Patents
Literature
883 results about "Rule matching" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
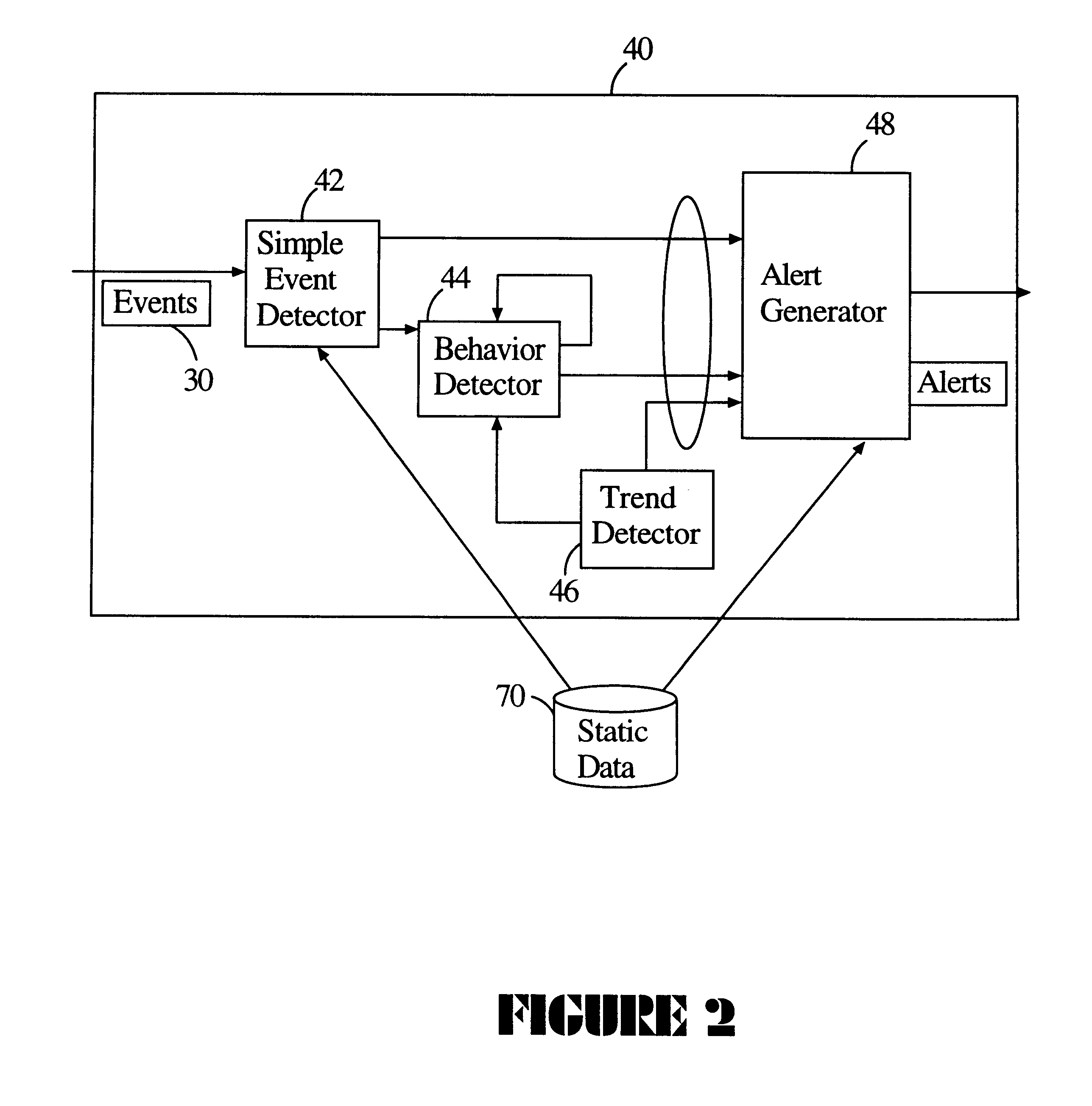
Matching rules. Matching rules are stateless. They perform passive filtering on the attribute values of an incoming event. A matching rule consists of a single predicate; if the predicate evaluates to true, the trigger actions, which are specified in the rule, run.
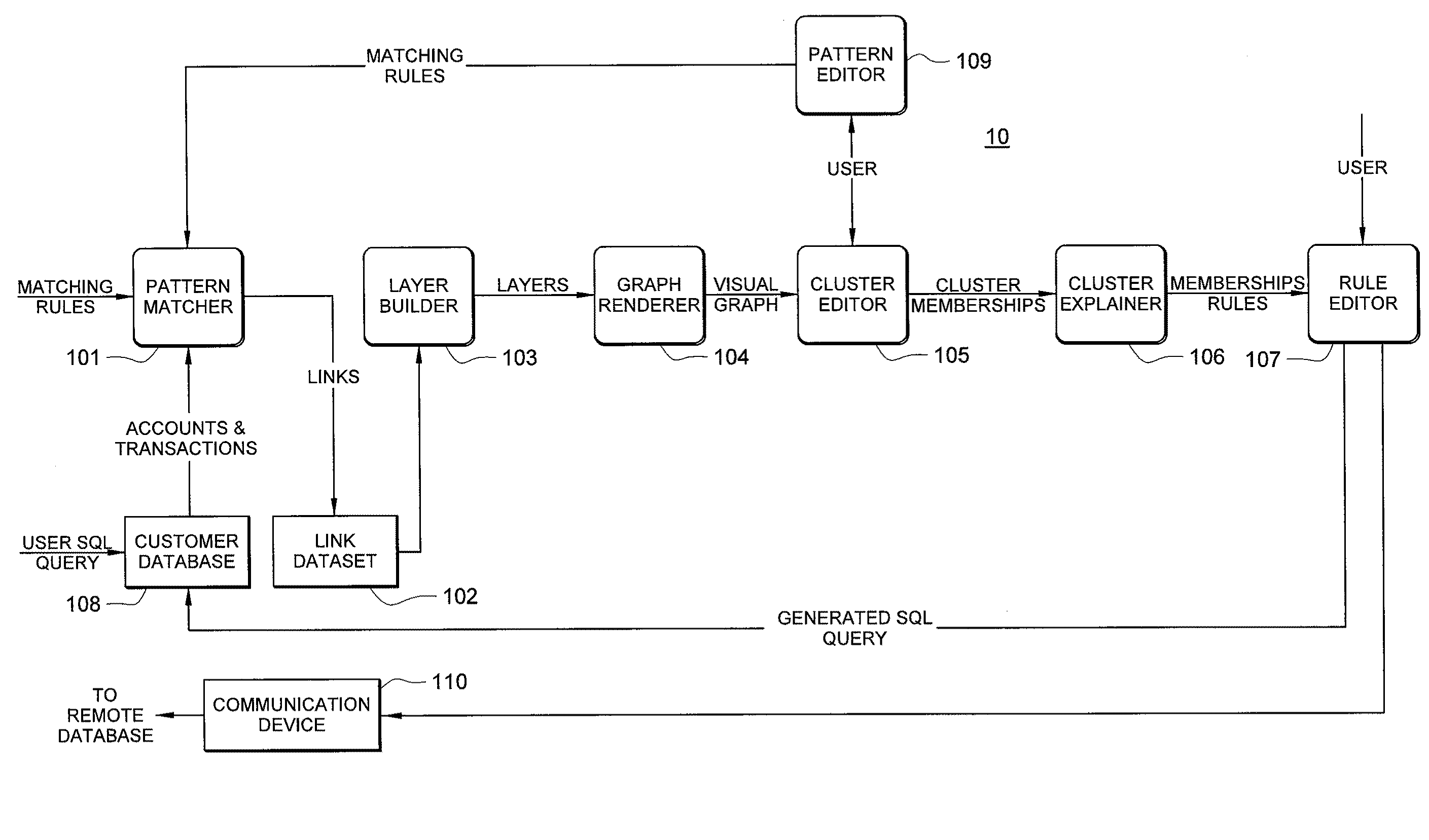
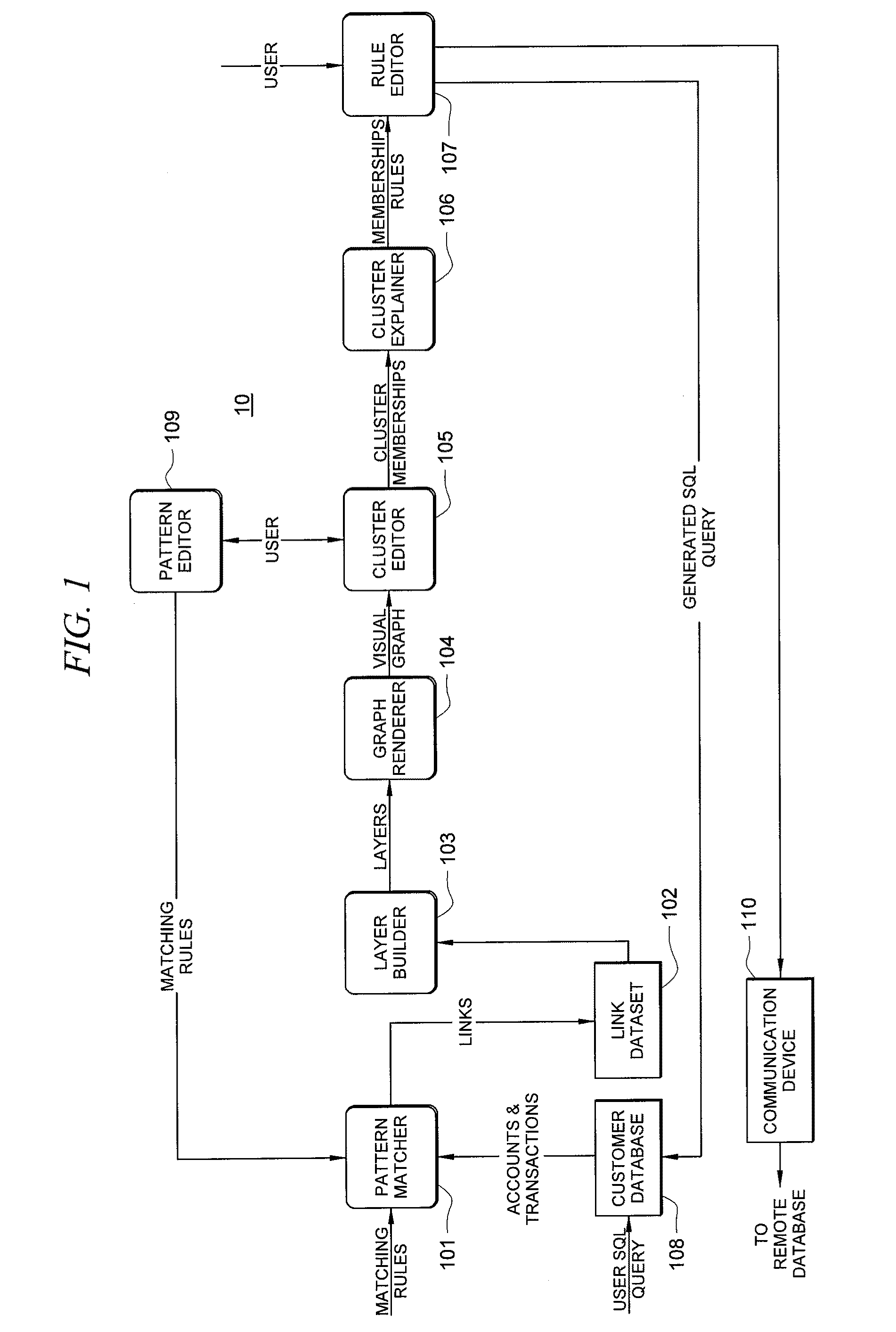
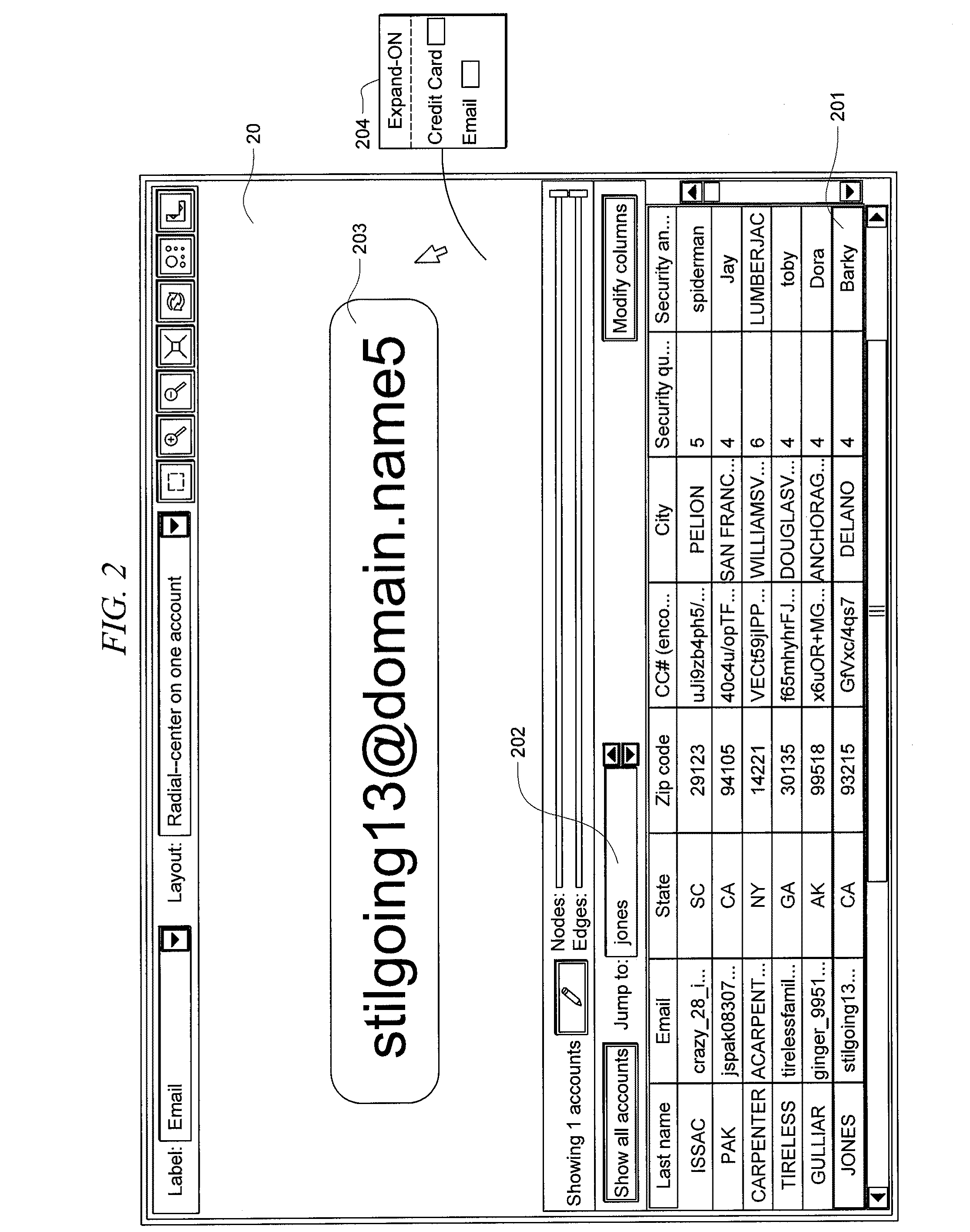
Systems and methods for fraud detection via interactive link analysis
ActiveUS20090044279A1Facilitate fraud detectionFinanceDigital data processing detailsHigh probabilitySystem identification
Fraud detection is facilitated by developing account cluster membership rules and converting them to database queries via an examination of clusters of linked accounts abstracted from the customer database. The cluster membership rules are based upon certain observed data patterns associated with potentially fraudulent activity. In one embodiment, account clusters are grouped around behavior patterns exhibited by imposters. The system then identifies those clusters exhibiting a high probability of fraud and builds cluster membership rules for identifying subsequent accounts that match those rules. The rules are designed to define the parameters of the identified clusters. When the rules are deployed in a transaction blocking system, when a rule pertaining to an identified fraudulent cluster is triggered, the transaction blocking system blocks the transaction with respect to new users who enter the website.
Owner:FAIR ISAAC & CO INC
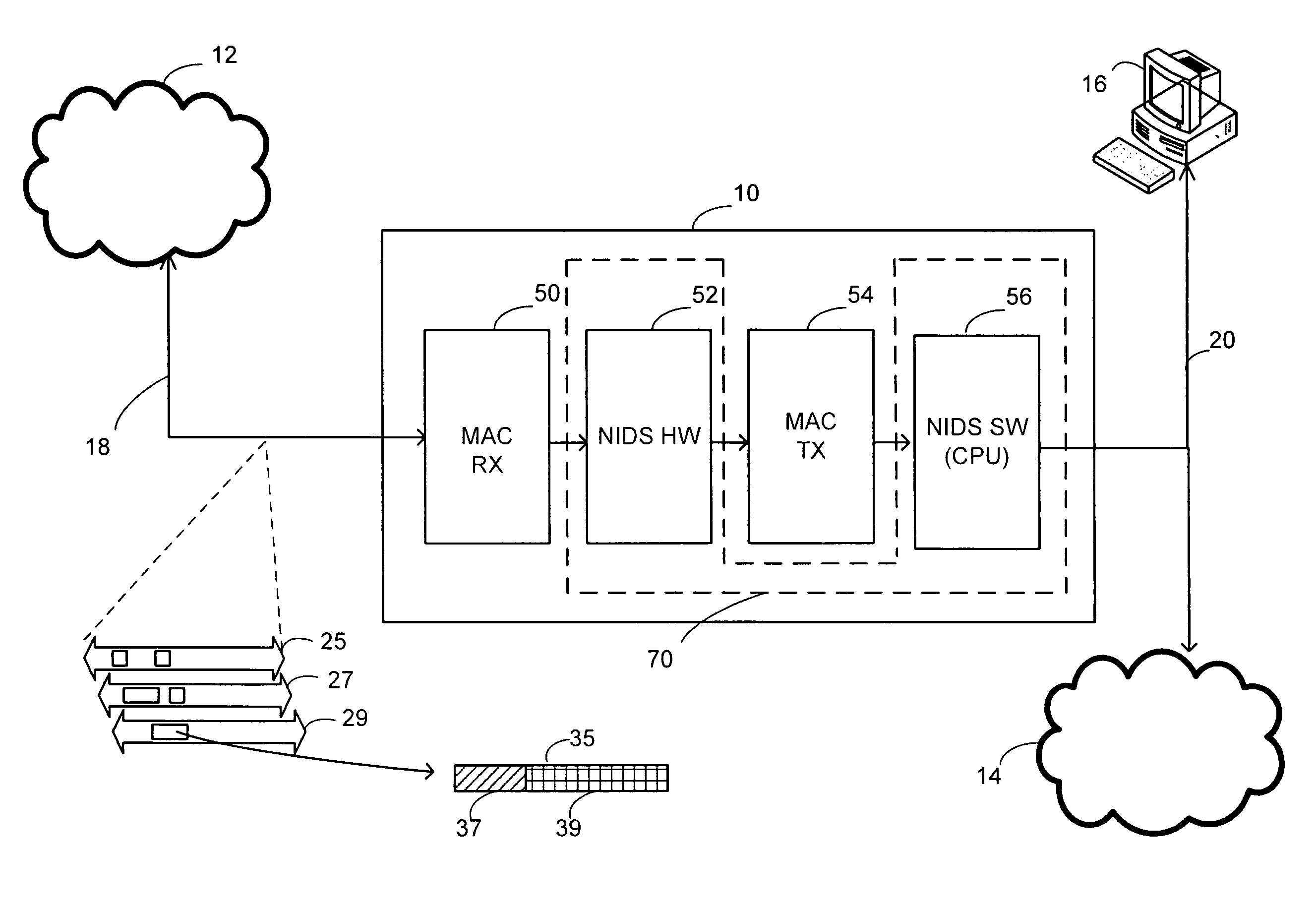
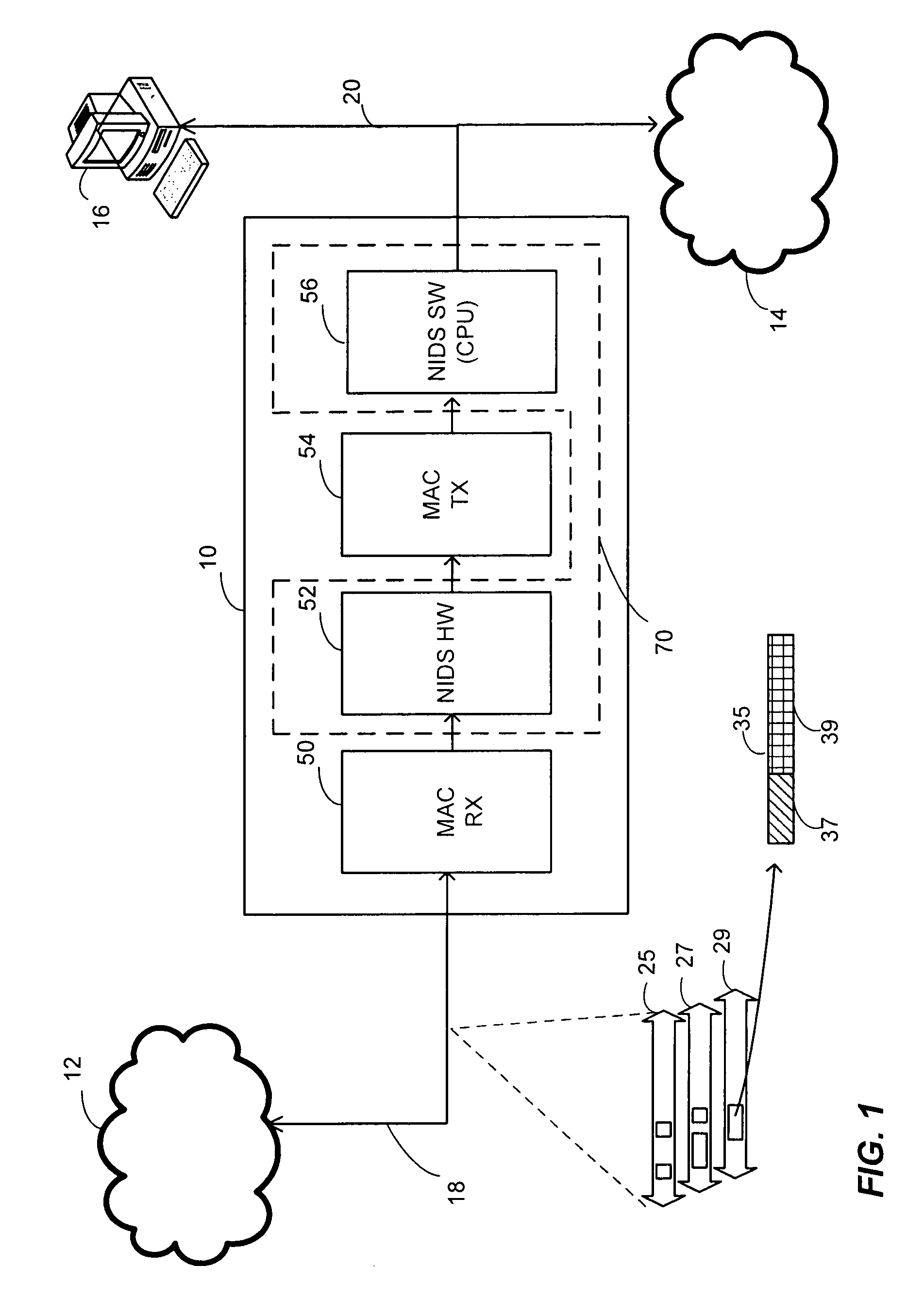
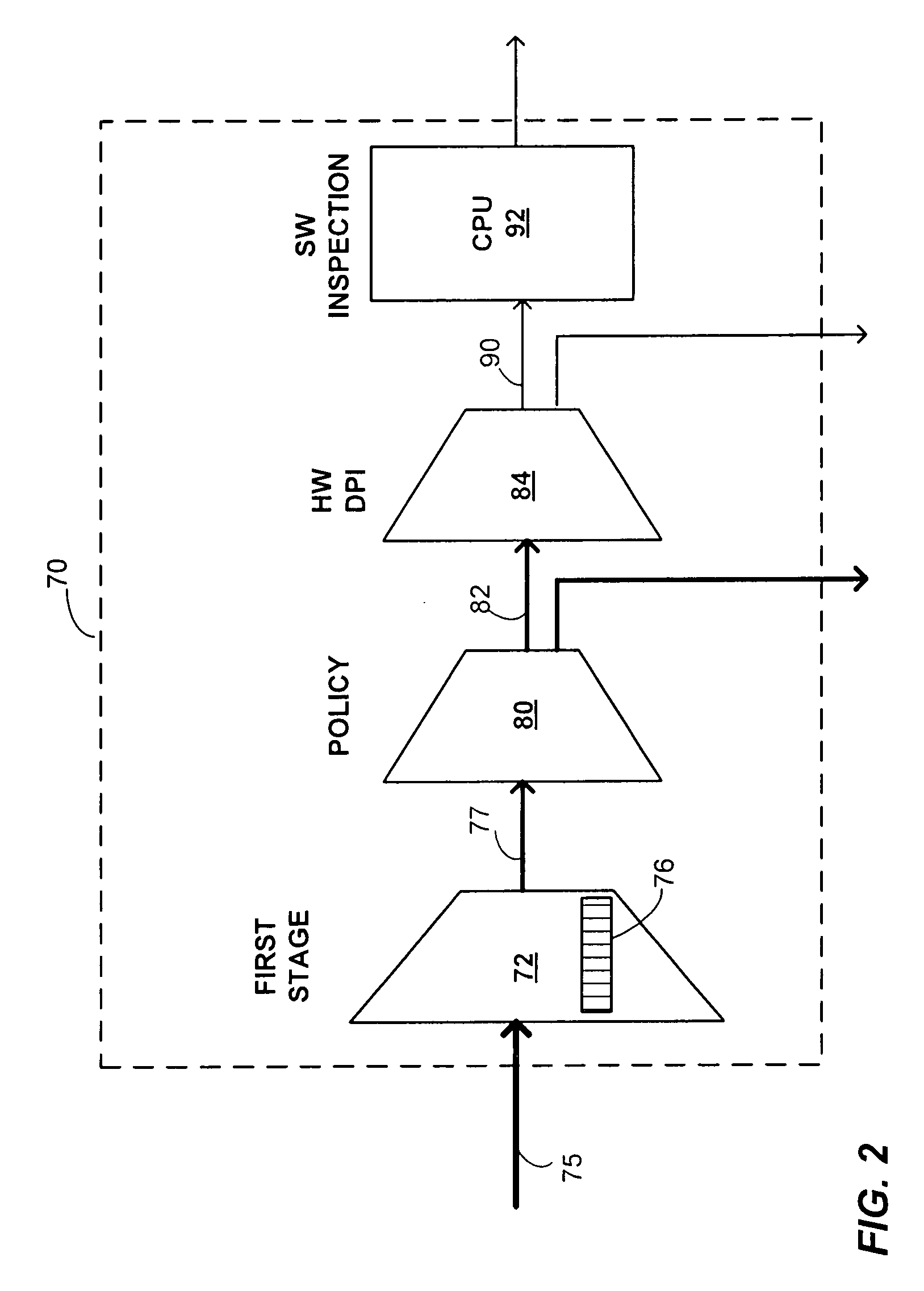
Method and Apparatus for Deep Packet Inspection for Network Intrusion Detection
ActiveUS20080201772A1Hardware monitoringMultiple digital computer combinationsComputer hardwareData stream
In a method of determining whether a data stream includes unauthorized data, the data stream is analyzed using a hardware filter to detect a presence of one or more of a first set of patterns in the data stream. It is determined whether a packet in the data stream belongs to one of a plurality of data flows to be further inspected based on the analysis of the data stream by the hardware filter. A set of rules is applied to the packet to produce rule match status data if it is determined that the packet belongs to one of the plurality of data flows to be further inspected. The packet is analyzed to determine if the packet includes unauthorized data using software stored on a computer-readable medium and implemented on a processor if the rule match status data indicates that the packet potentially includes unauthorized data.
Owner:MARVELL ISRAEL MISL
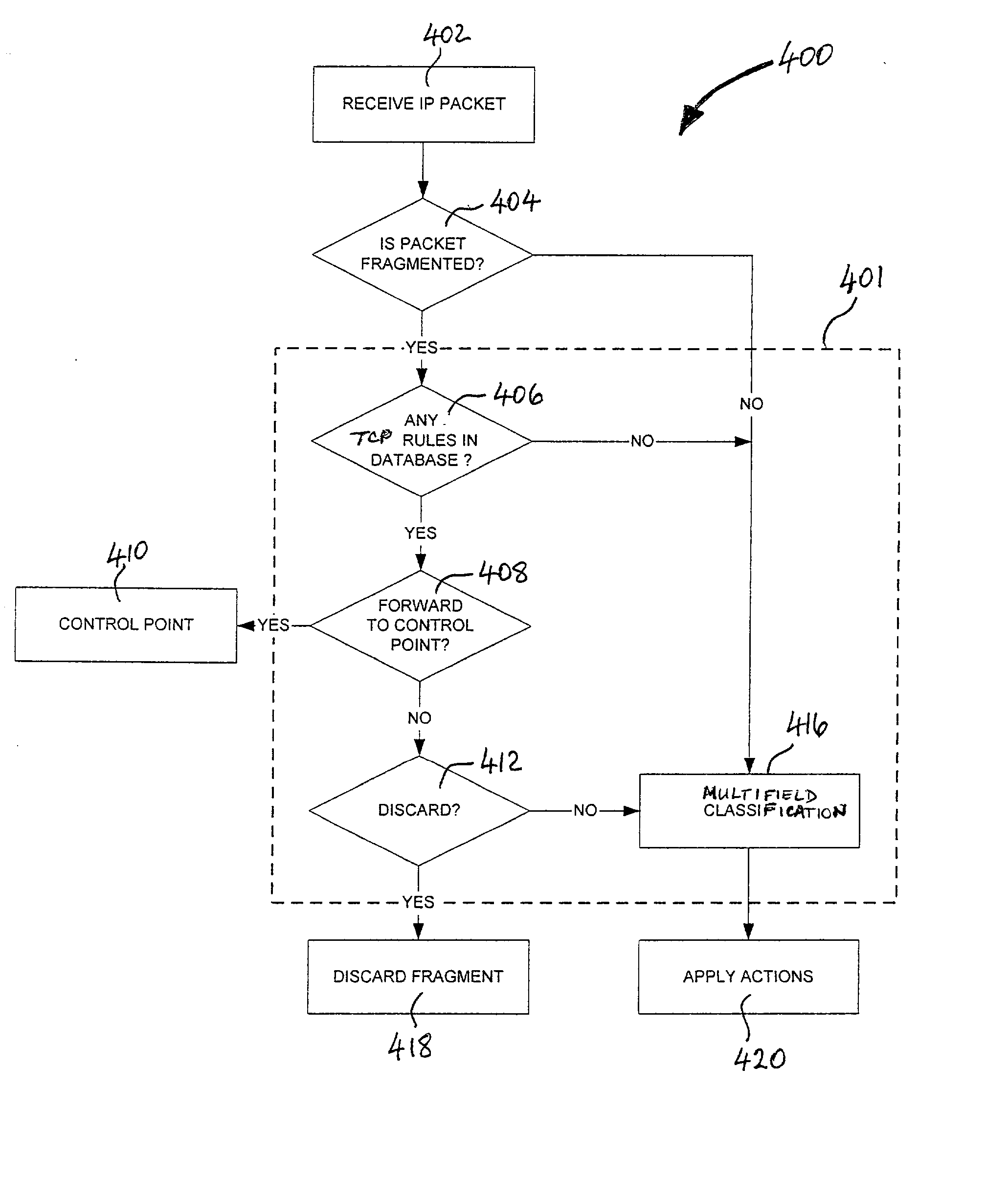
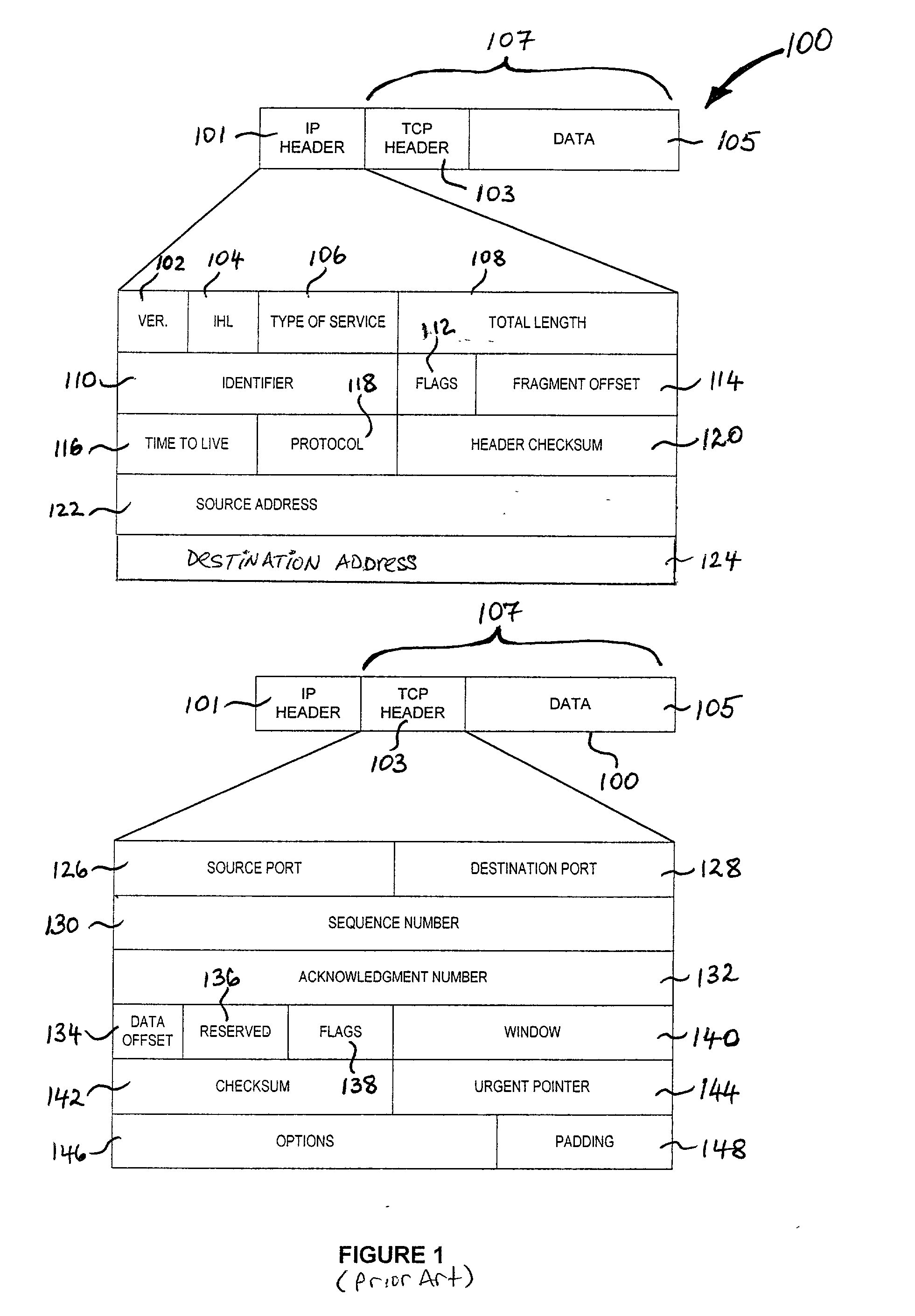
Classification support system and method for fragmented IP packets
InactiveUS20030126272A1Data processing applicationsMultiple digital computer combinationsSupporting systemWire speed
Owner:IBM CORP
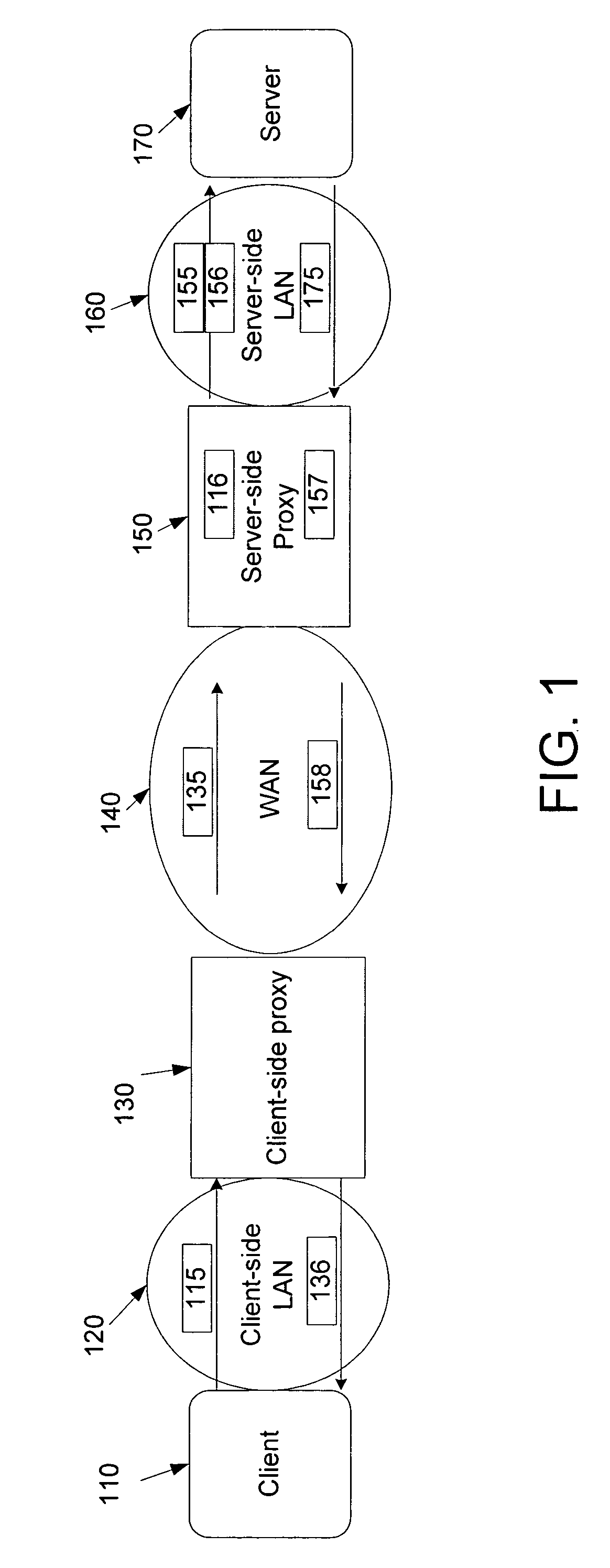
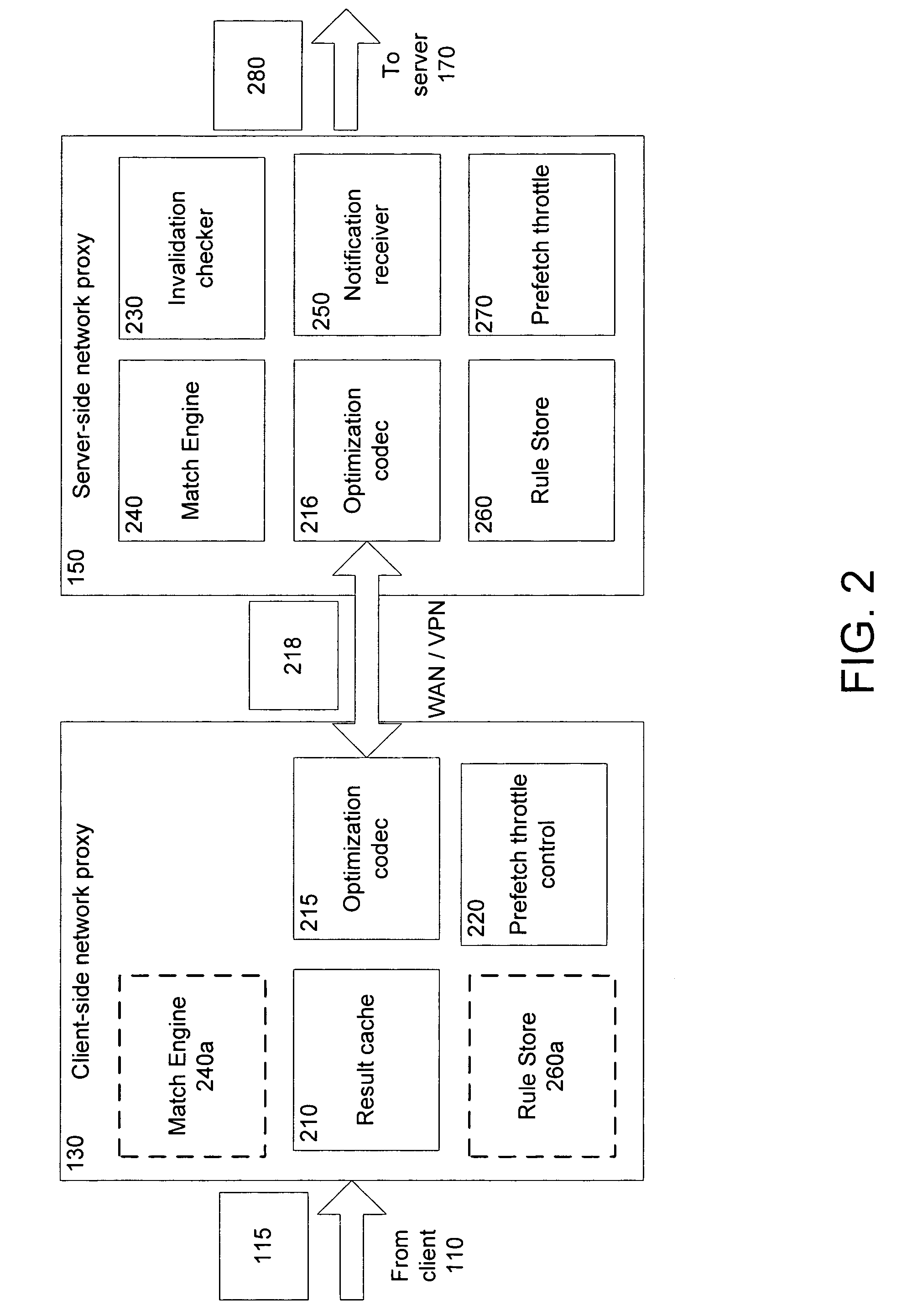
Rules-based transaction prefetching using connection end-point proxies
ActiveUS20060212524A1Increase speedReduce server latencyMultiple digital computer combinationsTransmissionClient-sideNetwork application
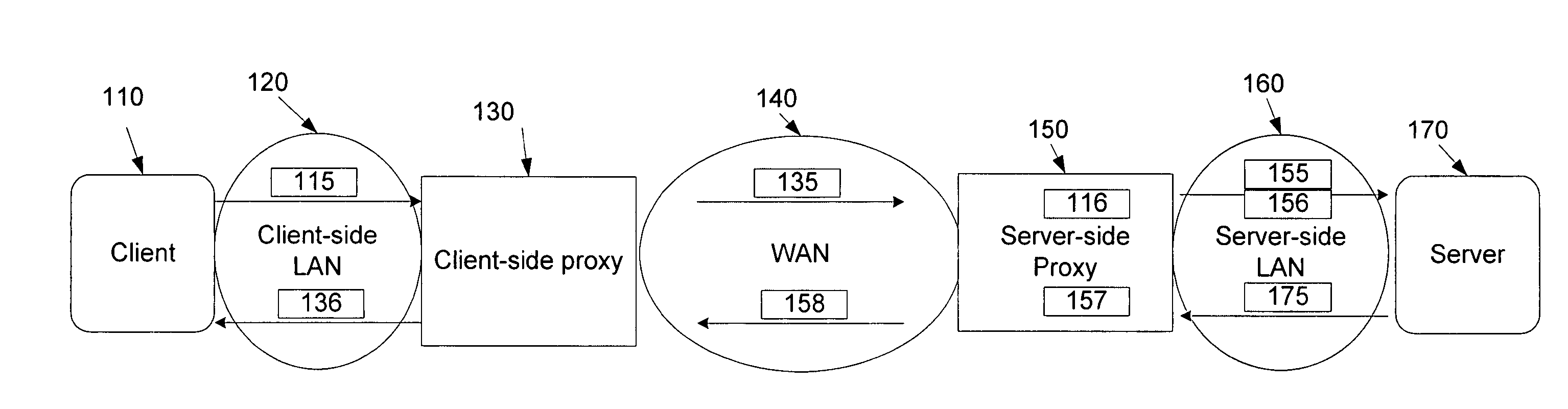
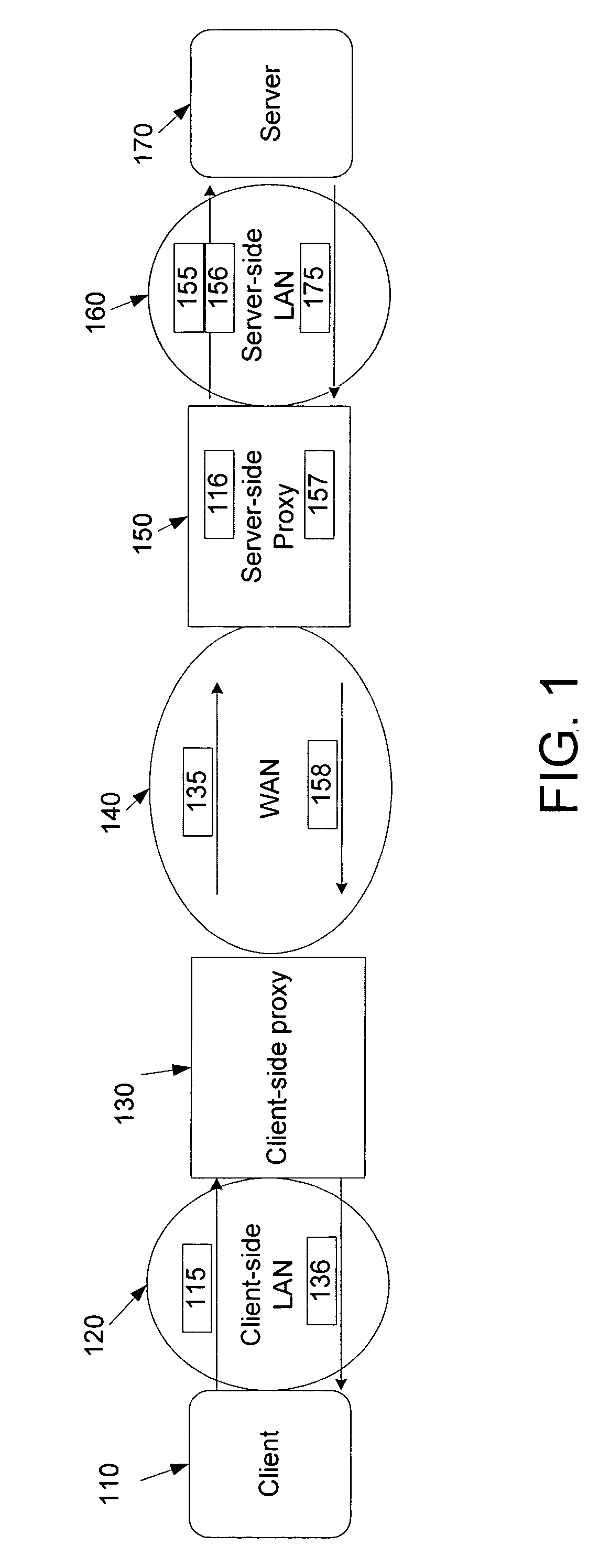
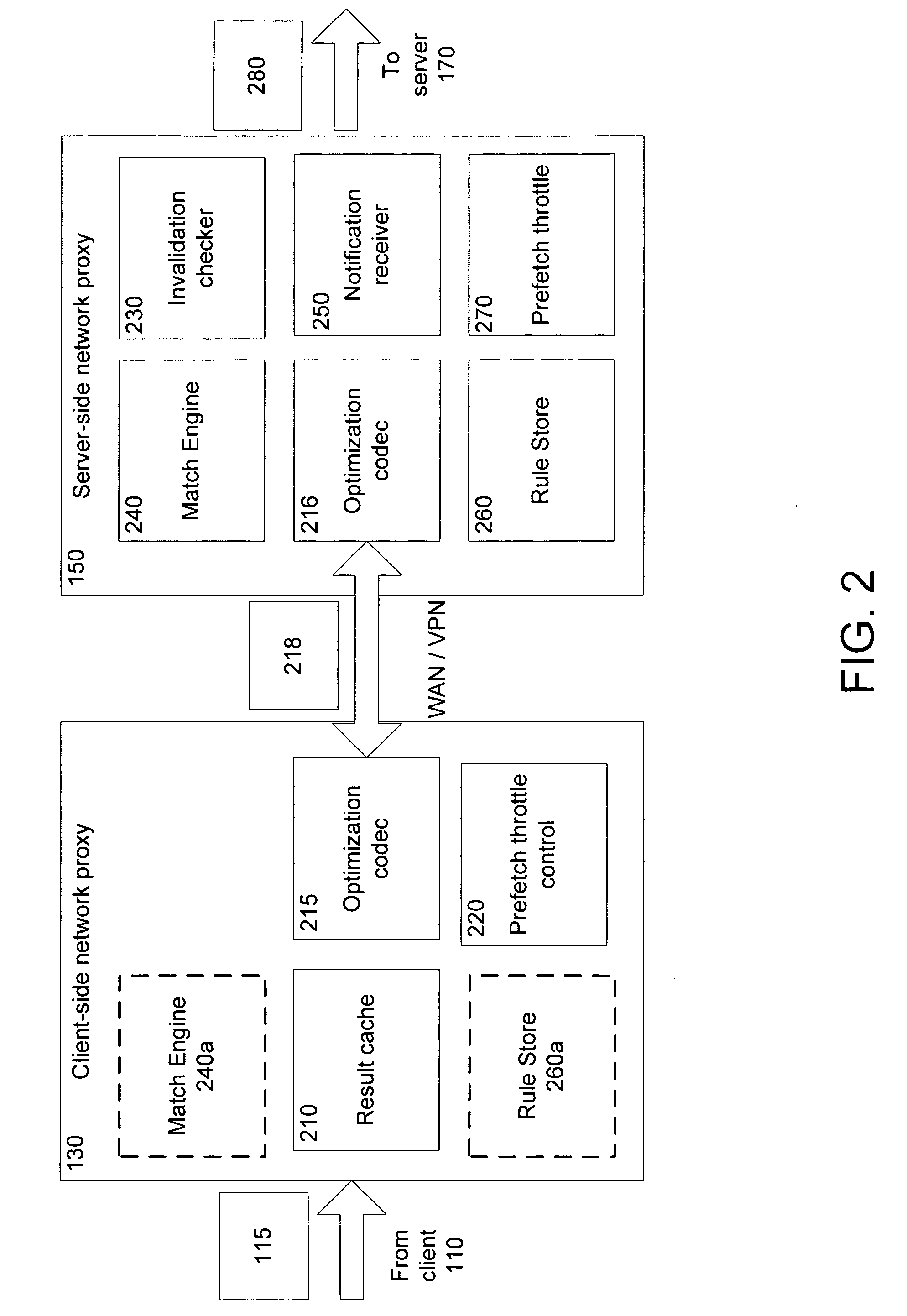
Network proxies reduce server latency in response to series of requests from client applications. Network proxies intercept messages clients and a server. Intercepted client requests are compared with rules. When client requests match a rule, additional request messages are forwarded to the server on behalf of a client application. In response to the additional request messages, the server provides corresponding response messages. A network proxy intercepts and caches the response messages. Subsequent client requests are intercepted by the network application proxy and compared with the cached messages. If a cached response message corresponds with a client request message, the response message is returned to the client application immediately instead of re-requesting the same information from the server. A server-side network proxy can compare client requests with the rules and send additional request messages. The corresponding response messages can be forwarded to a client-side network proxy for caching.
Owner:RIVERBED TECH LLC
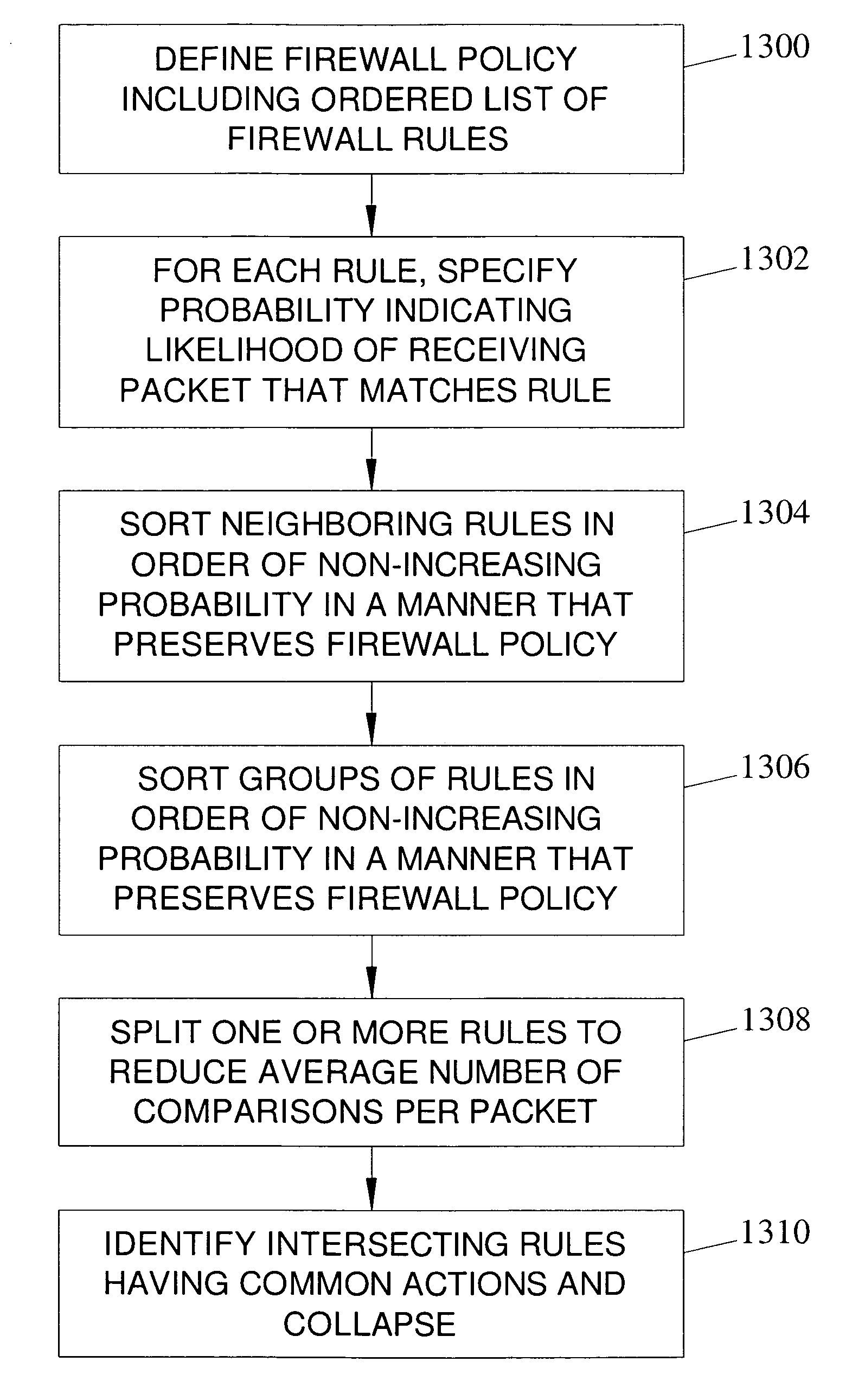
Methods, systems, and computer program products for network firewall policy optimization
ActiveUS20060248580A1Improve performanceLower latencyMultiplex system selection arrangementsData switching by path configurationComputer networkComputer program
Methods, systems, and computer program products for firewall policy optimization are disclosed. According to one method, a firewall policy including an ordered list of firewall rules is defined. For each rule, a probability indicating a likelihood of receiving a packet matching the rule is determined. The rules are sorted in order of non-increasing probability in a manner that preserves the firewall policy.
Owner:WAKE FOREST UNIV
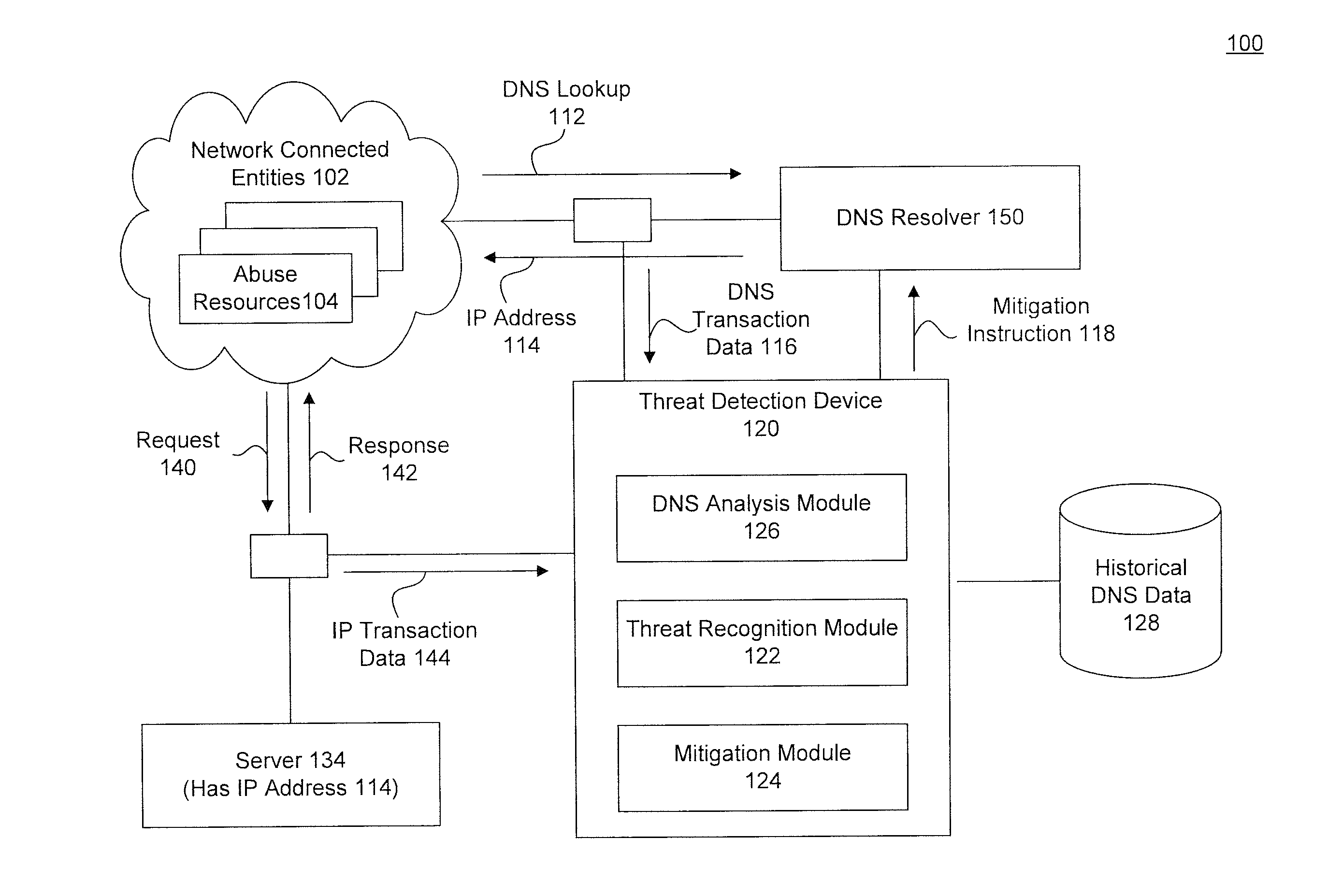
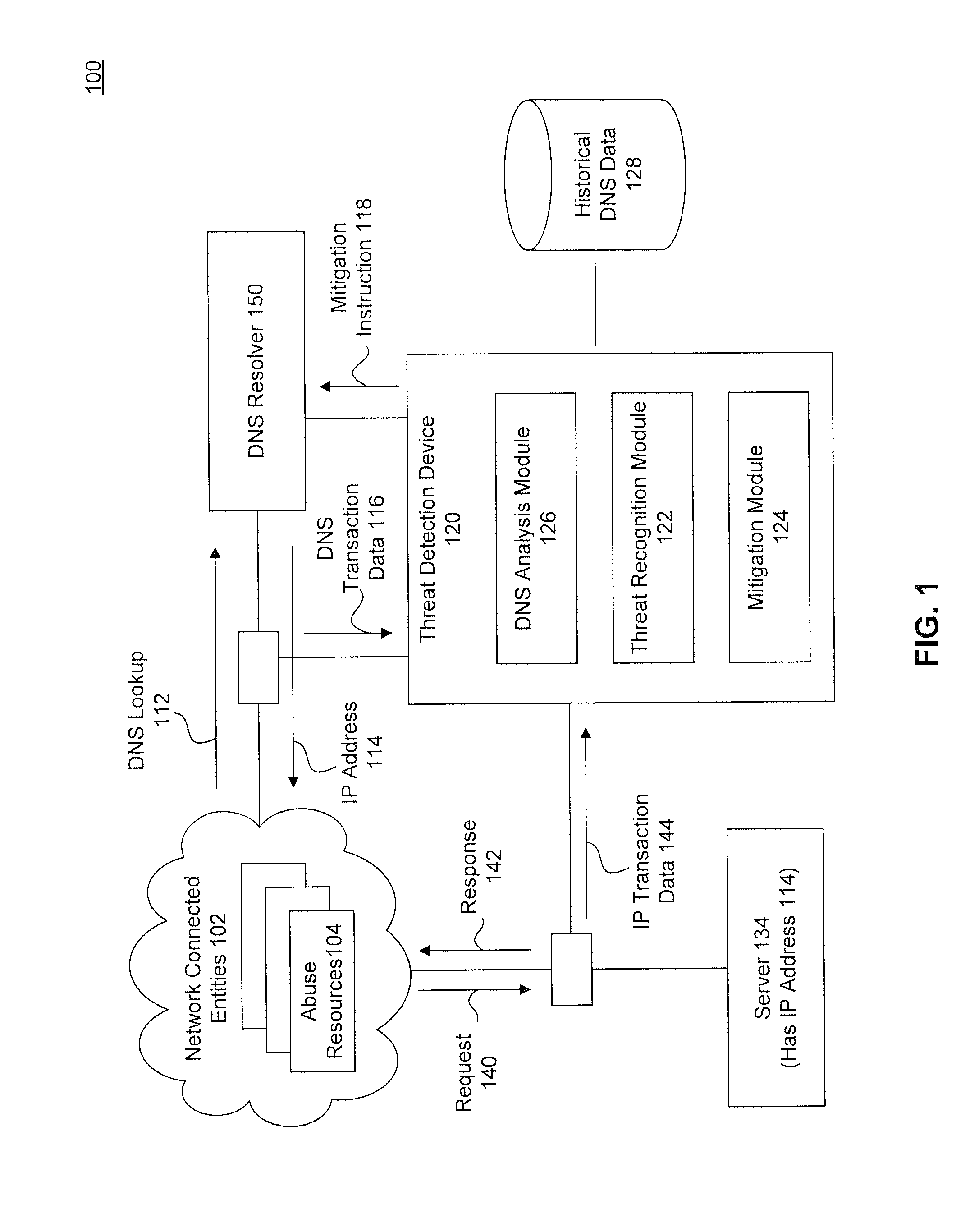
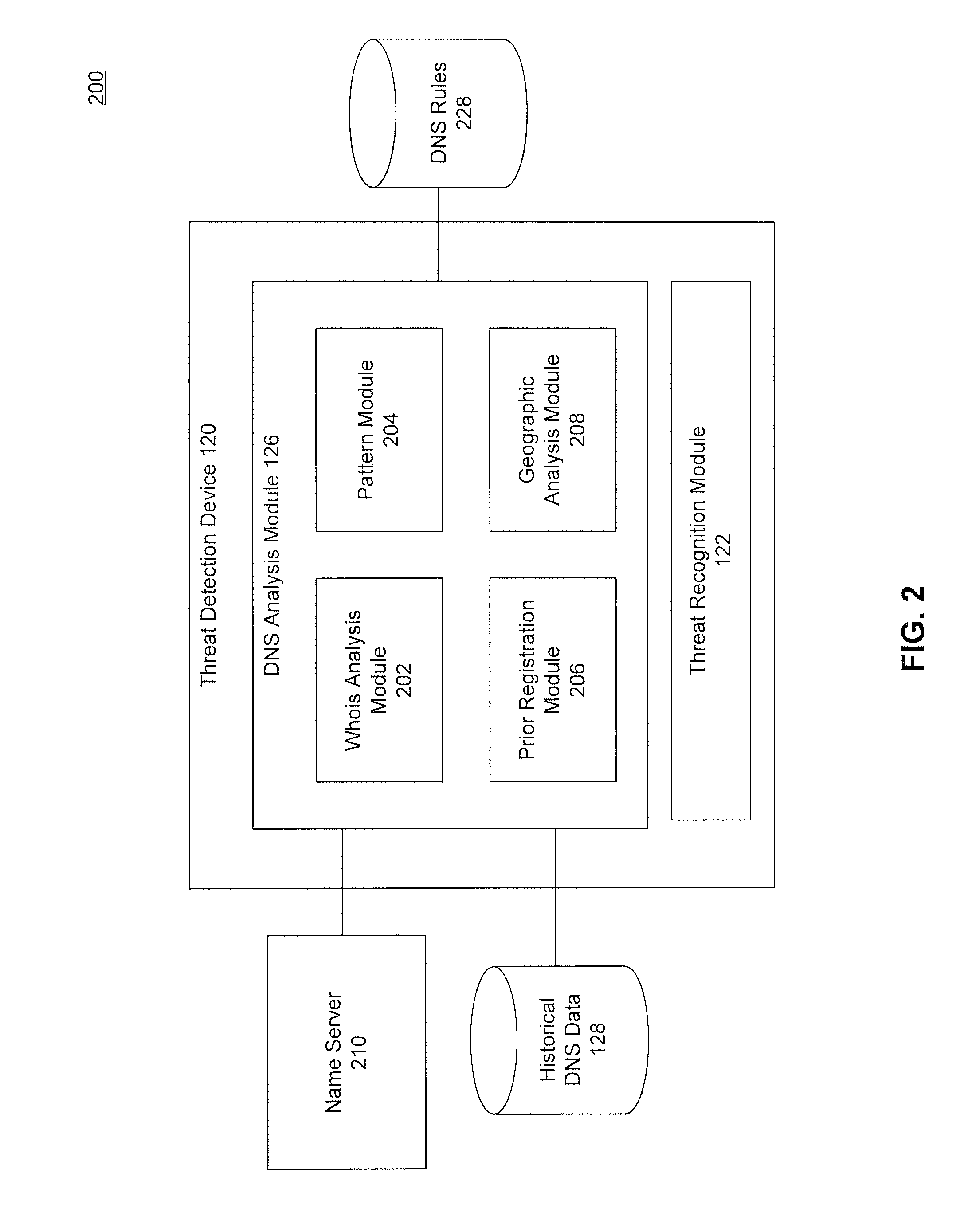
Network Threat Detection and Mitigation Using a Domain Name Service and Network Transaction Data
InactiveUS20150350229A1Memory loss protectionError detection/correctionDomain nameNetwork addressing
In an embodiment, a method detects an abuse to a network environment. In the method, real-time name service transaction data to resolve a domain name to a network address is collected from the network environment. Historical name service information for the domain name is retrieved. Transaction information describing data sent between the network environment and the network address is collected. The collected transaction information and the historical name service information is analyzed against at least one rule. When the collected transaction information and the historical name service information are determined to match at least one rule, the network address is determined to be is associated with a potential abuser of the network environment.
Owner:CISCO TECH INC
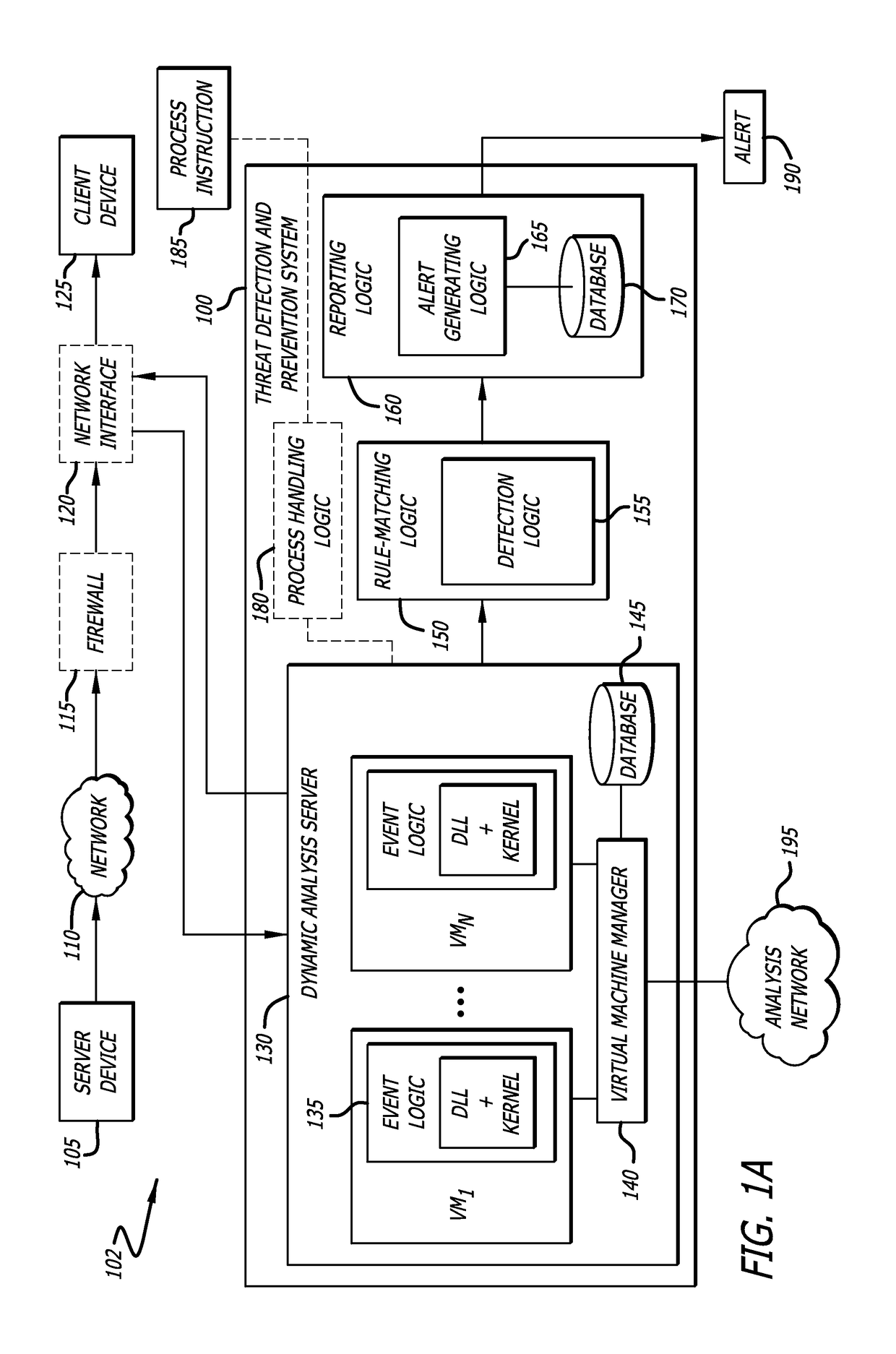
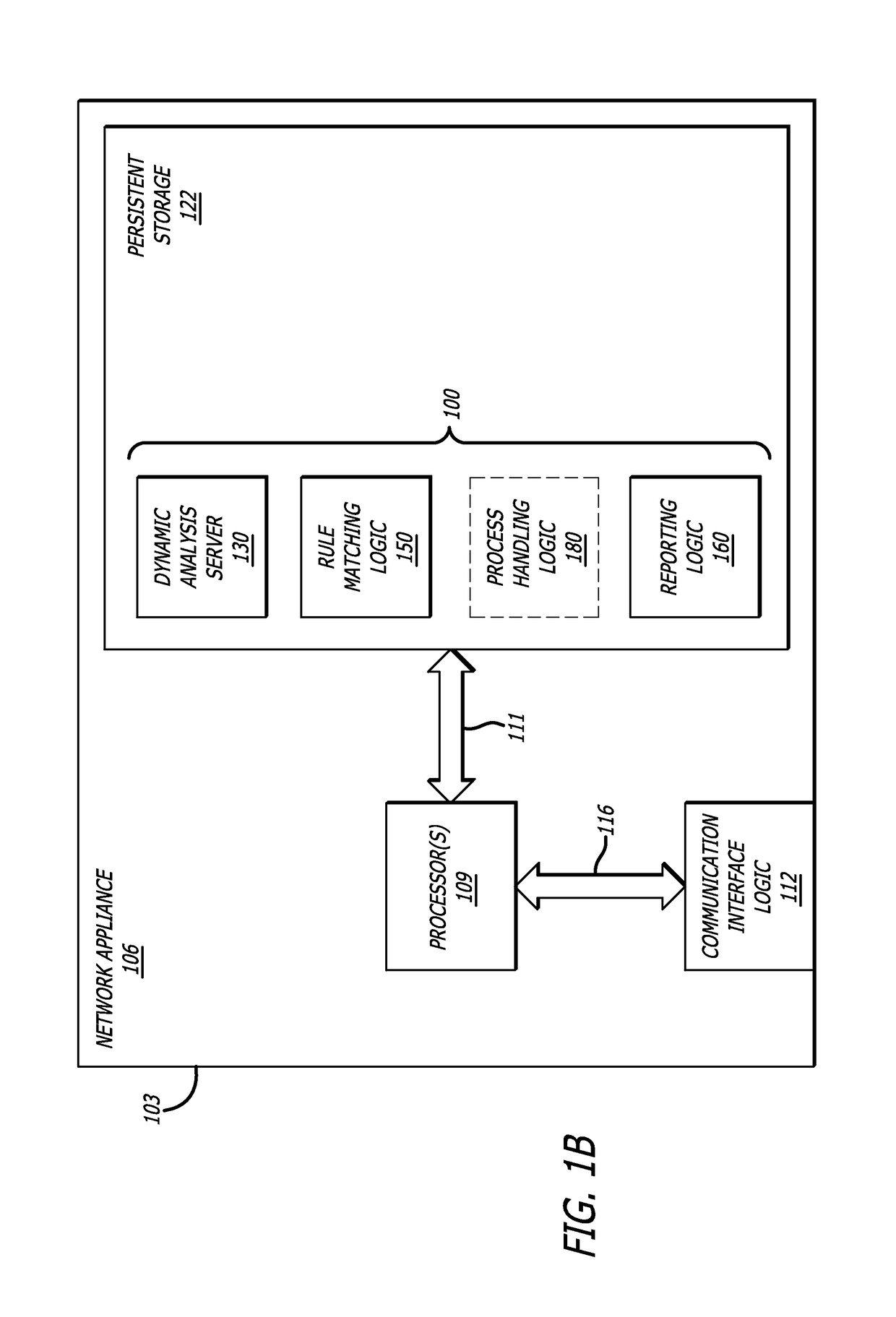
Method to detect application execution hijacking using memory protection
According to one embodiment, a system comprising a dynamic analysis server comprising one or more virtual machines is disclosed, wherein the one or more virtual machines may be configured to execute certain event logic with respect to a loaded module. The virtual machines may be communicatively coupled to a virtual machine manager and a database; and rule-matching logic comprising detection logic, wherein the detection logic is configured to determine (1) whether an access source is attempting to access a protected region such as a page guarded area; and (2) determine whether the access source is from the heap. The system further comprises reporting logic that is configured to generate an alert so as to notify a user and / or network administrator of a probable application-execution hijacking attack.
Owner:FIREEYE SECURITY HLDG US LLC
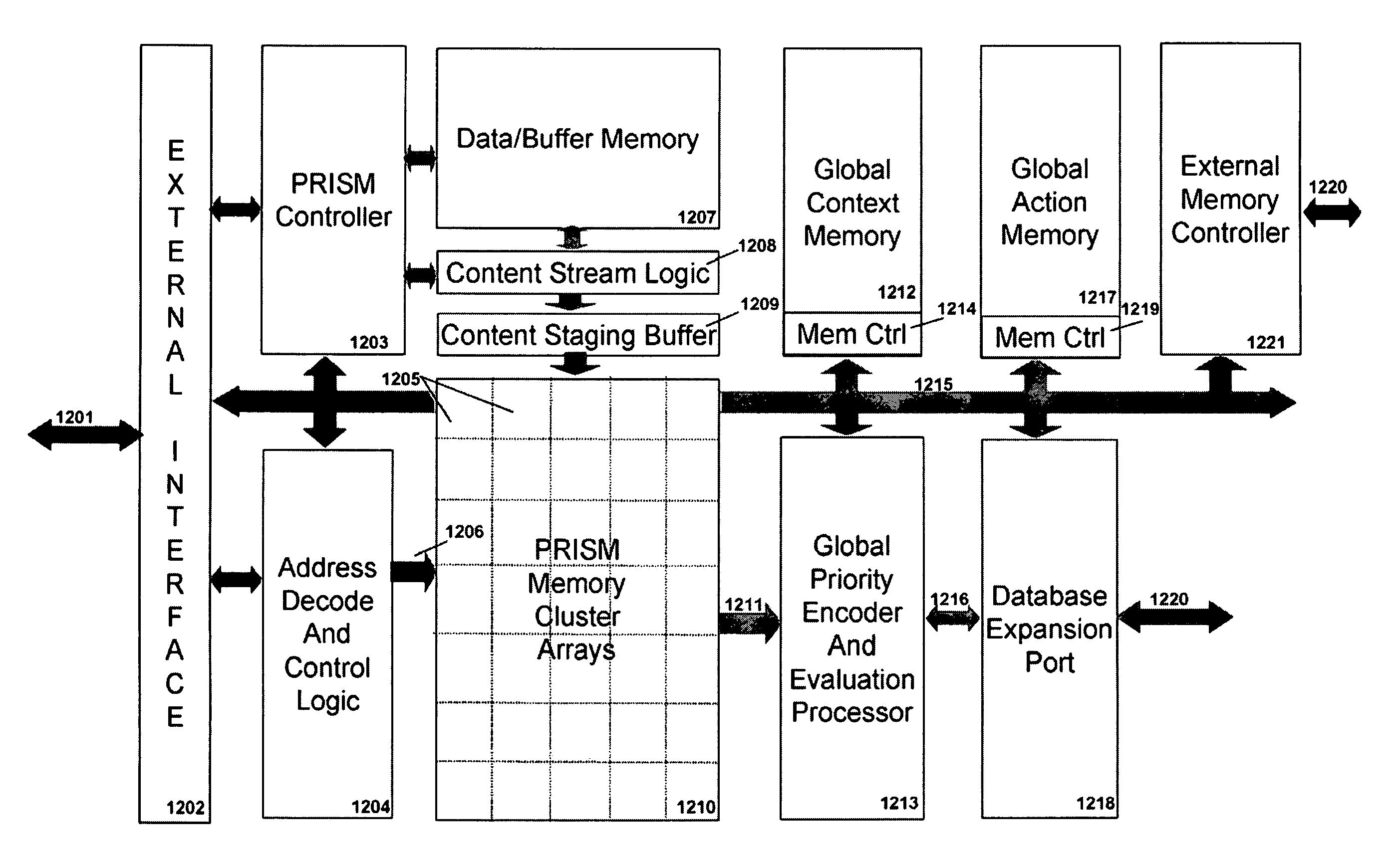
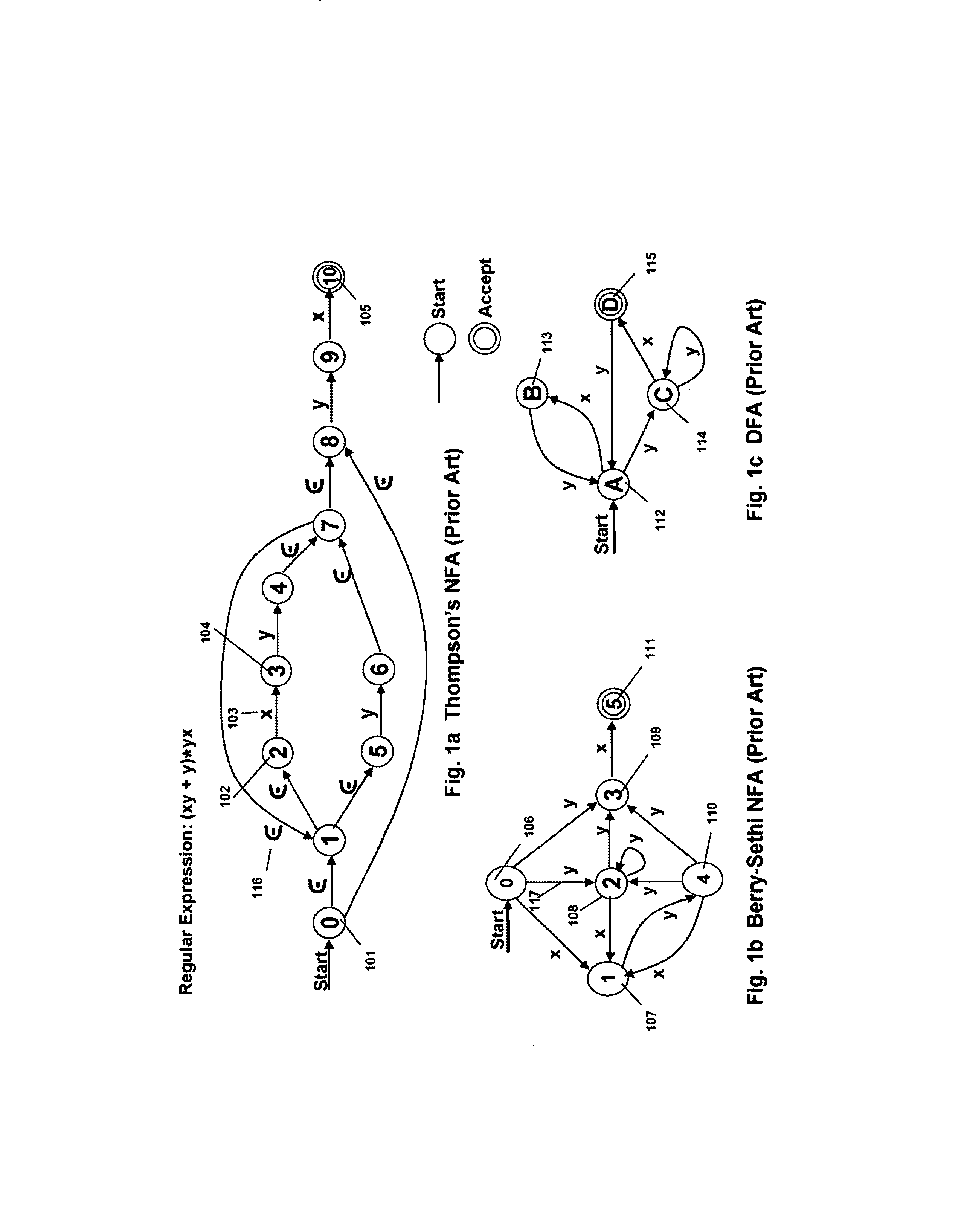
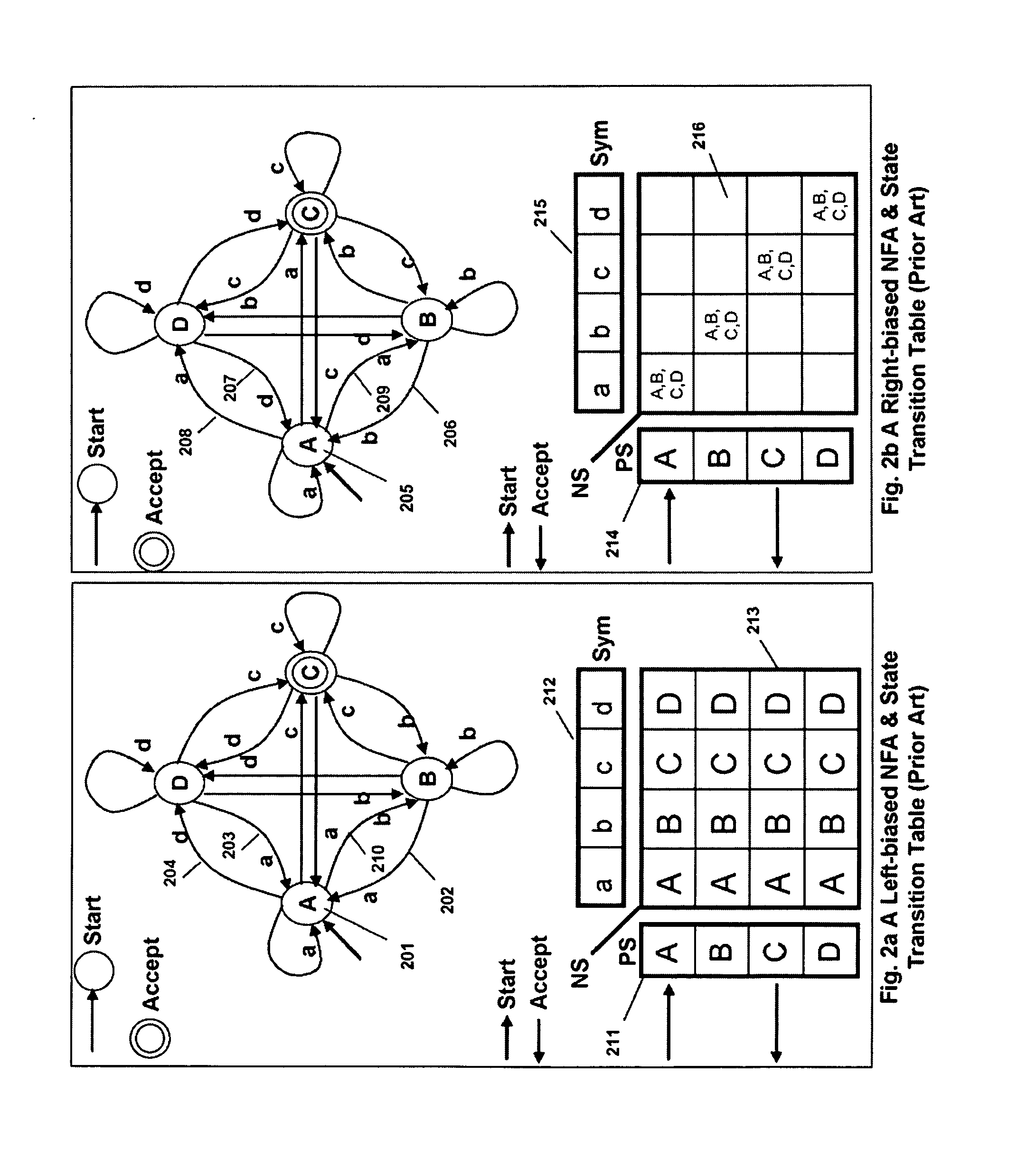
Complex symbol evaluation for programmable intelligent search memory
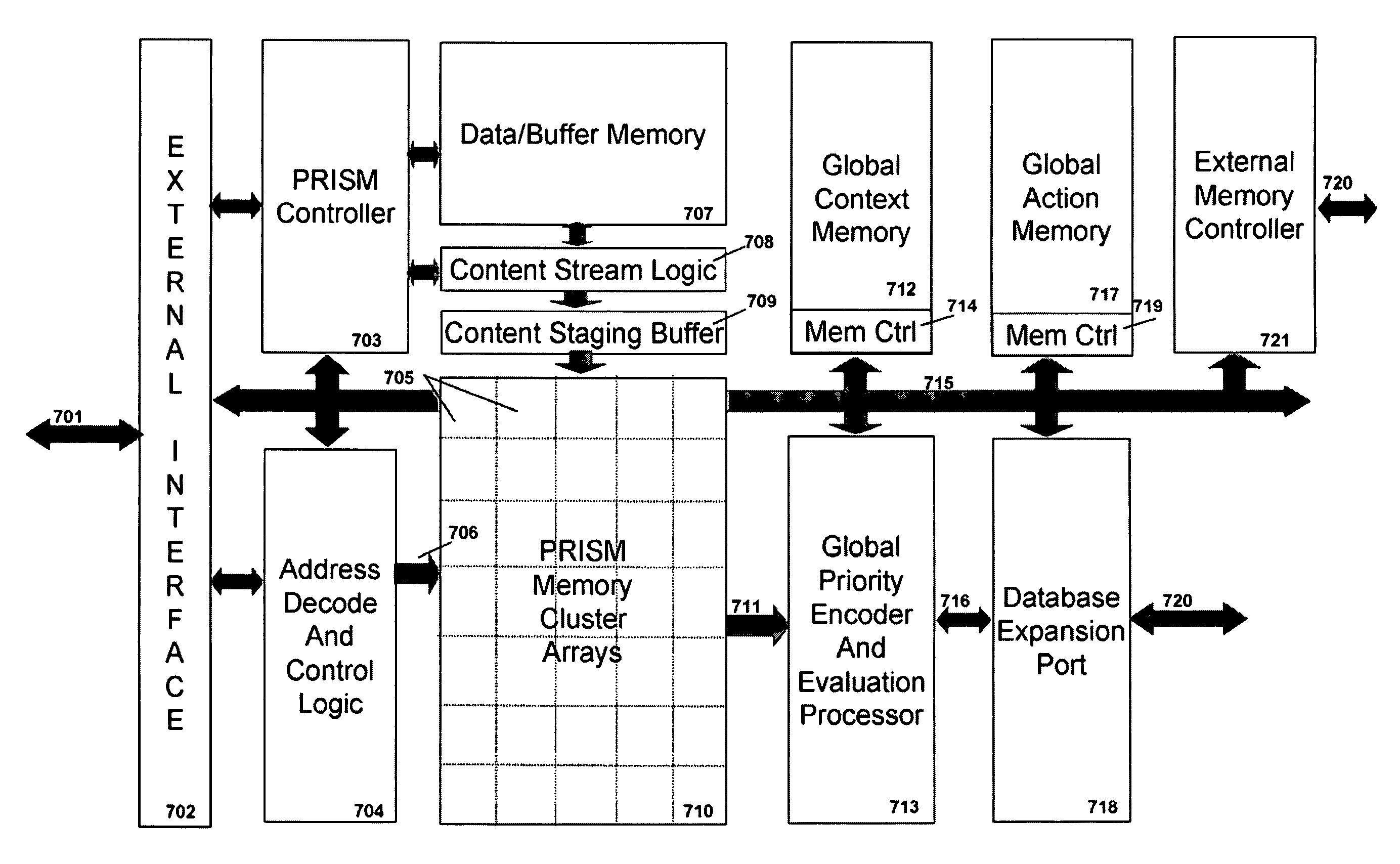
ActiveUS7827190B2Efficient and compact realizationDigital data information retrievalDigital data processing detailsTerm memoryMemory architecture
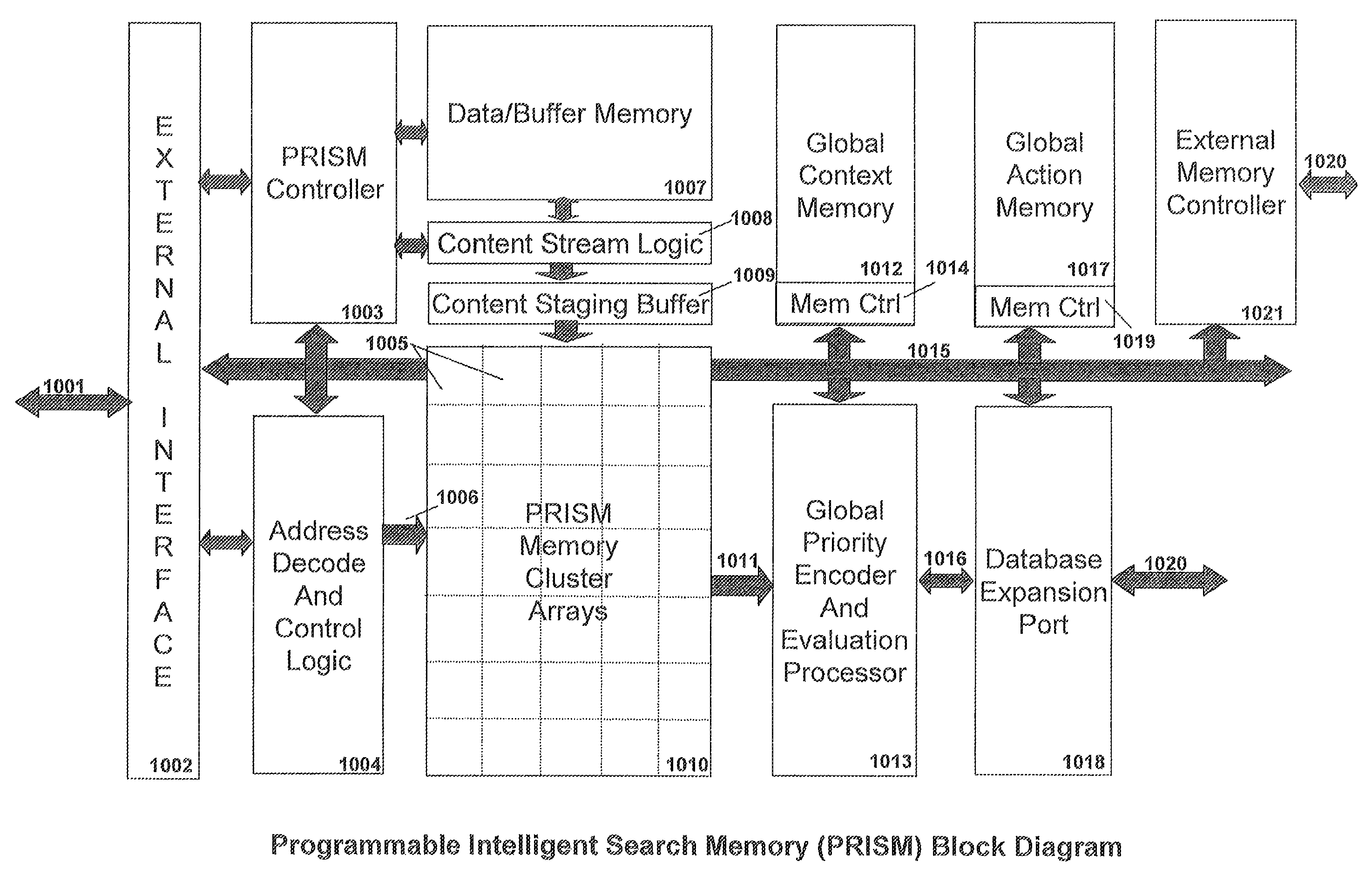
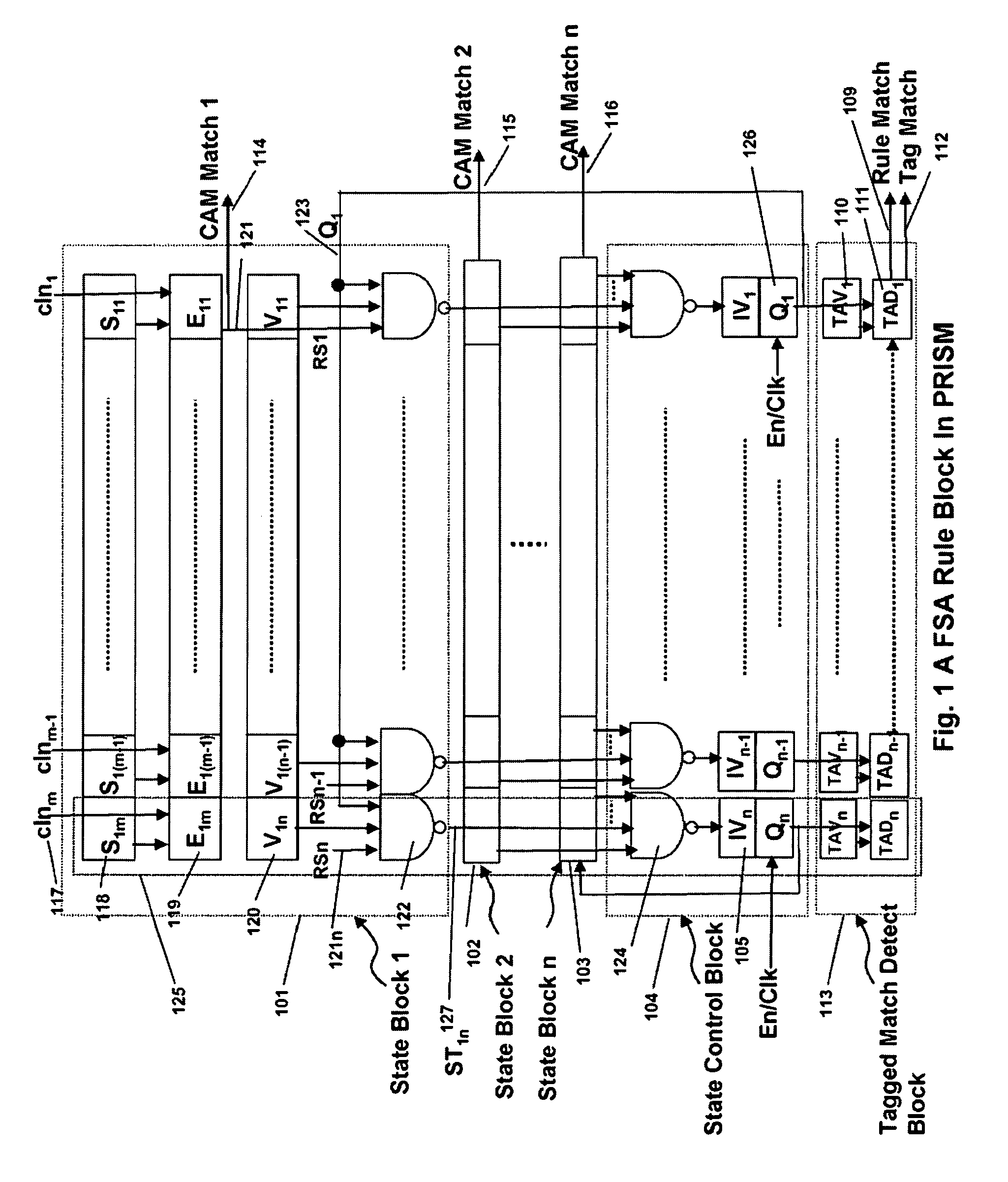
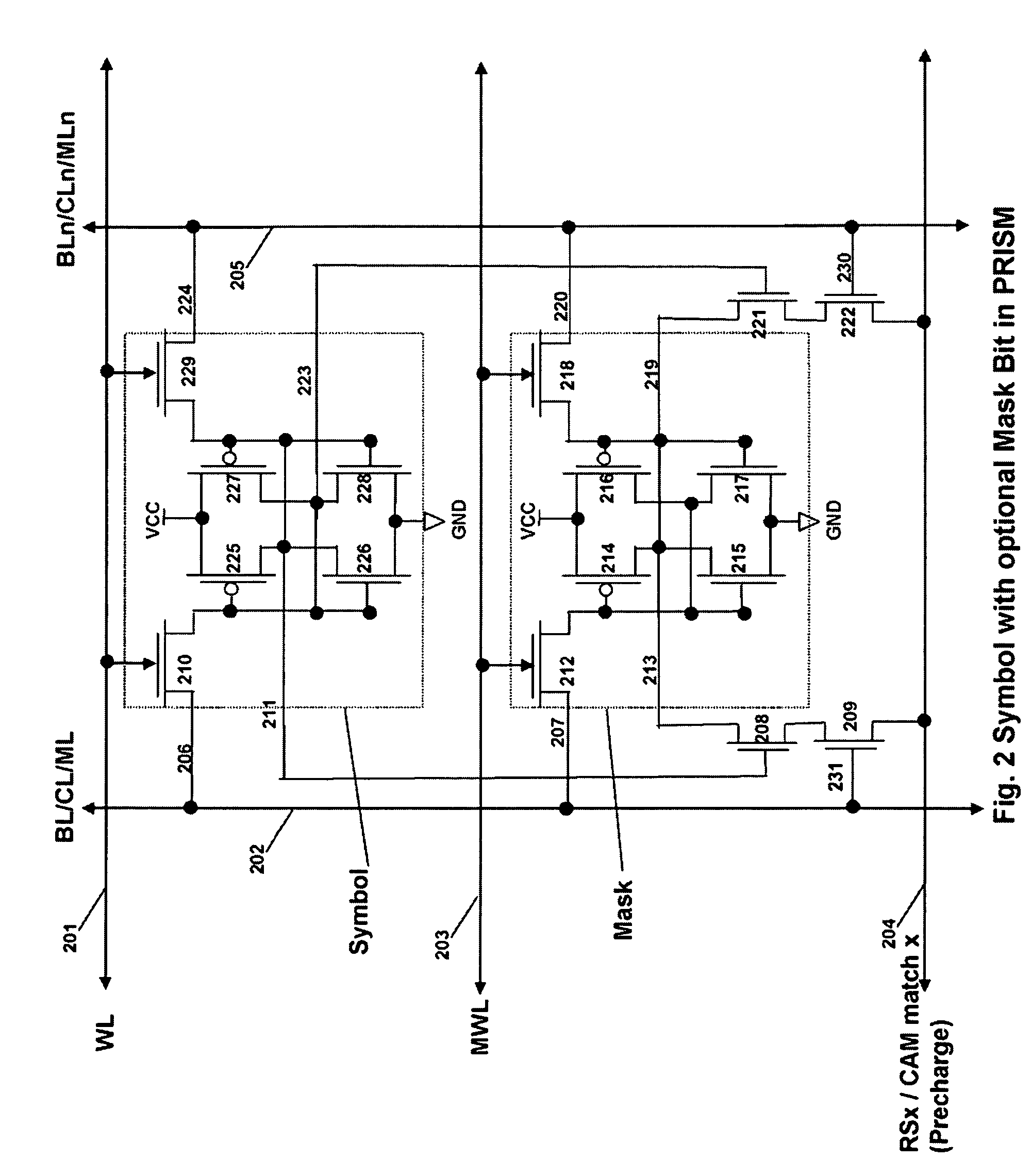
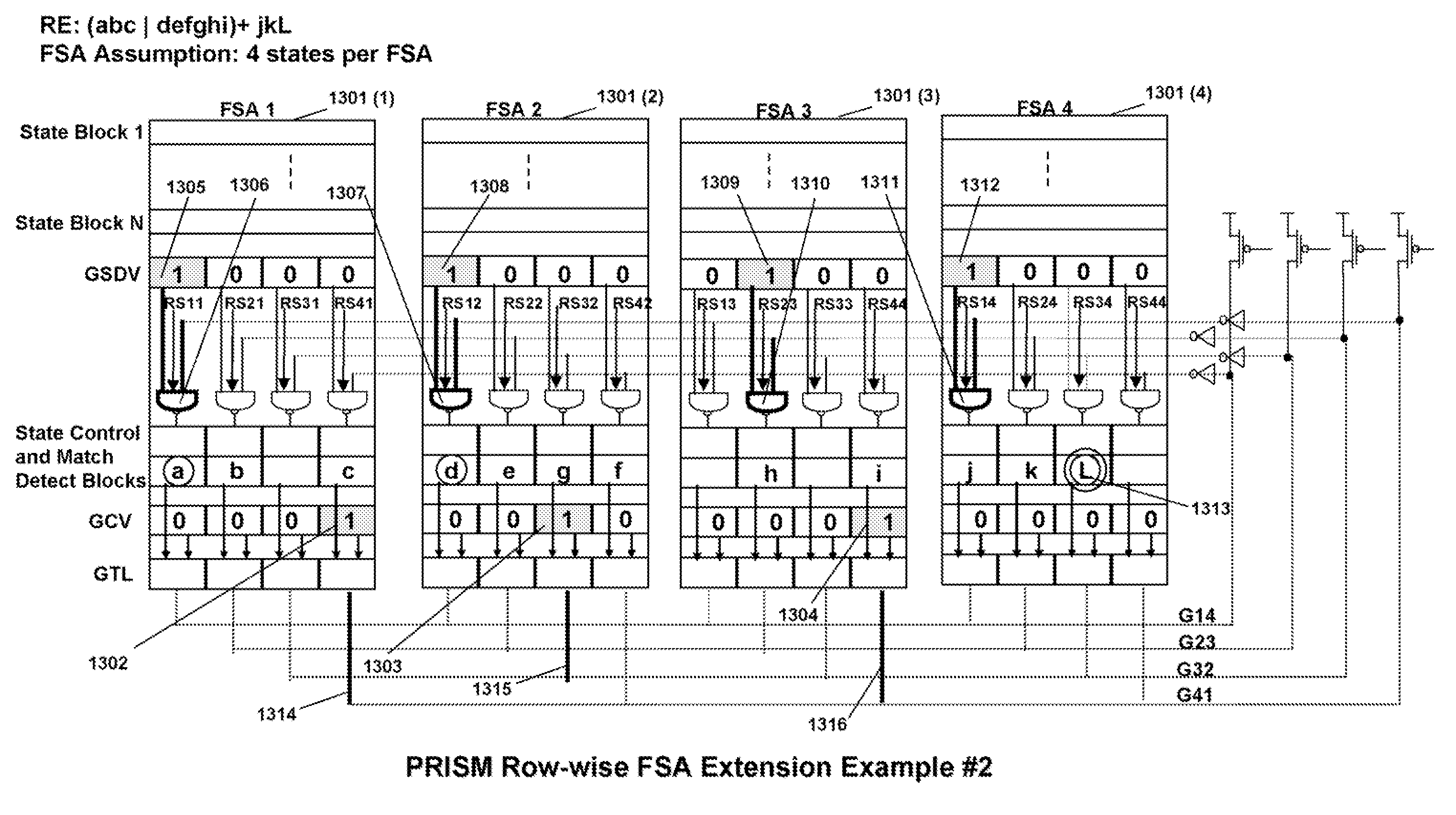
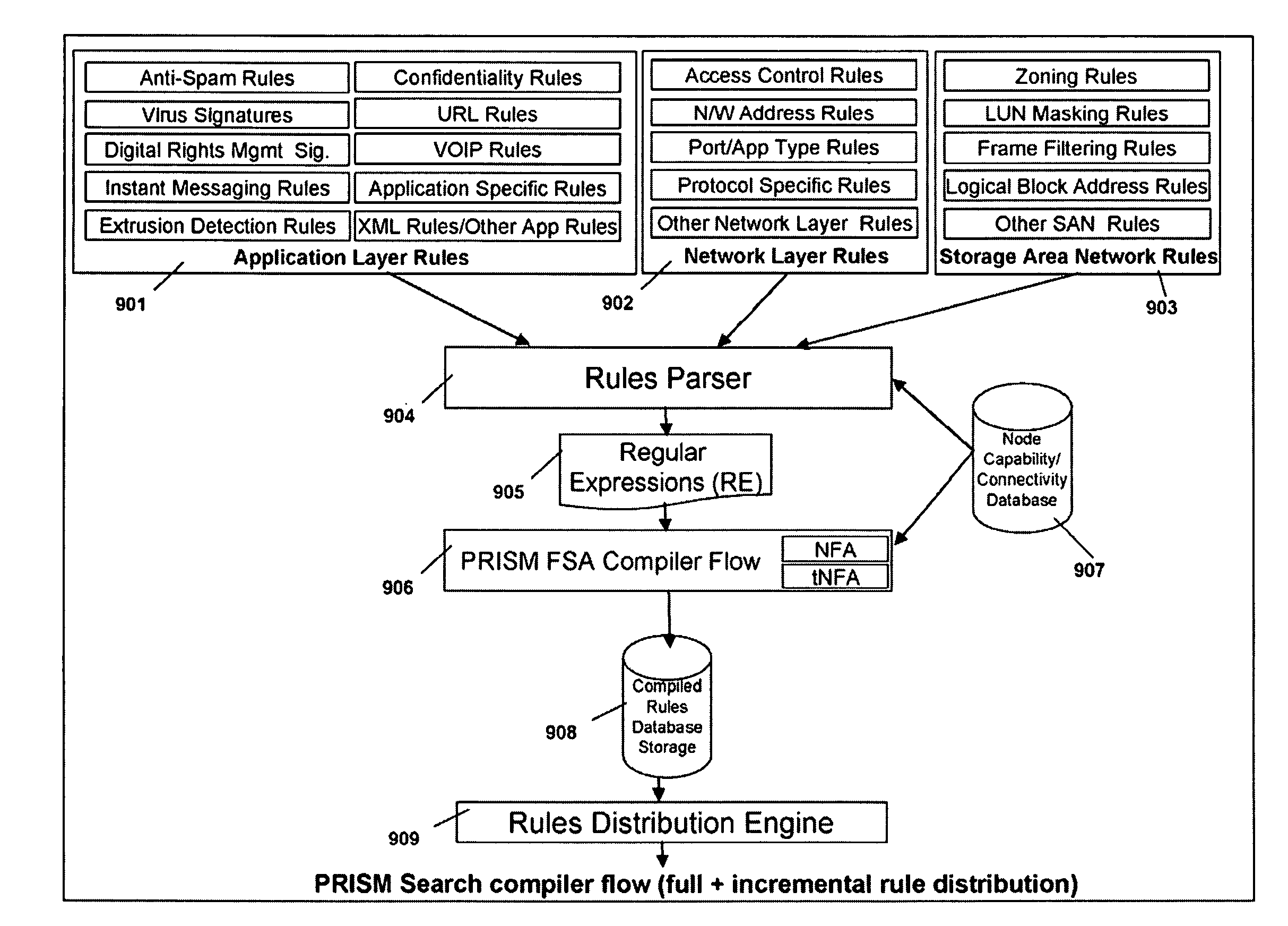
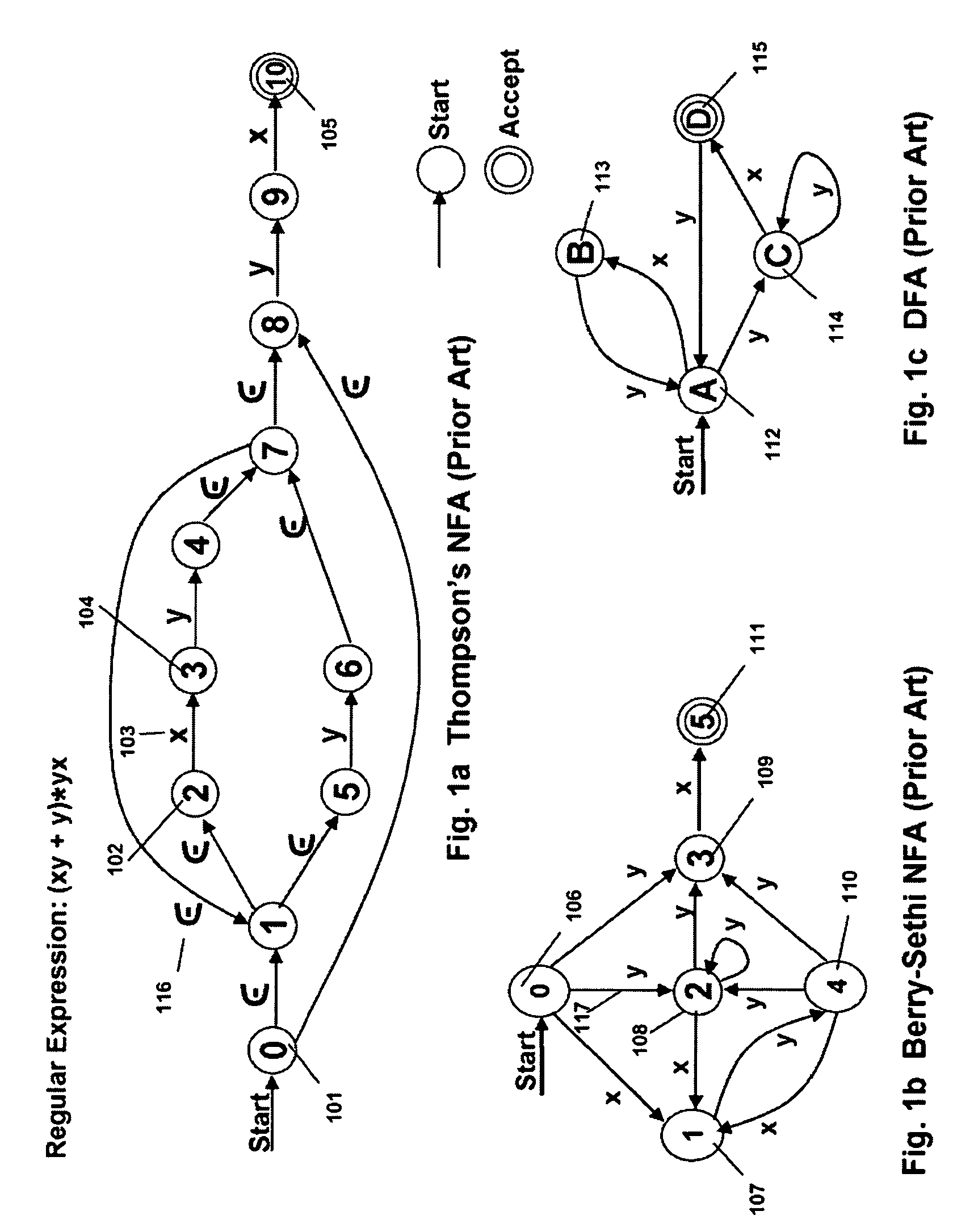
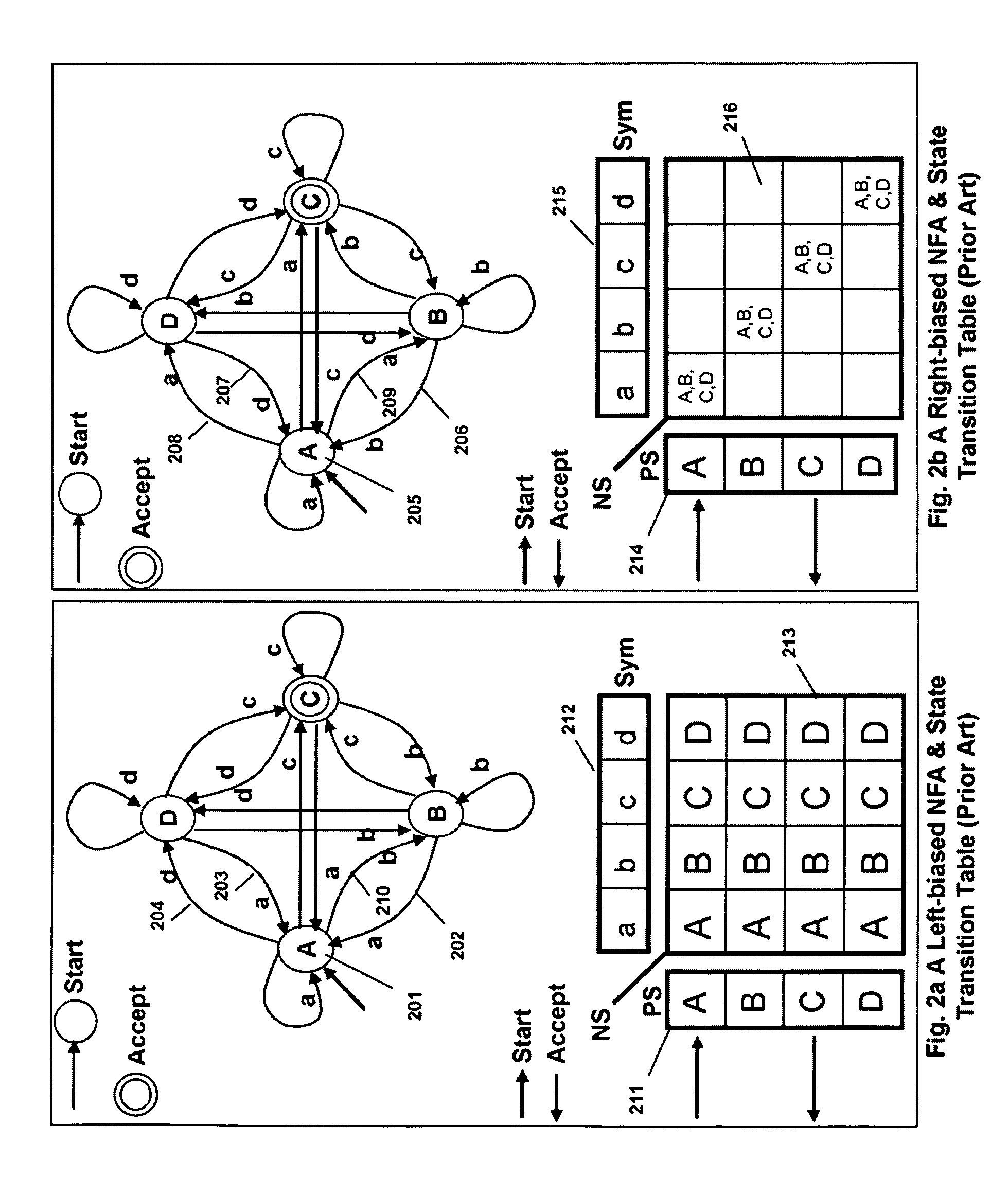
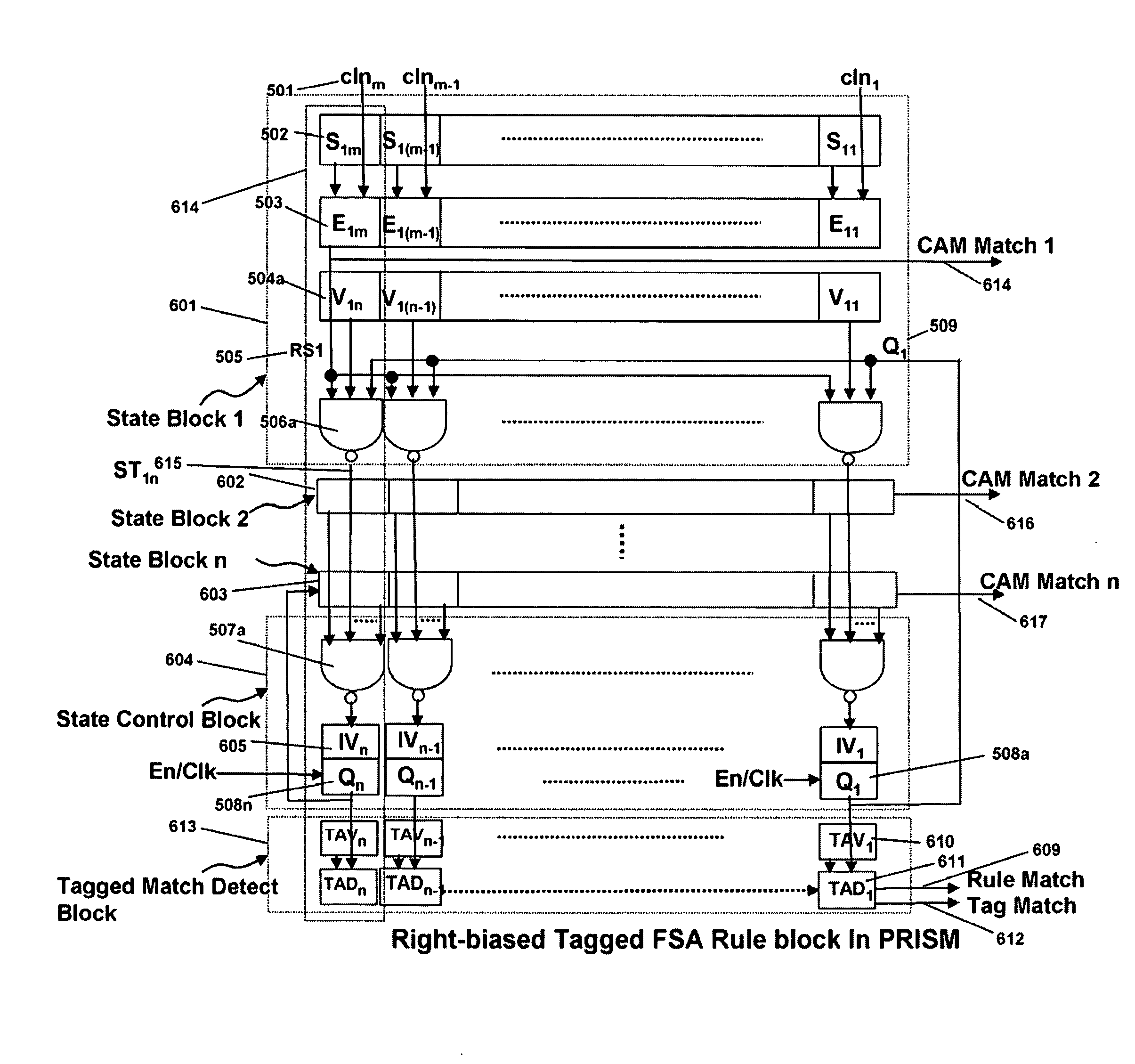
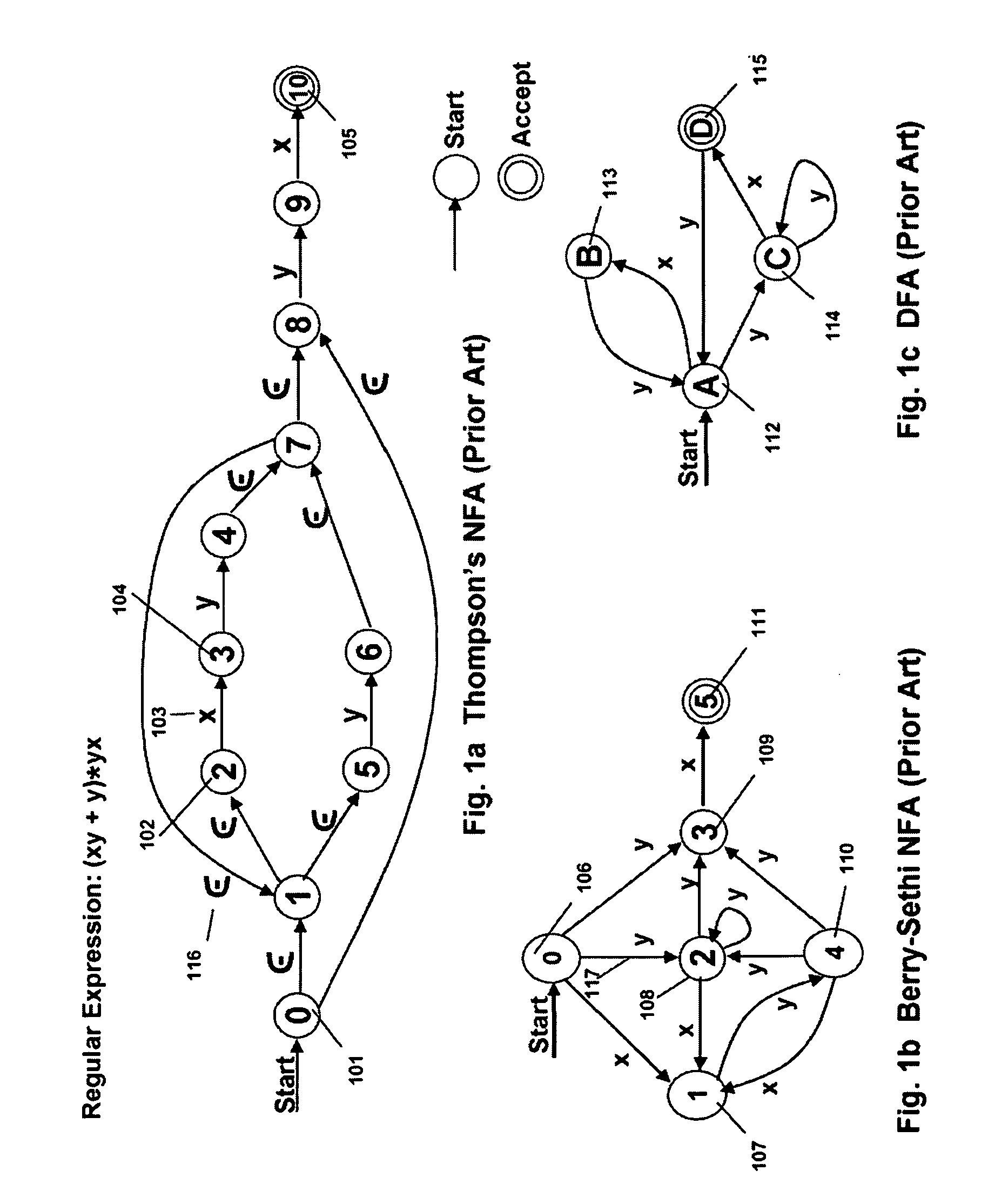
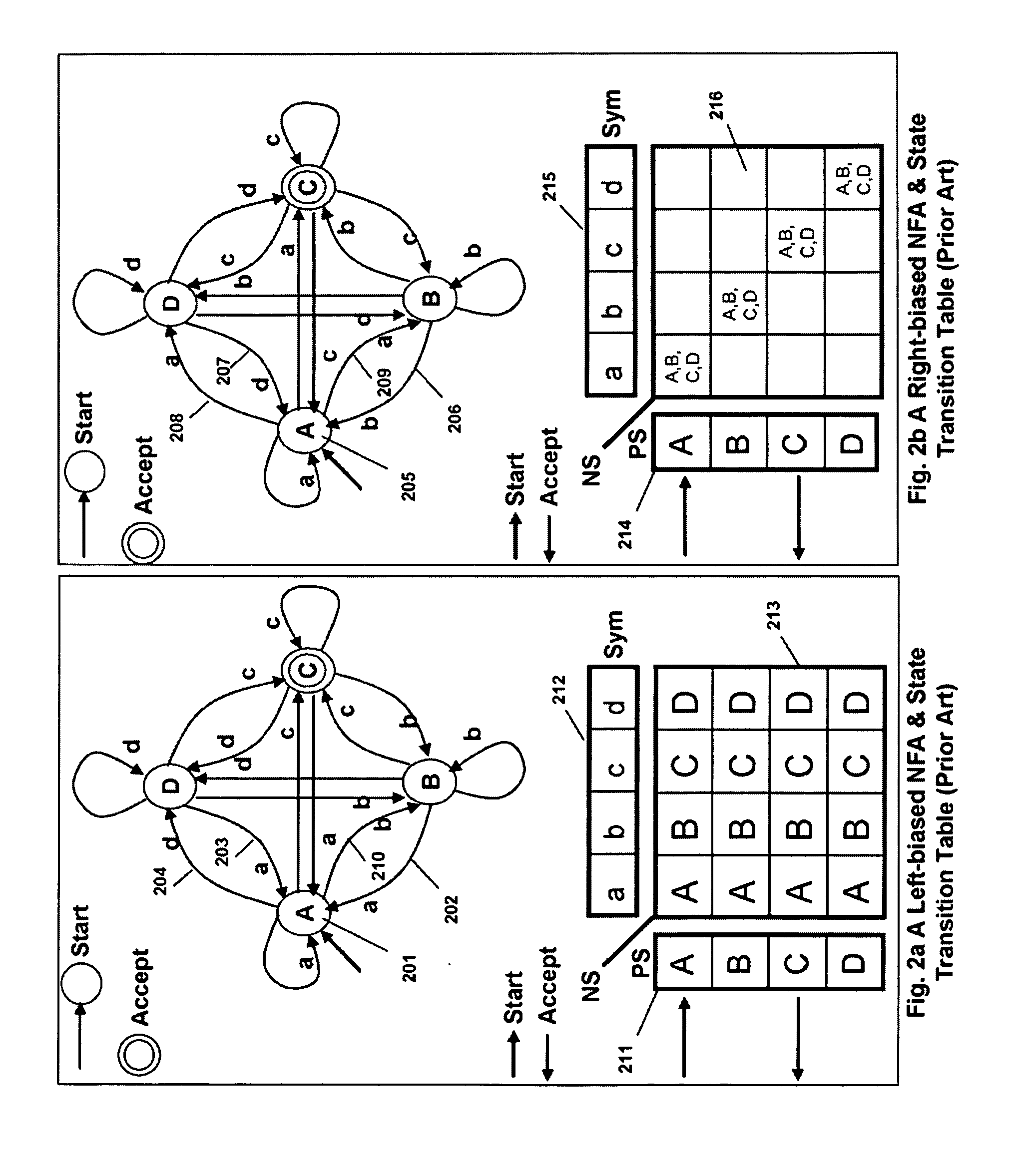
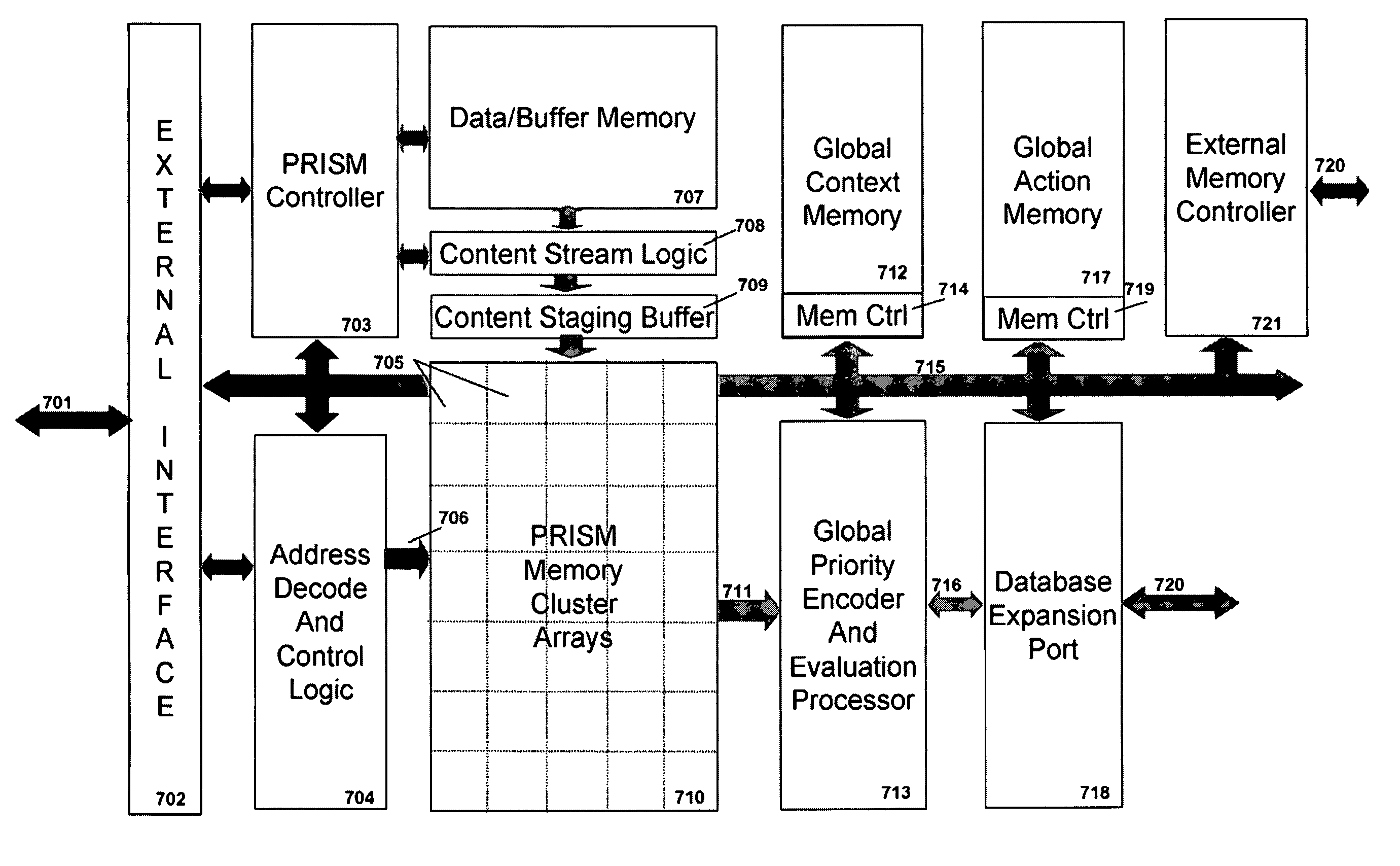
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken. Content search rules comprise of regular expressions which are converted to finite state automata and then programmed in PRISM for evaluating content with the search rules. The PRISM memory provides features for complex regular expression symbols like range detection, complement control, bit masking and the like and enables complex symbols and compact regular expression representation.
Owner:INFOSIL INC
Controlling A Network Interface Using Virtual Switch Proxying
Methods and systems for permitting a controller within a virtualization environment to control access to devices virtualized within hardware are described herein. For example, a NIC may be able to request rules that define how network traffic is managed at the NIC's virtual switch. In some arrangements, the NIC may transmit a query for the matching rule to a proxy, which may determine whether it has a rule matching the request. If the proxy does not have a matching rule, the proxy may query a controller for the matching rule, which may transmit the rule to the proxy. The proxy may update its store of rules and transmit the matching rule to the NIC. Upon receipt of the matching rule, the NIC may update the rules stored in its virtual switch and may process the packet in accordance with the matching rule.
Owner:CITRIX SYST INC
Embedded Programmable Intelligent Search Memory
ActiveUS20080140661A1Reduce classification overheadImprove performanceDigital data information retrievalDigital data processing detailsMulti processorMemory architecture
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken The PRISM content search memory is embedded in a single core or multi-core processors or in multi-processor systems to perform content search. PRISM accelerates content search by offloading the content search tasks from the processors. Content search rules comprise of regular expressions which are converted to finite state automata and then programmed in PRISM for evaluating content with the search rules.
Owner:INFOSIL INC
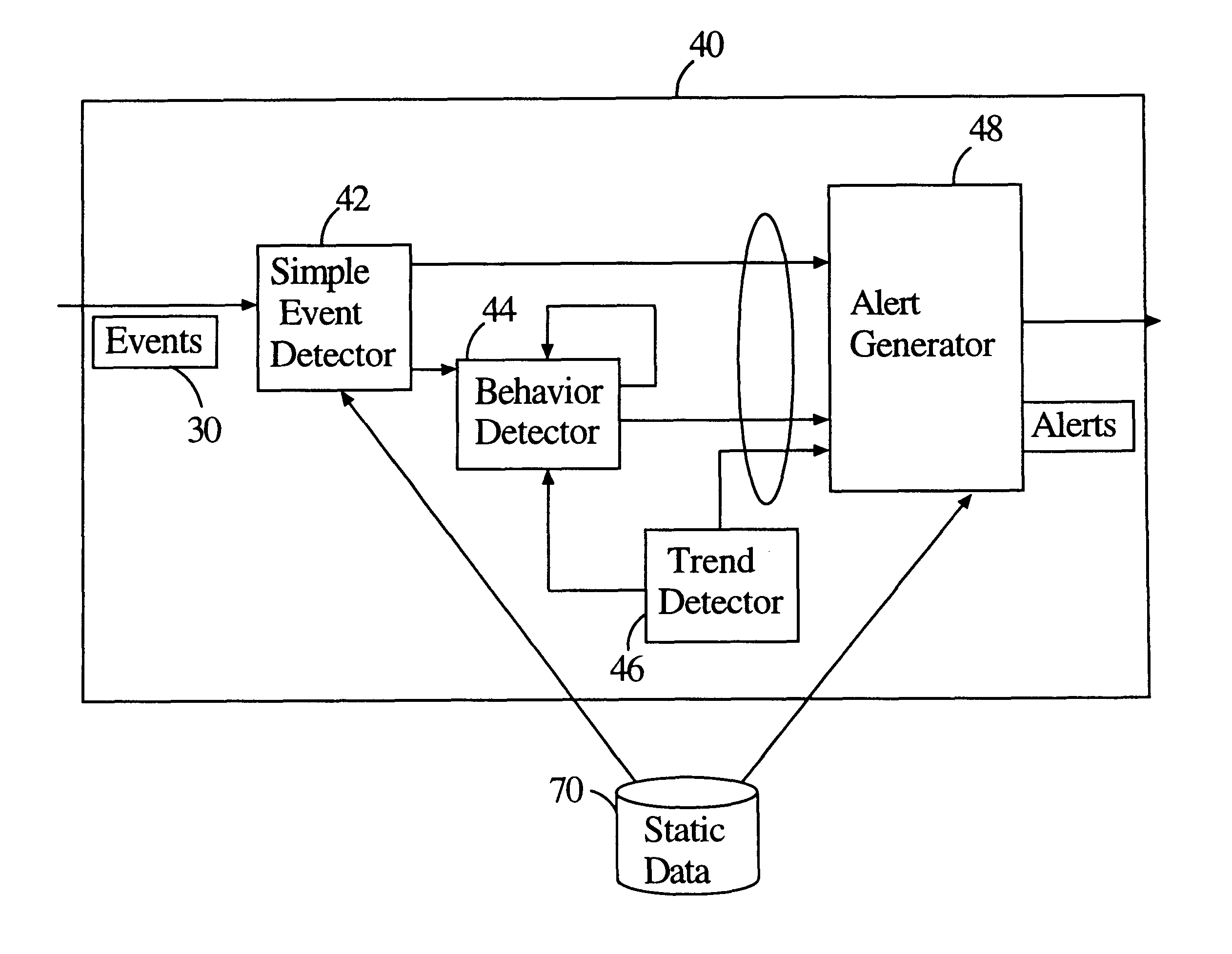
Method and system for capturing streaming data by an actionable information engine
The present invention captures streaming data and avoids continual retrieval. The invention only looks at data once, has a time dependency built into it, and data that is not consumed or relevant is discarded. The invention includes an engine processor that processes data according to stored information; stored rules that define engine operation, an input events module for receiving events which provides a plurality of events. Events are processed according to stored rules for generating a series of valid results when input events match the rules. Rule states that have been matched to an input event but have not produced a valid result are stored in state storage. The state of a rule as stored enables the engine to provide a valid result output upon a future reception of an input event necessary to complete the rule. Transaction log module monitors the operation of the engine for specified time period.
Owner:ELITY SYST
Rules-based transaction prefetching using connection end-point proxies
ActiveUS7853699B2Increase speedReduce latencyMultiple digital computer combinationsTransmissionApplication softwareClient-side
Owner:RIVERBED TECH LLC
FSA Context Switch Architecture for Programmable Intelligent Search Memory
ActiveUS20090049230A1Reduce overheadSoap detergents with organic compounding agentsDigital data information retrievalMemory architectureAutomaton
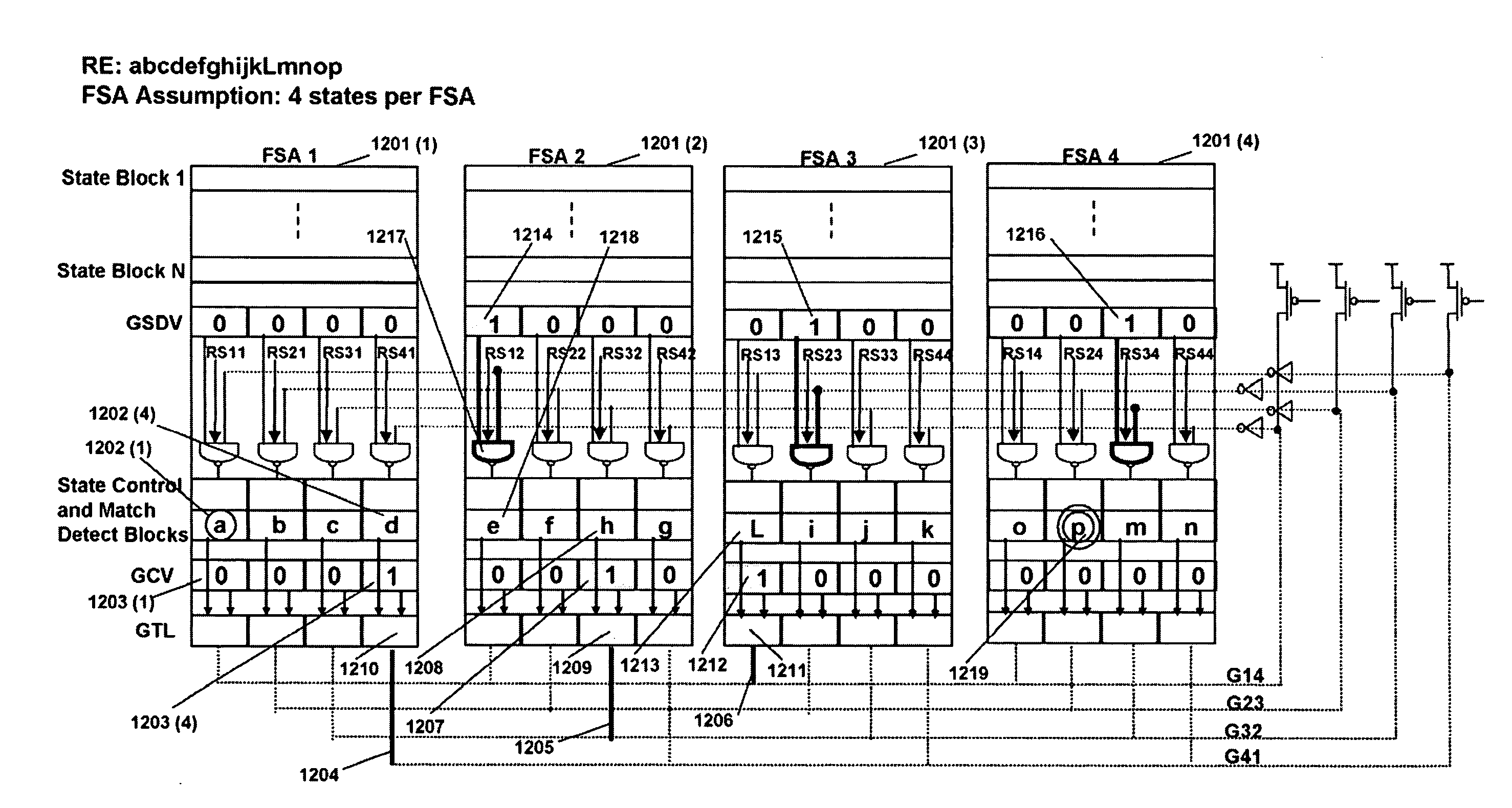
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken. Content search rules comprise of regular expressions which are converted to finite state automata (FSA) and then programmed in PRISM for evaluating content with the search rules. PRISM architecture comprises of a plurality of programmable PRISM Search Engines (PSE) organized in PRISM memory clusters that are used simultaneously to search content presented to PRISM. A context switching architecture enables transitioning of PSE states between different input contexts.
Owner:INFOSIL INC
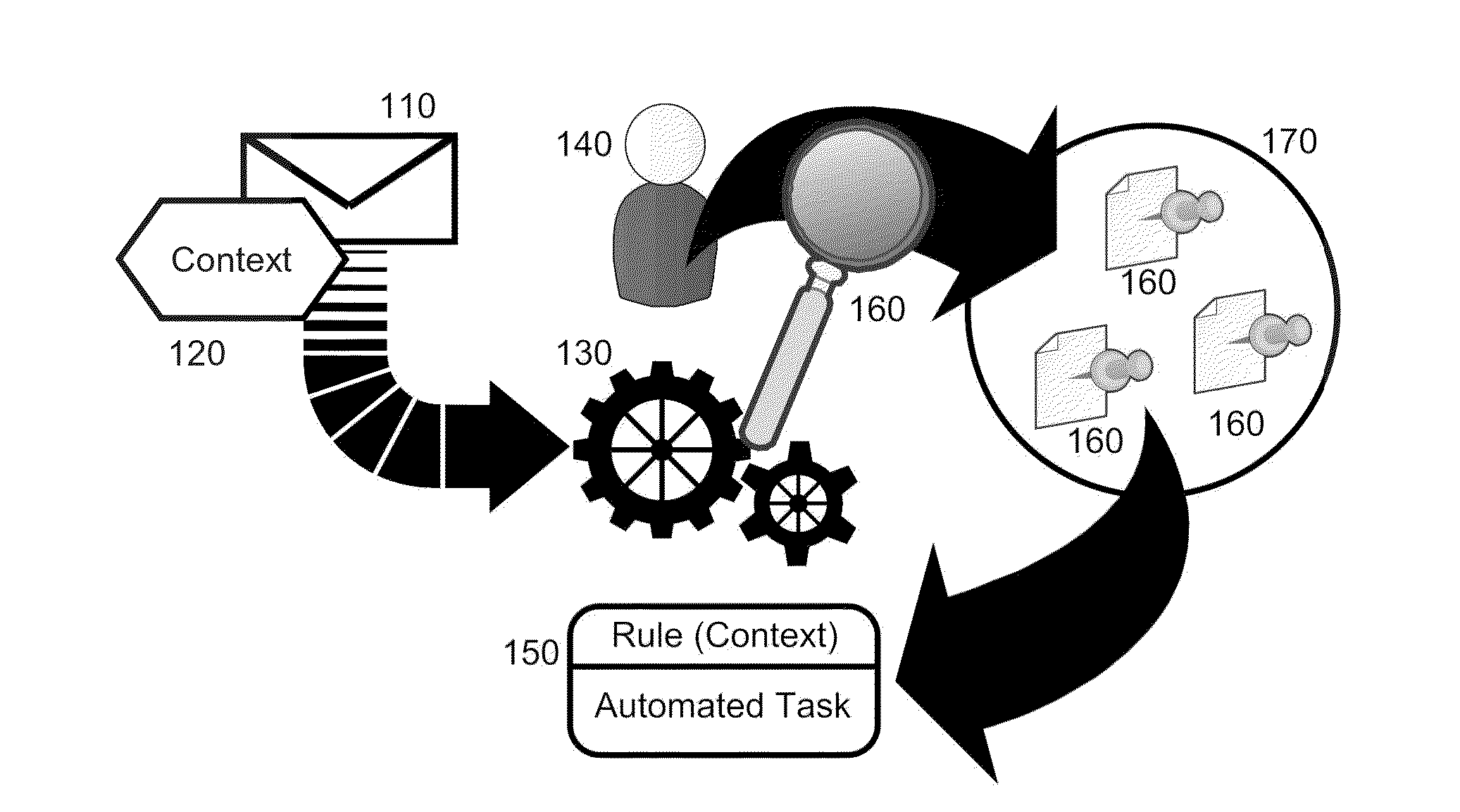
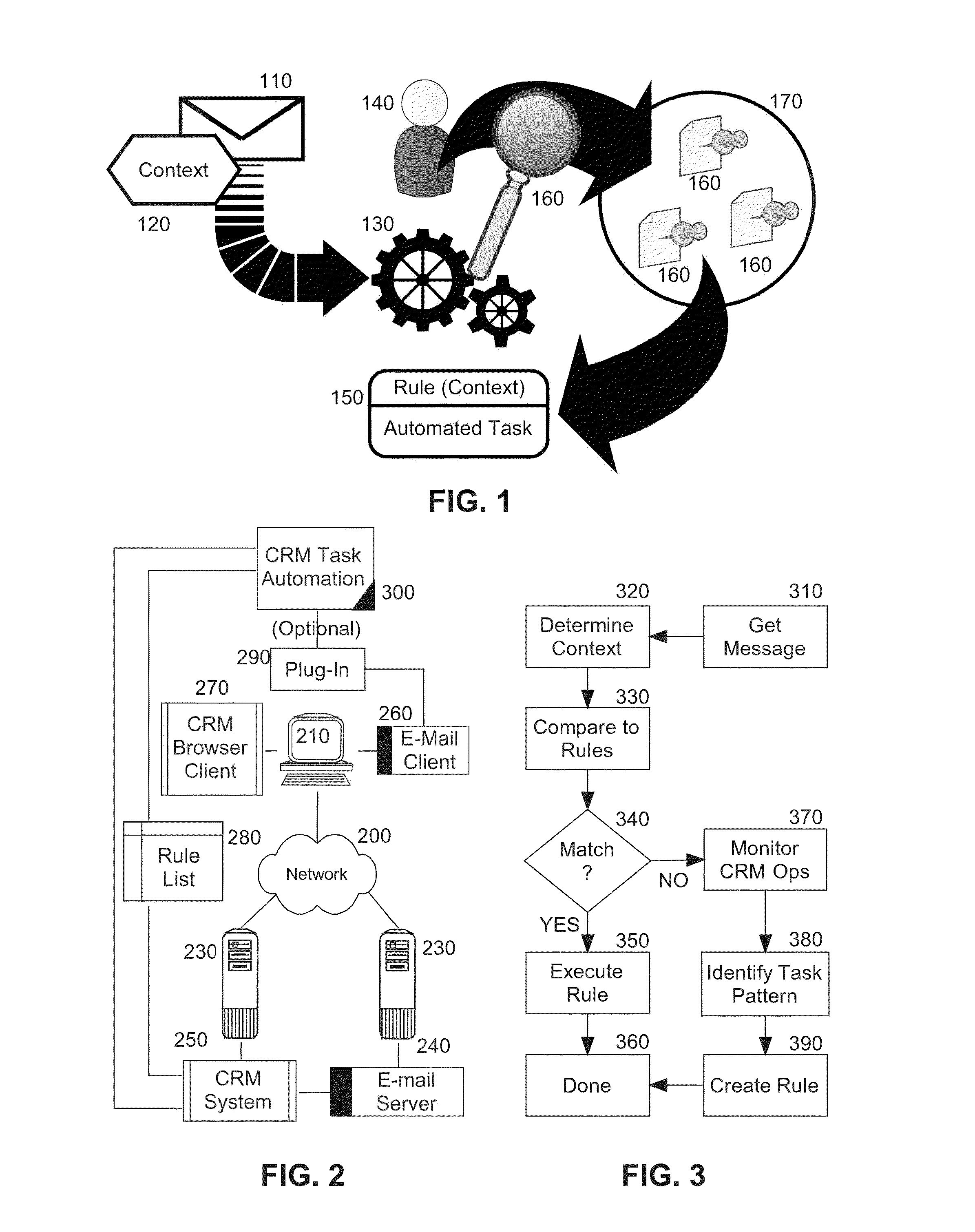
Automation of customer relationship management (CRM) tasks responsive to electronic communications
Embodiments of the invention provide a method, system and computer program product for automating customer relationship management (CRM) tasks responsive to inbound and outbound messages. In an embodiment of the invention, a method of automating CRM tasks responsive to inbound and outbound messages is provided. The method includes determining a context for a message such as an e-mail, monitoring a set of manual operations performed by an end user in a CRM application subsequent to the determination of the context of the message, grouping the set of manual operations into an automated task for the CRM application, and storing a rule associating the automated task with the context. Thereafter, in response to detecting receipt of a new message, a context is matched for the new message to the rule and the automated task associated with the rule is triggered.
Owner:SUGARCRM
Compiler for Programmable Intelligent Search Memory
ActiveUS20080140600A1Efficient and compact realizationReduce overheadDigital data information retrievalDigital storageMemory architectureAutomaton
Memory architecture provides capabilities for high performance content search. Content search rules comprise of regular expressions which are compiled to finite state automata and then programmed in Programmable Intelligent Search Memory (PRISM) for evaluating content with the search rules. A compiler compiles the content search rules for evaluation by PRISM memory. The PRISM memory architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken.
Owner:INFOSIL INC
FSA context switch architecture for programmable intelligent search memory
ActiveUS7890692B2Reduce overheadSoap detergents with organic compounding agentsDigital data information retrievalMemory architectureAutomaton
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken. Content search rules comprise of regular expressions which are converted to finite state automata (FSA) and then programmed in PRISM for evaluating content with the search rules. PRISM architecture comprises of a plurality of programmable PRISM Search Engines (PSE) organized in PRISM memory clusters that are used simultaneously to search content presented to PRISM. A context switching architecture enables transitioning of PSE states between different input contexts.
Owner:INFOSIL INC
Signature Search Architecture for Programmable Intelligent Search Memory
ActiveUS20080140662A1Improve performanceReduce overheadDigital data information retrievalDigital data processing detailsMemory architectureAutomaton
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. Content search rules comprise of regular expressions which are compiled to finite state automata (FSA) and further comprise of patterns of strings a first set of which are compiled to a compressed signature database and a second set of which are compiled into FSAs. The finite state automata are then programmed in Programmable Intelligent Search Memory (PRISM) programmable FSA rule blocks and the compressed signature database is programmed in the PRISM signature search engines for evaluating content with the content search rules. A compiler compiles the content search rules for evaluation by PRISM memory. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM), action(s) associated with the matched rule(s) are taken.
Owner:INFOSIL INC
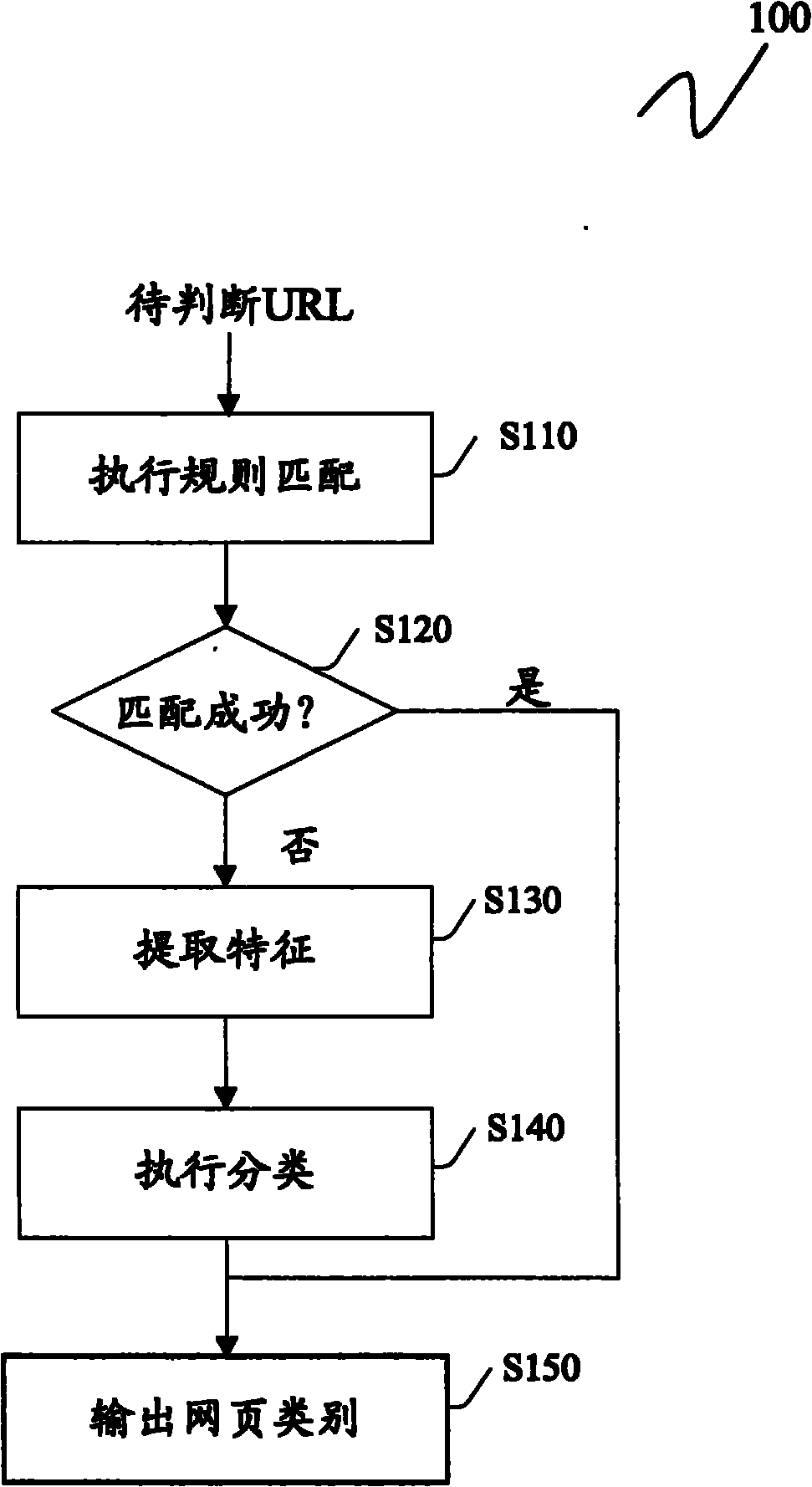
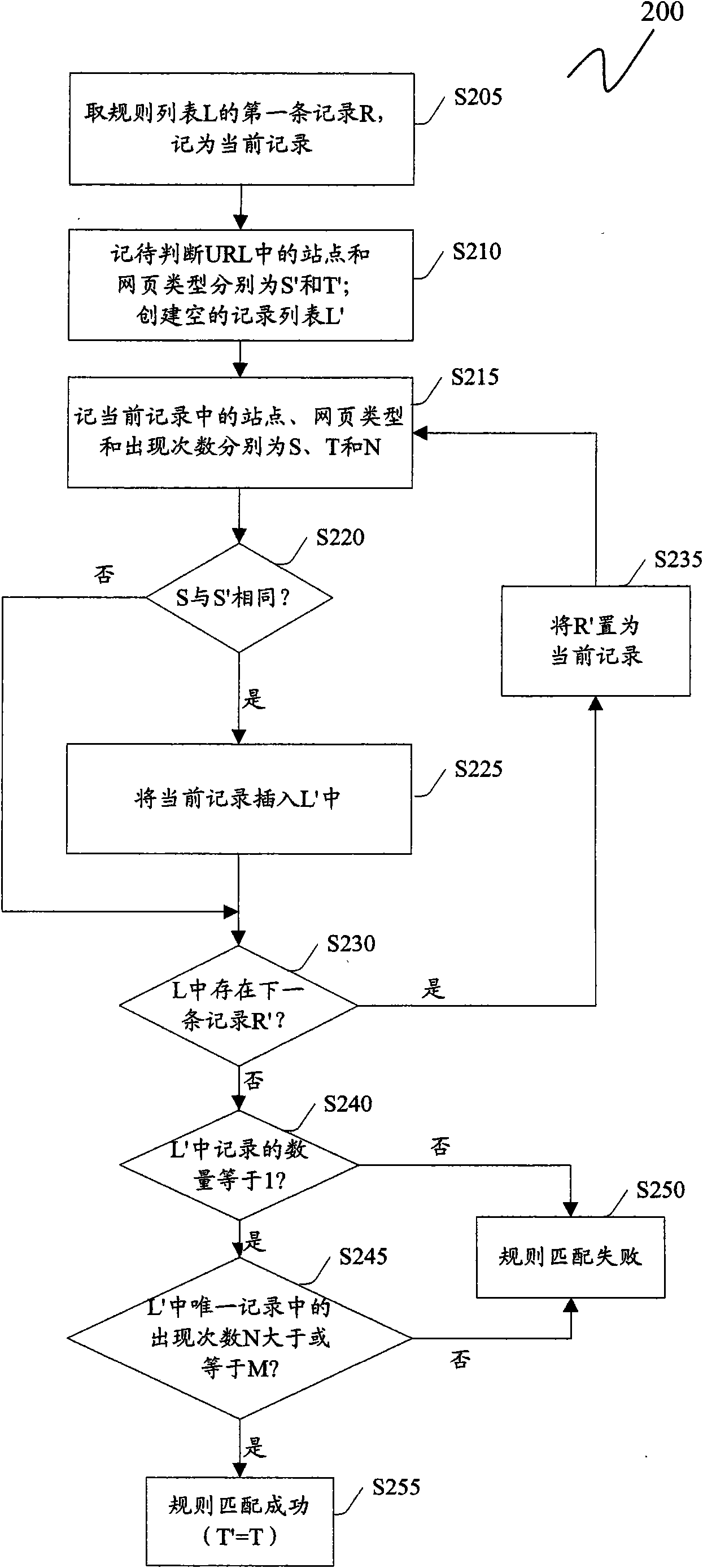
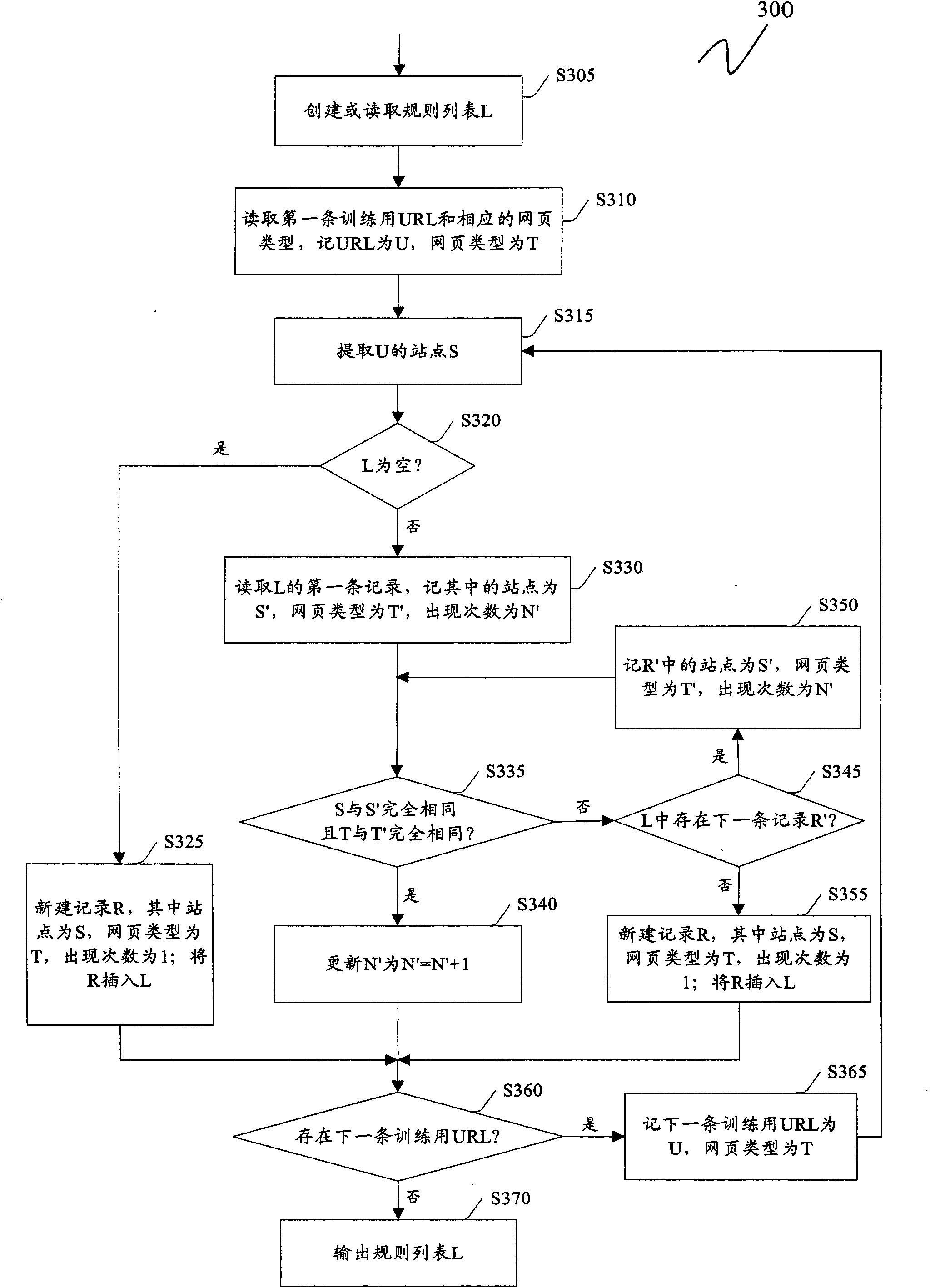
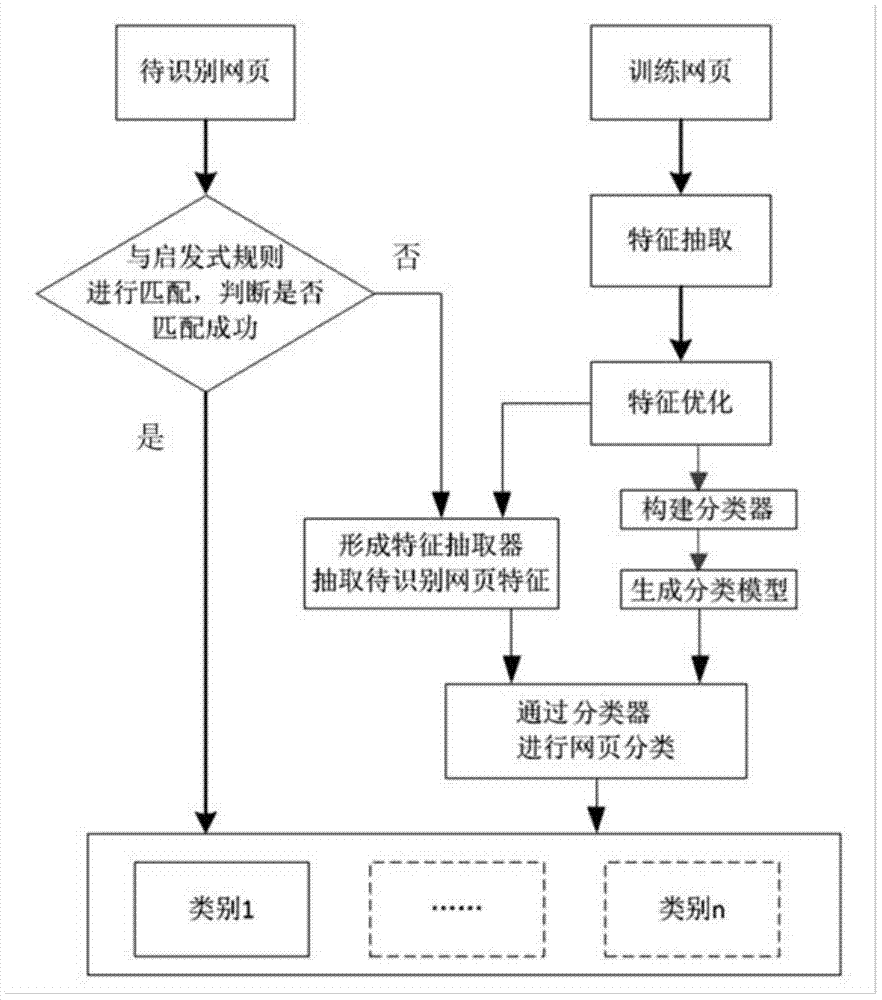
Method and device for judging type of webpage
InactiveCN101872347ARealize judgmentCharacter and pattern recognitionSpecial data processing applicationsFeature vectorMatch rule
The invention discloses a method and a device for judging the type of a webpage. The method comprises the following steps: carrying out rule matching in a prestored rule table on the basis of the URL of a webpage to be judged, wherein the rule list comprises a plurality of rule records for judging the type of the webpage; if the rule matching is successful, obtaining the type of the webpage to be judged according to the successfully matched rules; if the rule matching is unsuccessful, extracting predetermined features from the URL and / or HTML source codes of the webpage to be judged, and utilizing a classifier to classify the type of the webpage to be judged so as to obtain the type of the webpage to be judged on the basis of a feature vector composed of features selected from the extracted predetermined features. In the scheme of the invention, the invention can combines the advantages of a rule recognition scheme and a recognition scheme based on statistical learning, and can realize to judge the types of various webpage such as blogs, forums, news and the like.
Owner:FUJITSU LTD
Programmable Intelligent Search Memory
ActiveUS20080140912A1Efficient and compact realizationImprove application performanceDigital data information retrievalDigital storageMemory architectureAutomaton
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken. Content search rules comprise of regular expressions which are converted to finite state automata and then programmed in PRISM for evaluating content with the search rules.
Owner:INFOSIL INC
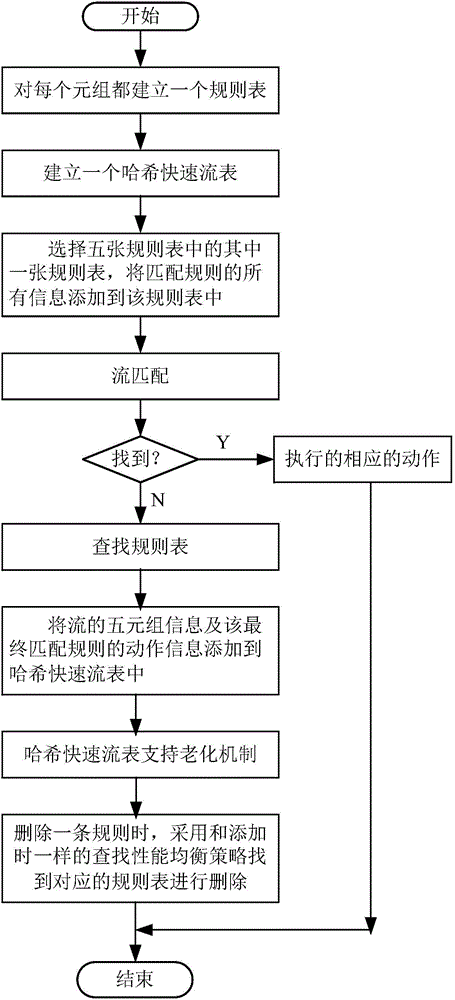
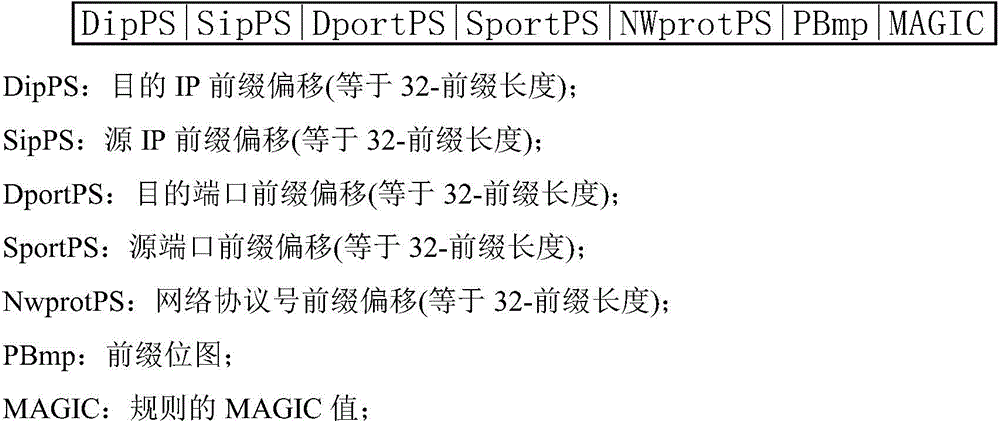
Implementation method for multi-field rule matching
ActiveCN104468381AImprove query real-time response speedSolve the problem of finding the best ruleData switching networksData compressionData stream
The invention discloses an implementation method for multi-field rule matching, and relates to the technical field of high-speed stream classification. The implementation method comprises the steps that firstly, a rule list is established for each tuple according to quintuple definition of IP message data streams, then a Hash rapid stream list is established, and all information matched with rules is added in the rule lists; secondly, IP message data stream matching is conducted, corresponding actions are executed if matched data streams are found, otherwise the rule lists are searched, and mask matching inquiries are conducted. According to the implementation method, the mode that a prefix extension Trie tree high in inquiring speed is improved, part of memory space is sacrificed, and data compression and the Hash list are combined is adopted, and thus under the premise that the inquiring speed is ensured, memory explosion caused by a large-capacity rule base can be avoided.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
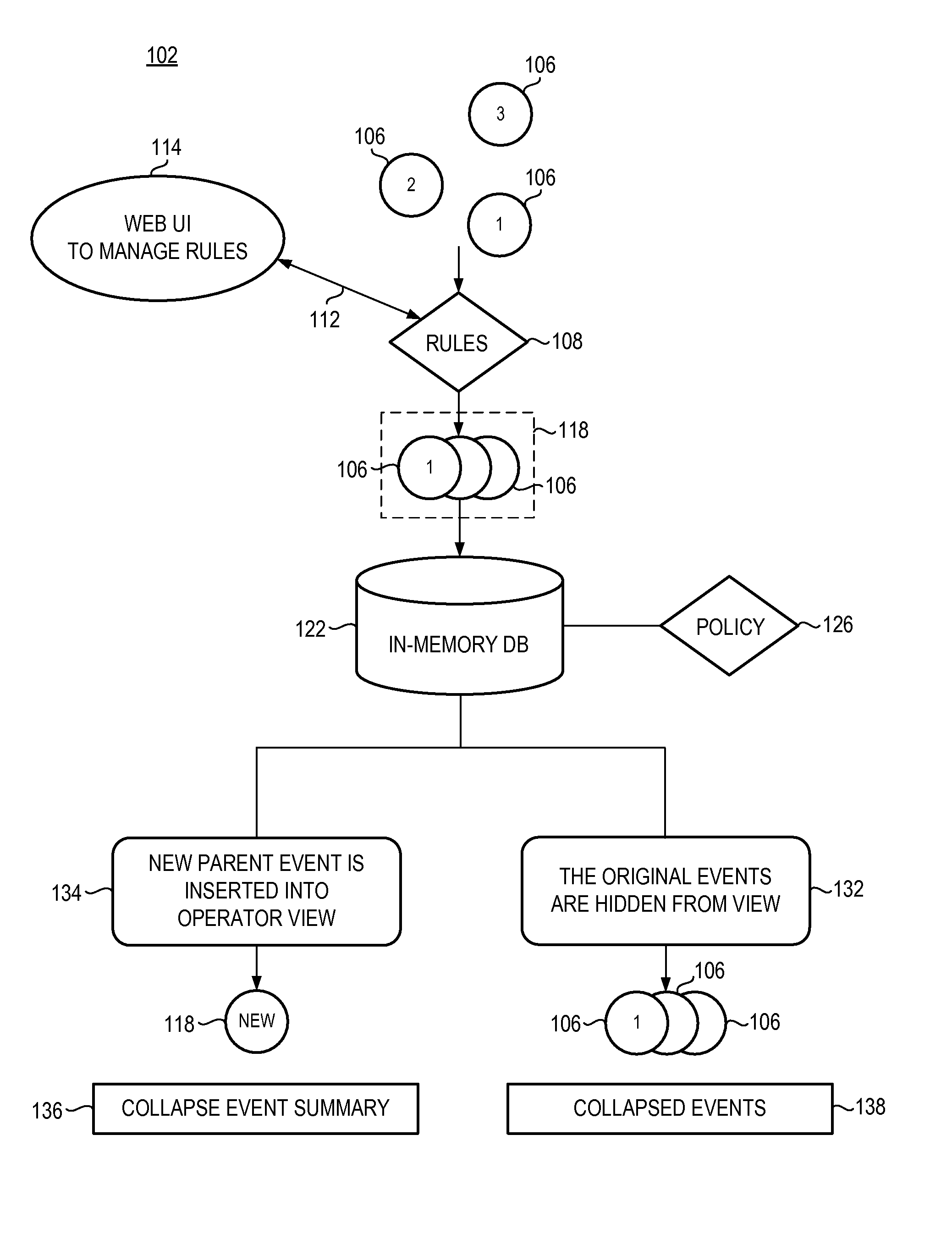
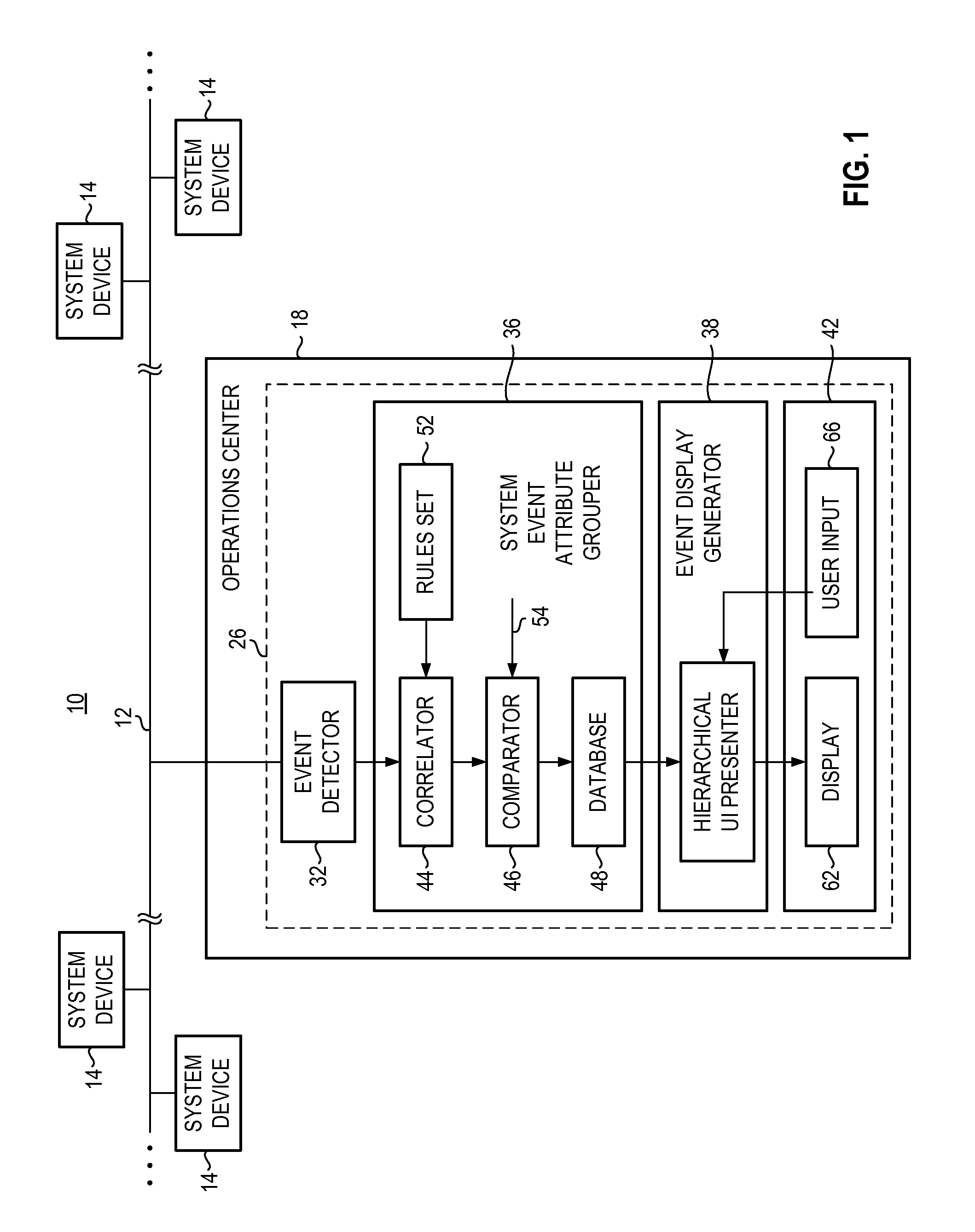
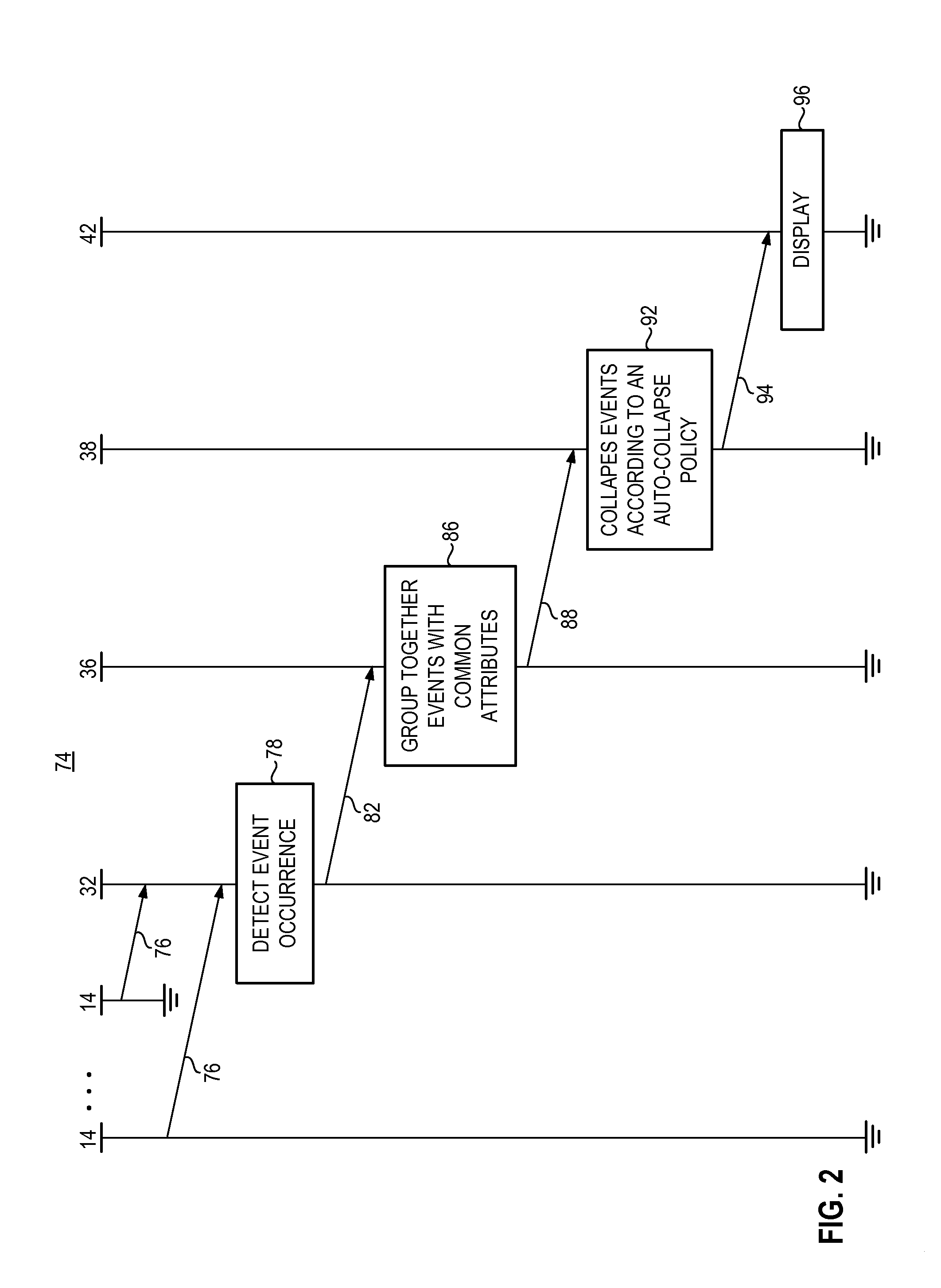
Apparatus, and associated method, for monitoring system events
InactiveUS20100030888A1Easy to identifyReadily able to resolveDigital computer detailsNon-redundant fault processingMonitoring systemSystem failure
An apparatus, and an associated method, for facilitating monitoring of a system, such as a system formed of an IT infrastructure. A detector detects the occurrence of system events, such as system faults or other anomalies. The detected events are matched with a set of rules, such by correlating attributes of the detected system events, to determine which events are related. Related events are grouped together into a group. An identification of the group is generated and displayed upon a display monitor. The individual events that comprise the group are hidden from view, i.e., collapsed behind the group identification.
Owner:HEWLETT PACKARD DEV CO LP
System and method for identifying webpage types
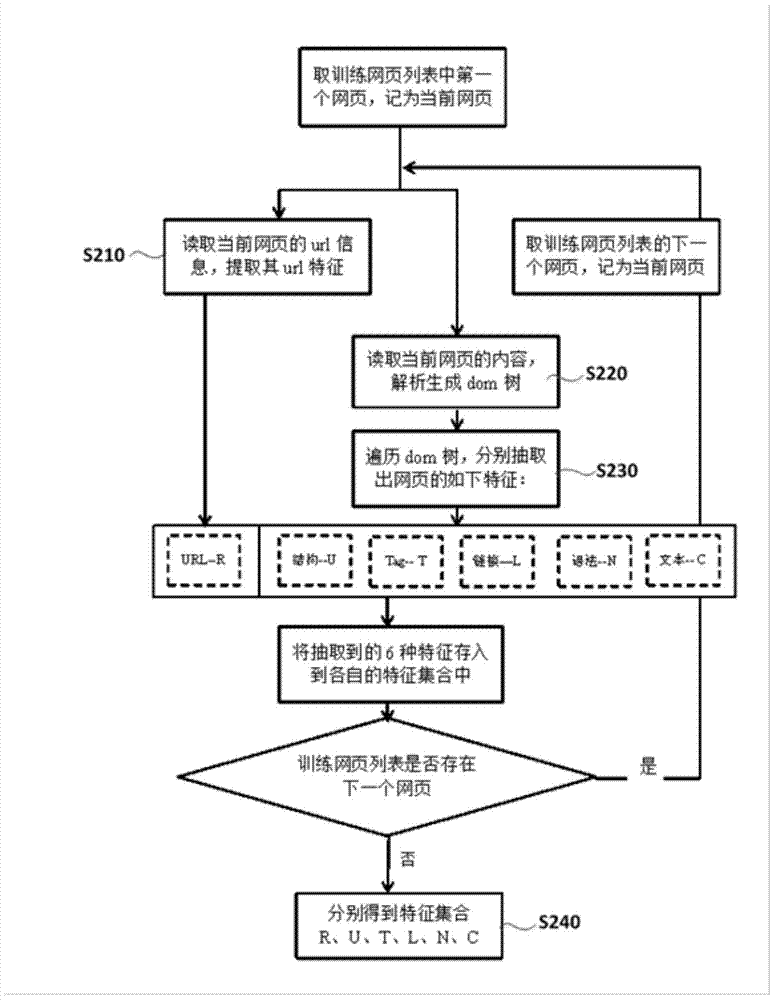
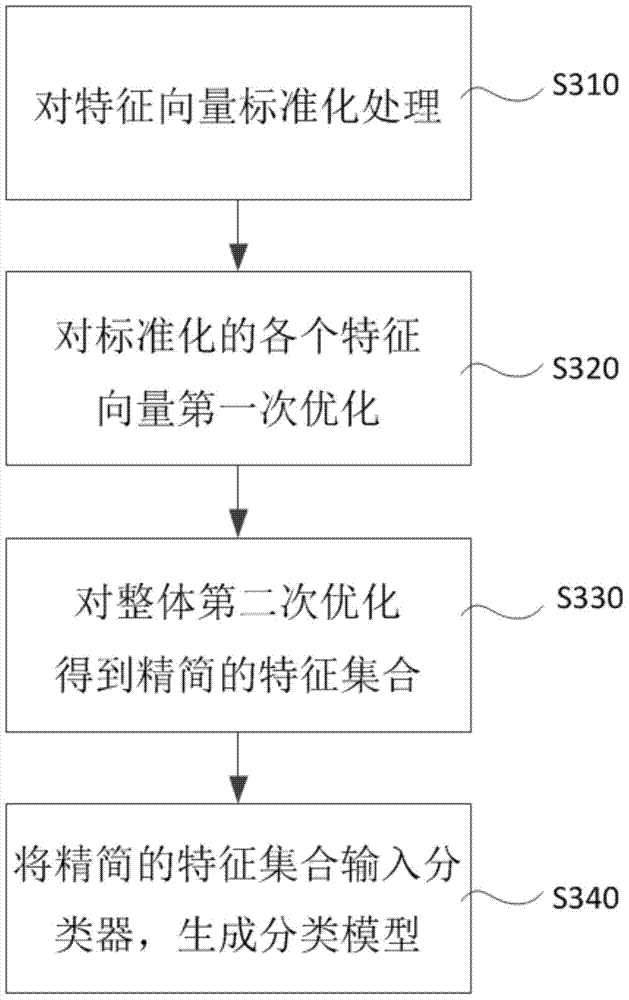
ActiveCN103544210AHigh speedImprove recognition accuracySpecial data processing applicationsWeb data retrieval using information identifiersFeature vectorTyping Classification
The invention relates to the field of network information retrieval and mining, in particular to a system and method for identifying webpage types. The method comprises the following steps that a heuristic rule is predefined, and a heuristic rule list is generated; a predetermined feature is extracted from a training webpage to form a standard feature vector which is optimized twice to form a simplified feature set, a classifier and a feature extractor are established, and a classification model is generated through the classifier; based on an URL and a source code of a webpage to be identified, rule matching is carried out on the heuristic rule list; if matching succeeds, the webpage type of the webpage to be identified is output; if matching fails, the classifier is used for carrying out webpage type classification on the webpage to be identified. The system and method for identifying webpage types are flexible and convenient to use, high in identifying speed and high in identifying accuracy, big change is of no need when a cross language webpage is identified, identifying efficiency is high, and high actual use value is achieved.
Owner:烟台中科网络技术研究所
Interval symbol architecture for programmable intelligent search memory
ActiveUS7831607B2Reduce overheadDigital data information retrievalDigital data processing detailsPrismMemory architecture
Memory architecture provides capabilities for high performance content search using regular expressions and patterns of strings. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken. Content search rules include of regular expressions which are converted to finite state automata and then programmed in PRISM for evaluating content with the search rules. The PRISM memory provides features for complex regular expression symbols like interval symbol, range detection, complement control, bit masking and the like and enables complex symbols and compact regular expression representation.
Owner:INFOSIL INC
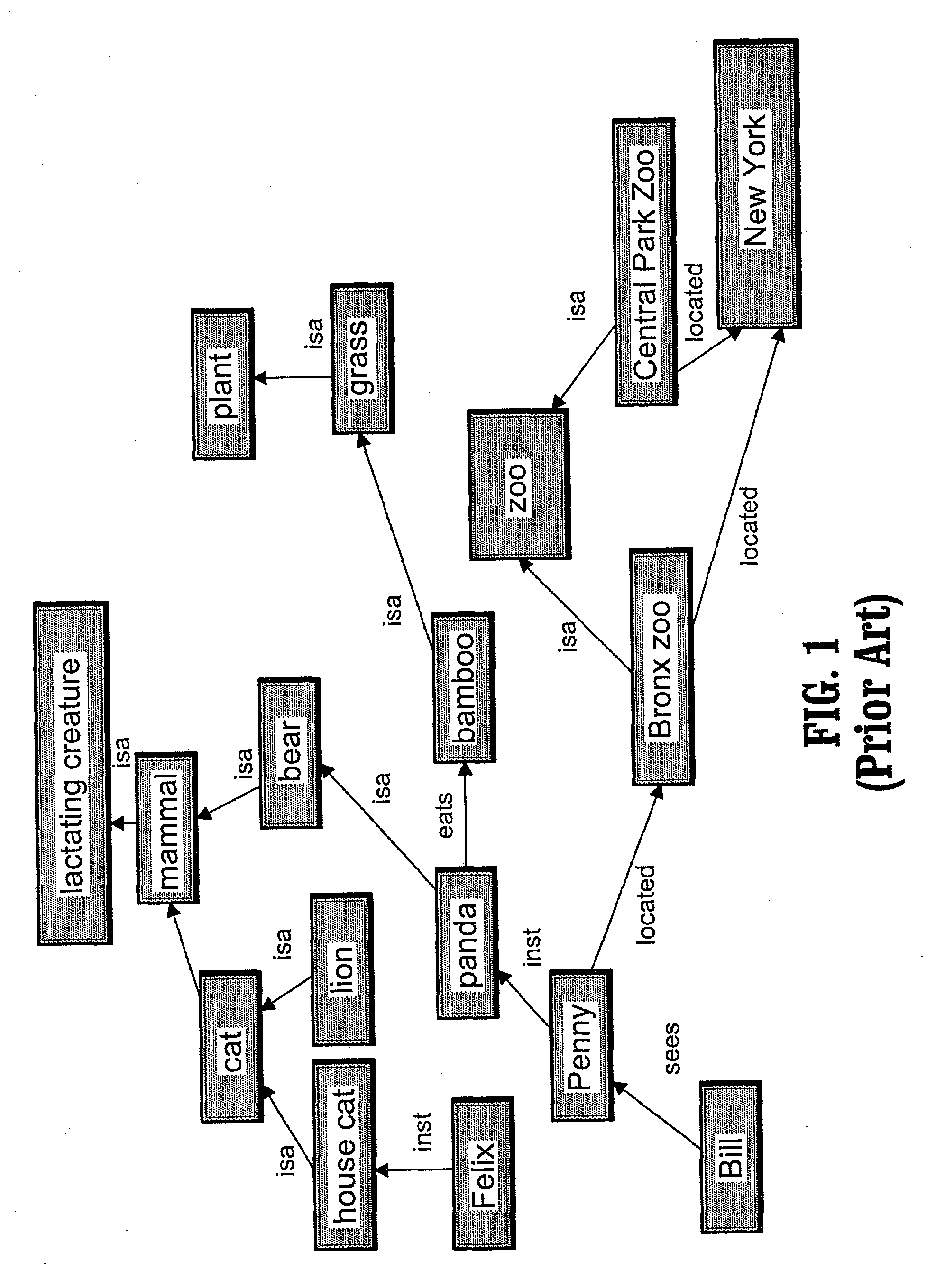
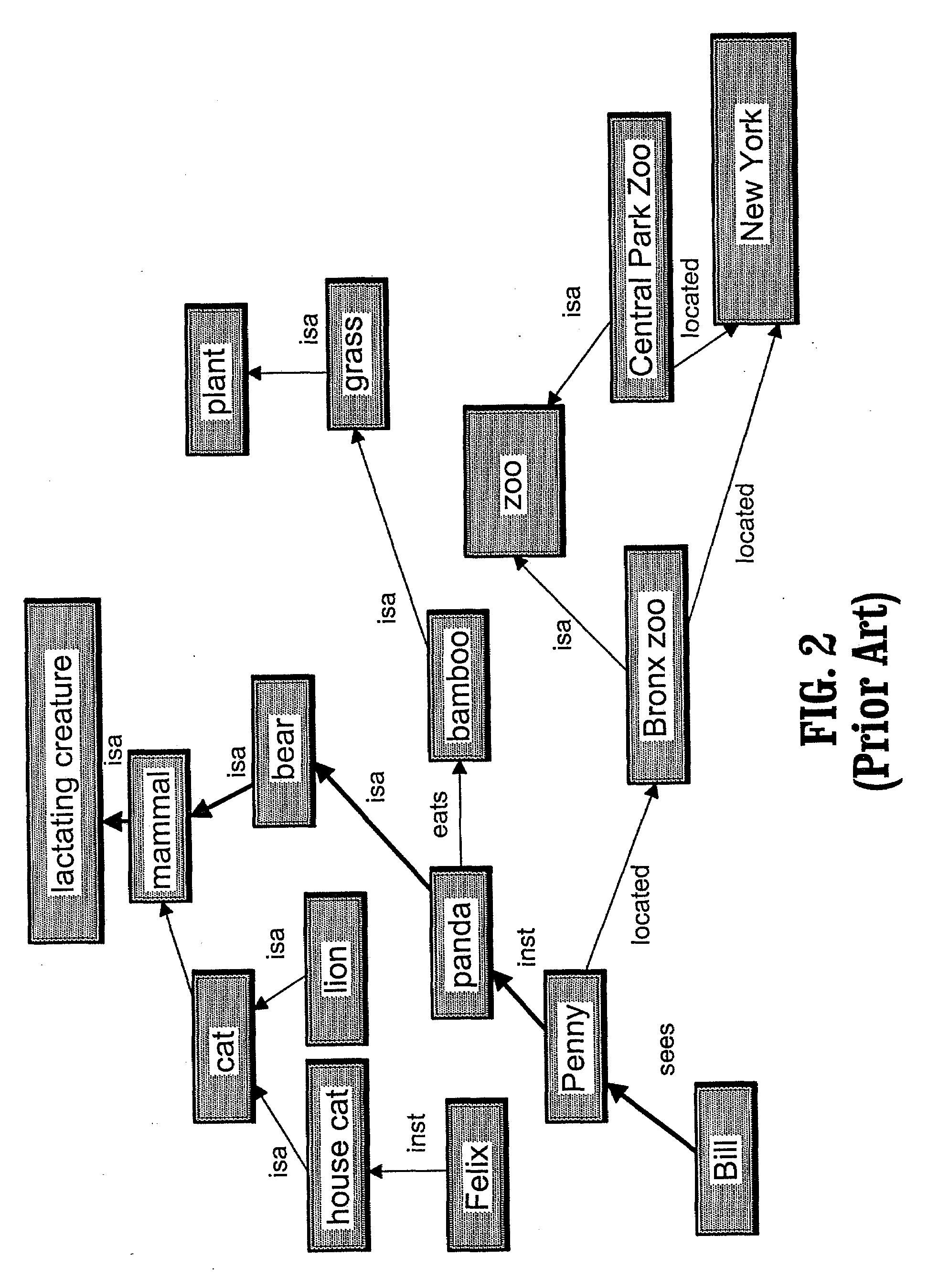
Method and knowledge structures for reasoning about concepts, relations, and rules
InactiveUS20090055342A1Data processing applicationsMultiple digital computer combinationsKnowledge structureMatch rule
A system and method for reasoning about concepts, relations and rules having a semantic network comprising at least one node from a predetermined set of node types, at least one link from a predetermined set of link types, and zero or more rules from a predetermined set of rule types, a subset of the rule types being matching rule types, each node and each link being associated with a set of zero or more rules; a network reasoning data structure having a reasoning type database having at least one regular expression, each of the regular expressions being a class of sequences having at least three node types and two link types, wherein the network reasoning data structure further has a context being a set of rules; and a reasoning engine having an activator for activating one or more activated paths in the semantic network, the set of activated paths having a common starting node in the semantic network, wherein the reasoning engine further has a validator for selecting a subset of the activated paths being valid paths, each rule from the set of rule matching types that is associated with one or more path elements on each valid path being matched by one or more rules in the context and wherein the reasoning engine further has a legal inferencer for selecting a subset of the set of valid paths being legal and valid paths, the legal and valid paths matching at least one of the regular expressions.
Owner:IBM CORP
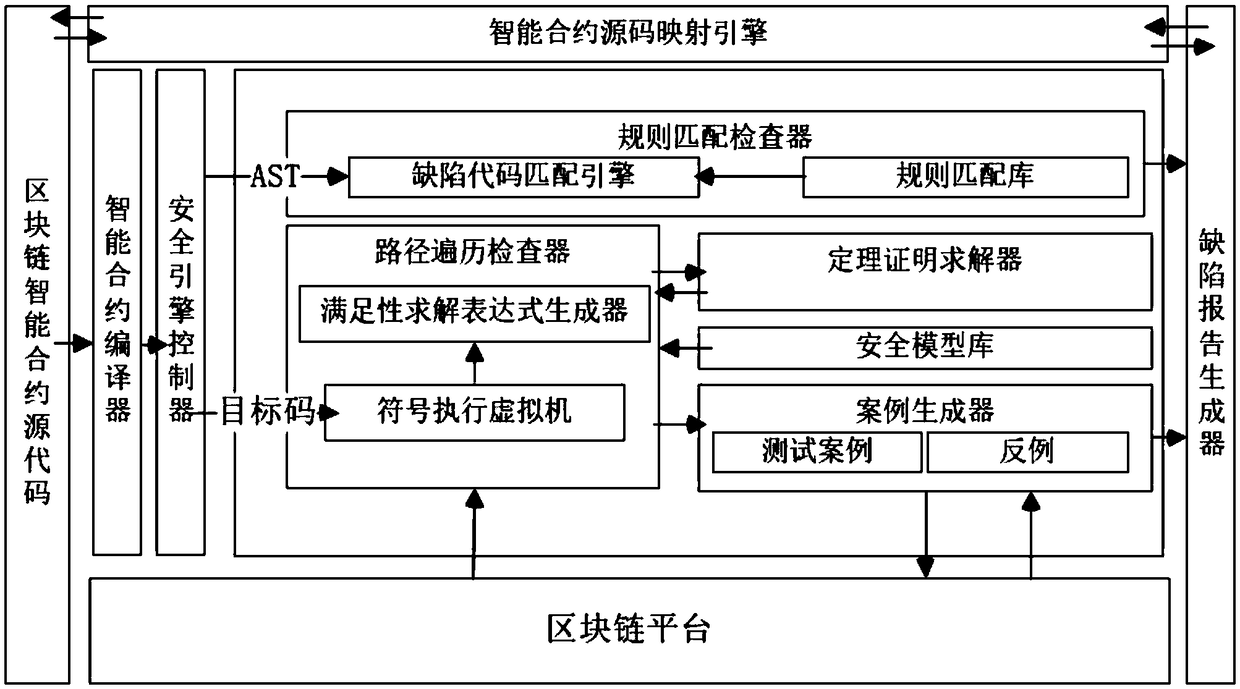
Automated intelligent contract code defect detection system and method
ActiveCN109063477AReliable checkSolve the problem of false positivesPlatform integrity maintainanceProtocol authorisationSoftware engineeringSmart contract
The invention discloses an automatic intelligent contract code defect detection system and method. Combining static code analysis with dynamic path traversal, together with independently extensible security model library and rule matching library, the defect code inspection is more complete, accurate and reliable, and the problem of missing report in defect code is solved. At that same time, the interface call of the bottom platform of the block chain is load in real time, and the generated t cases and counterexamples are used on the block chain platform to verify whet the defect code is a pseudo error or not, so that the defect code of the intelligent contract can be effectively and accurately found out, and the defect error code can be located to the specific position of the intelligentcontract source code through the source code mapping engine.
Owner:成都链安科技有限公司
Zero rating in wireless prepaid communications network
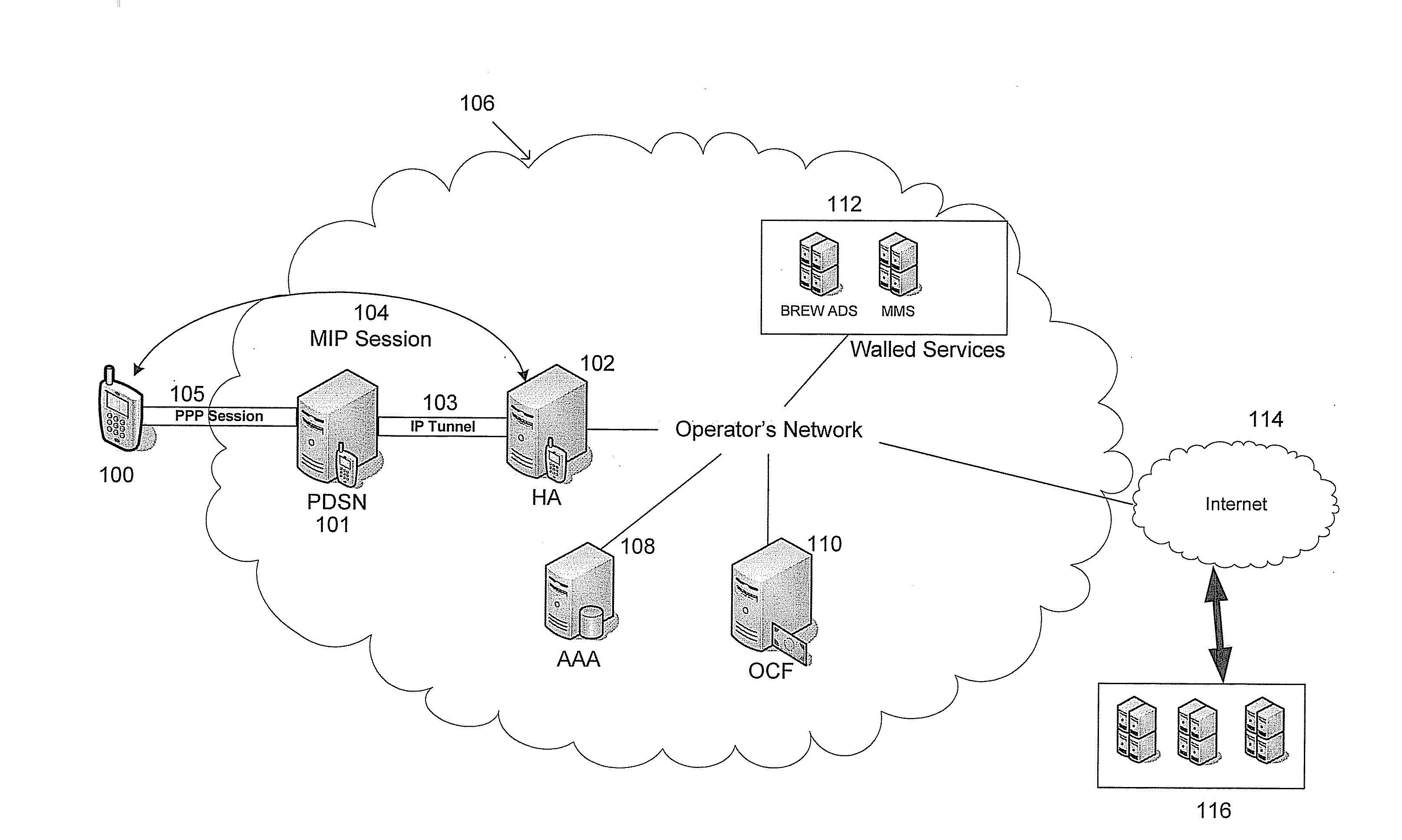
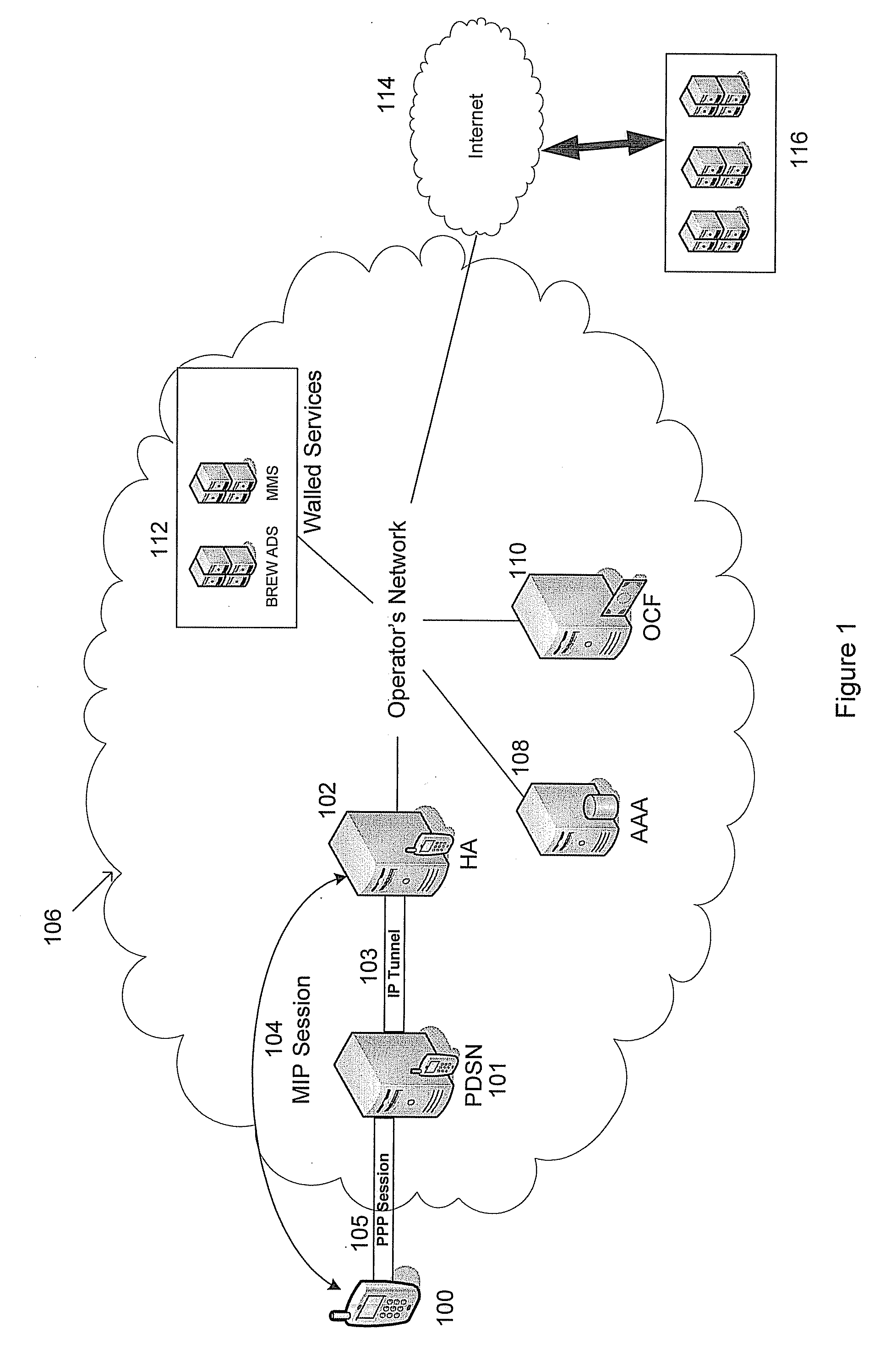
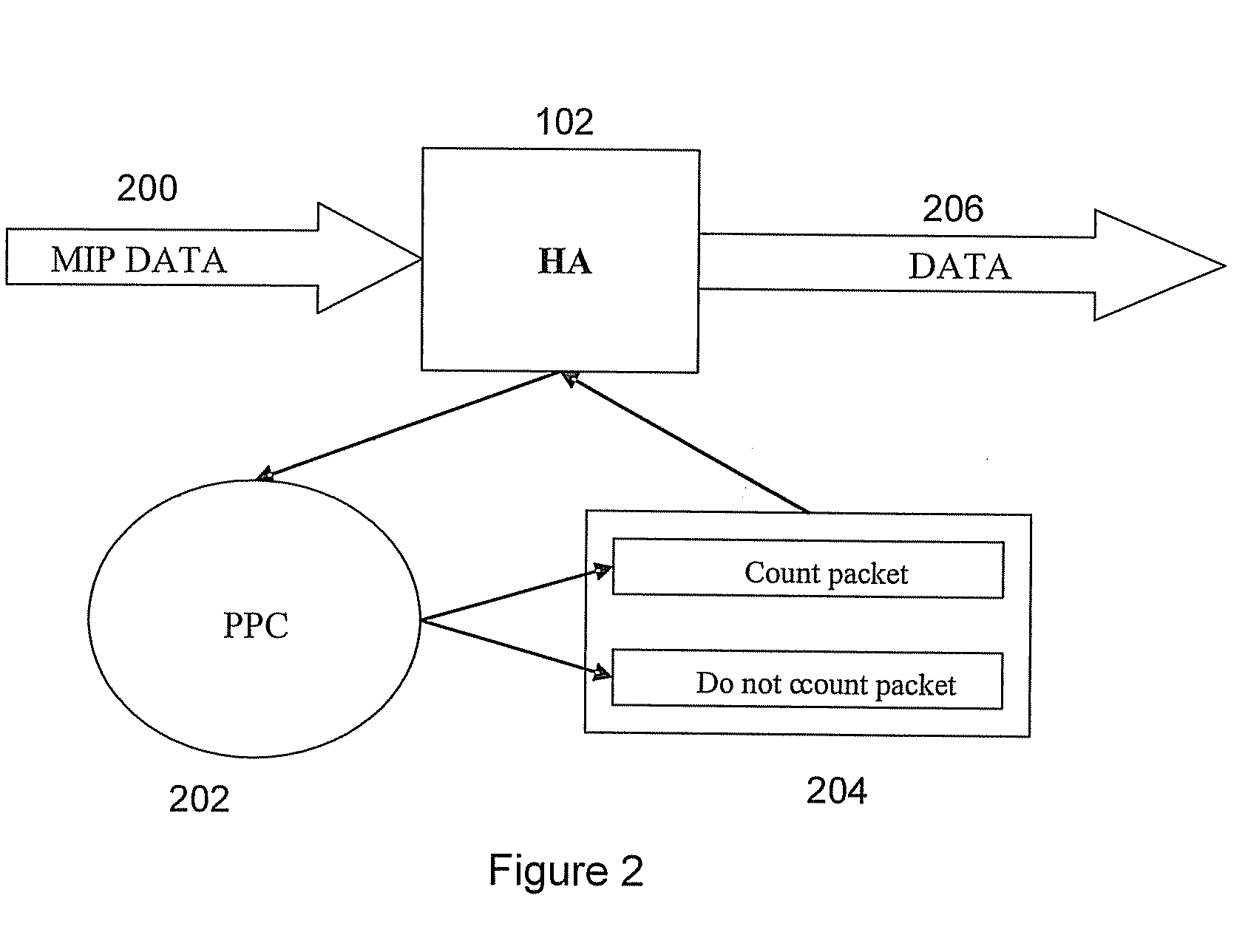
ActiveUS20090168660A1Metering/charging/biilling arrangementsAccounting/billing servicesNetwork packetZero-rating
This disclosure relates to methods and systems for monitoring network usage according to predetermined rules and calculating user charges based on the network usage. The described technique includes receiving a data packet, extracting parameters from the data packet and determining whether the extracted parameters match at least one rule in a rules engine. Charges for the data packet are calculated based on the matched rules. The data packet is forwarded on to its destination.
Owner:U S CELLULAR
FSA Extension Architecture for Programmable Intelligent Search Memory
ActiveUS20080140911A1Efficient and compact realizationReduce overheadDigital data information retrievalDigital storagePrismMemory architecture
Memory architecture provides capabilities for high performance content search. The architecture creates an innovative memory that can be programmed with content search rules which are used by the memory to evaluate presented content for matching with the programmed rules. When the content being searched matches any of the rules programmed in the Programmable Intelligent Search Memory (PRISM) action(s) associated with the matched rule(s) are taken. Content search rules comprise of regular expressions which are converted to finite state automata (FSA) and then programmed in PRISM for evaluating content with the search rules. PRISM architecture comprises of a plurality of programmable PRISM Search Engines (PSE), each capable of supporting a predetermined size FSAs. FSA extension architecture is created to extend the predetermined size limit of an FSA supported by PSE, by coupling multiple PSEs together to behave as a composite PSE to support larger FSAs.
Owner:INFOSIL INC
Threat intelligence oriented entity identification method and system
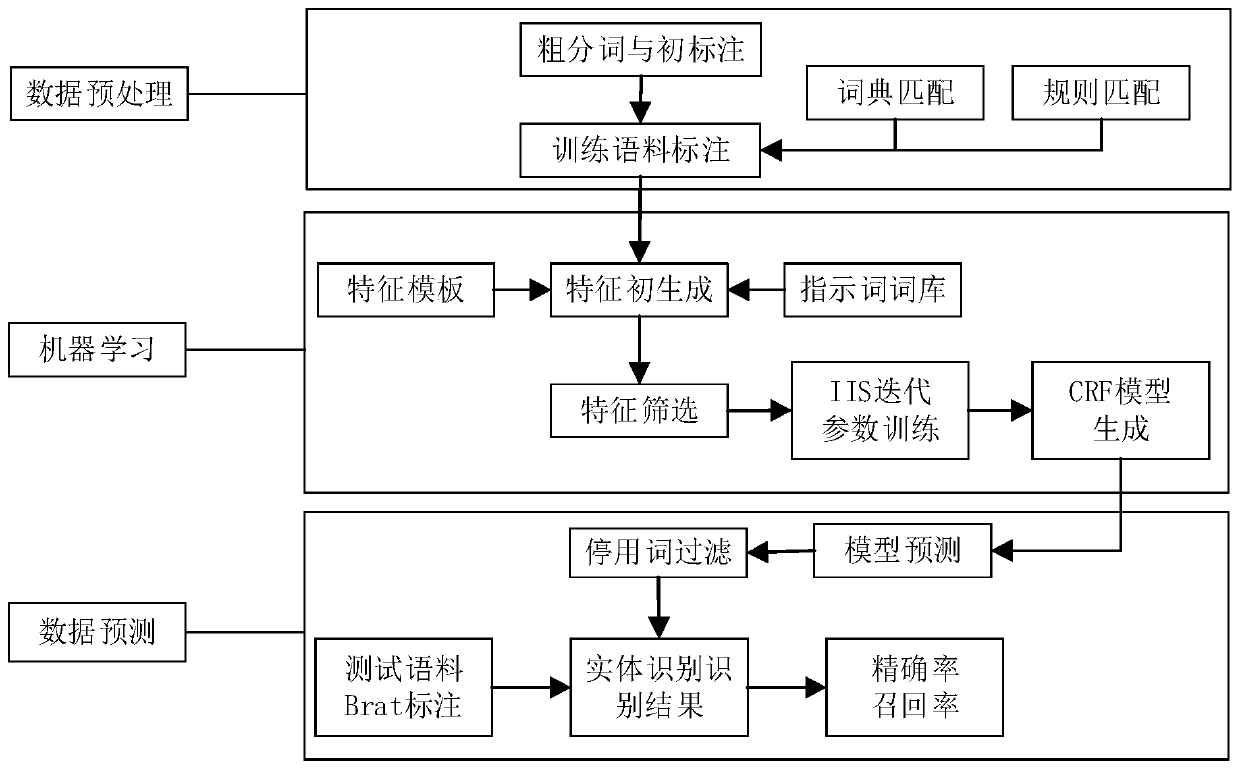
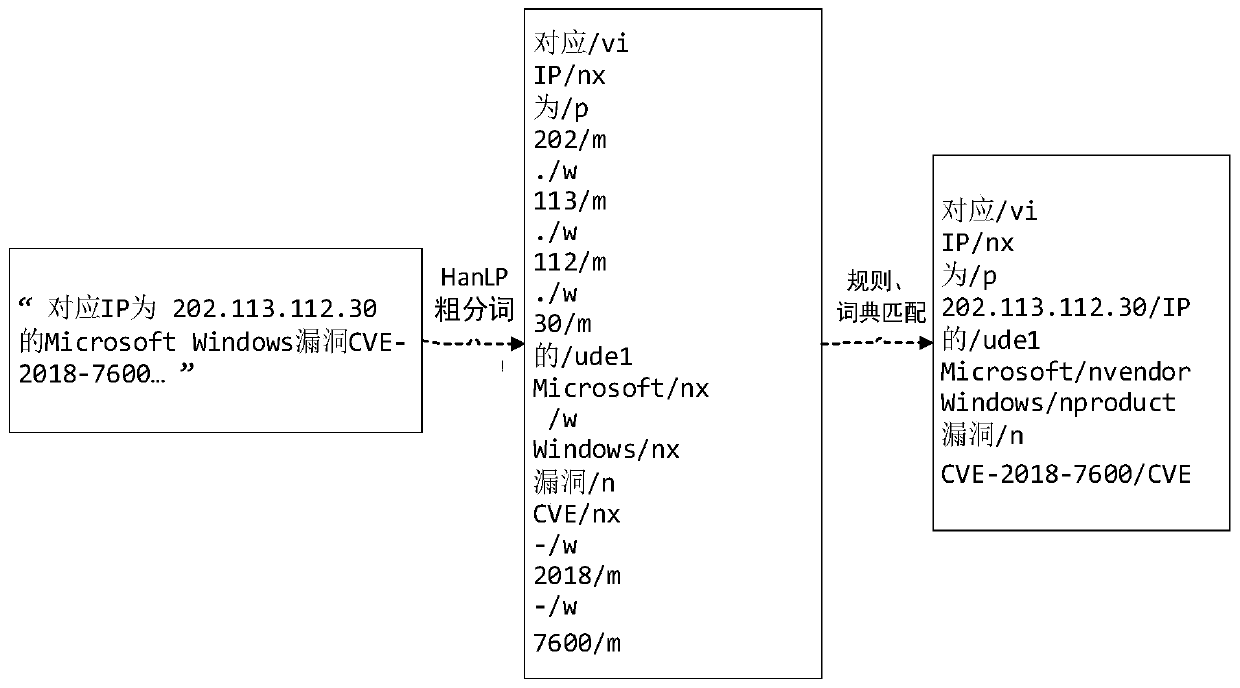
InactiveCN109858018AFitEasy to identifySpecial data processing applicationsCommon wordExtraction methods
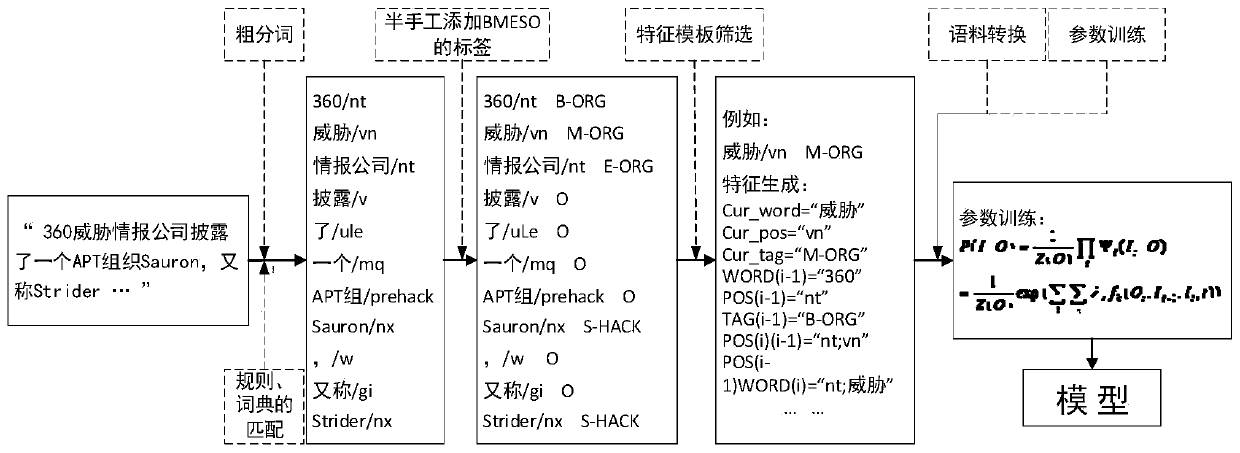
The invention relates to a threat intelligence oriented entity identification method and system. The method comprises the following steps: 1) performing coarse word segmentation on a threat information text serving as a training corpus; 2) constructing a threat information entity common word dictionary library and a rule library, and performing dictionary matching and rule matching on a coarse word segmentation result; 3) marking an entity label for each word based on a matching result to form a training set; 4) constructing a feature template, establishing an indication word bank to perfect the screening form of the feature template, generating context features for the training set by using the feature template, screening, and inputting the screened features into a machine learning modelto carry out parameter iterative training; and 5) performing coarse word segmentation, dictionary matching and rule matching on the threat information text to be identified, and performing entity identification by using the trained machine learning model. According to the threat information entity extraction method, the threat information entity extraction is completed by adopting a means of combining a rule, a dictionary and a model, so that the entity identification precision of the threat information is remarkably improved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Identifying and Securing Sensitive Data at its Source
ActiveUS20150324606A1Reduce processRelational databasesDigital data protectionClassification ruleData management
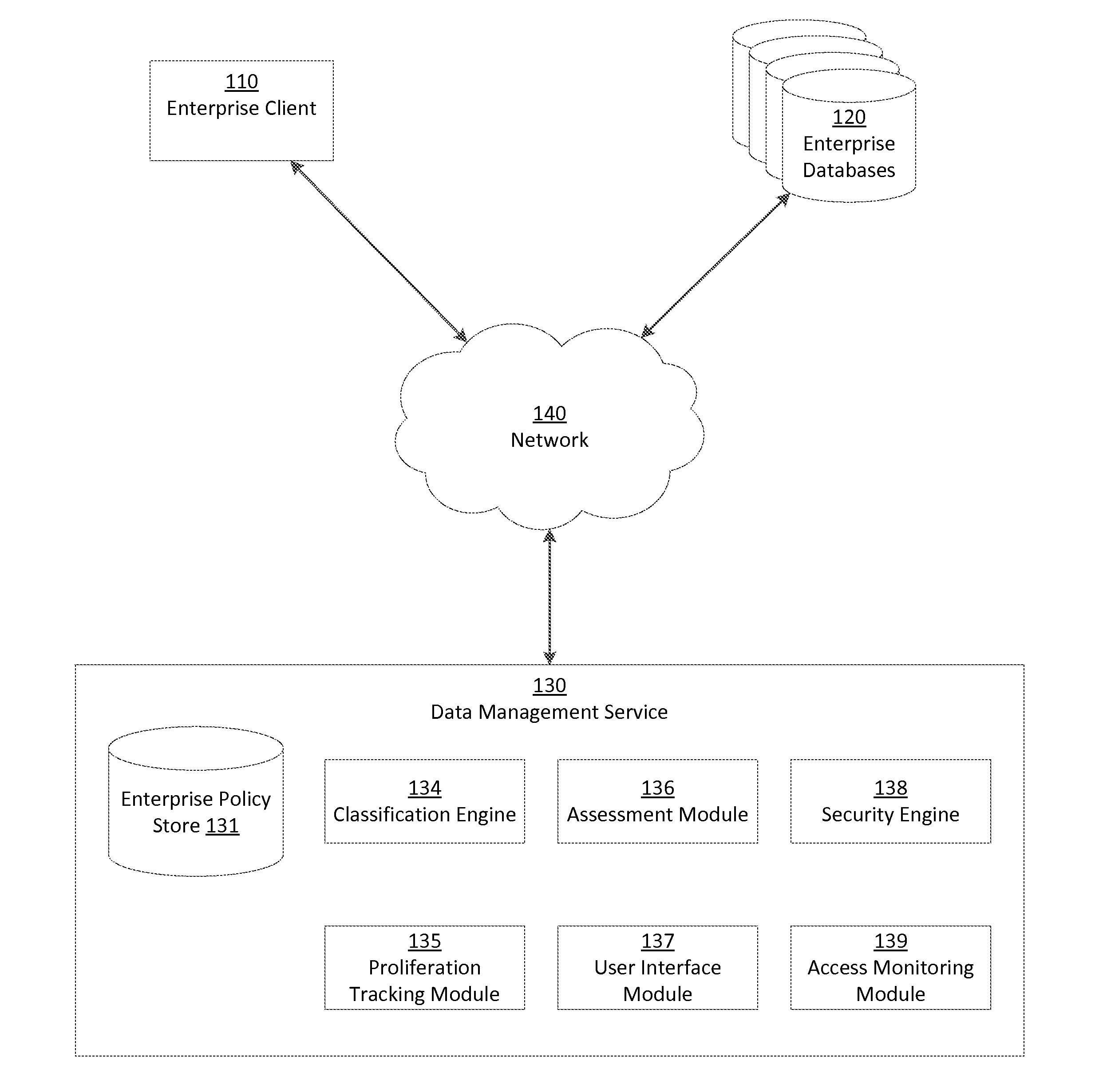
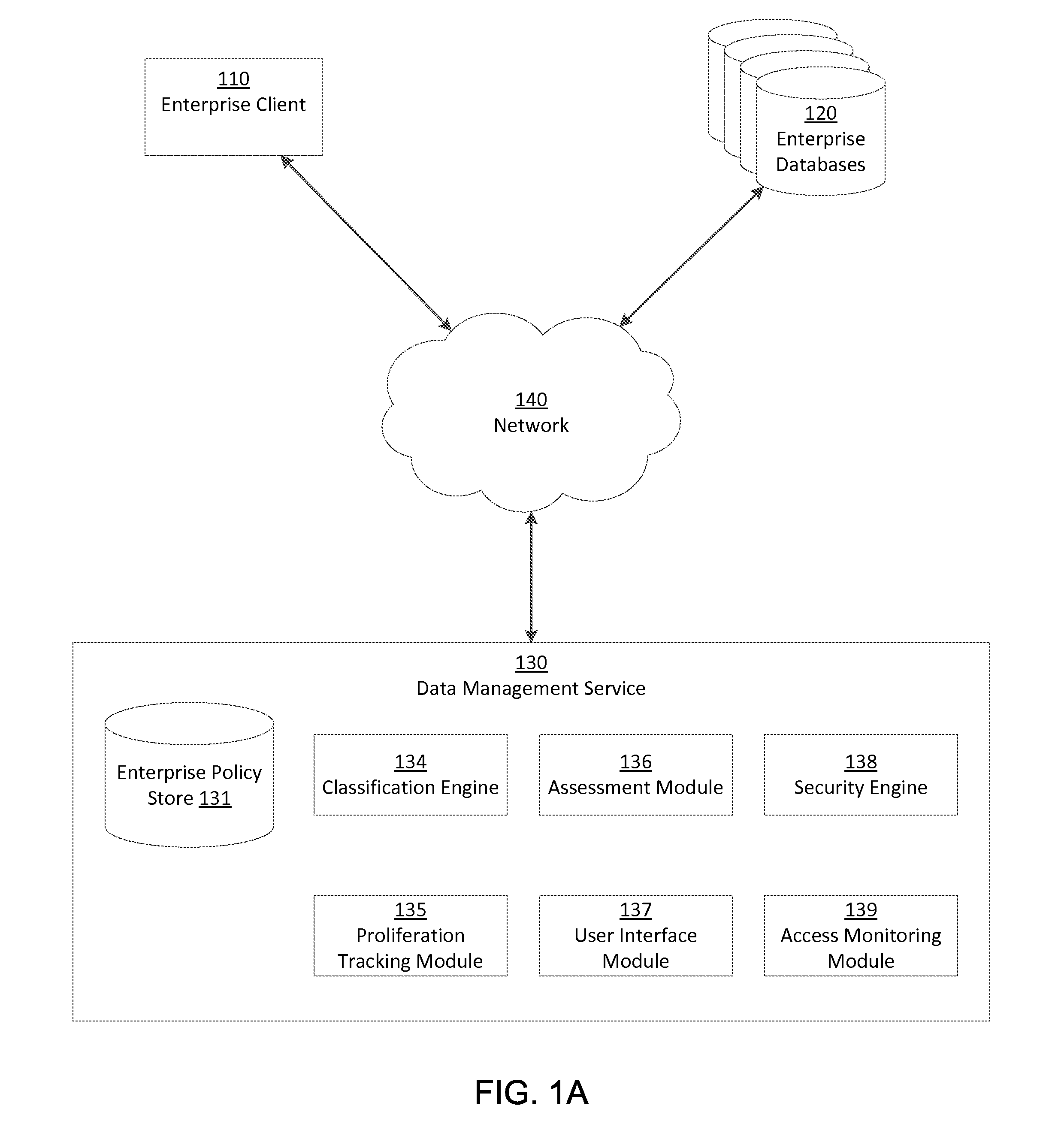
A data management service identifies sensitive data stored on enterprise databases according to record classification rules that classify a data record as having a sensitive data type if the data record includes fields matching at least one of the record classification rules. The data management service determines assessment scores for enterprise databases according to sensitive data records and protection policies on the enterprise databases. The data management service provides an interface that groups enterprise databases having common attributes or common sensitive data types and indicates aggregated assessment scores for the groups of enterprise databases. Through the interface with the grouped enterprise databases, an administrator apply protection policies to enterprise databases. To apply the protection policy, the data management service applies the protection policy to a source database from which dependent enterprise databases access the sensitive database.
Owner:INFORMATICA CORP
Rule matching method, device and system
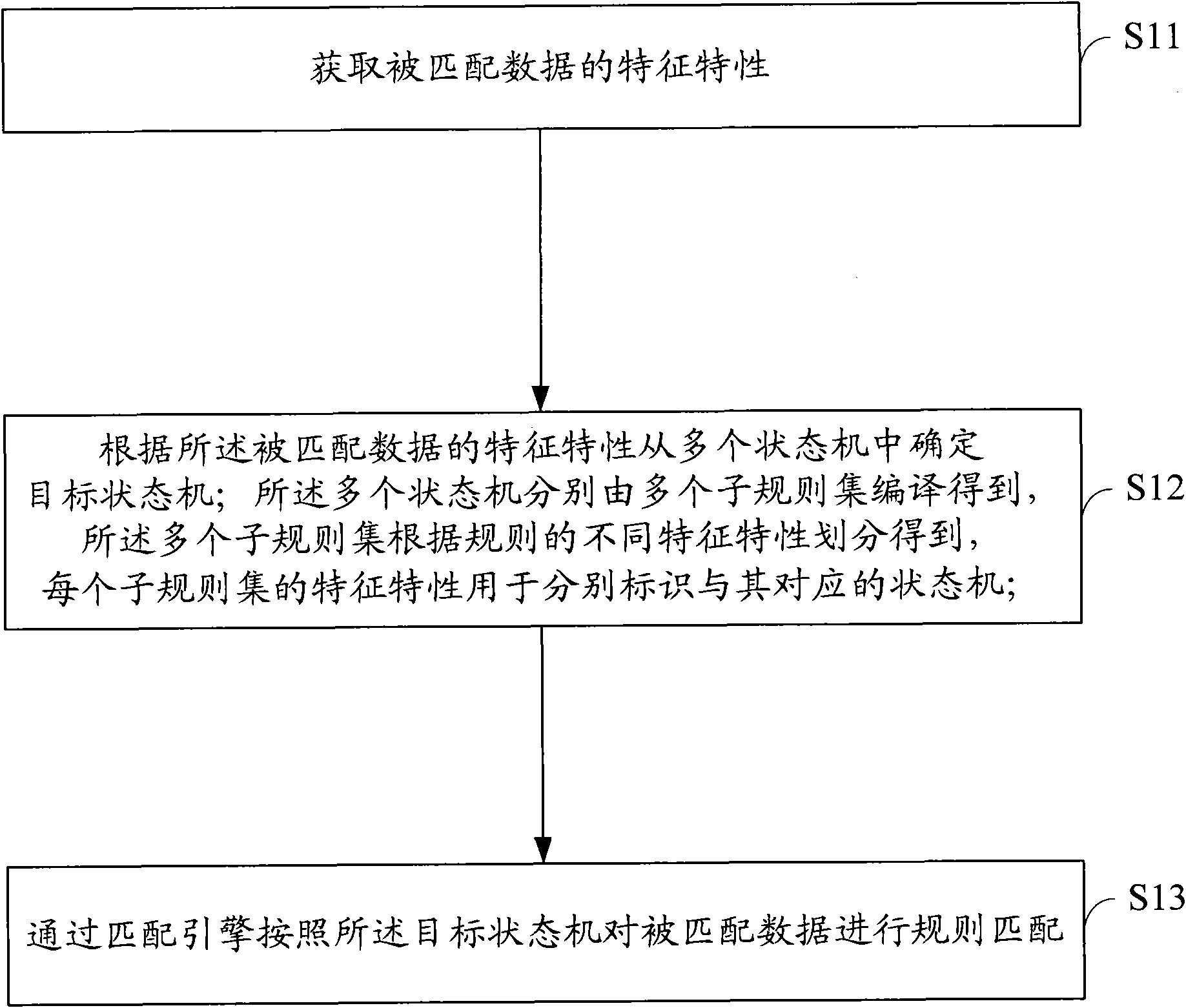
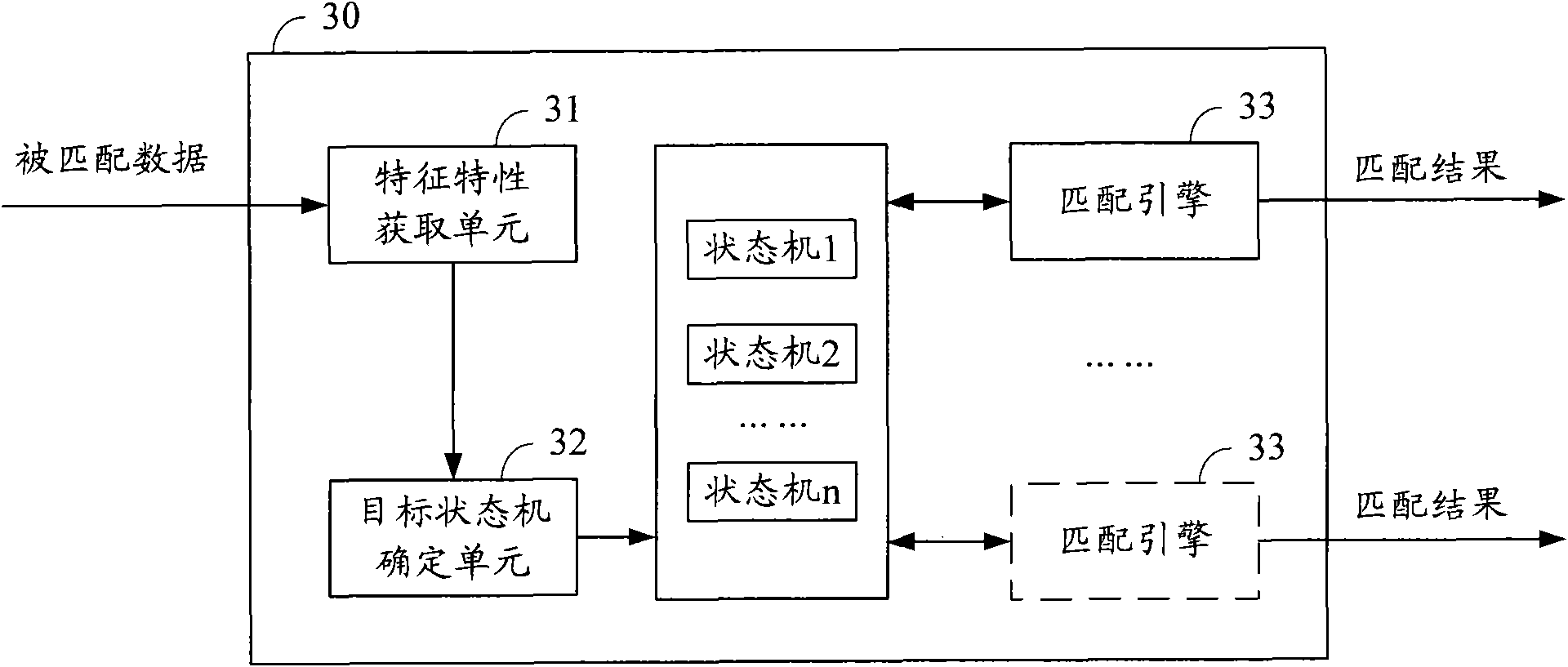
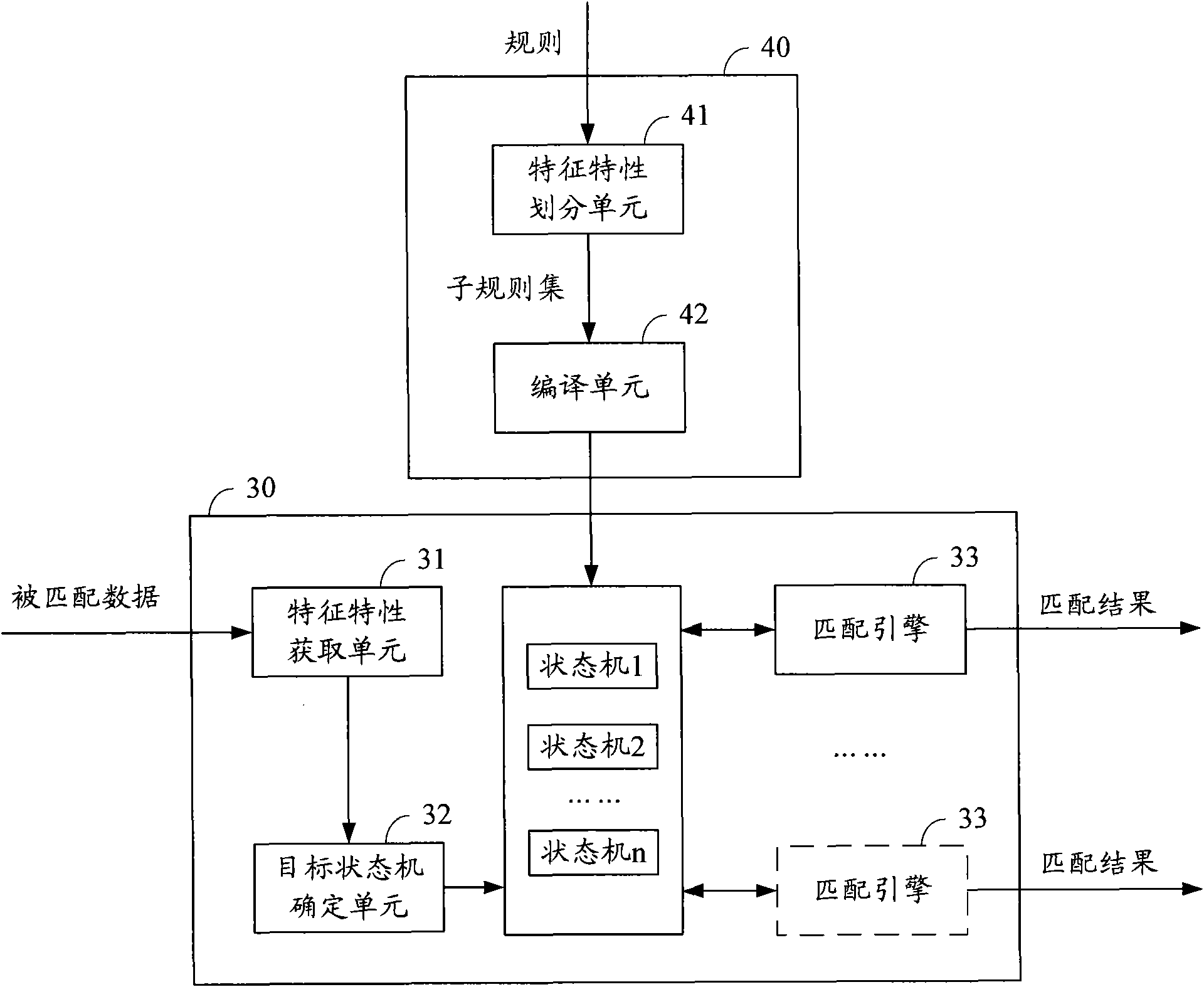
InactiveCN101841546AReduce the size of the rulesetReduce branchesTransmissionSpecial data processing applicationsFinite-state machineIdentifying goals
The embodiment of the invention discloses a rule matching method, a device and a system, wherein the rule matching method comprises the steps of: obtaining the characteristic of the matched data; determining the target state machine from a plurality of state machines according to the characteristic of the matched data; obtaining the plurality of state machines by compiling a plurality of sub-rulesets; obtaining the plurality of sub-rule sets according to the division of different characteristics of the rule; the characteristic of each sub-rule set is used for respectively identifying the state machine which corresponds to each sub-rule set; and carrying out the rule matching by matching an engine according to the target state machine. The embodiment of the invention effectively reduces the size of the rule set in the state machine and causes the branch of the state machine to reduce and the depth of the state to becomes small, thus being capable of reducing the matching period of therule matching and saving the cost and time of the system resources, and further increasing the matching efficiency.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com