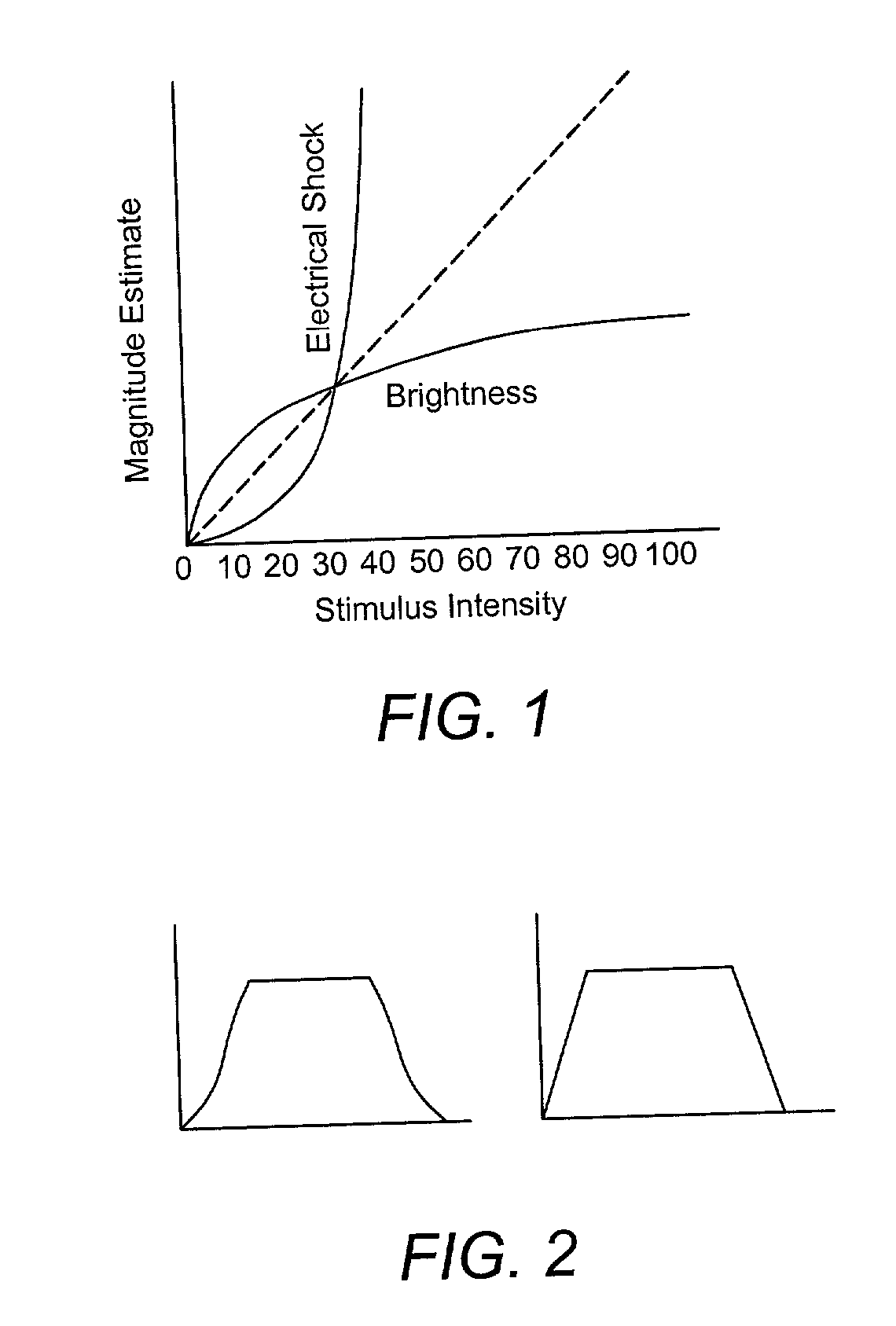
Patents
Literature
97 results about "Filter analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
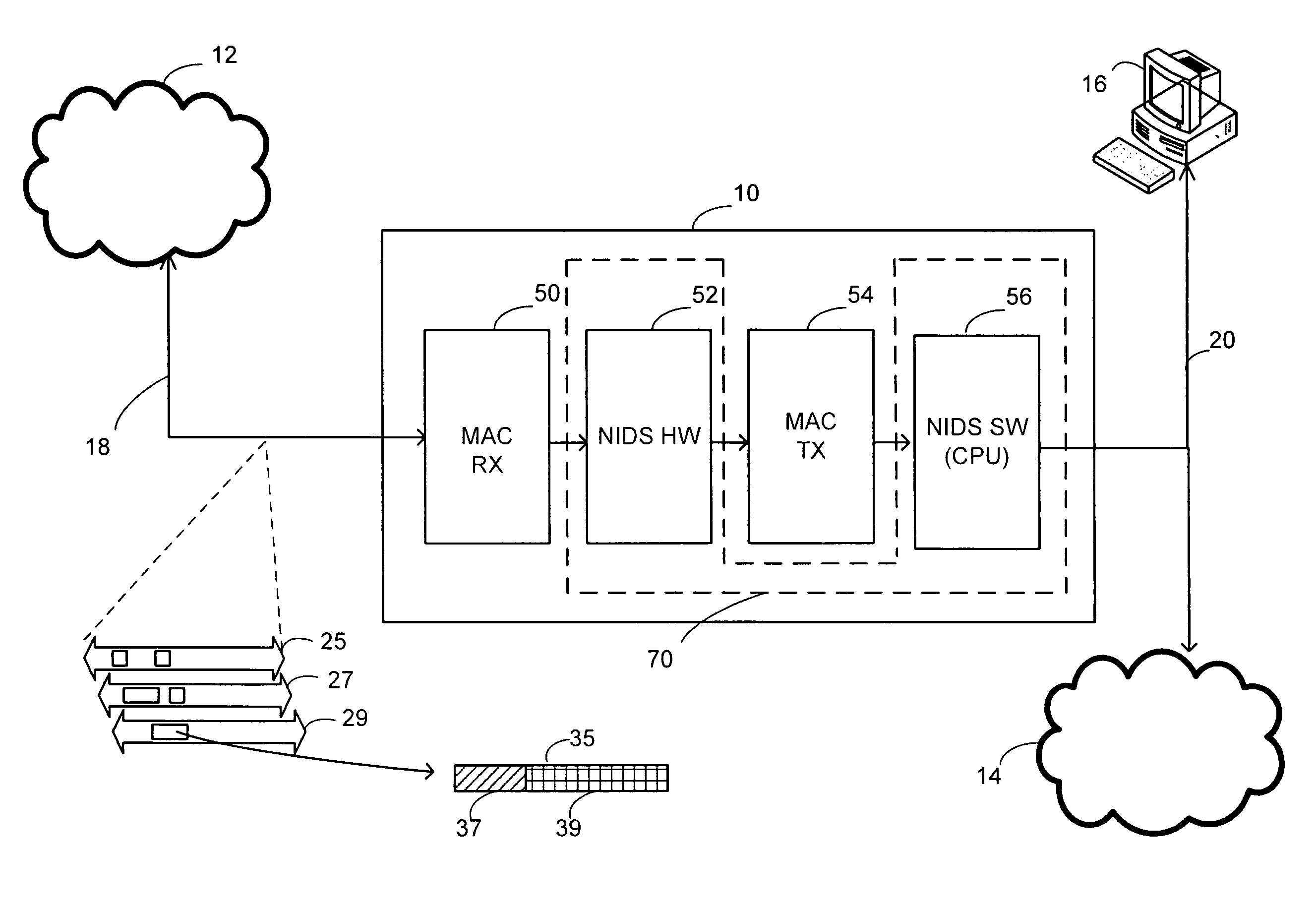
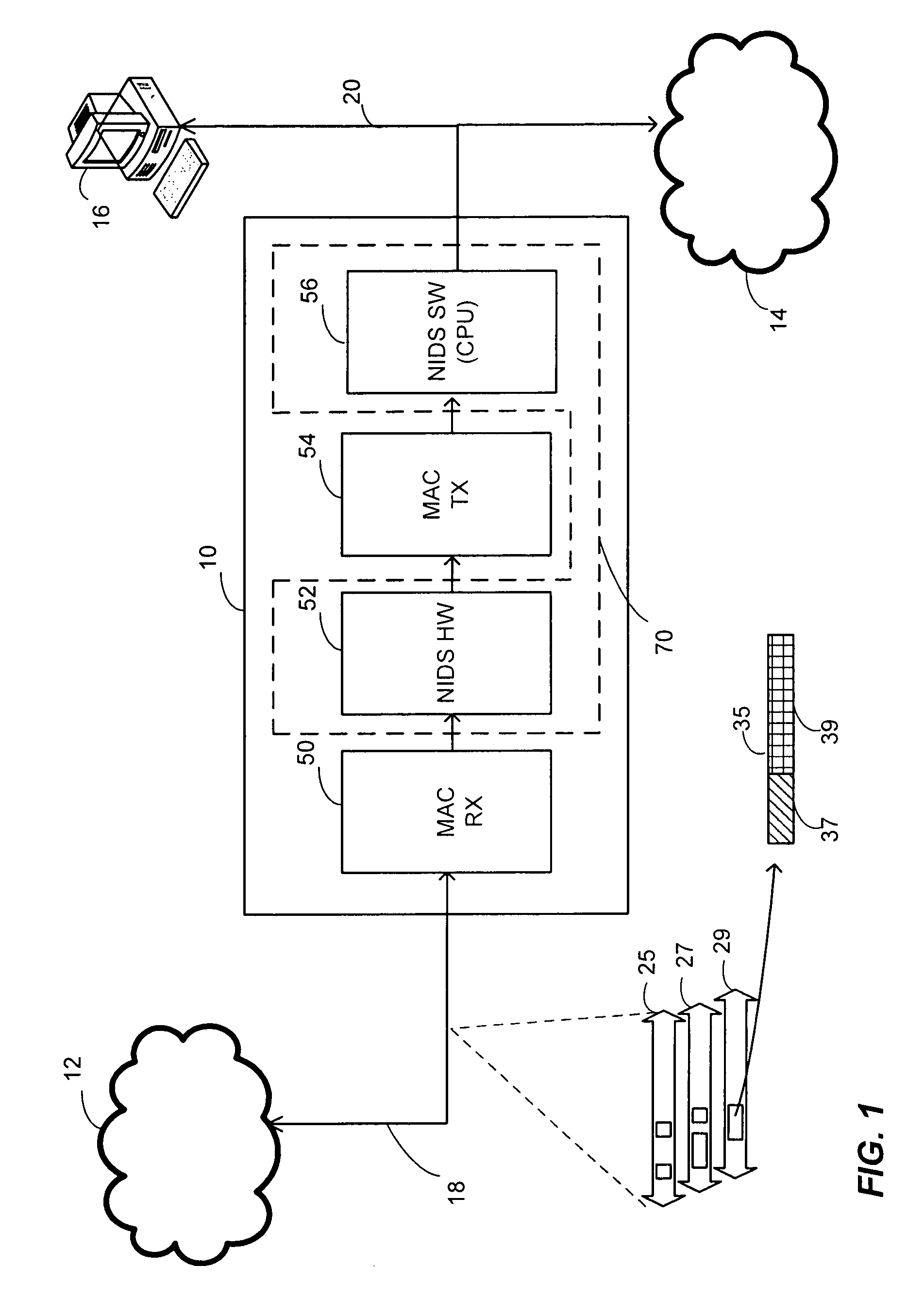
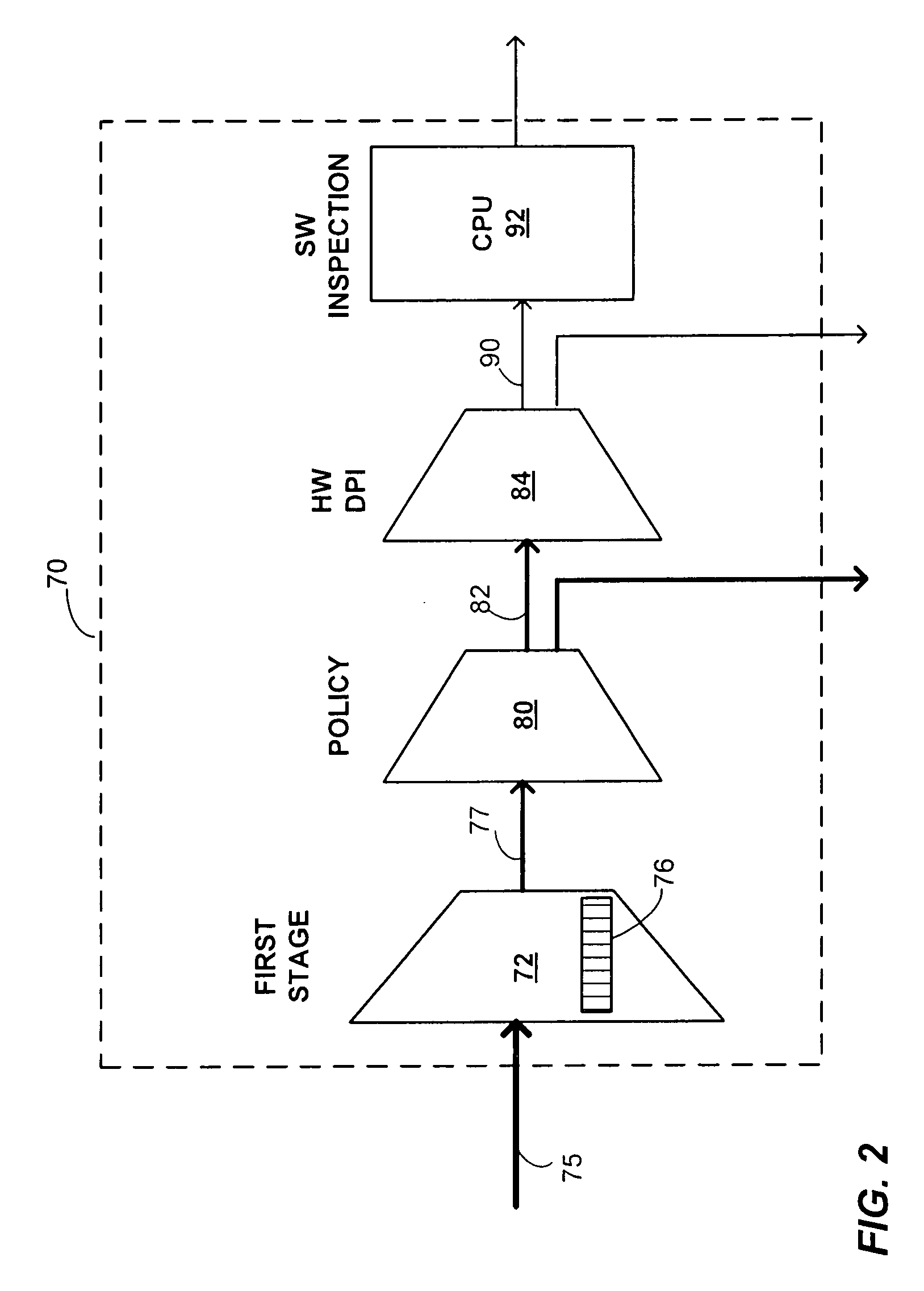
Method and Apparatus for Deep Packet Inspection for Network Intrusion Detection
ActiveUS20080201772A1Hardware monitoringMultiple digital computer combinationsComputer hardwareData stream
In a method of determining whether a data stream includes unauthorized data, the data stream is analyzed using a hardware filter to detect a presence of one or more of a first set of patterns in the data stream. It is determined whether a packet in the data stream belongs to one of a plurality of data flows to be further inspected based on the analysis of the data stream by the hardware filter. A set of rules is applied to the packet to produce rule match status data if it is determined that the packet belongs to one of the plurality of data flows to be further inspected. The packet is analyzed to determine if the packet includes unauthorized data using software stored on a computer-readable medium and implemented on a processor if the rule match status data indicates that the packet potentially includes unauthorized data.
Owner:MARVELL ISRAEL MISL
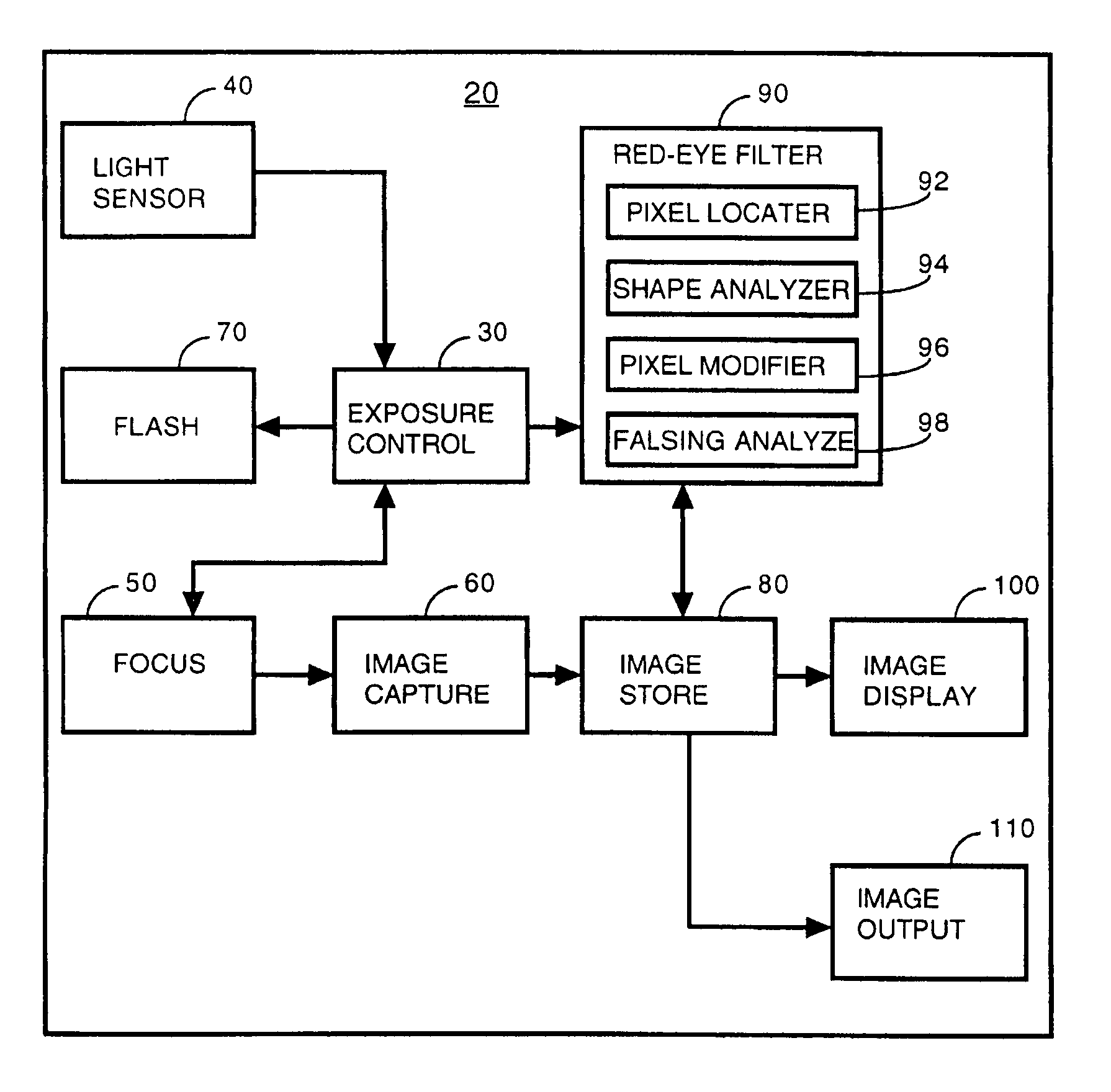
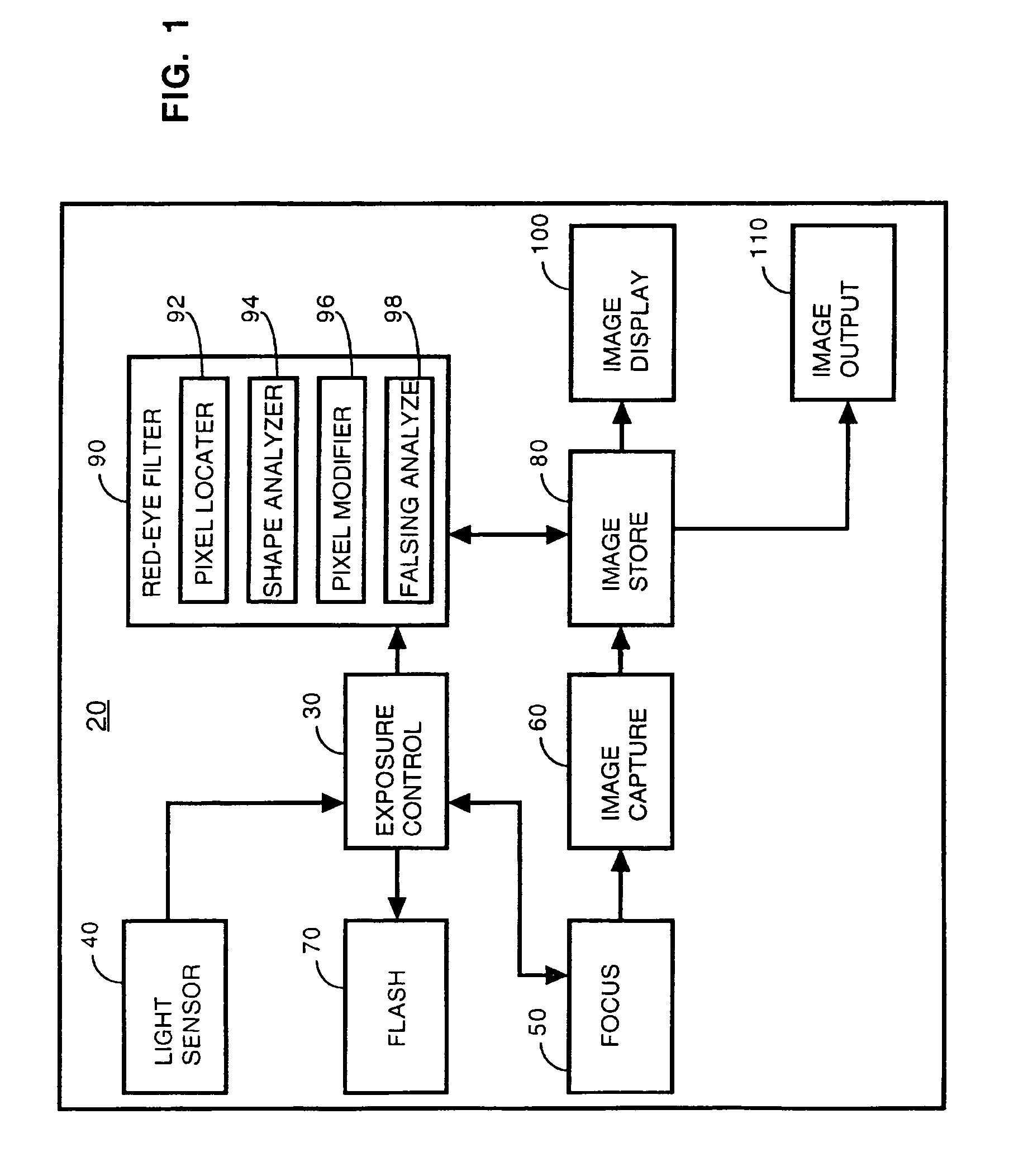
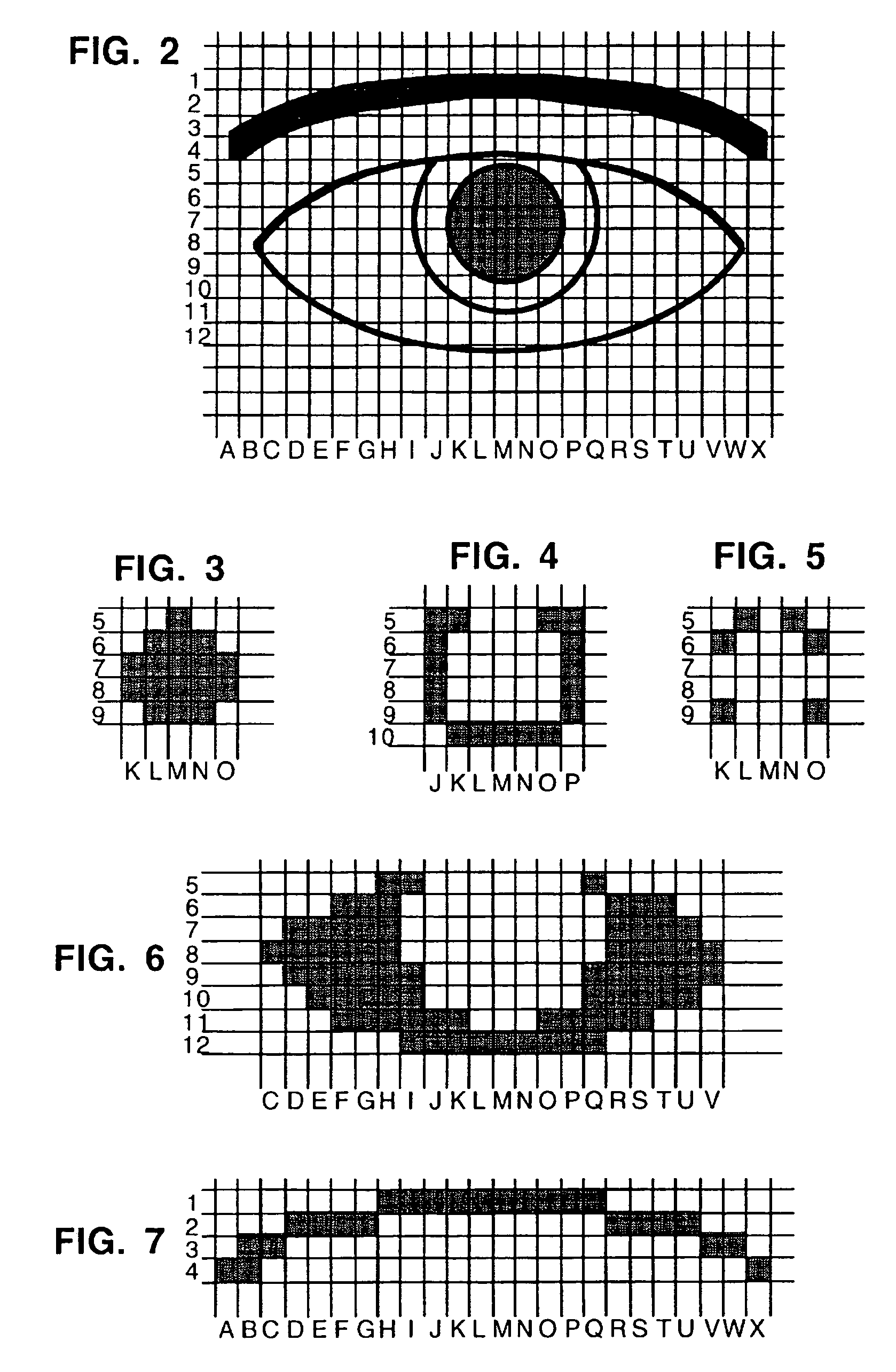
Image modification based on red-eye filter analysis
A digital camera has an integral flash and stores and displays a digital image. Under certain conditions, a flash photograph taken with the camera may result in a red-eye phenomenon due to a reflection within an eye of a subject of the photograph. A digital apparatus has a red-eye filter which analyzes the stored image for the red-eye phenomenon and modifies the stored image to eliminate the red-eye phenomenon by changing the red area to black. The modification of the image is enabled when a photograph is taken under conditions indicative of the red-eye phenomenon. The modification is subject to anti-falsing analysis which further examines the area around the red-eye area for indicia of the eye of the subject. The detection and correction can be optimized for performance and quality by operating on subsample versions of the image when appropriate.
Owner:FOTONATION LTD
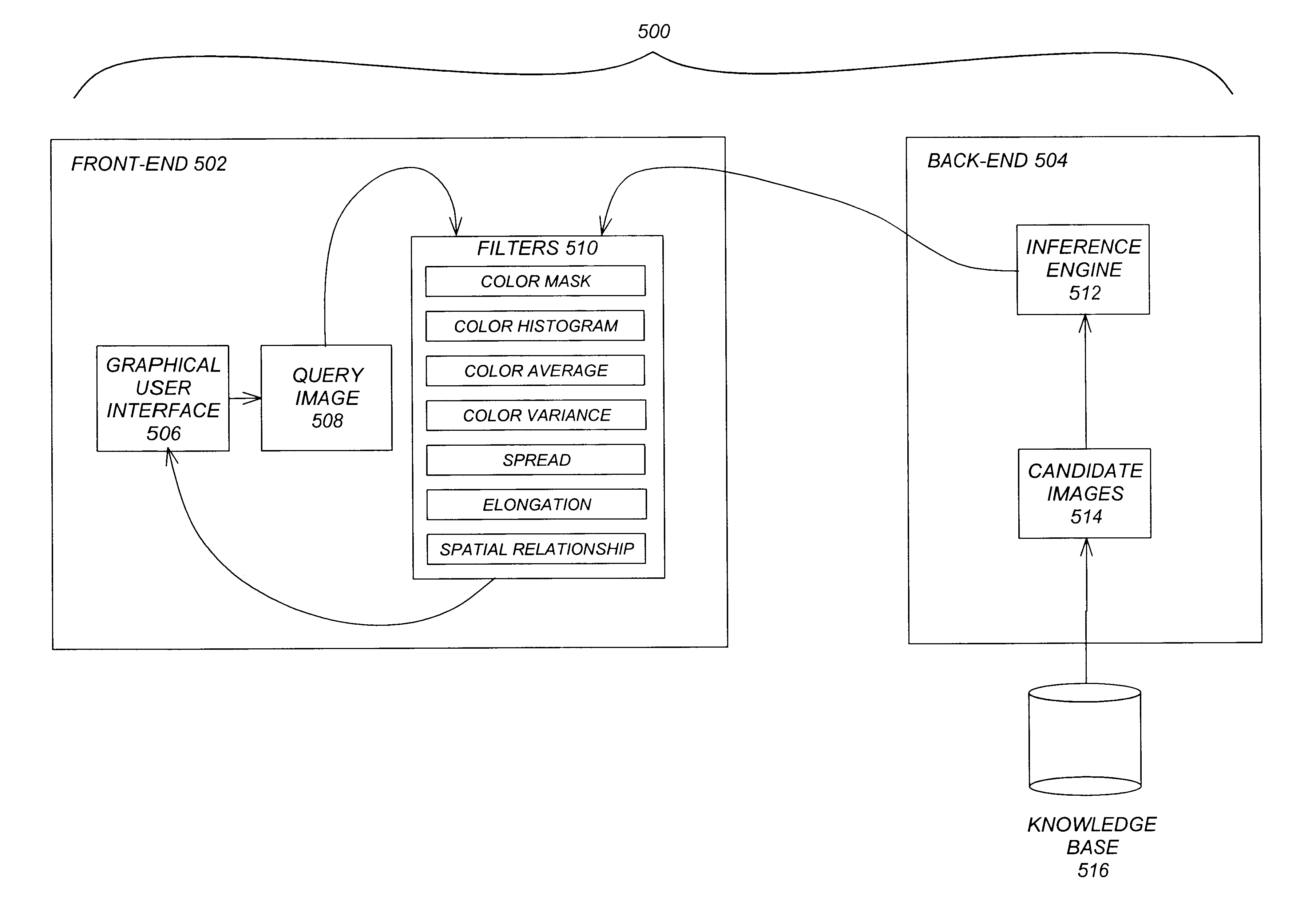
Perception-based image retrieval
InactiveUS6865302B2Data processing applicationsDigital data information retrievalAverage filterPattern perception
A content-based image retrieval (CBIR) system has a front-end that includes a pipeline of one or more dynamically-constructed filters for measuring perceptual similarities between a query image and one or more candidate images retrieved from a back-end comprised of a knowledge base accessed by an inference engine. The images include at least one color set having a set of properties including a number of pixels each having at least one color, a culture color associated with the color set, a mean and variance of the color set, a moment invariant, and a centroid. The filters analyze and compare the set of properties of the query image to the set of properties of the candidate images. Various filters are used, including: a Color Mask filter that identifies identical culture colors in the images, a Color Histogram filter that identifies a distribution of colors in the images, a Color Average filter that performs a similarity comparison on the average of the color sets of the images, a Color Variance filter that performs a similarity comparison on the variances of the color sets of the images, a Spread filter that identifies a spatial concentration of a color in the images, an Elongation filter that identifies a shape of a color in the images, and a Spatial Relationship filter that identifies a spatial relationship between the color sets in the images.
Owner:RGT UNIV OF CALIFORNIA
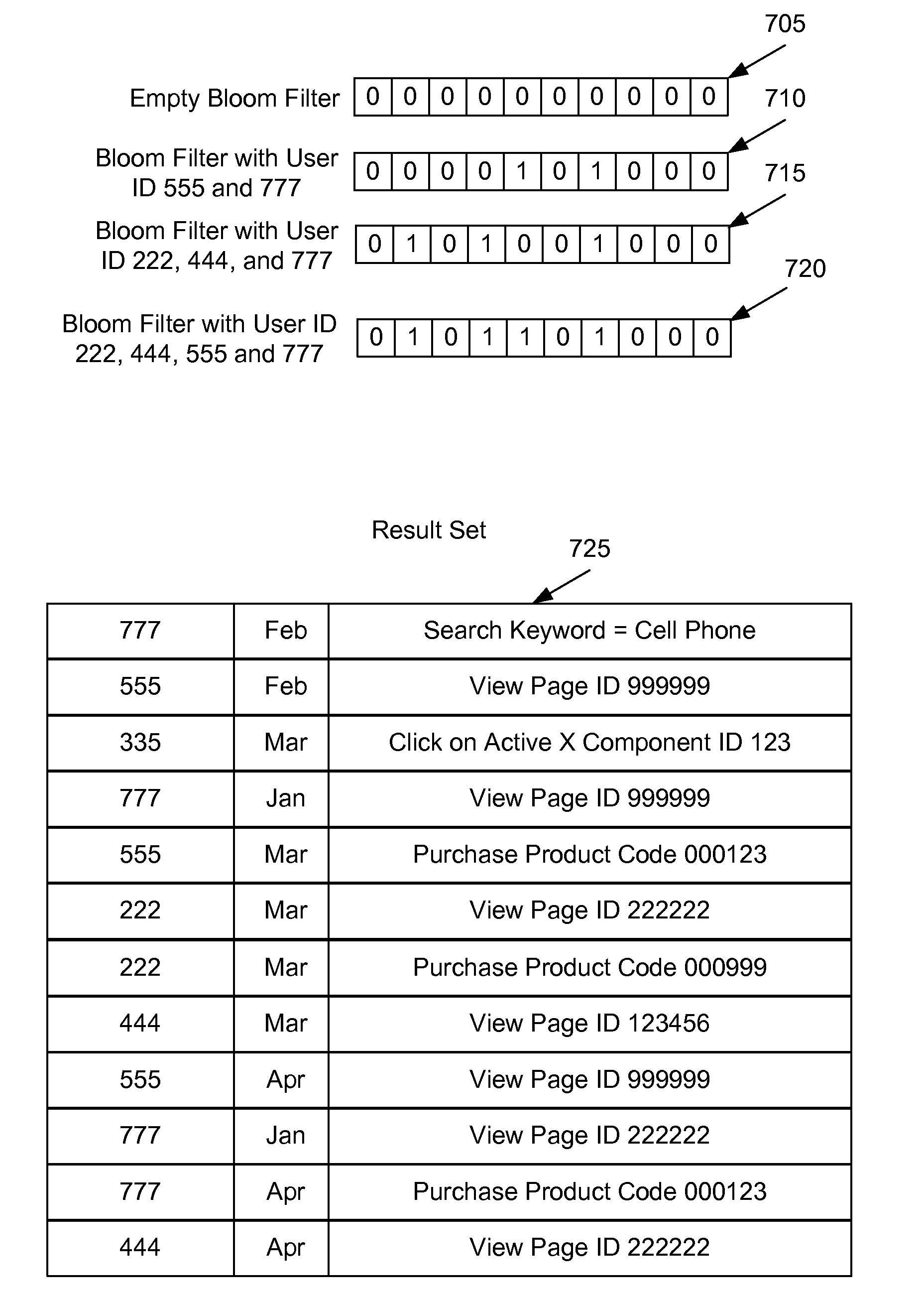
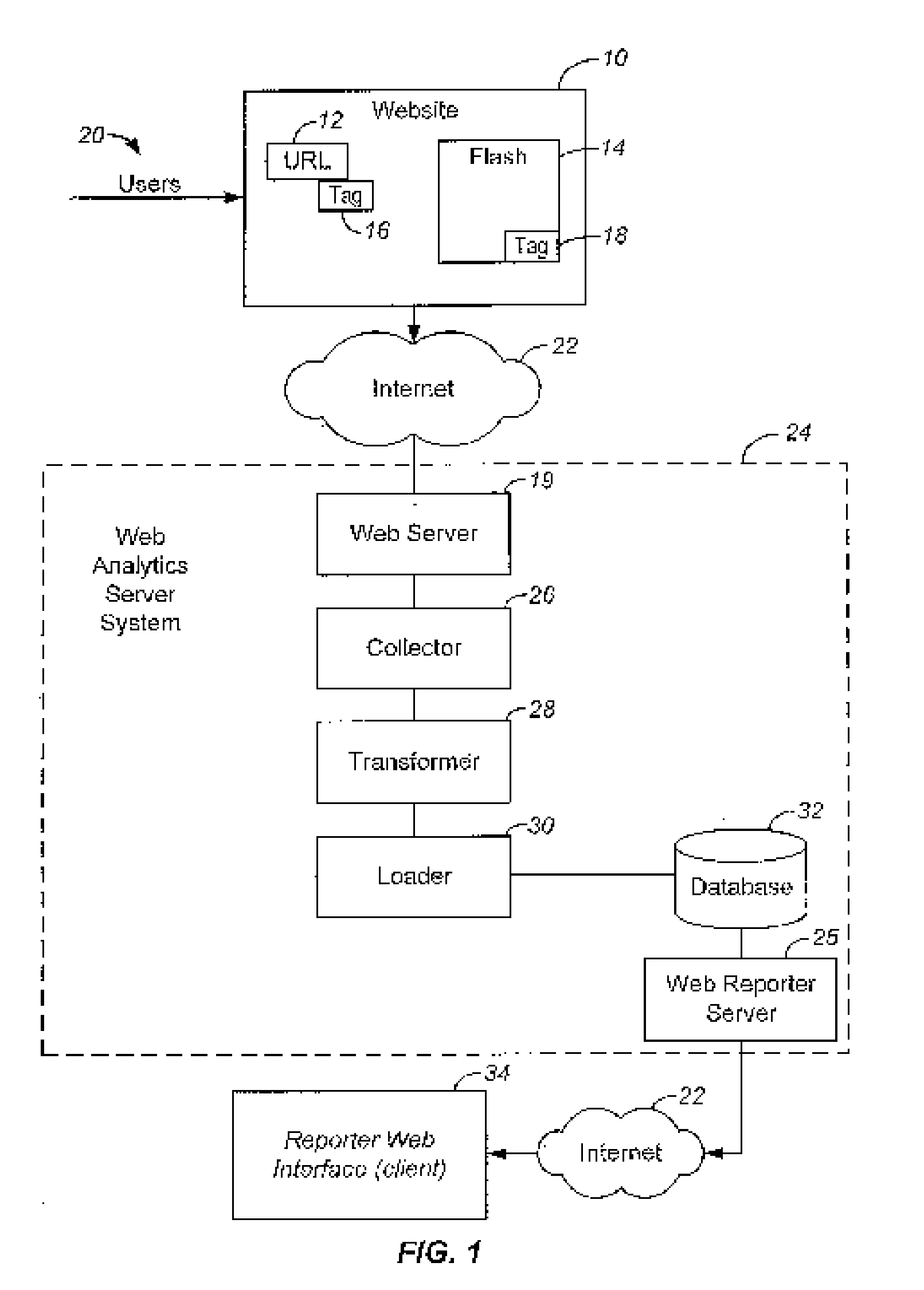
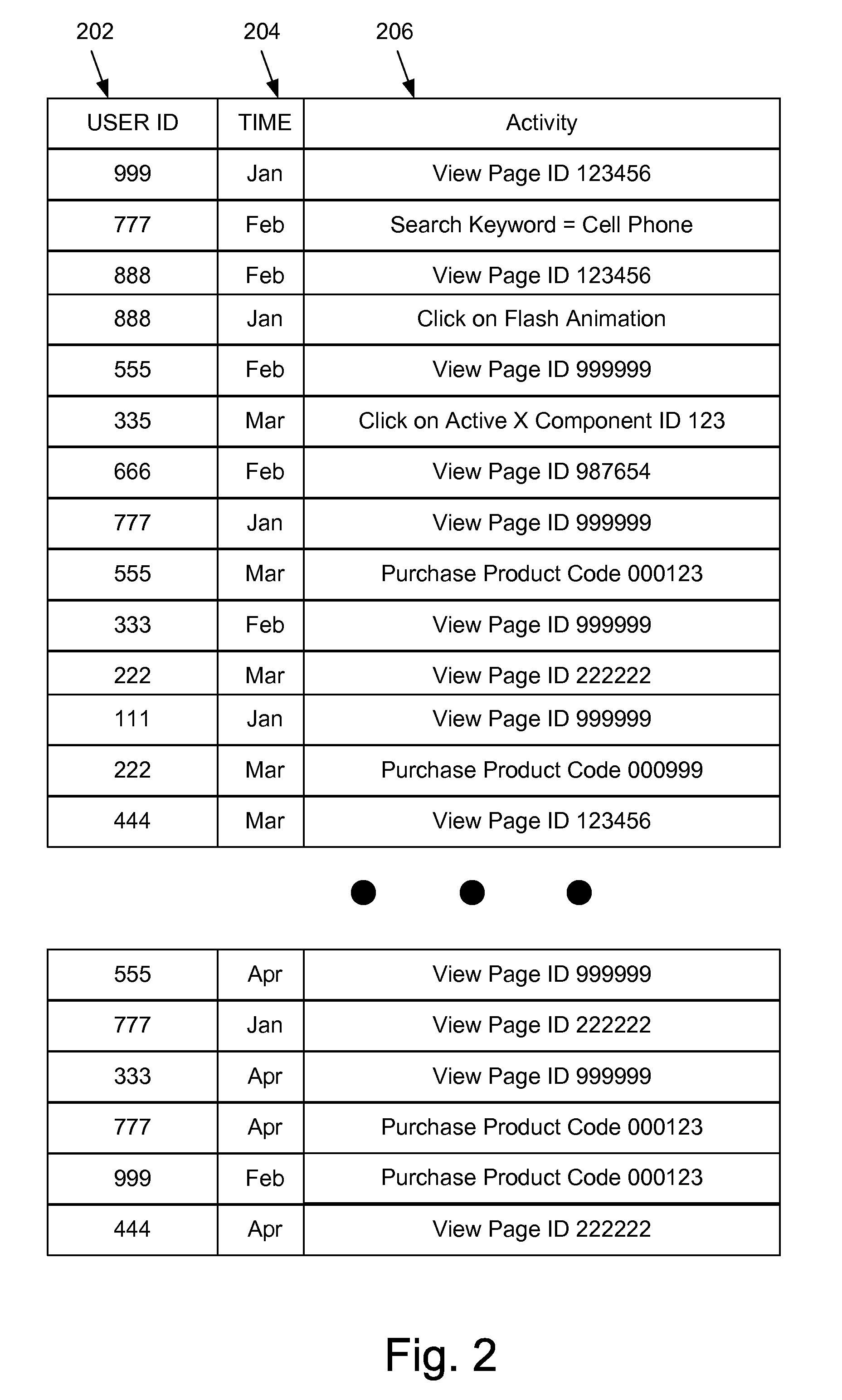
System and method of using a bloom filter in a web analytics application
ActiveUS20100070514A1Digital data processing detailsWebsite content managementWeb analyticsOnline and offline
Embodiments of the present invention are directed to the use of a Bloom Filter in a web analytics application. Large sets of data, obtained from on and offline sources, may be analyzed using a Bloom Filter to find desired patterns within the data. The use of a Bloom Filter in the analysis allows for a more efficient use of resources to perform the analysis.
Owner:ACOUSTIC LP
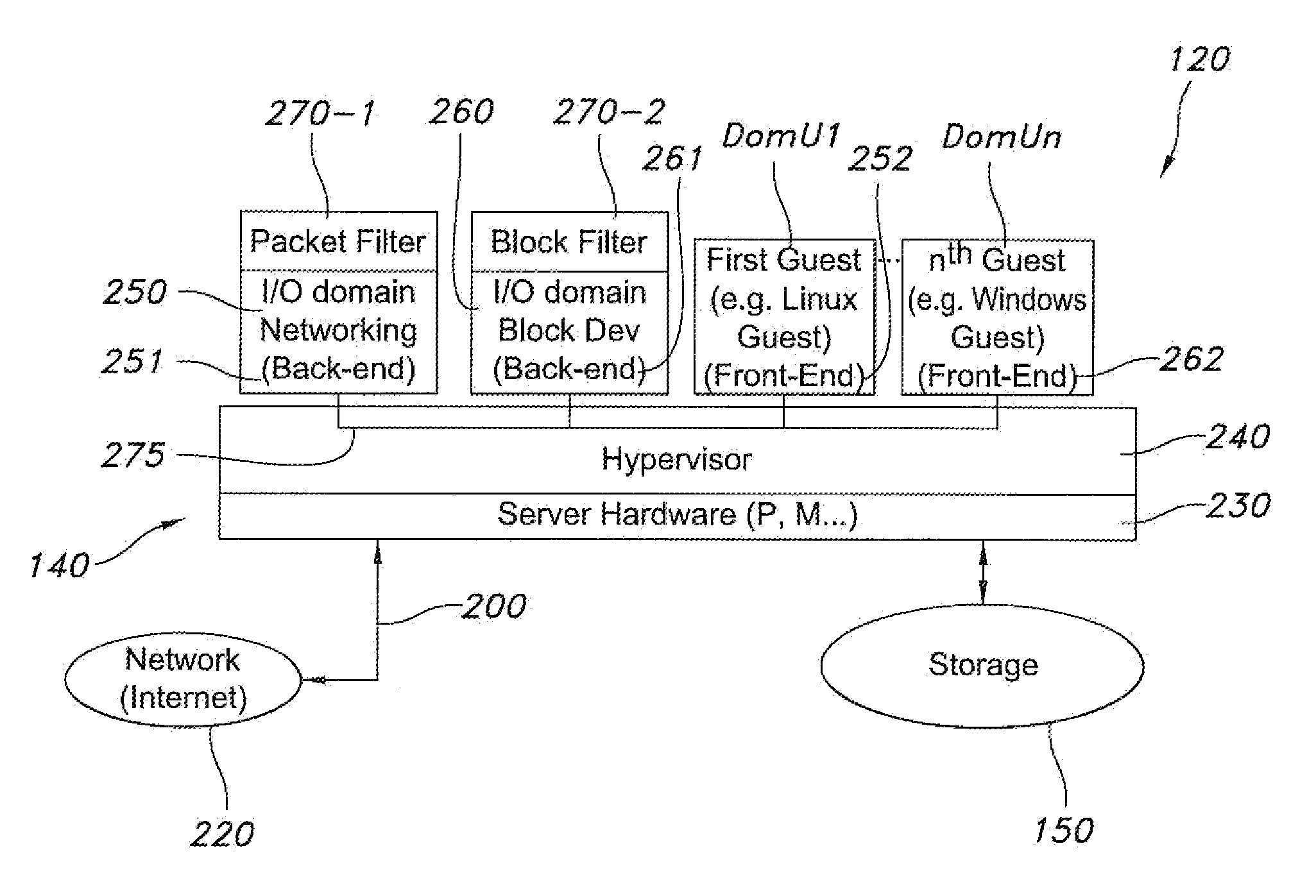
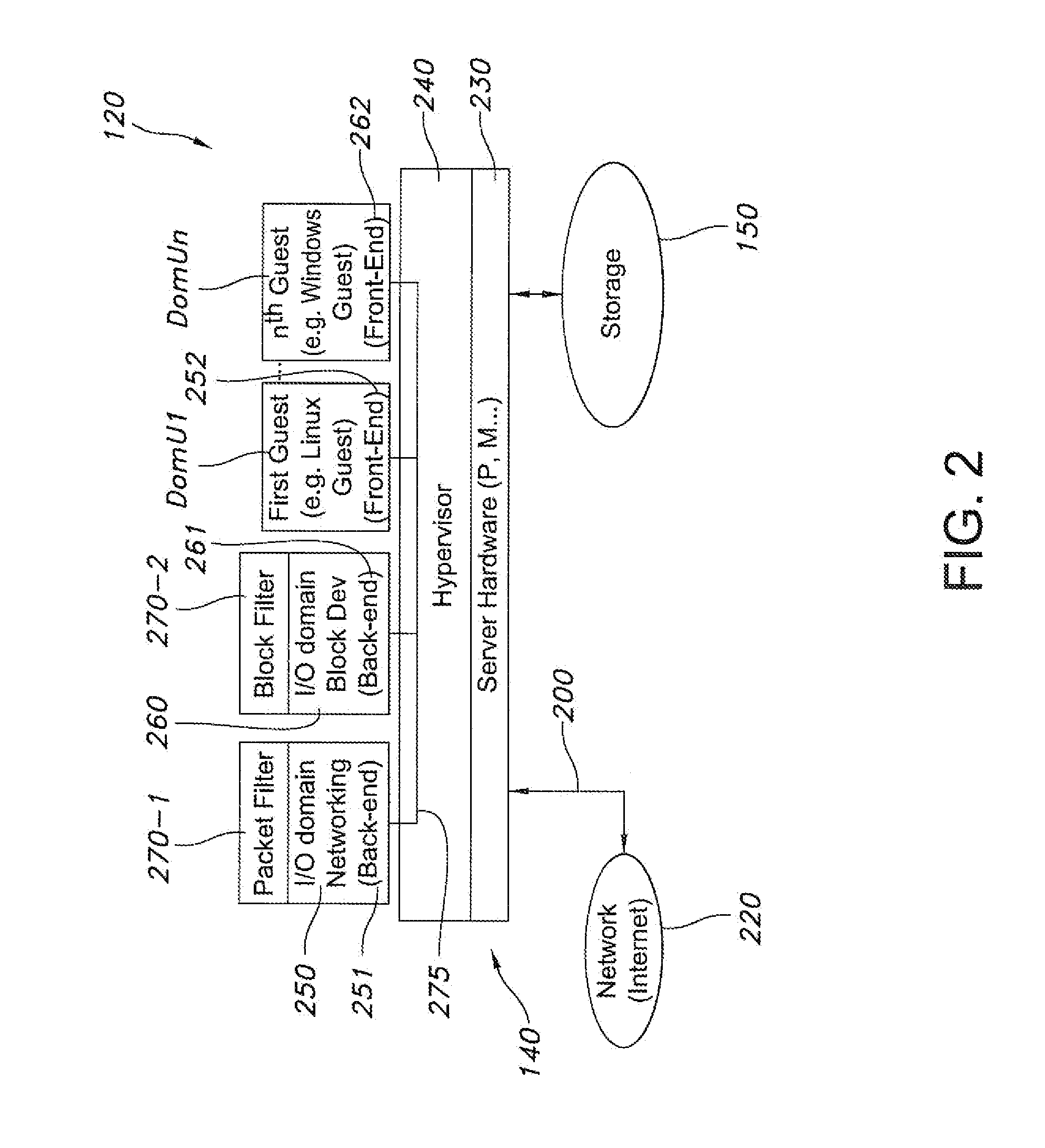
In-the-flow security services for guested virtual machines
InactiveUS20100100718A1Prevent server sprawlMinimize license requirementDigital computer detailsPlatform integrity maintainanceTraffic capacityOperational system
Methods and apparatus provide security to guest virtual machines configured on a hardware platform. A plurality of I / O domains are also configured on the hardware platform and connect between each of the guest virtual machines and a network connected to the hardware platform or remote or local storage available to the hardware platform. In this manner, the I / O domains are configured in the flow of the guest virtual machines as they utilize available resources, for instance, and are able to filter network or block level traffic, respectively. Representatively, one filter analyzes packets exchanged to and from the network, while the other filter analyzes internal traffic and may be a block-tap, stackable driver, virus scanning application, etc. Also, the guested virtual machines communicate with the I / O domains by way of a shared memory transport. Still other features contemplate drivers, operating systems, and computer program products, to name a few.
Owner:ORACLE INT CORP
Communicating information about the content of electronic messages to a server
InactiveUS20060031318A1Protect resourcesImprove accuracyMultiple digital computer combinationsData switching networksFilter analysisDistributed computing
Described are techniques and mechanisms for addressing unsolicited commercial, junk, or generally unwanted electronic messages. Very generally stated, a message server is provided that performs a message filtering analysis using resources local to the message server. The message server delivers to a remote device messages that do not fail the filter. In the situation where the message filtering analysis was incorrect, the remote device returns a notification of that fact to the message server with sufficient information that the message server can update its local resources accordingly.
Owner:QUALCOMM INC
Landslide dynamic identifying and monitoring technology based on synthetic aperture radar differential interferometry (D-InSAR)
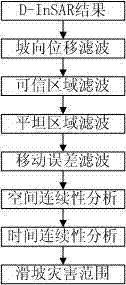
The invention discloses a landslide dynamic identifying and monitoring technology based on synthetic aperture radar differential interferometry (D-InSAR). The landslide dynamic identifying and monitoring technology solves practical problems in D-InSAR landslide disaster monitoring in alpine valley regions, and the information which means nothing to landslide identification can be filtered, so that a landslide area in which deformation happens is found out in a monitoring range. A method for extracting a landslide disaster range from D-InSAR monitoring results comprises the following steps of: extracting an area according with landslide moving characteristics from the D-InSAR monitoring results through a sloping filtering technology; analyzing a D-InSAR reliable area, and extracting reliable data from the monitoring results according to the reliable area; performing a filtering analysis method of flat areas and a filtering analysis method of movement errors; and performing a landslide identification method based on a time-space continuity technology.
Owner:BEIJING BEIKE ANDI TECH DEV
Method for the detection of viable microorganisms
InactiveUS20050202523A1Enhancing bacteria absorptionRapid visualizationBioreactor/fermenter combinationsBiological substance pretreatmentsMicroorganismExternal energy
Method for the detection and enumeration of viable microorganisms. A liquid that comprises one or more markers incorporated in a liquid sol-gel precursor, is provided. A transparent slide is coated with a thin uniform layer of the liquid sol-gel precursor composition. The microorganisms are separated from liquid sample to be analyzed by passing the sample through a filter, and then bringing the filter into close contact with the sol-gel coated slide. The filter is co-incubated with the sol-gel coated slide for a period of time and at a temperature suitable to promote uptake of the markers by the microorganisms. The gel-coated slide irradiated with an external energy source, so as to generate detectable signals emitted from the markers uptaken by the microorganisms. Image of the detectable signals emitted from the microorganisms are acquired, and analyzed using a computer system, in order to provide the identification and enumeration of the microorganisms.
Owner:BIOGEM OPTICAL LTD
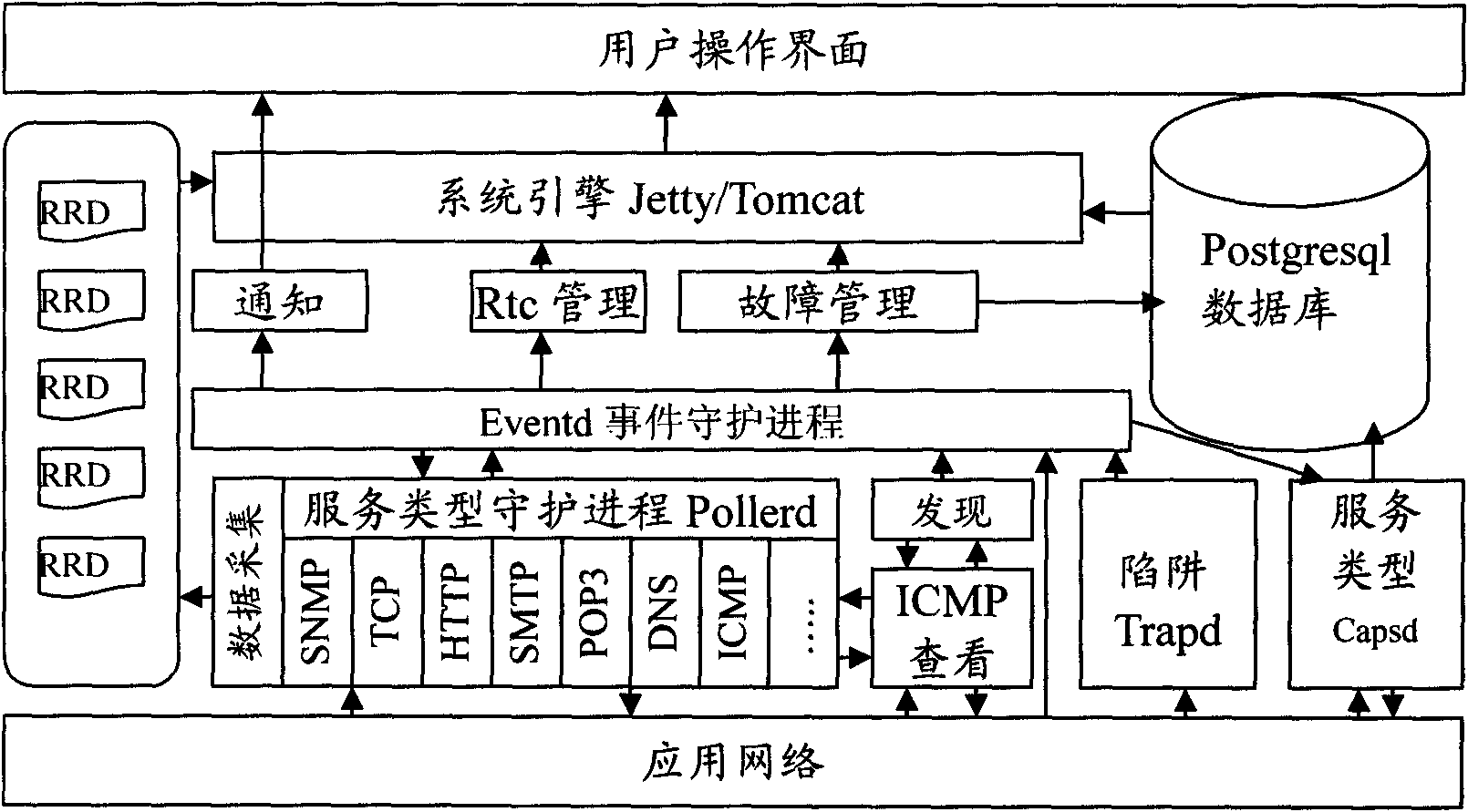
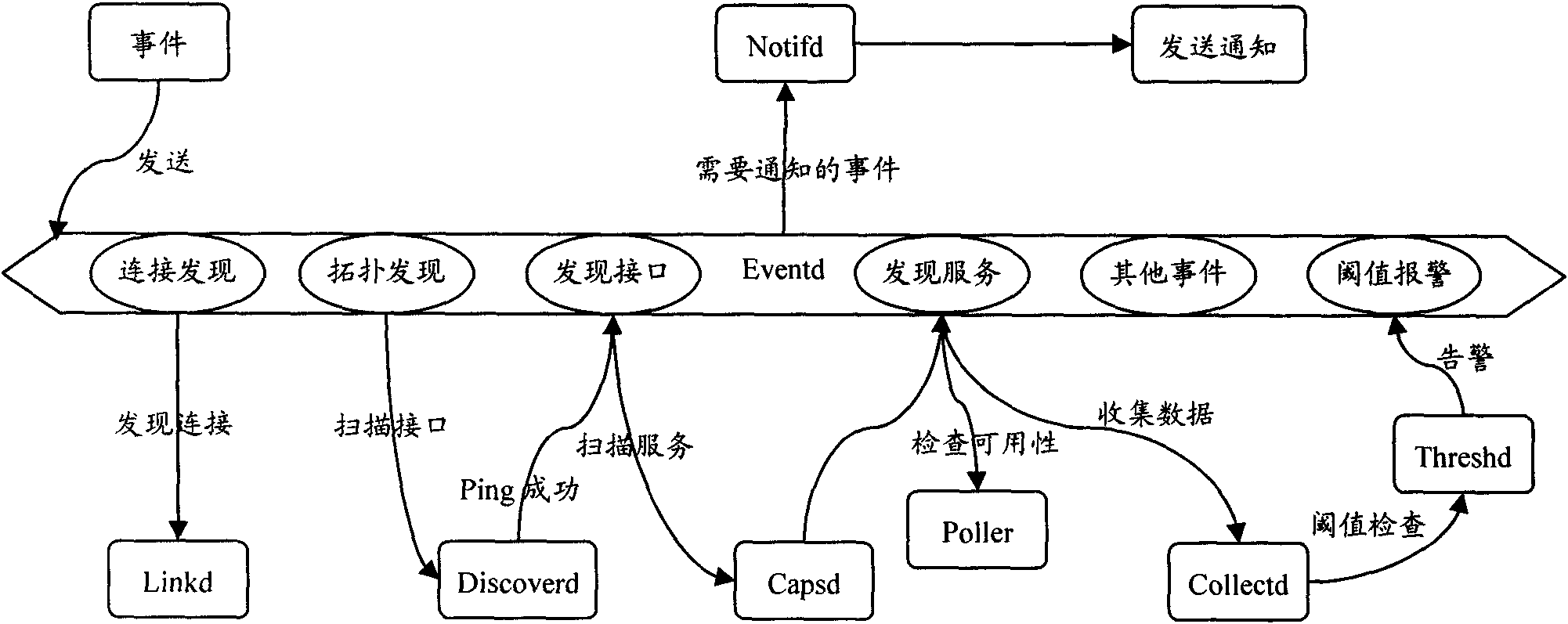
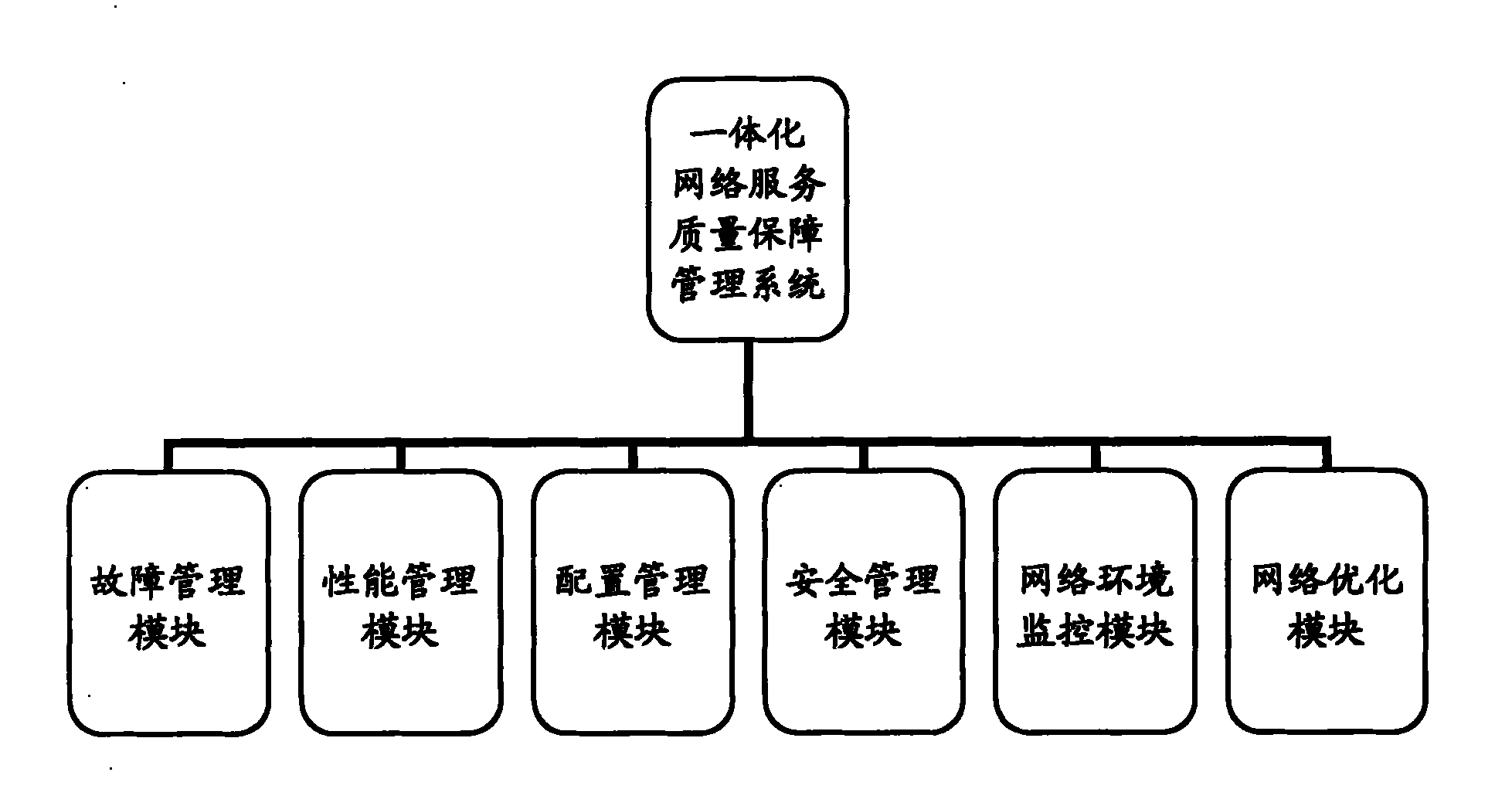
Integrated network quality of service assurance and management system
The invention relates to an integrated network quality of service assurance and management system, which comprises a database module, a daemon process module, a system engine module and a user operating interface module, wherein the daemon process module is connected with an out-of-system application network, and is connected with the user operating interface module by the system engine module; the database module is connected with the daemon process module and the system engine module respectively; and the daemon process module is also connected with the user operating interface module. The integrated network quality of service assurance and management system provided by the invention can realize background data collection and raw data filtering analysis by the daemon process module and realize foreground page display by the user operating interface module to enable a manager to realize the functions of network failure management, configuration management, performance management, security management and the like by accessing a user operating interface, integrates a plurality of functions, and is simply structured, low in cost, simple and convenient to operate and wide in application range.
Owner:CERTUS NETWORK TECHNANJING
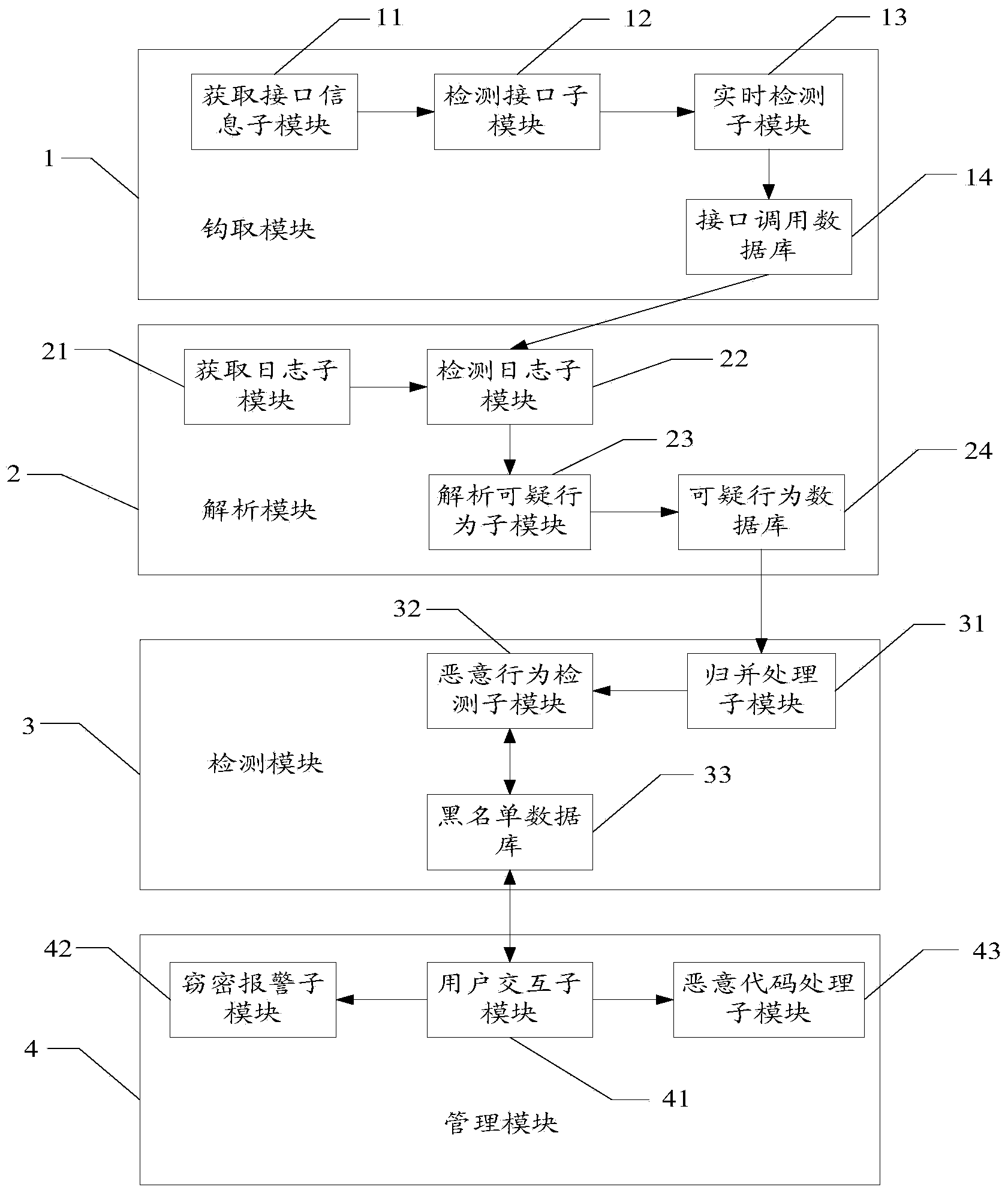
User privacy information protection method and user privacy information protection system
ActiveCN103716313AEffective monitoring of circulationProtect private dataTransmissionInternet privacyData information
The invention relates to a user privacy information protection method. The method comprises steps that: step 1, a pick-up module carries out interface calling operation to acquire basic interface information, and a redirection filtering method is employed to carry out filtering analysis on operation which may access to sensitive information; step 2, operation log data information sent by terminal equipment is received by a parsing module, information in an interface calling database is called, and an operation log of sensitive operation is recorded; step 3, processing on information in a suspected-behavior operation database is carried out by a detection module, information-stealing operation is screened out based on information of a black list database, and information-stealing operation behavior information is stored in the black list database, and step 4, information-stealing operation is processed according to the information-stealing operation behavior information stored in the black list database. According to the user privacy information protection method, an information-stealing behavior can be monitored, a latent information-stealing threat can be discovered, and the information-stealing operation is stopped; sensitive information circulation is monitored; and user privacy data can be comprehensively monitored and protected.
Owner:INST OF INFORMATION ENG CAS
Perception-based image retrieval
InactiveUS20010046332A1Data processing applicationsDigital data information retrievalAverage filterPattern perception
A content-based image retrieval (CBIR) system has a front-end that includes a pipeline of one or more dynamically-constructed filters for measuring perceptual similarities between a query image and one or more candidate images retrieved from a back-end comprised of a knowledge base accessed by an inference engine. The images include at least one color set having a set of properties including a number of pixels each having at least one color, a culture color associated with the color set, a mean and variance of the color set, a moment invariant, and a centroid. The filters analyze and compare the set of properties of the query image to the set of properties of the candidate images. Various filters are used, including: a Color Mask filter that identifies identical culture colors in the images, a Color Histogram filter that identifies a distribution of colors in the images, a Color Average filter that performs a similarity comparison on the average of the color sets of the images, a Color Variance filter that performs a similarity comparison on the variances of the color sets of the images, a Spread filter that identifies a spatial concentration of a color in the images, an Elongation filter that identifies a shape of a color in the images, and a Spatial Relationship filter that identifies a spatial relationship between the color sets in the images.
Owner:RGT UNIV OF CALIFORNIA
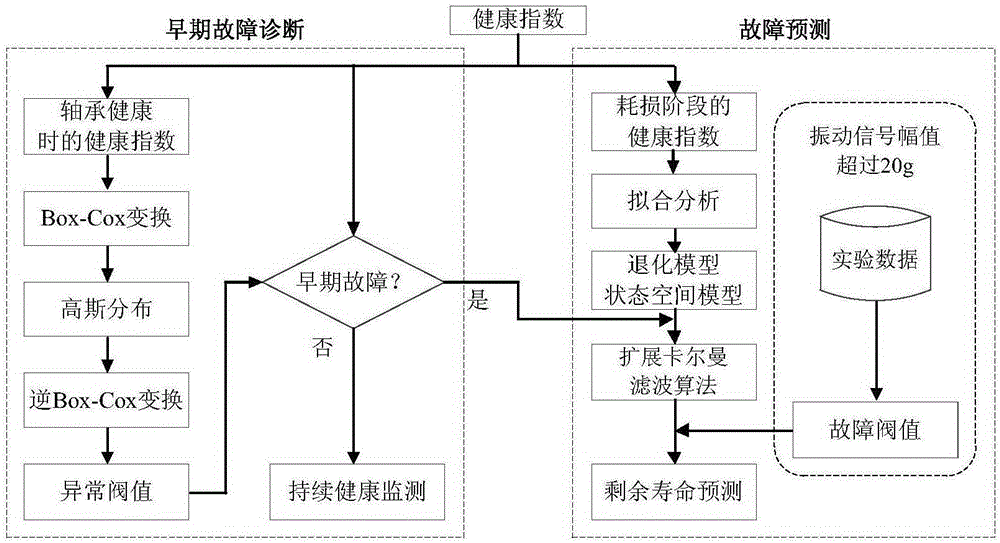
Bearing fault diagnosis and prediction method based on extended Kalman filtering algorithm
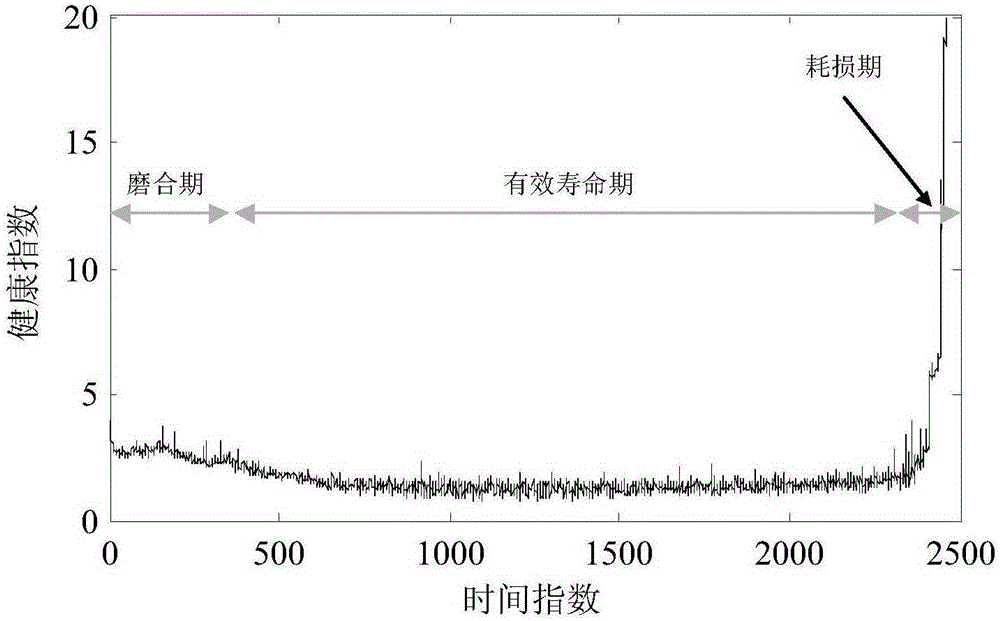
ActiveCN105300692AImprove forecast accuracyShort timeMachine bearings testingSpecial data processing applicationsHealth indexPredictive methods
The invention discloses a bearing fault diagnosis and prediction method based on an extended Kalman filtering algorithm, and the method comprises the following steps: 1) employing a full service life cycle vibration signal of a bearing; 2) constructing an AR model through the vibration signal, carrying out the filtering analysis of the vibration signal, and highlighting a signal correlated with a fault; 3) extracting energy information correlated with a wavelet packet coefficient through employing wavelet packet transformation, and constructing a feature character; 4) carrying out the calculation of a mahalanobis distance, constructing health indexes based on the mahalanobis distance, converting the non-negative and non-Gaussian distribution health indexes into Gaussian distribution data through Box-Cox transformation, and determining a related abnormal threshold range through the features of Gaussian distribution and the inverted Box-Cox transformation; 5) carrying out fitting analysis of health index data in a loss period, constructing a degeneration model and a status space model, updating model parameters through employing current data and the extended Kalman filtering algorithm, and predicting the remaining service life of the bearing. The method is higher in prediction precision, and is shorter in consumed time.
Owner:吴江市民福电缆附件厂
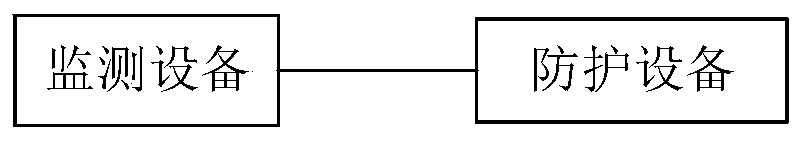
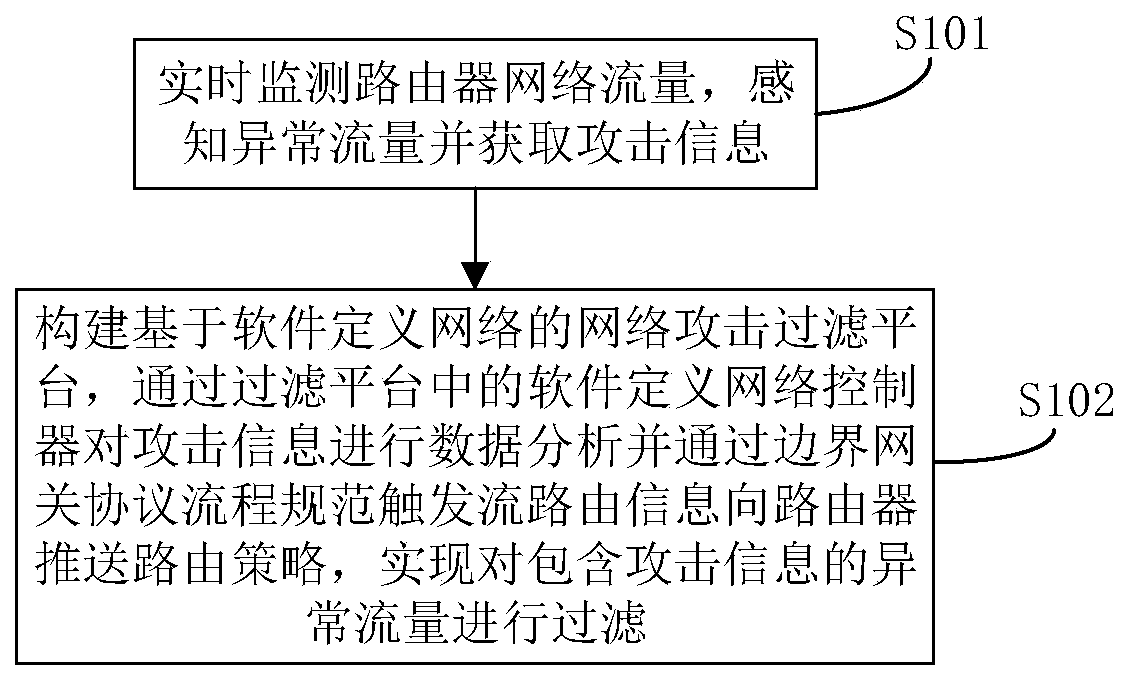
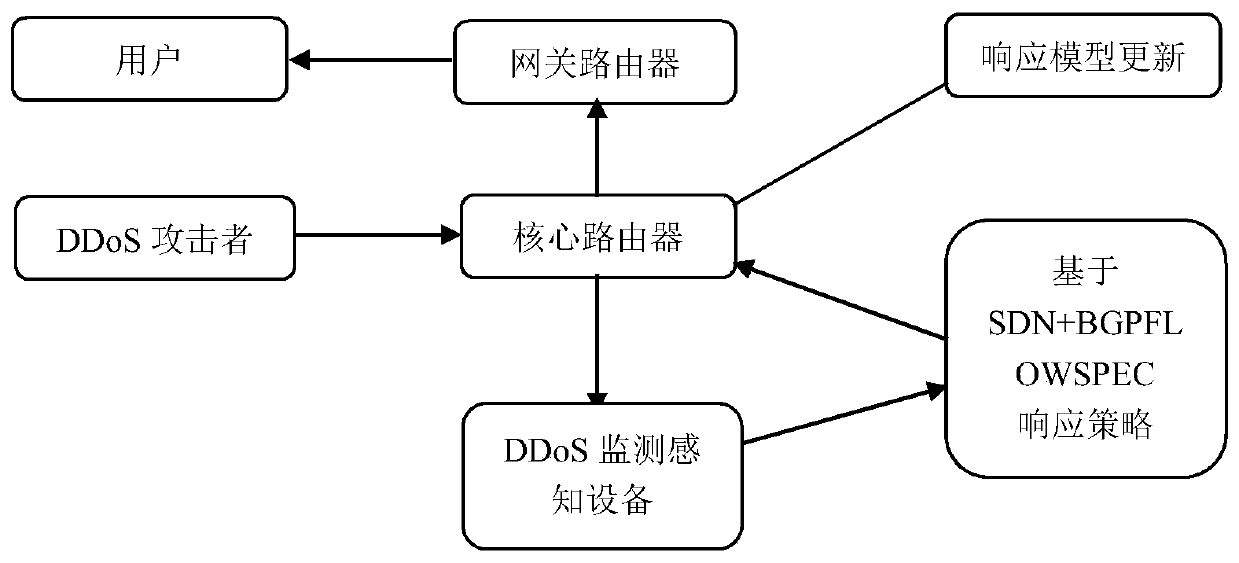
DDoS attack protection system and method based on SDN and BGP process specifications
The invention belongs to the technical field of network safety, and particularly relates to a DDoS (Distributed Denial of Service) attack protection system and method based on SDN (Software Defined Network) and BGP (Border Gateway Protocol) process specifications, comprising: a monitoring device for monitoring router network traffic in real time and detecting abnormal traffic through a sensing device to obtain attack information; protective device, receiving attack information of the monitoring equipment, a network attack filtering platform based on a software-defined network is used for protecting abnormal flow, and a software-defined network controller which is used for carrying out data analysis on attack information and pushing a routing strategy to a router through a boundary gatewayprotocol flow specification is arranged in the filtering platform, so that the abnormal flow accommodating the attack information is filtered. According to the method, attacks and services are distinguished, passing of the service flow is guaranteed while the attack flow is suppressed, flow filtering analysis is finer, the situation that a normal service system cannot be used due to the fact thatlegal flow and illegal flow flowing to a target host are completely blocked is avoided, and the method has important guiding significance for network safety communication.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
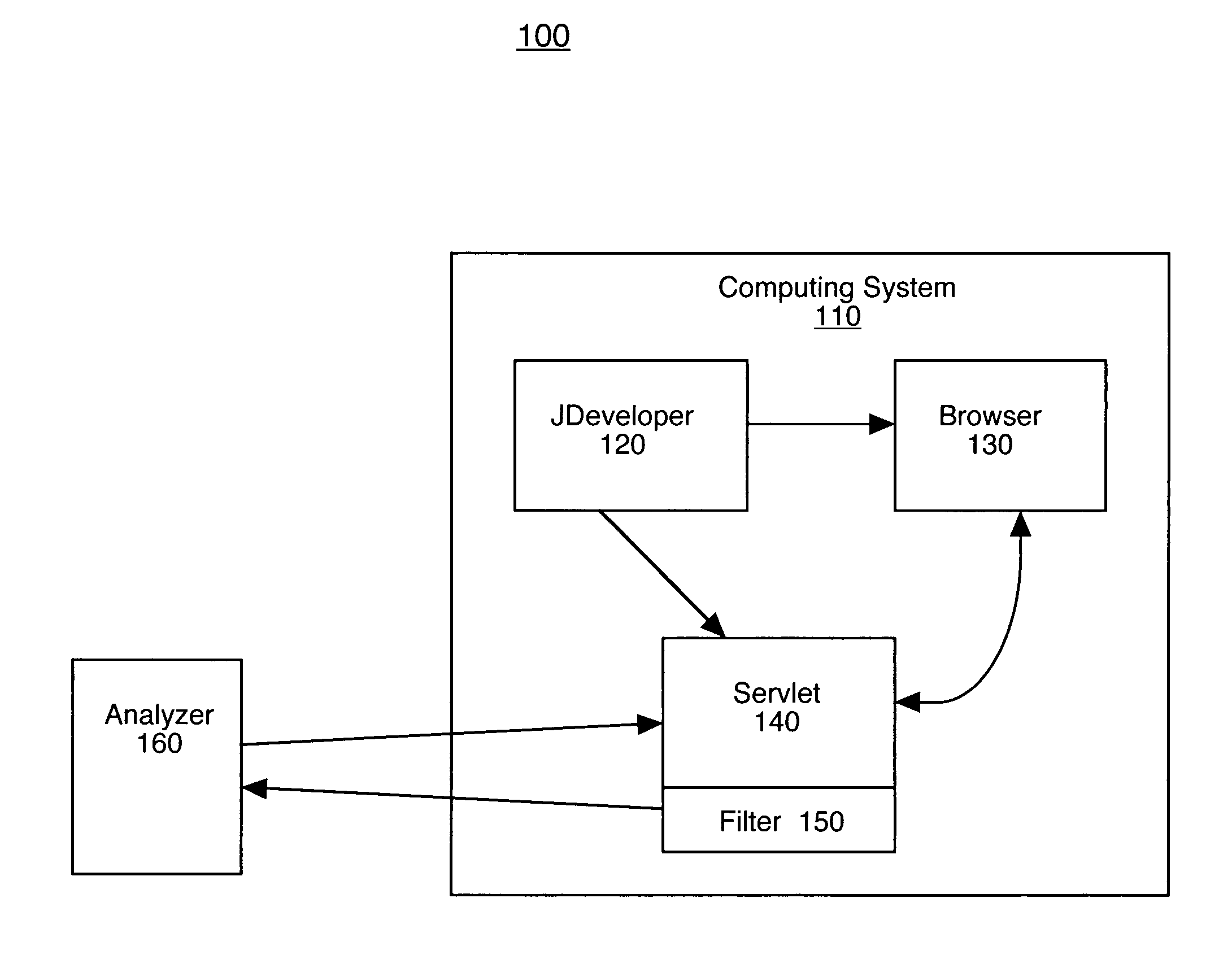
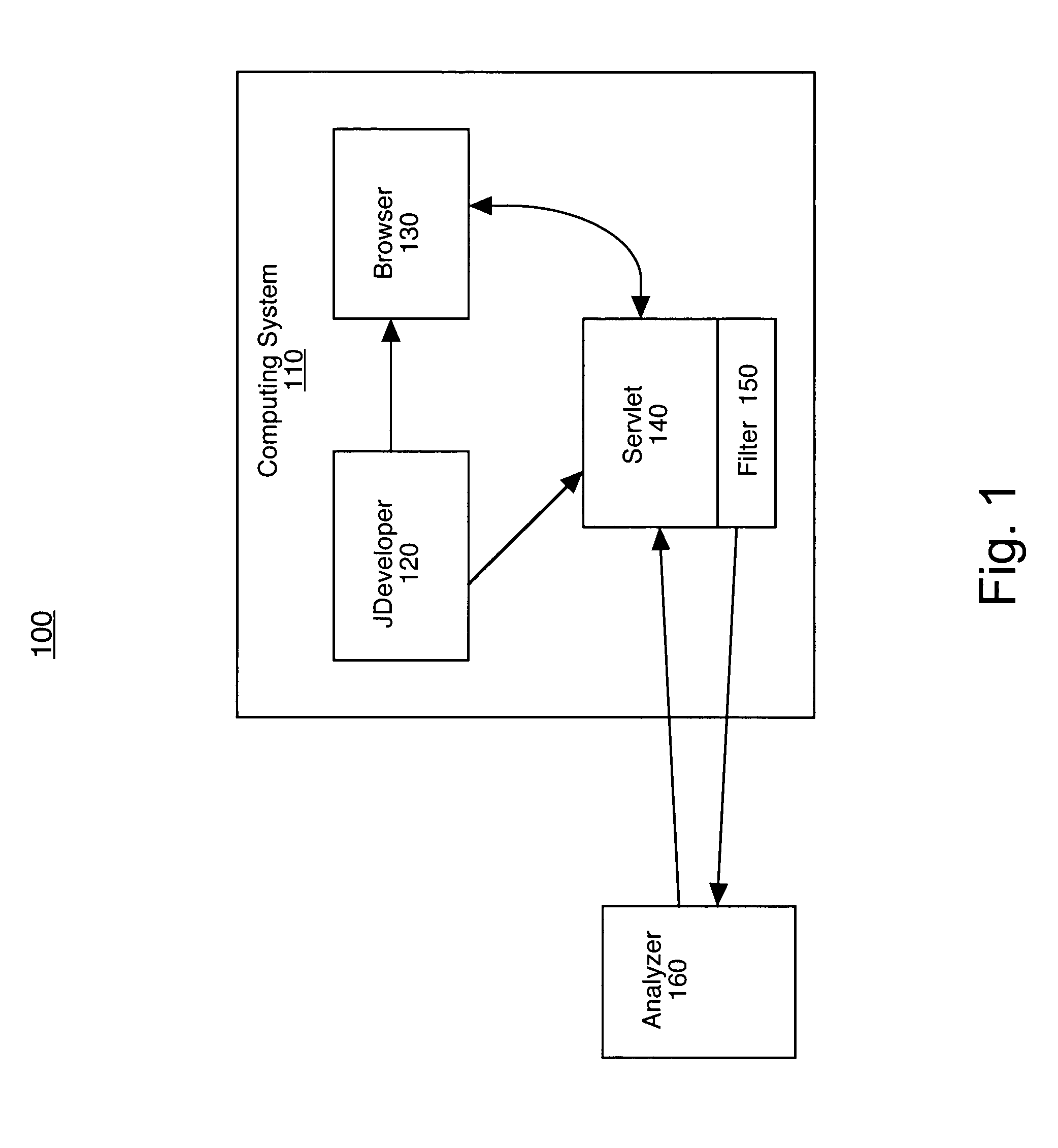
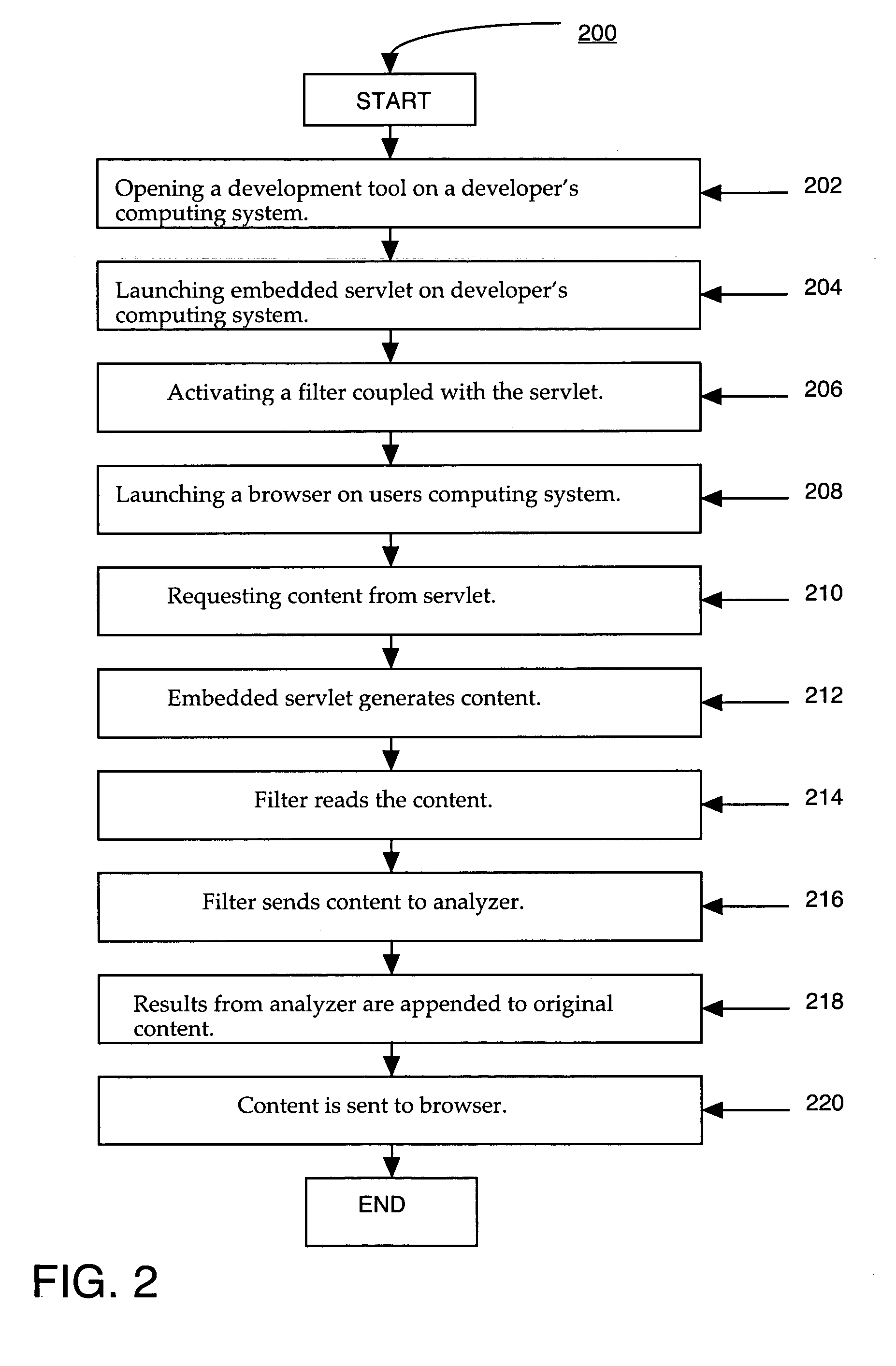
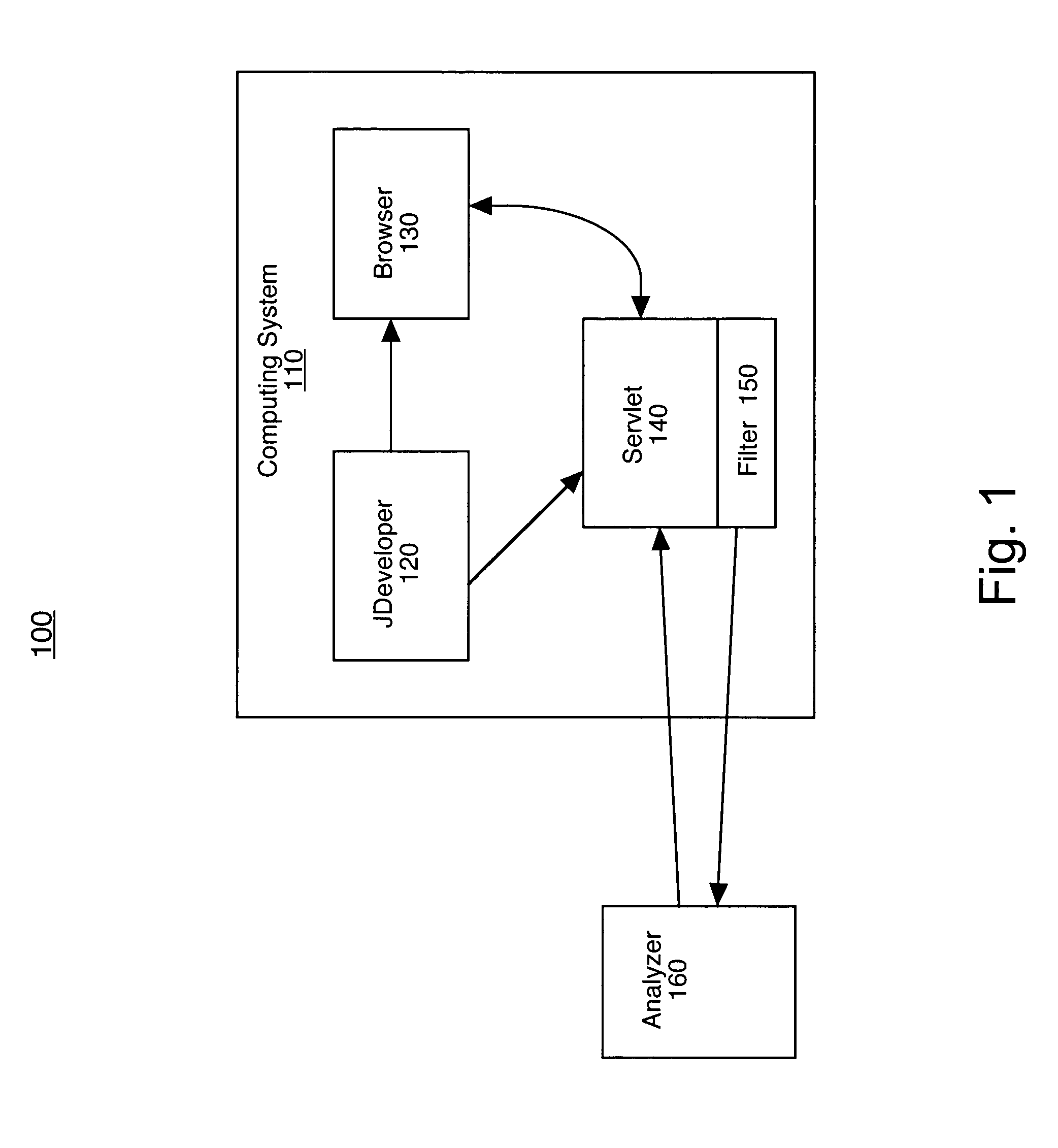
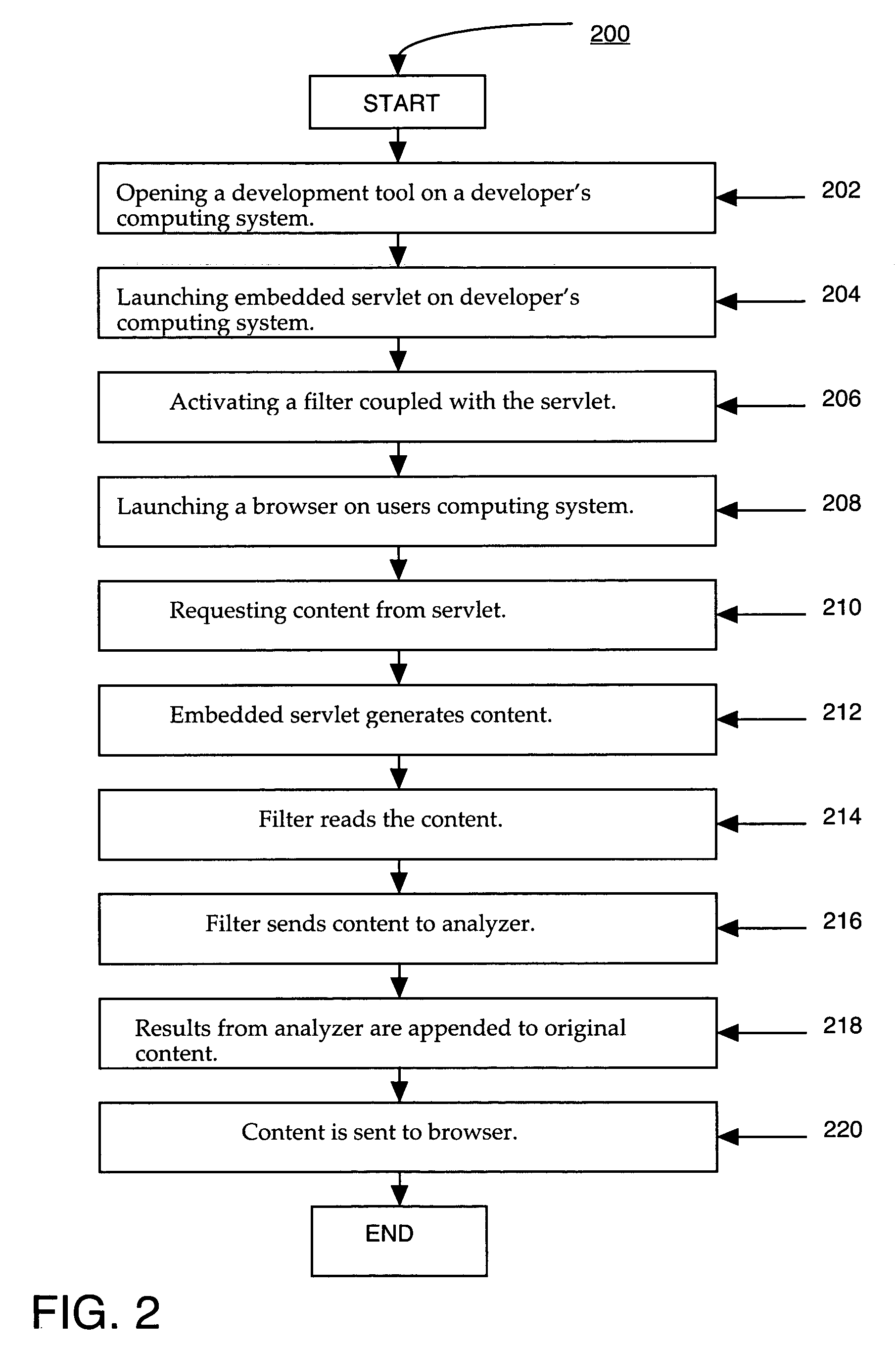
System and method for analyzing content on a web page using an embedded filter
ActiveUS20050216471A1Digital data information retrievalDigital data processing detailsFilter analysisWeb page
A method for analyzing content on a web page. In one method embodiment, the present invention accesses a web page having content. Additionally, the web page is processed through a filter wherein the filter transfers the content of the web page to an analyzer. The analyzer analyzes the content of the web page. The analyzer then returns the result of the analyzing to the server which appends the result of the analyzing to the content of the web page. The results are then displayed on the web page. In so doing, the ability to provide an analysis of the functionality of a web page at the time of development is provided.
Owner:ORACLE INT CORP
A safety protection system and method based on a CIP protocol in a PLC
ActiveCN109922085APrevent intrusionTo achieve the effect of safety protectionTransmissionFilter analysisProtection system
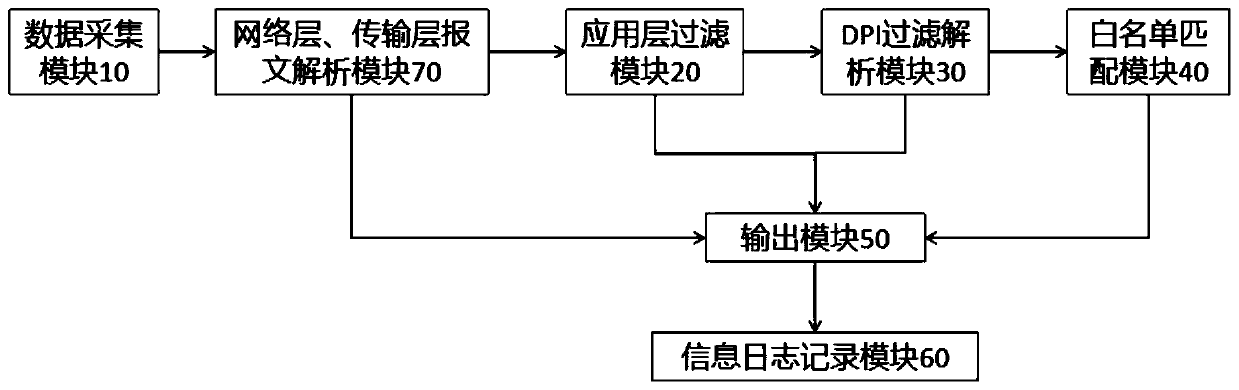
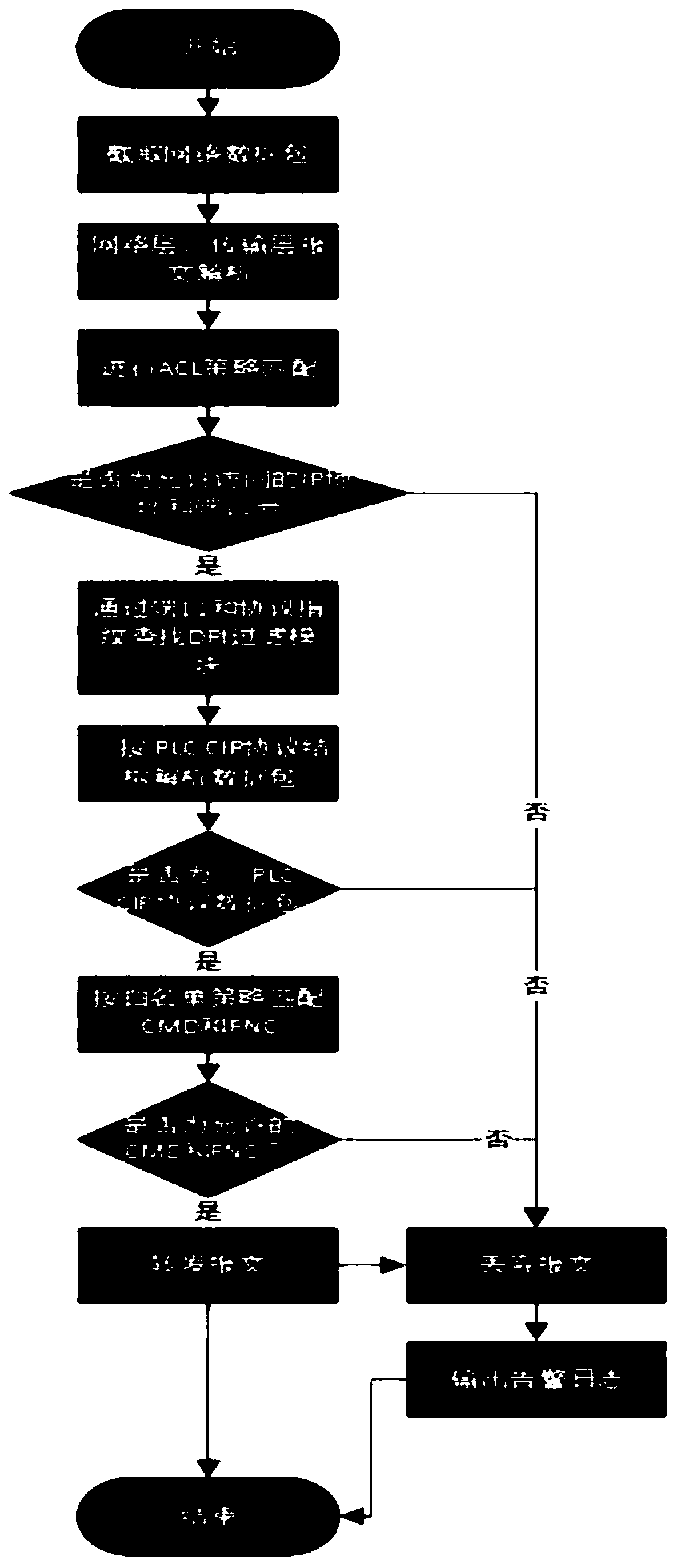
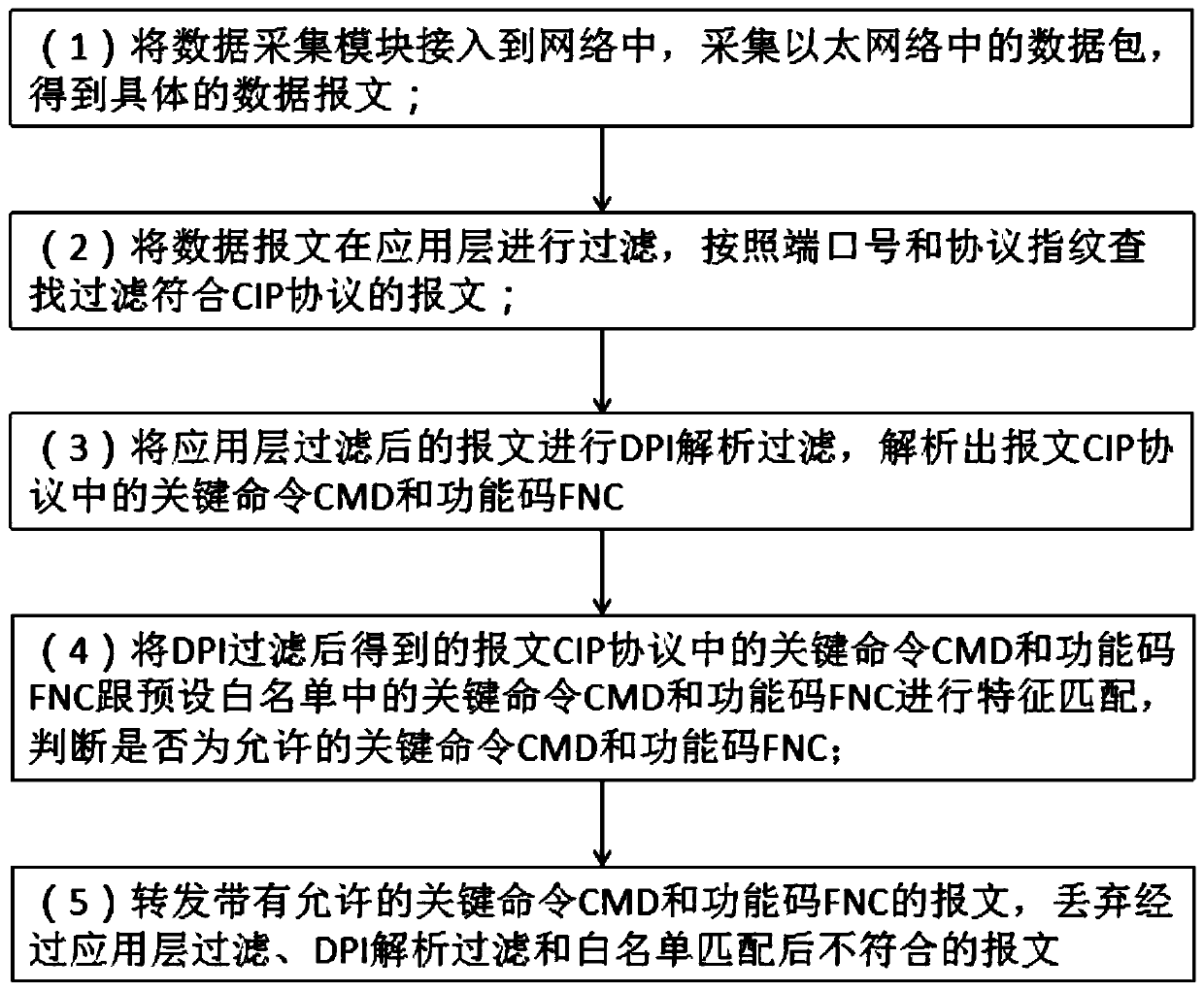
The invention discloses a safety protection system and method based on a CIP protocol in a PLC, and the system comprises a data collection module which is accessed to a network through a network interface, and is used for collecting a data packet in the Ethernet, obtaining a specific data message, and sending the obtained data message to an application layer filtering module; the application layerfiltering module is used for searching and filtering messages conforming to the CIP protocol and sending the messages to the DPI filtering and analyzing module; the DPI filtering and analyzing moduleis used for analyzing a key command CMD and a function code FNC in the CIP protocol and sending the key command CMD and the function code FNC to the white list matching module; the white list matching module is used for carrying out feature matching on the key command CMD and the function code FNC analyzed in the DPI filtering analysis module and the key command CMD and the function code FNC preset in the white list, and judging whether the key command CMD and the function code FNC are allowed or not; and the output module forwards or discards the message according to filtering judgment of the application layer filtering module, the DPI filtering analysis module and the white list matching module.
Owner:江苏亨通工控安全研究院有限公司
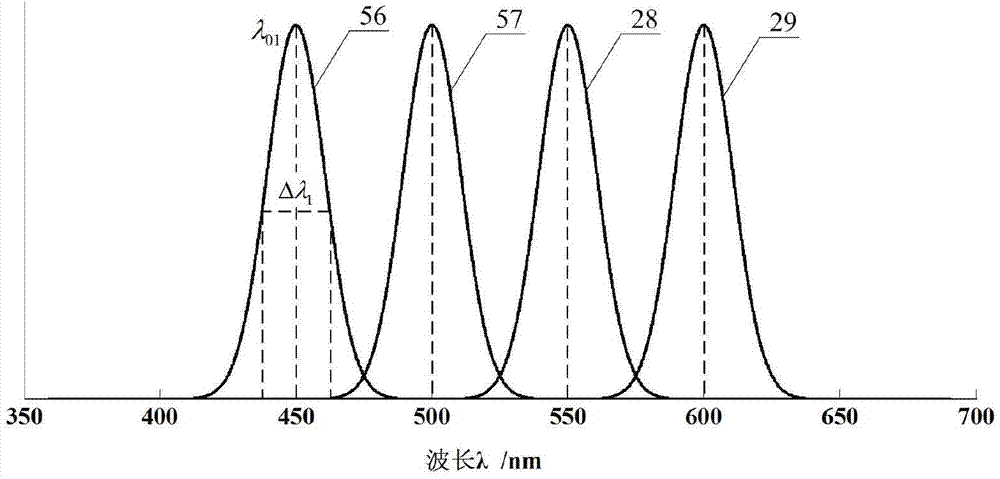
Optical fiber Fabry-Perot sensor multiplexing method and device based on multi-wavelength and low-coherence light source
ActiveCN103115636ALow costRealize multiplex demodulationConverting sensor output opticallyFilter analysisMulti wavelength
The invention discloses an optical fiber Fabry-Perot sensor multiplexing method and device based on a multi-wavelength and low-coherence light source. The optical fiber Fabry-Perot sensor multiplexing device comprises a light source module, 3dB couplers, an optical fiber Fabry-Perot sensor unit and a demodulation unit. The optical fiber Fabry-Perot sensor multiplexing method is characterized in that all channels of the light source module output low-coherence light with different wavelengths; N channel light passes through the corresponding 3dB couplers and then are irradiated to the corresponding optical fiber Fabry-Perot sensors, and reflected light re-passes the corresponding 3dB couplers and form a light beam through a multi-channel beam combiner to be irradiated into the demodulation unit; a demodulation interferometer achieves optical path difference scanning and outputs low-coherence interference fringes overlapped with all sensor cavity length information; and low-coherence interference fringe optical signals are converted to electric signals and then transmitted to a computer, the signals are subjected to filter analysis and decision algorithm processing, simultaneously all optical fiber Fabry-Perot sensor information is demodulated, and multiplexing of the optical fiber Fabry-Perot sensor is achieved. Compared with the prior art, the optical fiber Fabry-Perot sensor multiplexing method and device reduce system cost, support batch production, and can simultaneously and independently achieve multi-channel sensor multiplexing demodulation.
Owner:TIANJIN UNIV
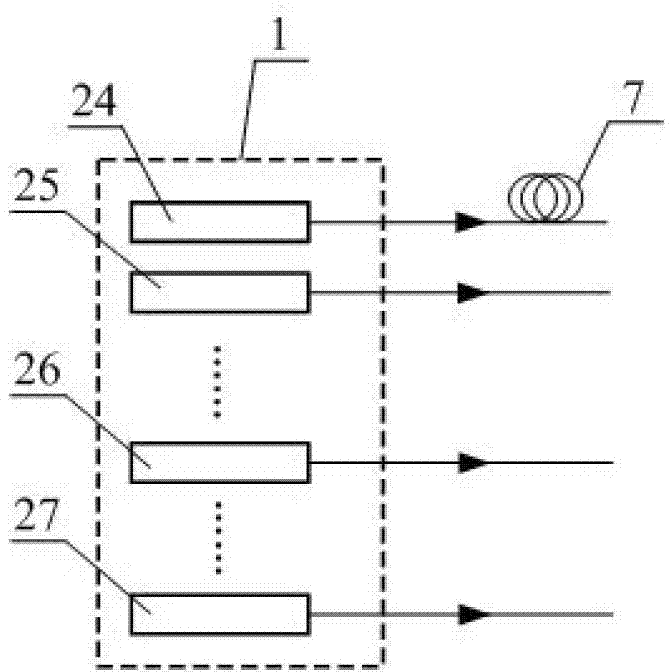
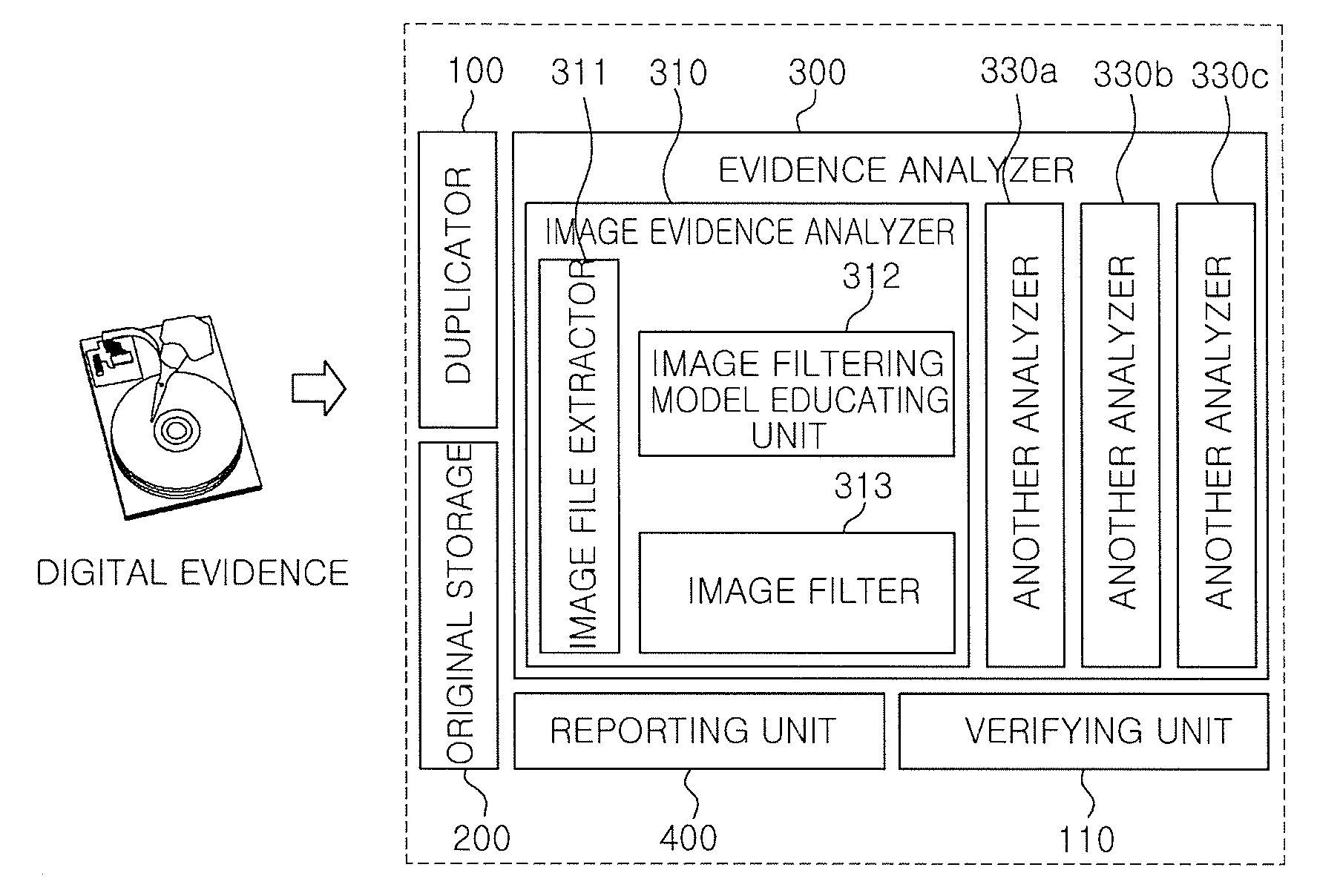
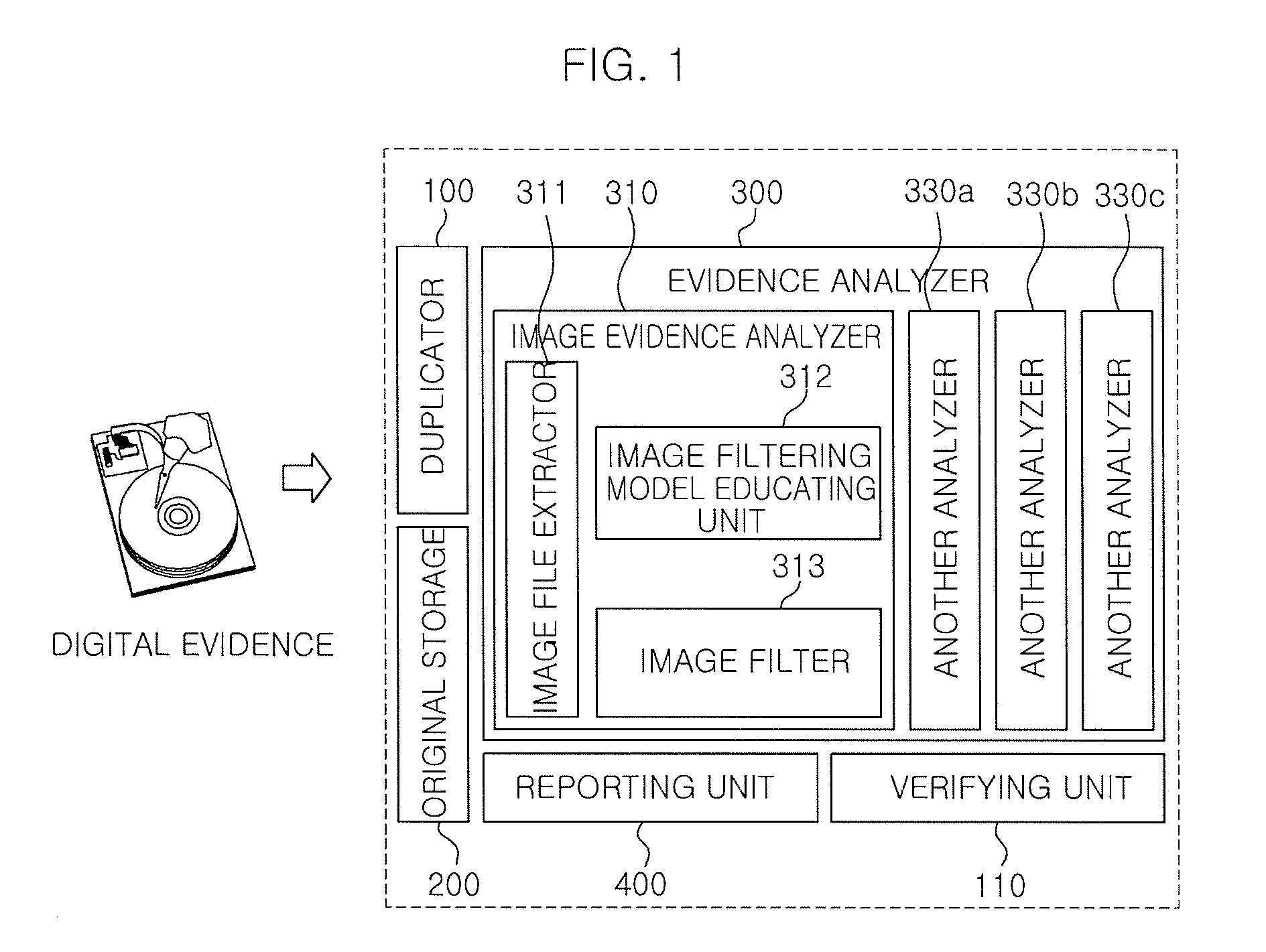
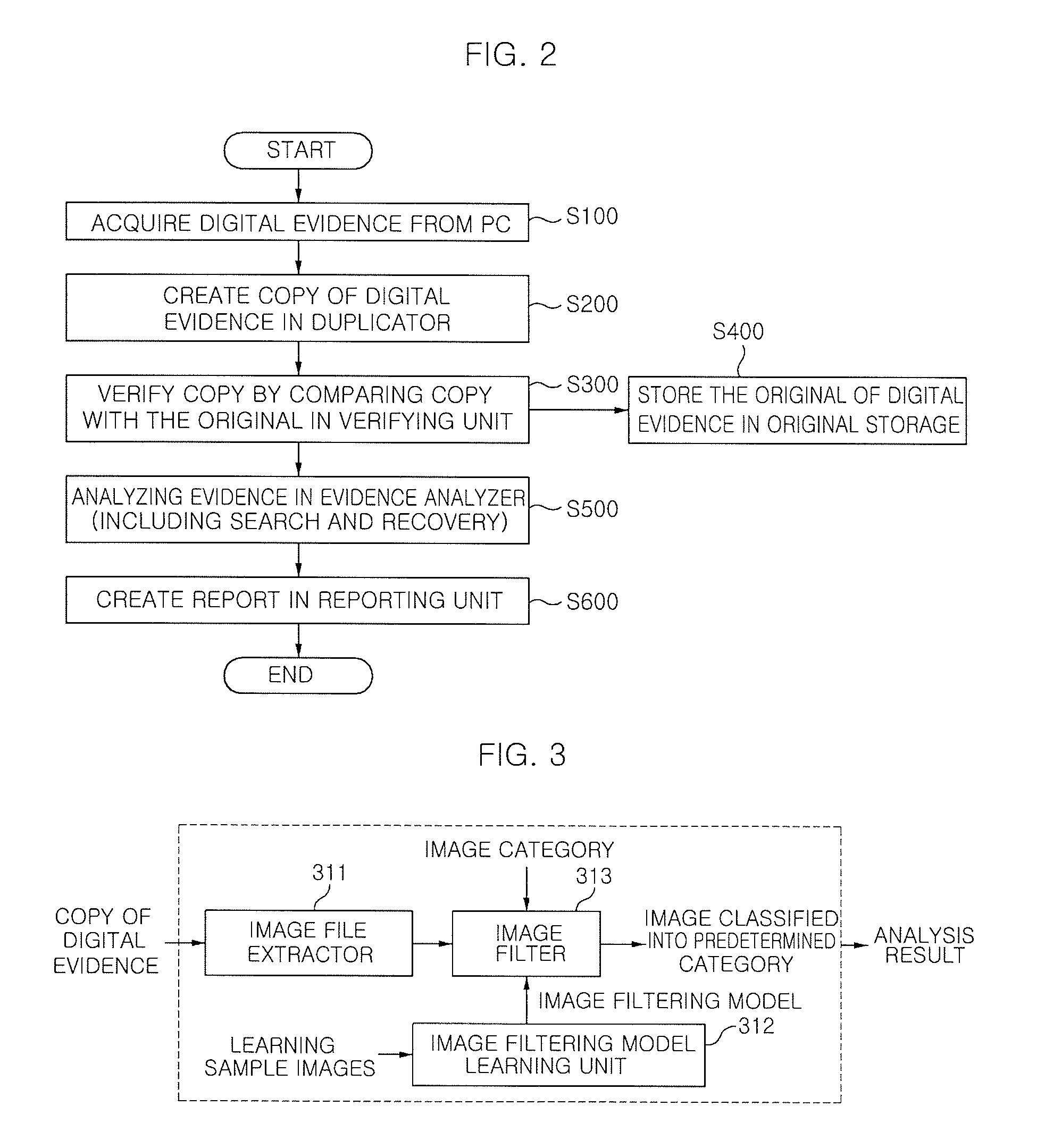
System for analyzing forensic evidence using image filter and method thereof
ActiveUS20090136140A1Simplify the analysis processEfficient executionProgram control using stored programsCharacter and pattern recognitionPattern recognitionLearning unit
The present invention provides a system for analyzing forensic digital evidence using an image filter and a method thereof. The system for analyzing forensic evidence using an image filter includes: a duplicator that creates a copy of digital evidence; a verifying unit that discriminates whether a copy and the original of the digital evidence are the same; an original storage that stores the original of the digital evidence; an evidence analyzer that classifies image files for the copy of the digital evidence stored in the original storage, on the basis of an image filtering model created by a learning model in accordance with predetermined categories, and then analyzes the evidence; and a reporting unit that creates a report about the result of evidence analysis. The image evidence analyzer includes an image file extractor, an image filtering model learning unit, an image filter, and a plurality of analyzers.
Owner:ELECTRONICS & TELECOMM RES INST
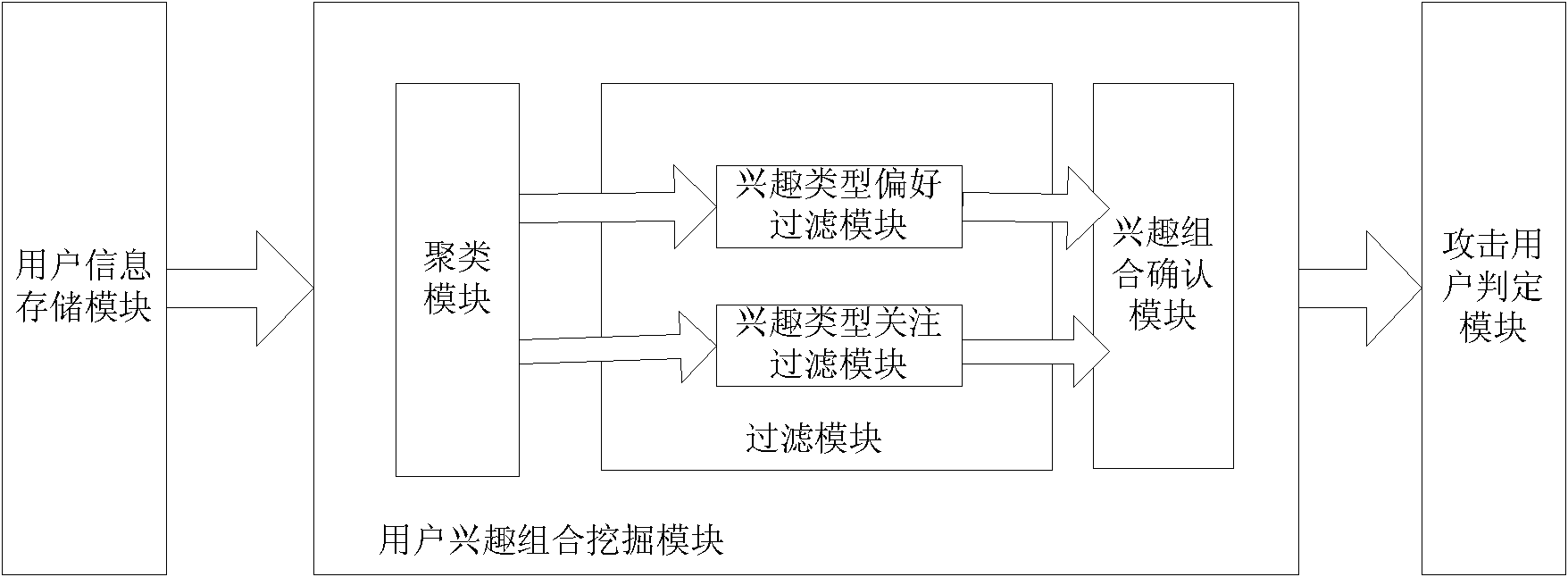
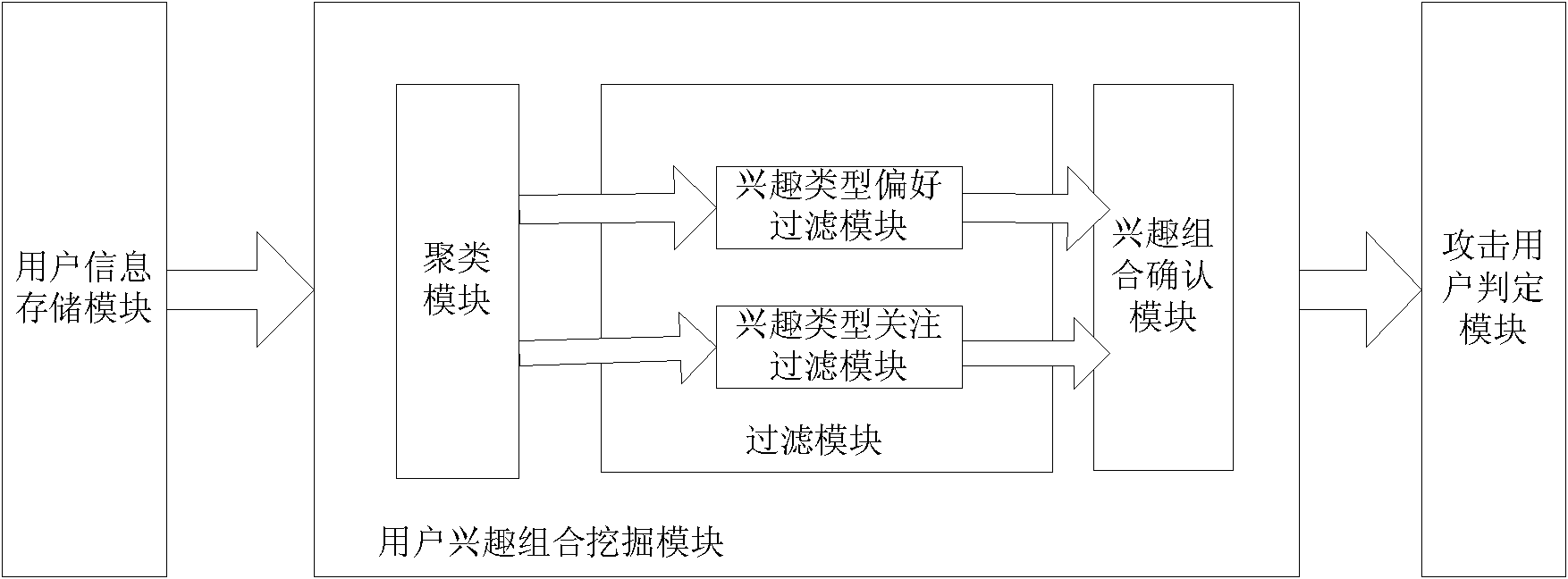
System and method for detecting attack of collaborative recommender based on interest combination
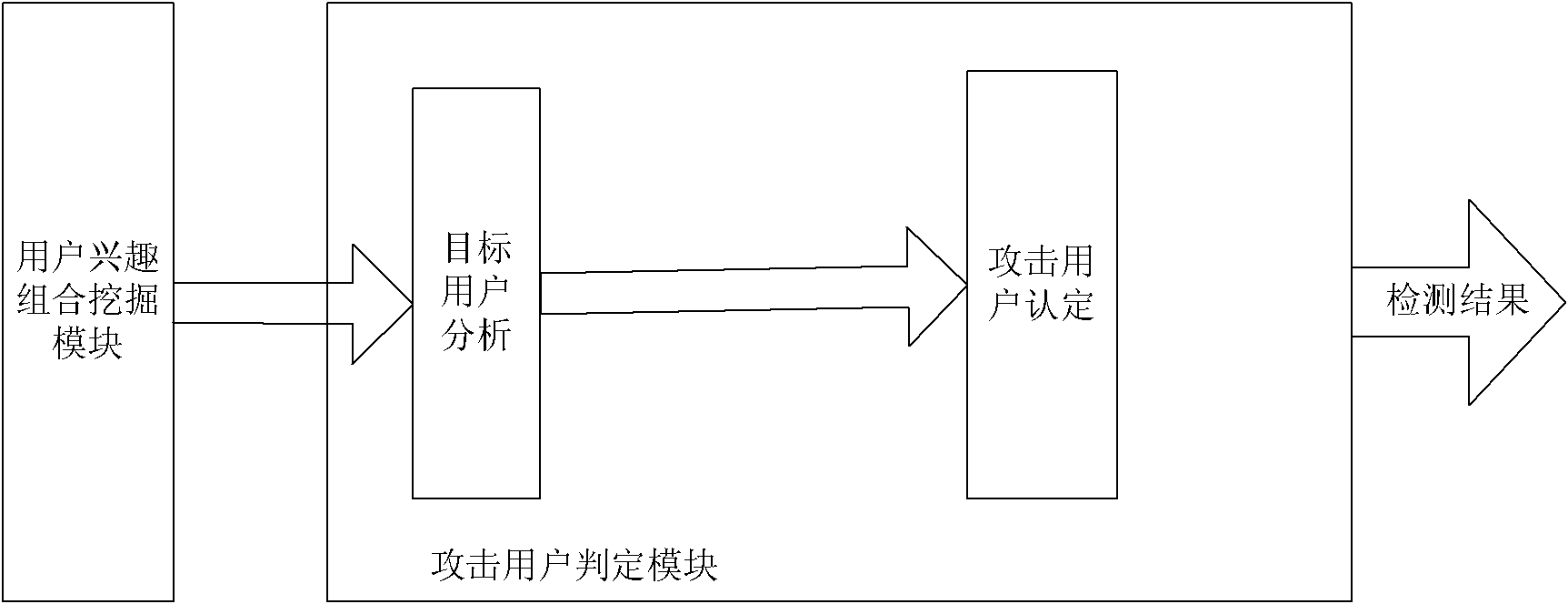
InactiveCN102118382AEasy to handleAvoid the problem of predicting specific attack modelsTransmissionSpecial data processing applicationsComputer moduleFilter analysis
The invention provides a system and method for detecting the attack of a collaborative recommender based on interest combination. The system comprises a user information record module, a user information storage module, a user interest combination mining module and an attack user judging module which are connected sequentially. The user interest combination mining module comprises a clustering module, a filtering module and an interest combination confirming module which are connected sequentially. The clustering module is connected with the user information storage module, and the interest combination confirming module is connected with the attack user judging module. The method comprises the following steps of: recording the existing grading information of a user; establishing a user-program grading matrix; carrying out cluster analysis, filter analysis and interest combination confirmation by the user interest combination mining module to obtain a standard user interest combination; analyzing a target user and determining the attack user by the attack user judging module; and finishing the determination of the attack user.
Owner:SOUTH CHINA UNIV OF TECH
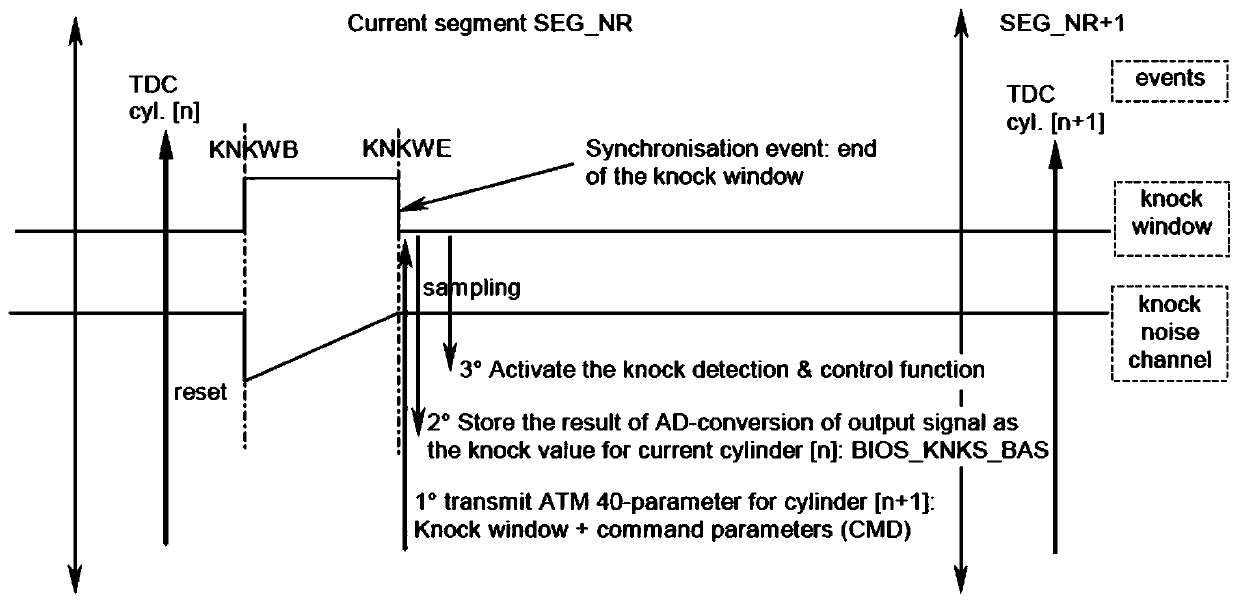
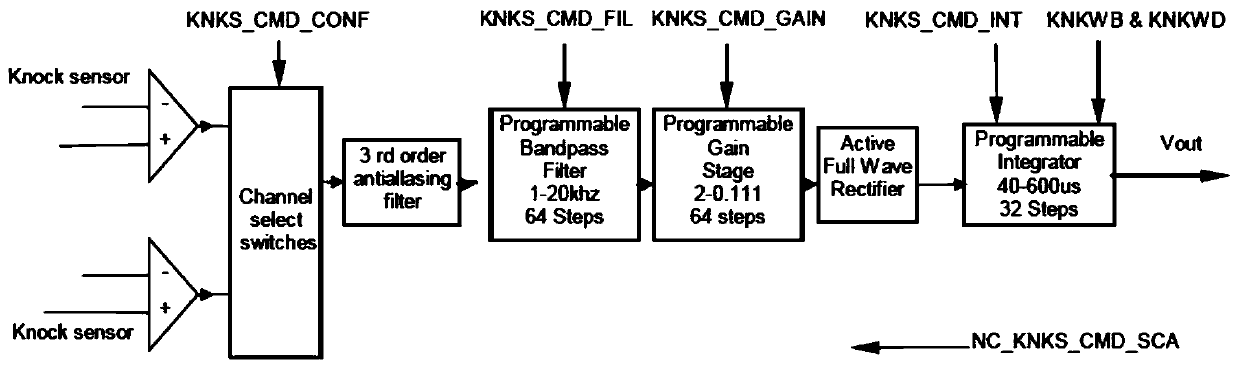
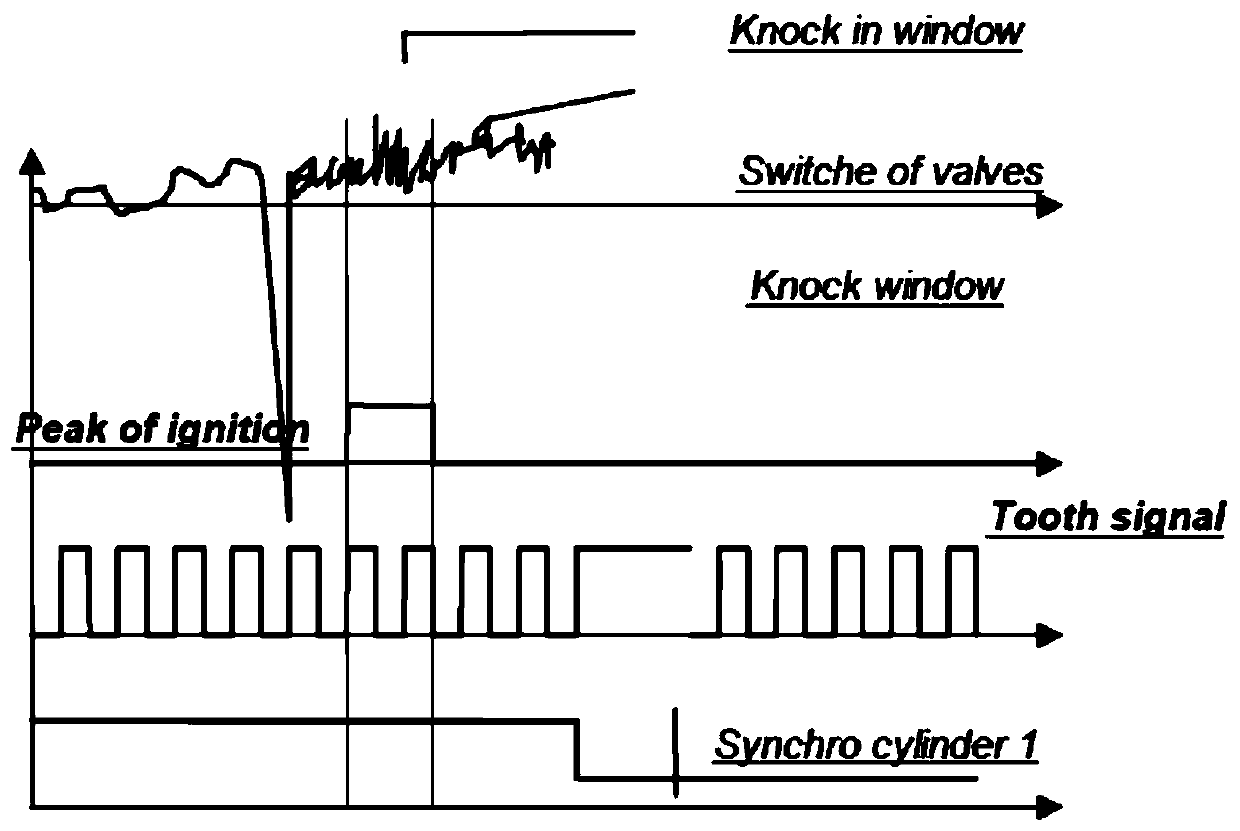
Automatic calibration method for engine knock
InactiveCN109973280AAccurately distinguish and analyze work shock situationAdapt to precise control requirementsMachines/enginesAdvancing/retarding ignitionExternal combustion engineFilter analysis
The invention discloses an automatic calibration method for engine knock. The automatic calibration method for engine knock comprises the steps of carrying out knock control matching by adopting engine knock intelligent-calibration, self-adaption and self-studying technologies; collecting the following equipment running data: temperature, rotate speed, oil consumption condition and ignition anglecondition; storing the data, and carrying out secondary analysis; and intelligently optimizing knock calibration. By adopting the technical scheme, the complex control logics such as cylinder detection, data analysis and processing are greatly simplified; and along with the development of a knock sensor technology and an electronic technology, the accuracy in signal acquisition is realized, and irrelevant noise can be eliminated through filter analysis in different ways and detonation sensor feedback signal processing in different ways, so that the engine work knock situation can be accuratelydiscriminated, control parameters such as advance angle of ignition are dynamically adjusted, the accuracy control requirement of a high-speed internal combustion engine is met, and the whole intelligent calibration process is realized.
Owner:HANTENG AUTOMOBILE CO LTD
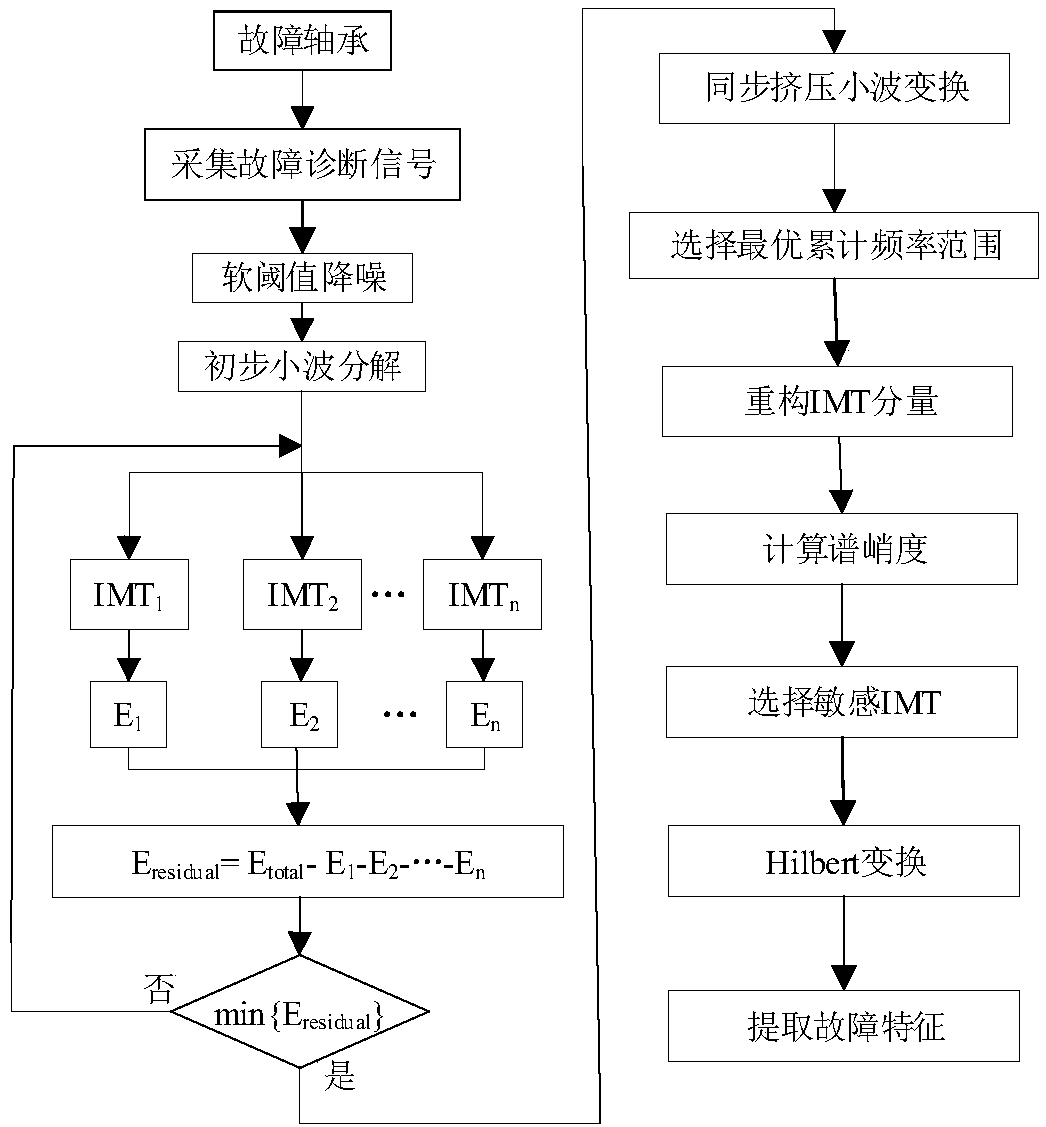
A rotary machine failure diagnosis method based on improved synchronous extrusion transformation
The invention discloses a rotary machine failure diagnosis method based on improved synchronous extrusion transformation. The method includes the following steps: step 1: filtering analysis is performed on a collected vibration signal with rotary machine failure characteristics, strong background noise influence is eliminated, a pure vibration signal is extracted; step 2: an optimal frequency range of the failure characteristic signal is extracted by utilizing a wavelet analysis method, the optimal frequency range is utilized, a time frequency ridge characteristic and a signal time frequency component of the vibration signal are extracted according to a synchronous extruding transformation method, the vibration signal is reconstructed, an optimal signal component is selected by utilizing aspectrum peak value method, and Hilbert transformation is performed to extract a failure characteristic. The frequency of the failure characteristic can be accurately determined through the optimal frequency center and range by adopting the rotary machine failure characteristic efficient extraction method based on improved extrusion wavelet transformation.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Diagnosis and improvement method for low-frequency abnormal sound of air conditioning compressor under idling working condition of blade electric vehicle
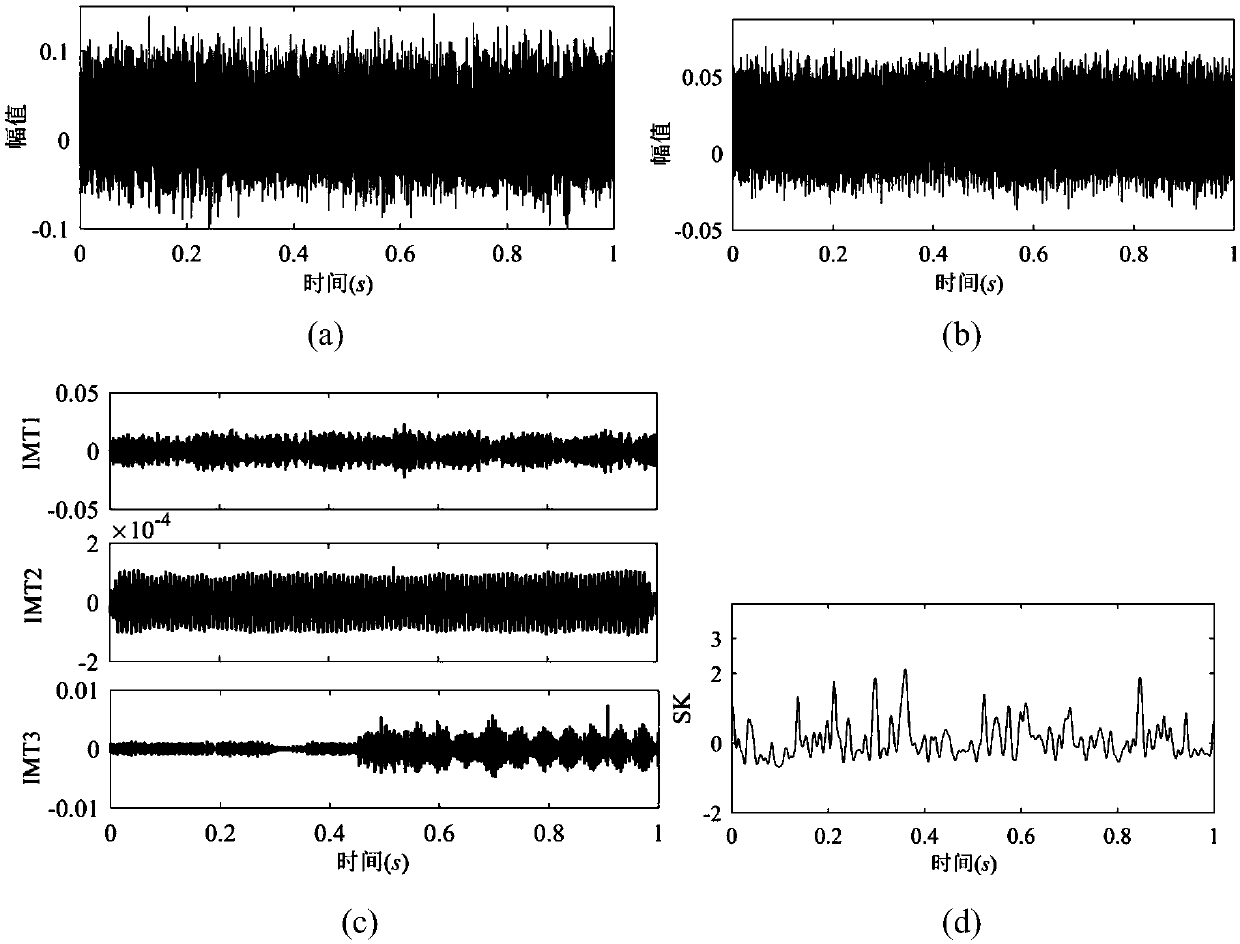
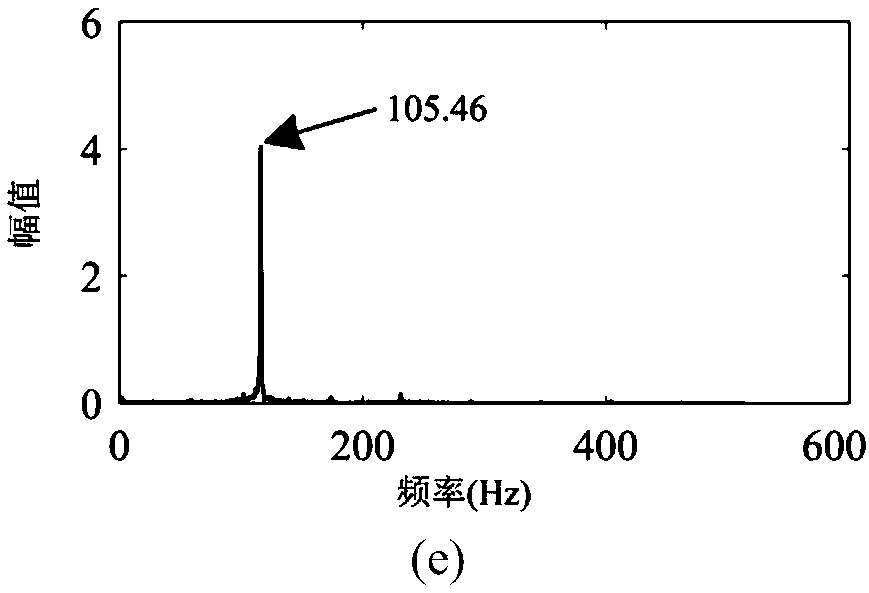
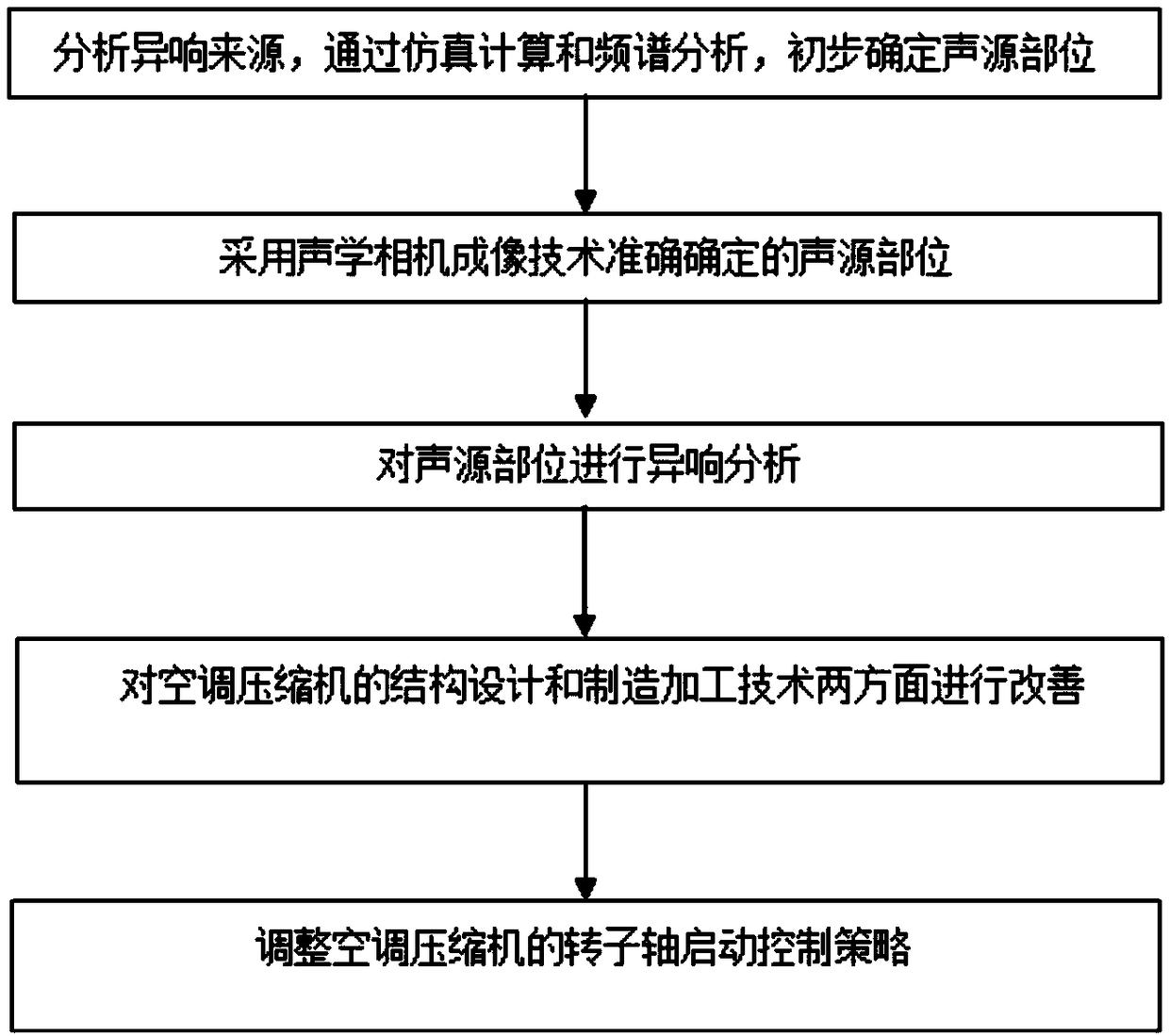
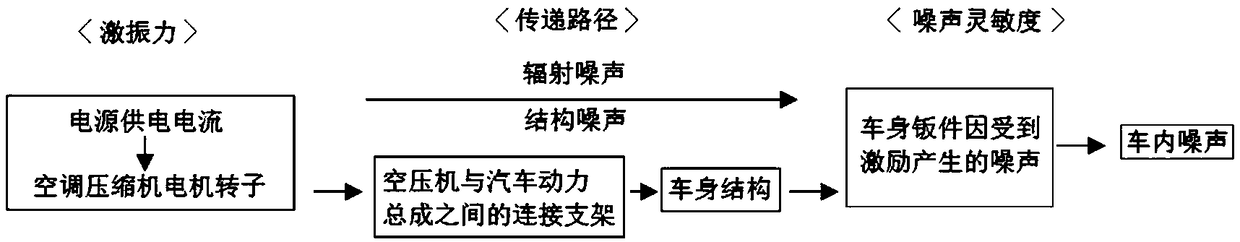
InactiveCN109026639AAbnormal noise problem solvingAbnormal noise problem solving directionRotary/oscillating piston combinations for elastic fluidsPump testingSound sourcesFrequency spectrum
The invention discloses a diagnosis and improvement method for low-frequency abnormal sound of an air conditioning compressor under an idling working condition of a blade electric vehicle. The diagnosis and improvement method mainly comprises the following steps that abnormal sound sources are analyzed, and through simulating calculation and spectral analysis, a sound source part is determined preliminarily; then a final sound source part is determined by adopting an acoustic camera imaging technology; then sound source noise analysis is performed, specifically, noise time domain and frequencydomain analysis, sound filter analysis and sound quality analysis are involved; a rotor shaft vibration frequency response test is performed on air conditioning compressors of the blade electric vehicle and a competitive vehicle model, and a structure which generates the noise of the blade electric vehicle is determined; then, a rotor shaft starting control strategy of the air conditioning compressor of the blade electric vehicle is adjusted, and rotor shaft positioning starting is changed to rotor shaft non-positioning starting; and finally, improvement is performed in two aspects of the structure design and the manufacturing machining technology of the air conditioning compressor of the blade electric vehicle. According to the diagnosis and improvement method, the abnormal noise of theair conditioning compressor can be effectively detected and lowered.
Owner:SOUTH CHINA UNIV OF TECH
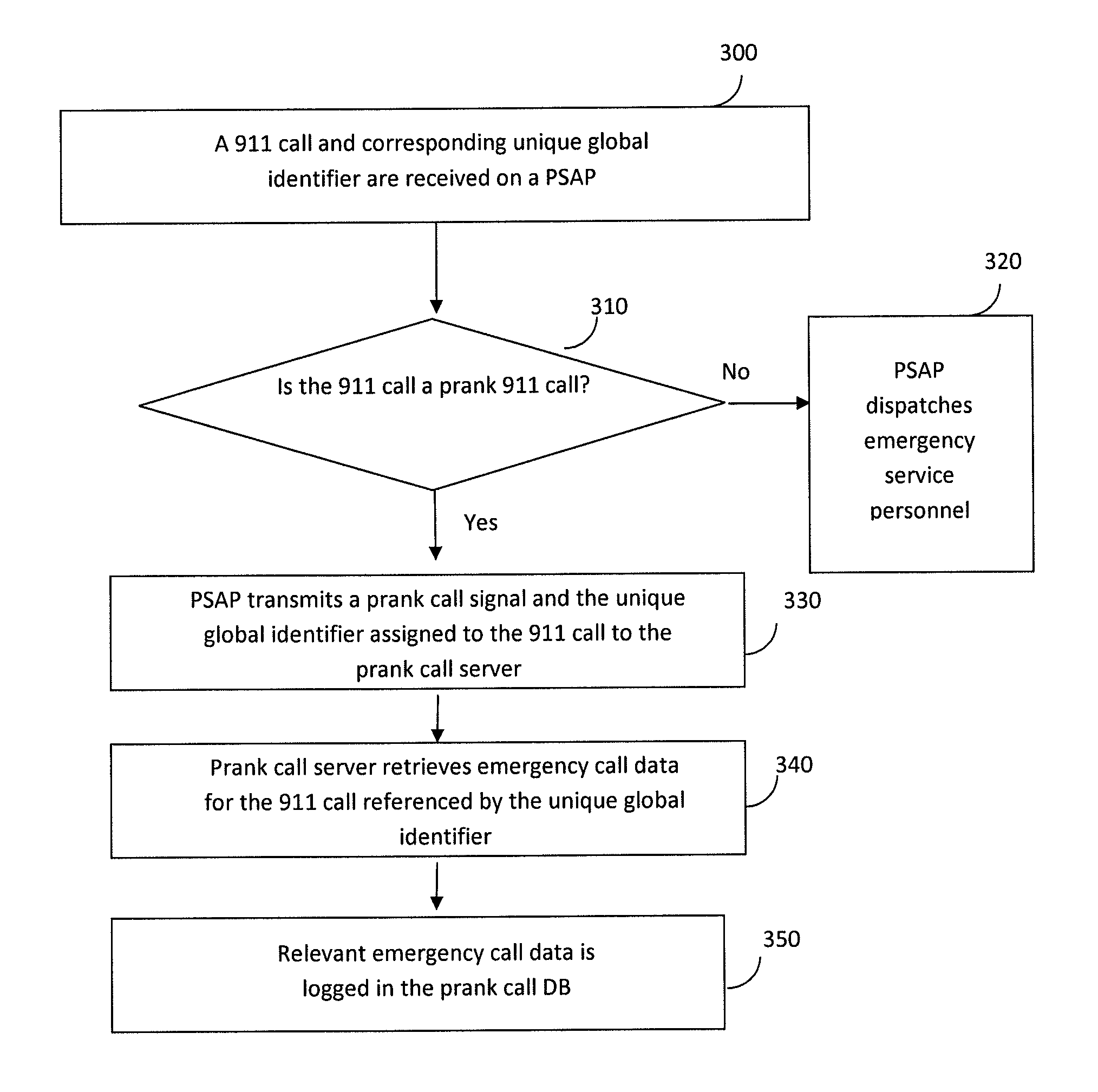
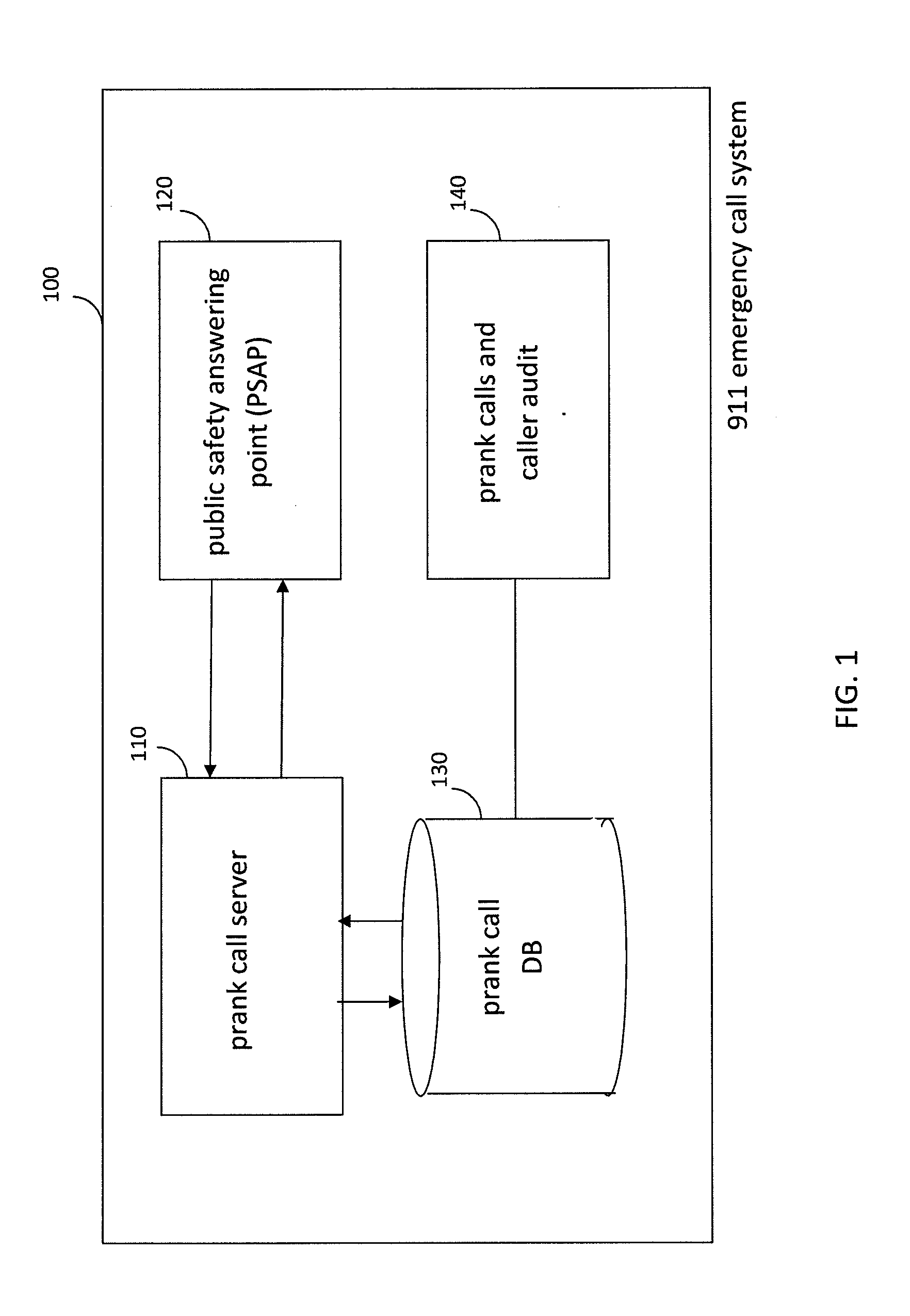
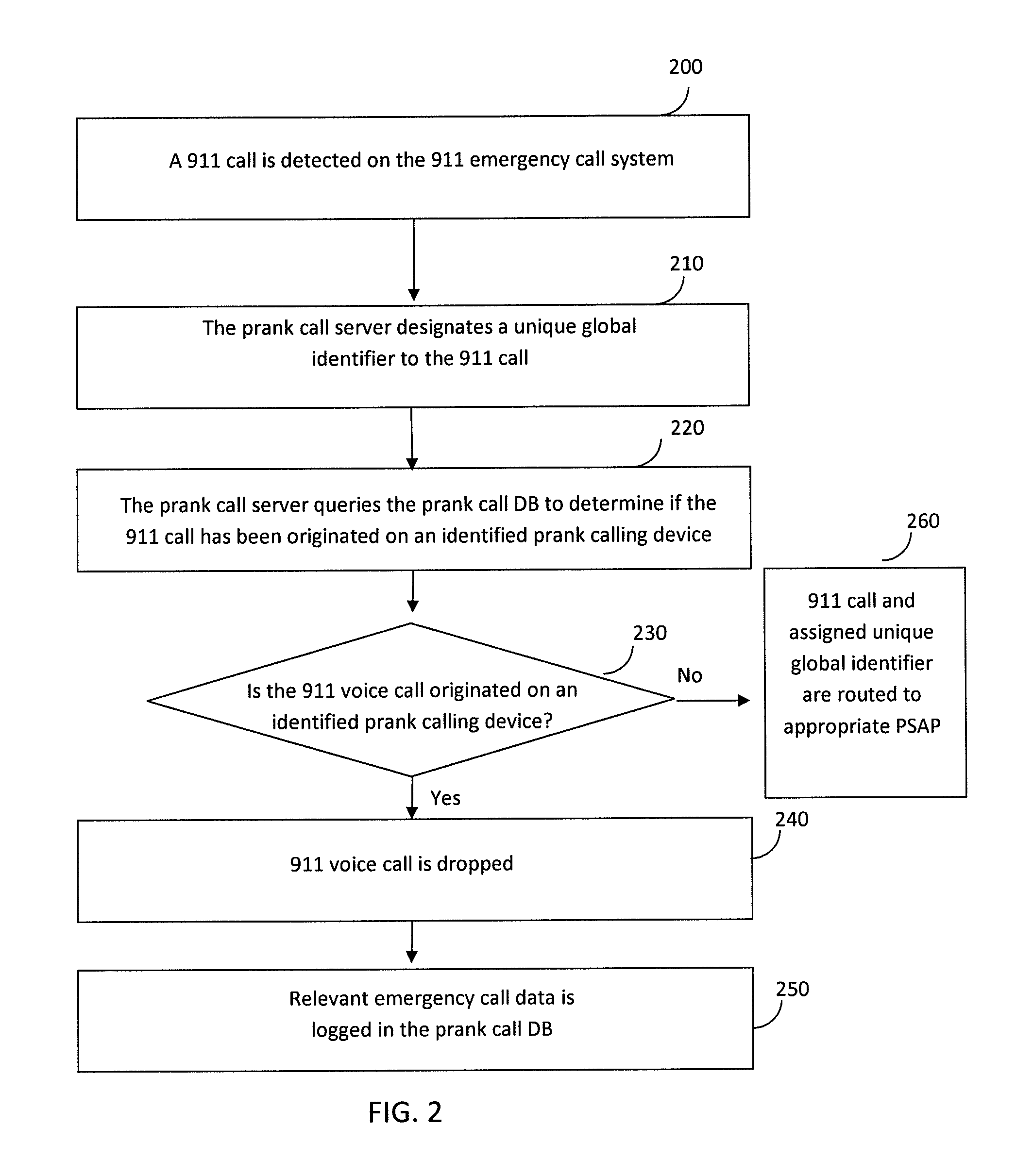
Unique Global Identifier Header for Minimizing Prank Emergency 911 Calls
A prank call server that performs 911 prank call filtering over a 911 emergency call system, prior to routing a 911 call to a PSAP. The inventive prank call server identifies prank calling devices, regardless of current service subscription, by retrieving and analyzing emergency call data pertaining to detected prank 911 calls. The prank call server assigns a unique global identifier to each 911 call detected on the 911 emergency call system. Unique global identifiers enable a PSAP to uniquely identify prank 911 calls that are identified thereon. A PSAP transmits a prank call signal and a relevant unique global identifier to the prank call server, for each prank 911 call that is detected. A prank call signal / unique global identifier combination triggers the prank call server to store all available call data for a referenced prank 911 call in to a prank call database, for subsequent prank call filtering analysis.
Owner:TELECOMM SYST INC
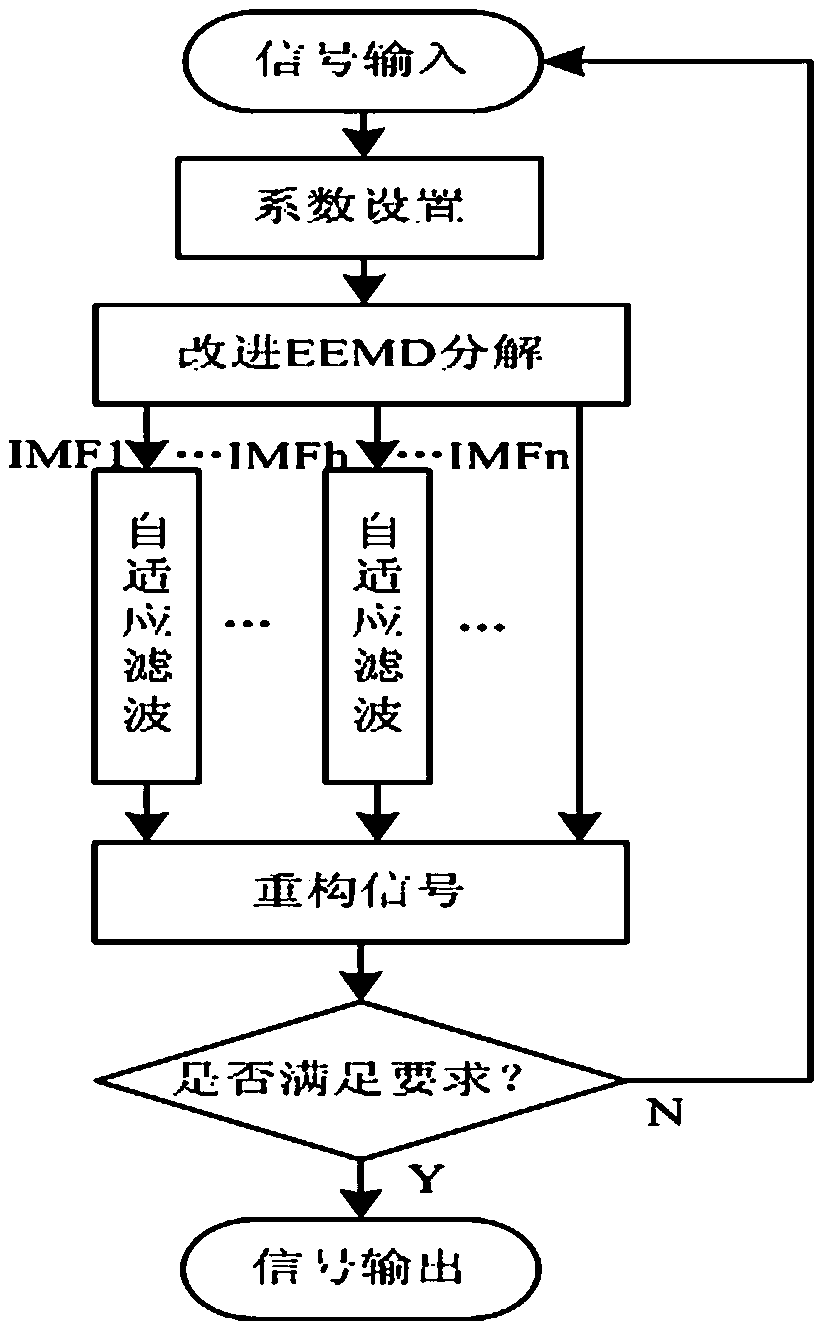
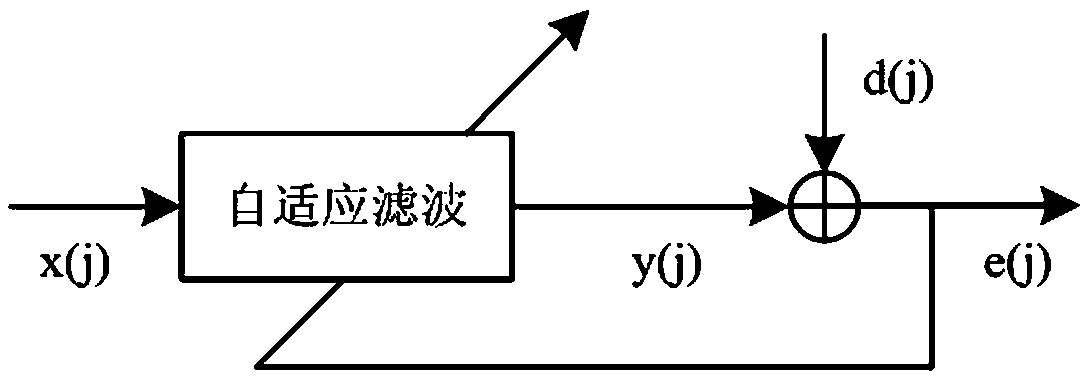
De-noising algorithm of laser range finding signals of power transmission circuit based on improved EEMD
InactiveCN107607835AImprove operational efficiencyOvercoming Mode Aliasing DisadvantagesFault locationElectromagnetic wave reradiationLaser rangingDecomposition
The invention provides a de-noising algorithm of laser range finding signals of a power transmission circuit based on the improved EEMD. Filtering analysis and de-noising processing carried out on noise-containing laser range finding signals of the power transmission circuit can be effectively achieved. The method comprises steps of firstly establishing a power transmission circuit laser range finding signal acquisition system; carrying out rapid EEMD decomposition on the power transmission circuit laser range finding signals obtained through the experiment so as to obtain a series of intrinsic mode functions IMFs; then, selecting different numbers of IMFs to carry out adaptive filtering de-noising according to different noise forms; and finally, adding the de-noised IMFs so as to reconstruct the expected power transmission circuit laser range finding signals. An experiment result proves that by use of the method, noise in the power transmission circuit laser range finding signals canbe effectively reduced; rapid and precise range finding can be performed on targets influencing operation of the power transmission circuit; and safety and stability of the operation of the power transmission circuit are improved.
Owner:STATE GRID CORP OF CHINA +1
Fluid identification method of frequency dispersion AVO related attribute inversion
The invention provides a fluid identification method of frequency dispersion AVO related attribute inversion. According to the method, inversion operation is performed on reservoir section seismic reflection coefficients, and longitudinal scanning and filtering analysis are performed on variable parameters obtained by the inversion operation so that frequency dispersion AVO related attributes are acquired, and fluid properties of reservoir sections are identified according to the frequency dispersion AVO related attributes. The method is suitable for complex reservoir section fluid identification so that the method has characteristics of being great in stability, high in identification accuracy, etc.
Owner:CHINA PETROLEUM & CHEM CORP +1
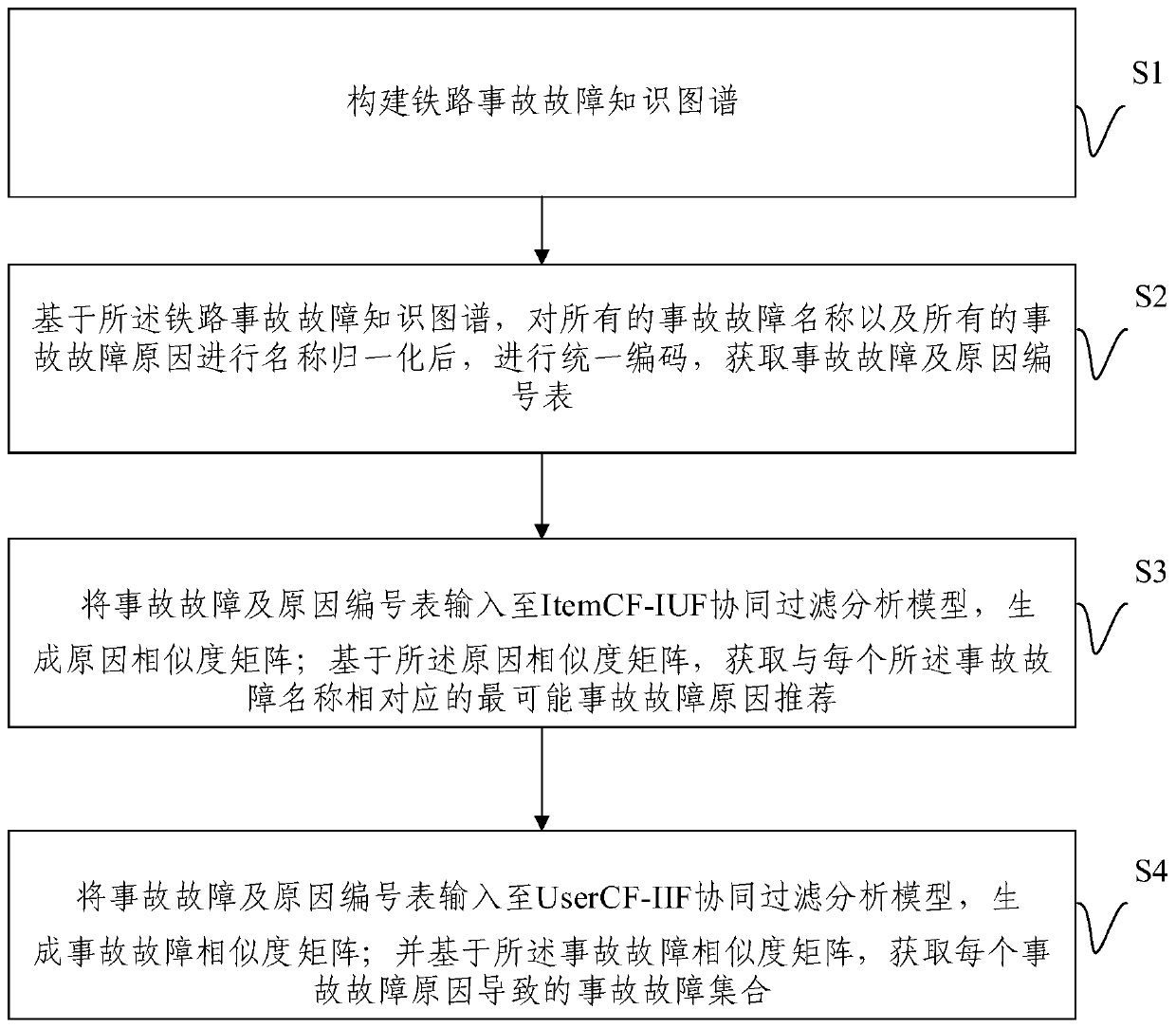
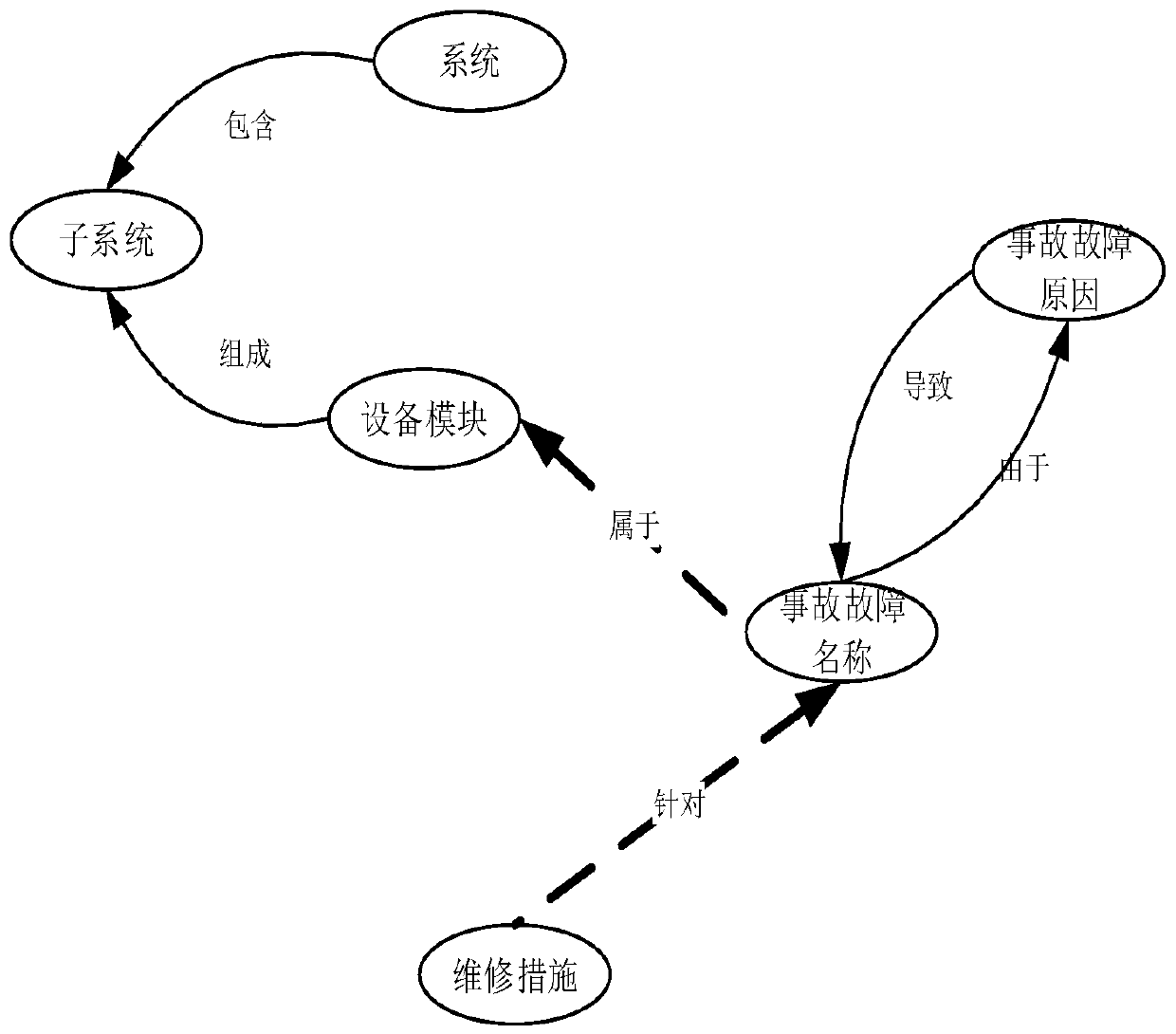
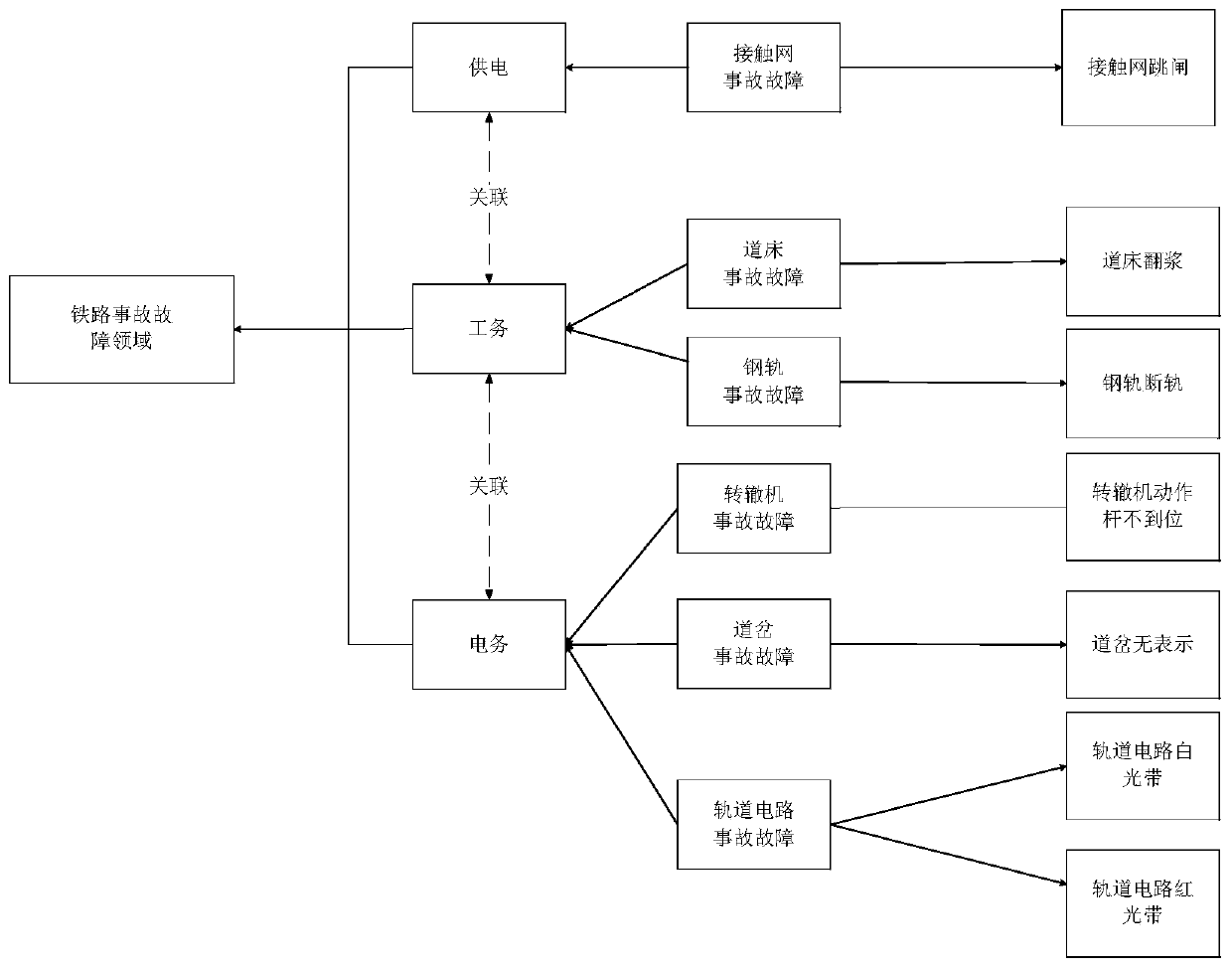
Railway accident fault correlation and accident fault reason analysis method and system
PendingCN111209472AImprove securityRealize intelligent operation and maintenanceDigital data information retrievalSpecial data processing applicationsAlgorithmFilter analysis
The embodiment of the invention provides a railway accident fault correlation and accident fault reason analysis method and system. The method comprises the steps of constructing a railway accident fault knowledge graph; based on the railway accident fault knowledge graph, performing name normalization on all accident fault names and all accident fault reasons, and then performing unified coding to obtain an accident fault and reason number table; inputting the accident fault and reason number table into a collaborative filtering analysis model to generate a reason similarity matrix; based onthe reason similarity matrix, obtaining the most possible accident fault reason recommendation corresponding to each accident fault name; inputting the accident fault and reason number table into a collaborative filtering analysis model to generate an accident fault similarity matrix; and based on the accident fault similarity matrix, obtaining an accident fault set caused by each accident fault reason. According to the embodiment of the invention, by fusing the knowledge graph and the recommendation algorithm, the accuracy of accident fault association and reason analysis is improved, and theguarantee of railway safety operation is enhanced.
Owner:INST OF COMPUTING TECH CHINA ACAD OF RAILWAY SCI +2
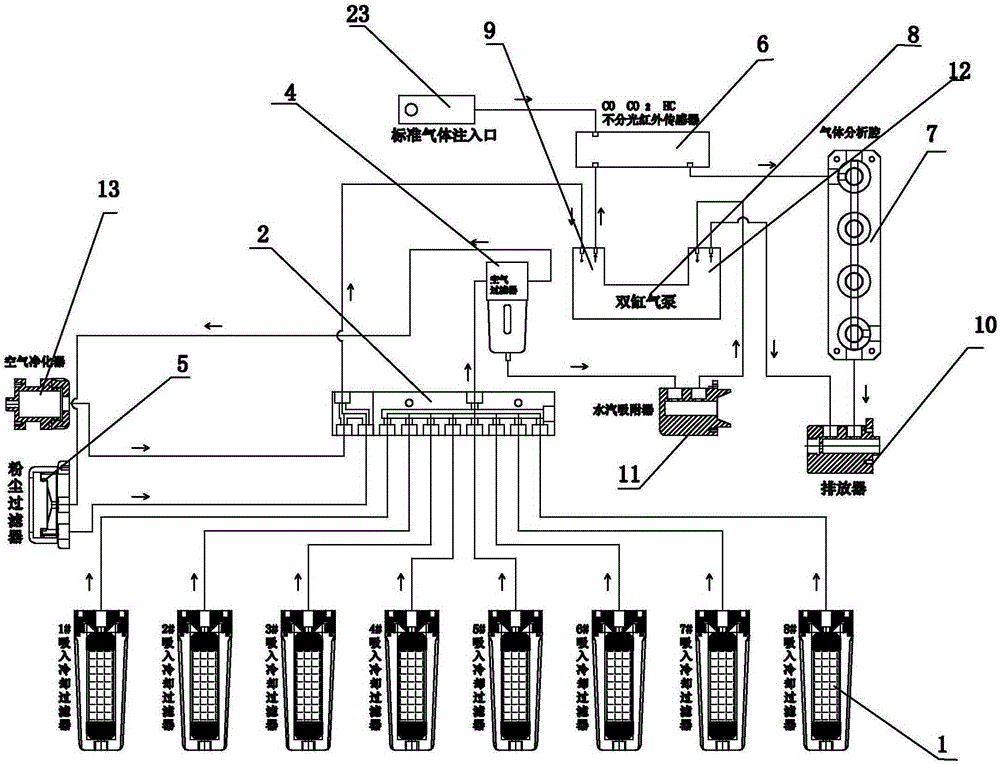
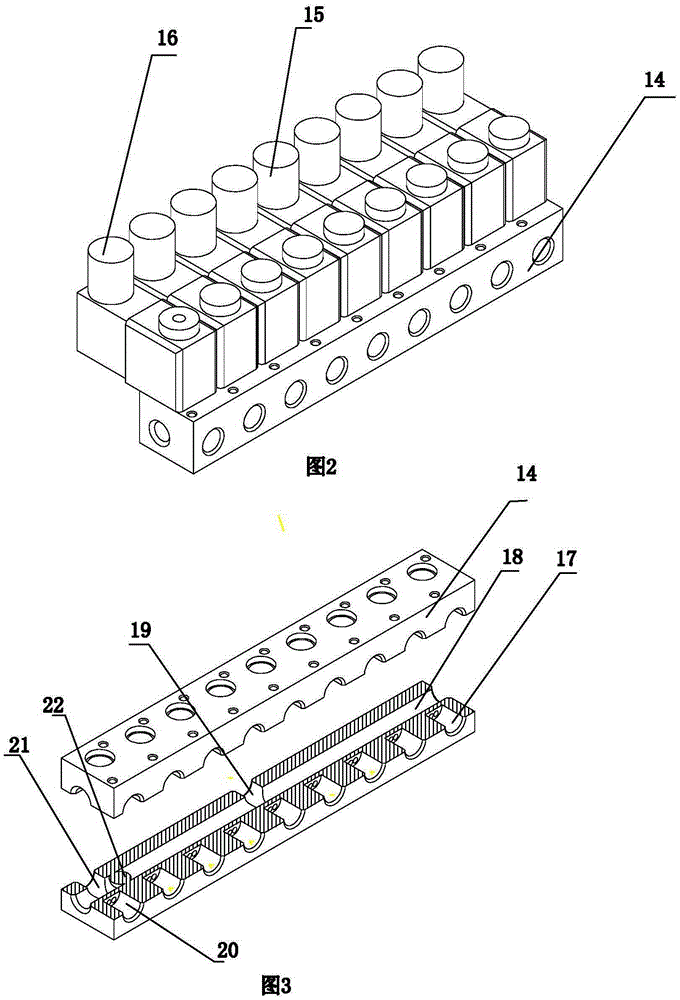
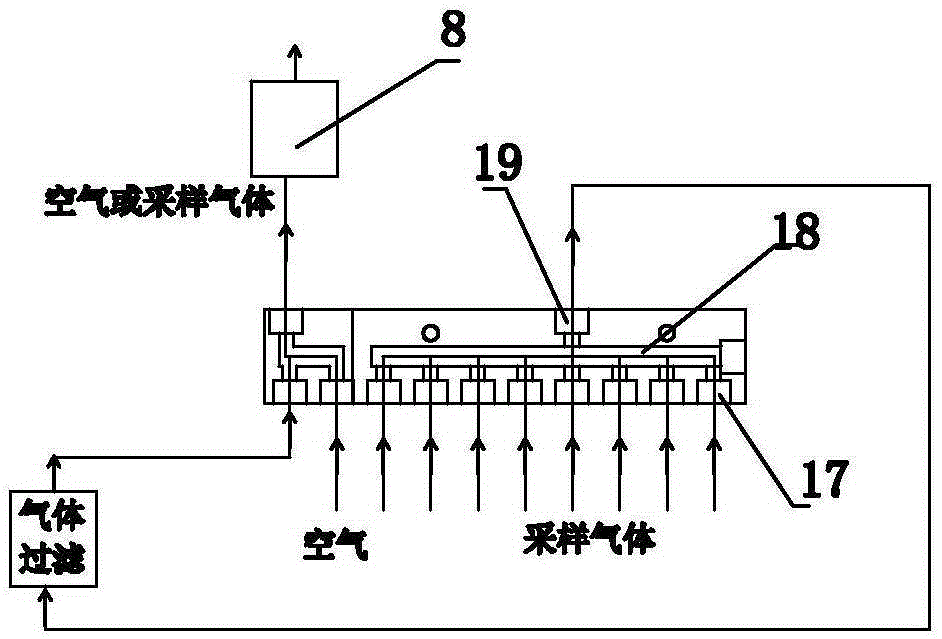
Multichannel routing inspection type diesel engine tail gas detection device
The invention discloses a multichannel routing inspection type diesel engine tail gas detection device. A plurality of cooling filters are connected with a gas distributor. A computer controls the gas distributor to gate one channel of gas to conduct the follow-up filtering analysis processing. The gas distributor is connected with a gas filter component and a gas analysis sensor component. The multichannel routing inspection type diesel engine tail gas detection device has the advantages that sampling gases exhausted from a diesel engine tail gas exhaust pipe is sent to the gas distributor after passing through the cooling filters; the gas distributor is controlled through the computer to gate the channel of the gas from the multiple channels to conduct the follow-up processing; the gated gas is subjected to moisture separation through an air filter, and filtered air enters a nondispersive infrared sensor after being further decontaminated and filtered through a dust filter; and the collection of components of oxygen, nitric oxide, nitrogen dioxide and sulfur dioxide is conducted through an electrochemical sensor in a gas analysis cavity, and then the sampling gases are exhausted through an exhausting device.
Owner:林琪 +1
Online monitoring system for grounding grid resistance
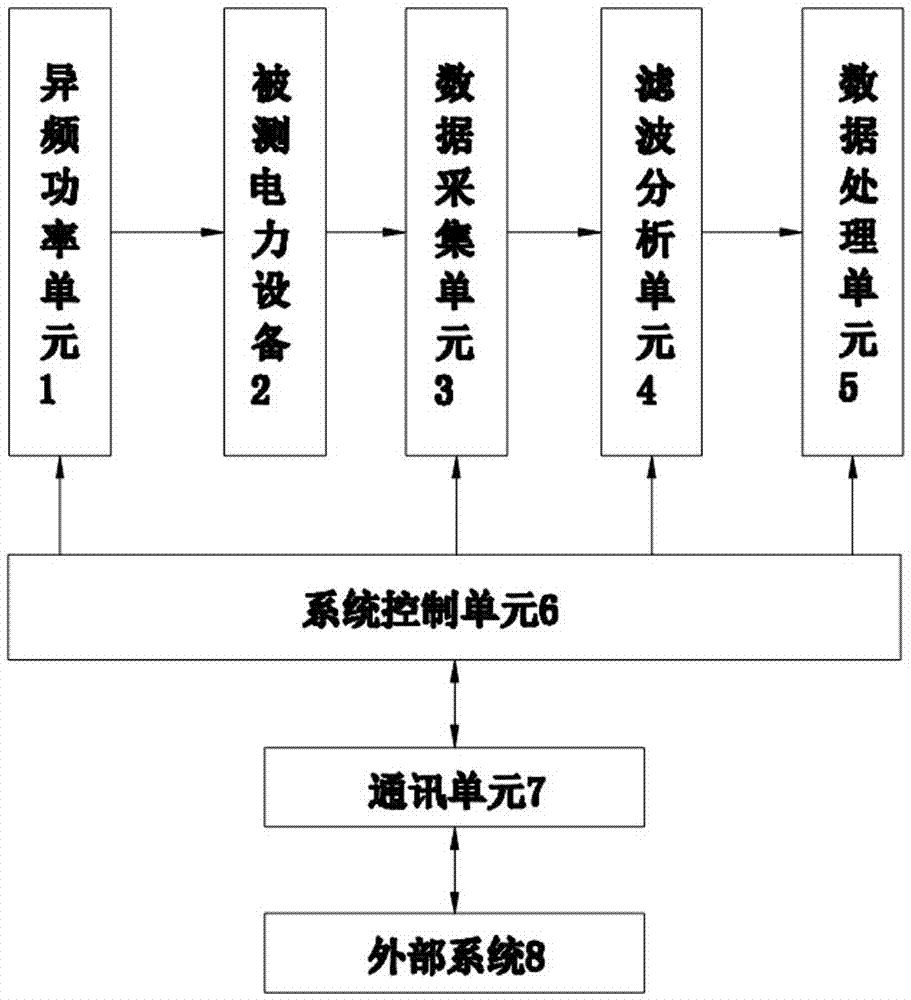
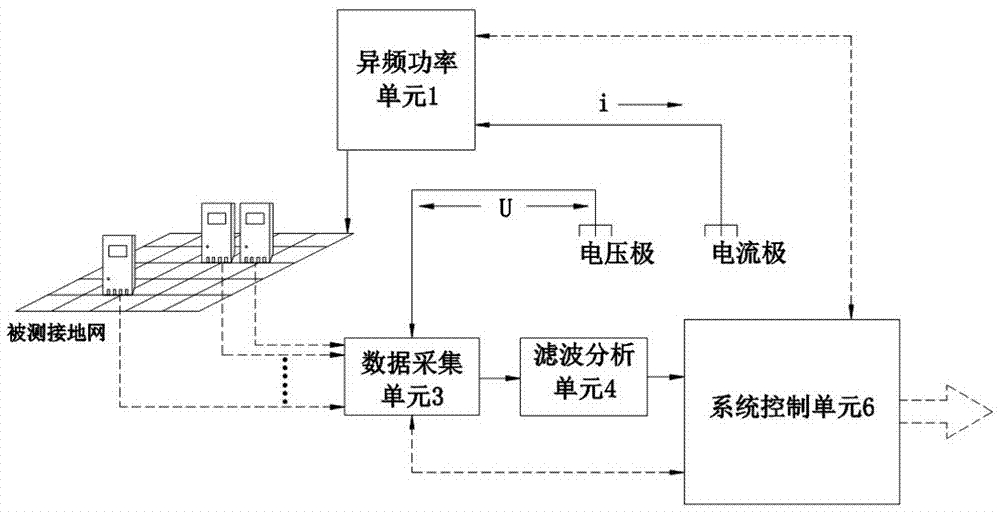
PendingCN107290592ASecurity real-time controlTimely monitoring of characteristic parametersEarth resistance measurementsElectric power systemElectric power equipment
The invention discloses an online monitoring system for grounding grid resistance, and relates to the technical field of power systems. The online monitoring system comprises a pilot power unit, a data acquisition unit, a filter analysis unit, a data processing unit, a system control unit, a communication unit and an external system, wherein the pilot power unit is connected with monitored power equipment, the monitored power equipment is connected with the data acquisition unit, the data acquisition unit is connected with the filter analysis unit, the filter analysis unit is connected with the data processing unit, and the system control unit is connected with the pilot power unit, the data acquisition unit, the filter analysis unit and the data processing unit respectively; and the system control unit is connected with the external system via the communication unit. The online monitoring system can timely monitor characteristic parameters of a grounding device, and timely monitor the grounding resistance indicator change trend of the grounding device, so that the relevant department can timely master the security of a grounding grid and formulate corresponding countermeasures, and personal and equipment safety accidents are effectively prevented.
Owner:河南天通电力有限公司
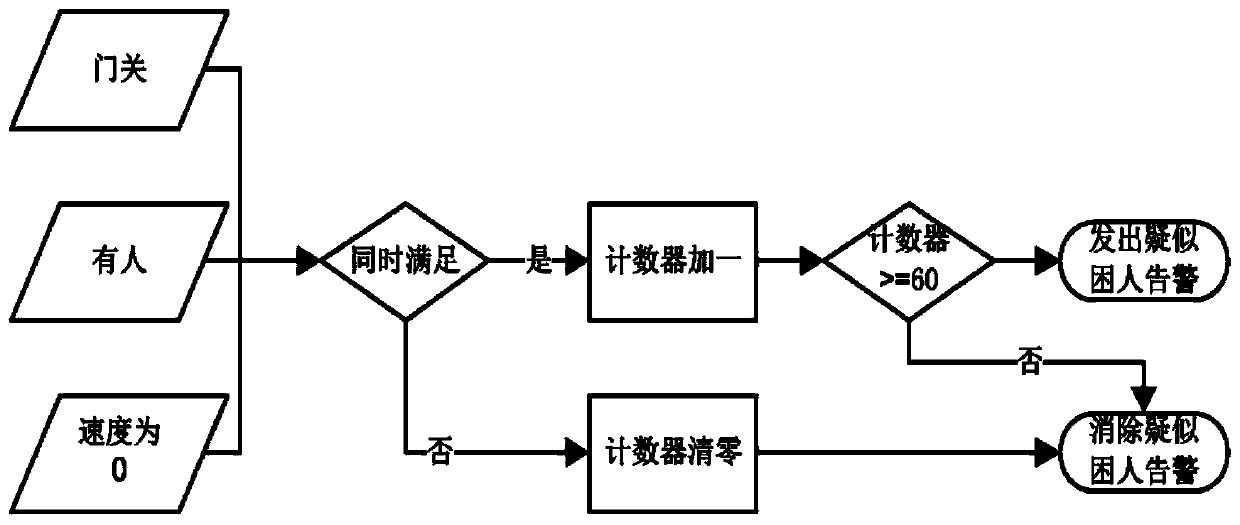
Big data analysis based trapping in elevator misinformation identification method
The invention relates to a big data analysis based trapping in an elevator misinformation identification method, and provides an alarming method when someone is trapped in an elevator based on the bigdata acquired by a sensor during the actual running of the elevator and combining the characteristics of the running big data of complicated equipment with the machine analysis theory. The method includes the steps of: establishing a deep neural network predication model; acquiring signals by an alarming service unit, and performing processing and analysis to the data; judging whether it is suspected trapped alarming, or not; if yes, sending the alarming information to the trapped alarming filtering service unit of the Internet of Things; performing real-time filtering analysis on the alarming based on the trapped alarming filtering service unit of the Internet of Things; judging whether someone is really trapped, or not according to the analysis result; and if someone is really trapped,feeding the trapped alarming information back to the alarming service unit, and informing the alarming information to a maintenance department by the alarming service unit, and meanwhile, starting theinformation storage service unit for information storage. According to the method, whether someone is really trapped can be distinguished in real time, and the trapped information can be informed inreal time and assistance can be given to the maintenance department, so that the trapped passenger can be rescued timely.
Owner:虏克电梯有限公司
System and method for analyzing content on a web page using an embedded filter
ActiveUS8140489B2Digital data information retrievalDigital data processing detailsFilter analysisWeb page
Owner:ORACLE INT CORP
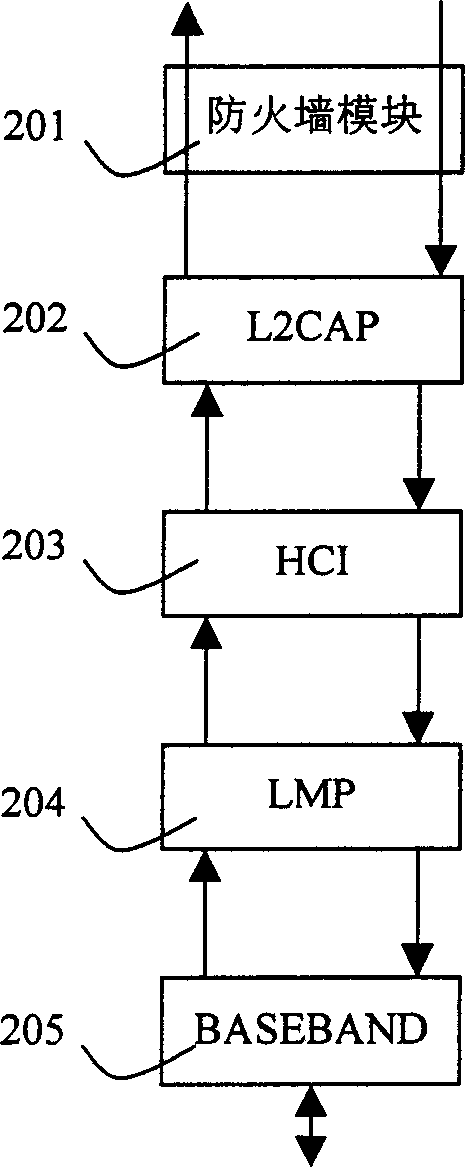
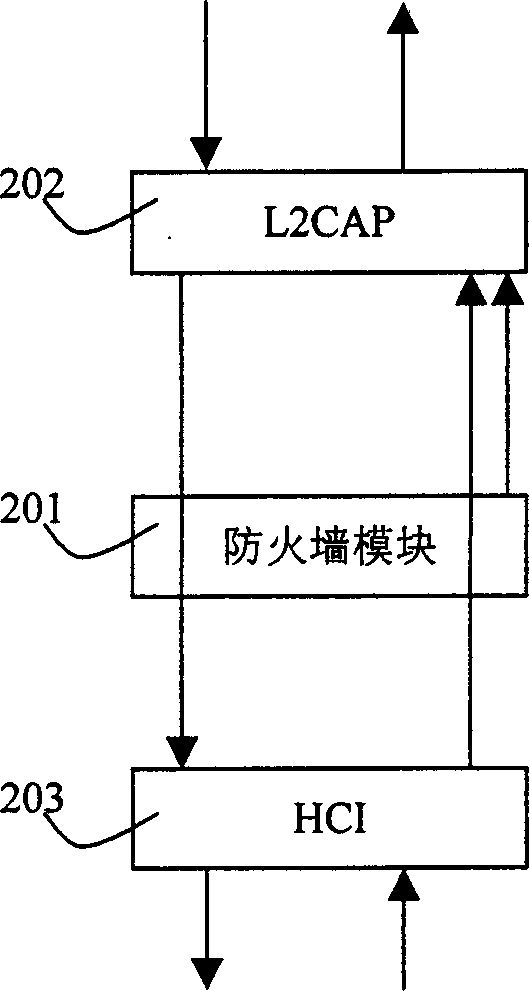
Safety protection module of mobile communication equipment and its processing method
InactiveCN1801807AEnsure accurate and credibleEnsure safetyTransmissionNetwork packetData information
Present invention discloses safety protection module and processing method using blue teeth transmission technique transmission technique mobile communication equipment,It contains increasing one fire wall module In blue teeth protocol stack mainframe control interface, proceeding filtering analyses to incoming data packet according to only blue teeth equipment address of each blue teeth equipment, to credible node , allowing establishing communications linkage to transmit data,to unlikelihood node preventing all data packet transmitted to said node prohibiting responses to said node transmitted data packet, Said invention aims at ensuring messages transmission only In creditable blue teeth equipment , preventing equipment connection attempt to local equipment connection, also prohibiting non - user original idea ' s connection with other equipment, Thereby effectively ensuring local equipment data information not be illegally filched.
Owner:YINGHUADA (SHANGHAI) ELECTRONIC CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com