Patents
Literature
3418 results about "Equipment Safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
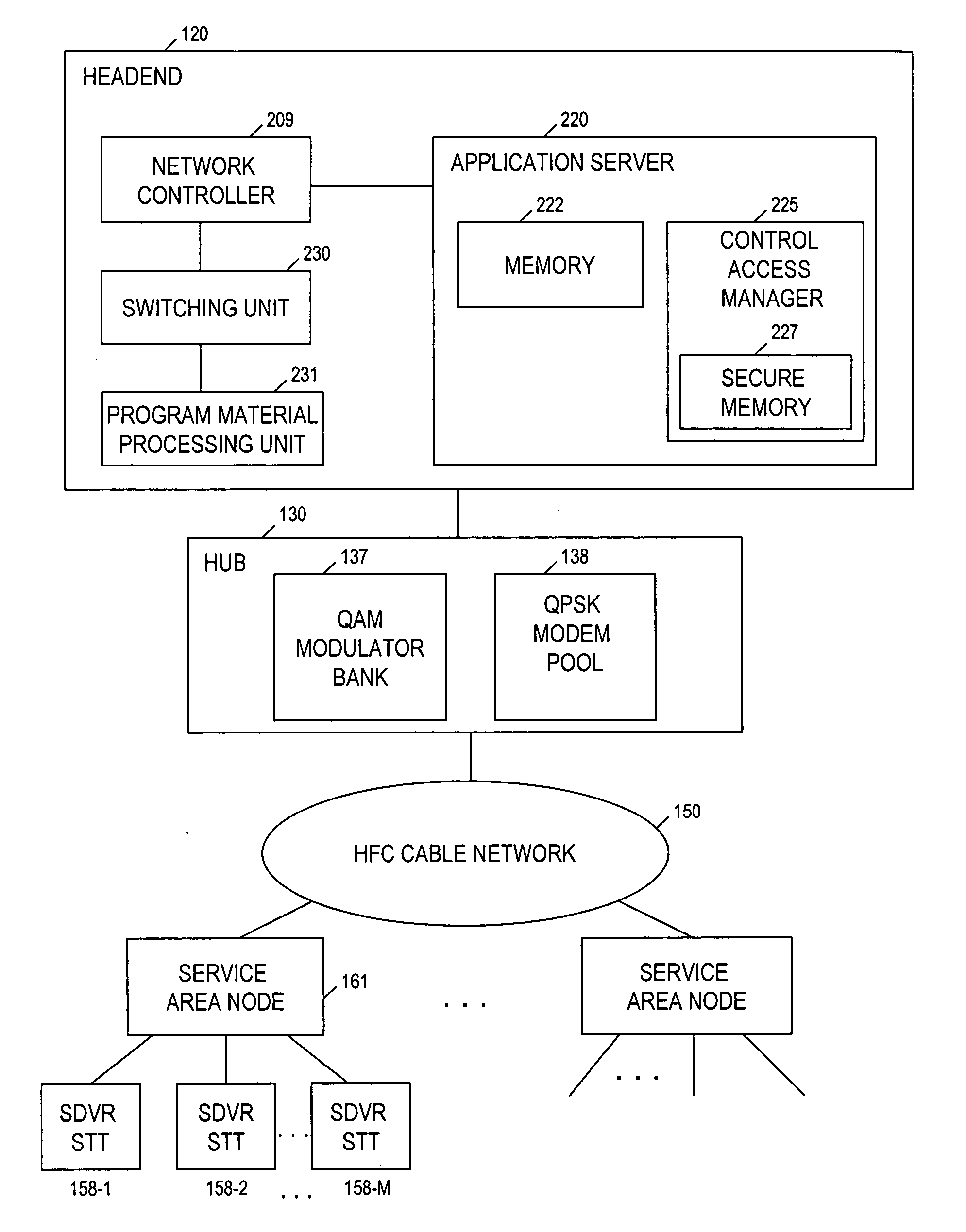
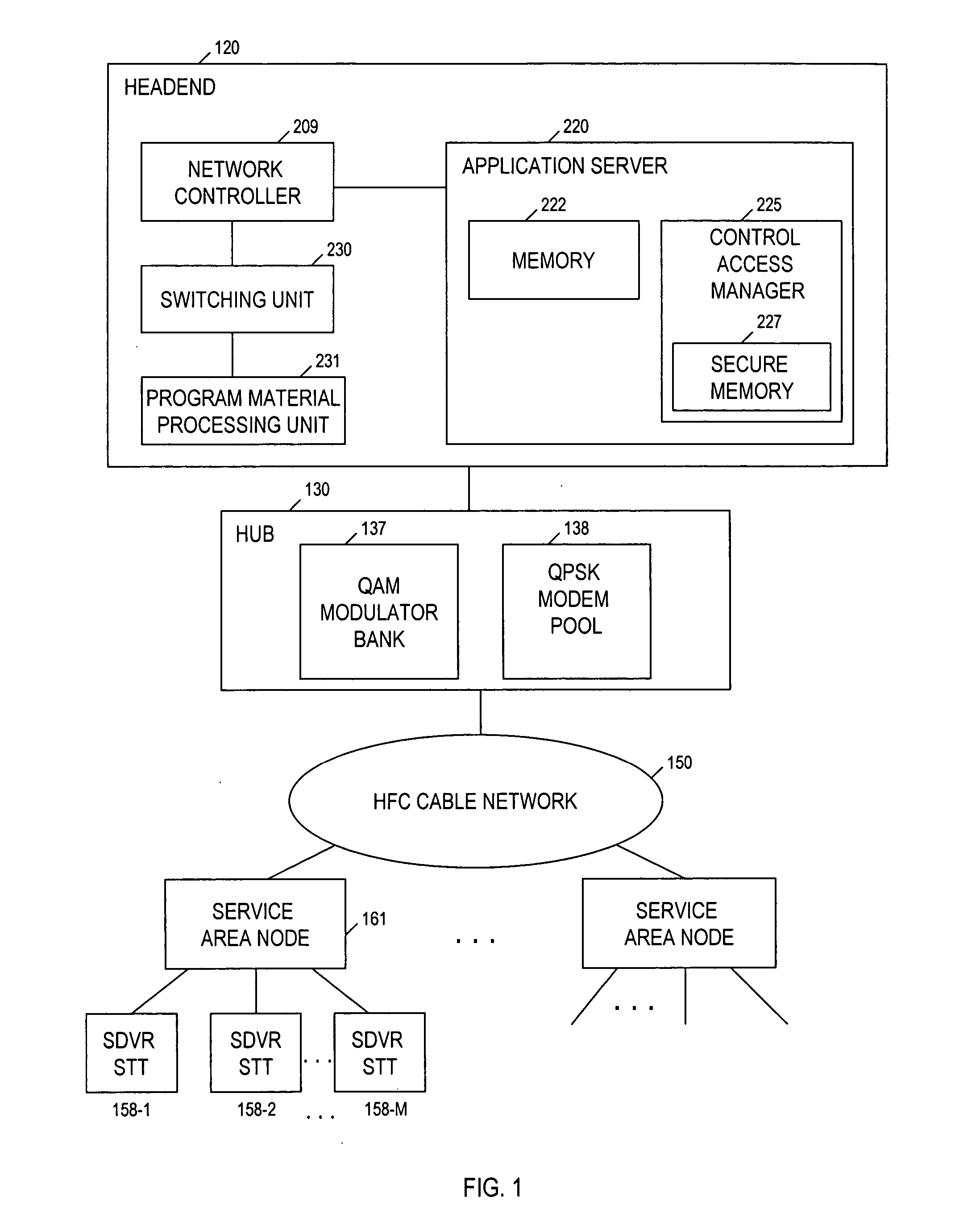
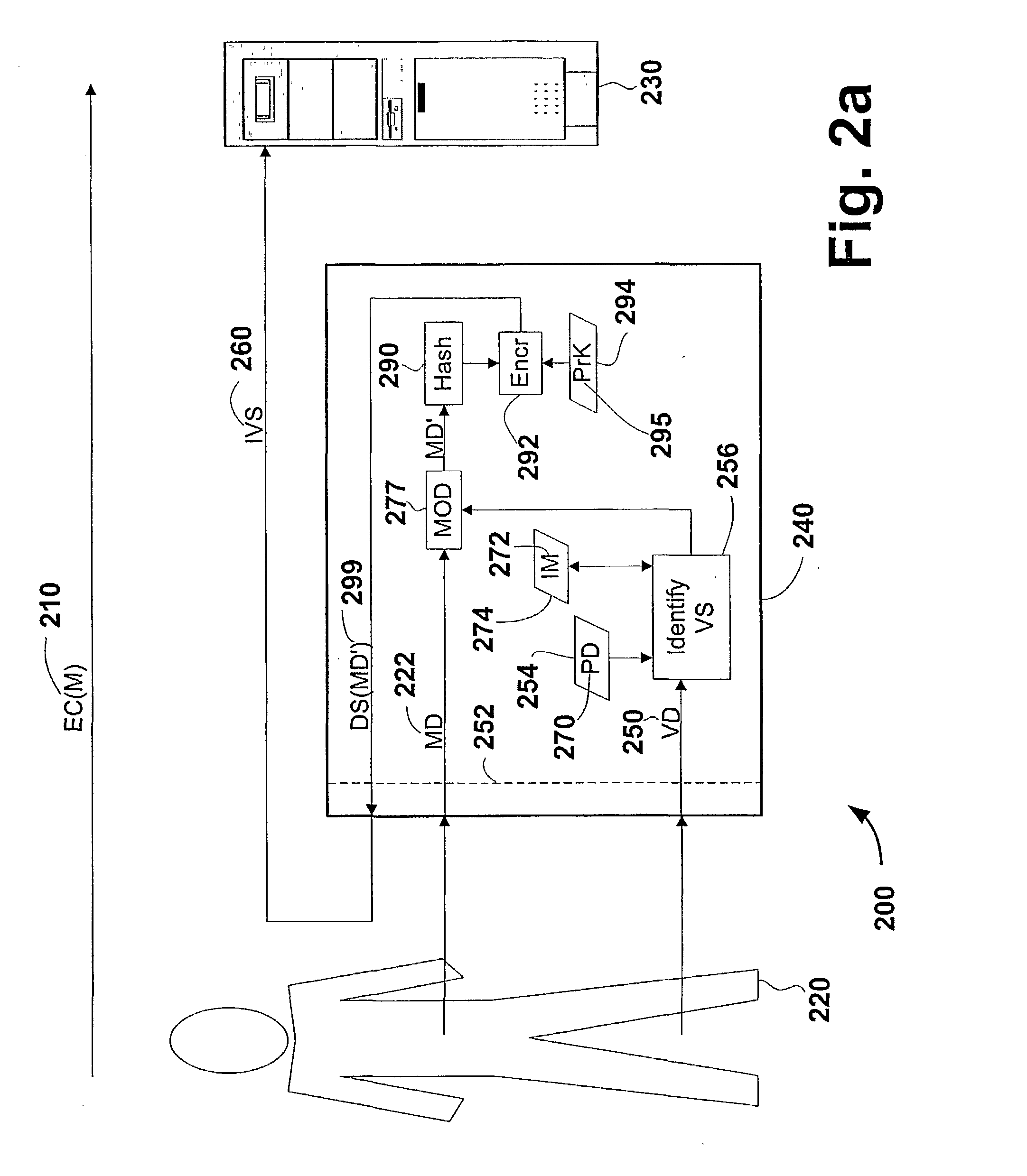
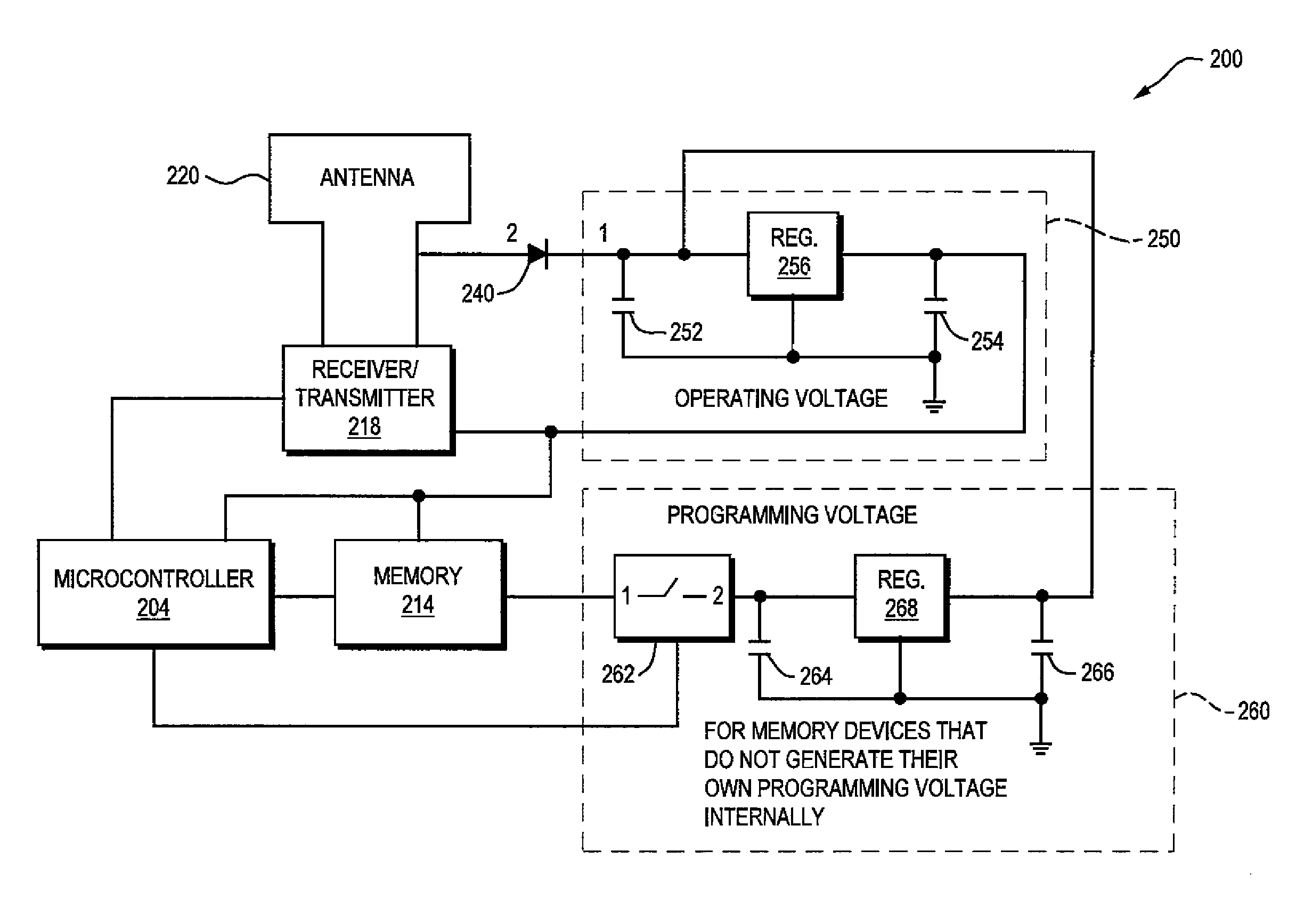
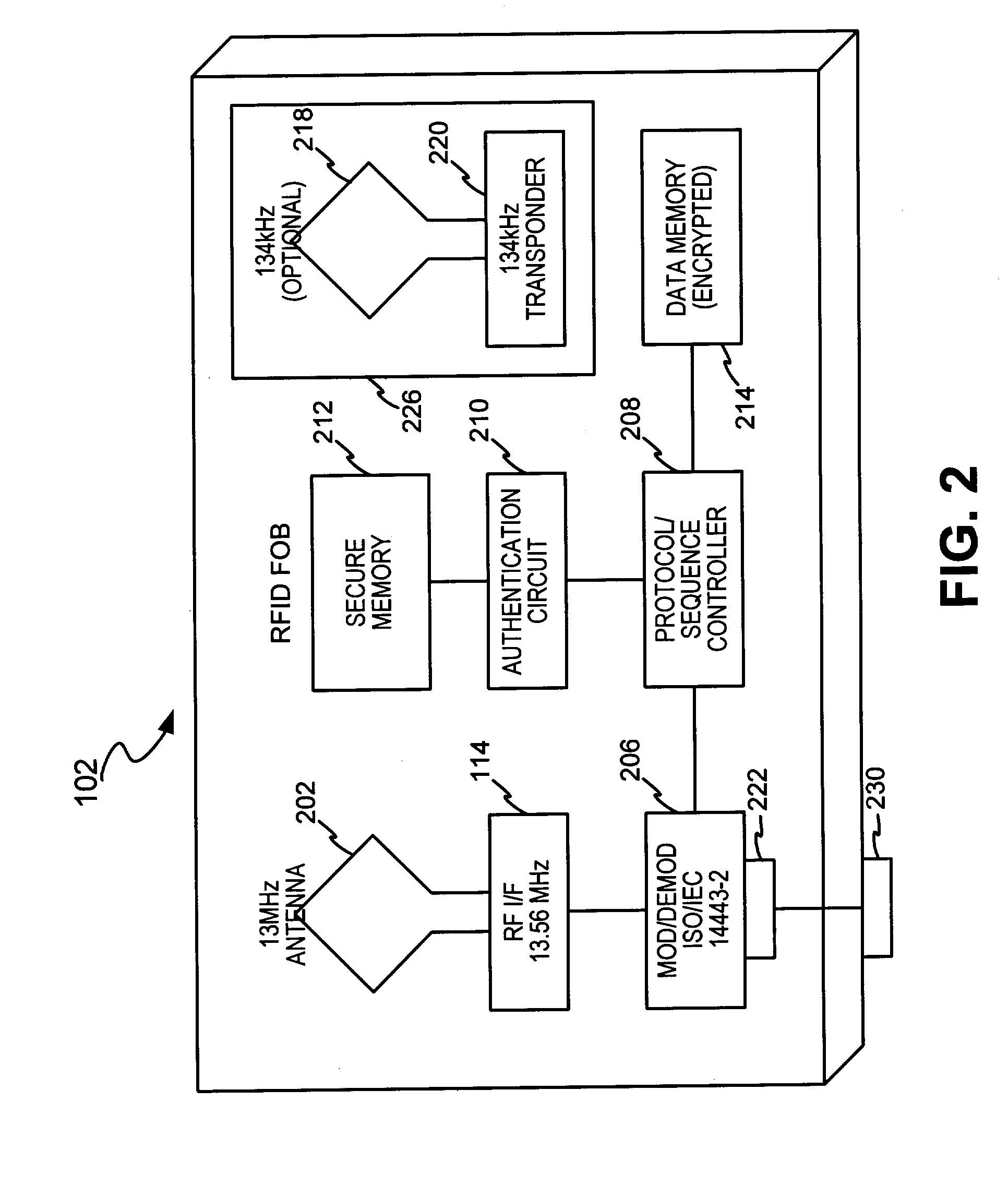
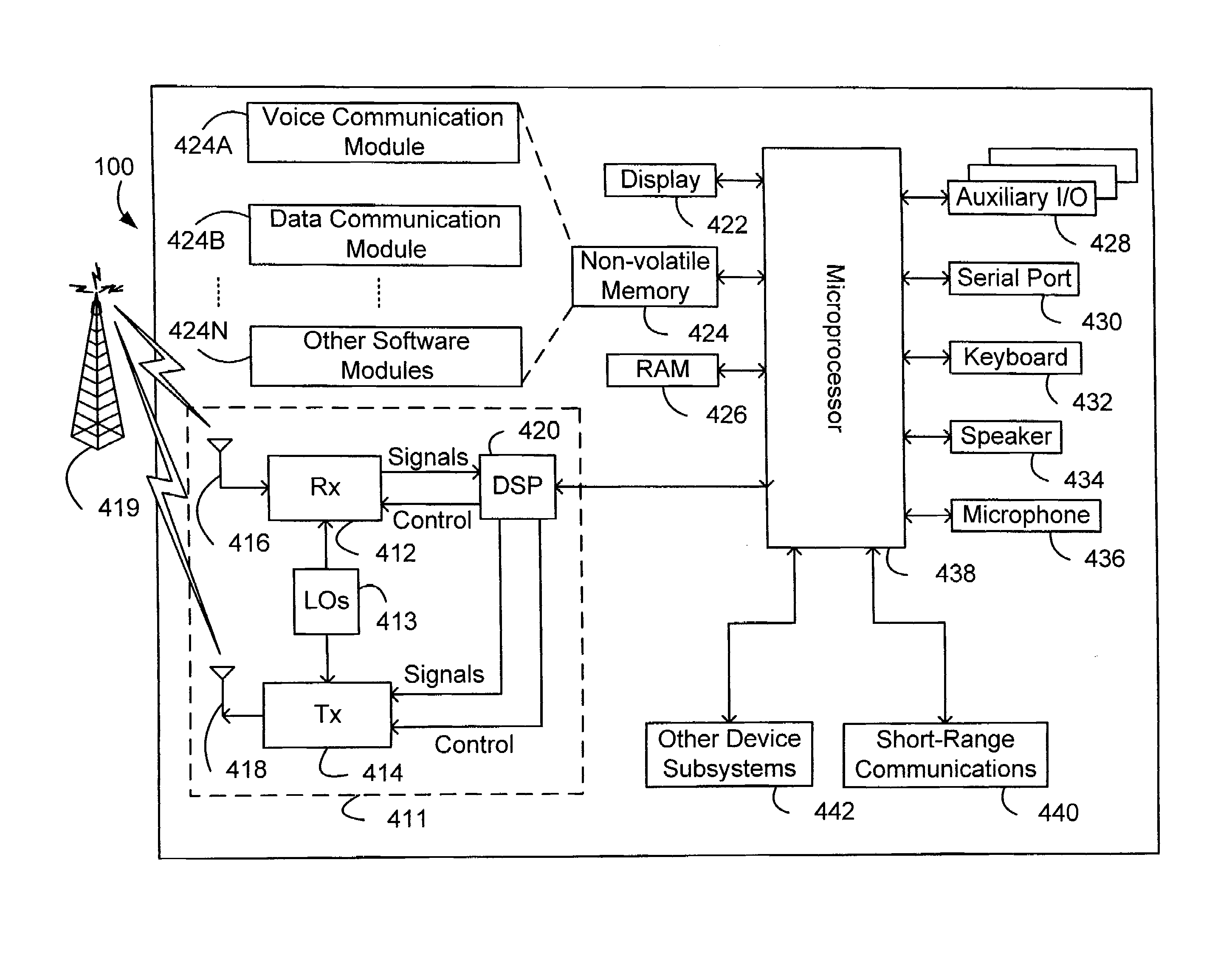
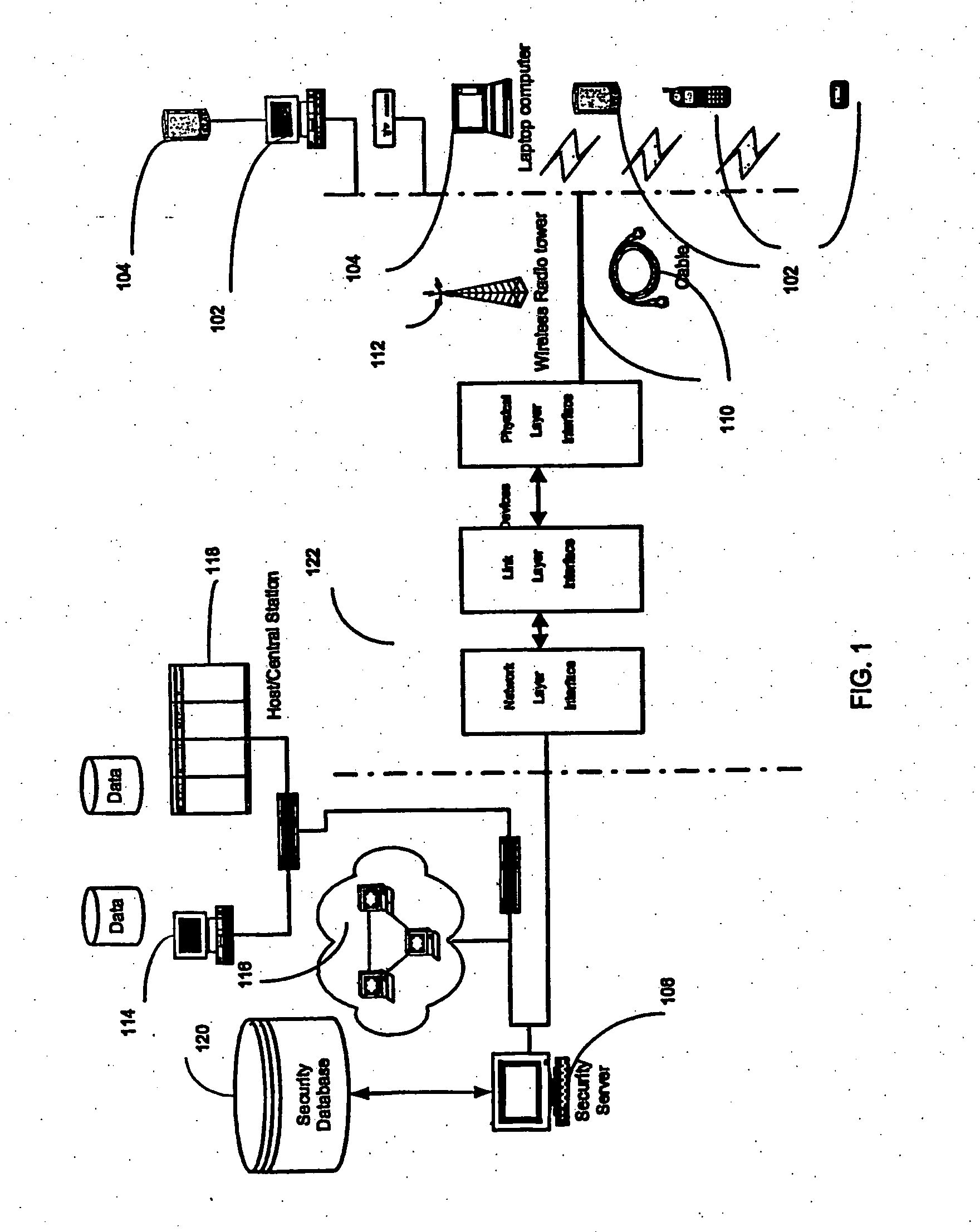
Technique for securely communicating programming content
ActiveUS20060047957A1Prevent illegal useEncryption apparatus with shift registers/memoriesDigital data processing detailsTime segmentSecurity level
A technique is provided for securely transferring programming content from a first device in a first layer, e.g., a trusted domain, to a second device in a second layer, e.g., outside the trusted domain. When a user requests that the first device transfer protected content to the second device, the first device needs to authenticate the second device. After the second device is authenticated, the first device may transfer to the second device the protected content, together with a rights file associated therewith. The rights file specifies the rights of the second device to use the protected content, according to its security level indicative of its security. These rights may concern, e.g., the number of times that the second device may subsequently transfer the protected content to other devices, the time period within which the second device may play the protected content, etc. The higher the security level of the second device is, the more rights accorded thereto. Indeed, the second device may need to meet a minimum security level requirement in order for it to receive or keep the protected content.
Owner:TIME WARNER CABLE ENTERPRISES LLC +1
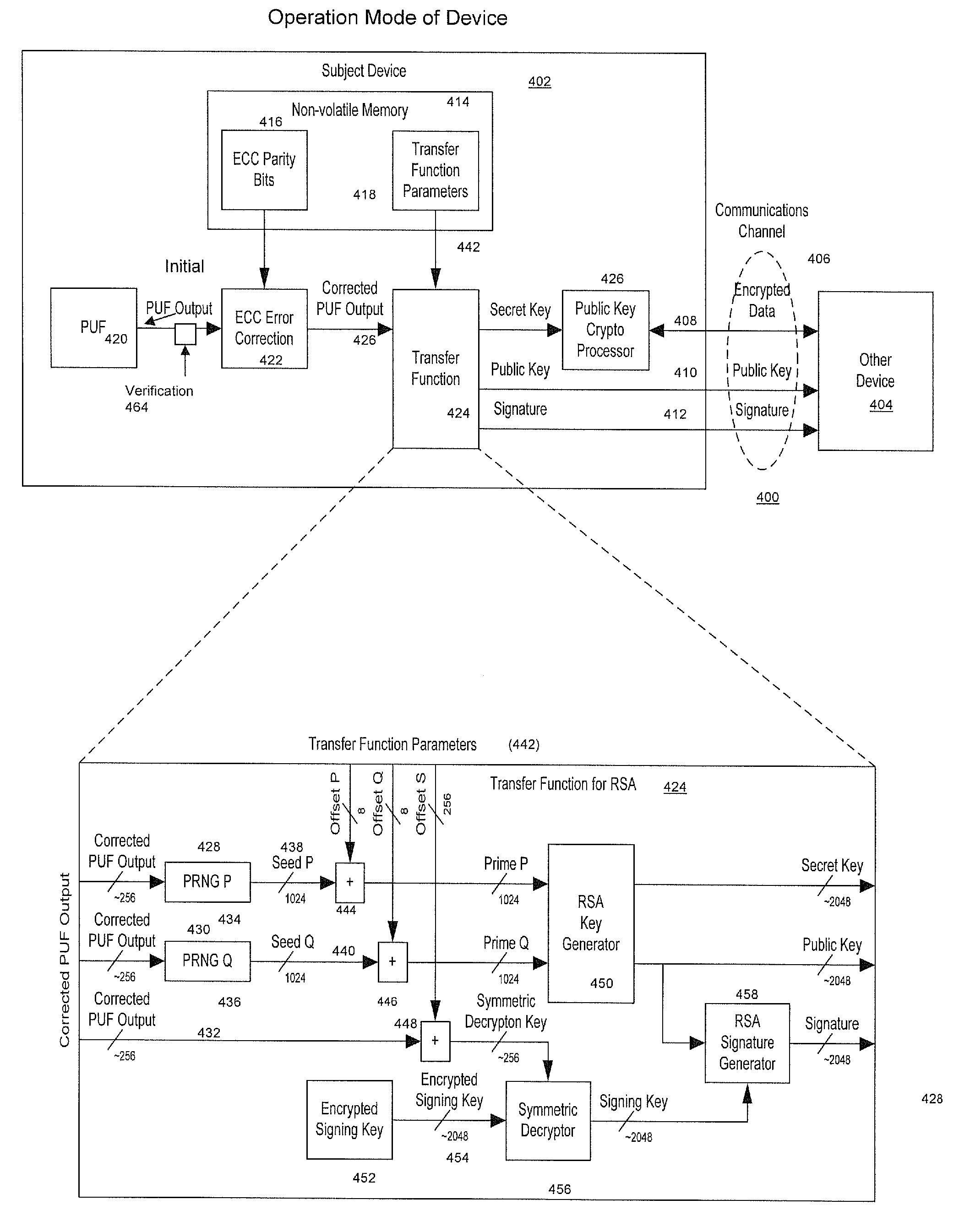
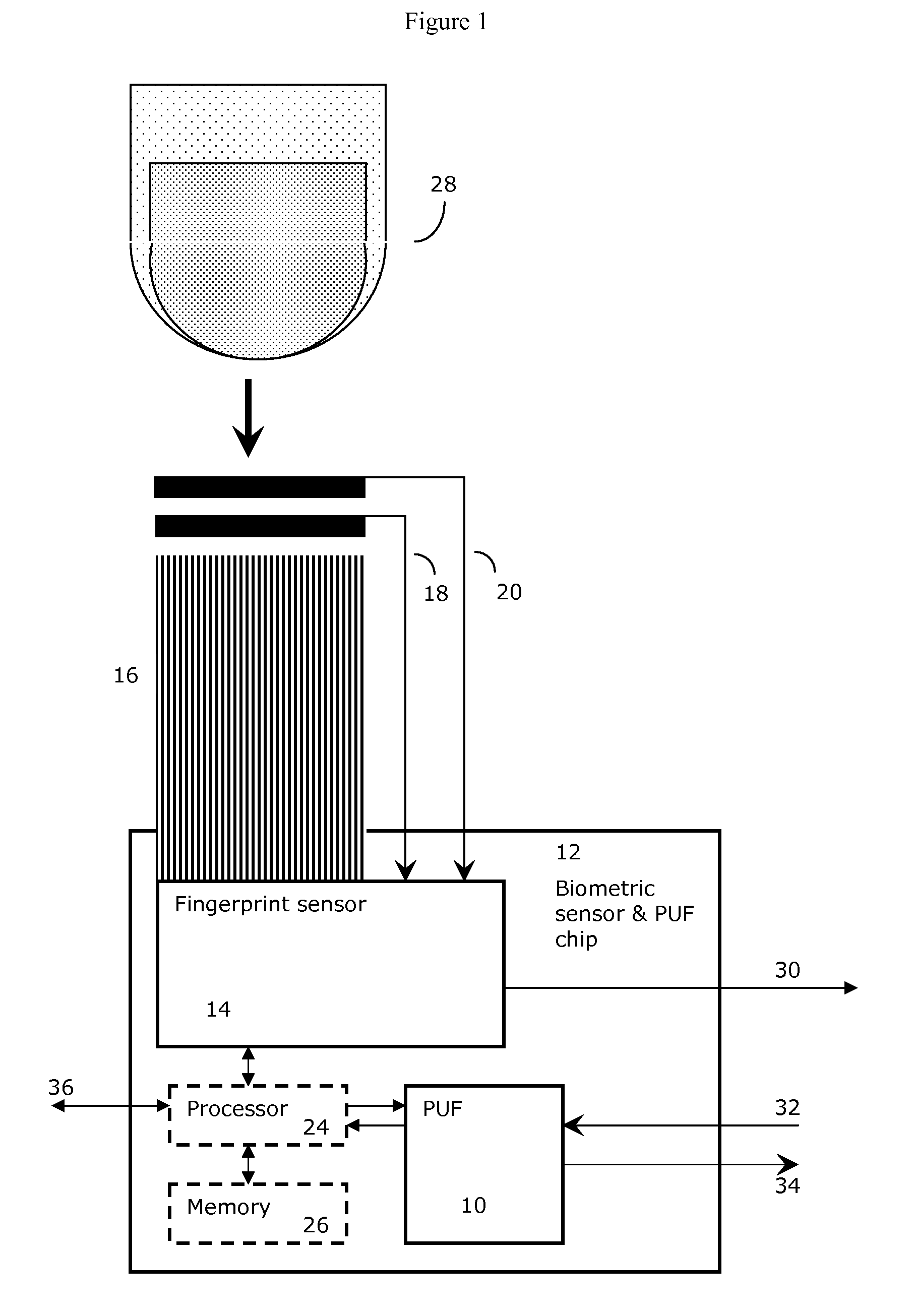
Method and System for Electronically Securing an Electronic Biometric Device Using Physically Unclonable Functions
InactiveUS20110002461A1Consume minimalCost of producingKey distribution for secure communicationElectric signal transmission systemsPhysical unclonable functionSecurity validation
A system for securing an integrated circuit chip used for biometric sensors, or other electronic devices, by utilizing a physically unclonable function (PUF) circuit. These PUF functions are in turn used to generate security words and keys, such as an RSA public or private key. Such a system can be used to protect biometric security sensors and IC chips, such as fingerprint sensors and sensor driver chips, from attack or spoofing. The system may also be used in an efficient method to produce unique device set-up or power-up authentication security keys. These keys can be generated on a low frequency basis, and then frequently reused for later security verification purposes. In operation, the stored keys can be used to efficiently authenticate the device without the need to frequently run burdensome security key generation processes each time, while maintaining good device security.
Owner:SYNAPTICS INC
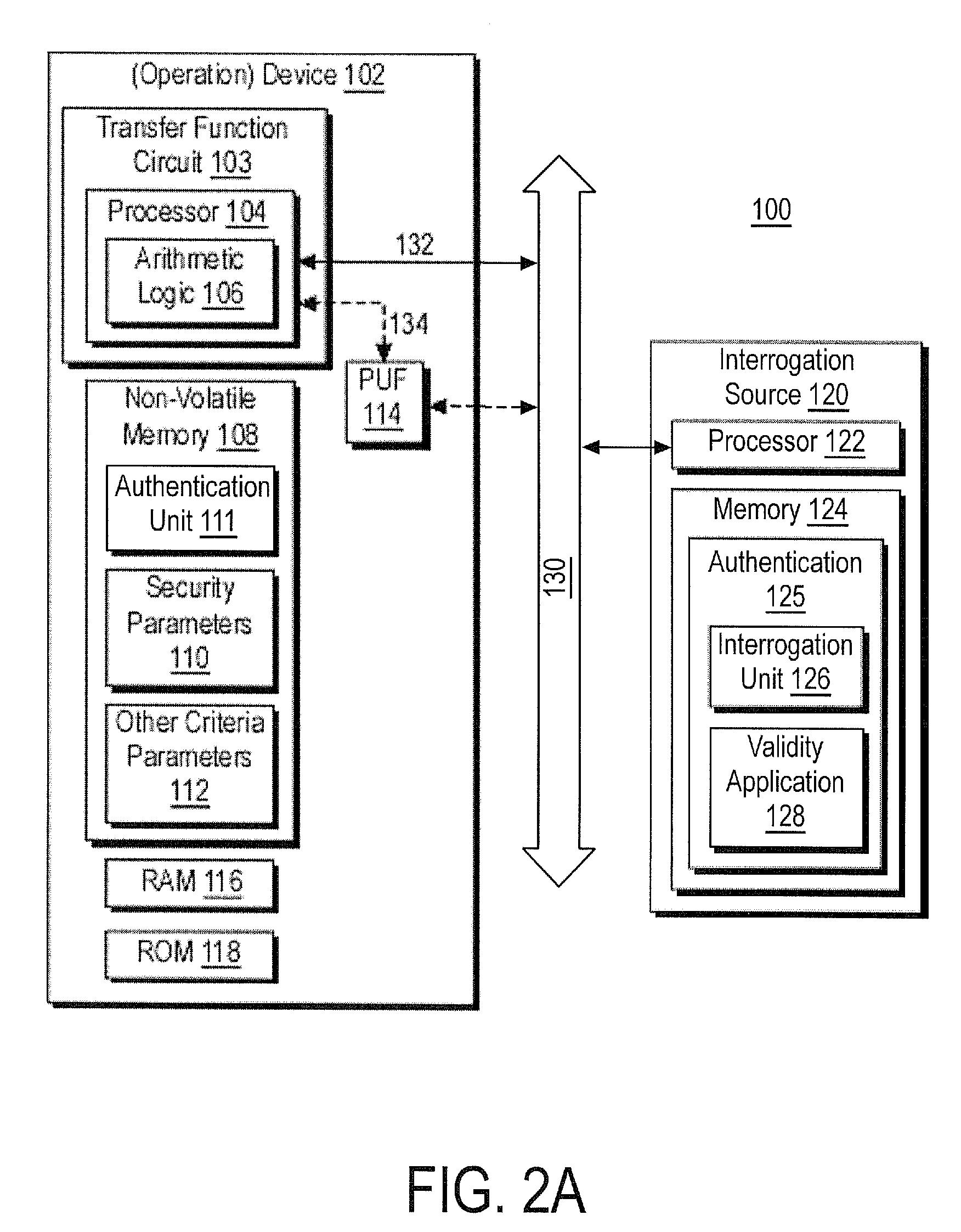
Trusted authentication digital signature (tads) system
Trusted entity authentication includes creating a public-private pair in a secure environment; storing the private key within a device during its manufacture in the secure environment; linking the public key with other information in the secure environment, receiving input within the device comprising verification data of an entity, identifying within the device a verification status based on the verification data and data prestored within the device; independent of the verification status identified, generating a digital signature for a message including an indication of the identified verification status using the private key; outputting the digital signature for transmission with an EC; identifying upon receipt of the EC the information linked with the public key by authenticating the message with the public key, and considering the identified information and the indicated verification status. The linked information includes device security aspects and the verification status regards entity authentication performed by the device.
Owner:FIRST DATA
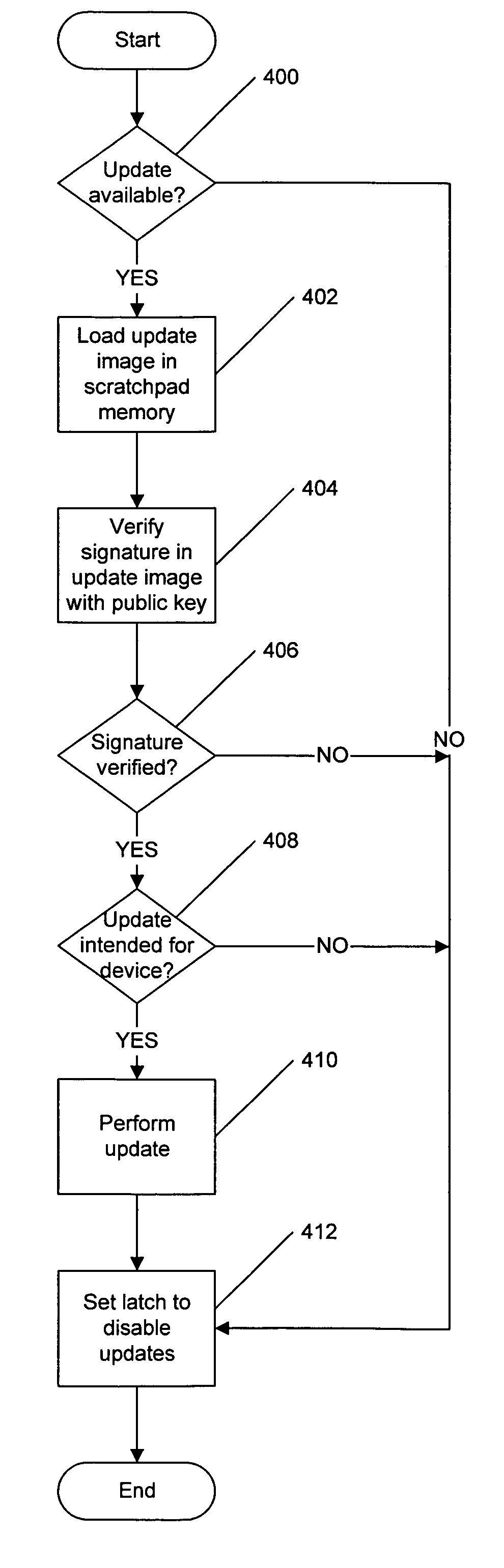
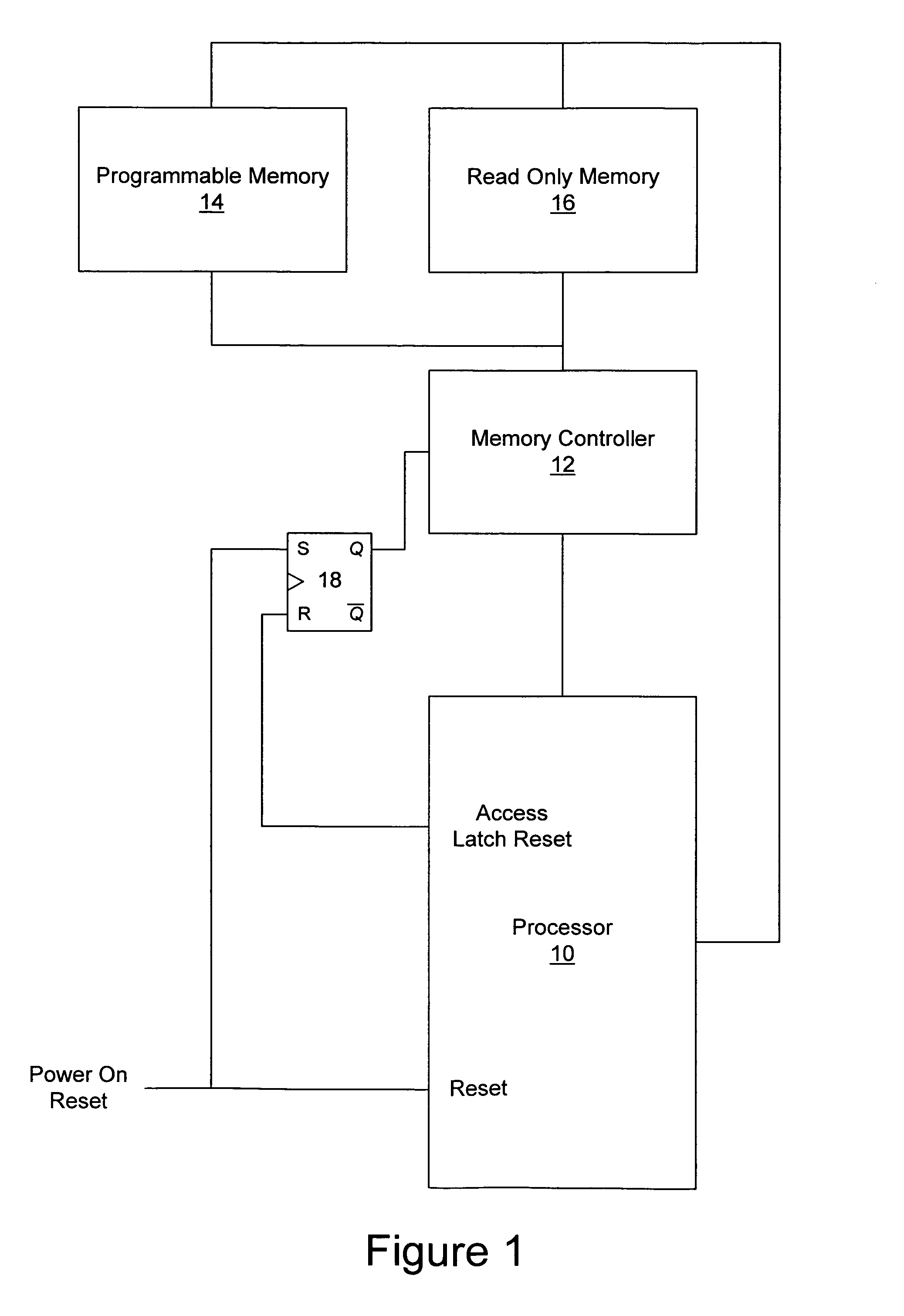
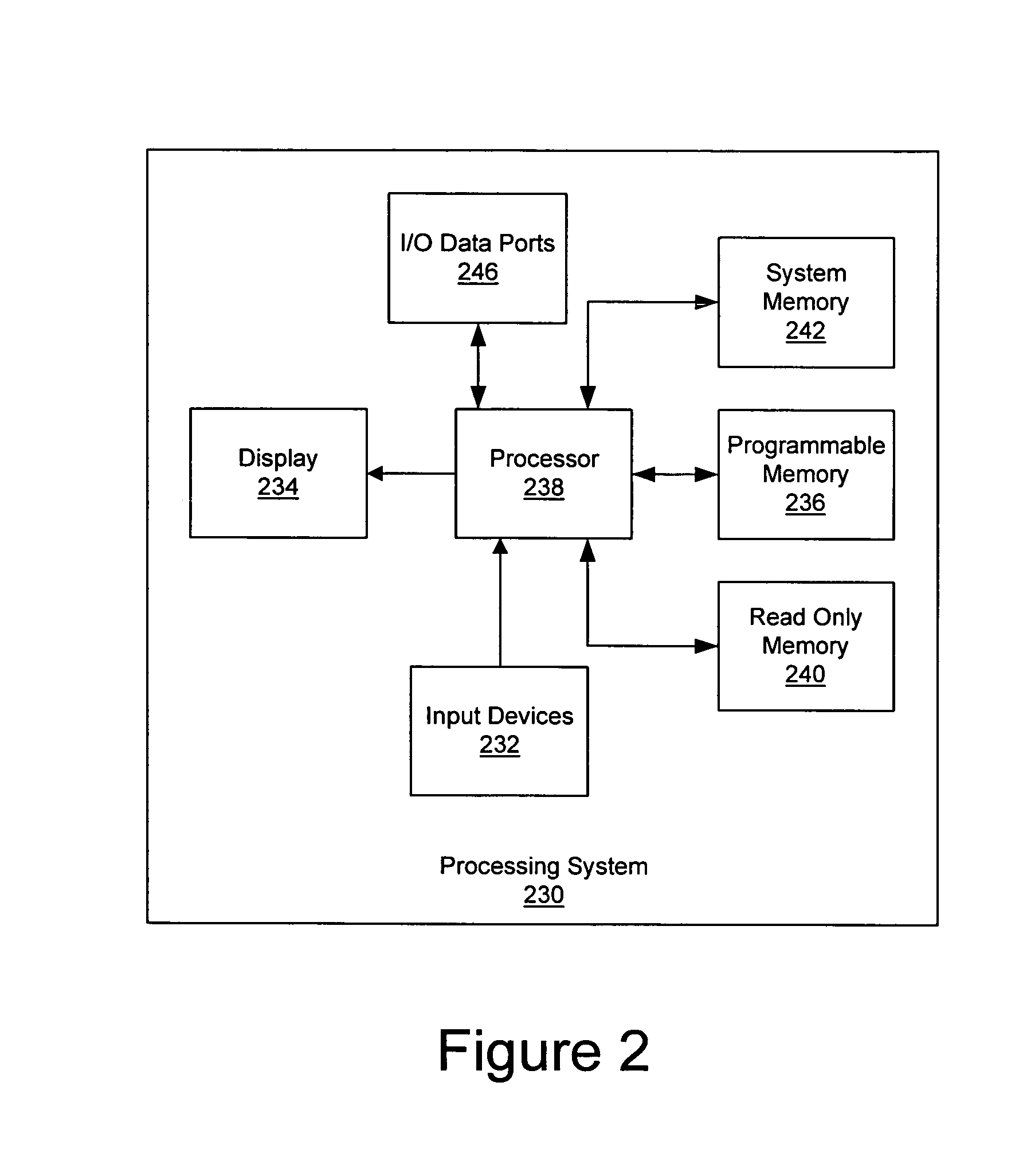
Methods, systems and computer program products for secure firmware updates
ActiveUS7069452B1Avoid accessReduce stepsDigital computer detailsUnauthorized memory use protectionData storeControl equipment
Methods, systems and computer program products which provide secure updates of firmware (i.e. data stored in a programmable memory device of a processing system) are disclosed. Updates of a programmable memory of a device may be controlled by providing an update window of finite duration during which the programmable memory may be updated. Access to the programmable memory may be based on the state of an access latch. The access latch may be set to allow access after a hardware reset of the device. An update control program may be executed to control access to the programmable memory and the latch reset to prevent access upon completion of the update control program. Verification of the update may be provided through encryption techniques and rules incorporated in certificates for application of updates to provide for selectively updating devices. Also disclosed are methods of securely providing differing functionality to generic devices.
Owner:IBM CORP
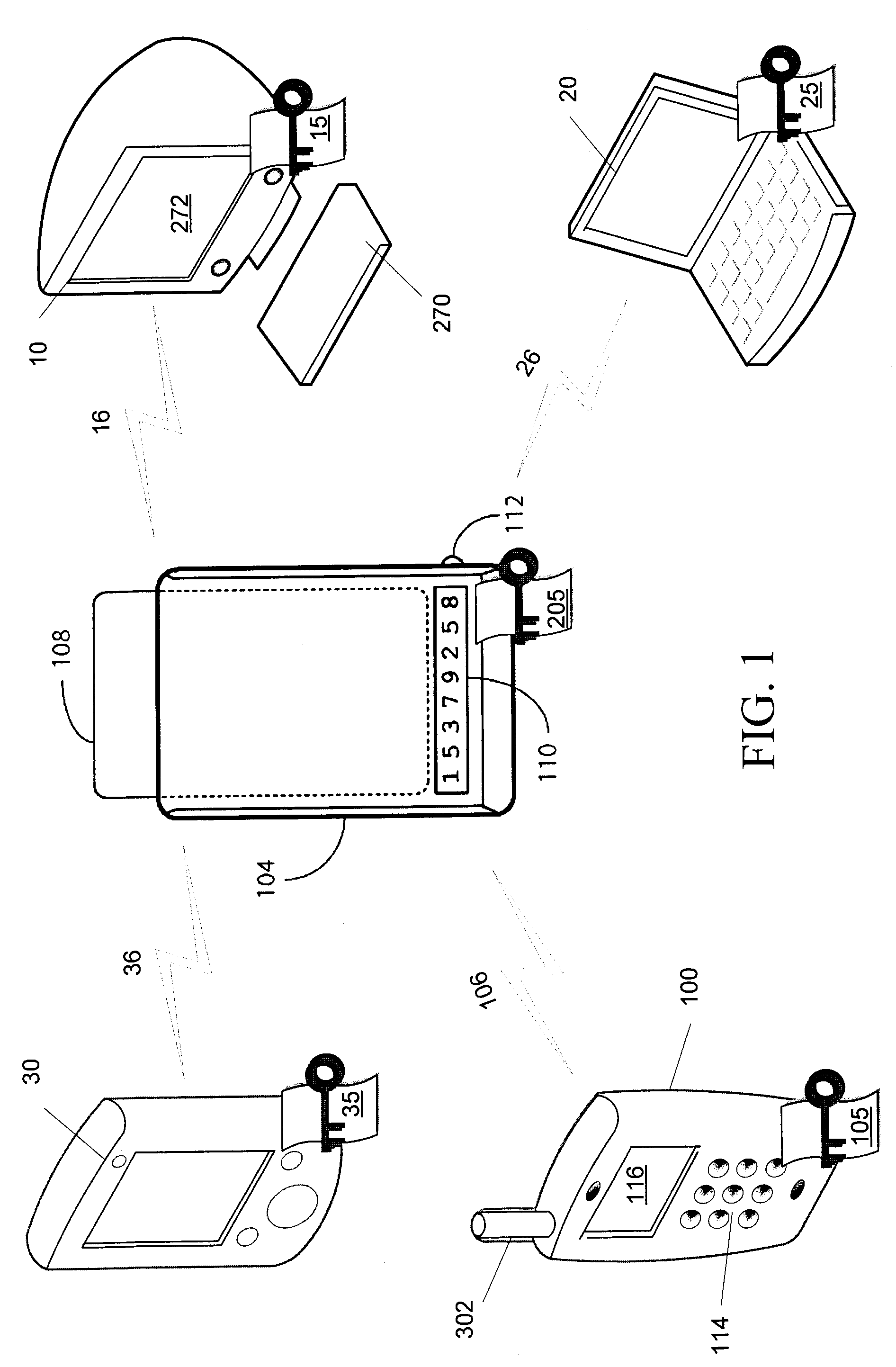
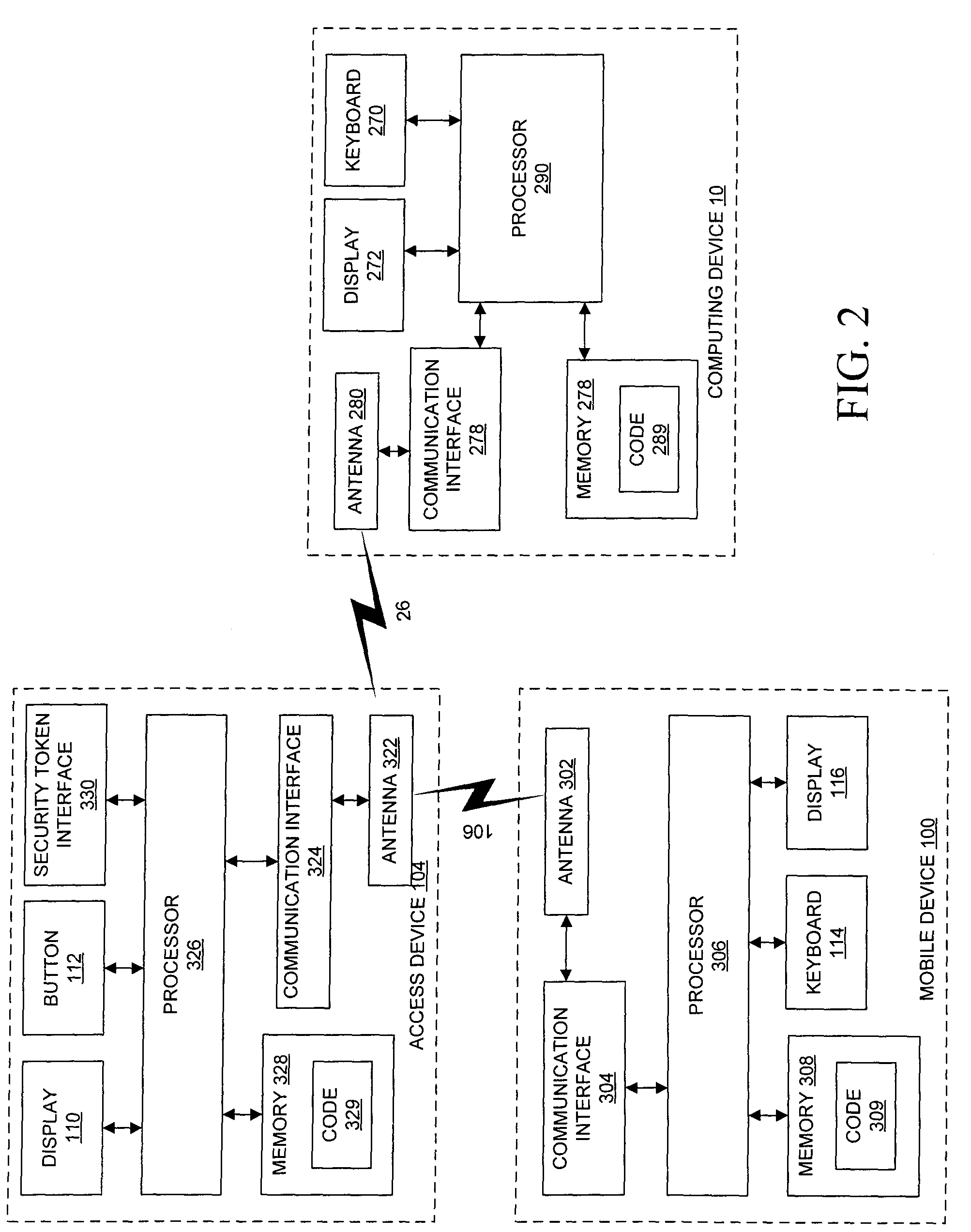
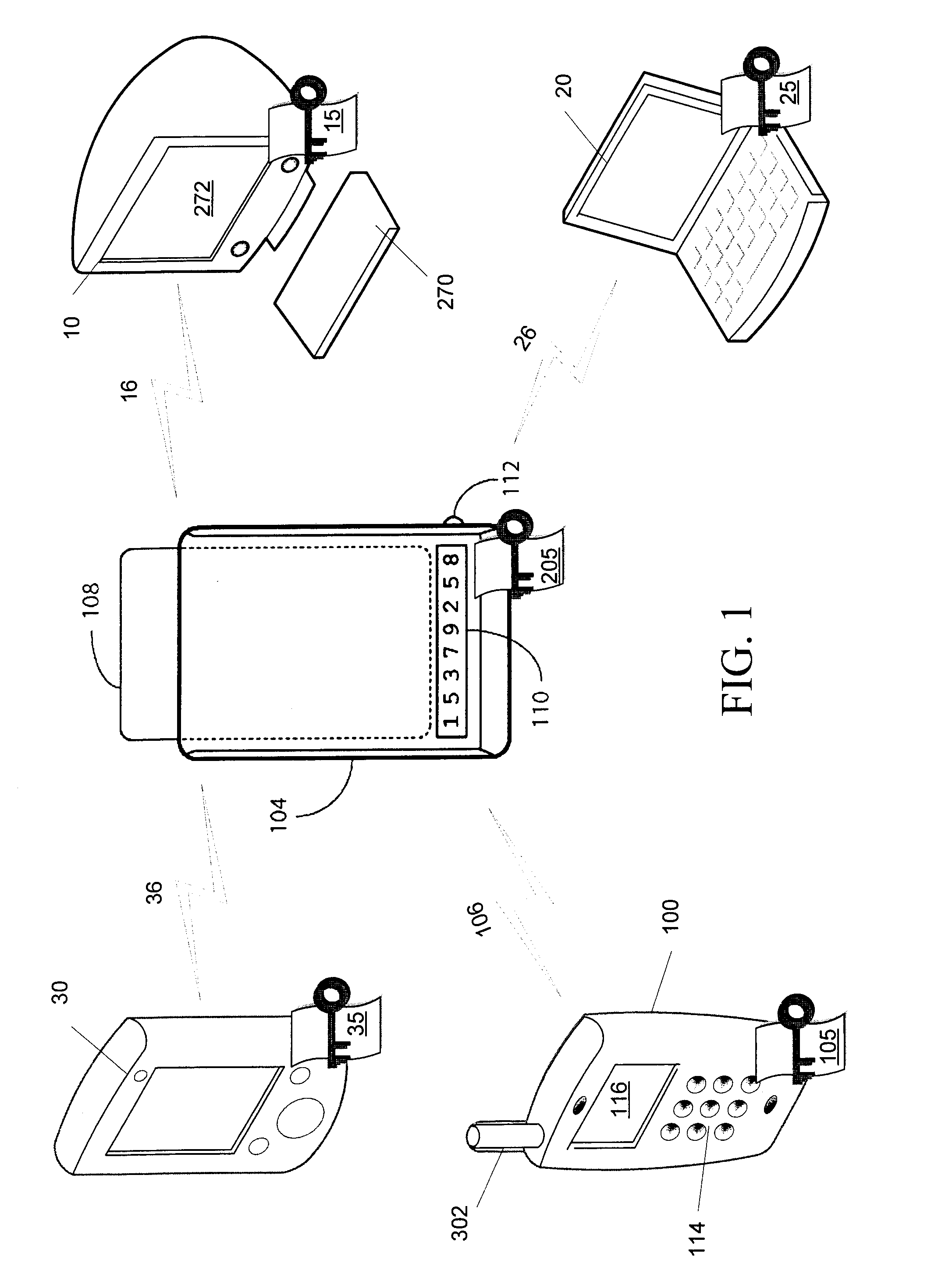
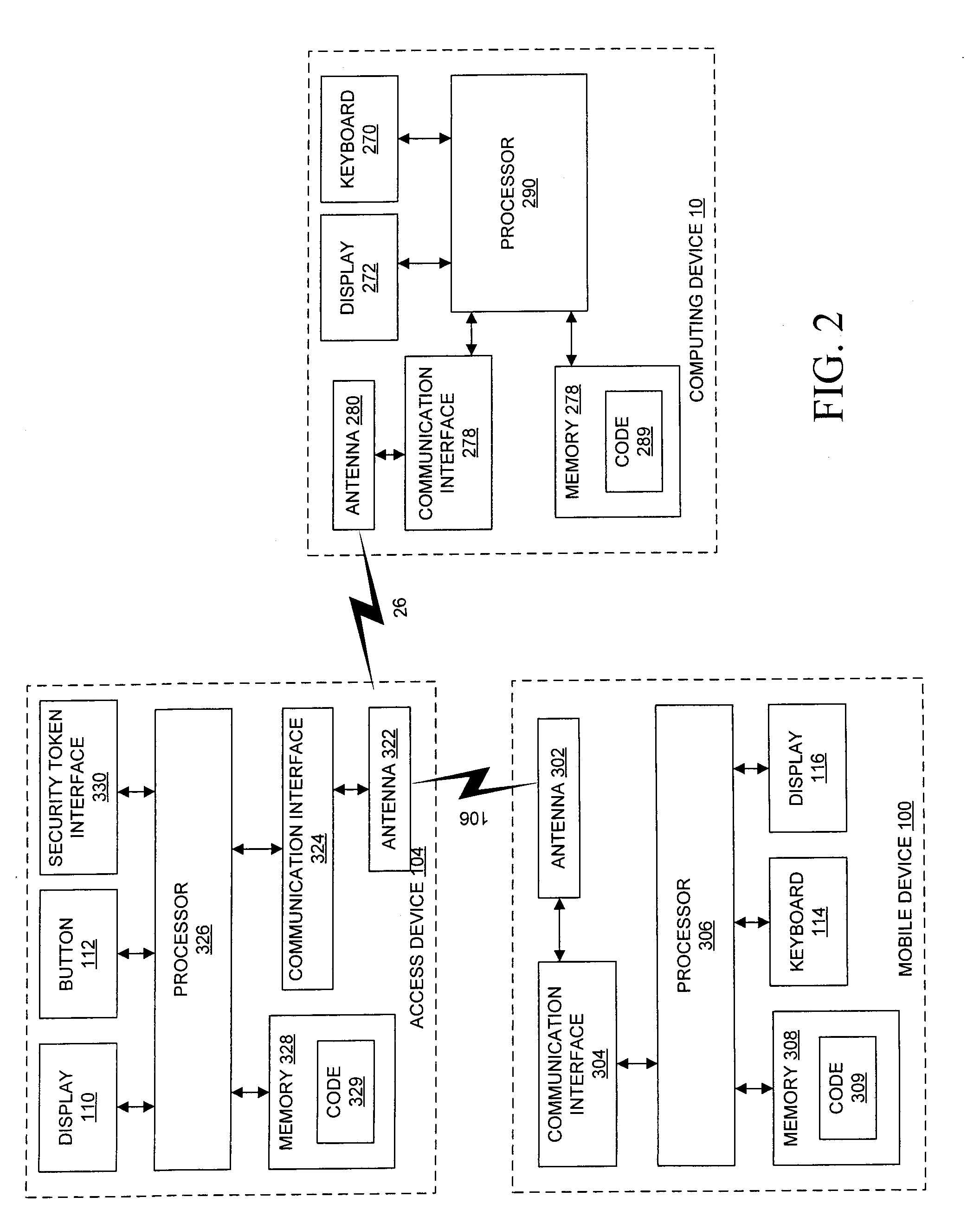
Management of multiple connections to a security token access device
ActiveUS20080016537A1Digital data processing detailsUnauthorized memory use protectionUser devicePairing
A security token access device, a user device such as a computing device or communications device, and a method for managing multiple connections between multiple user devices and the access device. The access device maintains connection information, including security information, for each user device securely paired with the access device. Each time a new user device is paired with the access device, the access device transmits a notification to the user devices already paired to the user device. A user may provide instructions to the access device to terminate a pairing with one of the user devices by overwriting at least a portion of the connection information associated with the designated user device. A user device may further request a listing of all user devices currently paired with the access device.
Owner:MALIKIE INNOVATIONS LTD
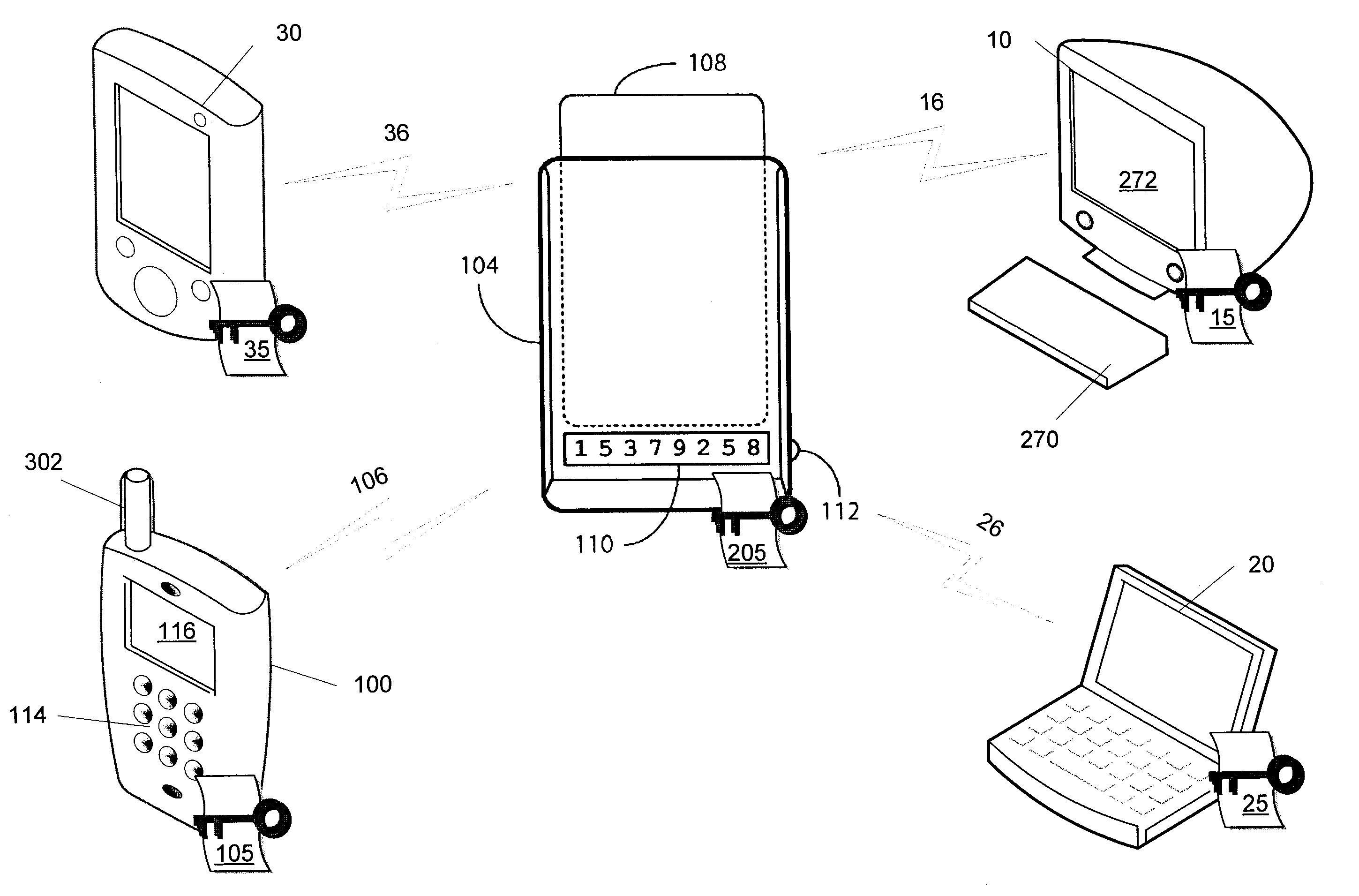
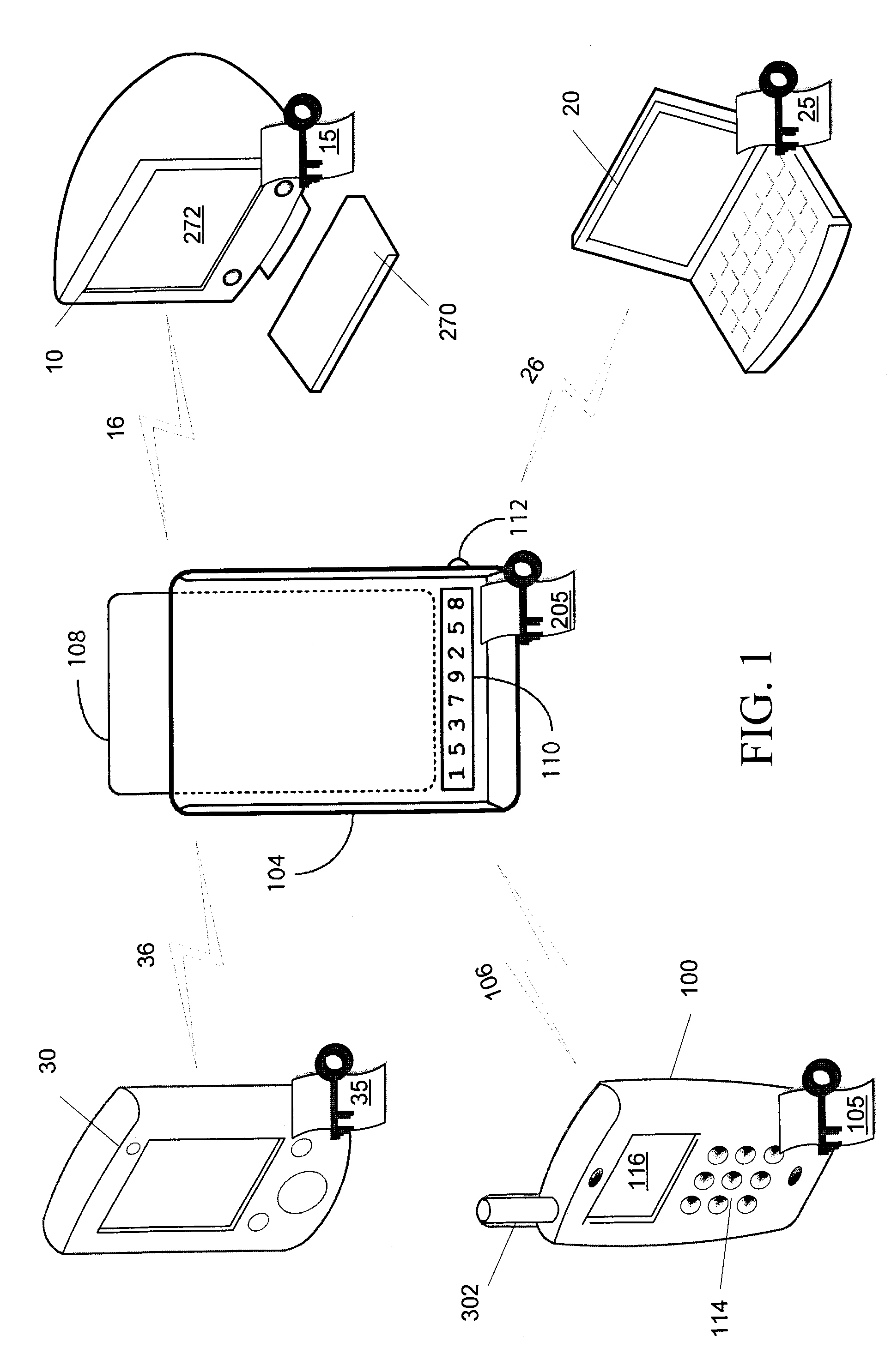
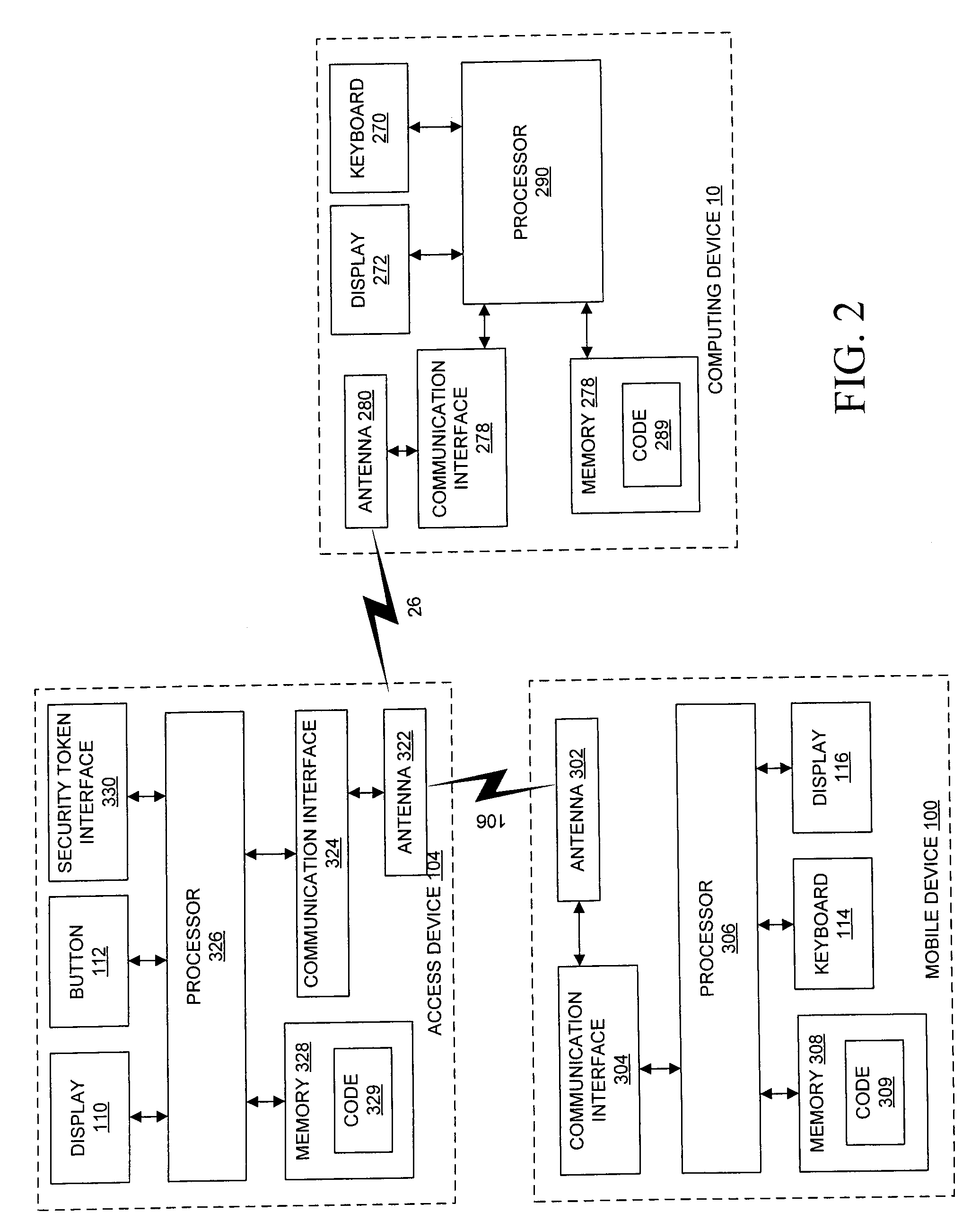
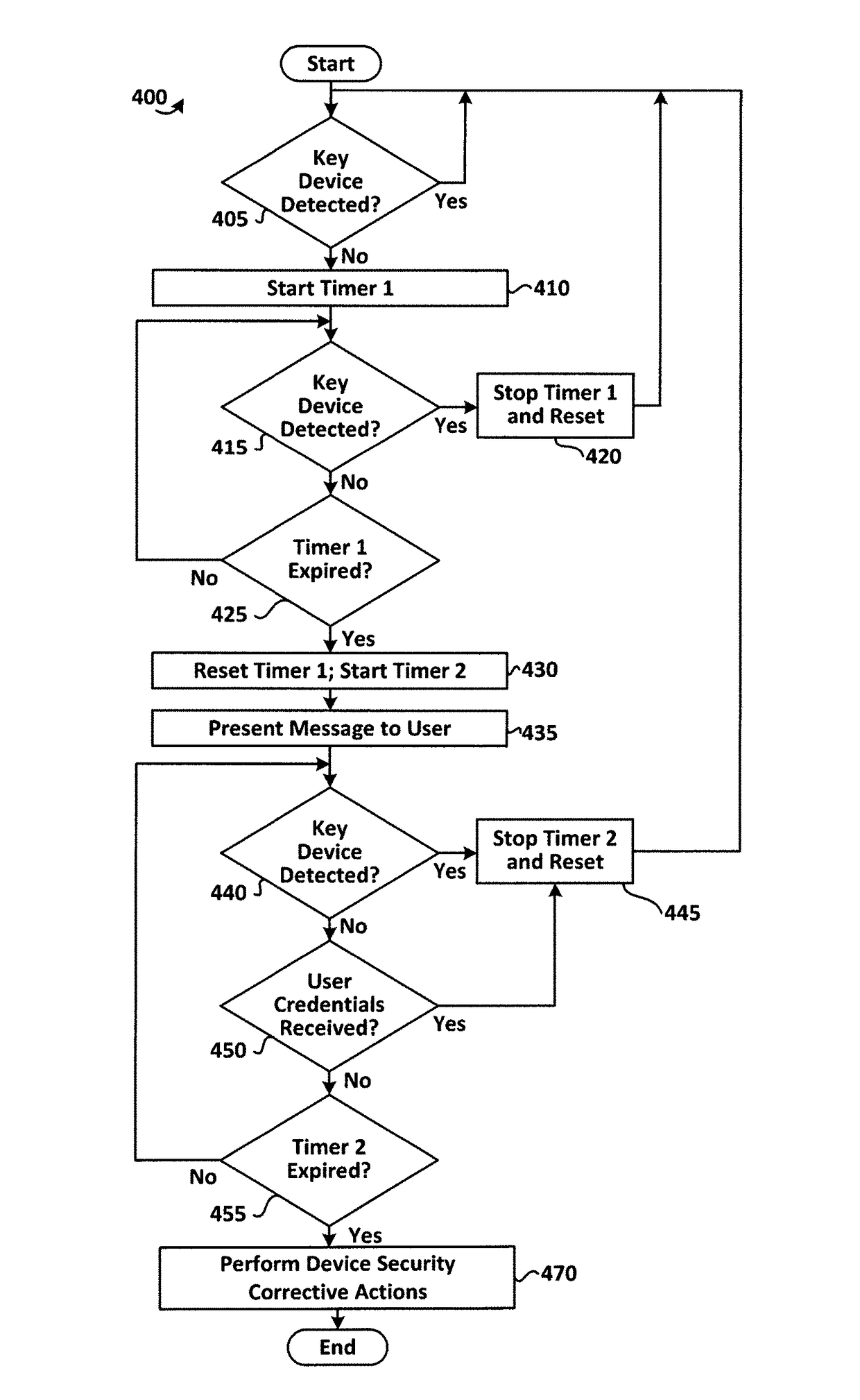
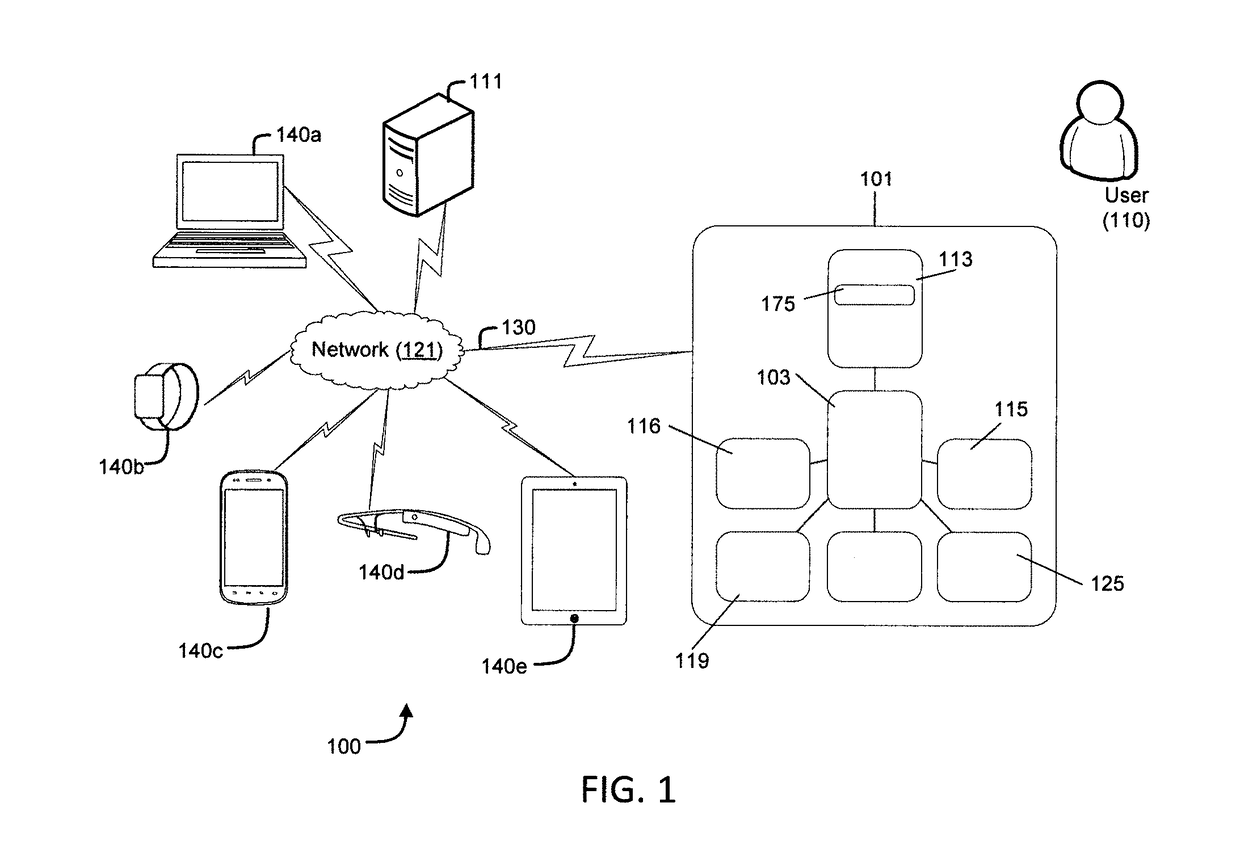
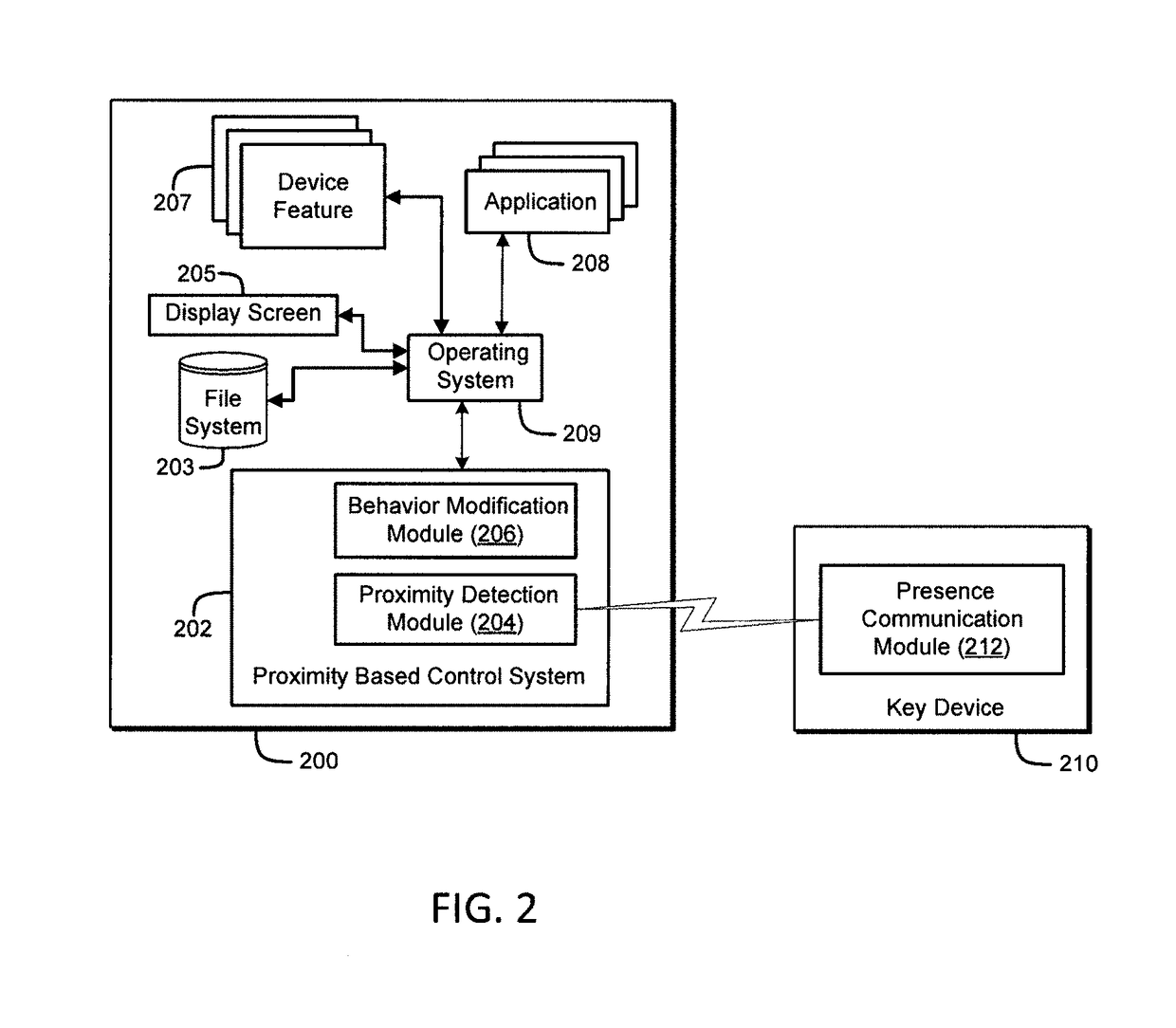
Method for performing device security corrective actions based on loss of proximity to another device
ActiveUS9763097B2Suppress lock mechanismImprove convenienceLocation information based serviceTransmissionComputer hardwareTime segment
The method disclosed herein provides for performing device security corrective action based on loss of proximity to another device, such as a key device. While a mobile communication device is locked, a mobile communication device determines whether or not a key device is within a specified distance. If the key device is not within the specified distance from the mobile communication device, a notification may be displayed on the mobile communication device. If a user responds to the notification, the user may prevent or alter the mobile communication device from performing at least one device security corrective action. If, however, the user does not respond to the notification within a specified time period, the at least one device security corrective action is performed on the mobile communication device.
Owner:LOOKOUT MOBILE SECURITY
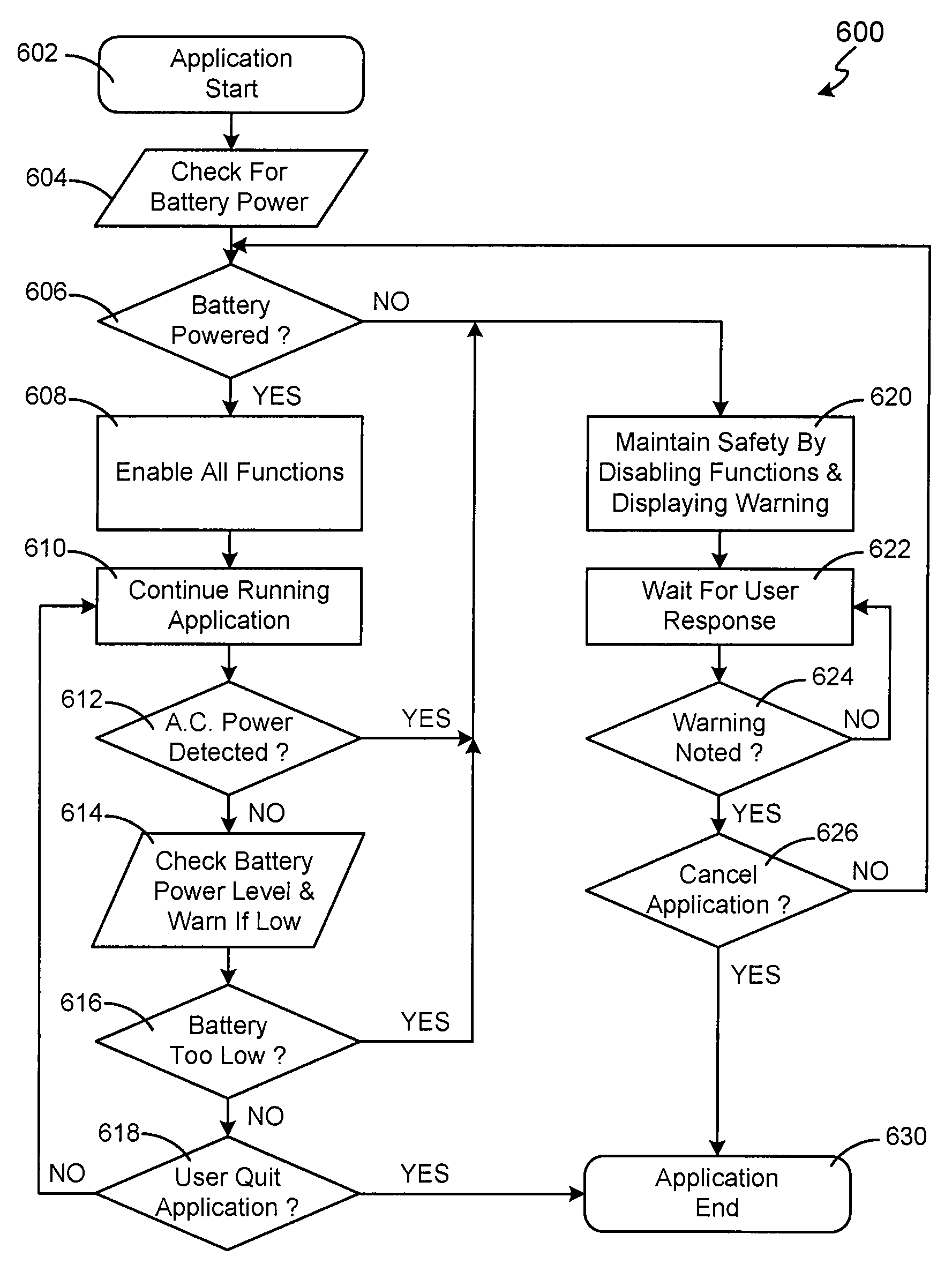
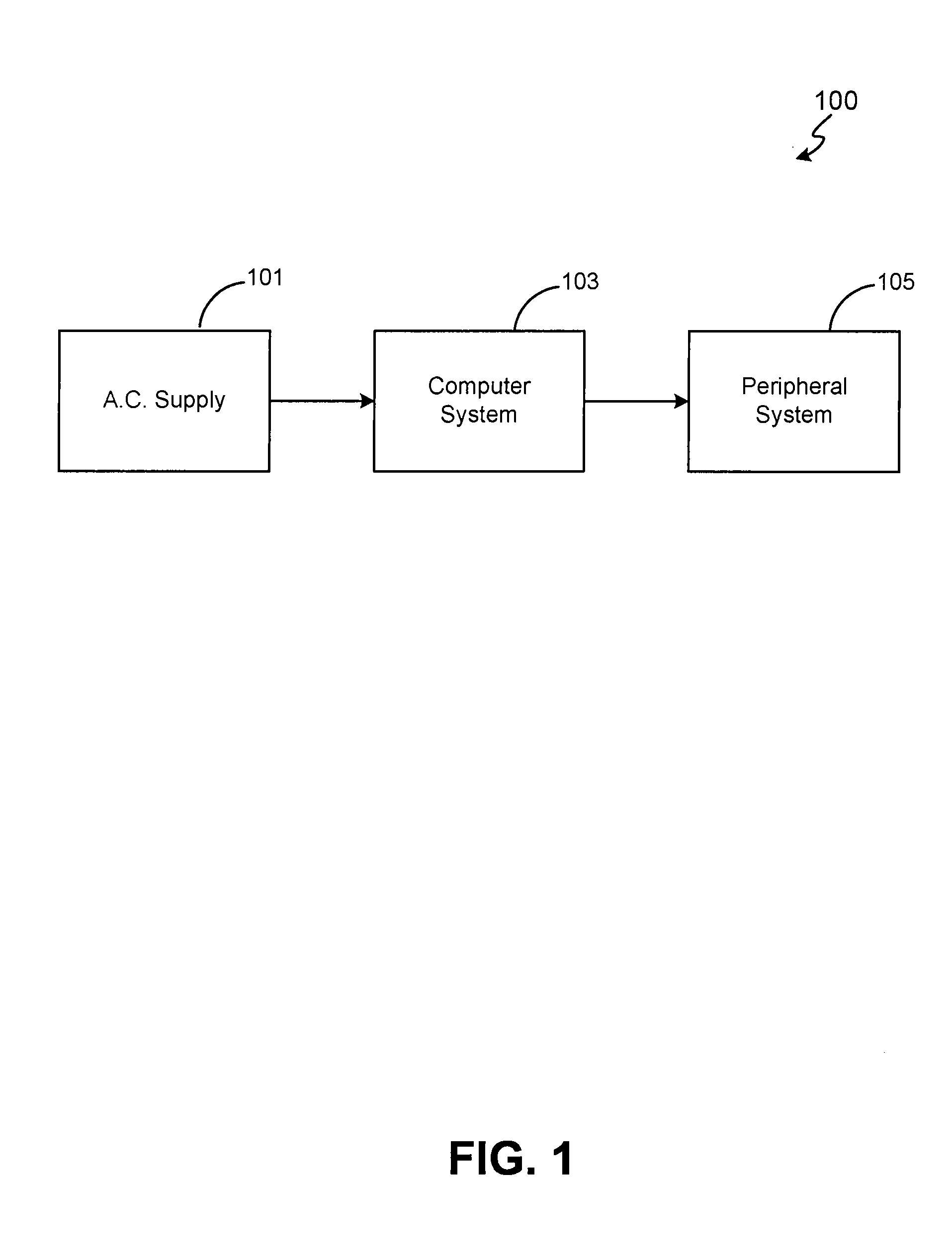
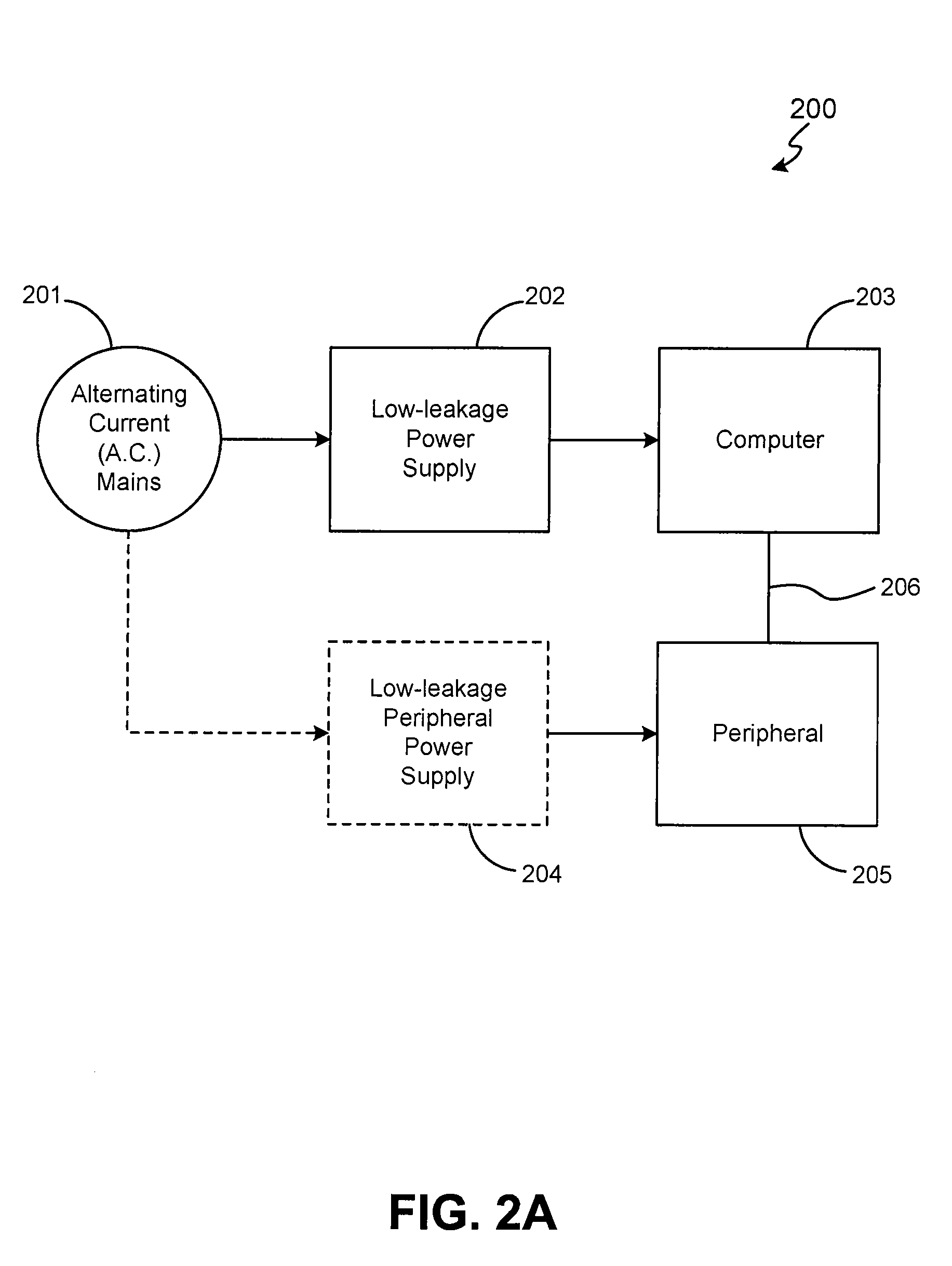
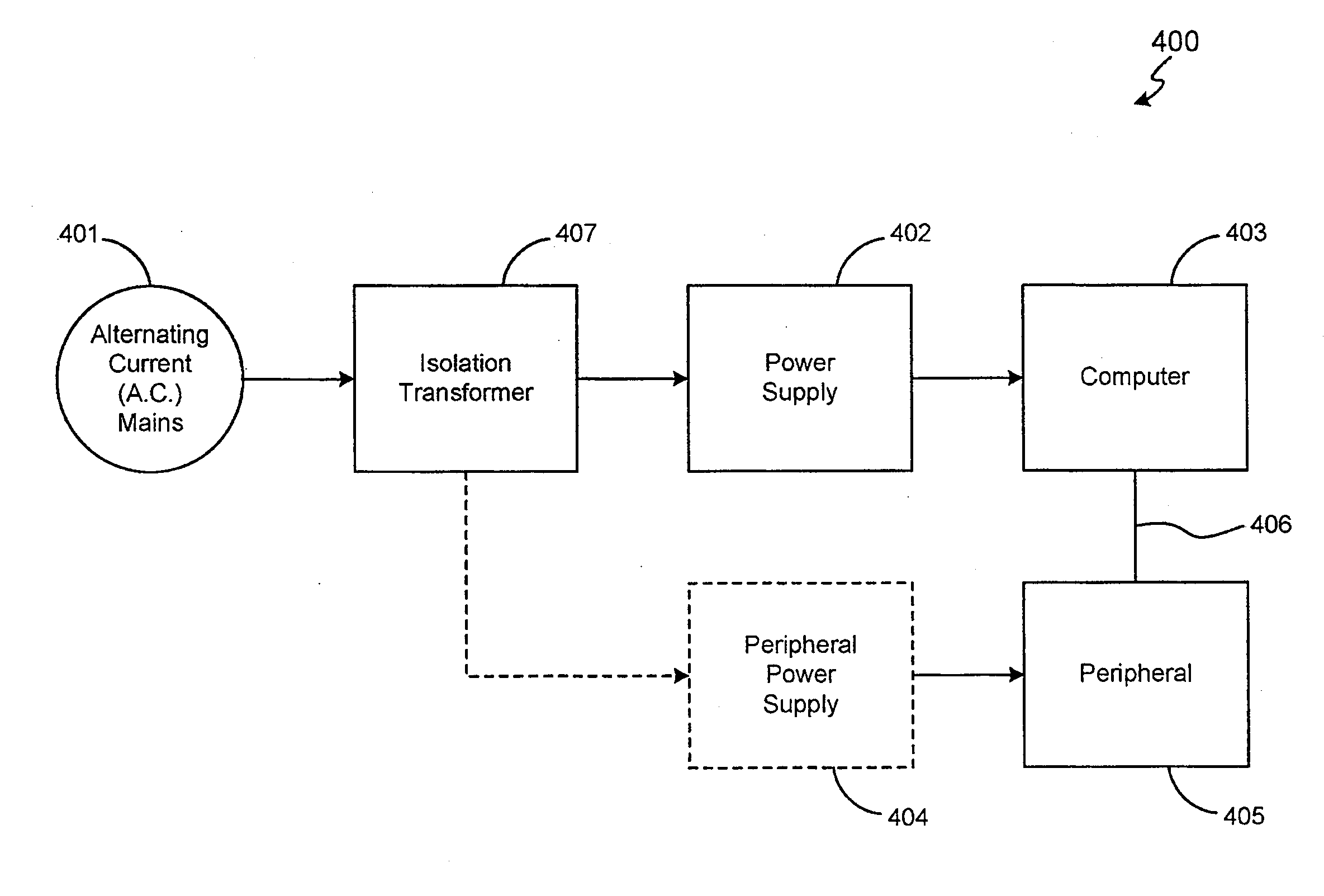
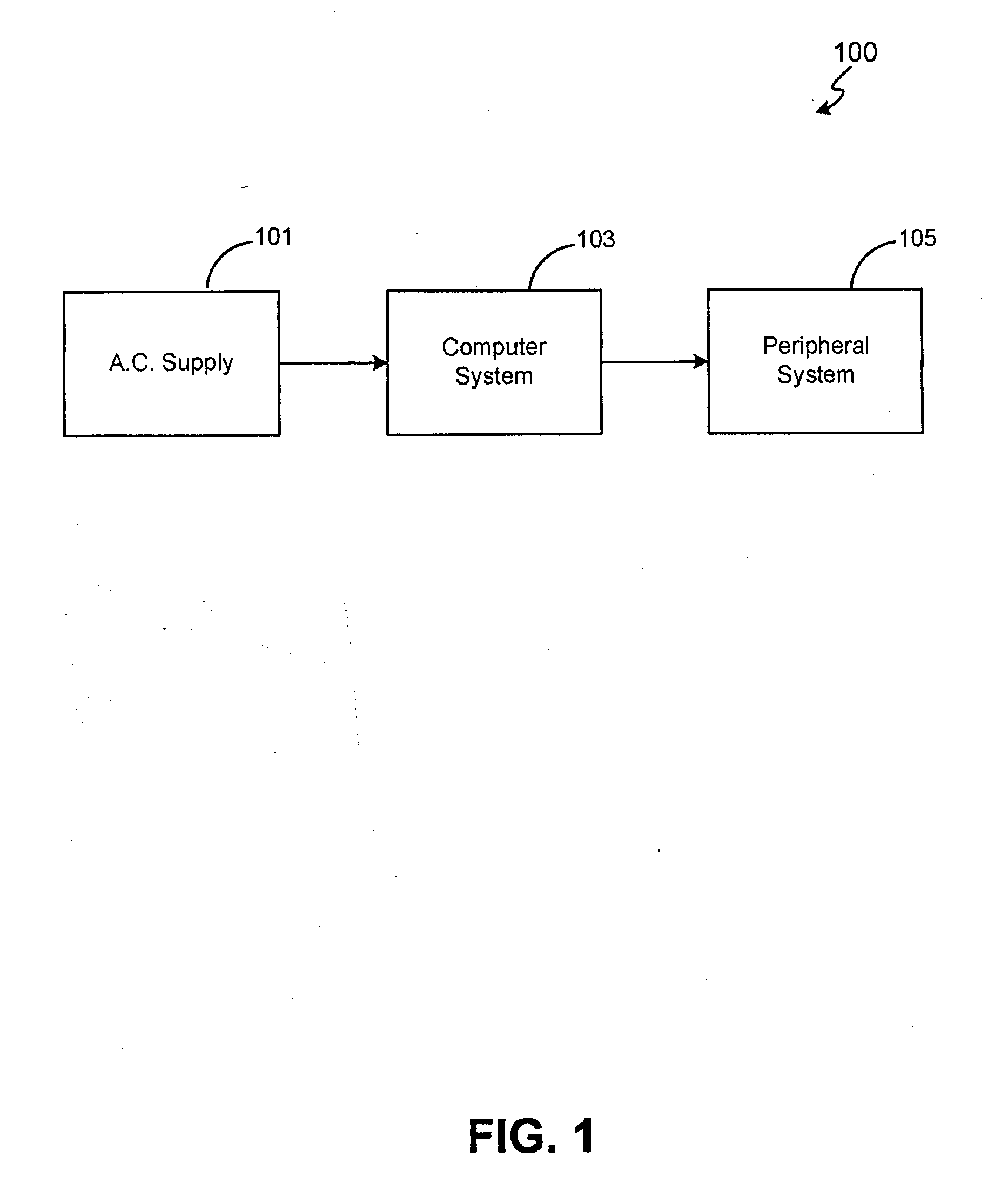
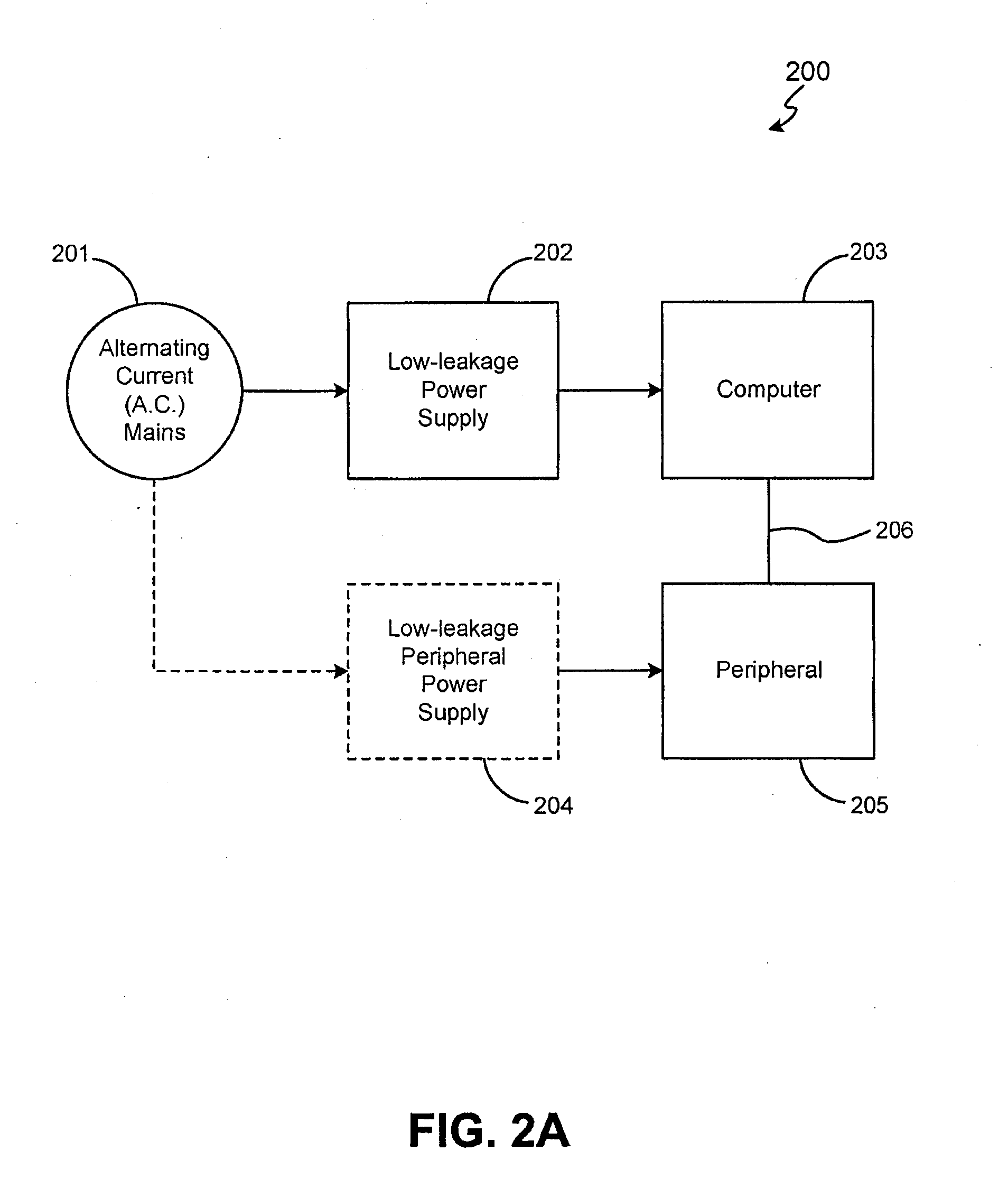
Method and system for enhancing safety with medical peripheral device by monitoring if host computer is AC powered
A method and system for enhancing computer peripheral safety is provided. In accordance with various aspects of the present invention, the exemplary method and system are configured to monitor and / or isolate alternating current (A.C.) supplies with and / or from any peripheral subsystems or devices. An exemplary method and system comprises an A.C. supply, a host computer system, and a peripheral subsystem or device connected to the host computer system, such as an ultrasound imaging and / or therapy peripheral, and an isolation subsystem configured for monitoring and / or isolating the A.C. supply from the peripheral subsystem or device. In accordance with an exemplary embodiment, an isolation subsystem comprises application software and associated modules and functions that when executed continuously monitors and / or polls the host computer's hardware and / or operating system for the presence of an isolated source, such as a battery, or an unisolated power source, such as through a battery charger and / or other connection path to the A.C. main supply. In accordance with other exemplary embodiments, an isolation subsystem can comprises a wireless or other safe / isolated electrical link for connecting a patient contact device, and / or a verification link or other verification mechanisms configured between an isolation transformer and host computer to monitor or observe usage to power the host computer and peripheral subsystem.
Owner:GUIDED THERAPY SYSTEMS LLC
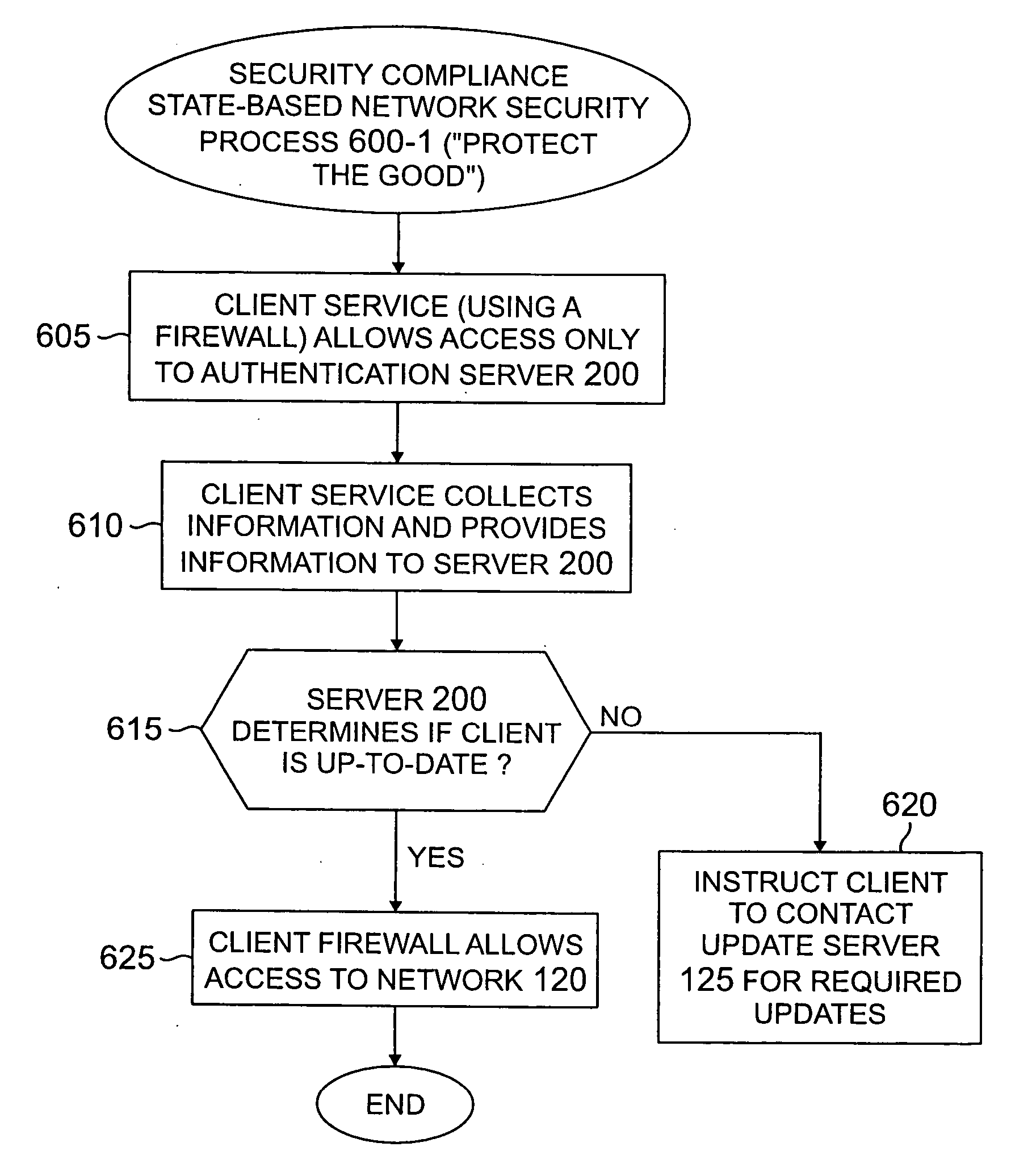
Method and apparatus for network security based on device security status
A method and apparatus are provided for network security based on a security status of a device. A security update status of a device is evaluated; and one or more of a plurality of security policies are selected to apply to the device based on the security update status. The available security philosophies may include, for example, a “protect the good” philosophy, an “encourage the busy” philosophy and a “shut off the non-compliant” philosophy. The security update status can evaluate, for example, a version level of one or more security features installed on the device or can be based on a flag indicating whether the device satisfies predefined criteria for maintaining one or more computer security protection features up-to-date.
Owner:AVAYA INC
Portable keying device and method
A portable encryption key installation system is disclosed that includes a portable keying device for installing a data communications encryption key in an electronic terminal. The portable keying device securely reprograms the encryption key in the electronic terminal without having to remove the terminal from its shipping container or ship the electronic terminal offsite. Furthermore, the portable keying device securely reprograms the encryption key in the electronic terminal without having to dismantle the terminal, deactivate any anti-tampering features, or re-bond the terminal.
Owner:HAND HELD PRODS
System for distributed intelligent remote sensing systems
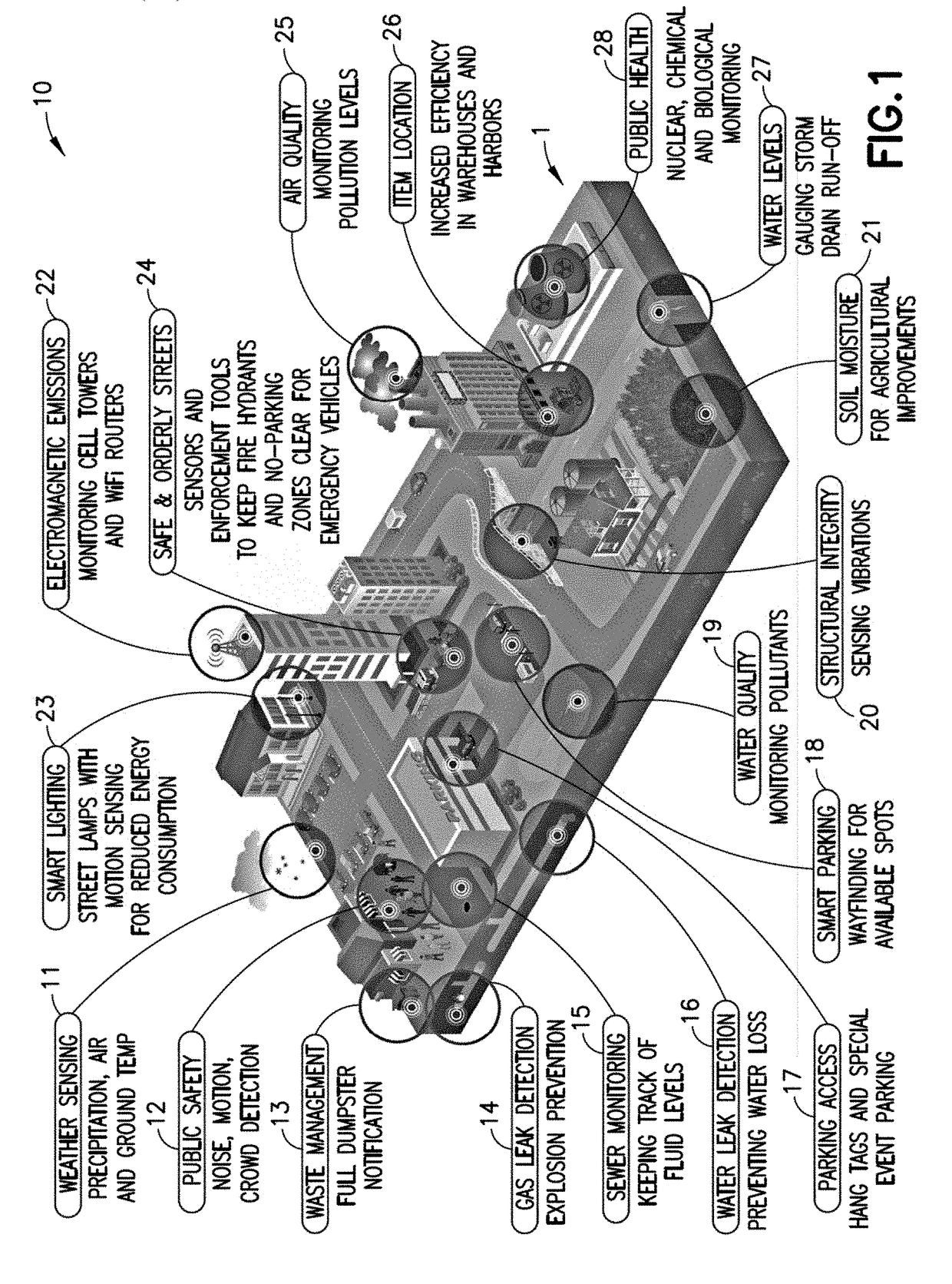
ActiveUS20180054490A1Detection of traffic movementPosition fixationDistributed intelligenceSystem of systems
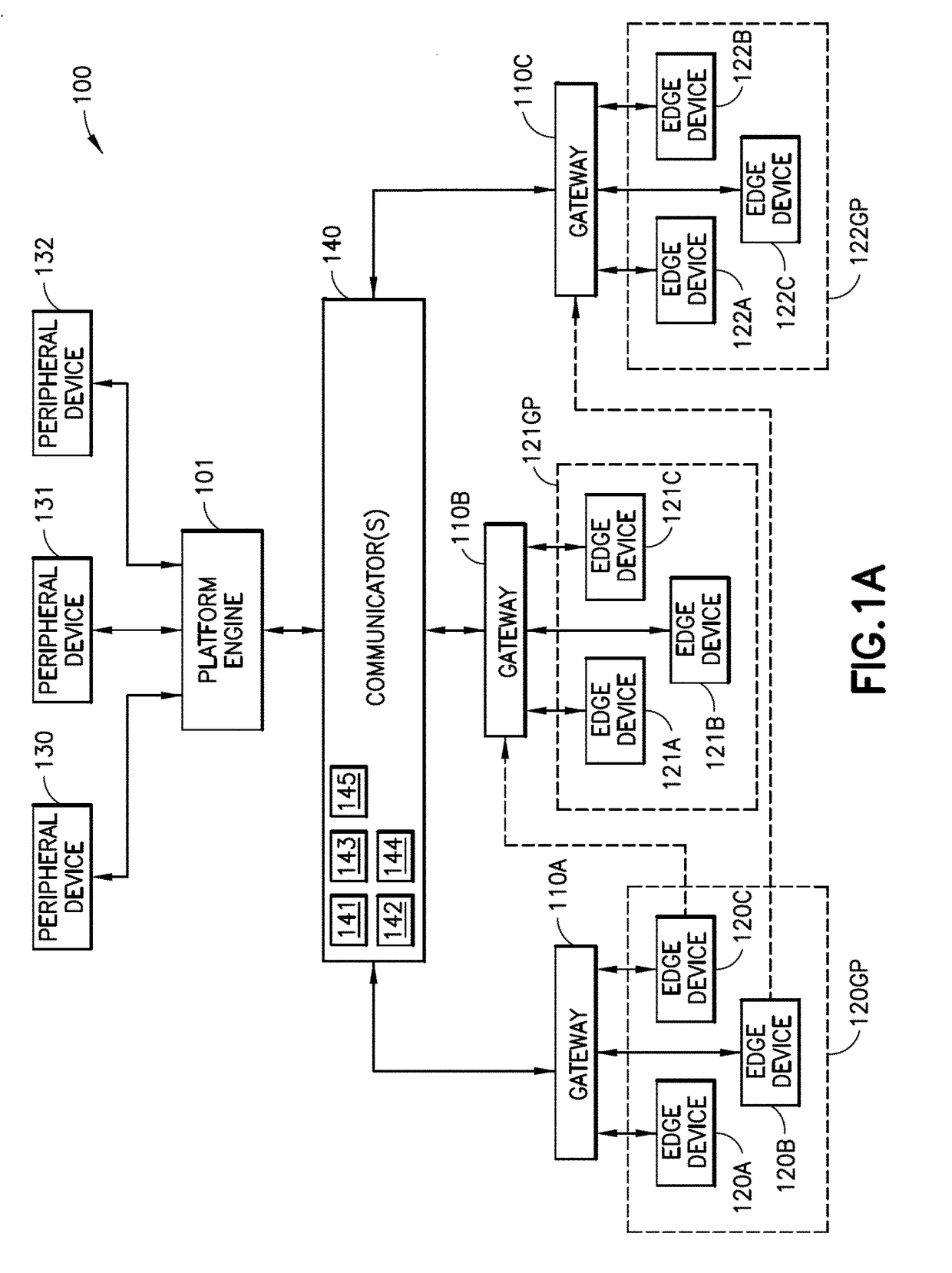
An Internet of things (IoT) system, including a distributed system of virtual machines, includes at least one IoT platform system control engine, that includes a platform system control engine secure system space and a IoT platform system control engine user defined space, at least one network node device that includes a network node device secure system space and an IoT network node device user defined space, and at least one edge device that includes an edge device secure system space and an edge device user defined space, where the secure system space of the control engine, the network node device, and the edge device are each configured to be secured to prevent unauthorized access, and the user defined spaces of the platform system control engine, the network node device and the edge device each define a respective virtual machine.
Owner:FYBR
A system and method for dynamic fob synchronization and personalization
InactiveUS20050033689A1Digital data processing detailsPayment architecturePersonalizationData synchronization
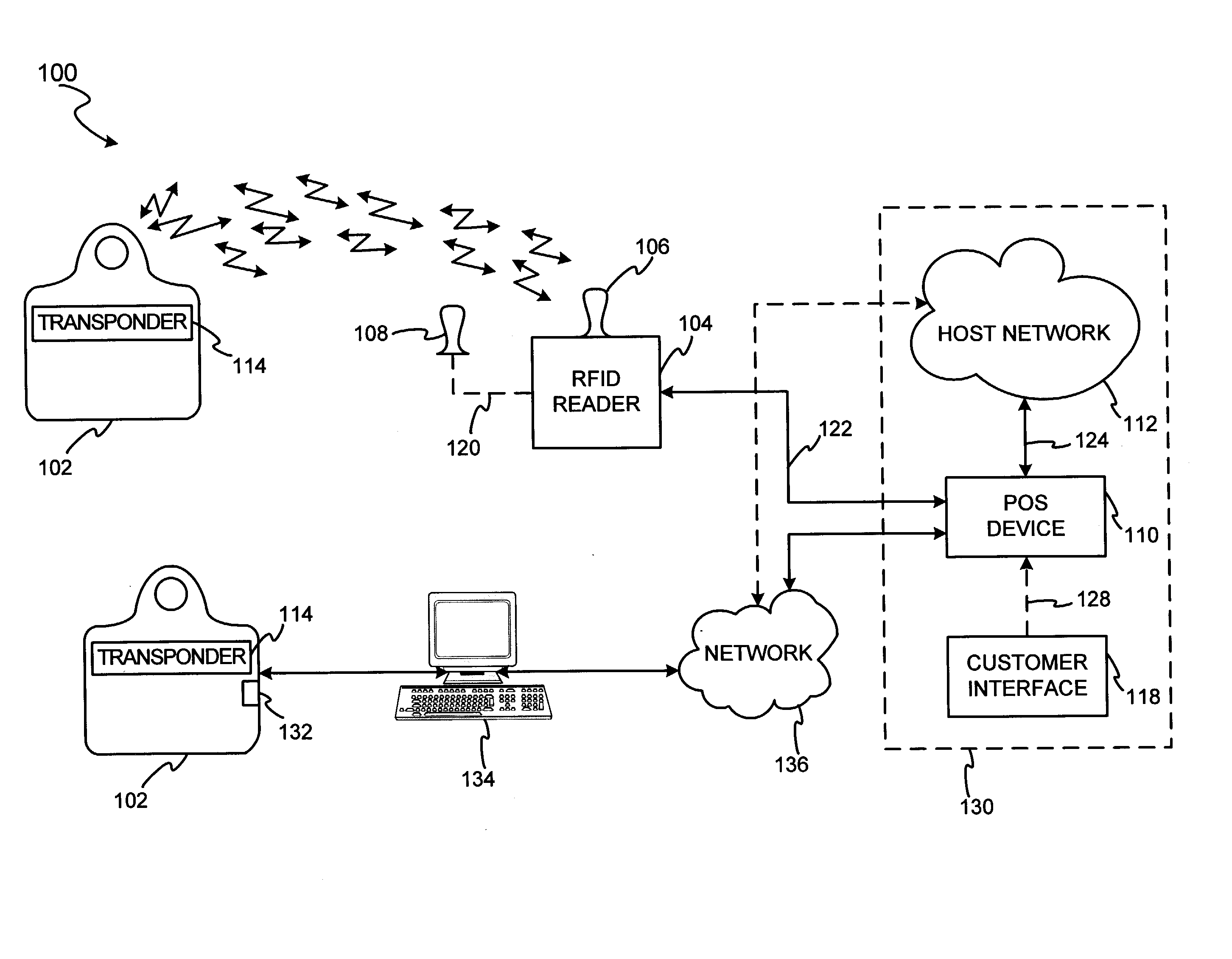
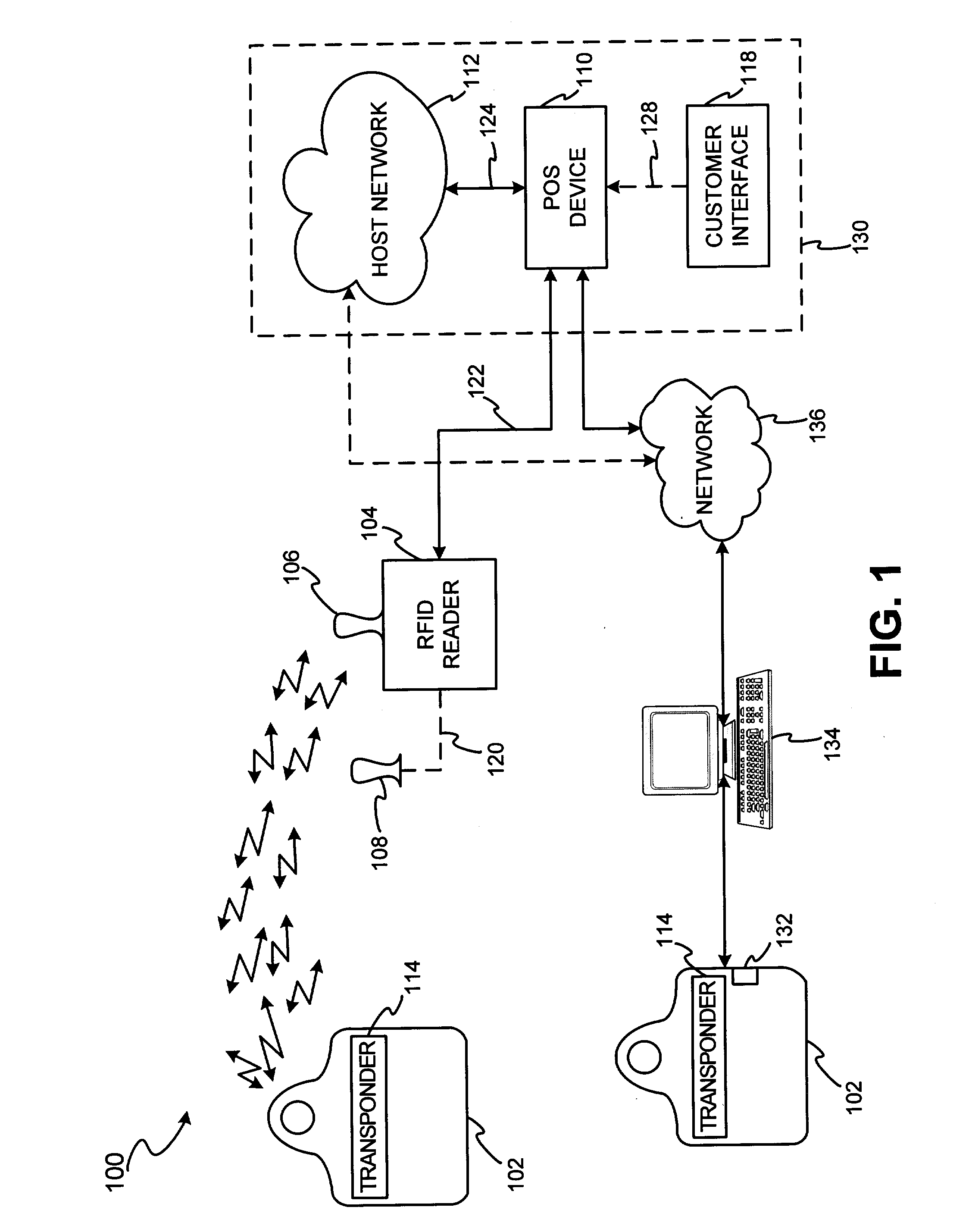
A system generally for personalizing and synchronizing fob data in the context of a distributed transaction system is disclosed. A dynamic fob synchronization system may comprise point of service (POS) devices configured with transponder-readers to initiate a transaction in conjunction with a fob, an enterprise data collection unit, and a fob object database update system. An exemplary dynamic synchronization system (DSS) may comprise various fob POS devices, a secure support client server, a fob object database update system (FODUS), one or more enterprise data synchronization interfaces (EDSI), an update logic system, one or more enterprise data collection units (EDCUs), and one or more fob POS devices configured to interoperably accept and interface with fobs. In an exemplary embodiment, DSS may comprise a personalization system and an account maintenance system configured to communicate with FODUS. Personalization of multi-function fobs may be accomplished using a security server configured to generate and / or retrieve cryptographic key information from multiple enterprise key systems during the final phase of the fob issuance process.
Owner:LIBERTY PEAK VENTURES LLC
Method and system for enhancing computer peripheral safety
A method and system for enhancing computer peripheral safety is provided. In accordance with various aspects of the present invention, the exemplary method and system are configured to monitor and / or isolate alternating current (A.C.) supplies with and / or from any peripheral subsystems or devices. An exemplary method and system comprises an A.C. supply, a host computer system, and a peripheral subsystem or device connected to the host computer system, such as an ultrasound imaging and / or therapy peripheral, and an isolation subsystem configured for monitoring and / or isolating the A.C. supply from the peripheral subsystem or device. In accordance with an exemplary embodiment, an isolation subsystem comprises application software and associated modules and functions that when executed continuously monitors and / or polls the host computer's hardware and / or operating system for the presence of an isolated source, such as a battery, or an unisolated power source, such as through a battery charger and / or other connection path to the A.C. main supply. In accordance with other exemplary embodiments, an isolation subsystem can comprises a wireless or other safe / isolated electrical link for connecting a patient contact device, and / or a verification link or other verification mechanisms configured between an isolation transformer and host computer to monitor or observe usage to power the host computer and peripheral subsystem.
Owner:GUIDED THERAPY SYSTEMS LLC
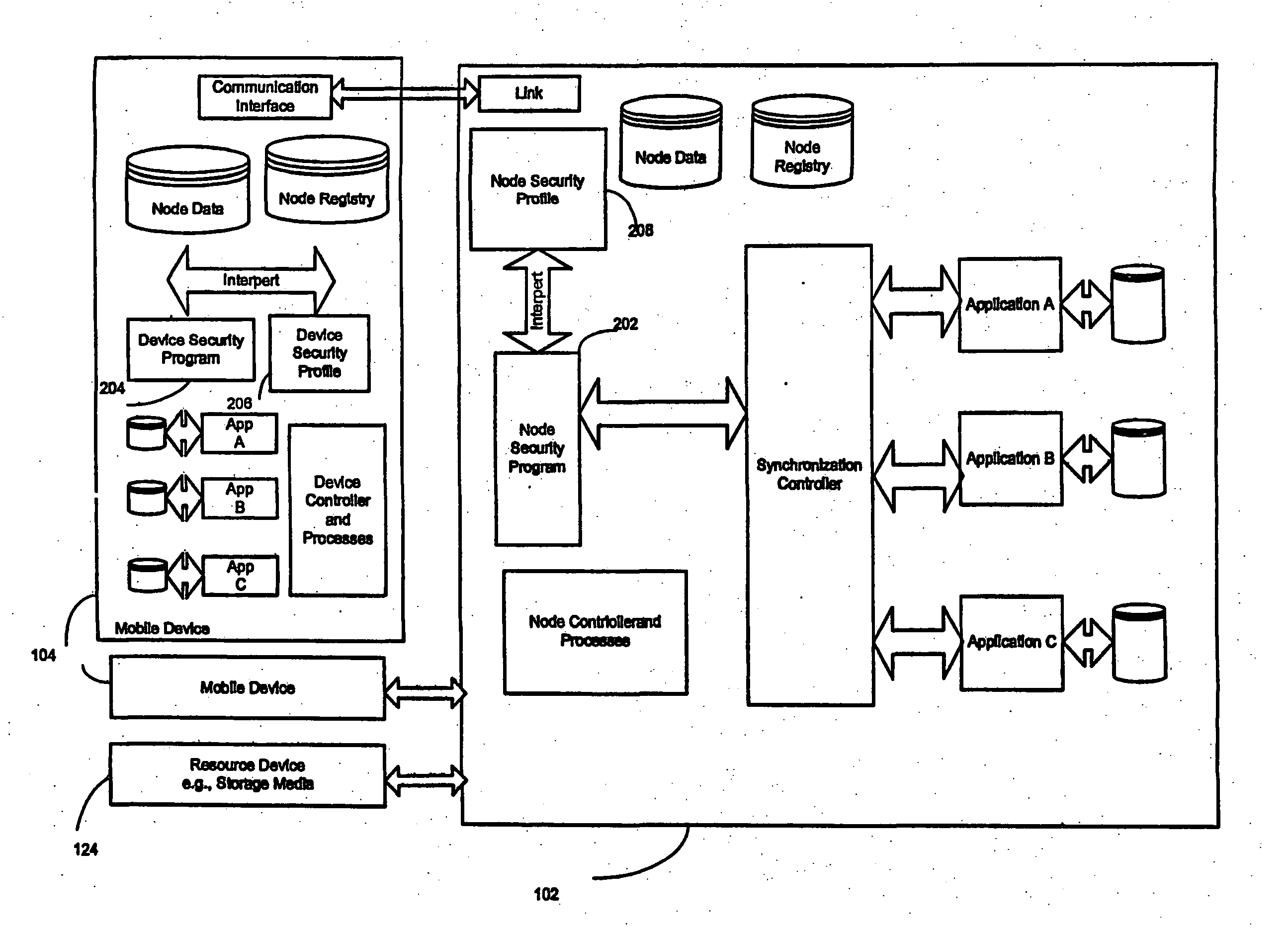
Enterprise-wide security system for computer devices
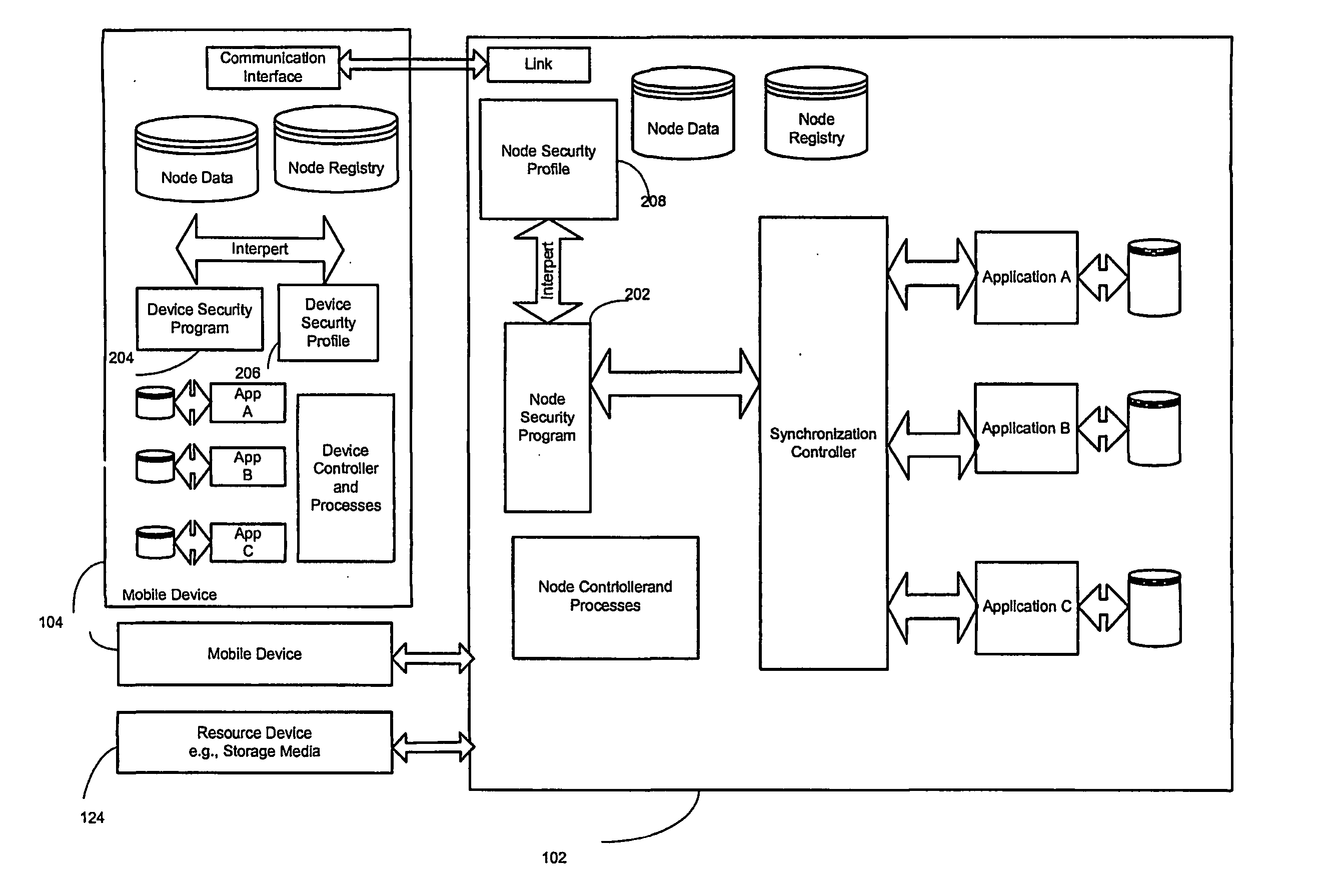
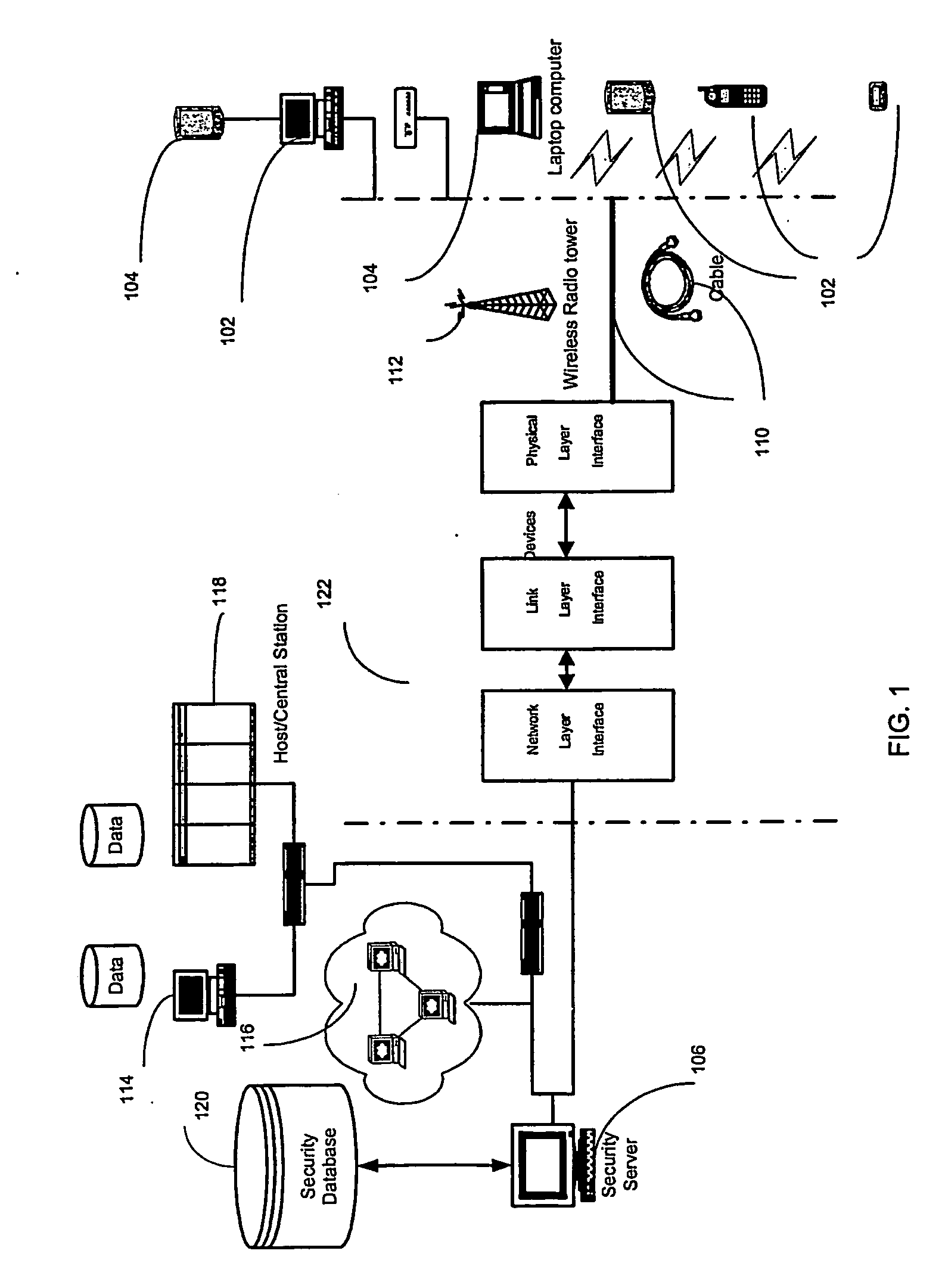
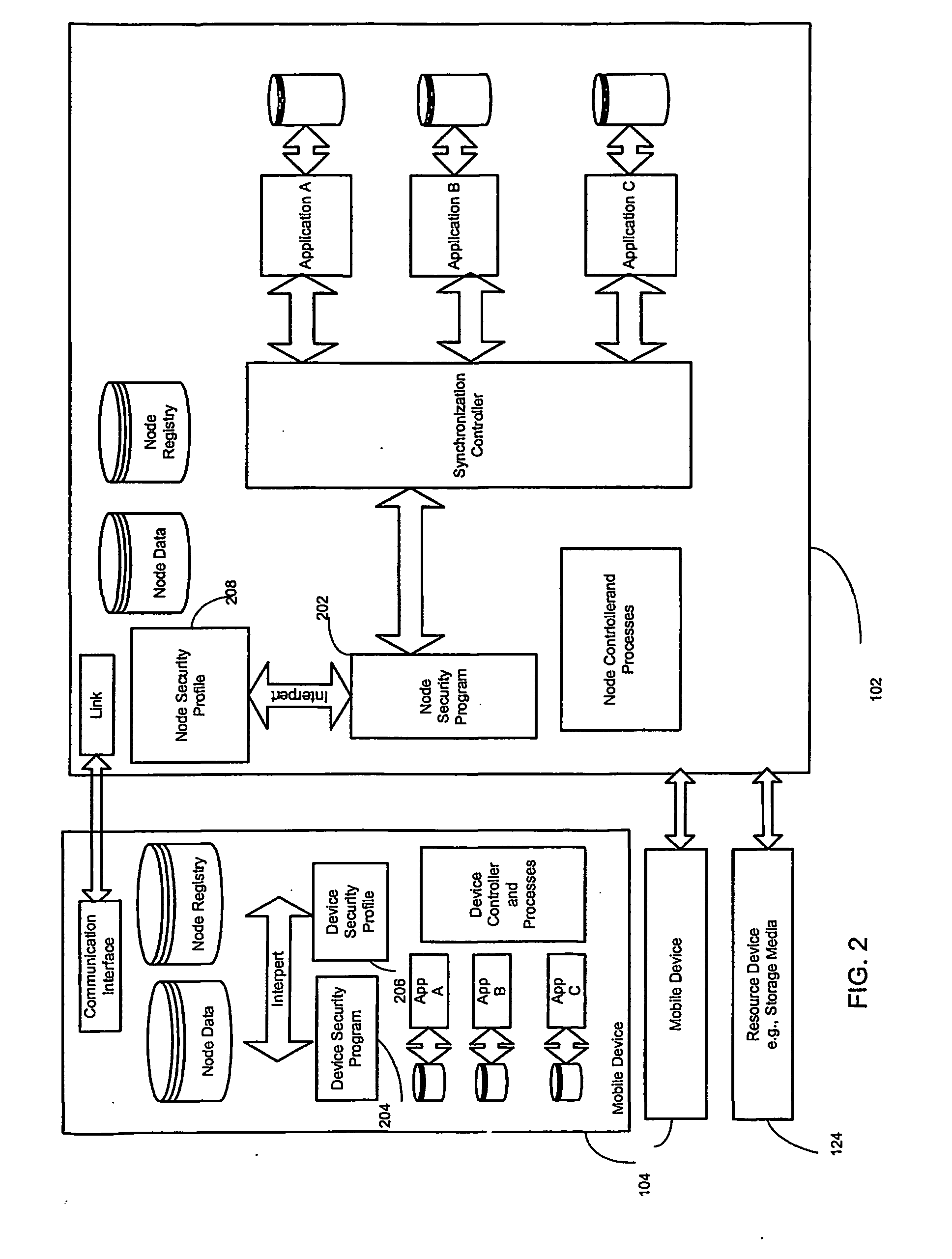
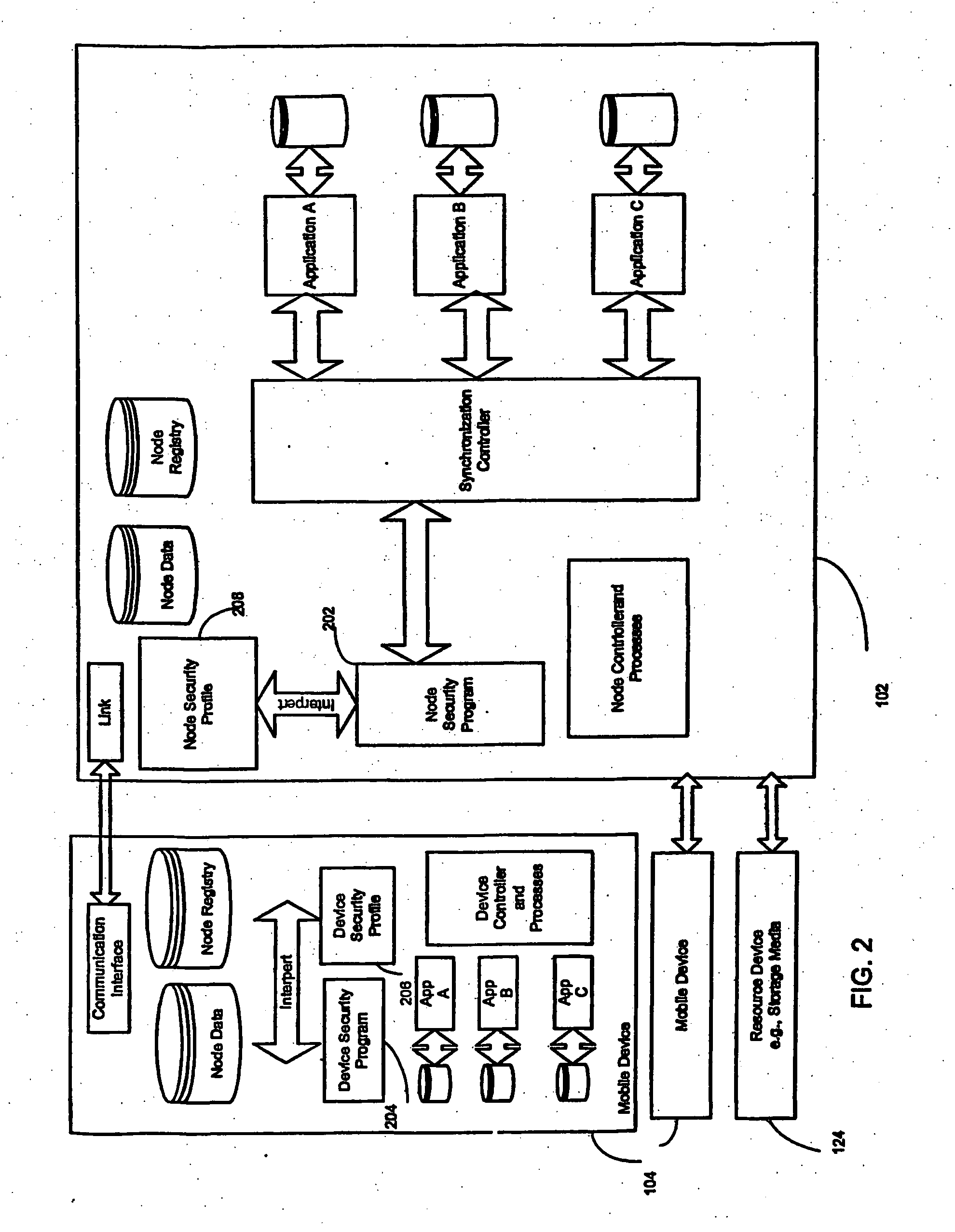
A system and method for securing data in mobile devices includes a computing node and a plurality of mobile devices. A node security program executed in the computing node interfaces with a device security program executed at a mobile device. The computing node is responsible for managing the security based on a node security profile interpreted by a node security program executed in the computing node. A device discovery method and arrangement also detects and locates various information about the mobile devices based on a scan profile.
Owner:TRUST DIGITAL +1
Management of multiple connections to a security token access device
ActiveUS8112794B2Digital data processing detailsUnauthorized memory use protectionUser devicePairing
A security token access device, a user device such as a computing device or communications device, and a method for managing multiple connections between multiple user devices and the access device. The access device maintains connection information, including security information, for each user device securely paired with the access device. Each time a new user device is paired with the access device, the access device transmits a notification to the user devices already paired to the user device. A user may provide instructions to the access device to terminate a pairing with one of the user devices by overwriting at least a portion of the connection information associated with the designated user device. A user device may further request a listing of all user devices currently paired with the access device.
Owner:MALIKIE INNOVATIONS LTD
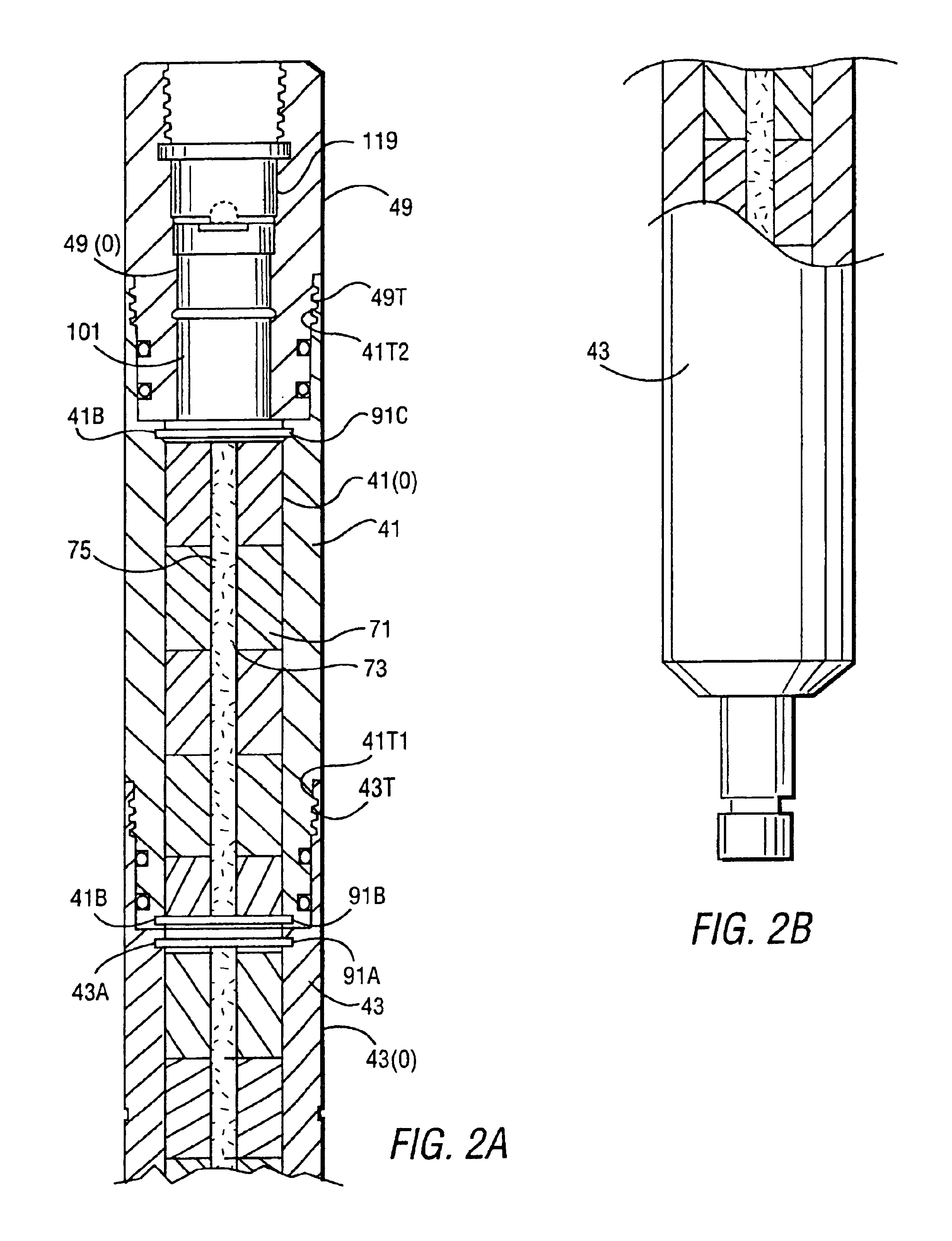
Thermal generator for downhole tools and methods of igniting and assembly
InactiveUS6925937B2Incandescent ignitionFluid removalElectricityElectrical resistance and conductance
Owner:ROBERTSON MICHAEL C
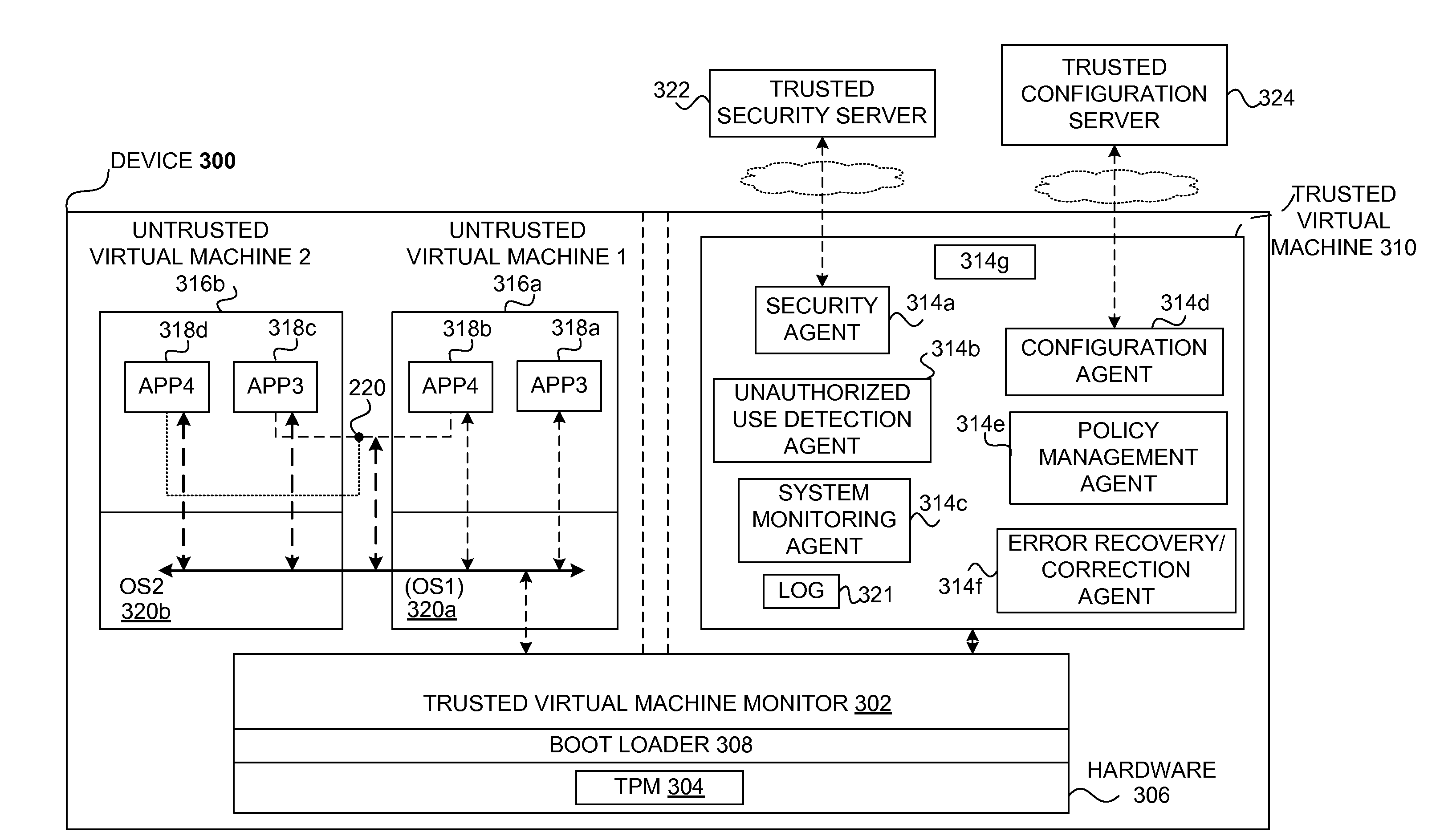
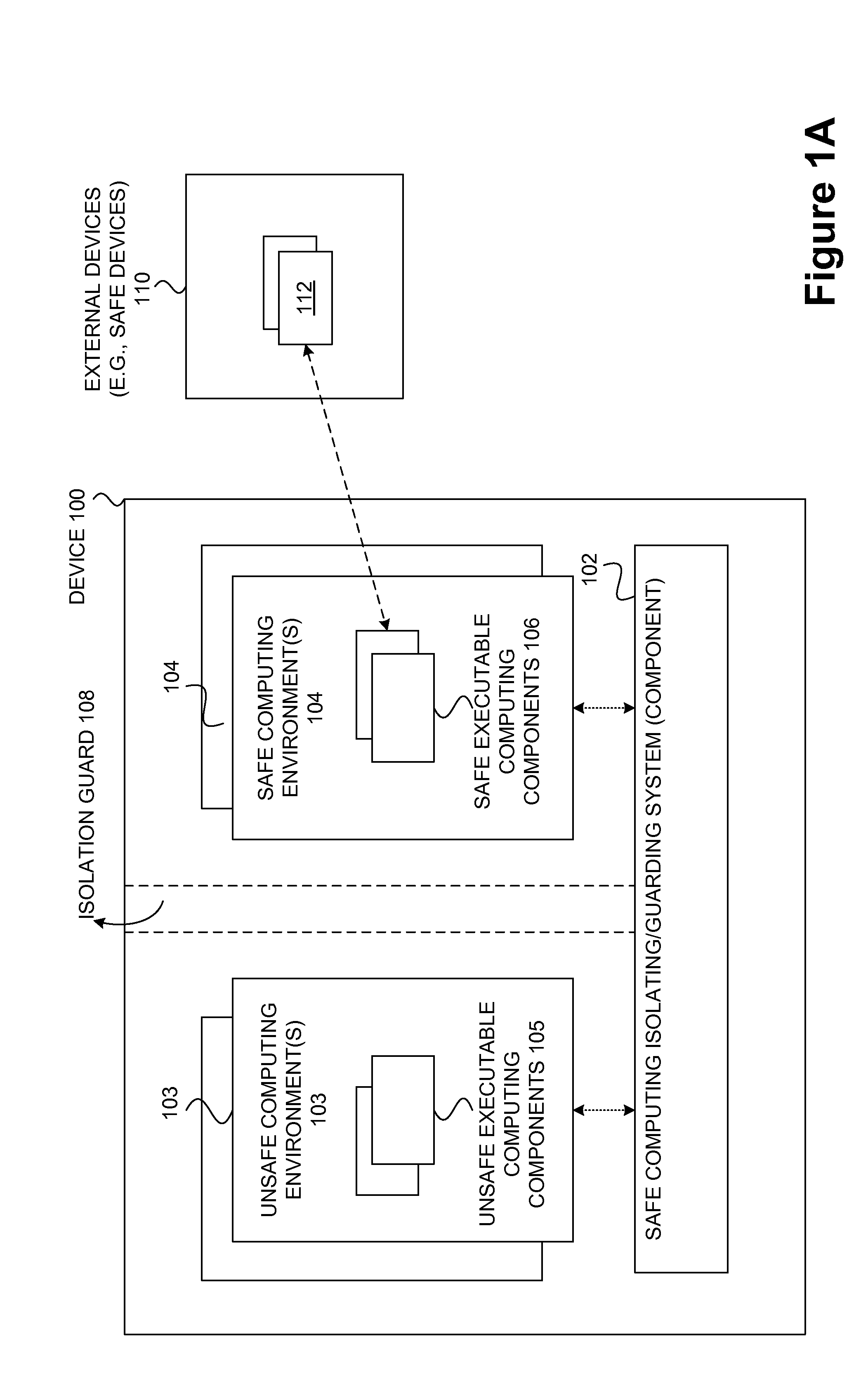
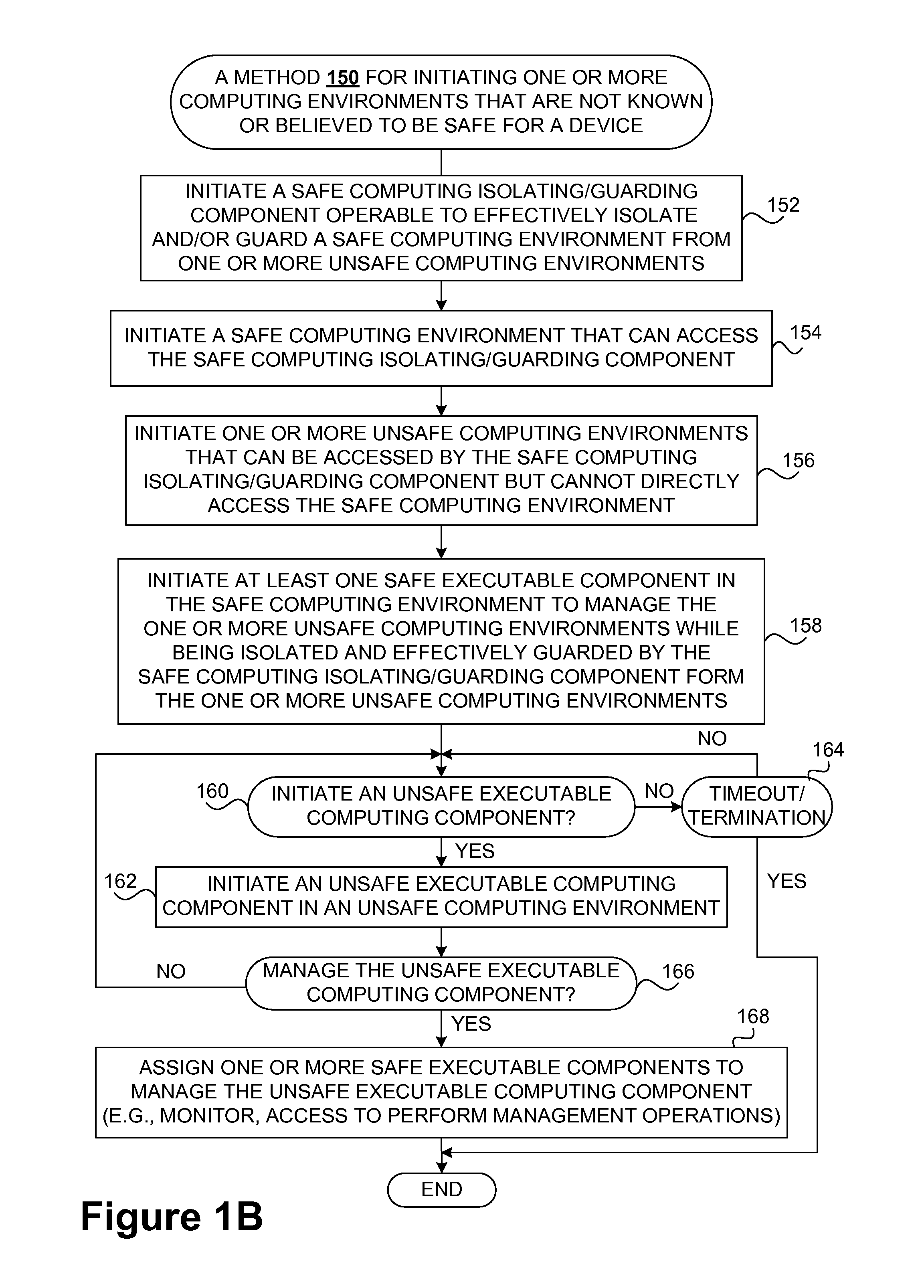
Safety and management of computing environments that may support unsafe components
InactiveUS20090265756A1Effectively guardEffective isolationMemory loss protectionError detection/correctionTrusted componentsTrusted Computing
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
Radio communication device and user authentication method for use therewith
ActiveUS6928166B2Imposing any operating burdenLevel of security can changeMultiple keys/algorithms usageUser identity/authority verificationConfidentialityUser authentication
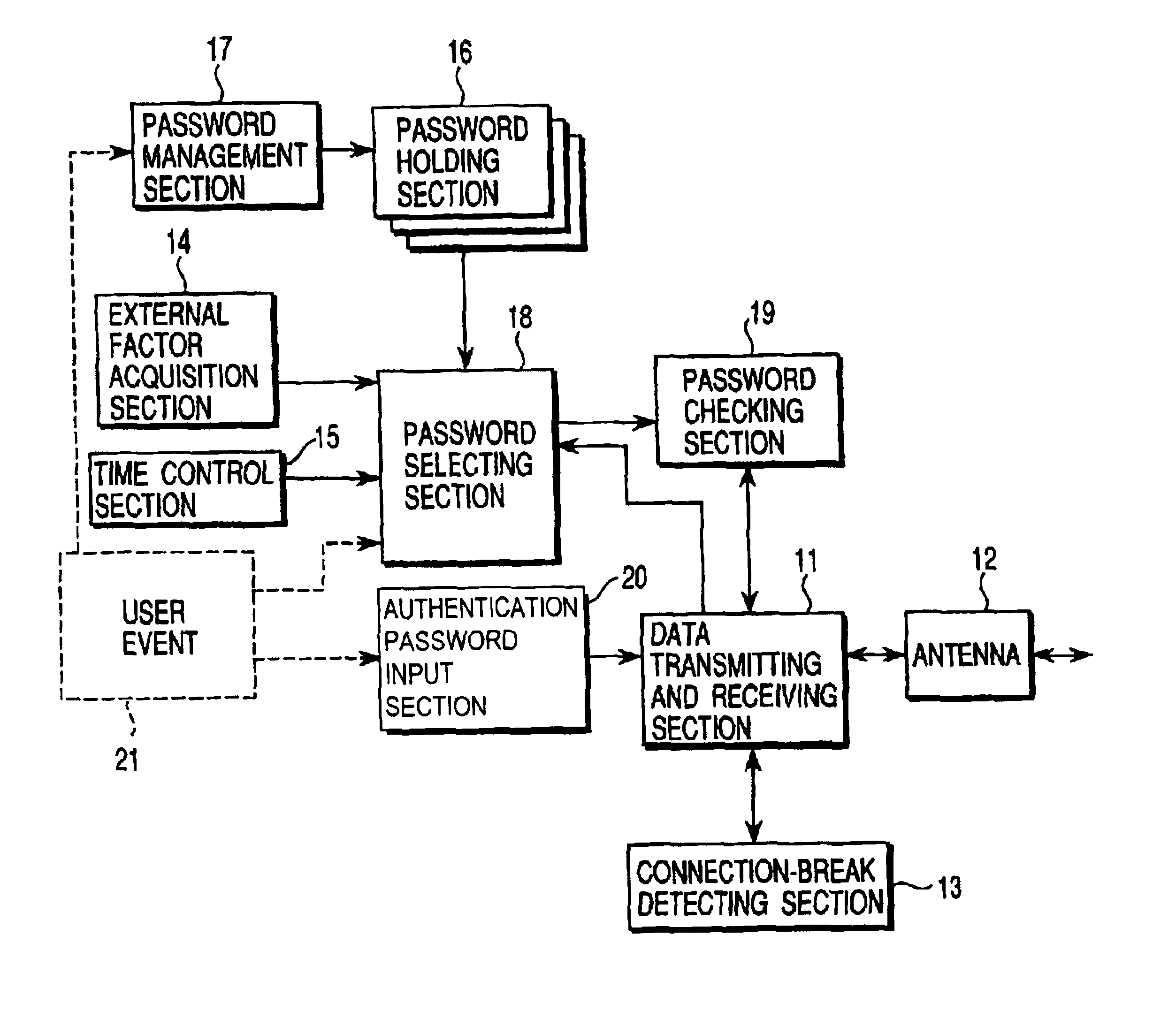
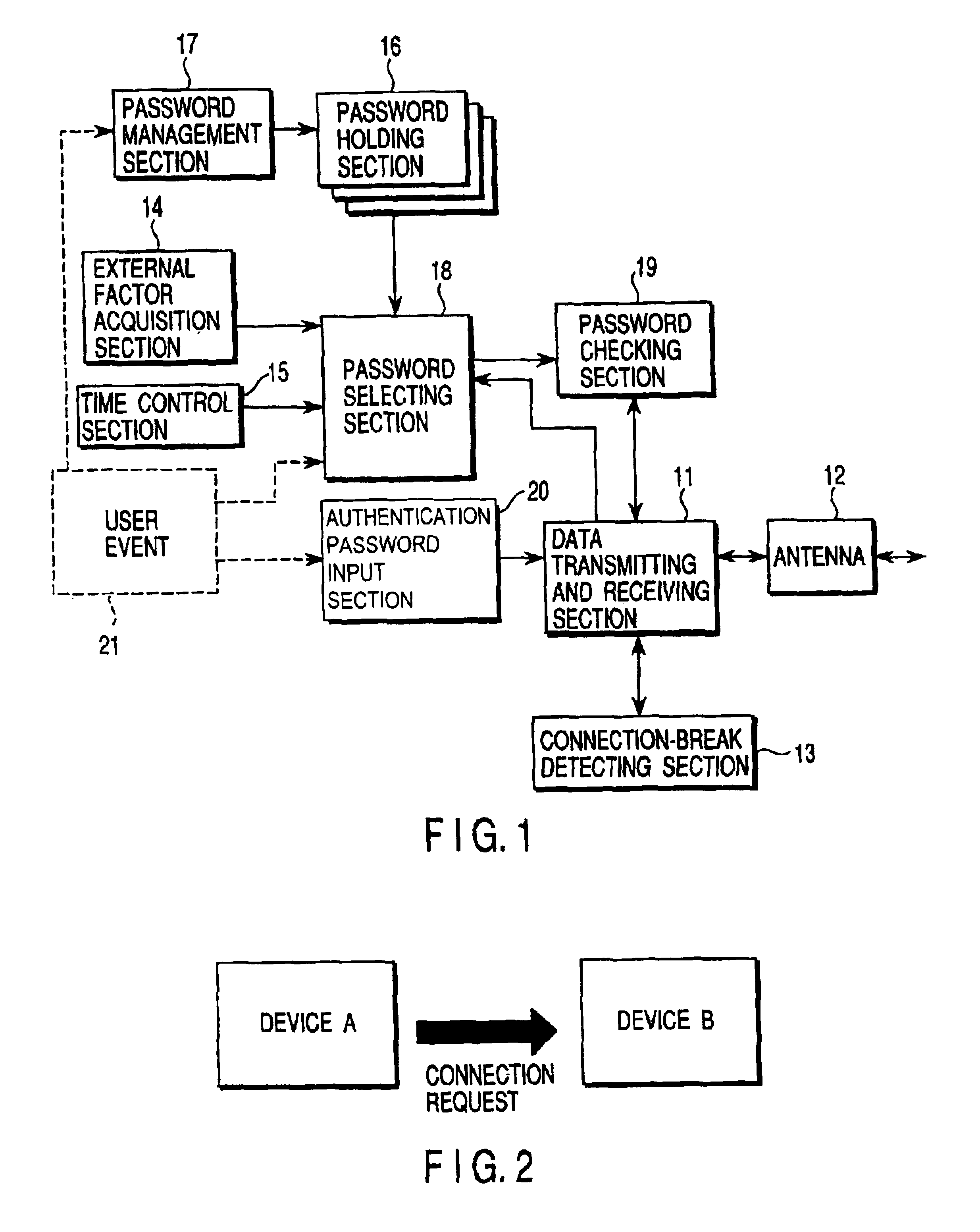
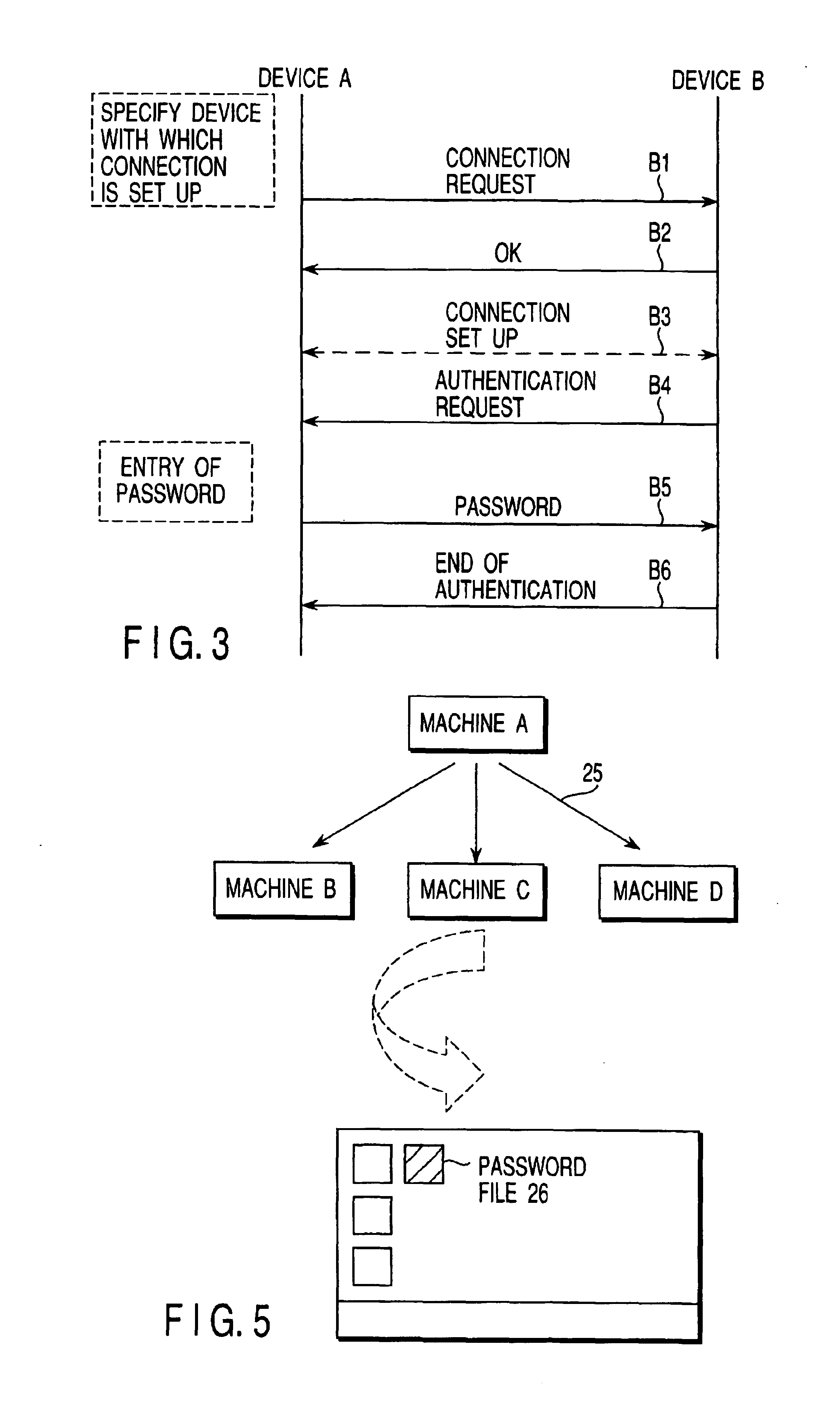
To allow flexible security level switching according communication situations, a password holding section holds a plurality of device authentication passwords, for example, a temporary password and a private password. The temporary password is valid only under a certain situation and the private password has a high level of confidentiality to increase the device security. A password management section allows the user to add a new password to the password holding section and delete an existing password therefrom. A password selecting section selects the most suitable password for current connection from among passwords in the password holding section according to a user event, information acquired by an external factor acquisition section, and information from a time control section. The selected password is output to a password checking section.
Owner:2BCOM LLC
Secured personal data handling and management system
ActiveUS20110224509A1Improvement has not been caseEasy to detectData processing applicationsDigital data processing detailsData providerData access
A system, method and personal apparatus for managing highly secured personal data is provided. The system and the personal apparatus are complementary, both providing highly secured personal data, mass, safe and secured data access, storage and management solutions, while serving the needs for managing and exchanging secured personal data with external services and data providers and with other such highly secured personal data users. The apparatus may be used independently of the system by securely connecting the apparatus to service providers. The apparatus, which is uniquely identified with a unique user, includes a sensor module comprising a plurality of biometric sensors for reading a plurality of personal biological identification parameters of the user and an authentication unit for positive authentication of the user's personal biological identification parameters stored in the authentication unit. The system is designed to securely serve the needs of conducting and maintaining multiple users' personal data access, storage, updating and retrieval capabilities. The method supports the safe and secured operation of the apparatus by its owner, in order to get access to the system and to exchange highly secured personal data with external pre-registered service providers and with other registered system users.
Owner:OS - NEW HORIZON PERSONAL COMPUTING SOLUTIONS
Method for evaluating lithium ion battery peak power online
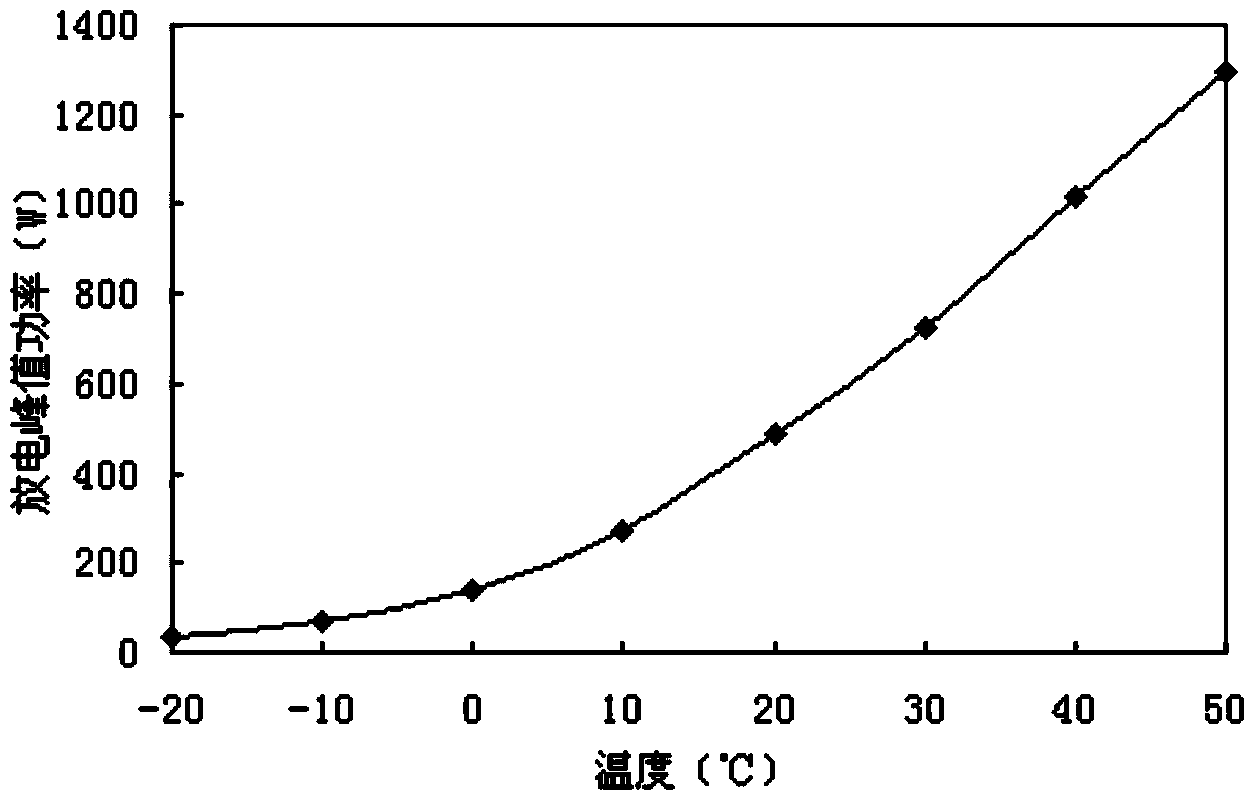
ActiveCN103675707AReduce the risk factorImprove stability and reliabilityElectric devicesElectrical testingElectrical batteryInternal resistance
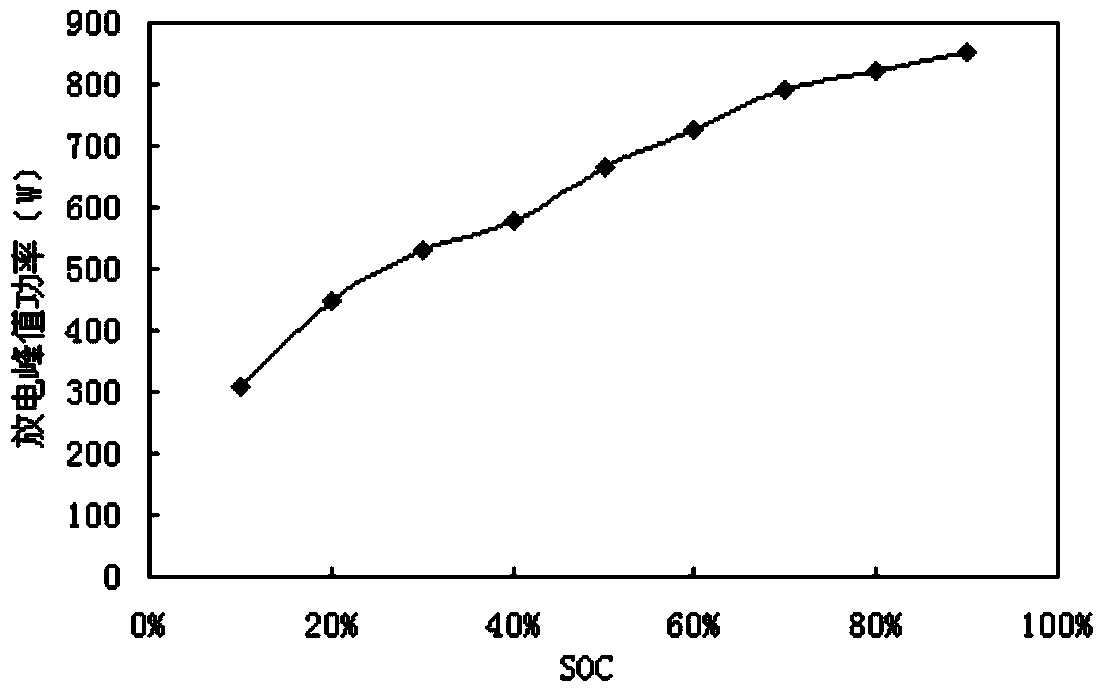
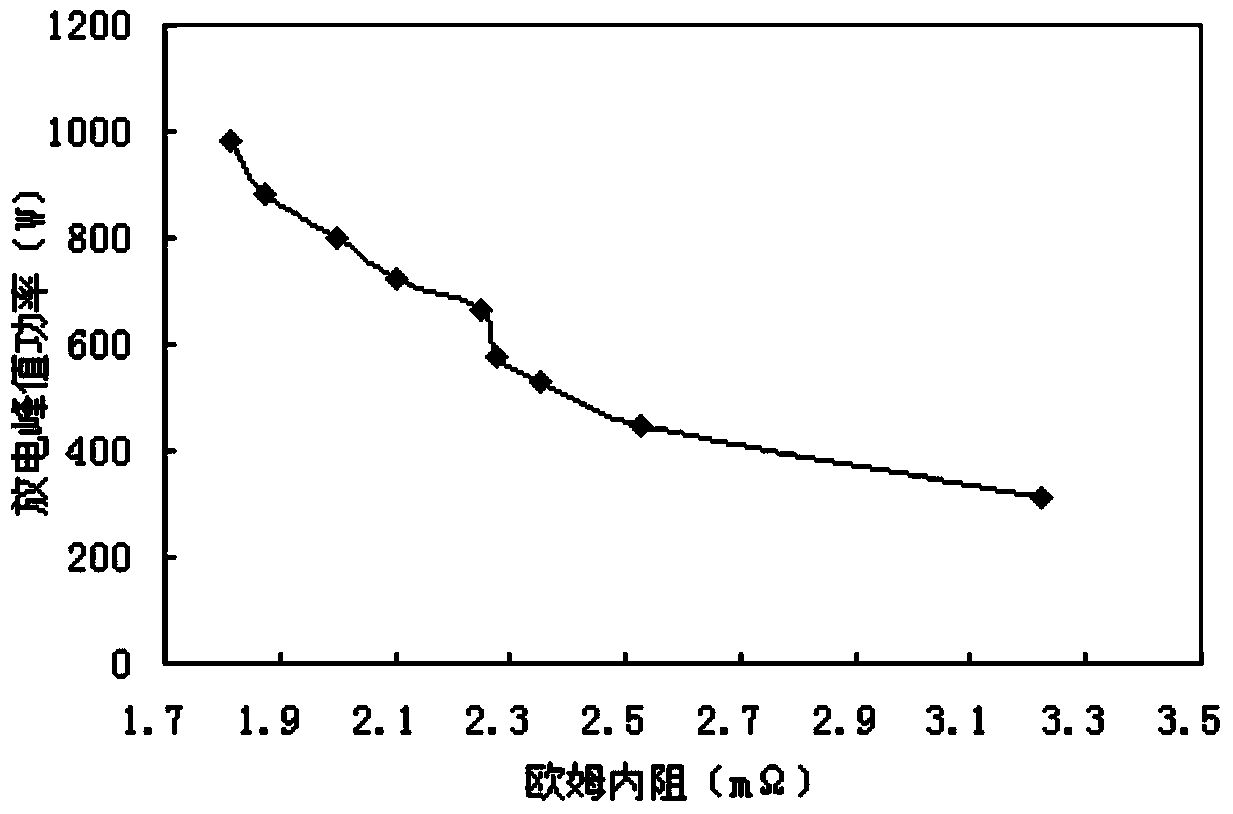
The invention discloses a method for evaluating lithium ion battery peak power online. The method comprises the following steps that influencing characteristic curves of the influence on lithium ion battery peak power by the charge state, Ohm internal resistance, temperature and sustainable time of a lithium ion battery are respectively built; all factors influencing the battery peak power are synthesized, and a battery peak power evaluation initial model is built; the battery peak power evaluation initial model is embedded into a vehicle-mounted terminal system, and the battery peak power evaluation initial model continues to be trained. The method has the advantages that the situations that due to the fact that the operation is not proper, and the battery is overcharged or overdischarged, the service life of the battery is shortened, and use cost is greatly increased are basically avoided through the method, the danger coefficient of the battery in the use process is lowered, and the reliability and stability of the operation of an electric vehicle are improved, and personal safety and equipment safety are guaranteed.
Owner:STATE GRID CORP OF CHINA +2
Message identification with confidentiality, integrity, and source authentication
InactiveUS7095855B1Encryption apparatus with shift registers/memoriesDigital data processing detailsComputer hardwareConfidentiality
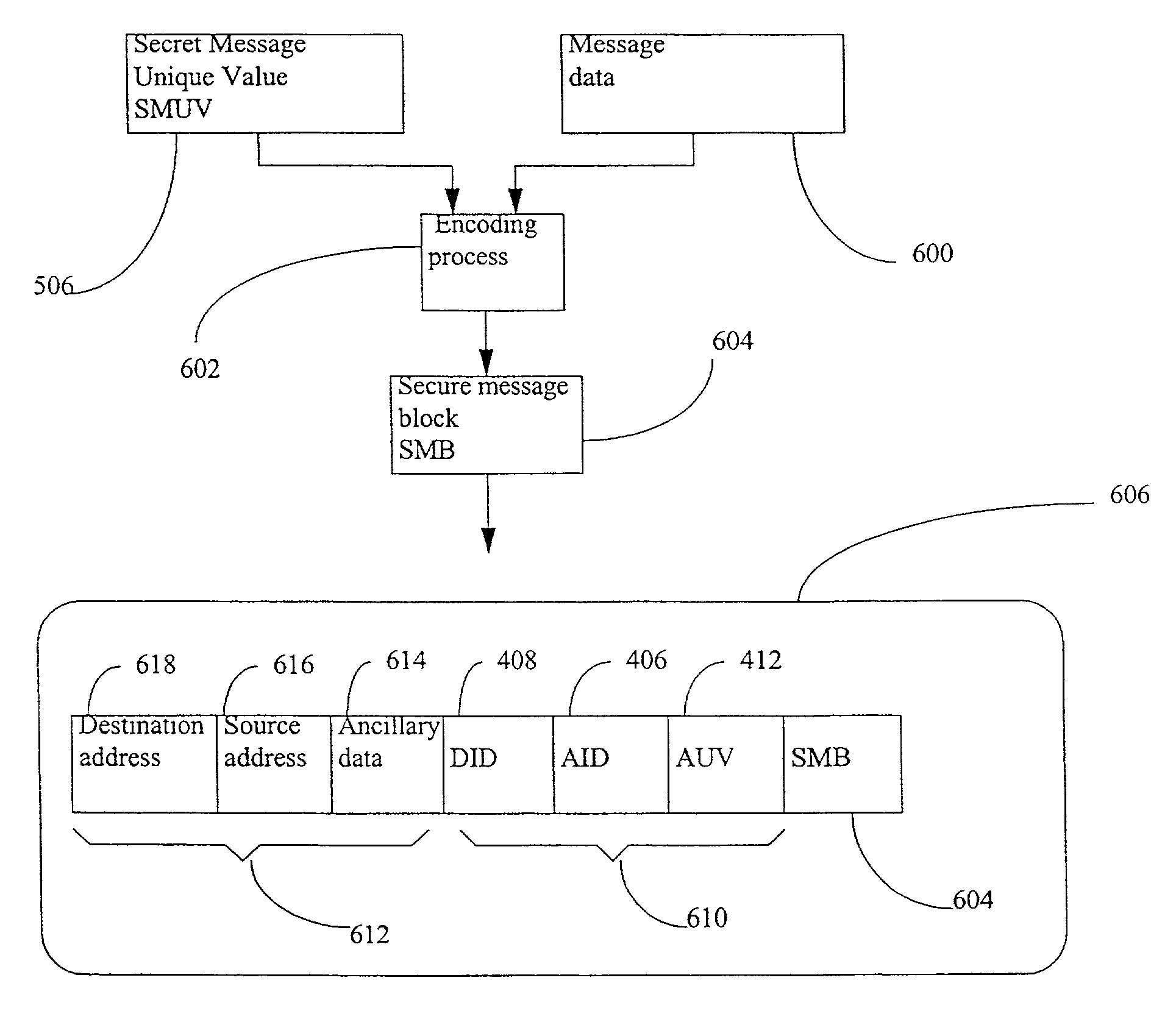
A method for securely encoding and transmitting a message by an originating device to one of a plurality of recipient devices, said message being associated with a particular one of a plurality of application running on the originating device. Transmission is generated by using a device identifier, an application identifier and an application value, of a message value; combining the message value with one or more first secret values, said secret values being known substantially only to the originating device and one or more intended recipient device of the message, to establish a secret message value; applying the secret message value and the message to an encoding process to form a secure message block, and combining an address with a device identifier, the application identifier, the application value and the secure message block, to form a secure message for transmission which is decodable by the one or more of said intended recipient devices which thereby recover the message, the address, the device identifier, the application identifier and the application value.
Owner:COLLINS LYAL SIDNEY
Management of multiple connections to a security token access device
ActiveUS20080016368A1Digital data processing detailsUnauthorized memory use protectionUser deviceInternet privacy
A system and method for automatically managing a connection between a user device and a security token access device. The access device is adapted to wirelessly communicate with a plurality of user devices and to be securely paired with at least one of the plurality of user devices, and is further adapted to maintain connection information relating to each of the plurality of user devices. The connection information comprises security information for each user device securely paired with the access device. The access device automatically manages a connection by maintaining a store of connection information comprising security information for each of a set of at least one securely paired user devices; determining whether one of the securely paired user devices is a stale device; and if it is determined that one of the securely paired user devices is a stale device, implementing a management protocol for handling the stale device.
Owner:MALIKIE INNOVATIONS LTD
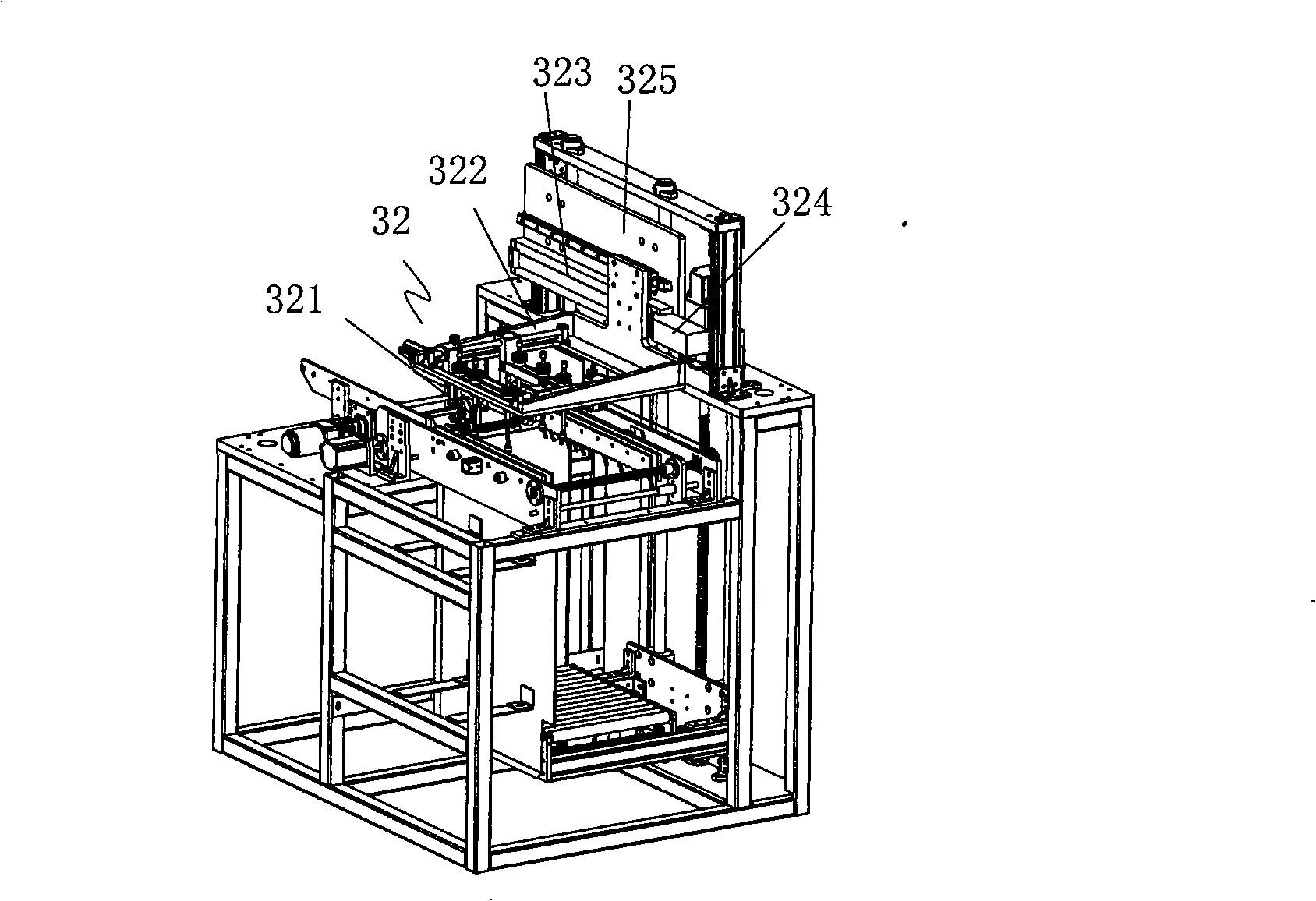
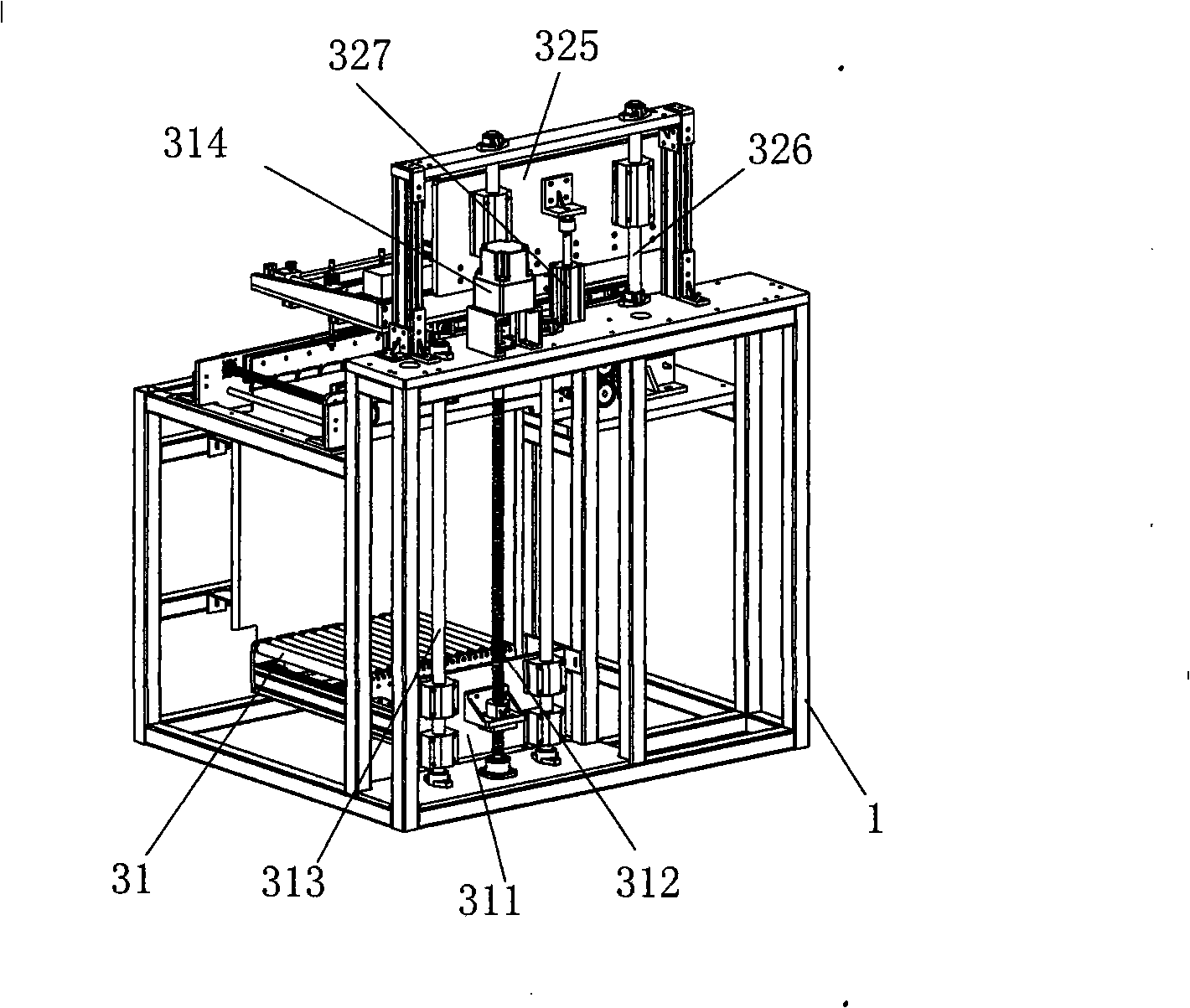
Appearance inspection machine for printed circuit board
InactiveCN101403709AThe detection process is fastImprove detection efficiencyMaterial analysis by optical meansSortingForeign matterEngineering
The invention provides a testing machine used for testing the appearance of a printing circuit board, comprising a frame which is provided with a transmission mechanism; the front end of the transmission mechanism is provided with an upper plate mechanism; the transmission mechanism is internally provided with two scanning mechanisms; a panel turnover mechanism is arranged between the two scanning mechanisms; the tail part of the transmission mechanism is butt-jointed with a sorting mechanism; and all mechanisms are controlled by control host machines cooperatively. The testing machine adopts a whole-line digital camera photographing technique to detect the defects on the printing circuit such as foreign matter, exposed copper, supplemented oil, scraping, poor gold-plating, character error, non-uniform green oil, non-uniform welding disc, non-uniform depth of channel, residual copper, omitted printing, developing and the like, automatically feeds and sorts the nondefective and waster, improves the simpleness and reliability of the operation, can observe the defects of the board in real-time by adopting a powerful image processing and analysis software system to provide a plurality of image processing and analysis systems, has quick detection speed, high detection efficiency, safe and reliable equipment, simple operation, is convenient and easy to be learned and meets the man-machine interaction.
Enterprise-wide security system for computer devices
InactiveUS20070186275A1Digital data processing detailsUser identity/authority verificationMobile deviceEnterprise level
A system and method for securing data in mobile devices (104) includes a computing mode (102) and a plurality of mobile devices (104). A node security program (202) executed in the computing node (102) interfaces with a device security program (204) executed at a mobile device (104). The computing node (102) is responsible for managing the security based on a node security profile (208) interpreted by a node security program (202) executed in the computing node (102). A device discovery method and arrangement (106) also detects and locates various information (120) about the mobile devices (104) based on a scan profile (206).
Owner:MUSARUBRA US LLC
Induction cooker heating device
PendingCN107726388ARealize the use effectSave separate placement spaceDomestic stoves or rangesLighting and heating apparatusElectricityComputer module
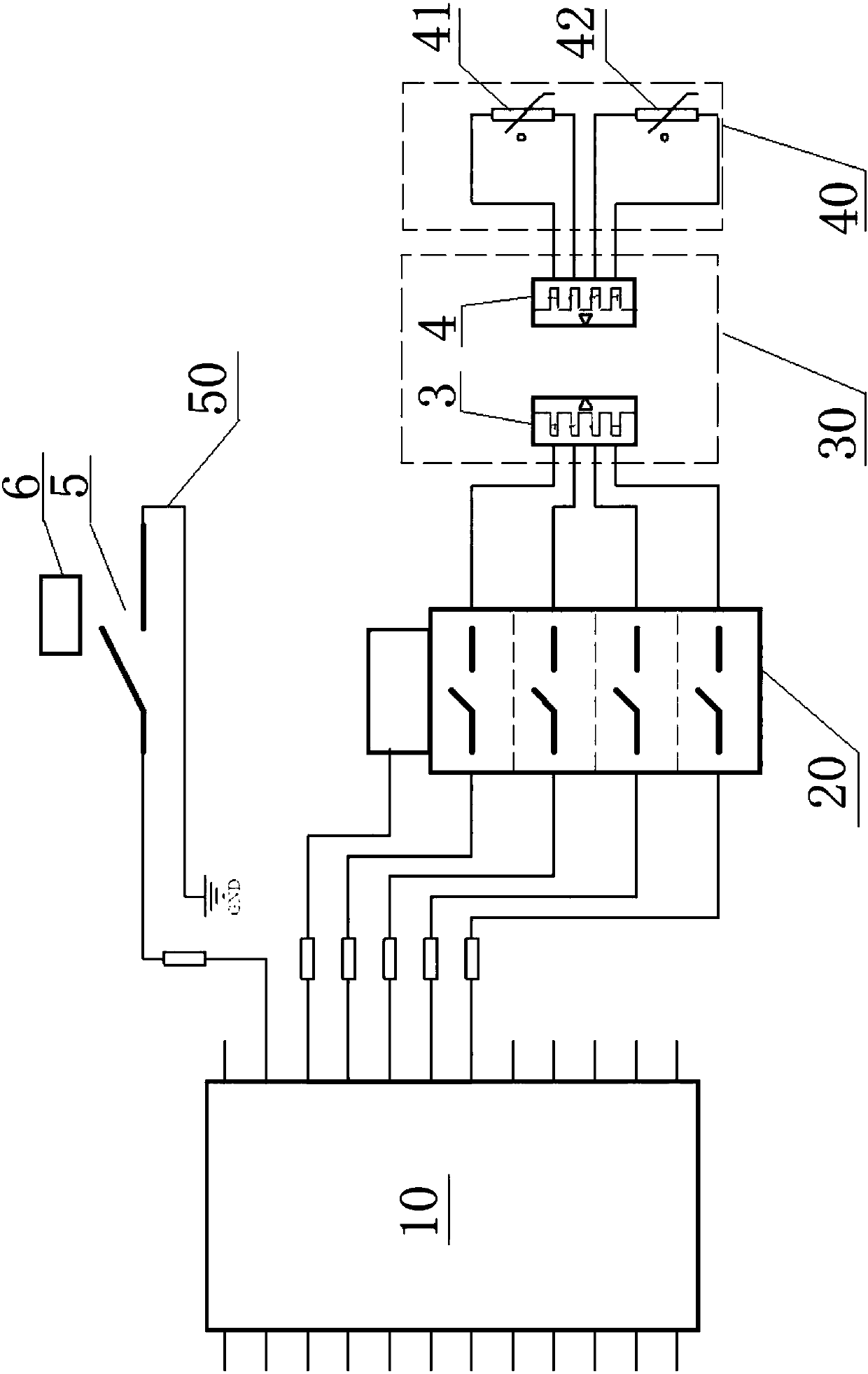
The invention discloses an induction cooker heating device. A main control chip module (10) connected with a heating control circuit is arranged in a cooker body (1), and the cooker body is provided with a circuit coupling interface A (3) of the heating control circuit. A sensor module (40) is arranged in a pot body (2), and a circuit coupling interface B (3) electrically connected with the sensormodule is arranged in the bottom of the pot body. When the bottom seat of the pot body is on the top of the cooker body, the circuit coupling interface B is jointed with the circuit coupling interface A, so that the main control chip module can be electrically connected with the sensor module so as to control heating. An induction cooker of the induction cooker heating device can be used alone orconduct combined use, the functions are complete, and the individual placement space of the induction cooker is saved. The assembly structure is consistent with user usages. During assembly, whetherthe pot body is assembled in place or not can be detected and short-circuit protection can be realized through a pot assembly detection module and a switching circuit module. Thus, the damage of a main control chip is prevented, and the equipment safety and reliability is high.
Owner:FOSHAN SHUNDE MIDEA ELECTRICAL HEATING APPLIANCES MFG CO LTD
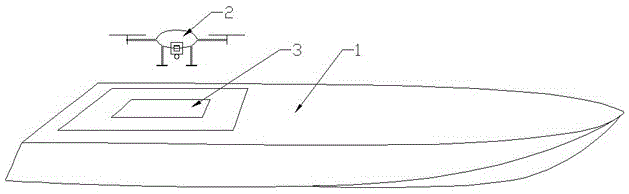
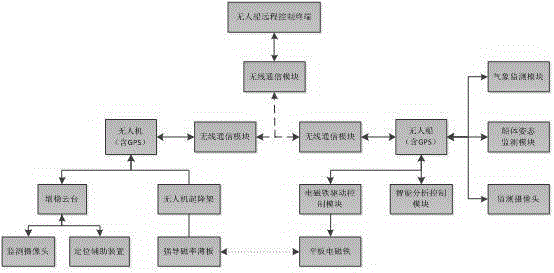
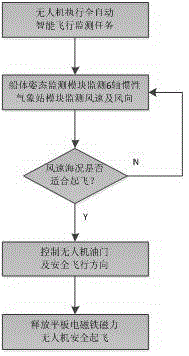
Take-off and landing system for unmanned ship-borne unmanned aerial vehicle
ActiveCN105059558AStable and reliable takeoff and landingRealize take-off and landing operationsArresting gearLaunching/towing gearRemote controlUncrewed vehicle
The invention provides a take-off and landing system for an unmanned ship-borne unmanned aerial vehicle, which exerts good stability and can effectively solve a problem that the unmanned aerial vehicle cannot safely take off and land on a bumpy unmanned ship. The take-off and landing system for the unmanned ship-borne unmanned aerial vehicle, provided by the invention, comprises a take-off and landing fixing device, a take-off and landing hanging device and a take-off and landing control device, wherein the take-off and landing fixing device is arranged on the unmanned ship; the take-off and landing hanging device is arranged on the unmanned aerial vehicle; the unmanned aerial vehicle takes off from and lands on the unmanned ship through use of the take-off and landing control device to control coordination between the take-off and landing fixing device and the take-off and landing hanging device; and the take-off and landing control device comprises a take-off and landing process monitoring camera, a meteorological monitoring module, a ship body posture monitoring module, a wireless communication module and a remote control terminal. The take-off and landing system for the unmanned ship-borne unmanned aerial vehicle, provided by the invention, can be applied to the technical field of safety of water area operation equipment.
Owner:ZHUHAI YUNZHOU INTELLIGENCE TECH COMPANY
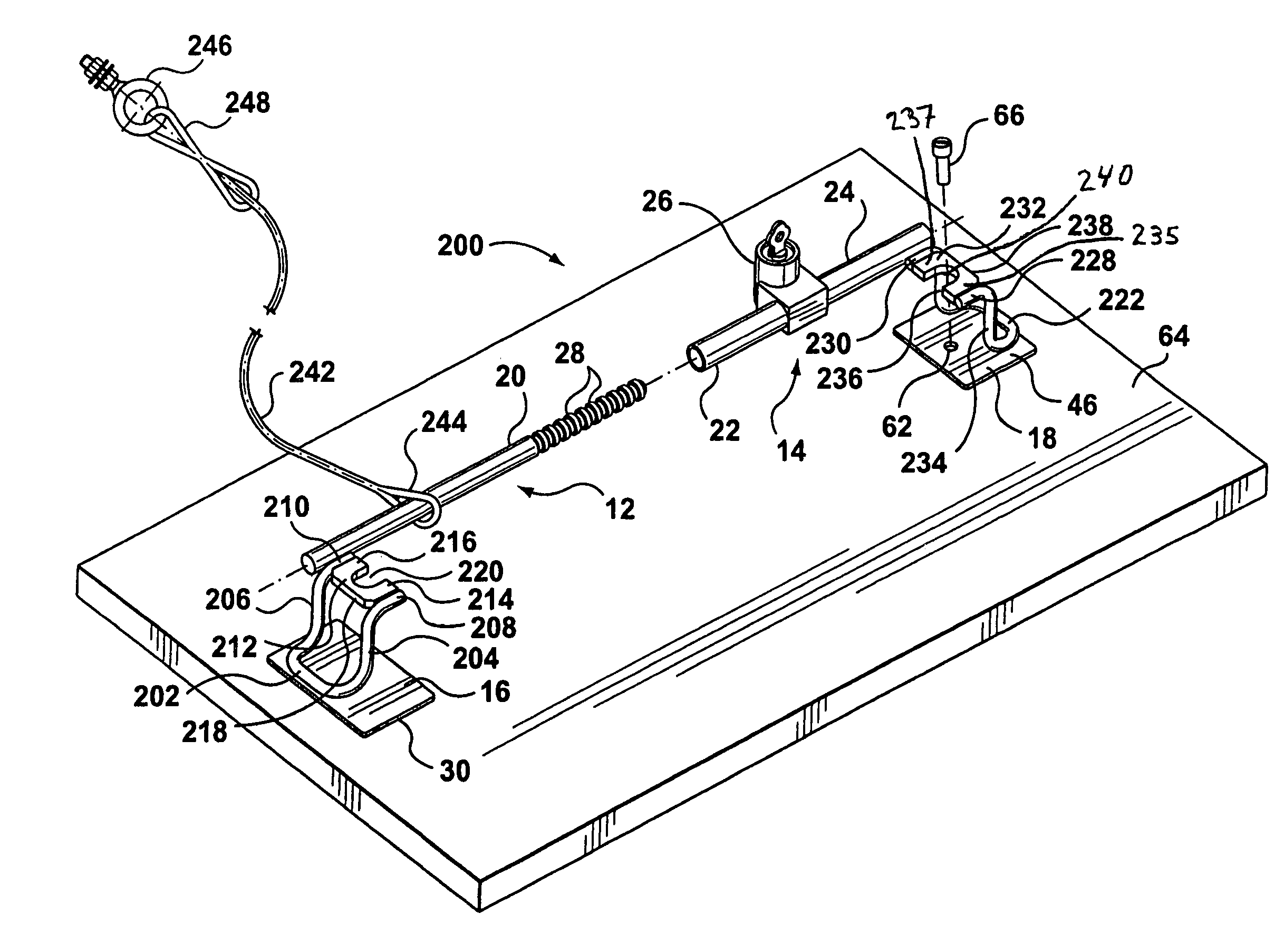
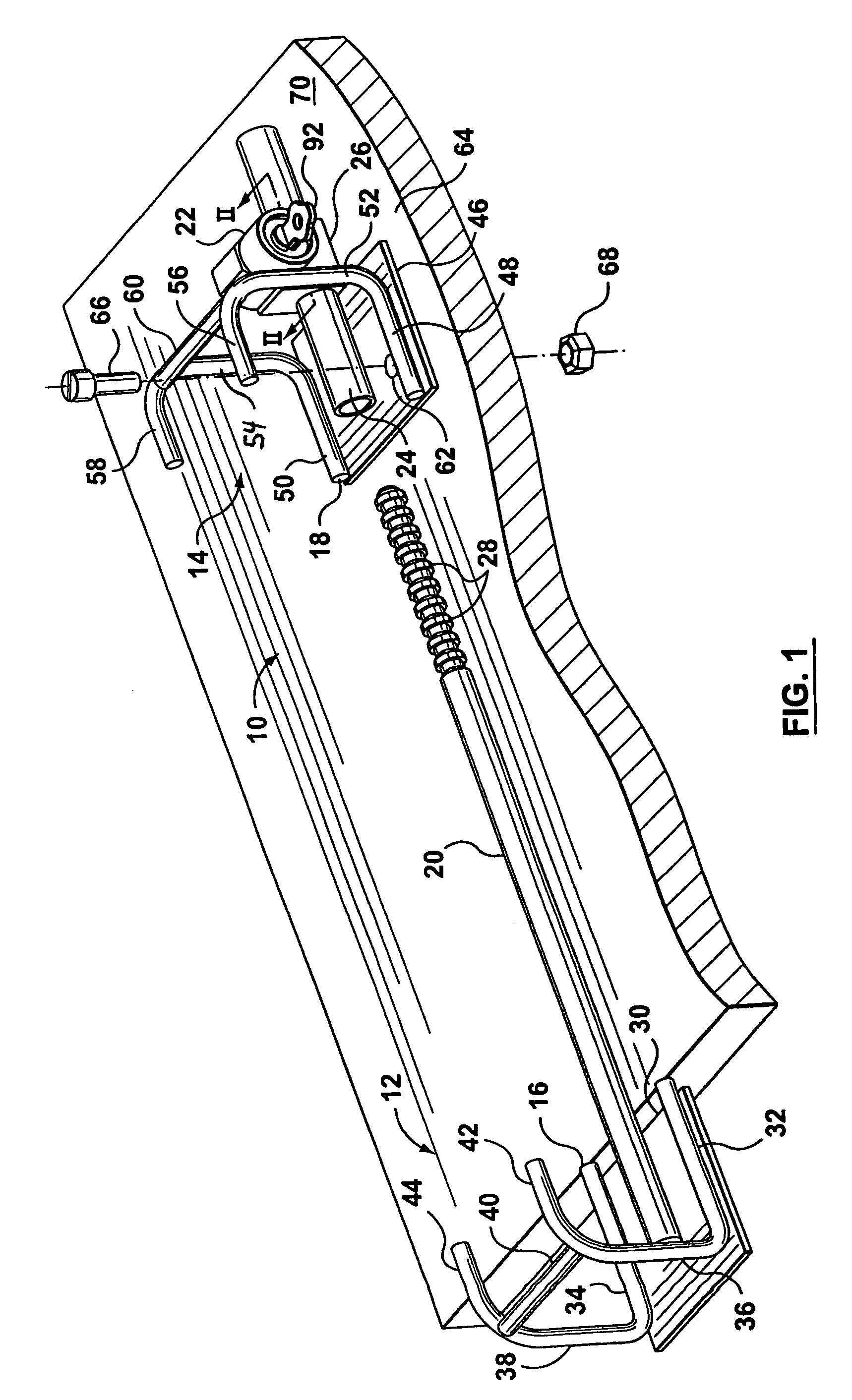
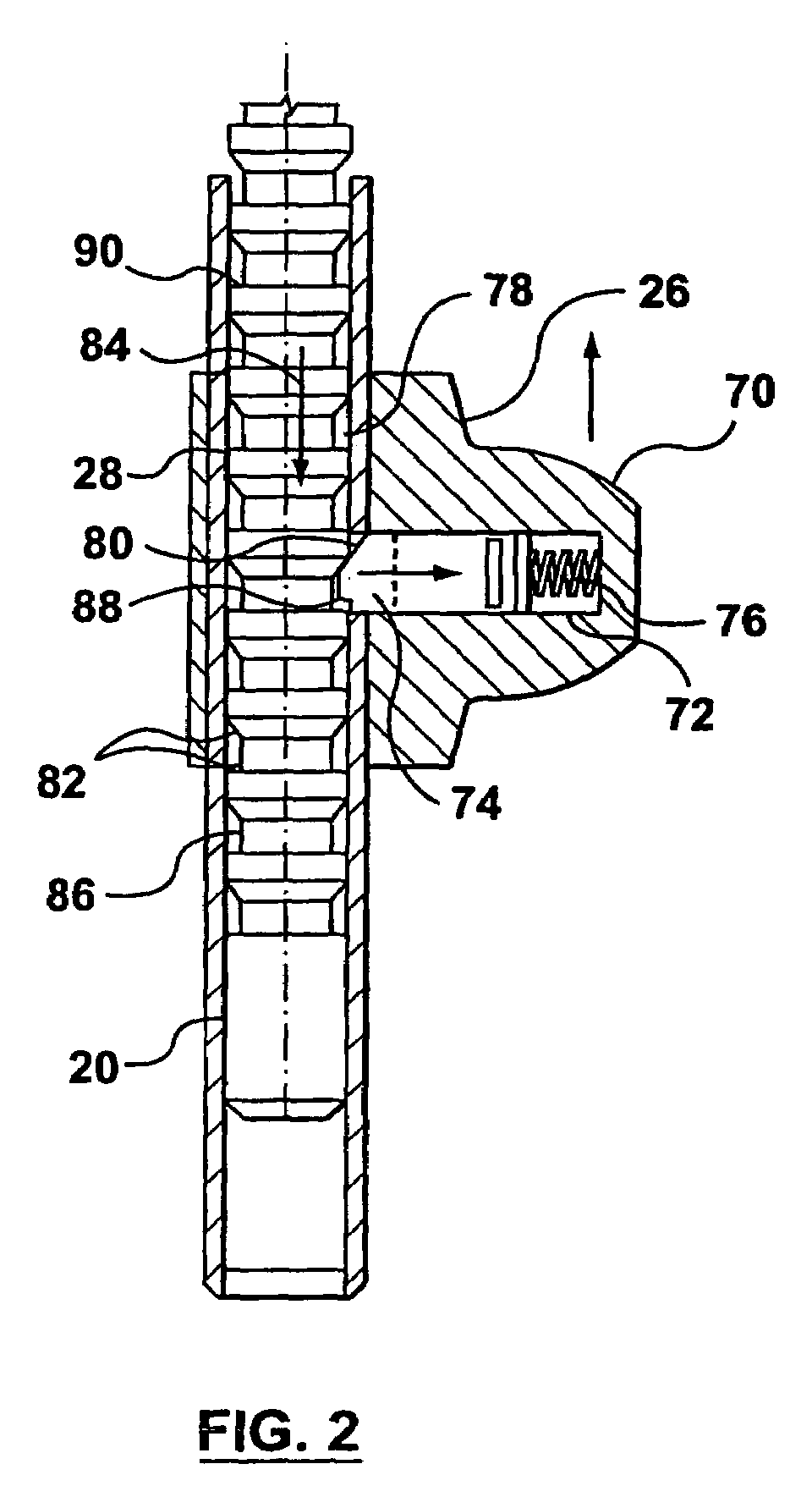
Equipment security device
A security device that can be used to secure devices, such as laptop computers, of varying sizes, and includes two securing members that are telescopically connected together and which have opposed restraining members for securing a device there between.
Owner:COMPUCAGE INT
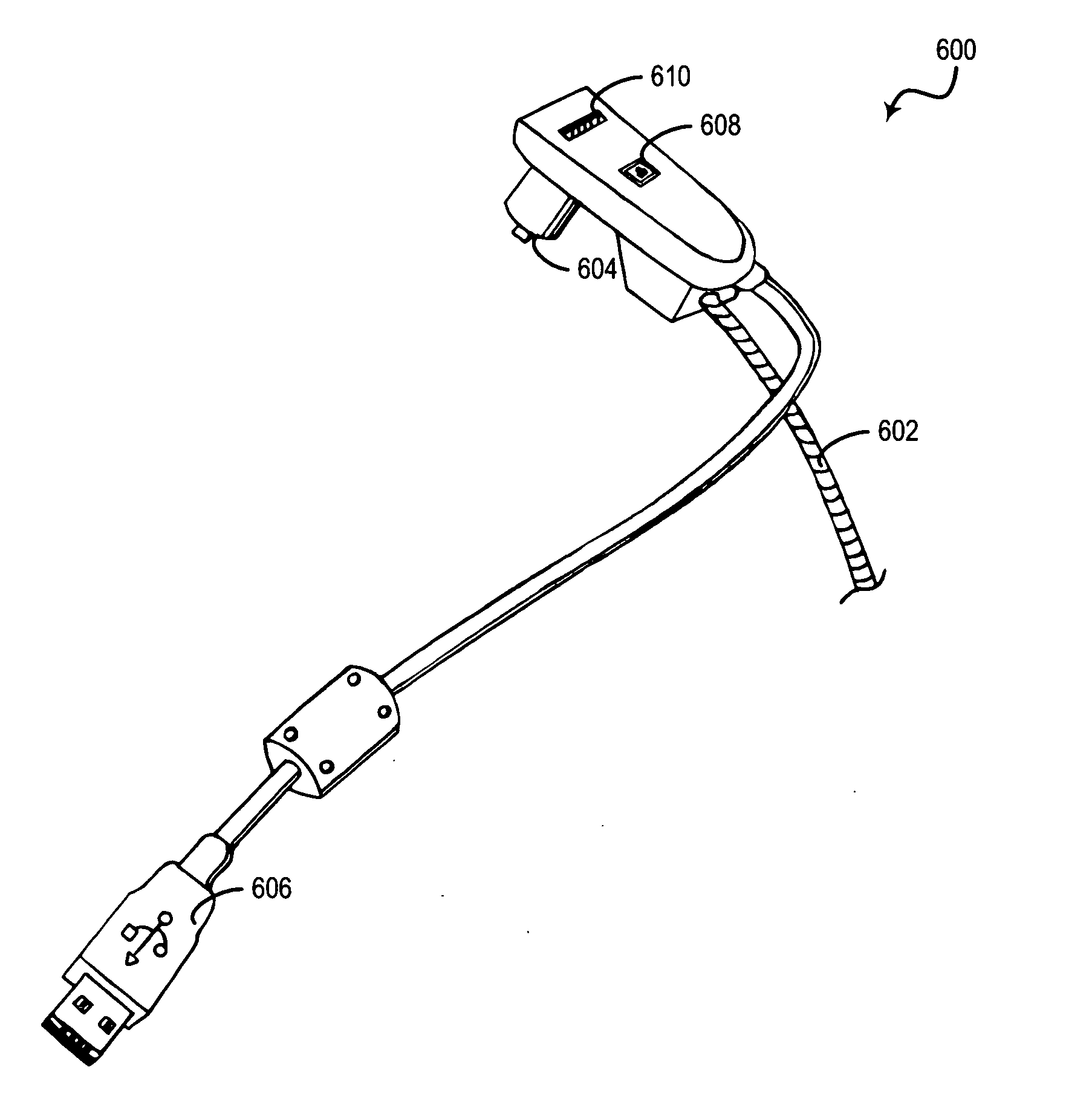
System and method for equipment security cable lock interface
A cable lock apparatus that is operated by the computer equipment that the apparatus is intended to protect, rather than by a key, is disclosed. According to a preferred embodiment of the invention, the cable lock is equipped with a hot-swappable computer interface, such as a Universal Serial Bus (USB) interface, for connecting to the computer. The user of the computer unlocks the cable lock by providing a password or other form of authentication to the computer. The computer transmits this authentication information, via the USB interface, to circuitry within the cable lock device, which validates the authentication information. If the authentication information validates properly, the cable lock device circuitry activates a motor or solenoid to mechanically release the cable lock.
Owner:LENOVO (SINGAPORE) PTE LTD
Network based device security and controls
ActiveUS20130333032A1Memory loss protectionError detection/correctionOperational systemInternet traffic
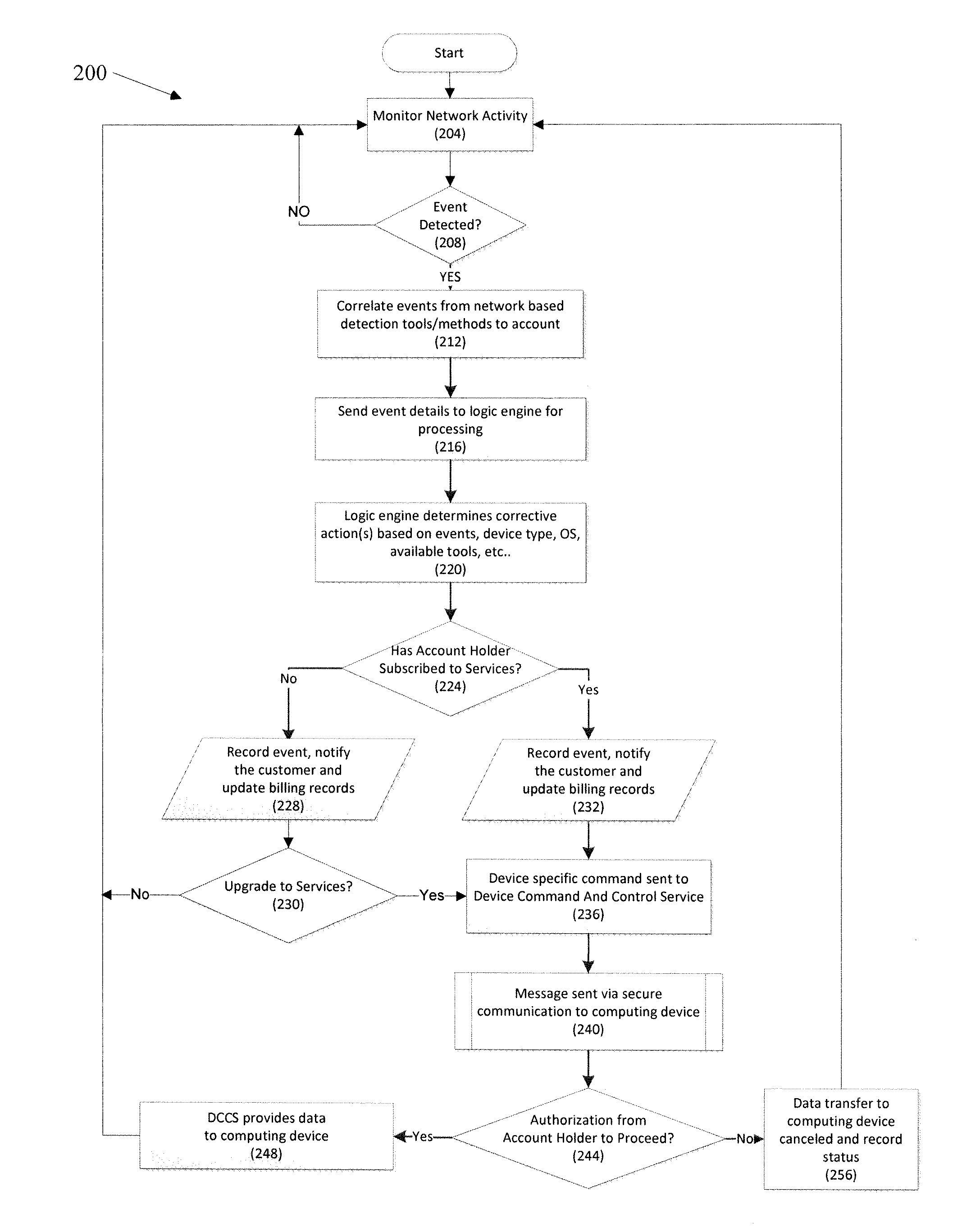
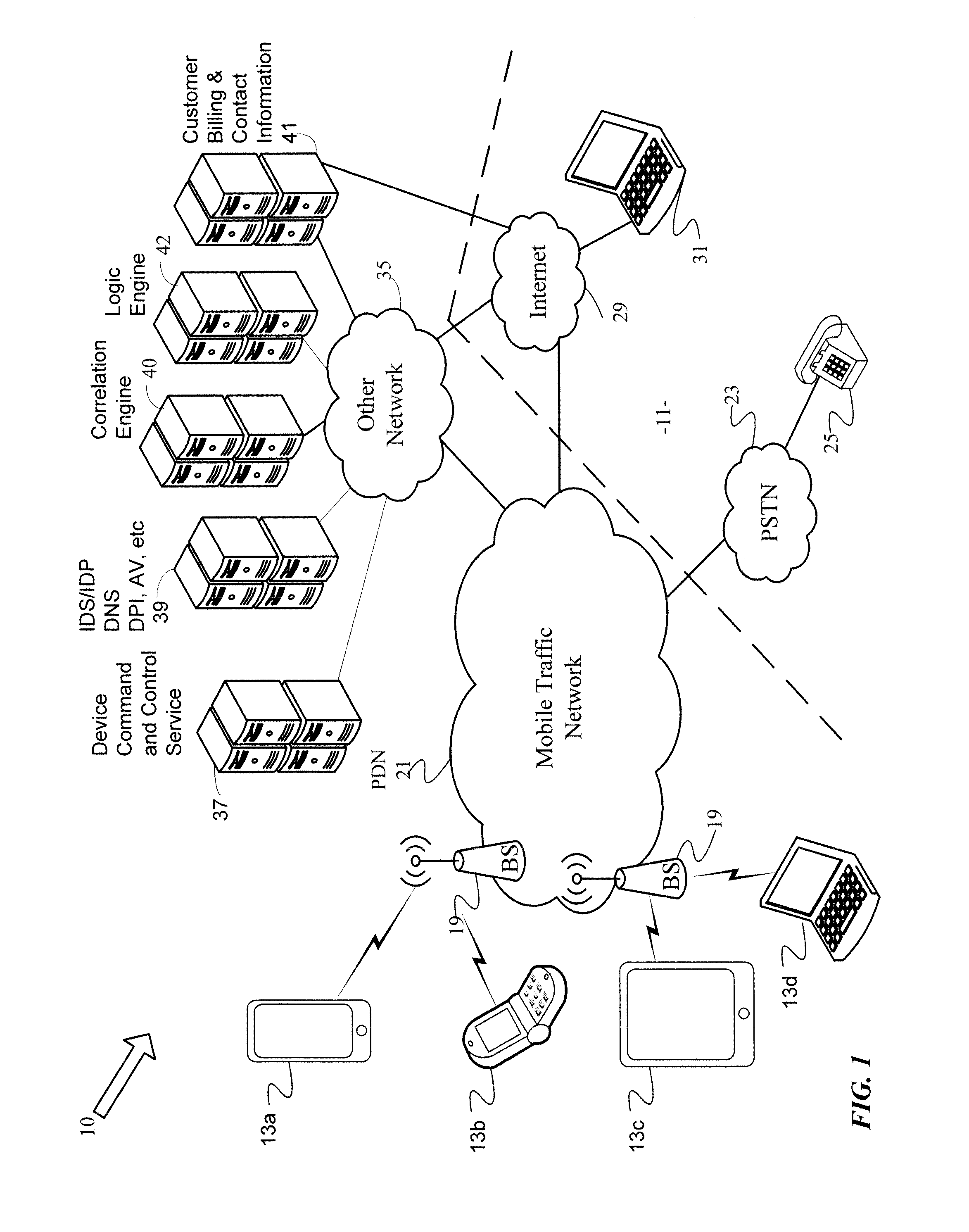
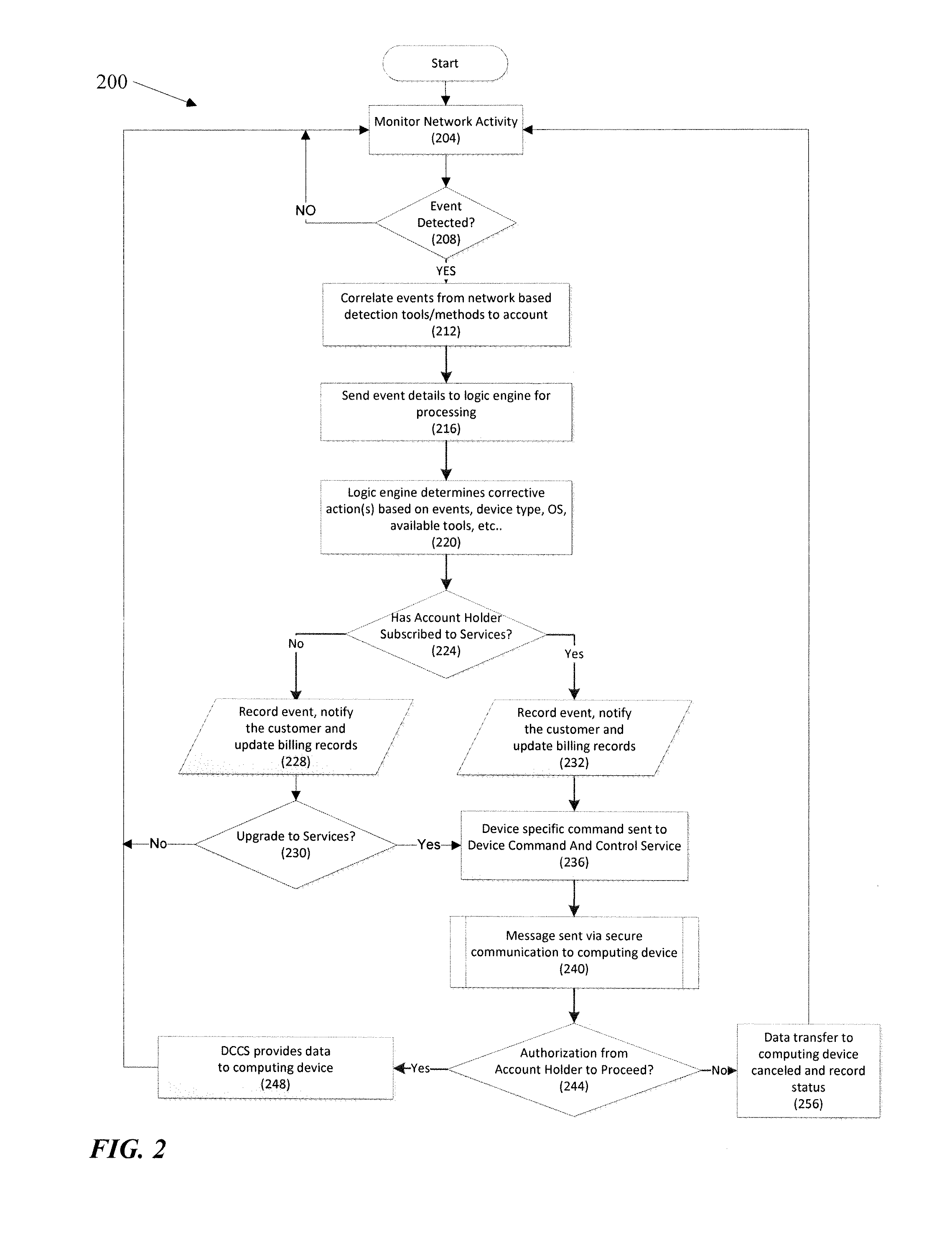
Protection against security attacks involves monitoring network traffic for a computing device security attack and determining whether there is a security event, using one or more network based security tools. Next, it is determined whether an event pattern involving two or more security events meets a predetermined criteria. Upon determining that there is a security attack, corrective action is tailored, based on the type of the computing device, the operating system of the computing device, the type of security attack, and / or the available protection tools. A course of action is performed depending on whether an account of the computing device includes a security protection service. If there is a security protection service, a message is sent over a secure link to the computing device. This message includes the corrective action to cure the computing device from the security attack.
Owner:CELLCO PARTNERSHIP INC +1
Method and system for controllably and selectively securing a portable computing device to a physical holding device
InactiveUS20060066438A1Readily apparentElectric signal transmission systemsImage analysisLocking mechanismControl signal
A method and system for controllably and selectively securing a portable computing device to a physical holding device includes a physical holding device for receiving a portable computing device. A locking mechanism locks the portable computing device to the physical holding device. A security application associates with the portable computing device for responding to an authorization input for generating an electronic locking mechanism control signal. An actuator mechanism responds to the electronic locking mechanism control signal to actuate the locking mechanism in locking the portable computing device to the physical holding device.
Owner:MOTION COMPUTING
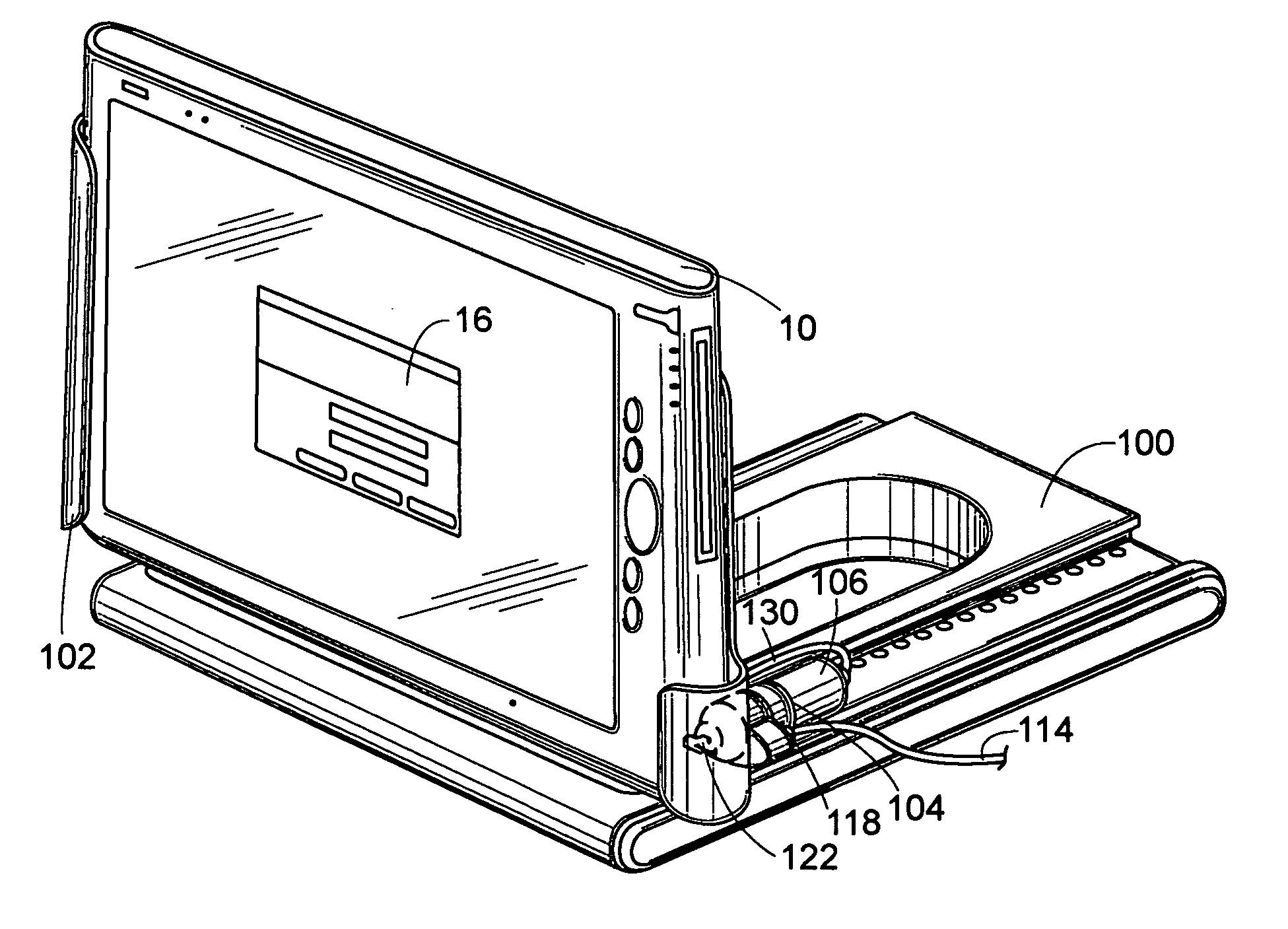
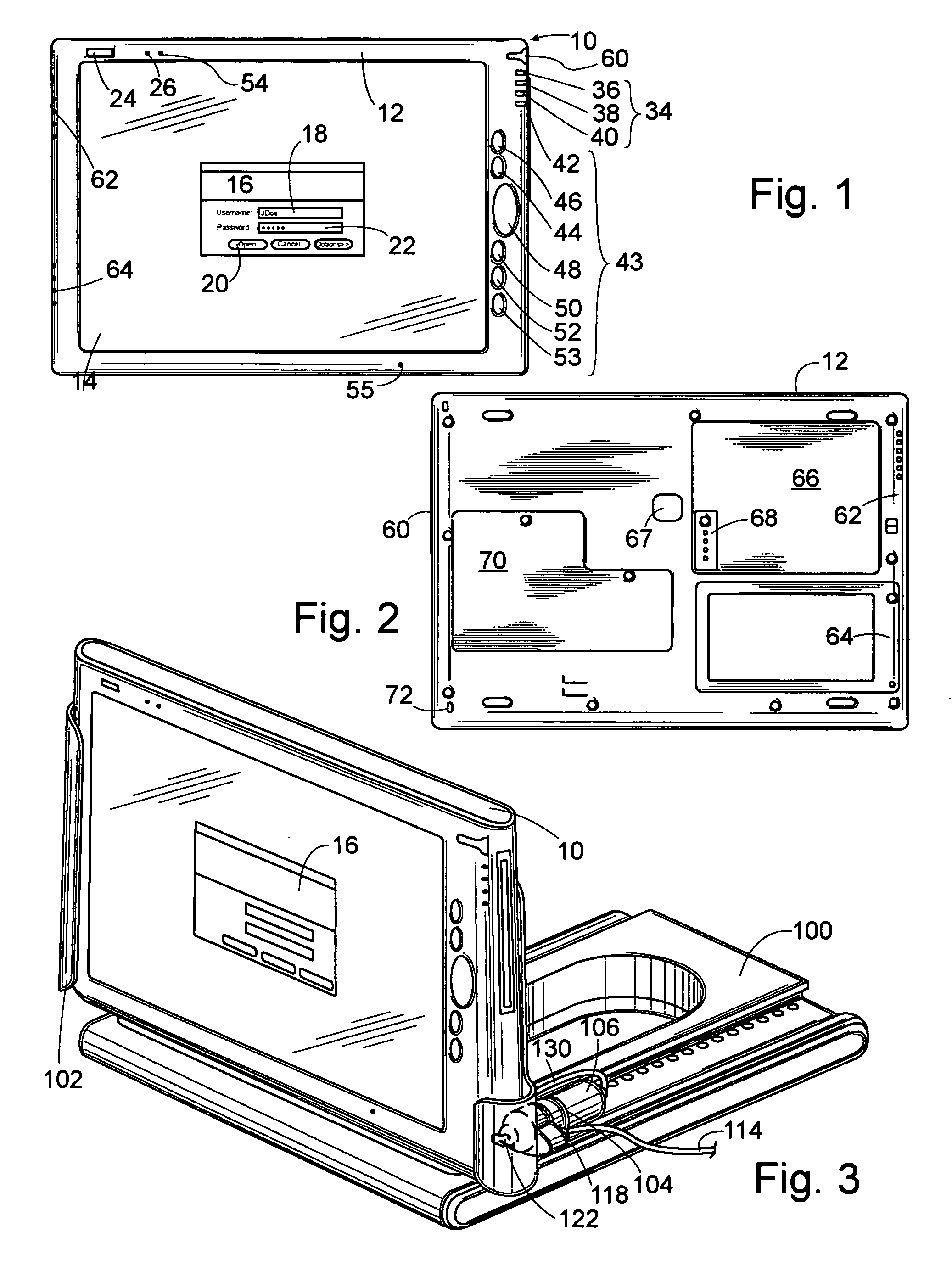
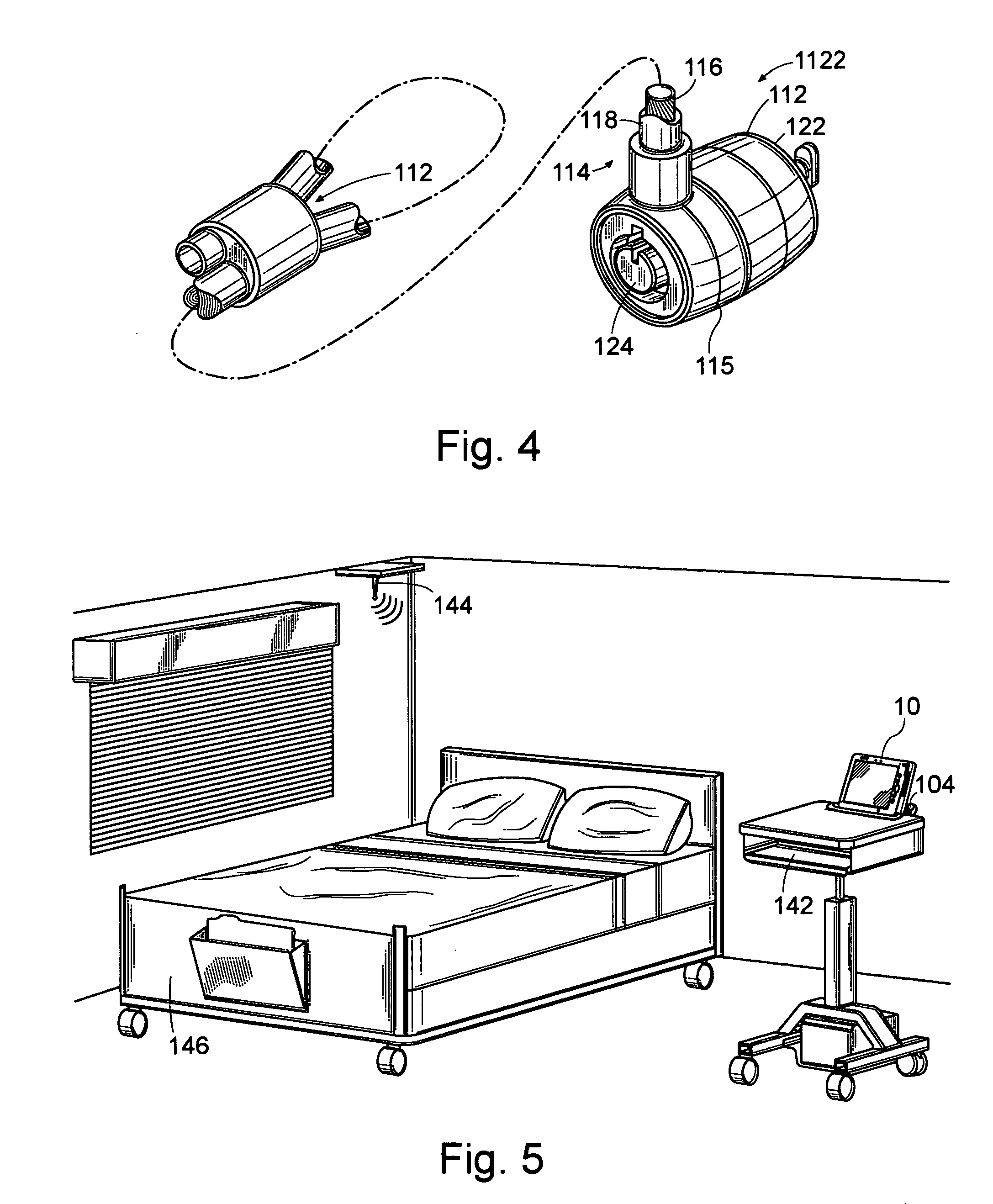
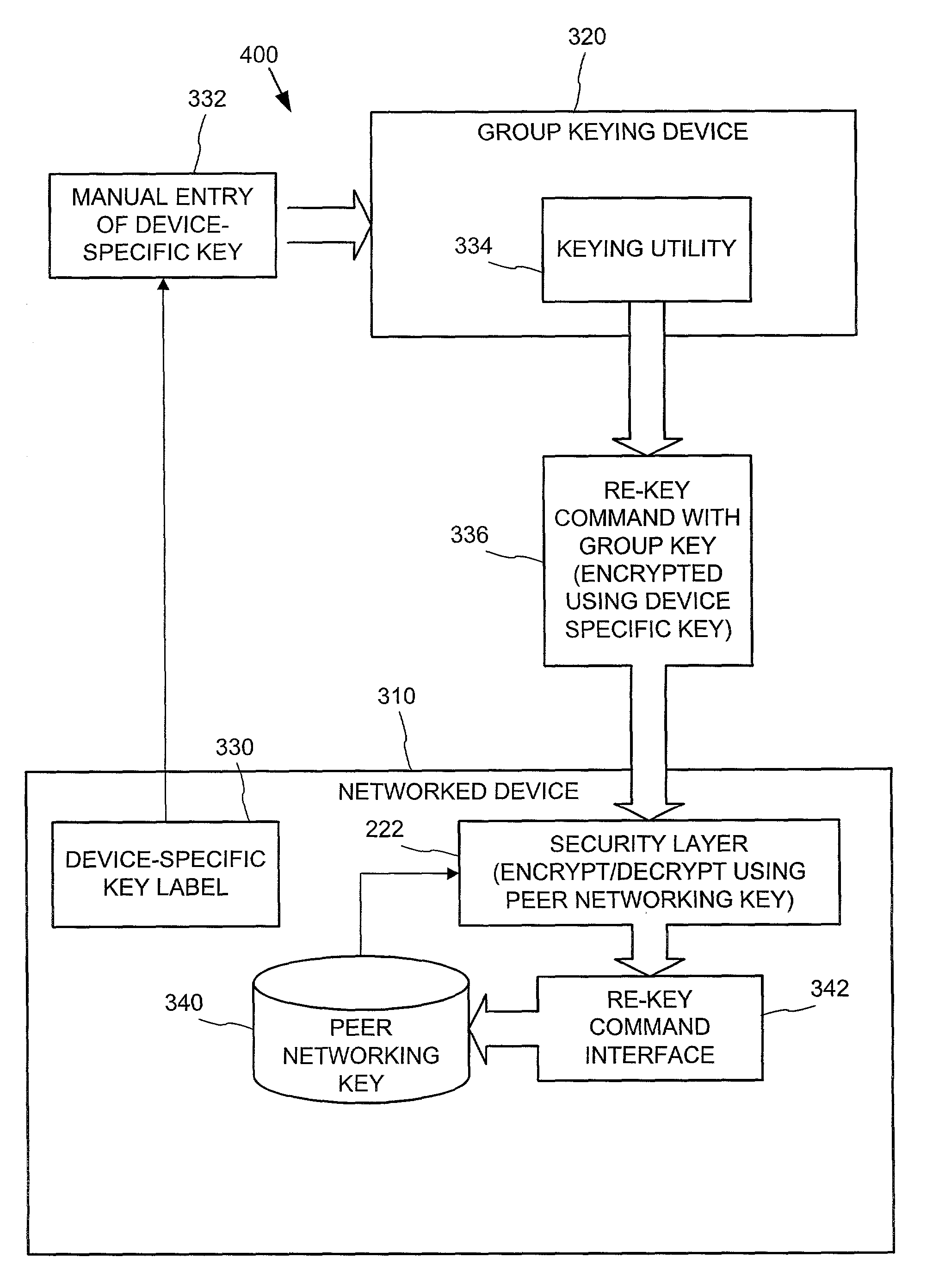
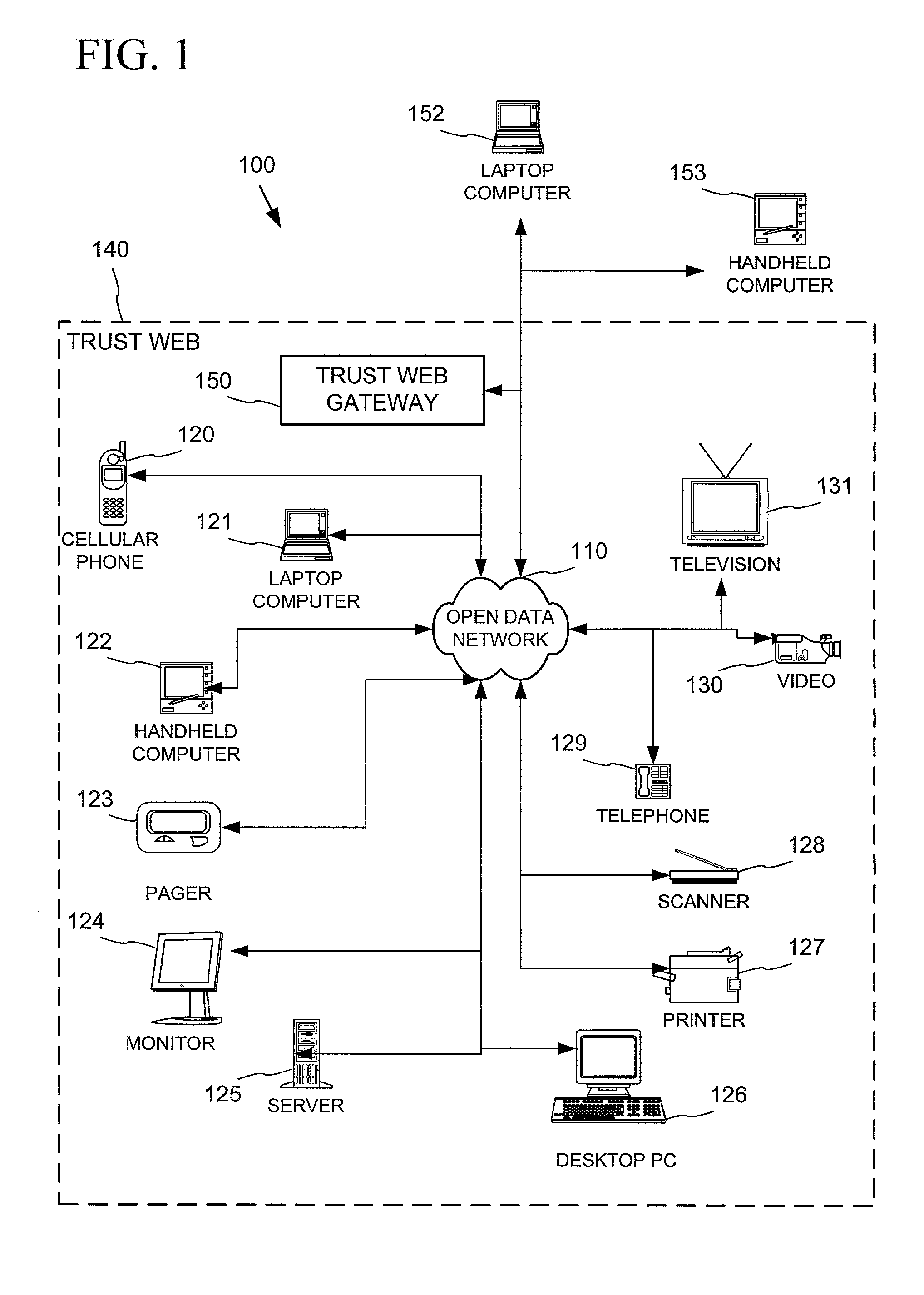
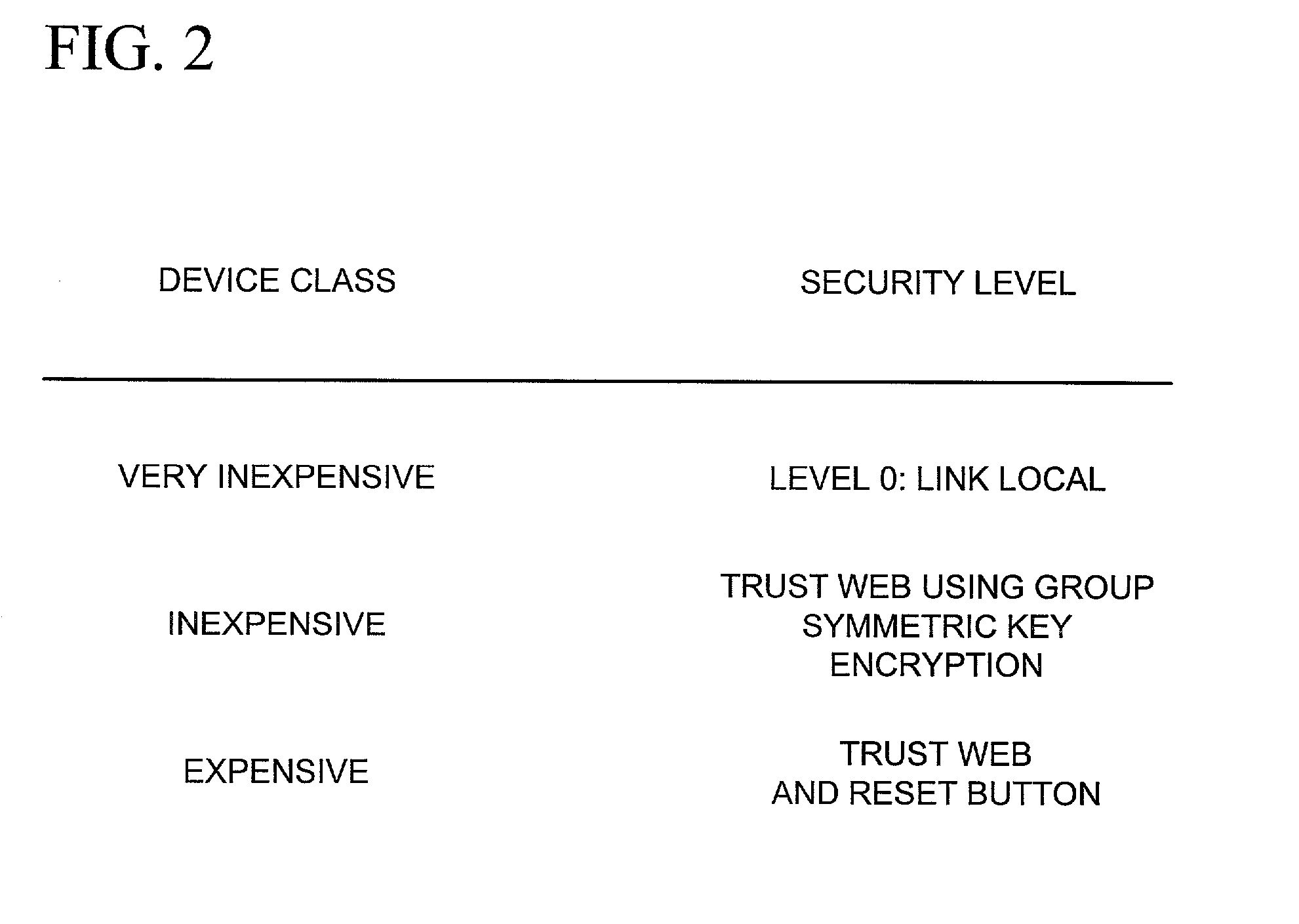
Establishing secure peer networking in trust webs on open networks using shared secret device key
InactiveUS7082200B2CostImprove connectivityKey distribution for secure communicationDigital data processing detailsS/KEYVia device
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com