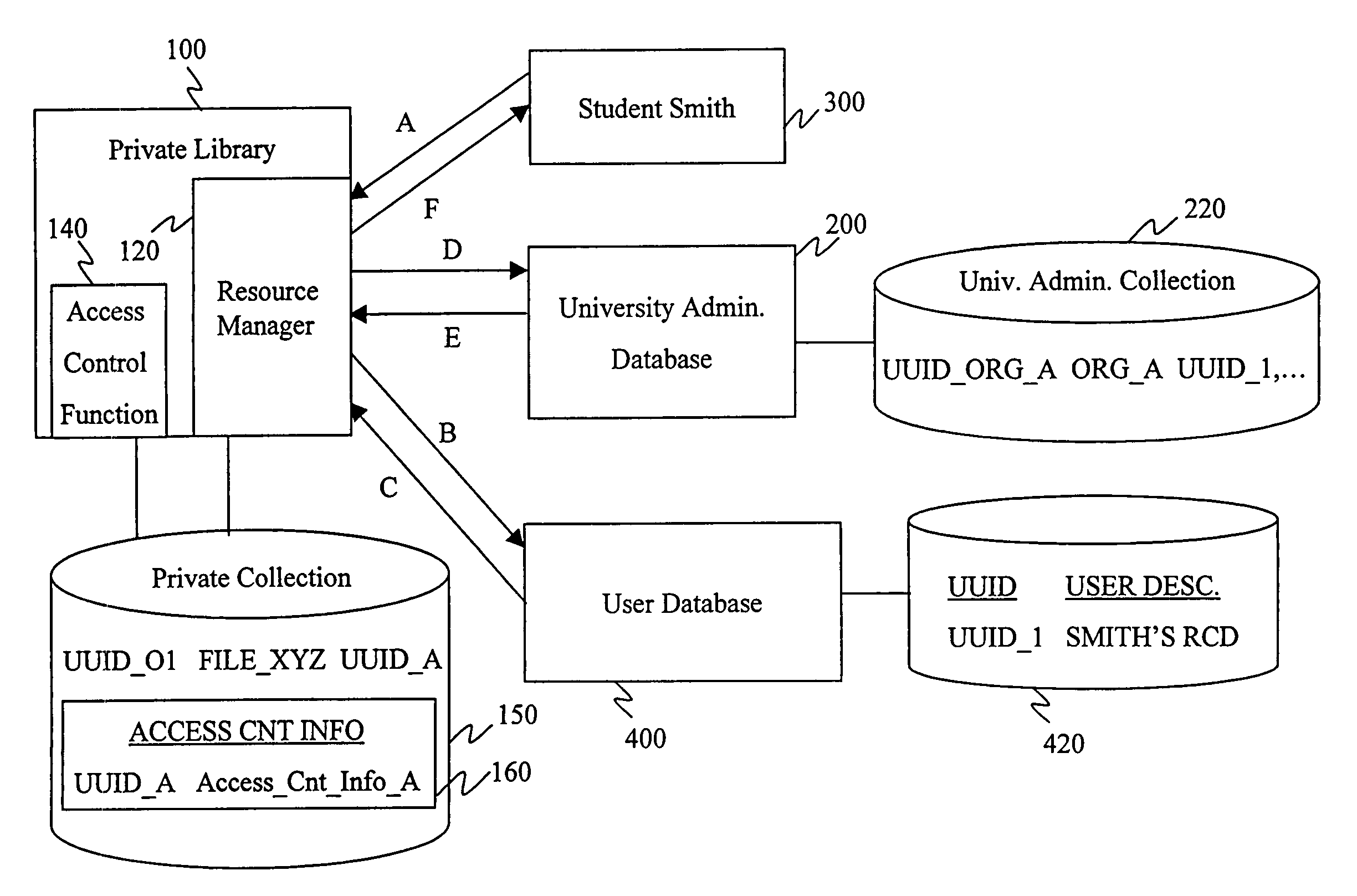
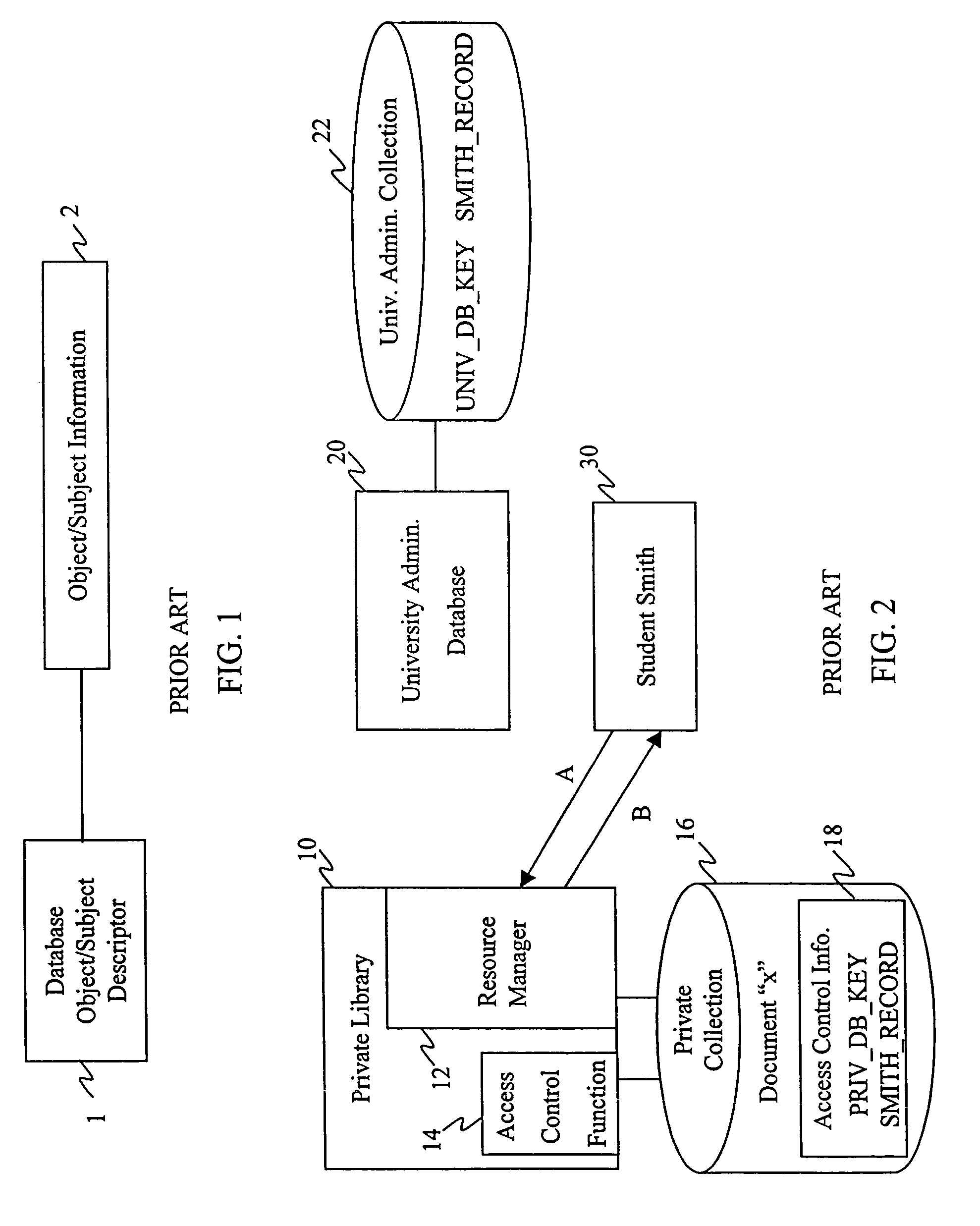
Distributed data structures for authorization and access control for computing resources
InactiveUS7331058B1Reduce significant administrative expenseSignificant expenseDigital data processing detailsUser identity/authority verificationArray data structureUniversally unique identifier
The invention relates to using a universally unique identifier in a database to uniquely identify, both within and outside of the database system, a user. A storage system, according to the invention, includes a first storage area having an object stored therein; and a second storage area having stored therein an object identifier that identifies the object. The object identifier is unique within and outside of the storage system, and can be a Universal Unique Identifier (UUID). The invention also relates methods for storing and retrieving objects identified based on the unique identifier.
Owner:IBM CORP
Methods and systems for creating and communicating with computer processes
InactiveUS20050132384A1Mechanism usedInterprogram communicationSecuring communicationUniversally unique identifierApplication programming interface
Disclosed are mechanisms for creating and communicating with computer processes. An application programming interface (API) presents services of the system to applications. The API is usable with all processes, local and remote, and is transparent with respect to the location of processes. A process table stores information about processes created using the system. The process table supports centralized process control and peer-to-peer process communication and synchronization. Each process is assigned a Universally Unique Identifier (UUID) that uniquely identifies the process no matter the computing device on which it runs. A parent UUID and a group UUID may be attached to the process and used for enforcing dependencies (e.g., for halting the process and all of its child processes) and for managing arbitrary, user-defined groups, respectively. A global event is associated with each process. When a process receives this event, it performs a controlled shutdown, cleans up, and reports status.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for building big data distributed log
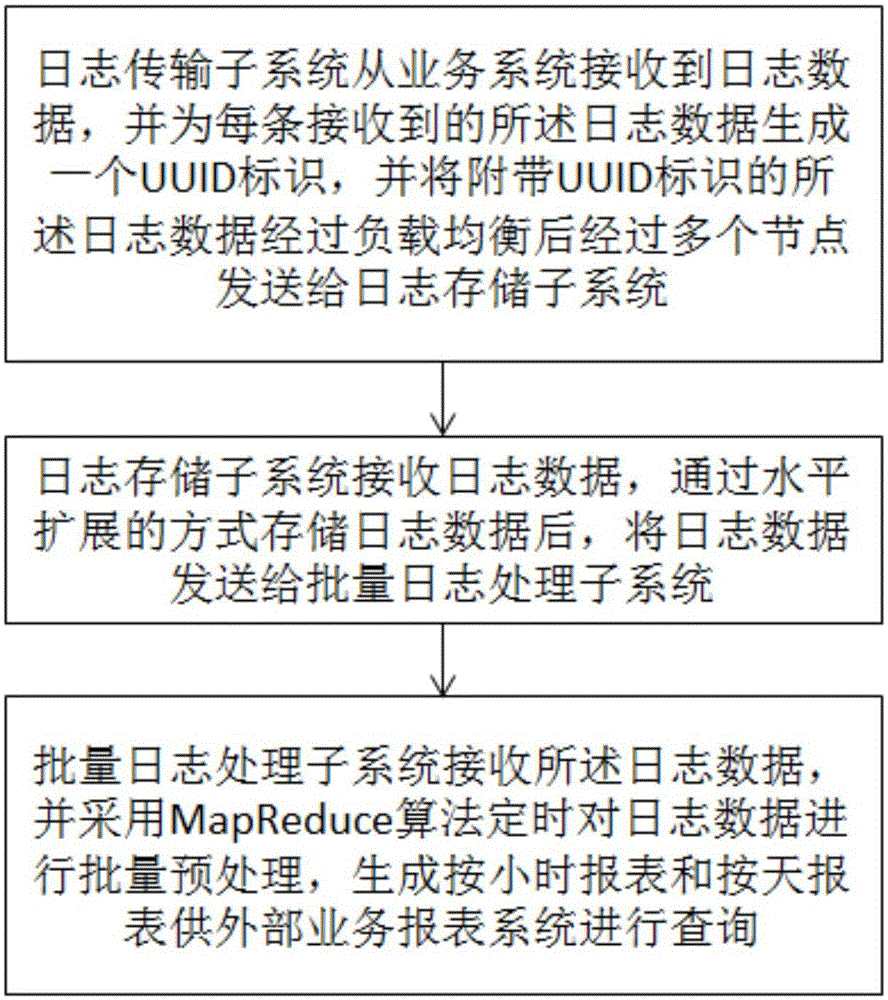
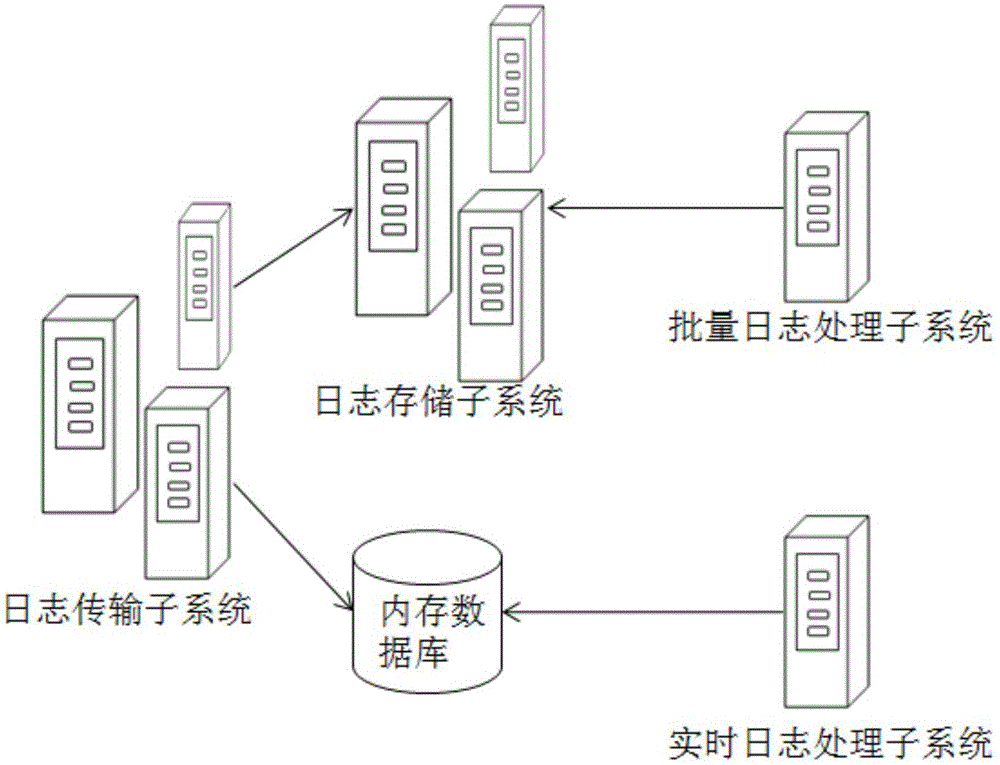
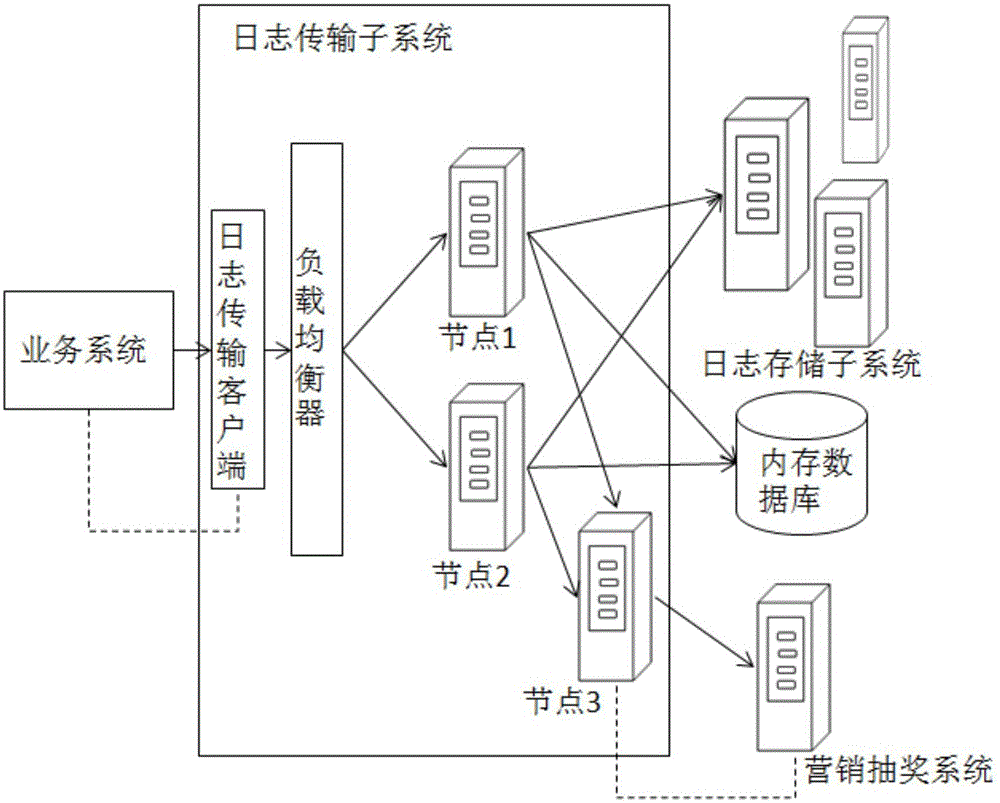
ActiveCN105138615AMeet reliabilitySatisfy real-timeDatabase management systemsDatabase distribution/replicationUniversally unique identifierMaintainability
The invention relates to a method and a system for building a big data distributed log. The method comprises the following steps that: 1, a log transmission sub system receives log data from a service system, generates a UUID (Universally Unique Identifier) for each piece of received log data, and sends the log data with the UUID to a log storage sub system through a plurality of nodes after the load balance; 2, the log storage system receives the log data, and stores the log data in a horizontal expansion mode; and 3, a mass log processing sub system extracts the log data stored in the log storage sub system, uses a MapReduce algorithm to regularly perform mass pre-processing on the log data, and generates a report by the hour and a report by the day to be required by an external service report system. The method and the system have the advantage that the requirements on the reliability, the real-time performance, the high performance, the high expandability and the maintainability of a log system under the big data condition can be met.
Owner:北京思特奇信息技术股份有限公司
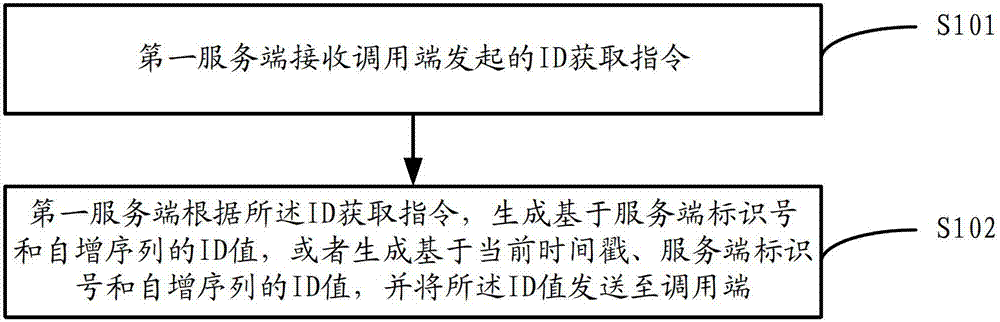
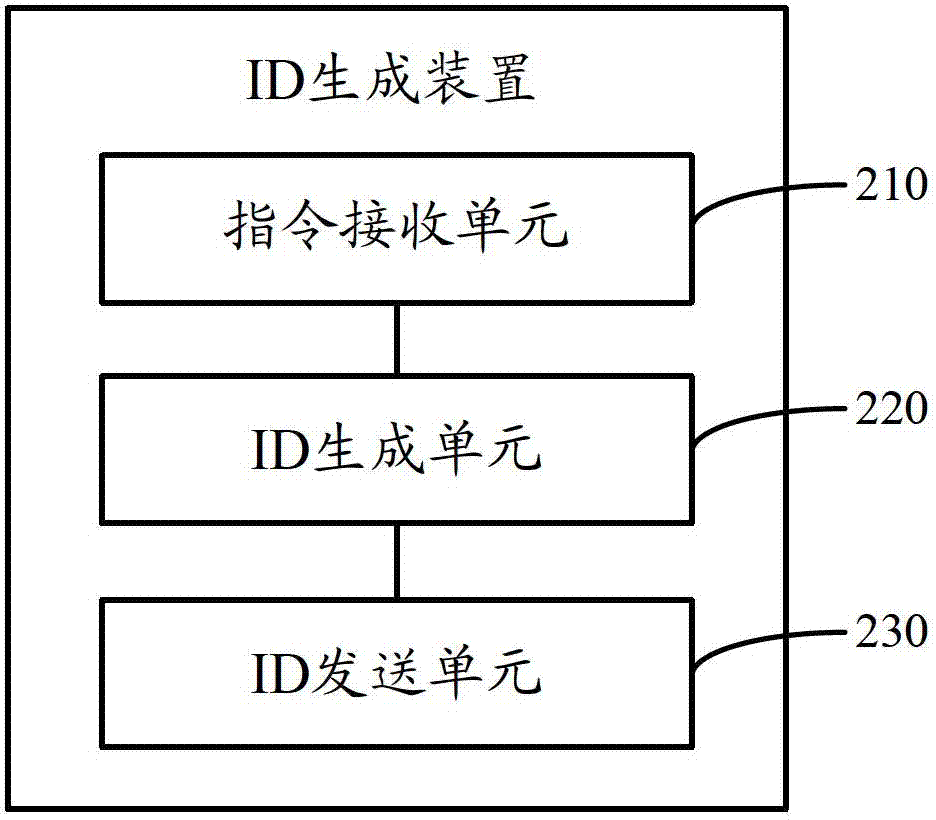
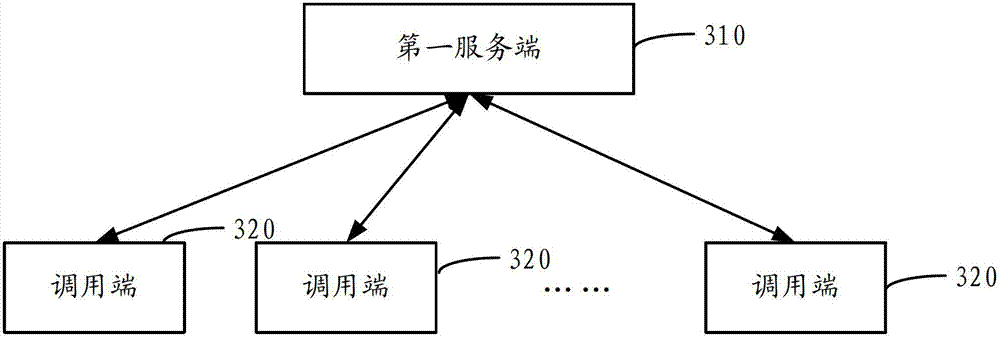
Method, equipment and system for generating ID
ActiveCN102769667AImprove performanceImprove reliabilityTransmissionExtensibilityUniversally unique identifier
The invention discloses a method, equipment and a system for generating an ID. The method comprises the following steps: a first service terminal receives an ID acquisition instruction initiated by calling terminals; according to the ID acquisition instruction, generating an ID value based on a service end identification number and a self-increasing sequence, or generating an ID value based on the current time stamp, a service end identification number and a self-increasing sequence; and transmitting the generated ID value to the calling terminals. According to the technical scheme provided by the invention, an overall unique ID is generated in a service-oriented manner, which is good in extendibility and high in serviceability and reliability; and besides, generated IDs are ensured to be sequential and incremental, the IDs are smaller than a UUID (Universally Unique Identifier) in occupied space, and the application is convenient and quick.
Owner:北京鸿享技术服务有限公司
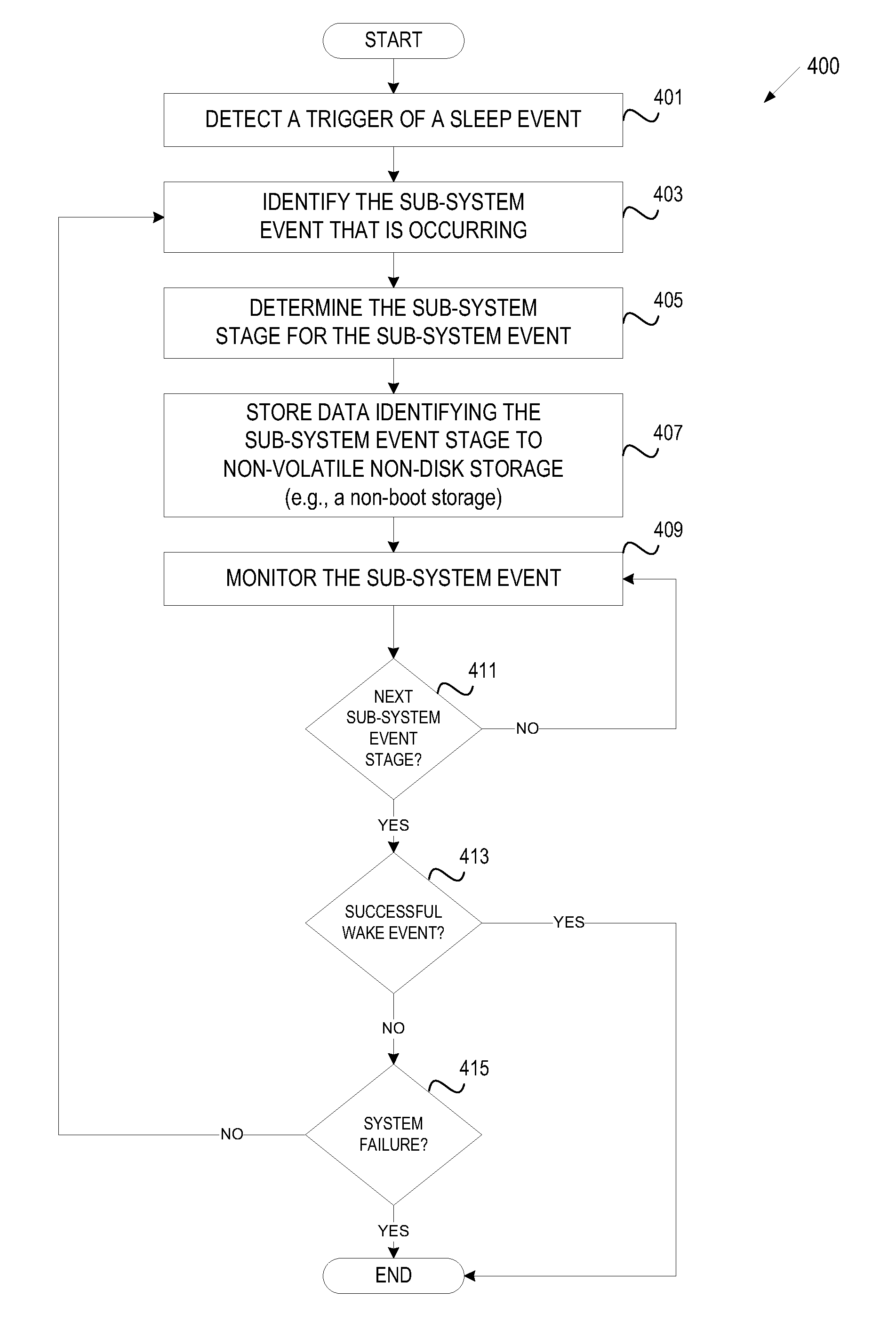
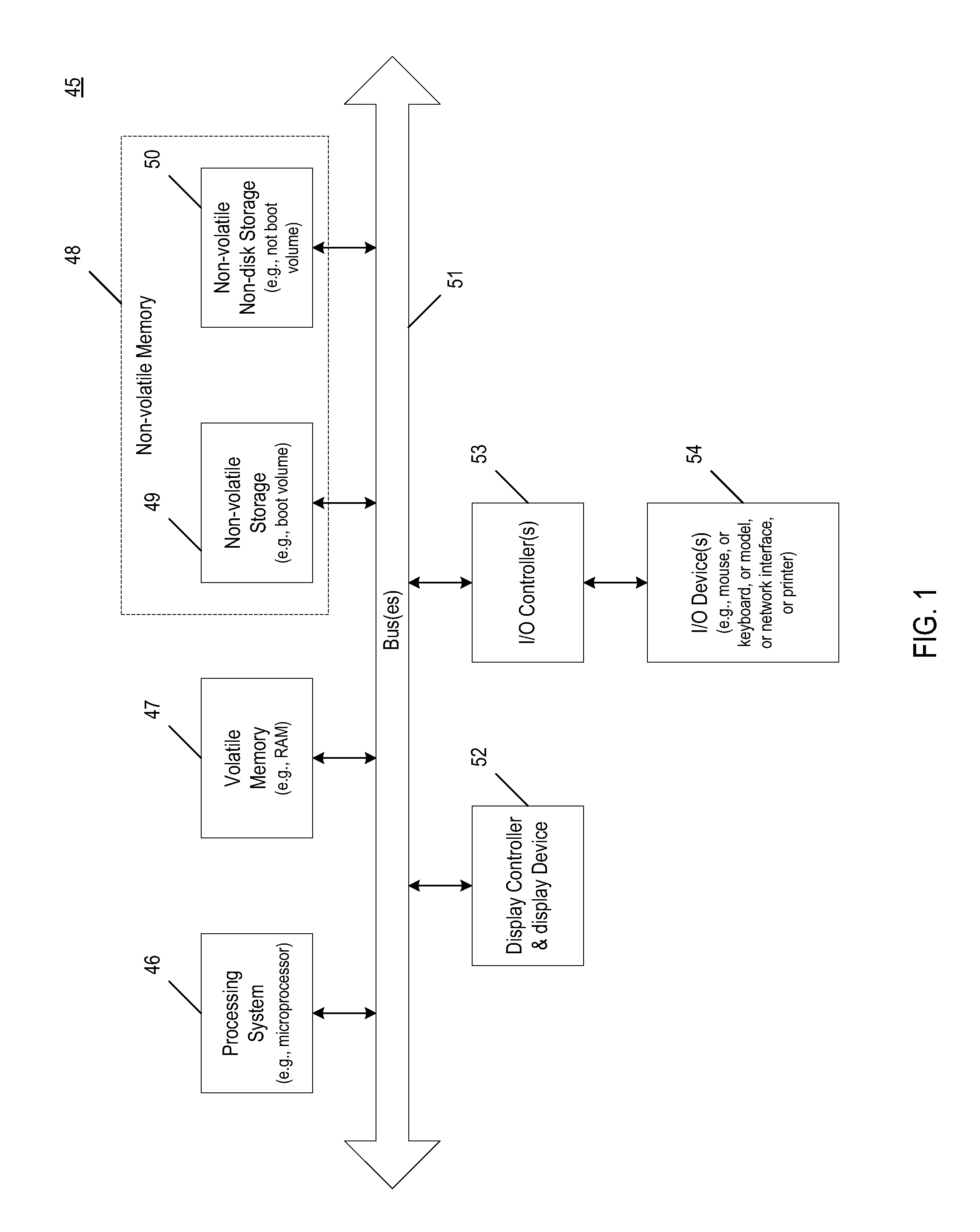
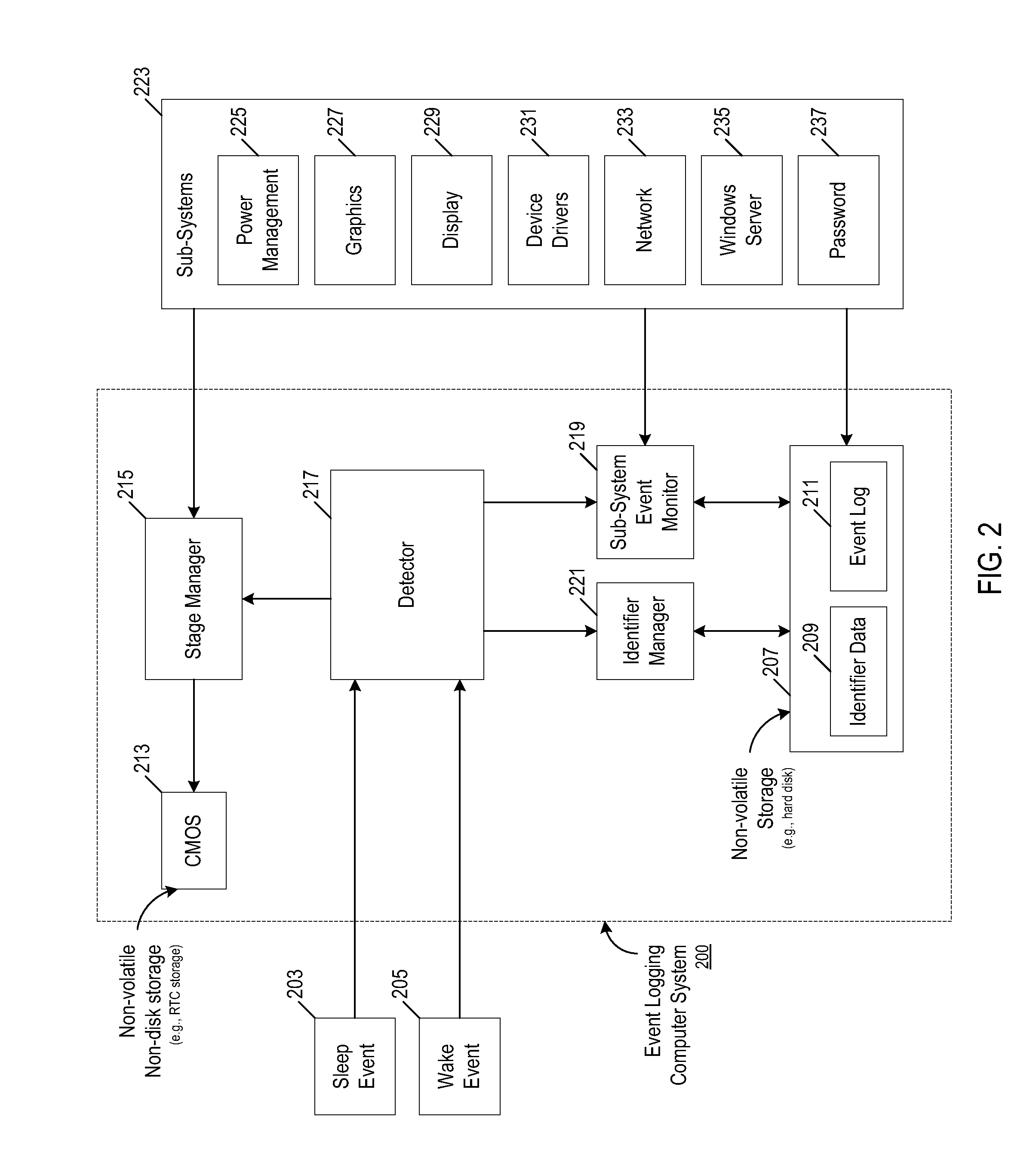
Sleep wake event logging
ActiveUS20100312946A1Error detection/correctionDigital data processing detailsUniversally unique identifierUnique identifier
A machine implemented method includes creating a universally unique identifier, detecting a trigger of a sleep event, and associating the universally unique identifier with the sleep event. The method monitors sub-system events that occur after a sleep event has been triggered and stores data in non-volatile non-disk storage (e.g., non-boot storage) identifying an event stage corresponding to the sub-system event that is occurring. The method determines whether a wake event has completed and logs each of the sub-system events using the universally unique identifier until a wake event has completed.
Owner:APPLE INC
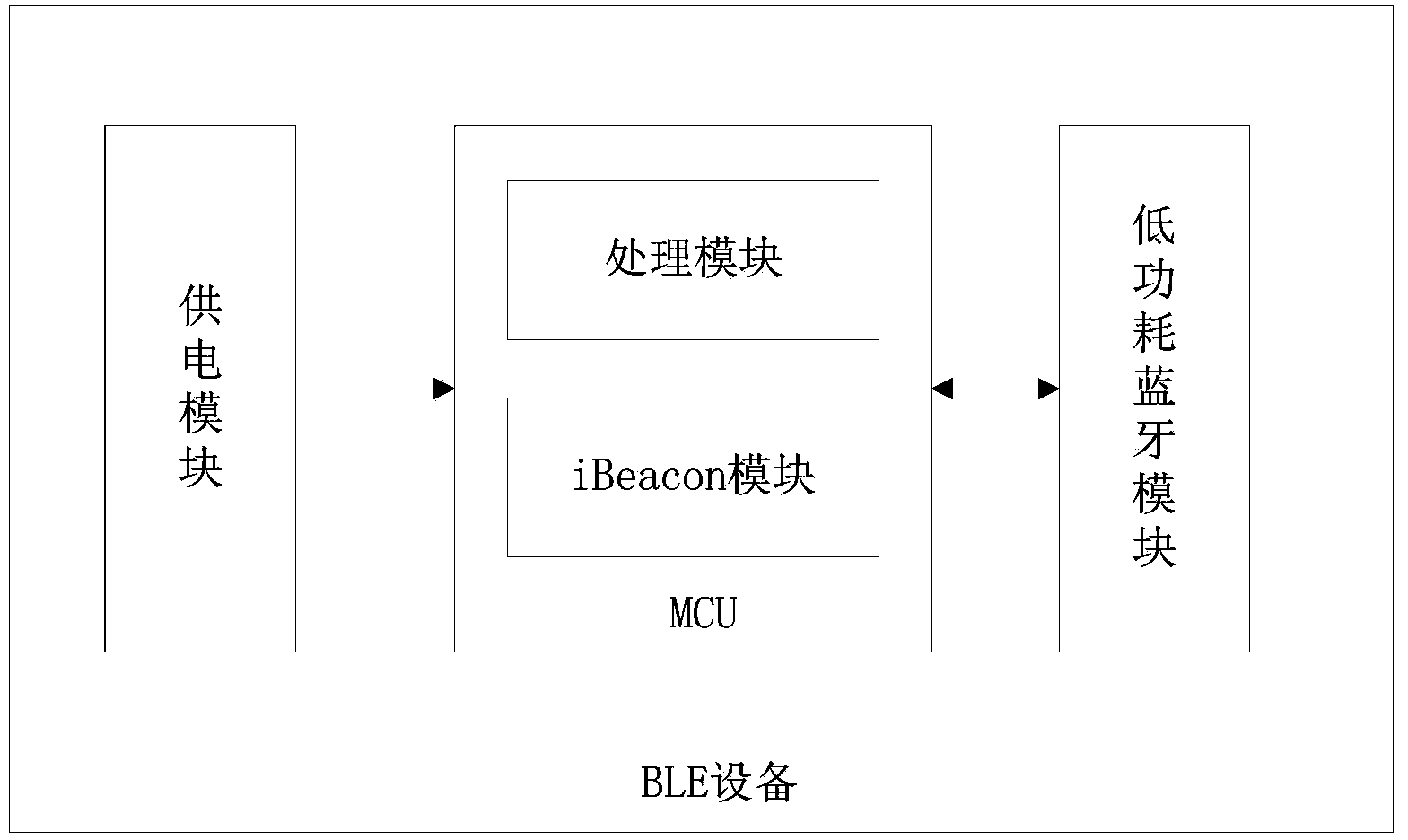
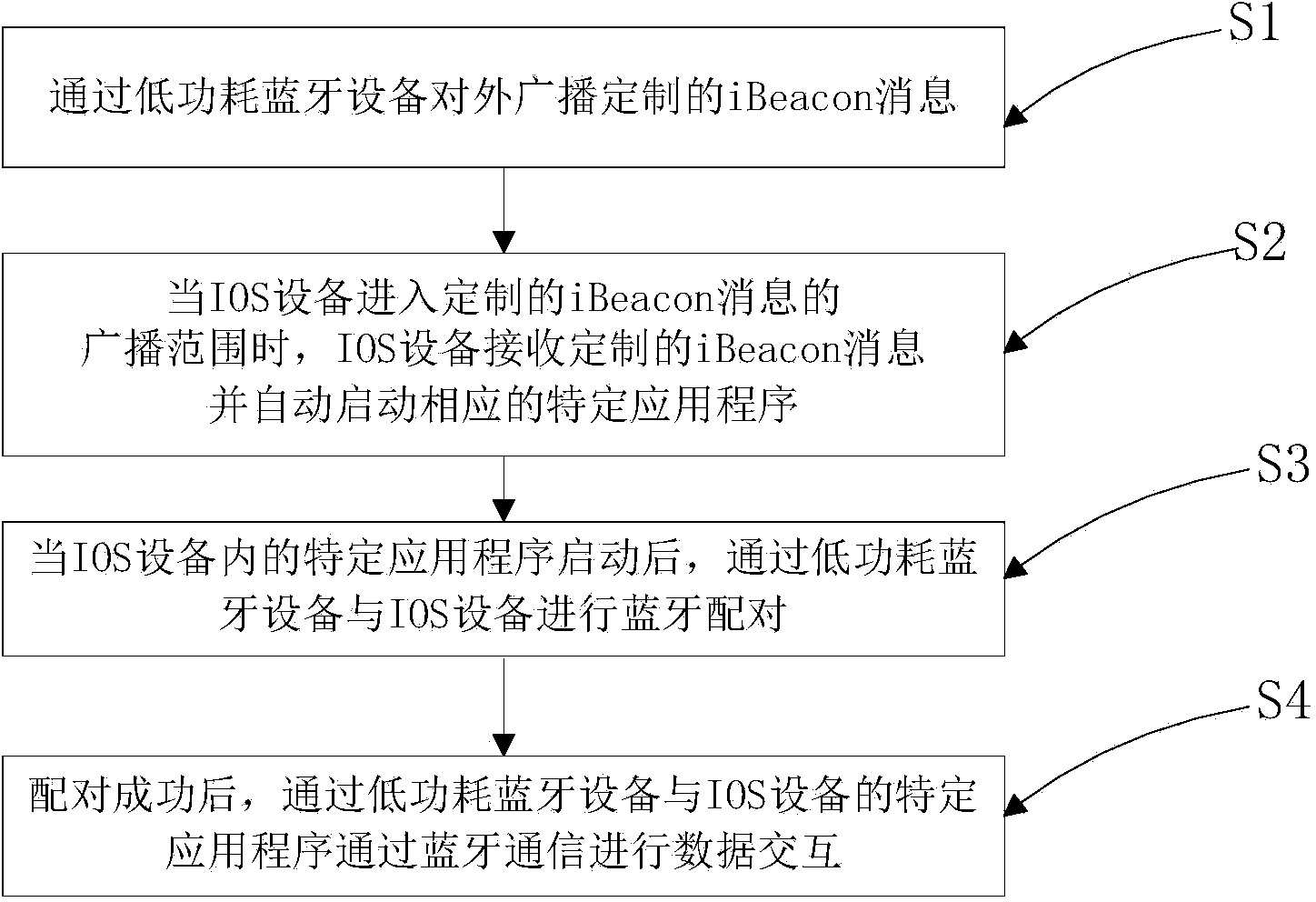
BLE (Bluetooth Low Energy) device, information safety device and automatic start-up method of application program
InactiveCN104077169AImprove experienceEasy to operateProgram loading/initiatingCommunications securityUniversally unique identifier
The invention discloses a BLE (Bluetooth Low Energy) device. The configuration of the BLE device is that an iBeacon base station is simulated, a custom iBeacon message is outwards broadcasted, and Bluetooth communication with an IOS device within the broadcasting range of the iBeacon message is built so as to conduct data interaction with a specific application program in the IOS device, wherein the iBeacon message comprises a universally unique identifier corresponding to the specific application program; the universally unique identifier is used for enabling the IOS device to automatically start up the specific application program to build the Bluetooth communication with the BLE device; the IOS system version of the IOS device is IOS 7.1 or above. The invention further provides an information safety device and an automatic start-up method of an application program. The BLE device, the information safety device and the automatic start-up method can realize the aims of the automatic start-up of the application program and the Bluetooth communication with the BLE device, solve the problems of being low in accuracy, low in efficiency, poor in user experience and the like when a plurality of devices simultaneously pair with each other, and meanwhile can prevent others from monitoring to a certain extent and improve communication security.
Owner:BEIJING SENSESHIELD TECH
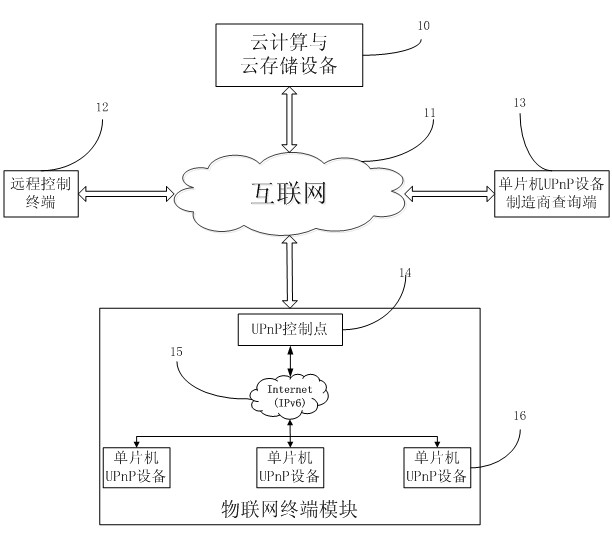
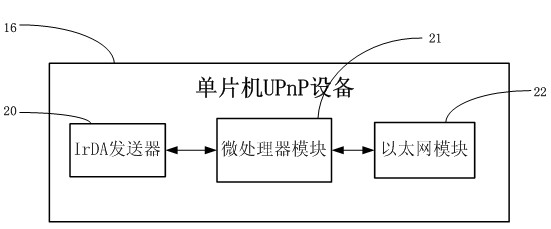
Realization method and device for intelligent home unified platform on basis of UPnP protocol
InactiveCN102694804AEnsure safetyLow costDigital data authenticationTransmissionMicrocontrollerUniversally unique identifier
The invention discloses a realization method and a device for intelligent home unified platform on the basis of a UPnP protocol. The realization method comprises the following steps: applying a unified naming manner to (Universally Unique Identifier) UUID of singlechip UPnP equipment; and binding the UUID of the UPnP equipment and the URL (Uniform Resource Locator) to a UUID+URL format character string. The device provided by the invention integrates an Internet of Things terminal, a cloud computer, cloud storage equipment, a remote control terminal and a singlechip UPnP equipment manufacturer inquiry terminal; and a singlechip UPnP equipment user controls the singlechip UPnP equipment, and the singlechip UPnP equipment manufacturer obtains the information of the singlechip UPnP equipment through accessing the URL. According to the method and device provided by the invention, through a singlechip, the Internet of Things terminal accesses a network, and the cost of building intelligent family network is greatly reduced. Moreover, the method provided by the invention is a method through which the UPnP equipment manufacturer can effectively track the product information.
Owner:SOUTH CHINA UNIV OF TECH
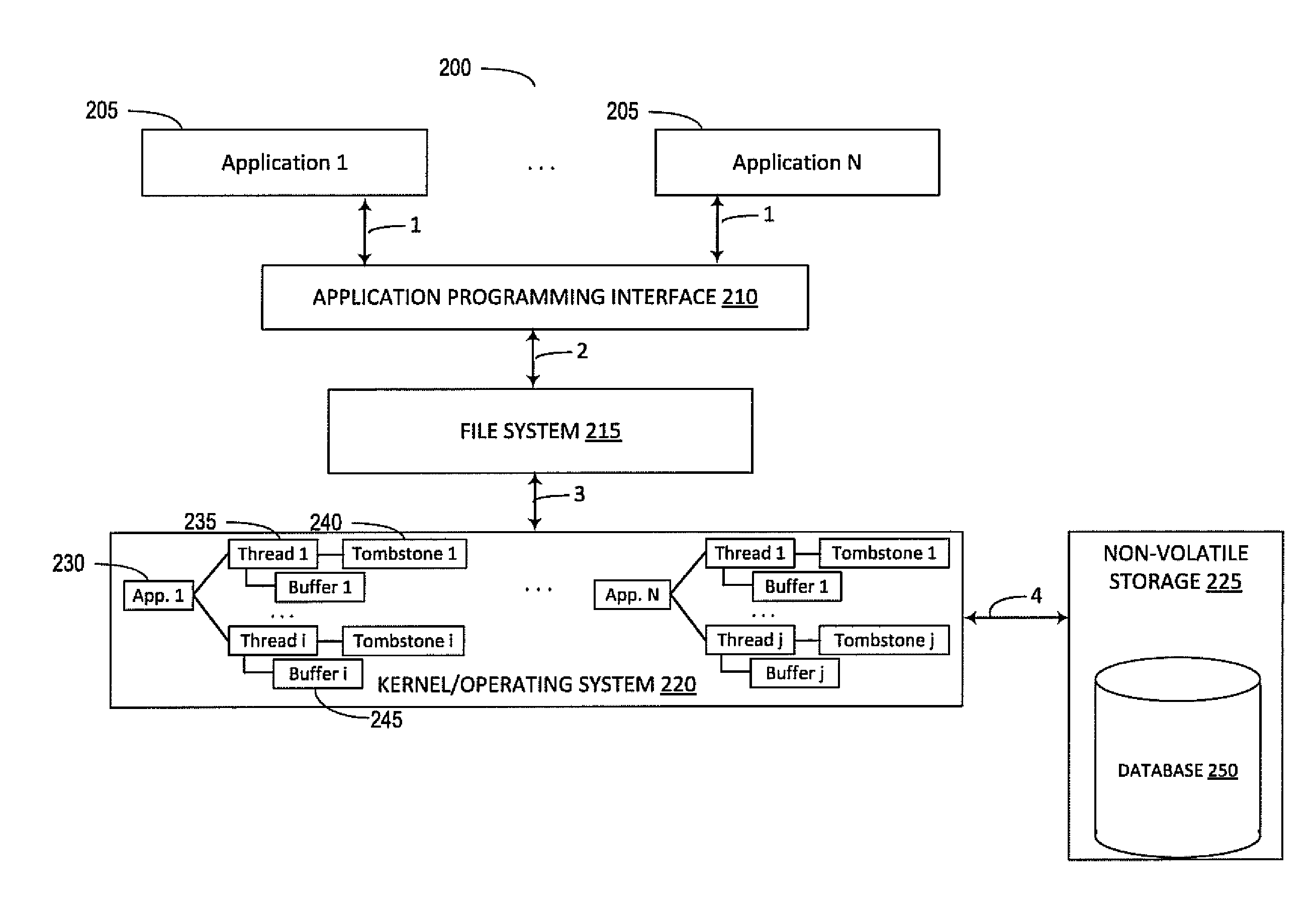
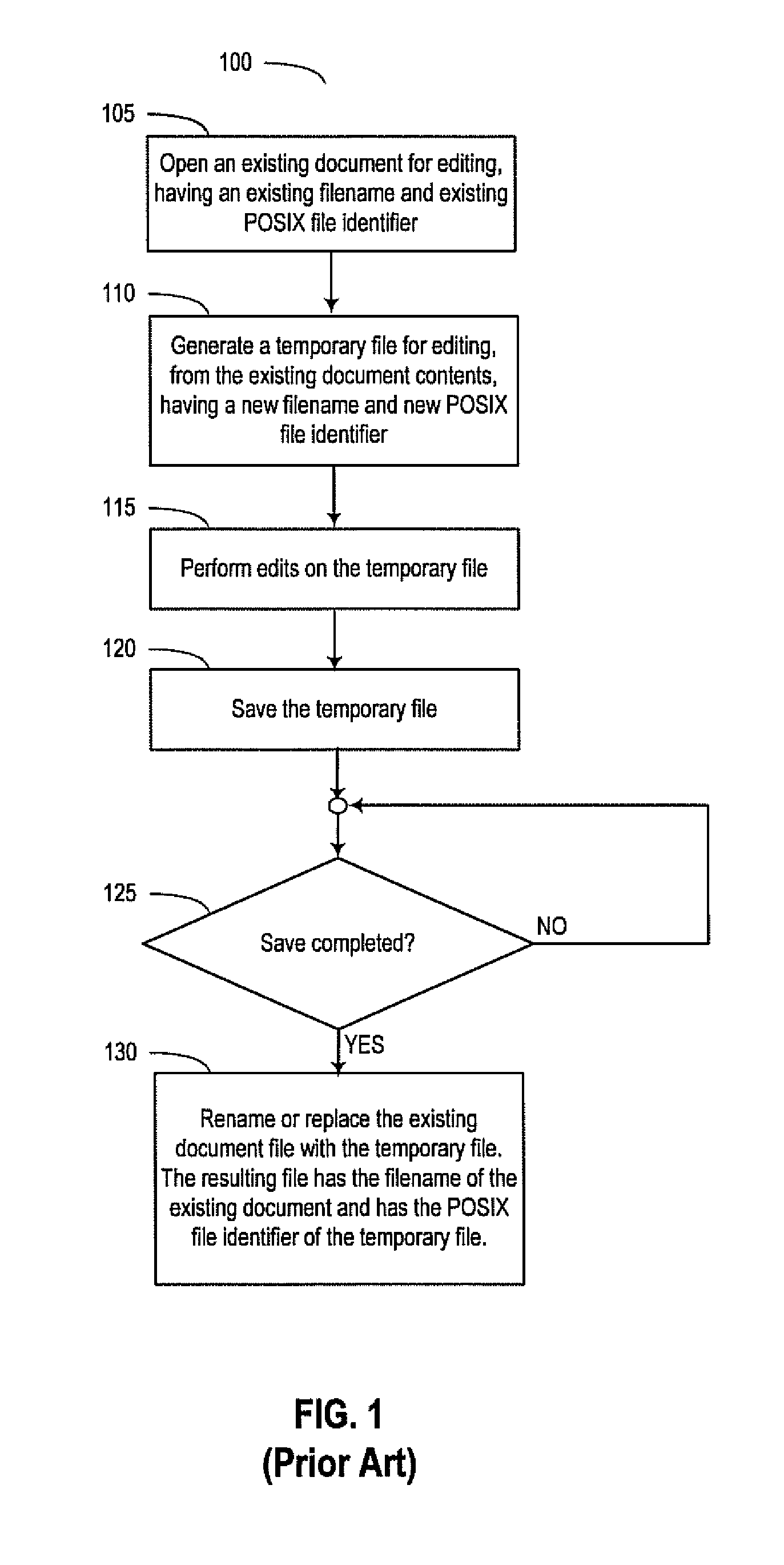
Document tracking for safe save operations
ActiveUS20150347440A1Operational securityDigital data information retrievalRedundant operation error correctionOperational systemFlash file system
Systems and methods are disclosed that track a document within a file system using document identifier (DOCID) that is preserved during safe save operations. The DOCID can be a universally unique identifier (UUID). The DOCID can be generated on a local file system or generated during a synchronization process with a remote synchronization service. Applications can opt in to document tracking. The kernel of the operating system can monitor file system operations on a per-application and per-thread basis and determine when a processing thread is about to perform a safe save. When a sequence of file system operations indicates that a safe save is to be performed, the kernel can generate and store a tombstone record that includes the DOCID and other metadata of the tracked document and pass the DOCID and metadata to the newly saved document.
Owner:APPLE INC
Ultra-low power consumption indoor and outdoor hybrid positioning system
InactiveCN105911578AReduce power consumptionLow power long rangeSatellite radio beaconingUsing reradiationUniversally unique identifierLongitude
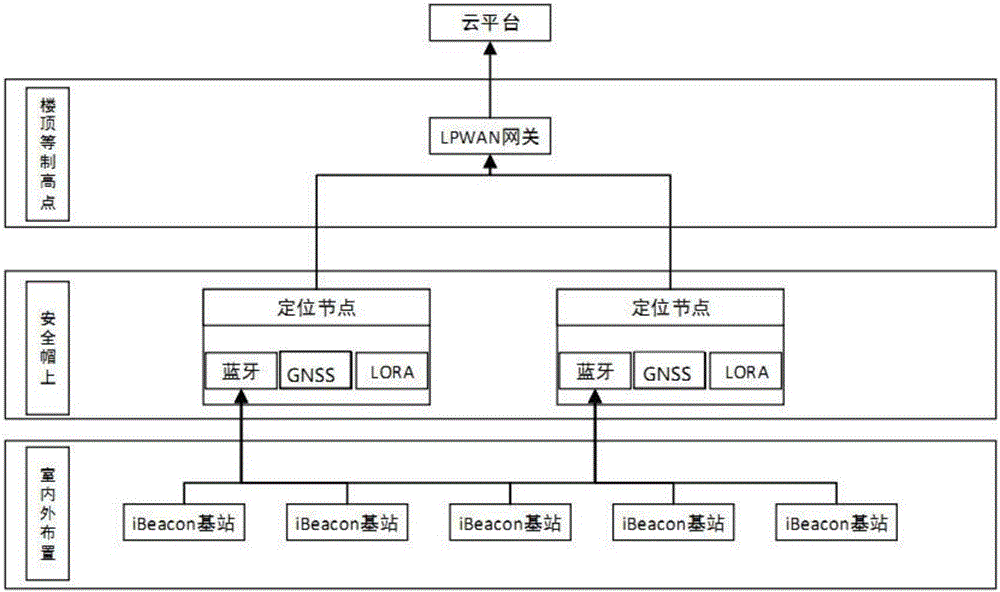
The invention discloses an ultra-low power consumption indoor and outdoor hybrid positioning system. The system comprises a plurality of iBeacon base stations which are arranged indoors and broadcast general unique identification codes through Bluetooth by preset signal intensities; a positioning node, wherein the positioning node is arranged on a moving object to be positioned, periodically monitors the plurality of general unique identification codes and the corresponding signal intensities around the positioning node through Bluetooth and outputs the monitored result by means of LoRa; a wireless gateway used for receiving the plurality of general unique identification codes and the signal intensity information and outputting the plurality of general unique identification codes and the signal intensity information through a mobile network; and a cloud platform used for receiving the plurality of general unique identification codes and the signal intensities and determining the latitude, longitude and indoor position of the moving object. According to the invention, by adopting the iBeacon technology based on Bluetooth indoors and adopting a GNSS positioning technology outdoors, precise positioning and seamless switching are realized, low power consumption and long distance transmission is realized by means of the LPWAN gateway, the positioning precision is high, the power consumption is low, the distance is long, and the system is suitable for large-scale popularization and application.
Owner:武汉慧联无限科技有限公司
Virtual serial cable
Techniques and systems for providing a virtual serial cable are provided. For example, computing device, a method, and a computer-program product may be provided. A computing device may include one or more data processors and a receiver for receiving a serial communication from a first serially-connected device located in a first location, wherein the first serially-connected device is assigned a first universally unique identifier, and wherein the serial communication includes a second universally unique identifier assigned to a second serially-connected device located in a second location. A non-transitory computer-readable storage medium may contain instructions which when executed on the one or more data processors, cause the one or more processors to obtain the second universally unique identifier, determine that the second universally unique identifier is assigned to the second serially-connected device, and create a virtual serial connection between the first serially-connected device and the second serially-connected device, wherein the virtual serial connection is established with the second serially-connected device based on the second universally unique identifier being assigned to the second serially-connected device. The computing device may include a transmitter for transmitting the serial communication to the second serially-connected device located in the second location, wherein the serial communication causes the second serially-connected device to perform an operation.
Owner:CITRIX SYST INC
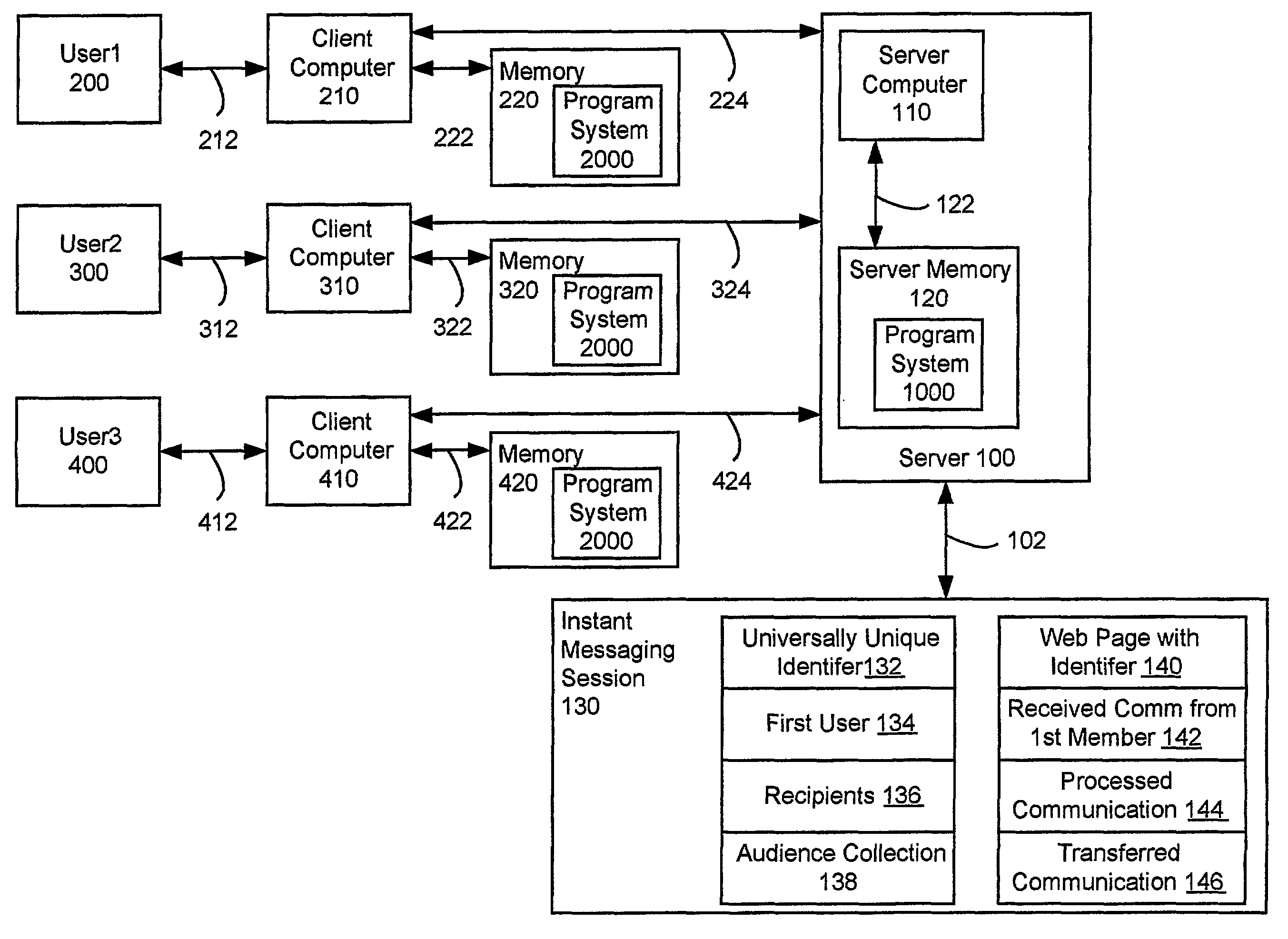
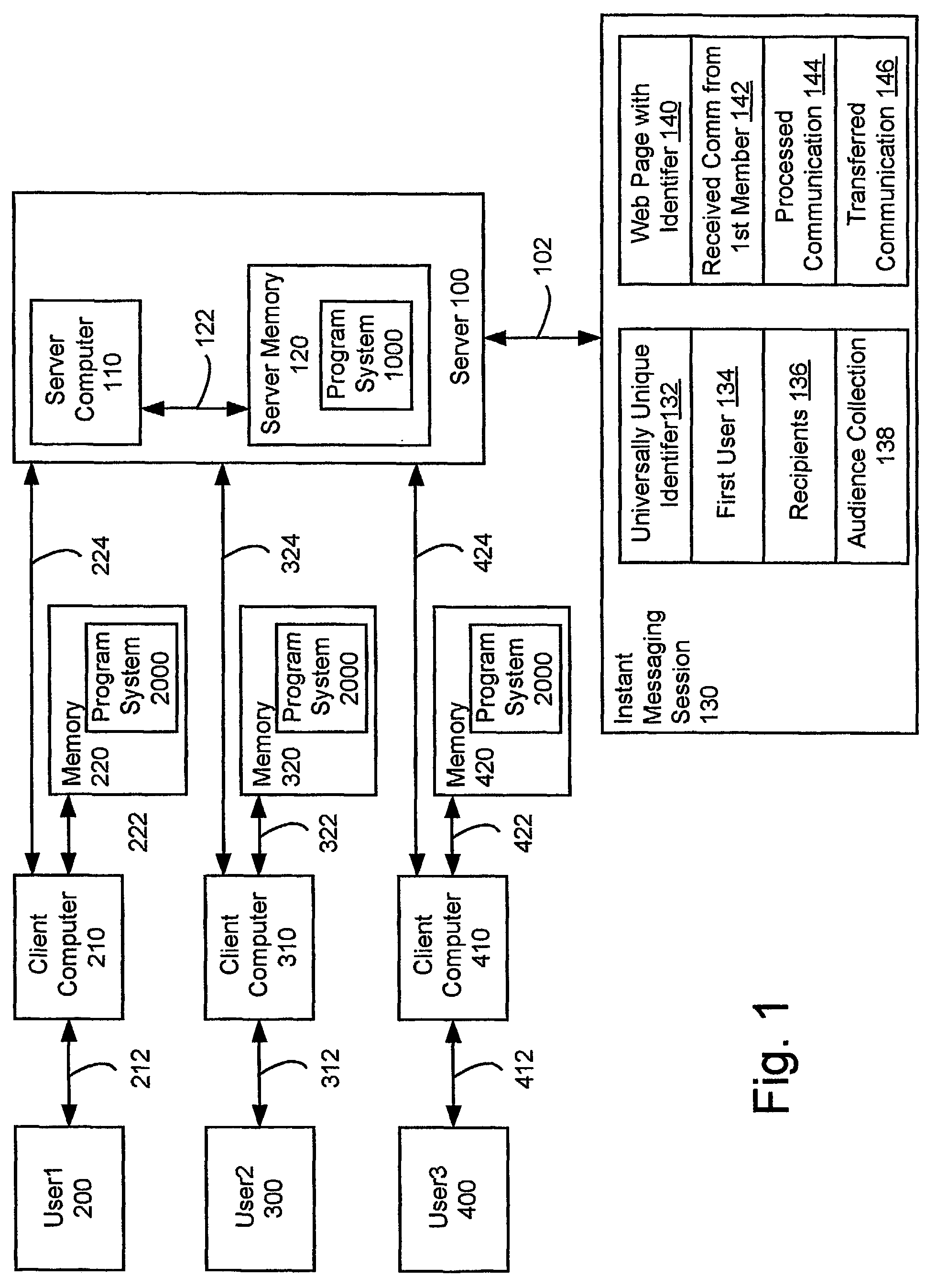
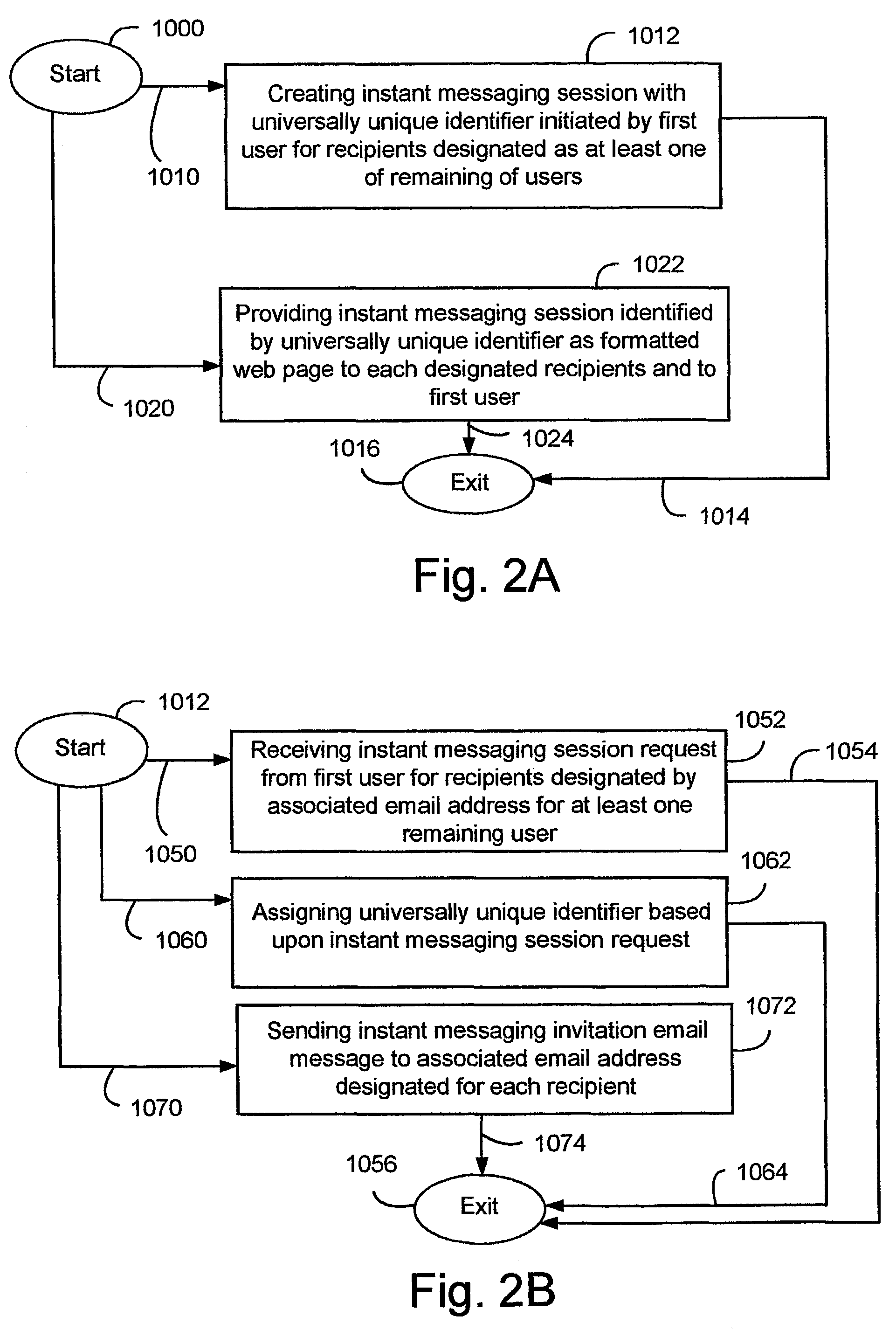
Email integrated instant messaging
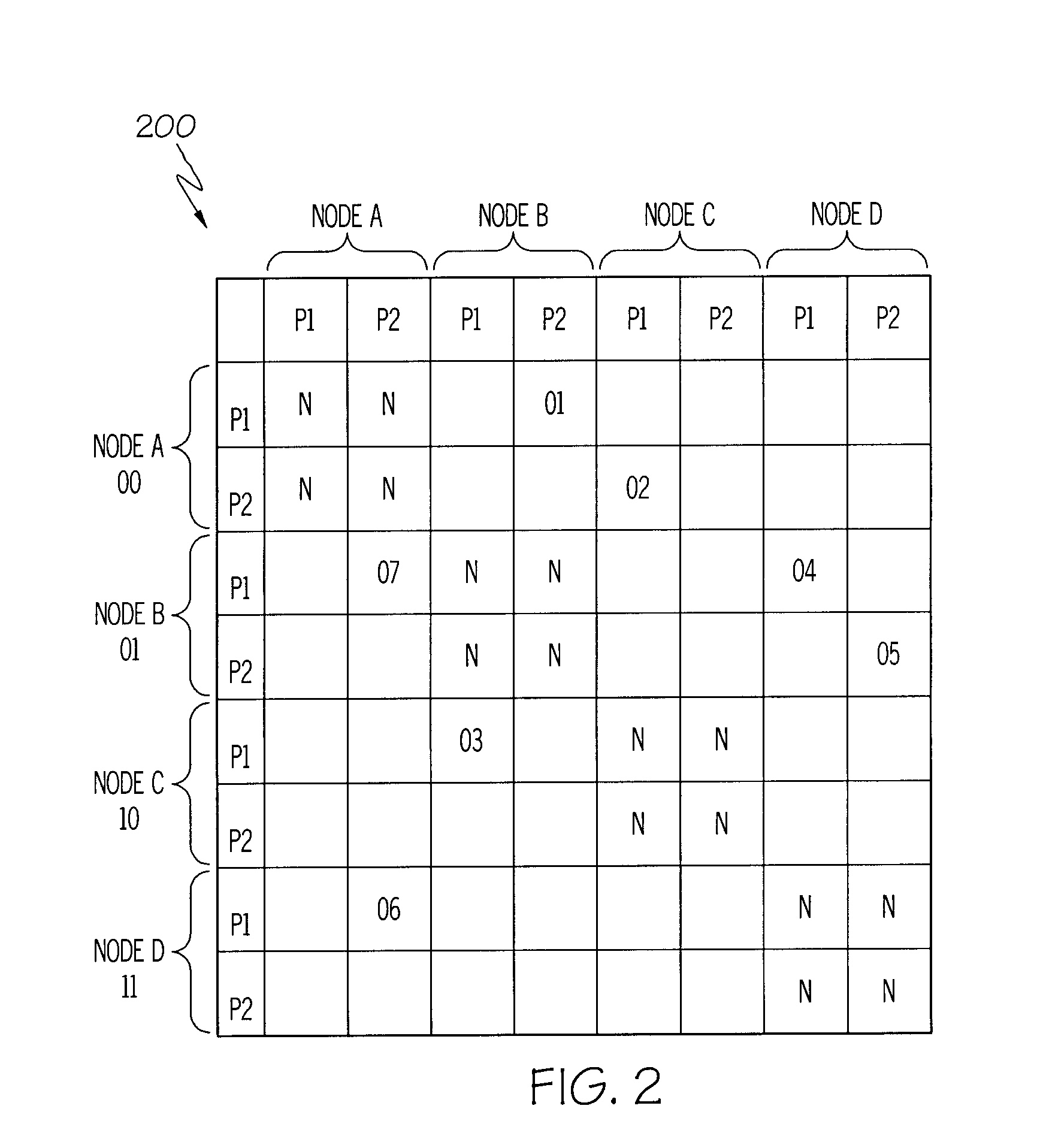
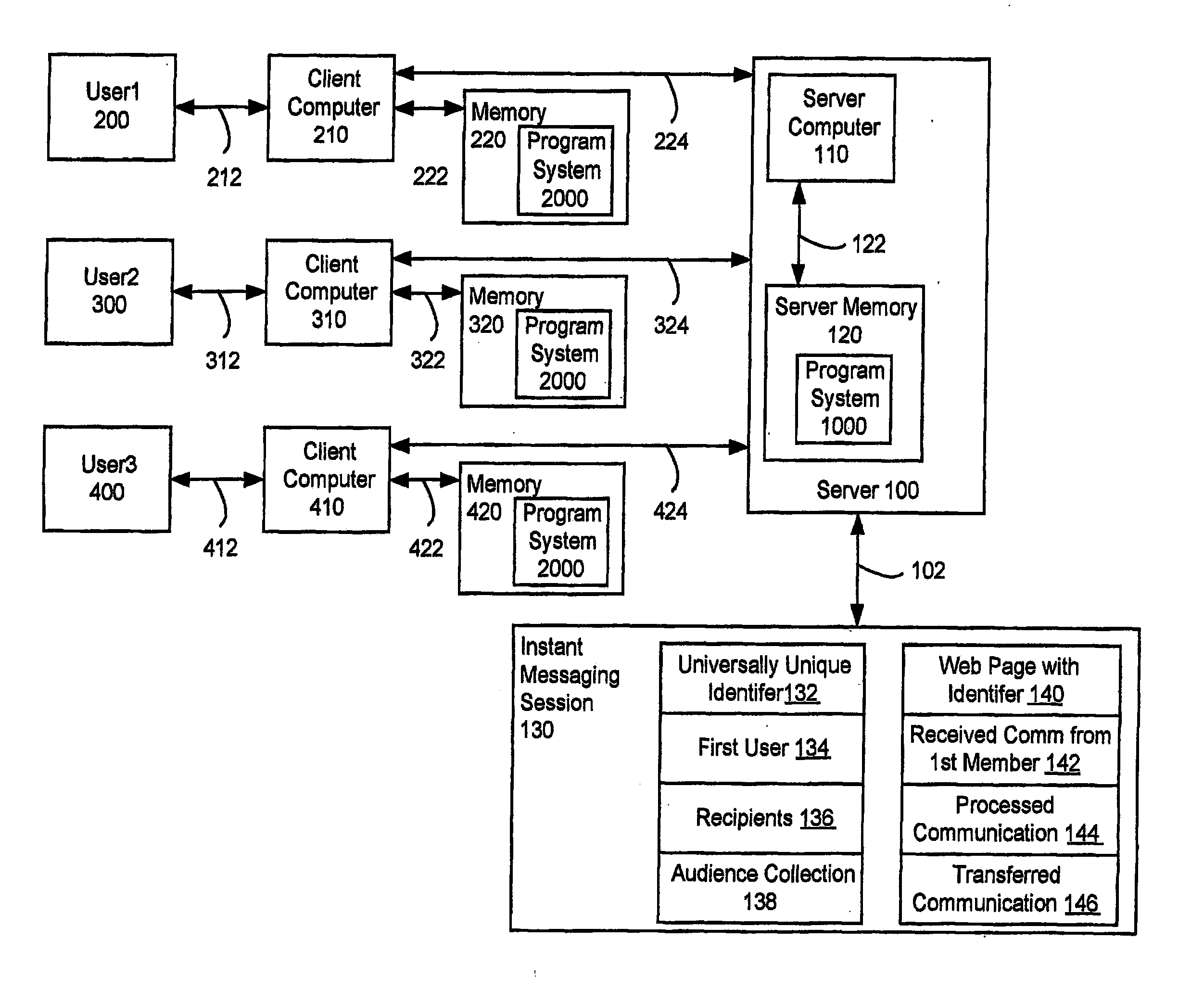
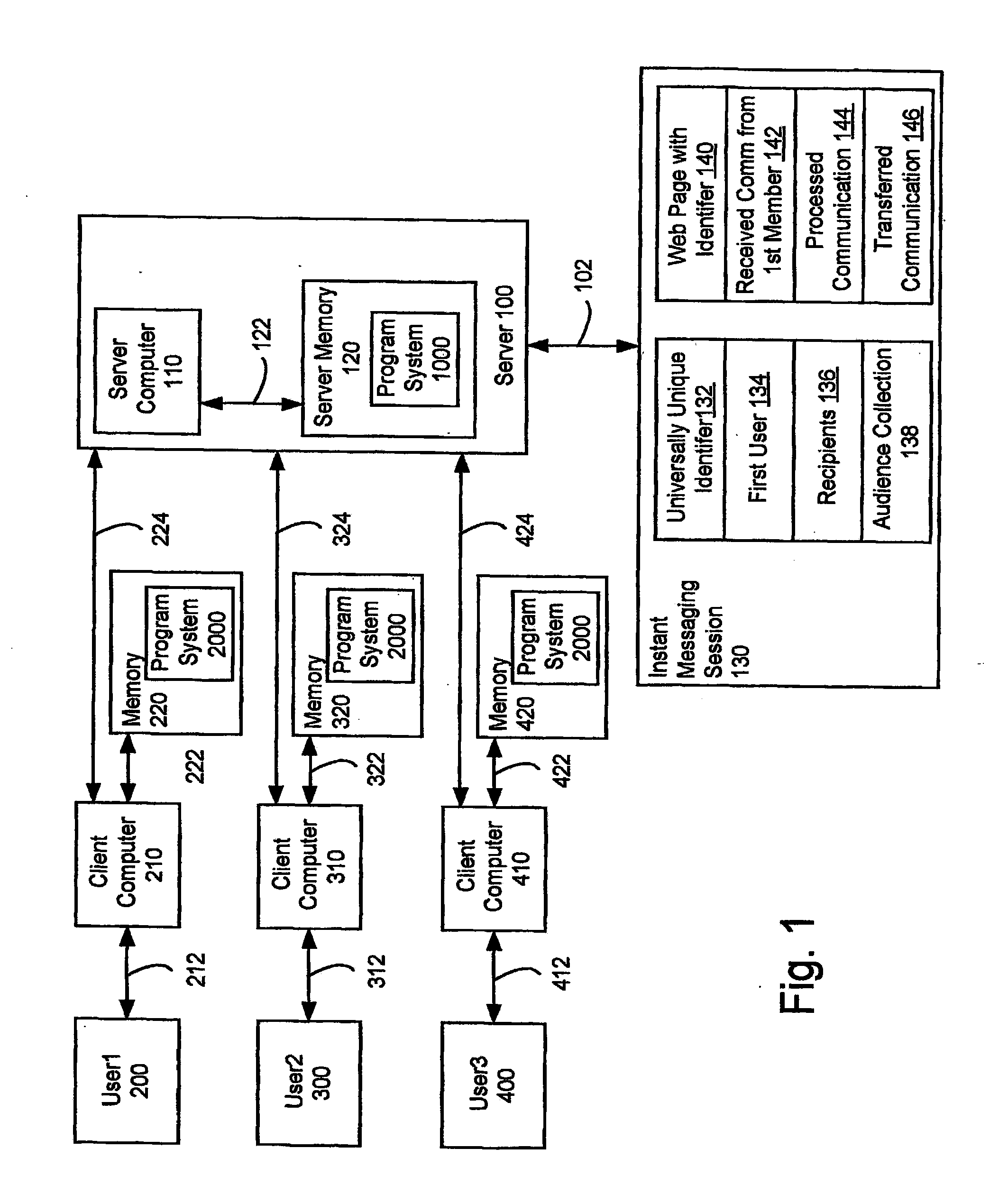
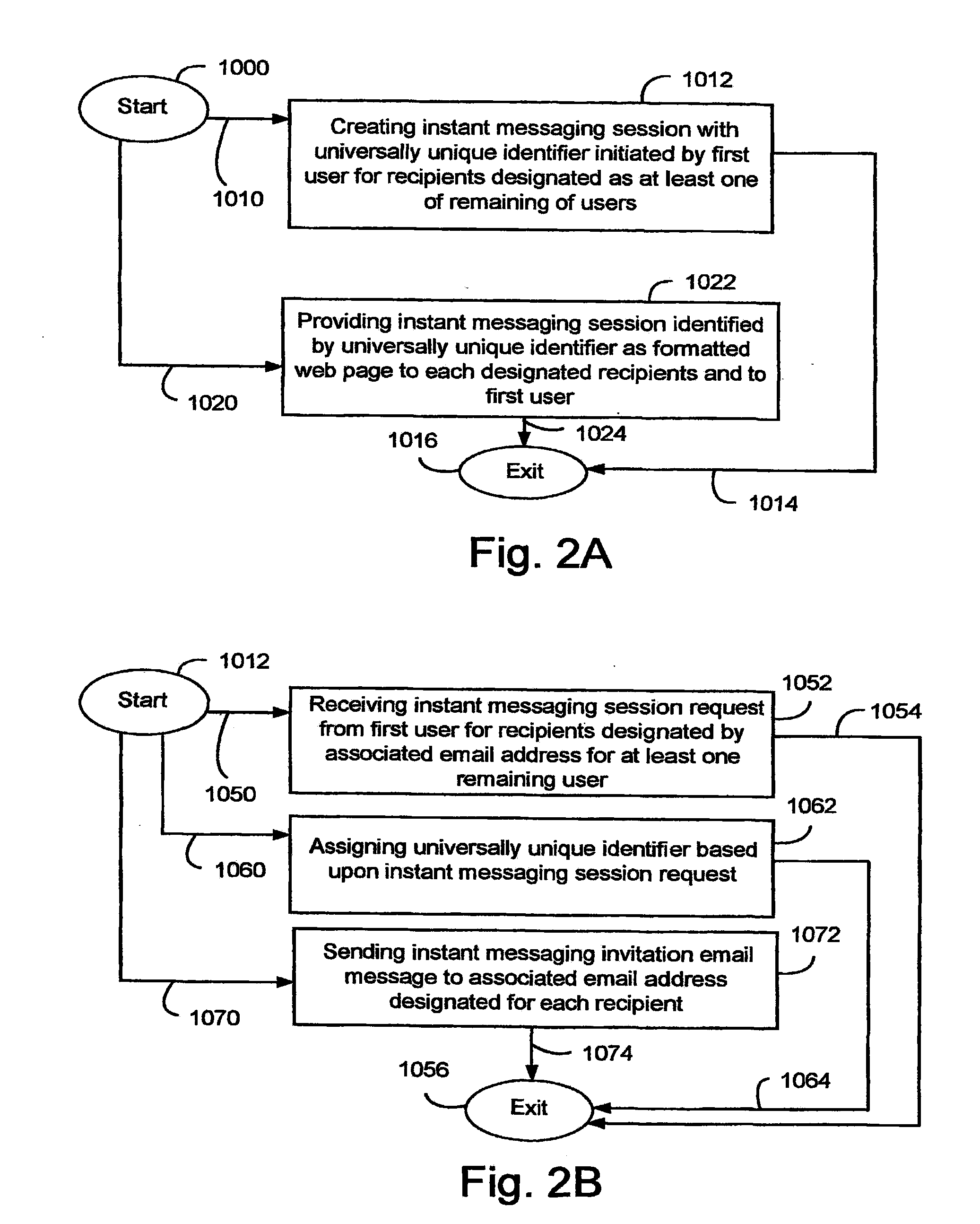
ActiveUS8001190B2Multiple digital computer combinationsOffice automationUniversally unique identifierMessage passing
A system and method supporting instant messaging which removes many of the problems and barriers to the use of instant messaging through the use of universally unique identifiers to web pages for instant messaging sessions, with recipients invited to the instant messaging session via email.
Owner:META PLATFORMS INC
System and method of implementing an object storage infrastructure for cloud-based services
ActiveUS9135269B2Easy retrievalWeb data indexingMultiple digital computer combinationsUniversally unique identifierCloud base
A method for storing objects in an object storage system includes the steps of establishing a network connection with a client over an inter-network, receiving an upload request indicating an object to be uploaded by the client, selecting at least two storage nodes on which the object will be stored, receiving the object from the client via the network connection, and streaming the object to each of the selected storage nodes such that the object is stored on each of the selected storage nodes. The method can also include writing an object record associating the object and the selected storage nodes to a shard of an object database and generating a Universally Unique Identifier (UUID). The UUID indicates the shard and the object ID of the object record, such that the object record can be quickly retrieved. Object storage infrastructures are also disclosed.
Owner:EGNYTE
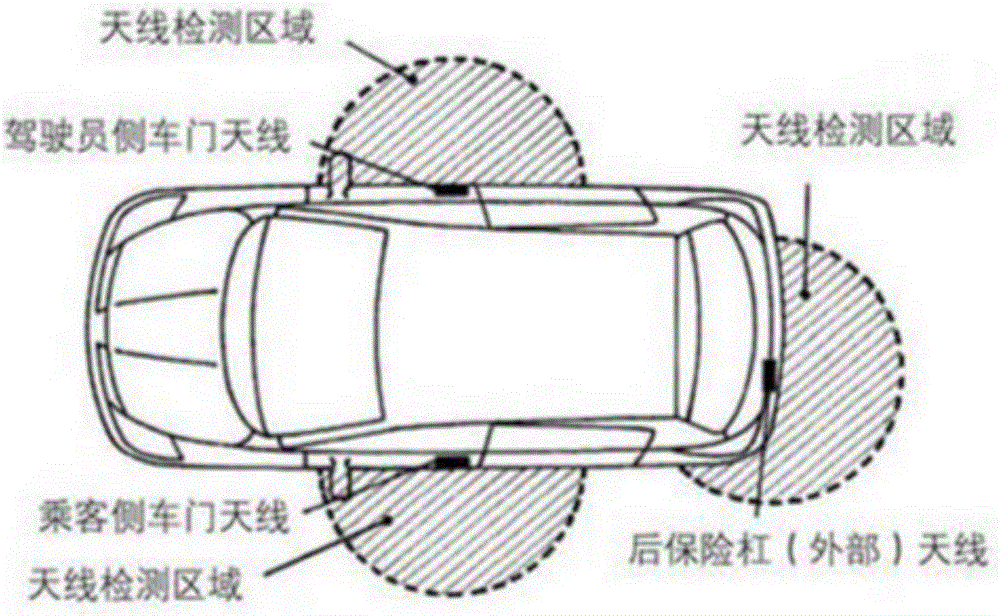
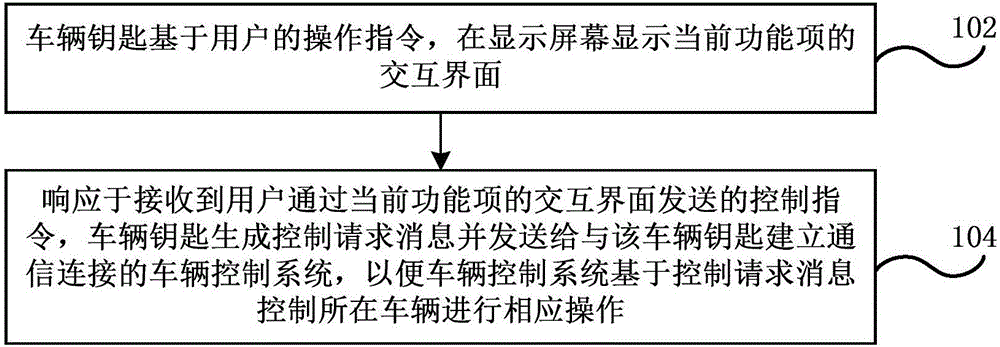
Vehicle control method, vehicle control system, vehicle key, vehicle, and vehicle system
ActiveCN106846563ARich remote control functionsMeet the remote control function requirementsAnti-theft devicesIndividual entry/exit registersOperating instructionUniversally unique identifier
The invention discloses a vehicle control method, a vehicle control system, a vehicle key, a vehicle, and a vehicle system. The method comprises: the vehicle key displays an interactive interface of a current function item on a display screen based on an operating instruction of a user, and a function list is set in the vehicle key, and comprises multiple function items and UUIDs (Universally Unique Identifiers) representing functions of the function items; in order to respond to a received control instruction sent by a user through the interactive interface of the current function item, the vehicle key generates a control request message and sends to the vehicle control system in communication connection with the vehicle key, so that the vehicle control system conveniently controls the vehicle to operate correspondingly based on the control request message, and the control message comprises the UUID representing the function of the current function item and the control instruction. According to the vehicle control method, the vehicle control system, the vehicle key, the vehicle, and the vehicle system provided by the invention, a remote control function of the vehicle key on the vehicle is enriched, the demand of the user on the remote control function of the vehicle under the overall background of mobile internet development can be met, and the user experience is improved.
Owner:ZHICHEAUTO TECH BEIJING
Framework and Method of Using Instant Messaging (IM) as a Search Platform
InactiveUS20070255795A1Multiple digital computer combinationsUniversally unique identifierUnique identifier
A framework and method to integrate a Search Service in an IM environment is provided. A Search Service is represented by one or more buddies or contacts of an IM user. An IM user performs inline search by adding a buddy representing a Search Service to a new or existing IM conversation, and inputting search query as a normal IM message. The Search Service sends the search results back as a regular IM message to all parties participating in the IM conversation. A Search Service implements and runs persistently one or more IM client simulators (SEIMCS) according to the communication and application protocol of an IM system. The Search Service defines one or more universally unique identifiers (UUIDs), registers one or more IM members with the UUIDs to an IM service. It logs in the defined IM members to the IM system and publishes these IM members. The framework allows a Search Service to work with any IM service, and an IM service can support any Search Service, wherein the Search Services and the IM services are operated independently. Neither IM client software nor IM system needs to be changed. No special indicators, prefix of IM message, search button or other actions need to be defined for performing search in an IM environment.
Owner:SOOKOOL
System and method for universal identification of biological samples
InactiveUS20050106619A1Bioreactor/fermenter combinationsBiological substance pretreatmentsUniversally unique identifierUnique identifier
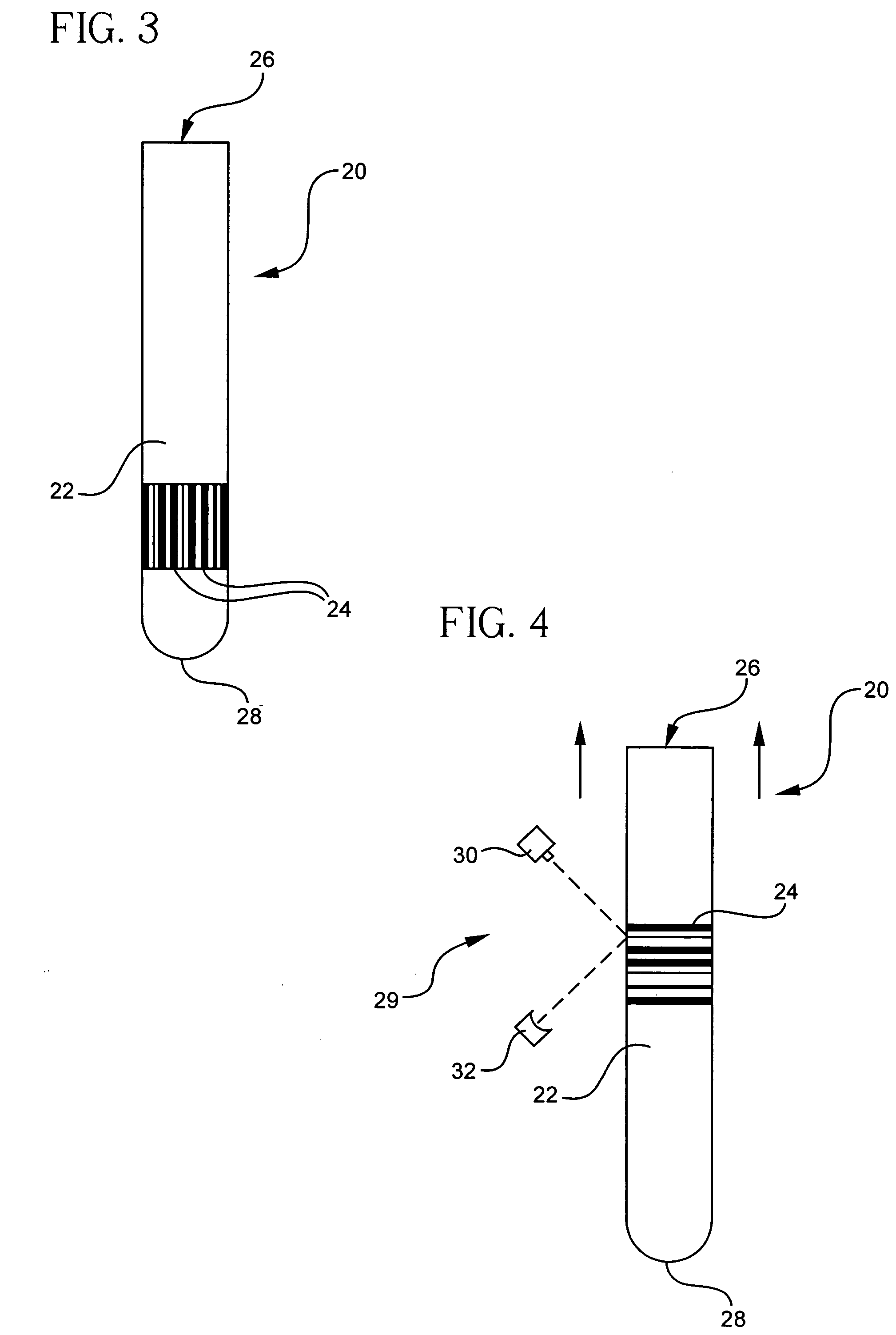
A system and method for identifying a biological sample associated with a container is disclosed. A universally unique identifier is associated with each container. In one or more embodiments, the identifier comprises one or more markings having a specular reflectance which differs from the specular reflectance of the outer surface of the container adjacent the markings. A detection apparatus detects the differences in specular reflectance light to identify the identifier associated with the container. The identifier is associated with certain information regarding the container and biological sample. From that point forward, any information about the contents of the container may be retrieved by searching on its container ID. Because the container ID is assured by its manufacturer to be universally unique, the container and sample may move from one organization to another under the same identifier, and information about the contents of the container may be shared by querying on its container ID. Practically, the sample ID becomes universal by virtue of presenting a universally-understood search key usable by anyone who needs to process the container. By suitably restricting access to sensitive database fields, patient confidentiality may more easily be assured since the marking on the specimen does not reveal any such information.
Owner:BECTON DICKINSON & CO
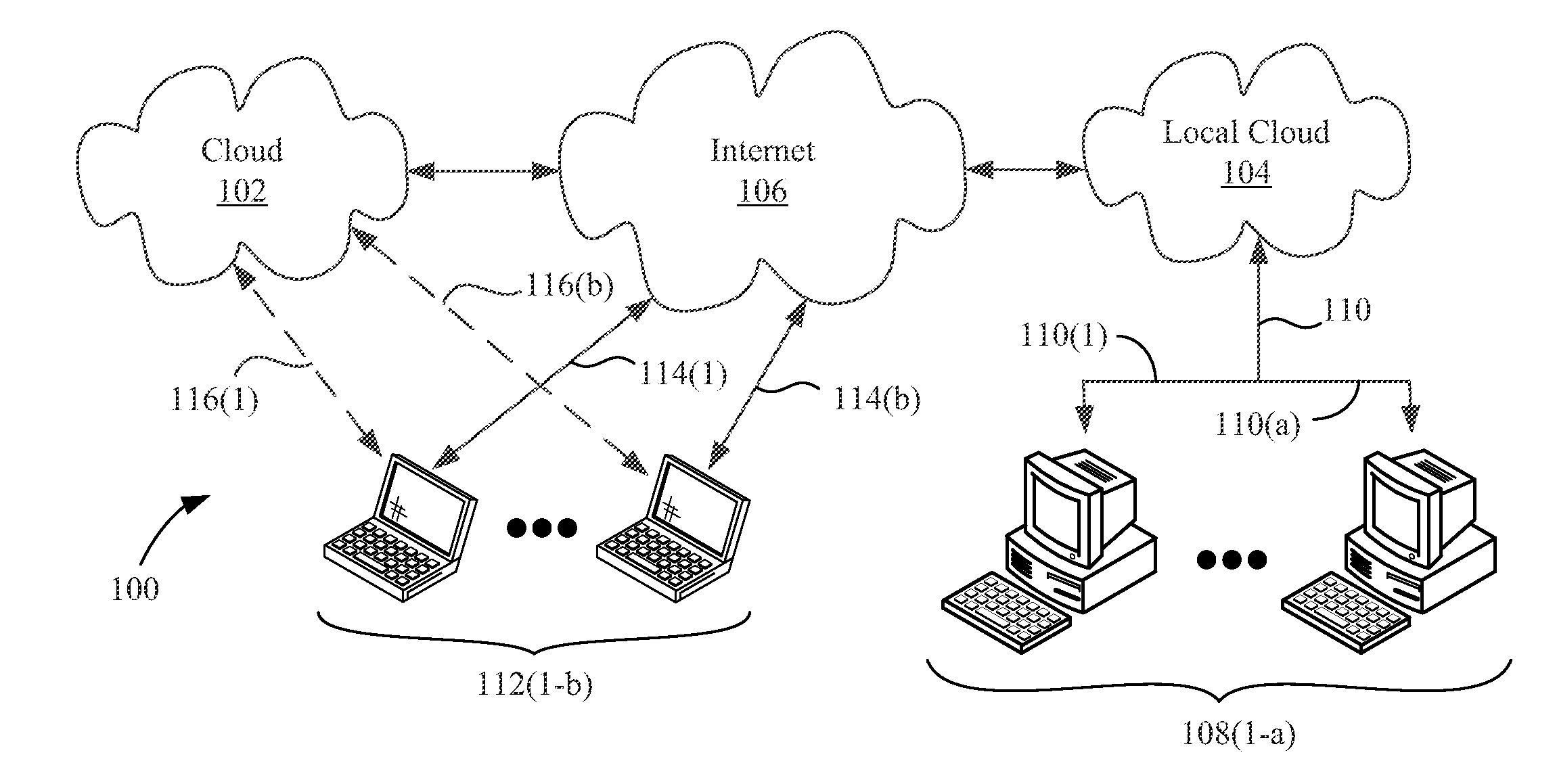
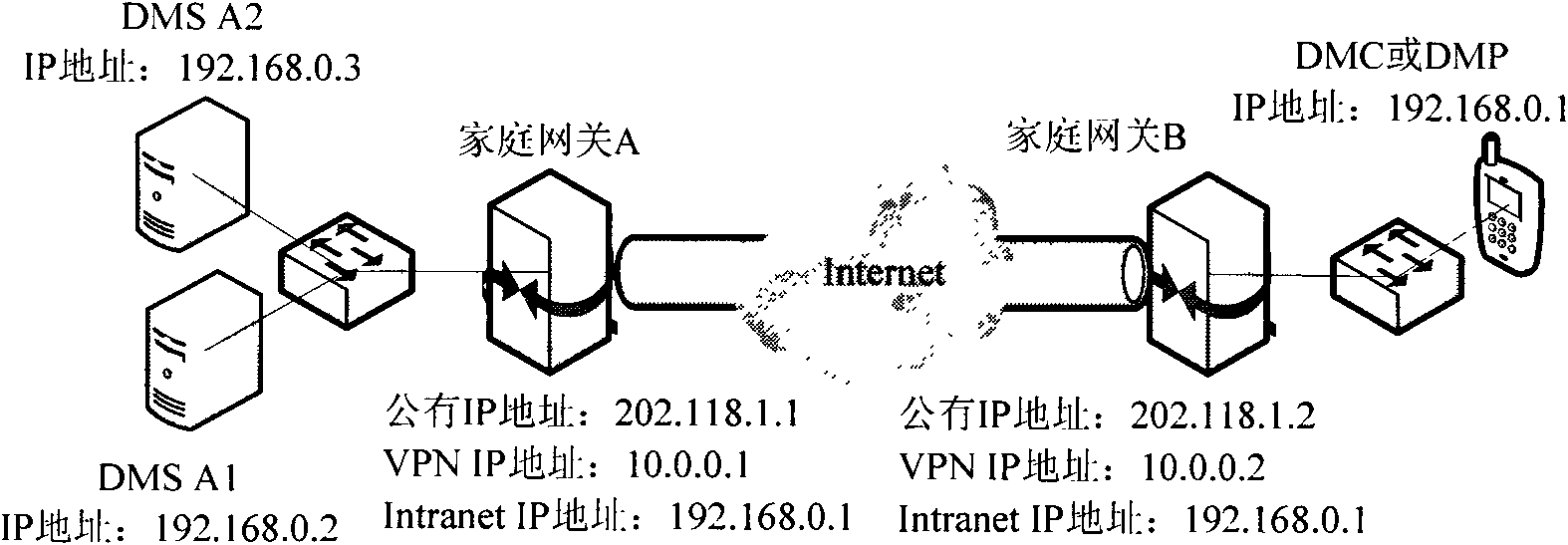
Inter-home digital living network alliance (DLNA) equipment discovering and controlling method and device
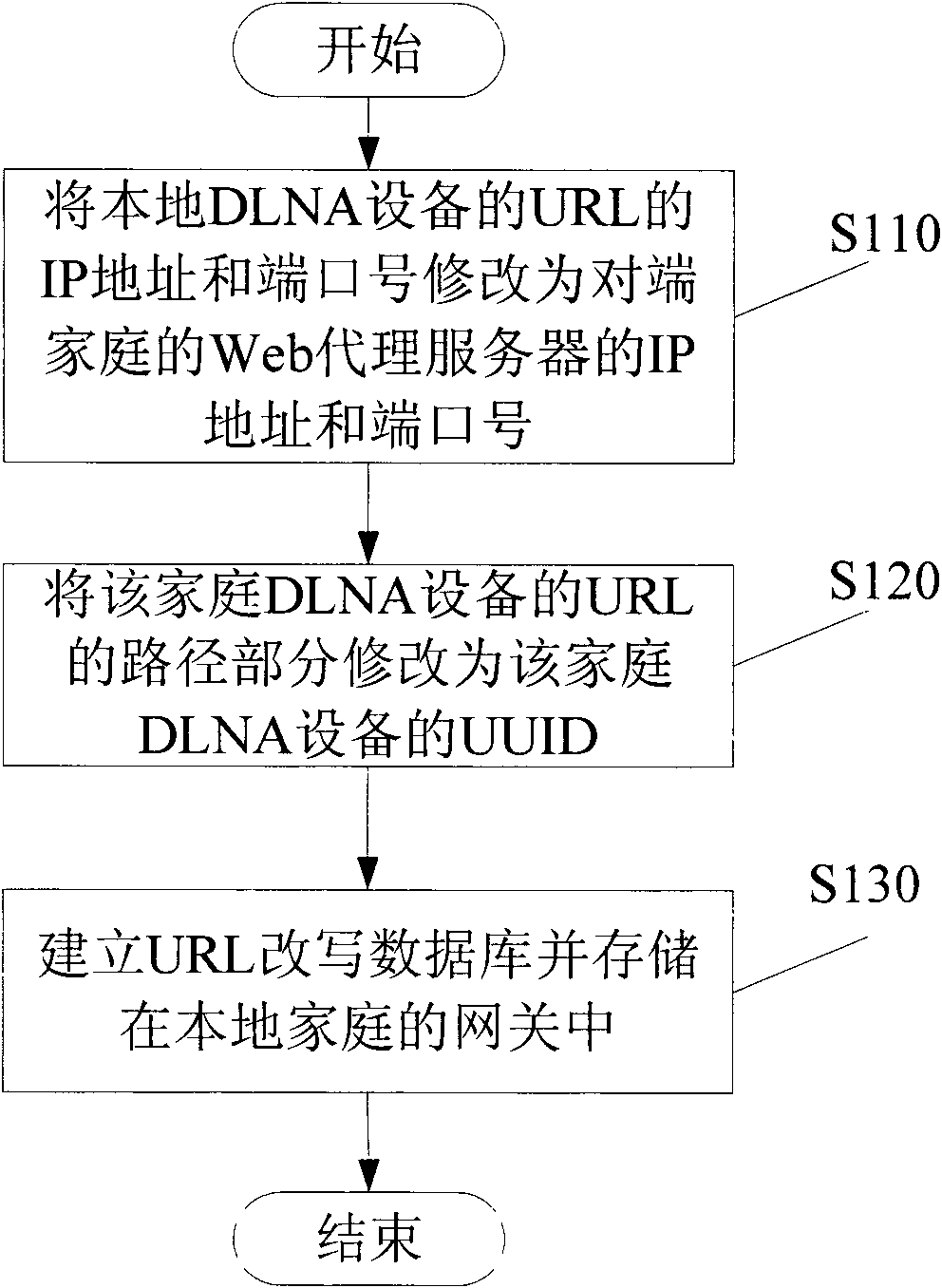
The invention provides a method for performing inter-home digital living network alliance (DLNA) equipment discovery between a local home and an opposite end home. The method comprises the following steps that: a simple service discovery protocol (SDDP) proxy in the opposite end home performs uniform resource locator (URL) rewriting on a retrieval response transmitted from the home DLNA equipmentbased on a universally unique identifier (UUID) of the home DLNA equipment after transmitting the received equipment retrieval multi-cast messages to the home DLNA equipment in the opposite end home in a multi-cast manner, and then transmits the retrieval response which is subjected to URL rewriting to the home DLNA equipment in the local home in a unicast manner, wherein during the URL rewriting, the internet protocol (IP) address and the port number of the URL in the retrieval response are rewritten to be the IP address of a Web proxy server and the port number of a monitored port in a gateway of the local home respectively; and the path part of the URL in the retrieval response is rewritten to be the UUID of the home DLNA equipment in the opposite end home.
Owner:NEUSOFT CORP
Arrangements for Auto-Merging Processing Components
InactiveUS20090063662A1Digital computer detailsTransmissionUniversally unique identifierAuto-configuration
In some embodiments a method for auto-configuring a network is disclosed. The method can include communicating with at least one node in a processing complex, receiving node connection data from the at least one node querying a node to verify at least a portion of the node connection data and auto-configuring system partitioning in response to the node connection data. In some embodiments the method can also include verifying the node connection data by transmitting a request for a universally unique identifier and a node identifier. The node identifier can be associated with the universally unique identifier. The node identifier can be utilized in data transmitted between nodes.
Owner:LENOVO GLOBAL TECH INT LTD
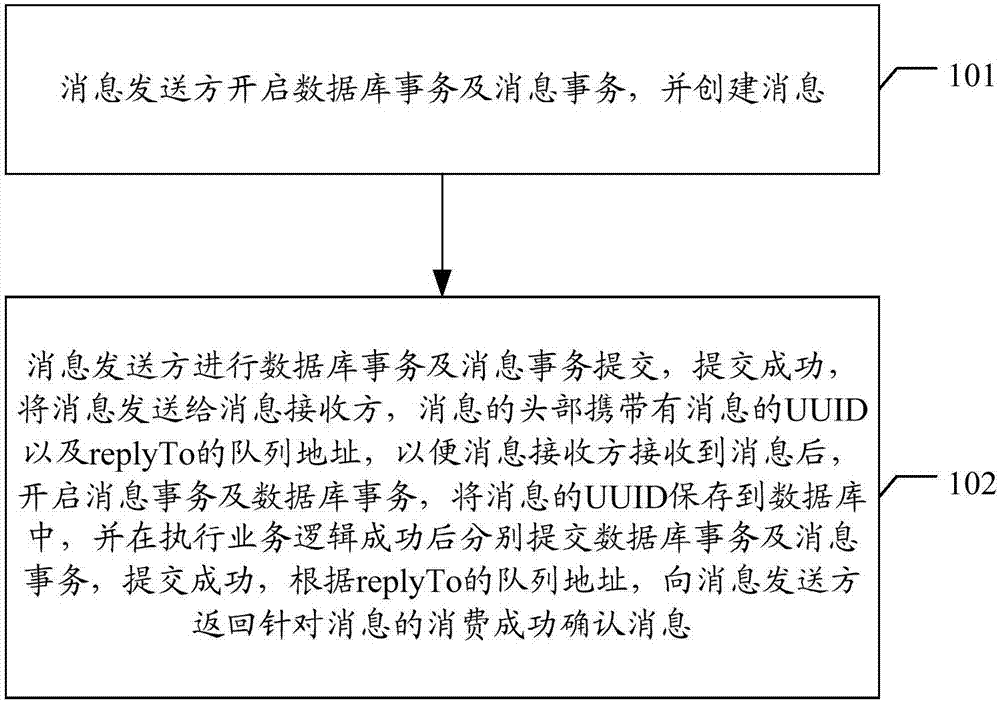
Queue message uniformity implementing method and device, equipment and storage medium
ActiveCN108009027AImprove performanceInterprogram communicationUniversally unique identifierDistributed computing
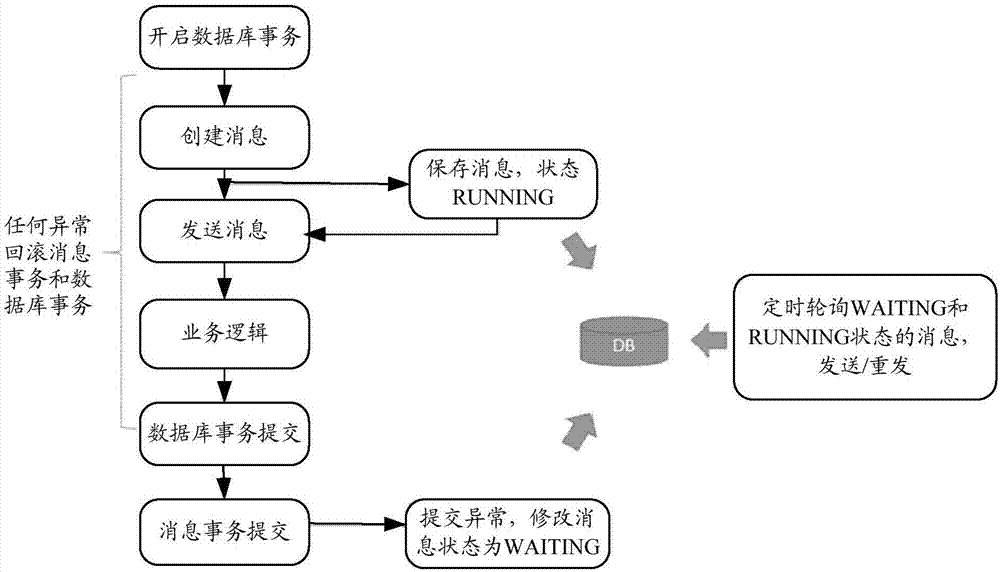
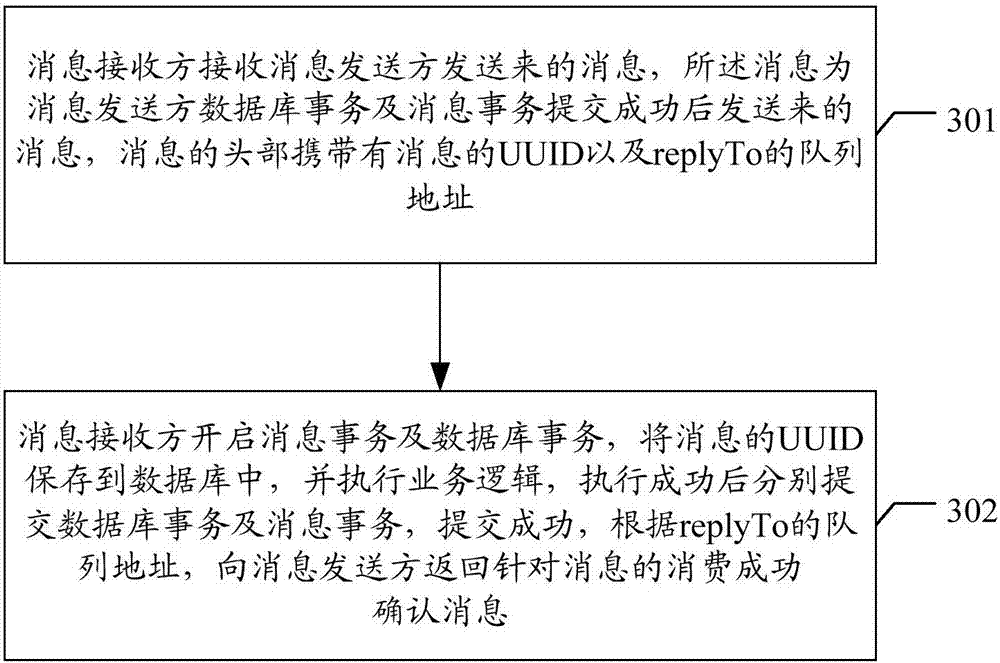
The invention discloses a queue message uniformity implementing method and device, equipment and a storage medium, wherein the method comprises: opening a database business and a message business by amessage sender, creating messages, submitting the database business and the message business, transmitting the messages to a message receiver if submission is successful, with headers of messages carrying a message UUID (universally unique identifier) and replayTo queue address; after the message receiver receives the messages, opening the message business and the database business, saving the UUIDs of the messages to a database, submitting the database business and the message business after business logic is successfully executed, and if submission is successful, returning a message-responding consumption success confirming message to the message sender according to the replyTo queue address. The queue message uniformity implementing method and device, the equipment and the storage medium according to the scheme provide a complete frame model of queue message uniformity so that system performance and the like are improved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
System and method for implementing video calls
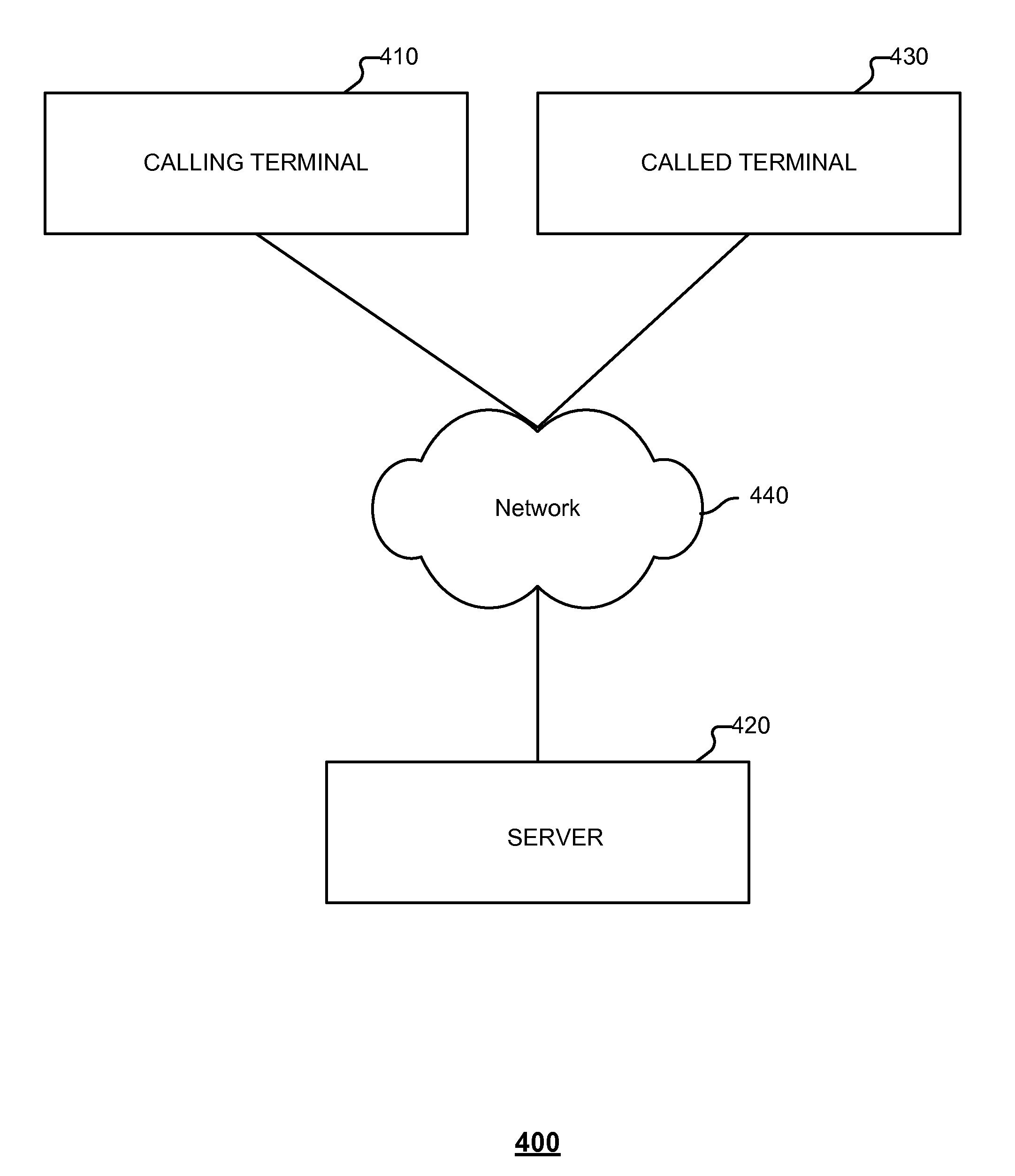
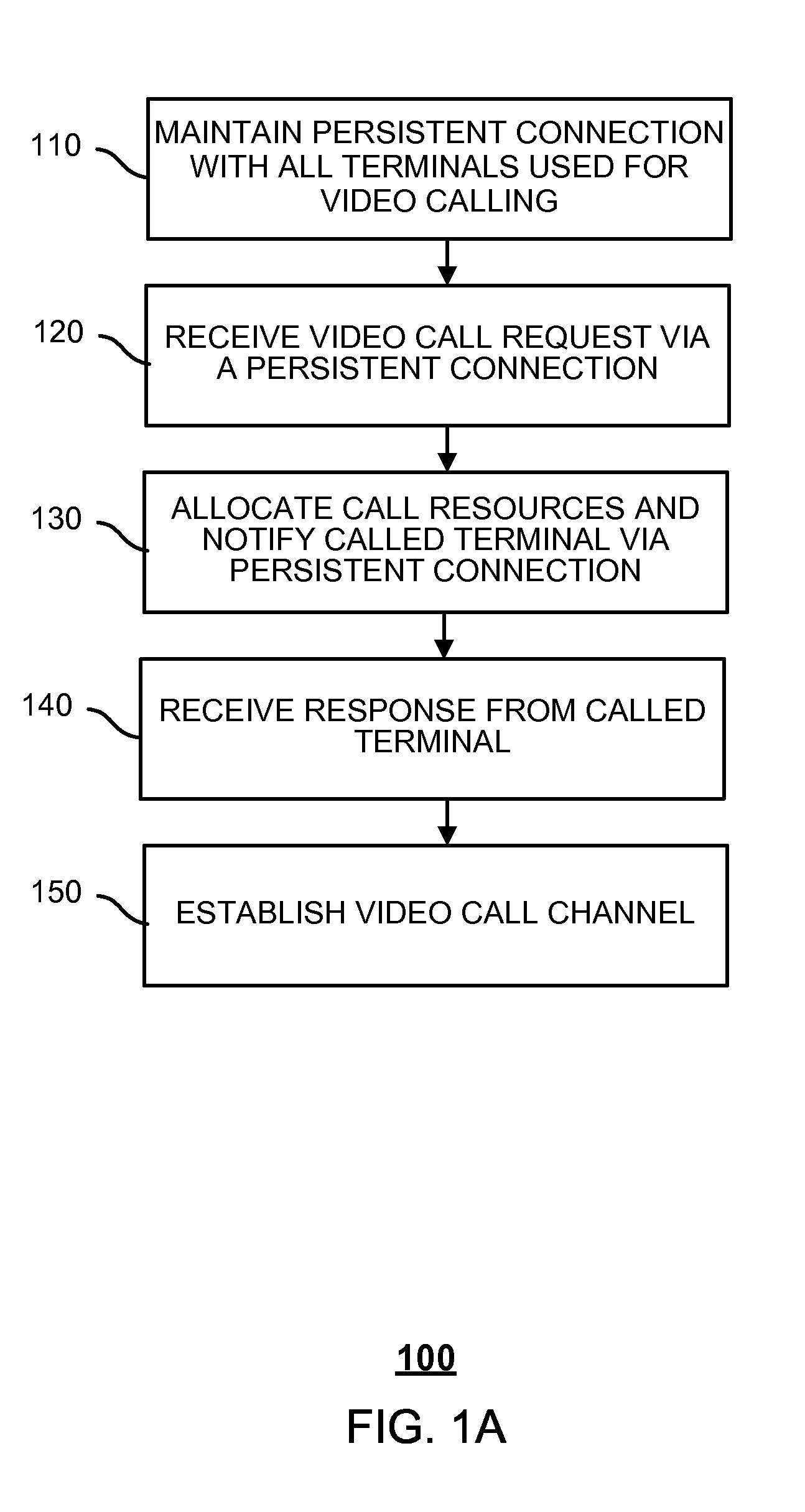
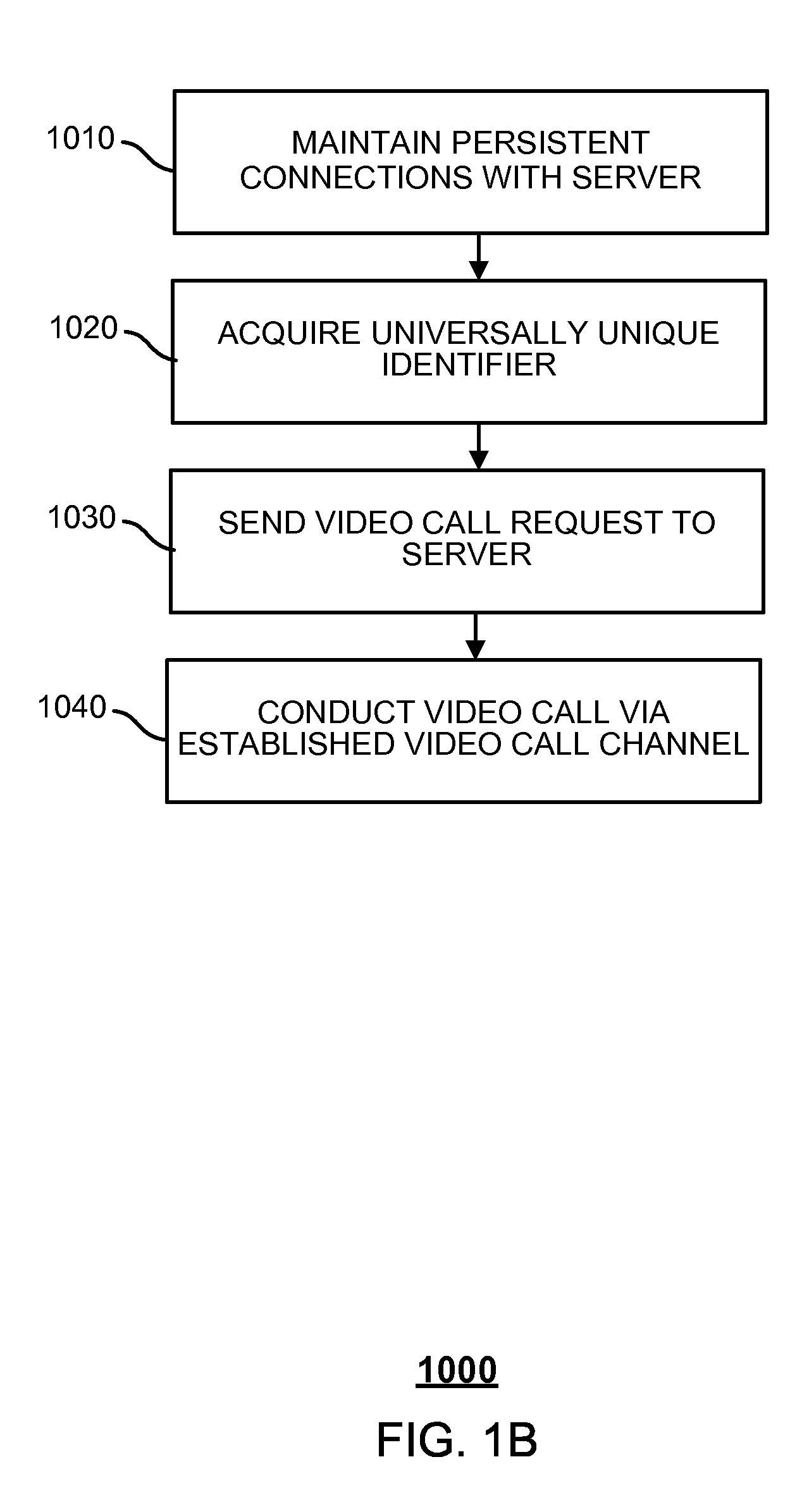
ActiveUS20150189227A1Sensing record carriersTwo-way working systemsCall terminationUniversally unique identifier
Embodiments of the present application relate to a method for implementing video calls, a system for implementing video calls, and a computer program product for implementing video calls. A method for implementing video calls is provided. The method includes maintaining persistent connections with a plurality of terminals used to make video calls, each terminal having a universally unique identifier, receiving a video call request from a calling terminal via one of the persistent connections, the video call request including the universally unique identifier of the calling terminal, equipment descriptive information of the calling terminal, and the universally unique identifier of a called terminal, notifying the called terminal via one of the persistent connections, the notification being based on the universally unique identifier of the called terminal, receiving a response from the called terminal, and establishing a video call channel based on the received response.
Owner:BANMA ZHIXING NETWORK HONGKONG CO LTD
Arrangements for auto-merging processing components
InactiveUS8180862B2Digital computer detailsTransmissionUniversally unique identifierComputer science
In some embodiments, a method for auto-configuring a network is disclosed. The method can include communicating with at least one node in a processing complex, receiving node connection data from the at least one node querying a node to verify at least a portion of the node connection data, and auto-configuring system partitioning in response to the node connection data. In some embodiments, the method can also include verifying the node connection data by transmitting a request for a universally unique identifier and a node identifier. The node identifier can be associated with the universally unique identifier. The node identifier can be utilized in data transmitted between nodes.
Owner:LENOVO GLOBAL TECH INT LTD
E-mail integrated instant messaging
InactiveUS20120030295A1Multiple digital computer combinationsOffice automationUniversally unique identifierWeb page
A system and method supporting instant messaging which removes many of the problems and harriers to the use of instant messaging through the use of universally unique identifiers to web pages for instant messaging sessions, with recipients invited to the instant messaging session via email.
Owner:META PLATFORMS INC
Dynamic uniform resource locator (URL) generator, generation method, dynamic-URL-based authentication system and method
ActiveCN102546165AOptimize generation methodConvenient paymentUser identity/authority verificationProtocol authorisationPaymentUniversally unique identifier
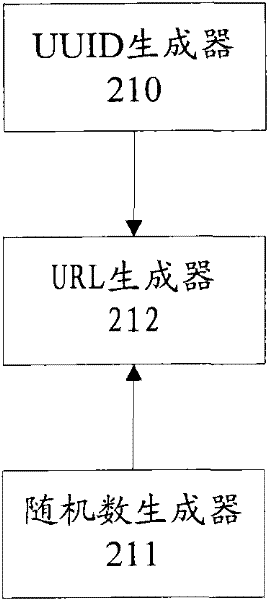
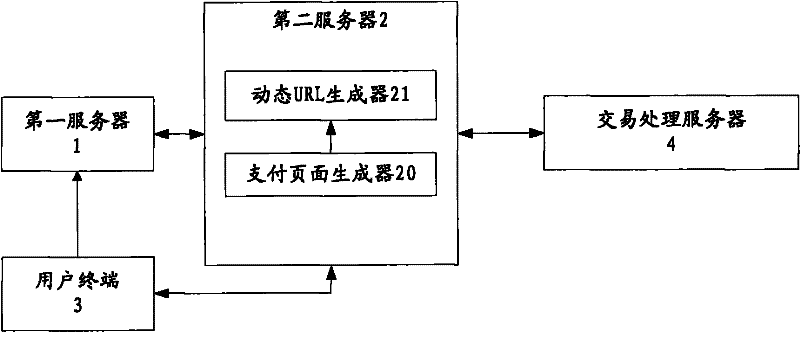
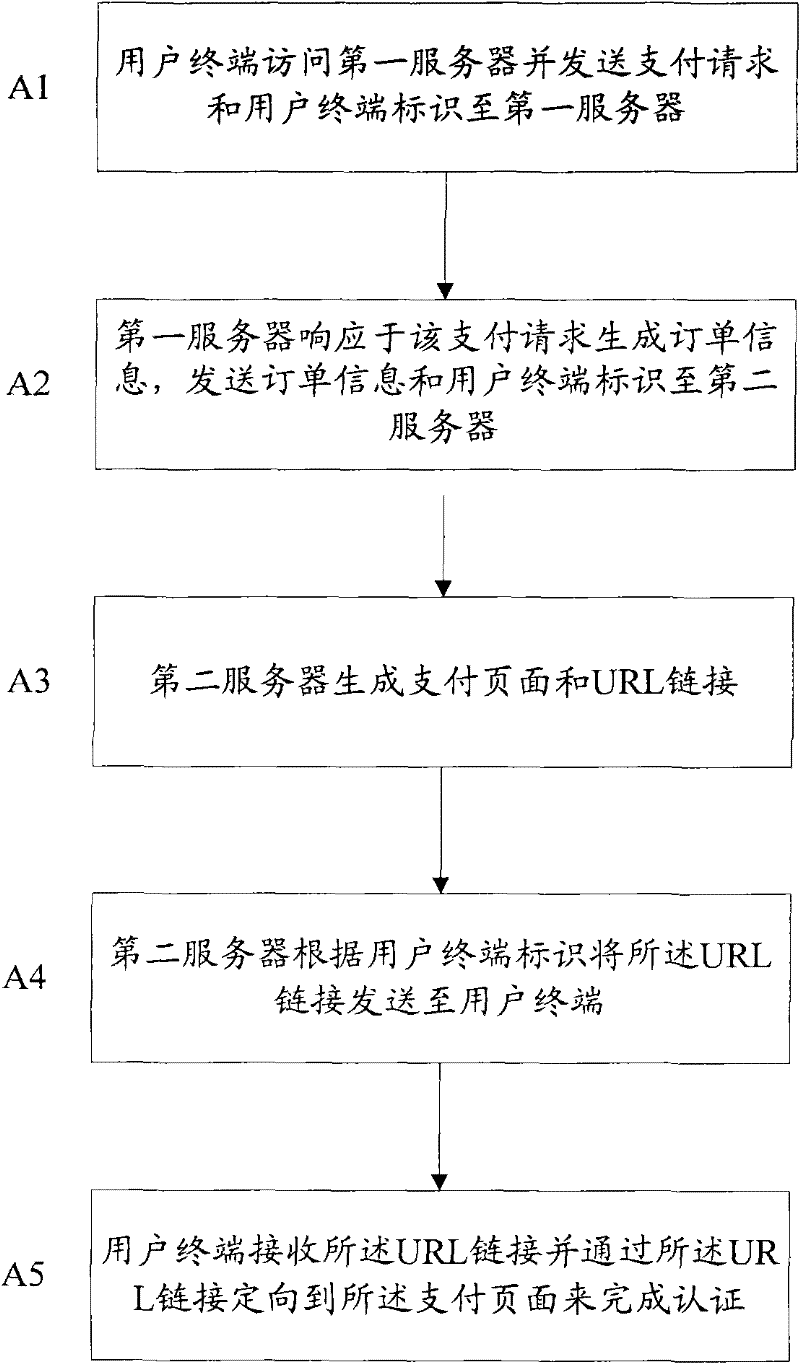
The invention provides a dynamic uniform resource locator (URL) generator, a dynamic URL generation method, a dynamic-URL-based authentication system and a dynamic-URL-based authentication method. The dynamic-URL-based authentication system comprises a first server, a second server and a user terminal, wherein the first server generates order information in response to a payment request transmitted by the user terminal, and transmits the order information and a user terminal identifier to the second server; the second server generates a payment page comprising the order information and a password input box, and a URL link which comprises a universally unique identifier (UUID) and a random number and is related to the payment page, and transmits the URL link to the user terminal according to the user terminal identifier; and the user terminal accesses the first server, transmits the payment request and the user terminal identifier to the first server, receives the URL link, and is oriented to the payment page through the URL link to finish authentication. The dynamic URL generator, the dynamic URL generation method, the authentication system and the authentication method are convenient to implement and high in safety and applicability.
Owner:CHINA UNIONPAY
Self-assignment of node identifier in a cluster system
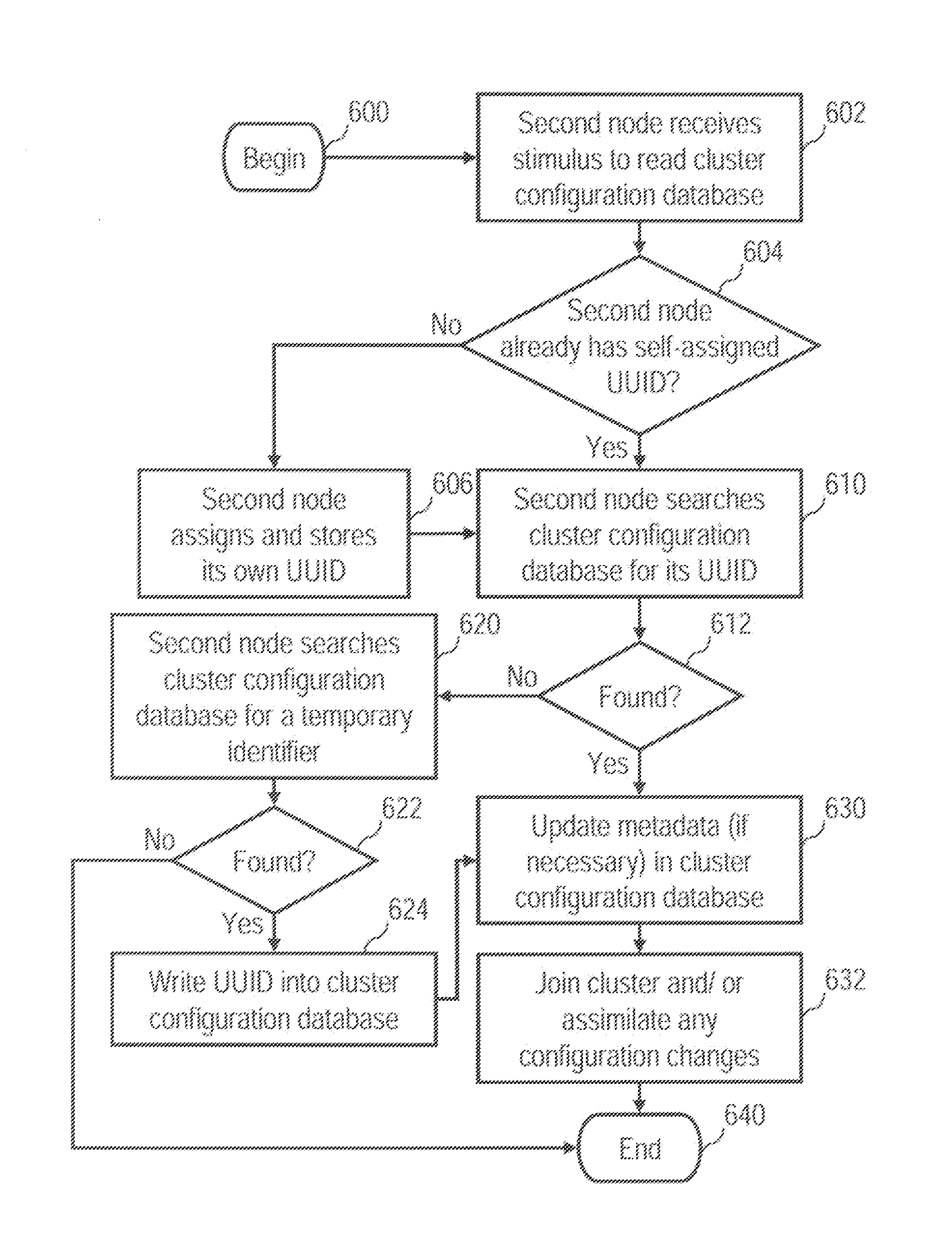
ActiveUS20120143887A1Digital data processing detailsTransmissionUniversally unique identifierCluster systems
In response to a stimulus indicating configuration of a node into a cluster of a plurality of nodes including the node, the node determines whether or not the node has a universally unique identifier (UUID), and if not, the node provides its own persistent self-assigned UUID. The node searches a cluster configuration database for a temporary identifier associated with the node. In response to the node locating the temporary identifier of the node in the cluster configuration database, the node writes its self-assigned UUID into the cluster configuration database and joins the cluster.
Owner:IBM CORP
Method and system for generating identification code
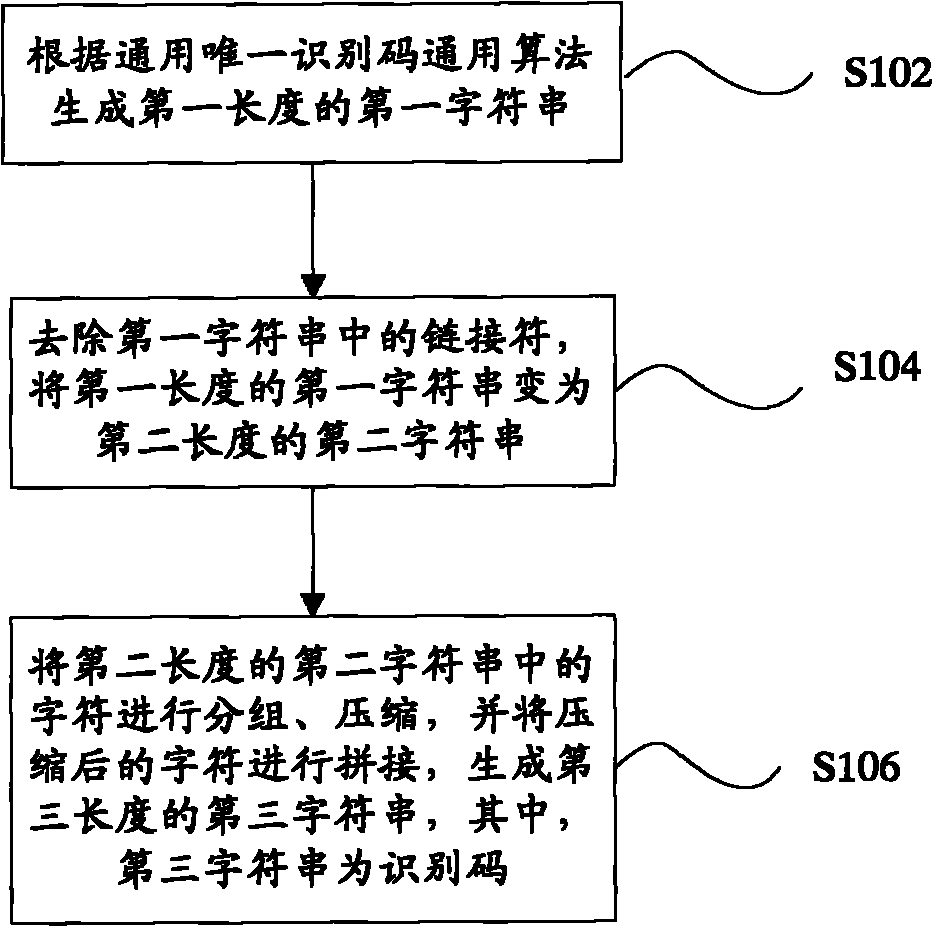
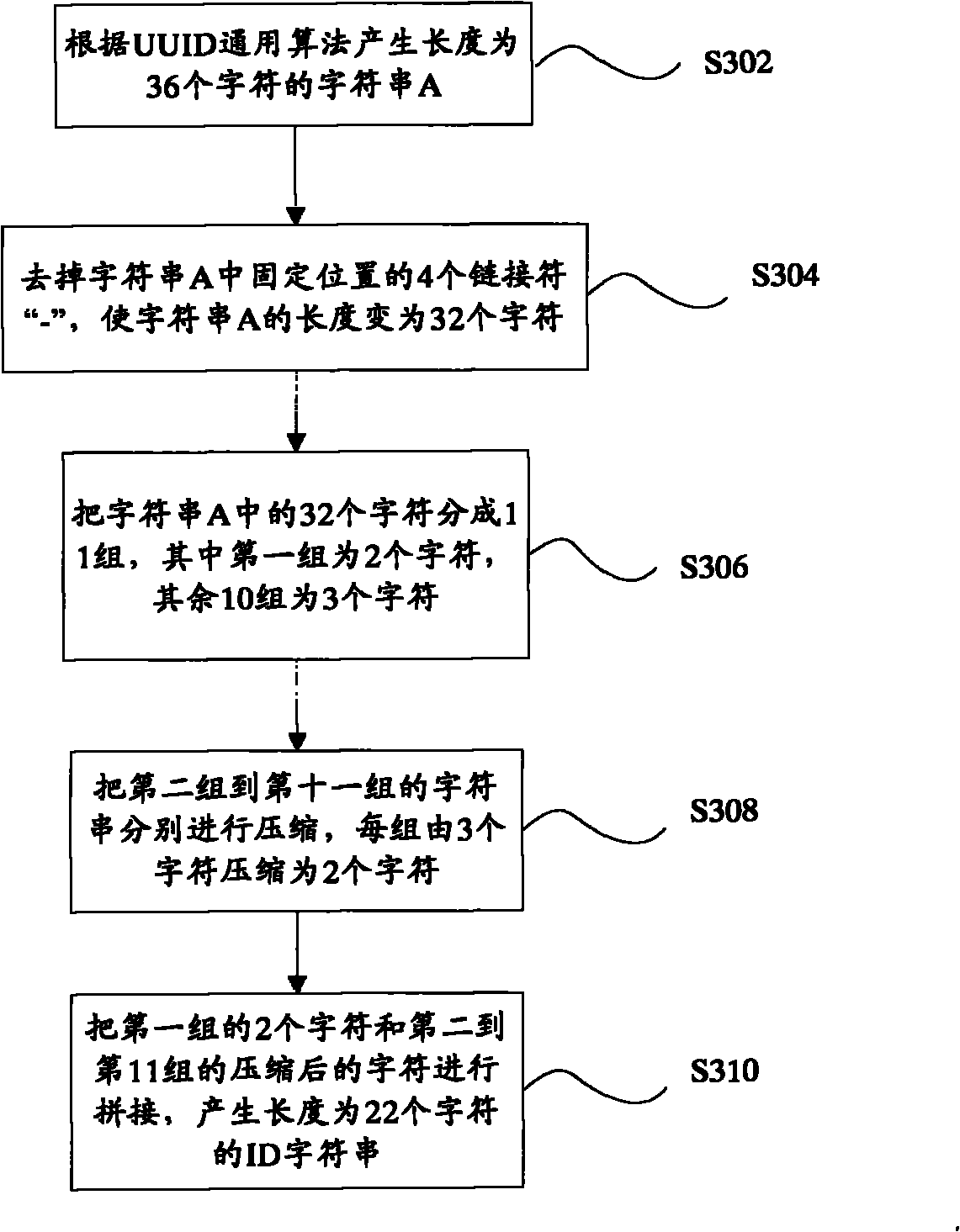
ActiveCN101976241AUniqueness guaranteedReduce the number of bytesSpecial data processing applicationsUniversally unique identifierAlgorithm
The invention provides a method for generating an identification code. The method comprises the following steps of: (S104) generating a first character string with a first length according to a universal algorithm of a universal unique identification code; (S104) removing a linking character in the first character string and changing the first character string with the first length into a second character string with a second length; and (S106) grouping and compressing characters in the second character string with the second length, and splicing the compressed characters to generate a third character string with a third length, wherein the third character string is an identification code. The invention also provides an identification code generation system. According to the technical scheme, the identification code generation system and the method can be realized, which not only can guarantee that the identification code generated in a distributed system has uniqueness, but also can effectively reduce the byte number occupied by the identification code so as to save the storage space and guarantee the data storage efficiency, and too much network flow cannot be increased.
Owner:YONYOU NETWORK TECH
Method for accessing to network by device of internet of things, device and system
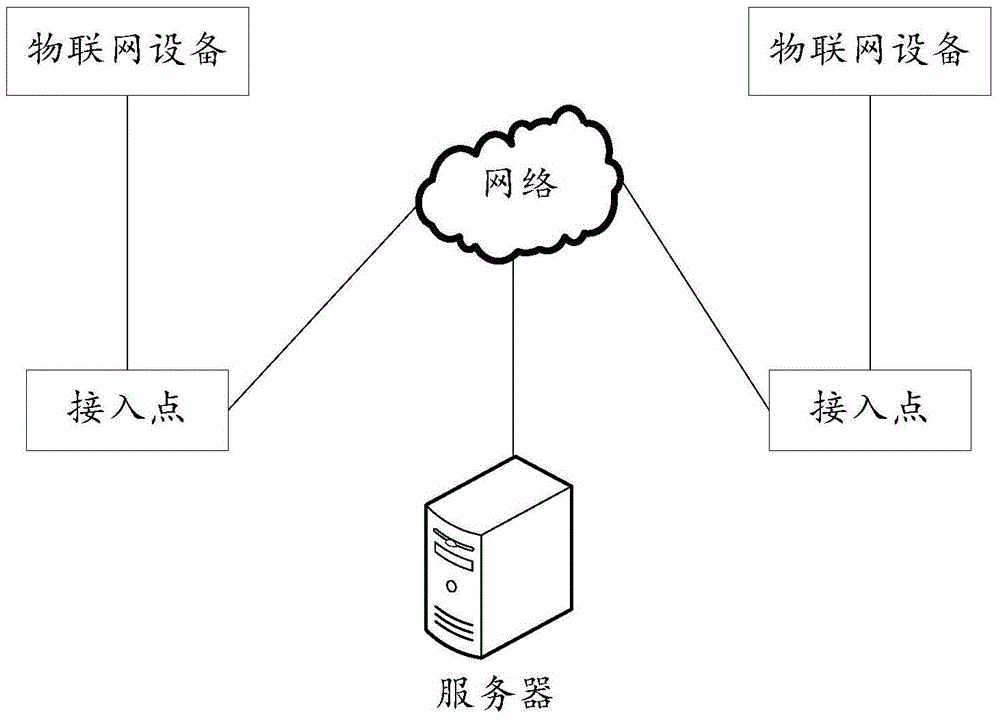
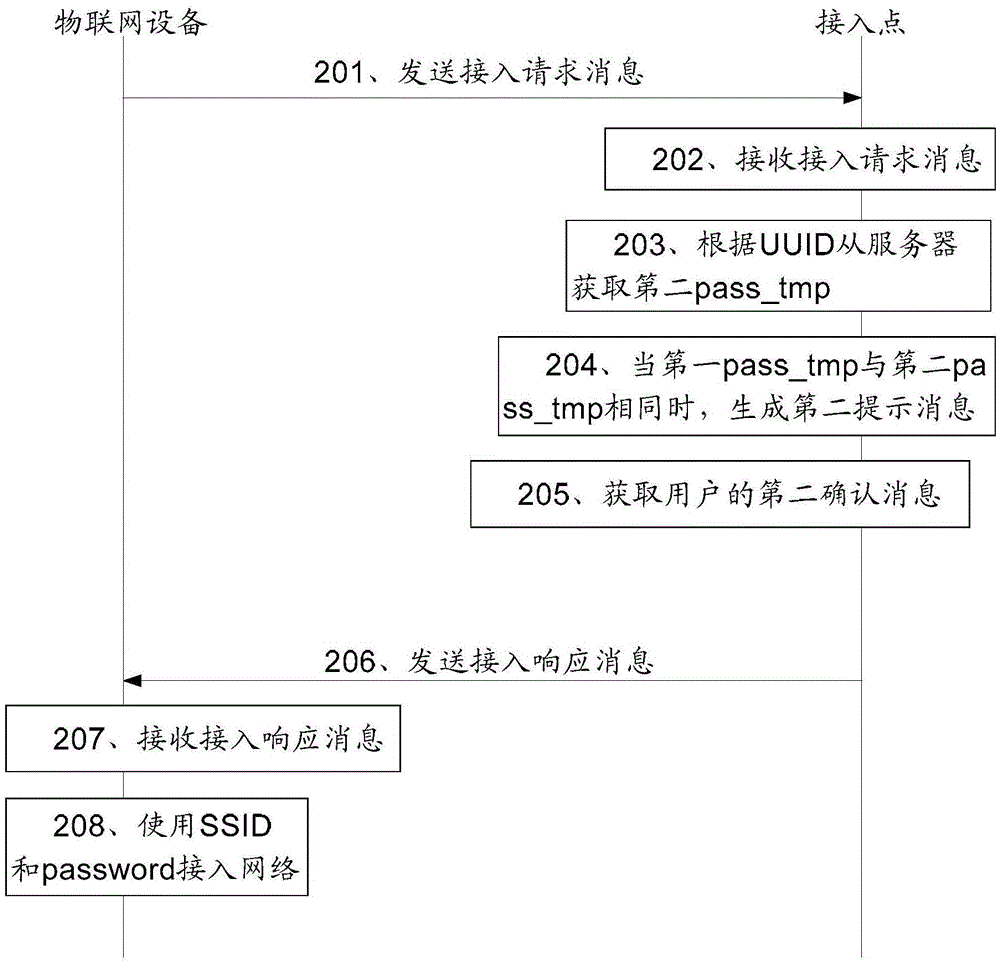
ActiveCN105578470AImprove access efficiencySecure AccessAssess restrictionNetwork topologiesUniversally unique identifierPassword
The invention provides a method for accessing to a network by a device of internet of things, a device and a system relating to the field of the internet of things. In adoption of the method, the device and system of the invention, the device of internet of things can securely access to the network, meanwhile, hardware devices provided to the device of internet of things are reduced, and the operation steps of a user are reduced. The method comprises following steps that: the device of internet of things sends an access request message to an access point; the access request message comprises a UUID (Universally Unique Identifier), a SSID (service set identifier) and first pass-tmp; the device of internet of things receives an access response message sent by the access point,; the access response message comprises a SSID and a password; and the device of internet of things accesses to the network by using the SSID and password. The method, the device and the system of the invention are used for accessing to the network by the device of internet of things.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com