Patents
Literature
15144results about How to "Operational security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
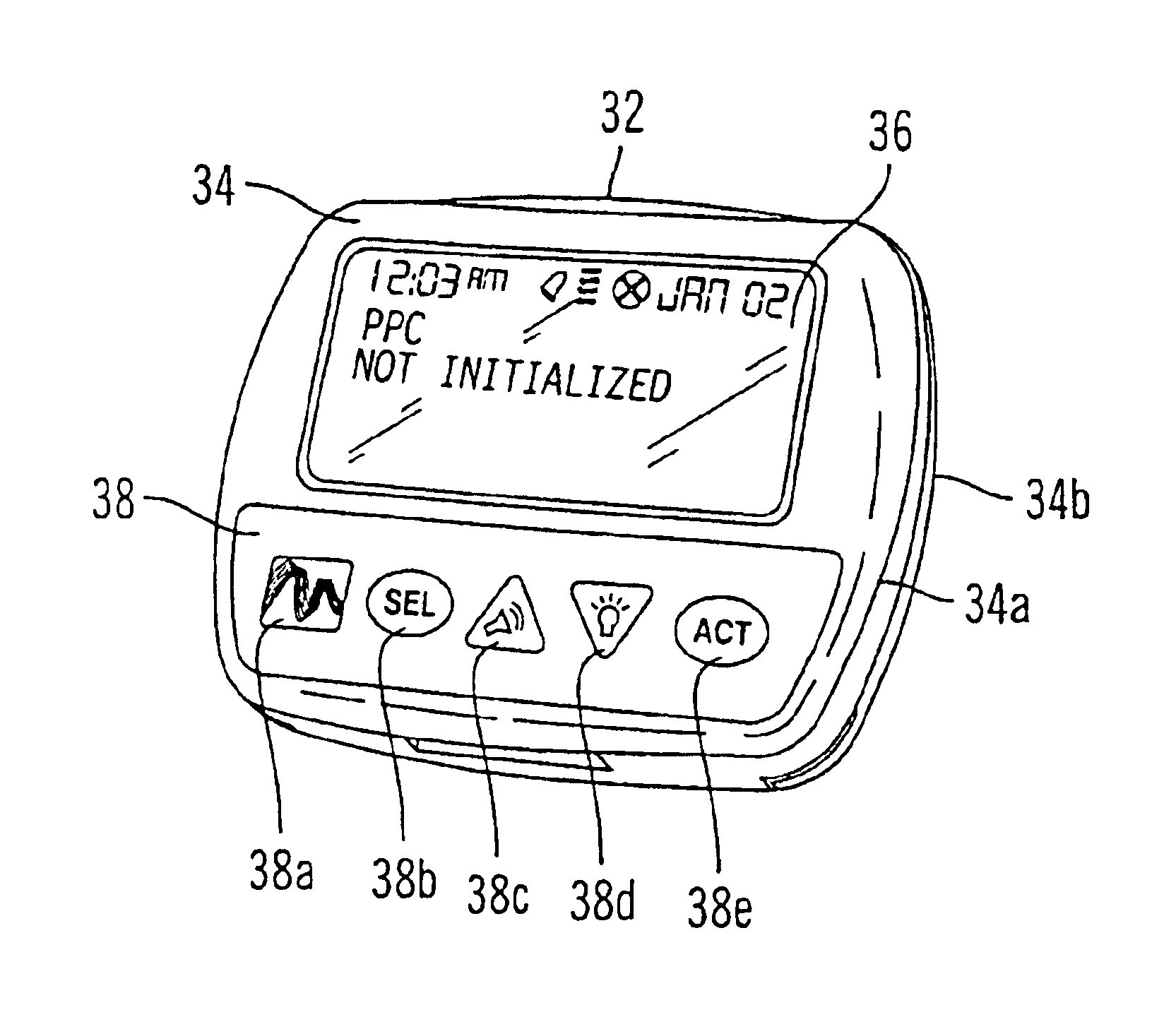
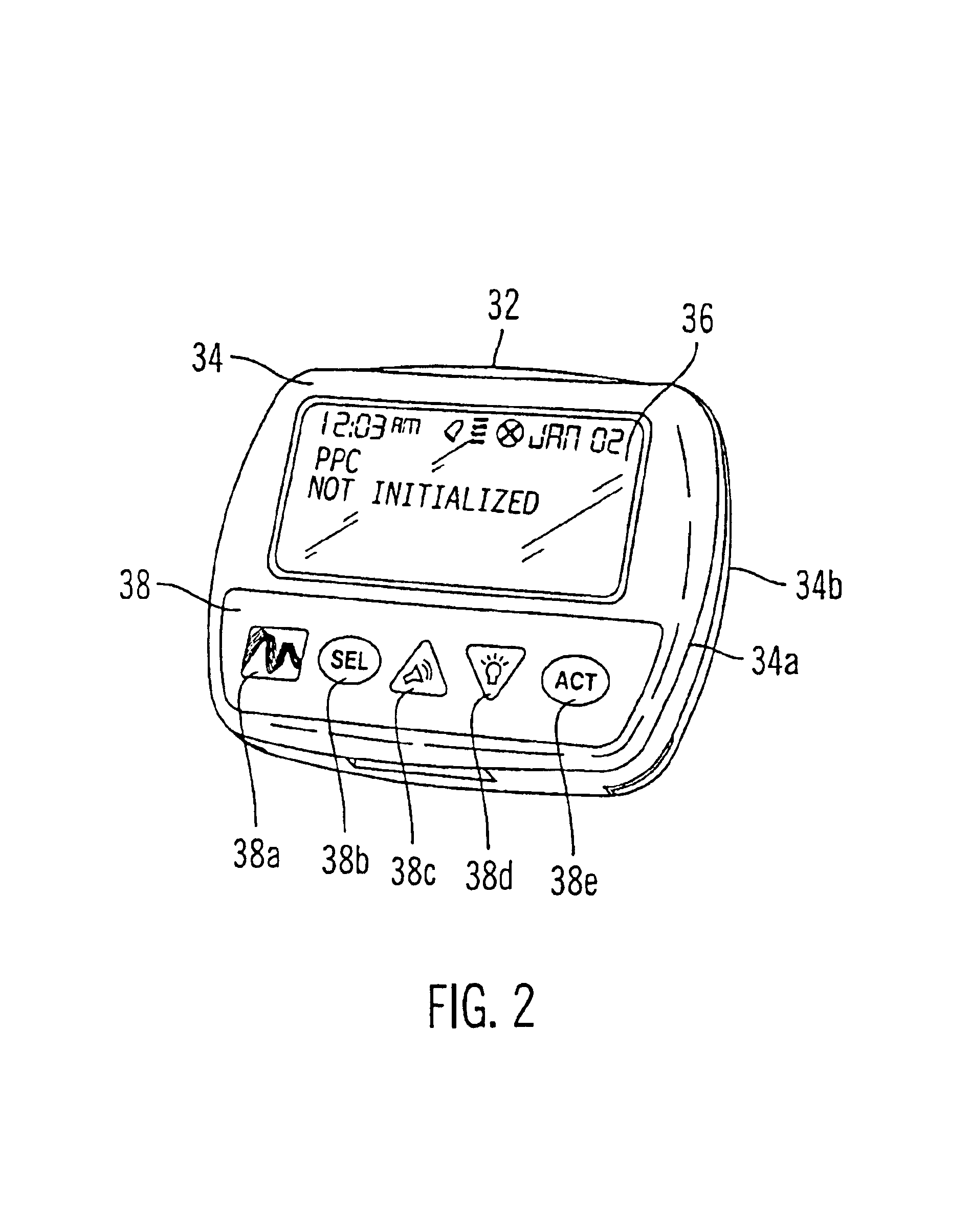
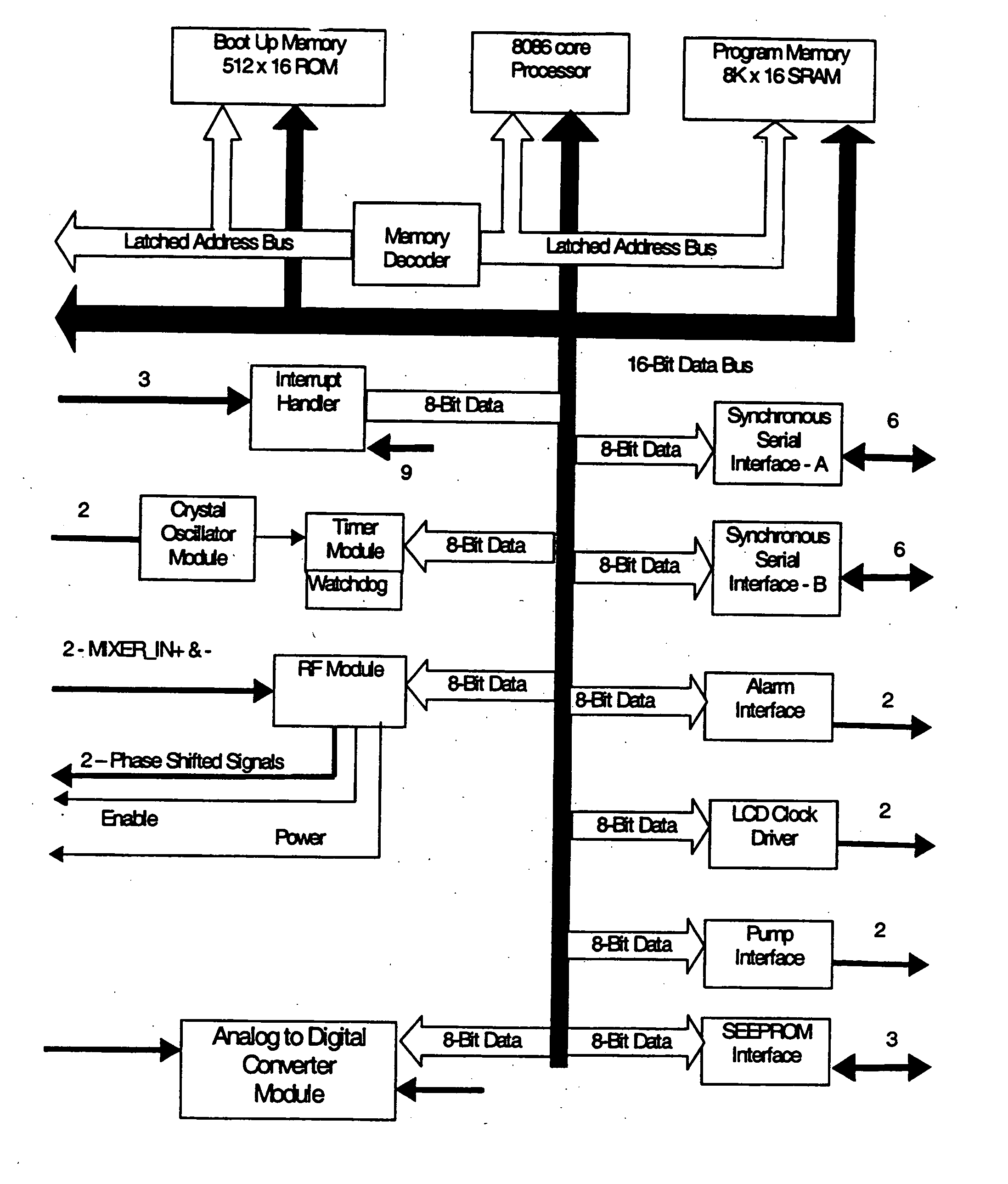
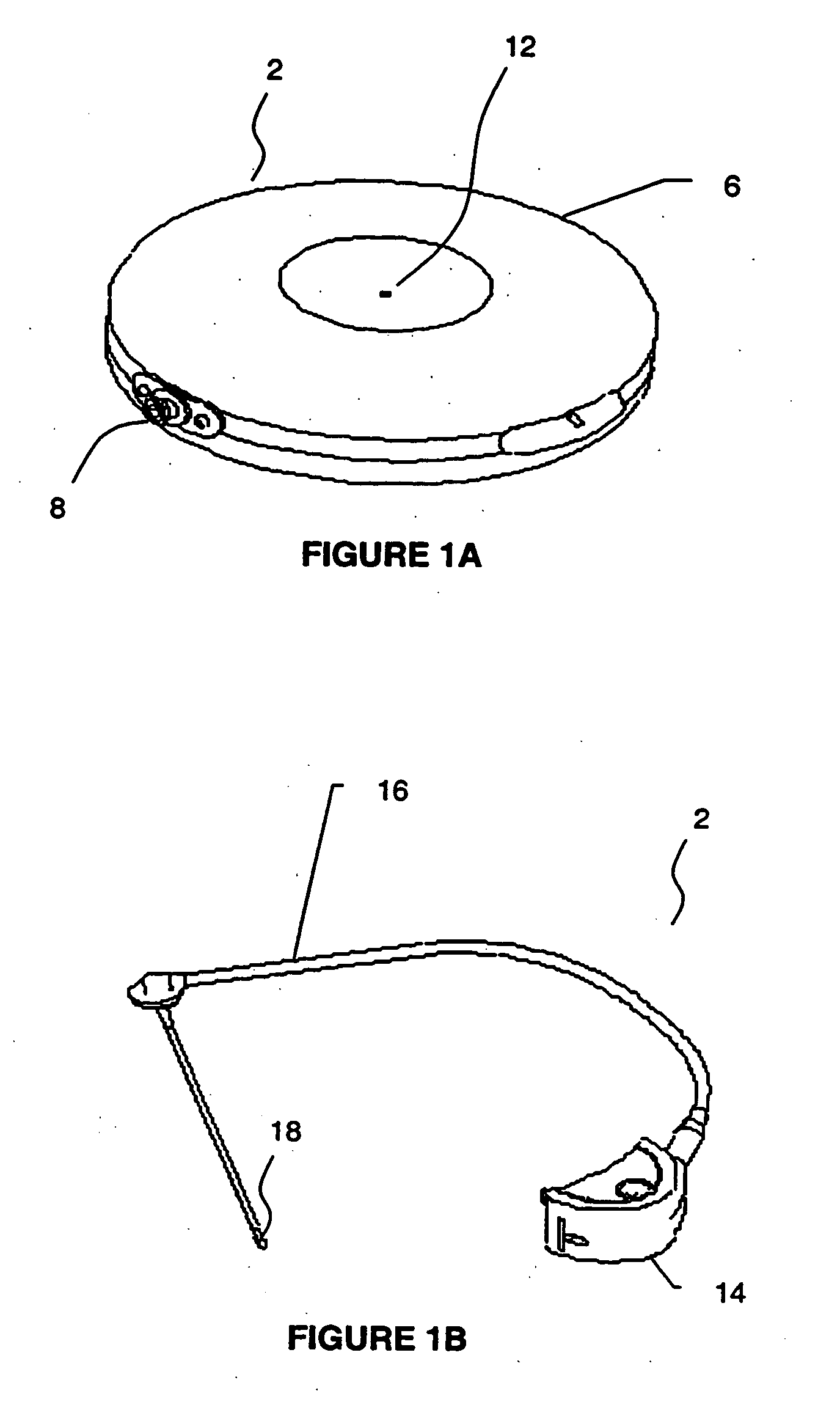
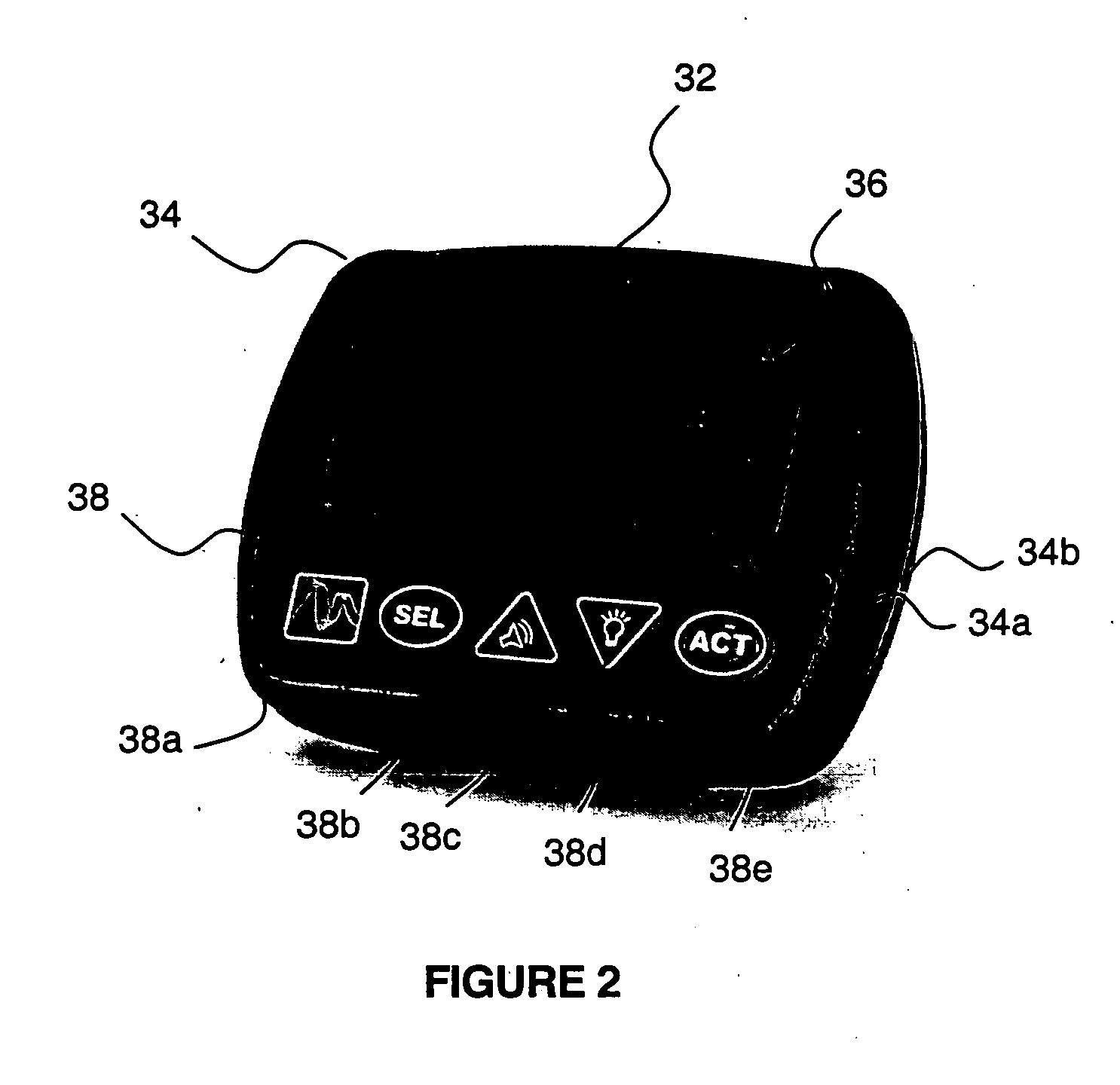
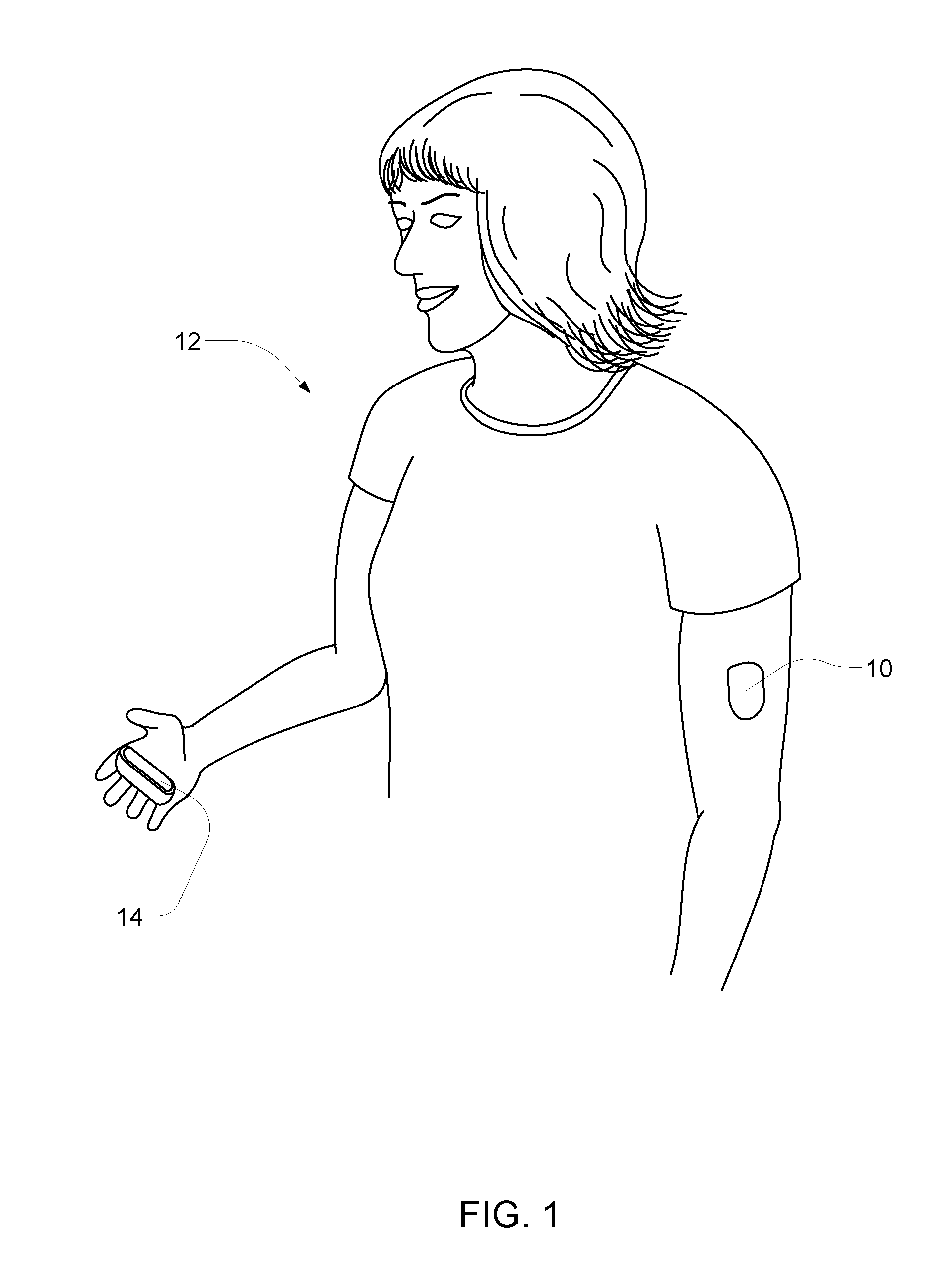
Microprocessor controlled ambulatory medical apparatus with hand held communication device
InactiveUS6873268B2Enhance user interfaceReduce system sizeEnergy efficient ICTElectrotherapyDrugs infusionHand held
An implantable infusion pump possesses operational functionality that is, at least in part, controlled by software operating in two processor ICs which are configured to perform some different and some duplicate functions. The pump exchanges messages with an external device via telemetry. Each processor controls a different part of the drug infusion mechanism such that both processors must agree on the appropriateness of drug delivery for infusion to occur. Delivery accumulators are incremented and decremented with delivery requests and with deliveries made. When accumulated amounts reach or exceed, quantized deliverable amounts, infusion is made to occur. The accumulators are capable of being incremented by two or more independent types of delivery requests. Operational modes of the infusion device are changed automatically in view of various system errors that are trapped, various system alarm conditions that are detected, and when excess periods of time lapse between pump and external device interactions.
Owner:MEDTRONIC MIMIMED INC
Microprocessor controlled ambulatory medical apparatus with hand held communication device
ActiveUS20050010269A1Enhance capacityReduce in sizeEnergy efficient ICTElectrotherapyTelemetry EquipmentBiomedical engineering
An implantable infusion pump possesses operational functionality that is, at least in part, controlled by software operating in two processor ICs which are configured to perform some different and some duplicate functions. The pump exchanges messages with an external device via telemetry. Each processor controls a different part of the drug infusion mechanism such that both processors must agree on the appropriateness of drug delivery for infusion to occur. Delivery accumulators are incremented and decremented with delivery requests and with deliveries made. When accumulated amounts reach or exceed, quantized deliverable amounts, infusion is made to occur. The accumulators are capable of being incremented by two or more independent types of delivery requests. Operational modes of the infusion device are changed automatically in view of various system errors that are trapped, various system alarm conditions that are detected, and when excess periods of time lapse between pump and external device interactions.
Owner:MEDTRONIC MIMIMED INC
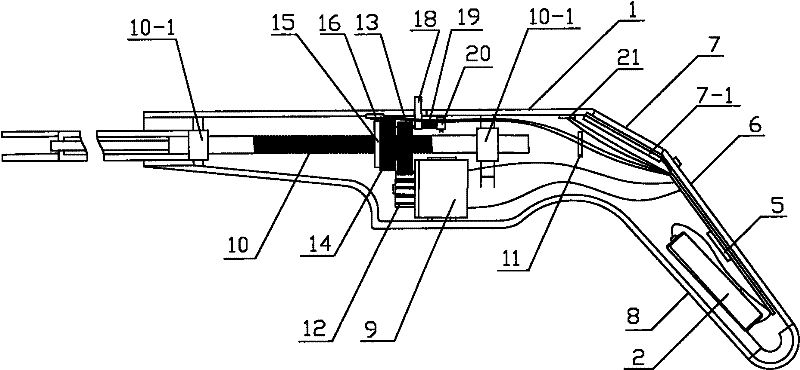
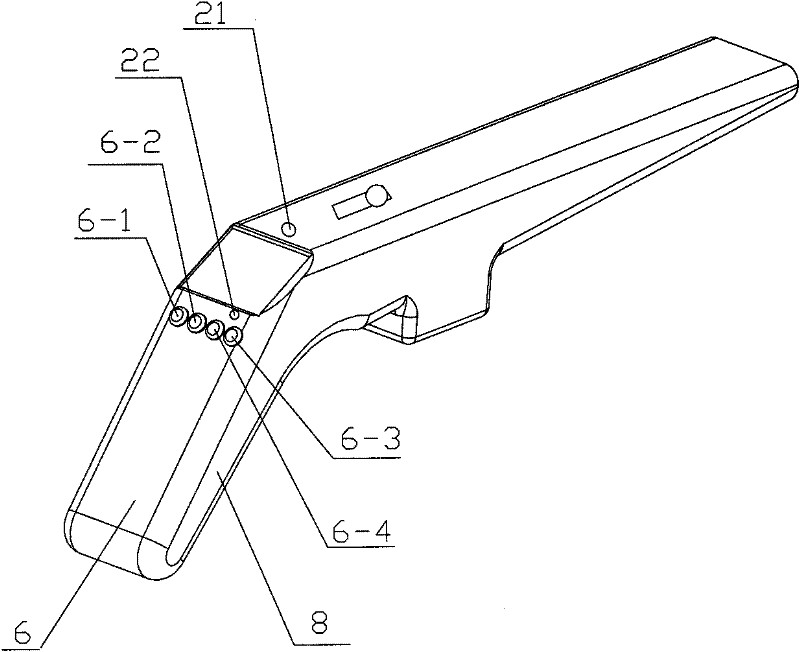
Numerically controlled surgical stapling apparatus
ActiveCN102228387AAccurate operationOperational securityNumerical controlSurgical staplesElectricityMemory chip
The invention relates to a numerically controlled surgical stapling apparatus comprising a clamping assembly, a housing and a main body assembly arranged in the housing. An electric driving device is arranged in the main body assembly. The stapling apparatus is characterized by further comprising a numerical control device which comprises a control board, a display screen and a sensing device, wherein at least one memory chip and a control chip are arranged on the control board; and the display screen is capable of displaying the values of operation parameters and clock information. The electric driving device is capable of receiving a signal produced by the numerical control device and drives a nail magazine to move toward a nail anvil until a predetermined closing gap, and further causes a suturing nail to reach a predetermined forming height after firing the suturing nail. The numerically controlled surgical stapling apparatus provided in the invention is capable of performing accurate and safe control on the transmission steps and the operation actions and also of clearly displaying the operation parameters so that a doctor can know the whole surgery process; therefore, human-machine conversation is made possible.
Owner:B J ZH F PANTHER MEDICAL EQUIP
Numerically controlled surgical stapling apparatus
ActiveCN102228387BAccurate operationOperational securitySurgical staplesNumerical controlMemory chipElectricity
The invention relates to a numerically controlled surgical stapling apparatus comprising a clamping assembly, a housing and a main body assembly arranged in the housing. An electric driving device is arranged in the main body assembly. The stapling apparatus is characterized by further comprising a numerical control device which comprises a control board, a display screen and a sensing device, wherein at least one memory chip and a control chip are arranged on the control board; and the display screen is capable of displaying the values of operation parameters and clock information. The electric driving device is capable of receiving a signal produced by the numerical control device and drives a nail magazine to move toward a nail anvil until a predetermined closing gap, and further causes a suturing nail to reach a predetermined forming height after firing the suturing nail. The numerically controlled surgical stapling apparatus provided in the invention is capable of performing accurate and safe control on the transmission steps and the operation actions and also of clearly displaying the operation parameters so that a doctor can know the whole surgery process; therefore, human-machine conversation is made possible.
Owner:B J ZH F PANTHER MEDICAL EQUIP
Patch-sized fluid delivery systems and methods
ActiveUS20070219480A1Reduce likelihoodOperational securityElectrotherapyFlexible member pumpsLoudspeakerMicrophone
A patch-sized fluid delivery device may include a reusable portion and a disposable portion. The disposable portion may include components that come into contact with the fluid, while the reusable portion may include only components that do not come into contact with the fluid. Redundant systems, such as redundant controllers, power sources, motor actuators, and alarms, may be provided. Alternatively or additionally, certain components can be multi-functional, such a microphones and loudspeakers that may be used for both acoustic volume sensing and for other functions and a coil that may be used as both an inductive coupler for a battery recharger and an antenna for a wireless transceiver. Various types of network interfaces may be provided in order to allow for remote control and monitoring of the device.
Owner:DEKA PROD LLP
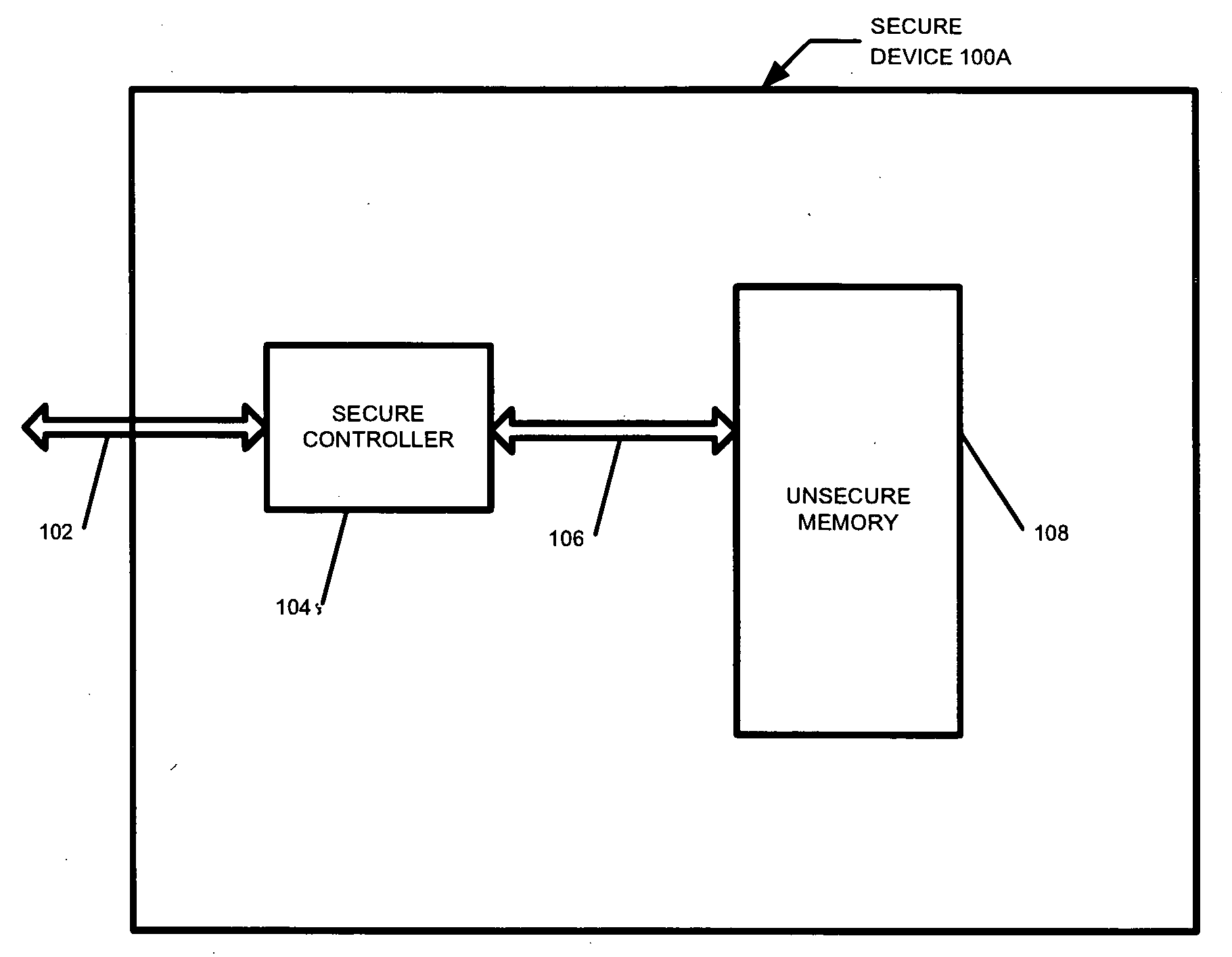
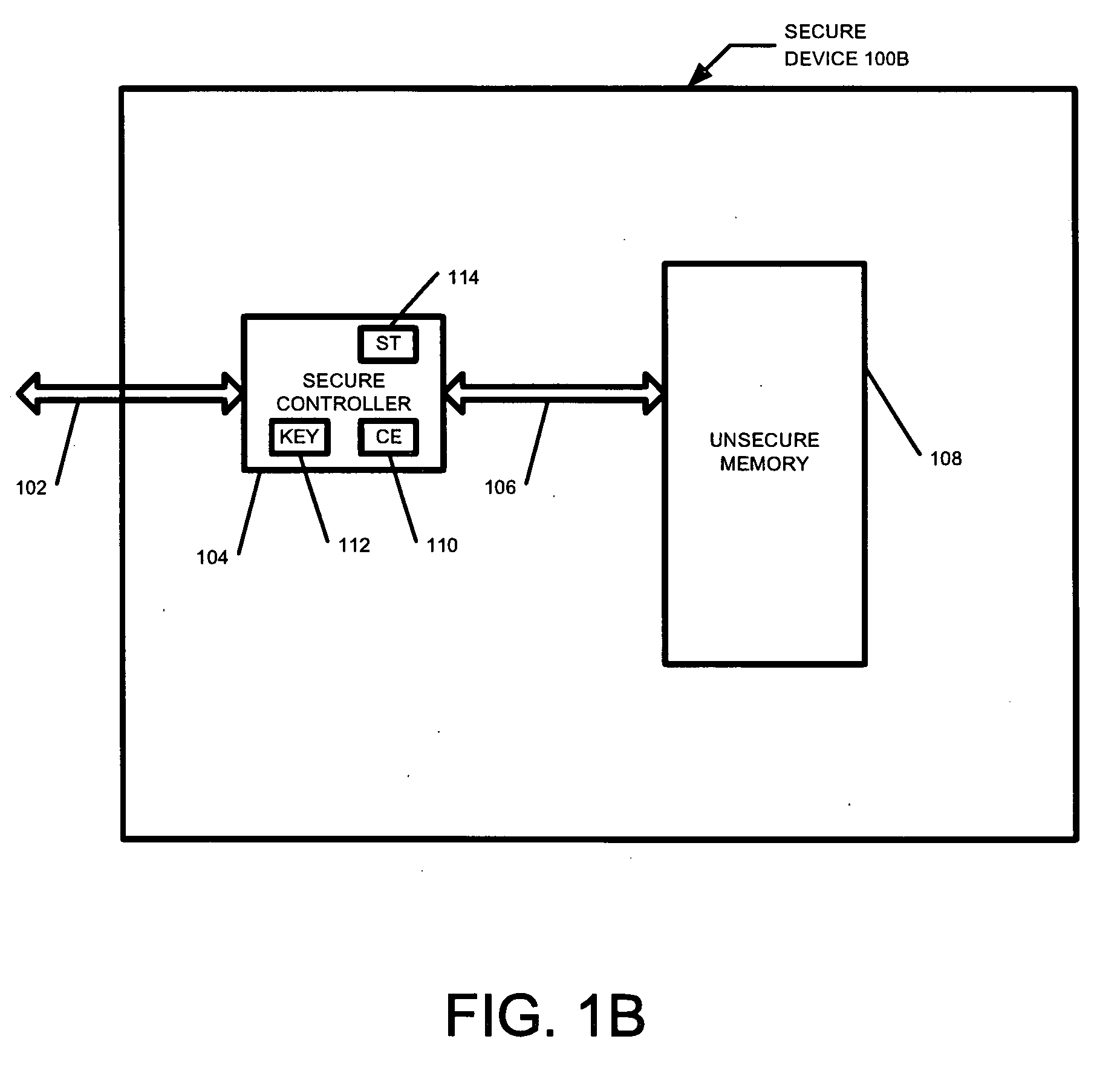
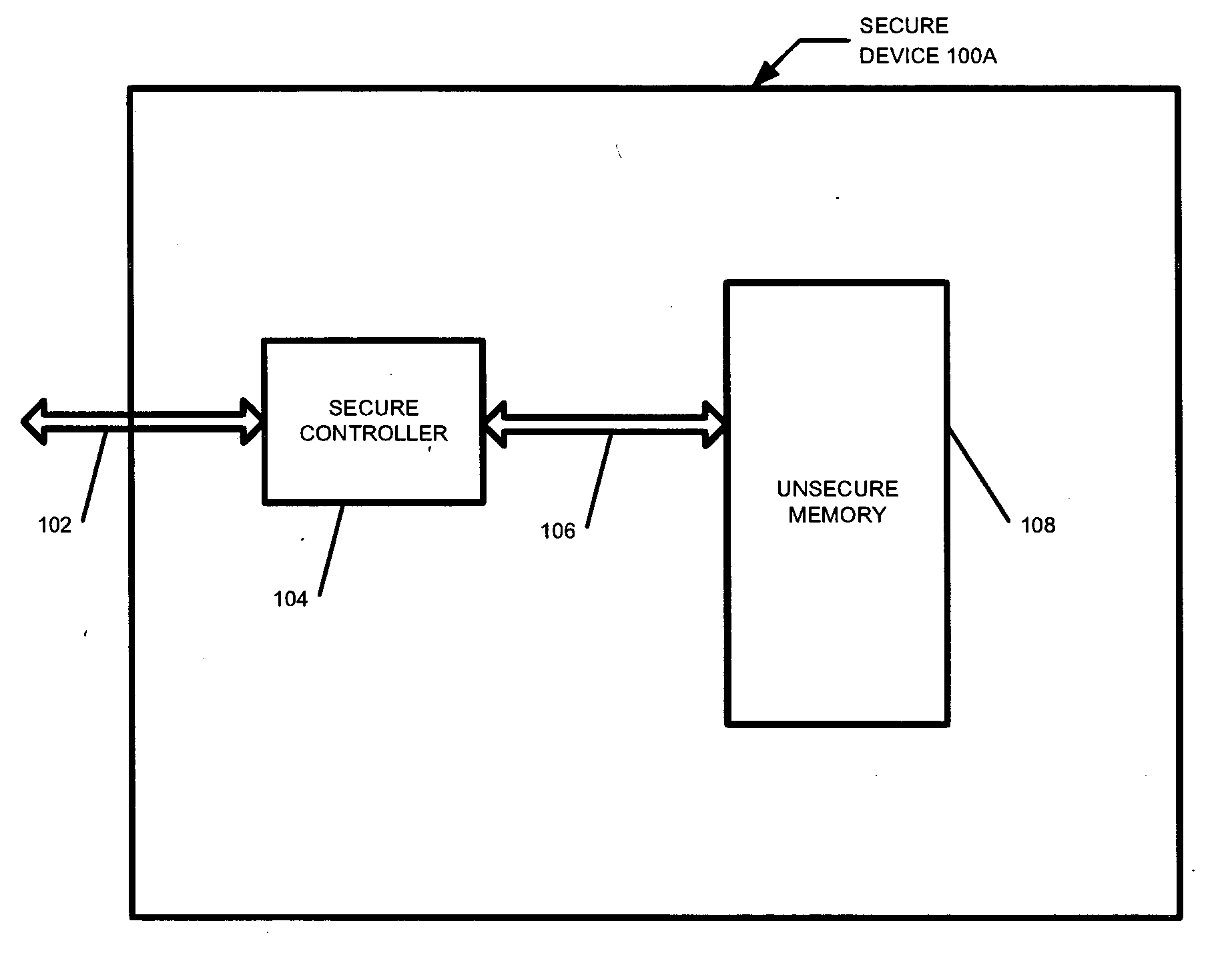
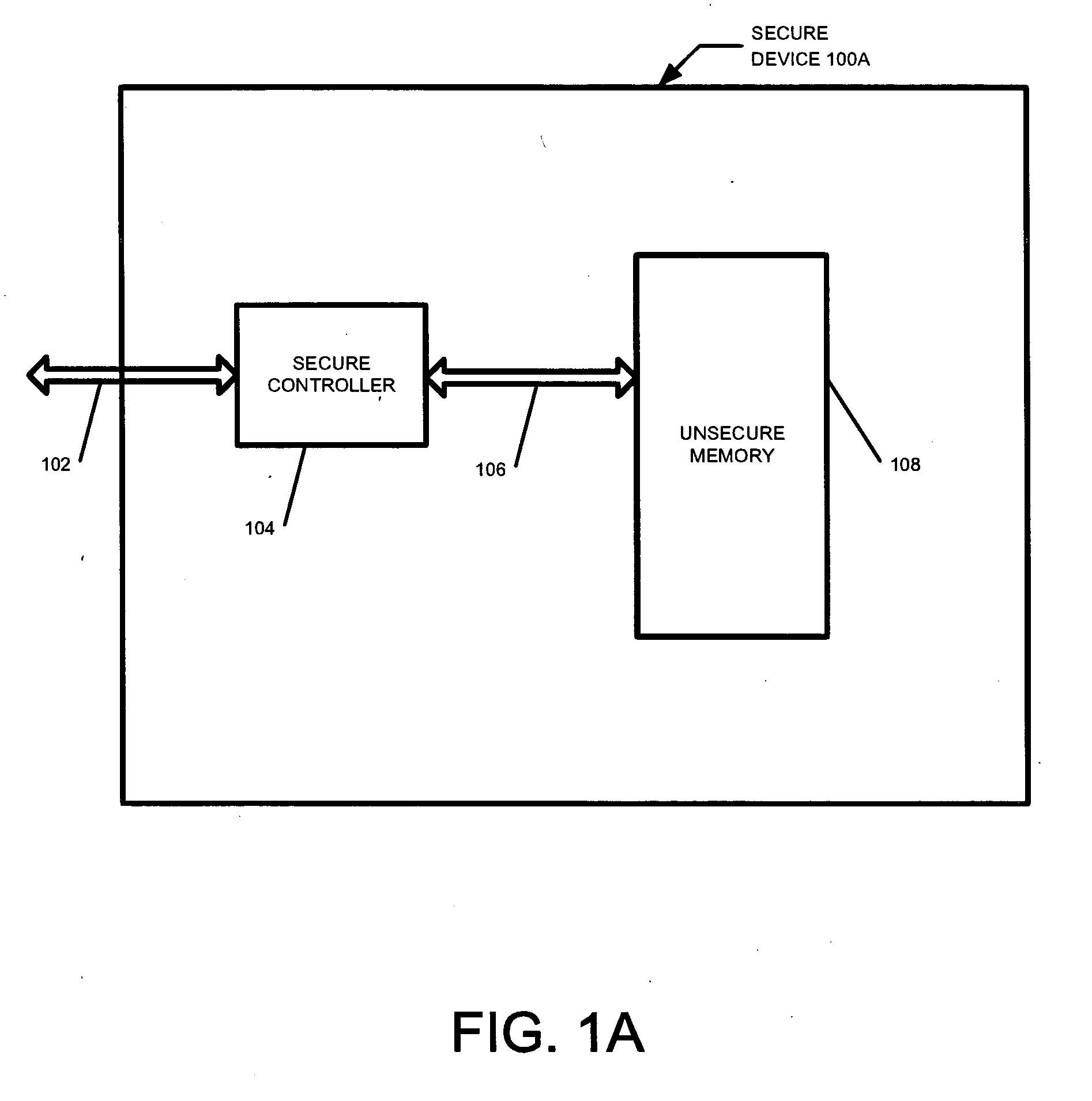
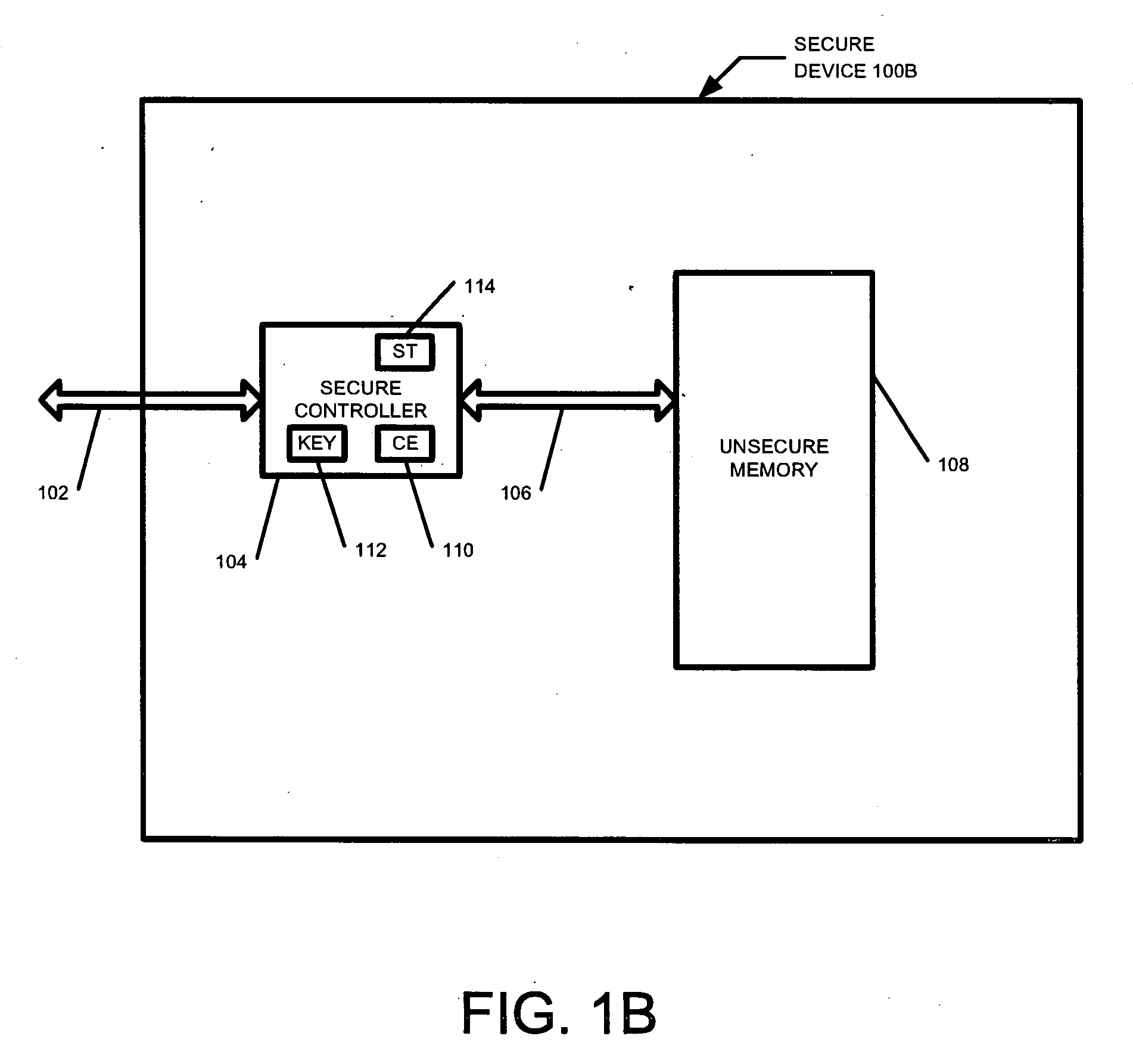
Secure yet flexible system architecture for secure devices with flash mass storage memory
InactiveUS20070061597A1Operational securityImprove security levelMemory architecture accessing/allocationUser identity/authority verificationLarge capacitySafety Equipment
A device with mass storage capability that uses a readily available non secure memory for the mass storage but has firmware (and hardware) that provides security against unauthorized copying of data. This is true even though the firmware itself is stored in the non secure mass storage memory, and therefore potentially vulnerable to hacking. An indication of the authenticity of the firmware must be present before it will be executed by the device. This protects the device contents from unauthorized duplication or tampering. Additional functionality can be added to the device with additional firmware applications, and the authenticity of those additional applications will also be verified before they will be executed. This further prevents unauthorized copying or tampering of secure content through any mechanisms that may be unscrupulously introduced. Any data within the mass storage memory may also be encrypted.
Owner:SANDISK TECH LLC +1
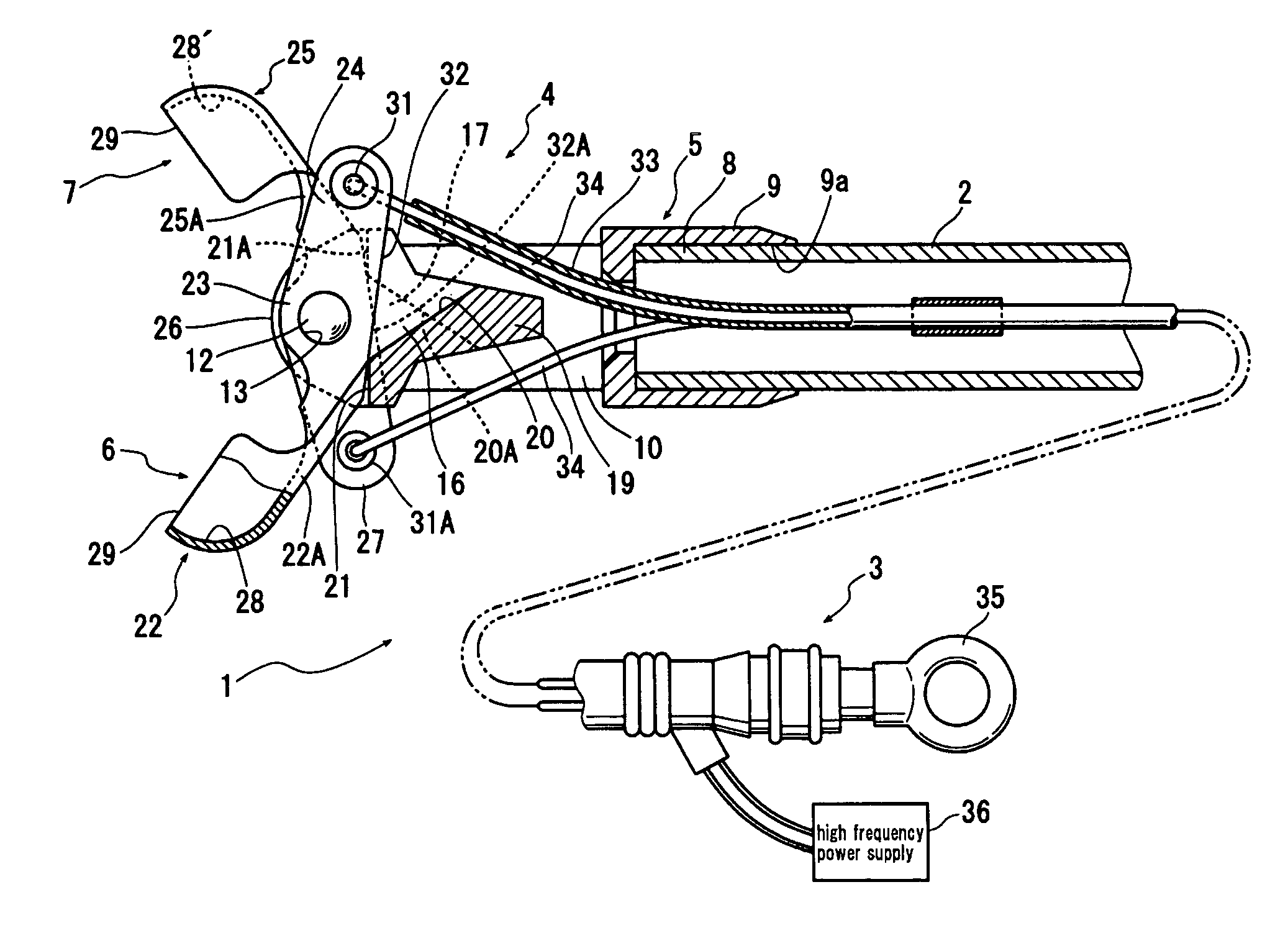
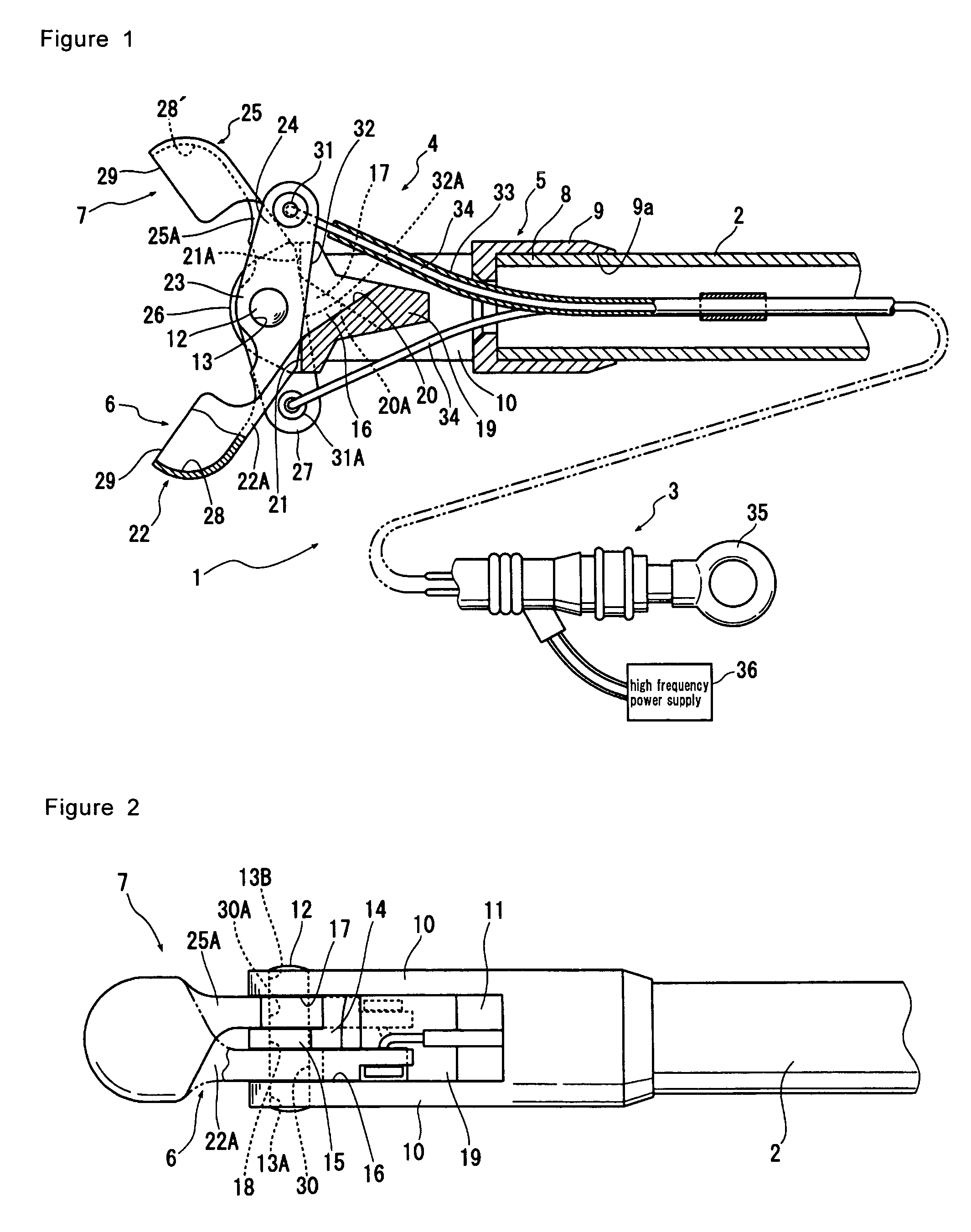
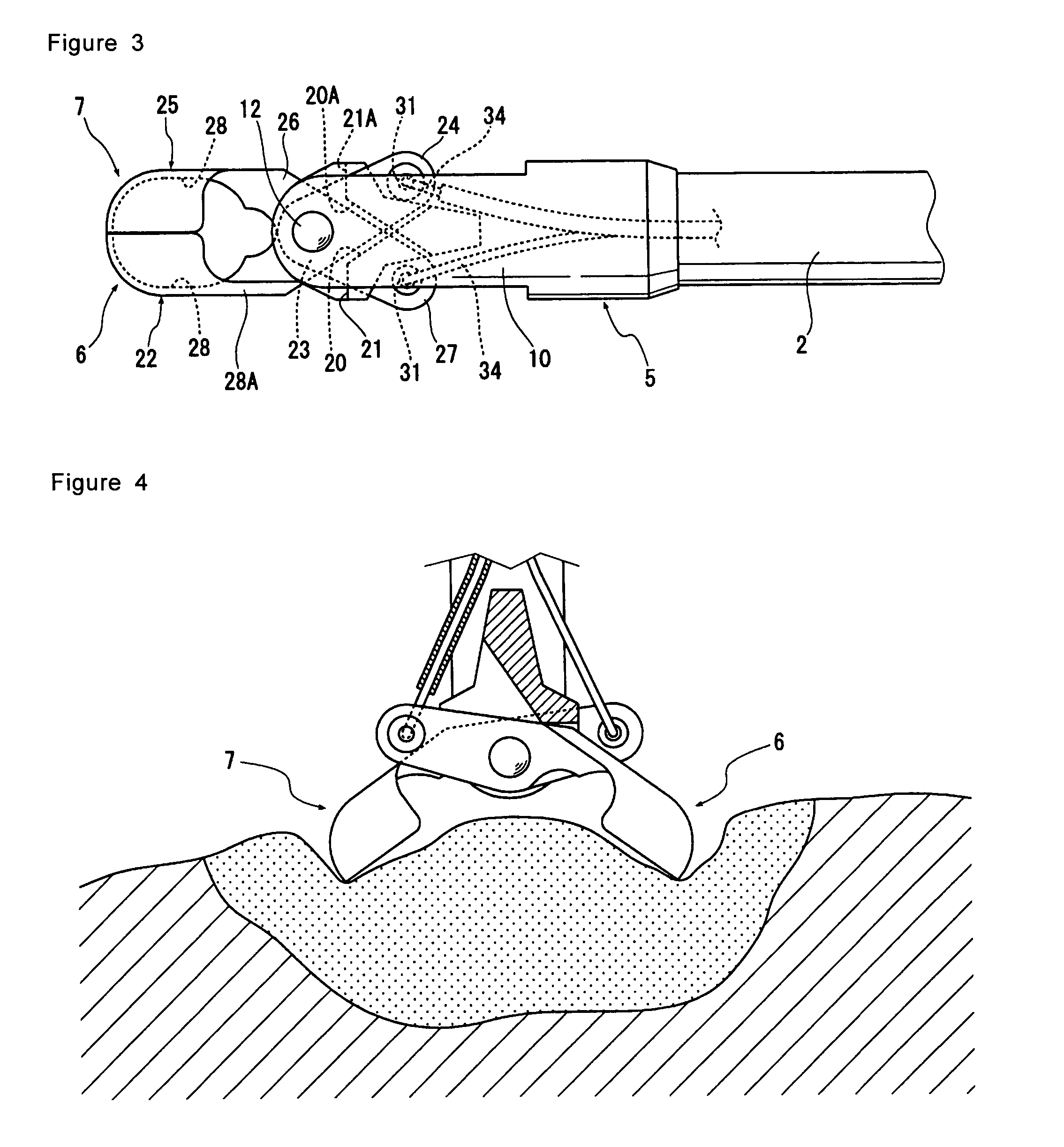
Bipolar high frequency treatment device
ActiveUS8562604B2Operational securitySafely operable bipolar high frequency treatmentVaccination/ovulation diagnosticsSurgical instruments for heatingElectricityForceps
Provided is a bipolar high frequency treatment device including a catheter tube insertable into a body through a treatment device passage of an endoscope; a first forceps blade and a second forceps blade at the top end of the catheter tube, which first forceps blade and second forceps blade can be opened and closed by operating from outside the body; a support member for supporting the first forceps blade and the second forceps blade so that the blades are able to open and close; and a voltage supplier for supplying a high frequency voltage to the first forceps blade and the second forceps blade, wherein the first forceps blade and the second forceps blade are electrically insulated with an insulating element.
Owner:KANEKA CORP
Lithium metal dispersion in electrodes
InactiveUS20050130043A1High specific capacityPromote circulationElectrode rolling/calenderingElectrode thermal treatmentLithium metalHost material
Electrodes, such as anodes and cathodes, can include a host material that is prelithiated or undergoes lithiation upon electrolyte introduction into a battery. Lithiation of the host material can occur by the agitation of lithium metal and a host material, the agitation of a lithium metal powder and a host material at a temperature greater than room temperature, the application of pressure to a lithium metal and host material mixture, contact of the host material with molten lithium metal, the lamination of lithium foil or lithium mesh onto an electrode containing the host material, or by lamination of lithium metal or mesh onto an electrode at elevated temperatures.
Owner:AEA TECH BATTERY SYST +1
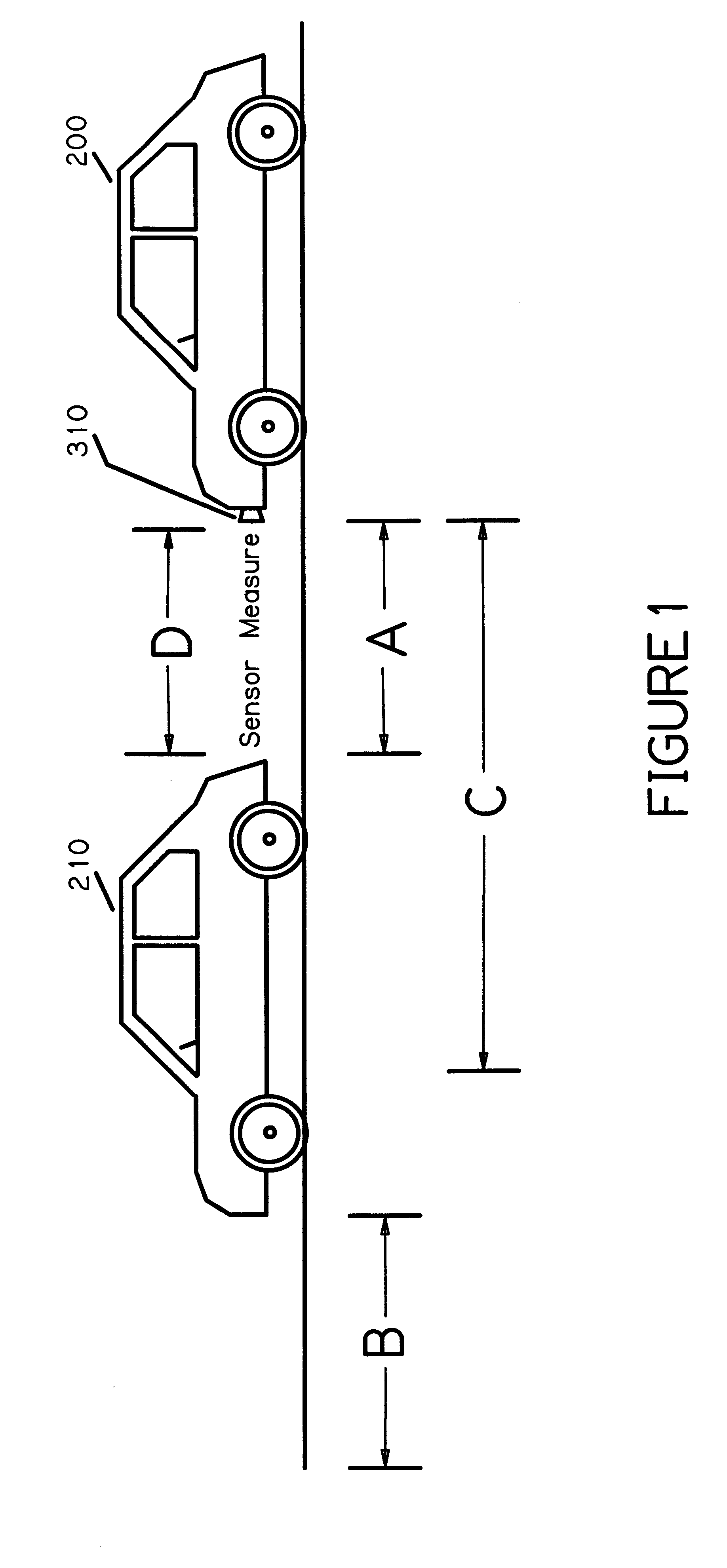
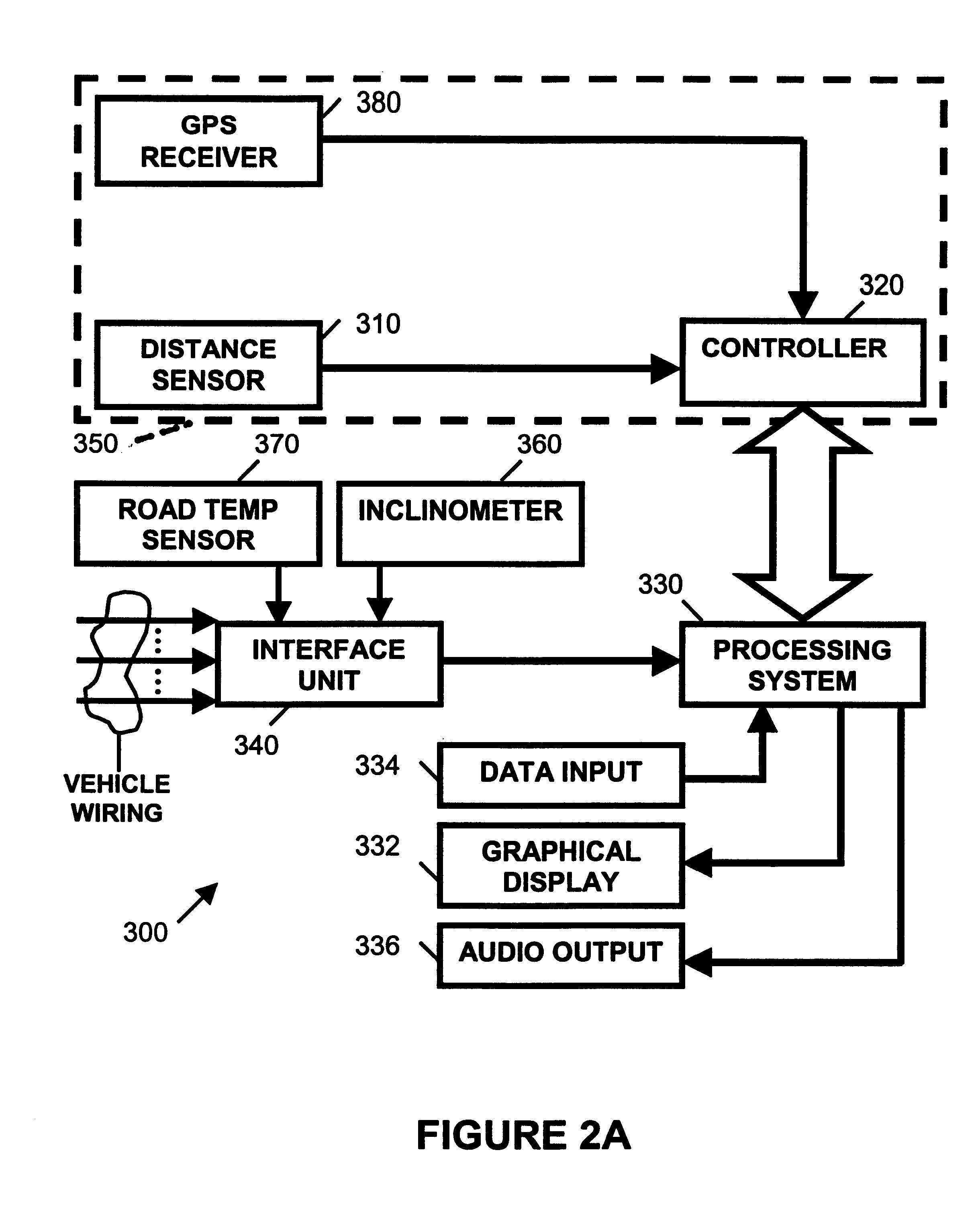
Vehicle-based headway distance training system
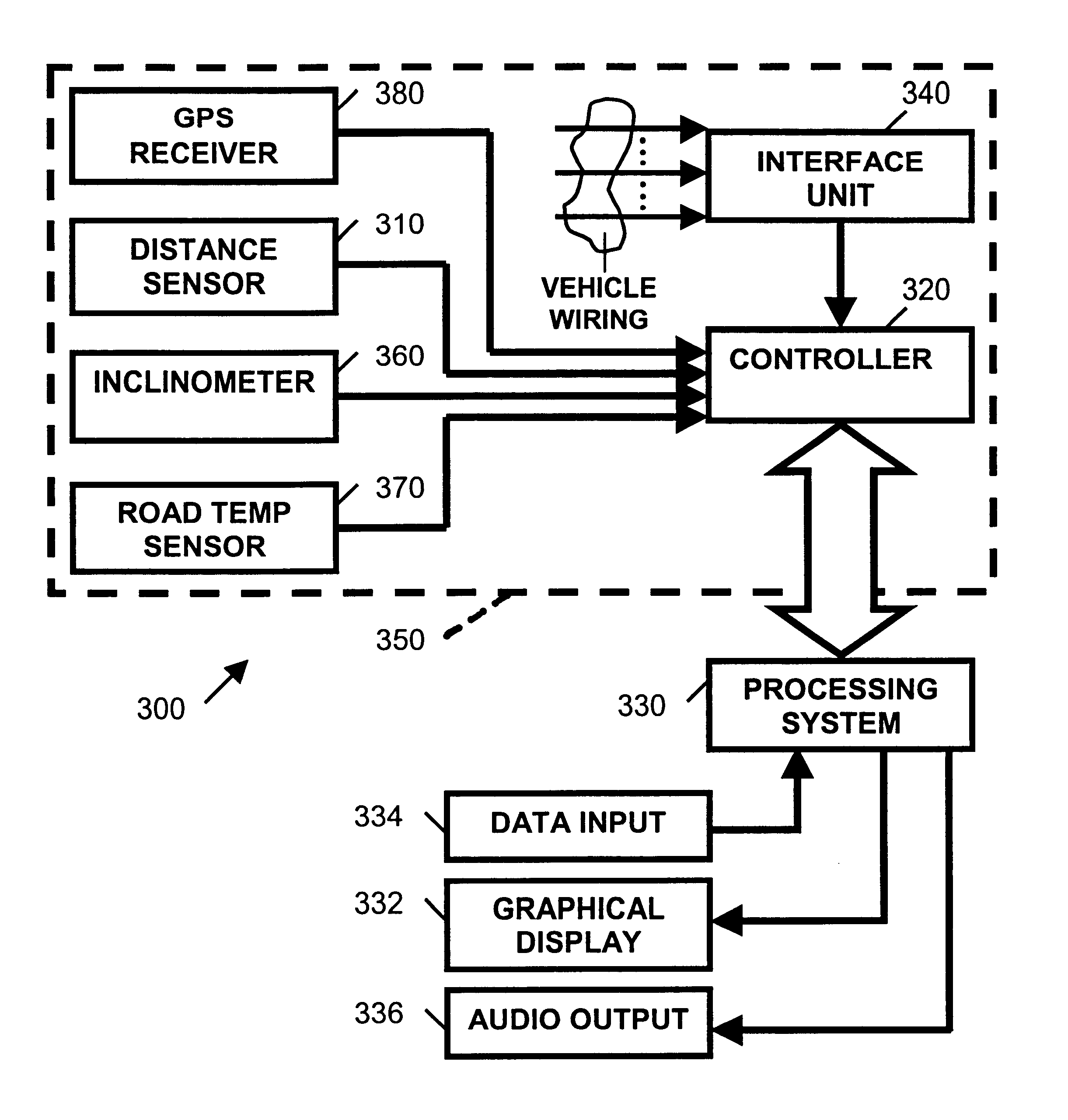
InactiveUS6679702B1Good choiceImprove safety performanceCosmonautic condition simulationsAnti-collision systemsGraphical displaySensor system
A vehicle-based headway collision avoidance training system (300) is provided that includes a sensor system (350) mounted to the training vehicle (200), a processing system (330), and an interface unit (340) coupled to the vehicle's wiring. The combination of processing system (330), a graphical display (332), a data input device (334), and an audio output device (336) provides a collection of special auditory and visual displays attended to by the student, and controls and displays used by the instructor that are unique for teaching headway safety in the context of a moving vehicle.
Owner:RAU PAUL S
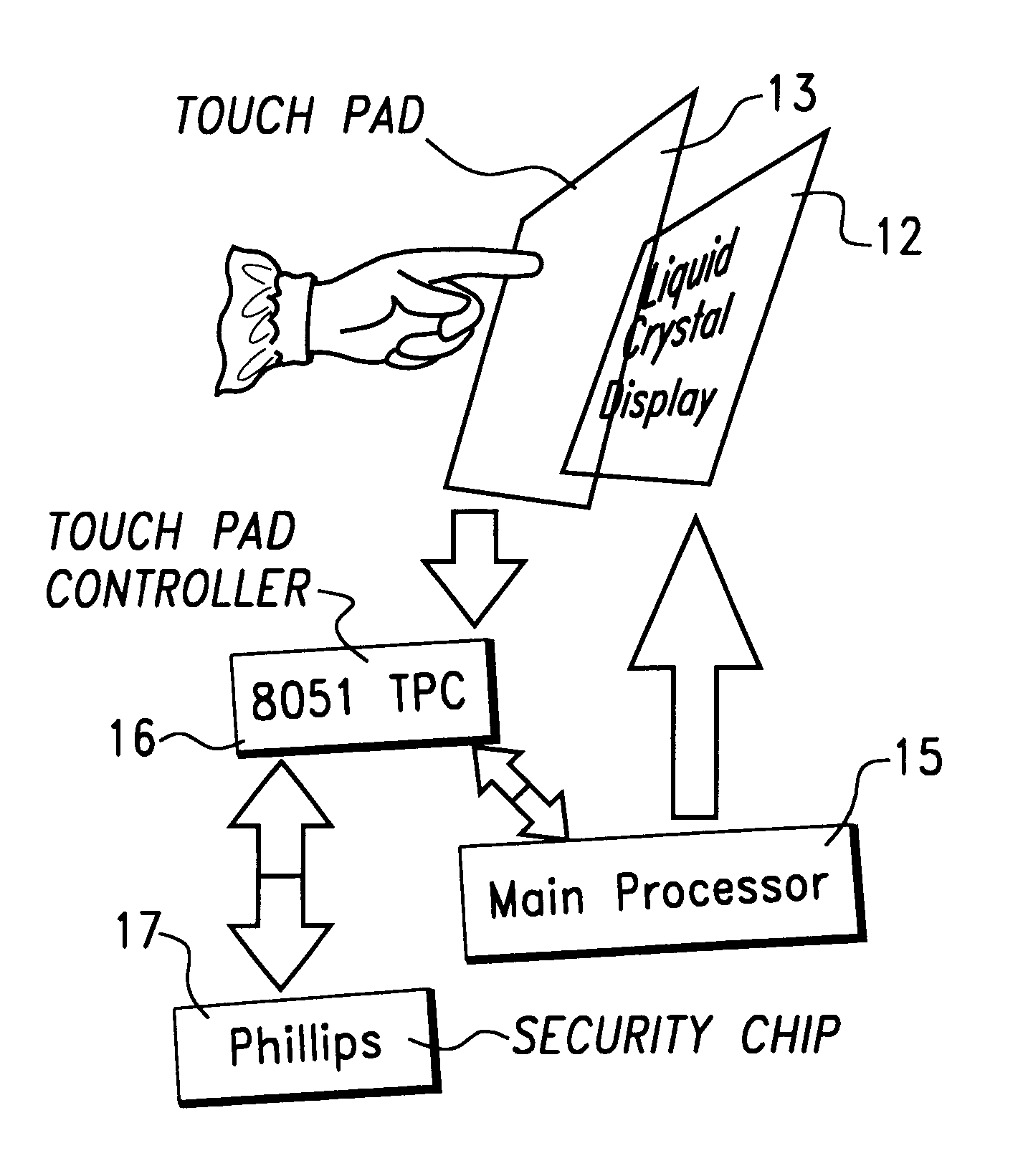
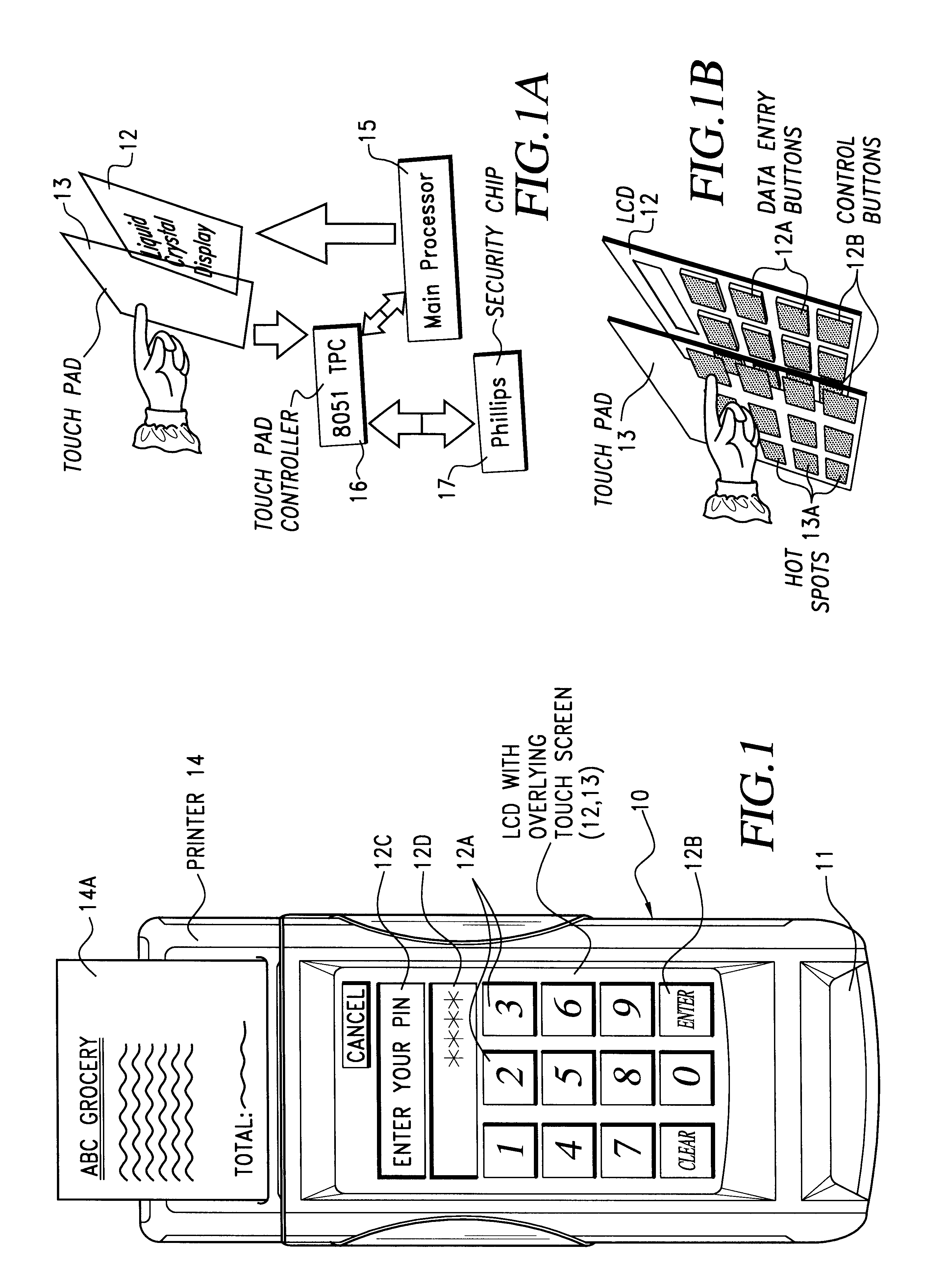
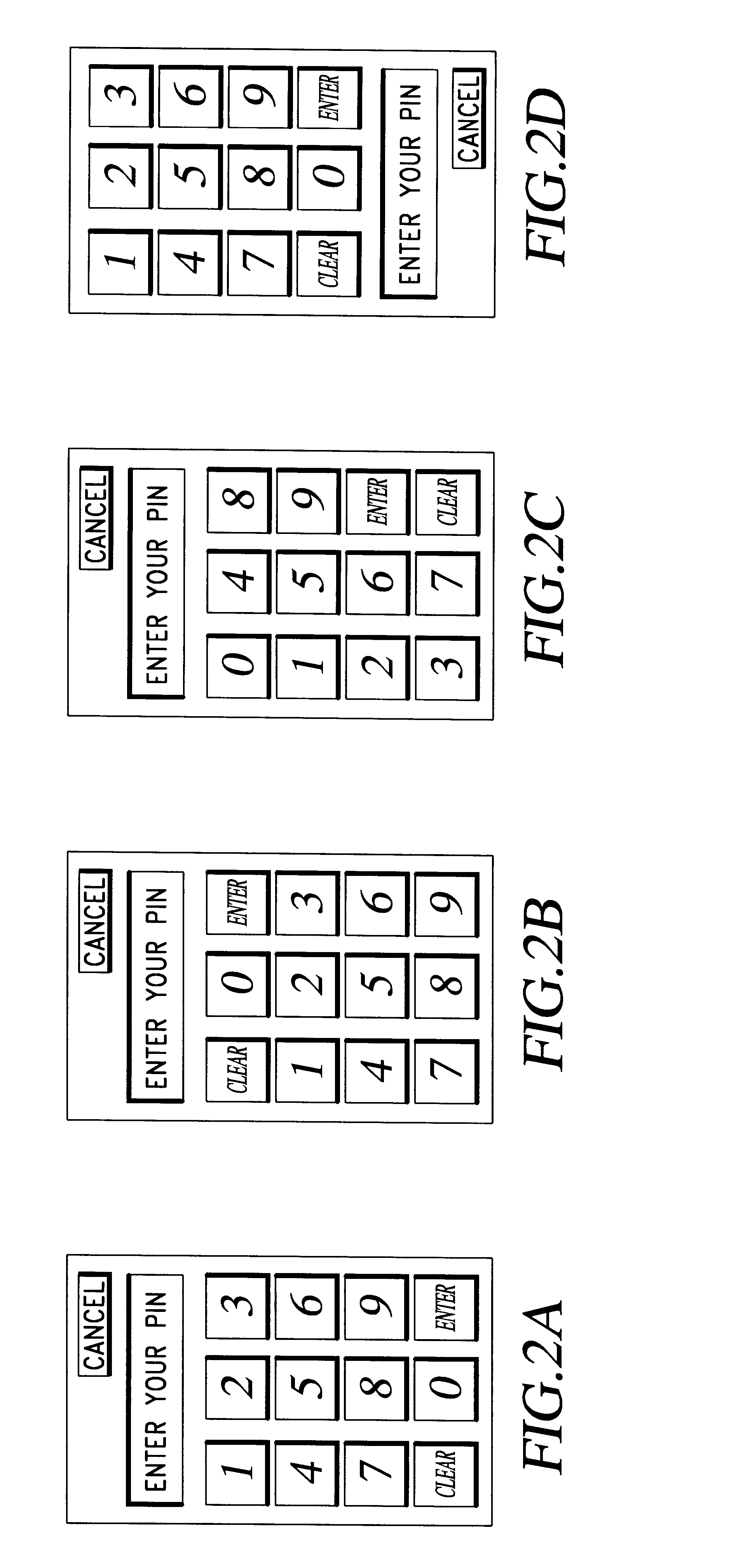
Method for secure pin entry on touch screen display
InactiveUS6549194B1None of methods is secureEffective preventionElectric signal transmission systemsMultiple keys/algorithms usageDisplay deviceTouchpad
A method for operating a combination touch pad and display screen device as a PINpad for entering a A plurality of numerical keypad layouts for the display screen are defined. Each keypad layout has a unique arrangement of decimal number locations differing from one layout to all others. For each PIN entry event a random one of the numerical keypad layouts is selected and displayed on the display screen.
Owner:HEWLETT PACKARD DEV CO LP
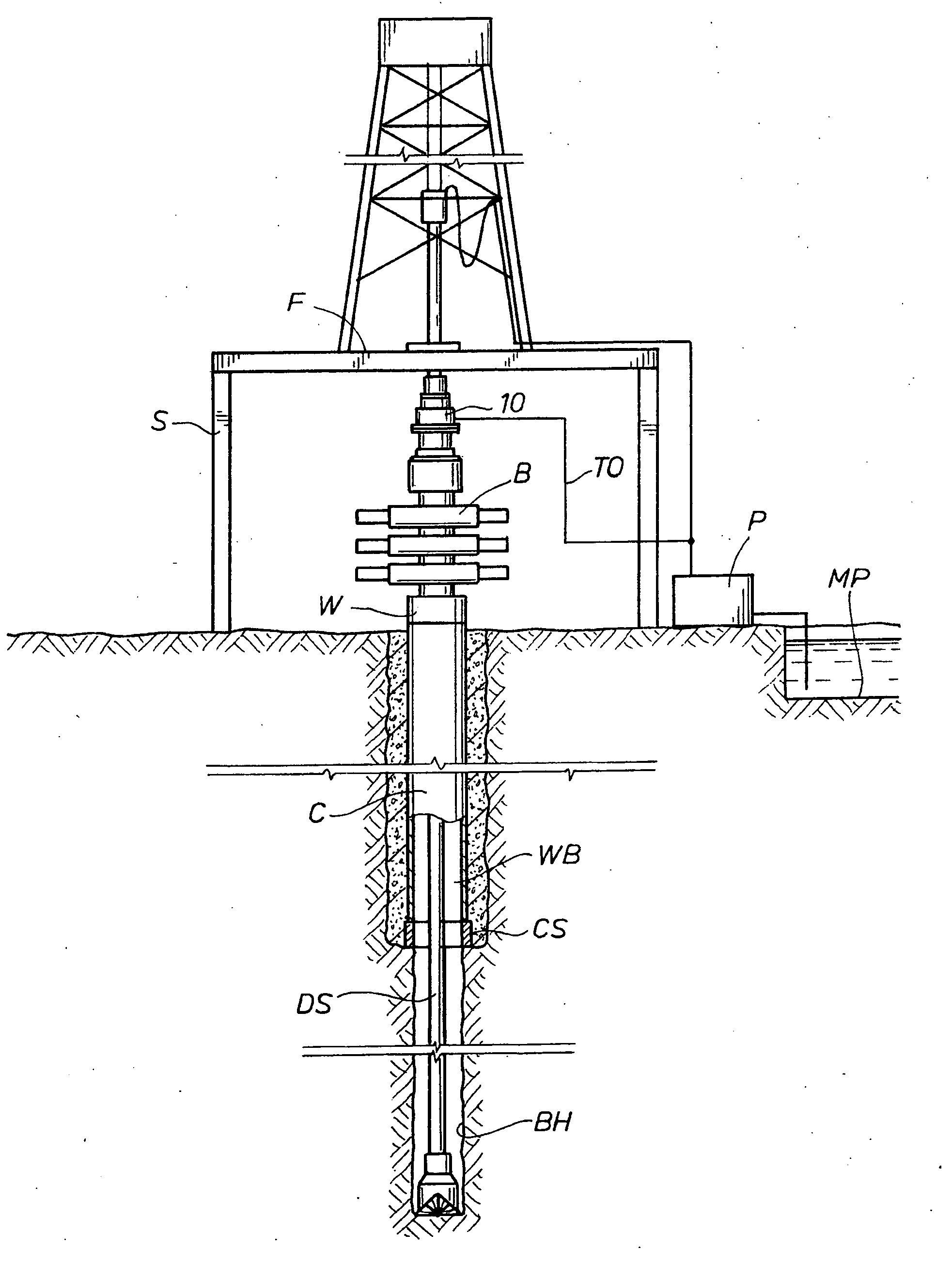
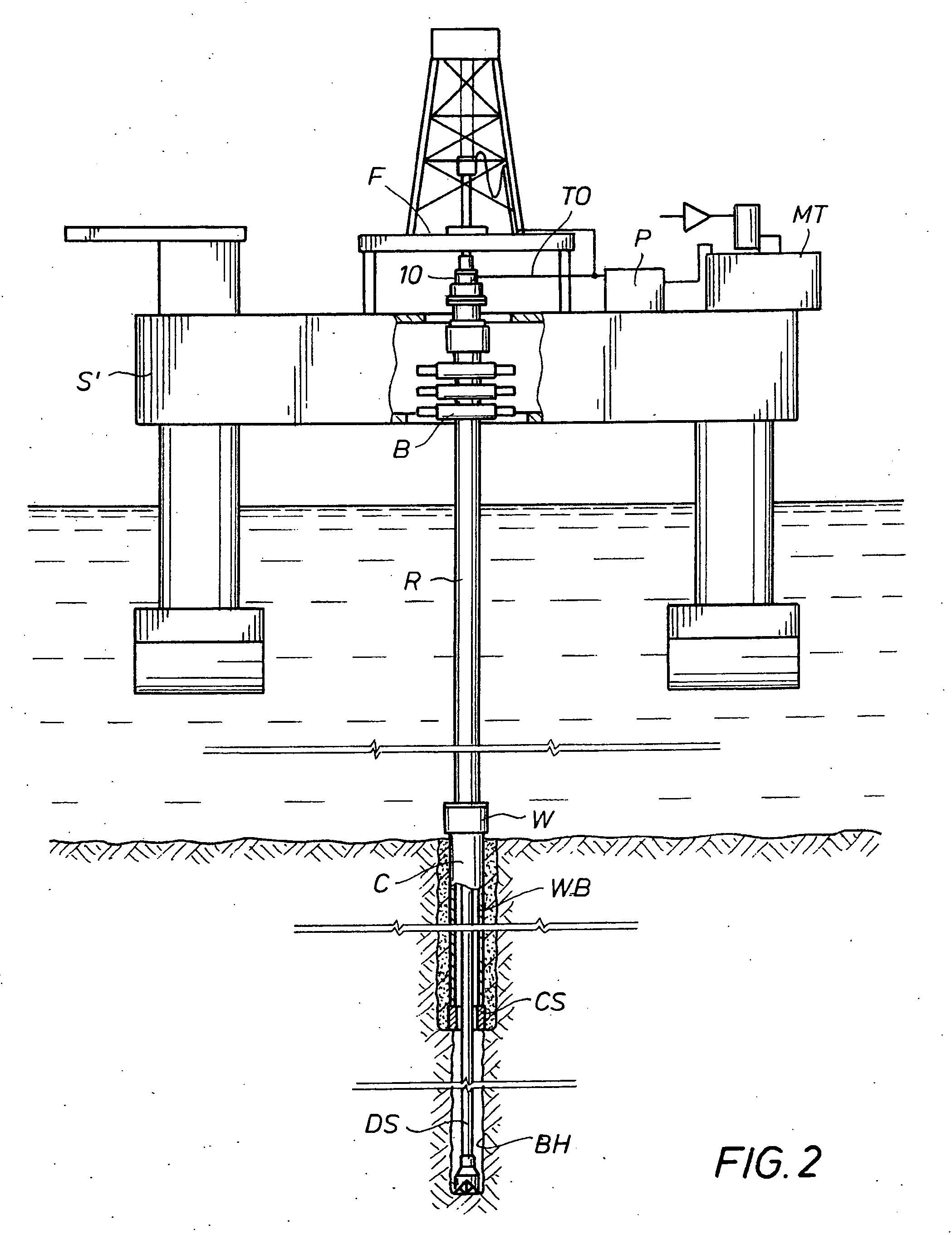
Drilling with a high pressure rotating control device
ActiveUS20110024195A1Operational securityHigh safety factorSurveyDrilling rodsWell drillingControl system
A Drill-To-The-Limit (DTTL) drilling method variant to Managed Pressure Drilling (MPD) applies constant surface backpressure, whether the mud is circulating (choke valve open) or not (choke valve closed). Because of the constant application of surface backpressure, the DTTL method can use lighter mud weight that still has the cutting carrying ability to keep the borehole clean. The DTTL method identifies the weakest component of the pressure containment system, such as the fracture pressure of the formation or the casing shoe leak off test (LOT). With a higher pressure rated RCD, such as 5,000 psi (34,474 kPa) dynamic or working pressure and 10,000 psi (68,948 kPa) static pressure, the limitation will generally be the fracture pressure of the formation or the LOT. In the DTTL method, since surface backpressure is constantly applied, the pore pressure limitation of the conventional drilling window can be disregarded in developing the fluid and drilling programs. Using the DTTL method a deeper wellbore can be drilled with larger resulting end tubulars, such as casings and production liners, than had been capable with conventional MPD applications.
Owner:WEATHERFORD TECH HLDG LLC
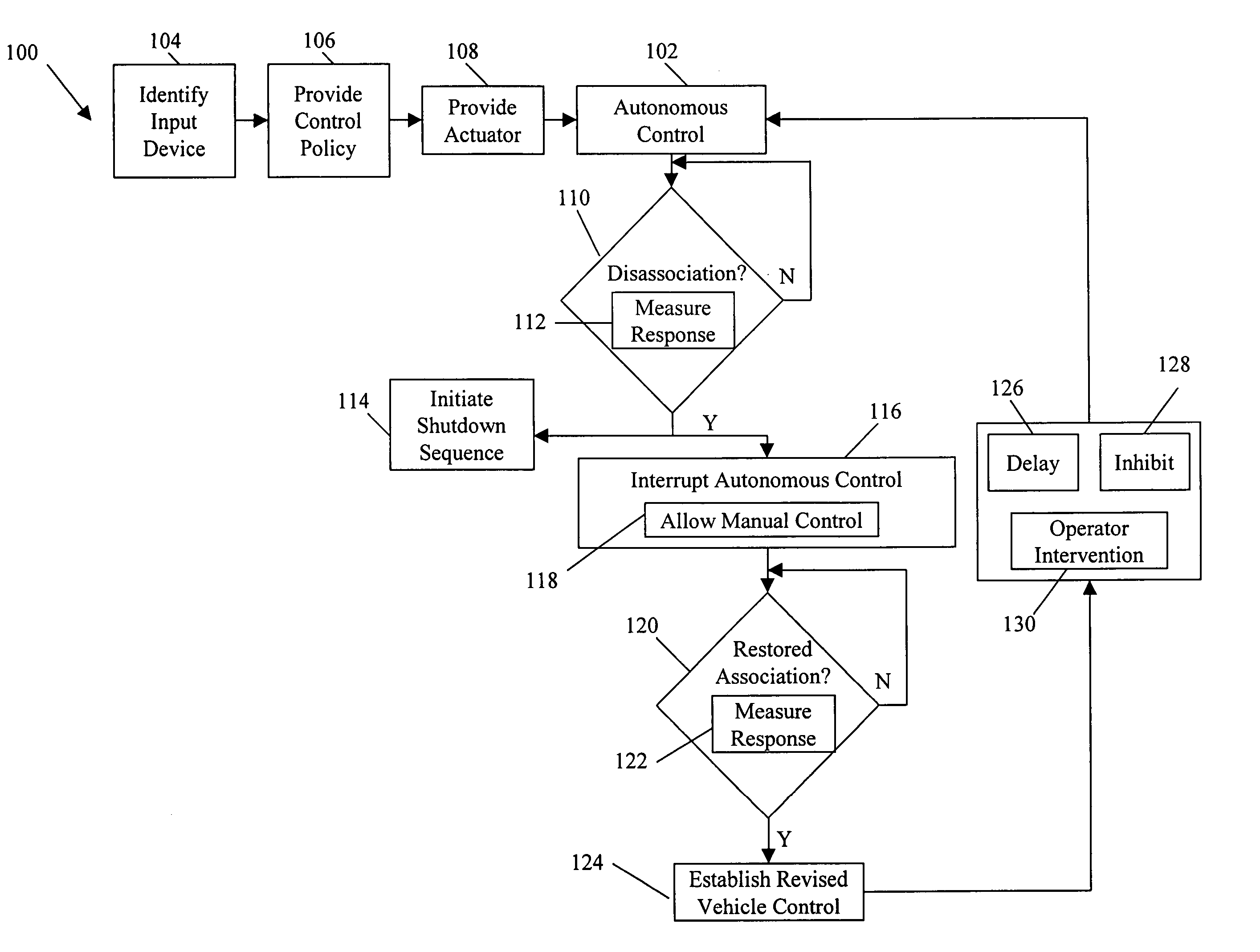
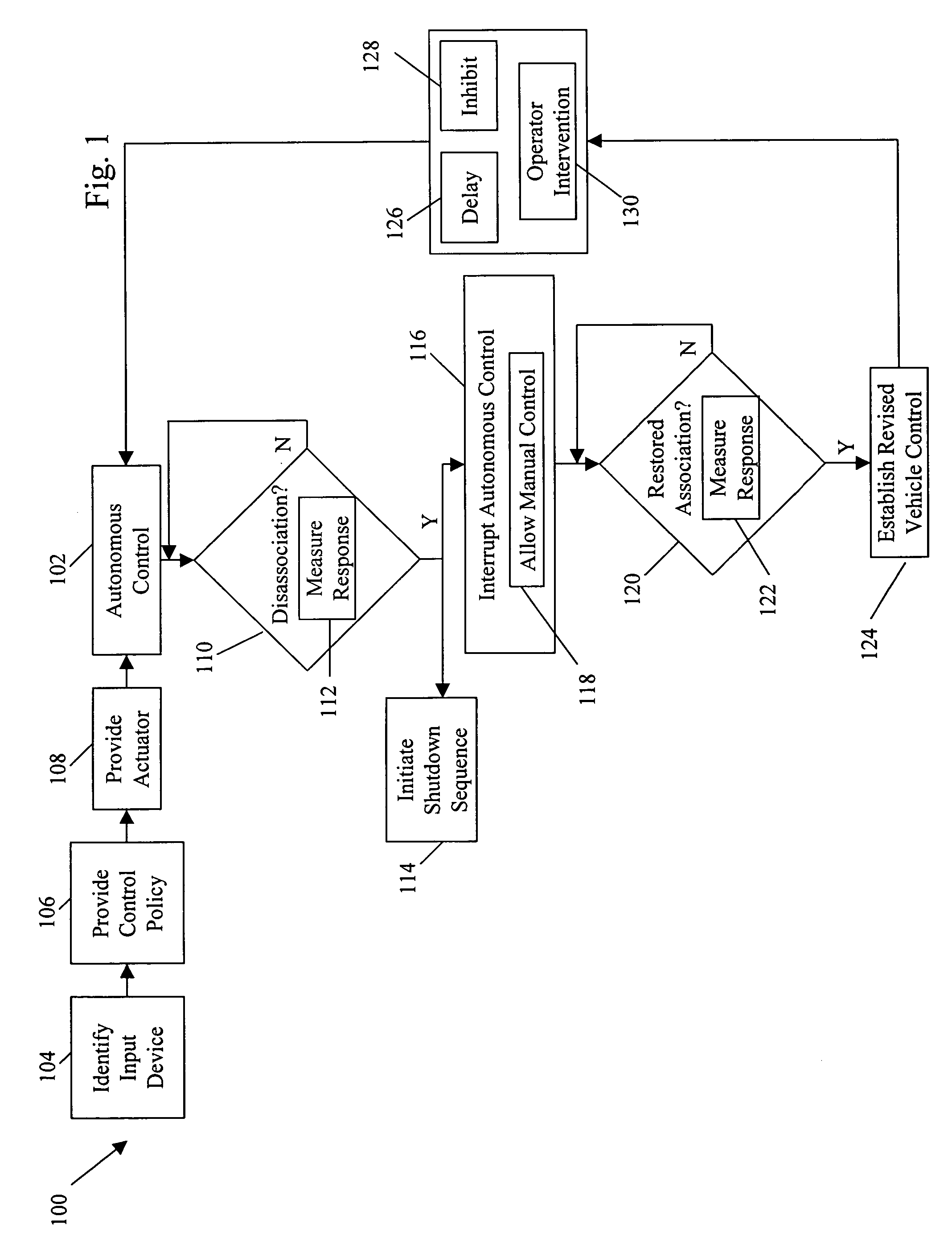
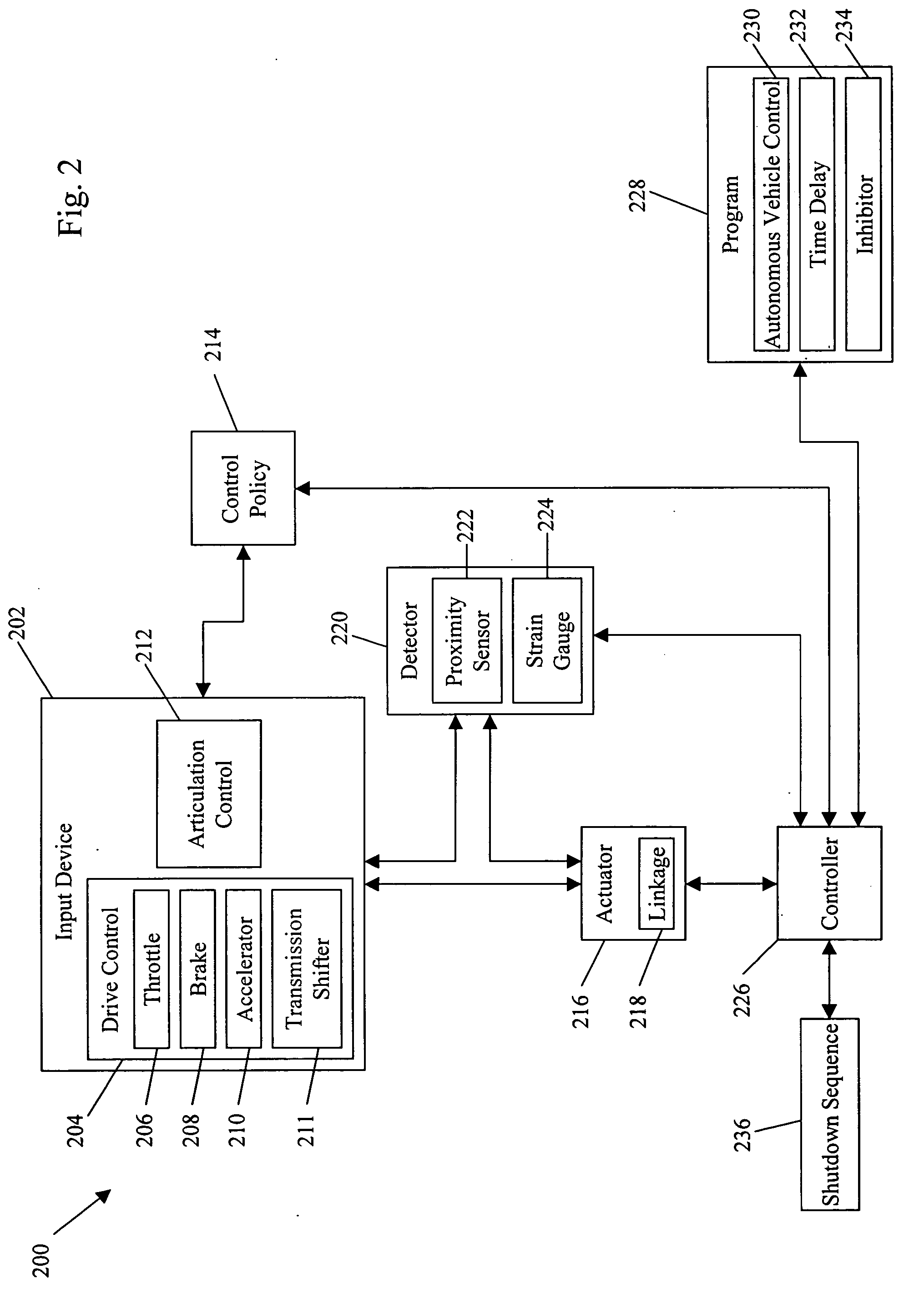
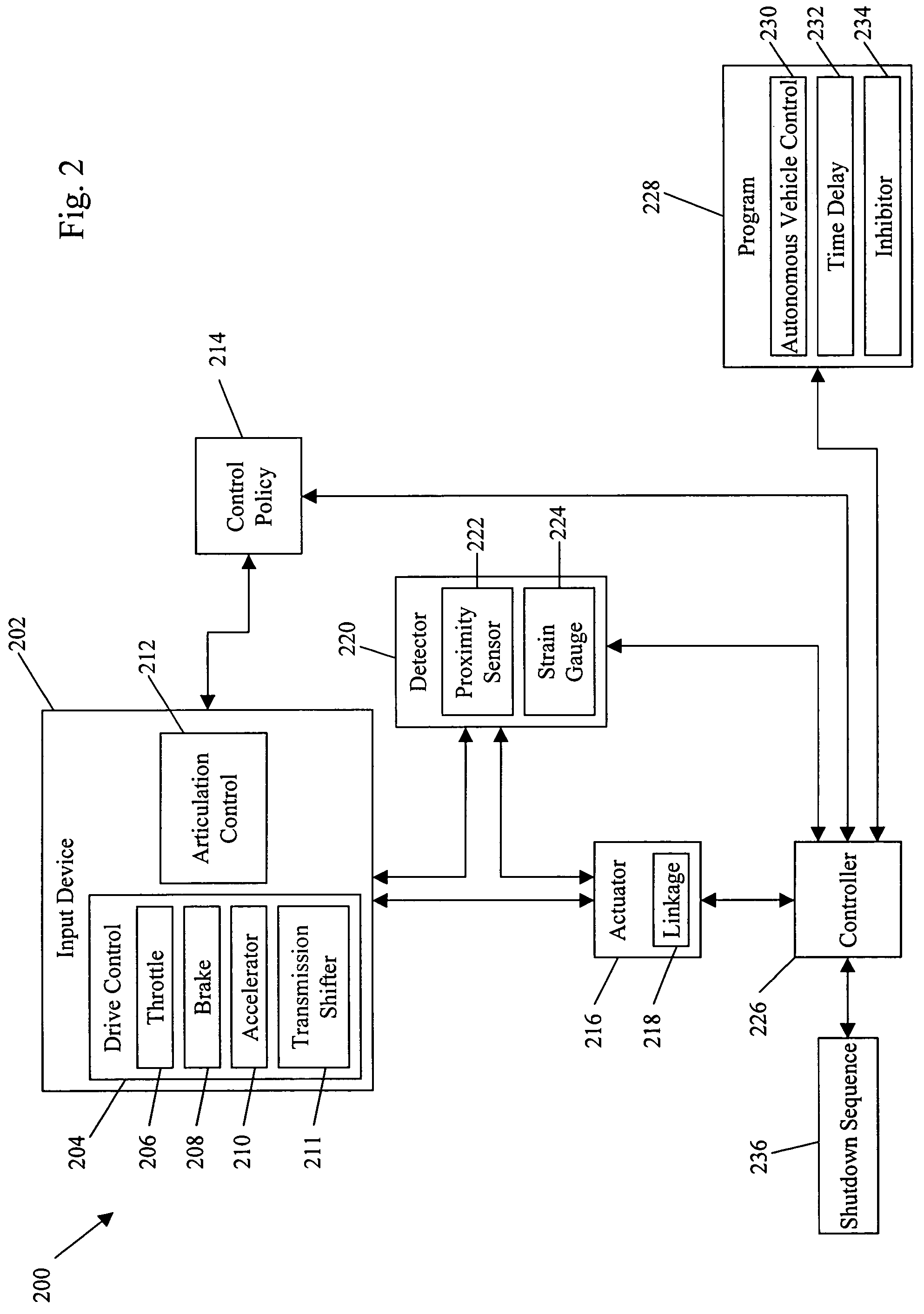
Systems and methods for control of an unmanned ground vehicle
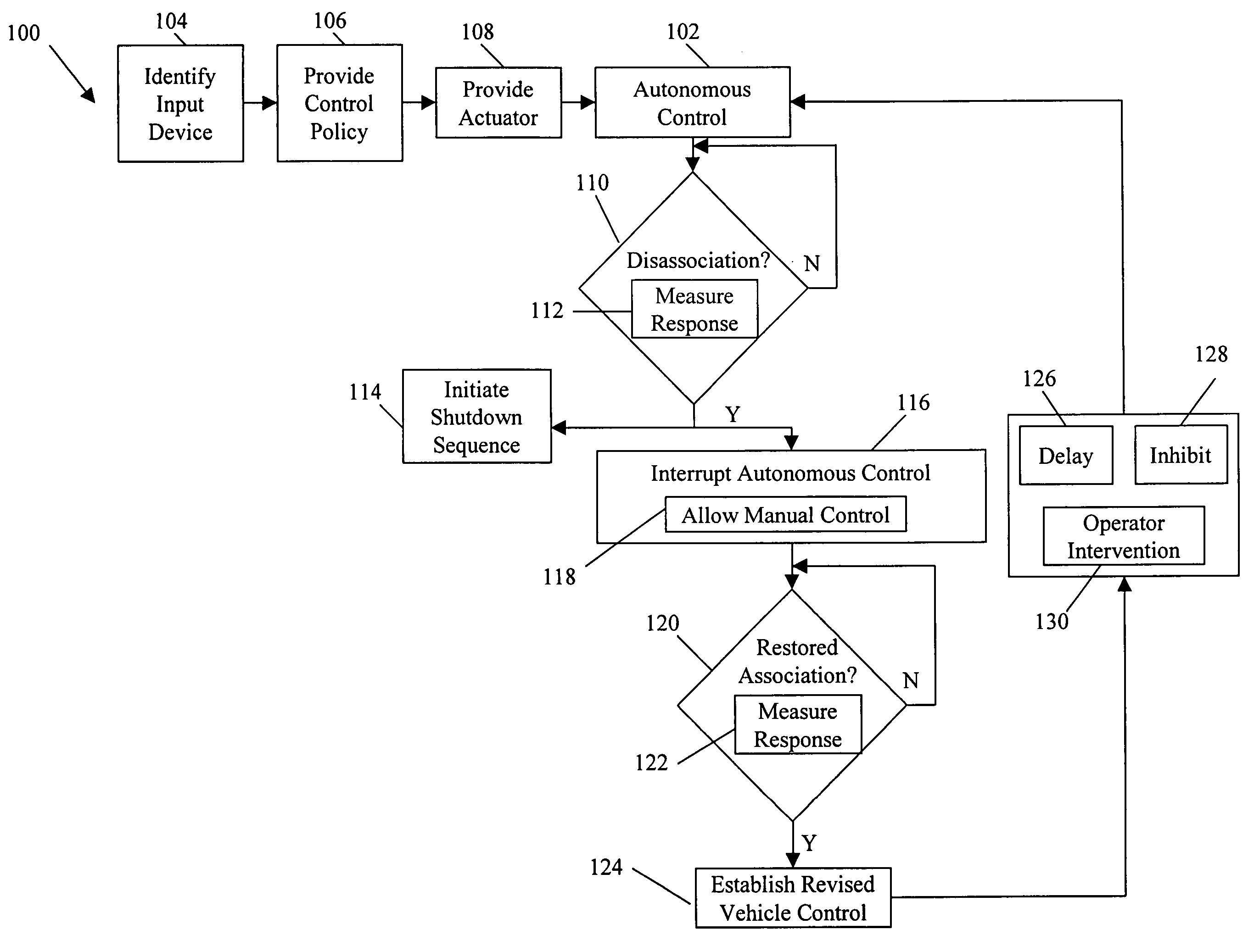
InactiveUS20060089766A1Improve securityDecrease and eliminates need for manual interventionDigital data processing detailsVehicle position/course/altitude controlEngineeringGround vehicles
Systems and methods for interruptible autonomous control of a vehicle. Autonomous control is achieved by using actuators that interact with input devices in the vehicle. The actuators (e.g., linkages) manipulate the input devices (e.g., articulation controls and drive controls, such as a throttle, brake, tie rods, steering gear, throttle lever, or accelerator) to direct the operation of the vehicle. Although operating autonomously, manual operation of the vehicle is possible following the detection of events that suggest manual control is desired. Subsequent autonomous control may be permitted, permitted after a prescribed delay, or prevented.
Owner:IROBOT CORP
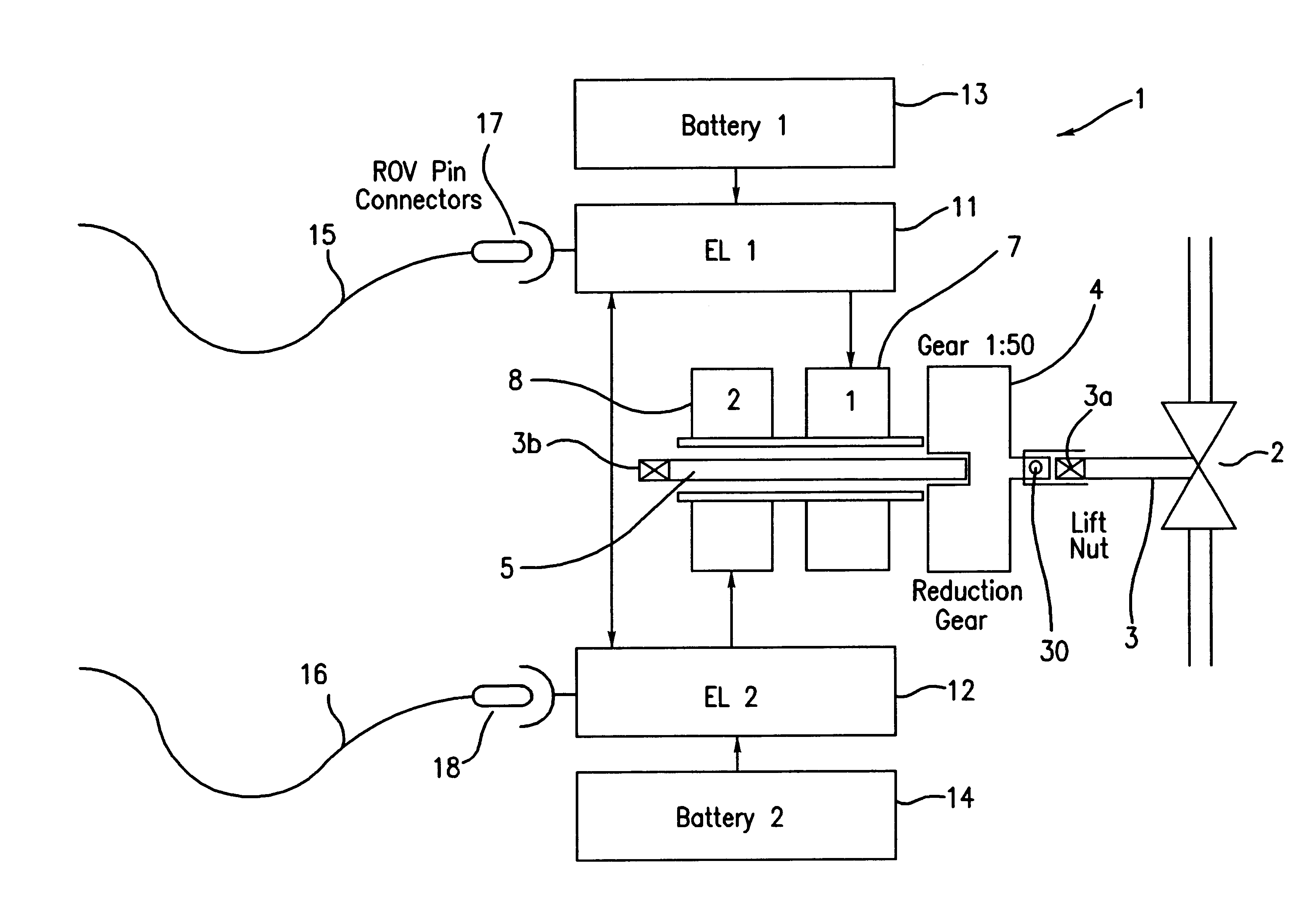
Electric actuator
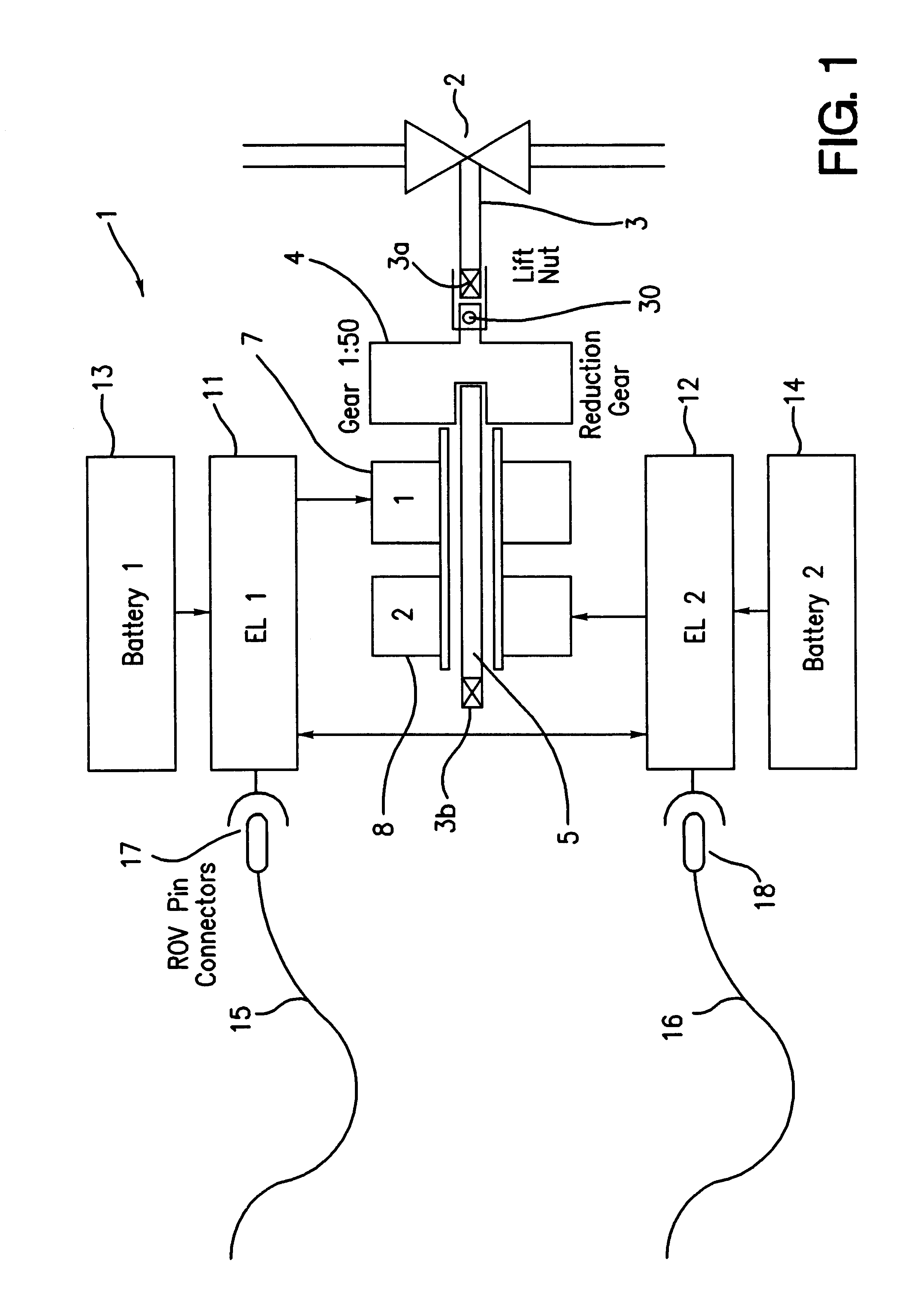
InactiveUS6595487B2More powerReduce power lossOperating means/releasing devices for valvesSealing/packingElectricityActuator
An actuator system for actuating a valve in a subsea environment comprises a valve spindle that is arranged to be coupled to an electric motor. To provide for power to the motor, at least one local electrical storage unit is provided. The system also includes a control unit comprising switching means for controlling the power to the motor. The control unit includes an intelligent processor and is arranged to receive signals from external sensors measuring a number of external and internal parameters, The actuator is preferable housed in a modular cage for easy replacement.
Owner:KONGSBERG OFFSHORE
Systems and methods for control of an unmanned ground vehicle
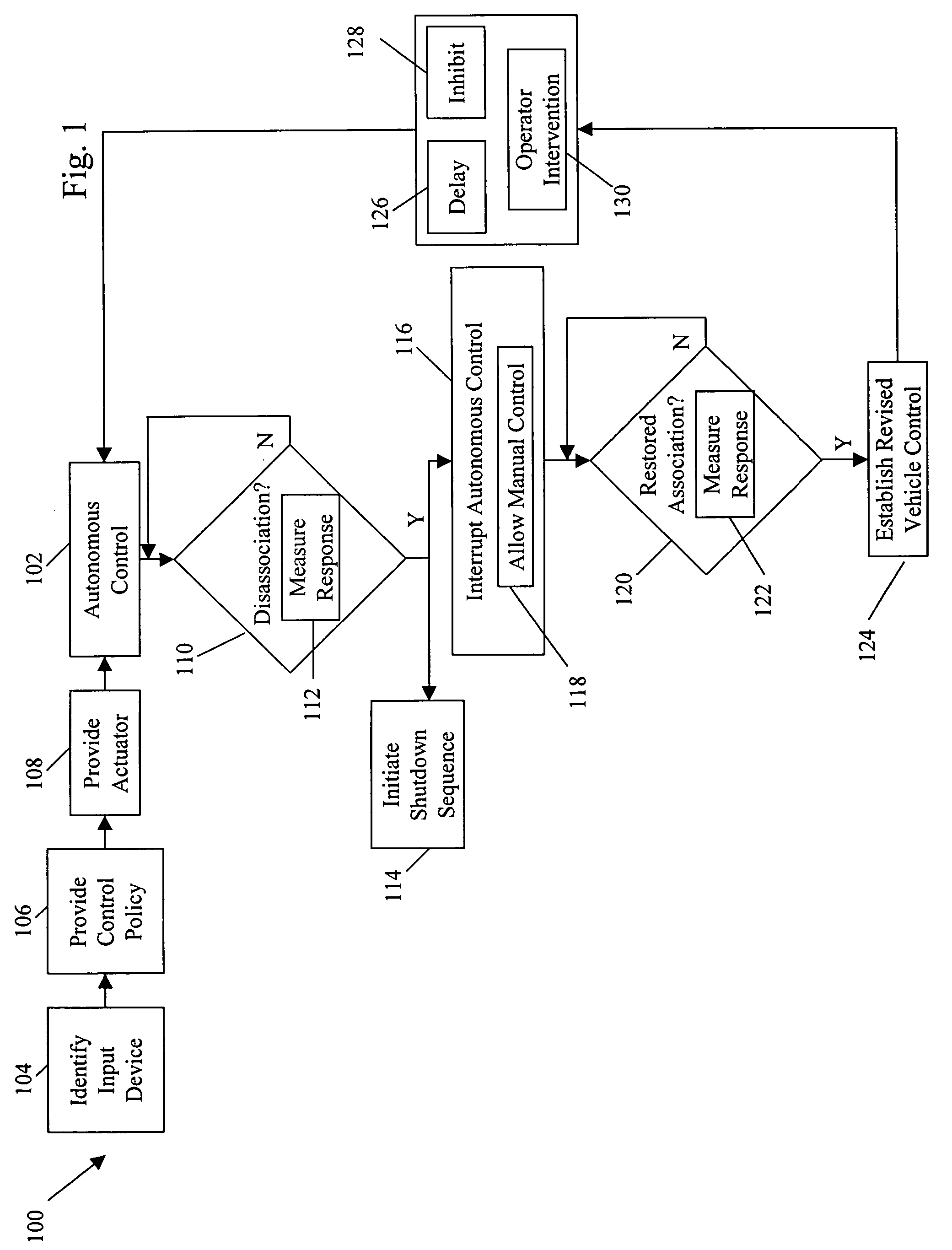
InactiveUS7499776B2Decrease and eliminates need for manual interventionImprove task efficiencyVehicle testingAnalogue computers for trafficEngineeringGround vehicles
Systems and methods for interruptible autonomous control of a vehicle. Autonomous control is achieved by using actuators that interact with input devices in the vehicle. The actuators (e.g., linkages) manipulate the input devices (e.g., articulation controls and drive controls, such as a throttle, brake, tie rods, steering gear, throttle lever, or accelerator) to direct the operation of the vehicle. Although operating autonomously, manual operation of the vehicle is possible following the detection of events that suggest manual control is desired. Subsequent autonomous control may be permitted, permitted after a prescribed delay, or prevented.
Owner:IROBOT CORP
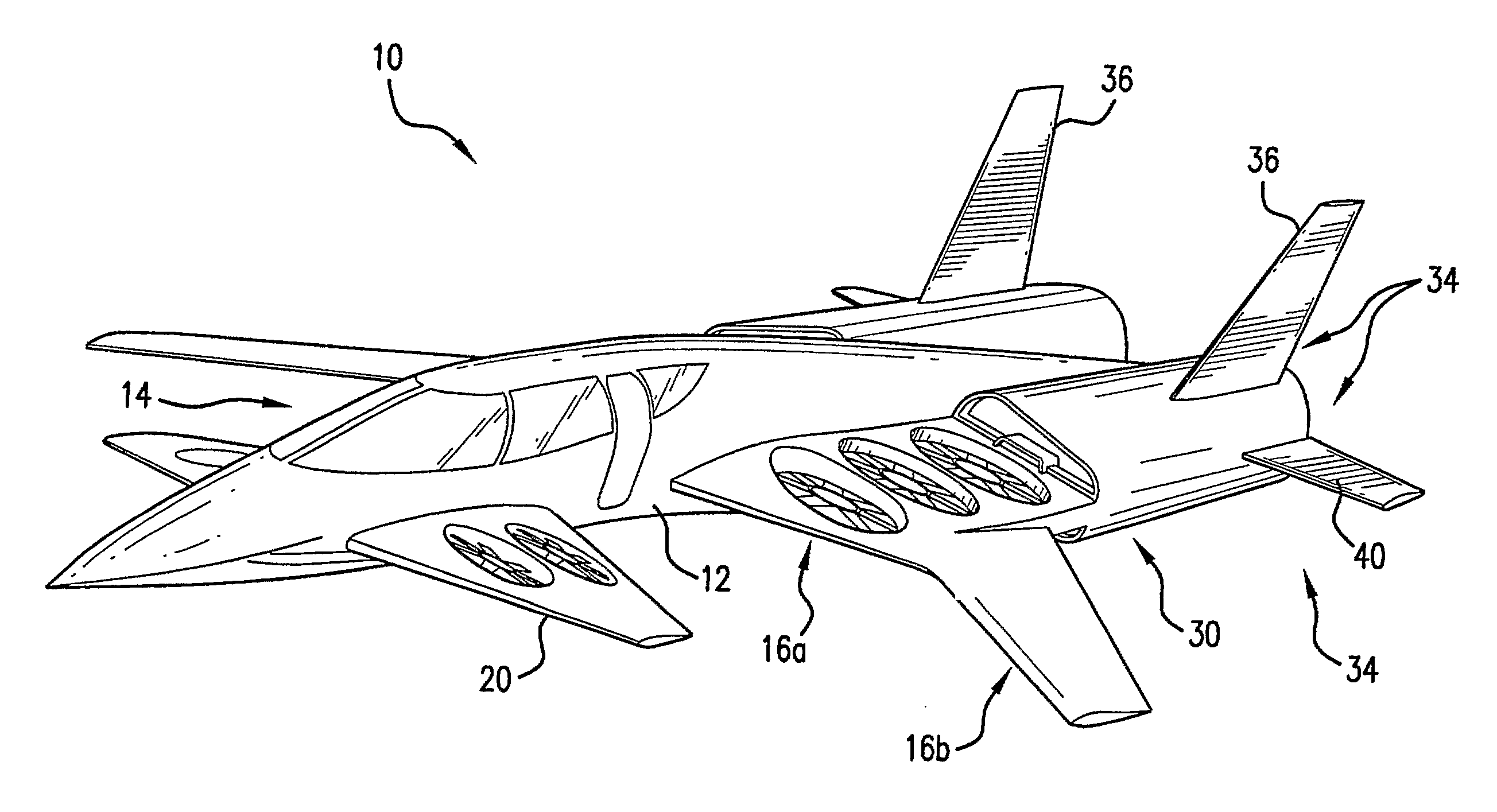
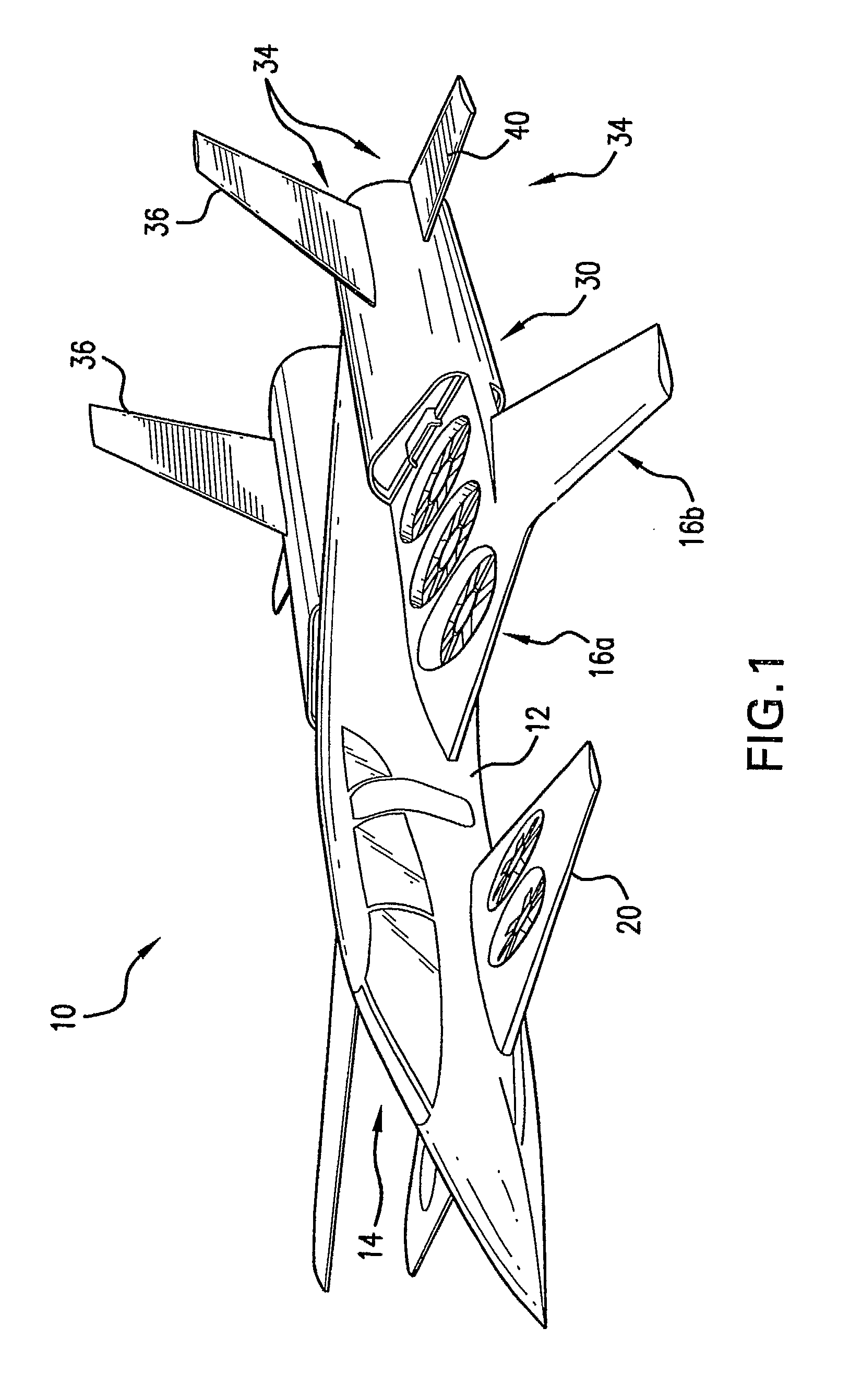
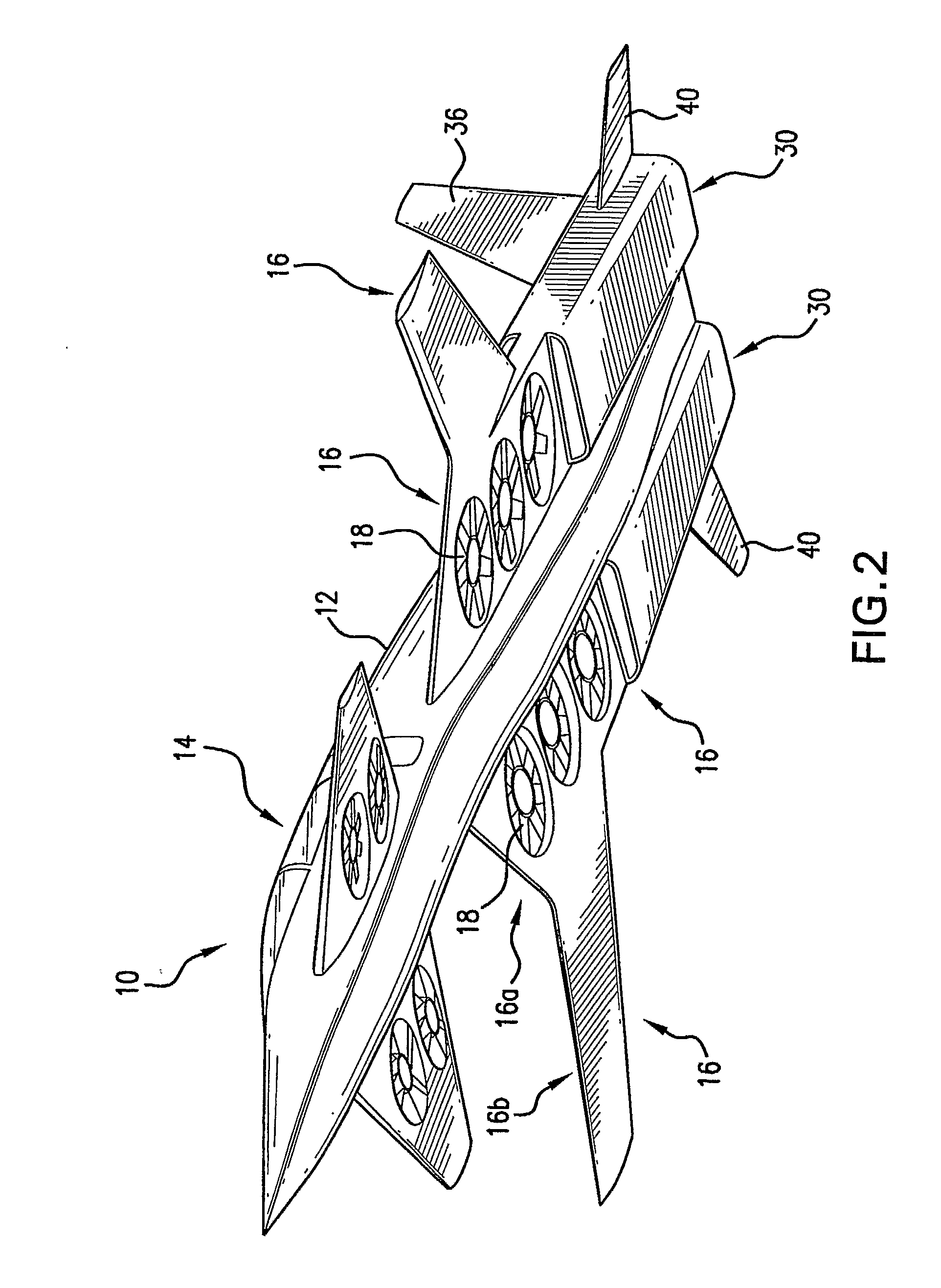
Hybrid jet/electric vtol aircraft
ActiveUS20130062455A1Improve efficiencyLess thrust capacityAircraft navigation controlEfficient propulsion technologiesJet aeroplaneElectricity
A fixed-wing VTOL aircraft features an array of electric lift fans distributed over the surface of the aircraft. A generator is (selectively) coupled to the gas turbine engine of the aircraft. During VTOL operation of the aircraft, the engine drives the generator to generate electricity to power the lifting fans. Power to the lifting fans is reduced as the aircraft gains forward speed and is increasingly supported by the wings.
Owner:SONIC BLUE AEROSPACE
Economical High Pressure Wear Resistant Cylinder That Utilizes A High Pressure Field For Strength
InactiveUS20160215774A1Easy to transportLighter and cheap materialPositive displacement pump componentsFluid removalWear resistantHydraulic fracturing
A high-pressure wear resistant cylinder that utilizes a high-pressure field for strength is an economical method of, or device for, handling very high pressures and the pumping of abrasive and corrosive fluids. The economic considerations are so favorable, that the invention may be considered a replacement part. The invention is suitable for a variety of applications, particularly a reciprocating flow work exchanger in the well stimulation or hydraulic fracturing industry. Using a high pressure field to strengthen the external surface (outside) of a pipe that is precision honed and plated or sleeved internally (inside), it is now possible to construct various high pressure machines in a relatively inexpensive manner. This invention makes it possible to use pipe with internal operating pressures greater than their nominal operating pressure ratings permit. This invention will be used in various high pressure piping and machinery applications.
Owner:TRINITY PUMPWORKS LLC
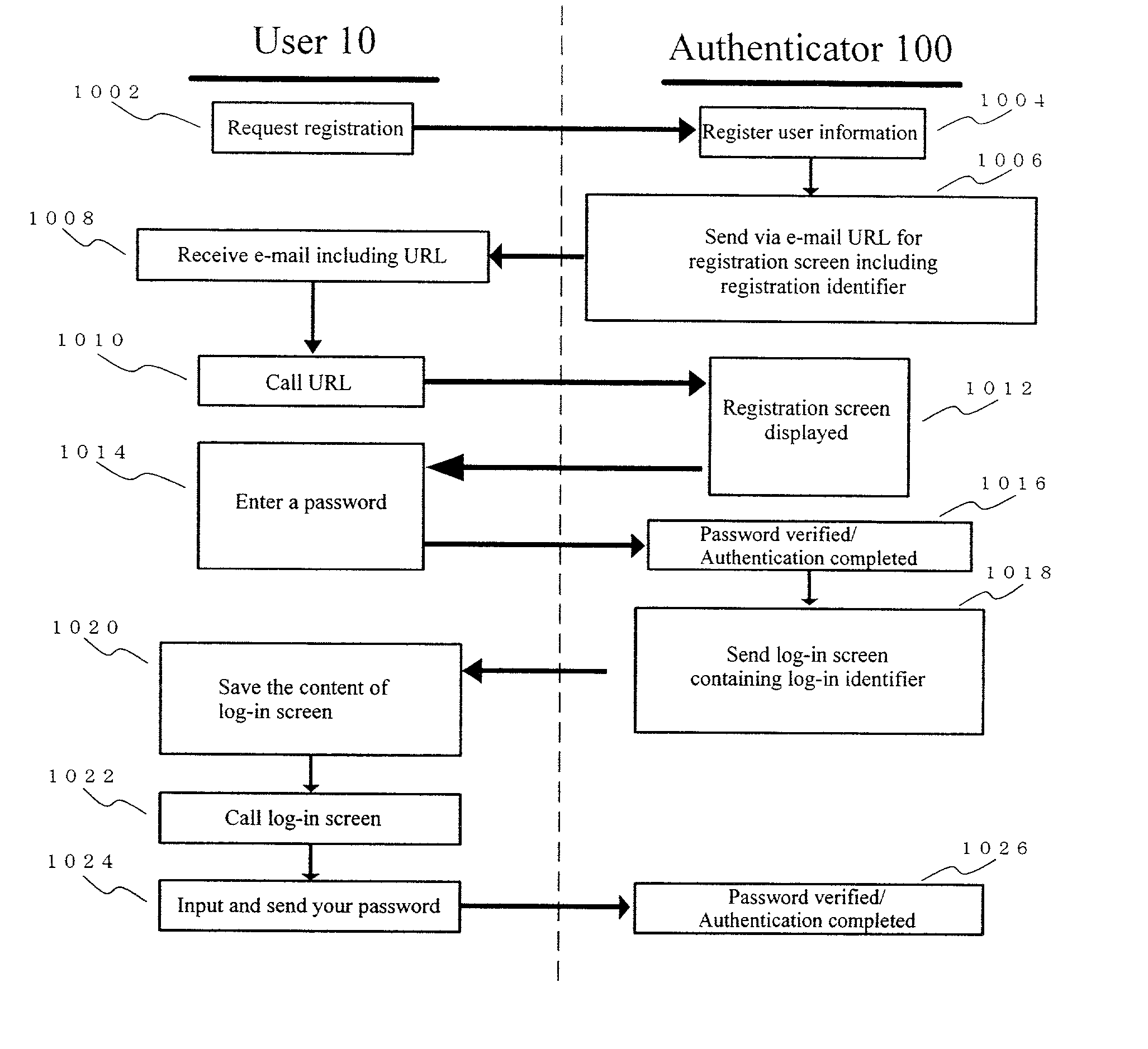
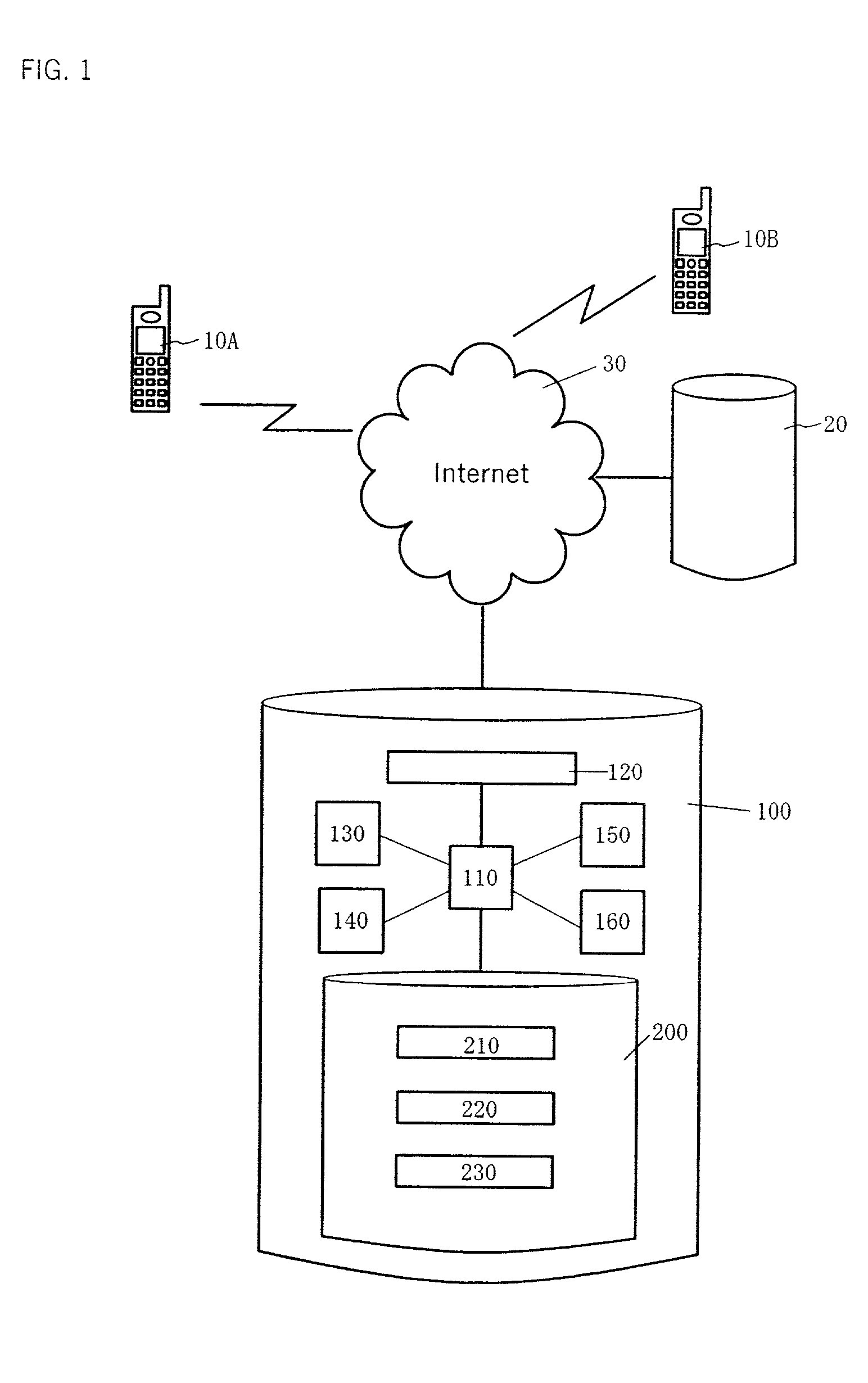
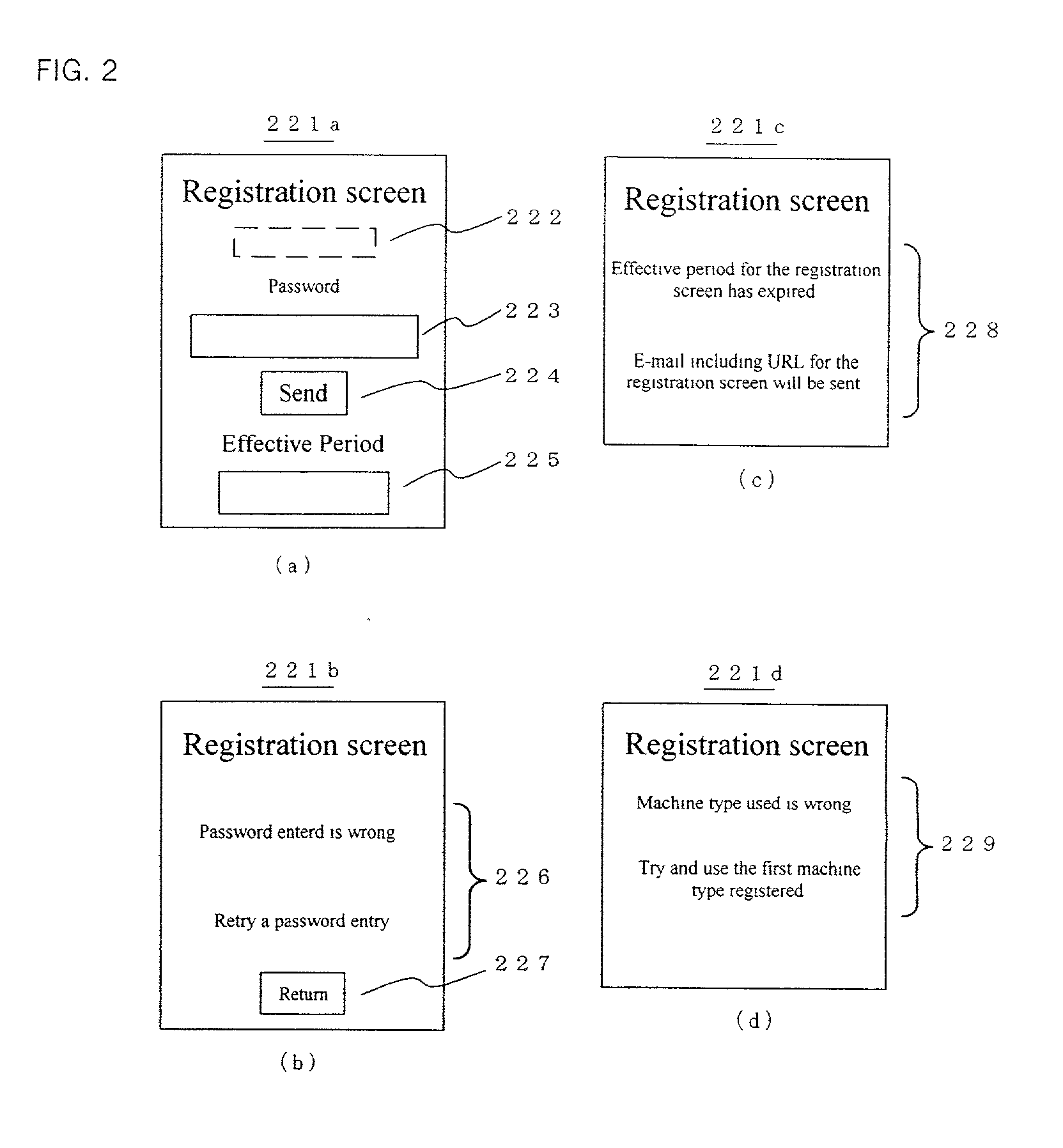
Authentication method and device
InactiveUS20020087892A1Operational securityDigital data processing detailsUser identity/authority verificationInternet privacyPassword
[PROBLEM] Person authentication and authentication device of the present invention aims at providing a user with services of easy, inexpensive, highly secure, and reliable person authentication. [MEANS TO SOLVE THE PROBLEMS]Authentication method adopted by the present invention comprises: a step that forwards to a communication device of a user a registration identifier that identifies the user and / or the communication device by including the identifier in an address of registration screen peculiar to the user and / or the communication device; and a step that, when the address is accessed, and a first password is entered and replied to the registration screen, authenticates the user based on the registration identifier and the first password; and a step that sends a login screen display to the user when the authentication step is successful, which the step is comprised of a step where the login screen display comprises a field for entering a second password, and a login identifier to identify the user and / or the communication device; and a step that authenticates the user based on the login identifier contained in the login screen display replied by the user, and the second password.
Owner:MORGAN STANLEY
Waterproof case for electronic device
InactiveUS20090032420A1Increased durabilityOperational securityOther accessoriesContainer/bottle contructionDisplay deviceEngineering
A waterproof case is provided for an electronic device having a touch panel display. The waterproof case includes an operating member for operating the touch panel display. The operating member includes: an operating portion which penetrates from the outer surface to inner surface of a wall forming the waterproof case in a watertight manner and which is disposed to be able to be pushed from the outer surface of the wall; an arm extending from a portion of the operating member, the portion being disposed inwardly from the wall, in the direction transverse to the direction in which the operating portion is pushed; and a contact portion which is provided to an end of the arm and is contacted with the touch panel display in response to the push of the operating portion.
Owner:SONY CORP
Integrated imager circuit comprising a monolithic array of single photon avalanche diodes
ActiveUS7262402B2Integrated inexpensivelyImprove good performanceOptical rangefindersSolid-state devicesSingle-photon avalanche diodeAvalanche diode
Owner:ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL)
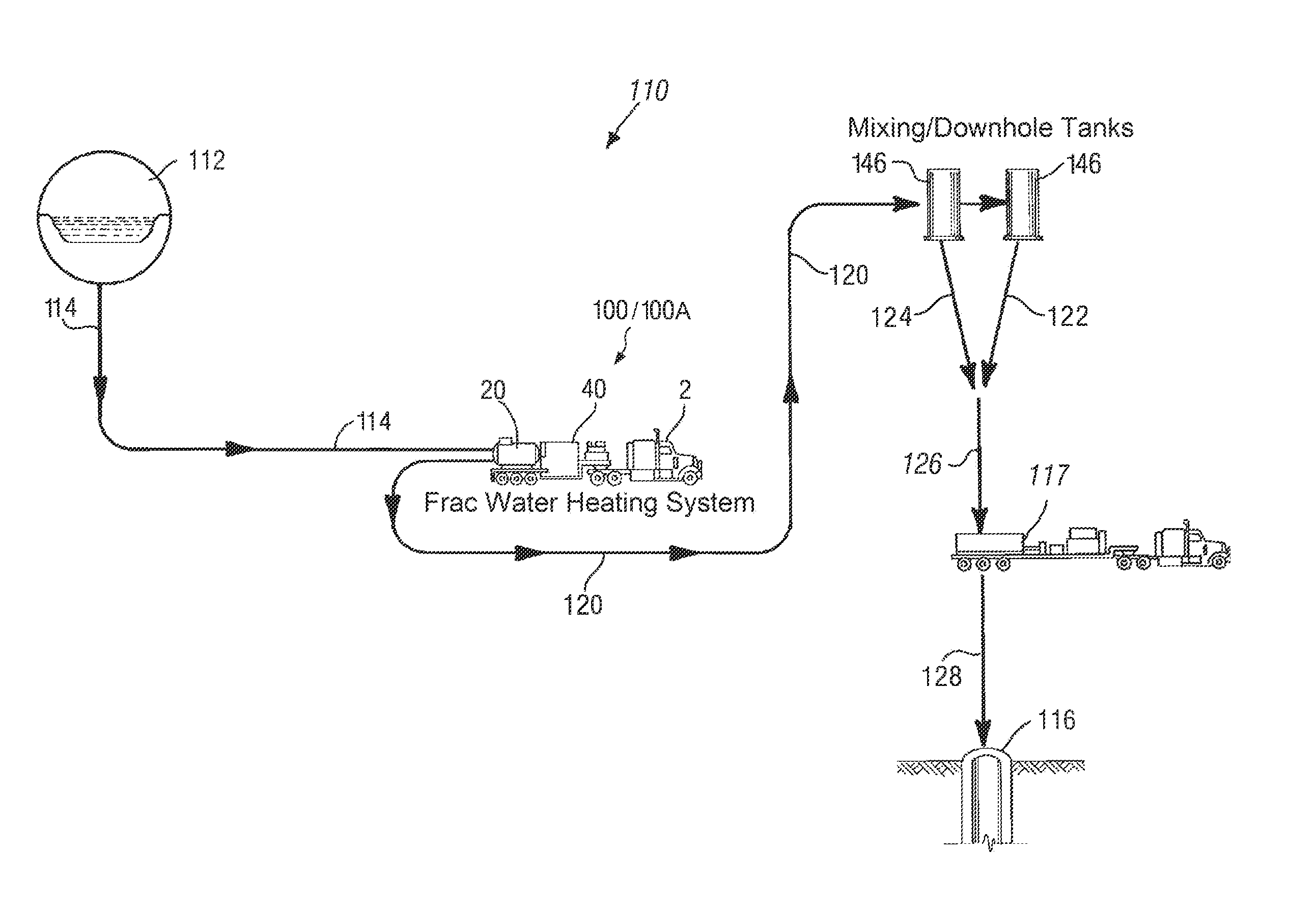
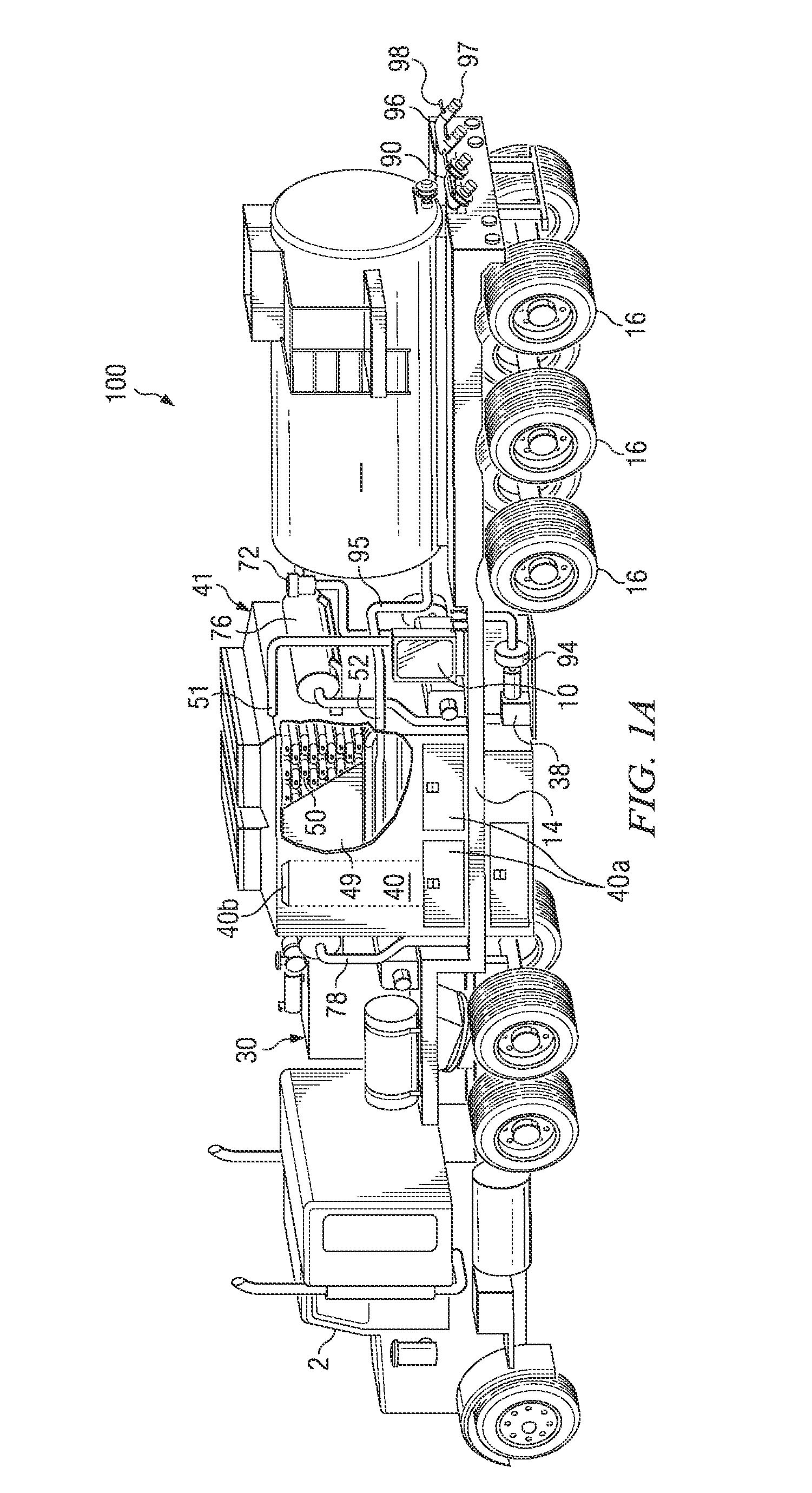
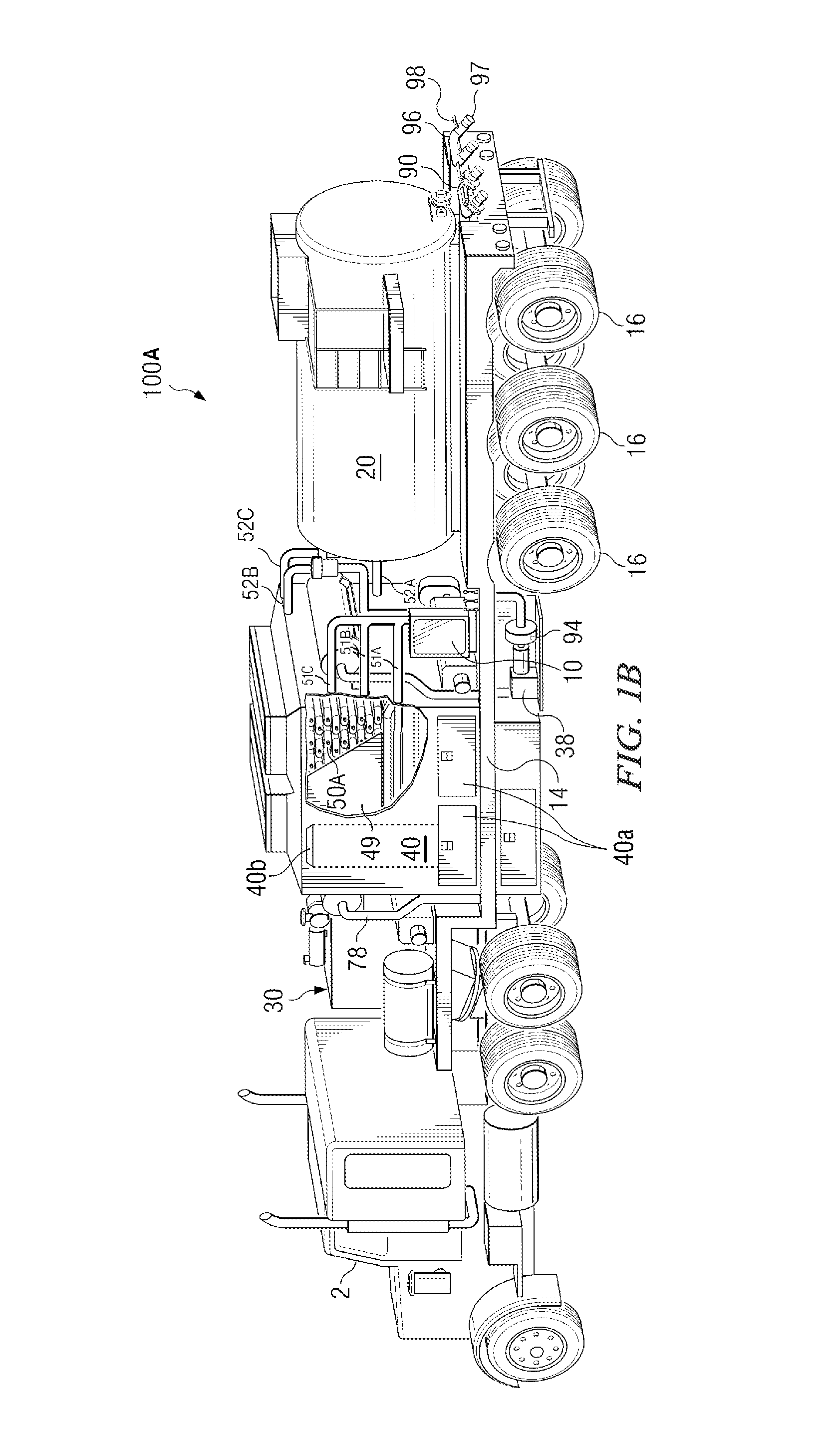
Frac water heating system and method for hydraulically fracturing a well
InactiveUS20140144641A1Safely and continuously heatingMaximize atomization and combustionInsulationFluid removalCombustion chamberFuel tank
The present invention overcomes many of the disadvantages of prior art mobile oil field heat exchange systems by providing an improved frac water heating system. The present invention is a self-contained unit which is easily transported to remote locations. In one embodiment, the present invention includes a single-pass tubular coil heat exchanger contained within a closed-bottom firebox having a forced-air combustion and cooling system. In another embodiment, the present invention includes multiple, single-pass heat exchanger units arranged in a vertically stacked configuration. The rig also includes integral fuel tanks, hydraulic and pneumatic systems for operating the rig at remote operations in all weather environments. In a preferred embodiment, the improved frac water heating system is used to heat water on-the-fly (i.e., directly from the supply source to the well head) to complete hydraulic fracturing operations. The present invention also includes systems for regulating and adjusting the fuel / air mixture within the firebox to maximize the combustion efficiency. The system includes a novel hood opening mechanism attached to the exhaust stack of the firebox.
Owner:CHANDLER RONALD L
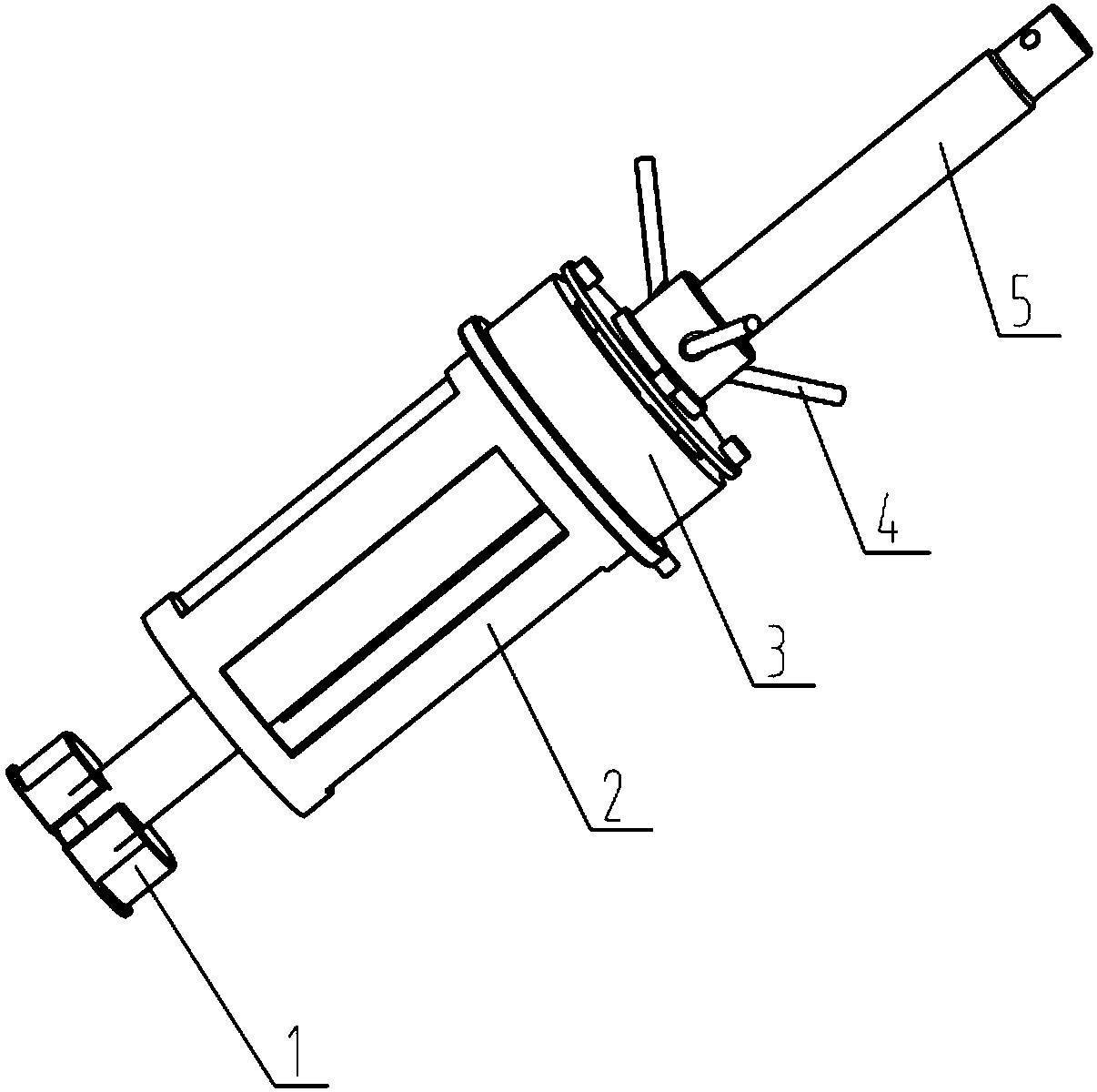
Thin-wall sliding sleeve disassembling fixture
PendingCN108555826AEasy loadingGuaranteed fitMetal-working hand toolsEngineeringMechanical engineering
The invention provides a thin-wall sliding sleeve disassembling fixture. The thin-wall sliding sleeve disassembling fixture comprises a puller nut and a puller screw. The puller screw is in threaded connection with the puller nut. One end of the puller screw is provided with a clamping jaw. The puller screw is in threaded connection with the clamping jaw. A bracket and a hydraulic system are installed between the puller nut and the clamping jaw. The bracket and the hydraulic system are sheathed on the puller screw. The bracket is adjacent to the clamping jaw. The hydraulic system is adjacent to the puller nut. Through controlling the hydraulic system to boost pressure and reduce pressure, the disassembly of a thin-wall sliding sleeve can be realized. The thin-wall sliding sleeve disassembling fixture is small in volume, light in weight, smooth and steady in movement, and safe and convenient in operation, and capable of preventing the deformation of the thin-wall sliding sleeve and thescratching of a hole wall in an disassembling process.
Owner:YANTAI JEREH PETROLEUM EQUIP & TECH CO LTD
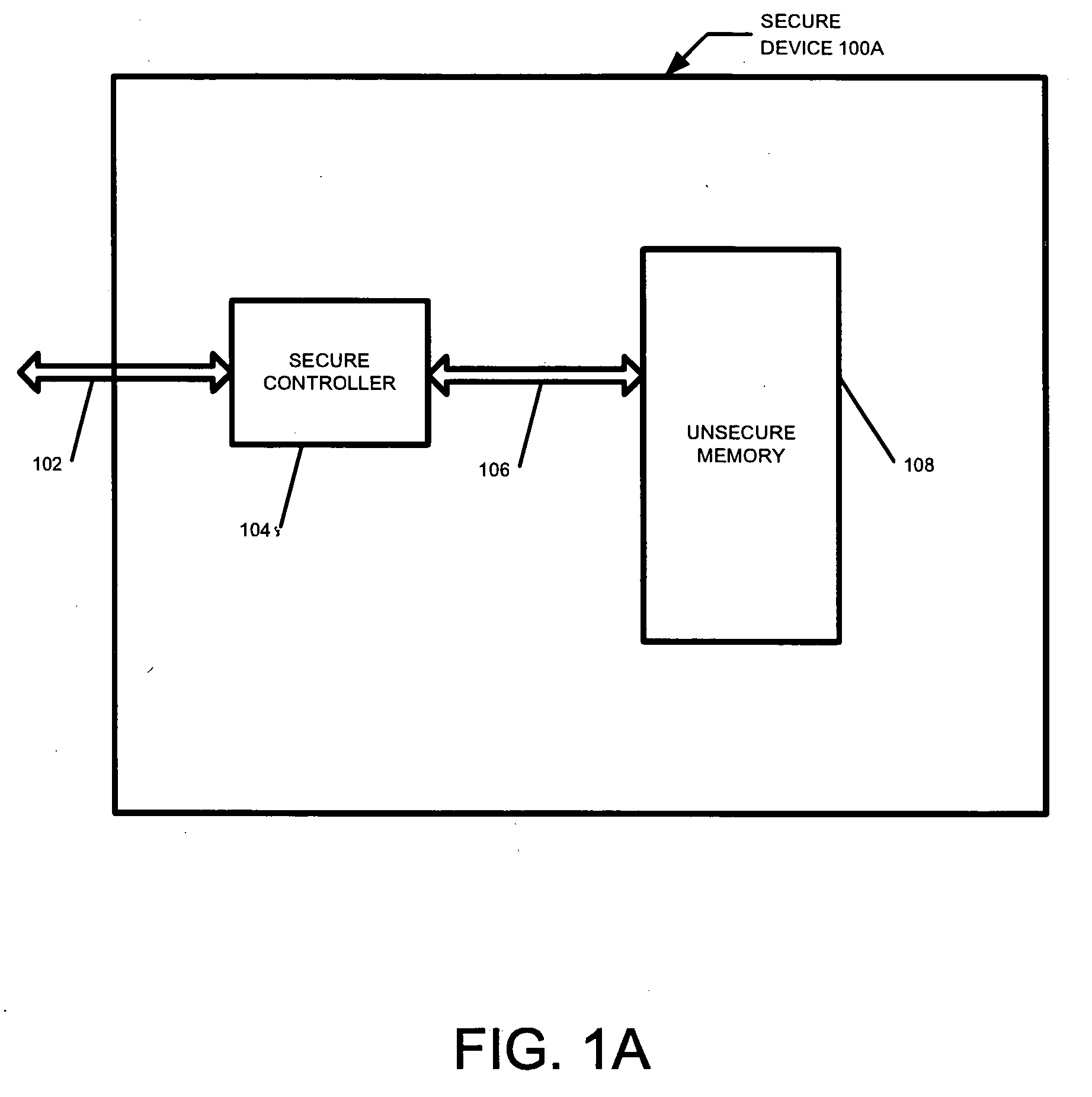
Methods used in a secure yet flexible system architecture for secure devices with flash mass storage memory
InactiveUS20070061581A1Operational securityImprove security levelMemory architecture accessing/allocationUser identity/authority verificationMass storageCopying
A device with mass storage capability that uses a readily available non secure memory for the mass storage but has firmware (and hardware) that provides security against unauthorized copying of data. This is true even though the firmware itself is stored in the non secure mass storage memory, and therefore potentially vulnerable to hacking. An indication of the authenticity of the firmware must be present before it will be executed by the device. This protects the device contents from unauthorized duplication or tampering. Additional functionality can be added to the device with additional firmware applications, and the authenticity of those additional applications will also be verified before they will be executed. This further prevents unauthorized copying or tampering of secure content through any mechanisms that may be unscrupulously introduced. Any data within the mass storage memory may also be encrypted.
Owner:SANDISK TECH LLC +1
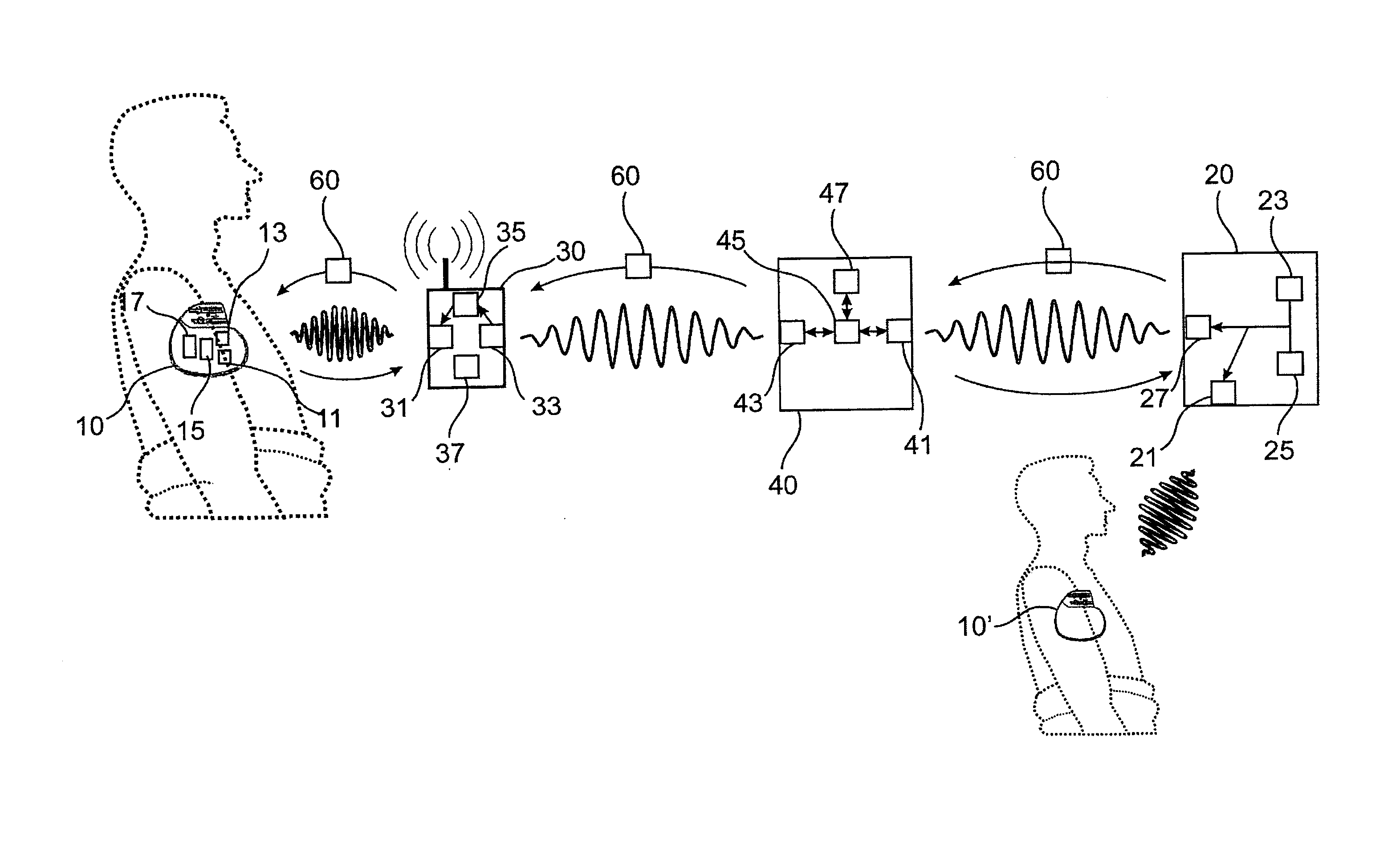
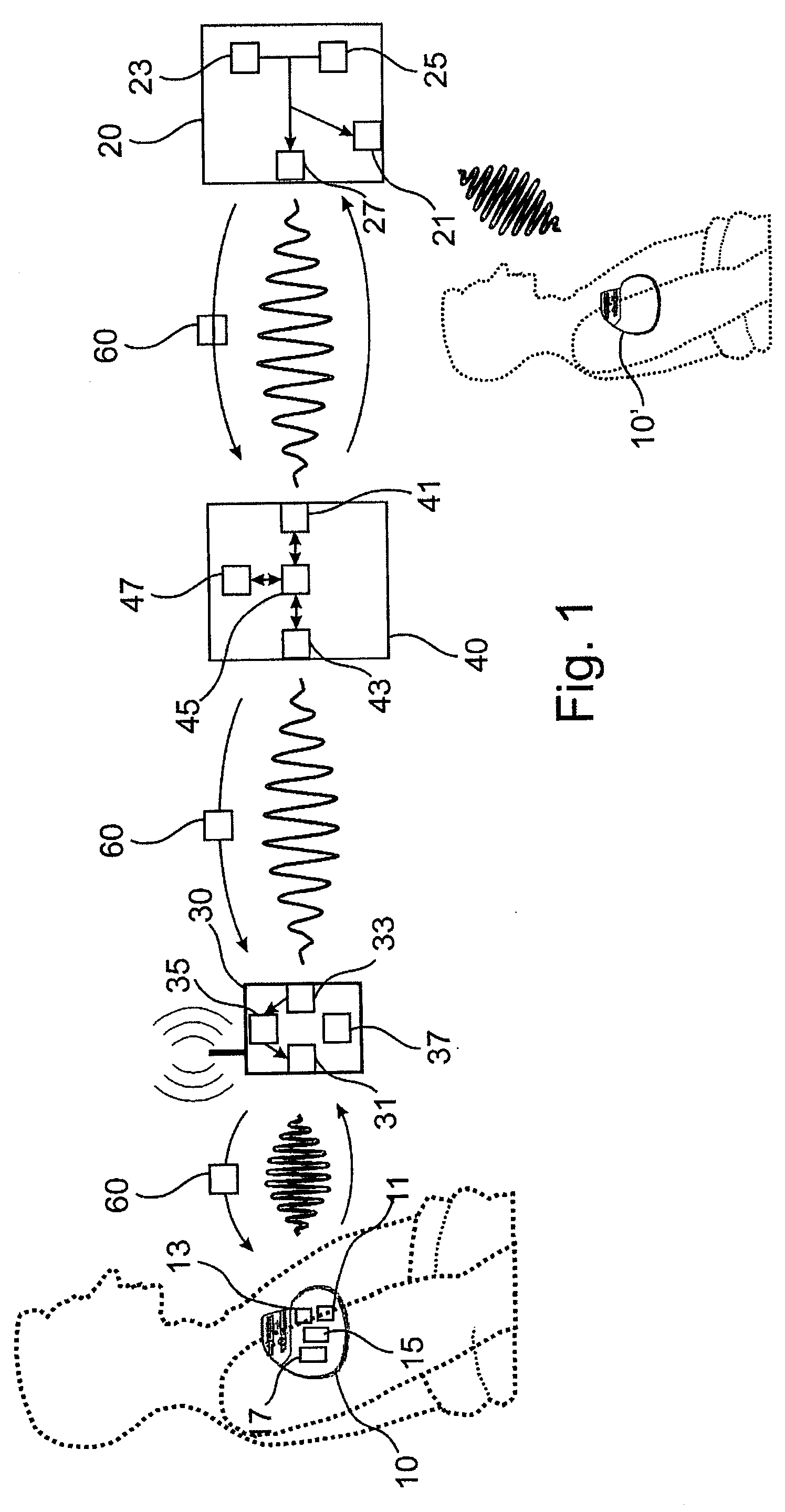
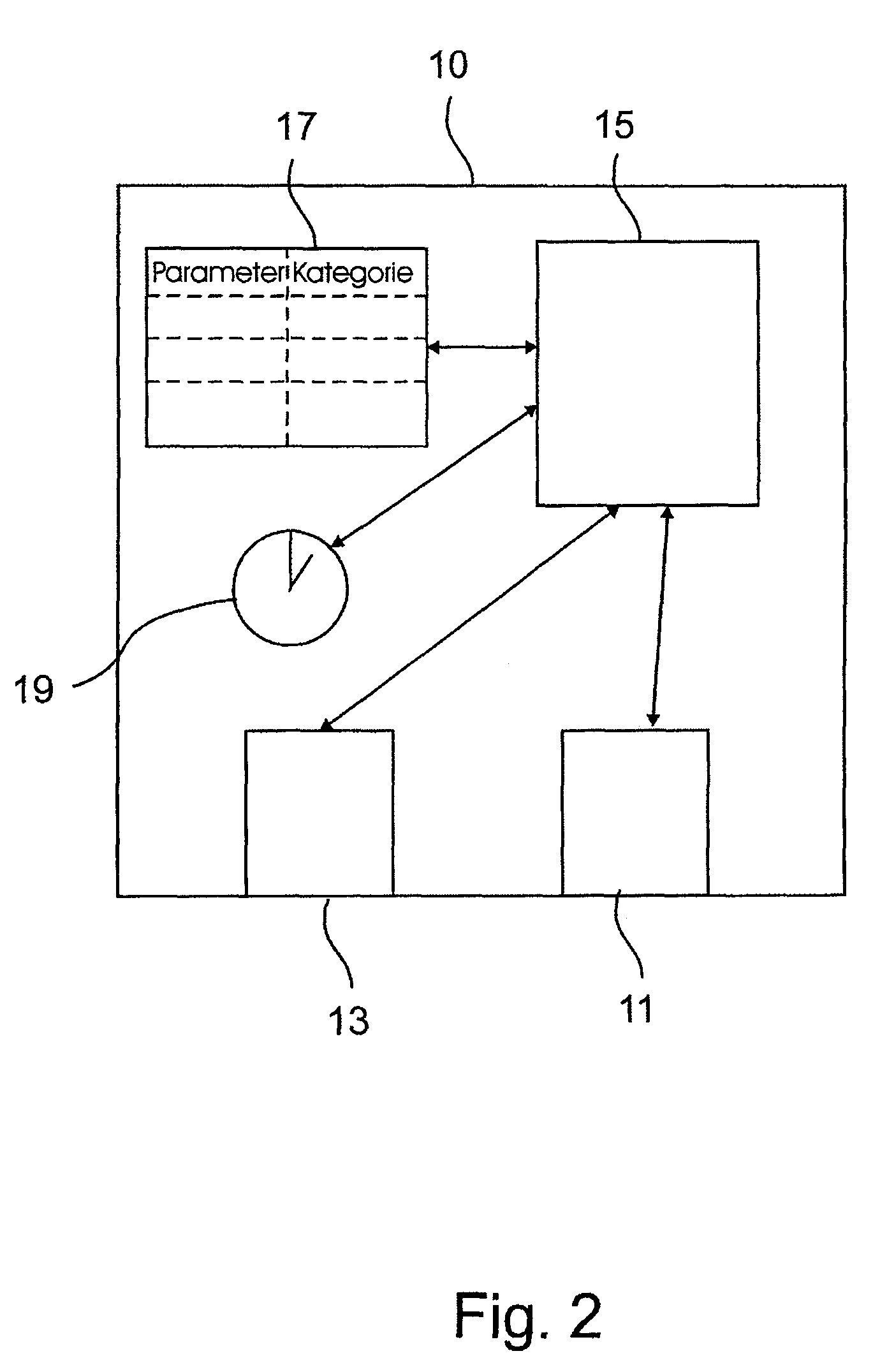
Method for secure reprogramming of clinically relevant parameters as part of remote programming of an electronic implant
The invention relates to a remotely programmable personal medical device, in particular a programmable implantable medical device, e.g., a cardiac pacemaker, a defibrillator, a cardioverter or the like. In addition, the invention relates to an arrangement for remote programming of such a personal medical device and a method for remote programming of a programmable personal medical device.
Owner:BIOTRONIK SE & CO KG
Registry verification for a mechanized store using radio frequency tags
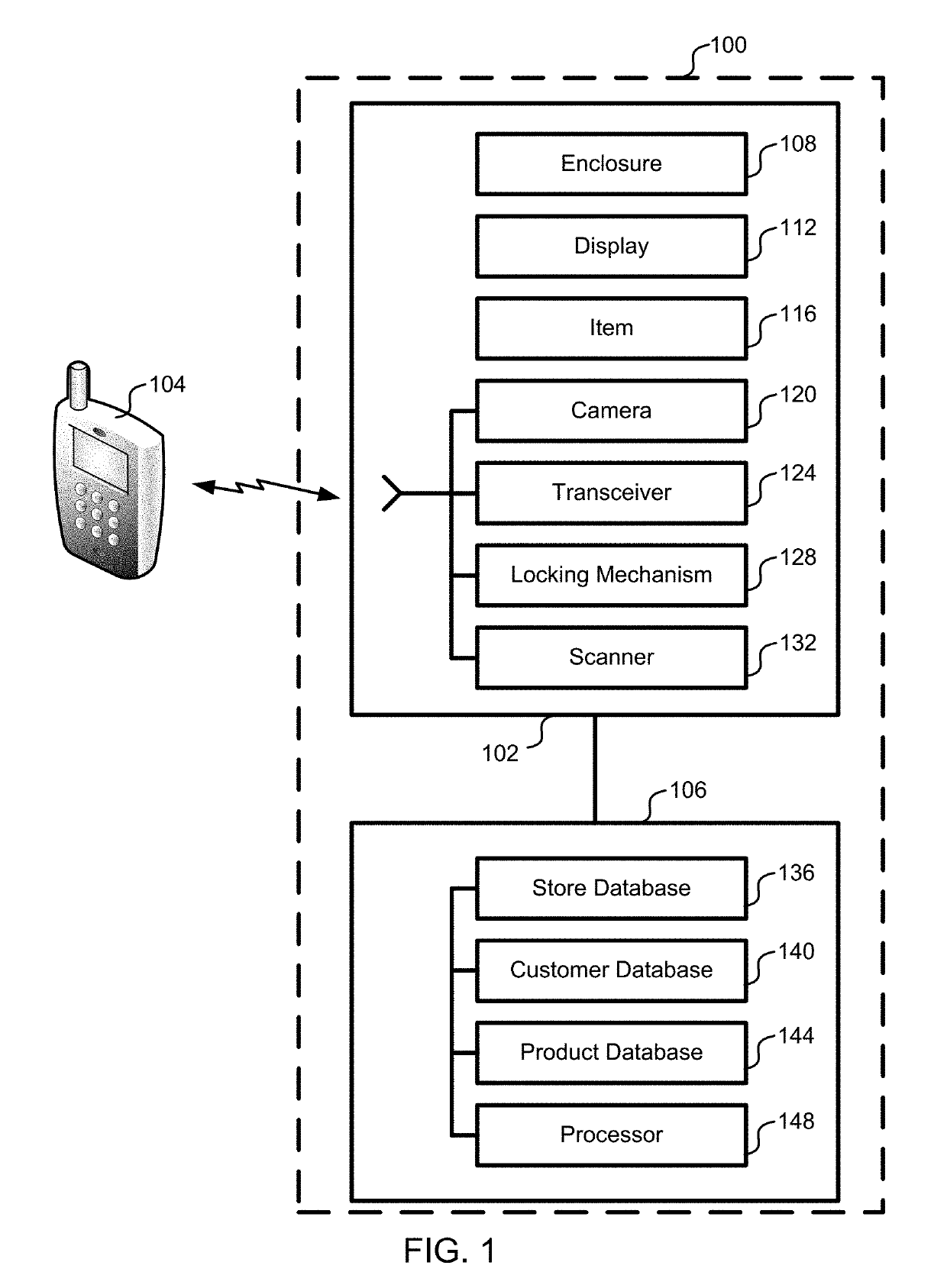
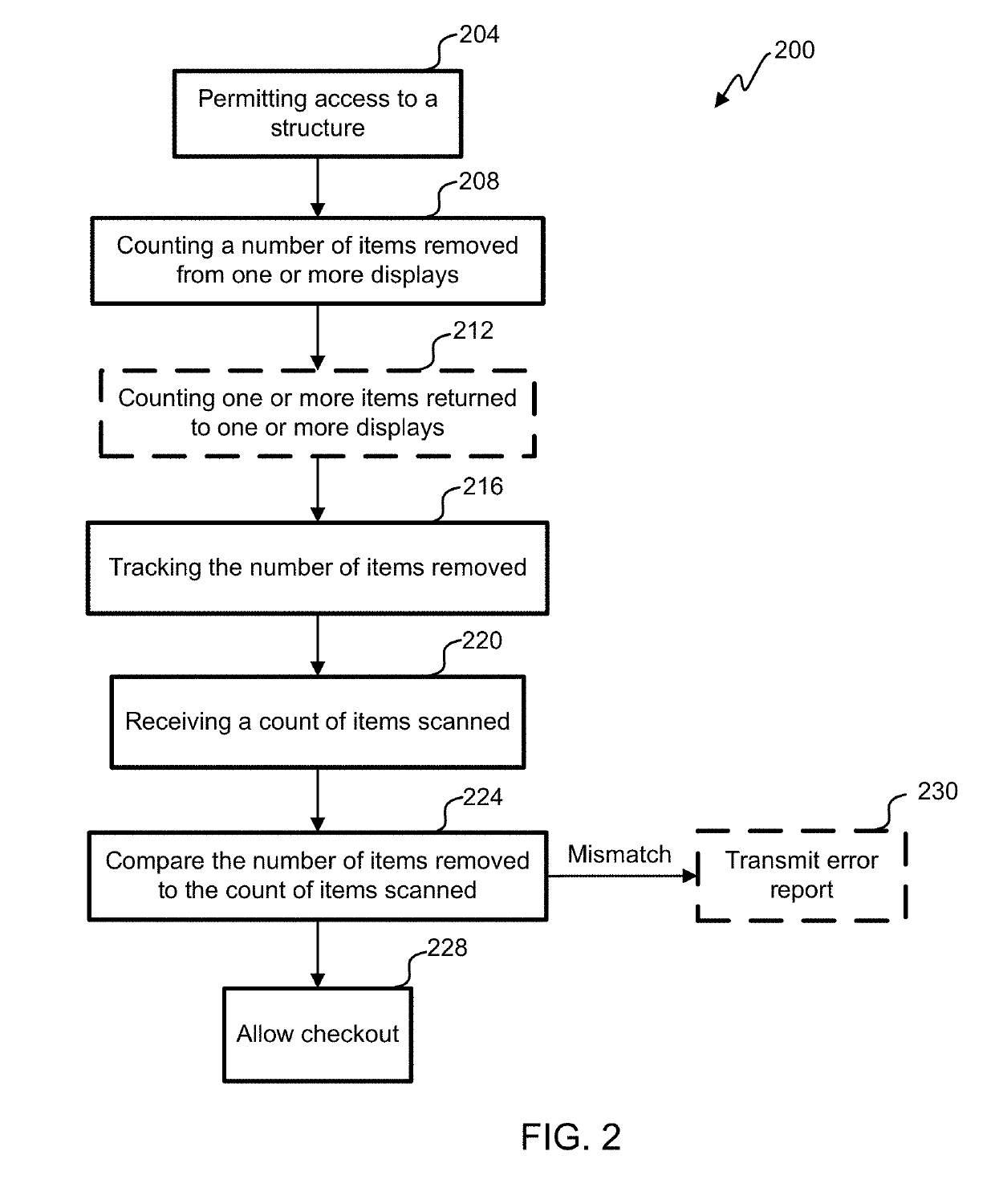
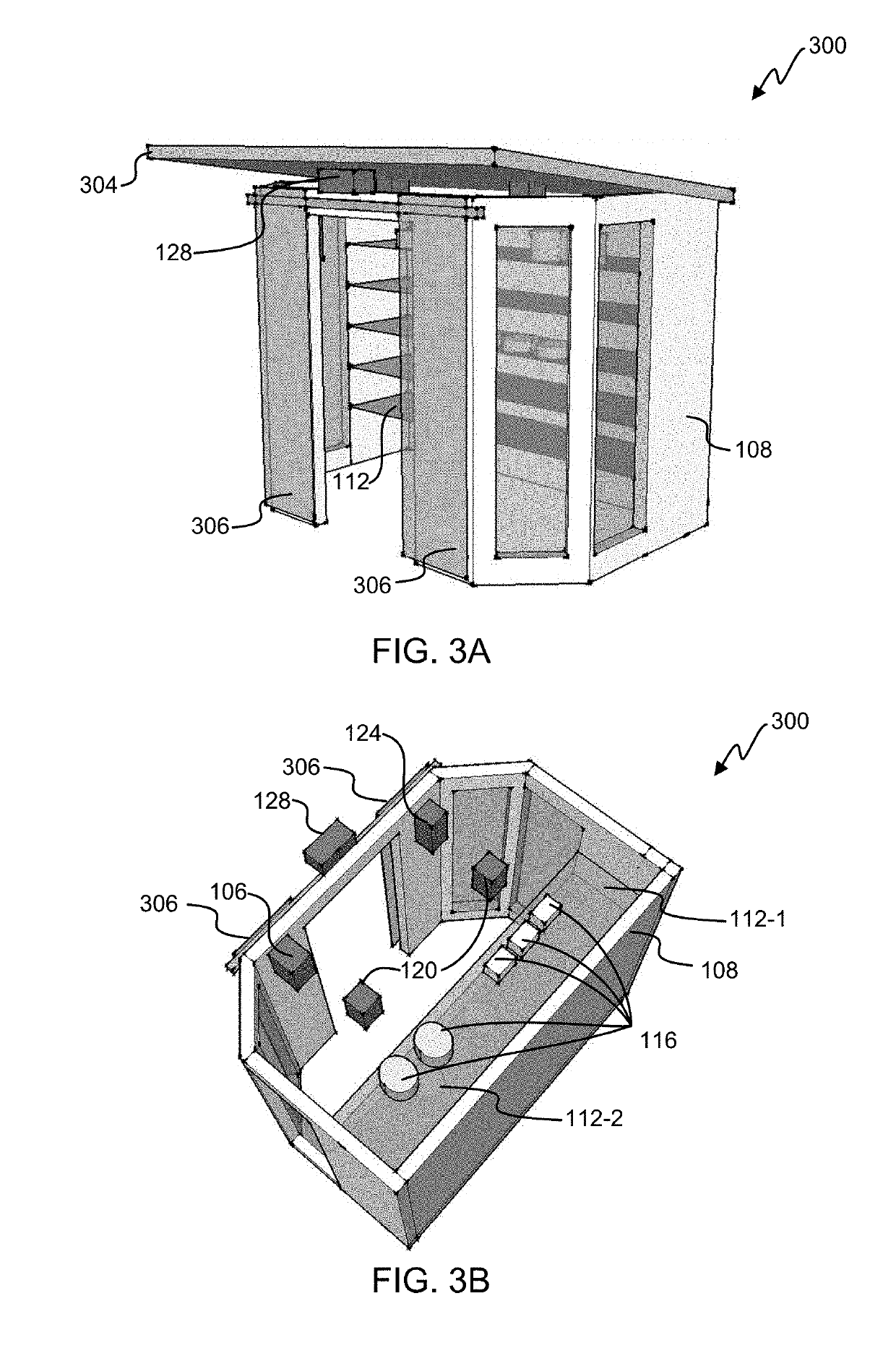
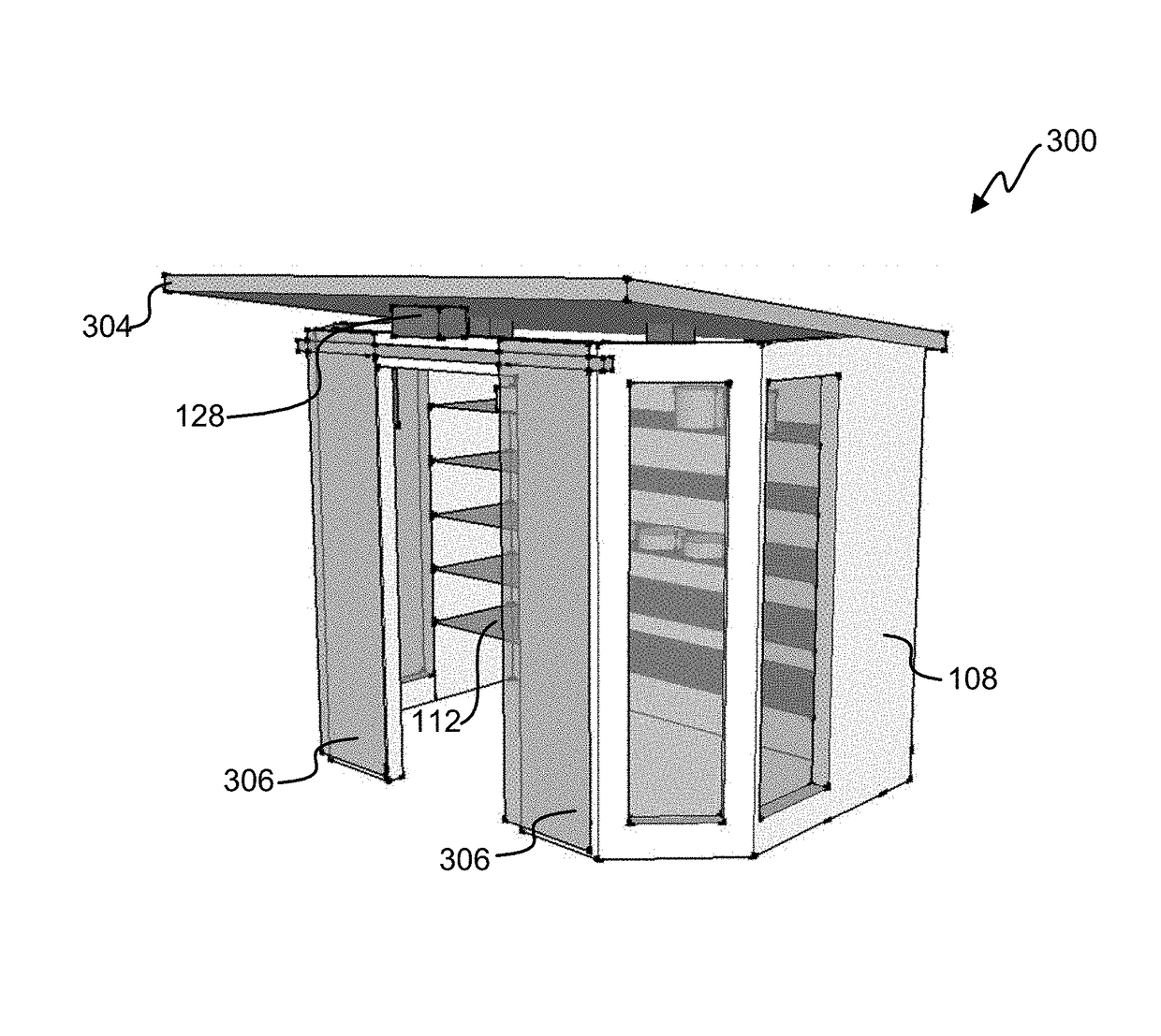
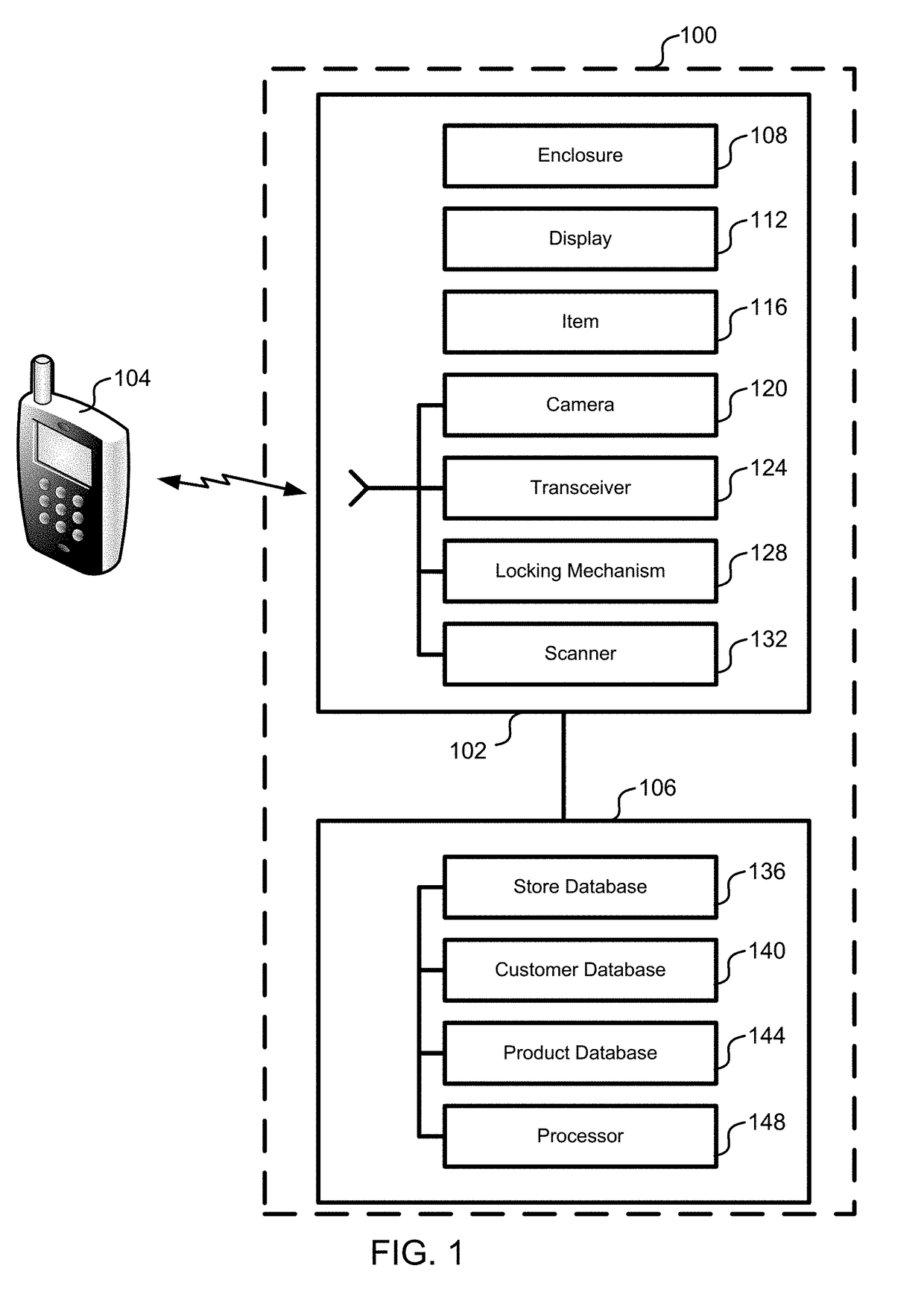
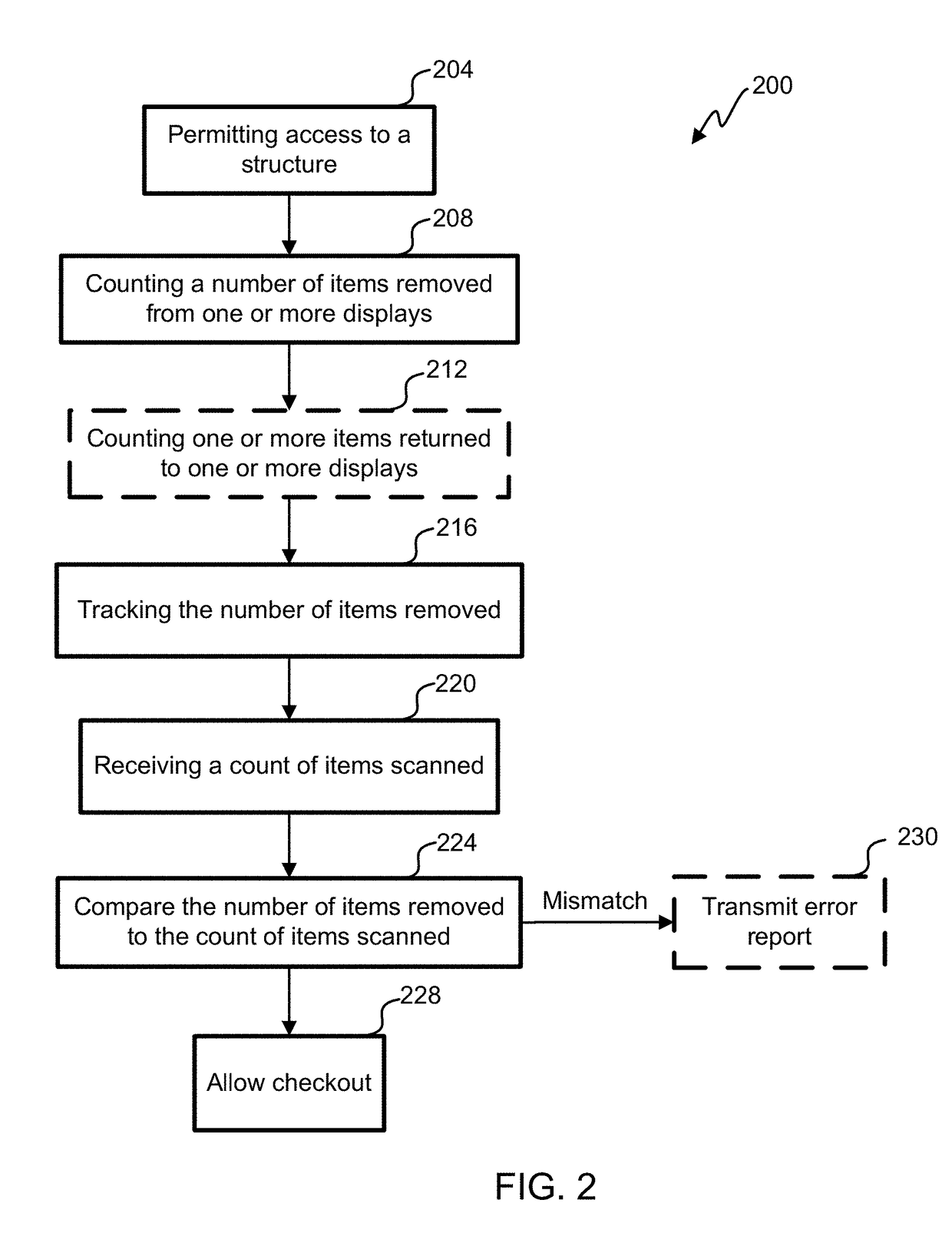
ActiveUS20190147709A1Reduce shop liftingReduce theftCash registersPayment architectureRadio frequencyComputer science
Registry verification is used in a mechanized store. A camera is used to count a first number of items taken by a user. Radio frequency tags are used to determine a second number of items. The first number of items is compared to the second number of items to reduce a likelihood of errors.
Owner:STANDARD COGNITION CORP
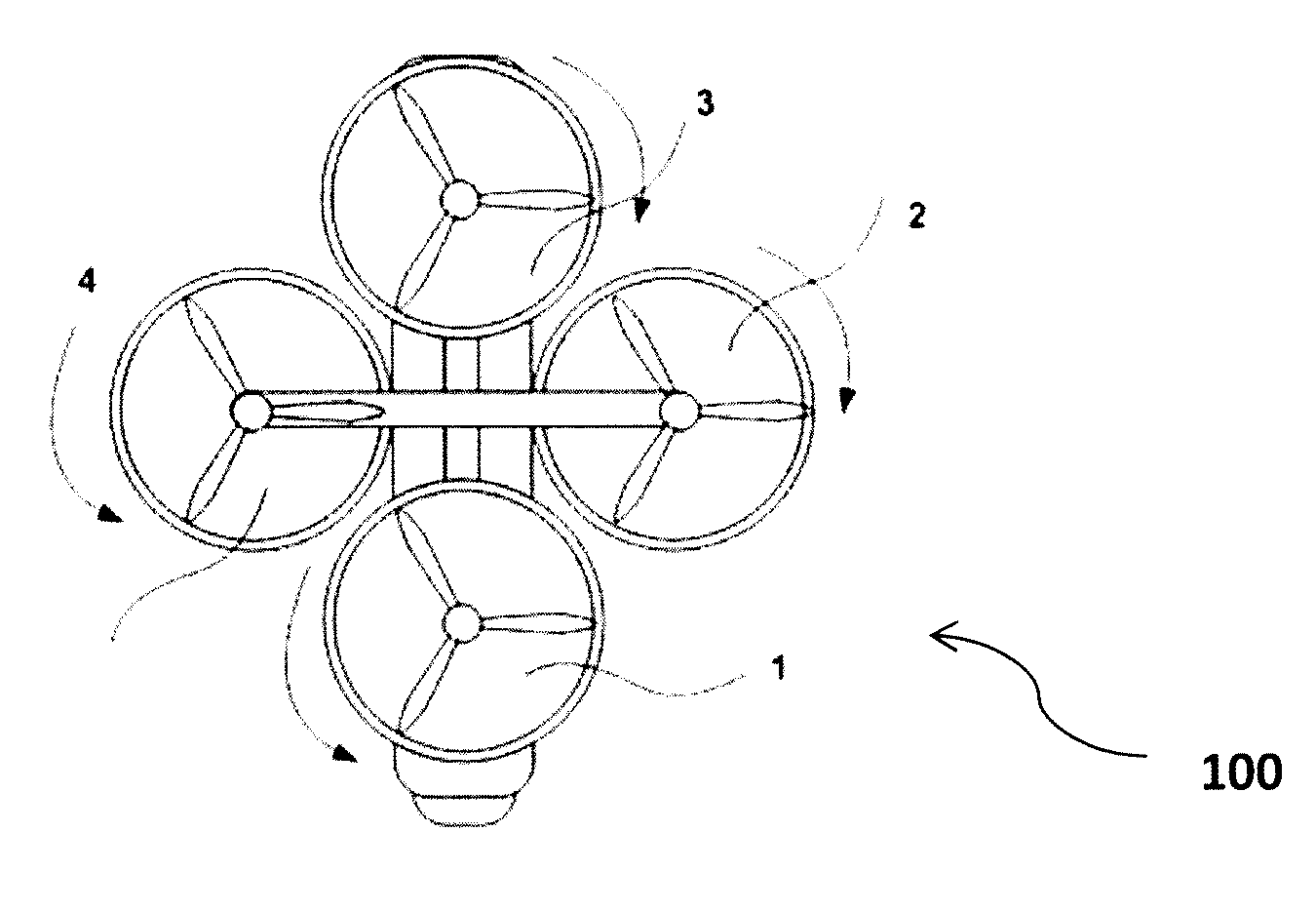
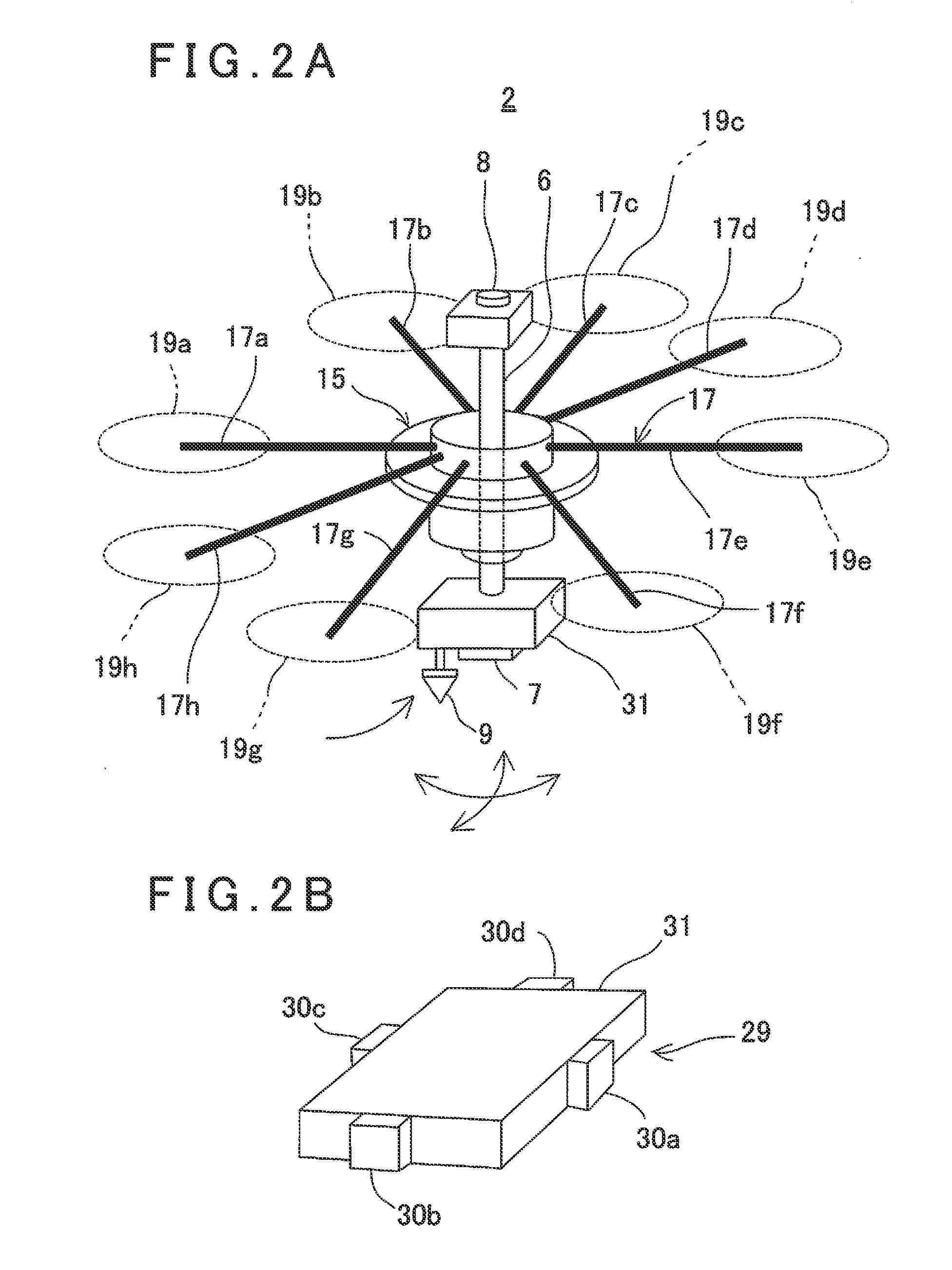
System and method for control of quadrotor air vehicles with tiltable rotors
InactiveUS20160023755A1Safe operationImprove controlPropellersUnmanned aerial vehiclesFlight vehiclePropeller
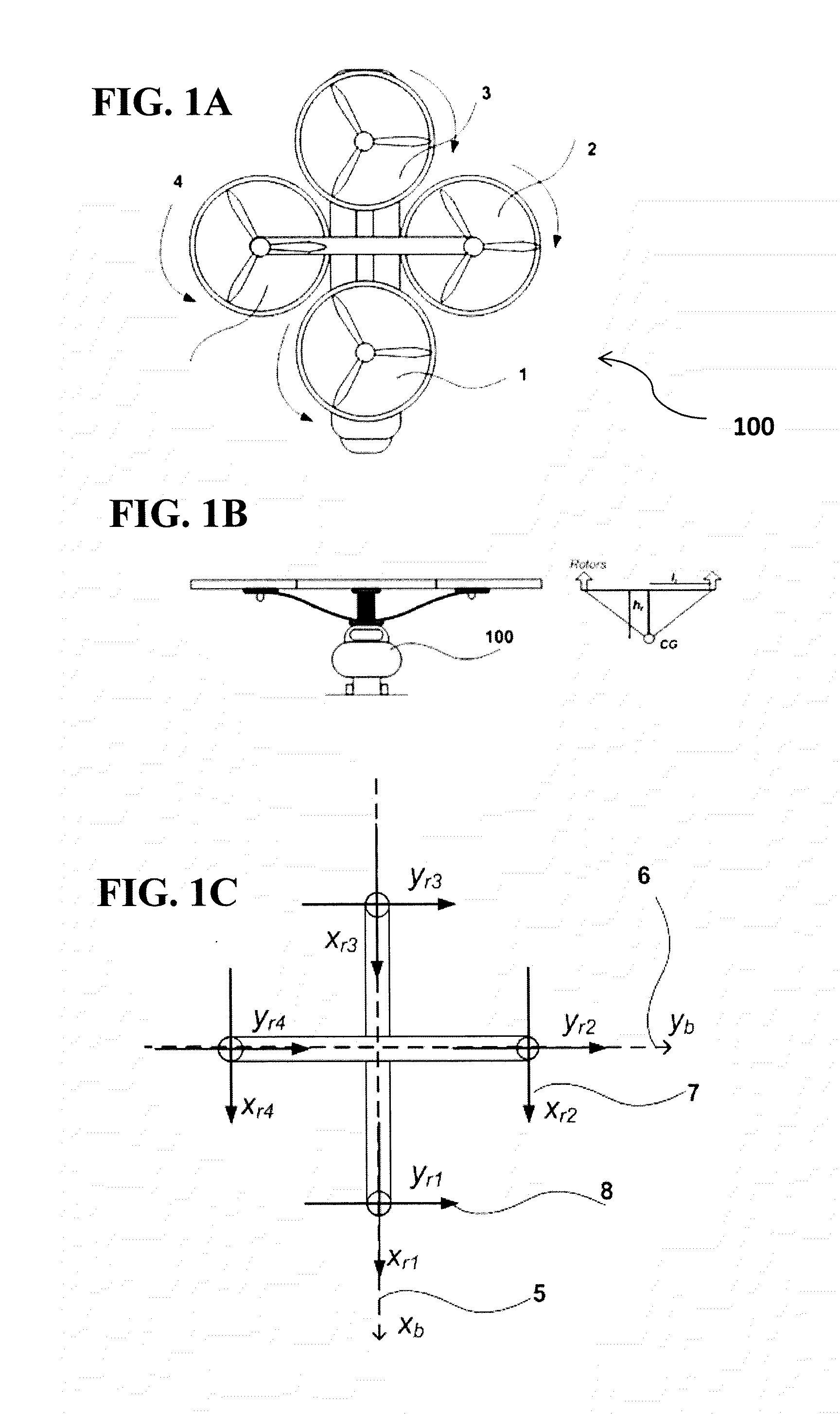
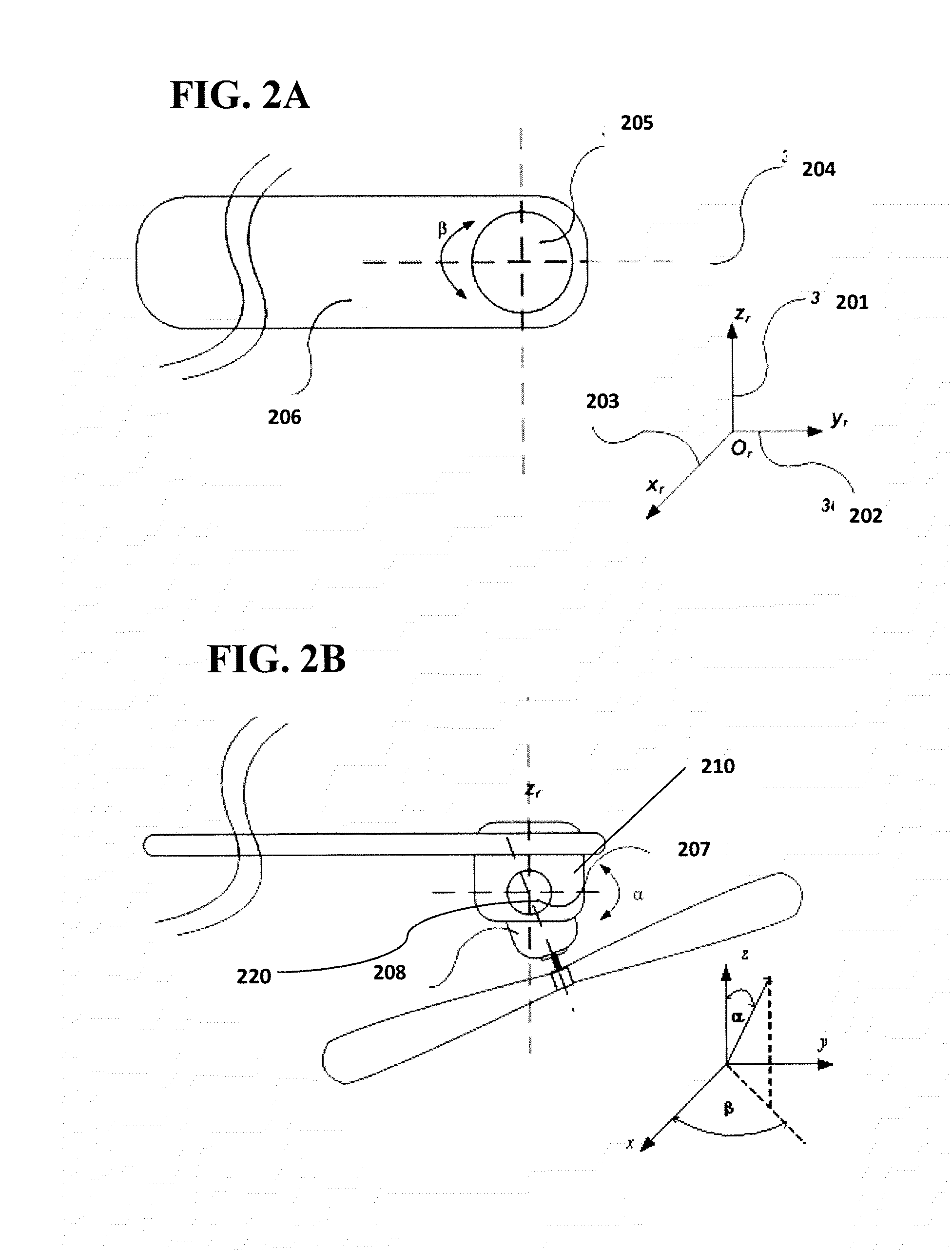
A system and method of controlling quadrotor air vehicles (QRAV) that may include an additional two degrees of freedom for each of the four propellers of the QRAV. Each of the four rotors may be allowed to rotate (tilt) around two local axes selected from the x-axis (roll), y-axis (pitch), and z-axis (yaw). Control of the quadrotor including the additional two degrees of freedom allows thrust of each rotor to be direct in any direction of a semi-sphere. As a result, total control inputs of the QRAV may be increased to twelve, enabling smooth control to achieve superior and precise maneuverability. Additionally, the system and method is fault tolerant and capable of handling failures of any of the rotors. Commands to the propellers may be fully decoupled and achieved independently thereby giving pilots better control to execute difficult maneuvers.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
Wireless local area network context control protocol
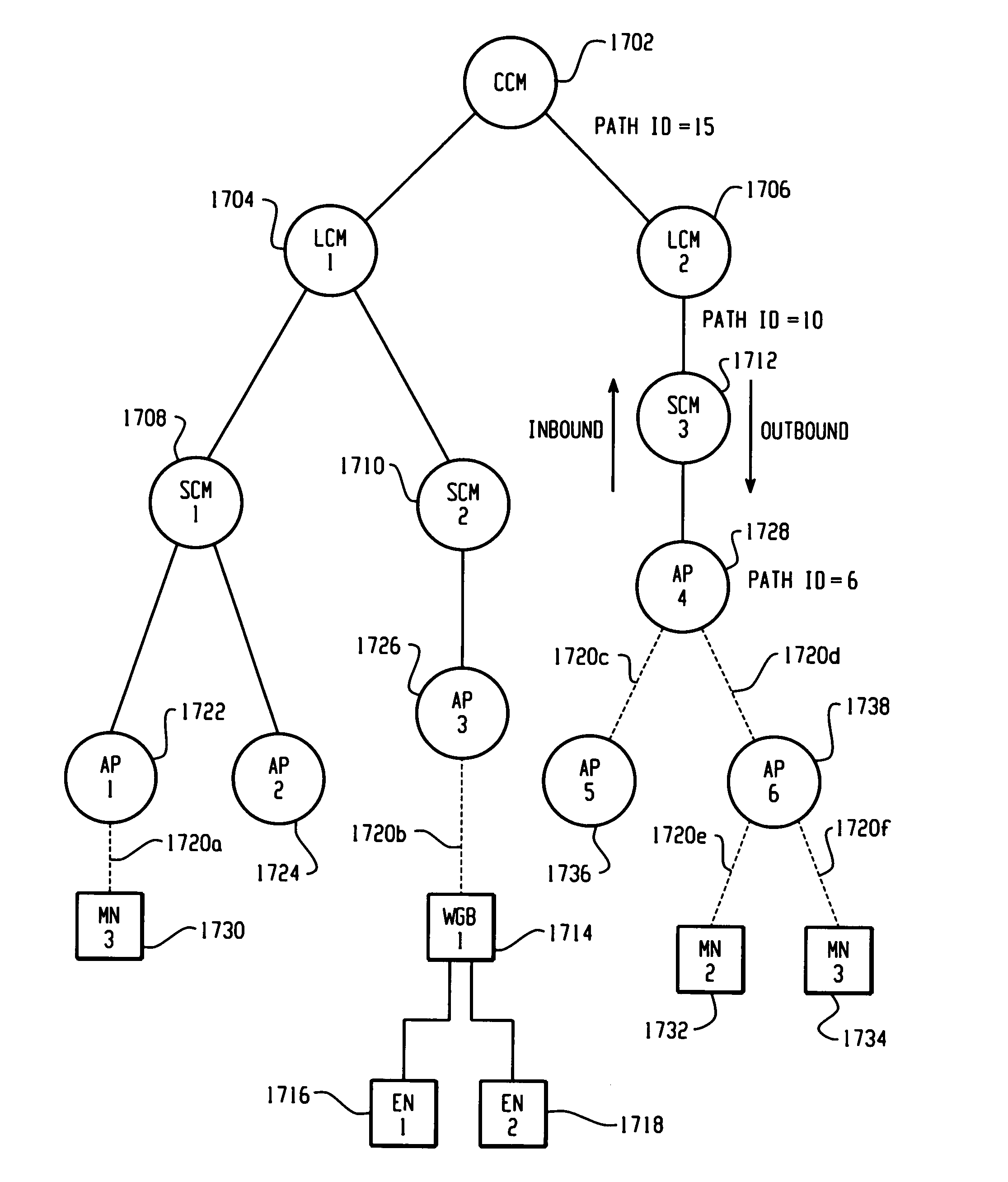
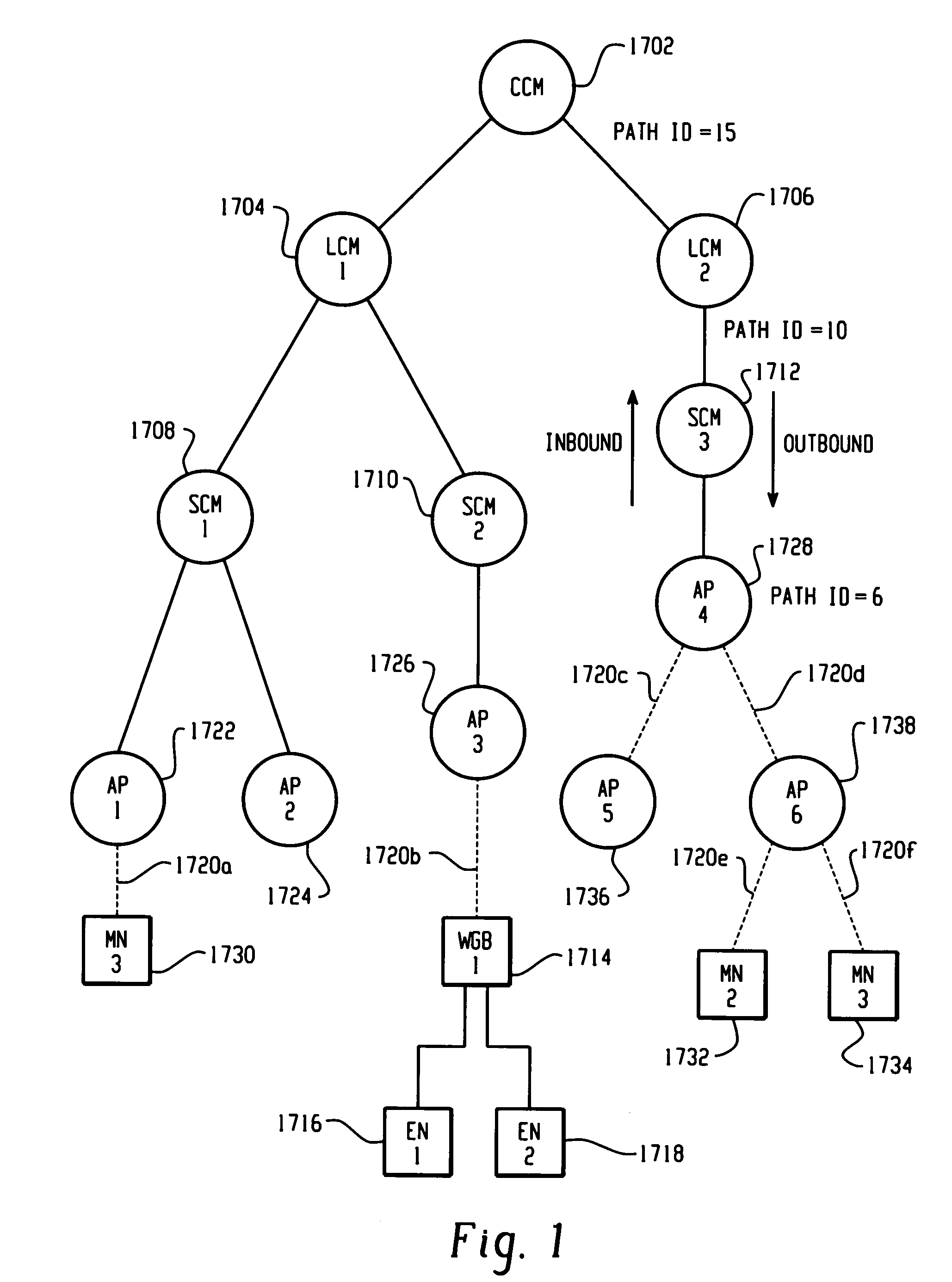
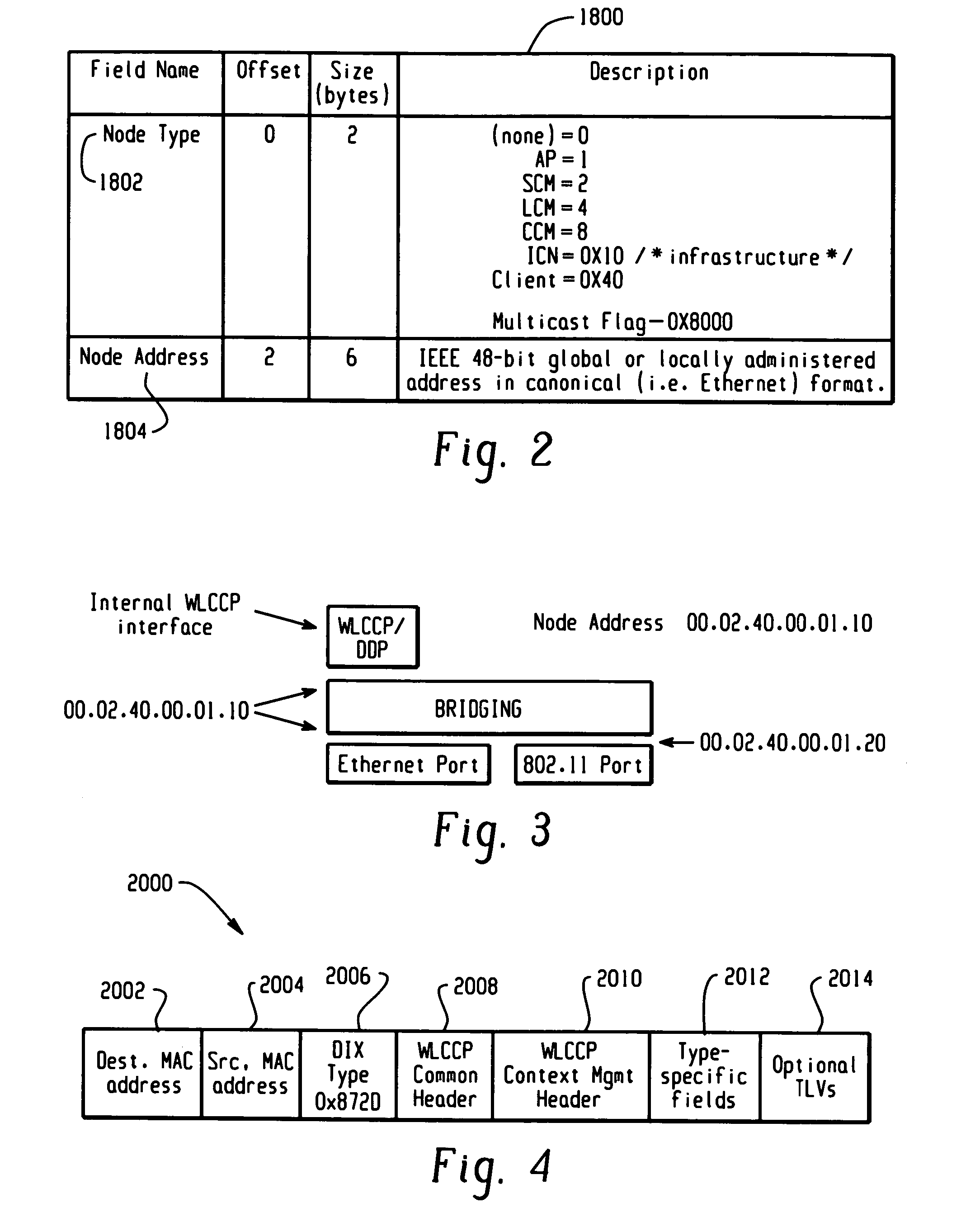
ActiveUS20050220054A1Easy to optimizeOperational securityNetwork topologiesDigital computer detailsPathPingMobile station
A Wireless LAN Context Control Protocol (WLCCP) is used to establish and manage a wireless network topology and securely manages the “operational context” for mobile stations in a campus network. The WLCCP registration protocol can automatically create and delete links in the network, securely distribute operational context, and reliably establish Layer 2 forwarding paths on wireless links. A single infrastructure node is established as the central control point for each subnet, and enables APs and MNs to select the parent node that provides the “least-cost path” to a backbone LAN. Context messages provide a general-purpose transport for context and management information. WLCCP “Trace” messages facilitate network diagnostic tools. Ethernet or UDP / IP encapsulation can be used for WLCCP messages. Ethernet encapsulation is employed for intra-subnet (e.g. AP-to-AP or AP-to-SCM) WLCCP messages. IP encapsulation is used for inter-subnet WLCCP messages and may also be used for intra-subnet WLCCP messages.
Owner:CISCO TECH INC
Facial-recognition vehicle security system
InactiveUS7602947B1Prevent theftEasily defeatedAnti-theft devicesCharacter and pattern recognitionDriver/operatorControl signal
A movable-vehicle security system includes a facial-recognition system including a scanner such as a television or infrared camera directed at the face of a person in the driver's seat, which system produces output control signals that are applied to enable or disable operation of the vehicle, with or without a key or other supplemental security system. In a particular embodiment, the system includes a camera mounted on the “third taillight” assembly (which is preferably mounted below the roof and inside the rear window), directed at the rear-view mirror, and coupled to a facial-recognition computer, which in turn is coupled (with appropriate security precautions) to an enabling element for the vehicle, such as a starter motor. In a further embodiment, the system can be coupled to various elements of the motive system to create an auto-starting car.
Owner:LEMELSON JEROME H +1
Registry verification for a mechanized store
ActiveUS9886827B2Difficult to manageTime period is limitedCharacter and pattern recognitionCash registersComputer scienceOperating system
Registry verification is used in a mechanized store. A camera is used to count a first number of items taken by a user. The items are scanned to determine a second number of items. The first number of items is compared to the second number of items to reduce a likelihood of errors.
Owner:STANDARD COGNITION CORP
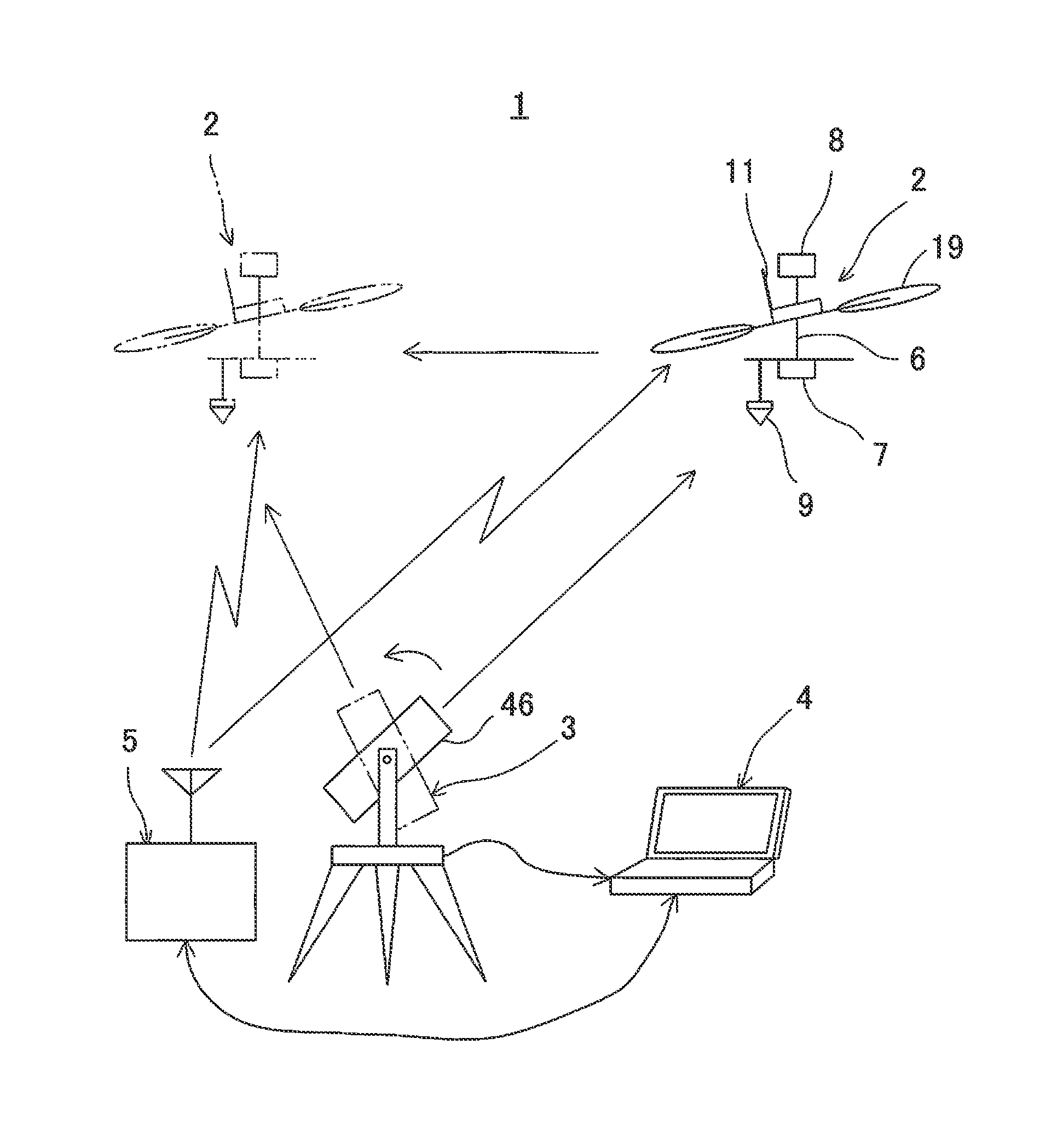
Flying Vehicle Guiding System And Flying Vehicle Guiding Method
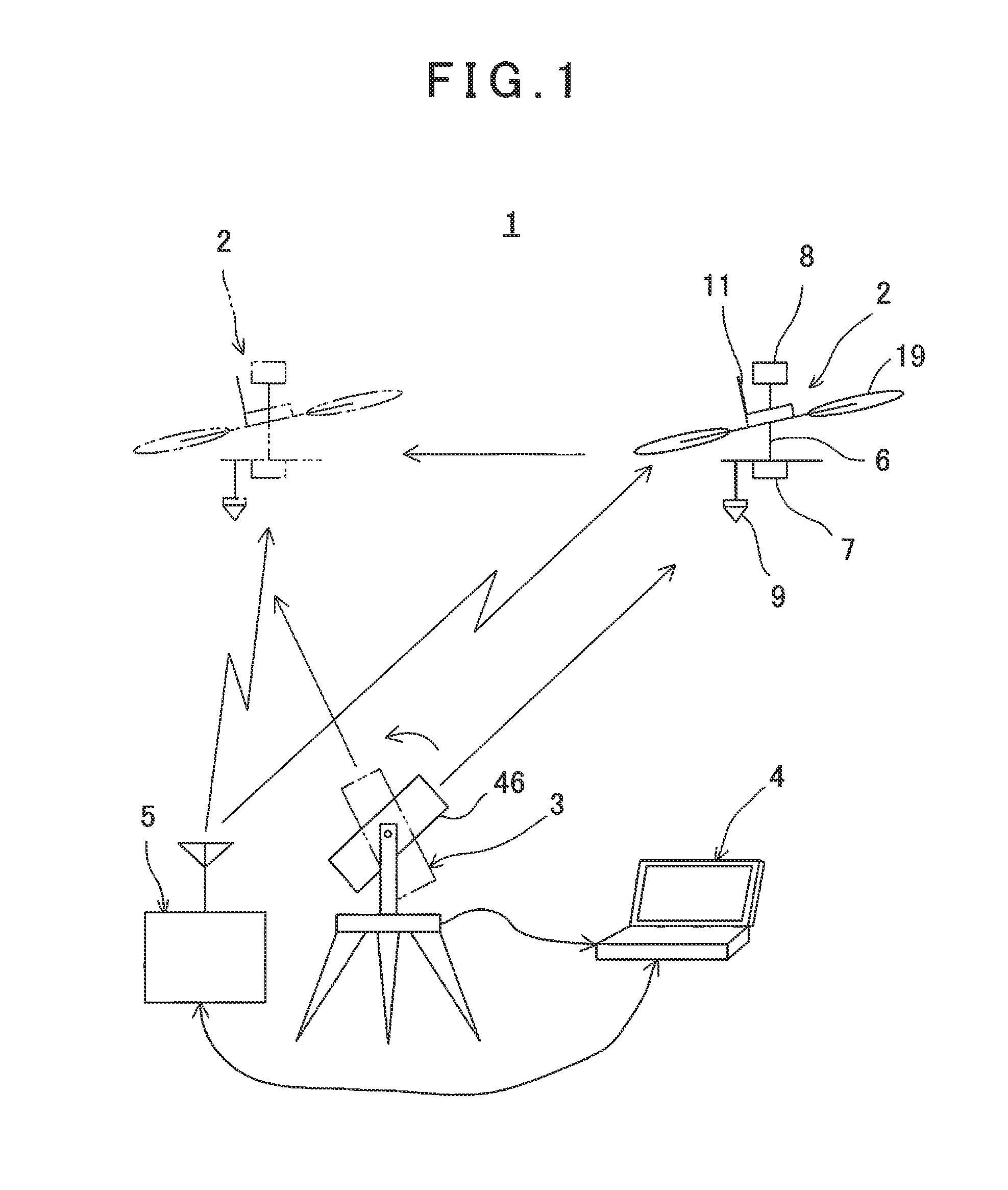
ActiveUS20140371952A1Improve image processing capabilitiesOperational securityDigital data processing detailsPhotogrammetry/videogrammetrySurvey instrumentFlight vehicle
A flying vehicle guiding system, which comprises a remotely controllable flying vehicle system, a surveying instrument being able to measure distance, angle, and track, and a ground base station for controlling a flight of the flying vehicle system based on measuring results by the surveying instrument, wherein the flying vehicle system has a retro-reflector as an object to be measured, wherein the surveying instrument has a non-prism surveying function for performing distance measurement and angle measurement without a retro-reflector, a prism surveying function for performing distance measurement and angle measurement with respect to the retro-reflector, and a tracking function for tracking the retro-reflector and for performing distance measurement and angle measurement, wherein the surveying instrument performs non-prism measurement on a scheduled flight area, the ground base station sets a safe flight area based on the results of the non-prism measurement, and controls so that the flying vehicle system flies in the safe flight area based on the results of tracking measurement by de surveying instrument.
Owner:KK TOPCON
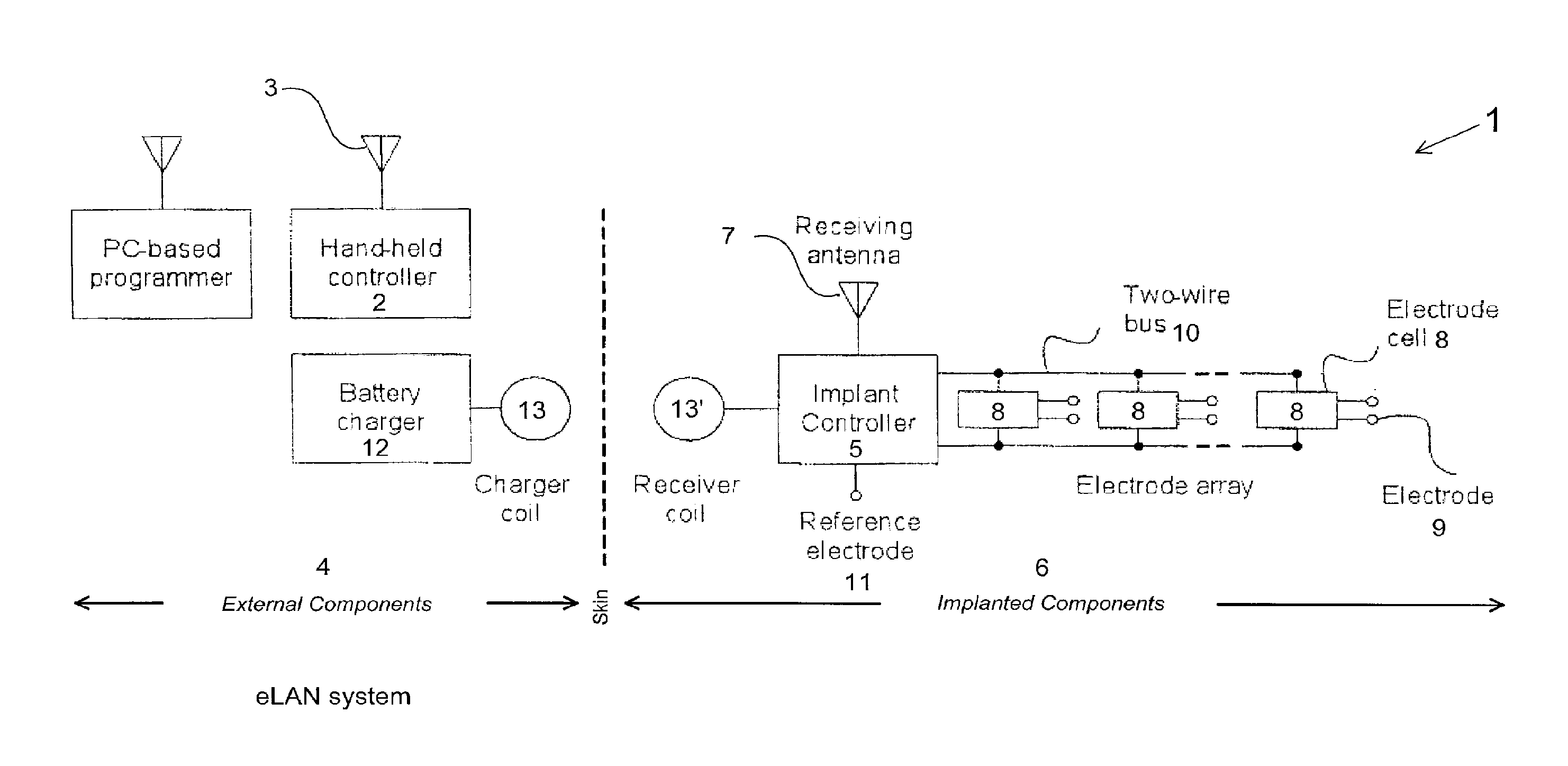
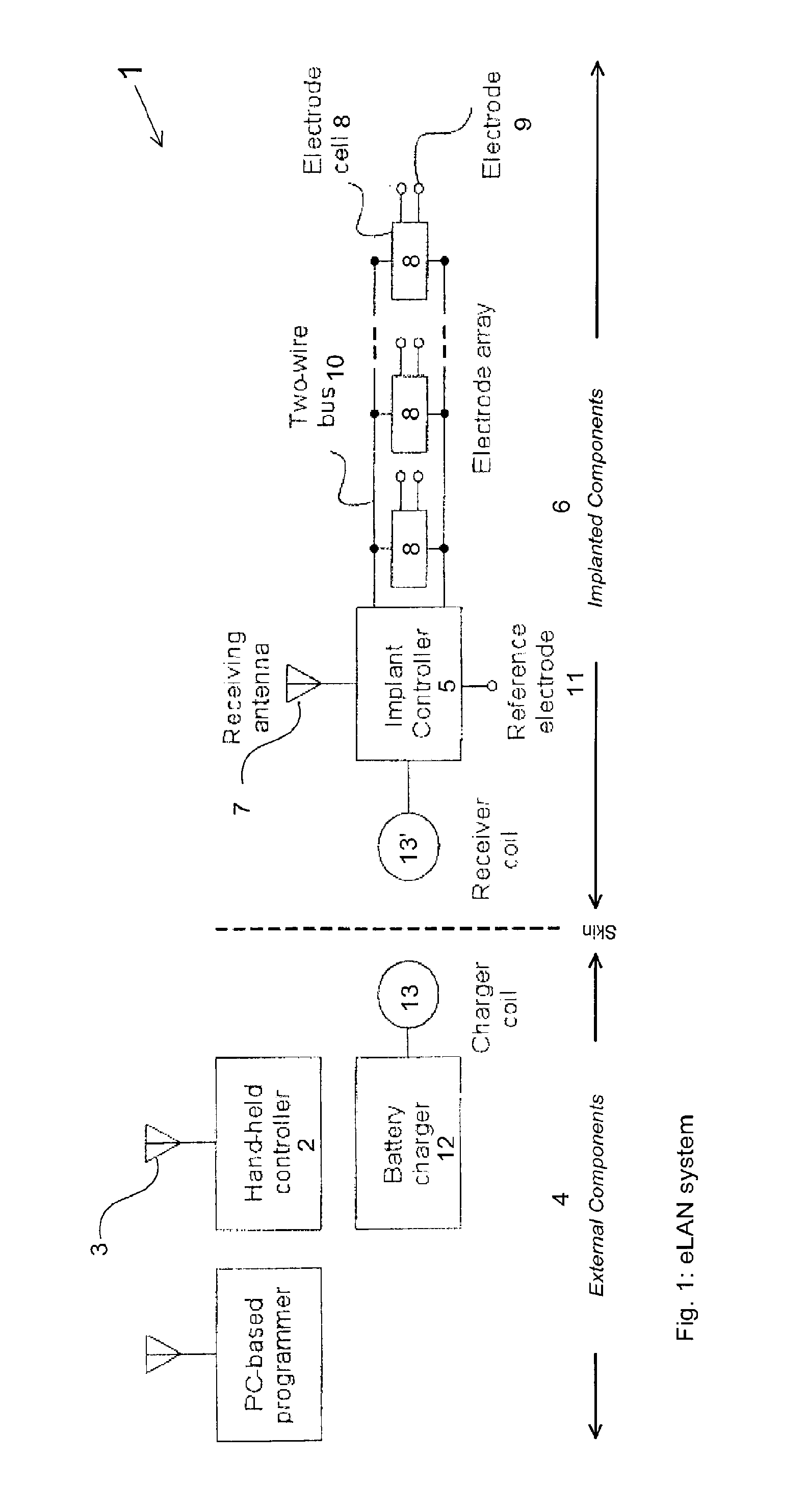
Neuro-stimulation
ActiveUS20120161945A1Easy to addEasy to replaceElectric signal transmission systemsInternal electrodesControl logicElectrical and Electronics engineering
The invention is a distributed implantable neuro-stimulation system, comprising an implant controller including control logic to transmit two time-varying power signals, varying between two levels and out of phase with the other, and a command signal modulated onto at least one of the power signals. One or more electrode cells, each having control logic to extract charge from the power signals and recover commands from the command signal. A two-wire bus interconnecting the implant controller and all the electrode cells, to carry one of the time varying signals in each of the two wires, and to carry the command signal.
Owner:SALUDA MEDICAL PTY LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com