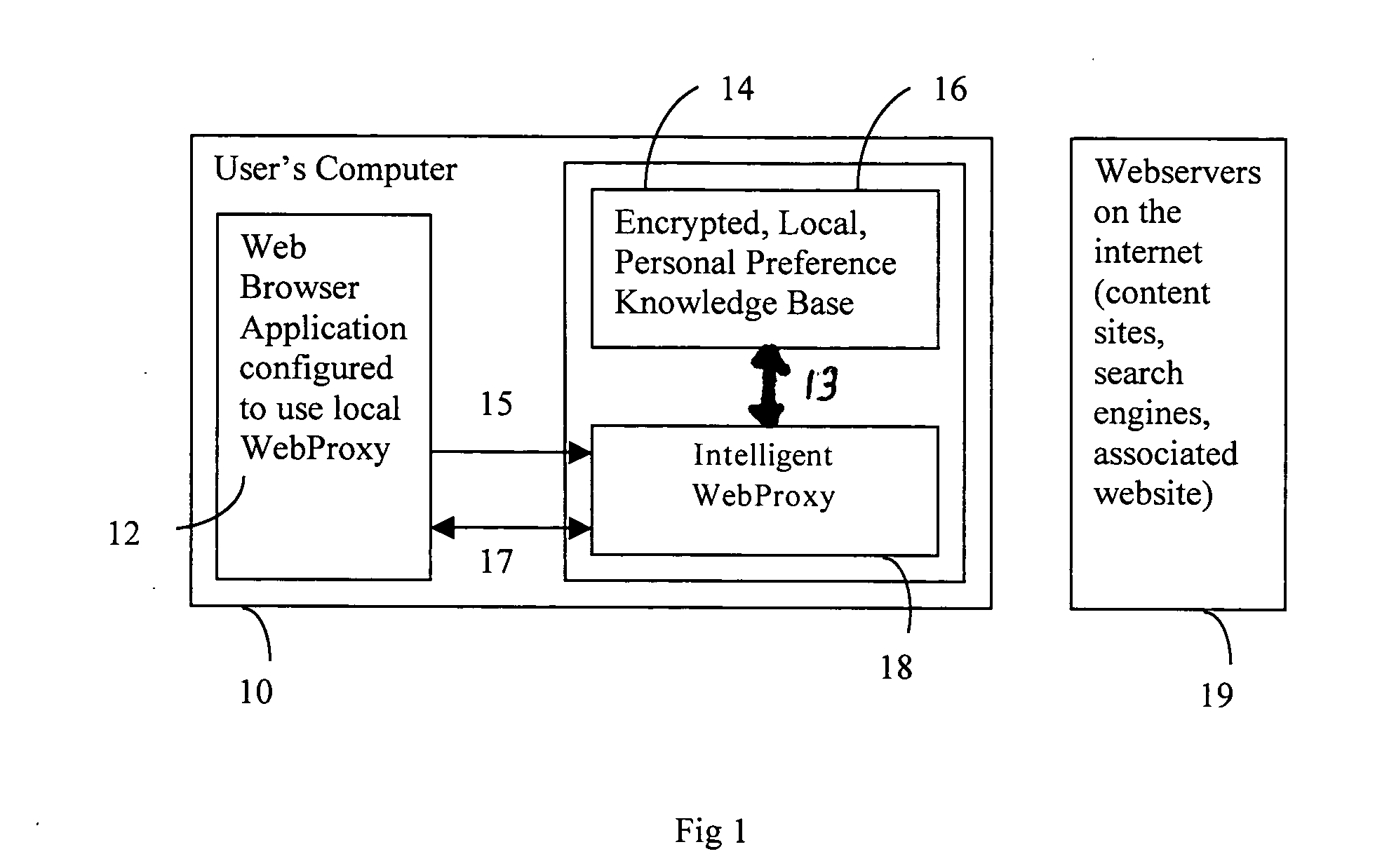
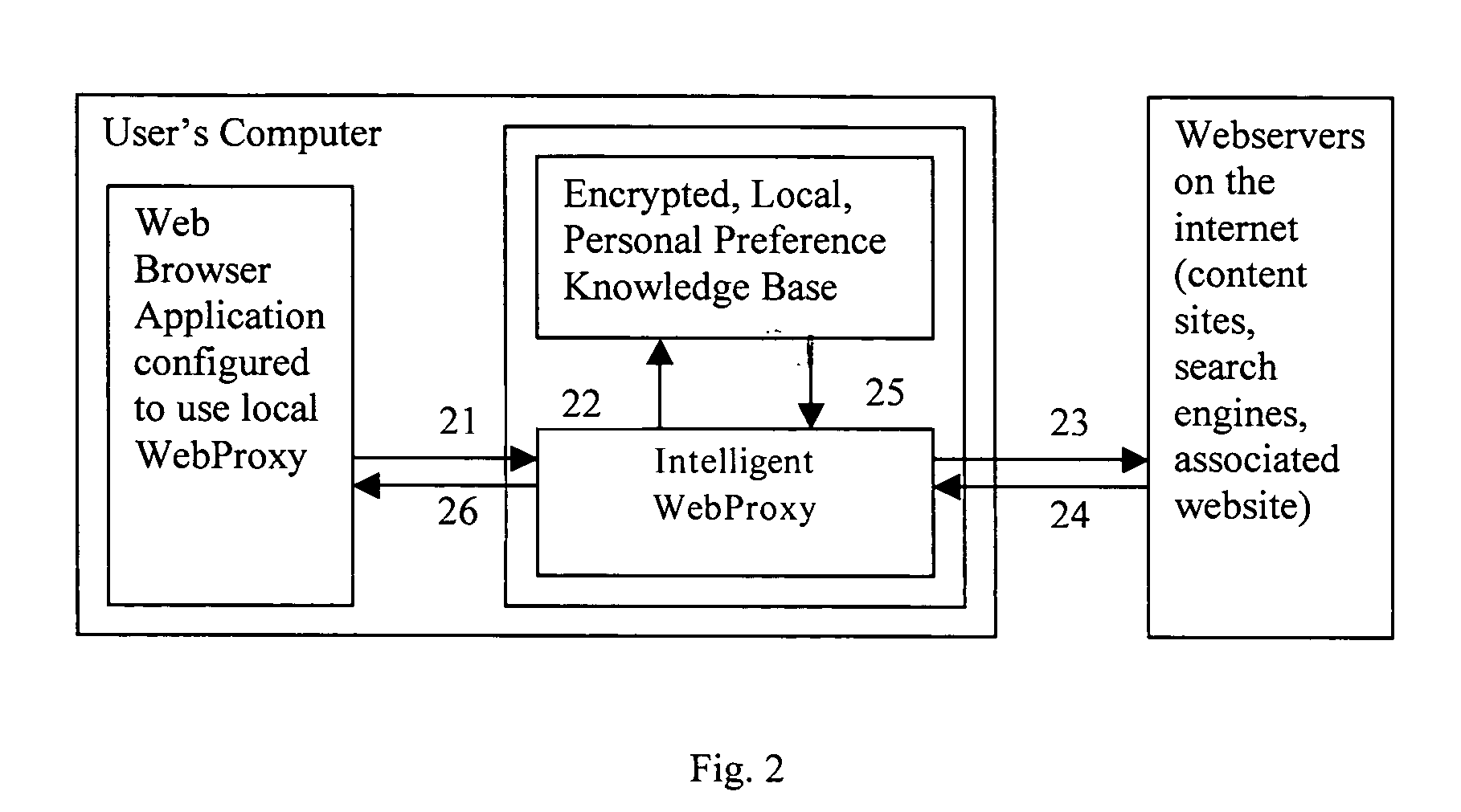
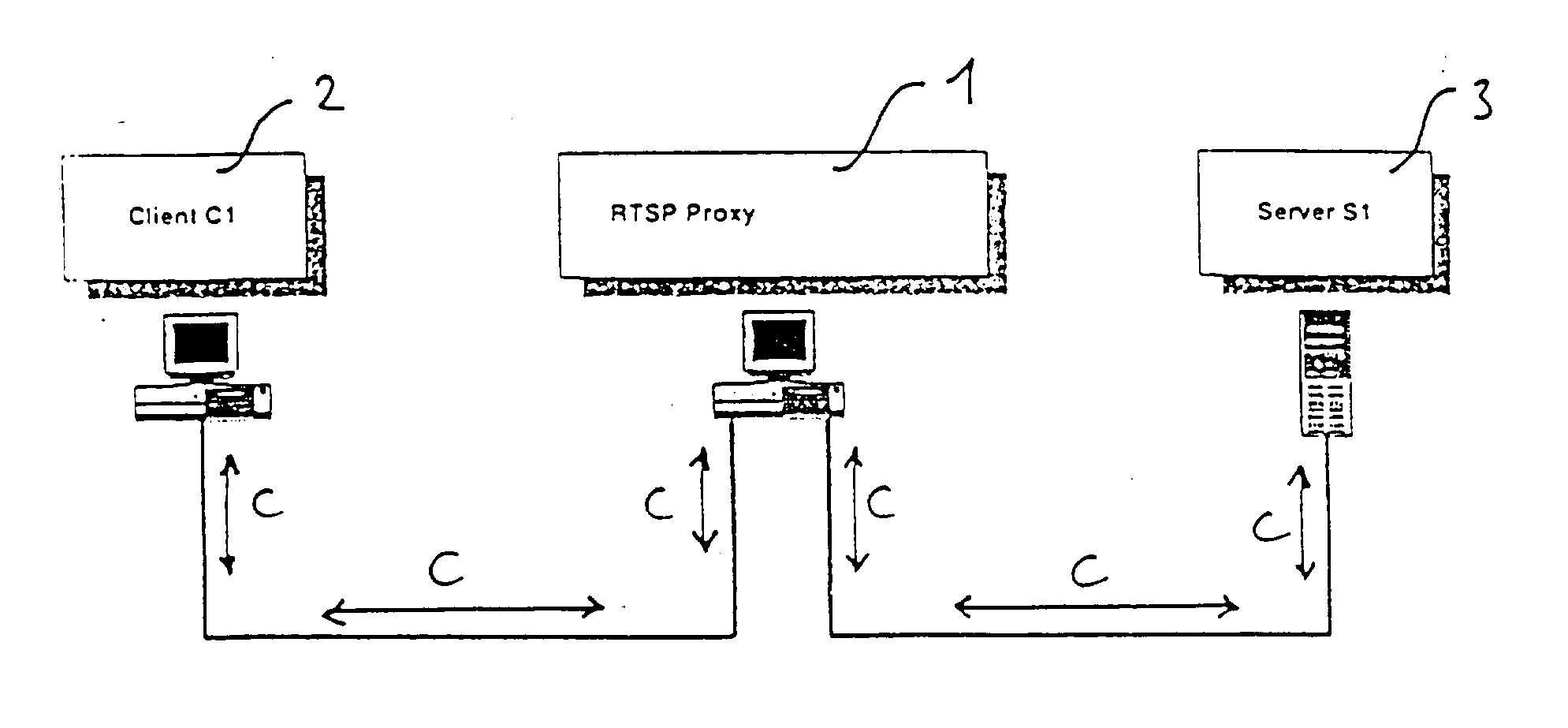
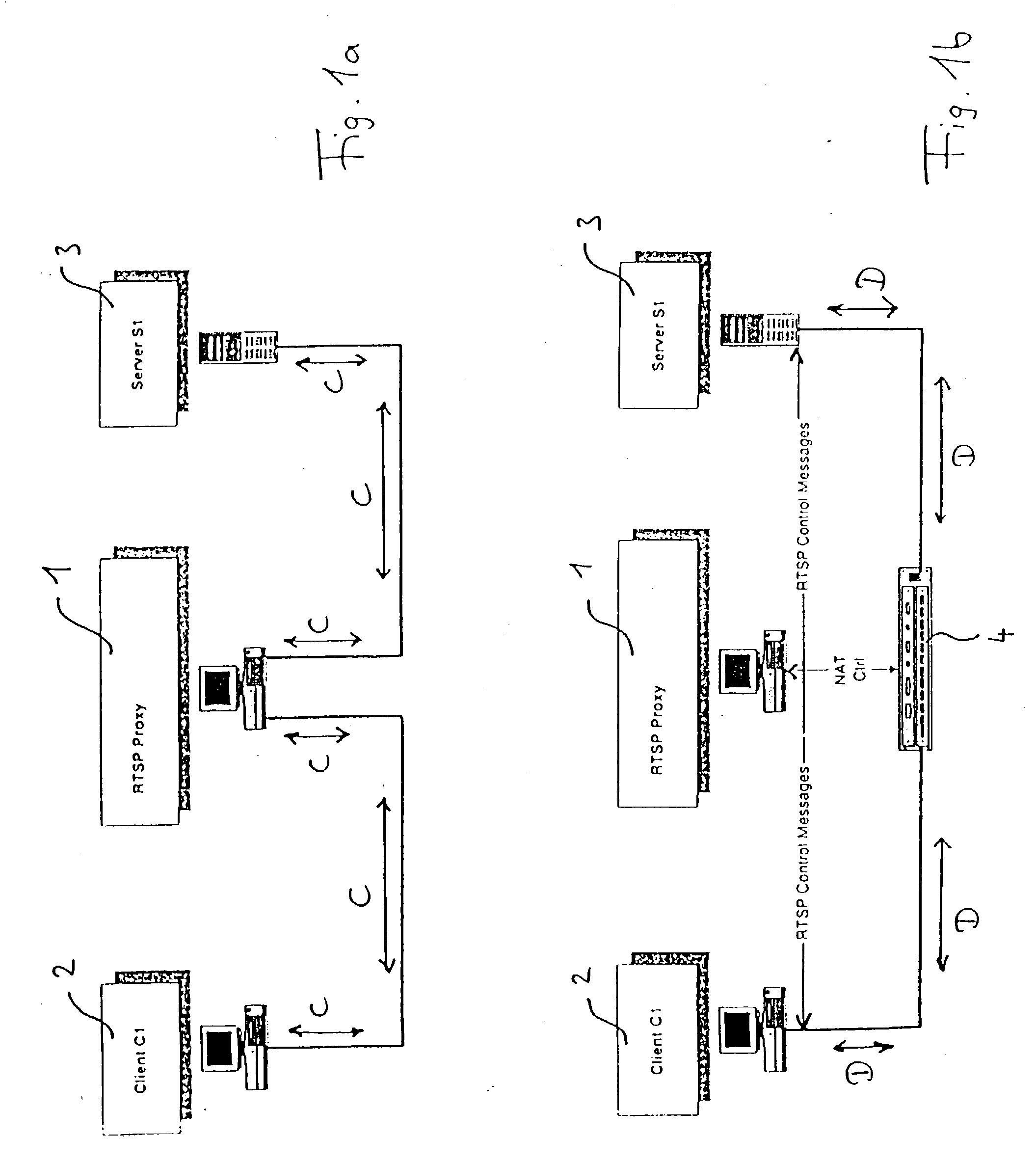
Patents
Literature
126 results about "Web proxy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
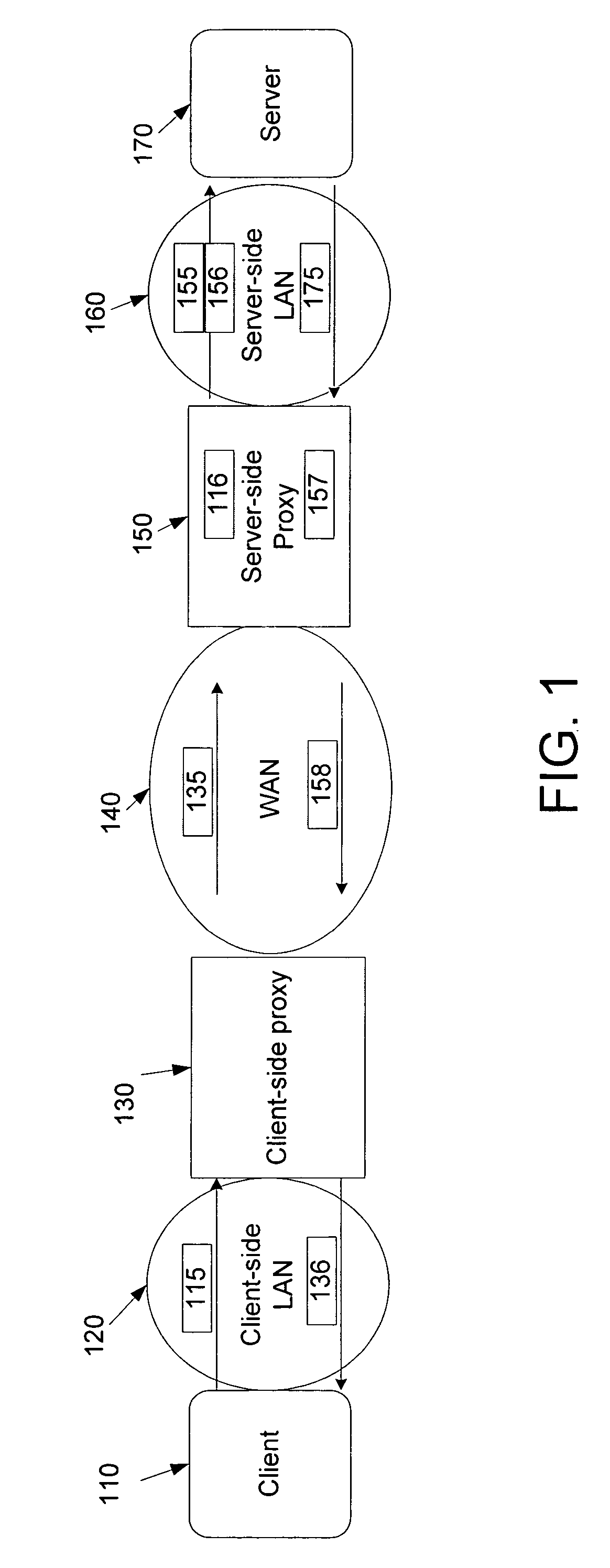
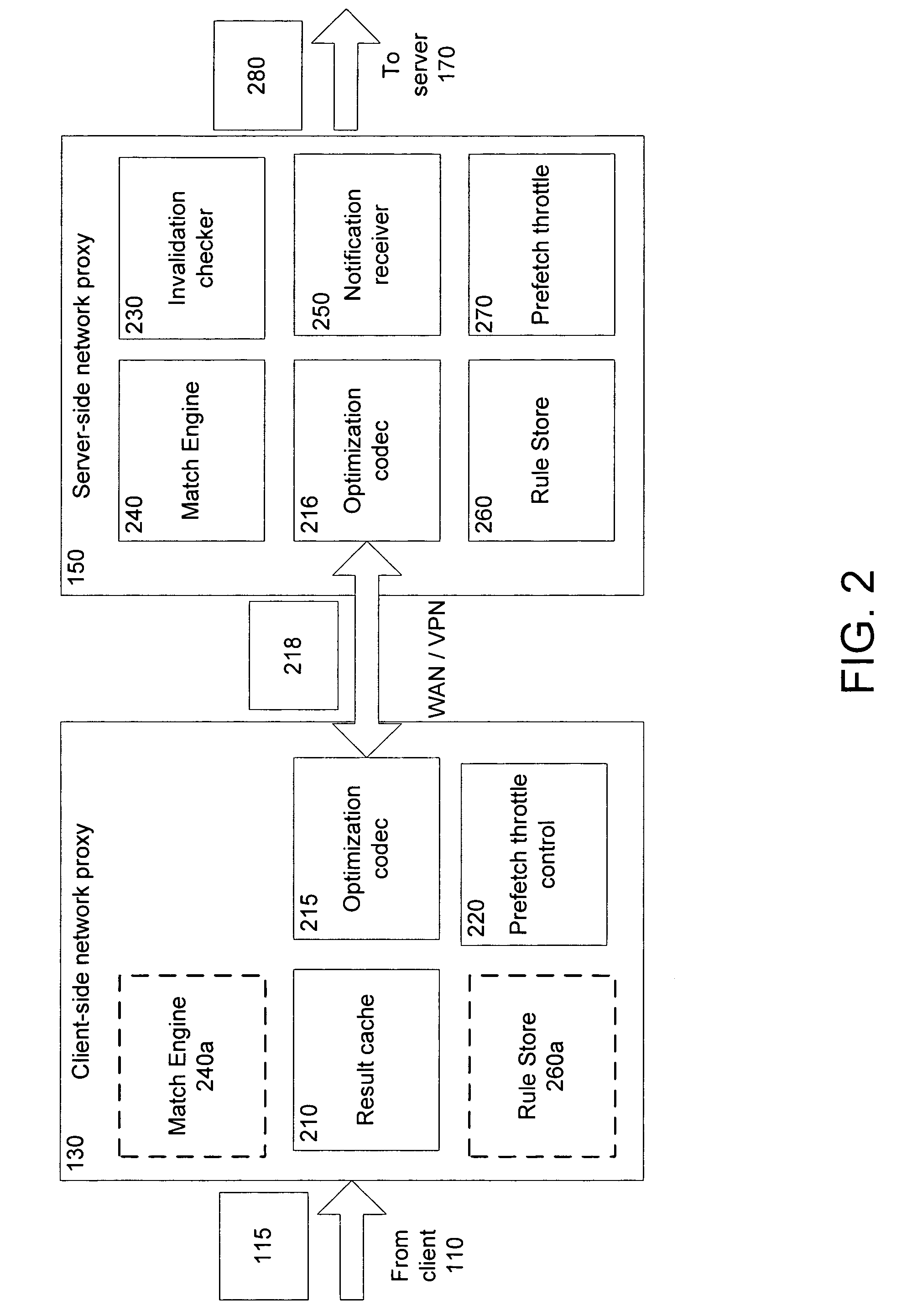
Rules-based transaction prefetching using connection end-point proxies
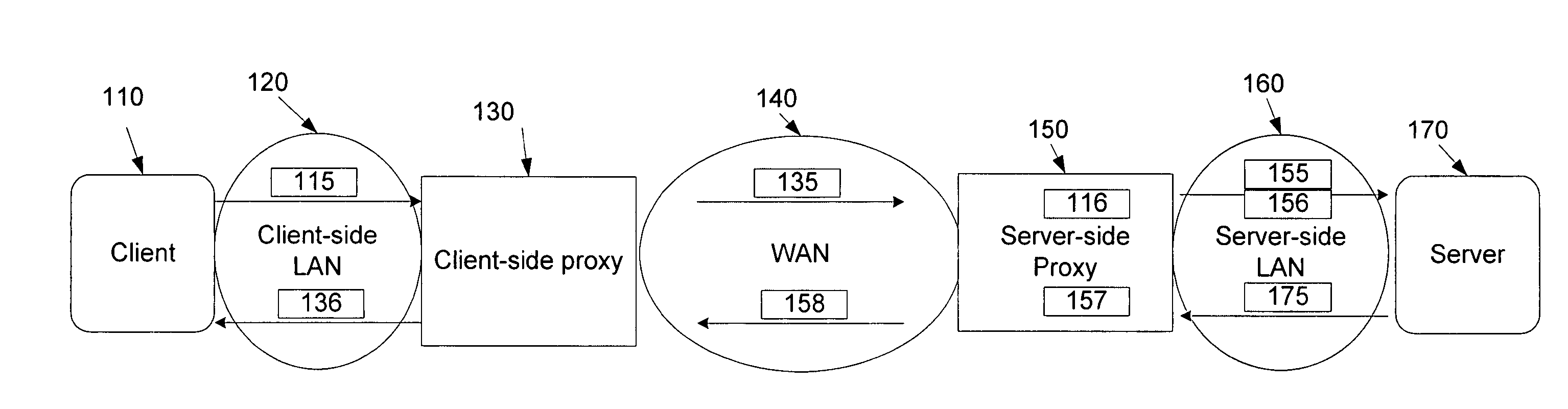
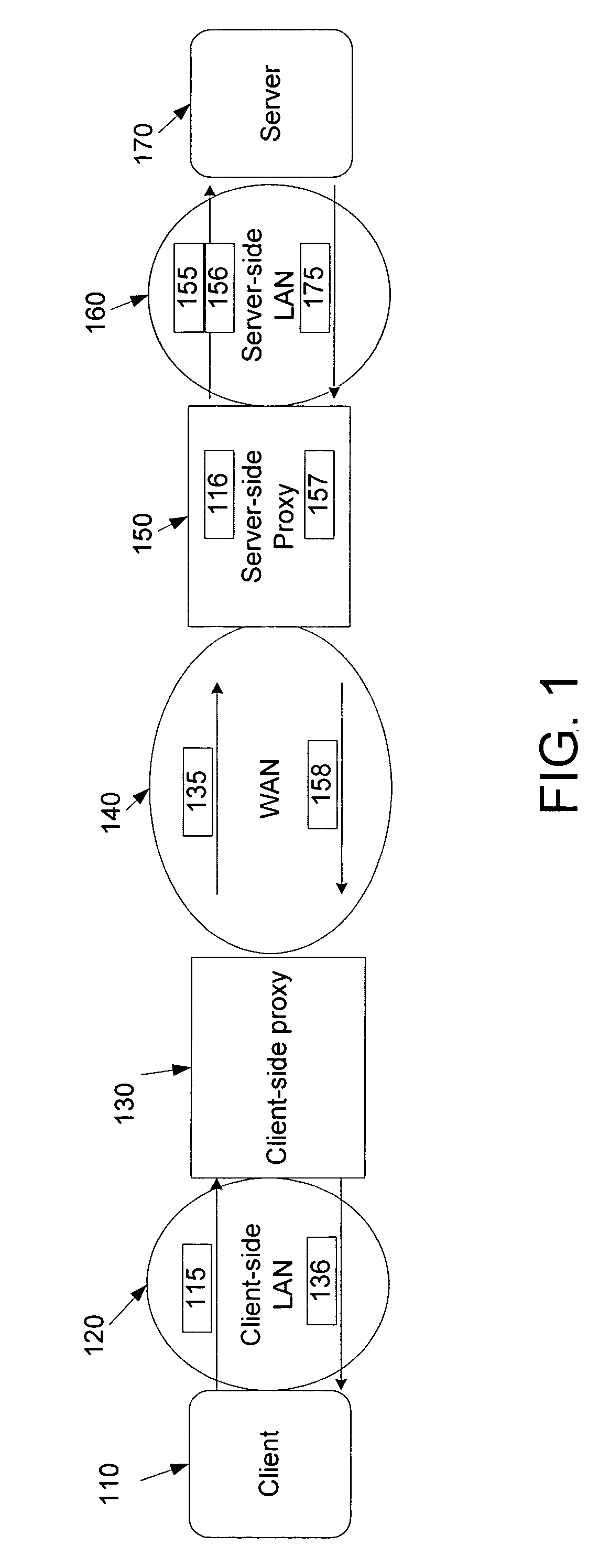
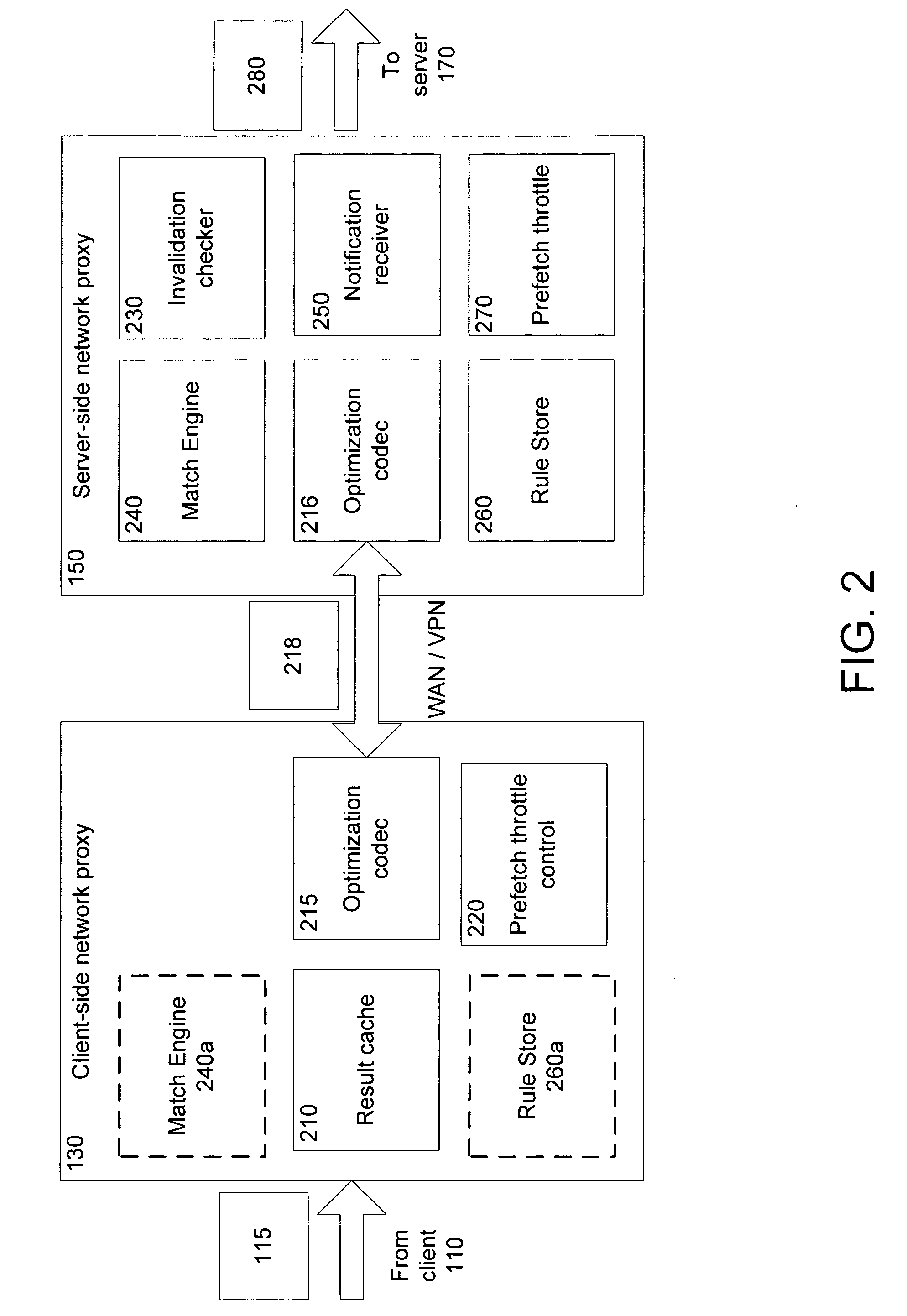
ActiveUS20060212524A1Increase speedReduce server latencyMultiple digital computer combinationsTransmissionClient-sideNetwork application
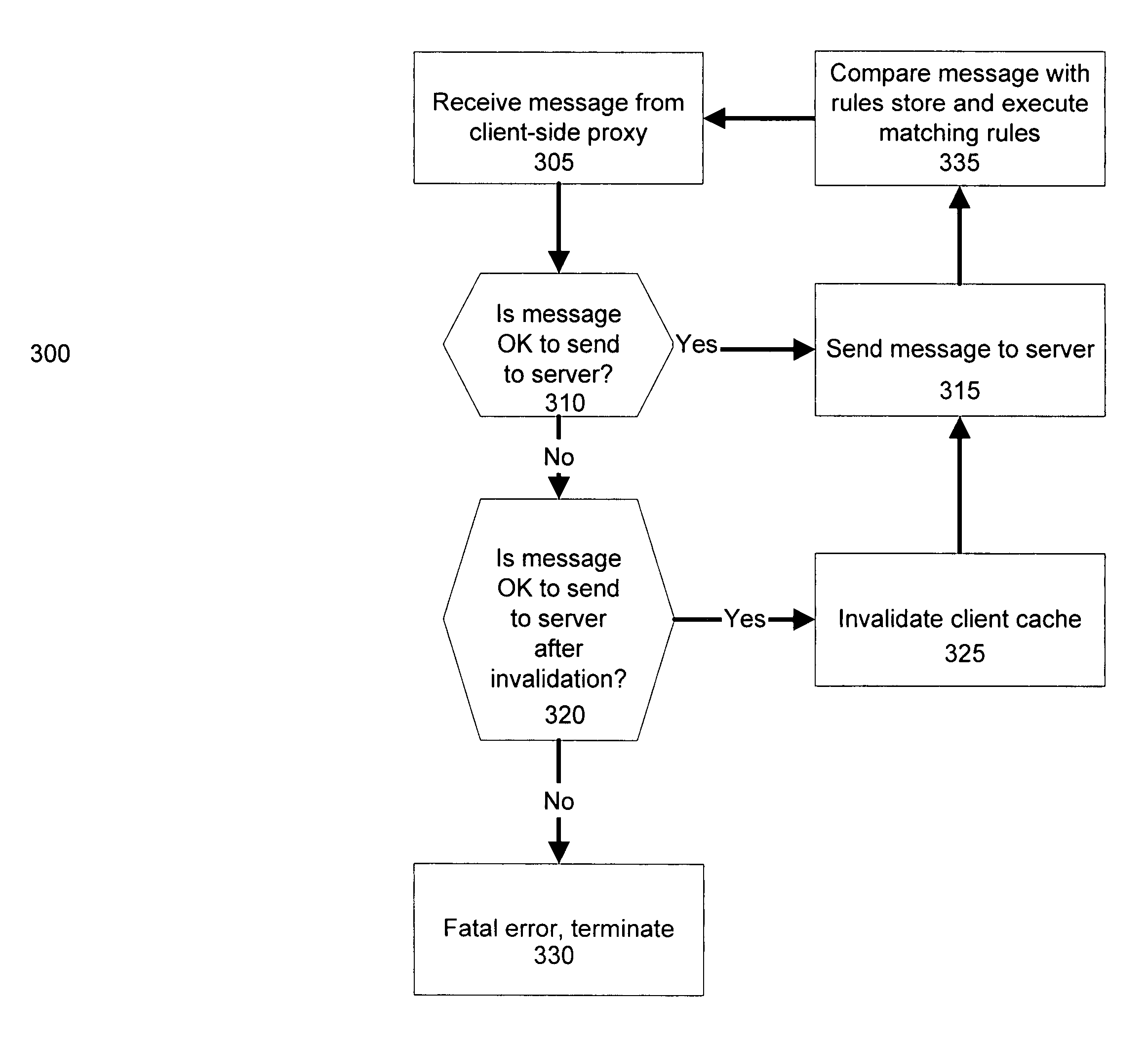
Network proxies reduce server latency in response to series of requests from client applications. Network proxies intercept messages clients and a server. Intercepted client requests are compared with rules. When client requests match a rule, additional request messages are forwarded to the server on behalf of a client application. In response to the additional request messages, the server provides corresponding response messages. A network proxy intercepts and caches the response messages. Subsequent client requests are intercepted by the network application proxy and compared with the cached messages. If a cached response message corresponds with a client request message, the response message is returned to the client application immediately instead of re-requesting the same information from the server. A server-side network proxy can compare client requests with the rules and send additional request messages. The corresponding response messages can be forwarded to a client-side network proxy for caching.
Owner:RIVERBED TECH LLC
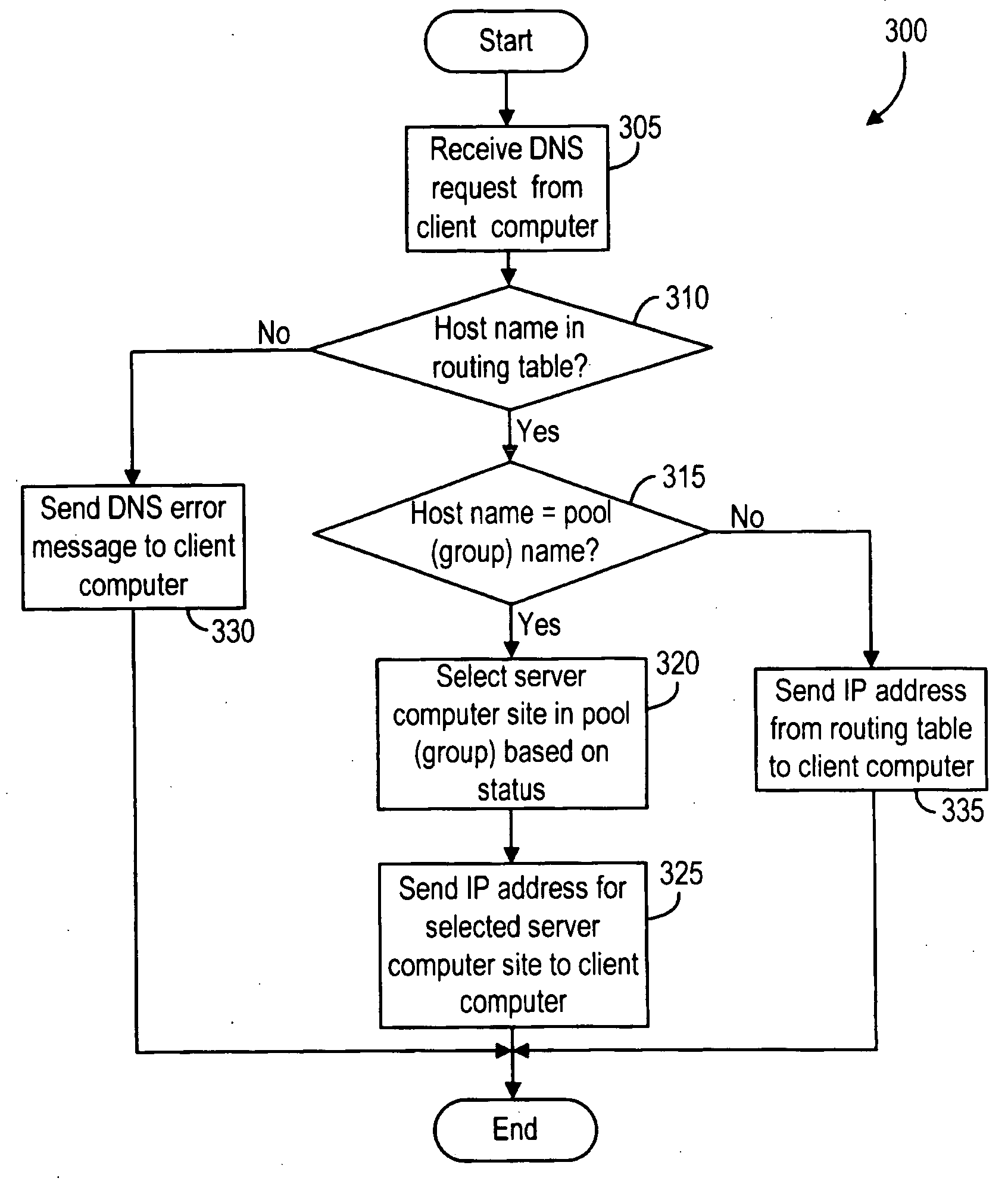
System and method for distributing load among redundant independent stateful World Wide Web server sites
InactiveUS20050021848A1Overcome limitationsPerformance issueResource allocationMultiple digital computer combinationsFailoverLoad Shedding
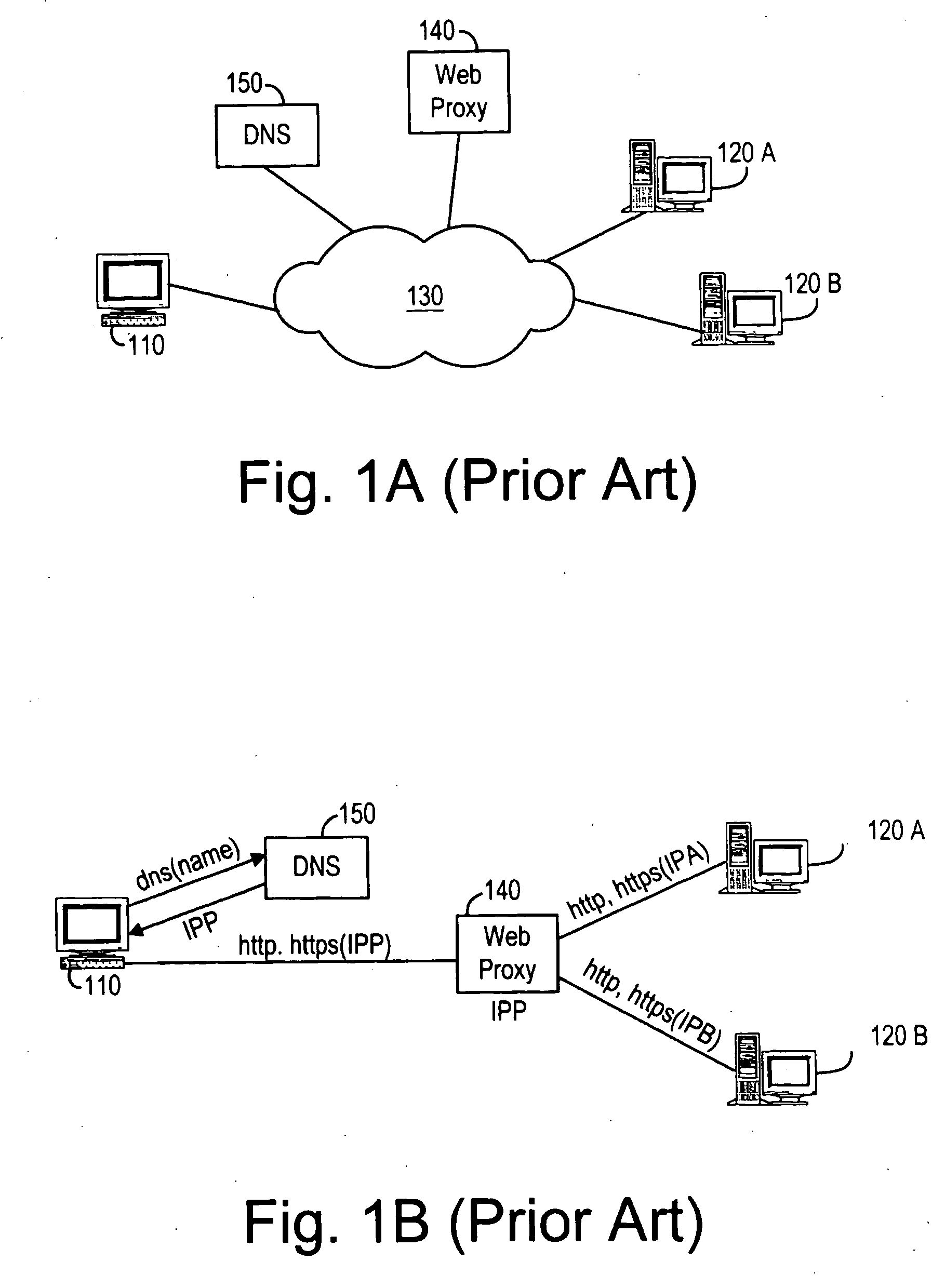
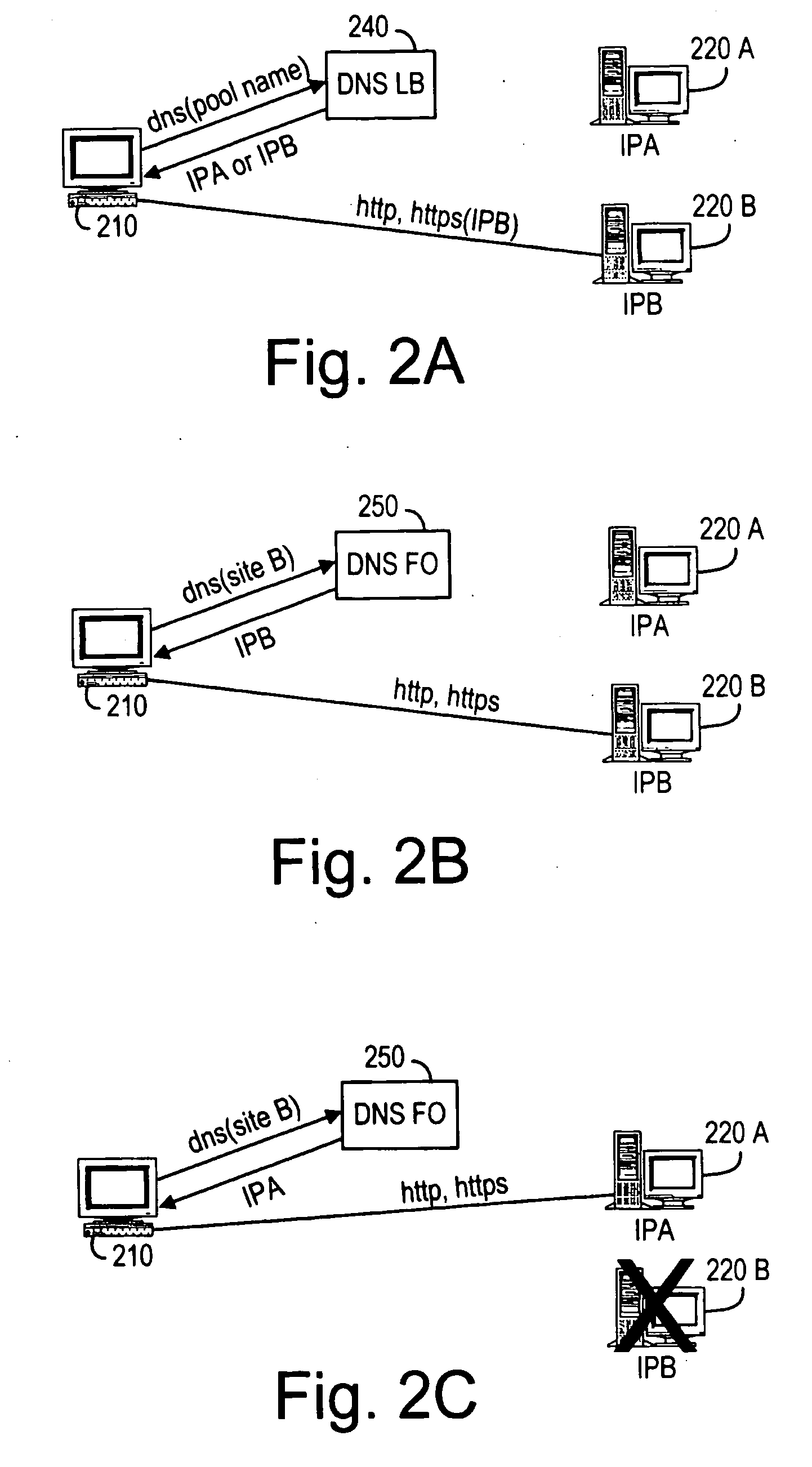
The present invention provides a system and method for distributing load among redundant, independent, stateful web server sites that overcome the limitations of prior art solutions. This is accomplished by constructing the server computer to respond to an initial connection request from a client computer with the name of a server computer site, pool or group selected based on various criteria. The server computer site, pool and group names are maintained in DNS nameservers with load balancing and failover capabilities. As a result, the single-point-of-failure and performance issues introduced by prior art web proxy servers are eliminated. In addition, since the session state information is only maintained on the selected server computer site, the need to synchronize web proxy server state with server computer state is eliminated.
Owner:HTC CORP
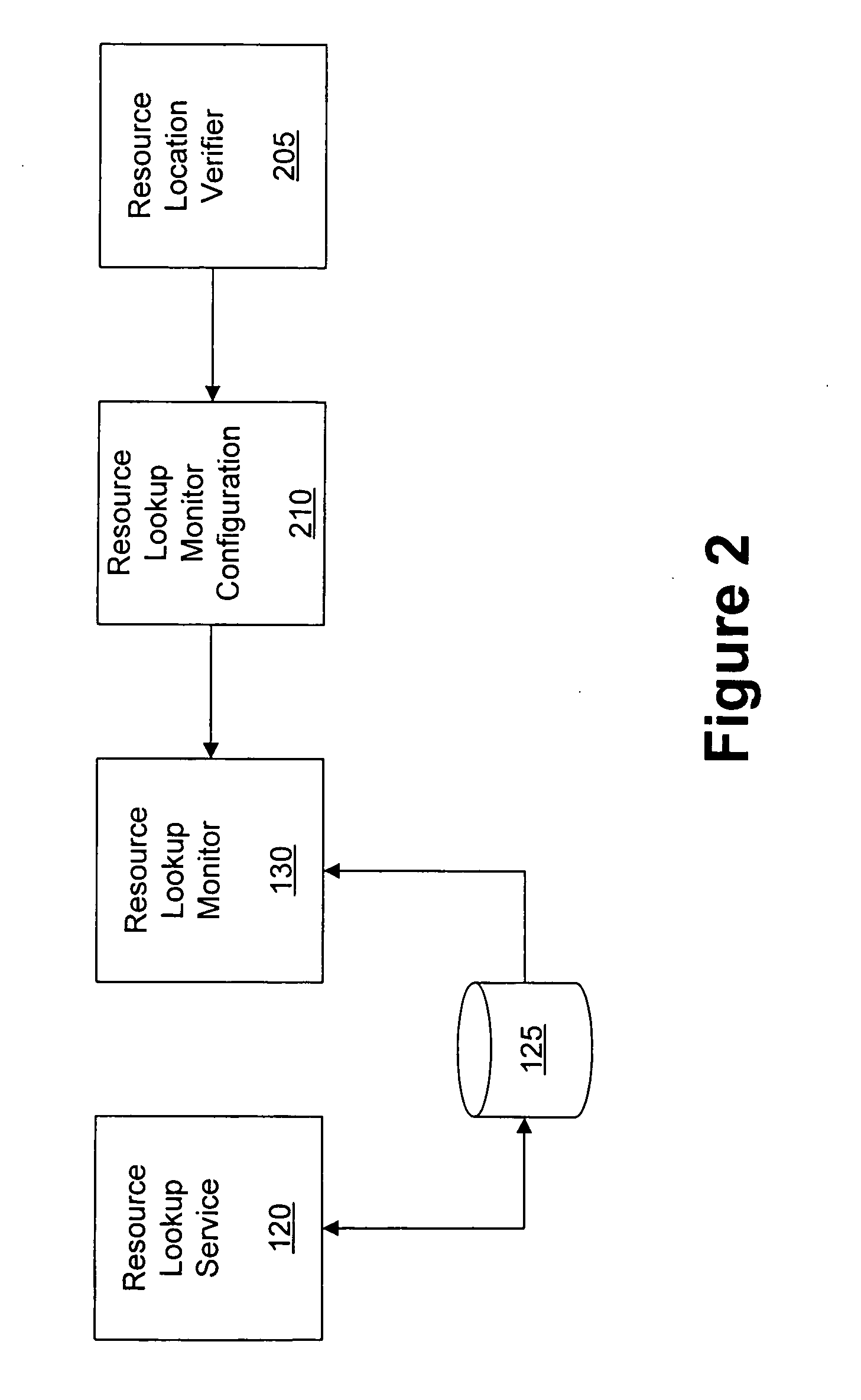
Pre-fetching resources based on a resource lookup query
InactiveUS20050240574A1Digital data information retrievalSpecial data processing applicationsResource basedClient-side
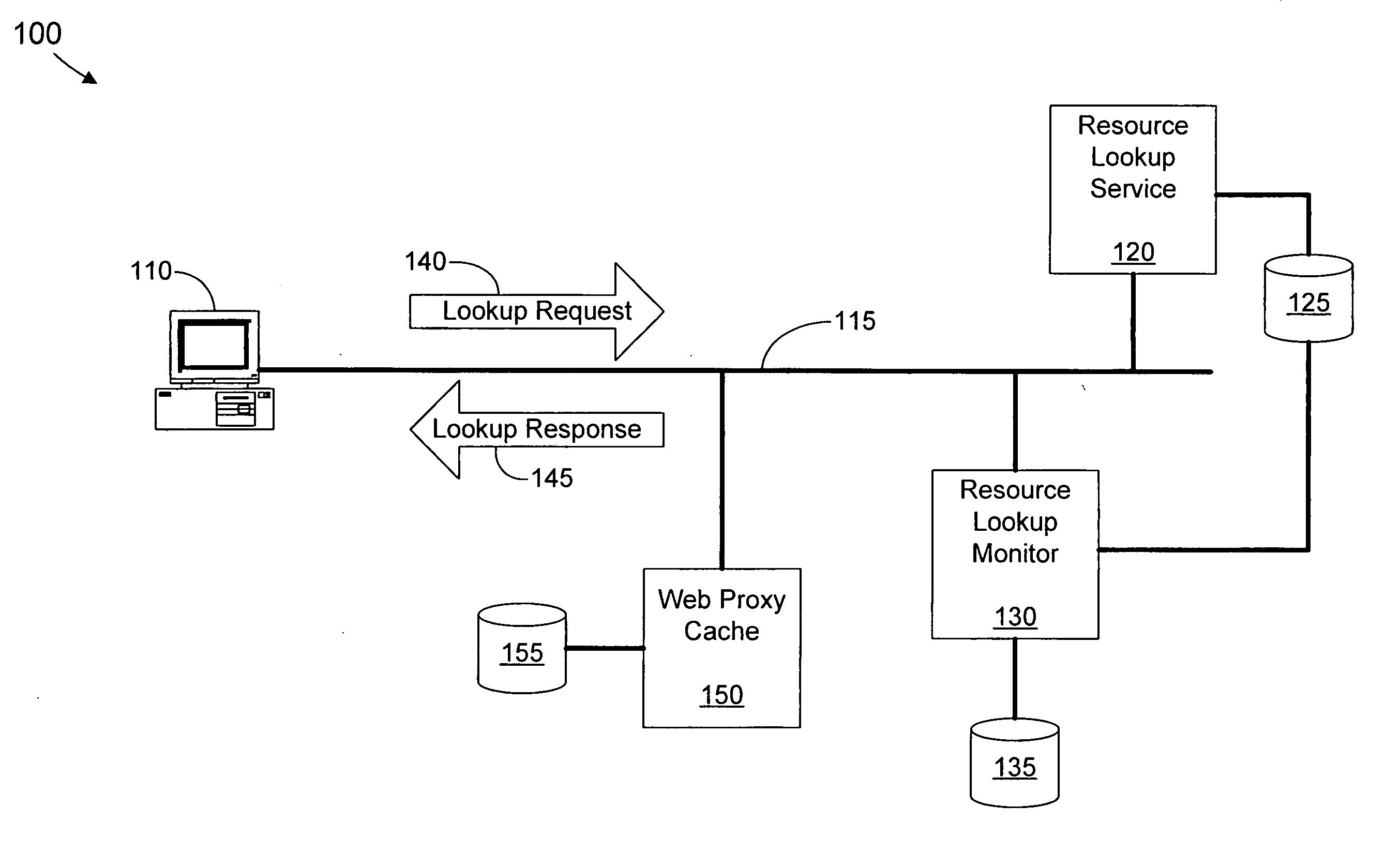
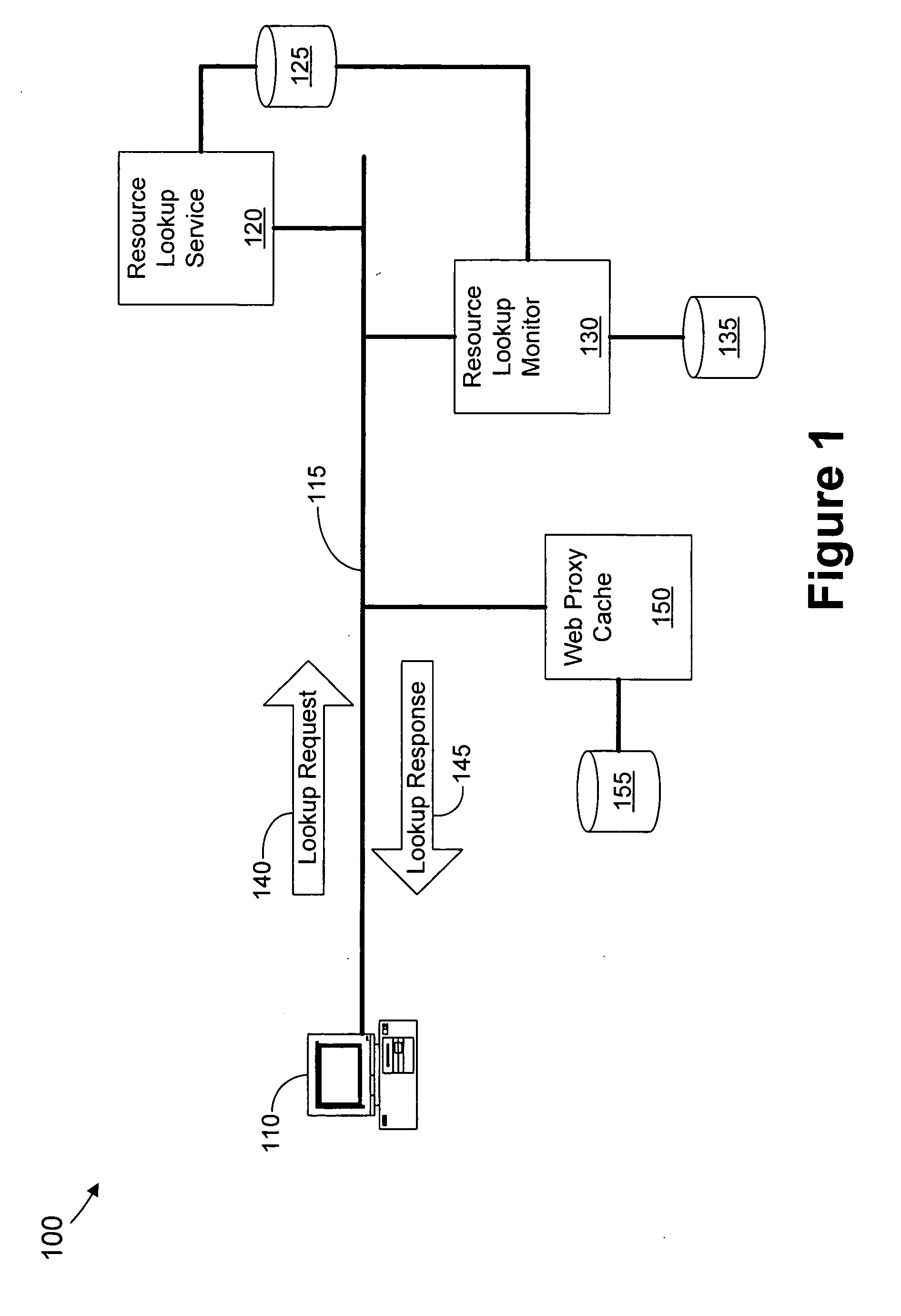
A method and apparatus are provided for pre-fetching resources based upon a query request to a resource lookup service. A monitoring application snoops for requests / replies from clients. Web content is pre-fetched via a web proxy based on the requests. Thus, the web content is made available to the client more efficiently.
Owner:IBM CORP
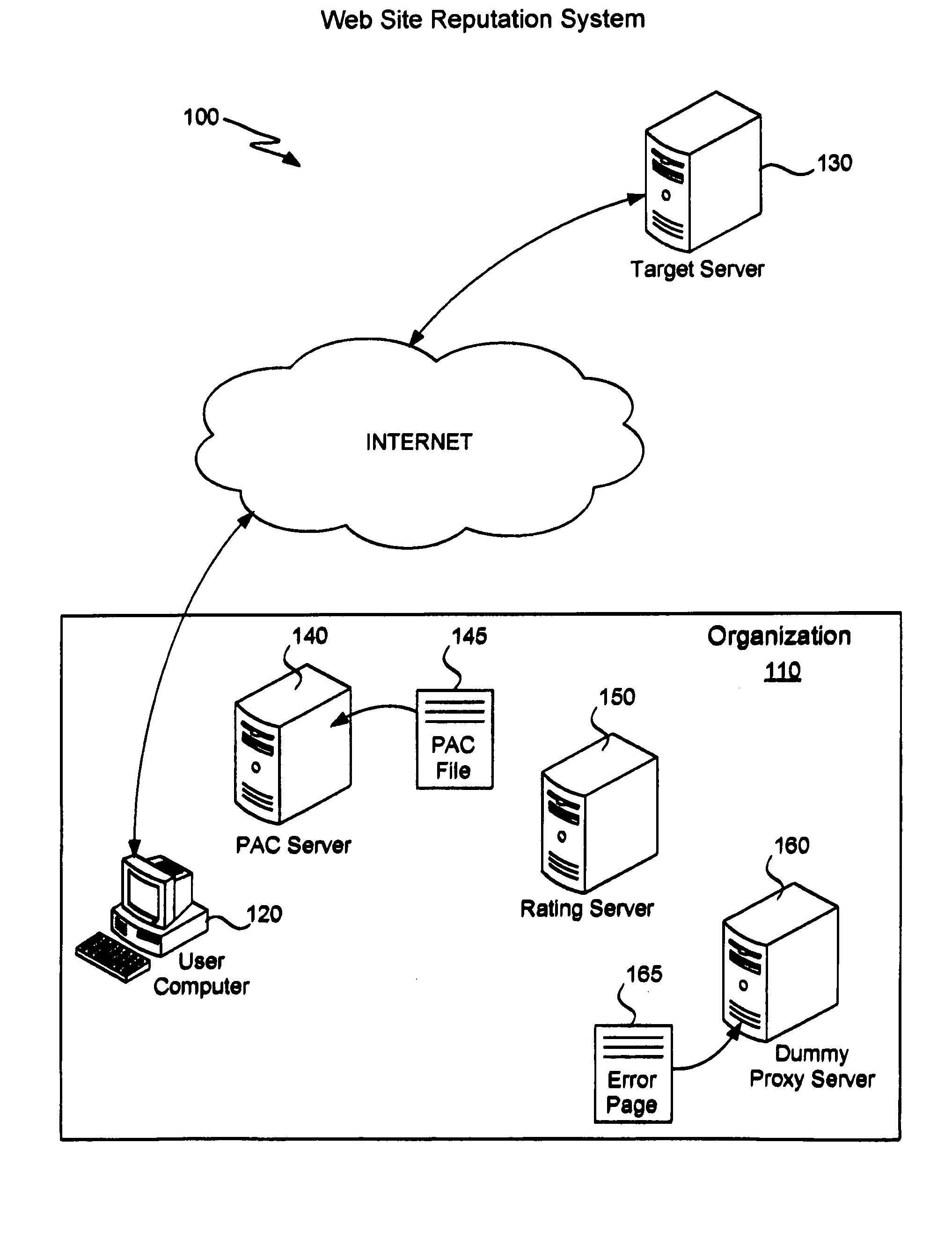
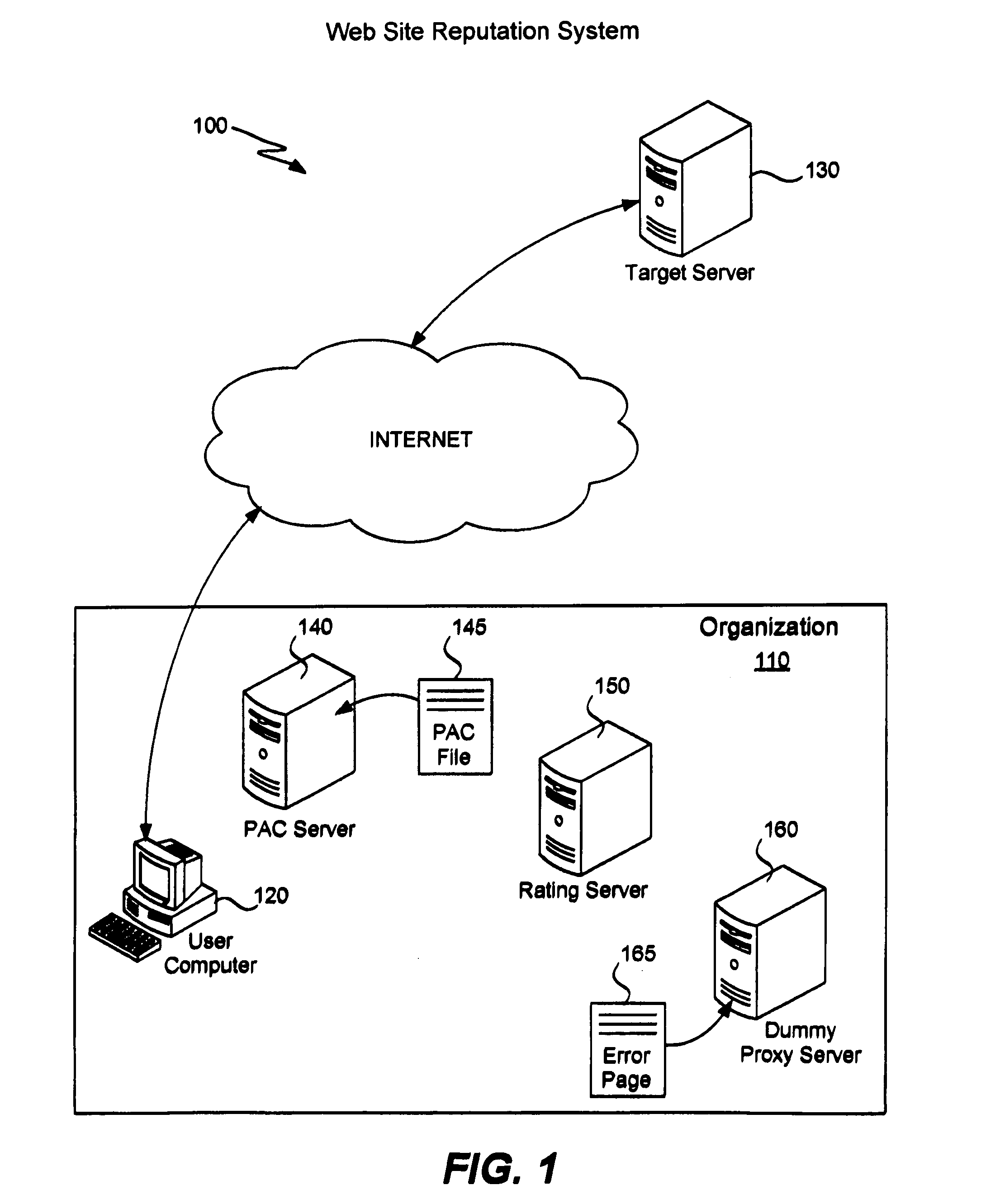
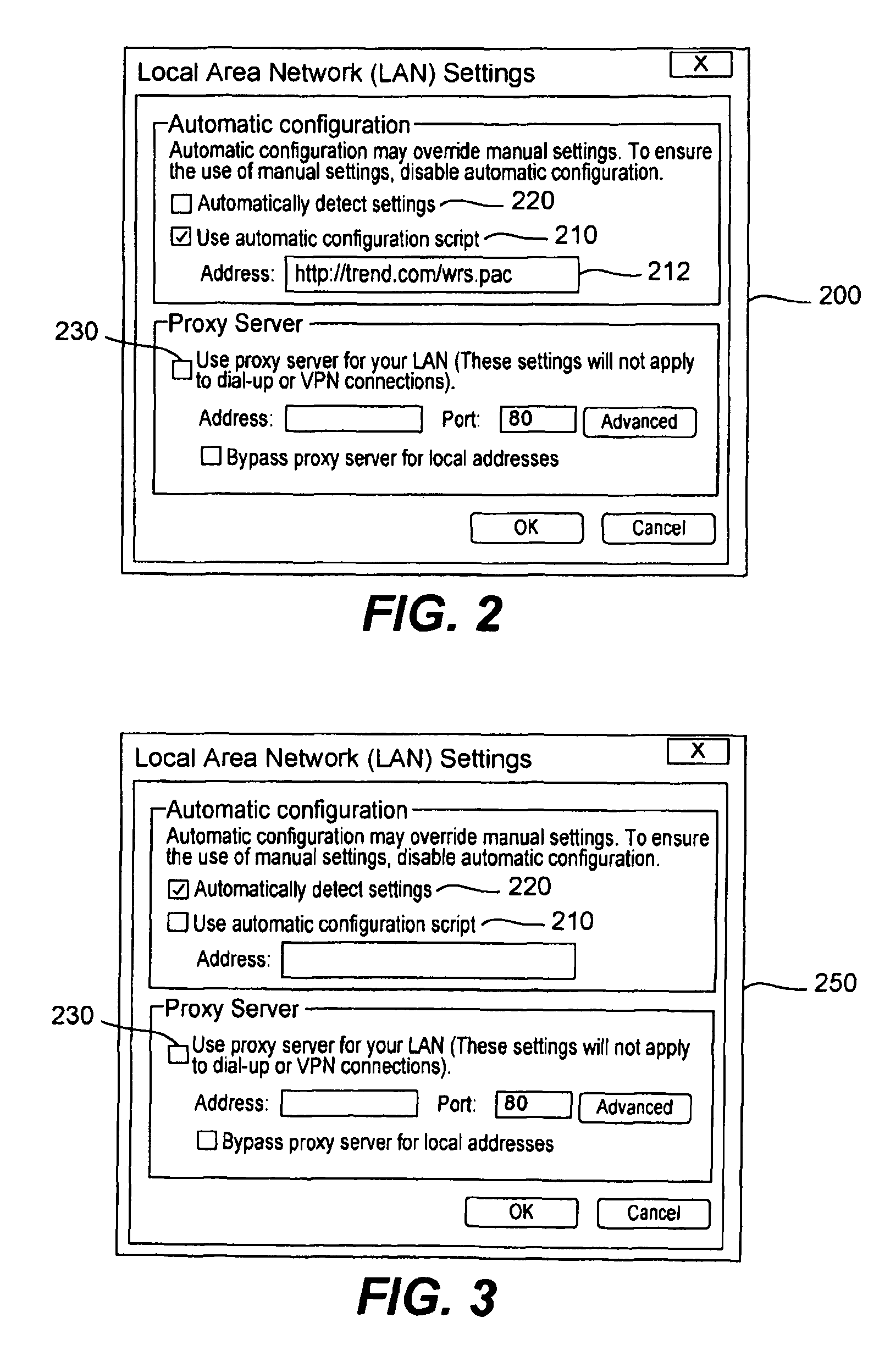
Web site reputation service using proxy auto-configuration
ActiveUS8527631B1Easy to useMultiple digital computer combinationsProgram controlAuto-configurationWeb browser
A Web site reputation service automatically redirects a browsing request for analysis by a rating server. On the browsing request, a proxy autoconfiguration (PAC) file is downloaded from a PAC server to a Web browser of a user computer. The function of the PAC file is executed, sending a request to a rating server along with a host name of a target Web site. The function does not immediately return a proxy server, but first requests a rating of the Web site. A rating result associated with the Web site is produced by the rating server. The rating server returns the rating result and the function returns an address of a proxy server to the Web browser based upon the rating result. A user can enable the Web Proxy Autodiscovery Protocol to use the service. Access control may be implemented by applying an HTTP authentication mechanism on the Web server that hosts the PAC file.
Owner:TREND MICRO INC
Systems and methods for providing resource allocation in a networked environment
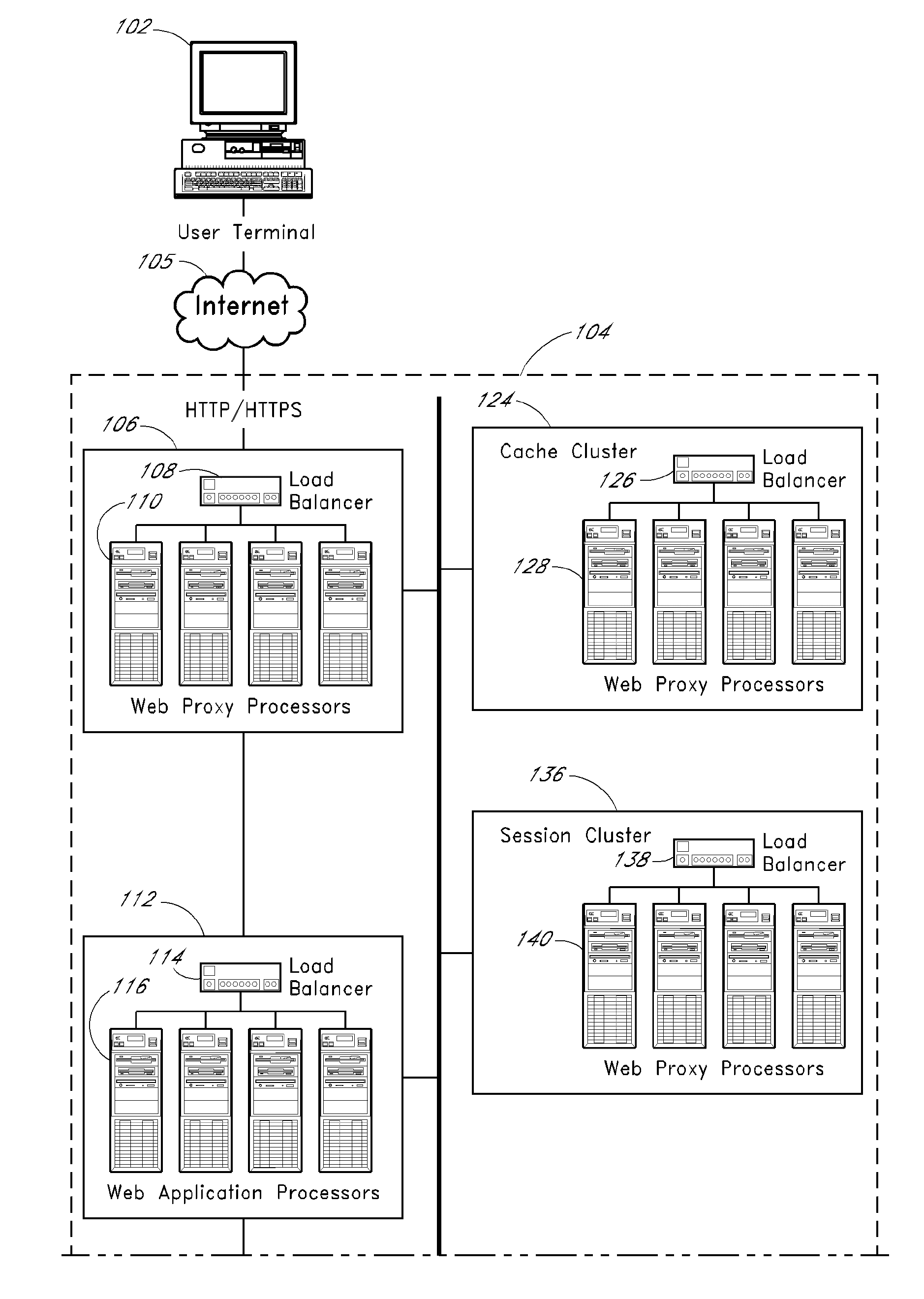
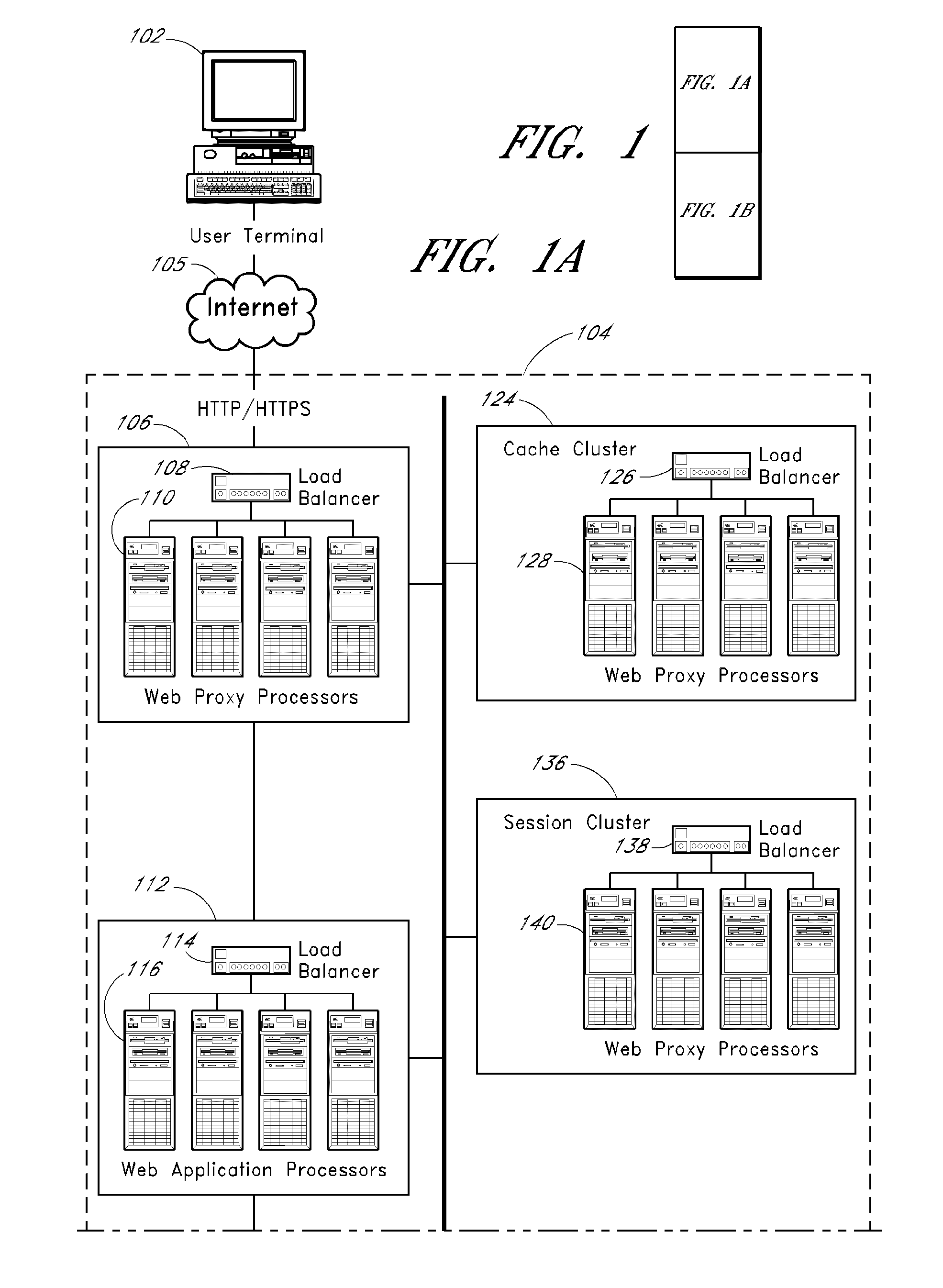
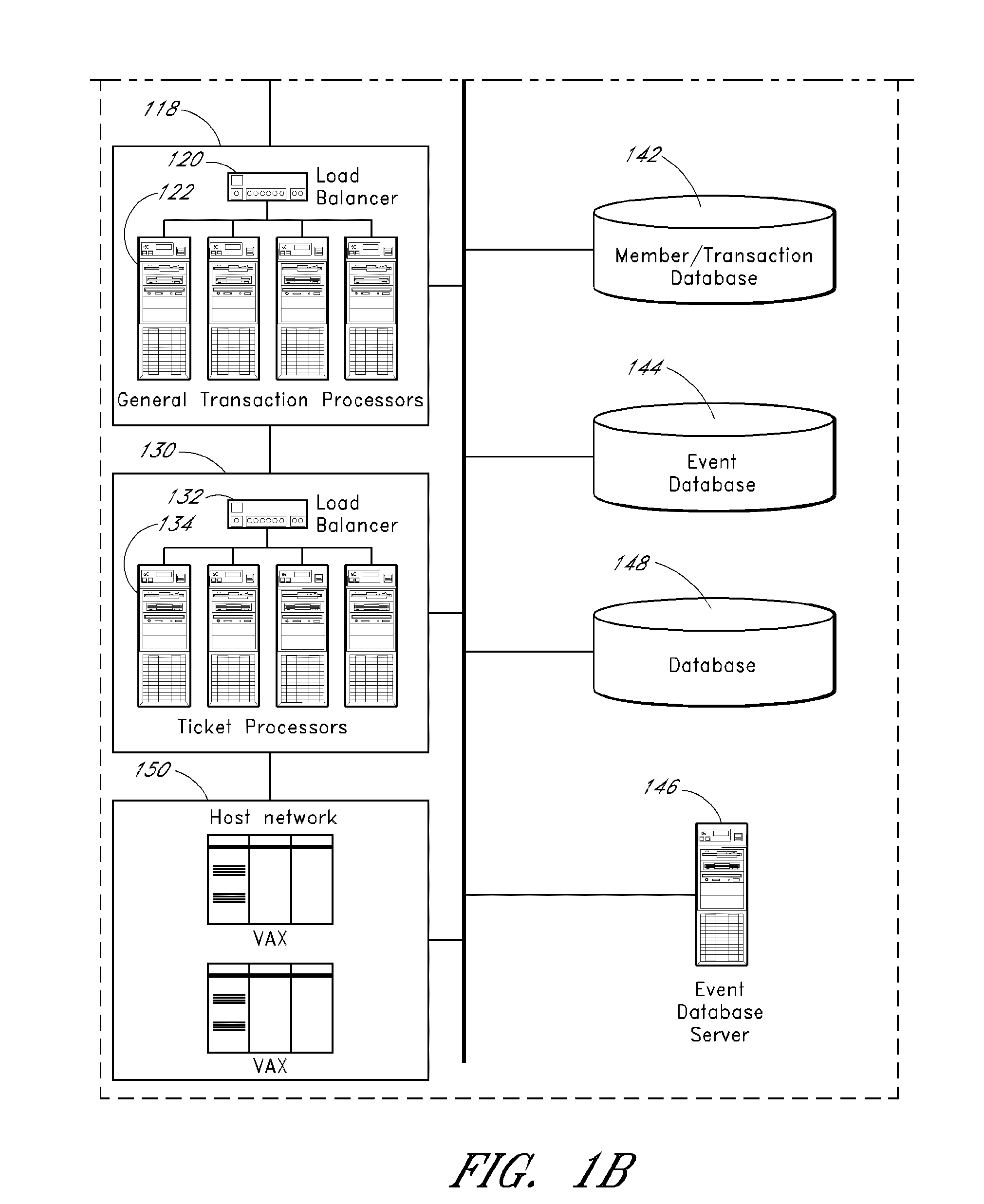
ActiveUS20090164635A1Increase purchase offer amountAbility to utilizeFinanceDigital data processing detailsWeb siteNetworked system
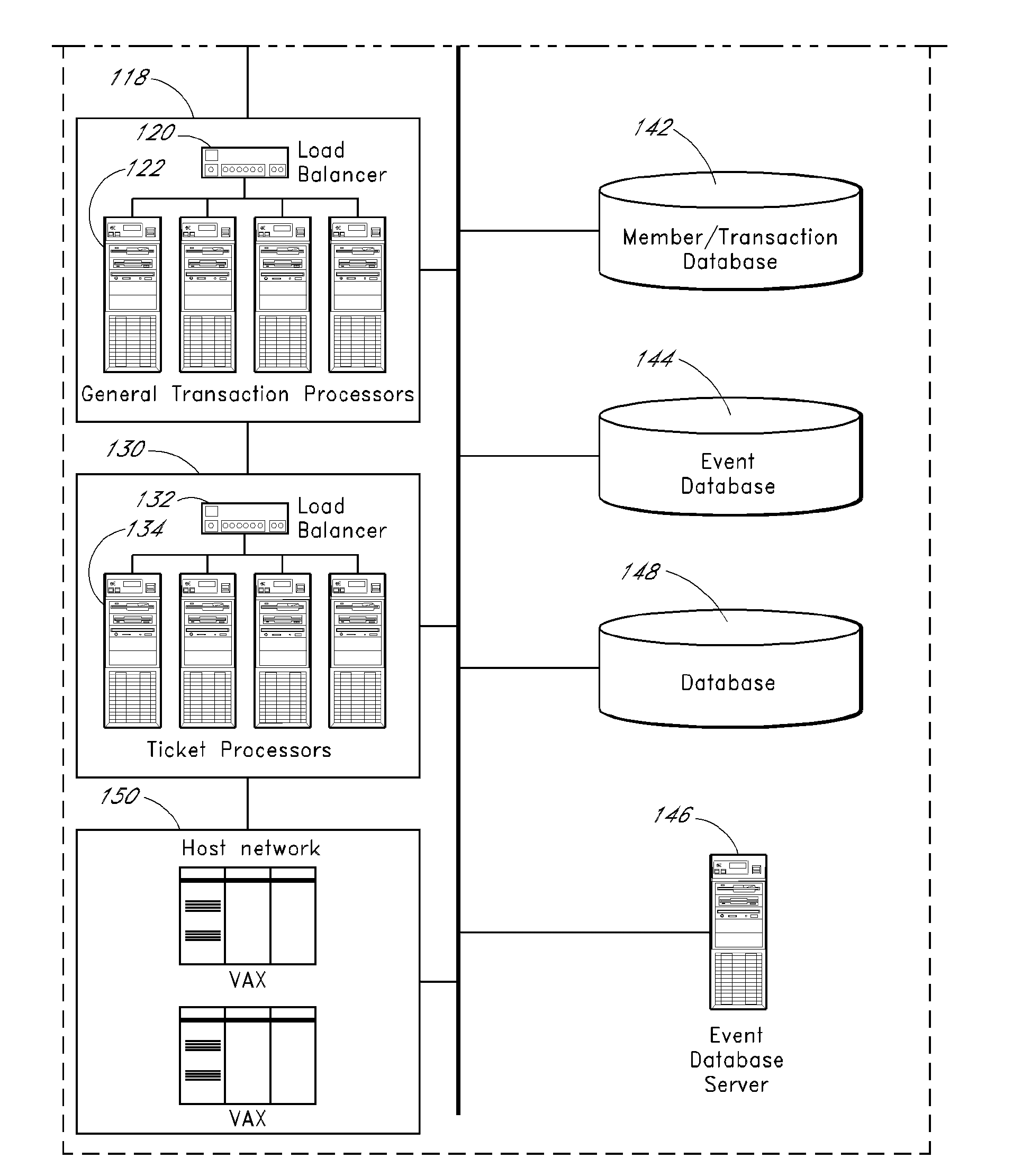
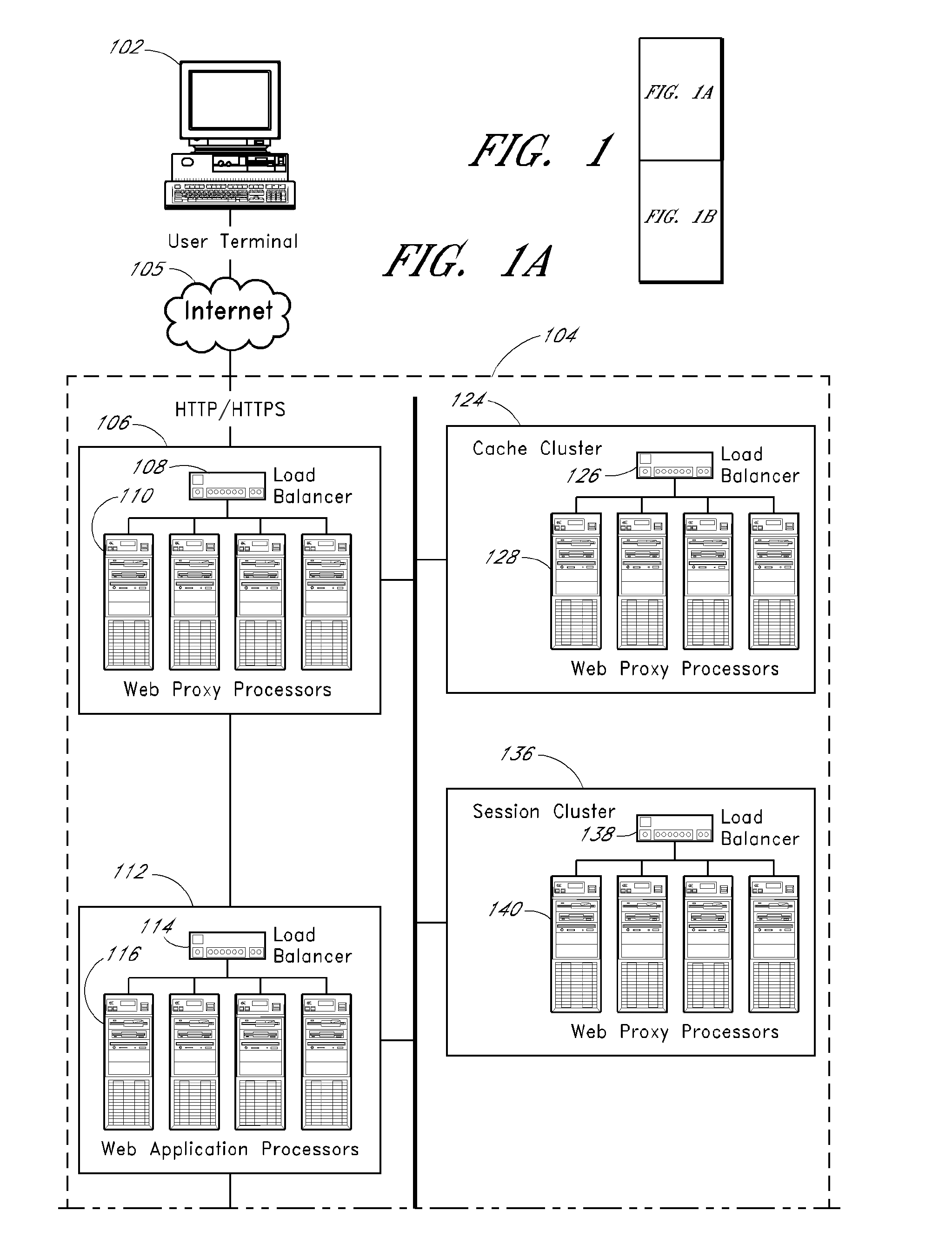
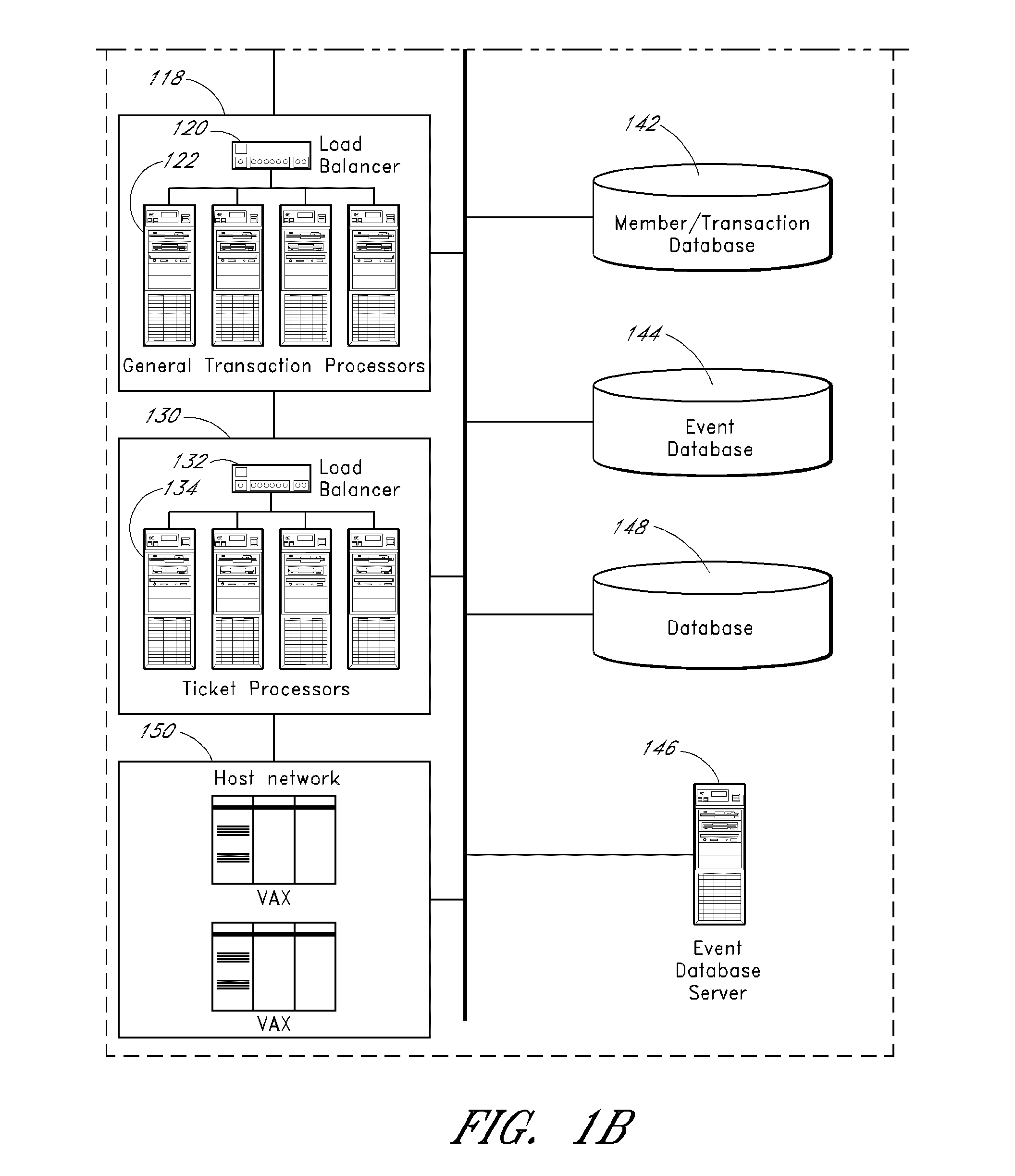
Methods and systems for allocating resources, such as computer controlled resources, in a networked system are described. An example system includes a network interface, an item database, a load balancer, a web proxy processor configured to selectively block or route an inbound user browser request, a cache cluster system configured to cache data and states for access by other system components, and program code stored in computer readable memory configured to store a session identifier on a user terminal associated with a user browser, process an item acquisition request from the user browser while the browser is accessing a first website, transmit to the browser an indication that the acquisition request is accepted if the acquisition request meets a predefined criterion, if the acquisition request is accepted then automatically transmit to the browser an offer to transfer the item to another, use the session identifier for identification, and determine if a transfer instruction has been received from the browser.
Owner:LIVE NATION ENTERTAINEMENT INC
Rules-based transaction prefetching using connection end-point proxies
ActiveUS7853699B2Increase speedReduce latencyMultiple digital computer combinationsTransmissionApplication softwareClient-side
Owner:RIVERBED TECH LLC
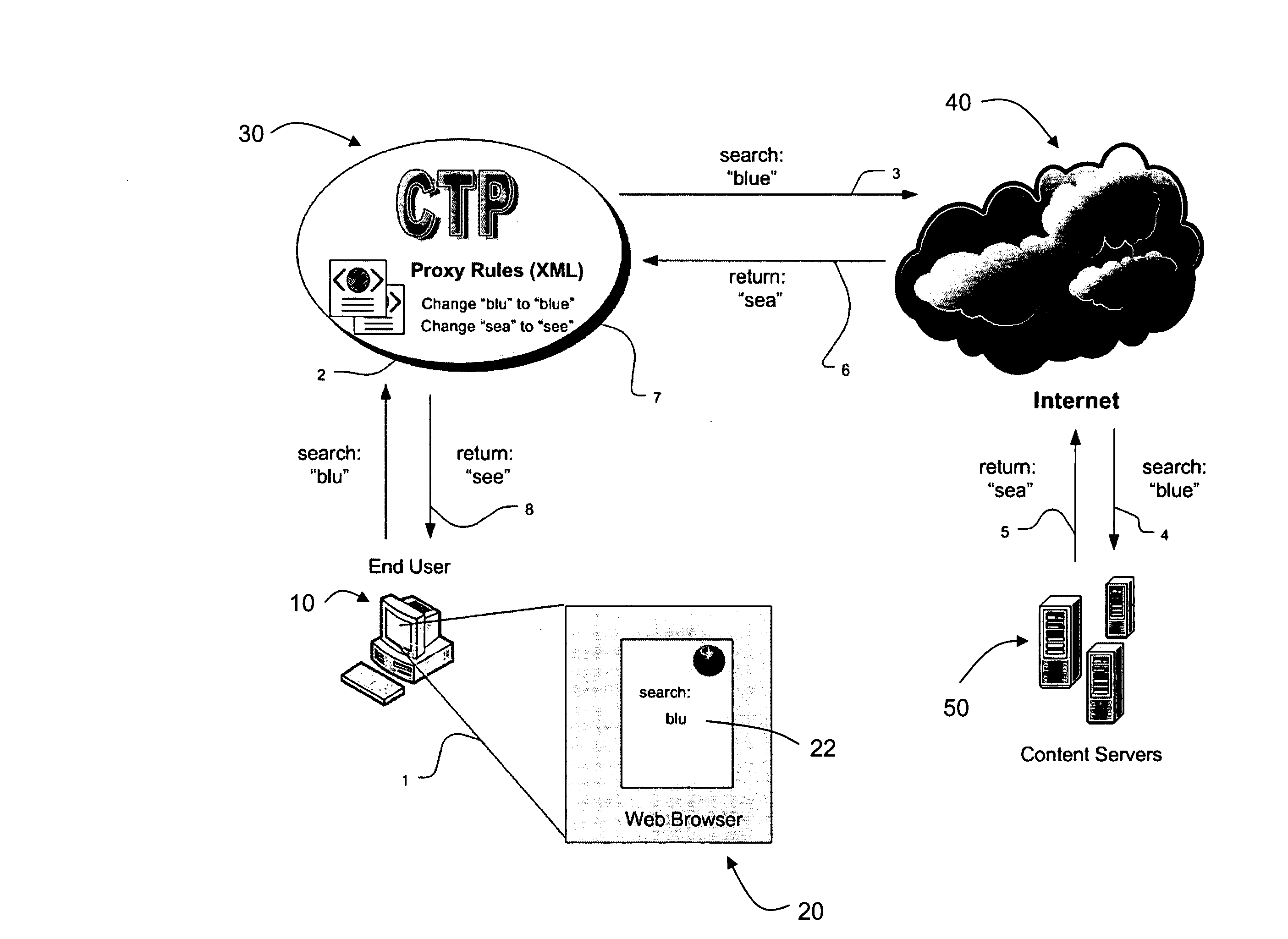
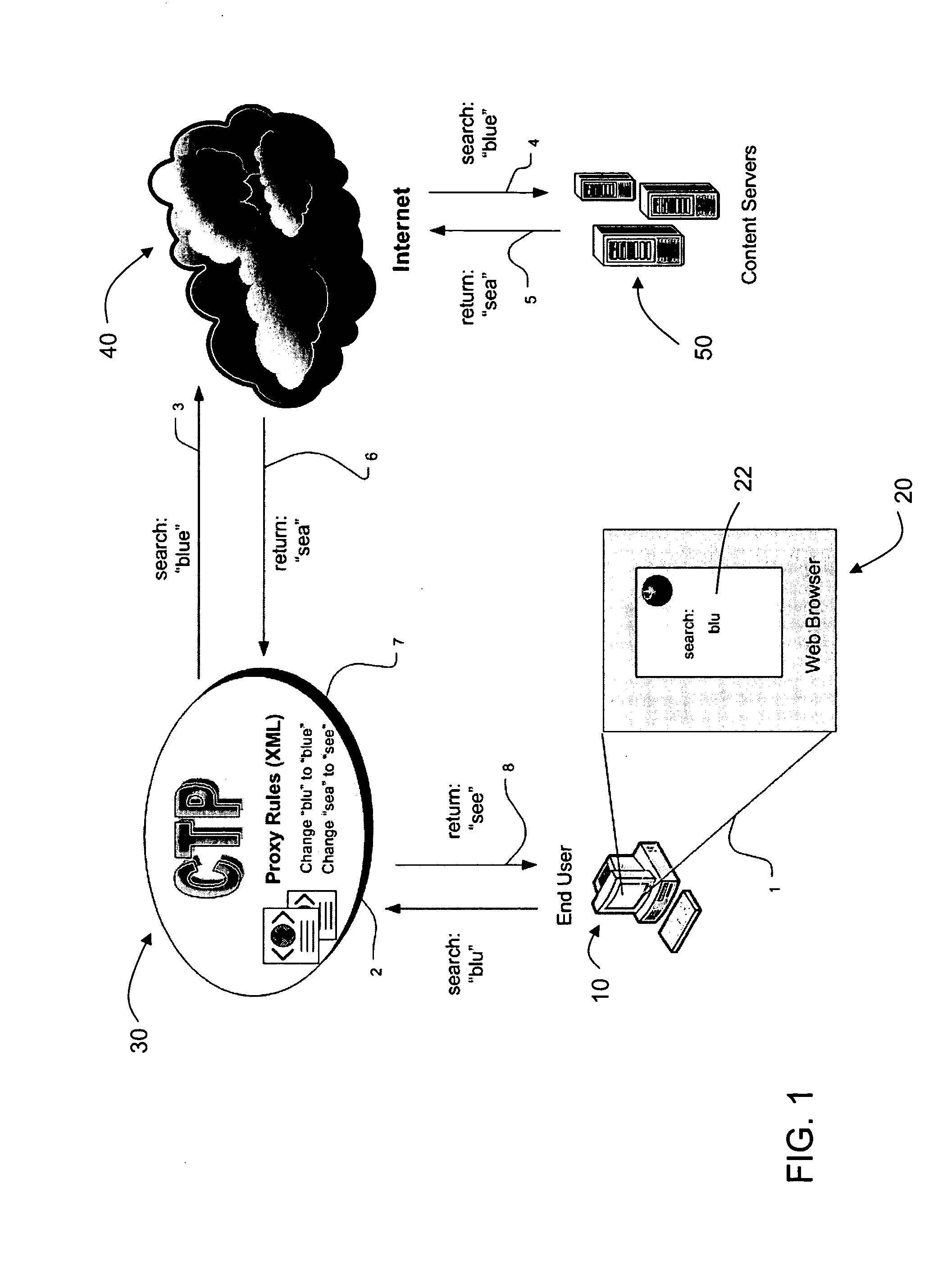
Content transform proxy
InactiveUS20080183902A1Computer security arrangementsMultiple digital computer combinationsWeb browserClient-side
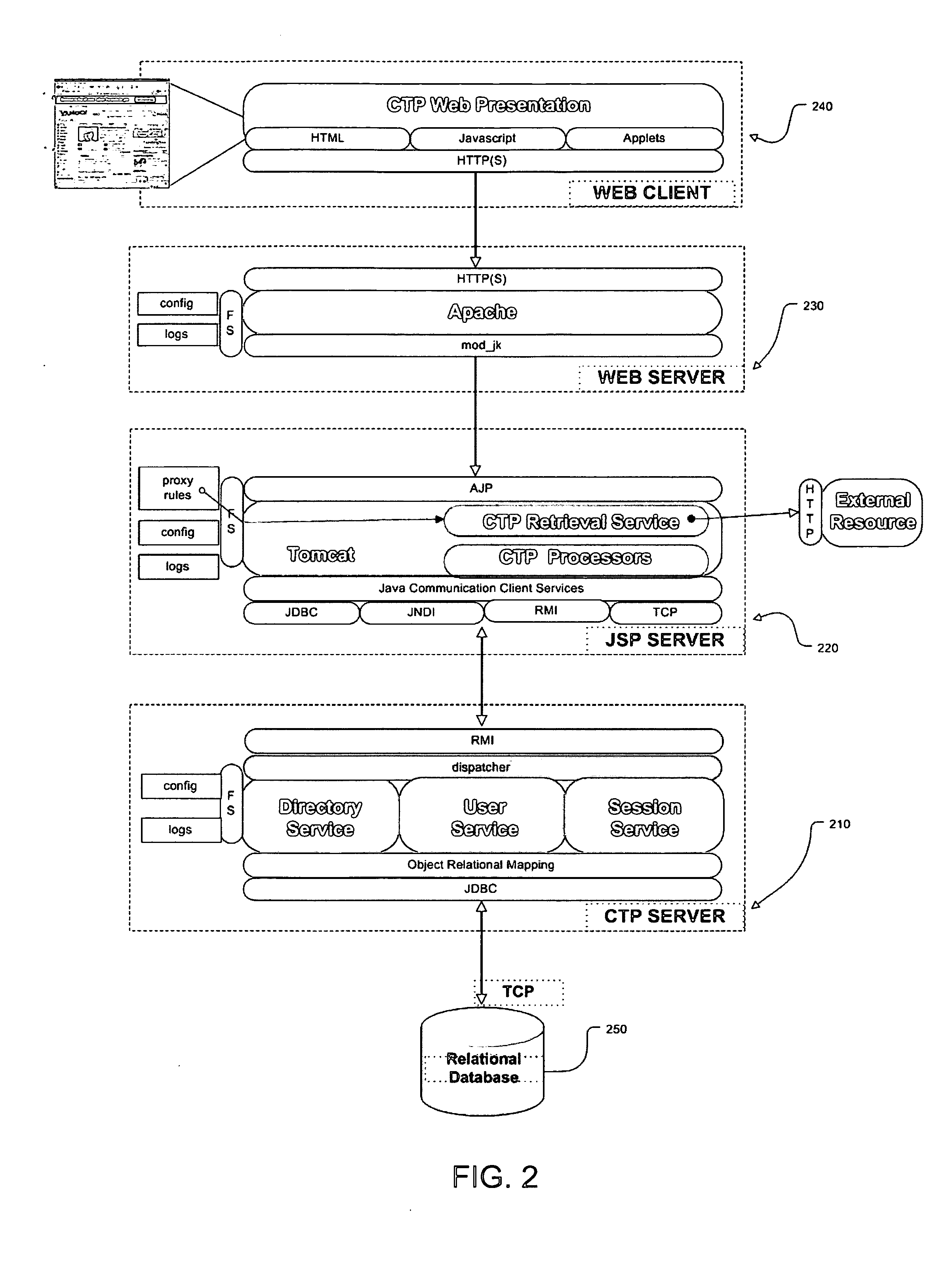
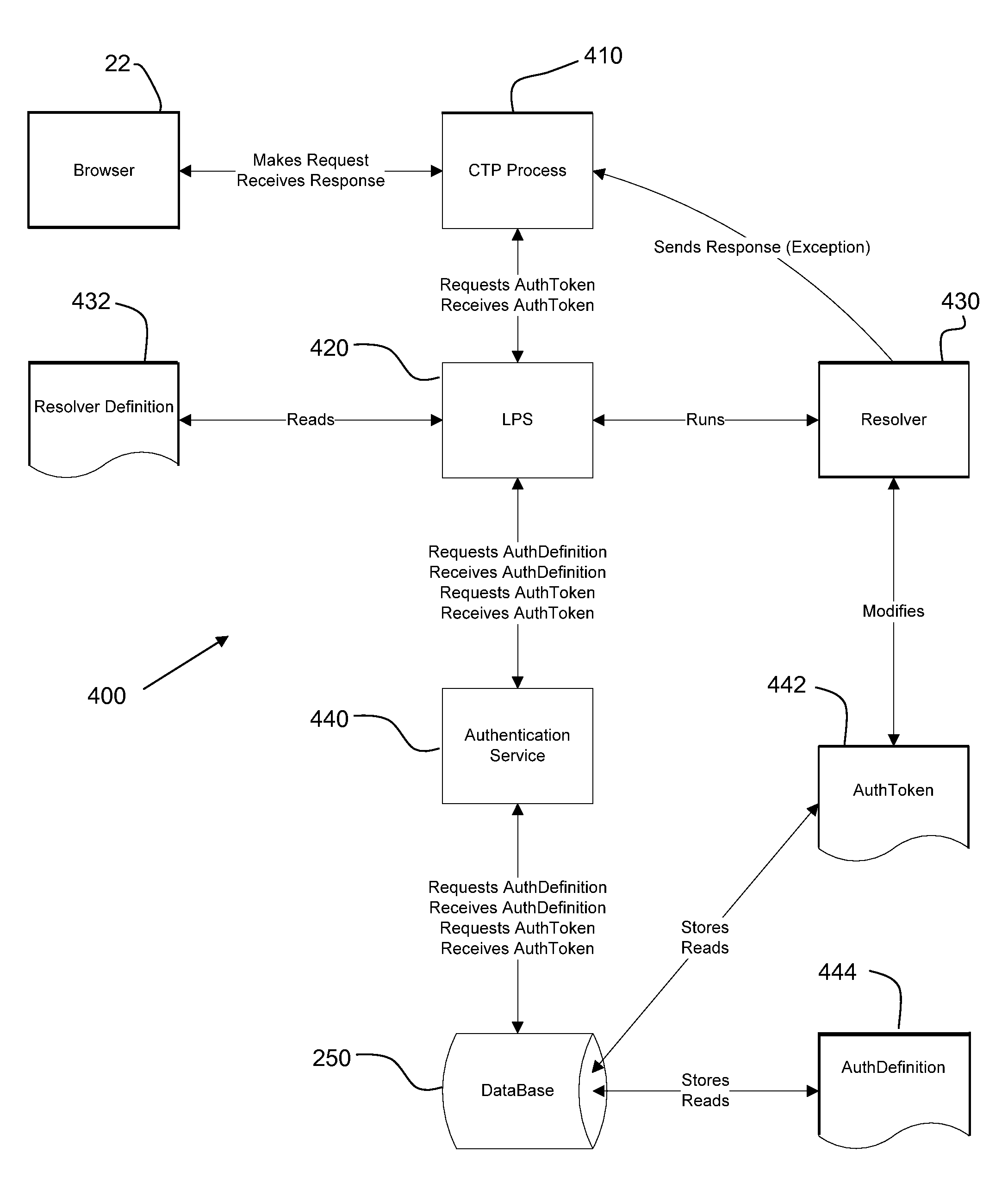
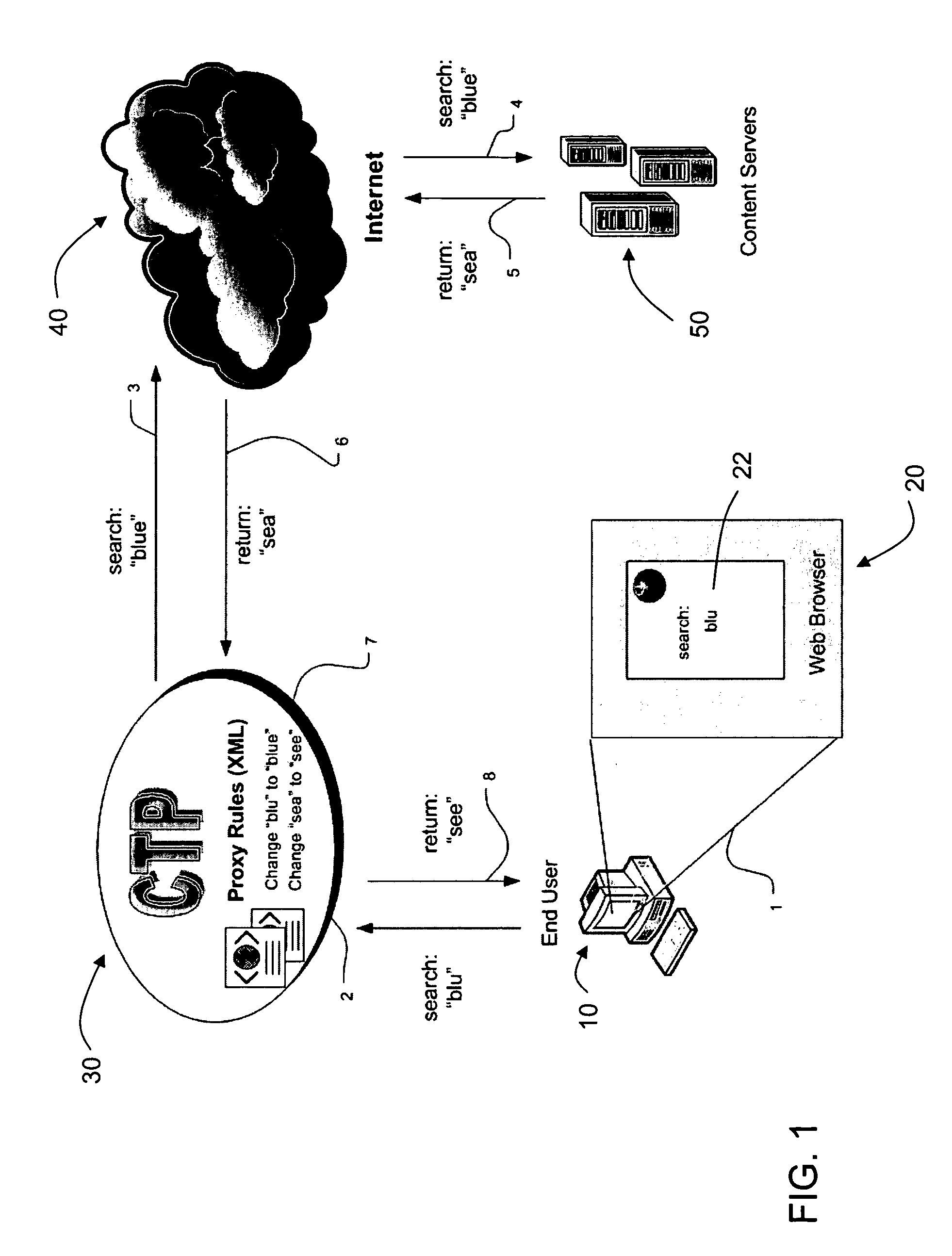
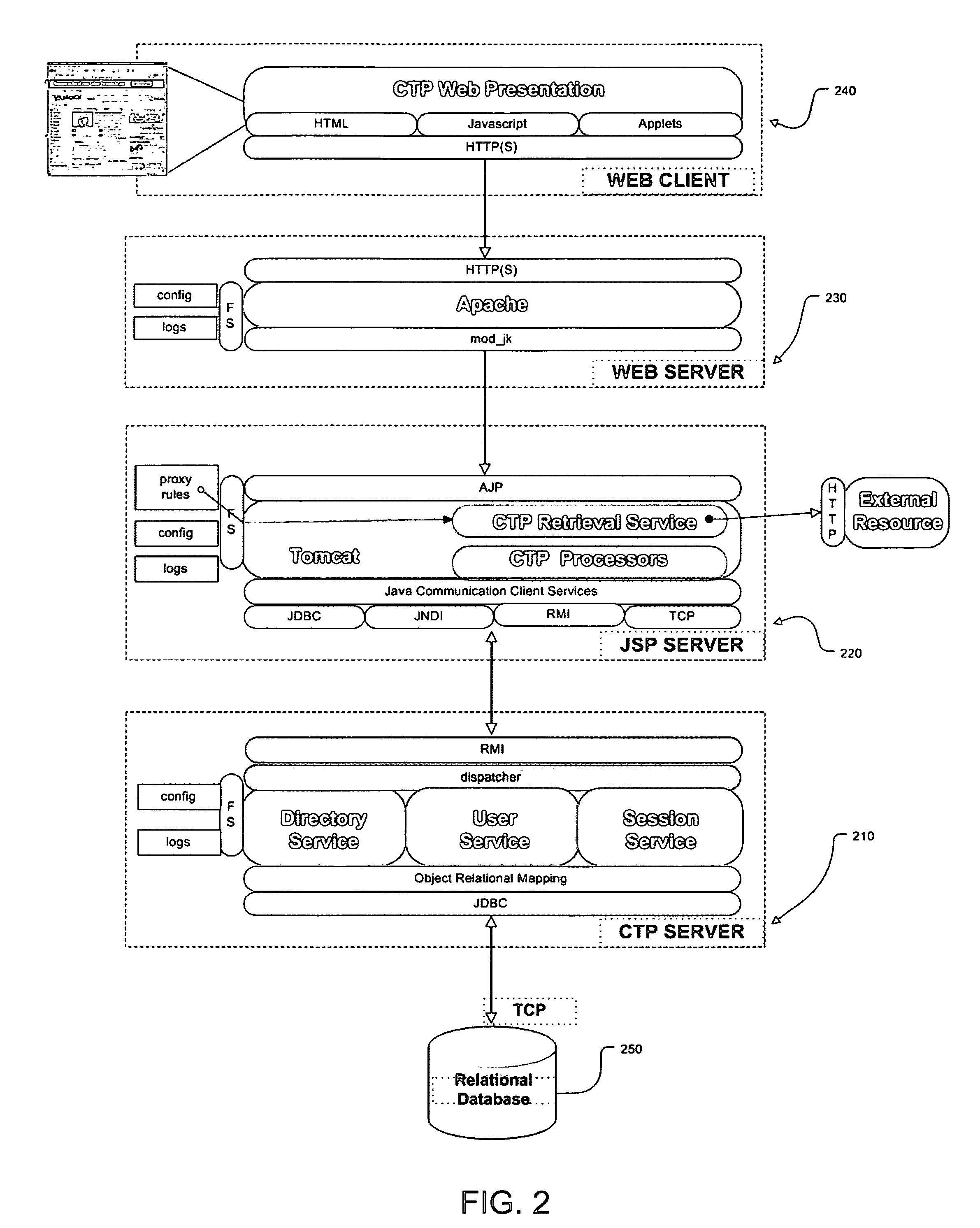
The Content Transform Proxy (CTP) service is an advanced Web proxy service, the basic function of which is to modify incoming HTTP requests having a server-side destination and / or outgoing HTTP responses. The CTP service is implemented by the CTP program, which resides on a host in a data communications network between an end user (the Web client) and a content server that the client is attempting to access. The HTTP request and / or an HTTP response is modified by making an HTTP request on the client side using a client web browser, processing the HTTP request on the server side using outgoing proxy rules, passing on the processed HTTP transaction to the server-side destination, returning the results of the processed HTTP request from the server-side destination, processing the HTTP response on the server side using incoming proxy rules, and returning the processed HTTP response to the client web browser on the client side.
Owner:FGM
Computer network security system employing portable storage device
ActiveUS7228438B2Easy to useRaise security concernsUser identity/authority verificationUnauthorized memory use protectionUniform resource locatorClient machine
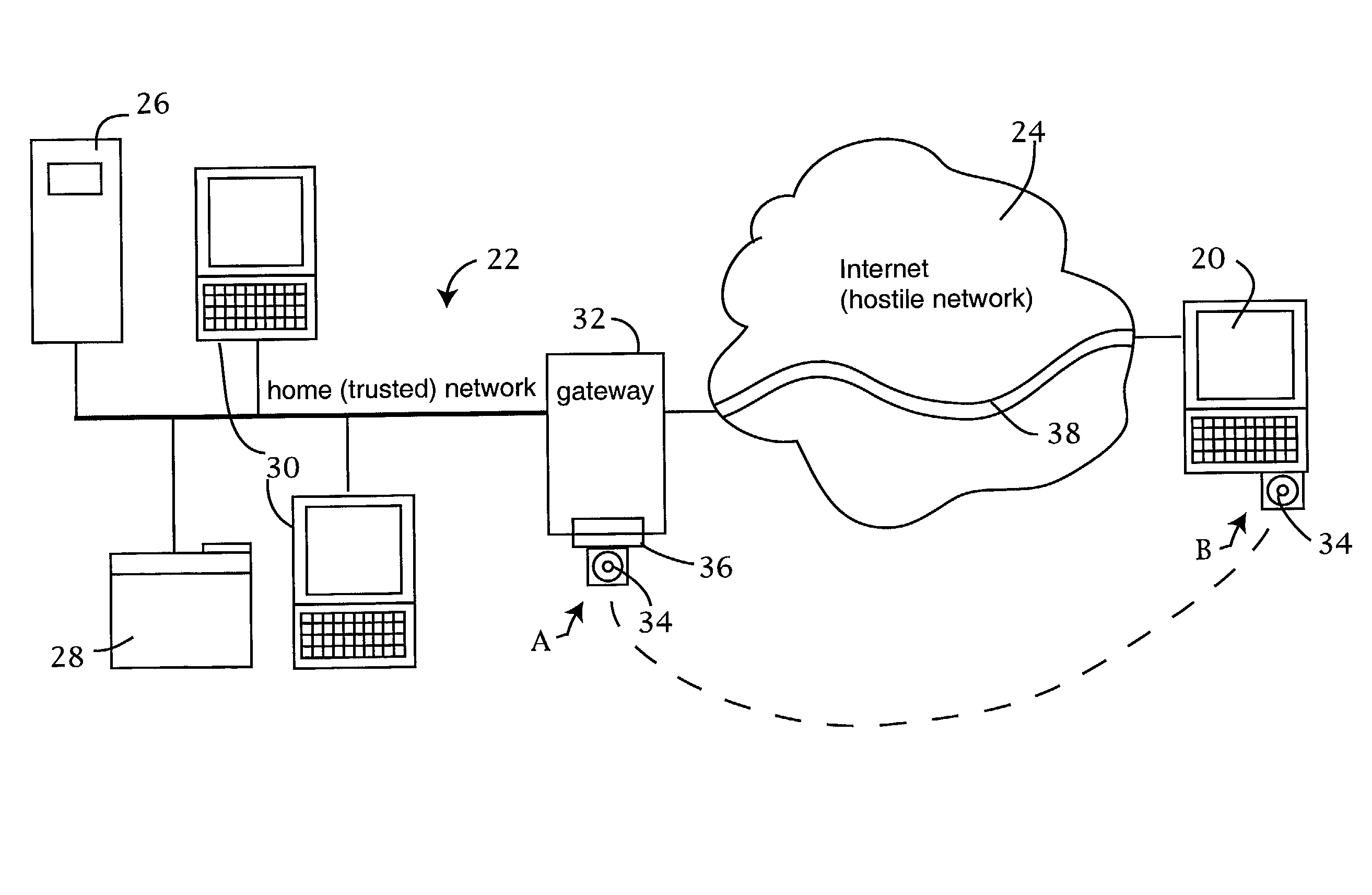
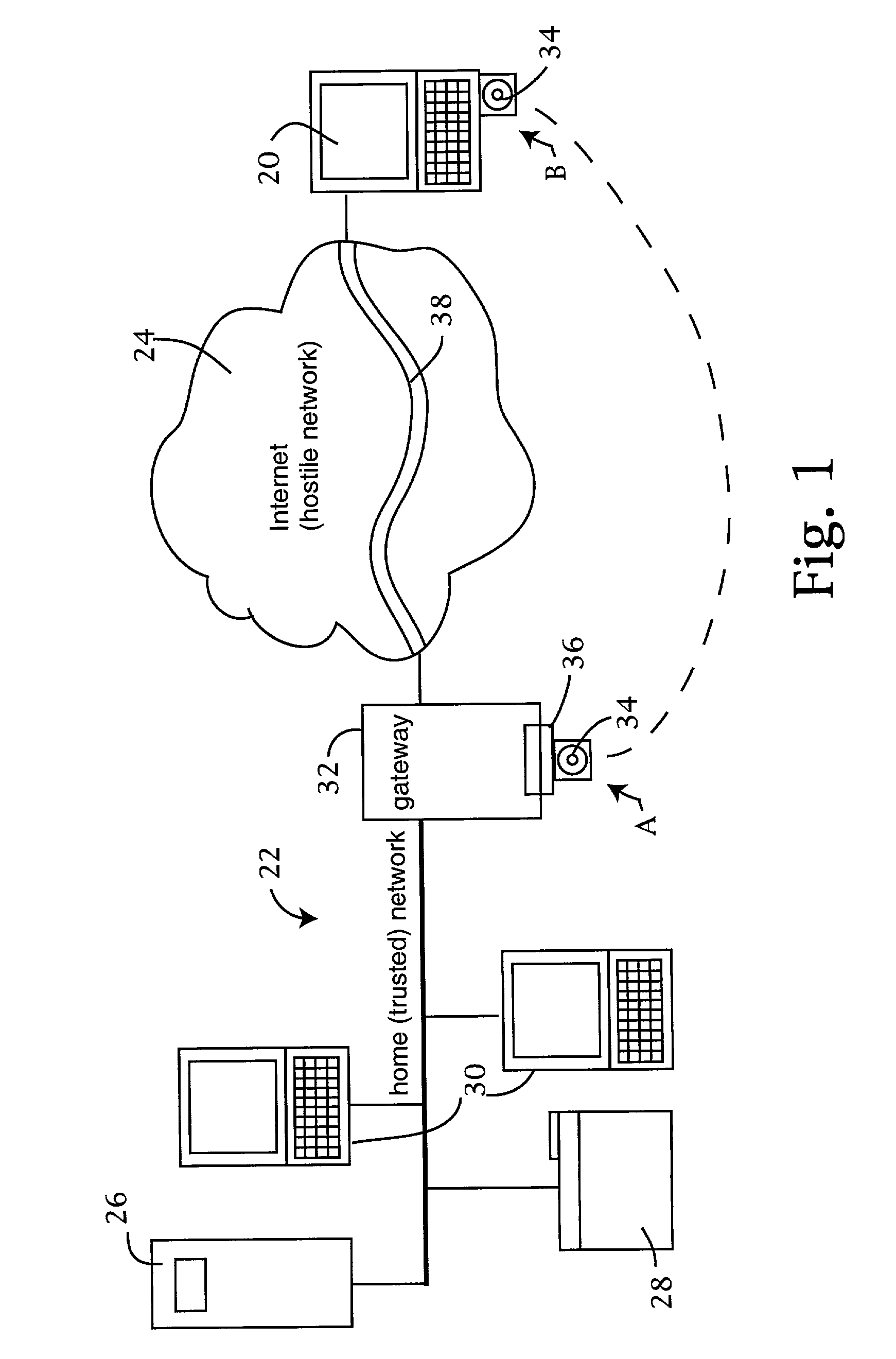
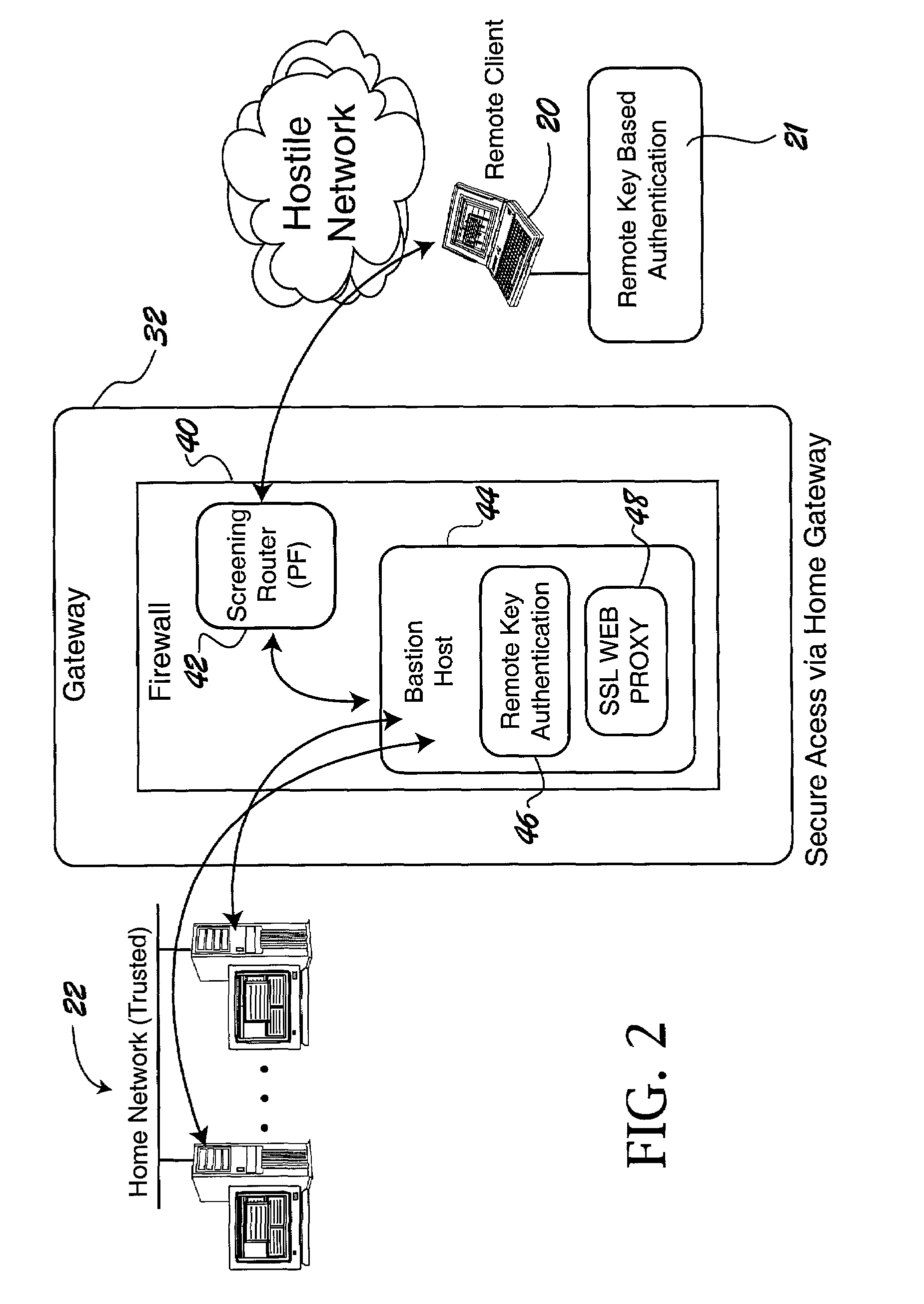
The trusted computer network is protected behind a gateway that includes a bastion host and screening router which blocks all URLs associated with the trusted network. The bastion host includes a remote client authentication mechanism and web proxy component that verifies and translates incoming URL requests from authenticated remote clients. Authentication is performed using one-time passwords that are stored on a portable storage device. The user configures the portable storage device by operating configuration software from the protected side of the gateway. The portable storage device also stores plug-in software to enable the client computer to properly retrieve the one-time password and exchange authentication messages with the bastion host. Further security is obtained by basing the one-time password on an encrypted version of the user's PIN. A symmetric key used to encrypt the PIN is stored in a protected area within the portable storage device.
Owner:SOVEREIGN PEAK VENTURES LLC
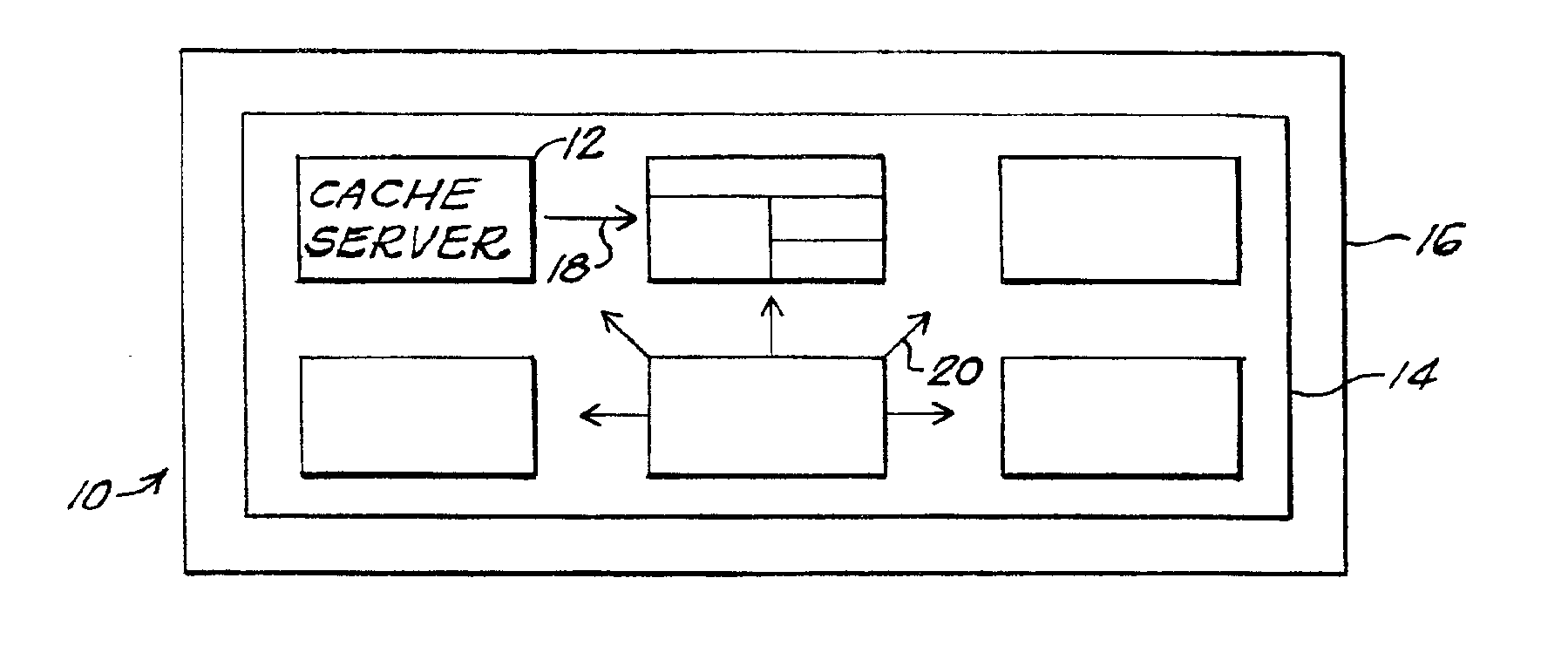
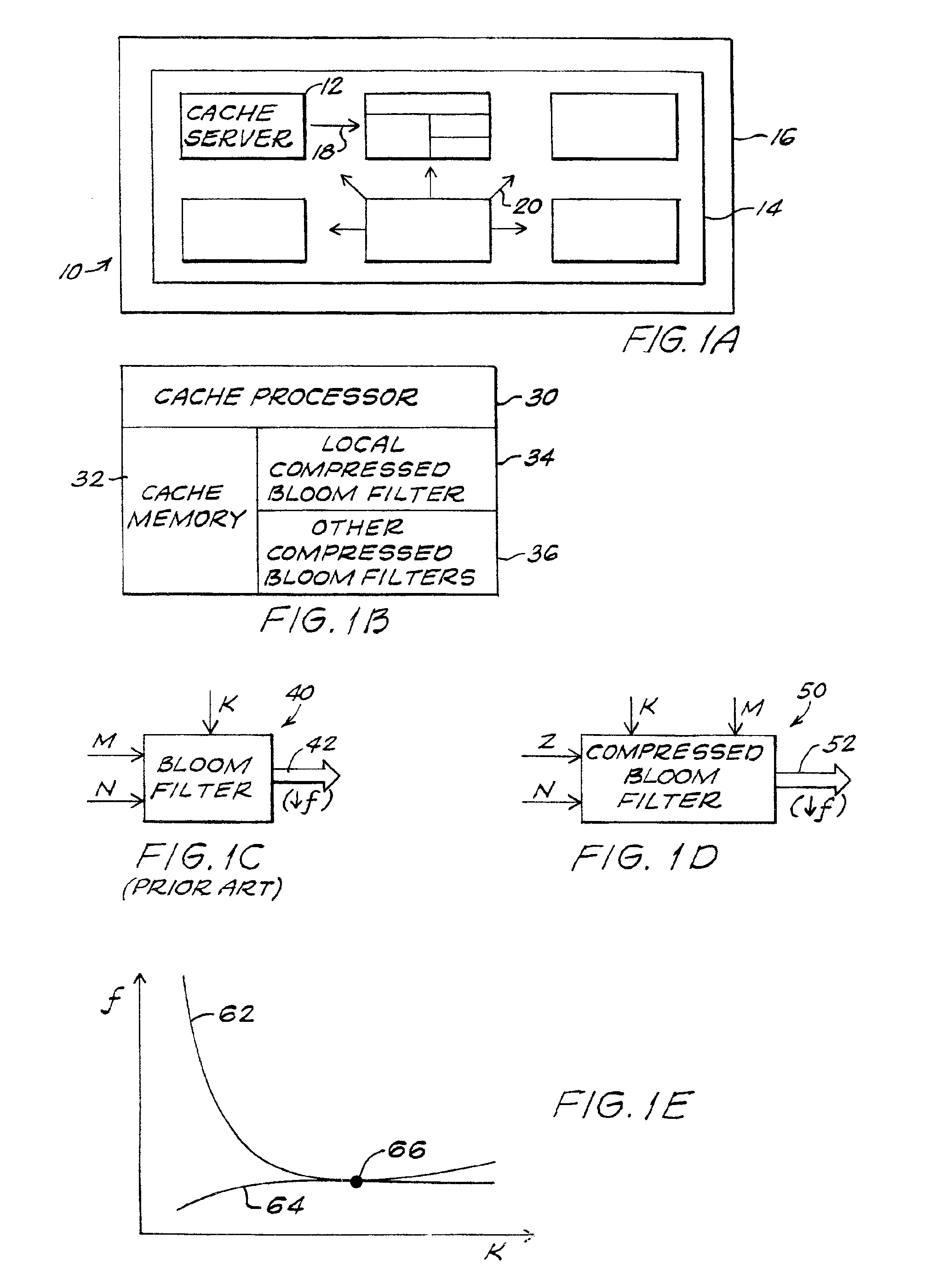
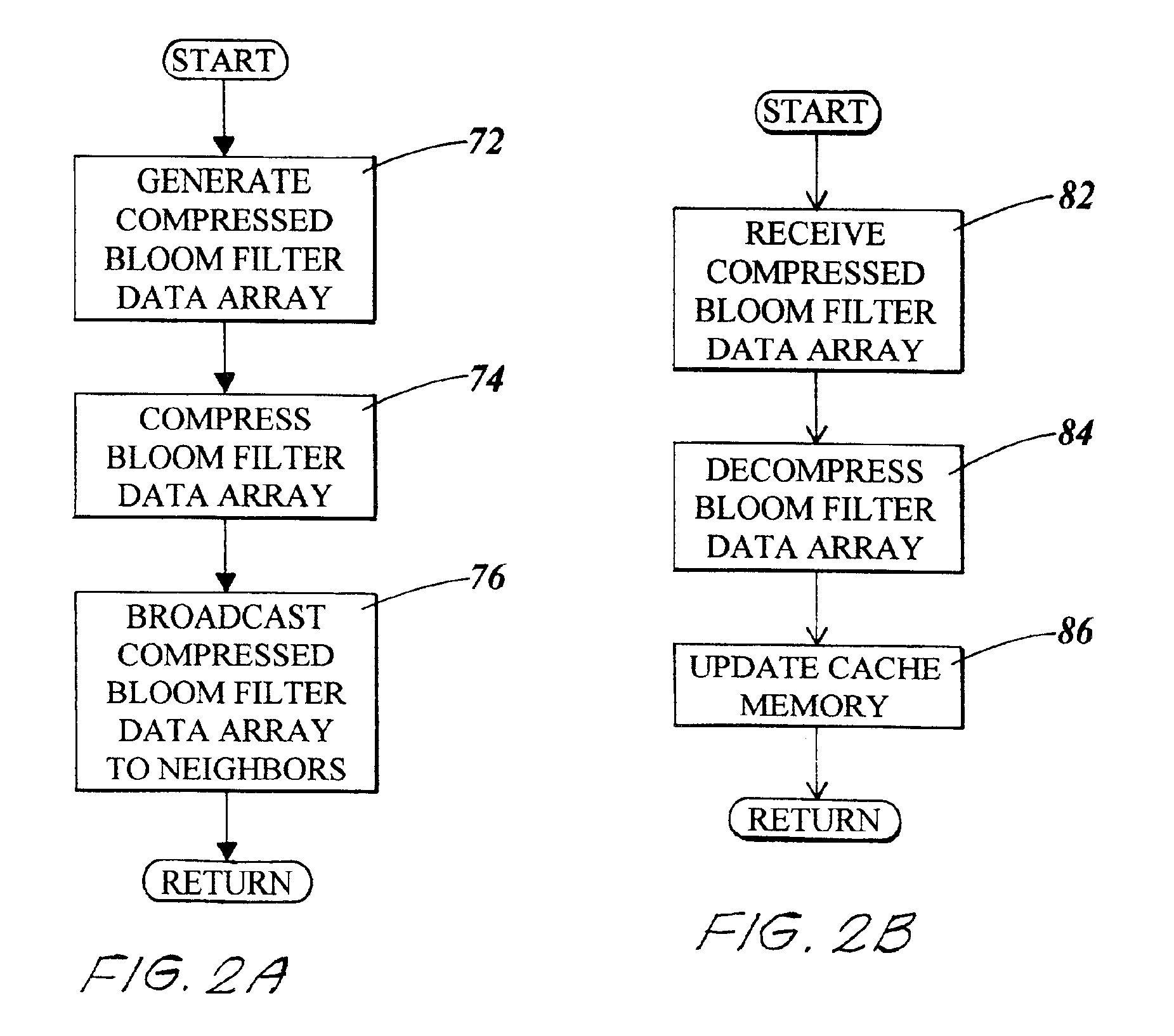
Distributed, compressed Bloom filter Web cache server
InactiveUS6920477B2Minimizing rateReduce false alarm rateData processing applicationsMultiple digital computer combinationsArray data structureWeb cache
Compressed Bloom filters that act as a message as well as a data structure provide smaller false positive rates, reduced bits broadcast and / or reduced computational overhead in distributed Web proxy servers and other distributed networks.
Owner:BREED AUTOMOTIVE TECH INC +1
Method for remote access to intranet Web server and Web proxy server
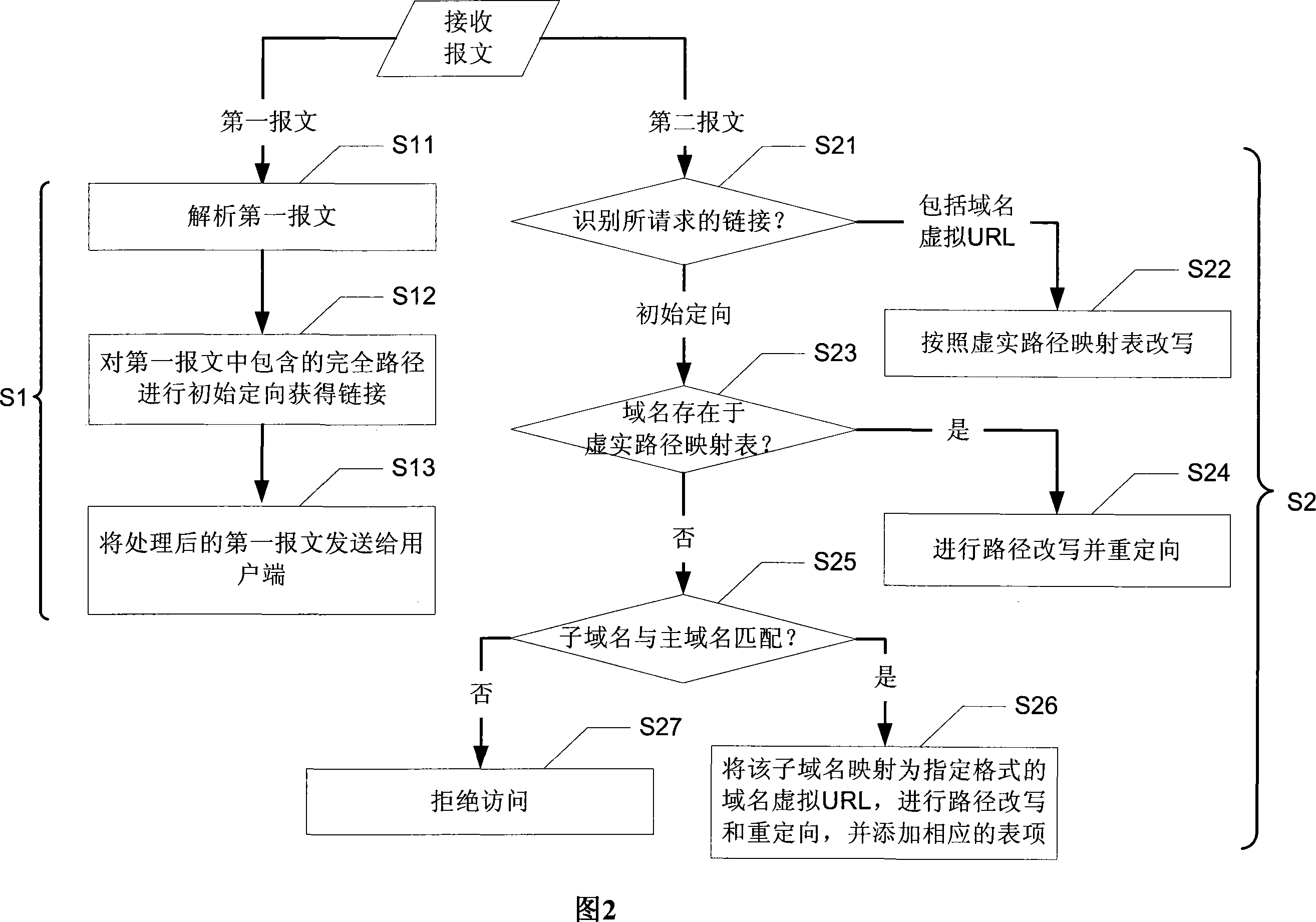
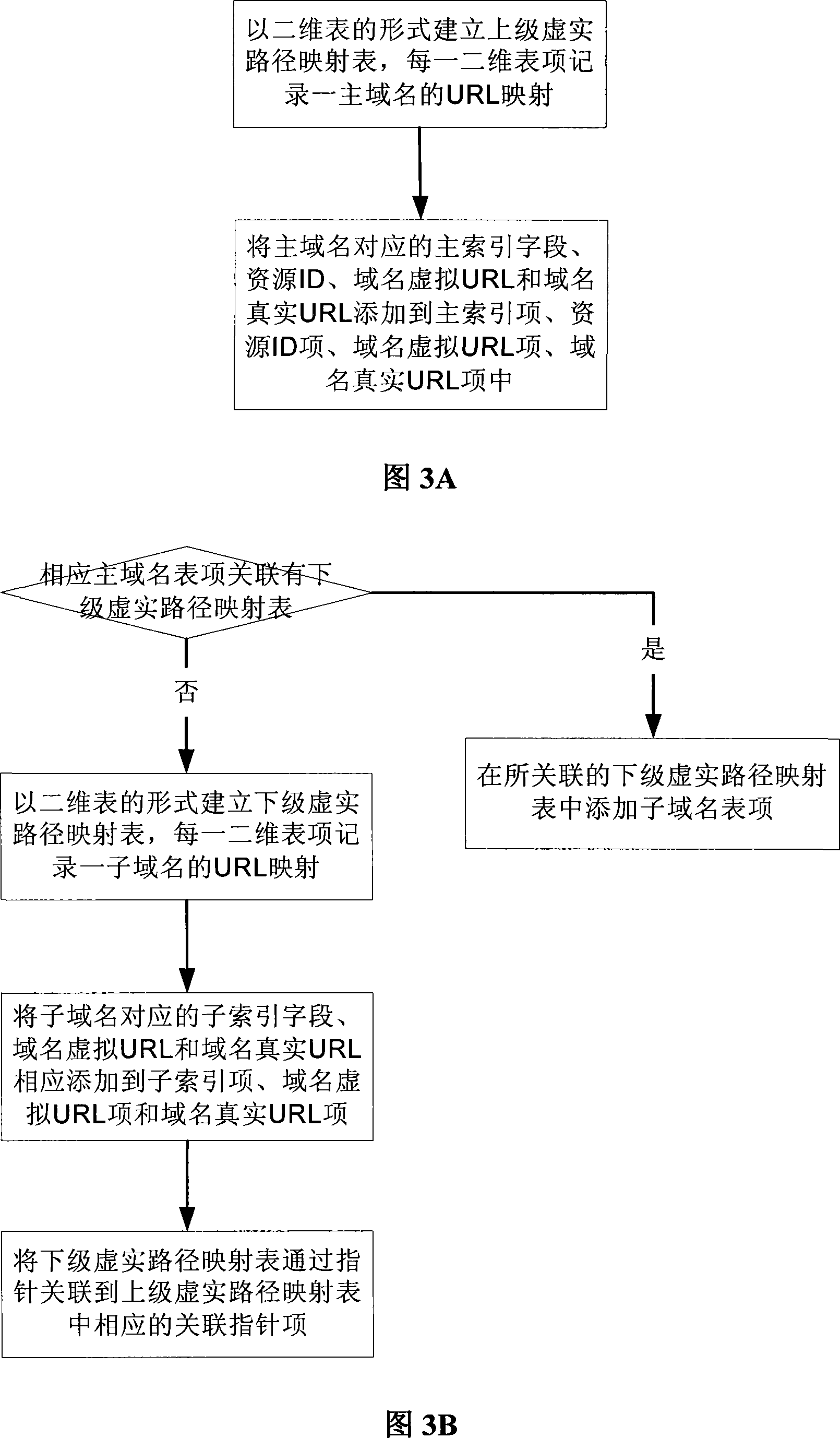
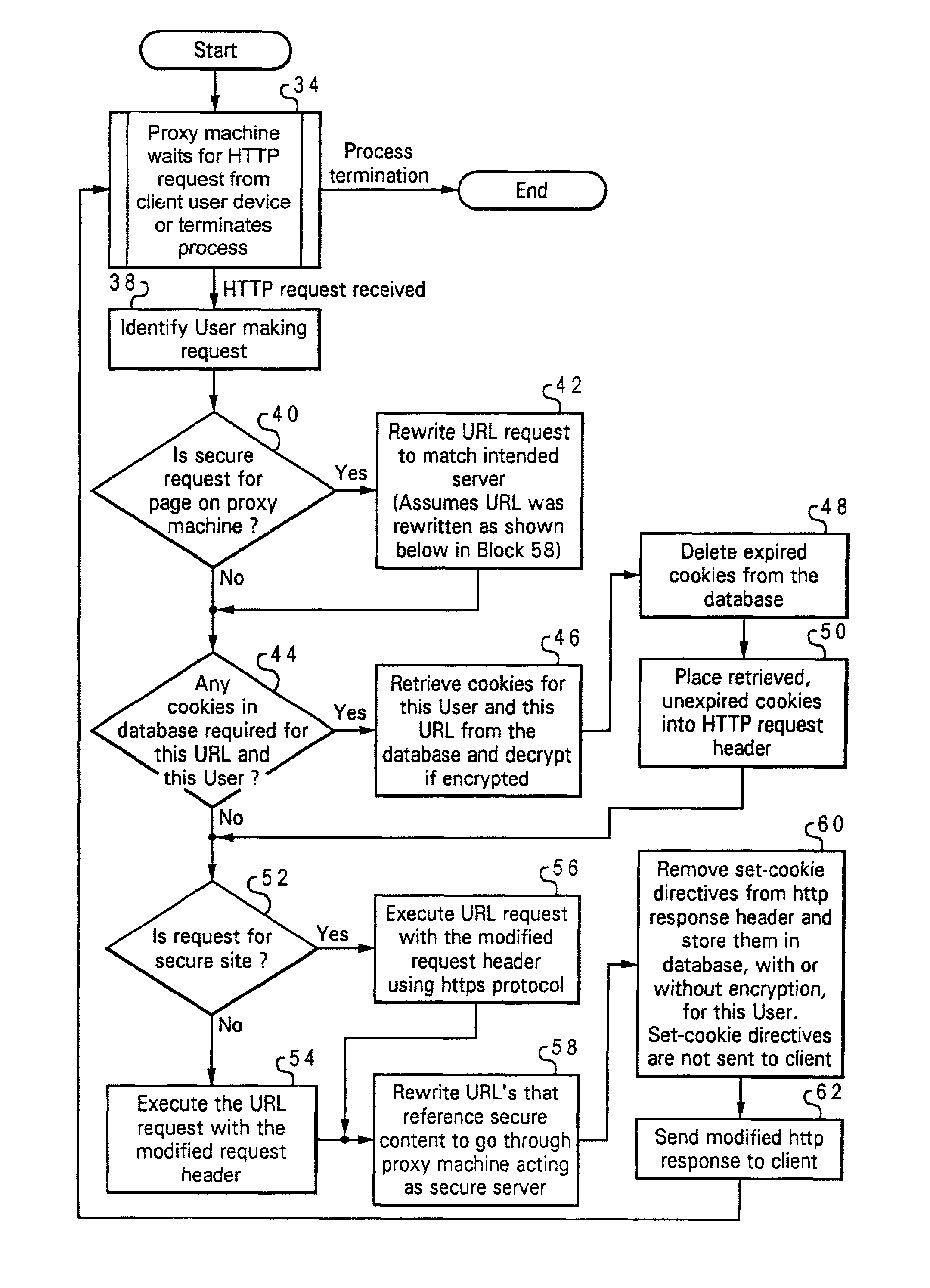
ActiveCN101242336AAvoid confusionRealize differentiated rewritingNetworks interconnectionDomain nameWeb service
The invention discloses a method for remote accessing intranet web server, a web proxy server gateway executes the steps: initially orienting a complete path contained a first message sent to the user terminal by a web server to obtain a link; carrying out a rewrite from domain name virtual URL to a domain name real URL for a second message sent to the user terminal by a web server, or extracting the domain name from a initial orienting complete path to directly perform a reorienting or perform a specified format virtual URL mapping and reorienting for a sub domain name when a preset fuzzy policy match succeeds. The invention also discloses a web proxy server. The invention can avoid a Cookie confusion of a user terminal, increases processing efficiency of the web proxy server, and reduce a processing cost of the system.
Owner:NEW H3C TECH CO LTD
Application prioritization in a stateless protocol
InactiveUS20040006602A1Multiple digital computer combinationsSecuring communicationTraffic capacityBalancing network
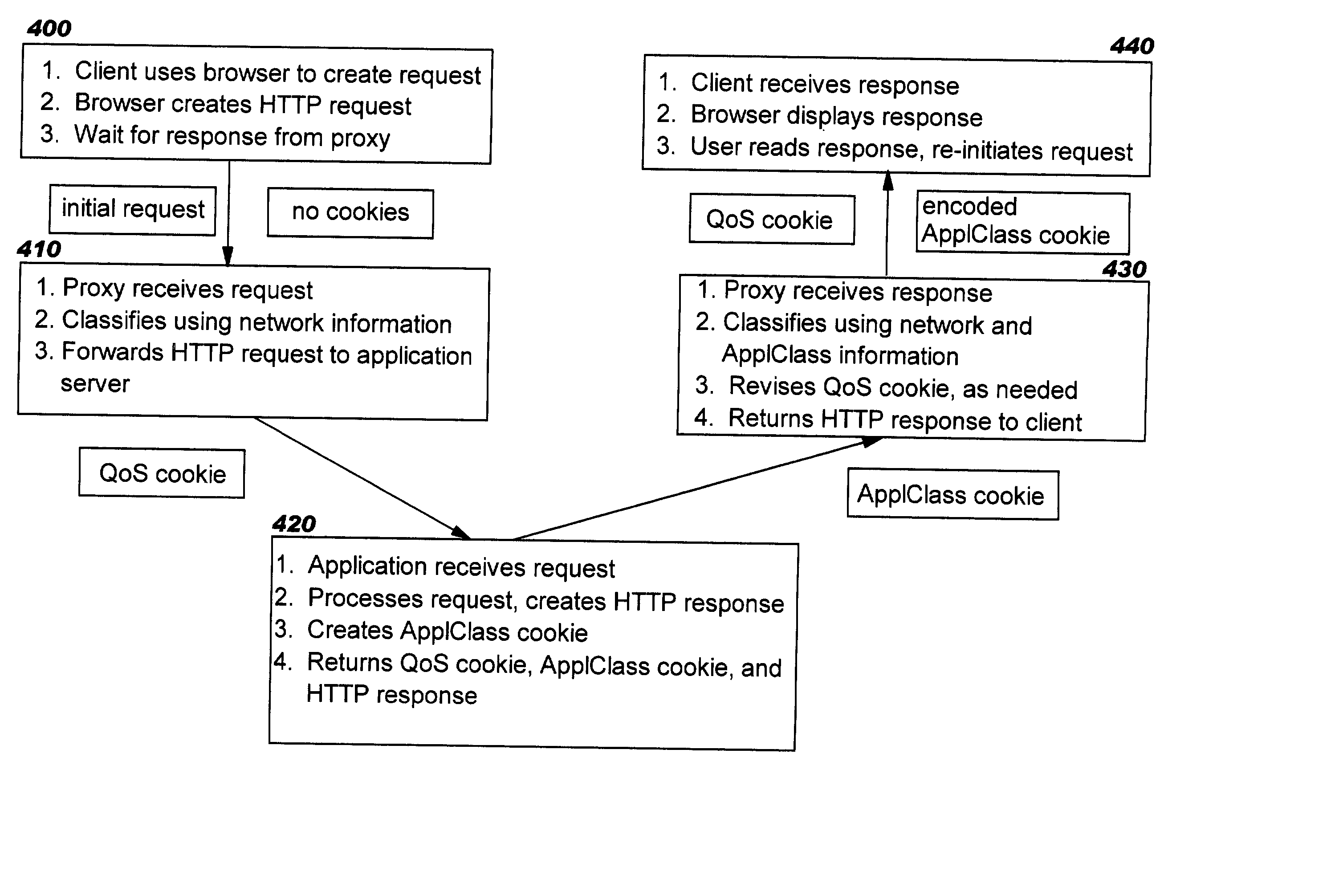
Techniques are disclosed that enable an application to prioritize its traffic in an application-specific manner, such that traffic which is most important to this application can be prioritized over traffic that is less important to this application, where this prioritization information is reflected in differential treatment of the traffic within the network. An application conveys relative priority information for its traffic to a Web proxy or edge server, and this device then consults stored policy information to determine how the traffic should be prioritized in the network. The Web proxy also ensures that usage of network resources is balanced among multiple applications. Cookies are used for transmitting priority information between the edge server and application in an efficient manner.
Owner:IBM CORP
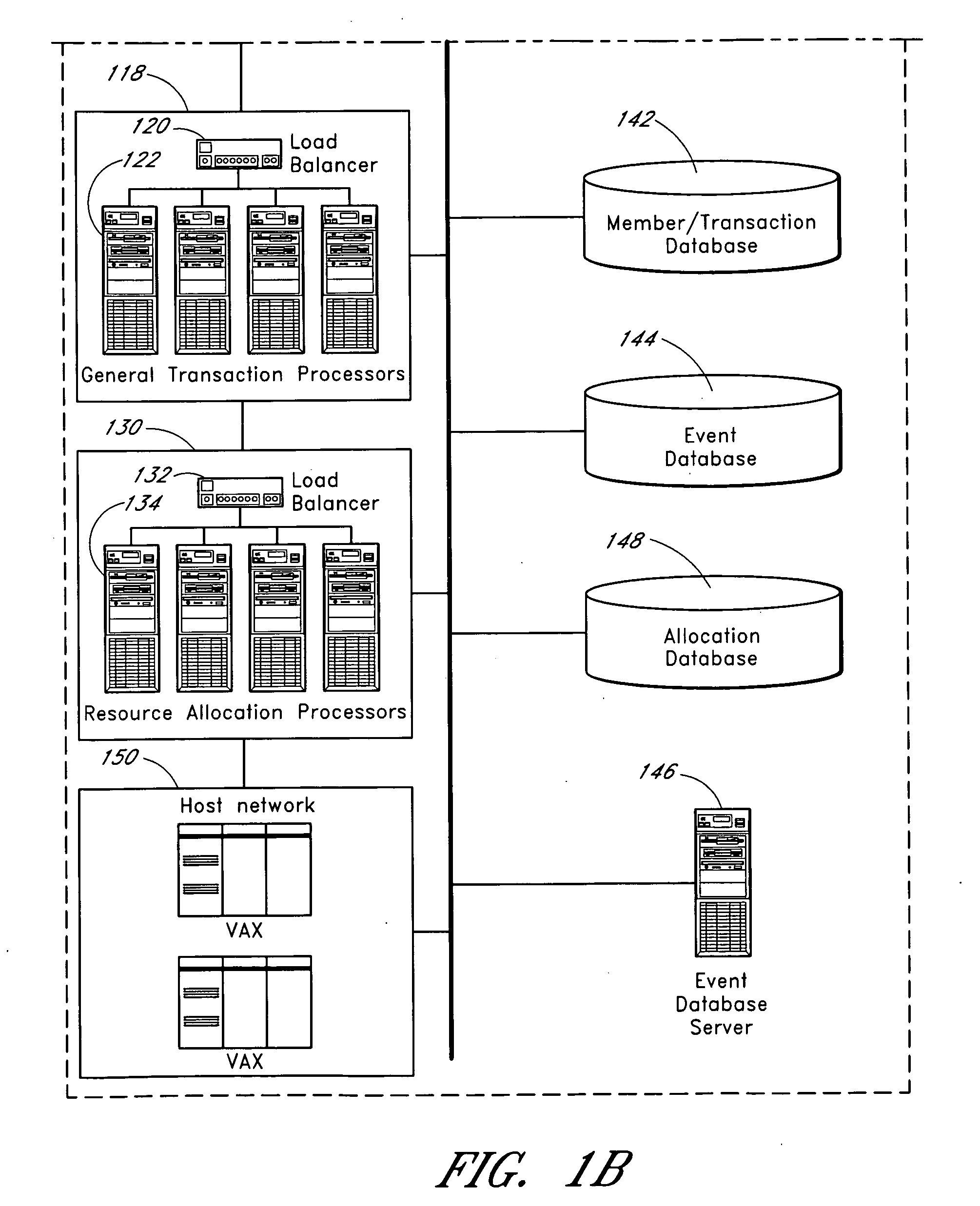
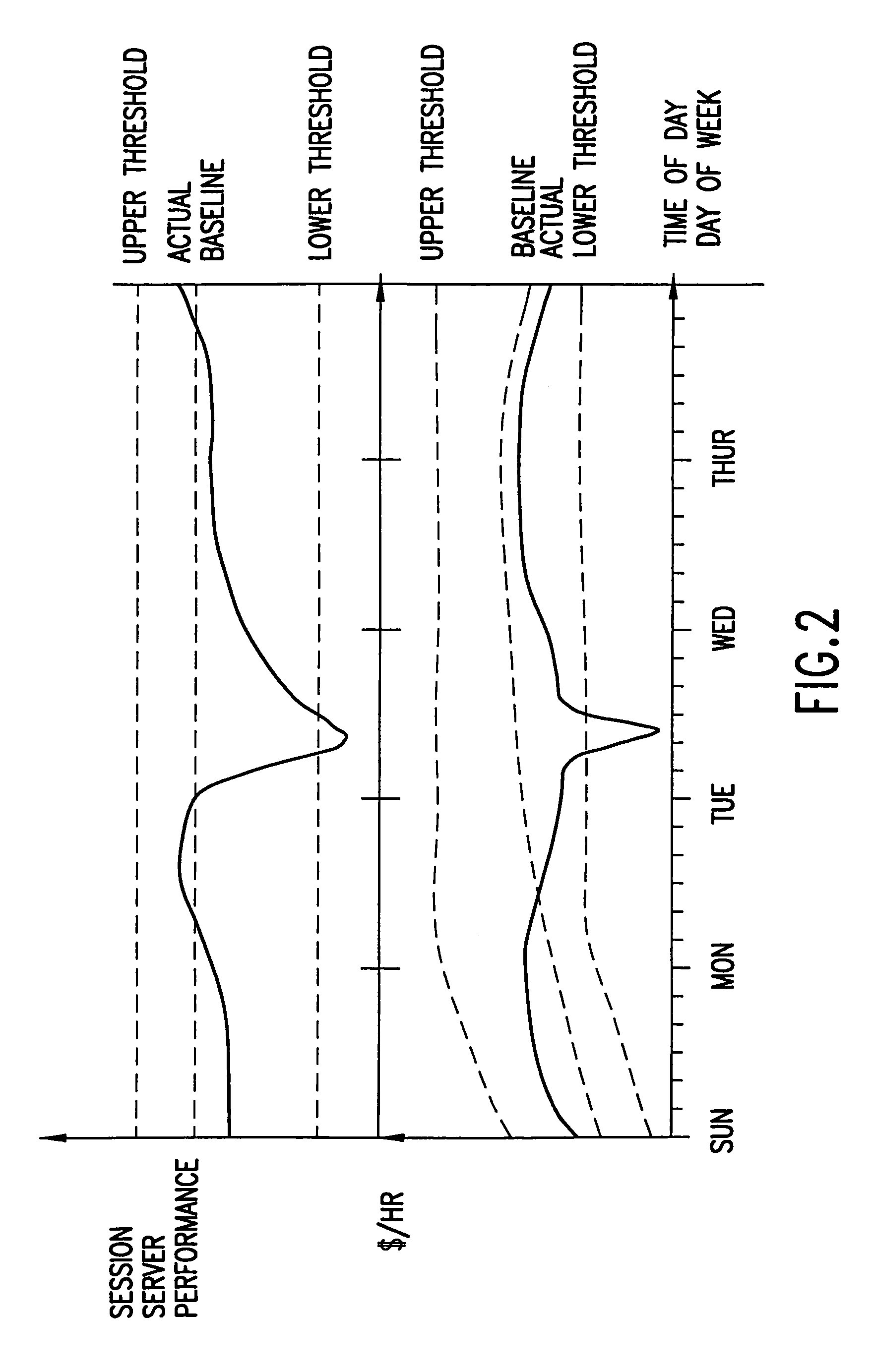
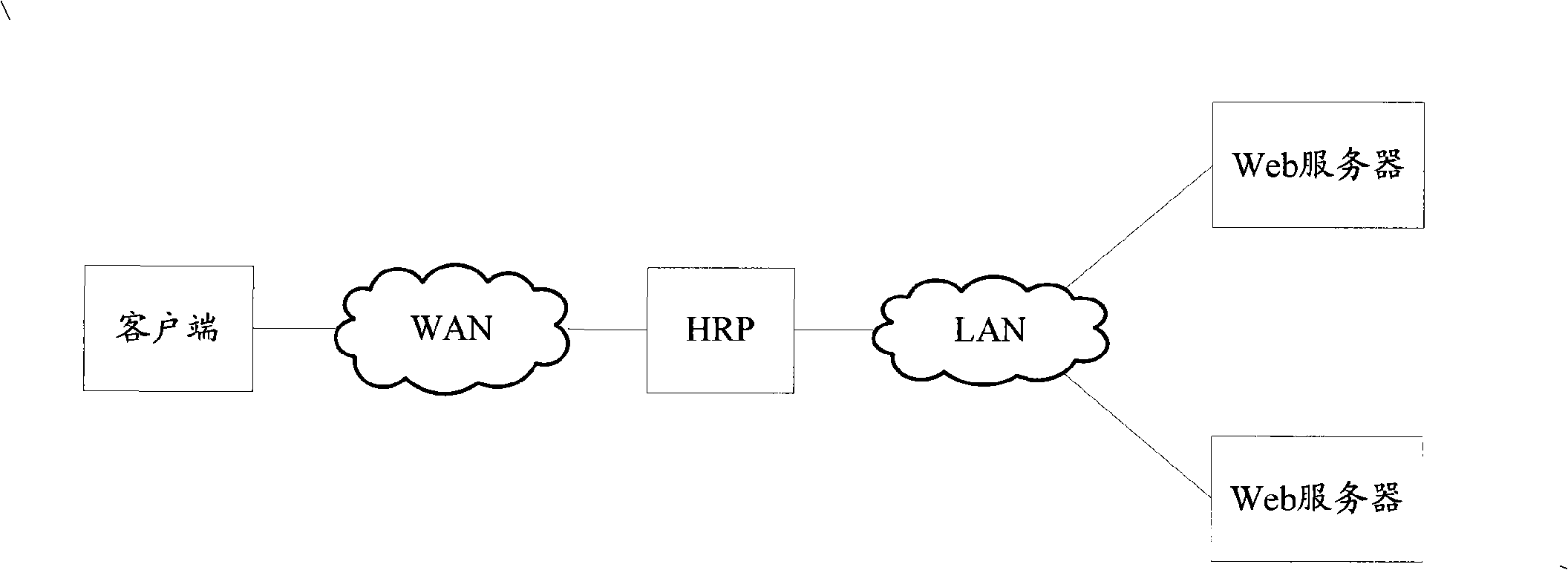
Process control system
A computer system configured to provide process control is described herein. The computer system optionally includes a web proxy system, including a load balancer, and a cache cluster. An interface is configured to receive a user search query. A search engine is configured to receive the user query and to identify one or more corresponding events. An interface is configured to display identified events to the user and to receive a user selection of a first event. A data store is configured to store item requests received from a plurality of users for the first event, including corresponding request timing data. An optional servo system is configured to suggest an assignment of items with respect to the first event based at least in part on the number of prior item requests and corresponding request timing data.
Owner:LIVE NATION ENTERTAINEMENT INC
Method of authentication processing during a single sign on transaction via a content transform proxy service
InactiveUS7647404B2Computer security arrangementsMultiple digital computer combinationsWeb browserClient-side
The Content Transform Proxy (CTP) service is an advanced Web proxy service, the basic function of which is to modify incoming HTTP requests having a server-side destination and / or outgoing HTTP responses. The CTP service is implemented by the CTP program, which resides on a host in a data communications network between an end user (the Web client) and a content server that the client is attempting to access. The HTTP request and / or an HTTP response is modified by making an HTTP request on the client side using a client web browser, processing the HTTP request on the server side using outgoing proxy rules, passing on the processed HTTP transaction to the server-side destination, returning the results of the processed HTTP request from the server-side destination, processing the HTTP response on the server side using incoming proxy rules, and returning the processed HTTP response to the client web browser on the client side.
Owner:FGM
Assessment of content delivery services using performance measurements from within an end user client application
A system for measuring and monitoring performance of online content is provided. In one embodiment, the system includes an intermediary device, such as a web proxy, that receives client requests for content, such as requests for web pages. The device obtains the requested content, modifies it by applying one or more performance optimizations, and serves it to the client. The device also inserts code into the content for execution by the client to gather and report data reflecting, e.g., how quickly the client is able to get and process the content. The code includes information identifying the modifications the device made, and this is reported with the timing data, so that the effect on performance can be analyzed. In other embodiments, the device selects one of multiple versions of content, and the inserted code contains information identifying the selected version. The foregoing are merely examples; other embodiments are described herein.
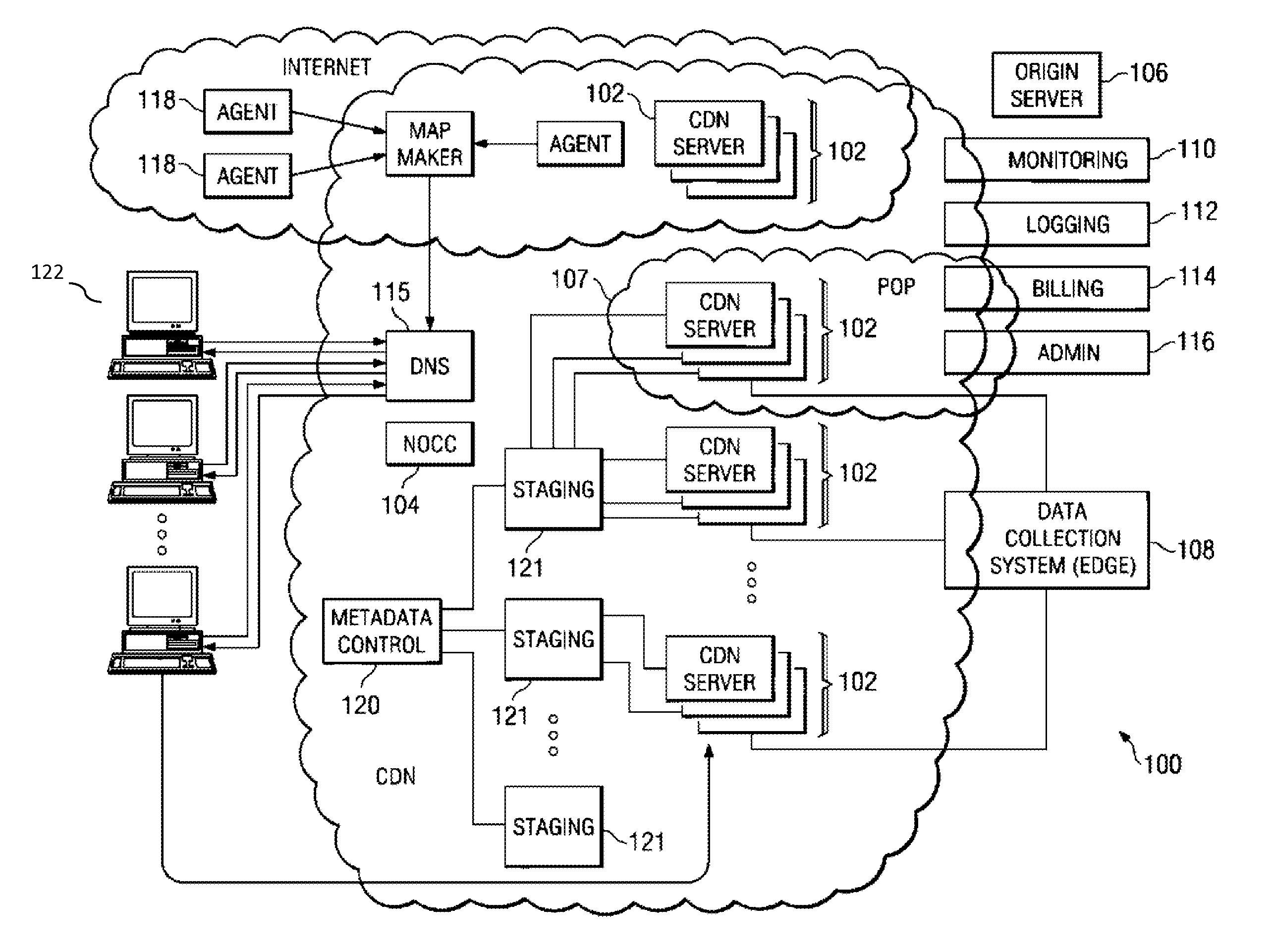
Owner:AKAMAI TECH INC
Real time data distribution system
InactiveUS20100088126A1Increase resourcesComplete banking machinesDrawing from basic elementsReal-time dataDistribution system
Owner:TICKETMASTER
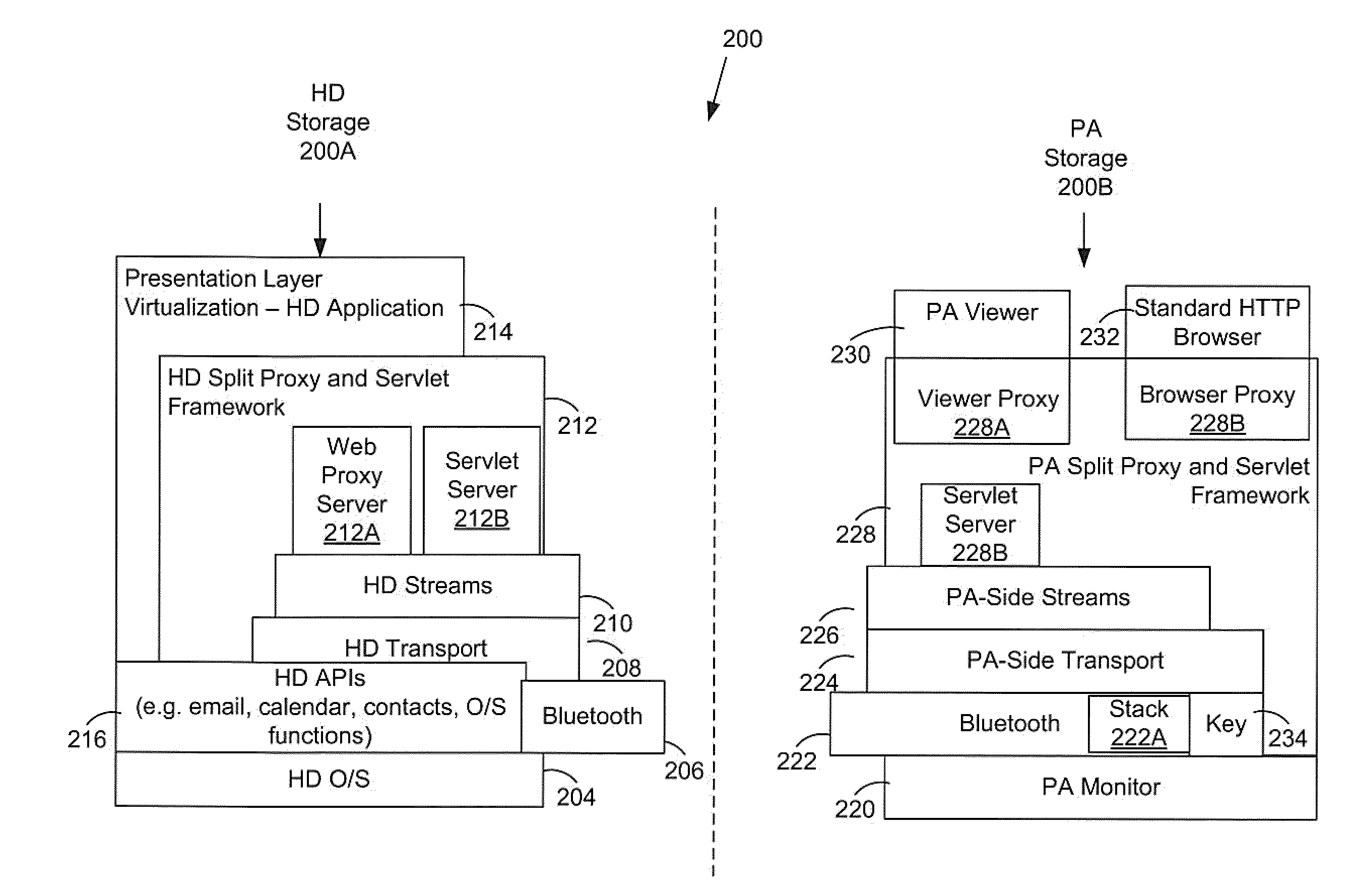
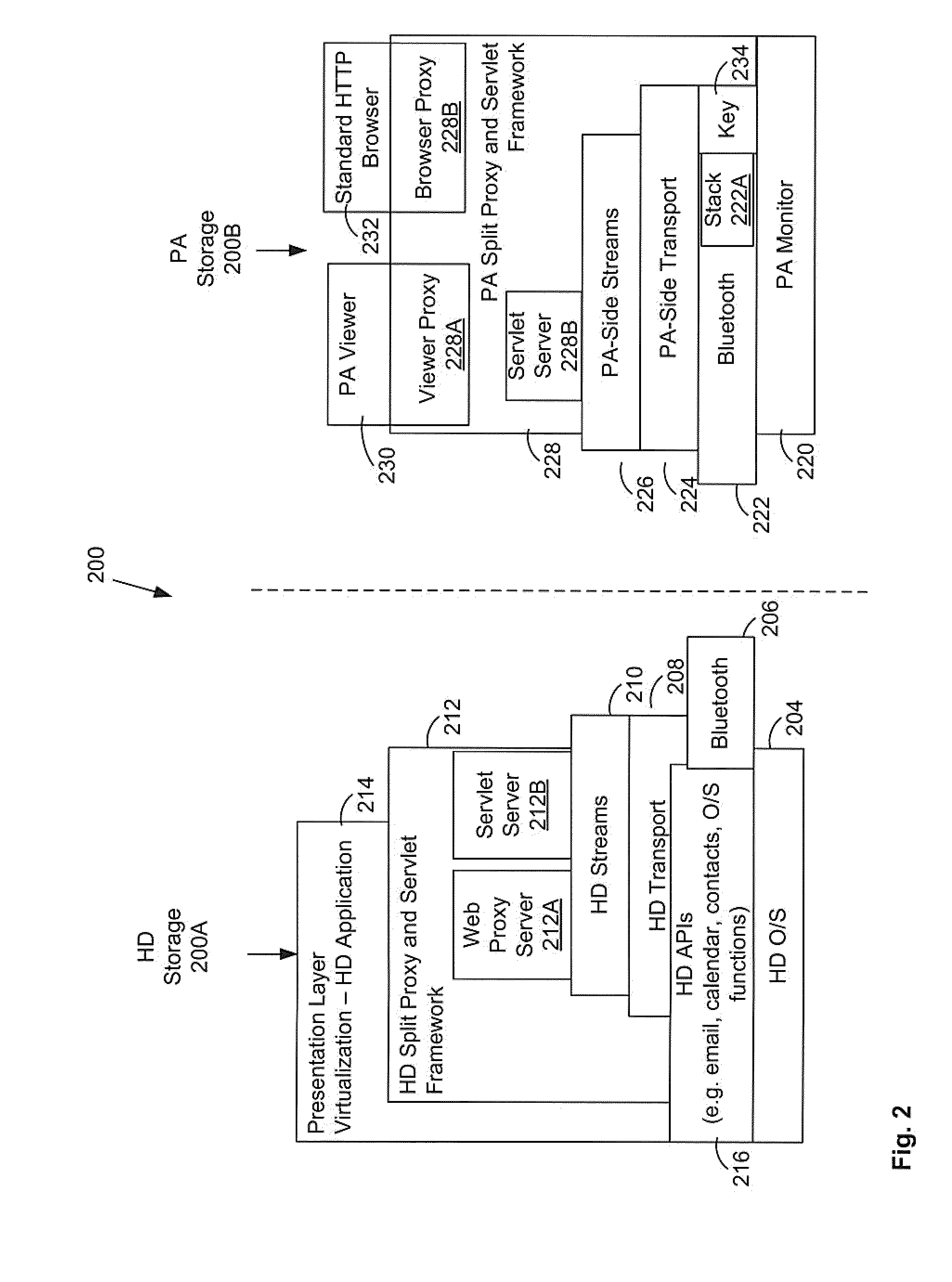
Secured presentation layer virtualization for wireless handheld communication device having endpoint independence
ActiveUS20100306528A1Computer security arrangementsMultiple digital computer combinationsPrivate networkTechnical standard
The connectivity and security of wireless handheld devices (HDs) can he leveraged to provide a presentation appliance (PA) (e.g. a laptop) with an ability to securely communicate with an enterprise's private network. A split-proxy server, with part of it executing on the HD and a part executing on the PA, implements a full HTTP 1.1 compliant Internet / Web Proxy to couple the PA for communication through the HD. Support for the pragmatic keep-alive header, the CONNECT method, socket connection sharing, and thread pooling, enables a fully functional browsing environment to access web-based applications that are built on standard Internet technologies without the need for re-rendering or re-writing the user interfaces to suit the HD. In addition, Intranet web-based applications are made securely accessible without the need for additional VPN and remote access technologies. The PA may be configured to prevent residual storage of sensitive data on the PA.
Owner:MALIKIE INNOVATIONS LTD
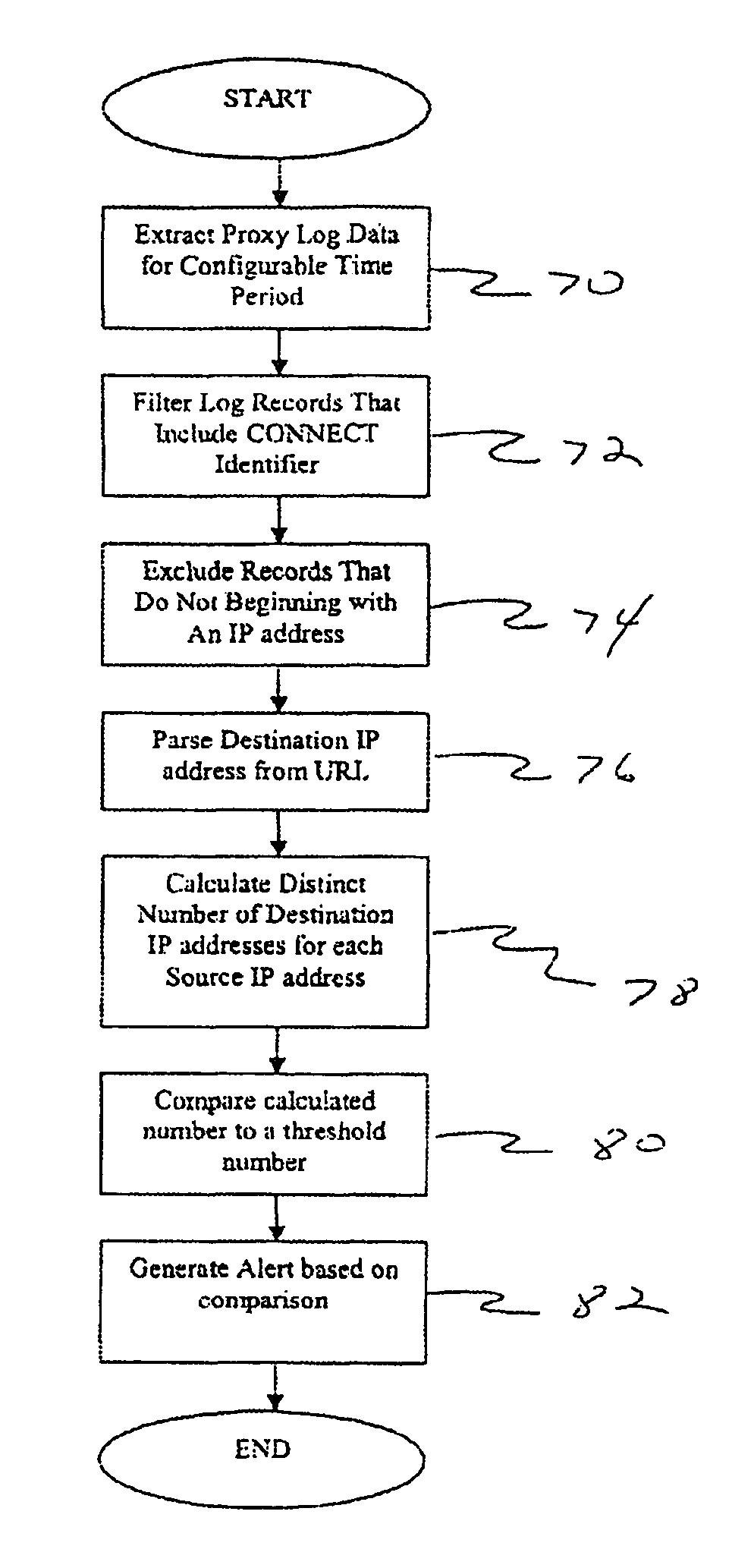
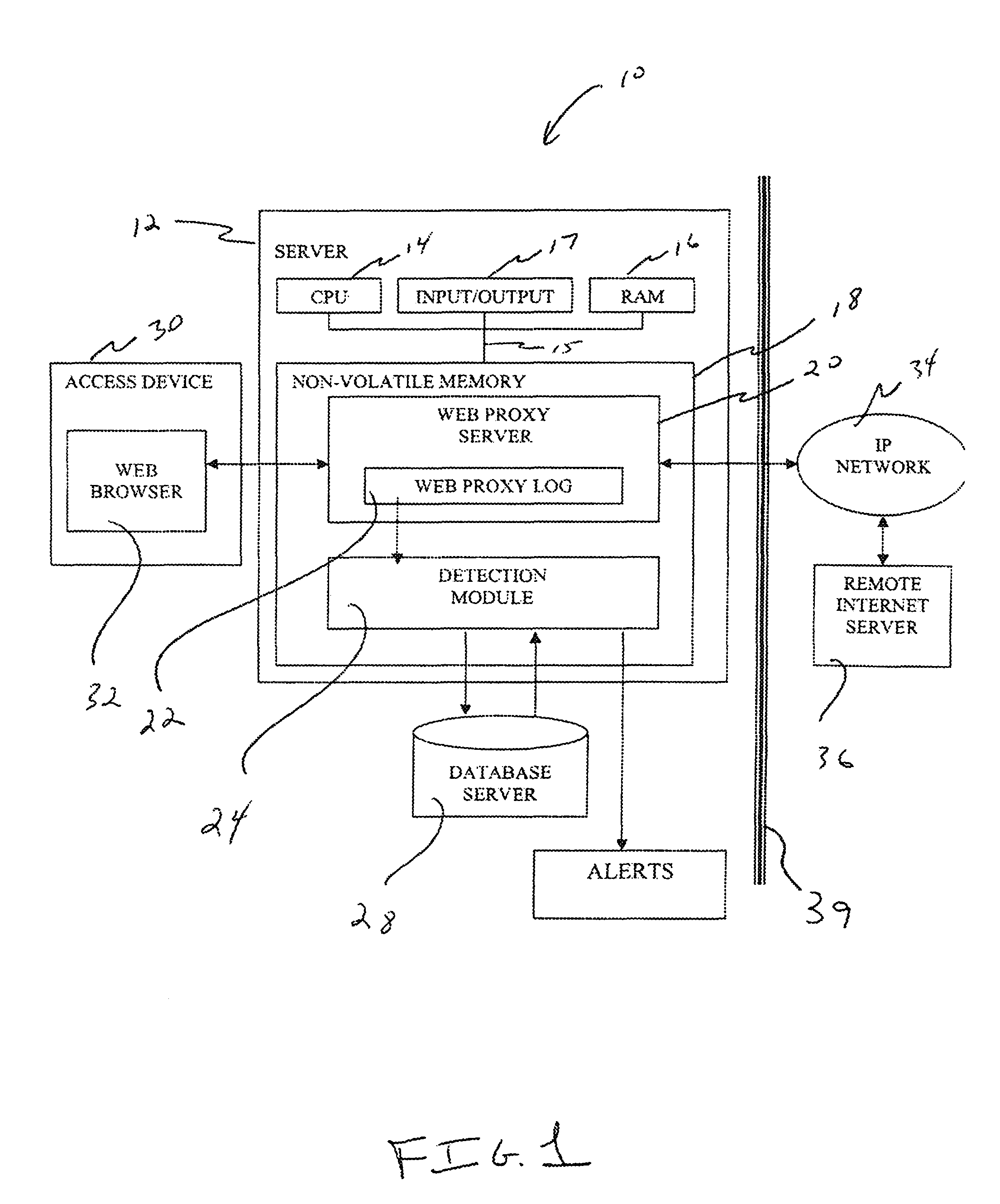
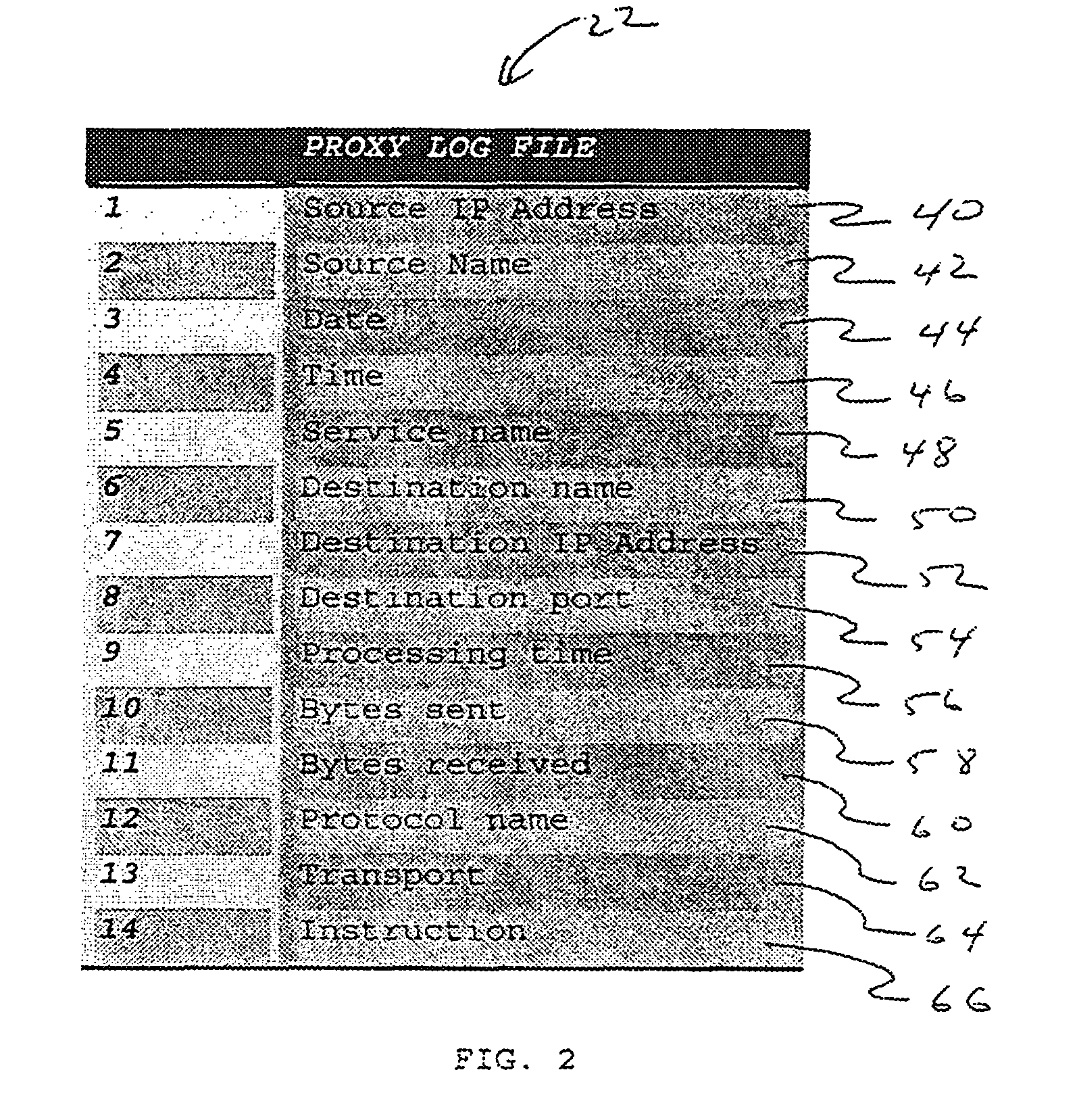
Detecting anomalous web proxy activity
InactiveUS7661136B1Detect presenceReducing false positiveMemory loss protectionUnauthorized memory use protectionUniform resource locatorEnd user
A method, system and apparatus for detecting anomalous web proxy activity by end-users are disclosed. The techniques include analyzing records from a web proxy log and determining whether the records contain anomalous end-user activity by inspecting a uniform resource locator and a connect instruction included therein. The techniques also include generating an alert in response to the analysis.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
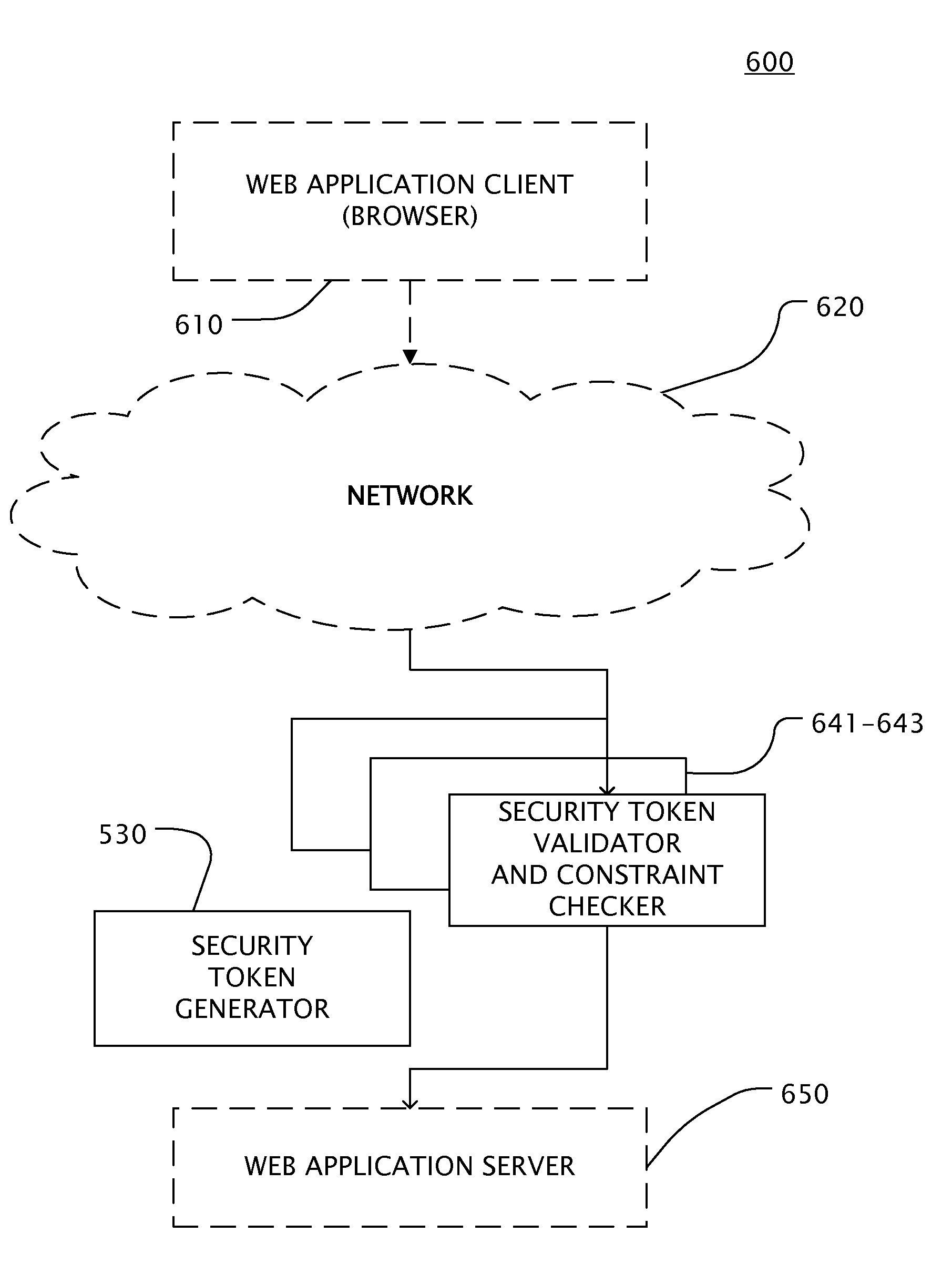
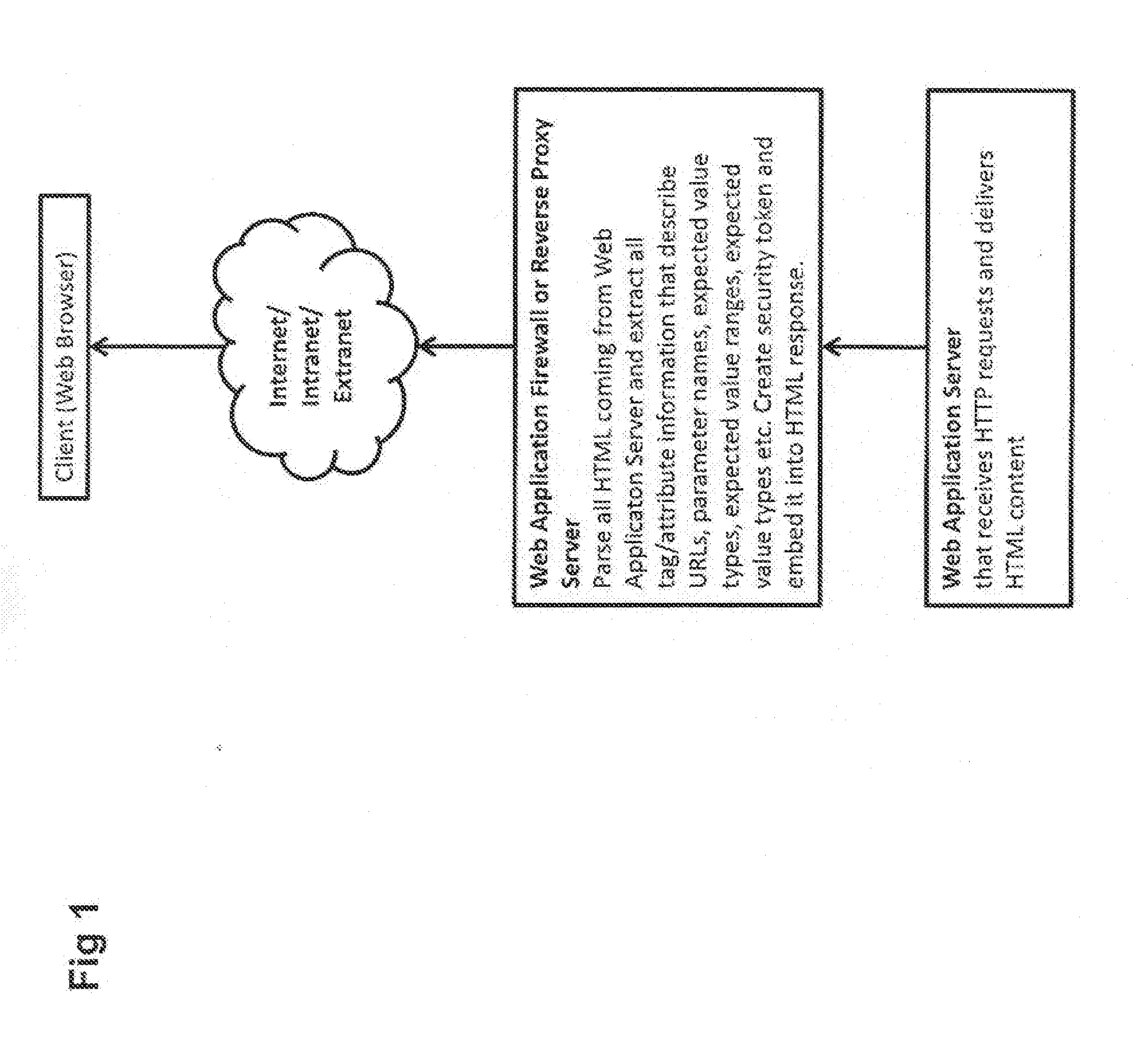
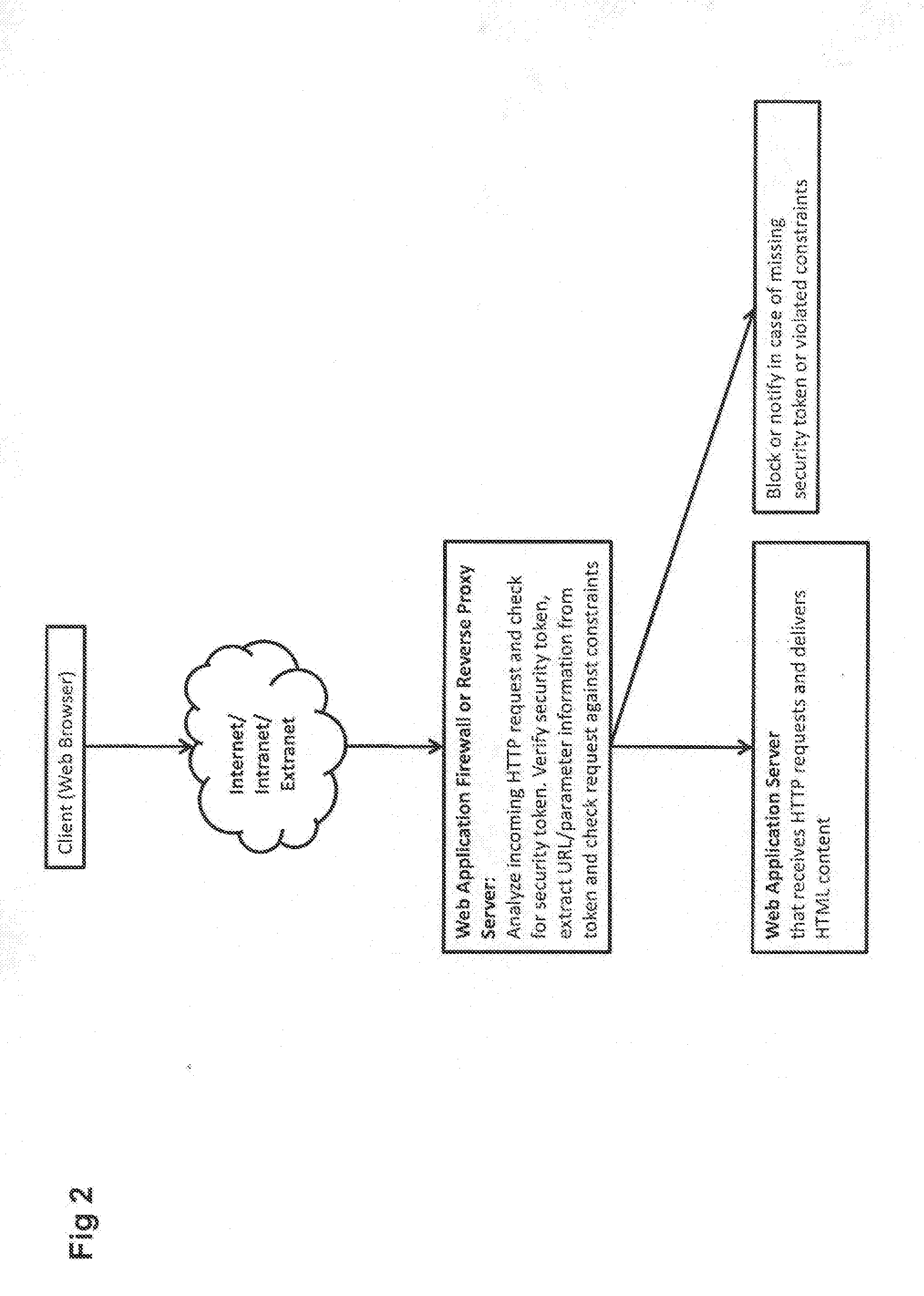
Web application security filtering
InactiveUS20100332837A1Simple and efficientLess sensitiveDigital data processing detailsUser identity/authority verificationWeb applicationApplication server
User inputs and / or Uniform Resource Identifier (URI), historically and popularly referred to as Universal Resource Locator (URL), requests in a content description language are passed through a security service (Web application firewall or a reverse Web proxy server) that is placed in front of Web application servers in order to protect the servers from hacking attempts. For validating Webform user inputs and / or URI requests and parameters the content description language is enriched by the security service with additional security tokens that are dynamically created based on the content being transferred. The user receives the information and returns input with the security tokens. The security service can then verify all provided user input data against the constraints described in the corresponding security token. As a result, the method may block the HTTP request or create log messages or notification events in reaction to violations of the user input data compared to the constraints in the security token.
Owner:PHION
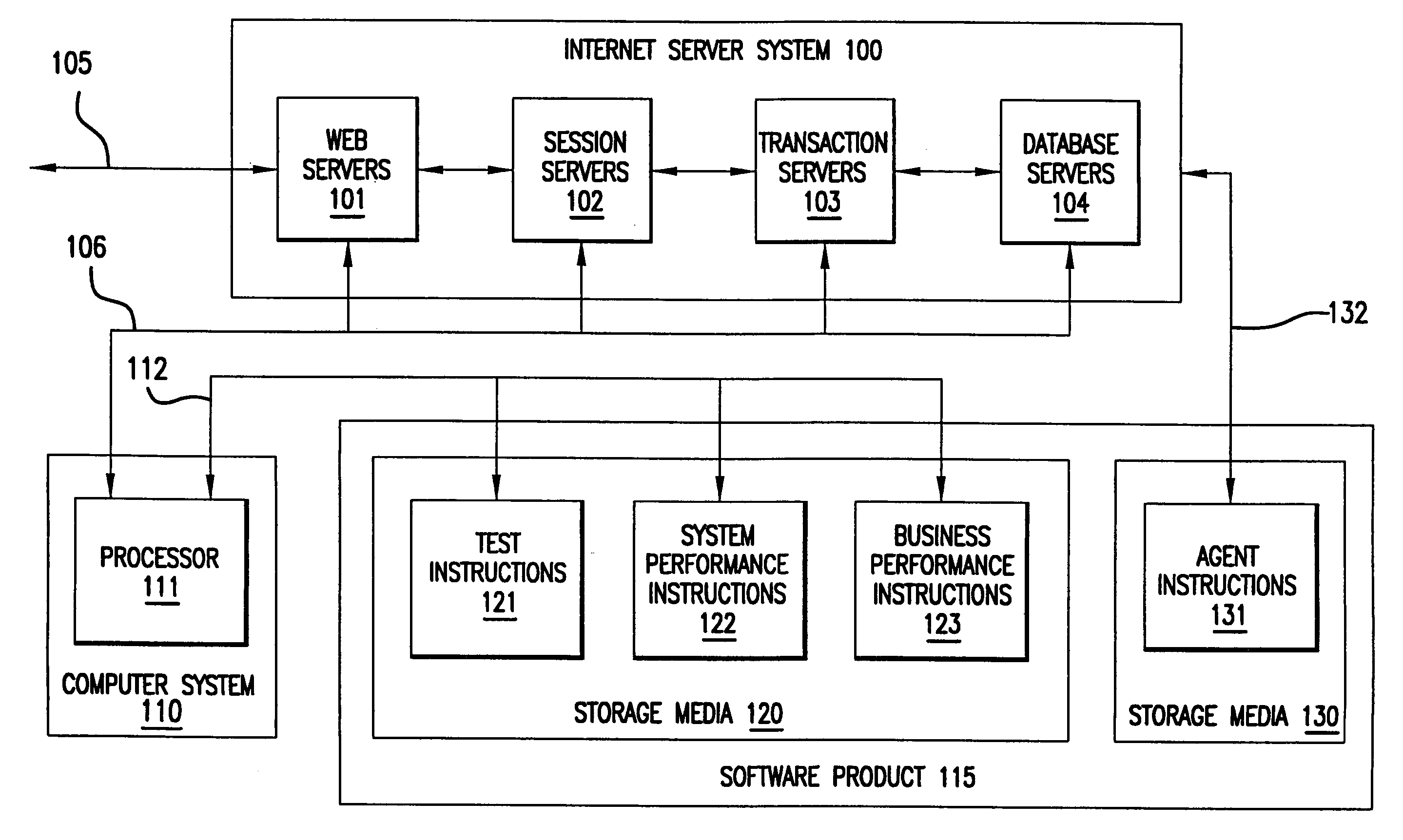
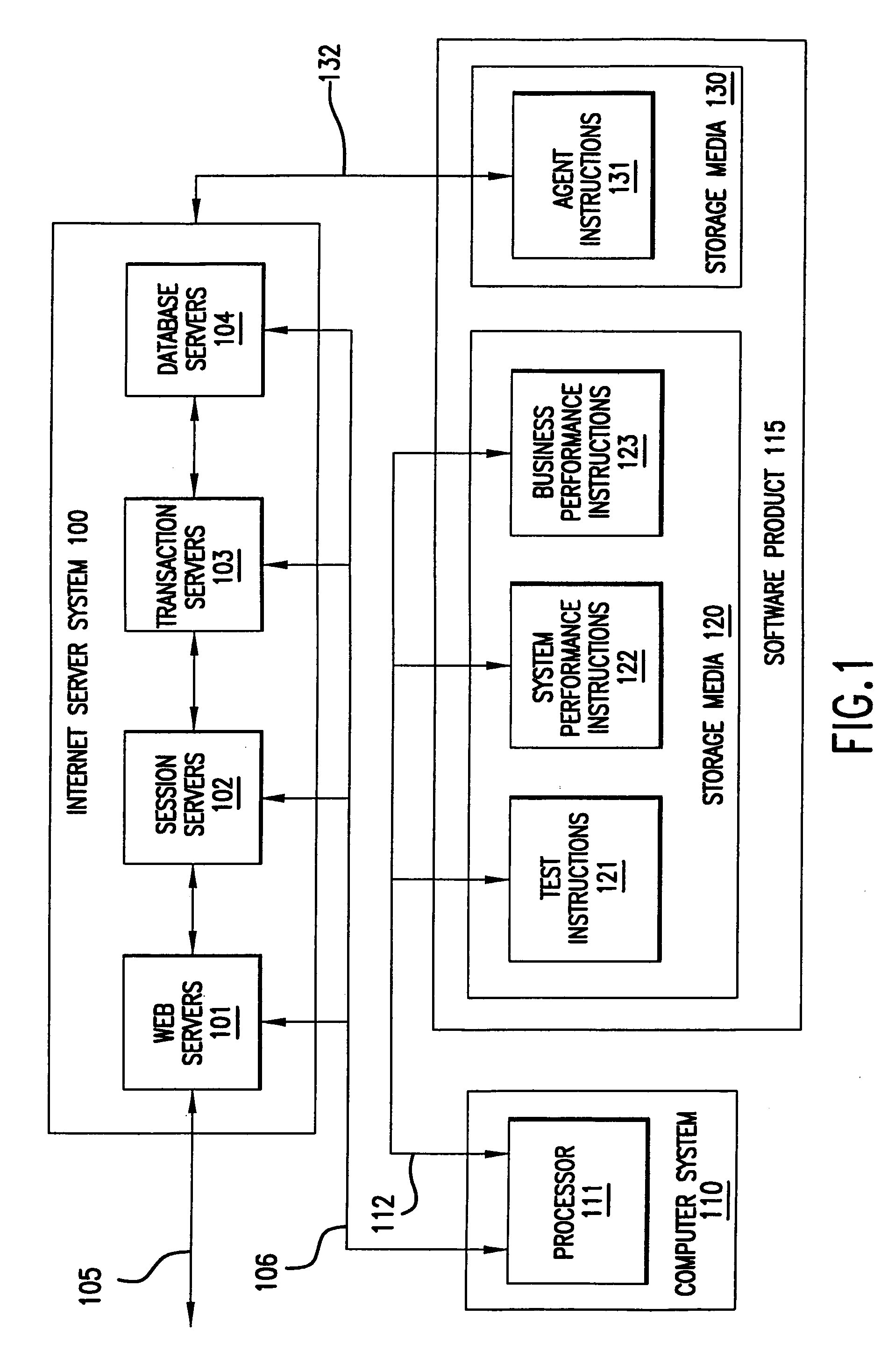
Filtering web proxy for recording web-based transactions that supports secure HTTP steps
A software product tests and monitors an Internet server system. Advantageously, the software product communicates with a web browser without the need for other client software to configure transactions. The user of the web browser is guided through web pages to record, edit, and playback transactions. Recording may occur over a secure connection. The software product performs automated tests using the transactions in addition to measuring both system performance data and business performance data. The software product generates alarms when thresholds are exceeded. The test data, performance data, and alarms are correlated in time and presented graphically to the user.
Owner:VIAVI SOLUTIONS INC
Systems and methods for providing resource allocation in a networked environment
Owner:LIVE NATION ENTERTAINEMENT INC
Method and device for improving accessing speed of network resource
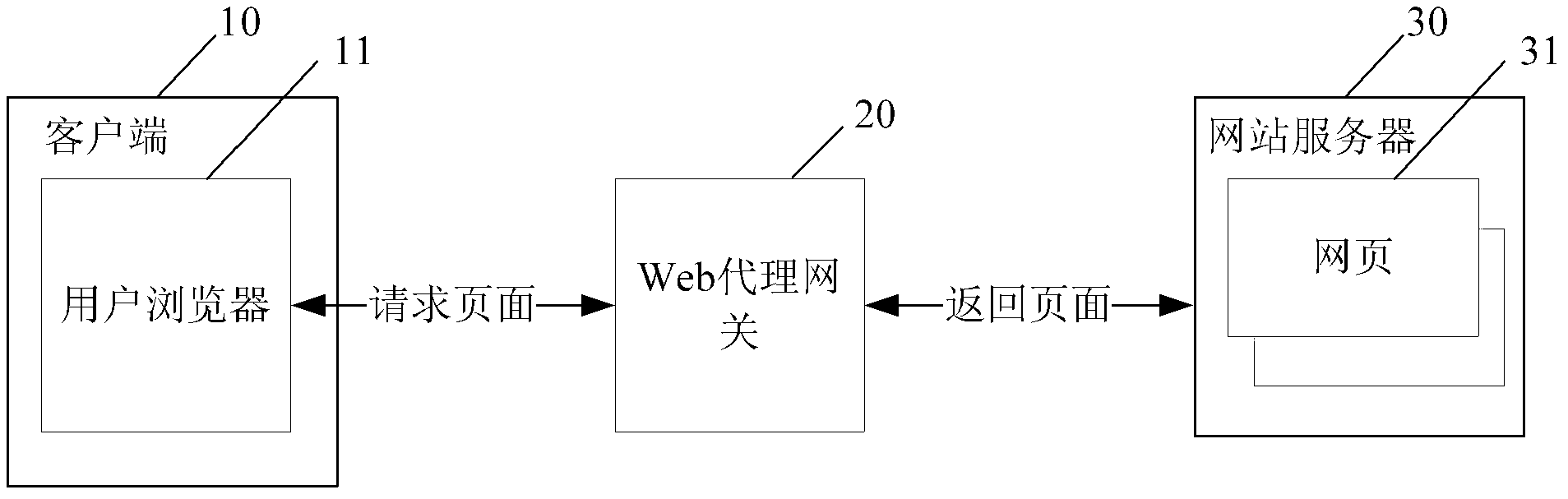
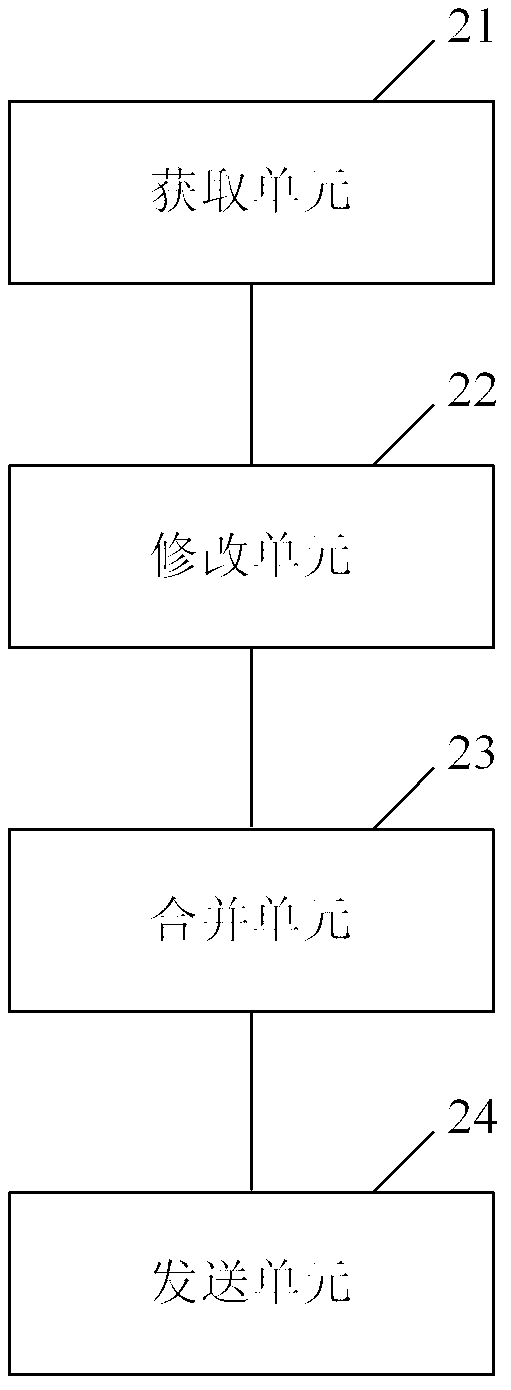
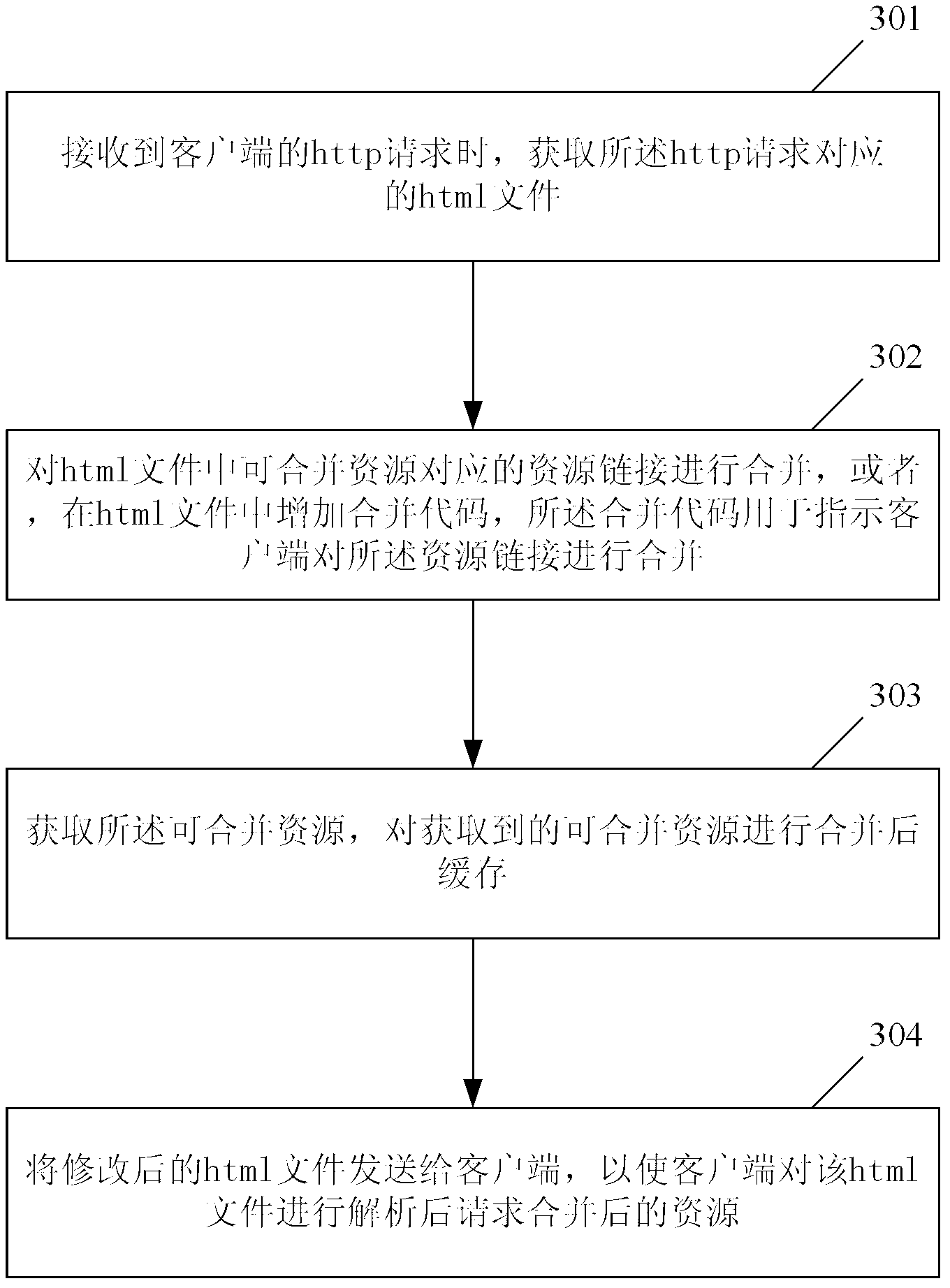
ActiveCN103327033AReduce the number of requestsImprove download speedTransmissionClient-sideHyper text transport protocol
The invention provides a method and a device for improving an accessing speed of a network resource, belonging to the technical field of an internet. The method comprises the followings steps: when receiving an http (Hyper Text Transport Protocol) request of a client, obtaining an html (Hypertext Markup Language) file corresponding to the http request; merging resource links corresponding to resources capable of being merged in the html file; or adding a merging code into the html file, wherein the merging code is used for indicating the client to merge the resource links; obtaining the resources capable of being merged, and merging and buffering the obtained resources capable of being merged; and sending a modified html file to the client so as to analyze the html file by the client and require the merged resources. According to the method and the device disclosed by the invention, the html file is modified on a web proxy gateway and the resources capable of being merged are merged so that the client can require aiming at the merged resources; therefore, each resource does not need to independently send out the request, the requiring times of a browser are reduced and the accessing speed of the network resource is improved.
Owner:重庆云流未来科技有限公司
Tool for personalized search
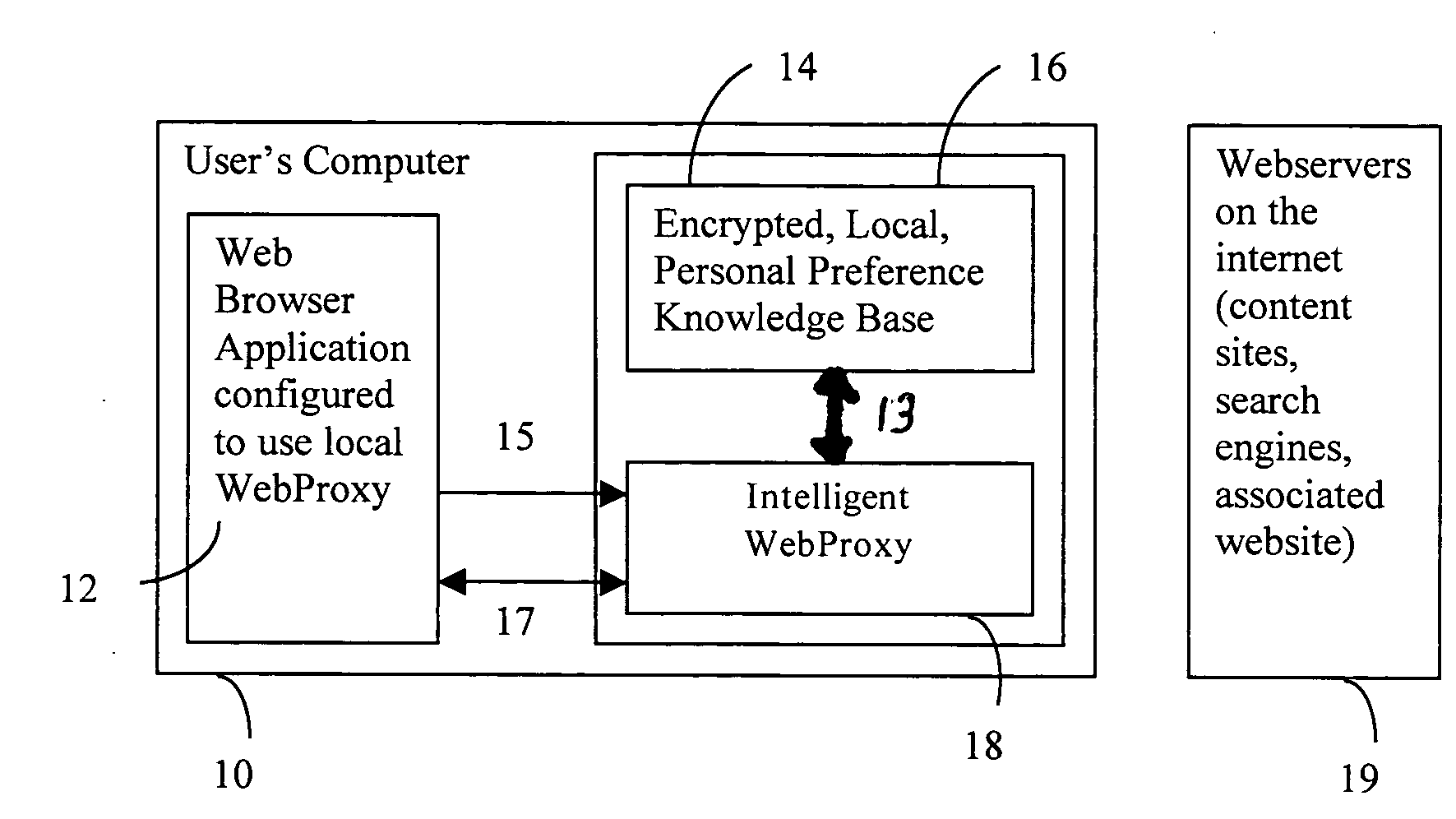
ActiveUS20090063475A1Fine tune customizationDigital data information retrievalDigital data processing detailsPersonalized searchPersonal knowledge base
Owner:PENDSE SUDHIR
Method, network and network proxy for transmitting information
ActiveUS20030163520A1Multiple digital computer combinationsTransmissionTime conditionData information
The invention is directed to a method of transmitting data information and control information each having a source address and a destination address, from a server, having a server address, to a client, having a client address. The method comprises the steps of transmitting the control information from the server to the client via a network proxy that has a network proxy address, and transmitting the data information from the server to the client not via the network proxy. This system has the advantage that, on one hand, the data information is transmitted directly and therefore without any additional delay due to the network proxy, so that the throughput of the data information is maintained. In particular, a video stream can be sent over the network under real-time conditions. Additionally and on the other hand, the invention provides the advantages achievable by using a network proxy. In particular, the functions offered by a network proxy may still be available in connection with a continuous media service. For example the server providing the media stream may change over time without the client noticing the change. This allows e.g. load-balancing during stream transmission without perturbation at the client side.
Owner:HULU
Pre-fetching web proxy
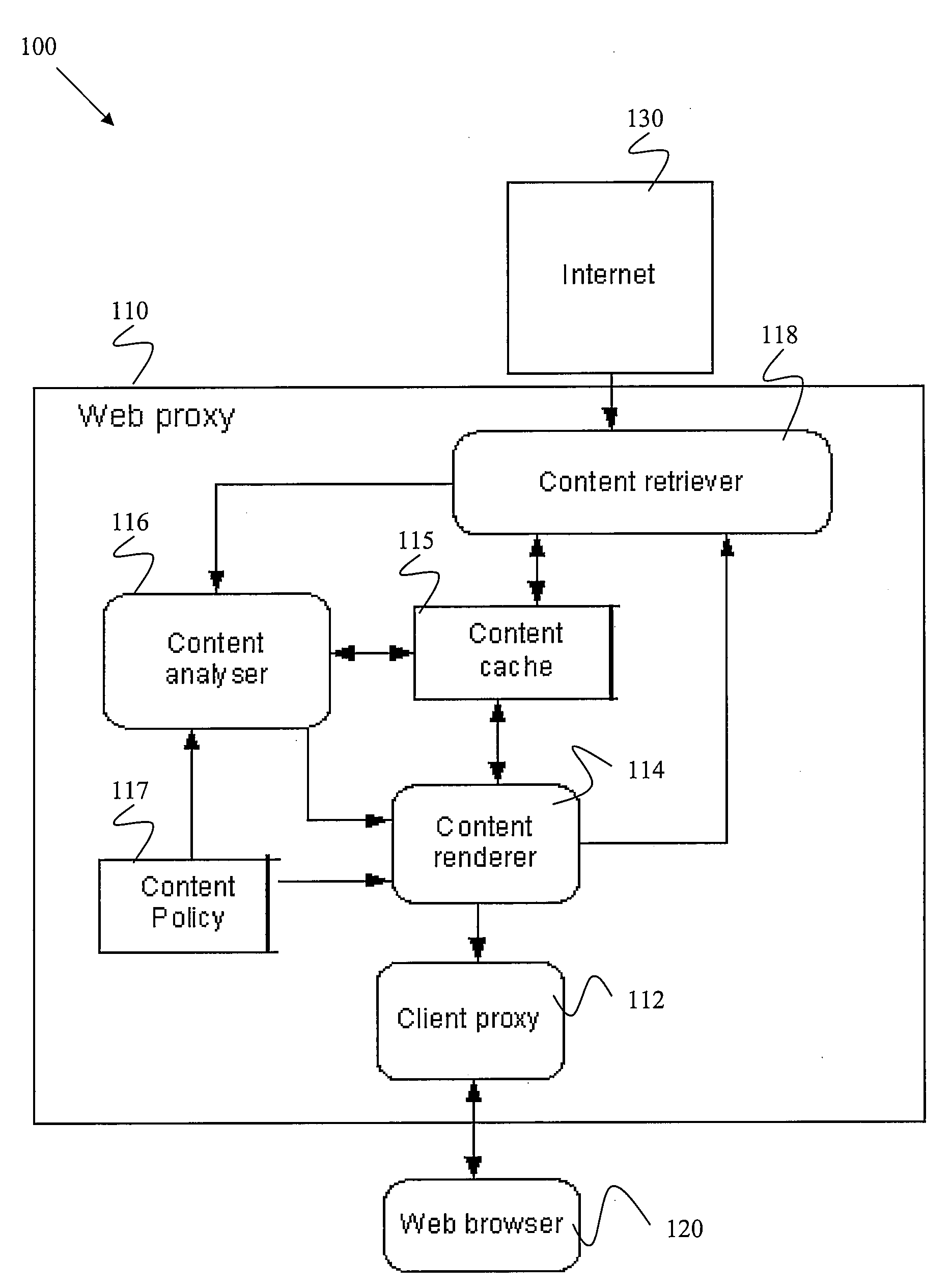
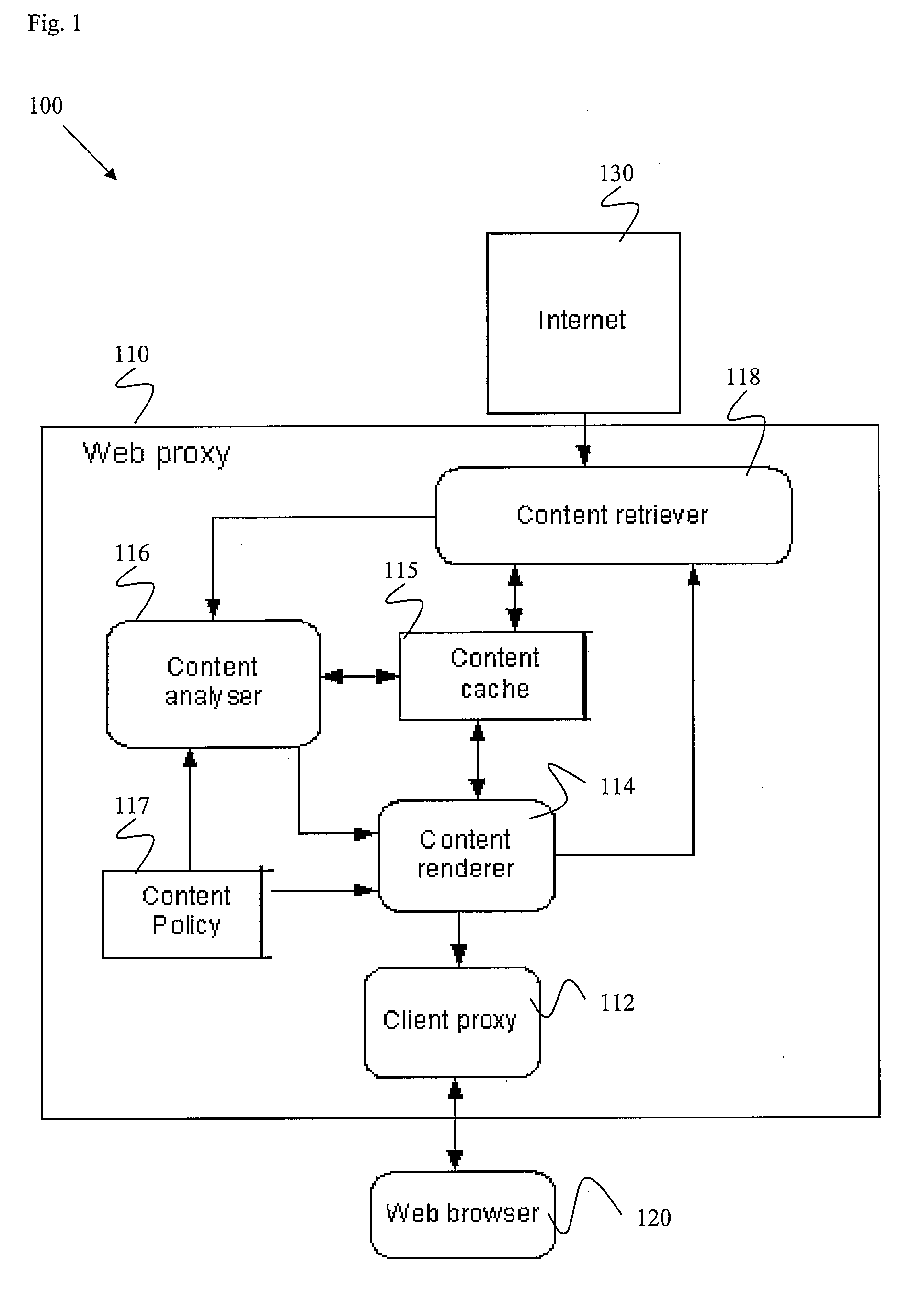
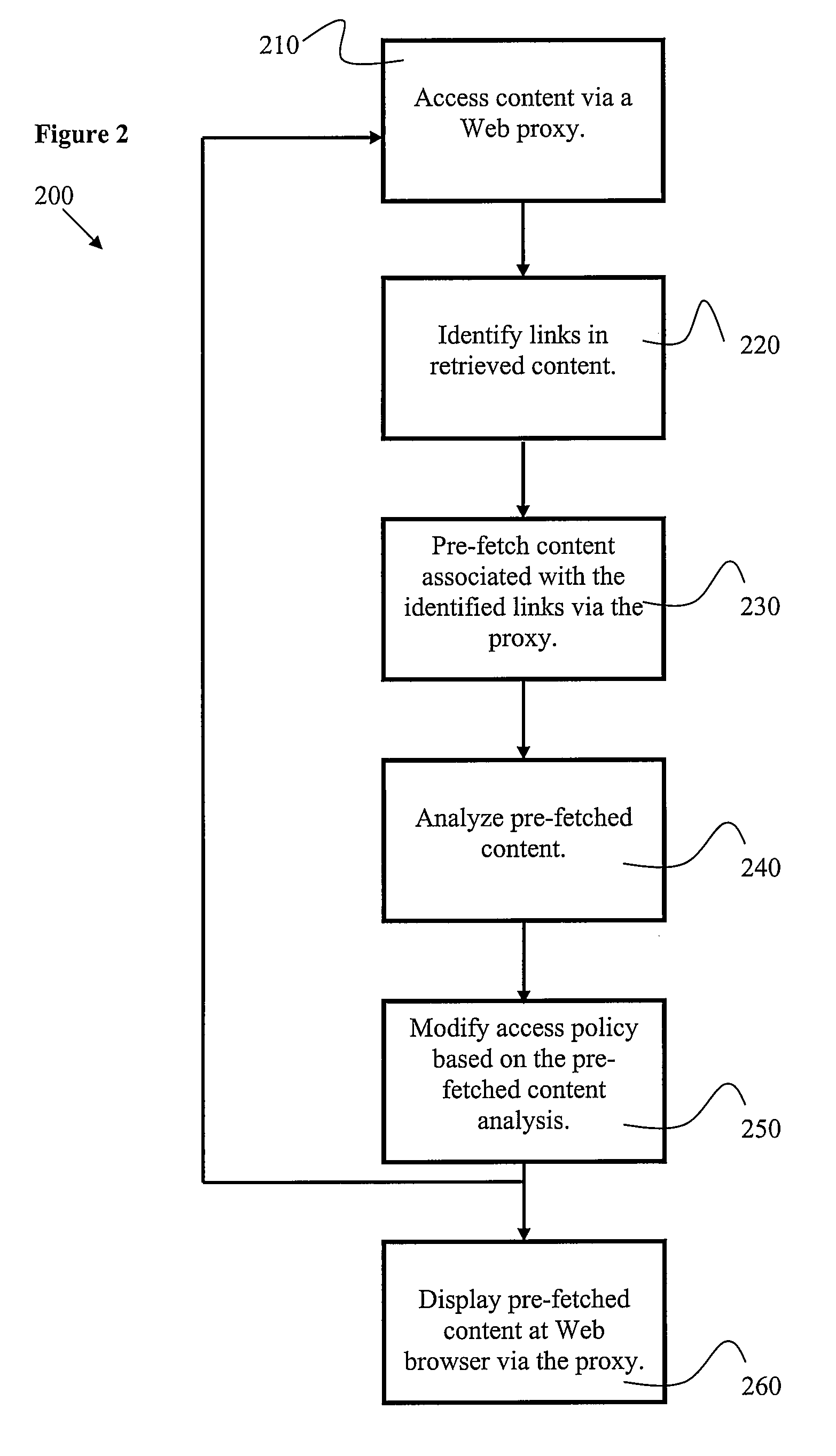
ActiveUS20080235239A1Digital data information retrievalMemory loss protectionNetwork onContent retrieval
Certain embodiments of the present invention provide methods and systems for providing access to network content. Certain embodiments provide a proxy system for providing access to network content. The system includes a content retriever for retrieving a first content on a network. The content retriever is configured to pre-fetch additional content linked or connected to the first content. The system also includes a content analyzer for analyzing the first content and the pre-fetched additional content according to a content policy and allowing access to the first content and the pre-fetched additional content in accordance with the content policy. The system further includes a content renderer for rendering allowed content for provision to a user upon user request. The renderer can also modify links to content based on a status of the linked content.
Owner:SOPHOS
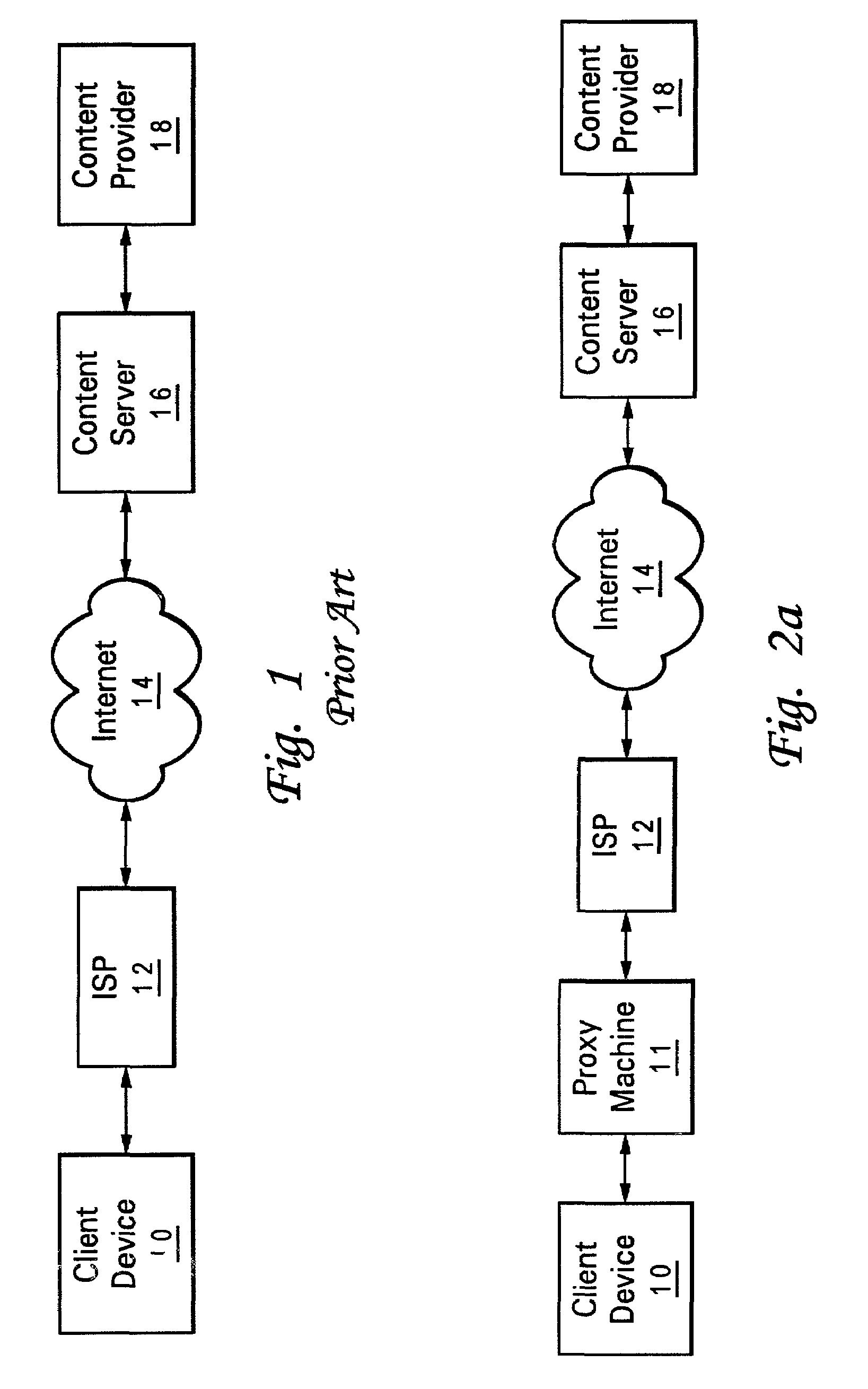
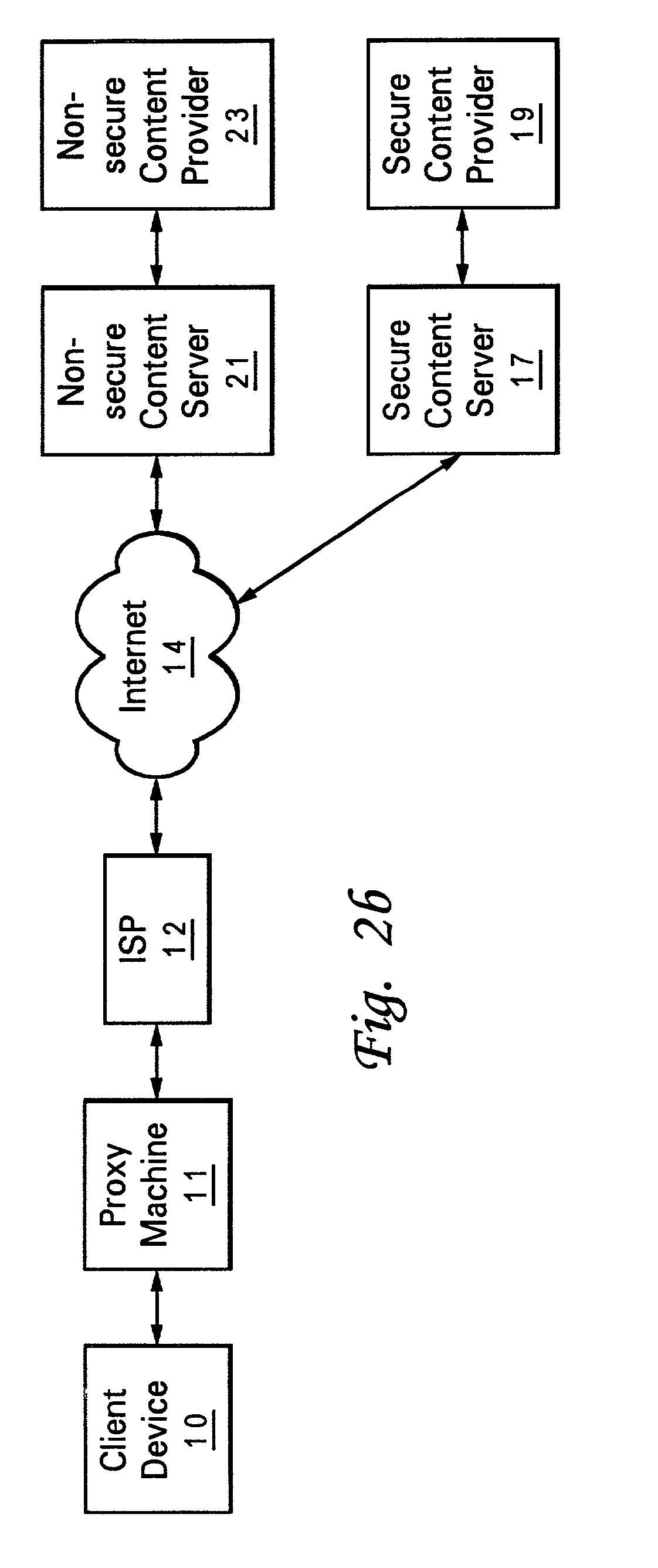
System and method for transcoding support of web content over secure connections
A method and system using for establishing an intermediary connection between a client device and a secure website using a web proxy machine. In the preferred embodiment, a secure connection is established between the web proxy and the secure content server. A response from the content server, typically in HTML format, is sent to the proxy machine through a secure connection. The proxy machine is then able to manipulate the secure response from the secure server, in ways such as transcoding the response to a format readable by the user device, storing sensitive financial data in cookies in the proxy machine, and to return a response from the content provider to the client device with or preferably without cookies.
Owner:IBM CORP
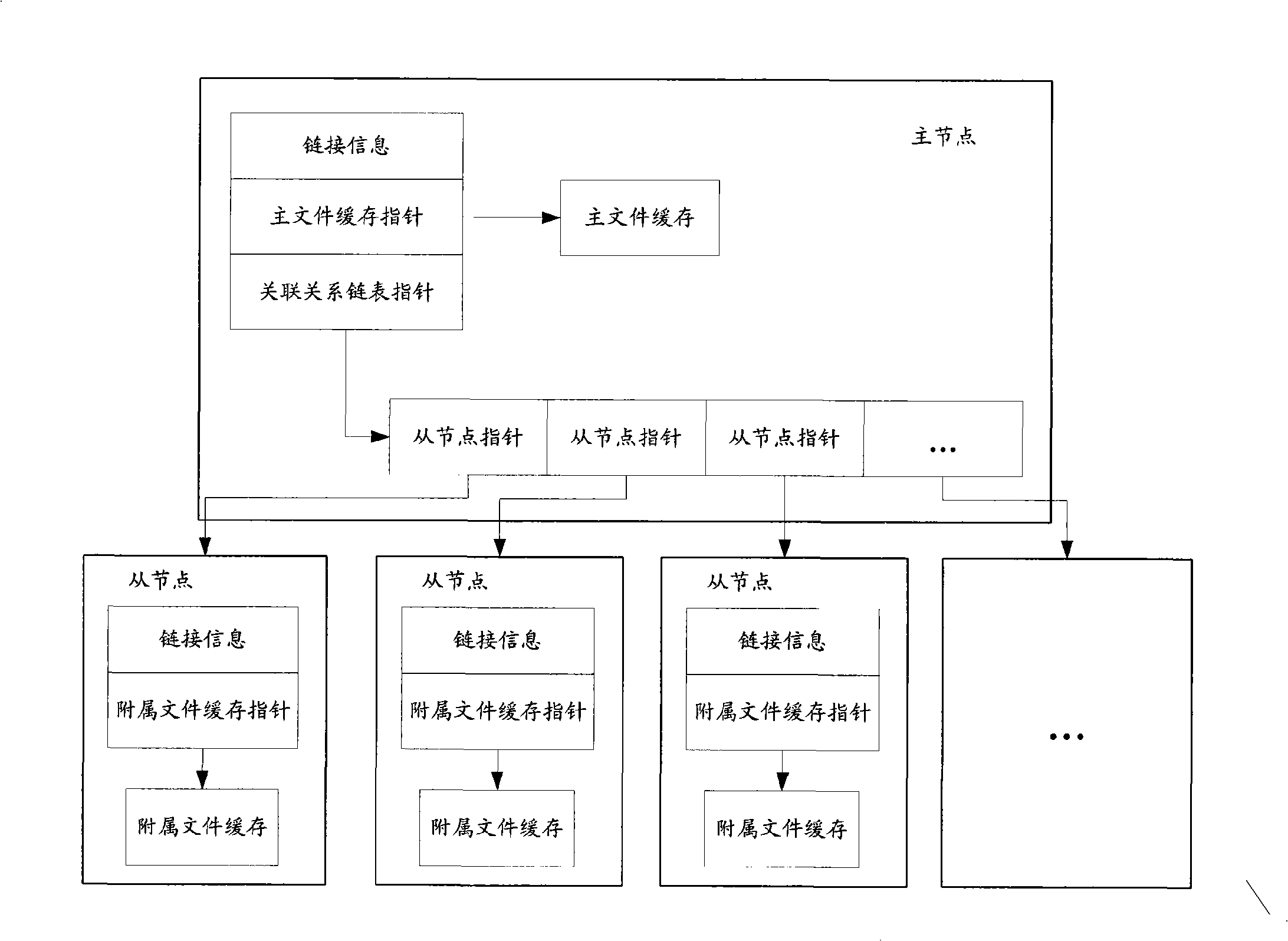
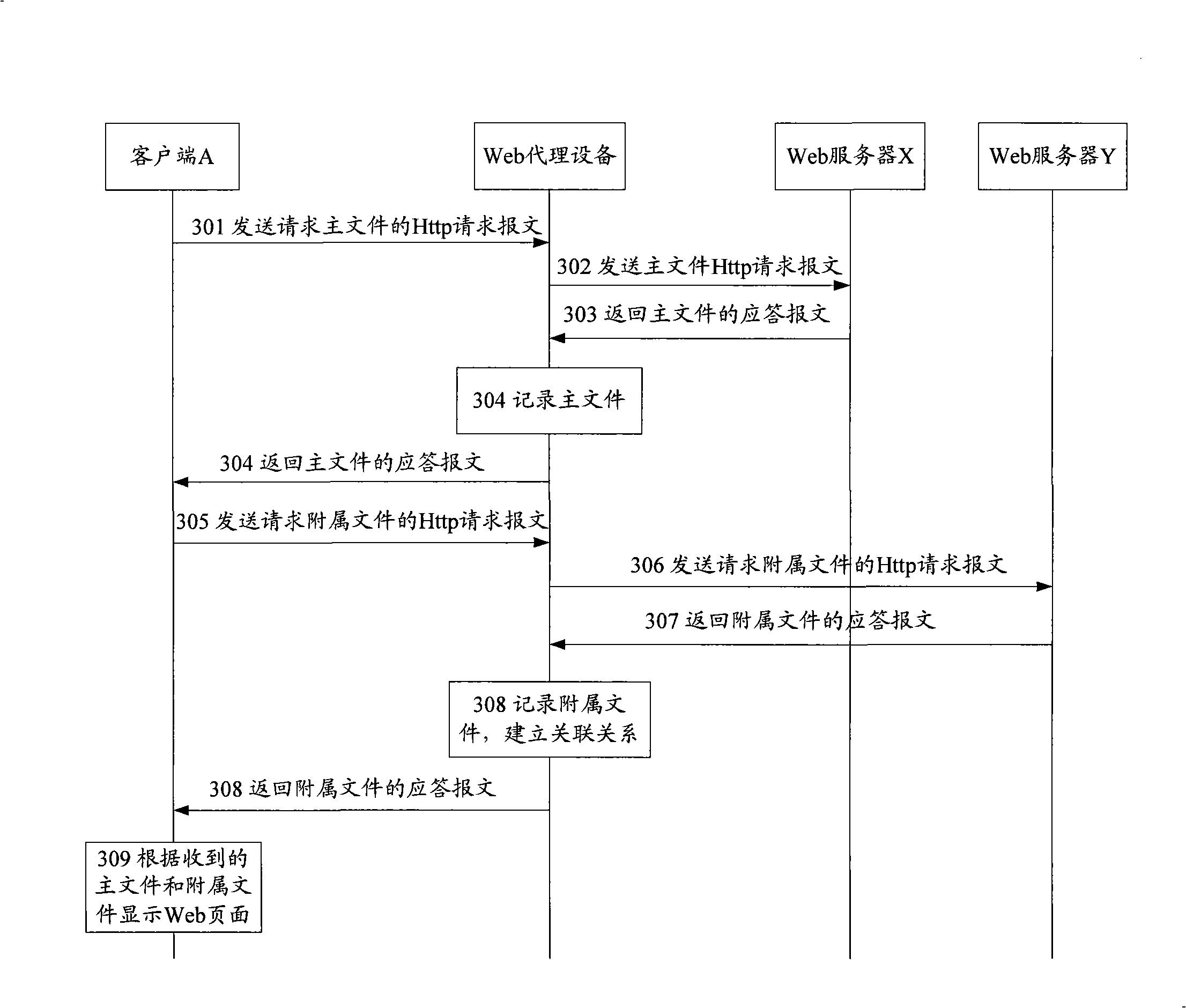
Method for updating Webpage and Web proxy device
ActiveCN101287013AQuick responseSolve the technical problem that the URL address of the attached file cannot be obtained by parsing the response messageData switching networksClient-sideWeb page
The invention discloses a method for updating Web pages and Web proxy equipment. The technical proposal of the invention mainly comprises the steps that: incidence relation between a Web page and a URL address of an embed subsidiary file of the Web page is recorded according to the URL address of the subsidiary file carried by an Http request message; when the Http request message of the Web page is received, the incidence relation is utilized to actively update the subsidiary file of the Web page, which leads a client to directly acquire the updated subsidiary file, thus promoting the response speed of the whole system to return to the Web page. In the technical proposal of the invention, the URL address of the embed subsidiary file of the Web page is obtained without need of resolving the Web page in a response message, thereby solving the technical problem that the URL address of the subsidiary file cannot be obtained by resolving the Web page of the response message in the prior art.
Owner:NEW H3C TECH CO LTD
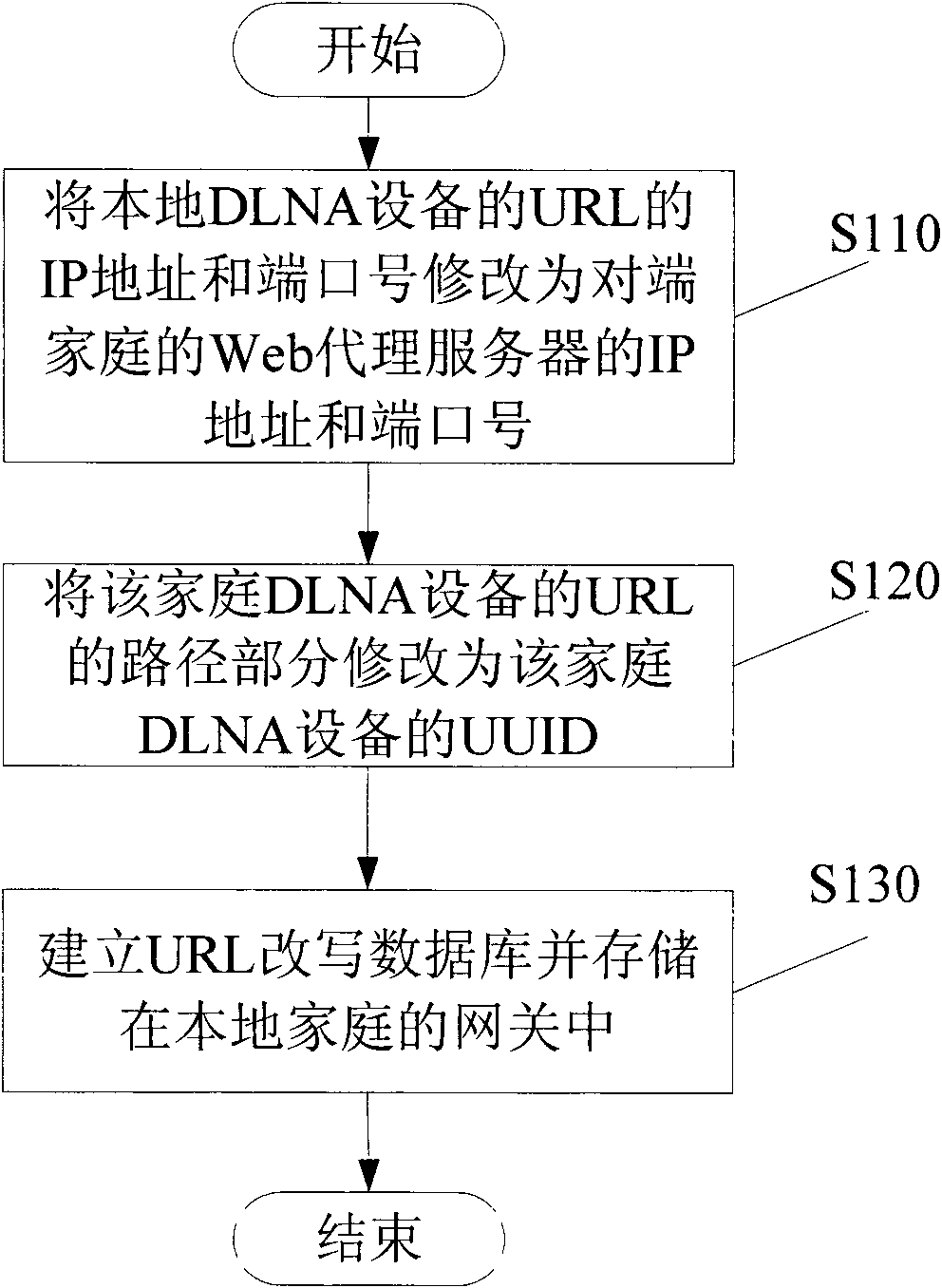
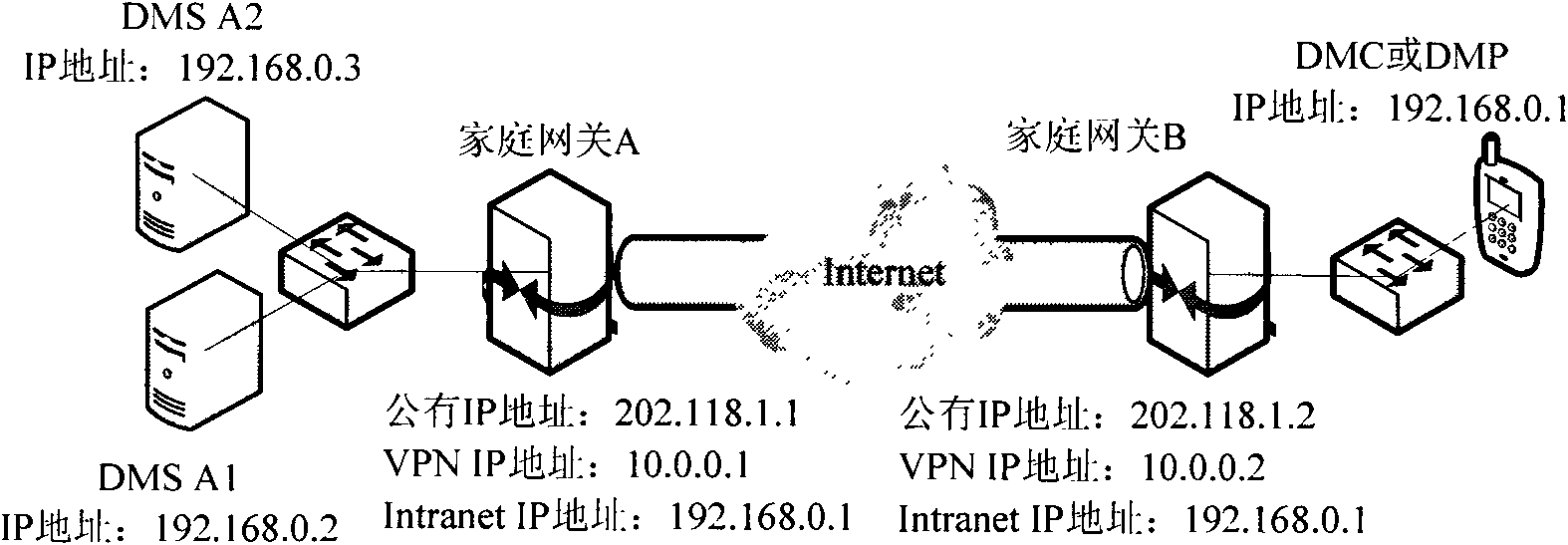
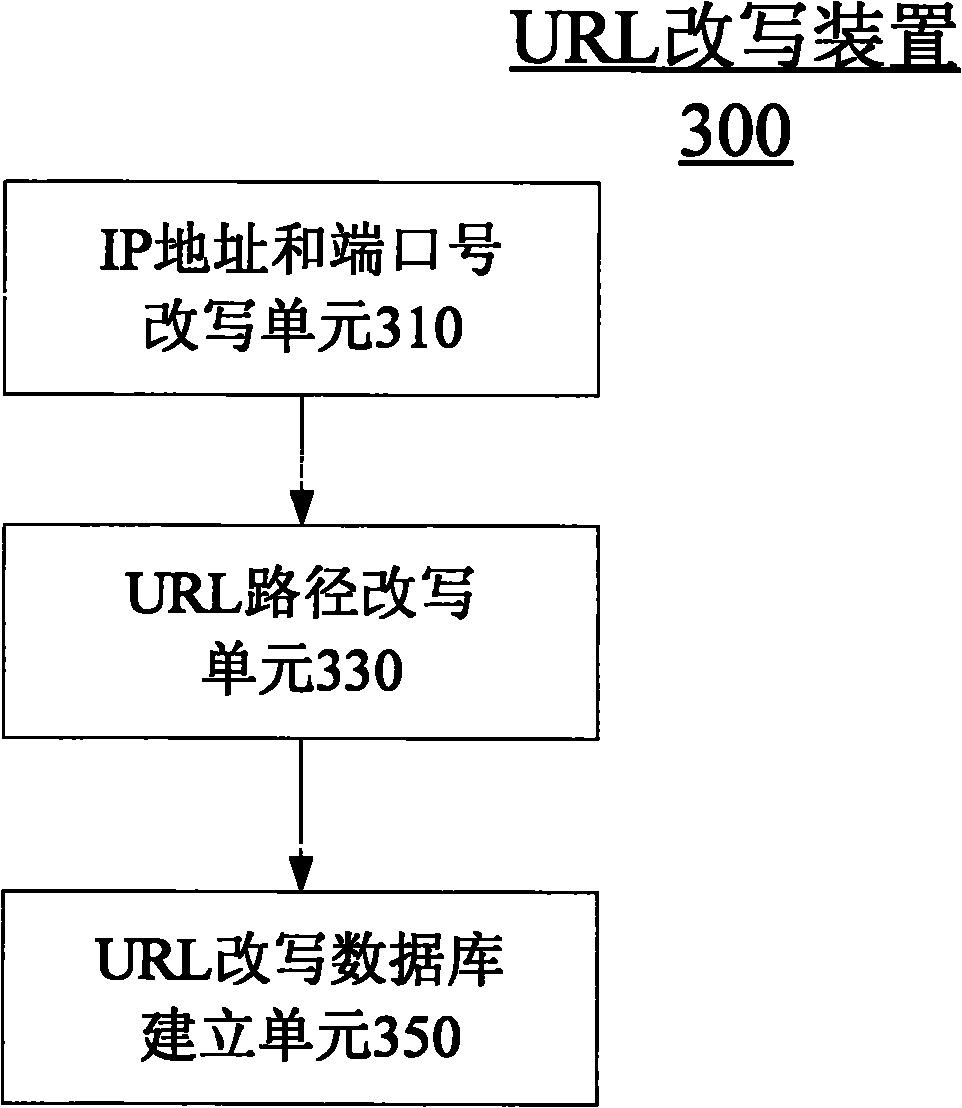
Inter-home digital living network alliance (DLNA) equipment discovering and controlling method and device
The invention provides a method for performing inter-home digital living network alliance (DLNA) equipment discovery between a local home and an opposite end home. The method comprises the following steps that: a simple service discovery protocol (SDDP) proxy in the opposite end home performs uniform resource locator (URL) rewriting on a retrieval response transmitted from the home DLNA equipmentbased on a universally unique identifier (UUID) of the home DLNA equipment after transmitting the received equipment retrieval multi-cast messages to the home DLNA equipment in the opposite end home in a multi-cast manner, and then transmits the retrieval response which is subjected to URL rewriting to the home DLNA equipment in the local home in a unicast manner, wherein during the URL rewriting, the internet protocol (IP) address and the port number of the URL in the retrieval response are rewritten to be the IP address of a Web proxy server and the port number of a monitored port in a gateway of the local home respectively; and the path part of the URL in the retrieval response is rewritten to be the UUID of the home DLNA equipment in the opposite end home.
Owner:NEUSOFT CORP
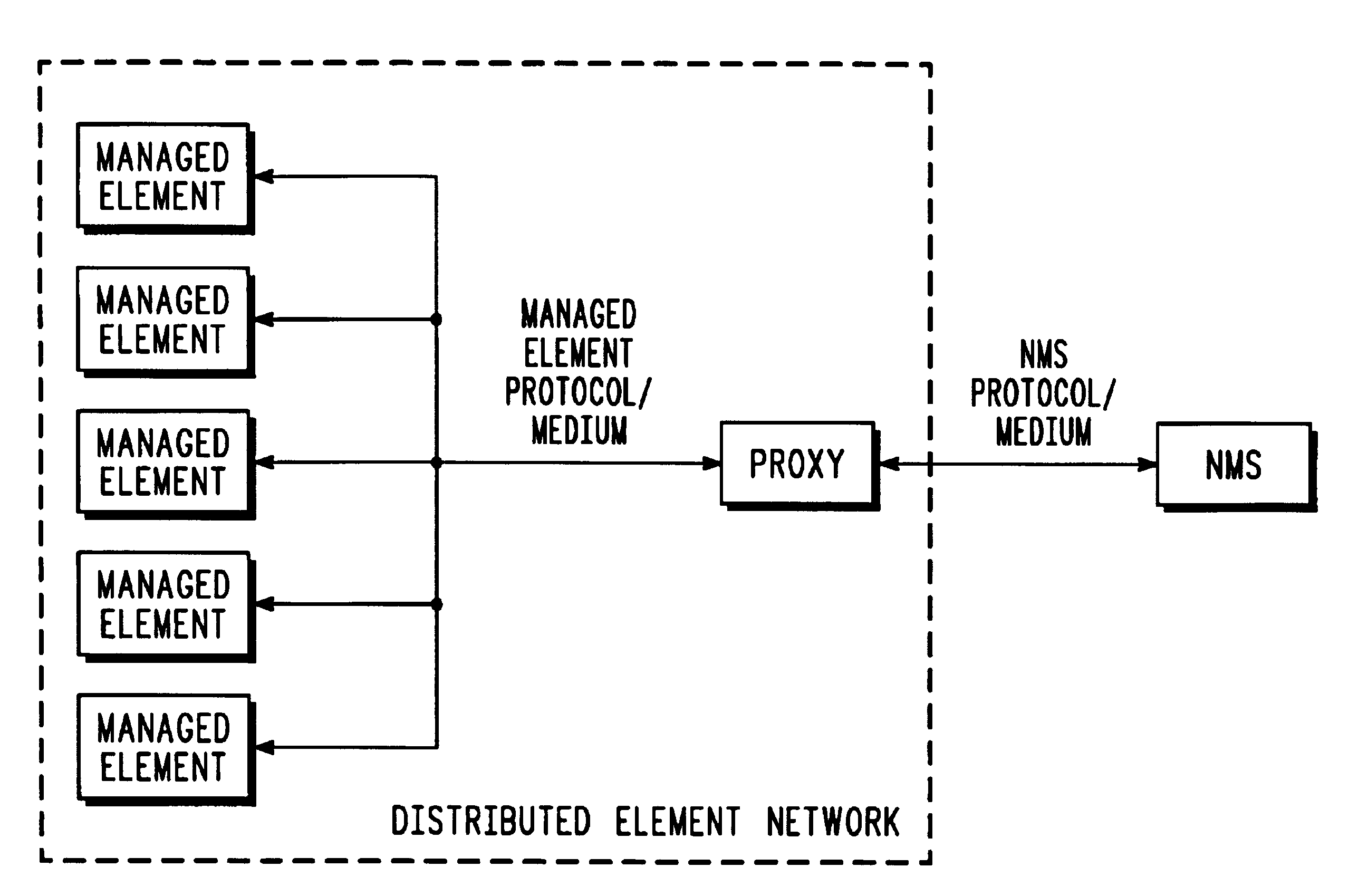
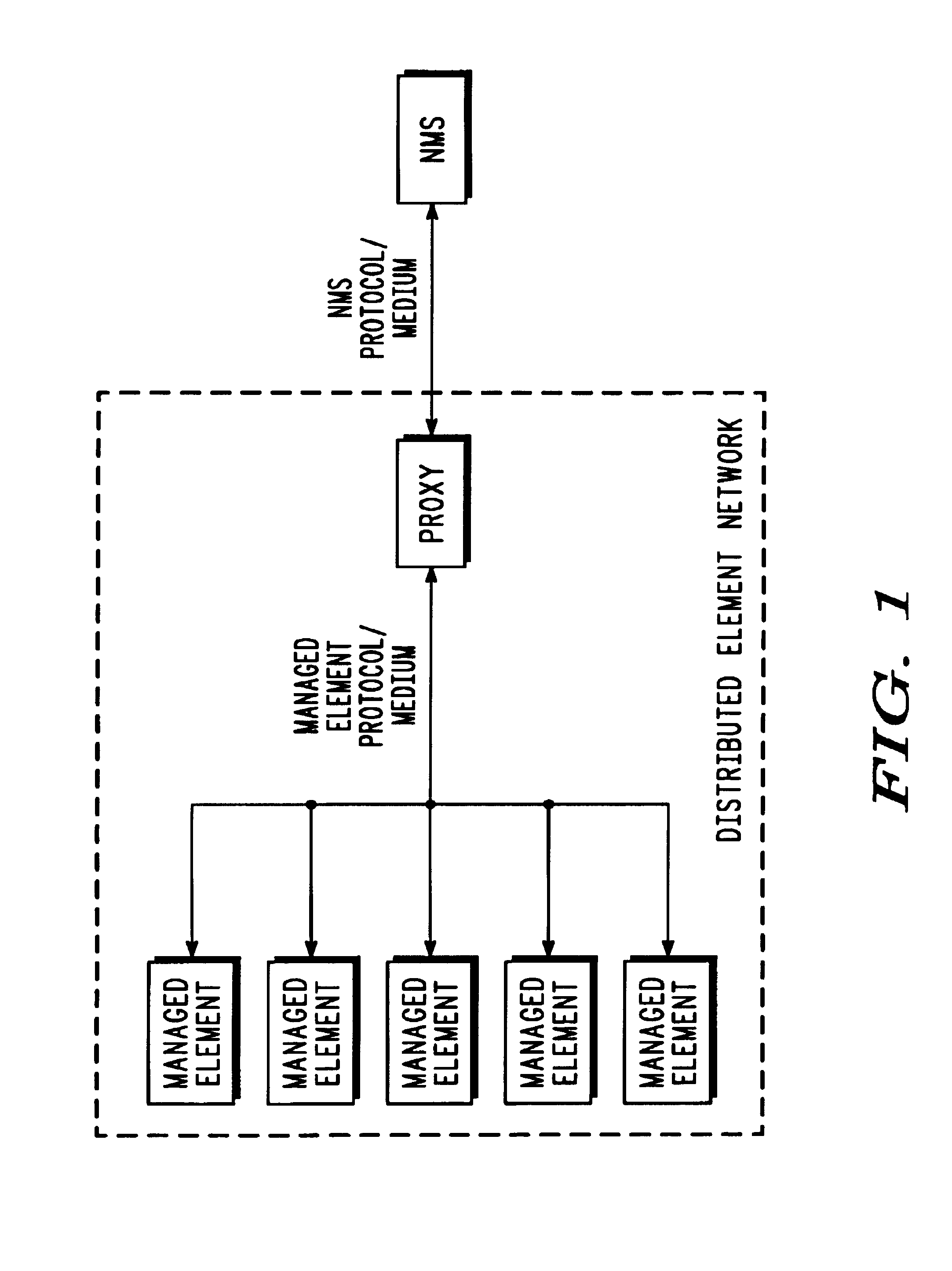
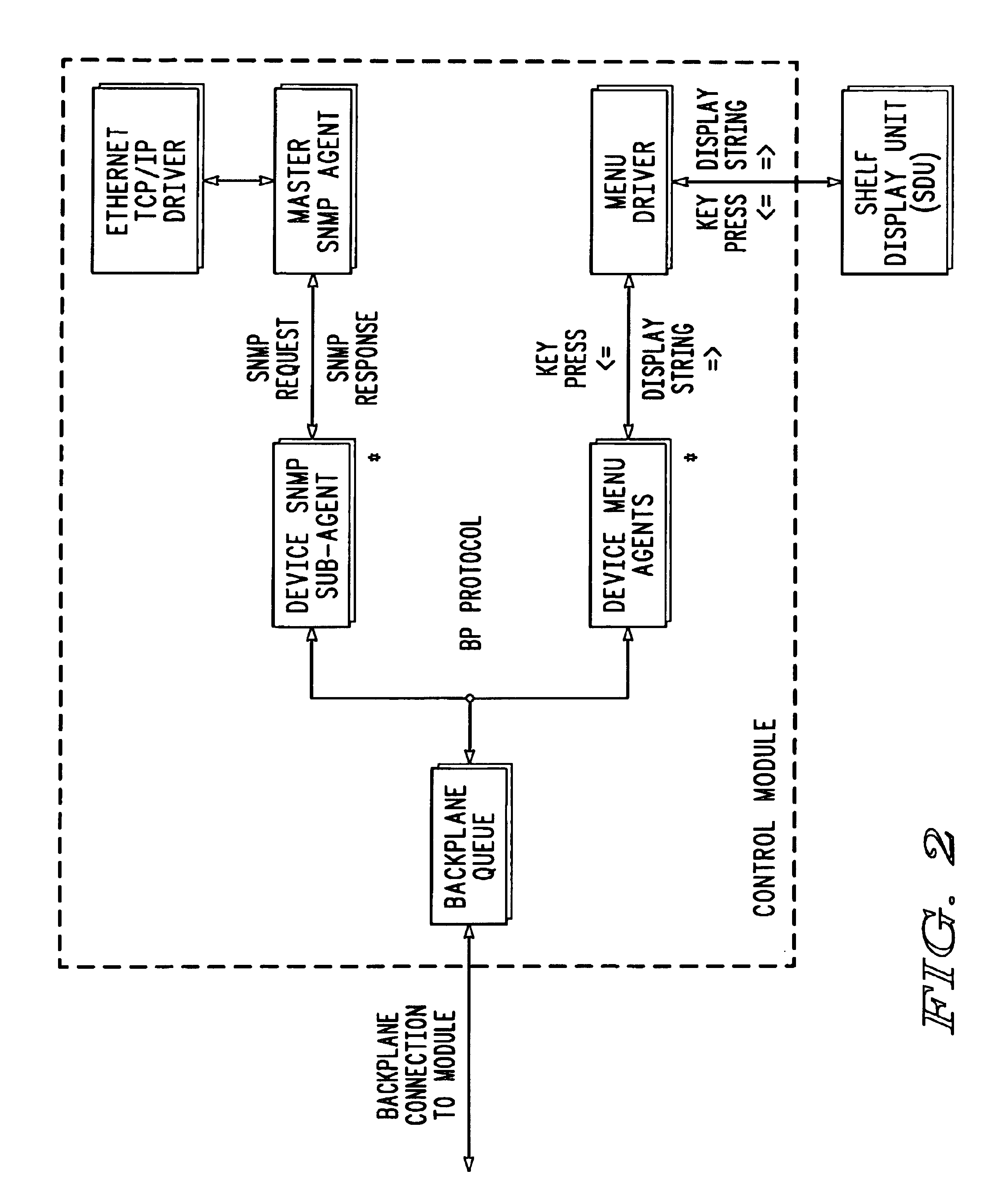
Distributed element network management
InactiveUS6963911B2Simple taskFree laborMultiple digital computer combinationsData switching networksNetwork agentNetwork management
A network of managed elements, in which code necessary for the integration of the elements into the network is contained in the elements themselves. A network proxy polls the elements to determine the presence of a new element or a revision to the code of an existing element. When found, code is copied from the element to the proxy, which serves as an interface between the elements and a network management system.
Owner:GOOGLE TECH HLDG LLC
Application Prioritization in a Stateless Protocol
InactiveUS20080034052A1Multiple digital computer combinationsElectric digital data processingEdge serverStateless protocol
Techniques are disclosed that enable an application to prioritize its traffic in an application-specific manner, such that traffic which is most important to this application can be prioritized over traffic that is less important to this application, where this prioritization information is reflected in differential treatment of the traffic within the network. An application conveys relative priority information for its traffic to a Web proxy or edge server, and this device then consults stored policy information to determine how the traffic should be prioritized in the network. The Web proxy also ensures that usage of network resources is balanced among multiple applications. Cookies are used for transmitting priority information between the edge server and application in an efficient manner.
Owner:IBM CORP
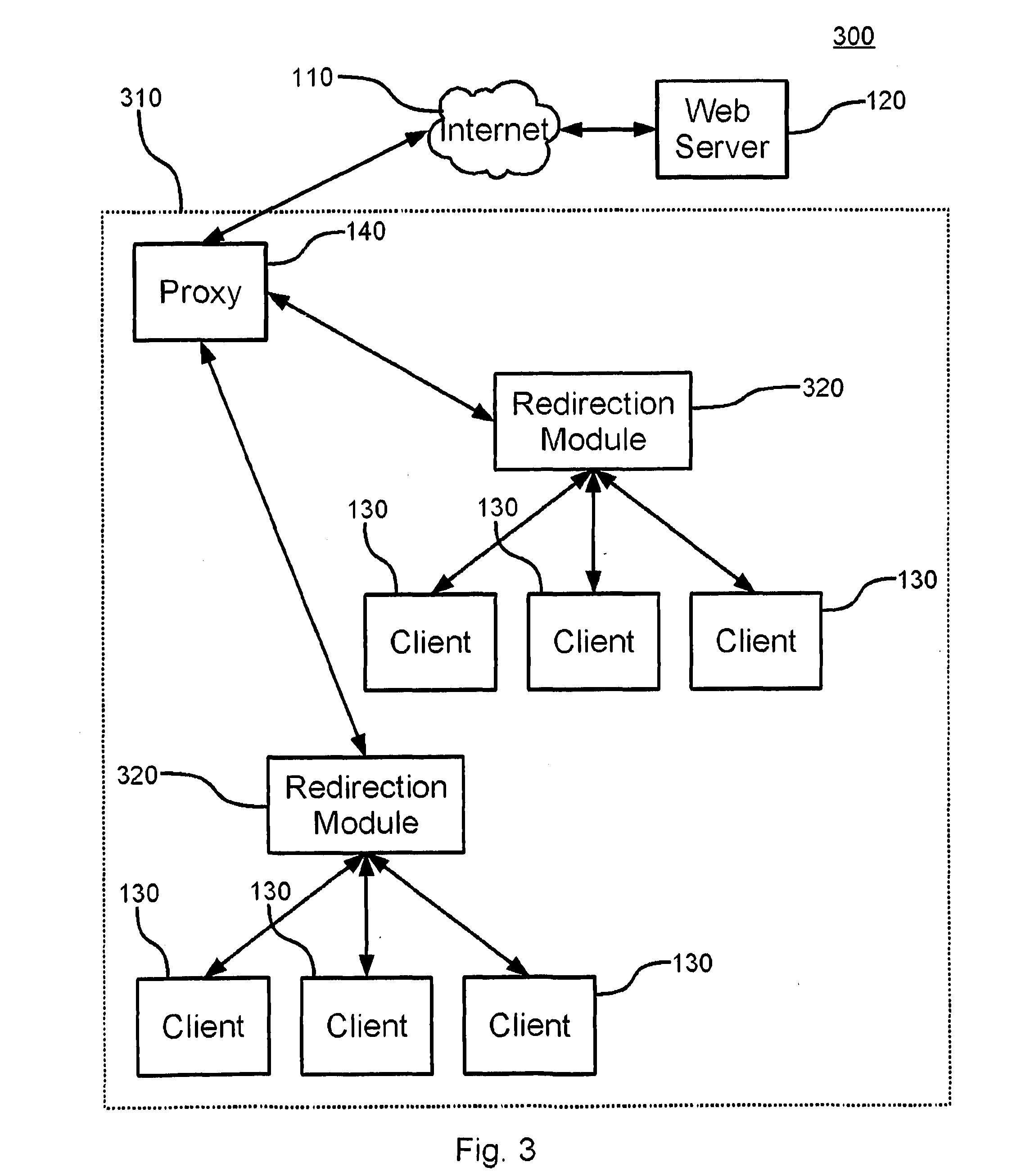
Transparent web proxy
InactiveUS20110119331A1Multiple digital computer combinationsTransmissionInternet communicationWeb service
Disclosed is a system and method for providing a transparent proxy for Internet communications. A filtering and redirection module receives IP requests from at least one client, reads and saves the destination of the IP requests, and rewrites the destination of the IP request to the destination of a proxy module. Upon being unable to read, or otherwise determine, a destination for an IP request, the proxy module accesses destination information about the IP request from the filtering and redirection module. The proxy module then transmits the IP request to a web server at the original destination.
Owner:INTERDIGITAL CE PATENT HLDG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com